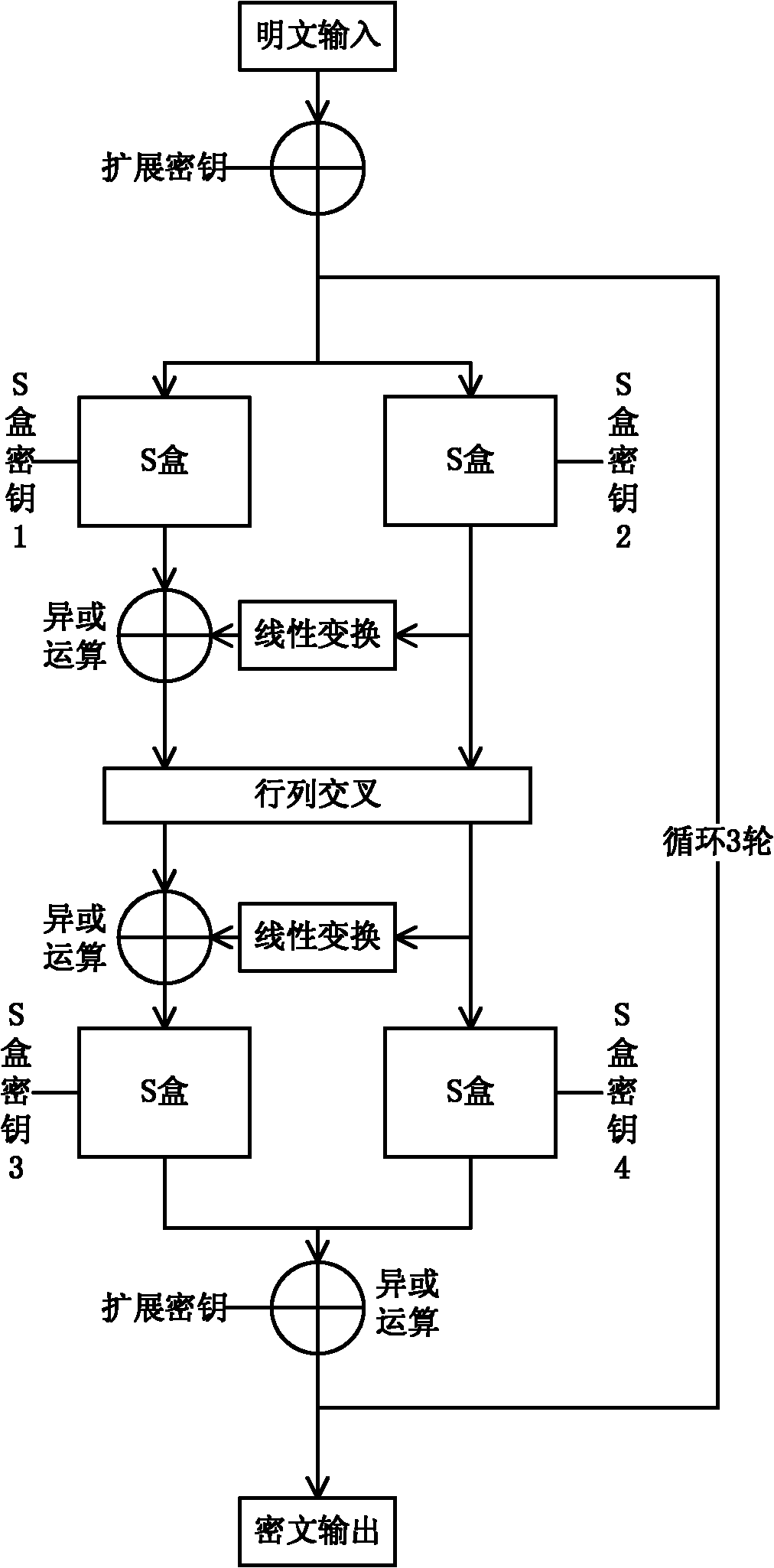
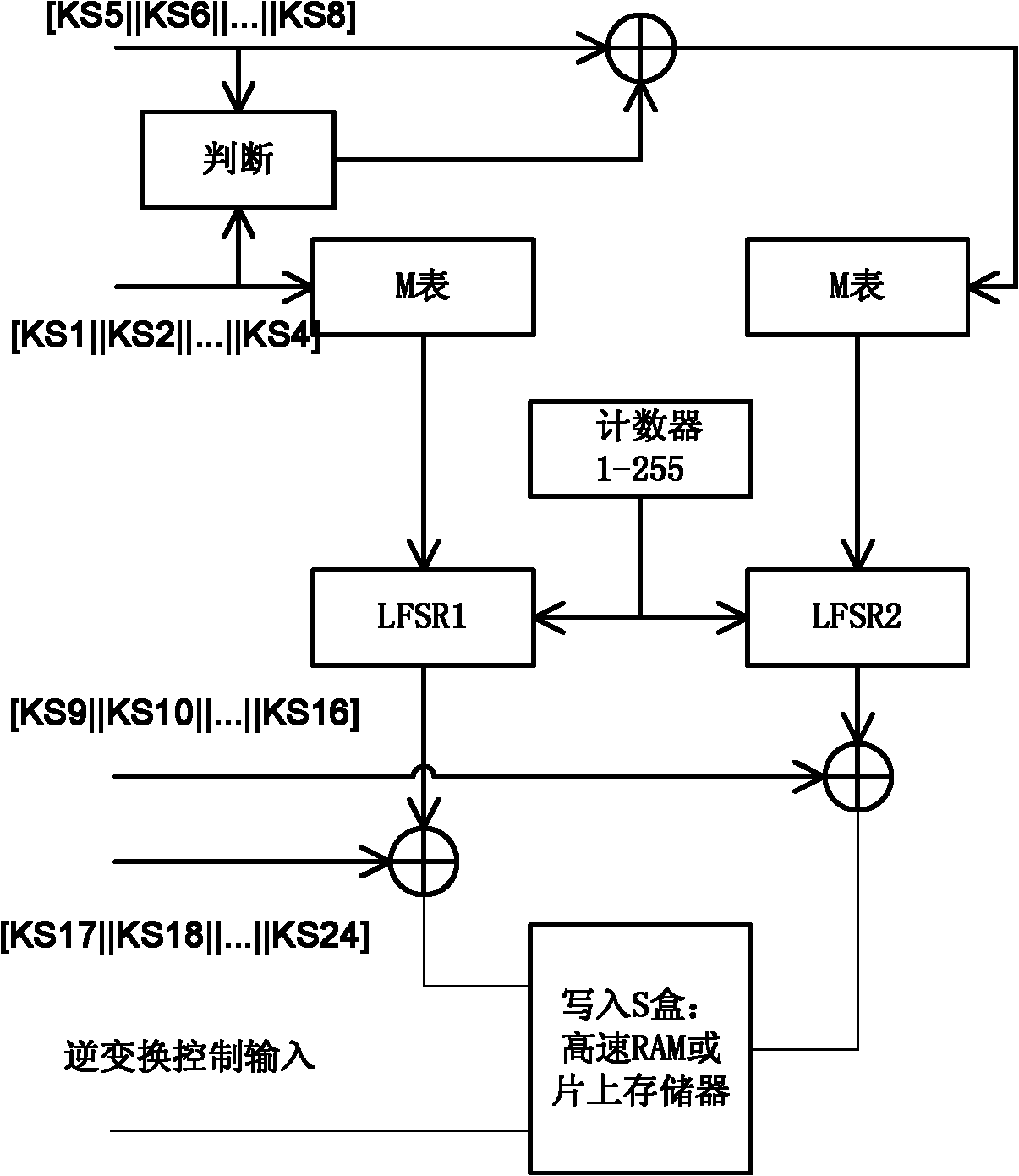
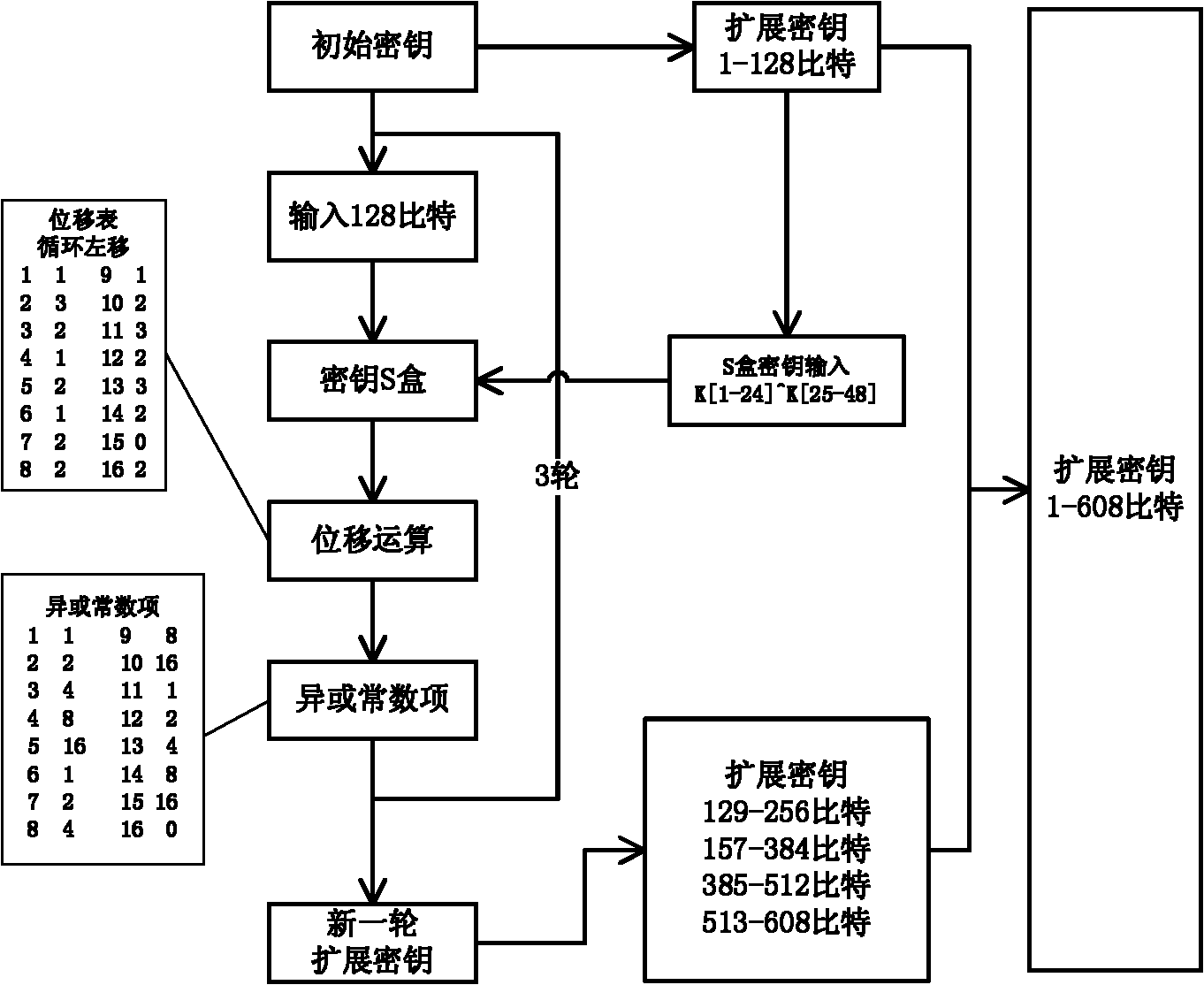
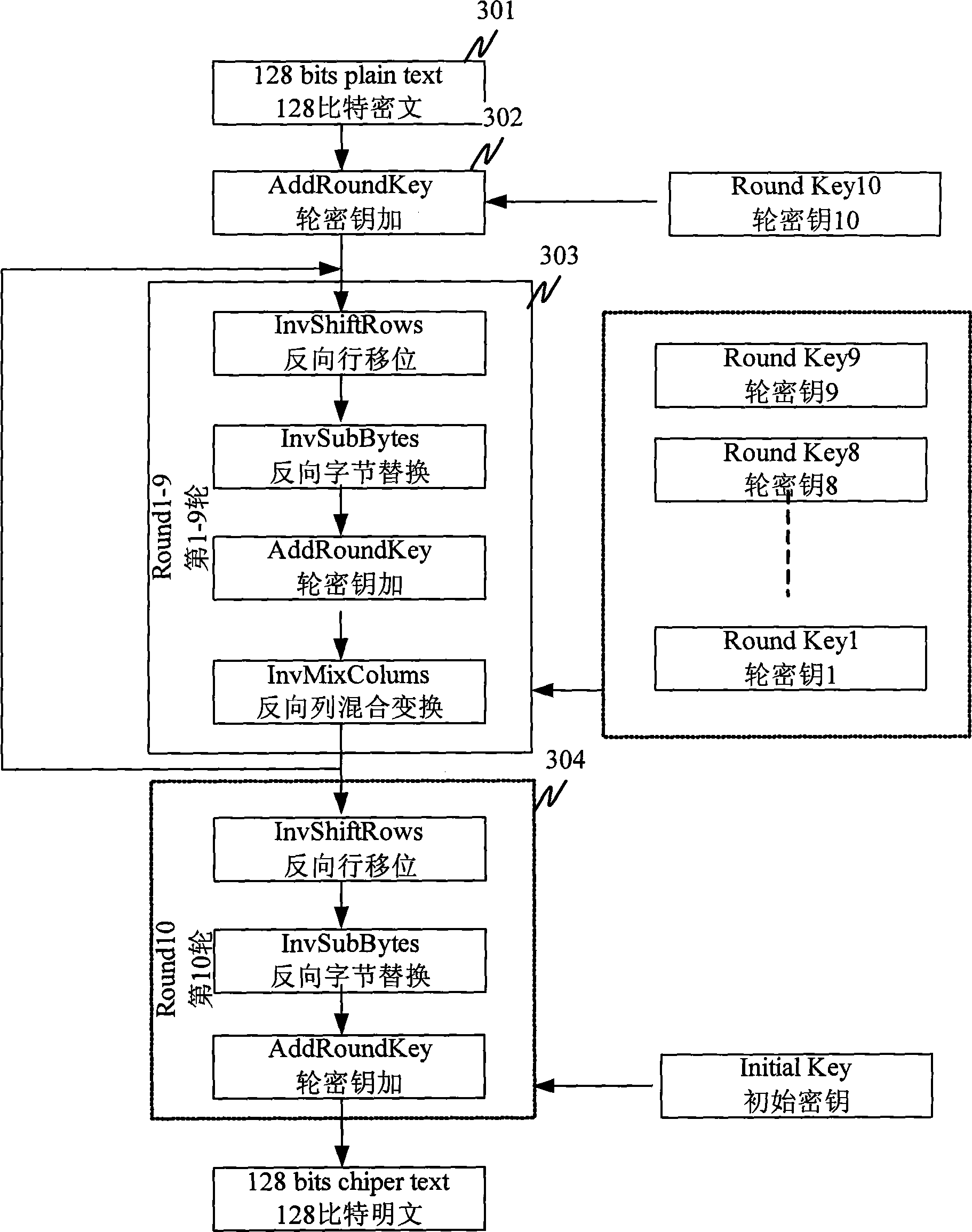
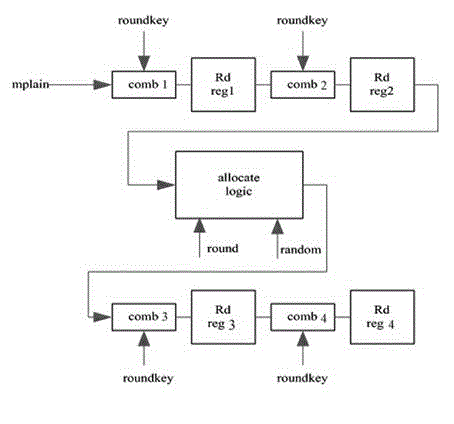
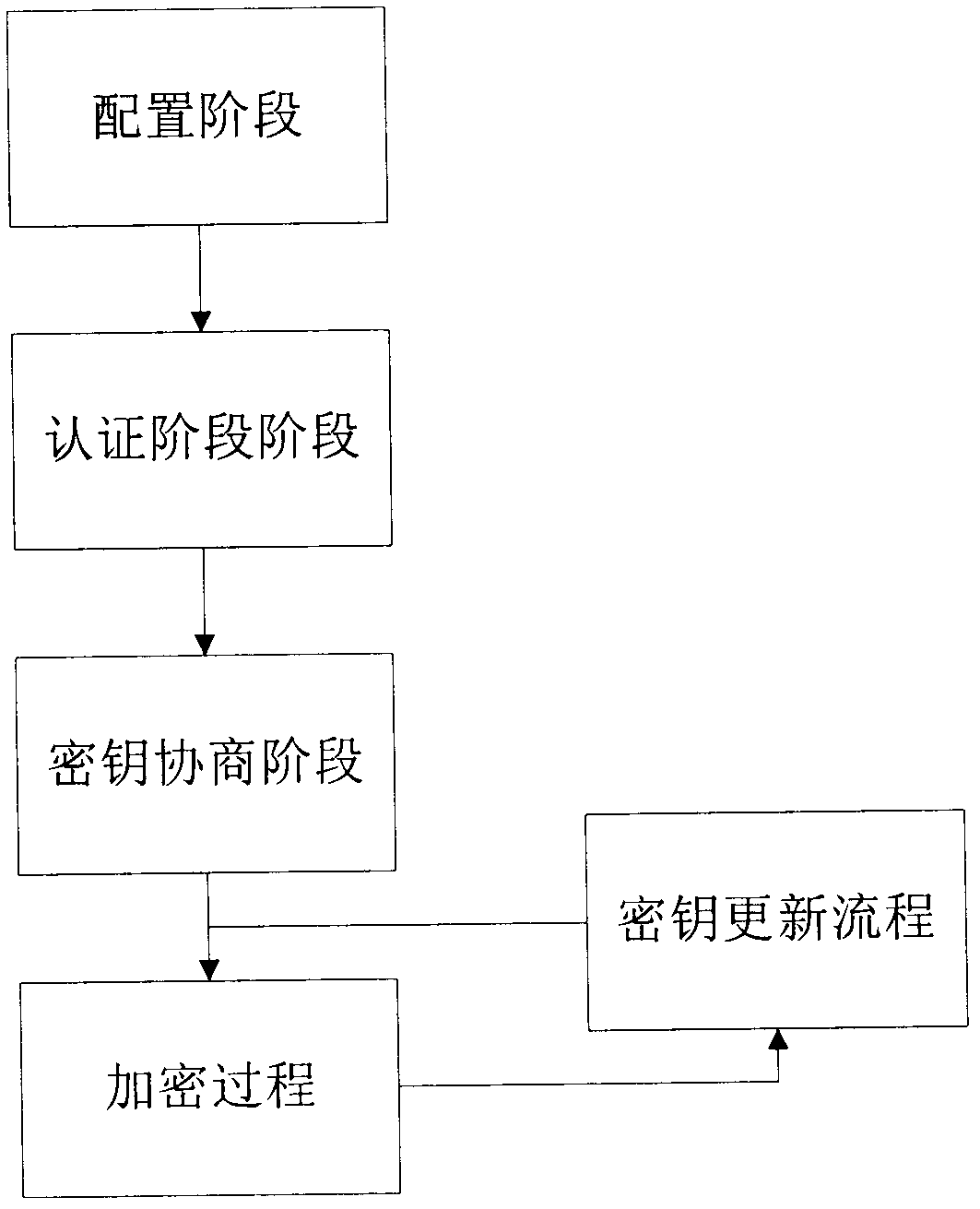
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
366 results about "Advanced Encryption Standard" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
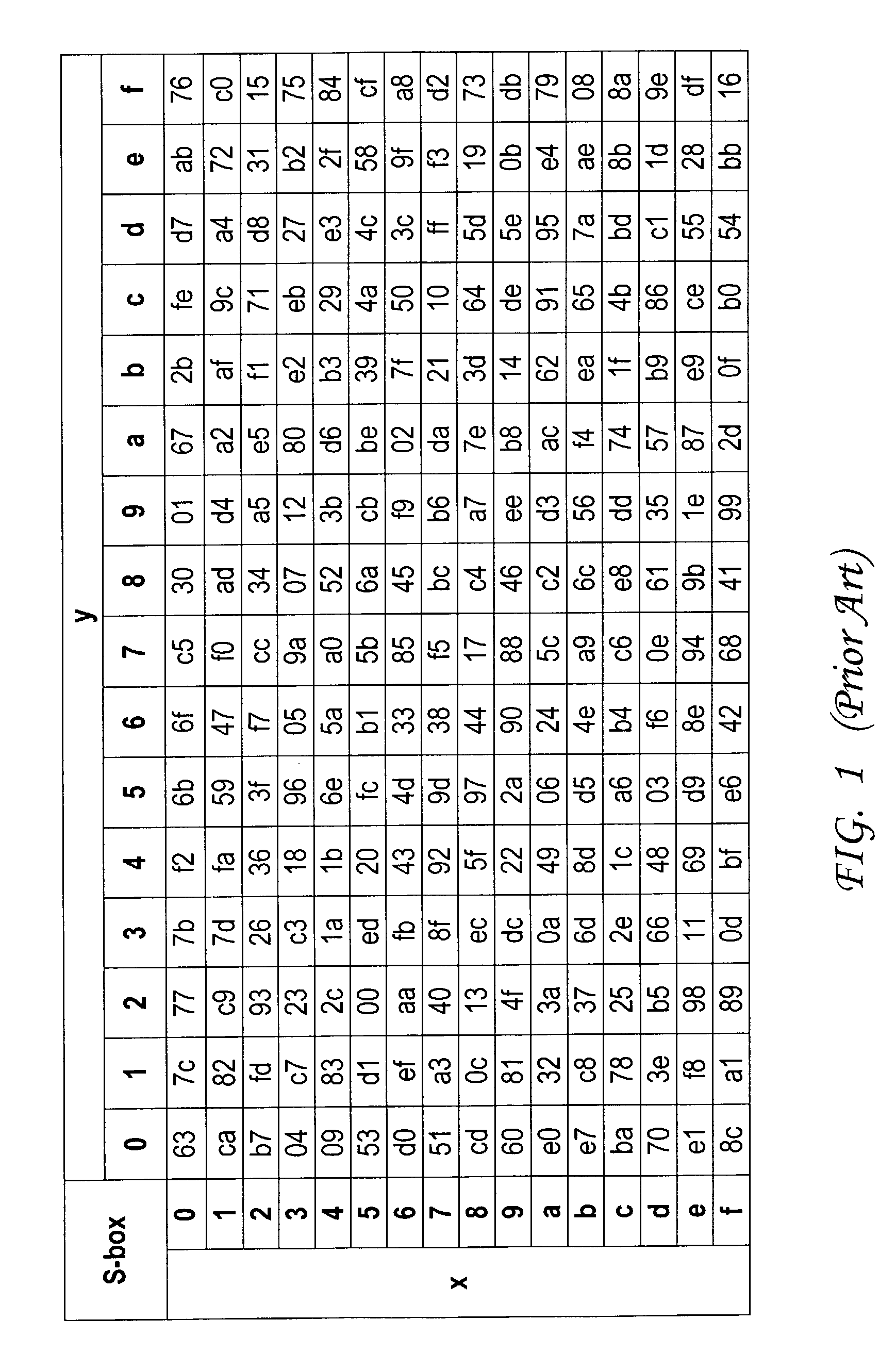
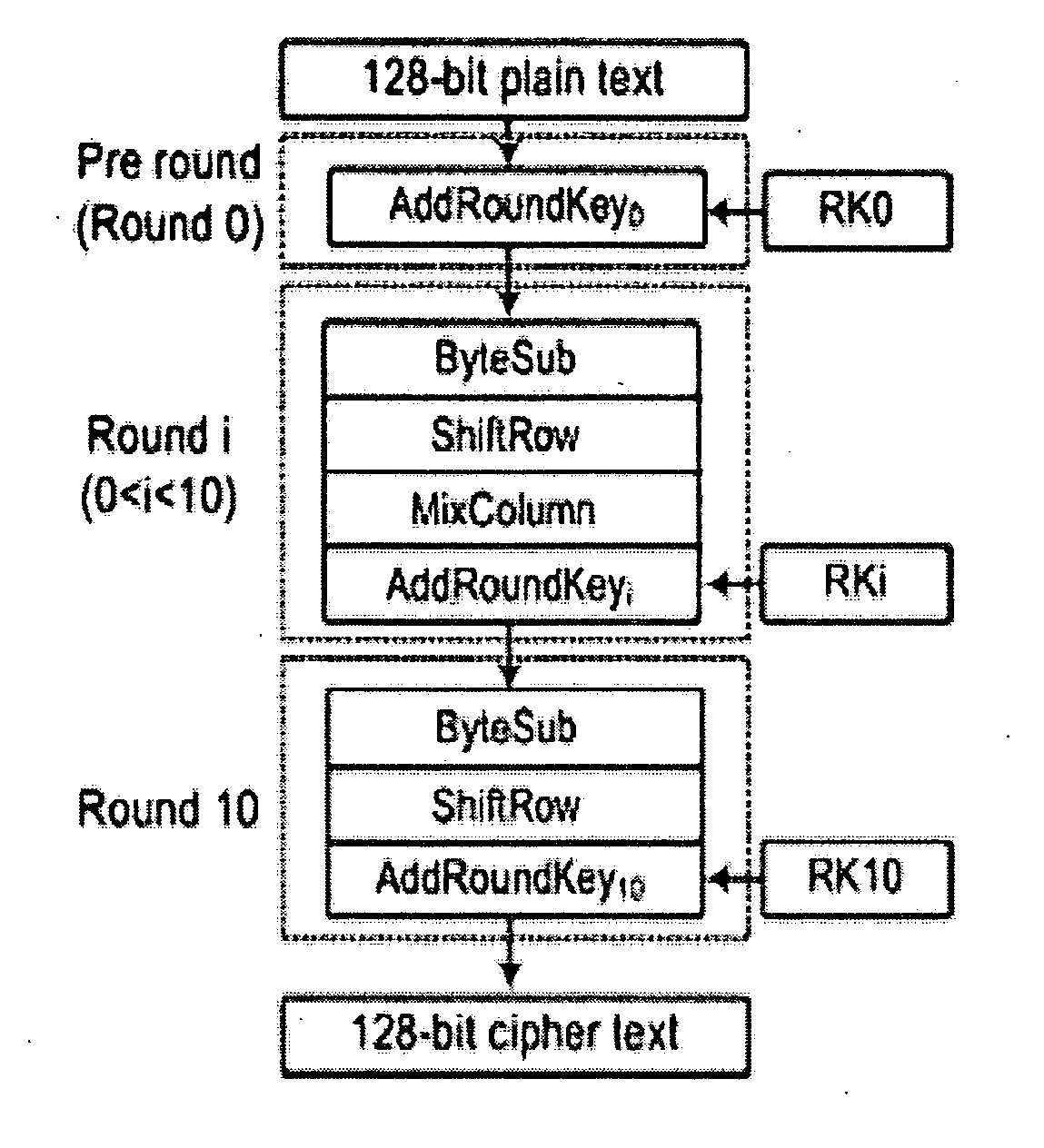
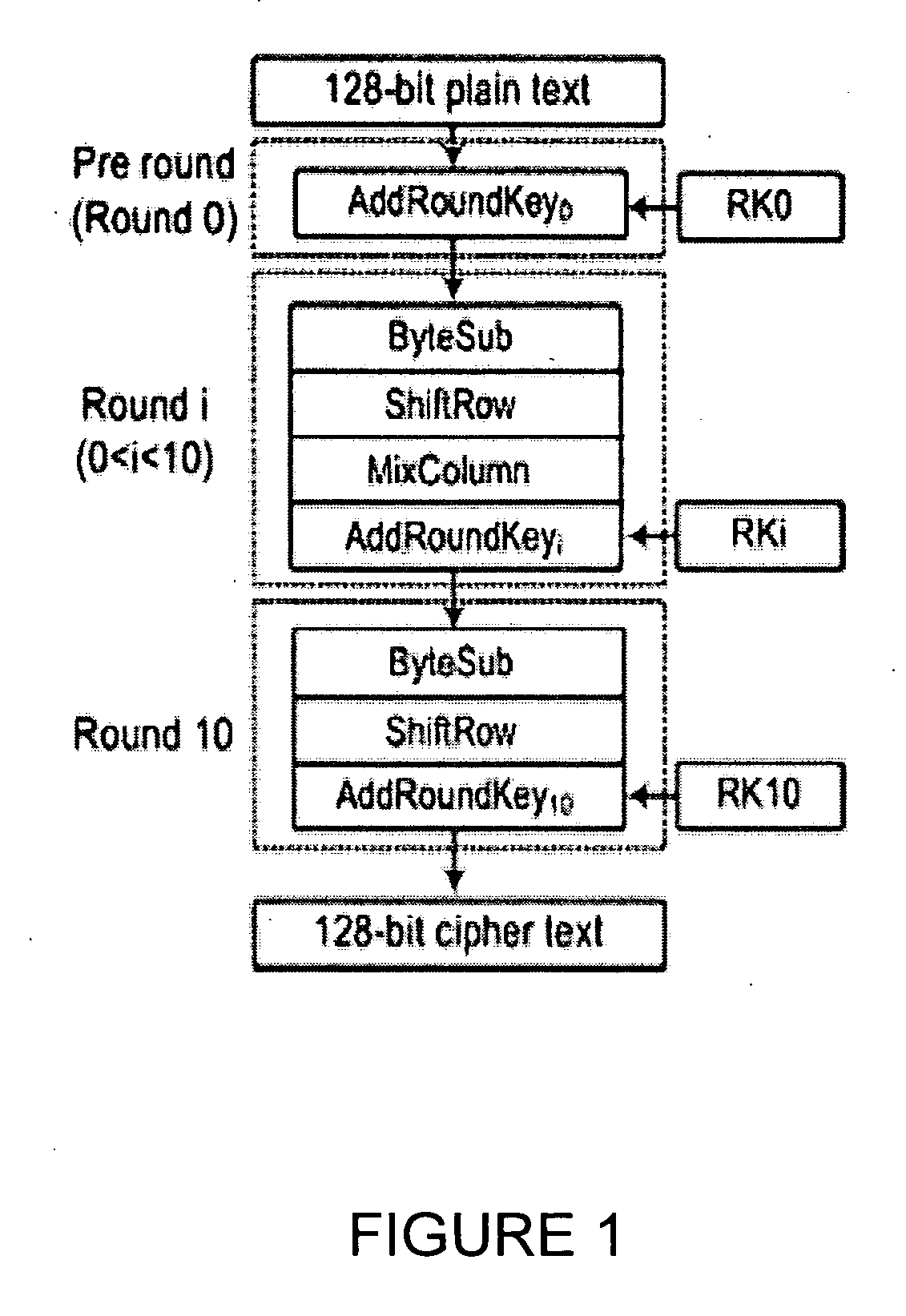
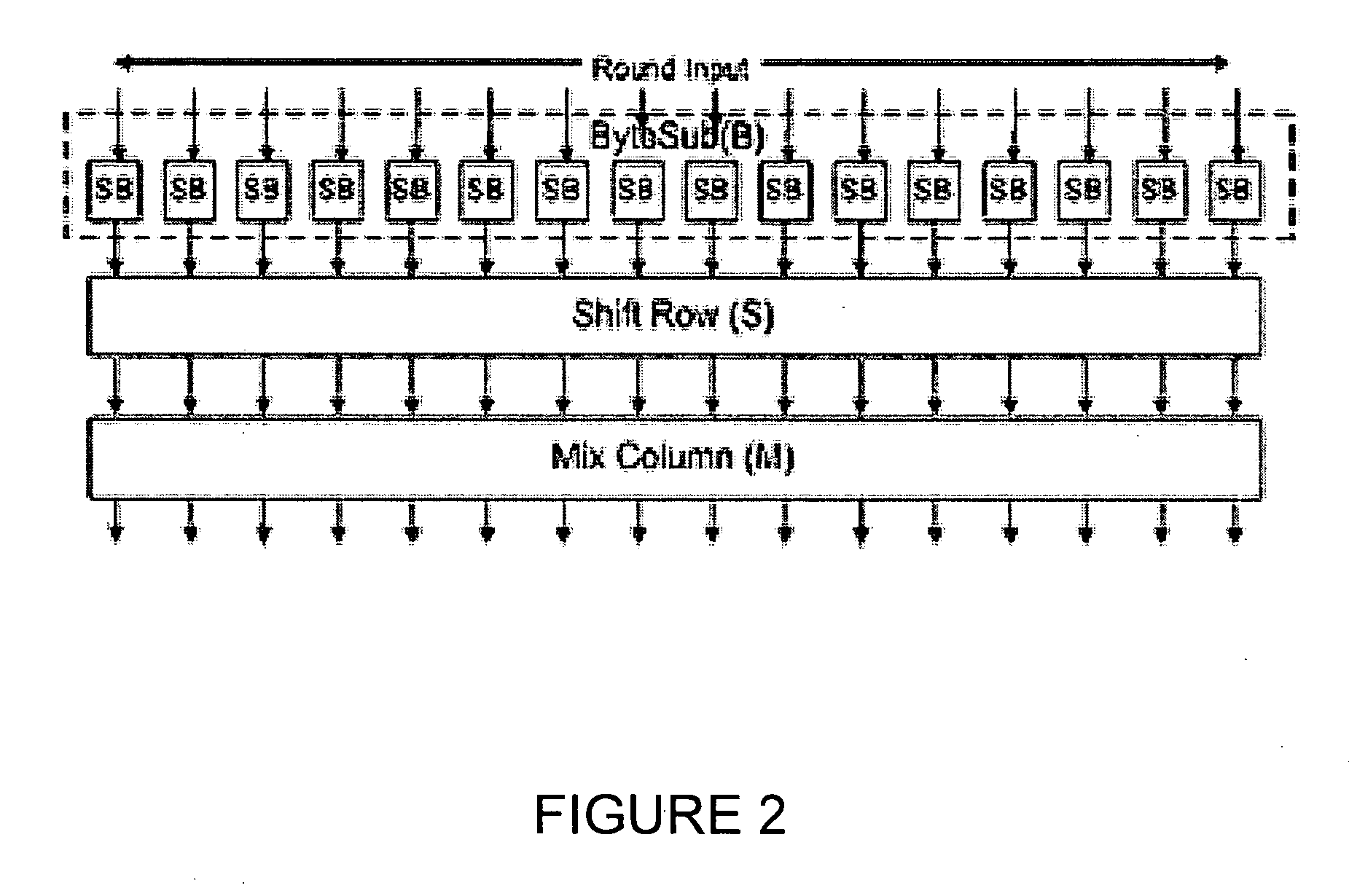
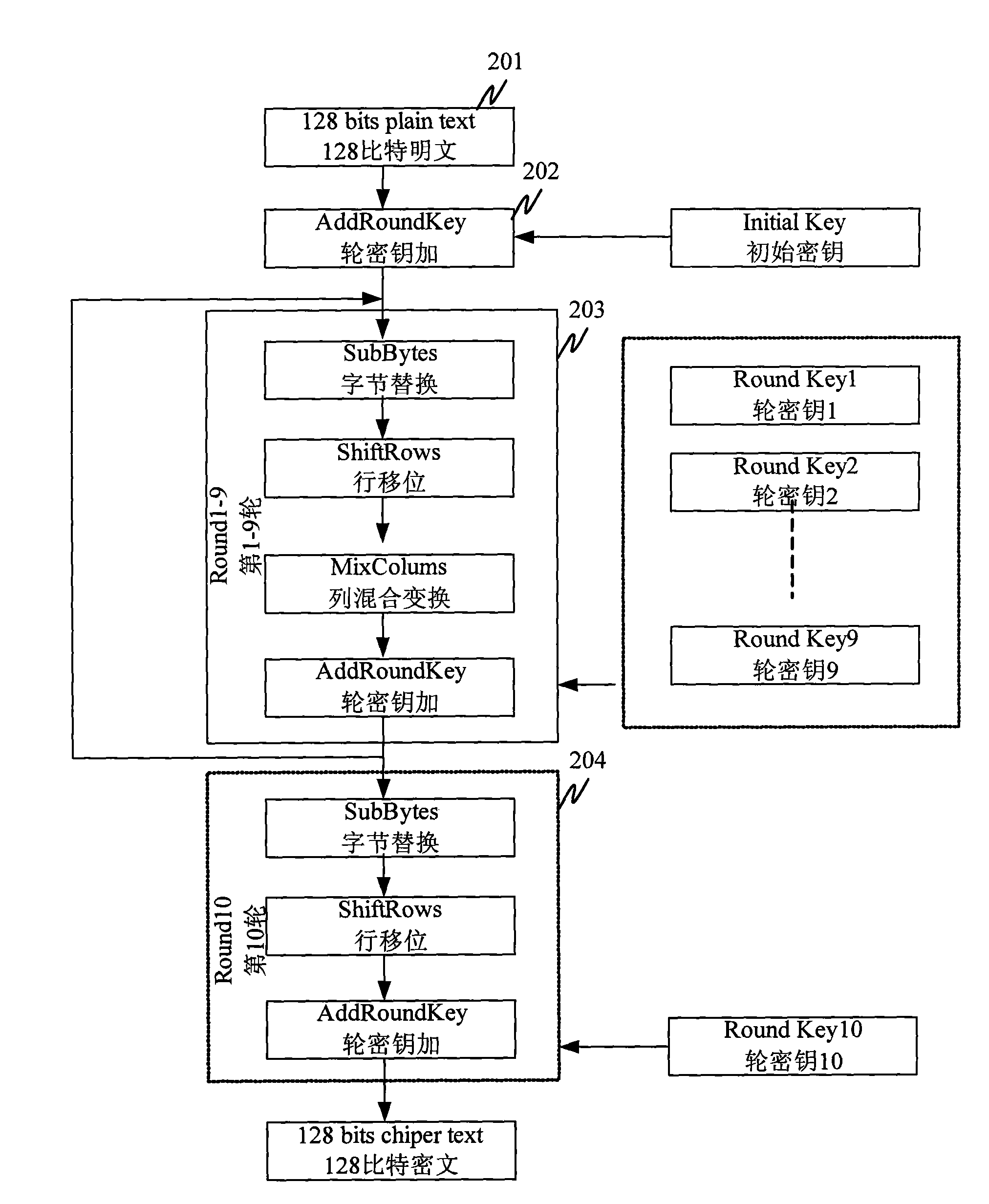
The Advanced Encryption Standard (AES), also known by its original name Rijndael ([ˈrɛindaːl]), is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
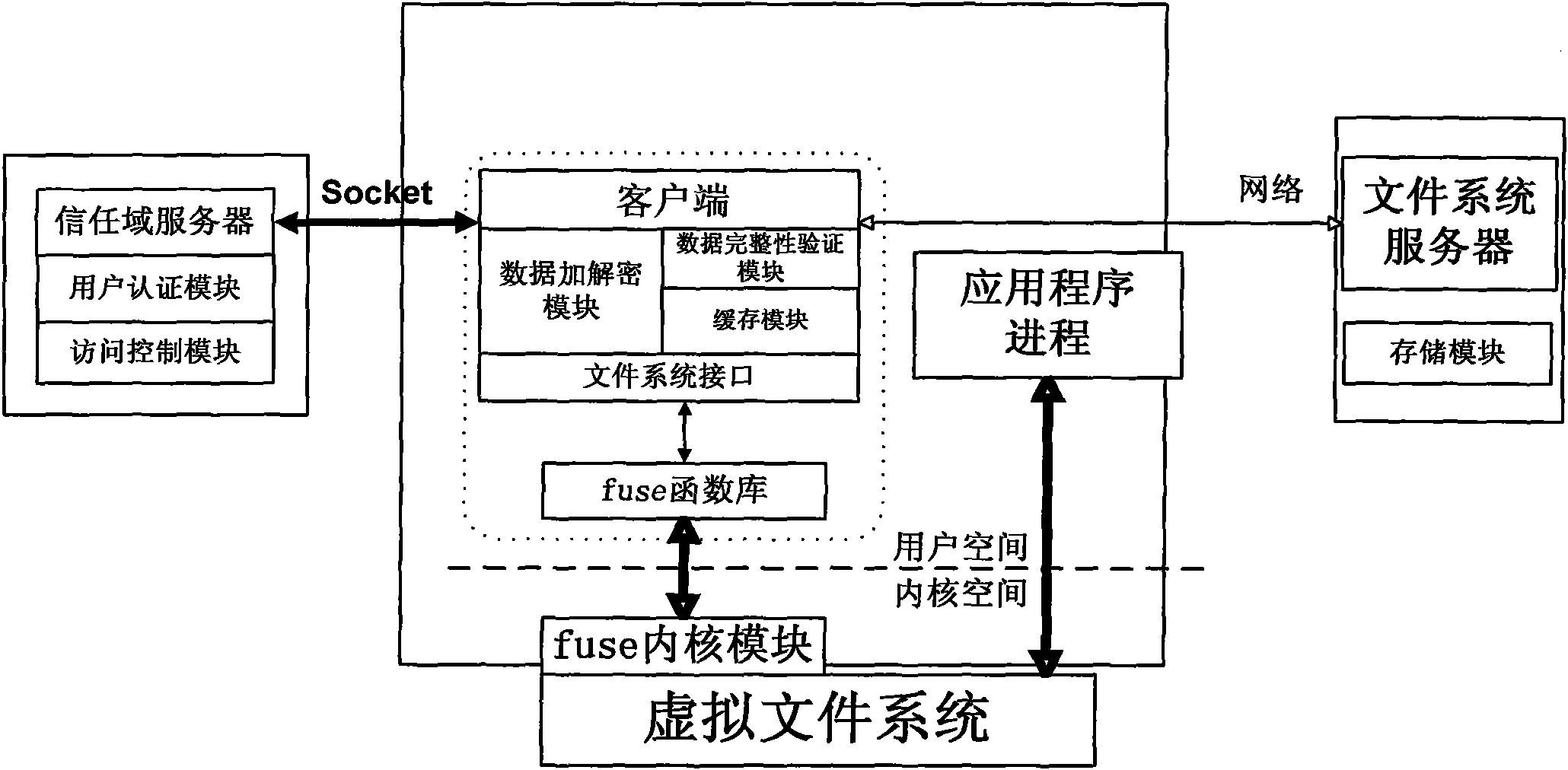
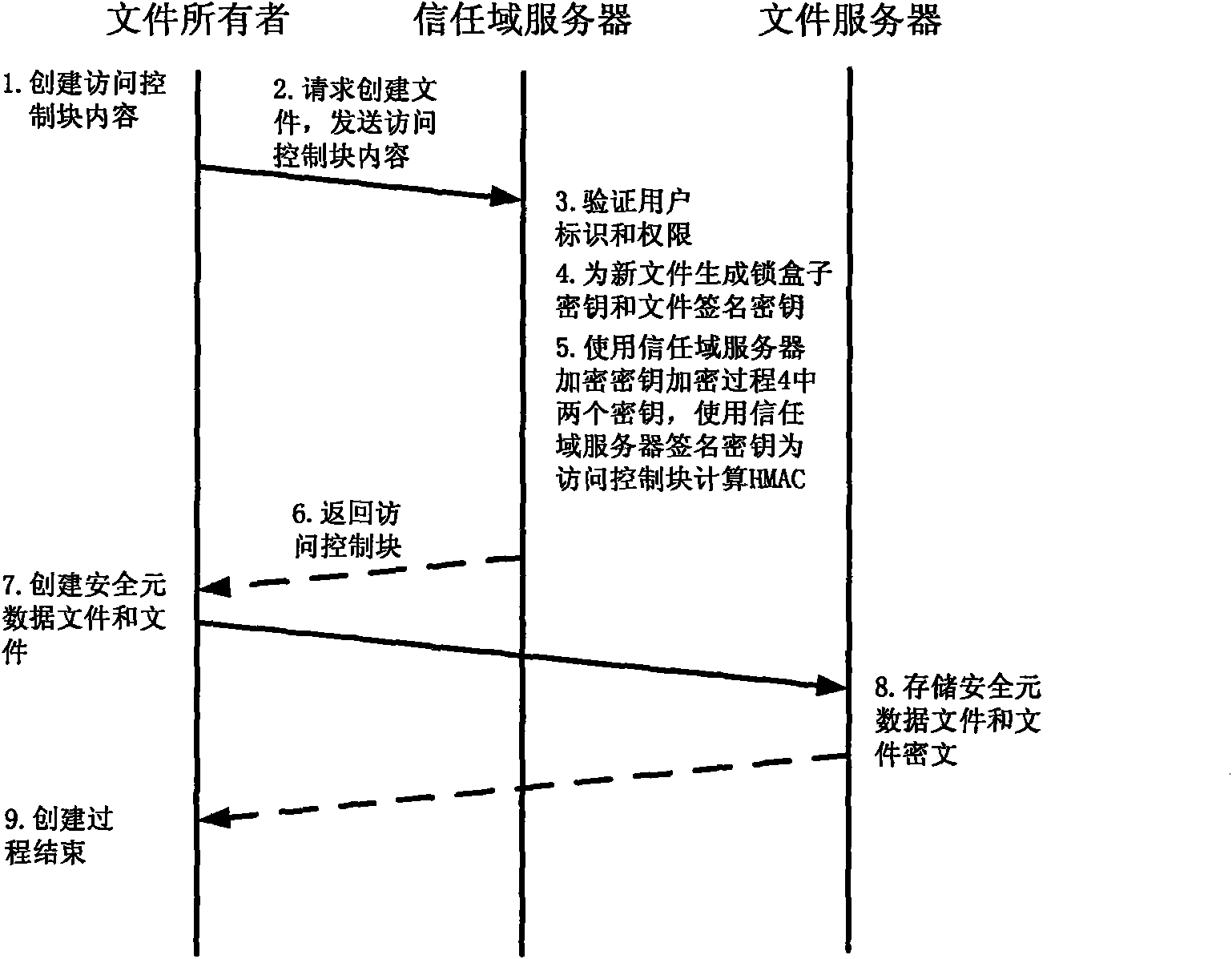
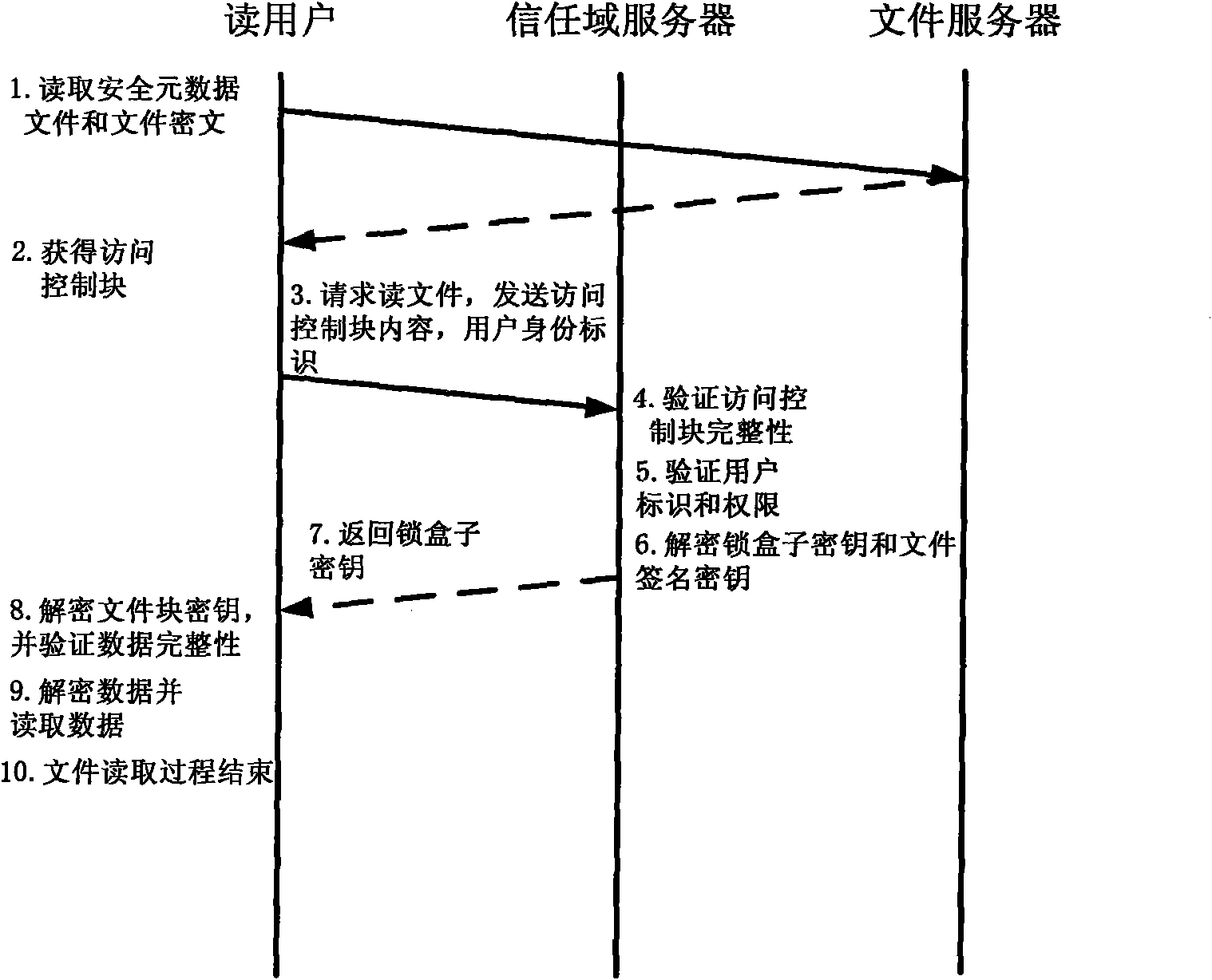
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
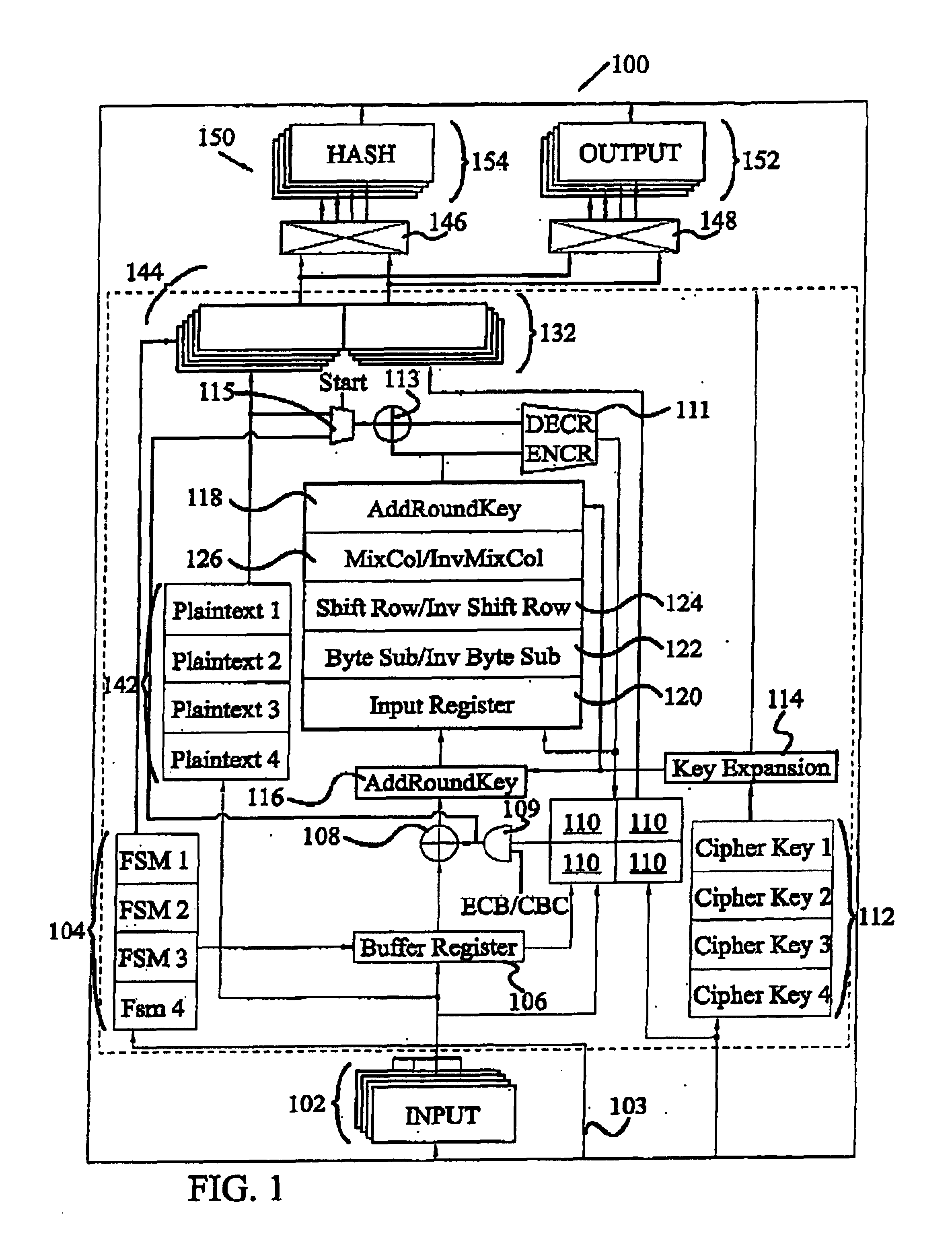
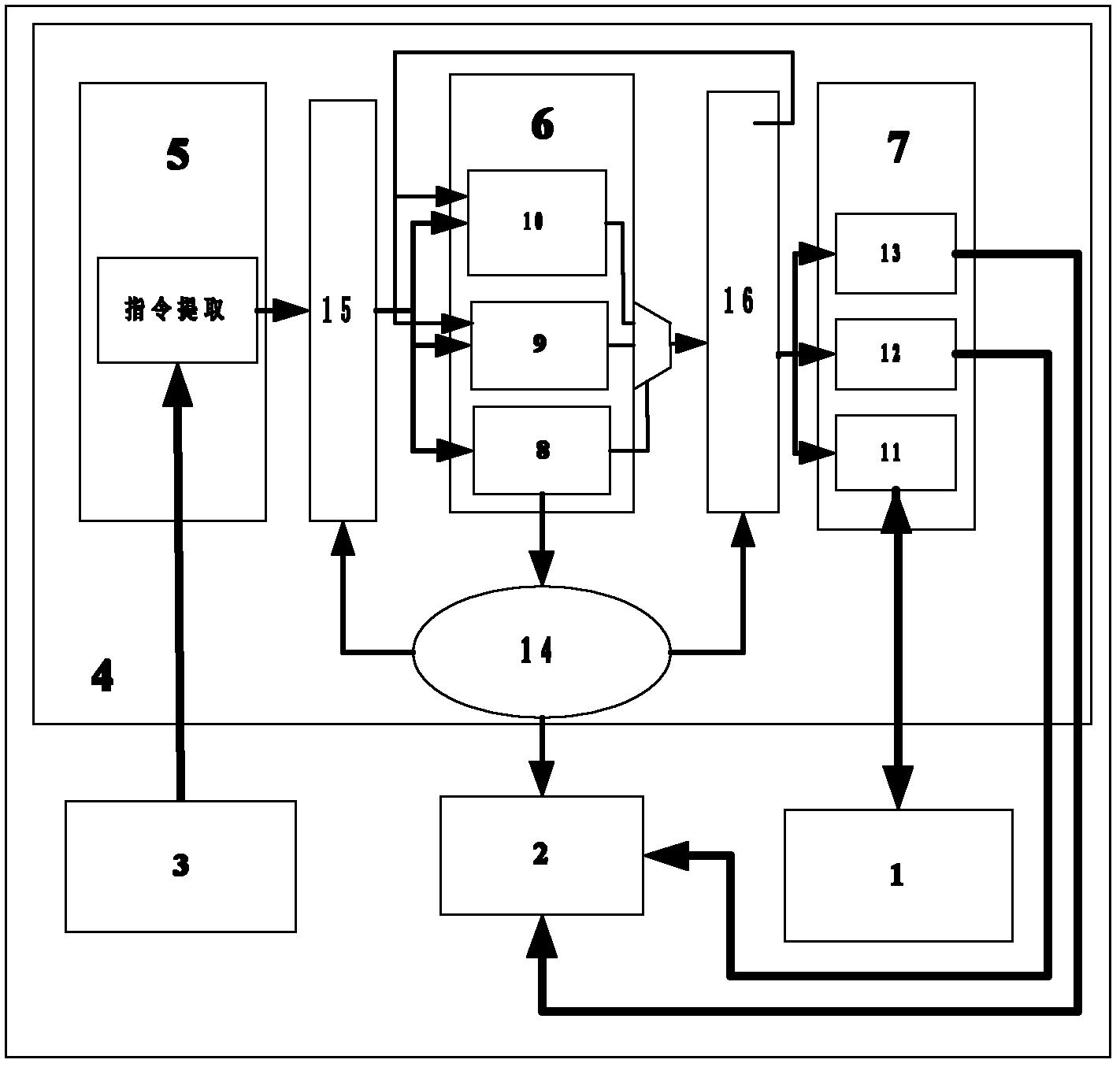
Circuit and method for implementing the advanced encryption standard block cipher algorithm in a system having a plurality of channels
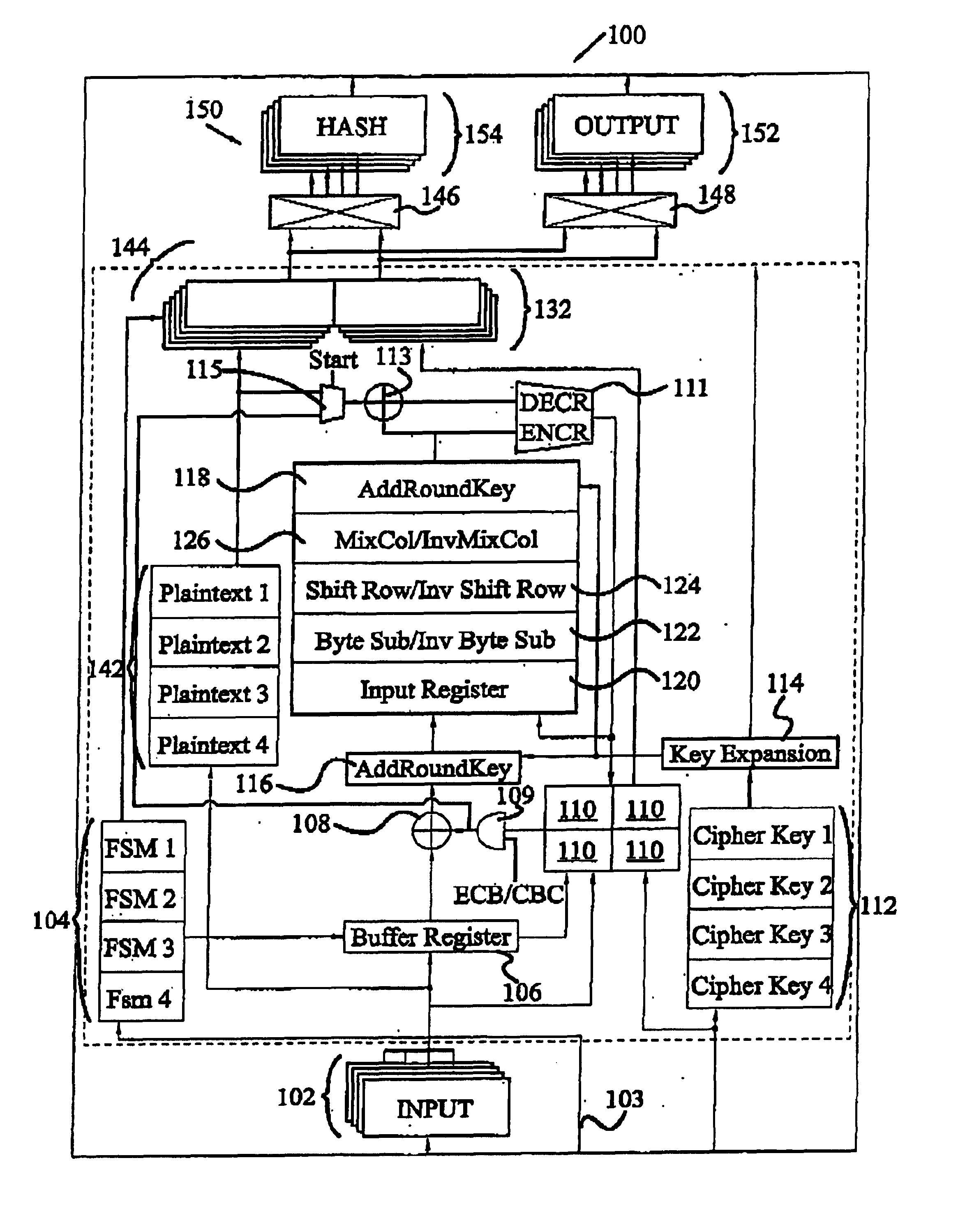
InactiveUS6937727B2Efficient implementationGenerate efficientlyEncryption apparatus with shift registers/memoriesUser identity/authority verificationS-boxAdvanced Encryption Standard
A circuit includes a single circuit portion for implementing the Advanced Encryption Standard (AES) block cipher algorithm in a system having a plurality of channels. The circuit portion includes a circuit for individually generating, on the fly, the round keys used during each round of the AES block cipher algorithm. The circuit portion also includes shared logic circuits that implement the transformations used to encrypt and decrypt data blocks according to the AES block cipher. The single circuit portion encrypts or decrypts data blocks from each of the plurality of system channels in turn, in round-robin fashion. The circuit portion also includes a circuit for determining S-box values for the AES block cipher algorithm. The circuit additionally implements an efficient method for generating round keys on the fly for the AES block cipher decryption process.
