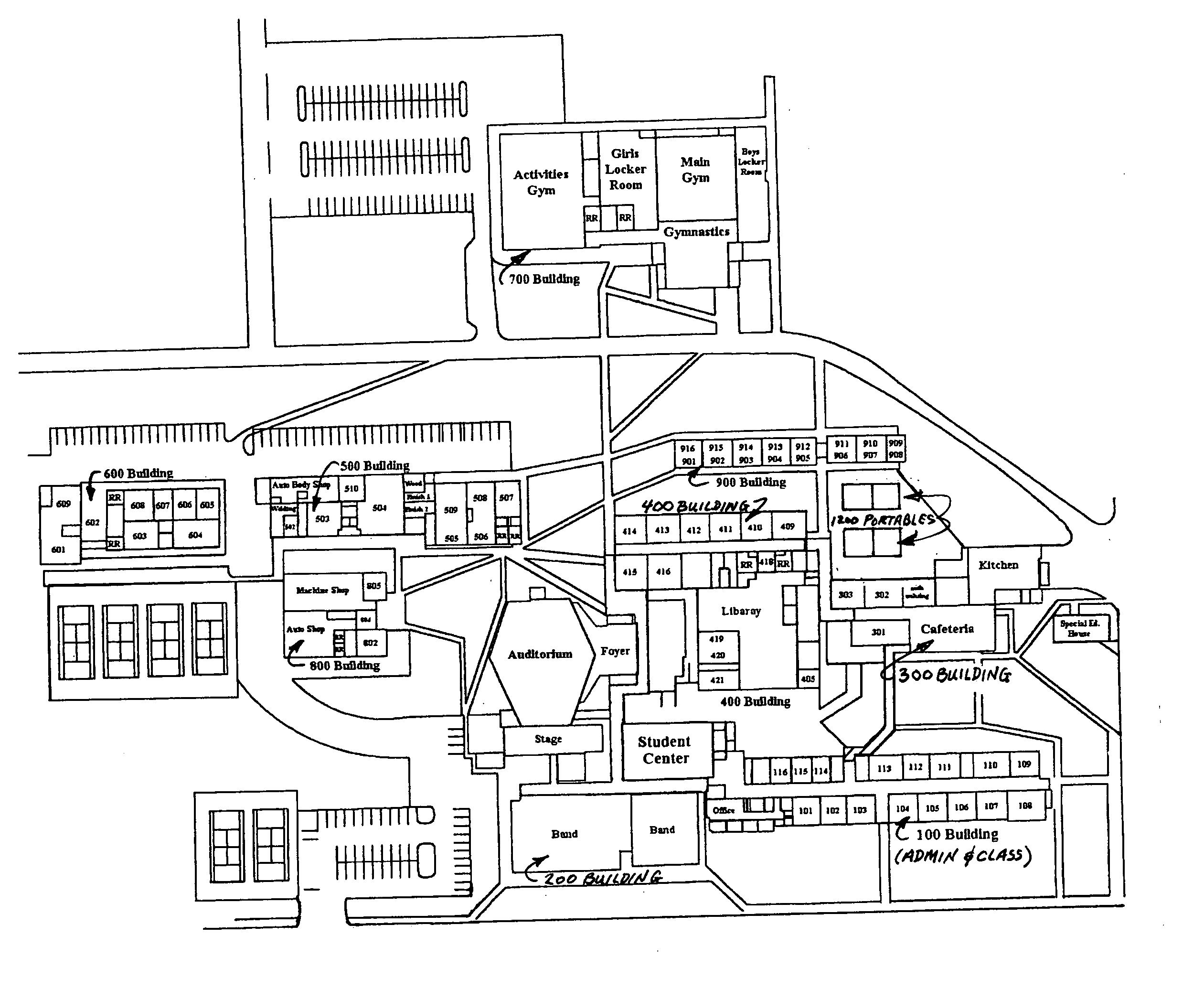
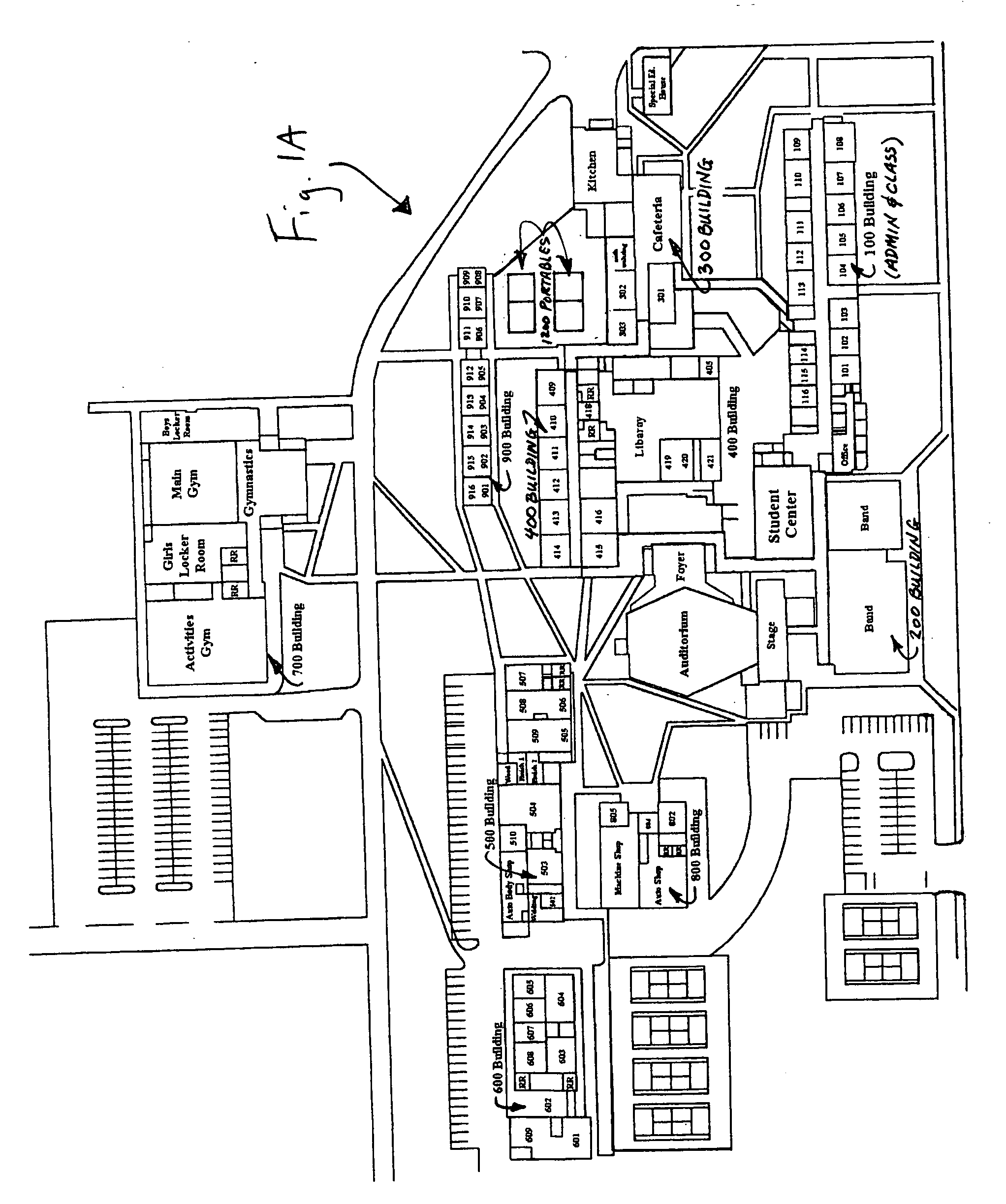
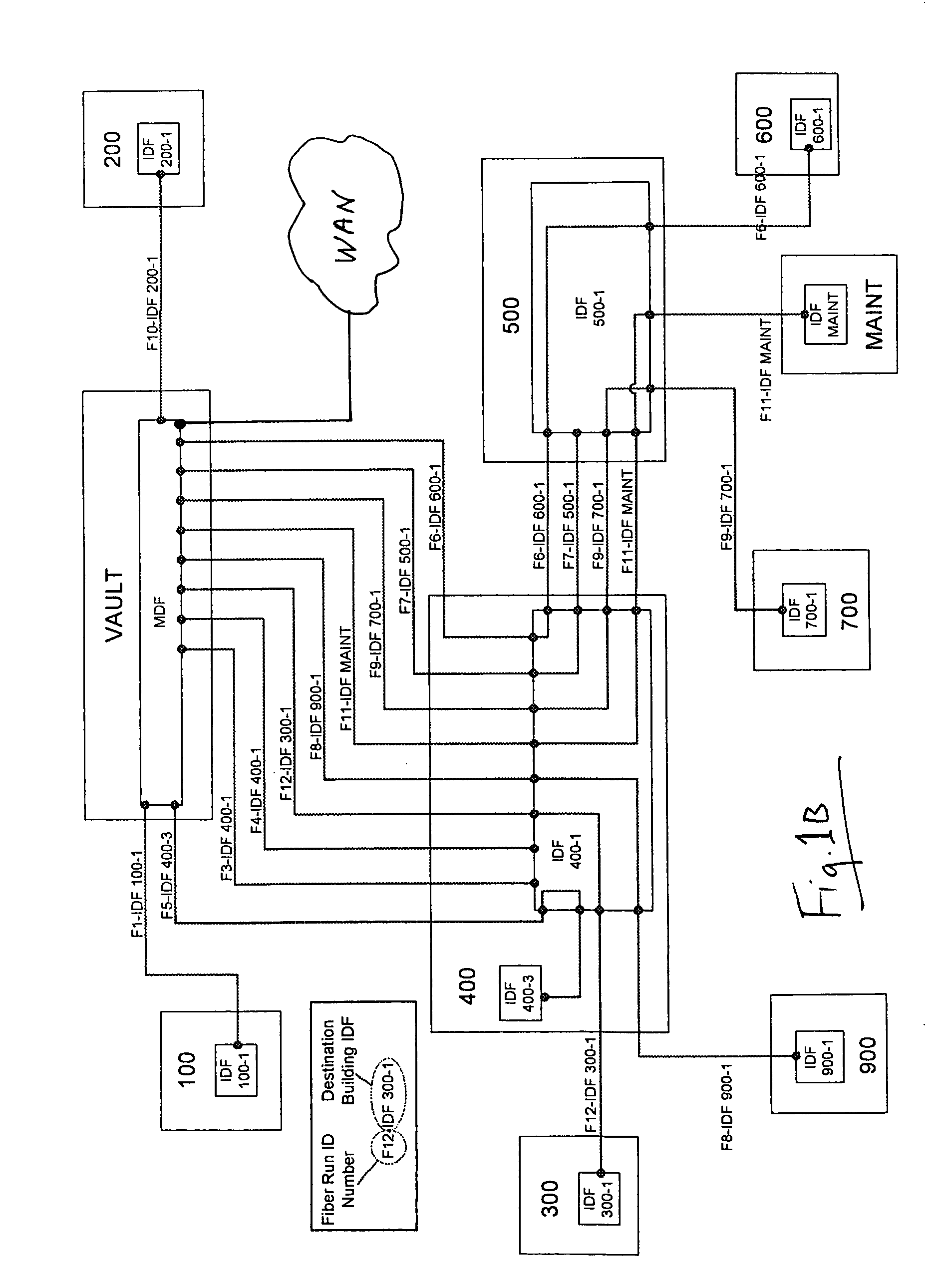
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30839 results about "Wireless" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
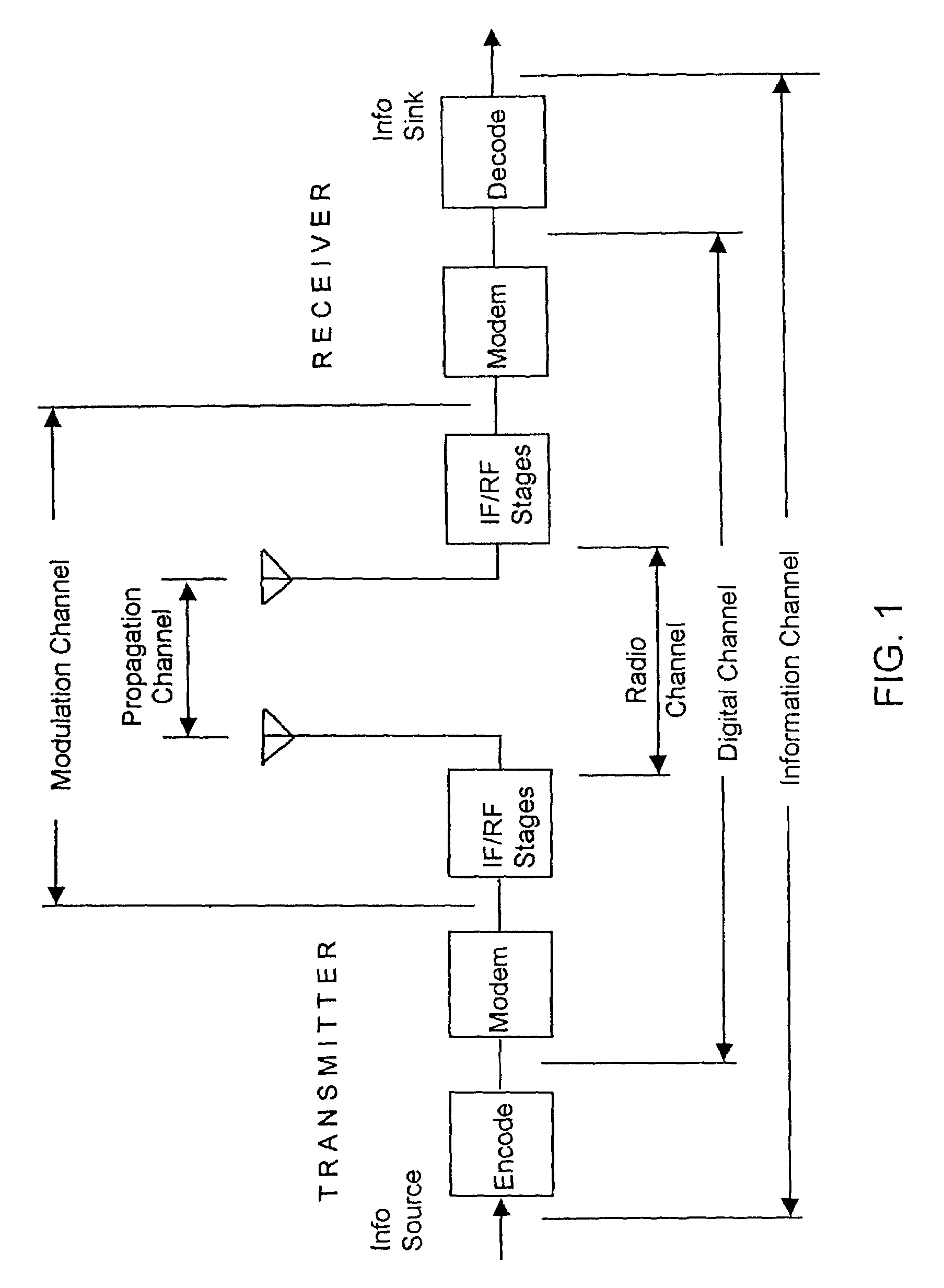
Wireless communication is the transfer of information or power between two or more points that are not connected by an electrical conductor. The most common wireless technologies use radio waves. With radio waves distances can be short, such as a few meters for Bluetooth or as far as millions of kilometers for deep-space radio communications. It encompasses various types of fixed, mobile, and portable applications, including two-way radios, cellular telephones, personal digital assistants (PDAs), and wireless networking. Other examples of applications of radio wireless technology include GPS units, garage door openers, wireless computer mouse, keyboards and headsets, headphones, radio receivers, satellite television, broadcast television and cordless telephones. Somewhat less common methods of achieving wireless communications include the use of other electromagnetic wireless technologies, such as light, magnetic, or electric fields or the use of sound.
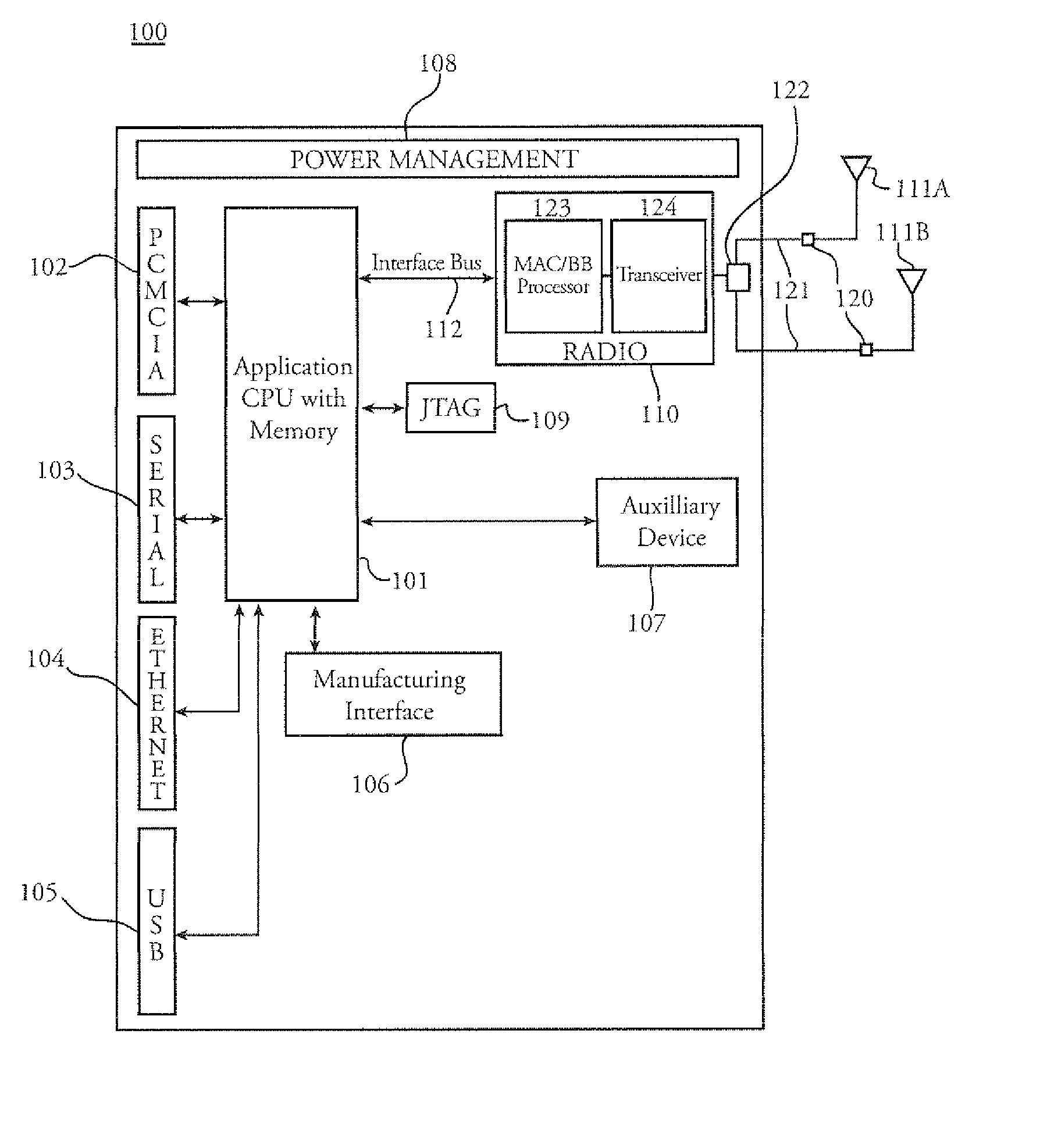
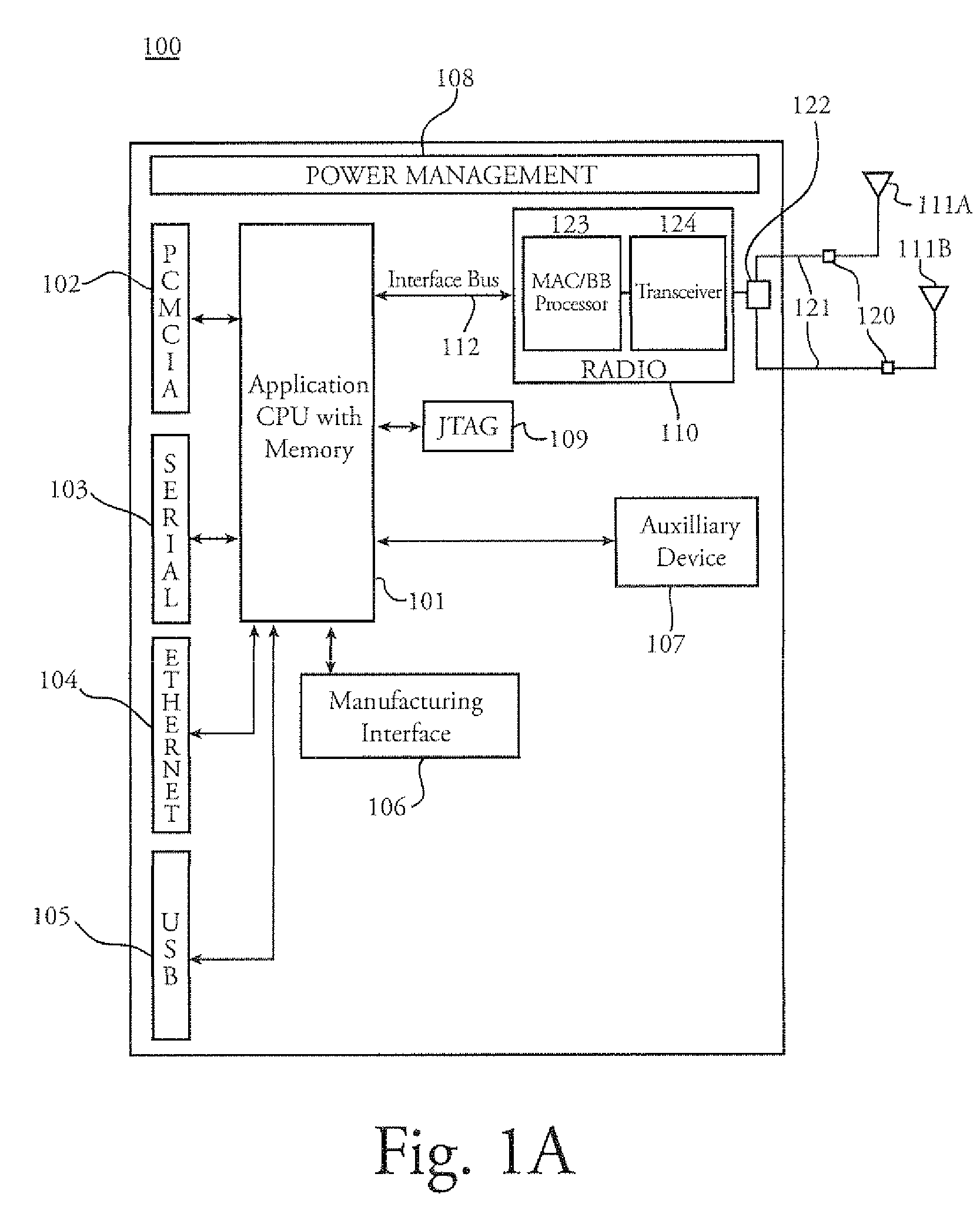
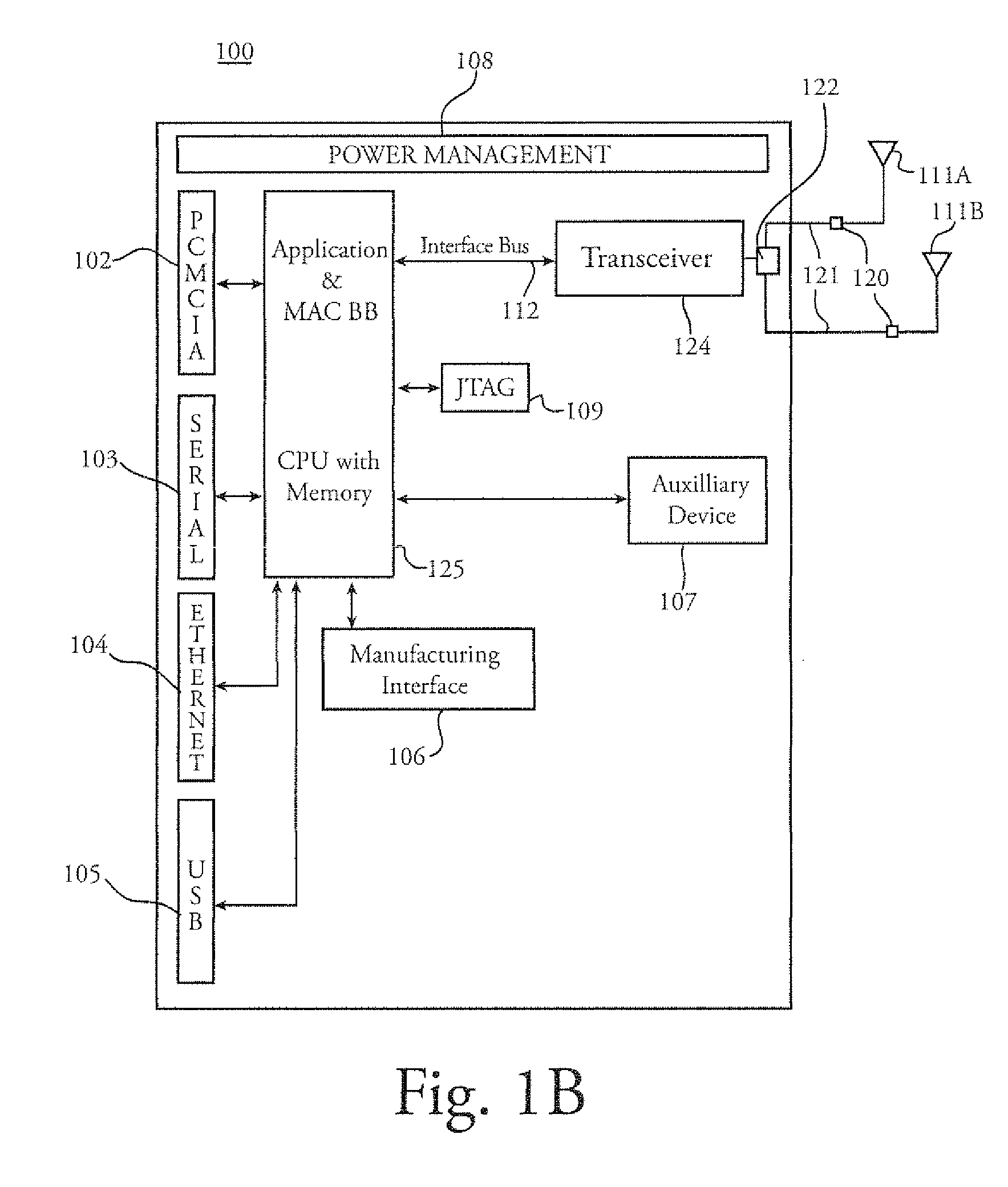
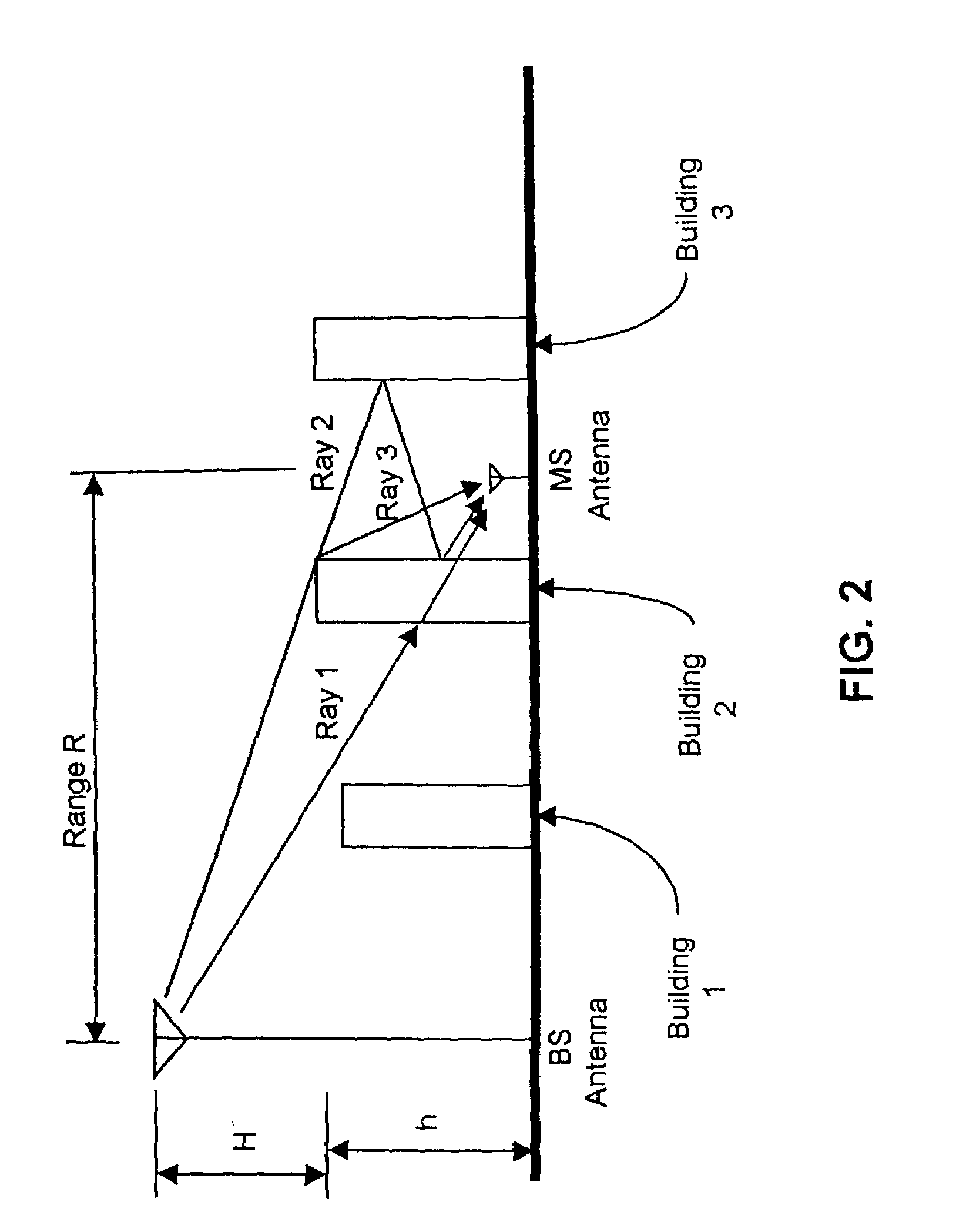
Wireless location using multiple location estimators
InactiveUS6249252B1Effectively and straightforwardly resolvedAmbiguity and conflictDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
