Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5051 results about "Confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
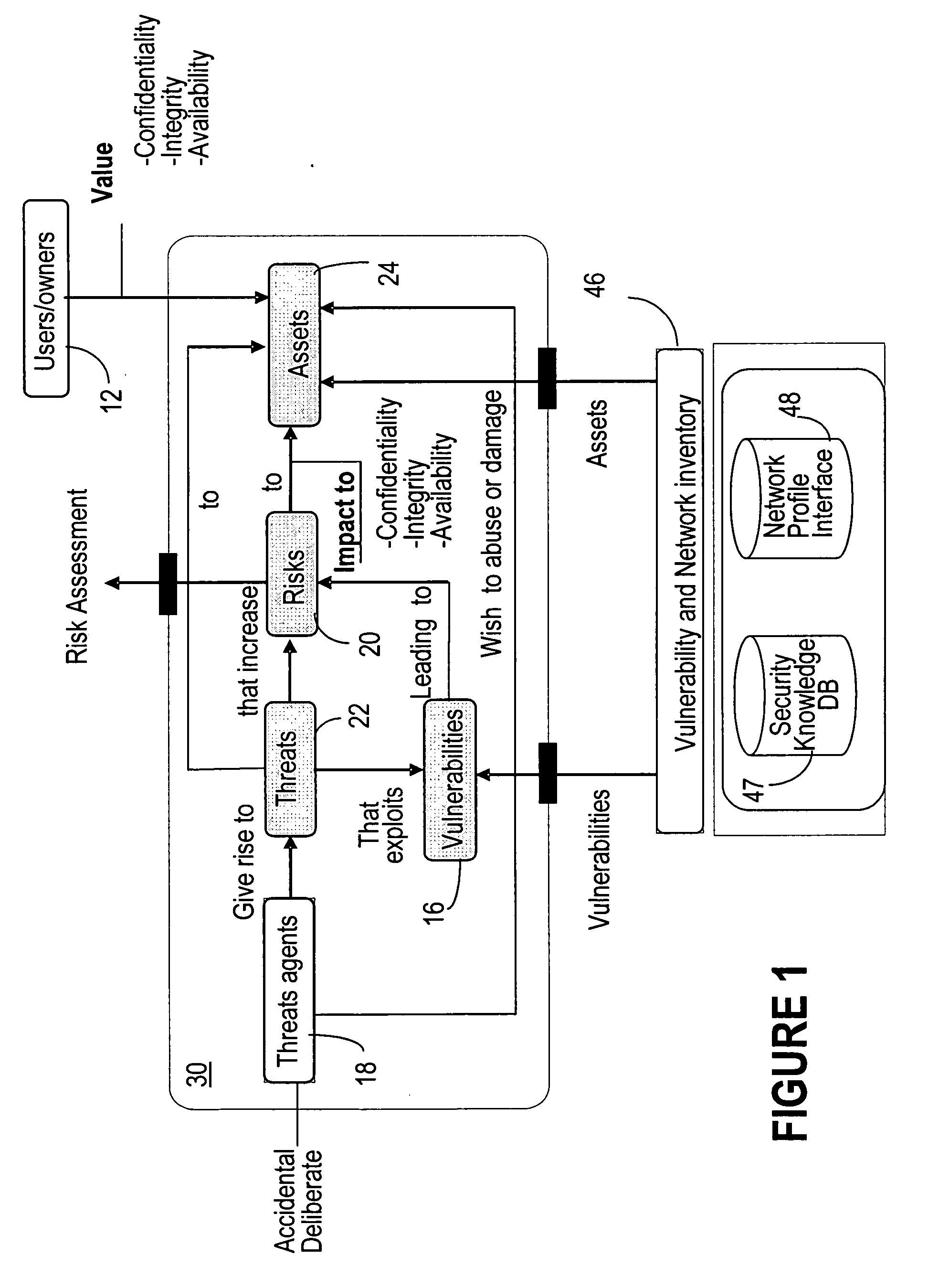
Confidentiality involves a set of rules or a promise usually executed through confidentiality agreements that limits access or places restrictions on certain types of information.
Method and apparatus for the secure distributed storage and retrieval of information
InactiveUS6192472B1Data processing applicationsPublic key for secure communicationActive faultConfidentiality
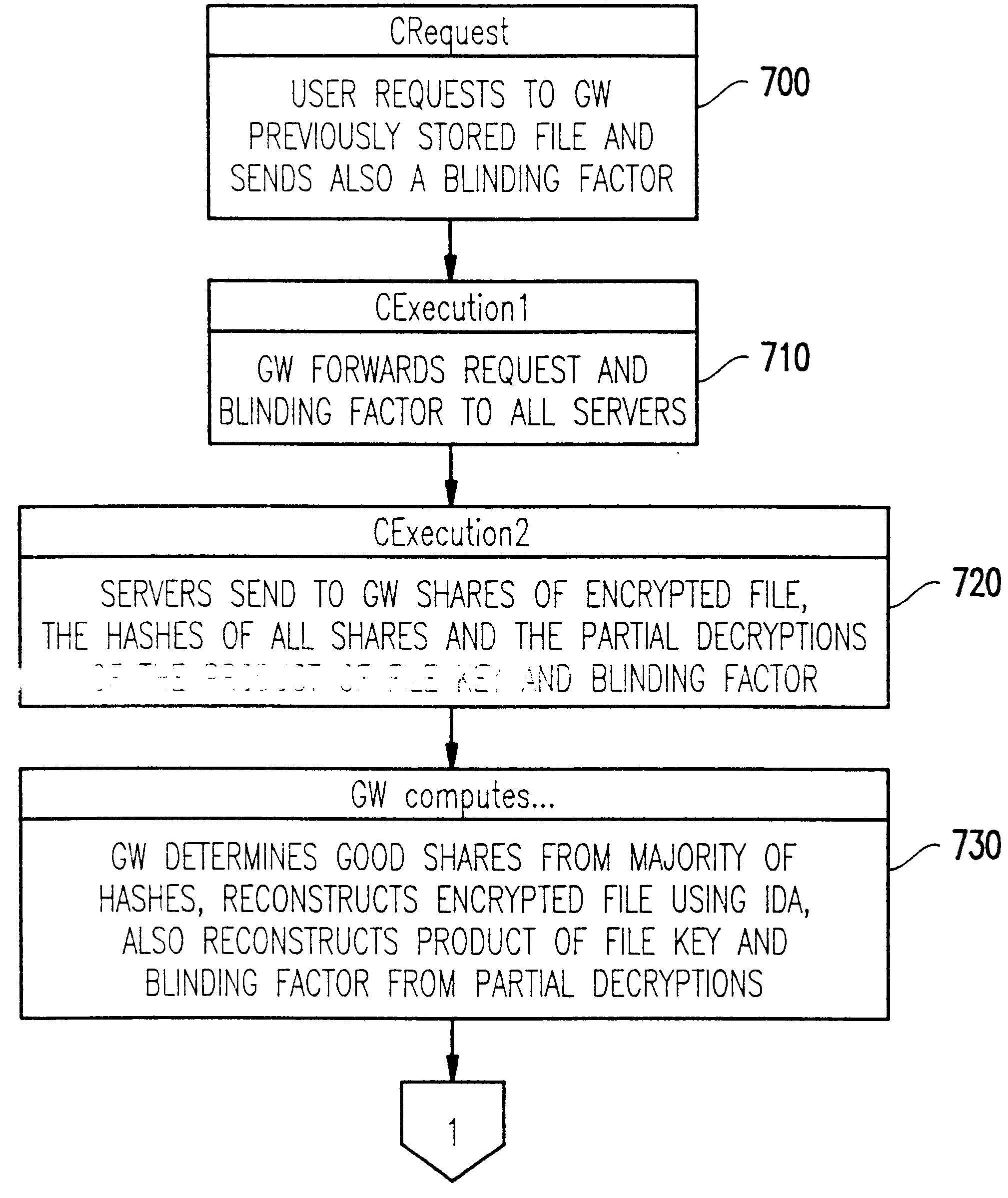
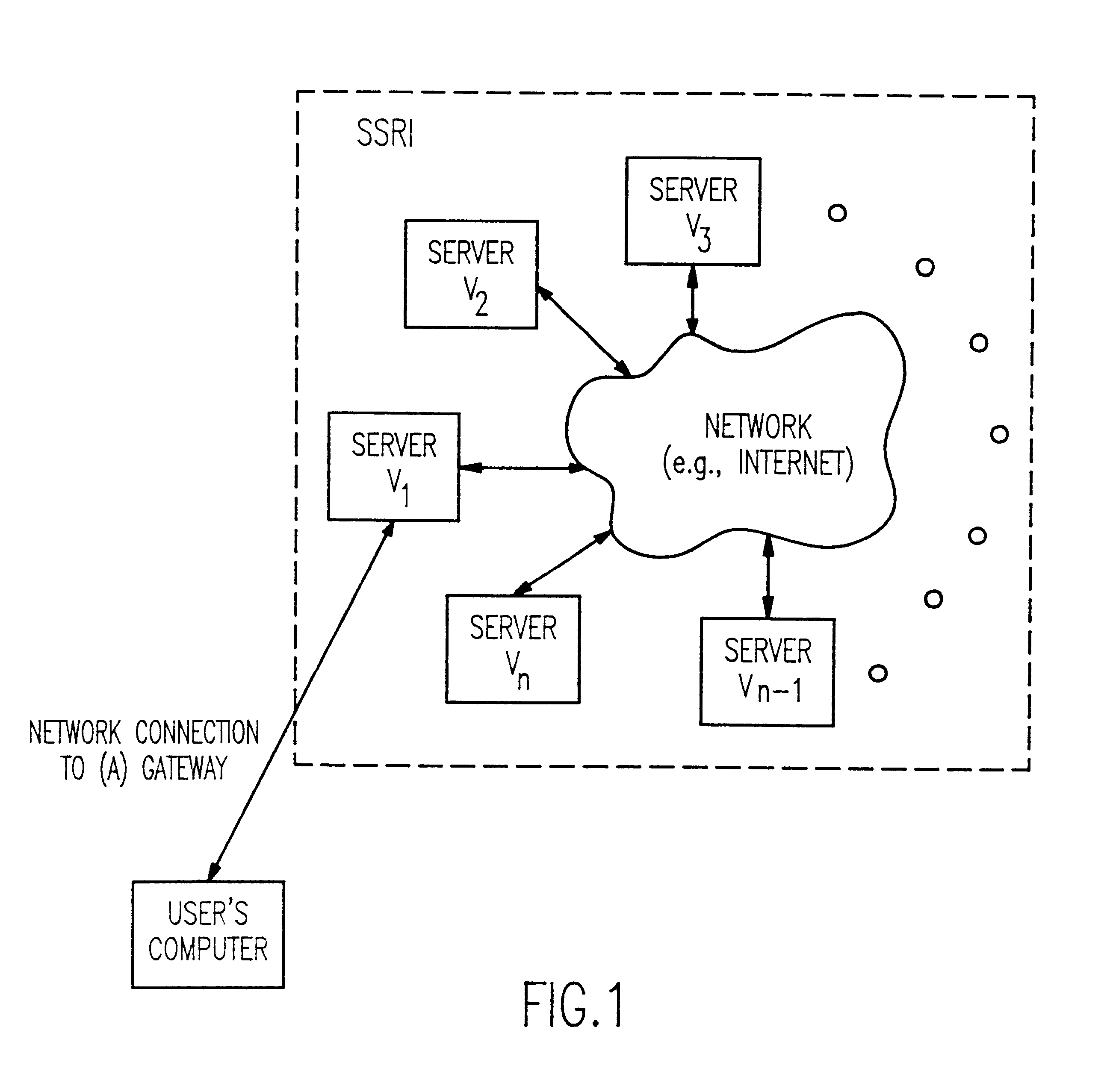
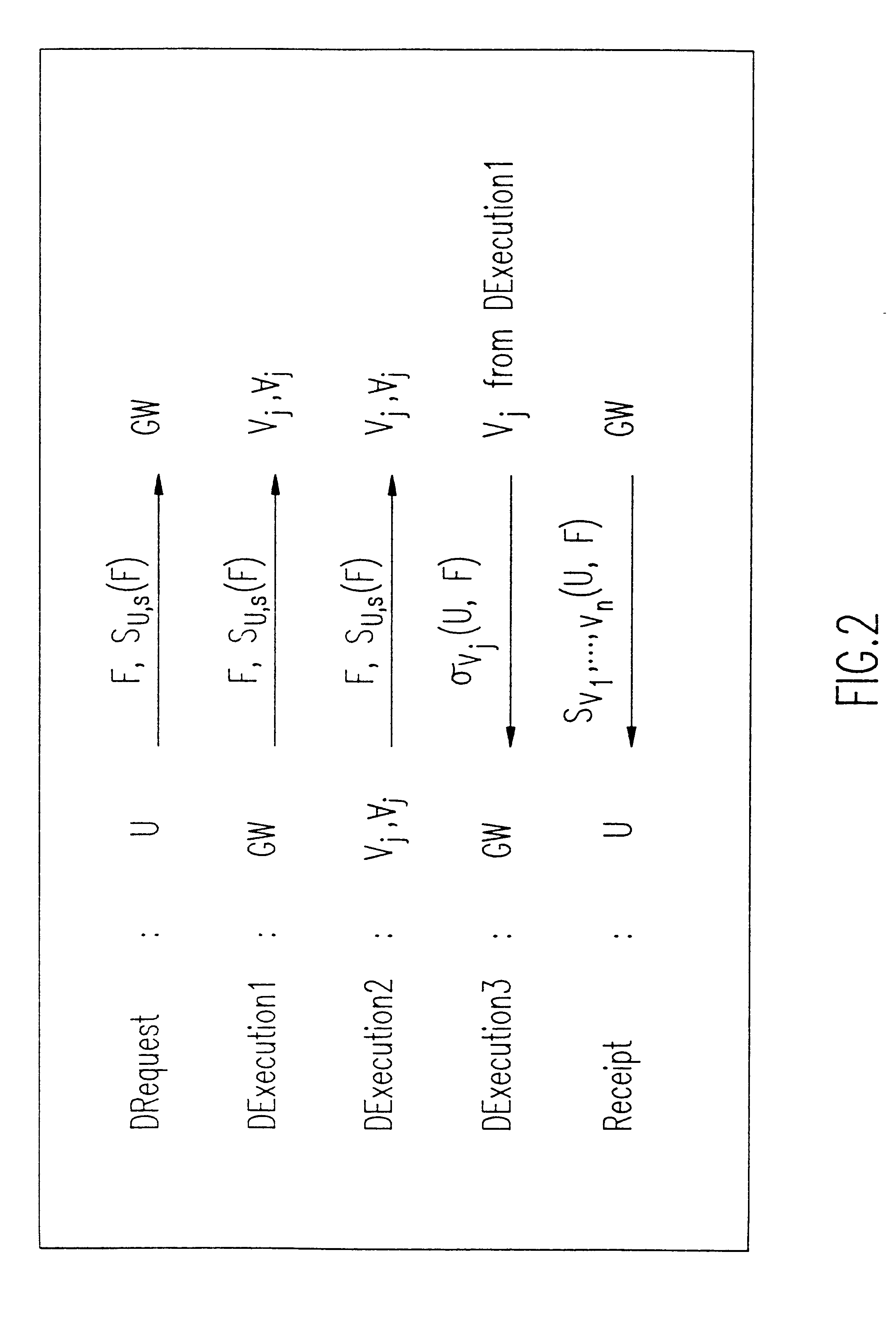
A solution to the general problem of Secure Storage and Retrieval of Information (SSRI) guarantees that also the process of storing the information is correct even when some processors fail. A user interacts with the storage system by depositing a file and receiving a proof that the deposit was correctly executed. The user interacts with a single distinguished processor called the gateway. The mechanism enables storage in the presence of both inactive and maliciously active faults, while maintaining (asymptotical) space optimailty. This mechanism is enhanced with the added requirement of confidentiality of information; i.e., that a collusion of processors should not be able to learn anything about the information. Also, in this case space optimality is preserved.
Owner:IBM CORP
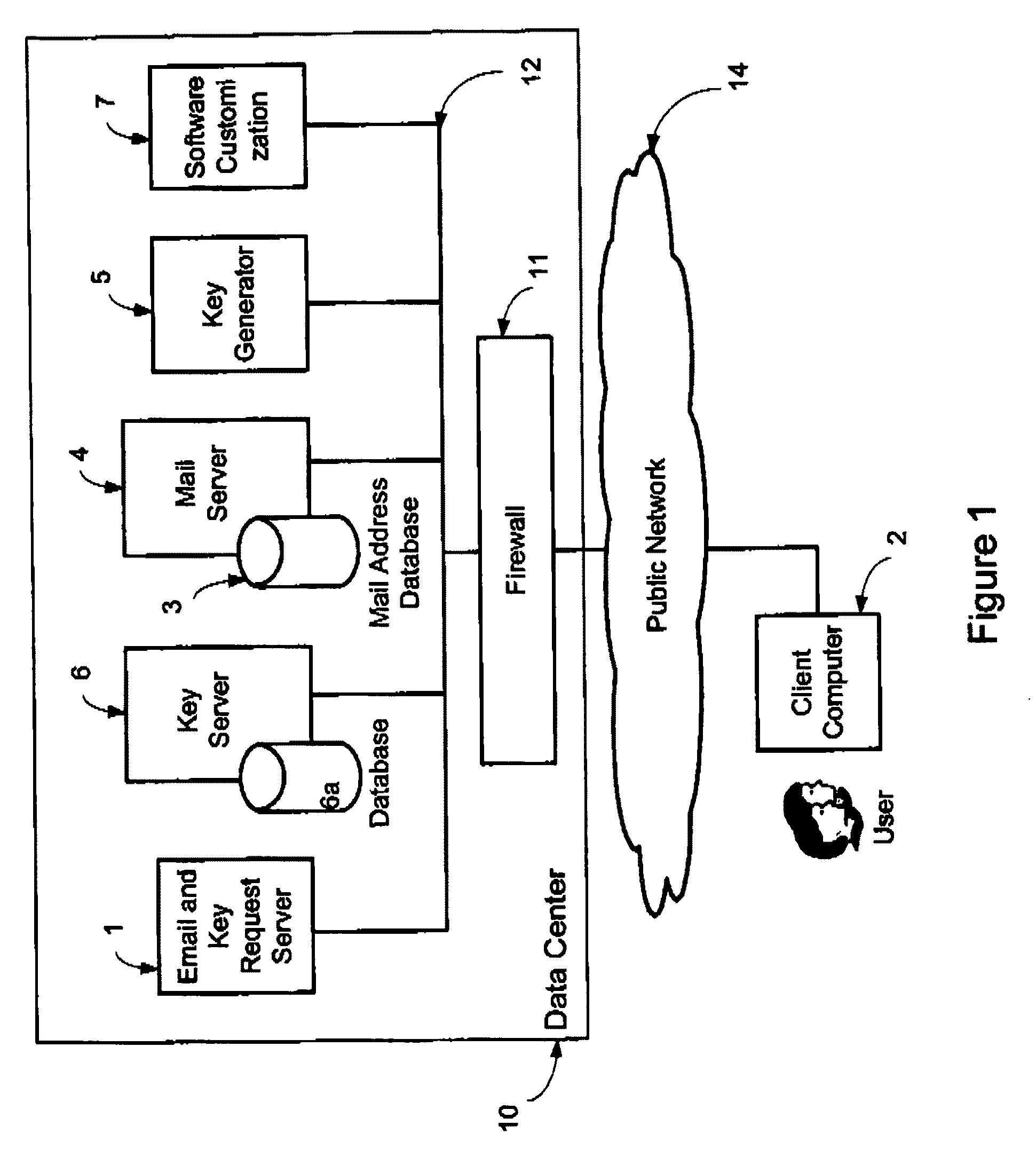
System and method for secure electronic communication services
InactiveUS20090198997A1Easy accessSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageScalable systemEmail address
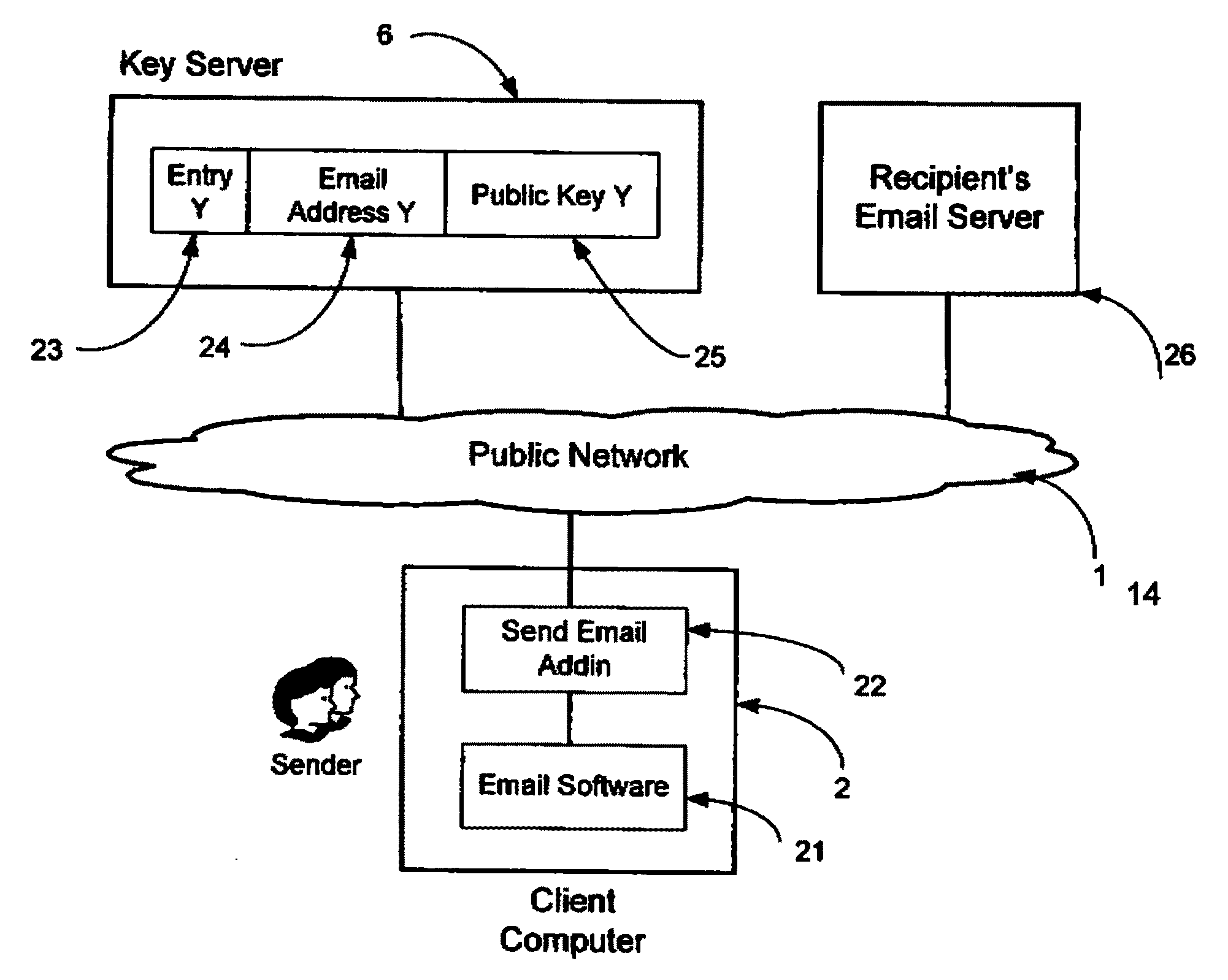
A system, method and software module for secure electronic communication services, wherein a public key (25) of private-public-key pair (30,25) is associated with an email address (24), internet name or other registered unique identifier; the registered user of the unique identifier holds the private-key (30) securely, and the respective public-key (25) is made accessible on a key server (6) for look-up and retrieval by other users, for encryption of communications to be sent to the holder of the private-key, and optionally for message confidentiality, message integrity and authentication of sender and recipient, without requiring certificates. A distributed and scalable system is provided by a server network (600; 401, 501) for registration, key distribution and management preferably using a kDNS server hierarchy (601,602,603) or a key-DNS server hierarchy (701,702,) and associated protocols so that public-keys of recipients can be searched and retrieved over the internet based on the recipients email address or other unique identifier, thus facilitating secure communication between users in different network domains and organizations.
