Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10393 results about "Access method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An access method is a function of a mainframe operating system that enables access to data on disk, tape or other external devices. They were introduced in 1963 in IBM OS/360 operating system. Access methods provide an application programming interface (API) for programmers to transfer data to or from device, and could be compared to device drivers in non-mainframe operating systems, but typically provide a greater level of functionality.
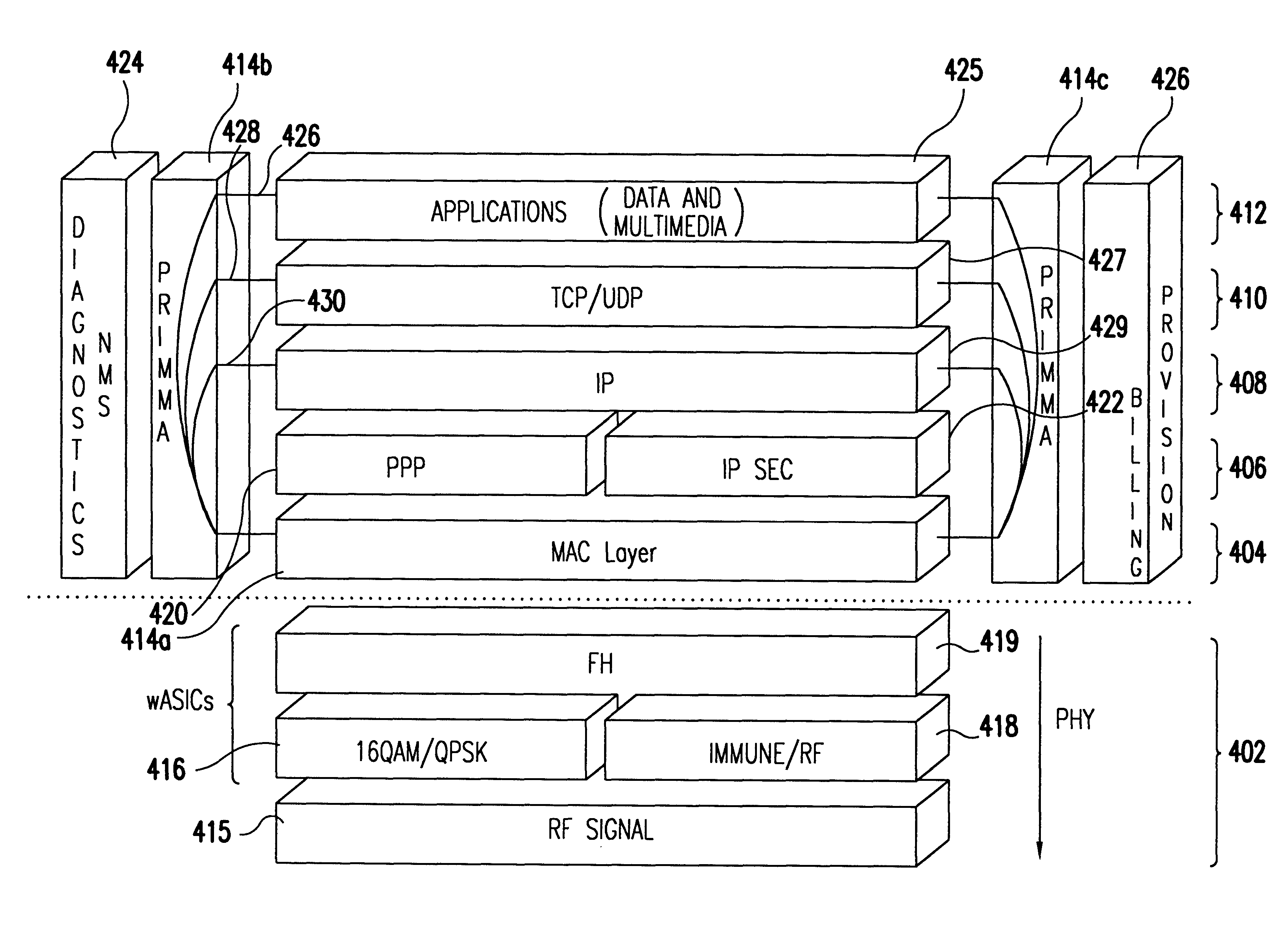
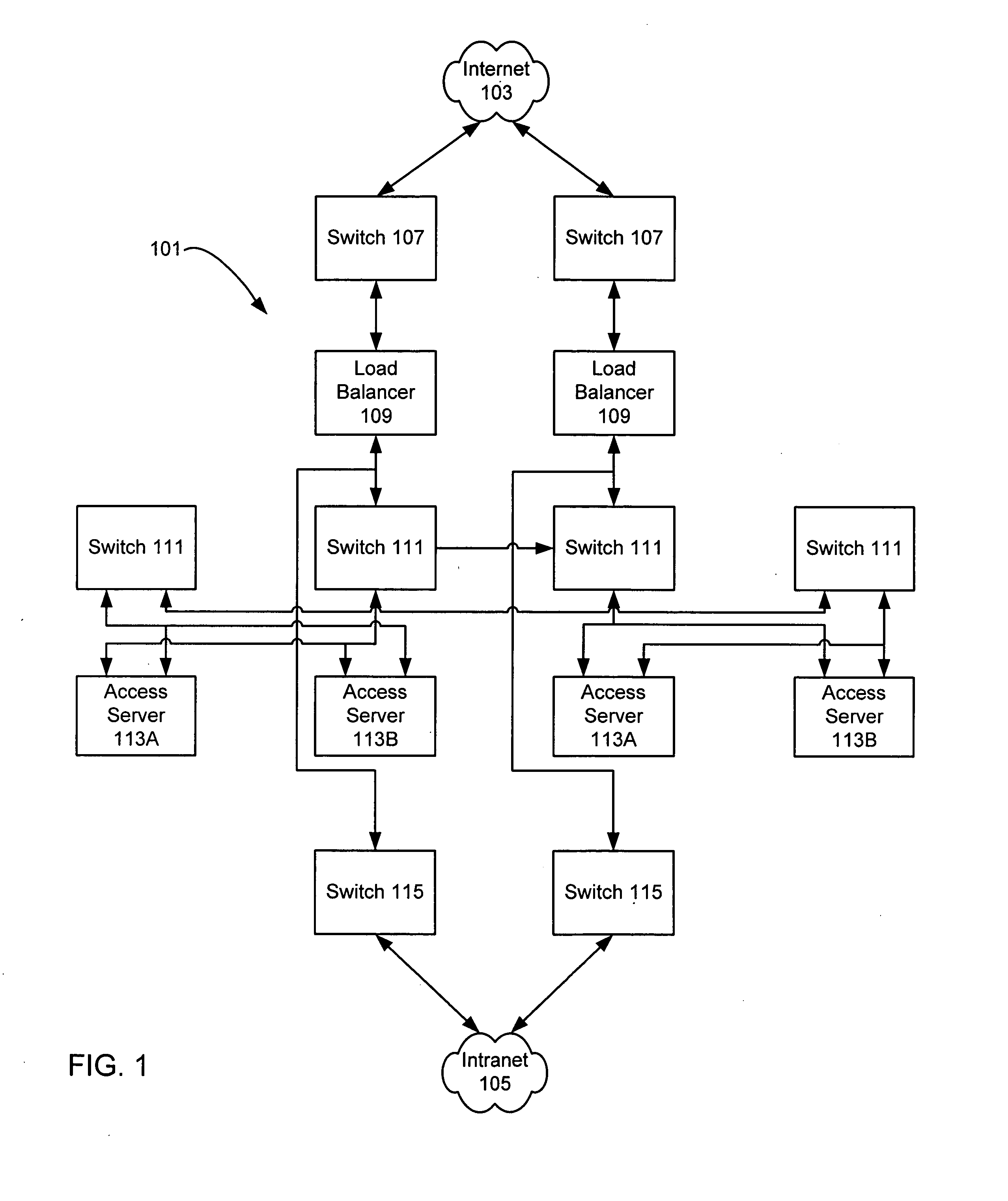
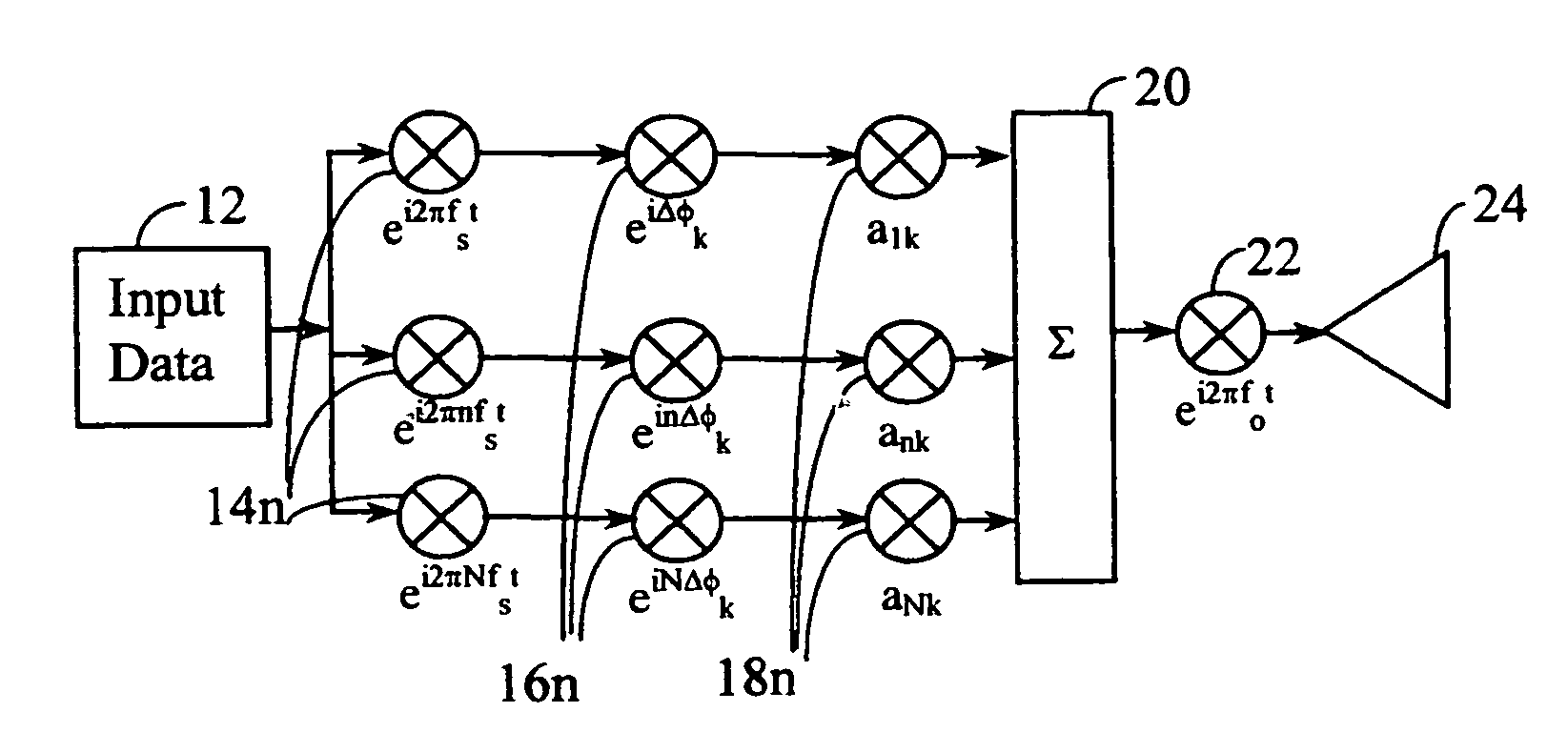
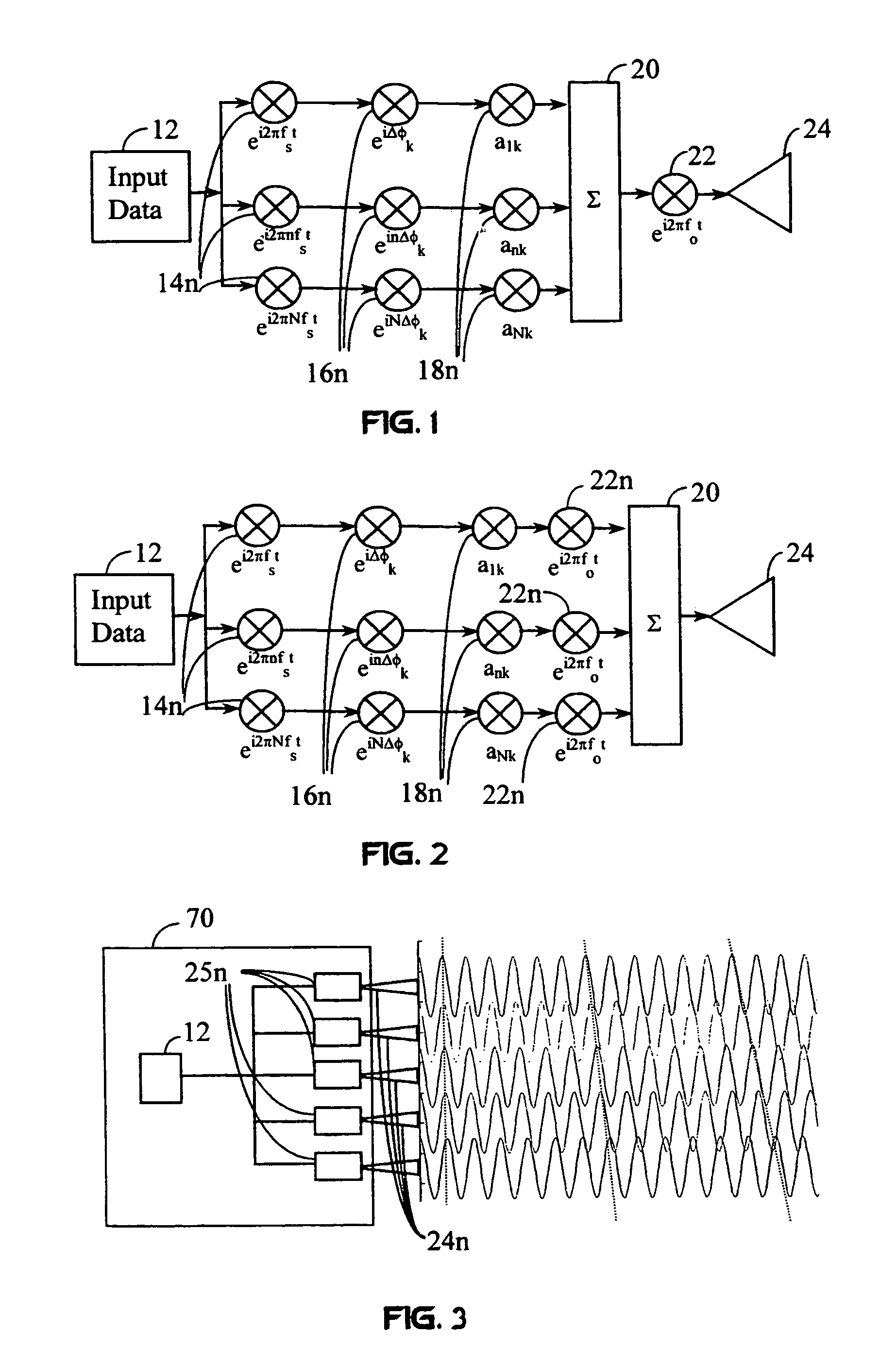
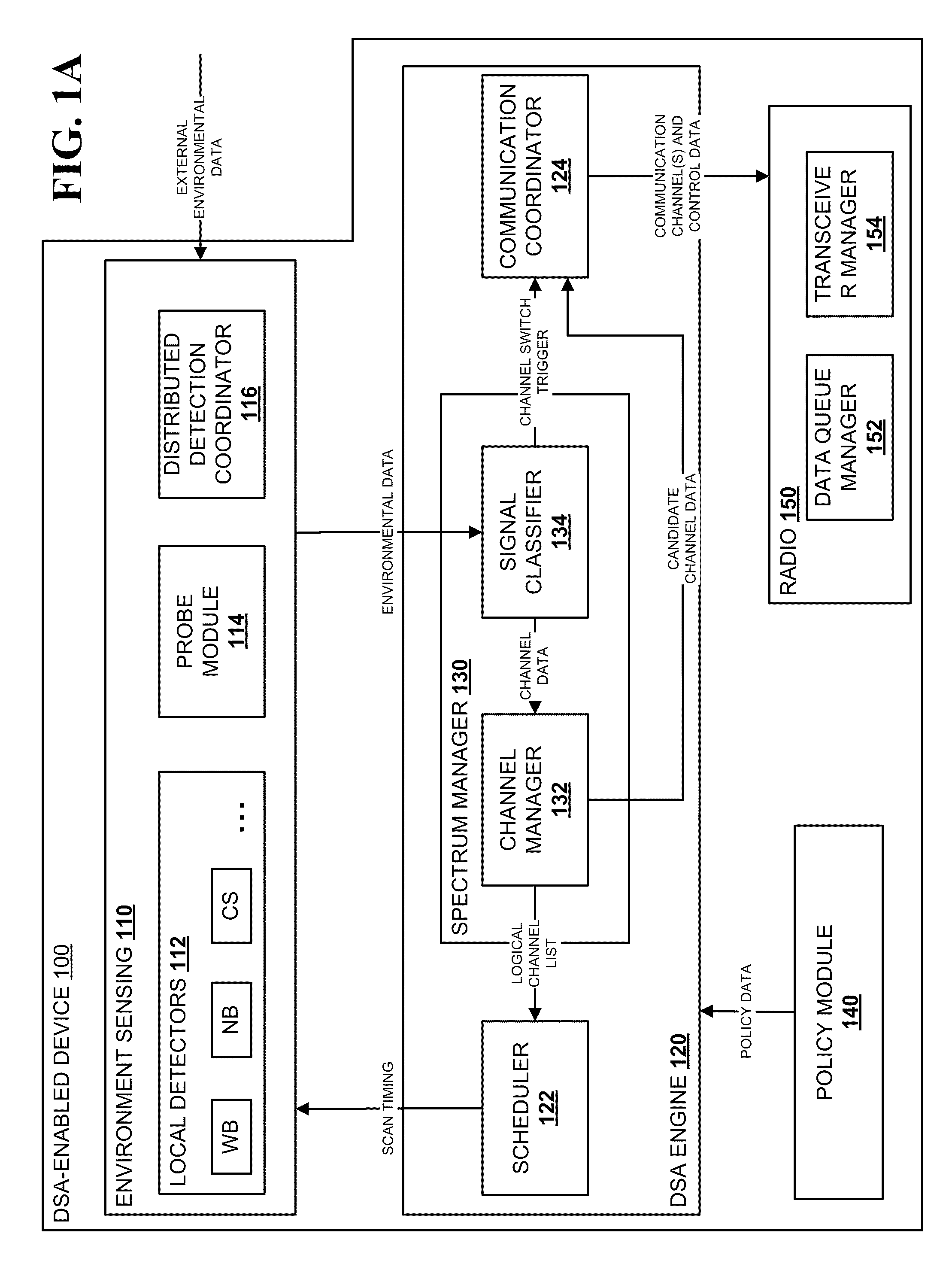
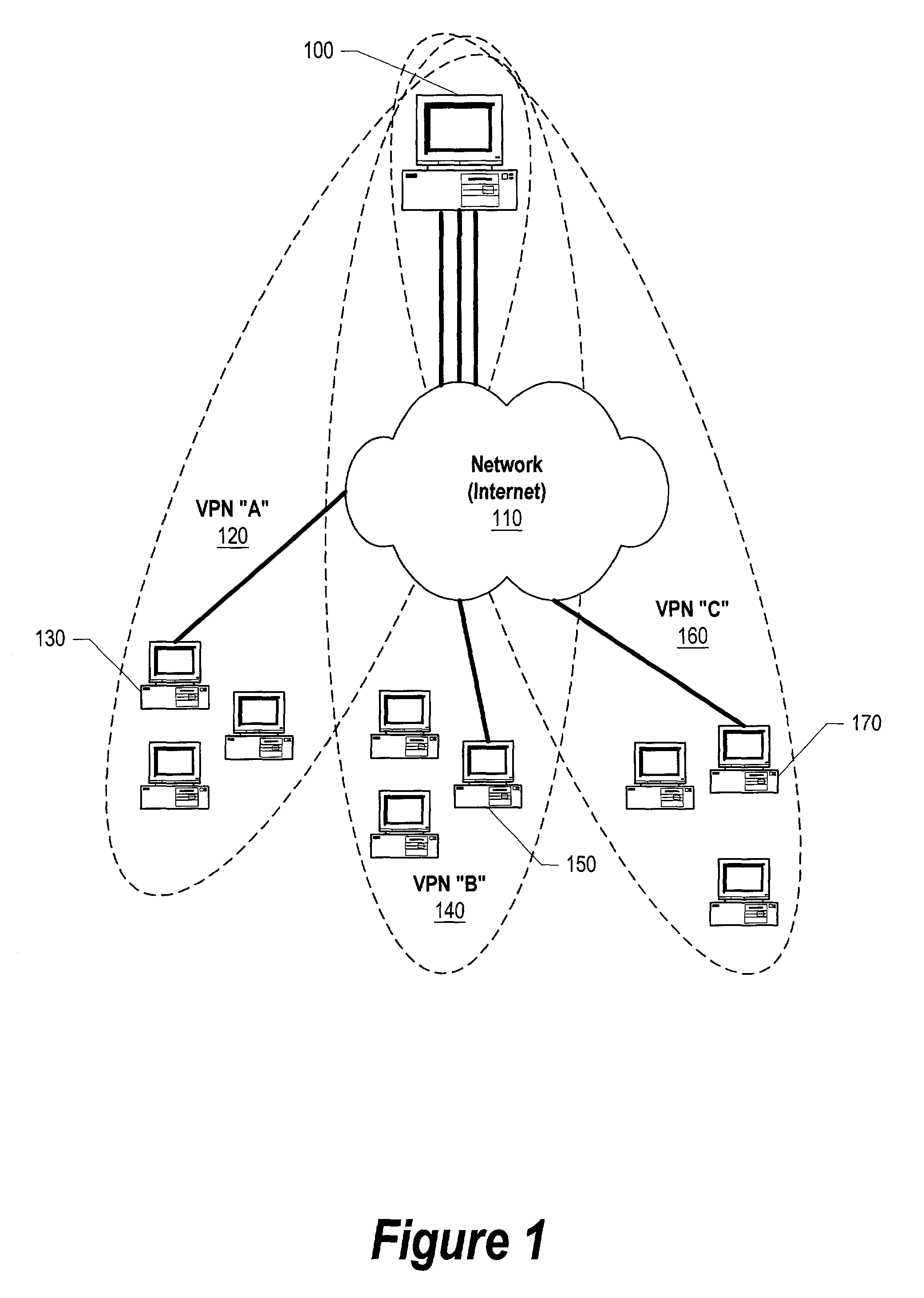
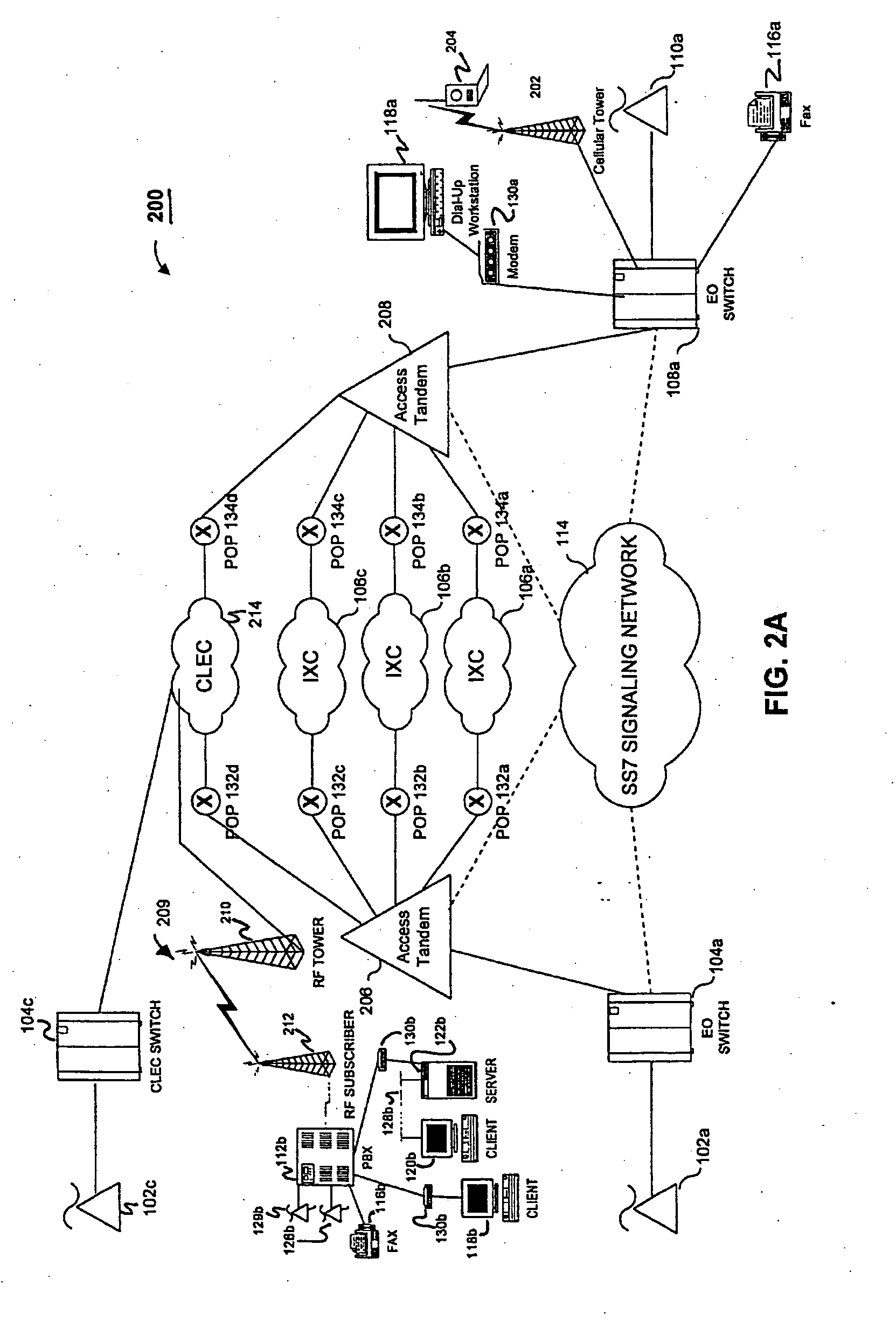
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
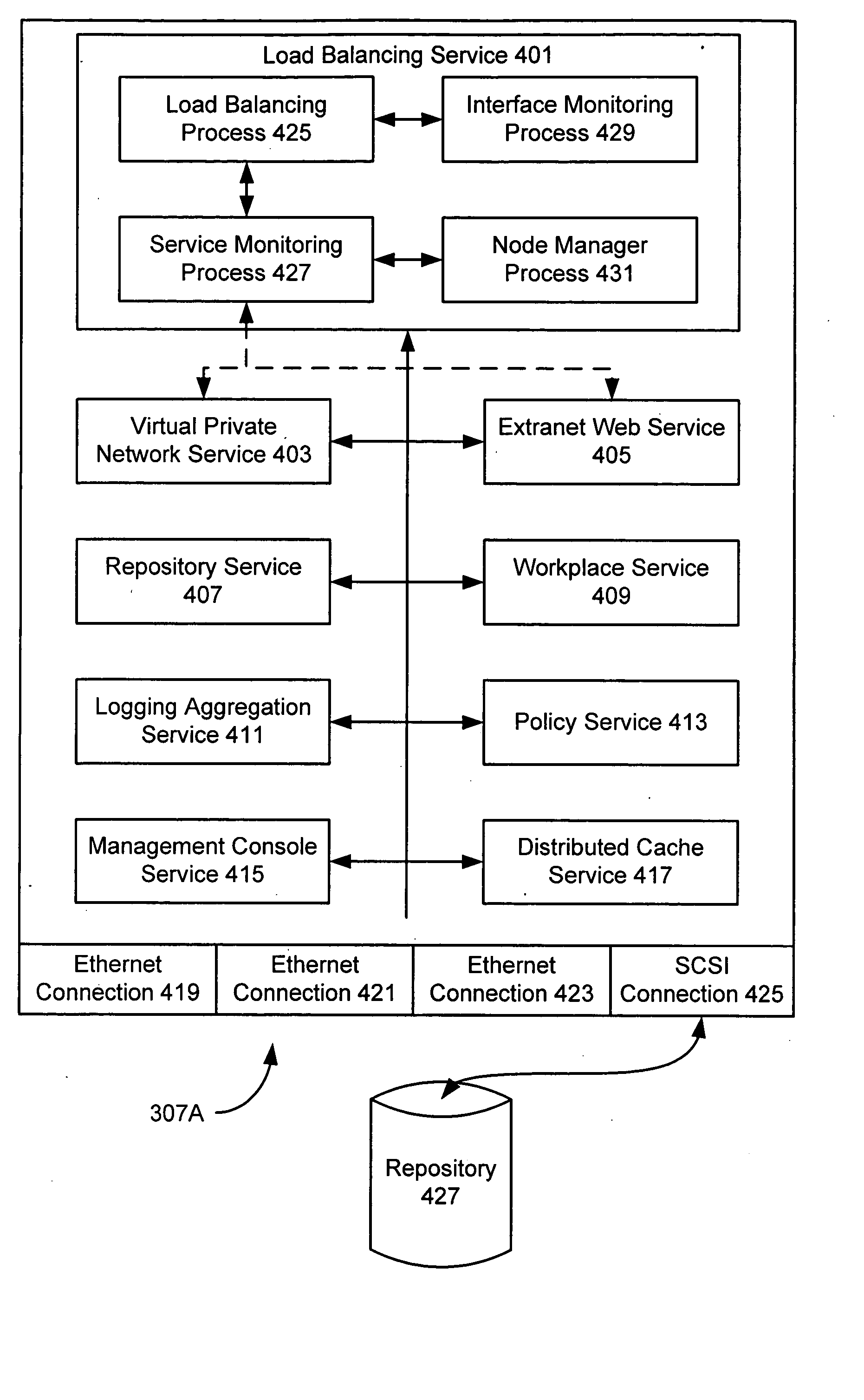
Network appliance
InactiveUS20050132030A1Low costReduce overheadError detection/correctionDigital computer detailsAccess methodClient-side
A network appliance is described that can provide a variety of software services, including both platform services, such as access method services, and a load balancing service. A network may include a network appliance that both provides one or more platform services and acts as a load balancer. When two or more such appliances are used together, they can replace a substantial portion of a conventional network. For example, when a network appliance receives a client communication, its load balancer service can determine whether one of its own platform services will process the communication or forward the communication to another network appliance for processing. Moreover, if the load balancing service of a network appliance fails, another network appliance can provide load balancing. Similarly, if another service of a network appliance fails, then the network appliance may continue to provide load balancing but forward communications requiring the failed service to another network appliance for processing.