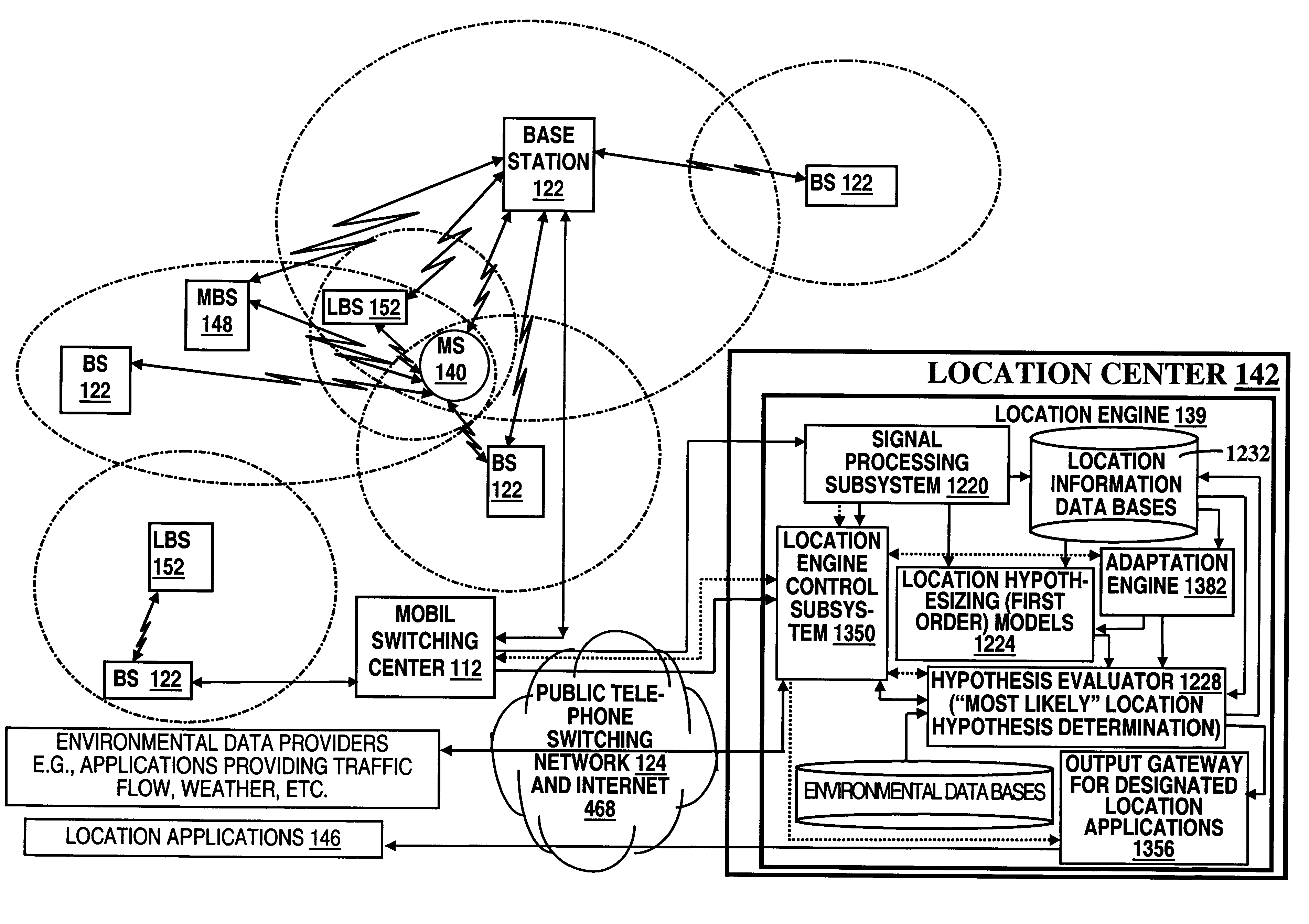
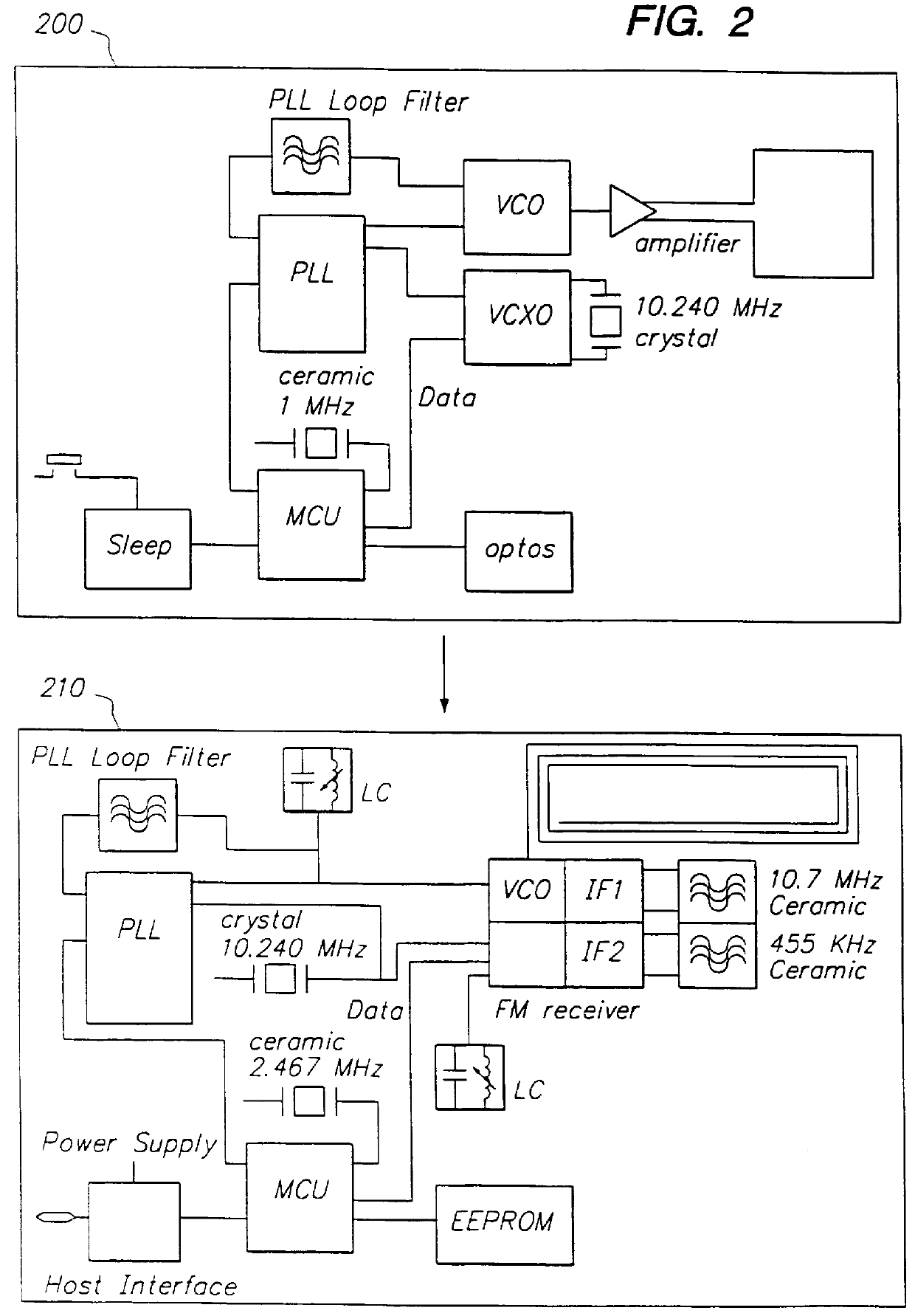
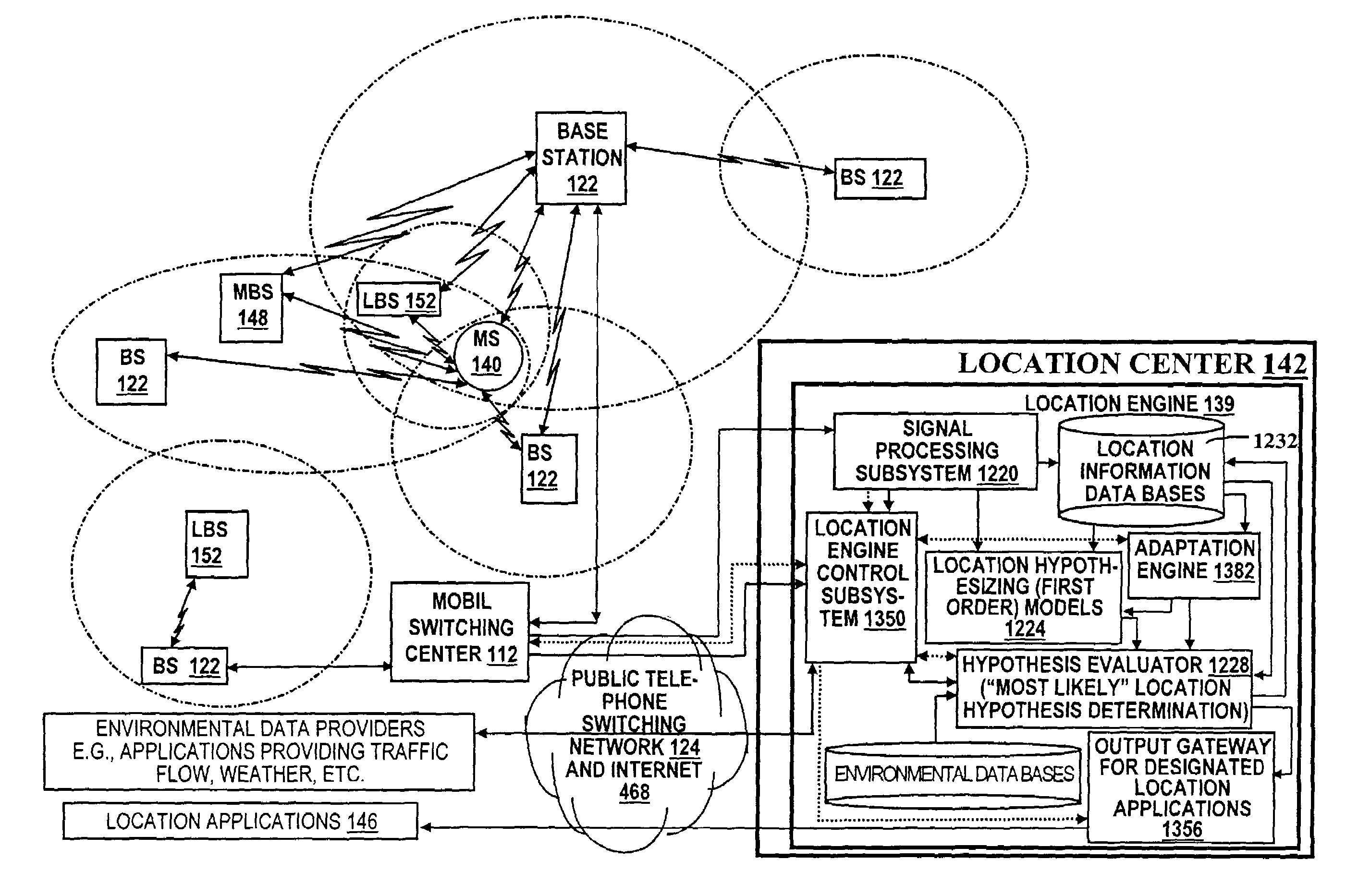
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; (5) GPS signals, (6) angle of arrival, (7) super resolution enhancements, and (8) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signing environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
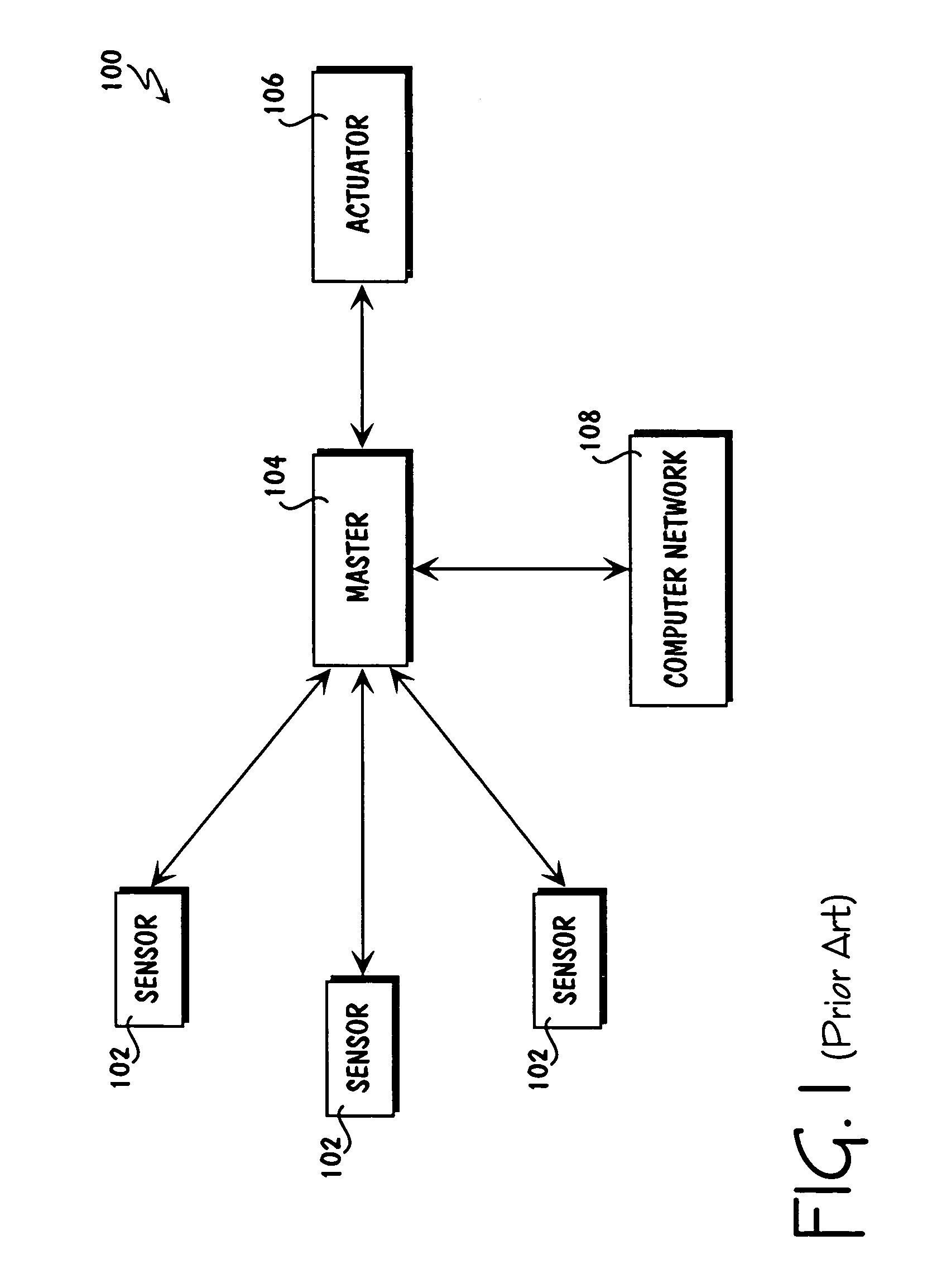
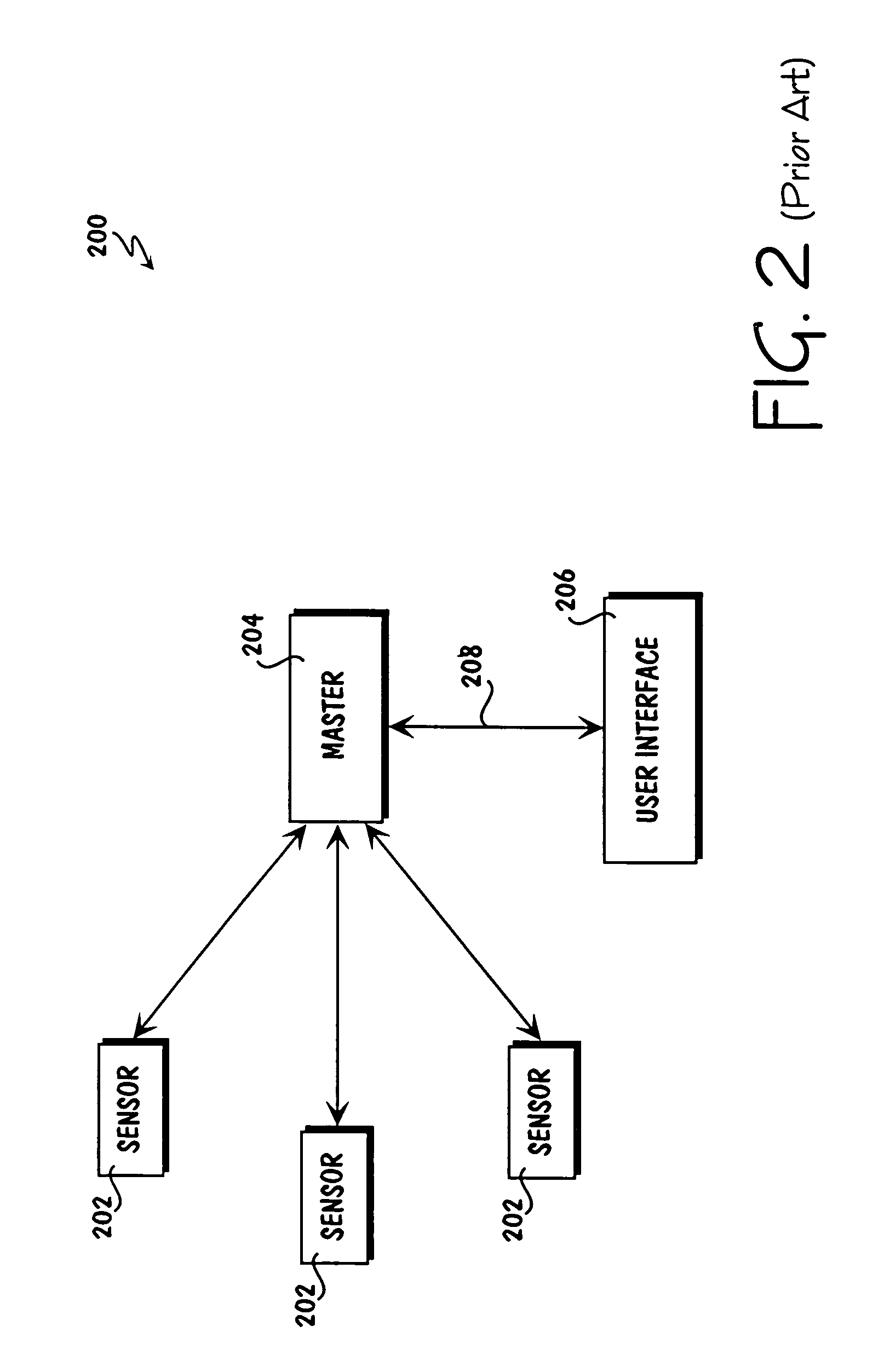
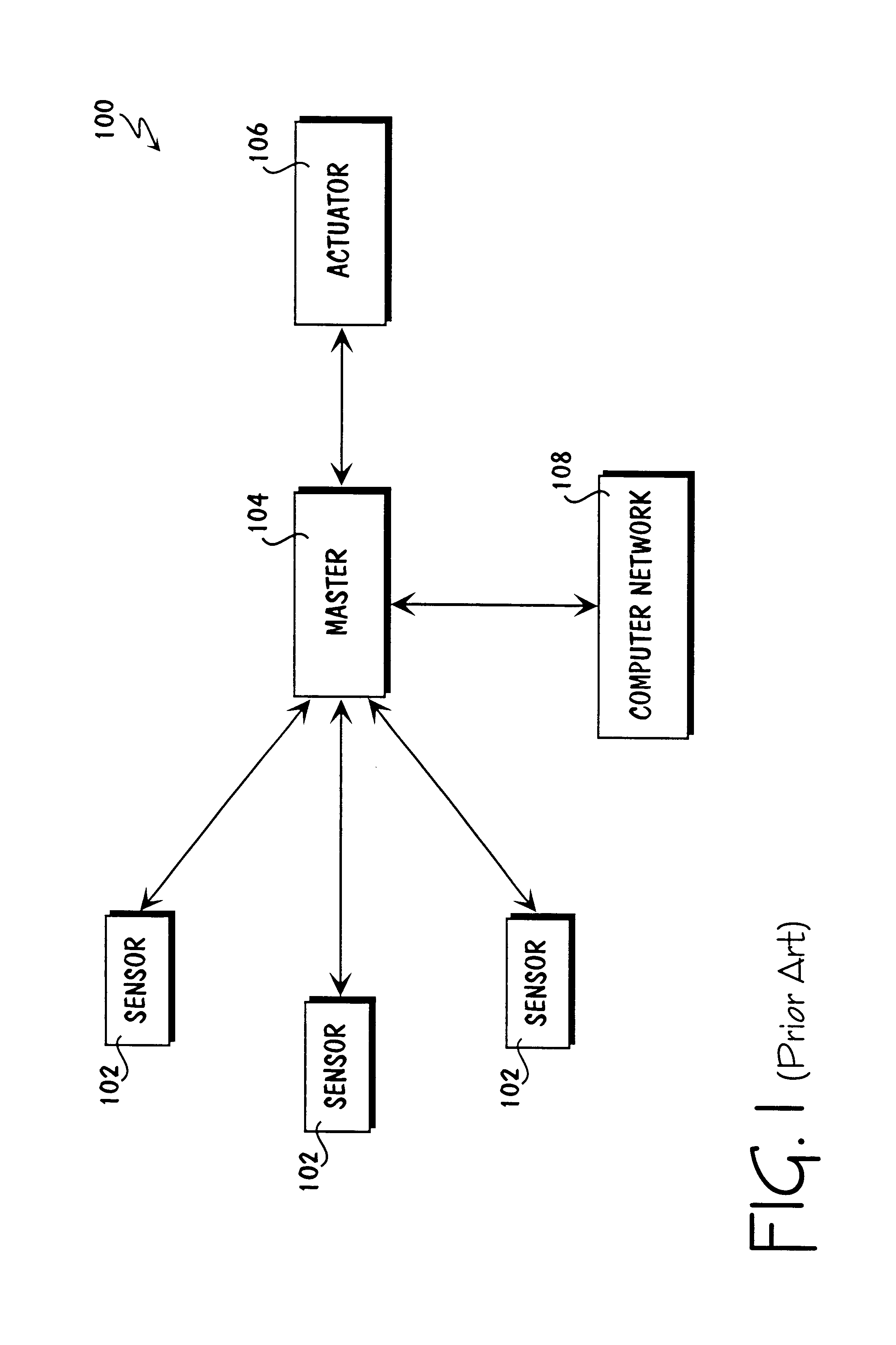
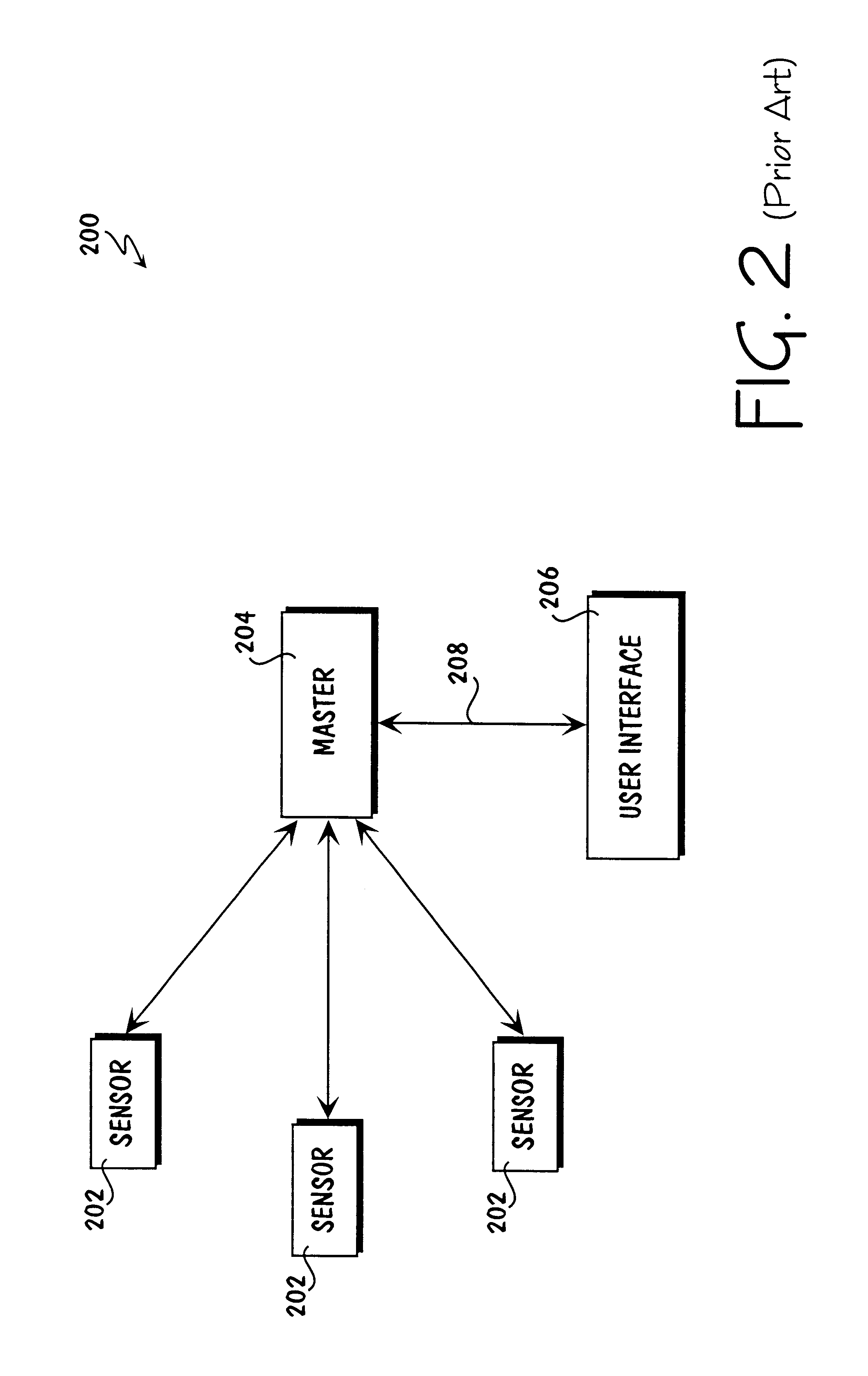
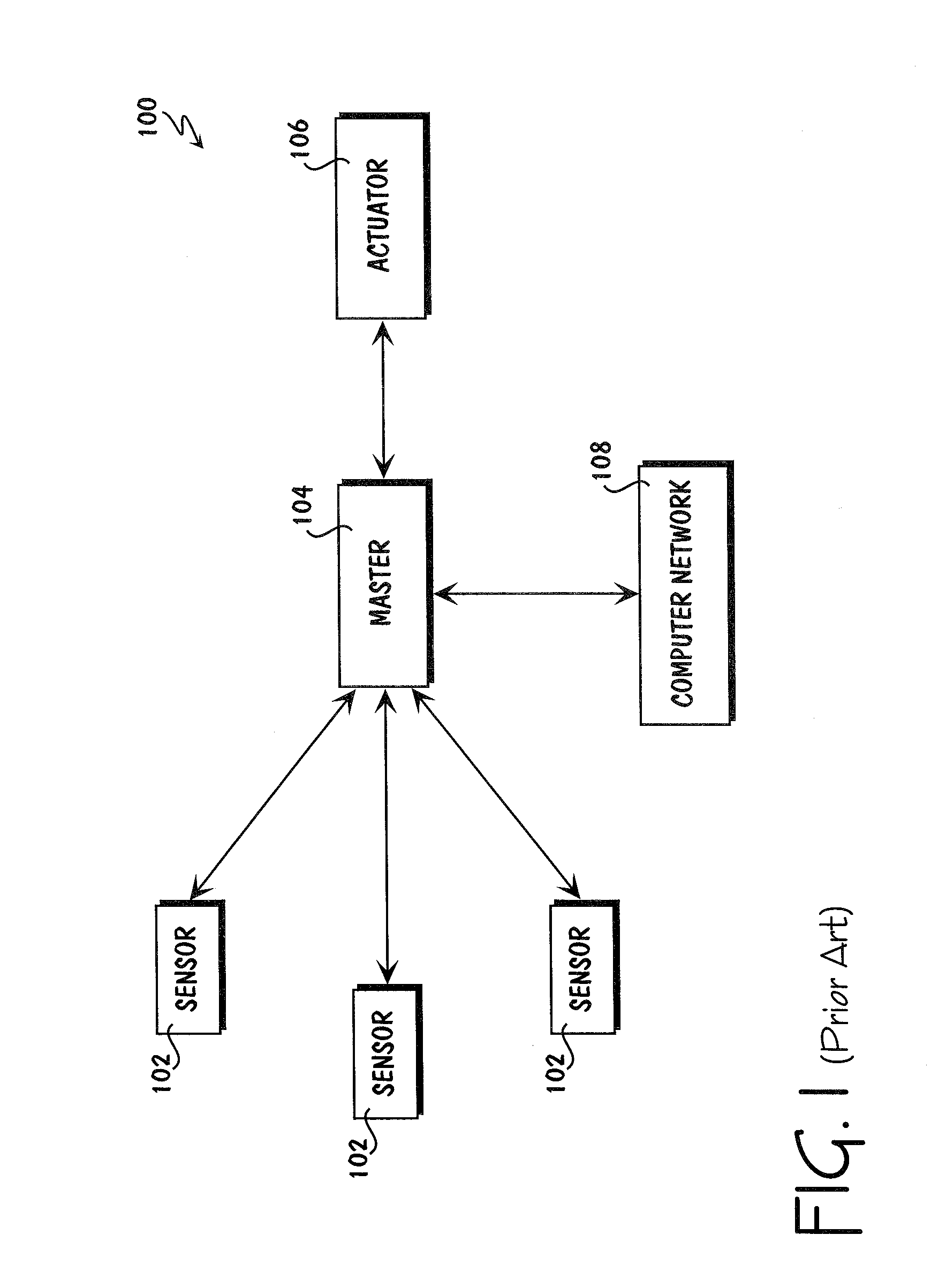
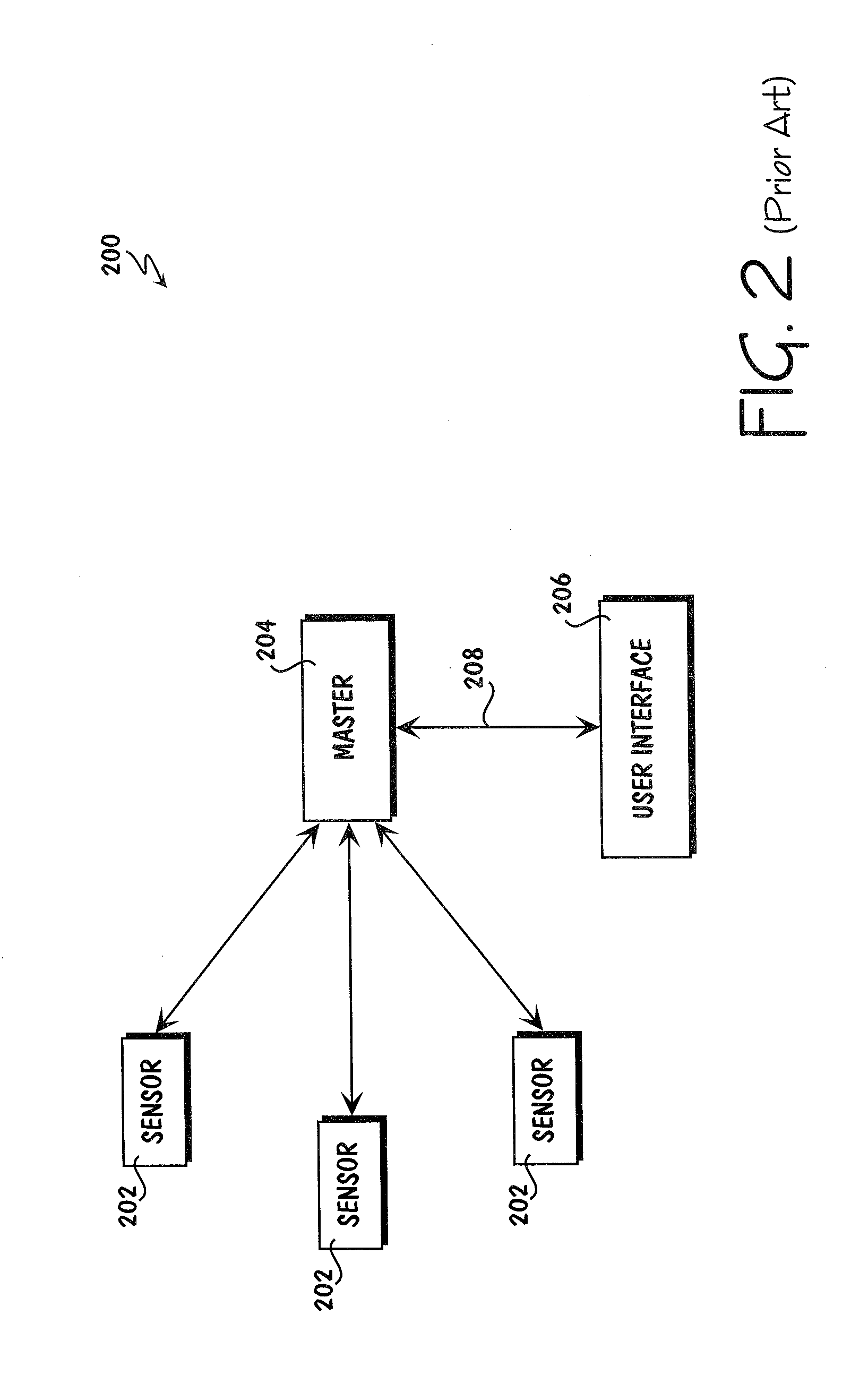
Method for collecting and processing data using internetworked wireless integrated network sensors (WINS)
InactiveUS7020701B1High reliability accessEasy to operateEnergy efficient ICTPower managementReconfigurabilityMonitoring and control
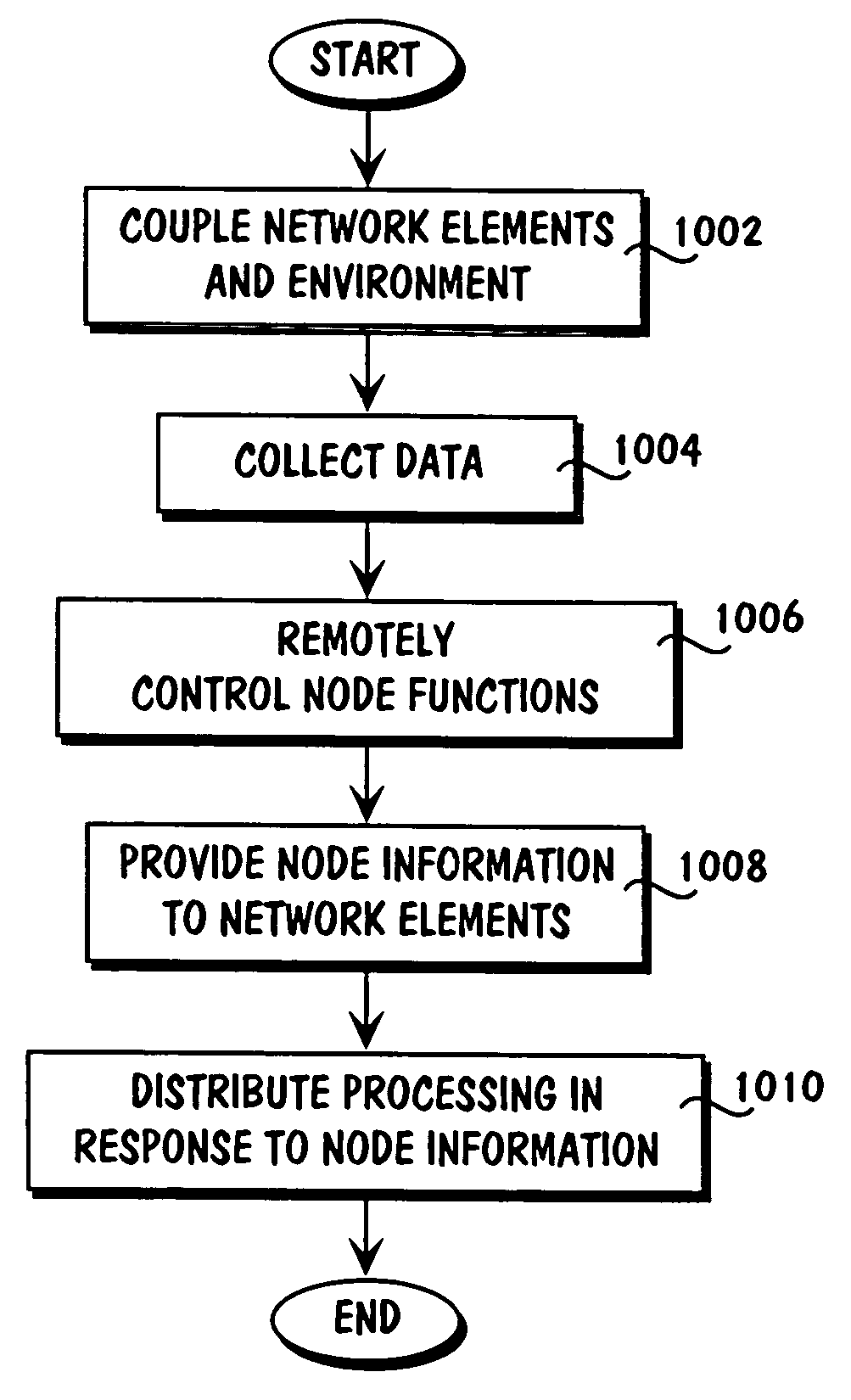
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
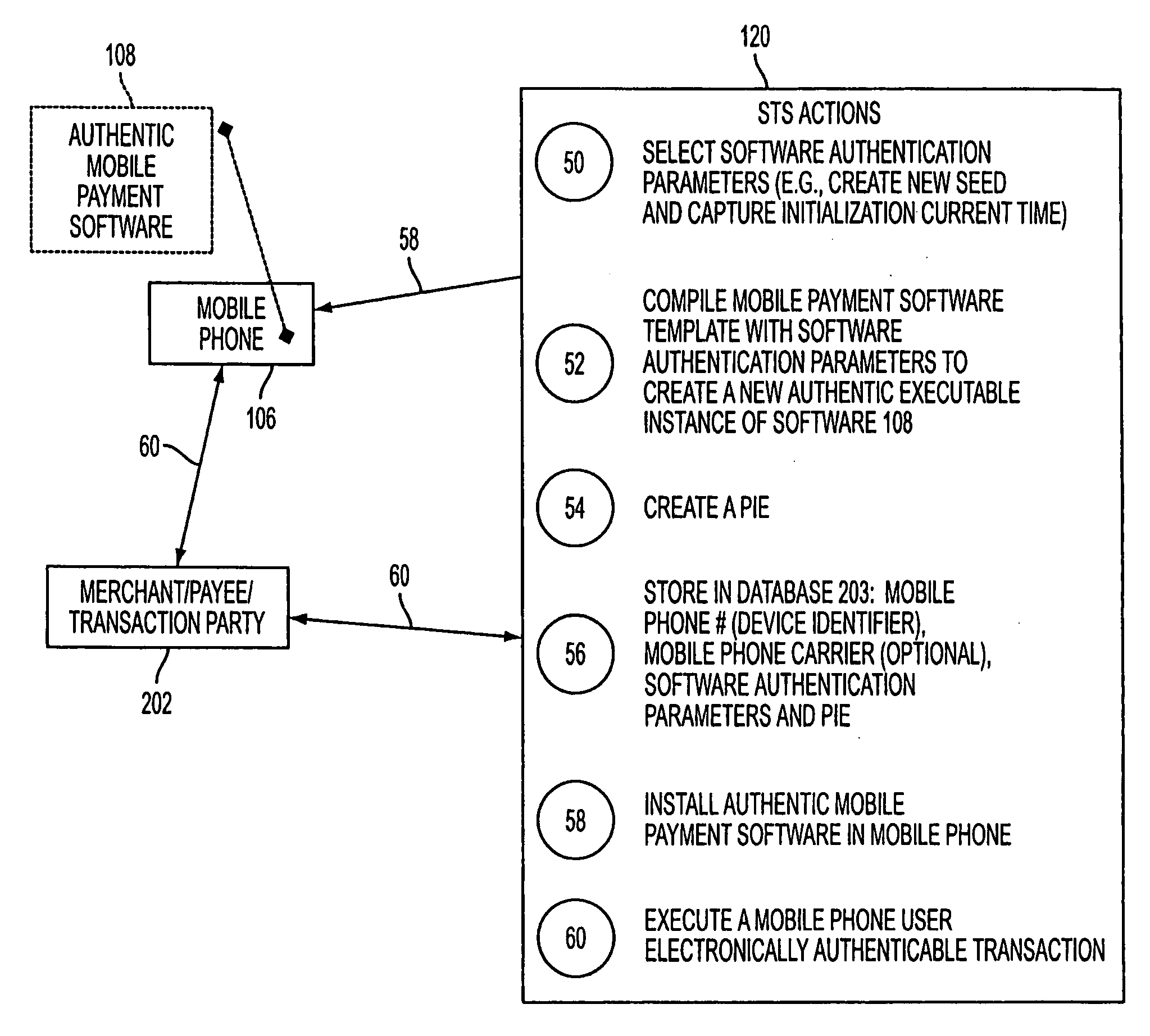
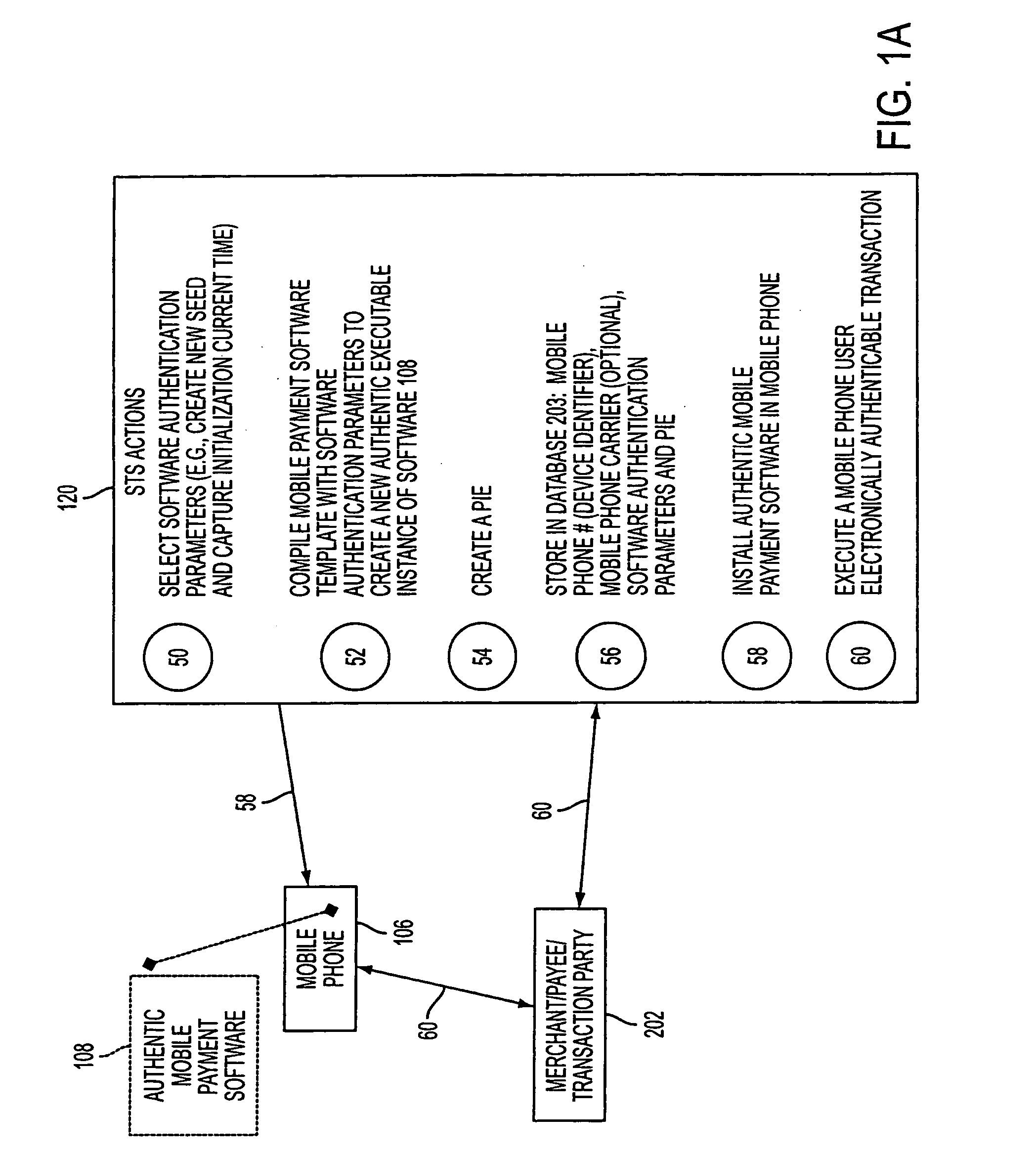
Wireless wallet
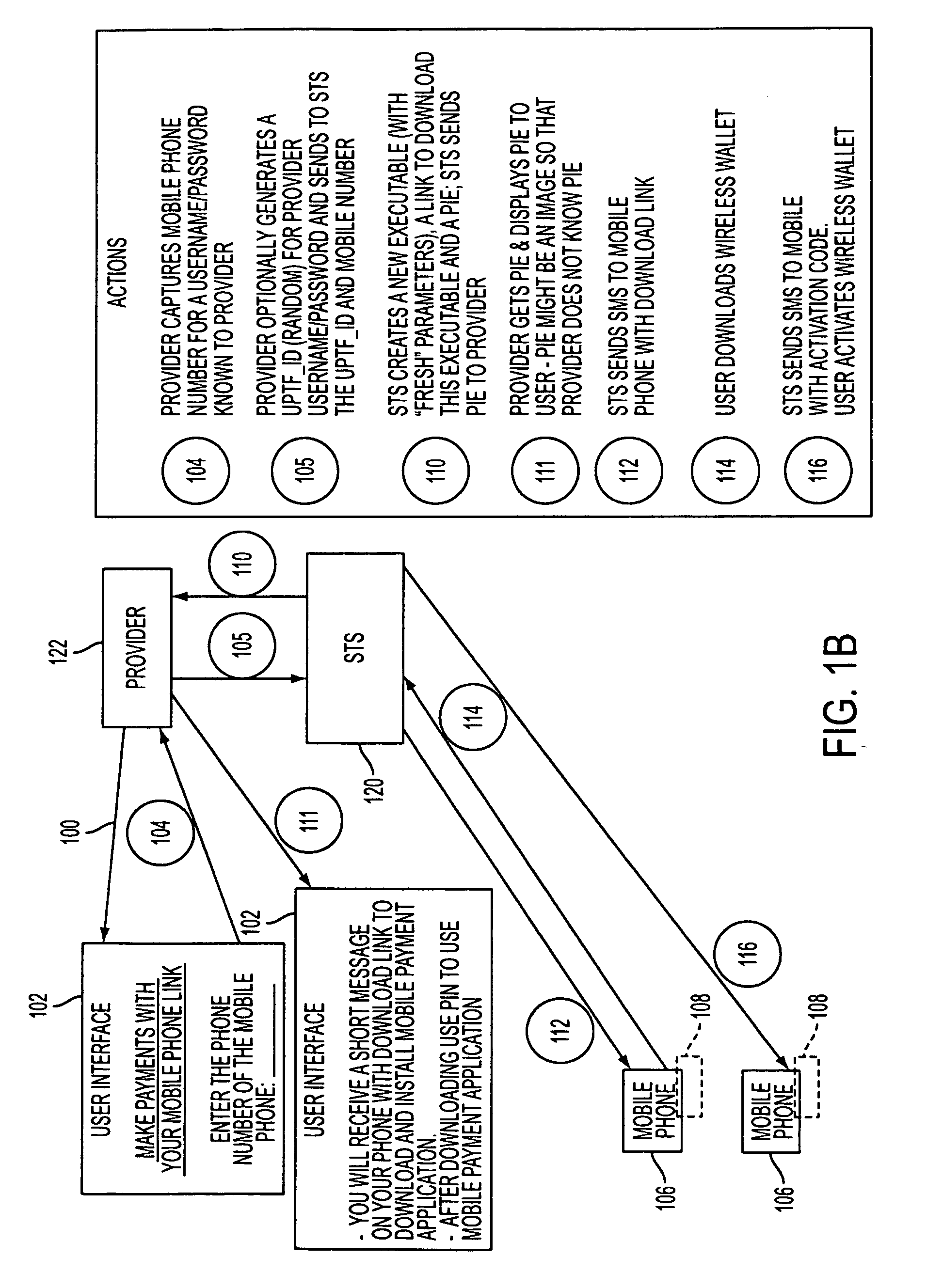
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
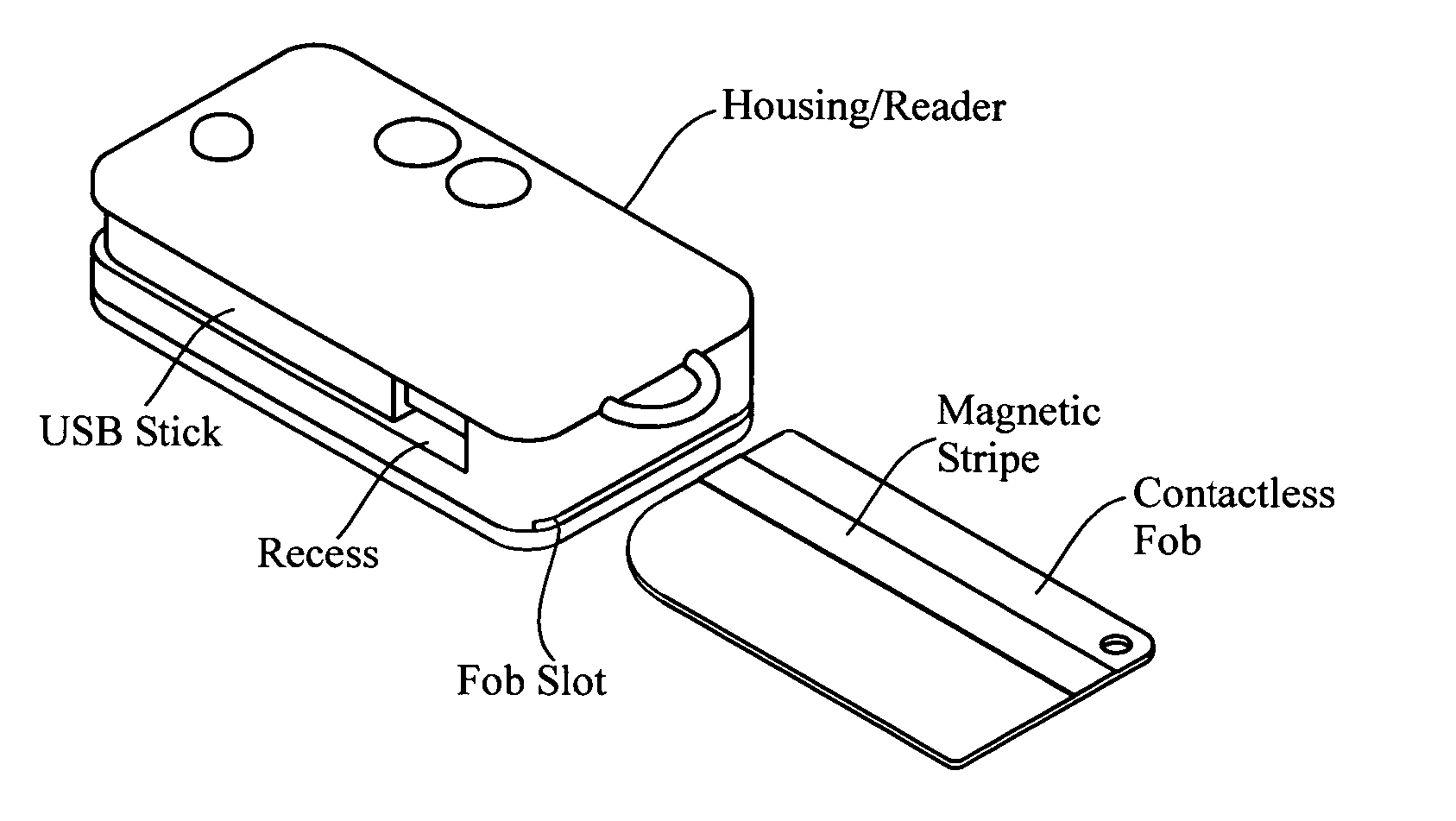
RFID reader with multiple interfaces
InactiveUS20060219776A1Anti-theft devicesSensing by galvanic contactsPersonalizationContactless smart card
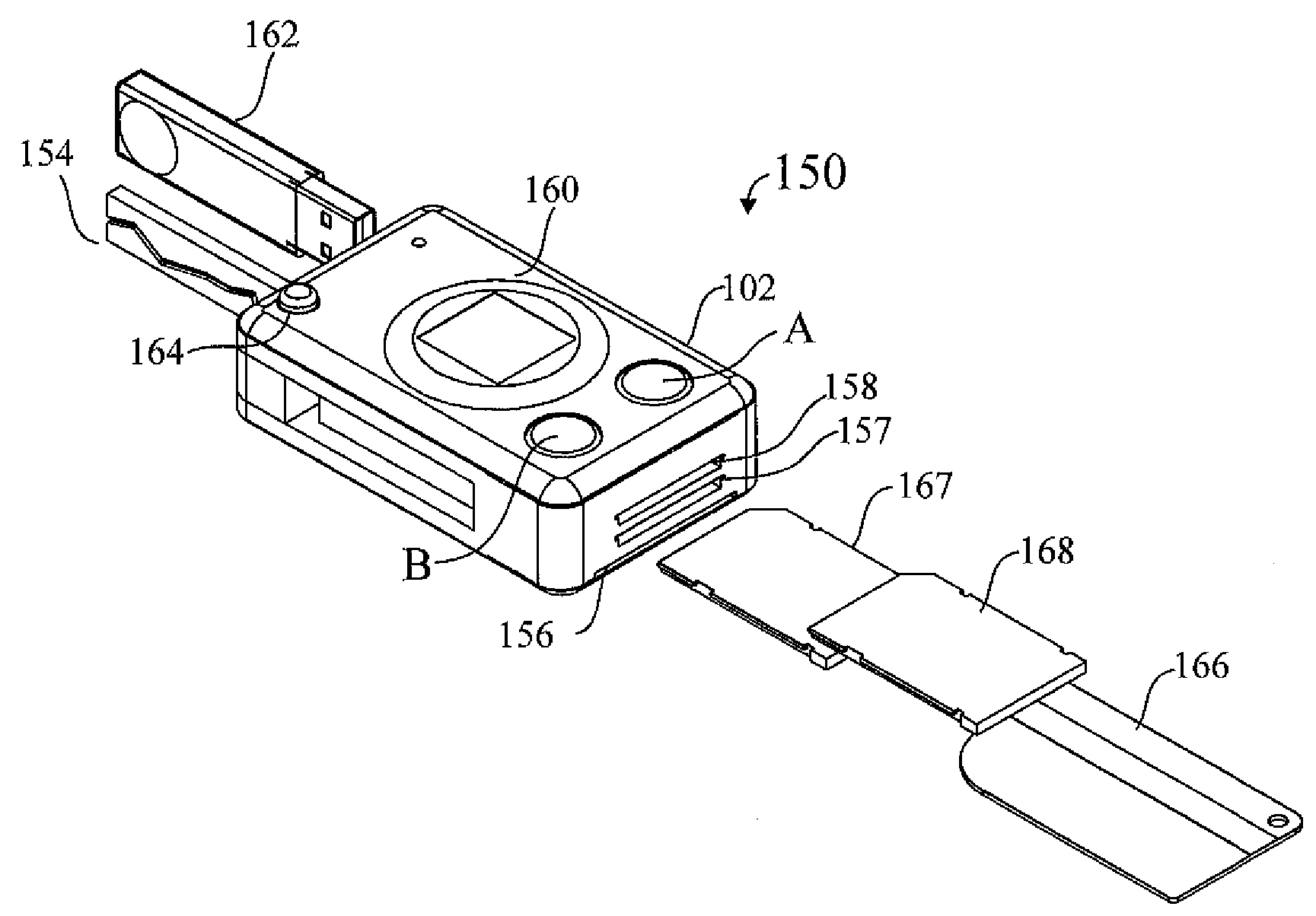
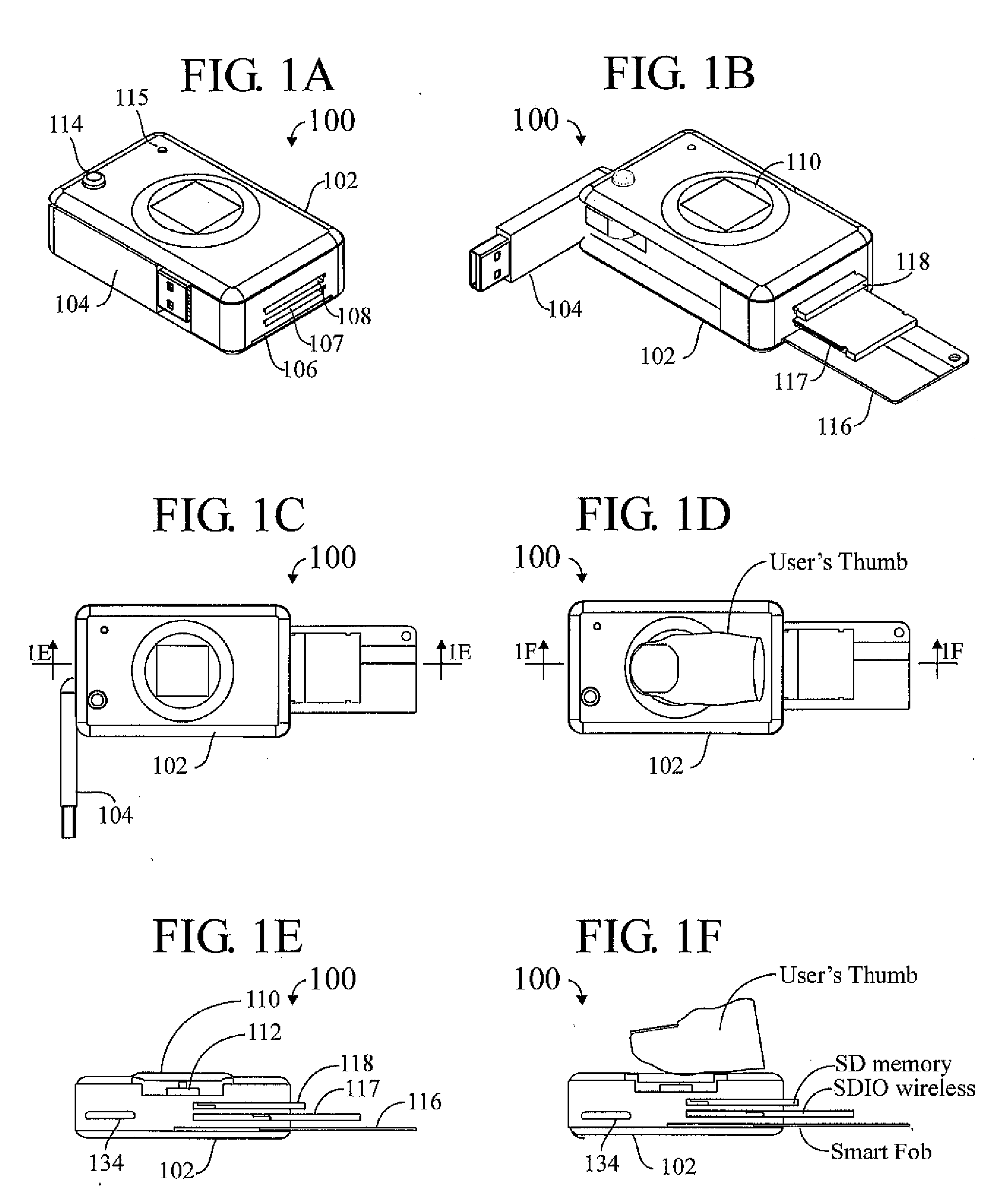
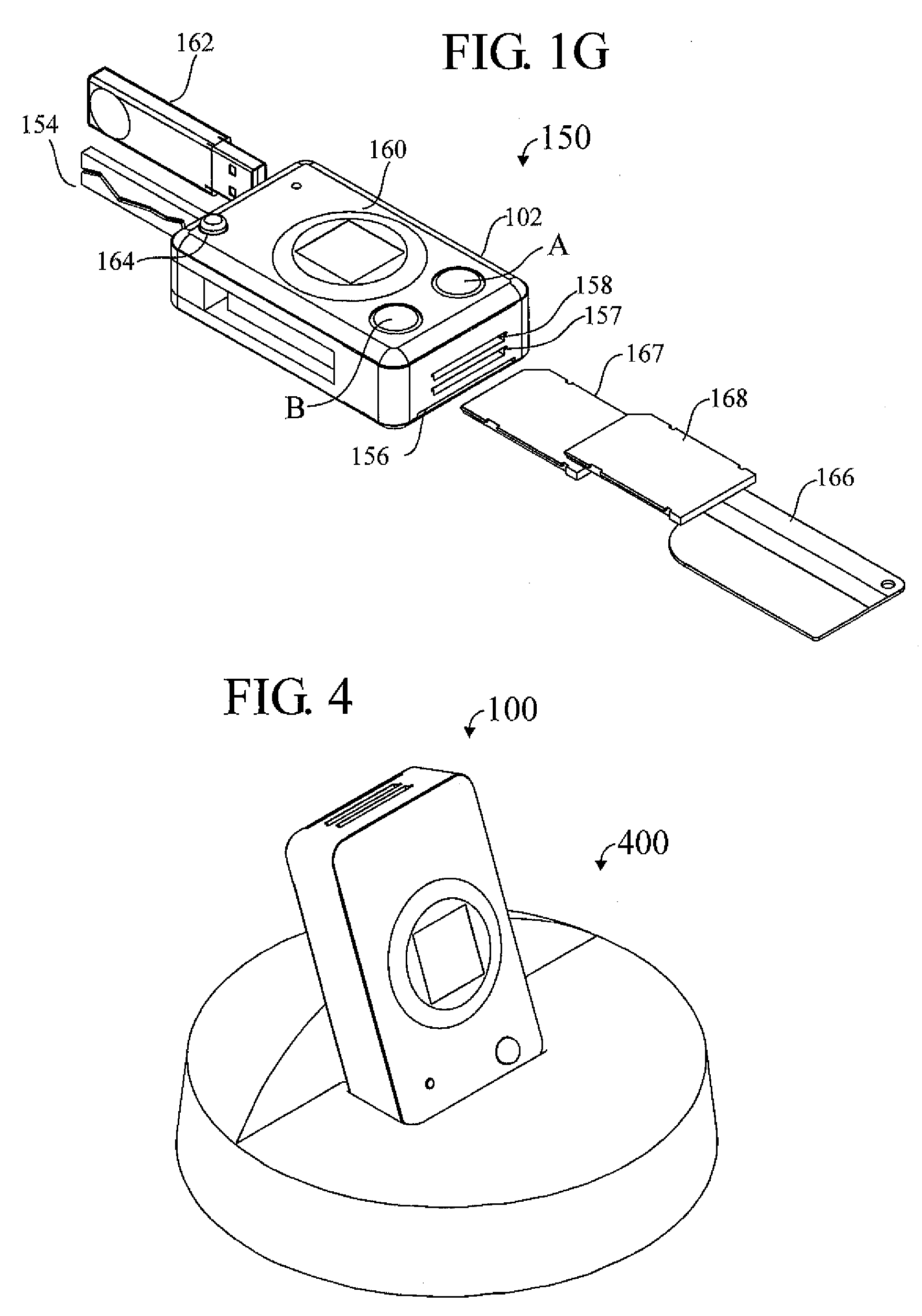
