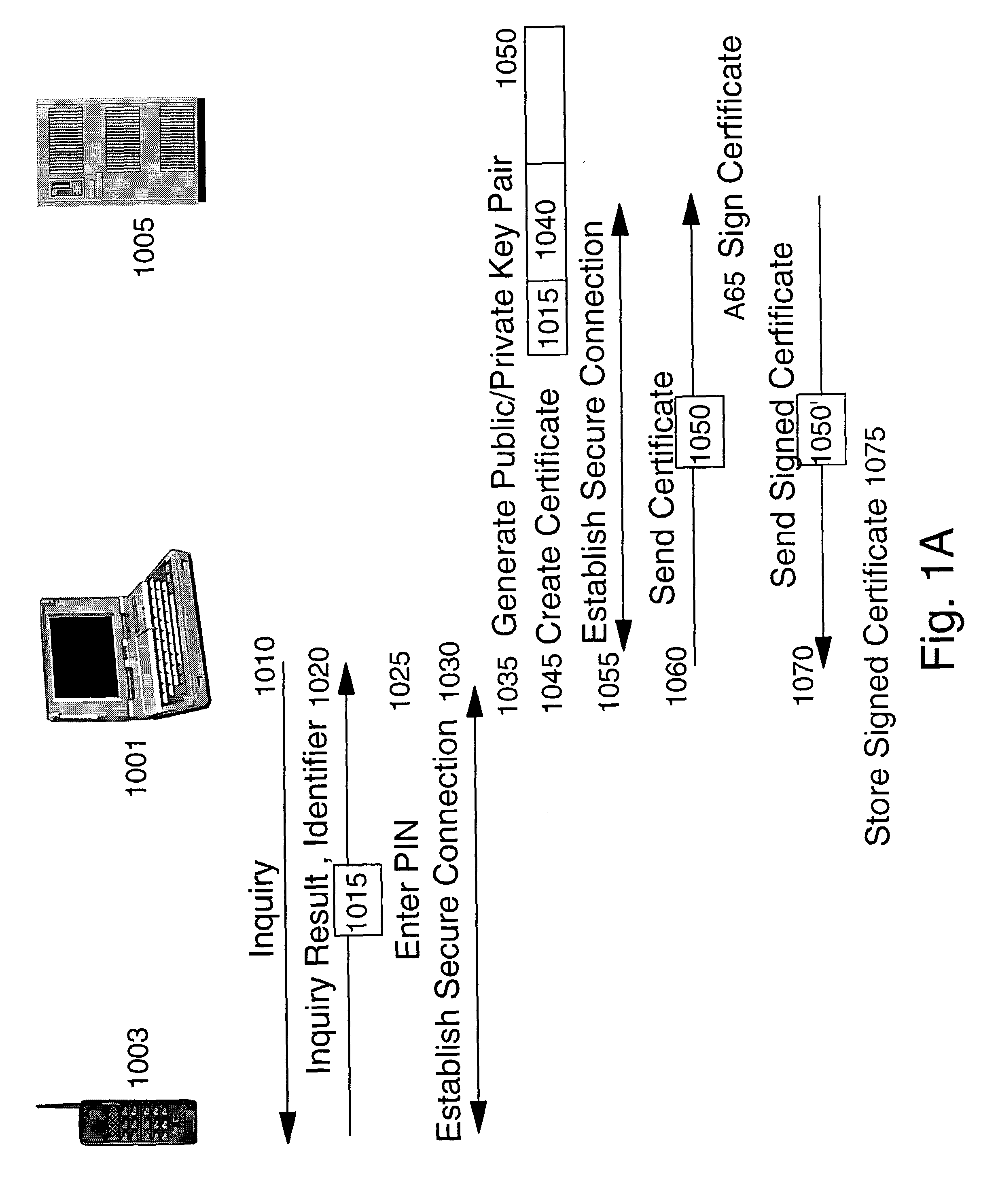
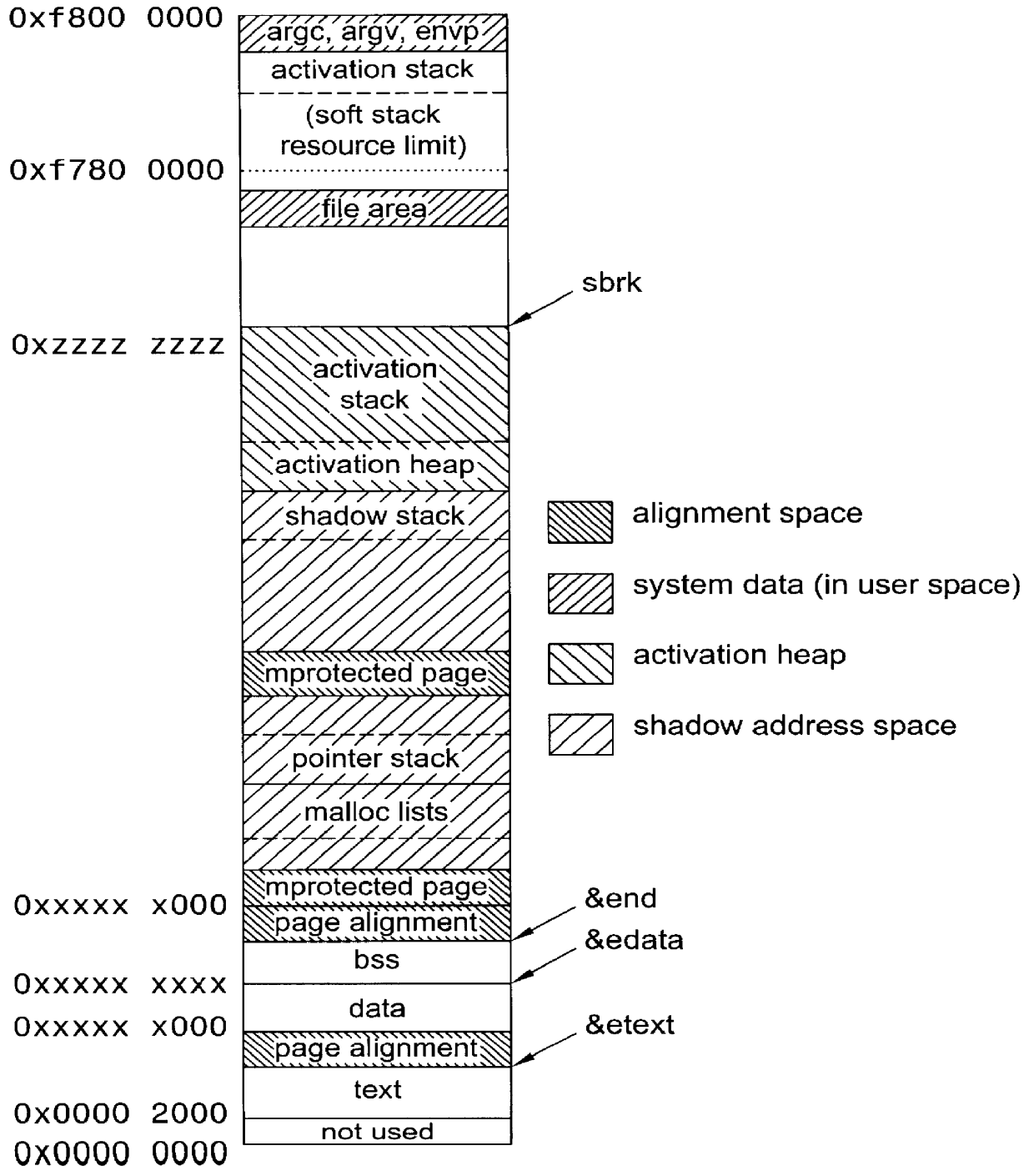
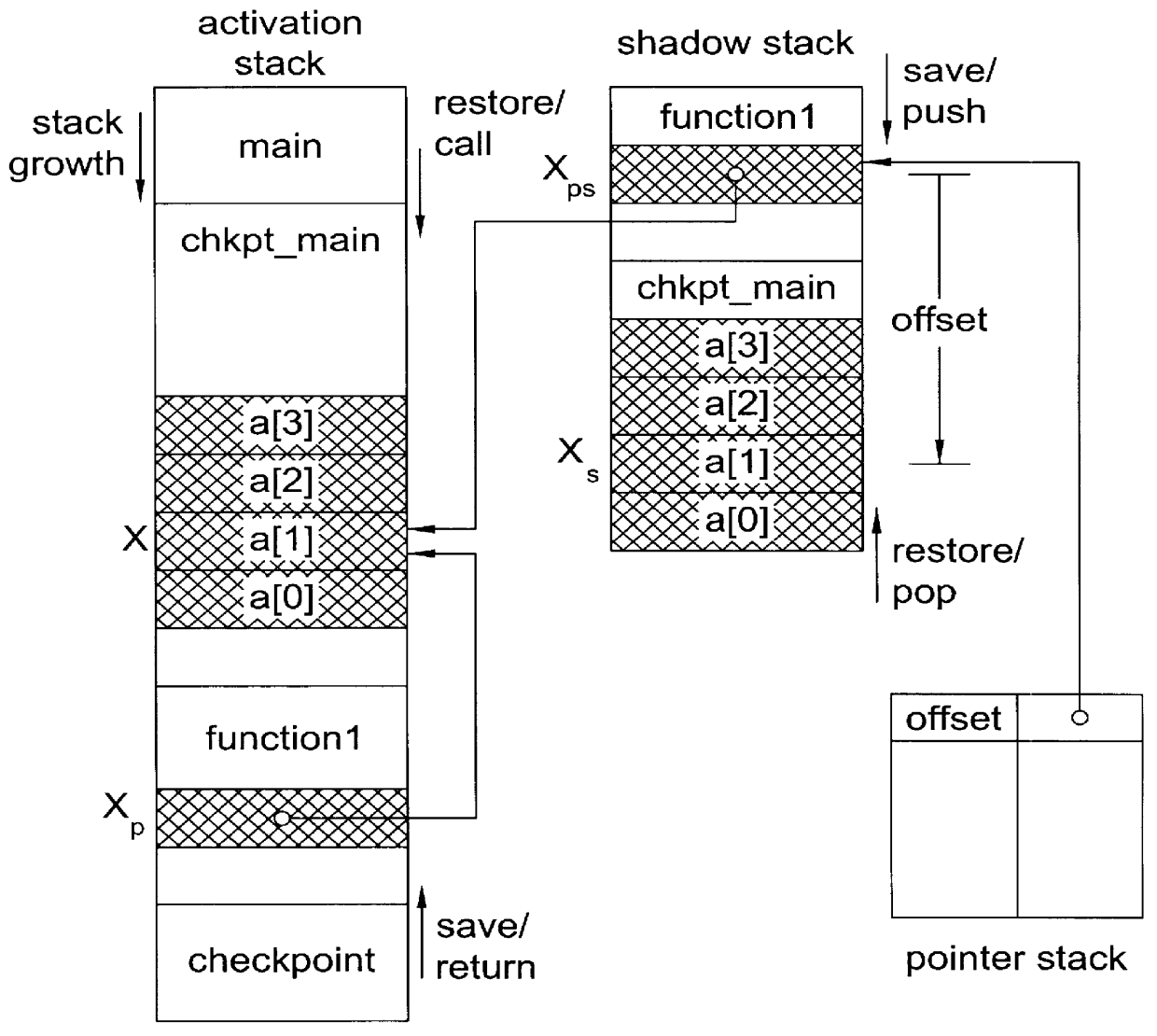
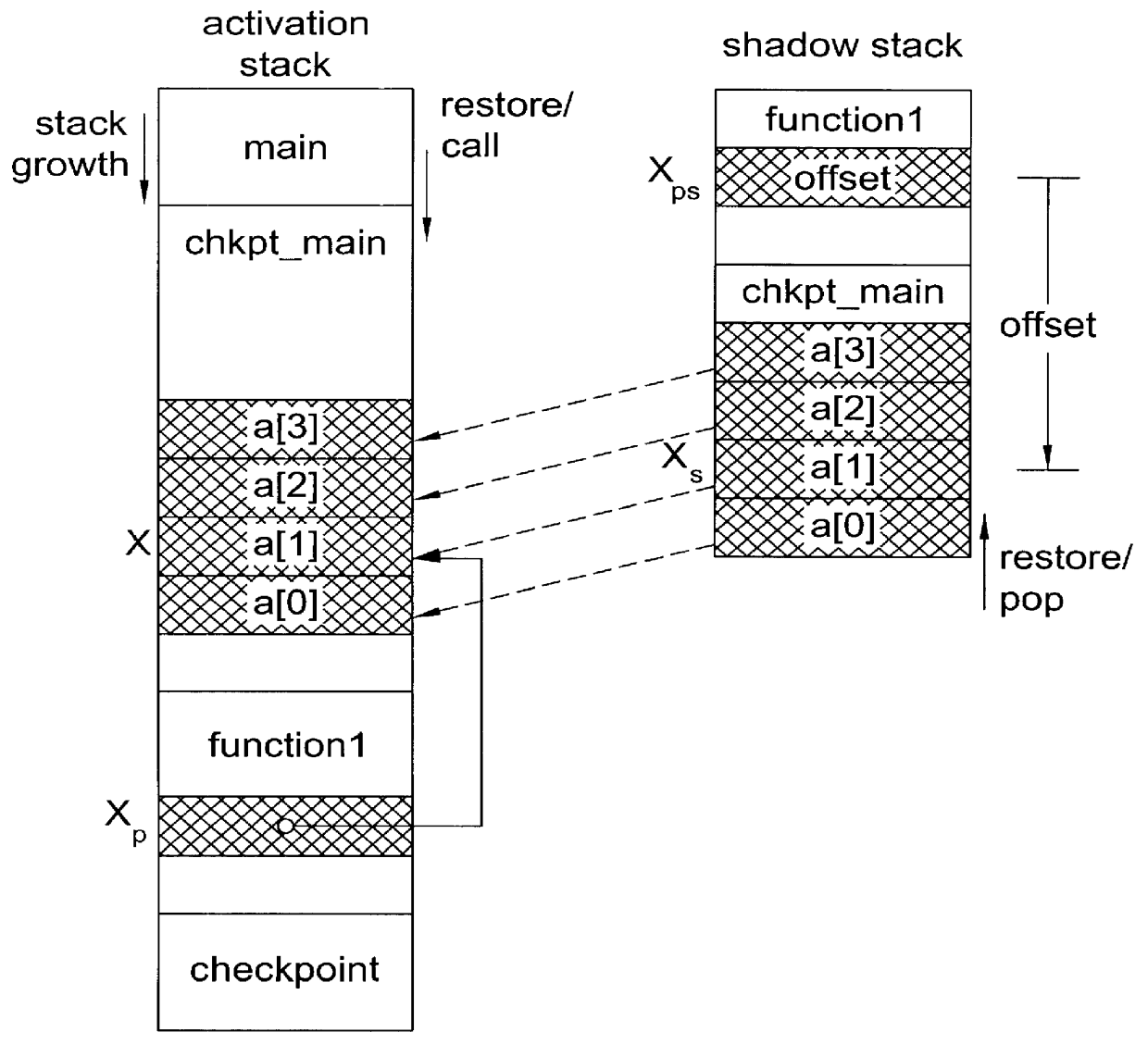
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
19268results about How to "Reduce overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
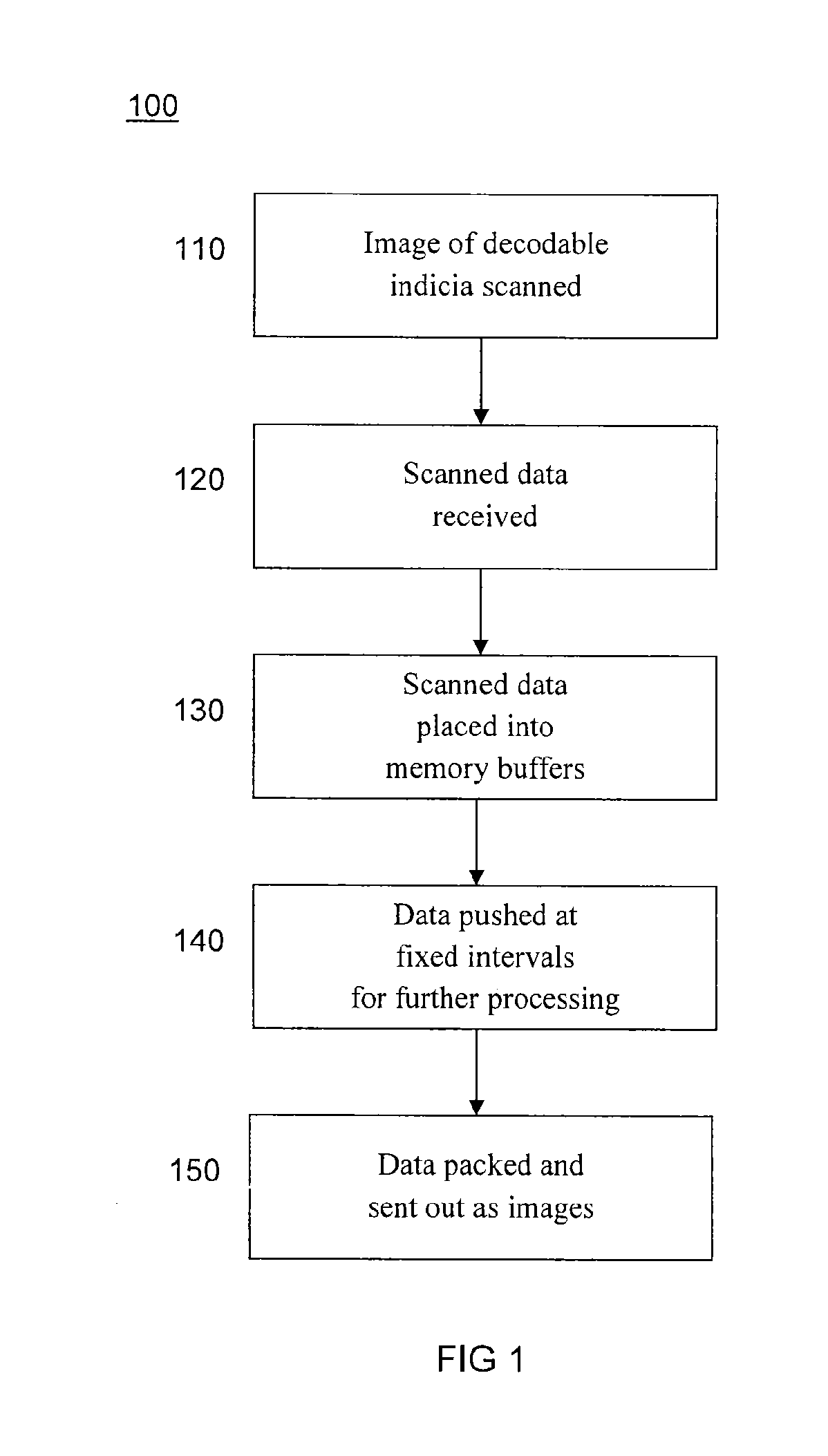
Data processing system and method
InactiveUS6215898B1Reduce overheadHigh sensitivityImage enhancementImage analysisStatic random-access memoryHigh memory
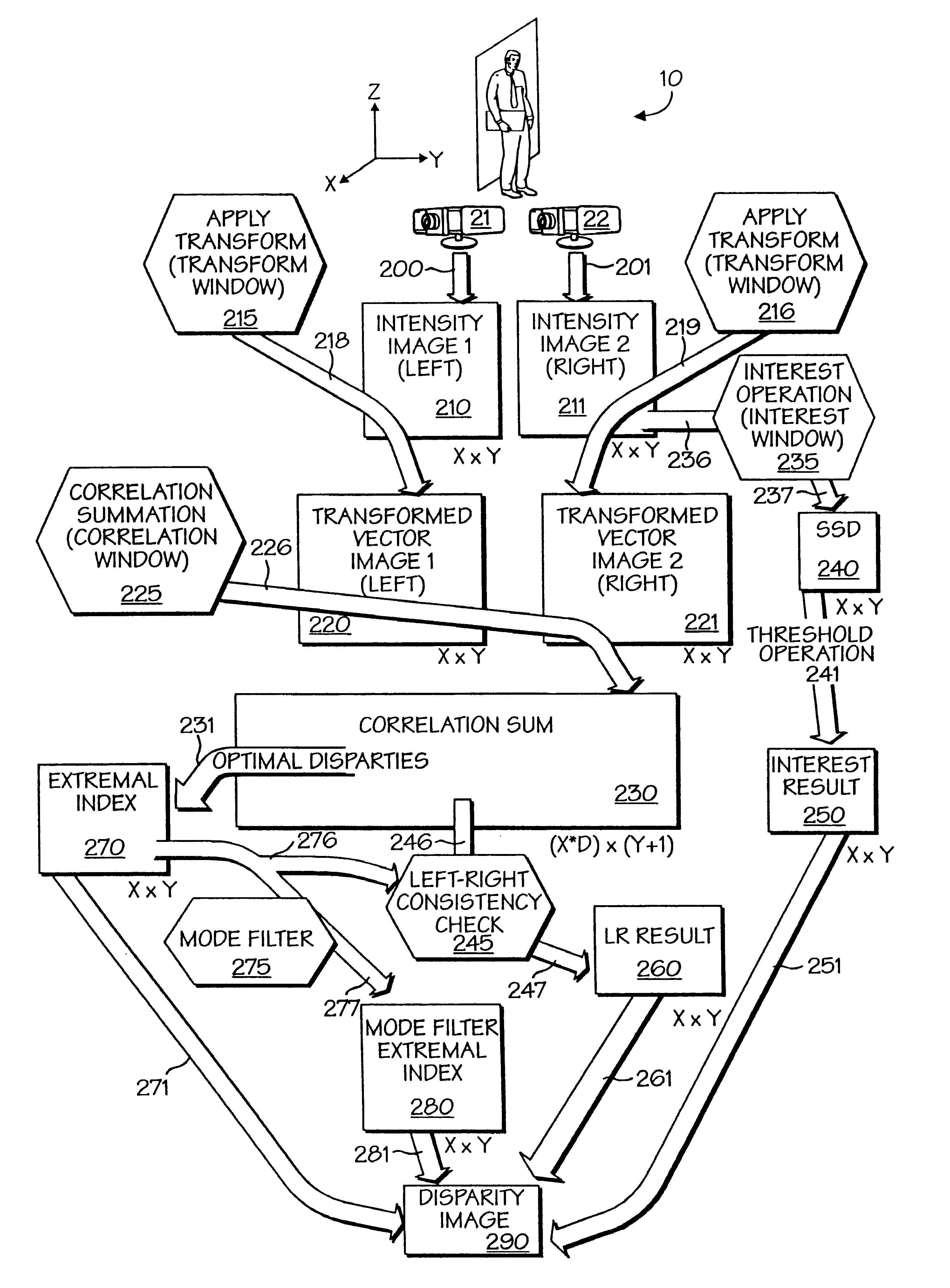
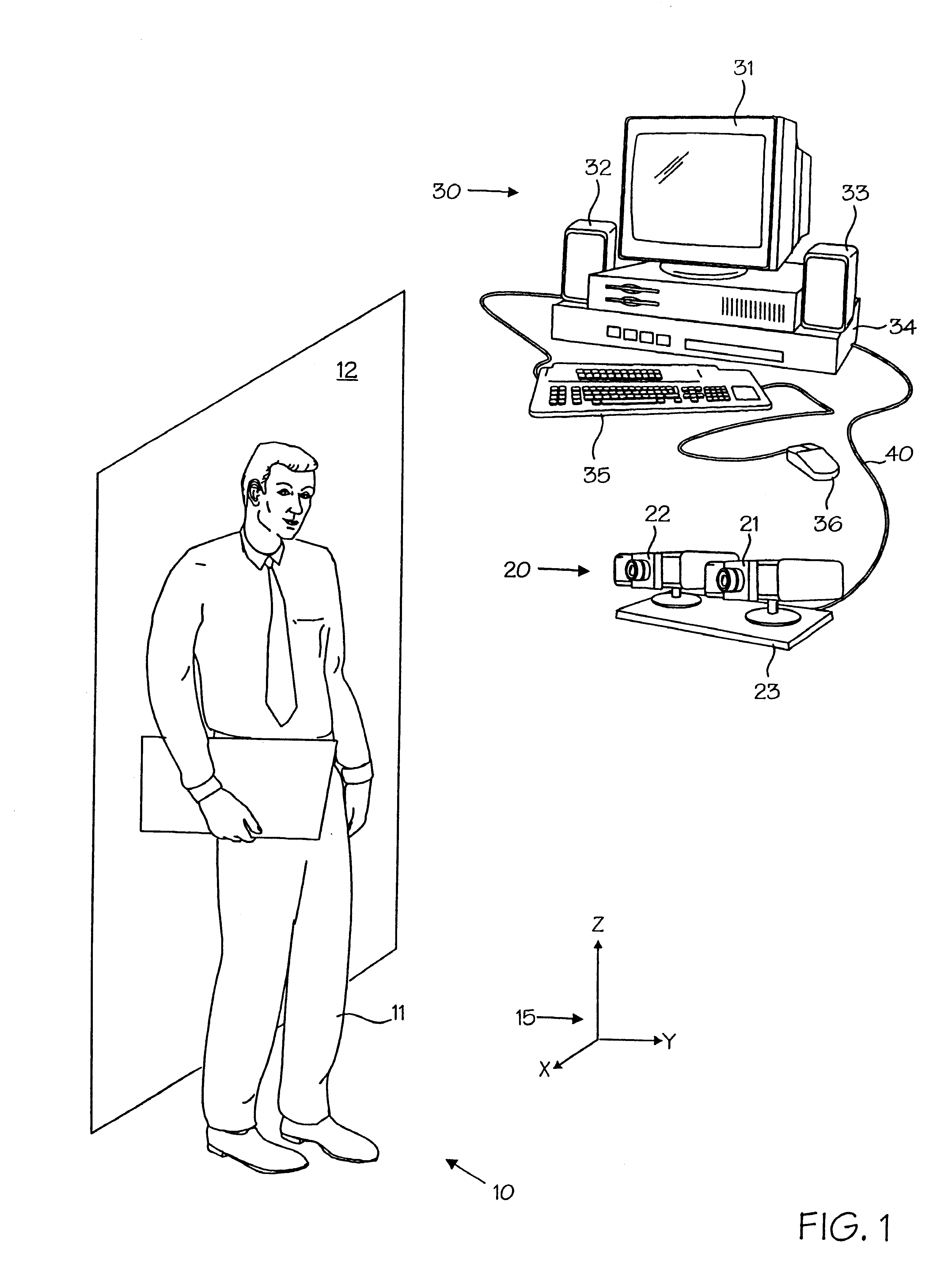
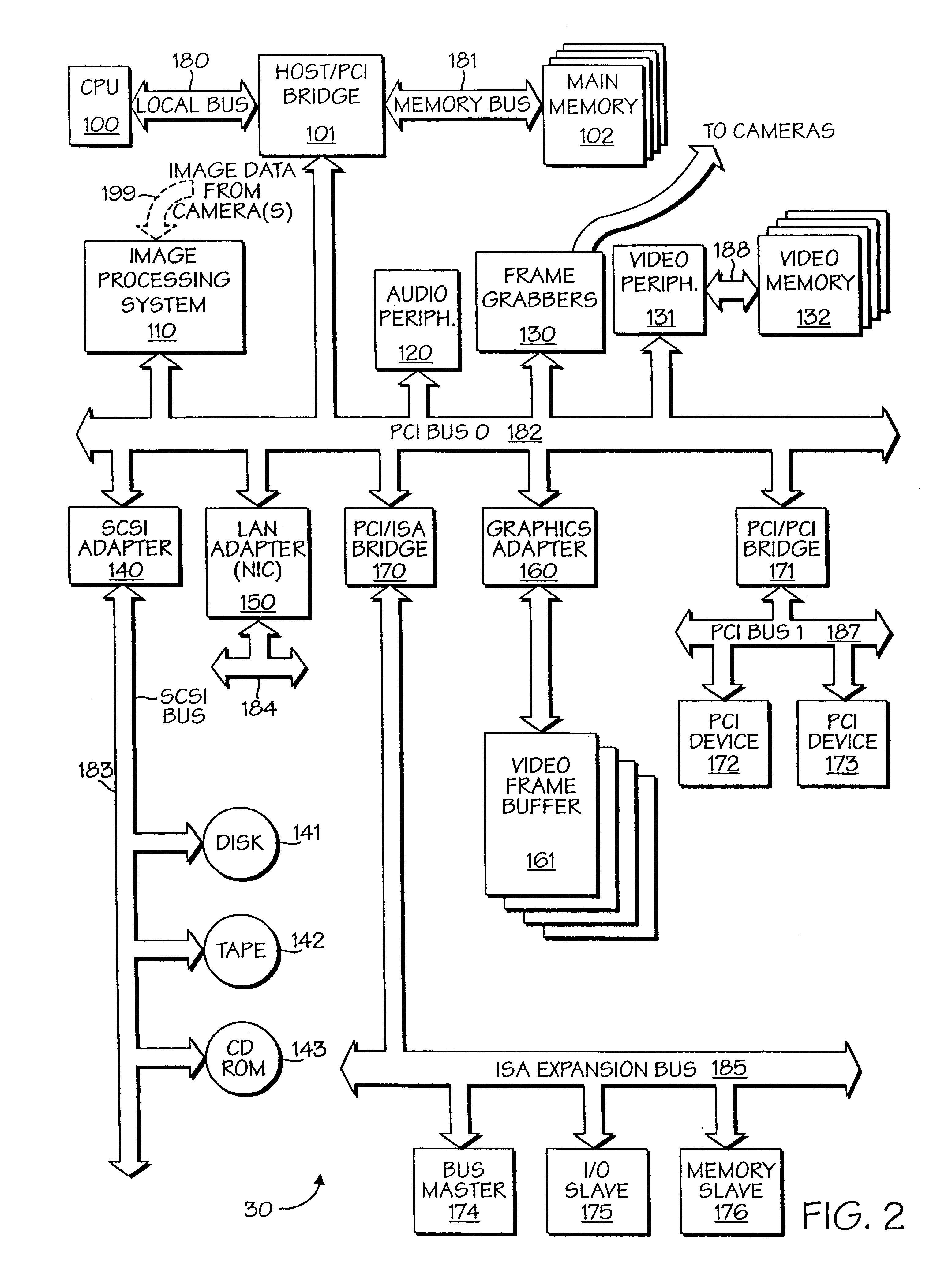
A powerful, scaleable, and reconfigurable image processing system and method of processing data therein is described. This general purpose, reconfigurable engine with toroidal topology, distributed memory, and wide bandwidth I / O are capable of solving real applications at real-time speeds. The reconfigurable image processing system can be optimized to efficiently perform specialized computations, such as real-time video and audio processing. This reconfigurable image processing system provides high performance via high computational density, high memory bandwidth, and high I / O bandwidth. Generally, the reconfigurable image processing system and its control structure include a homogeneous array of 16 field programmable gate arrays (FPGA) and 16 static random access memories (SRAM) arranged in a partial torus configuration. The reconfigurable image processing system also includes a PCI bus interface chip, a clock control chip, and a datapath chip. It can be implemented in a single board. It receives data from its external environment, computes correspondence, and uses the results of the correspondence computations for various post-processing industrial applications. The reconfigurable image processing system determines correspondence by using non-parametric local transforms followed by correlation. These non-parametric local transforms include the census and rank transforms. Other embodiments involve a combination of correspondence, rectification, a left-right consistency check, and the application of an interest operator.
