Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2184results about How to "Increase opportunities" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
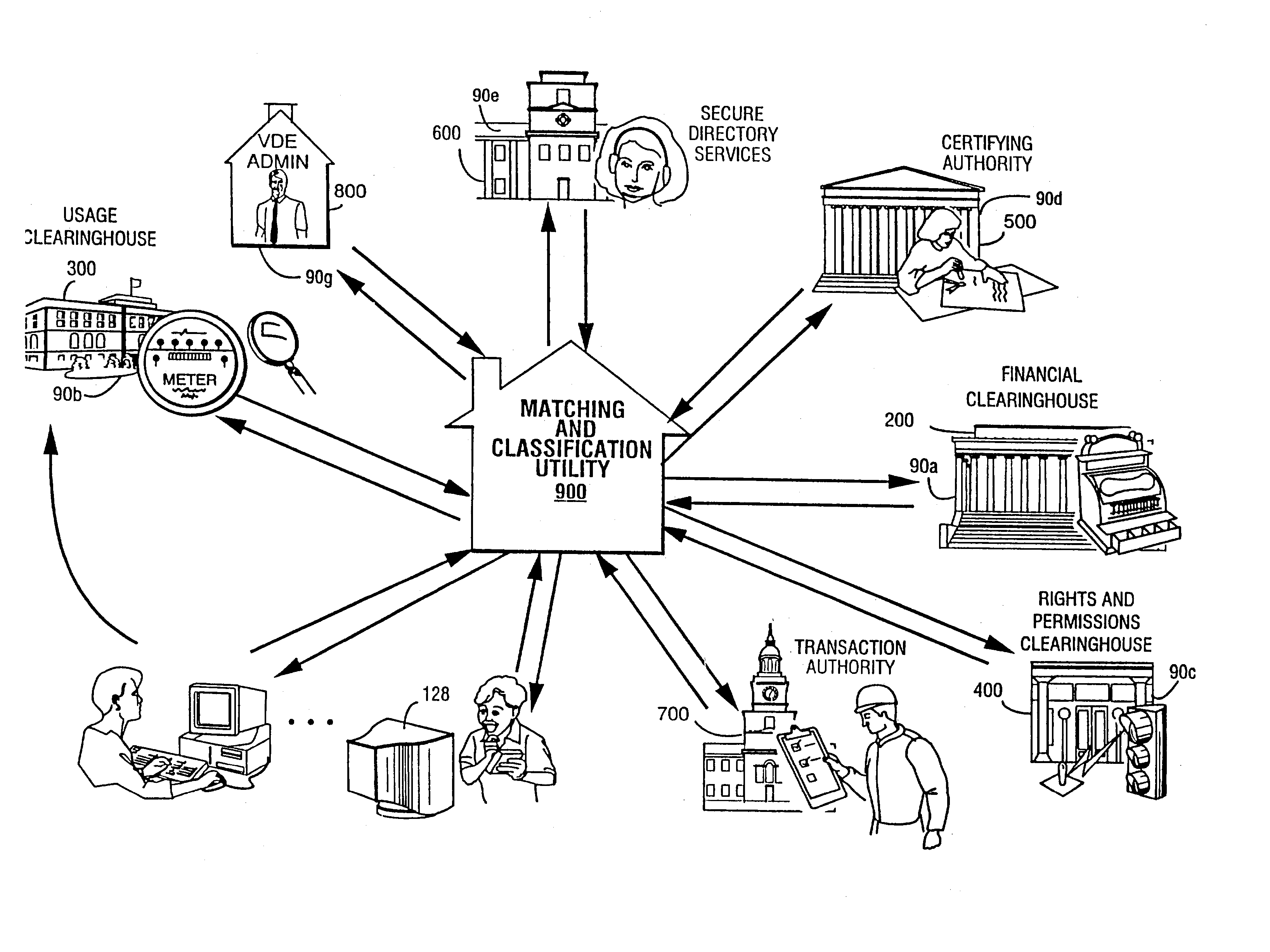
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
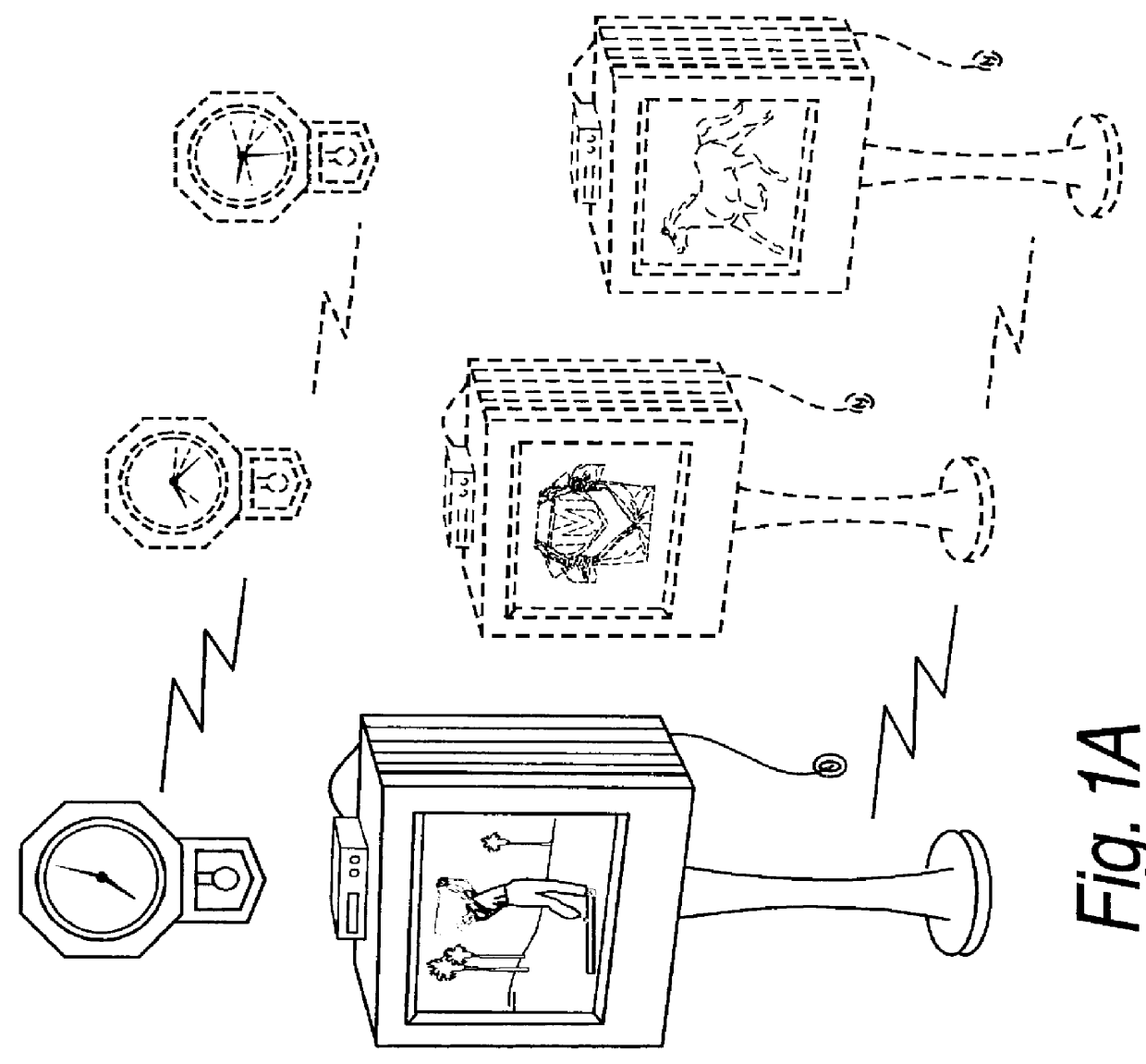
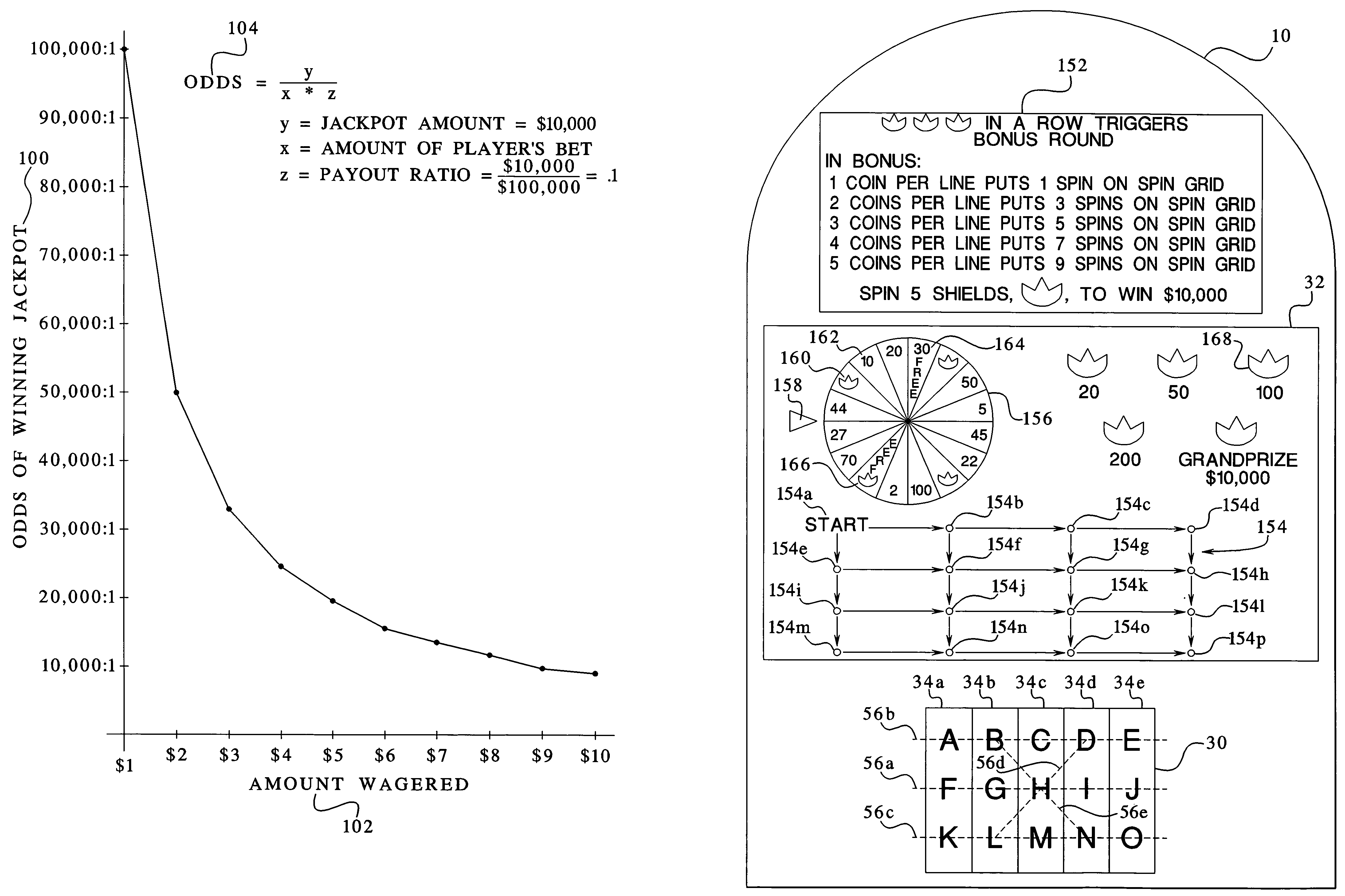
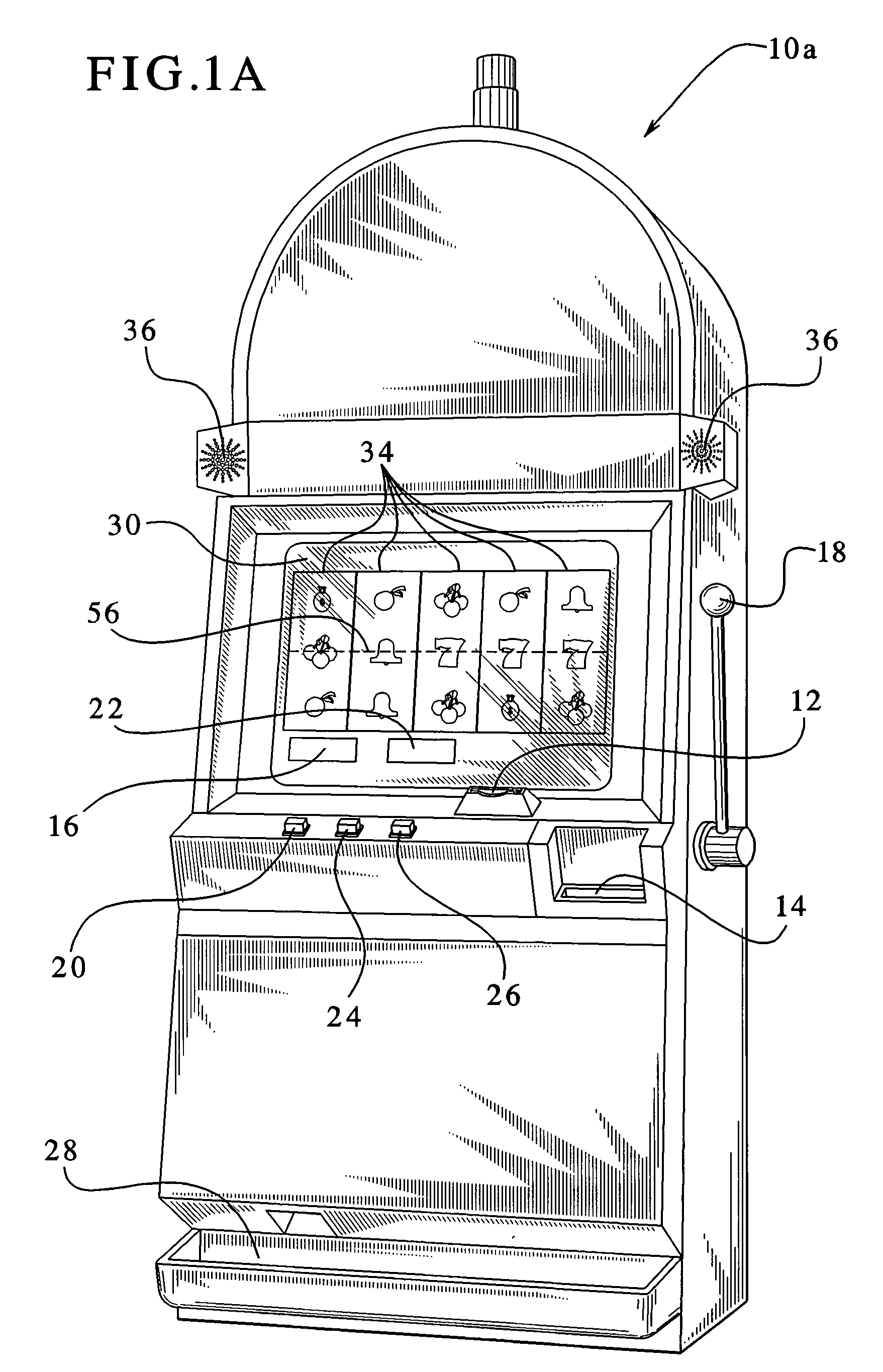
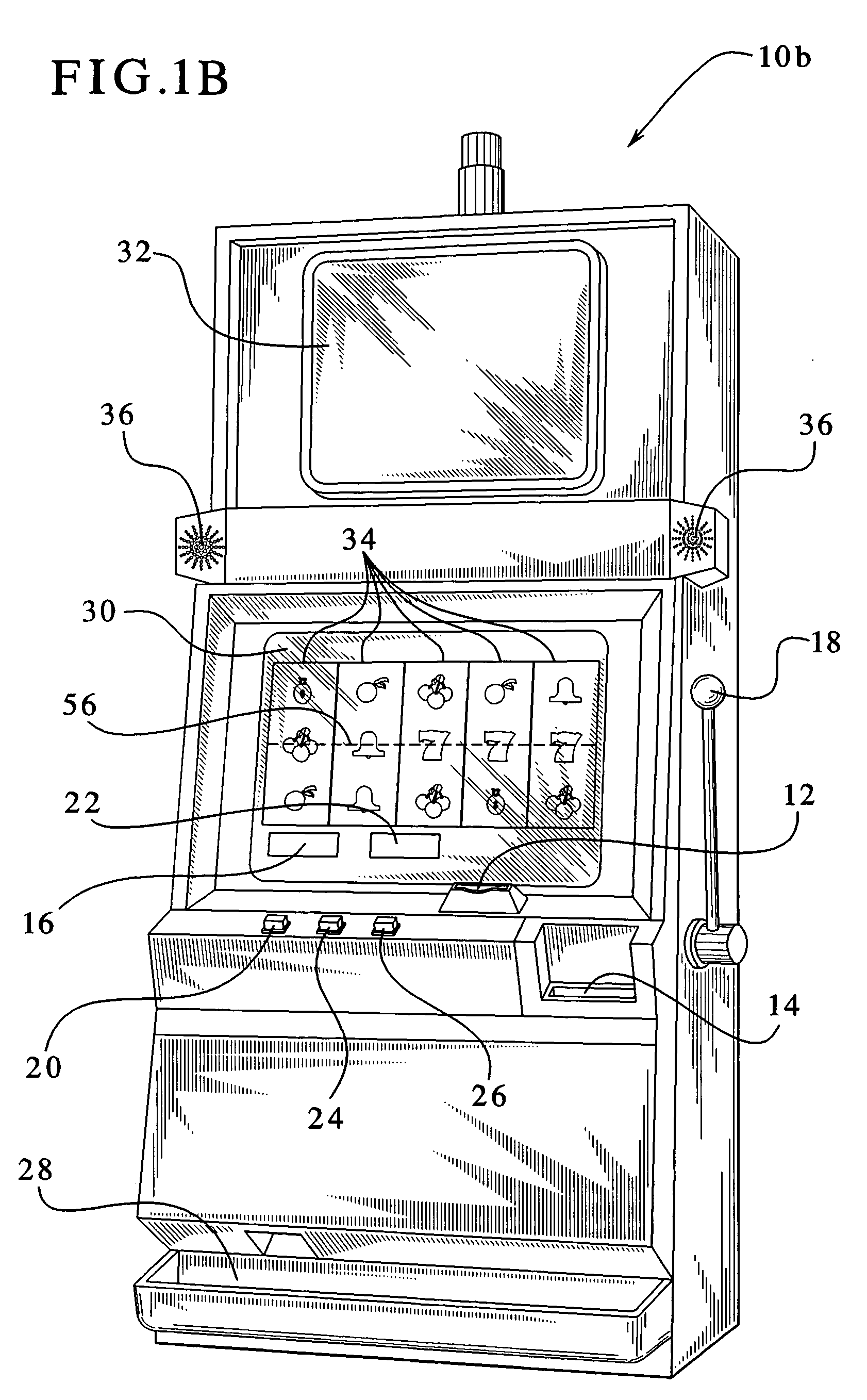
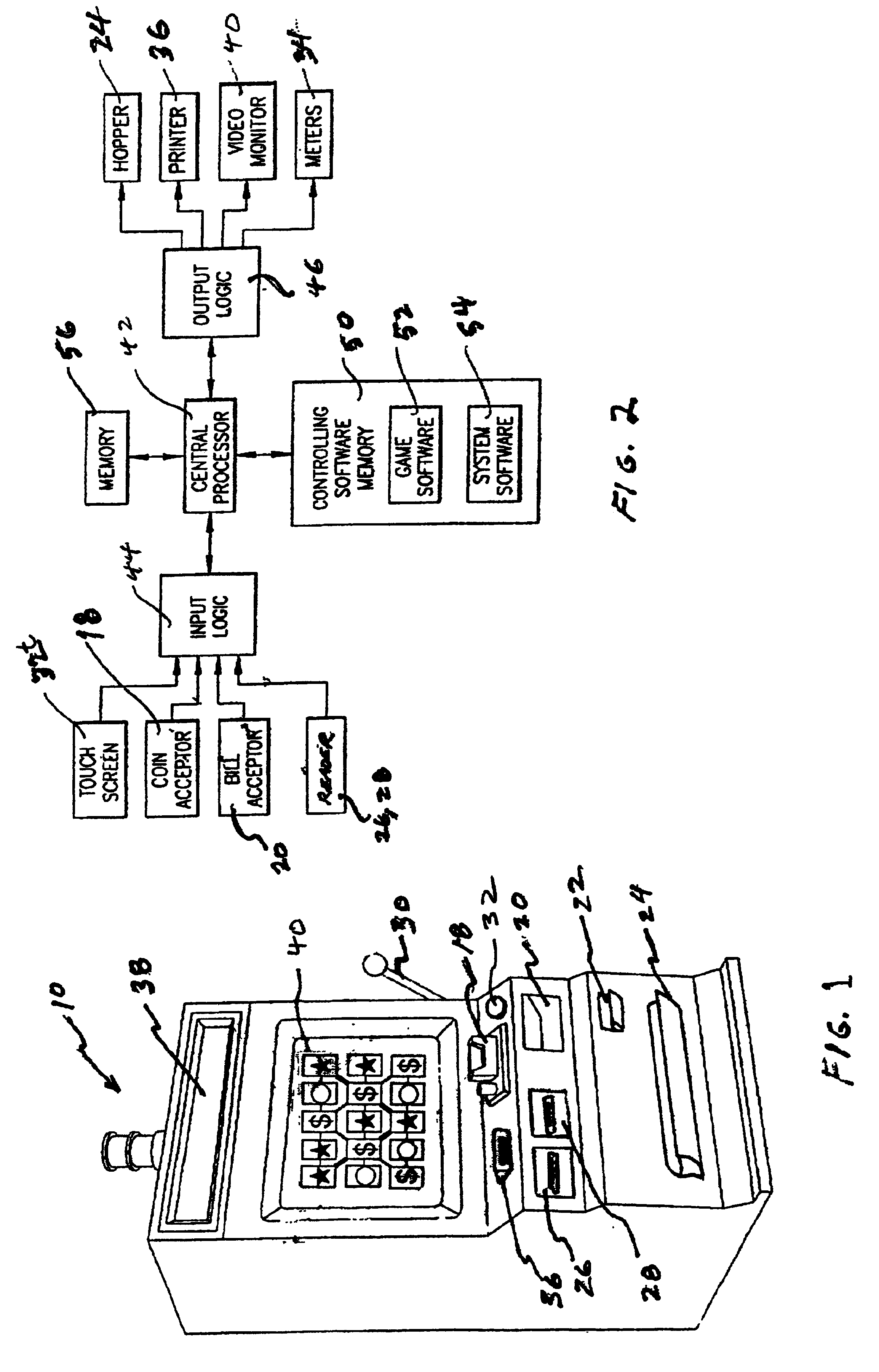
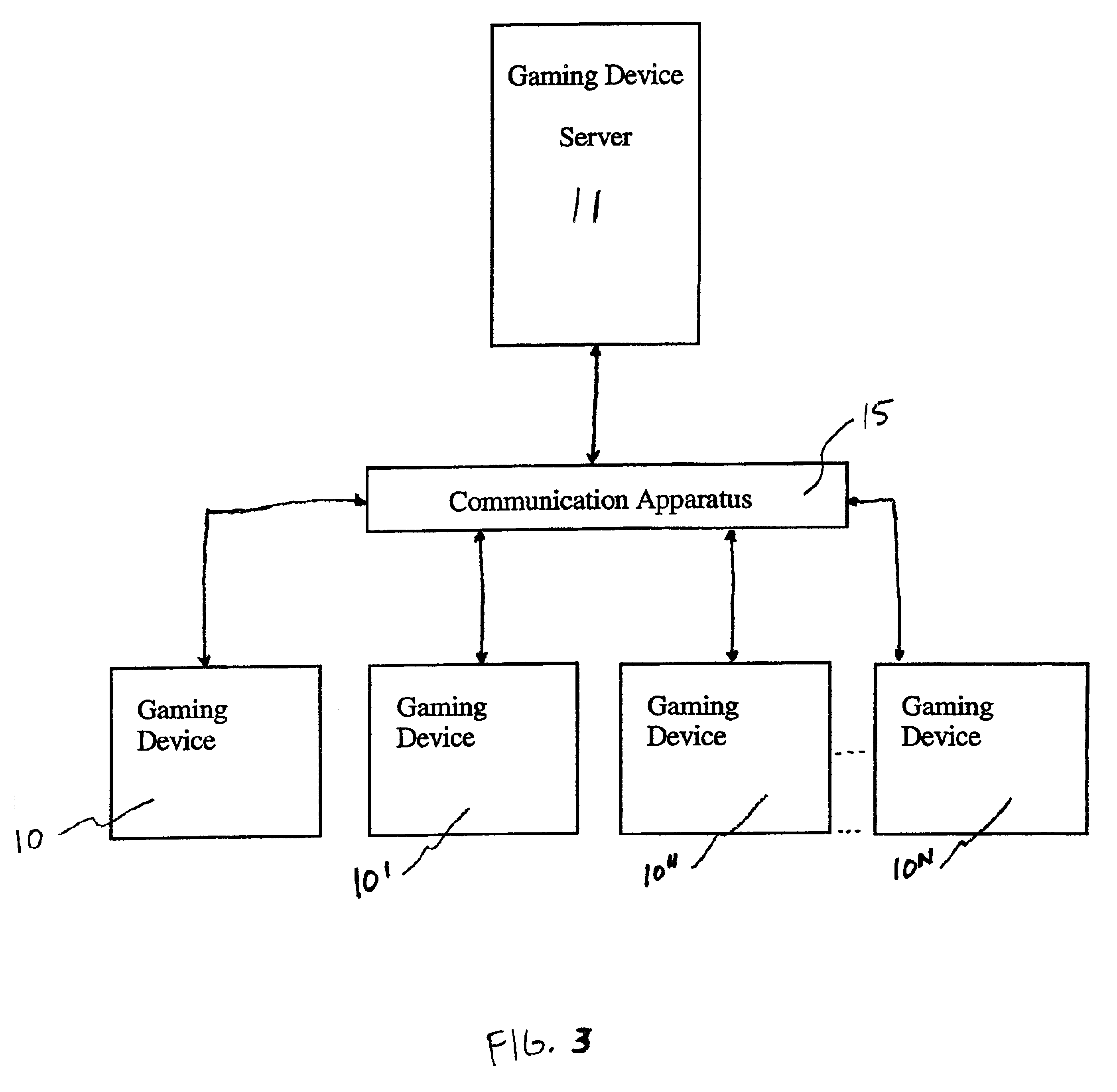
Gaming device having odds of winning which increase as a player's wager increases
InactiveUS7029395B1Raise the possibilityBetter oddsApparatus for meter-controlled dispensingVideo gamesOddsHuman–computer interaction
The present invention provides a gaming device, wherein the game requires the same average investment from a player to win an award, including a jackpot award, regardless of the amount that the player bets at any one time. The award can be unchanging, e.g., $10,000, each time a player plays the gaming device. The award can also vary such as with a progressive jackpot, i.e., the jackpot builds until a player “hits” the jackpot. The game enables the average investment necessary to win the jackpot to be uniform by varying the odds of winning the jackpot as the player's bet varies. That is, a player betting less money needs to play the game more times, on average, to win the jackpot. Likewise, a player betting more money needs to play the game less times, on average, to win the jackpot. The average overall bet or investment thus remains constant despite the player's betting habits or betting ability.