A pocket-size RFID reader apparatus having a contactless interface and a slot for insertion of a contactless smart card fob, and having a biometric sensor, thereby providing two levels of personalization. The apparatus may have a wireless interface; and a slot for insertion of a wireless SD I / O device. The apparatus may have a slot for insertion of an external memory device. The apparatus may have a mechanical connection (contact) interface. The apparatus may also have an RF interface for reading an electronic immobilizer within the apparatus.
Owner:DPD PATENT TRUST
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
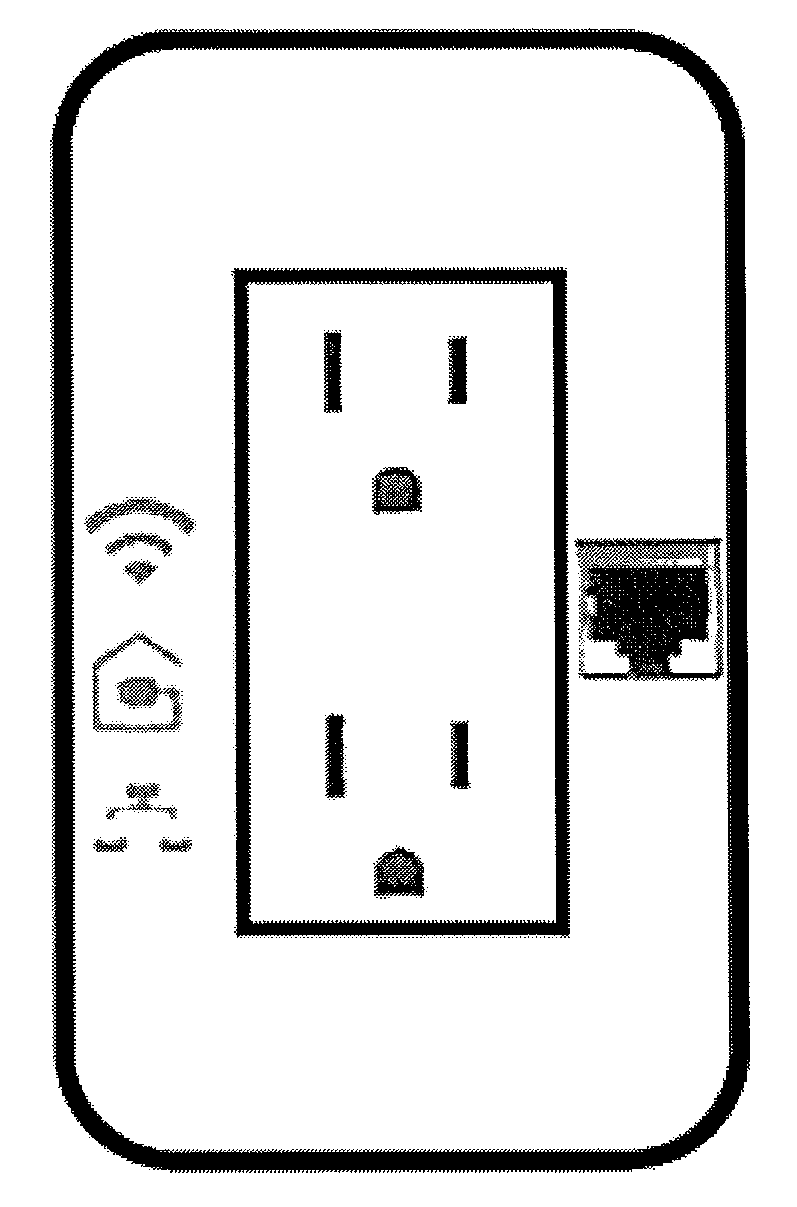
Power receptacle wireless access point devices for networked living and work spaces
Owner:UBIQUITI INC
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
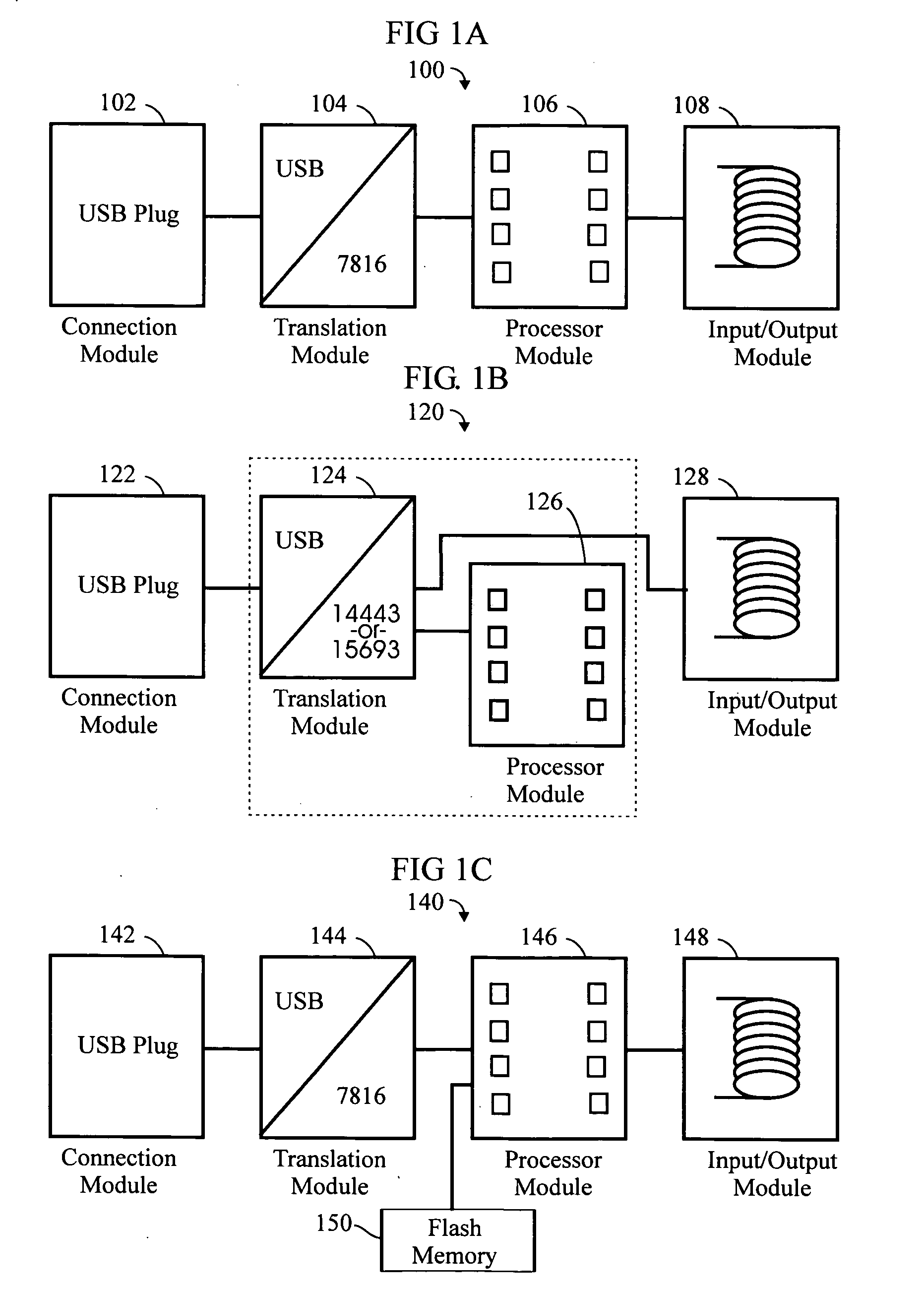
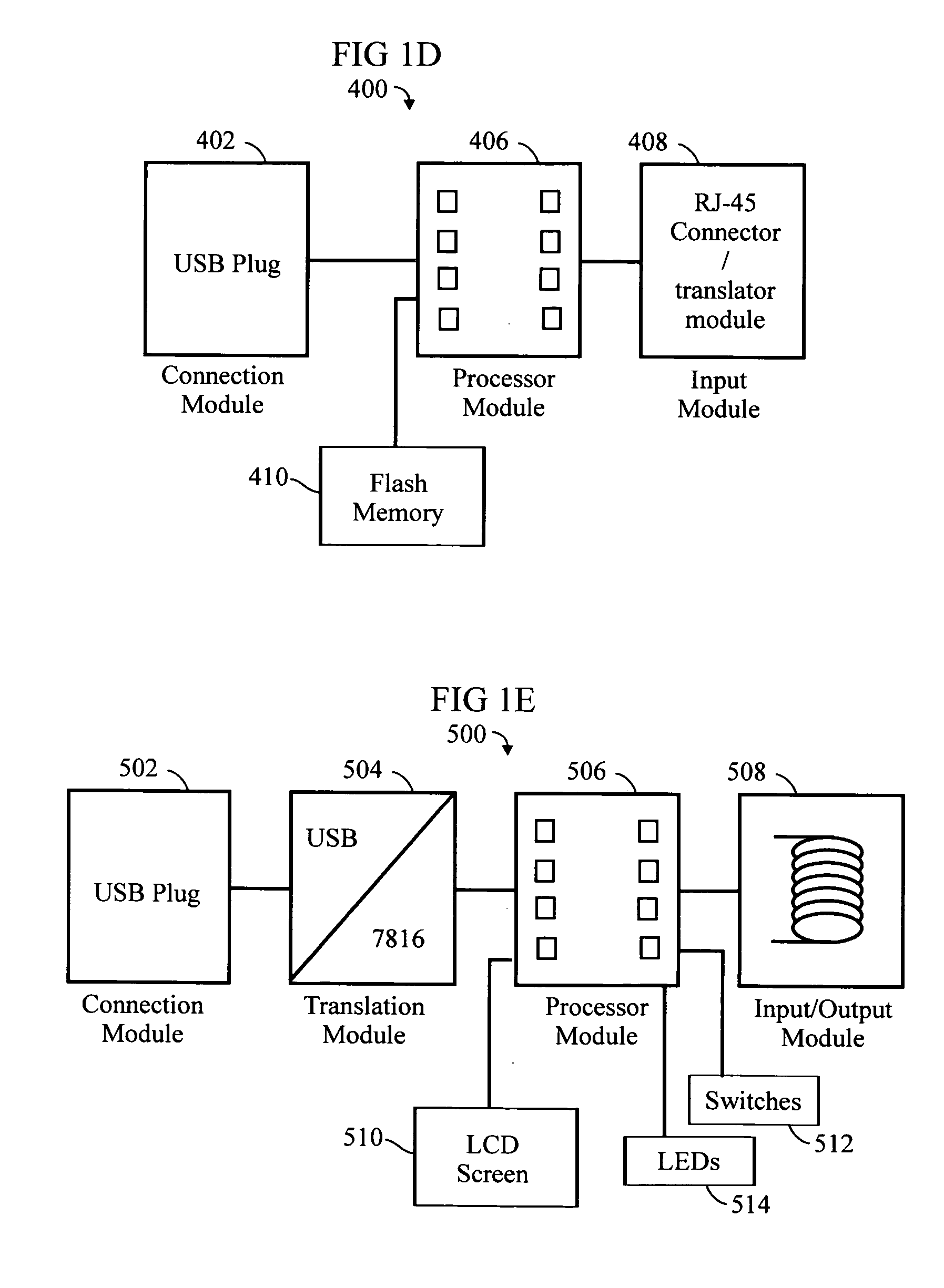
RFID token with multiple interface controller
InactiveUS20060208066A1Acutation objectsBroadcast information characterisationComputer moduleSmart card
An RFID token apparatus has a connection module for interfacing with an appliance capable of communicating and interacting with remote servers and networks, a translation module for moving signals between a USB interface and a smart card interface, a processor module which may be capable of operating as a dual-interface (DI) chip; and an input / output module having at least one RF antenna and a modulator. An RFID-contactless interface according to ISO 14443 & ISO 15693 and / or NFC. A wireless interface according to Zigbee, Bluetooth, WLAN 802.11, UWB, USB wireless and / or any similar interface. An RFID reader apparatus has a housing; a slot for a contact or contactless fob; and a USB stick alternately protruding from the housing and retracted within the housing.