Owner:INTEL CORP
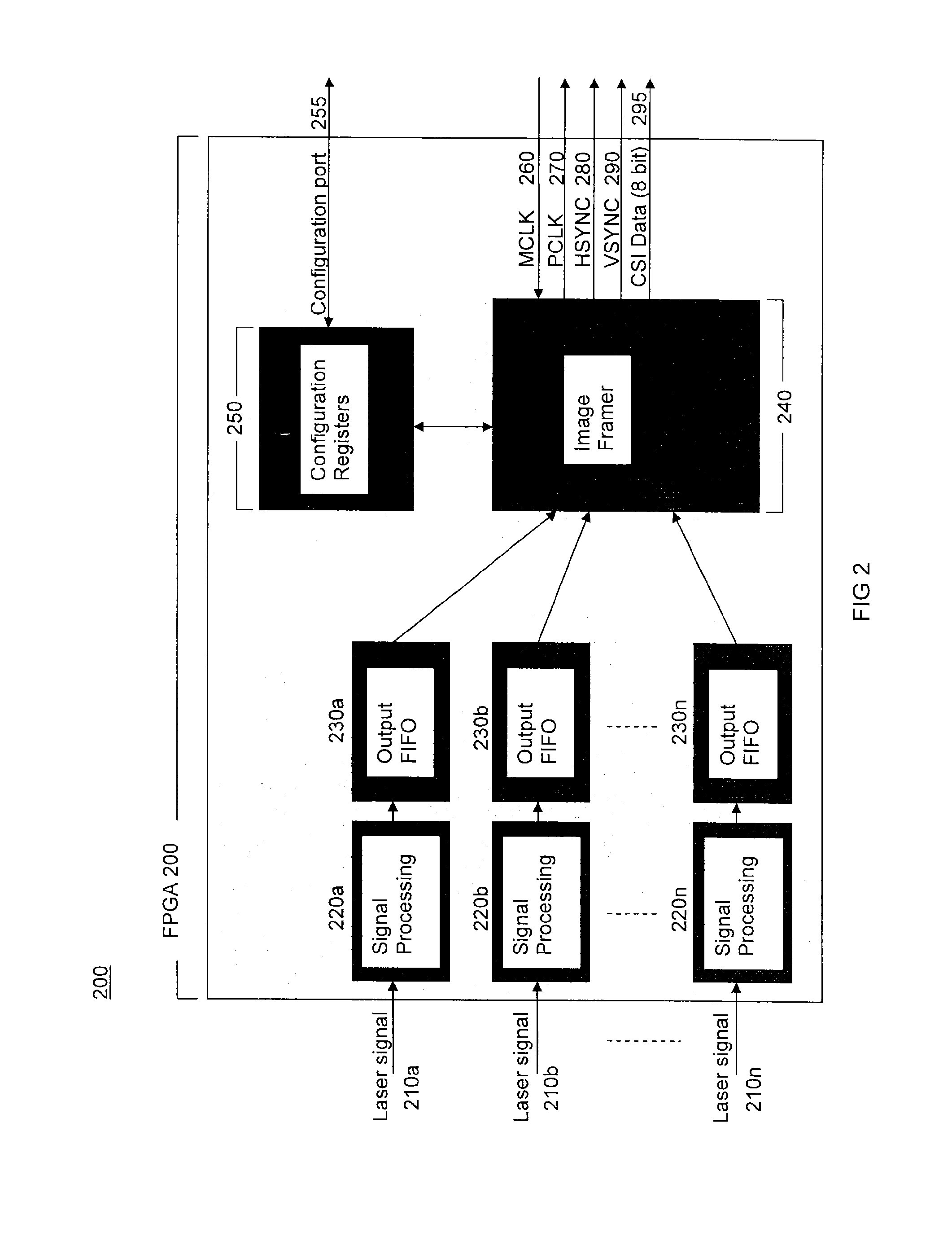
Method of using camera sensor interface to transfer multiple channels of scan data using an image format
ActiveUS20150053768A1Solve the slow scanning speedSolve excessive overheadCharacter and pattern recognitionRecord carriers used with machinesLaser scanningEngineering
Owner:HONEYWELL INT INC
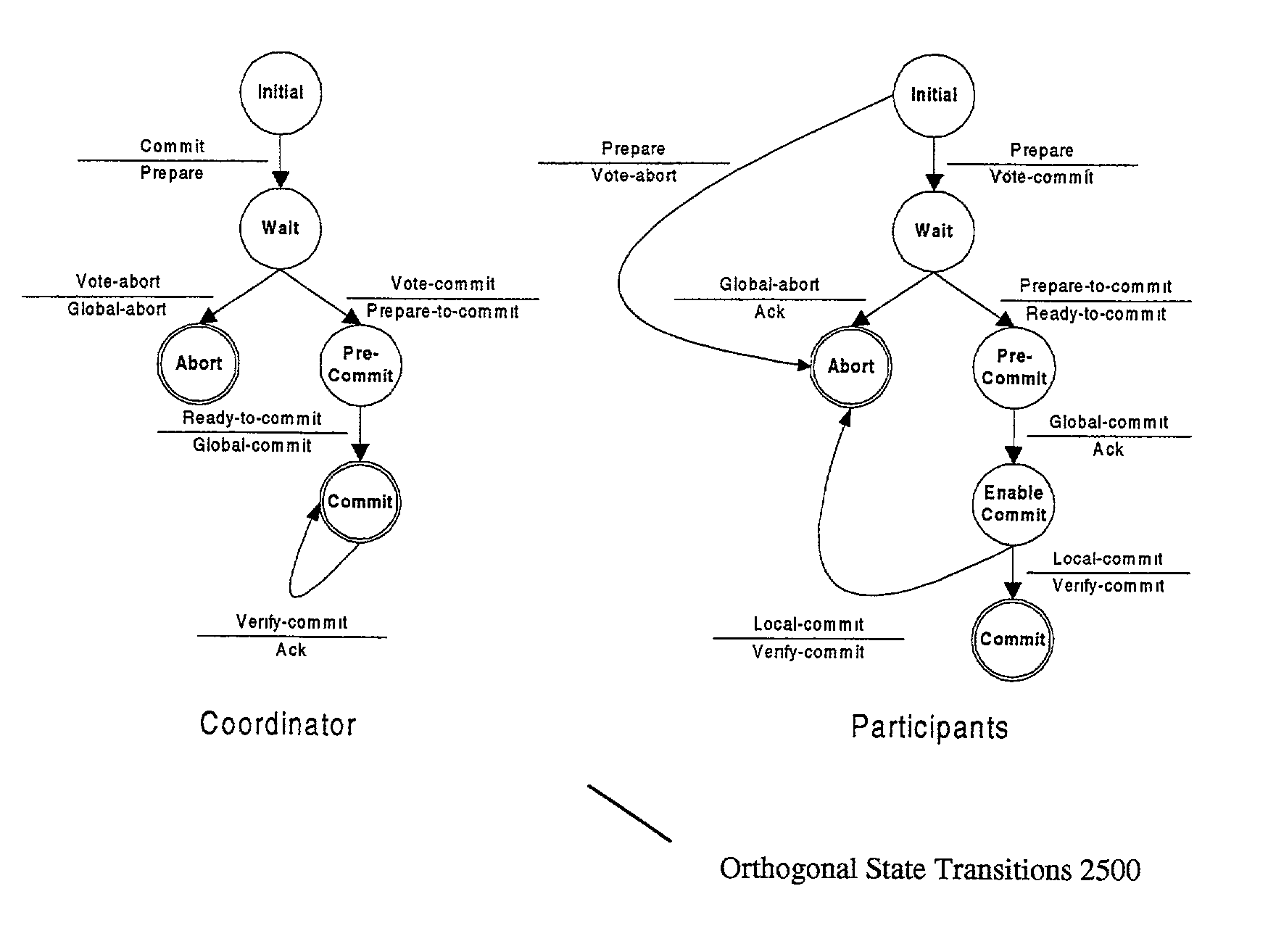
Asynchronous transcription object management system
ActiveUS7206805B1Avoid modificationReduce in quantityData processing applicationsMultiple digital computer combinationsManagement systemDistributed computing
Described herein is a system for executing distributed transactions. A coordinator and one or more participants cooperate to execute a distributed transaction, the distributed transaction including for each participant a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. Before each participant commits the transaction, the participants determine that the coordinator has committed the transaction. The coordinator commits the transaction after receiving acknowledgment from all the participants that they will commit the transaction. To determine whether the coordinator has committed the transaction, a participant transmits a message to the coordinator to acknowledge that it will commit the distributed transaction. The participant commits its respective transaction if it receives an acknowledgement from the coordinator. For the particular transaction being executed by a participant, the participant prevents other transactions from modifying a data item affected by the particular transaction. The participant will prevent such modifications until termination criteria for the particular transaction is satisfied, in which case the participant terminates the transaction.
Owner:ORACLE INT CORP
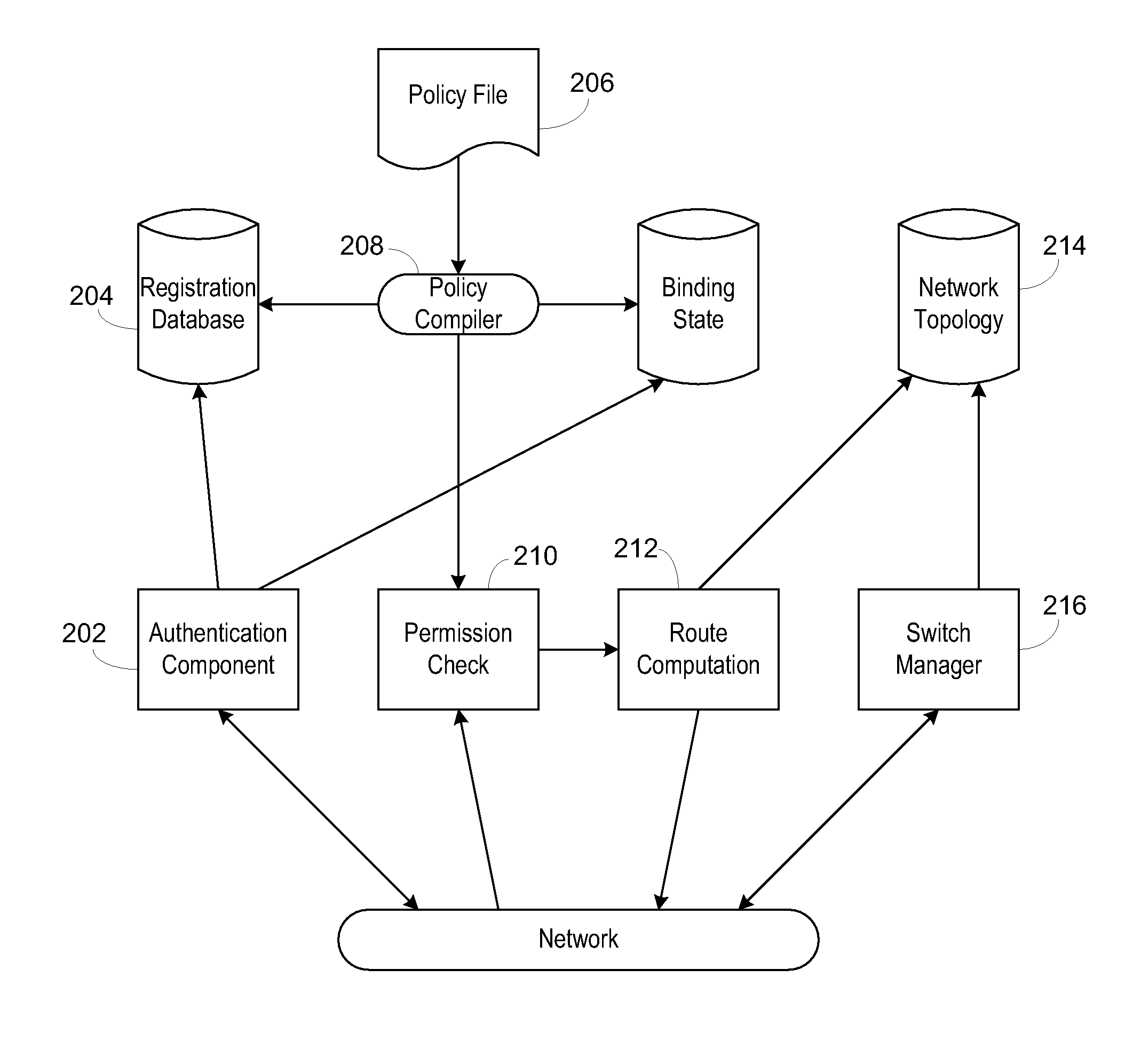
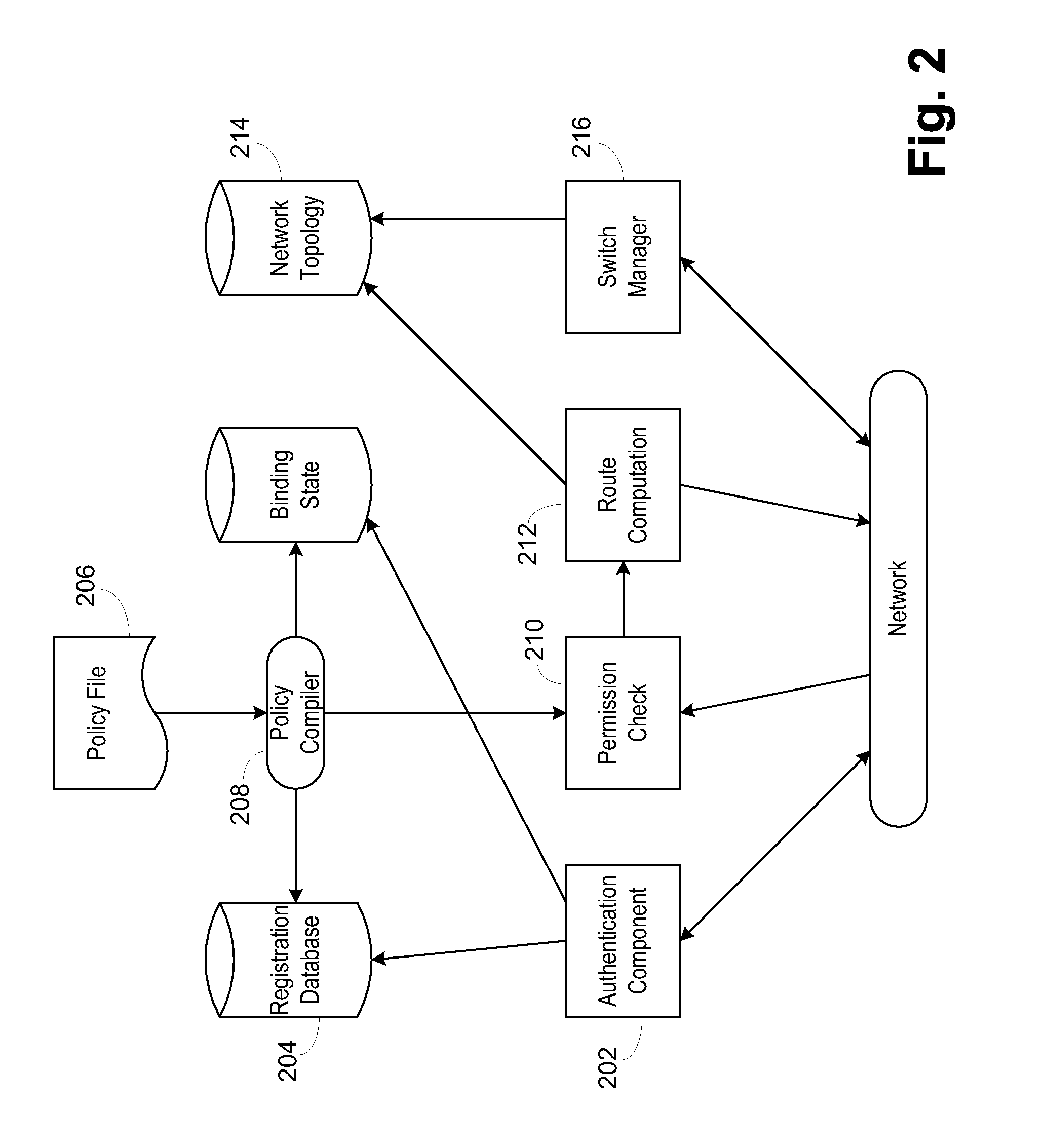
Secure network switching infrastructure
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
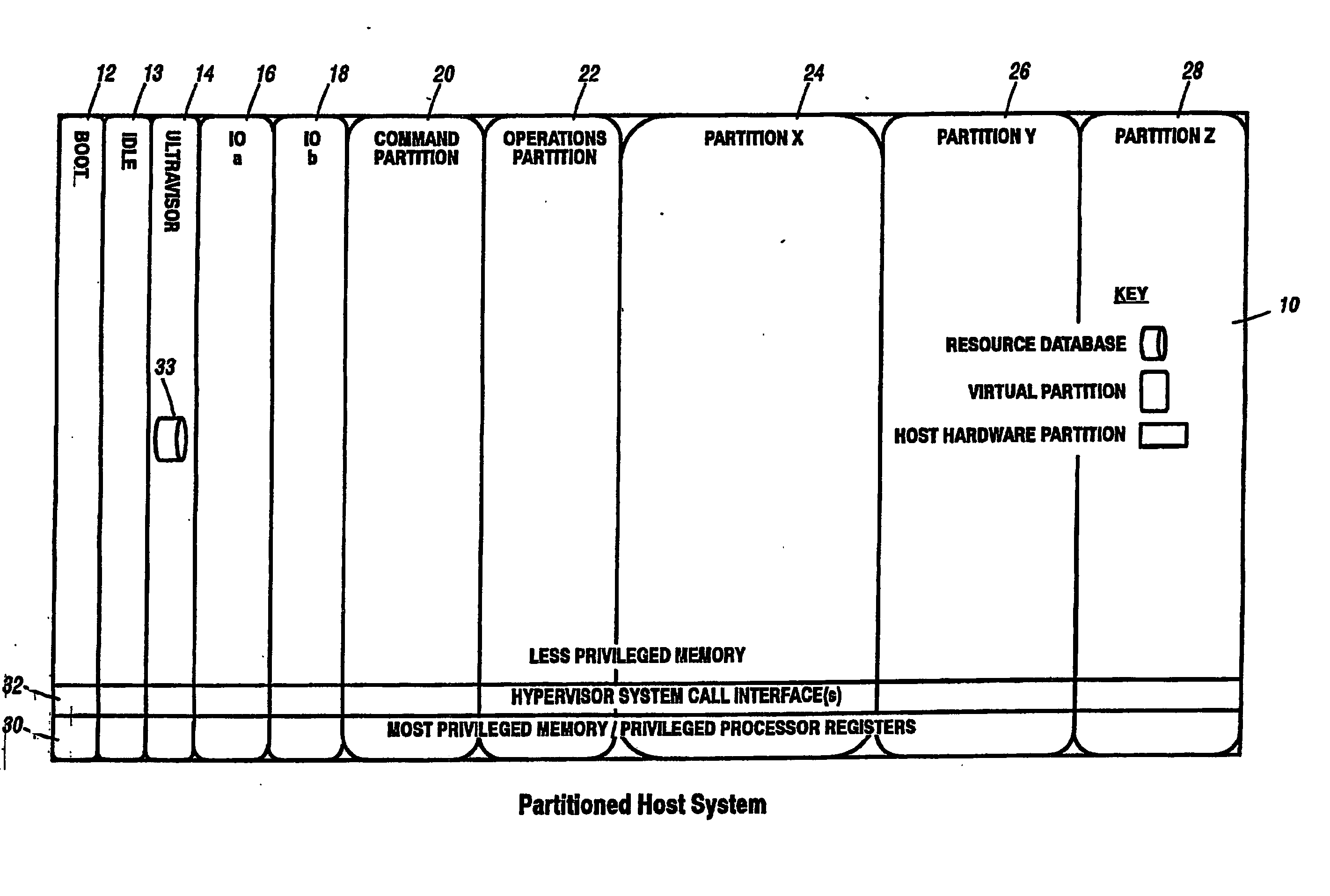
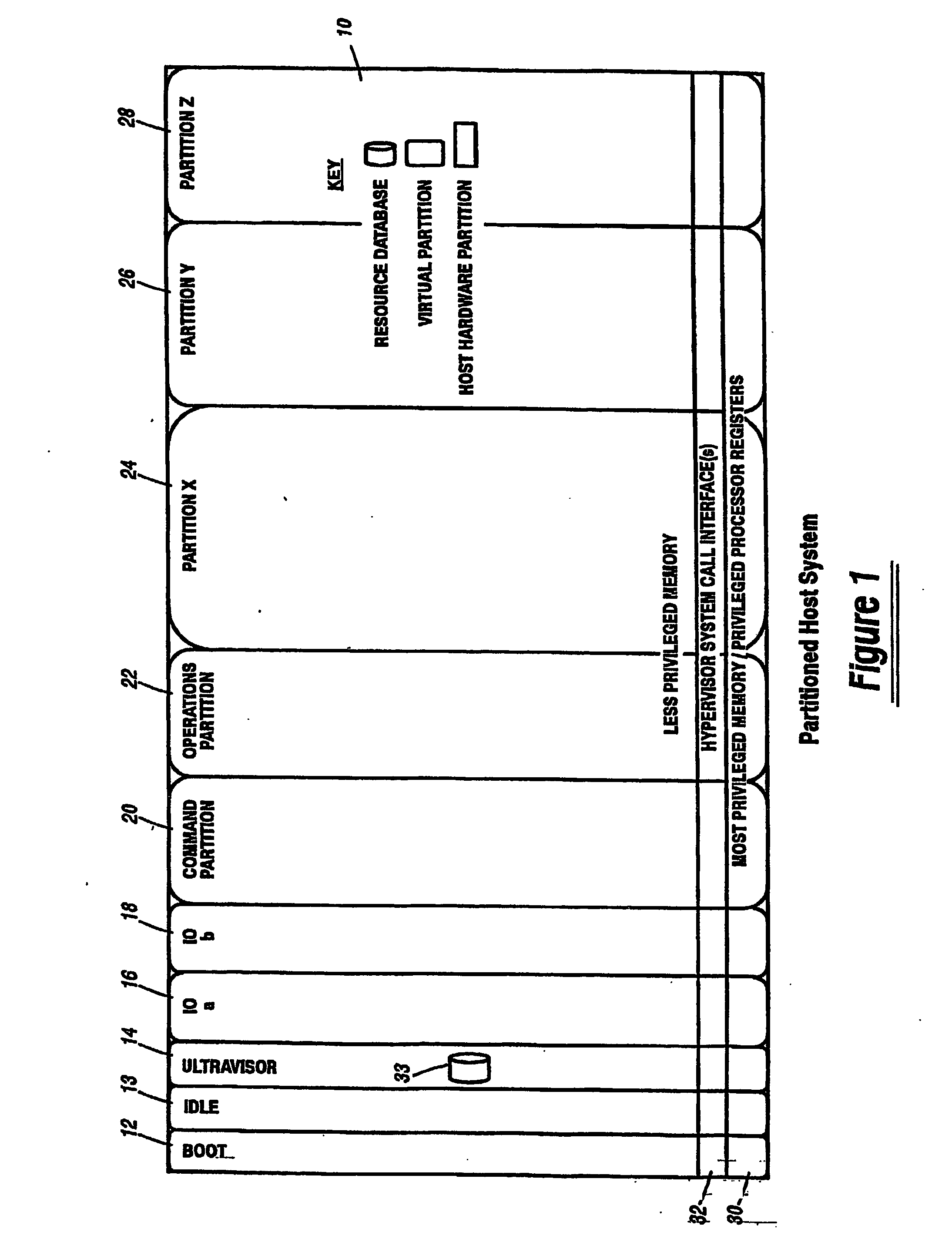
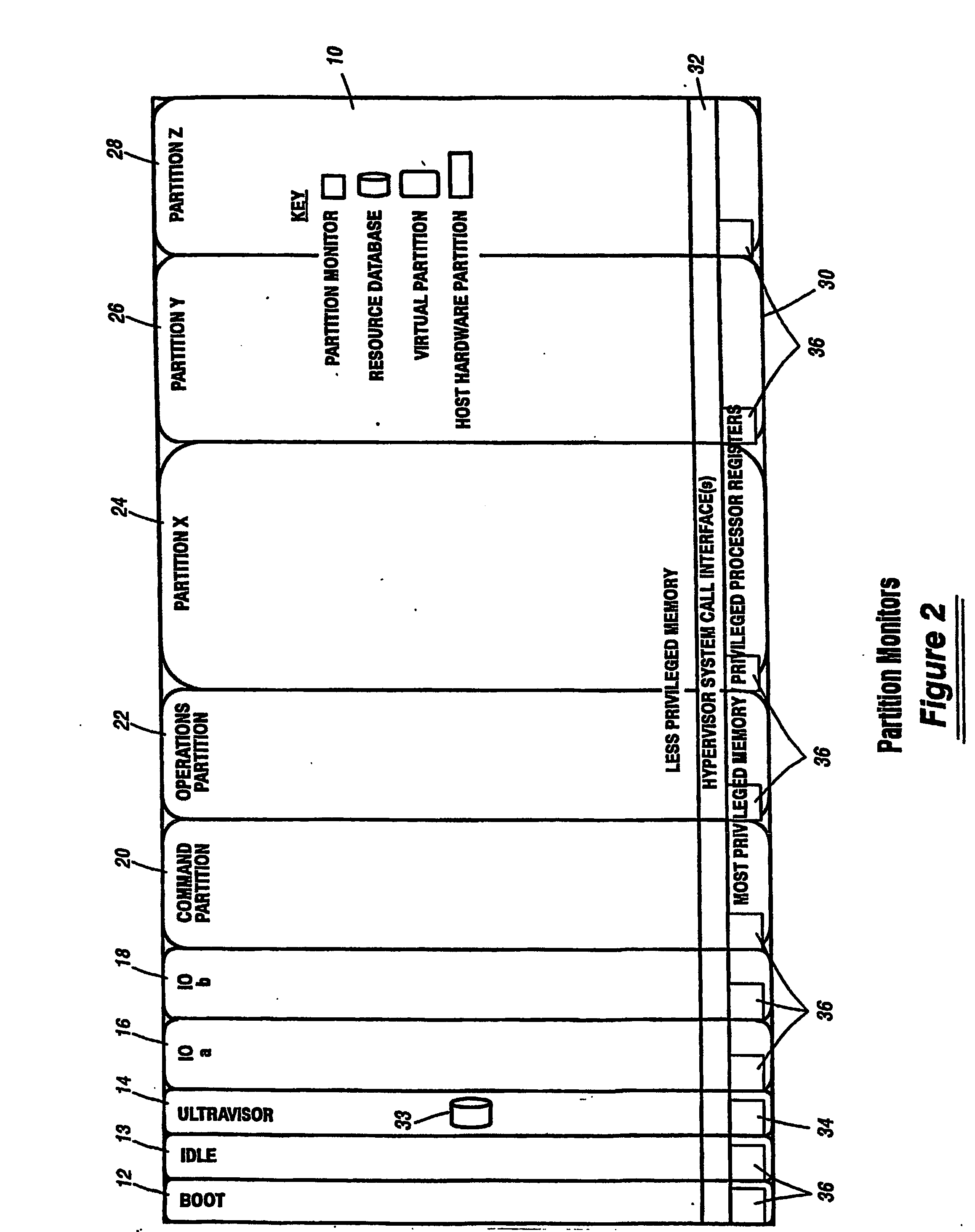
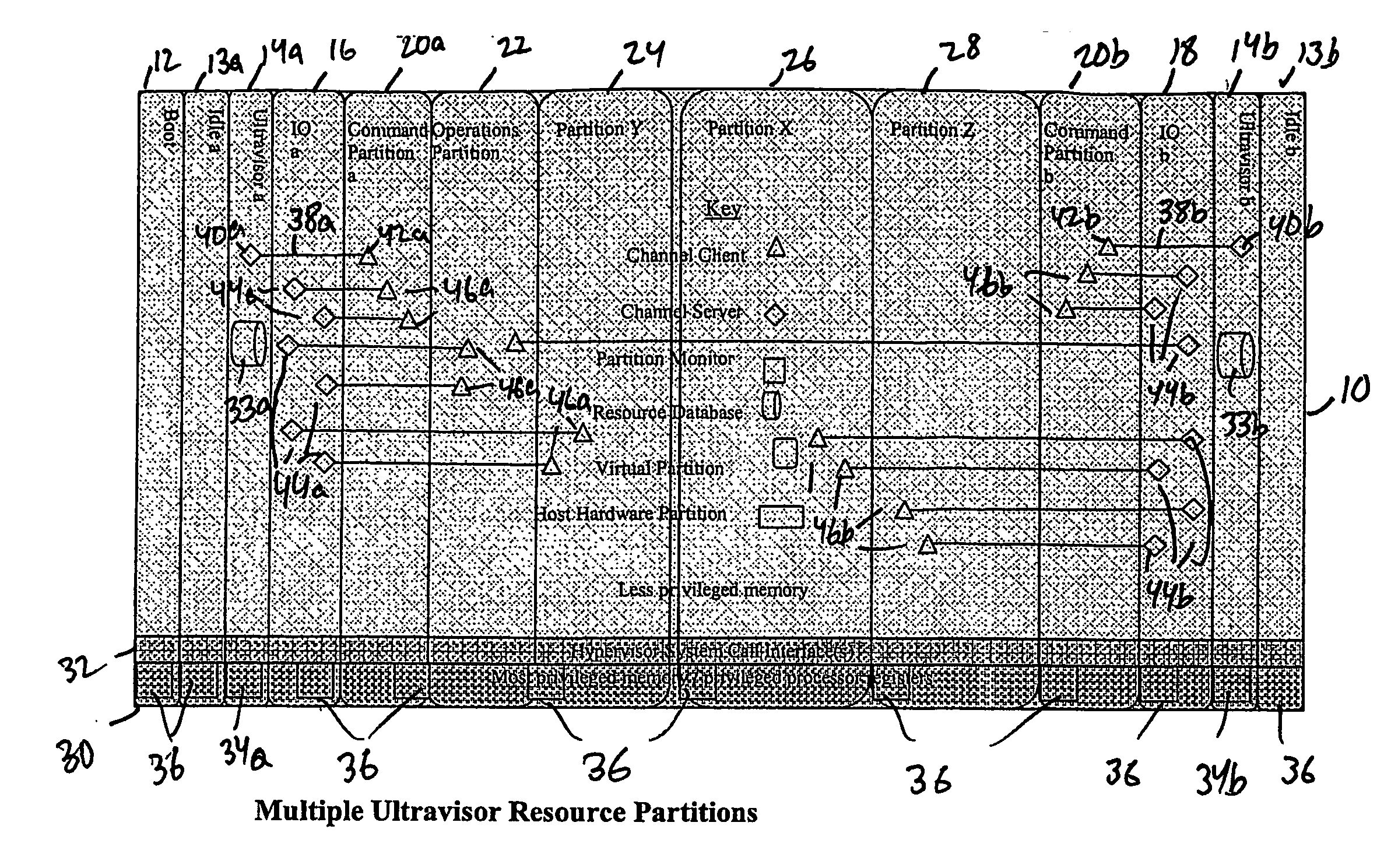
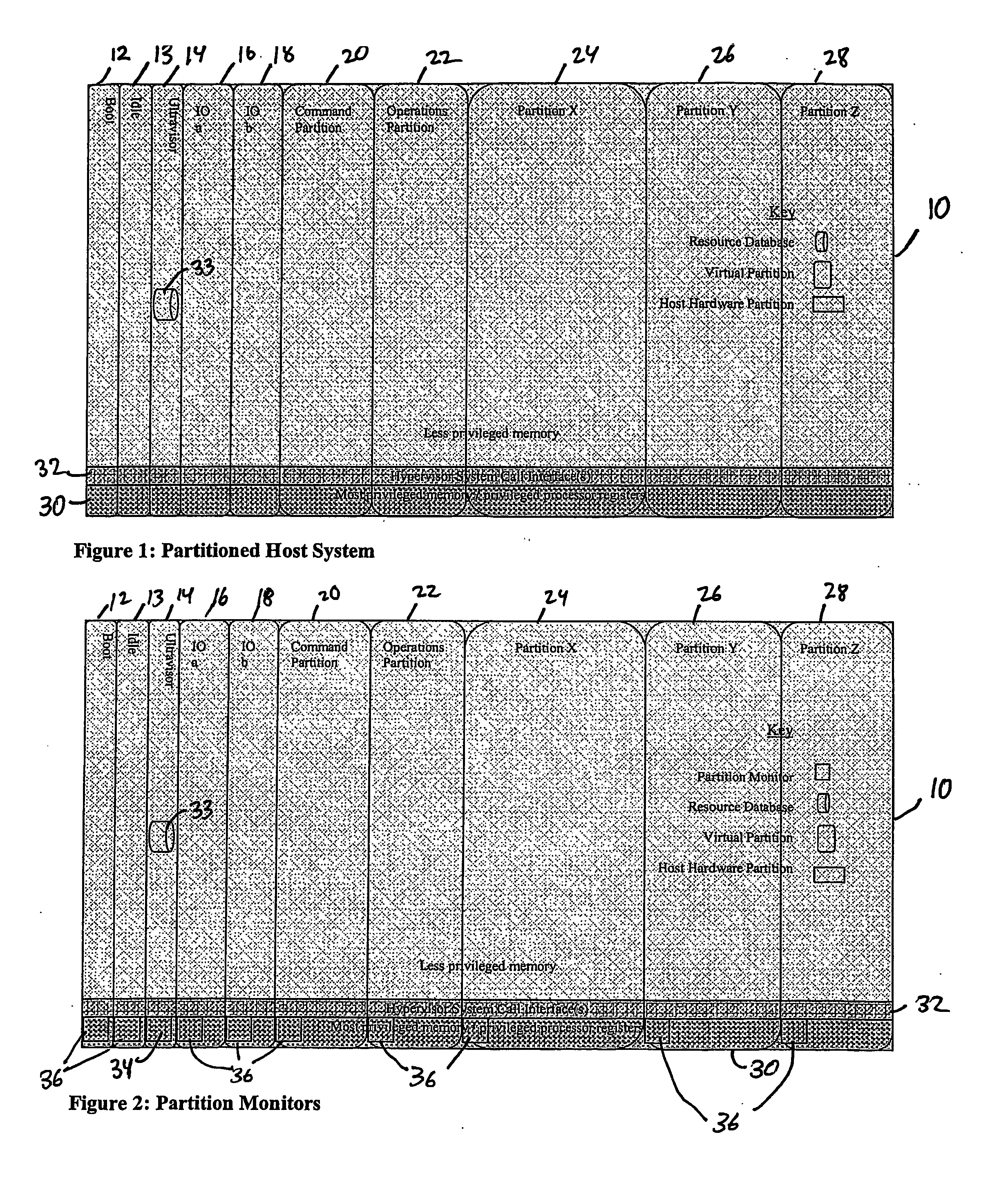
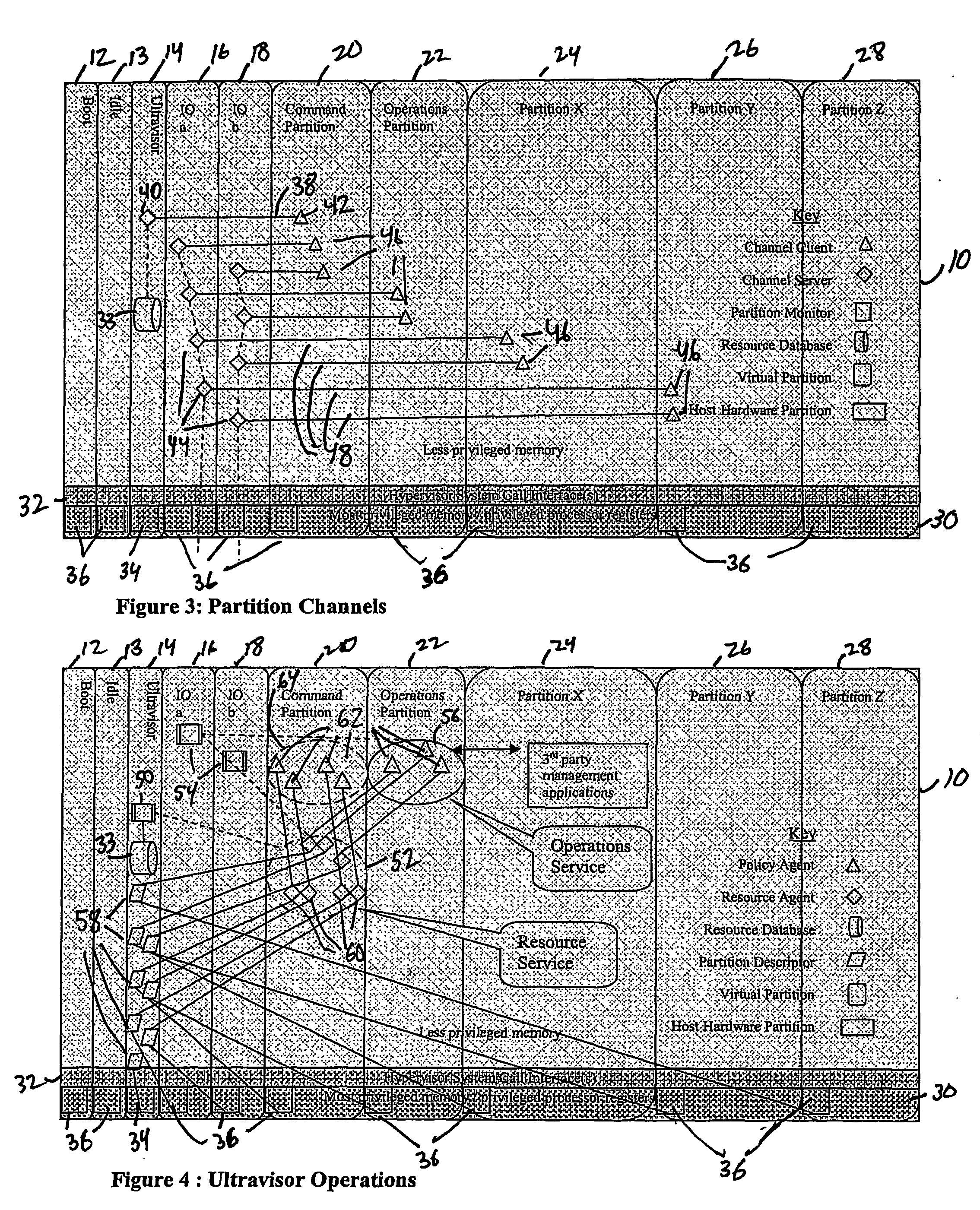
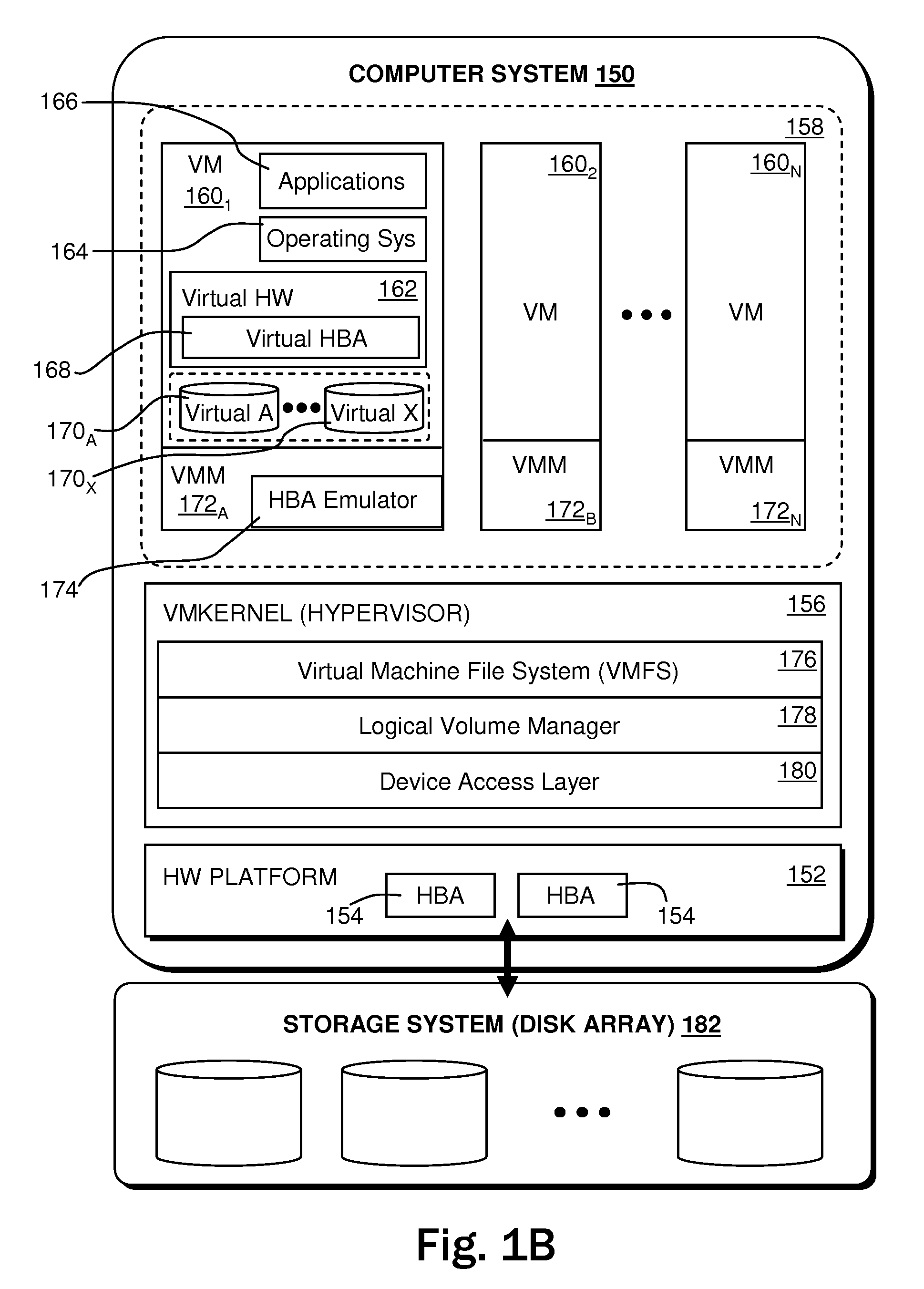
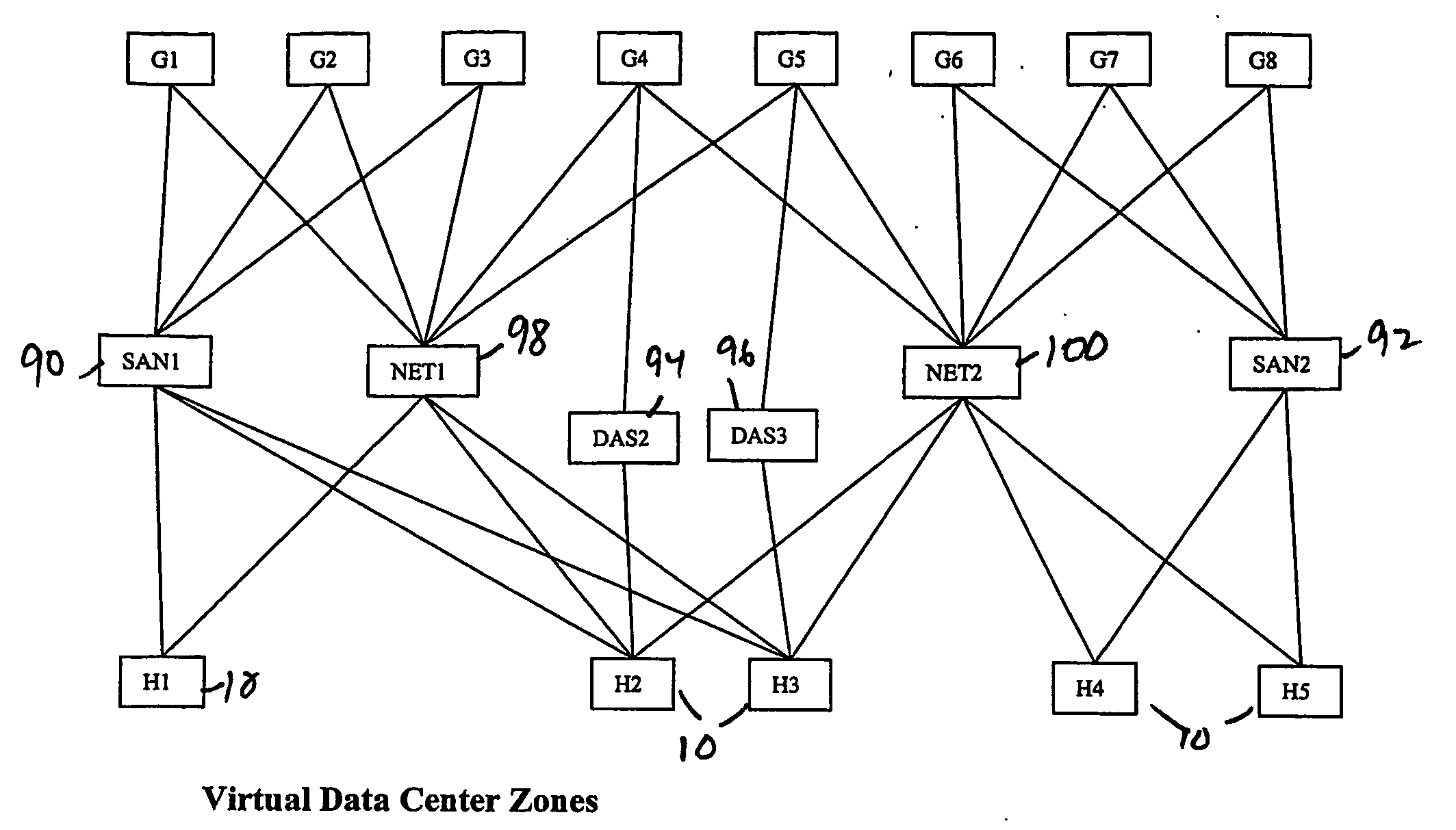
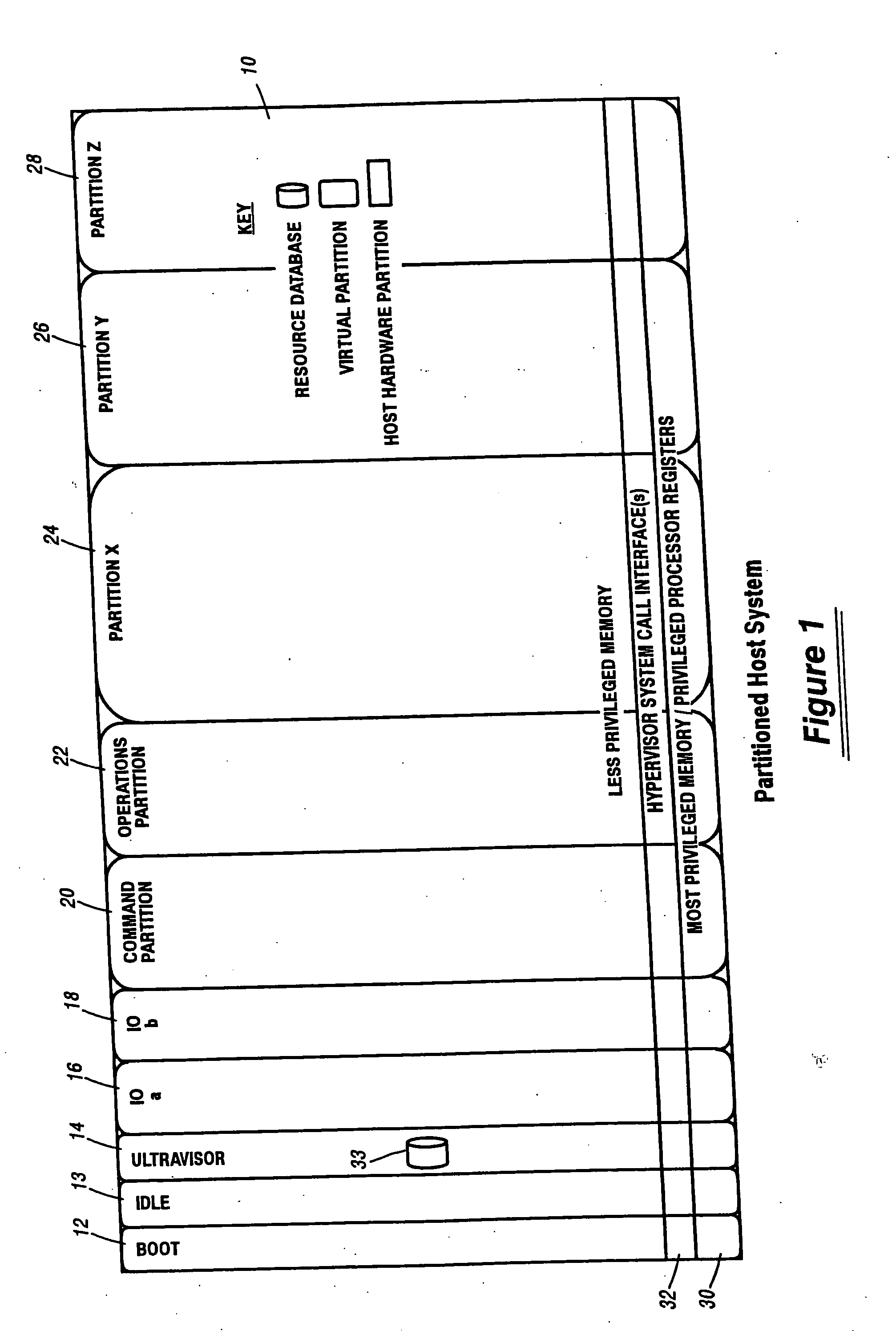
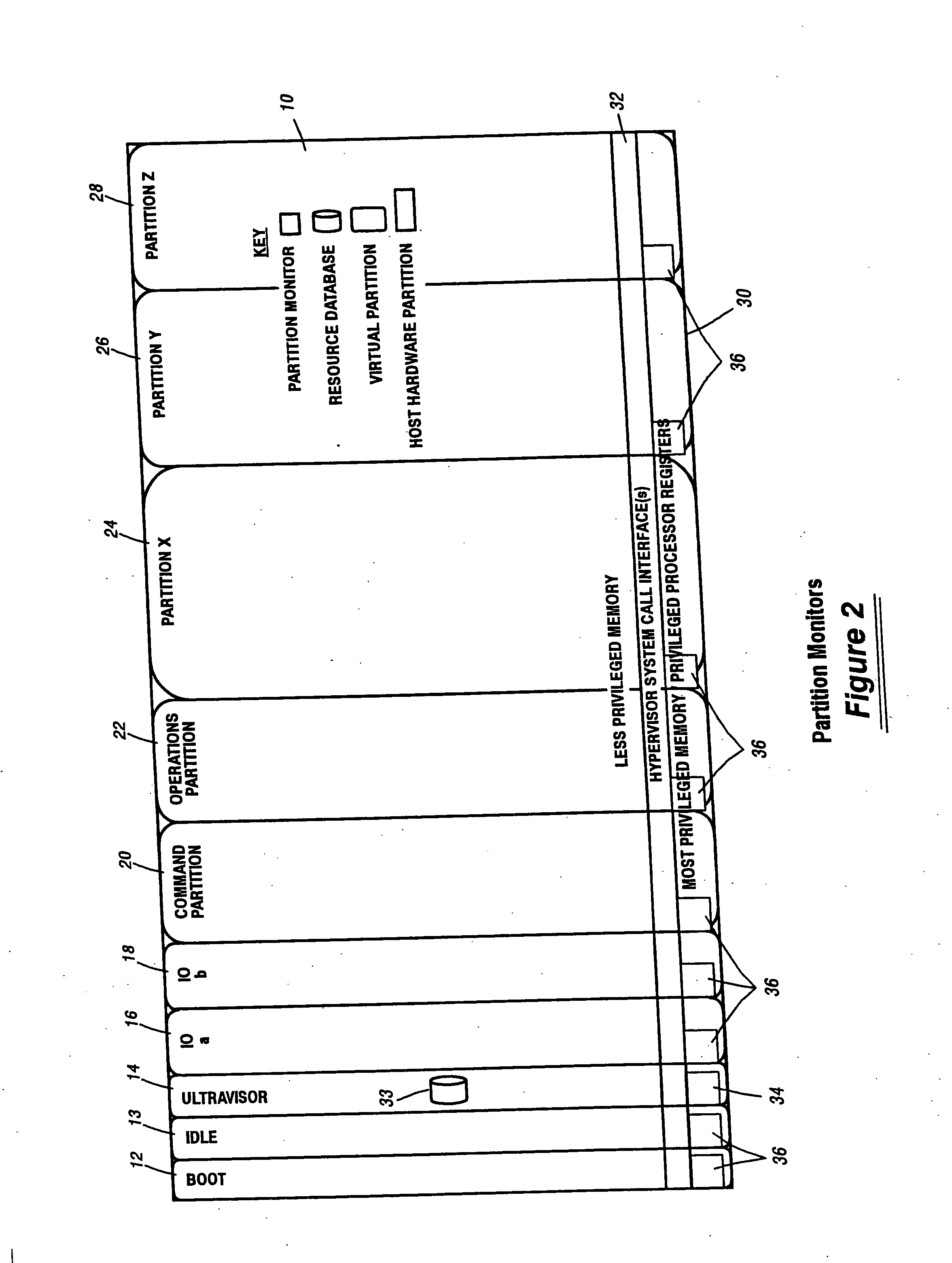
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
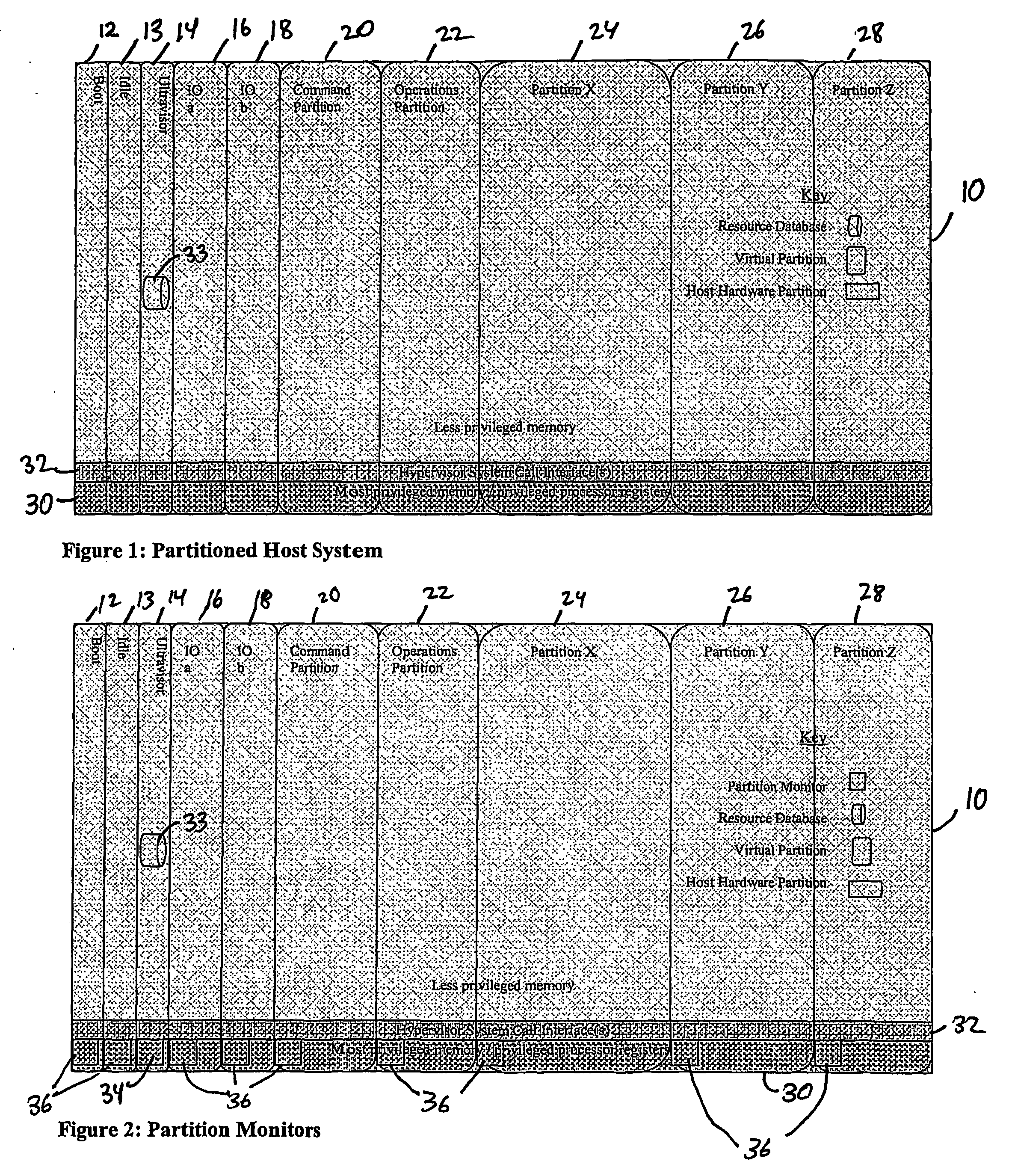
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
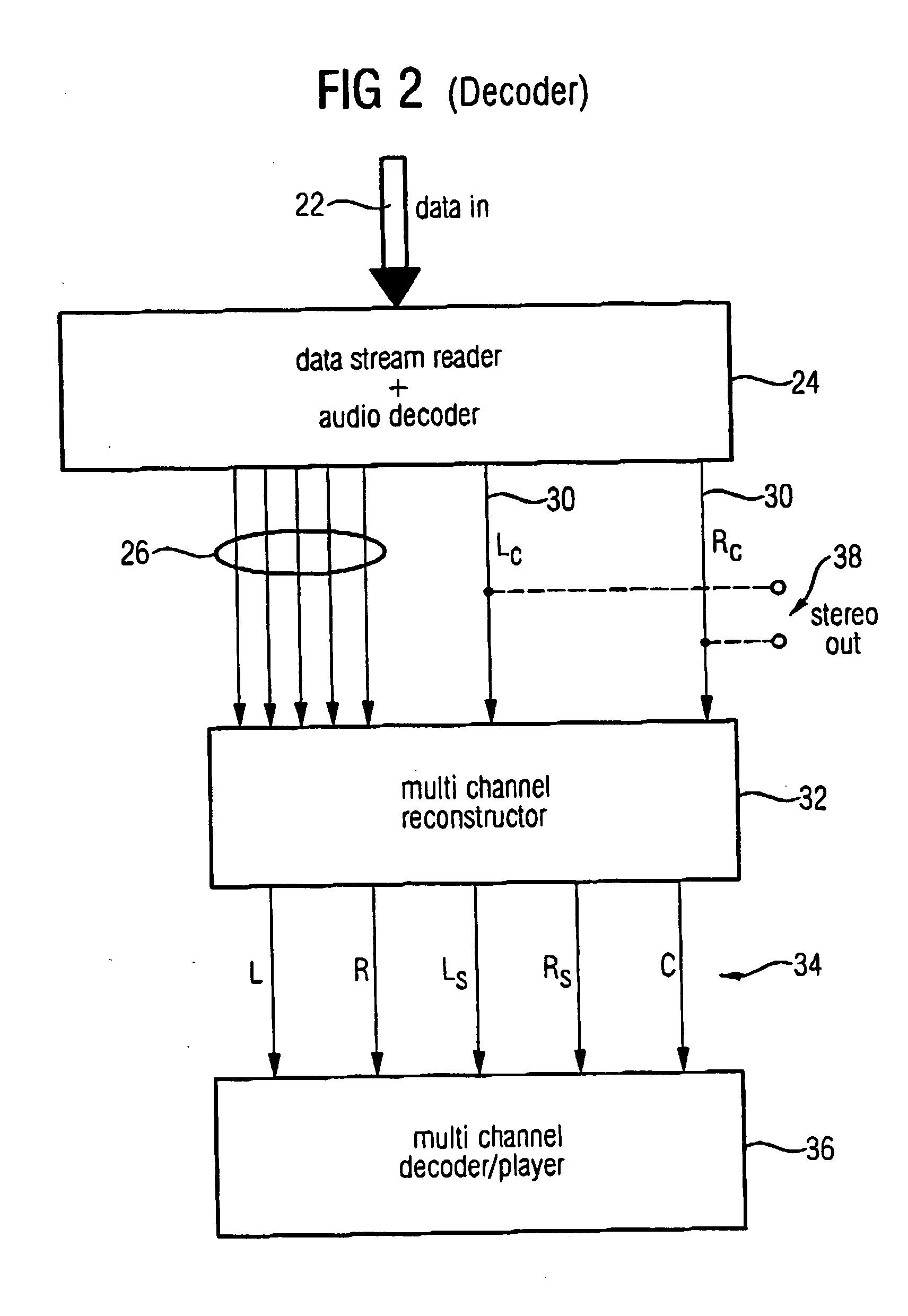
Compatible multi-channel coding/decoding
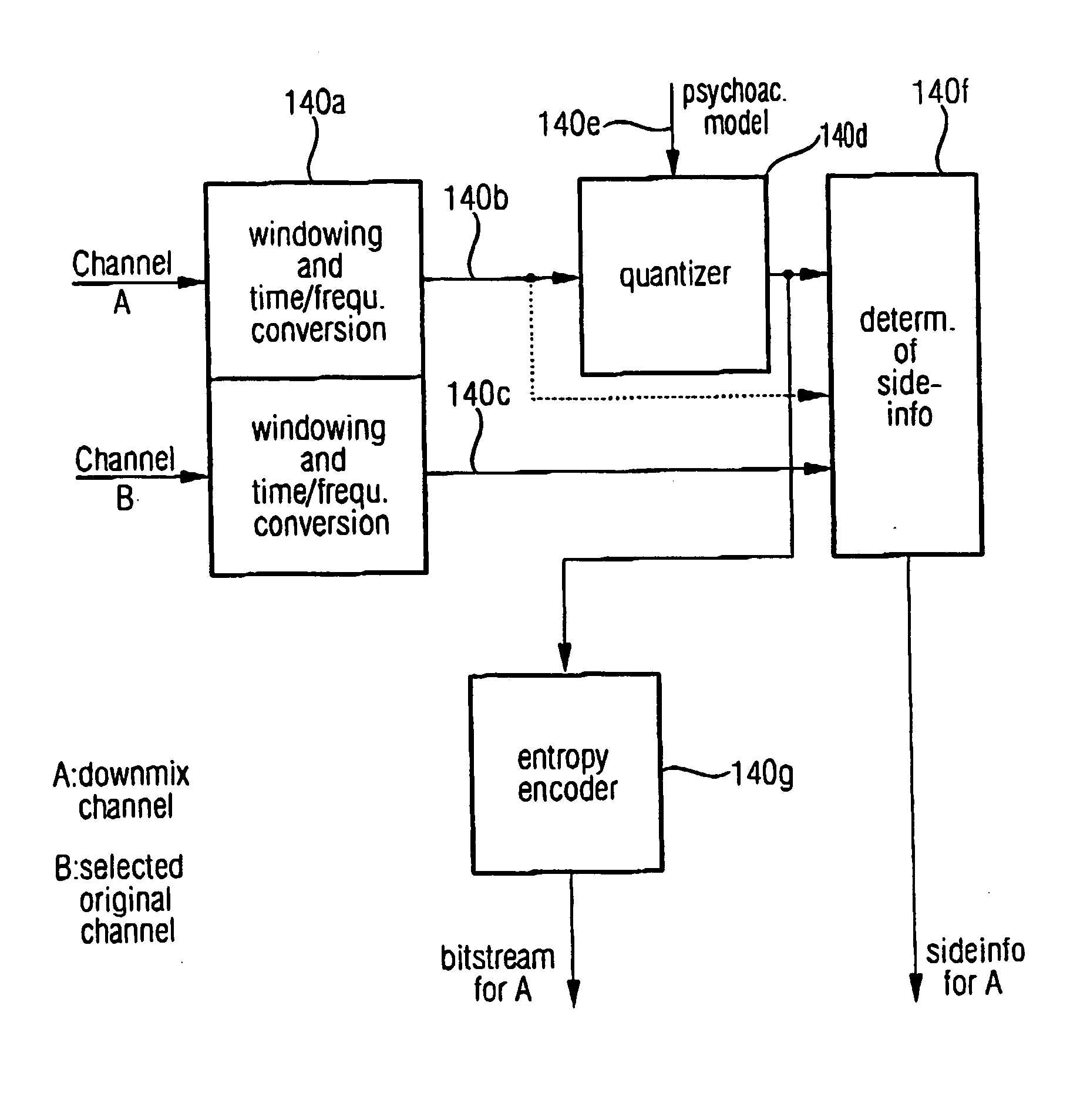
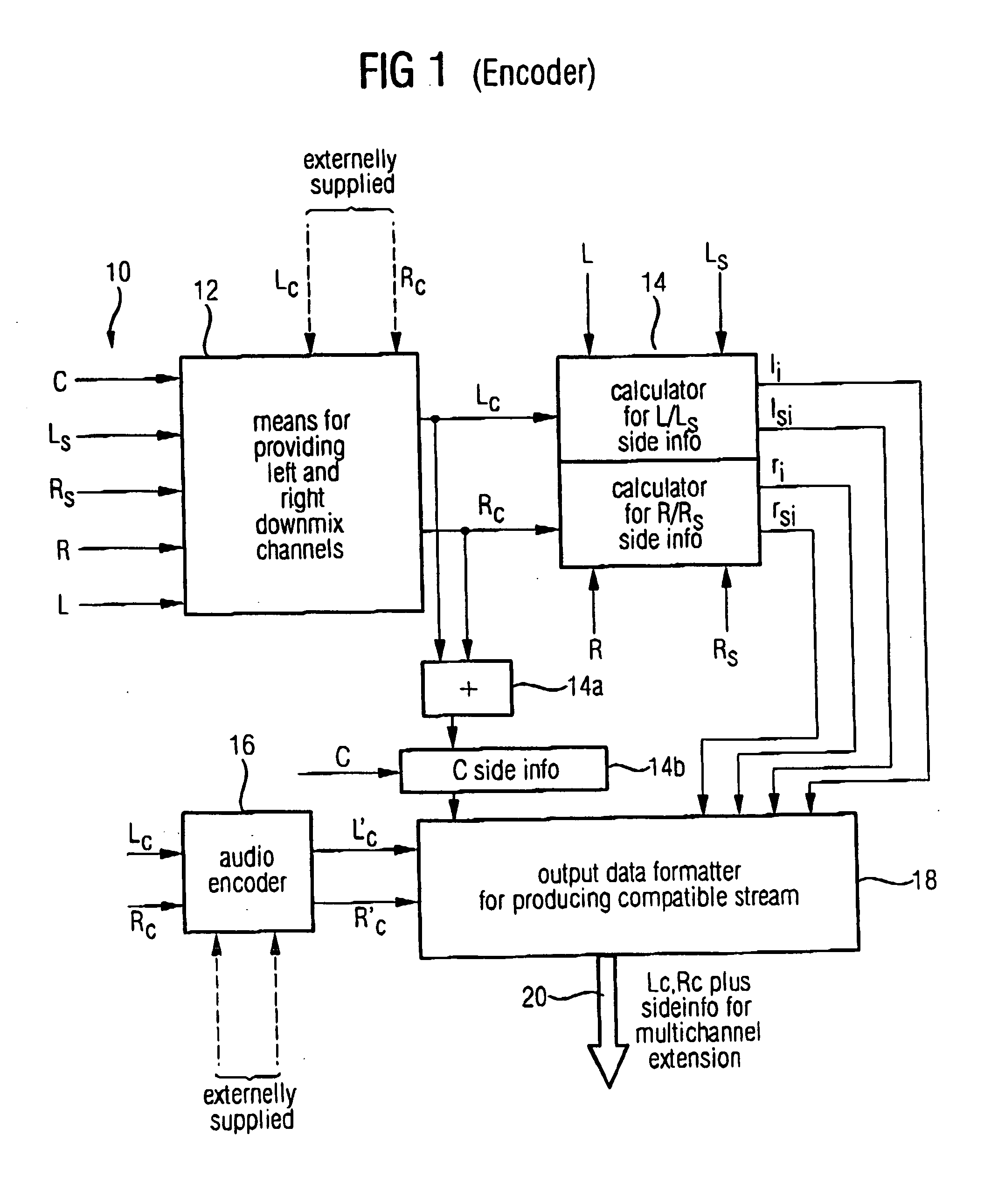
ActiveUS20050074127A1Suitable for processingEfficient and artifact-reduced encodingSpeech analysisStereophonic systemsSide informationComputer science