Owner:IGT
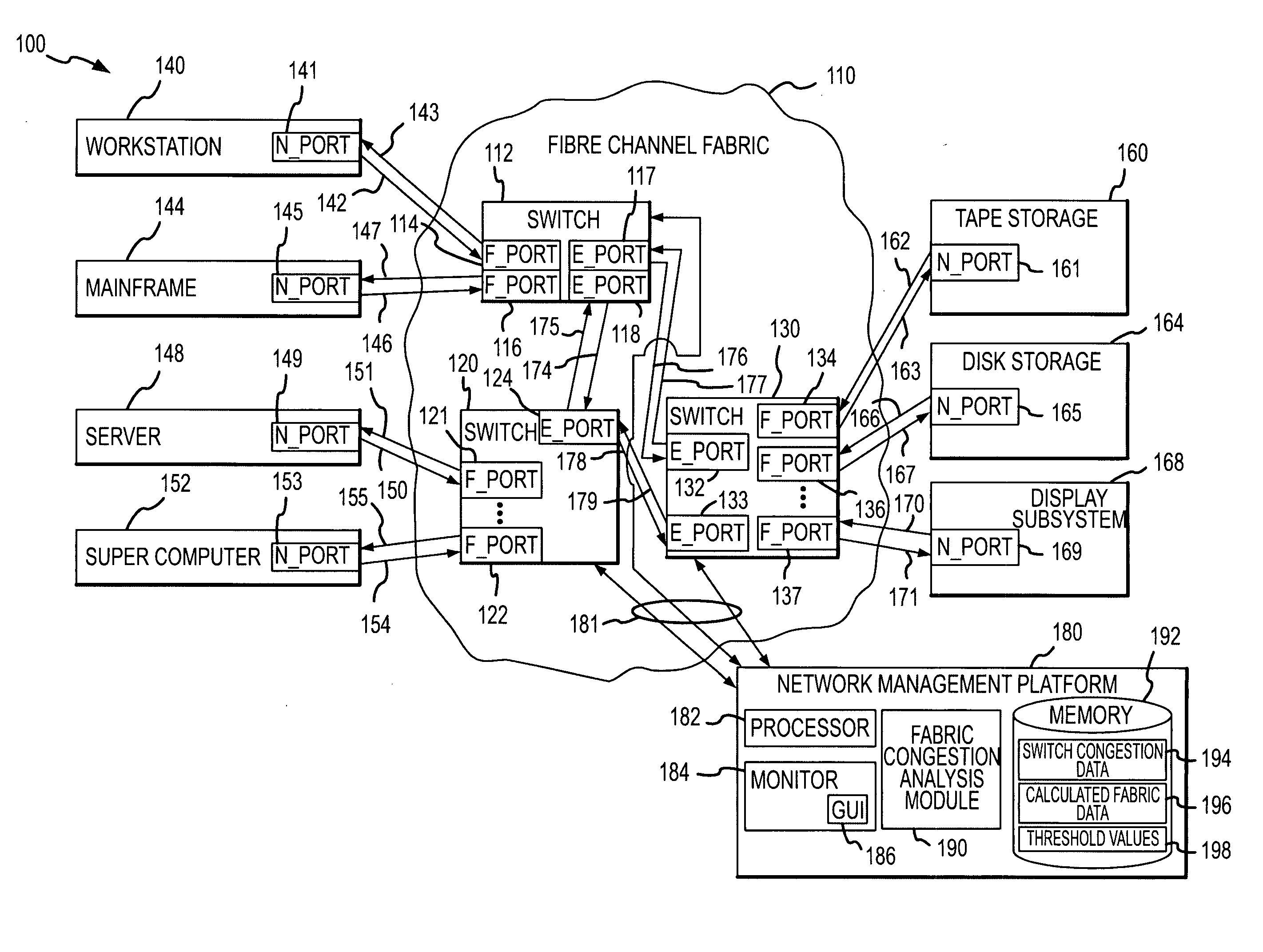
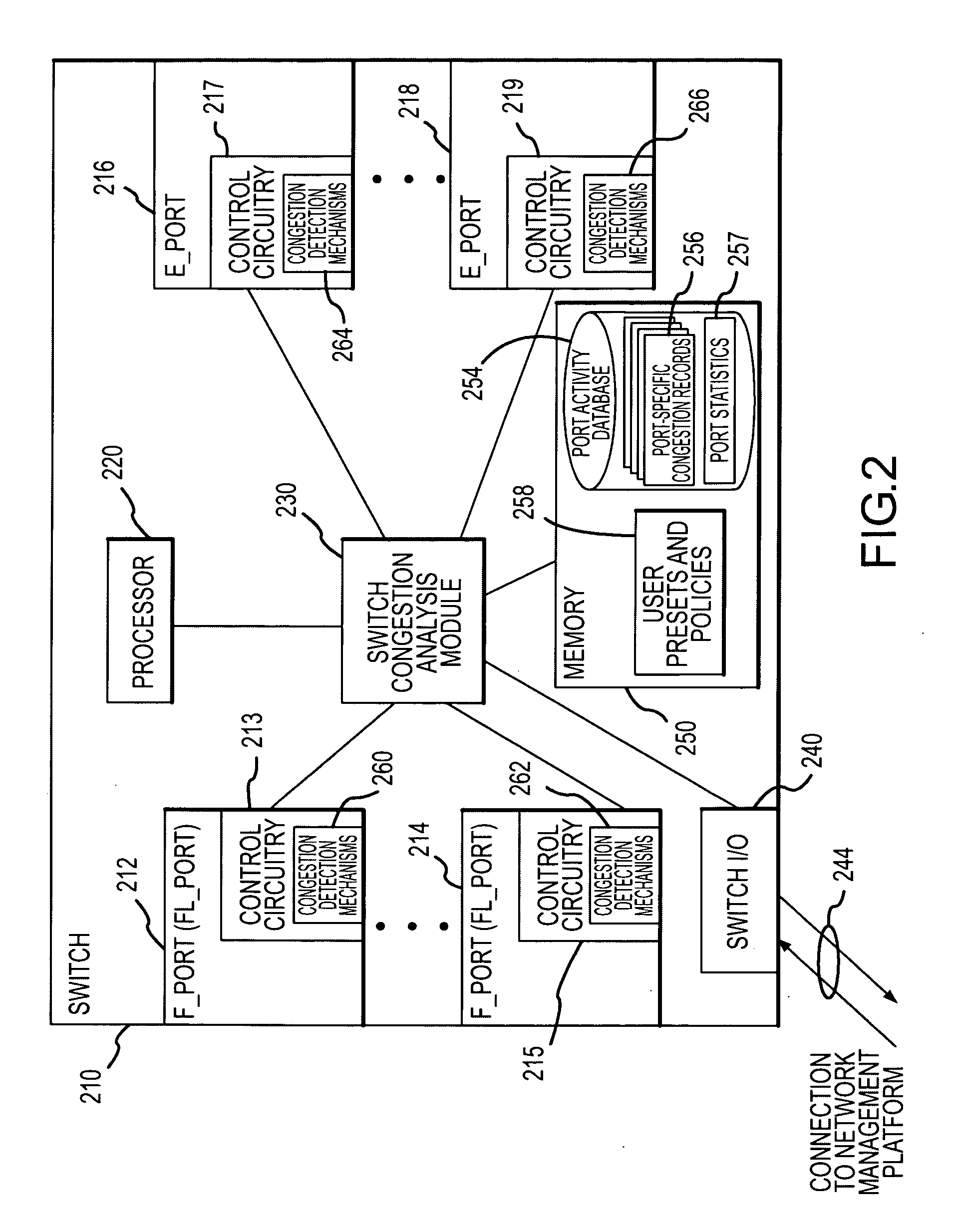
Method of detecting and monitoring fabric congestion
InactiveUS20050108444A1Effective isolationDisplay is generatedData switching networksInput/output processes for data processingTraffic capacityTraffic congestion
A system for detecting, monitoring, reporting, and managing congestion in a fabric at the port and fabric levels. The system includes multi-port switches in the fabric with port controllers that collect port traffic statistics. A congestion analysis module in the switch periodically gathers port statistics and processes the statistics to identify backpressure congestion, resource limited congestion, and over-subscription congestion at the ports. A port activity database is maintained at the switch with an entry for each port and contains counters for the types of congestion. The counters for ports that are identified as congested are incremented to reflect the detected congestion. The system includes a management platform that periodically requests copies of the port congestion data from the switches in the fabric. The switch data is aggregated to determine fabric congestion including the congestion level and type for each port and congestion sources.
Owner:MCDATA CORP
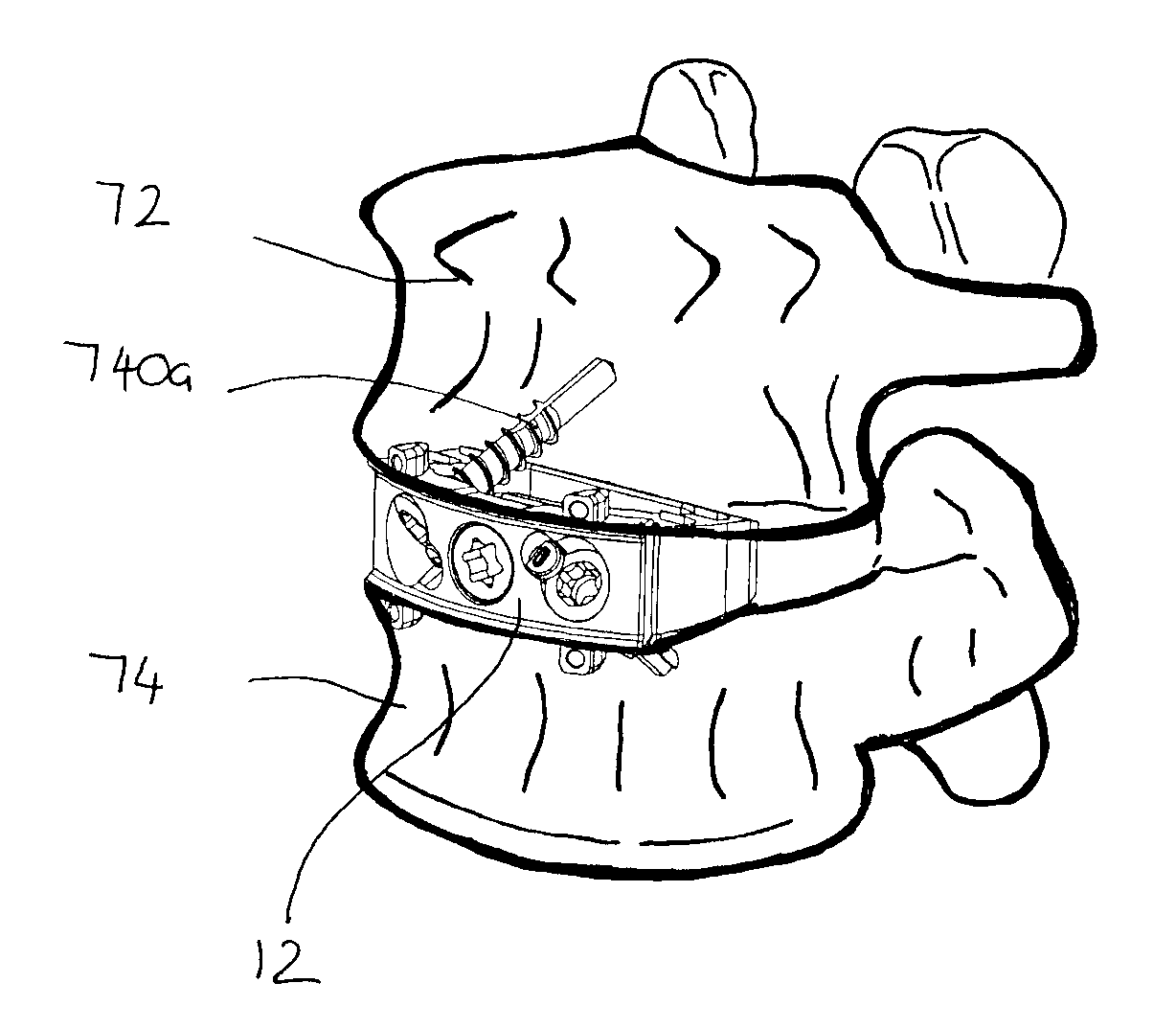
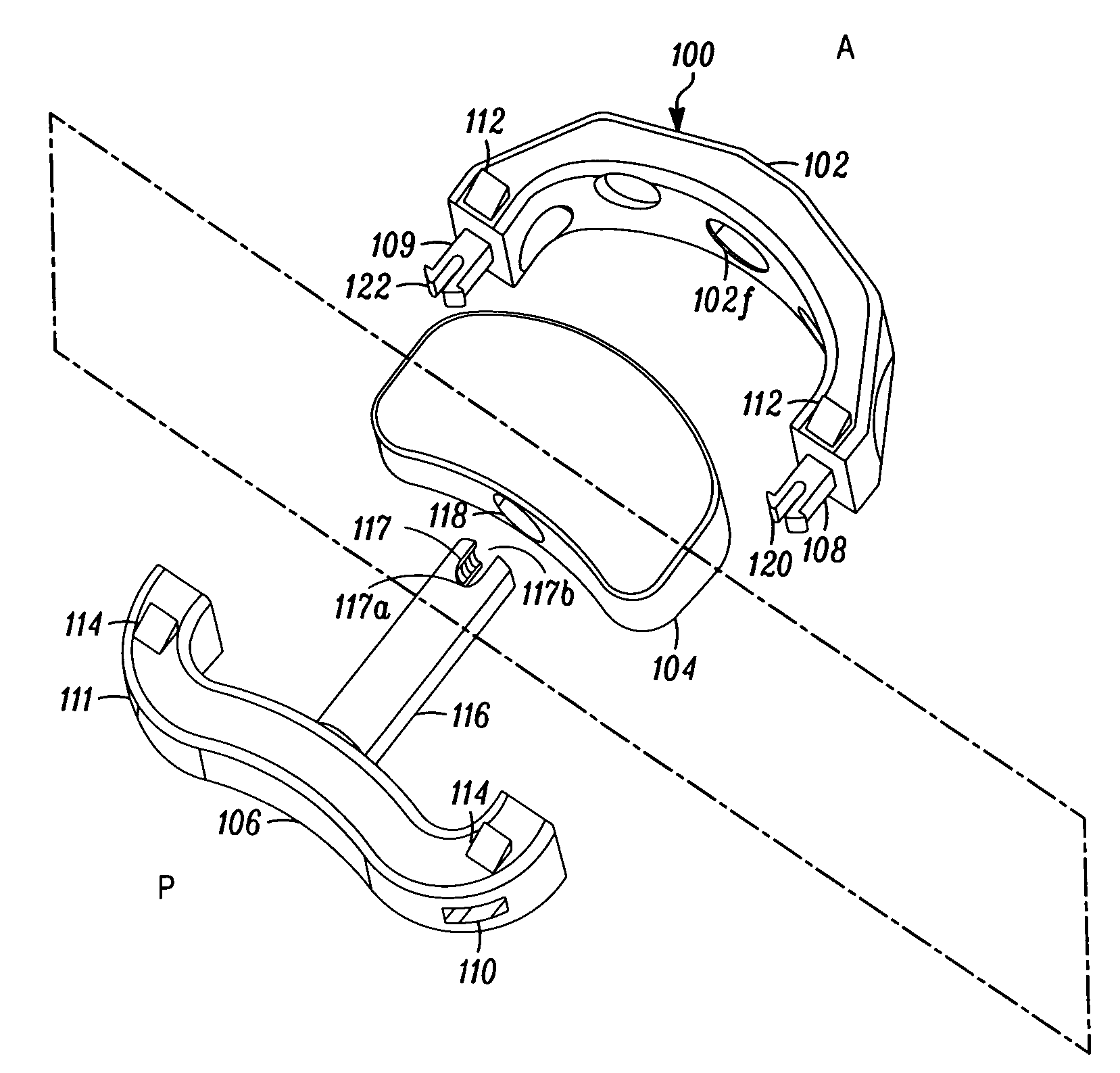
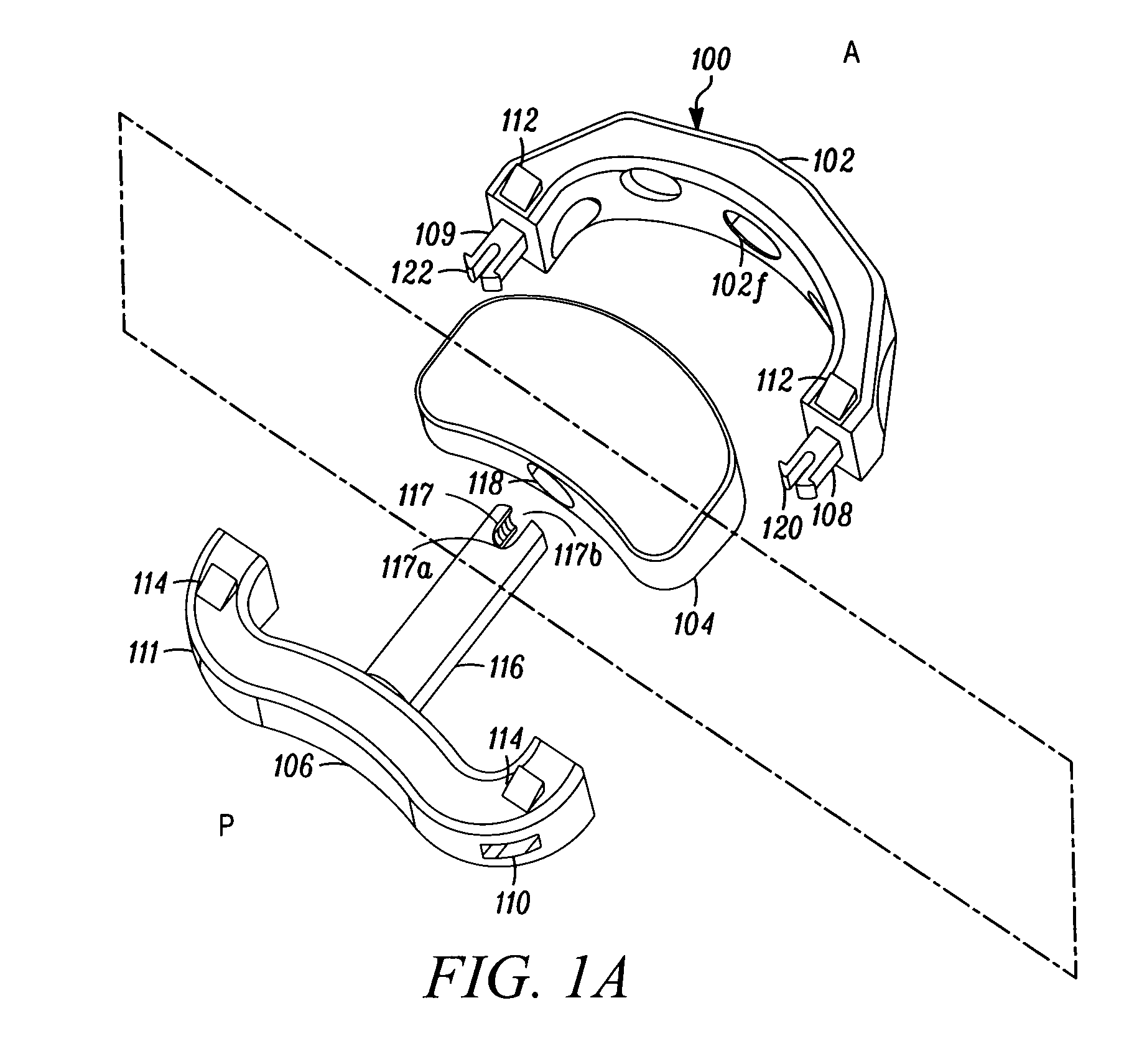
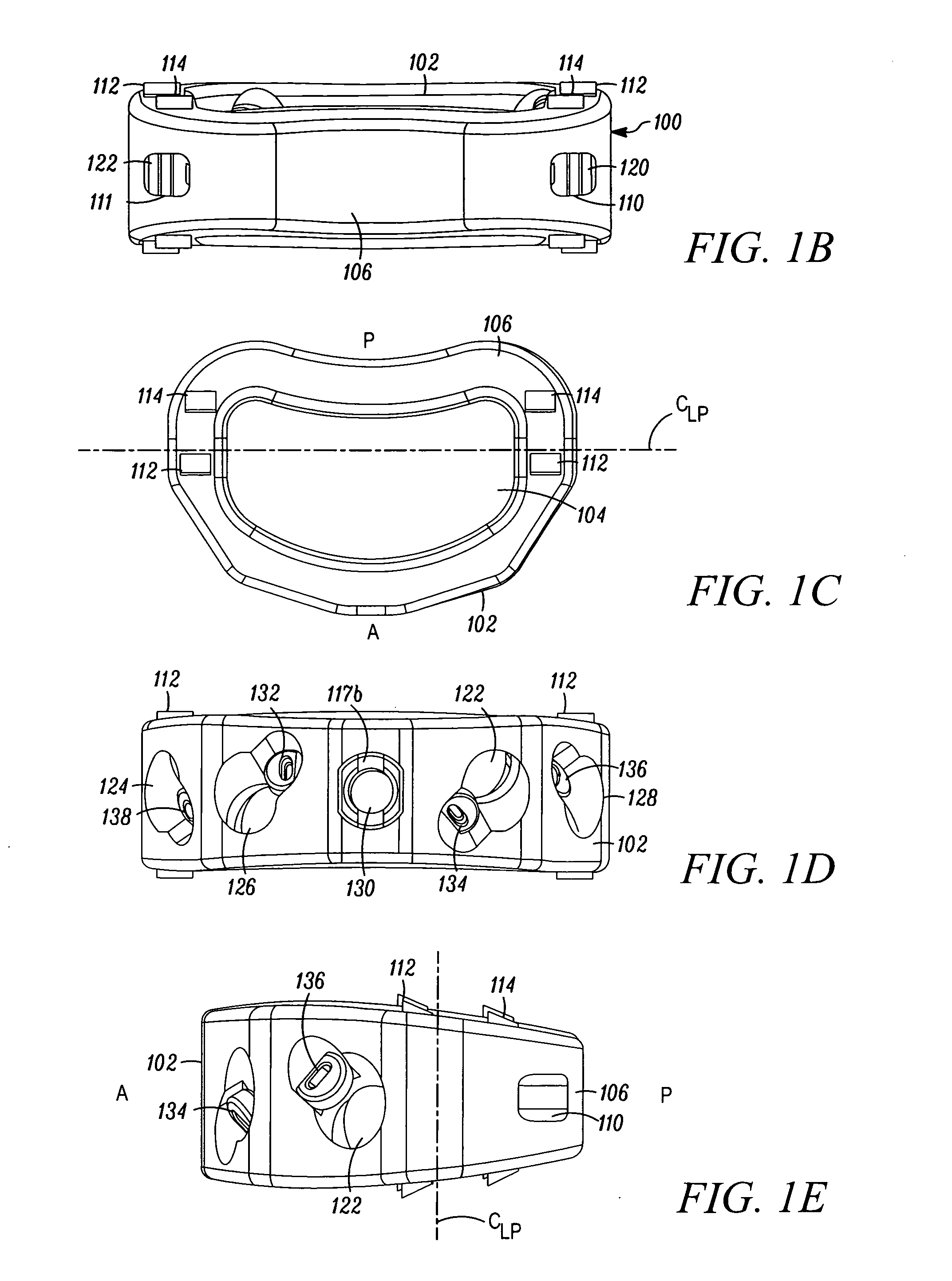
Orthopaedic Implants and Prostheses
InactiveUS20090210062A1Small sizeAdjustable sizeSuture equipmentsBone implantSurgical siteSurgical department
Disclosed herein are spinal implants particularly useful in interbody fusion surgery. One embodiment pertains to a plate configured to establish desired lordosis and / or disc height that may be implanted and secured to a superior and inferior vertebral body. The plate may be interlocked with a spacer component to form a single implant. Also disclosed is an anti-backout mechanism that helps prevent fixators from backing out upon securement of the plate in the spine. Kits comprising different sizes and inclination angles of components are disclosed, which can assist the surgeon in preoperatively assembling an implant to best fit in the surgical site of the patient.
Owner:THALGOTT JOHN +1
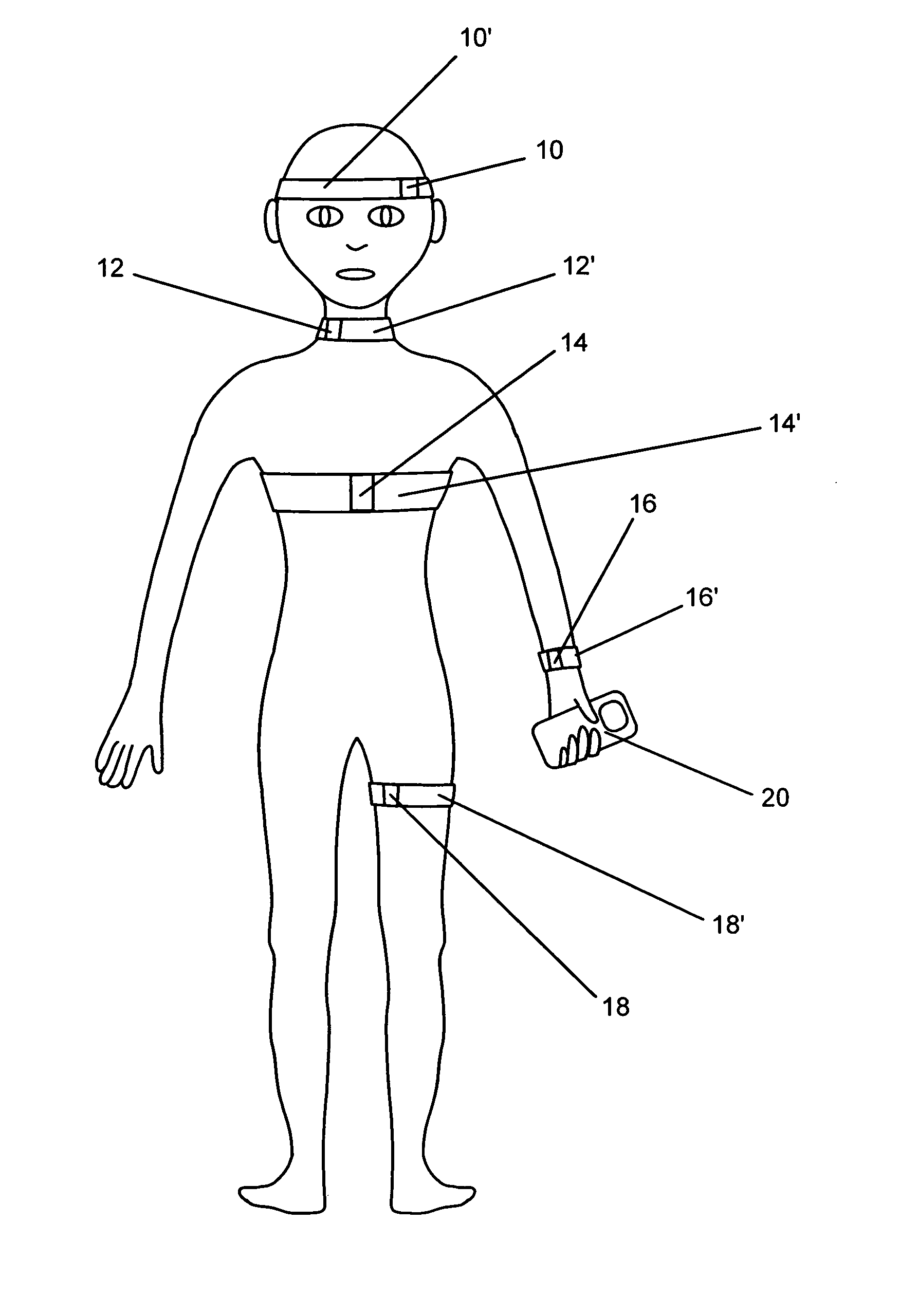
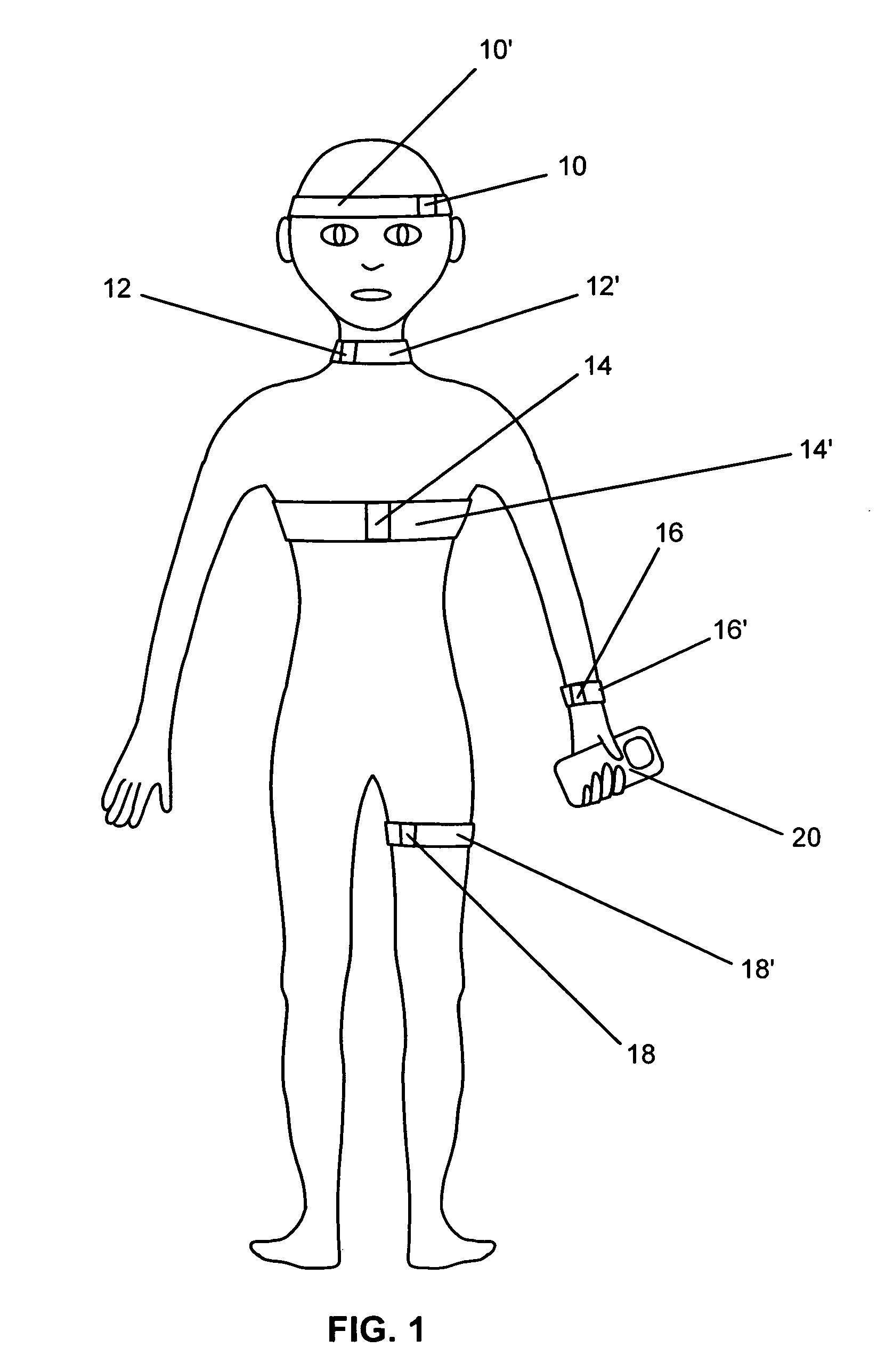
Systems and methods for non-invasive detection and monitoring of cardiac and blood parameters
InactiveUS20060100530A1Easy to detectEffective assessmentBlood flow measurement devicesCatheterData acquisitionNon invasive
Methods and systems for long term monitoring of one or more physiological parameters such as respiration, heart rate, body temperature, electrical heart activity, blood oxygenation, blood flow velocity, blood pressure, intracranial pressure, the presence of emboli in the blood stream and electrical brain activity are provided. Data is acquired non-invasively using ambulatory data acquisition techniques.
