Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1425 results about "File sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
File sharing is the practice of distributing or providing access to digital media, such as computer programs, multimedia (audio, images and video), documents or electronic books. File sharing may be achieved in a number of ways. Common methods of storage, transmission and dispersion include manual sharing utilizing removable media, centralized servers on computer networks, World Wide Web-based hyperlinked documents, and the use of distributed peer-to-peer networking.
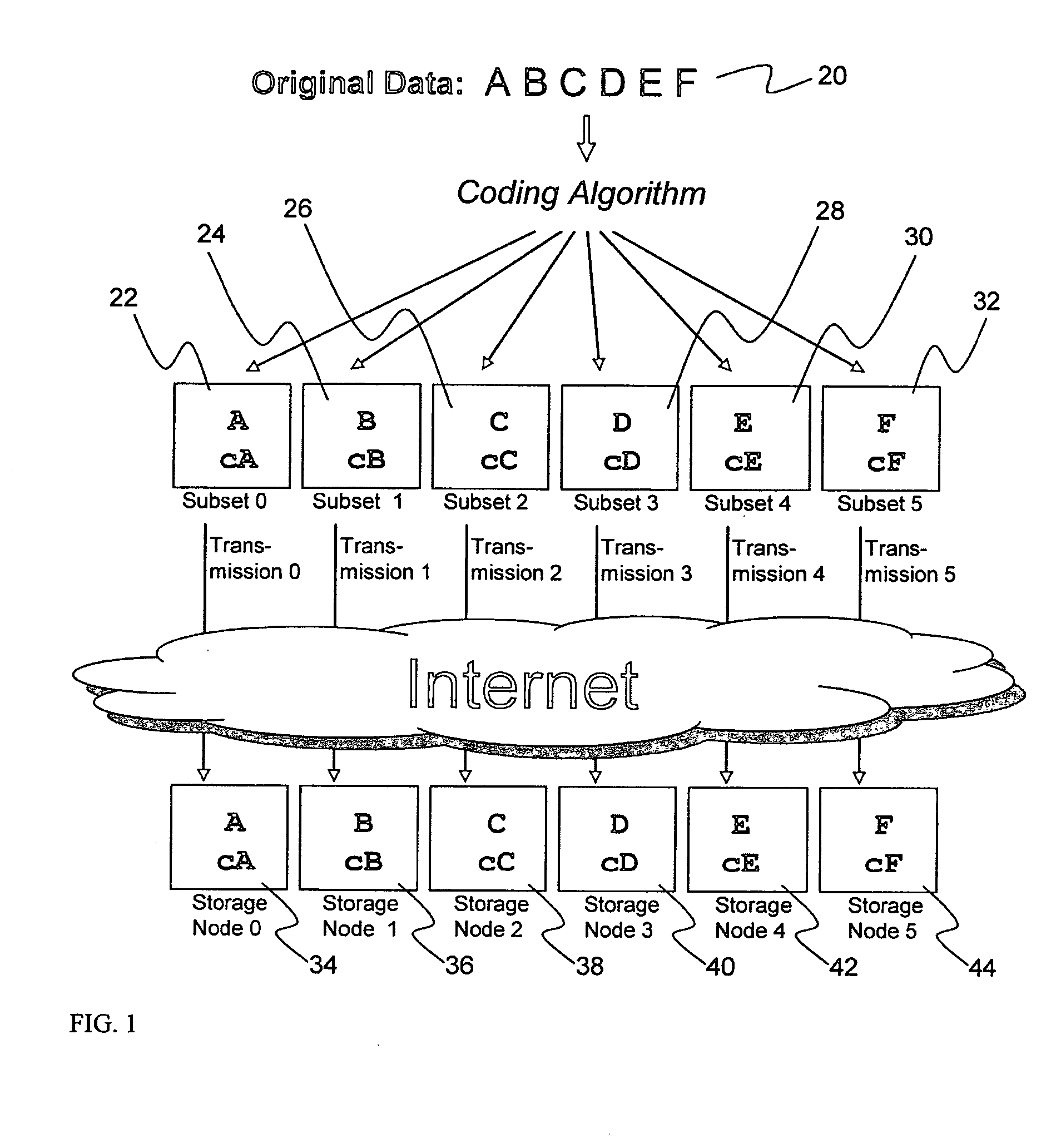
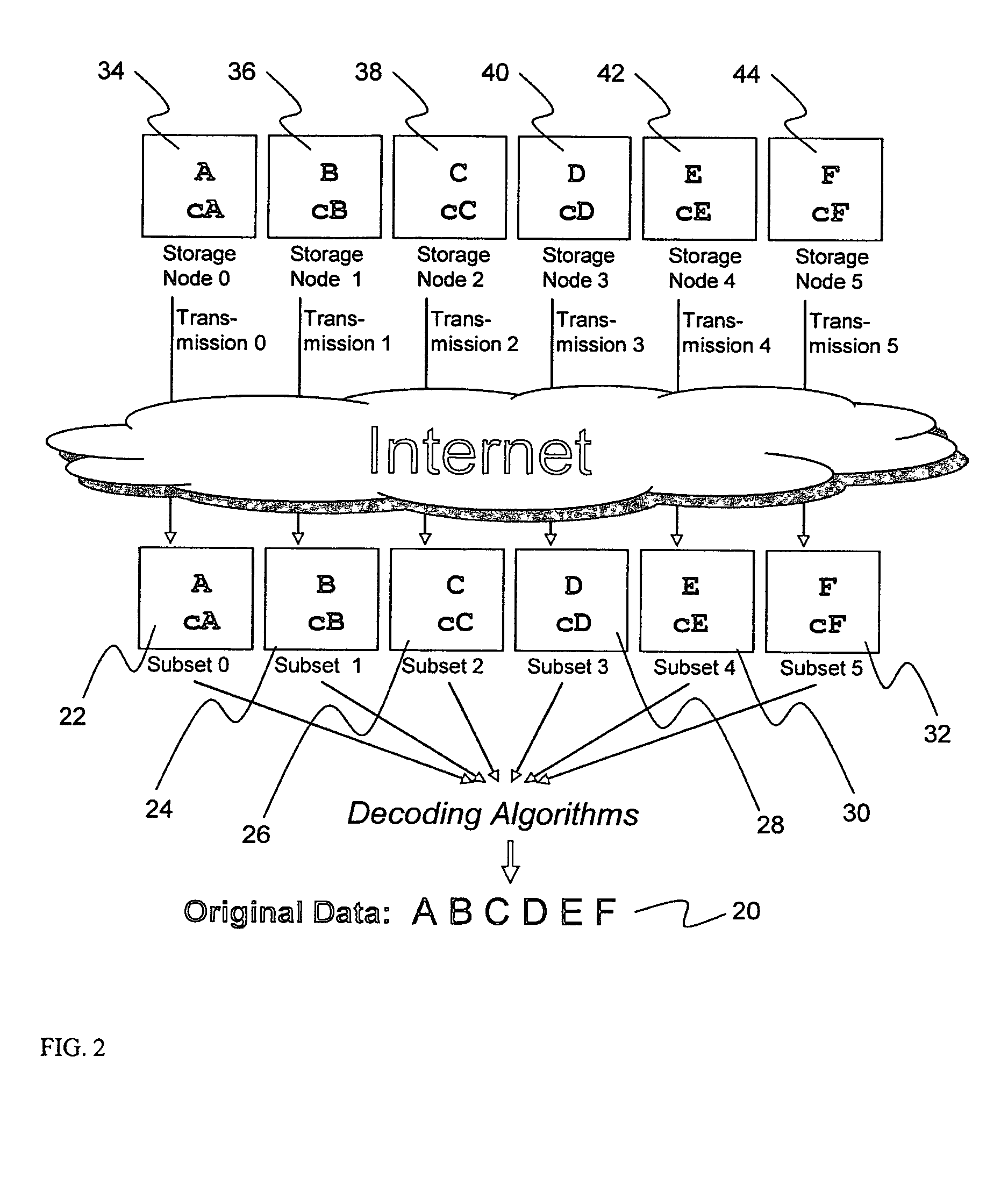
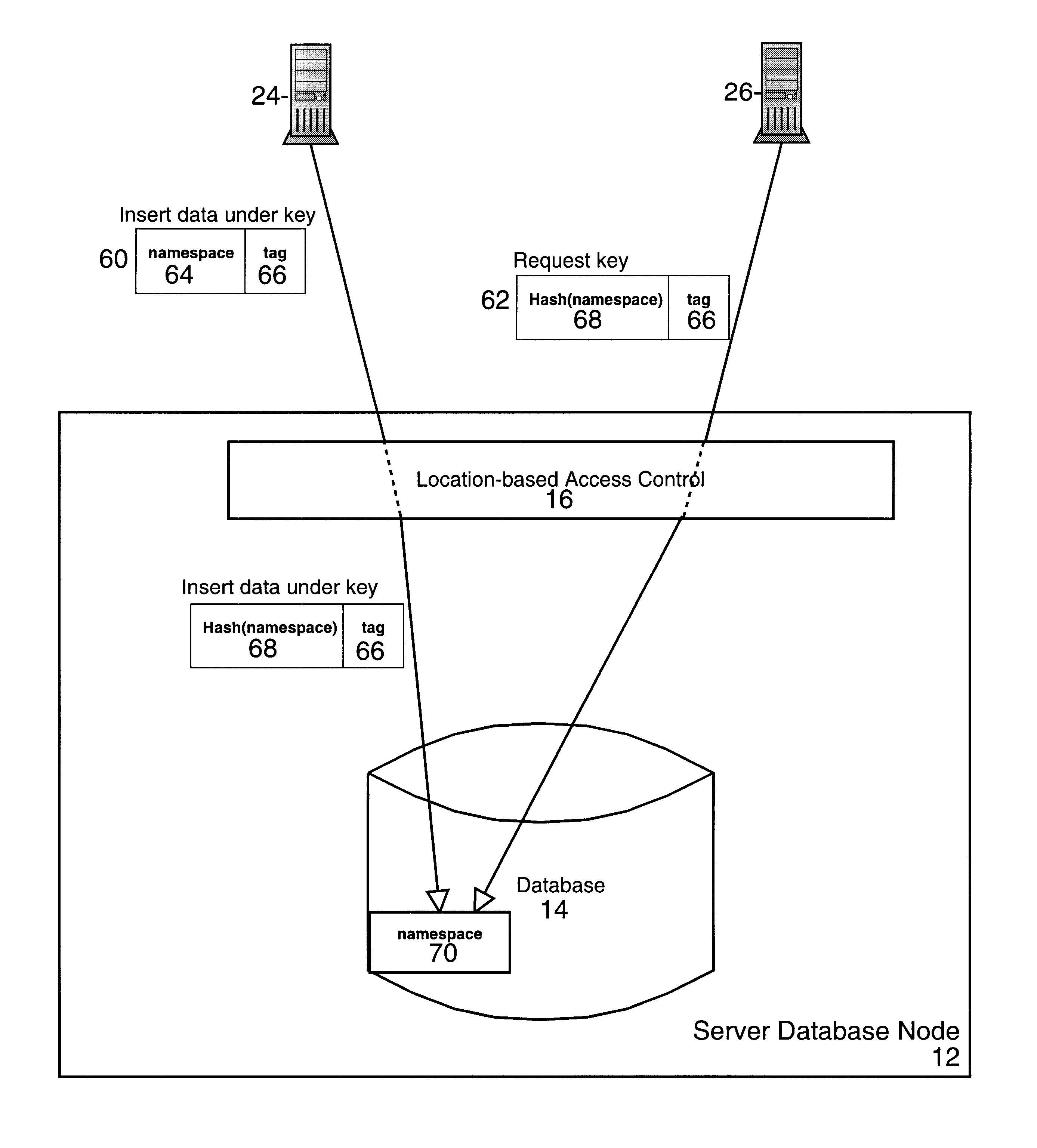
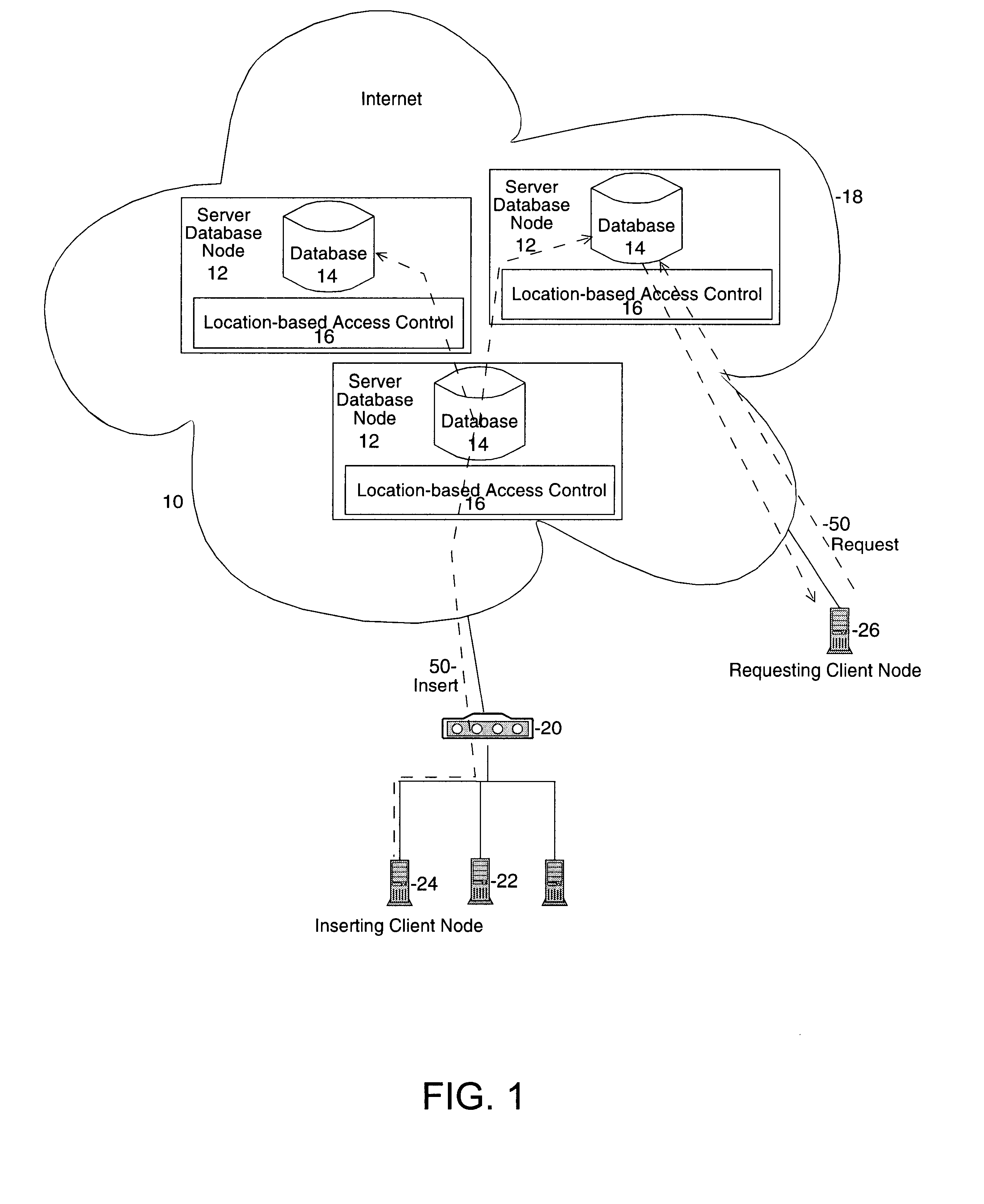
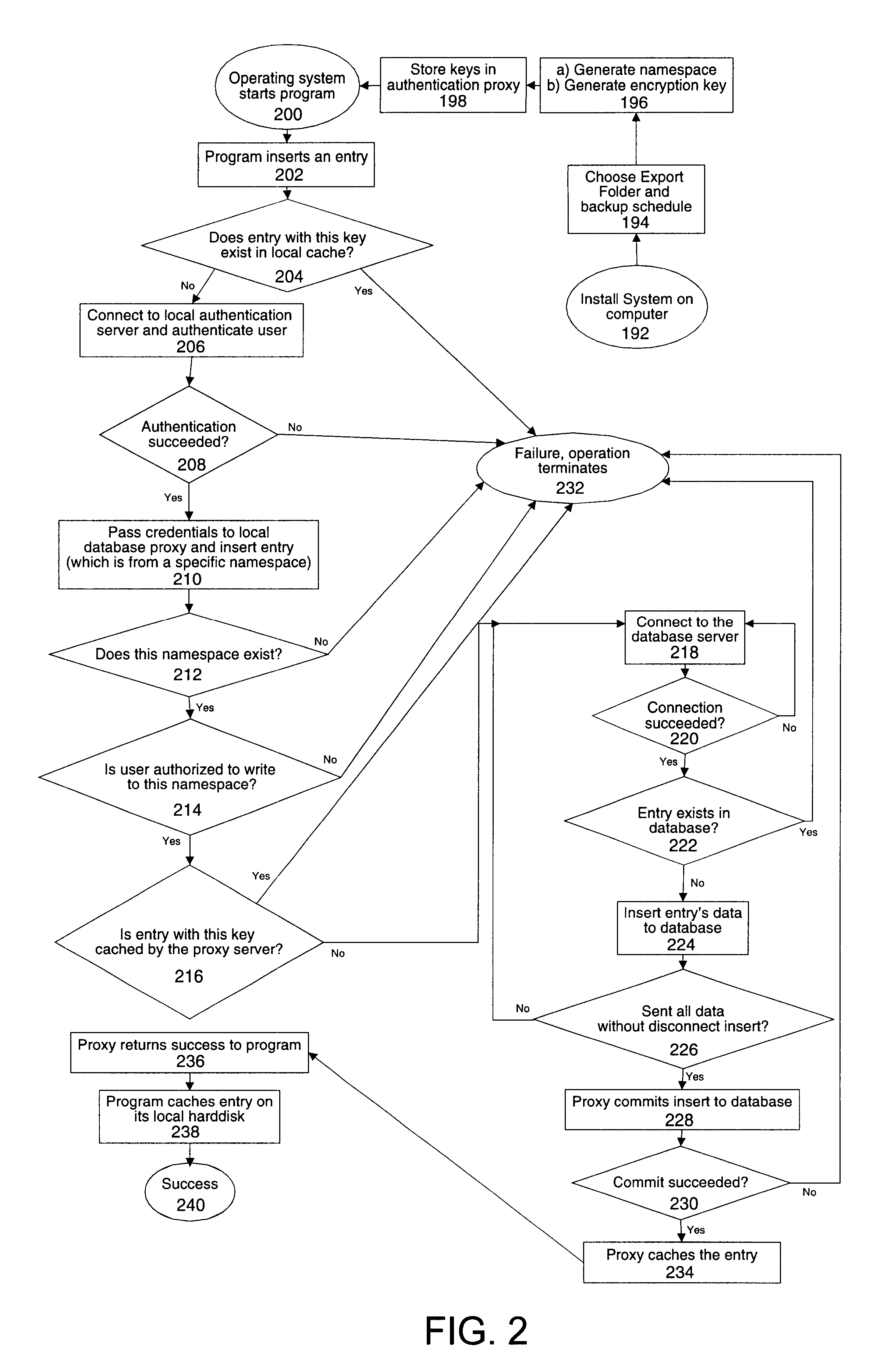
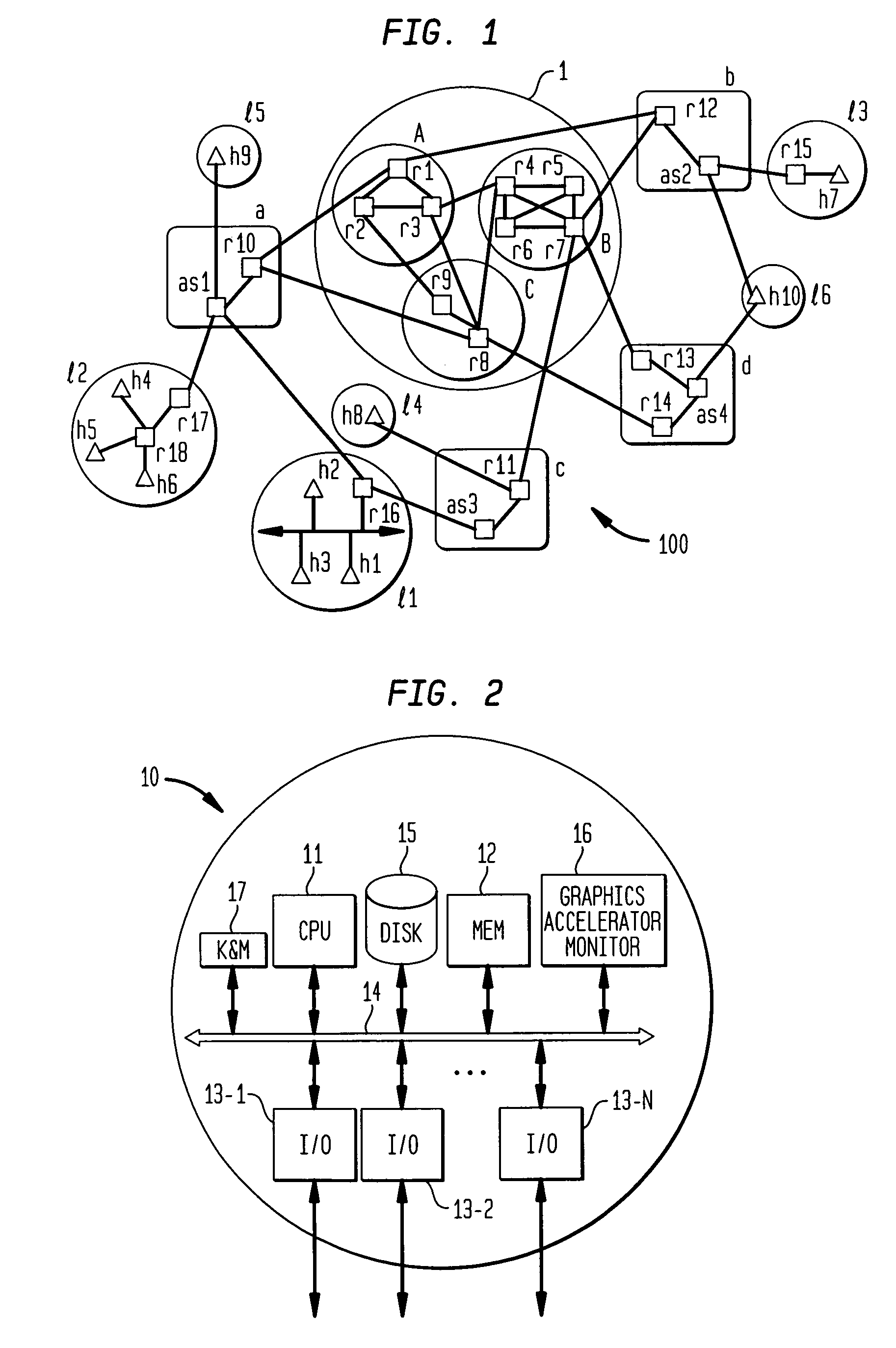
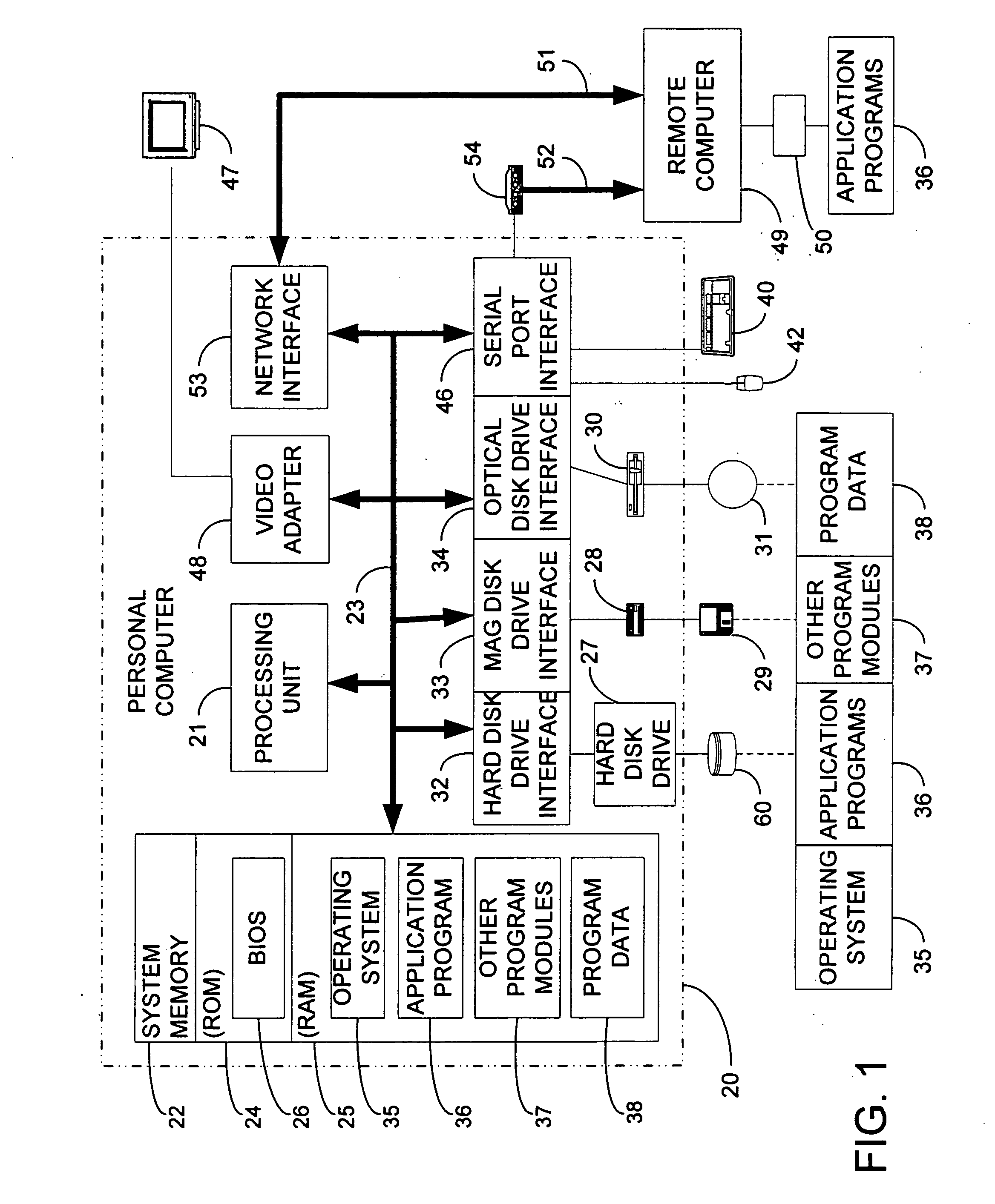
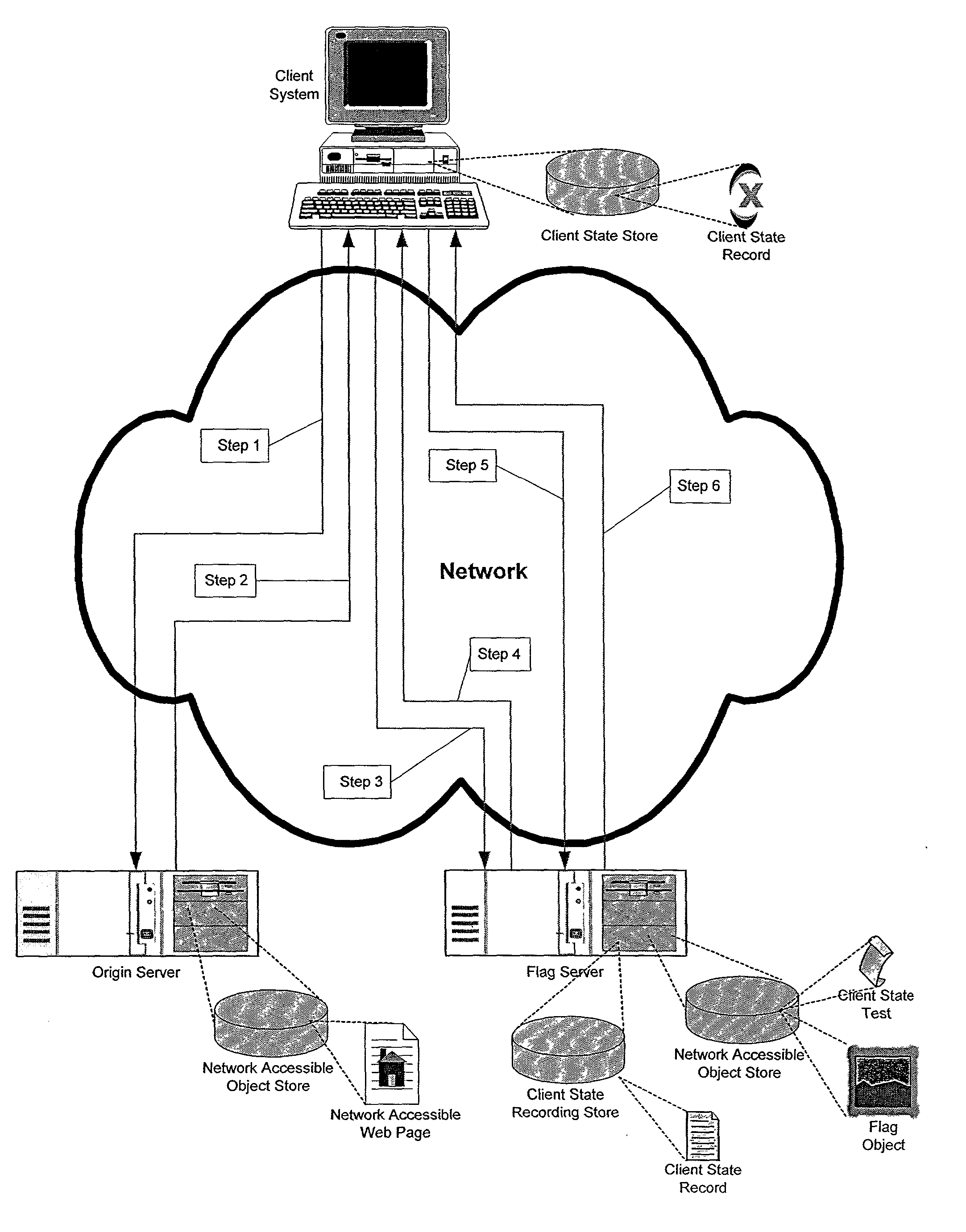
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
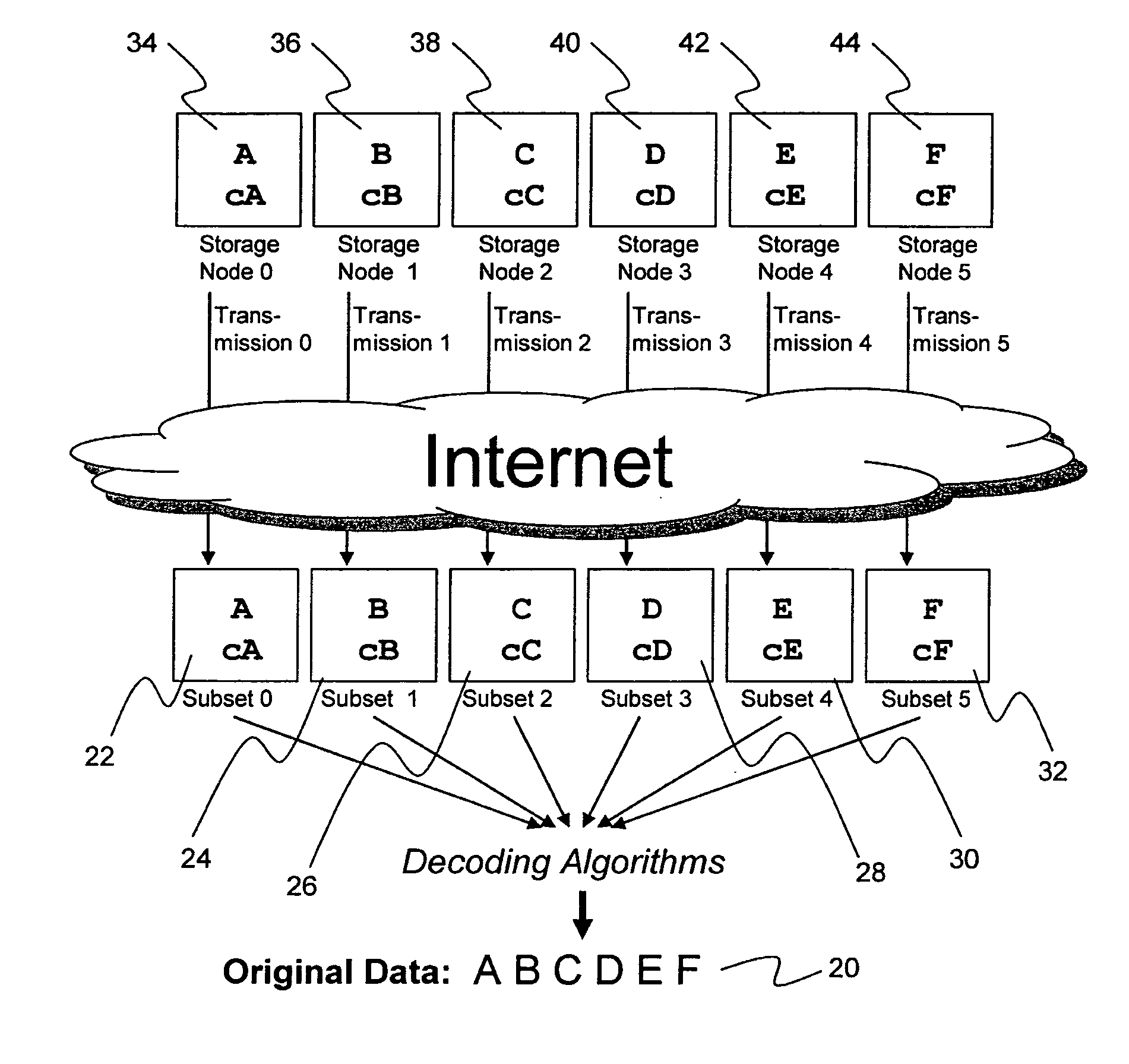
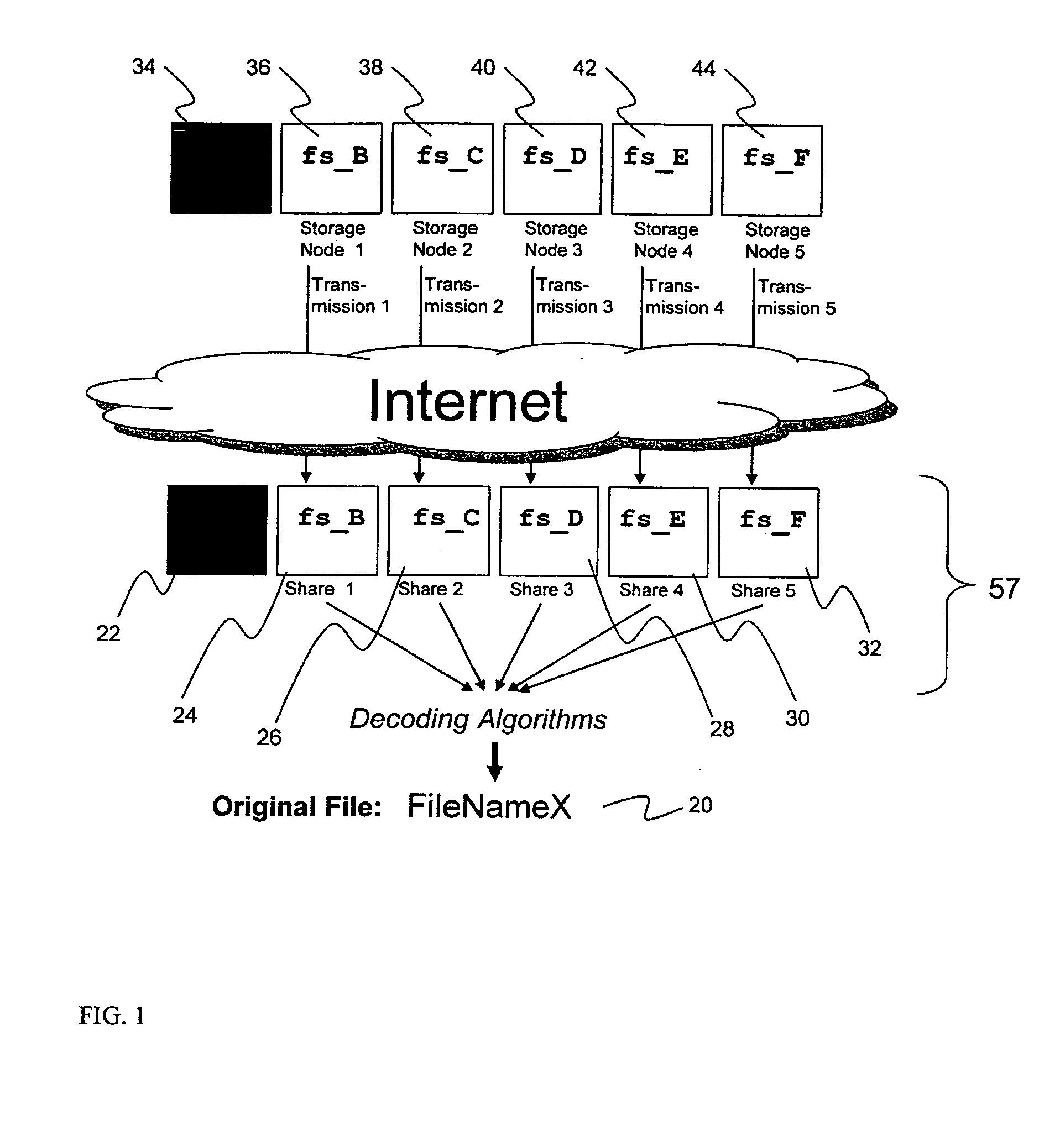
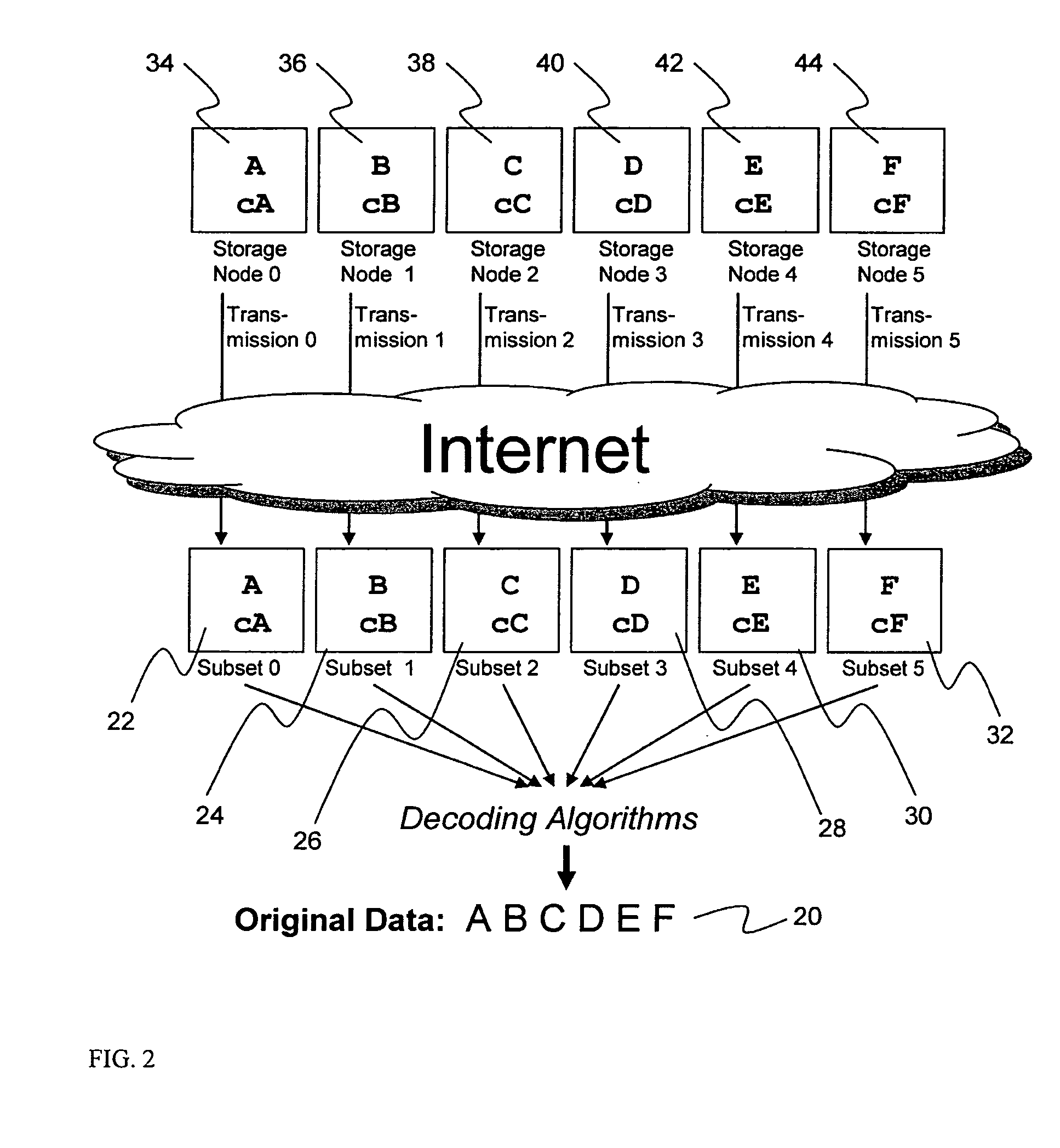
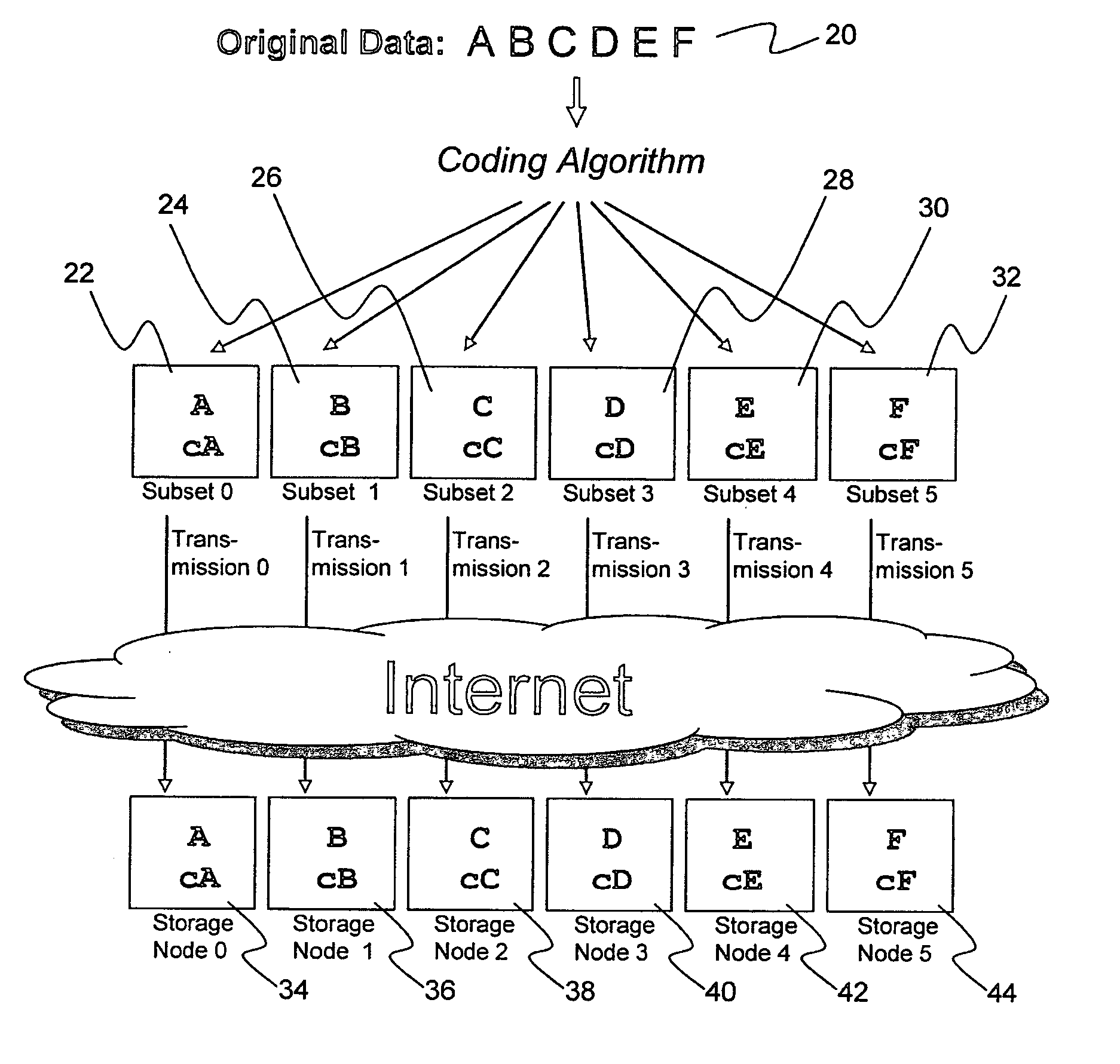
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
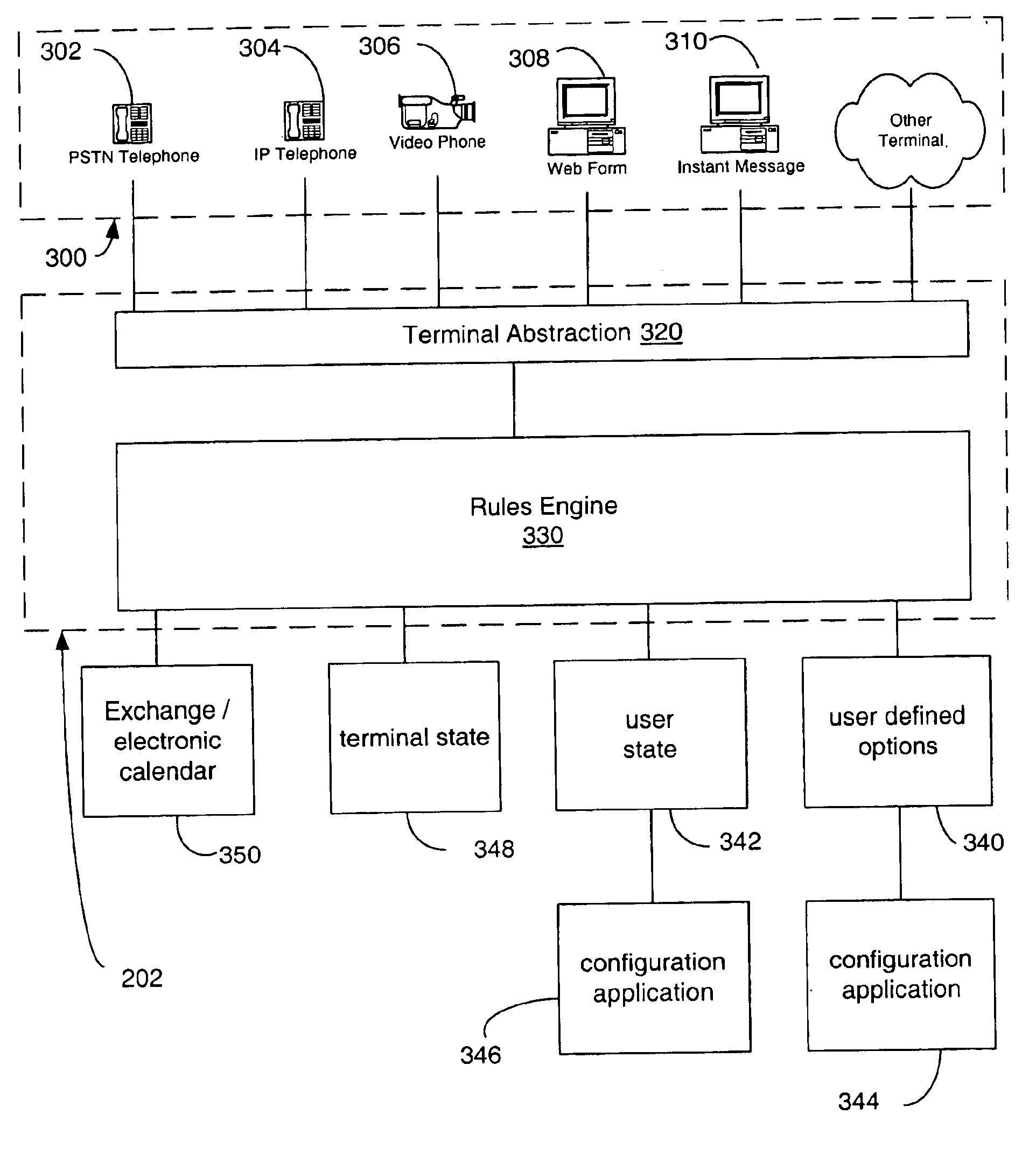
Multi-access mode electronic personal assistant
InactiveUS6895558B1Digital data information retrievalMultiplex communicationVocal responseData access