In processing a multi-channel audio signal having at least three original channels, a first downmix channel and a second downmix channel are provided, which are derived from the original channels. For a selected original channel of the original channels, channel side information are calculated such that a downmix channel or a combined downmix channel including the first and the second downmix channels, when weighted using the channel side information, results in an approximation of the selected original channel. The channel side information and the first and second downmix channels form output data to be transmitted to a decoder, which, in case of a low level decoder only decodes the first and second downmix channels or, in case of a high level decoder provides a full multi-channel audio signal based on the downmix channels and the channel side information. Since the channel side information only occupy a low number of bits, and since the decoder does not use dematrixing, an efficient and high quality multi-channel extension for stereo players and enhanced multi-channel players is obtained.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV +1
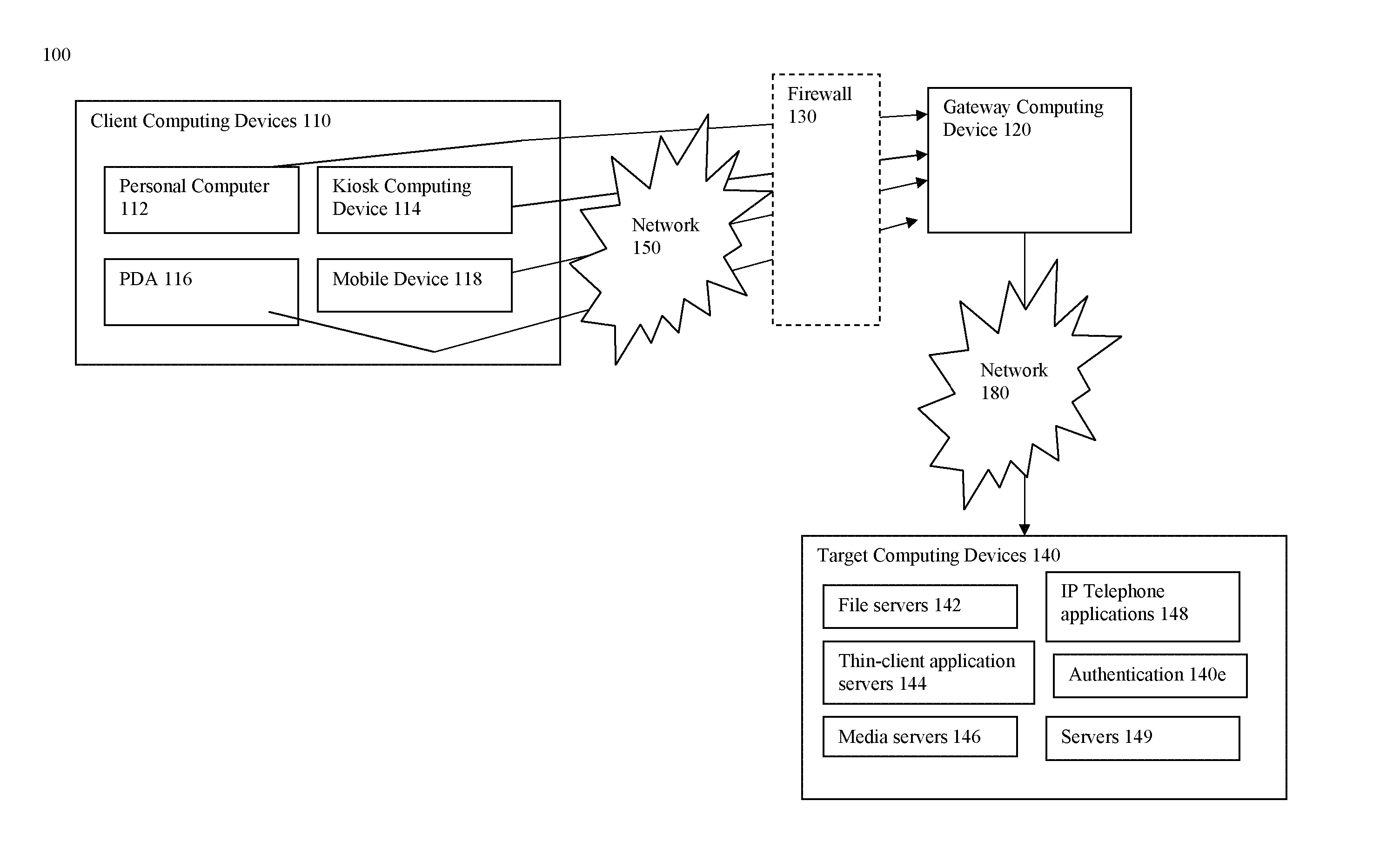
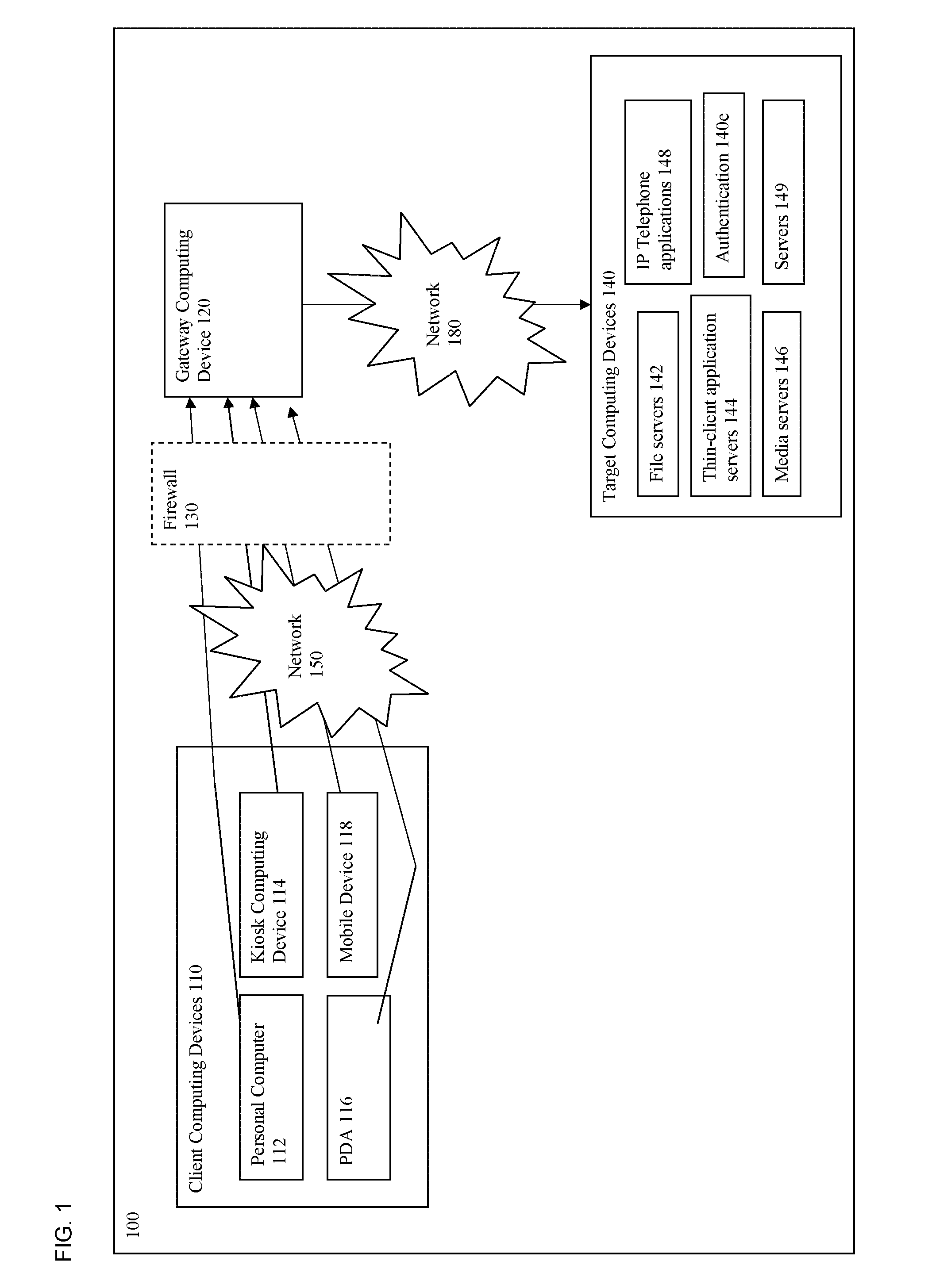
A method and systems for securing remote access to private networks
ActiveUS20060037071A1Reduce the burden onImprove experienceMultiple digital computer combinationsProgram controlPrivate networkNetwork address translation
A method for securing remote access to private networks includes a receiver intercepting from a data link layer a packet in a first plurality of packets destined for a first system on a private network. A filter intercepts from the data link layer a packet in a second plurality of packets transmitted from a second system on the private network, destined for an system on a second network. A transmitter in communication with the receiver and the filter performing a network address translation on at least one intercepted packet and transmitting the at least one intercepted packet to a destination.
Owner:CITRIX SYST INC
Network appliance
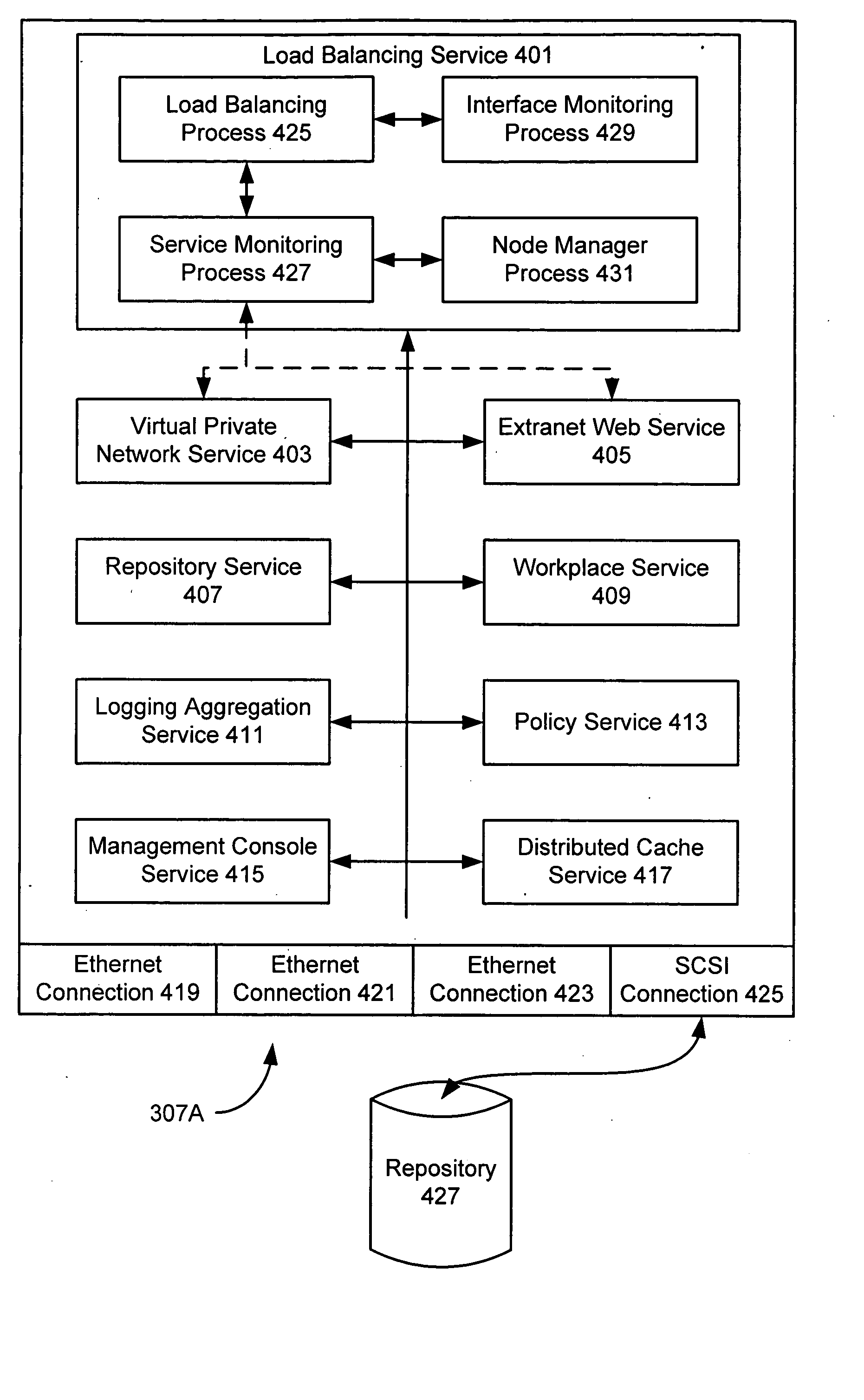
InactiveUS20050132030A1Low costReduce overheadError detection/correctionDigital computer detailsAccess methodClient-side
A network appliance is described that can provide a variety of software services, including both platform services, such as access method services, and a load balancing service. A network may include a network appliance that both provides one or more platform services and acts as a load balancer. When two or more such appliances are used together, they can replace a substantial portion of a conventional network. For example, when a