Owner:TOPOSIS CORP
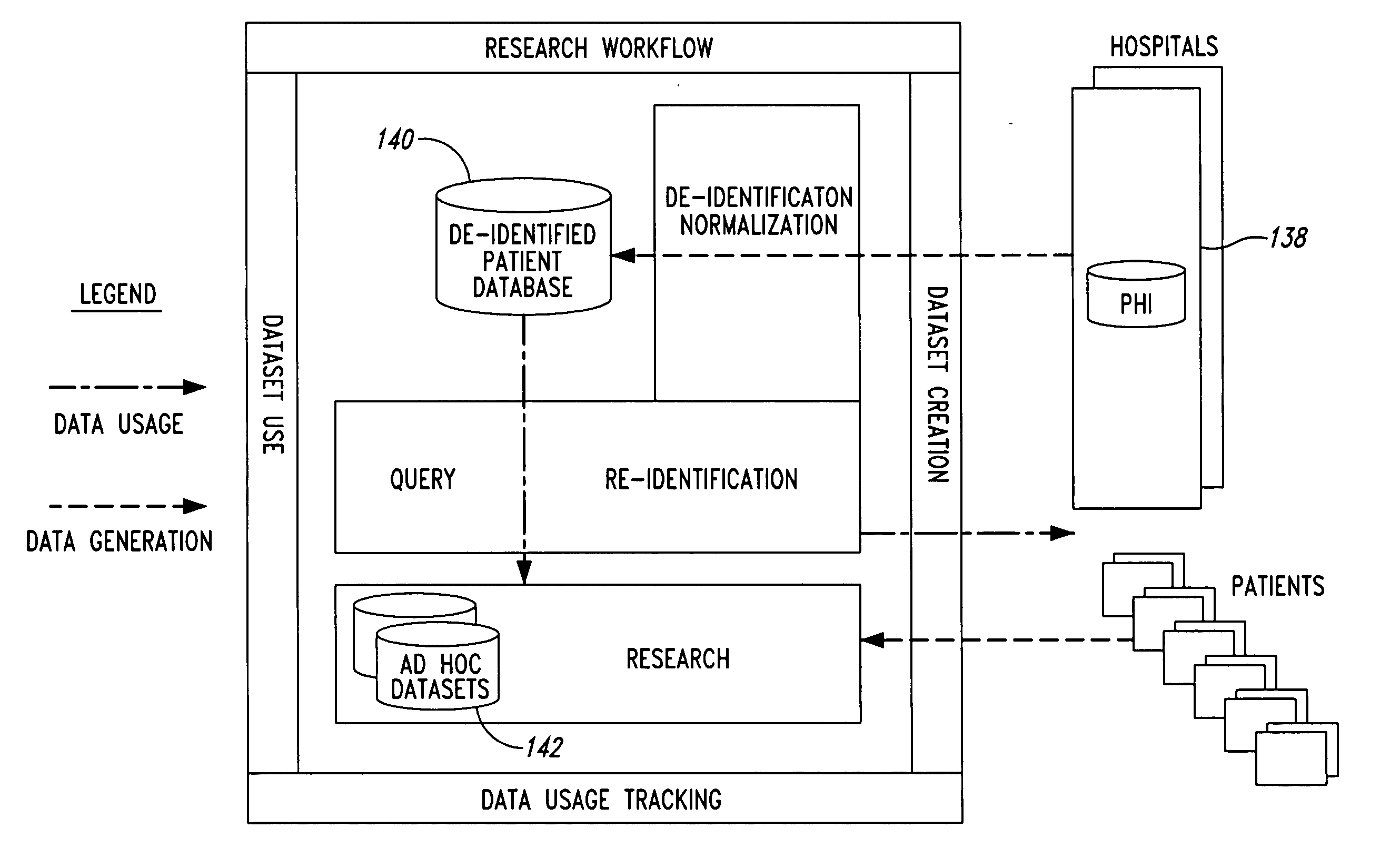
System and method for controlling access and use of patient medical data records
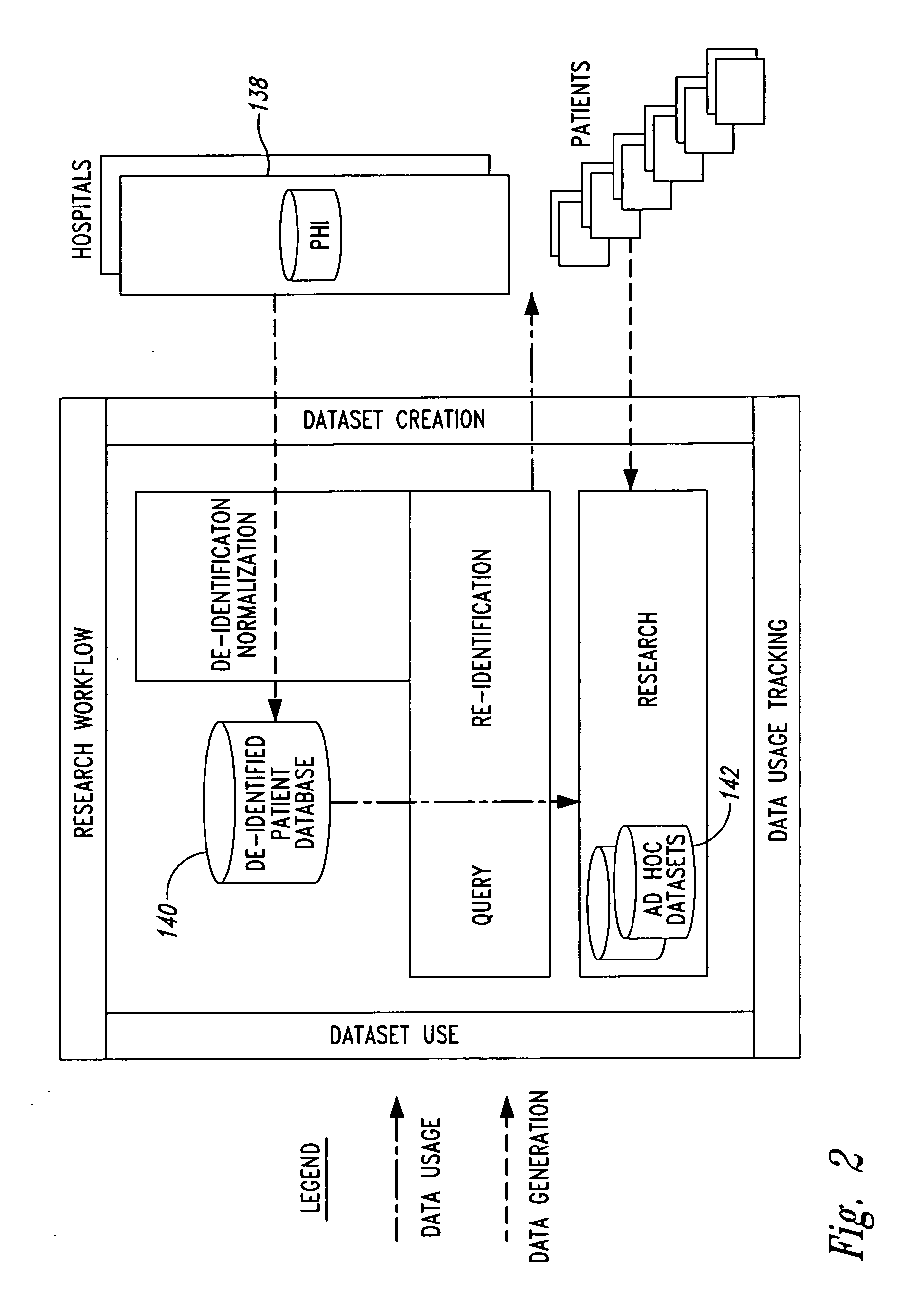
InactiveUS20050236474A1Prohibitive to printComputer security arrangementsPatient personal data managementConfidentialityPatient database
A system for processing patient health information (PHI) protects the confidentiality of PHI to achieve regulatory compliance. The PHI contains patient medical data and associated patient identification data. A de-identification agent extracts patient medical data and separates from all identification data to create de-identified patient data. A key is generated that allows subsequent reassociation of the patient medical data and the patient identification data. The de-identified patient data base may be queried for patient screening purposes. Patient queries are processed only if the study or patient screening has been authorized by appropriate authorities, such as an internal review board. Patients whose medical characteristics conform with the patient query are selected for possible use in a study. If re-identification of the selected patients is necessary, and authorized, the key may be used to provide the necessary reassociation. A data log records all access to patient data.
Owner:CONVERGENCE CT
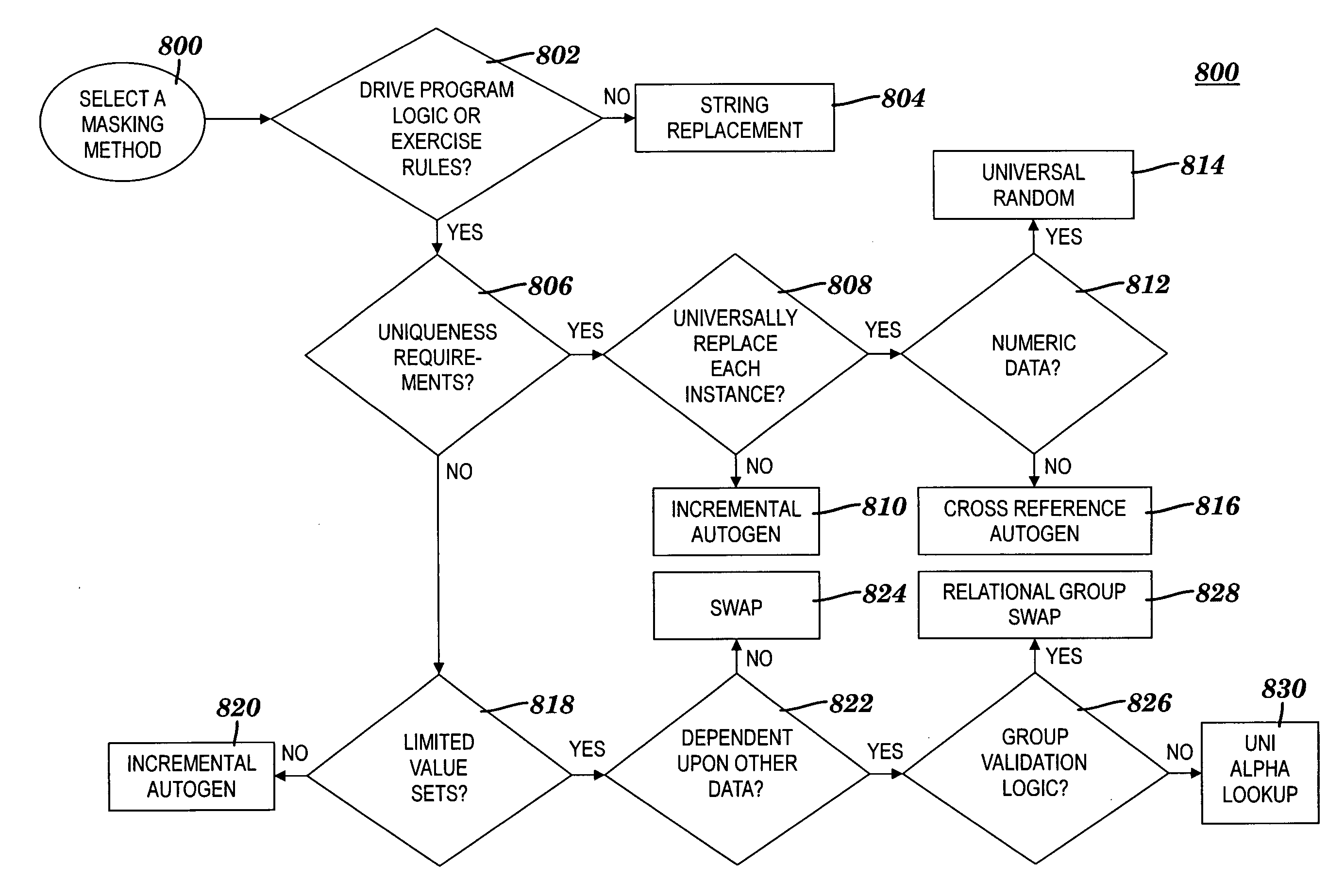
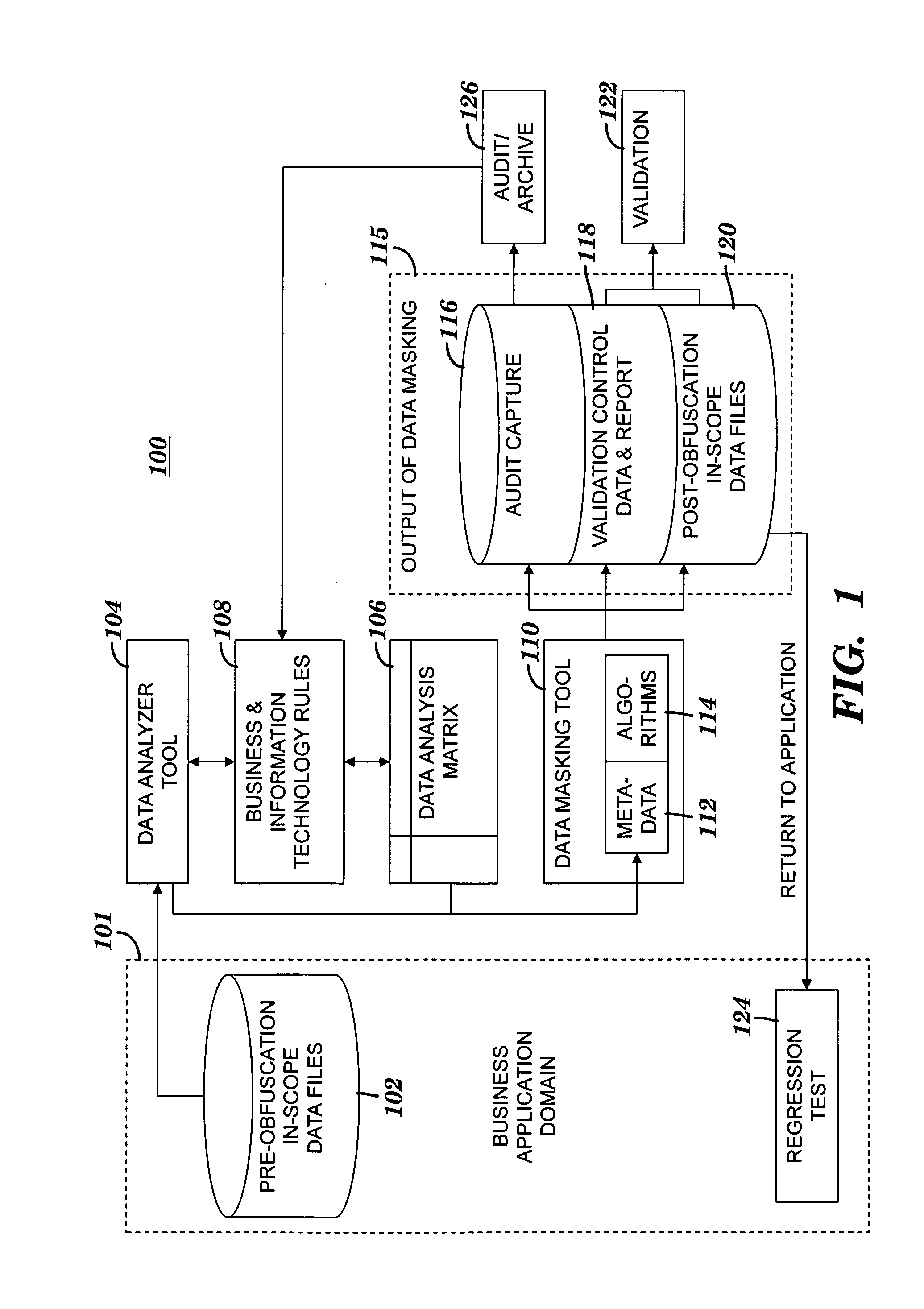
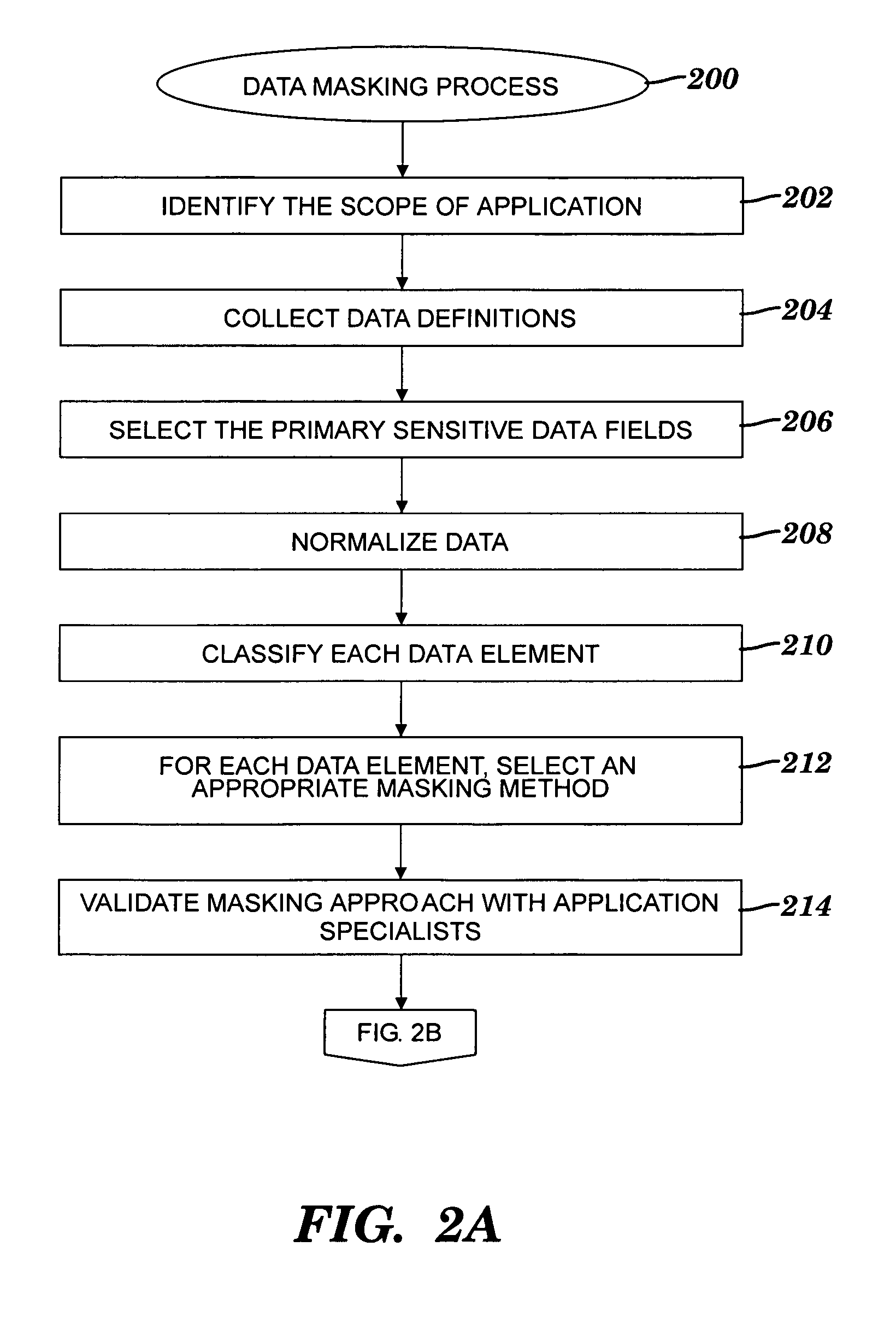
Obfuscating sensitive data while preserving data usability
InactiveUS20090132419A1Computer security arrangementsSecuring communicationConfidentialityData field
A method and system for obfuscating sensitive data while preserving data usability. The in-scope data files of an application are identified. The in-scope data files include sensitive data that must be masked to preserve its confidentiality. Data definitions are collected. Primary sensitive data fields are identified. Data names for the primary sensitive data fields are normalized. The primary sensitive data fields are classified according to sensitivity. Appropriate masking methods are selected from a pre-defined set to be applied to each data element based on rules exercised on the data. The data being masked is profiled to detect invalid data. Masking software is developed and input considerations are applied. The selected masking method is executed and operational and functional validation is performed.
Owner:IBM CORP
Methods, software programs, and systems for electronic information security
InactiveUS7395436B1Digital data processing detailsUser identity/authority verificationConfidentialityDigital signature
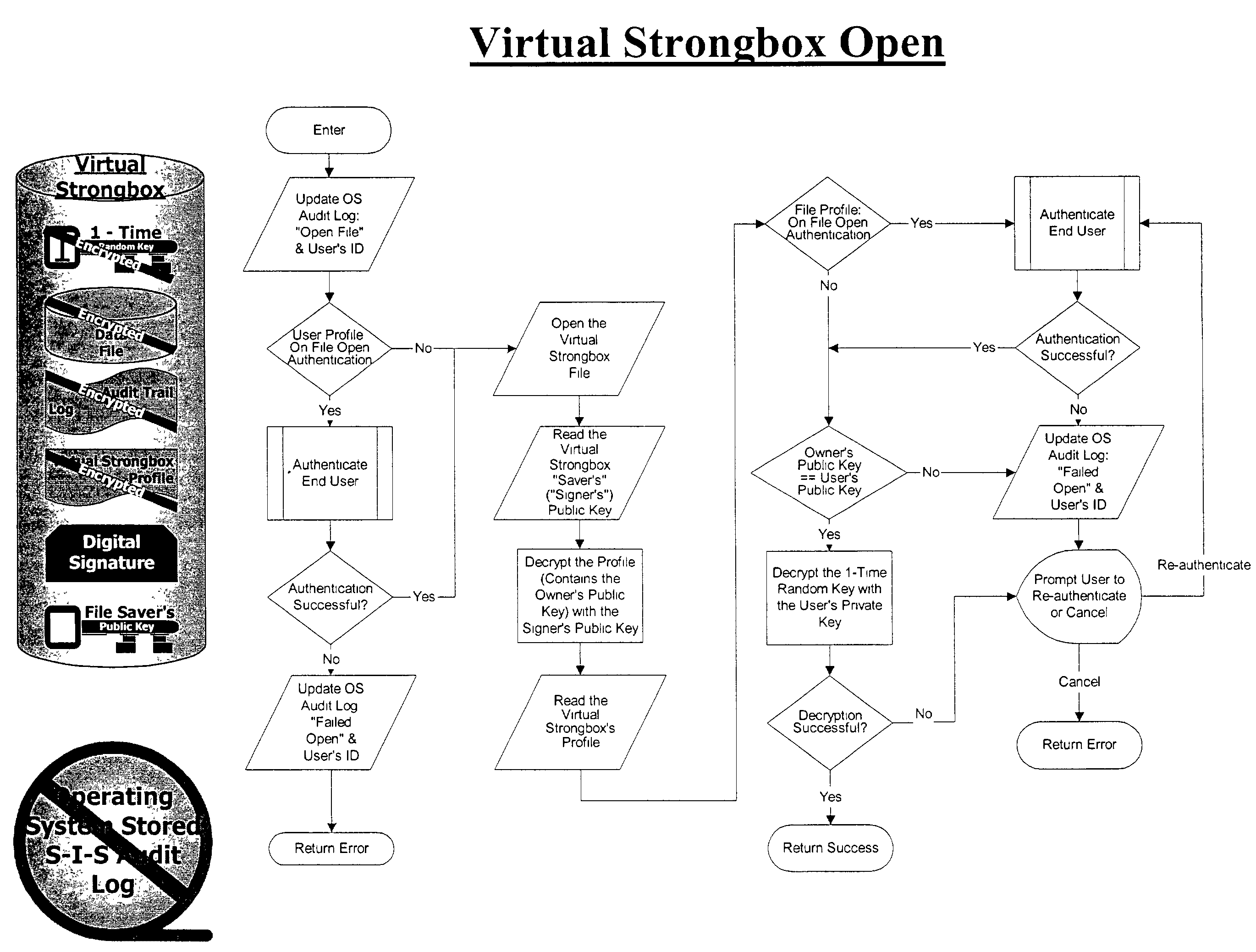
The present invention relates to various methods, software programs, and systems for electronic information security. More particularly, these various methods, software programs, and systems may serve to protect information security by providing an integrated system that helps ensure confidentiality, integrity, accountability, and ease of use. Certain embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a file container for storing: (a) a data file, which data file is encrypted with a one-time random encryption key; (b) the one-time random encryption key, which one-time random encryption key is encrypted with a public key portion of a public key / private key pair associated with an owner of the file container; (c) an audit trail log of the history of the file container, which audit trail log is encrypted with the one-time random encryption key with which the data file is encrypted; (d) a digital signature based upon a hash of the combined data file and the audit trail log, which hash is encrypted with a private key portion of a public key / private key associated with a writer / creator of the file container; and (e) a profile associated with the file container. Additional embodiments of the present invention relate to methods, software programs, and systems for electronic information security utilizing a fully integrated system for user authentication, virus scanning, time / date certification, encryption / decryption, digital signatures, stored document protection, transmitted document protection, and delivery verification.
Owner:KENEISYS
Protecting Information Using Policies and Encryption
ActiveUS20130097421A1Ensure confidentialityAvoid data lossDigital data protectionSecuring communicationDocumentation procedureConfidentiality
A technique and system protects documents at rest and in motion using declarative policies and encryption. Encryption in the system is provided transparently and can work in conjunction with policy enforcers installed at a system. A system can protect information or documents from: (i) insider theft; (ii) ensure confidentiality; and (iii) prevent data loss, while enabling collaboration both inside and outside of a company.
