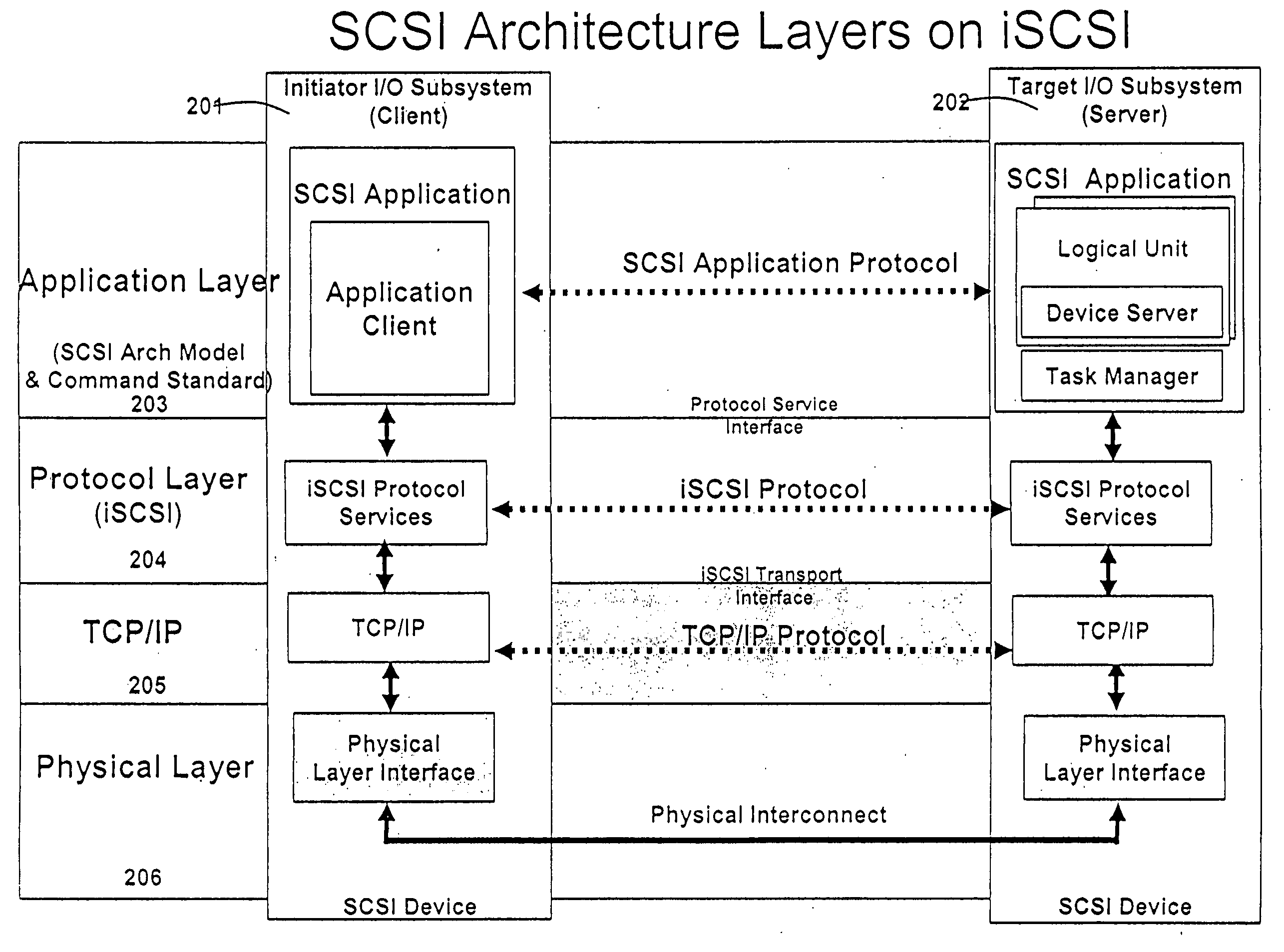
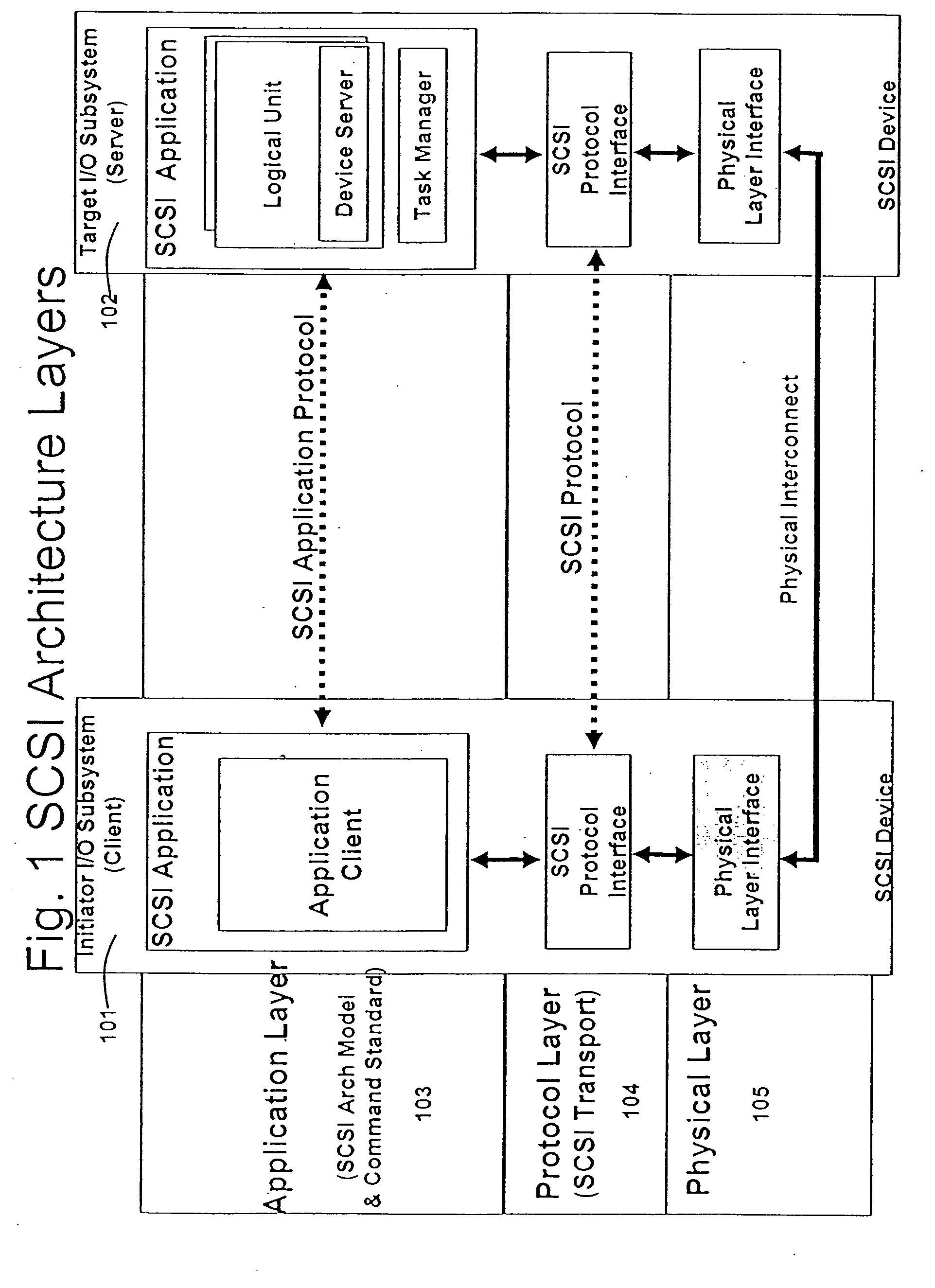
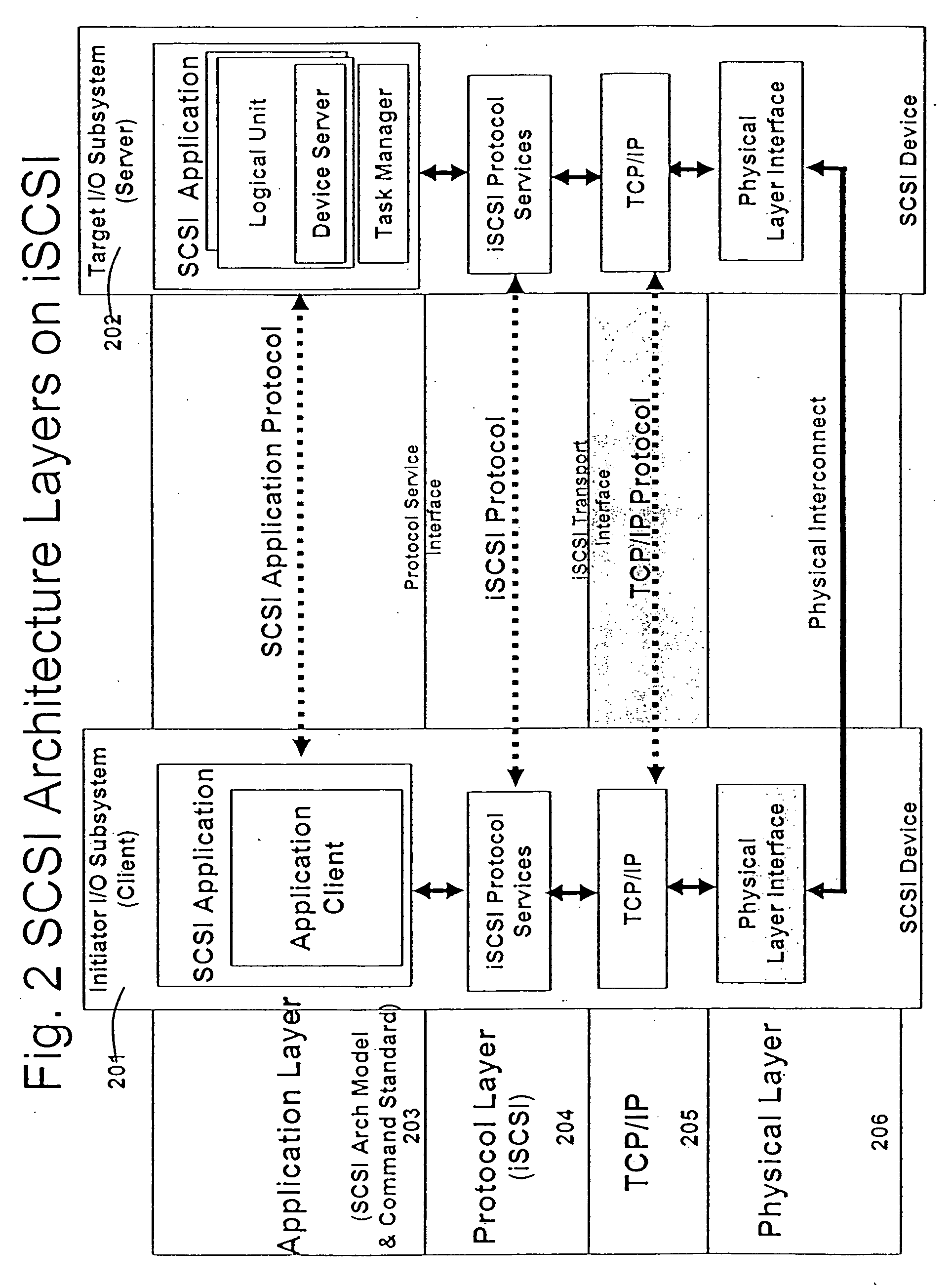
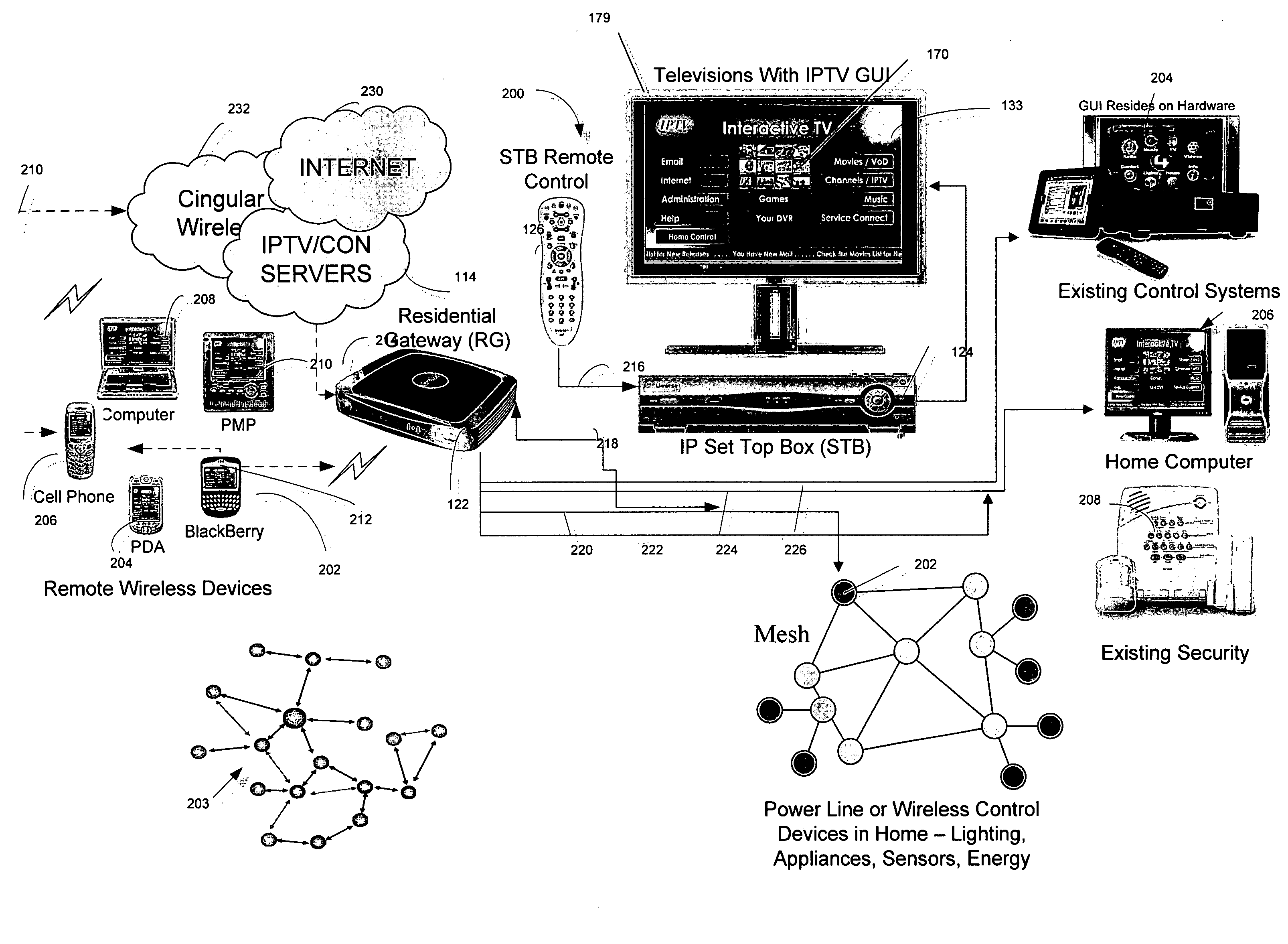
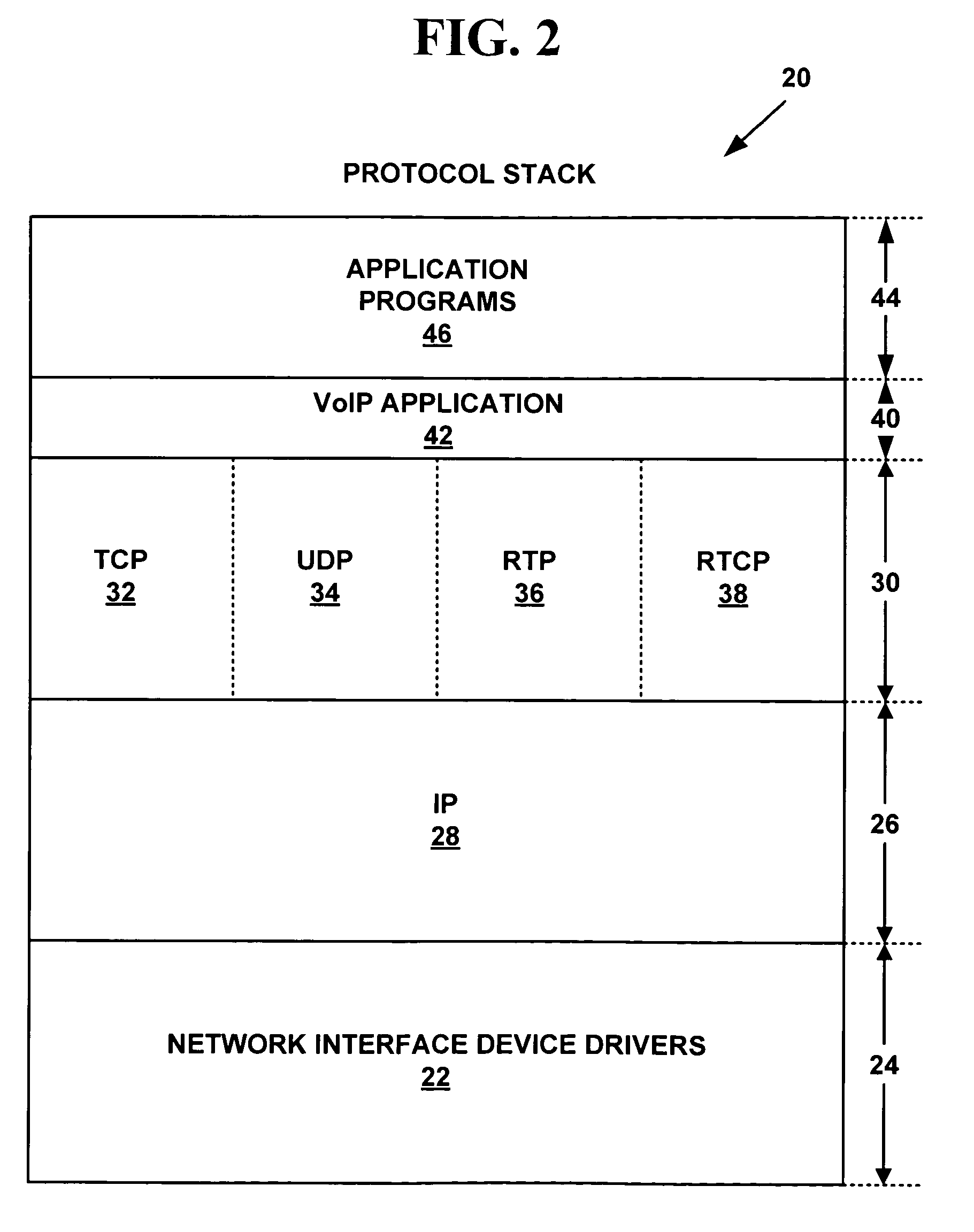
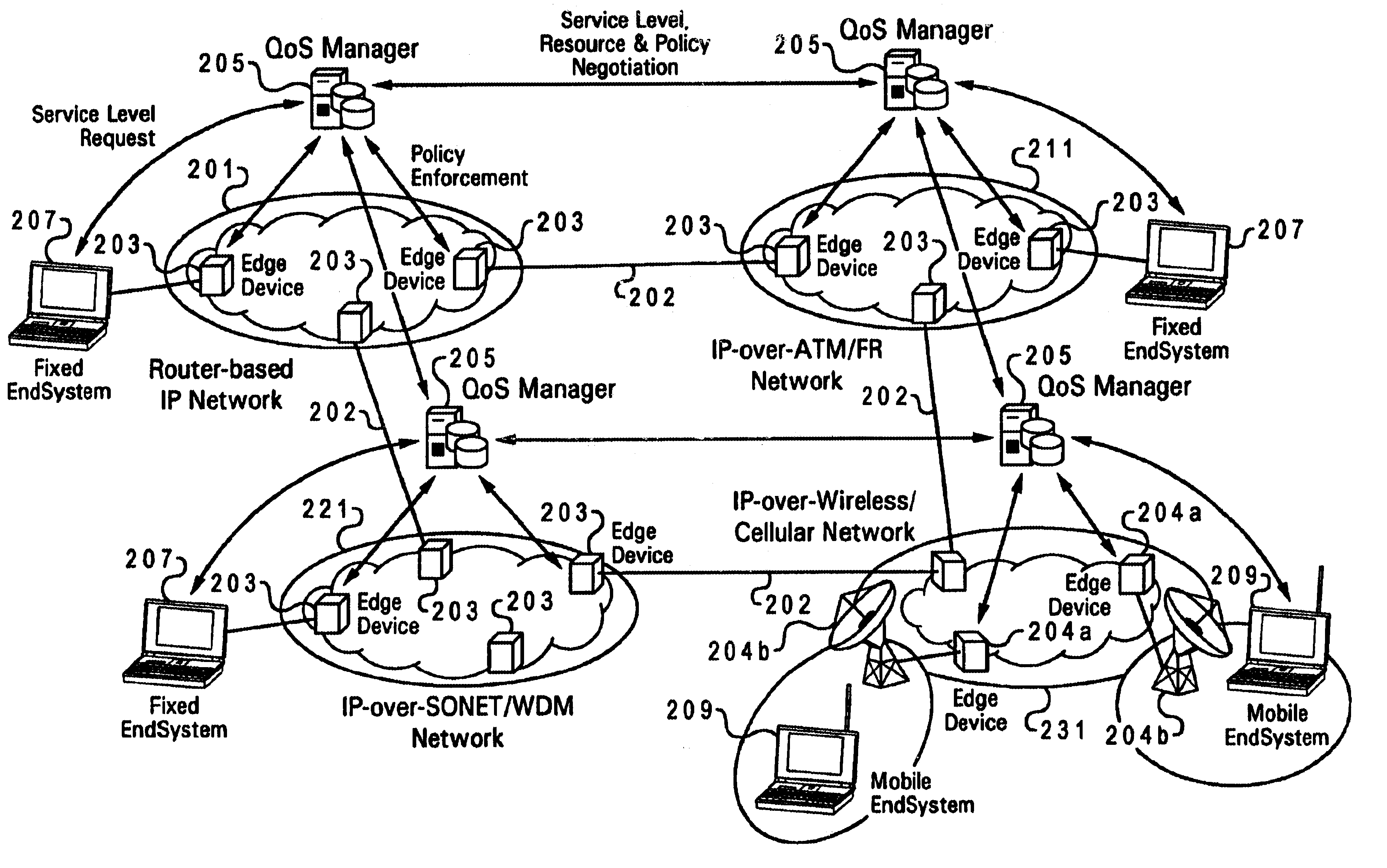
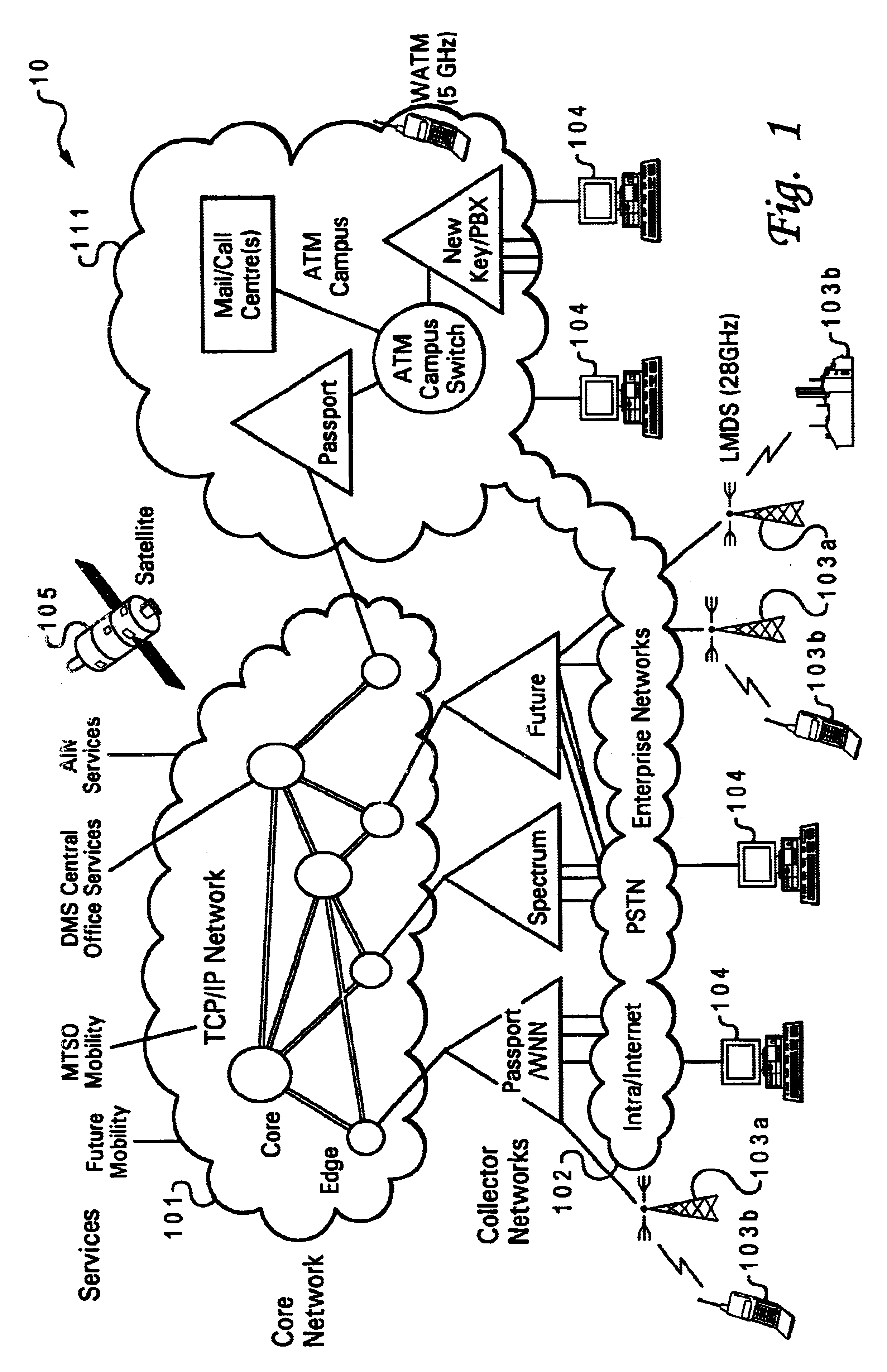
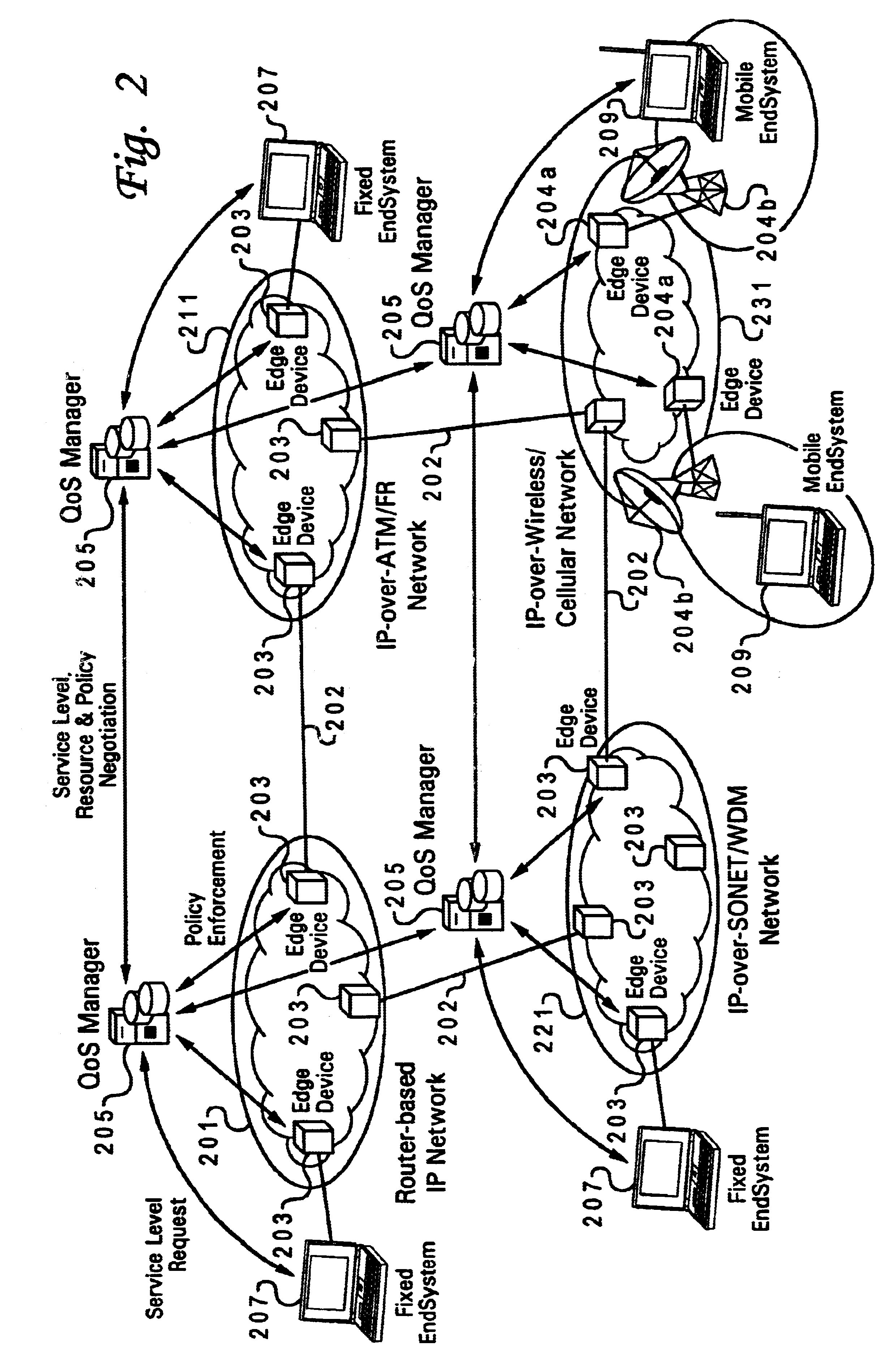
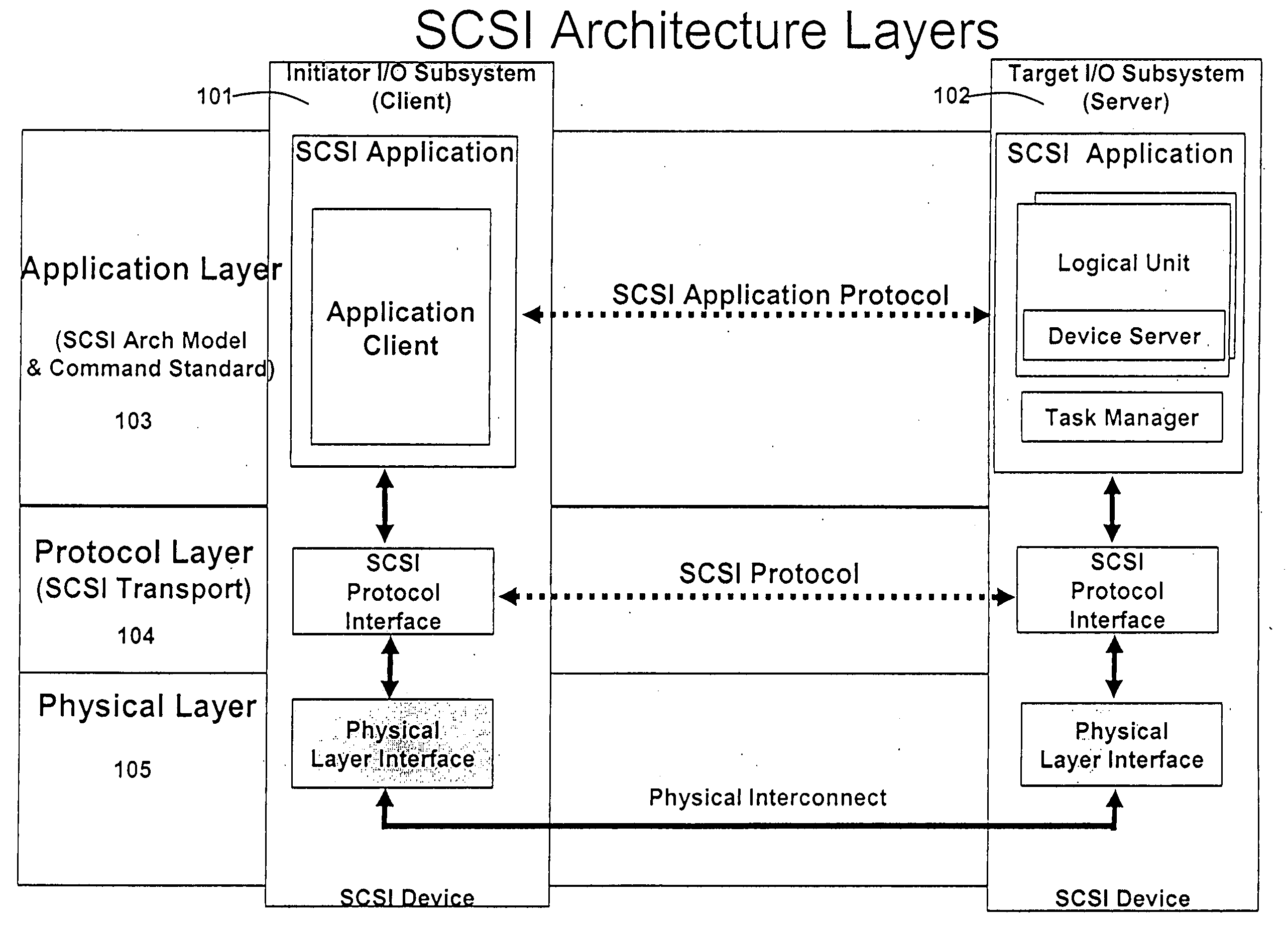
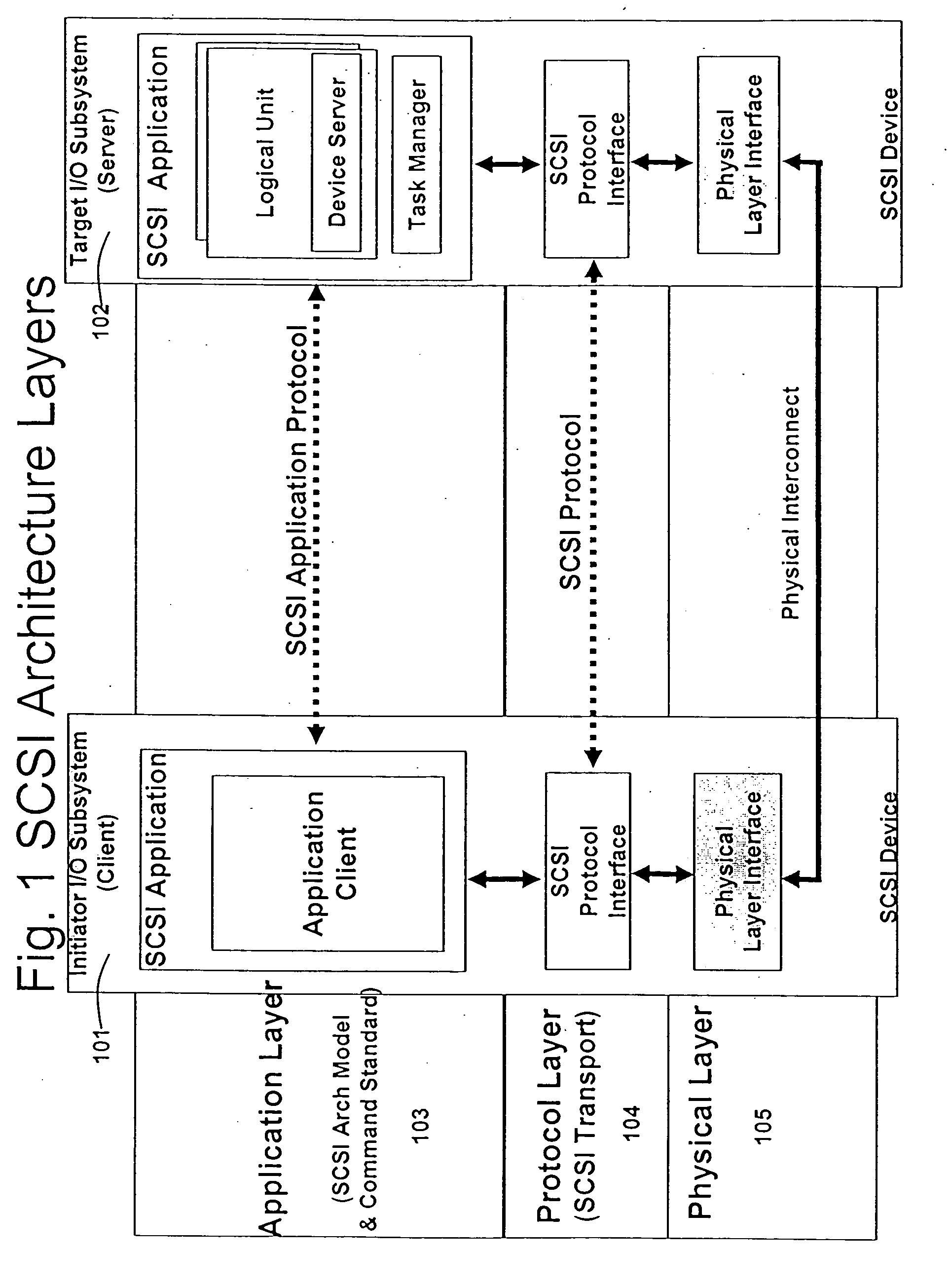
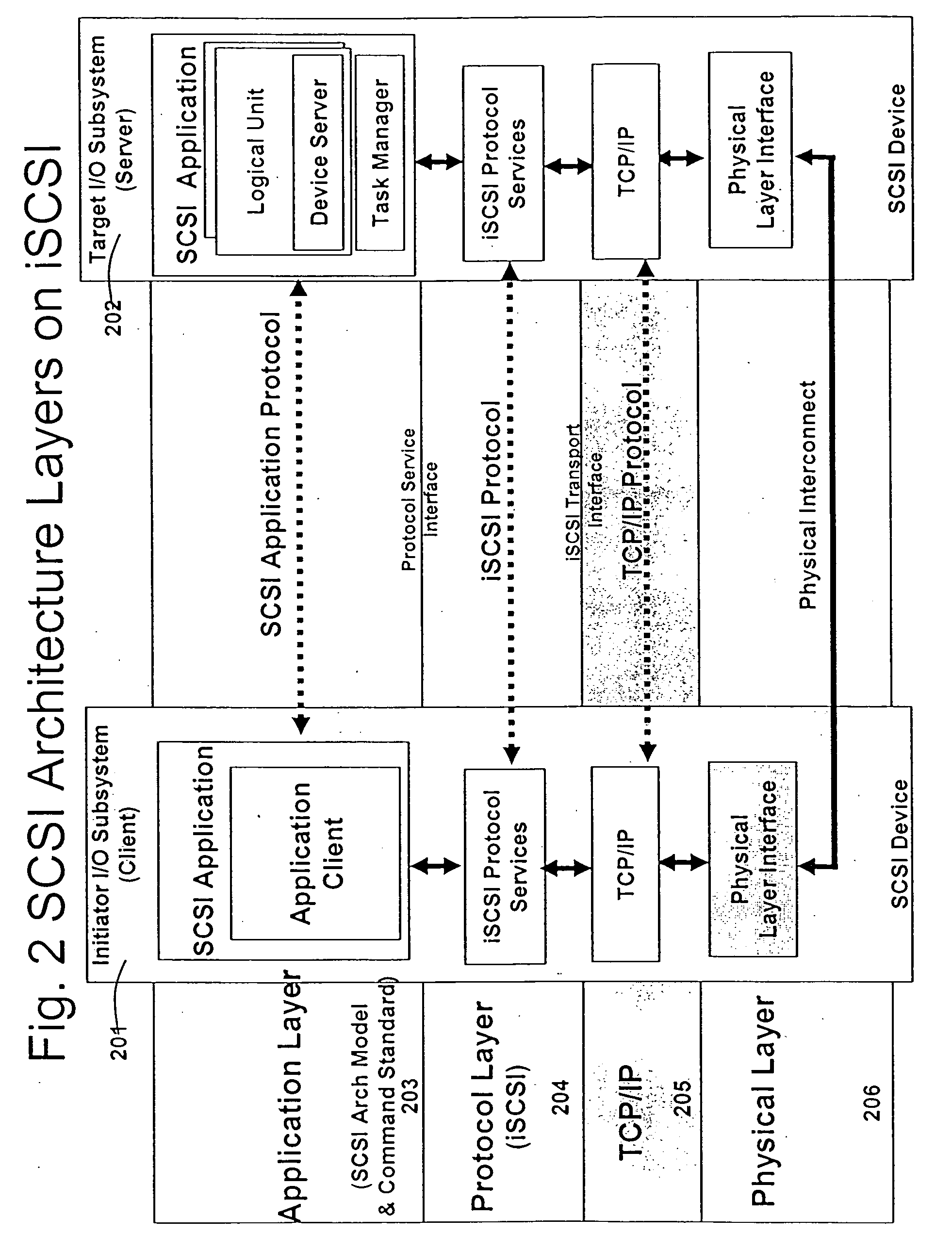
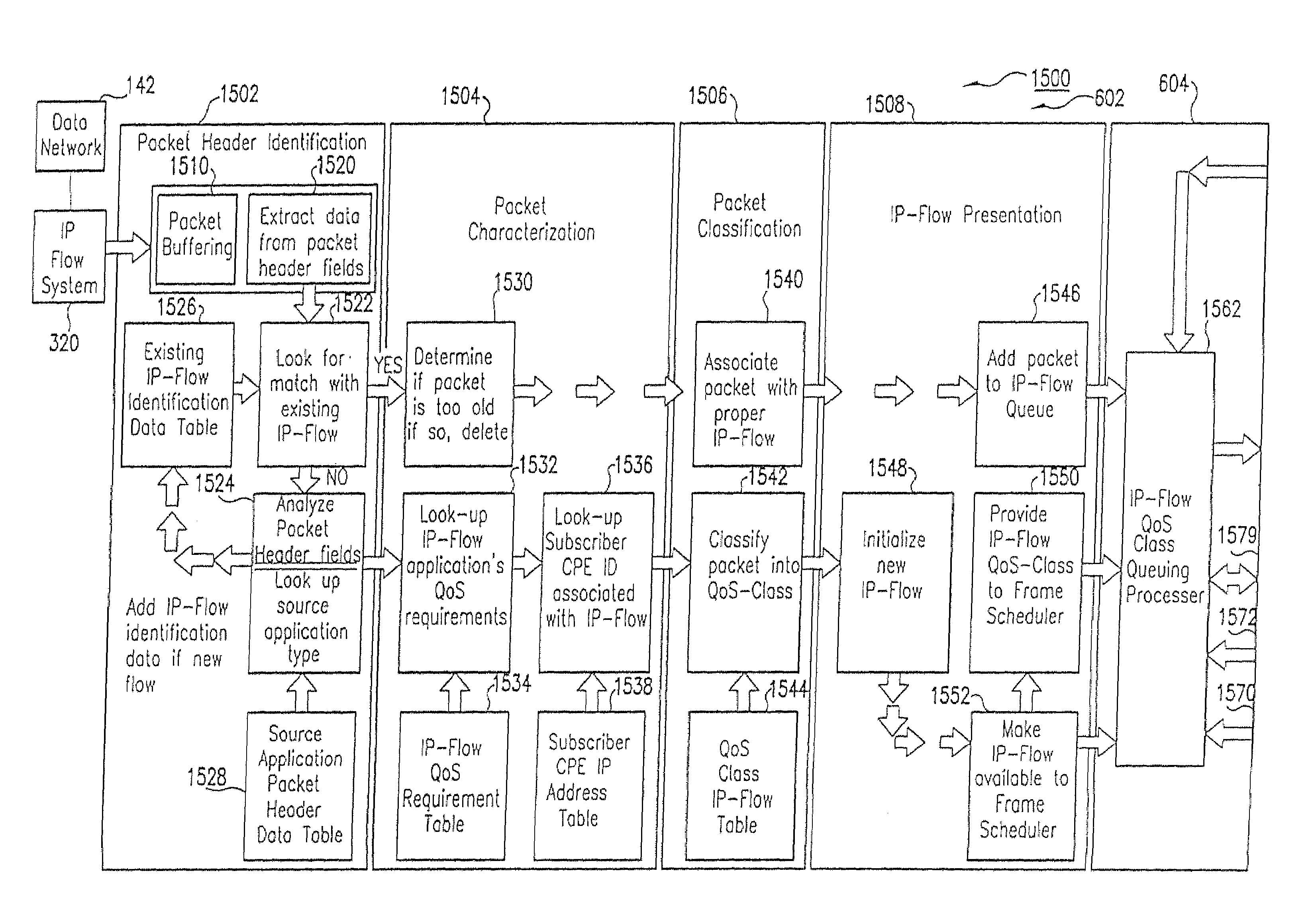
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
14148 results about "Internet Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
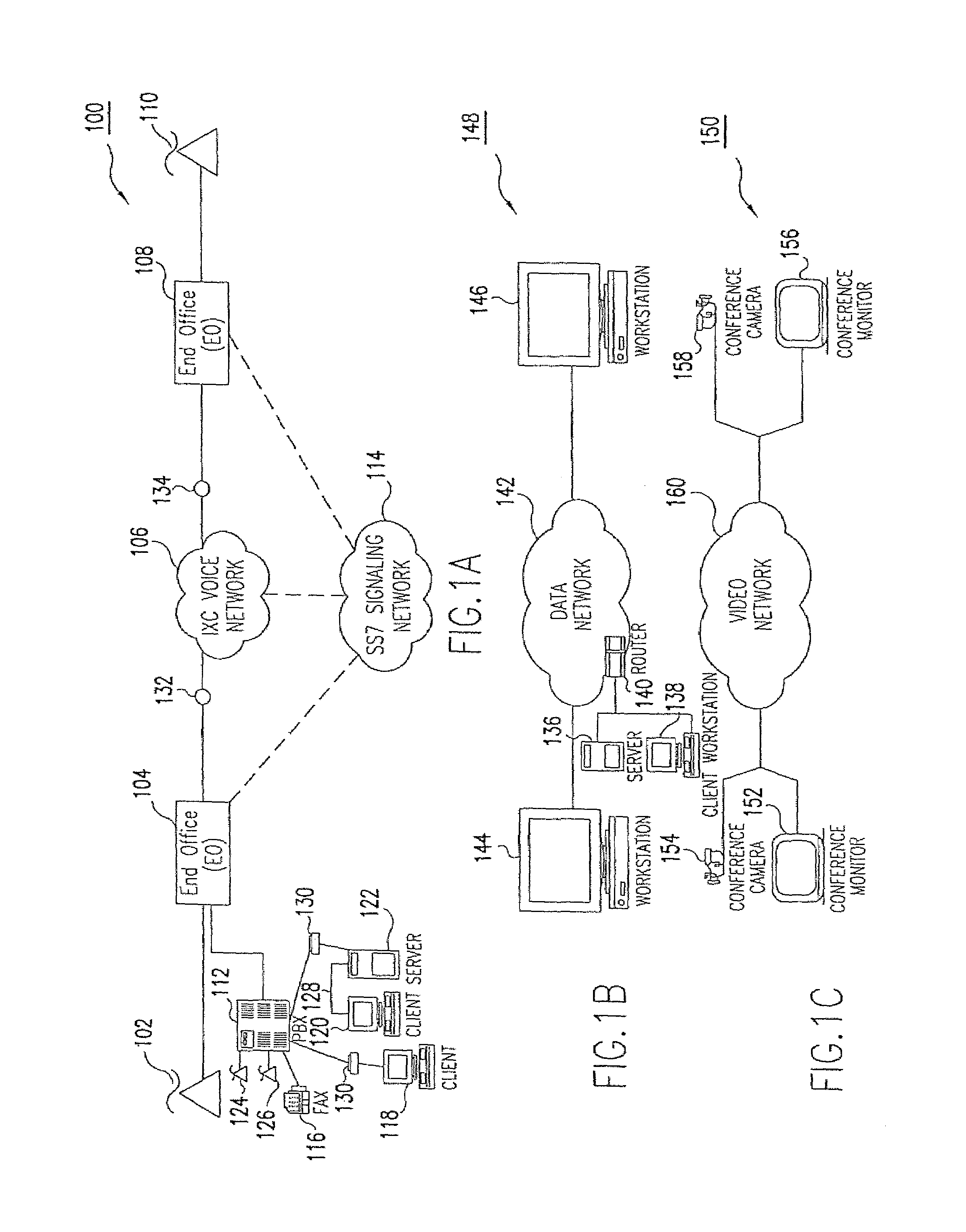
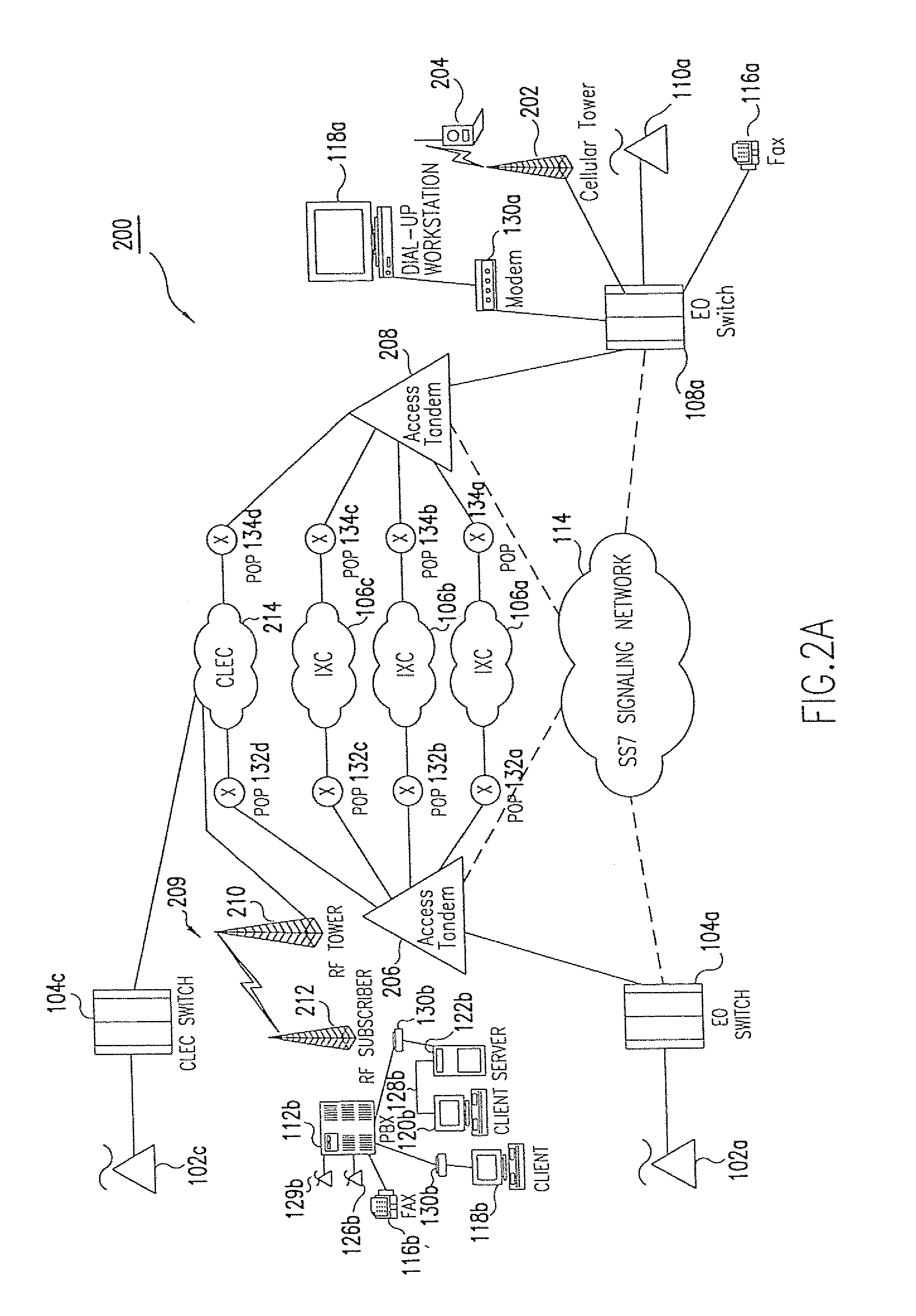
The Internet Protocol (IP) is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet.
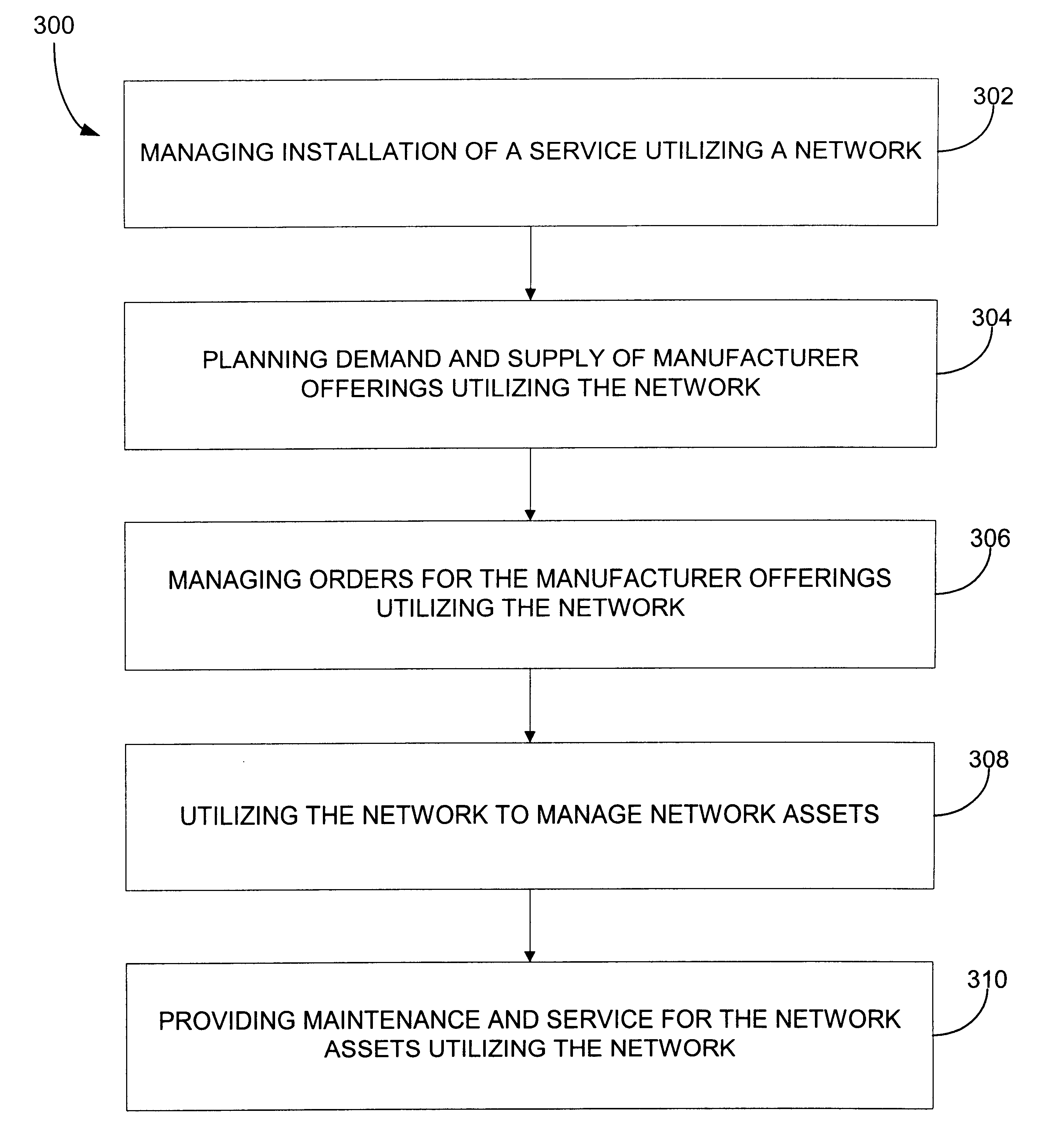
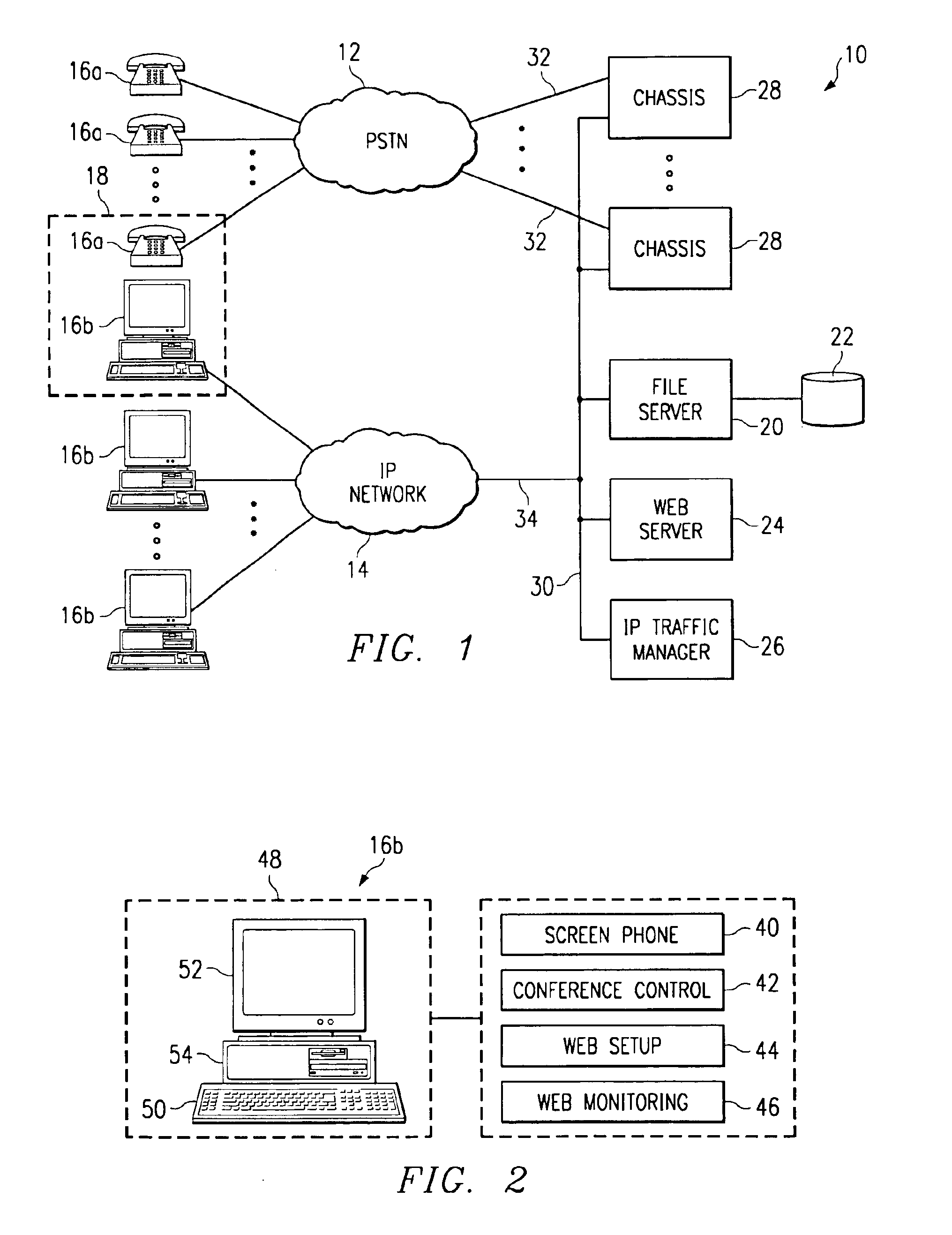
Providing collaborative installation management in a network-based supply chain environment
InactiveUS6606744B1Interconnection arrangementsSpecial service for subscribersWeb applicationService provision
A system, method and article of manufacture are provided for collaborative installation management in a network-based supply chain environment. According to an embodiment of the invention, telephone calls, data and other multimedia information are routed through a network system which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. The system includes integrated Internet Protocol (IP) telephony services allowing a user of a web application to communicate in an audio fashion in-band without having to pick up another telephone. Users can click a button and go to a call center through the network using IP telephony. The system invokes an IP telephony session simultaneously with the data session, and uses an active directory lookup whenever a user uses the system. Users include service providers and manufacturers utilizing the network-based supply chain environment.