Owner:EXCELIS INC
Advanced encryption standard (AES) engine with real time S-box generation
ActiveUS20050058285A1Good encryptionDifferent operationalEncryption apparatus with shift registers/memoriesSecret communicationShift registerS-box
An advanced encryption standard (AES) engine with real time S-box generation includes a Galois field multiplier system in a first mode responsive to a first data block for generating an AES selection (S-box) function by executing the multiplicative increase in GF1(2m) and applying an affine over GF(2) transformation to obtain a subbyte transformation; and a shift register system for transforming the subbyte transformation to obtain a shift row transformation; the Galois field multiplier system is responsive in a second mode to the shift row transformation to obtain a mix column transformation and add a round key for generating in real time an advanced encryption standard cipher function of the first data block.
Owner:ANALOG DEVICES INC +1
Advanced encryption standard (AES) hardware cryptographic engine
ActiveUS7295671B2Reduce in quantityKey distribution for secure communicationMultiple keys/algorithms usageS-boxAdvanced Encryption Standard
A cryptographic method and related implements the Rijndael—AES encryption standard. In one improvement, the decryption round keys are generated on a round by round basis from the final Nk round keys saved from a previous encryption key scheduling operation. Latency and memory requirements are thereby minimized. S-boxes for the AES key generation and cipher operation itself, may be implemented multiple times in different ways with different power signatures, with a pseudo-random selection of the pathway for the different bytes to be substituted. The premix operation occurs simultaneously with the generation of first round keys, and a dummy circuit with substantially identical timing as the real premix circuitry adds power consumption noise to the premix.