Owner:NEXTLABS
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
Method for implementing safe storage system in cloud storage environment
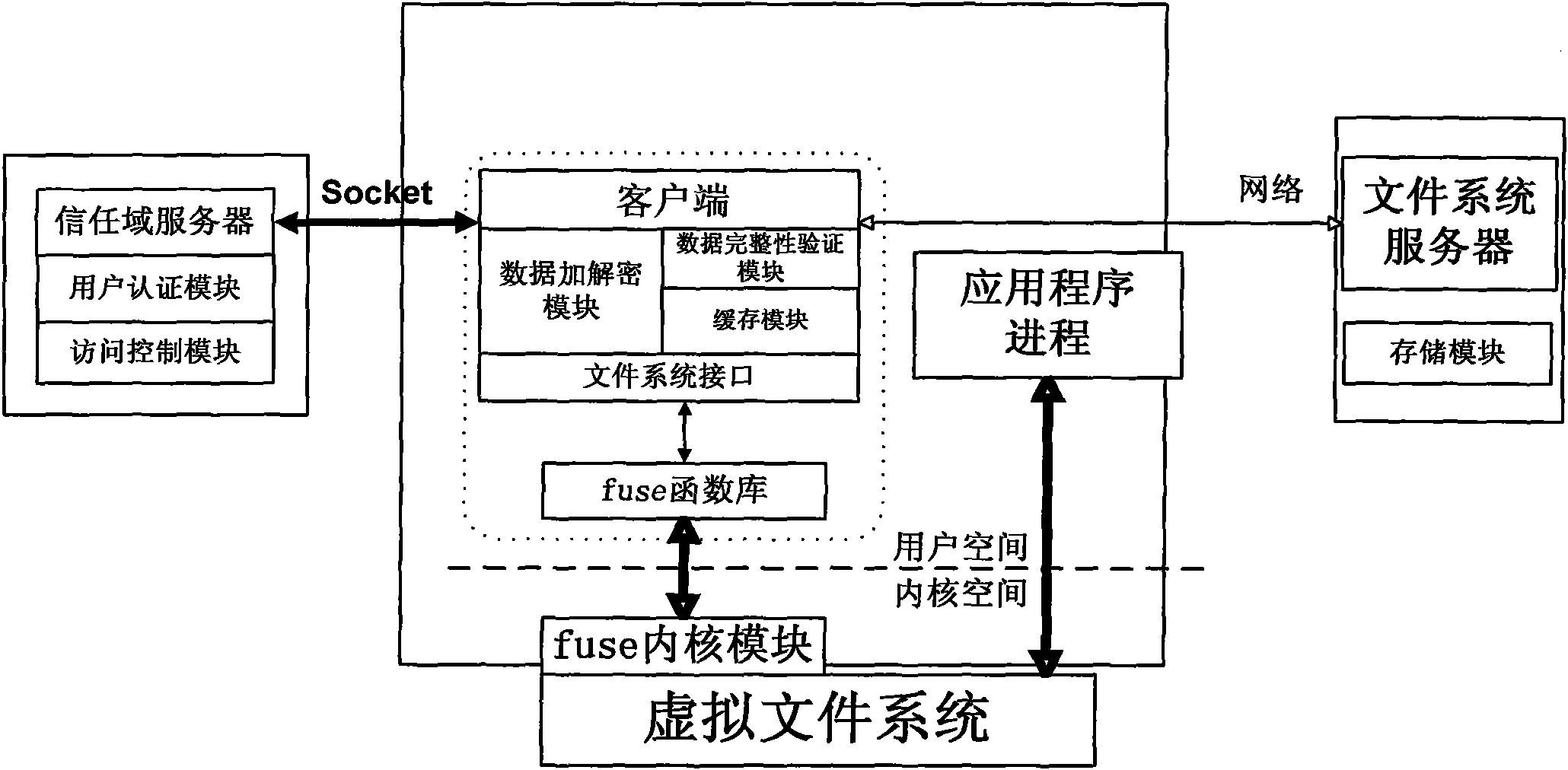
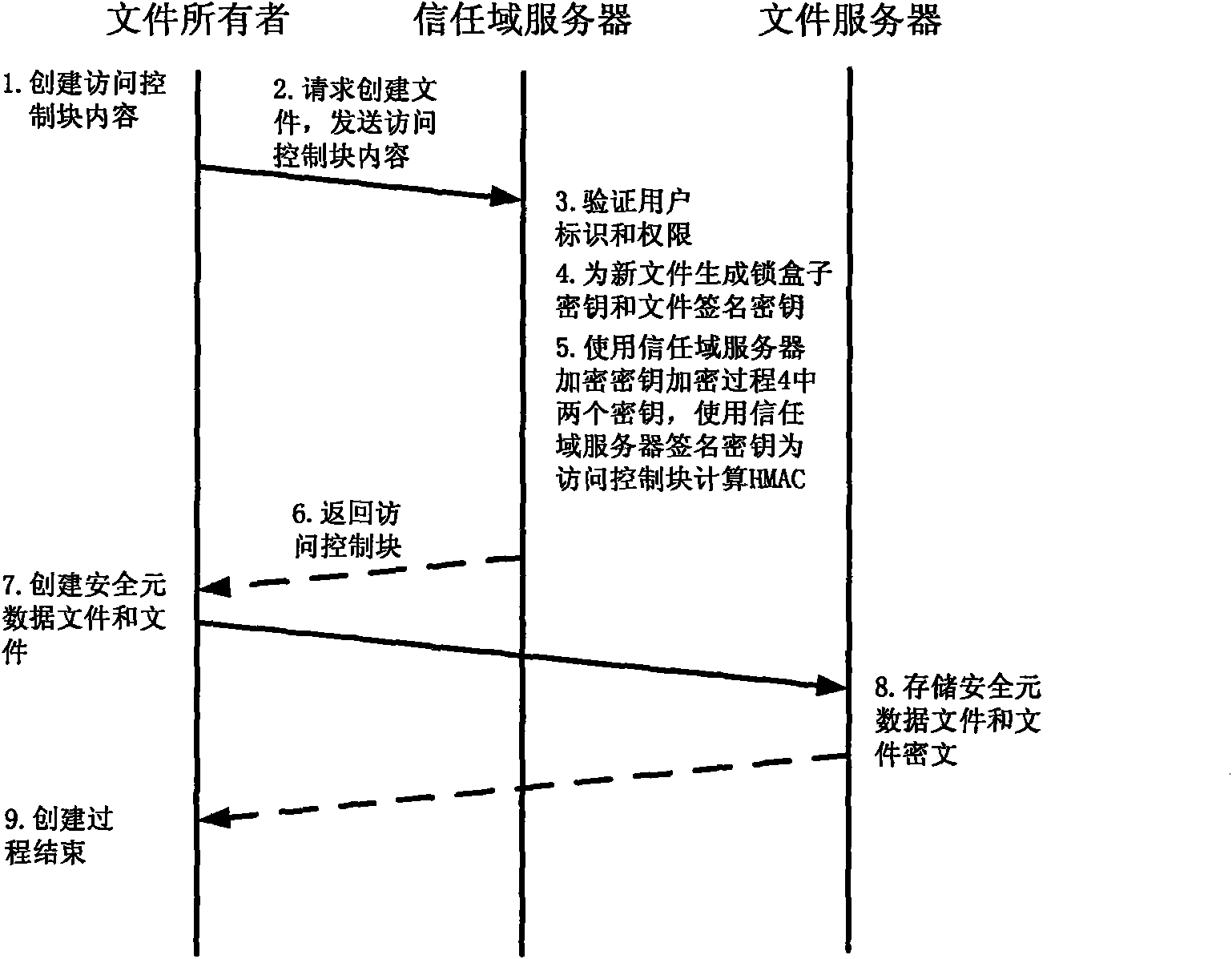
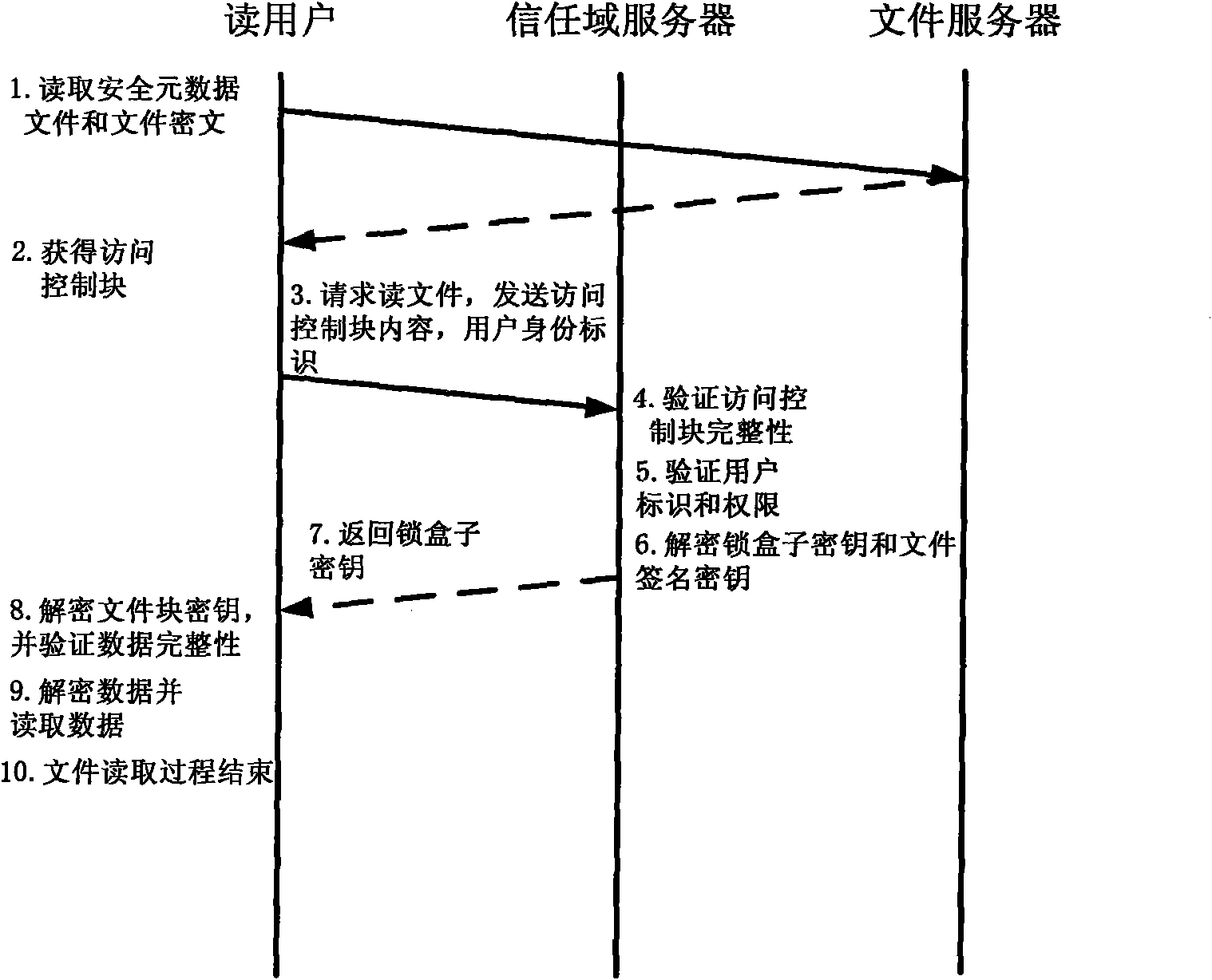
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
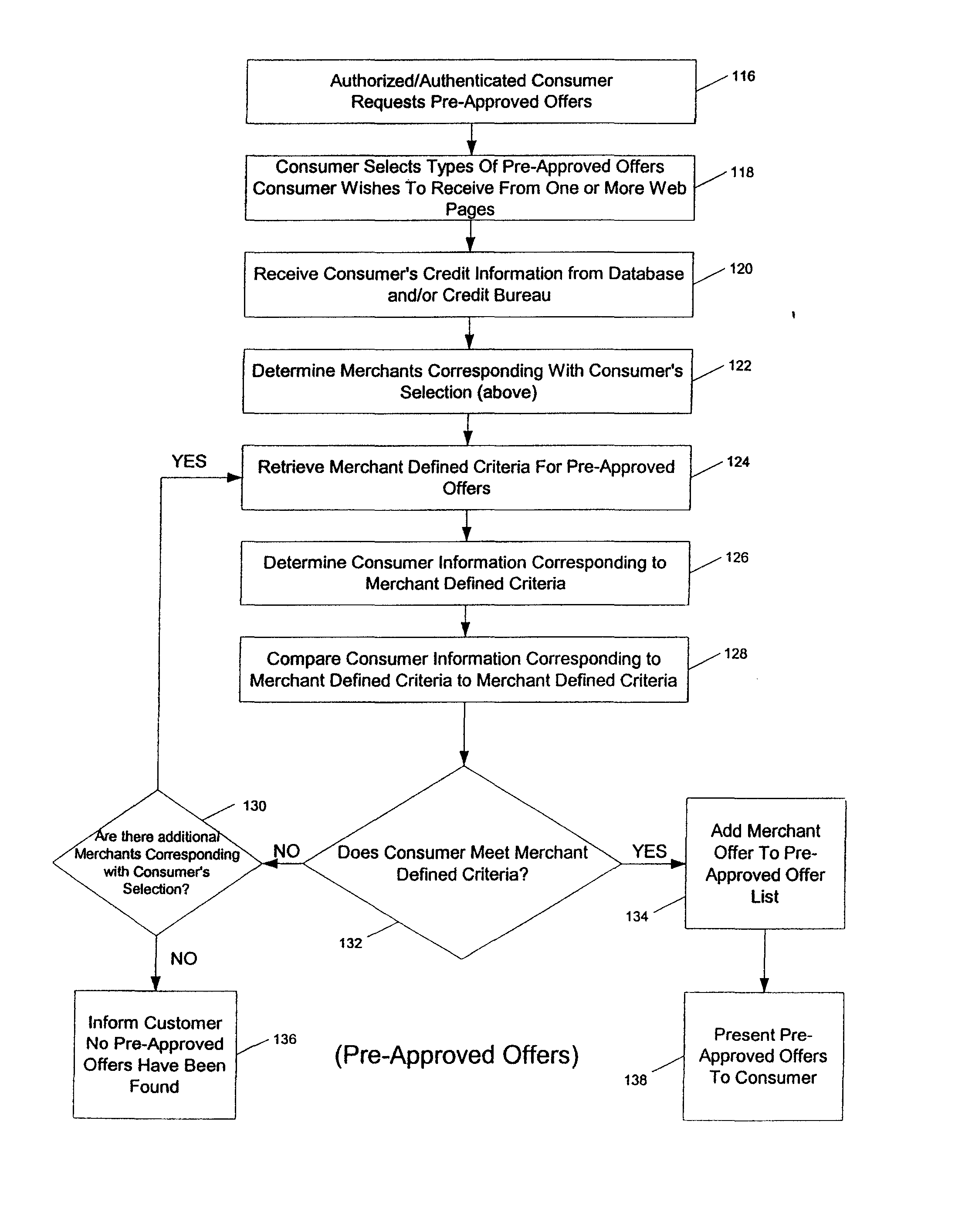
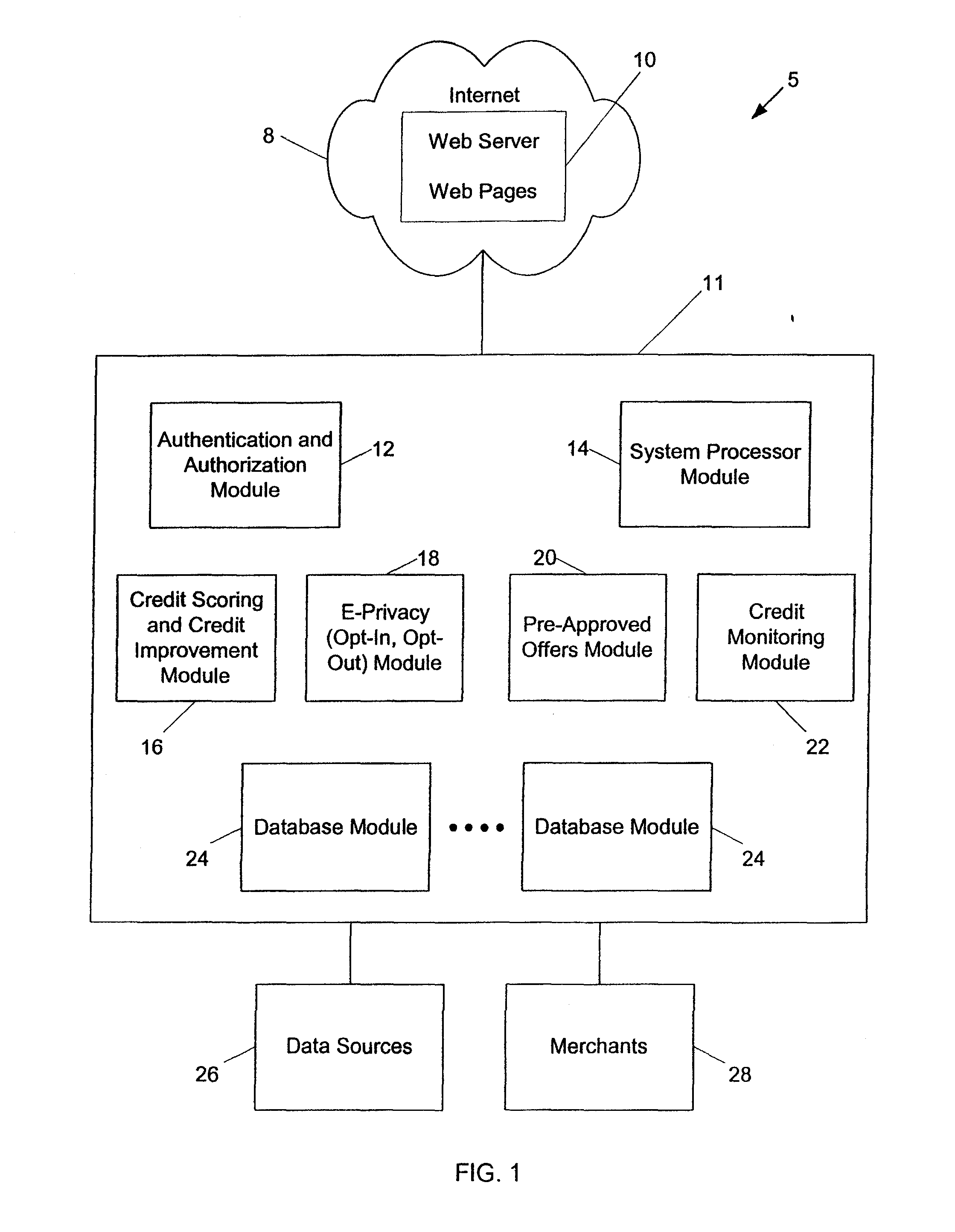
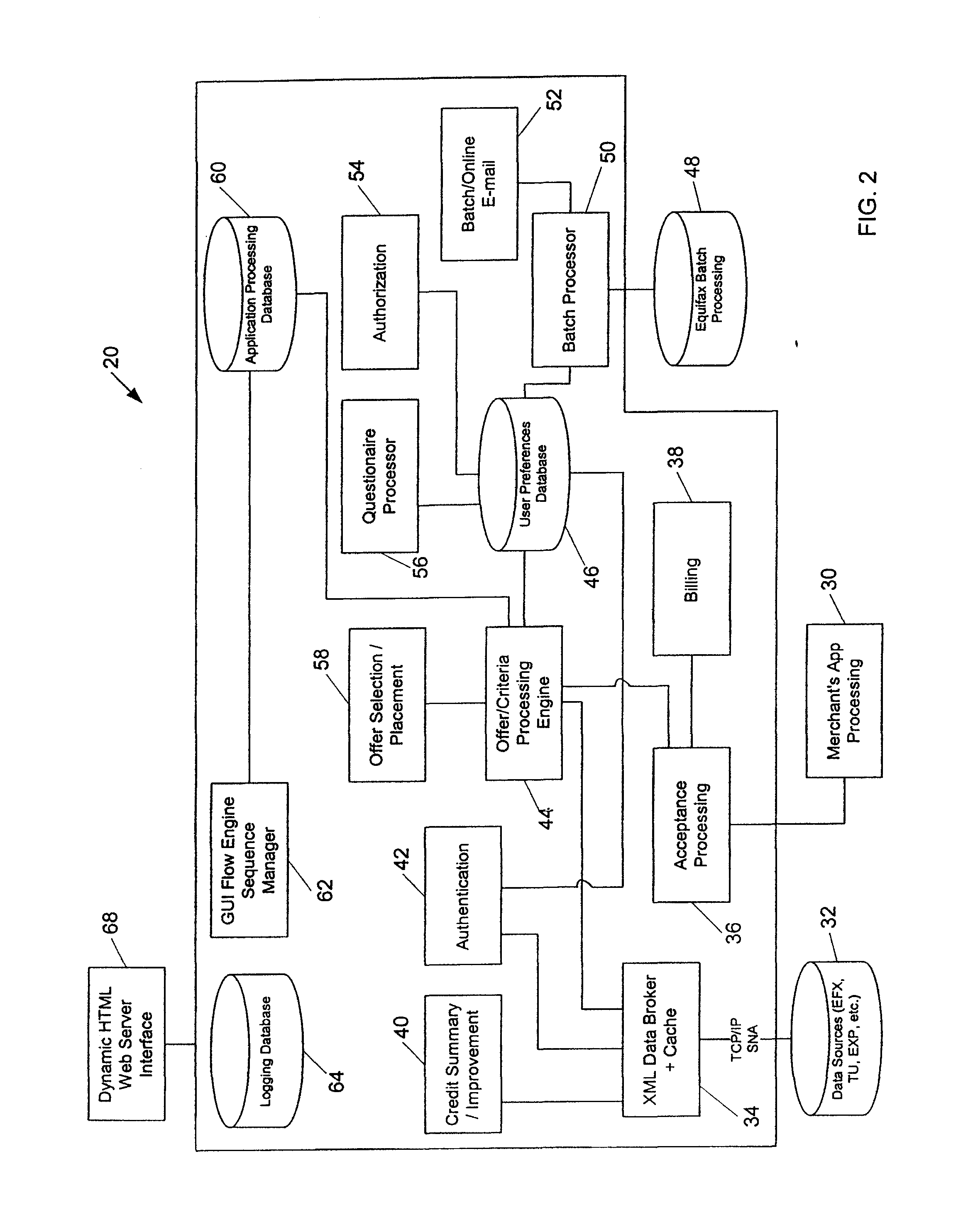
Systems and methods for providing consumers anonymous pre-approved offers from a consumer-selected group or merchants
InactiveUS20070299771A1Increase ratingsFinanceBuying/selling/leasing transactionsThird partyConfidentiality
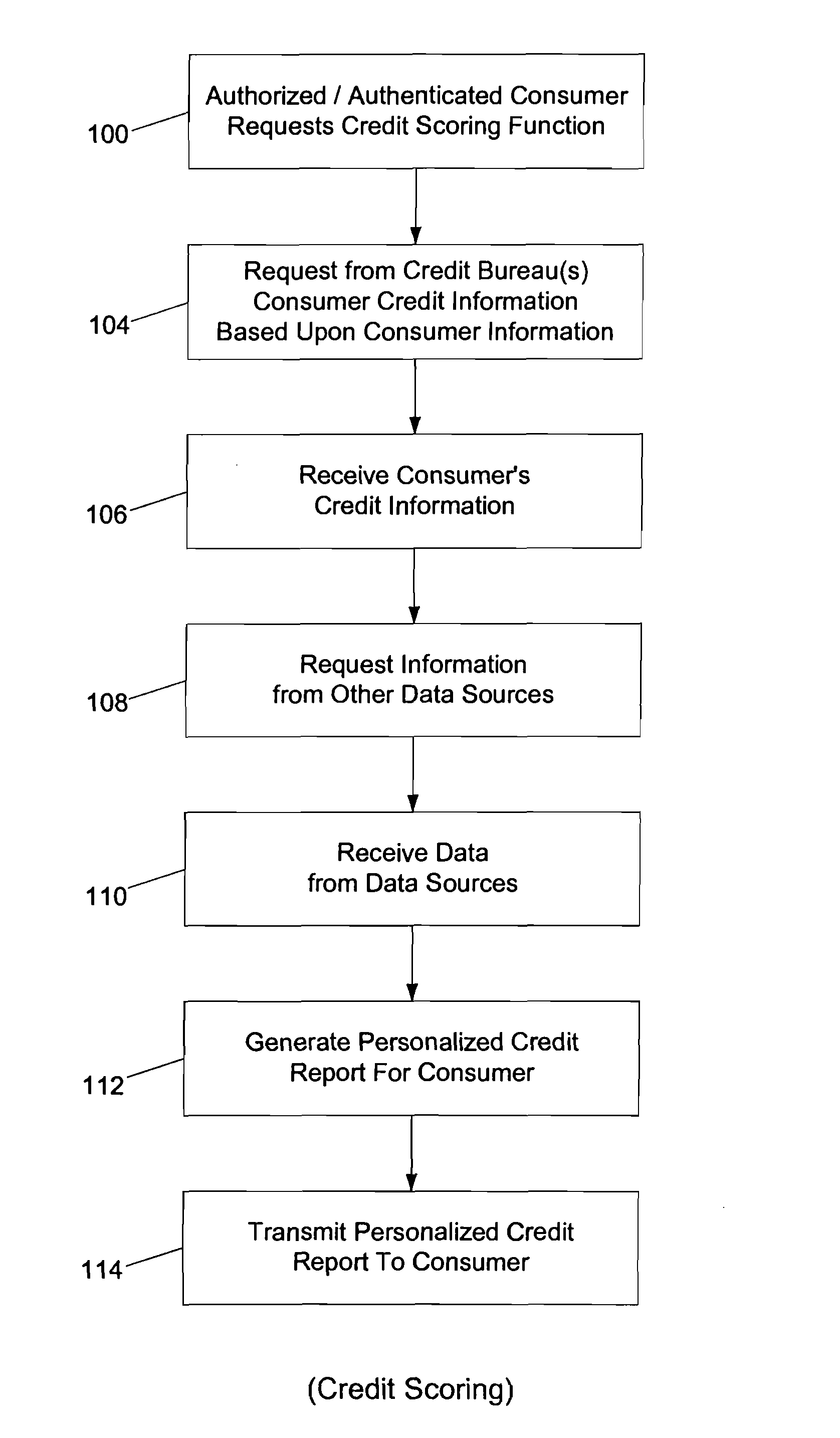
The system and method of the present invention provides consumers with credit information including information which can help the consumer evaluate the consumer's credit report or credit worthiness. The present invention can also provide consumers with suggestions to help consumers better their credit rating. The system and method of the present invention also provide consumers with pre-approved credit offers from a consumer-selected group of merchants, where the consumers are anonymous to the merchants, and the merchants do not receive copies of the consumer's credit report. Additional functions of the present invention include allowing users to opt-out or opt-into solicitation lists, and enabling users to automatically monitor their credit report. The present invention offers these services through a third party agent of the consumer which can be accessible to the consumer via the Internet. Through this agency relationship, the third party can request consumer information and determine pre-approved offers from a plurality of merchants while protecting the confidentiality of consumer credit information without negative consequences on a consumer's credit.