network appliance receives a client communication, its load balancer service can determine whether one of its own platform services will process the communication or forward the communication to another network appliance for processing. Moreover, if the load balancing service of a network appliance fails, another network appliance can provide load balancing. Similarly, if another service of a network appliance fails, then the network appliance may continue to provide load balancing but forward communications requiring the failed service to another network appliance for processing.
Owner:AVENTAIL A WHOLLY OWNED SUBSIDIARY OF SONICWALL
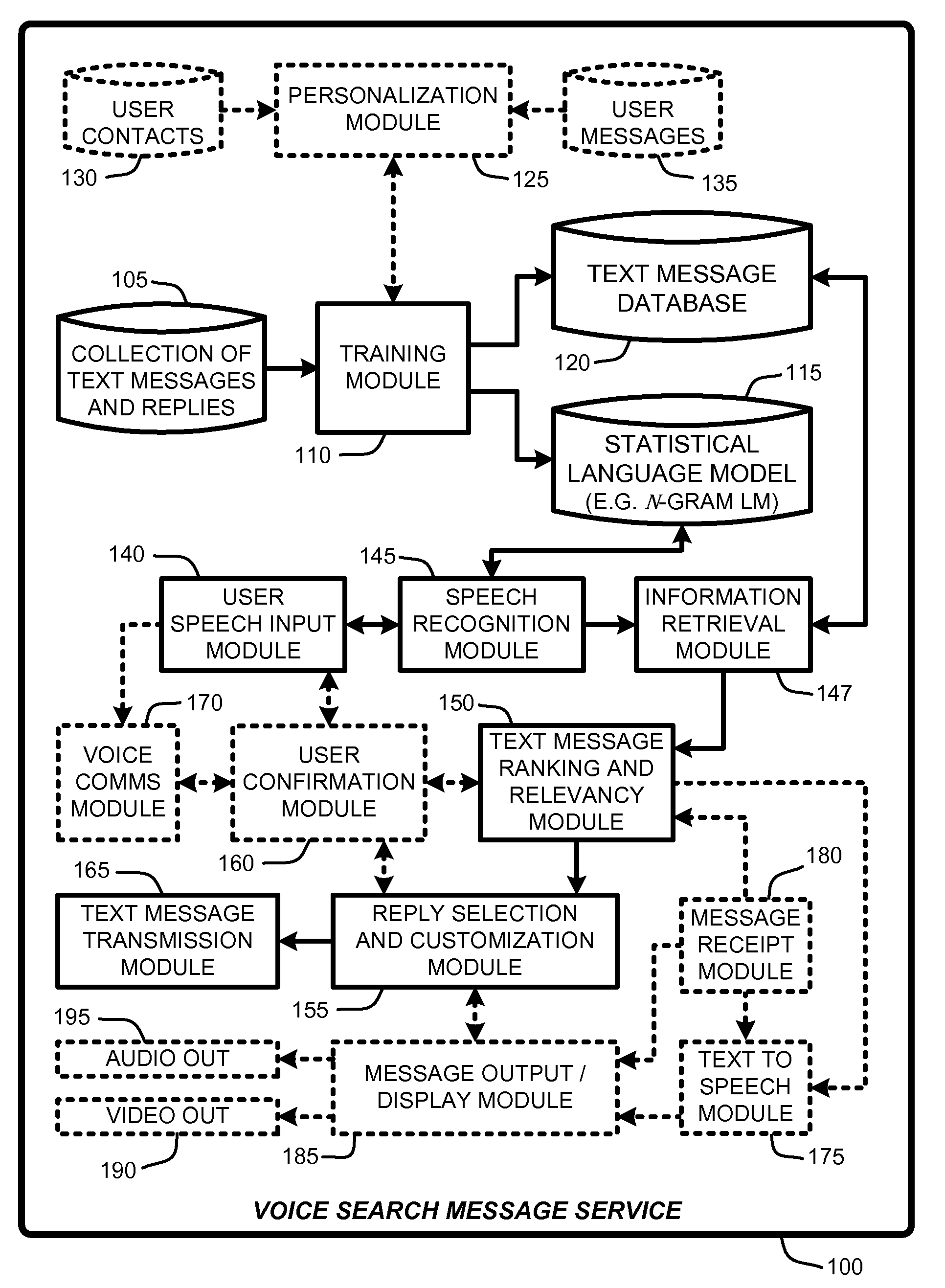
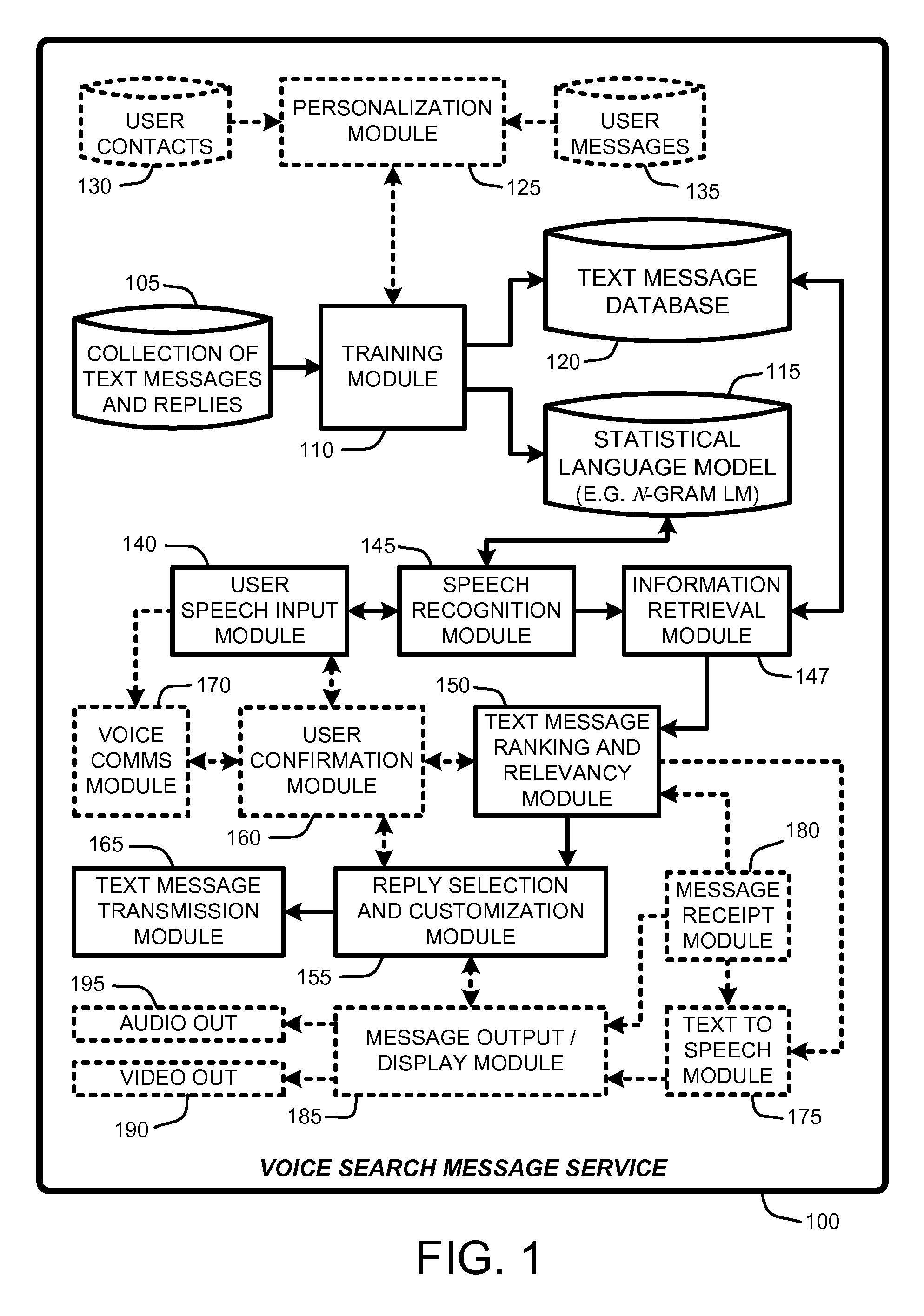
Replying to text messages via automated voice search techniques
Owner:MICROSOFT TECH LICENSING LLC
Low overhead fault tolerance through hybrid checkpointing and replay
ActiveUS20100107158A1Reduce overheadReduce needSoftware simulation/interpretation/emulationSpecial data processing applicationsVirtualizationLow overhead
A virtualized computer system provides fault tolerant operation of a primary virtual machine. In one embodiment, this system includes a backup computer system that stores a snapshot of the primary virtual machine and a log file containing non-deterministic events occuring in the instruction stream of the primary virtual machine. The primary virtual machine periodically updates the snapshot and the log file. Upon a failure of the primary virtual machine, the backup computer can instantiate a failover backup virtual machine by consuming the stored snapshot and log file.
Owner:VMWARE INC
Monitoring latency of a network to manage termination of distributed transactions
InactiveUS7290056B1Reduce in quantityReduce the numberMultiple digital computer combinationsTransmissionStateless protocolFinancial transaction
Described herein is a system for executing distributed transactions. A participant and a coordinator cooperate to execute a distributed transaction, the distributed transaction including a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. The distributed transaction may be terminated when communication between the participant and coordinator regarding the transaction does not occur within a time period. The time period may reflect the time required for a coordinator to send a message and a participant to acknowledge receipt of the message, and the time for the participant to perform operations executed for the transaction. The latency of network traffic between the participant and the coordinator is monitored, and the time periods adjusted accordingly. In addition, the amount of time required for the participant to execute operations for the transaction is monitored, and the time periods adjusted accordingly.