Owner:ATMEL CORP
Data cipher processors, AES cipher systems, and AES cipher methods using a masking method
ActiveUS20050207571A1Small sizeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesOriginal dataAdvanced Encryption Standard
Data cipher processors, advanced encryption standard (AES) cipher system, and AES cipher methods using a masking method perform round operations using a round key, a plain text, a cipher text, and masking data. Some of the round operations are implemented over a composite Galois Field GF(•). Original data and predetermined masking data are processed according to a predetermined rule. Sub-byte transformation operations used in the cipher method and system may include an affine transformation, an inverse affine transformation, an isomorphic transformation, and an inverse isomorphic transformation which are linear transformations, and an inverse transformation that is a non-linear transformation.
Owner:SAMSUNG ELECTRONICS CO LTD
Invariance based concurrent error detection for the advanced encryption standard
ActiveUS20070014395A1Protection attackPublic key for secure communicationSecret communicationThroughput degradationAdvanced Encryption Standard
Advanced Encryption Standard (AES) is an encryption algorithm for securing sensitive unclassified material by U.S. Government agencies and, as a consequence the de facto encryption standard for commercial applications worldwide. Performing concurrent error detection (CED) for protection of such a widely deployed algorithm is an issue of paramount importance. We present a low-cost CED method for AES. In this method, we make use of invariance properties of AES to detect errors. For the first time, the invariance properties of the AES, which are for the most part used to attack the algorithm, are being used to protect it from fault attacks. Our preliminary ASIC synthesis of this architecture resulted in an area overhead of 13.8% and a throughput degradation of 16.67%.
Owner:POLYTECHNIC INST OF NEW YORK
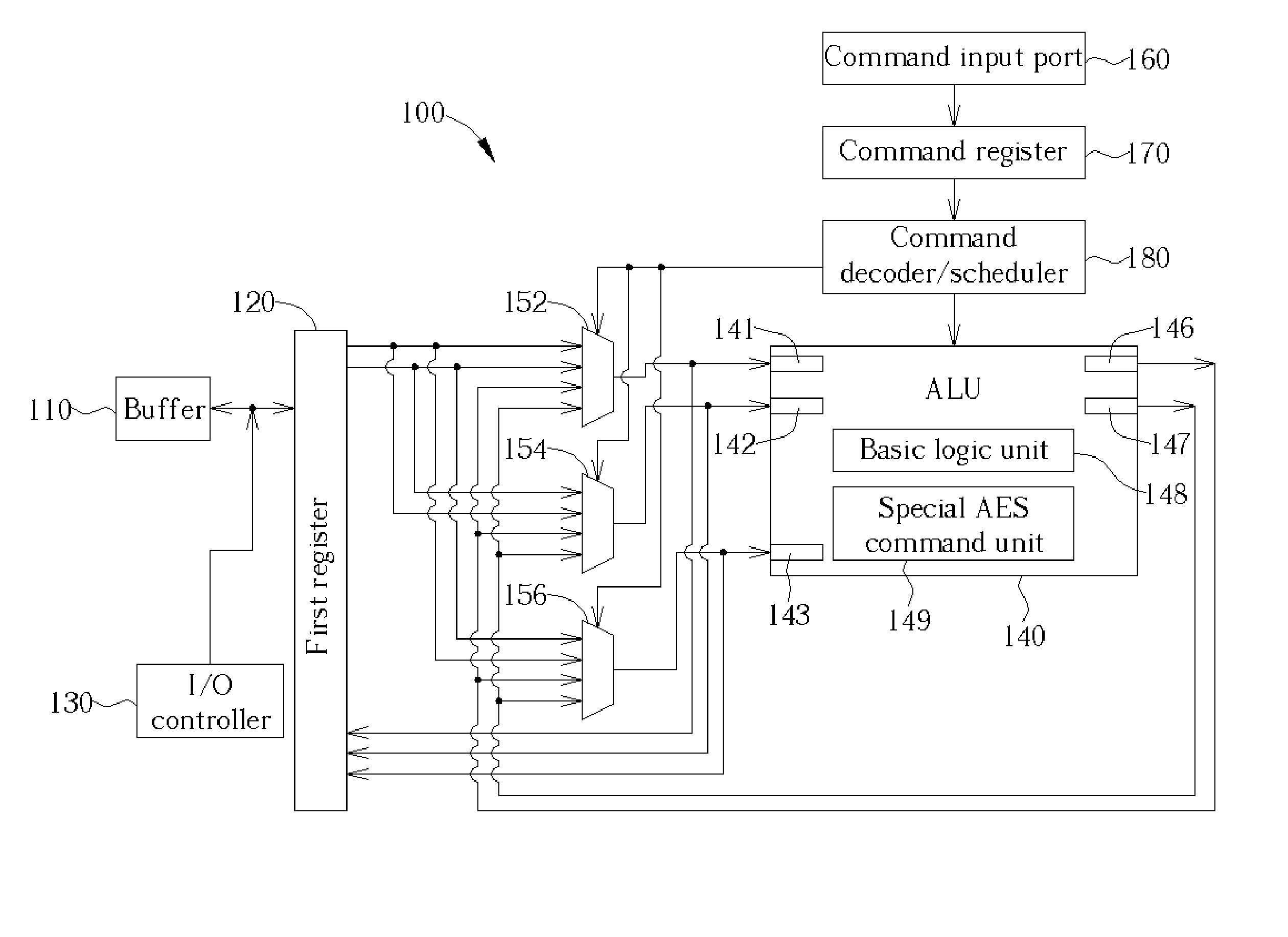
Method for implementing advanced encryption standards using a very long instruction word architecture processor