Owner:BRODY ROBERT M +2
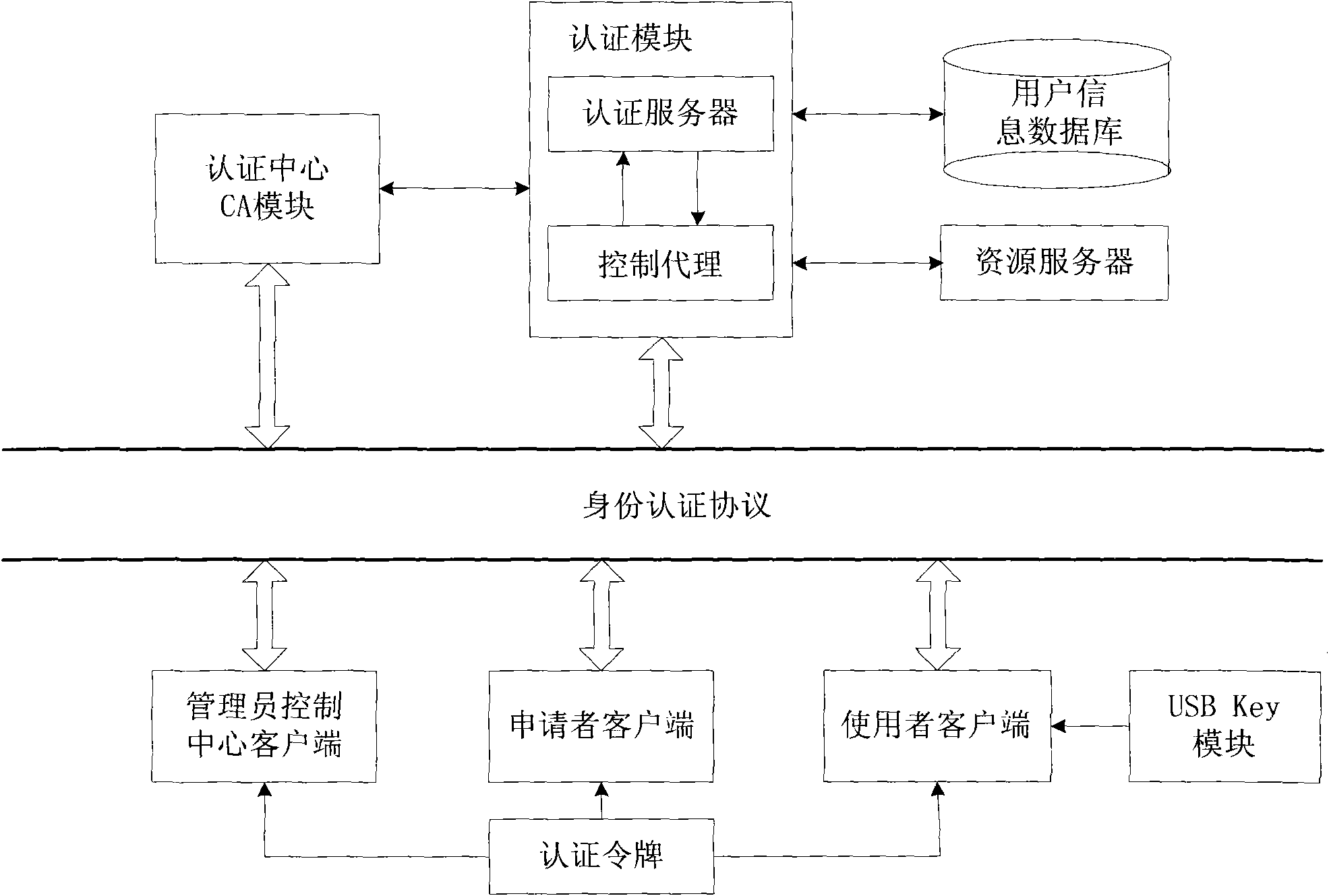
Network identity authentication system and method
InactiveCN101674304AEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
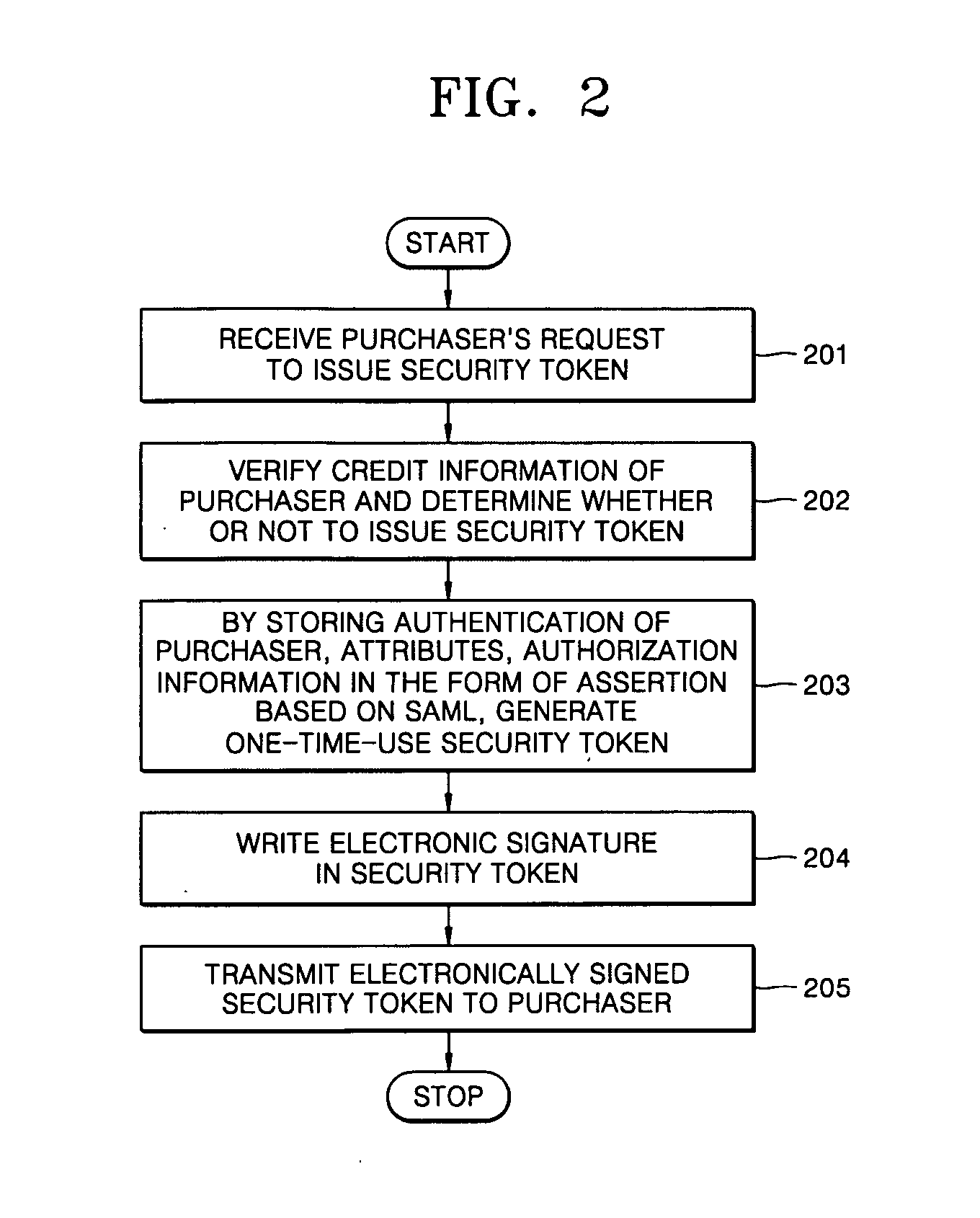
Method for electronic commerce using security token and apparatus thereof
InactiveUS20050097060A1Securing communicationPayments involving neutral partyConfidentialityExtensible markup
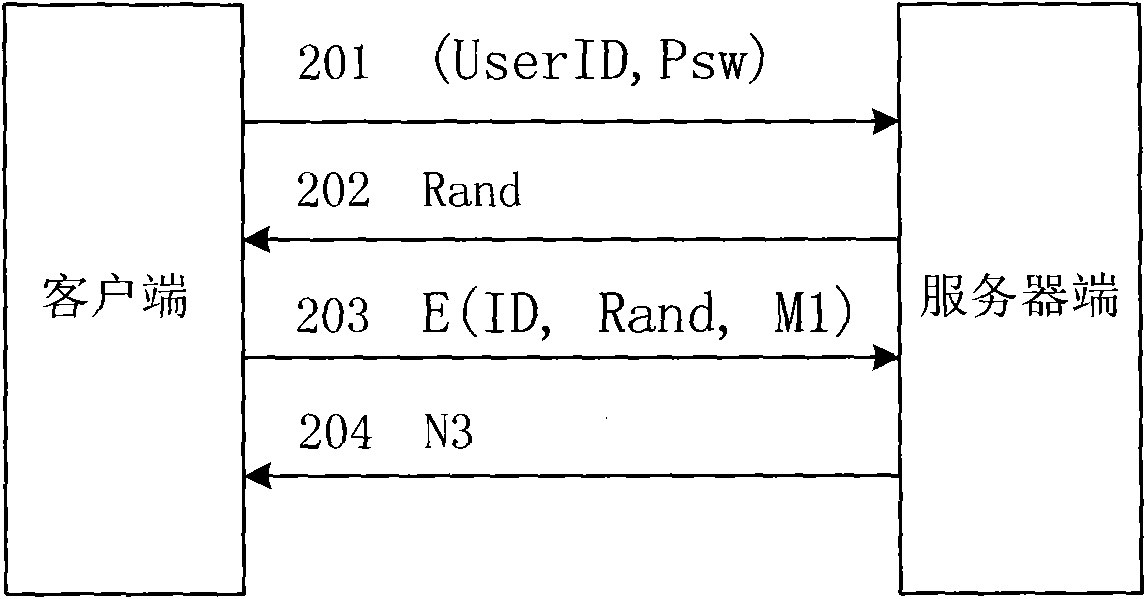
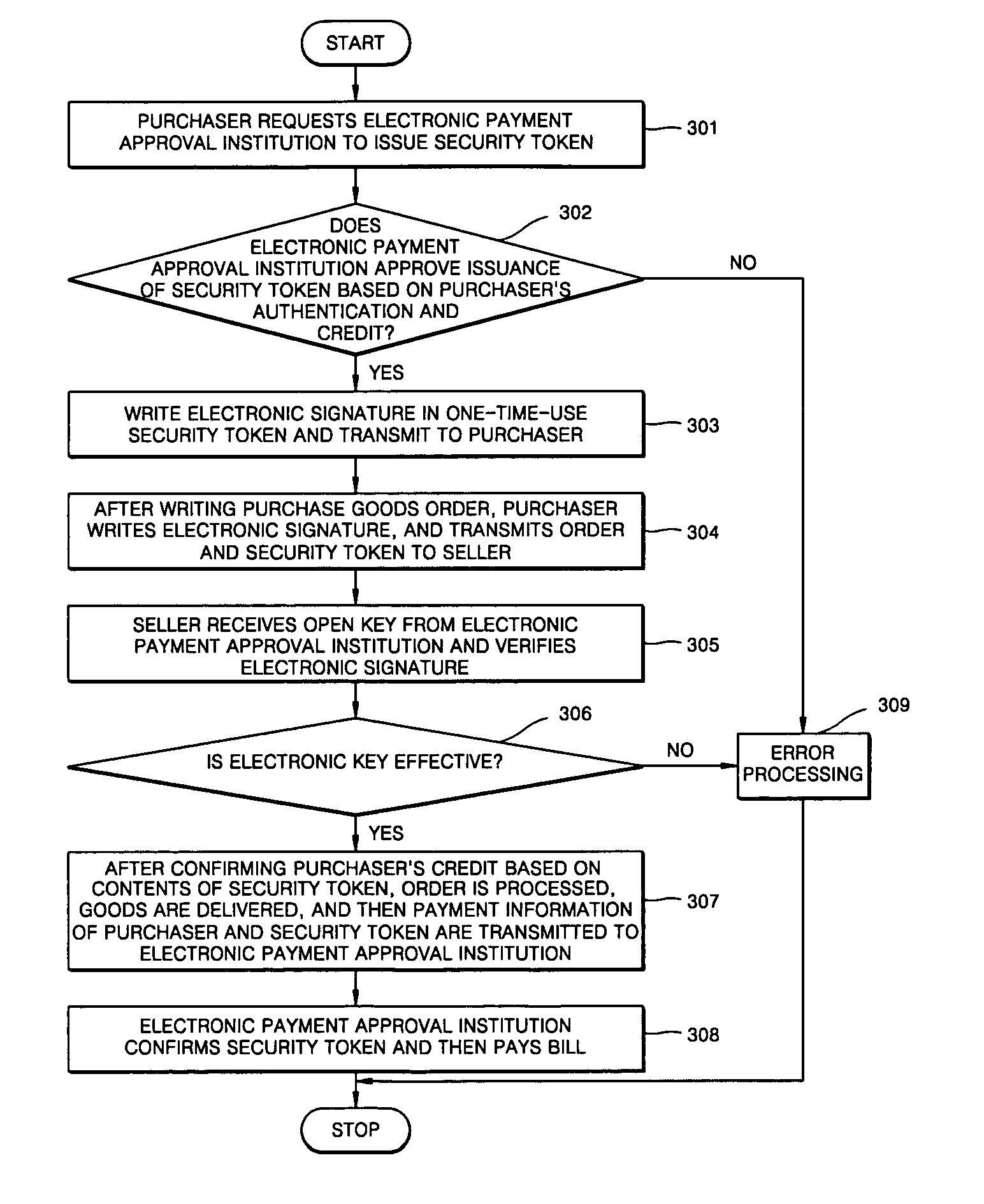
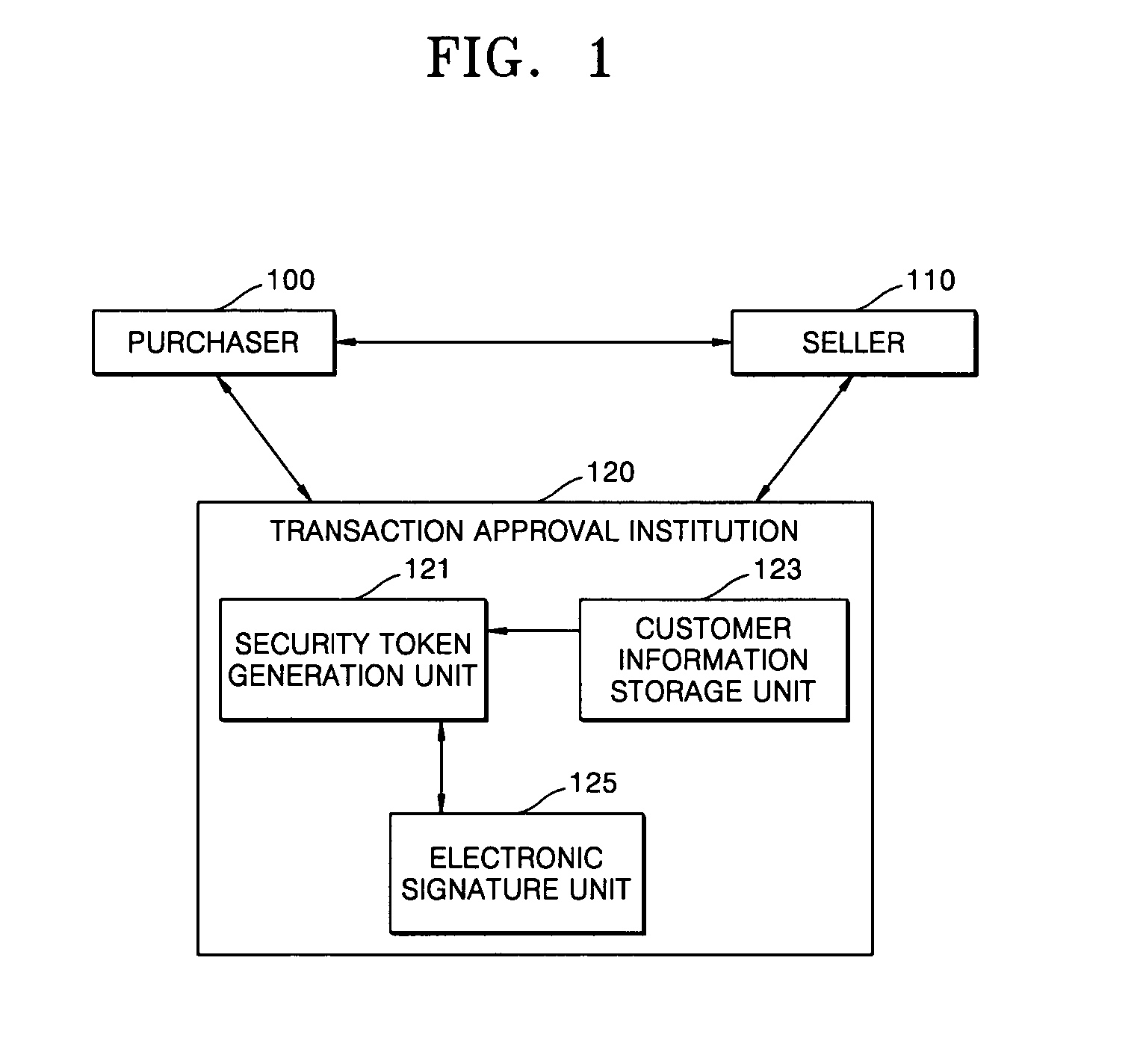
A method for electronic commerce using a security token and an apparatus thereof are provided. The electronic commerce method using a security token comprises a transaction approval institution generating a security token based on a security assertion markup language (SAML), using credit information of a purchaser who requests to issue a security token, and transmitting the security token to the purchaser; the purchaser writing an electronic signature on an order and transmitting the order together with the security token to a seller; the seller verifying the received order and security token, and then delivering goods according to the order to the purchaser; and the transaction approval institution performing payment for the seller and the purchaser. The method can solve the problems of personal information leakage and privacy infringement that may happen when a purchaser sends his personal information to a seller for electronic commerce. Since the token is one-time-use data, even if a security token sent is counterfeited or stolen, the loss can be minimized. In addition, by writing an extensible markup language (XML) electronic signature in the security token, authentication, integrity, and non-repudiation for a transmitted message can be guaranteed and through simple object access protocol (SOAP) security technology, confidentiality is maintained.
Owner:ELECTRONICS & TELECOMM RES INST
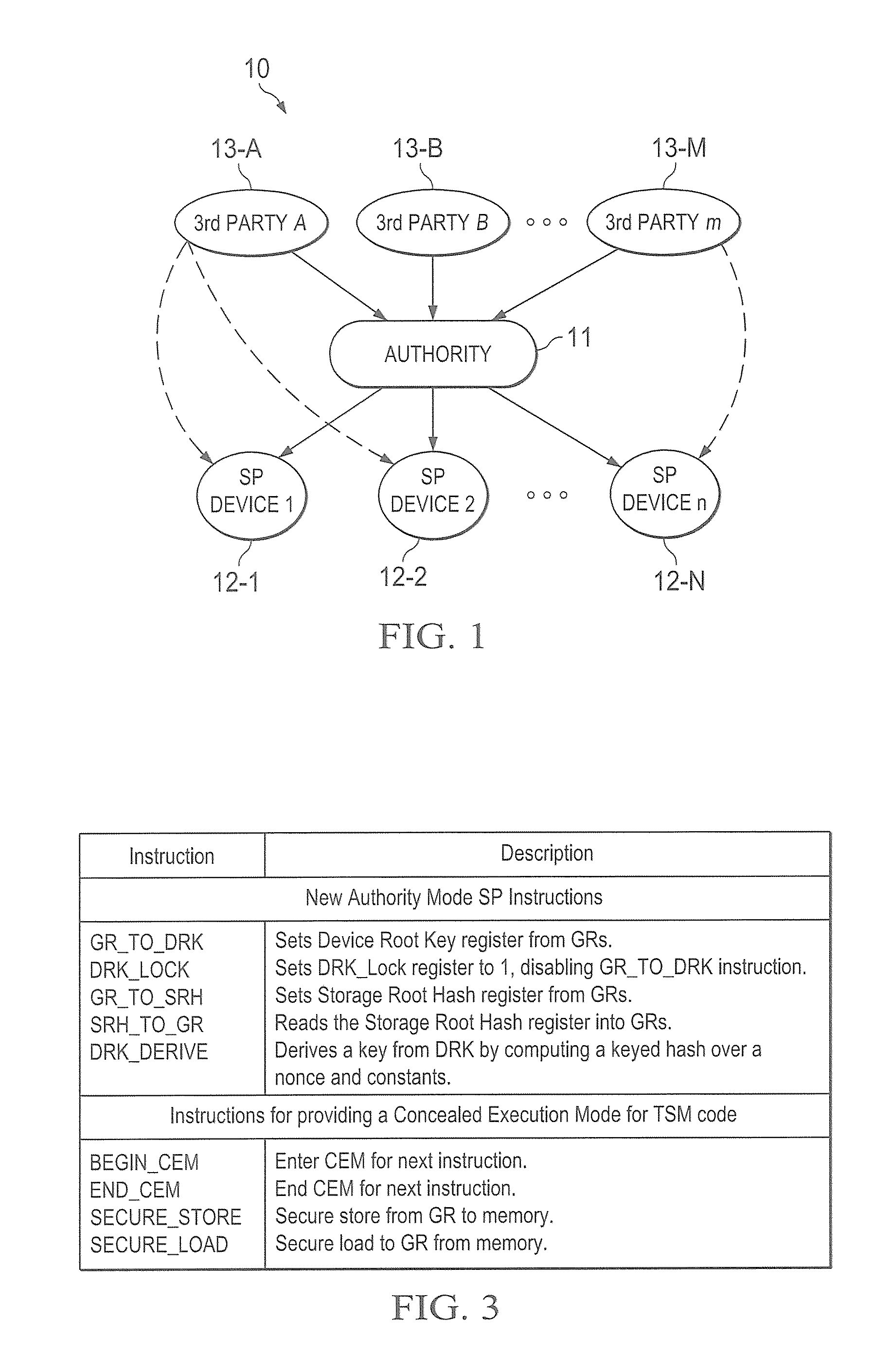
Hardware trust anchors in sp-enabled processors
ActiveUS20100042824A1User identity/authority verificationDigital computer detailsOperational systemConfidentiality
A trust system and method is disclosed for use in computing devices, particularly portable devices, in which a central Authority shares secrets and sensitive data with users of the respective devices. The central Authority maintains control over how and when shared secrets and data are used. In one embodiment, the secrets and data are protected by hardware-rooted encryption and cryptographic hashing, and can be stored securely in untrusted storage. The problem of transient trust and revocation of data is reduced to that of secure key management and keeping a runtime check of the integrity of the secure storage areas containing these keys (and other secrets). These hardware-protected keys and other secrets can further protect the confidentiality and / or integrity of any amount of other information of arbitrary size (e.g., files, programs, data) by the use of strong encryption and / or keyed-hashing, respectively. In addition to secrets the Authority owns, the system provides access to third party secrets from the computing devices. In one embodiment, the hardware-rooted encryption and hashing each use a single hardware register fabricated as part of the computing device's processor or System-on-Chip (SoC) and protected from external probing. The secret data is protected while in the device even during operating system malfunctions and becomes non-accessible from storage according to various rules, one of the rules being the passage of a certain time period. The use of the keys (or other secrets) can be bound to security policies that cannot be separated from the keys (or other secrets). The Authority is also able to establish remote trust and secure communications to the devices after deployment in the field using a special tamper-resistant hardware register in the device, to enable, disable or update the keys or secrets stored securely by the device.
