Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
12511 results about "Application server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
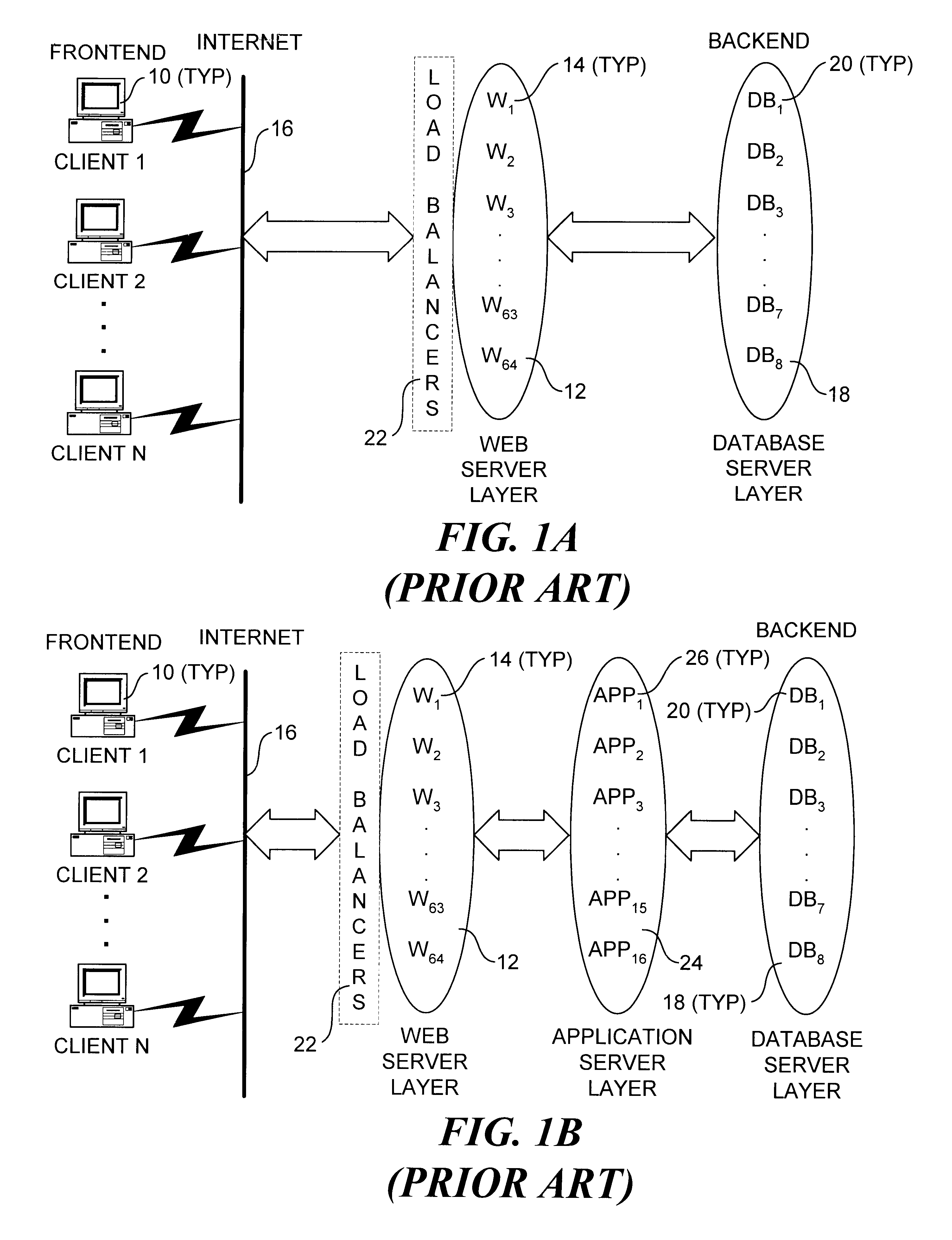
An application server is a software framework that provides both facilities to create web applications and a server environment to run them. Application Server Frameworks contain a comprehensive service layer model. An application server acts as a set of components accessible to the software developer through a standard API defined for the platform itself. For Web applications, these components are usually performed in the same running environment as their web server(s), and their main job is to support the construction of dynamic pages. However, many application servers target much more than just Web page generation: they implement services like clustering, fail-over, and load-balancing, so developers can focus on implementing the business logic.
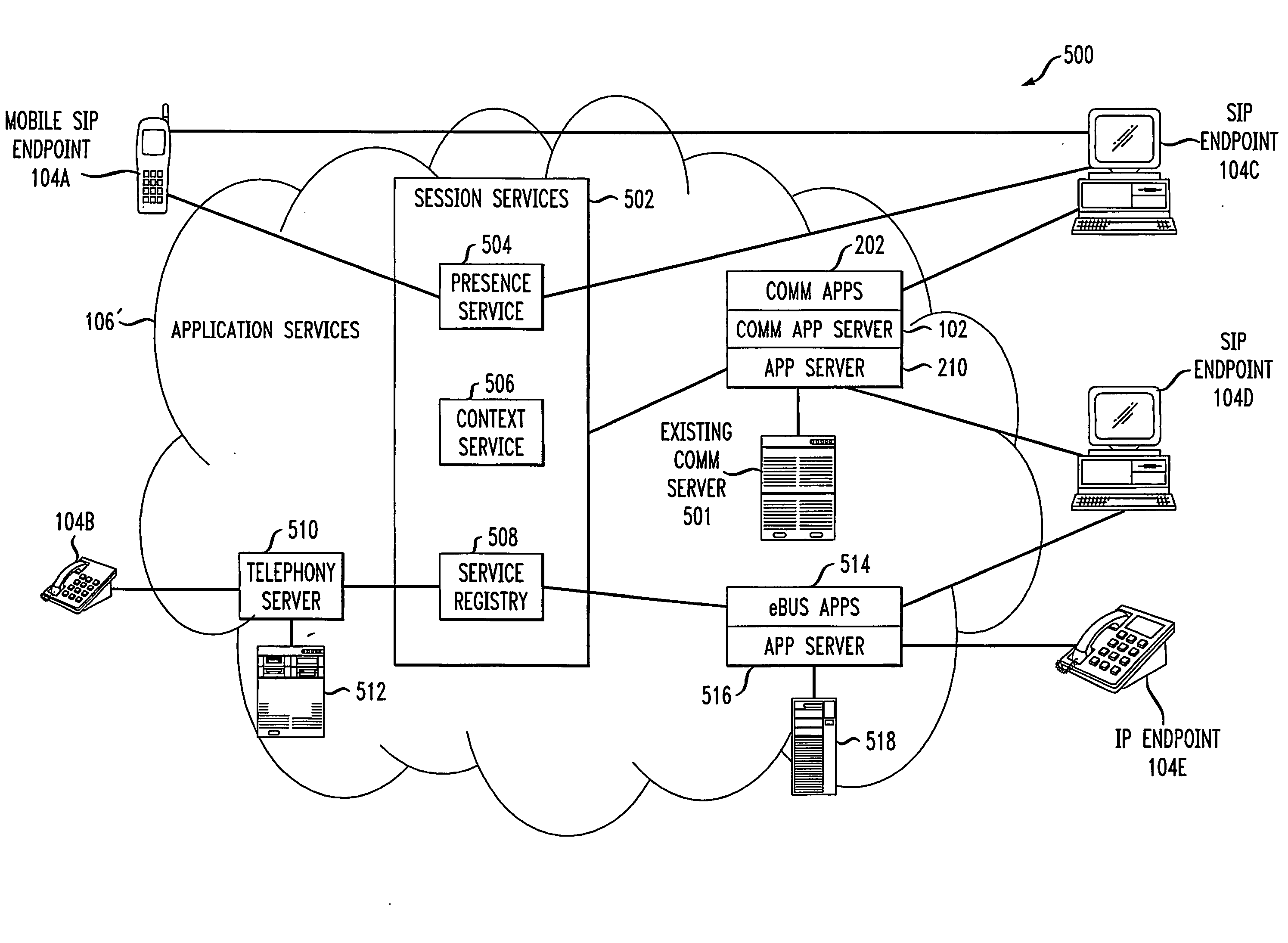
Communication application server for converged communication services
ActiveUS20080086564A1Multiple digital computer combinationsAutomatic exchangesApplication serverCommunications system
A communication application server for supporting converged communications in a communication system. The communication application server is responsive to communication service requests from external endpoints, applications or other c requesting entities, and in one embodiment comprises at least first and second components. The first component is operative: (i) to process a given one of the communication service requests to identify at least one corresponding communication service supported by the communication application server, (ii) to determine one or more executable communication tasks associated with the identified communication service; and (iii) to establish communication with one or more external servers to carry out execution of at least a subset of the one or more executable communication taks associated with the communication service. The second component is coupled between the first component and the one or more external servers, and provides, for each of the external servers, a corresponding interface for connecting the communication application server to the external server.
Owner:AVAYA INC
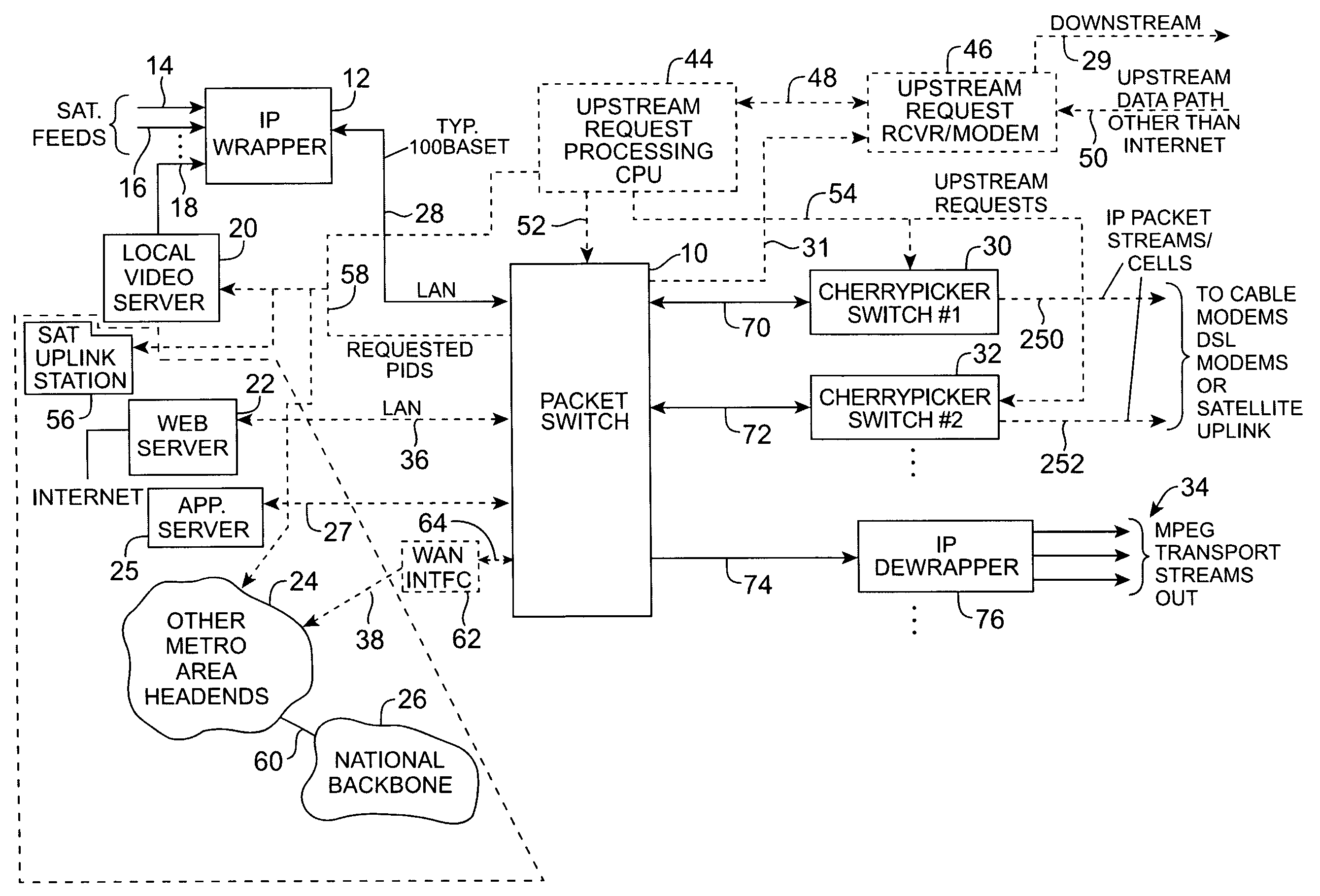
Headend cherrypicker multiplexer with switched front end
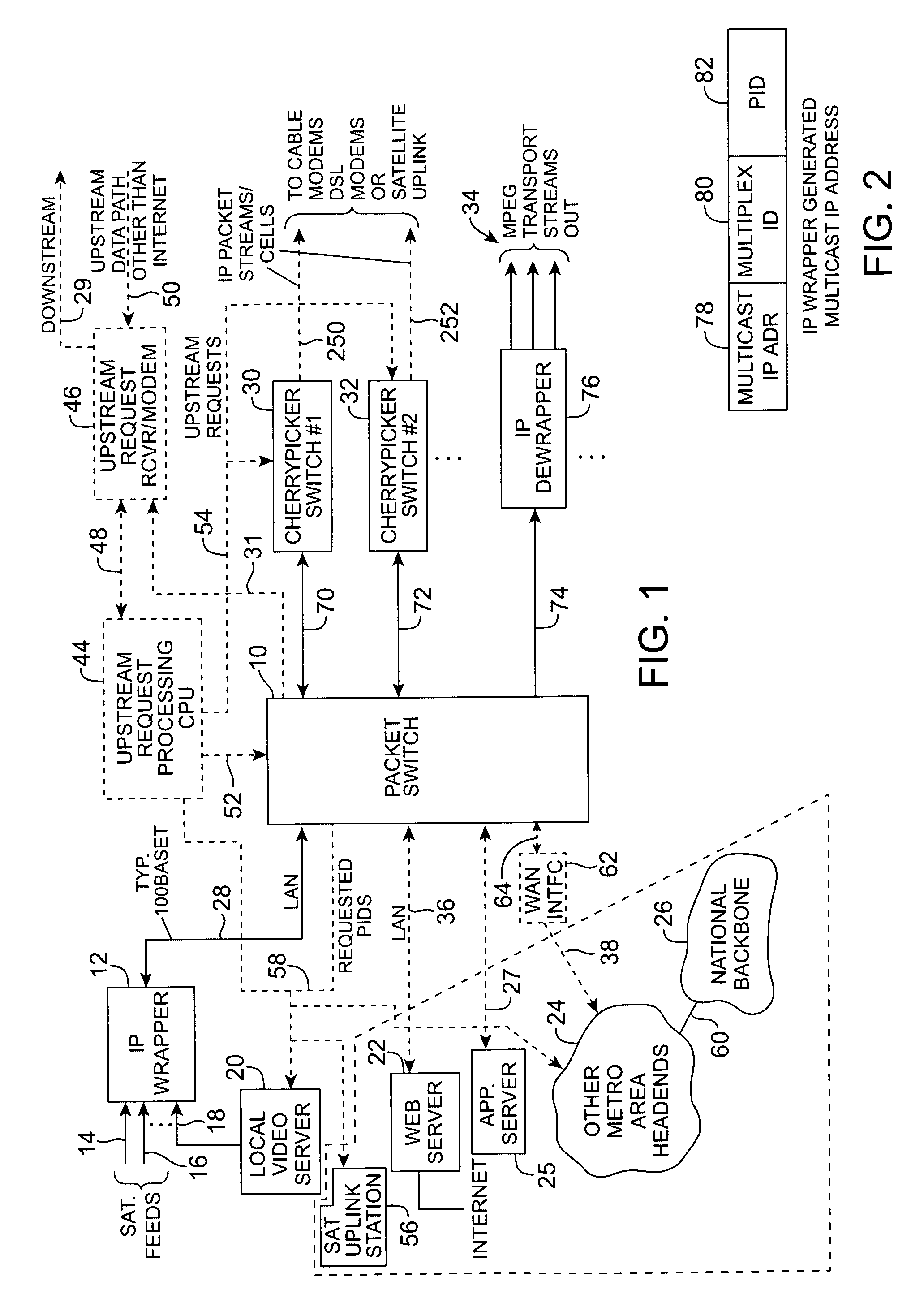
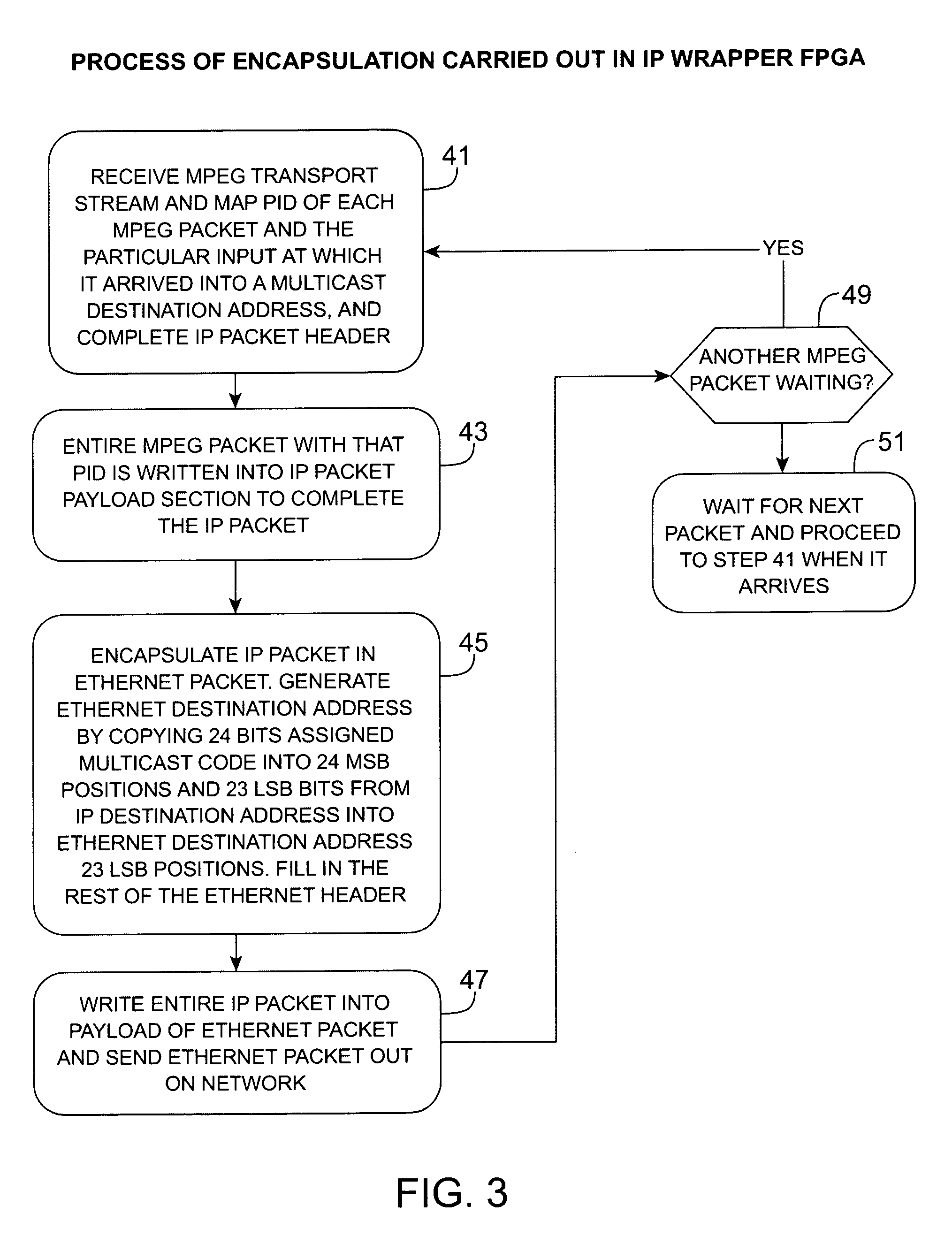
InactiveUS7039048B1Low costEasily scaledBroadband local area networksTime-division multiplexMPEG transport streamModem device
A headend or central office or satellite uplink facility for receiving upstream video-on-demand requests and MPEG transport streams containing video program data and packetizing said video data into TCP / IP or UDP / IP packets and LAN packets and routing them through a switch to one or more cherrypicker multiplexers. Each cherrypicker multiplexer receives LAN packets, depacketizes the MPEG data, partially or fully decompresses the data and recompresses the data to another smaller bandwidth, and repacketizes the data into MPEG packets or TCP / IP or UDP / IP packets. The repacketized TCP / IP or UDP / IP packets are transmitted directly to the customer as TCP / IP or UDP / IP packet data. MPEG packets generated by the cherrypicker multiplexer are, optionally, encapsulated in LAN packets addressed to an IP dewrapper circuit. There, they are depacketized back to MPEG packets and transmitted to the appropriate transmitter or modem for transmitting to a customer. Internet data and data from application servers, referred to as iData, can also be transmitted to customers through the cherrypicker multiplexers or a downstream modem, and upstream iData can be received through the modem.
Owner:GOOGLE TECH HLDG LLC
Network caching system for streamed applications
InactiveUS20030009538A1Data processing applicationsMultiple digital computer combinationsApplication serverNetwork packet
A network caching system for streamed applications provides for the caching of streamed applications within a computer network that are accessible by client systems within the network. Clients request streamed application file pages from other client systems, proxy servers, and application servers as each streamed application file is stored in a cache and used. Streamed application file page requests are broadcast to other clients using a multicast packet. Proxy servers are provided in the network that store a select set of streamed application file pages and respond to client requests by sending a response packet containing the requested streamed application file page if the streamed application file page is stored on the proxy server. Streamed application servers store all of the streamed application file pages. Clients try to send requests to streamed application servers as a last resort. Clients can concurrently send requests to other clients, to a proxy server, and to a streamed application server. Clients measure the response time to the clients requests placing a positive weighting on the more responsive request path and sending subsequent requests to the more positively weighted request path first.
Owner:NUMECENT HLDG
Internet database system
InactiveUS6523036B1Data processing applicationsDigital data processing detailsApplication serverHash function
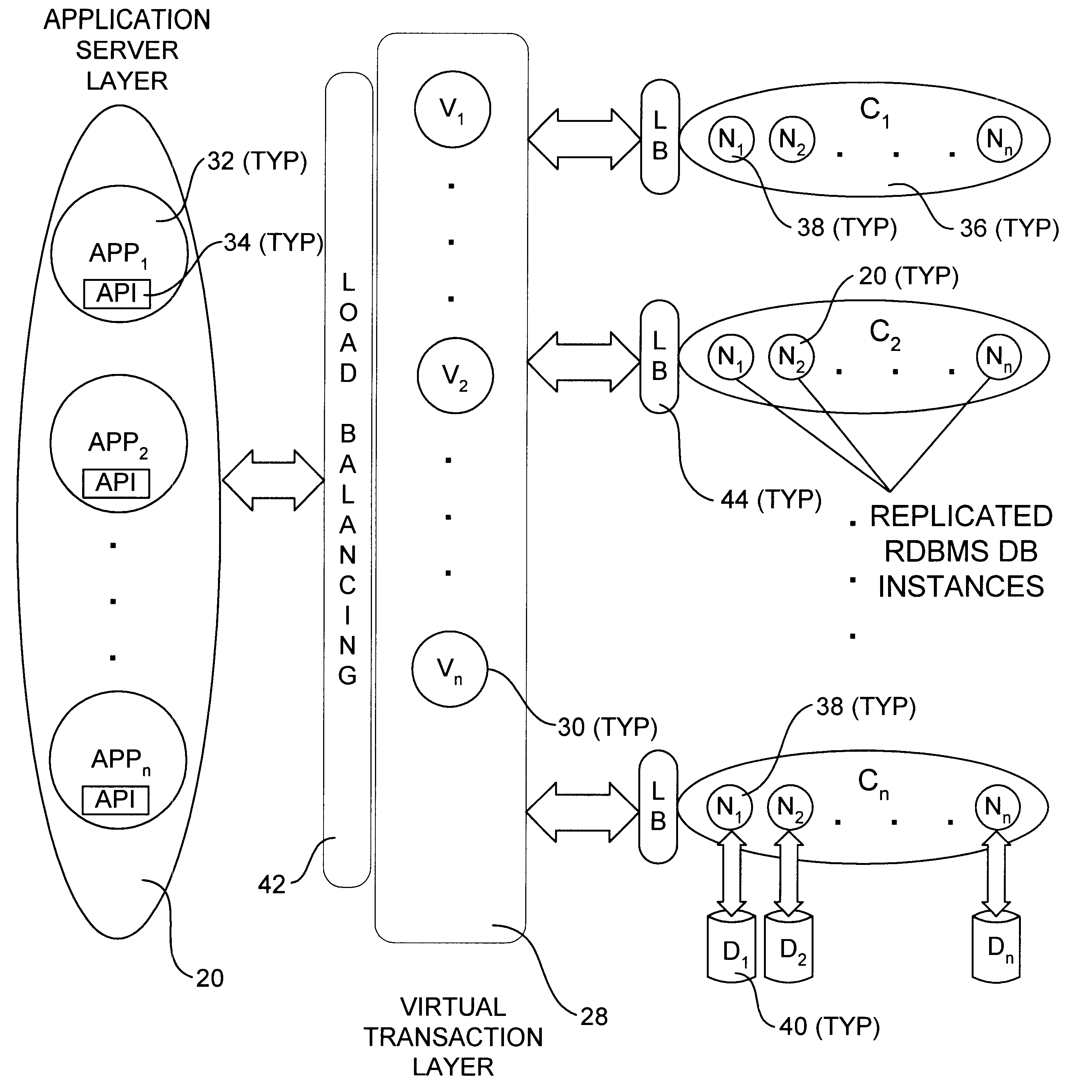
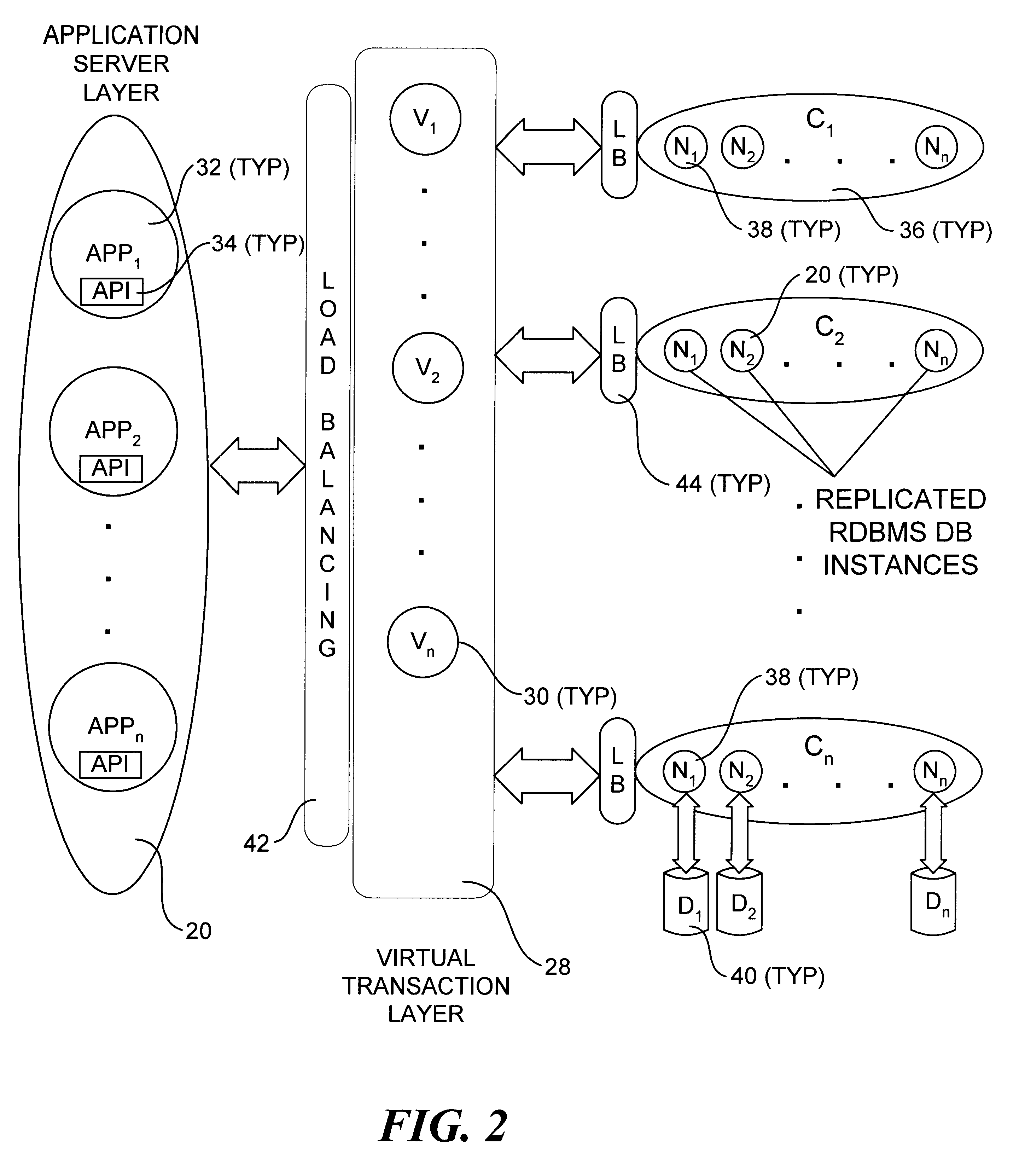
An incrementally-scalable database system and method. The system architecture enables database servers to be scaled by adding resources, such as additional servers, without requiring that the system be taken offline. Such scaling includes both adding one or more computer servers to a given server cluster, which enables an increase in database read transaction throughput, and adding one or more server clusters to the system configuration, which provides for increased read and write transaction throughput. The system also provides for load balancing read transactions across each server cluster, and load balancing write transactions across a plurality of server clusters. The system architecture includes an application server layer including one or more computers on which an application program(s) is running, a database server layer comprising two or more server clusters that each include two or more computer servers with replicated data, and an intermediate "virtual transaction" layer that includes at least two computers that facilitate database transactions with one or more databases operating in the database server layer. Data in the database(s) are evenly distributed across the server clusters in fragmented mutually exclusive subsets of data based on a hashing function. An application program interface is provided so as to enable application programs to perform a full range of database transactions without regard for where data is stored, or what database(s) is operating in the database server layer.