InactiveUS20050147239A1Encryption apparatus with shift registers/memoriesInternal/peripheral component protectionArithmetic logic unitProcessor register
A method for implementing Advanced Encryption Standards (AES) by a very long instruction word (VLIW) architecture processor. The method includes inputting the instructions for AES into the processor, decoding and scheduling the input instructions, controlling at least one of a plurality of multiplexers to output data from a first register of the processor and / or an arithmetic logic unit to the first register and / or the arithmetic logic unit according to the decoded and scheduled instructions, controlling the arithmetic logic unit to perform operations, and outputting results of the operations to the plurality of the multiplexers.
Owner:ADMTEK INCORPORATED
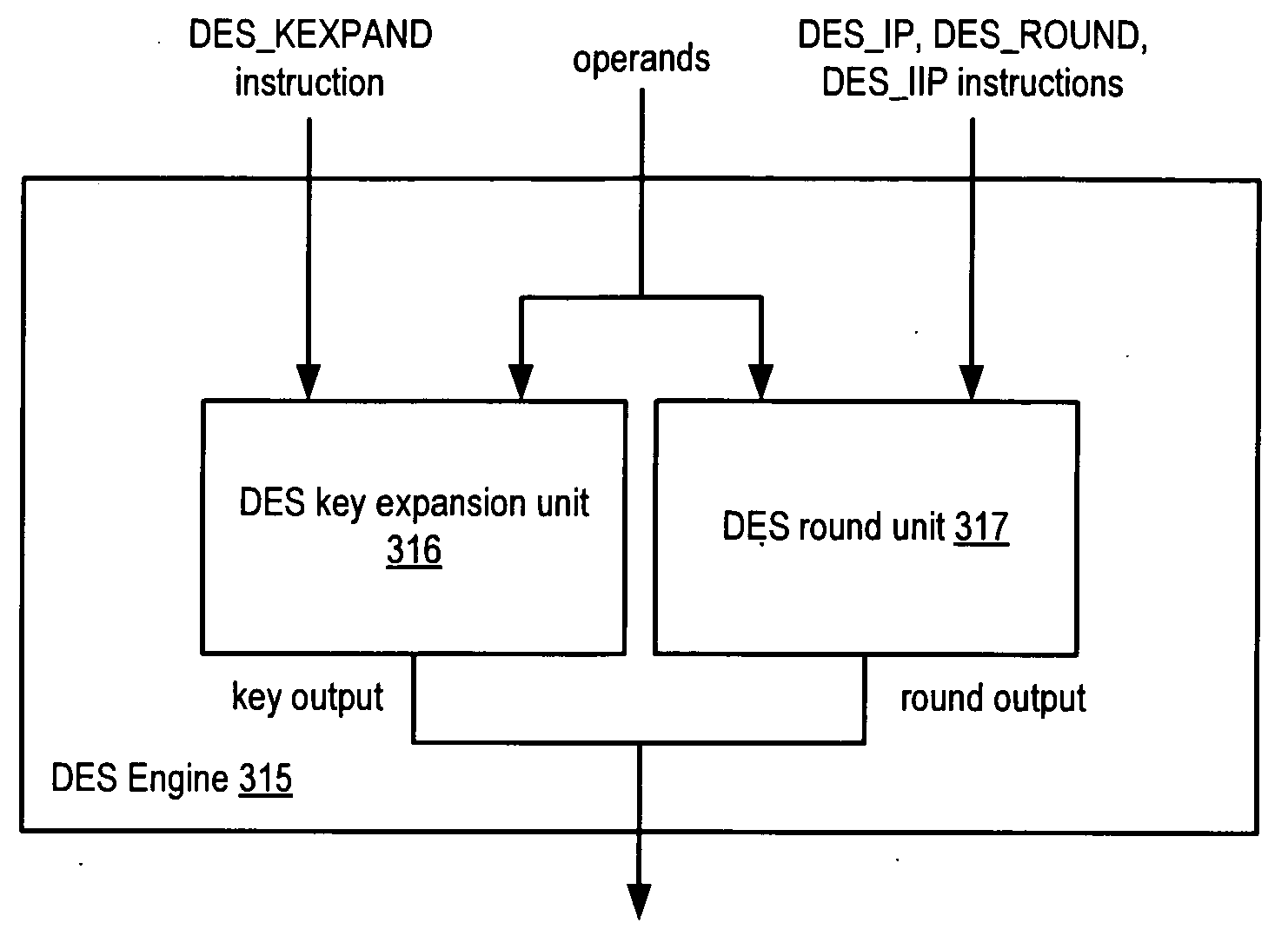
Apparatus and method for implementing instruction support for the advanced encryption standard (AES) algorithm
InactiveUS20100250965A1Unauthorized memory use protectionHardware monitoringInformation processingComputer hardware
A processor including instruction support for implementing the Advanced Encryption Standard (AES) block cipher algorithm may issue, for execution, programmer-selectable instructions from a defined instruction set architecture (ISA). The processor may include a cryptographic unit that may receive instructions for execution. The instructions include one or more AES instructions defined within the ISA. In addition, the AES instructions may be executable by the cryptographic unit to implement portions of an AES cipher that is compliant with Federal Information Processing Standards Publication 197 (FIPS 197). In response to receiving a first AES encryption round instruction defined within the ISA, the cryptographic unit may perform an encryption round of the AES cipher on a first group of columns of cipher state having a plurality of rows and columns. A maximum number of columns included in the first group may be fewer than all of the columns of the cipher state.