Owner:THE TRUSTEES FOR PRINCETON UNIV +1
Threshold and identity-based key management and authentication for wireless ad hoc networks
InactiveUS20060023887A1Reduce usageReduce resource requirementsKey distribution for secure communicationPublic key for secure communicationConfidentialityWireless ad hoc network
As various applications of wireless ad hoc network have been proposed, security has become one of the big research challenges and is receiving increasing attention. The present invention provides for a distributed key management and authentication approach by deploying the recently developed concepts of identity-based cryptography and threshold secret sharing. Without any assumption of pre-fixed trust relationship between nodes, the ad hoc network works in a self-organizing way to provide the key generation and key management service, which effectively solves the problem of single point of failure in the traditional public key infrastructure (PKI)-supported system. The identity-based cryptography mechanism provided not only to provide end-to-end authenticity and confidentiality, but also saves network bandwidth and computational power of wireless nodes.
Owner:UNIVERSITY OF CINCINNATI
Methods and systems for obfuscating data and computations defined in a secure distributed transaction ledger
ActiveUS20160261404A1Digital data protectionCommunication with homomorphic encryptionConfidentialityDistributed transaction
Aspects of the present invention provide systems and methods that facilitate computations that are publically defined while assuring the confidentiality of the input data provided, the generated output data, or both using homomorphic encryption on the contents of the secure distributed transaction ledger. Full homomorphic encryption schemes protect data while still enabling programs to accept it as input. In embodiments, using a homomorphic encryption data input into a secure distributed transaction ledger allows a consumer to employ highly motivated entities with excess compute capability to perform calculations on the consumer's behalf while assuring data confidentiality, correctness, and integrity as it propagates through the network.
Owner:DELL PROD LP
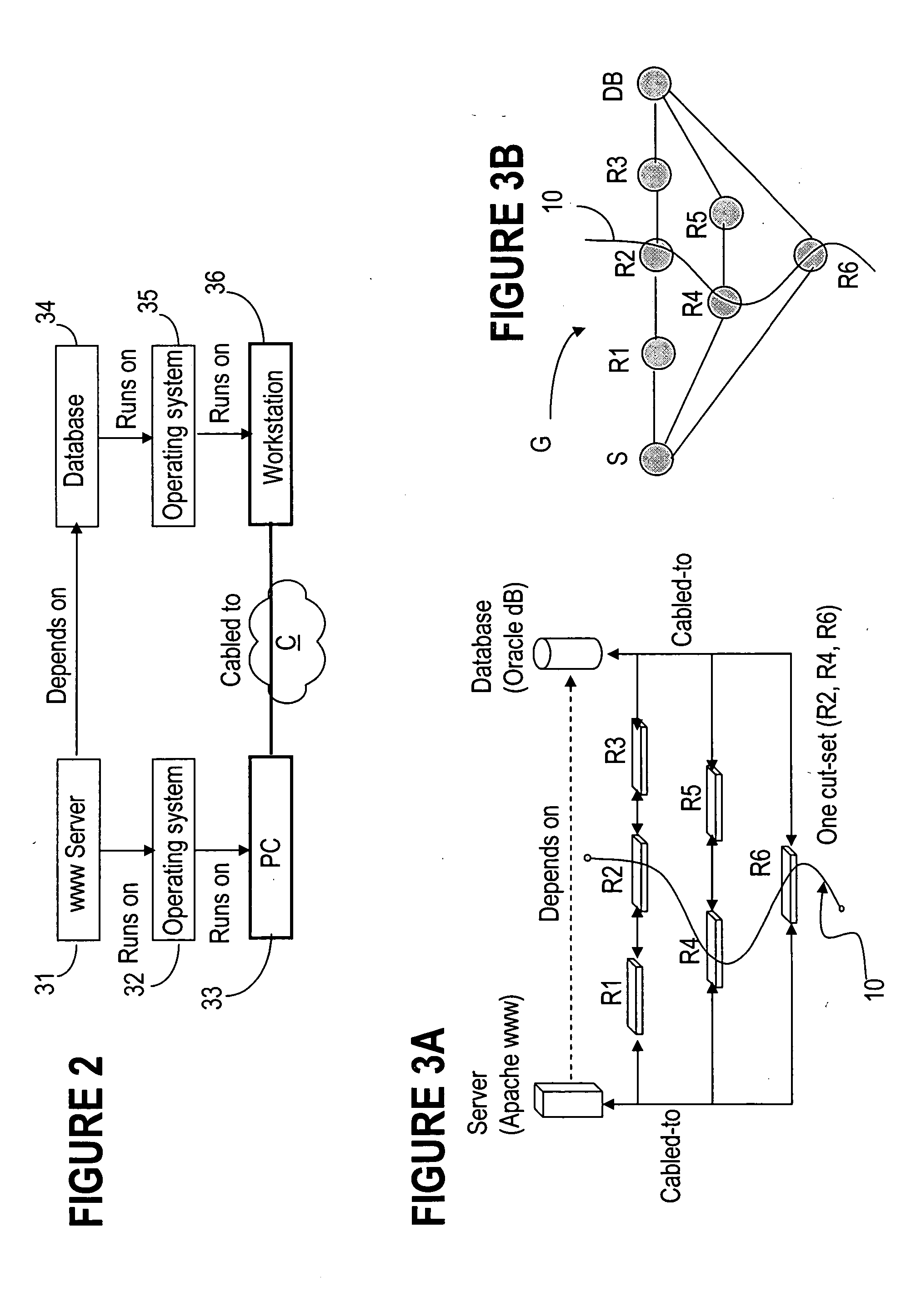
Application of cut-sets to network interdependency security risk assessment
InactiveUS20070067845A1Memory loss protectionError detection/correctionTraffic capacityRisk profiling
The invention is directed to providing threat and risk analysis for a network that has a high degree of inter-relationships and interdependencies among the assets comprising it, using a “cut set” enumeration method. The identified cut sets are used as the basis to the threat and risk analysis, since each cut set may affect the traffic between two dependent assets in the network, and thereby affect the security state of the dependent assets themselves. The affected security state may be confidentiality, integrity, availability, or other network or security relevant parameter.
Owner:ALCATEL LUCENT SAS
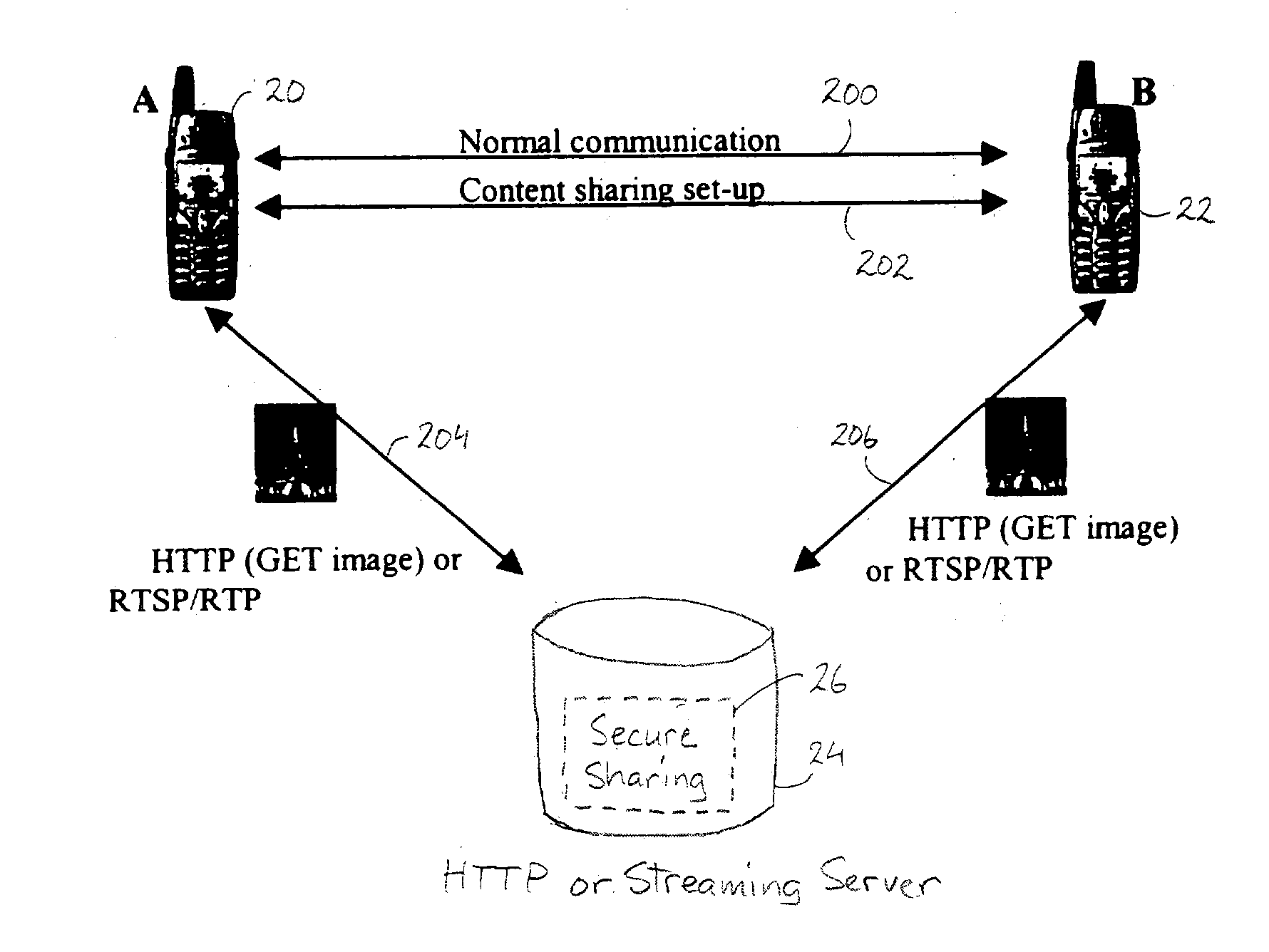
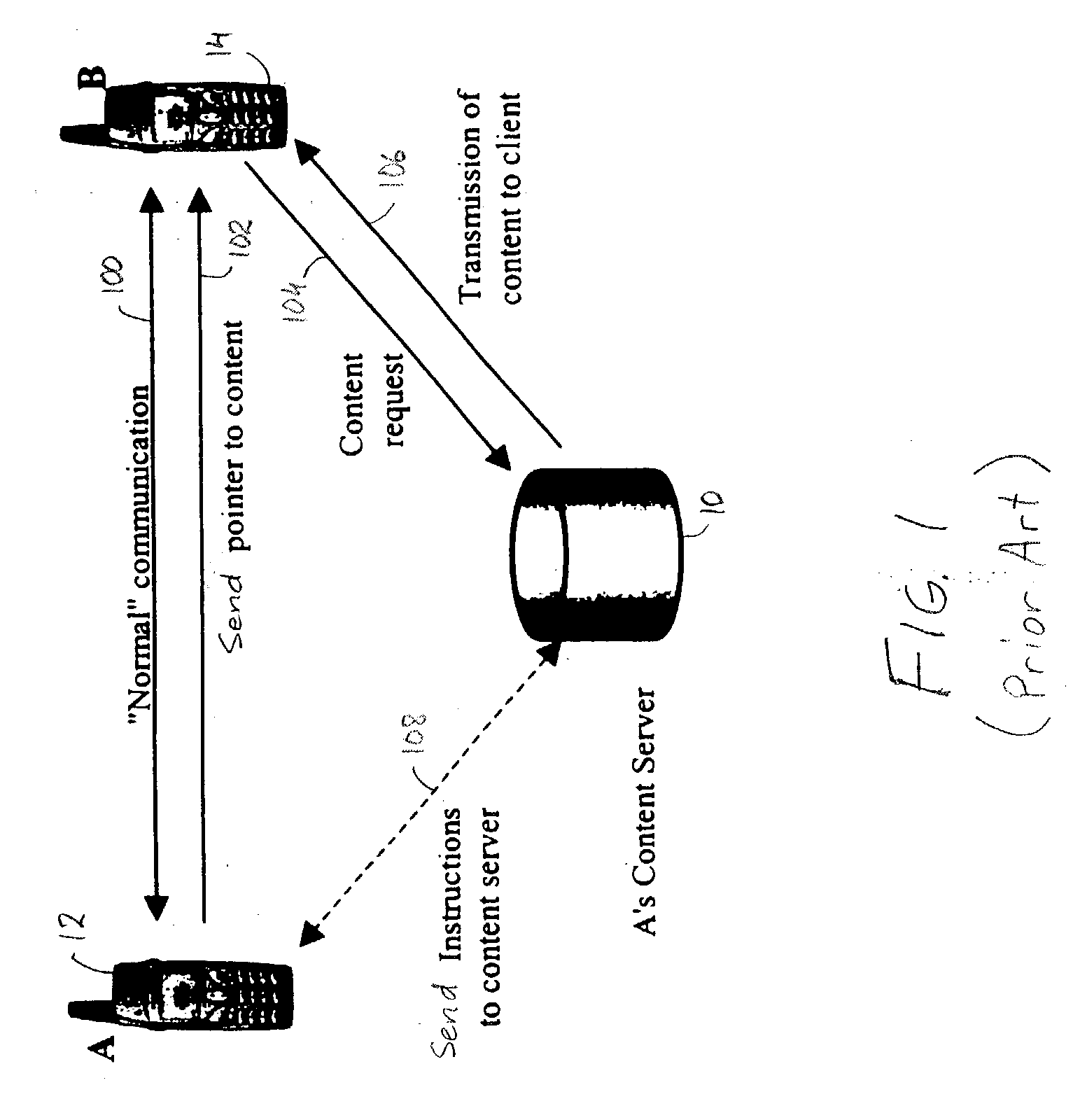
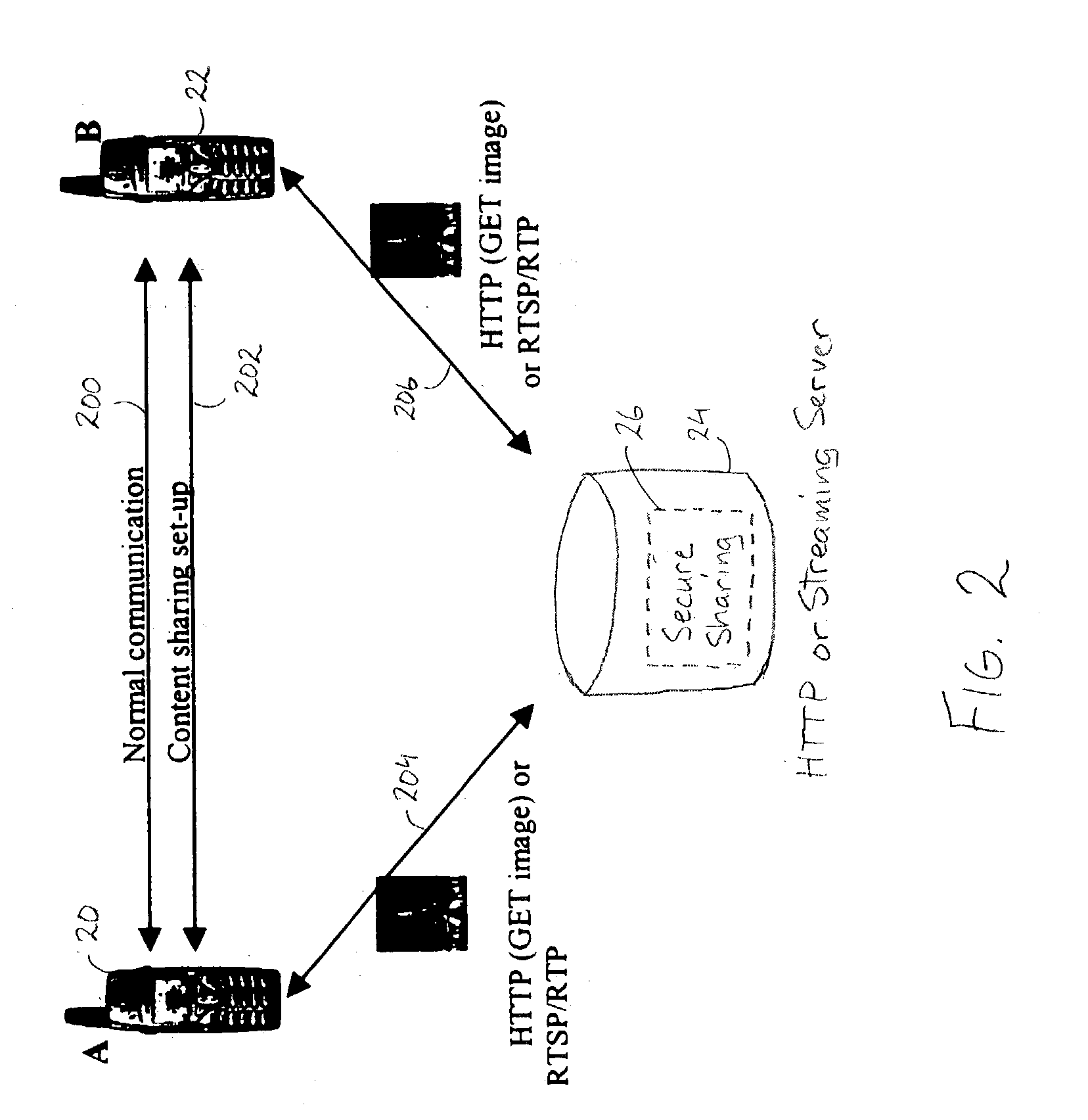
Secure content sharing in digital rights management
InactiveUS20040019801A1Digital data processing detailsDigital data protectionConfidentialityHeterogeneous network
Method and system for securely sharing content in real-time systems over heterogeneous networks. Cryptographic mechanisms of the content are used to protect the confidentiality and the integrity of the content. The confidentiality / integrity protection may be performed either before storing the content on the content server (i.e., pre-encryption), or by the content server while the content is being sent (i.e., real-time encryption).
Owner:TELEFON AB LM ERICSSON (PUBL)
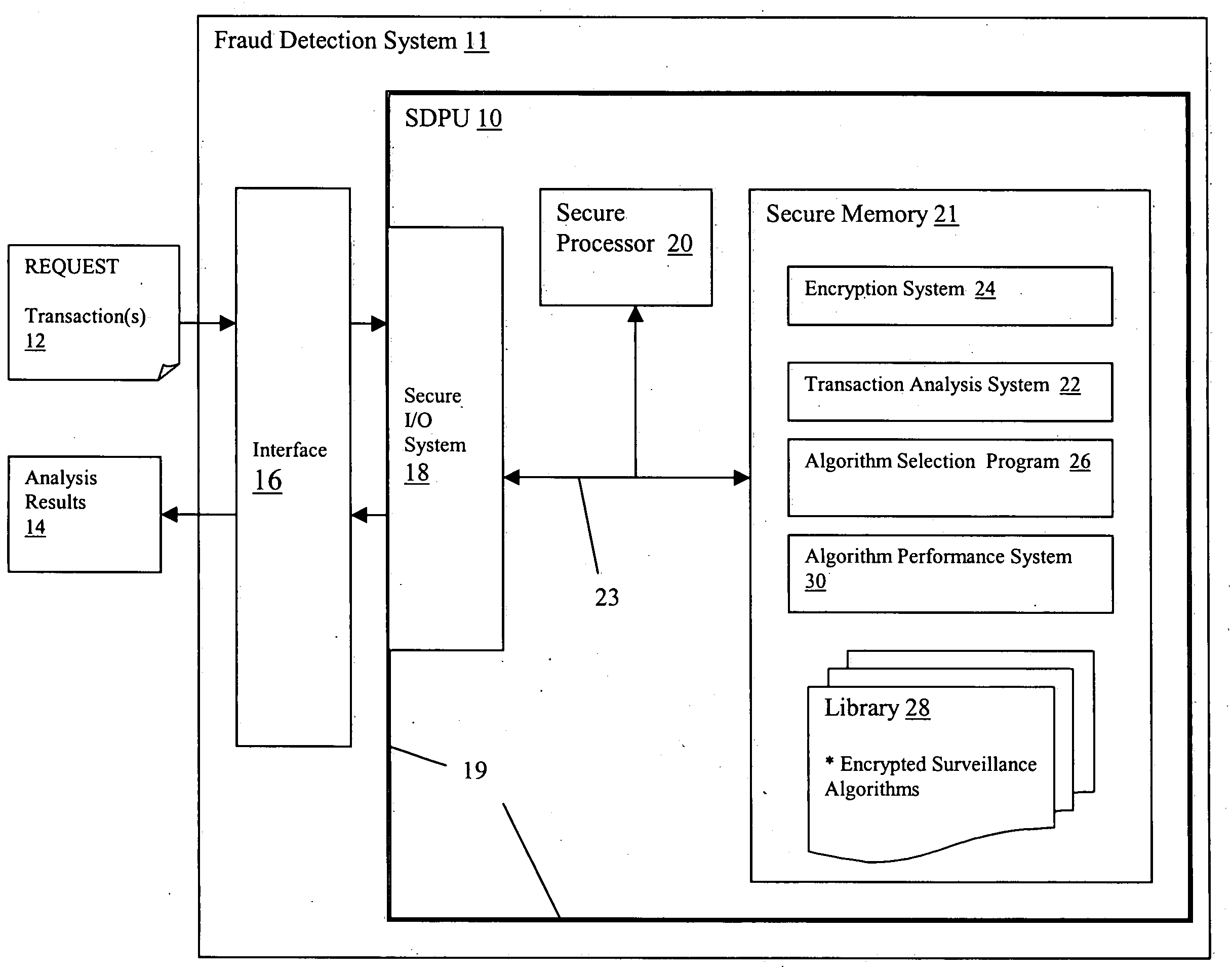
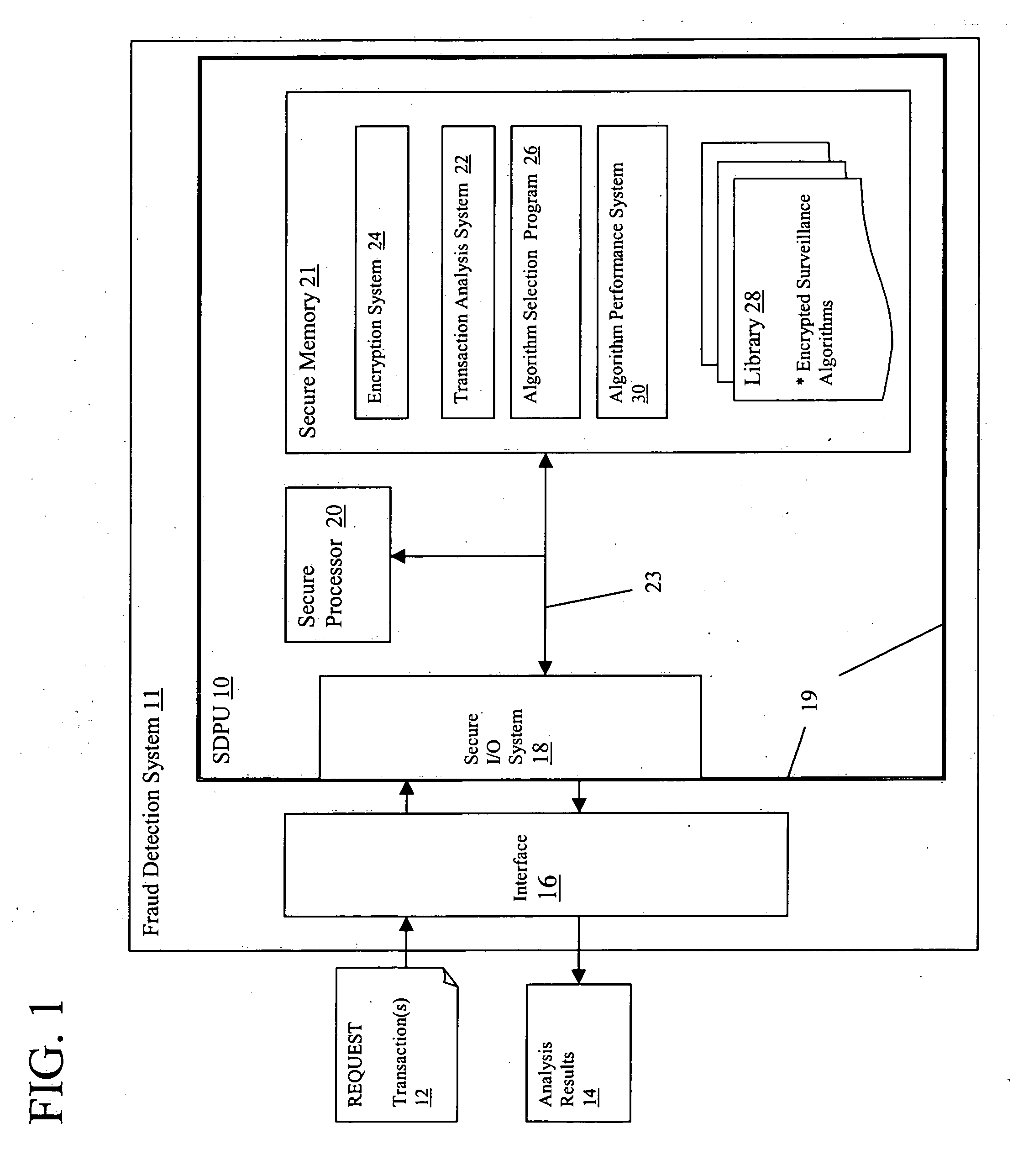
Confidential fraud detection system and method
ActiveUS20050091524A1Easy to detectDigital data processing detailsCryptography processingInternet privacyConfidentiality
Various embodiments for maintaining security and confidentiality of data and operations within a fraud detection system. Each of these embodiments utilizes a secure architecture in which: (1) access to data is limited to only approved or authorized entities; (2) confidential details in received data can be readily identified and concealed; and (3) confidential details that have become non-confidential can be identified and exposed.