Owner:EMC IP HLDG CO LLC
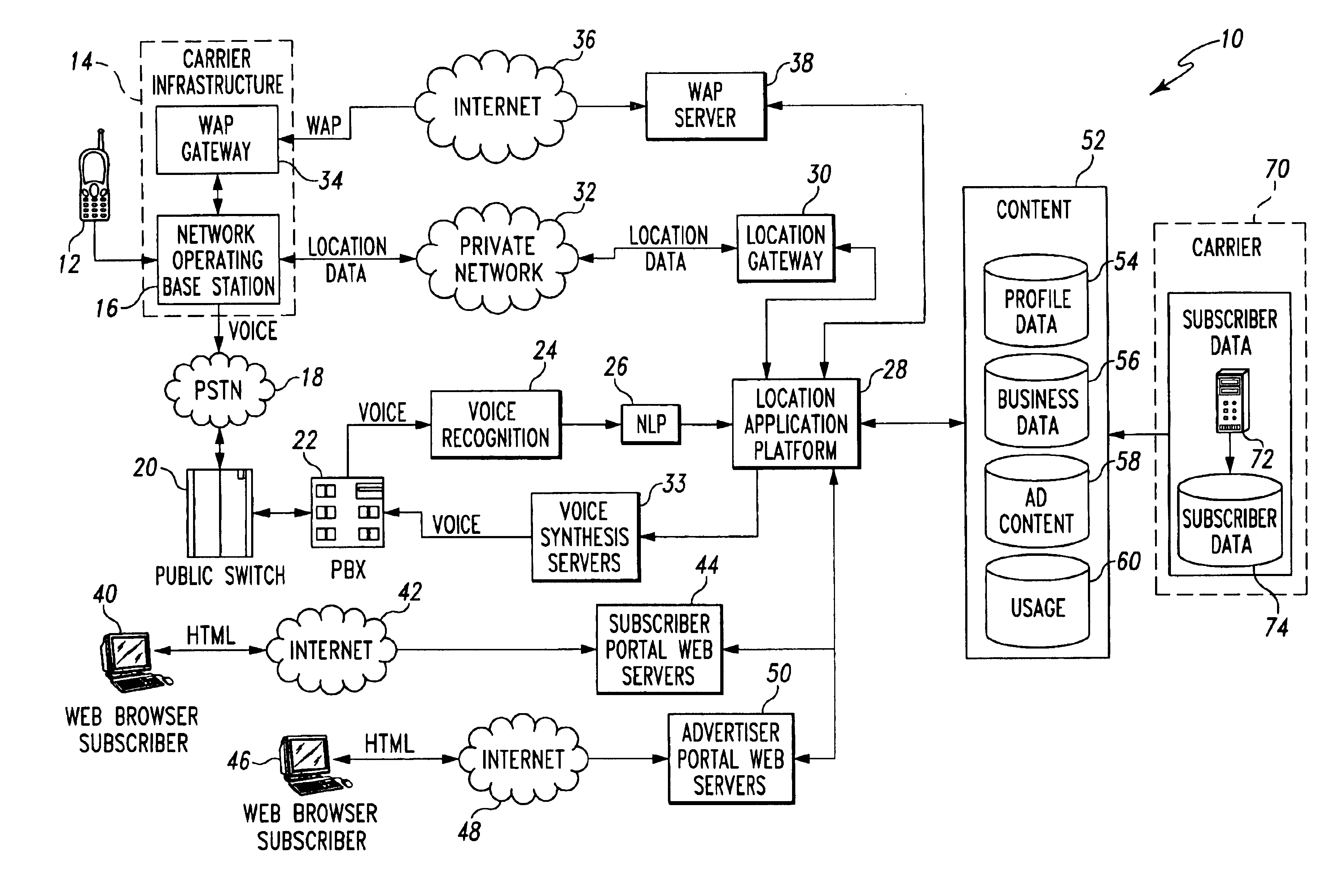
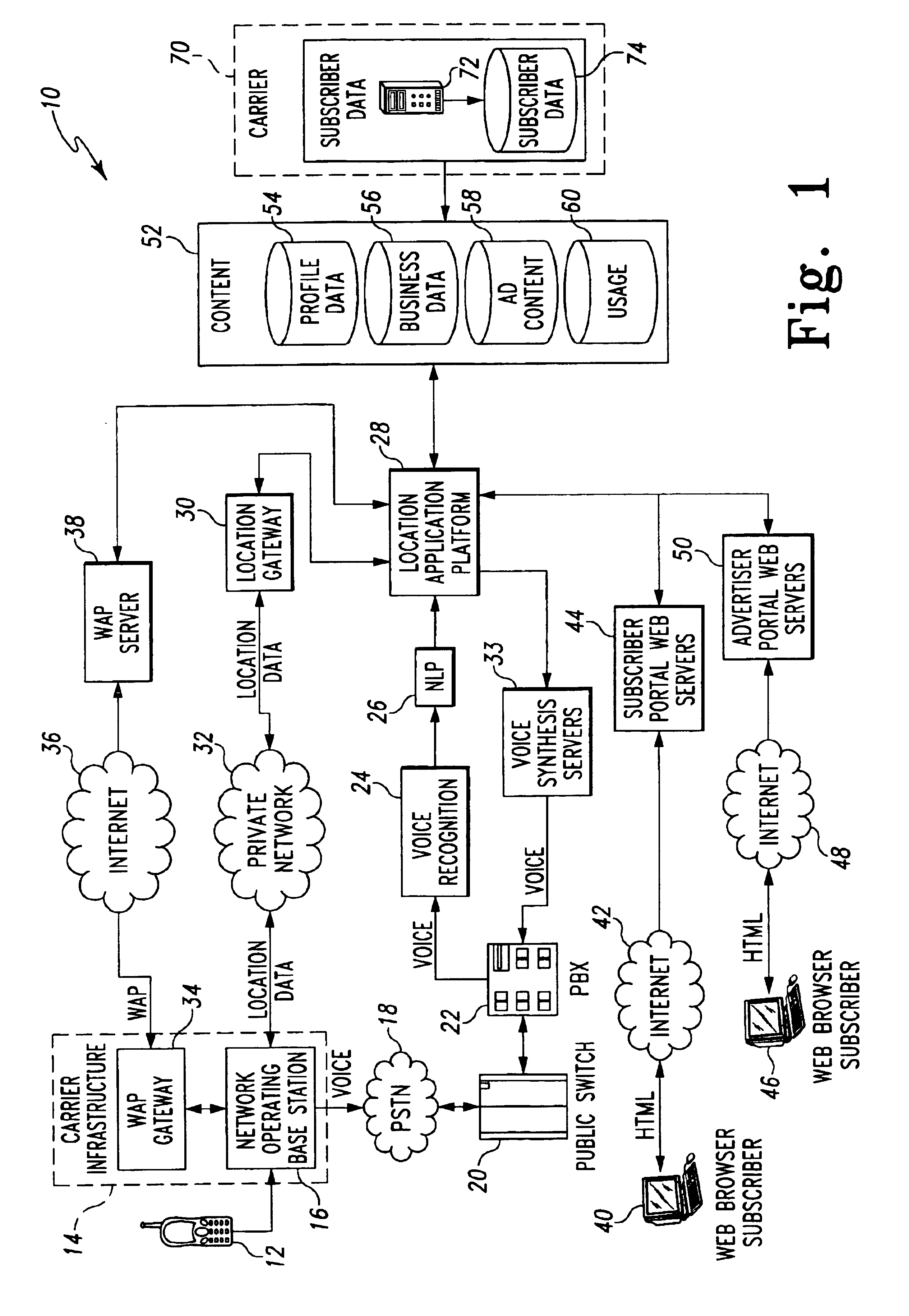
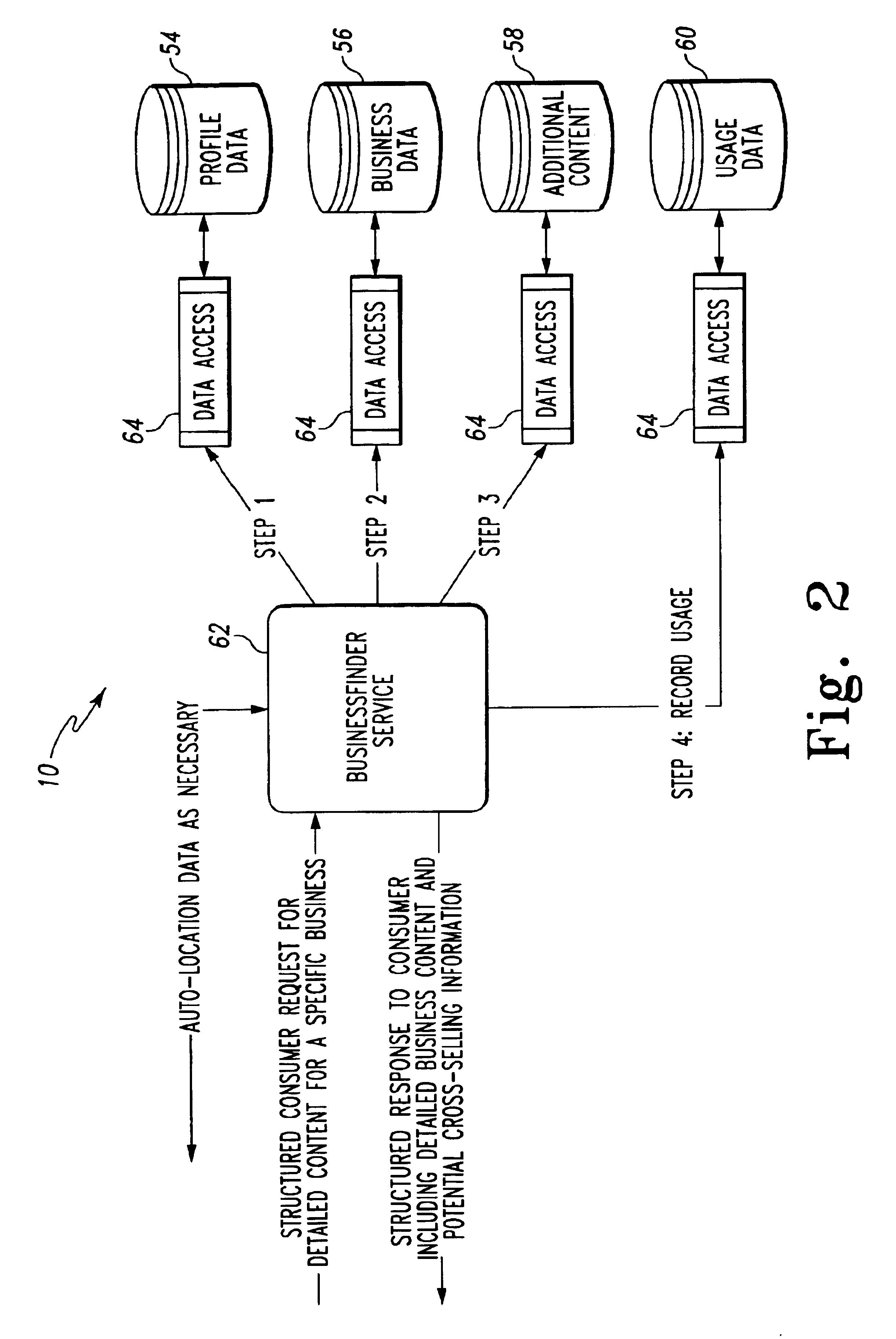
Location-based services
InactiveUS6944447B2Multiple digital computer combinationsSubstation equipmentCommunications systemApplication server
The present invention discloses a method and system for providing location-based services to a remote terminal that is connected to various types of communication systems. A tailored request for information is generated with the remote terminal. In addition, a geographic indicator associated with the remote terminal is also generated in the preferred embodiment. The tailored request for information and the geographic indicator are transmitted to a location-based application server. A structured response to the tailored request for information is generated with the location-based application server, wherein the structured response is based on the geographic indicator of the remote terminal. The structured response is the transmitted to the remote terminal using one of several different types of communication protocols and / or mediums.
Owner:ACCENTURE GLOBAL SERVICES LTD
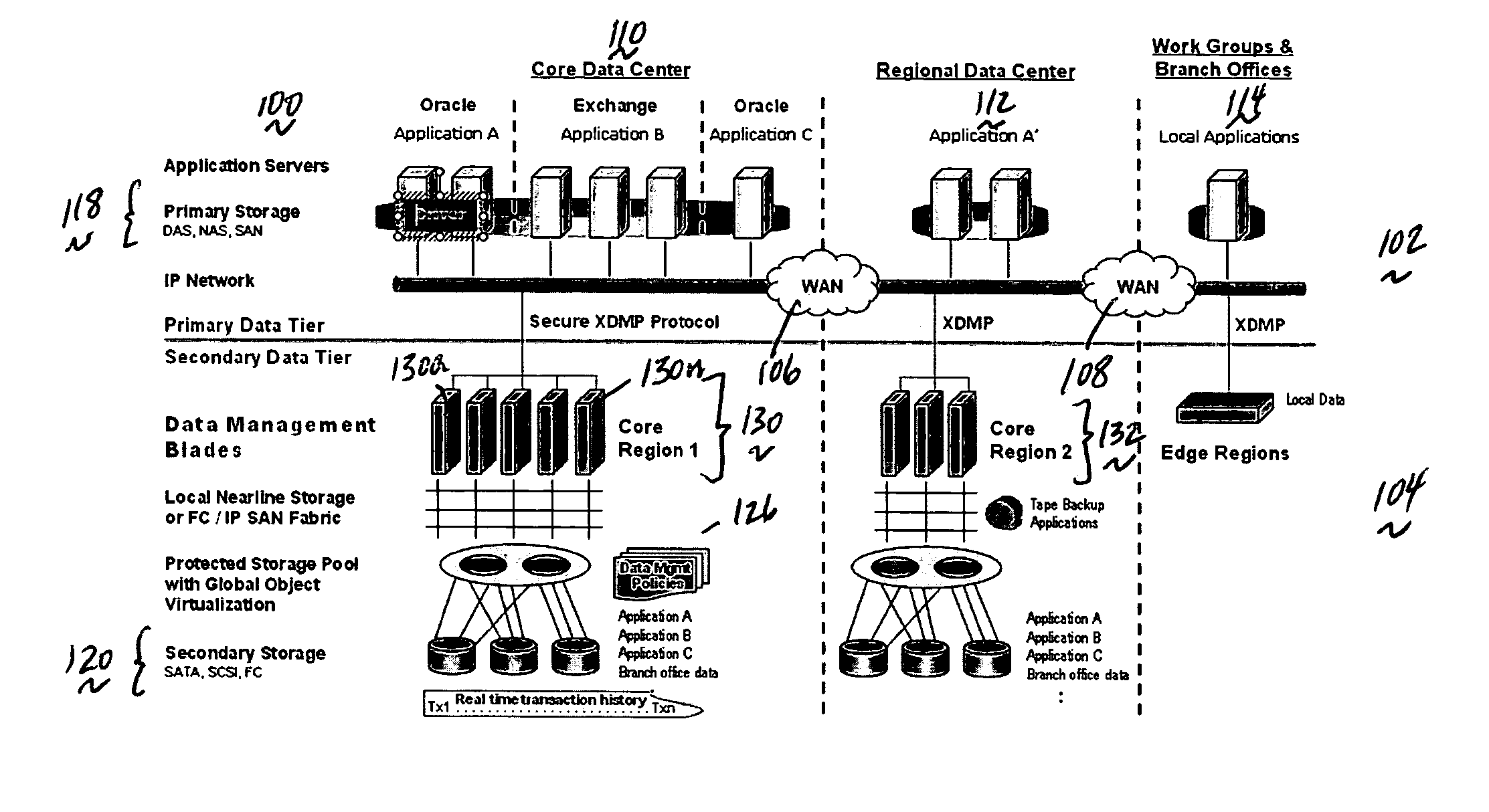
System for moving real-time data events across a plurality of devices in a network for simultaneous data protection, replication, and access services
ActiveUS20050262097A1Efficiently parallel processEfficiently route application-aware data changeDigital data information retrievalDigital data processing detailsData connectionData stream
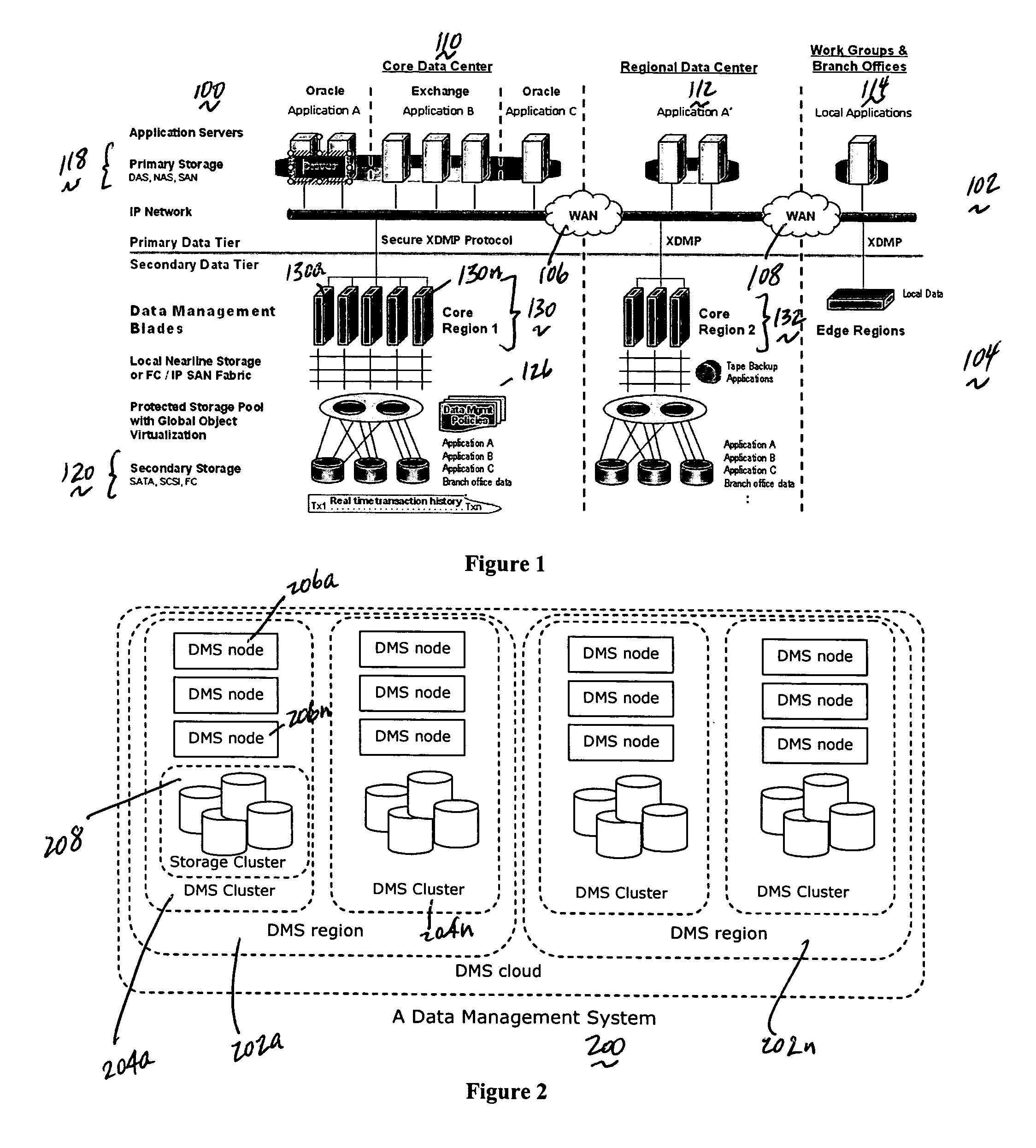
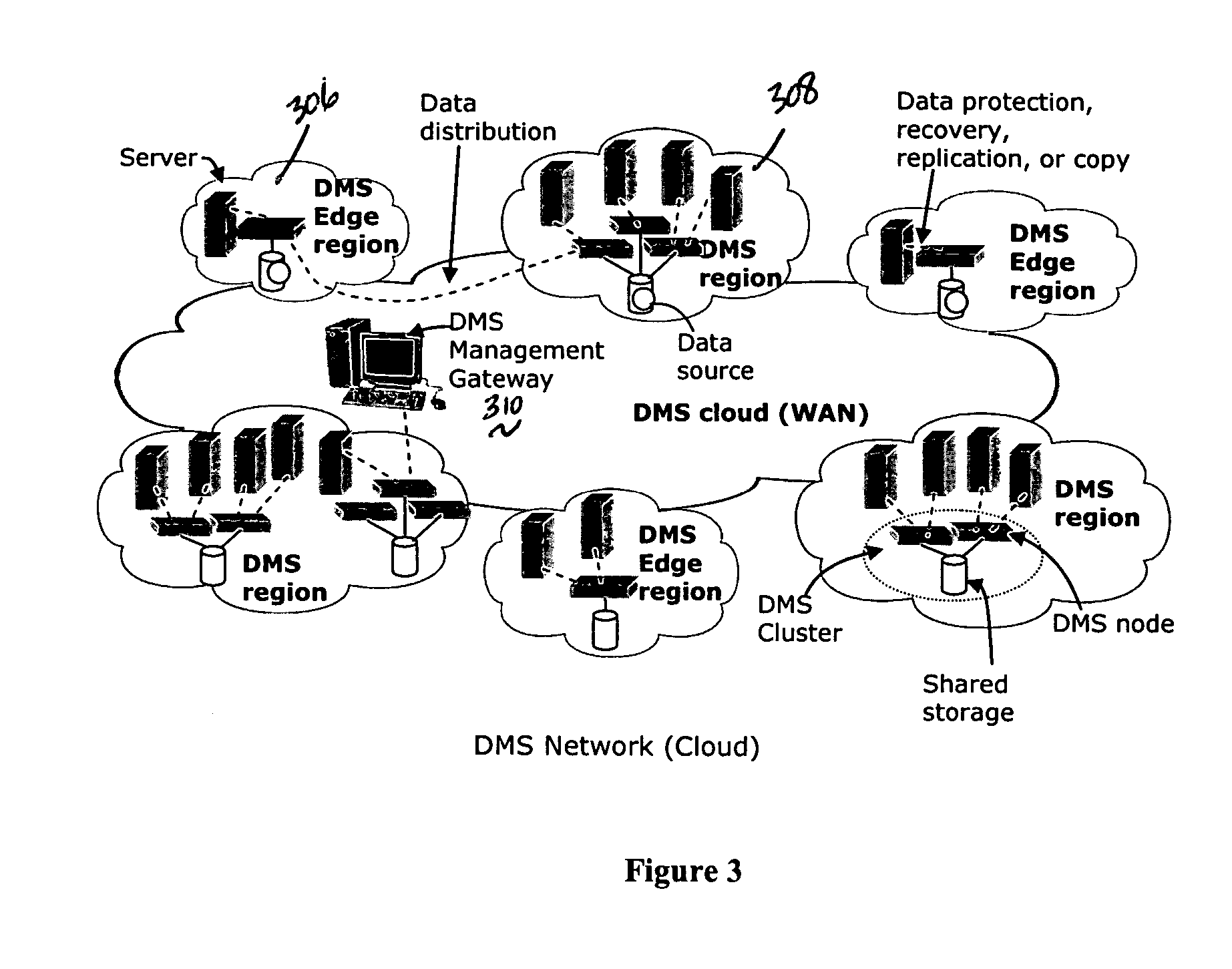
A data management system or “DMS” provides a wide range of data services to data sources associated with a set of application host servers. The data management system typically comprises one or more regions, with each region having one or more clusters. A given cluster has one or more nodes that share storage. To facilitate the data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver provides a method and apparatus for capturing real-time data transactions in the form of an event journal that is provided to the data management system. The driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. Using the streams generated in this manner, the DMS offers a wide range of data services that include, by way of example only: data protection (and recovery), disaster recovery (data distribution and data replication), data copy, and data query and access.
Owner:QUEST SOFTWARE INC
IP-based services for circuit-switched networks
ActiveUS20050058125A1Multiplex system selection arrangementsInterconnection arrangementsRadio access networkVoice over IP
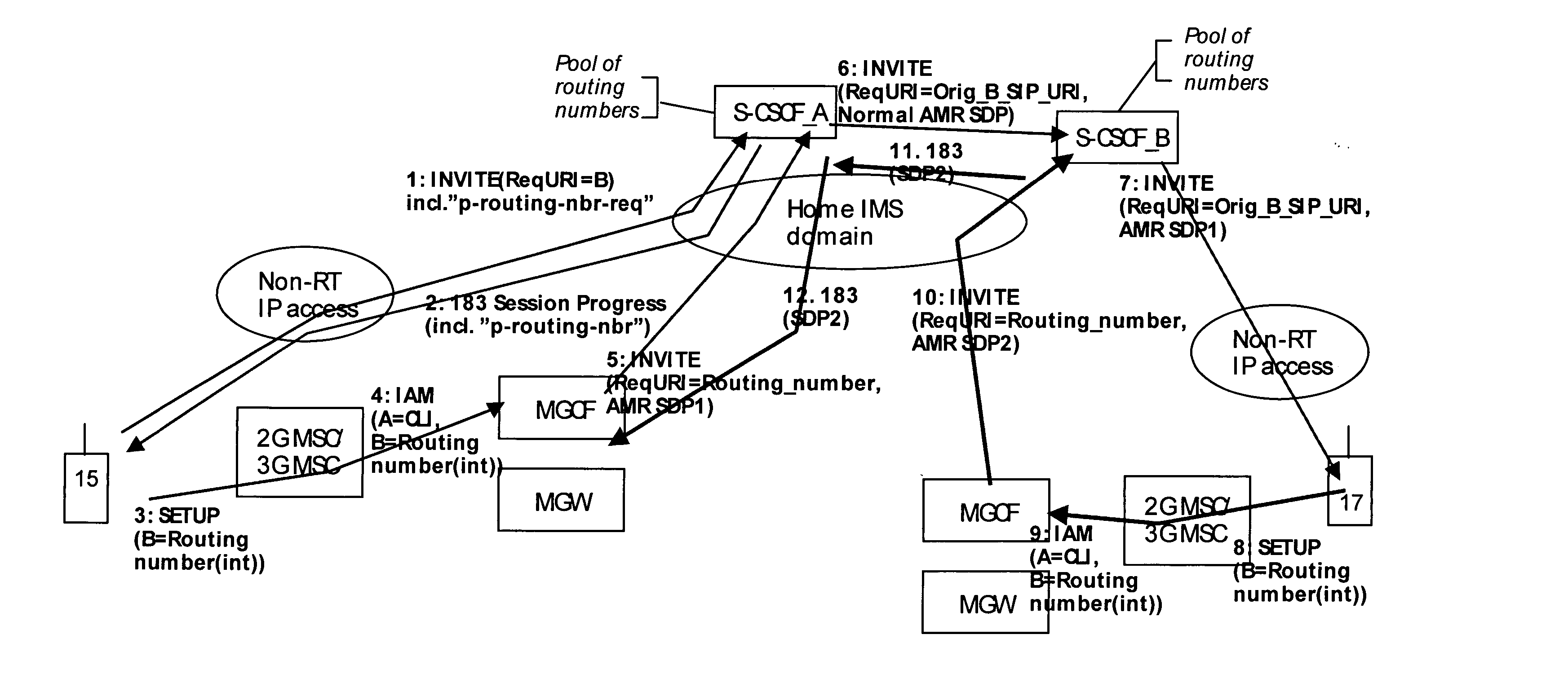
A mechanism for providing a connection from an IP-based network to a circuit-switched network, such as a GSM network is disclosed. A temporary routing number for the circuit-switched network, such as an E.164 number, is delivered to a user terminal, and a circuit-switched call leg is established from the user terminal to the IP-based network using the routing number. Thereby, IMS-services are provided for end users which are located in the radio access network not having sufficient QoS required for voice over IP. In the example of a conference call service, a request for a conference call may forwarded via a data channel or data path to an application server which provides that conference call service. The application server then selects a conference routing number and returns the routing number to the conference host terminal via the data channel. Using the received conference routing number, the conference host terminal can then set up a circuit-switched connection as a call leg of the conference call.
Owner:NOKIA TECHNOLOGLES OY
Integrated mobile application server and communication gateway
InactiveUS20060258397A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunication interfacePayment
A system is provided that includes a request module adapted to receive a request from an initiation interface initiated by a user and a user profile module adapted to associate the request with a user profile of the user. The user profile includes at least a payment plan selected by the user and an identification number of the user. The system also includes a payment interface adapted to submit a payment demand to the payment plan and a mobile communication interface adapted to transmit a confirmation to a mobile communication network for transmission to a wireless device associated with the identification number. In the system, the initiation interface may be a wireless device, a magnetic swipe reader, a wireless barcode reading device, an RFID interface, a website, and / or a web banner interface. A method of operating a server is provided. A computer-readable storage medium containing a set of instructions for a processor is provided.
Owner:SHOPTEXT INC
System and method for enabling application server request failover
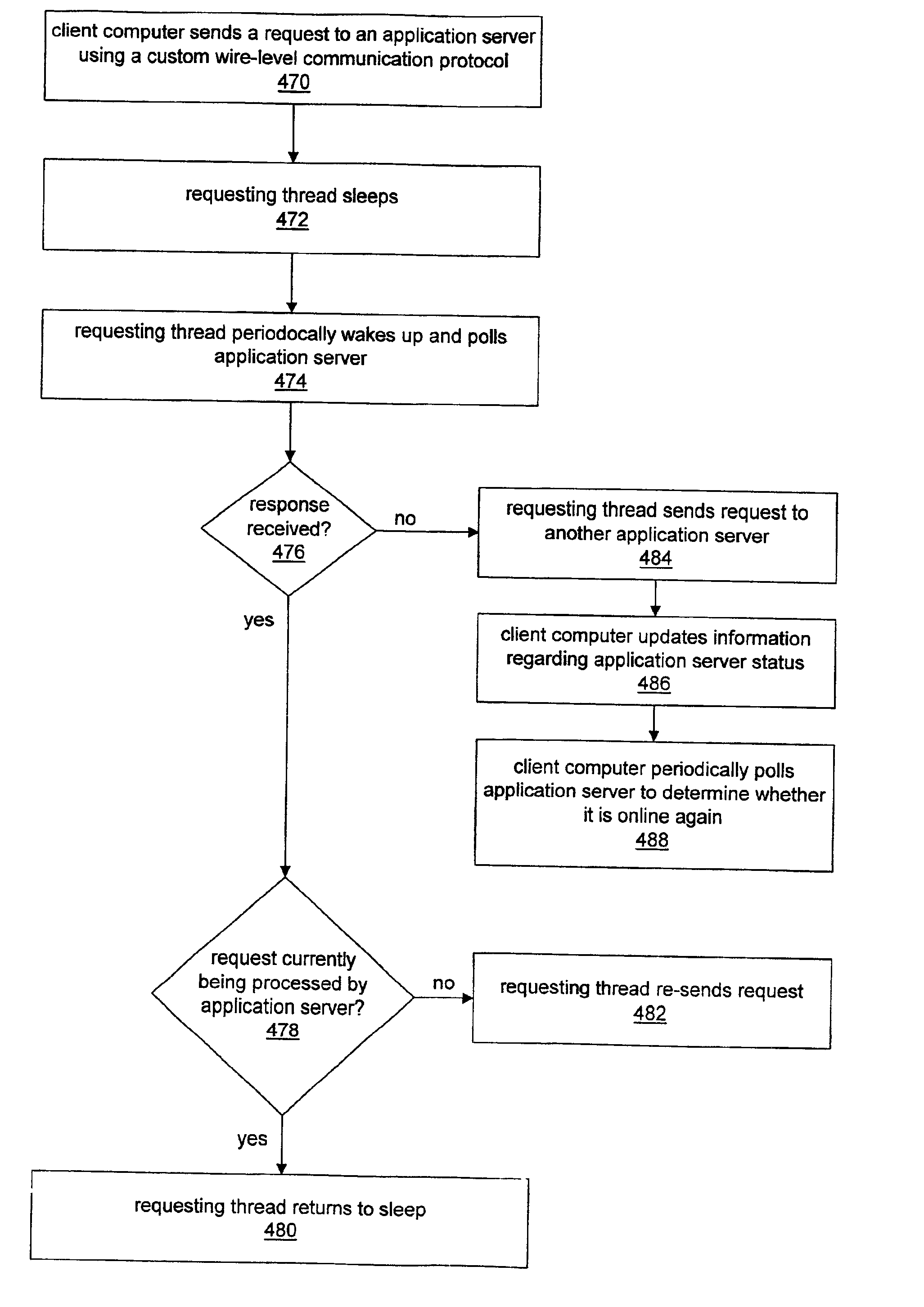
InactiveUS6859834B1Resource allocationMultiple digital computer combinationsFailoverApplication server
System and method for enabling application server request failover. For each application server request to be performed by a client computer, a requesting thread may be operable to utilize a custom wire-level communication protocol. Request failure detection mechanisms may be built into the custom wire-level communication protocol so that a requesting thread detects a failed request much sooner than if the thread utilized a standard communication protocol and relied on the client computer operating system for notification of failed requests. After sending a request to an application server, a requesting thread may be operable to “sleep” and then periodically wake up to poll the application server computer to determine whether the request has failed. If the requesting thread receives a response from the application server computer indicating that the request is not currently being processed, then the requesting thread may re-send the request. Receiving no response to the poll message may indicate that the application server computer is offline, e.g., due to a failure. The requesting thread may redirect the request to another application server computer if necessary.