Owner:DPD PATENT TRUST
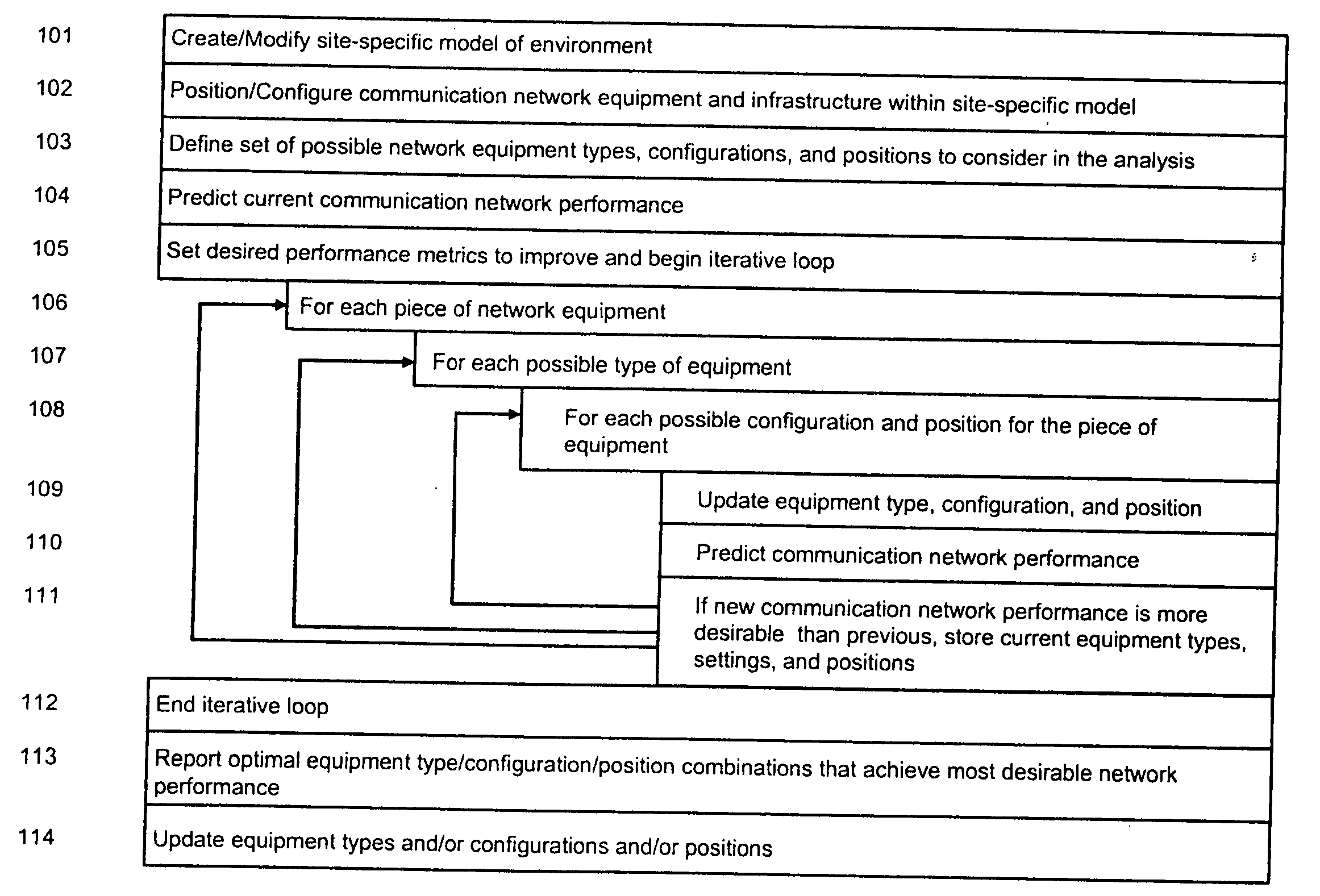
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
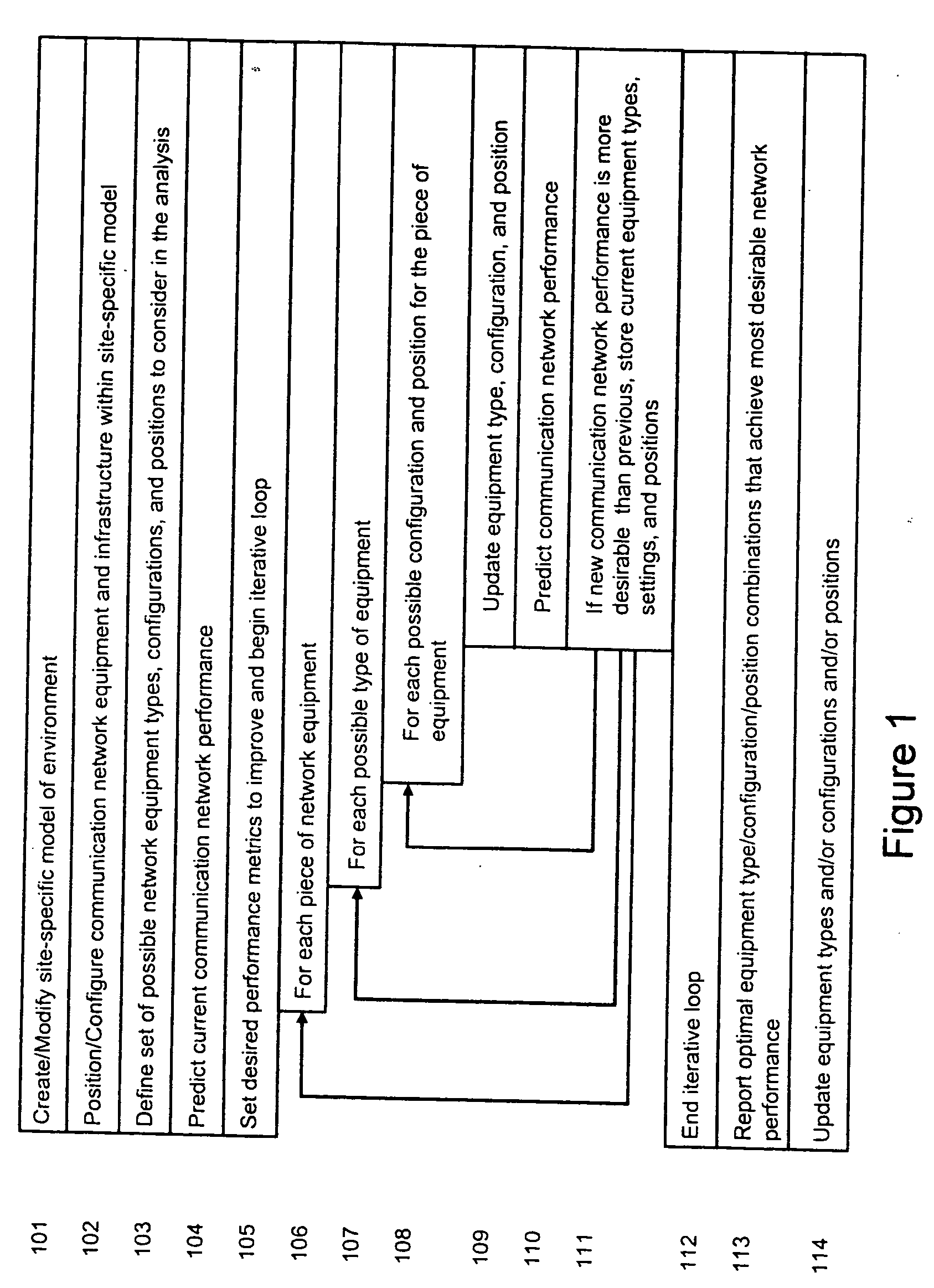
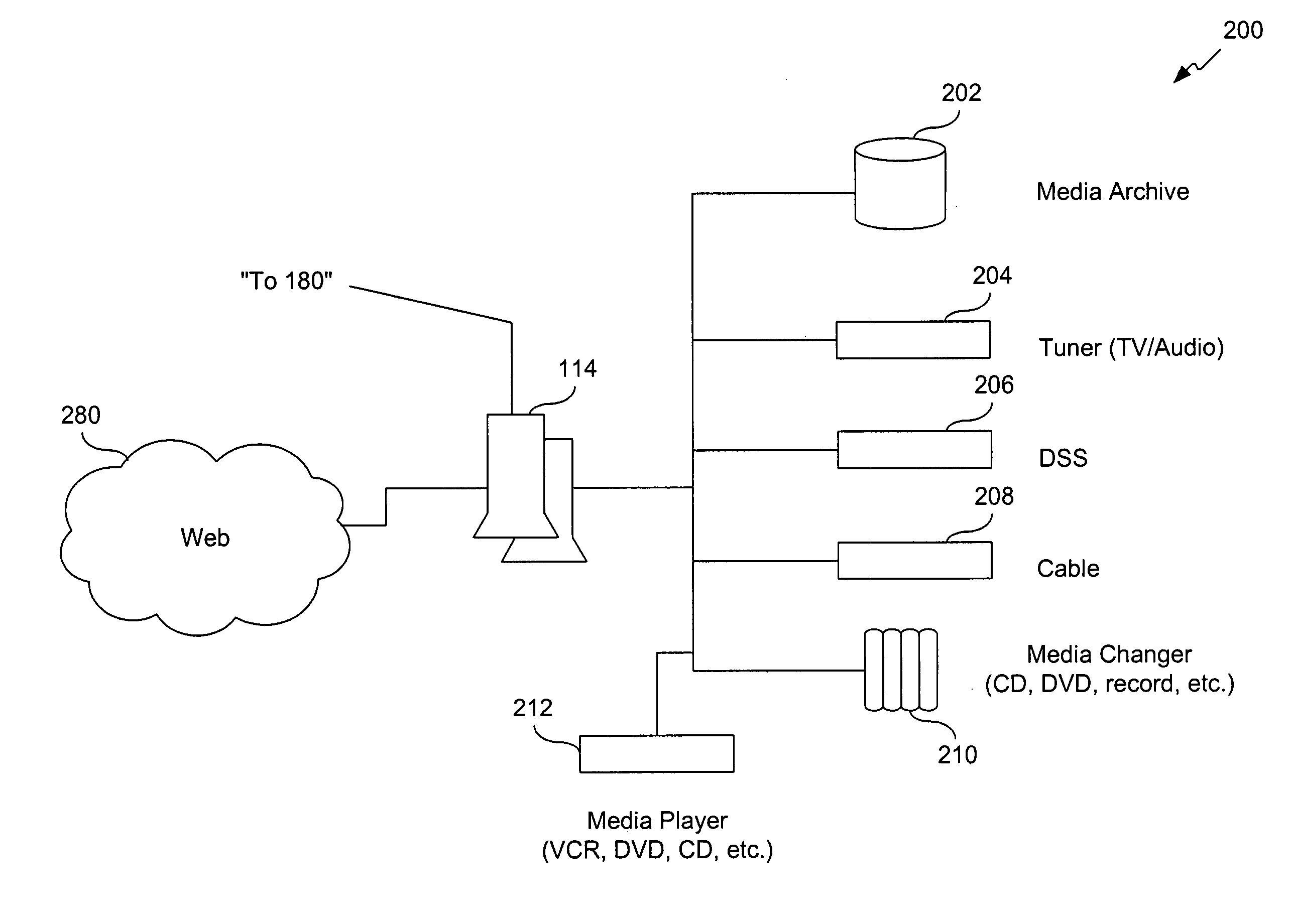
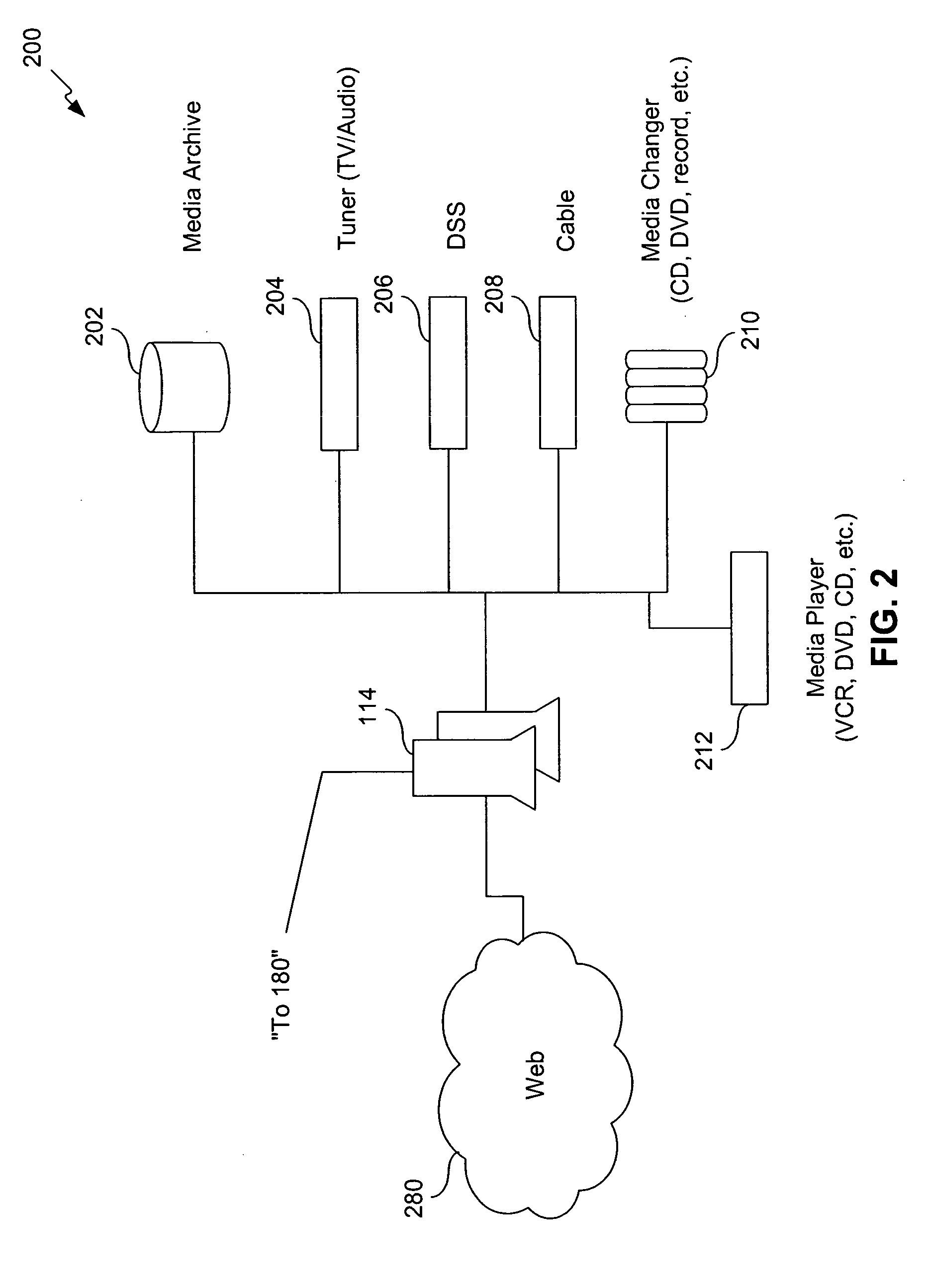
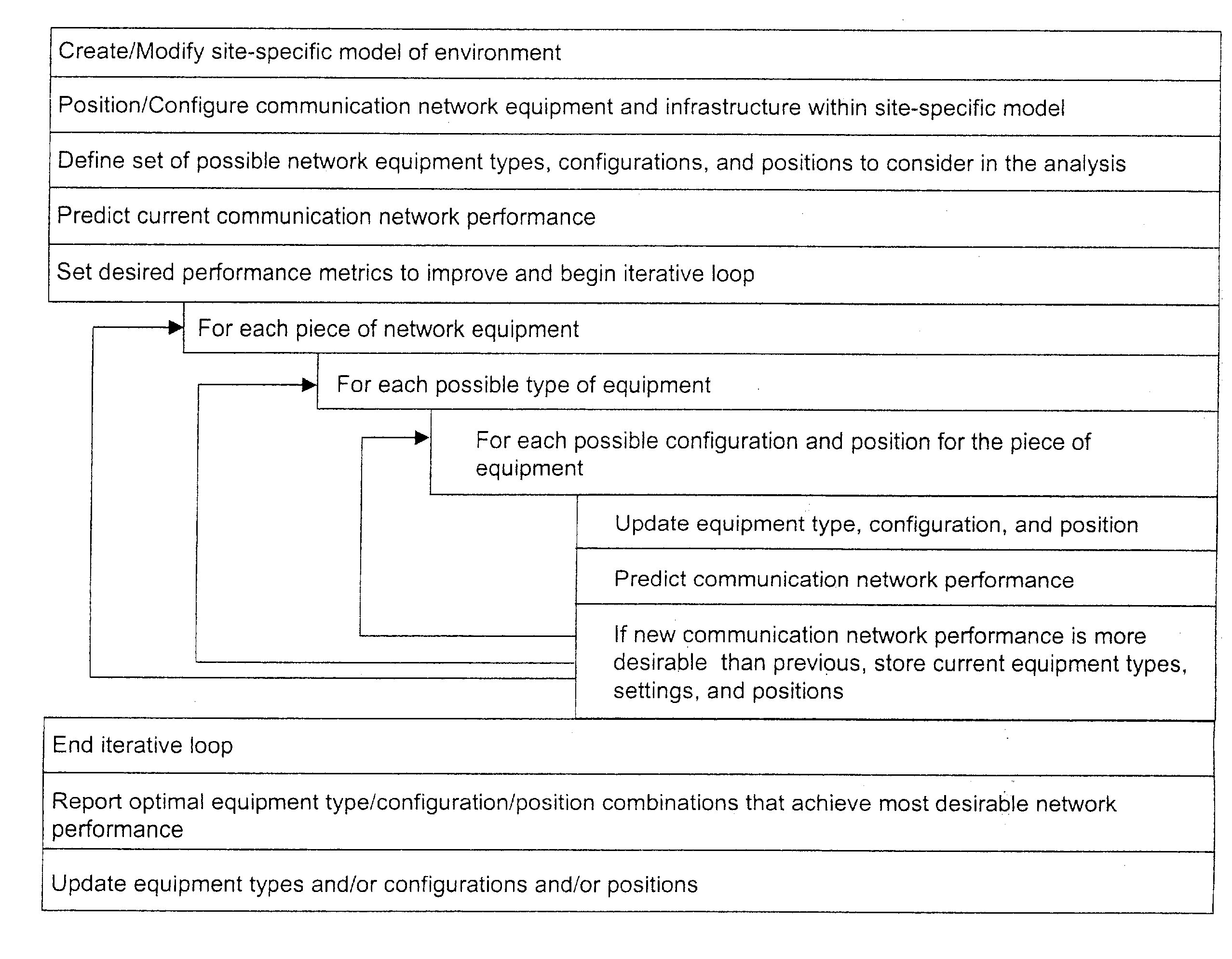
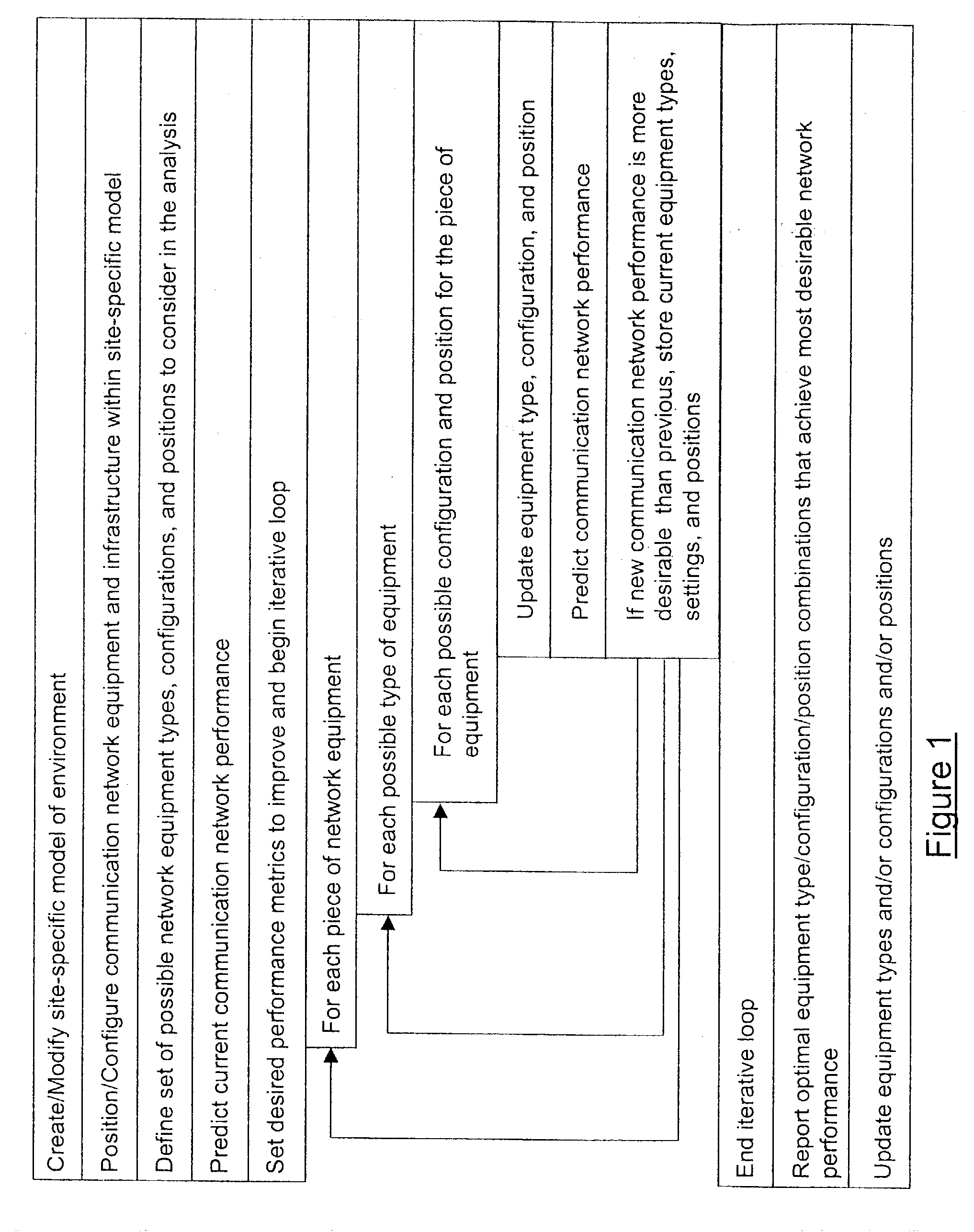
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
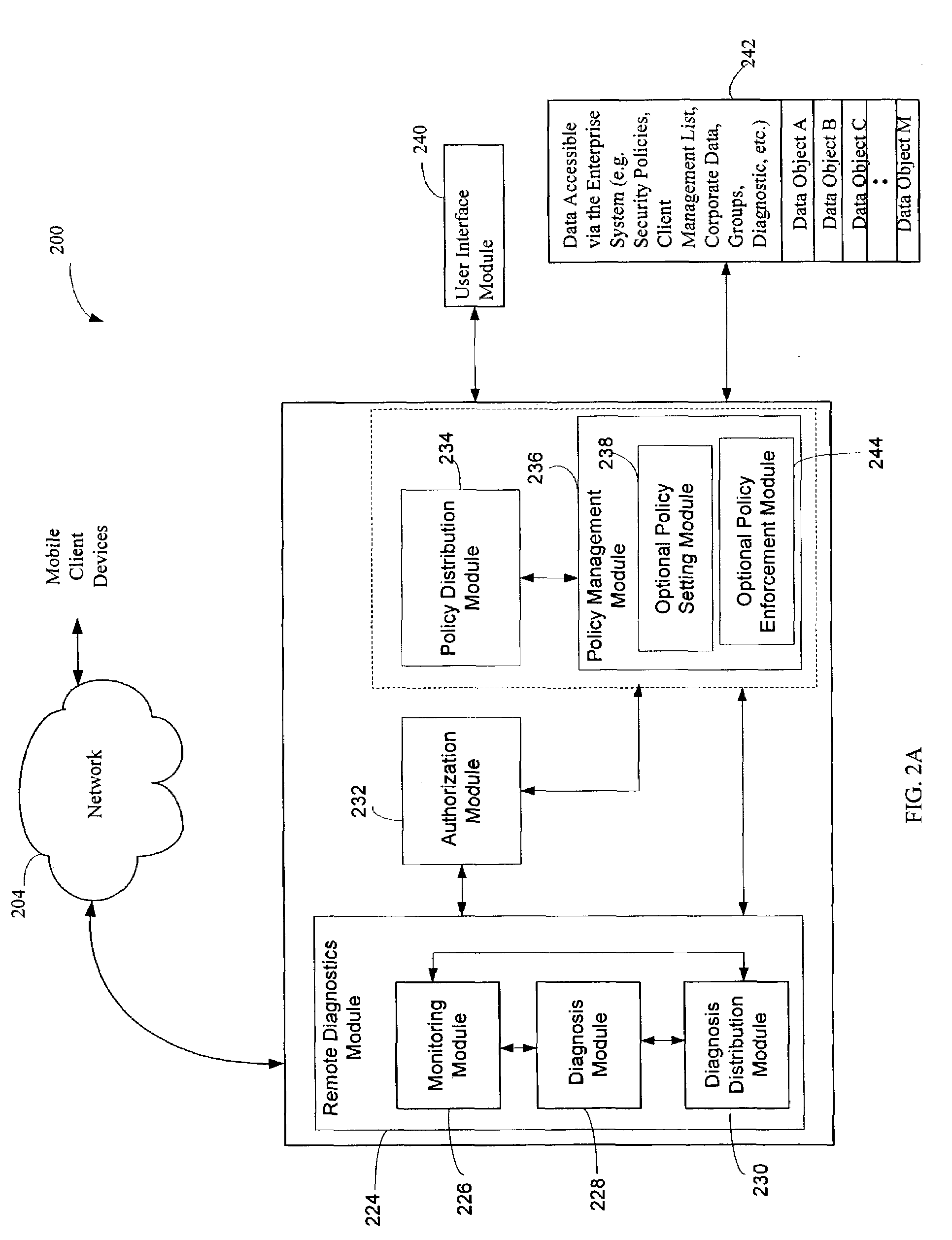
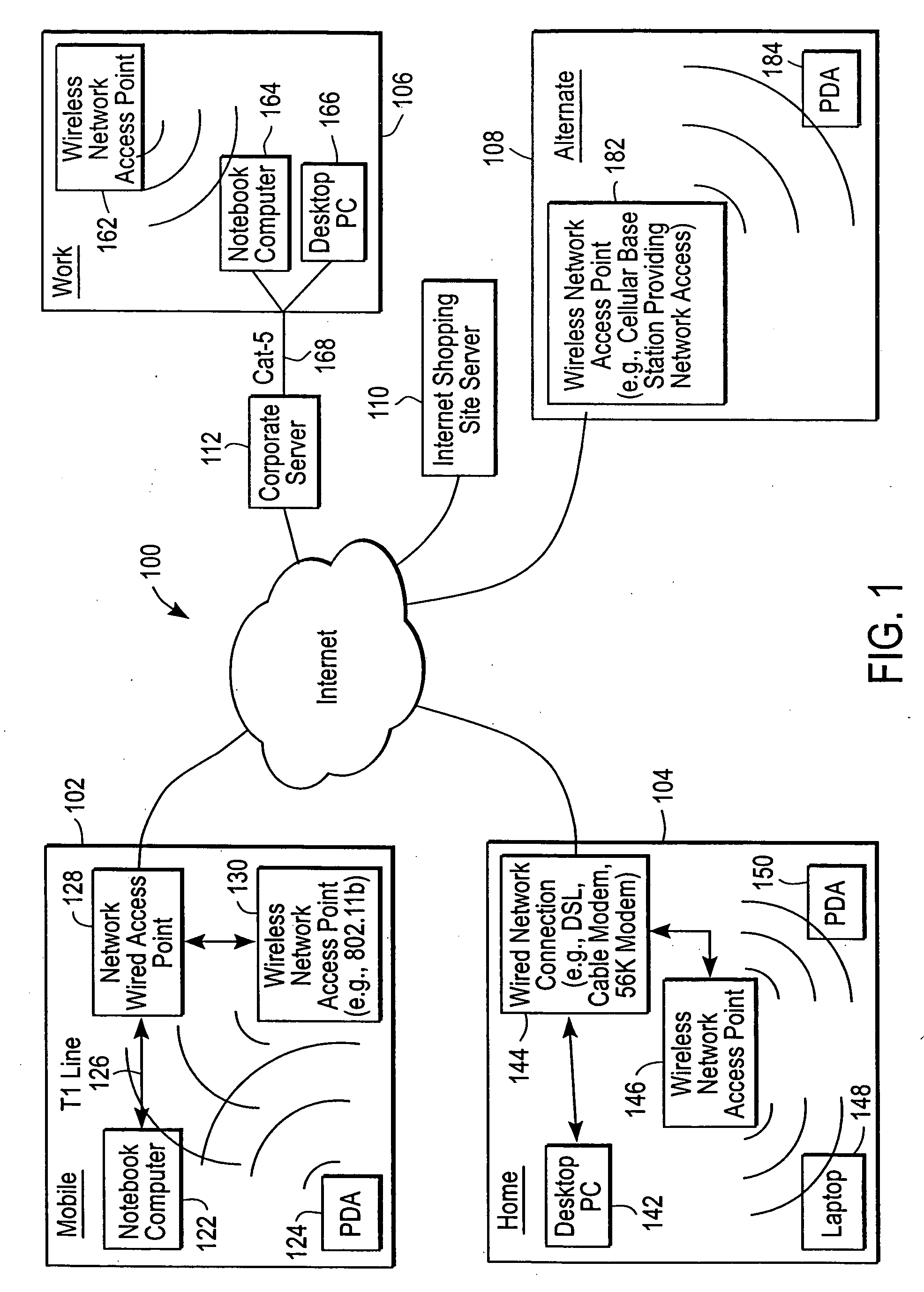
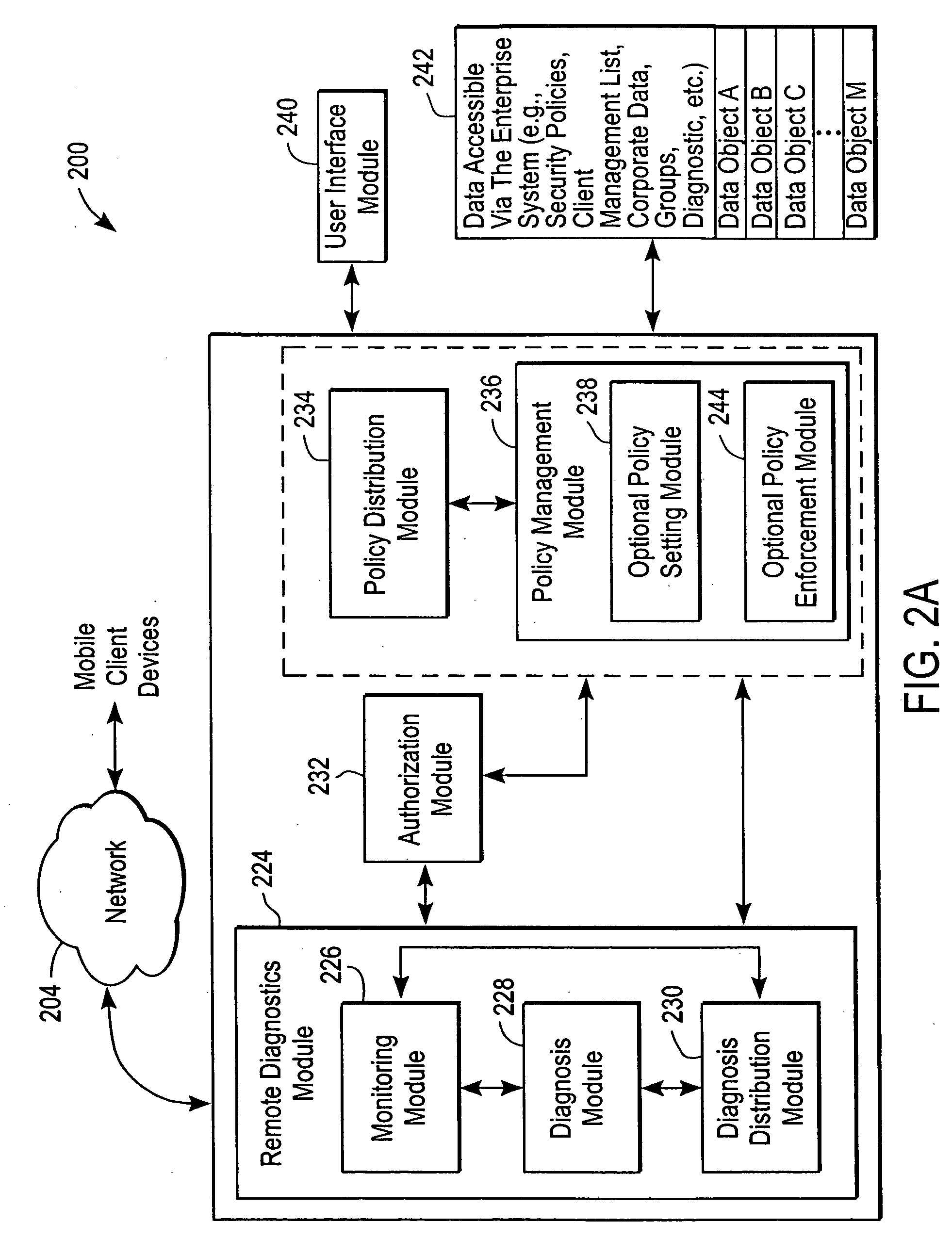
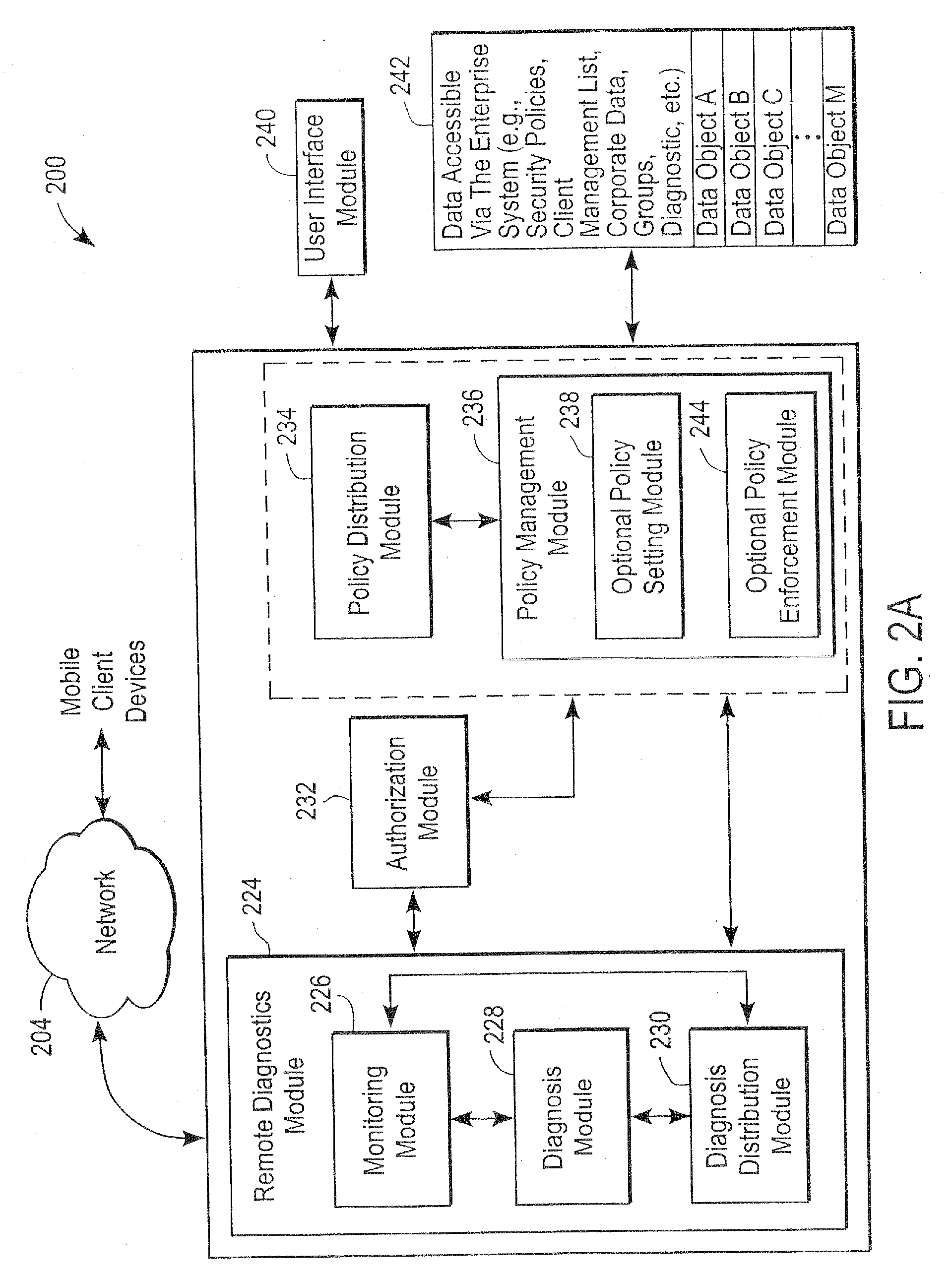
Administration of protection of data accessible by a mobile device
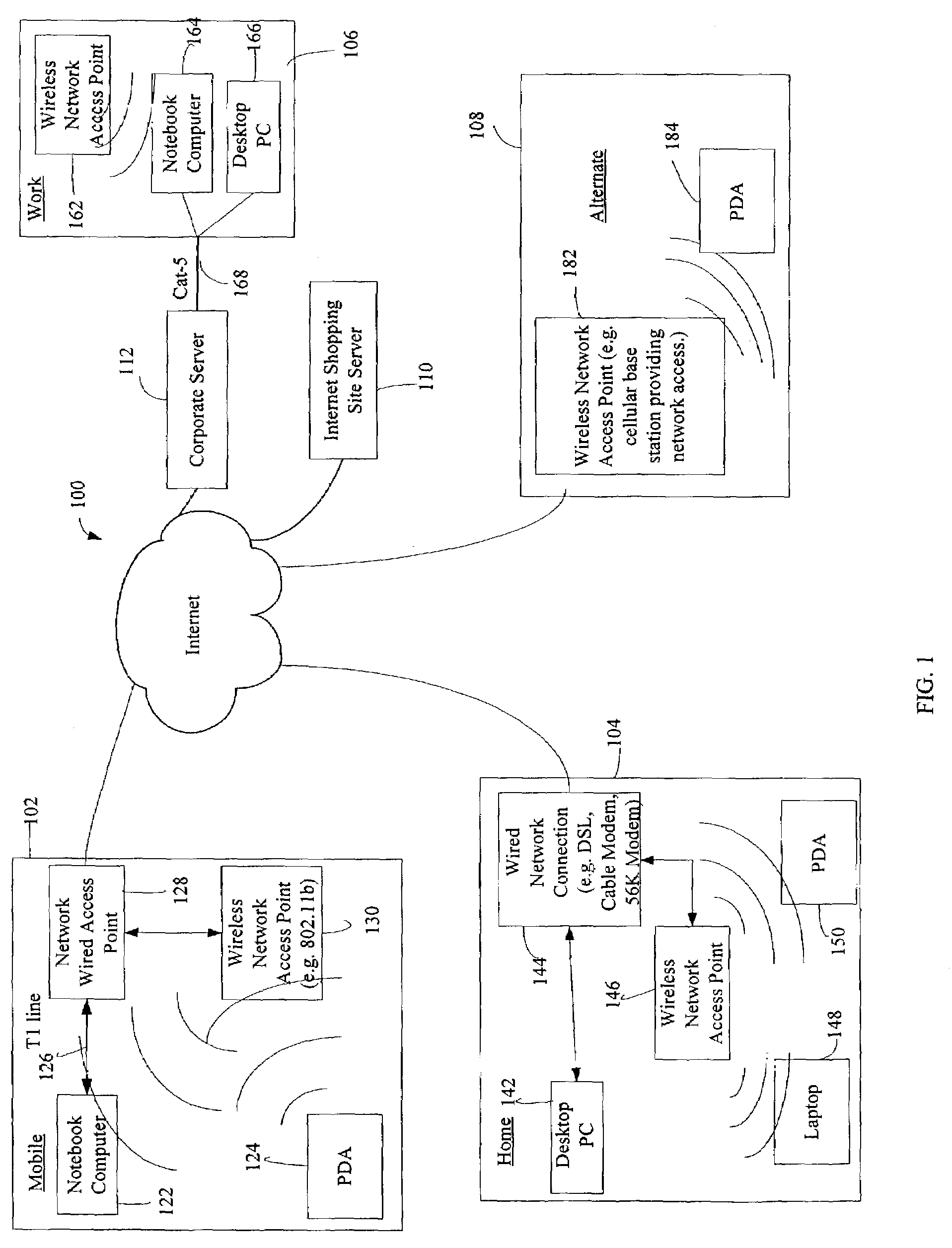
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
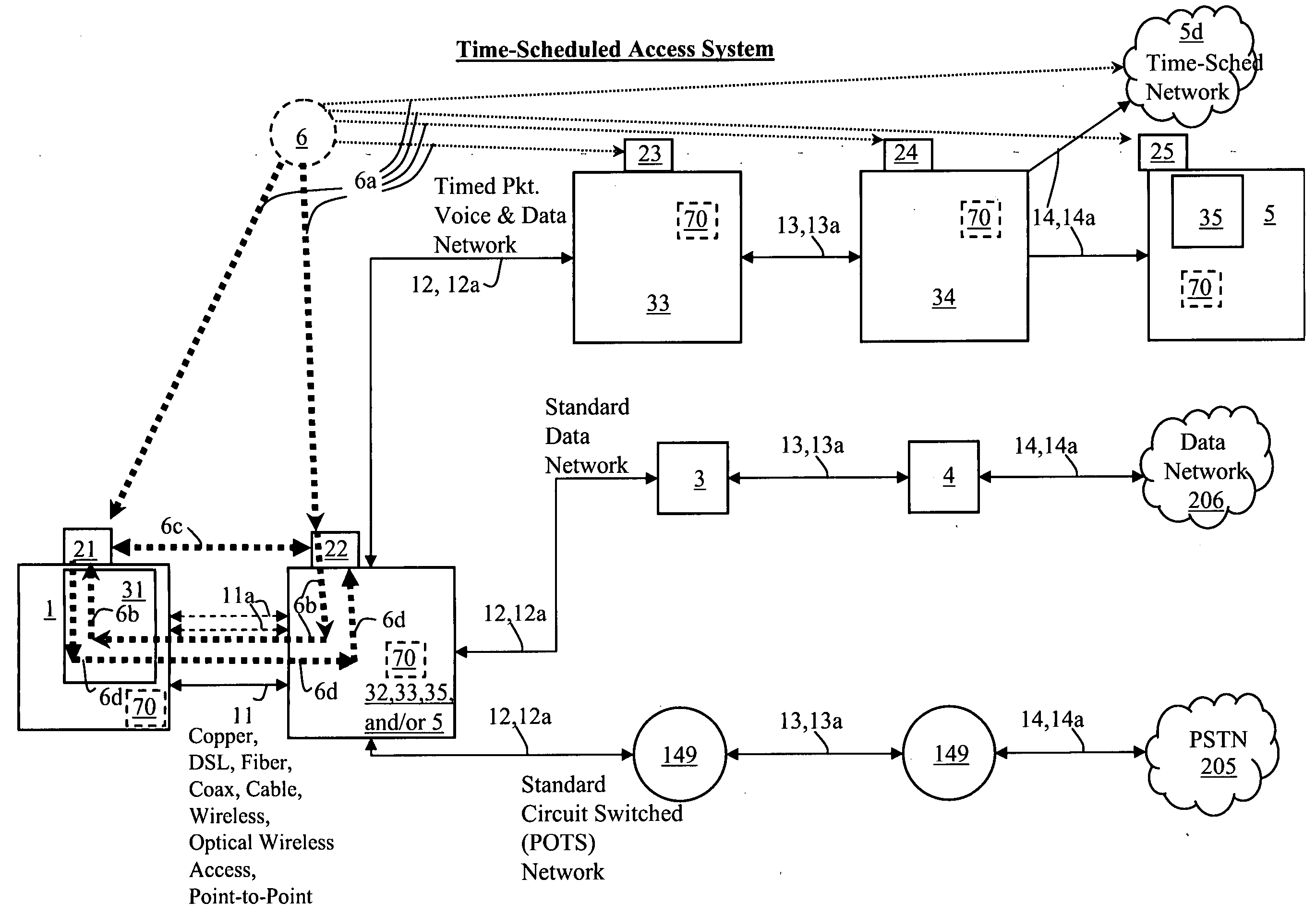
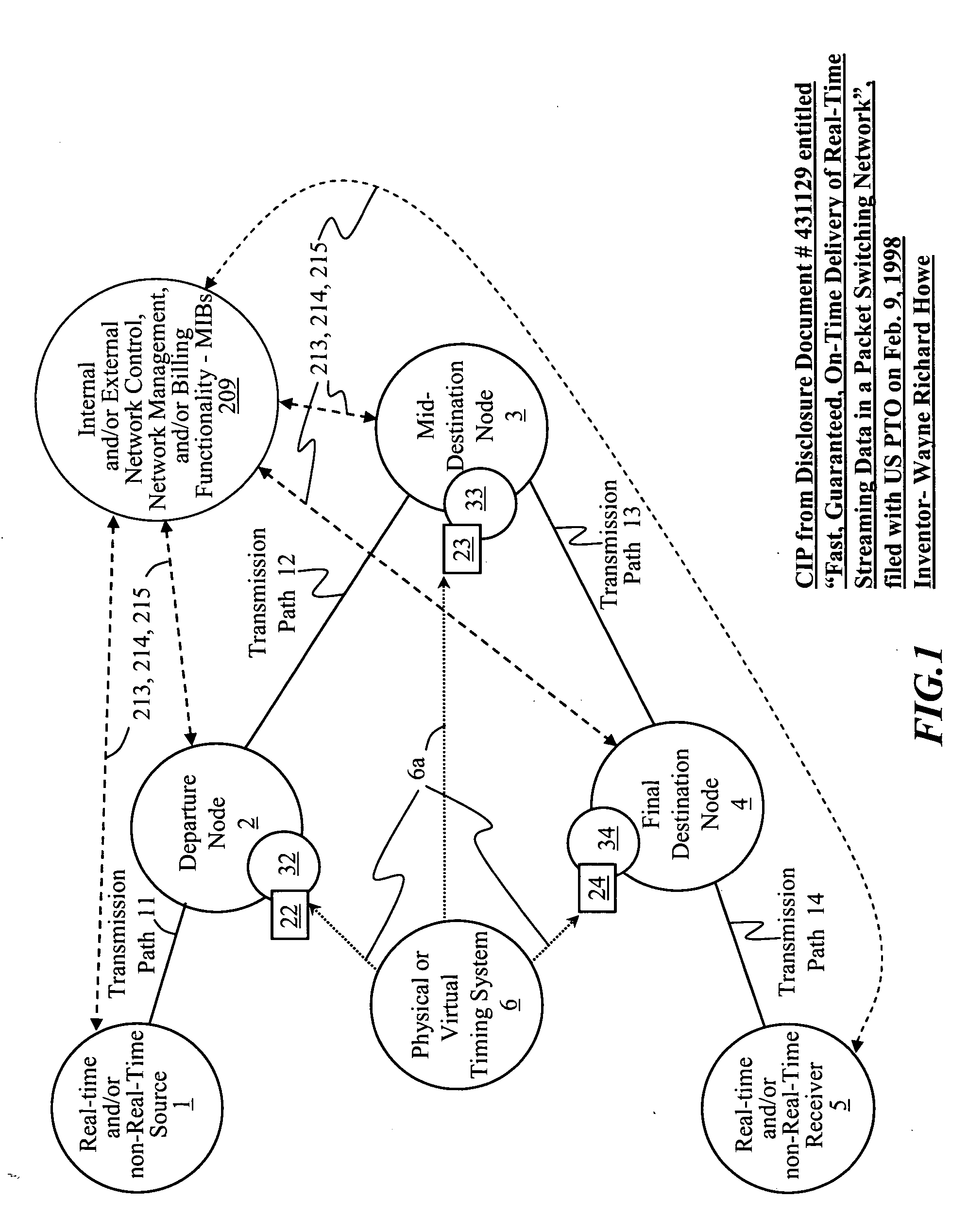
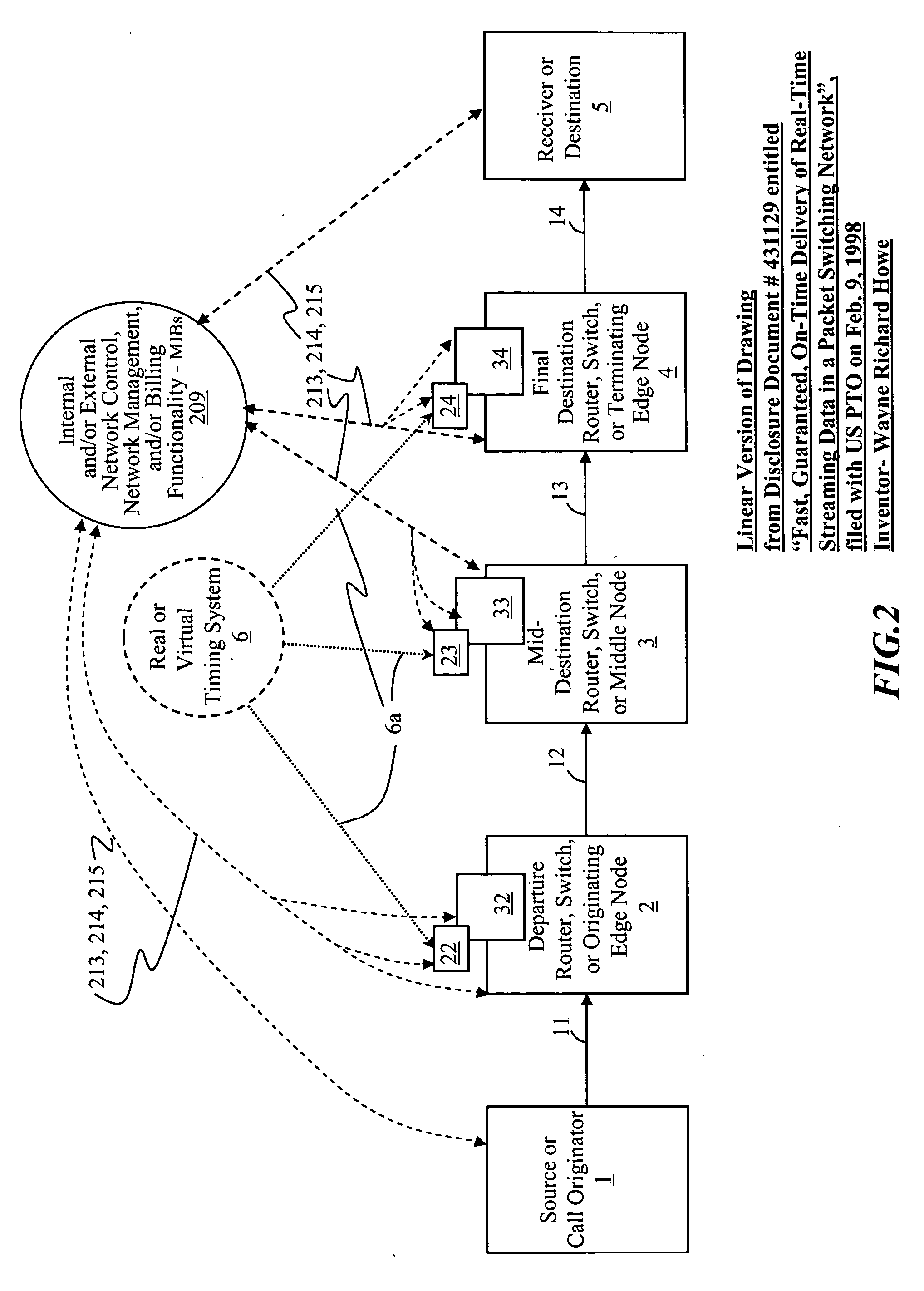
Time-scheduled and time-reservation packet switching
InactiveUS20050058149A1Optimum advantage and efficiencyImprove accuracyMultiplex system selection arrangementsTime-division multiplexData packTime schedule
Systems, methods, devices, processes, procedures, algorithms, networks, and network elements are described for time-scheduled and / or time-reserved dat networks. Invention provides capabilities for synchronizing data networks and / or data network links; for establishing time-schedules, time-reservations, time-schedule reservations, and / or reservation time-slots for packets, cells, frames, and / or datagrams; and for transferring, transmitting, switching, routing, and / or receiving time-sensitive, high-reliability, urgent, and / or other time-scheduled, time-reserved, time-allocated, and / or time-scheduled-reservation packets, cells, frames, and / or datagrams, such as real-time and high-priority messages over these networks. The invention(s) enables packet-, cell-, datagram- and / or frame-based networks to thereby efficiently, reliably, and in guaranteed real-time, to switch and / or route data such as voice, video, streaming, and other real-time, high-priority, high-reliability, and / or expedited data with guaranteed delivery and guaranteed quality of service. Networks may be fixed, point-to-point, mobile, ad-hoc, optical, electrical, and / or wireless.
Owner:HOWE WAYNE RICHARD
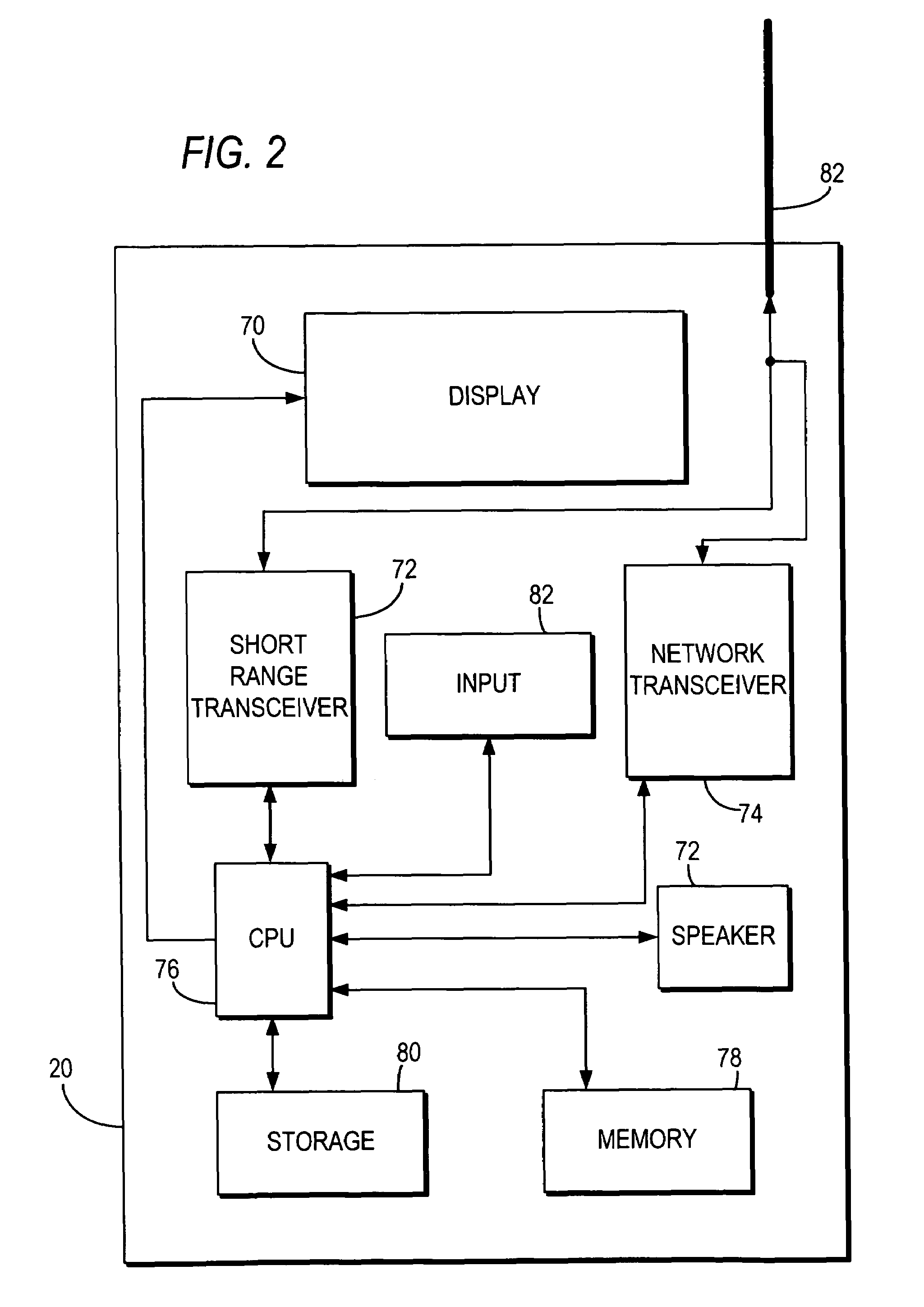
Medical device wireless adapter
The invention relates generally to a medical device wireless adapter, and more particularly, to a module that adapts an existing legacy or newly designed medical device to a healthcare provider's wireless infrastructure.
Owner:WELCH ALLYN INC
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
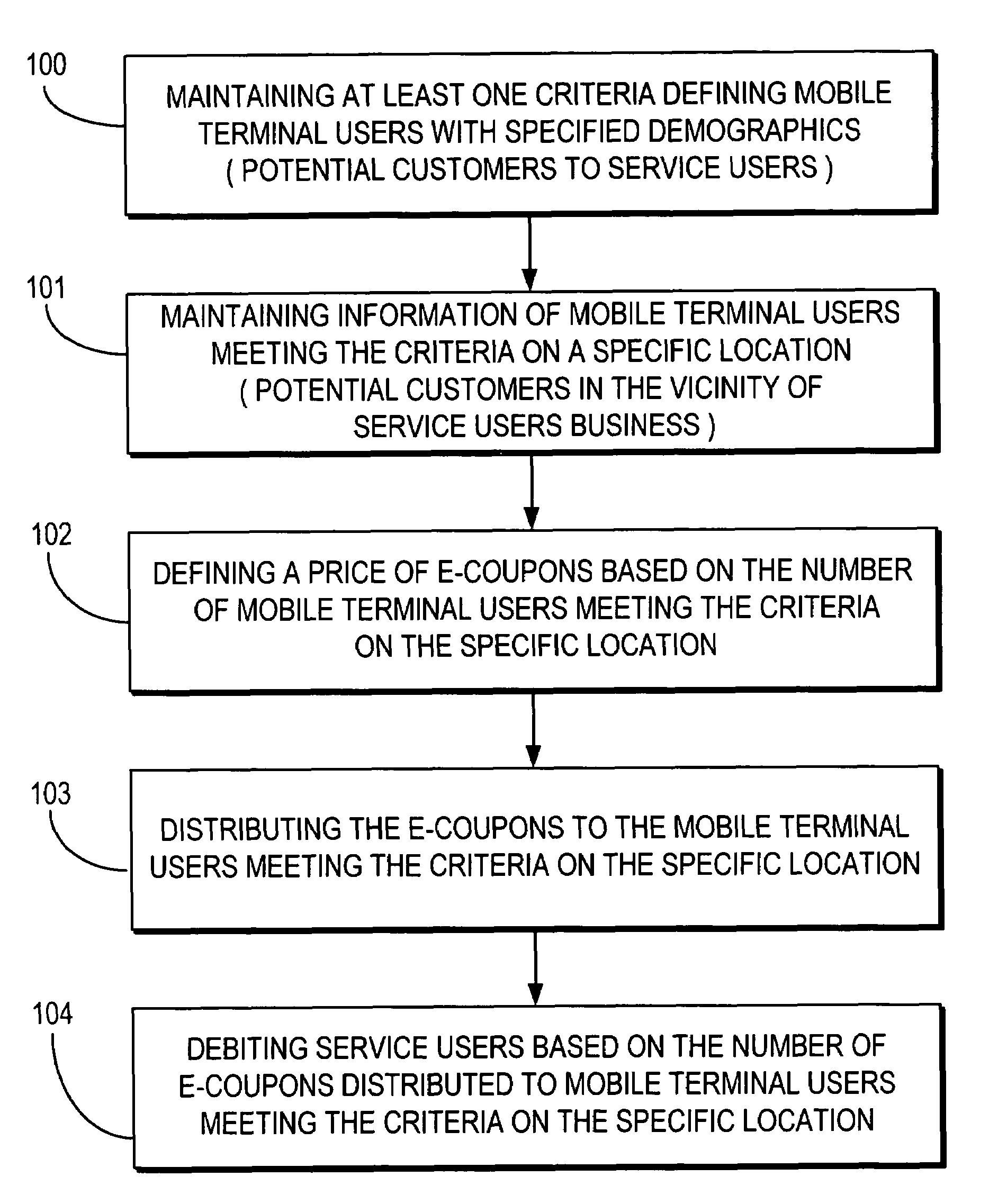