Owner:UNIV OF WASHINGTON +1
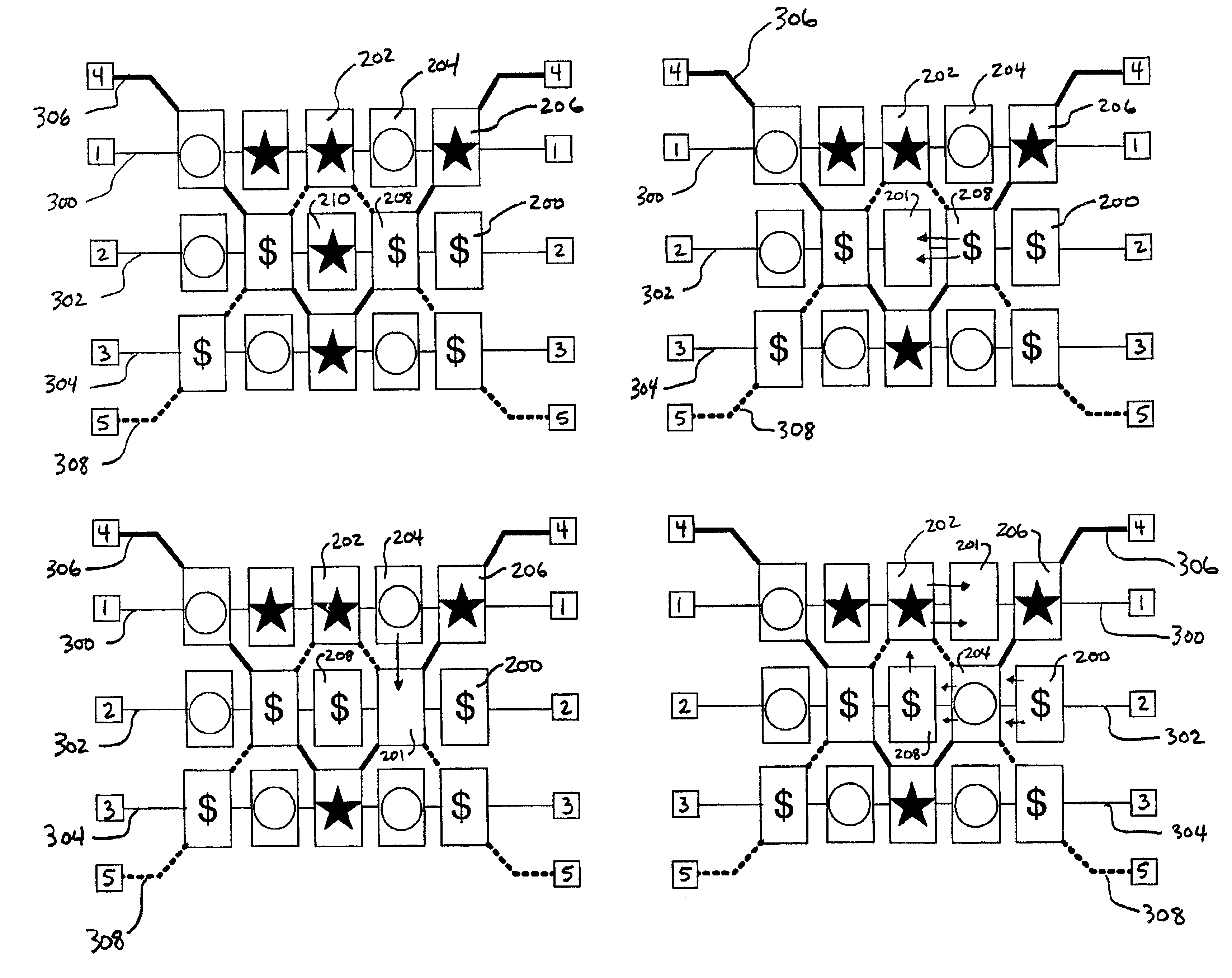
Gaming methods and apparatus using interchangeable symbols
InactiveUS6855054B2Increase opportunitiesLimited amount of timeCard gamesApparatus for meter-controlled dispensingHuman–computer interactionArtificial intelligence
Owner:IGT
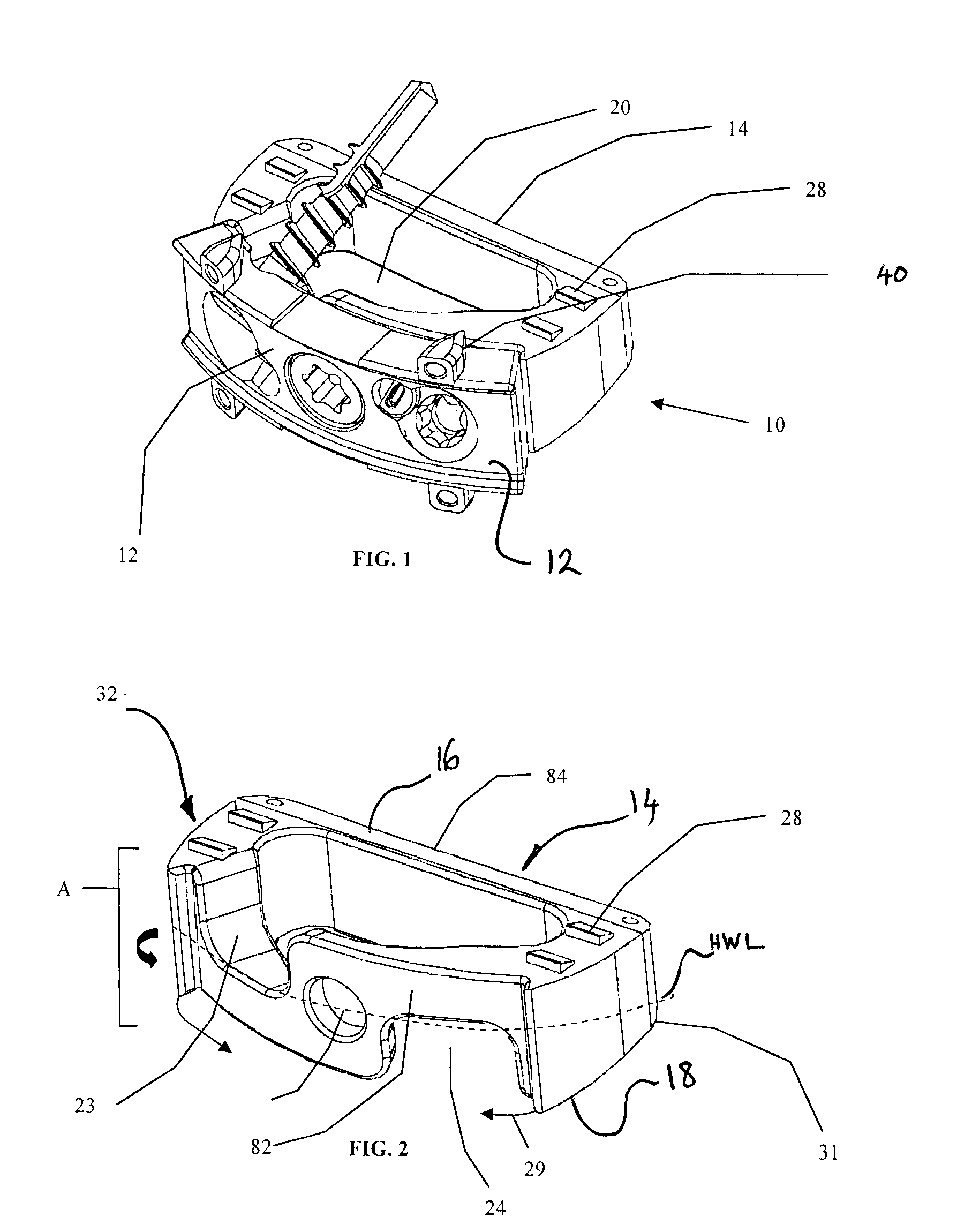
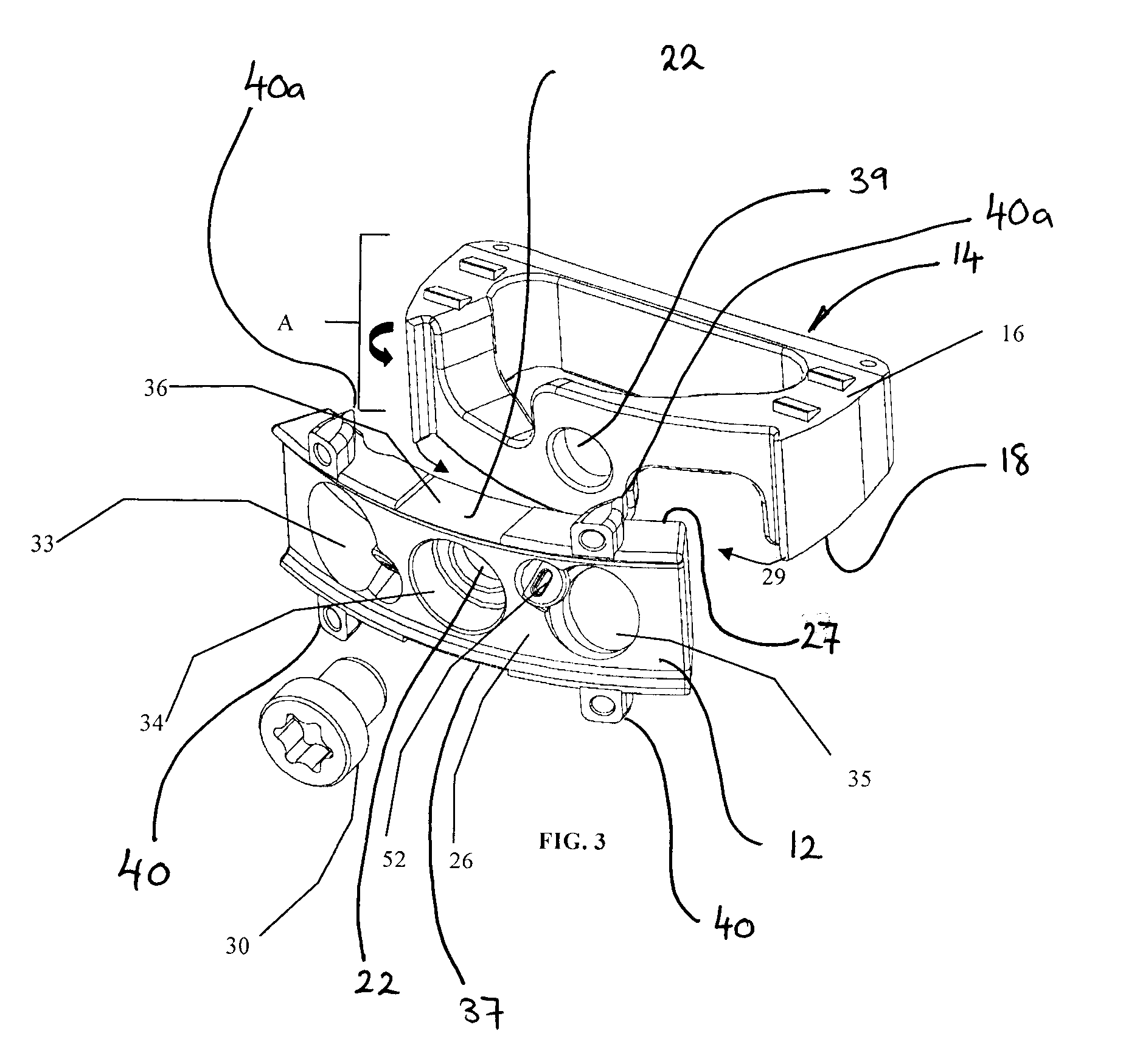
Orthopaedic Implants and Prostheses
Disclosed herein are modular spinal implants having components which are interlocked together to form a single implant. Specifically exemplified herein are implants that are sectioned along a longitudinal plane. Implants are disclosed which include channels for inter-fragmentary association with an elongate bone screw and which allow for angular variability of the screw relative to the channel. Also disclosed is an anti-backout mechanism that helps prevent fixators from backing out upon securement of the implant in the spine. Kits comprising different sizes and inclination angles of components are disclosed, which can assist the surgeon in preoperatively assembling an implant to best fit in the surgical site of the patient.
Owner:SURGICRAFT LTD
Portable GPS navigation device
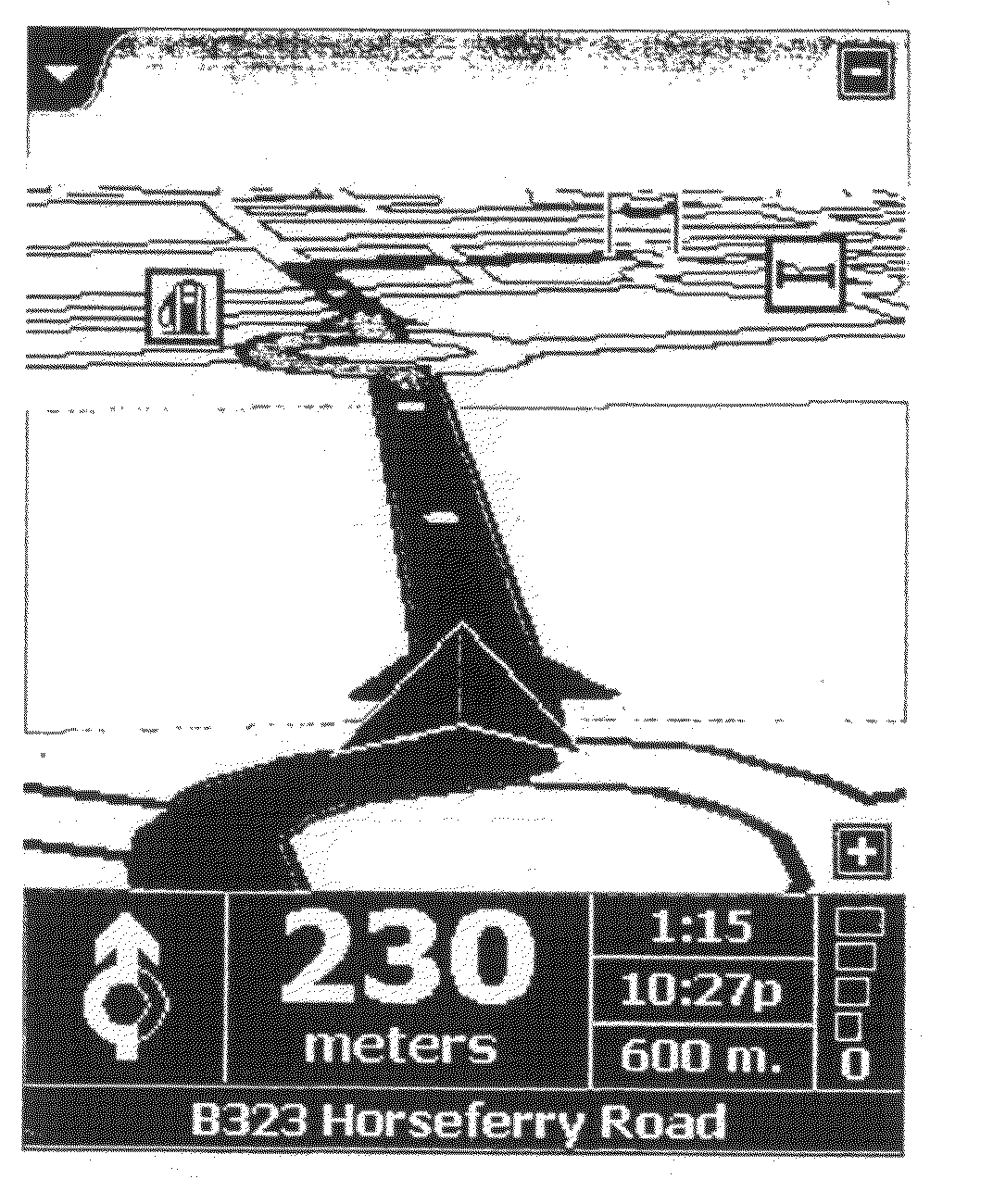
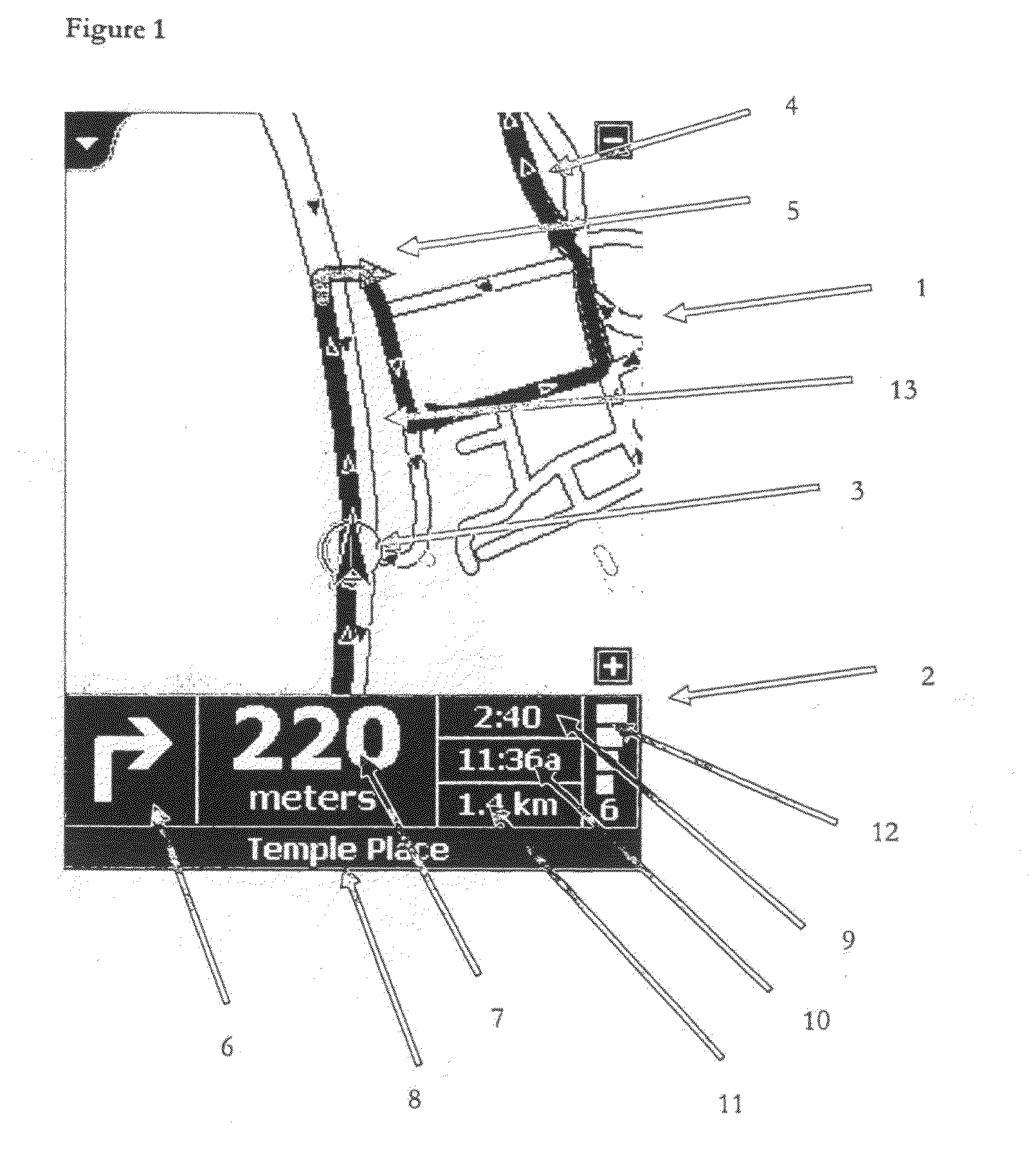
ActiveUS20110153209A1Fast informationSufficient cognitive loadInstruments for road network navigationControl with pedestrian guidance indicatorTransceiverWireless transceiver
A portable GPS navigation device displays map information and navigation instructions; the device (a) includes a two-way wireless transceiver operable to connect to a mobile telephone; (b) is operable to enable a user to control one or more functions of the mobile telephone and (c) includes an audio output and a microphone to enable a voice call to be made using the mobile telephone.
Owner:TOMTOM NAVIGATION BV
Resource scheduling method and system
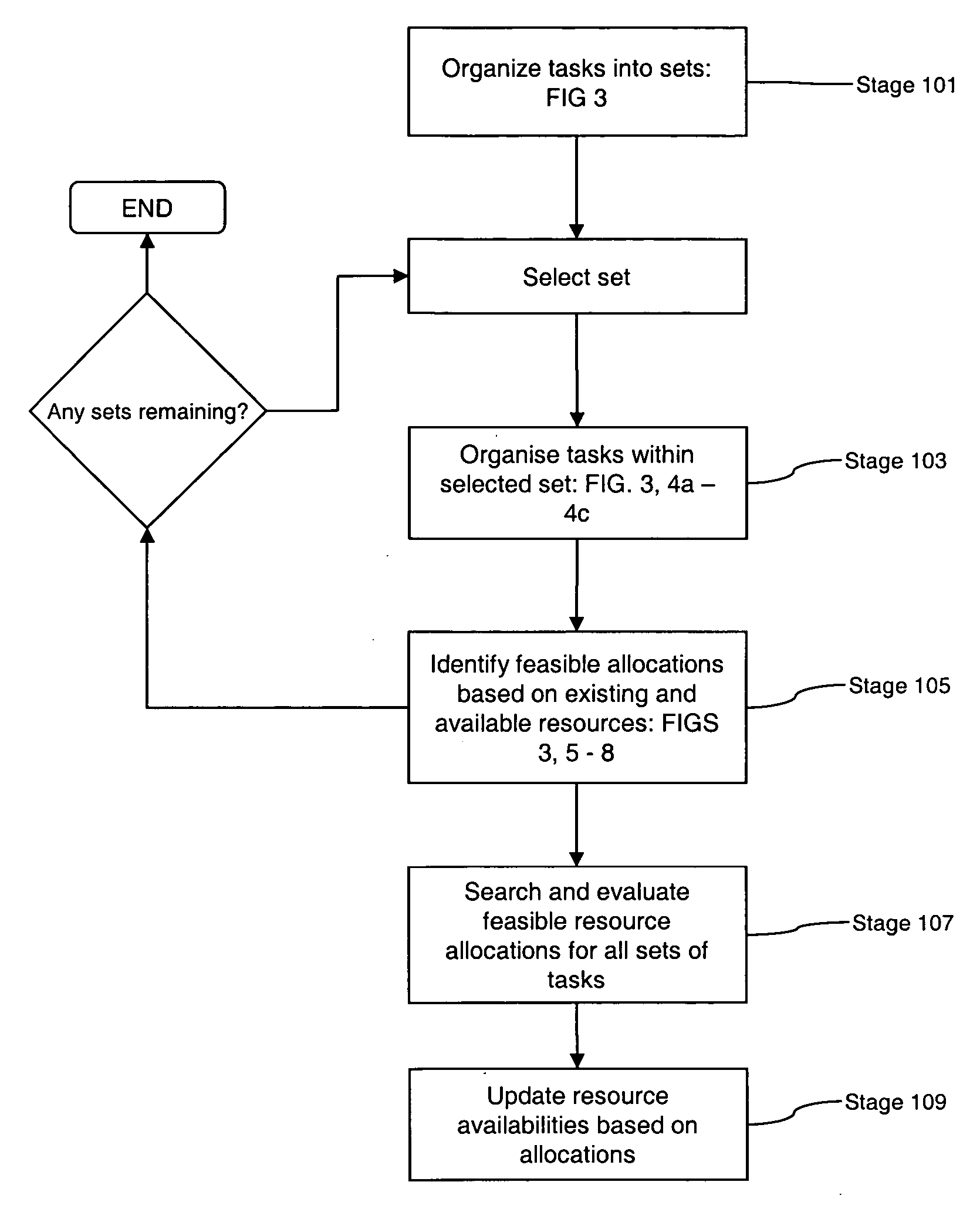
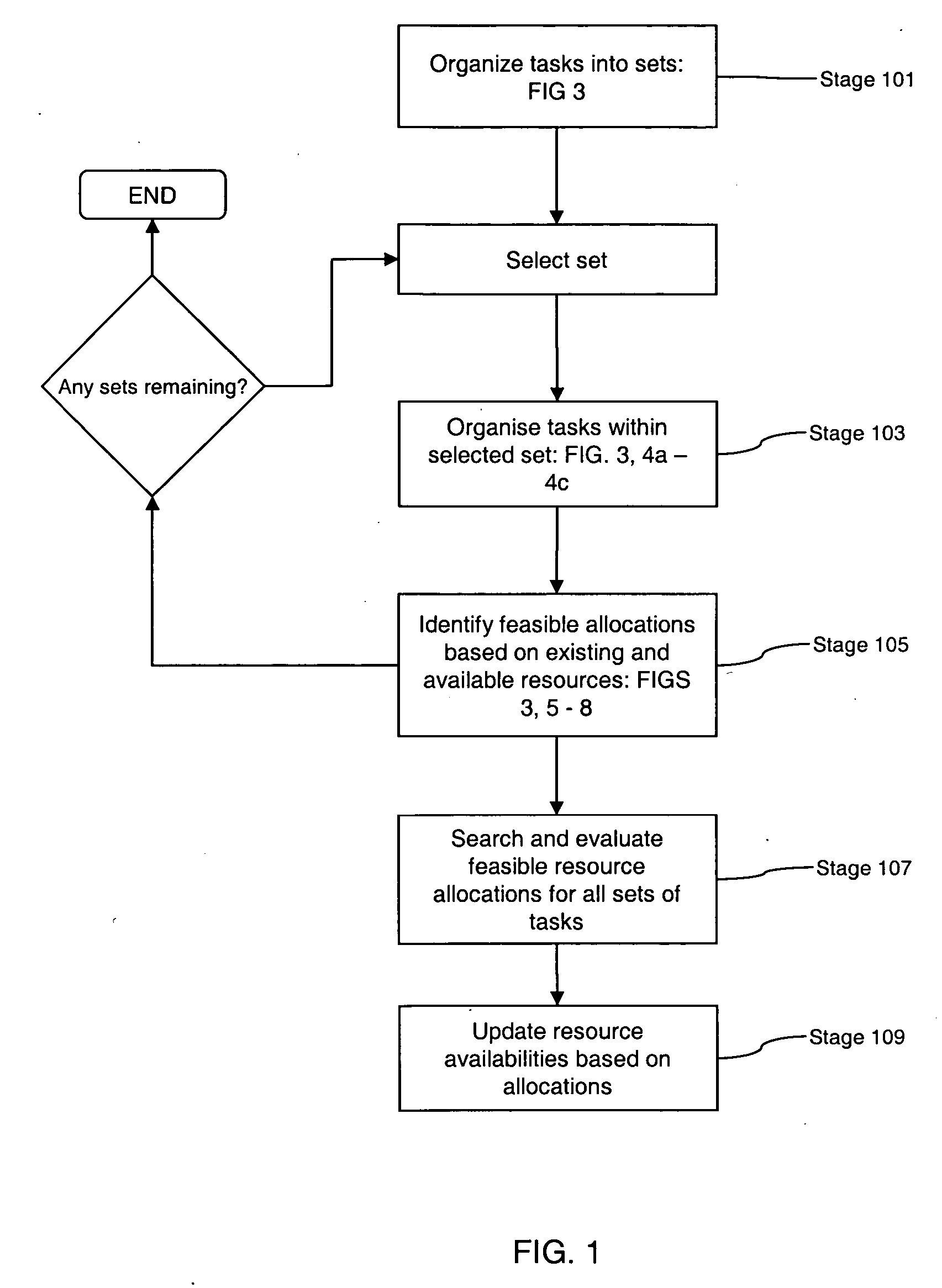
ActiveUS20070021998A1Reduce the amount of calculationIncrease opportunitiesDigital computer detailsMultiprogramming arrangementsResource poolDistributed computing
Embodiments of the invention are concerned with scheduling resources to perform tasks requiring a plurality of capabilities or capabilities and capacities, and has particular application to highly changeable or uncertain environments in which the status and the composition of tasks and / or resources changes frequently. Embodiments provide a method for use in a scheduling process for scheduling allocation of resources to a task, each resource having a plurality of attributes, wherein the task has one or more operational constraints including a required plurality of capabilities, and a performance condition associated therewith. The method comprises: receiving data indicative of a change to the status of the scheduling process; in response to receipt of the status data, reviewing the attributes of individual resources so as to identify combinations of resources able to collectively satisfy said capability requirements of the task; evaluating each identified combination of resources in accordance with a performance algorithm so as to identify an associated performance cost; selecting a combination of resources whose identified performance cost meets the performance condition; and scheduling said task on the basis of said selected combination of resources. In embodiments of this aspect of the invention, changes to resource configurations are effected as part of the scheduling process. These changes can be made dynamically, in response to the occurrence of events that have a bearing on the scheduling process, and involve aggregating resources together so as to create, essentially, a new resource pool from which selection can be made.