Owner:ORACLE INT CORP
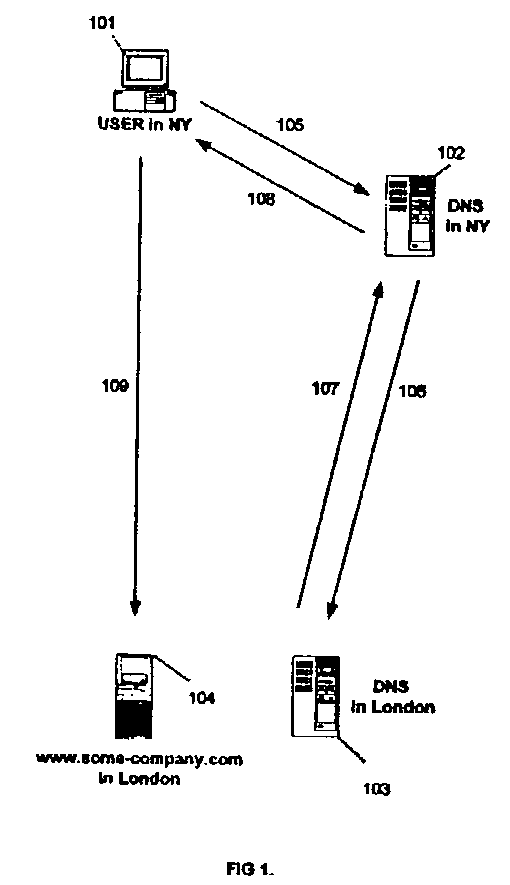
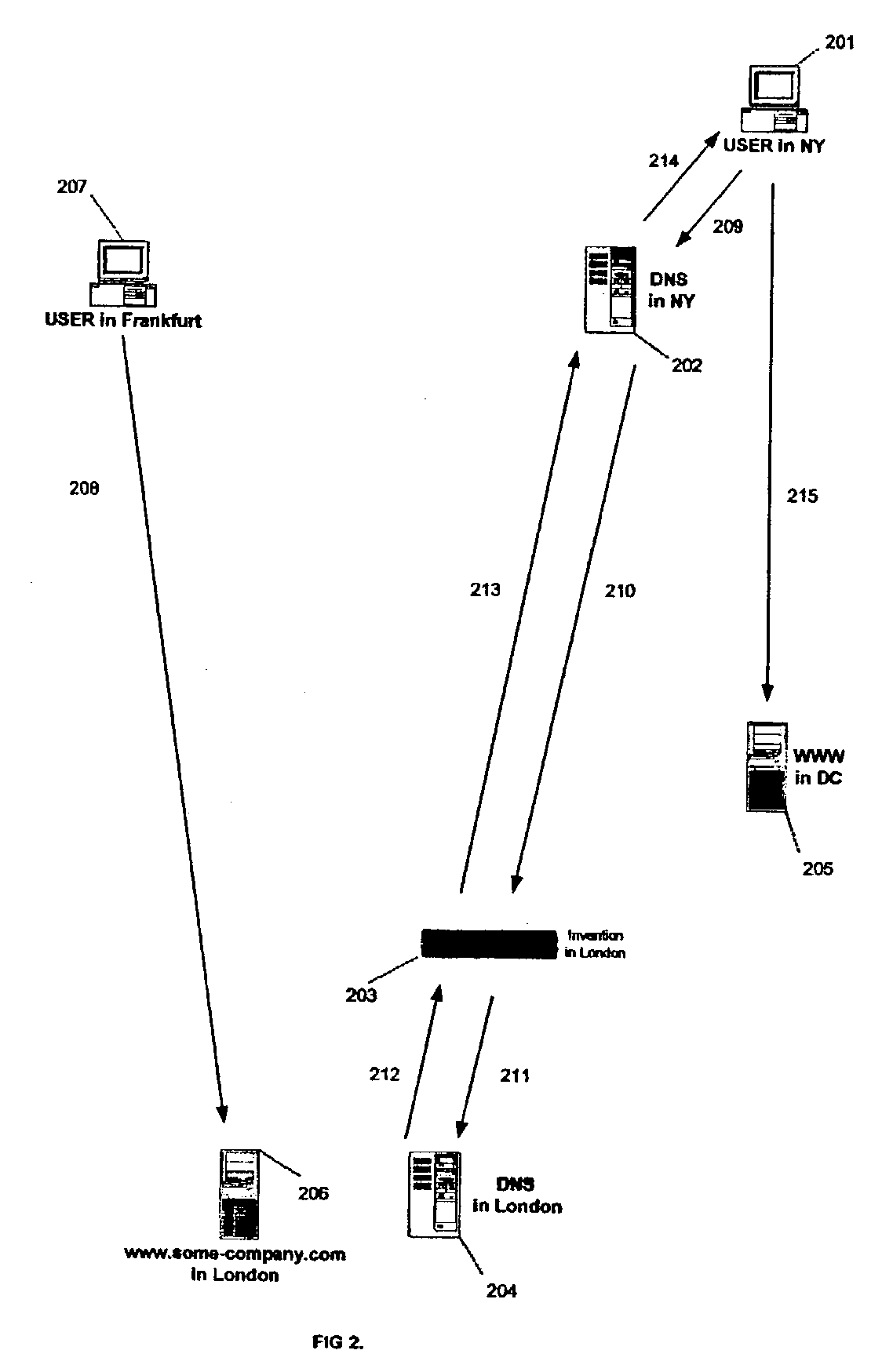
Apparatus and method for transparent selection of an Internet server based on geographic location of a user
ActiveUS7310686B2Data processing applicationsMultiple digital computer combinationsApplication serverGeolocation
This invention is an apparatus and a method that selects the optimum location of a service on the Internet according to the user's geo-location and the configuration of the invention by transparently altering the DNS messages. In the preferred embodiment, the invention operates at OSI model's data link layer and it is located in front of the DNS server so that it does not require any modification in the existing DNS or IP network setup or on the application servers. It provides a fast and transparent method of locating an Internet service without the overhead of server scripts, HTTP redirects, or extra steps by the user to find the desired location or content.
Owner:BUSHNELL HAWTHORNE
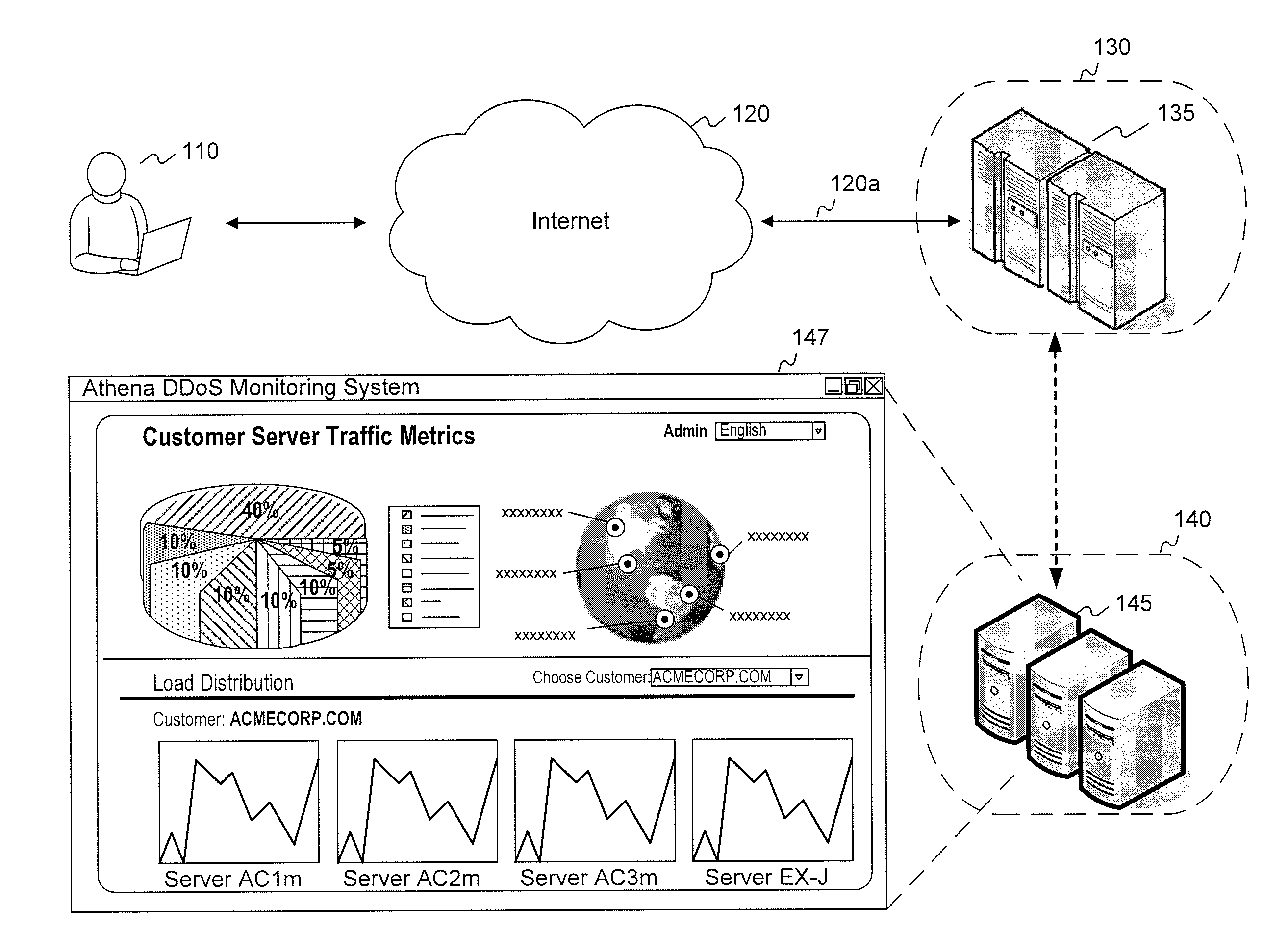
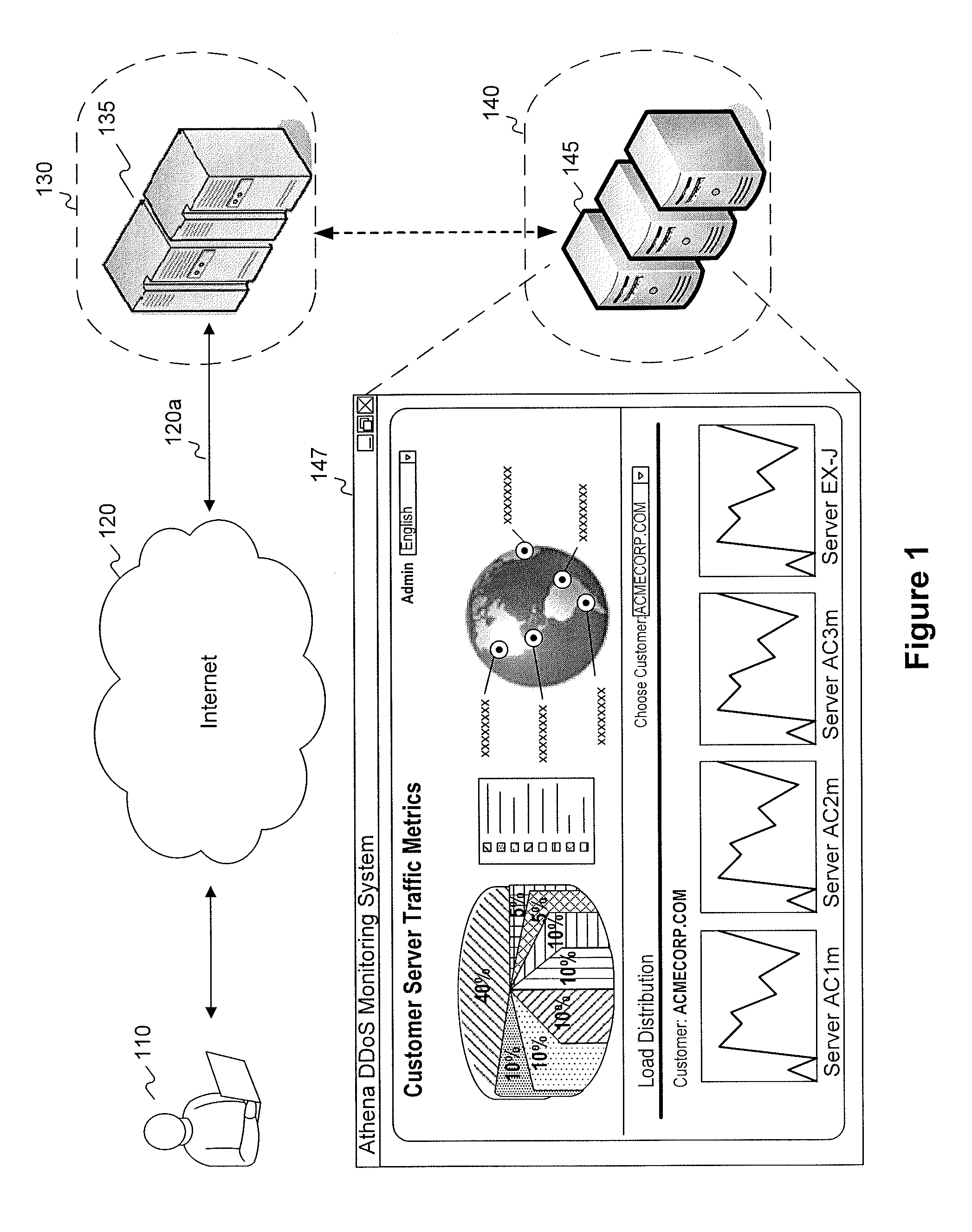
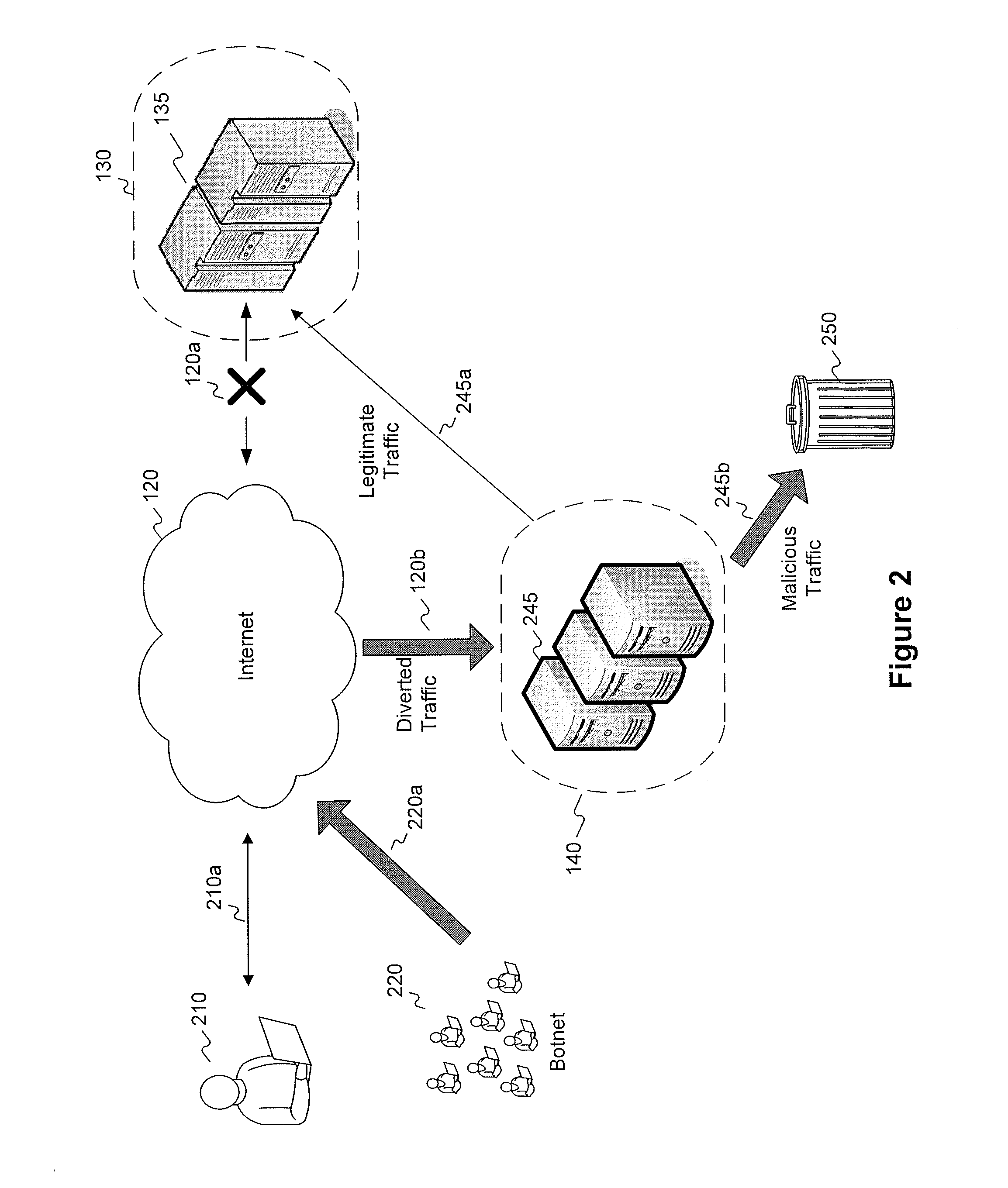
Active validation for ddos and ssl ddos attacks
InactiveUS20120174196A1Memory loss protectionError detection/correctionApplication serverClient-side
Methods and systems for detecting and responding to Denial of Service (“DoS”) attacks comprise: detecting a DoS attack or potential DoS attack against a first server system comprising one or more servers; receiving, at a second server system comprising one or more servers, network traffic directed to the first server system; subjecting requesting clients to one or more challenge mechanisms, the challenge mechanisms including one or more of challenging requesting clients to follow through HTTP redirect responses, challenging requesting clients to request Secure Sockets Layer (SSL) session resumption, or challenging requesting clients to store and transmit HTTP cookies; identifying one or more non-suspect clients, the one or more suspect clients corresponding to requesting clients that successfully complete the one or more challenge mechanisms; identifying one or more suspect clients, the one or more suspect clients corresponding to requesting clients that do not successfully complete the one or more challenge mechanisms; and forwarding, by the second server system, traffic corresponding to the one or more non-suspect clients to the first server system. Once a client has been validated, clients may communicate directly with application servers in a secure manner by transparently passing through one or more intermediary proxy servers.
Owner:VERISIGN
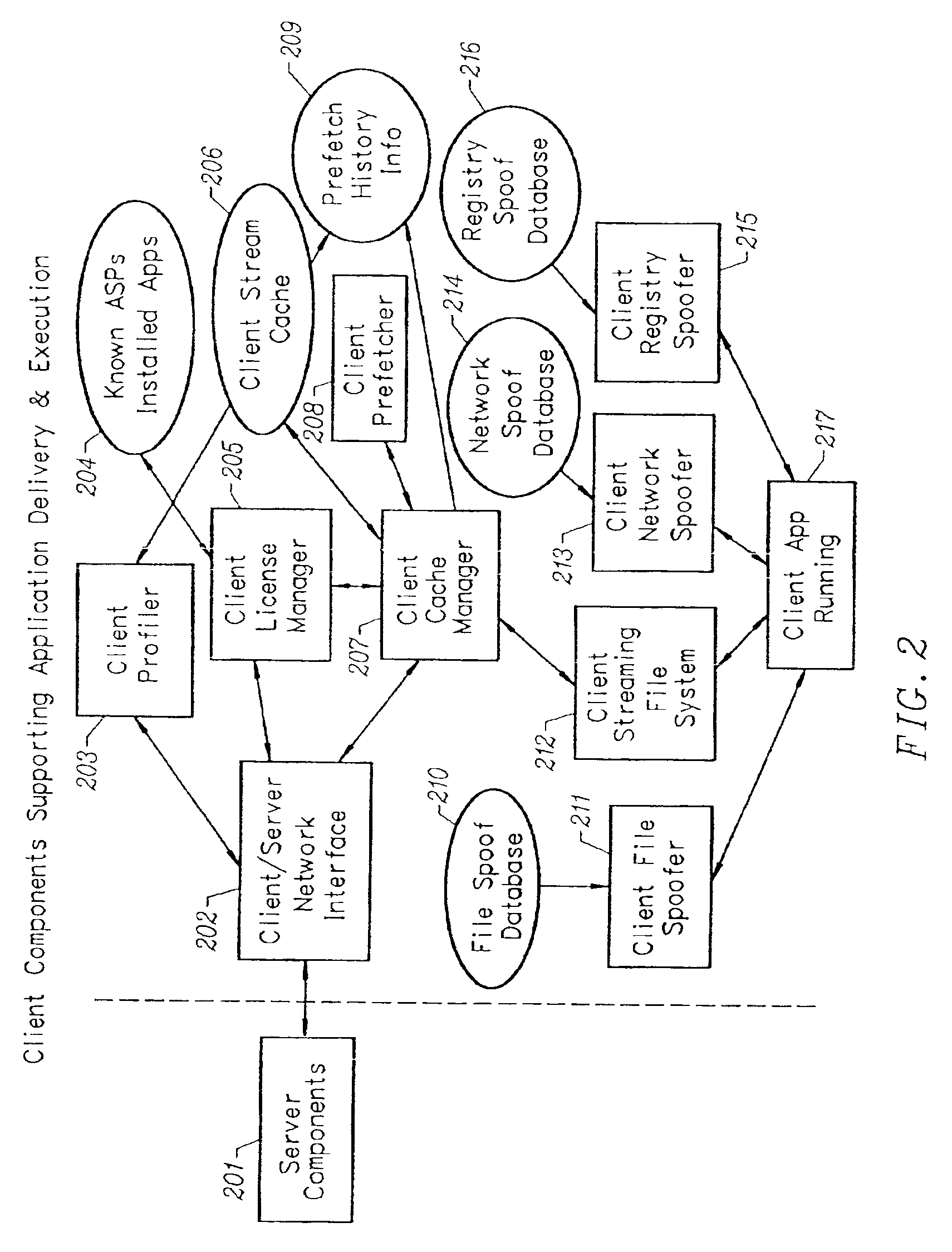
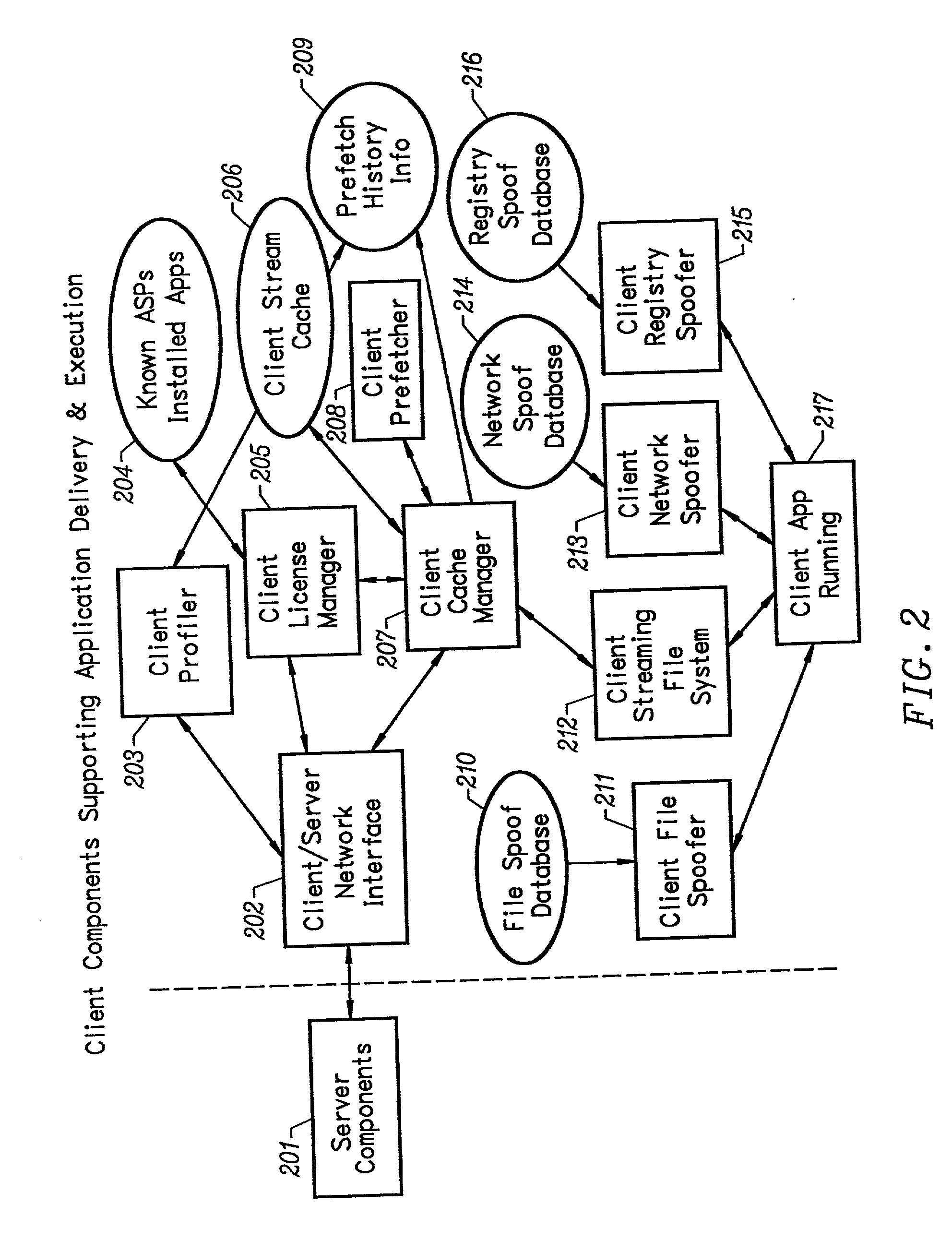
Client-side performance optimization system for streamed applications
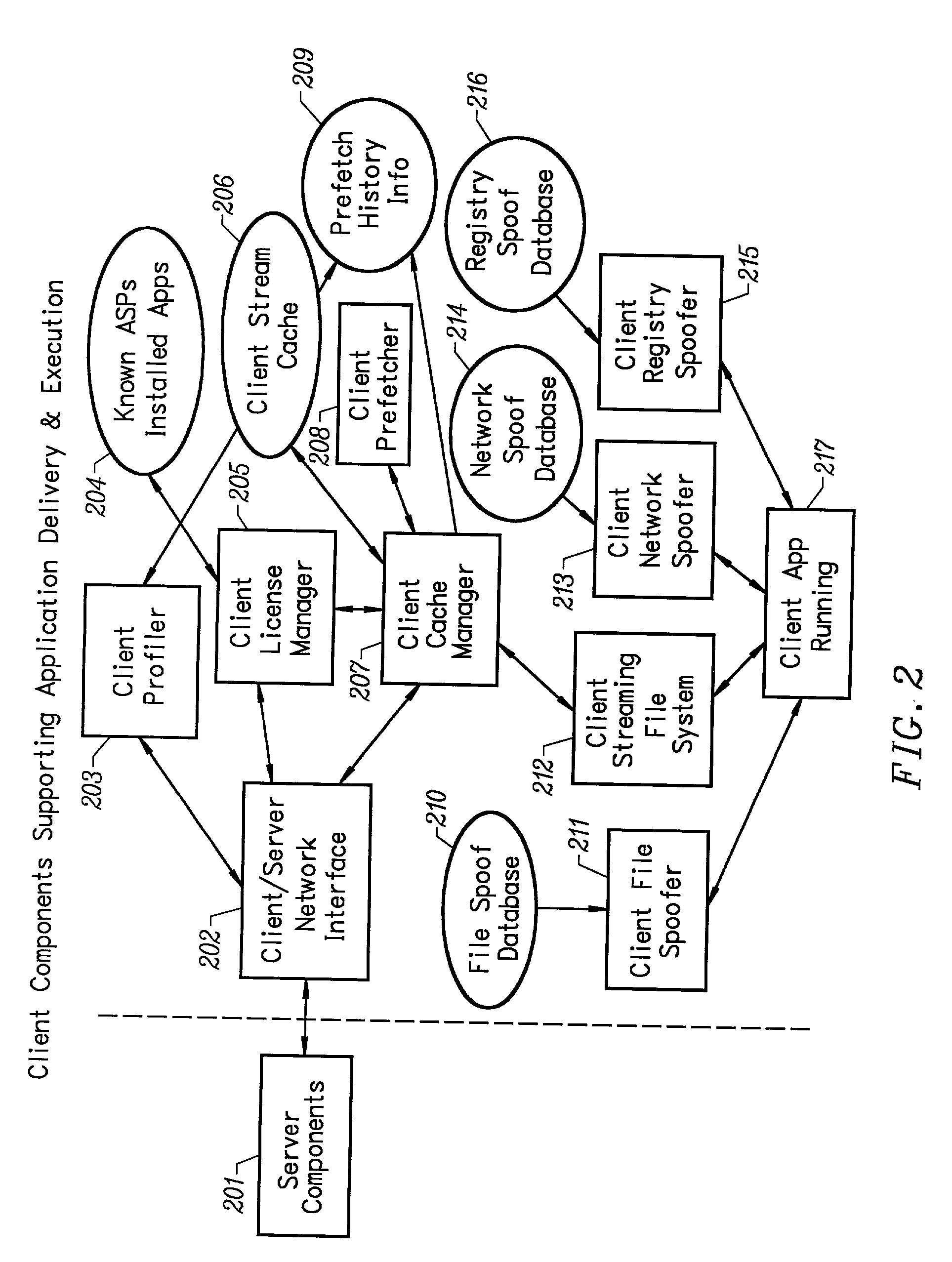
InactiveUS6959320B2Efficiently stream and executeEasily integrates into client system 's operating systemMultiple digital computer combinationsProgram loading/initiatingApplication serverData file
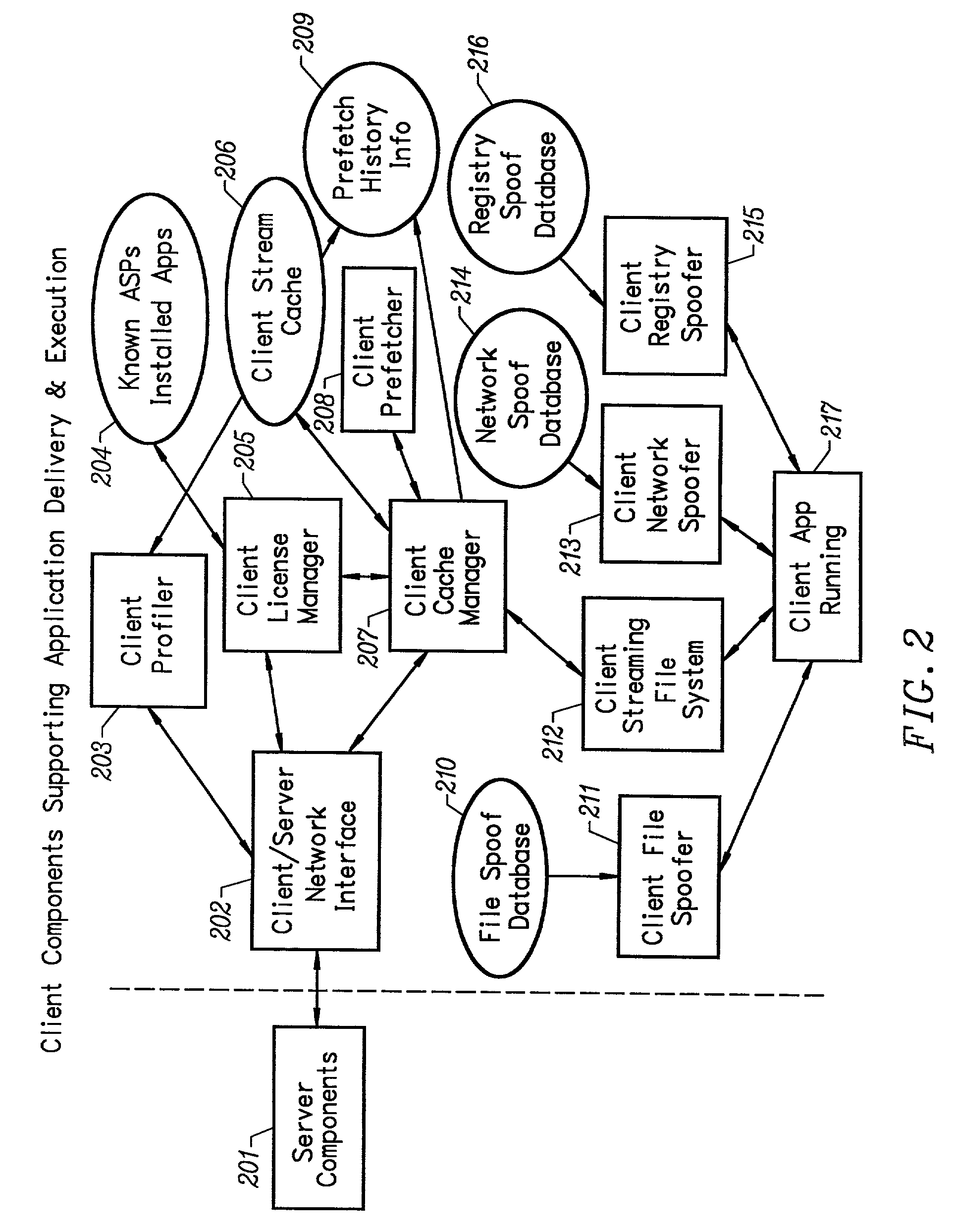
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
Systems and Methods for Facilitating Distributed Authentication
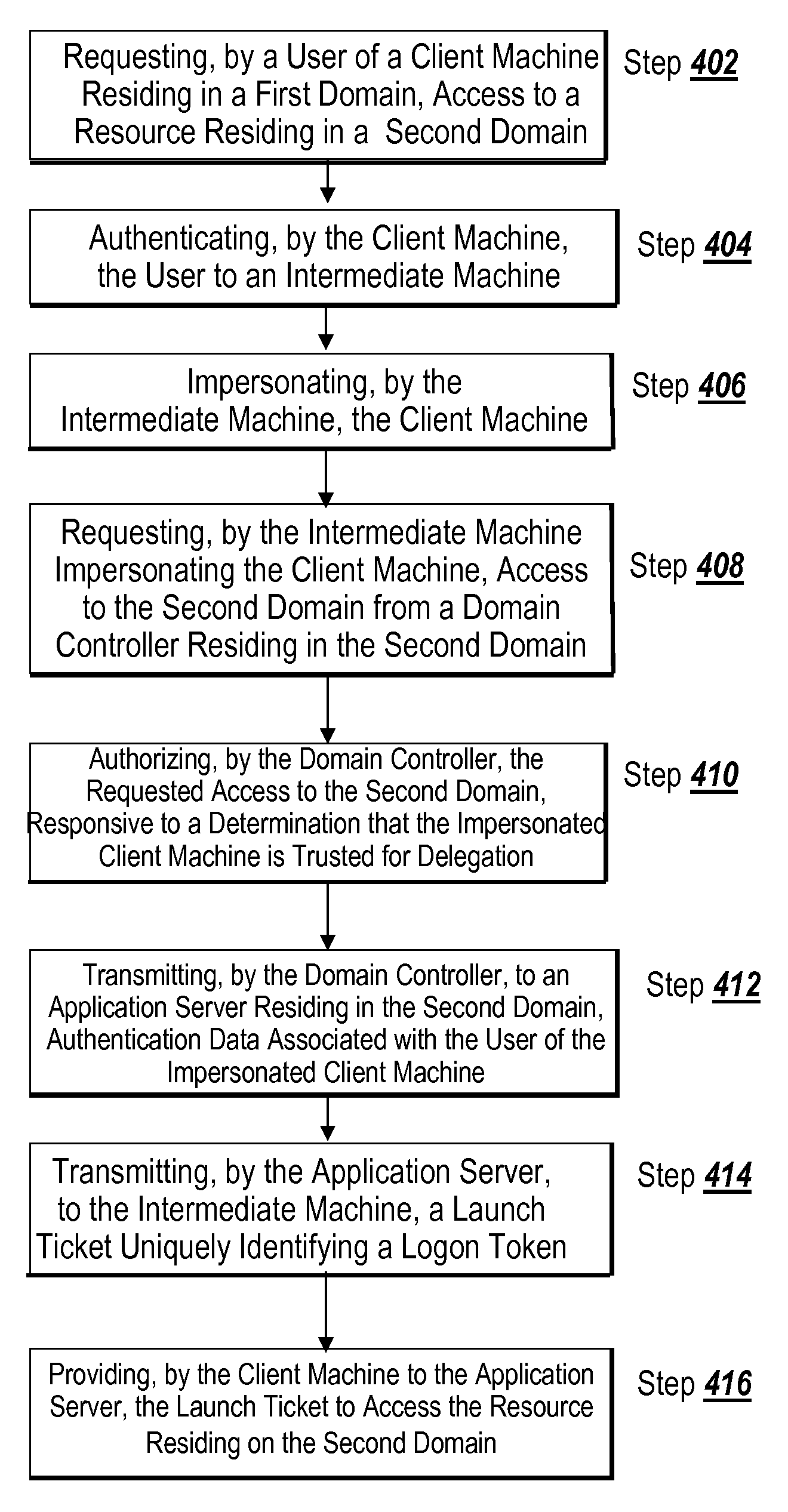
ActiveUS20070107048A1Digital data processing detailsUser identity/authority verificationApplication serverClient-side
A method for facilitating distributed authentication includes the step of requesting, by a user of a client machine residing in a first domain, access to a resource residing in a second domain. The client machine authenticates the user to an intermediate machine. The intermediate machine impersonates the client machine. The intermediate machine impersonating the client machine requests access to the second domain from a domain controller residing in the second domain. The domain controller authorizes the requested access, responsive to a determination that the impersonated client machine is trusted for delegation. The domain controller transmits to an application server residing in the second domain, authentication data associated with the impersonated client machine. The application server transmits, to the intermediate machine, a launch ticket uniquely identifying a logon token. The client machine provides, to the application server, the launch ticket to access the resource residing in the second domain.