Owner:AVENTAIL A WHOLLY OWNED SUBSIDIARY OF SONICWALL
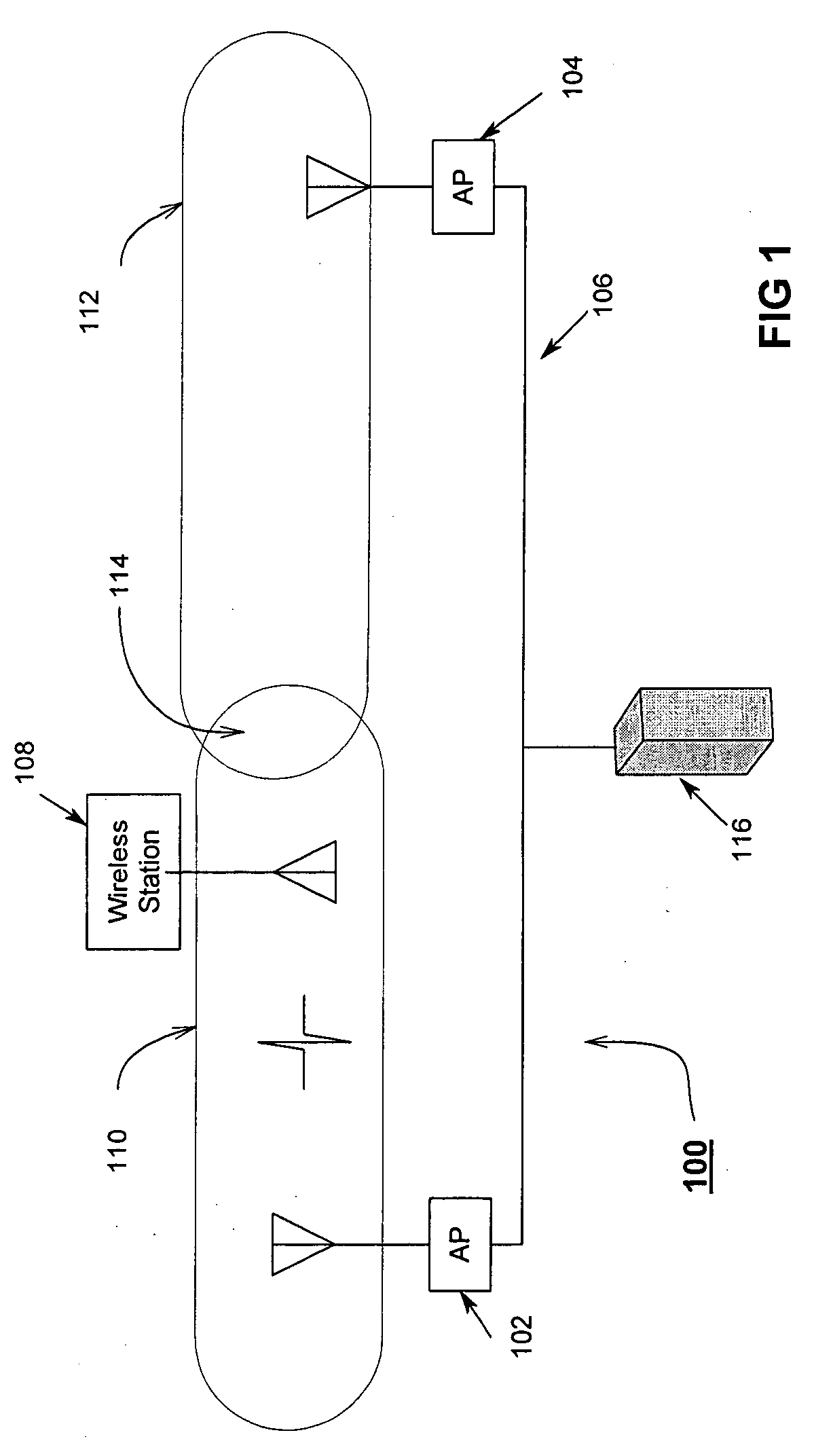
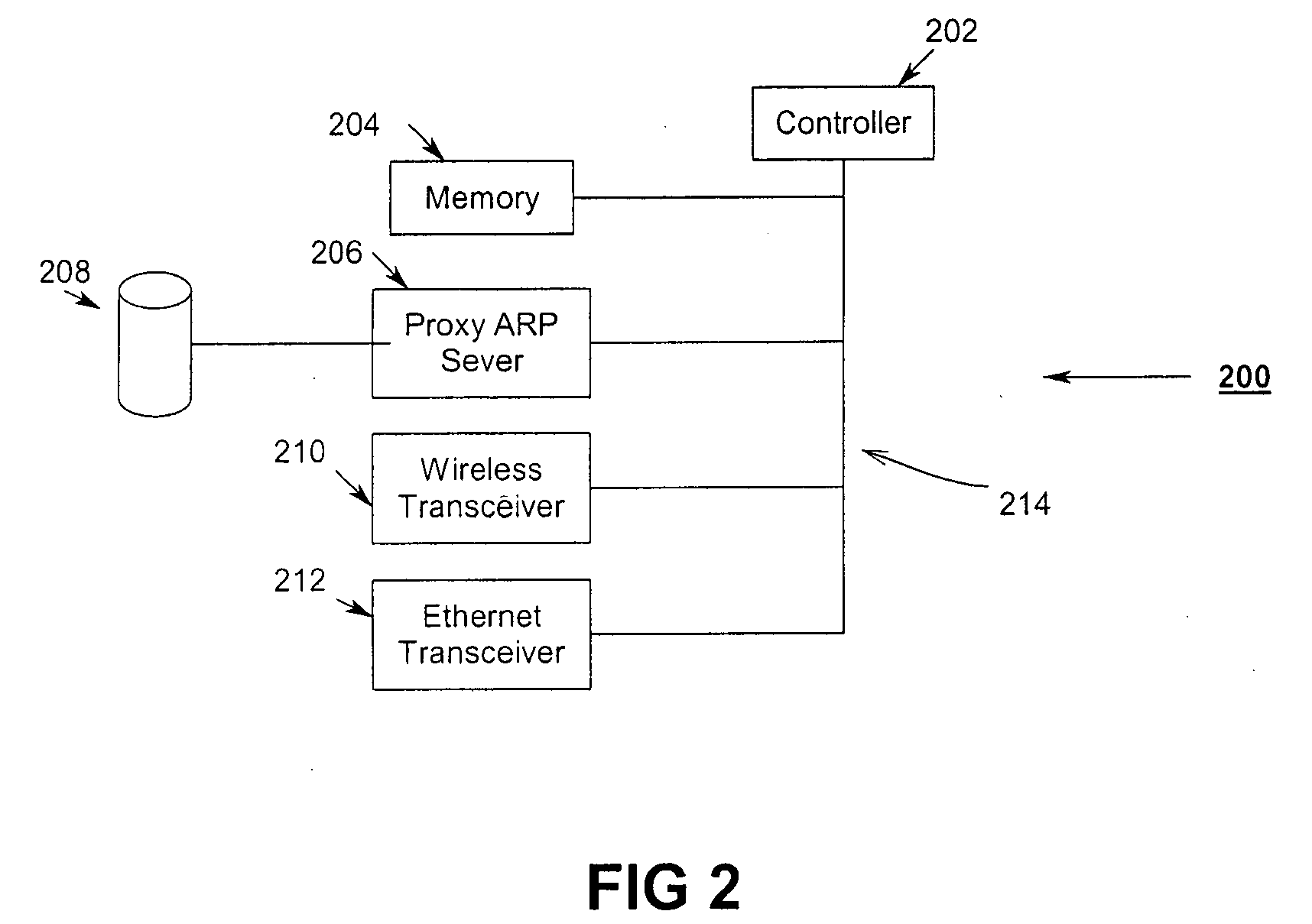
Uniform power save method for 802.11e stations
ActiveUS20050018624A1Delay minimizationFast sampling rateEnergy efficient ICTPower managementAccess methodClient-side
A power-save QSTA notifies an Access Point (AP) that its operating in a automatic power-save delivery (APSD) mode and negotiates a periodic wakeup schedule and a scheduled startup time with the AP. Wakeup times are synchronized with the 802.11 Timer Synchronization Function (TSF). The AP automatically sends frames to the QSTA when it determines the QSTA is in an awake state, otherwise downlink frames are buffered. The AP uses a combination poll+EDCF access method wherein at the start of each wakeup period the AP sends a poll to the QSTA, the poll having a flag that indicates to the QSTA if the AP has a downlink fame buffered for the QSTA. In addition, a Proxy ARP Server in an AP maintains IP / MAC bindings for associated clients so that when the AP receives a proxy ARP request for a client, the AP may respond for the client.
Owner:CISCO TECH INC
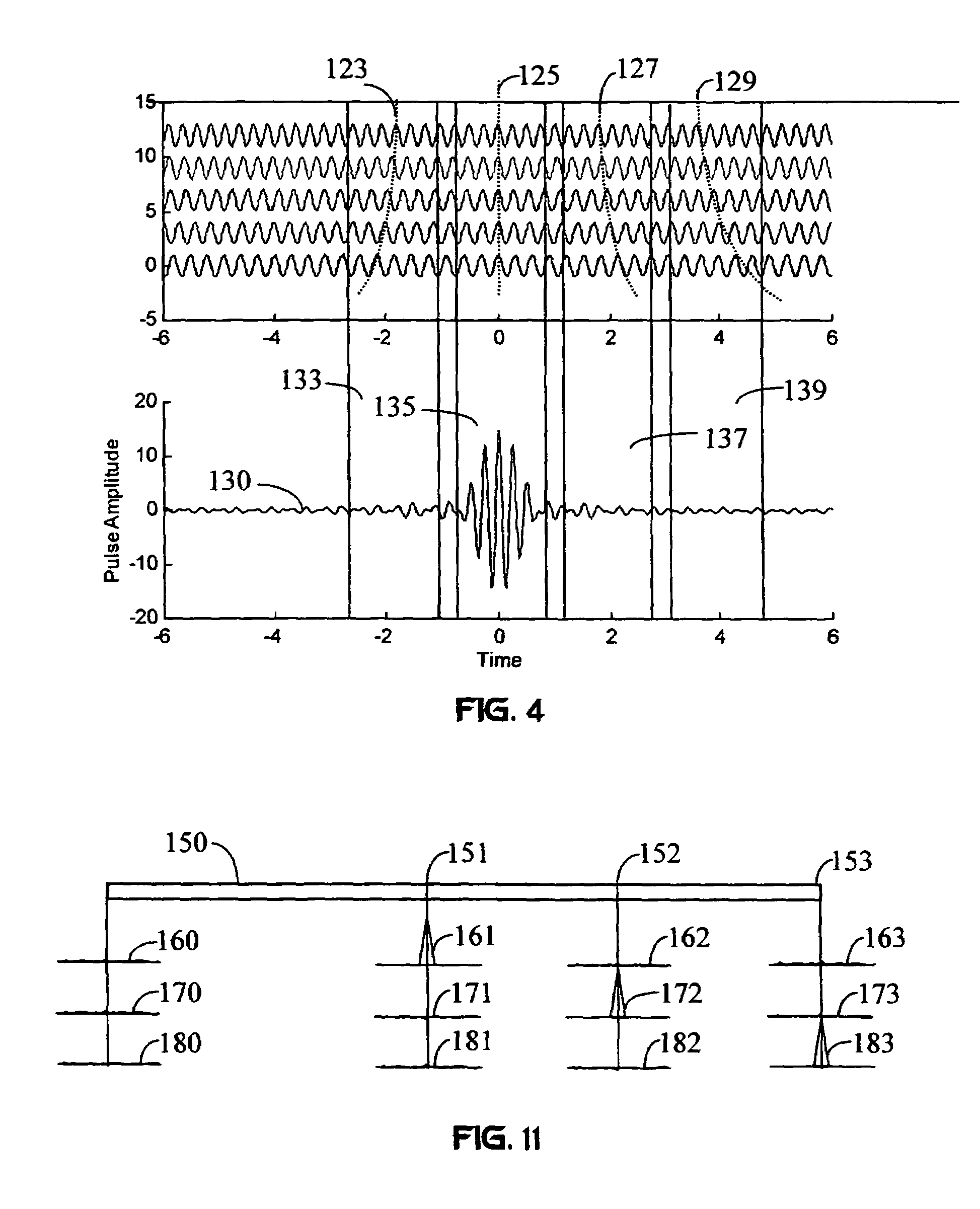
Multiple access method and system
InactiveUS7010048B1Reduce decreaseLower Level RequirementsFrequency diversityWavelength-division multiplex systemsFiberPulse envelope
A wireless communication system transmits data on multiple carriers simultaneously to provide frequency diversity. Carrier interference causes a narrow pulse in the time domain when the relative phases of the multiple carriers are zero. Selection of the frequency separation and phases of the carriers controls the timing of the pulses. Both time division of the pulses and frequency division of the carriers achieves multiple access. Carrier interferometry is a basis from which other communication protocols can be derived. Frequency hopping and frequency shifting of the carriers does not change the pulse envelope if the relative frequency separation and phases between the carriers are preserved. Direct sequence CDMA signals are generated in the time domain by a predetermined selection of carrier amplitudes. Each pulse can be sampled in different phase spaces at different times. This enables communication in phase spaces that are not detectable by conventional receivers. The time-dependent phase relationship of the carriers provides automatic scanning of a beam pattern transmitted by an antenna array. In waveguide communications, the carrier frequencies and phase space may be matched to the chromatic dispersion of an optical fiber to increase the capacity of the fiber.
Owner:DEPARTMENT 13 INC
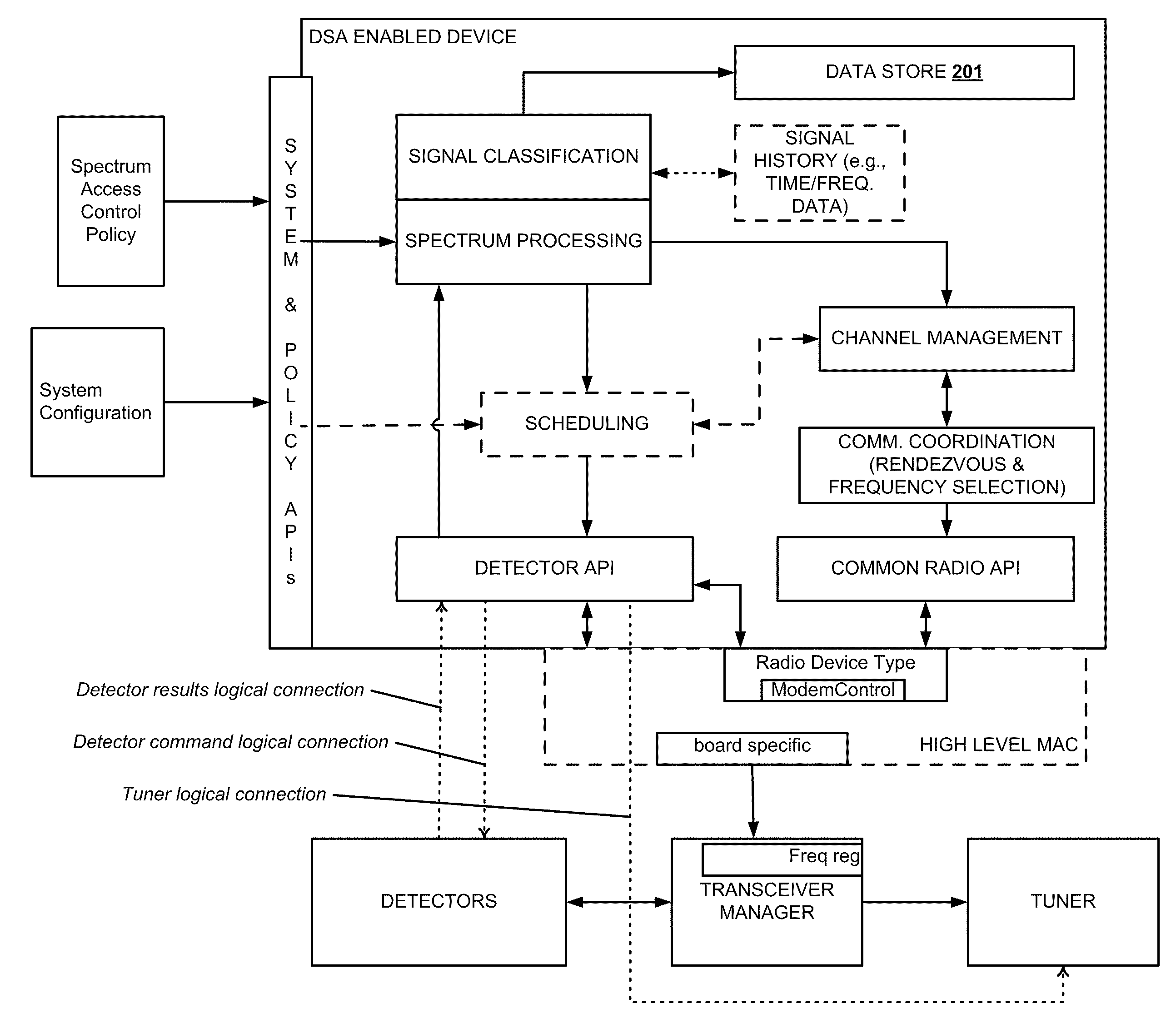
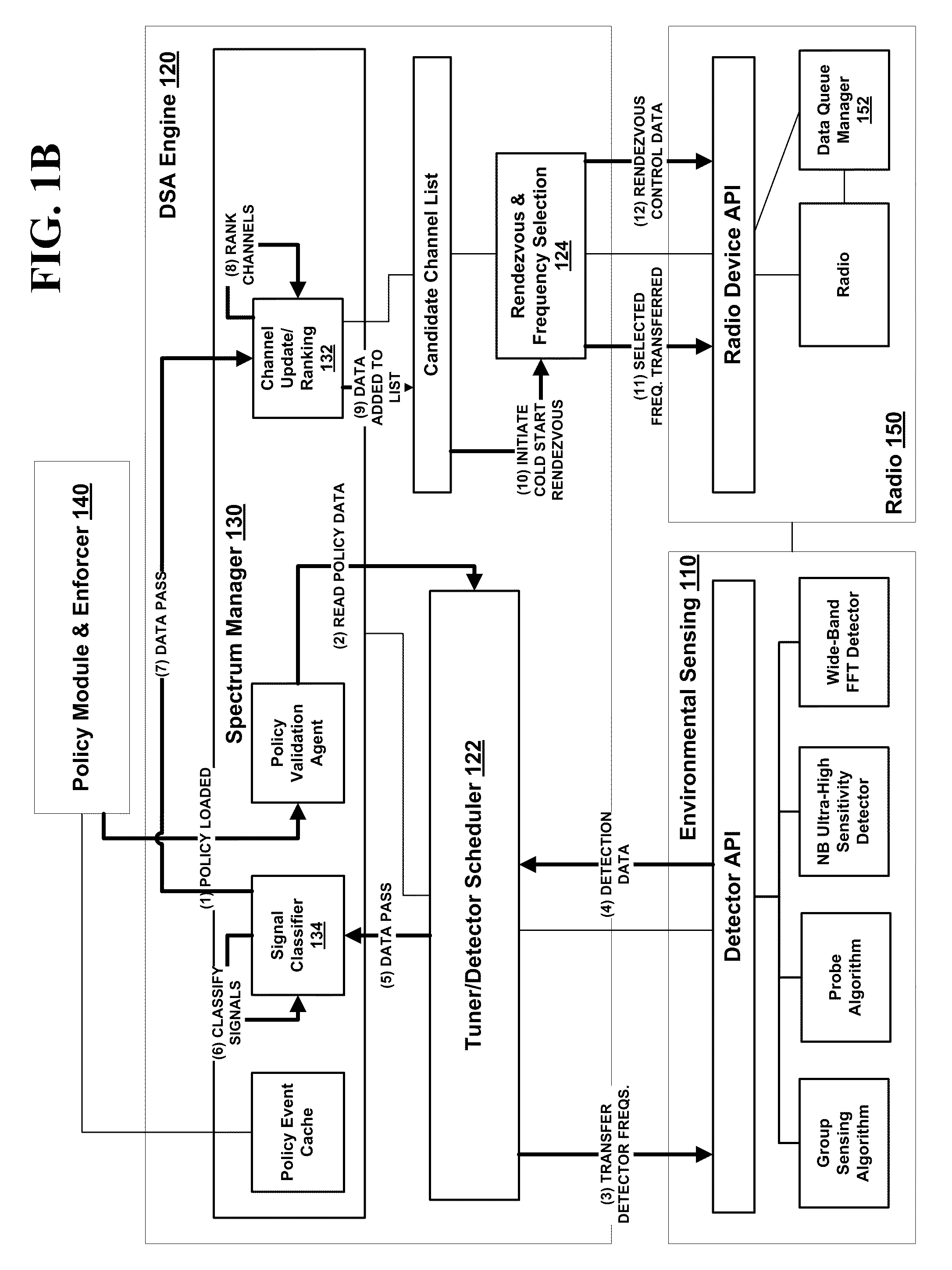
Method and System for Dynamic Spectrum Access
InactiveUS20100173586A1Reduce the valueReduce valueSpectral gaps assessmentTransmission monitoringAccess methodTelecommunications
Methods and systems for dynamic spectrum access (DSA) in a wireless network are provided. A DSA-enabled device may sense spectrum use in a region and, based on the detected spectrum use, select one or more communication channels for use. The devices also may detect one or more other DSA-enabled devices with which they can form DSA networks. A DSA network may monitor spectrum use by cooperative and non-cooperative devices, to dynamically select one or more channels to use for communication while avoiding or reducing interference with other devices.
Owner:SHARED SPECTRUM
Data communication method, communication system and mobile terminal
InactiveUS20090316811A1Reduce PAPRReduce power consumptionNetwork traffic/resource managementTransmission path divisionAccess methodCommunications system
In a communications system which complies with LTE including a base station 2 which transmits data by using an OFDM (Orthogonal Frequency Division Multiplexing) method as a downlink access method, and a mobile terminal 3, in a case in which an uplink scheduling request signal SR is transmitted by using an S-RACH when an Ack / Nack signal is being transmitted by using an Ack / Nack exclusive channel, the transmission of the Ack / Nack signal is stopped while the uplink scheduling request signal SR is transmitted.
Owner:MITSUBISHI ELECTRIC CORP
Security access method and apparatus
InactiveUS6877097B2Electric signal transmission systemsDigital data processing detailsComputer hardwareWireless transmission
Owner:ACTIVIDENTITY
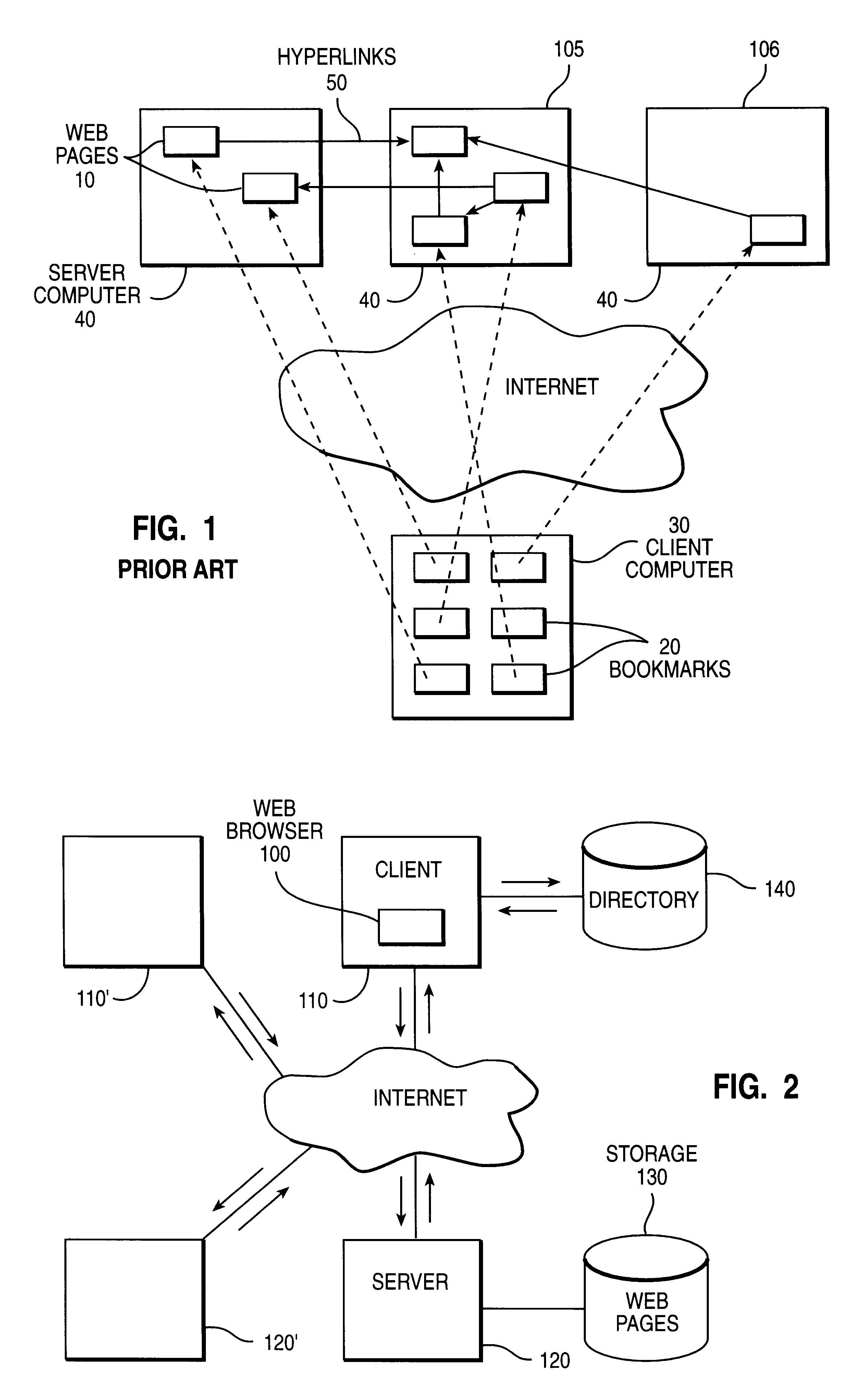
Management of and access to information and other material via the world wide web in an LDAP environment
InactiveUS6209036B1Data processing applicationsMultiple digital computer combinationsHyperlinkService improvement
Provided is a method and apparatus for improved access to material via the World Wide Web Internet service. Web page URLs are stored as attribute-values of directory objects and Web page hyperlinks to those directory objects are provided together with access logic responsive to the hyperlinks for retrieving the URLs for use by a client. This indirect access to Web pages via hyperlinks to directories has significant advantages for Web page organization and facilitates more flexible methods of Web page access than the known use of hyperlinks which include URLs pointing directly to the target Web pages.