A system enables communication between server resources and a wide spectrum of end-terminals to enable access to the resources of both converged and non-converged networks via voice and / or electronically generated commands. An electronic personal assistant (ePA) incorporates generalizing / abstracting communications channels, data and resources provided through a converged computer / telephony system interface such that the data and resources are readily accessed by a variety of interface formats including a voice interface or data interface. A set of applications provides dual interfaces for rendering services and data based upon the manner in which a user accesses the data. An electronic personal assistant in accordance with an embodiment of the invention provides voice / data access to web pages, email, file shares, etc. A voice-based resource server authenticates a user by receiving vocal responses to one or more requests variably selected and issued by a speaker recognition-based authentication facility. Thereafter an application proxy is created.
Owner:MICROSOFT TECH LICENSING LLC
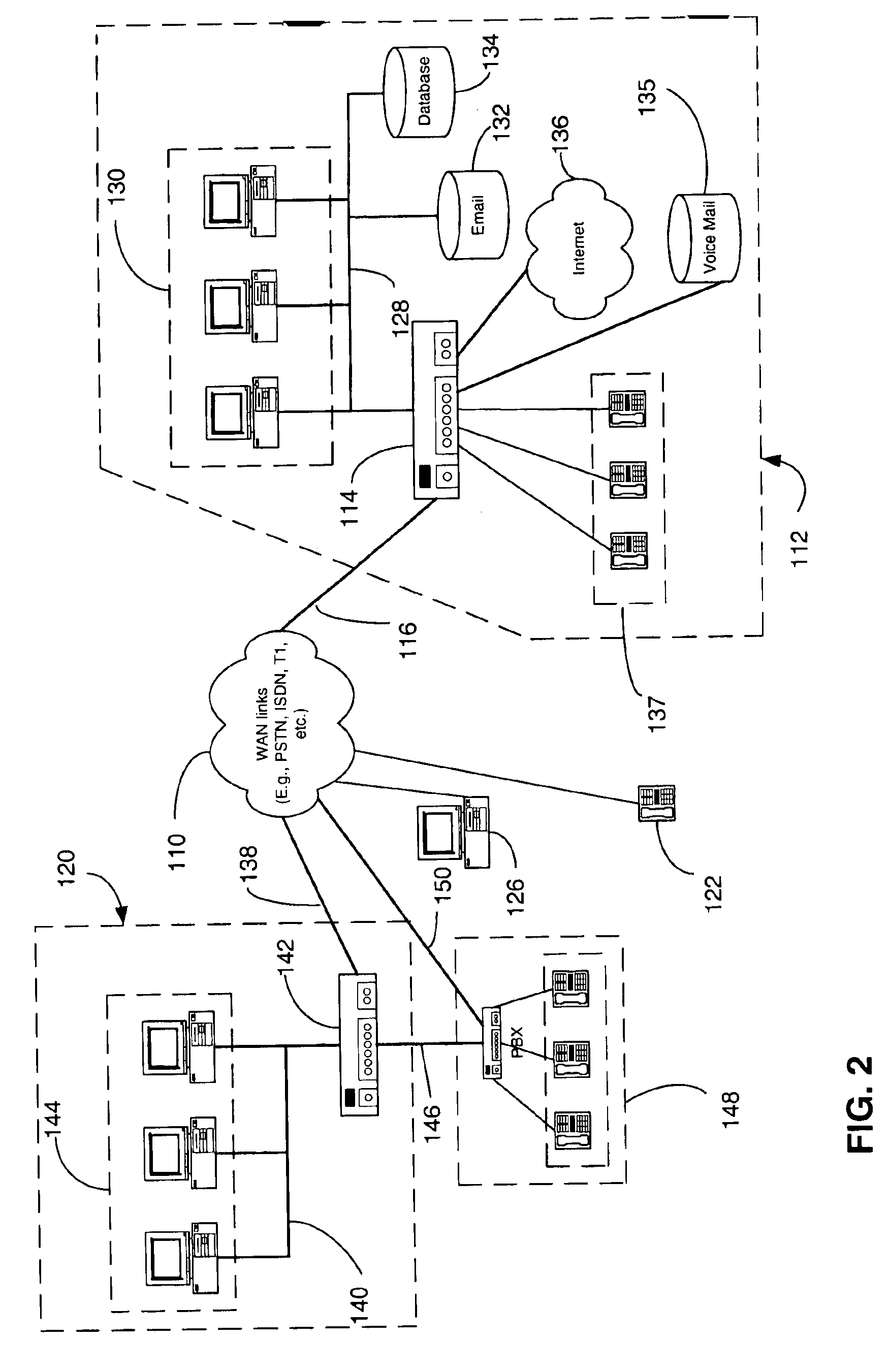
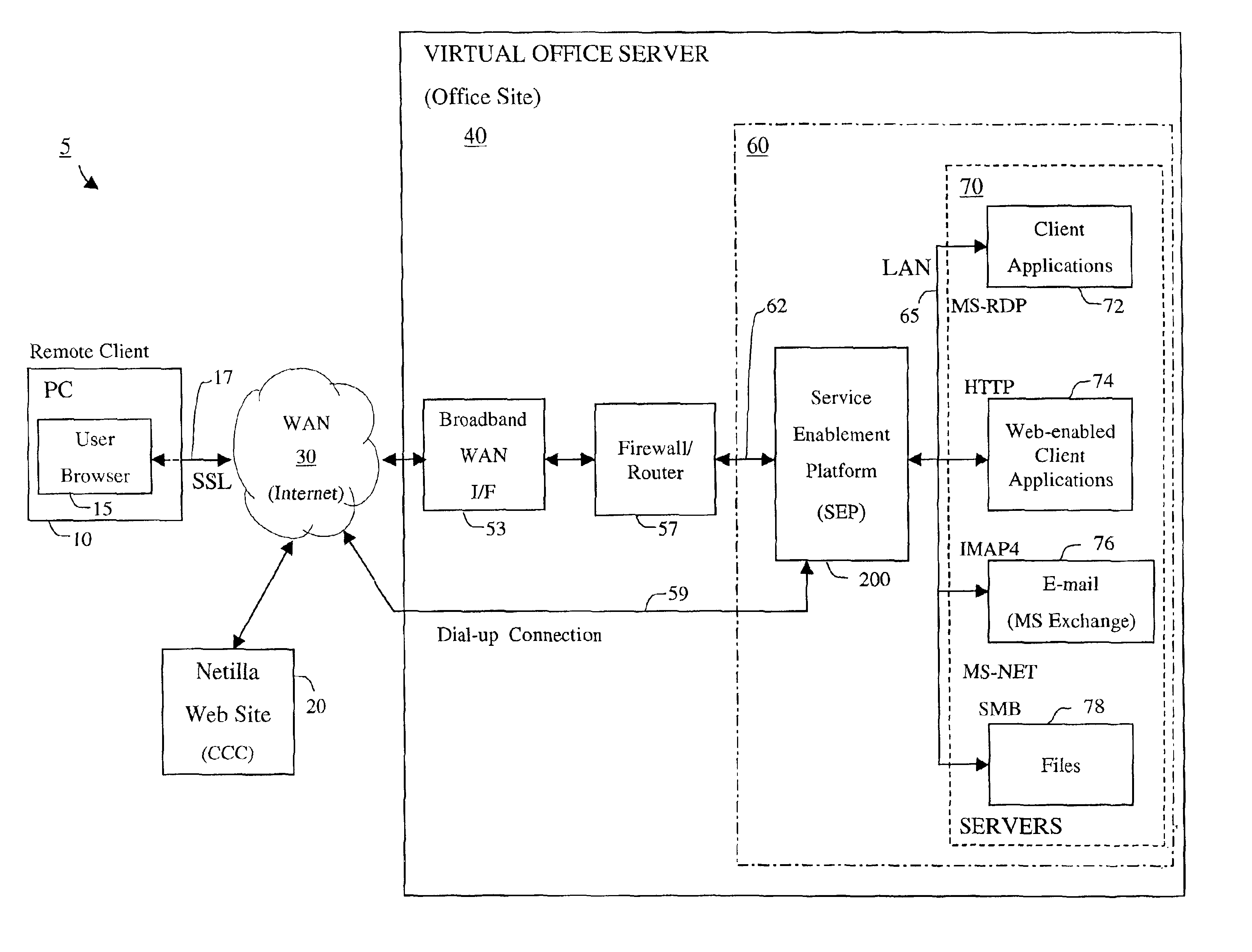
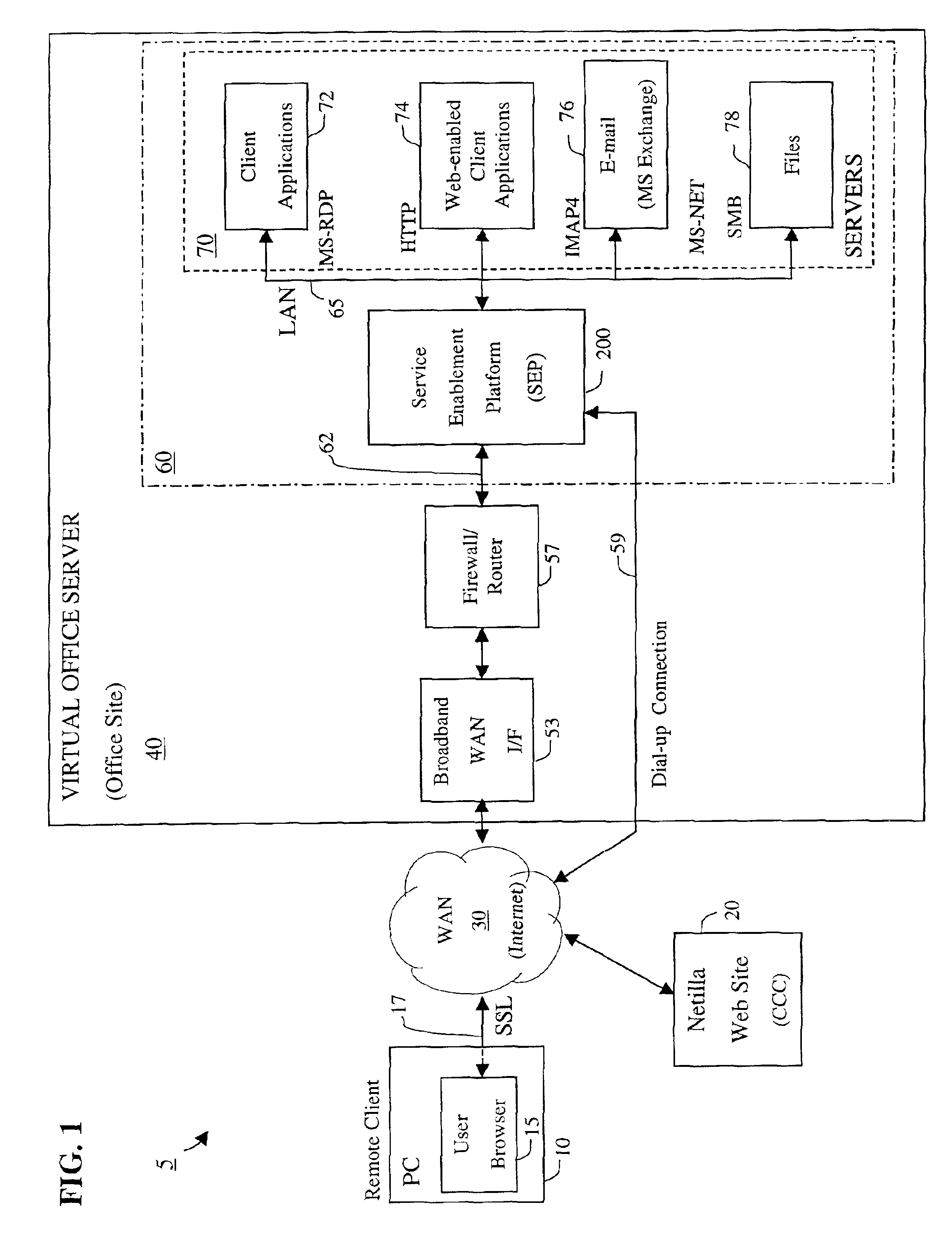
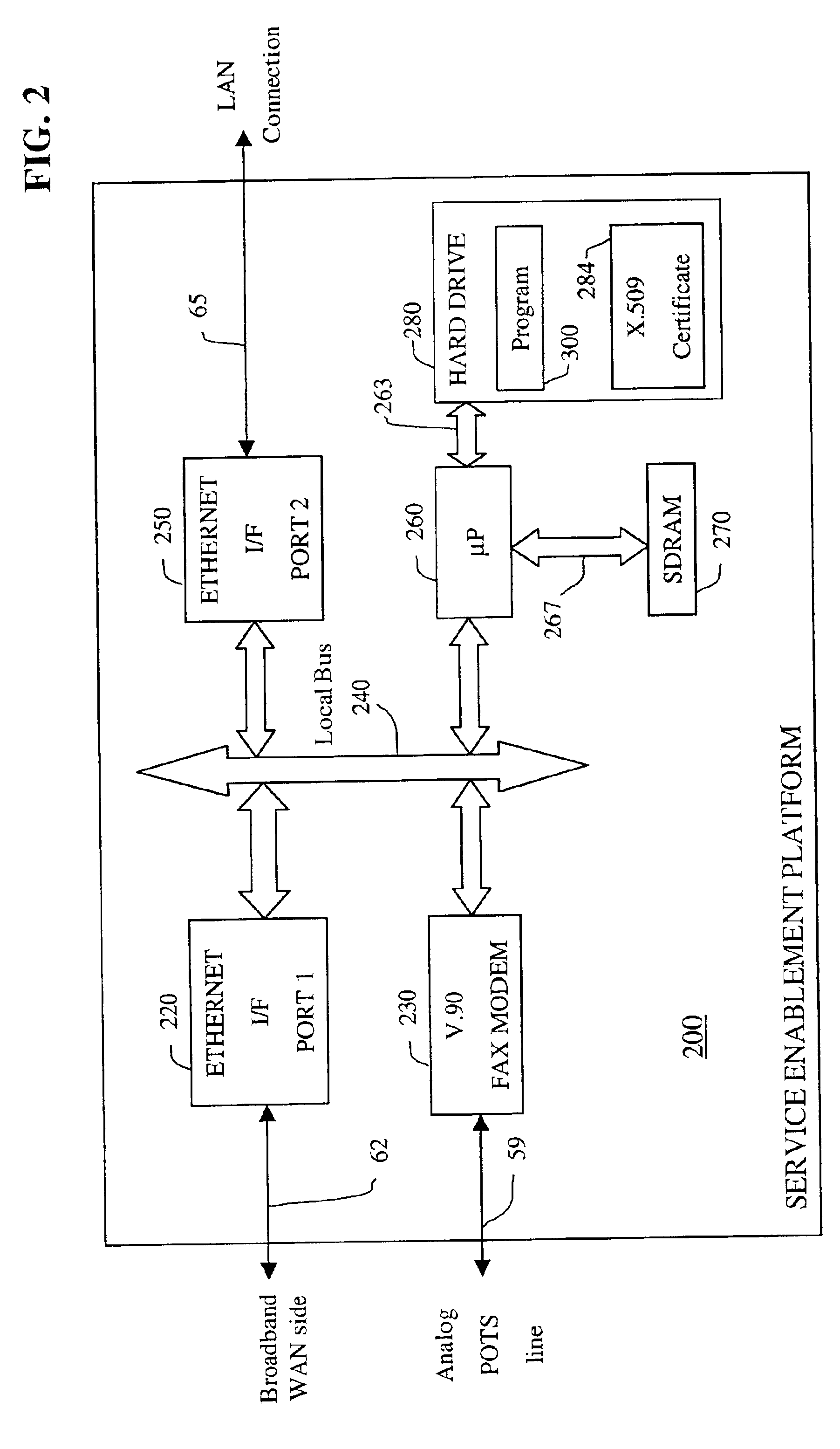
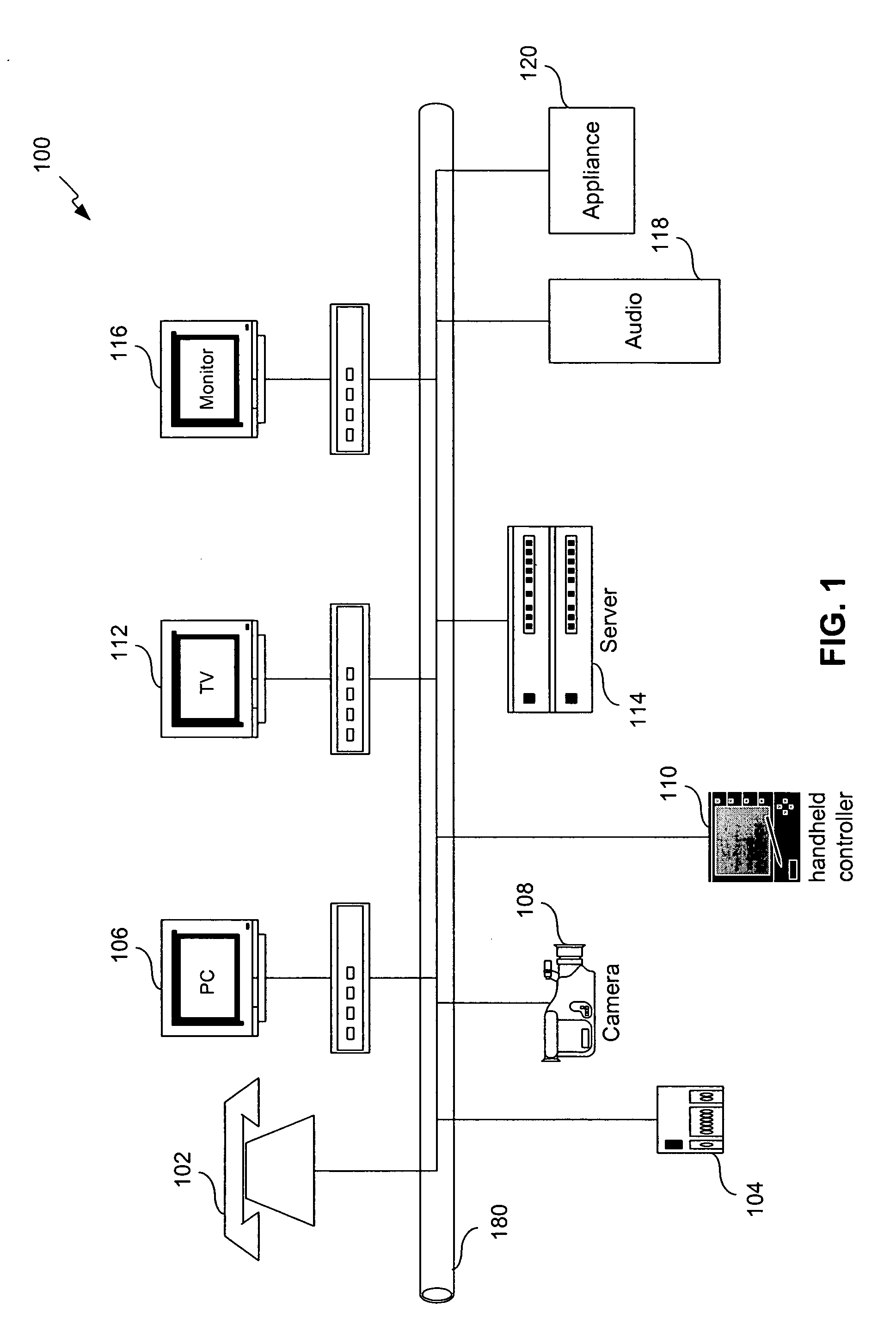