Owner:ORACLE INT CORP
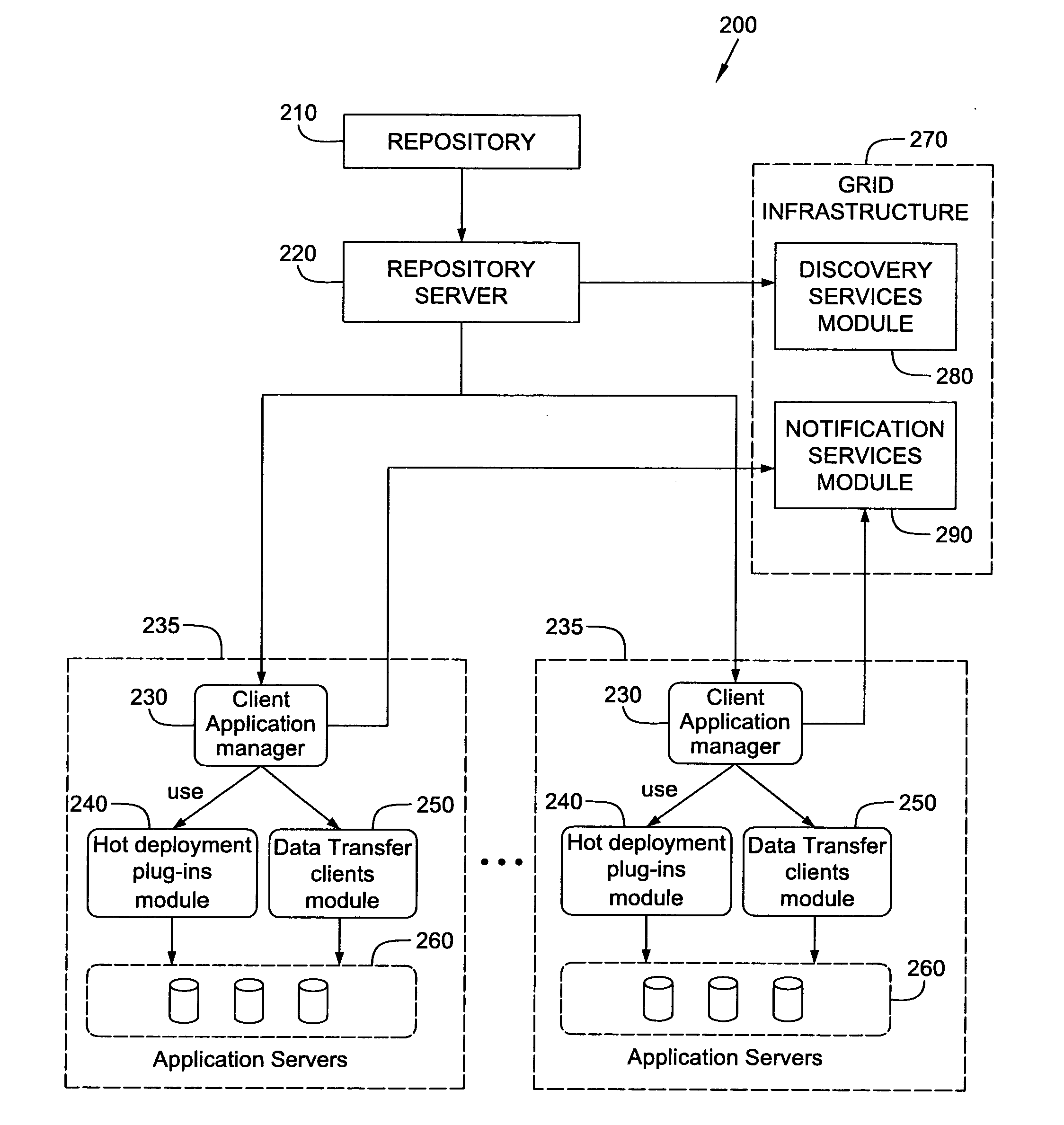
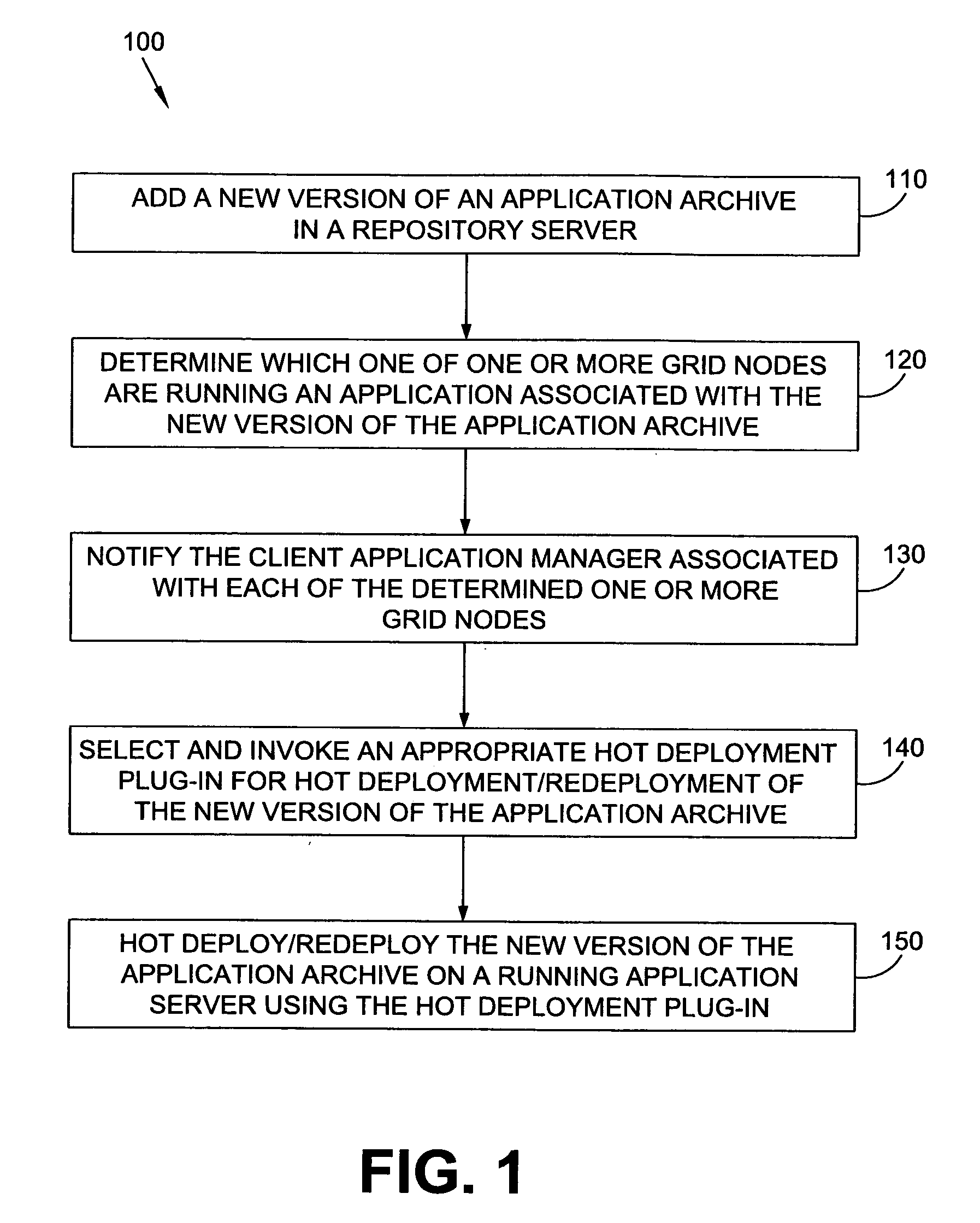
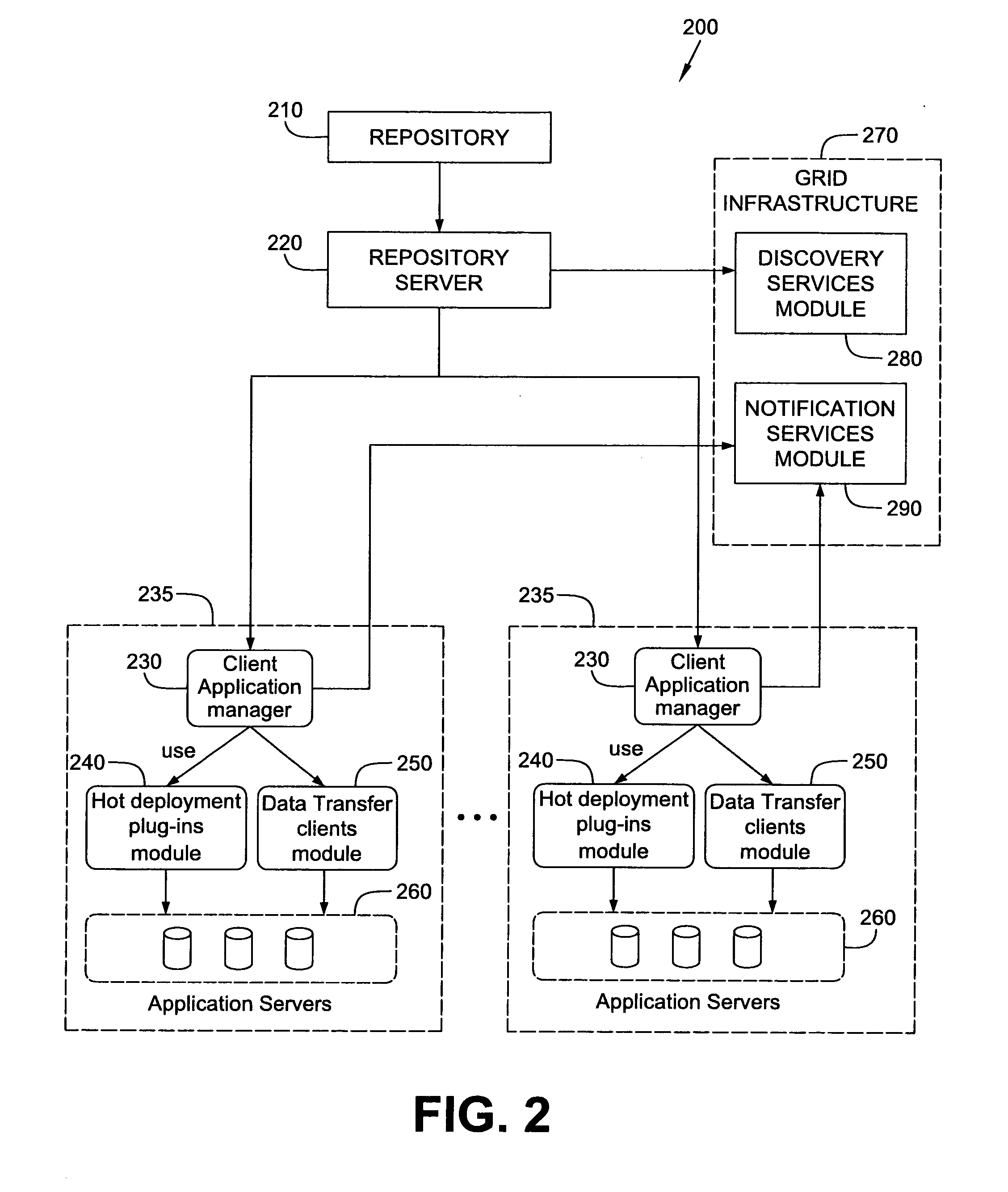
System and method for hot deployment/redeployment in grid computing environment
ActiveUS20080162674A1Reduce chanceReduce overheadSoftware engineeringDigital computer detailsApplication serverProgram management
A technique for hot deploying / redeploying applications in a grid computing environment to improve operating efficiency and reduced overhead. In one example embodiment, this is accomplished by notifying a client application manager associated with each of one or more grid nodes about a type of data transfer protocol to use upon receiving a new version of an application release bundle by a repository server. The new version of the application release bundle is then hot deployed / redeployed on running one or more application servers in the associated grid using an appropriate hot deployment plug-in based on the data transfer protocol by each client application manager.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
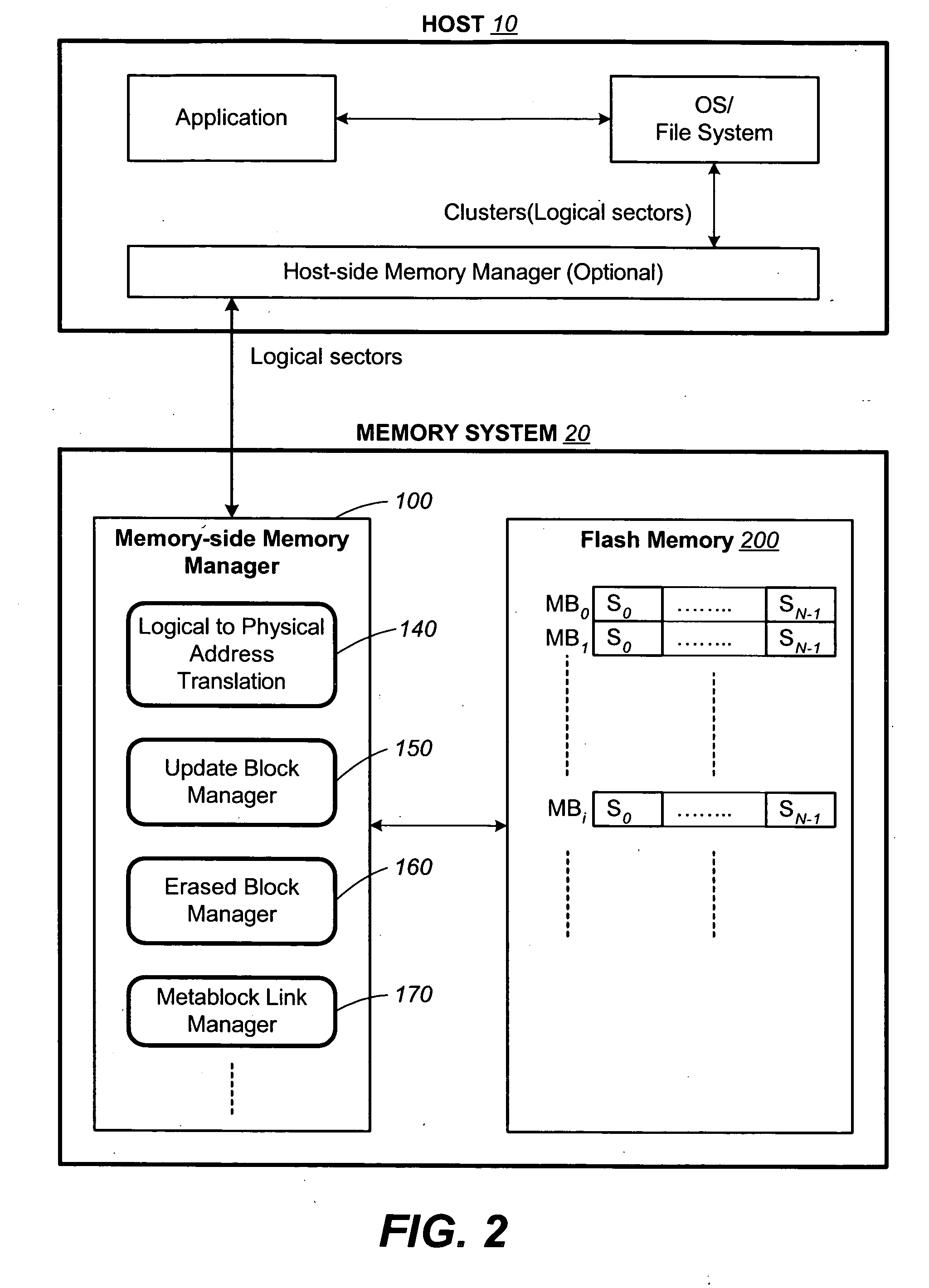
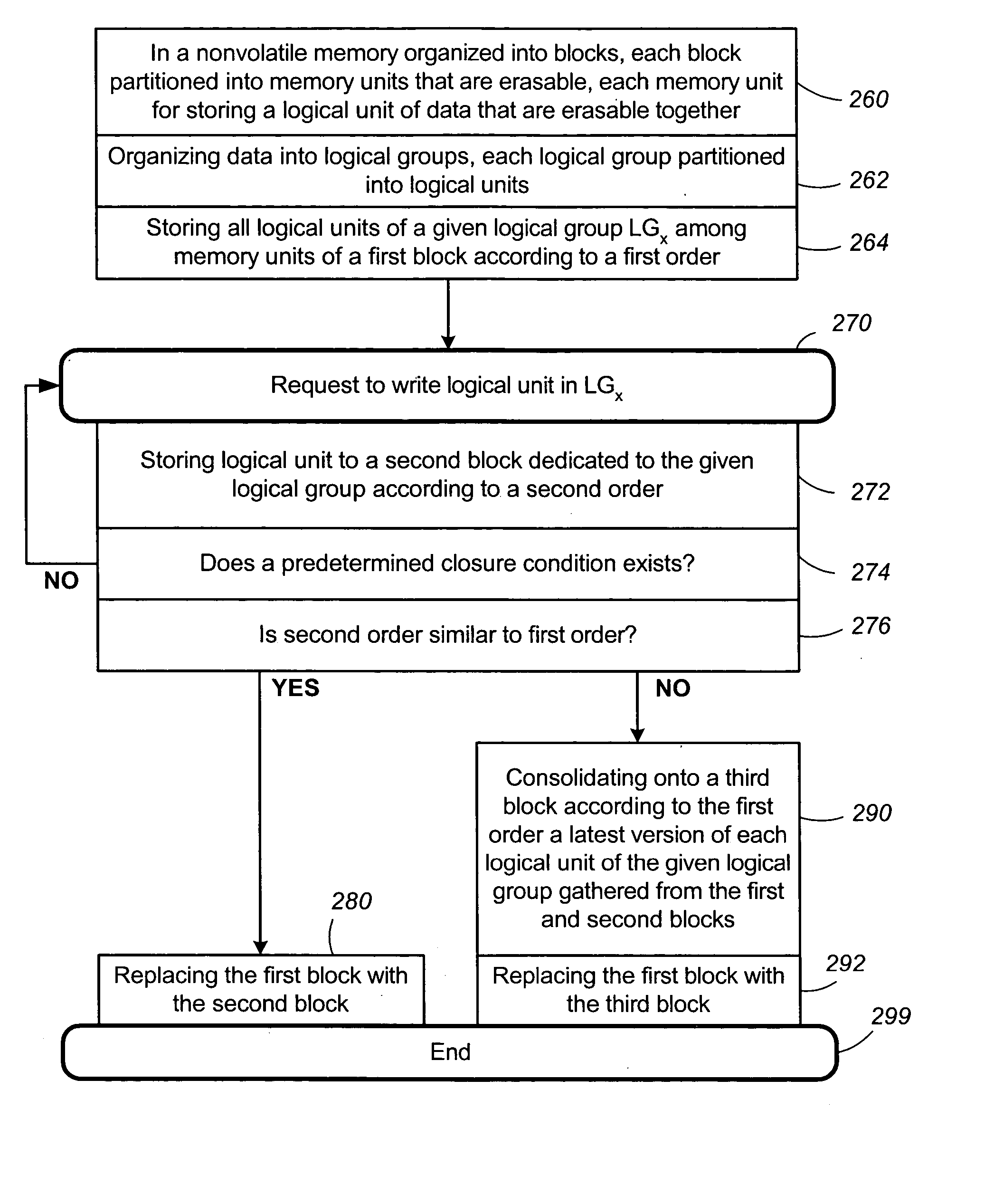
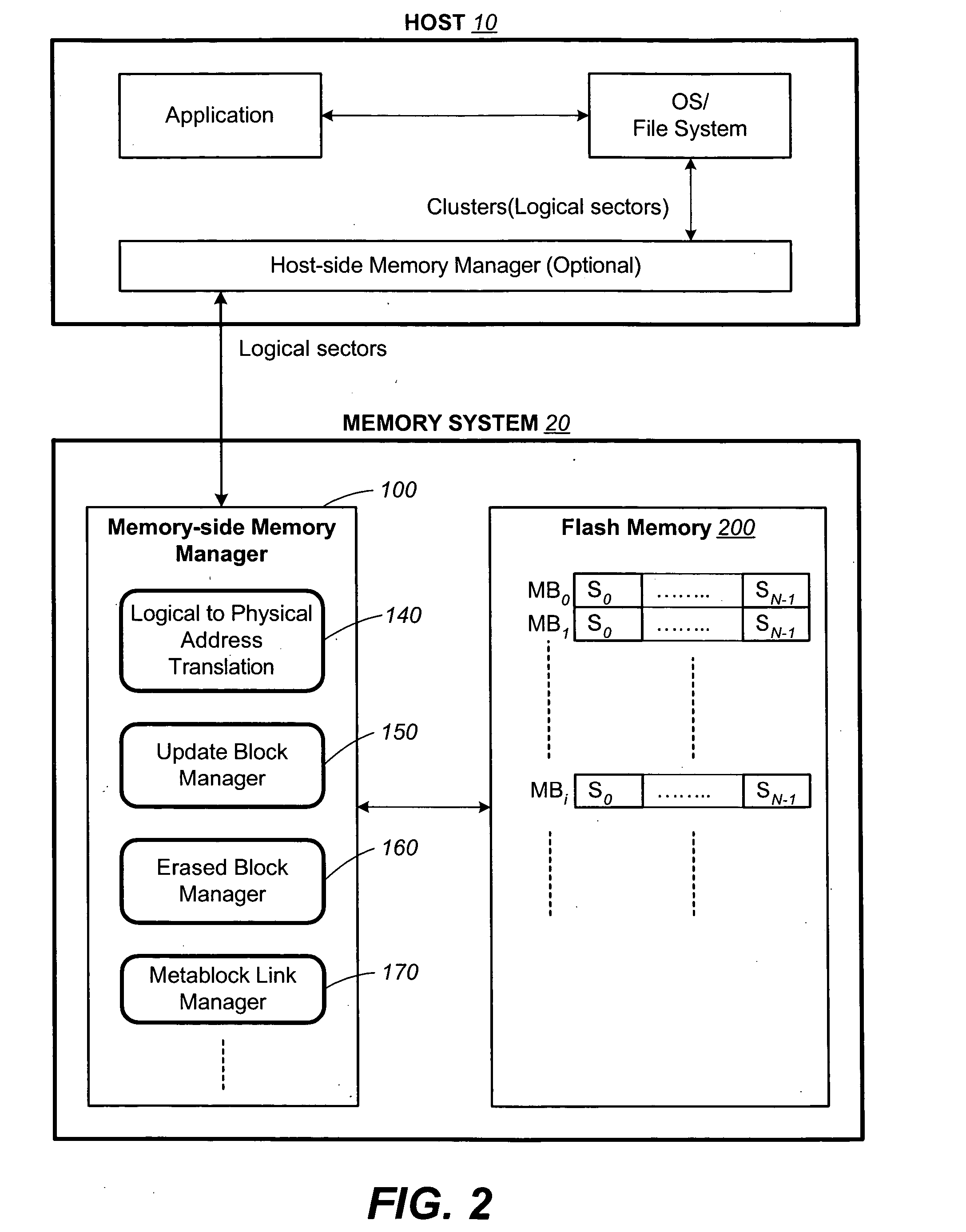
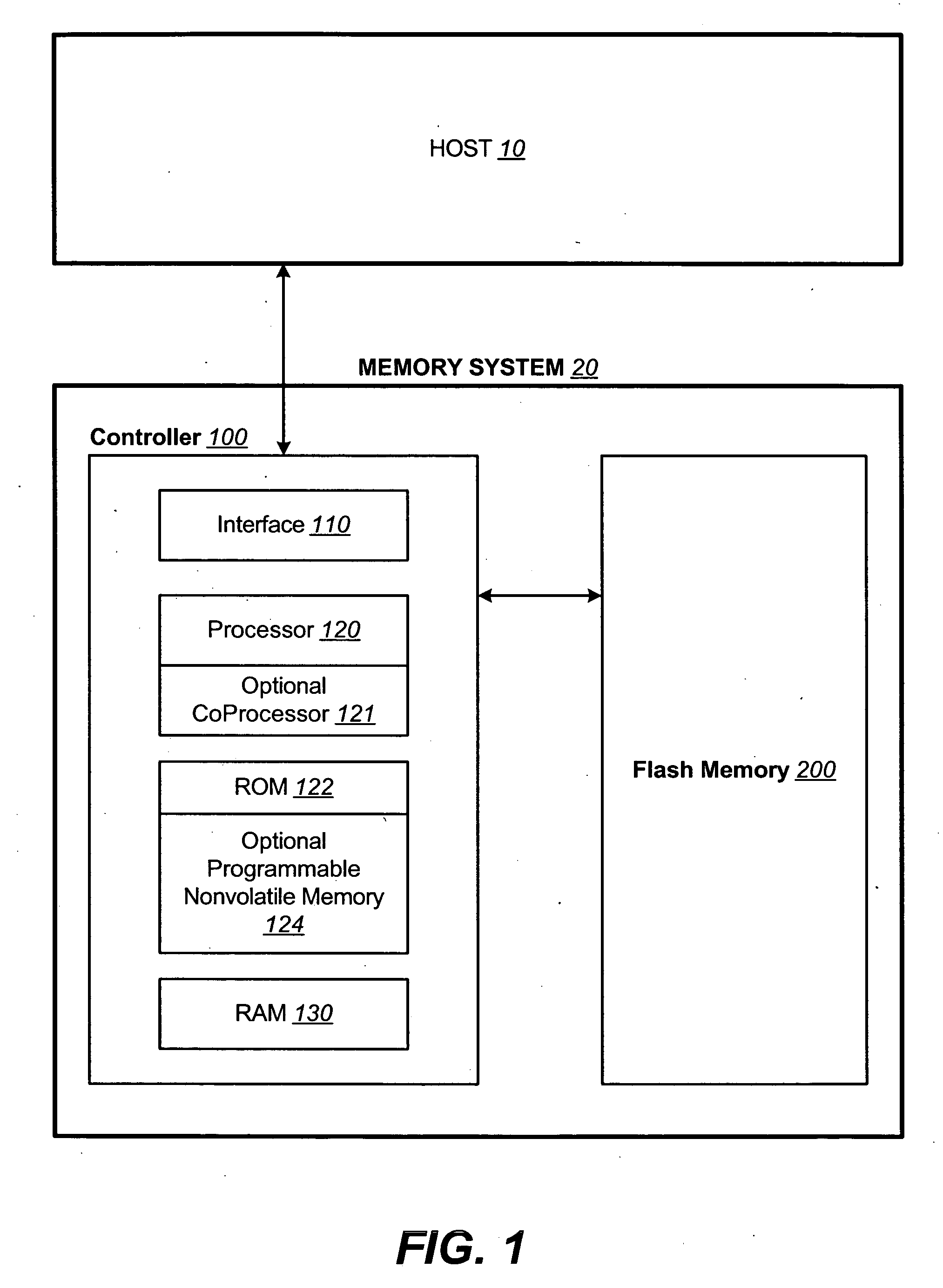
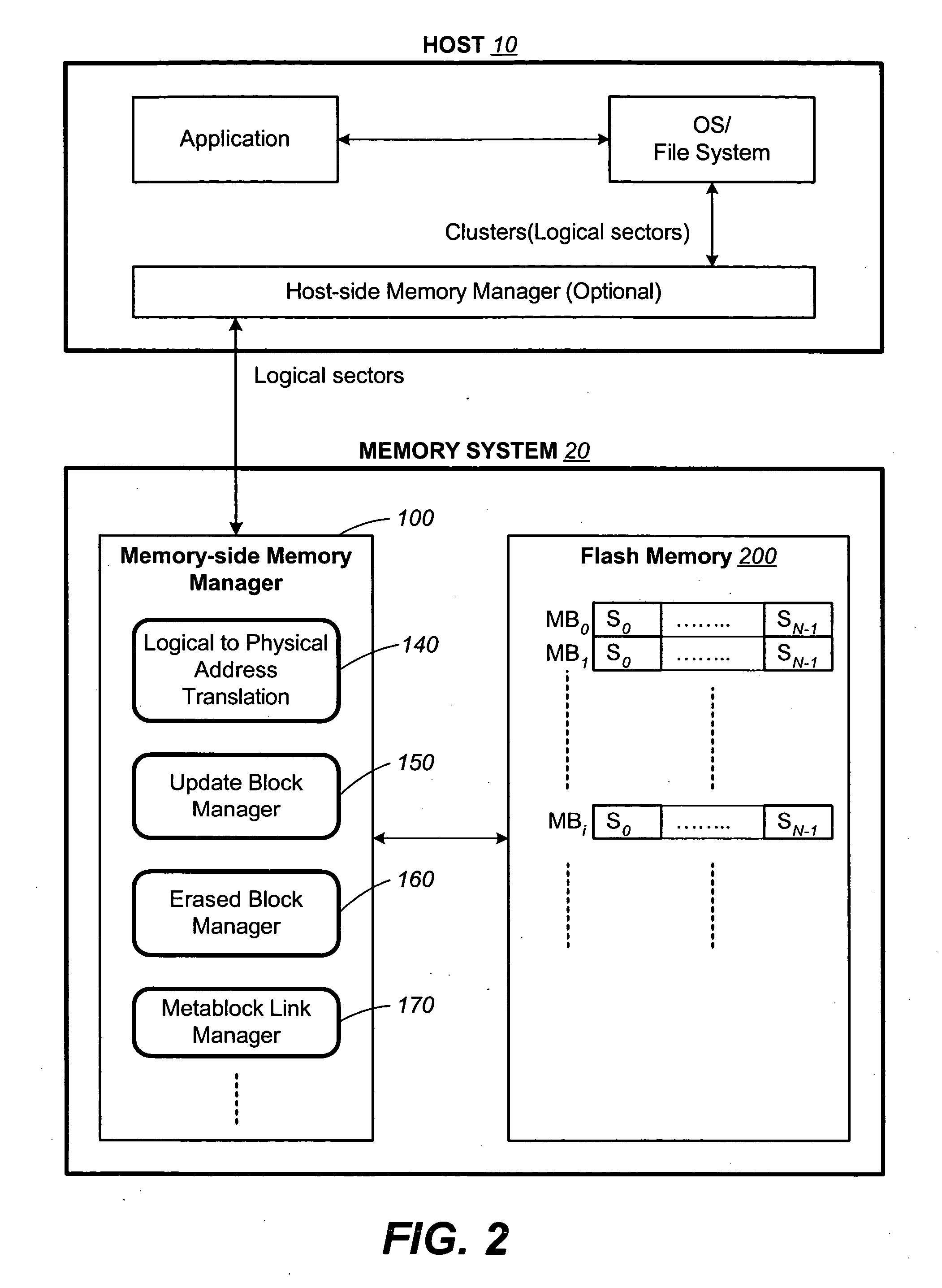
Non-volatile memory and method with non-sequential update block management
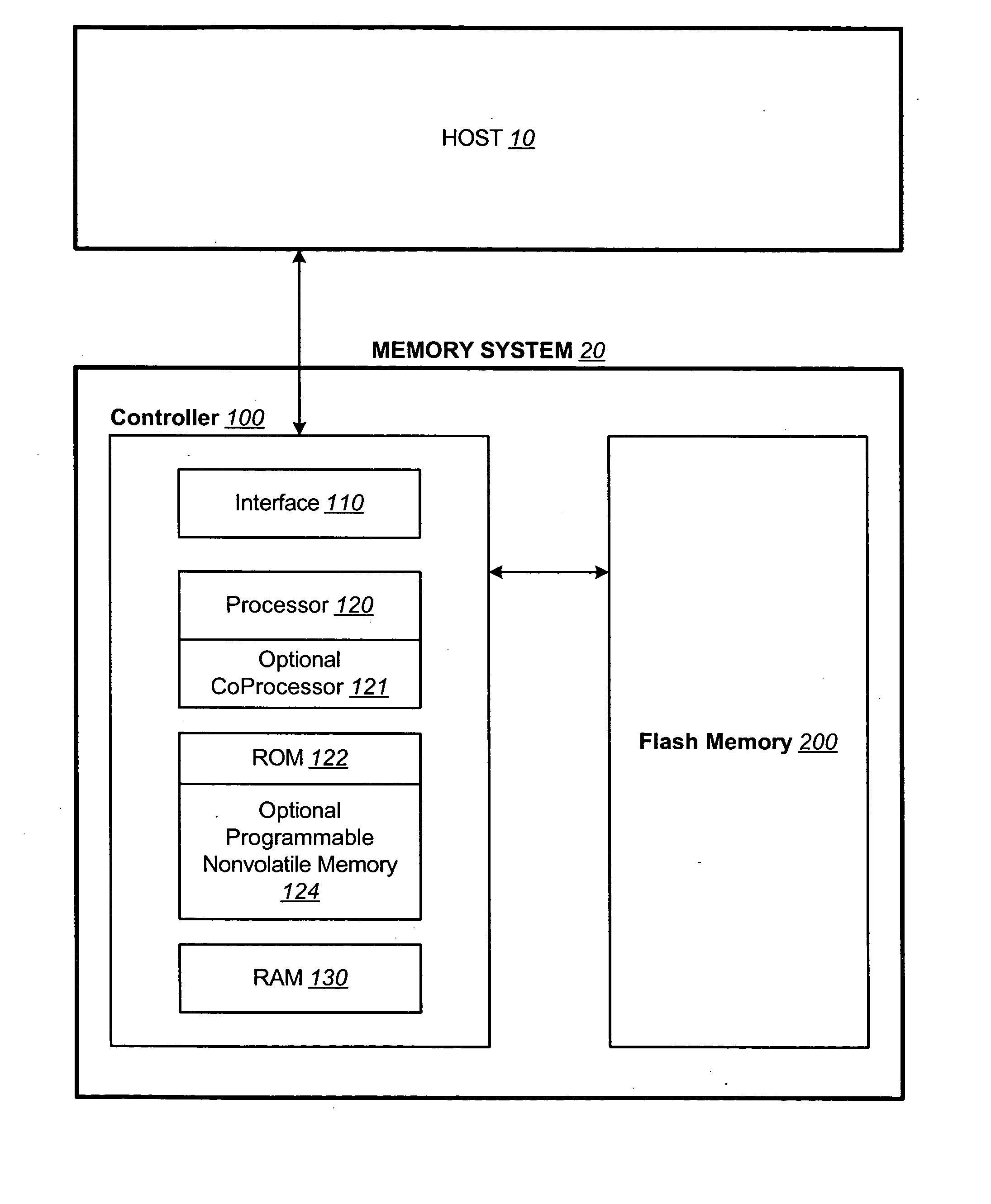
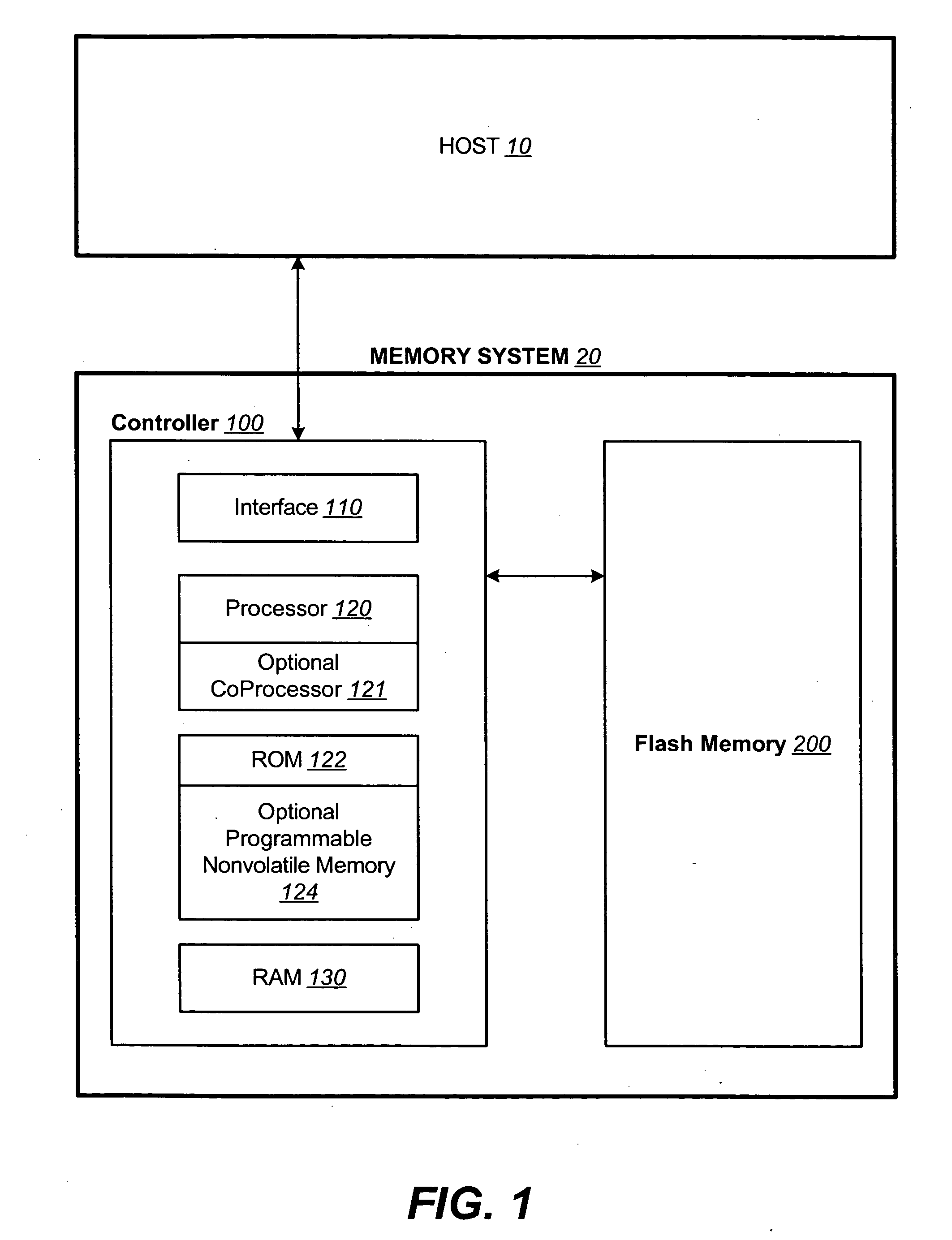
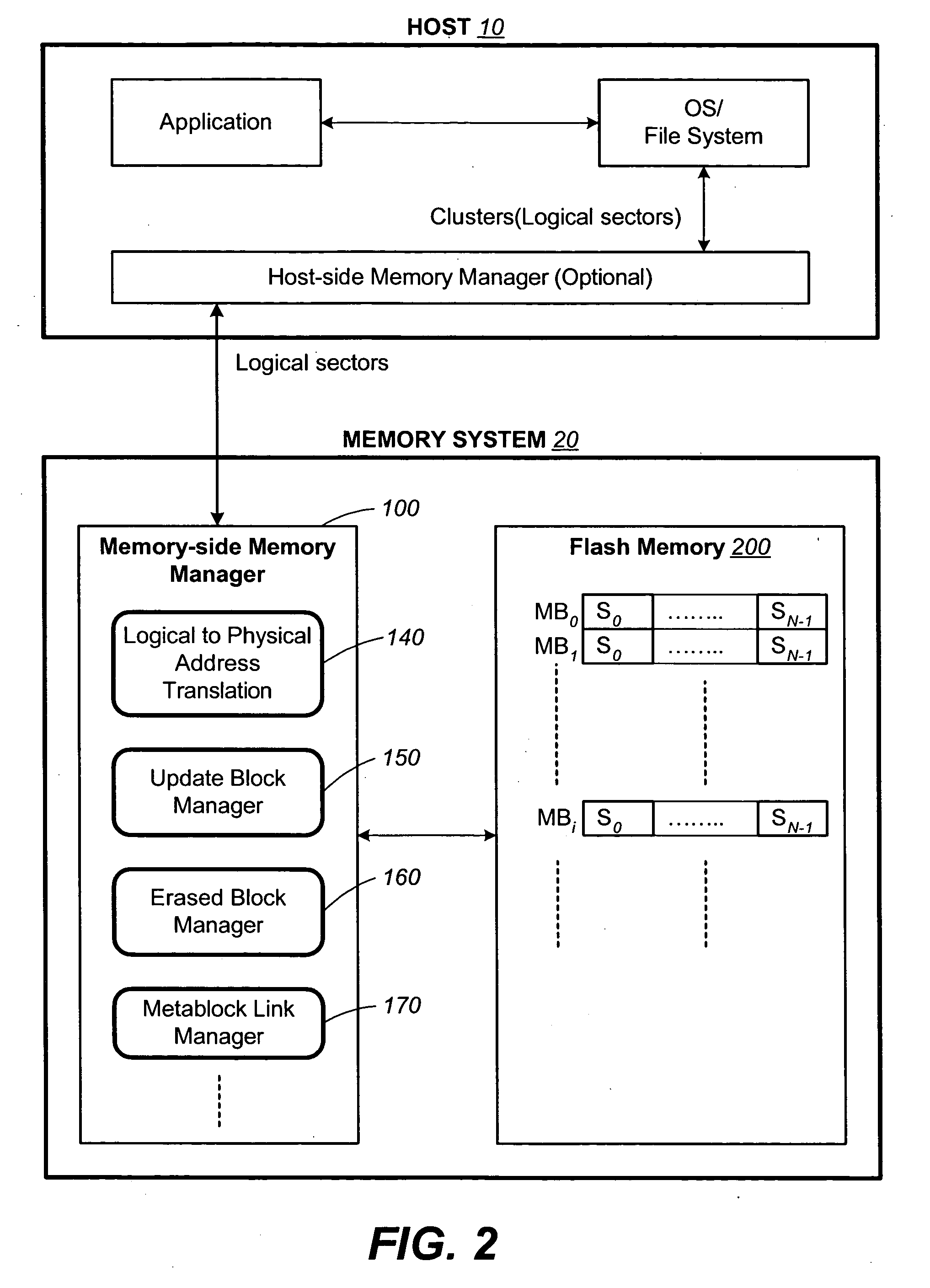
InactiveUS20050141312A1Good ECCExtra level of reliabilityMemory architecture accessing/allocationMemory adressing/allocation/relocationLogic cellOperating system
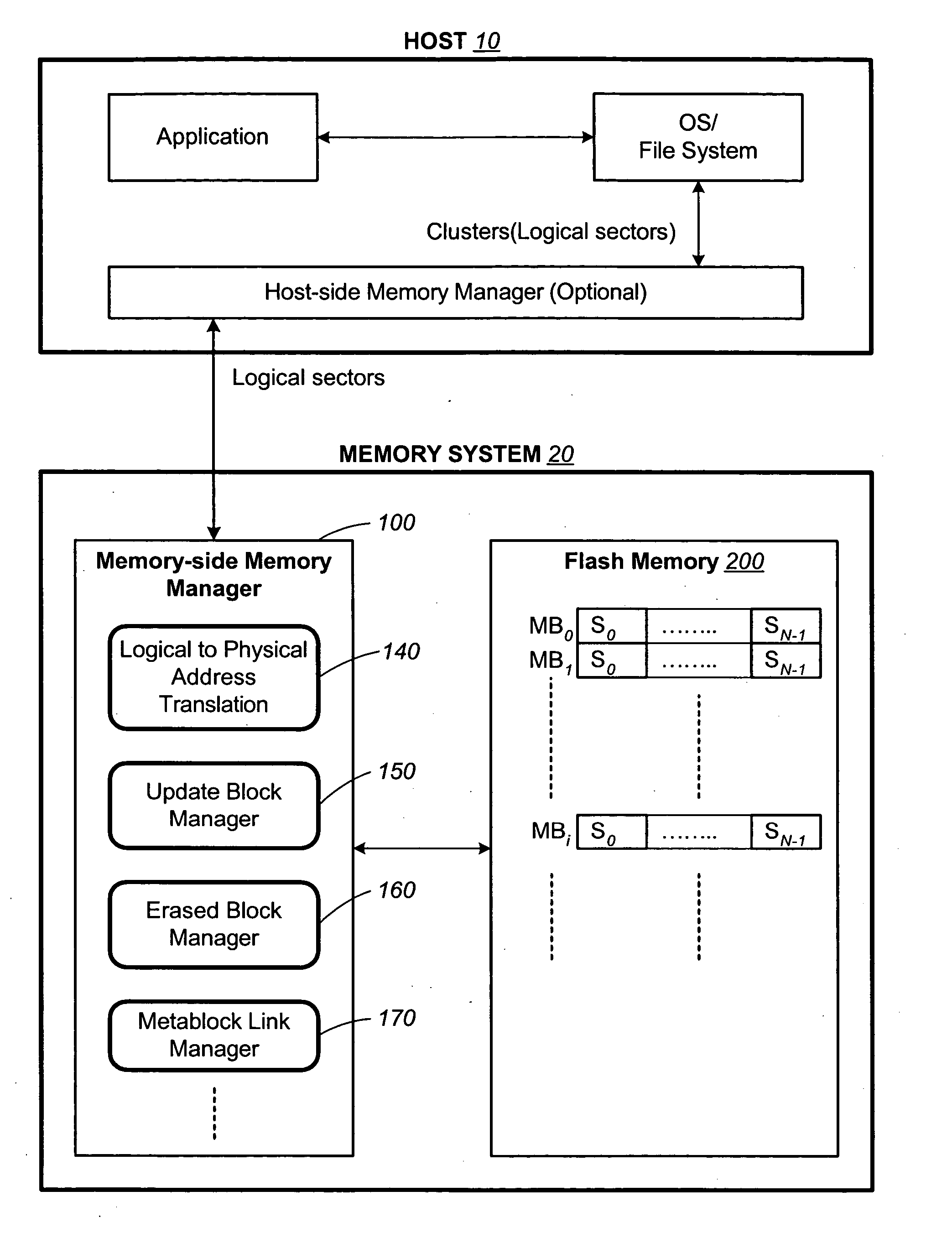
In a nonvolatile memory with block management system that supports update blocks with non-sequential logical units, an index of the logical units in a non-sequential update block is buffered in RAM and stored periodically into the non-volatile memory. In one embodiment, the index is stored in a block dedicated for storing indices. In another embodiment, the index is stored in the update block itself. In yet another embodiment, the index is stored in the header of each logical unit. In another aspect, the logical units written after the last index update but before the next have their indexing information stored in the header of each logical unit. In this way, after a power outage, the location of recently written logical units can be determined without having to perform a scanning during initialization. In yet another aspect, a block is managed as partially sequential and partially non-sequential, directed to more than one logical subgroup.
Owner:SANDISK TECH LLC
Non-volatile memory and method with block management system
ActiveUS20050144360A1Increase efficiencyReduce overheadMemory architecture accessing/allocationMemory adressing/allocation/relocationManagement systemNon-volatile memory