Owner:IBM CORP
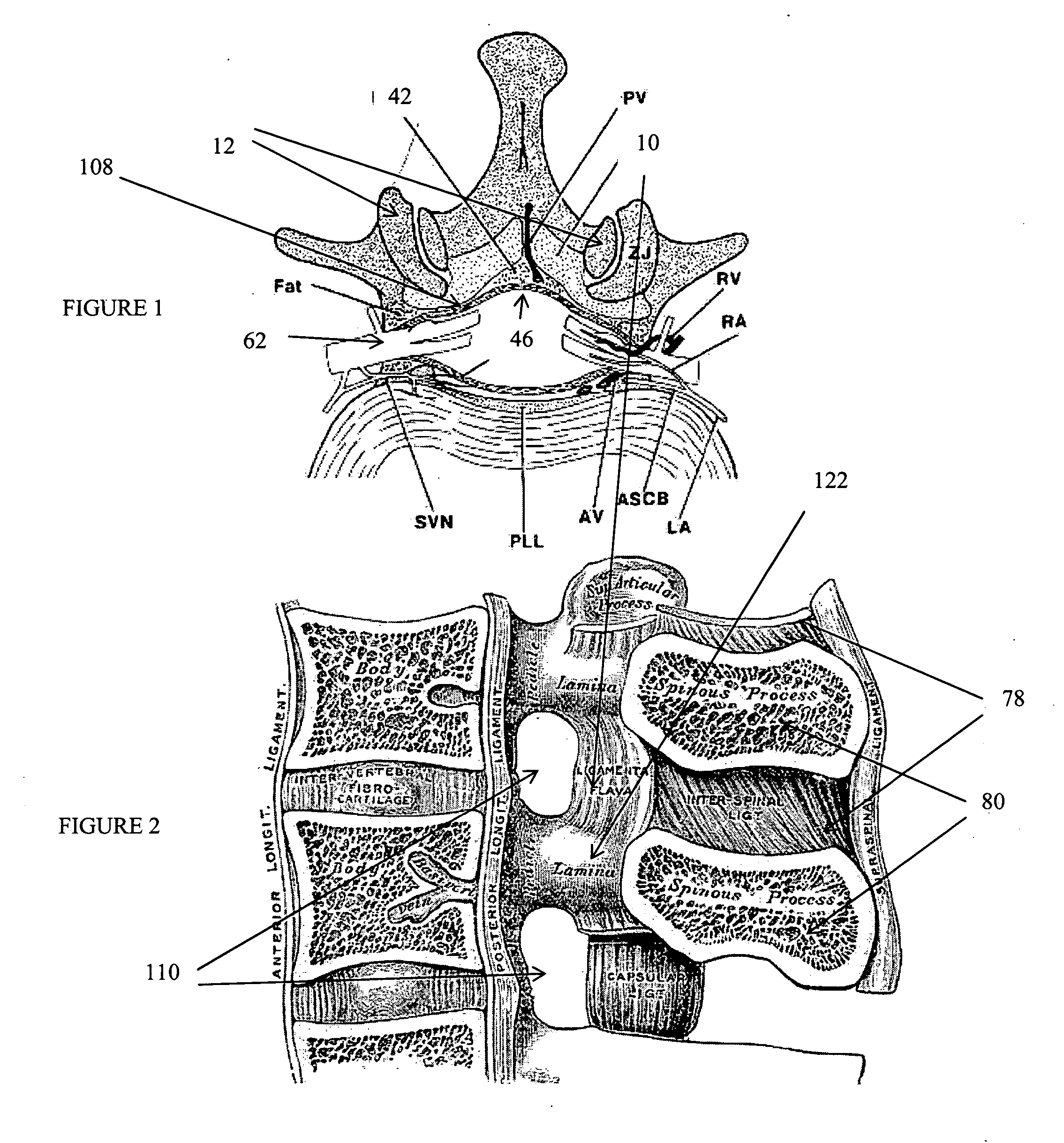
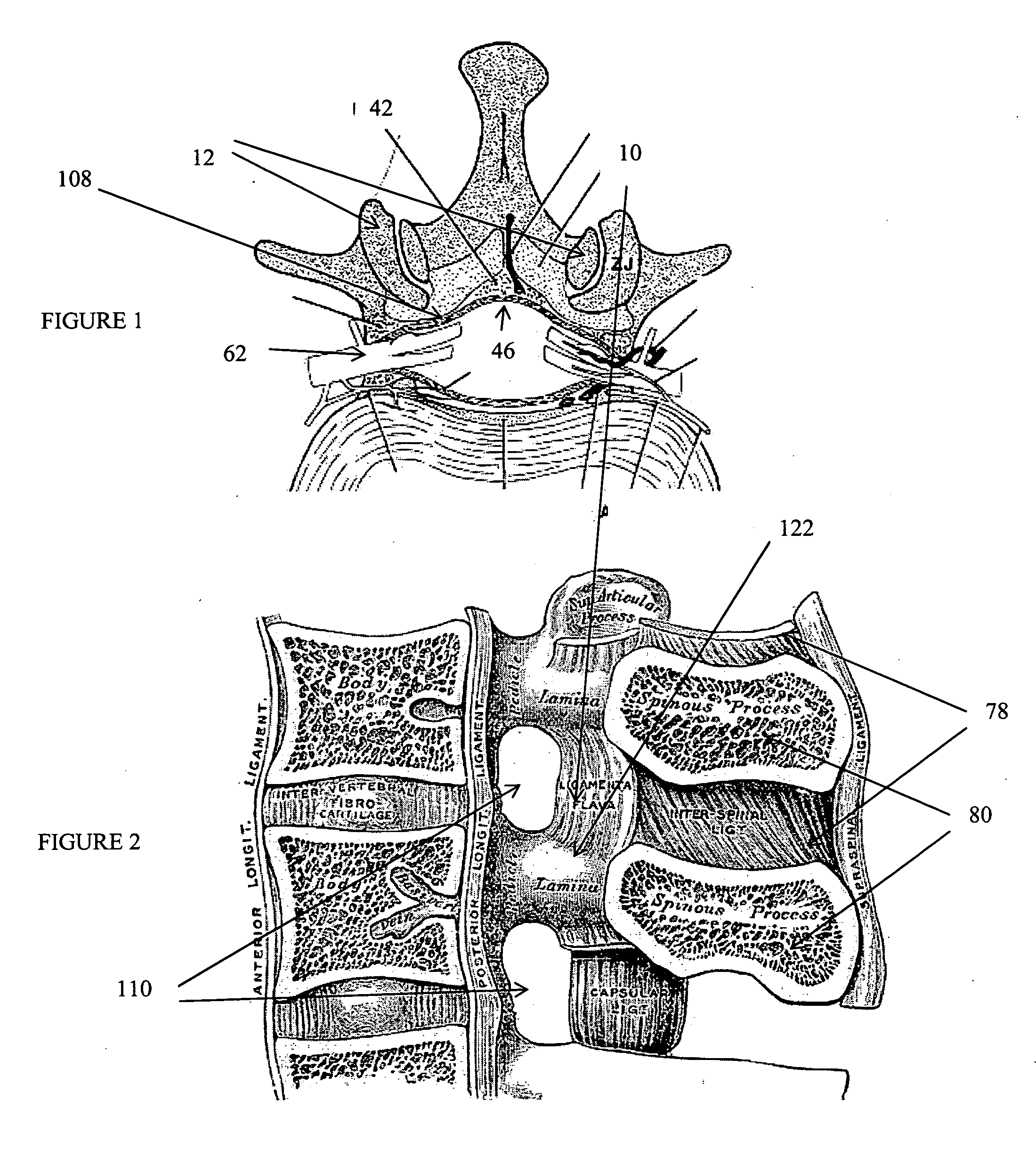
Devices and methods for tissue access
ActiveUS20060089633A1Easy to disassembleEliminate needCannulasAnti-incontinence devicesSurgical departmentNerve stimulation
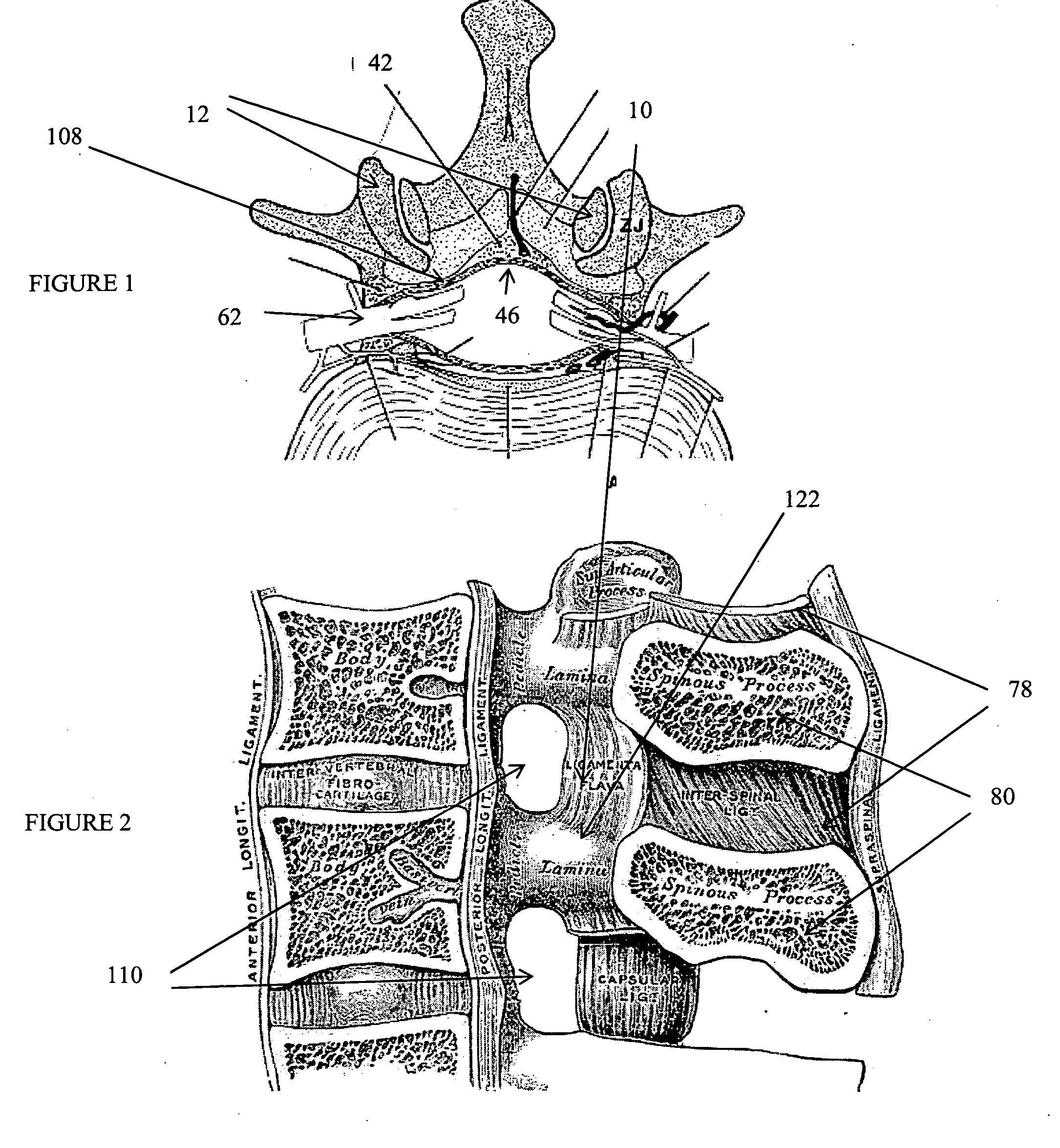
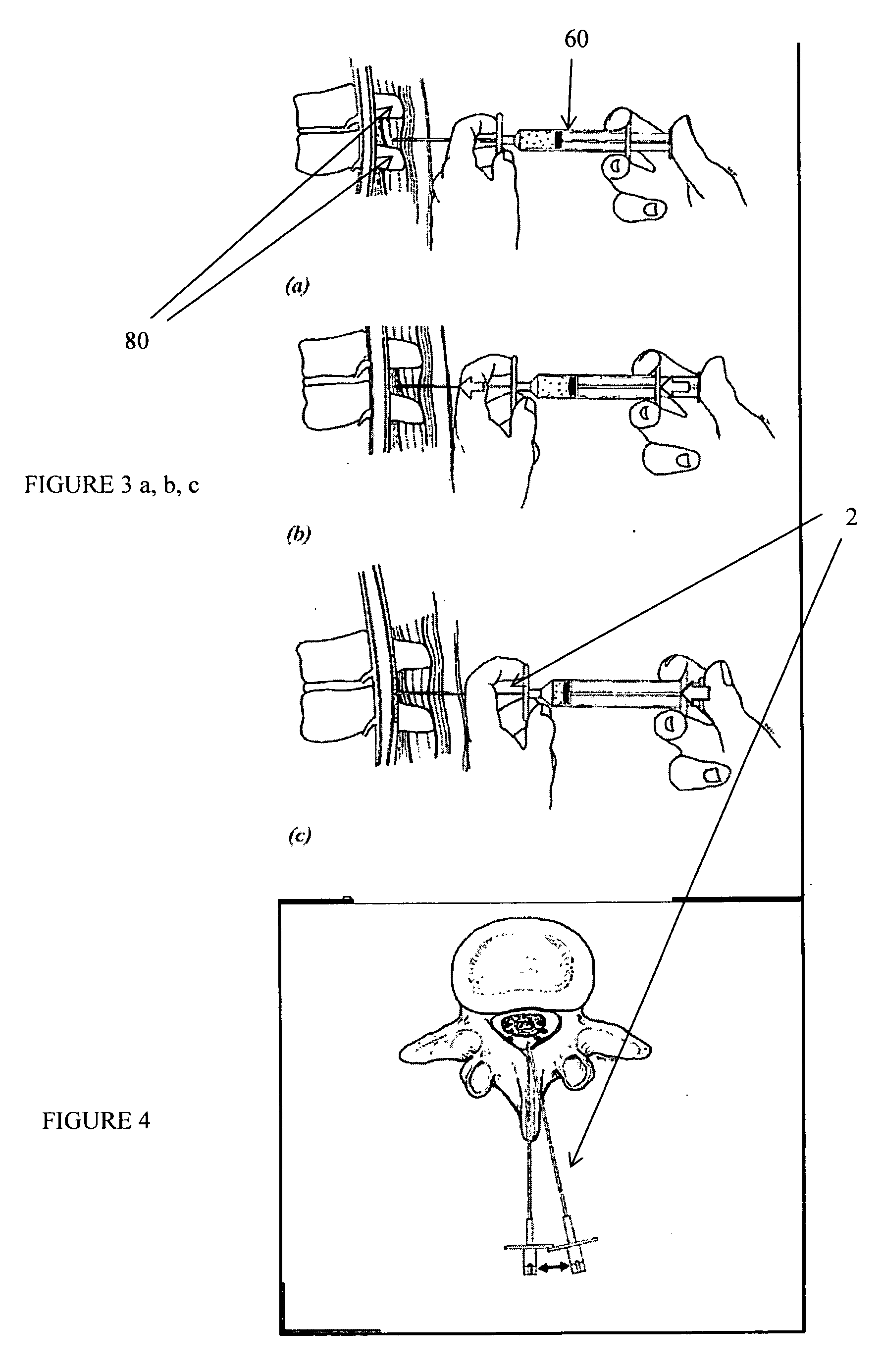
Methods and apparatus are provided for selective surgical removal of tissue, e.g., for enlargement of diseased spinal structures, such as impinged lateral recesses and pathologically narrowed neural foramen. In one variation, tissue may be ablated, resected, removed, or otherwise remodeled by standard small endoscopic tools delivered into the epidural space through an epidural needle. Once the sharp tip of the needle is in the epidural space, it is converted to a blunt tipped instrument for further safe advancement. A specially designed epidural catheter that is used to cover the previously sharp needle tip may also contain a fiberoptic cable. Further embodiments of the current invention include a double barreled epidural needle or other means for placement of a working channel for the placement of tools within the epidural space, beside the epidural instrument. The current invention includes specific tools that enable safe tissue modification in the epidural space, including a barrier that separates the area where tissue modification will take place from adjacent vulnerable neural and vascular structures. In one variation, a tissue abrasion device is provided including a thin belt or ribbon with an abrasive cutting surface. The device may be placed through the neural foramina of the spine and around the anterior border of a facet joint. Once properly positioned, a medical practitioner may enlarge the lateral recess and neural foramina via frictional abrasion, i.e., by sliding the abrasive surface of the ribbon across impinging tissues. A nerve stimulator optionally may be provided to reduce a risk of inadvertent neural abrasion. Additionally, safe epidural placement of the working barrier and epidural tissue modification tools may be further improved with the use of electrical nerve stimulation capabilities within the invention that, when combined with neural stimulation monitors, provide neural localization capabilities to the surgeon. The device optionally may be placed within a protective sheath that exposes the abrasive surface of the ribbon only in the area where tissue removal is desired. Furthermore, an endoscope may be incorporated into the device in order to monitor safe tissue removal. Finally, tissue remodeling within the epidural space may be ensured through the placement of compression dressings against remodeled tissue surfaces, or through the placement of tissue retention straps, belts or cables that are wrapped around and pull under tension aspects of the impinging soft tissue and bone in the posterior spinal canal.
Owner:SPINAL ELEMENTS INC +1
Devices and methods for tissue access
InactiveUS20060095028A1Improve securityAvoid injuryEar treatmentCannulasAccess methodSurgical removal
Methods and apparatus are provided for selective surgical removal of tissue. In one variation, tissue may be ablated, resected, removed, or otherwise remodeled by standard small endoscopic tools delivered into the epidural space through an epidural needle. The sharp tip of the needle in the epidural space, can be converted to a blunt tipped instrument for further safe advancement. The current invention includes specific tools that enable safe tissue modification in the epidural space, including a barrier that separates the area where tissue modification will take place from adjacent vulnerable neural and vascular structures. A nerve stimulator may be provided to reduce a risk of inadvertent neural abrasion.
Owner:BAXANO
Devices and methods for tissue access
InactiveUS20060122458A1Enabling symptomatic reliefApproach can be quite invasiveCannulasDiagnosticsSurgical departmentNerve stimulation
Methods and apparatus are provided for selective surgical removal of tissue, e.g., for enlargement of diseased spinal structures, such as impinged lateral recesses and pathologically narrowed neural foramen. In one variation, tissue may be ablated, resected, removed, or otherwise remodeled by standard small endoscopic tools delivered into the epidural space through an epidural needle. Once the sharp tip of the needle is in the epidural space, it is converted to a blunt tipped instrument for further safe advancement. A specially designed epidural catheter that is used to cover the previously sharp needle tip may also contain a fiberoptic cable. Further embodiments of the current invention include a double barreled epidural needle or other means for placement of a working channel for the placement of tools within the epidural space, beside the epidural instrument. The current invention includes specific tools that enable safe tissue modification in the epidural space, including a barrier that separates the area where tissue modification will take place from adjacent vulnerable neural and vascular structures. In one variation, a tissue removal device is provided including a thin belt or ribbon with an abrasive cutting surface. The device may be placed through the neural foramina of the spine and around the anterior border of a facet joint. Once properly positioned, a medical practitioner may enlarge the lateral recess and neural foramina via frictional abrasion, i.e., by sliding the tissue removal surface of the ribbon across impinging tissues. A nerve stimulator optionally may be provided to reduce a risk of inadvertent neural abrasion. Additionally, safe epidural placement of the working barrier and epidural tissue modification tools may be further improved with the use of electrical nerve stimulation capabilities within the invention that, when combined with neural stimulation monitors, provide neural localization capabilities to the surgeon. The device optionally may be placed within a protective sheath that exposes the abrasive surface of the ribbon only in the area where tissue removal is desired. Furthermore, an endoscope may be incorporated into the device in order to monitor safe tissue removal. Finally, tissue remodeling within the epidural space may be ensured through the placement of compression dressings against remodeled tissue surfaces, or through the placement of tissue retention straps, belts or cables that are wrapped around and pull under tension aspects of the impinging soft tissue and bone in the posterior spinal canal.