Owner:SUN MICROSYSTEMS INC
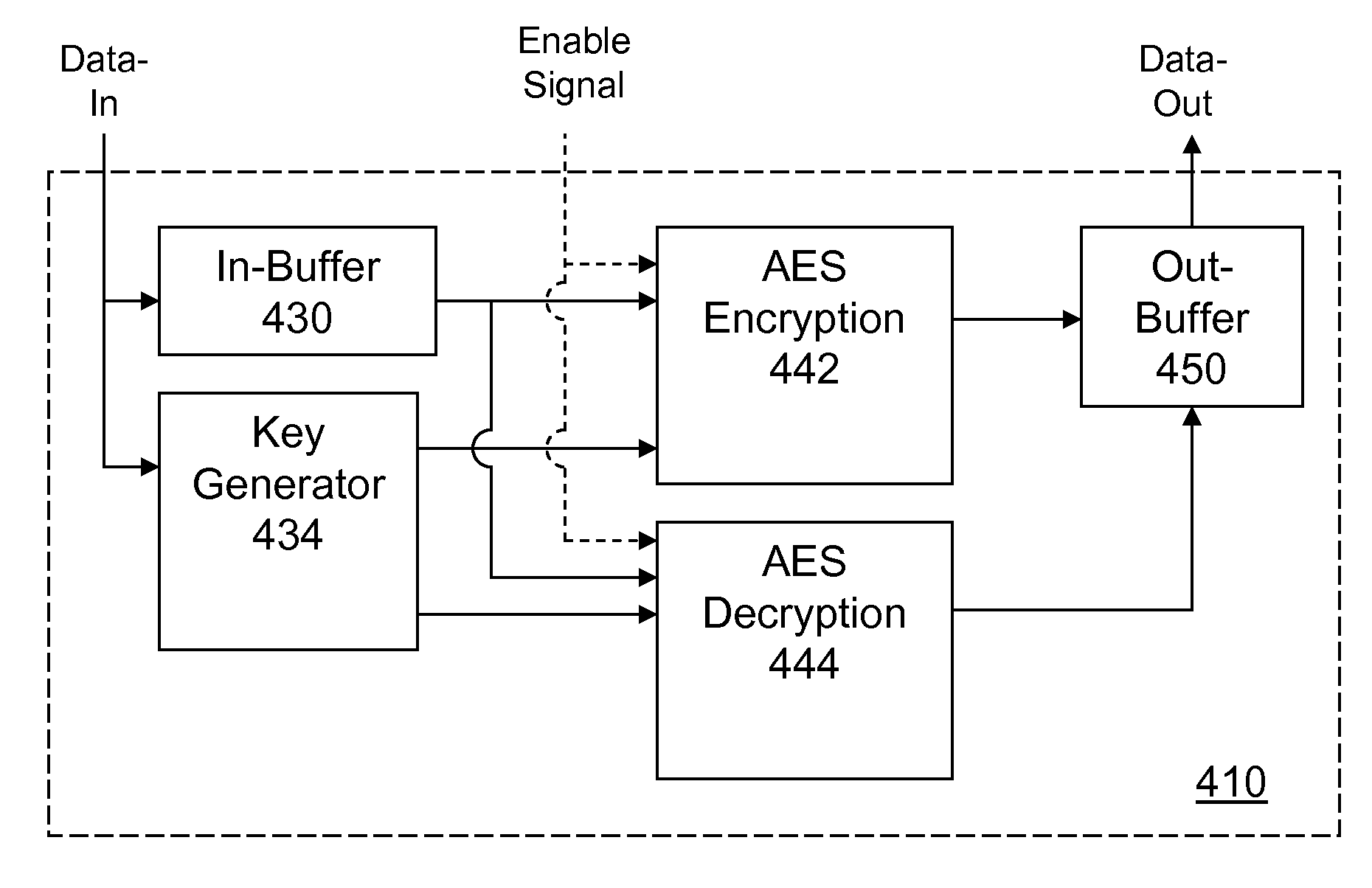
Portable Electronic Storage Devices with Hardware Security Based on Advanced Encryption Standard
InactiveUS20080192928A1Improve securityUnauthorized memory use protectionInternal/peripheral component protectionKey sizeAdvanced Encryption Standard
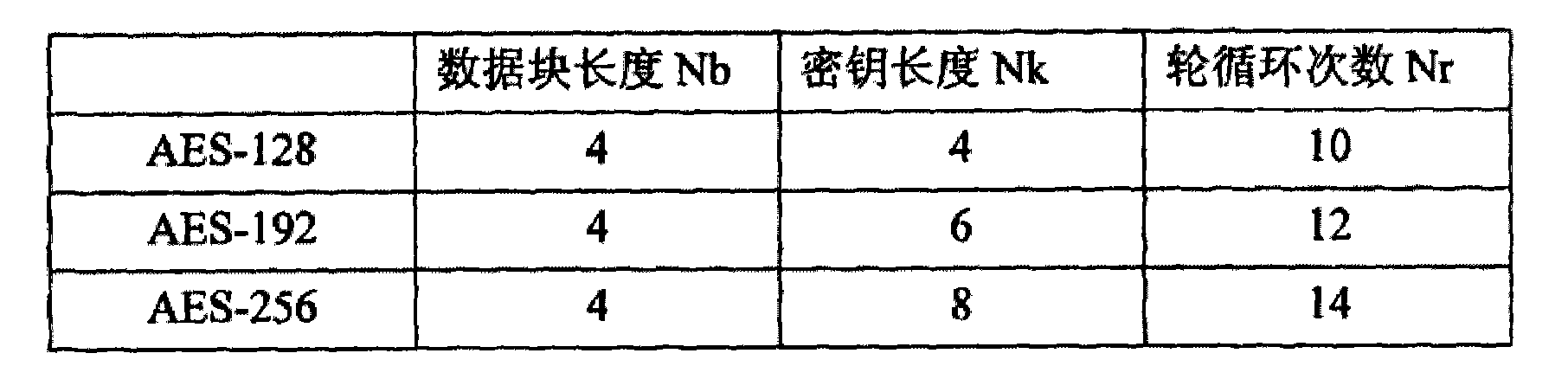
Portable electronic storage devices with hardware based security are described. According to one exemplary embodiment of the present invention, a portable electronic storage device (PESD) comprises a security engine integrated thereon. The security engine is configured to provide data encryption, data decryption, and encryption / decryption key (referred to as a key) generation according to a security standard (e.g., Advance Encryption Standard (AES)). AES is a symmetric encryption algorithm processing data in block of 128 bits. Under the influence of a key, a 128-bit data block is encrypted by transforming the data block in a unique way into a new data block of the same size. AES is symmetric sine the same key is used for encryption and the reverse transformation (i.e., decryption). The only secret necessary to keep for security is the key. AES may use different key-lengths (i.e., 128-bit, 192-bits and 256-bits).
Owner:SUPER TALENT ELECTRONICS
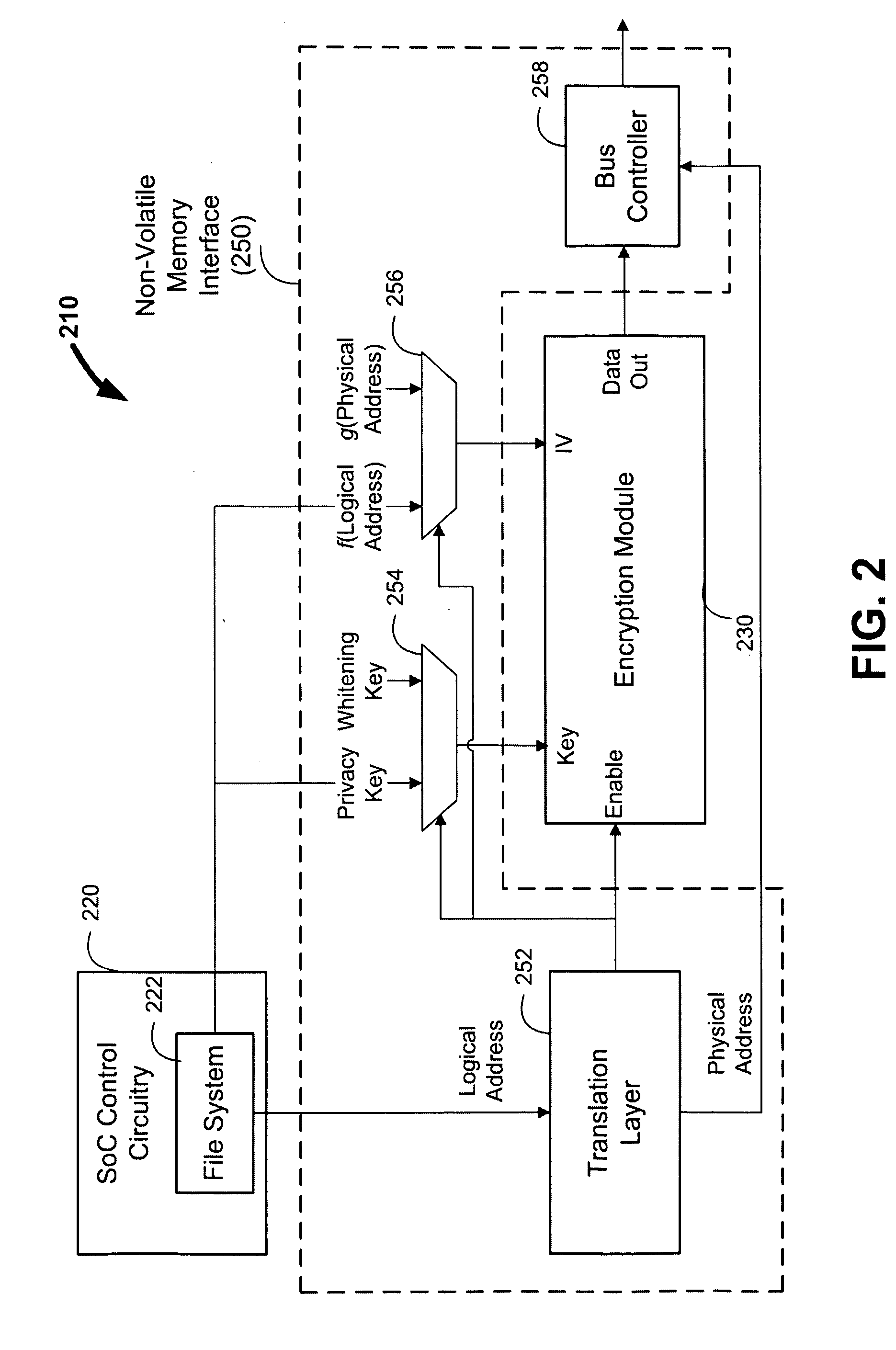
Data whitening for writing and reading data to and from a non-volatile memory
ActiveUS20100229005A1Increase randomnessReduce the possibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMemory interfaceAdvanced Encryption Standard
Systems, apparatuses, and methods are provided for whitening and managing data for storage in non-volatile memories, such as Flash memory. In some embodiments, an electronic device such as media player is provided, which may include a system-on-a-chip (SoC) and a non-volatile memory. The SoC may include SoC control circuitry and a memory interface that acts as an interface between the SoC control circuitry and the non-volatile memory. The SoC can also include an encryption module, such as a block cipher based on the Advanced Encryption Standard (AES). The memory interface can direct the encryption module to whiten all types of data prior to storage in the non-volatile memory, including sensitive data, non-sensitive data, and memory management data. This can, for example, prevent or reduce program-disturb problems or other read / write / erase reliability issues.
Owner:APPLE INC
System and method for executing Advanced Encryption Standard (AES) algorithm
ActiveUS7106860B1Improve performanceSecret communicationCoding/ciphering apparatusState of artComputer hardware
A system and method is presented for enciphering information using the Advanced Encryption Standard (AES) algorithm in which a subprocessor is configured to manipulate data as it is being loaded into the subprocessor memory. Thus, unlike implementations in the prior art, which require complete loading of data into a subsystem memory before data manipulation thereby creating a potential bottleneck in memory, this invention reduces the potential bottleneck in memory.
Owner:SYNAPTICS INC
Wireless intelligent network protocol with ultra-low power consumption
ActiveCN102761941ALow costReduce power consumptionPower managementNetwork topologiesFault toleranceLine sensor
The invention discloses a wireless intelligent sensor network protocol (ATZGB-SleepTree) with ultra-low power consumption. The protocol includes a physical layer, an MAC (media access control) layer, a link layer, a network layer and an application layer according to an OSI (open system interconnection) reference model. A traditional wireless sensor protocol and even an existing ZigBee protocol are quite difficult to meet the requirements of low power consumption, low cost, high fault tolerance and the like of a wireless sensor, and under the circumstance, the ATZGB-SleepTree protocol arises at the historic moment. The ATZGB-SleepTree constructs a wireless network which is low in cost and power consumption, high in sensitivity, reliability and real-time control and transmission, highly flexible in work pattern and configuration, automated in link management, capable of achieving AES (advanced encryption standard) data encryption, supportive to multiple bands and multiple wireless rates and capable of achieving synchronous sleep and synchronous wake-up of all nodes of the whole network, routing fault-tolerance and automatic recovery and is used for substituting for traditional wireless and cable network transmission modes.