Owner:CITRIX SYST INC
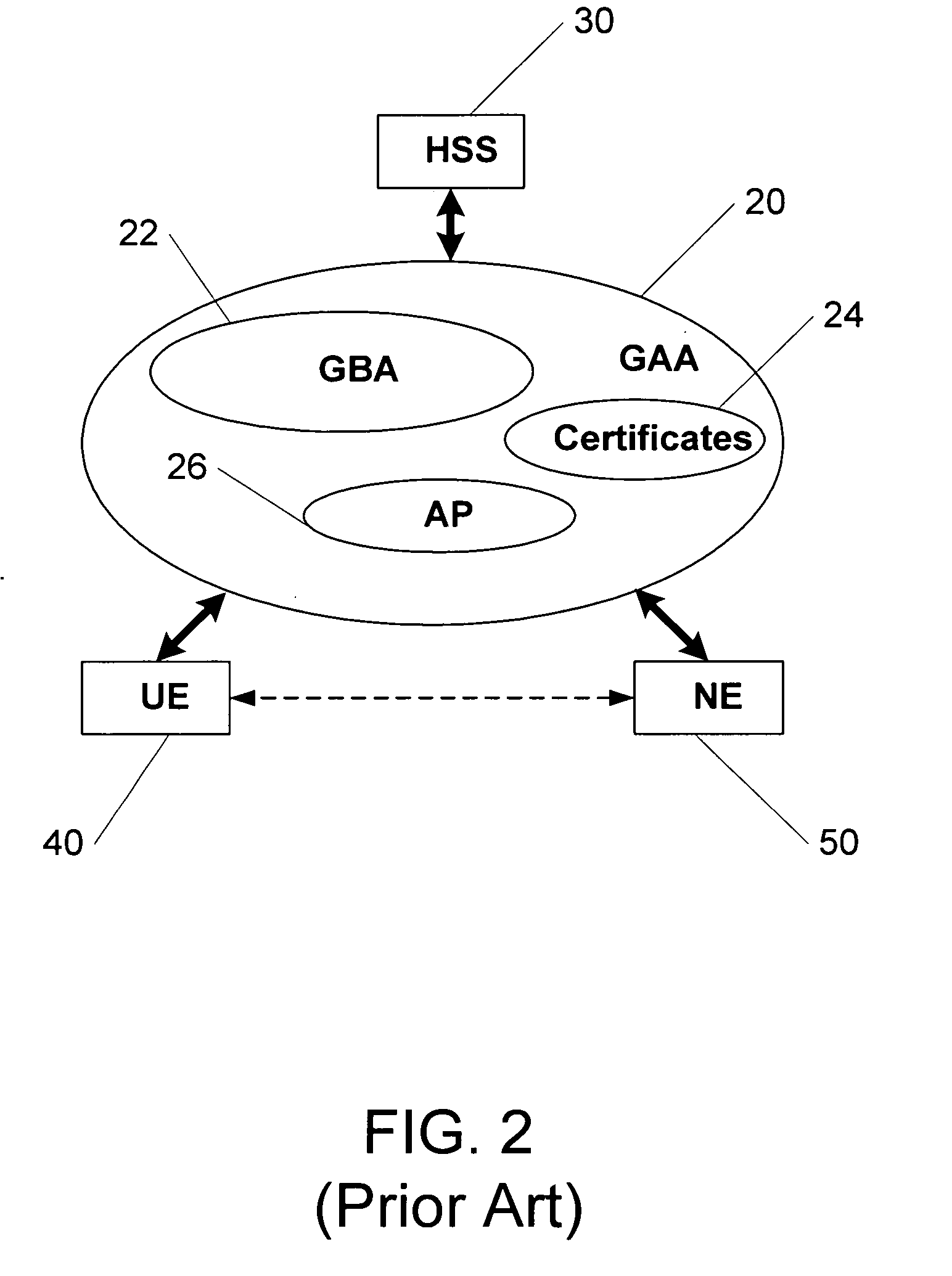
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
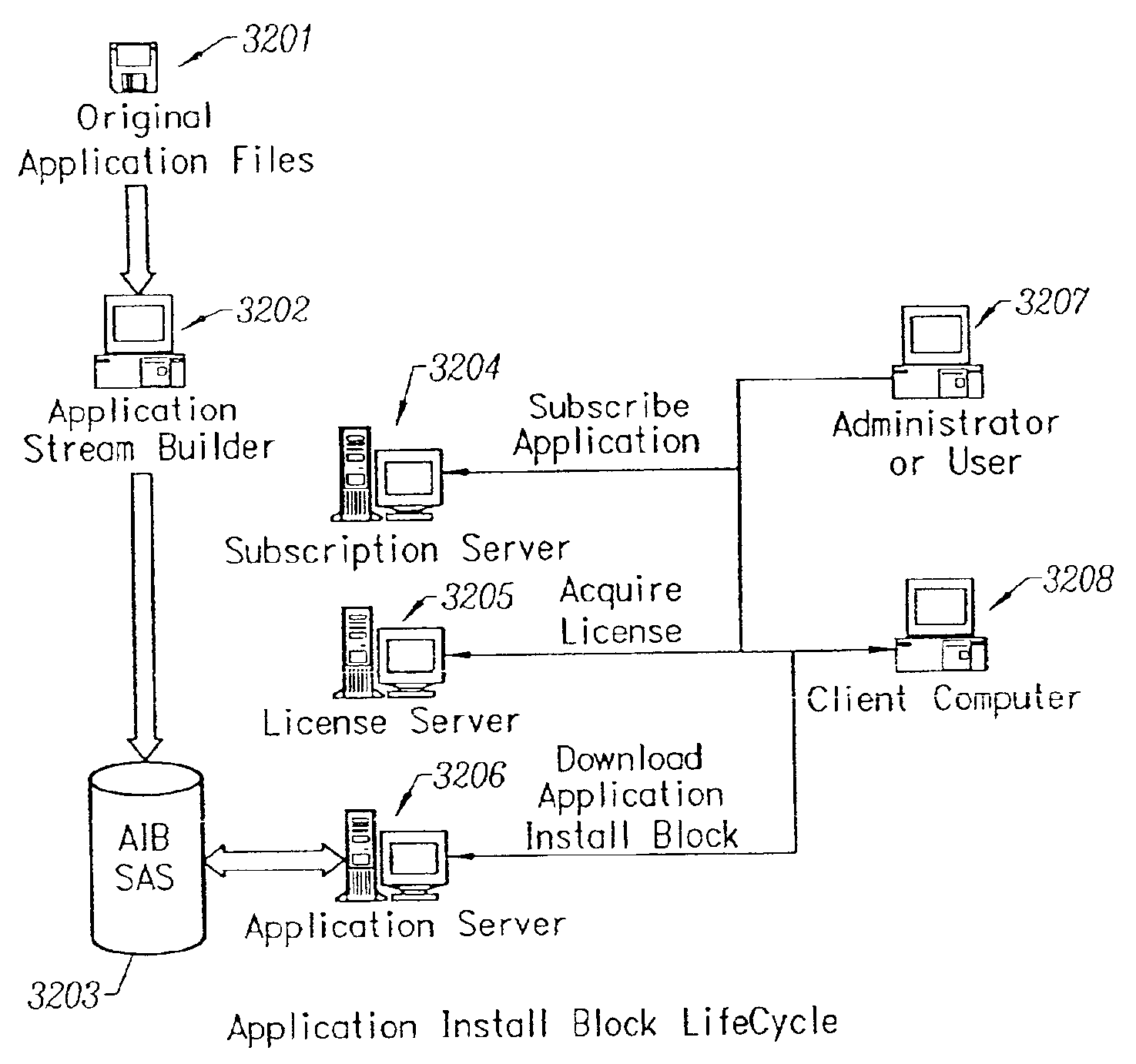
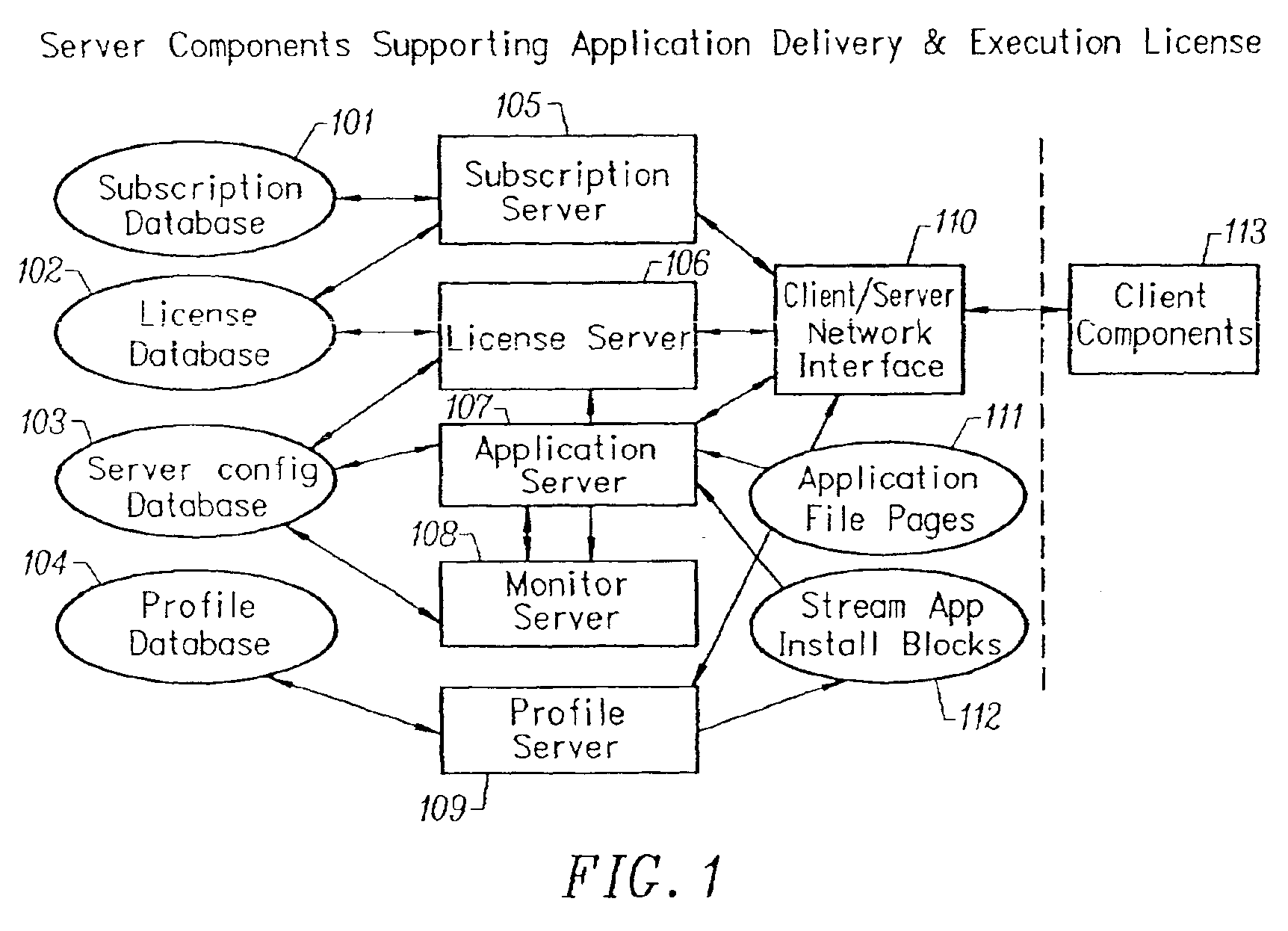
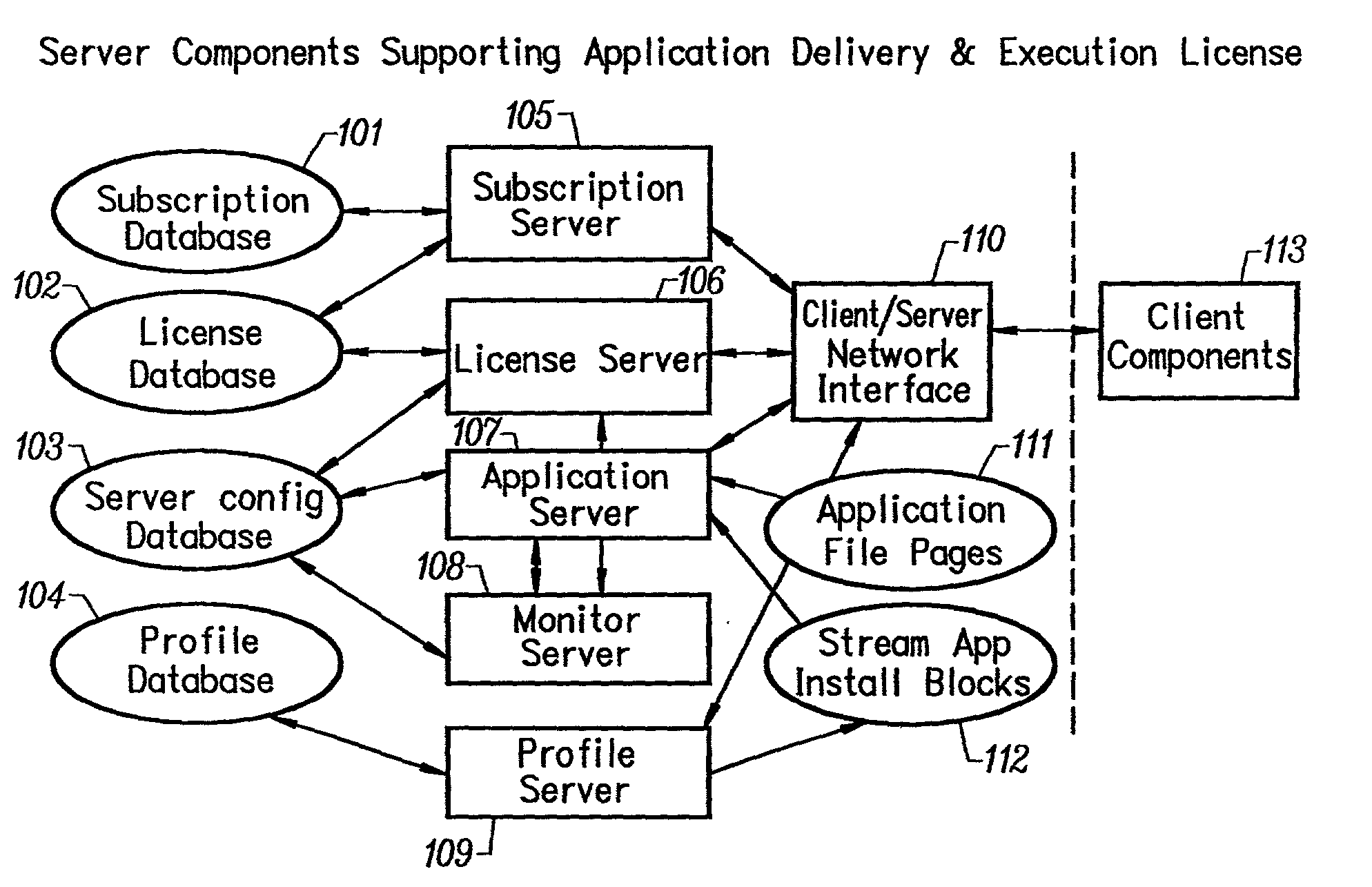
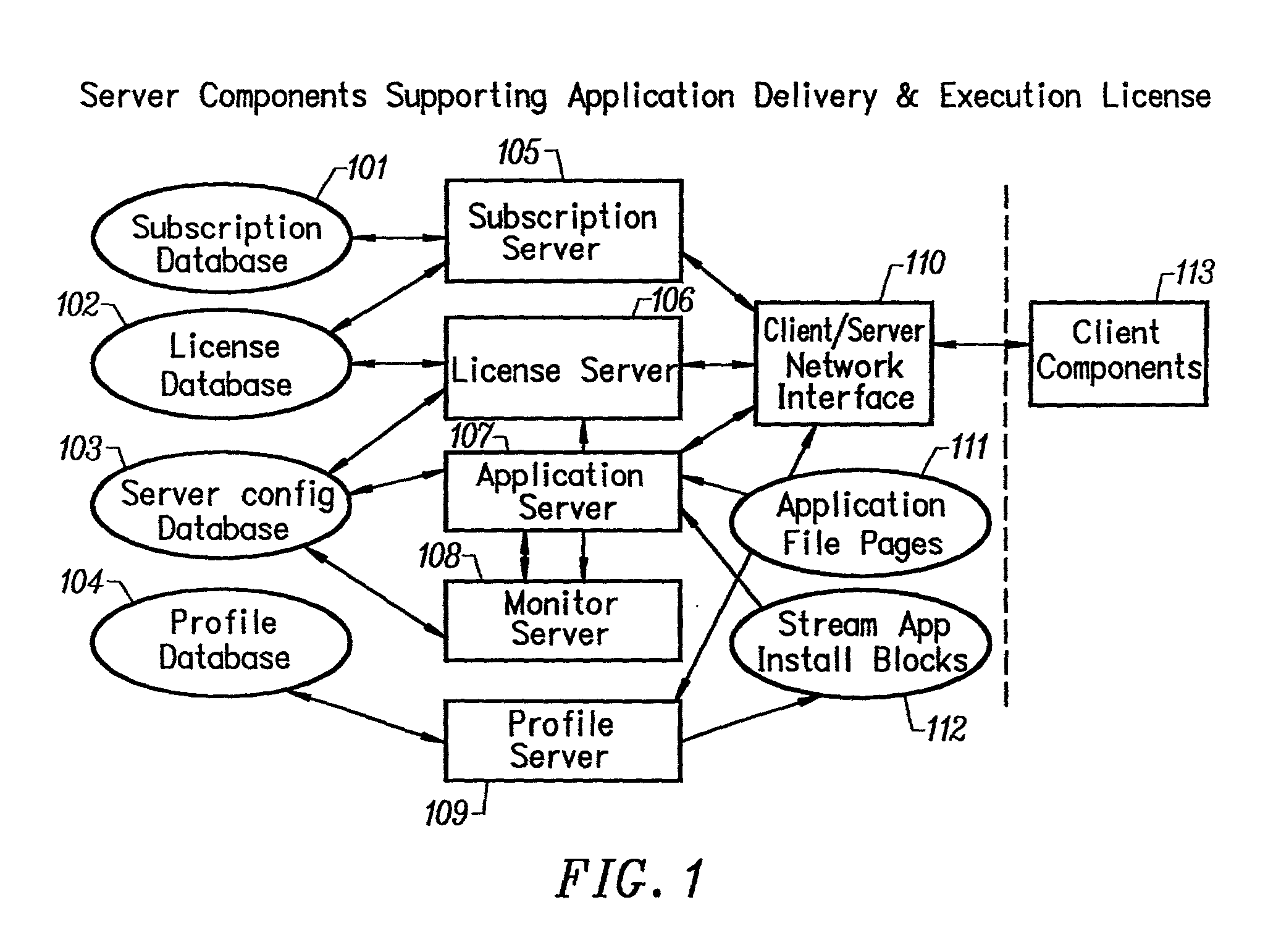
Intelligent network streaming and execution system for conventionally coded applications
InactiveUS7062567B2Multiple digital computer combinationsDigital data authenticationIntelligent NetworkApplication server
An intelligent network streaming and execution system for conventionally coded applications provides a system that partitions an application program into page segments by observing the manner in which the application program is conventionally installed. A minimal portion of the application program is installed on a client system and the user launches the application in the same ways that applications on other client file systems are started. An application program server streams the page segments to the client as the application program executes on the client and the client stores the page segments in a cache. Page segments are requested by the client from the application server whenever a page fault occurs from the cache for the application program. The client prefetches page segments from the application server or the application server pushes additional page segments to the client based on the pattern of page segment requests for that particular application. The user subscribes and unsubscribes to application programs, whenever the user accesses an application program a securely encrypted access token is obtained from a license server if the user has a valid subscription to the application program. The application server begins streaming the requested page segments to the client when it receives a valid access token from the client. The client performs server load balancing across a plurality of application servers. If the client observes a non-response or slow response condition from an application server or license server, it switches to another application or license server.
Owner:NUMECENT HLDG
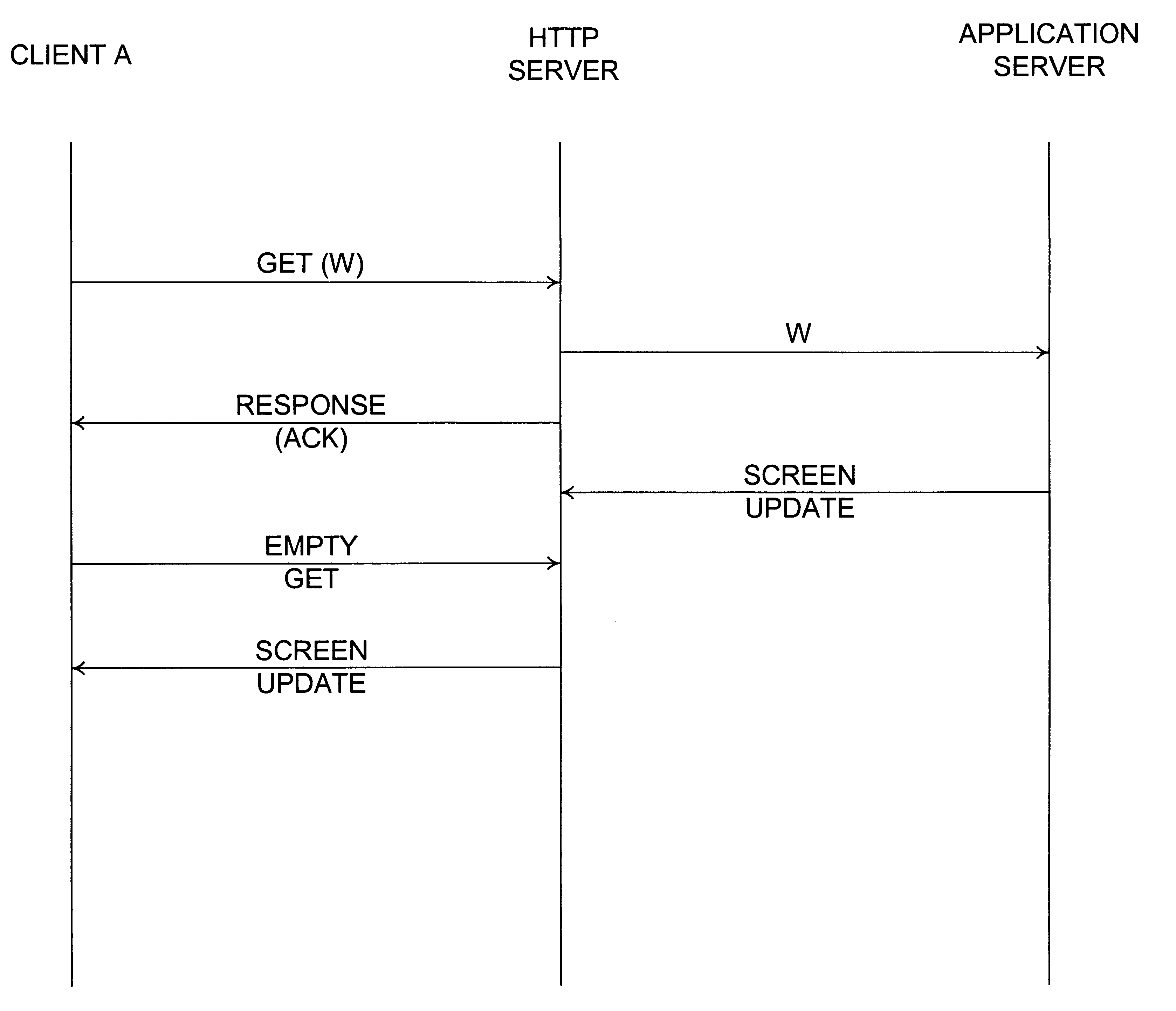
Emulating a persistent connection using http
InactiveUS6789119B1Optimize networkIncrease the burdenMultiple digital computer combinationsSecuring communicationApplication serverComputer science
An apparatus, method and computer program product for emulating a persistent connection using http. According to one embodiment, the method includes receiving an empty get from a first client; receiving a get from a second client, the get containing data to be sent to the first client; and sending a response to the first client, in response to the empty get, the response containing the data. According to another embodiment, the method includes receiving, from a client, a get containing first data to be sent to an application server; sending the first data to the application server; sending an ack response to the client in response to the get; receiving a response from the application server, the response containing second data to be sent to the client; waiting for an empty get from the client; receiving an empty get from the client; and sending the second data to the client in response to the empty get. According to another embodiment, the method includes receiving, from a client, a get containing first data to be sent to an application server; sending the first data to the application server; sending an ack response to the client in response to the get; receiving an empty get from the client; receiving a response from the application server, the response containing second data to be sent to the client; and sending the second data to the client in response to the empty get.