Owner:BAXANO
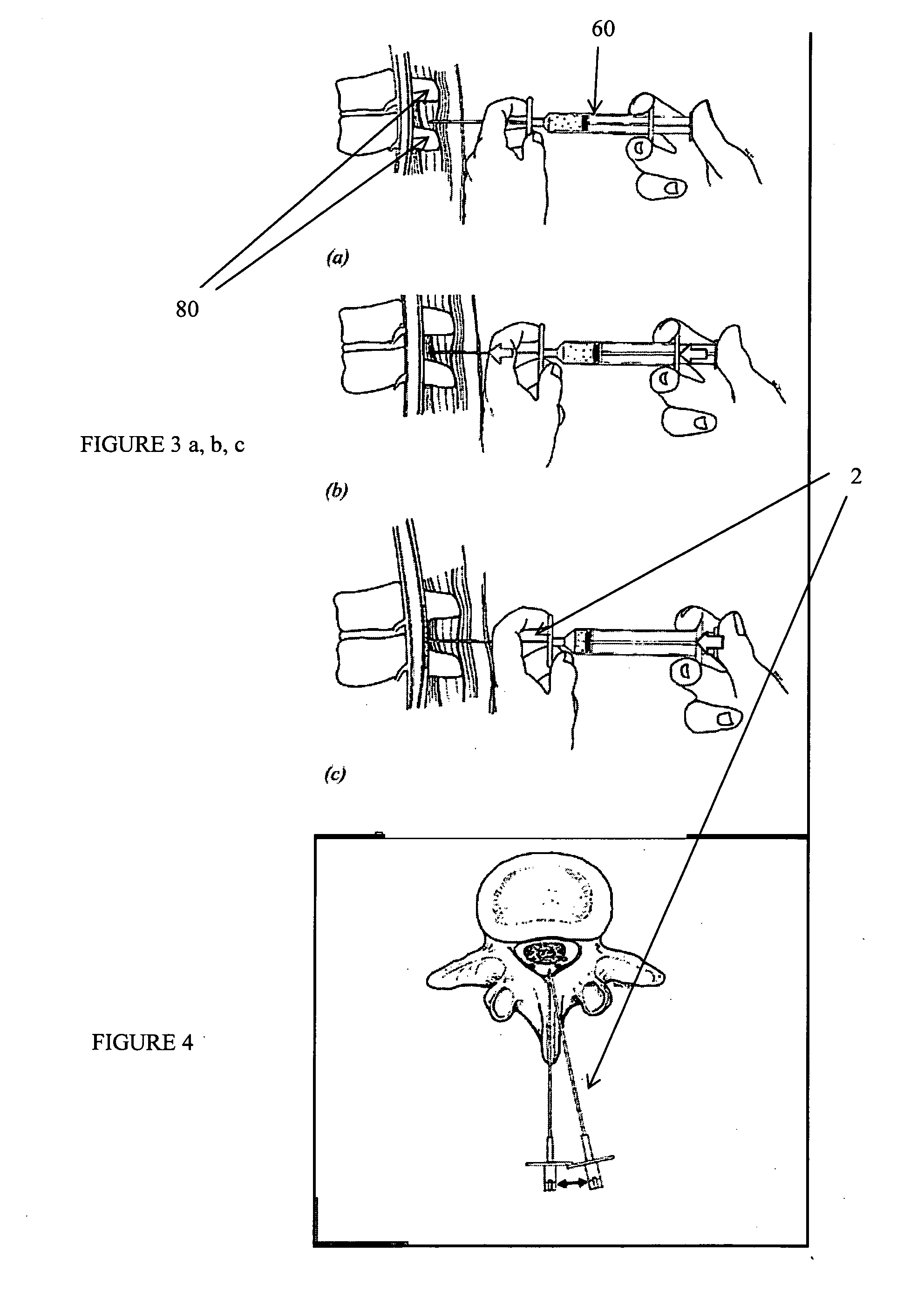
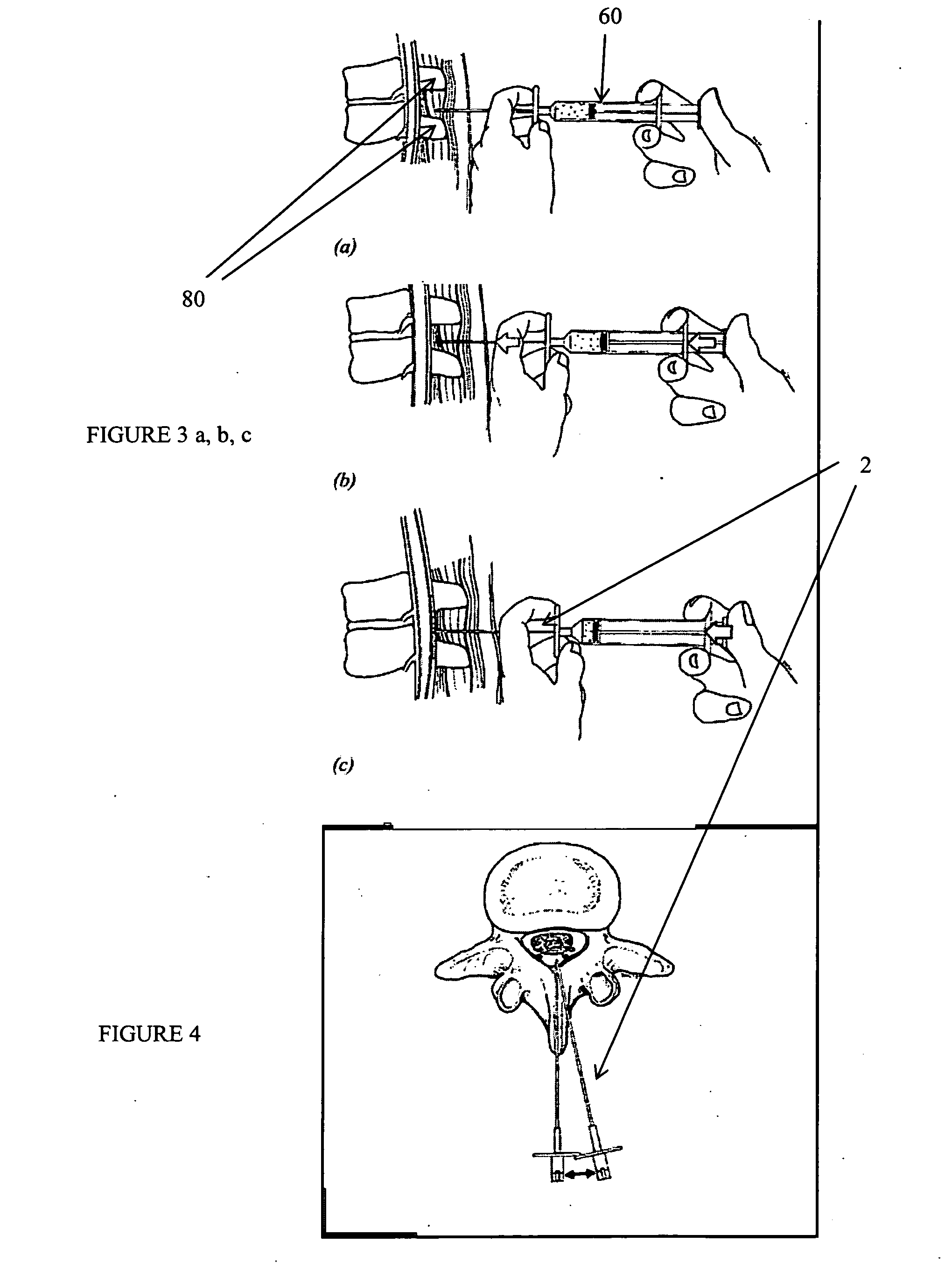
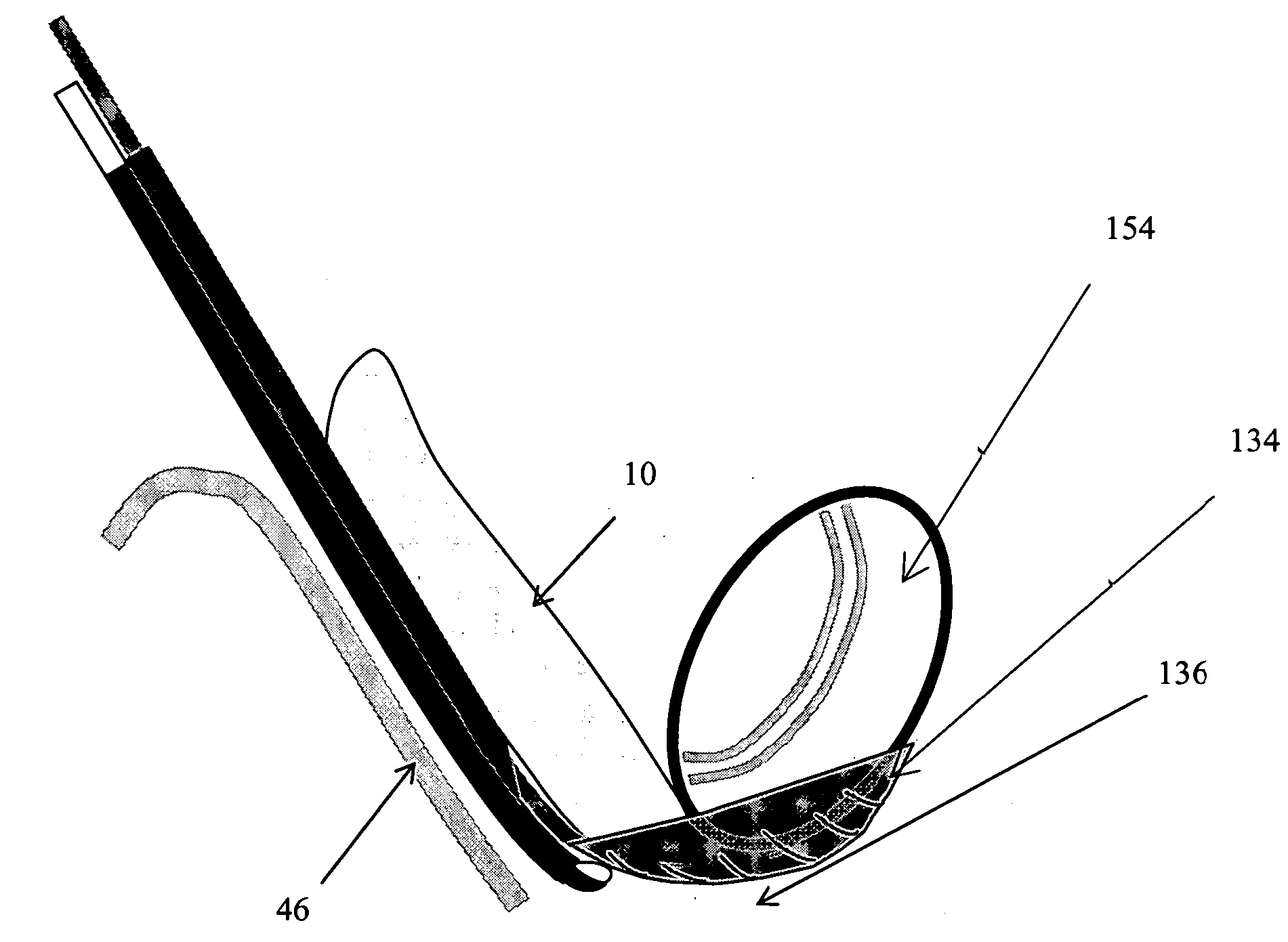
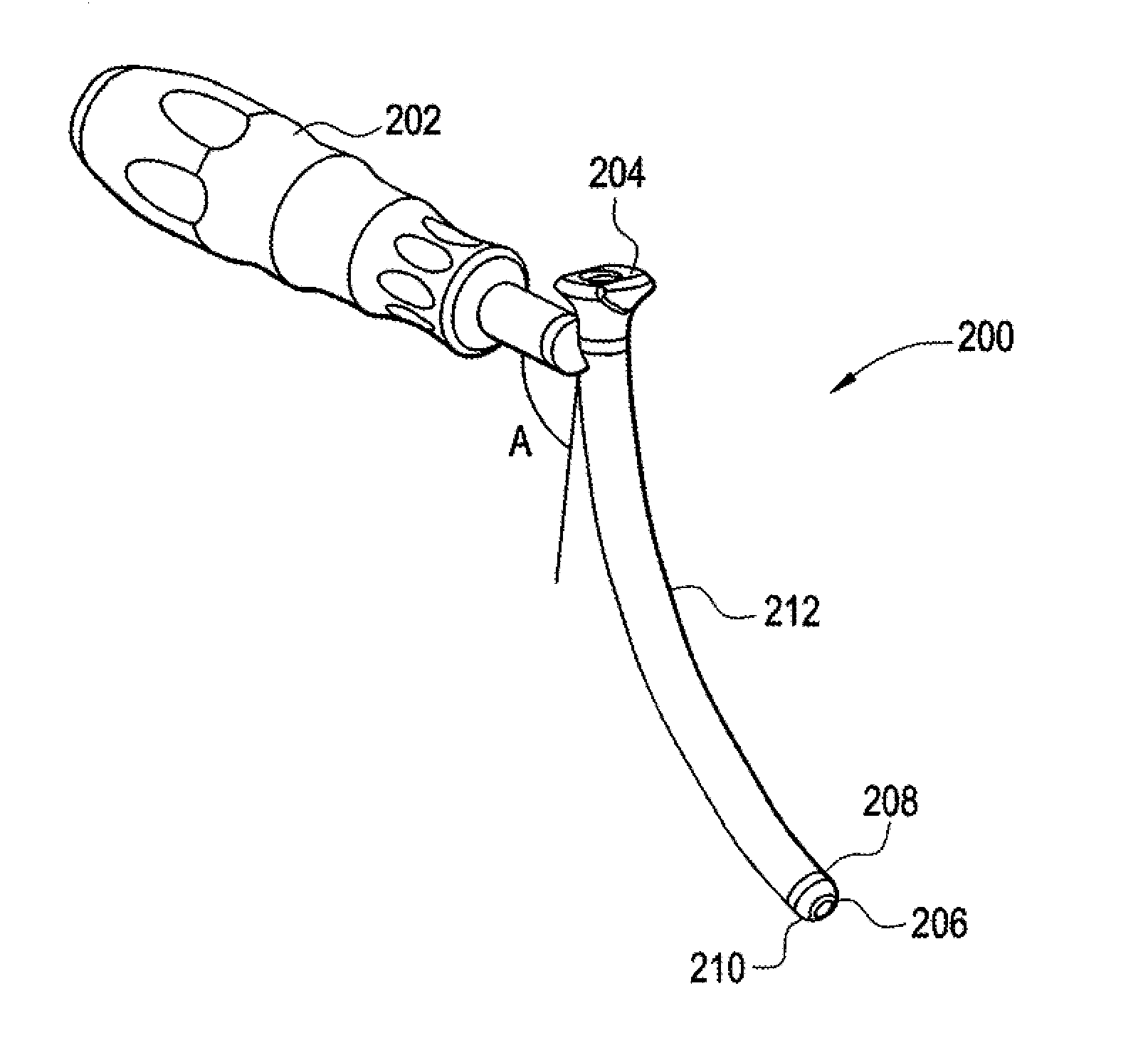
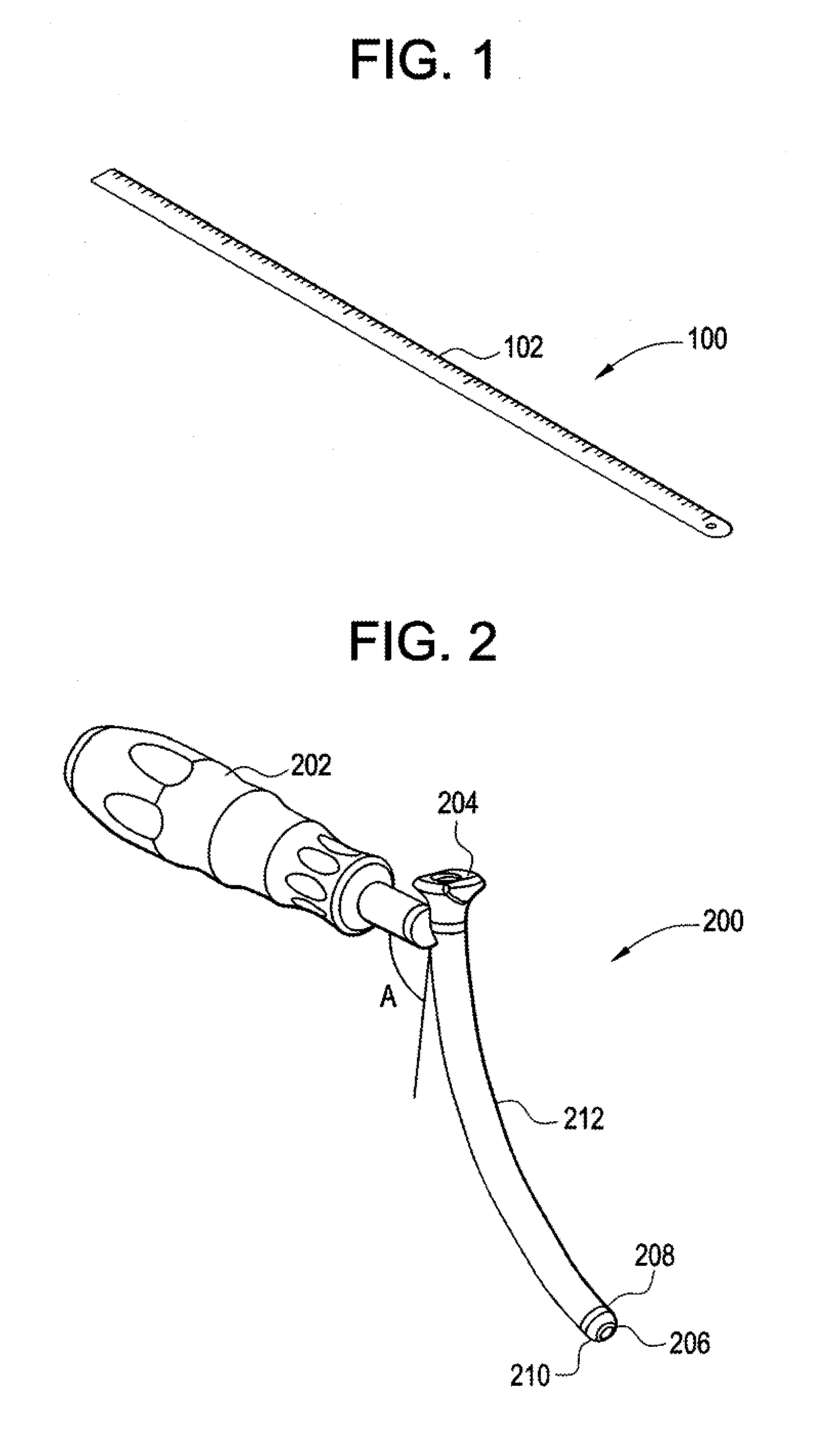
Curviliner spinal access method and device
InactiveUS20080221586A1Avoid complicationsOperating roomEar treatmentSurgical needlesProximateAccess method
A curvilinear spinal access device for performing a procedure on a spine of a patient is disclosed. The device includes a working portal configured to be advanced toward a surgical site located at the spine of the patient. The working portal includes a distal end and a proximate end, a working portal housing having an open interior channel disposed between the distal end and the proximate end, an exterior channel disposed on an outside surface of the working portal housing and between the distal end and the proximate end. The distal end is configured to be disposed at the surgical site and the proximate end is disposed away from the surgical site. The housing has a curved shape defined between the proximate end and the distal end, wherein the proximate end is disposed with respect to the distal end. The working channel is configured to allow advancement of at least one surgical tool and / or at least one implant toward the surgical site.
Owner:ALPHATEC SPINE INC
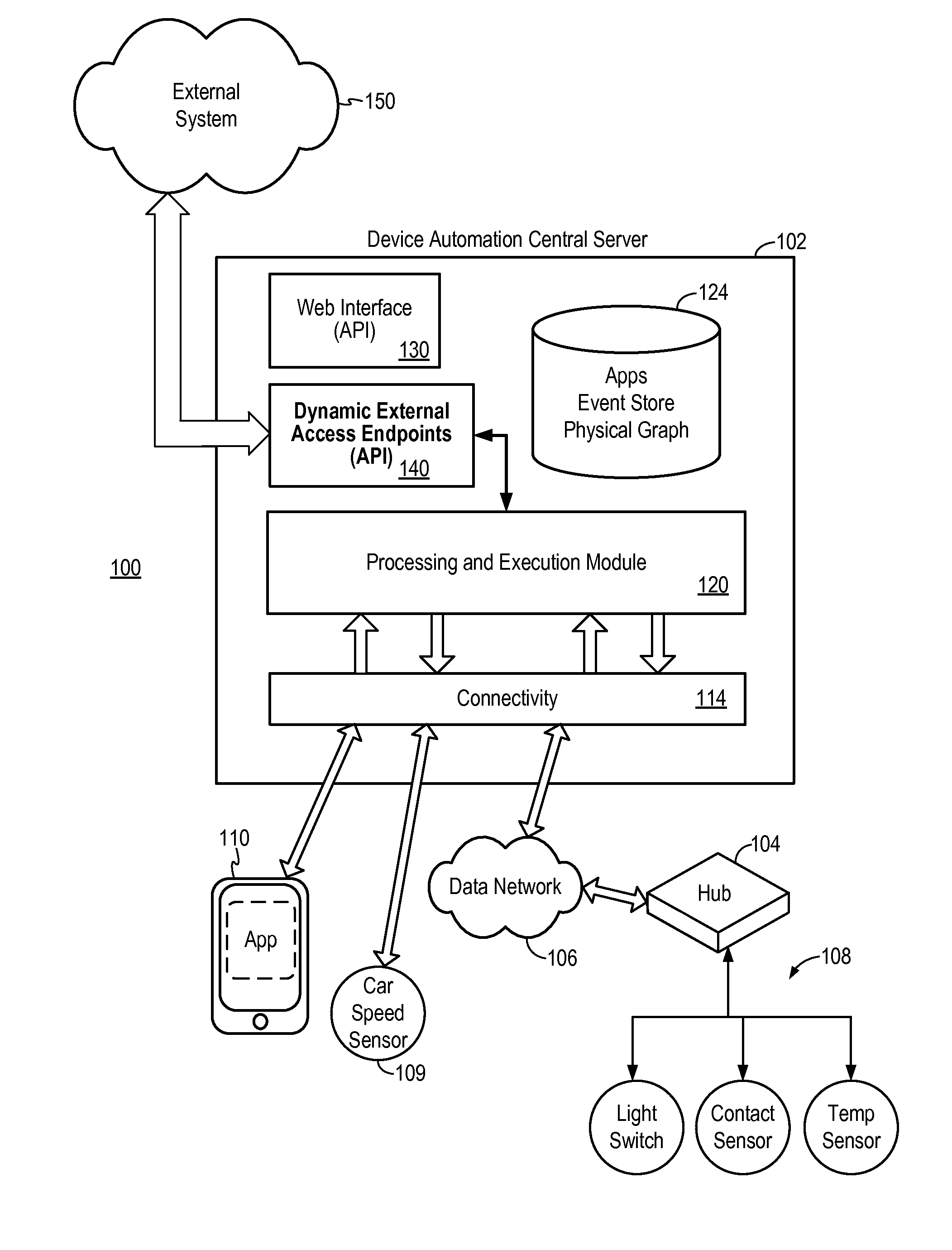
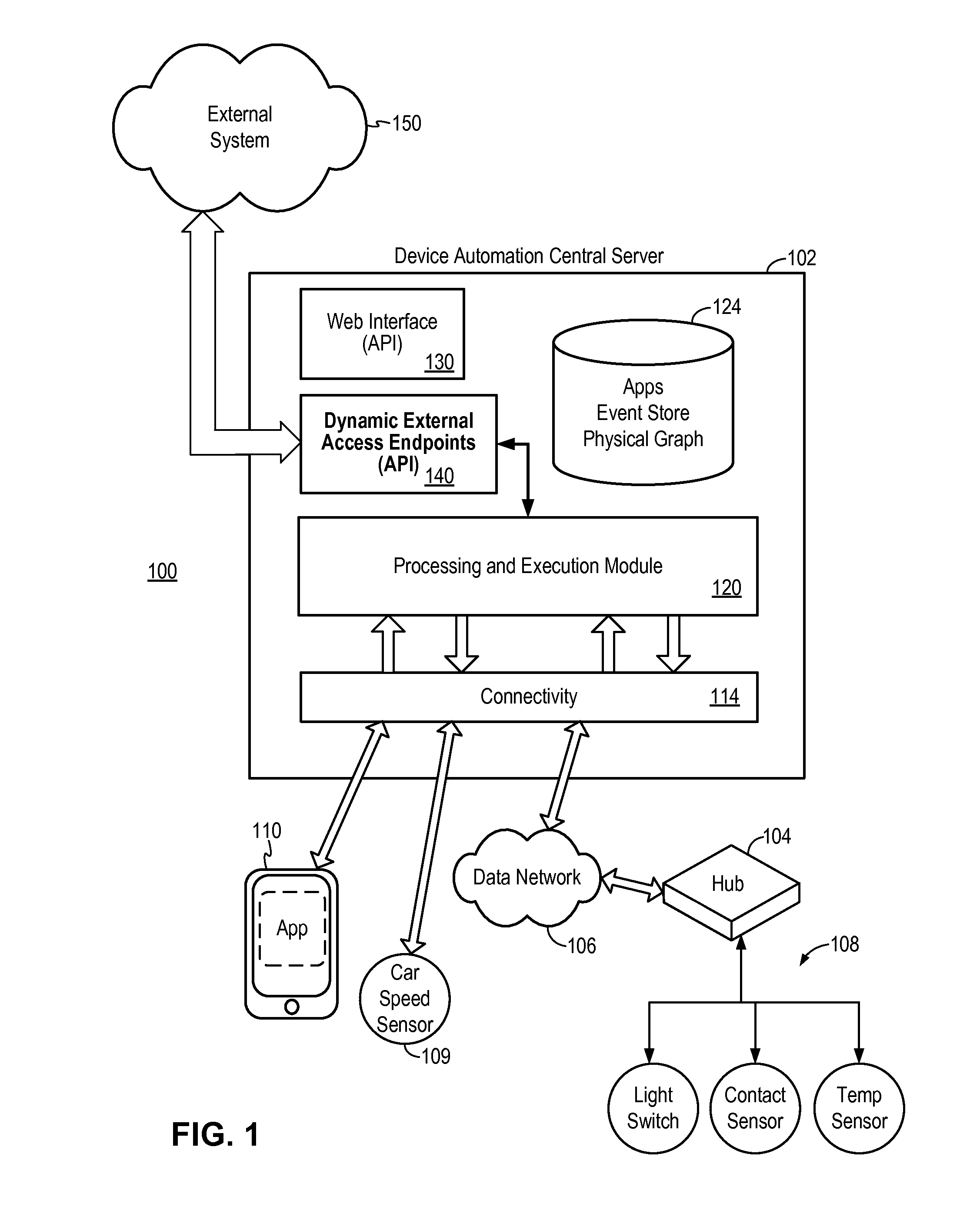
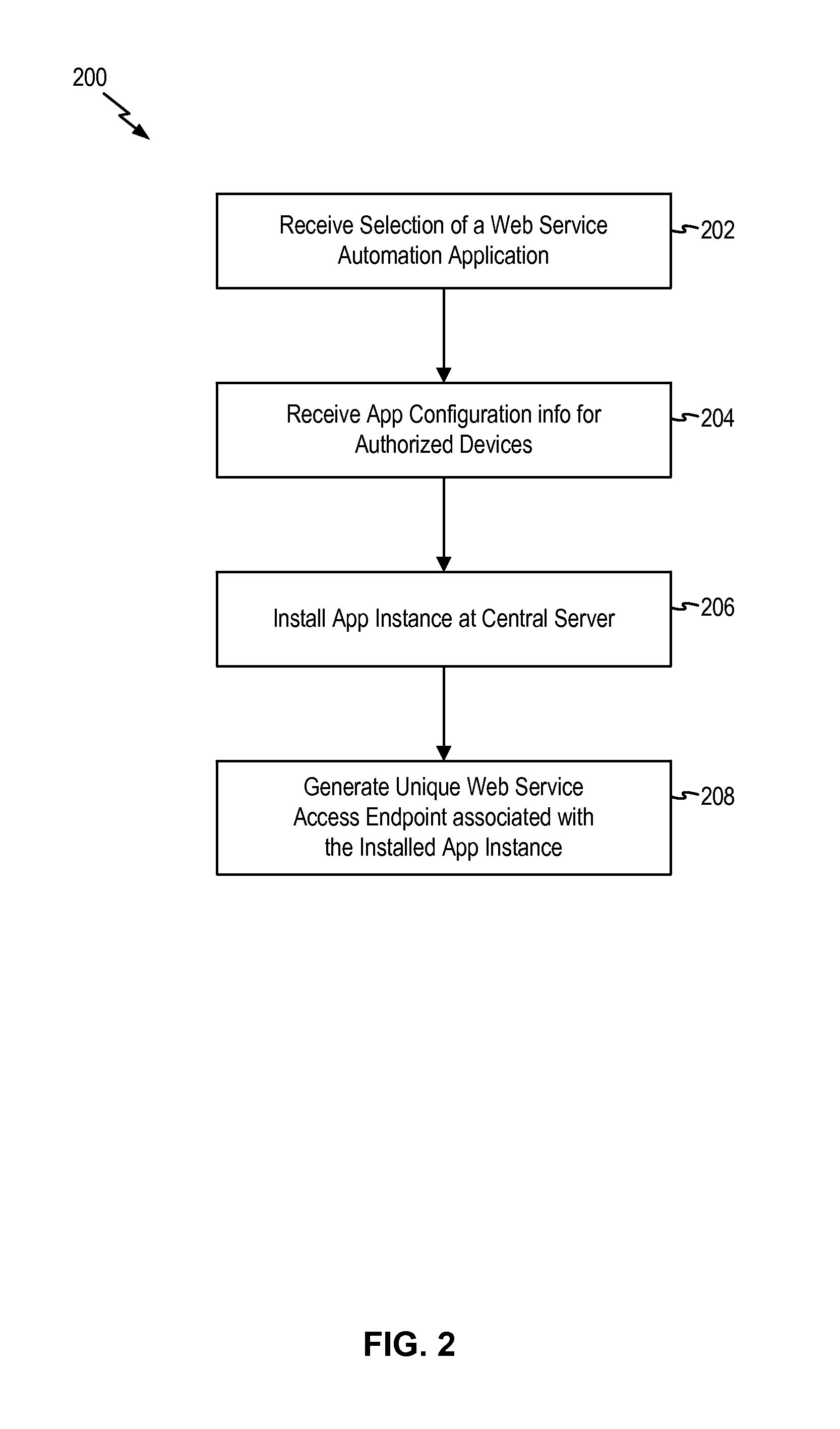
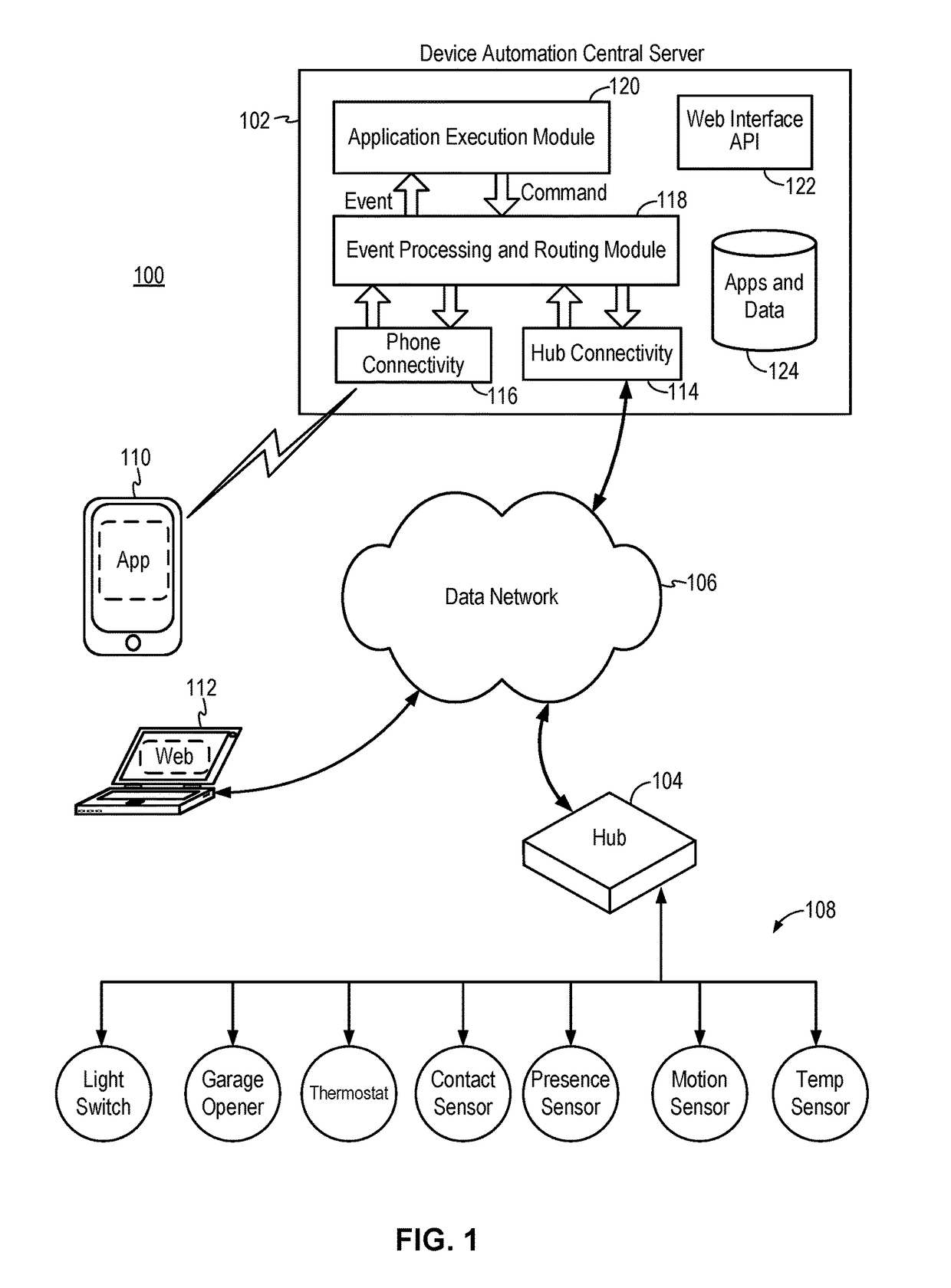
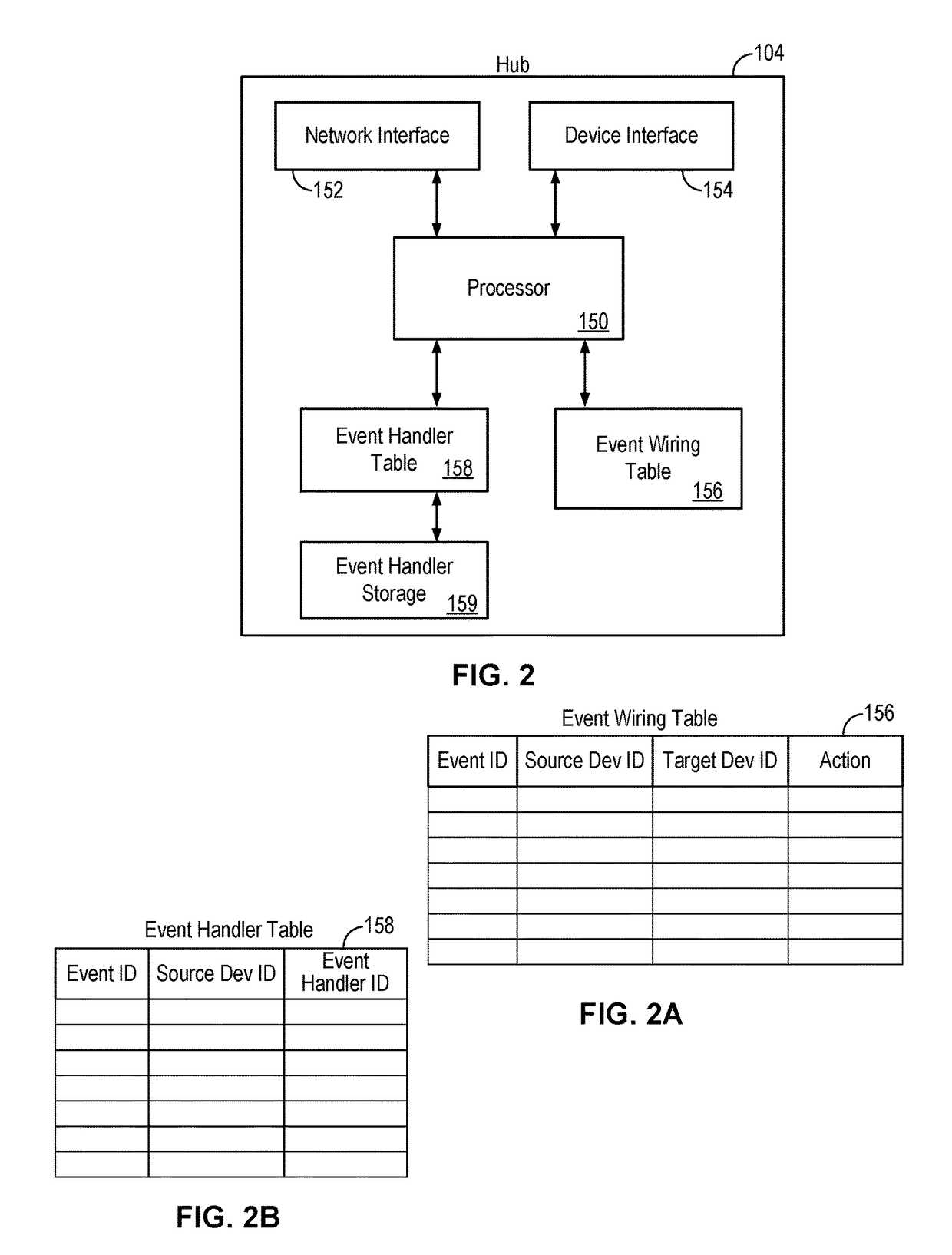
Secure external access to device automation system
A secure external access method provides an external system with access to a device automation system implementing automatic control of one or more devices in an automation environment. The external access method enables external system access to devices only when the devices have been authorized for external access and the external system has the proper authentication credential. External access endpoints are dynamically defined by the web service automation applications and are unique to each installed instance of the web service automation application.