A non-volatile memory system is organized in physical groups of physical memory locations. Each physical group (metablock) is erasable as a unit and can be used to store a logical group of data. A memory management system allows for update of a logical group of data by allocating a metablock dedicated to recording the update data of the logical group. The update metablock records update data in the order received and has no restriction on whether the recording is in the correct logical order as originally stored (sequential) or not (chaotic). Eventually the update metablock is closed to further recording. One of several processes will take place, but will ultimately end up with a fully filled metablock in the correct order which replaces the original metablock. In the chaotic case, directory data is maintained in the non-volatile memory in a manner that is conducive to frequent updates. The system supports multiple logical groups being updated concurrently.
Owner:SANDISK TECH LLC
Para-virtualized computer system with I/0 server partitions that map physical host hardware for access by guest partitions
InactiveUS20070061441A1Improve efficiencyImprove securityError detection/correctionDigital computer detailsOperational systemSystem call
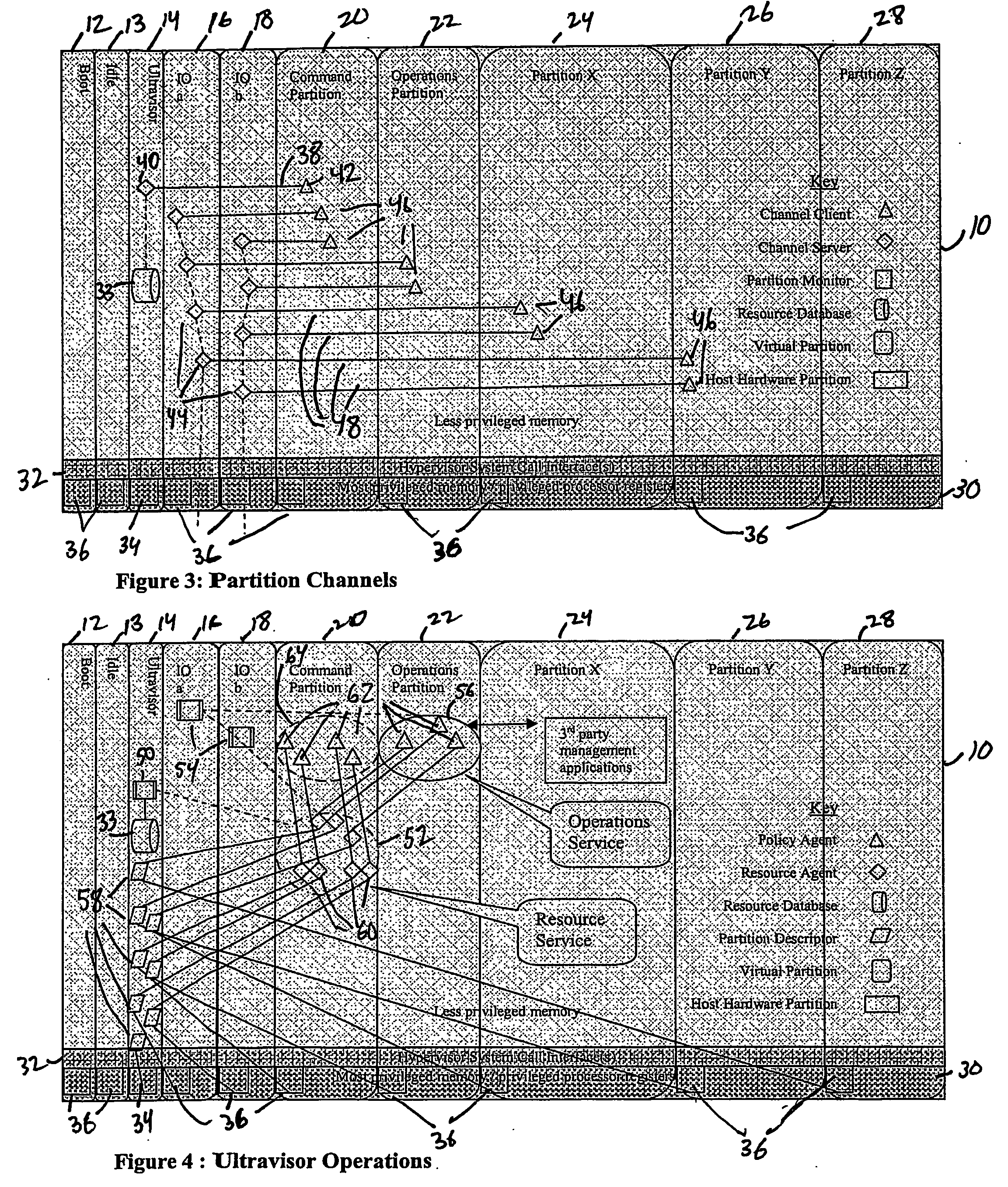
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Non-volatile memory and method with control data management
ActiveUS20050144365A1Good ECCExtra level of reliabilityMemory architecture accessing/allocationMemory adressing/allocation/relocationManagement systemMulti state
In a nonvolatile memory with block management system, critical data such as control data for the block management system is maintained in duplicates. Various methods are described for robustly writing and reading two copies of critical data in multi-state memory. In another aspect of the invention, a preemptive garbage collection on memory block containing control data avoids an undesirable situation where a large number of such memory blocks need be garbage collected at the same time.
Owner:SANDISK TECH LLC
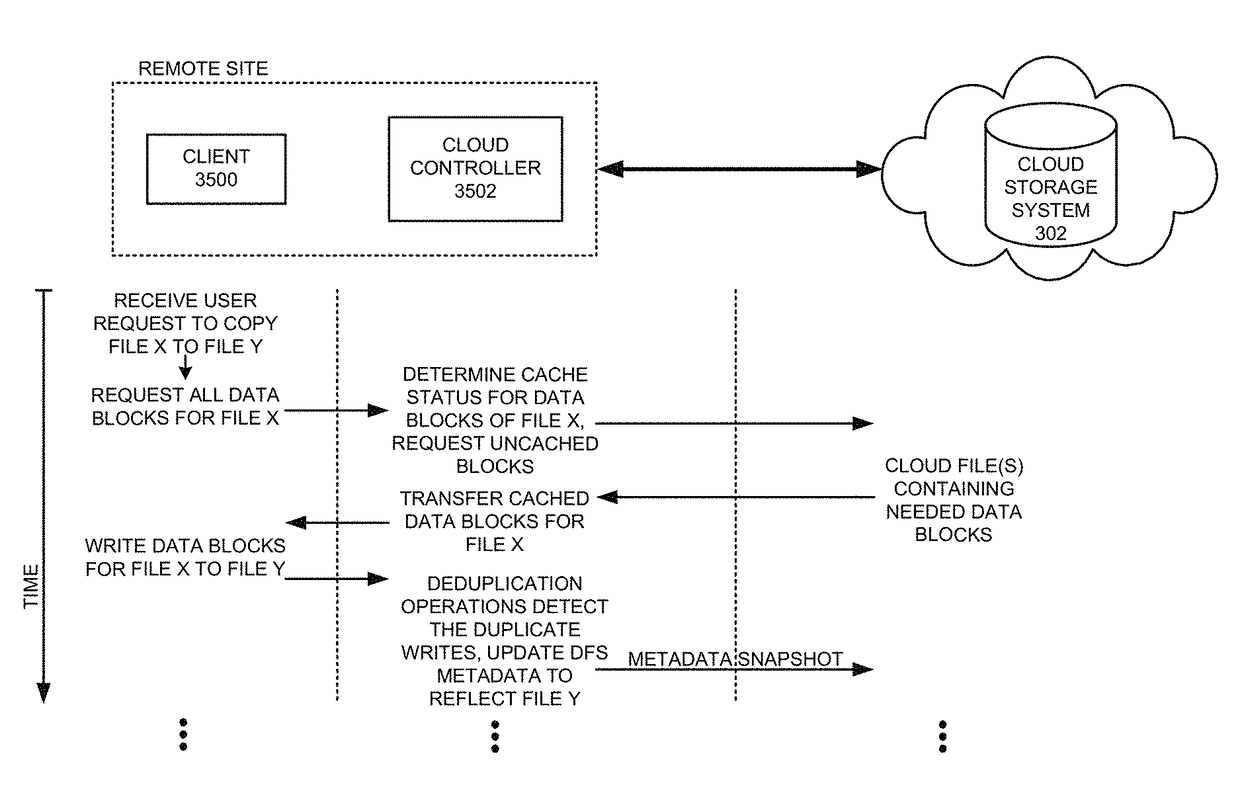
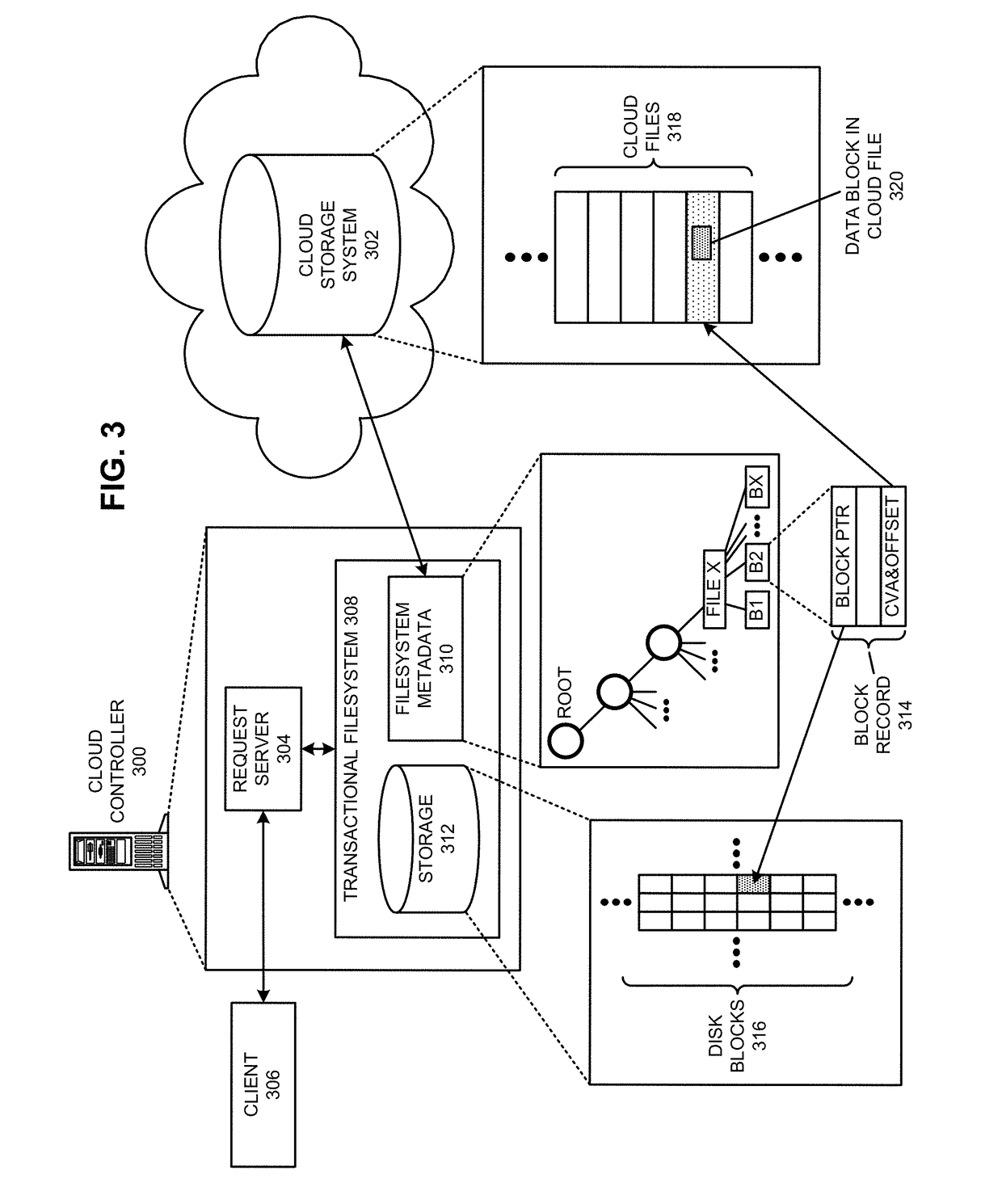
Executing a cloud command for a distributed filesystem
ActiveUS9811532B2Reduce perceived command execution timeReduce administrative burdenInput/output to record carriersDigital data information retrievalFile systemData file
The disclosed embodiments disclose techniques for executing a cloud command for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. During operation, a cloud controller presents a distributed-filesystem-specific capability to a client system as a file in the distributed filesystem (e.g., using a file abstraction). Upon receiving a request from the client system to access and / or operate upon this file, the client controller executes an associated cloud command. More specifically, the cloud controller initiates a specially-defined operation that accesses additional functionality for the distributed filesystem that exceeds the scope of individual reads and writes to a typical data file.