Owner:CISCO TECH INC +1
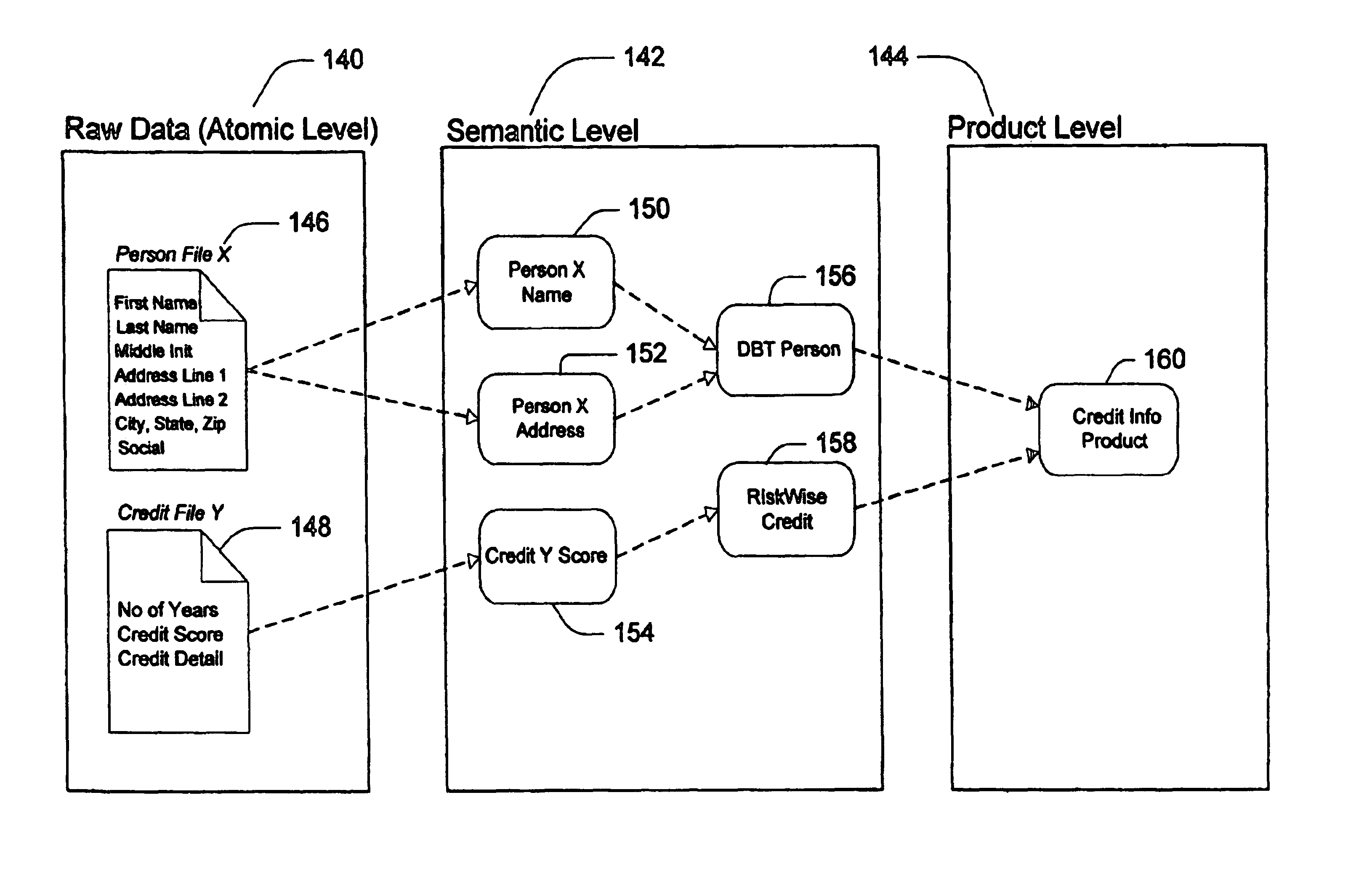
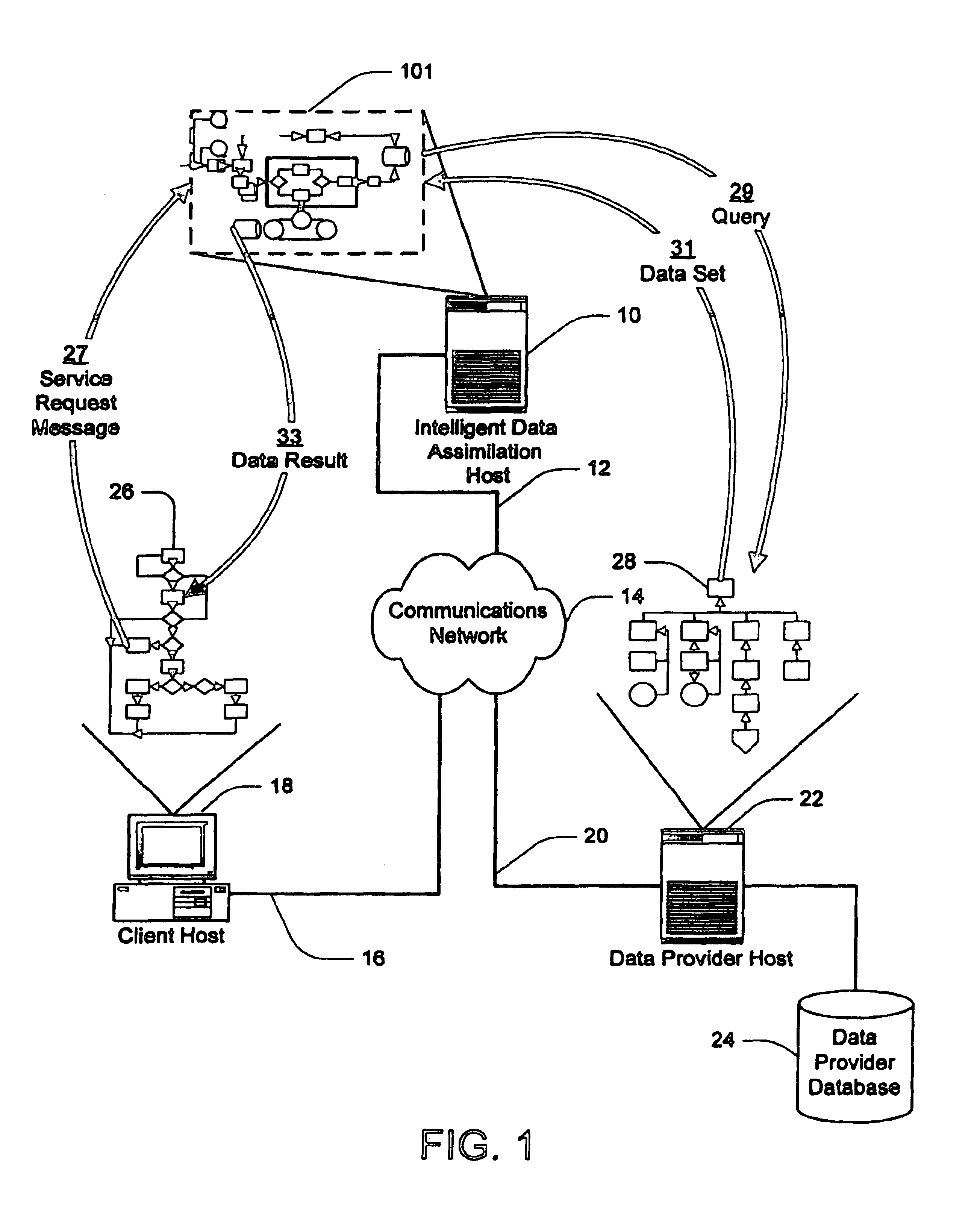
Method and apparatus for intelligent data assimilation
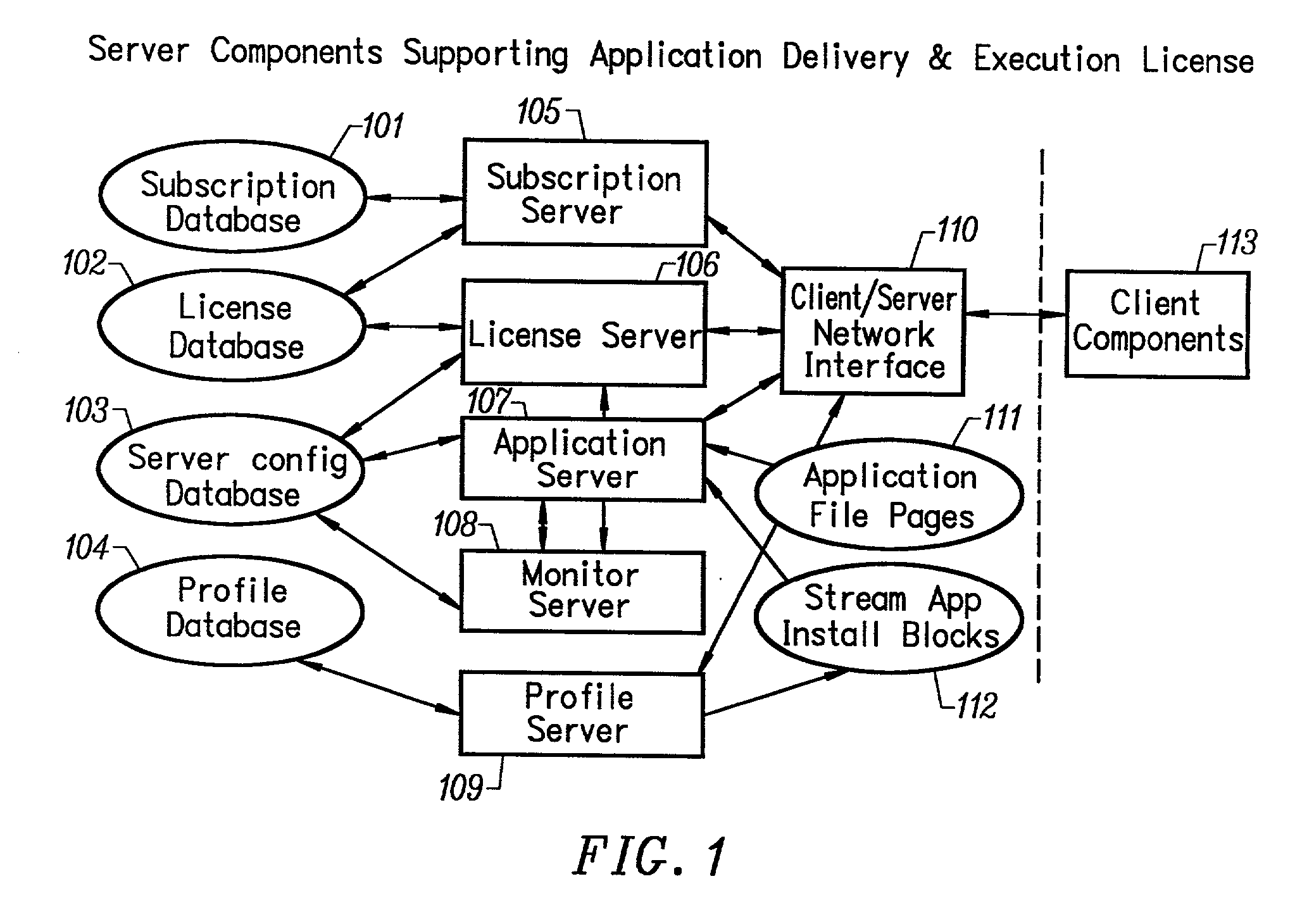
InactiveUS6847974B2Data processing applicationsWebsite content managementGraphical user interfaceApplication server
An intelligent data assimilation system including an ontology description, workflows, and logical search objects. The logical search objects operably connect to external and internal data providers and return search results using an ontology describing atomic data objects and semantic objects. The semantic objects are grouped into larger semantic structures by workflows to create customized services that return search results termed data products. Services are accessed through an application server capable of responding to service requests from different types of data clients. Graphical user interfaces provide facilities for creating logical search objects and aggregating logical search objects into workflows and services.
Owner:US SEARCH COM
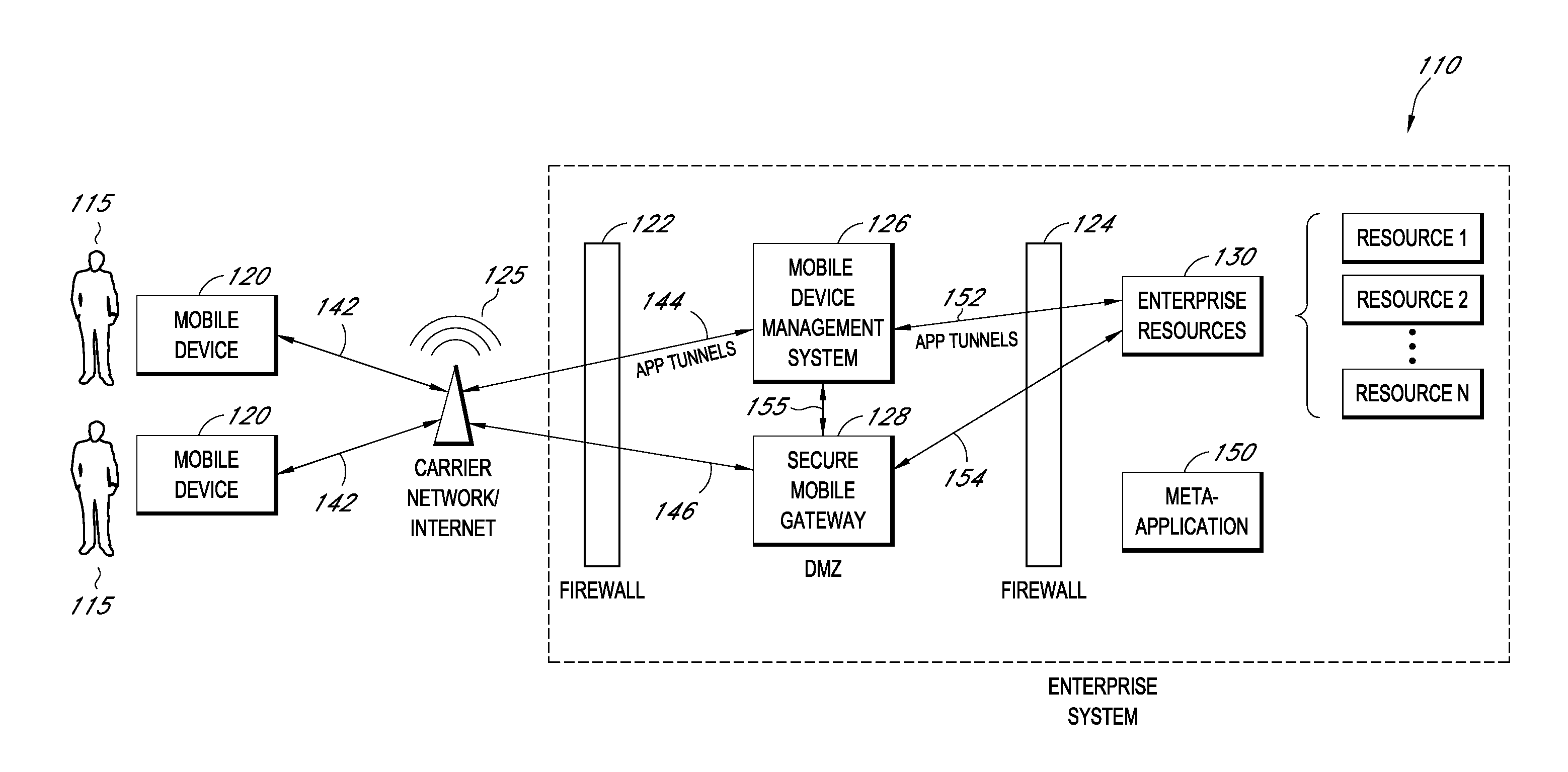
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
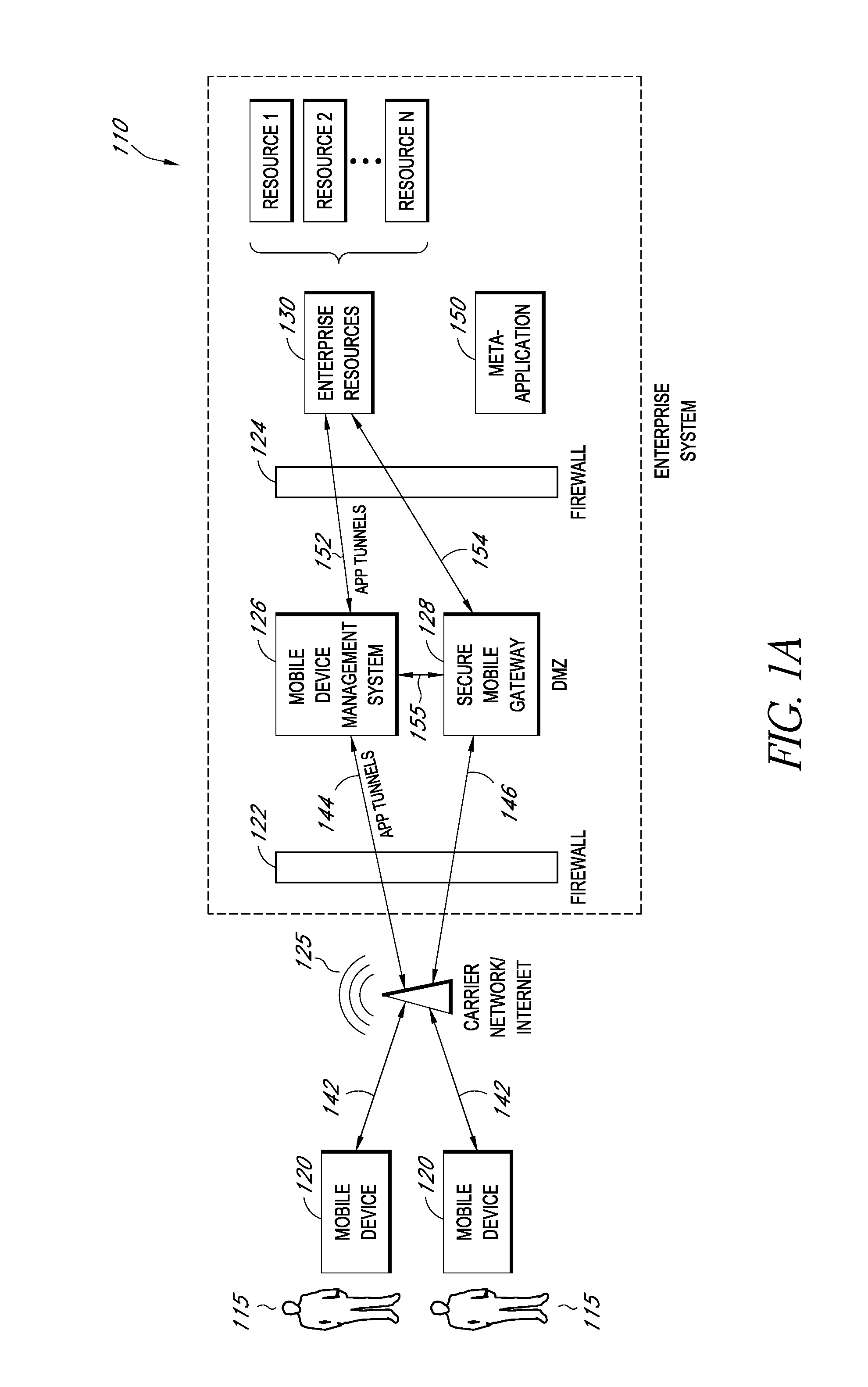
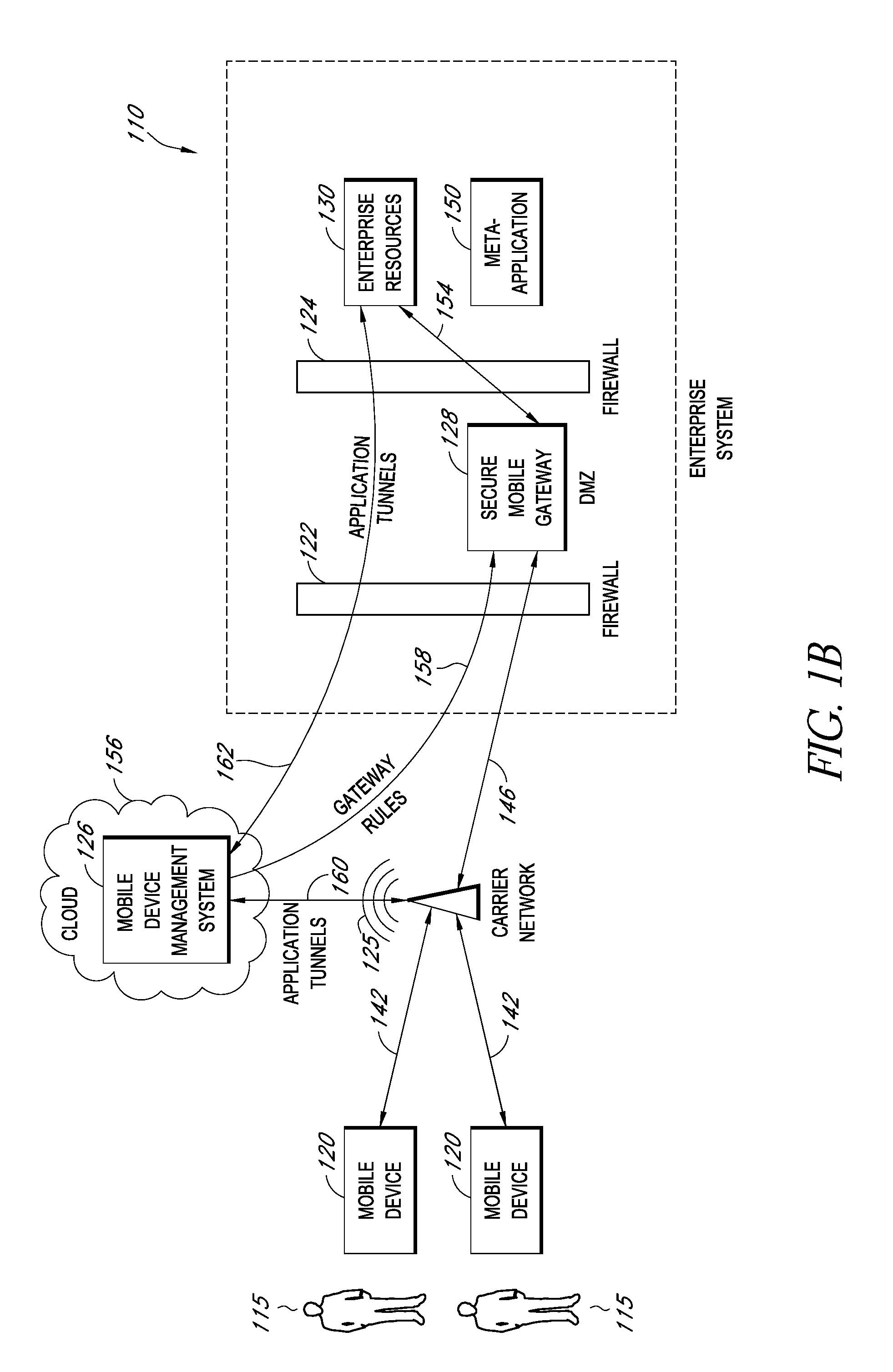
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Systems and methods for IMS user sessions with dynamic service selection
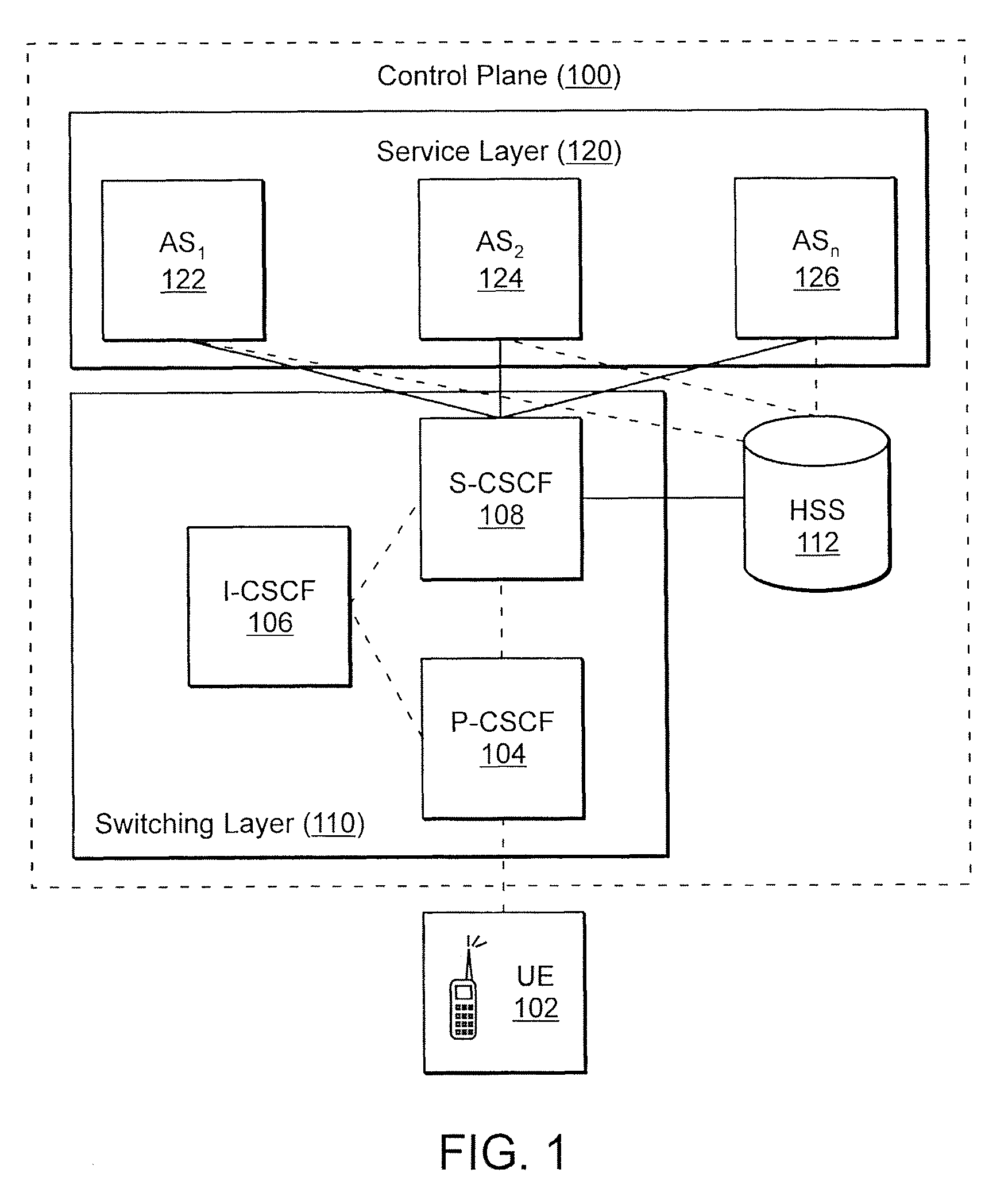
ActiveUS7856226B2Multiplex system selection arrangementsSpecial service provision for substationApplication serverSession control
Owner:AYLUS NETWORKS
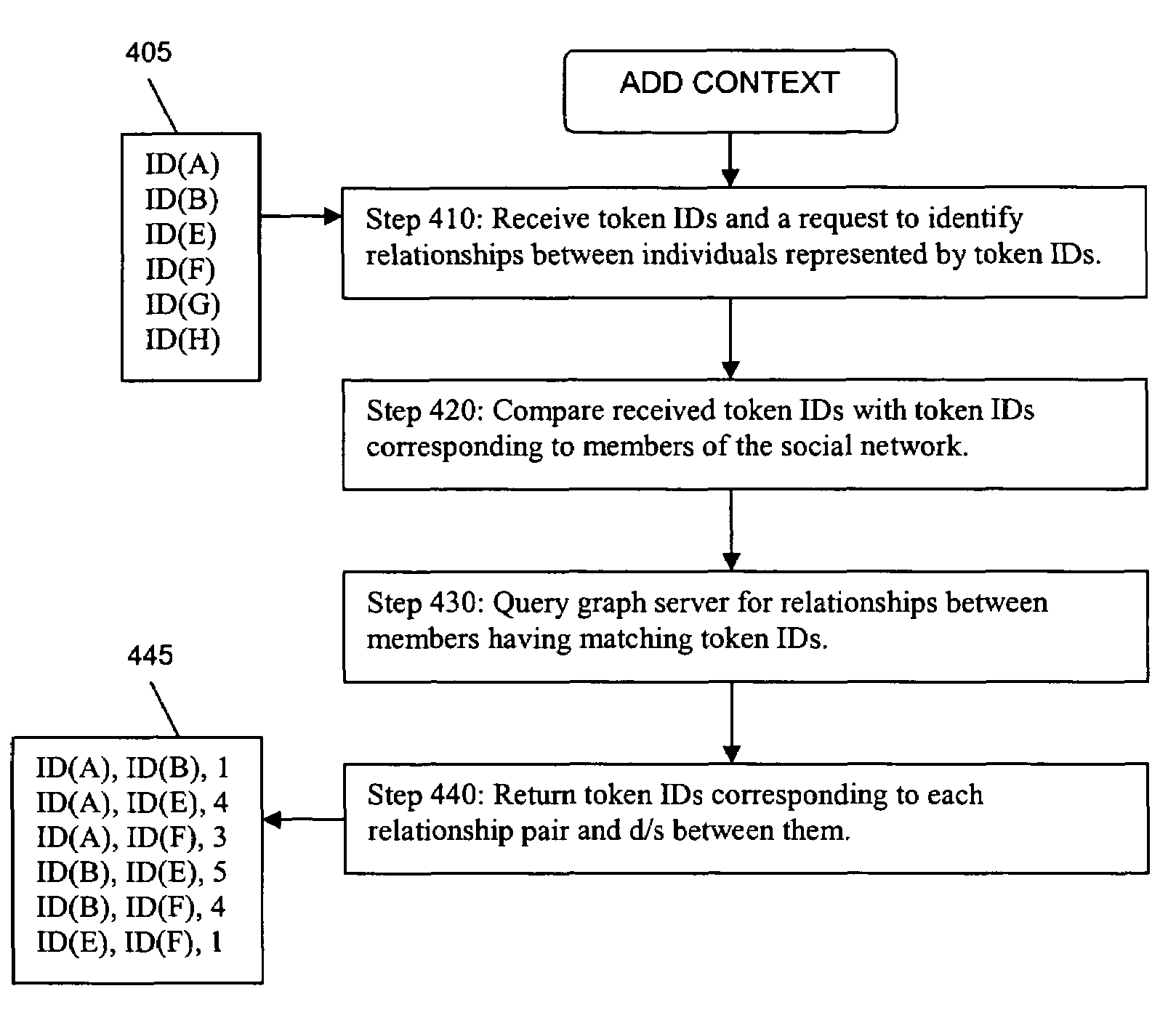
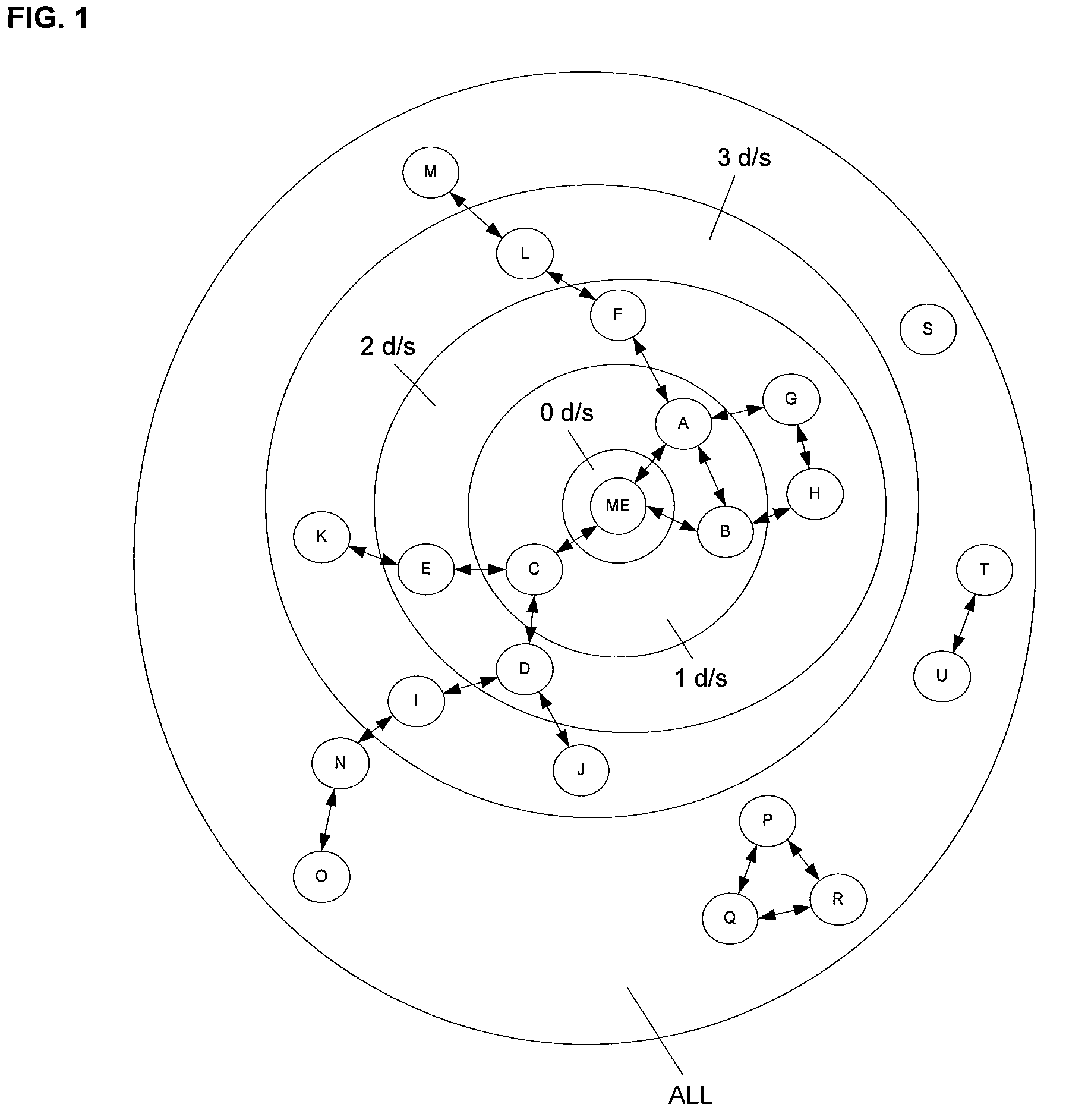
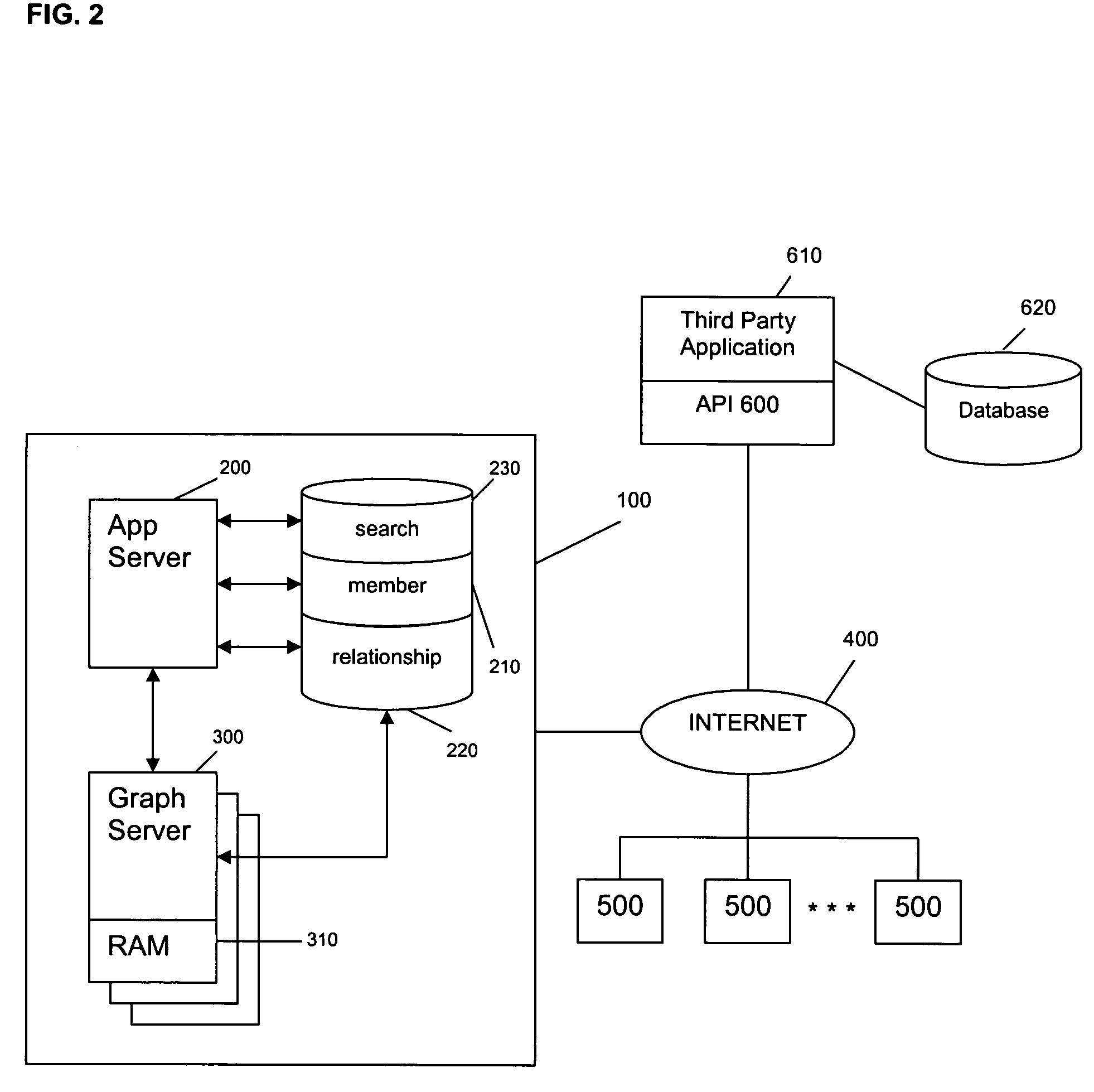
Method for sharing relationship information stored in a social network database with third party databases
Social network information maintained in a first database is shared with a second database. The operators of the second database use the social network information to better manage services provided to their customers and target particular information to their customers. The process begins with a request made to an application server of the first database by an application server of the second database, for social network information relevant to a set of individuals. The request includes identifying information of each individual in the set. The first database is then searched for matches with the identifying information in the request. If matches are found, the social network information relevant to those individuals for whom matches are found is shared with the second database.