Owner:TRIMBLE MRM
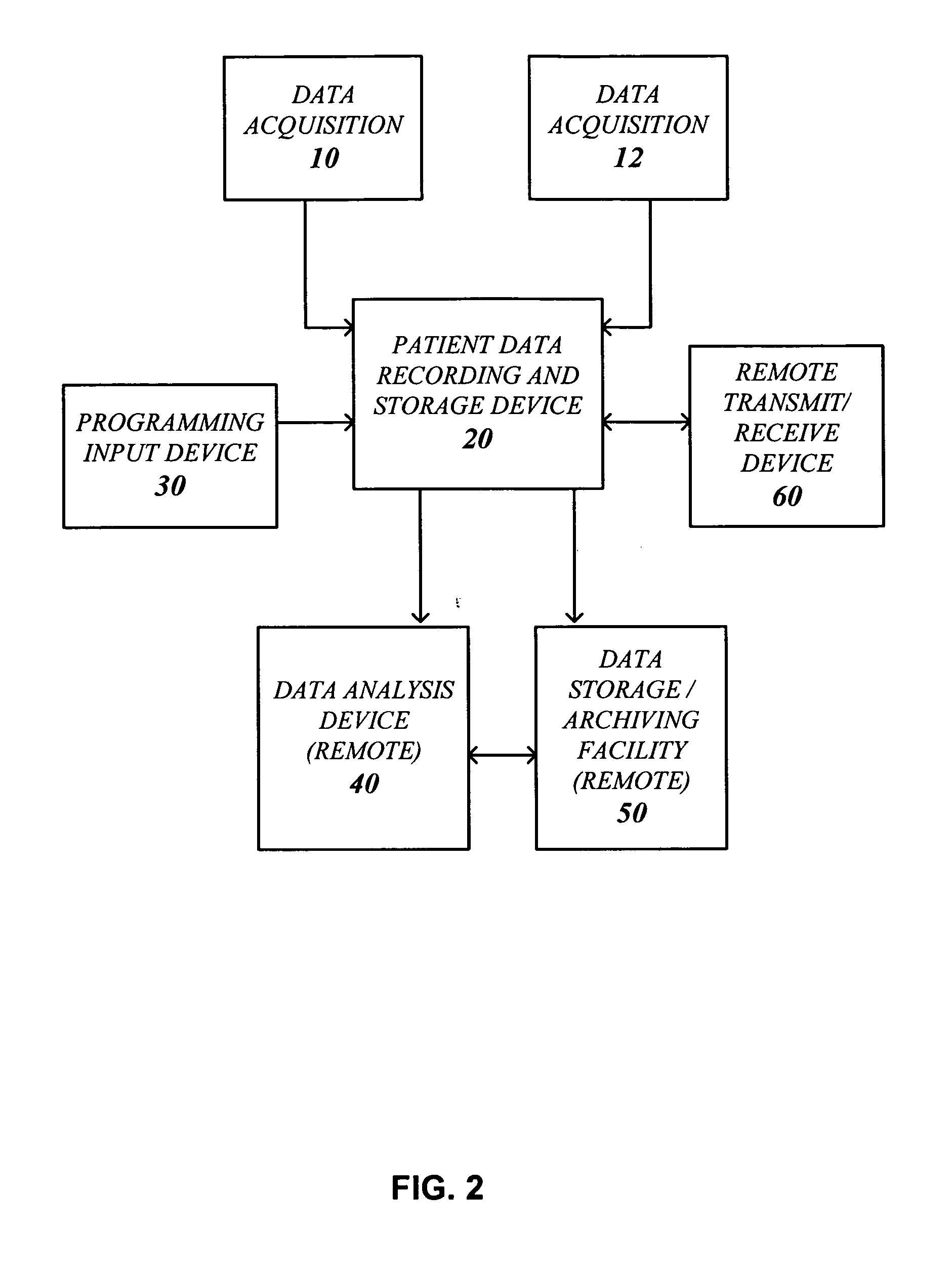
System and process for non-invasive collection and analysis of physiological signals
ActiveUS20050124864A1Simple signal processingCost-effectivePerson identificationCatheterDiseaseSleep Walking
A system and method for detecting, monitoring and analyzing physiological characteristics. Signals from a subject are acquired from a suite of sensors, such as temperature, carbon dioxide, humidity, light, movement, electromagnetic and vibration sensors, in a passive, non-invasive manner. The signals are processed, and physiological characteristics are isolated for analysis. The system and method are to analyze sleep patterns, as well as to prevent bed sores or detect conditions such as illness, restless leg syndrome, periodic leg movement, sleep walking, or sleep apnea. However, numerous other applications of the invention are also disclosed.
Owner:BEST BUY HEALTH INC
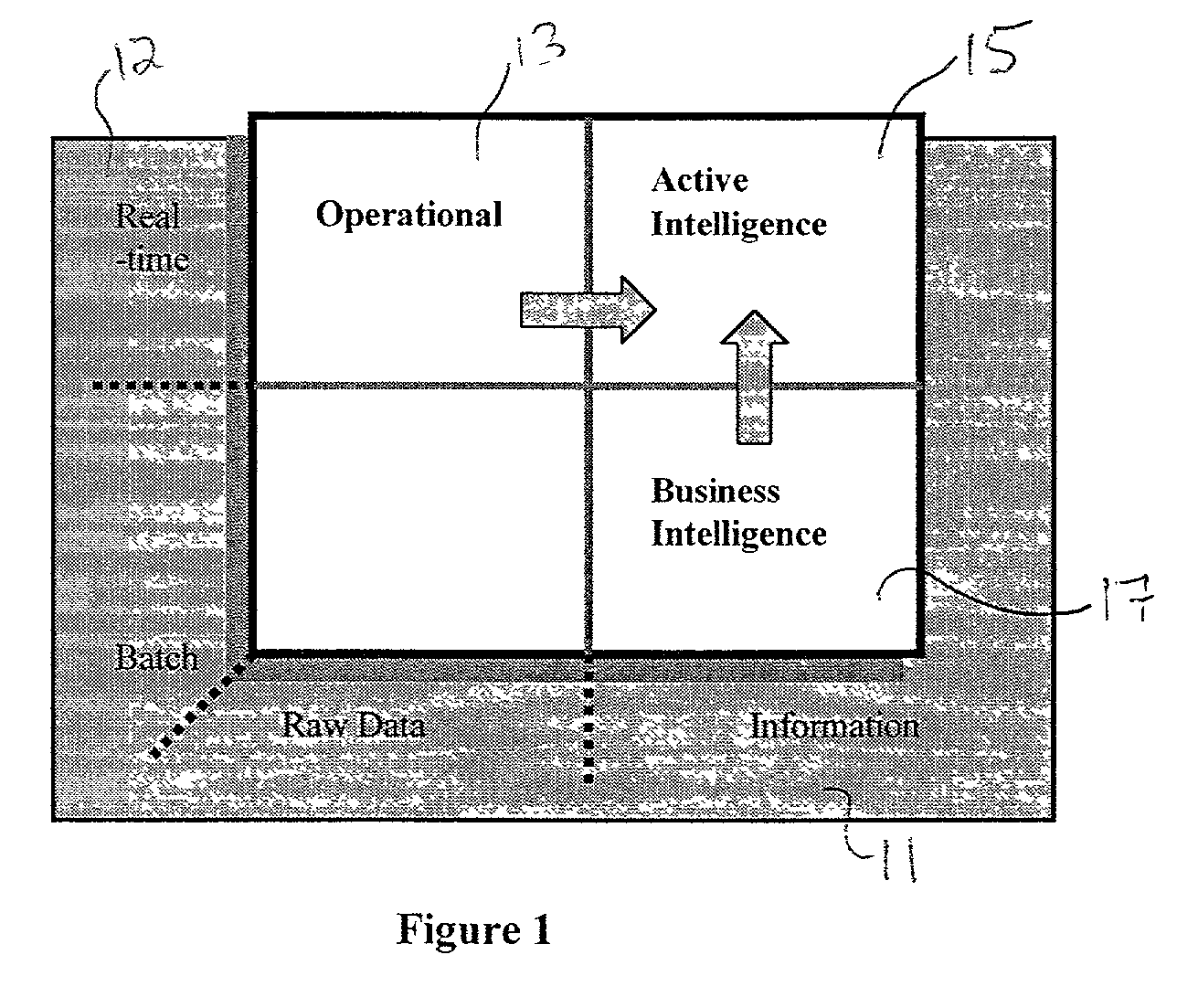
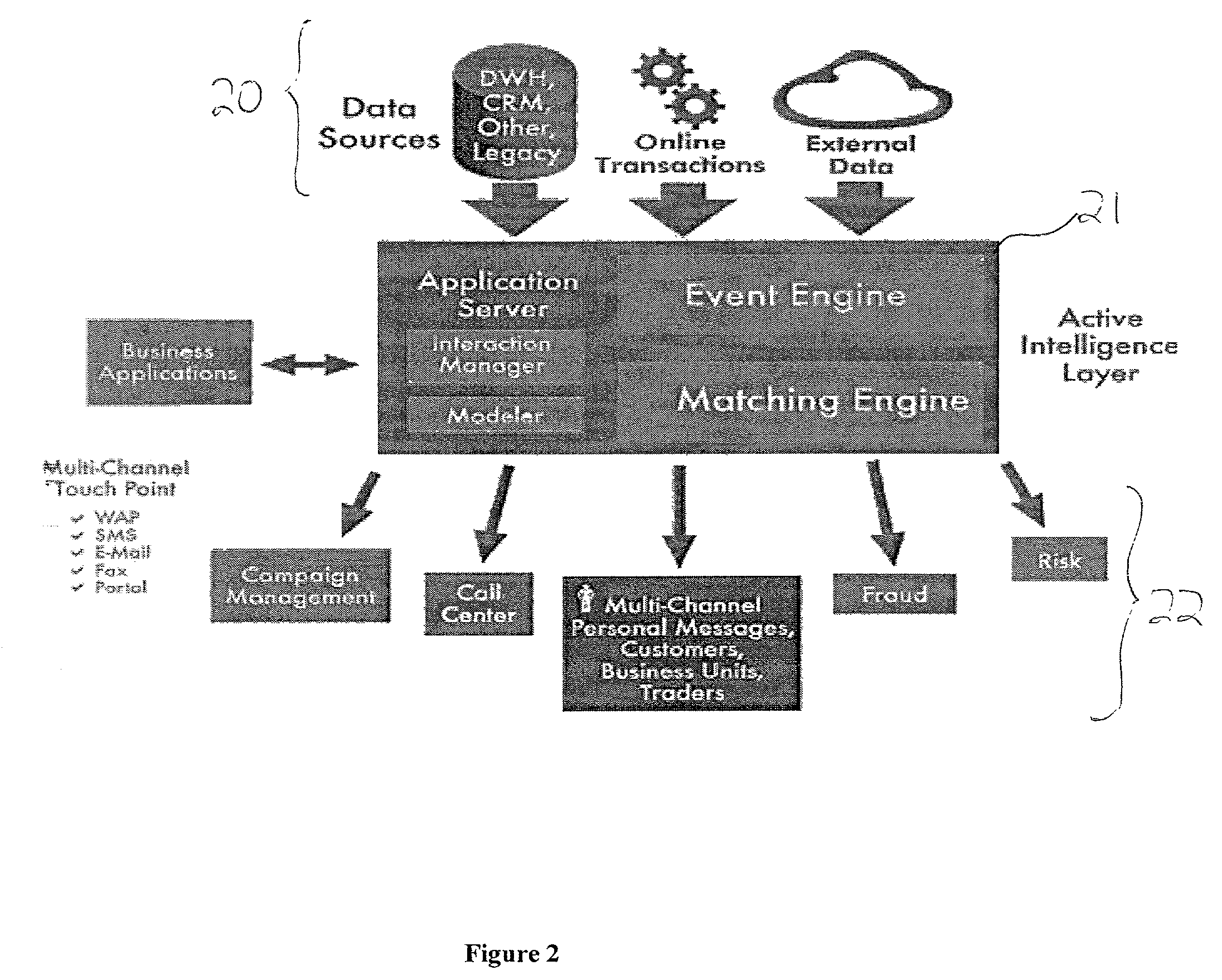
System and method for analyzing and utilizing data, by executing complex analytical models in real time
InactiveUS6965886B2Efficiently distributedIncrease opportunitiesDigital computer detailsOffice automationOperational systemReal-time data
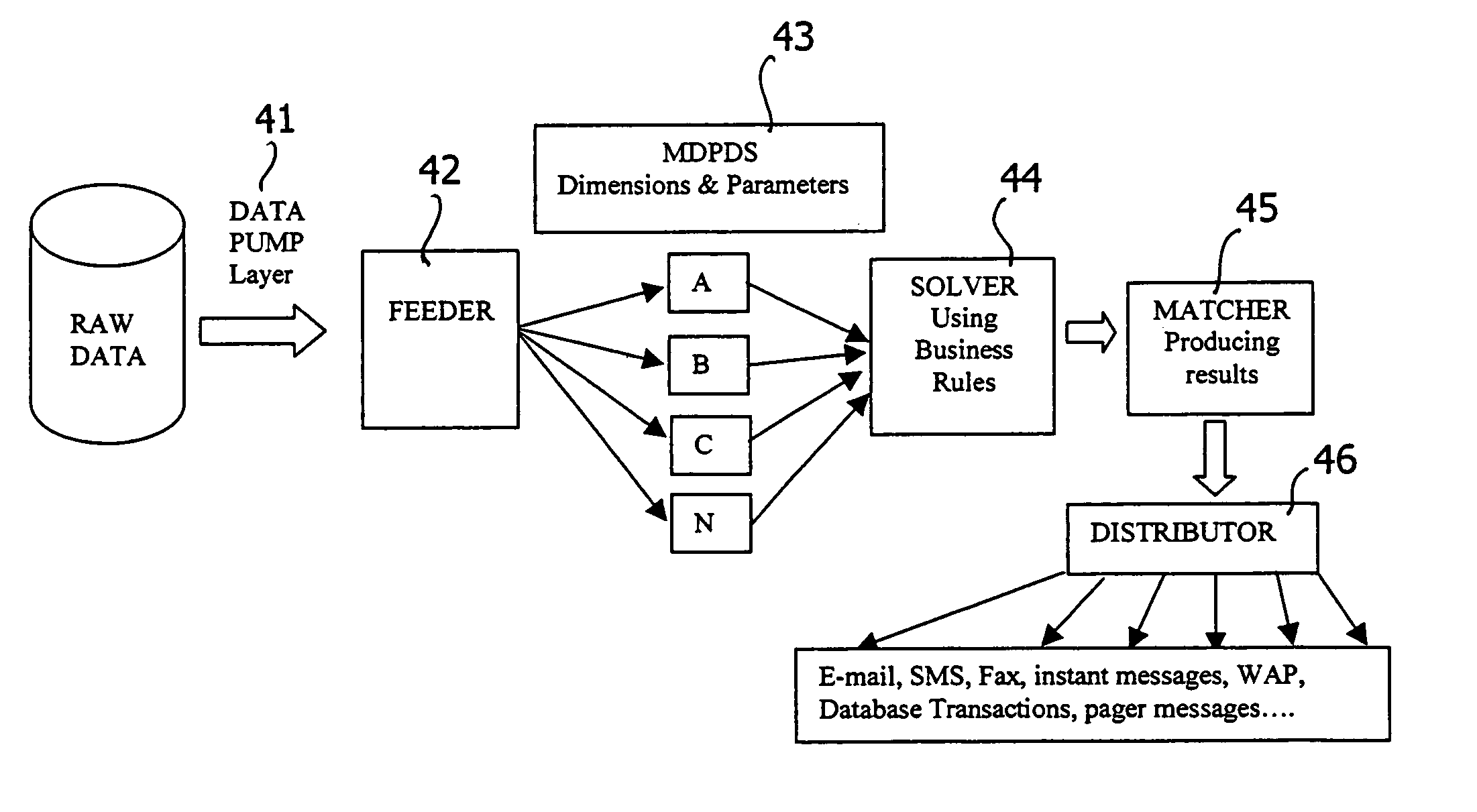
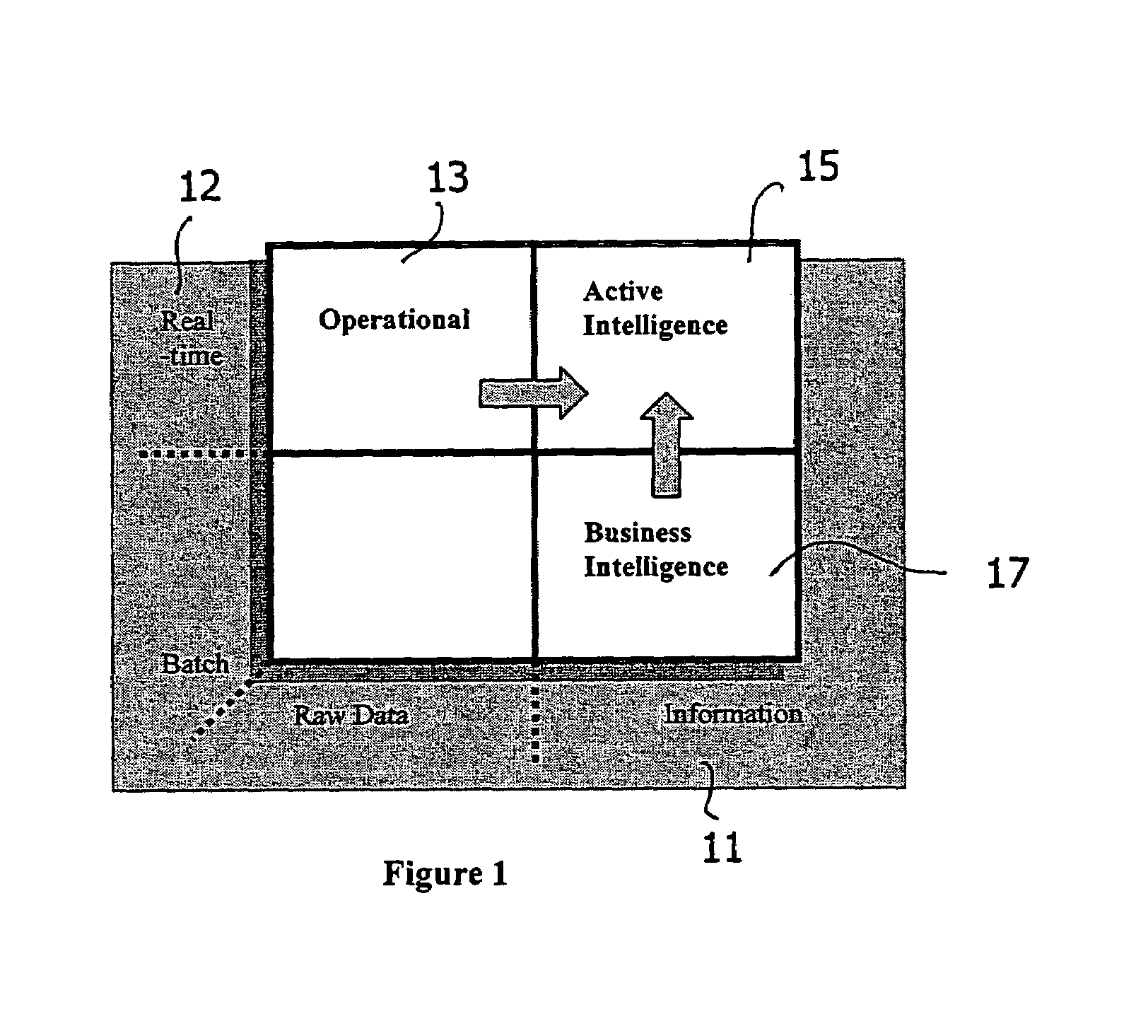
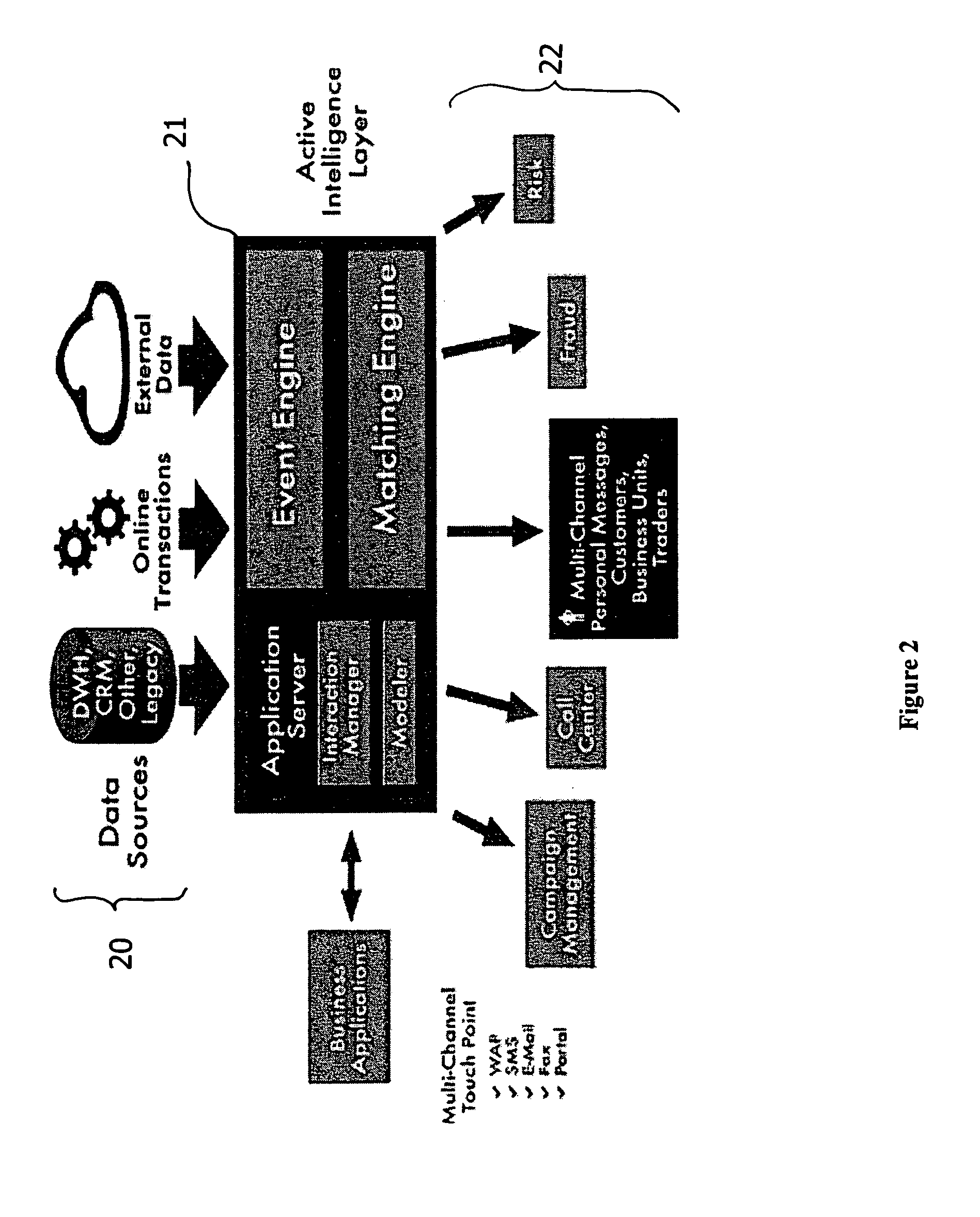
A system and method for collecting, filtering, analyzing, distributing and effectively utilizing highly relevant events (such as key business events) in real time, from huge quantities of data. The present invention analyzes both historic and real-time data stemming from operational activity, by interfacing with internal data repositories (such as Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM)), external data sources (such as suppliers and clients), and real time operational systems in order to create an Active Intelligence Platform. This Active Intelligence Platform is positioned as a layer between the organization's data sources and its applications, monitoring inputs and relaying only the important data items to the relevant individuals and / or systems. This allows individuals and systems to respond immediately and effectively to key events.