Owner:SAMSUNG ELECTRONICS CO LTD
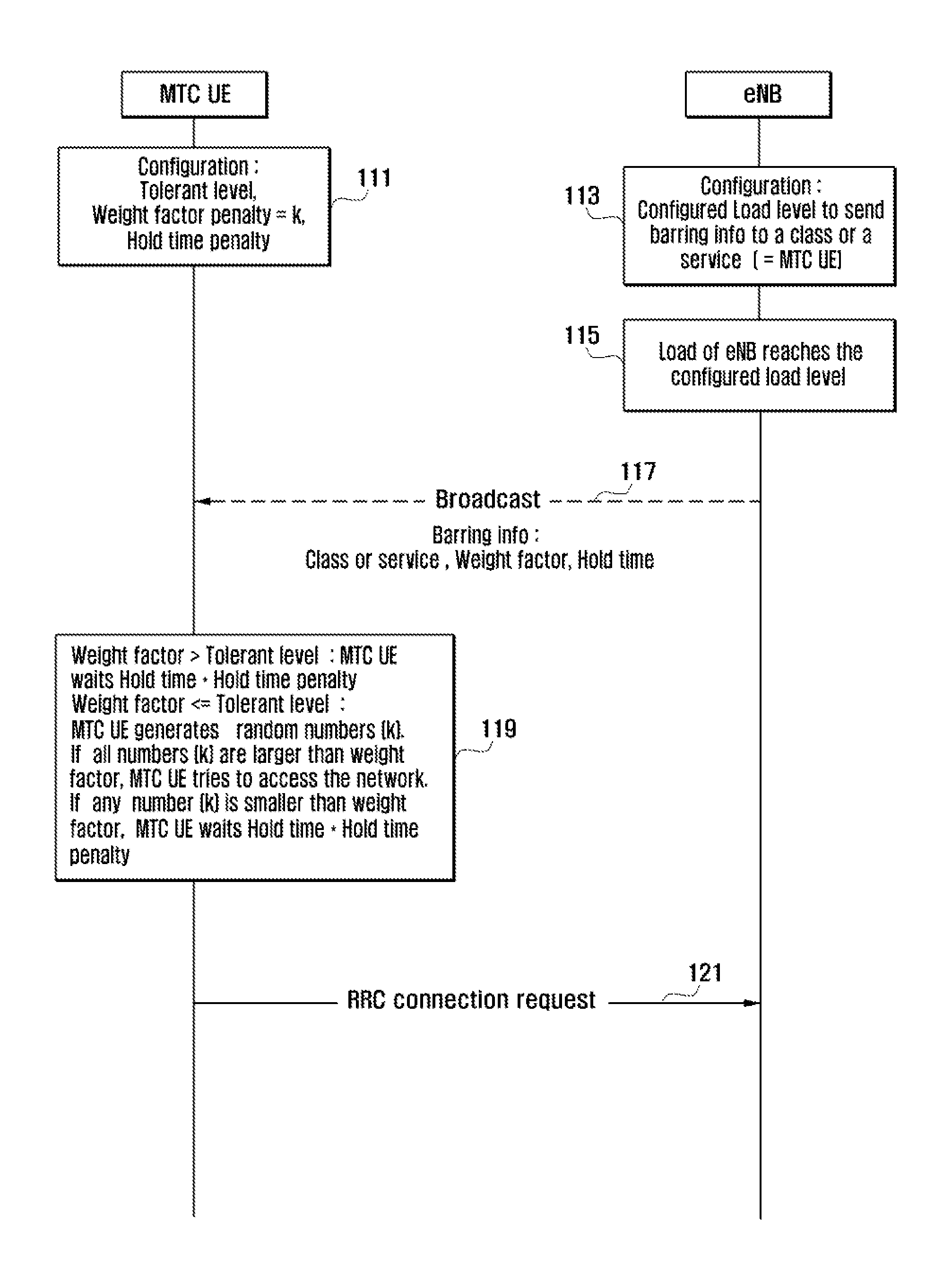
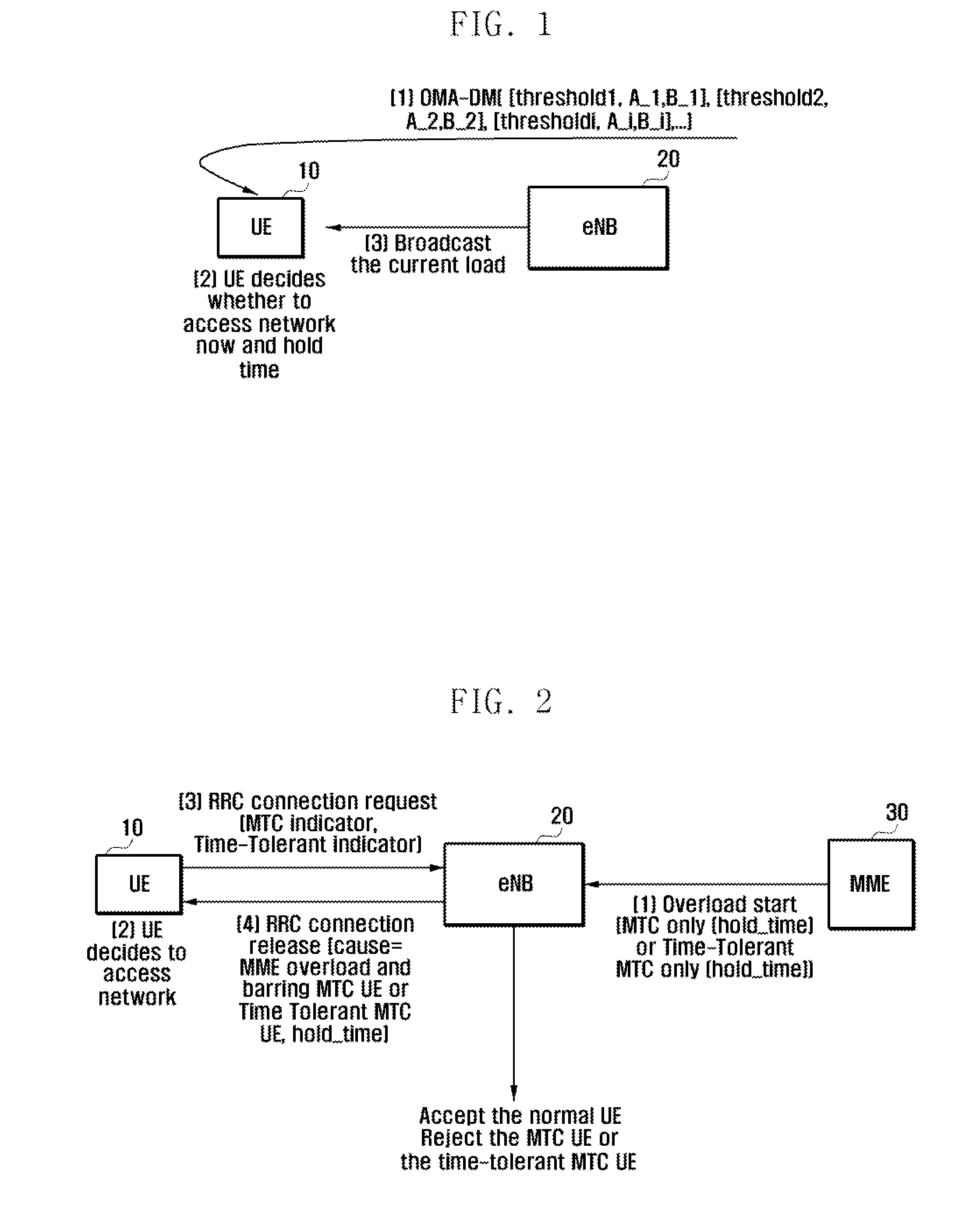
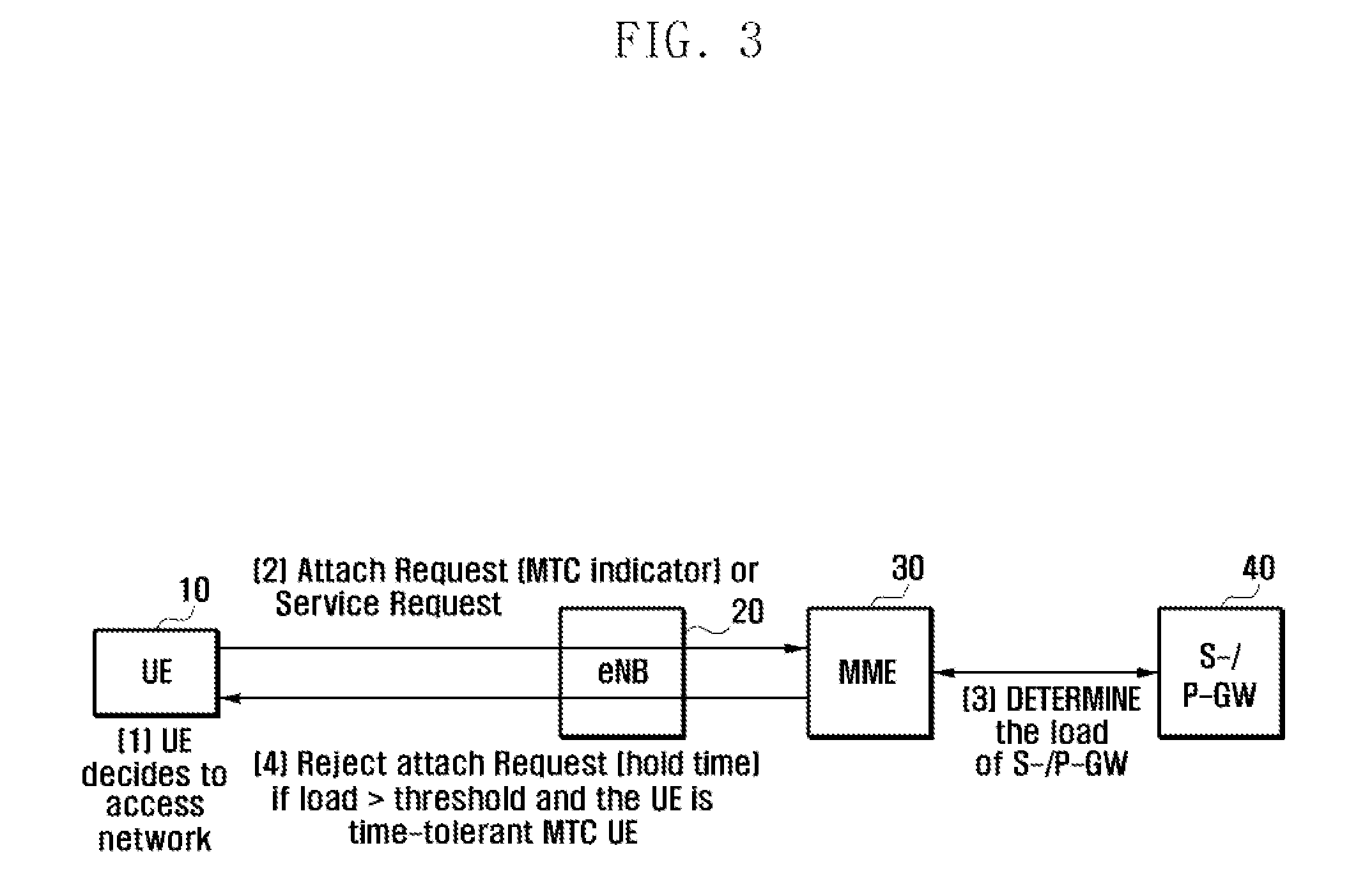
Method and apparatus for controlling network access of ue in wireless communication system
ActiveUS20110199898A1Controlling access barring efficientlyHigh network loadError preventionFrequency-division multiplex detailsAccess methodCommunications system
A method and an apparatus for controlling network access of a User Equipment (UE) based on the network's load and time tolerance (delay tolerance) are provided. A network access method for a terminal in a wireless communication system includes sending an access request message containing a time-tolerant indicator at a predefined time, determining, when a reject message is received, a cause value and a hold time contained in the reject message, and re-sending the access request message after the hold time elapses.
Owner:SAMSUNG ELECTRONICS CO LTD
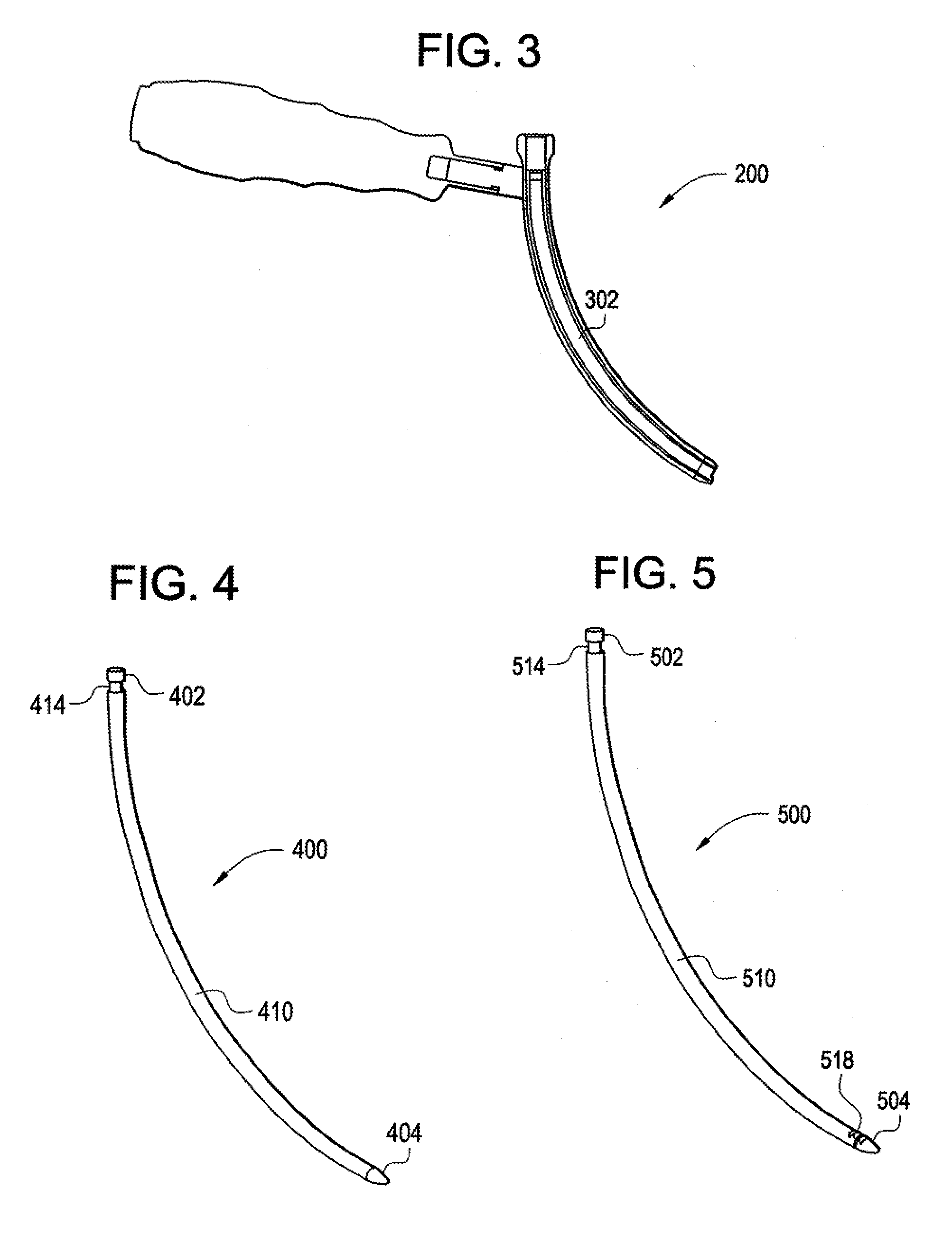
Curvilinear spinal access method and device
A curvilinear spinal access device having an expandable working portal. The device includes a slide having a channel with an open top and a movable top sized to cover the open top of the channel forming an expandable working portal with a proximal end and a distal end. The movable top can be moved between a closed position and an open position, wherein in the closed position the movable top blocks direct visualization between the proximal end and the distal end of the expandable working portal and in the open position movement of the movable top results in direct visualization from the proximal end to the distal end of the expandable working portal.
Owner:ALPHATEC SPINE INC
Sitemap Access Method, Product, And Apparatus
InactiveUS20080005127A1Easy to understandSaving distribution costDigital computer detailsTransmissionAccess methodUser interface
When a network request such as a resource location request, search engine request, and WHOIS request to process input having a resource identifier is received a user interface can then be provided to perform a request to access and display at least one sitemap corresponding to said resource identifier while performing the network request.
Owner:MEC MANAGEMENT LLC
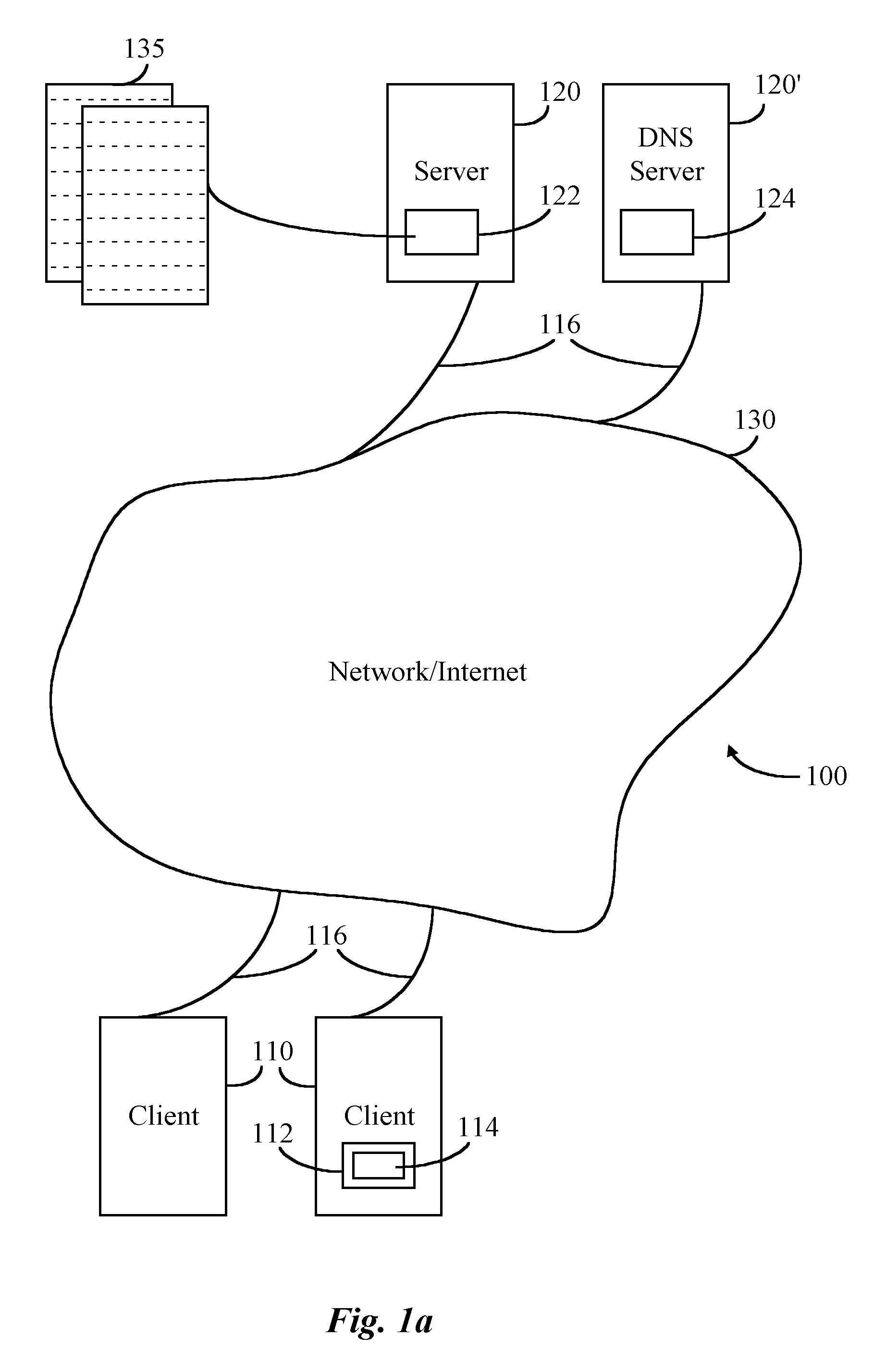
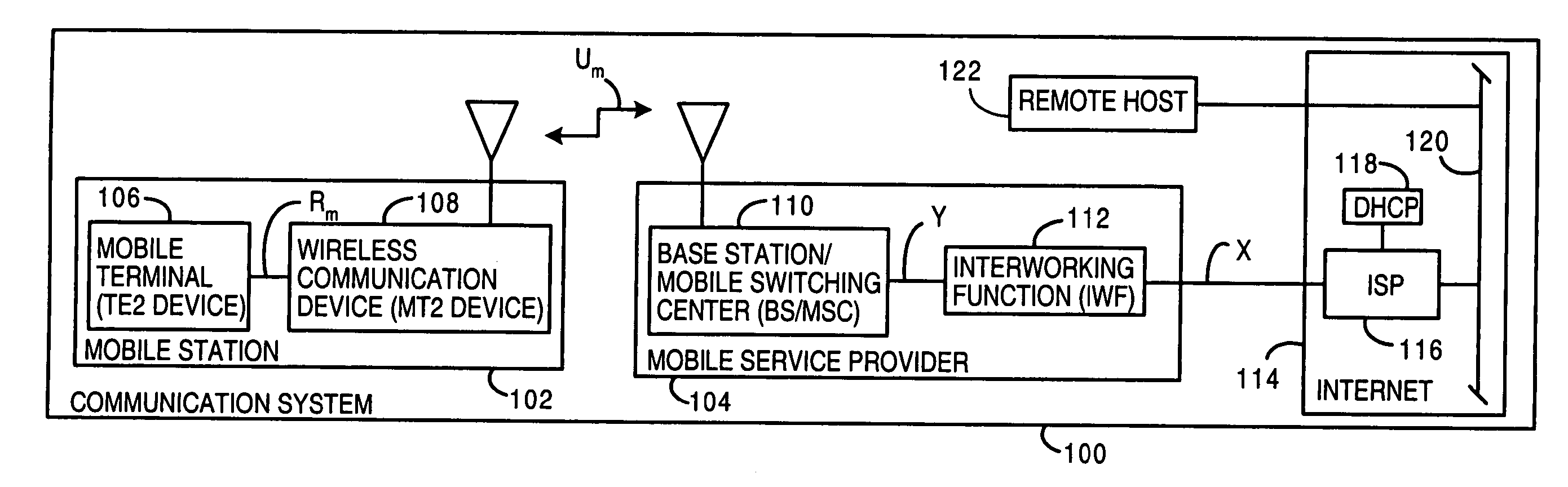
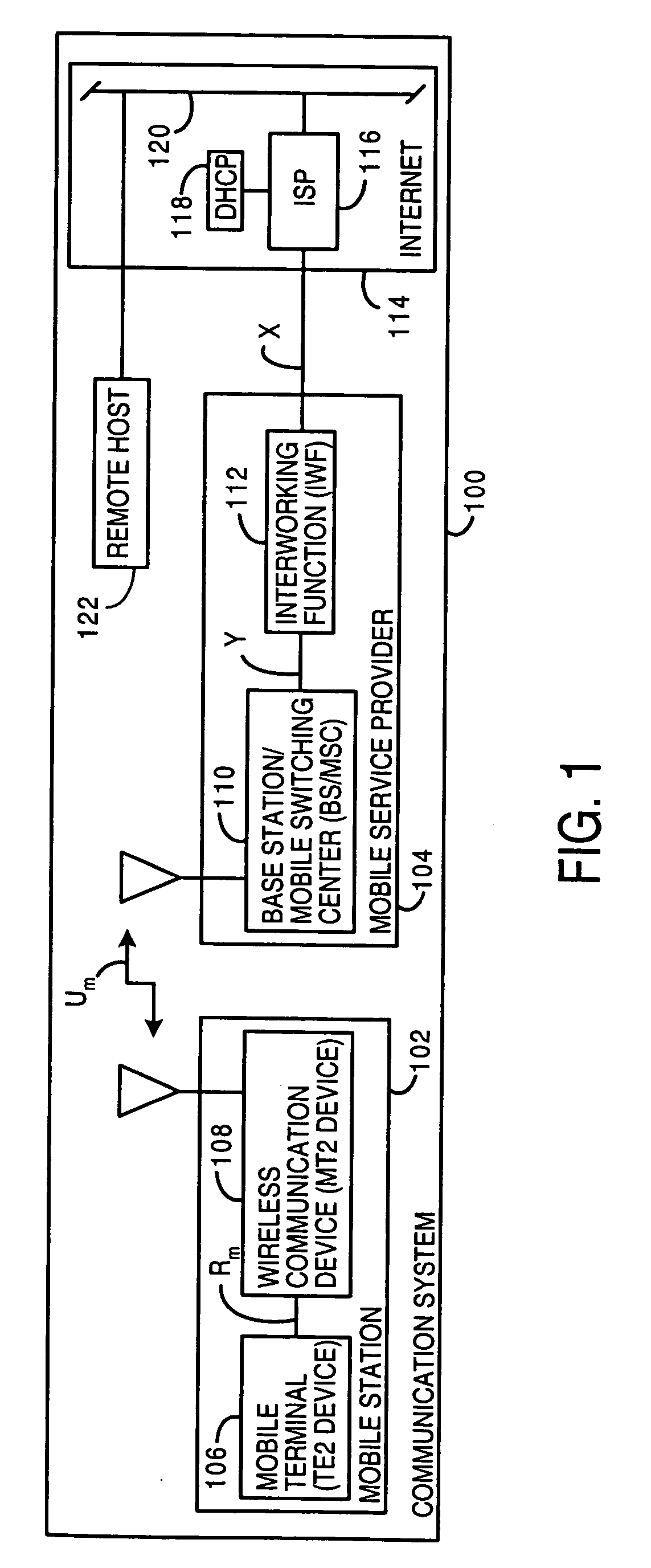
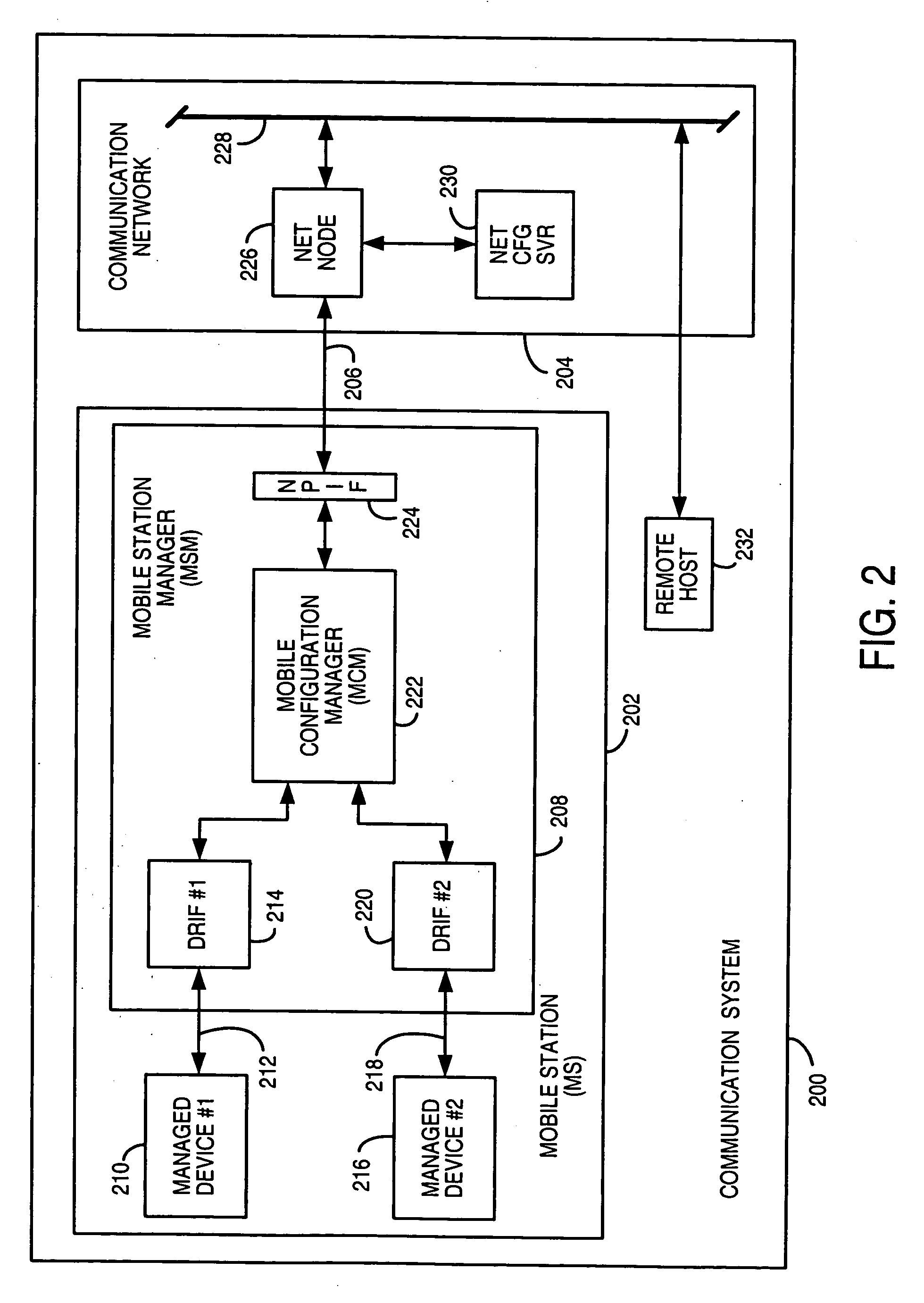
Dynamically provisioned mobile station and method therefor
Multimode mobile station includes mobile configuration manager, device interface, and network interface to dynamically provision network configuration for mobile TE2-type mobile terminals and accomodates multiple protocols over multiple carrier access methods over Um interface and multiple access methods over Rm interface. A method for communicating between endpoints, where a mobile node obtains a unique configuration from a network for a managed device. The mobile node dynamically provisions the configuration for the connected managed device, in response to device request or network notice. The node adapts messages over Rm interface for TE2 signals and over Um interface for a wireless protocol.