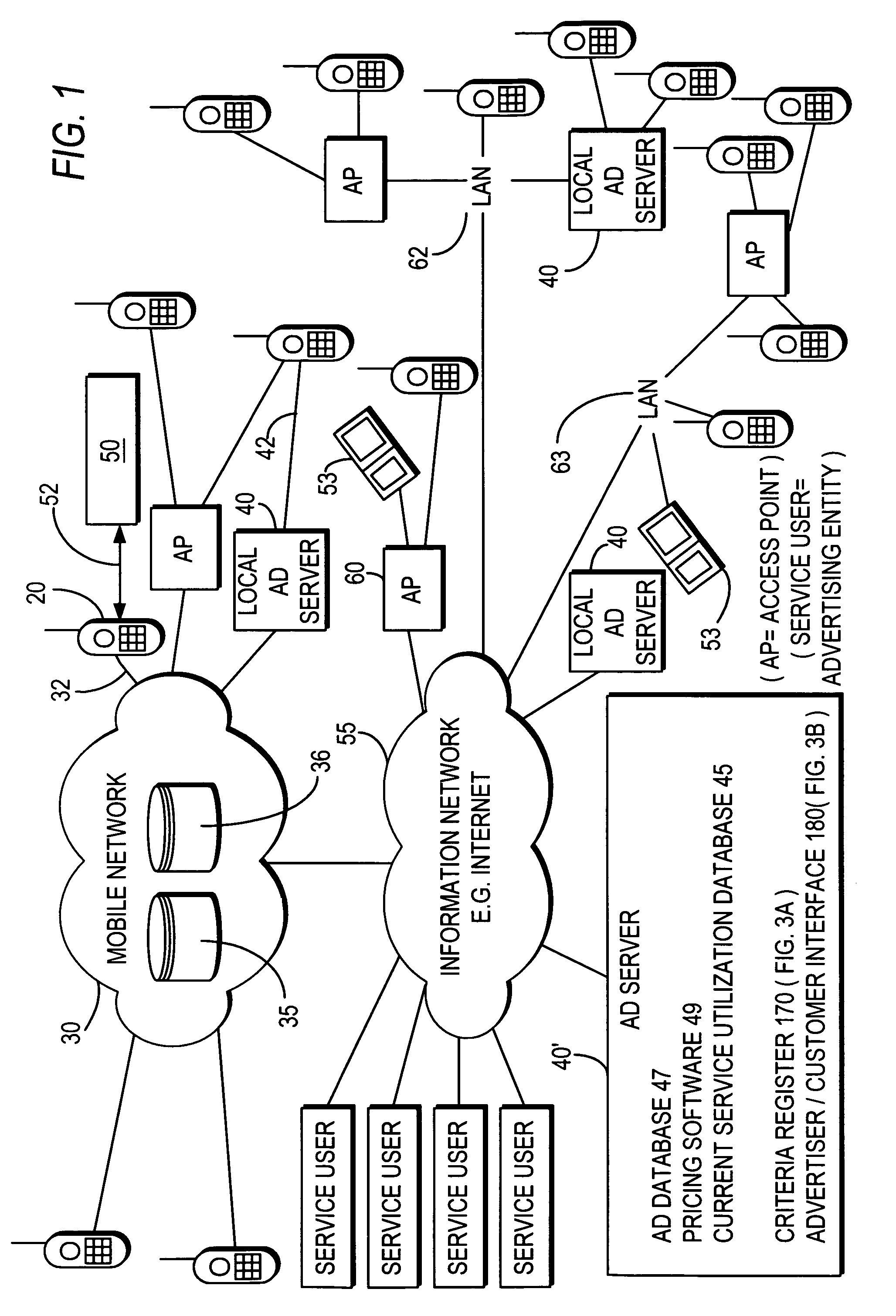
Real-time wireless e-coupon (promotion) definition based on available segment
Advertising messages are provided to mobile terminals of those users identified by user information as meeting certain criteria, such as users fitting particular user profiles and / or users located in a particular desired location. The content of the advertising messages is dynamically generated based on the number of mobile terminals to whom the advertising message is to be sent and the advertising message is sent to the identified mobile terminals over a mobile network or a short range communication signal. In the latter case, location information may be sent to the mobile terminal along with an advertising message. Where the content of an advertising message comprises an electronic coupon, the value of the coupon depends on the number of mobile terminals to whom the advertising message is to be sent. A mobile terminal user can redeem an electronic coupon by transmitting it from his mobile terminal to a coupon redemption terminal.
Owner:NOKIA TECH OY
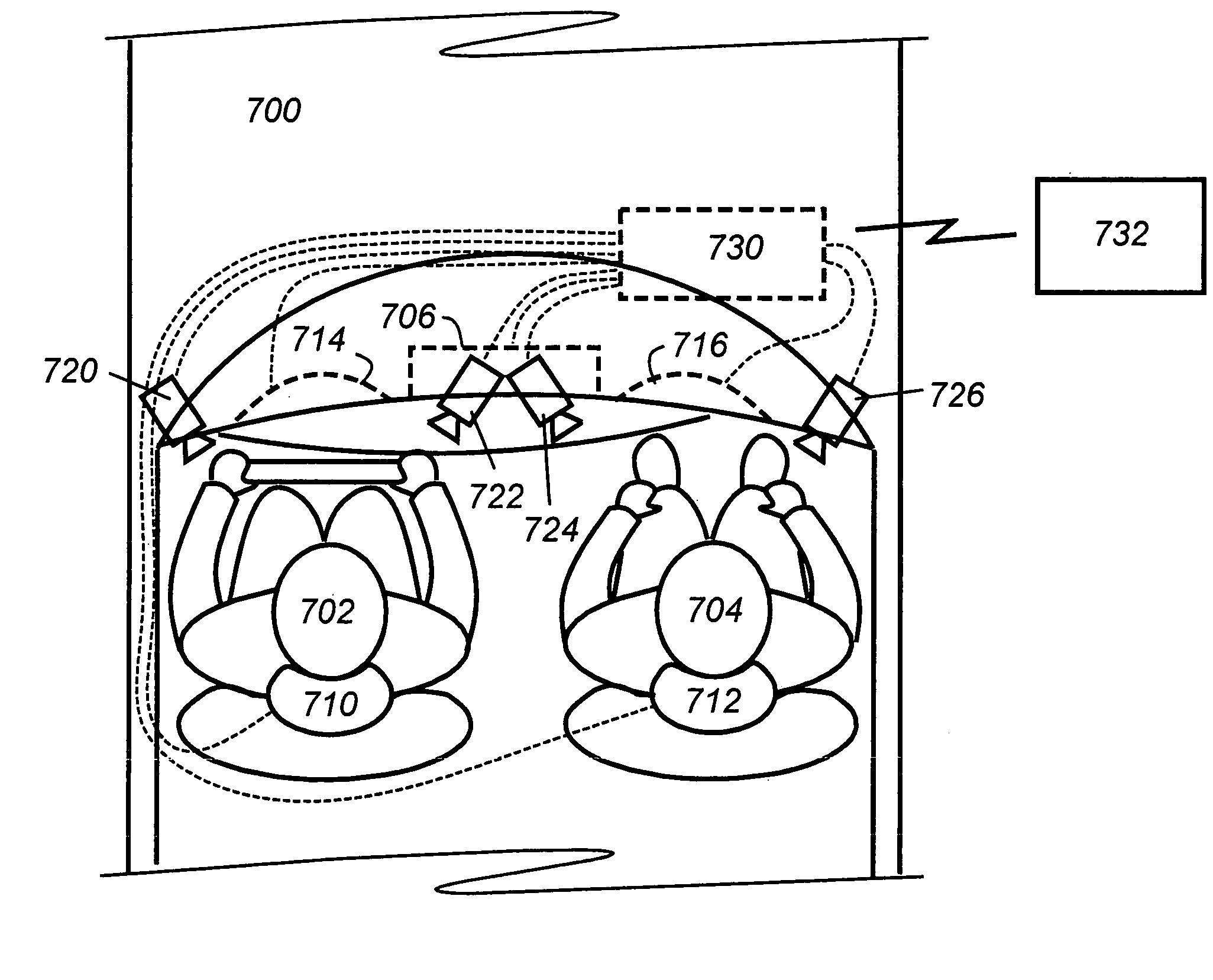
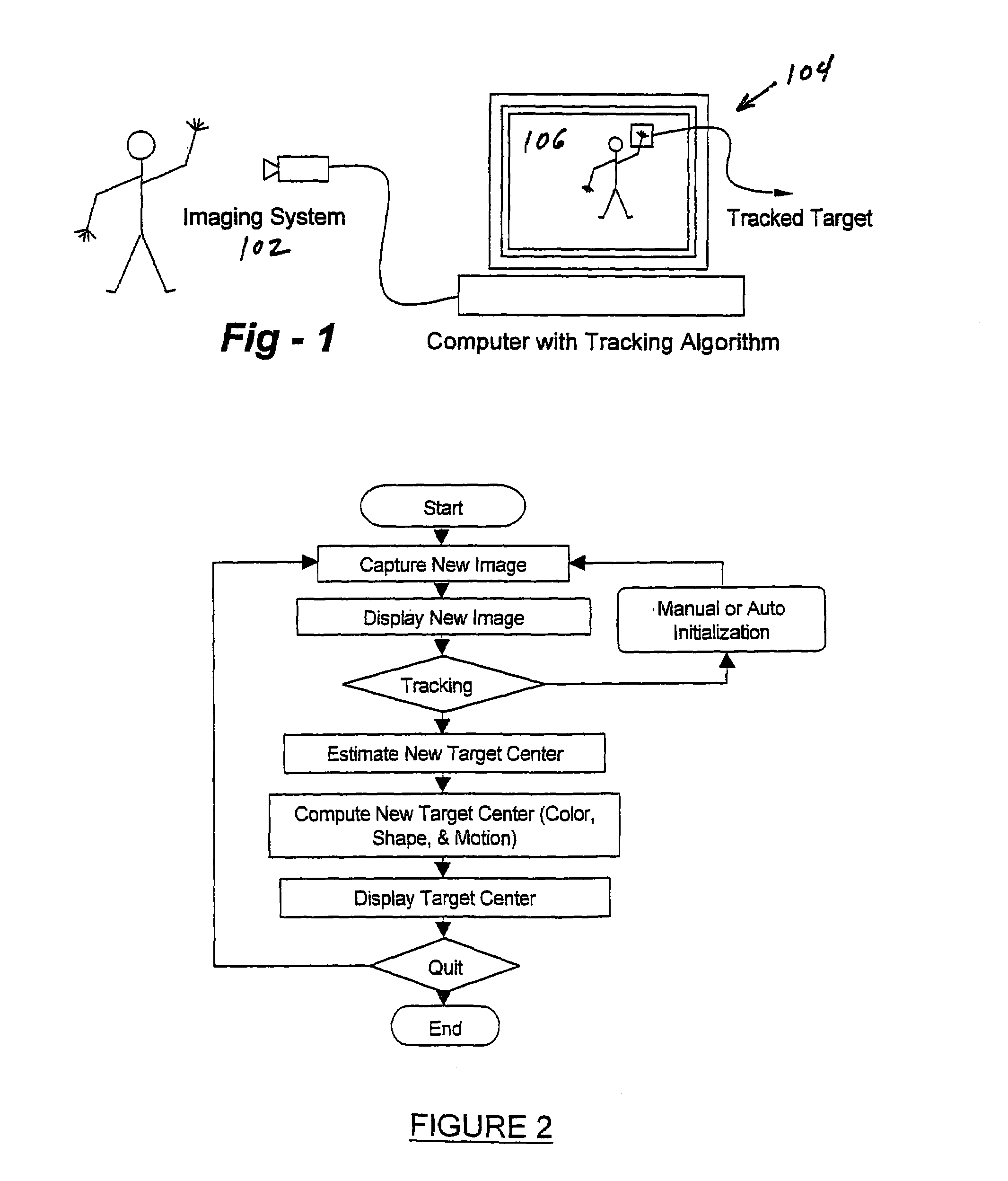
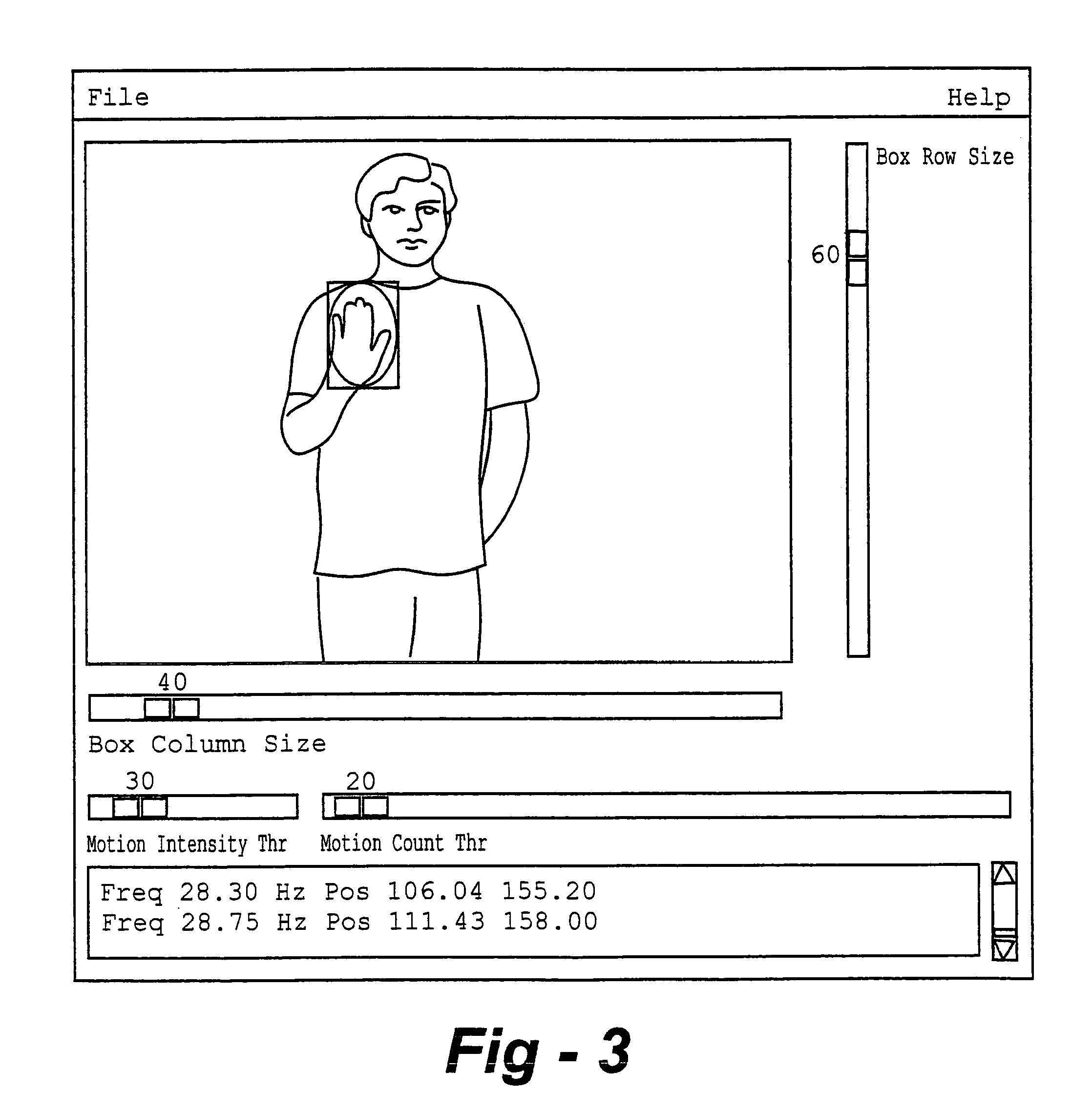
Tracking and gesture recognition system particularly suited to vehicular control applications
InactiveUS7050606B2Realize automatic adjustmentImage enhancementImage analysisDriver/operatorControl system
A system and method tracks the movements of a driver or passenger in a vehicle (ground, water, air, or other) and controls devices in accordance with position, motion, and / or body or hand gestures or movements. According to one embodiment, an operator or passenger uses the invention to control comfort or entertainment features such the heater, air conditioner, lights, mirror positions or the radio / CD player using hand gestures. An alternative embodiment facilitates the automatic adjustment of car seating restraints based on head position. Yet another embodiment is used to determine when to fire an airbag (and at what velocity or orientation) based on the position of a person in a vehicle seat. The invention may also be used to control systems outside of the vehicle. The on-board sensor system would be used to track the driver or passenger, but when the algorithms produce a command for a desired response, that response (or just position and gesture information) could be transmitted via various methods (wireless, light, whatever) to other systems outside the vehicle to control devices located outside the vehicle. For example, this would allow a person to use gestures inside the car to interact with a kiosk located outside of the car.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