Owner:ACTIMIZE
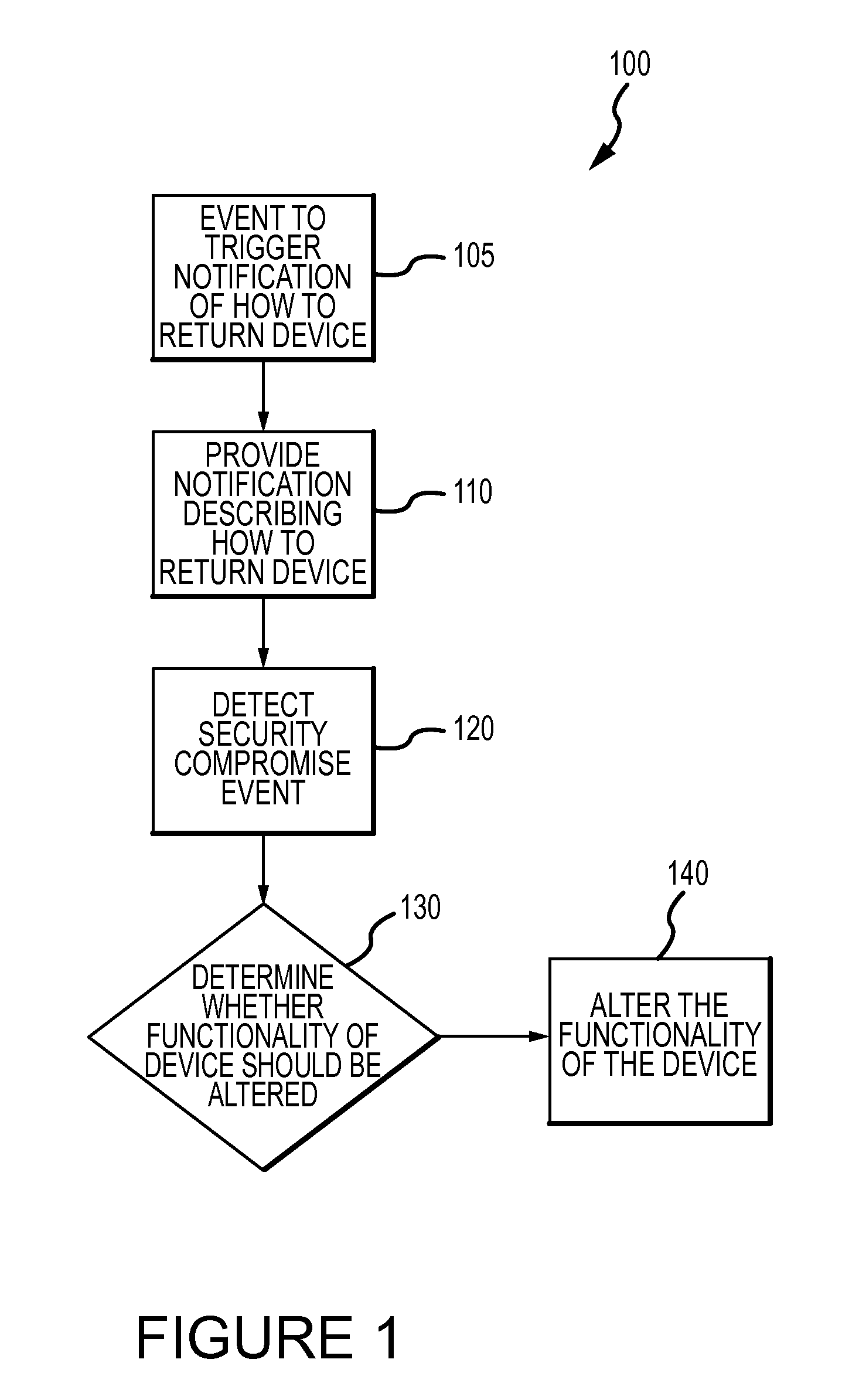
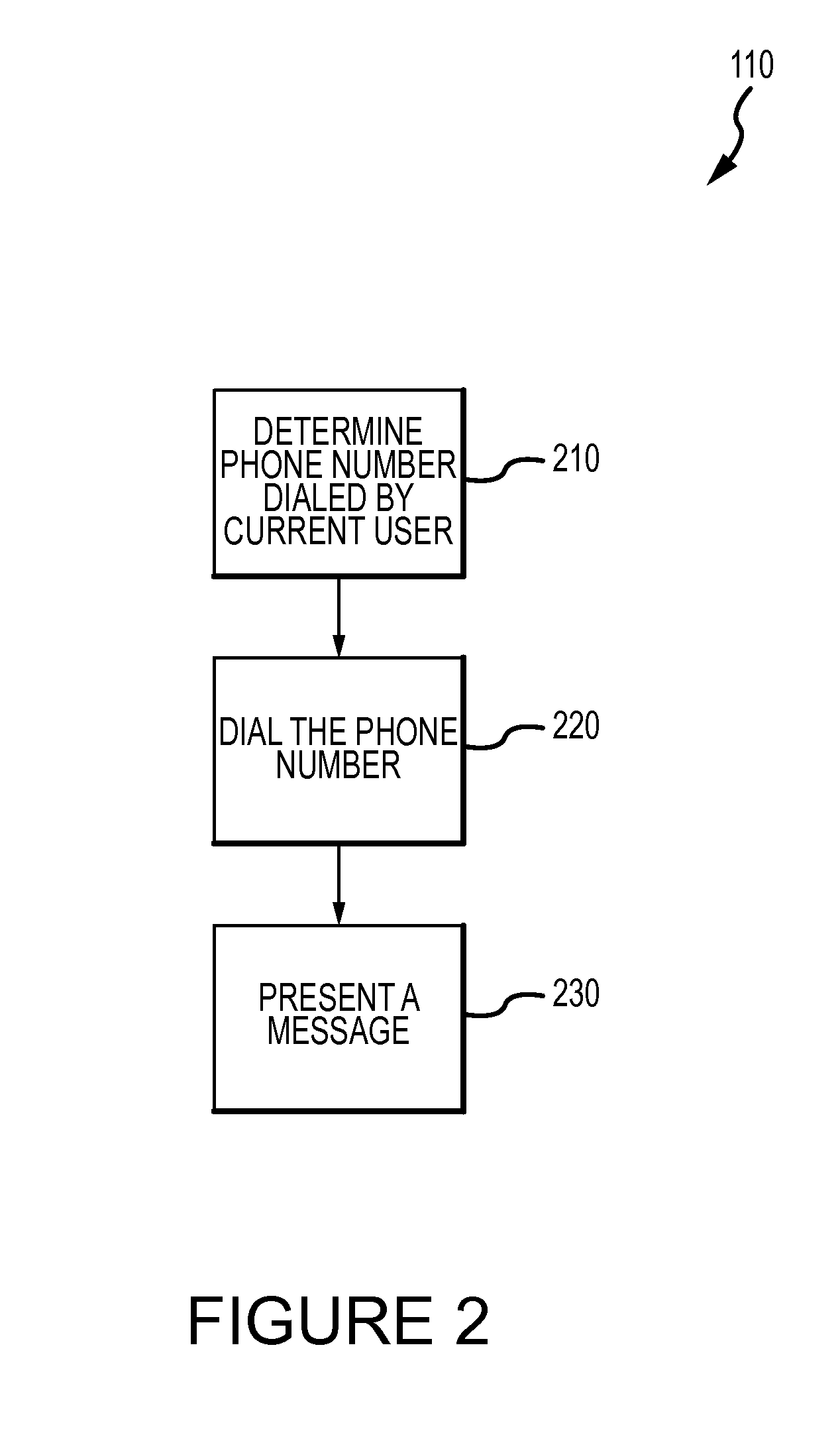
Method for mitigating the unauthorized use of a device
ActiveUS20090253410A1Raise the possibilityIncrease opportunitiesUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDevice MonitorLocal environment
The invention is directed to systems and methods for detecting the loss, theft or unauthorized use of a device and / or altering the functionality of the device in response. In one embodiment, a device monitors its use, its local environment, and / or its operating context to determine that the device is no longer within the control of an authorized user. The device may receive communications or generate an internal signal altering its functionality, such as instructing the device to enter a restricted use mode, a surveillance mode, to provide instructions to return the device and / or to prevent unauthorized use or unauthorized access to data. Additional embodiments also address methods and systems for gathering forensic data regarding an unauthorized user to assist in locating the unauthorized user and / or the device.
Owner:BLANCCO TECH GRP IP OY
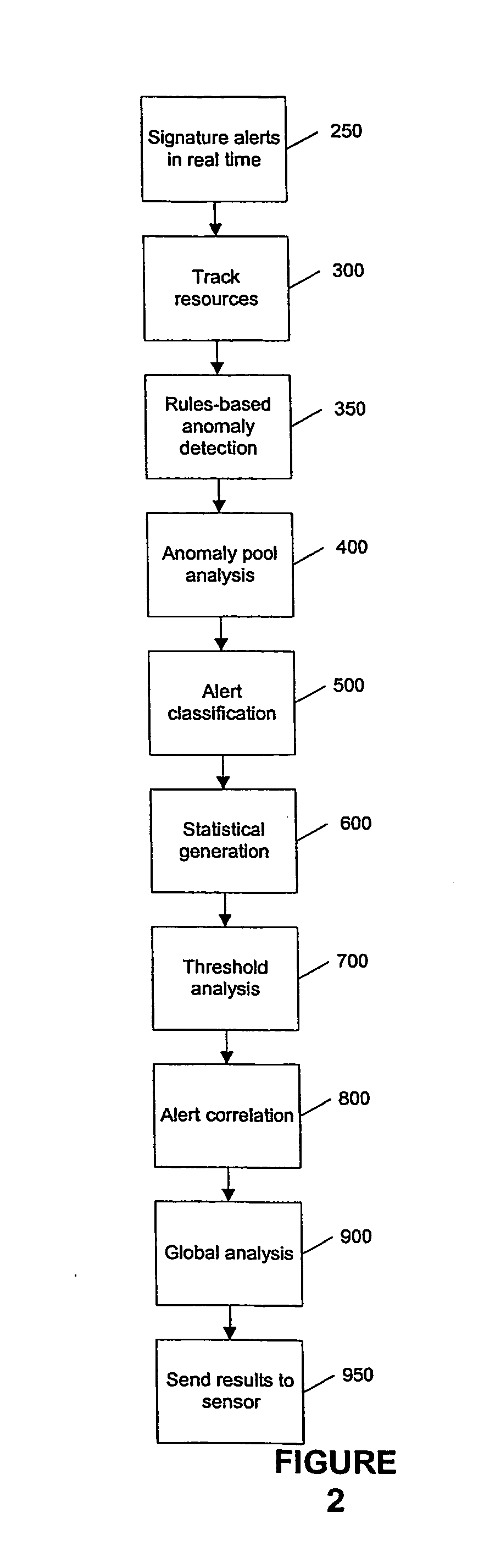
Adaptive behavioral intrusion detection systems and methods
ActiveUS20050044406A1Increase opportunitiesMicrobiological testing/measurementDigital data processing detailsApplication serverInternet traffic
Systems and methods for analyzing historical network traffic and determining which traffic does not belong in a network are disclosed. Intrusion detection is performed over a period of time, looking for behavioral patterns within networks or information systems and generating alerts when these patterns change. The intrusion detection system intelligently forms correlations between disparate sources to find traffic anomalies. Over time, behaviors are predictive, and the intrusion detection system attempts to predict outcomes, becoming proactive instead of just reactive. Intrusions occur throughout whole information systems, including both network infrastructure and application servers. By treating the information system as a whole and performing intrusion detection across it, the chances of detection are increased significantly.
Owner:MASERGY COMMUNICATIONS
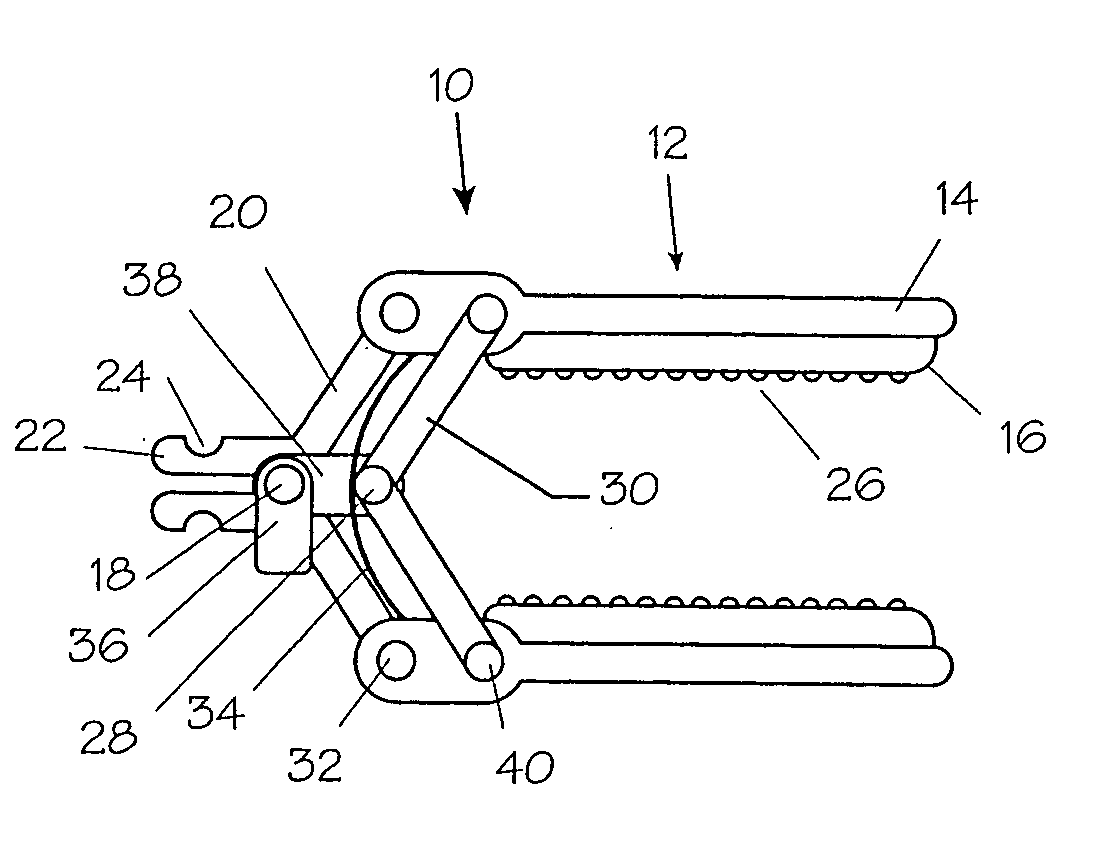
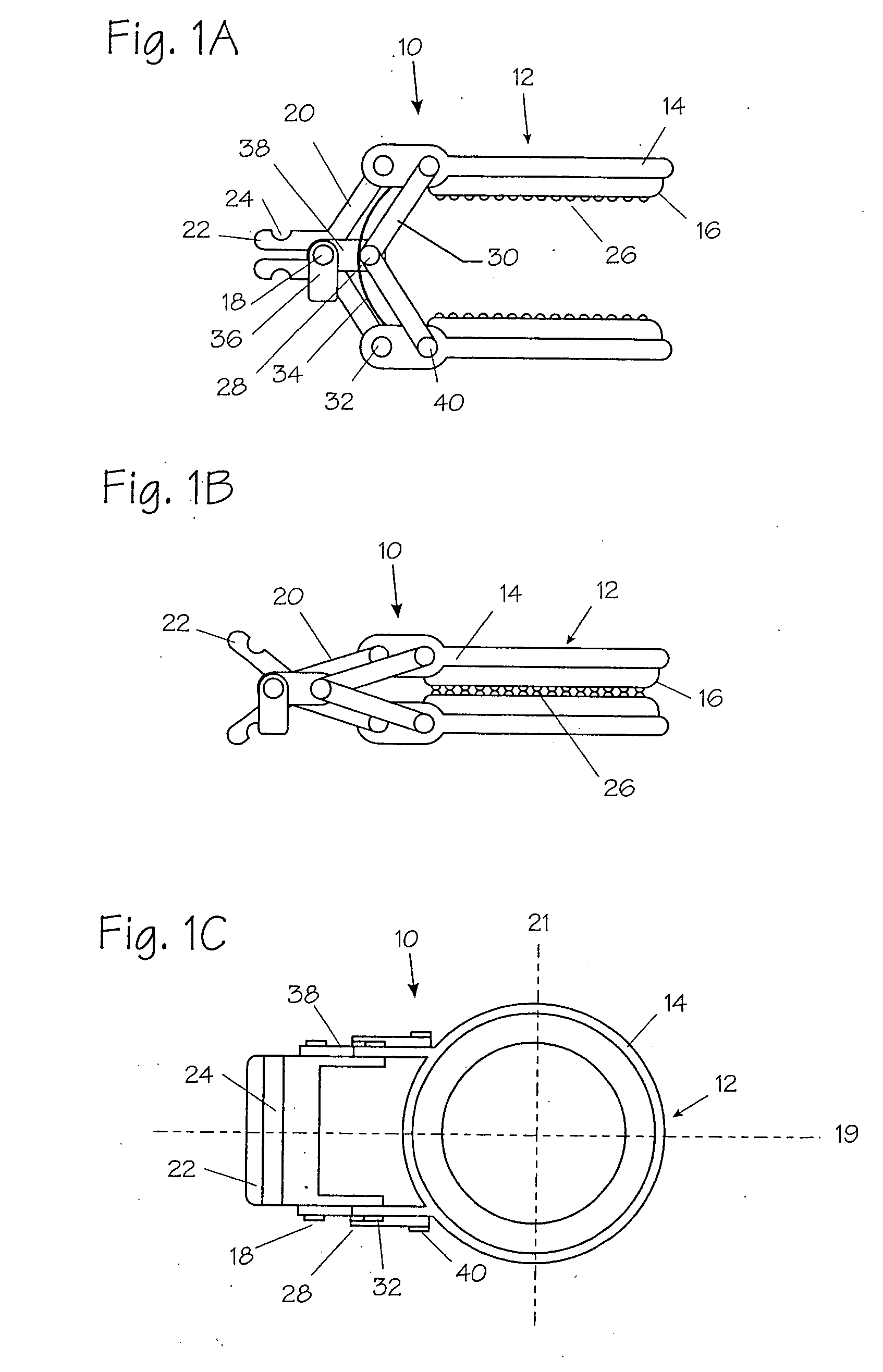
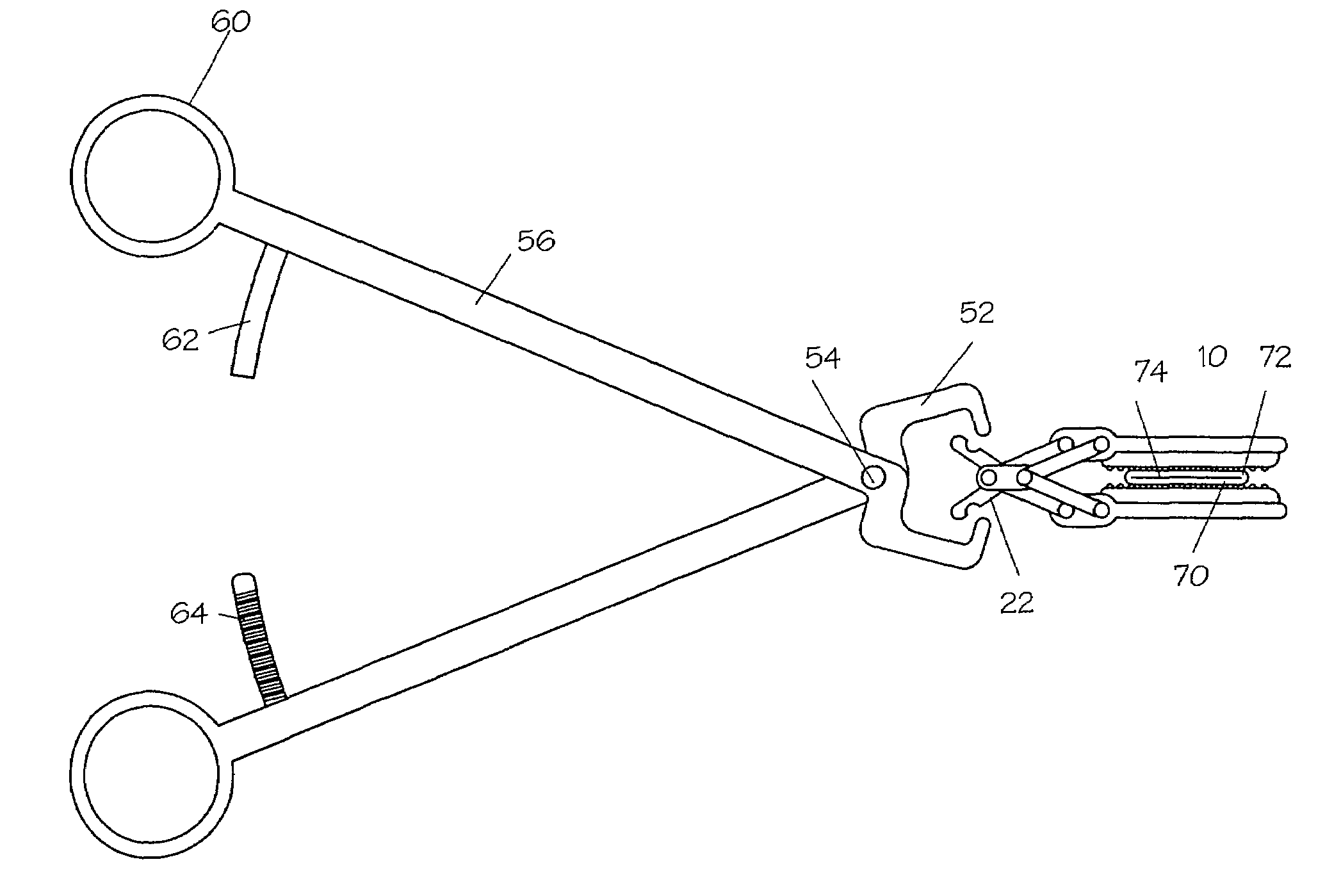
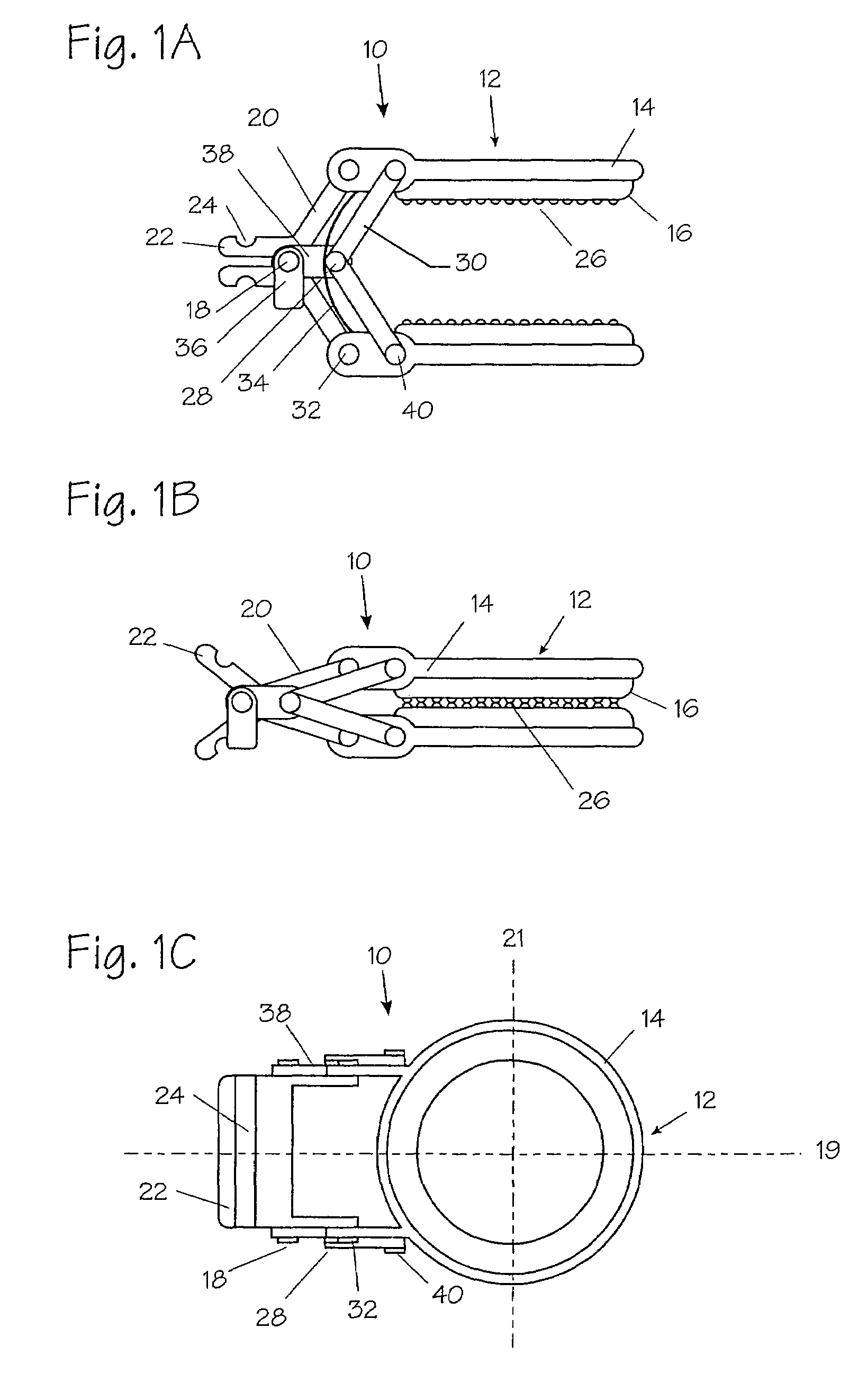
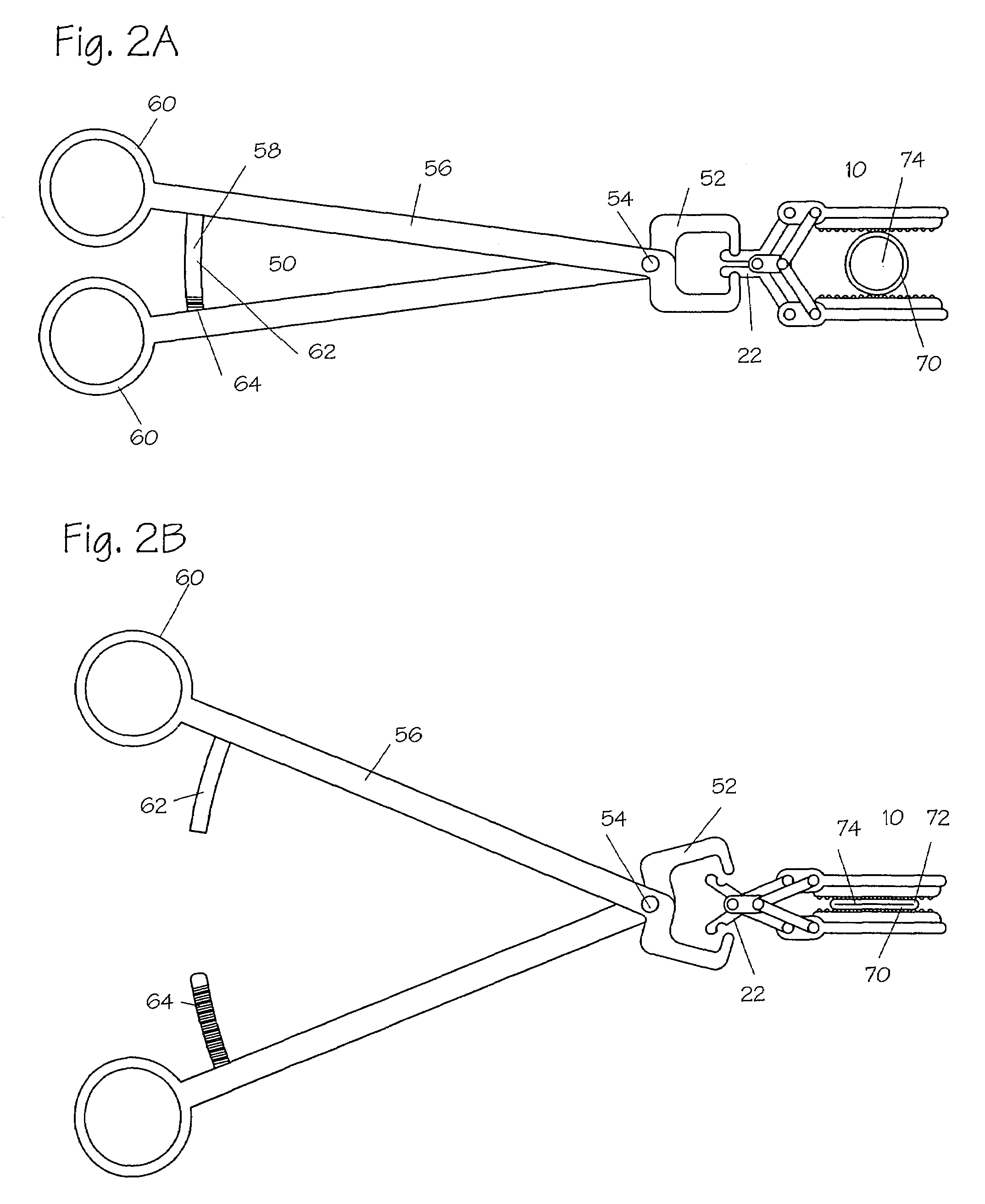
Method and apparatus for vascular and visceral clipping
InactiveUS20050251183A1Convenient treatmentMinimizing chanceSnap fastenersClothes buttonsTrauma surgeryLarge intestine
Devices and methods for achieving hemostasis and leakage control in hollow body vessels such as the small and large intestines, arteries and veins as well as ducts leading to the gall bladder and other organs. The devices and methods disclosed herein are especially useful in the emergency, trauma surgery or military setting, and most especially during damage control procedures. In such cases, the patient may have received trauma to the abdomen, extremities, neck or thoracic region. The devices utilize removable or permanently implanted, broad, soft, parallel jaw clips with minimal projections to maintain vessel contents without damage to the tissue comprising the vessel. These clips are applied using either standard instruments or custom devices that are subsequently removed leaving the clips implanted, on a temporary or permanent basis, to provide for hemostasis or leakage prevention, or both. These clips overcome the limitations of clips and sutures that are currently used for the same purposes. The clips come in a variety of shapes and sizes. The clips may be placed and removed by open surgery or laparoscopic access.