Owner:IBM CORP
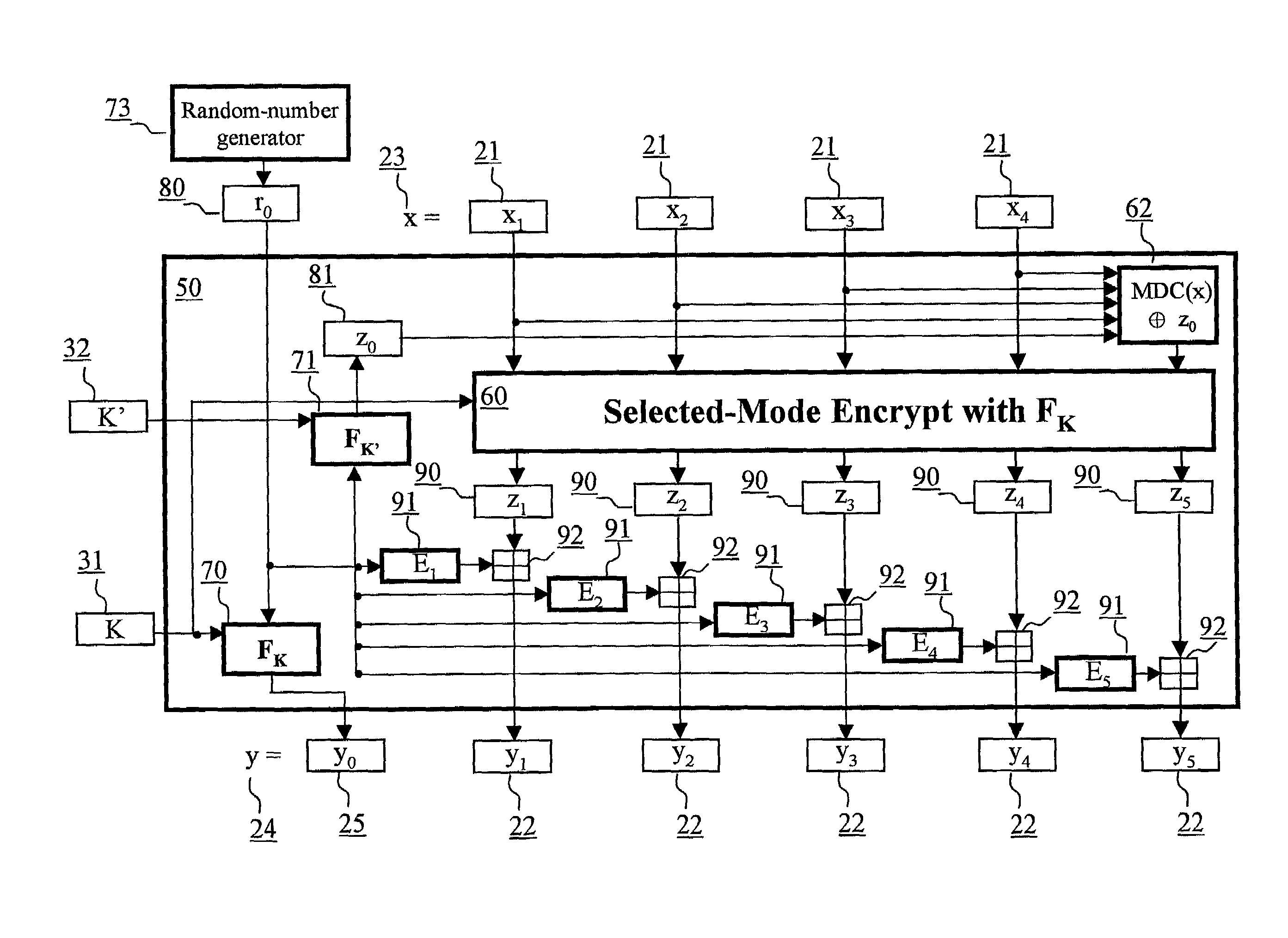
Block encryption method and schemes for data confidentiality and integrity protection
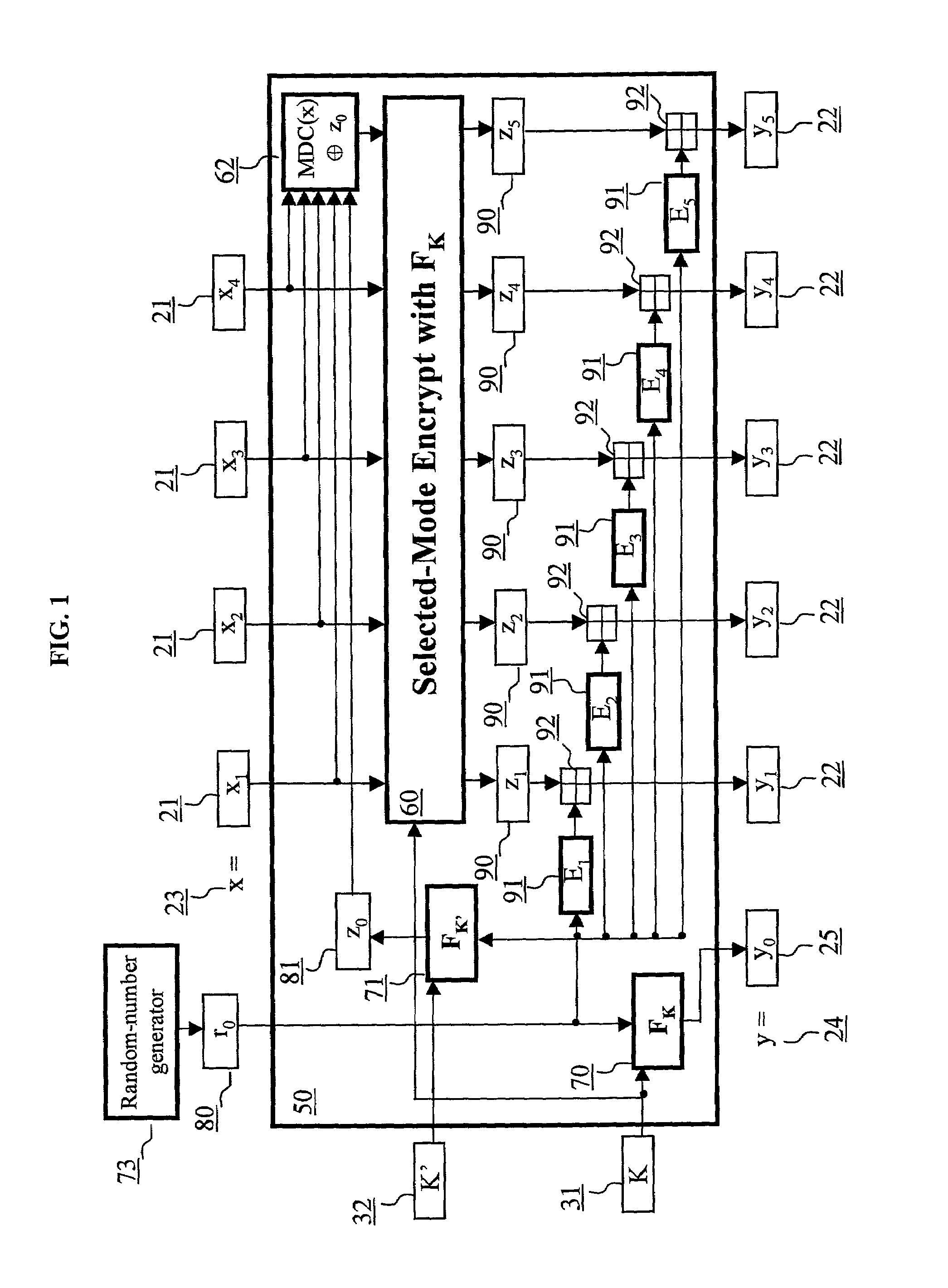
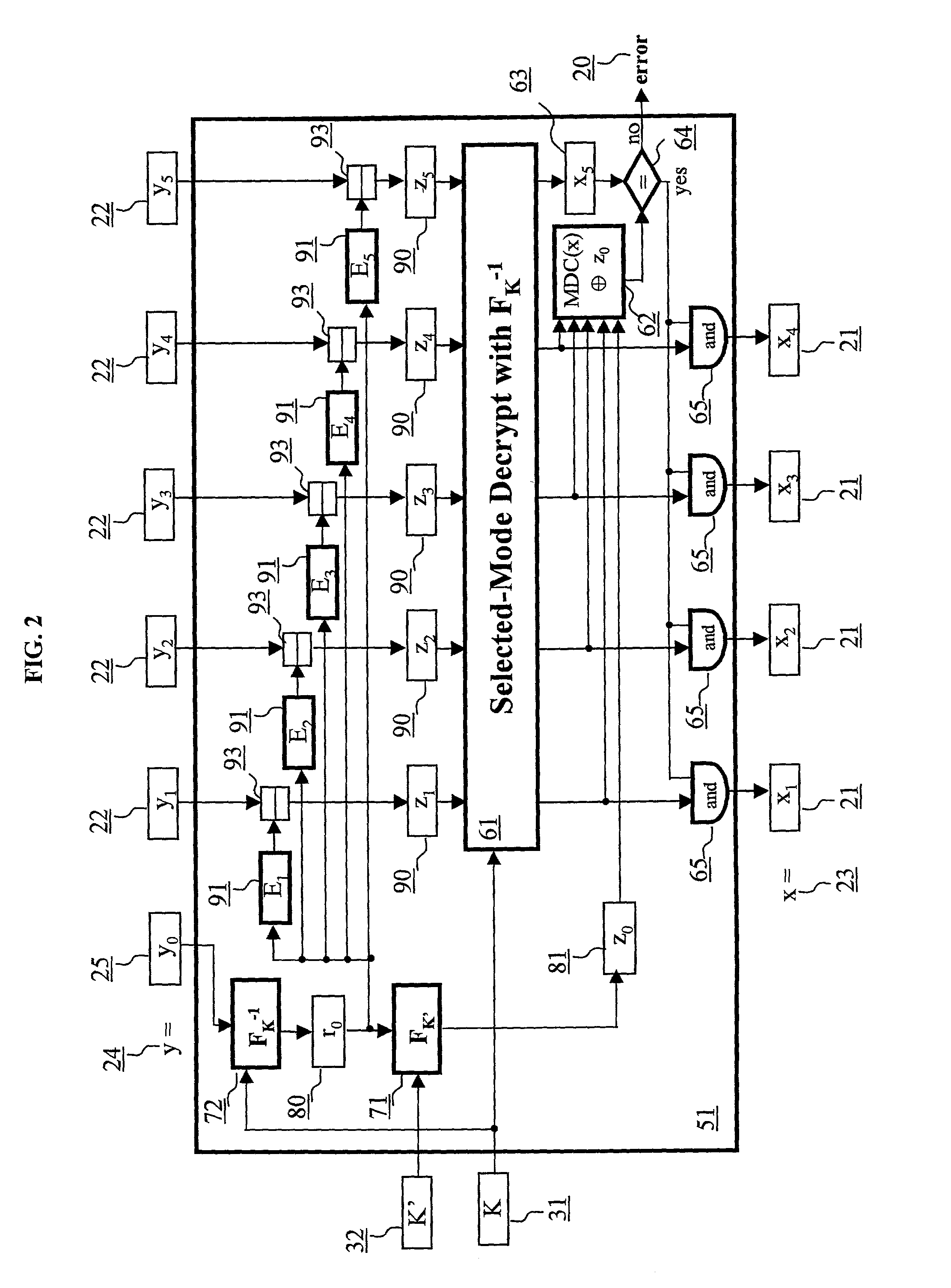
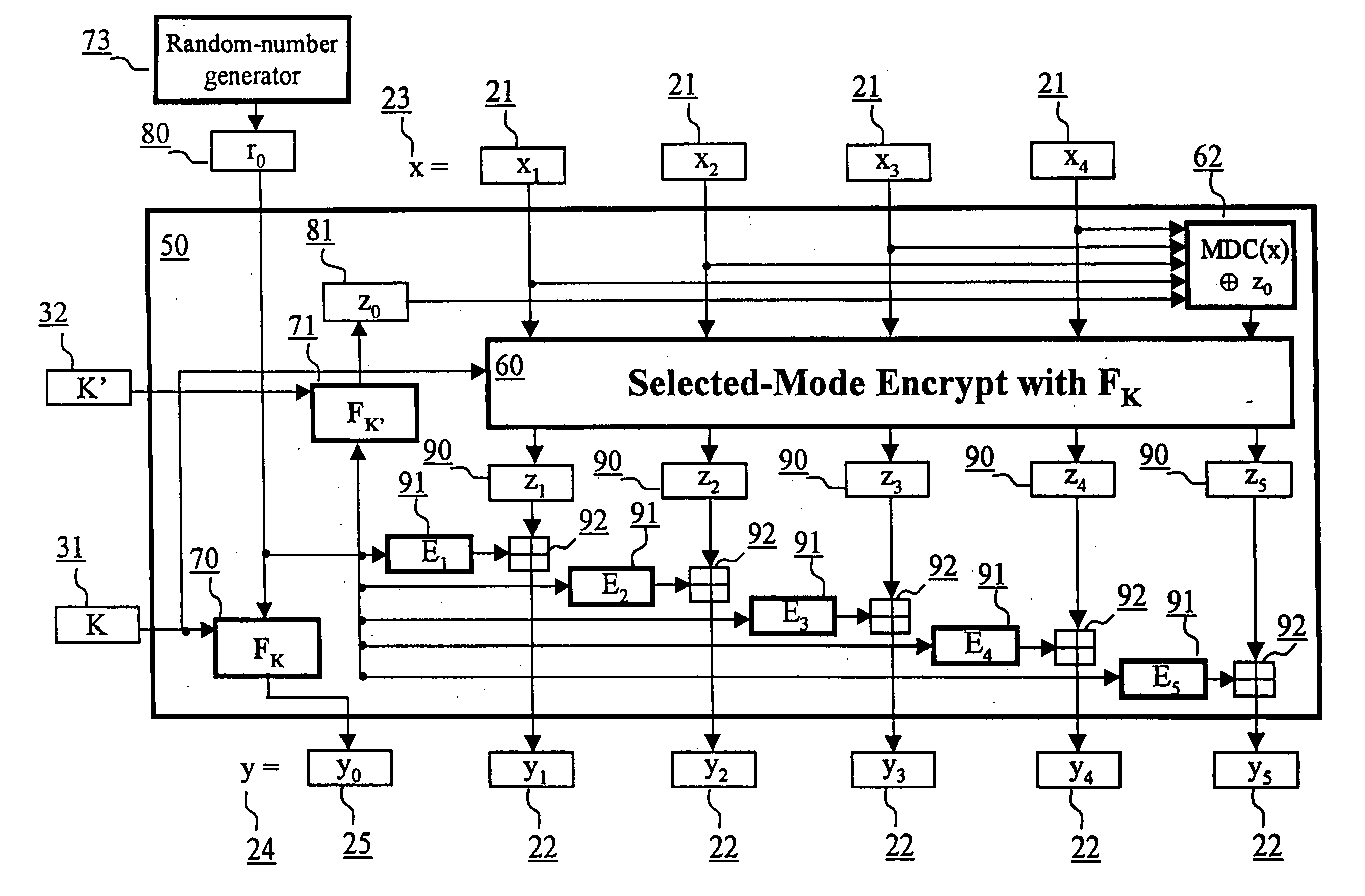
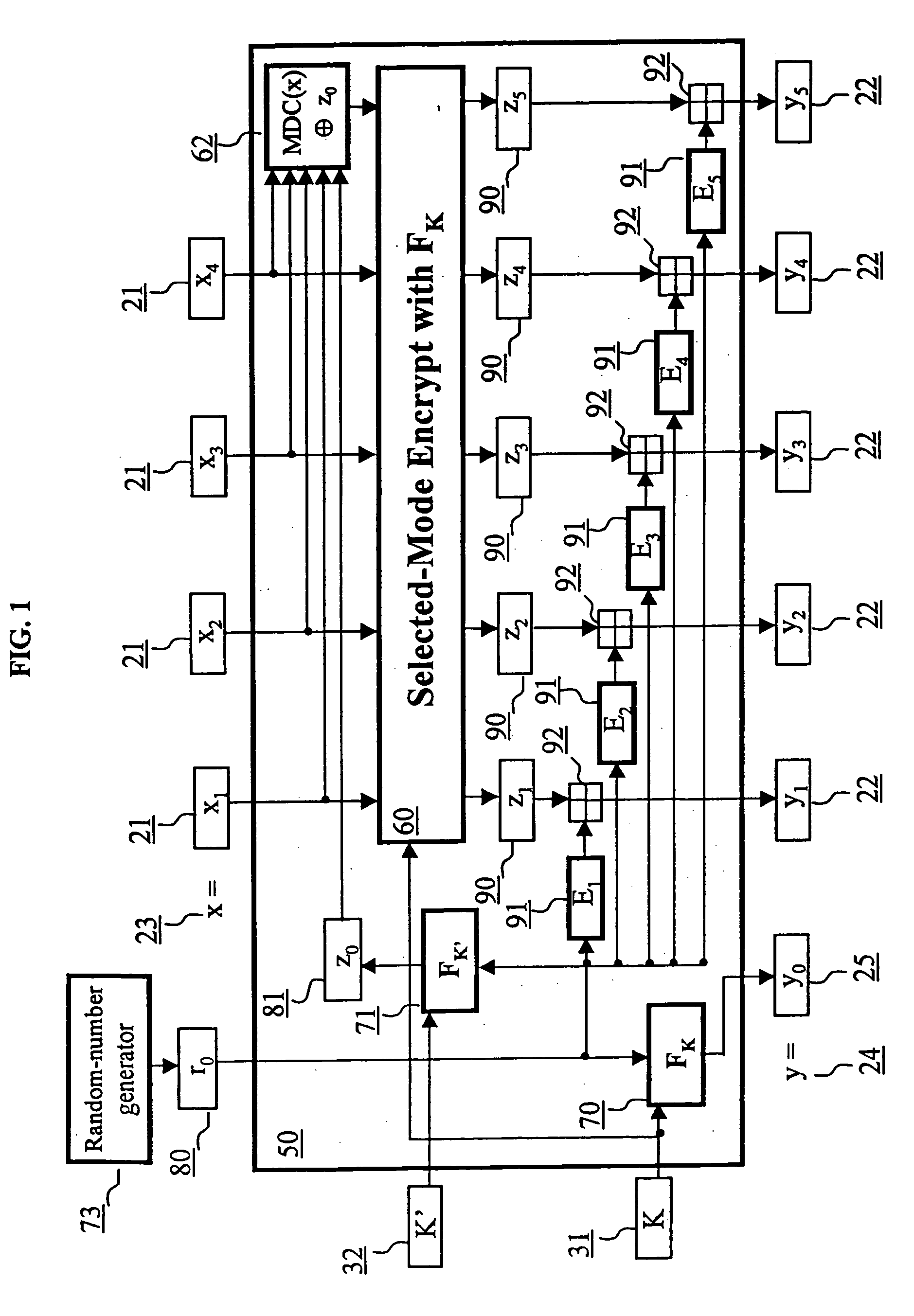
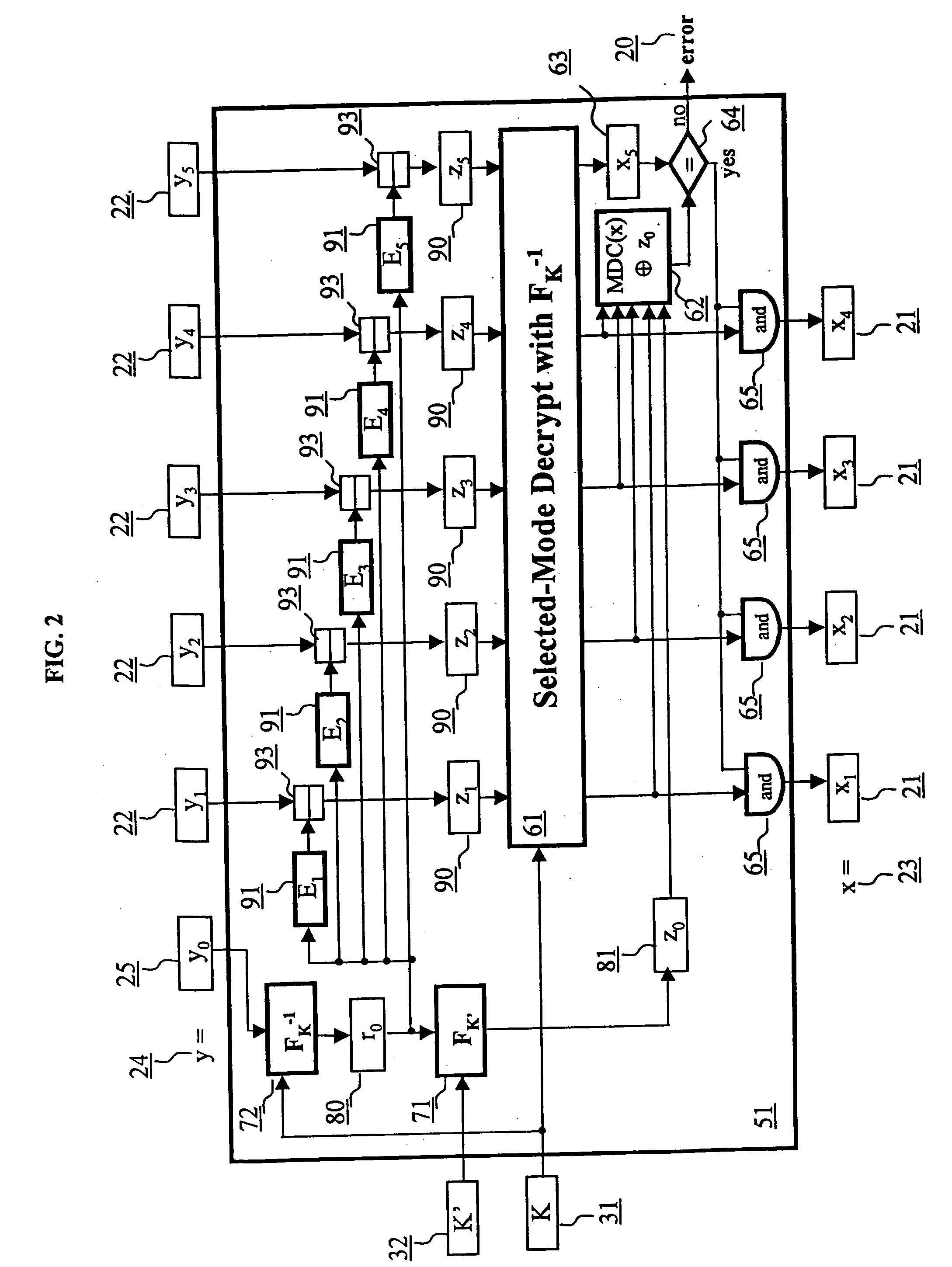
ActiveUS6973187B2Encryption apparatus with shift registers/memoriesUser identity/authority verificationPower applicationComputer hardware
A block encryption method and schemes (modes of operation) that provide both data confidentiality and integrity with a single cryptographic primitive and a single processing pass over the input plaintext string by using a non-cryptographic Manipulation Detection Code function for secure data communication over insecure channels and for secure data storage on insecure media. The present invention allows, in a further aspect, software and hardware implementations, and use in high-performance and low-power applications, and low-power, low-cost hardware devices. The block encryption method and schemes of this invention allow, in yet a further aspect, encryption and decryption in parallel or pipelined manners in addition to sequential operation. In a yet further aspect, the block encryption method and schemes of this invention are suitable for real-time applications.