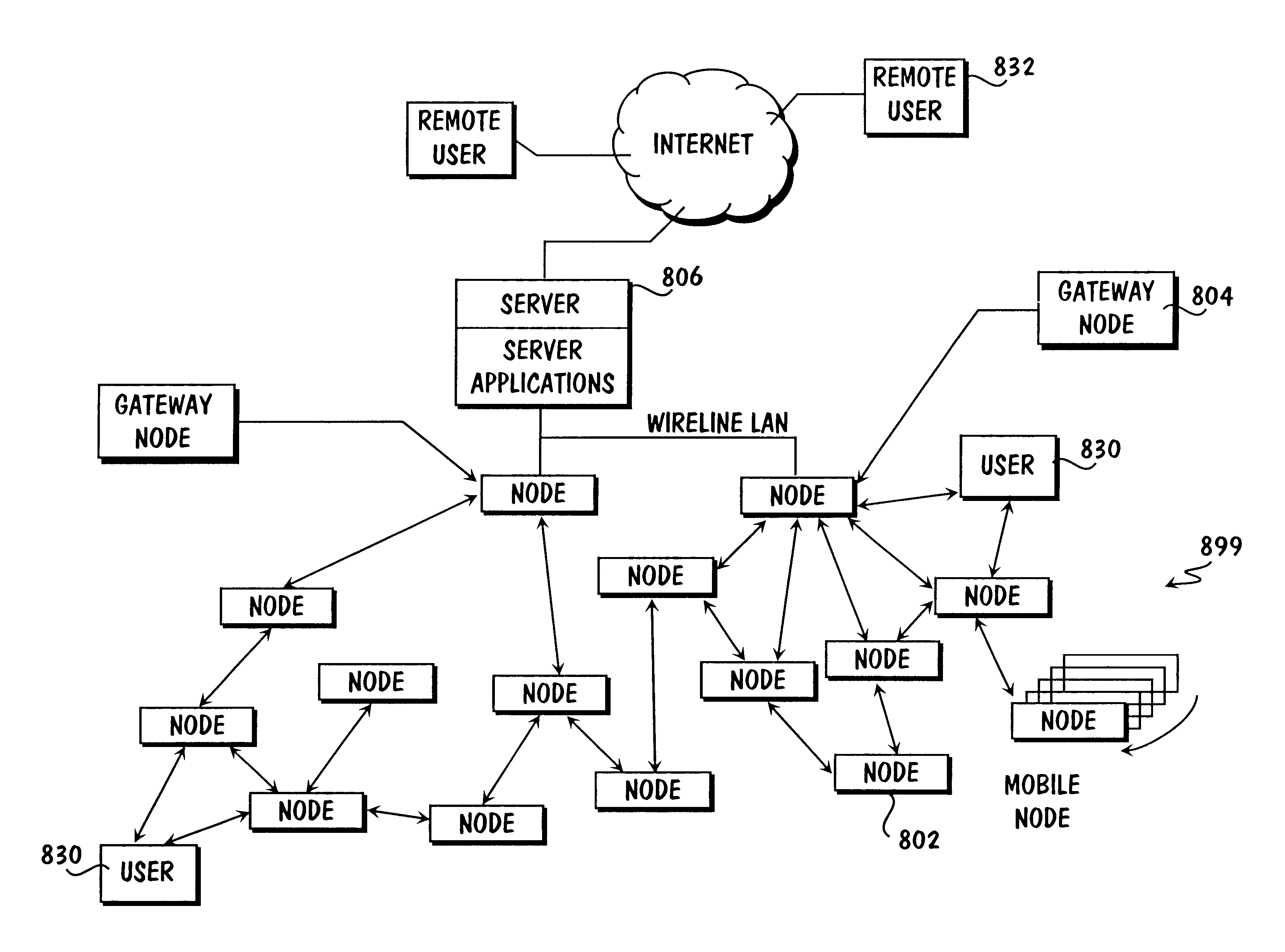
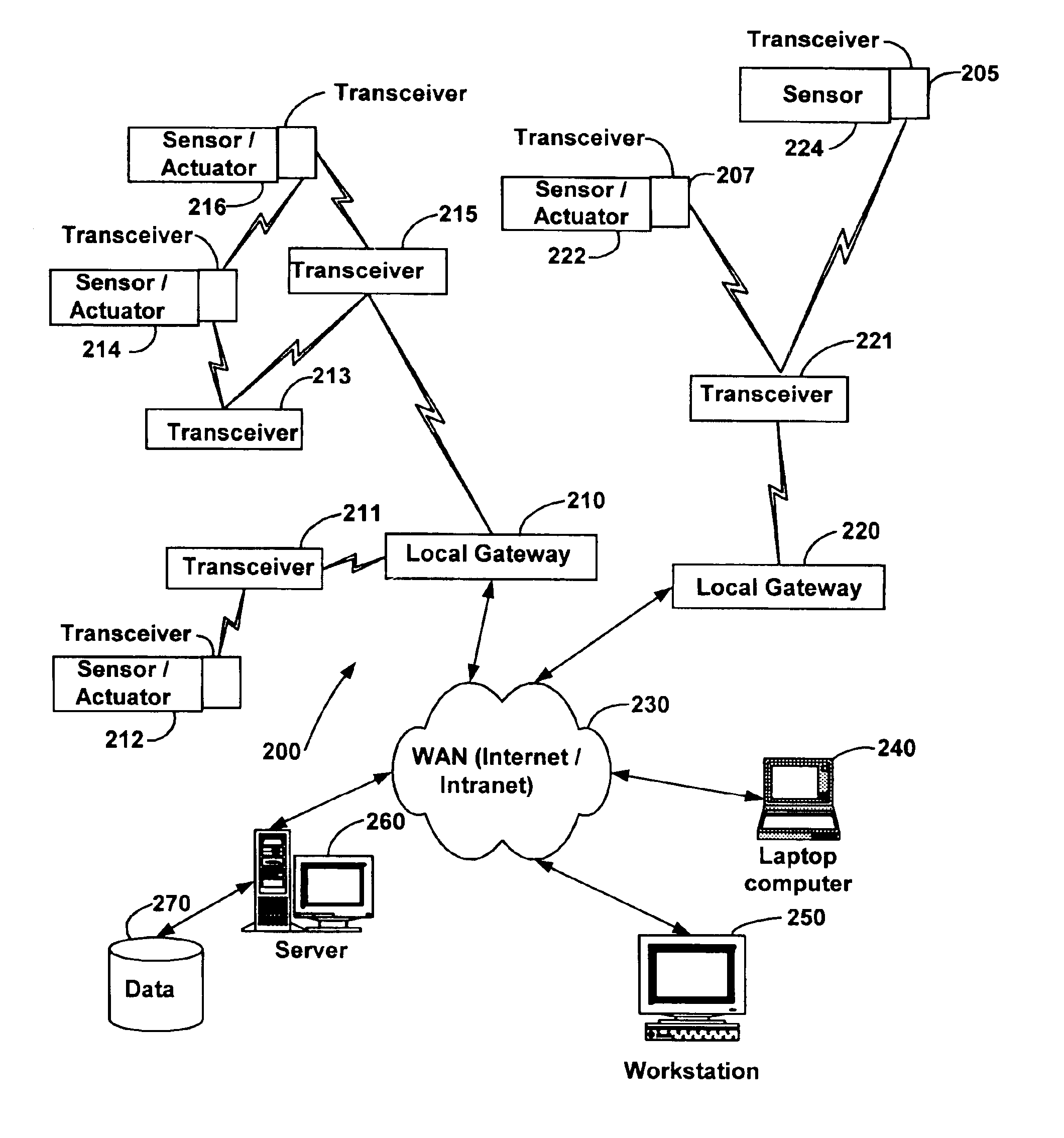
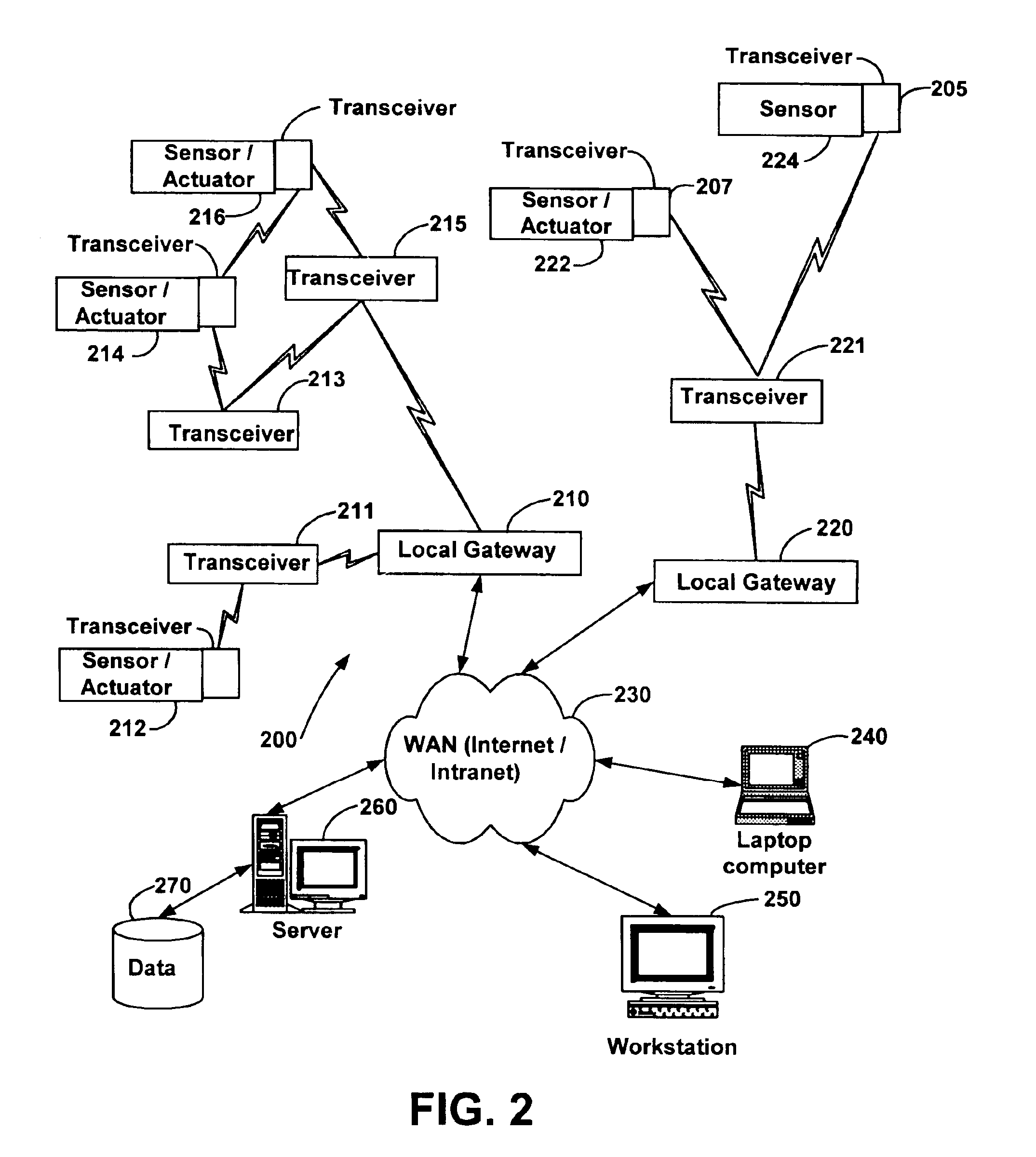
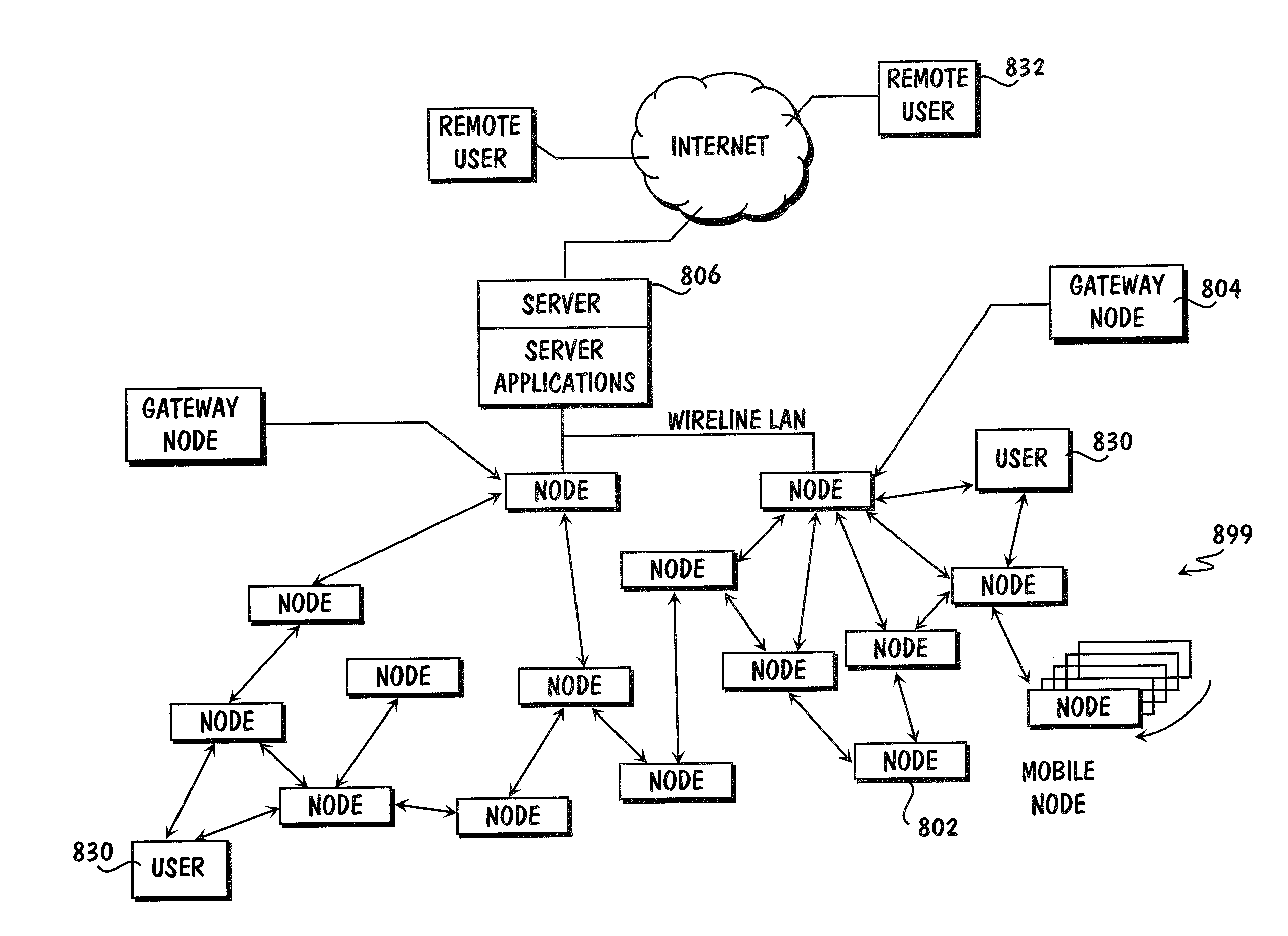
System and method for monitoring and controlling remote devices
InactiveUS6914893B2Easy to integrateEasily mapped into the packet protocolActive radio relay systemsElectric testing/monitoringTransceiverTelecommunications link
The present system is directed to a computerized system for monitoring and controlling remote devices by transmitting data between the remote systems and a gateway interface via a packet message protocol system. The system comprises one or more remote sensors to be read and possibly one or more actuators to be remotely controlled. The remote sensor(s) / actuator(s) then interface with uniquely identified remote transceivers that transmit and / or receive data. If necessary in individual applications, signal repeaters may relay information between the transceiver(s) and the gateway interface. Communication links between the remote transceivers and the gateway interface are preferably wireless but may also be implemented via a mixture of wireless and wired communication links. To successfully communicate between the transceiver(s) and the gateway interface, the present invention receives a plurality of RF signal transmissions containing a packet protocol via RF signals that includes sender and receiver identifiers, a description of the packet itself, a message number, any commands, the data, and an error detector. In addition, the packet protocol can be easily integrated with alternate data communication protocols for use with systems other than the Internet.
Owner:SIPCO
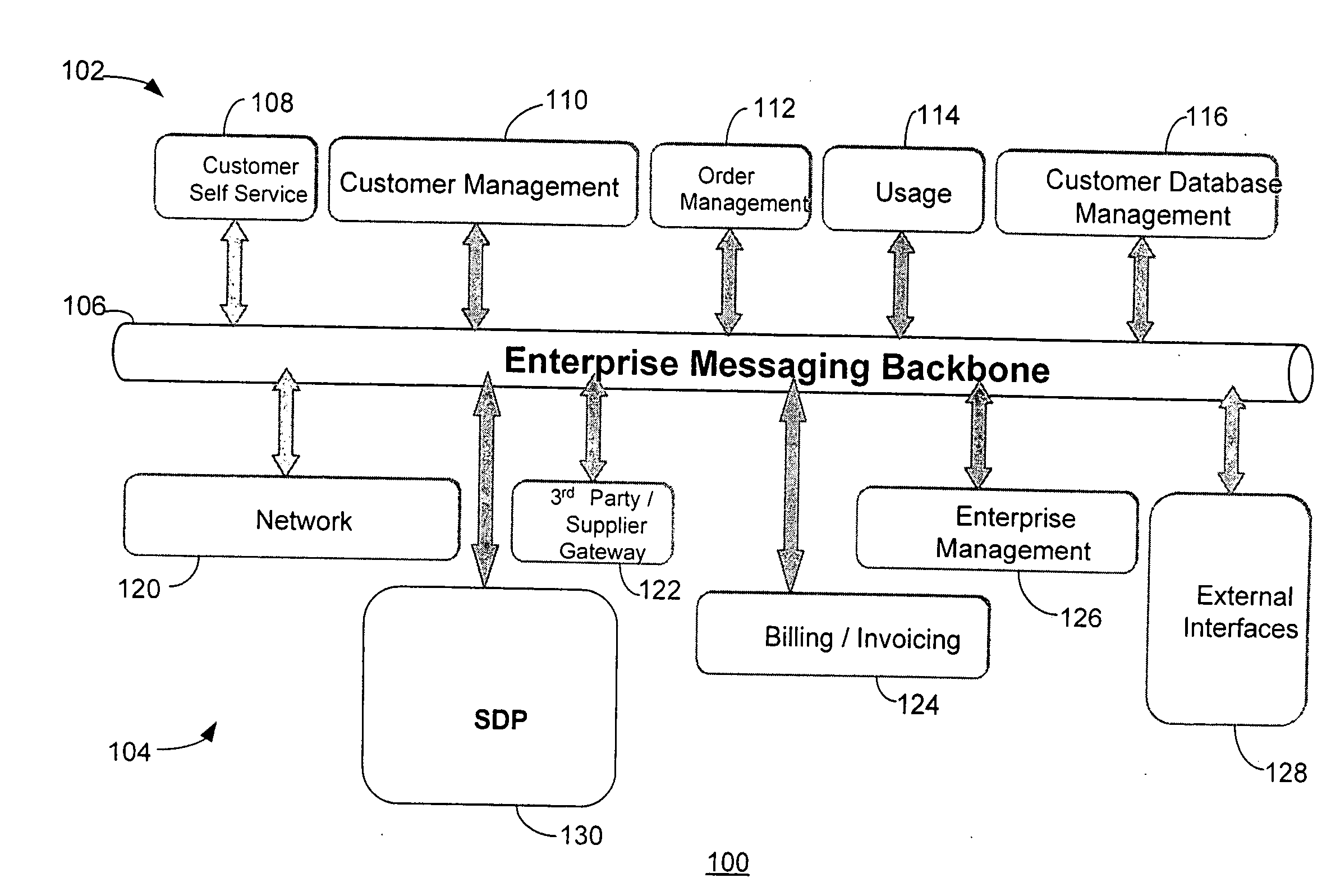
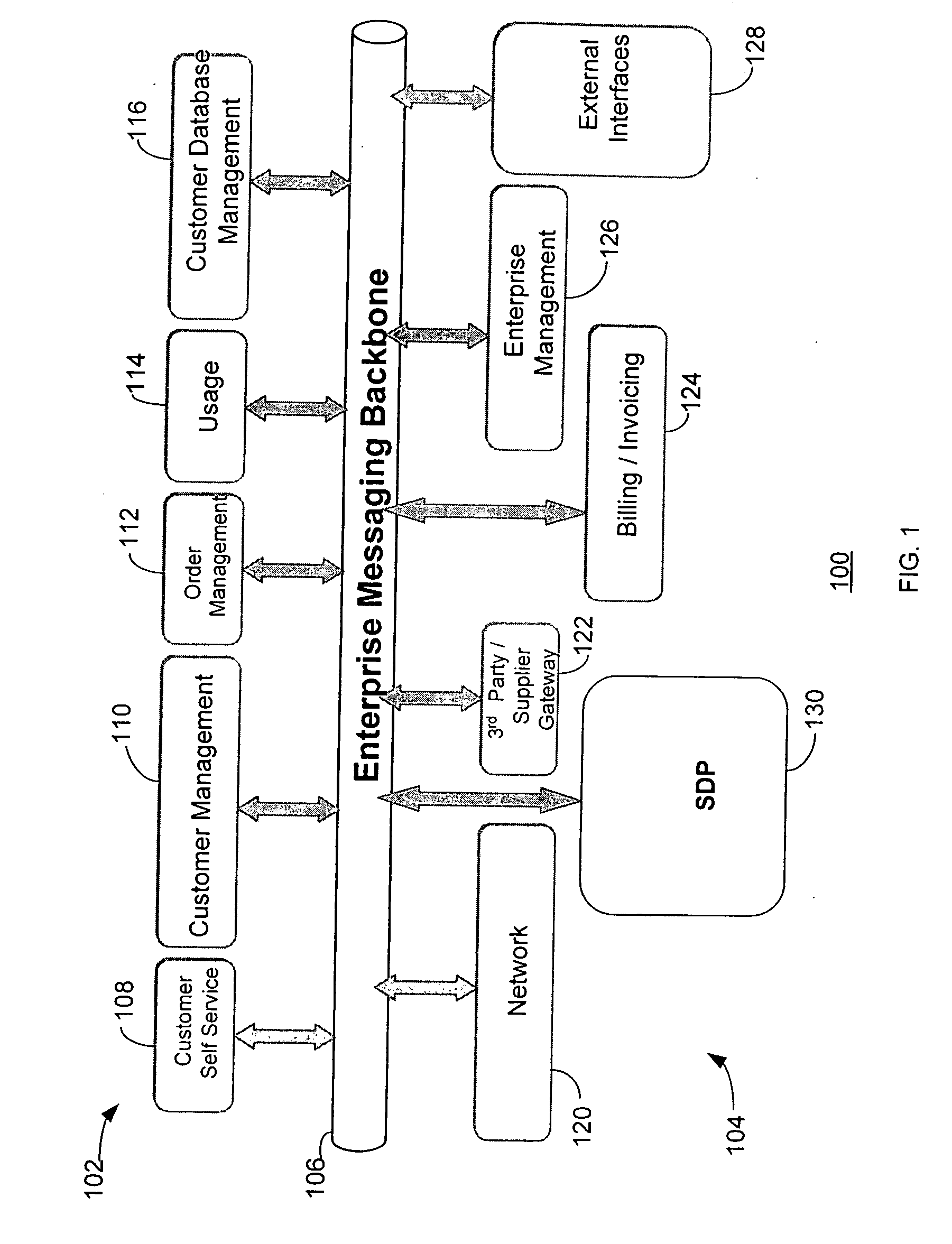
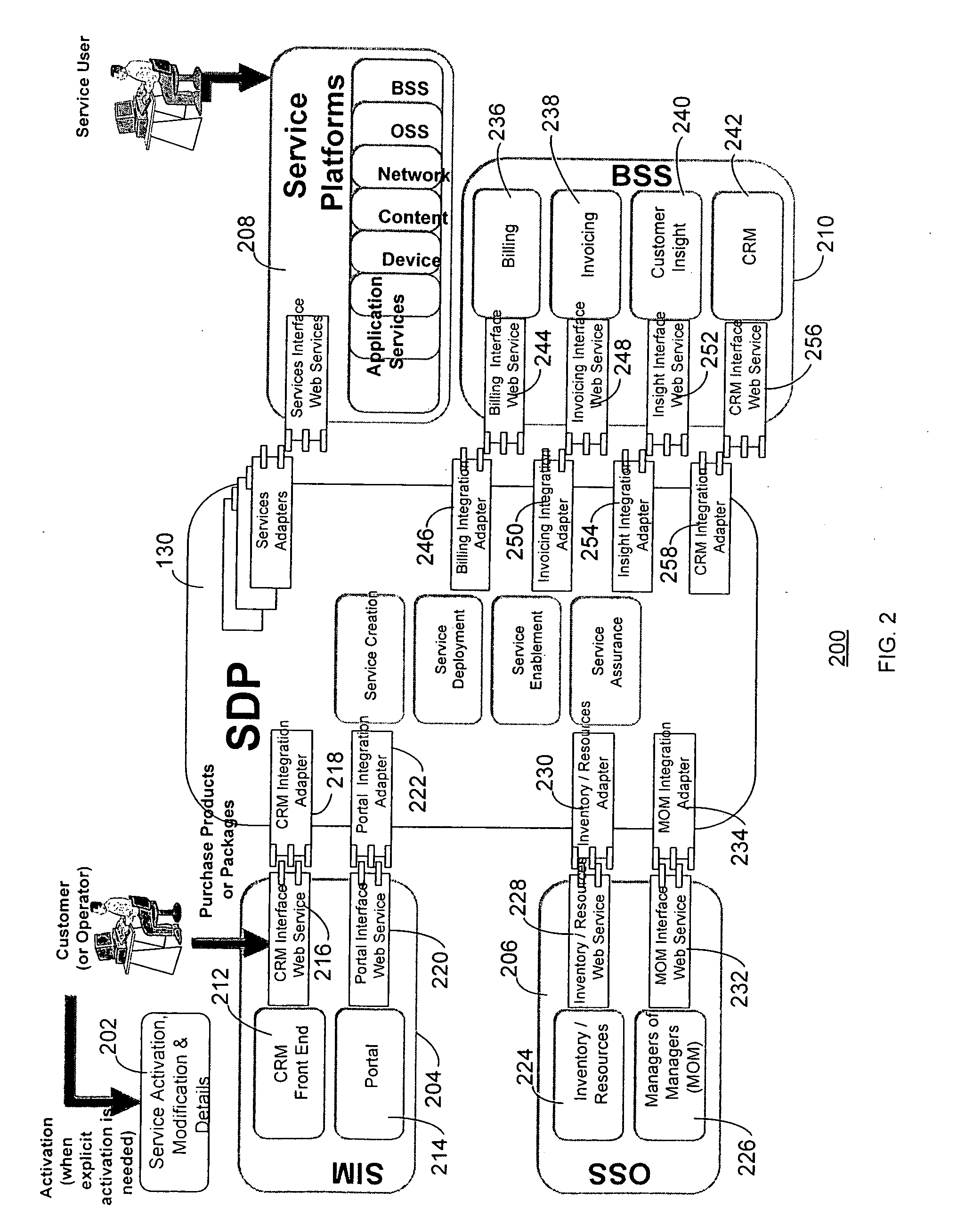
Service delivery platform
InactiveUS20070150480A1Easy to deployQuick serviceTechnology managementBilling/invoicingEngineeringUser equipment
A service delivery platform is disclosed, including method and apparatus for managing the delivery of a variety of services to customers or subscribers. Exemplary services that may be managed using the service delivery platform include telecommunication services such as cable, wire line and wireless services. The service delivery platform creates, hosts, and manages services over different channels and end user devices. The implementation of the service delivery platform will dramatically simplify service deployment and management, and allow an enterprise to develop new services more rapidly with the reduced development efforts.