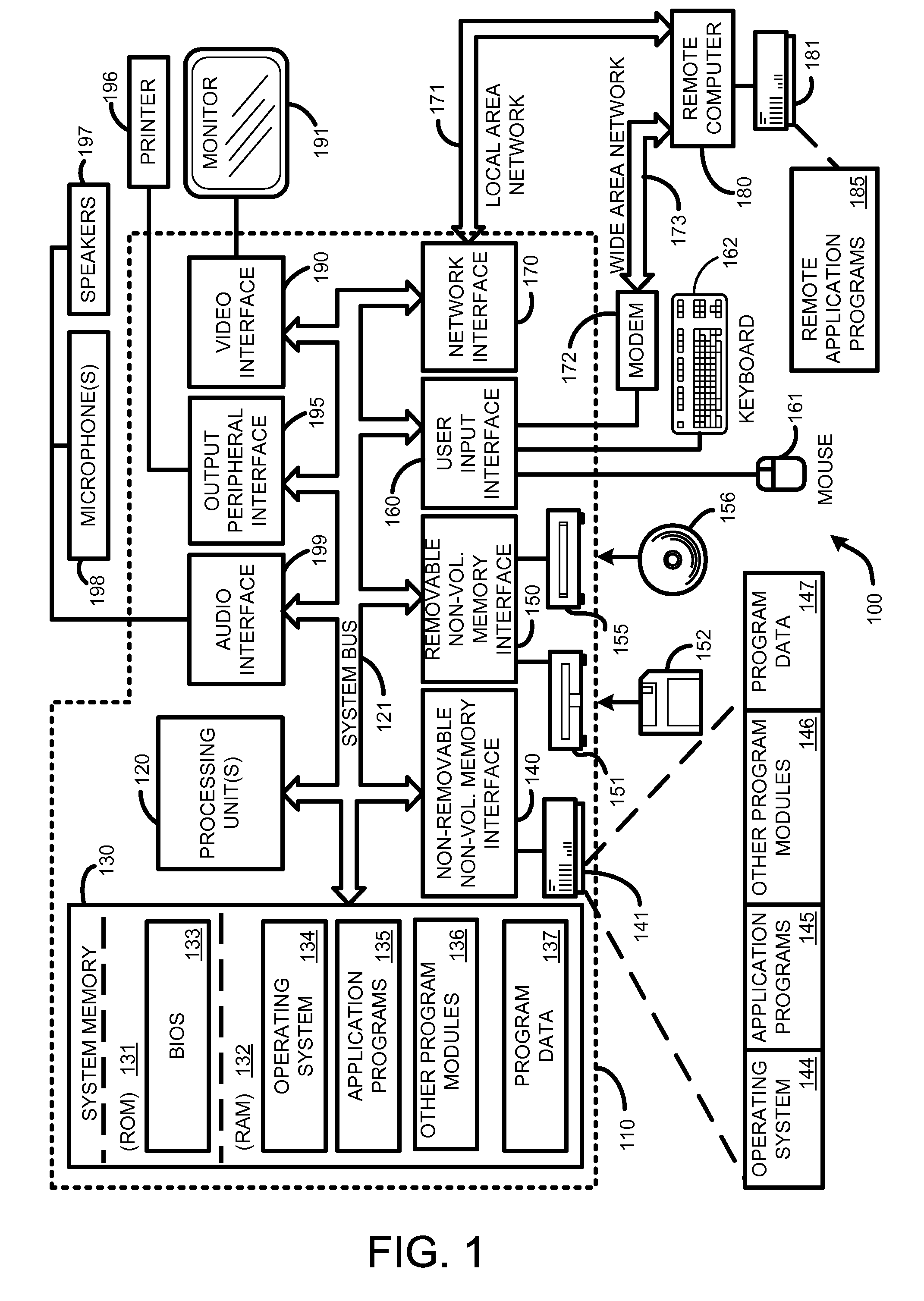
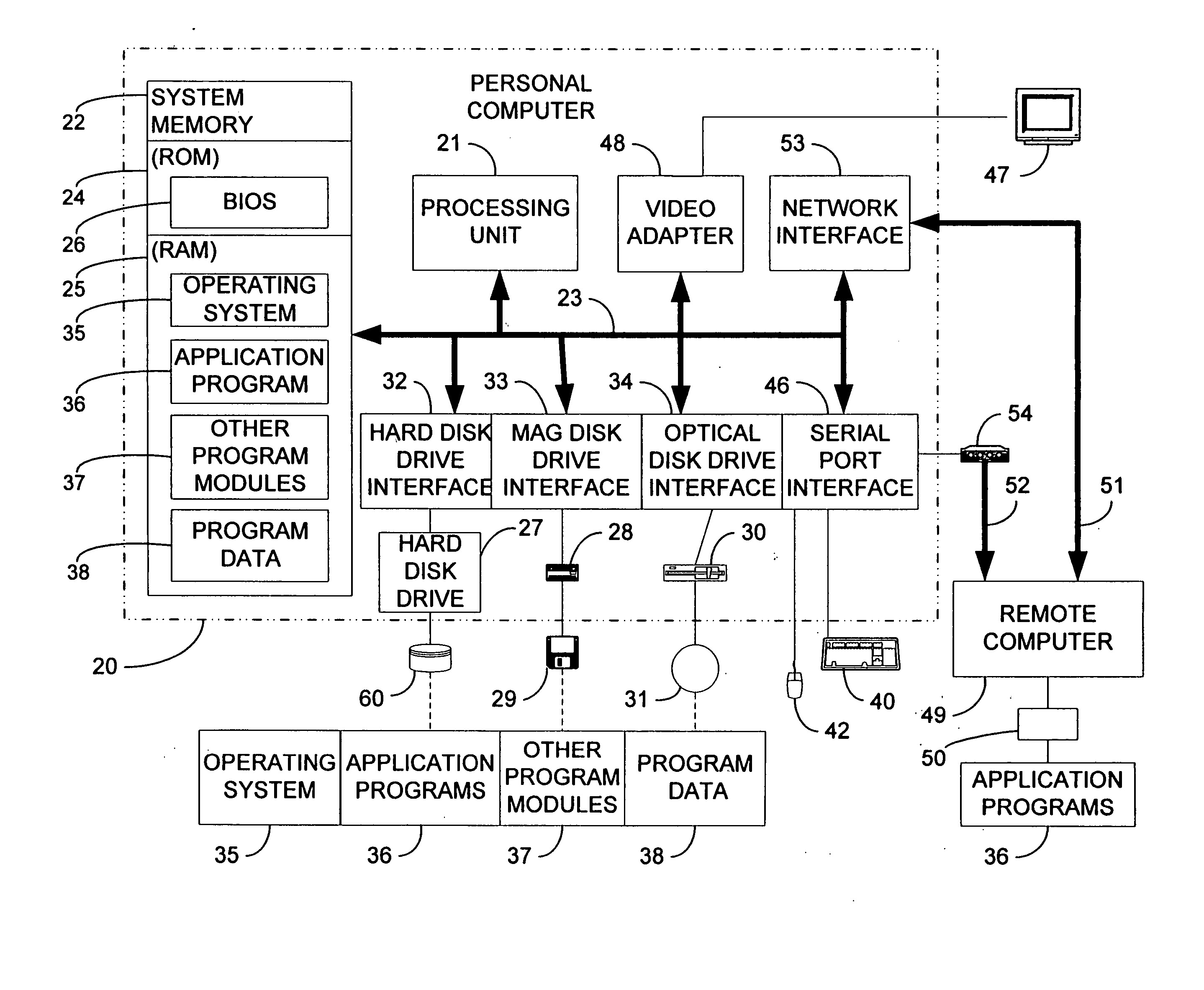
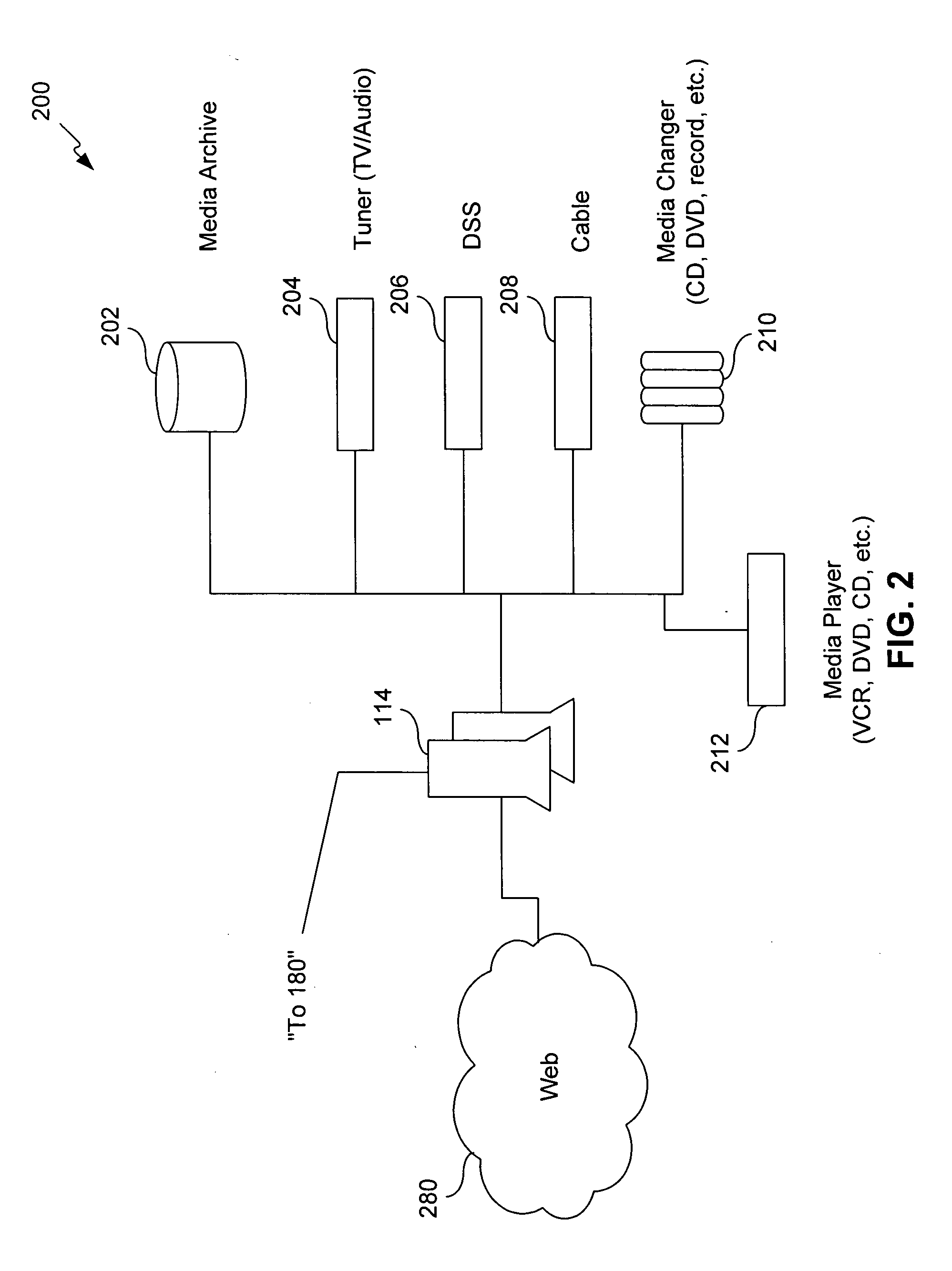
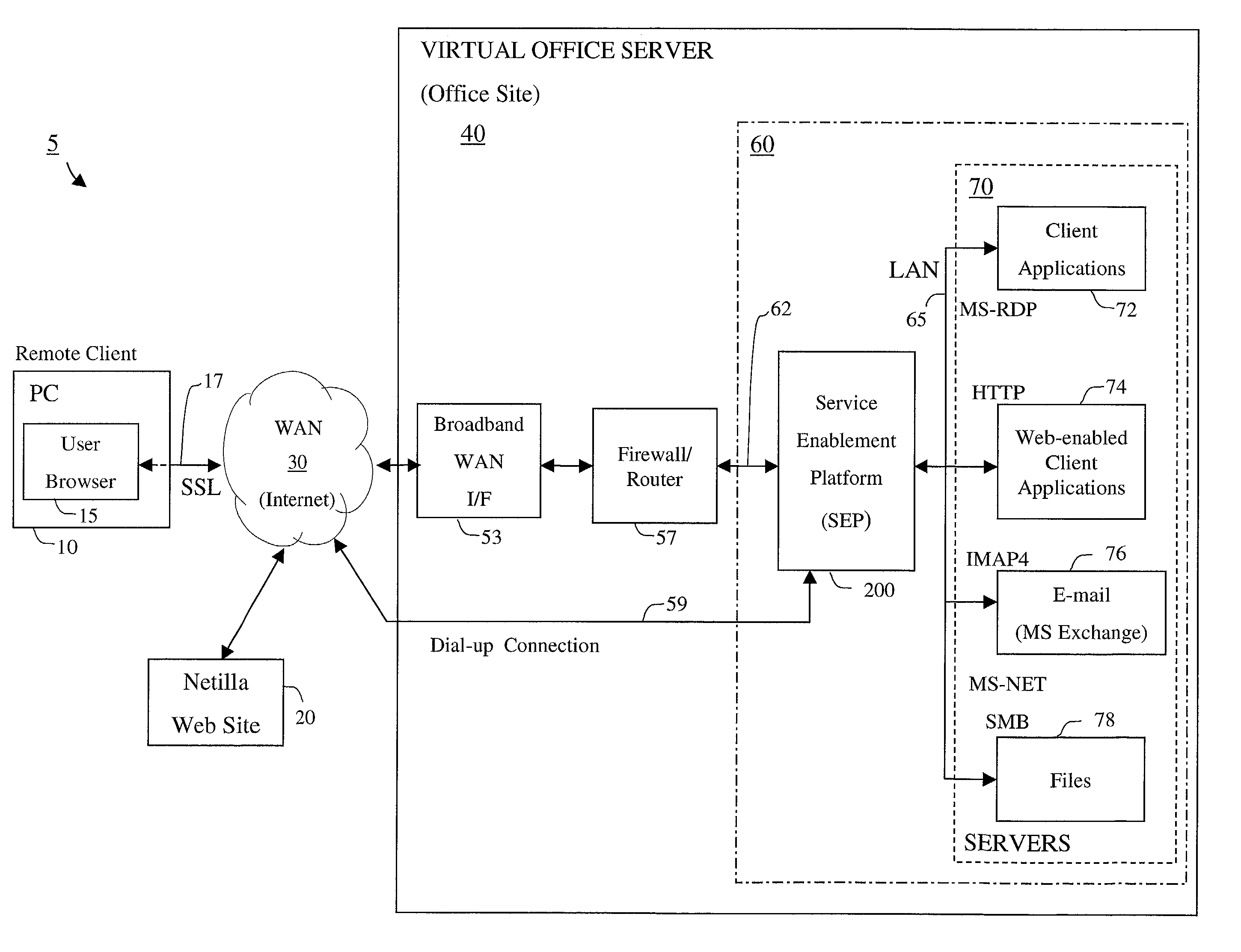
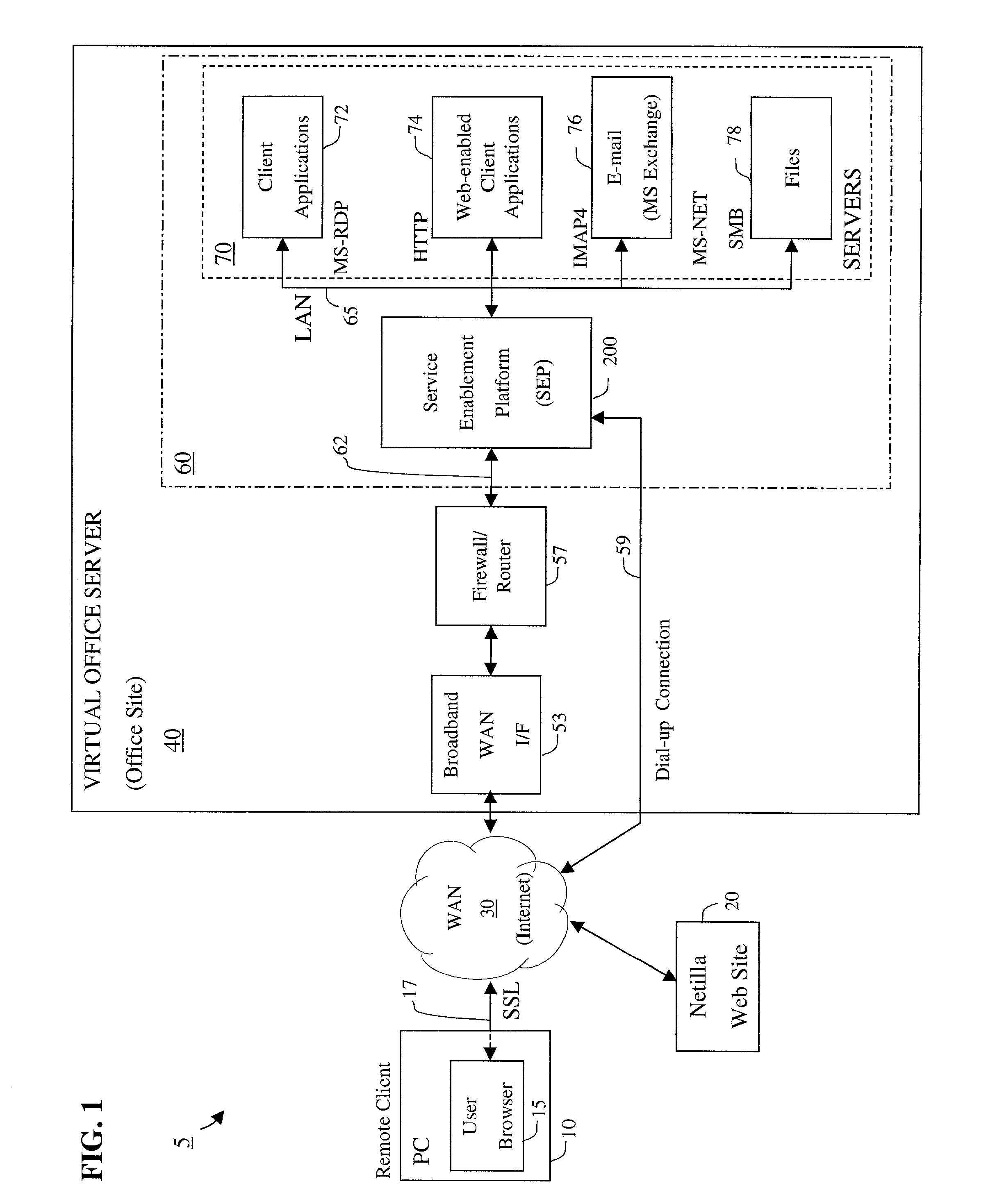
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6920502B2Readily and easily accommodateExpanding processing and storage capacityMultiple digital computer combinationsProgram controlCA protocolNetwork connection
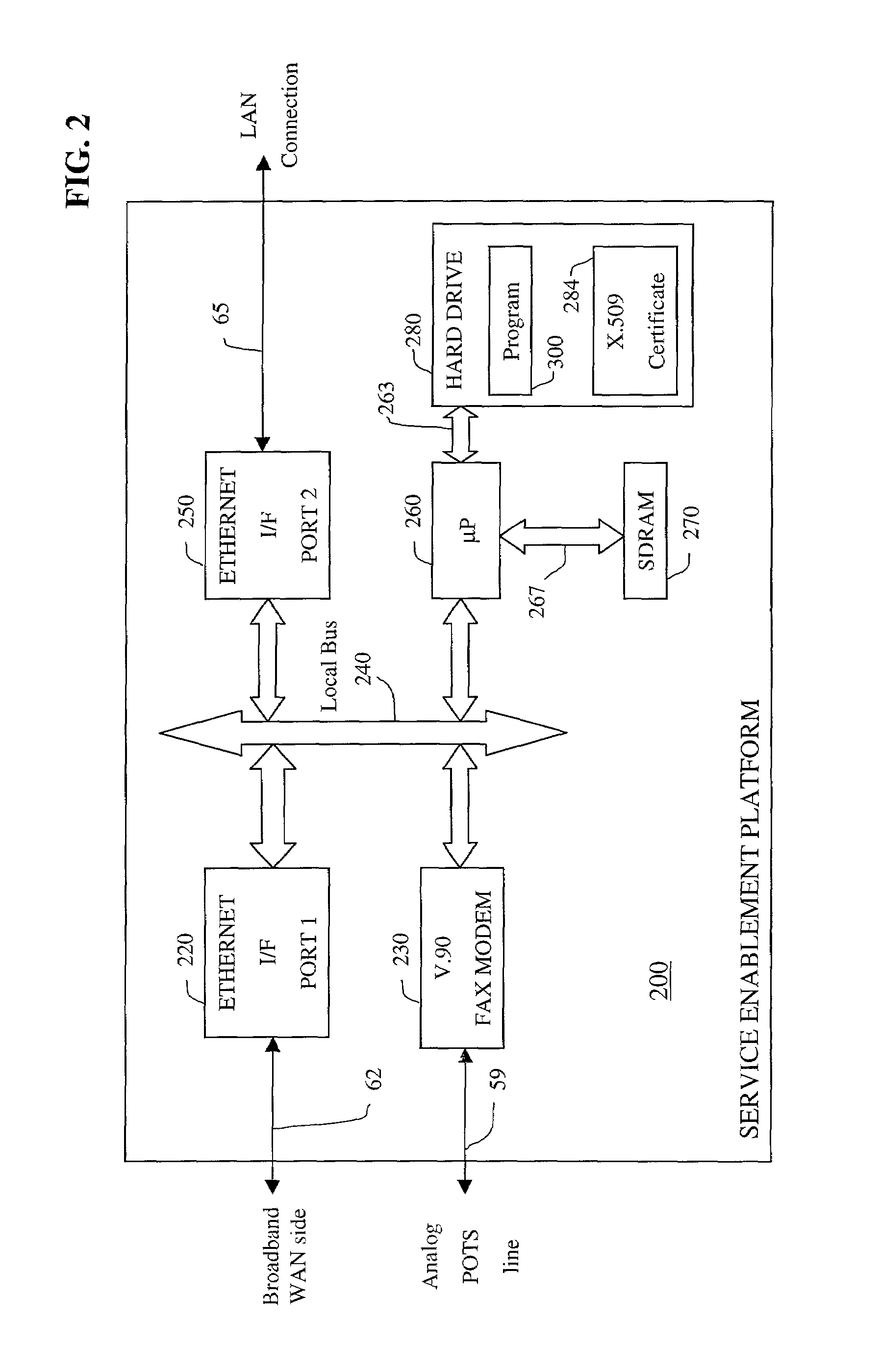
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
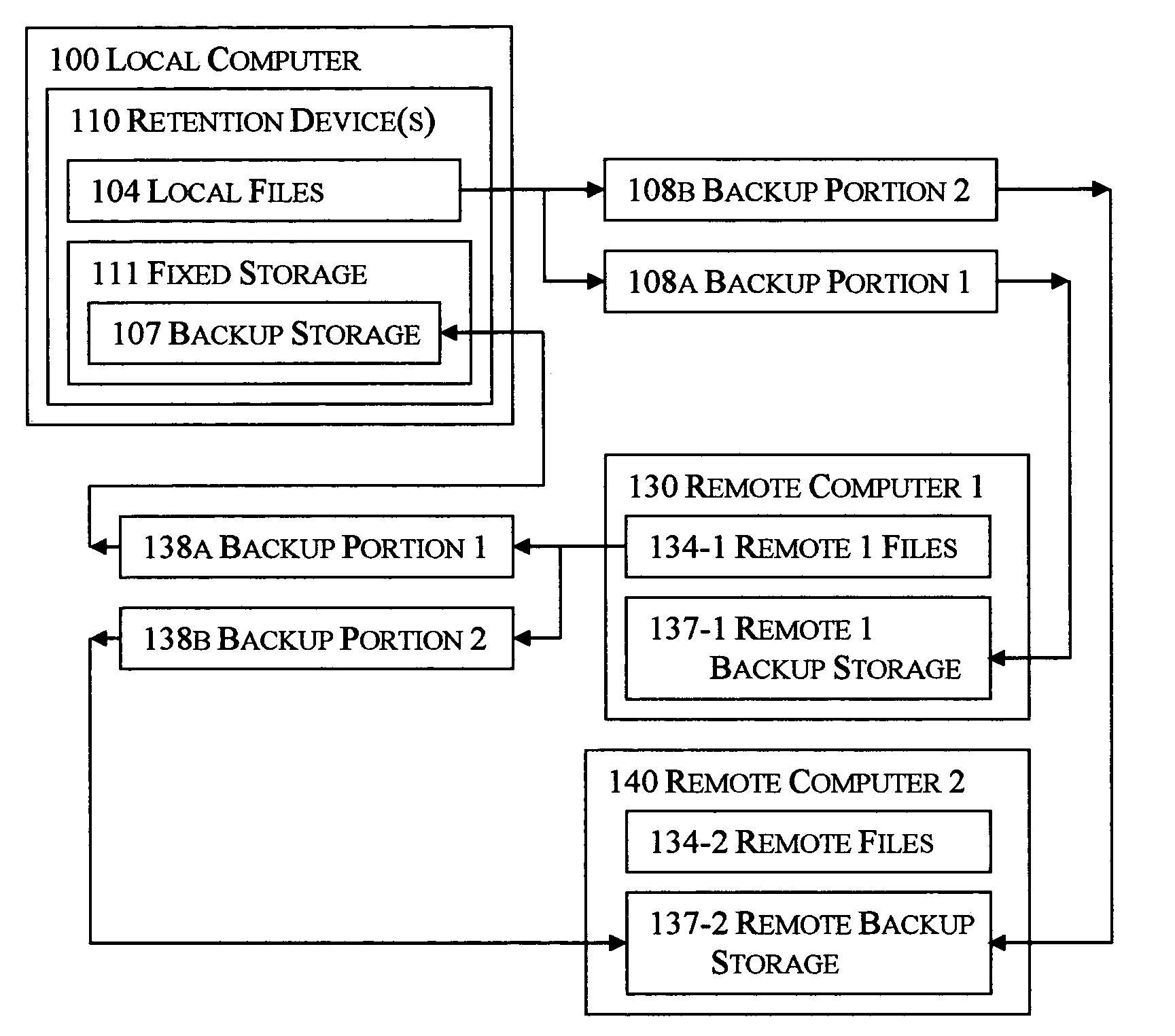
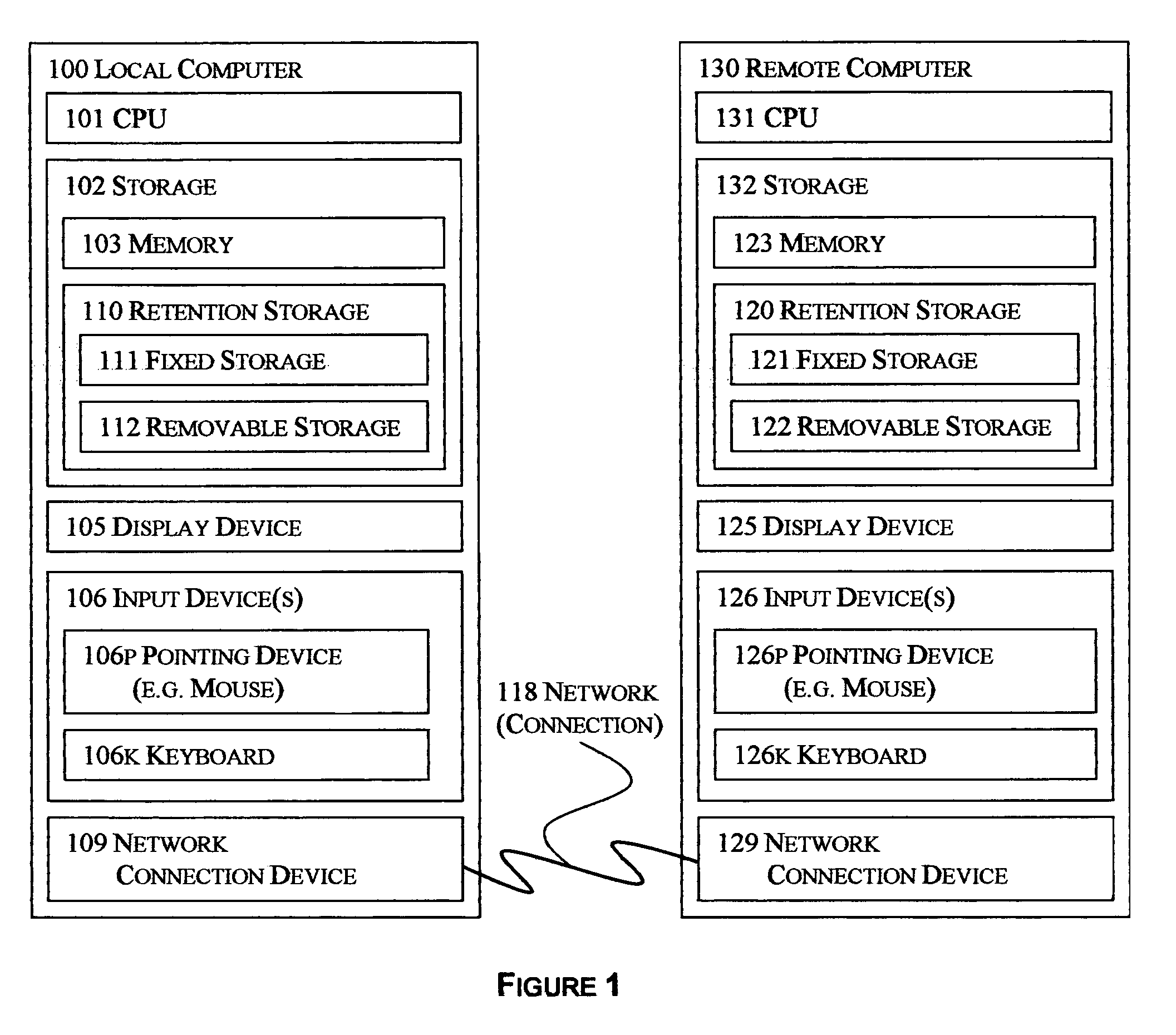
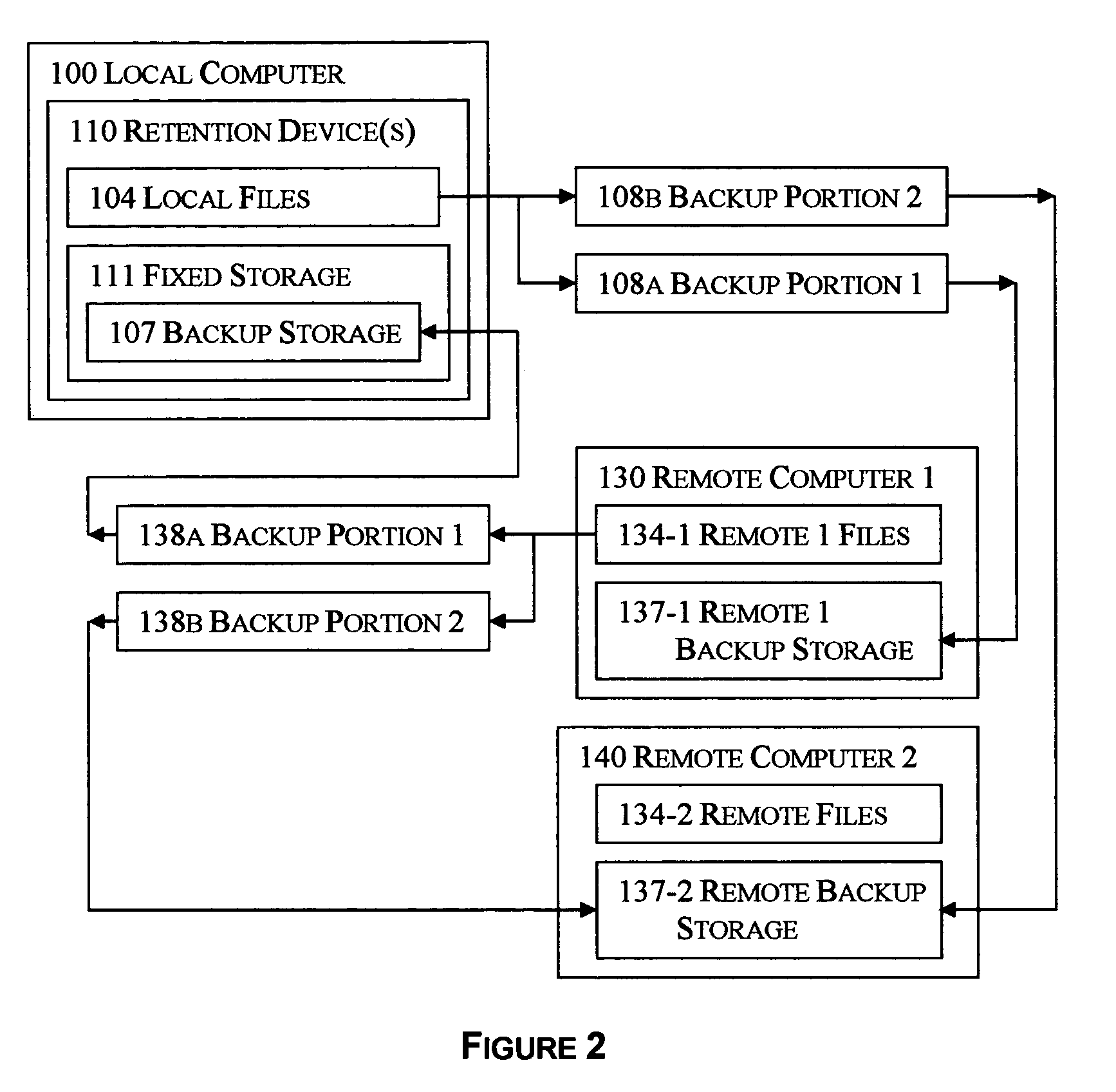
Selective reciprocal backup
InactiveUS7330997B1Risk minimizationIncrease probabilityError detection/correctionMemory systemsNetwork connectionApplication software
The disclosed technology applies the principle of anonymous reciprocity to facilitate remote backups. A local computer stores other computer's backup files, while storing backup copies of local files on other computers connected through a network. Each computer may securely maintain and manage storage for other computers' files. Application may be constrained to a local area network, or work on the Internet. The disclosed technology works in a peer-to-peer environment; no central server is required. The same disclosed technology may also apply to file sharing.