Owner:北京云天创科技有限公司
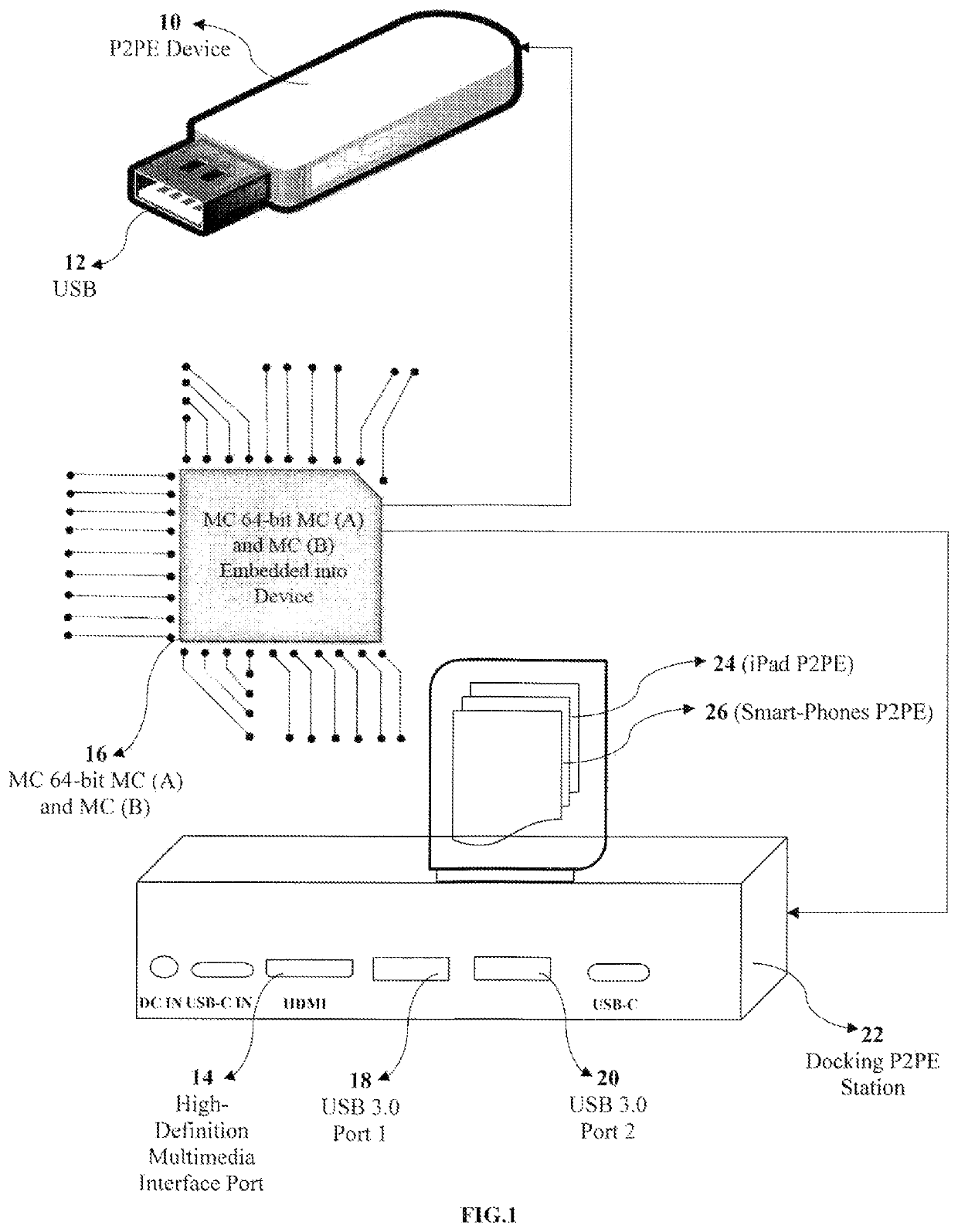
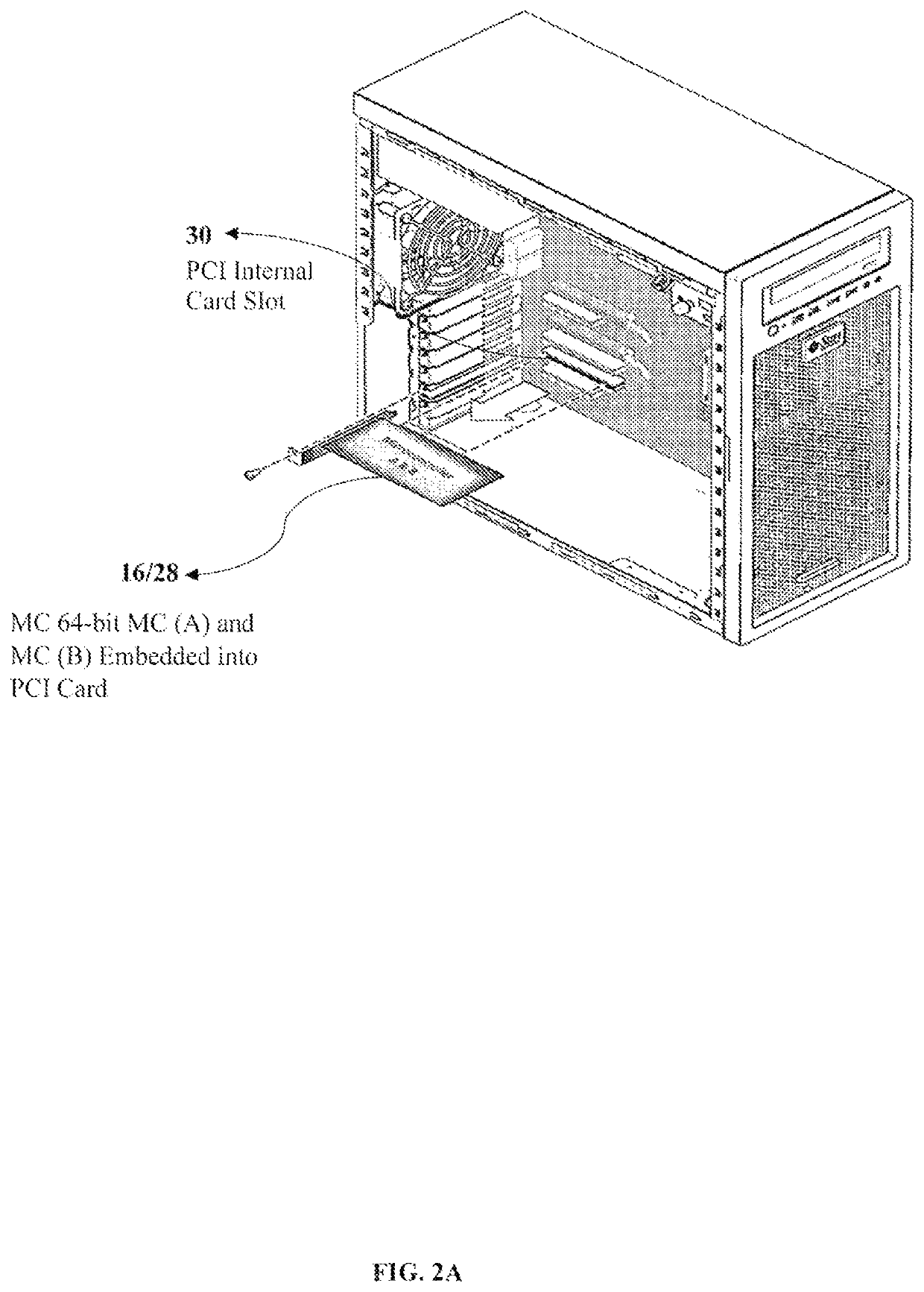
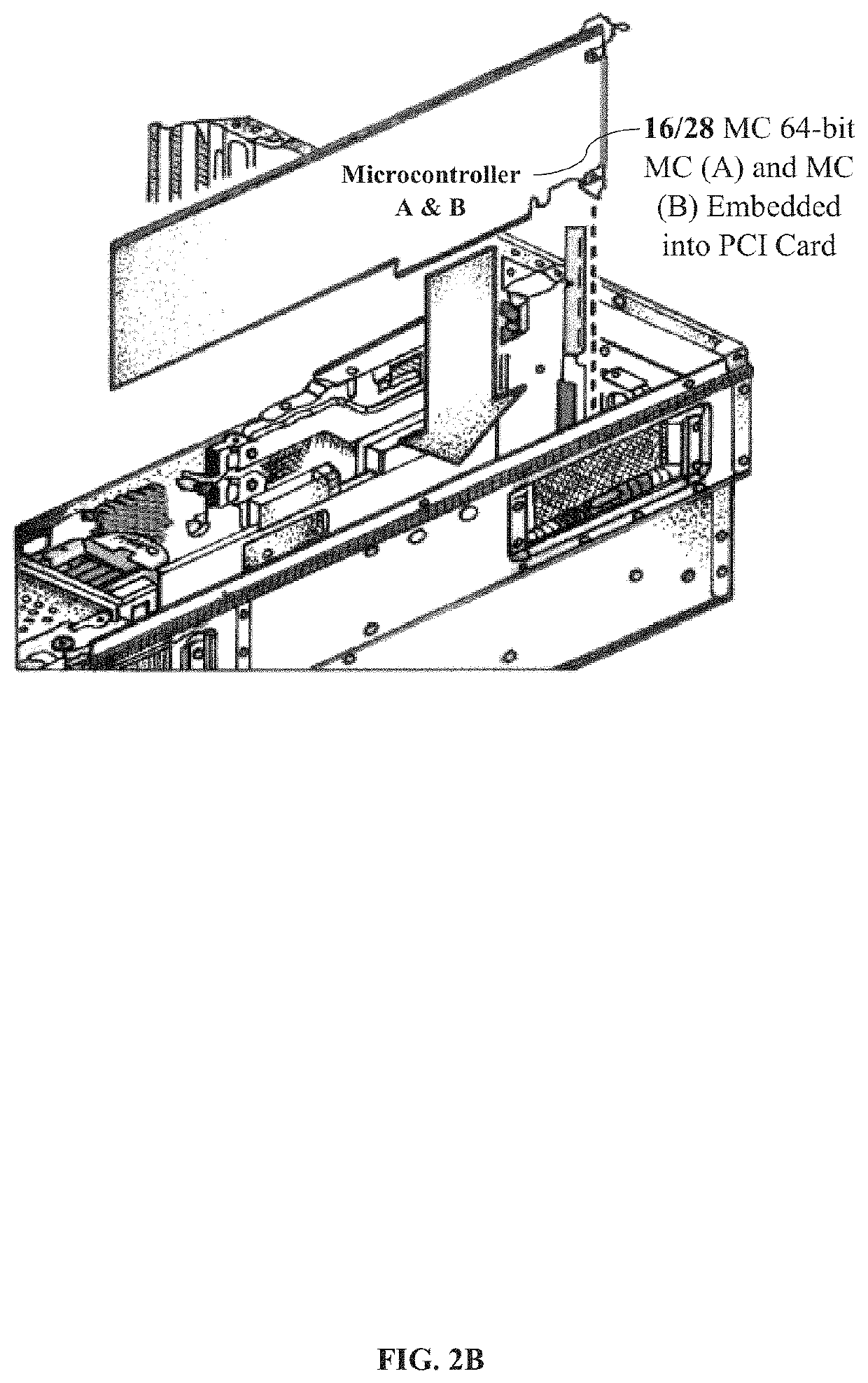
Methods, system and point-to-point encryption device microchip for AES-sea 512-bit key using identity access management utilizing blockchain ecosystem to improve cybersecurity
ActiveUS10673617B1Facilitate communicationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesMicrocontrollerComputer architecture
A combined system and not a system separately having a complex system hardware architecture and software with levels of complexity of P2PE, IAM, and BCE. A microcontroller (MC) 64-bit using MC (A) and MC (B) embedded into a device using point-to-point encryption (P2PE) to communicate with the novel IAM blockchain software and a central server database to track all registered and non-registered IoT devices in the BCE. The present invention includes a MC 64-bit method of MC (A) and MC (B) having an advanced encryption standards (AES) strong encryption algorithm (SEA) of 512-bit key utilizing the blockchain ecosystem (BCE), IoT identity to validate transactions between the authentication, and identity of the IoT devices. The MC 64-bit of MC (A) and MC (B) employs a novel AES-SEA 512-bit key to generate a real-time randomly validation symmetrical key encryption in rounds of 10 bits, sending data into the central server and the IAM blockchain software to authenticate each device, track IoT devices, MC entries, and validations. Once the encryption AES-SEA 256-bit key is generated in the MC (A) and the encryption AES-SEA 256-bit key is generated in MC (B), the communication between the MC (A) and MC (B) will generate the AES-SEA 512-bit key with 10 bits; the pseudo-random number process is modified using a time based to be programmed with a timer which has an input of the clock frequency. The MC 64-bit of MC (A) and MC (B) is programmed in a master mode and slave mode; therein providing a novel system of circuit hardware using an AES-SEA 512-bit key and AES 2048 algorithm key to generate PKI certifications for validation, authentication, and authorization through the BCE.
Owner:CYBER ALIENS LLC
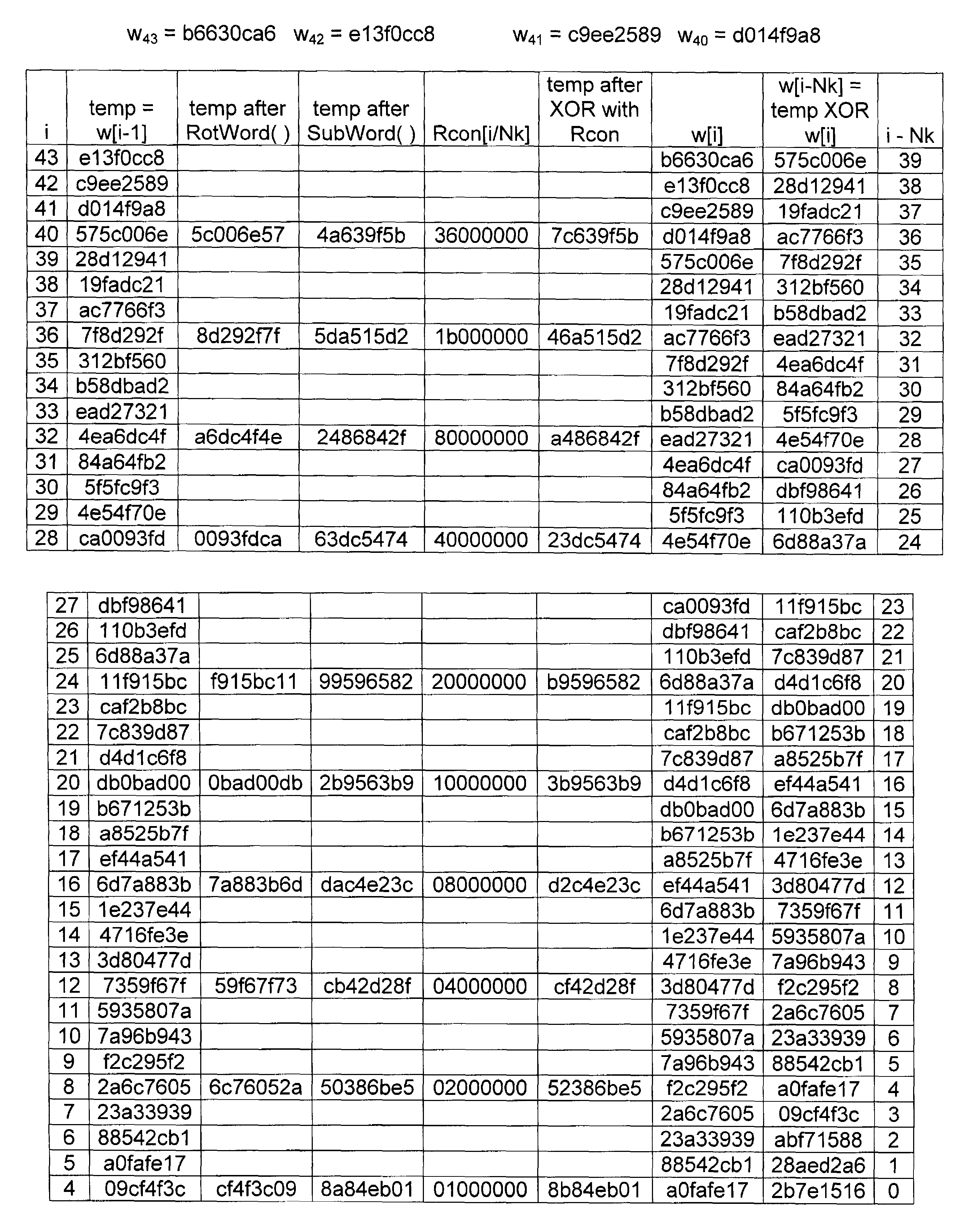
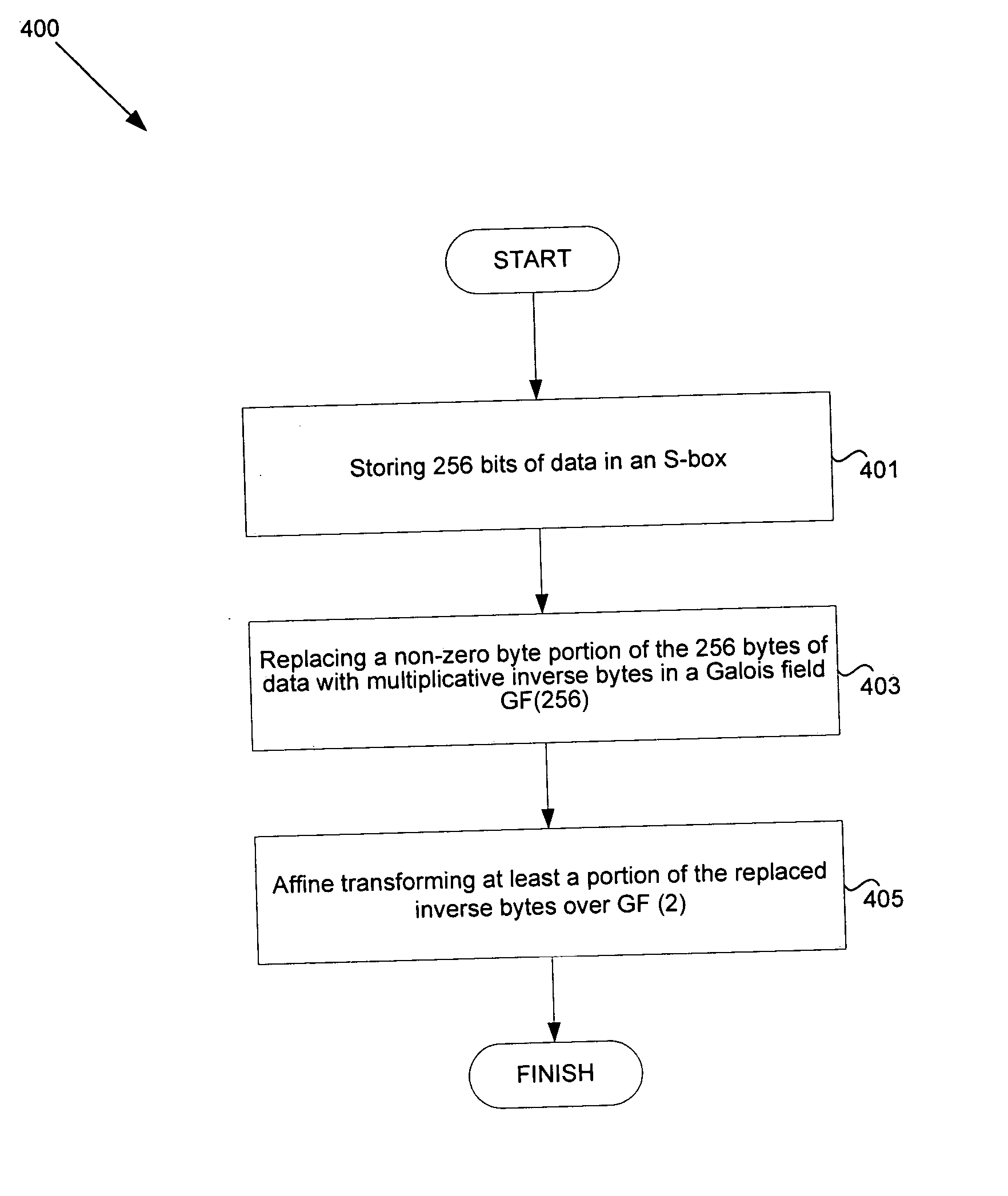
Method and system for implementing substitution boxes (S-boxes) for advanced encryption standard (AES)
Systems and methods for implementing Advanced Encryption Standard (AES) are disclosed herein. Aspects of the method may comprise storing 256 bytes of data. A non-zero byte portion of the 256 bytes of data may be replaced with multiplicative inverse bytes in a Galois field GF(256) and the replaced inverse bytes may be affine transformed over GF (2). The affine transformed bytes may be affine inverse transformed, and the affine inverse transformed bytes may be multiplicatively inversed over GF(256). The affine transformation over GF(2) may be determined as a matrix multiplication and addition of (1 1 0 0 0 1 1 0). If the 256 bytes comprise a zero byte, the zero byte from the 256 bytes of data may be mapped to the zero byte portion of the 256 bytes of data.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Data security confidentiality method under cloud environment
ActiveCN105354507AGuaranteed ownershipEnsuring Safety and ReliabilityDigital data protectionDigital data authenticationThird partyConfidentiality
The present invention discloses a data security confidentiality method under a cloud environment. The method is based on an independent third-party authentication and storage device and a terminal security detection program, wherein, the third-party authentication and storage device comprises a self-controlled chip and a memory; a program that runs on the self-controlled chip comprises a control module and a file system module; the memory comprises an encrypted memory area and an ordinary memory area; the control module accessed the encrypted memory area of the memory; the ordinary memory area comprises the terminal security detection program; the encrypted memory area comprises identity authentication information, a key and an algorithm software carrier; the key adopts an encryption mode of associating an AES (Advanced Encryption Standard) symmetric key with an RSA (Rivest Shamir Adleman) asymmetric key; and a fingerprint identifier is arranged on the third-party authentication and storage device. The data security confidentiality method under the cloud environment disclosed by the present invention guarantees data not to be stolen and tampered in the cloud environment, and improves security and confidentiality of user data in a terminal and a service terminal.
Owner:ZHEJIANG YUANWANG SOFTWARE
Block cipher encryption and decryption method
InactiveCN102025484AIncreased confusionImprove throughputEncryption apparatus with shift registers/memoriesS-boxAdvanced Encryption Standard
The invention provides a block cipher encryption and decryption method belonging to the field of data encryption and decryption. The algorithm of the invention designs a symmetric encryption structure, especially the S-box design in the invention can configure S transformation required for encryption and S inverse transformation required for decryption without additional circuit resources, thereby being beneficial to the implementation of an encryption / decryption integrated hardware circuit and consuming fewer area resources compared with the AES (advanced encryption standard) encryption / decryption integrated circuit. The complicated S box structure of the algorithm can resist the traditional known attack methods. In case of a small number of encryption rounds (three rounds), a high encryption speed can be provided, and decryption can be carried out at the same speed by using the same encryption and decryption hardware. The algorithm is especially suitable for realizing an ASIC (application specific integrated circuit), and can realize an ASIC chip based on the encryption and decryption special-purpose algorithm. Besides, the invention can be also used for the design of IP cores on FPGA (field programmable gate array). Compared with the AES algorithm, the invention consumes fewer resources on FPGA and has higher speed.