Owner:ACCENTURE GLOBAL SERVICES LTD
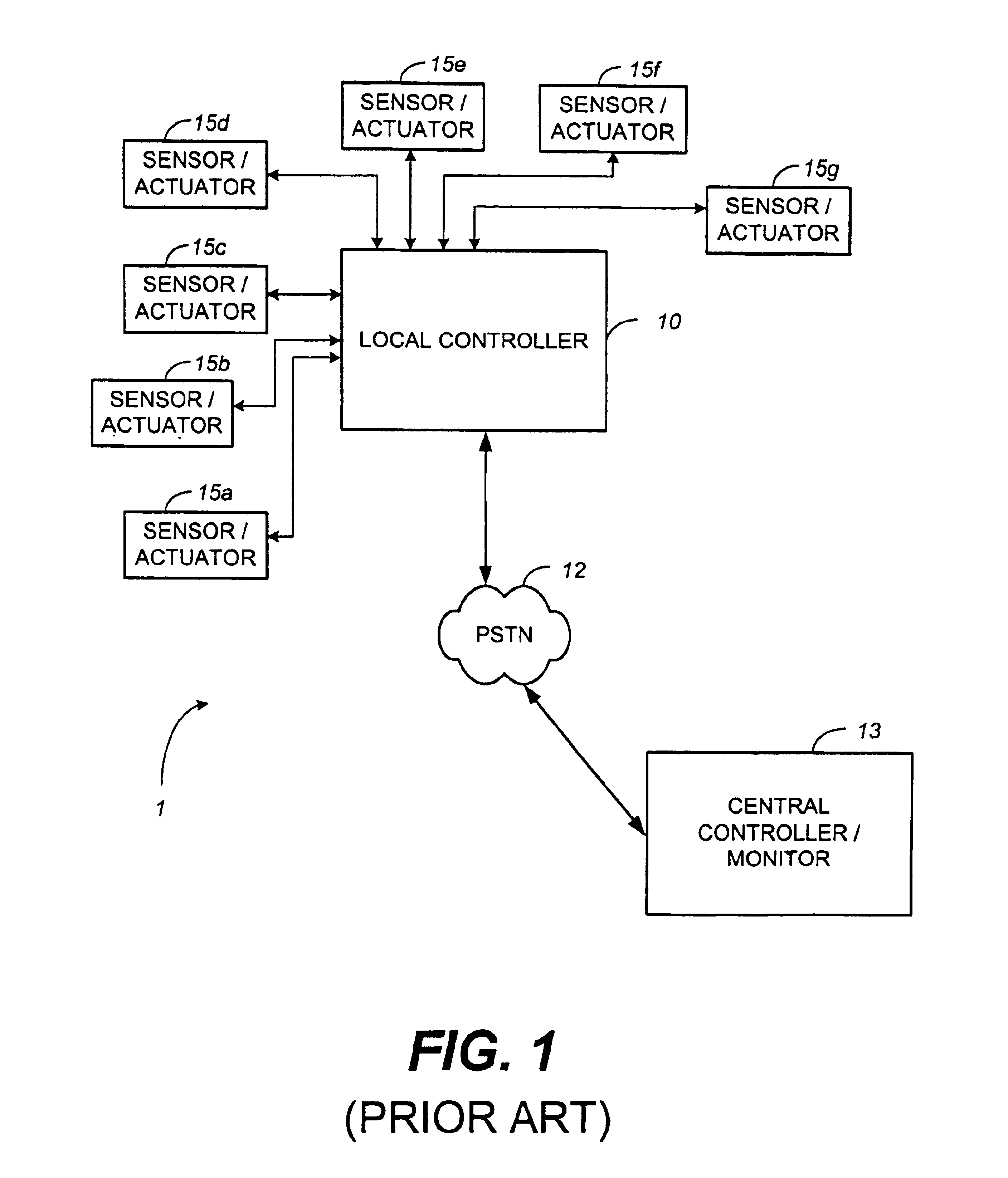
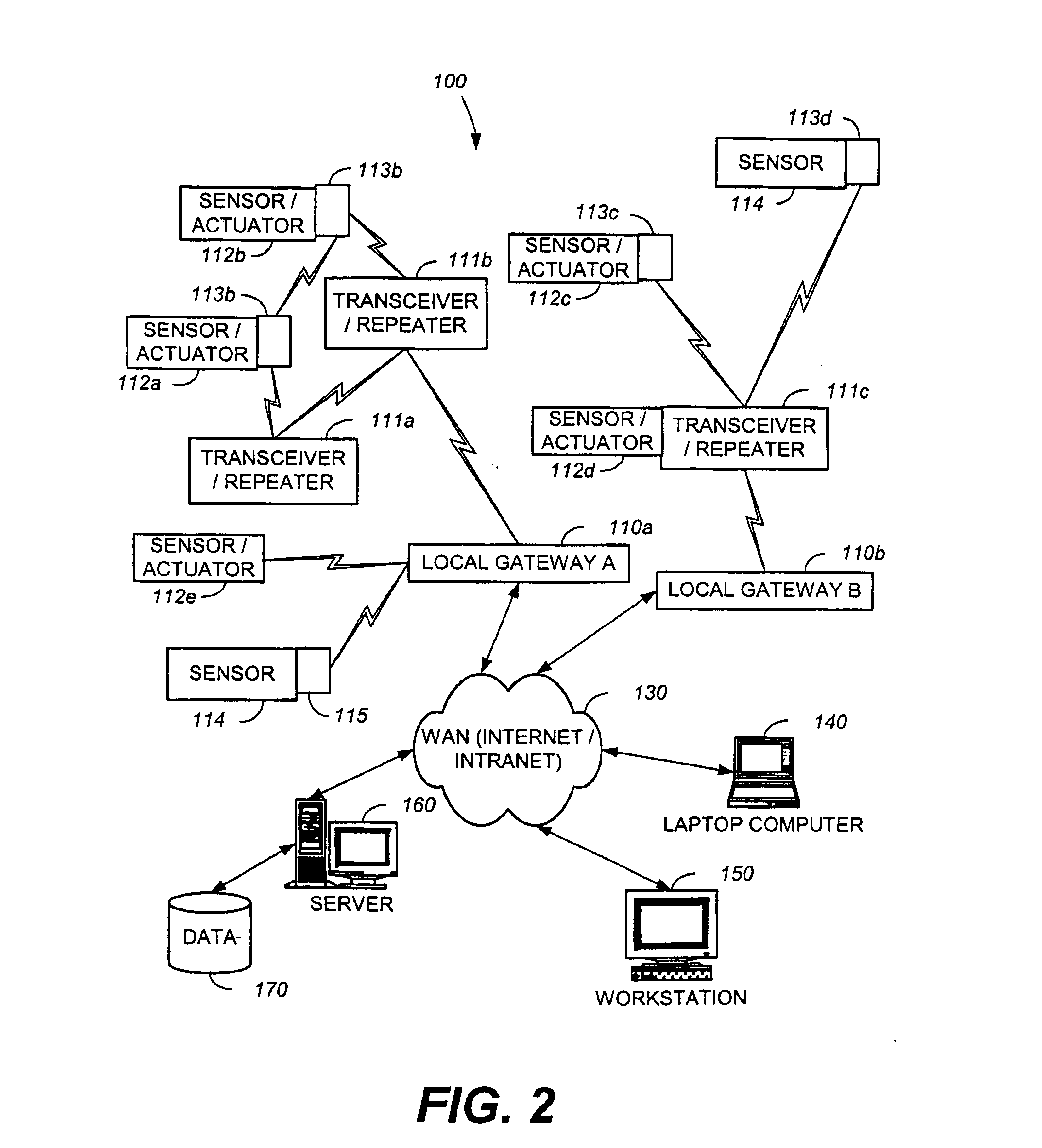
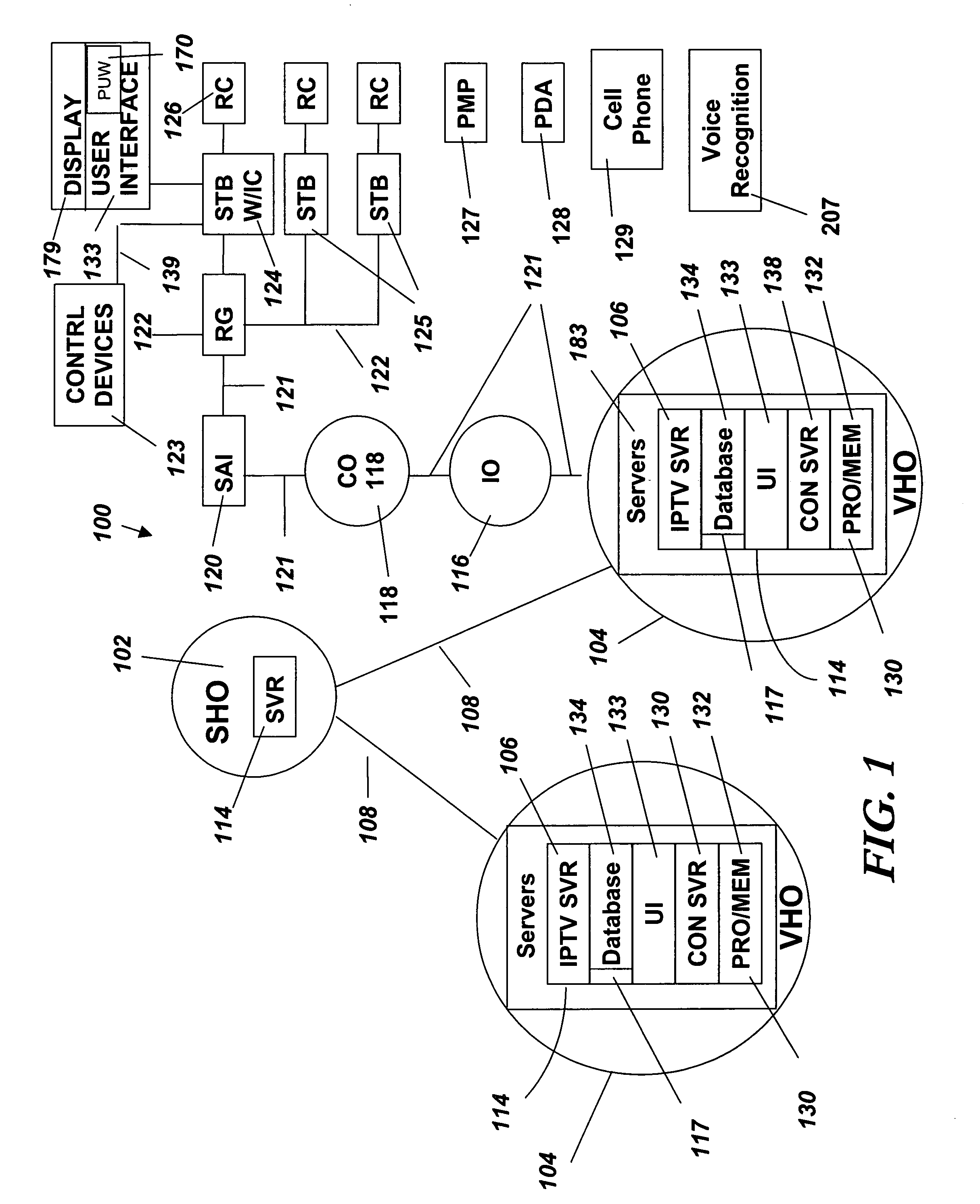
System and method for monitoring and controlling residential devices
InactiveUS6891838B1Closed feedback loopIntegrated inexpensivelyElectric signal transmission systemsNetwork topologiesControl signalActuator
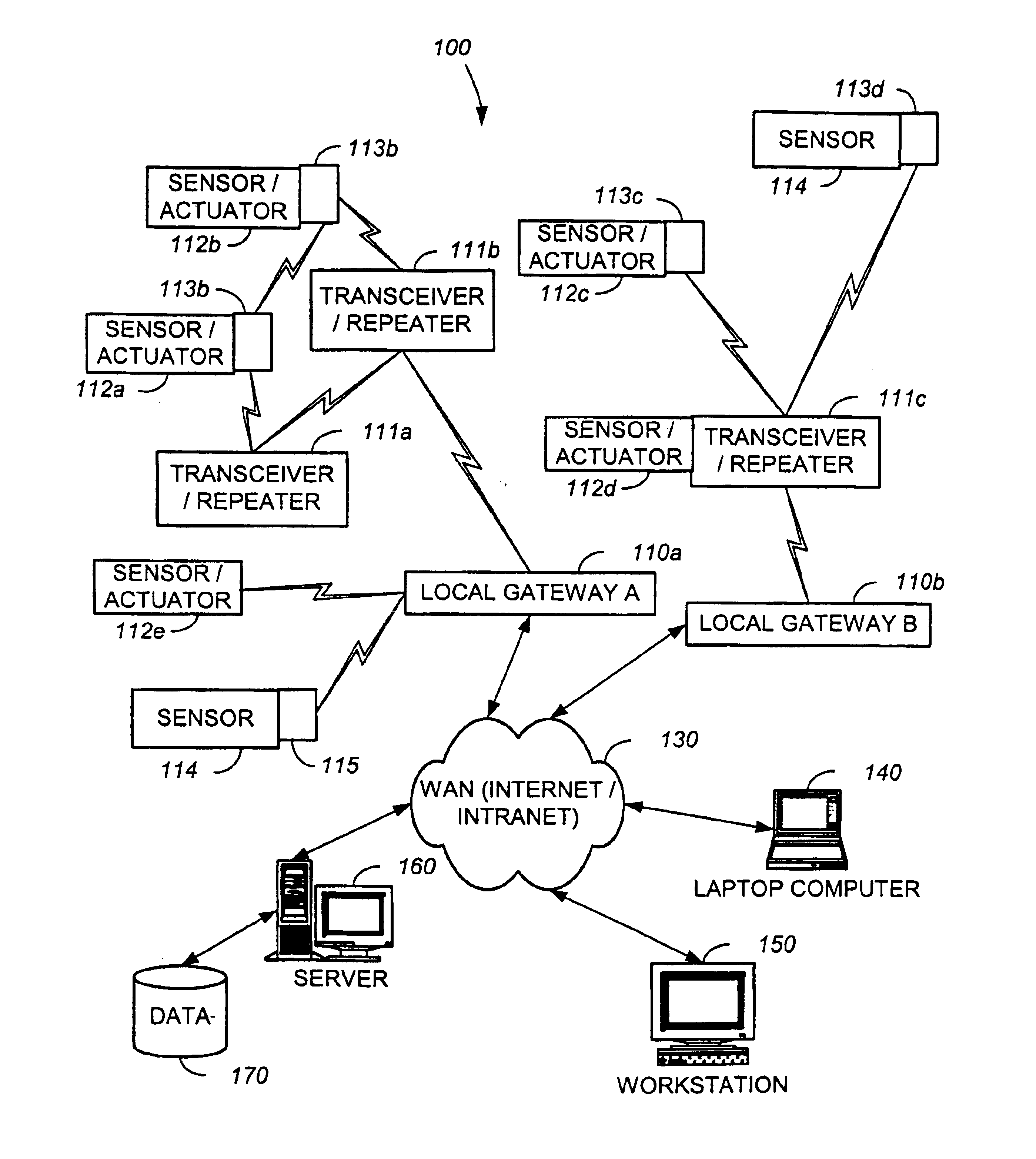
The present invention is generally directed to a system and method for monitoring and controlling a host of residential automation systems. The system is implemented by using a plurality of wireless communication devices configured to relay both data and command encoded signals through the wireless network of communication devices interposed between integrated sensors / actuators and a gateway device. In accordance with a preferred embodiment, the gateway translates the data encoded signals and embeds the information in a data packet using terminal control protocol / Internet protocol to communicate the data to a computing device on a wide area network. The computing device may comprise data collection and or control algorithms as desired. The computing device may forward command signals to the gateway device. In response thereto, the gateway may convert the command signals into appropriate command encoded signals for wireless transmission to a designated actuator integrated in a residential system. The present invention can also be viewed as providing a method for monitoring and controlling residential systems. In its broadest terms, the method can be described as: sensing a parameter; generating a wireless signal; traversing a wireless network to a gateway interconnected with a wide area network; communicating the parameter to a computing device on the network; generating a control signal; communicating the control signal to the gateway; converting the control signal; and broadcasting the control signal such that an appropriate actuator is energized.
Owner:SIPCO
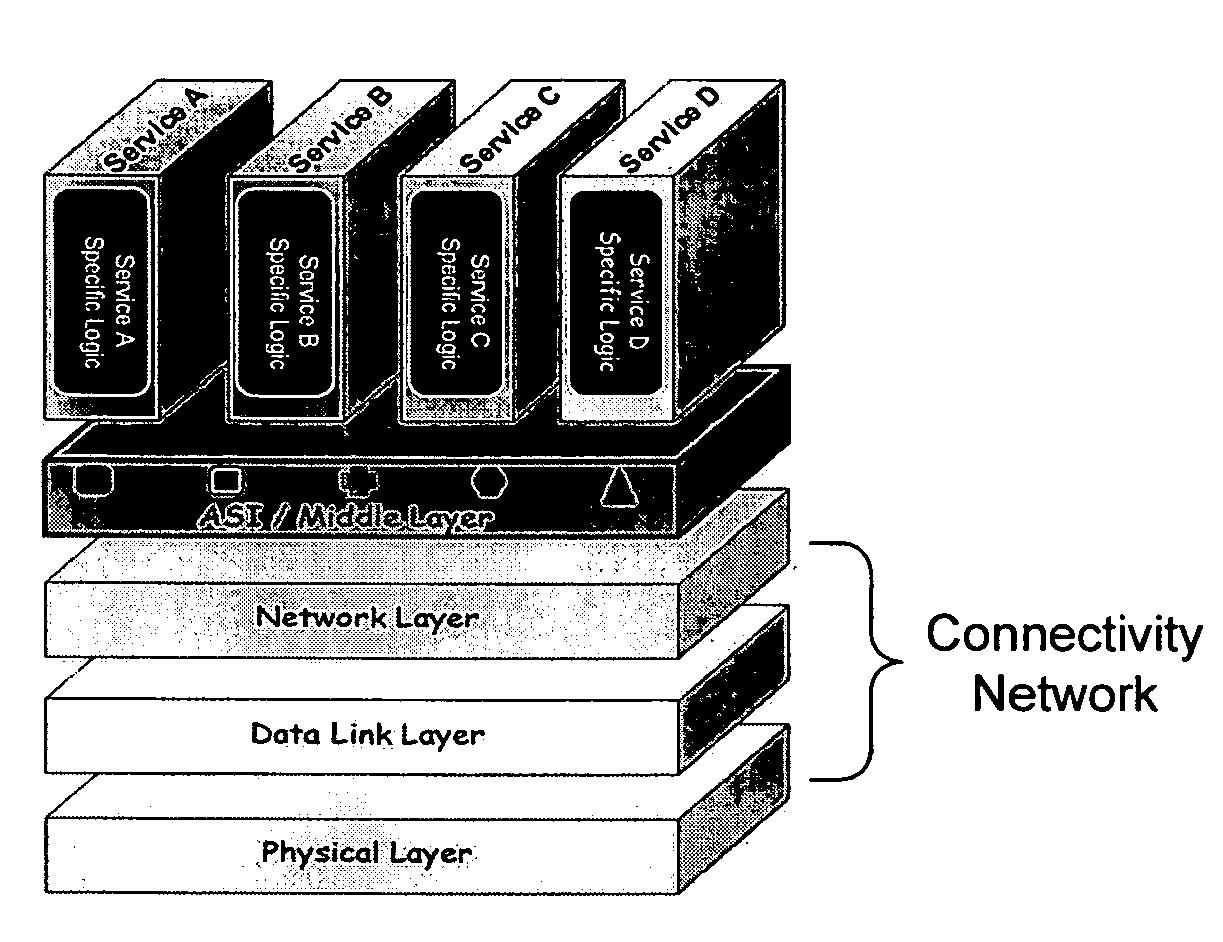
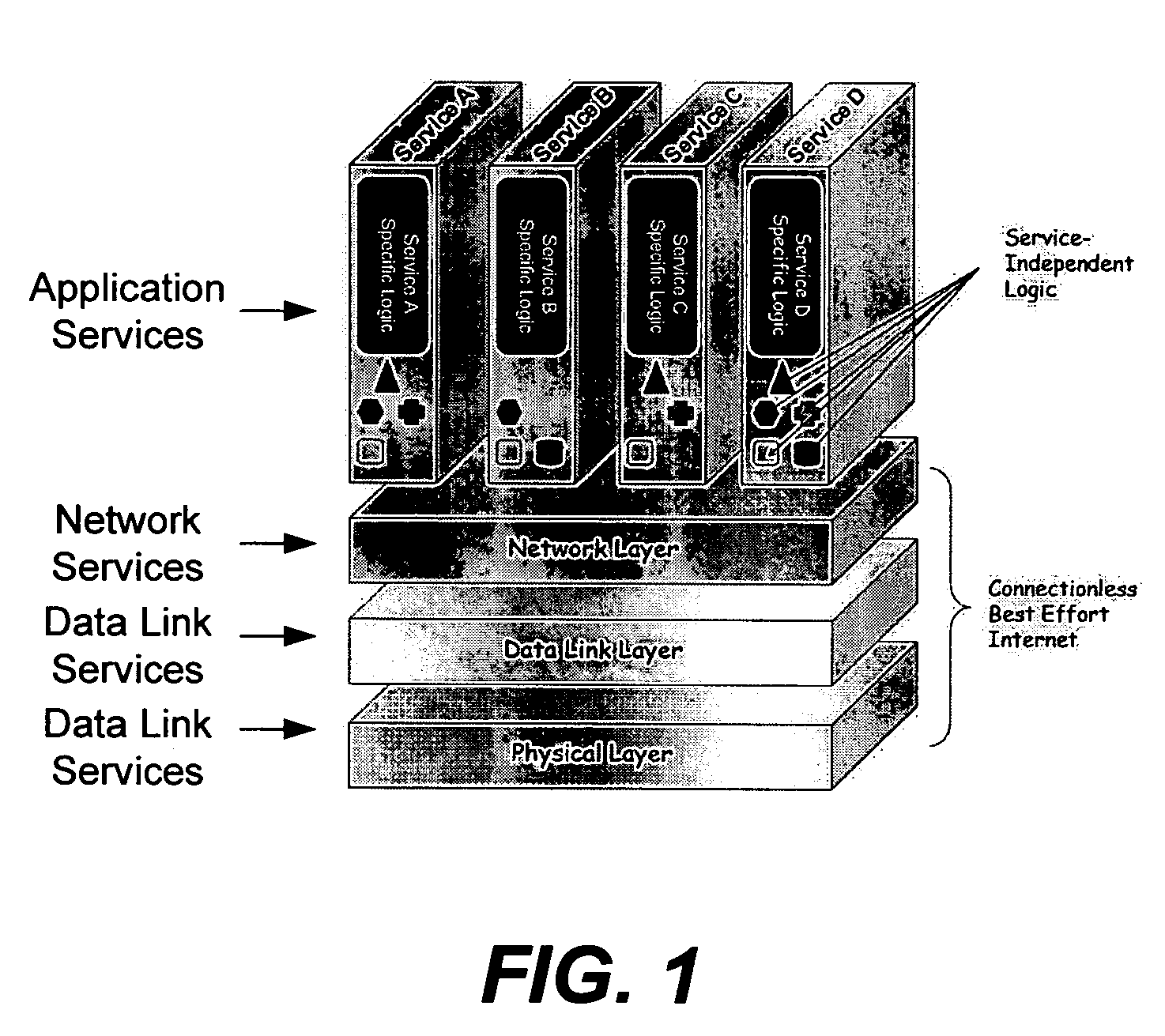
Application services infrastructure for next generation networks including one or more IP multimedia subsystem elements and methods of providing the same
A system for supporting a plurality of different applications utilizing a next generation network having a network layer includes an application services middleware between the applications and the network layer that includes a plurality of common infrastructure elements usable by the different applications. The common infrastructure elements provide both services associated with use of the network and services that are not associated with use of the network. At least one of the common infrastructure elements is an Internet Protocol (IP) Multimedia Subsystem (IMS) element.
Owner:BELLSOUTH INTPROP COR
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
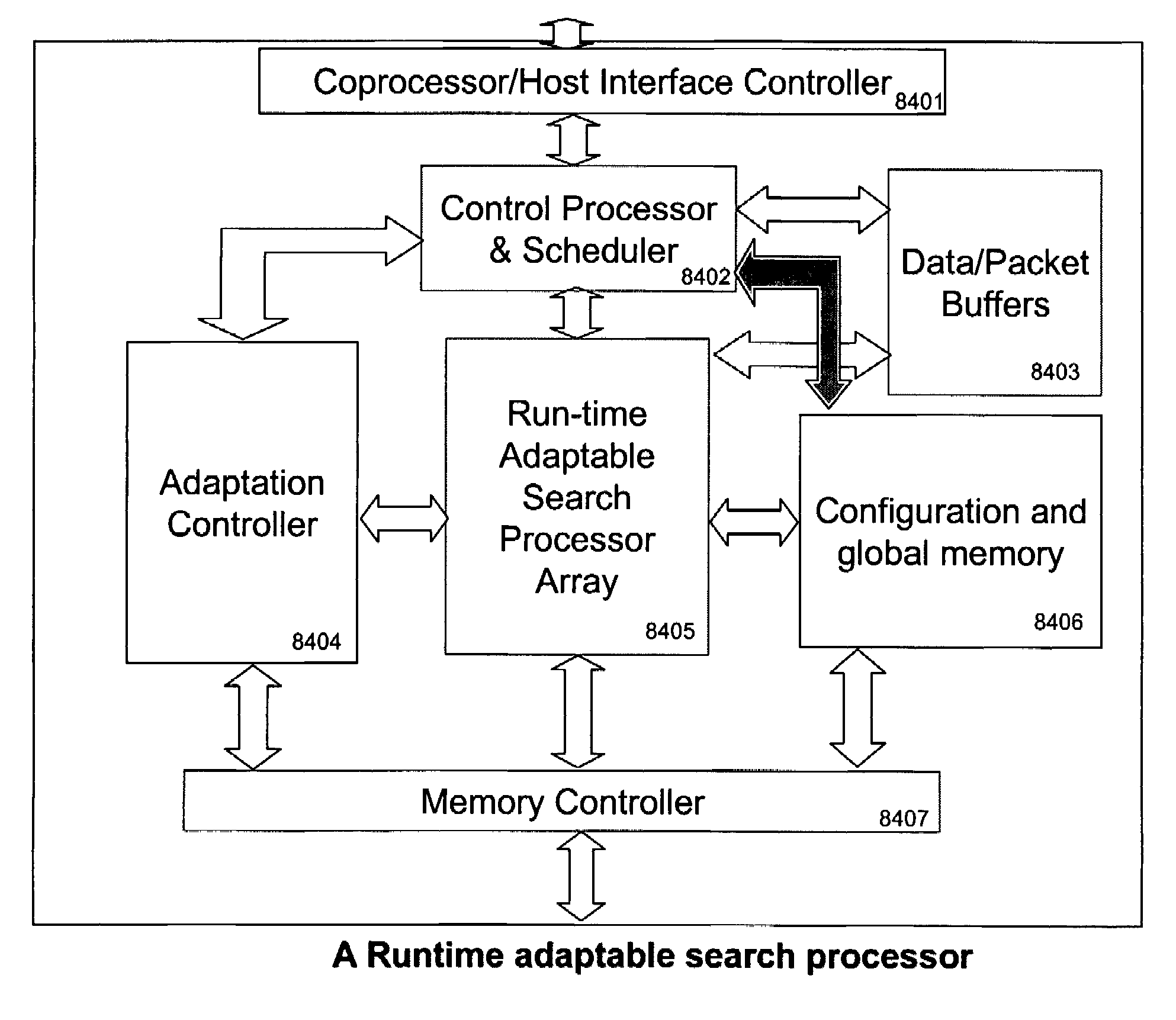
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
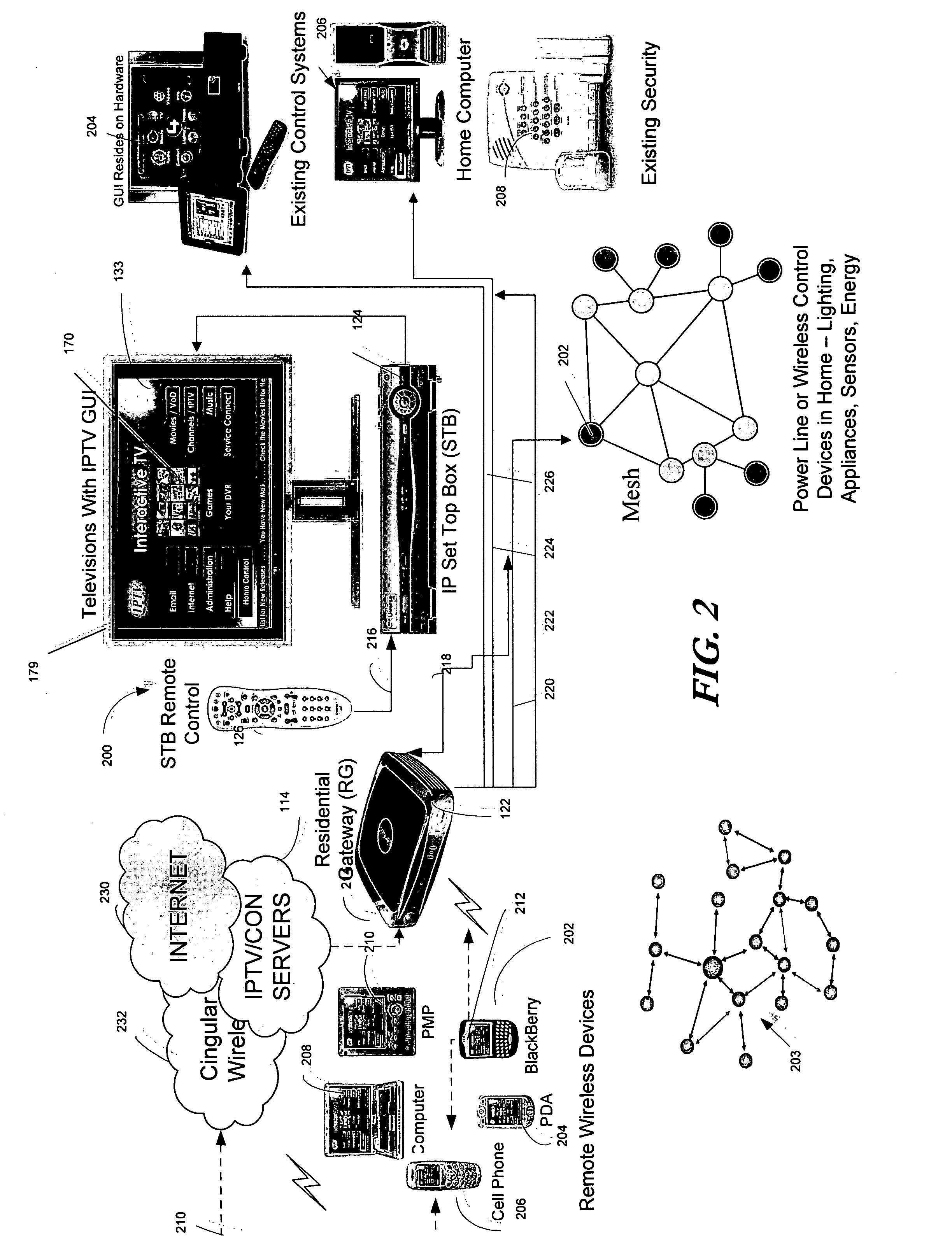
Home automation system and method
InactiveUS20070192486A1Television system detailsColor television detailsTelevision systemDevice status
In one embodiment a method is disclosed for interacting with a controllable device in an internet protocol television (IPTV) system. The method receives at a control server, device state data for the controllable device from a first client device in the IPTV network; accesses user interface (UI) data from a database accessible to the control server; reflects the device state data in the UI data at the control server; and sends the UI data from an IPTV server to the first client device. In another embodiment a system is disclosed for interacting with a controllable device in an internet protocol television (IPTV) system. The system receives at a control server, device state data for the controllable device from a first client device in the IPTV network; accesses user interface (UI) data from a database at the control server; reflects the device state data in the UI at the control server; and sends the UI from an IPTV server to the first client device.
Owner:SBC KNOWLEDGE VENTURES LP
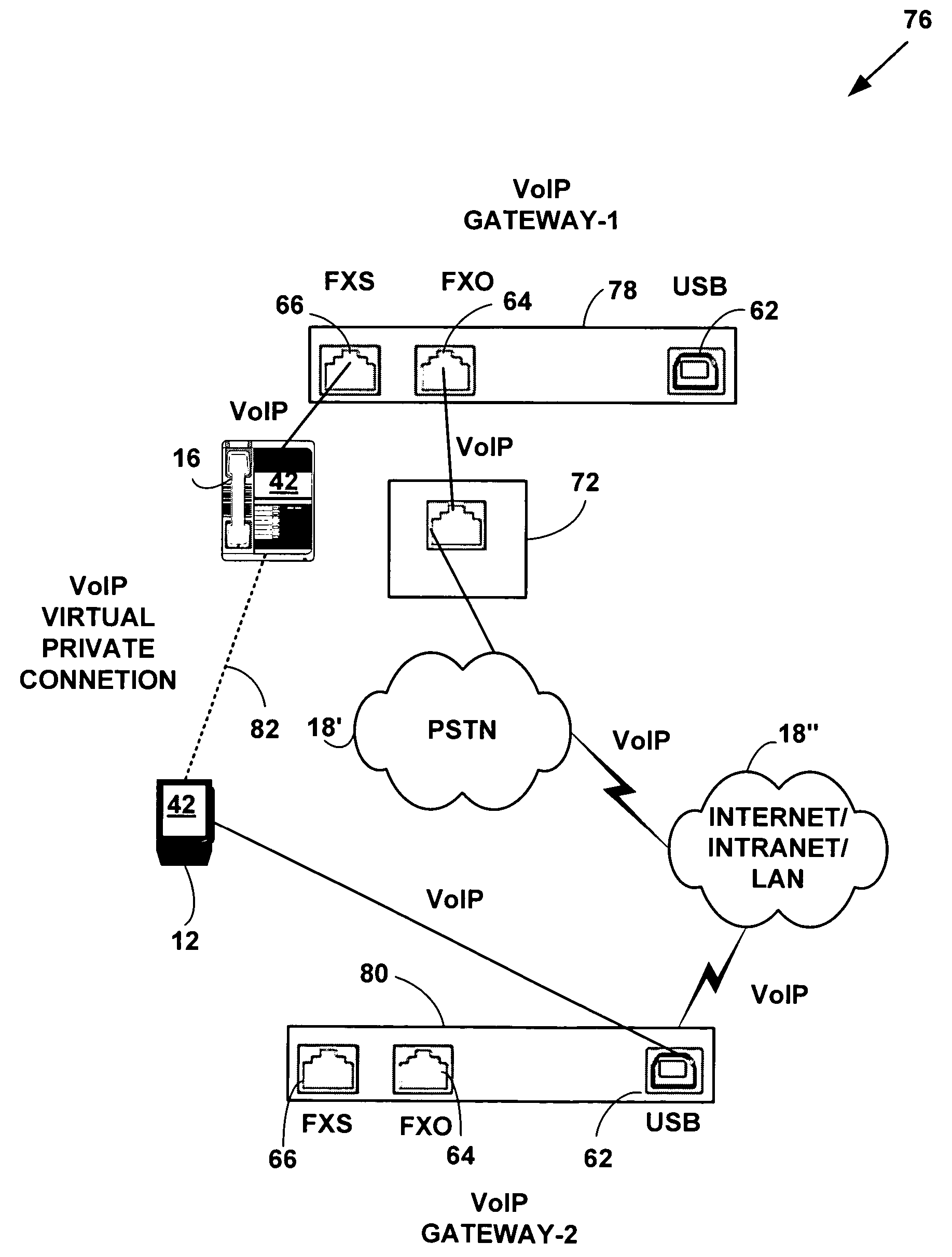
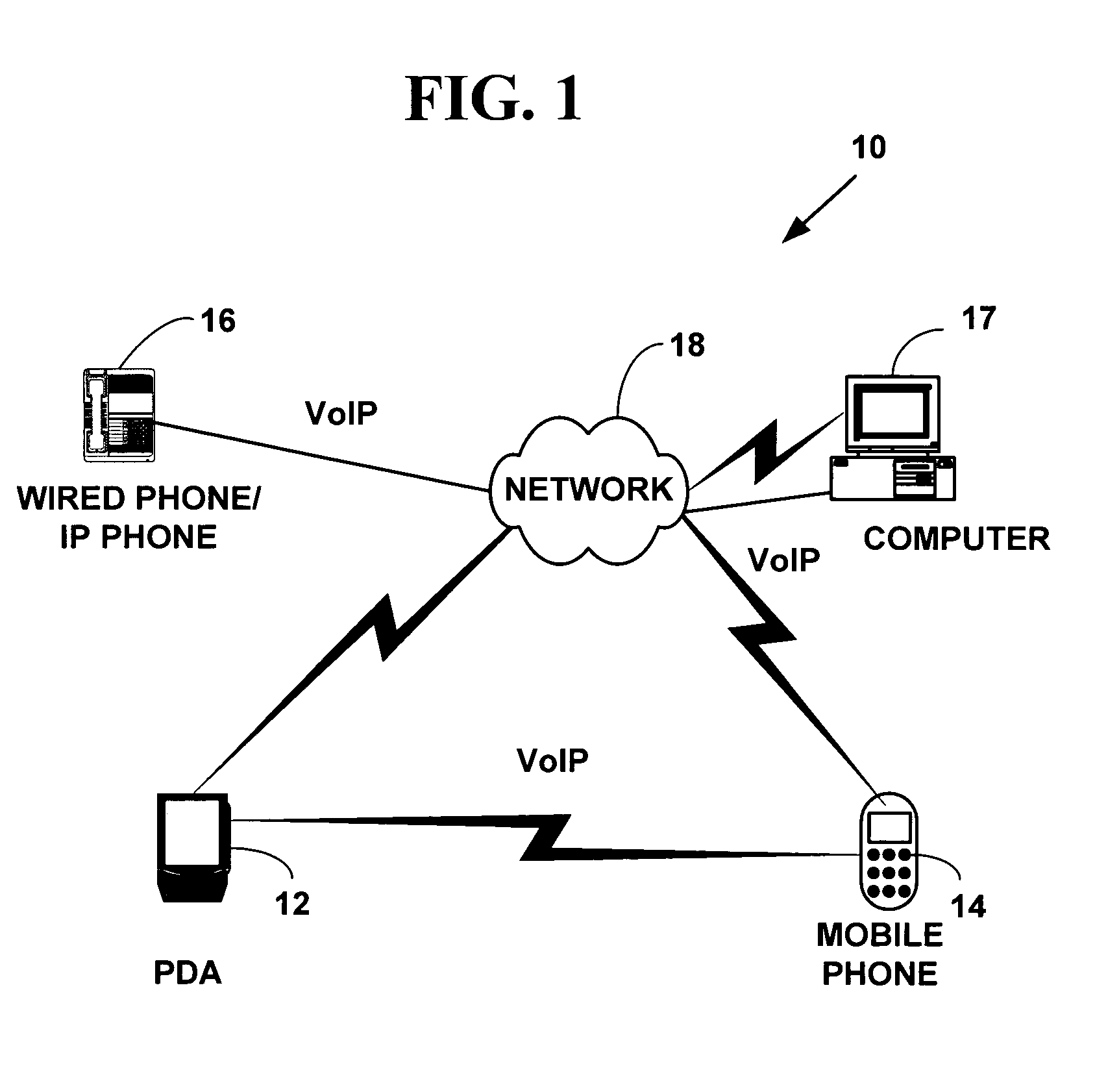
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
Method and system for wireless QOS agent for all-IP network
A wireless quality of service (QoS) agent for an all-Internet Protocol (IP) network. The QoS agent couples to an all-IP network. The coupling means includes communication means for transfer of information between the agent and a QoS manager of the all-IP network. The agent is also able to seamlessly extend QoS support for multimedia applications from wireline to wireless and control QoS of the multimedia applications sent over wireless connections on the all-IP network.