Owner:PANZURA LLC
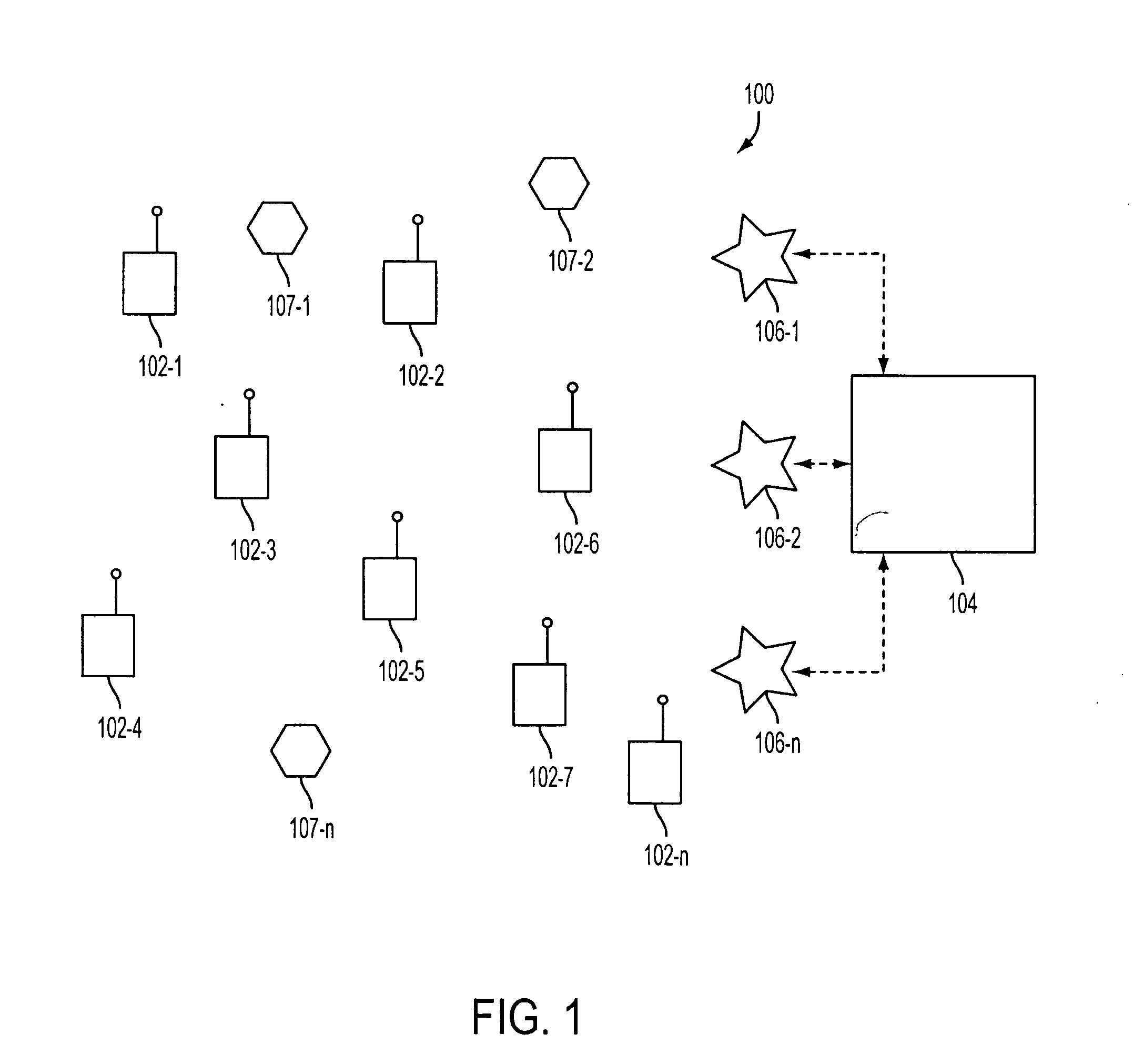
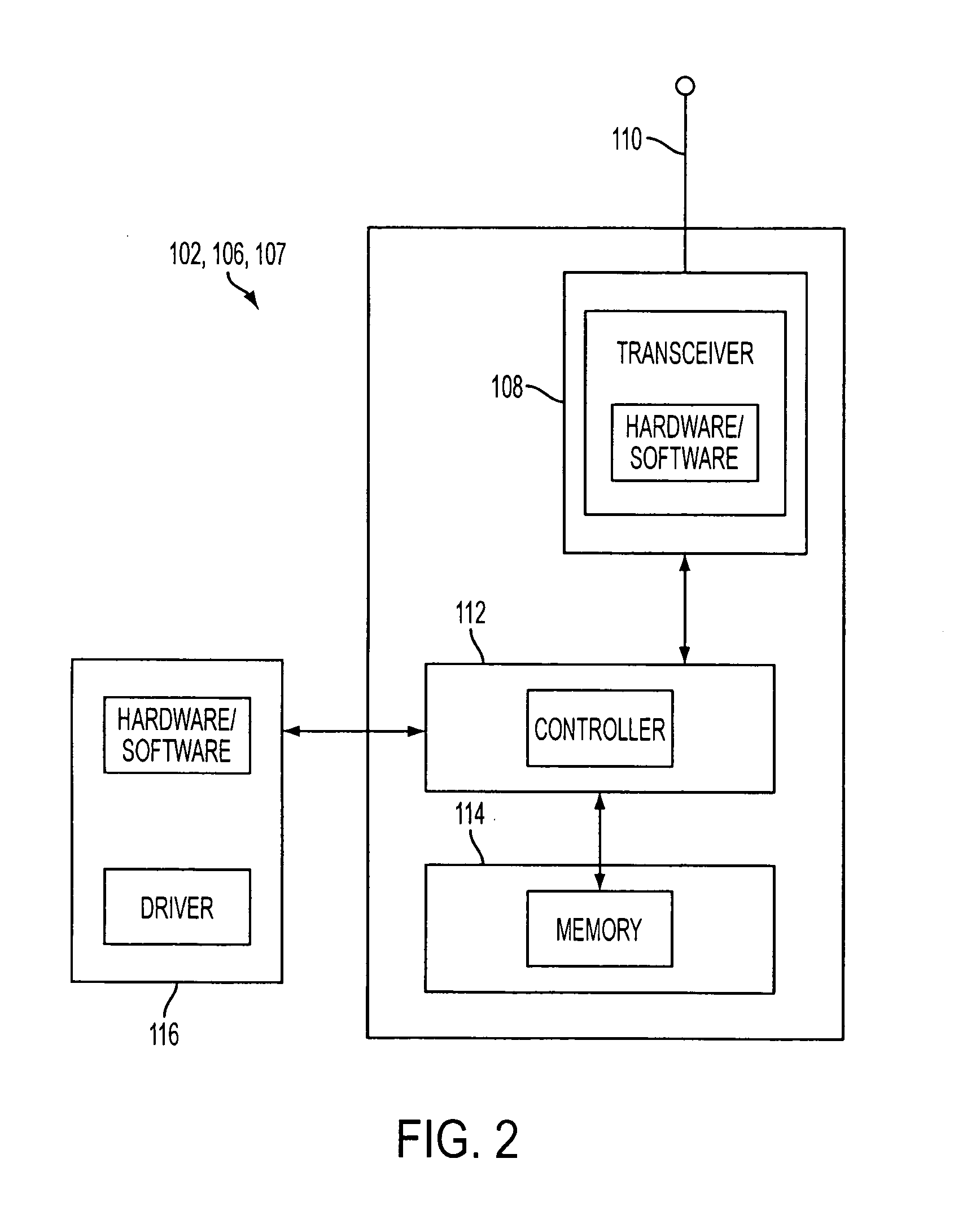
Method and apparatus for efficiently initializing secure communications among wireless devices
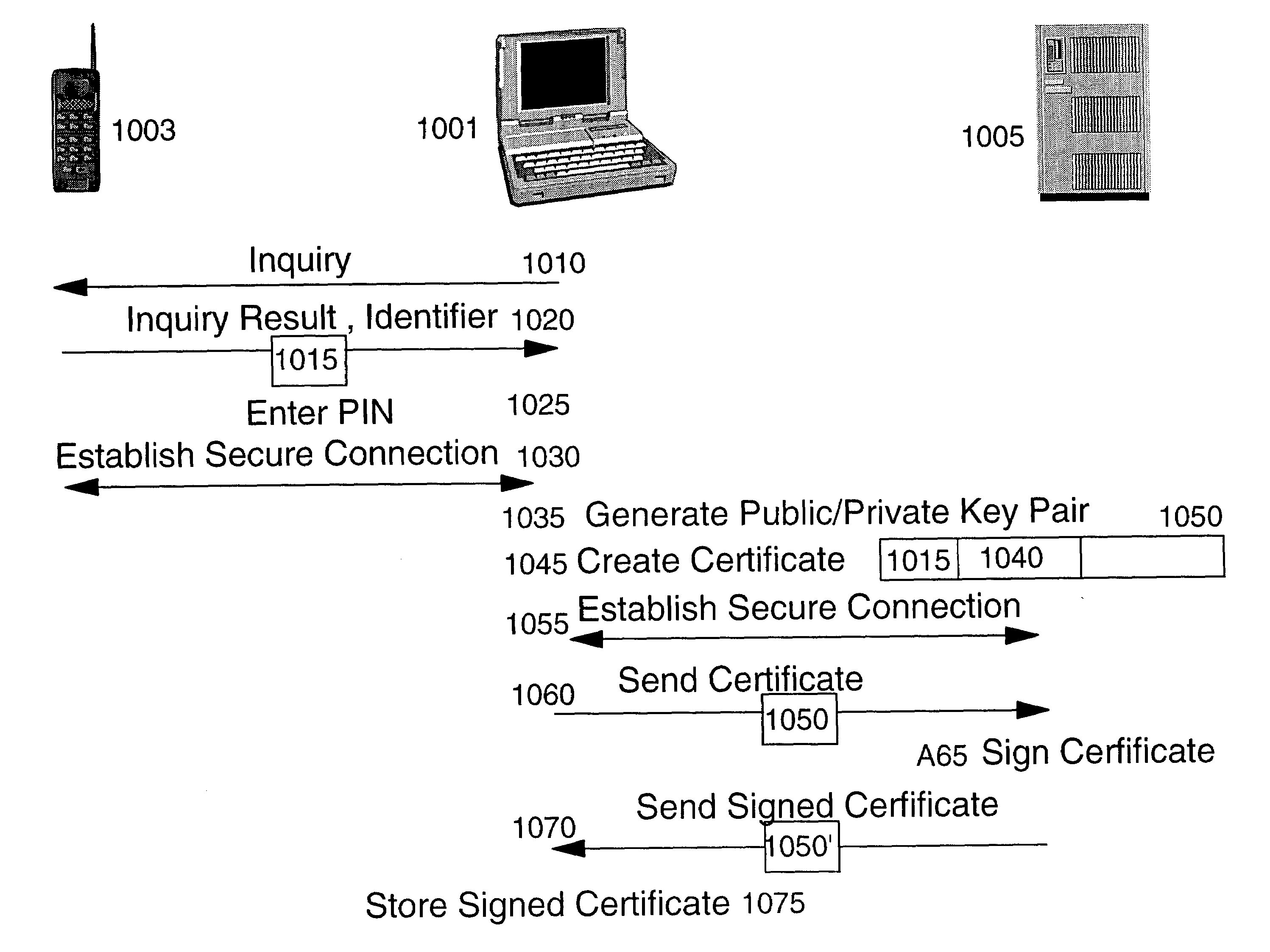
InactiveUS6886095B1Efficient administrationEliminating inflexibilityUser identity/authority verificationRadio/inductive link selection arrangementsSecure communicationRadio networks
A method and system for efficiently establishing secure communications between mobile devices in a radio network. The present invention utilizes public key cryptography and unique hardware identifiers to enable authorizations for access to wireless networks, such as picocells. The present invention prevents the mobile user from maintaining a plurality of secrets such as user identifier / password pairs, PINs, or encryption keys, for access to each device to which he might require access.
Owner:IBM CORP
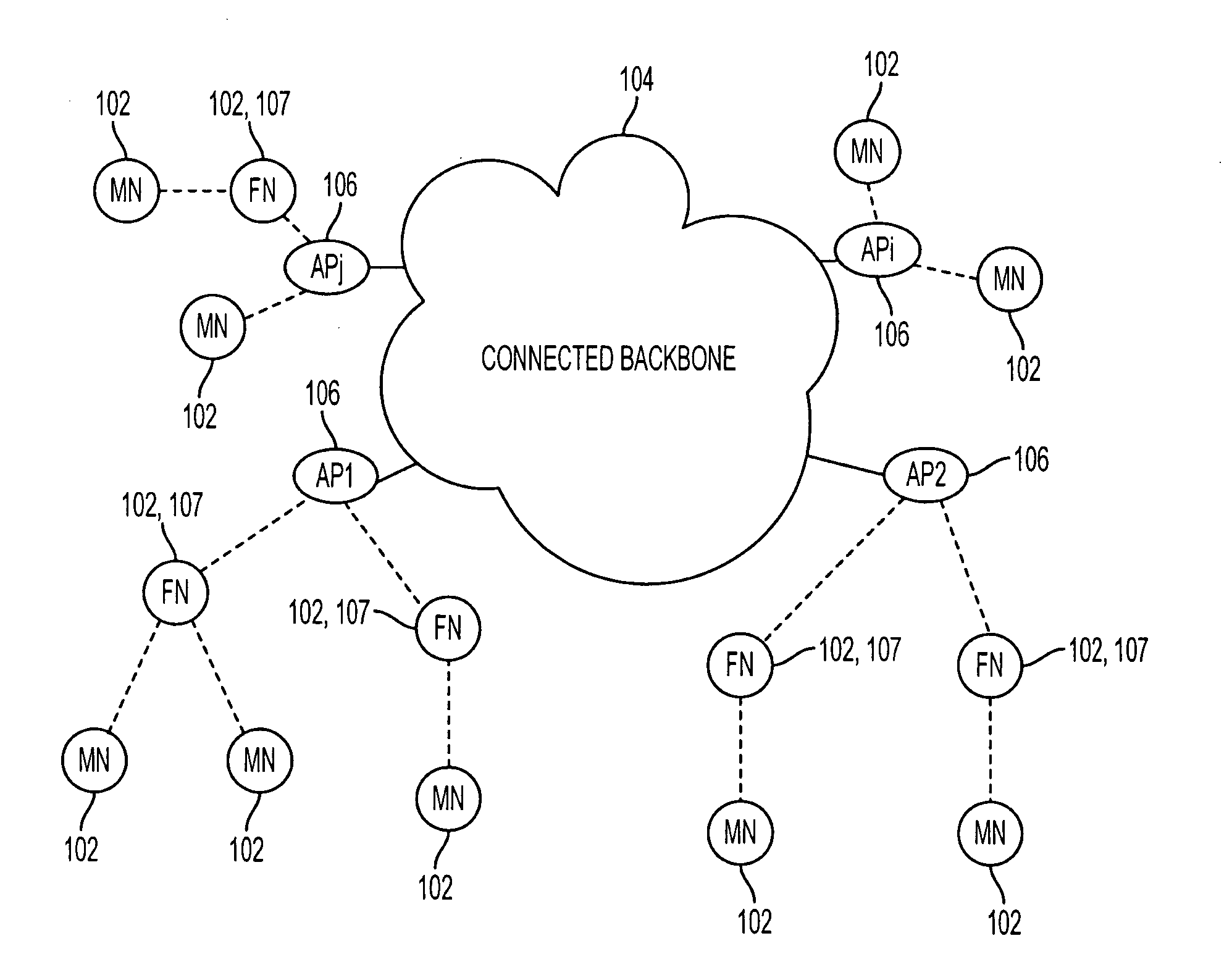
System and method to support multicast routing in large scale wireless mesh networks
ActiveUS20060098607A1Quick changeReduce overheadMultiplex system selection arrangementsNetwork topologiesTree rootWireless mesh network
Provided is a system and method for a multicast routing algorithm to work in infrastructure based mesh networks. It chooses access points, fixed infrastructure gateway nodes connected to each other and / or the global internet via a wired / wireless backbone, as a group of local multicast group leaders to form a multicast group leader cloud. Each local multicast group leader is elected on-demand according to the local multicast group member's request. Each local multicast group leader forms a local multicast tree rooted at this leader connecting all multicast group members associated with the AP. The processes of electing and maintaining local multicast trees rooted at APs enable efficient coordination with underlying unicast routing to exploit the advantages of fixed infrastructure nodes. Therefore, routing overhead and multicast tree convergence time are reduced. The method can support large networks with fast topology change due to fast convergence and reduced routing overhead.
Owner:ARRIS ENTERPRISES LLC
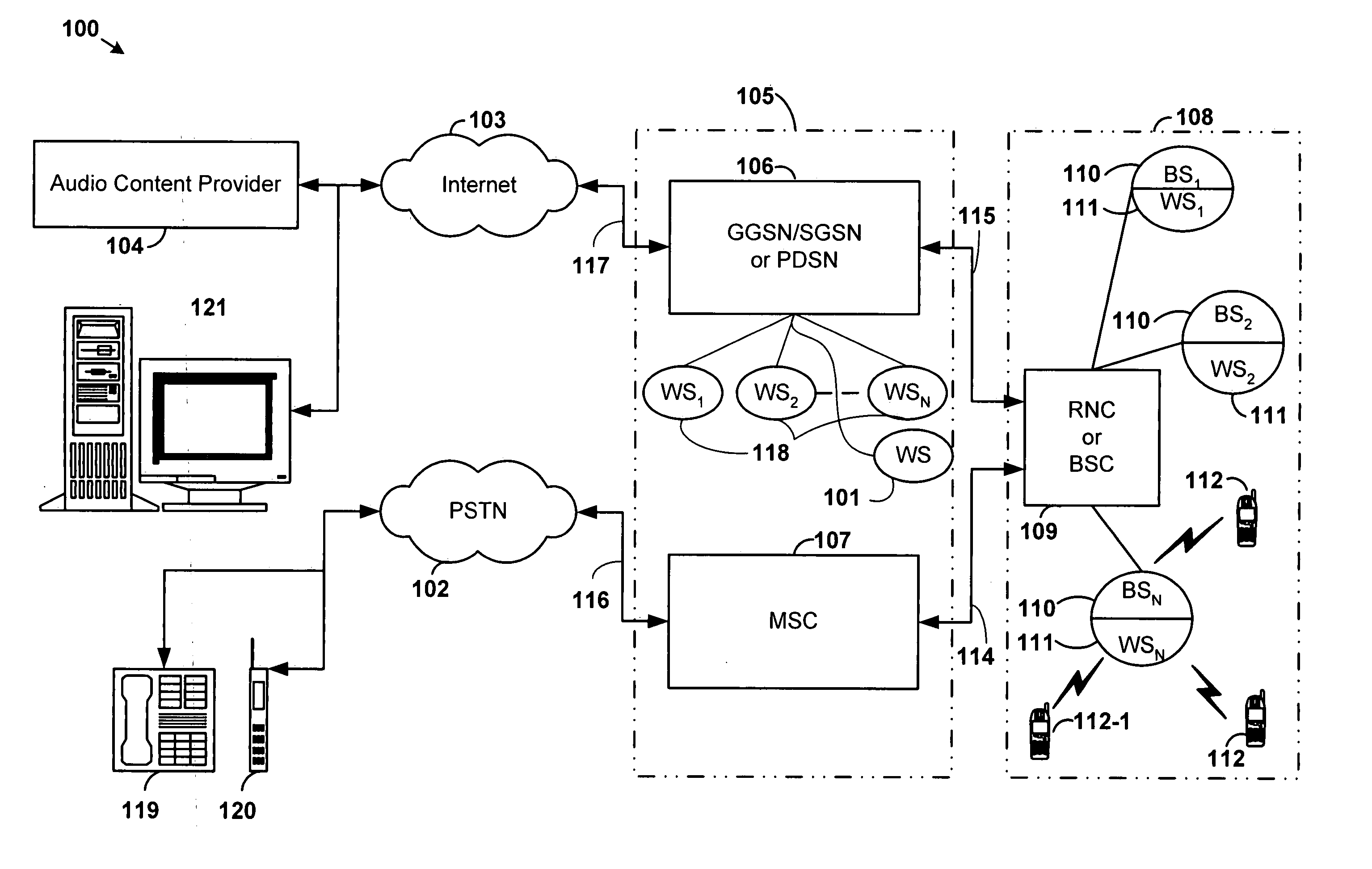
System and method for wireless delivery of audio content over wireless high speed data networks
InactiveUS20050245243A1Easy to useEfficient use ofNetwork traffic/resource managementSpecial service for subscribersPersonalizationThird generation
A system and method that facilitate efficient use of 3G high-speed data networks while providing for personalized audio content selection and coordinated distribution of selected content are disclosed. The invention categorizes audio content to be delivered over wireless networks such that the categories correspond to a different delivery priority. In an illustrative three-category implementation, category 1 content has the highest delivery priority for delivery as soon as possible, category 2 content has the next highest delivery priority for delivery, and category 3 content, such as music, audio books and so on, has the least urgent delivery priority. The categories are used to coordinate audio content delivery to efficiently use available bandwidth and network resources by delivering content at off-peak times. The invention also allows the downloading process to be interruptible such that it can be resumed at about the point of an interruption to conserve resources.
Owner:LUCENT TECH INC
Scalable partition memory mapping system
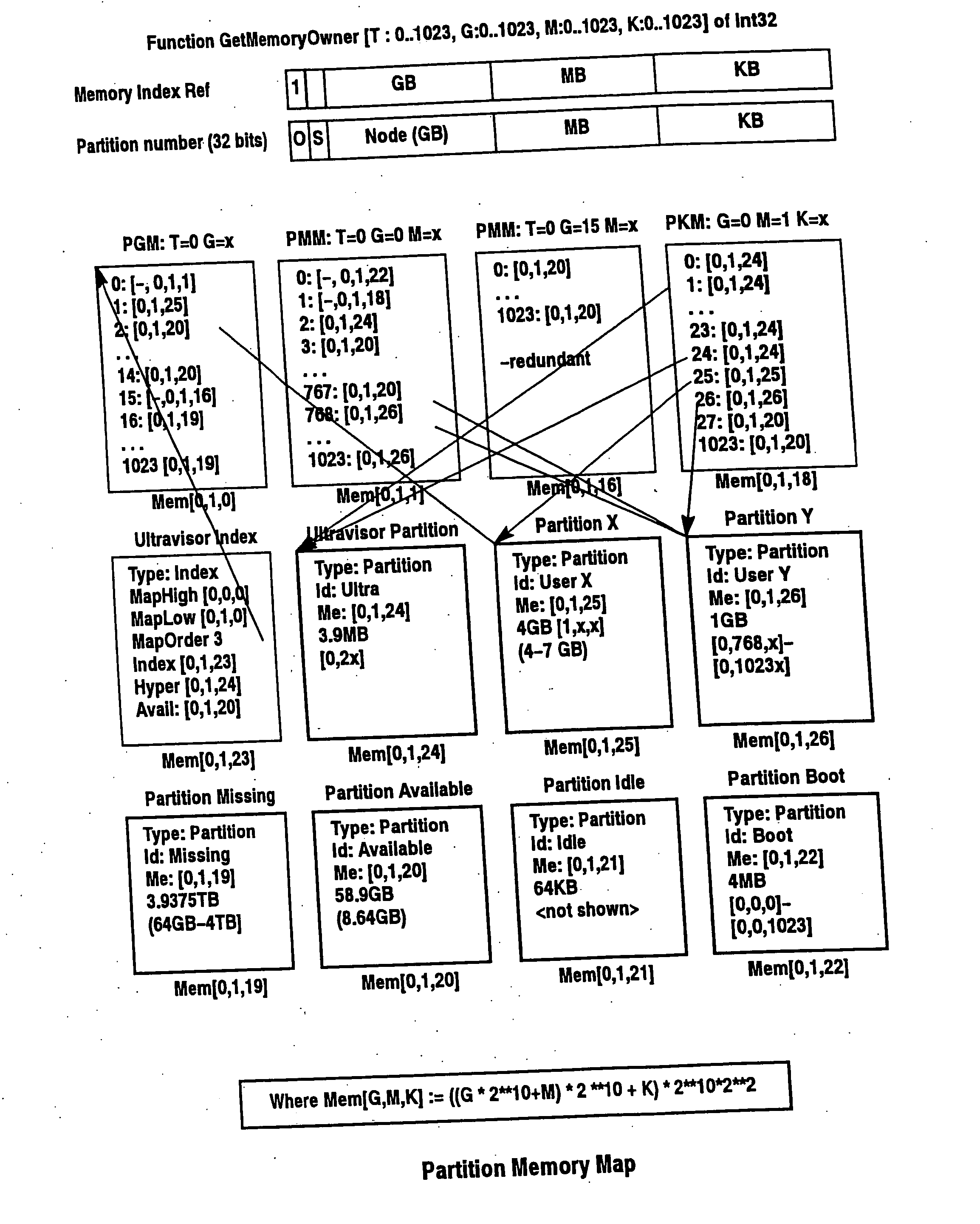
InactiveUS20070067366A1Improve efficiencyImprove securityMemory architecture accessing/allocationSoftware simulation/interpretation/emulationIn-memory databaseOperational system
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. A scalable partition memory mapping system is implemented in the ultravisor partition so that the virtualized system is scalable to a virtually unlimited number of pages. A log (210) based allocation allows the virtual partition memory sizes to grow over multiple generations without increasing the overhead of managing the memory allocations. Each page of memory is assigned to one partition descriptor in the page hierarchy and is managed by the ultravisor partition.
Owner:UNISYS CORP
Non-volatile memory and method with memory planes alignment
InactiveUS20050141313A1Good ECCExtra level of reliabilityMemory architecture accessing/allocationMemory adressing/allocation/relocationComputer architectureLogic cell
A non-volatile memory is constituted from a set of memory planes, each having its own set of read / write circuits so that the memory planes can operate in parallel. The memory is further organized into erasable blocks, each for storing a logical group of logical units of data. In updating a logical unit, all versions of a logical unit are maintained in the same plane as the original. Preferably, all versions of a logical unit are aligned within a plane so that they are all serviced by the same set of sensing circuits. In a subsequent garbage collection operation, the latest version of the logical unit need not be retrieved from a different plane or a different set of sensing circuits, otherwise resulting in reduced performance. In one embodiment, any gaps left after alignment are padded by copying latest versions of logical units in sequential order thereto.
Owner:SANDISK TECH LLC
Method for managing resources in high capacity wireless communication system
ActiveUS20110090855A1Improve efficiencyReduces contention overheadError preventionNetwork traffic/resource managementClear to sendMulti input
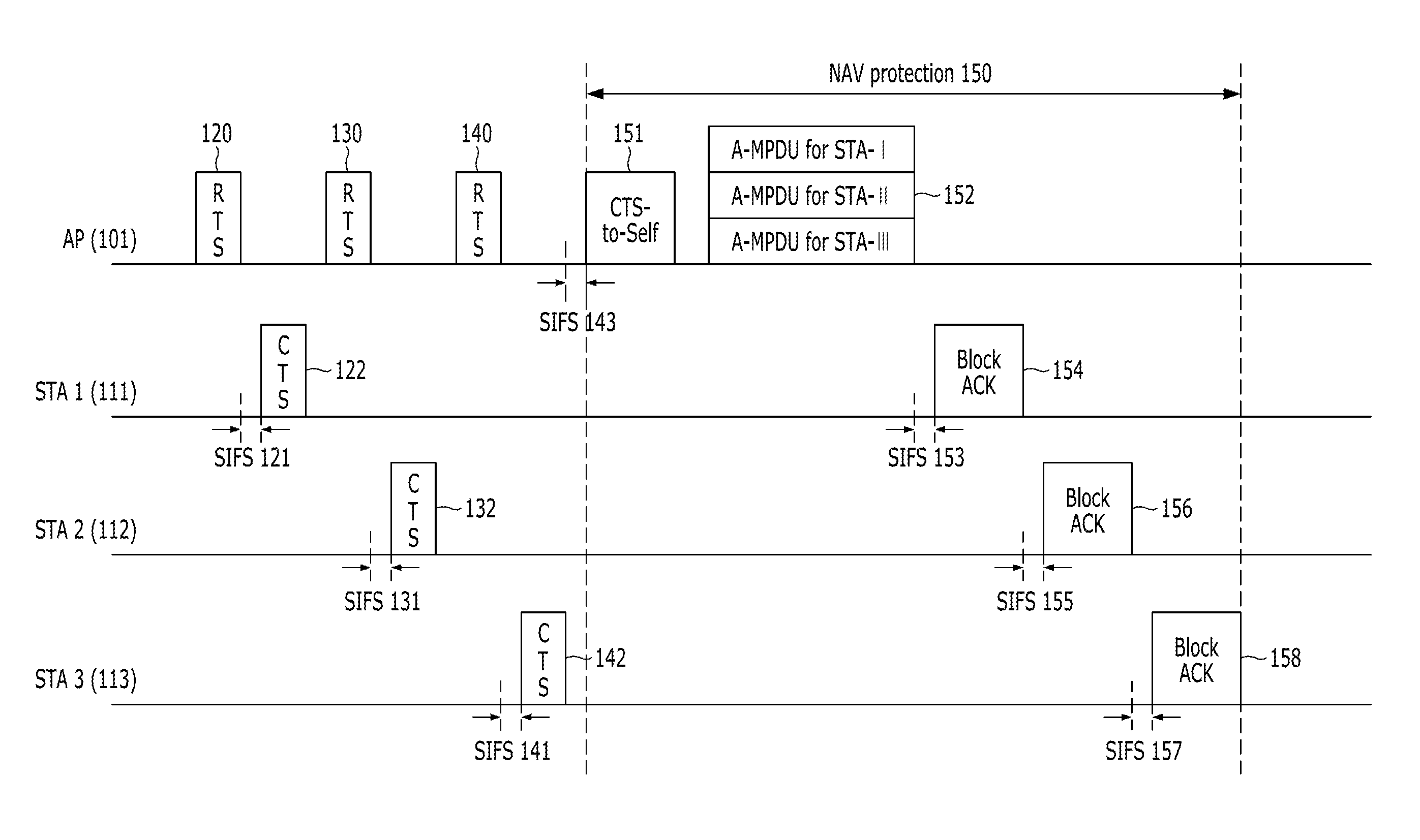
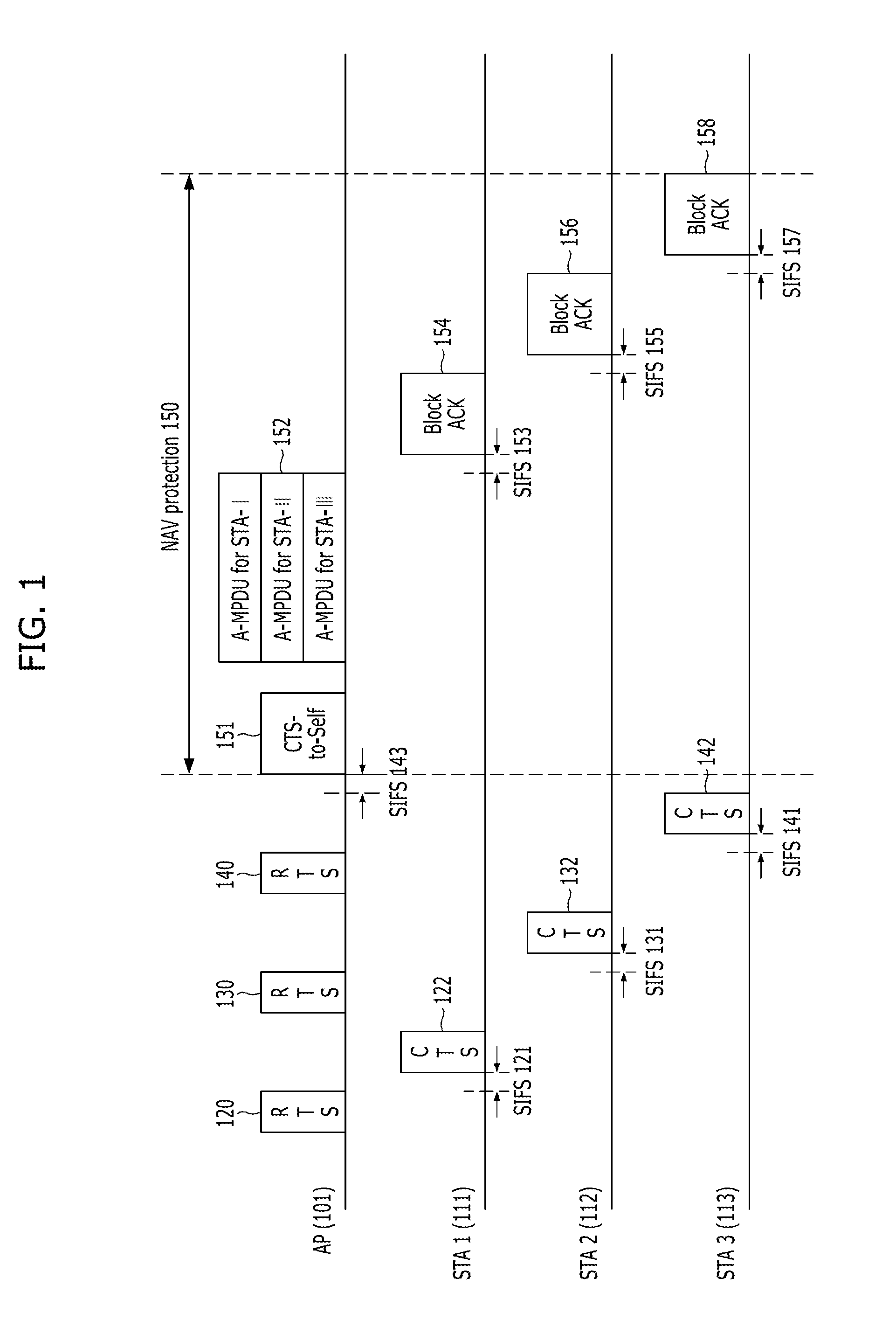
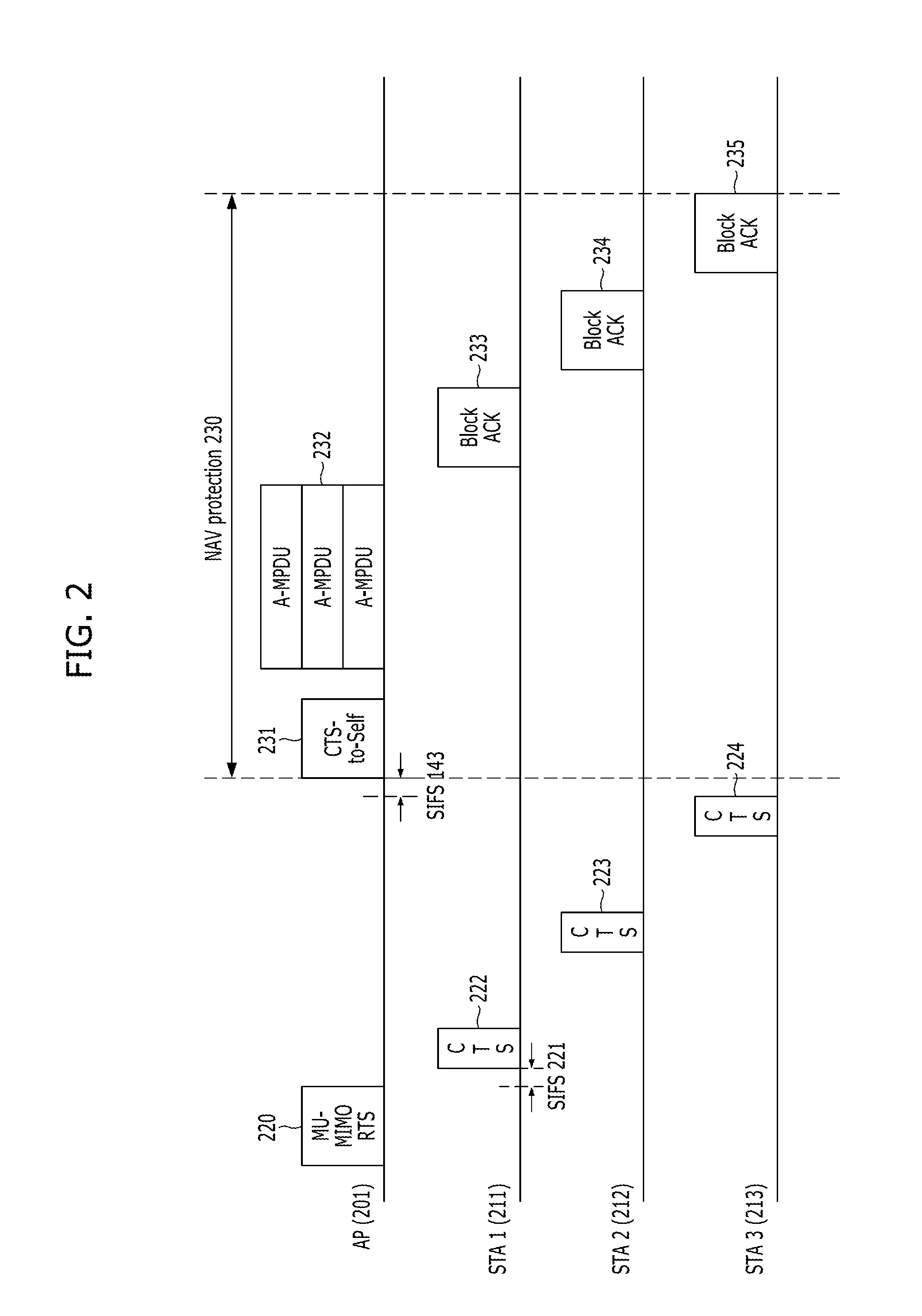
Provided is a method for managing resource in a high capacity wireless communication system capable of communicating with two or more users in a multi-input multi-output (MIMO) scheme when a base station transmits data. The includes: transmitting a MU-MIMO request-to-send (RTS) message to stations intending to transmit data in the MIMO scheme, and sequentially receiving a clear-to-send (CTS) message from stations intending to receive the data; transmitting a transmission ACK message to the stations, wherein the transmission ACK message includes information which prevents data collision during a time of data transmission to the stations and ACK signal; and configuring data to be transmitted to the stations into aggregated packets (A-MPDUs), transmitting the A-MPDUs to the stations in the MIMO scheme, and receiving a block ACK message from the stations.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for efficiently initializing mobile wireless devices
InactiveUS6980660B1Efficient administrationEliminating inflexibilityKey distribution for secure communicationDigital data processing detailsSecure communicationUnique identifier
A method and system for enabling wireless devices distributed throughout an enterprise to be efficiently initialized for secure communications. The method and system utilize well known public key cryptography and machine unique identifiers to establish a secure channel and initialize the wireless devices.