Owner:VDG
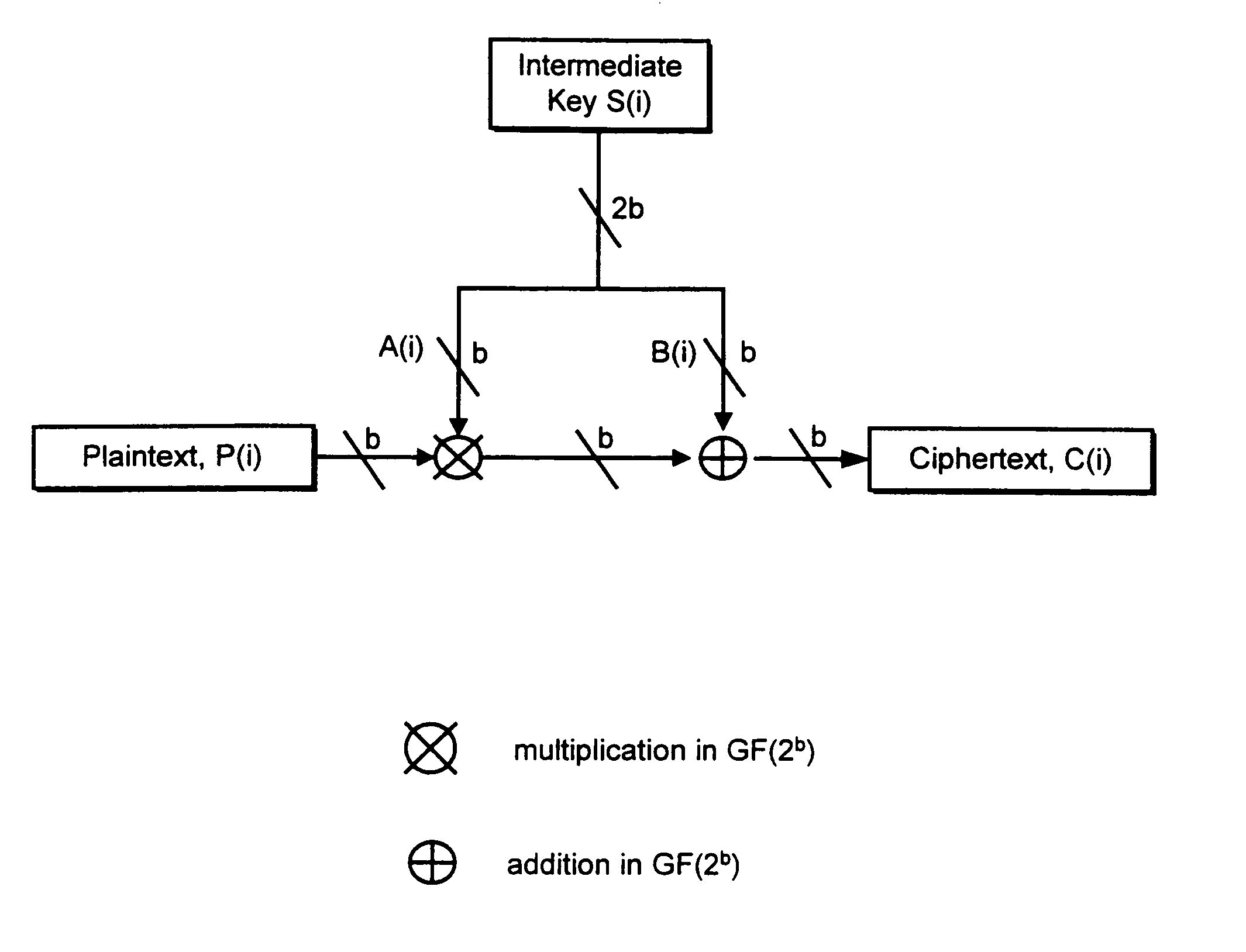
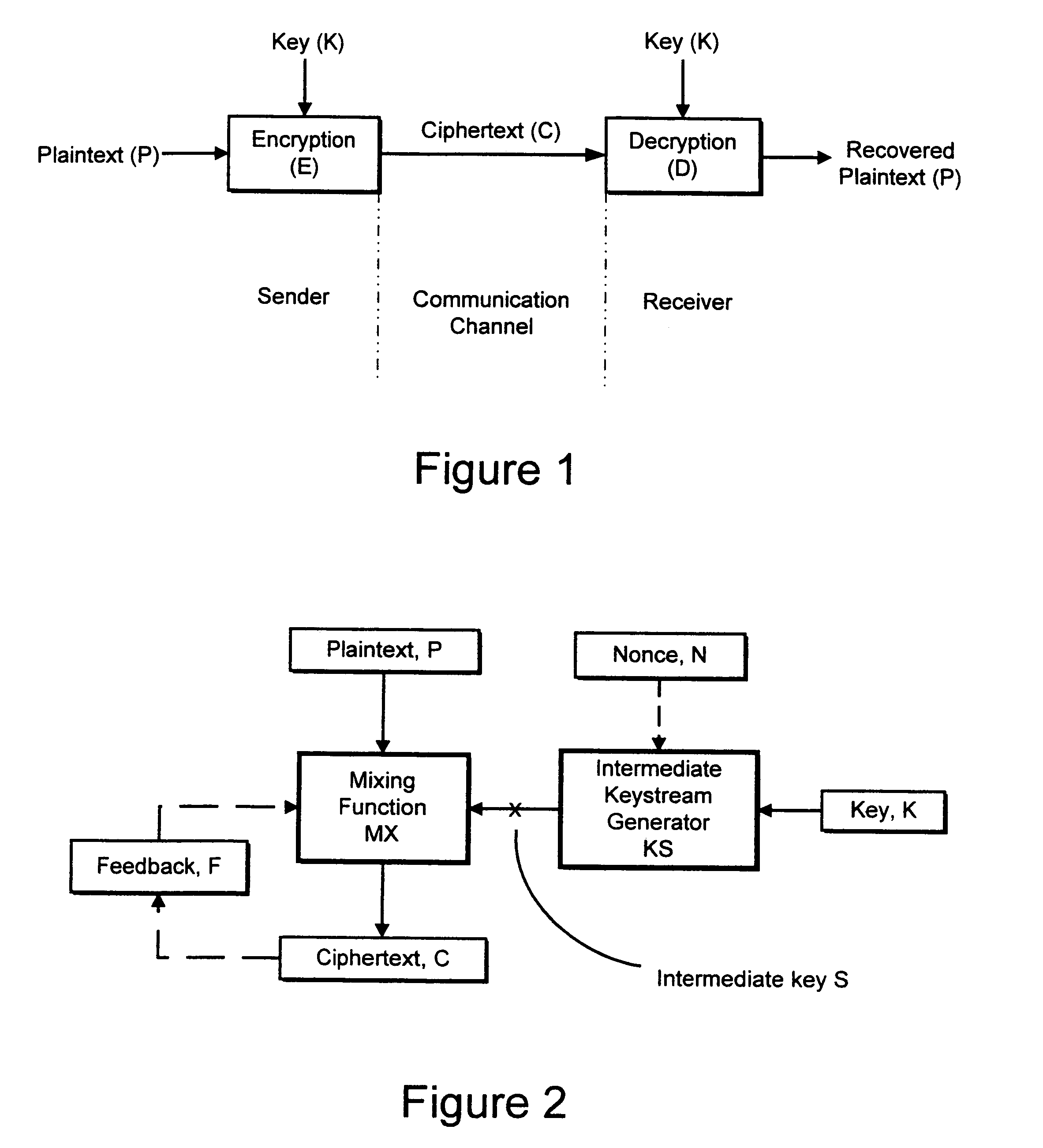
Cryptographic apparatus and method
InactiveUS7177424B1Quick implementationEasy to operateEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPlaintextComputer hardware
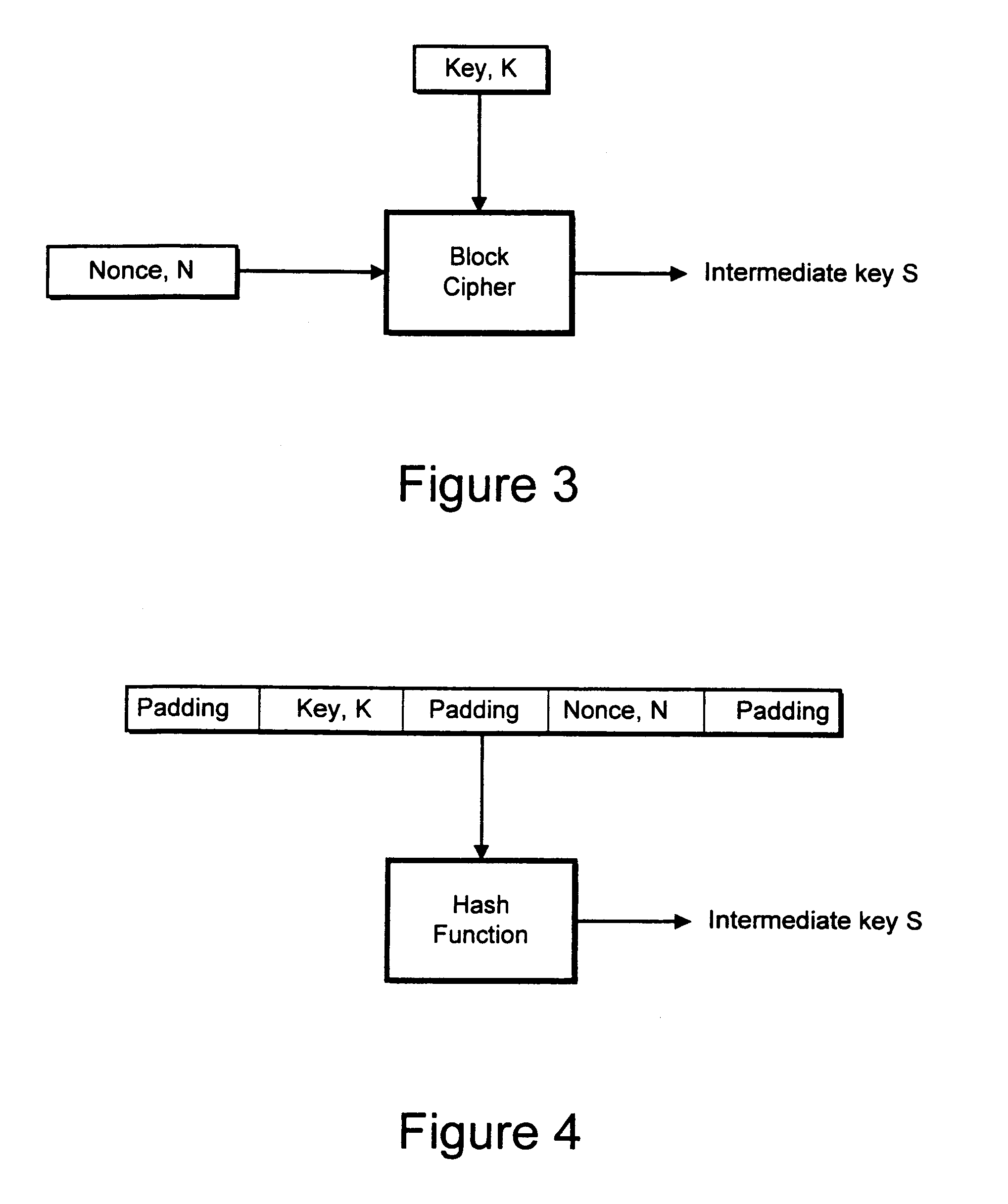
An encryption system comprises a pseudo-random number generator (KS) for generating a long pseudo-random sequence (S) from a shorter encryption key (K) and, if necessary, a nonce value (N), and a mixing function (MX) for combining the sequence with a plaintext message (P) on a block-by-block basis, where successive blocks (S(i)) of 128 bits of the sequence are combined with successive 64-bit blocks of plaintext (P(i)) to produce successive 64-bit blocks of ciphertext. The blockwise use of a long pseudo-random sequence preserves the advantages of a block cipher in terms of data confidentiality and data integrity, as well as benefiting from the speed advantages of a stream cipher.
Owner:HITACHI LTD
Credit management for electronic brokerage system
InactiveUS6985883B1Maintaining anonymitySpecial service provision for substationFinanceConfidentialityData mining
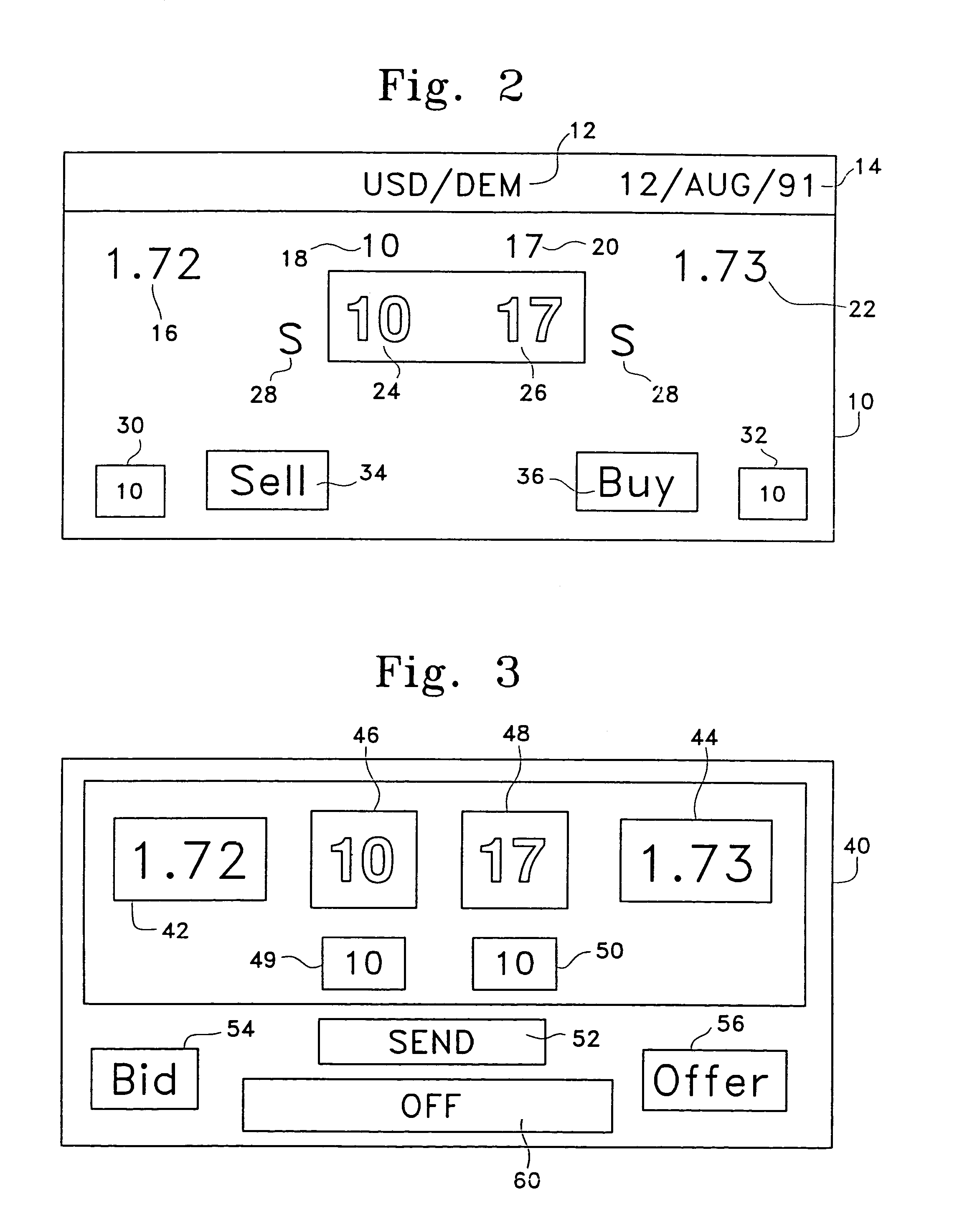
An anonymous trading system (FIG. 1) identifies the best bids and offers (QuoteSubmit, FIG. 3) from those counterparties (WS A1a1) with which each party (WS A1fb1, WS A1b2, ... WS A2a2) is currently eligible to deal, while maintaining the anonymity of the potential counterparty and the confidentiality of any specific credit limitations imposed by the anonymous potential counterparty. To that end, each bid or offer (QuoteSubmit, FIG. 3) for a particular type of financial instrument is prescreened by the system for compatibility with limited credit information (for example, a one bit flag indicating whether a predetermined limit has already been exceeded) and an anonymous “Dealable” price (24,26) is calculated for each of the traders (WS A1b, . . . WS A2a) dealing with that particular financial instrument.
Owner:EBS DEALING RESOURCES
Systems and methods for providing consumers anonymous pre-approved offers from a consumer-selected group of merchants
ActiveUS7720750B2Increase ratingsFinanceBuying/selling/leasing transactionsThird partyConfidentiality
Owner:EQUIFAX INC
Block encryption method and schemes for data confidentiality and integrity protection
InactiveUS20060056623A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPower applicationComputer hardware
Owner:VDG
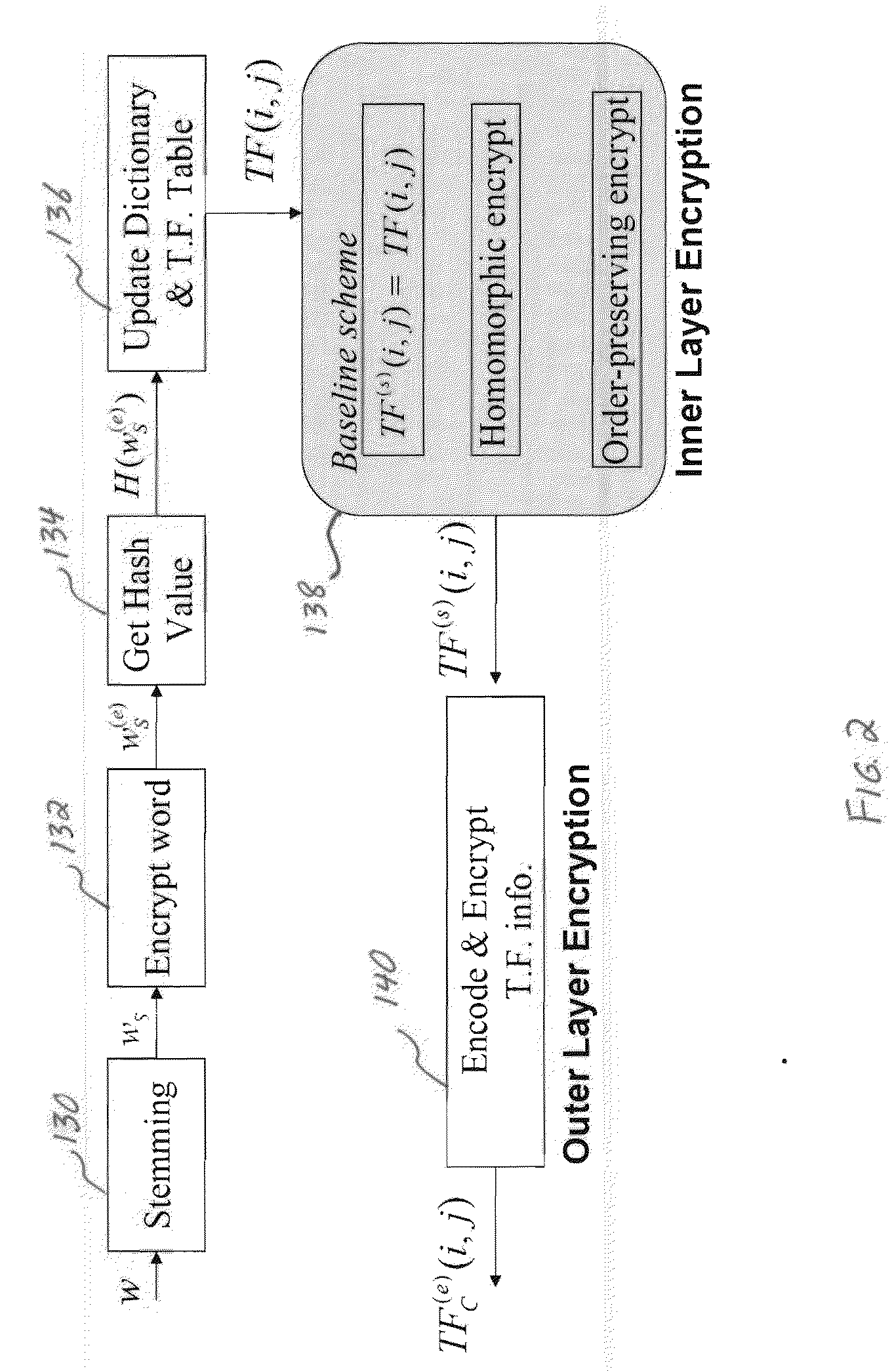
System and method for confidentiality-preserving rank-ordered search
InactiveUS20100146299A1Avoid contactWeb data indexingDigital data processing detailsConfidentialityComputerized system
A confidentiality preserving system and method for performing a rank-ordered search and retrieval of contents of a data collection. The system includes at least one computer system including a search and retrieval algorithm using term frequency and / or similar features for rank-ordering selective contents of the data collection, and enabling secure retrieval of the selective contents based on the rank-order. The search and retrieval algorithm includes a baseline algorithm, a partially server oriented algorithm, and / or a fully server oriented algorithm. The partially and / or fully server oriented algorithms use homomorphic and / or order preserving encryption for enabling search capability from a user other than an owner of the contents of the data collection. The confidentiality preserving method includes using term frequency for rank-ordering selective contents of the data collection, and retrieving the selective contents based on the rank-order.
Owner:UNIV OF MARYLAND
Method and system for protecting electronic data in enterprise environment
ActiveUS7921284B1Facilitate restrictive accessEasy accessComputer security arrangementsTransmissionConfidentialitySecurity level
Even with proper access privilege, when a secured file is classified, at least security clearance (e.g. a clearance key) is needed to ensure those who have the right security clearance can ultimately access the contents in the classified secured file. According to one embodiment, referred to as a two-pronged access scheme, a security clearance key is generated and assigned in accordance with a user's security access level. A security clearance key may range from most classified to non-classified. Depending on implementation, a security clearance key with a security level may be so configured that the key can be used to access secured files classified at or lower than the security level or multiple auxiliary keys are provided when a corresponding security clearance key is being requested. The auxiliary keys are those keys generated to facilitate access to secured files classified respectively less than the corresponding security or confidentiality level.