Owner:QUALCOMM INC
Secured device access in a device automation system
ActiveUS20170078298A1Service provisioningProgram loading/initiatingAccess methodSoftware engineering
Owner:SAMSUNG ELECTRONICS CO LTD
Secure access method and system
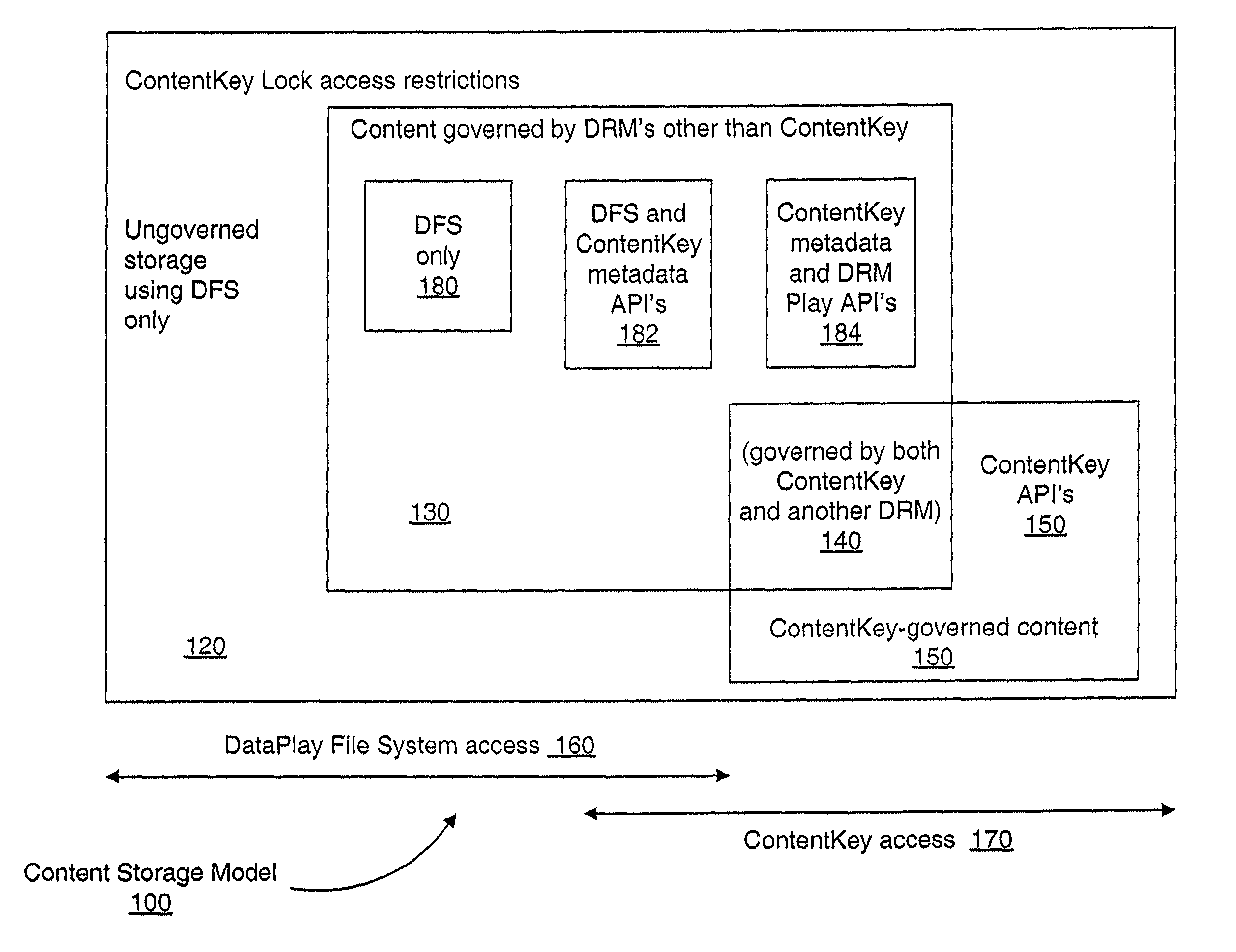
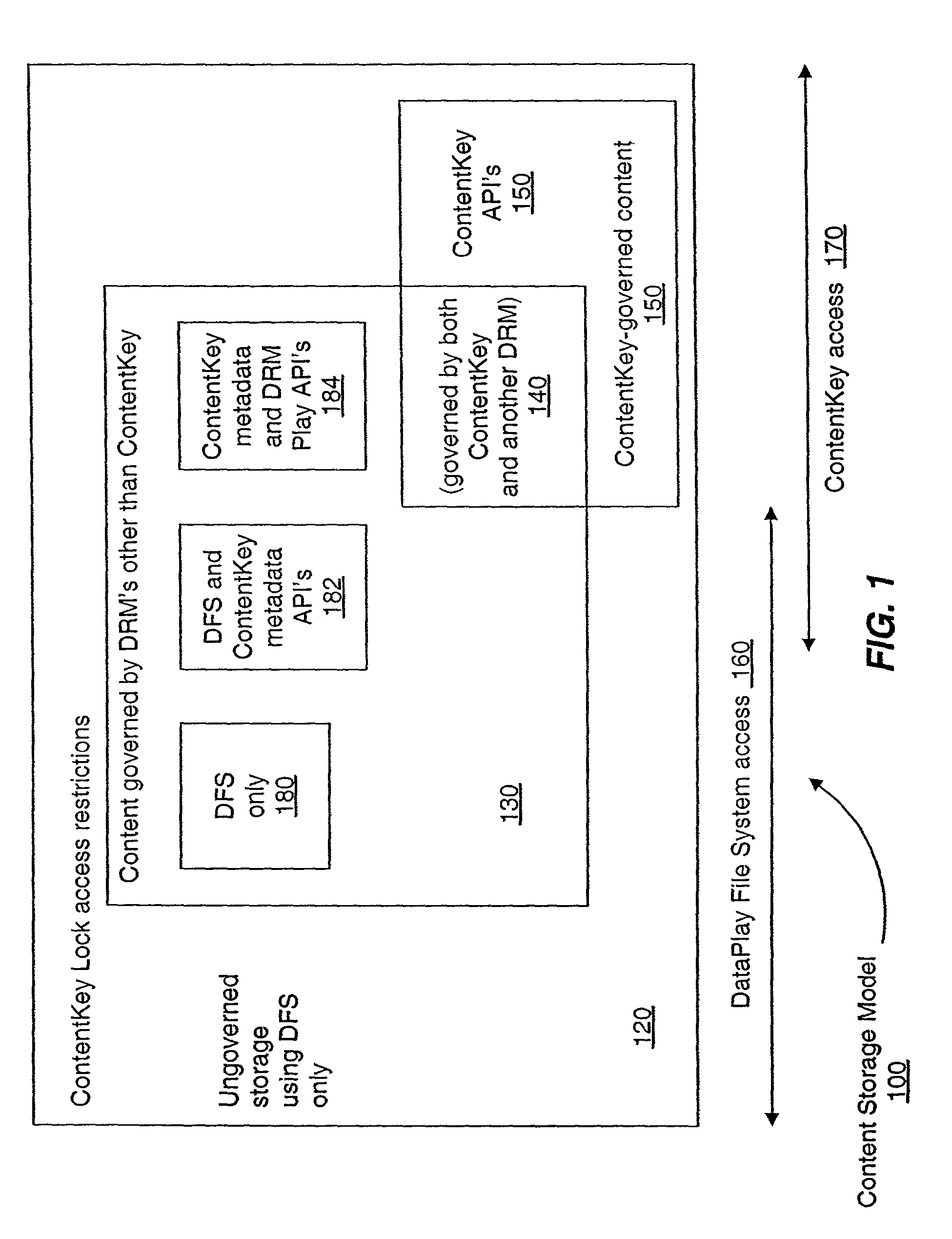
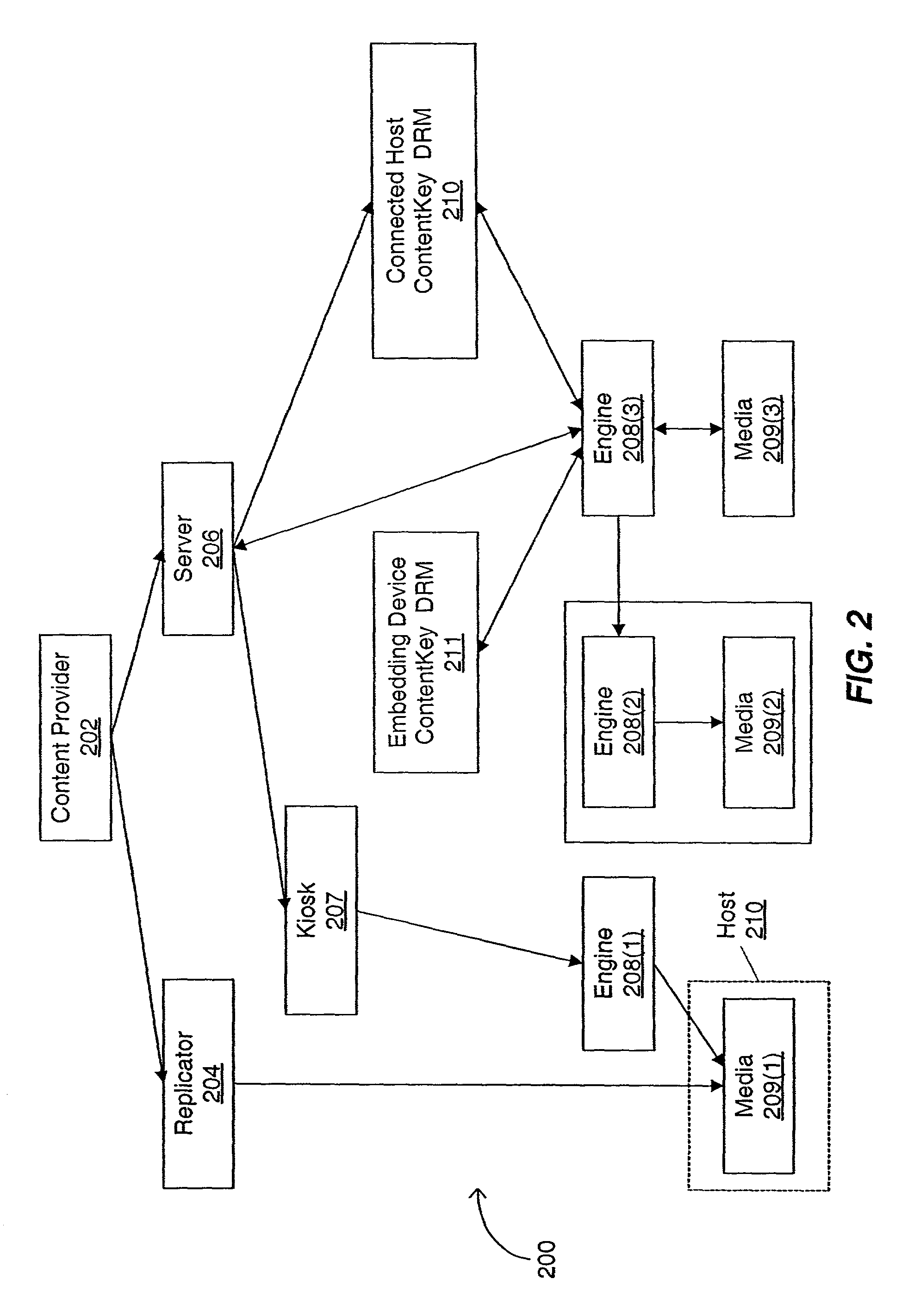
A secure electronic content system and method is provided. The system includes a controller including an interface component, a host system coupled to the controller, the host system configured to present content under predetermined conditions, the host system operable with a navigation protocol, the host system further including a system manager operable with an associations component configured to be at least partially run by the host system, a translator configured to provide meanings and generate commands within the host system at least a first digital rights management (DRM) component configured to provide encoding and access rules for the content; and a file system component including a file system application programming interface (API) configured to provide a logical interface between a plurality of components.
Owner:DATAPLAY
Personal assistant application access method and system
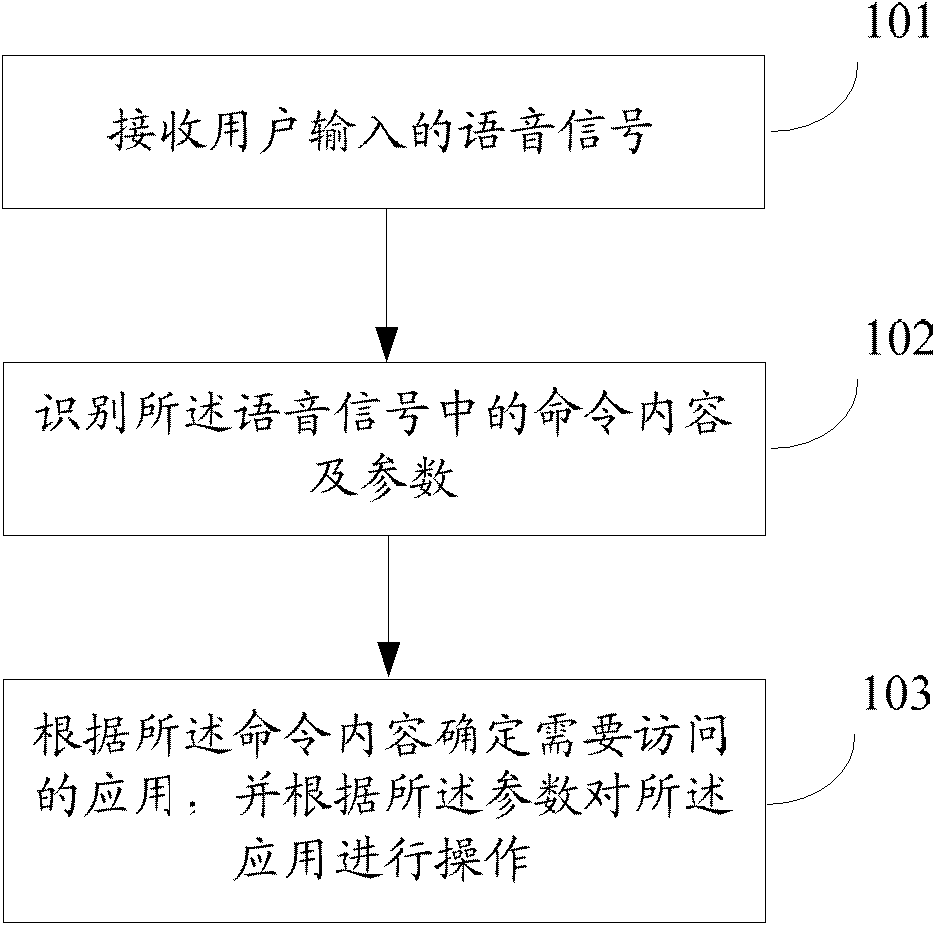
InactiveCN102510426ARealize the function of personal virtual assistantEfficient shortcut command orientationSpeech analysisSubstation equipmentAccess methodUser input
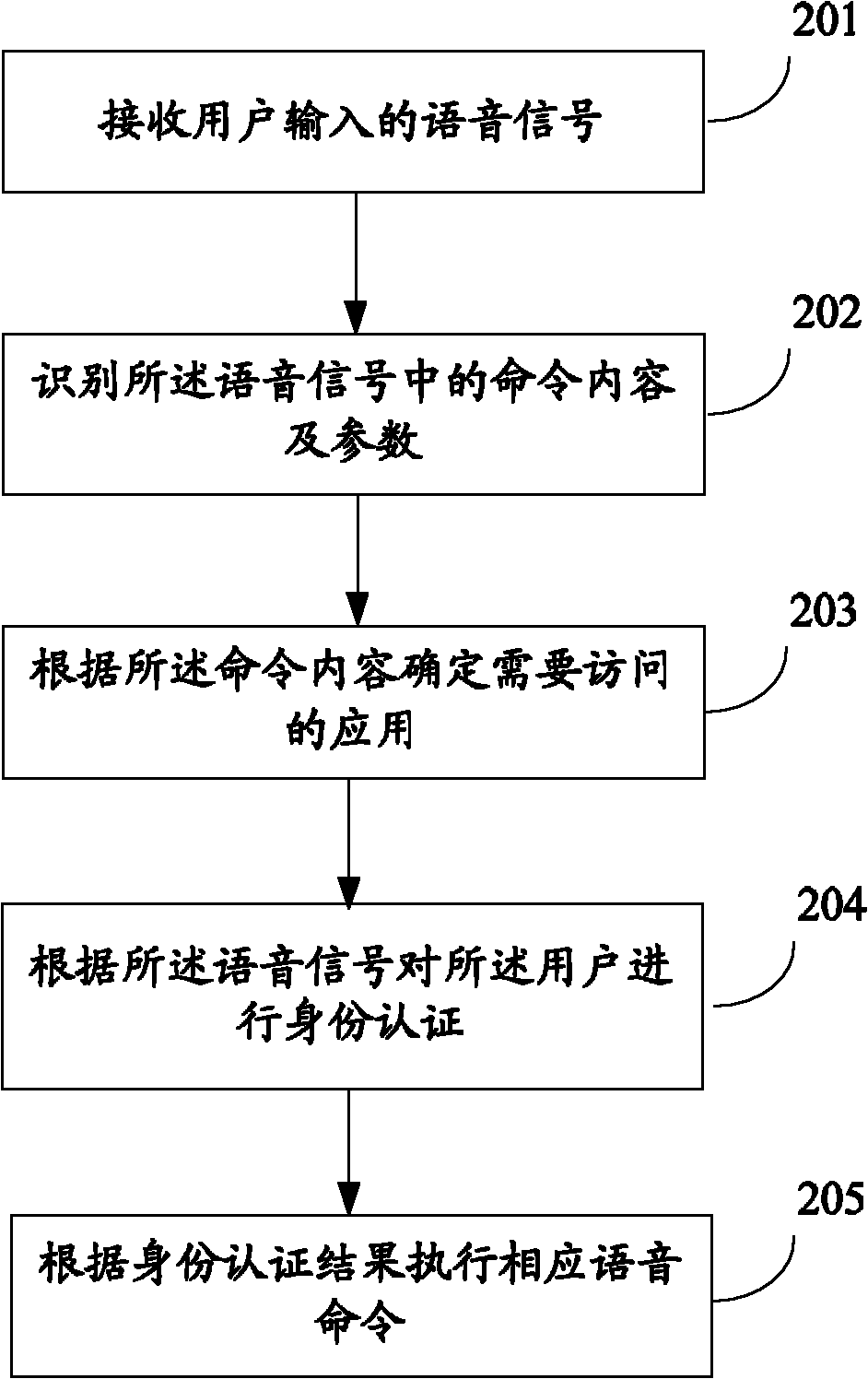
The invention relates to the technical field of application access and discloses a personal assistant application access method and system. The method comprises the following steps: receiving a voice signal input by a user; identifying command content and parameters in the voice signal; according to the command content, determining application which needs to access; and according to the parameters, operating the application. By utilizing the personal assistant application access method and system disclosed by the invention, the human-computer interaction efficiency can be improved.
Owner:IFLYTEK CO LTD
Conditional access method and device
InactiveUS6070796AInput/output for user-computer interactionAcutation objectsComputer hardwareAccess method
PCT No. PCT / FR96 / 01269 Sec. 371 Date Feb. 20, 1998 Sec. 102(e) Date Feb. 20, 1998 PCT Filed Aug. 8, 1996 PCT Pub. No. WO97 / 07448 PCT Pub. Date Feb. 27, 1997A conditional access device for use in connection with a host electronic equipment. The device includes a pointer peripheral containing one or more integrated circuit card coupler units. In addition, it also includes a device for acquiring personal information about a user. The personal information is locally compared with information stored in the integrated circuit card without passing through the host equipment.
Owner:SIRBU CORNEL
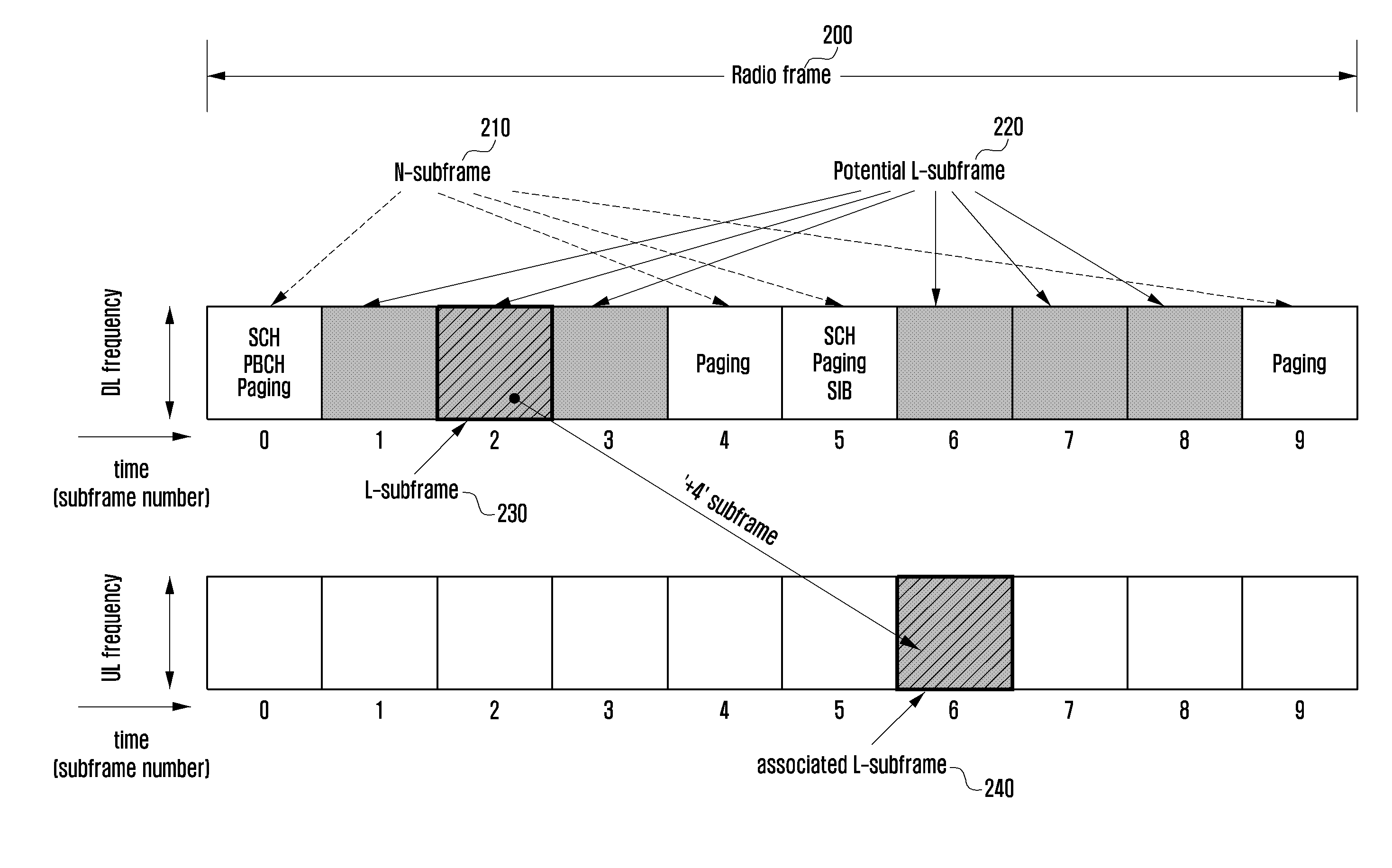
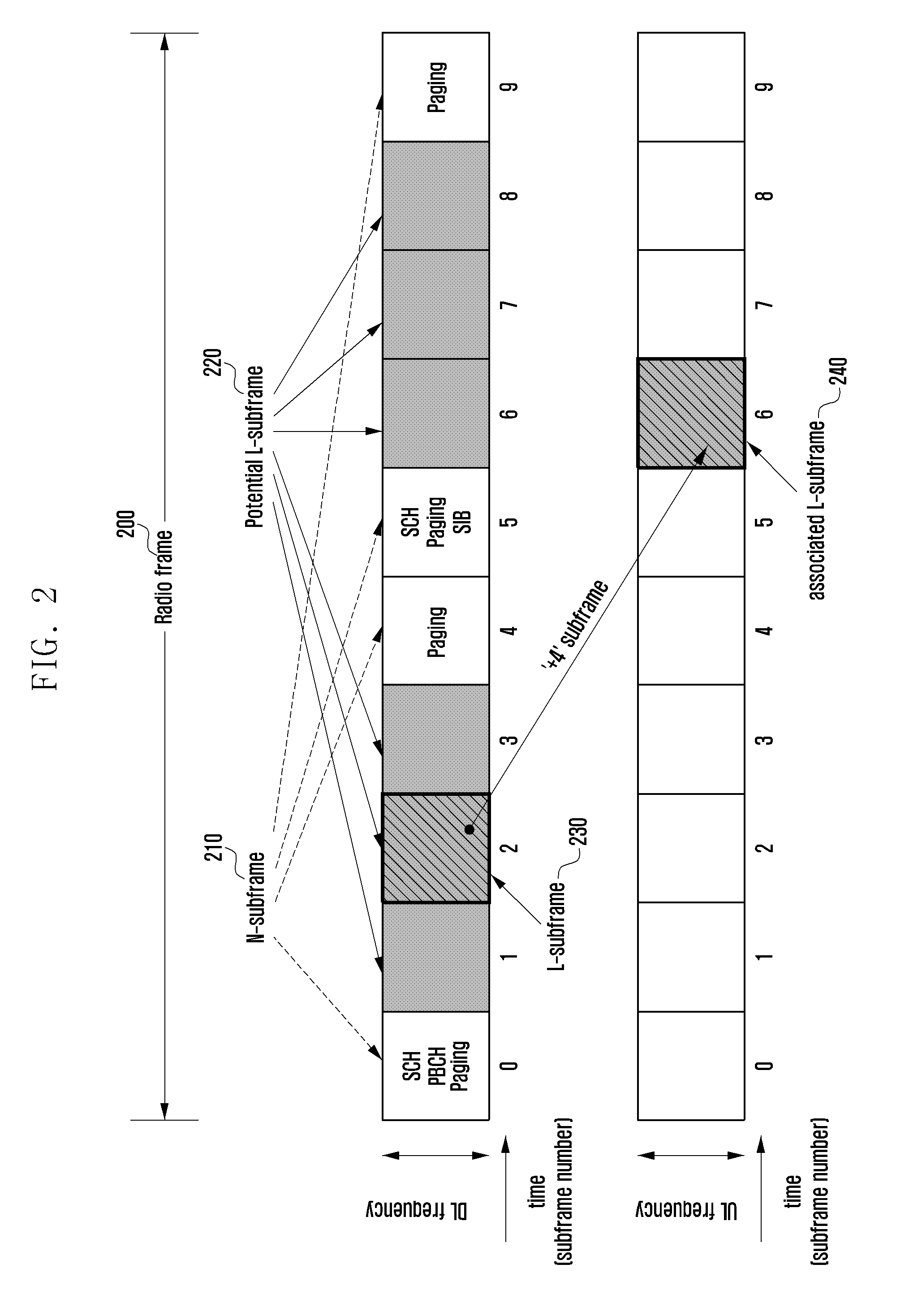
System access method and apparatus of a narrowband terminal in a wireless communication system supporting wideband and narrowband terminals
ActiveUS20130077582A1Synchronisation arrangementWireless commuication servicesCellular radioAccess method
A system access method of a narrowband terminal is provided for supporting both wideband and narrowband terminals in a cellular radio communication system. The method includes broadcasting a Shared CHannel (SCH) for a terminal to acquire system synchronization; transmitting a Low-end Master Information Block (L-MIB) including control information on an L-subframe configuration for supporting a second type terminal and a sub-band configuration of the L-subframe; transmitting a Low-end System Information Block (L-SIB) including information on downlink reception and uplink transmission of the second type terminal; and performing a random access procedure, when an attach request is received from one of the first type terminals and the second type terminals.