Owner:IBM CORP
System and method for providing checkpointing with precompile directives and supporting software to produce checkpoints, independent of environment constraints
InactiveUS6161219AReduce overheadViable and practicalSoftware testing/debuggingSpecific program execution arrangementsOperational systemMinimum time
A method for portable checkpointing comprising the steps of: pre-compiling an input source code; and outputting an associated output source code which includes support for portable checkpointing. The portability of the checkpoints allows migration between systems with different hardware, software, and operating systems. The portable checkpoints are stored in a Universal Code Format (UCF) and are selectively activated at the next potential checkpoint marker after a MinTBC (Minimum Time Between Checkpoints) timer expires.
Owner:UNIV OF IOWA RES FOUND
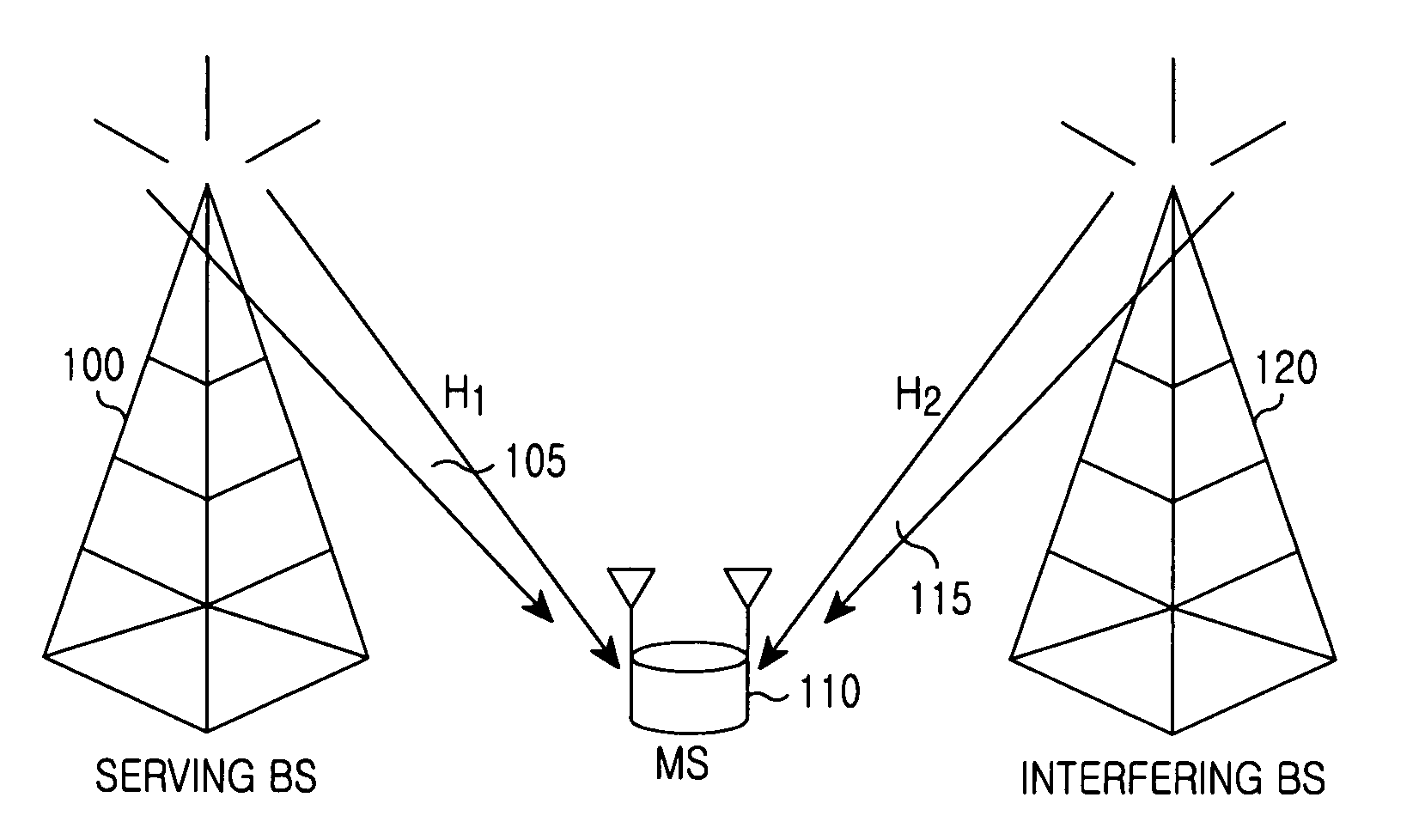
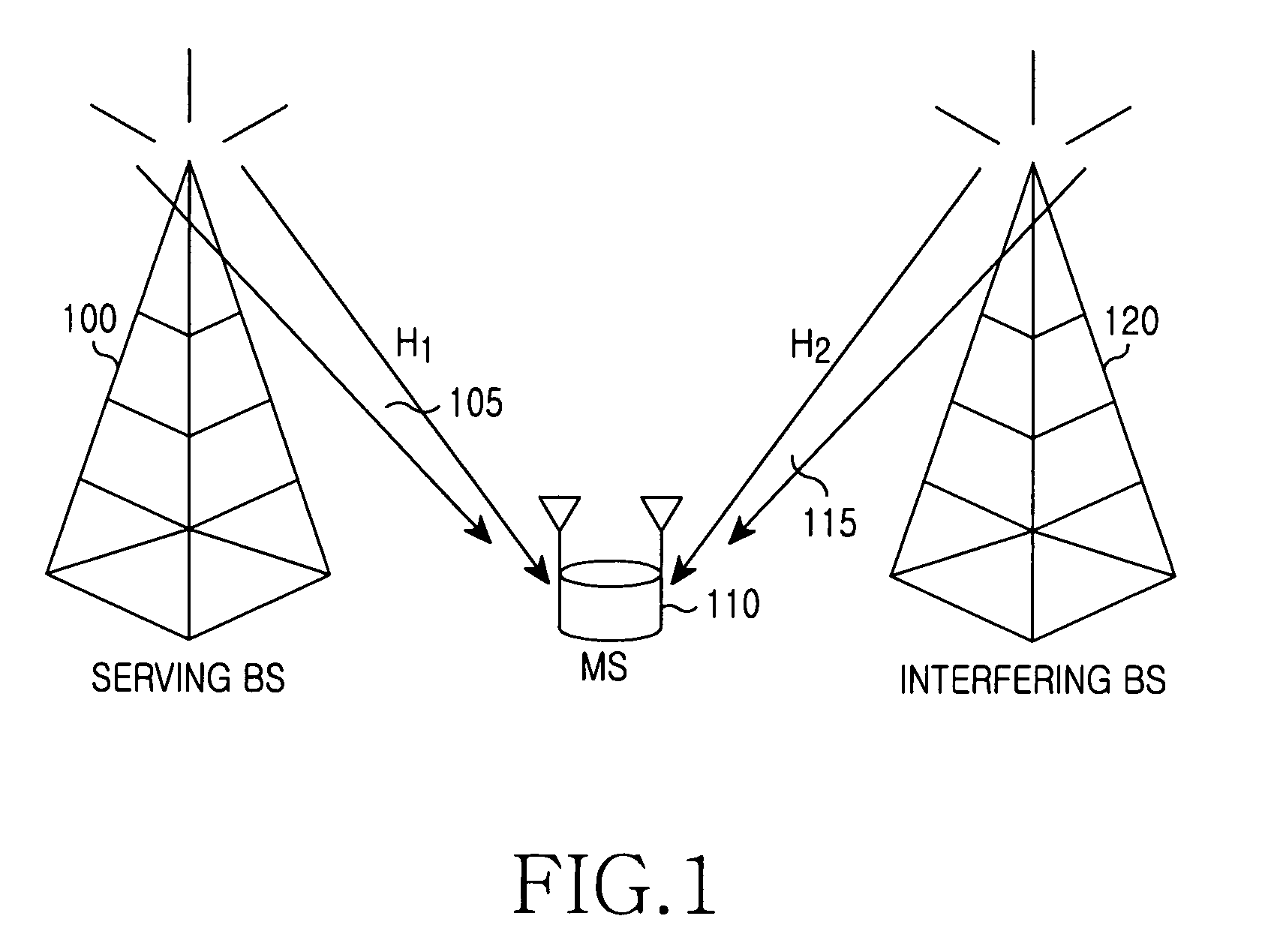
Method and apparatus for transmitting control information for interference mitigation in multiple antenna system
ActiveUS20100232539A1Guaranteed normal transmissionReduce overheadSite diversityOrthogonal multiplexMobile stationPrecoding matrix
A multiple antenna system including a mobile station and a base station are operable to perform a method for transmitting control information for interference mitigation. A Mobile Station (MS) can transmit control information for interference mitigation. The MS determines a first Precoding Matrix Index (PMI) and a second PMI for interference from an adjacent Base Station (BS). Based on a correlation level from correlation values between one of the first PMI and second PMI and the remaining PMIs in the codebook, the MS determines a level of a subset of PMIs, and feeds back information indicating the correlation level.
Owner:SAMSUNG ELECTRONICS CO LTD
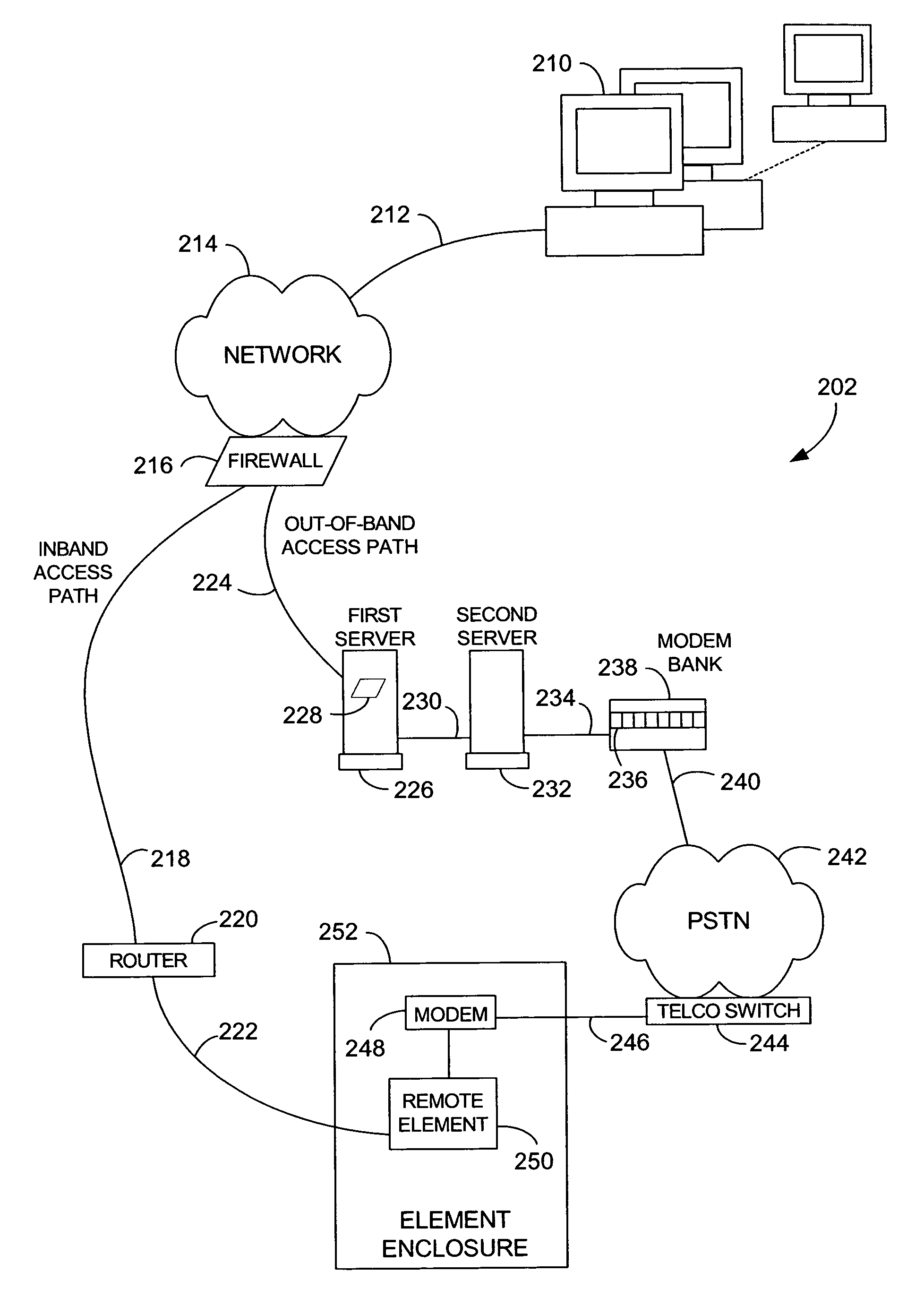
Method and system for providing secure, centralized access to remote elements
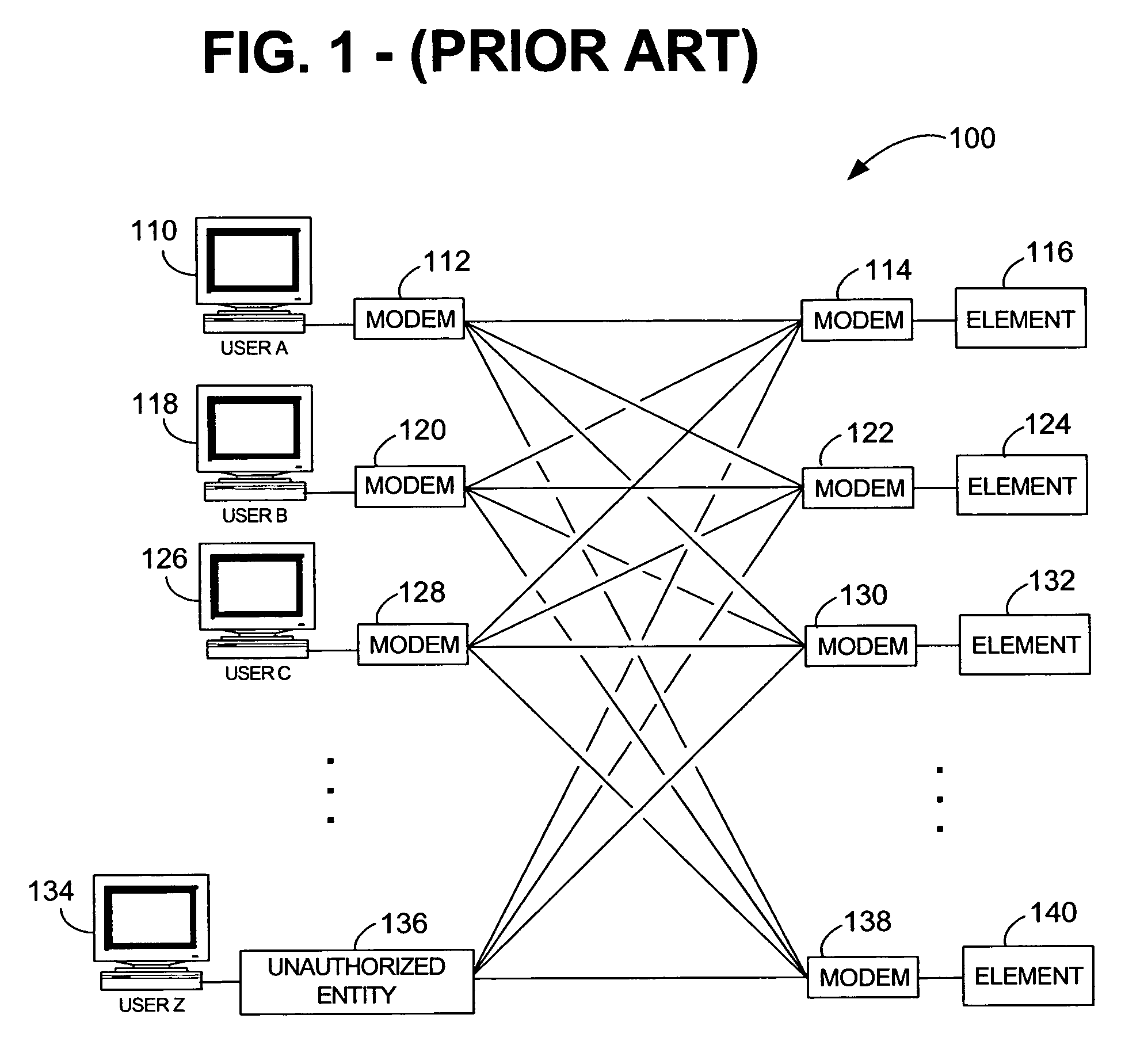
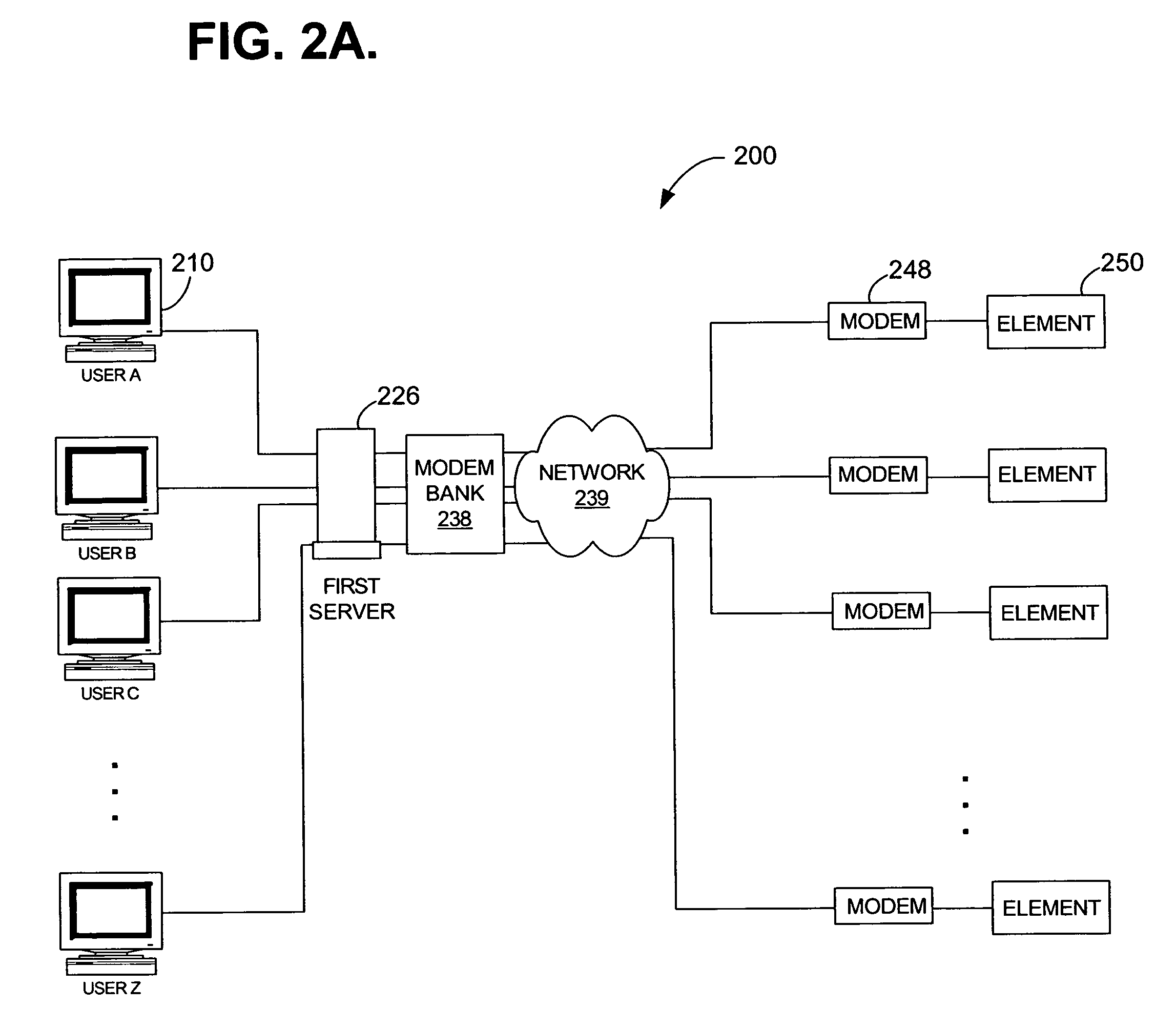
ActiveUS7640581B1Reduce overheadReduce eliminateMultiple digital computer combinationsProgram controlNetwork elementSecurity Measure
A system and method for establishing centralized, out-of-band access to remote network elements is provided. Status and other information can be securely retrieved from the remote elements. One or more servers observe and manage a plurality of remote elements using modem-to-modem communications between a modem bank and a remote modem. Requests are submitted through a central mediation point, thereby allowing central control of user profiles and a collection of security audit log information. One or more authentication mechanisms provide enforced security measures and trusted communication paths between a user and a remote element. Remote elements can be securely monitored and administered from a central location.
Owner:CENTURYLINK INTPROP
Method and device for controlling RRC state
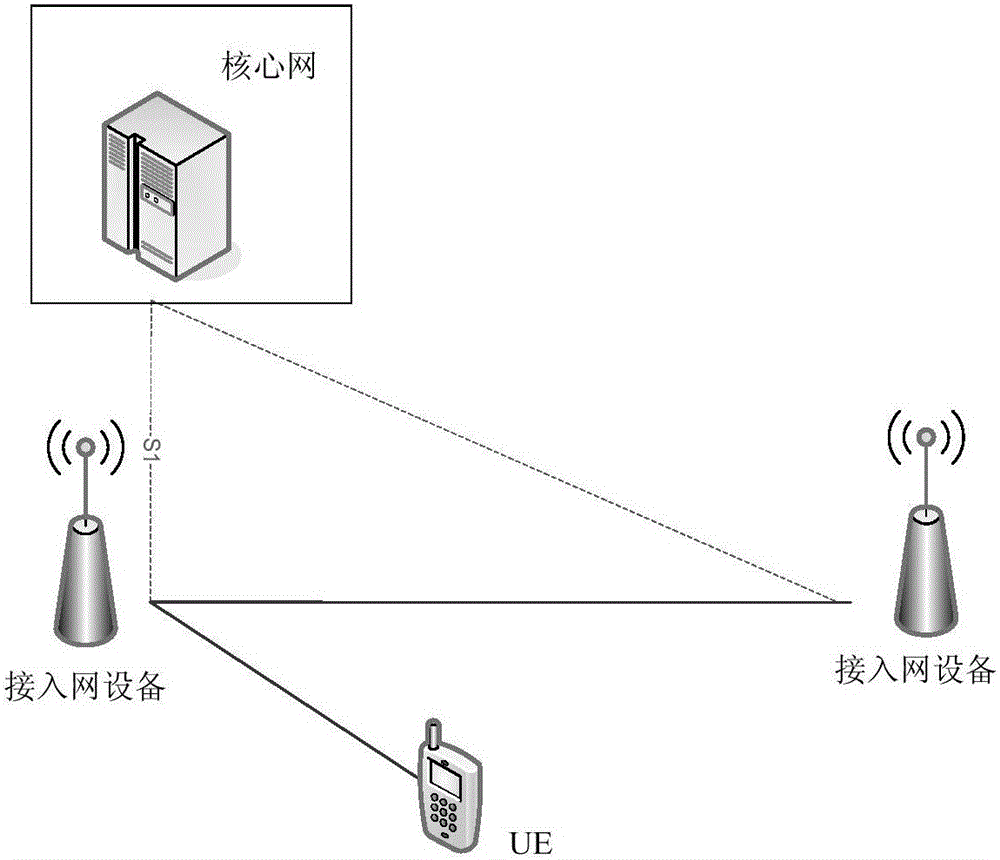
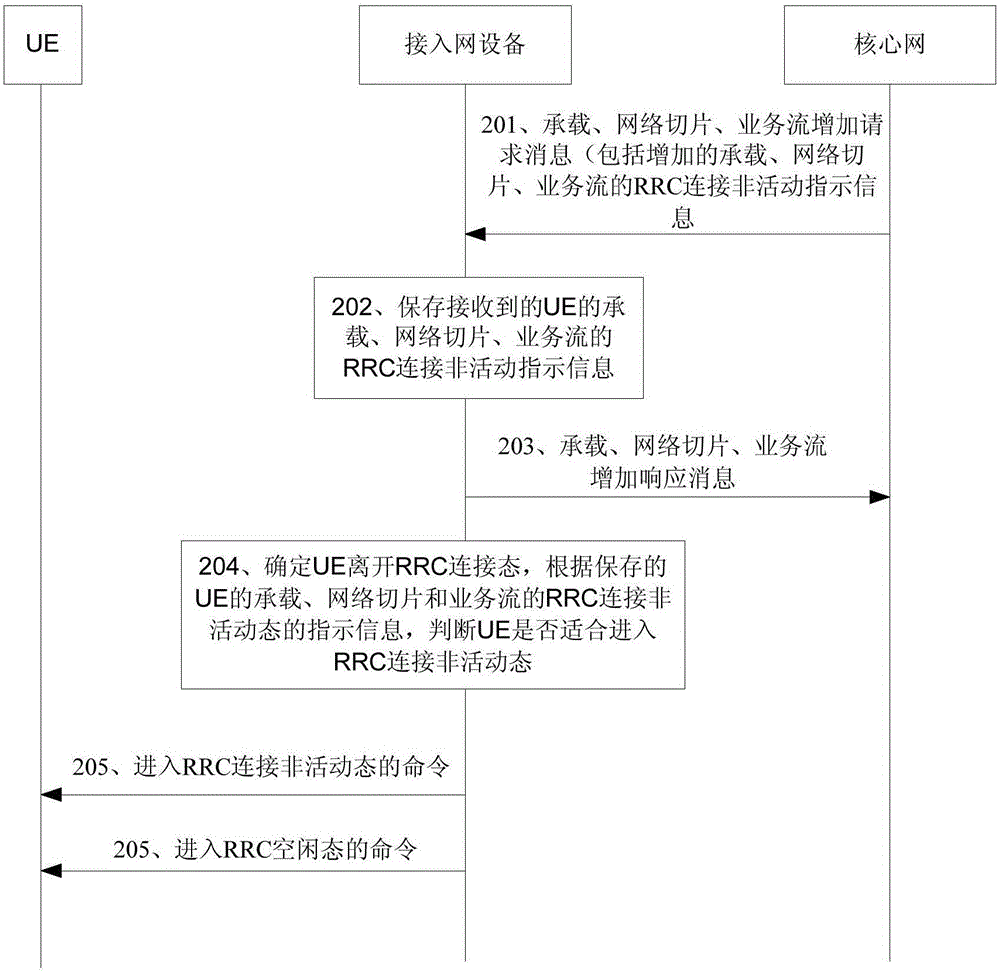
ActiveCN105898894AReduce overheadImprove performanceAssess restrictionConnection managementAccess networkComputer science
The embodiment of the invention discloses a method and device for controlling a RRC (Radio Resource Control) state. An access network device obtains indication information of a RRC connection inactive state of UE; when the UE leaves a RRC connected state, the access network device determines that the UE enters the RRC connection inactive state or a RRC idle state based on the indication information of the RRC connection inactive state; and when that the UE enters the RRC connection inactive state is determined, the access network device stores contextual information of the UE and sends an instruction of entering the RRC connection inactive state to the UE to enable the UE to enter the RRC connection inactive state. In the abovementioned method, the access network device can control the UE to enter a suitable RRC state based on the condition of the UE, thereby reducing signaling overheads and improving system performance.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com