Owner:ACCENTURE GLOBAL SERVICES LTD
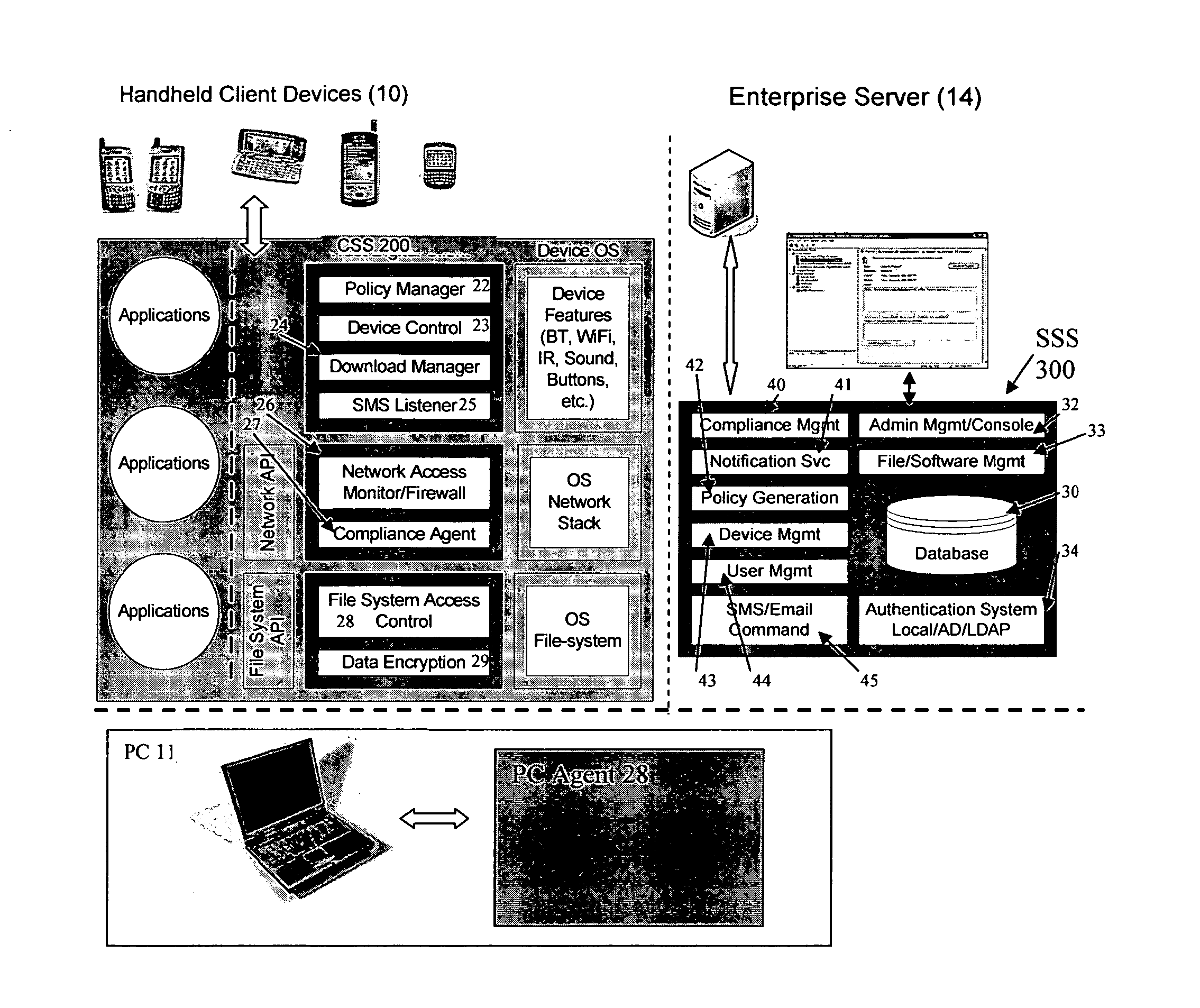
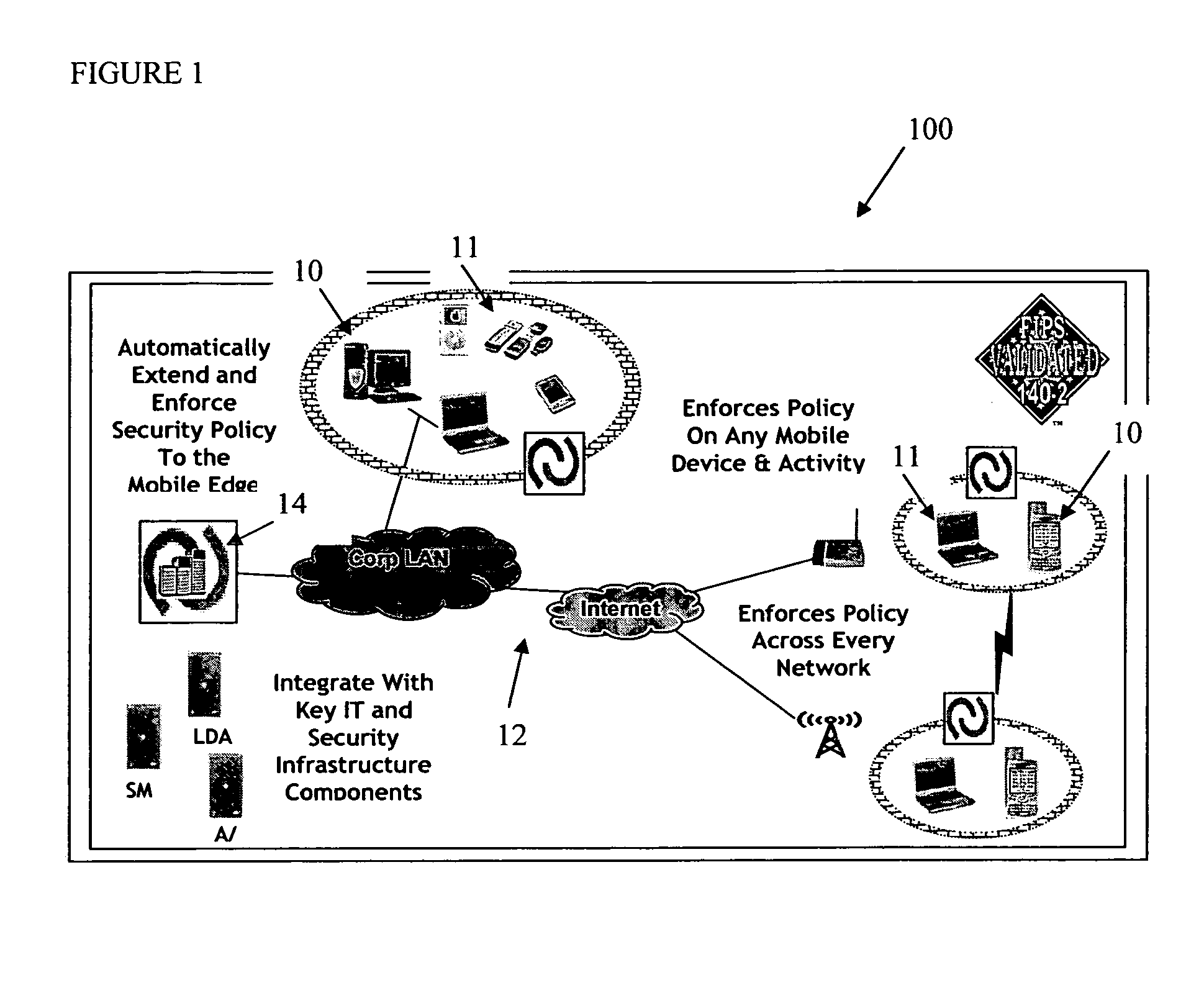
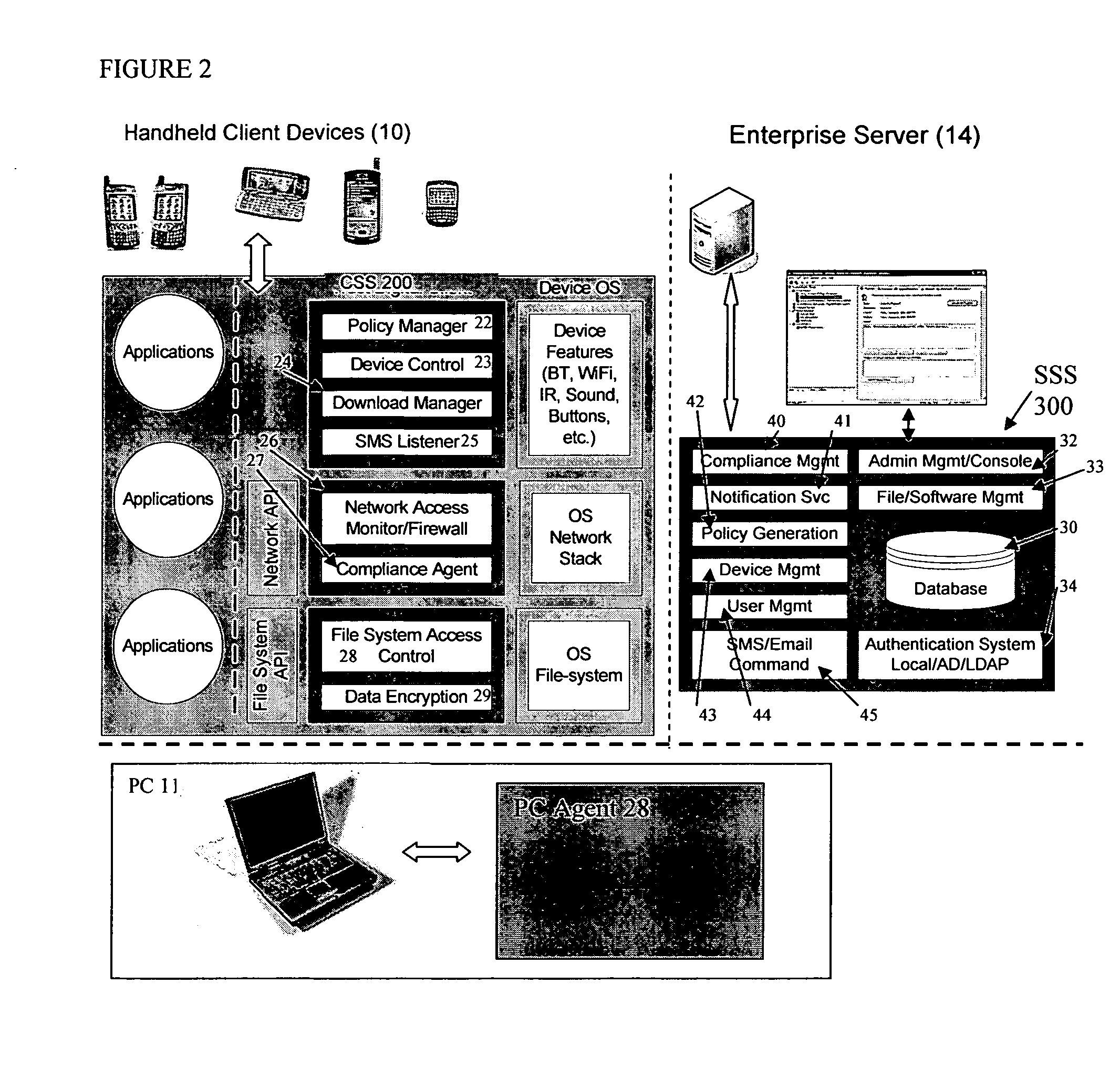
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
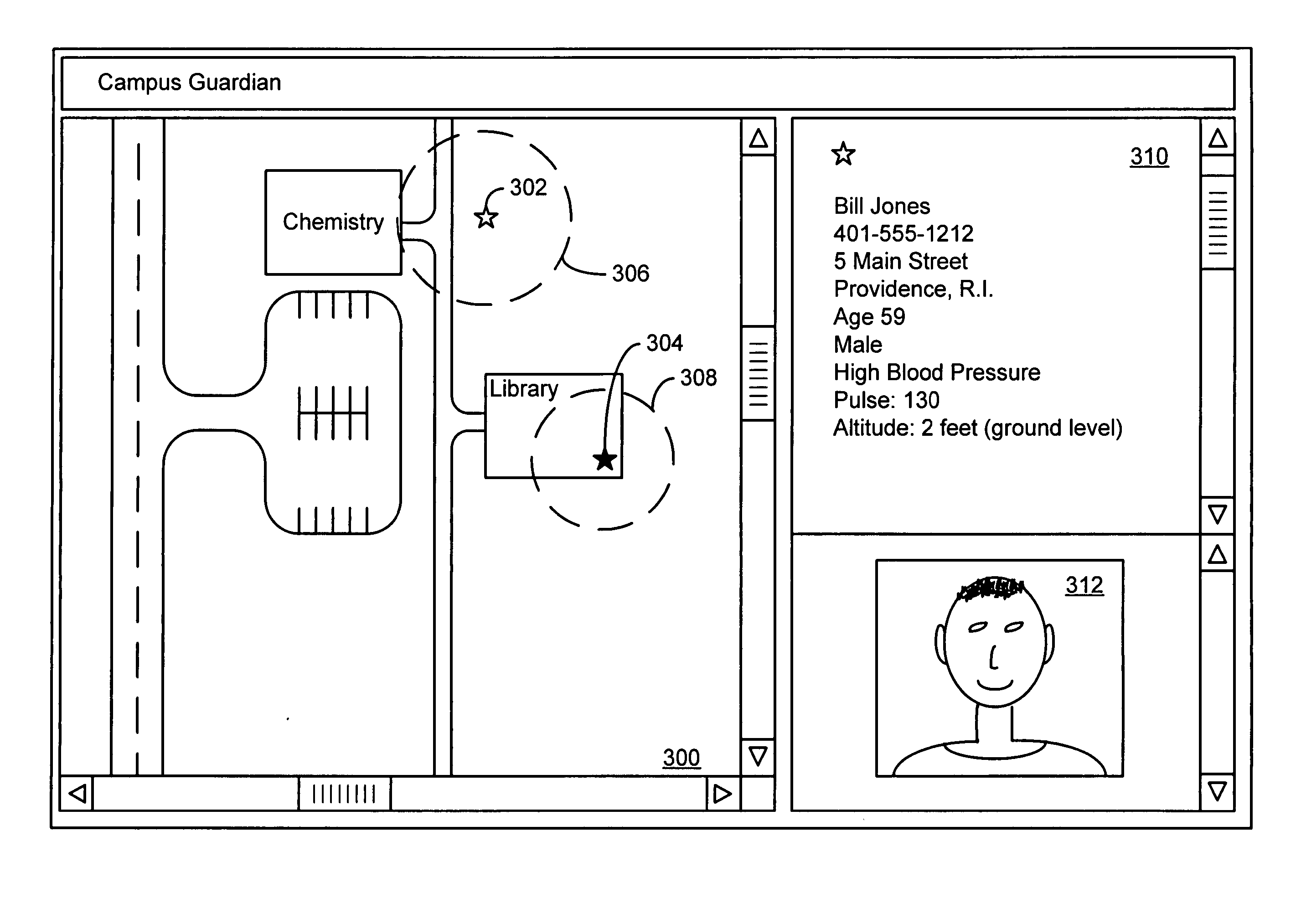
Wireless virtual campus escort system
InactiveUS20050075116A1Bioelectric signal measurementNavigational calculation instrumentsVirtual campusSecurity guard
Owner:AMERICAN TRAFFIC SOLUTIONS
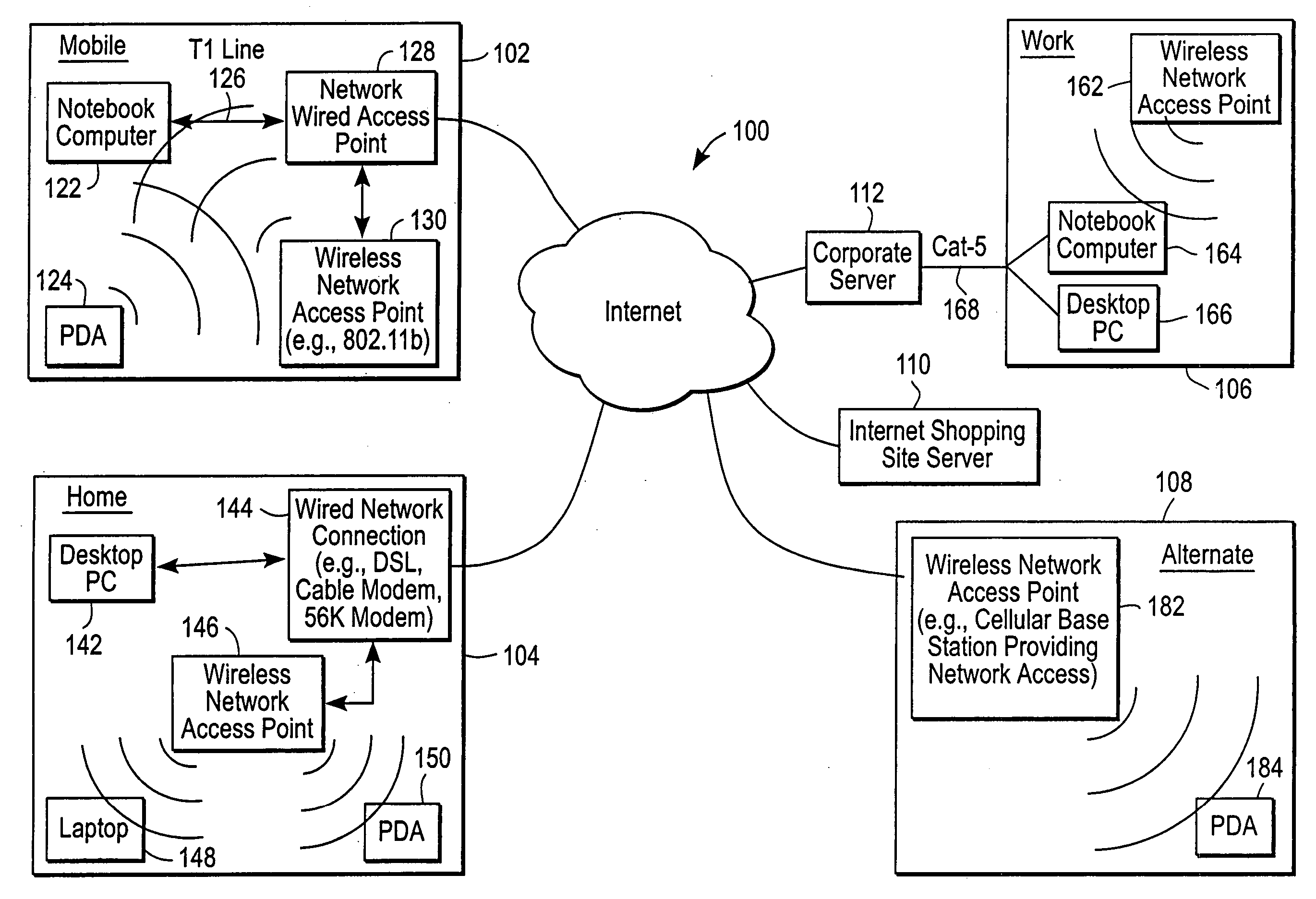
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS20060053447A1Facilitate transmission and receptionTelevision system detailsColor television detailsControl signalDisplay device
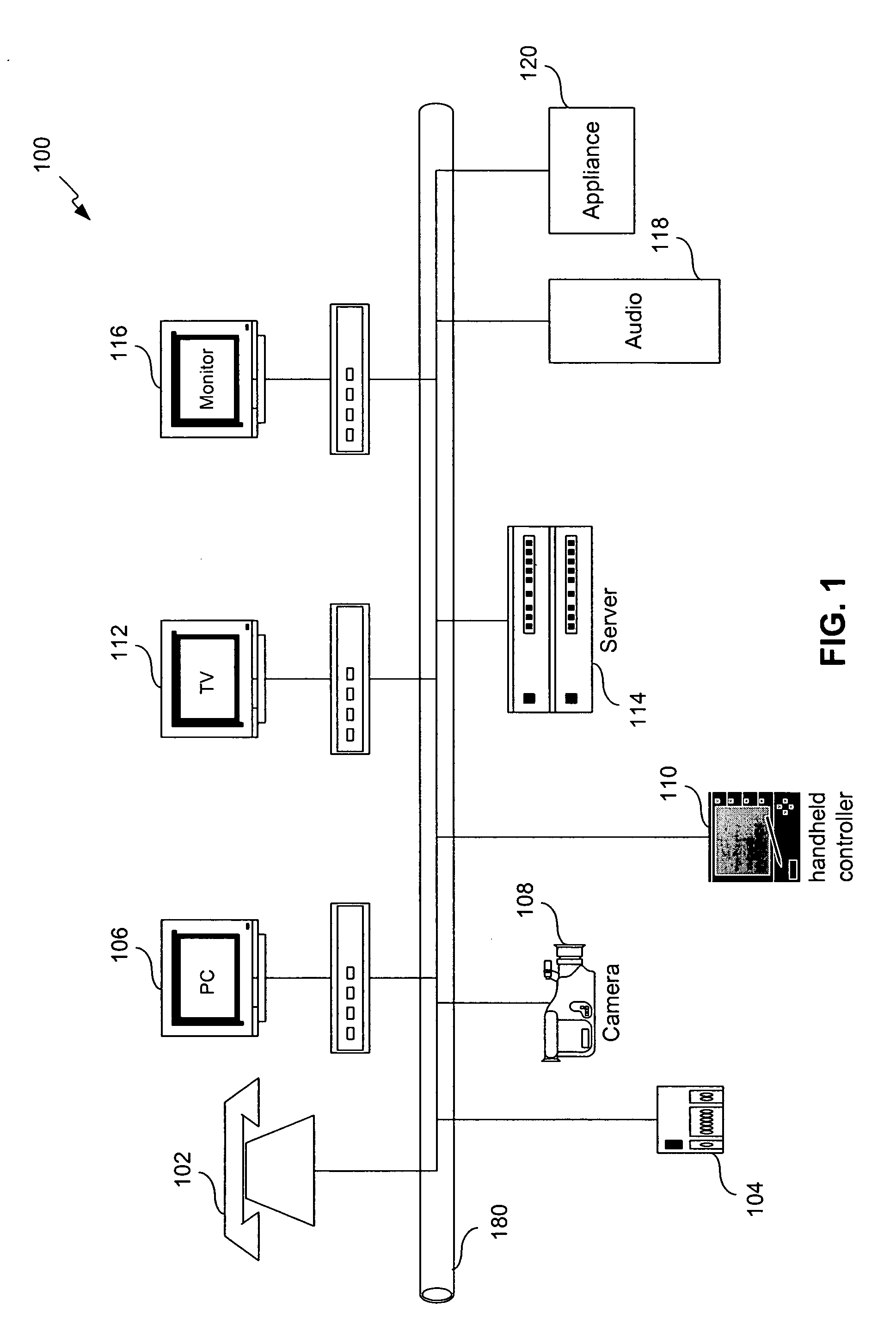
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
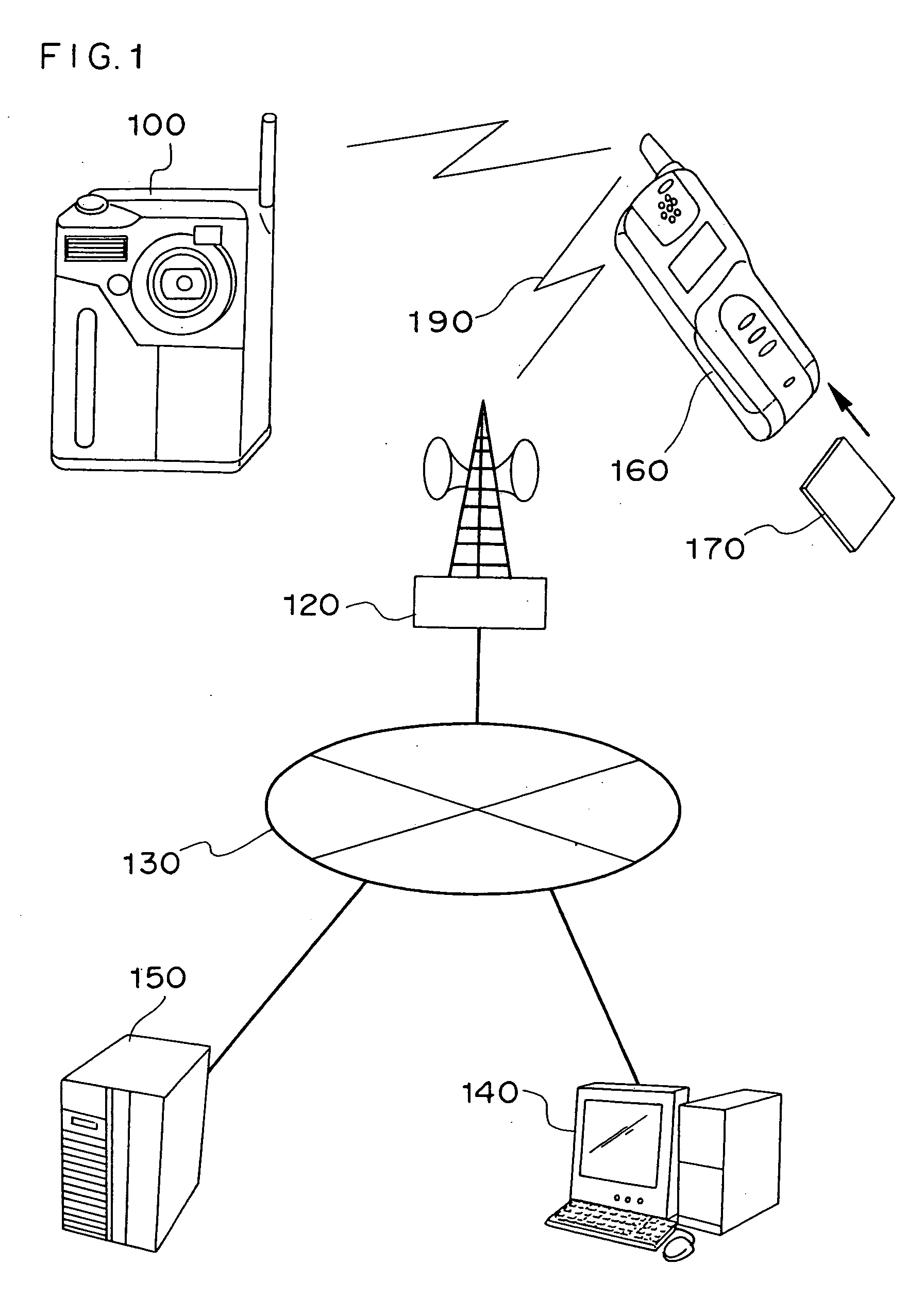
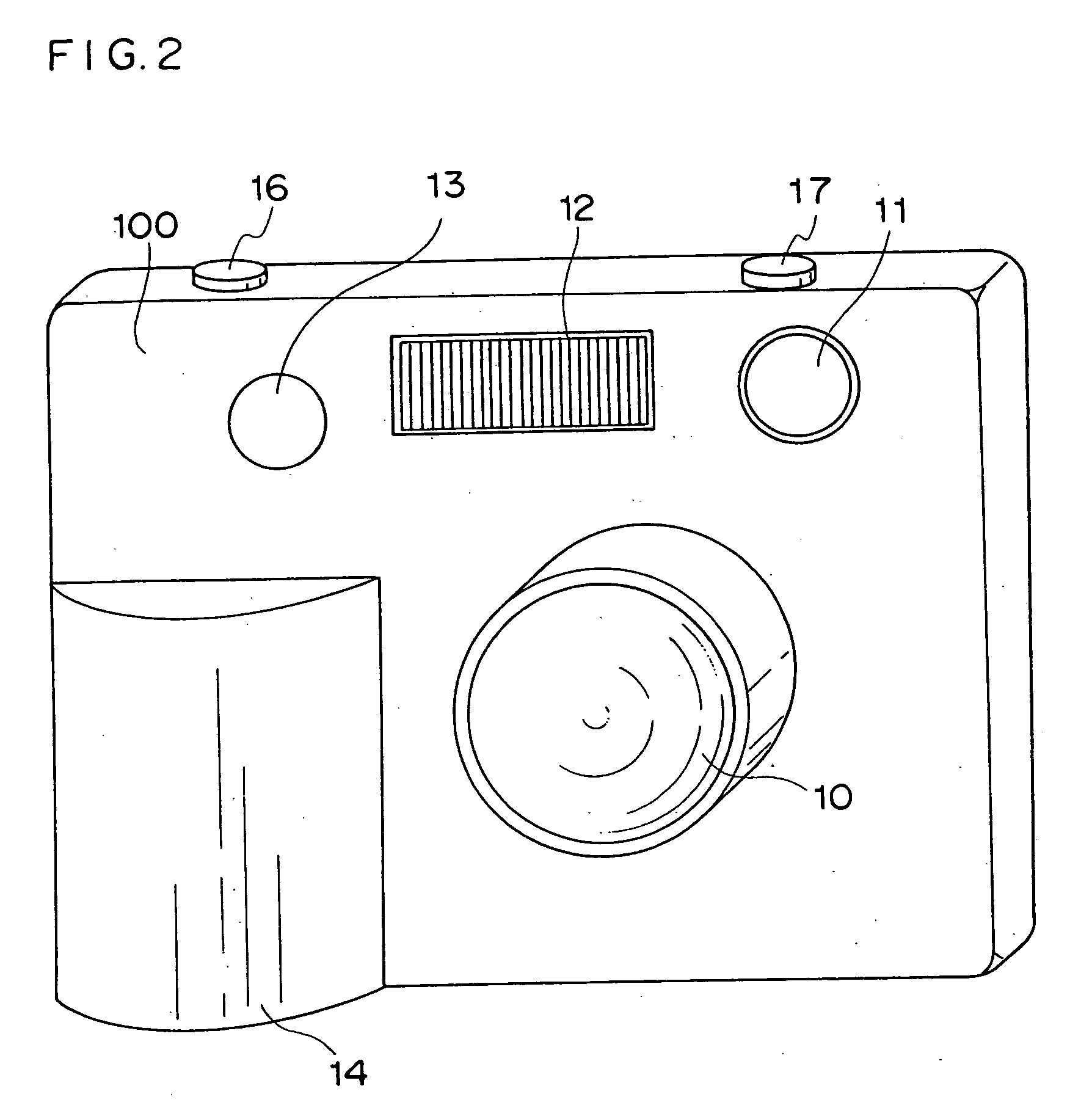
Electronic apparatus, electronic camera, electronic device, image display apparatus, and image transmission system
ActiveUS20050001024A1Speed up user identificationAvoid mistakesTelevision system detailsElectric signal transmission systemsComputer hardwareTransfer system
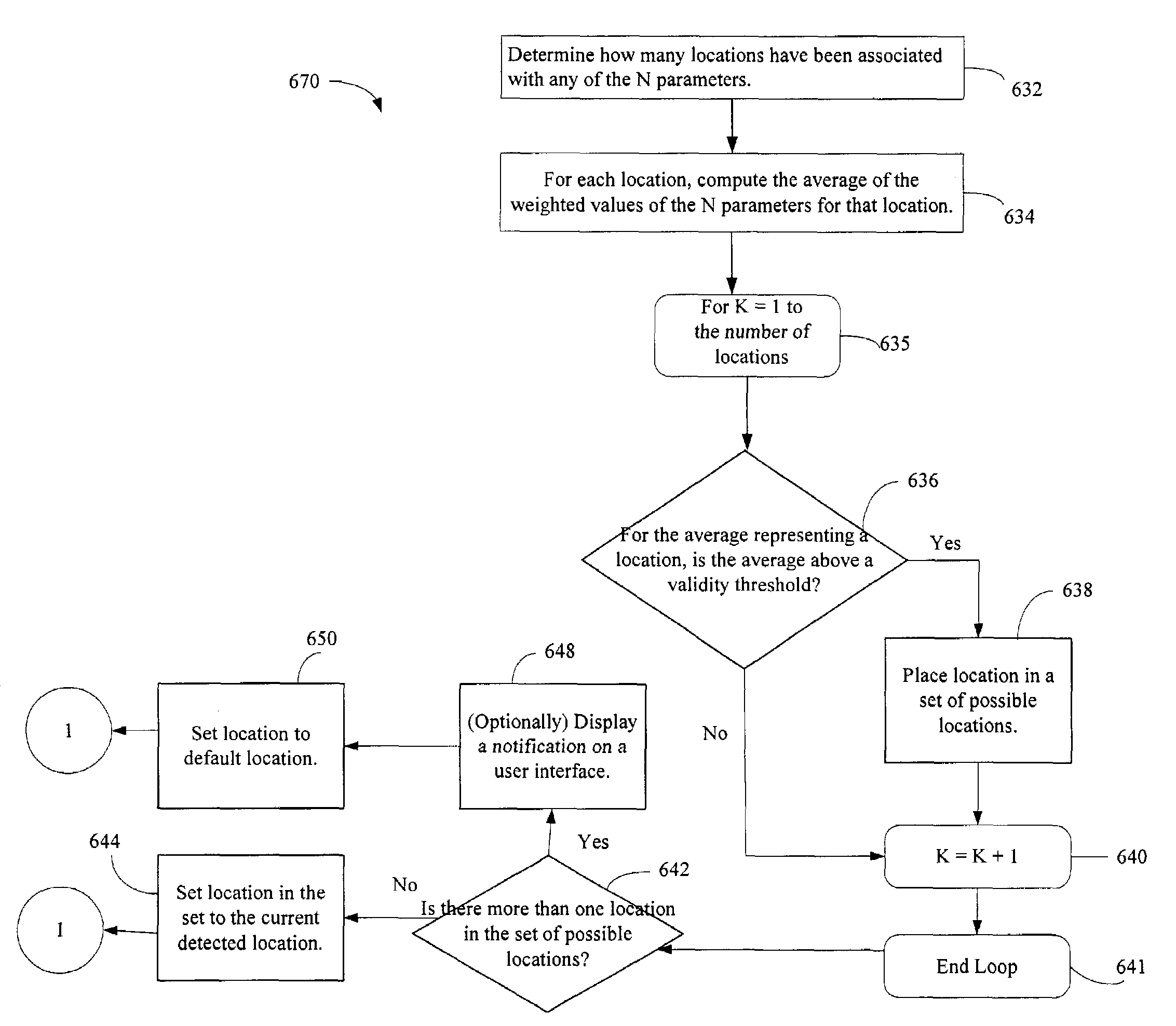
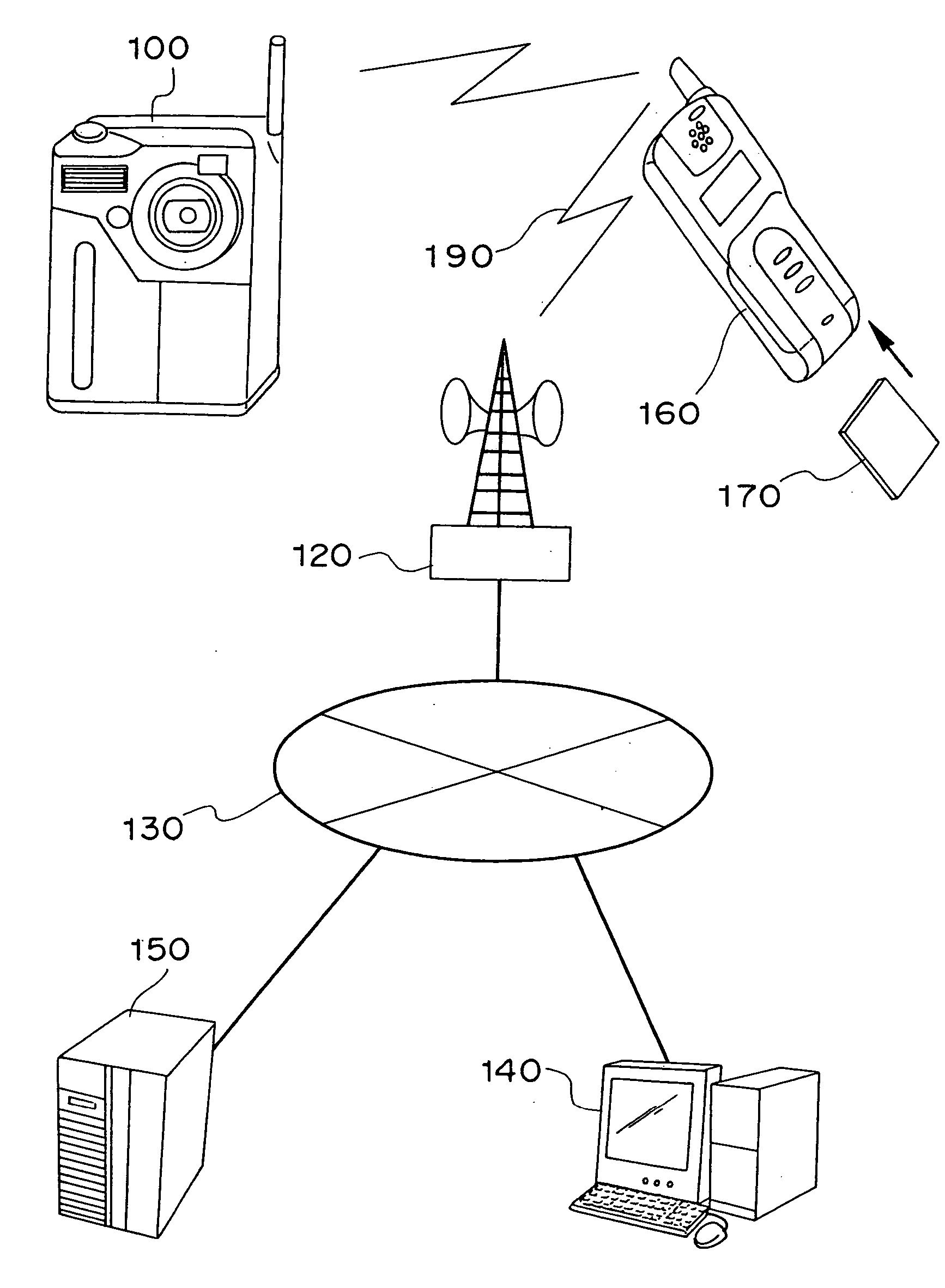
In an electronic apparatus having a user identification function or in a user identification method, an electronic apparatus and an electronic instrument having stored therein user personal information communicate in wireless with each other so as to enable the electronic apparatus to automatically identify the electronic apparatus user. If the electronic apparatus identifies a plurality of possible users, the electronic apparatus automatically selects the user by executing specific user identification processing.
Owner:NIKON CORP
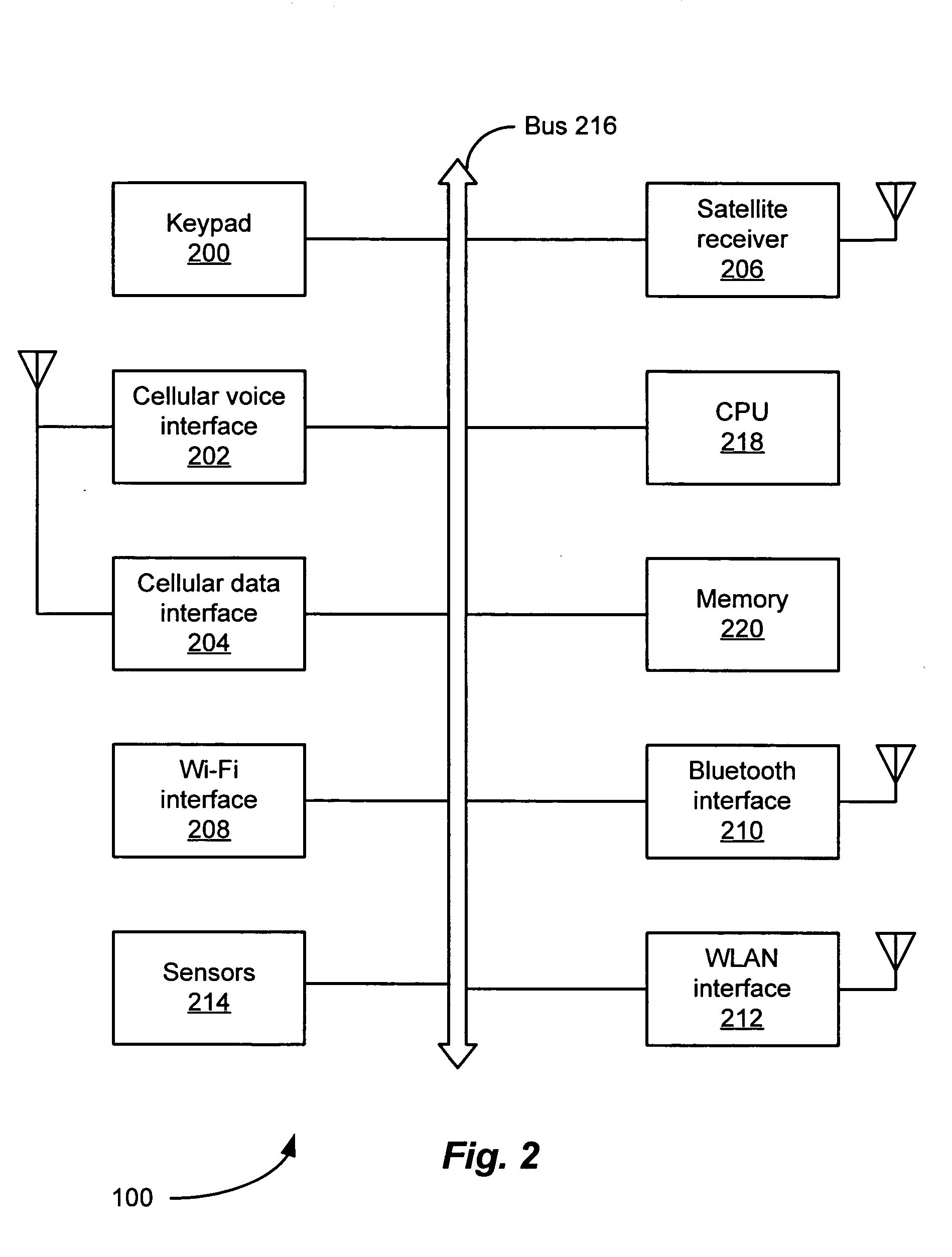
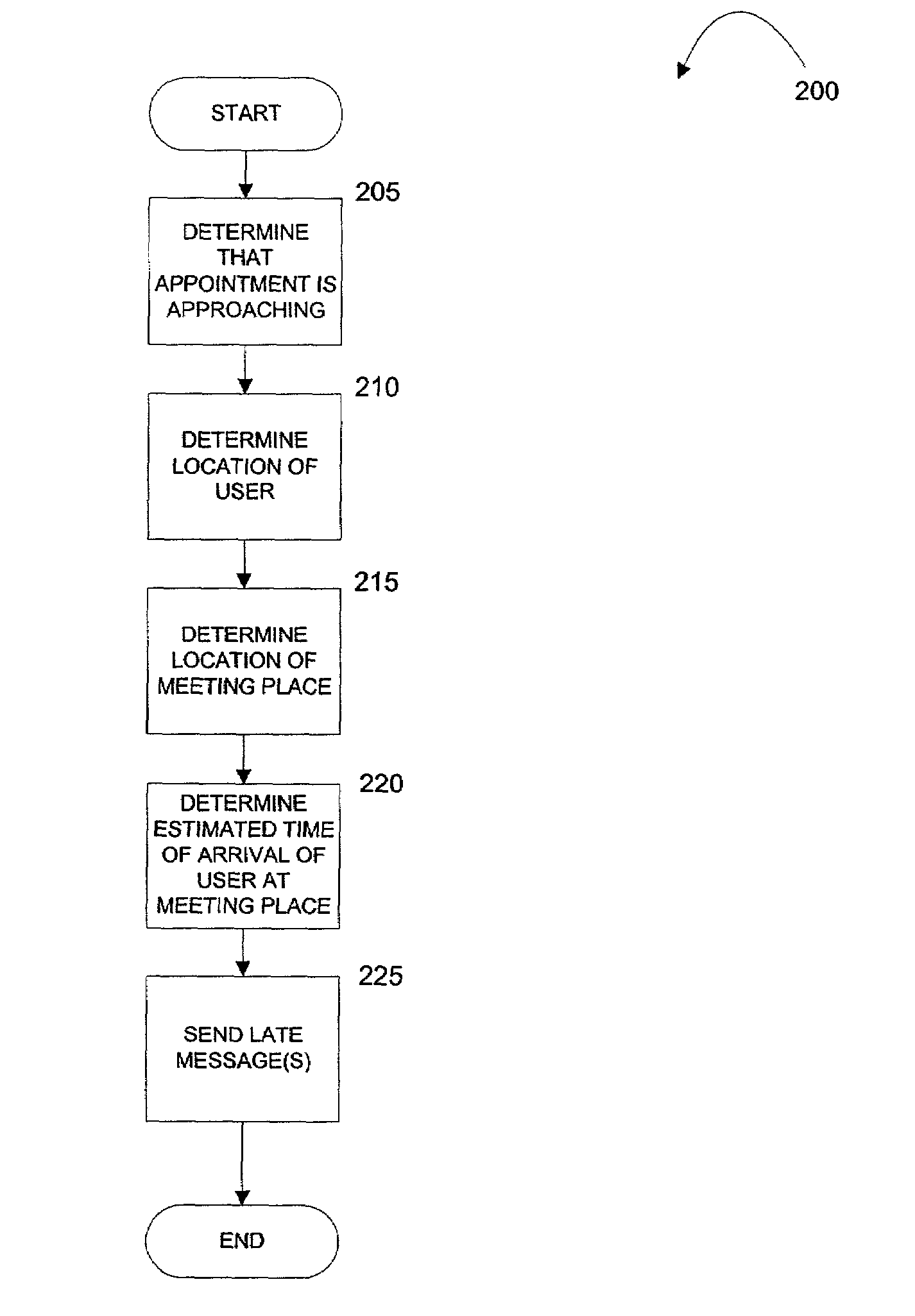
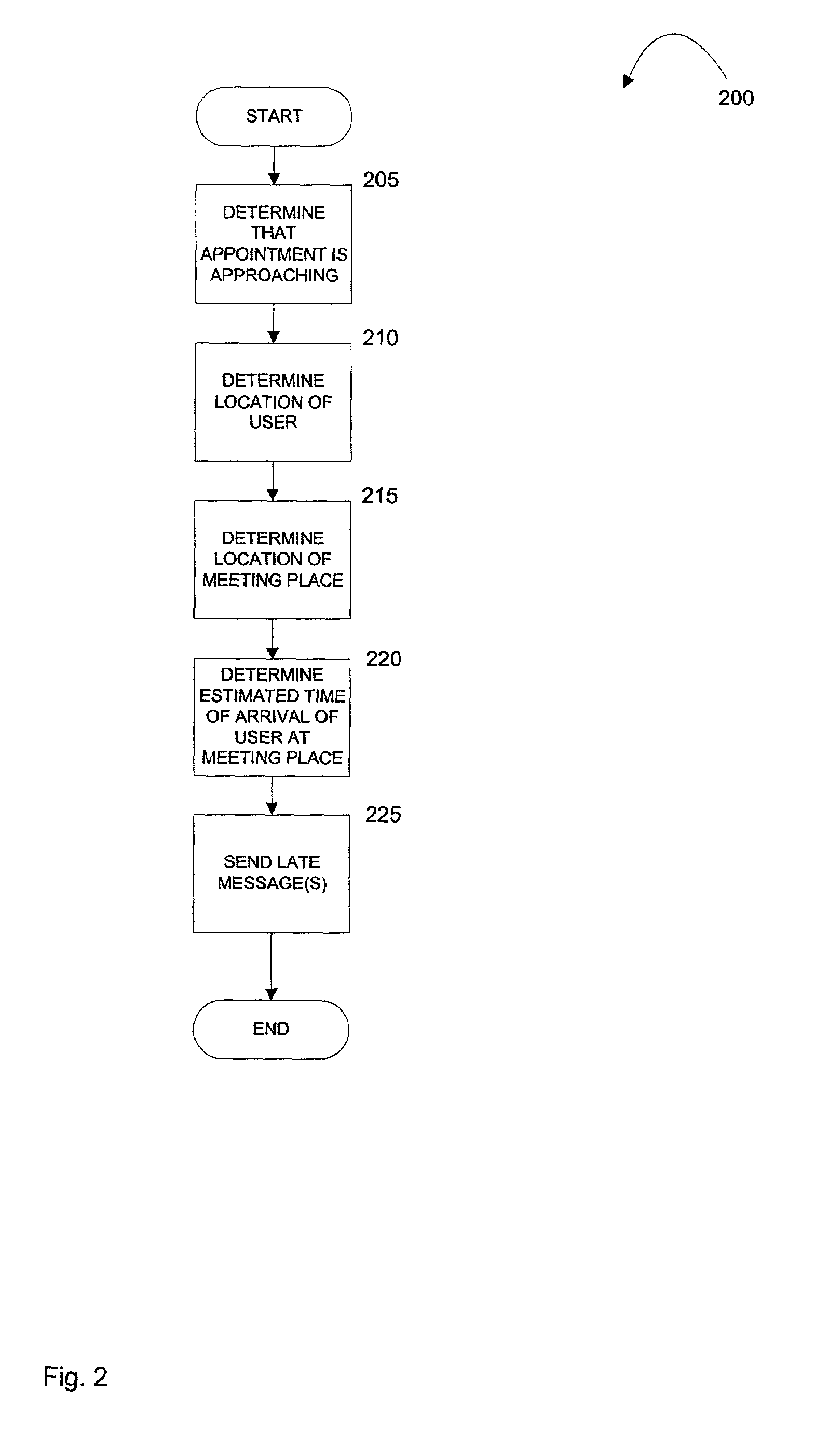
Location and time sensitive wireless calendaring
ActiveUS7139722B2Instruments for road network navigationRoad vehicles traffic controlStart timePager
A computer-implemented method provides location-sensitive and time-sensitive calendaring to a wireless device, such as a cellphone, pager, PDA, etc. A user's calendar is maintained with a number of appointments, start times and end times for the appointments, meeting place and a list of attendees for the appointments. When the present time reading is within a predetermined minimum of a meeting start time of an appointment of a calendar of a user, the location of the user is determined based on the location of the wireless device. The location of the meeting place is also determined. Using historical data (of the user or others), the estimated time of arrival of the user at the meeting place is determined. If the estimated time of arrival is after the meeting start time, then a late message may be sent to the user and / or to the other meeting attendees.