Owner:ODOM GARY
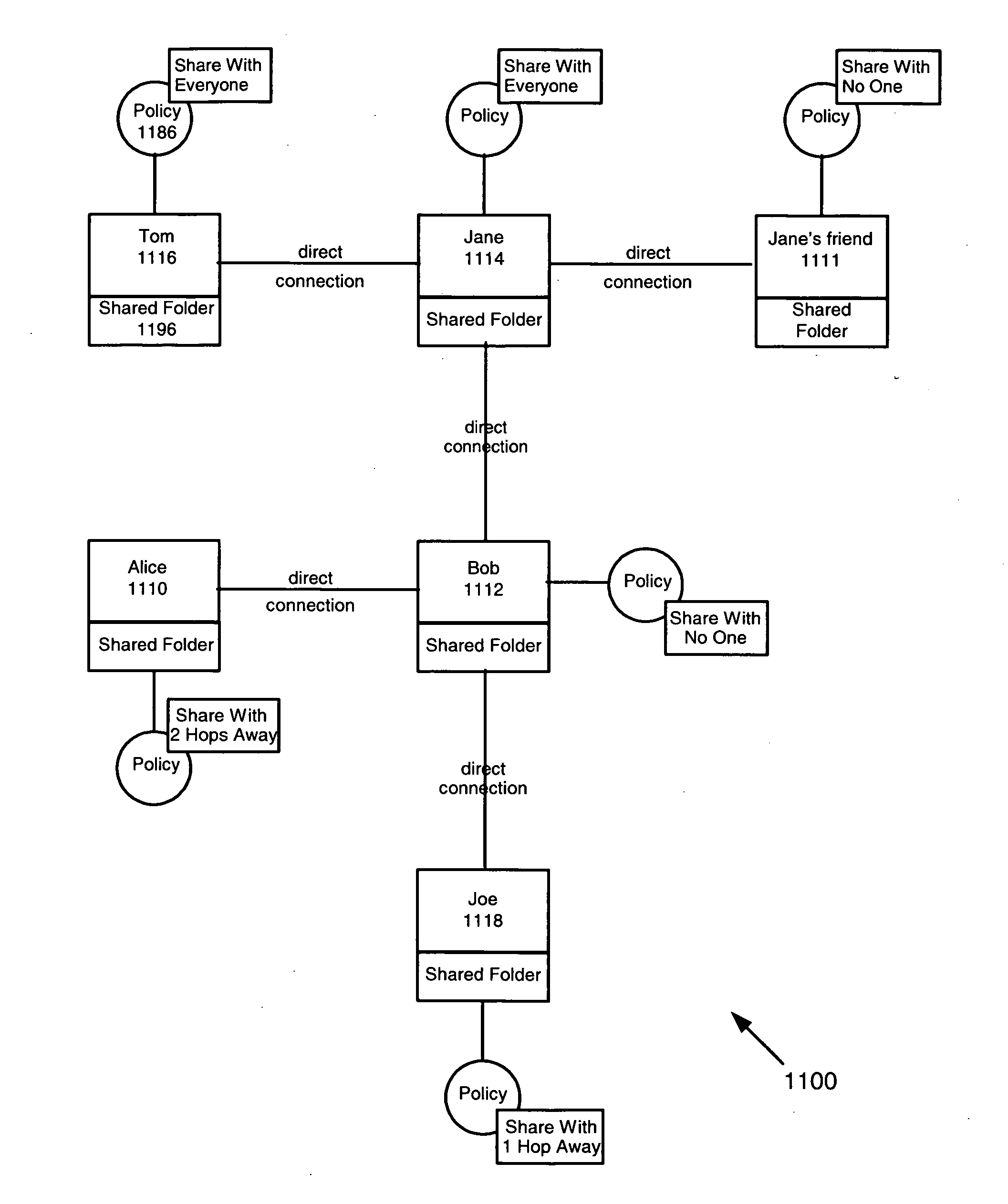
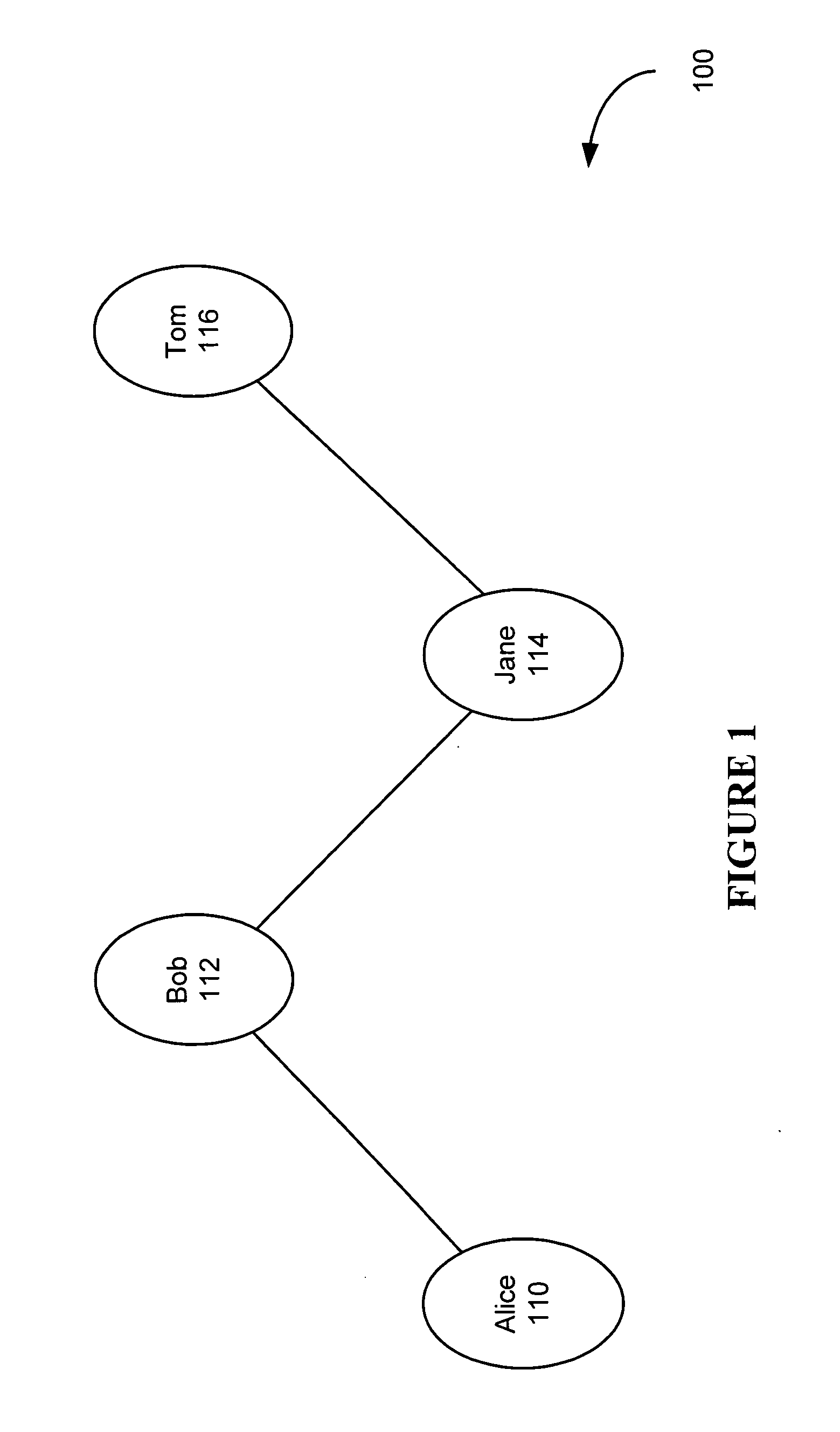
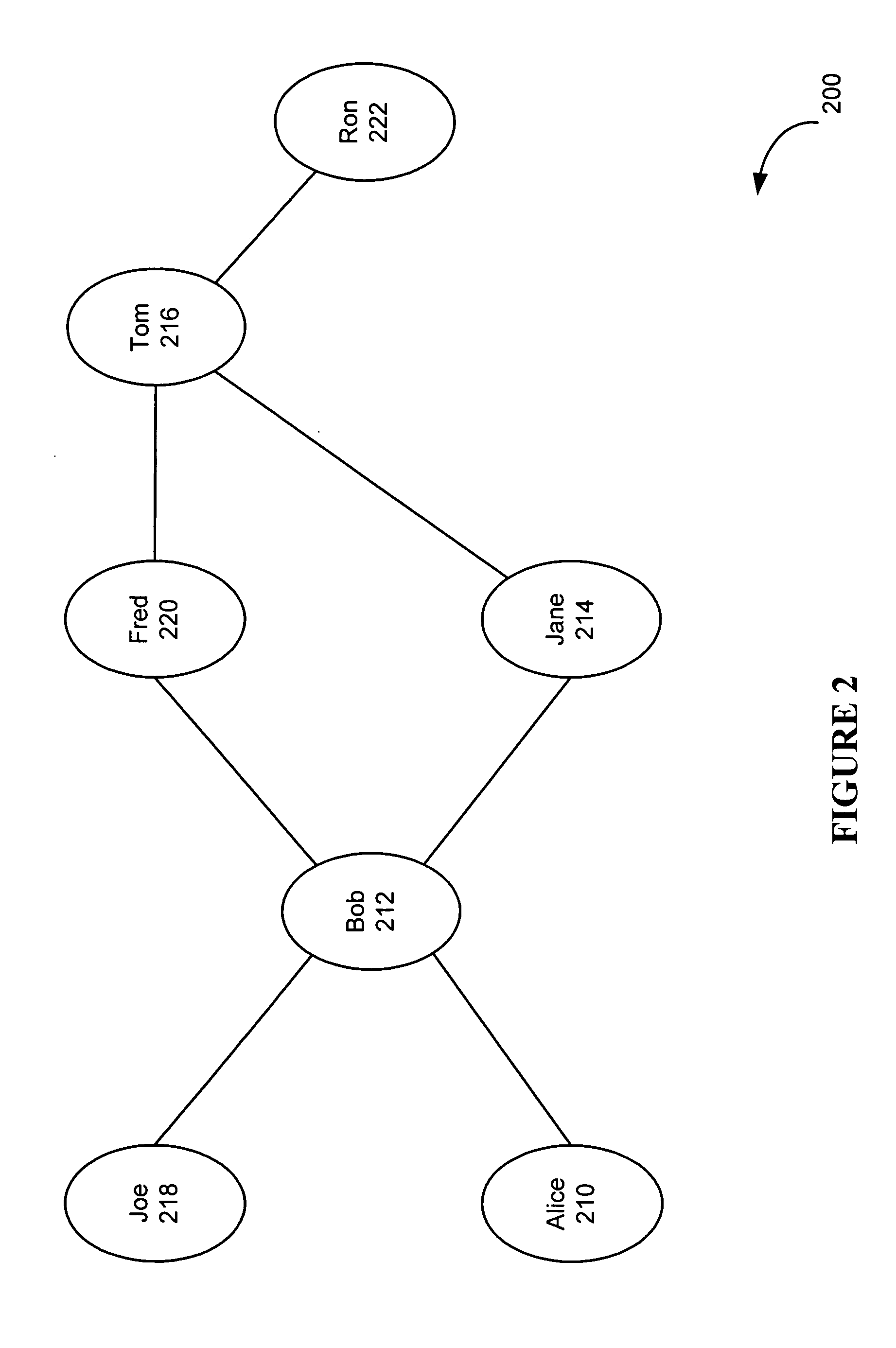
System and method for developing and using trusted policy based on a social model
InactiveUS20060248573A1Digital data processing detailsUser identity/authority verificationInternet privacyFile sharing
A trust policy is constructed based upon a social relationship between real-world entities. The trust policy may determined based upon a social network and social network maps. The social network map provides a framework to determine social distances. The trust policy provides quick and secure access to desired or trusted nodes while providing security from entities outside the trusted sphere of nodes. The trust policy determined by the social distance may be used for various types of applications including filtering unwanted e-mail, providing secure access to resources, and accessing protected services. File sharing, referral querying, advertisement targeting, announcement targeting, access control, and various applications may be limited using the constructed trust policy.
Owner:CONTENTGUARD HLDG
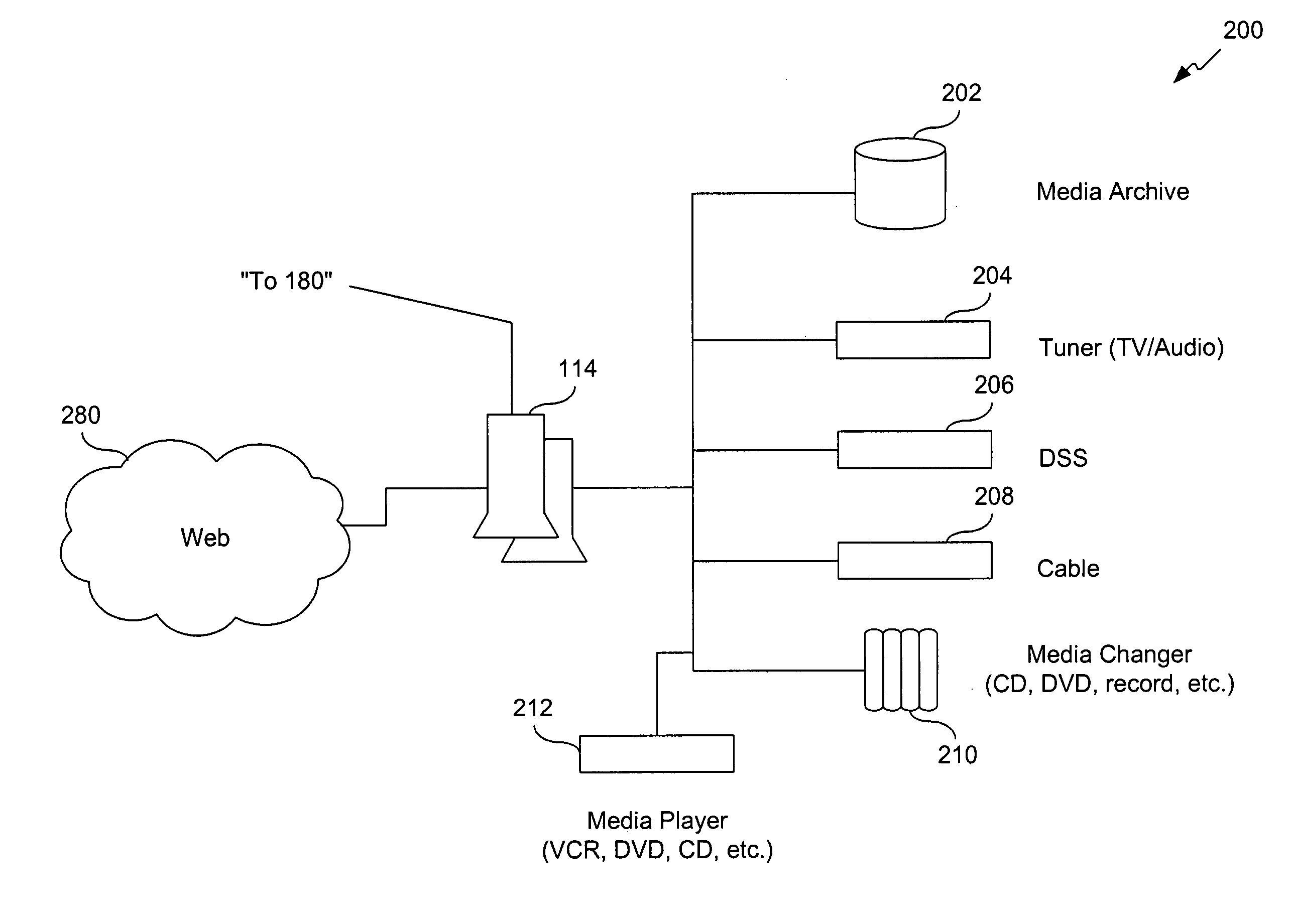
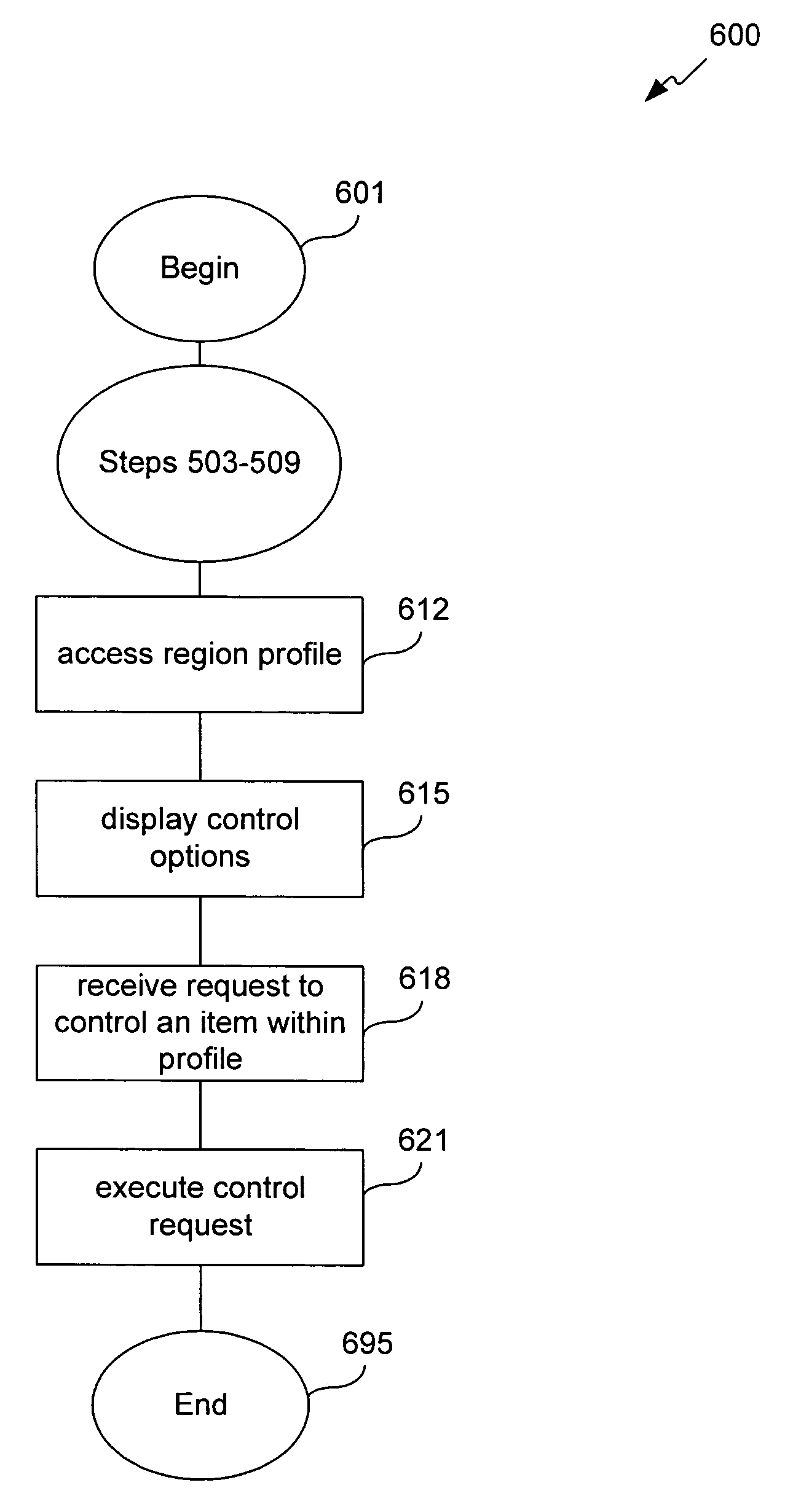
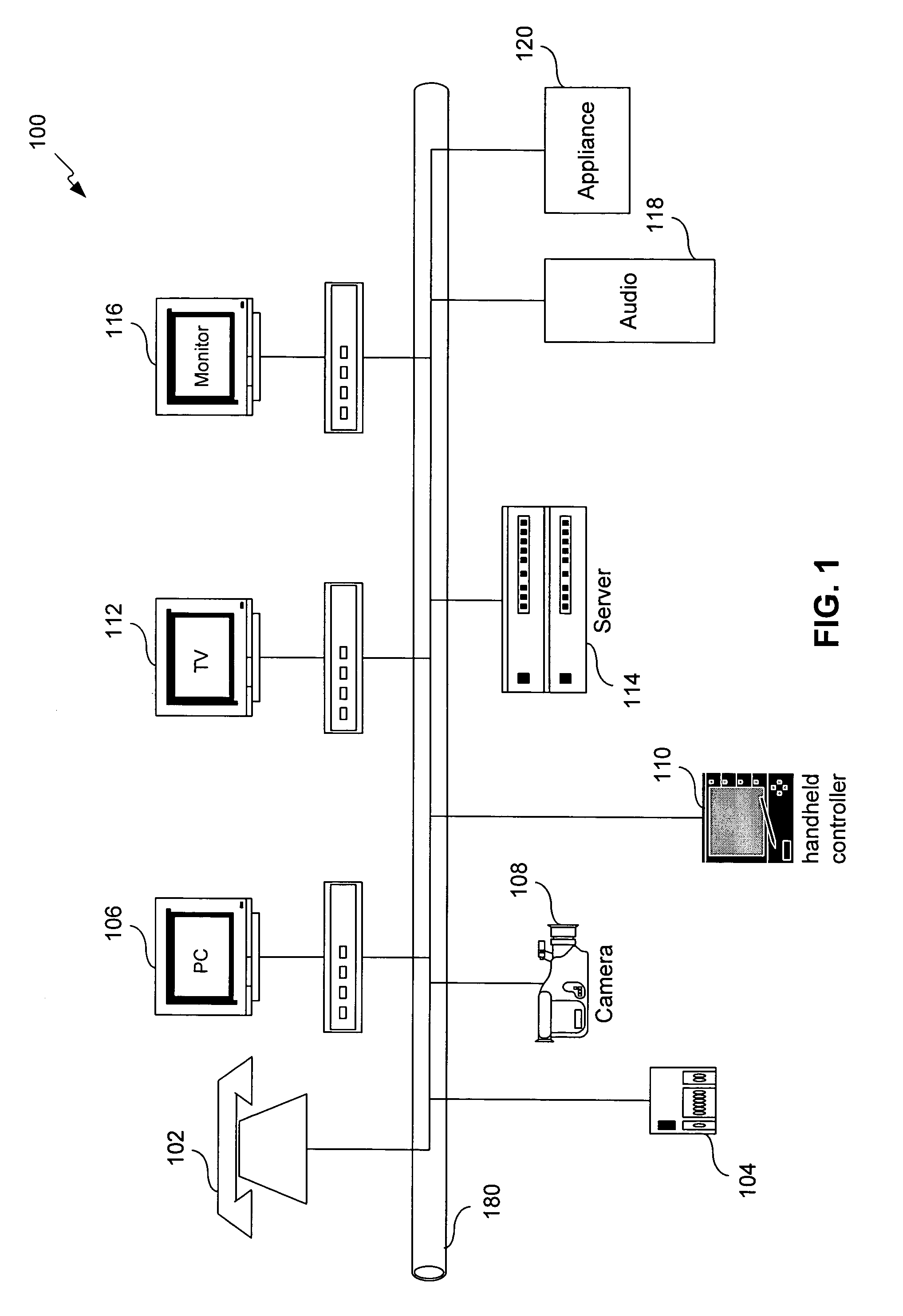
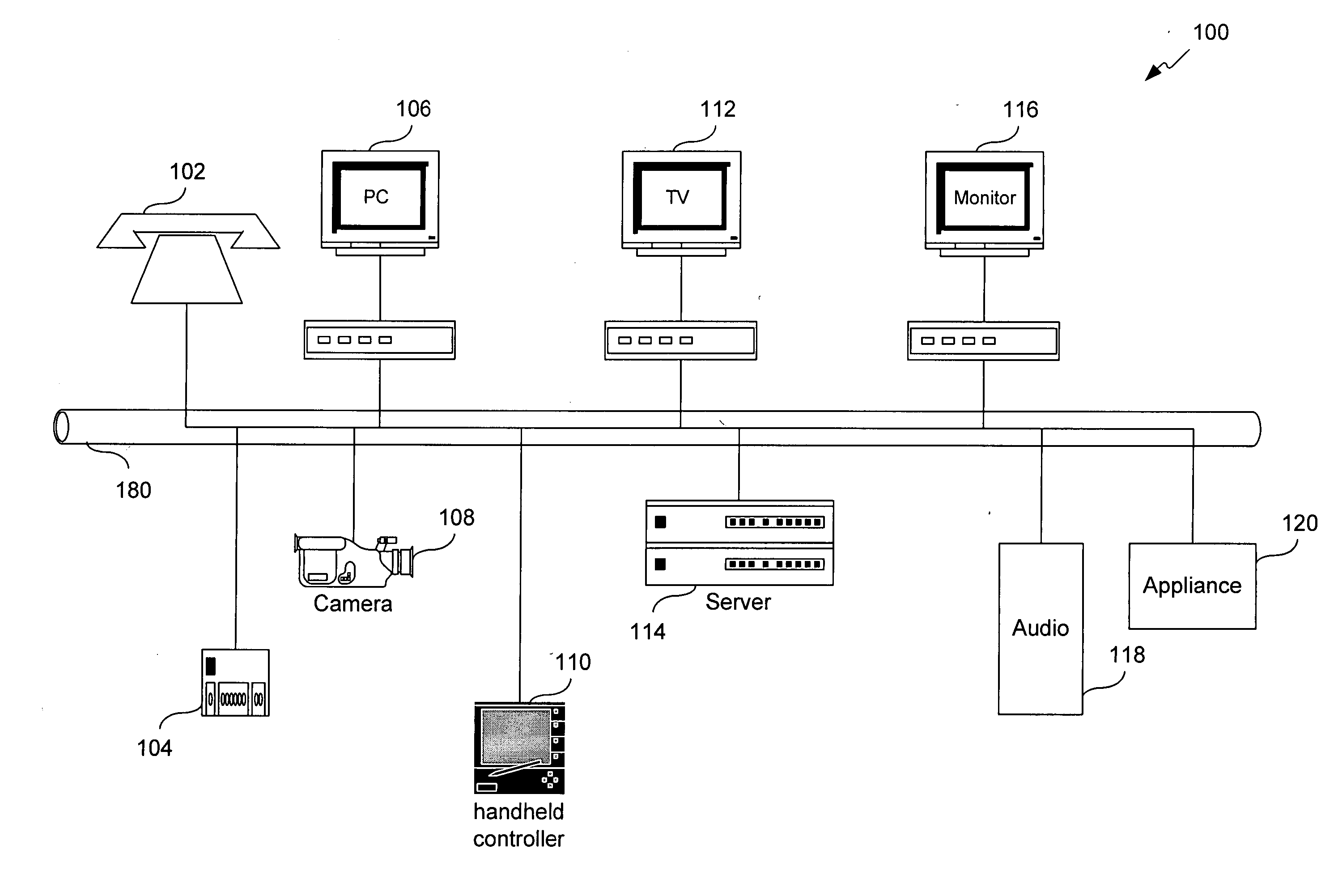
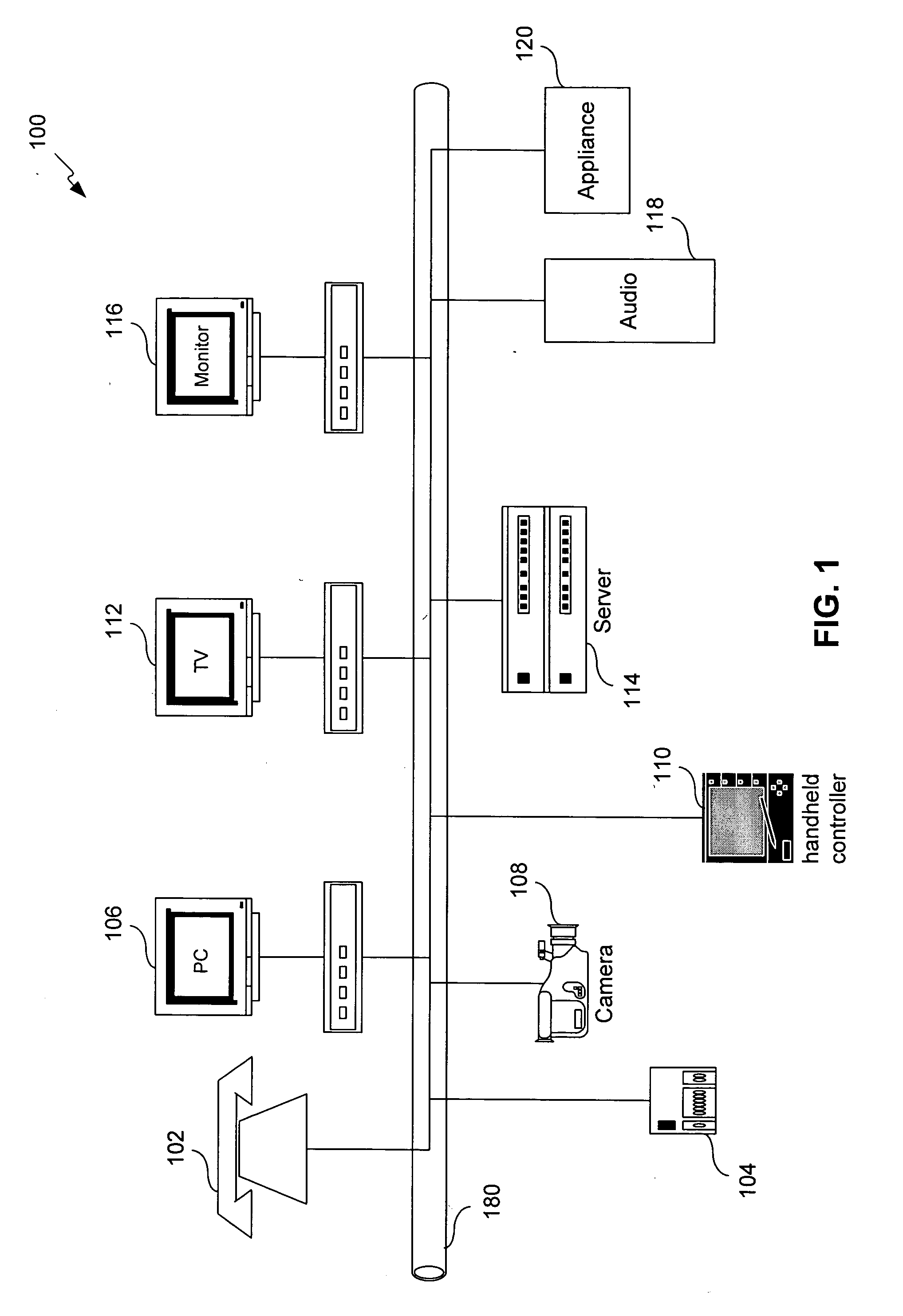
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS20060053447A1Facilitate transmission and receptionTelevision system detailsColor television detailsControl signalDisplay device
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for improved data sharing and content transformation
InactiveUS20050234864A1Easy to shareNeed can be fittedDigital data information retrievalDigital data processing detailsThird partyInternet privacy
A user's personal computer can be turned into a personal network server for easily sharing personal digital information with other people using a wide variety of devices. There are a variety of alternative ways in which such file sharing on the user's computer can be implemented, such as with a client-side server approach, a hosted server approach, and an automated publish approach. Depending upon a variety of factors, the requested shared data may be intelligently and dynamically transformed to better fit the requesting party's needs. Programming interfaces are available to third parties that allow for access to the shared data and for providing customized instructions on what to do when transforming the data.