Owner:SAMSUNG ELECTRONICS CO LTD
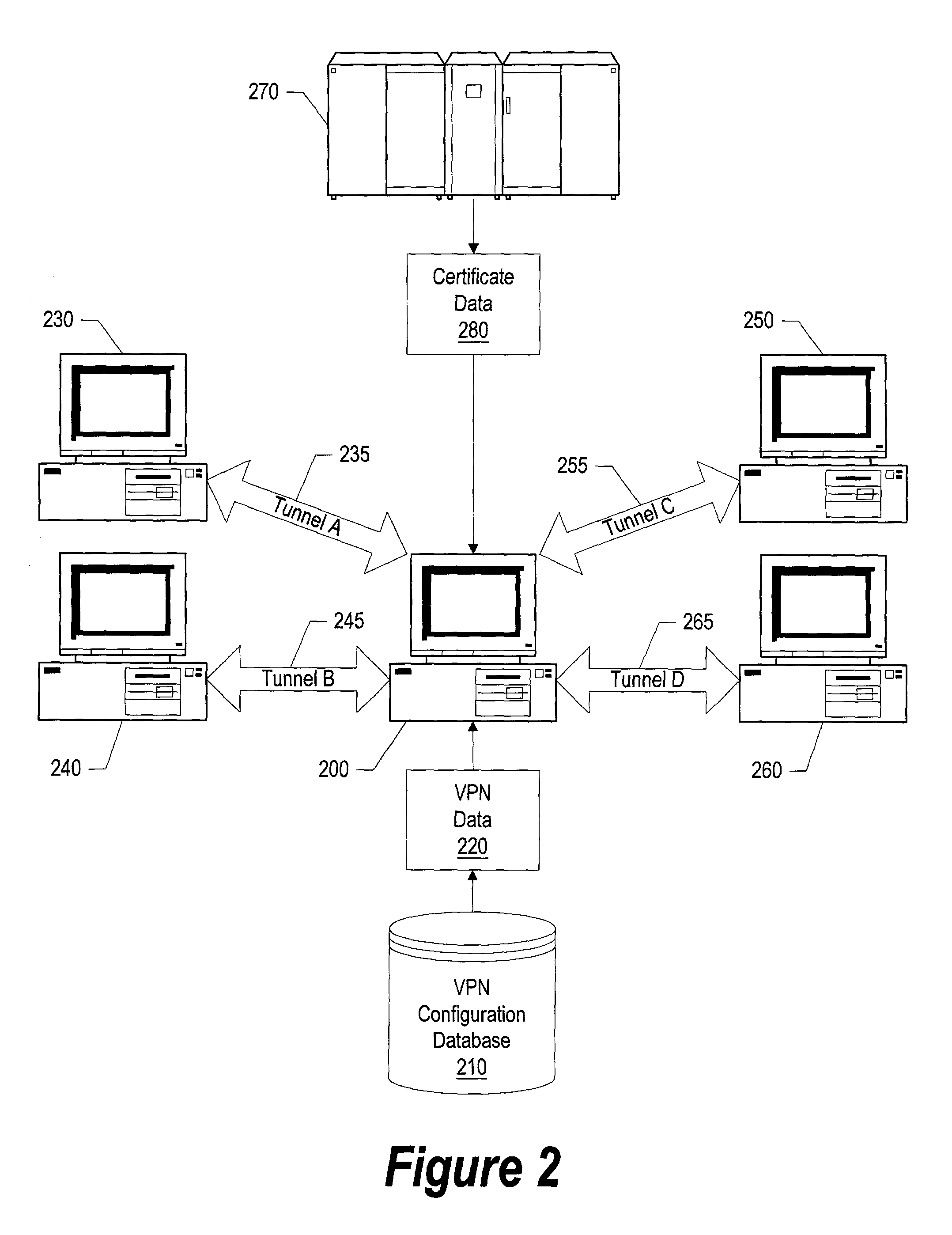
System and method for dynamically determining CRL locations and access methods
ActiveUS7003662B2User identity/authority verificationComputer security arrangementsAccess methodEngineering
A system and method for dynamically determining a CRL location and protocol. CRL location names and protocols are retrieved from a digital certificate data structure which includes a network servers that contain the CRL file. A determination is made as to whether any of the servers reside in the current domain, in which case the server is used because the data is more secure. If no locations are within the current domain, Internet servers outside the current domain are analyzed. Security parameters may be established that restrict which Internet servers can be used to retrieve the data. The security parameters may also include which access methods may be used to retrieve data since some access methods provide greater security than other access methods. A security parameter may also be based upon both the access method and the name, or address, of the Internet server.
Owner:TREND MICRO INC
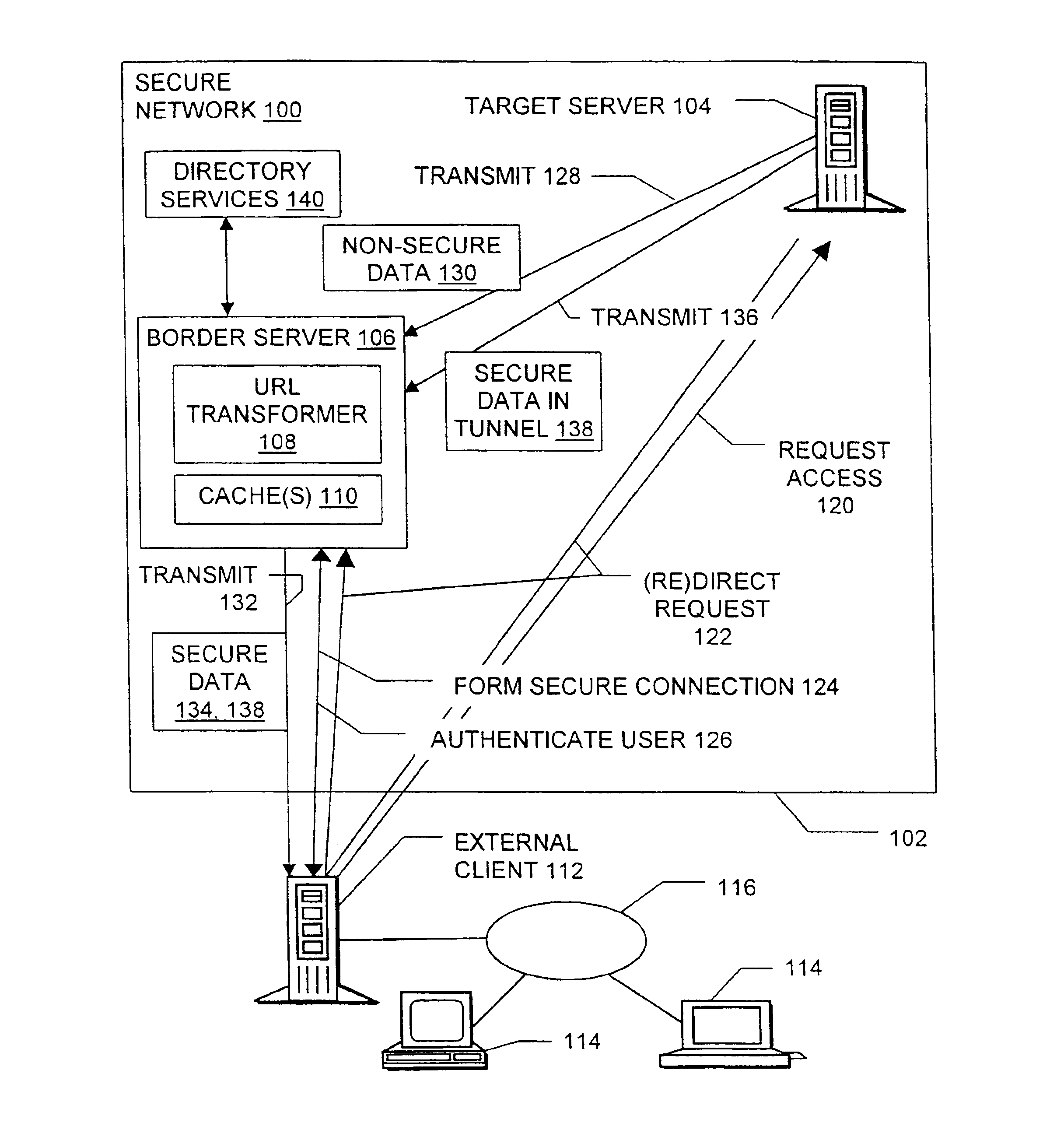
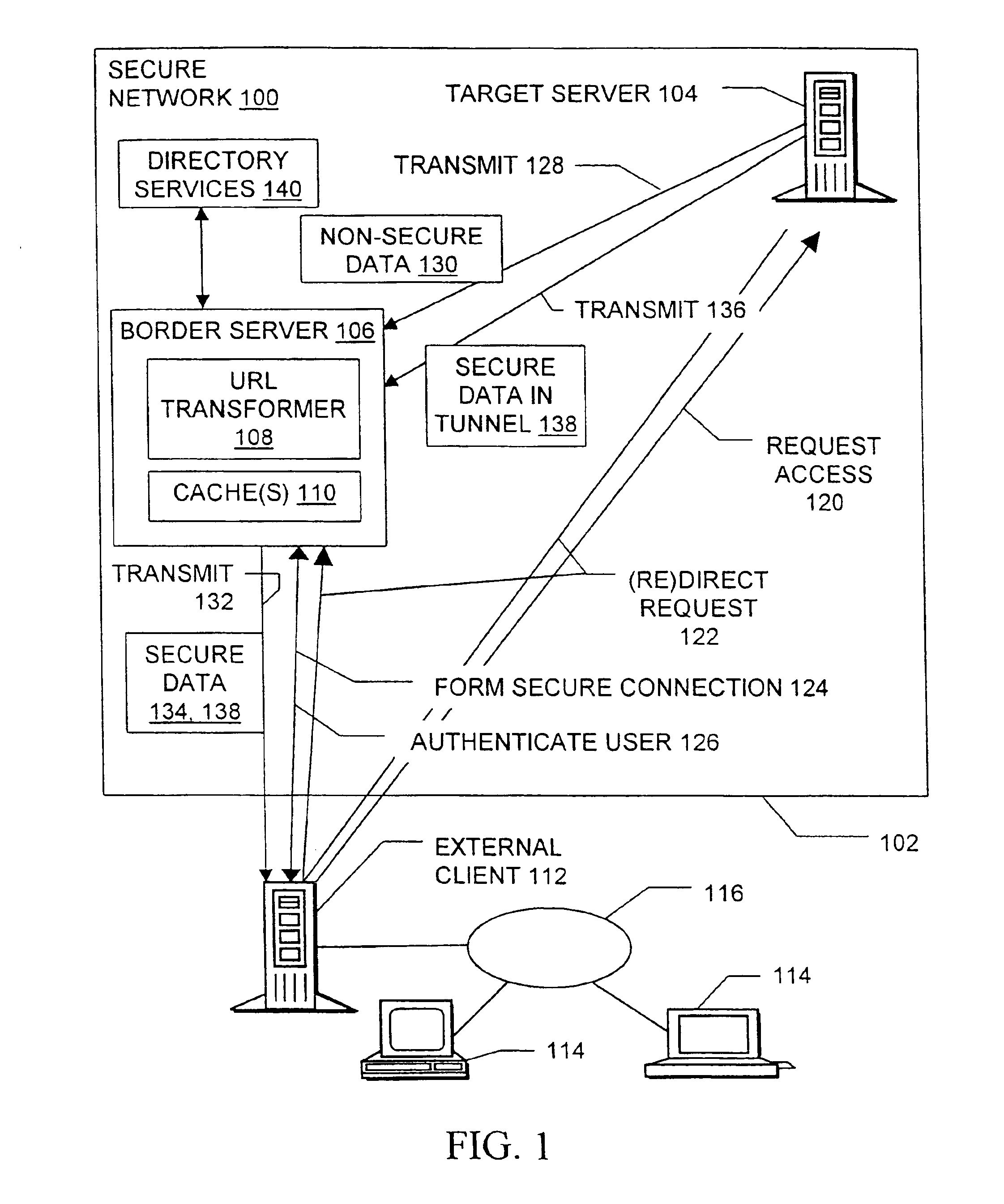
Secure intranet access
InactiveUS6950936B2Secure transmissionDigital data processing detailsUser identity/authority verificationAccess methodPrivate network
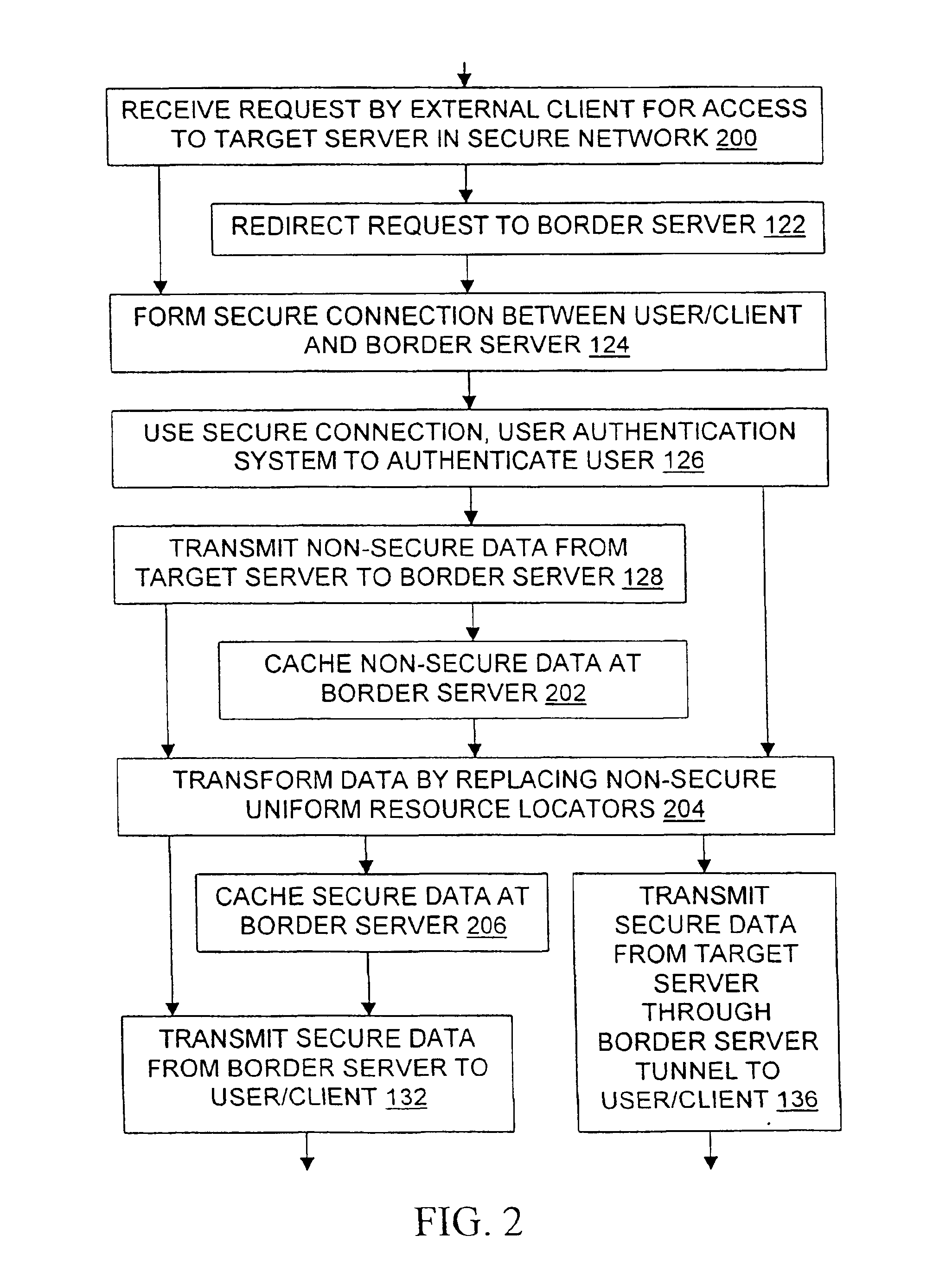
Methods, signals, devices, and systems are provided for secure access to a network from an external client. Requests for access to confidential data may be redirected from a target server to a border server, after which a secure sockets layer connection between the border server and the external client carries user authentication information. After the user is authenticated to the network, requests may be redirected back to the original target server. Web pages sent from the target server to the external client are scanned for non-secure URLs such as those containing “http: / / ” and modified to make them secure. The target server and the border server utilize various combinations of secure and non-secure caches. Although tunneling, may be used, the extensive configuration management burdens imposed by virtual private networks are not required.
Owner:RPX CORP
Pass-through write policies of files in distributed storage management
ActiveUS20070266056A1Data processing applicationsDigital data information retrievalAccess methodStorage management
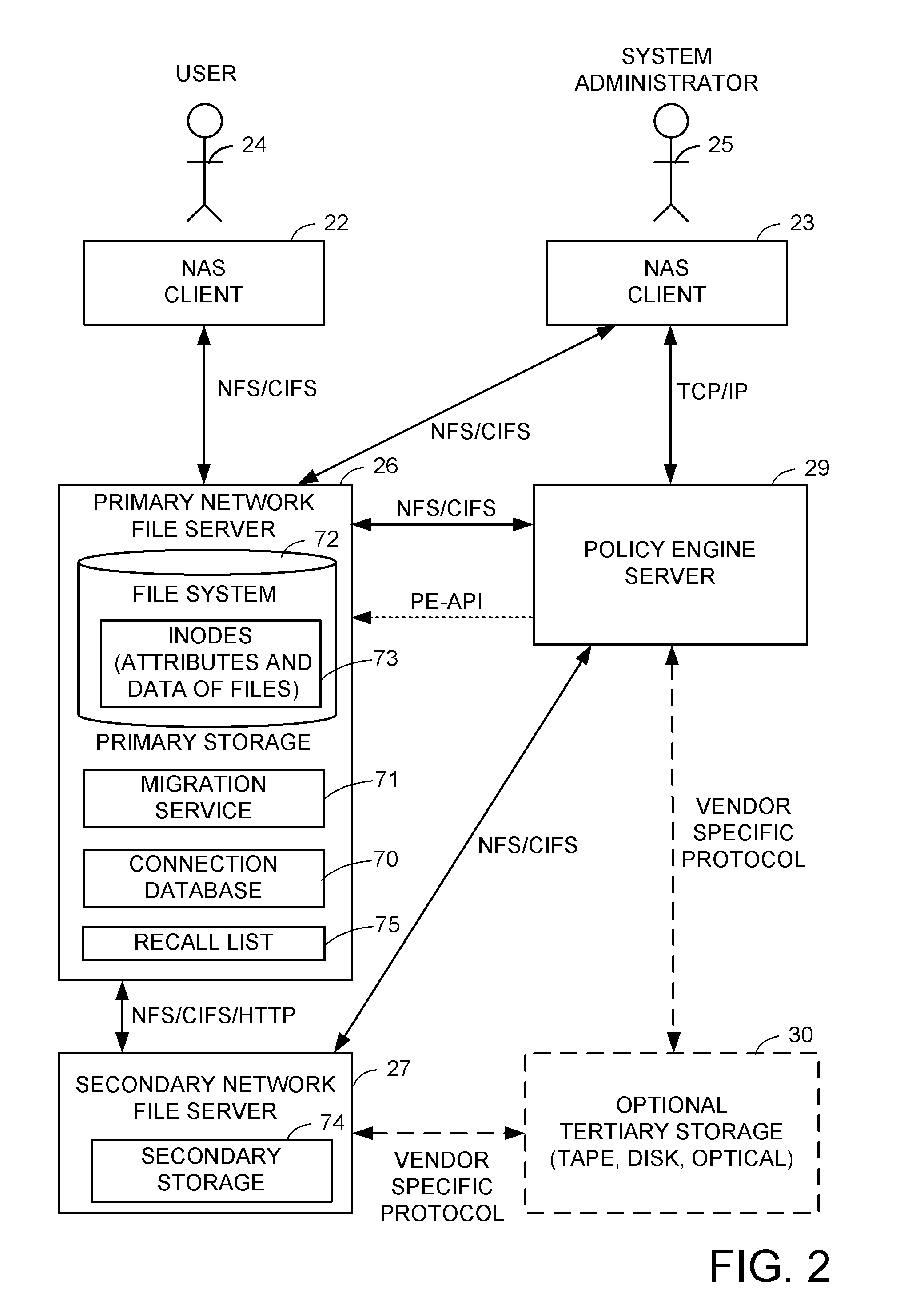
A hierarchical storage system includes file servers and a policy engine server. Offline attributes are added to file system inodes in a primary file server, file system parameters are added in the primary server, offline read and write access method fields are added to a connection database, and the primary file server uses these attributes and parameters for selecting a particular read method or write method for access to an offline file or section of an offline file. The write methods follow a “write recall full” policy, a “pass-through write” policy, a “pass-through multi-version” policy, or a “directory write pass-through” policy. The pass-through multi-version policy results in a new offline version of a file each time that a client opens and writes to a multi-version file. The directory write pass-through policy results in a new offline file when a file is created within a write pass-through directory.
Owner:EMC IP HLDG CO LLC
Systems and methods for limiting web site access
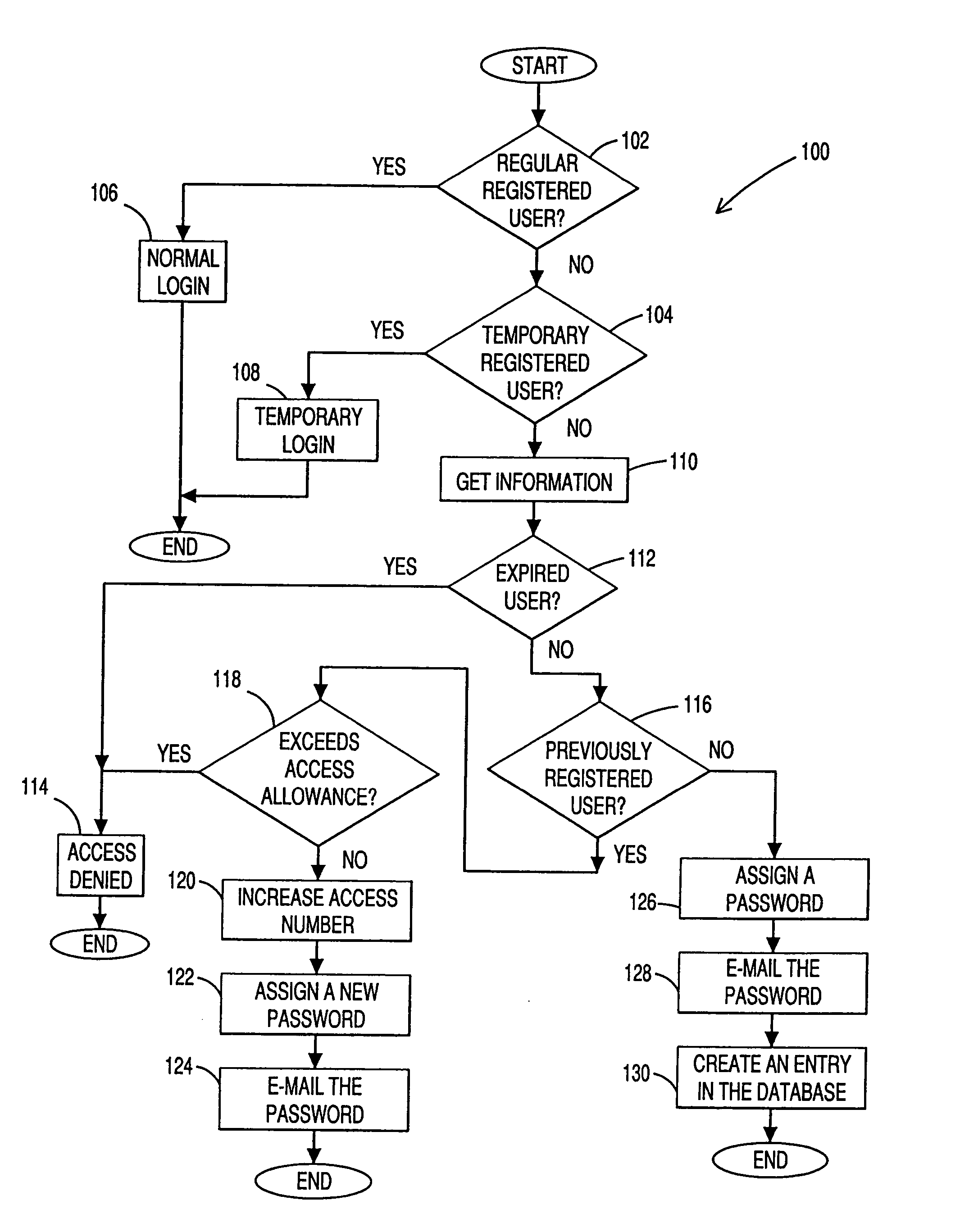
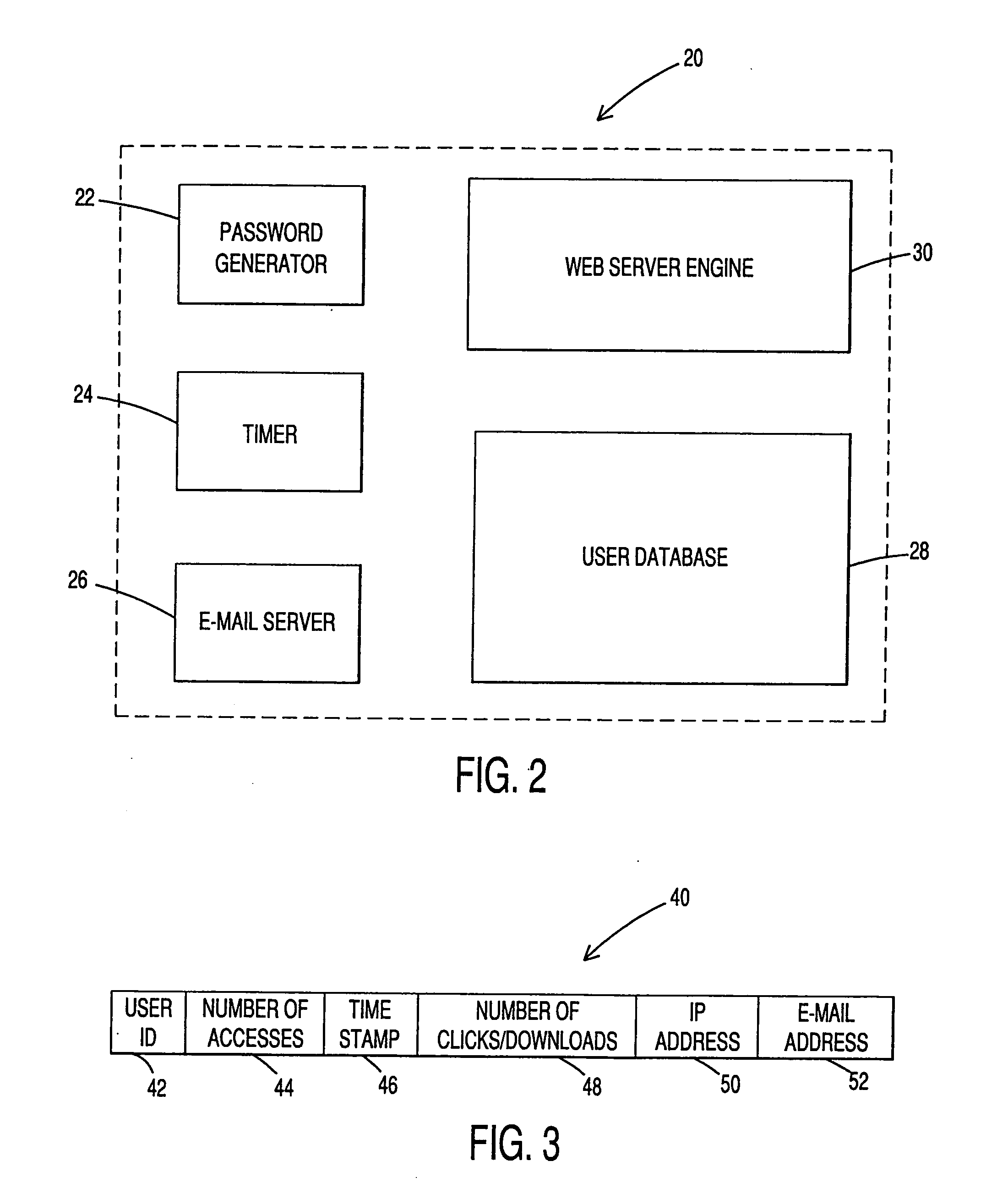
InactiveUS20060031503A1Limited durationDigital data processing detailsUnauthorized memory use protectionWeb siteAccess method
Methods relate to providing limited temporary access to a web site to visitors who desire to experience all the features provided by this site before becoming a member. The temporary access privileges may be limited by duration, which is counted from the initial access request, or by number of accesses. At the end of the temporary access period, the visitor may be given additional access privileges before being permanently denied access. The user may be identified either by the IP address assigned to the user device or by the user's e-mail address.