Owner:INTELLECTUAL VENTURES I LLC
Information security apparatus
ActiveUS20100031065A1Low costImprove output stabilityError preventionRandom number generatorsComputer hardwareTamper resistance
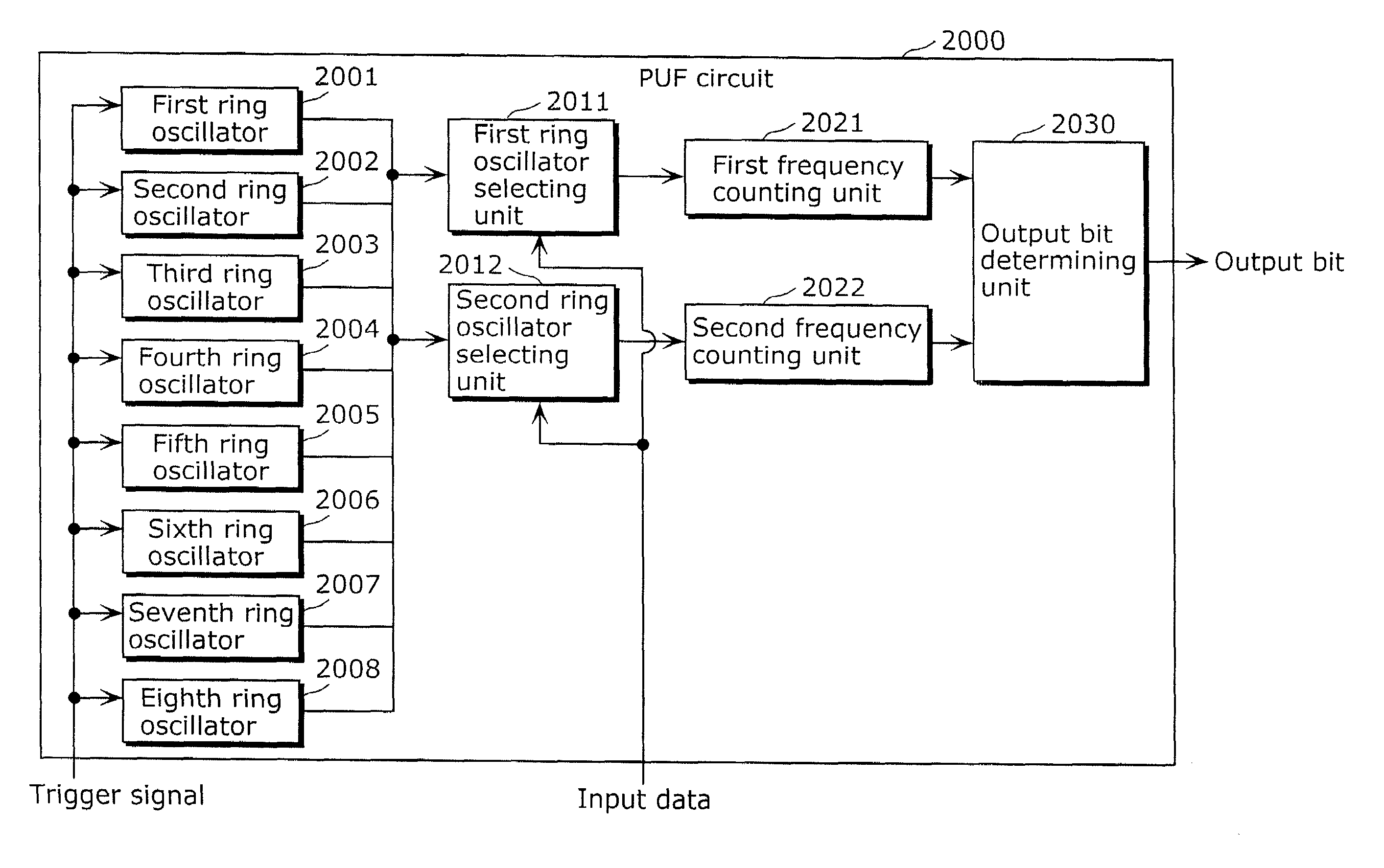
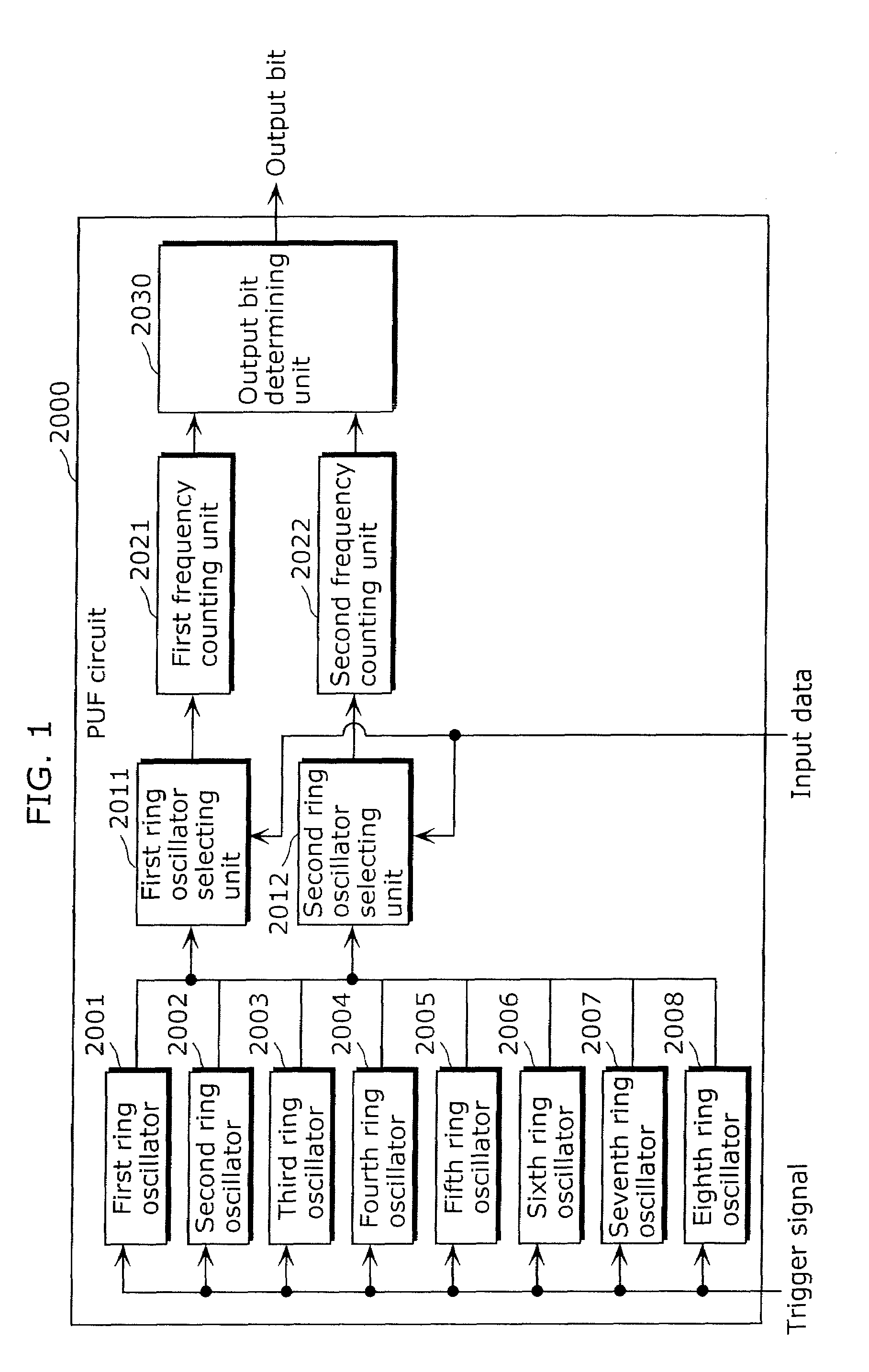
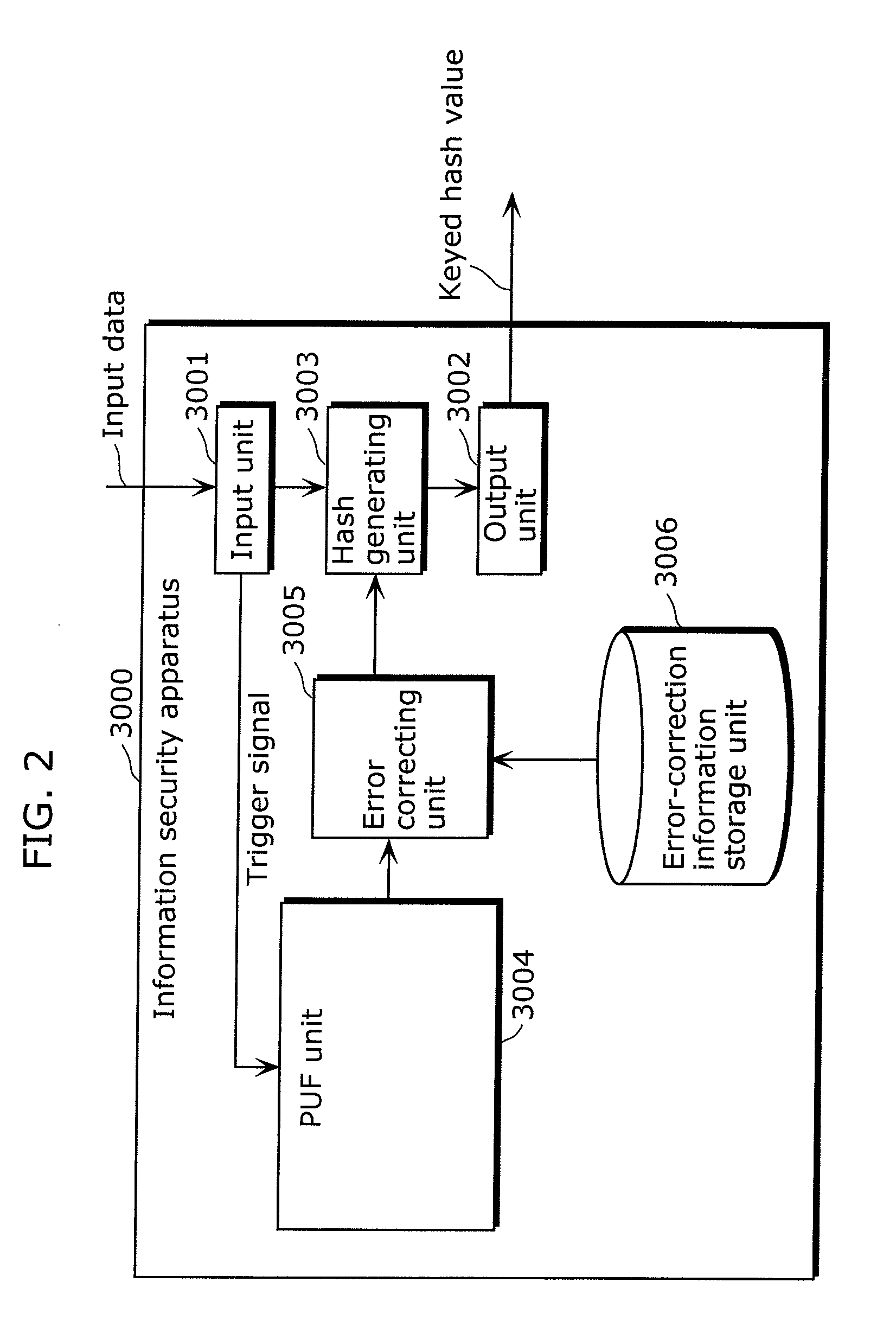
Provided is an information security apparatus (1100) that has enhanced stability and confidentiality of a hash key. The information security apparatus (1100) includes an information generating PUF unit (1104) that has tamper resistance set, using physical characteristics, so as to output a preset hash key, a partial error-correction information storage unit (1107) that stores partial error-correction information, an error correcting PUF unit (1106) that has tamper-resistance set, using physical characteristics, so as to output error-correcting PUF information, an error-correction information generating unit (1108) that generates error-correction information using partial correction information and the error-correcting PUF information, and an error correcting unit (1105) that corrects an error for the hash key outputted from the information generating PUF unit (1104) and outputs an error-corrected hash key.
Owner:PANASONIC CORP
Method and system for file transfer
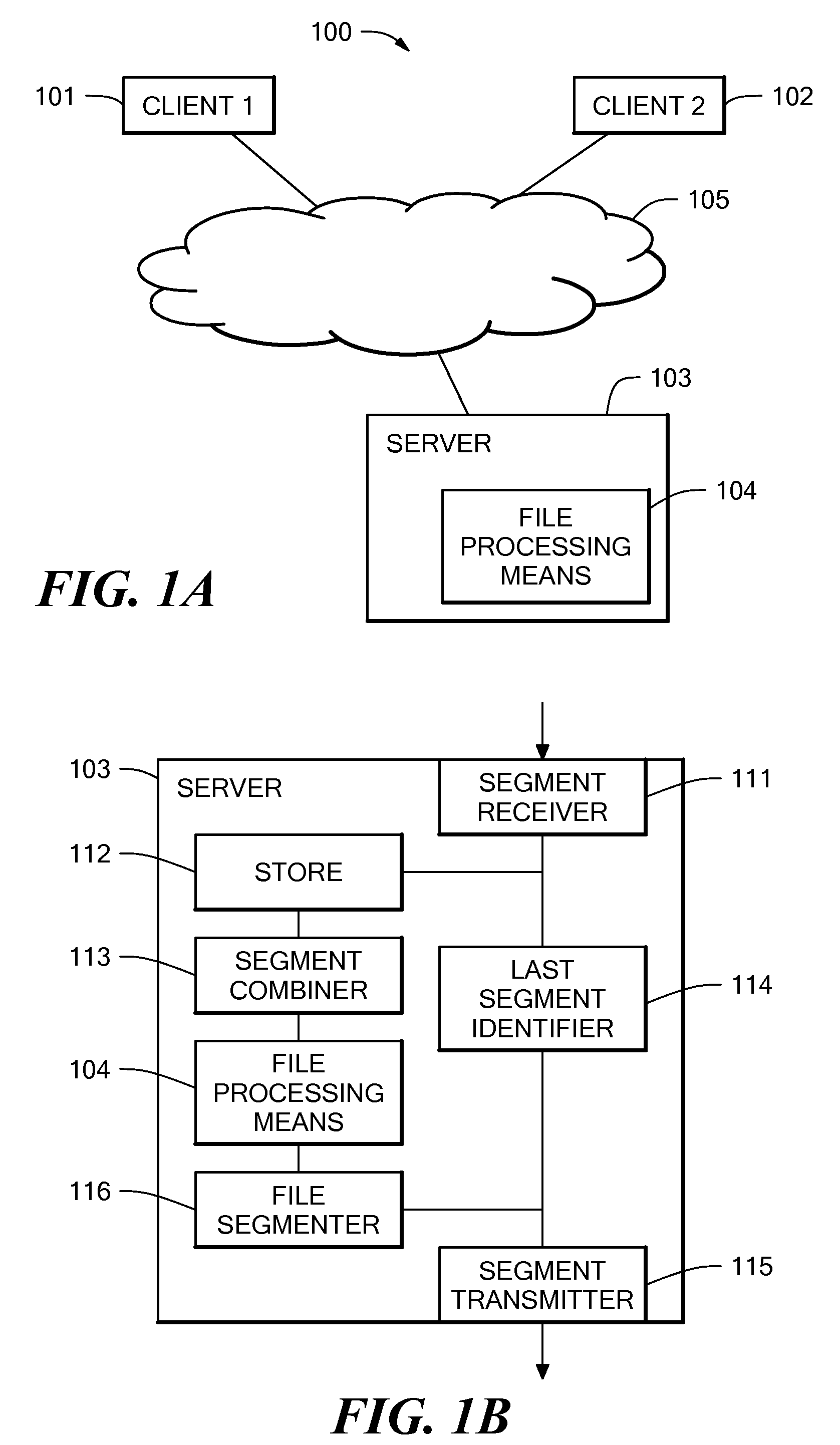
ActiveUS20080040503A1Reduce transmission delayMultiple digital computer combinationsTransmissionAnti virusConfidentiality
A method and system for file transfer are provided in which a file is transferred between a source client and a destination client via a middle server. The server receives segments of a file from the source client and stores the segments of the file as they are received. The server also forwards the segments of the file to a destination client as they are received, with the exception of one segment. The server combines the segments to form the whole file and applies a process to the whole file. The process may be for example an authorisation process such as an anti-virus check, a confidentiality check, or a content validity check. If the file passes the process, the remaining excepted segment is forwarded to the destination client.
Owner:IBM CORP
One-Way Router
A one-way router combines benefits of a network diode and router, and thus can route data between networks of varying confidentiality and / or integrity in a secure, one-way fashion. Secure routing is provided transparently so that the router is compatible with standard network applications by synthesizing responses for standard network protocols to provide many-to-many network connections while preventing bidirectional data flow. Separate network stacks are provided for each connected network, and the network stacks are separated from each other by data diodes that enforce one-way data flow. The one-way router can be implemented in hardware or software, and provides architectural flexibility to customize levels of assurance, performance, reliability, and cost.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
Application-layer security method and system
InactiveUS7313822B2Avoid attackMemory loss protectionUnauthorized memory use protectionConfidentialityApplication software
The present invention secures applications from executing illegal or harmful operation requests received from a distrusted environment, thereby, preventing an application from damaging itself, other applications, performance, files, buffers, databases, and confidentiality of information. An operation reverse engineering layer is positioned in front of an application in a trusted environment and between the application and the incoming application operation requests that are received from an unknown or distrusted environment. The operation reverse engineering layer checks the requests for either form, content, or both, to insure that only legal and harmless requests will pass to the given application. Hardware, software, or both, are employed to implement the operation reverse engineering layer.
Owner:KAVADO
High-safety portable payment receiving device
ActiveCN103956006ASecure Proximity Electronic PaymentsSecure paymentCash registersMicrocontrollerPayment
The invention discloses a high-safety portable payment receiving device which comprises a storage module, a payment information reading and setting module, a terminal user identity recognition module, a communication module, an input-output module and a microcontroller. The invention further discloses a high-safety portable payment receiving method for the device. The high-safety portable payment receiving method comprises the steps of setting, payment receiving and payment. When the device is worn, the method can also comprise the step of wearing verification. The device and the method perform user identity pre-setting through a biosensor and perform authentication and recognition through the biosensor when being used, a step of manually inputting passwords and other information to perform login authentication is omitted, multiple-step operation in the payment receiving process is also remarkably decreased, convenient, fast and safe adjacent electronic payment receiving is achieved, the safety, confidentiality and usability are greatly improved, and an application range of population is widened. In addition, the device can be a watch, a bracelet, a ring or other wearable styles, can also built in a wearable accessory and is convenient and fashionable.
Owner:JINLING INST OF TECH
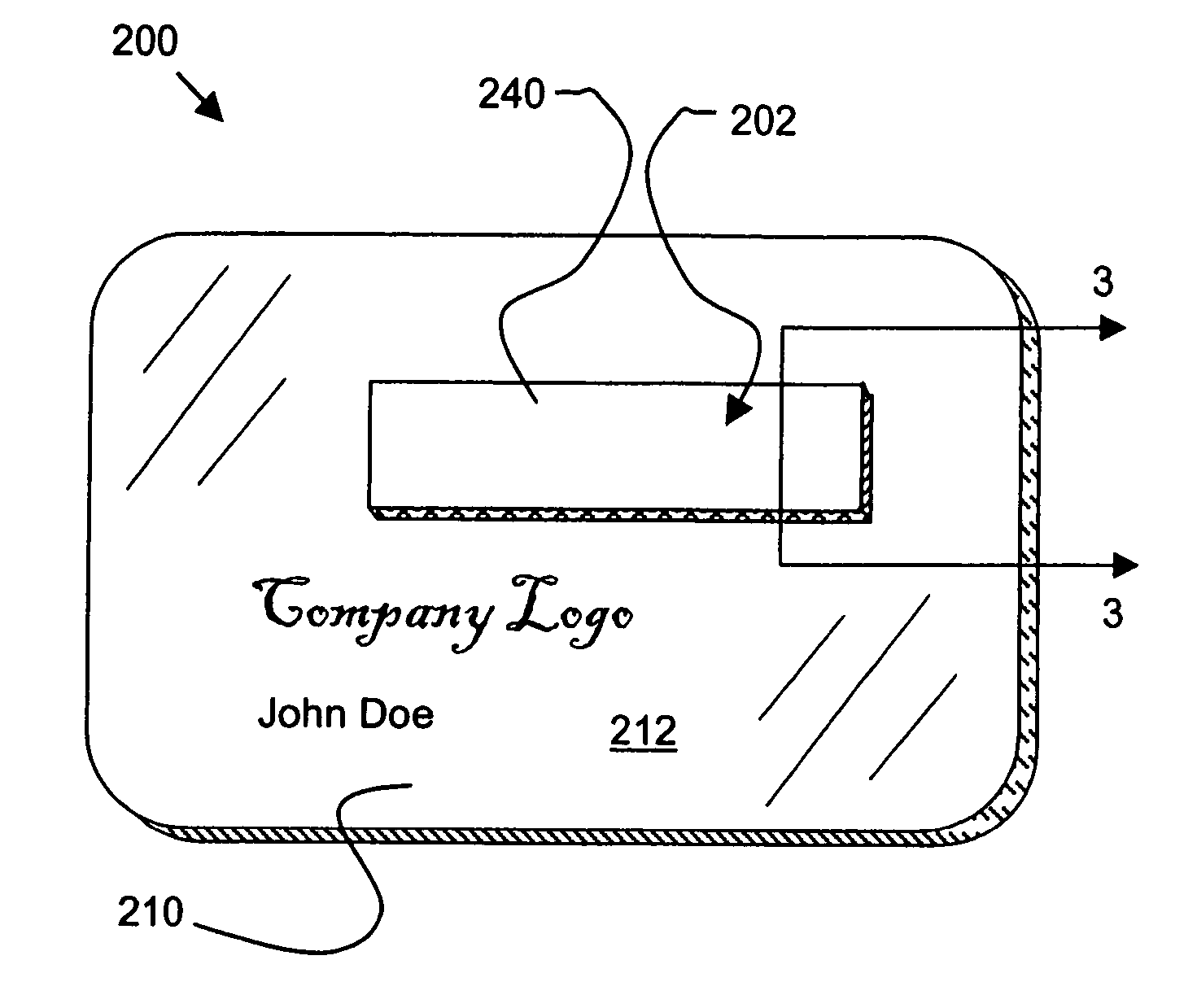
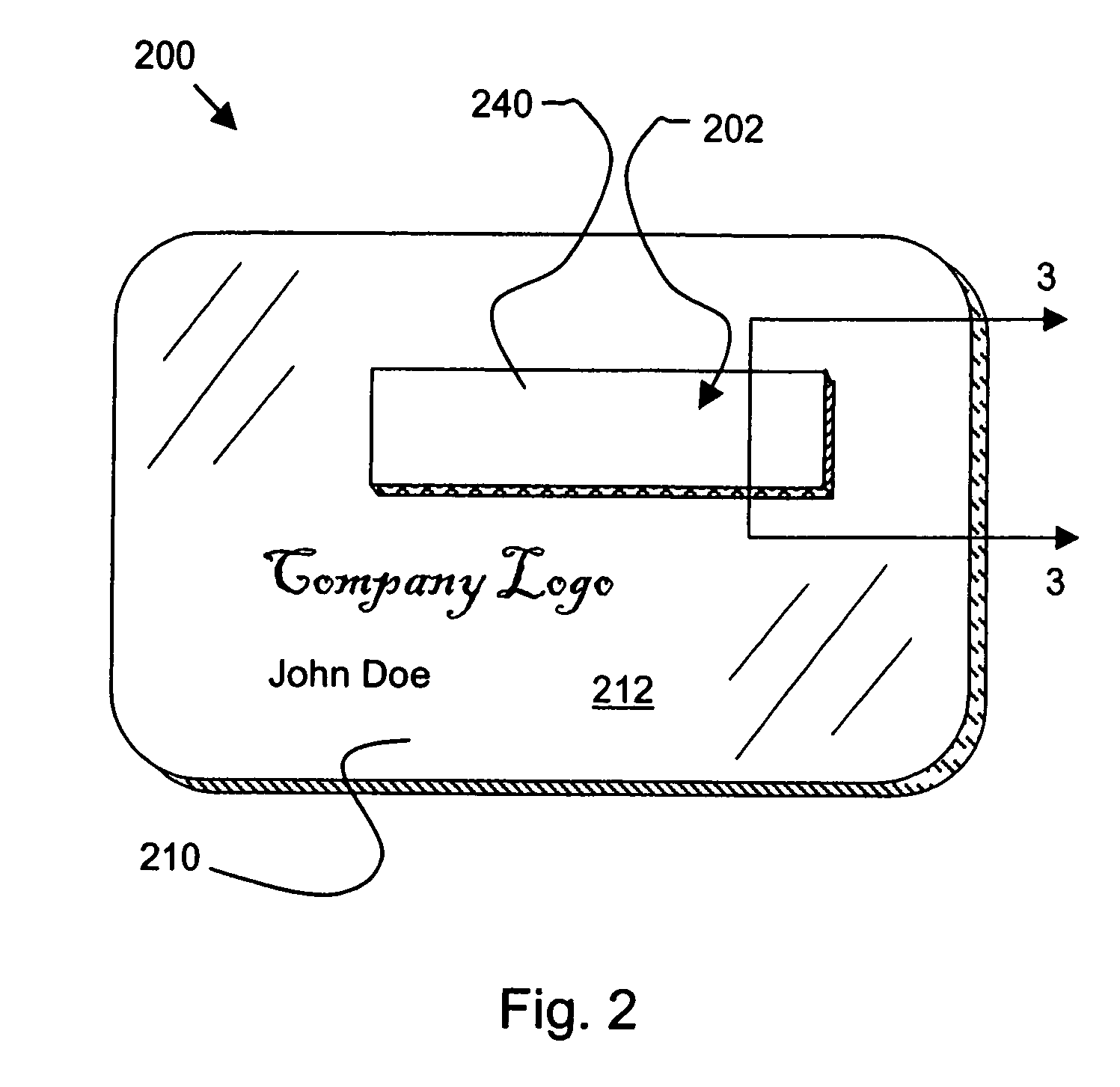
Security label, secured article and method for making the label and article
InactiveUS20050230960A1Improve tamper resistanceReduces and minimizesStampsOther printing matterConfidentialityAdhesive
A tamper-resistant secure label, article and associated method. A label for overlying information comprises an adhesive layer for adhering the label to a substrate. The adhesive layer includes a structural adhesive that ensures that an initial removal precludes re-adhering using the adhesive layer. The label may further include an obscuring layer to selectively block visual access to the information and maintain the confidentiality of the information until the obscuring layer is removed.
Owner:AVERY DENNISON CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com