Owner:BEIHANG UNIV
Method and system for extending advanced encryption standard (AES) operations for enhanced security
InactiveUS20060050887A1Improve securityImprove encryption securitySecret communicationSecuring communicationComputer hardwareCommunications system
In a wireless communication system, a method and system for extending Advanced Encryption Standard (AES) operations for enhanced security are provided. In an AES encryption operation, an initial state may be modified by XORing with an initial modifier before a first processing round and a final state may be modified by XORing with a final modifier after a final processing round. The output of a MixColumns function performed during AES decryption operation rounds may be modified by XORing with a corresponding round modifier. In an AES decryption operation, an initial state may be modified by XORing with a decoded final modifier before a first processing round and a final state may be modified by XORing with a decoded initial modifier after a final processing round. The input of an InvMixColumns function performed during AES decryption operation rounds may be modified by XORing with a corresponding decoded round modifier.
Owner:AVAGO TECH INT SALES PTE LTD
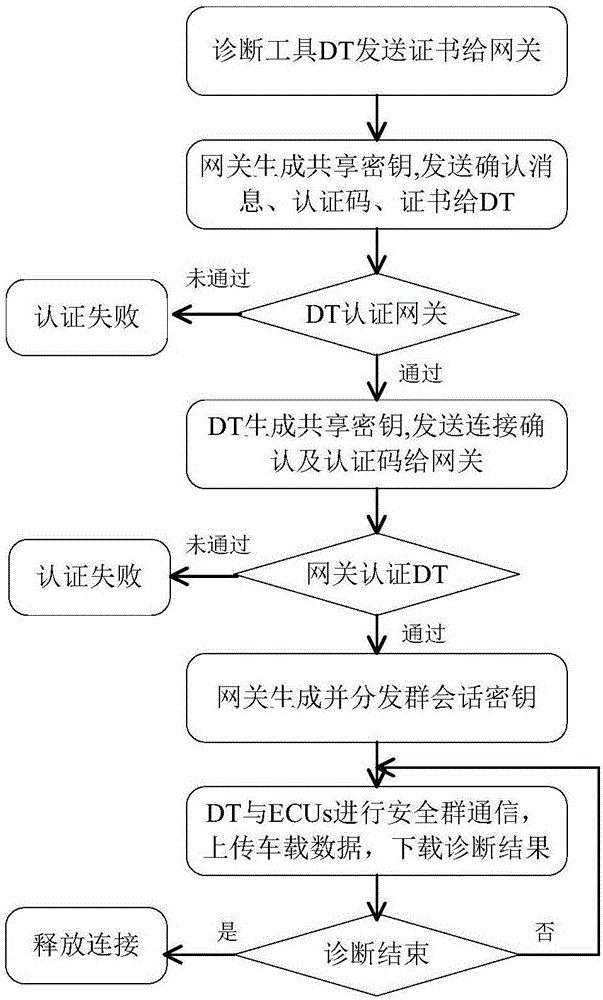
Security access and secret communication method of vehicle-mounted remote diagnostic services
InactiveCN106357681APrevent unauthorized accessFast communication processingTransmissionArea networkControl area
The invention discloses a security access and secret communication method of vehicle-mounted remote diagnostic services. An electronic control unit gateway is taken as a bridge, and bidirectional authentication of the gateway and a diagnostic tool, shared key negotiation and a gateway issued group dialogue secret key are taken as a framework and an AES (Advanced Encryption Standard) encryption and HMAC (Hash Message Authentication Code) authentication algorithm facing a CAN (Controlled Area Network) are taken as the basis to establish security connection between an electronic control unit and the diagnostic tool. By adopting the security access and secret communication method of the vehicle-mounted remote diagnostic services, provided by the invention, a security connection mechanism of the CAN and remote applications can be provided, and illegal access to vehicle-mounted parts by the remote diagnostic services can be prevented.
Owner:HEFEI UNIV OF TECH
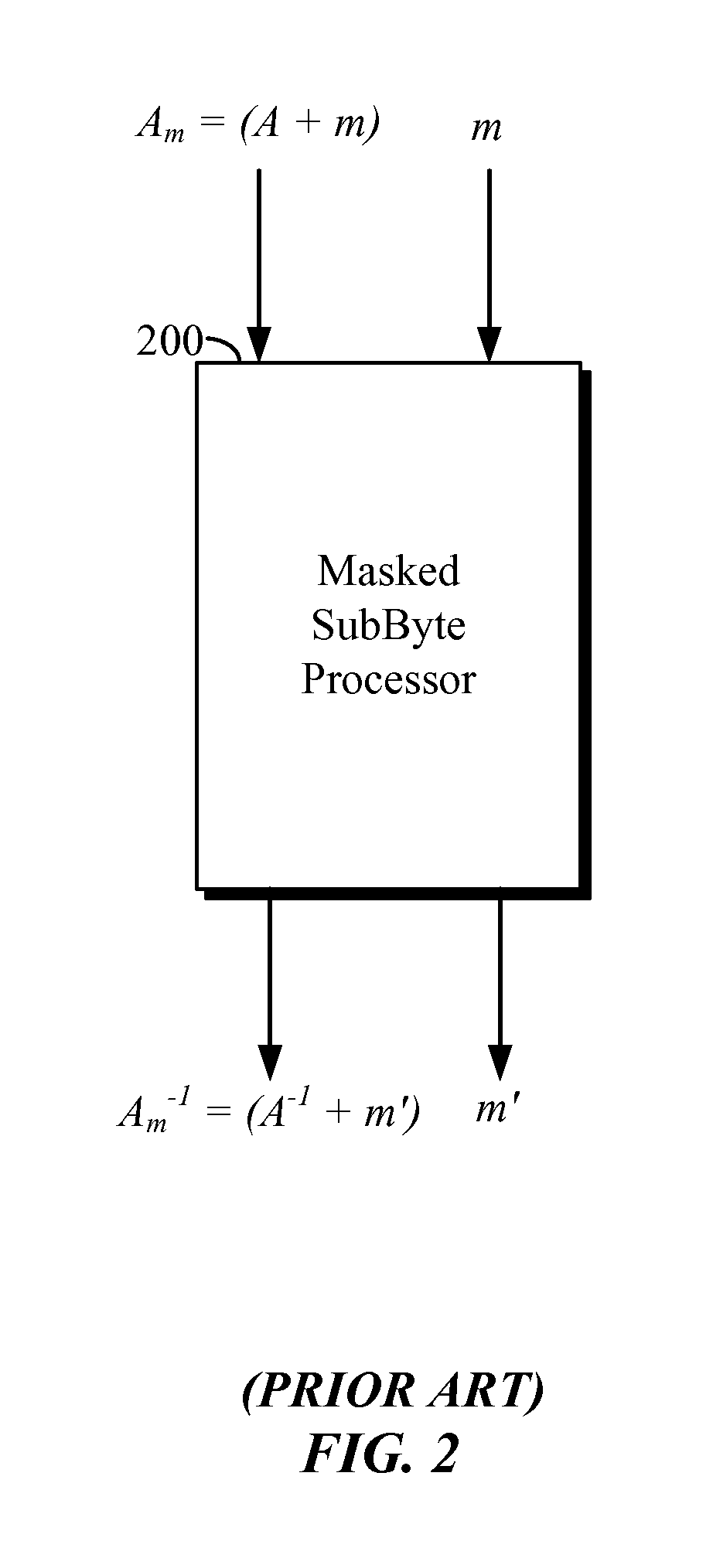
Cryptographic cipher with finite subfield lookup tables for use in masked operations
InactiveUS20160269175A1Encryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPlaintextCiphertext
Various features pertain to cryptographic ciphers such as Advanced Encryption Standard (AES) block ciphers. In some examples described herein, a modified masked AES SubBytes procedure uses a static lookup table that is its own inverse in GF(22). The static lookup table facilitates computation of the multiplicative inverse during nonlinear substitution operations in GF(22) In an AES encryption example, the AES device combines plaintext with a round key to obtain combined data, then routes the combined data through an AES SubBytes substitution stage that employs the static lookup table and a dynamic table to perform a masked multiplicative inverse in GF(22) to obtain substituted data. The substituted data is then routed through additional cryptographic AES stages to generate ciphertext. The additional stages may include further SubBytes stages that also exploit the static and dynamic tables. Other examples employ either a static lookup table or a dynamic lookup table but not both.
Owner:QUALCOMM INC
Data encryption transmission method and system
InactiveCN102333093AImprove securityFast encryption and decryptionEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextNetwork communication
The invention is applicable to the field of network communication, and provides a data encryption transmission method and system. The data encryption transmission method comprises the following steps: A. a server dynamically generates a DES (data encryption standard) key based on a data encryption algorithm (DEA), and encrypts the DES key by an RSA (Rivest, Shamir and Adleman) public key which is dynamically generated by a client side so as to generate an RSA encrypted ciphertext; B. the client side decrypts the received RSA encrypted ciphertext so as to obtain the DES key; and C. a message transferred between the server and the client side is compressed according to a ZLIB algorithm, and then the DES key encrypts the compressed message. The data encryption transmission method has the beneficial effects that the RSA and DES encryption algorithms are combined together, namely the message is encrypted according to the DES algorithm and meanwhile the DES key is encrypted according to the RSA algorithm so as to integrate the advantage of fast encryption and decryption speed of the DES algorithm and the advantage of high safety of the RSA algorithm; and meanwhile the message is compressed according to the ZLIB algorithm so as to realize safe and efficient data encryption transmission.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
Multimode reconfigurable encryption method based on advanced encryption standard (AES) encryption algorithm
InactiveCN102185692AAvoid Side Channel AttacksEasy to operateEncryption apparatus with shift registers/memoriesComputer hardwareS-box
The invention discloses a multimode reconfigurable encryption method based on an advanced encryption standard (AES) encryption algorithm. In the method, five operating modes are provided for a user to select, and an all-random S box generation way and a biased random S box generation way are provided. The method comprises the following steps of: judging whether the operating mode and an S box selected by the user are rational or not; if the selected operating mode and the selected S box are irrational, prompting the user to perform reselection; if the selected operating mode and the selected S box are rational, further calculating the smallest encryption round number according to the differential uniformity and nonlinearity of the generated S box, and determining a final encryption round number according to the requirements of the user; selecting a source file for an encryption or decryption operation; and finally storing the encrypted or decrypted data file, and providing the encrypted or decrypted data file for the user to view. By the method, side channel attacks possibly on encryption realized by adopting hardware are effectively avoided, and an operating way of the reconfigurable encryption method is optimized; the method is applied to the configuration of a set of reconfigurable software encryption system, and the reconfiguration and integration of block ciphers into the same software system; and convenience is brought to operations and management.
Owner:BEIHANG UNIV
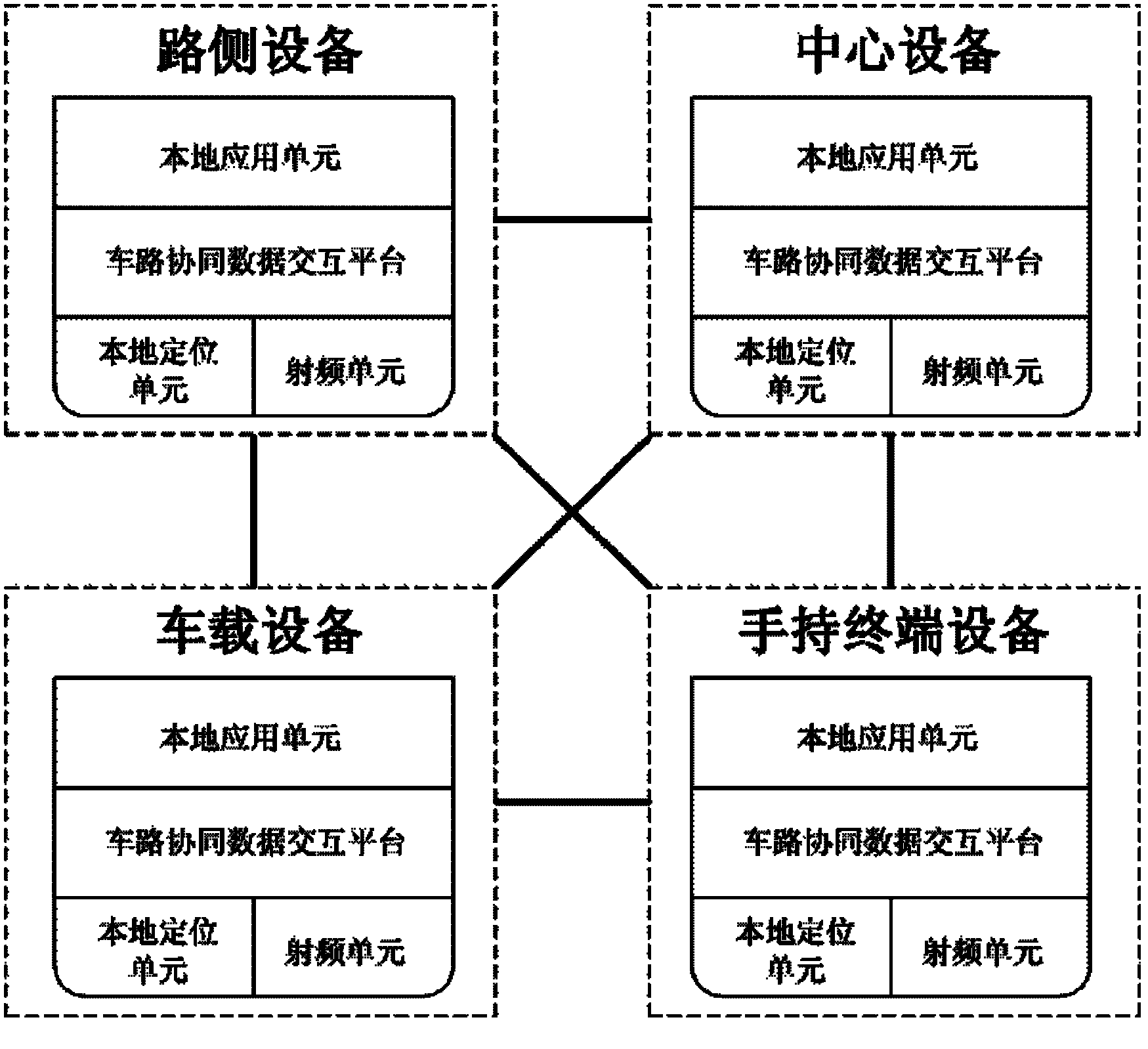
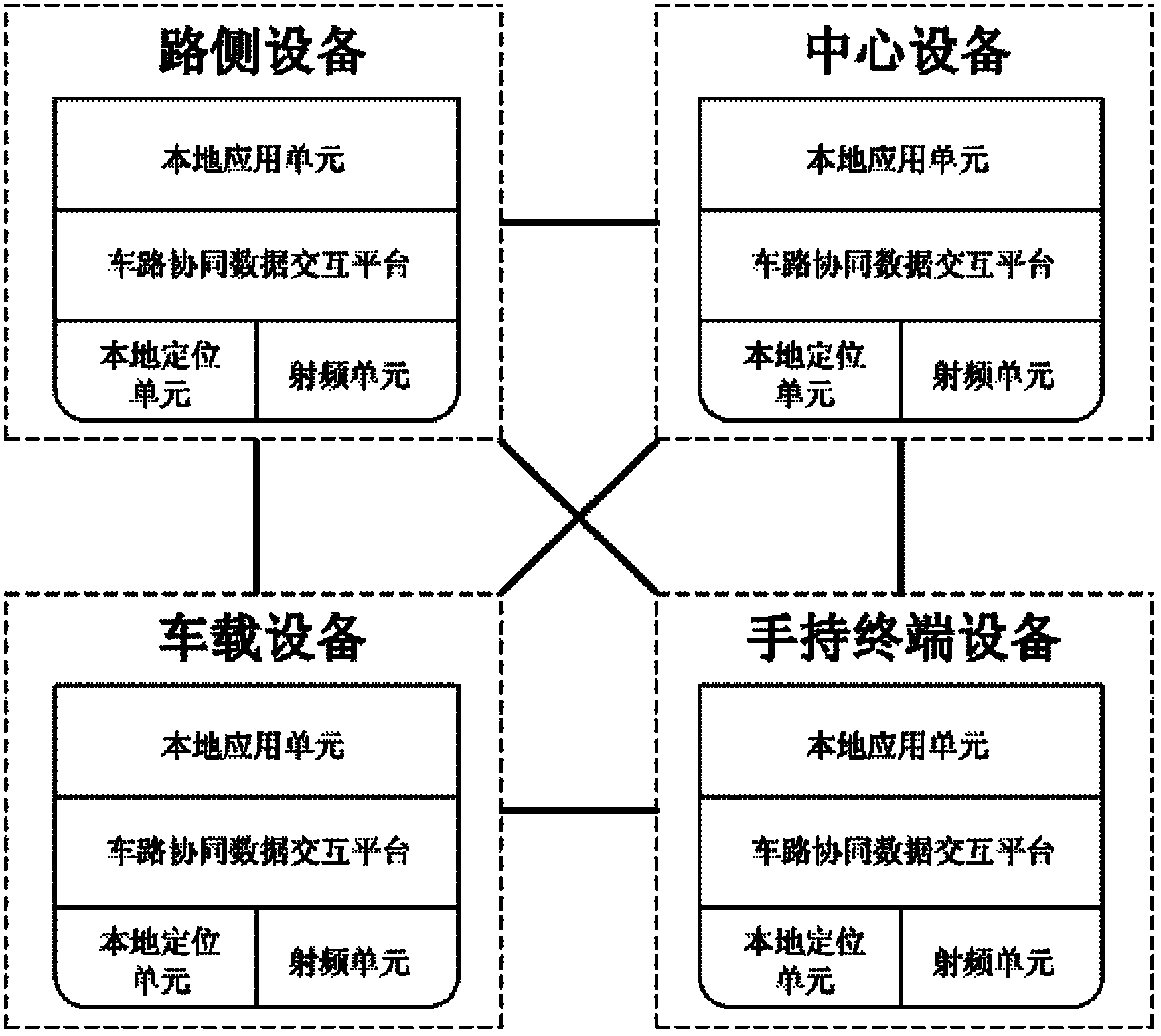
Vehicle-road collaborative data interactive system by means of multi-mode wireless communication
ActiveCN102622872AImprove traffic efficiencyImprove traffic safetyRoad vehicles traffic controlWireless transmissionHand held
The invention discloses a vehicle-road collaborative data interactive system by means of multi-mode wireless communication, which belongs to the field of intelligent transportation, comprises road testing equipment, central equipment, vehicular equipment and hand-held terminal equipment, and is operated in a Windows operation system environment. The vehicle-road collaborative data interactive system has the advantages that 1) realizing data interaction among transportation participants; 2) meeting diversified demands of the transportation participants on transportation communication; 3) integrating various information interactive modes in various vehicle-road collaborative systems including vehicle-vehicle / vehicle-road communication; 4) reliability and soundness of a vehicle-road collaborative communication network are effectively guaranteed by communication control, and the problems of topology high-speed transformation, communication barrier and the like are effectively adapted to; and 5) safety and reliability of data are guaranteed by means of AES (advanced encryption standard) encryption and CRC (cyclic redundancy check) data check, external attack is eliminated, and data loss in wireless transmission is detected.