Owner:SHAPIRO AARON M
Method and system for asynchronous transmission, backup, distribution of data and file sharing
InactiveUS6662198B2Easy to shareSolve the real problemDigital data information retrievalData processing applicationsOperational systemFile sharing
A system and method is provided for asynchronously sharing, backing up, and distributing data based on immutable entries. The system which is layered upon an existing operating system automatically stores, queues and distributes requested data among users.
Owner:ZOTECA
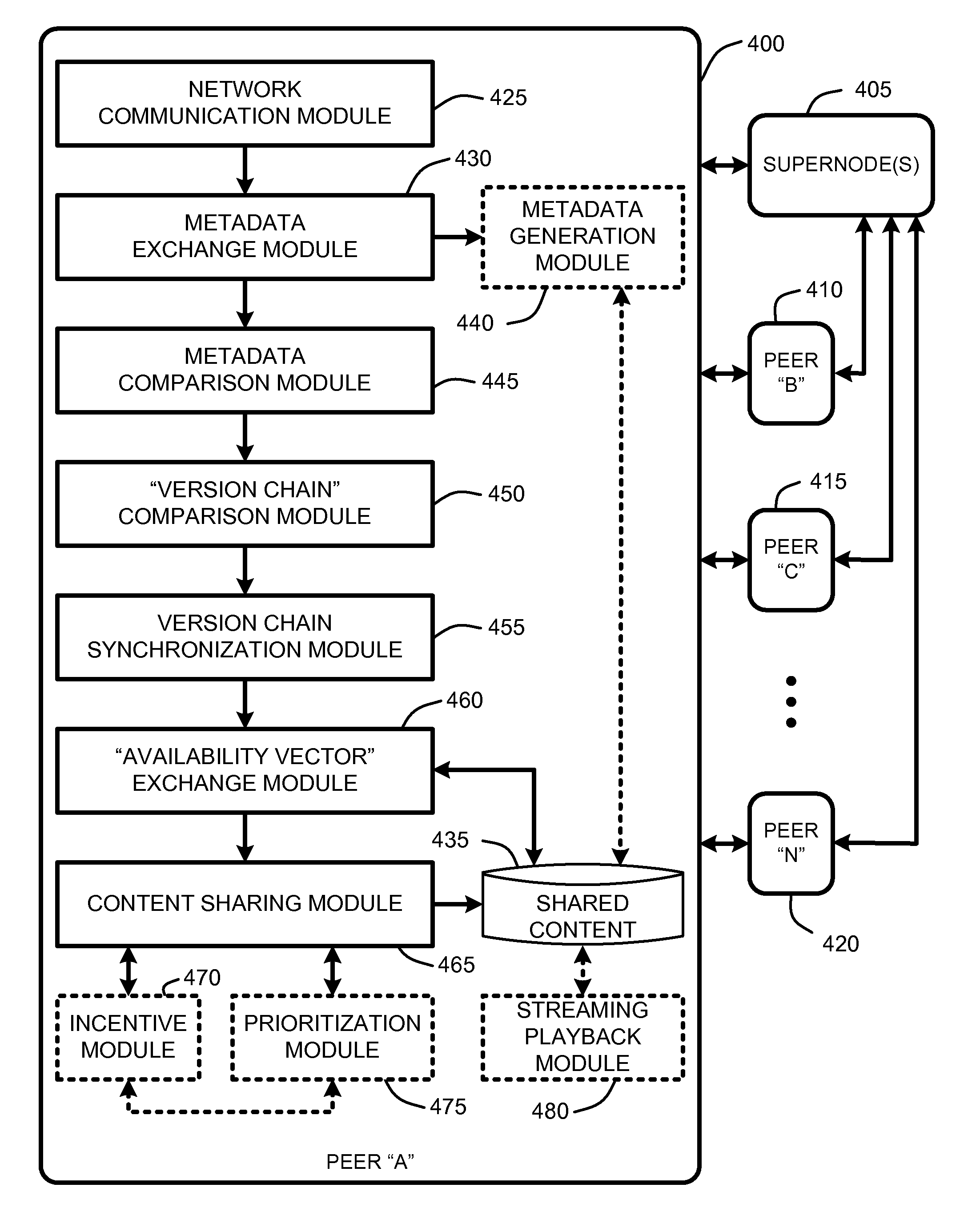
Versioning synchronization for mass p2p file sharing
InactiveUS20080005195A1Digital data information retrievalSpecial data processing applicationsDirectory structureFile sharing
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and accompanying methods for providing, through a centralized server site, an integrated virtual office environment, remotely accessible via a network-connected web browser, with remote network monitoring and management capabilities
InactiveUS6981041B2Expanding processing and storage capacityEasy to scaleMultiple digital computer combinationsData switching networksCA protocolNetwork connection
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. During initial operation, the SEP, operating under a default profile, establishes, over an analog connection to the WAN, a management session with the site to obtain customer WAN access information, then tears down the analog connection and establishes a broadband WAN connection through which the SEP re-establishes its prior session and obtains a client certificate and its customized profile. The SEP then re-initializes itself to that particular profile.
Owner:AEP NETWORKS
Entertainment device configured for interactive detection and security vigilant monitoring in communication with a control server
InactiveUS20070256105A1Facilitate transmission and receptionClosed circuit television systemsBurglar alarmSensor arrayEngineering
Home security detectors configured with the control components of the home comprising interactive detectors enhanced to support location-awareness and home occupant-awareness and functionality. The system includes at least one motion sensor configured with communication devices operatively arranged to transmit information about any motion of occupants in the various sections of the home as part of the information about the occupancy of the home during an emergency. At least one sensor is provided in various rooms of a home each sensing a state of the home. A central communication device is coupled, wired or wirelessly, directly or indirectly, to each home sensor configured to transmit the state of the home. The number of occupants in the home are determined by at least one body heat sensor and at least one heartbeat sensor each configured with the interactive detectors to detect the presence of emergency and home occupants and to know the present situations such as their heartbeats, such that the number of occupants and their locations are determinable from the number of detected body heat and their security and safety conditions are determinable by their heartbeats. The detection method includes the steps of sensing a state of the home and transmitting the state of the home to at least a server. Images of the home are captured by at least a camera means configured with at least a MOS and / or CMOS based active sensor array for producing real-time images and stored in the server for wireless retrieval. The images ideally include at least an intruder of the home. The server is configured with a central processor for enabling controlling security vigilance monitoring and for enabling rapid distribution of detection data, voice, and other detection signals within the monitoring environment. The system establishes a network which includes configuring home audio / visual devices, media destination means such as televisions, monitors, PDAs, notepads, notebooks, MP3, wireless stereo, cell phones etc for the detection means. The control server supports video / audio servings, telephony, messaging, file sharing, internetworking, and security monitoring and allows home occupants to access and control the home network environment from any location within a controlled residential, commercial / industrial and / or non-residential, commercial / industrial environment with at least a computer means such as a cell phone.
Owner:COSTA VERDI SERIES 63 OF ALLIED SECURITY TRUST I
System and method for shared integrated online social interaction
InactiveUS7234117B2Enhanced interactionImprove identityOffice automationAnimationModularityNetwork communication
Owner:MICROSOFT TECH LICENSING LLC
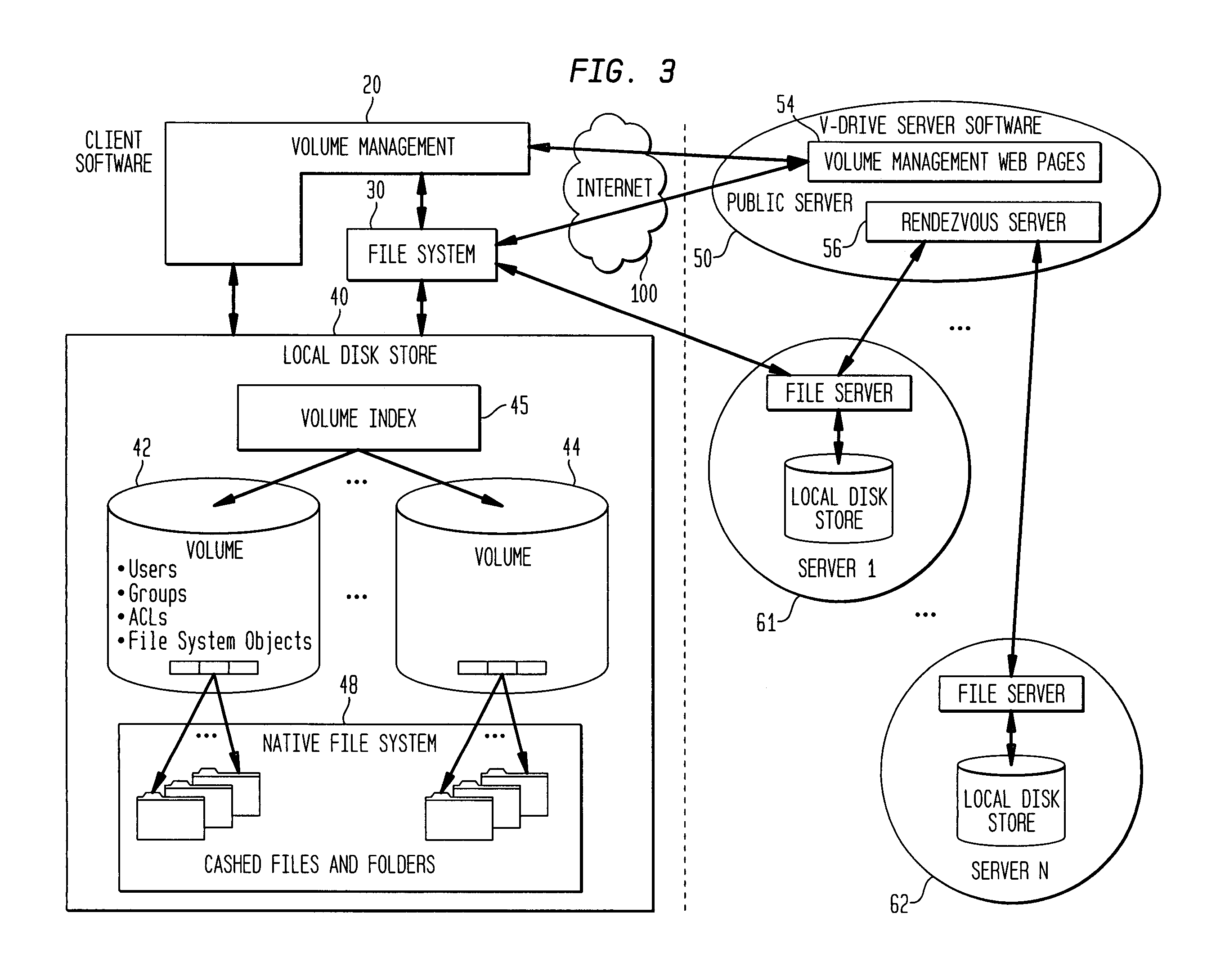
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
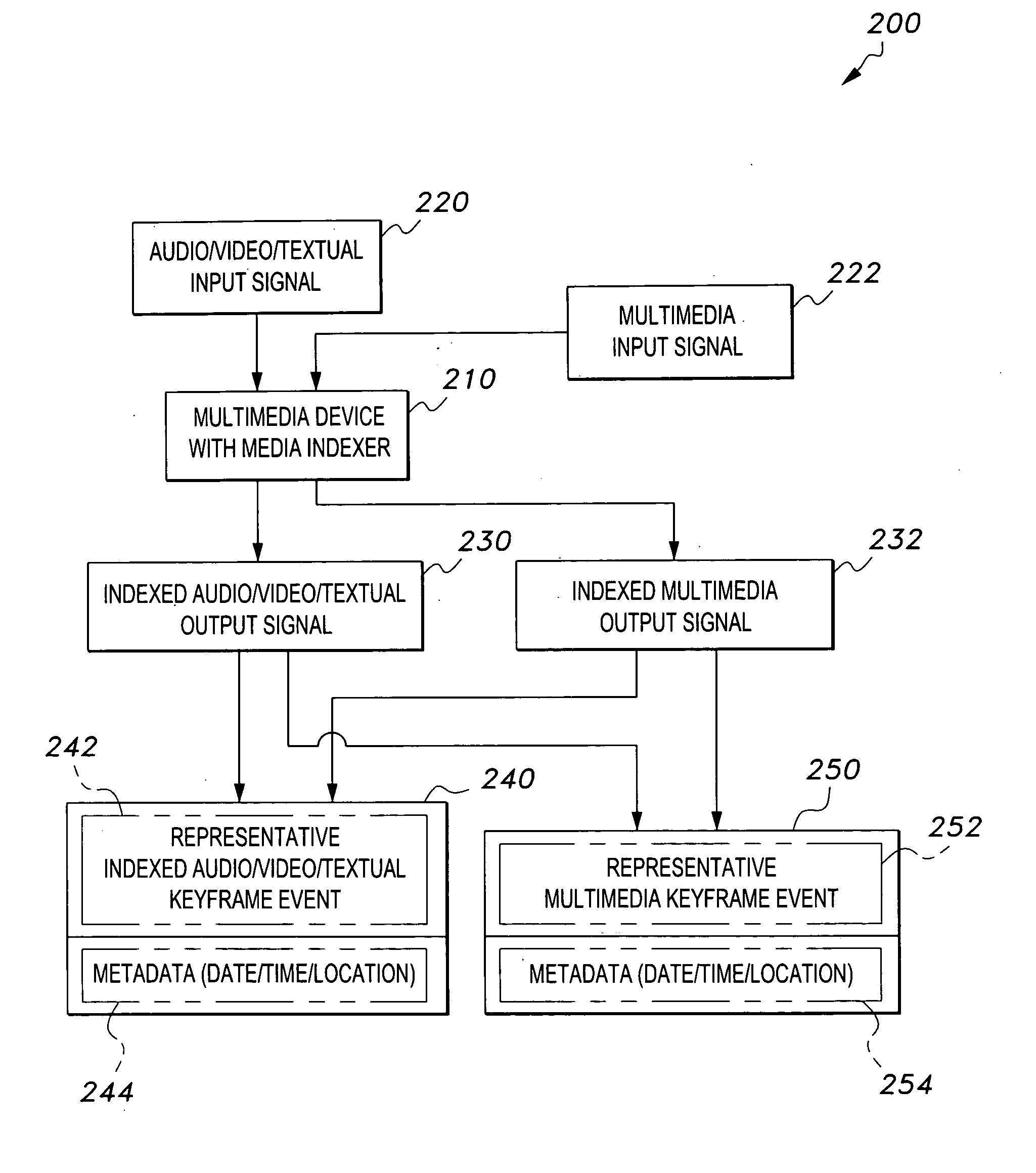
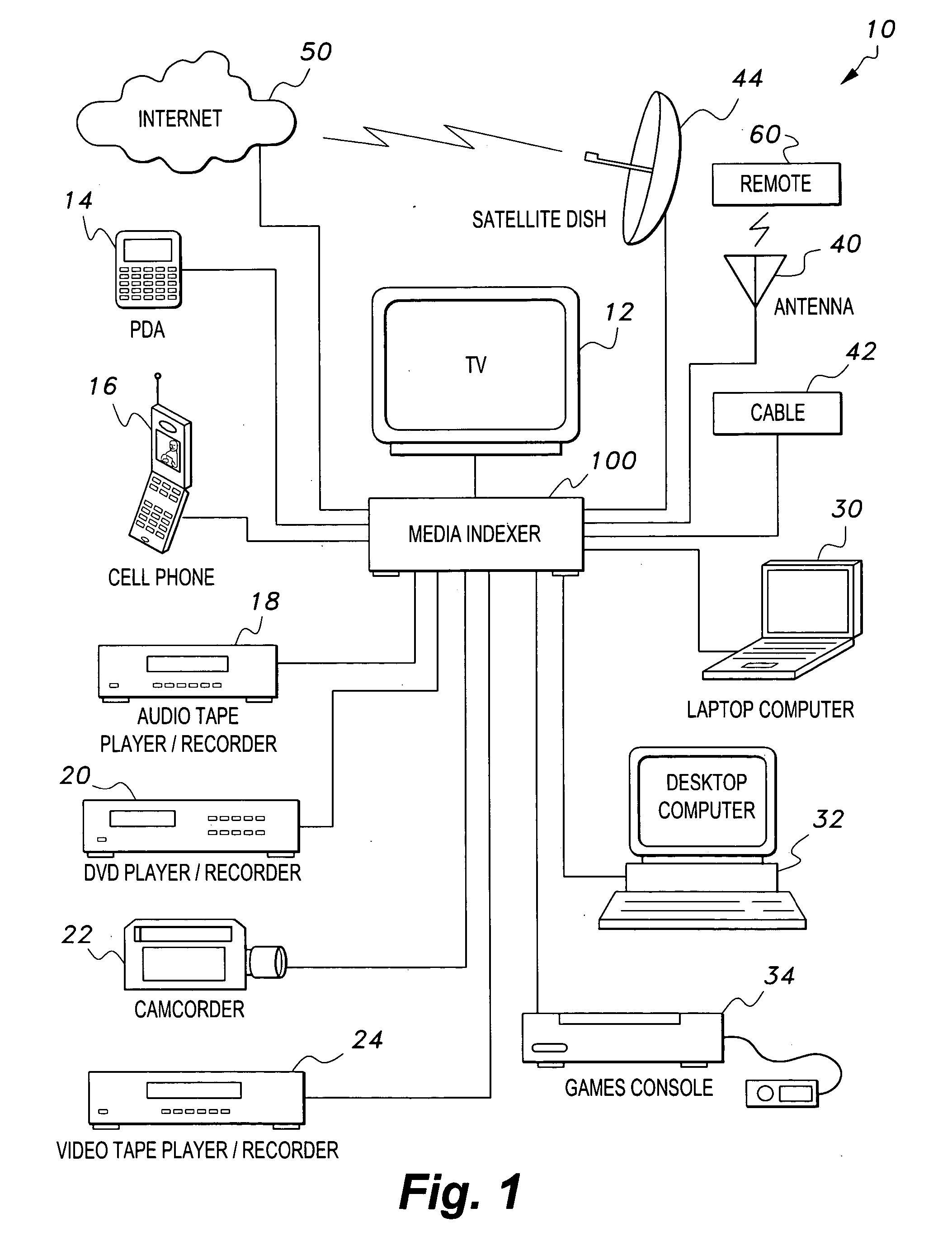
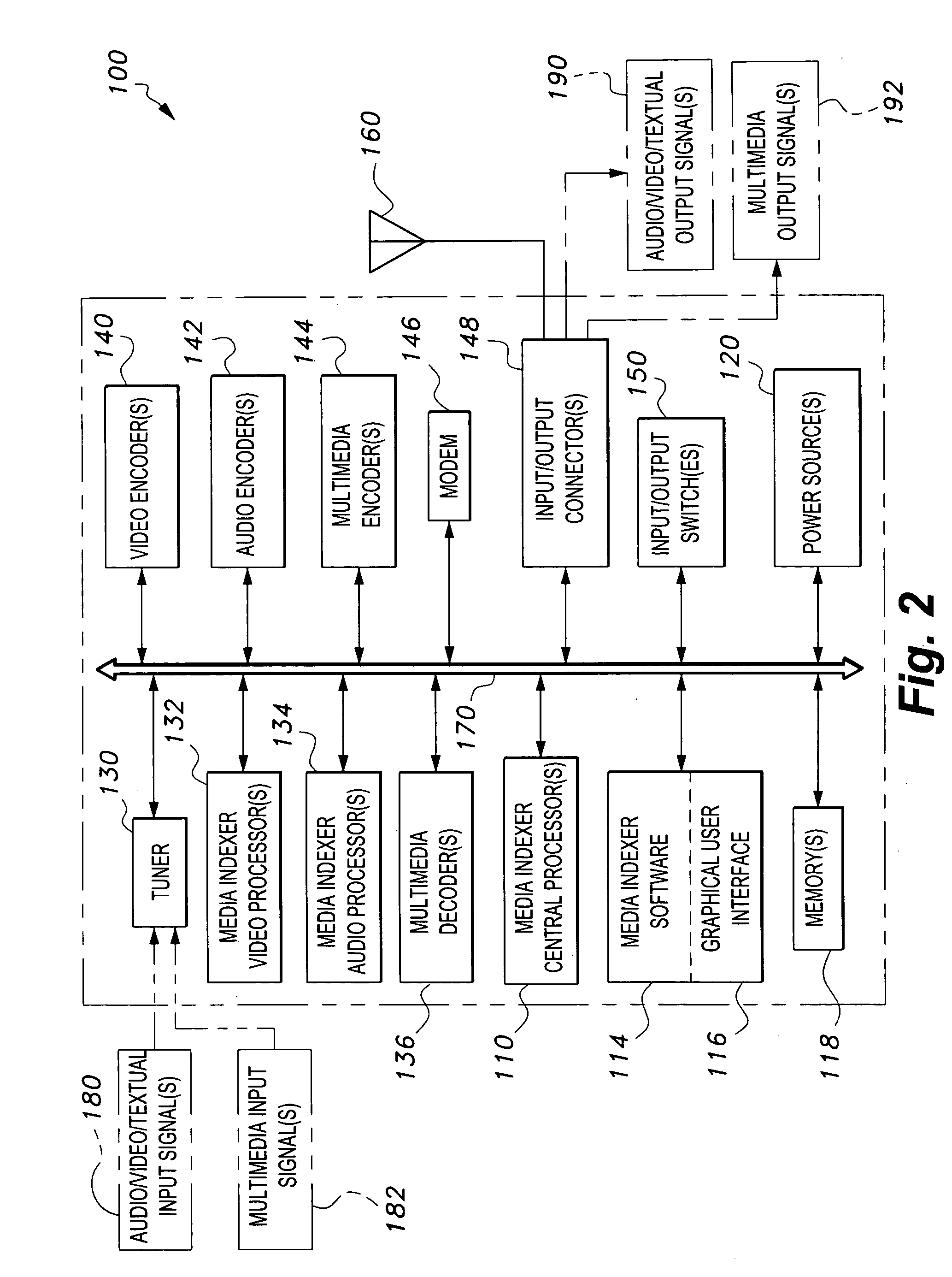
Media indexer
InactiveUS20050033758A1Inexpensive and dependable and fully effectiveTelevision system detailsPeptide/protein ingredientsData operationsFile sharing
A media indexer method, a media indexer, and / or a media indexer computer useable medium. The media indexer includes a central processor and a memory carrying thereon media indexer software which carries out steps including receiving a media signal, identifying keyframes of the media signal, establishing metadata for each identified keyframe, tagging each identified keyframe with metadata established for the associated keyframe, and outputting the media signal in a form unchanged from the received media signal, and / or a form including identified keyframes of the received media signal, each identified keyframe including a representative media keyframe event with metadata associated with the corresponding media keyframe event. The media indexer can generate parallel index signals that are synchronized to the time rate of the received media signal, and can input and output data using standard compatible file formats for file sharing and data manipulations with other compatible files and software.