Owner:DAMAGE CONTROL SURGICAL TECH
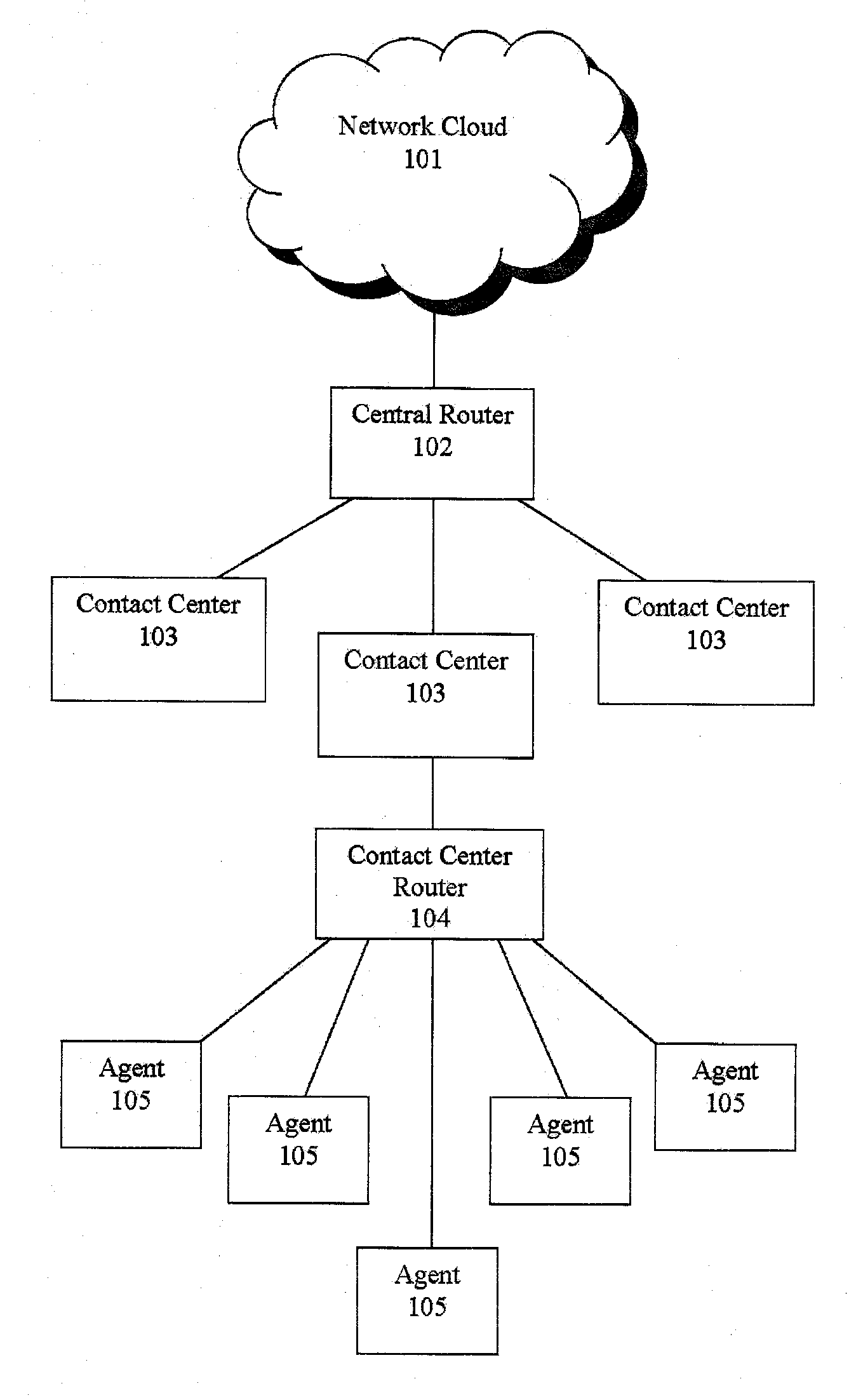
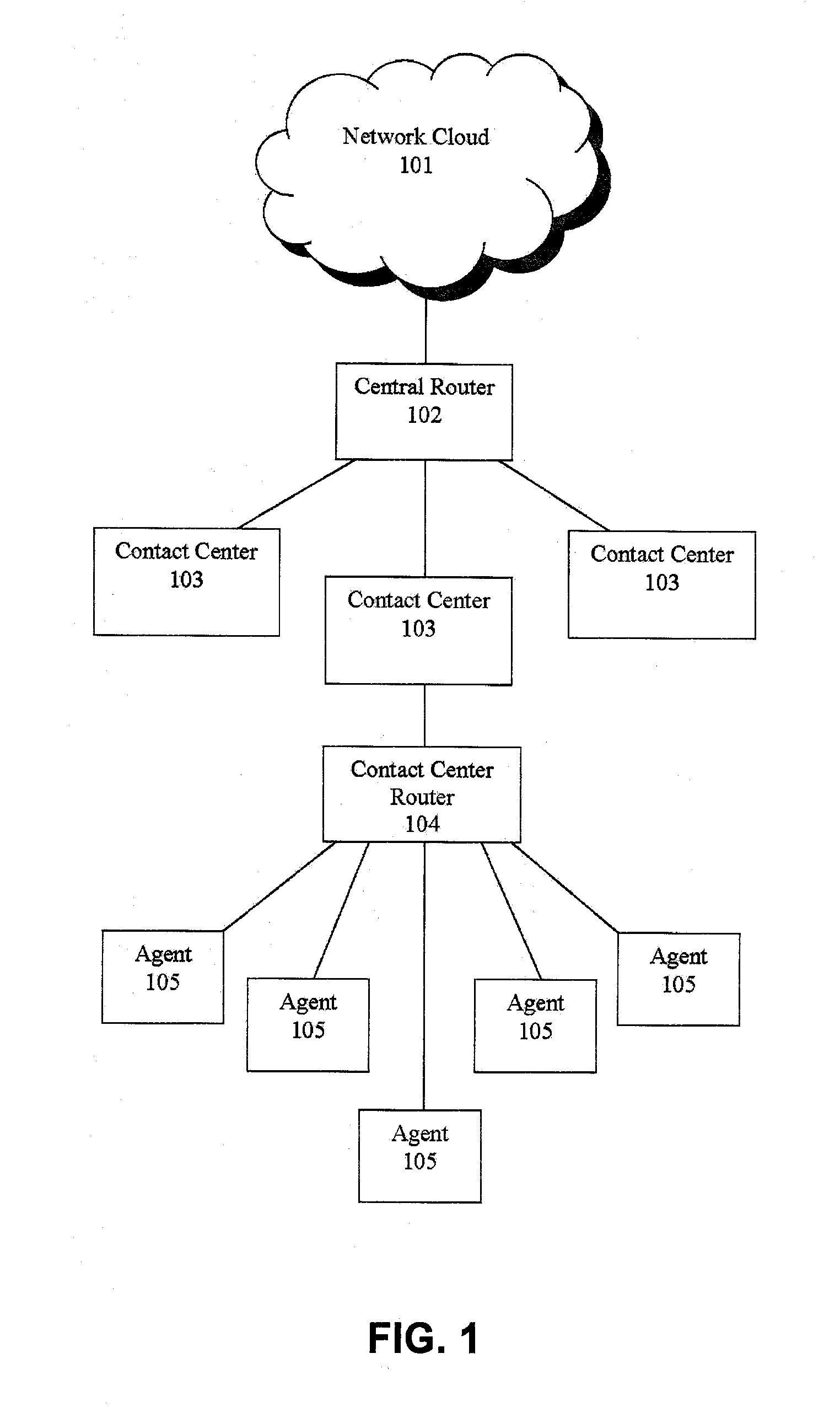
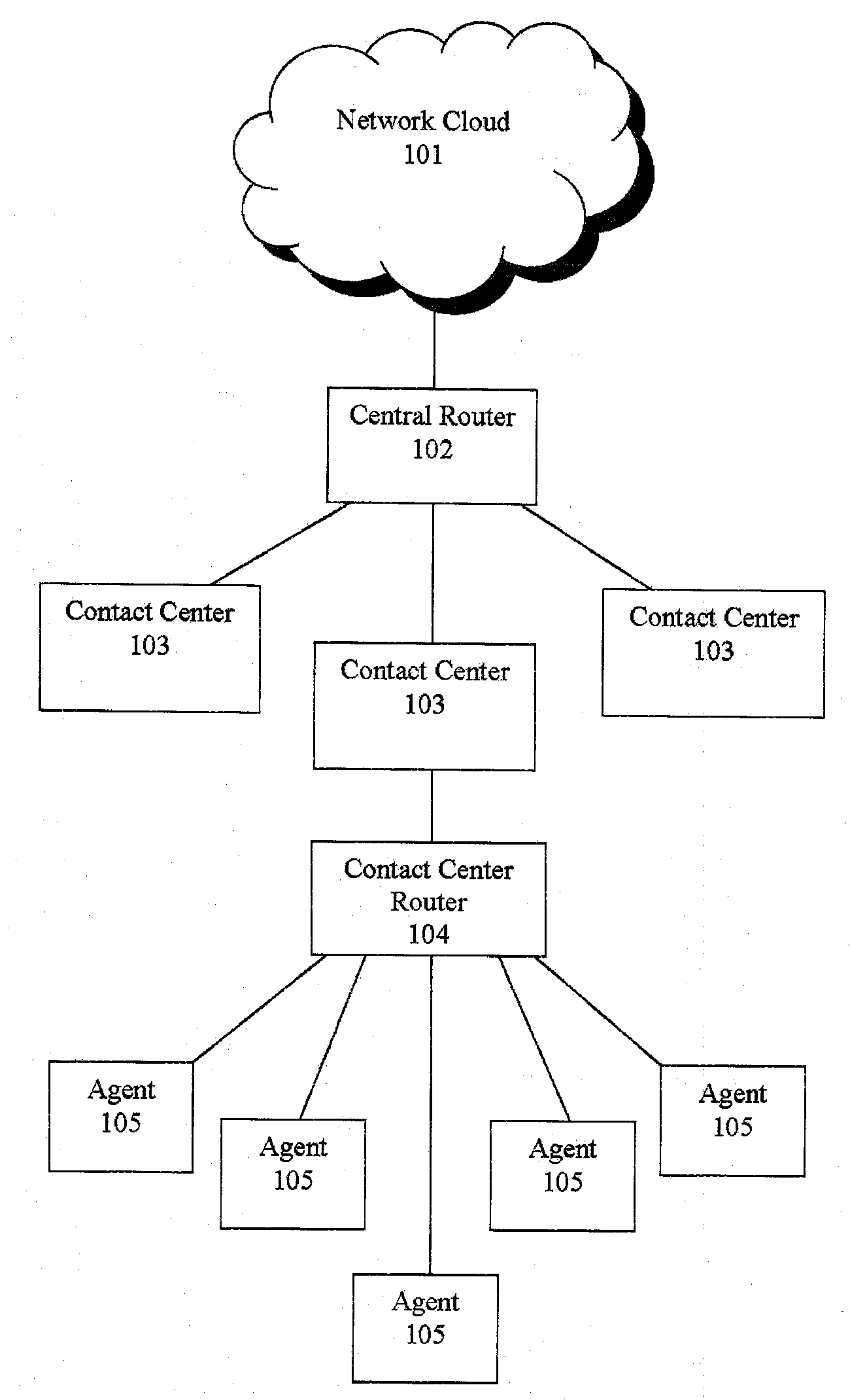
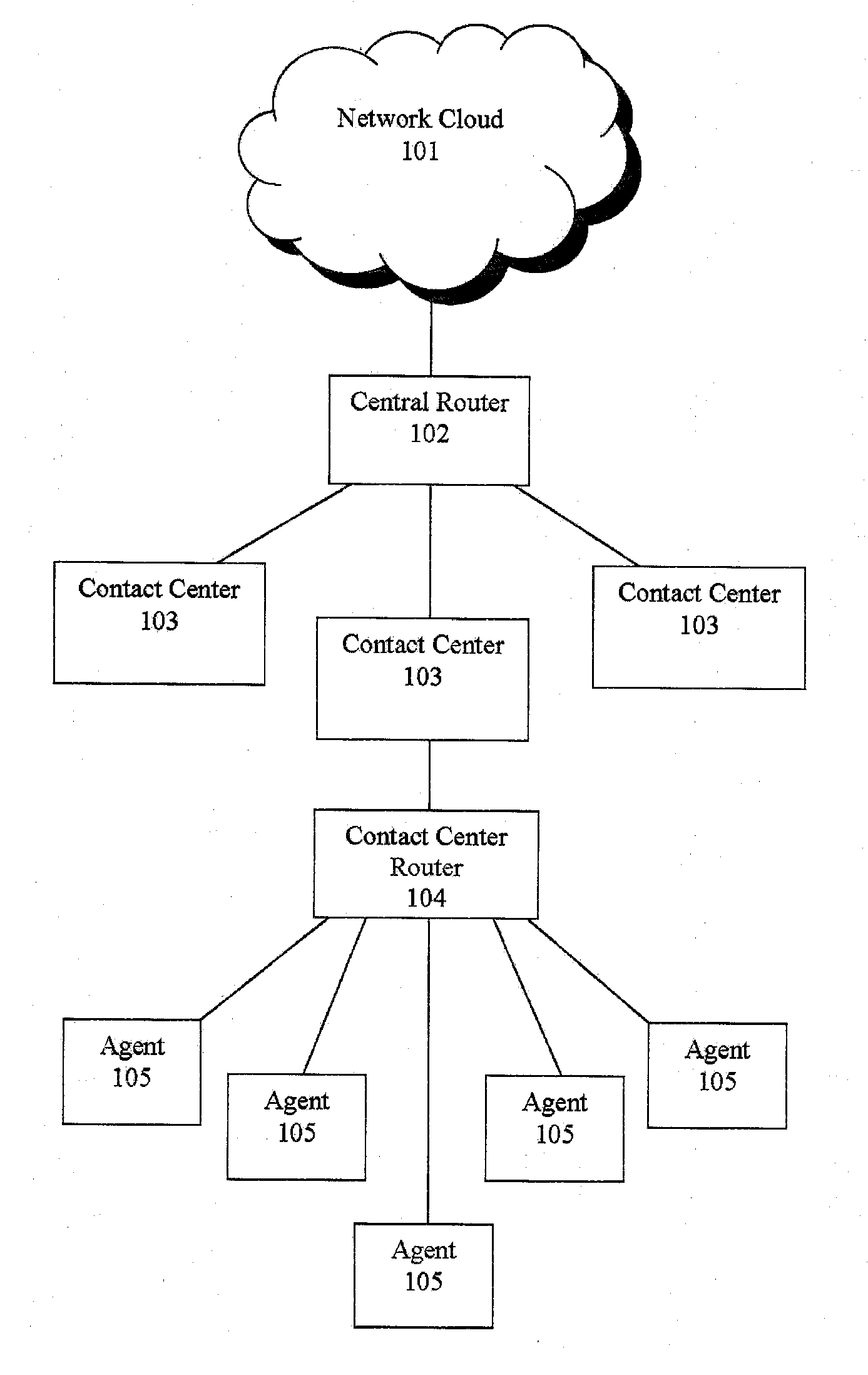
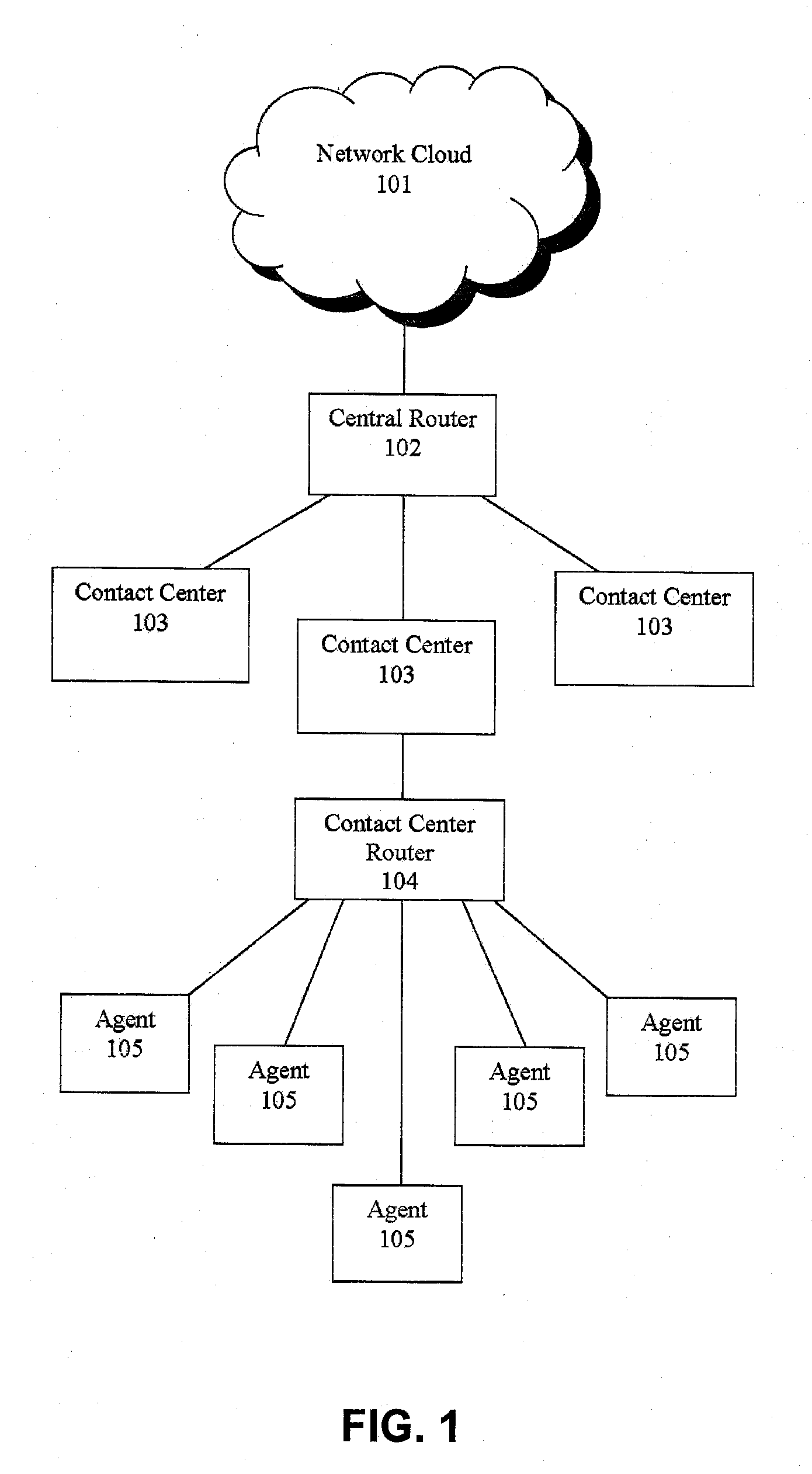
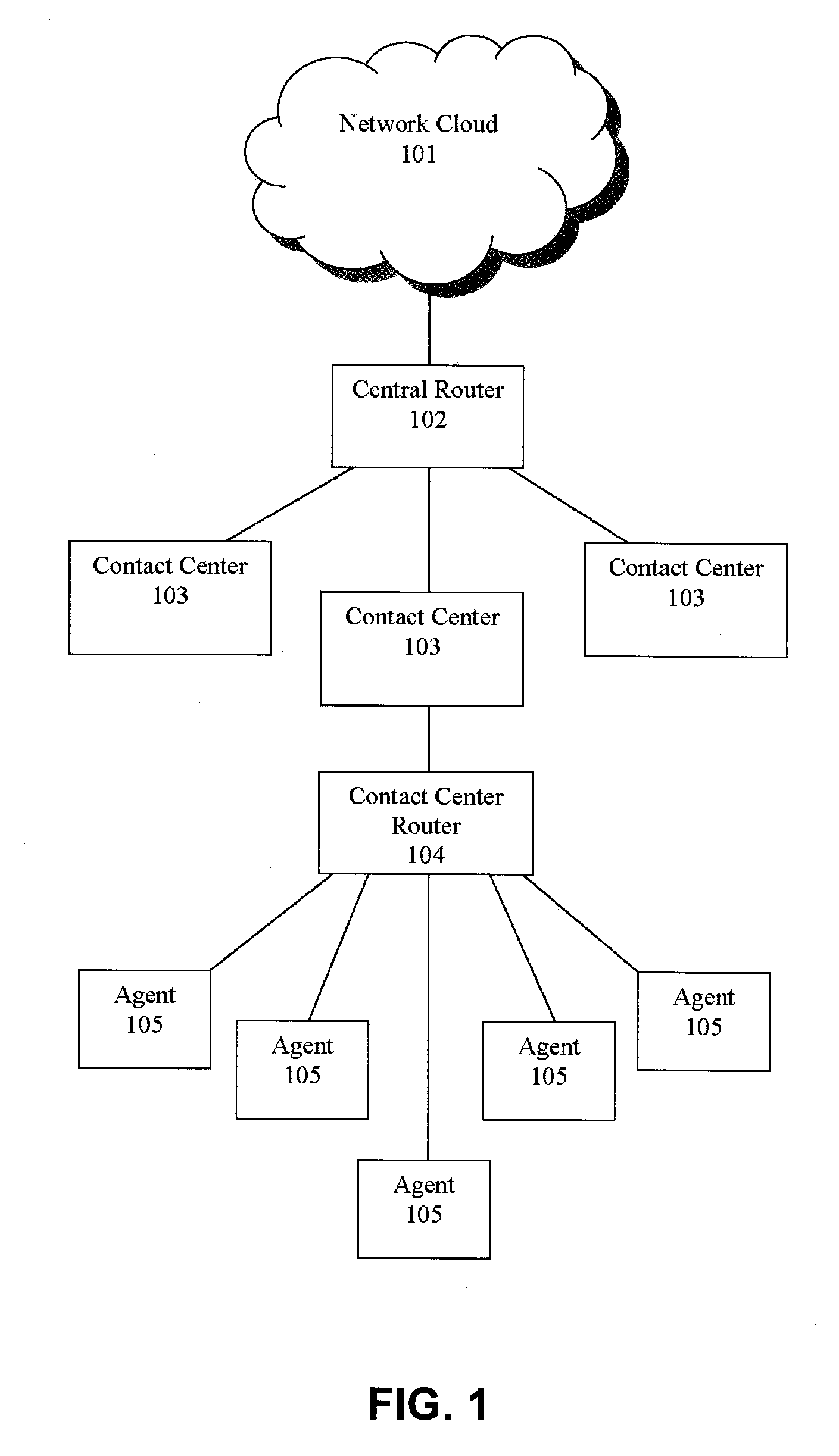
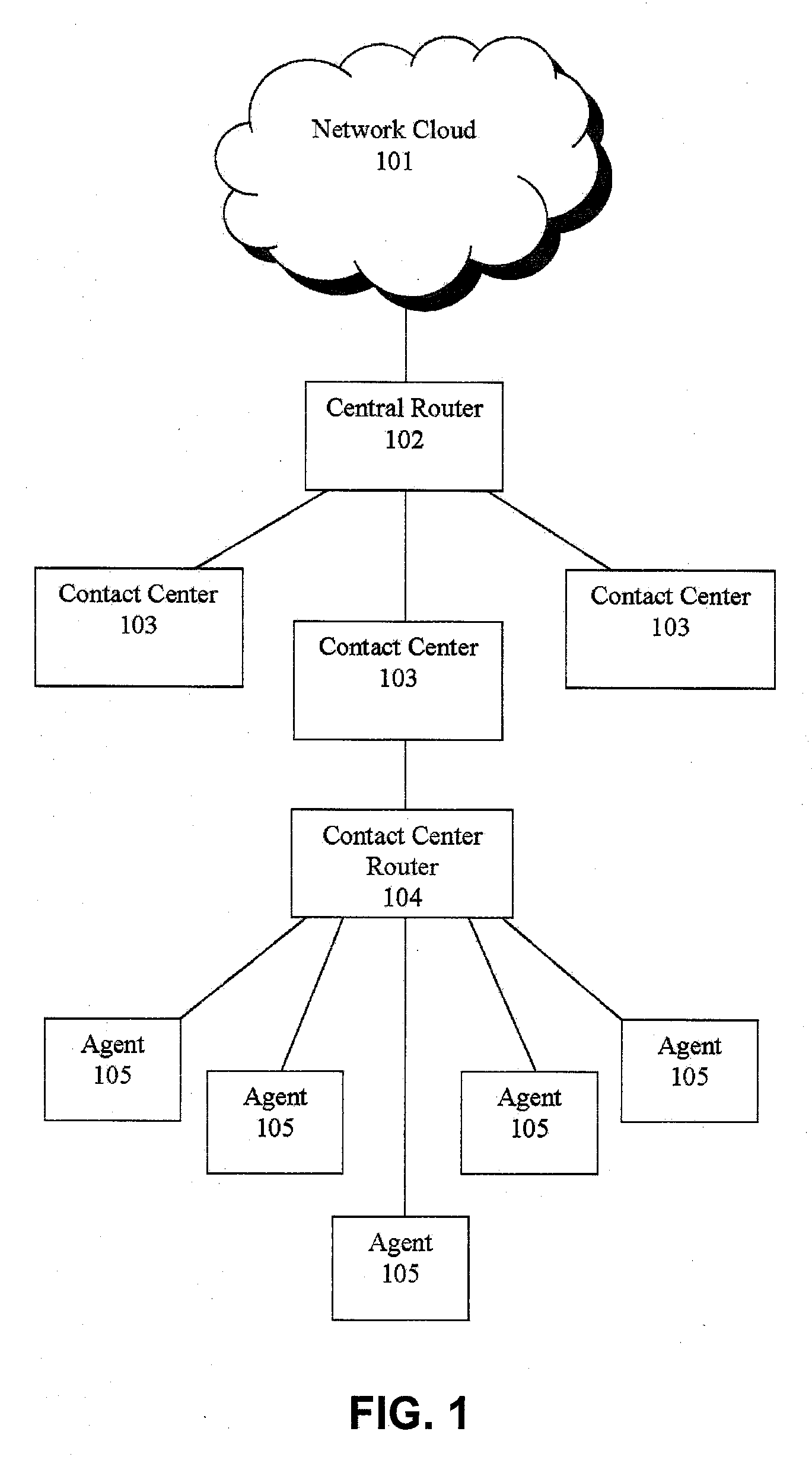
Jumping callers held in queue for a call center routing system
ActiveUS20090190749A1Extend connection timeQuick serviceManual exchangesAutomatic exchangesPattern matchingDemographic data
Methods and systems are provided for routing callers to agents in a call-center routing environment. An exemplary method includes identifying caller data for a caller in a queue of callers, and jumping or moving the caller to a different position within the queue based on the caller data. The caller data may include one or both of demographic data and psychographic data. The caller can be jumped forward or backward in the queue relative to at least one other caller. Jumping the caller may further be based on comparing the caller data with agent data via a pattern matching algorithm and / or computer model for predicting a caller-agent pair outcome. Additionally, if a caller is held beyond a hold threshold (e.g., a time, “cost” function, or the like) the caller may be routed to the next available agent.