Owner:BELLSOUTH INTPROP COR
Method and apparatus for providing visitors with a personalized itinerary and managed access to attractions
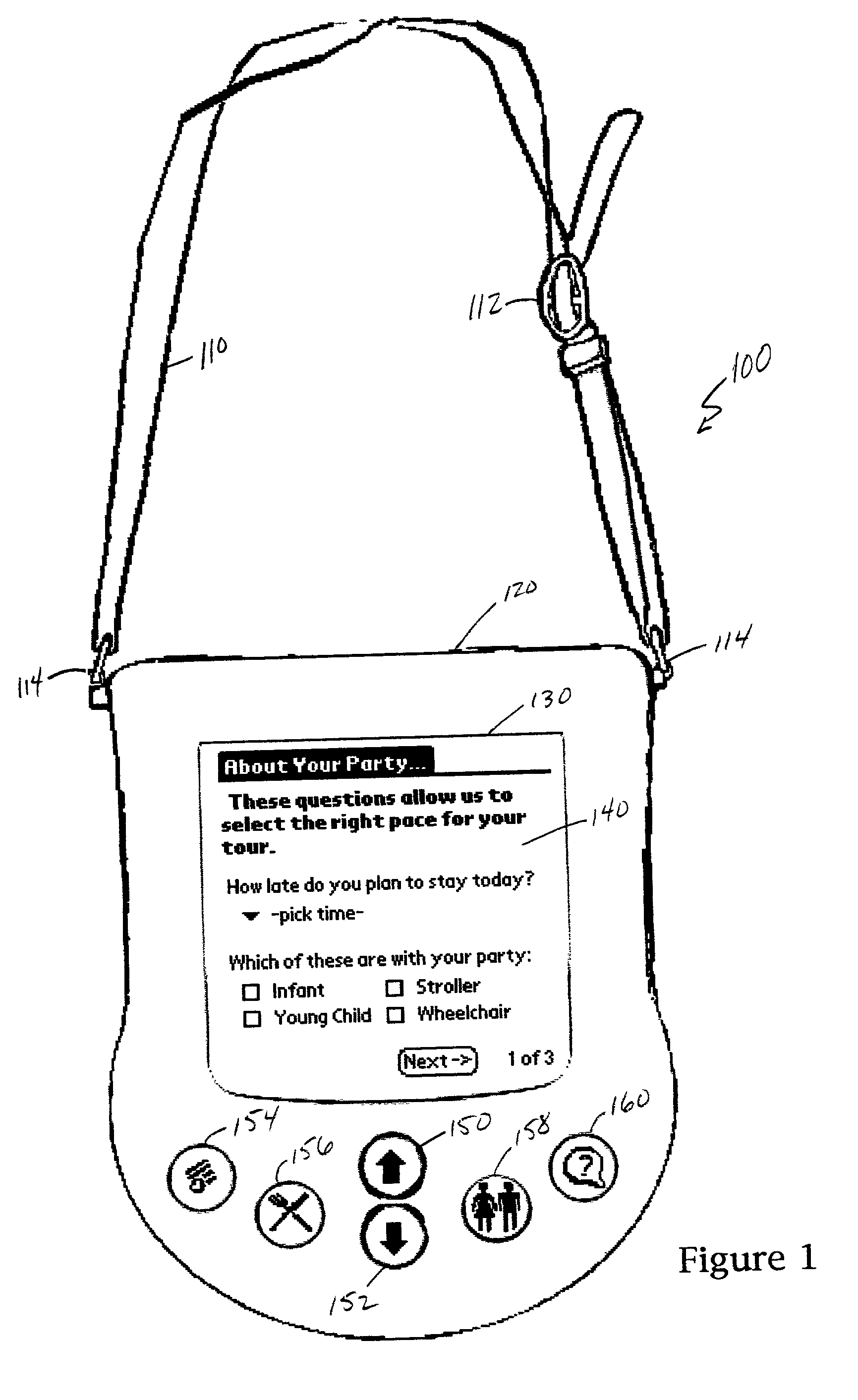
ActiveUS20020174003A1Reduce the possibilityShorten the timeRoad vehicles traffic controlReservationsPersonalizationAccess method
A method is disclosed for creating itineraries for a party of visitors to a facility, the facility having multiple attractions. Visitors give answers to questions about their preferences, which is combined with authoritative information about their admission privileges, and information stored about the attractions and facility, to generate an itinerary. The method can be executed by a portable, handheld computer which asks the questions, accepts the answers, and processes them into an itinerary which is both portable and dynamic, adjusting in real time to schedule changes and unscheduled attraction closures. In an alternative embodiment, the itinerary can be generated as the result of an Internet transaction, or through an interaction with a facility employee. The itinerary may be presented to the party in printed form, such as a schedule or ticket book. If a facility has an access control system that uses a central database, the itinerary can generated as records in the database, thereby allowing parallel use of prior art access methods.
Owner:AGILE JOURNEYS LLC
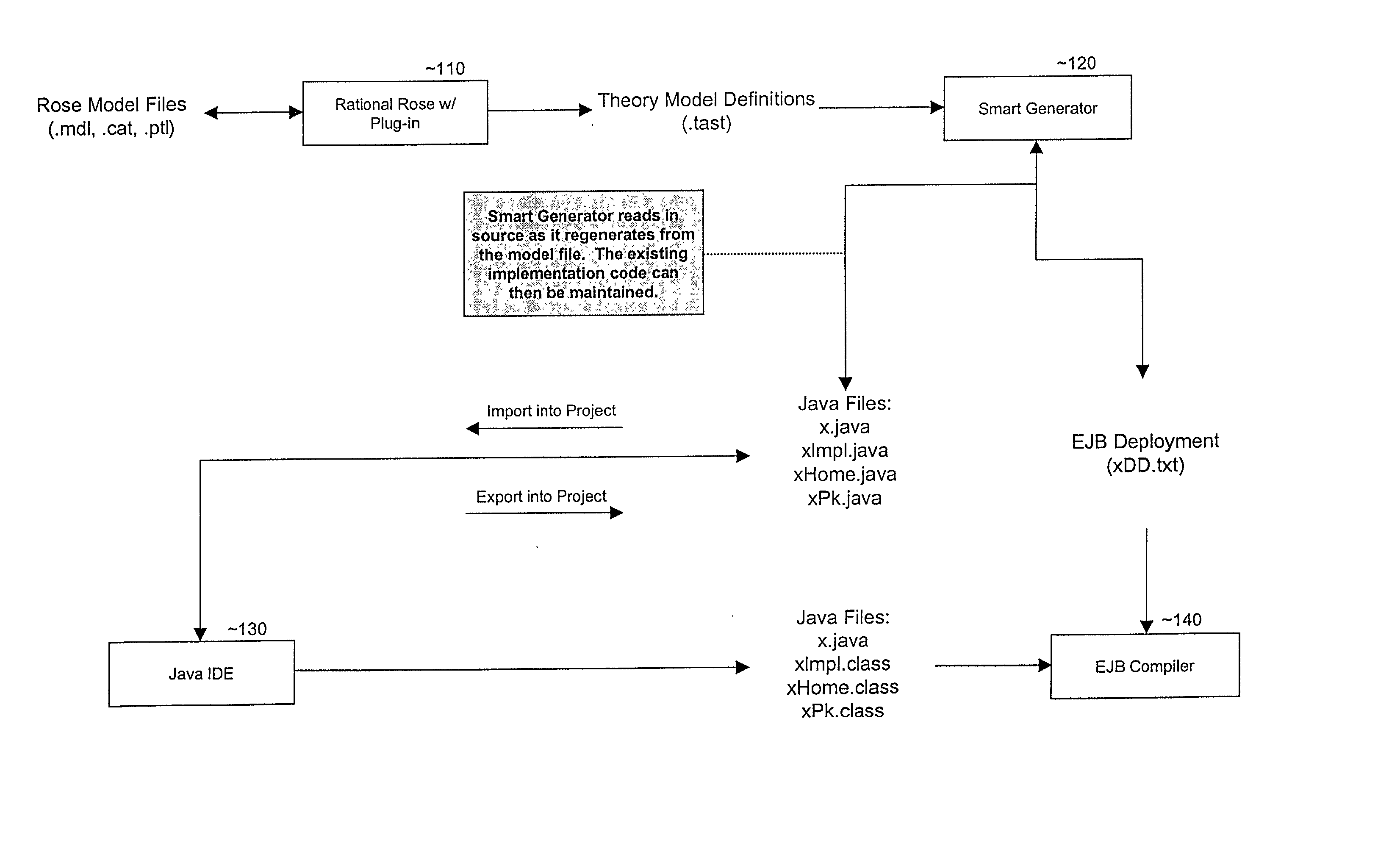
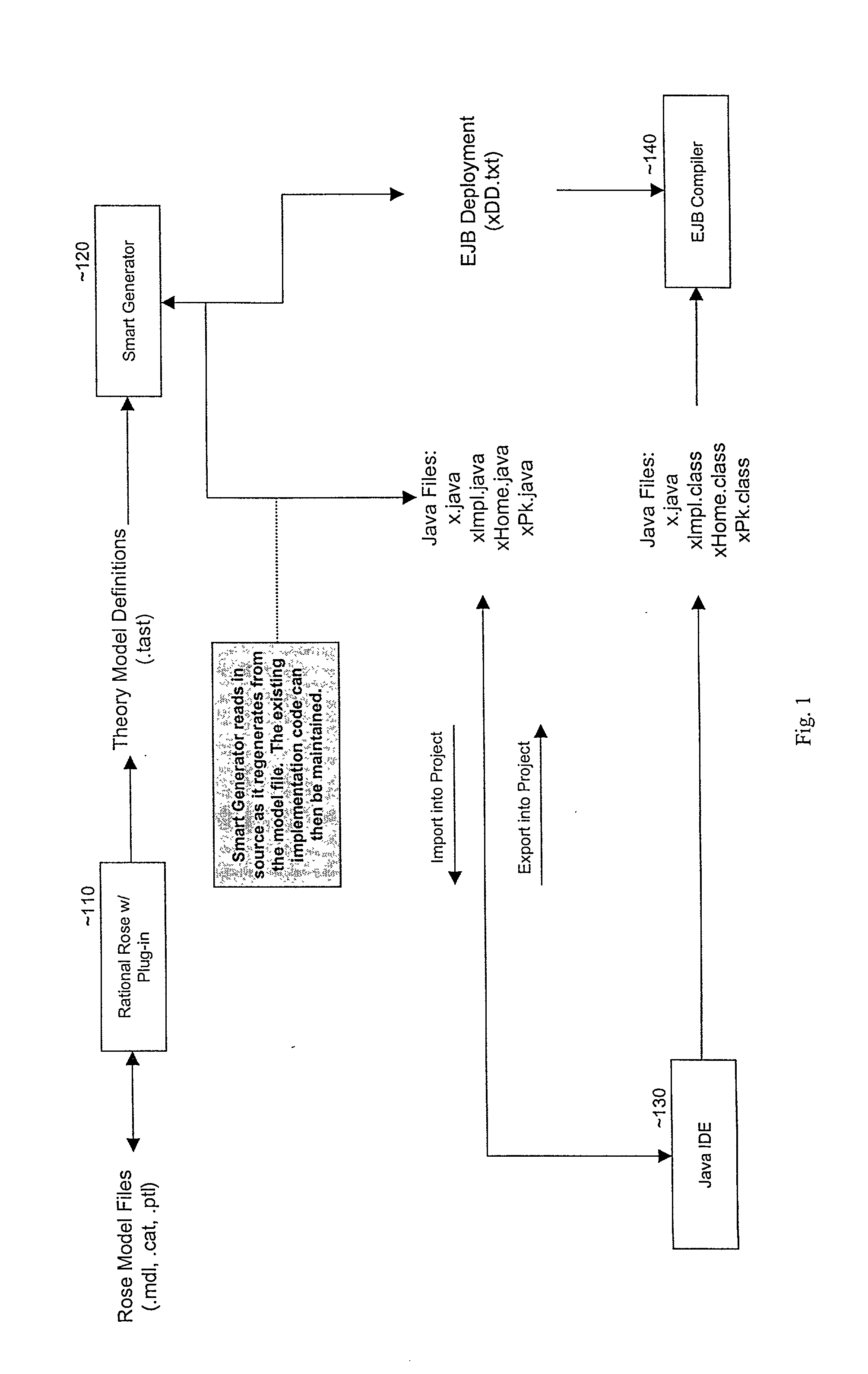
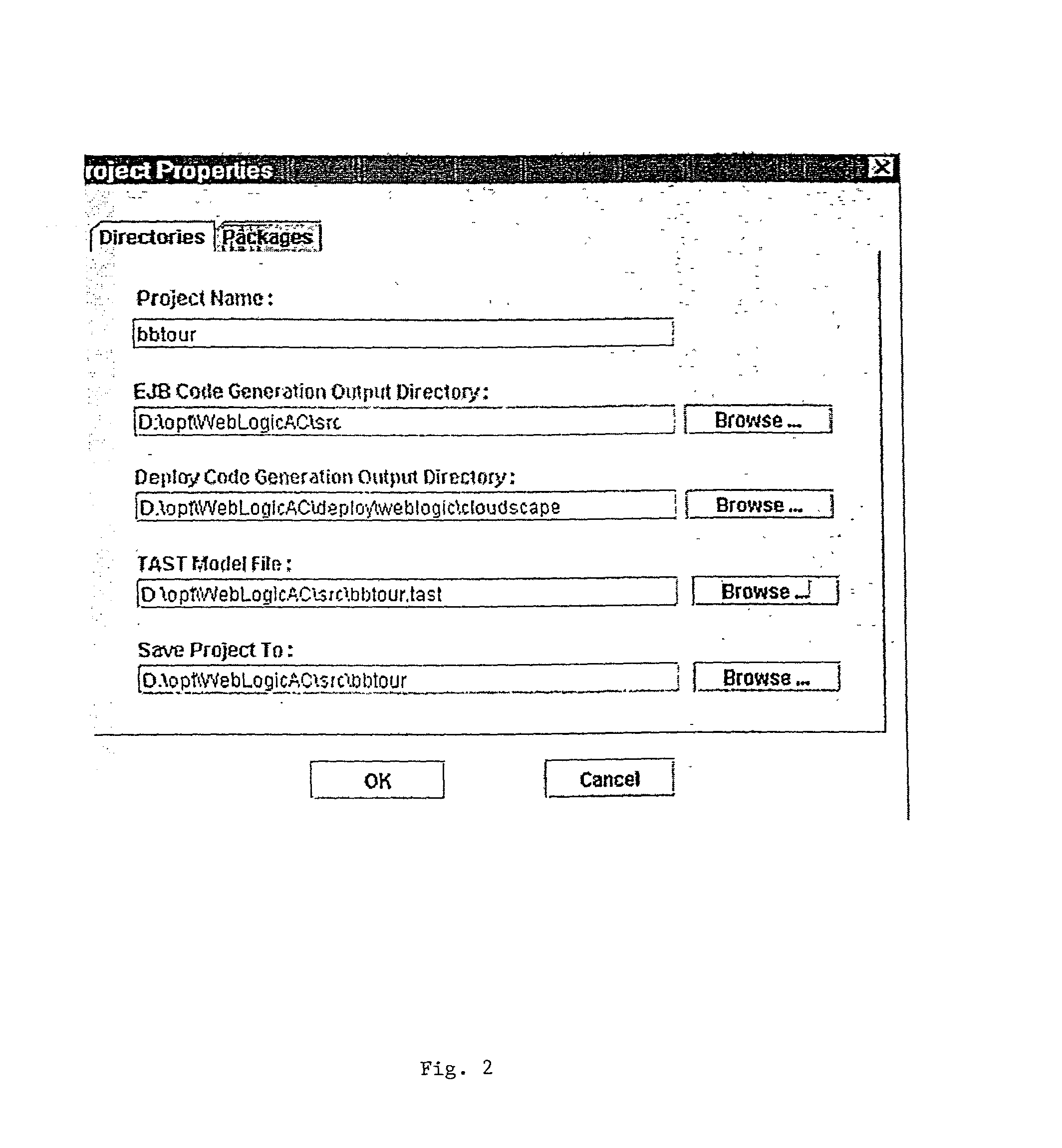
Smart generator
ActiveUS20020147763A1Laborious taskDigital data information retrievalMultiple digital computer combinationsAccess methodDEVS
The Smart Generator of the present invention allows the designer / developer / user to model the EJB components in a natural way without being concerned with implementation-specific details. The developer models the business objects using a UML drawing tool and the Smart Generator creates a set of classes that implements these objects with reference to the Enterprise JavaBeans specification. That is, the Smart Generator automatically create access methods and handling containment of references from the UML diagram.
Owner:ORACLE INT CORP
Method of universal file access for a heterogeneous computing environment
ActiveUS7774391B1Simple methodReduce the numberData processing applicationsFile access structuresOperational systemAuto-configuration
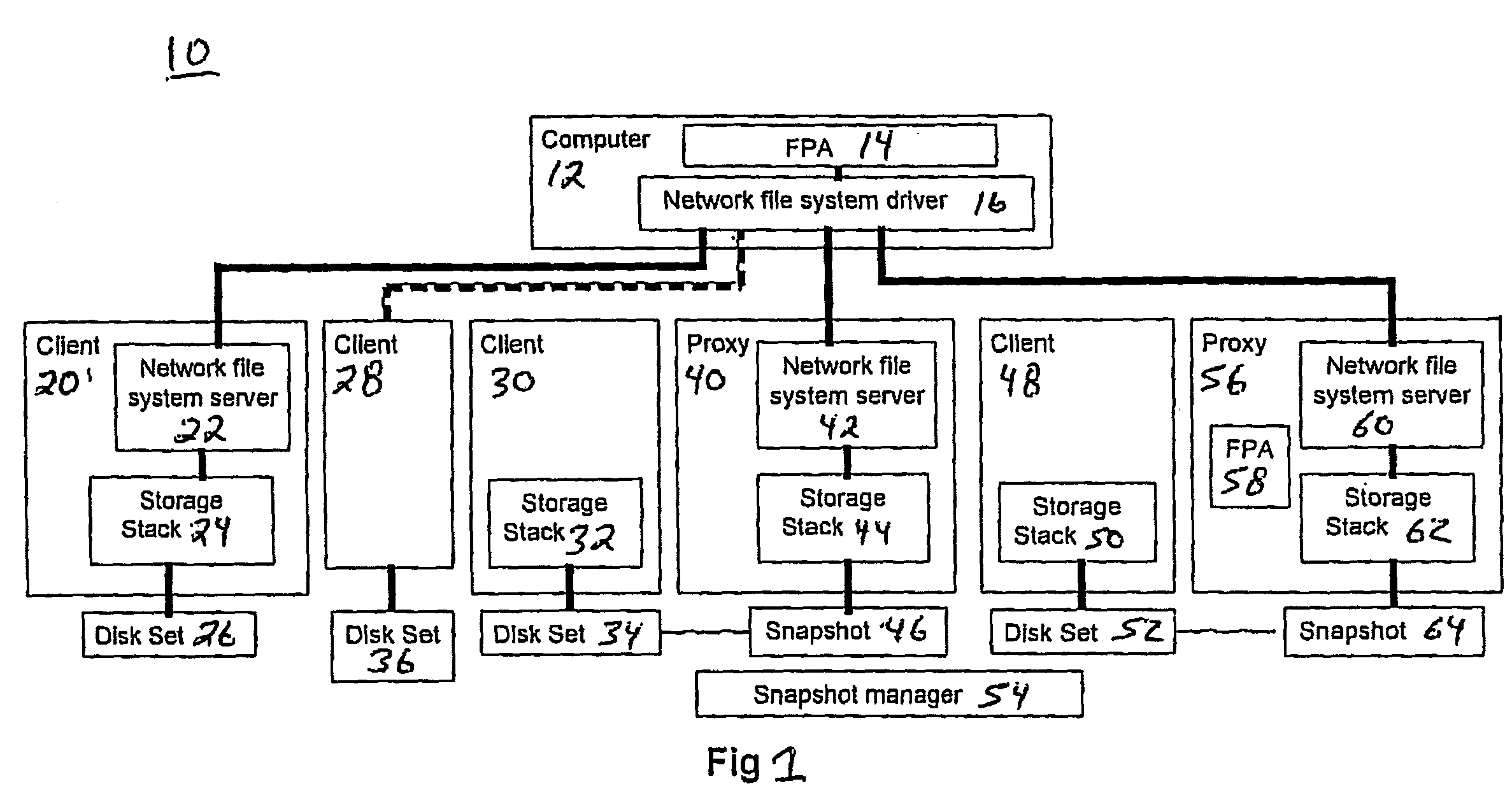
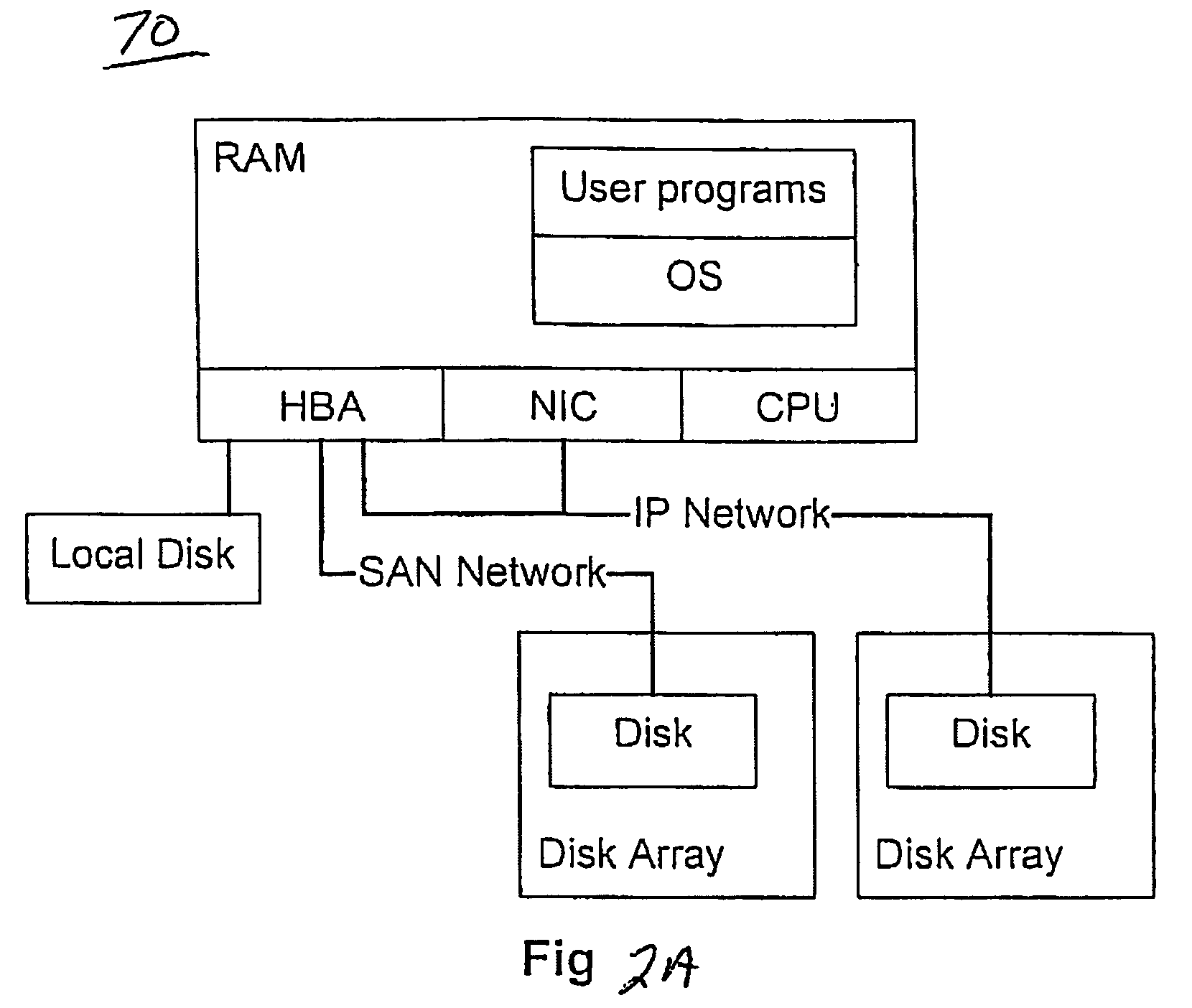
An architecture and system are described that provide a unified file access service within in a managed computing environment composed of diverse networks, computing devices, and storage devices. The service provides mechanisms for remotely accessing the file systems of any managed computer or disk snapshot, independently of the computer's current state (powered on, suspended or powered off), its location within the environment, its hardware type (virtual vs. physical), its operating system type, and its file system formats. The system isolates centralized FPAs from the details of clients, proxies and storage elements by providing a service that decomposes offloaded file system access into two steps. A FPA or a requester acting on behalf of the FPA first expresses the disk set or the computer containing the file systems it wishes to access, along with requirements and preferences about the access method. The service figures out an efficient data path satisfying the FPA's needs; and then automatically configures a set of storage and computing resources to provide the data path. The service then replies with information about the resources and instructions for using them. The FPA then accesses the requested file systems using the returned information.
Owner:VMWARE INC
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PtMP) transmission system architecture
InactiveUS20050232193A1Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceCode division multiple access
Owner:INTELLECTUAL VENTURES I LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com