Owner:BAXTER BRENT A
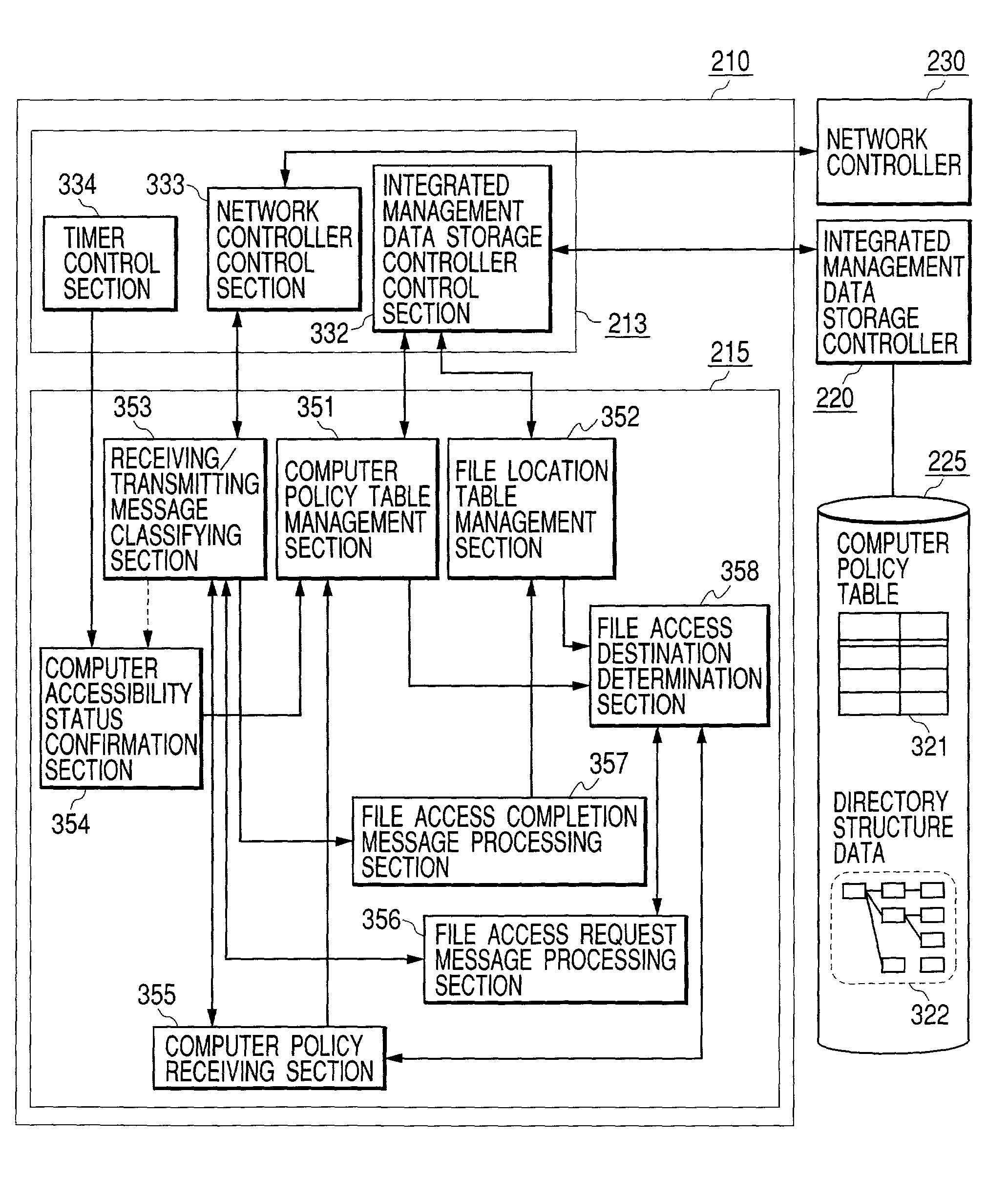
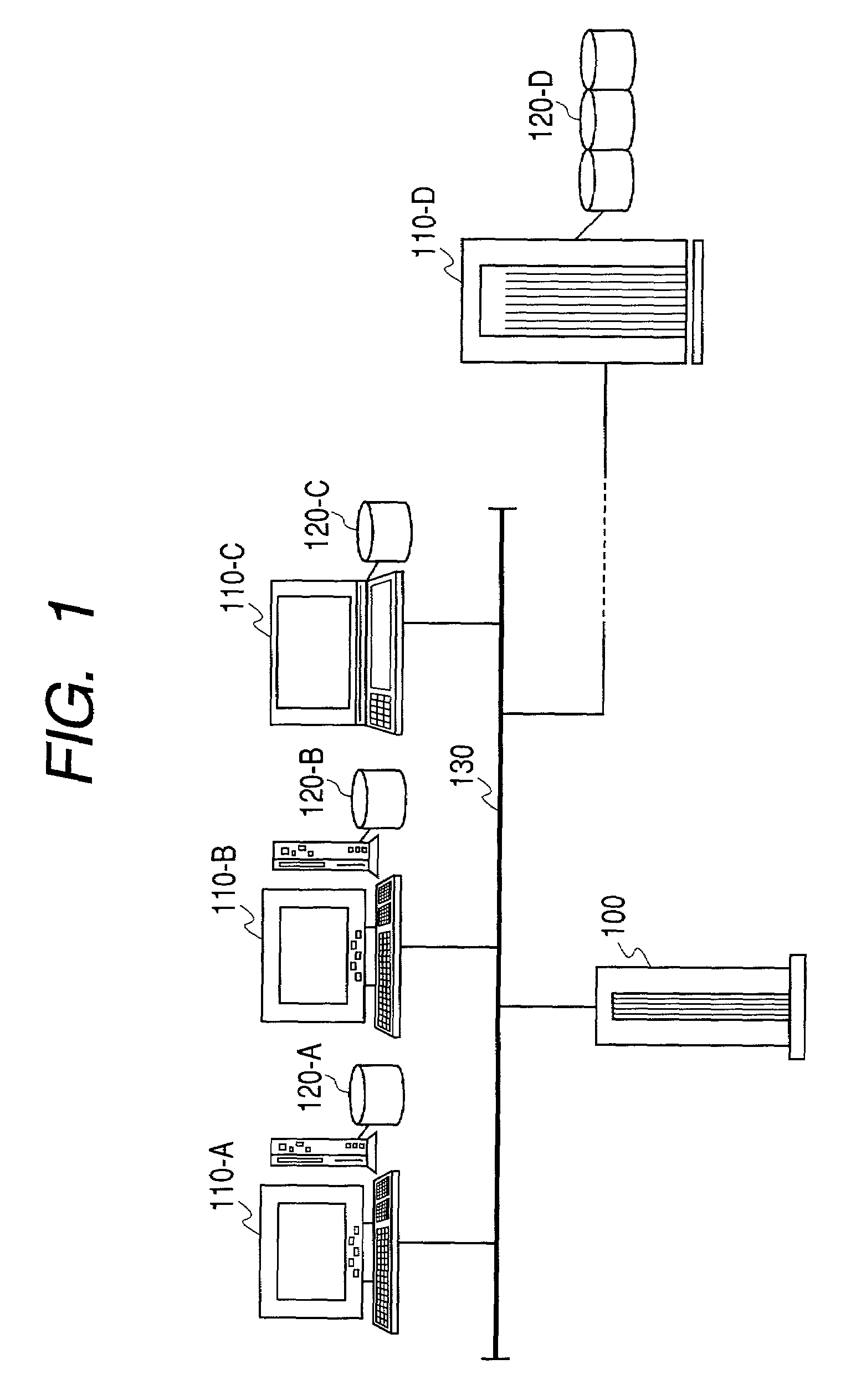
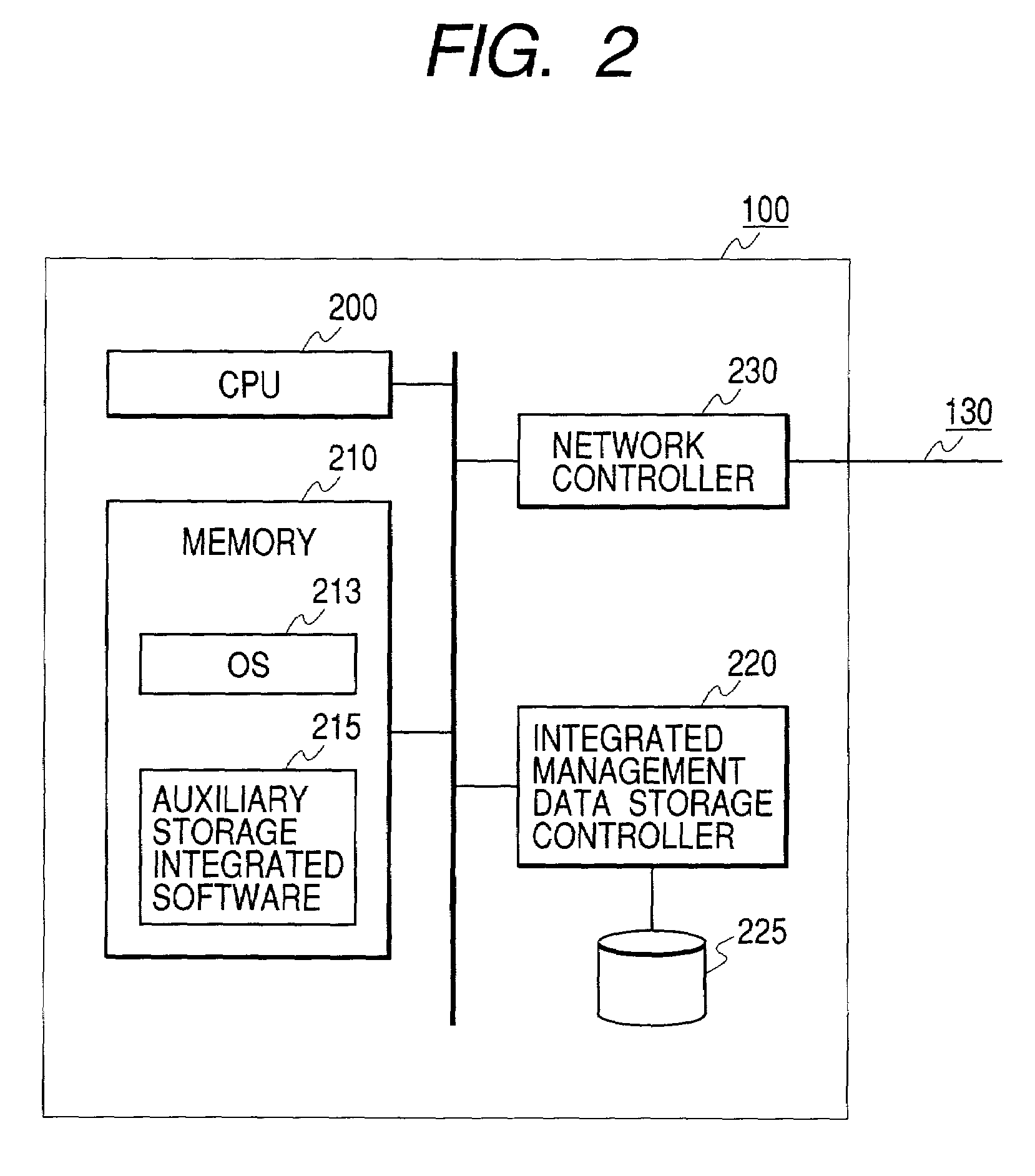
Storage management integrated system and storage control method for storage management integrated system
InactiveUS7120757B2Easy to implementImprove fitInput/output to record carriersDigital computer detailsStorage managementAccessibility
It is intended to achieve an arrangement wherein, when file information of shared disks which are distributed in a plurality of computers connected to a network are used, operating conditions at the time of accessing shared disks can be defined, thus enabling users to easily share files without being bothered by setting-up, or operations of computers located on the other side when they are to perform file sharing.In order to achieve the above-stated arrangement, a storage management integrated server 100 is provided in a network, and respective computers register conditions, an accessibility states and use types pertaining to shared volume to be offered to the server. Thereafter, when a certain computer is to make a file accessing to a shared volume, the computer makes an inquiry to the storage management integrated server for an adequate access destination, determines, on the basis of a response from the server, computers which are suitable to the access source, and makes direct accesses to such computers.
Owner:HITACHI LTD
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS7184848B2Facilitate transmission and receptionTelevision system detailsColor television detailsControl signalNetwork connection
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
File sharing in P2P group shared spaces
InactiveUS20050091289A1Reduce usageManaged quickly and effectivelySpecial service provision for substationData processing applicationsVisual presentationSystem usage
A computer implemented method and system enable users to share files in a server-less shared space. By providing access to such spaces via a visual presentation, the system renders content available for access by other group members. Access is sometimes provided through propagation of metadata or other uniquely identifying indicia associated with the shared space to all group members.
Owner:MICROSOFT TECH LICENSING LLC
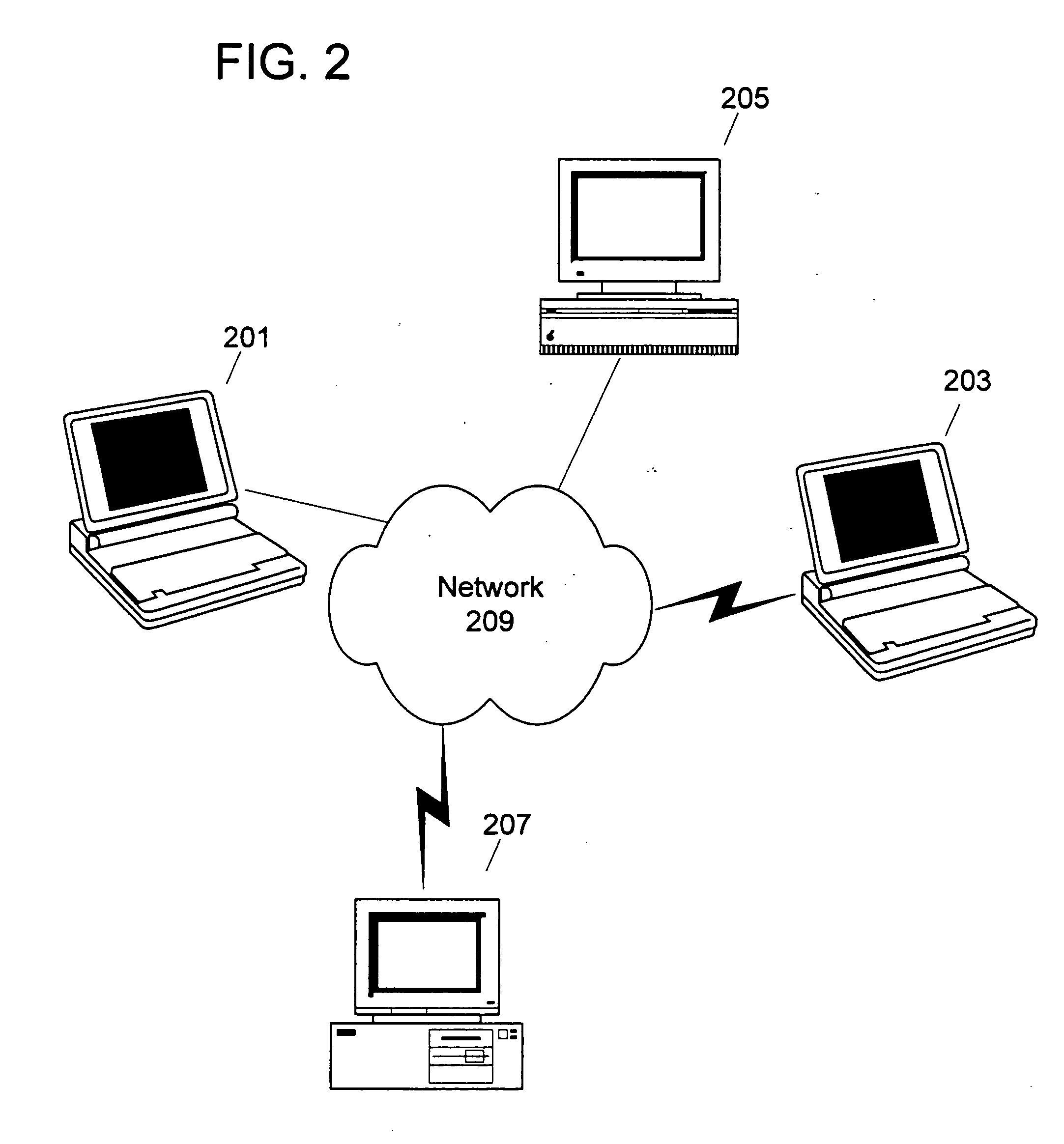
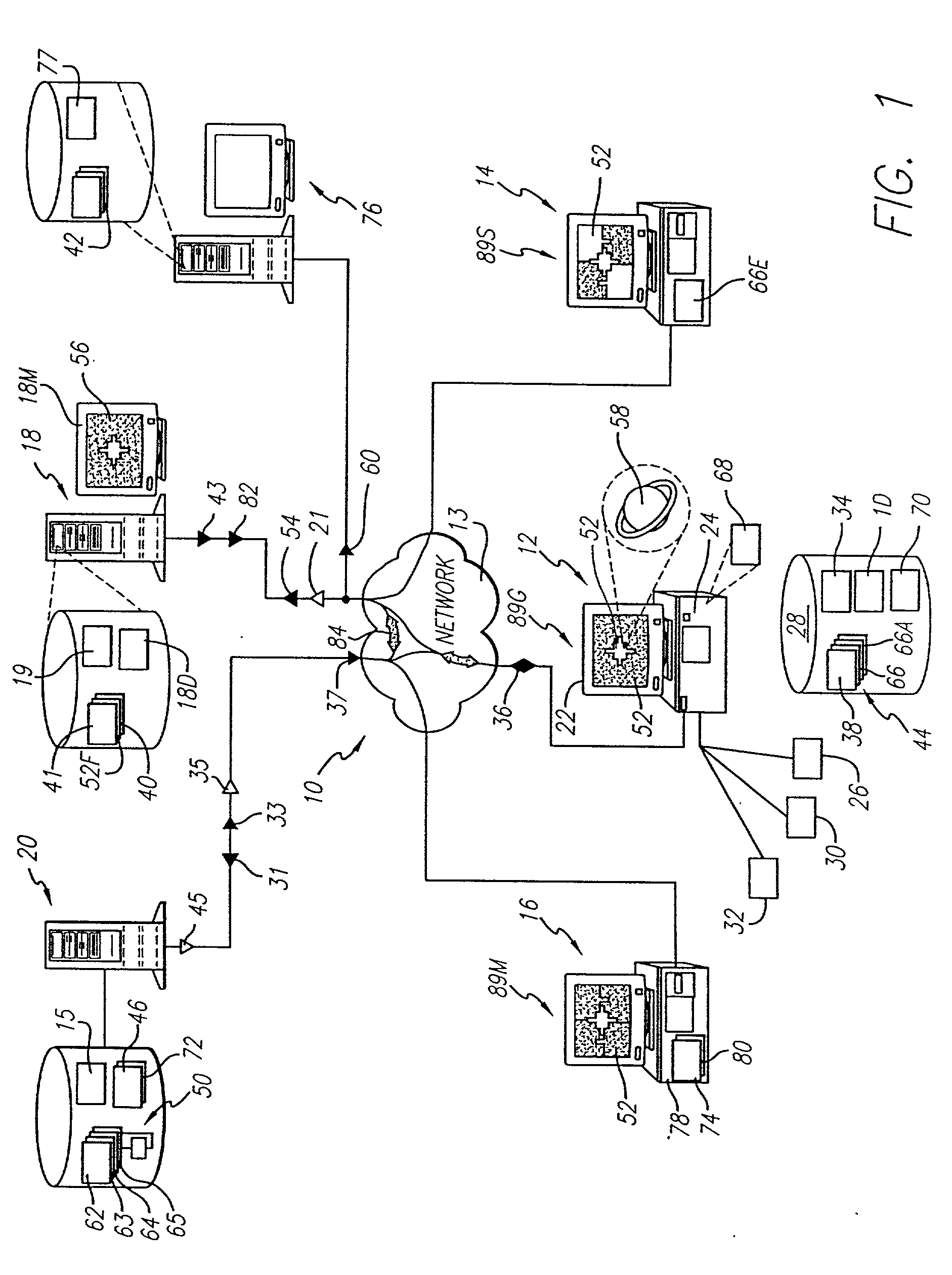
Organizing content on a distributed file-sharing network
InactiveUS20020046232A1Digital data information retrievalMultiple digital computer combinationsIndexing ServiceFile sharing
A system for and method of locating desired files in distributed file sharing over a computer network is disclosed, whereby each file 6 is categorized according to the content of the file 6 and information about files 6 resides on at least one central index server 3. Client terminals 1 publish files 6 for other client terminals 1 in the computer network 2. The central index servers 3 store the list of files 6 in the system. Client terminals 1 query the central index servers 3 to determine the set of files 6 currently available in the system. A central index server 3 returns a list of files 6 and file locations which match the query results and are currently available. The client terminal 1 issuing the search can retrieve the file 6 from the search results by requesting it from one of the client terminals 1 specified in the search results.
Owner:FILECAT
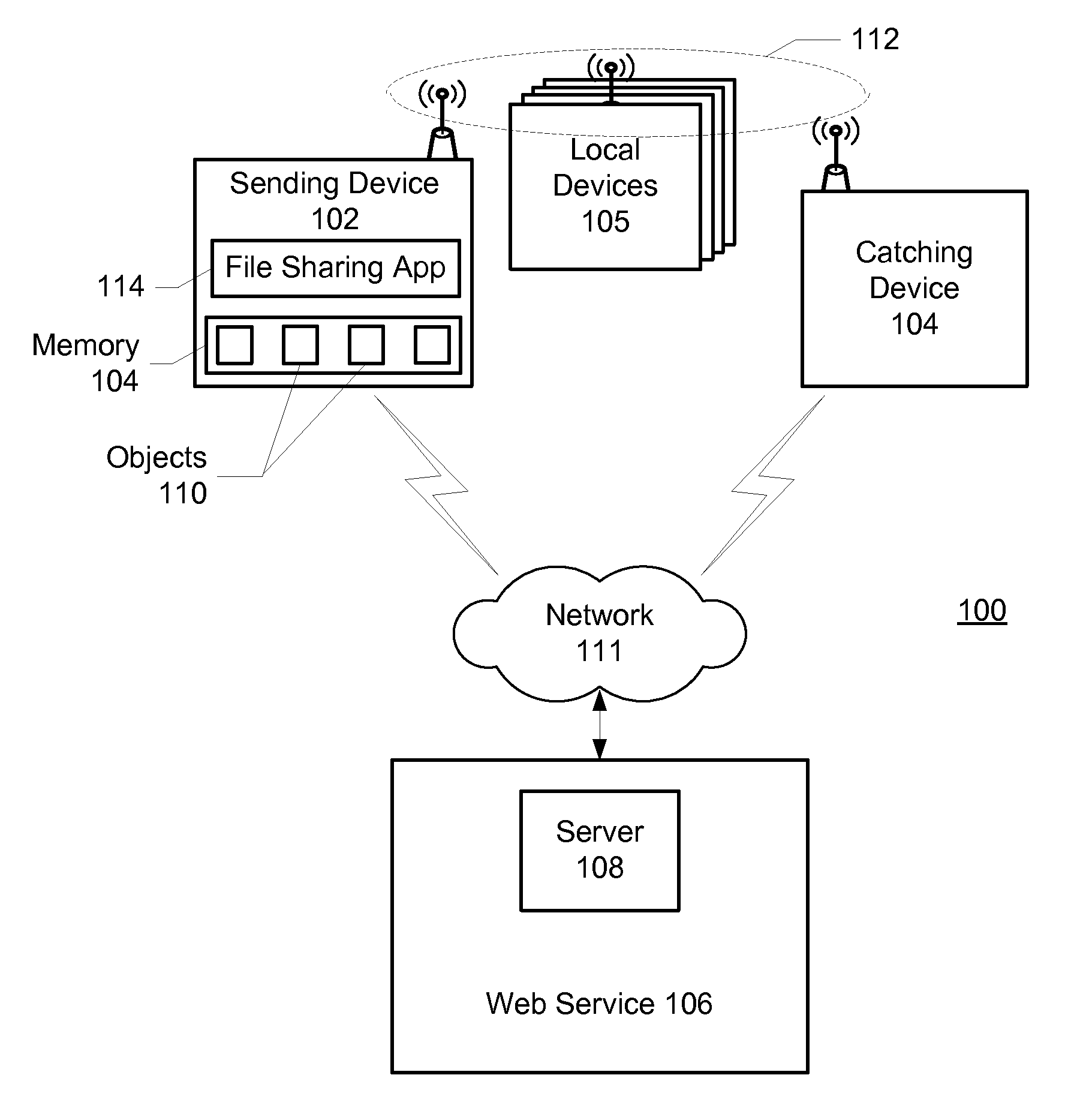
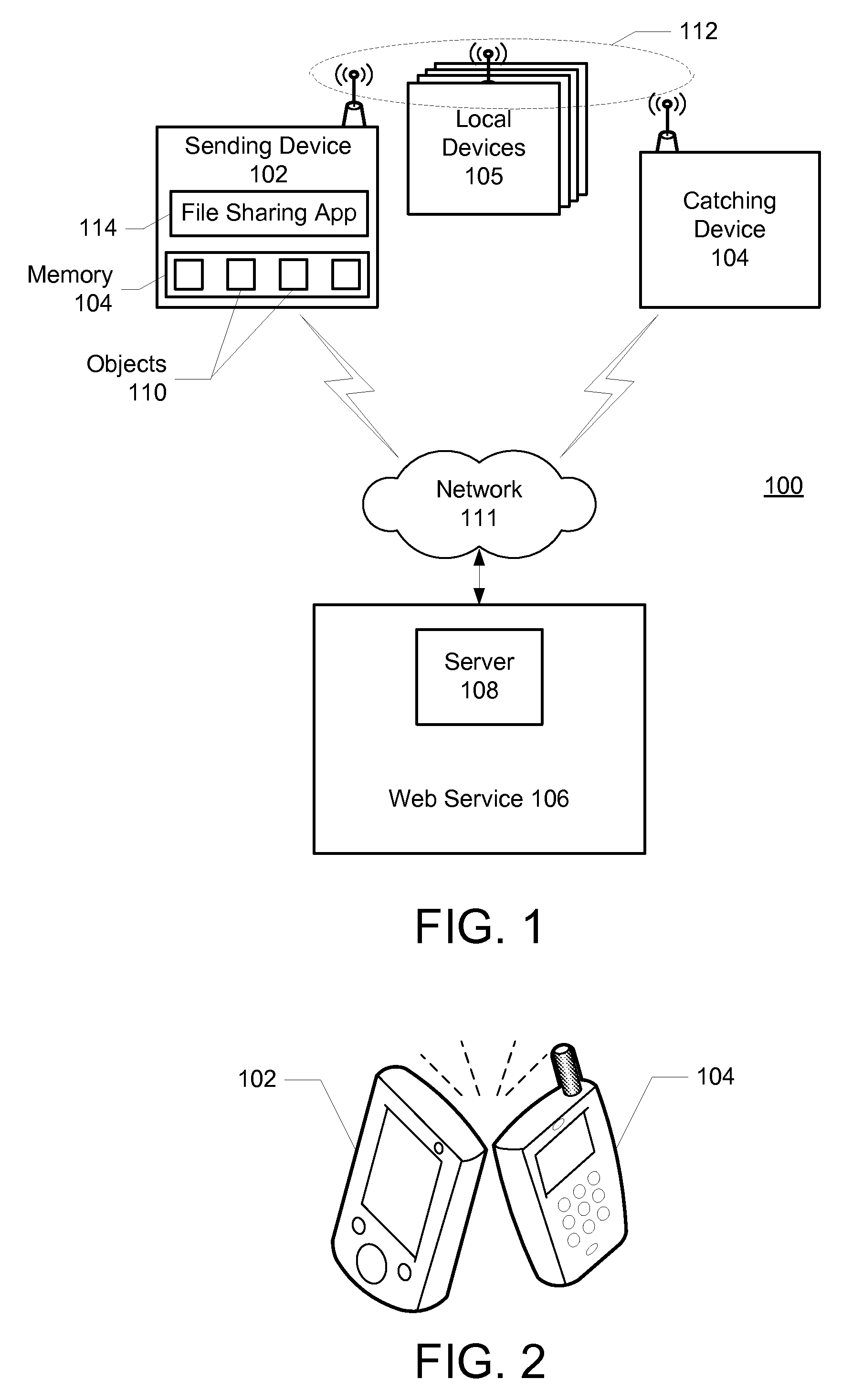
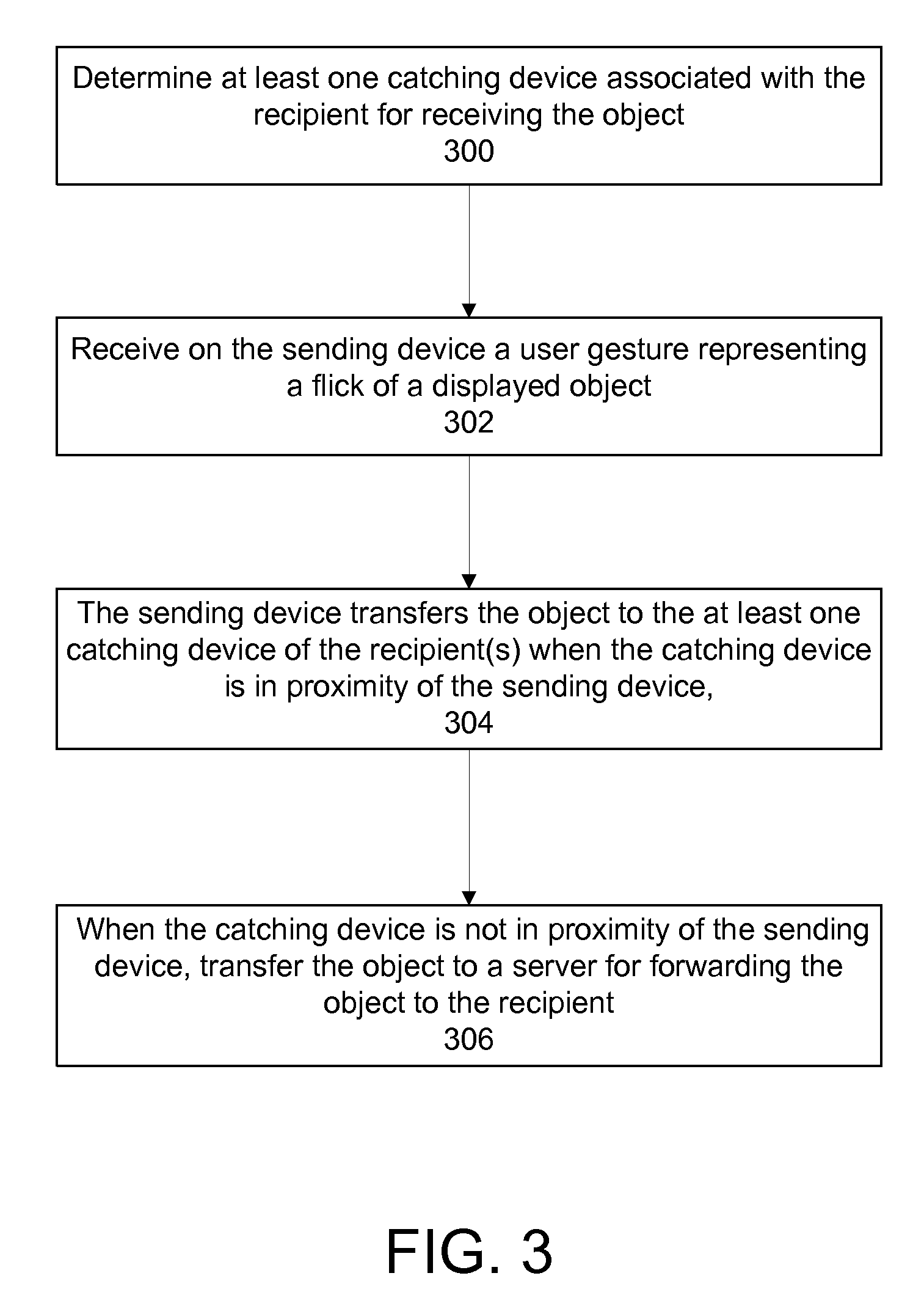
File sharing between devices
ActiveUS20100257251A1Services signallingMultiple digital computer combinationsFile sharingWorld Wide Web
Methods and systems for transferring an object from a sending device to a recipient comprises determining at least one catching device associated with the recipient for receiving the object; receiving on the sending device a user gesture representing a flick of a displayed object; transferring the object from the sending device directly to the catching device of the recipient when the catching device is in proximity of the sending device; and when the catching device is not in proximity of the sending device, transferring the object to a server for forwarding the object to the recipient.
Owner:GOOGLE LLC
Collaborative communication platforms
InactiveUS20060095514A1Rule out the possibilityWidely distributedMultiple digital computer combinationsOffice automationCommunications systemFile sharing
A collaborative communication system is disclosed. The collaborative communication system integrates a number of electronic. communication tools to meet the collaborative communication needs for an enterprise, family members or friends. All communications are within the system. According to one aspect of the collaborative communication system, registered users in the system are provided public, group and private arenas or domains. Depending on the privacy, communications with others may be conducted in any one of these domains. According to another aspect of the collaborative communication system, communications with others can be conducted through electronic internal mail (herein “i-mail”), instant messaging and file sharing. In particular, the i-mail operates on identifiers pertaining to registered users, thus eliminating the possibility of the registered users receiving unwanted email from other users outside the system.