Owner:BLACKBERRY LTD
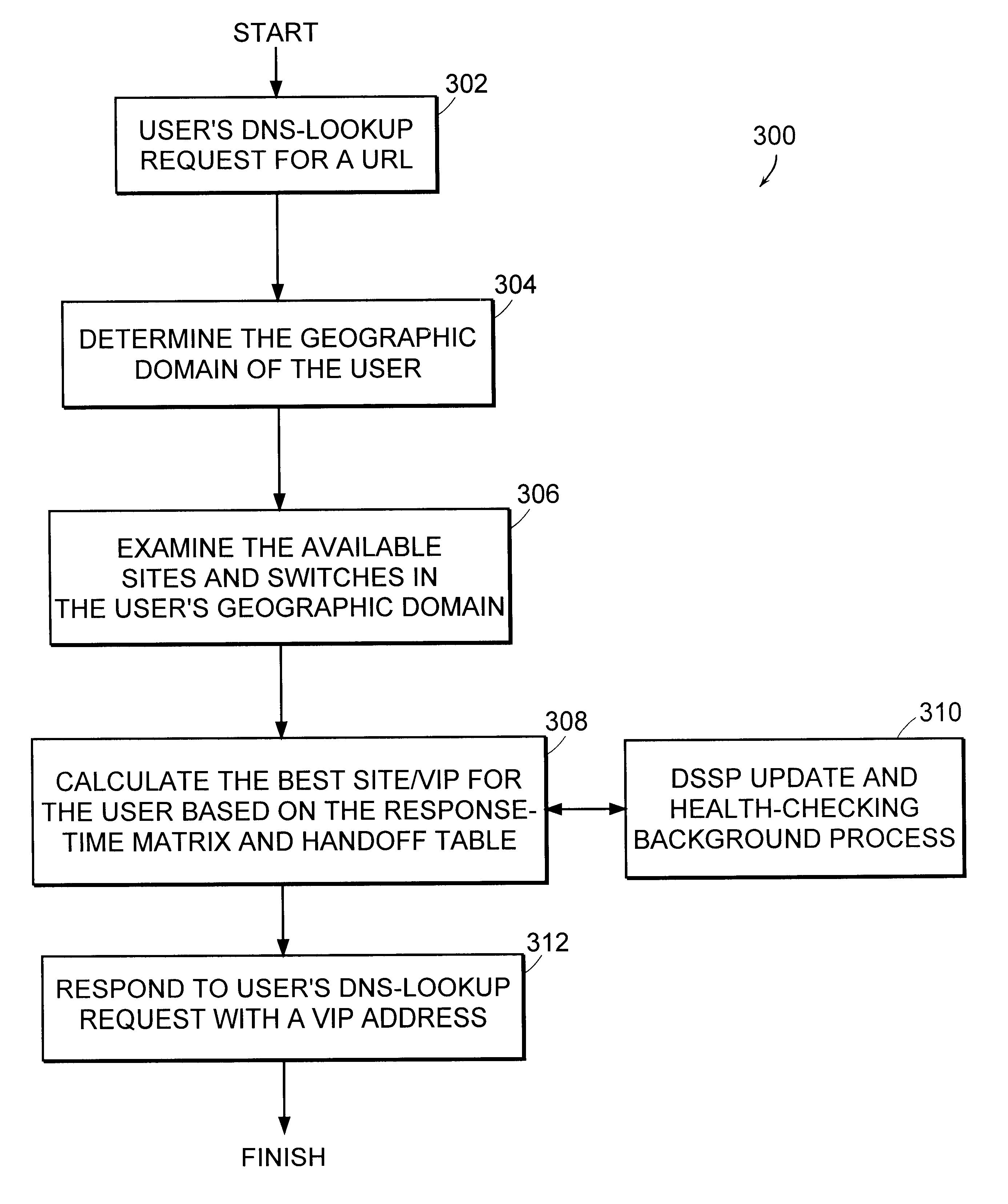
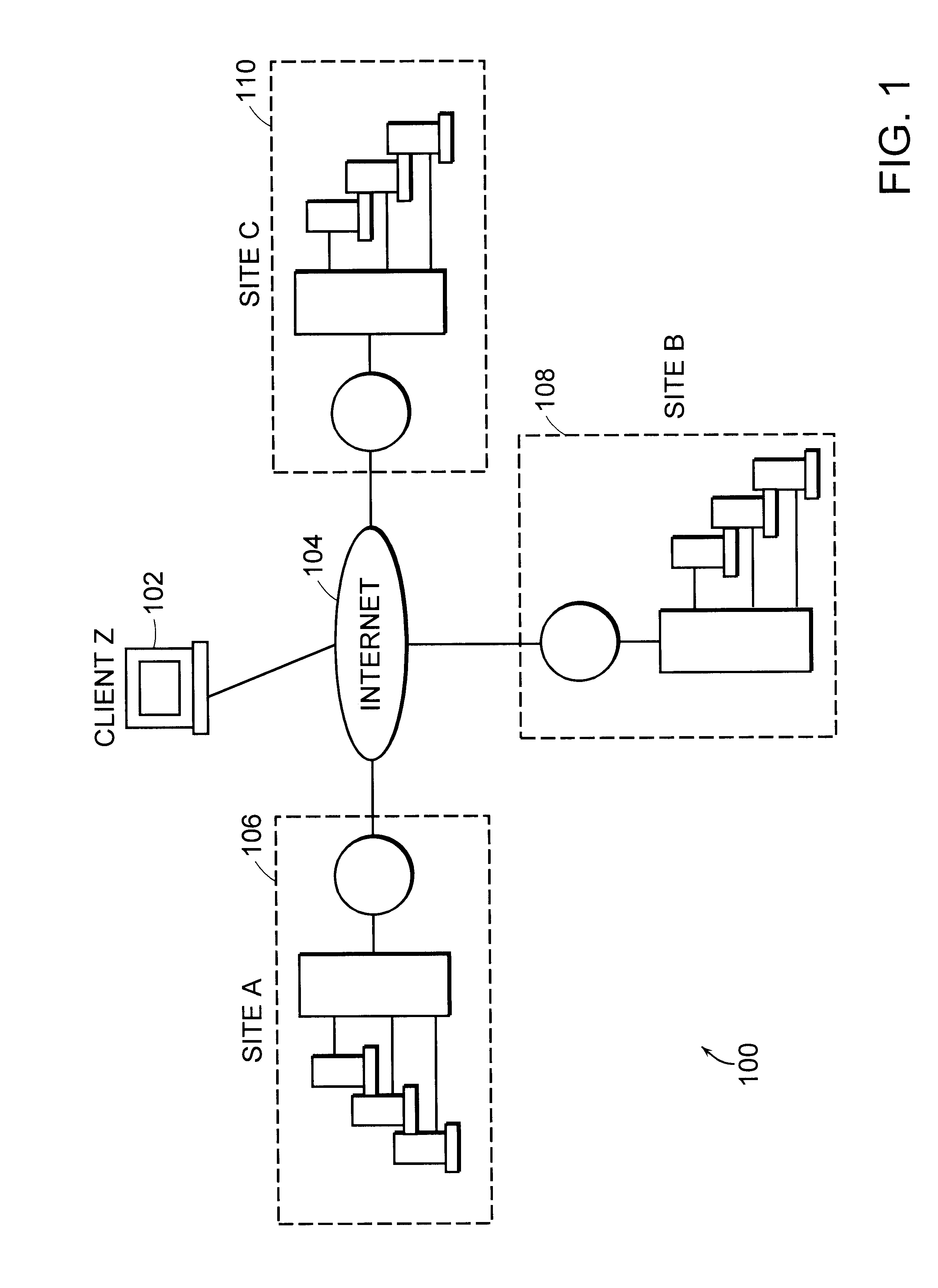
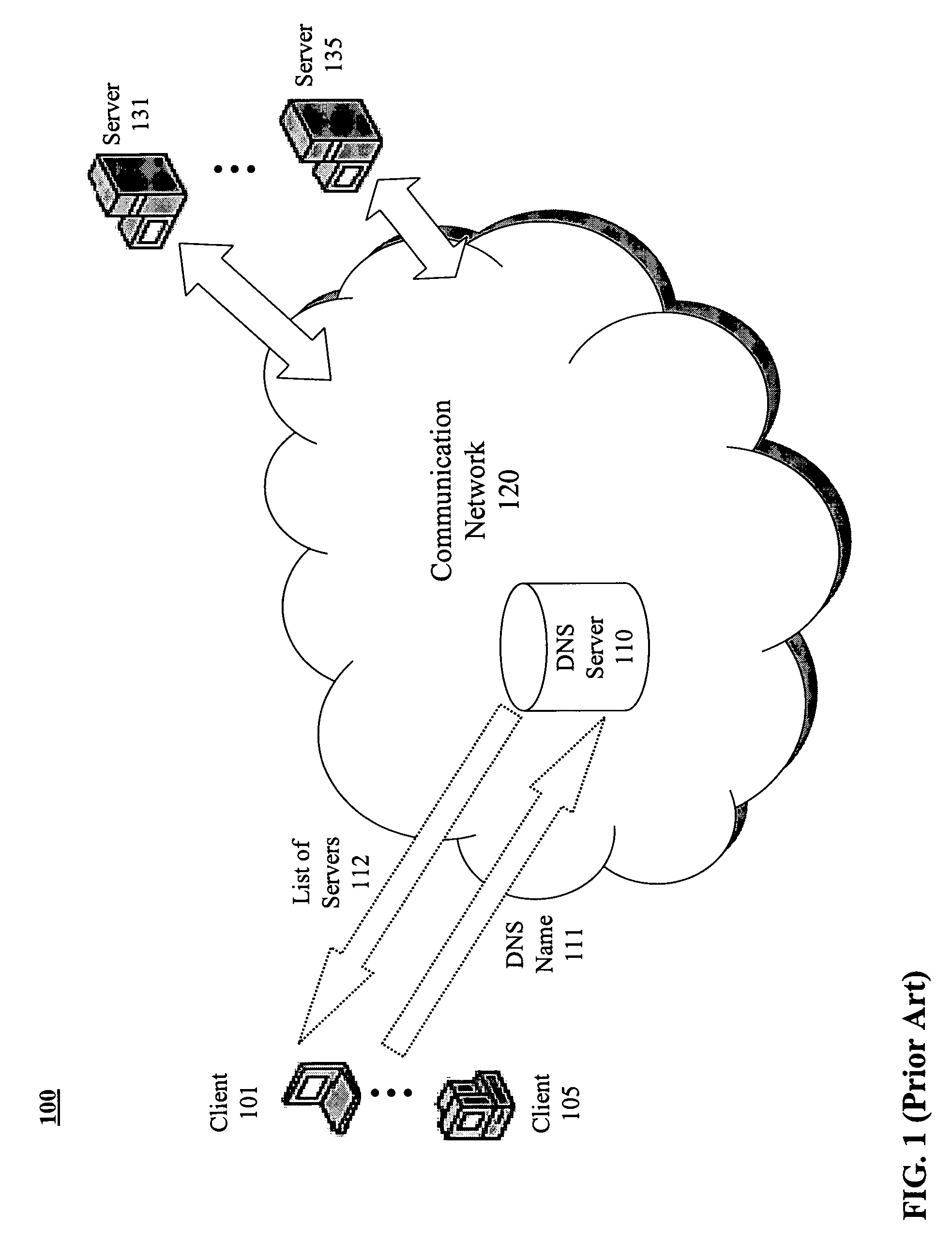
Distributed load-balancing internet servers
The actual site that serves the Web pages to a client in response to a URL domain name is automatically and transparently selected from a list of many switches each having identical data storage. In a peer hand-off process, a switch receives domain name server lookup request for a particular virtual Internet protocol (VIP) domain name. The switch examines the source IP-address for the domain name server request, examines the user's IP-address, and determines if there is server site that is geographically close to that user. The switch examines an ordered hand-off table corresponding to the domain. The switch chooses a next remote server (or its own VIP) in line based on, (a) the remote server location compared to domain name server request source, (b) the remote servers' weights, and (c) the remote server that experienced the previous hand-off. The switch then sends the domain name server response back to client domain name server with the IP-addresses in an ordered list.
Owner:RADWARE
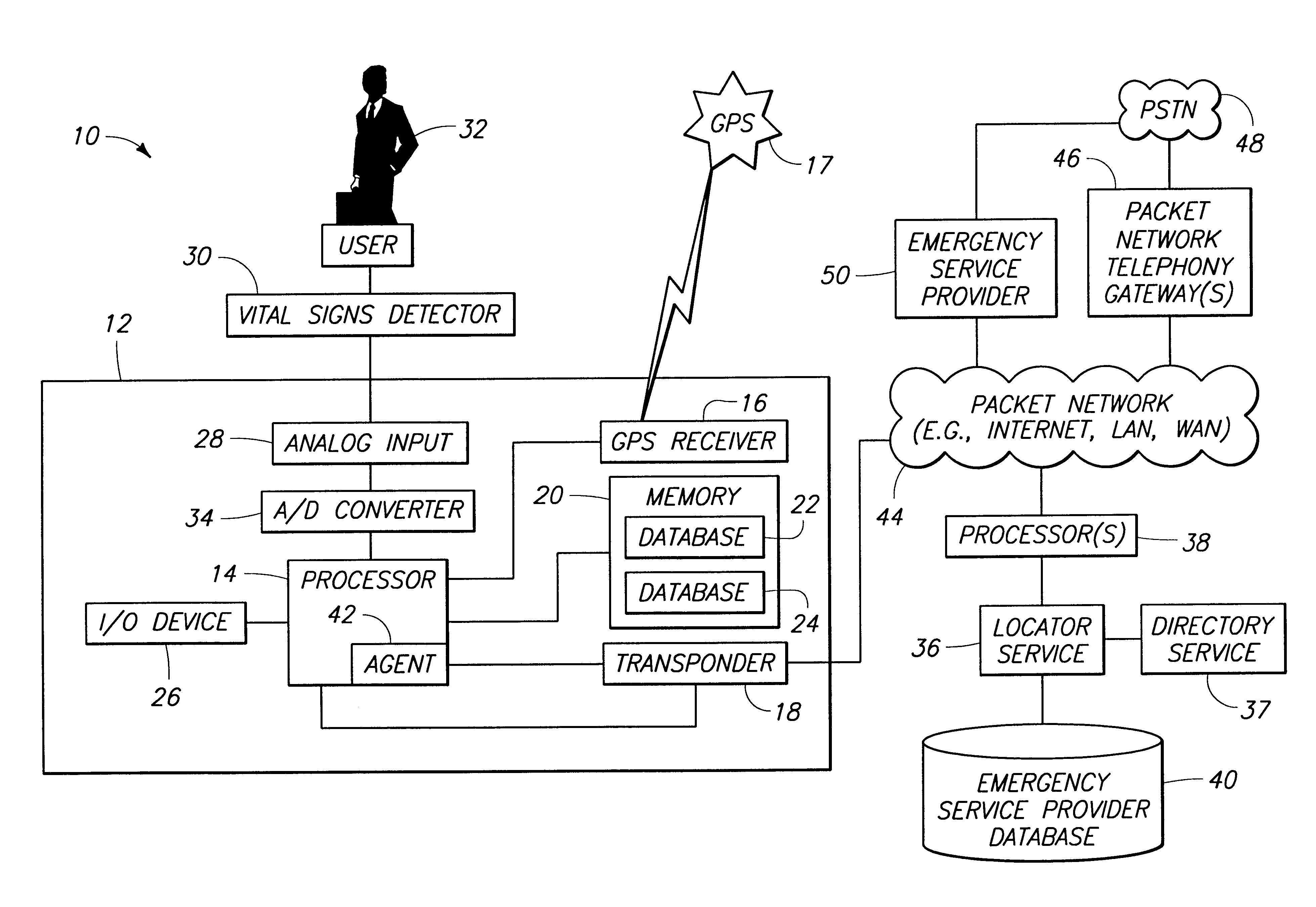
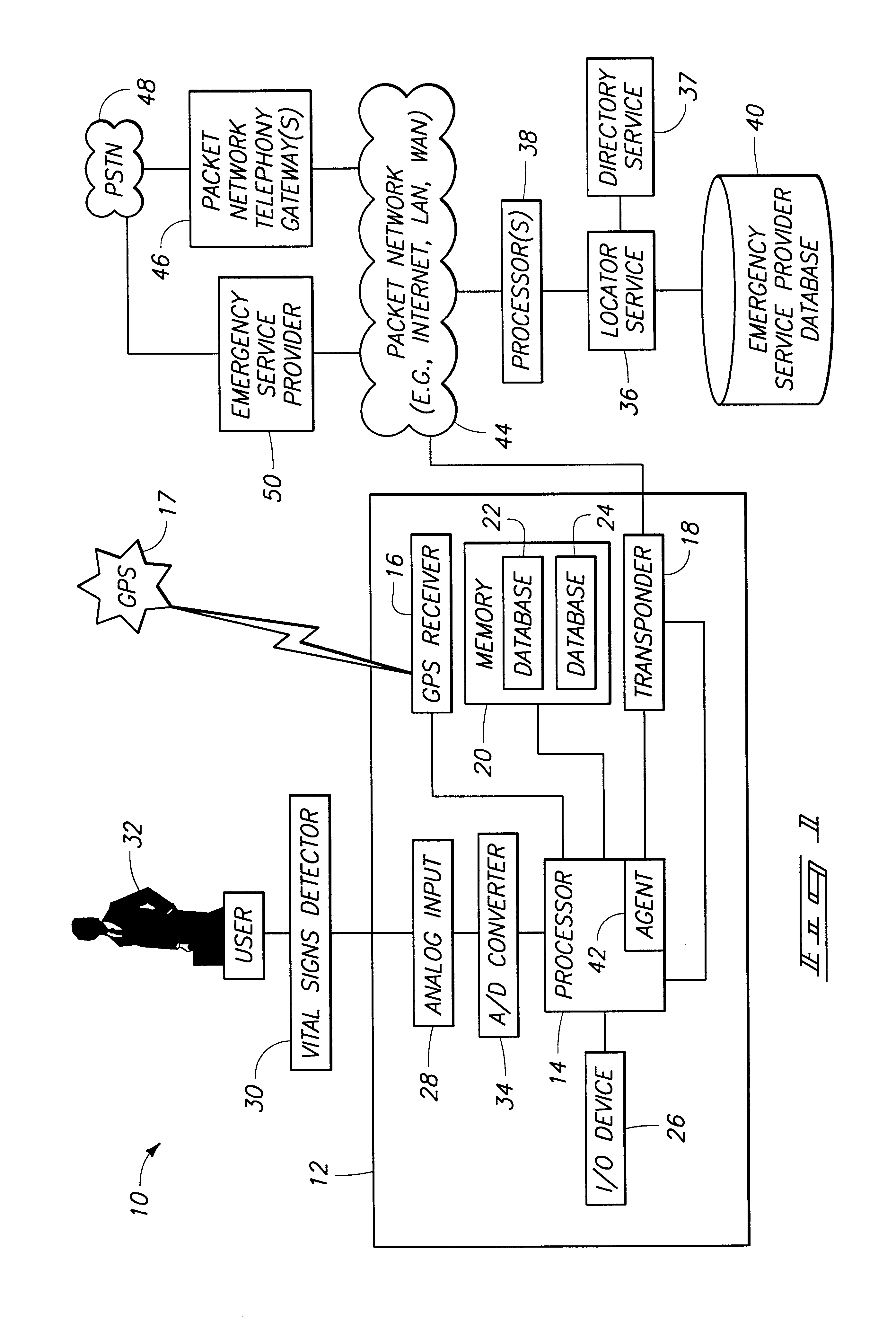
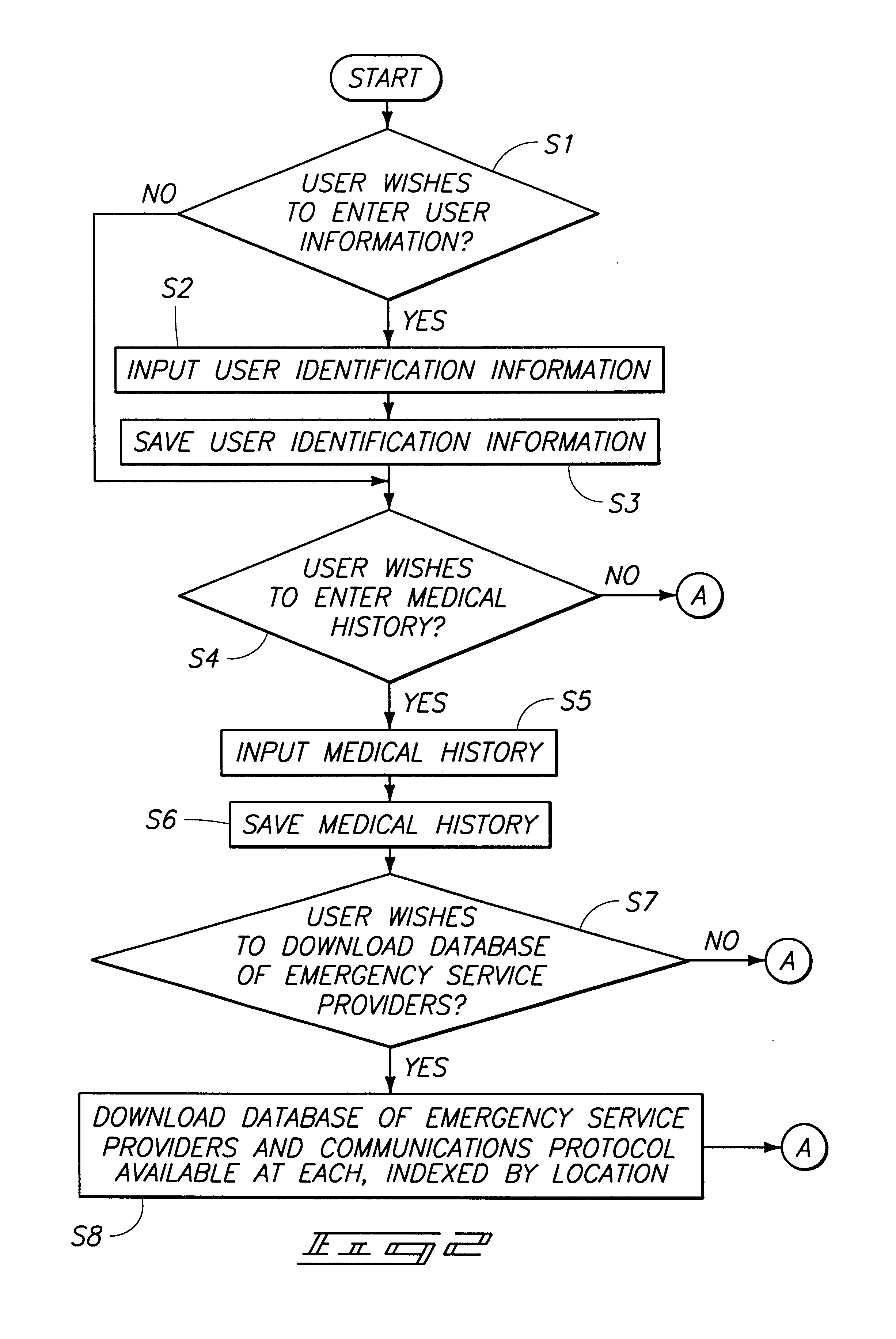
Mobile data device and method of locating mobile data device
InactiveUS6868074B1Rapid diagnosisEmergency connection handlingPosition fixationGps receiverMobile device
A method including providing a PDA having a processor, a memory coupled to the processor, a GPS receiver coupled to the processor and a RF transponder capable of communicating using Internet Protocol; storing user identification information in the memory; storing medical history information in the memory; determining location using the GPS receiver; transmitting the determined location to a service using the RF transponder; and in response to a request of emergency service by a user of the PDA, contacting the service and transmitting an emergency request to the service using the RF transponder. A PDA comprising a processor; a memory coupled to the processor; a GPS receiver coupled to the processor; and a wireless transponder capable of communicating using Internet Protocol, the PDA being configured to store user identification information in the memory, store medical history information in the memory, determine location using the GPS receiver, transmit the determined location to a service using the wireless transponder, and, in response to a request of emergency service by a user of the PDA, contact the service and transmit an emergency request to the service using the wireless transponder.