Owner:META PLATFORMS INC
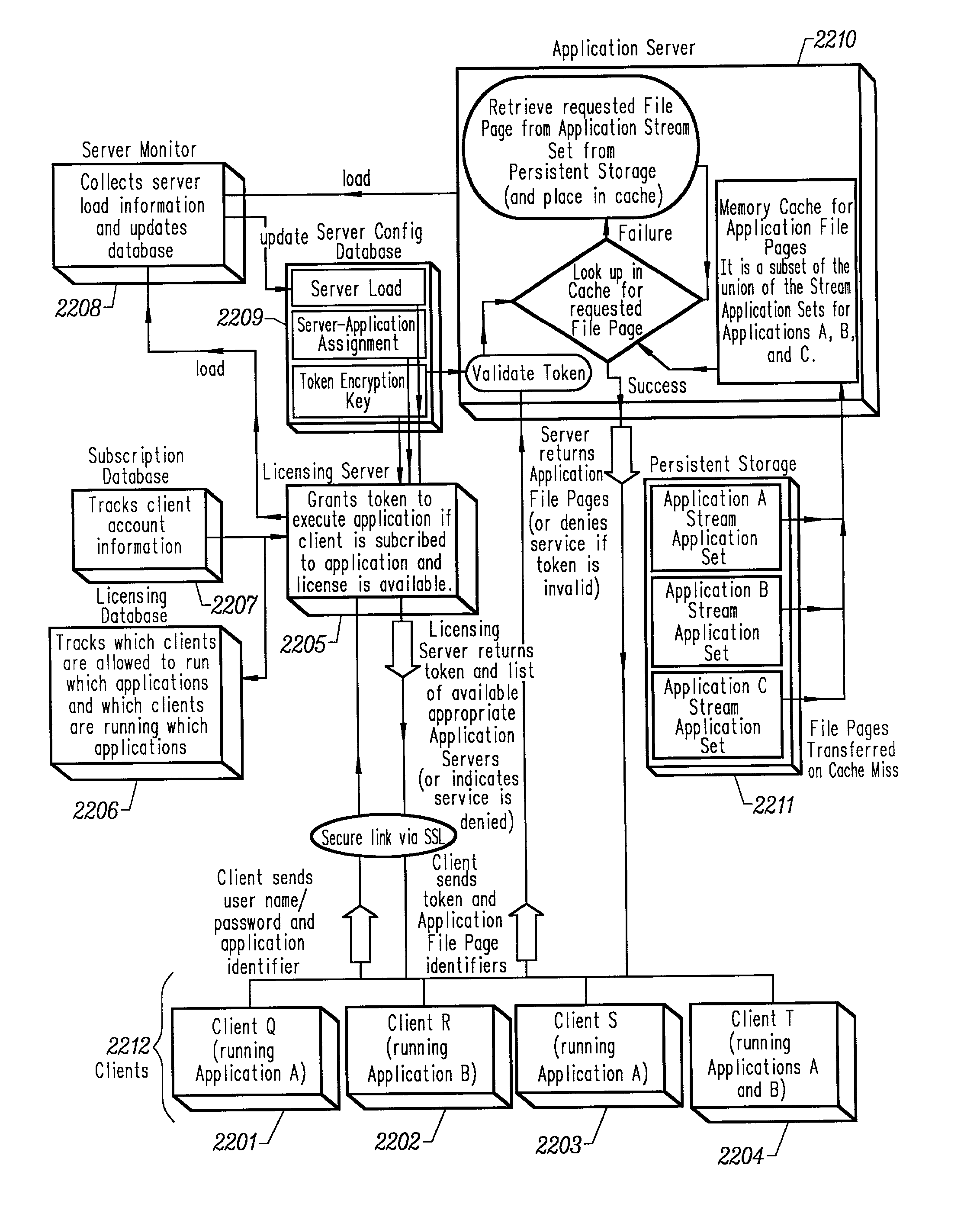
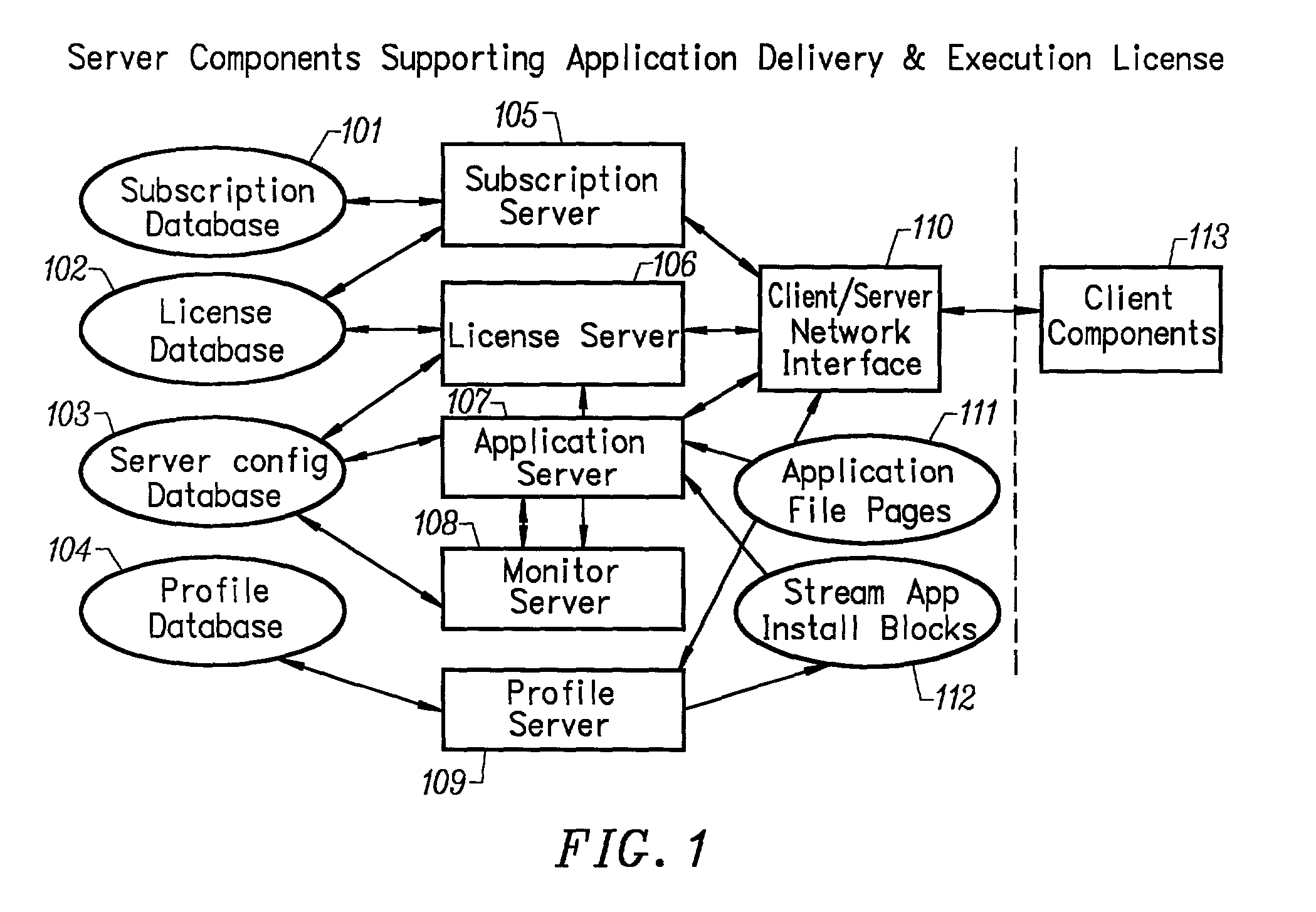
Optimized server for streamed applications
ActiveUS20030004882A1Efficient deliveryEasy maintenanceComputer security arrangementsSecret communicationApplication serverThe Internet
An optimized server for streamed applications provides a streamed application server optimized to provide efficient delivery of streamed applications to client systems across a computer network such as the Internet. The server persistently stores streamed application program sets that contain streamed application file pages. Client systems request streamed application file pages from the server using a unique set of numbers common among all servers that store the particular streamed application file pages. A license server offloads the streamed application server by performing client access privilege validations. Commonly accessed streamed application file pages are stored in a cache on the streamed application server which attempts to retrieve requested streamed application file pages from the cache before retrieving them from persistent storage. Requested streamed application file pages are compressed before being sent to a client as well as those stored in the cache.
Owner:NUMECENT HLDG
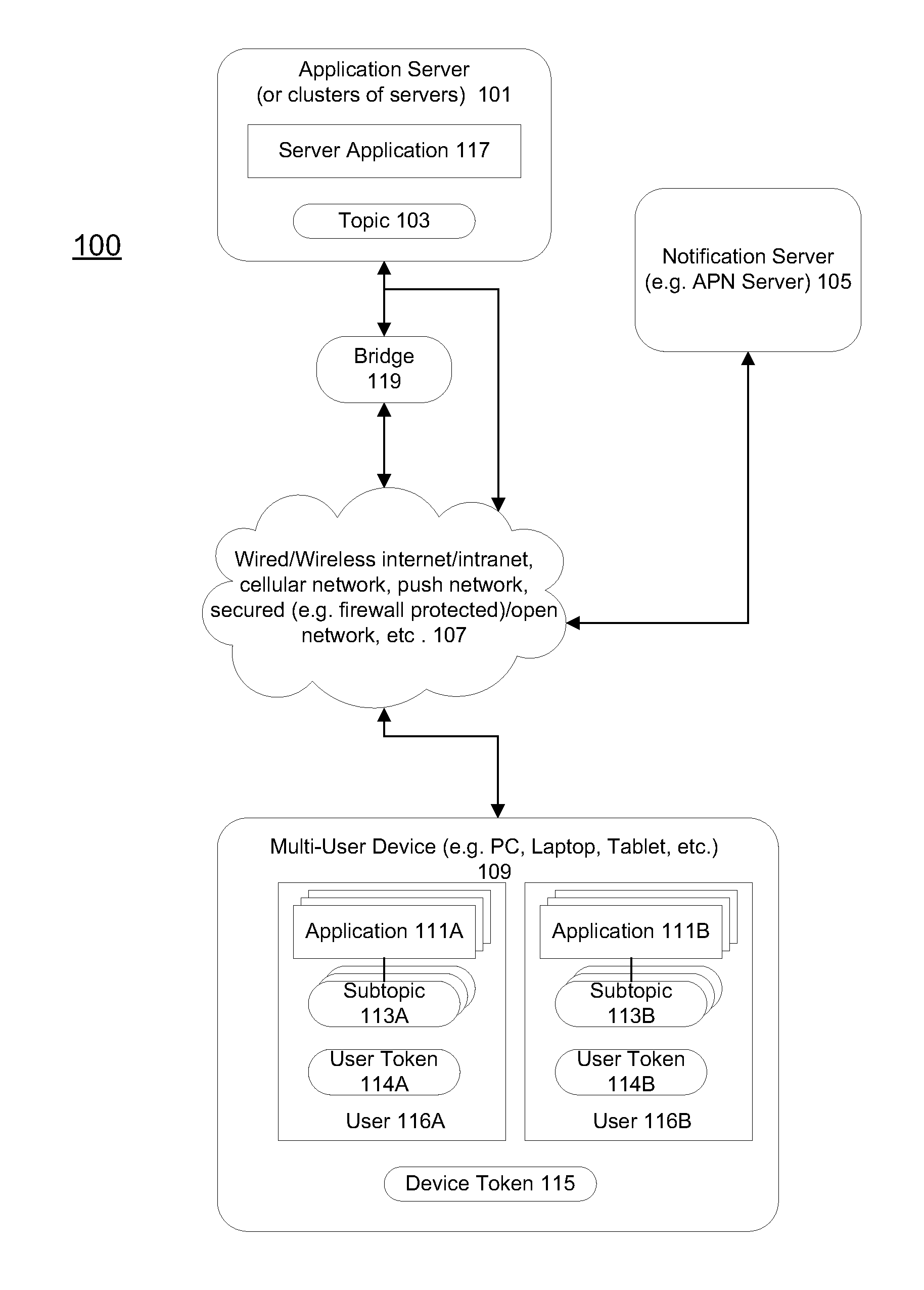
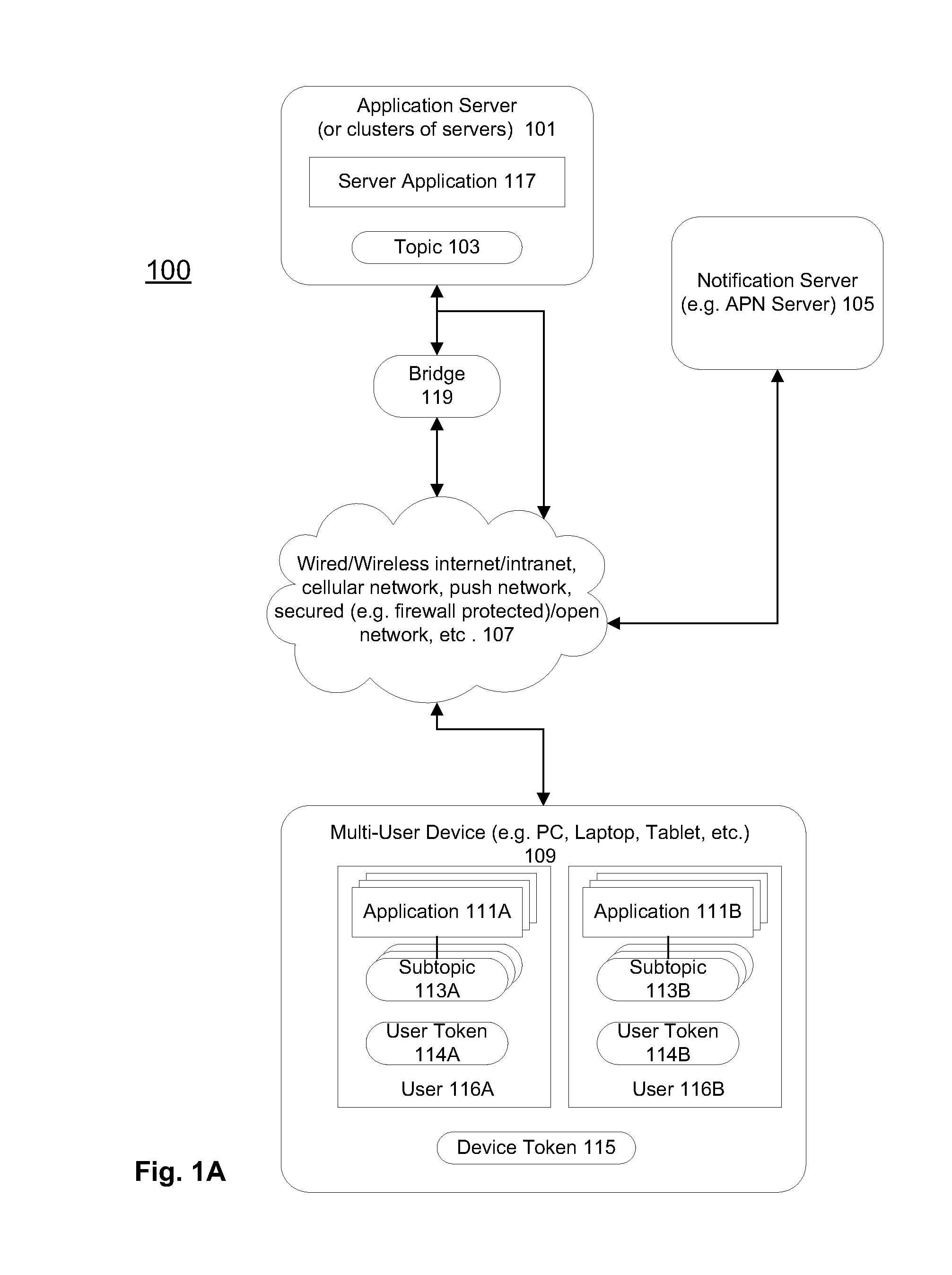
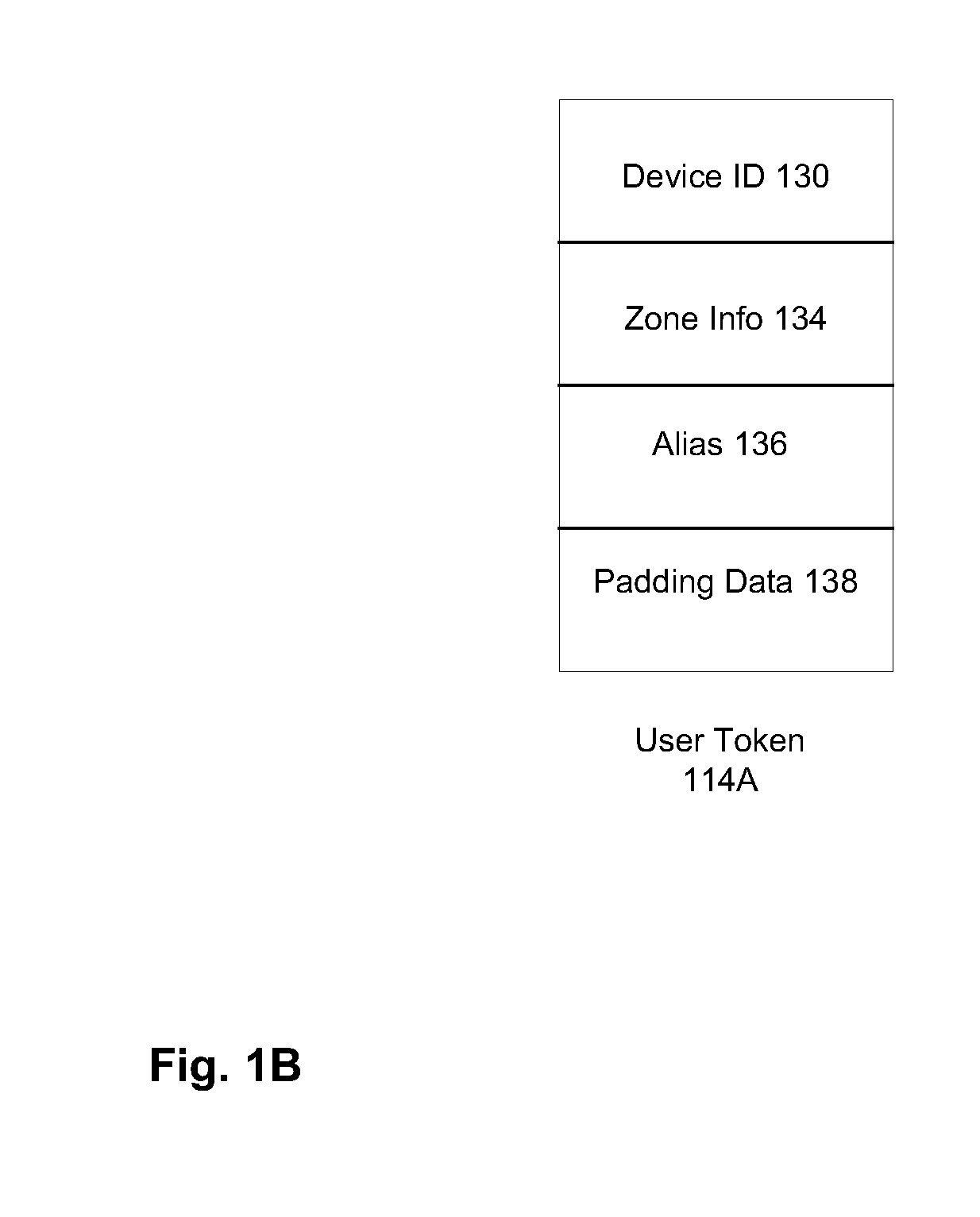
Message Push Notification Client Improvements For Multi-User Devices
ActiveUS20120173610A1Efficient deliveryMinimizing resource usageSpecial service provision for substationMultiple digital computer combinationsApplication serverClient-side
Methods and apparatuses that generate a subtopic identifier identifying a client application within a client device that can support multiple users are described. The client application may be associated with a server application hosted in one or more application servers. Notification services may be registered with the application servers from the client application to forward identifiers associated with the client application for one of the multiple users to the server application to enable the server application to push notification messages to the client device selectively for the client application for that user. When receiving a notification message from the application server, the notification message may be examined to forward the notification message directly to the client application for that user without invoking other applications in the client device if the notification message carries a subtopic identifier of the client application.
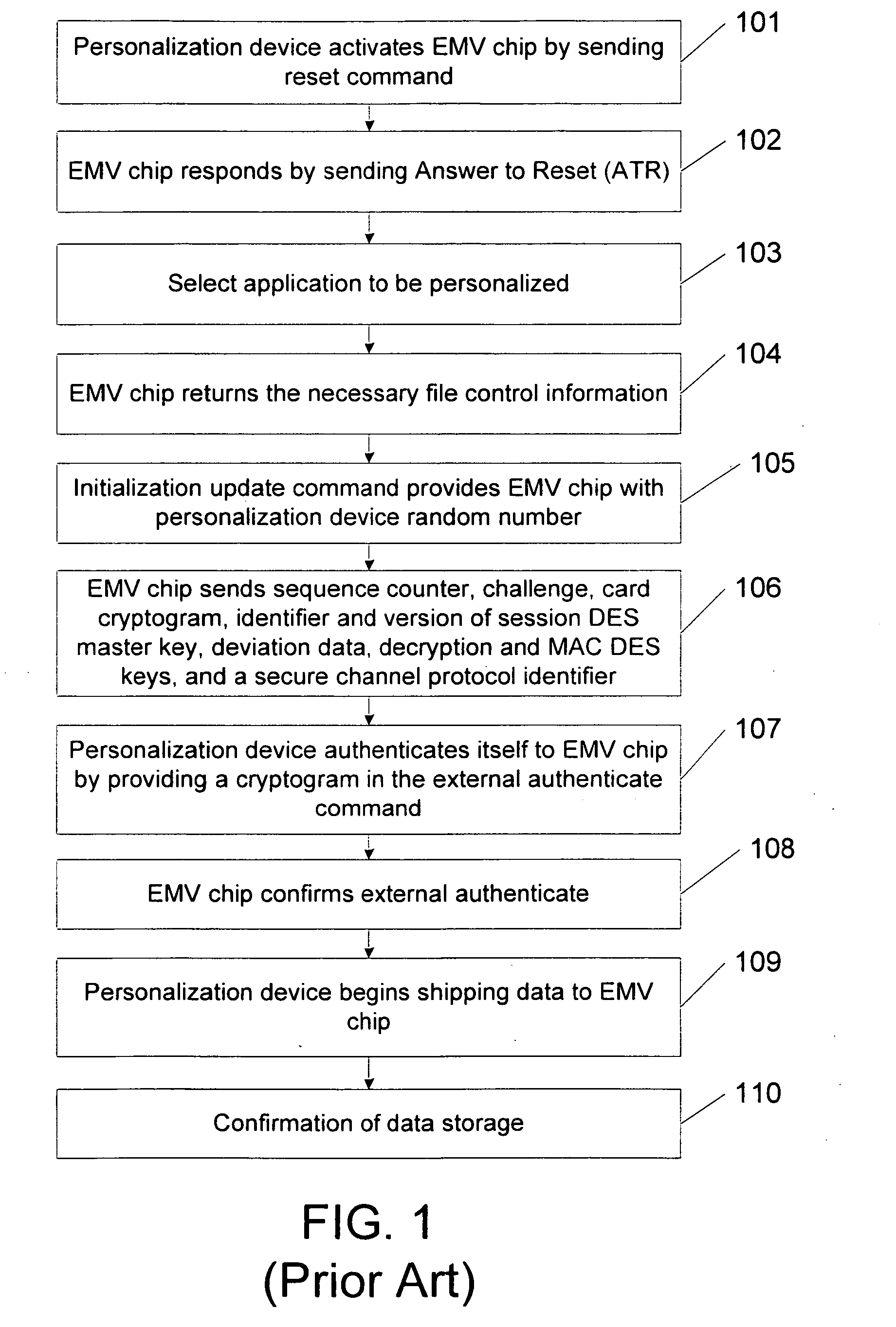
Owner:APPLE INC
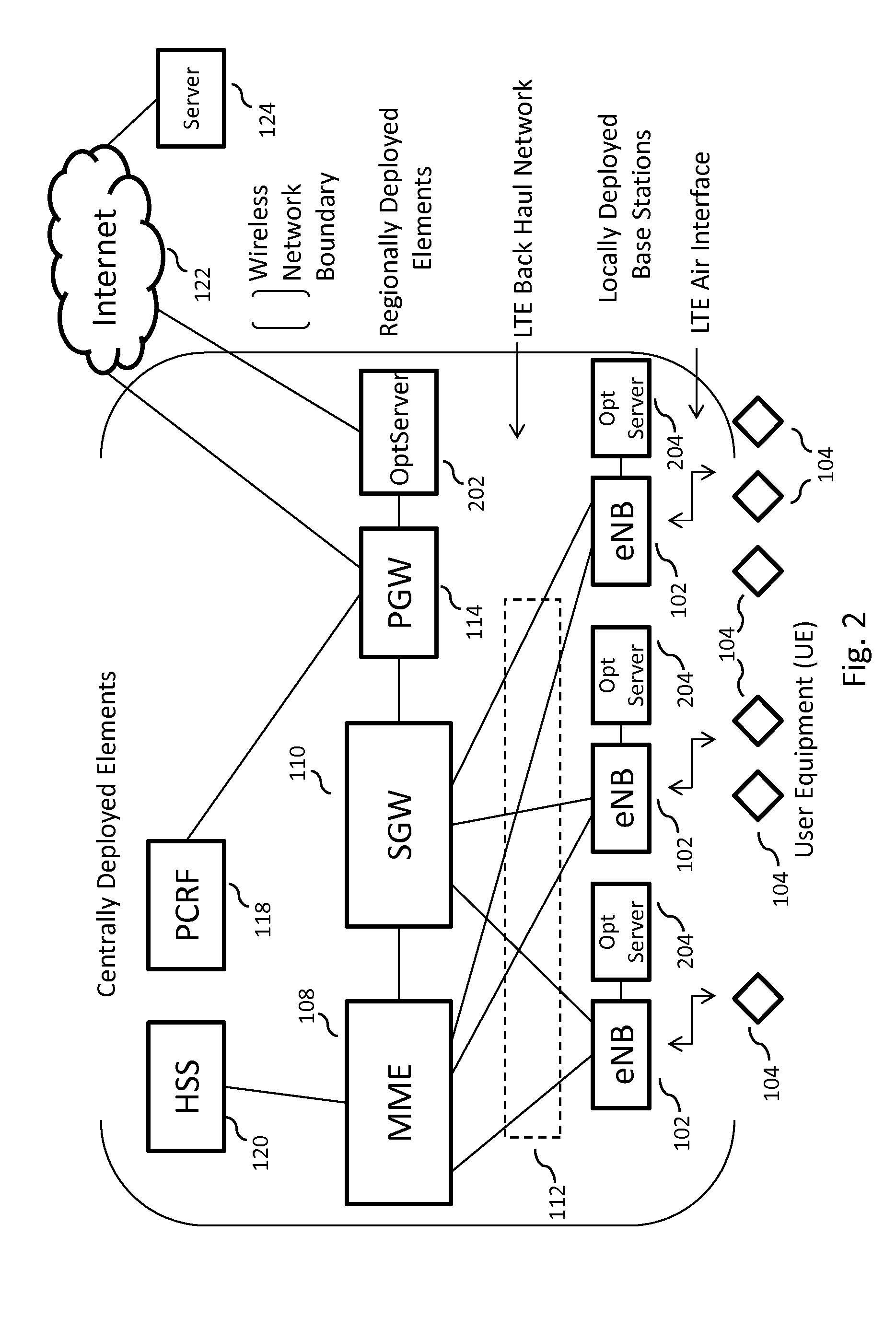
Optimized broadband wireless network performance through base station application server
ActiveUS20140003394A1Reduce time delayHigh bandwidthPower managementSpatial transmit diversityWireless mesh networkApplication server
Owner:ALL PURPOSE NETWORKS INC
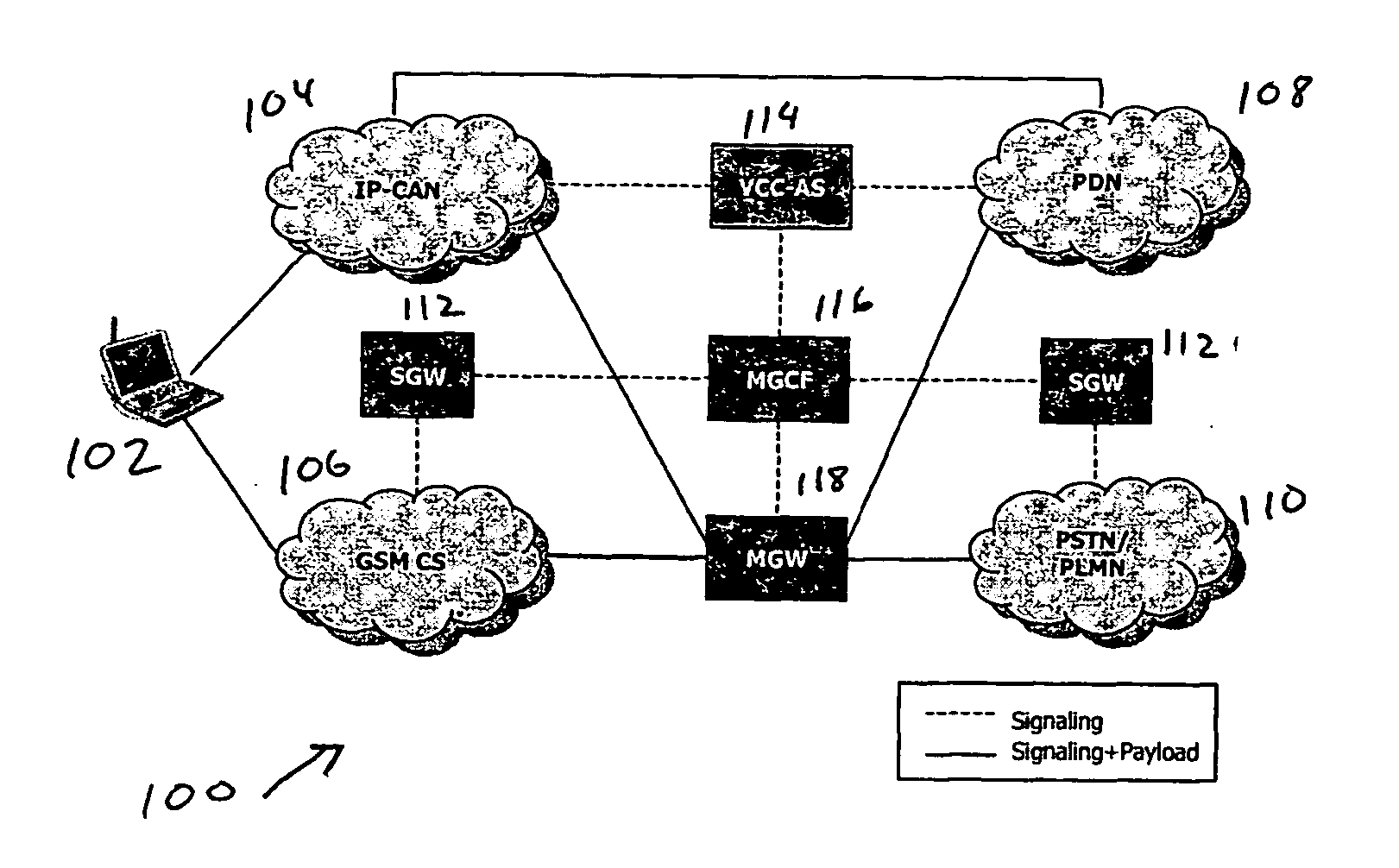
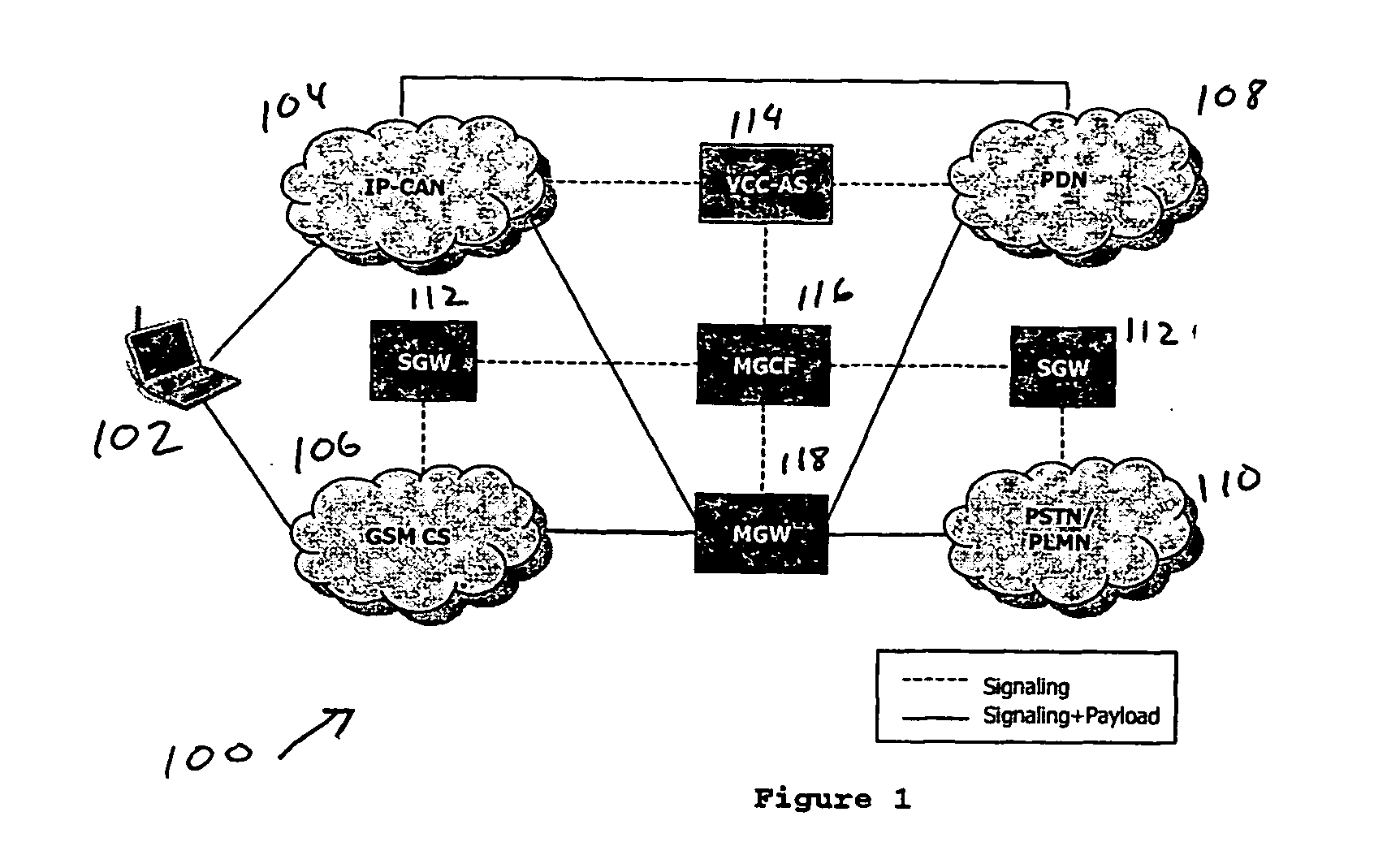
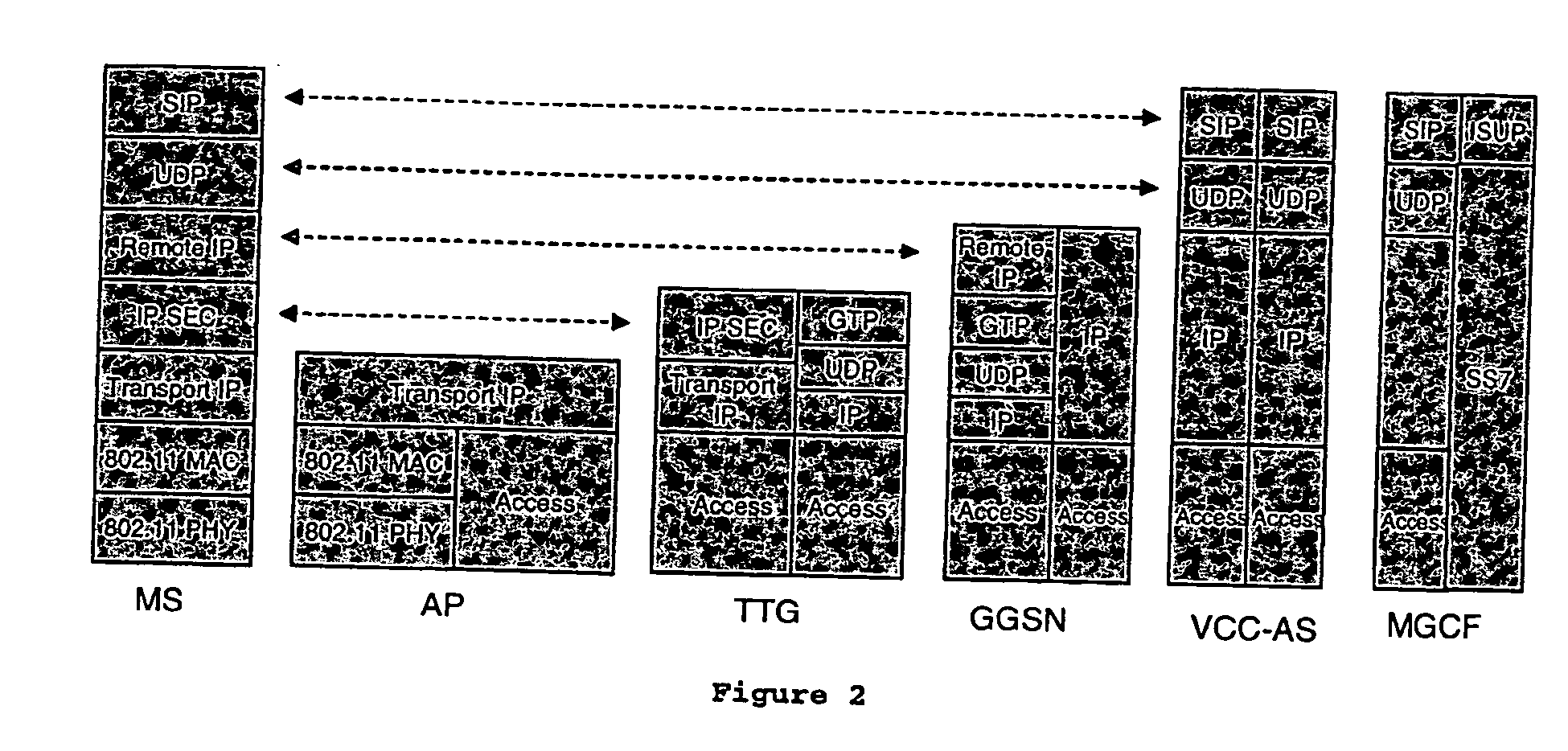
Voice call continuity application server between IP-CAN and CS networks
InactiveUS20070014281A1Accurate processingMultiplex system selection arrangementsConnection managementAccess networkApplication server
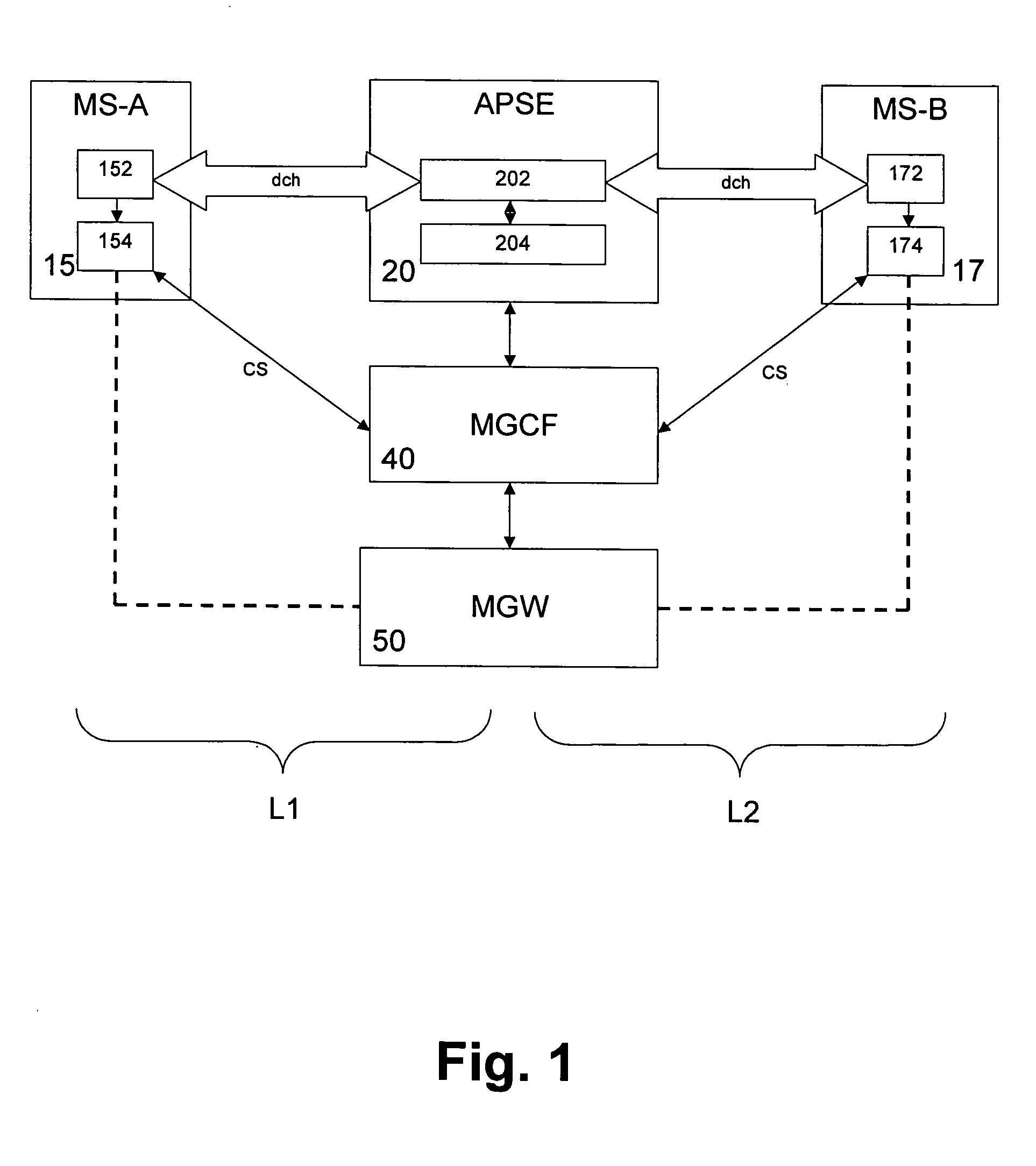
A system and method for continuous voice calls when a user switches between packet data and circuit switched access networks. In one example embodiment, the present innovations include an interworking system that supports voice call continuity for a user that moves between IP-CAN and CS networks (e.g., PSTN or GSM). In one example embodiment, the present innovations comprise a voice call continuity application server (VCC-AS) that serves as an anchor point for a voice call (i.e., it is the node from which a handover is initiated) and controls and handles voice calls to and from the user equipment (UE) regardless of the access network.
Owner:INTELLINET TECH
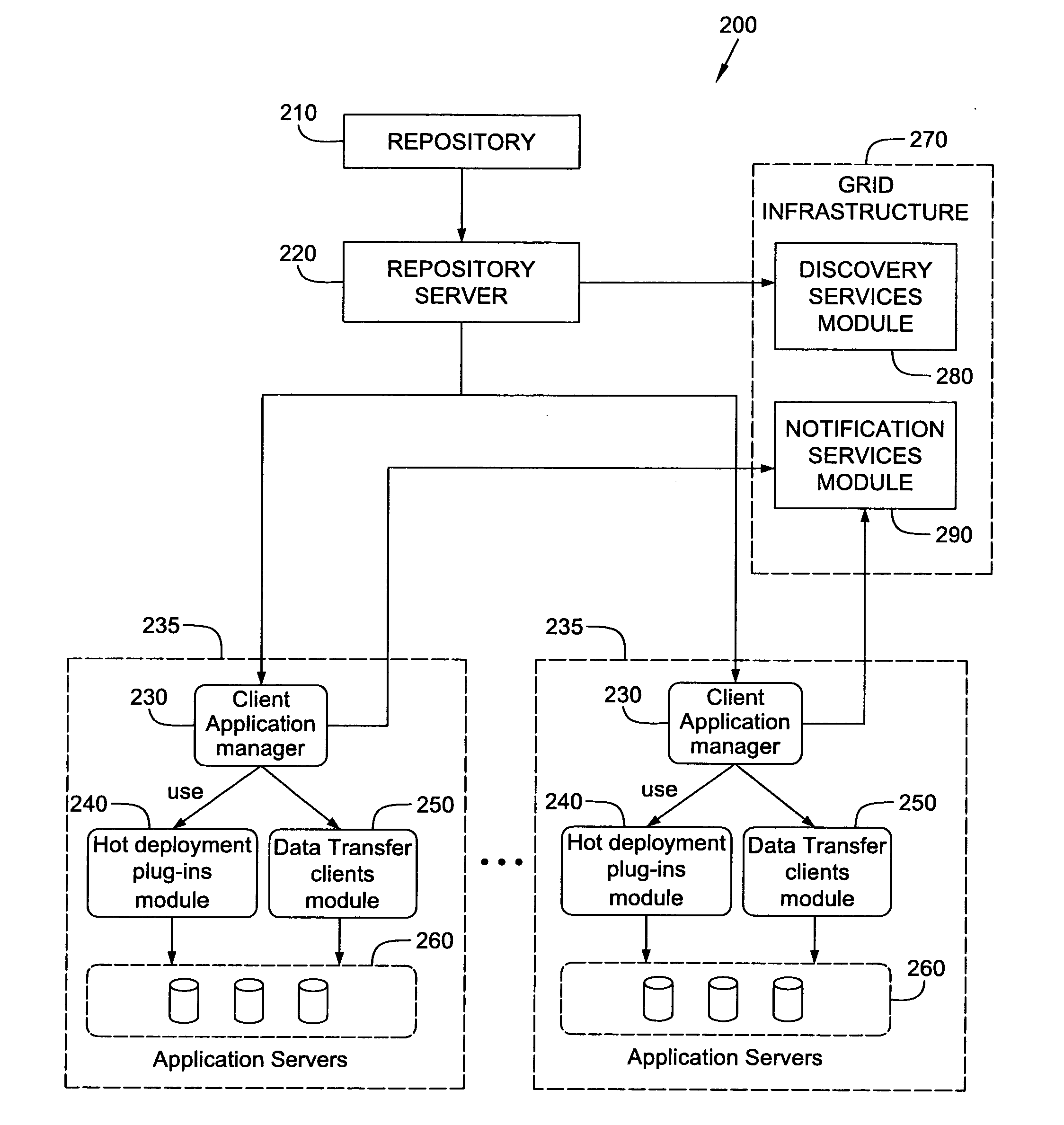