Owner:BCS SOFTWARE LLC
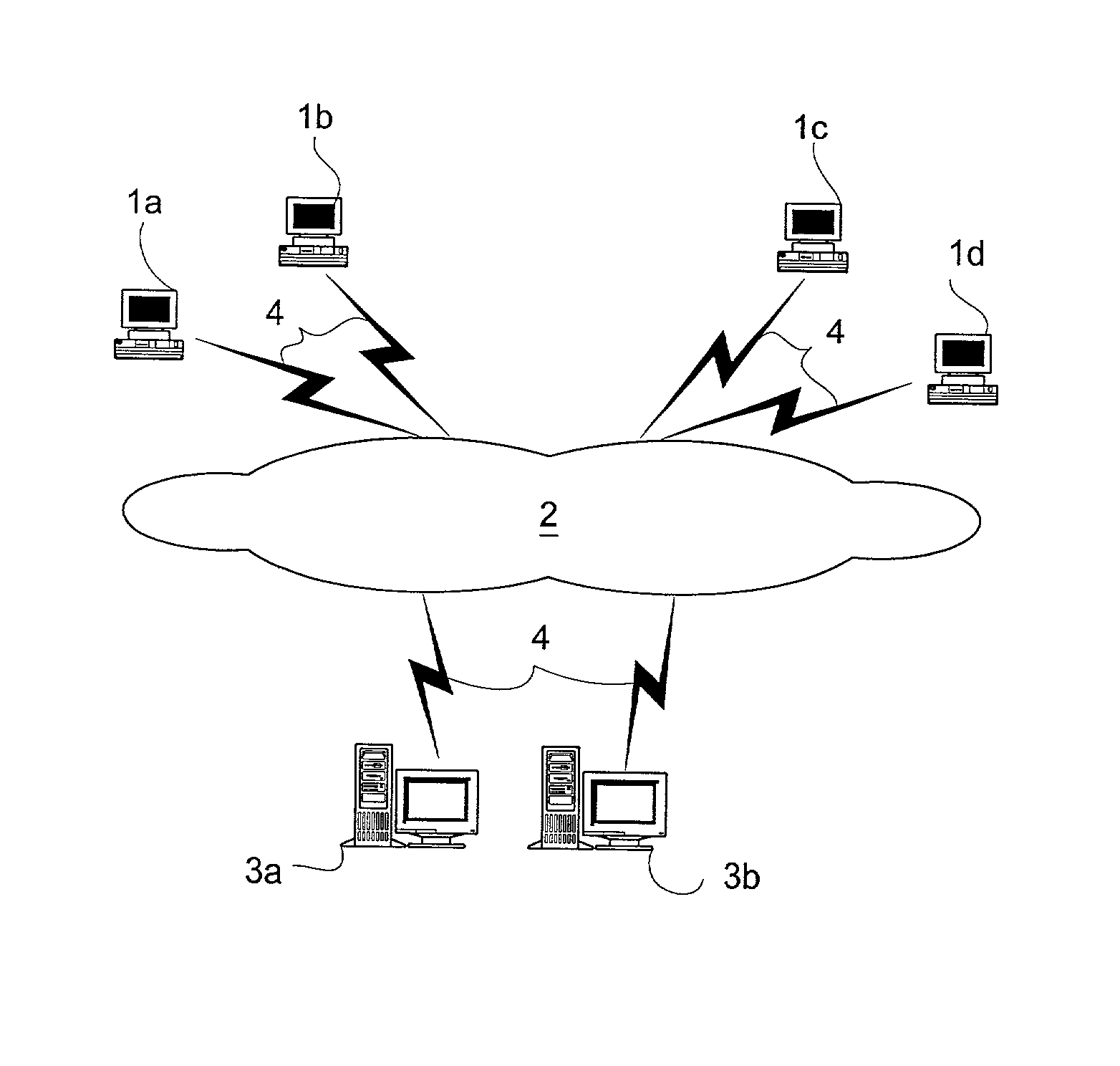
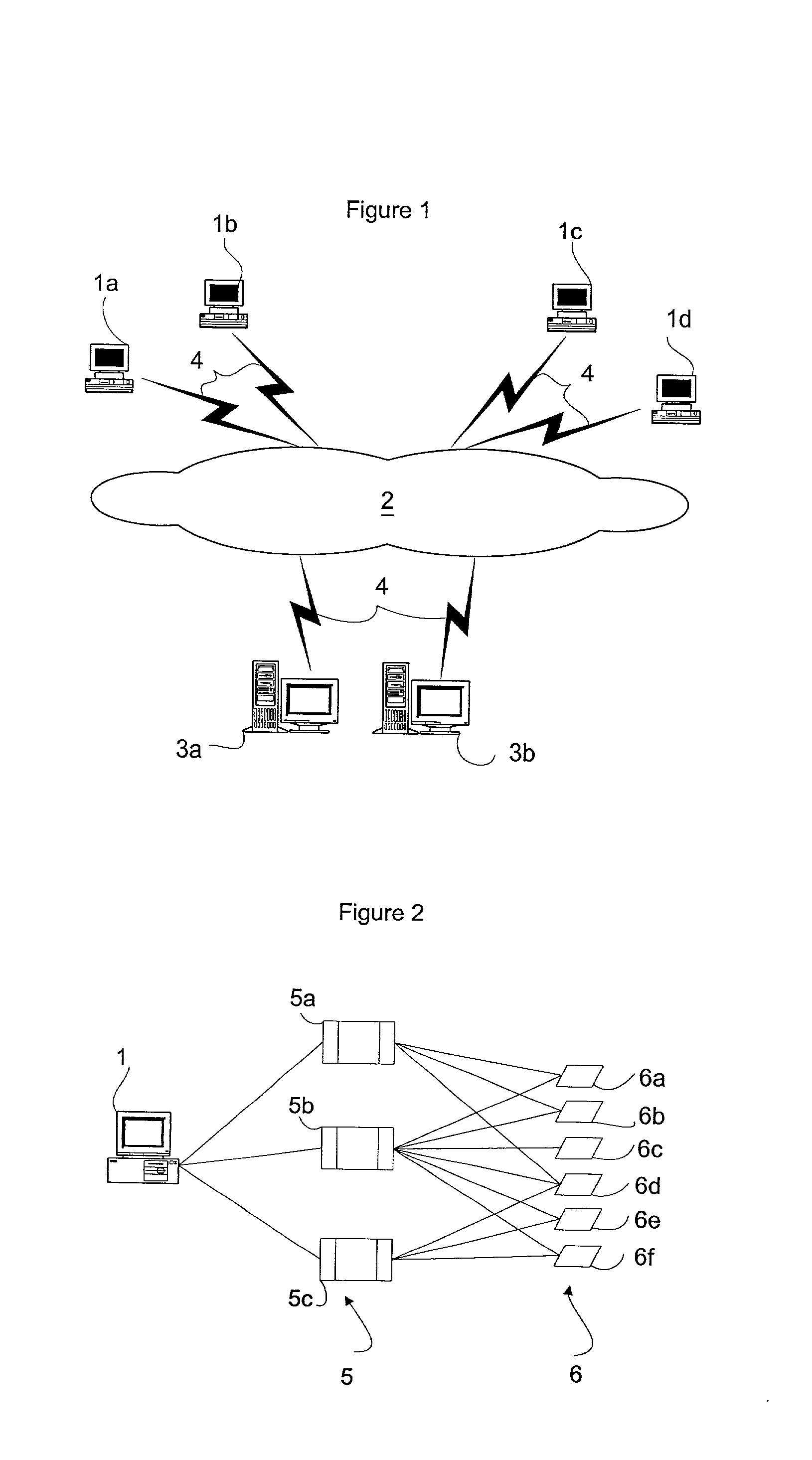
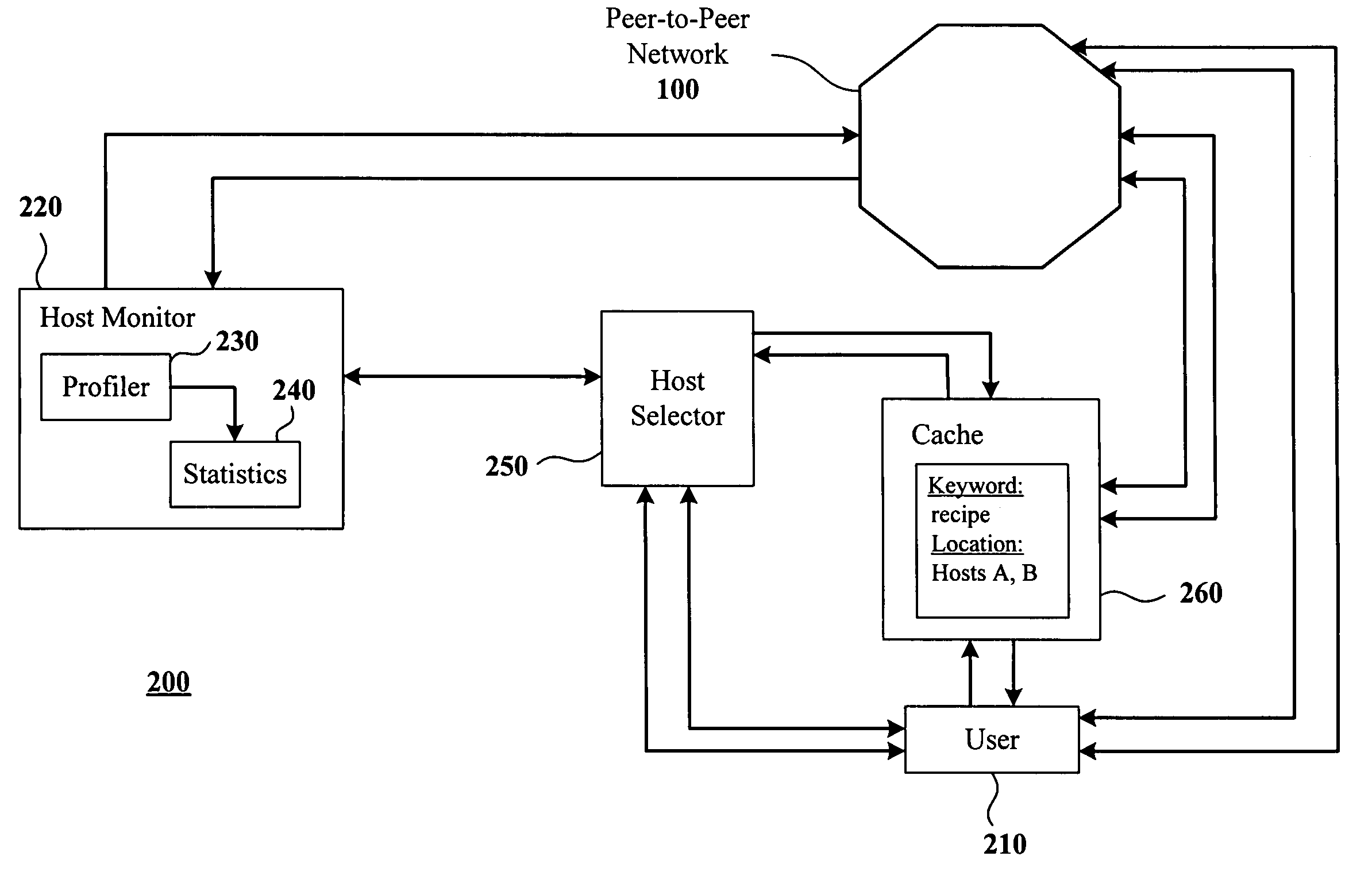
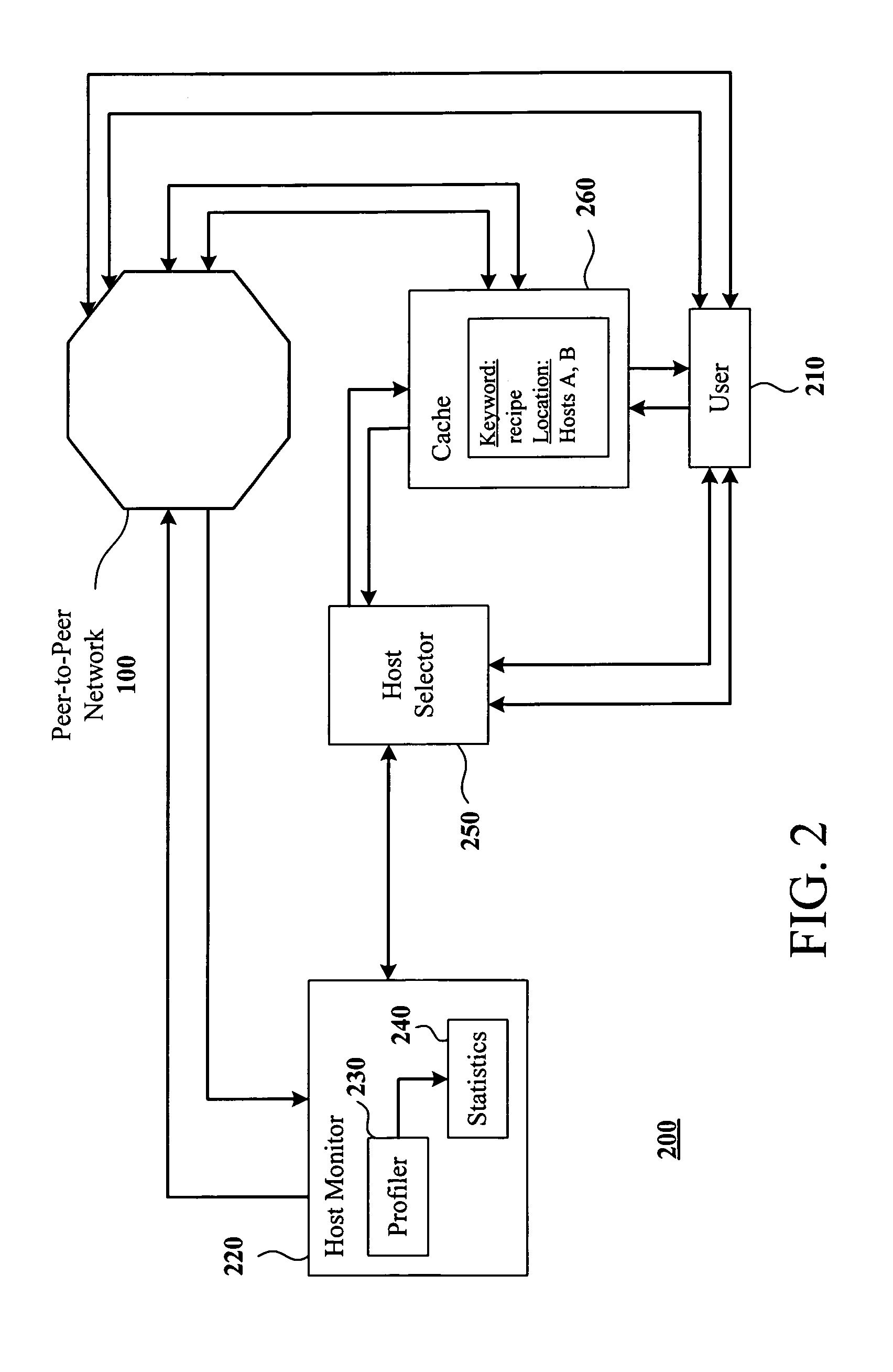
System and method for searching peer-to-peer computer networks by selecting a computer based on at least a number of files shared by the computer
InactiveUS7089301B1Increase opportunitiesStable network environmentData processing applicationsWeb data indexingEntry pointFile sharing
A method and system for intelligently directing a search of a peer-to-peer network, in which a user performing a search is assisted in choosing a host which is likely to return fast, favorable results to the user. A host monitor monitors the peer-to-peer network and collects data on various characteristics of the hosts which make up the network. Thereafter, a host selector ranks the hosts using the data, and passes this information to the user. The user then selects one or more of the highly-ranked hosts as an entry point into the network. Additionally, a cache may collect a list of hosts based on the content on the hosts. In this way, a user may choose to connect to a host which is known to contain information relevant to the user's search. The host selector may be used to select from among the hosts listed in the cache.
Owner:MOON GLOW SERIES 82 OF ALLIED SECURITY TRUST I
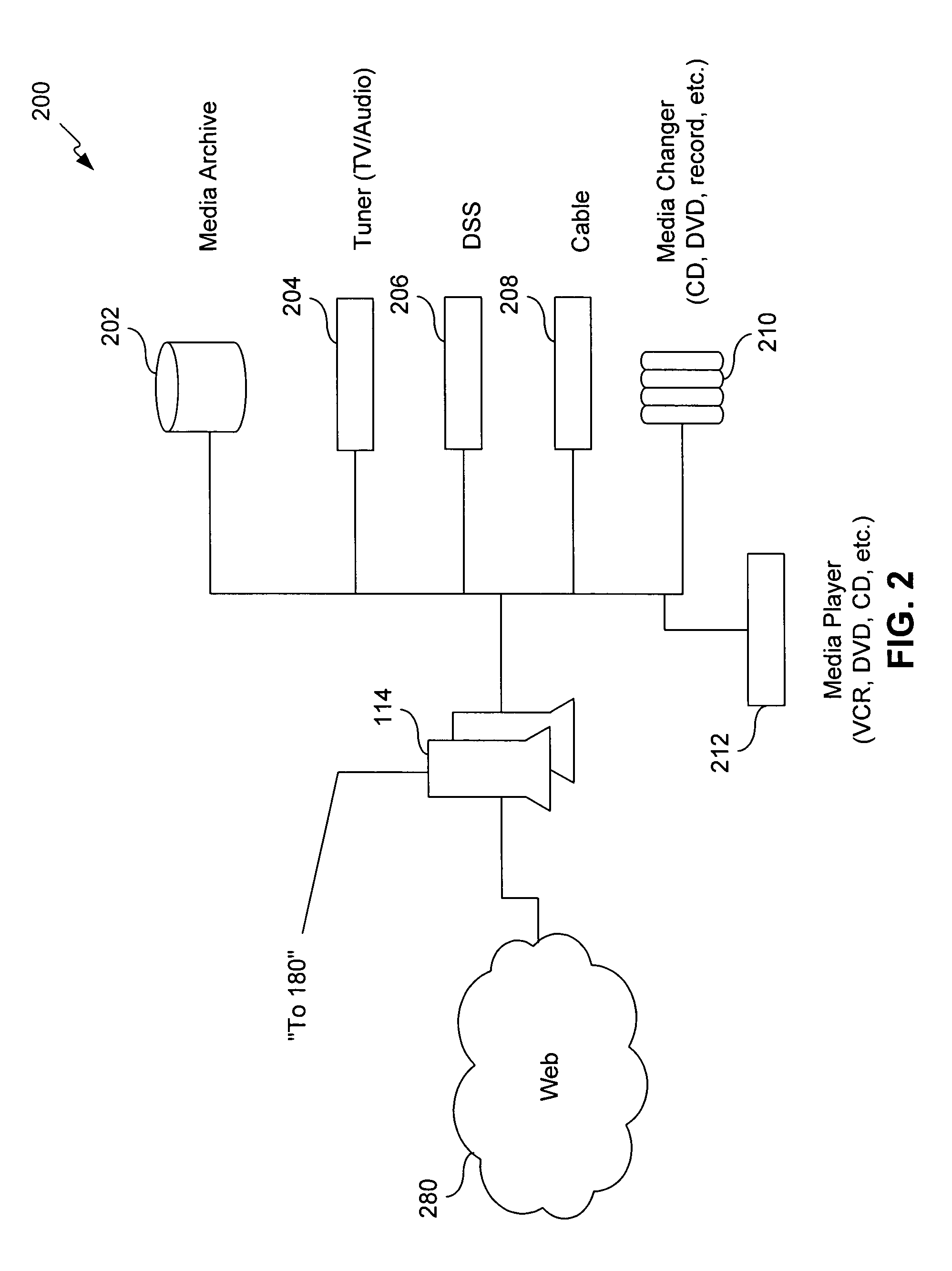
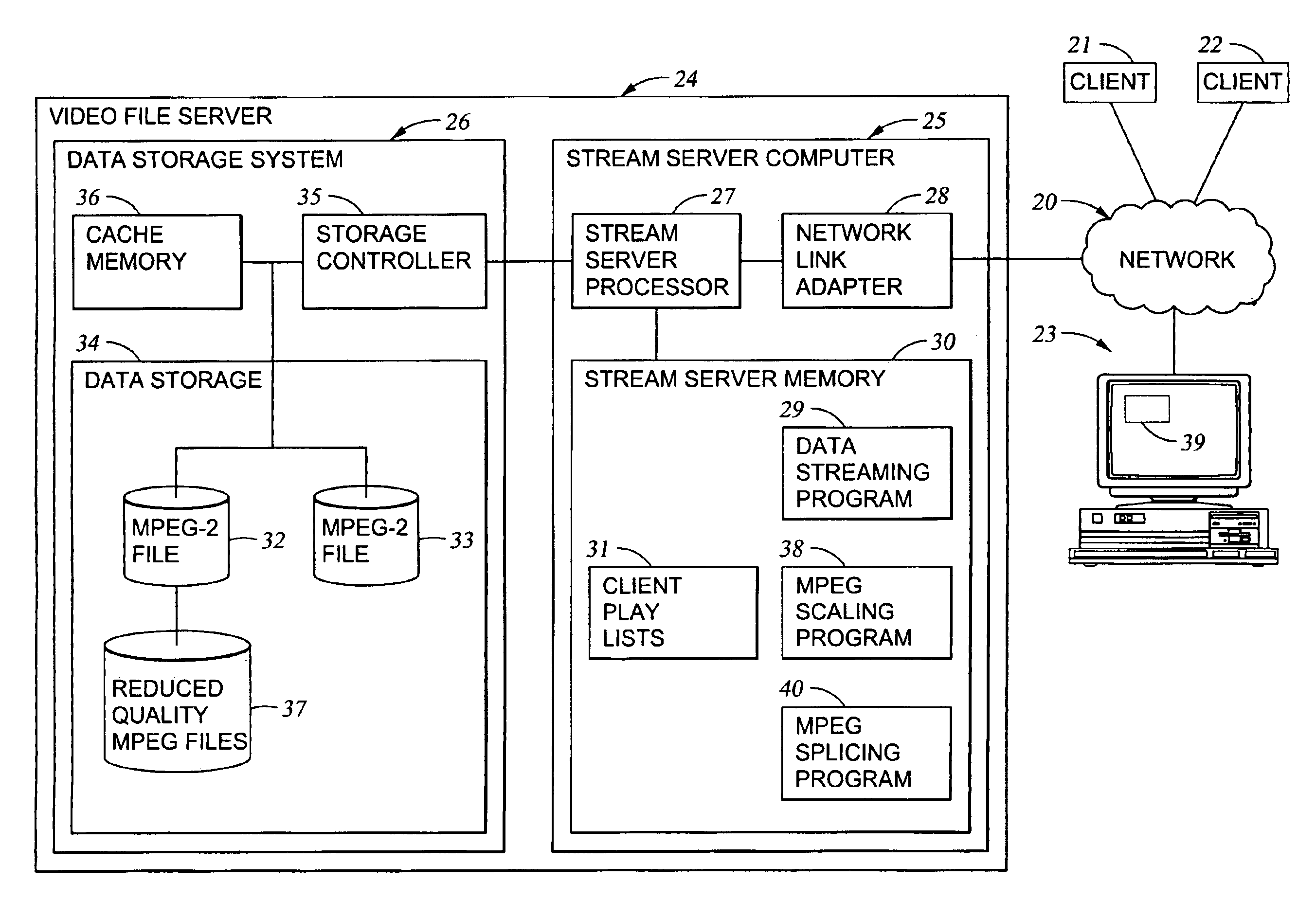
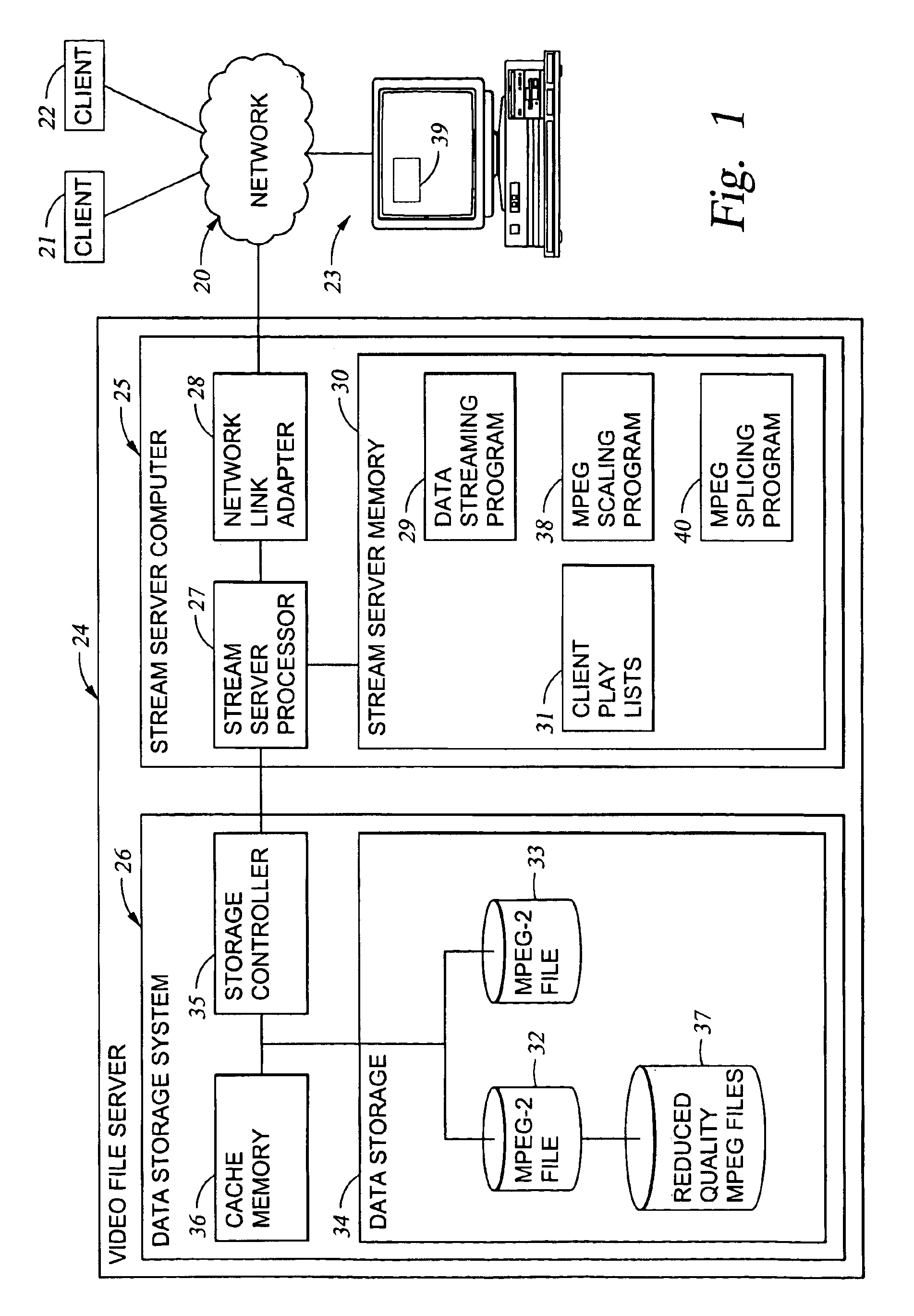
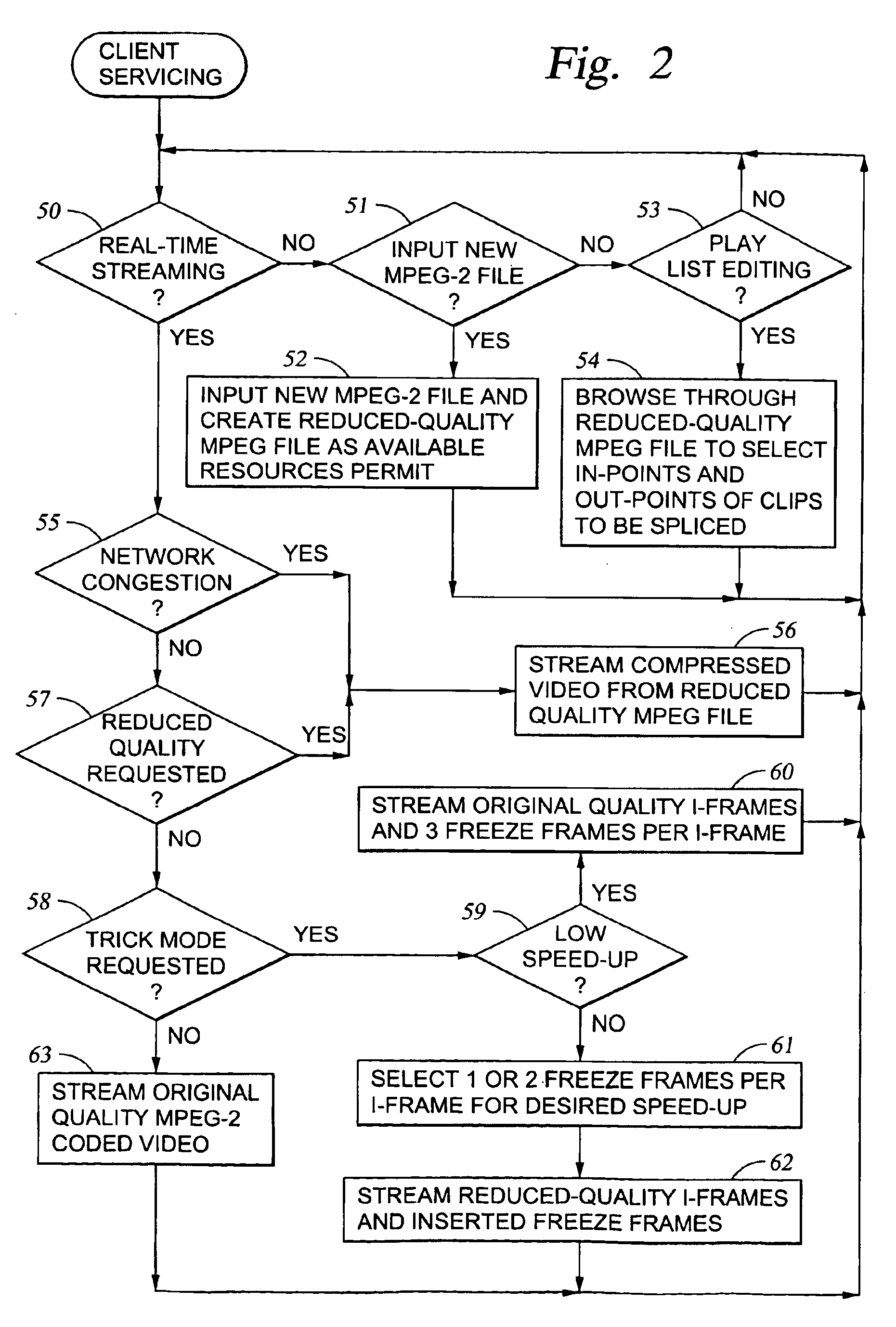
Processing of MPEG encoded video for trick mode operation
InactiveUS6871006B1Television system detailsPulse modulation television signal transmissionVisual presentationMPEG transport stream
Original-quality MPEG coded video is processed to produce reduced-quality MPEG coded video for trick mode operation by removing non-zero AC DCT coefficients from the 8×8 blocks of I-frames of the MPEG coded video to produce I-frames of reduced-quality MPEG coded video, and inserting freeze frames in the reduced-quality MPEG coded video. Preferably, the coded video is stored in a main file, a fast-forward file and a fast-reverse file. The fast forward file and the fast reverse files contain reduced-quality I frames corresponding to original-quality I frames in the main file. A reading of the main file produces an MPEG transport stream for an audio-visual presentation at a normal rate, a reading of the fast-forward file produces an MPEG transport stream of the audio-visual presentation in a forward direction at a fast rate, and a reading of the fast-reverse file produces an MPEG transport stream of the audio-visual presentation in a reverse direction at a fast rate. Preferably, the files share a volume that includes at least one GOP index associating the corresponding I frames of the files.
Owner:EMC IP HLDG CO LLC
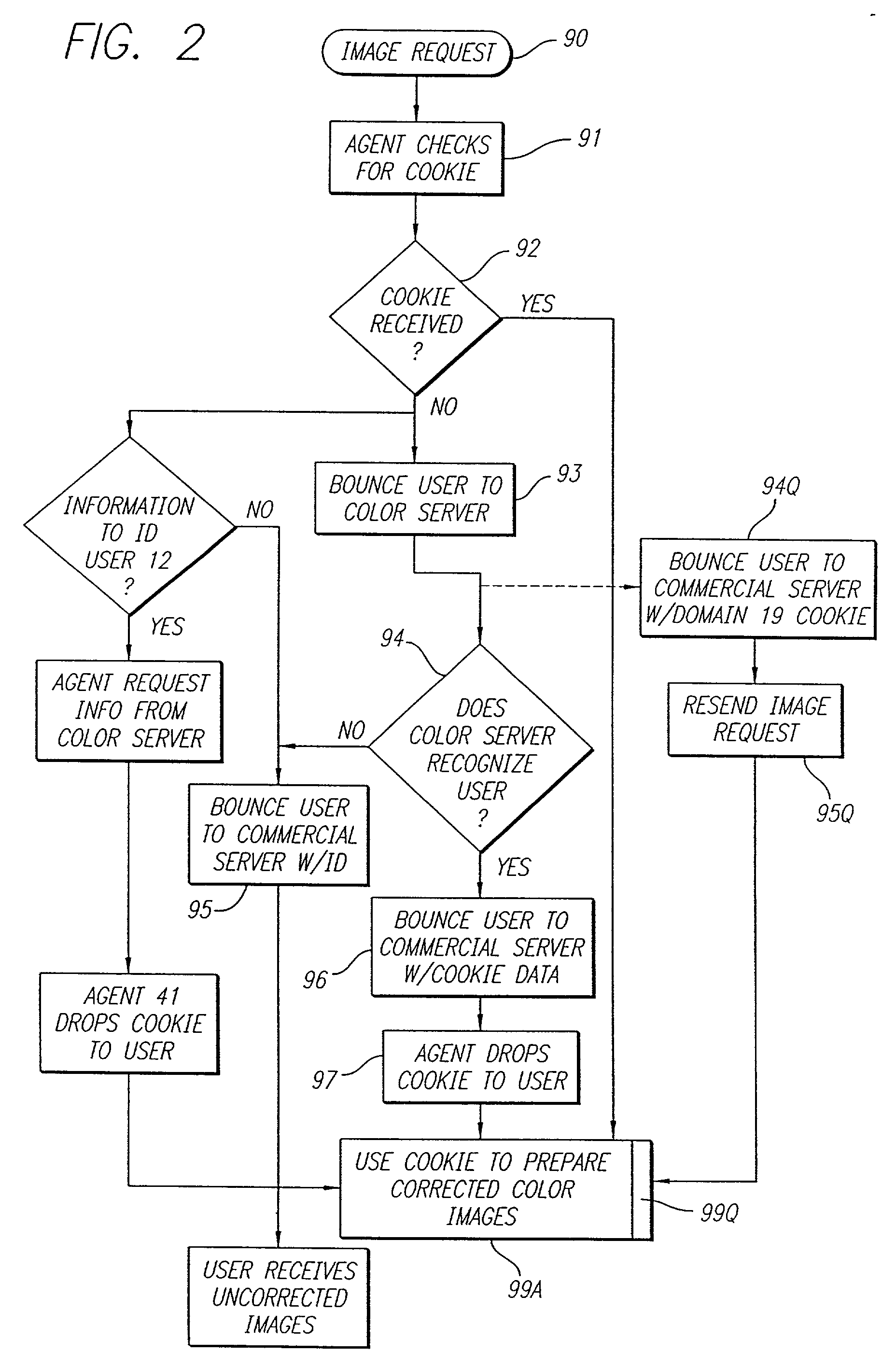
Image sharing for instant messaging
InactiveUS20020126135A1Retain controlImage enhancementCathode-ray tube indicatorsImage sharingFile sharing
Owner:RPX CORP +1
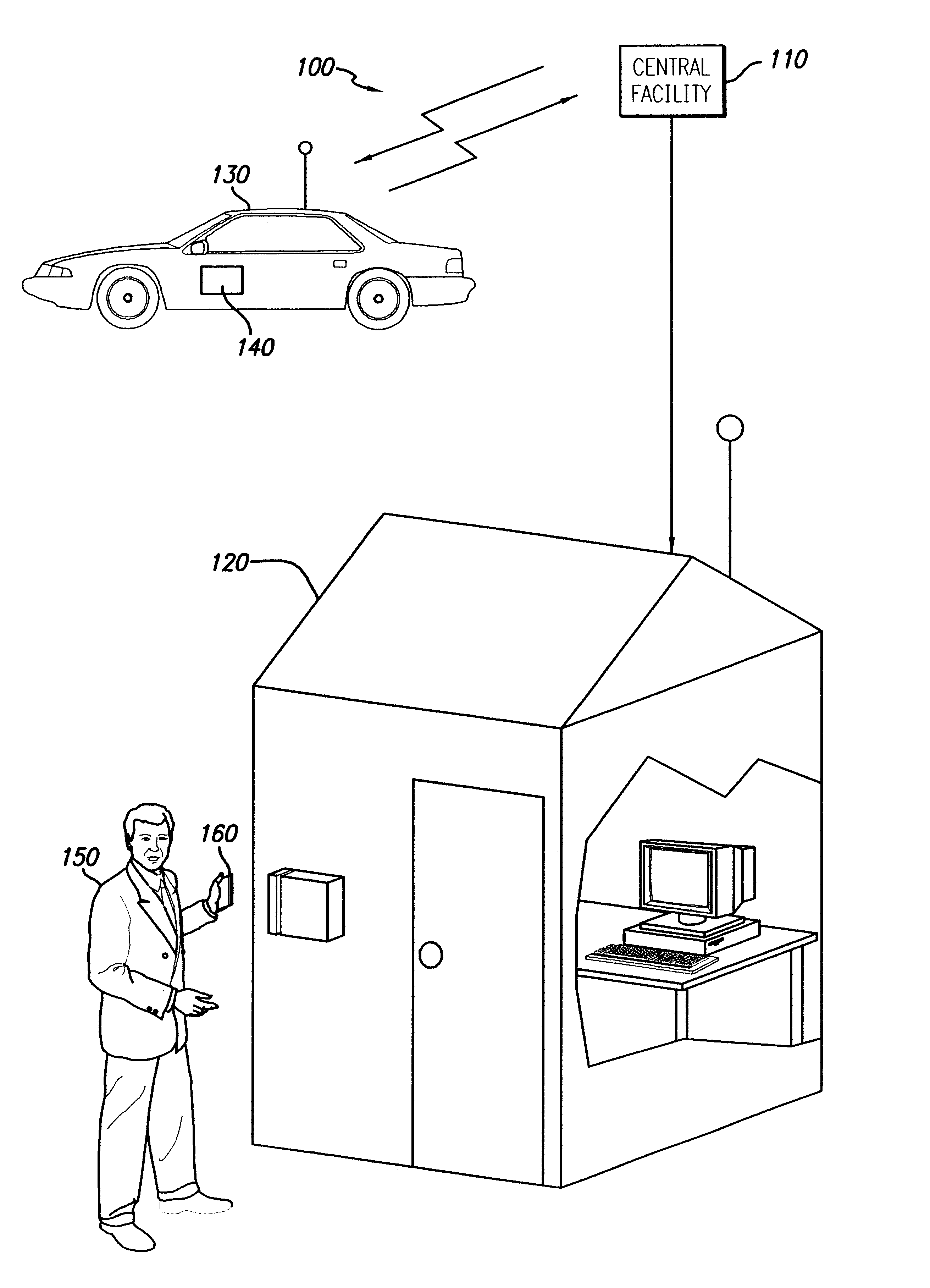
Method for efficient vehicle allocation in vehicle sharing system
InactiveUS6975997B1Minimize the numberMaximize convenienceCharging stationsReservationsIn vehicleMonitoring system
A system for sharing a fleet of vehicles among a plurality of users, where in preferred embodiments the shared vehicles are electrically powered, the system comprising a system control computer that assigns vehicles in response to requests by users, and monitors system performance, a computer subsystem through which users request vehicles for trips, and a vehicle subsystem within each vehicle that is in communication with the system control computer allowing the system control computer to monitor the location and status of each vehicle in the vehicle sharing fleet.