Owner:VERIZON PATENT & LICENSING INC
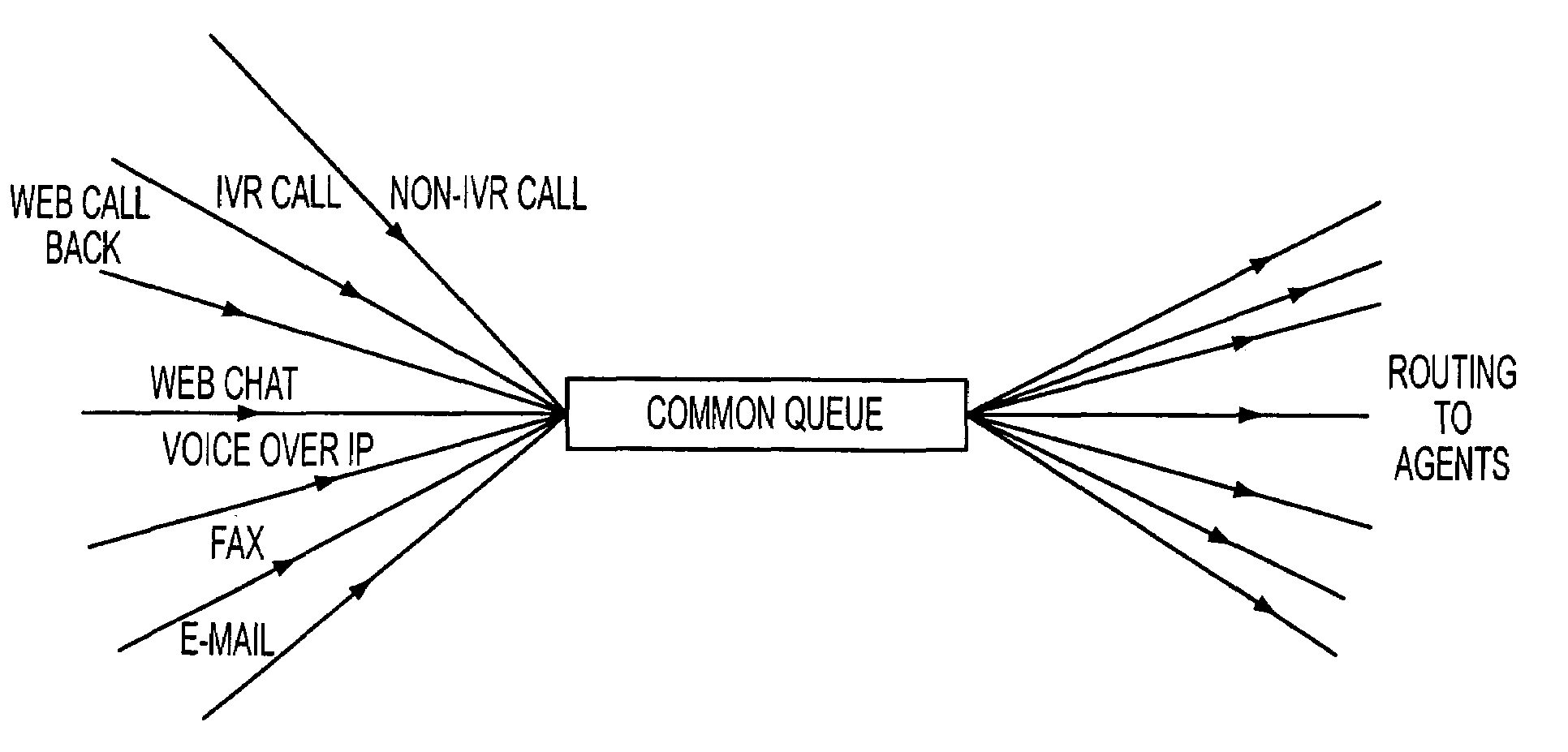
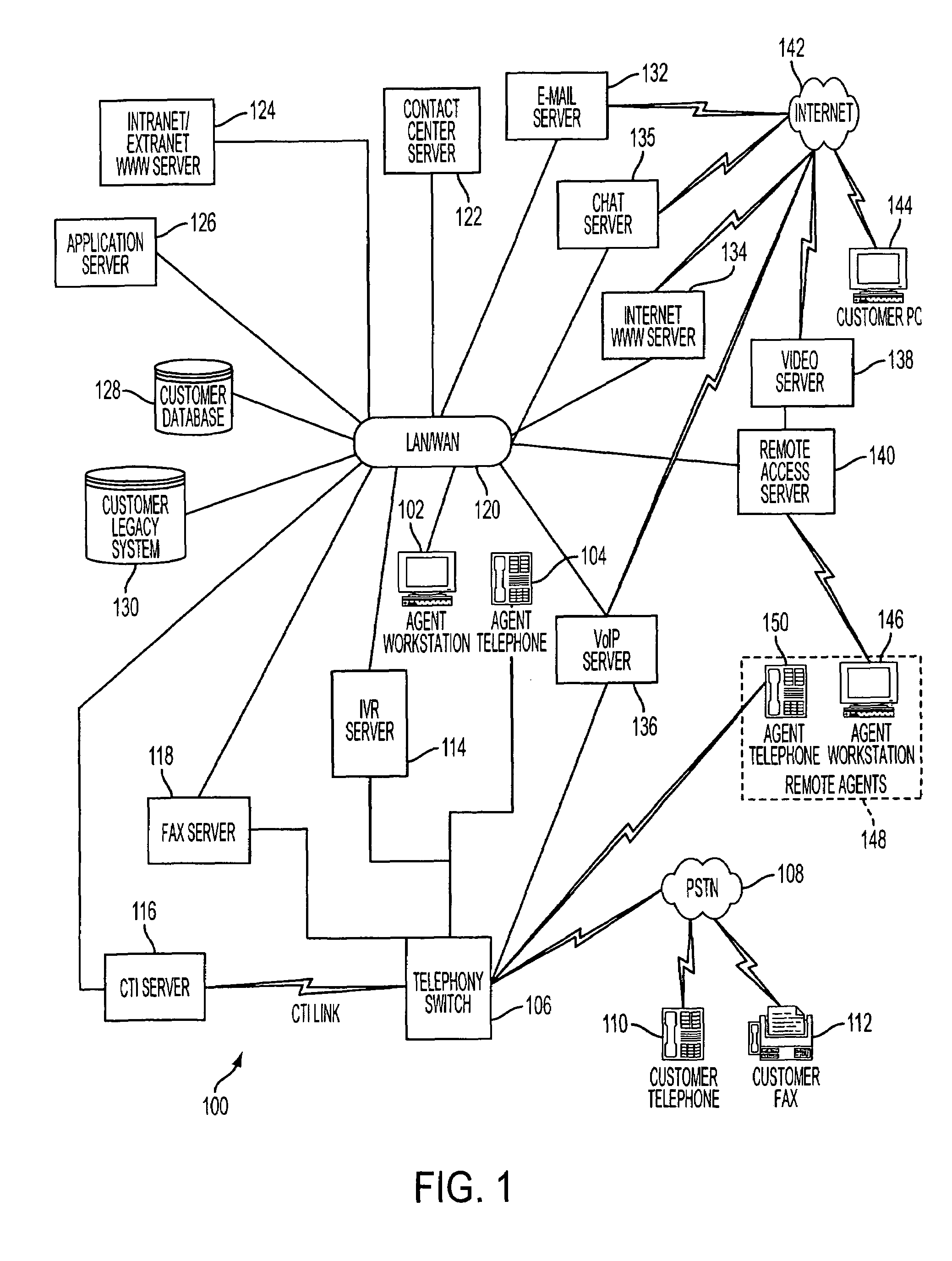
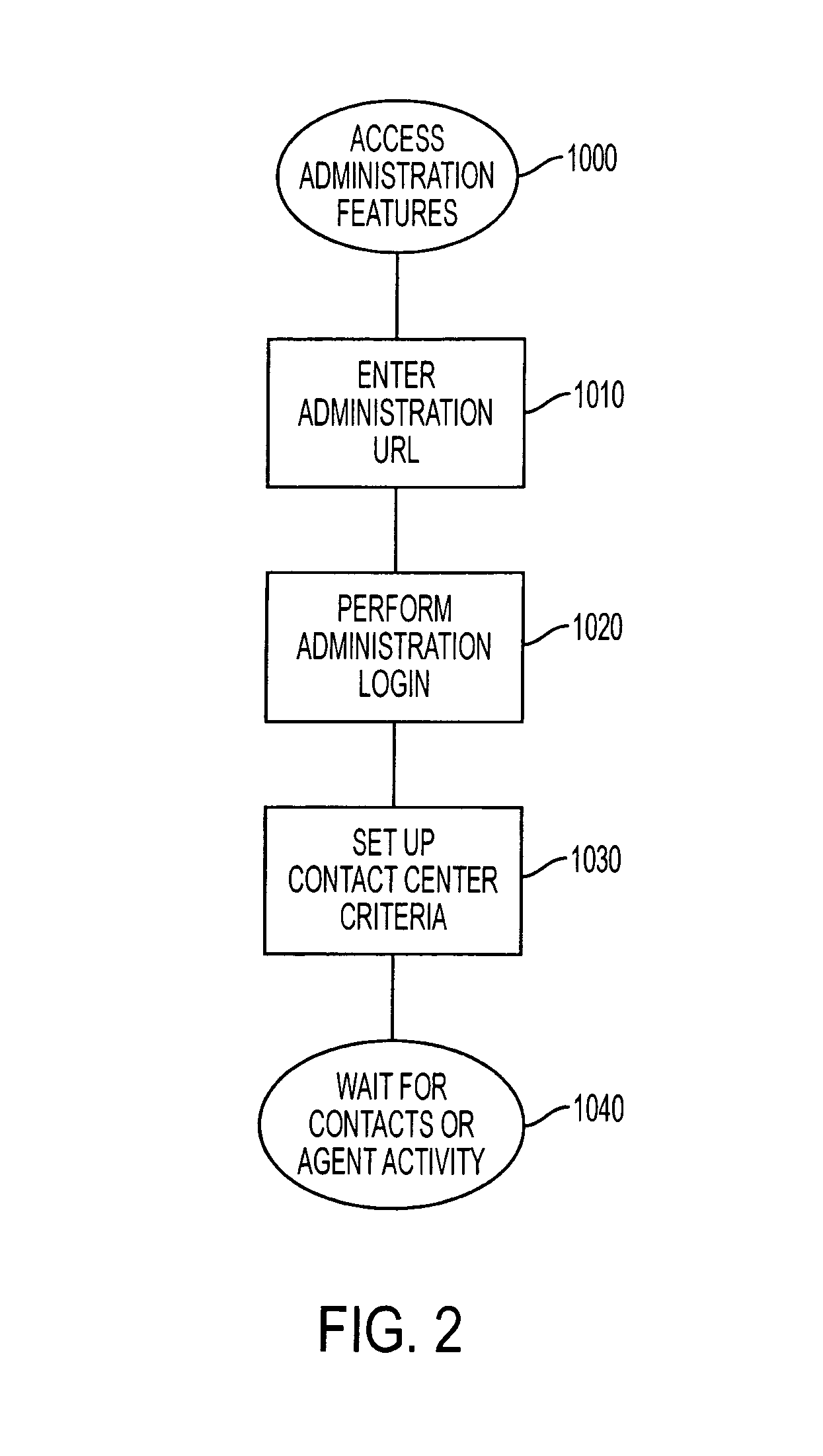
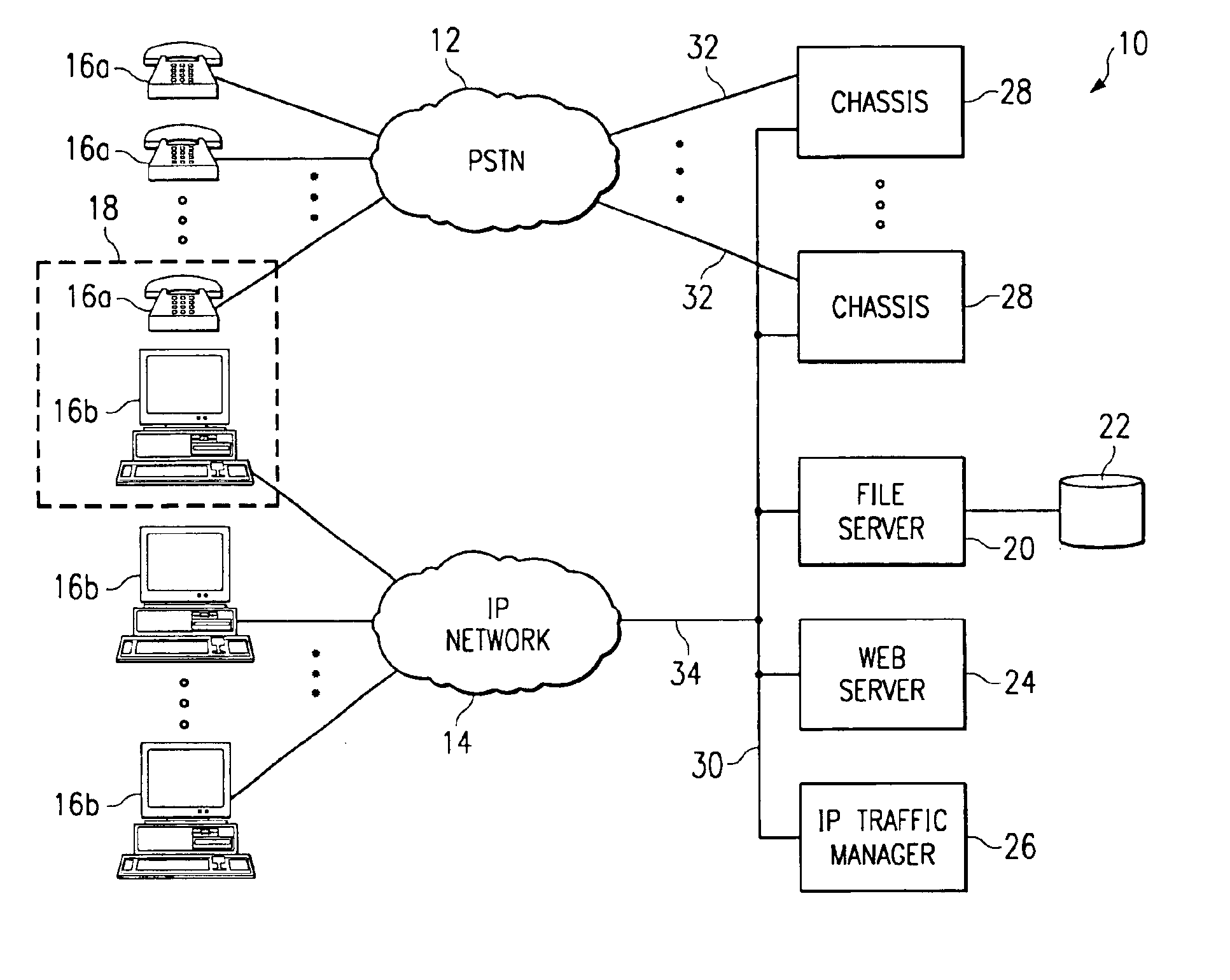
Contact center system capable of handling multiple media types of contacts and method for using the same
InactiveUS7092509B1Efficiently and effectively handlingManual exchangesAutomatic exchangesMedia typeContact center
A contact center system and method employing a plurality of agent workstations, and which includes a queuing component, capable of receiving contacts of different media-types, such as telephone calls, e-mails, facsimiles, web chat, voice over internet protocol, and so on, and maintaining the different media types contacts in a common queue while awaiting routing to the agent workstations. The system further comprises a routing component which routes the queued contacts to the agents based on criteria of the contacts, criteria of the agents, or both. A media changing component of the system is capable of changing a media-type of any of the media-type contacts to generate a changed media-type contact, while the queuing component is capable of entering the changed media-type contact in the common queue, and the routing component is capable of routting the queued changed media-type contact to at least one of the workstations. A contact handling component initiates an event at any of the workstations in response to the contact being routed to the workstation, so that an agent at the workstation can handle the contact as appropriate.
Owner:MICROLOG
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Method and computer program product for internet protocol (IP)-flow classification in a wireless point to multi-point (PtMP) transmission system
InactiveUS7251218B2Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceWireless access point
A system and method for Internet Protocol (IP) flow classification group IP flows in a packet-centric wireless point to multi-point telecommunications system is disclosed. The method comprises analyzing an IP flow in a packet-centric manner, classifying the IP flow, scheduling the IP flow for transmission over a shared wireless bandwidth between a wireless base station and at least one subscriber customer premises equipment (CPE) station, allocating the shared wireless bandwidth to a communication of the IP flow between the wireless base station and a subscriber CPE station so as to optimize end-user quality of service (QoS) associated with the IP flow.
Owner:INTELLECTUAL VENTURES I LLC
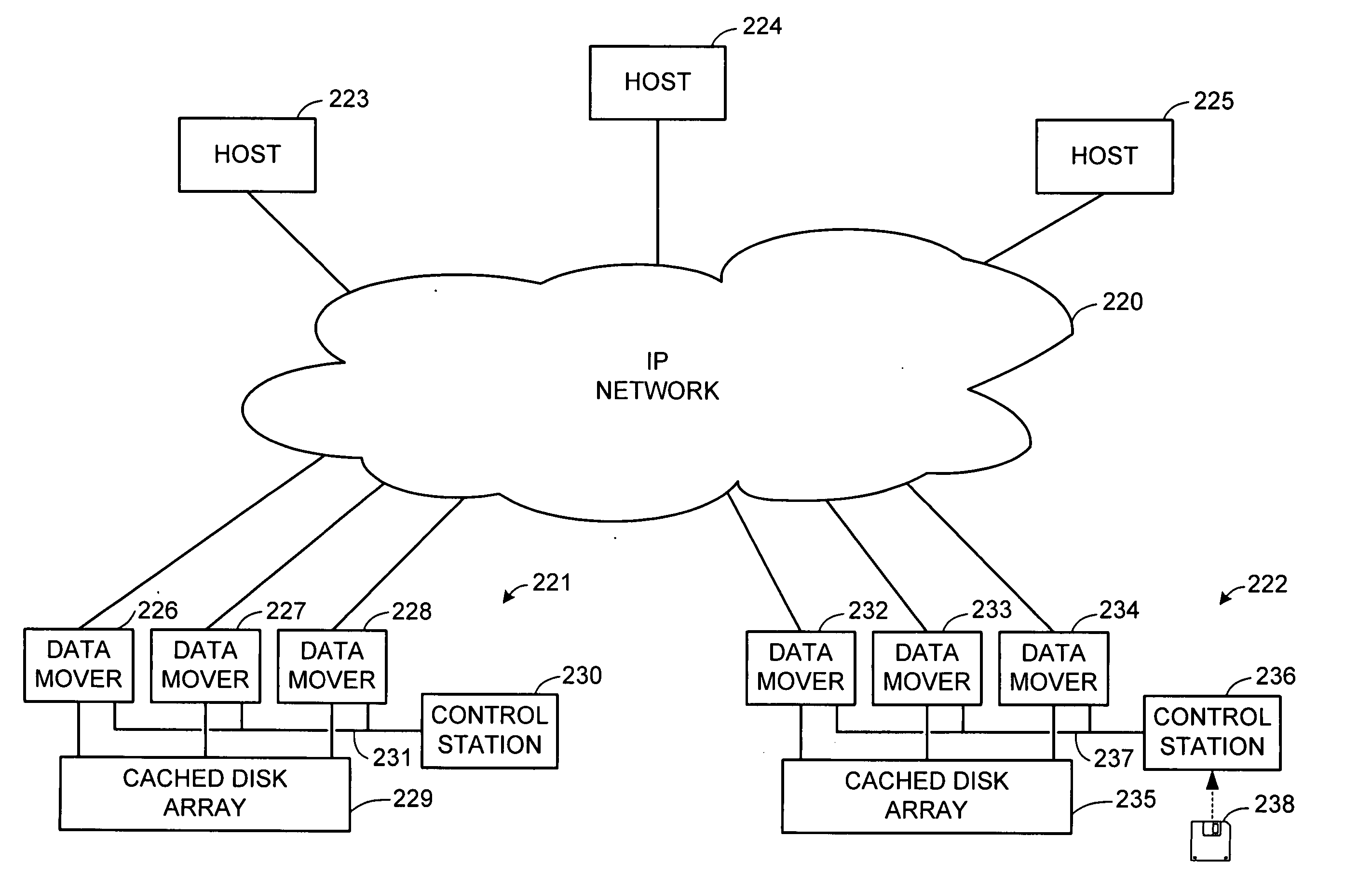
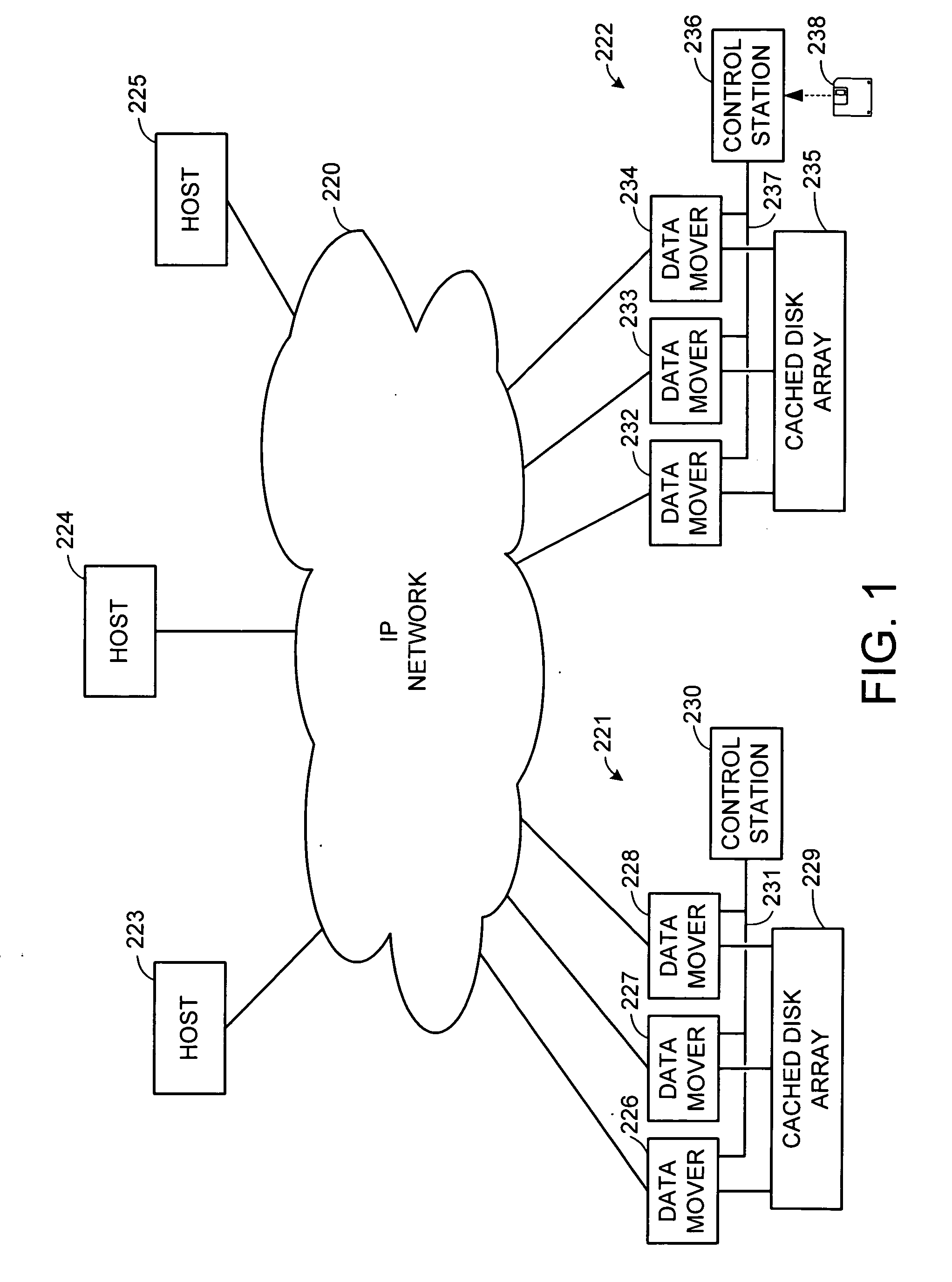
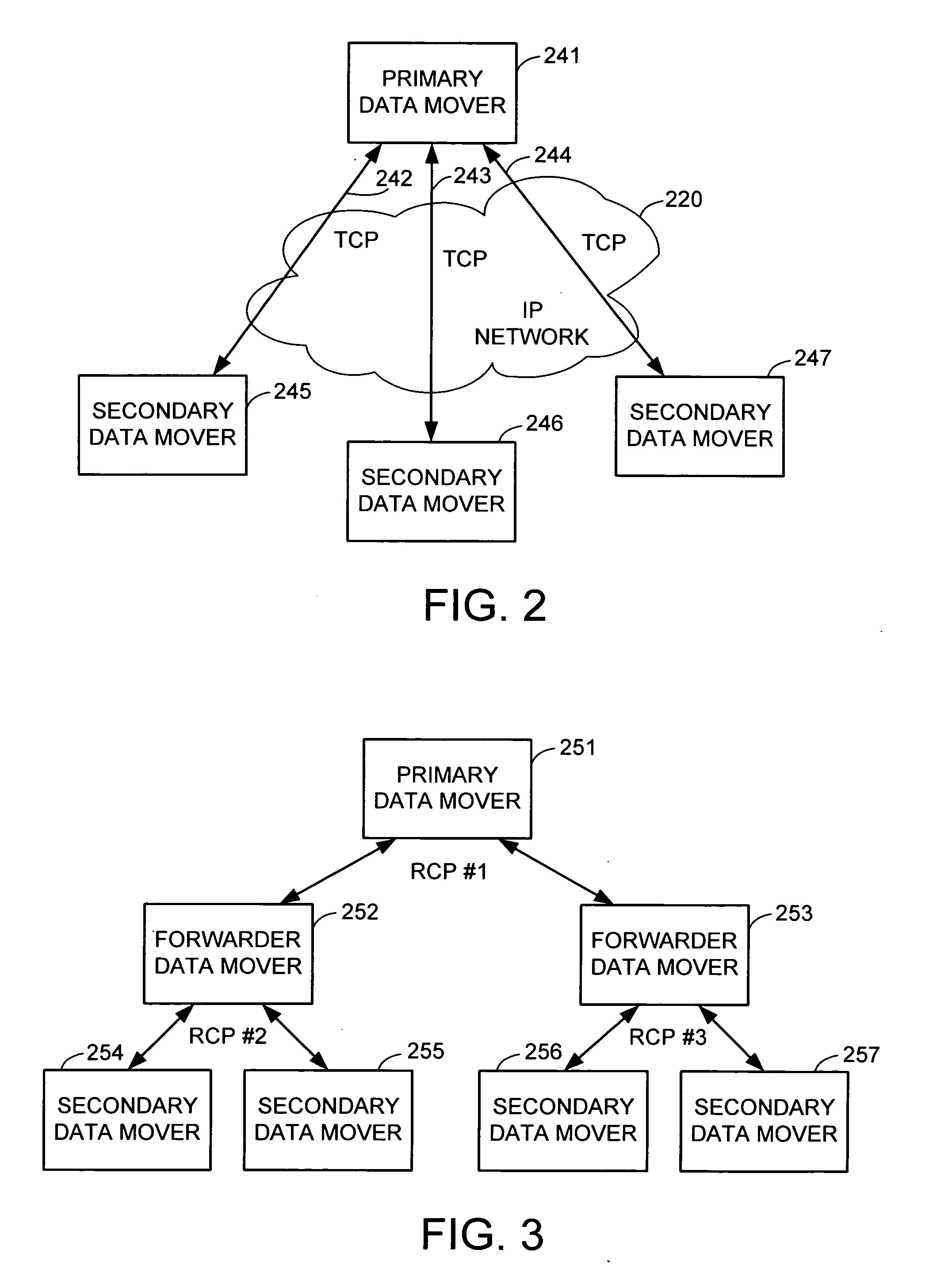
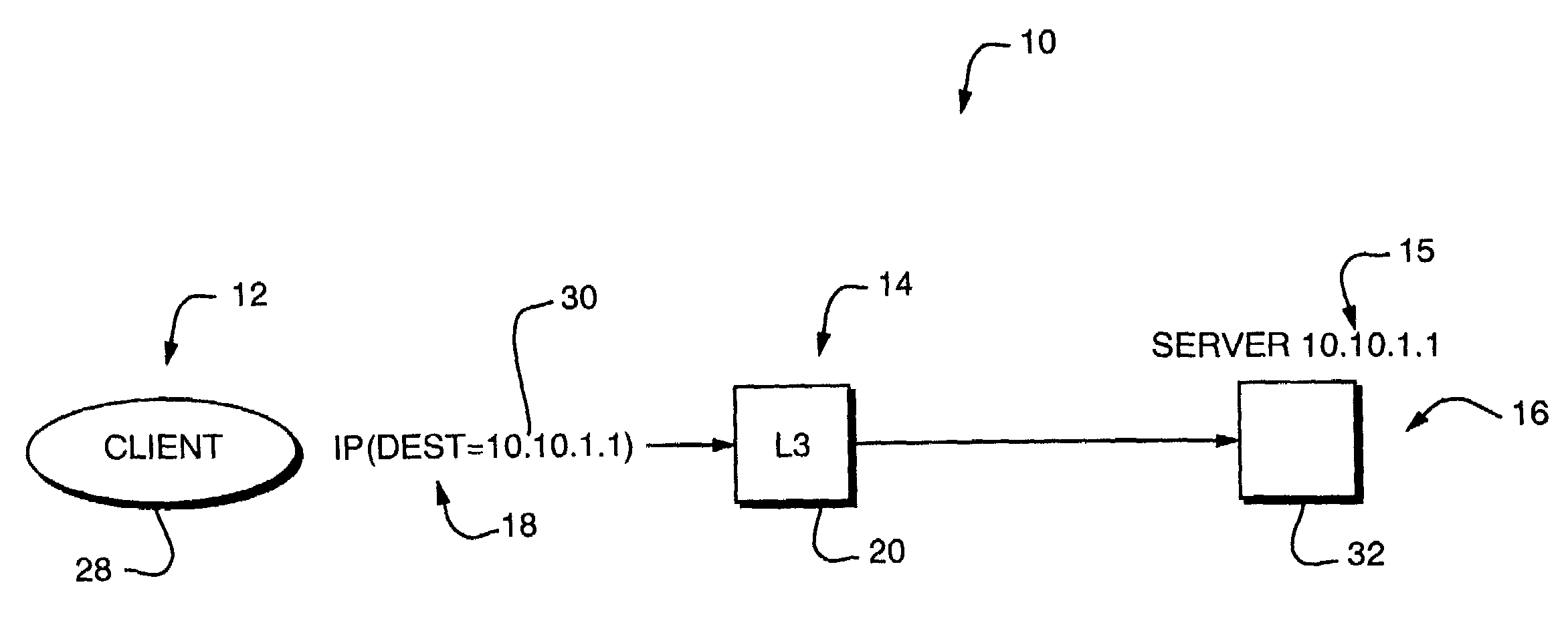
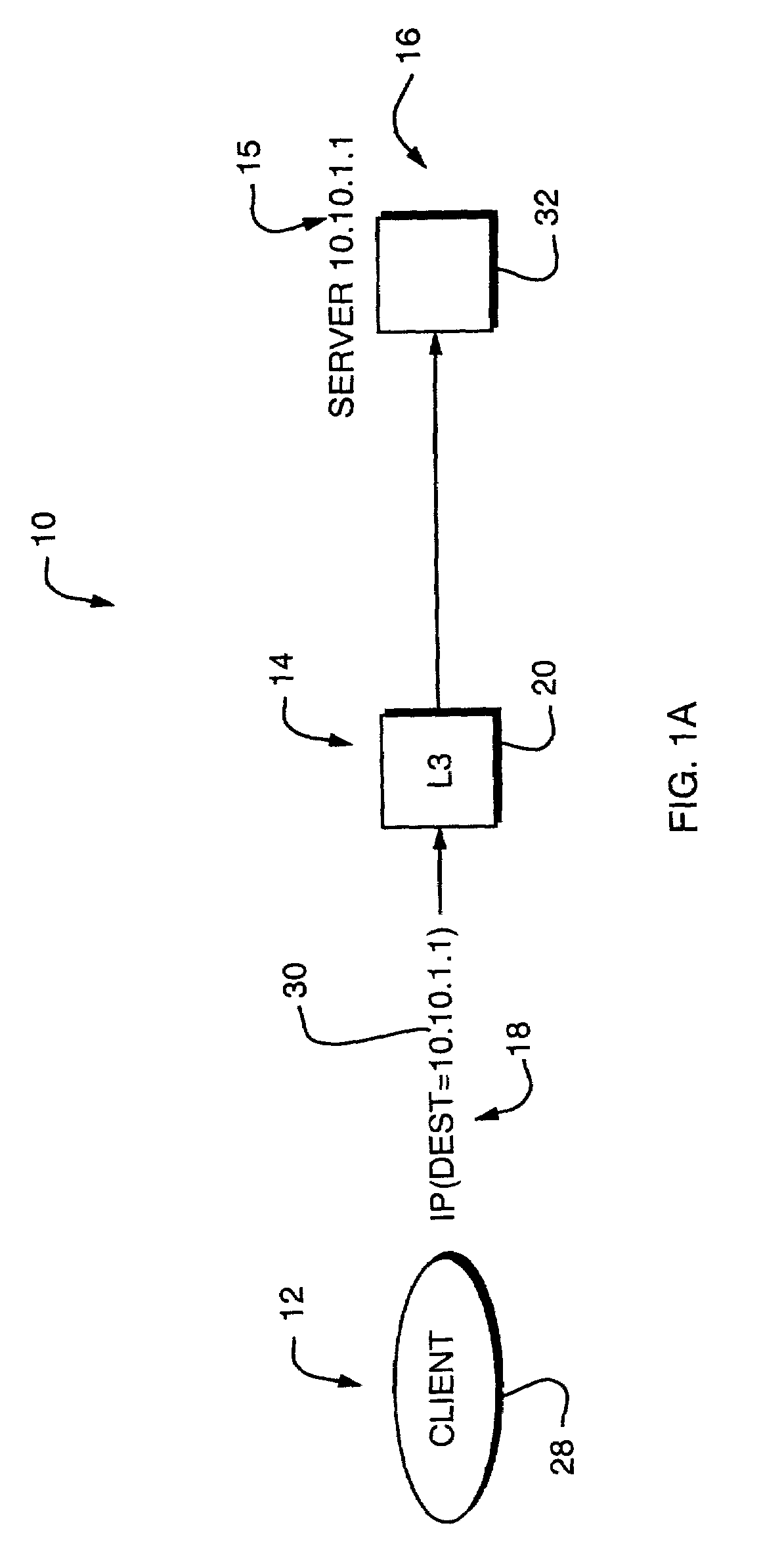
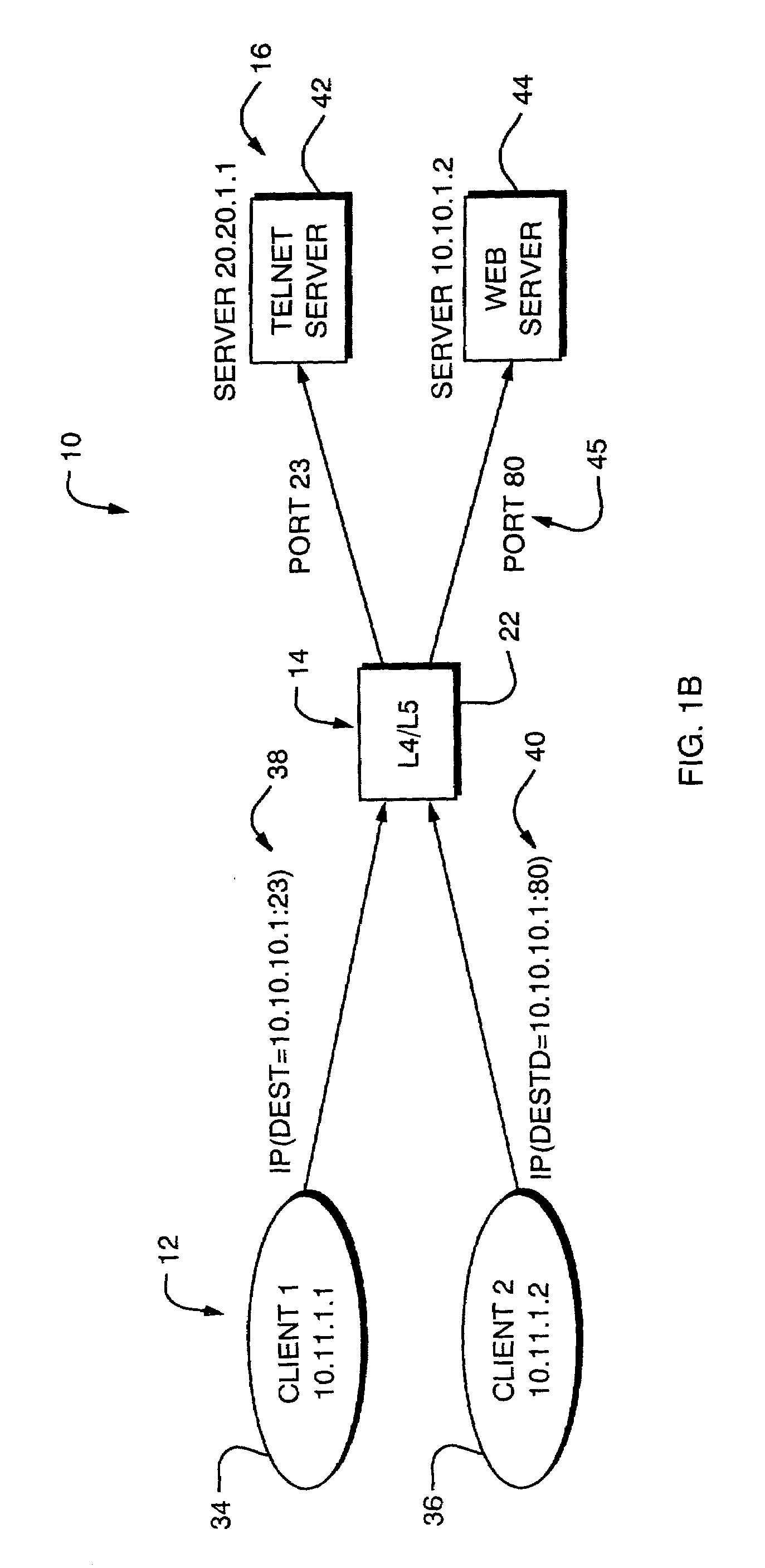
Internet protocol based disaster recovery of a server
For disaster recovery of a file server at an active site, the files that define the user environment of the file server are replicated to a virtual server at a disaster recovery site. To switch over user access from the active site to the disaster recovery site, the disaster recovery system determines whether there are sufficient network interfaces and file system mounts at the disaster recovery site. If so, the required resources are reserved, and user access is switched over. If not, an operator is given a list of missing resources or discrepancies, and a choice of termination or forced failover. Interruptions during the failover can be avoided by maintaining a copy of user mappings and a copy of session information at the disaster recovery site, and keeping alive client-server connections and re-directing client requests from the active site to the disaster recovery site.