Owner:BELLSOUTH INTPROP COR +1
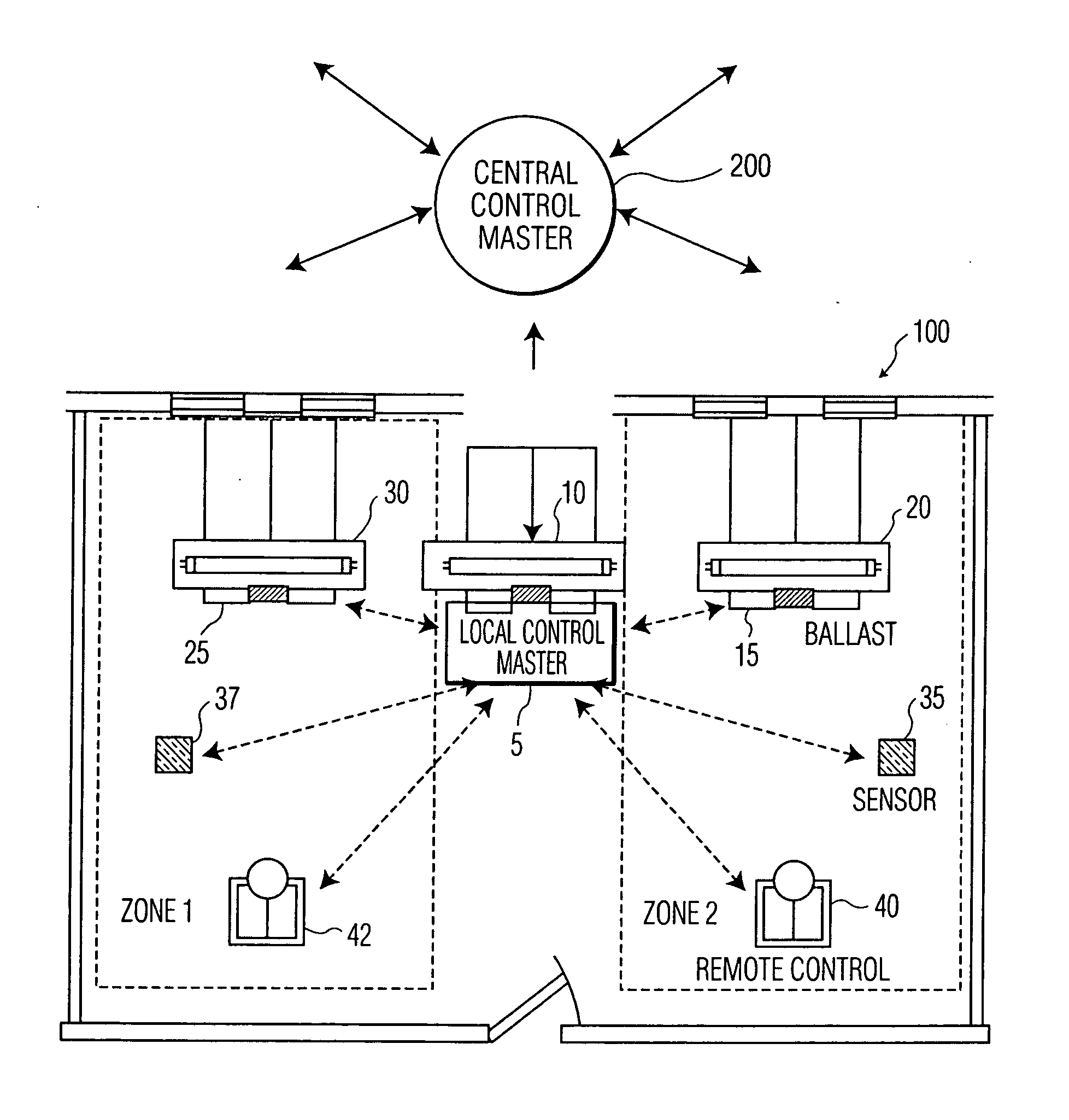
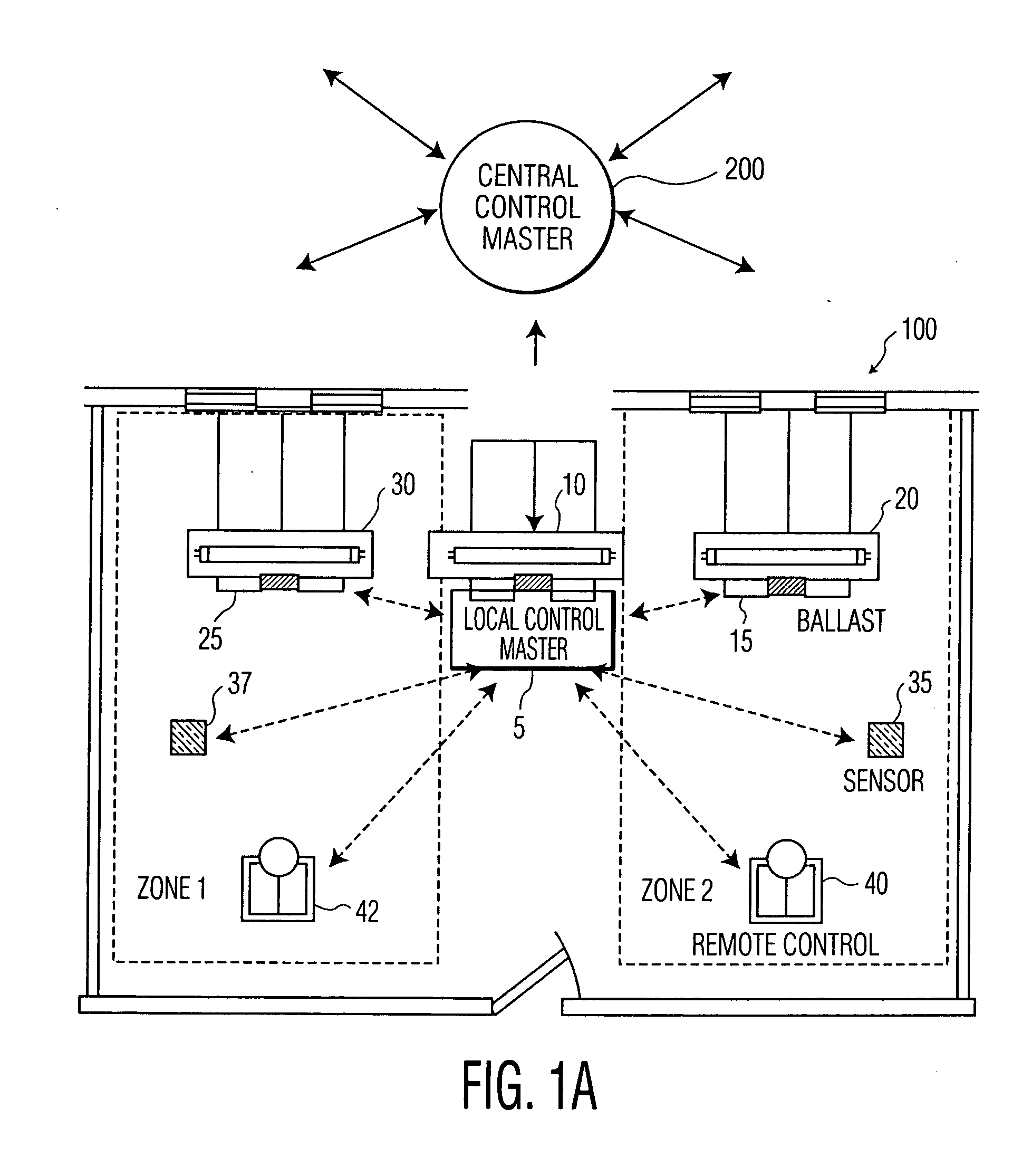
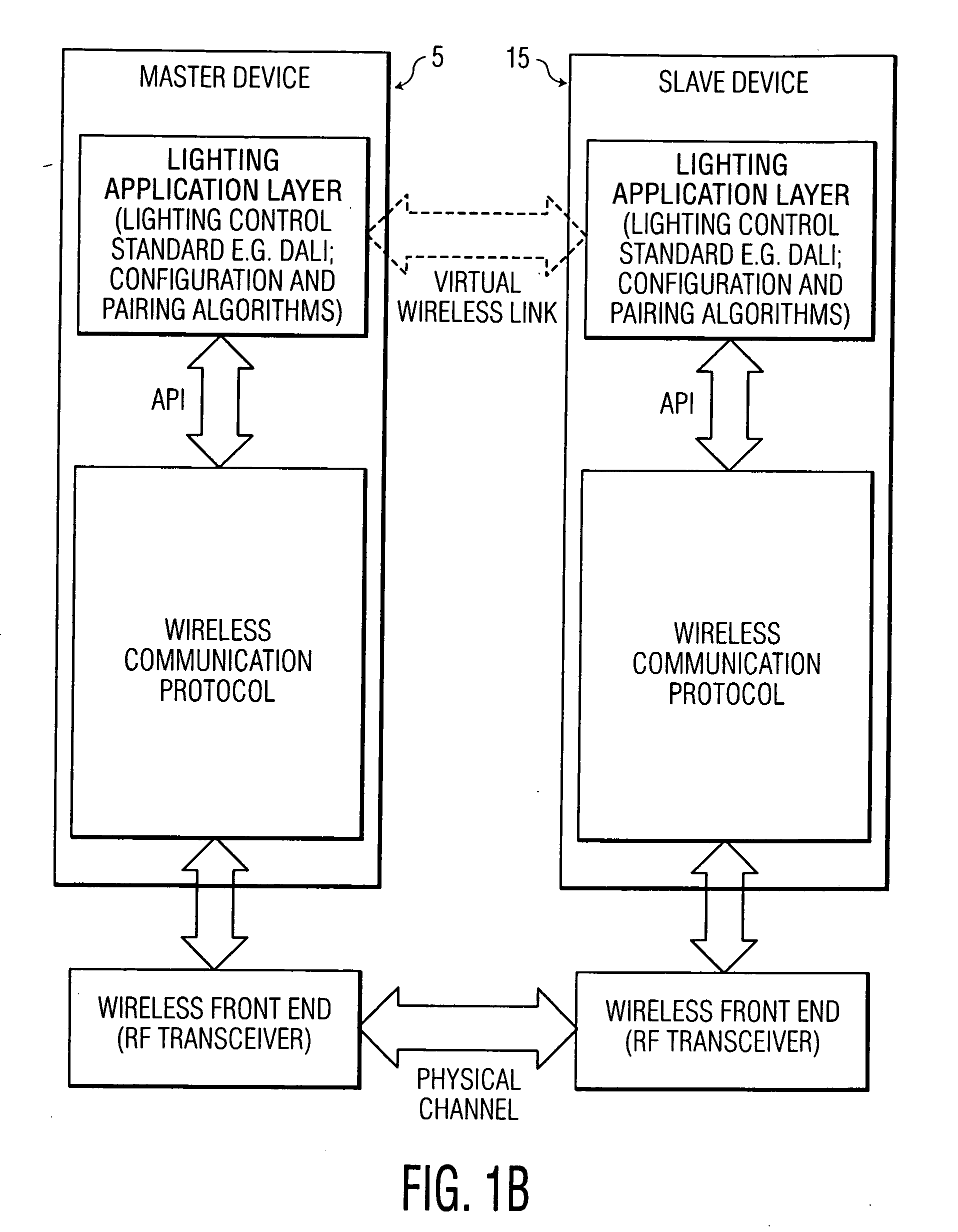
Master-slave oriented two-way rf wireless lighting control system
InactiveUS20060044152A1Telemetry/telecontrol selection arrangementsElectronic switchingEffect lightEngineering
A lighting control system network and method of providing same including a remote control unit having a RF signal transmitter and a RF receiver and a number of lighting control units, each of the lighting control units having a RF signal transmitter, a RF receiver, and a lighting unit associated therewith. The remote control unit and the lighting control units are configured in a master-slave oriented network. One of the lighting control units is configured as a master in the network and the remaining lighting control units and the remote control unit are configured as slaves in the network. The lighting control units and the remote control units communicate bi-directionally with each other over RF wireless links. The network may include sensors for detecting an environmental or system parameter. Multiple instances of the lighting control network may be interfaced together to form a building-wide network.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
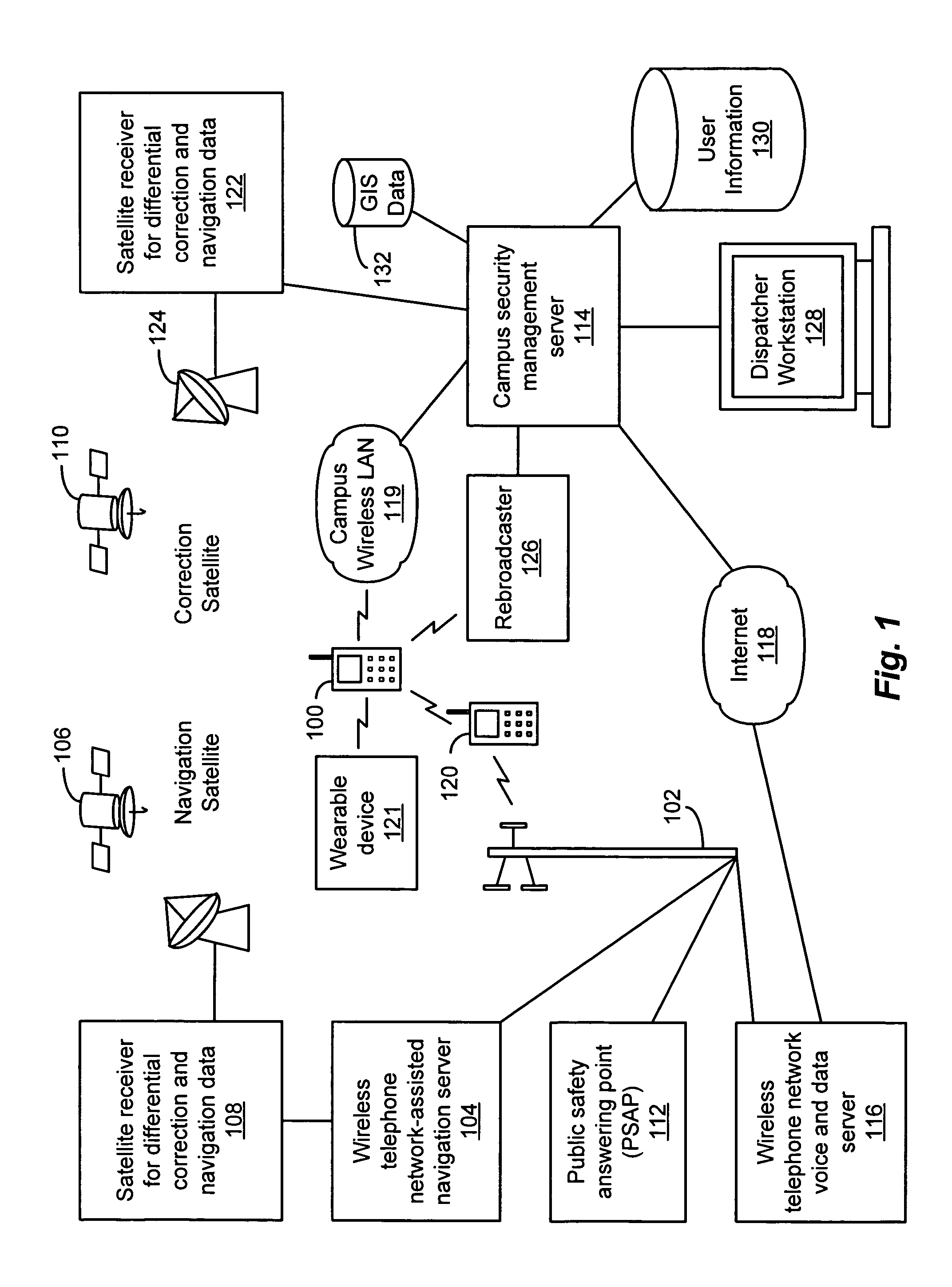
Computer-enabled, networked, facility emergency notification, management and alarm system
ActiveUS20060109113A1Avoid lostSpread quicklyElectric transmission signalling systemsBurglar alarmOutdoor areaNetwork link
Secure, verifiable, computer-enabled, LAN / WAN / Wireless networked, facility emergency notification, rapid alert management, and occupant alarm systems for public, private, and government buildings, and outdoor areas for which there is a need for rapid alerts to occupants or attendees of the occurrence of impending or in-progress dangerous or threatening events. The inventive system is a highly flexible rapid alert initiation, management and archival system comprising computer-enabled and network-linked apparatus, software, and methods enabling rapid dissemination from a central station or decentralized location of alerts of the occurrence of threatening or dangerous events in a series of hierarchical, increasing levels of directed action to be taken by the occupants, and permits monitoring and controlling activity of occupants during the event, archiving event data, including audio or / and video recordings until the situation returns to normal and an all clear signal is given. Databases provide site plans to assist in the response planning and execution.
Owner:SIEMENS SWITZERLAND
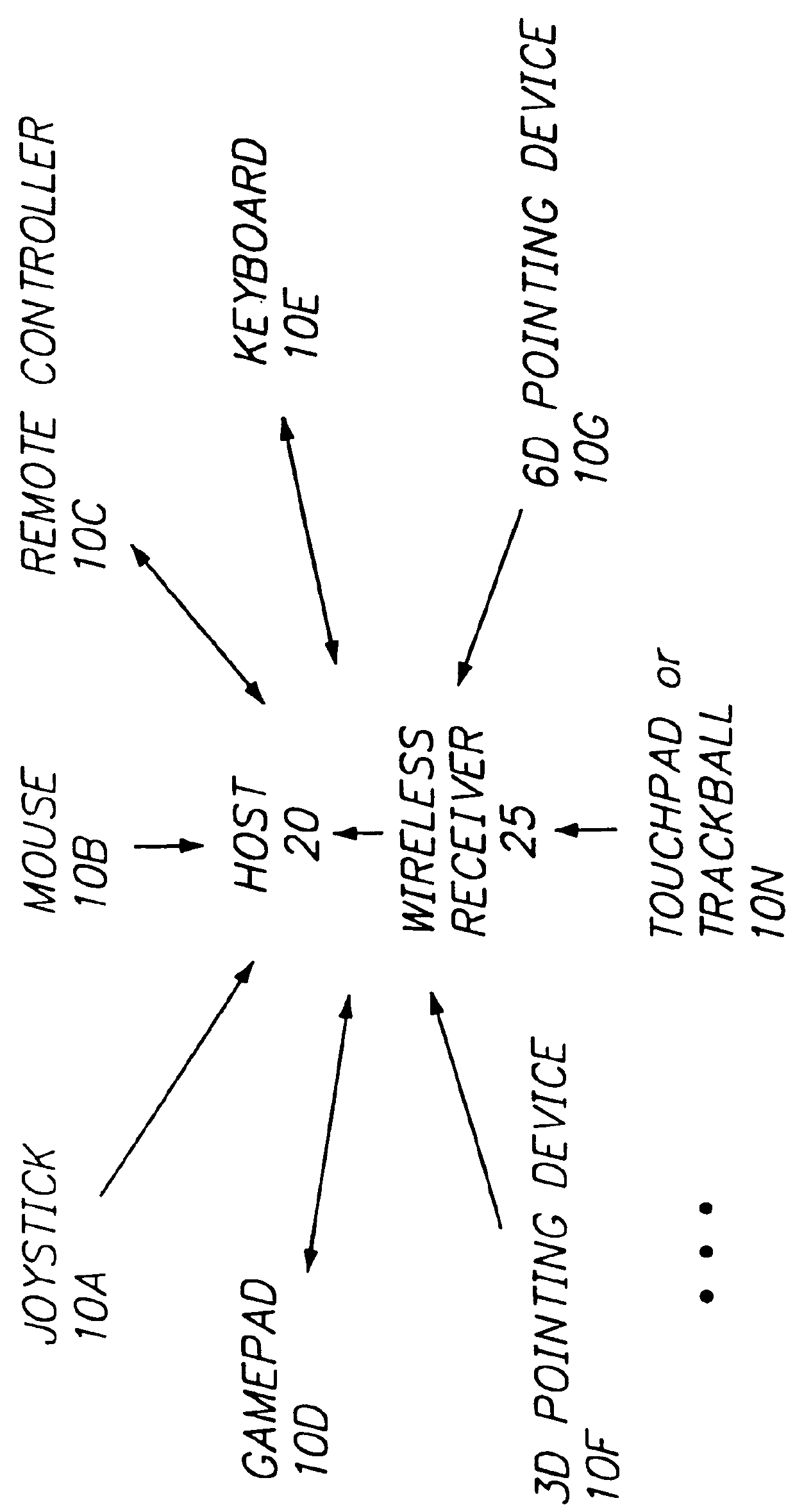
Wireless peripheral interface
InactiveUS6078789ASolve insufficient bandwidthTime-division multiplexRadio transmissionComputer hardwareJoystick
A method and apparatus for establishing a standardized communications protocol for wireless communications between a host and one or more peripheral devices such as joysticks, mice, gamepads, remote controllers or other devices including establishing a standard message format for messages communicated between a host and the peripheral devices, establishing a plurality of unique data types for associated peripheral devices, and prioritizing communications between the host and such peripherals to permit rapid and effective communication therebetween.
Owner:LOGITECH EURO SA
Geographic location using multiple location estimators
InactiveUS7298327B2Overcome inaccurate recognitionThe result is accurate and reliableDirection finders using radio wavesBeacon systems using radio wavesTerrainHeuristic
A location system is disclosed for commercial wireless telecommunication infrastructures. The system is an end-to-end solution having one or more location centers for outputting requested locations of commercially available handsets or mobile stations (MS) based on, e.g., CDMA, AMPS, NAMPS or TDMA communication standards, for processing both local MS location requests and more global MS location requests via, e.g., Internet communication between a distributed network of location centers. The system uses a plurality of MS locating technologies including those based on: (1) two-way TOA and TDOA; (2) pattern recognition; (3) distributed antenna provisioning; and (4) supplemental information from various types of very low cost non-infrastructure base stations for communicating via a typical commercial wireless base station infrastructure or a public telephone switching network. Accordingly, the traditional MS location difficulties, such as multipath, poor location accuracy and poor coverage are alleviated via such technologies in combination with strategies for: (a) automatically adapting and calibrating system performance according to environmental and geographical changes; (b) automatically capturing location signal data for continual enhancement of a self-maintaining historical data base retaining predictive location signal data; (c) evaluating MS locations according to both heuristics and constraints related to, e.g., terrain, MS velocity and MS path extrapolation from tracking and (d) adjusting likely MS locations adaptively and statistically so that the system becomes progressively more comprehensive and accurate. Further, the system can be modularly configured for use in location signaling environments ranging from urban, dense urban, suburban, rural, mountain to low traffic or isolated roadways. Accordingly, the system is useful for 911 emergency calls, tracking, routing, people and animal location including applications for confinement to and exclusion from certain areas.
Owner:TRACBEAM
Apparatus for internetworked wireless integrated network sensors (WINS)
InactiveUS20100148940A1High reliability accessEasy to operateAntenna supports/mountingsDigital computer detailsReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives
ActiveUS20040143428A1Significant valueEasy to explainGeometric CADProgram controlHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
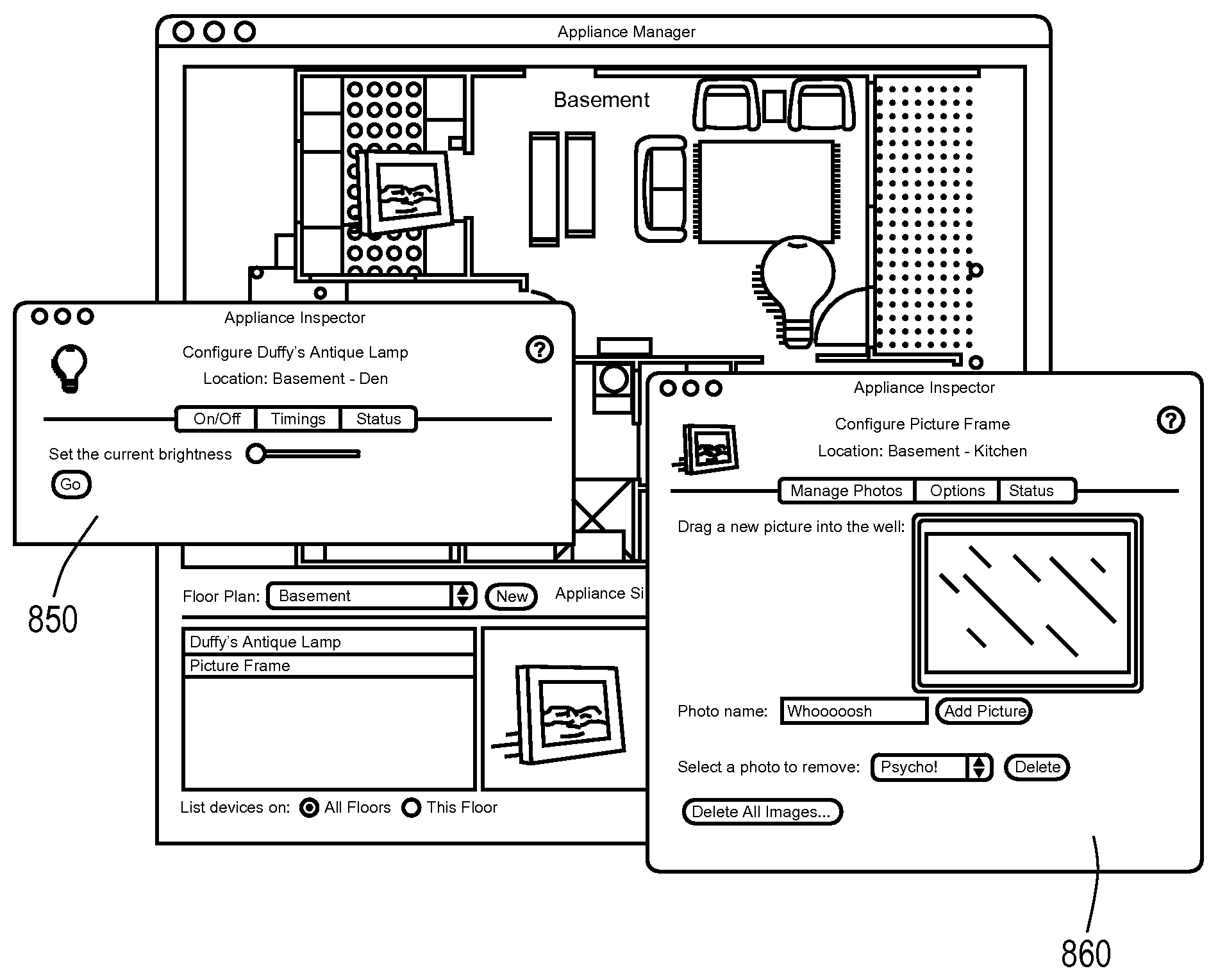
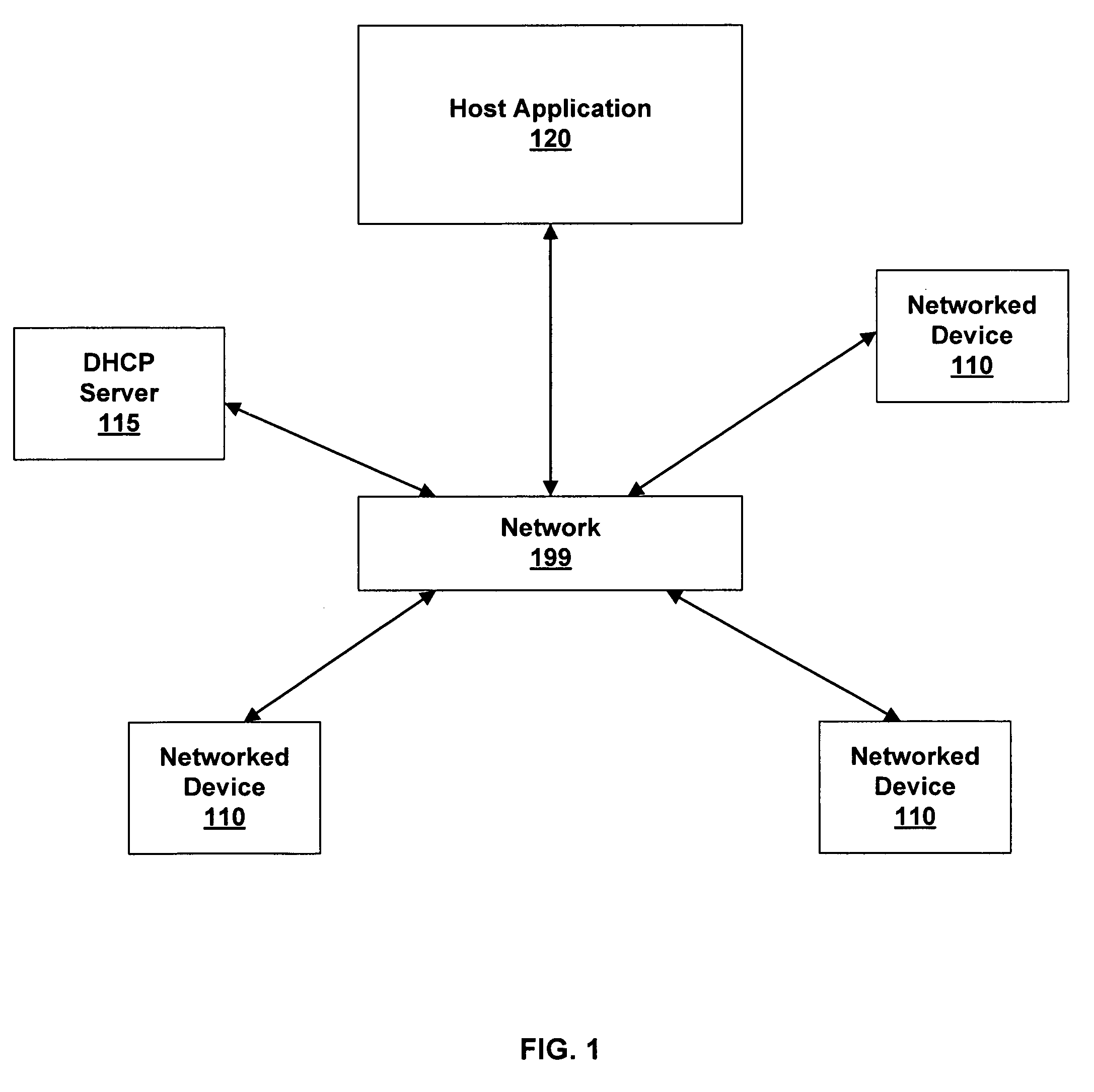
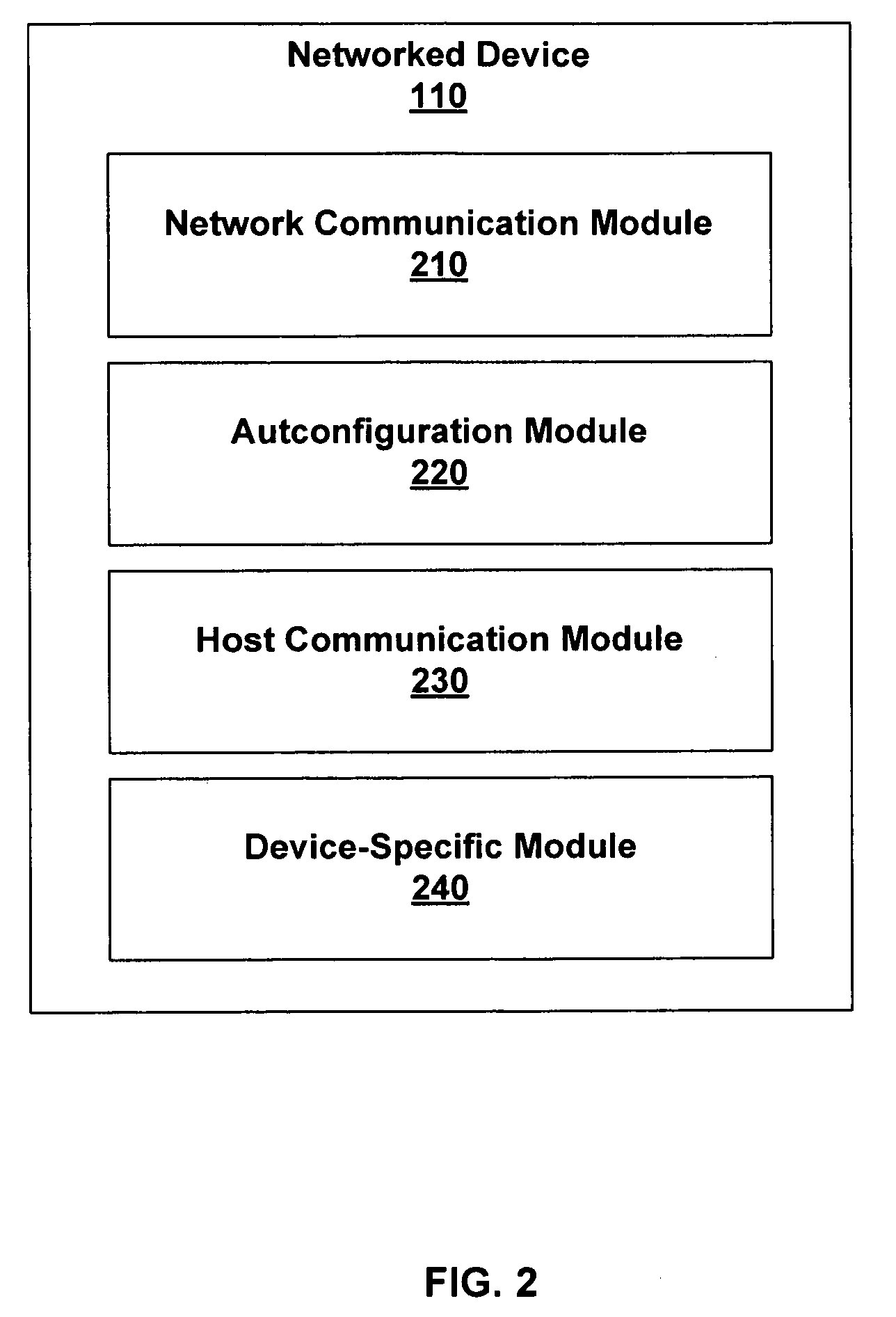
Wireless home and office appliance management and integration
ActiveUS7730223B1Minimal set-upUser managementDigital computer detailsElectric light circuit arrangementGraphicsPersonal computer
The present invention provides systems and methods for managing and controlling networked devices. A system comprises a host application executing on, for example, a personal computer, and one or more networked devices executing a client application. A networked device includes a consumer appliance equipped with network capability, a digital device such as MP3 players and DVRs, an electronically-controlled device such as a light circuit or other type of circuit, and the like. The host application automatically establishes communication with the networked device. The networked device configures a user interface for user control of the networked device. The host application provides a graphical layout of the networked device.
Owner:APPLE INC
Administration of protection of data accessible by a mobile device
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com