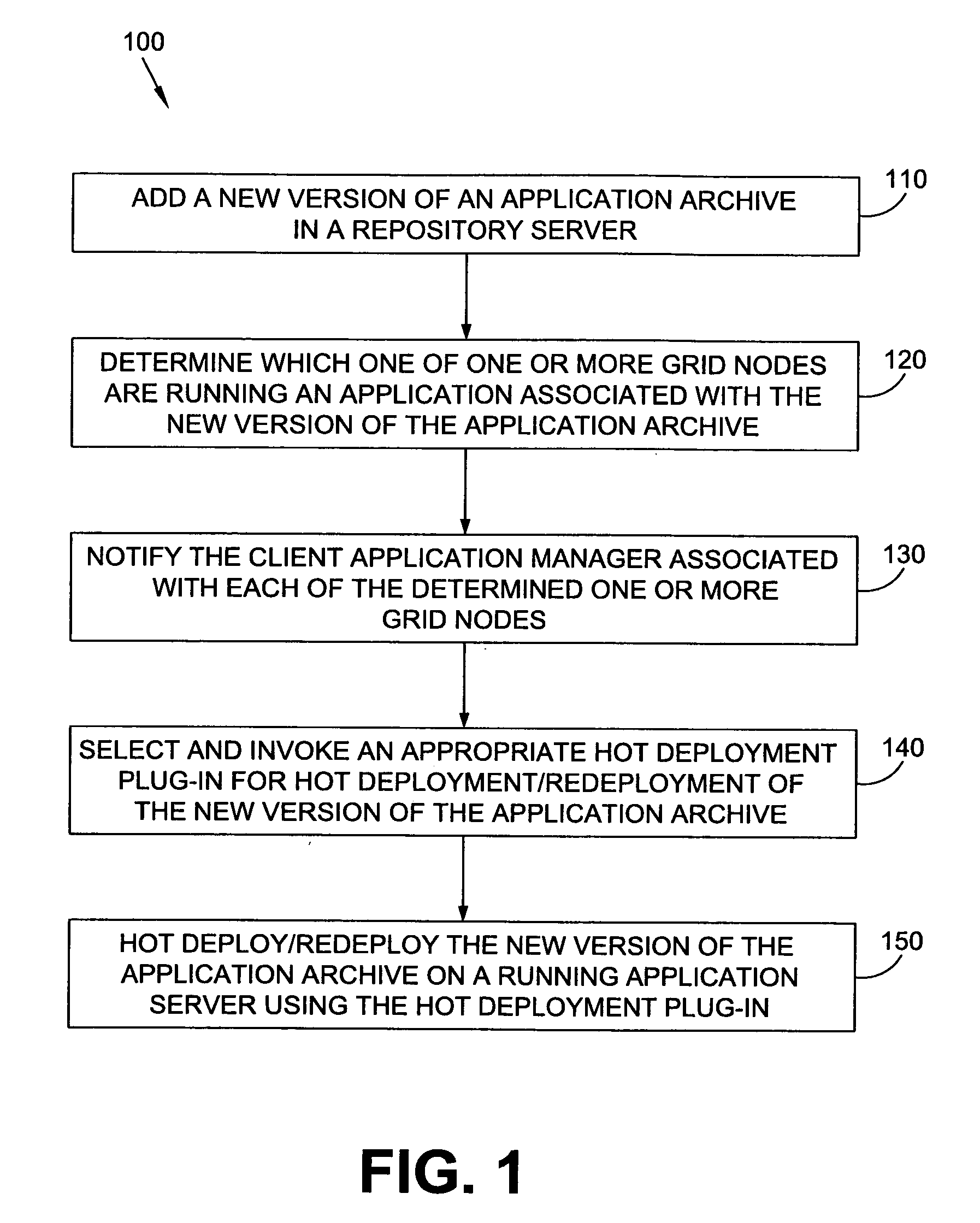
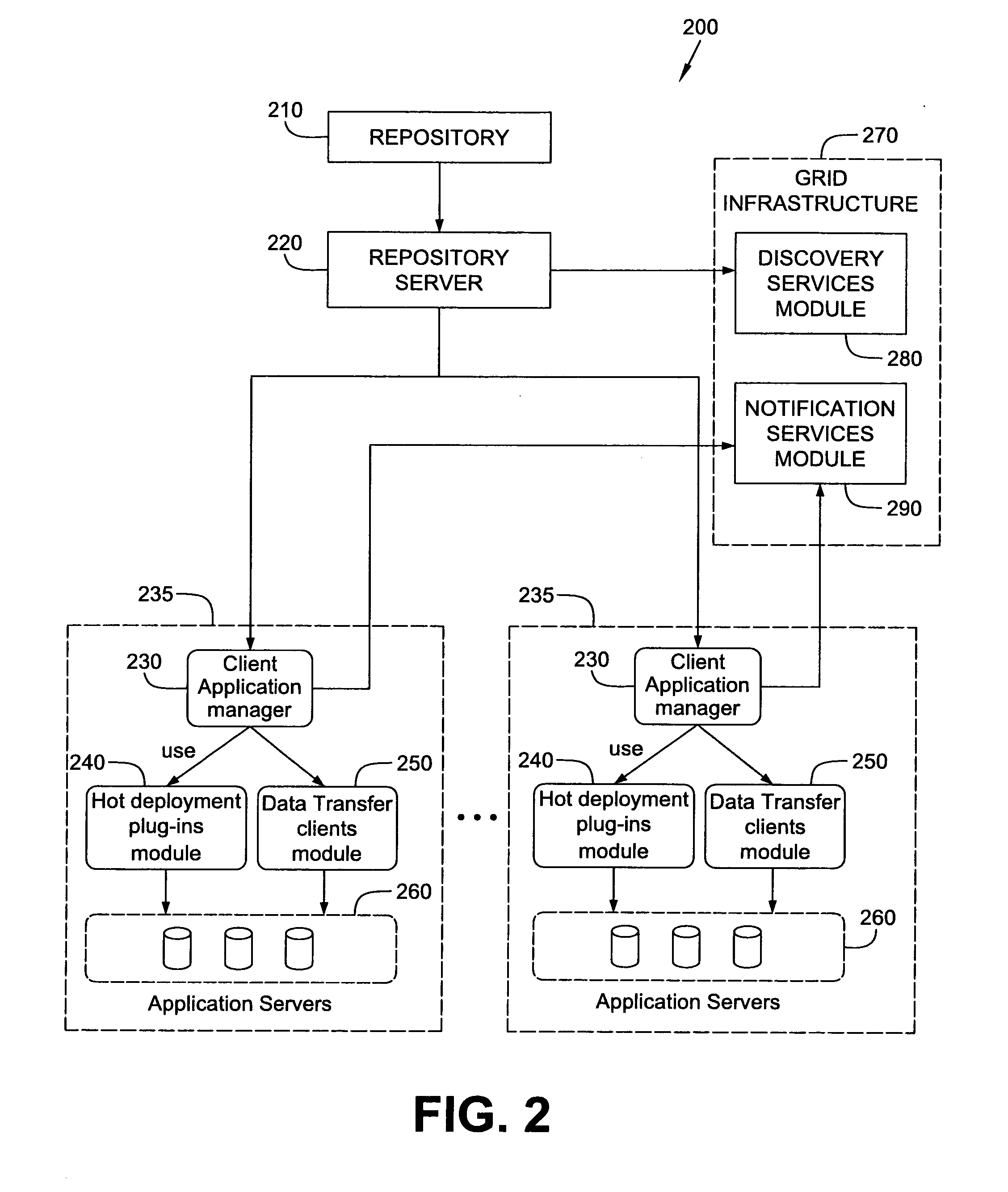
System and method for hot deployment/redeployment in grid computing environment
ActiveUS20080162674A1Reduce chanceReduce overheadSoftware engineeringDigital computer detailsApplication serverProgram management
A technique for hot deploying / redeploying applications in a grid computing environment to improve operating efficiency and reduced overhead. In one example embodiment, this is accomplished by notifying a client application manager associated with each of one or more grid nodes about a type of data transfer protocol to use upon receiving a new version of an application release bundle by a repository server. The new version of the application release bundle is then hot deployed / redeployed on running one or more application servers in the associated grid using an appropriate hot deployment plug-in based on the data transfer protocol by each client application manager.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and apparatus for a multimedia value added service delivery system
InactiveUS20080192736A1Easy to produceLess-costly to operateElectronic editing digitised analogue information signalsCarrier indicating arrangementsApplication serverTelecommunications network
A multimedia multi-service platform for providing one or more multimedia value added services in one or more telecommunications networks includes one or more application servers configured to operate in part according to a service program. The platform also includes one or more media servers configured to access, handle, process, and deliver media. The platform further includes one or more logic controllers and one or more management modules.
Owner:ONMOBILE GLOBAL LTD
Adaptive behavioral intrusion detection systems and methods
ActiveUS20050044406A1Increase opportunitiesMicrobiological testing/measurementDigital data processing detailsApplication serverInternet traffic
Systems and methods for analyzing historical network traffic and determining which traffic does not belong in a network are disclosed. Intrusion detection is performed over a period of time, looking for behavioral patterns within networks or information systems and generating alerts when these patterns change. The intrusion detection system intelligently forms correlations between disparate sources to find traffic anomalies. Over time, behaviors are predictive, and the intrusion detection system attempts to predict outcomes, becoming proactive instead of just reactive. Intrusions occur throughout whole information systems, including both network infrastructure and application servers. By treating the information system as a whole and performing intrusion detection across it, the chances of detection are increased significantly.
Owner:MASERGY COMMUNICATIONS
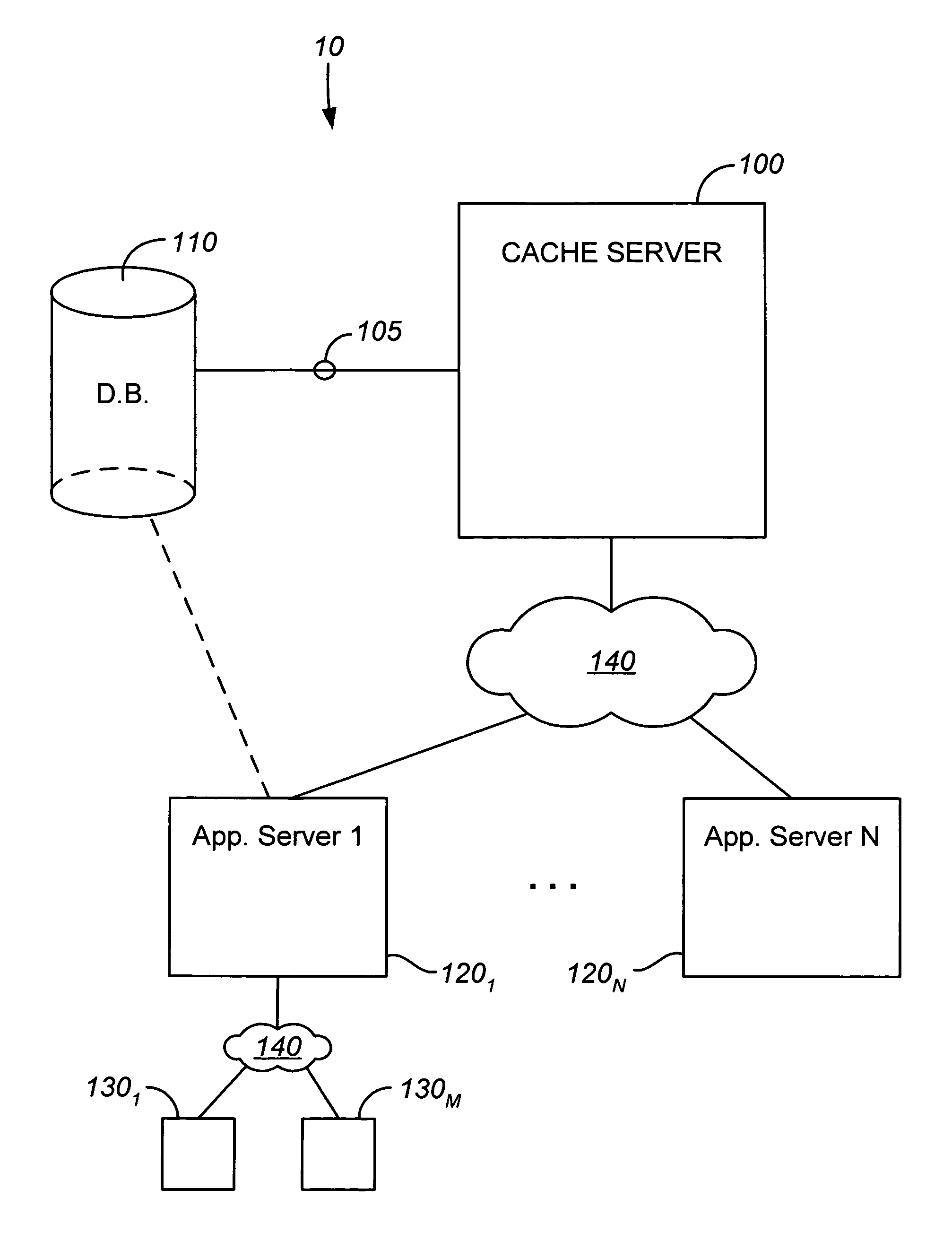
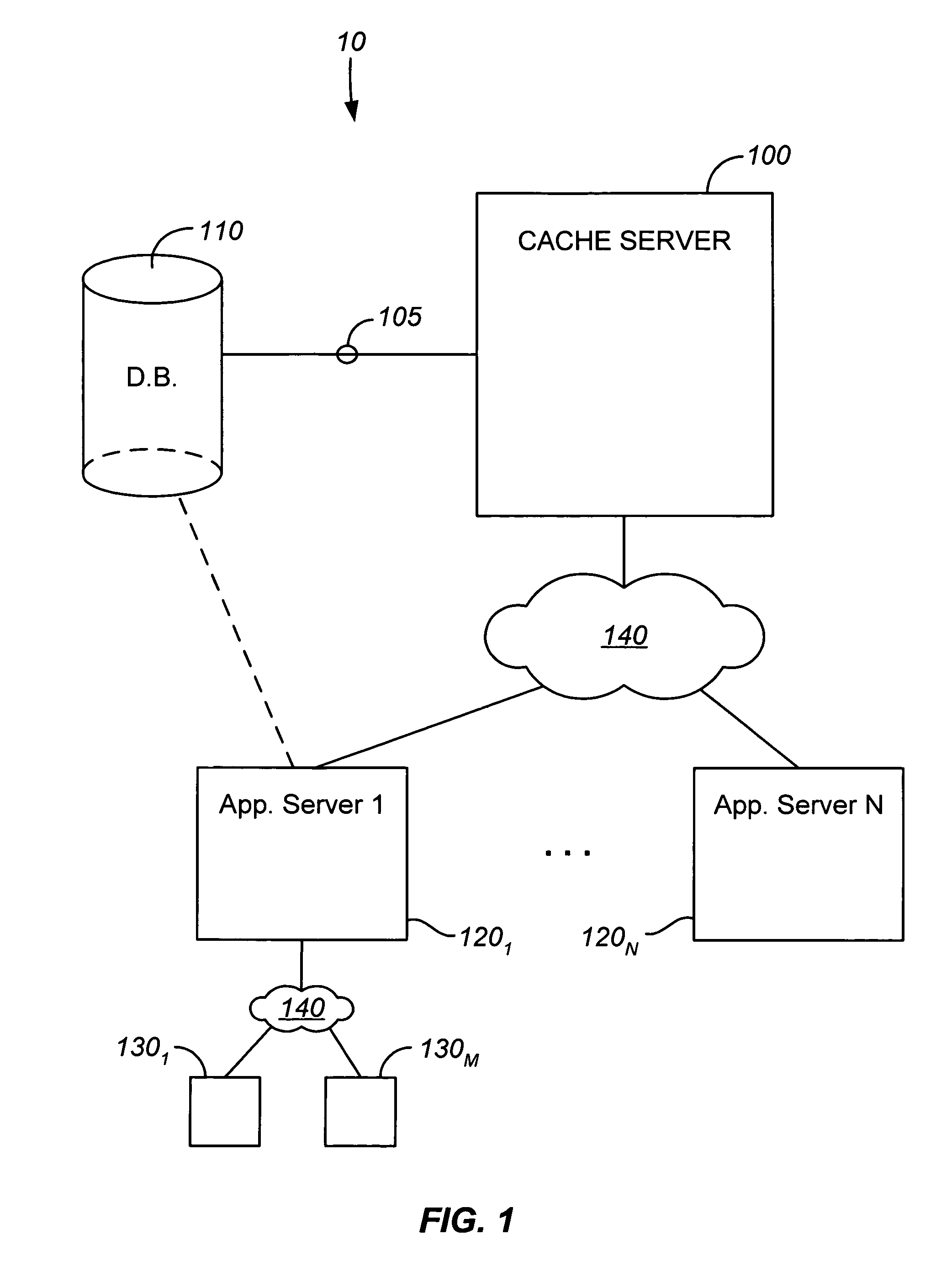
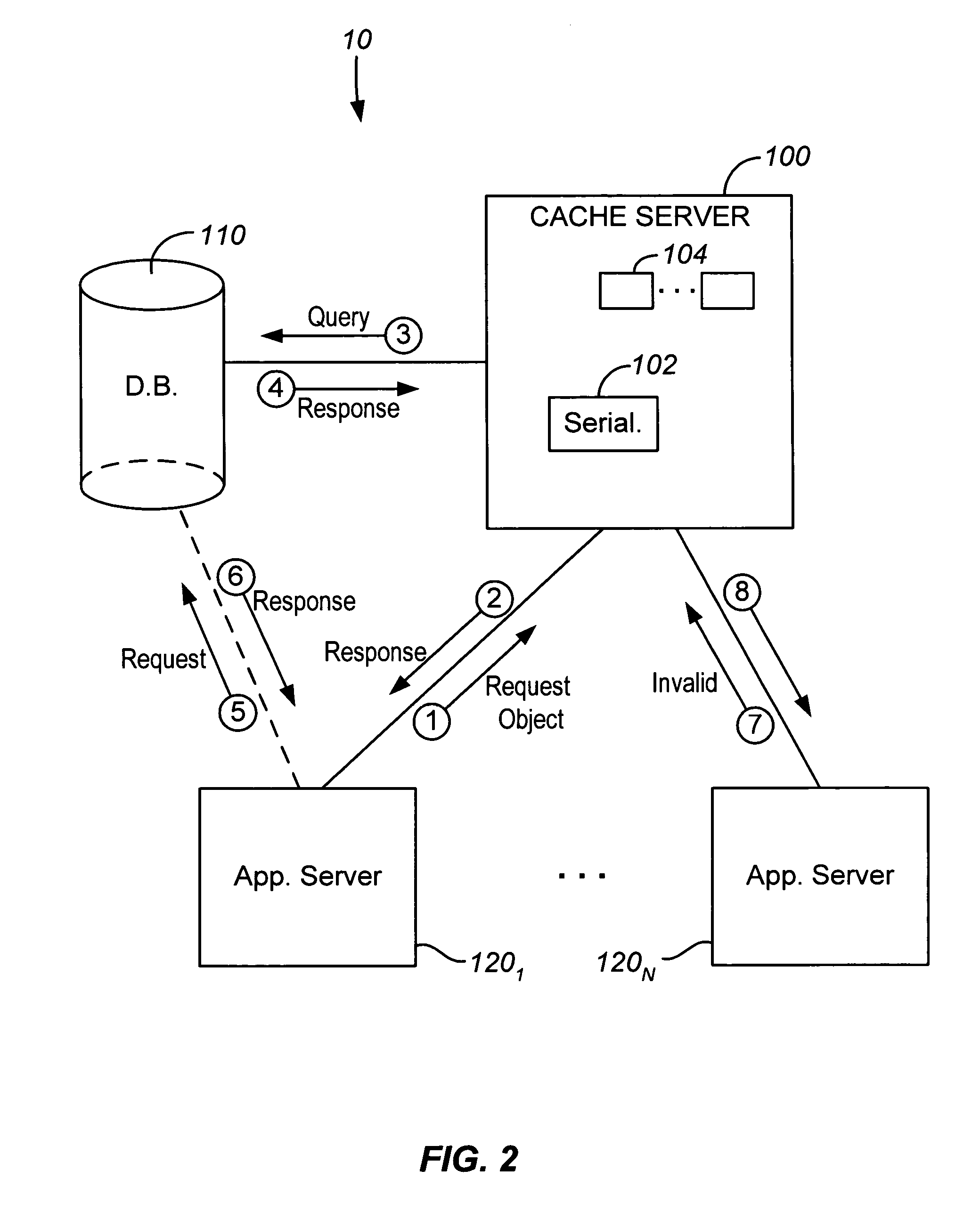
Java object cache server for databases
ActiveUS7209929B2Reduce loadReduce processing loadData processing applicationsDigital data processing detailsApplication serverCache server
A cache server is provided in a network for storing Java objects for retrieval by one or multiple application servers. Application server(s) are configured to request an object from the cache server, rather than requesting the Java object directly from a database, so as to reduce processing load on the database and free up database resources. Responsive to a request for a Java object from an application server, e.g., in an HTTP request, the cache server determines if the object is stored in memory and if so, serializes the requested object and sends the serialized object to the requesting server, e.g., in an HTTP response. The requesting server then deserializes the Java object. If the object is not stored in memory, the cache server instantiates the object (typically by requesting the object from the database), serializes the instantiated object and sends it to the requesting server. Cache coherency methods are also provided.