Owner:EMC IP HLDG CO LLC
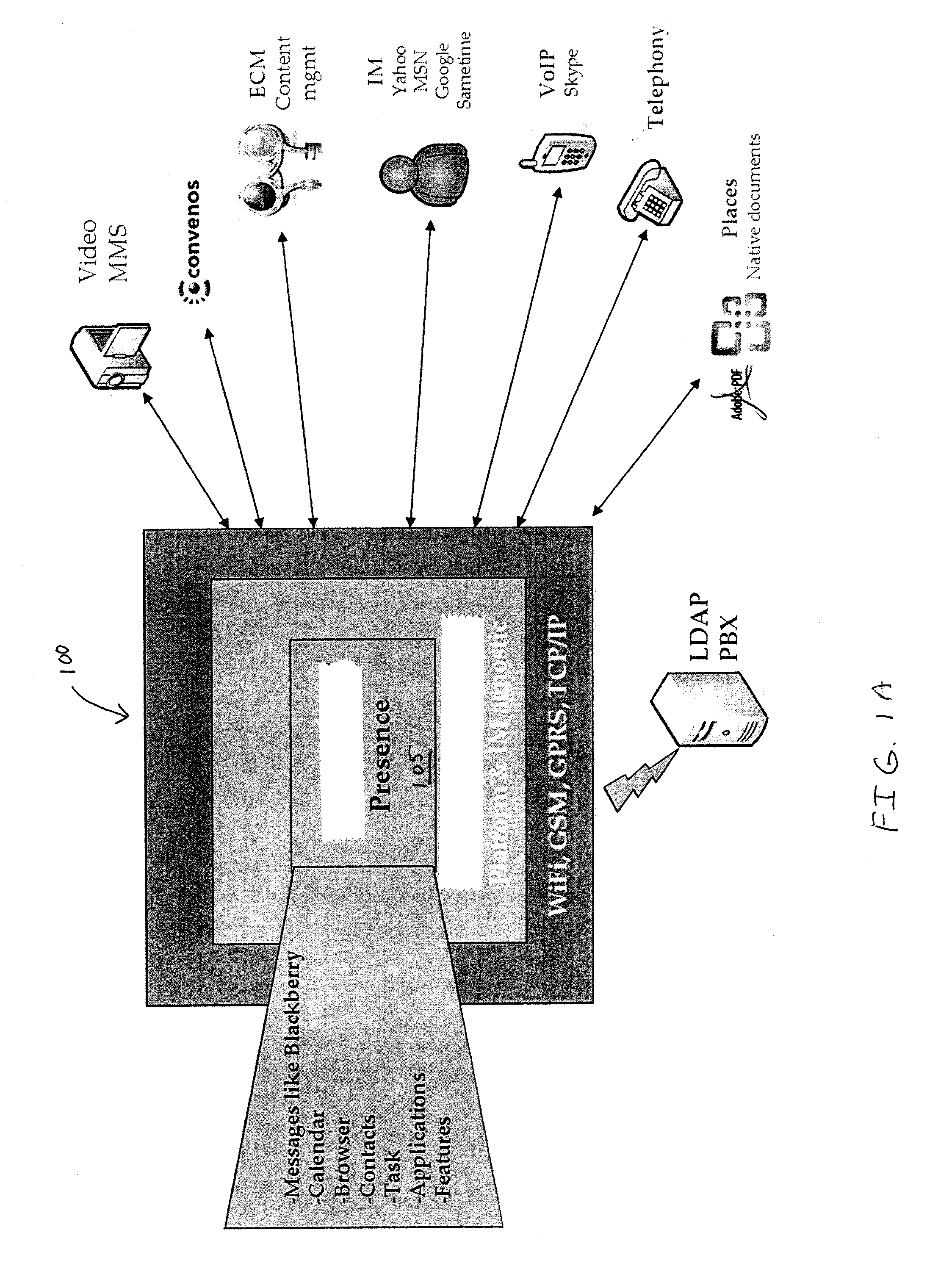
Apparatus, system, method, and computer program product for collaboration via one or more networks
InactiveUS20090019367A1Work well togetherFacilitate conferencing and collaborationDigital data protectionMultiple digital computer combinationsVirtual conferenceSpeech sound
A collaboration architecture supports virtual meetings, including web conferencing and collaboration. Presence information is aggregated from different types of communication services to provide a generic representation of presence. In one implementation, collaboration lifecycle management is provided to manage meetings over the lifecycle of a project. Audio options include voice over internet protocol (VoIP) and conventional PTSN phone networks, which are supported in one implementation by an audio conferencing server.
Owner:CONVENOUS
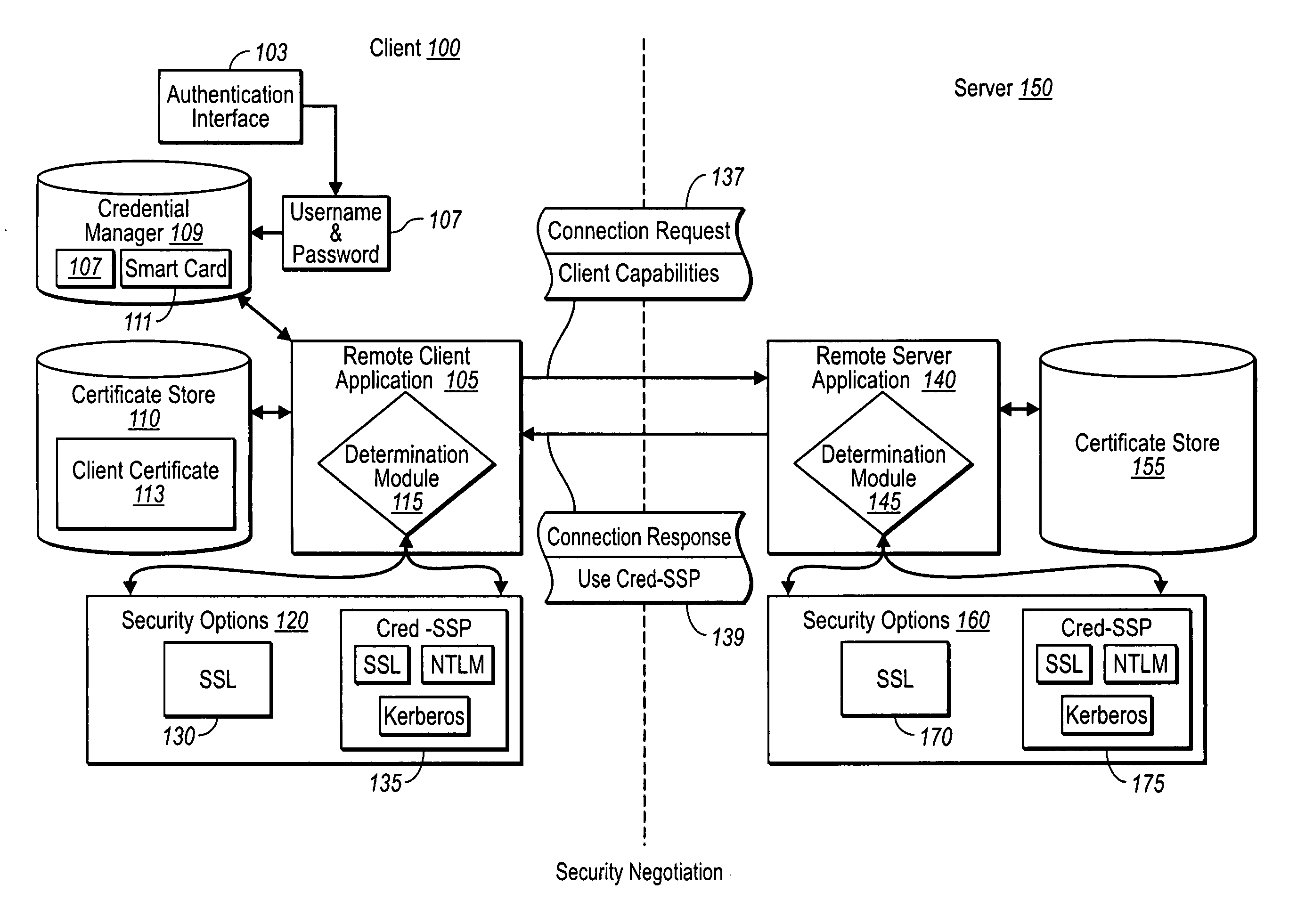
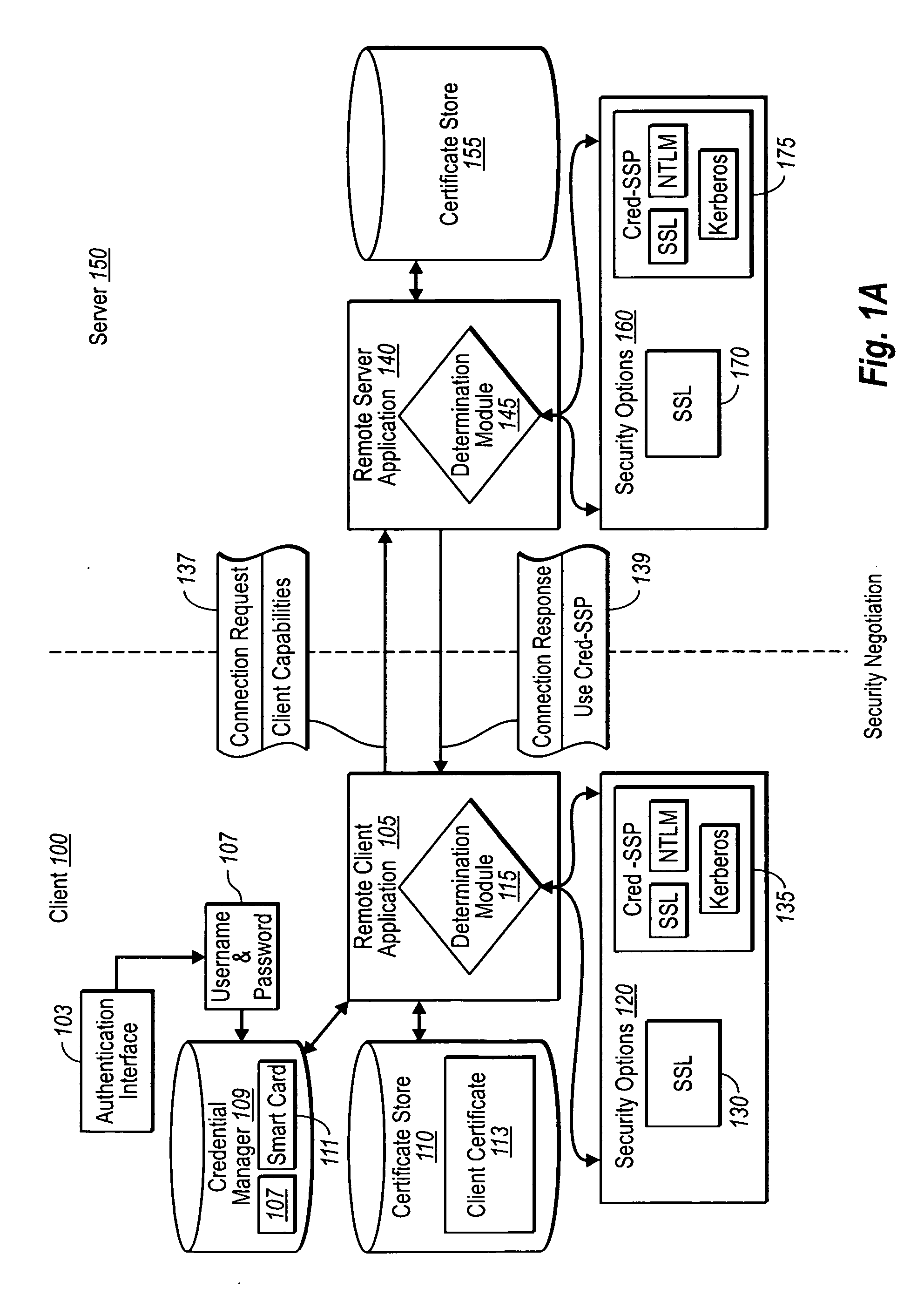
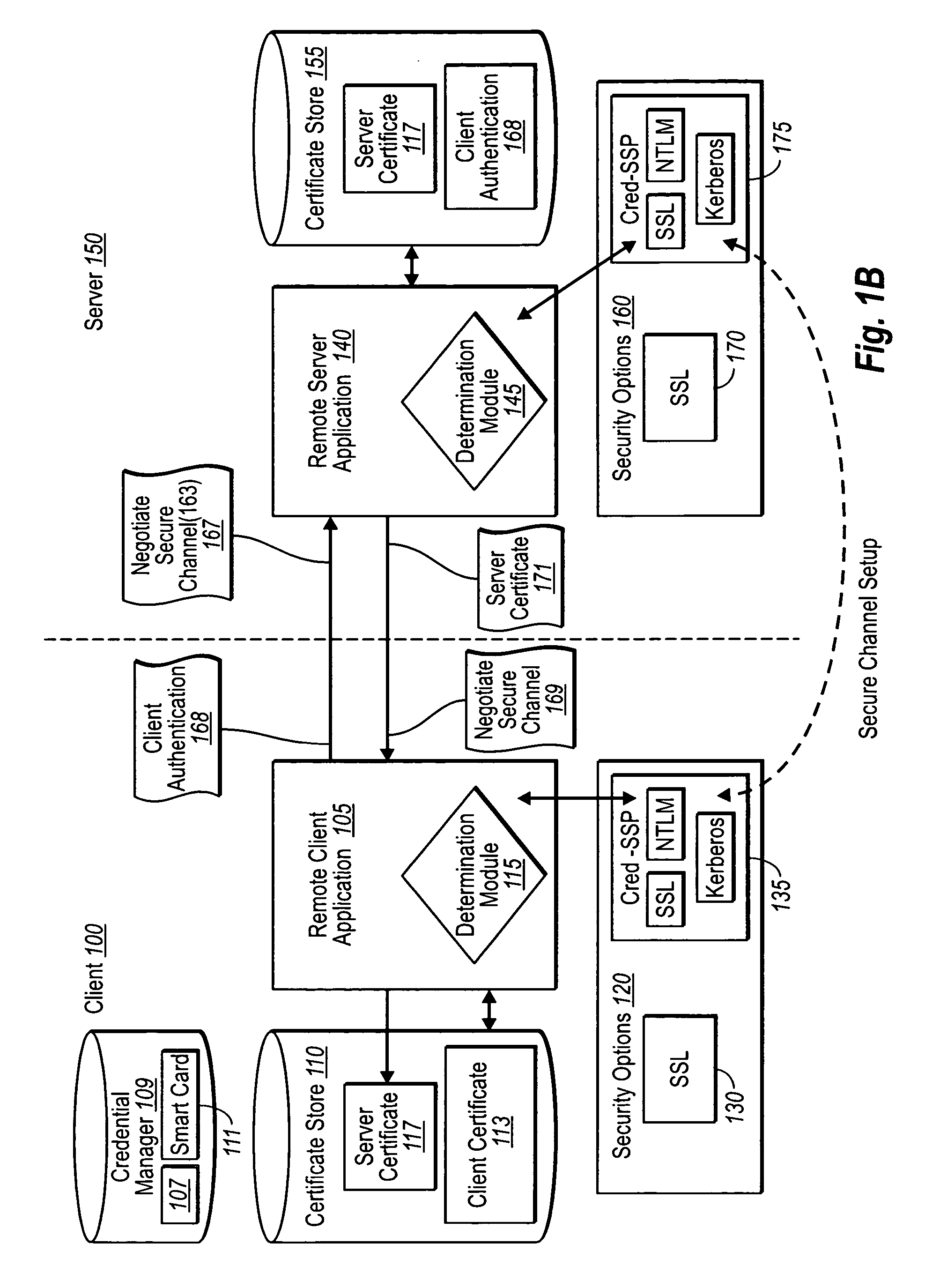
Creating secure interactive connections with remote resources
ActiveUS20070061878A1Easy to adaptDigital data processing detailsUser identity/authority verificationSecure communicationClient-side
Implementations of the present invention efficiently establish secure connections between a client and server, at least in part by authenticating the client and server early on in the connection setup phases. A client initiating a connection with a server identifies the secure communication protocols enabled at the client, and identifies these protocols in a connection request it sends to the server. The server processes the message and responds with a communication protocol it deems appropriate for the connection. The client and server then exchange appropriate authentication information, and then establish a connection session that implements the chosen communication protocol, and encrypts messages using the negotiated communication protocol. Additional implementations relate to reestablishing dropped connections behind virtual Internet Protocol addresses, without necessarily having to recommit much connection resource overhead.
Owner:MICROSOFT TECH LICENSING LLC
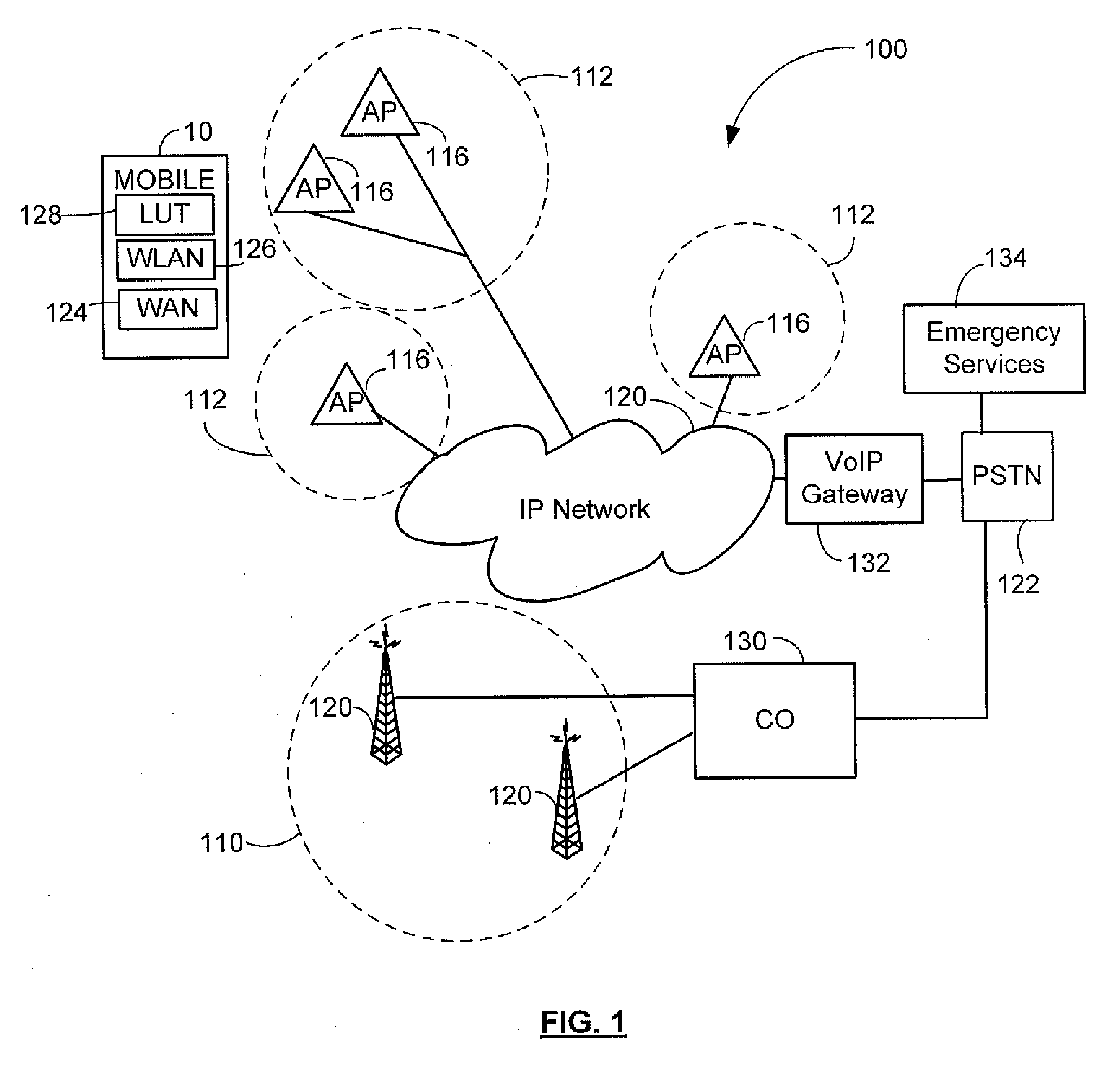
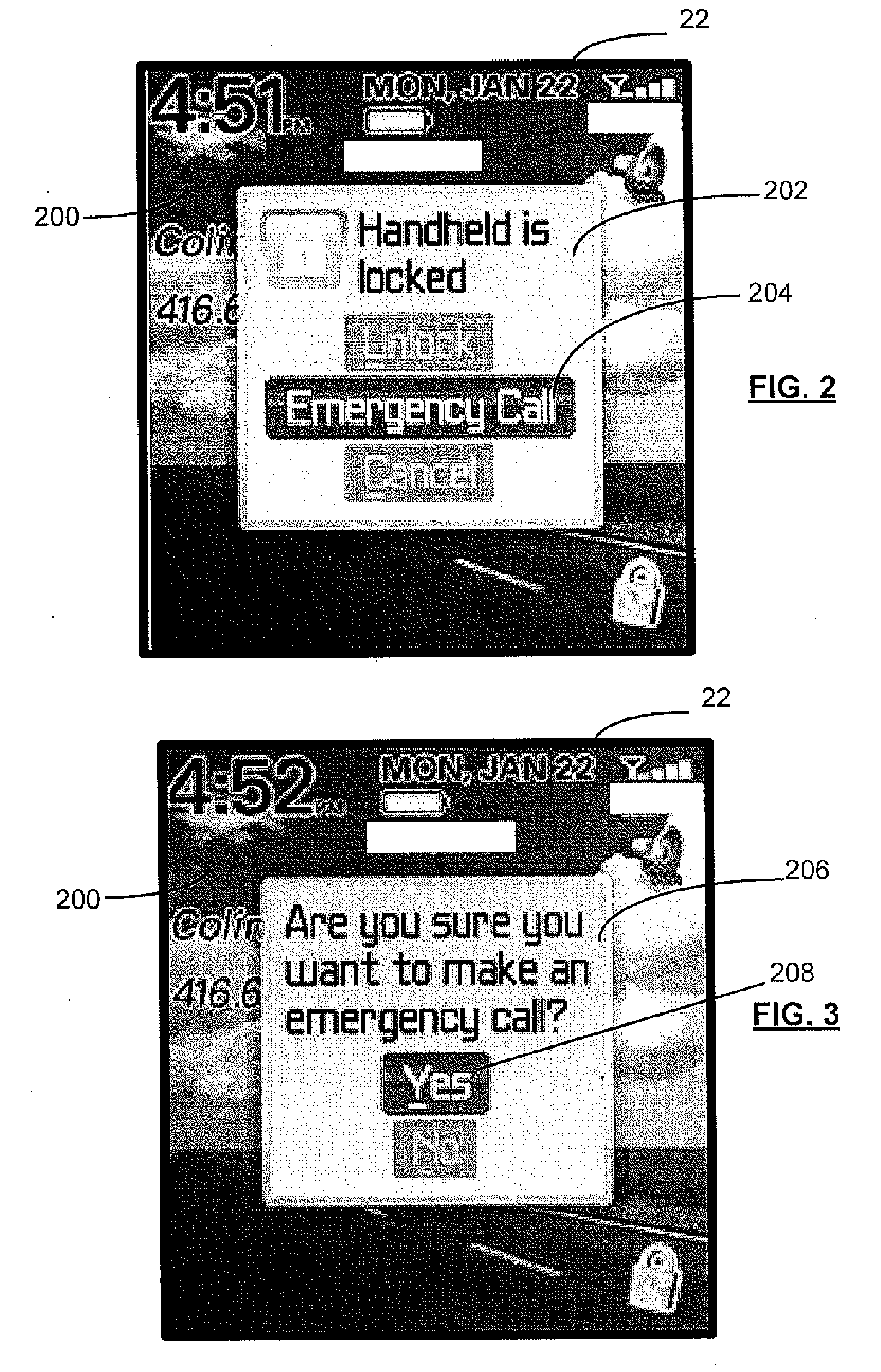
Emergency number selection for mobile communications device
ActiveUS20080200142A1Devices with wireless LAN interfaceSubstation equipmentTelecommunicationsBeacon frame
Automatically selecting an emergency number for use by a mobile communications device enabled for Voice Over Internet Protocol (VoIP) communications, including: receiving at the mobile communications device a geographic indicator in a beacon frame transmitted from a wireless access point of a wireless local area network that is connected to an Internet Protocol network; and determining from a plurality of emergency numbers stored in a storage element of the mobile communications device a selected emergency number in dependence on the received geographic indicator.
Owner:MALIKIE INNOVATIONS LTD
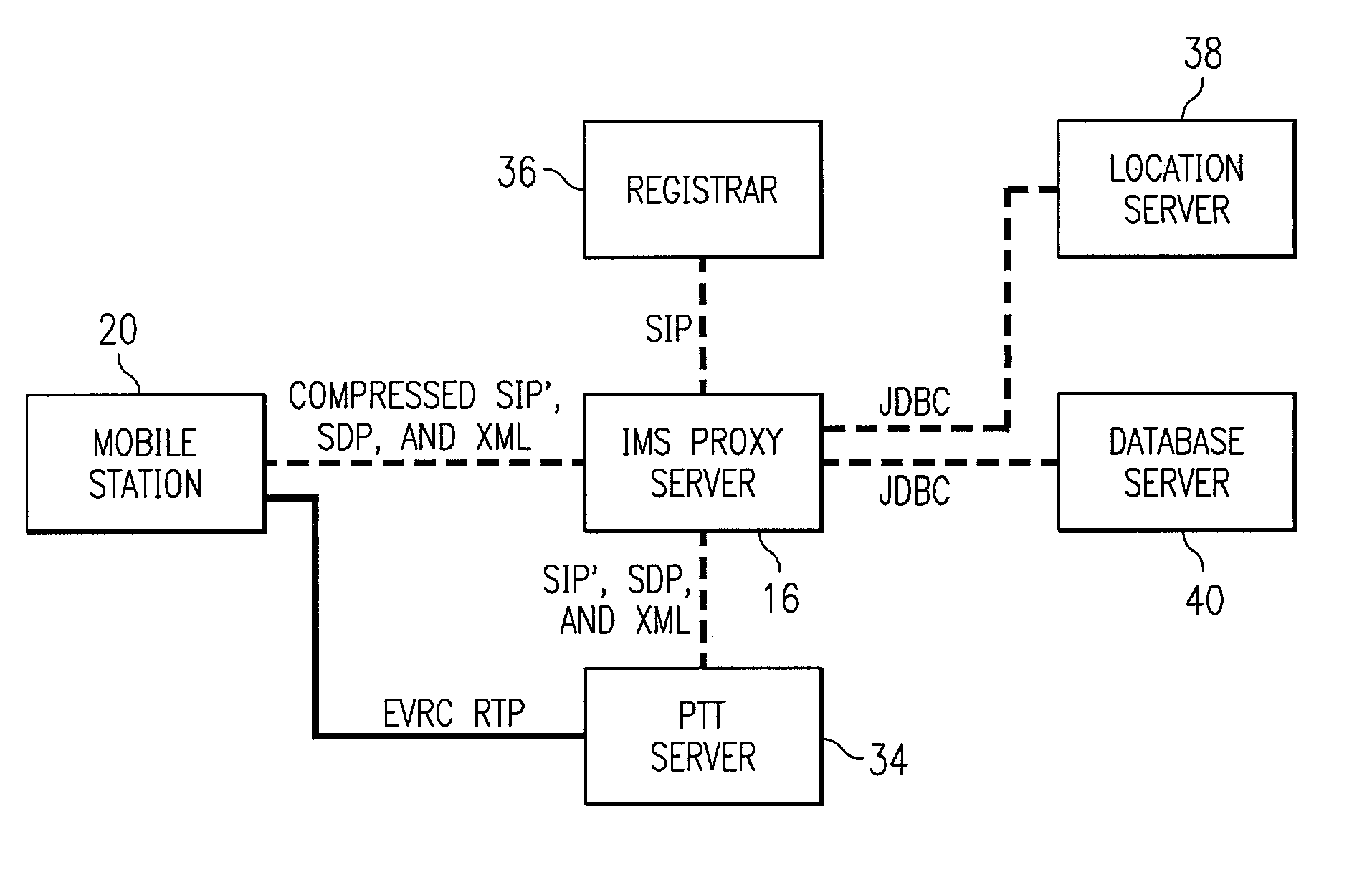
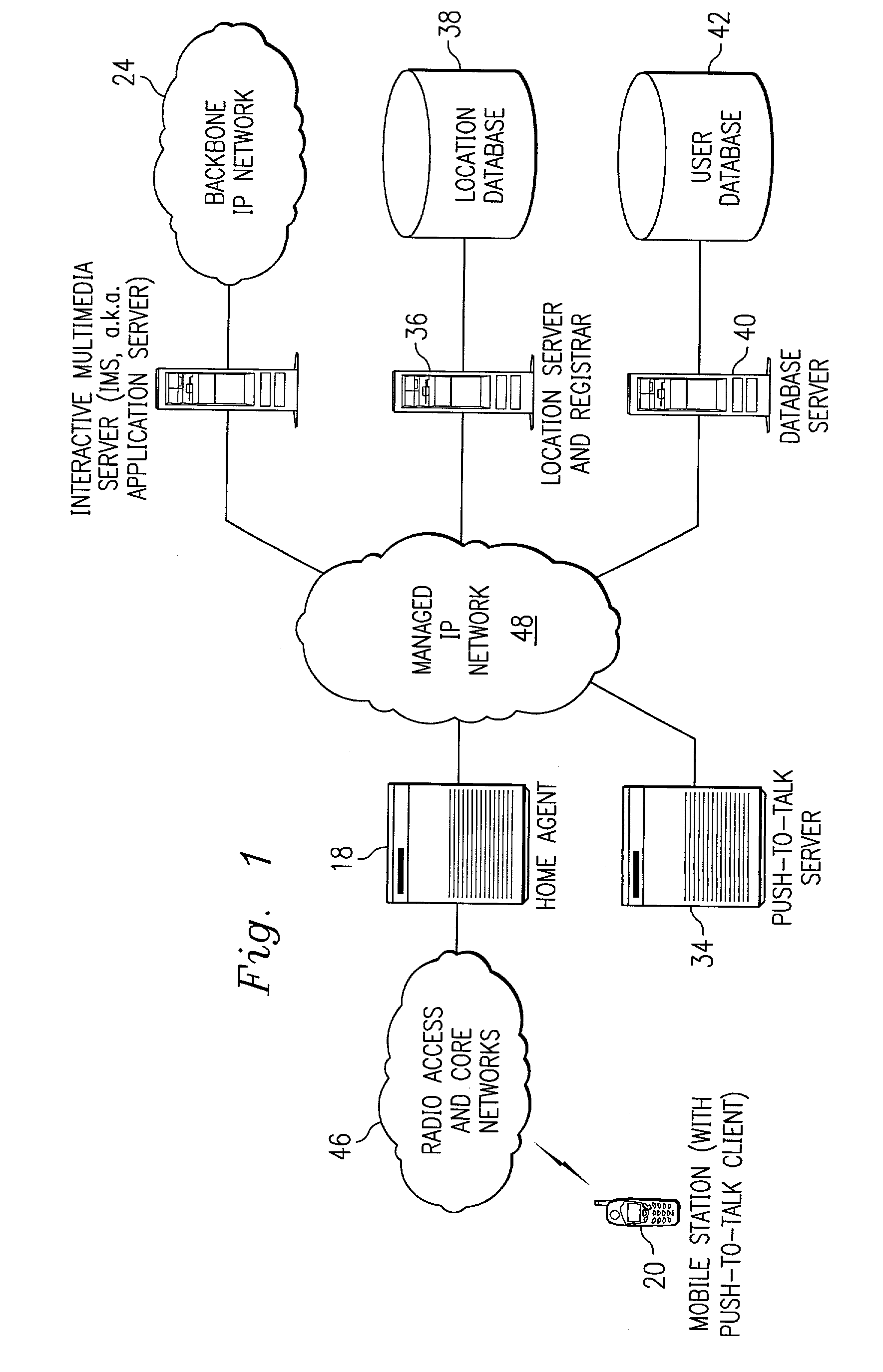
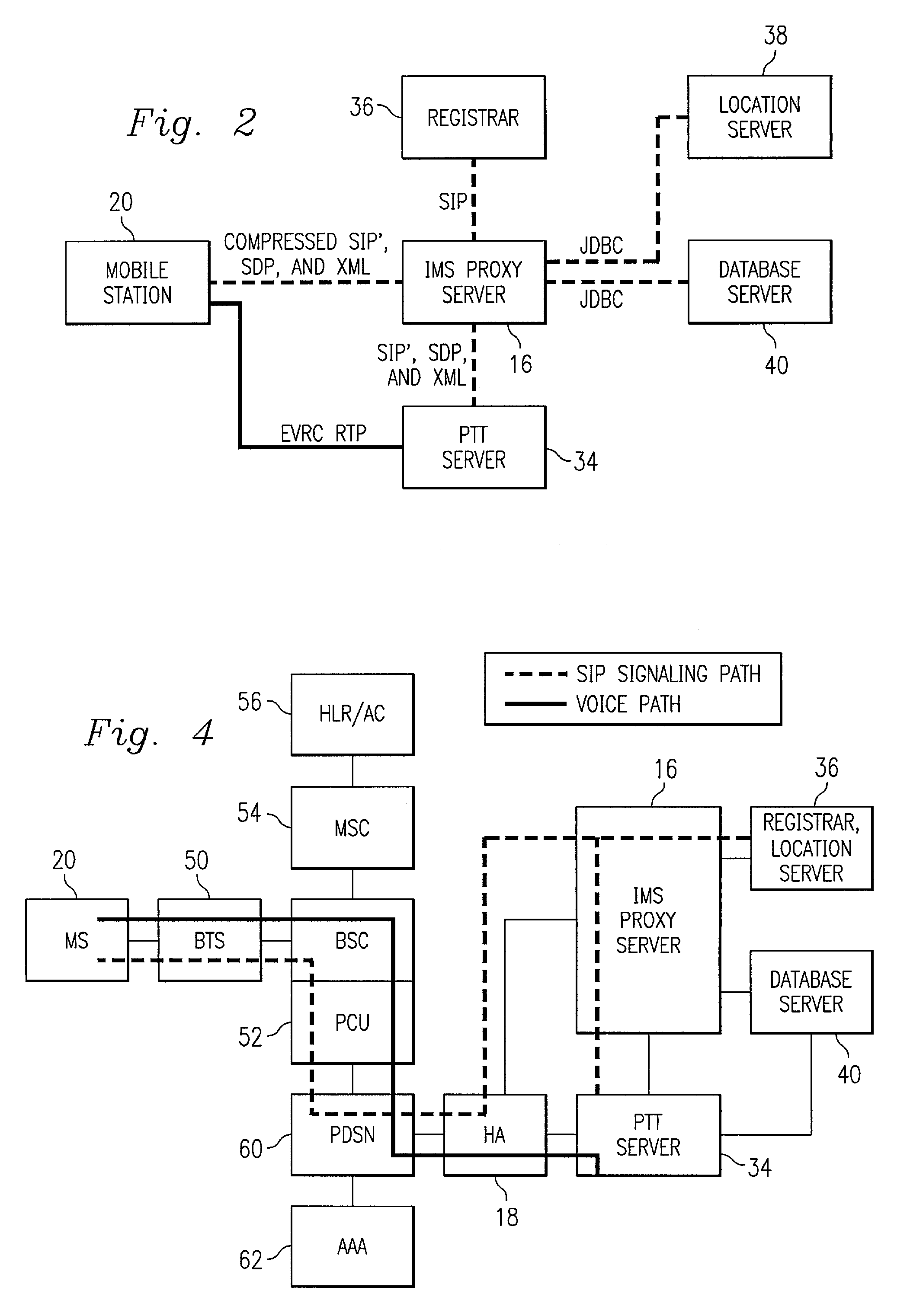
Push-to-talk wireless telecommunications system utilizing a voice-over-IP network
ActiveUS7170863B1Multiplex system selection arrangementsSpecial service provision for substationSession Initiation ProtocolTelecommunications network
A method and system to provide push-to-talk from one user to another in a wireless packet data telecommunications network is described. The system may include: a wireless communication network including push-to-talk (PTT) functionality, with a Session Initiation Protocol (SIP) Proxy Server; a SIP Registrar and Location Server operable to store contact addresses of active mobile devices; a Realtime Transport Protocol (RTP) Media Gateway (PTT Server) operable to function as a call endpoint for each of a plurality of mobile devices wherein the plurality of mobile devices are segmented into membership groups, the PTT Server further operable to multicast a communication from one member of the group to the other members of the group; and an Internet Protocol (IP) network interconnecting the SIP Proxy server, the SIP Registrar and Location Server, and the PTT Server.