Owner:RGT UNIV OF CALIFORNIA
System and method for peer to peer synchronization of files
InactiveUS20060242206A1Currency is bulkyMinimum configuration effortDigital data information retrievalData processing applicationsFile synchronizationOperational system
A system and related techniques provide a seamless, peer-to-peer file synchronization capability for sharing files, folders, directories or other stored content between machines. According to embodiments of the invention in one regard, a sync engine or other file management logic may be integrated into the operating system or other resources of a user's desktop, laptop, network-enabled cellular device or other computer, client, machine or other hardware. The sync engine may accept user designations of files, folders, directories or other contents which they wish to share, sync or roam between two or more selected machines, on an automatically consistent basis. The sync engine or other control logic may maintain a file system log to record the state of files which have been designated for sharing, to indicate for example whether a transmission of the file has been made, to which target machine or machines it has been transmitted, and other variables regarding the state of file or other content. According to embodiments of the invention in one regard, the sync engine may apply version management logic when files located on a target or destination machine, may, for example, reflect newer or more complete content than the file which is designated for roaming to that machine, or other under conditions. A user may therefore readily and with a comparative minimum of configuration effort select and effectuate the sharing of a set of frequently used or otherwise desired files to an arbitrary set of machines which they own or use, without a need to invoke a remote server or other control or storage to back up and synchronize that content.
Owner:MICROSOFT TECH LICENSING LLC
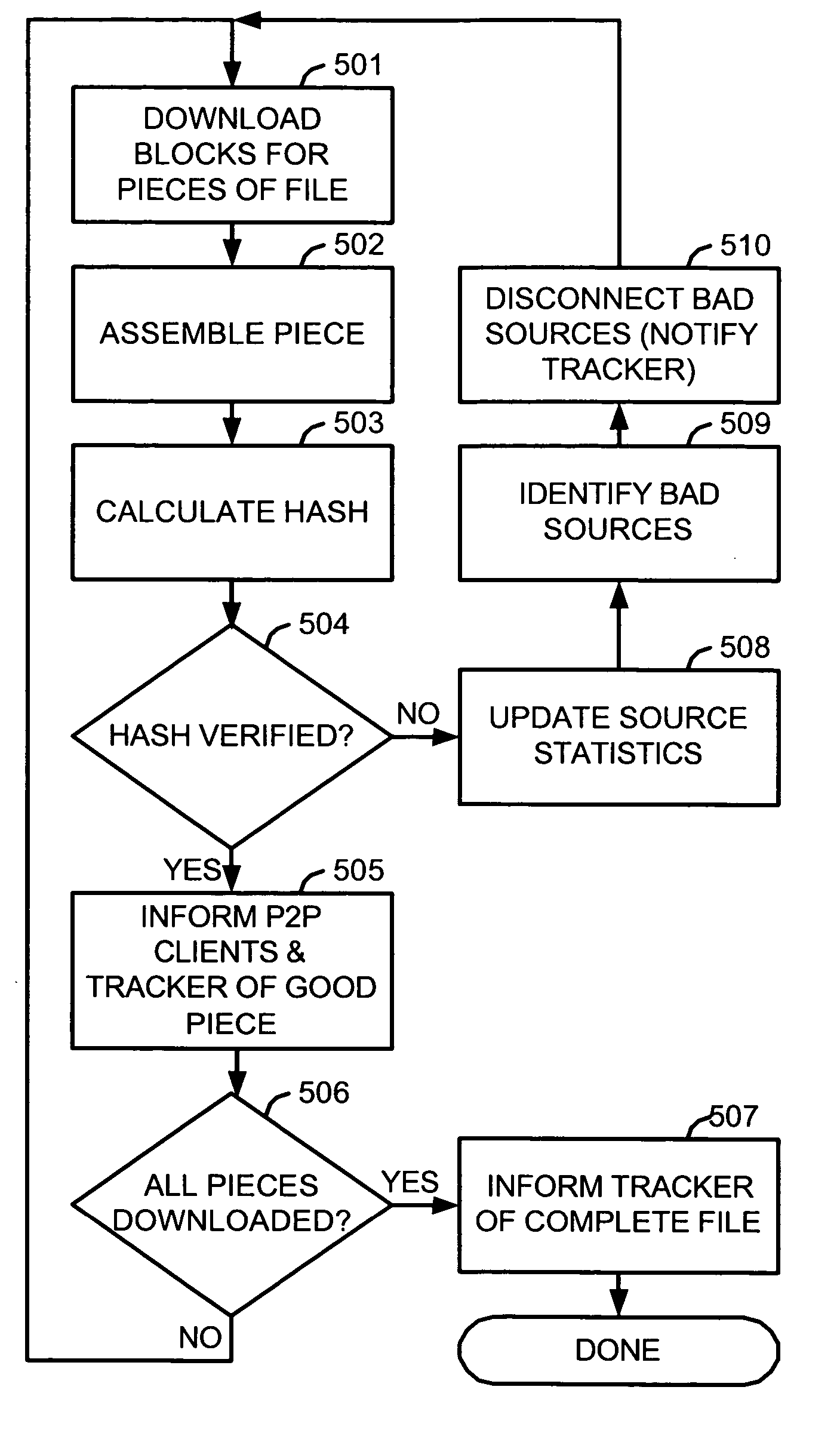
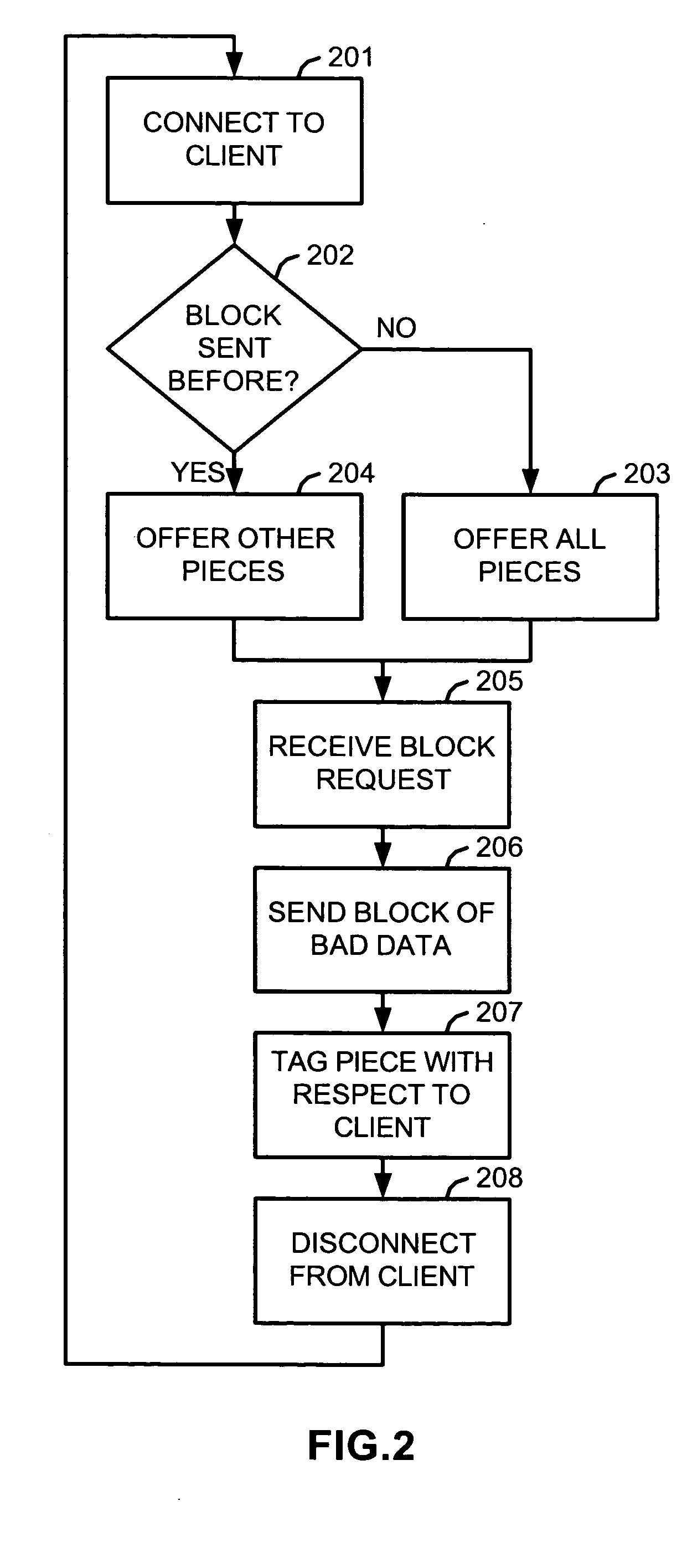
Corruption and its deterrence in swarm downloads of protected files in a file sharing network
InactiveUS20050203851A1Reduce in quantityIncrease the difficultyComputer security arrangementsTransmissionClient-sideFile sharing
A method and apparatus for corrupting a swarm download in a file sharing network provides corrupt data in response to a request for a portion of a file so that when portions received from various sources are assembled, the assembled product cannot be verified and the process must be repeated. To defeat the method, bad sources are identified and disconnected or otherwise ignored, or good sources are identified and given higher priorities. In another method for deterring unauthorized copying of a protected file in a P2P network, a P2P client offering the protected file is choked with agents connecting to it so that its upload capacity is diluted. In another method, false sources for a protected file are injected into a file sharing network so as to dilute the legitimate sources, making them more difficult to find.
Owner:MACROVISION CORP
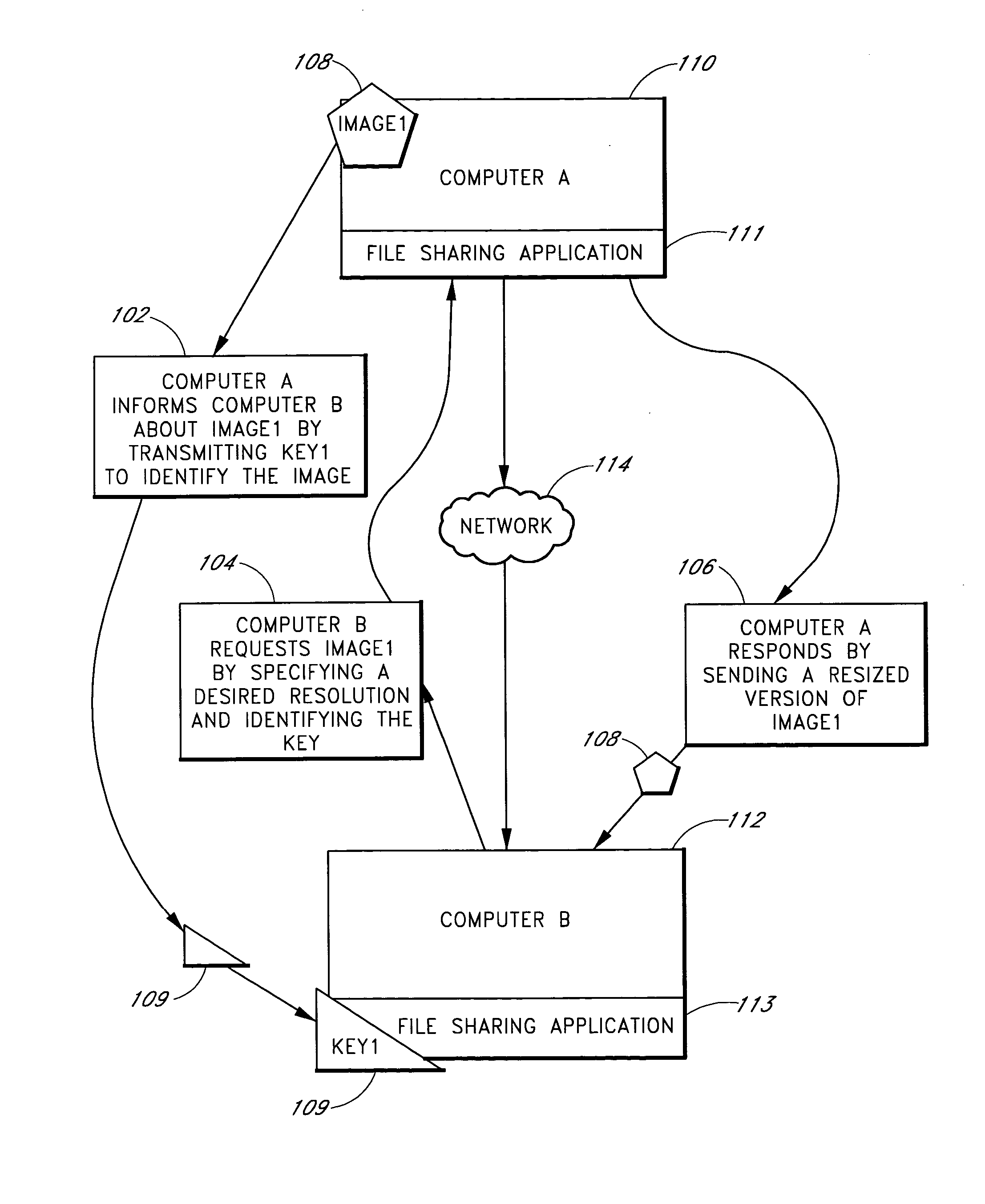
Methods and systems for image sharing over a network
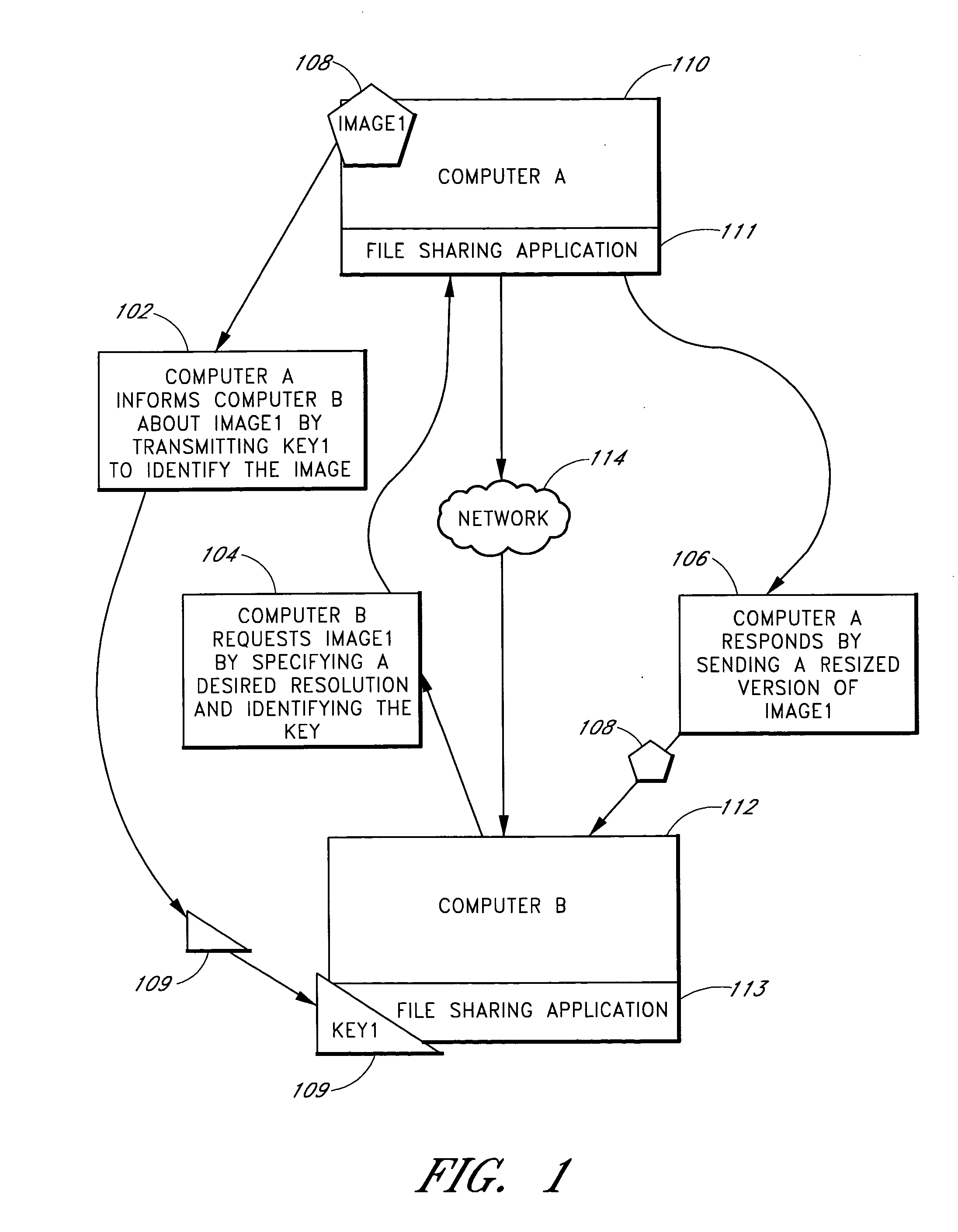
InactiveUS20050052685A1Shorten the timeHigh resolutionData processing applicationsDigital data processing detailsComputer graphics (images)Image resolution
Methods and systems are provided for sharing images over a network. A first user selects an image for sharing and designates an image recipient. Metadata for the first image is transmitted from the first user's terminal to the image recipient's terminal. At least partly in response to receiving the metadata, the image recipient's terminal transmits a request for the first image at a first resolution to the first user's terminal. In response to the request, the first user's terminal transmits the first image at the requested first resolution to the image recipient's terminal.
Owner:GOOGLE LLC
Method, system, and computer program product for managing controlled residential or non-residential environments
InactiveUS20050055472A1Transmission easilyEasy to receiveTelevision system detailsColor television detailsControl signalNetwork connection
A control server, or similar central processor, manages the distribution of data (including audio and video), voice, and control signals among a plurality of devices connected via a wired and / or wireless communications network. The devices include audio / visual devices (such as, televisions, monitors, PDAs, notepads, notebooks, MP3, portable stereo, etc.) as well as household appliances (such as, lighting, ovens, alarm clocks, etc.). The control server supports video / audio serving, telephony, messaging, file sharing, internetworking, and security. A portable controller allows a user to access and control the network devices from any location within a controlled residential and / or non-residential environment, including its surrounding areas. The controllers are enhanced to support location-awareness and user-awareness functionality.
Owner:MICROSOFT TECH LICENSING LLC
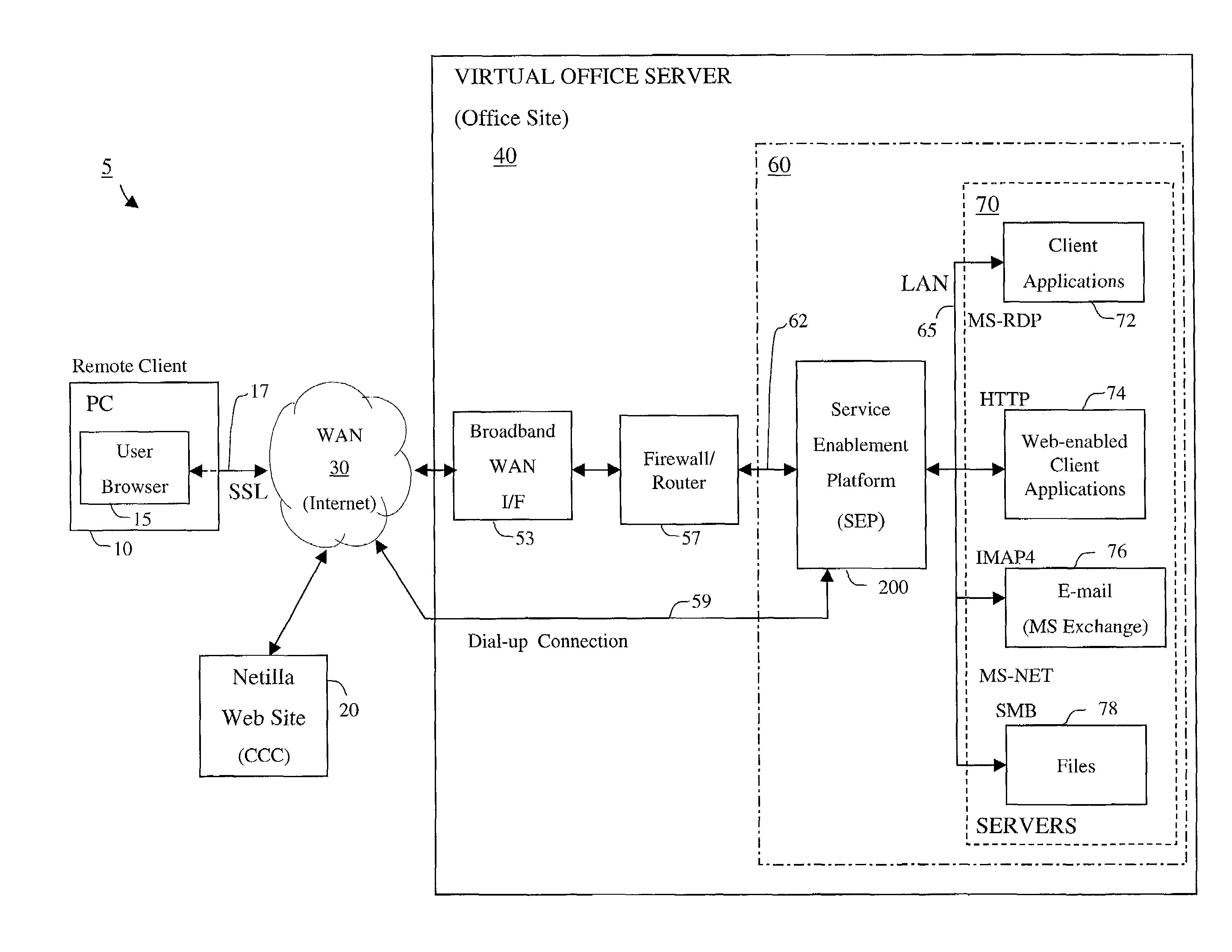
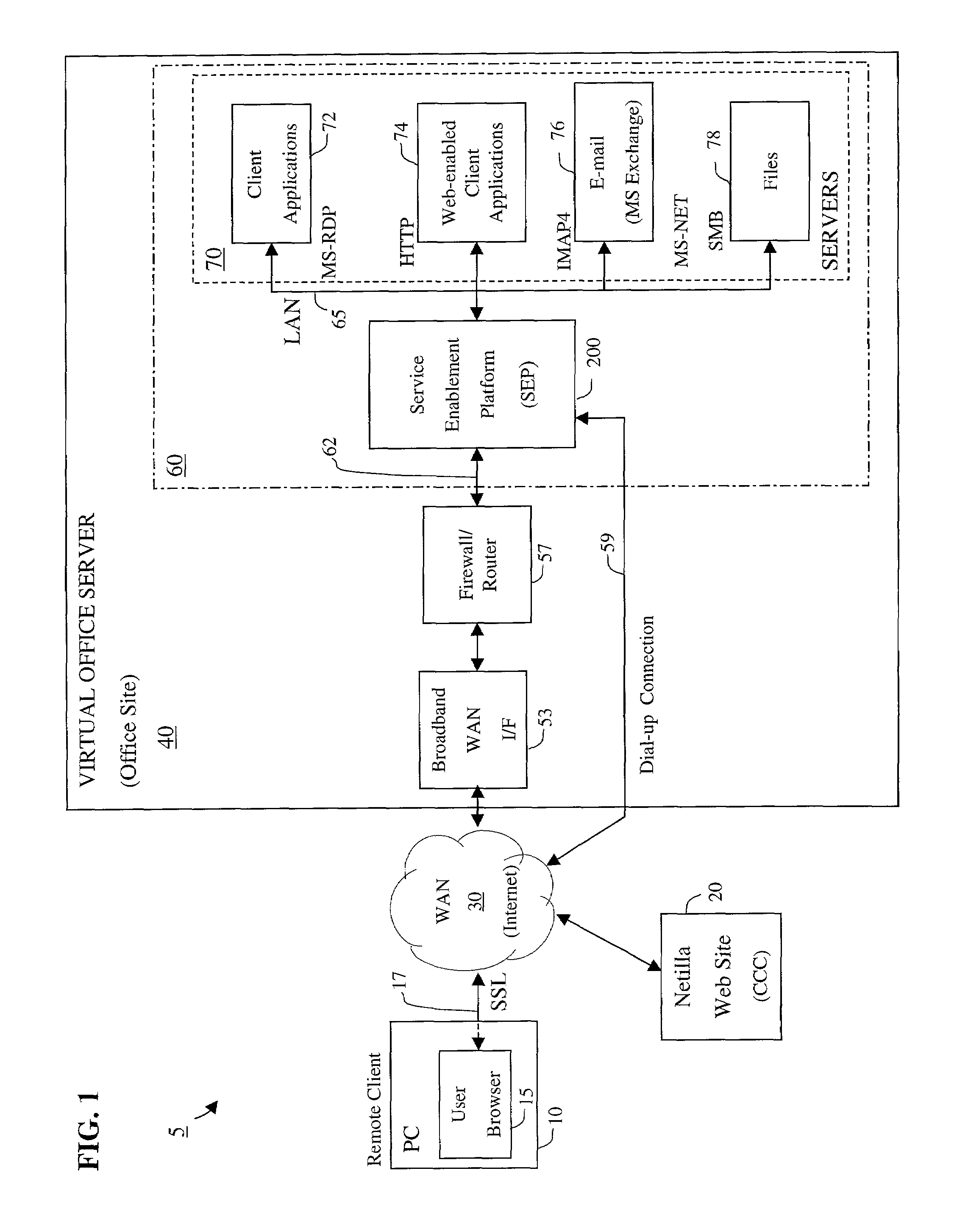
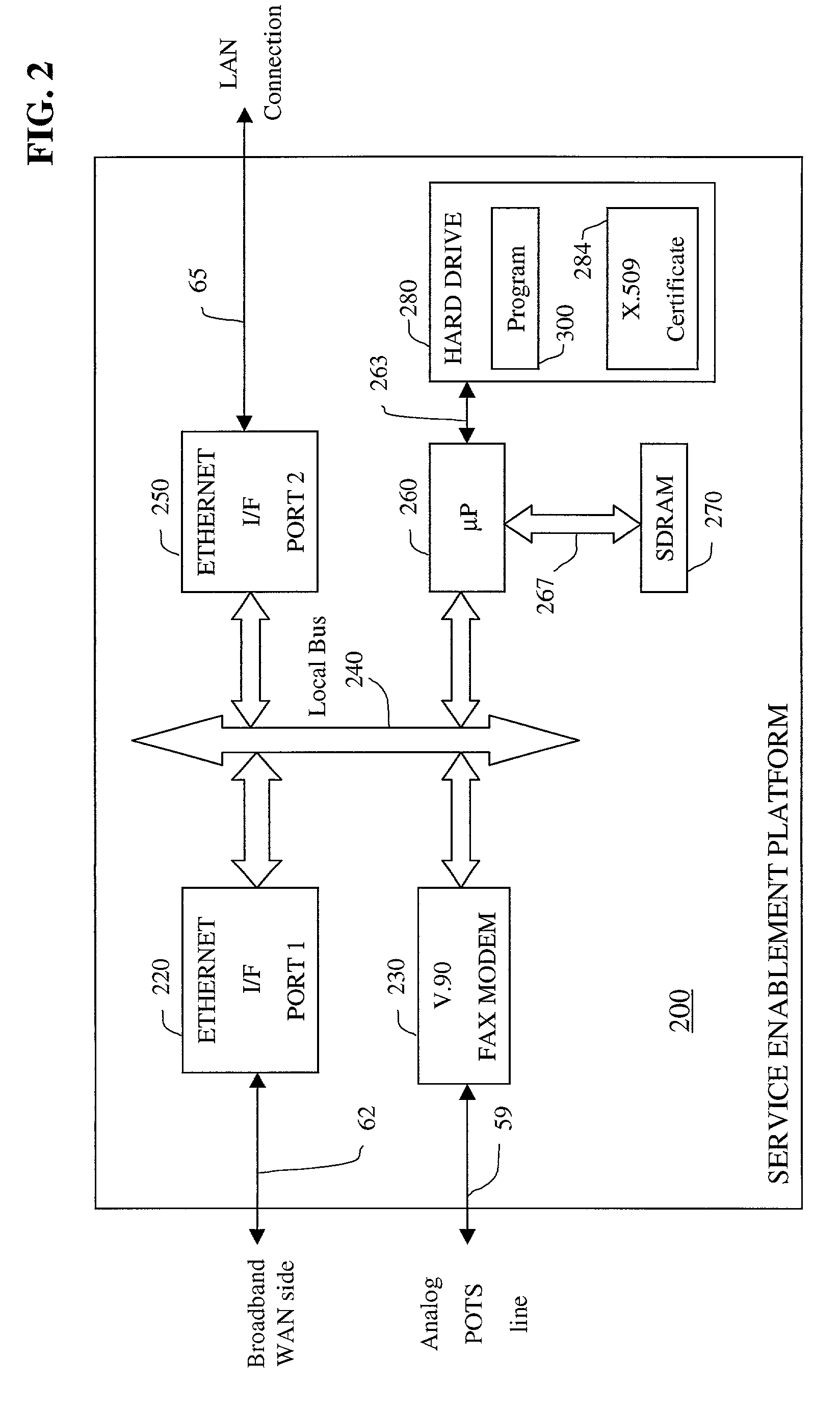
Apparatus and accompanying methods for providing, through a centralized server site, a secure, cost-effective, web-enabled, integrated virtual office environment remotely accessible through a network-connected web browser
InactiveUS7111060B2Readily and easily accommodateReadily and easilyMultiple digital computer combinationsTransmissionNetwork connectionVirtual office
Apparatus and accompanying methods for use therein for implementing an integrated, virtual office user environment, through an office server(s), through which a remotely stationed user can access typical office network-based applications, including e-mail, file sharing and hosted thin-client programs, through a remotely located network, e.g., WAN, connected web browser. Specifically, a front end, namely a service enablement platform (SEP), to one or more office servers on a LAN is connected to both the WAN and LAN and acts both as a bridge between the user and his(her) office applications and as a protocol translator to enable bi-directional, web-based, real-time communication to occur between the browser and each such application. The SEP translates user input originating from the browser into application-specific protocols and applies a result to a corresponding office application server.
Owner:AEP NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com