Owner:AFINITI LTD
Shadow queue for callers in a performance/pattern matching based call routing system
ActiveUS20100054453A1Increase opportunitiesShorten the construction periodManual exchangesAutomatic exchangesPattern matchingBase calling
Methods and systems are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. A method for routing callers includes routing a caller, if agents are available, to an agent based on a pattern matching algorithm (which may include performance based matching, pattern matching based on agent and caller data, computer models for predicting outcomes of agent-caller pairs, and so on). Further, if no agents are available for the incoming caller, the method includes holding the caller in a shadow queue, e.g., a set of callers. When an agent becomes available the method includes scanning all of the callers in the shadow queue and matching the agent to the best matching caller within shadow queue.
Owner:AFINITI LTD +1
Pooling callers for a call center routing system
InactiveUS20090190745A1Extend connection timeQuick serviceManual exchangesAutomatic exchangesPattern matchingDistributed computing
Methods and systems are provided for routing callers to agents in a call-center routing environment. An exemplary method includes routing a caller from a pool of callers based on at least one caller data associated with the caller, where a pool of callers includes, e.g., a set of callers that are not chronologically ordered and routed based on a chronological order or hold time of the callers. The caller may be routed from the pool of callers to an agent, placed in another pool of callers, or placed in a queue of callers. The caller data may include demographic or psychographic data. The caller may be routed from the pool of callers based on comparing the caller data with agent data associated with an agent via a pattern matching algorithm and / or computer model for predicting a caller-agent pair outcome. Additionally, if a caller is held beyond a hold threshold (e.g., a time, “cost” function, or the like) the caller may be routed to the next available agent.
Owner:AFINITI LTD
Routing callers out of queue order for a call center routing system
InactiveUS20090190750A1Extend connection timeAdjustable weightManual exchangesAutomatic exchangesPattern matchingDistributed computing
Methods and systems are provided for routing callers to agents in a call-center routing environment. An exemplary method includes identifying caller data for a caller of a plurality of callers in a queue, and routing the caller from the queue out of queue order. For example, a caller that is not at the top of the queue may be routed from the queue based on the identified caller data, out of order with respect to the queue order. The caller may be routed to another queue of callers, a pool of callers, or an agent based on the identified caller data, where the caller data may include one or both of demographic and psychographic data. The caller may be routed from the queue based on comparing the caller data with agent data associated with an agent via a pattern matching algorithm and / or computer model for predicting a caller-agent pair outcome. Additionally, if a caller is held beyond a hold threshold (e.g., a time, “cost” function, or the like) the caller may be routed to the next available agent.
Owner:AFINITI LTD
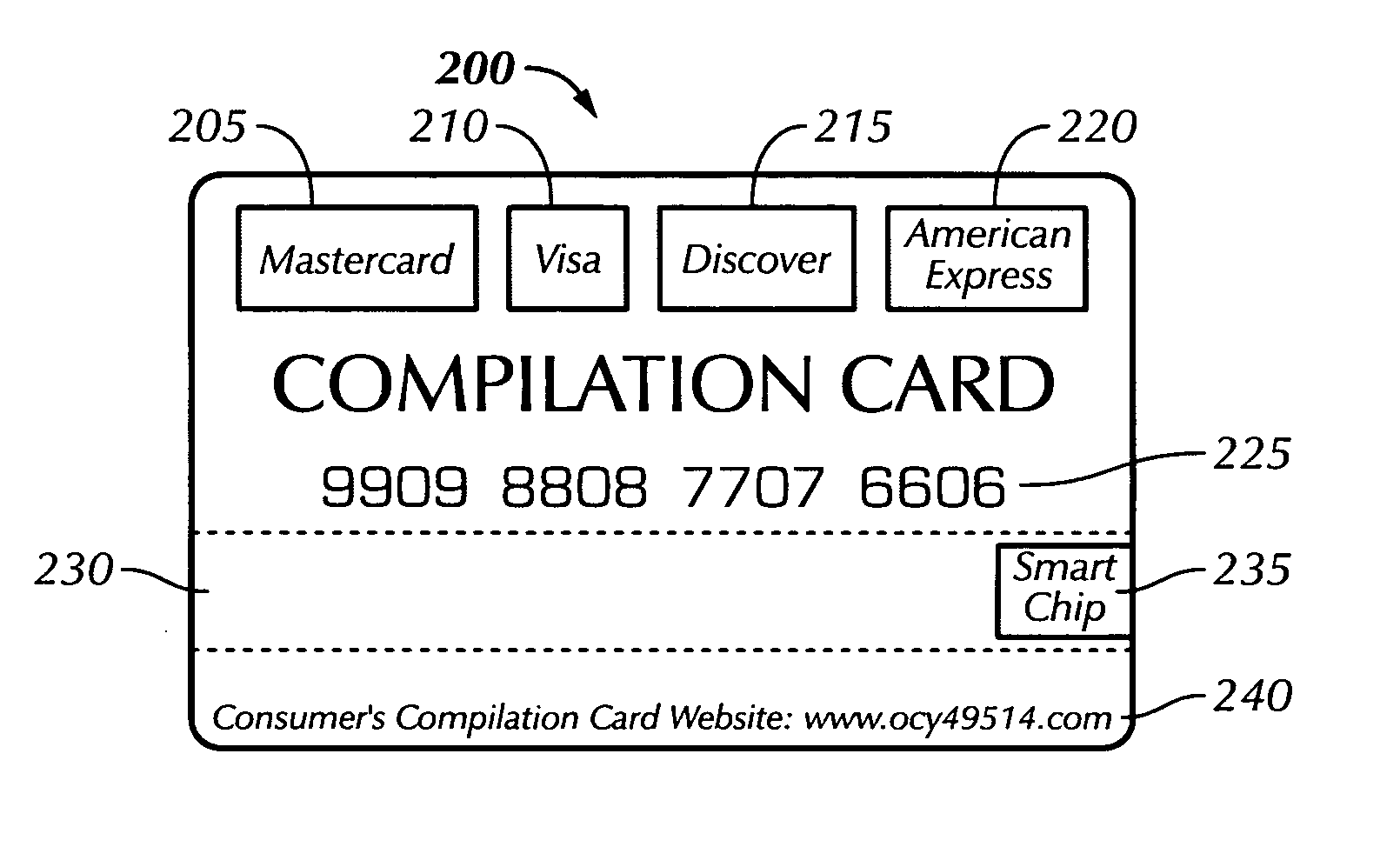
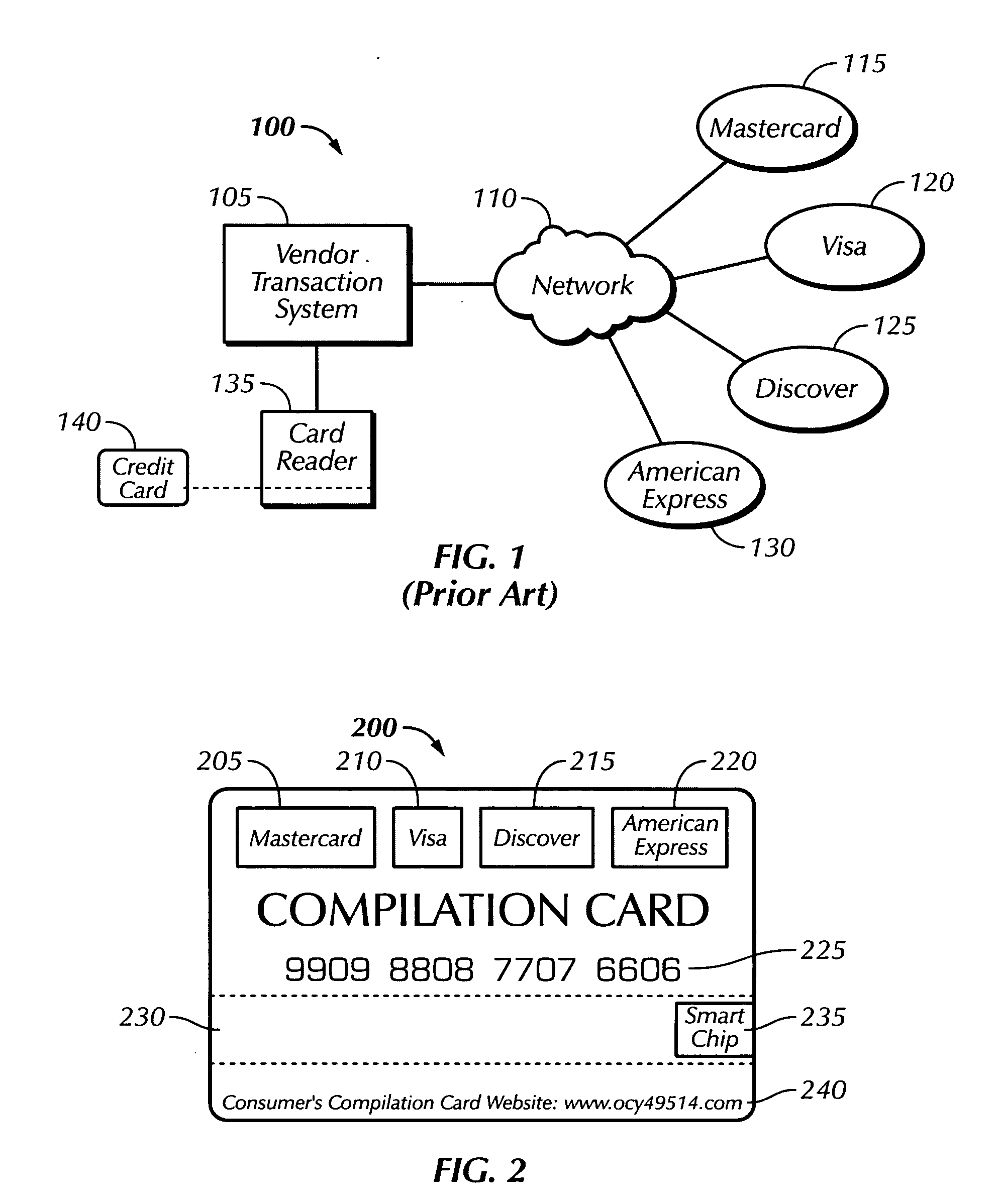
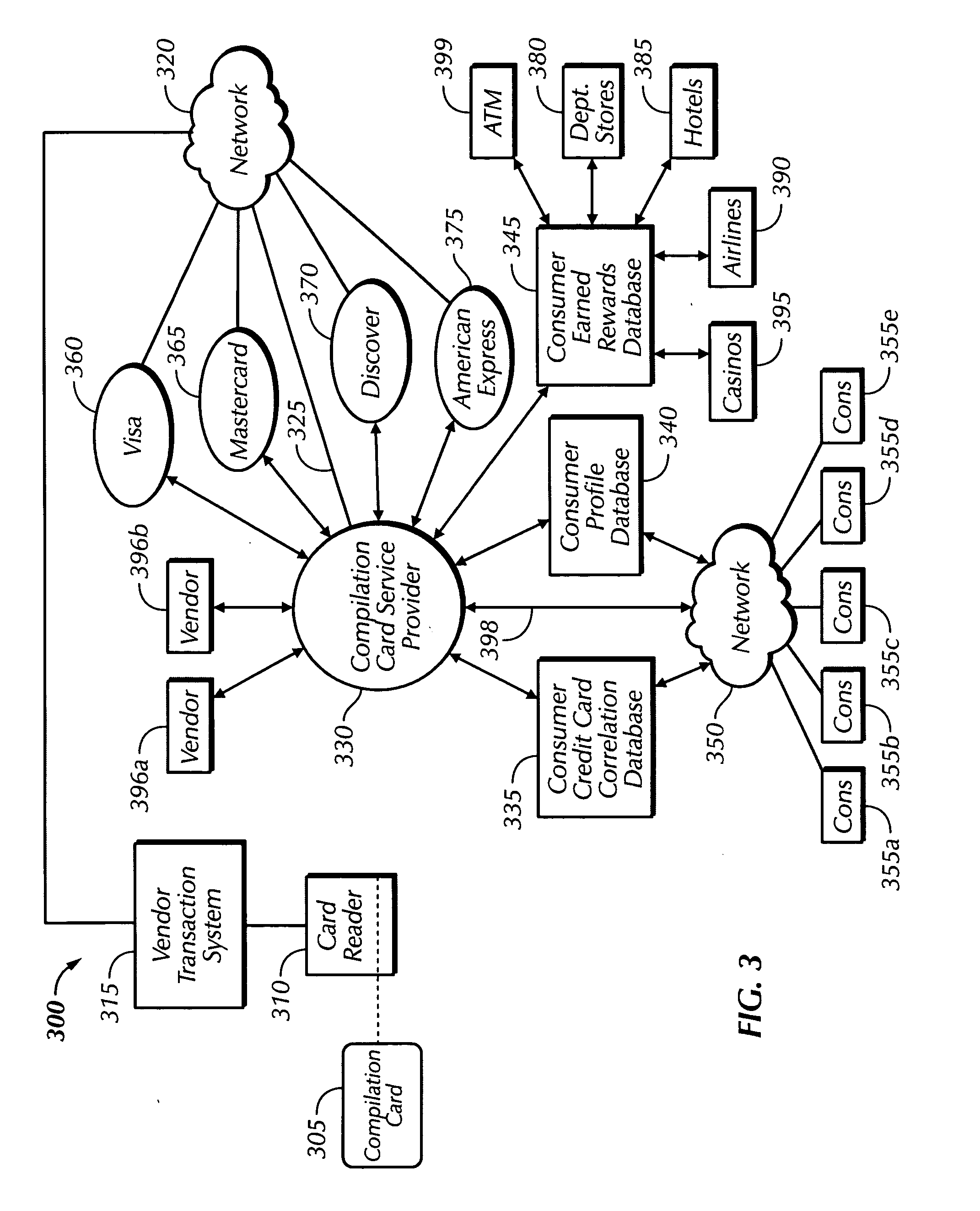
Method and apparatus for monetizing personal consumer profiles by aggregating a plurality of consumer credit card accounts into one card
A computer-implemented method of using one of a plurality of existing credit card accounts belonging to a consumer includes providing account data to a single service provider for a plurality of existing credit card accounts belonging to the consumer and providing the consumer with a compilation credit card associated with the plurality of existing credit card accounts of the consumer. the method also includes storing predefined preferences of the consumer regarding credit card selectivity, the consumer performing a credit card transaction and selecting one existing credit card account among the plurality of existing credit card accounts to which to charge the credit card transaction based on the stored predefined preferences of the consumer.
Owner:MENDELOVICH ISAAC F
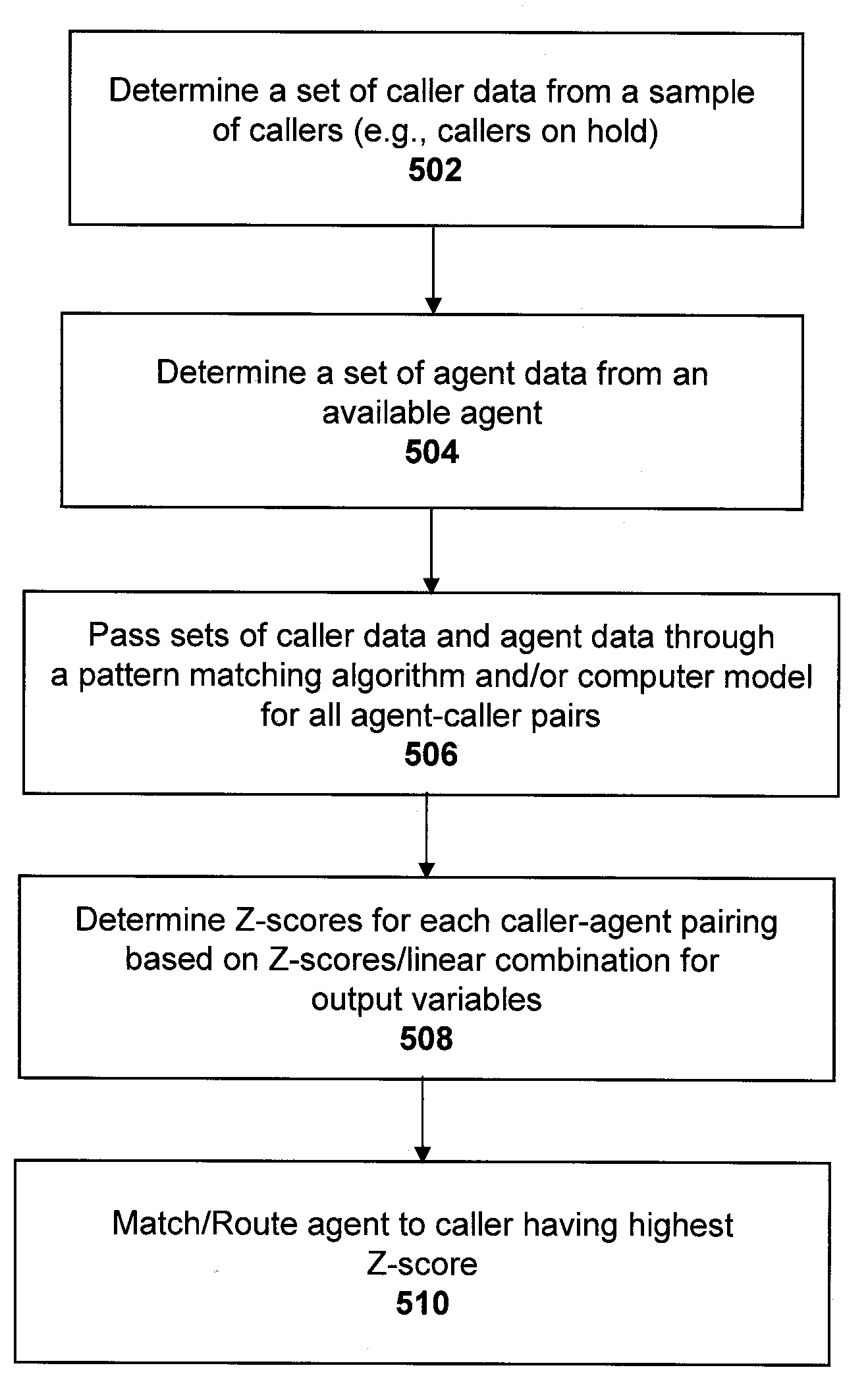
Call routing methods and systems based on multiple variable standardized scoring
ActiveUS20090190747A1Increase incomeLow costManual exchangesAutomatic exchangesPattern matchingContact center
Systems and methods are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. An exemplary method includes combining multiple output variables of a pattern matching algorithm (for matching callers and agents) into a single metric for use in the routing system. The pattern matching algorithm may include a neural network architecture, where the exemplary method combines output variables from multiple neural networks. The method may include determining a Z-score of the variable outputs and determining a linear combination of the determined Z-scores for a desired output. Callers may be routed to agents via the pattern matching algorithm to maximize the output value or score of the linear combination. The output variables may include revenue generation, cost, customer satisfaction performance, first call resolution, cancellation, or other variable outputs from the pattern matching algorithm of the system.
Owner:AFINITI LTD
Methods for matching, selecting, and/or classifying based on rights management and/or other information
InactiveUS20030046244A1Efficiently implementedFacilitate organized dissemination of digital contentAdvertisementsRelational databasesQualitative propertyPre-existing
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
Delivery particle
Owner:THE PROCTER & GAMBLE COMPANY
Agent satisfaction data for call routing based on pattern matching alogrithm
ActiveUS20100054452A1Reducing attritionLow costManual exchangesAutomatic exchangesPattern matchingContact center
Methods and systems are disclosed for routing callers to agents in a contact center with an intelligent routing system. An exemplary method includes routing callers to agents based on a pattern matching algorithm utilizing caller data and agent data, where the agent data includes agent satisfaction data from past agent-caller pairings. The agent satisfaction data may be obtained via surveys of the agents regarding their satisfaction with past agent-caller contacts. The agent satisfaction data may be used by the pattern matching algorithm in an attempt to increase agent satisfaction for future calls, thereby potentially reducing attrition of agents and cost to the call center, increasing morale of the agents, and so on. The agent satisfaction data and output from past agent-caller pairings may be weighted by the contact center against other agent data and caller data for a desired mixing of output variables.
Owner:AFINITI LTD
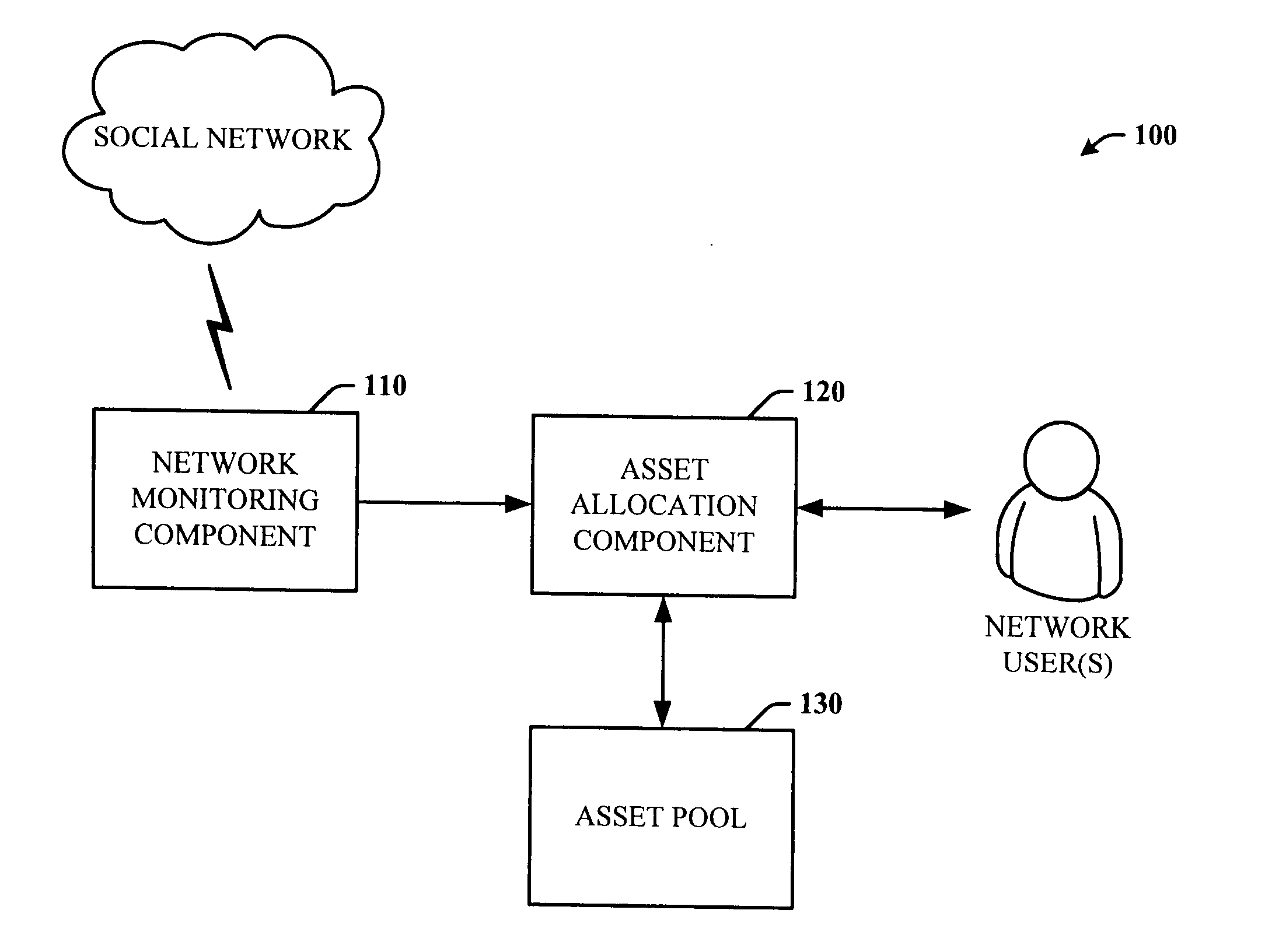
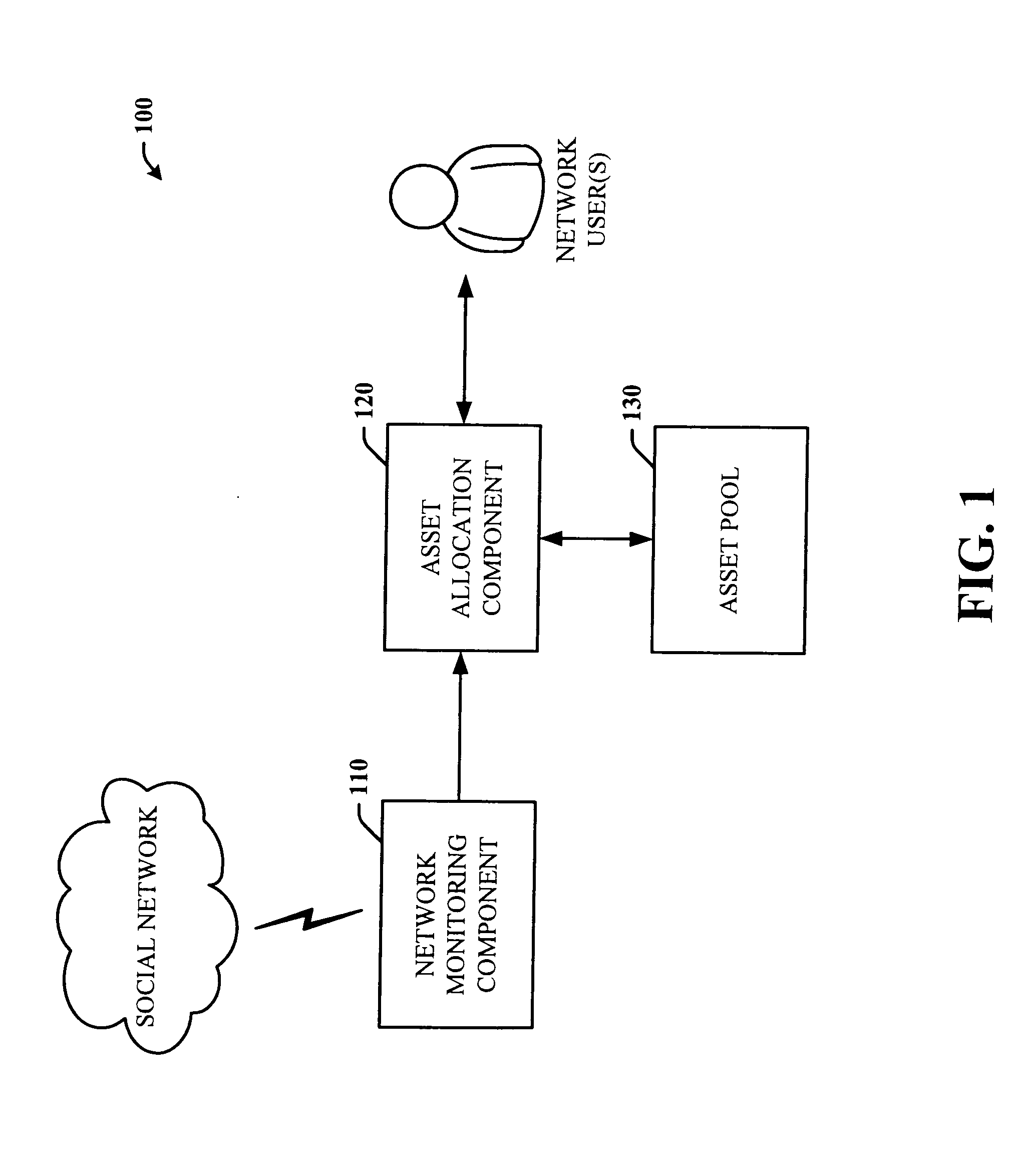
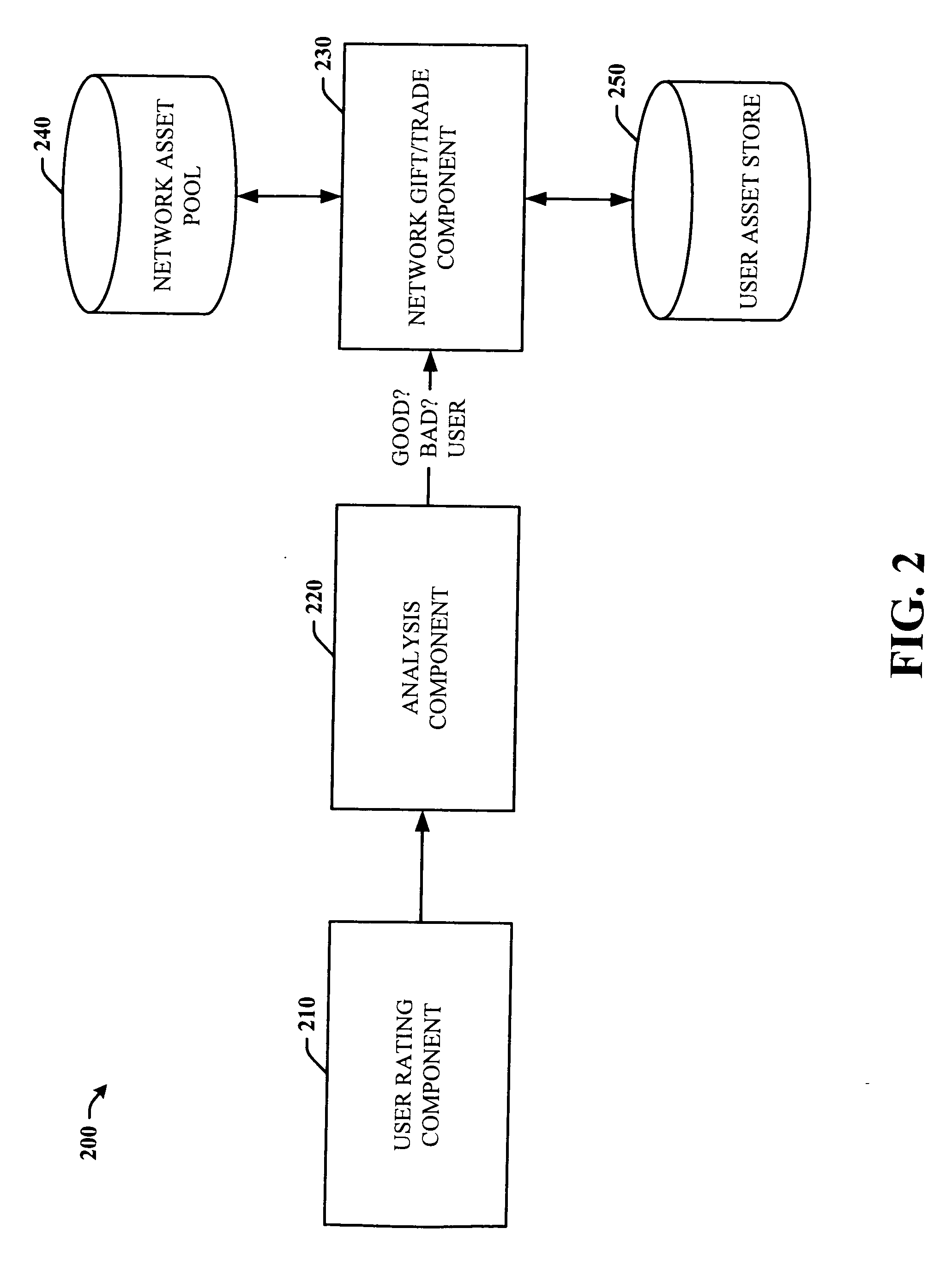
Systems and methods to facilitate self regulation of social networks through trading and gift exchange
ActiveUS20060190281A1Easy to usePromote self-regulationDigital computer detailsComputer security arrangementsInternet privacySocial internet of things
The subject invention provides a unique system and method that facilitates self-regulation of a social network system based at least in part on user behavior, and in particular on good or desirable user behavior. The system and method involve monitoring user behavior such as user activity and user interactions with other users and the network itself. Several factors can be weighed to determine whether the user behavior is good. Network assets or rights can be allocated to good users in the form of gifts or trade exchange opportunities whereas less desirable or bad users may not receive such gifts or trade opportunities or assets and rights might be revoked from them. By watching user behavior and promoting good behavior in this manner, the social network can be managed and self-regulated to optimize the utilization and distribution of both limited and unlimited assets (e.g., network created and user created assets or resources).