Owner:TSINGHUA UNIV
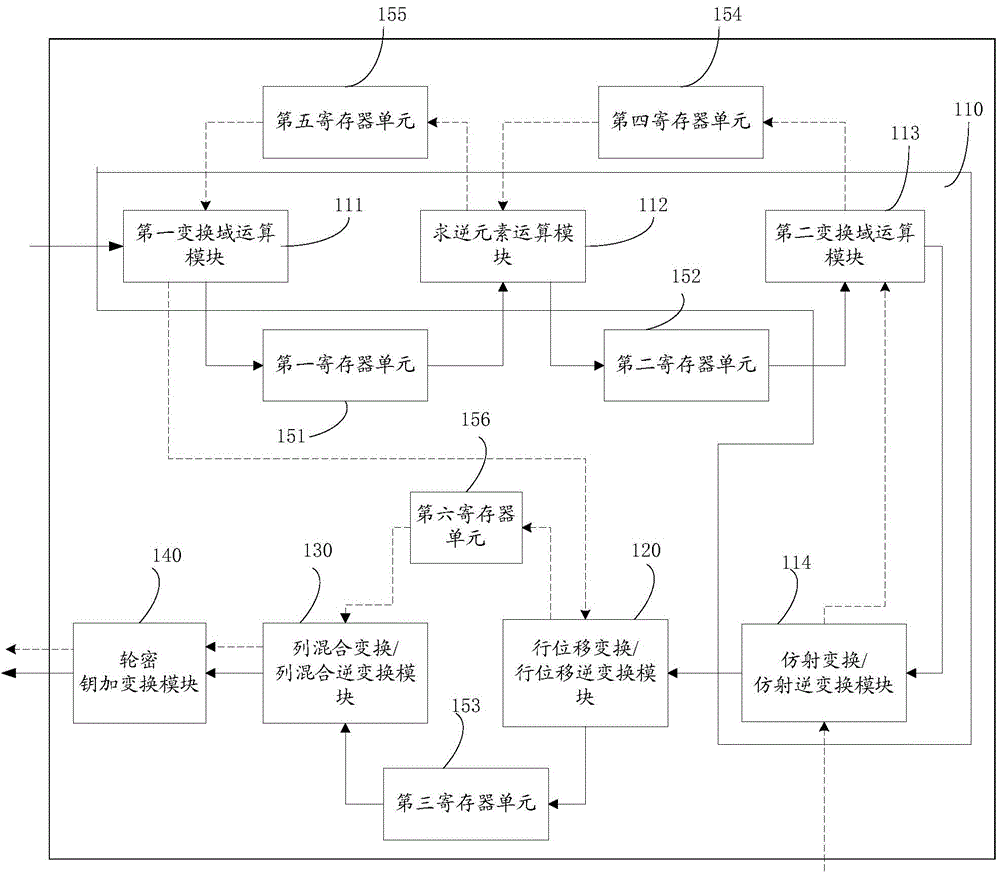
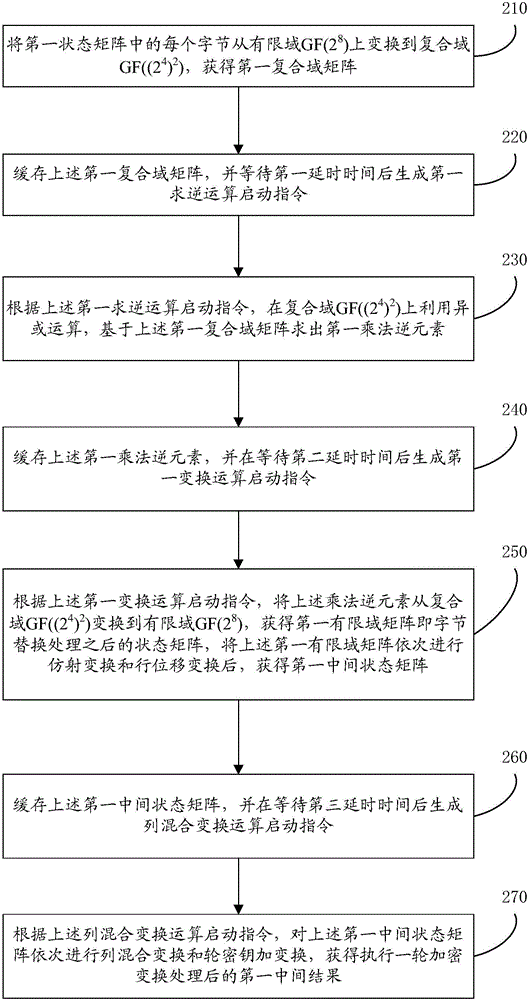
Device based on AES (advanced encryption standard) encryption/decryption algorithm and pipelining control method
InactiveCN104639314AAvoid duplicationImprove design efficiencyEncryption apparatus with shift registers/memoriesExclusive orAdvanced Encryption Standard
The invention provides a device based on AES (advanced encryption standard) encryption / decryption algorithm and a pipelining control method. The method comprises the following steps that a first composite domain matrix is buffered, and in addition, a first inversion operation starting instruction is generated after the waiting for the first delay time; exclusive-or operation is utilized in a composite domain GF((2<4>)<2>) according to the first inversion operation starting instruction, and a first multiplicative inverse element is solved on the basis of the first composite domain matrix; the first multiplicative inverse element is cached, and in addition, a first transform operation starting instruction is generated after the waiting for the second delay time; according to the first transform operation starting instruction, the first multiplicative inverse element is transformed into a finite domain GF(2<8>) from the composite domain GF((2<4>)<2>), and a first finite domain matrix is obtained; the first finite domain matrix is sequentially subjected to affine transformation and line shift transformation, and a first middle state matrix is obtained. The device and the method solve the problem that the defects in the aspects of area, power consumption and velocity exist when the existing hardware is used for realizing an AES algorithm.
Owner:SHENZHEN INST OF ADVANCED TECH
Method and device for improving digital encryption standard resisting differential power analysis
InactiveCN102983964ADestroy correlationTo achieve the purpose of resisting power analysisEncryption apparatus with shift registers/memoriesPlaintextPower analysis
The invention discloses a method and a device for improving a digital encryption standard resisting differential power analysis. In an S-box function processing step of standard 16-time operation for digital encrypting a 64-bit plaintext, a new S-box function represented by SM-Box is set in the following way. According to the invention, through the adoption of the S-box function transformed by different random numbers, relevance between real key information and a power curve is destroyed and great difficulty is caused in information obtaining of power analysis so as to achieve a purpose of resisting the power analysis. According to the invention, by using a covering technology, the plaintext is pre-covered before encryption operation and the random numbers are covered in each operation, so that attack caused by information leakage is effectively prevented, and the capacity of resisting differential power analysis attack is enhanced.
Owner:DATANG MICROELECTRONICS TECH CO LTD
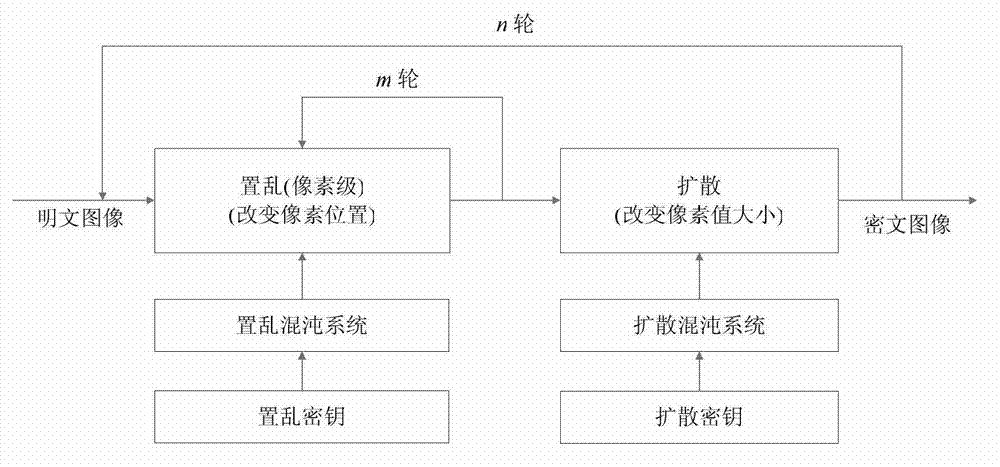
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
Instruction optimization method and processor for AES (Advanced Encryption Standard) symmetric encryption algorithm
InactiveCN102221990AImprove execution efficiencySave storage spaceMachine execution arrangementsCode spaceAssembly line
The invention discloses an instruction optimization method and an instruction processor for AES (Advanced Encryption Standard) symmetric encryption algorithm, wherein the instruction processor mainly comprises four parts of: a data memory, a code memory, a register file and an assembly line, wherein the assembly line comprises an addressing unit, a decoding unit, an execution unit and an assembly line controller. With the instruction optimization method, in the aspect of execution efficiency is reduced by 57.3x% relative to an ARM (Advanced RISC Machines) processor in a way that the clock periodicity required for AES_ASIP performing AES encryption algorithm is counted through periodic emulation, so that the execution efficiency of the algorithm is greatly improved; and in the aspect of code space, the instruction code occupies 783 bytes of memory space on the ARM processor, while the instruction code on the AES_ASIP just occupies 416 bytes of memory space, so that 46.6x% of code memory space is saved.
Owner:SHANDONG UNIV
Device and method for implementing AES encryption and decryption
InactiveCN102035641ASmall scaleSave hardware resourcesEncryption apparatus with shift registers/memoriesComputer hardwareAdvanced Encryption Standard
The invention provides a device and a method for implementing AES (advanced encryption standard) encryption and decryption. The method comprises the following steps of: receiving data to be encrypted or decrypted, and copying the data to be encrypted or decrypted into a state matrix; adding the state matrix and an initial key; performing Nr-1 round transformation on the state matrix added with the initial key; and performing incomplete round transformation on the state matrix subjected to Nr-1 round transformation so as to complete the encryption or decryption processing, wherein Nr is the round number required by encryption and decryption. The invention provides a device and a method for implementing AES encryption and AES decryption; meanwhile, the circuit scale can be greatly reduced.
Owner:ZTE CORP
Improved SM4 parallel encryption and decryption communication method based on GPU (Graphics Processing Unit)
ActiveCN105490802AFast implementationImprove securityEncryption apparatus with shift registers/memoriesComputer hardwareData stream
The invention discloses an improved SM4 parallel encryption and decryption communication method based on a GPU (Graphics Processing Unit). The encryption and decryption method comprises the following steps: using an AES (Advanced Encryption Standard)-128 key expansion algorithm to generate an expanded subkey needed by an SM4 encryption algorithm; improving a round function in the SM4 encryption algorithm; and using the parallel computing power of the GPU, improving the SM4 encryption algorithm into a form of parallel encryption. By adopting the encryption and decryption communication method of the invention, the security and the speed of implementation can be effectively improved, real-time and parallel encryption can be performed on data, and the encryption speed can be improved, so that normal transmission of data flow can be guaranteed and the processing delay can be reduced.
Owner:桂林蓝港科技有限公司
Enhanced MASK code method for resisting DES (data encryption standard) power consumption attack
ActiveCN102752103AWon't leakSmall design areaEncryption apparatus with shift registers/memoriesLogical operationsOperation mode
The invention relates to an enhanced MASK code method for resisting DES (data encryption standard) power consumption attack, comprising the steps as follows: step 1, realizing two rounds of DES (data encryption standard) calculations with a pipeline operation mode, realizing a calculating circuit by means of a first calculating circuit and a second calculating circuit which are mutually independent and isolated; step 2, realizing the DES (data encryption standard) calculation processes from the third round to the fourteenth round by means of a random positioning logical operation mode; step 3, realizing the last two rounds of DES (data encryption standard) calculations by means of a pipeline operation mode, and realizing the calculating circuit by means of a third calculating circuit and a fourth calculating circuit which are mutually independent and isolated, wherein each round of the DES (data encryption standard) calculations in step 1 to 3 is calculated with a MASK code method. The method provided by the invention not only reduces the design area of the chip, but also completely solves the problem in the prior art in which the two adjacent rounds of the MASK code solutions have a Hamming distance leakage, and keeps the sensitive information between wheels from leakage, and simultaneously keeps the Hamming distance and other sensitive information between two adjacentwheels from leakage, and effectively resists the power consumption attack.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Method for encryption authentication on Ad hoc network transmission layer protocol
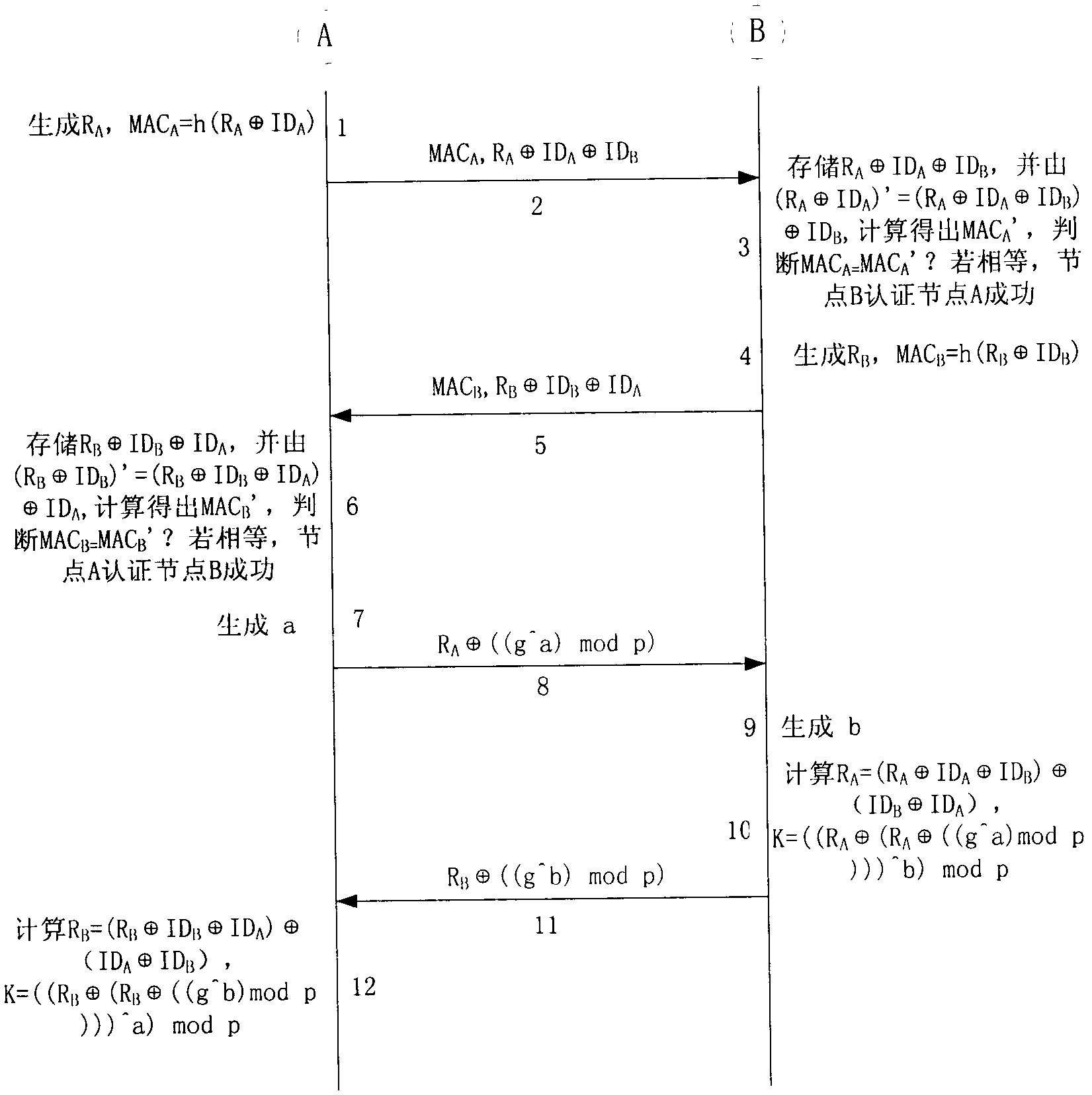
ActiveCN101980558AImplement identity authenticationLittle overheadNetwork traffic/resource managementWireless network protocolsHand shakesExclusive or
The invention discloses a method for encryption authentication on an Ad hoc network transmission layer protocol, which comprises five parts and 18 steps, wherein the five parts are a configuration stage, an authentication stage, a key negotiation stage, an encryption process and a key update flow. The encryption authentication method of the invention is applied to a hand shaking process in the end-to-end communication between two nodes in a multihop Ad hoc network, wherein the two nodes pass through message authentication code verification (MAC) for mutual verification; after the authentication successes, key negotiation is performed by using an elliptic curve diffie-hellman (ECDH) algorithm; and a subsequent message is encrypted by using a shared key acquired in the key negotiation process as a key material and by using an advanced encryption standard (AES) algorithm, and a key update flow is initiated in a communication process. In the authentication and key negotiation process, an exclusive or gate (XOR) algorithm is used for encrypting authentication information and key negotiation information, the safety is high, the efficiency is high, the system expense is small, and the encryption strength is high; and thus, the method has a promising application prospect in the technical field of wireless networks.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com