Owner:APPLE INC
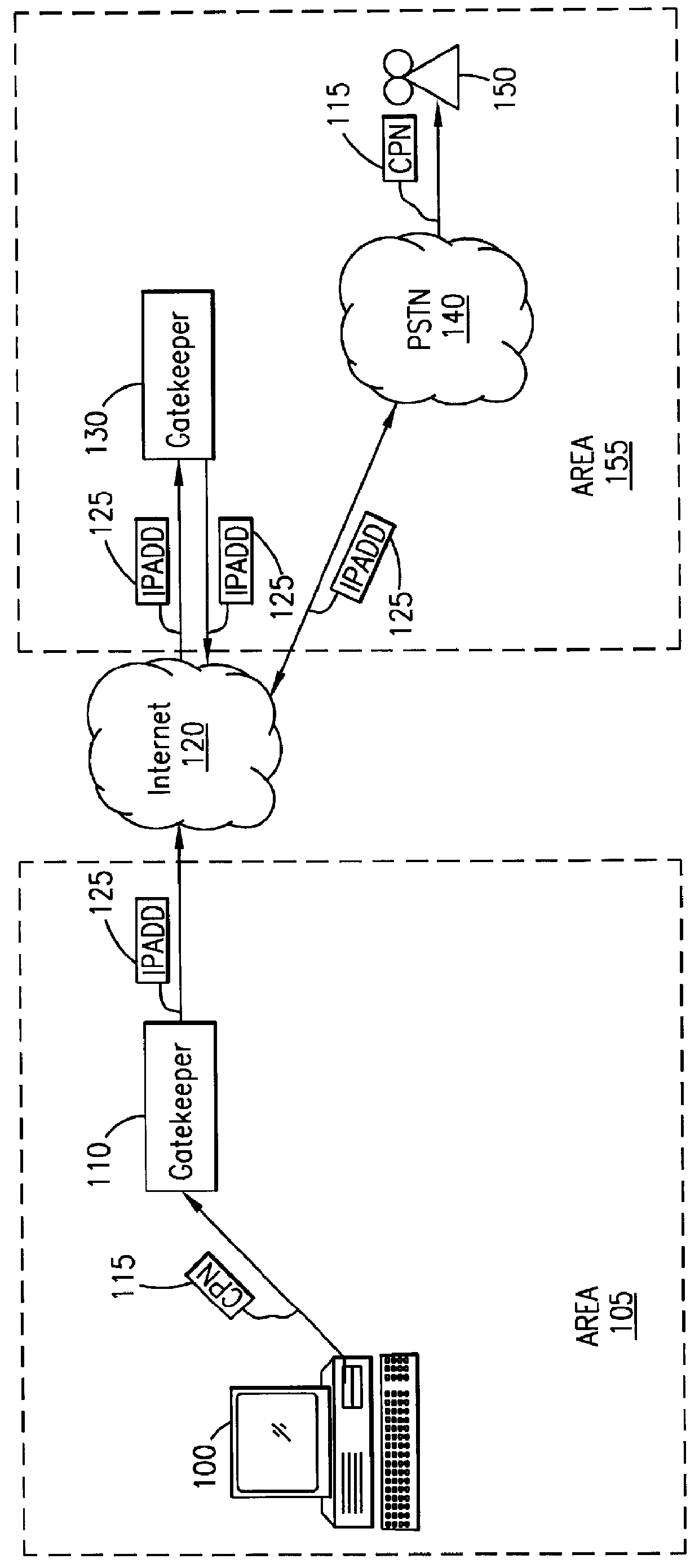
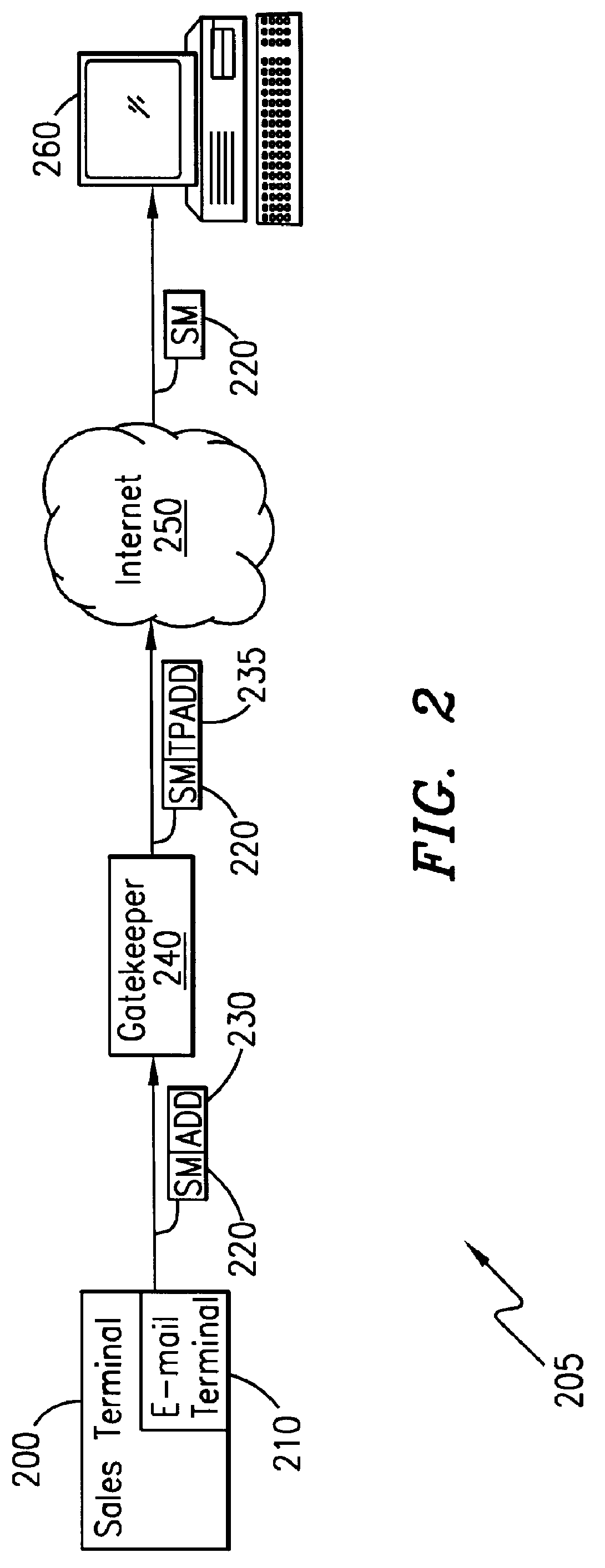
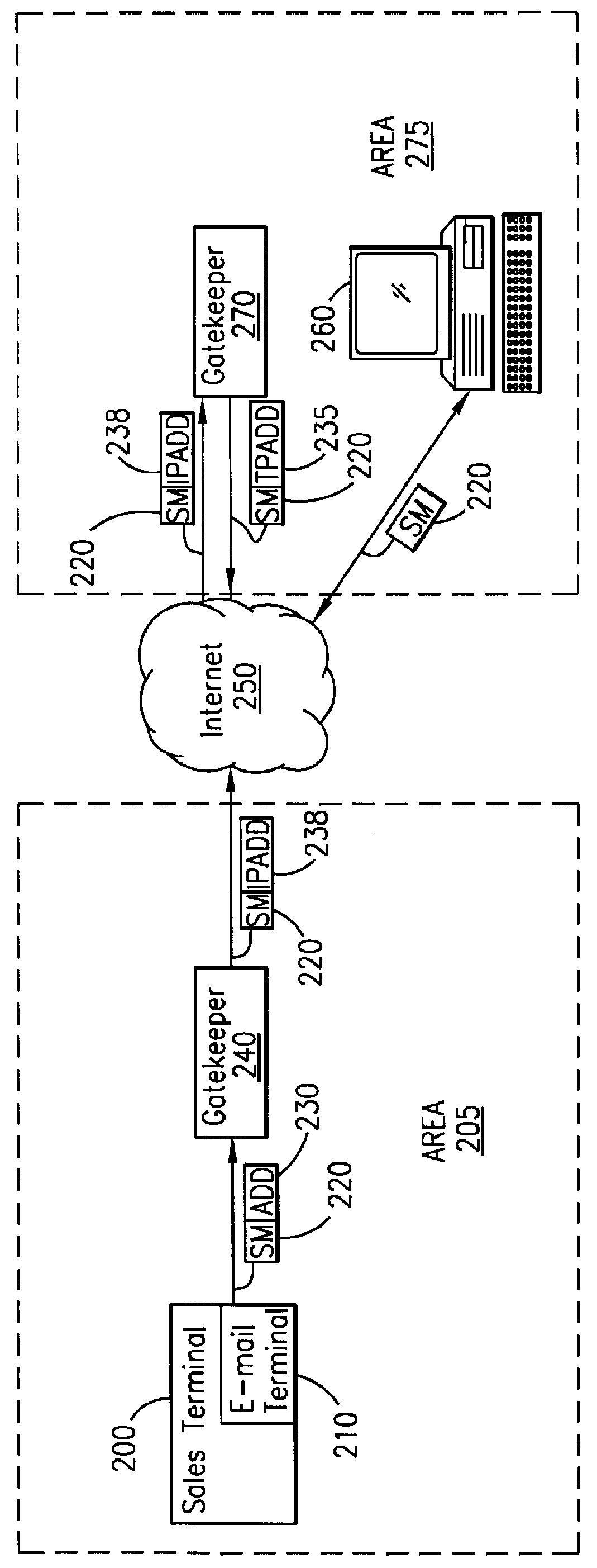
System and method for sending a short message containing purchase information to a destination terminal
InactiveUS6067529AEfficient and cost-effectiveReliable deliveryComplete banking machinesCash registersMulticast addressComputer terminal
A telecommunications system and method is disclosed for providing a substantially immediate electronic receipt after a consumer has made a purchase. When a consumer makes a purchase, the sales terminal, which is attached with a short message / e-mail sending capable terminal, can generate and route a short message along with the detailed purchase information to a transport address or alias address associated with the consumer via a Gatekeeper for the Internet for the area that the sales terminal is located in. Upon receipt of the short message, the Gatekeeper can then convert the alias address to the transport address, if the alias address is given and the consumer does not want the short message sent to the alias address, and forward the short message through the Internet to that transport address (or alias address) as an Internet Protocol datagram for storage and retrieval of the short message by the consumer either immediately or at a later time.
Owner:ERICSSON INC
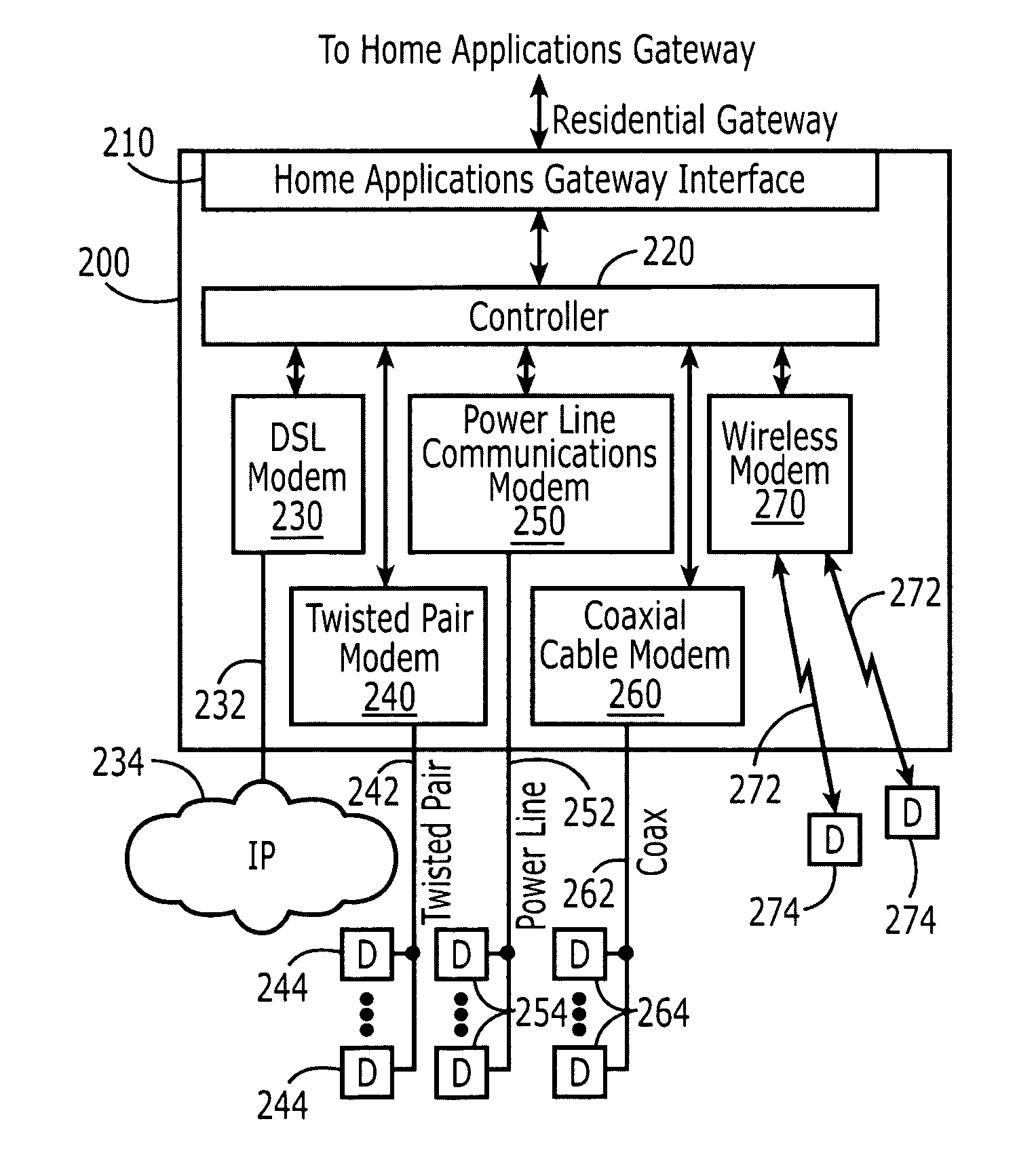
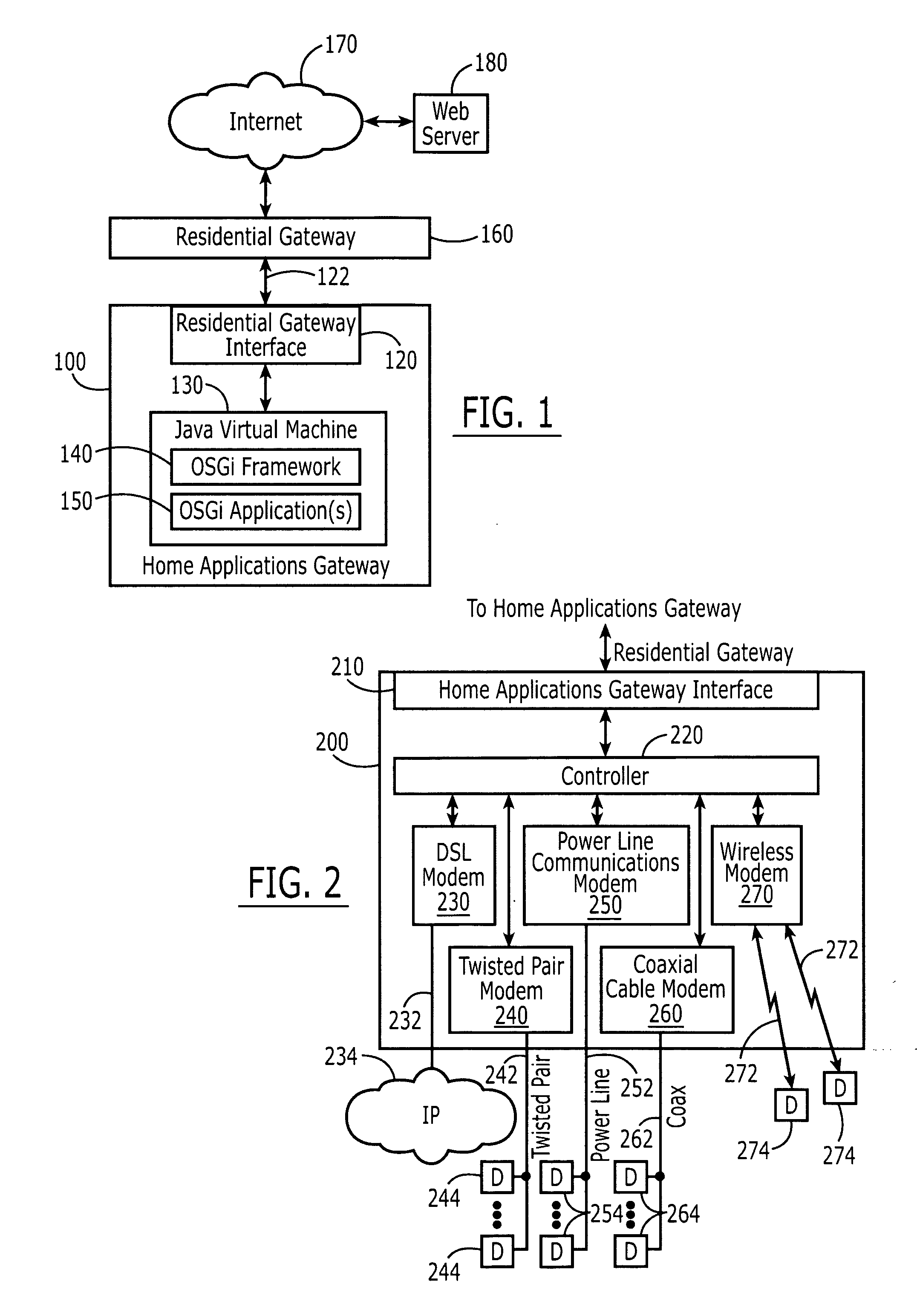
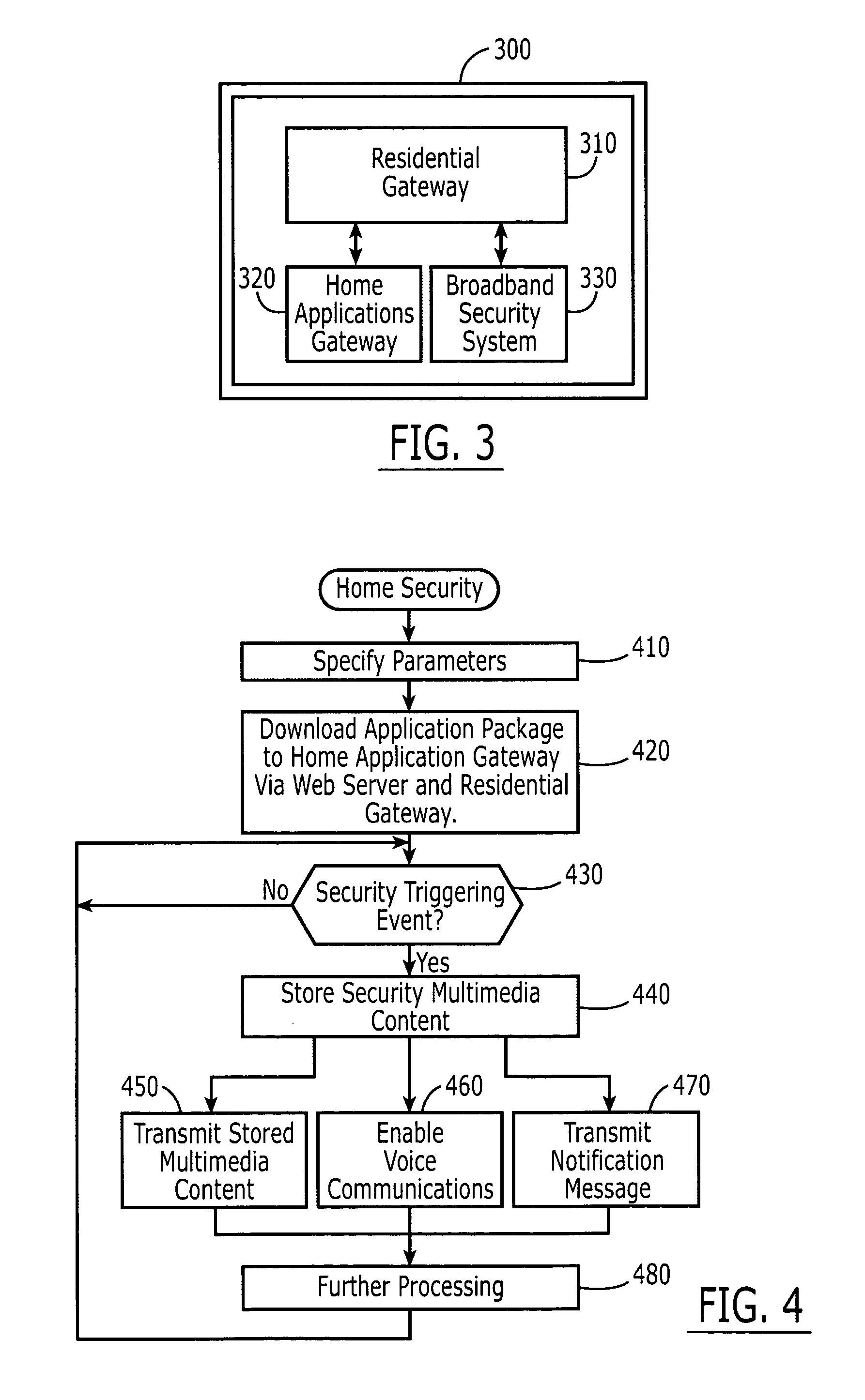
Broadband home applications gateway/residential gateway systems, methods and computer program products
A home applications gateway includes a residential gateway interface that is configured to connect to a residential gateway, and a Java Virtual Machine (JVM) that includes an Open Services Gateway initiative (OSGi) framework configured to execute OSGi Java applications that are downloaded and life cycle managed from a Web server through the residential gateway interface. The OSGi Java applications can include a video monitoring application that is configured to provide in-home and out-of-home access to Internet Protocol (IP)-based home video cameras and video files captured by the IP-based home video cameras, at a Web page. The OSGi Java applications can further include a lighting control application that is configured to control activation and deactivation of home lighting from the Web page. The OSGi Java applications can also include a home monitoring and control application that is configured to monitor home sensors and take action upon their activation.
Owner:BELLSOUTH INTPROP COR
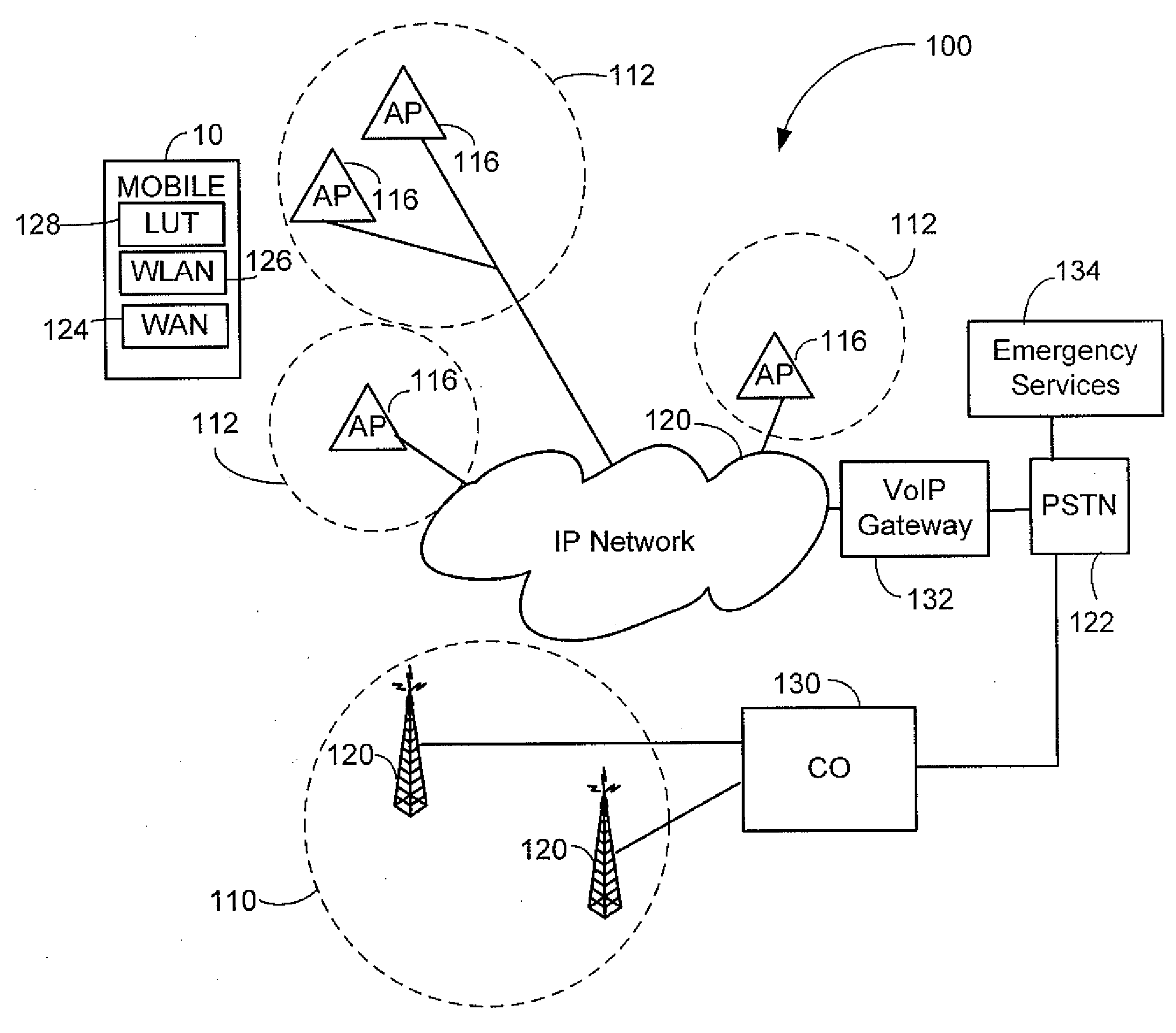
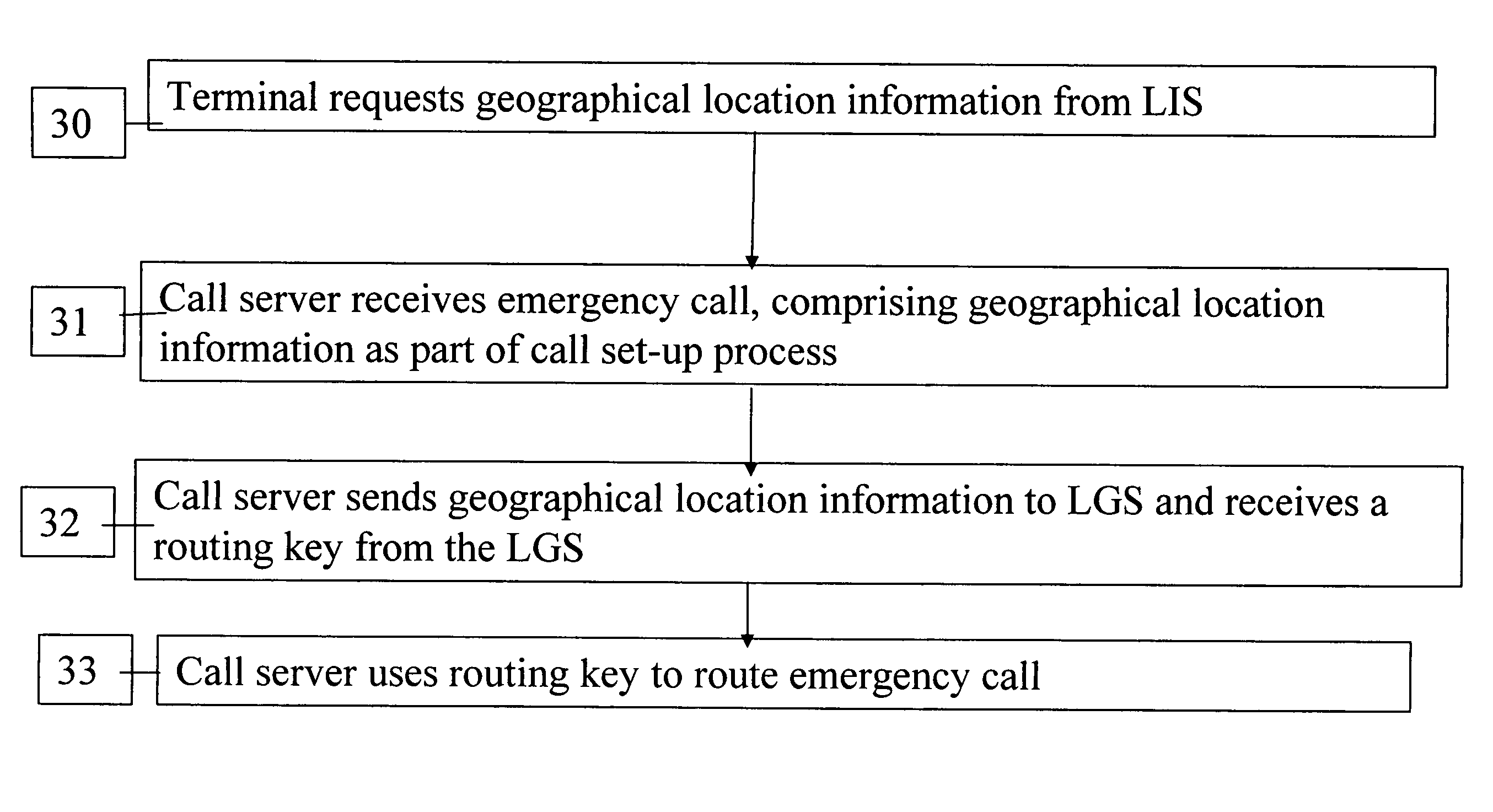
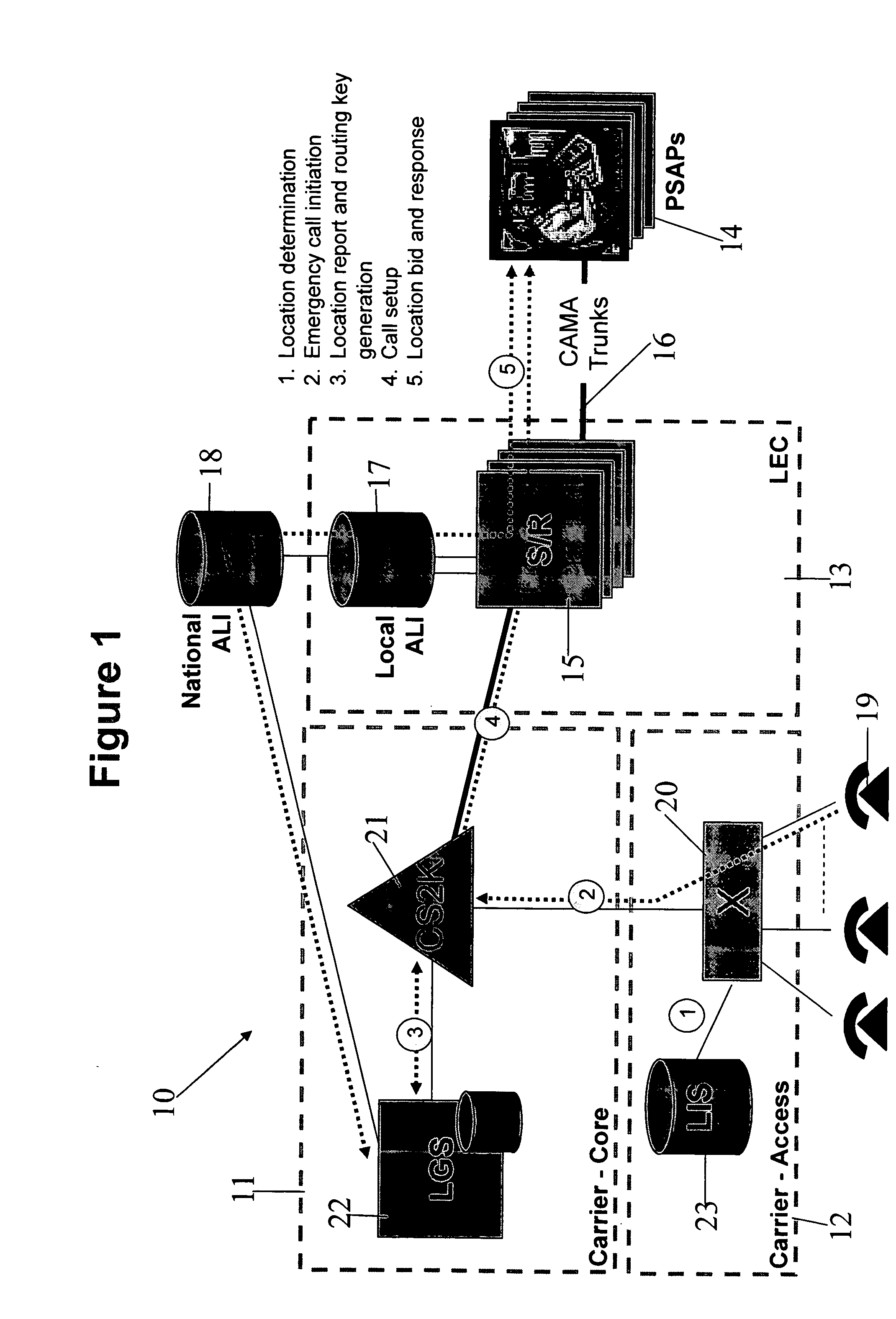
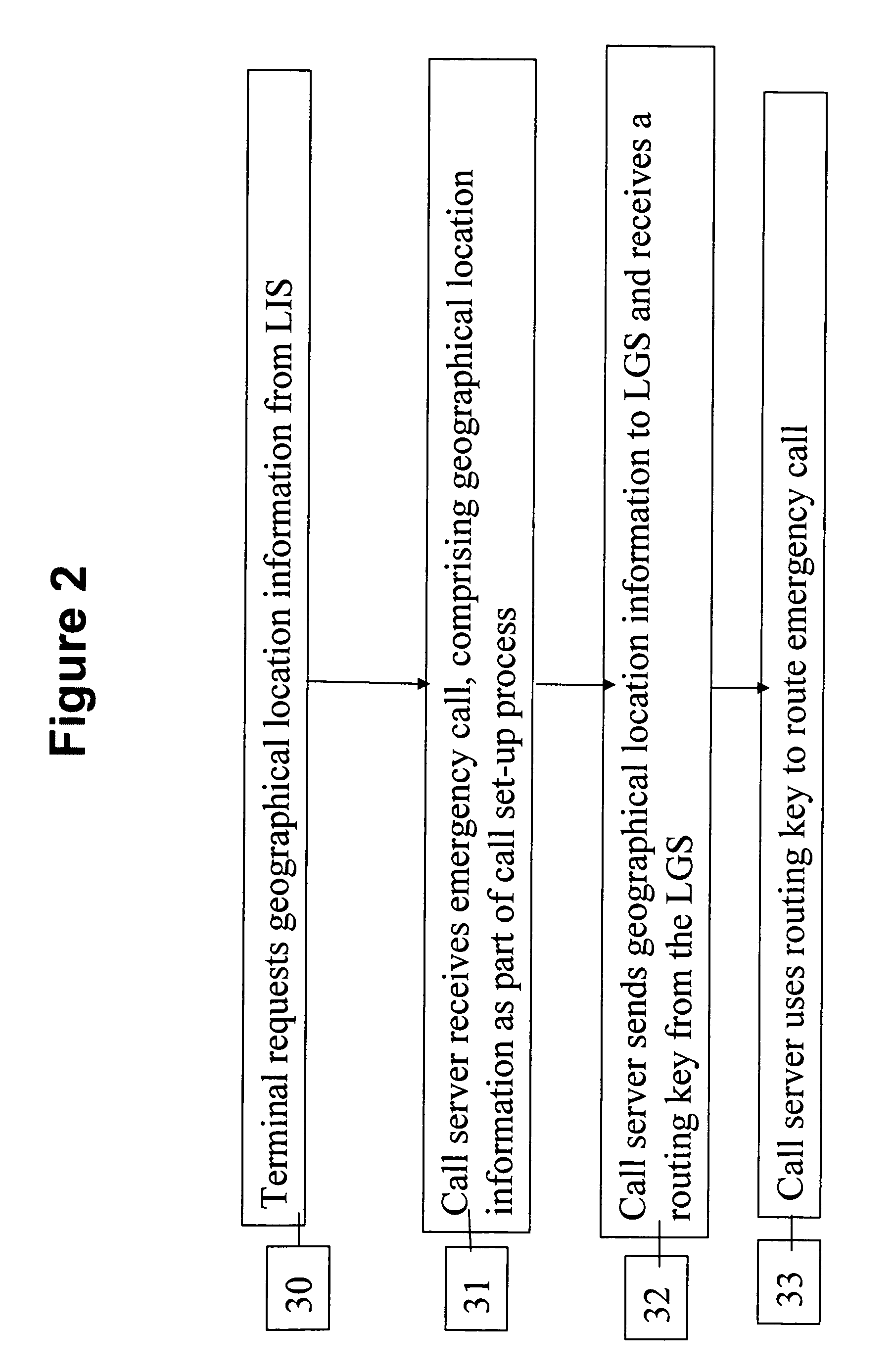
Determining the geographical location from which an emergency call originates in a packet-based communications network
ActiveUS20050190892A1Reduce needLow costSpecial service for subscribersNetwork connectionsCommunications systemSpeech sound
In order that emergency service vehicles can be dispatched to the correct destination promptly, accurate information about the location of the caller is needed. Another problem concerns routing emergency calls to the correct destination. For emergency calls a universal code is used such as 911 in North America and 112 in Europe. This universal code cannot be used to identify the destination of the call. These problems are particularly acute for nomadic communications systems such as voice over internet protocol communications networks. That is because user terminals change network location. These problems are solved by enabling the geographical location of the emergency caller to be determined by entities within a packet-based network without the need for modification of existing emergency services network infrastructure.