Owner:MICROSOFT TECH LICENSING LLC
Pooling callers for matching to agents based on pattern matching algorithms
ActiveUS20100111287A1Increase probabilityShorten the construction periodManual exchangesAutomatic exchangesPattern matchingHigh probability
Methods and systems are provided for routing callers to agents in a call-center routing environment. An exemplary method includes identifying caller data for at least one of a set of callers on hold and causing a caller of the set of callers to be routed to an agent based on a comparison of the caller data and the agent data. The caller data and agent data may be compared via a pattern matching algorithm and / or computer model for predicting a caller-agent pair having the highest probability of a desired outcome. As such, callers may be pooled and routed to agents based on comparisons of available caller and agent data, rather than a conventional queue order fashion. If a caller is held beyond a hold threshold the caller may be routed to the next available agent. The hold threshold may include a predetermined time, “cost” function, number of times the caller may be skipped by other callers, and so on.
Owner:AFINITI LTD
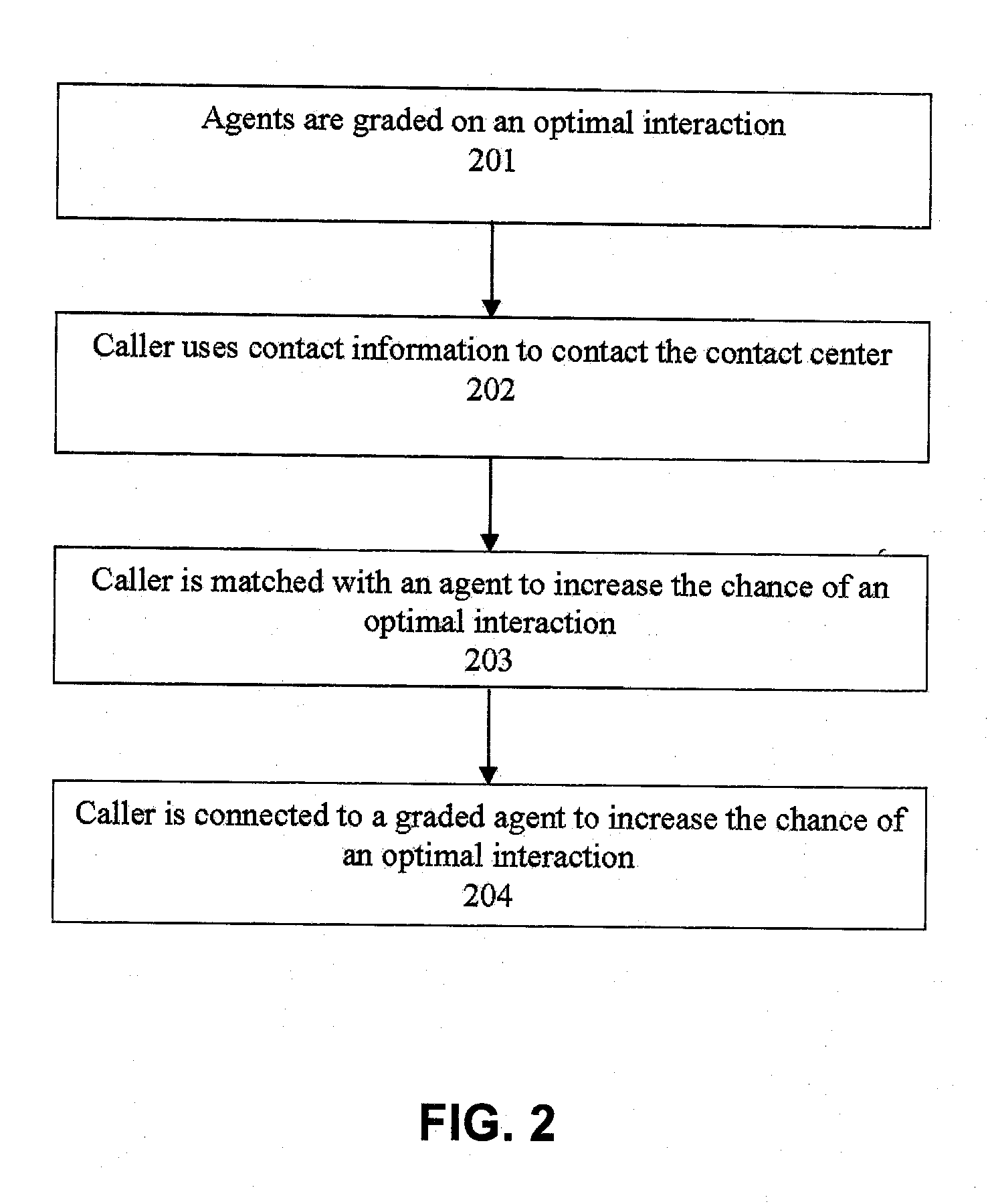
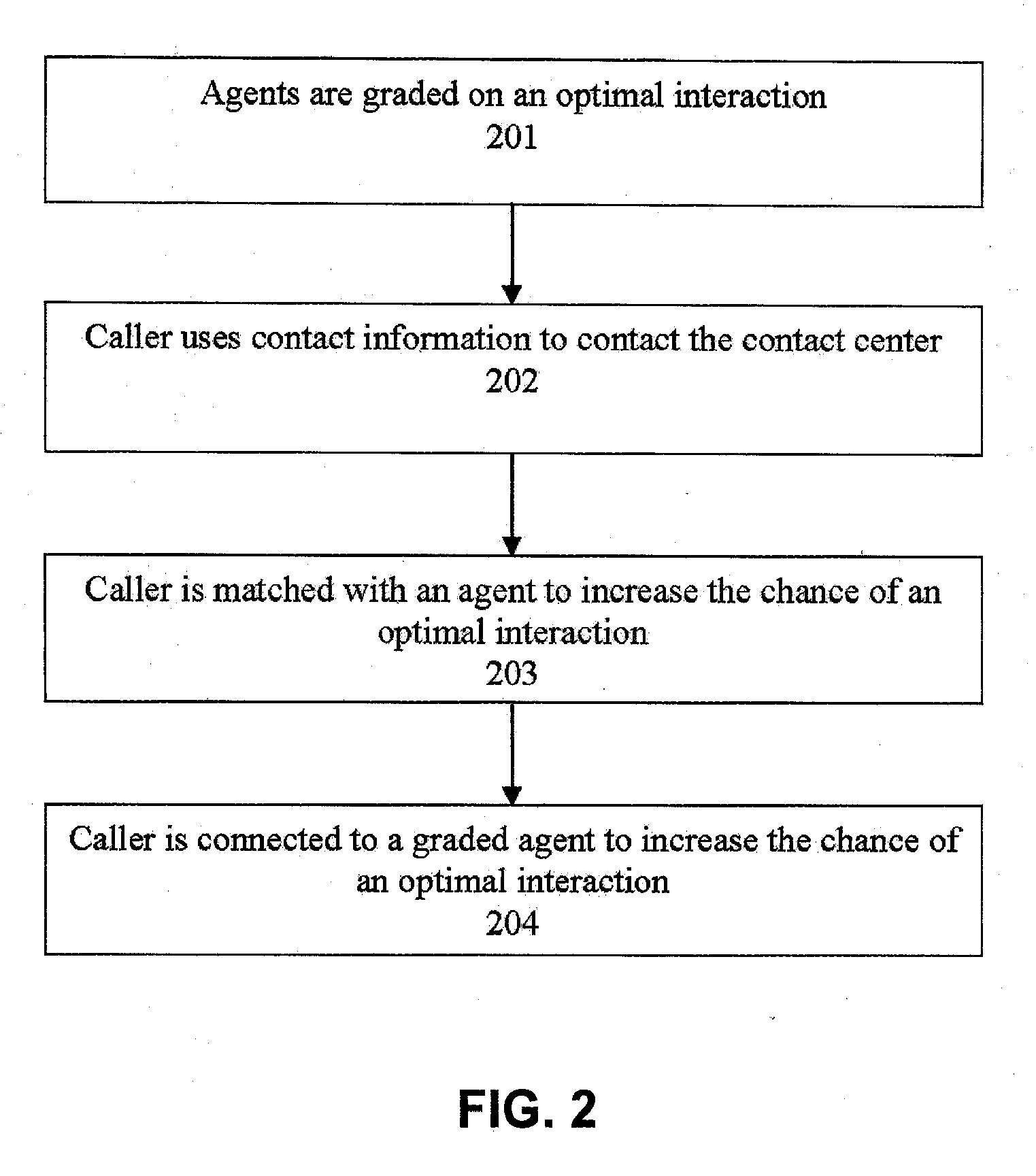
Systems and methods for routing callers to an agent in a contact center
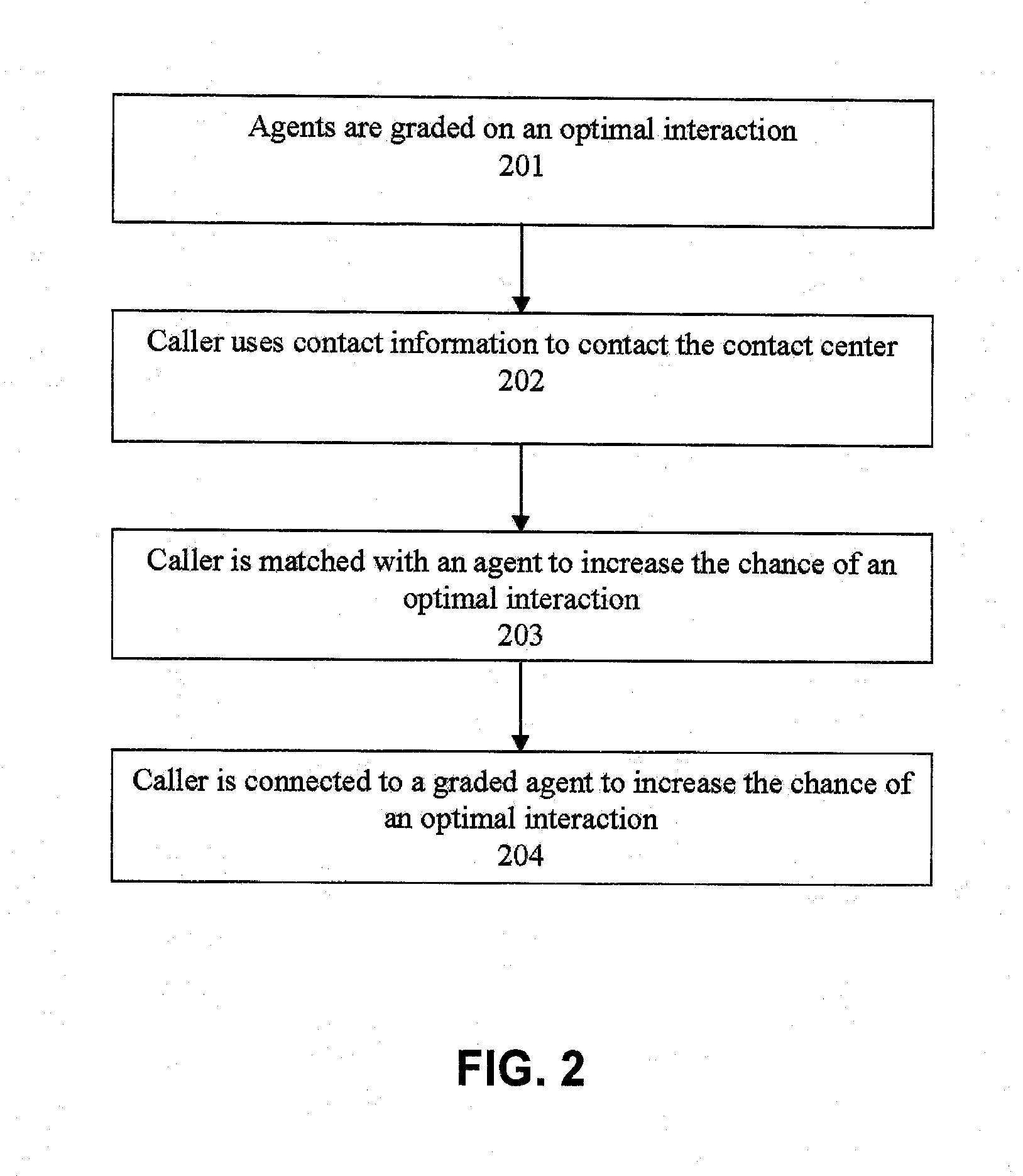
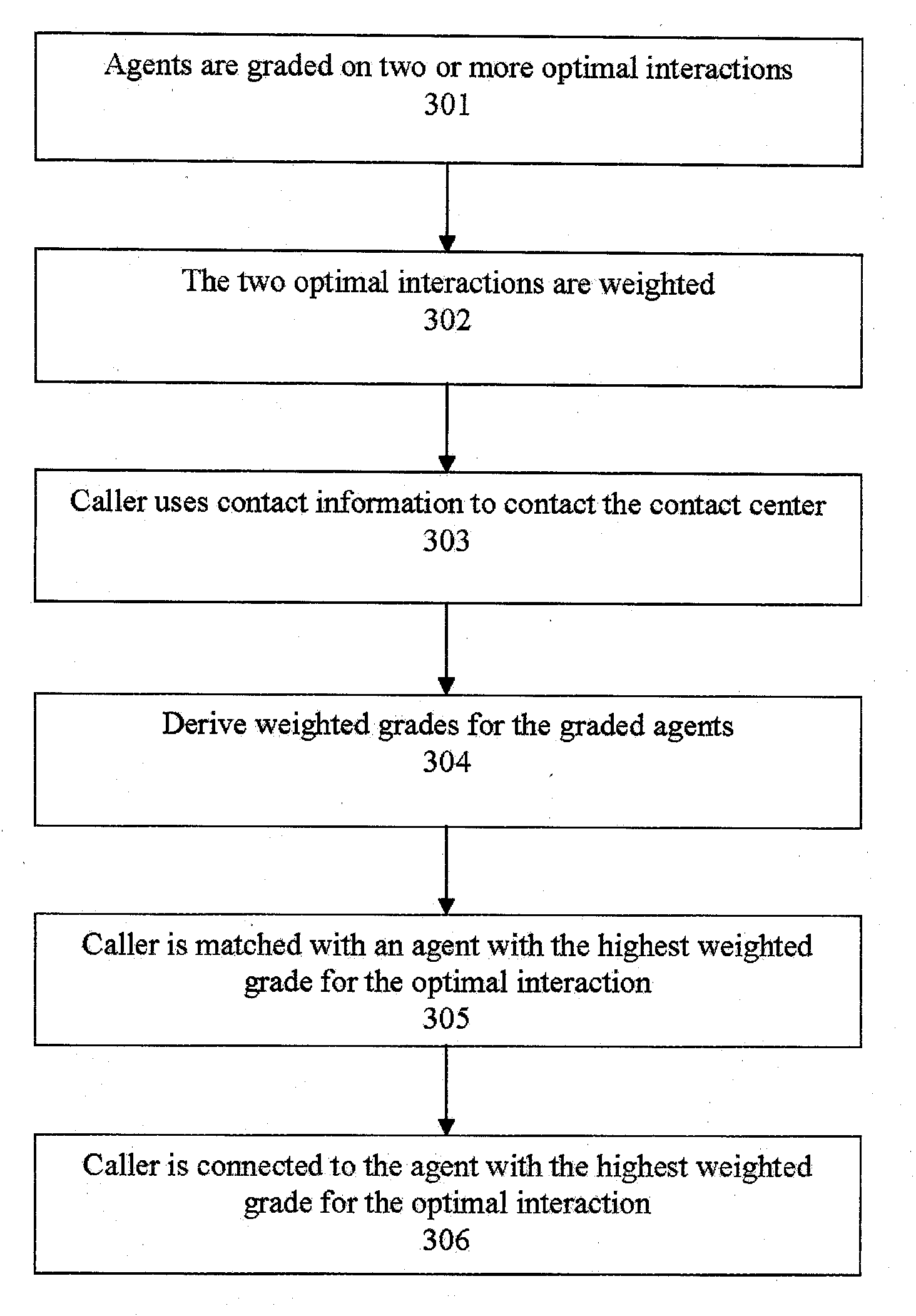
ActiveUS20090190748A1Increase opportunitiesShorten the construction periodManual exchangesAutomatic exchangesPattern matchingContact center
Methods are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. One or more agents are graded on achieving an optimal interaction, such as increasing revenue, decreasing cost, or increasing customer satisfaction. Callers are then preferentially routed to a graded agent to obtain an increased chance at obtaining a chosen optimal interaction. In a more advanced embodiment, caller and agent demographic and psychographic characteristics can also be determined and used in a pattern matching algorithm to preferentially route a caller with certain characteristics to an agent with certain characteristics to increase the chance of an optimal interaction.
Owner:AFINITI LTD
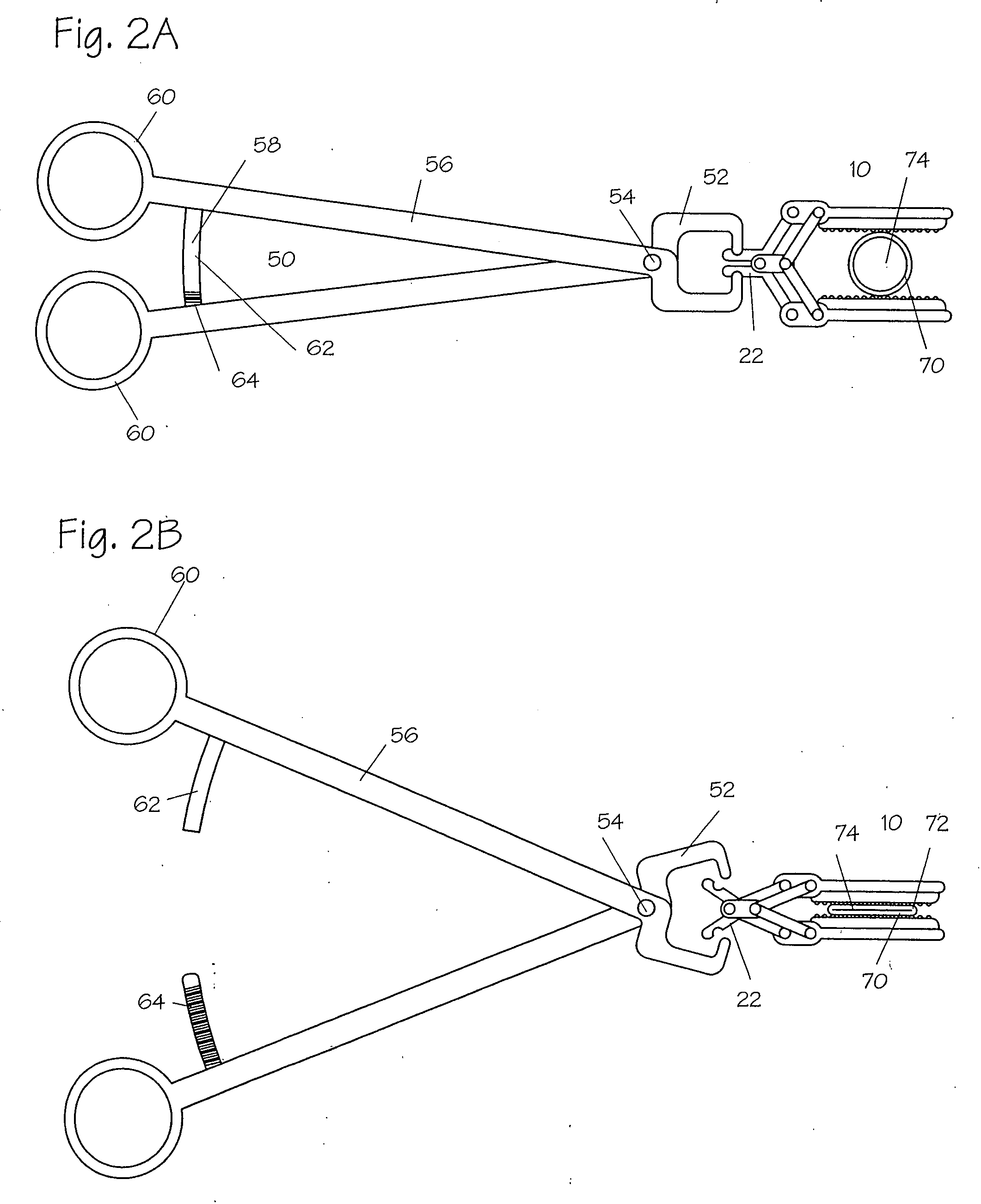
Method and apparatus for vascular and visceral clipping
InactiveUS7322995B2Convenient treatmentMinimizing chanceSnap fastenersClothes buttonsTrauma surgeryChest region
Devices and methods for achieving hemostasis and leakage control in hollow body vessels such as the small and large intestines, arteries and veins as well as ducts leading to the gall bladder and other organs. The devices and methods disclosed herein are especially useful in the emergency, trauma surgery or military setting, and most especially during damage control procedures. In such cases, the patient may have received trauma to the abdomen, extremities, neck or thoracic region. The devices utilize removable or permanently implanted, broad, soft, parallel jaw clips with minimal projections to maintain vessel contents without damage to the tissue comprising the vessel. These clips are applied using either standard instruments or custom devices that are subsequently removed leaving the clips implanted, on a temporary or permanent basis, to provide for hemostasis or leakage prevention, or both. These clips overcome the limitations of clips and sutures that are currently used for the same purposes. The clips come in a variety of shapes and sizes. The clips may be placed and removed by open surgery or laparoscopic access.
Owner:DAMAGE CONTROL SURGICAL TECH
Social network based virtual assembly places
InactiveUS20130031475A1Improve compatibilityIncrease opportunitiesOffice automationVideo gamesSocial media networkVirtual world
A method of providing virtual meeting environments for user controlled avatars. Each avatar is associated with user information from at least one social network (Facebook), and the user's profile picture and sex controls the general appearance of the avatars. The avatar's appearance can also be customized according to their user's social network relationships such as friends, friends of friends, or strangers. Various online virtual events, such as virtual parties, meeting rooms and the like may be created, and other social network users invited to participate by sending their avatars to the meeting environment. There the avatars may move about and interact with one another according to real-world rules, such as the rule that only avatars that are portrayed as physically being closely associated to each other in the virtual world may chat or interact, as well as exchange social network user information. Virtual environment search engines are also provided.
Owner:PLAYSTUDIOS
System and method for analyzing and utilizing data, by executing complex analytical models in real time
InactiveUS20030084053A1Increase opportunitiesMinimizing system resourceDigital data processing detailsDigital computer detailsAnalytic modelCustomer relationship management
A system and method for collecting, filtering, analyzing, distributing and effectively utilizing highly relevant events (such as key business events) in real time, from huge quantities of data. The present invention analyzes both historic and real-time data stemming from operational activity, by interfacing with internal data repositories (such as Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM)), external data sources (such as suppliers and clients), and real time operational systems in order to create an Active Intelligence Platform. This Active Intelligence Platform is positioned as a layer between the organization's data sources and its applications, monitoring inputs and relaying only the important data items to the relevant individuals and / or systems. This allows individuals and systems to respond immediately and effectively to key events.
Owner:ACTIMIZE
Systems and methods for routing callers to an agent in a contact center
ActiveUS20090190746A1Increase opportunitiesShorten the construction periodManual exchangesAutomatic exchangesPattern matchingContact center
Methods are disclosed for routing callers to agents in a contact center, along with an intelligent routing system. One or more agents are graded on achieving an optimal interaction, such as increasing revenue, decreasing cost, or increasing customer satisfaction. Callers are then preferentially routed to a graded agent to obtain an increased chance at obtaining a chosen optimal interaction. In a more advanced embodiment, caller and agent demographic and psychographic characteristics can also be determined and used in a pattern matching algorithm to preferentially route a caller with certain characteristics to an agent with certain characteristics to increase the chance of an optimal interaction.
Owner:AFINITI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com