Owner:SALESFORCE COM INC
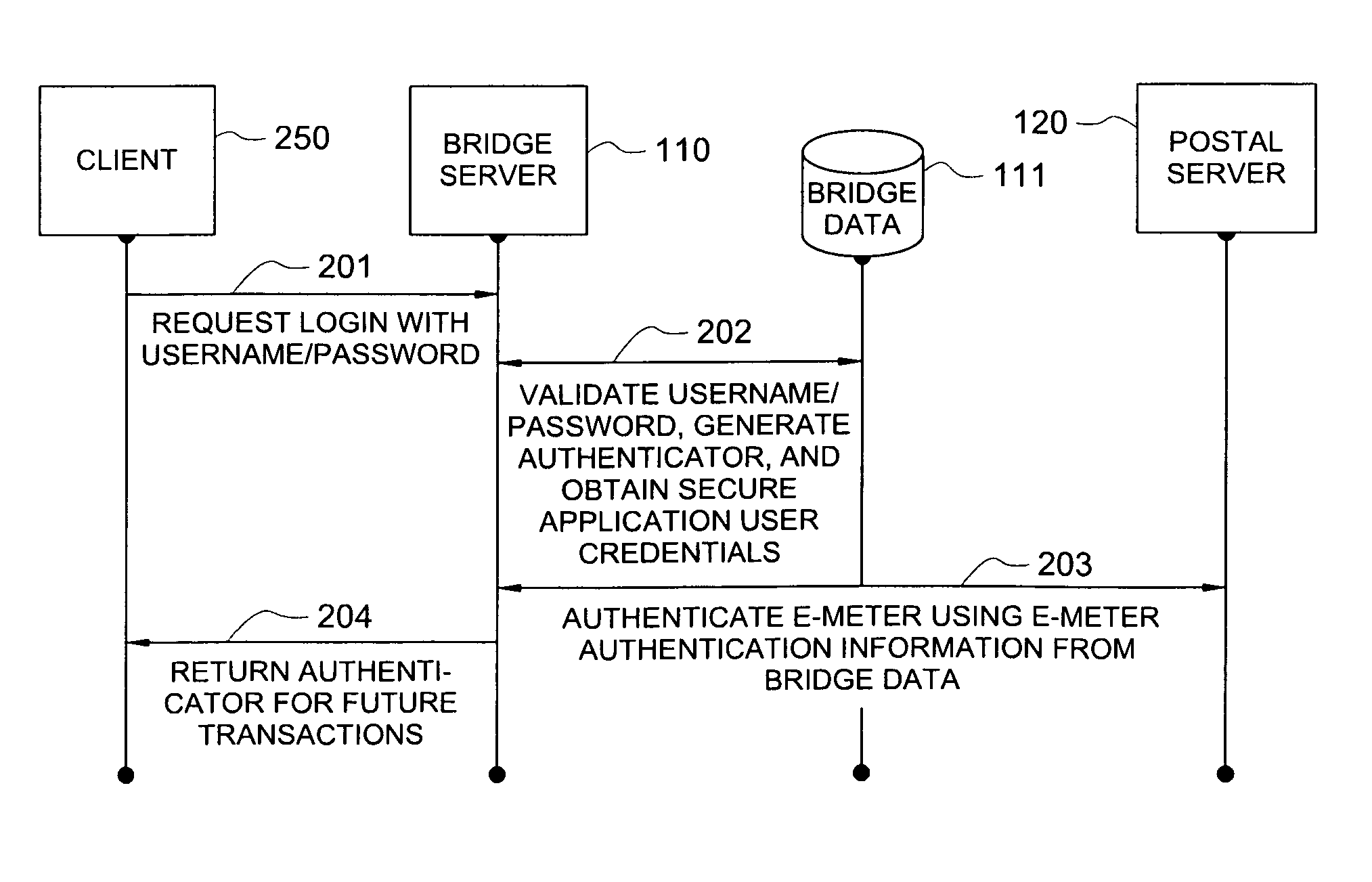
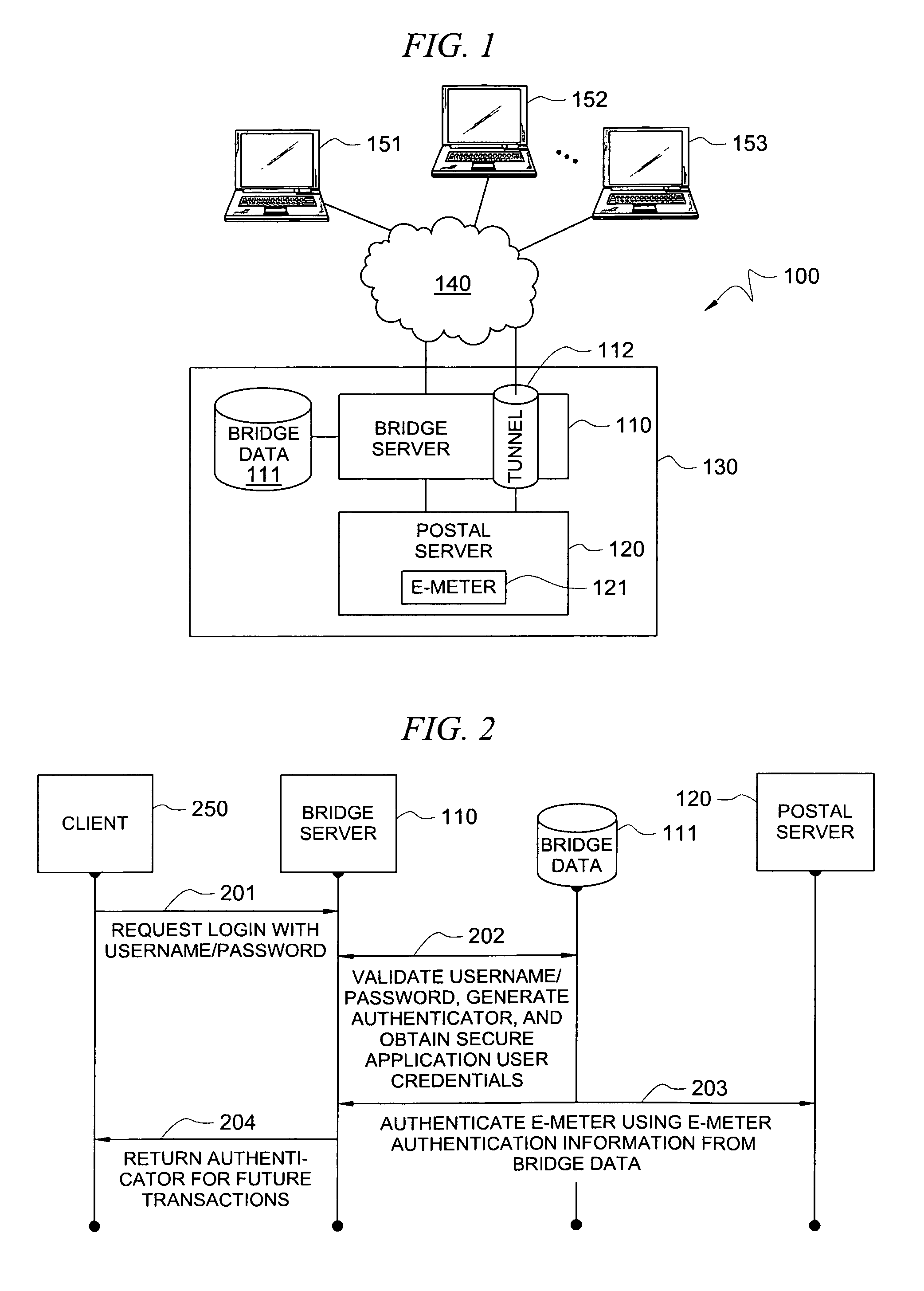
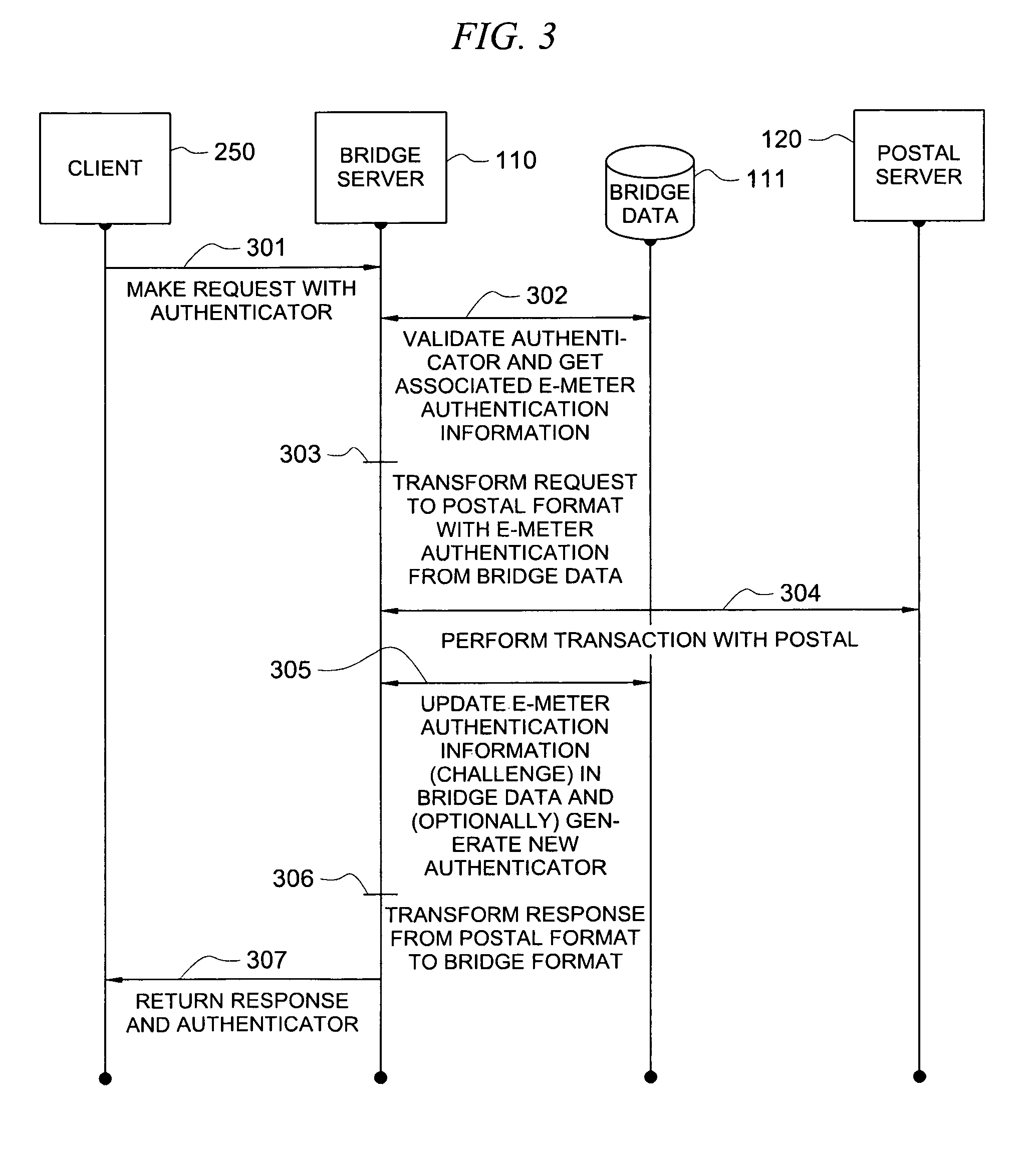
Secure application bridge server
ActiveUS8046823B1Easy to implementConvenient to accommodateDigital data processing detailsComputer security arrangementsApplication serverCryptographic protocol
Systems and methods are provided which implement a bridge server to provide user access to one or more secure applications. A bridge server of embodiments is disposed between a user and a secure application and invokes bridge server security protocols with respect to the user and secure application security protocols with respect to the secure application. In operation according to embodiments, client applications will link into a bridge server, the user will be authenticated by the bridge server, and a valid user will be correlated to an account of the secure application by the bridge server. Bridge servers of embodiments facilitate providing features with respect to secure application user access unavailable using the secure application security protocols.
Owner:AUCTANE INC
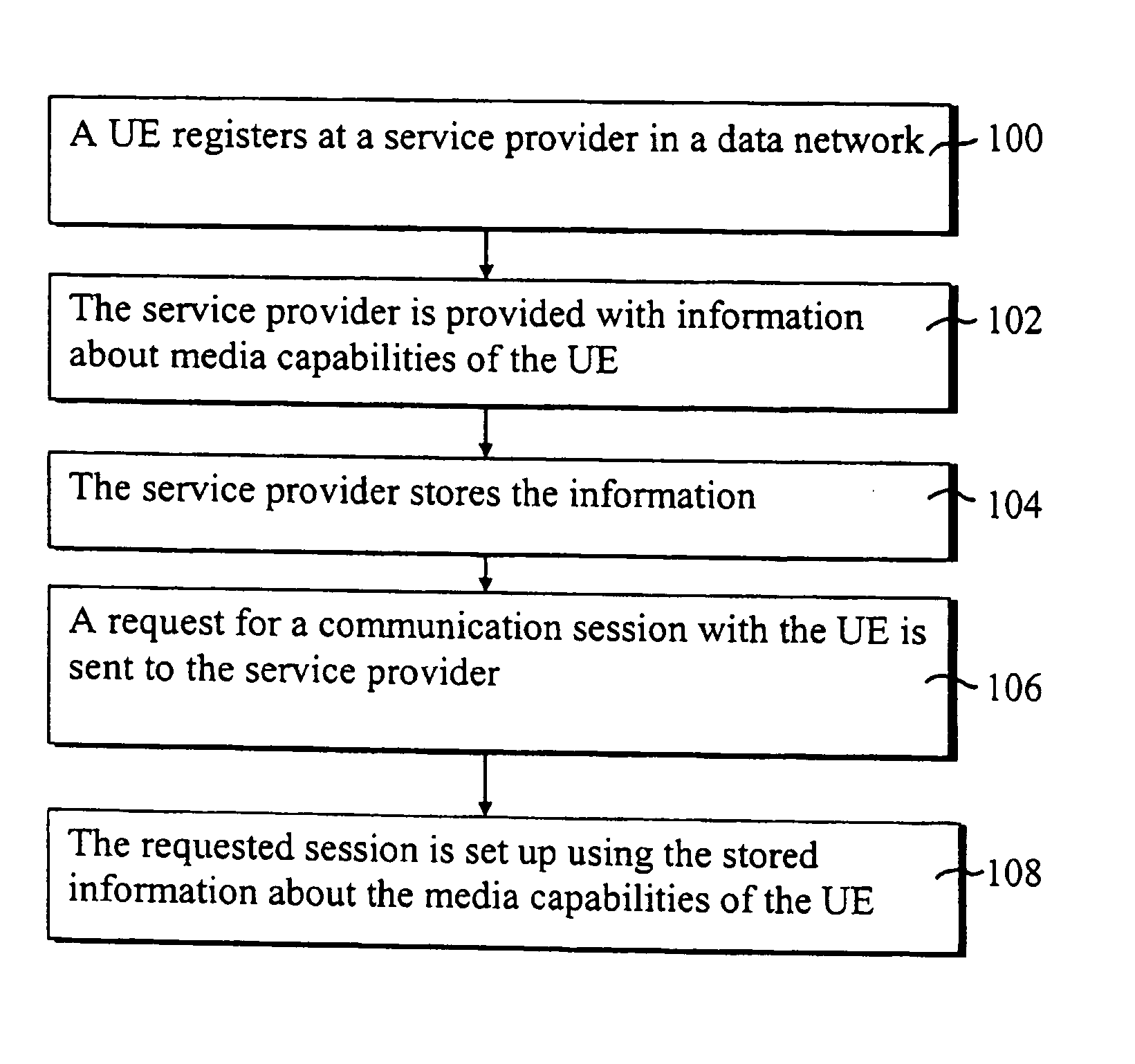
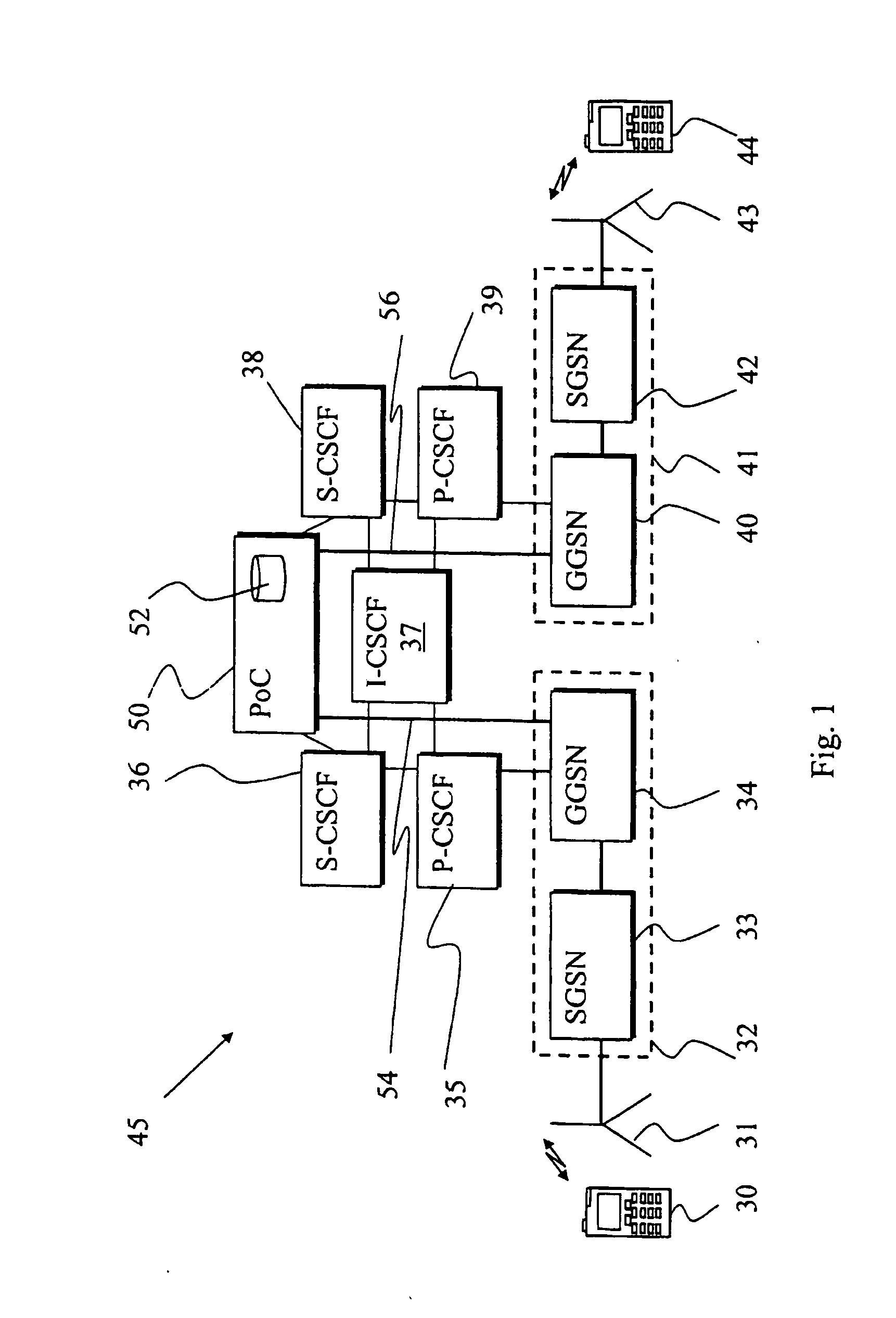
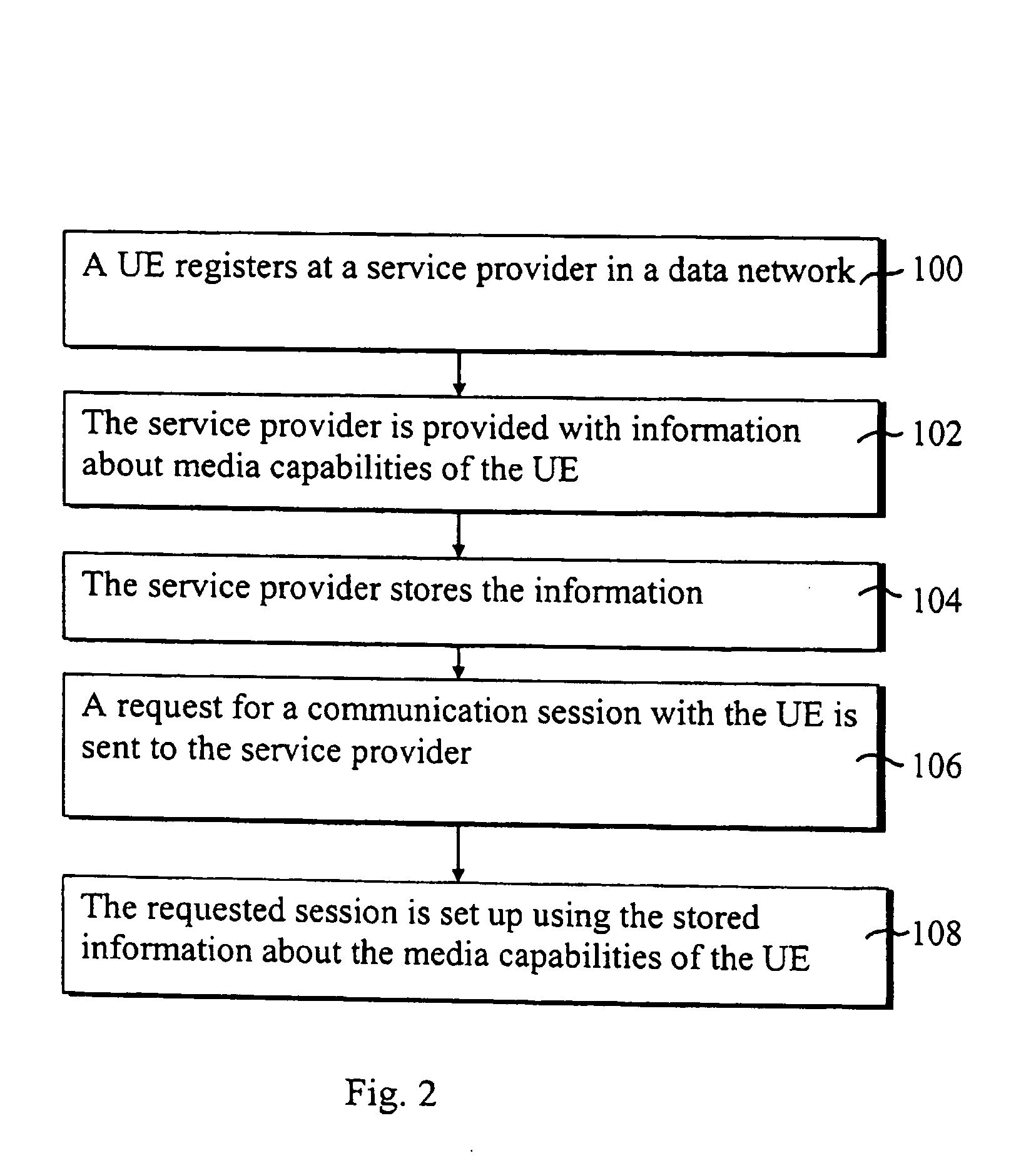
Setting up communication sessions
ActiveUS20050041578A1Resources delayingDelaying sessionError preventionNetwork traffic/resource managementApplication serverCommunications system
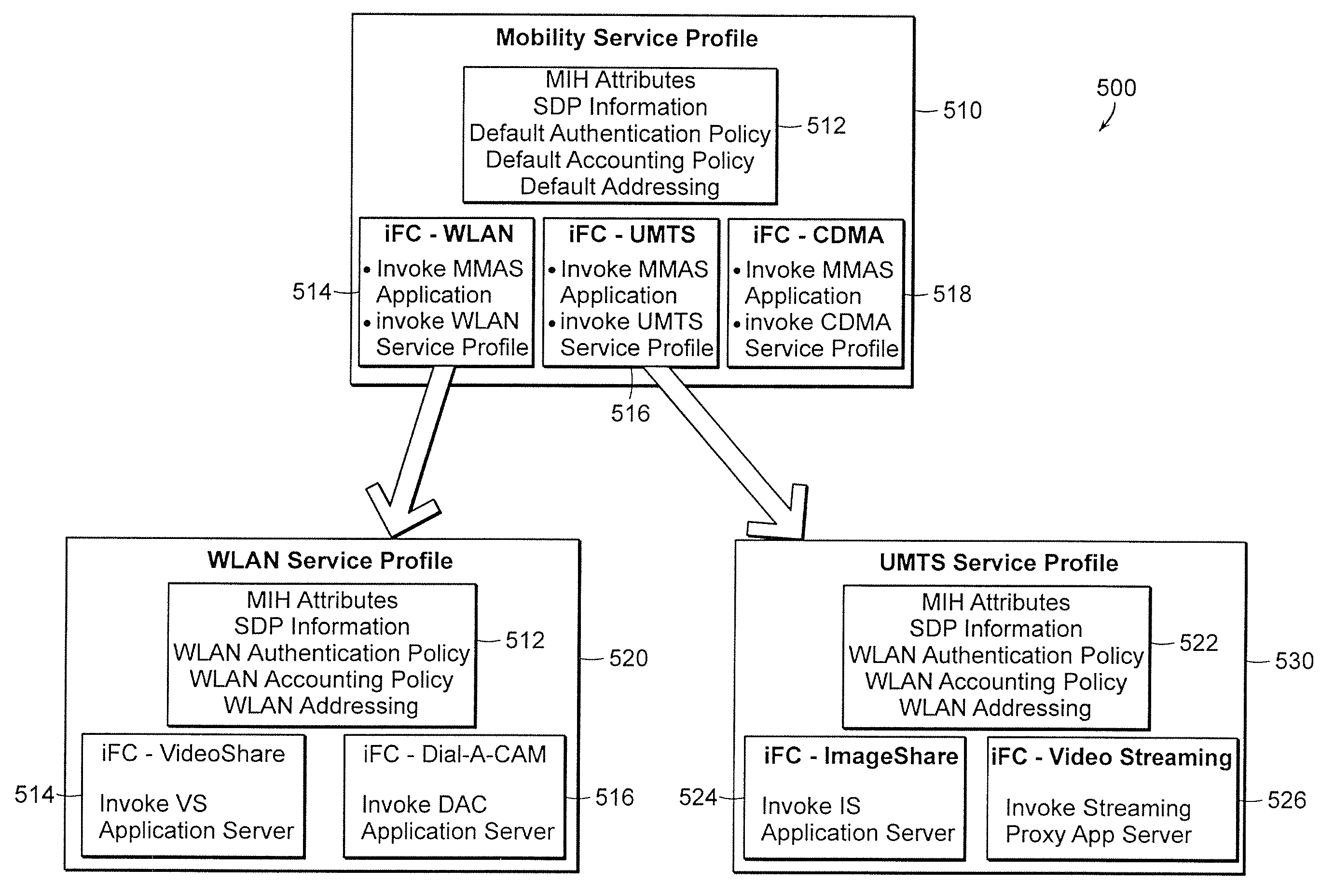
A method for setting up data sessions in a communication system is provided. The method comprises registering at least one user equipment with a service provider where after information about media capabilities is communicated between the at least one user equipment and the service provider and then stored. The method comprises further sending a request for a data session with at least one user equipment and using the stored information when setting up the requested data session. A communication system, an application server and a user equipment configured to operate accordingly are also provided.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com