Owner:AVAYA INC
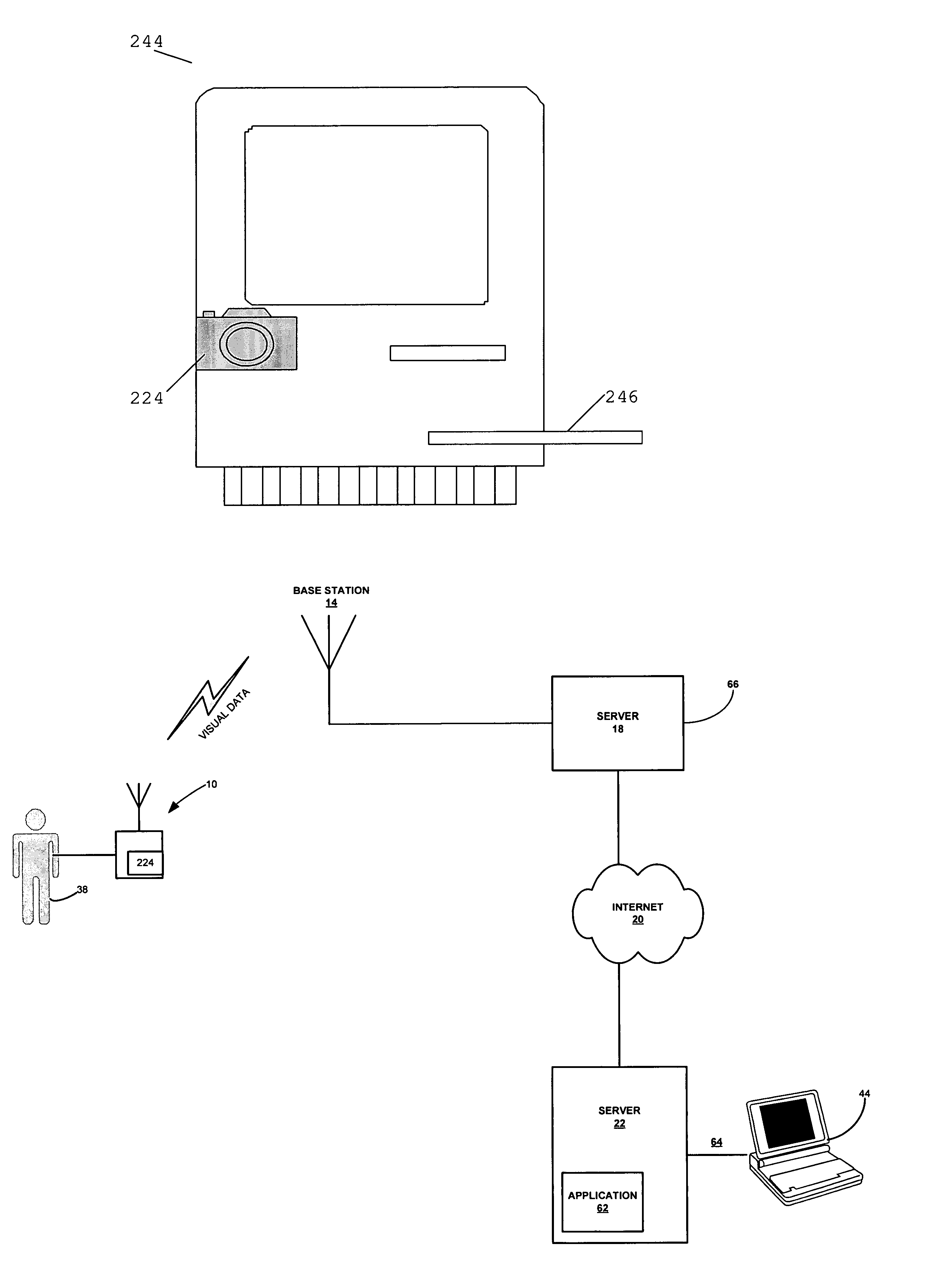
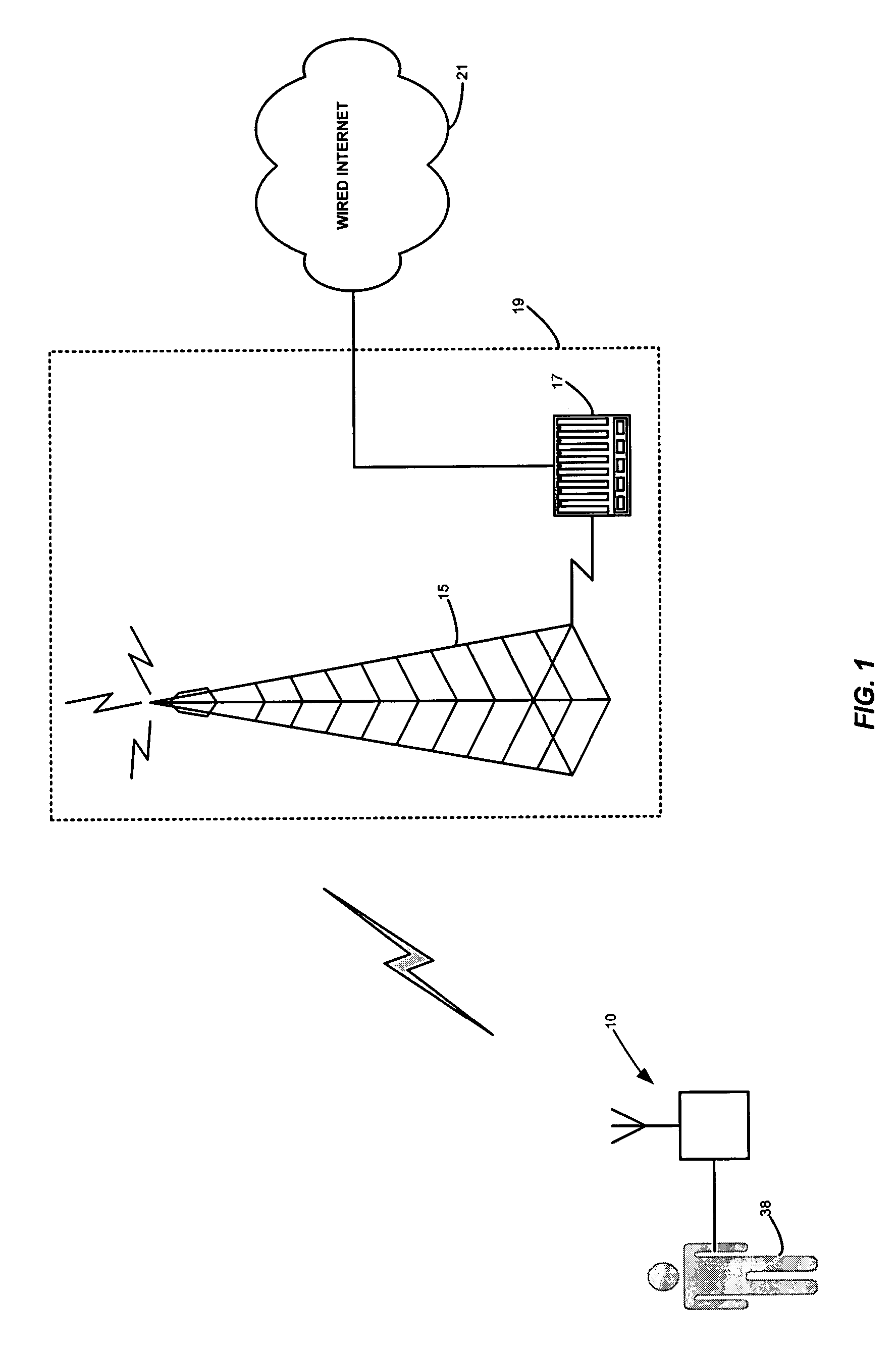
Method and apparatus for health and disease management combining patient data monitoring with wireless internet connectivity
InactiveUS7156809B2Maintain abilityReduced functionalityPhysical therapies and activitiesBioelectric signal measurementOperational systemPatient data
Embodiments of the invention provide a method and apparatus for a wireless health monitoring system for interactively monitoring a disease or health condition of a patient by connecting a mobile phone to or with a digital camera and / or a medical monitoring device. The health related data or visual information from the camera is transmitted to a server using standard internet protocols and may be integrated with various operating systems for handheld or wireless devices, especially those with enhanced capabilities for handing images and visual data.
Owner:KONINK PHILIPS ELECTRONICS NV +1
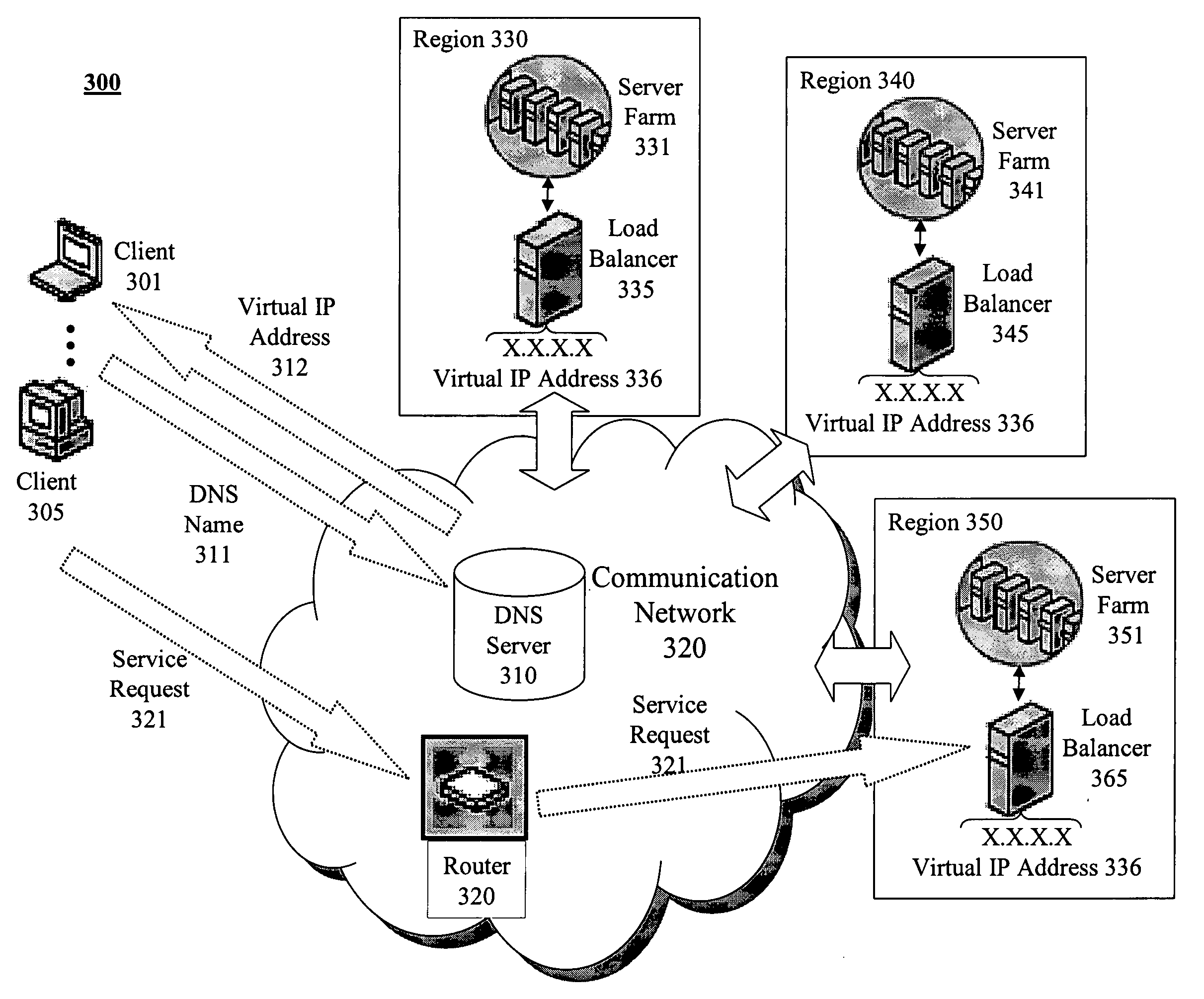
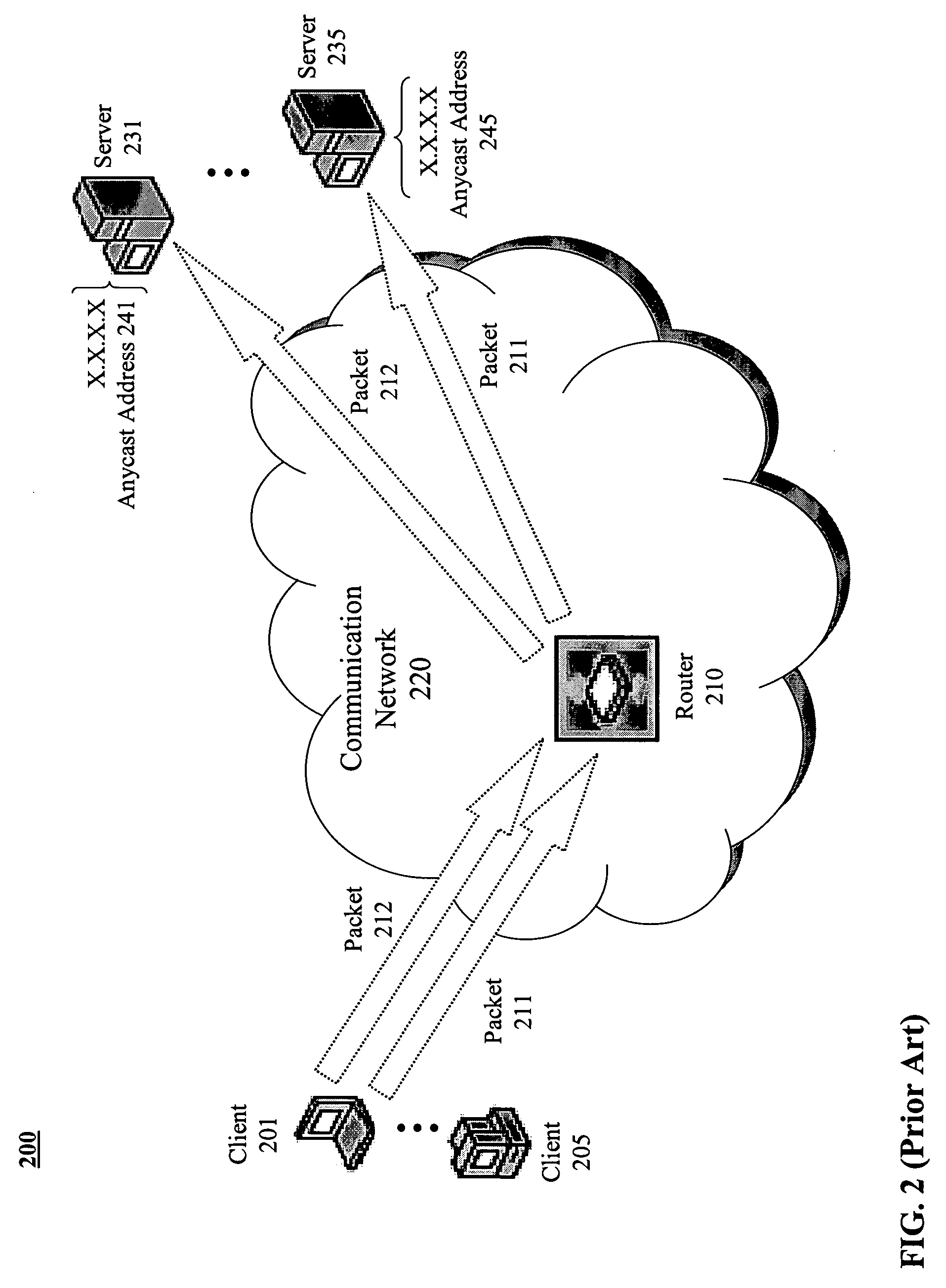
Configurable geographic prefixes for global server load balancing
ActiveUS7496651B1Traffic loadMultiprogramming arrangementsMultiple digital computer combinationsGeographic regionsIp address
In a load balancing system, user-configurable geographic prefixes are provided. IP address prefix allocations provided by the Internet Assigned Numbers Authority (IANA) and associated geographic locations are stored in a first, static database in a load balancing switch, along with other possible default geographic location settings. A second, non-static database stores user-configured geographic settings. In particular, the second database stores Internet Protocol (IP) address prefixes and user-specified geographic regions for those prefixes. The specified geographic region can be continent, country, state, city, or other user-defined region. The geographic settings in the second database can override the information in the first database. These geographic entries help determine the geographic location of a client and host IP addresses, and aid in directing the client to a host server that is geographically the closest to that client.
Owner:AVAGO TECH INT SALES PTE LTD
Geo-locating load balancing
Methods and apparatus are provided for geo-locating load balancing. According to one embodiment, a communication network architecture includes multiple servers, multiple load balancers, and multiple geographically dispersed communication devices. The servers provide services to the communication devices within the communication network. The load balancers each service a shared virtual Internet Protocol (IP) address common to all of the load balancers and perform load balancing of service requests on behalf of two or more of the servers that are located geographically proximate to the load balancer. The communication devices are communicatively coupled with the load balancers and are configured to issue service requests intended for any of the servers to the shared virtual IP address, whereby, upon issuing a service request, a communication device is directed to a particular server selected by a load balancing routine that is associated with a load balancer that is closest to the communication device.
Owner:LEVEL 3 COMM LLC
Internet-enabled conferencing system and method accommodating PSTN and IP traffic
InactiveUS6876734B1Special service provision for substationMultiplex system selection arrangementsStart timeTTEthernet
Owner:EMEETING NET
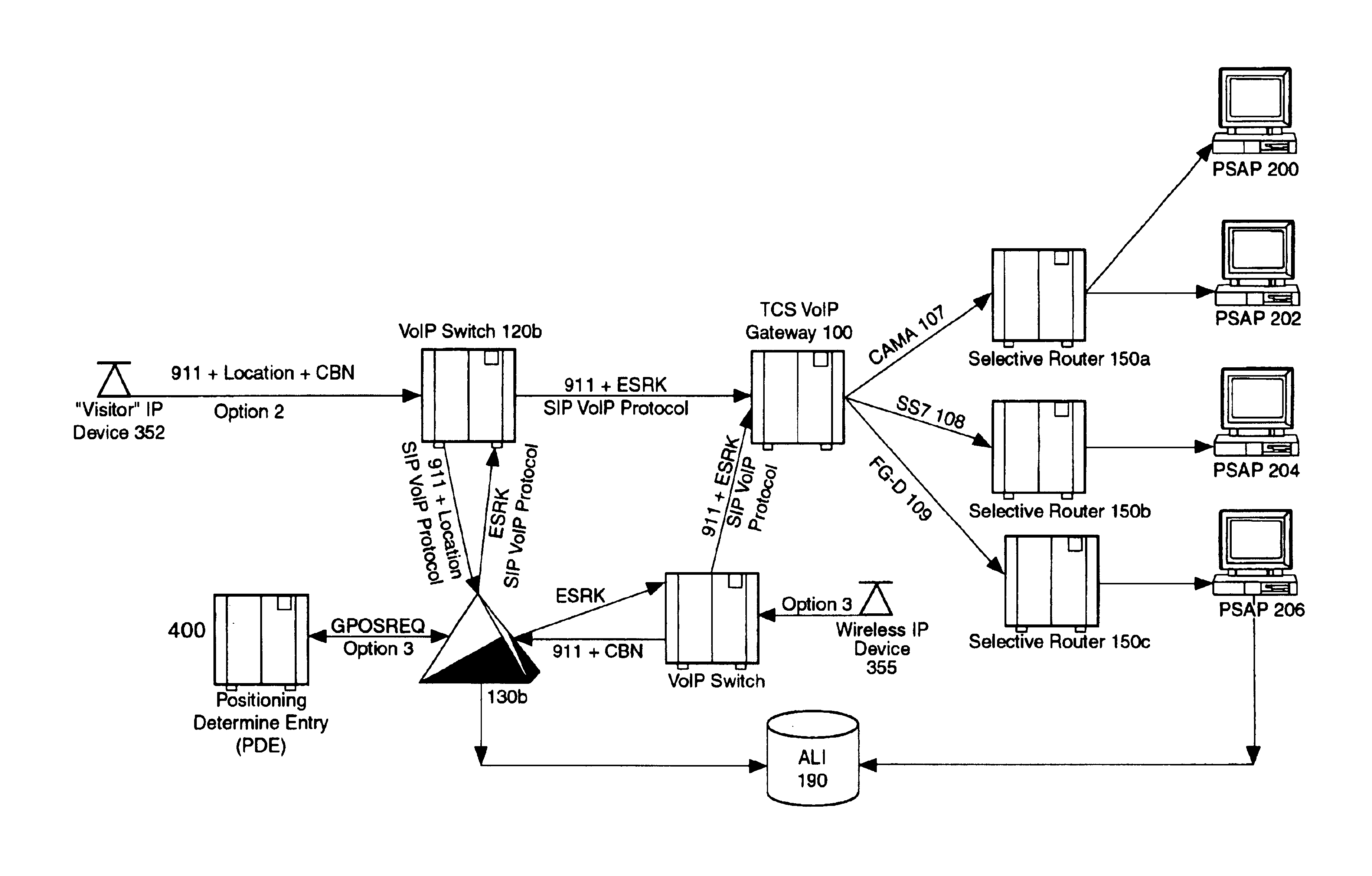
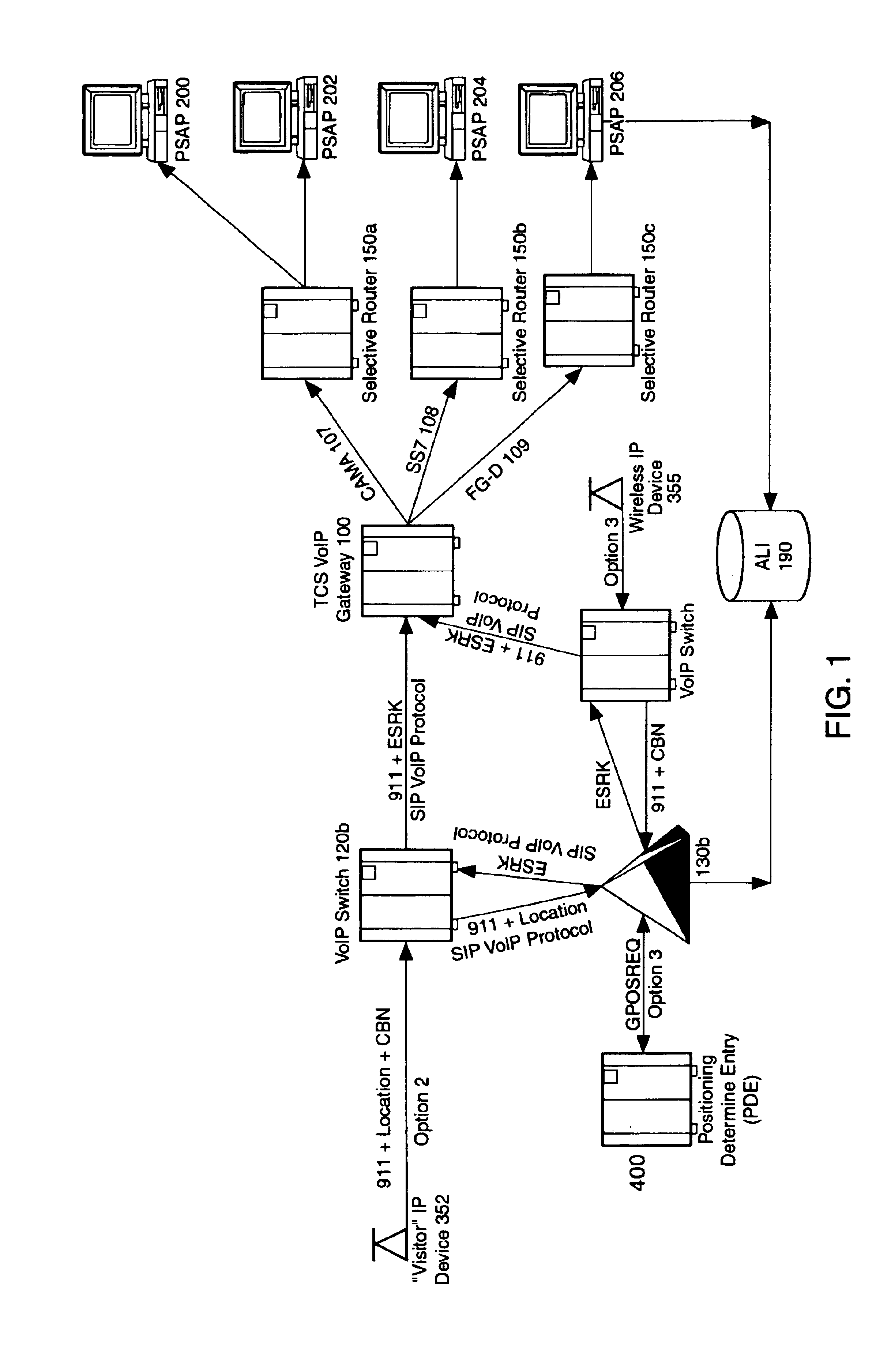
Enhanced E911 location information using voice over internet protocol (VoIP)
An E-9-1-1 voice-over-IP (VoIP) solution is provided wherein a 911 call from a wireless VoIP device is routed directly to the correct Public Safety Answer Point (PSAP) via dedicated trunks, together with correct location information and call-back number. VoIP gateways are implemented locally, at least one per LATA, and accept VoIP packetized data inbound, and convert it to standard wireline voice calls. Calls are routed to an IP address at the VoIP gateway, which then egresses the call to a voice port at a selective router. Dedicated voice trunks (CAMA, SS7, FG-D) are installed between each local VoIP gateway and appropriate selective routers. An Automatic Location Identification (ALI) database is provisioned with ESRKs dedicated for VoIP use. TCP / IP circuits may be established between some or all of the various local VoIP gateways.
Owner:TELECOMM SYST INC
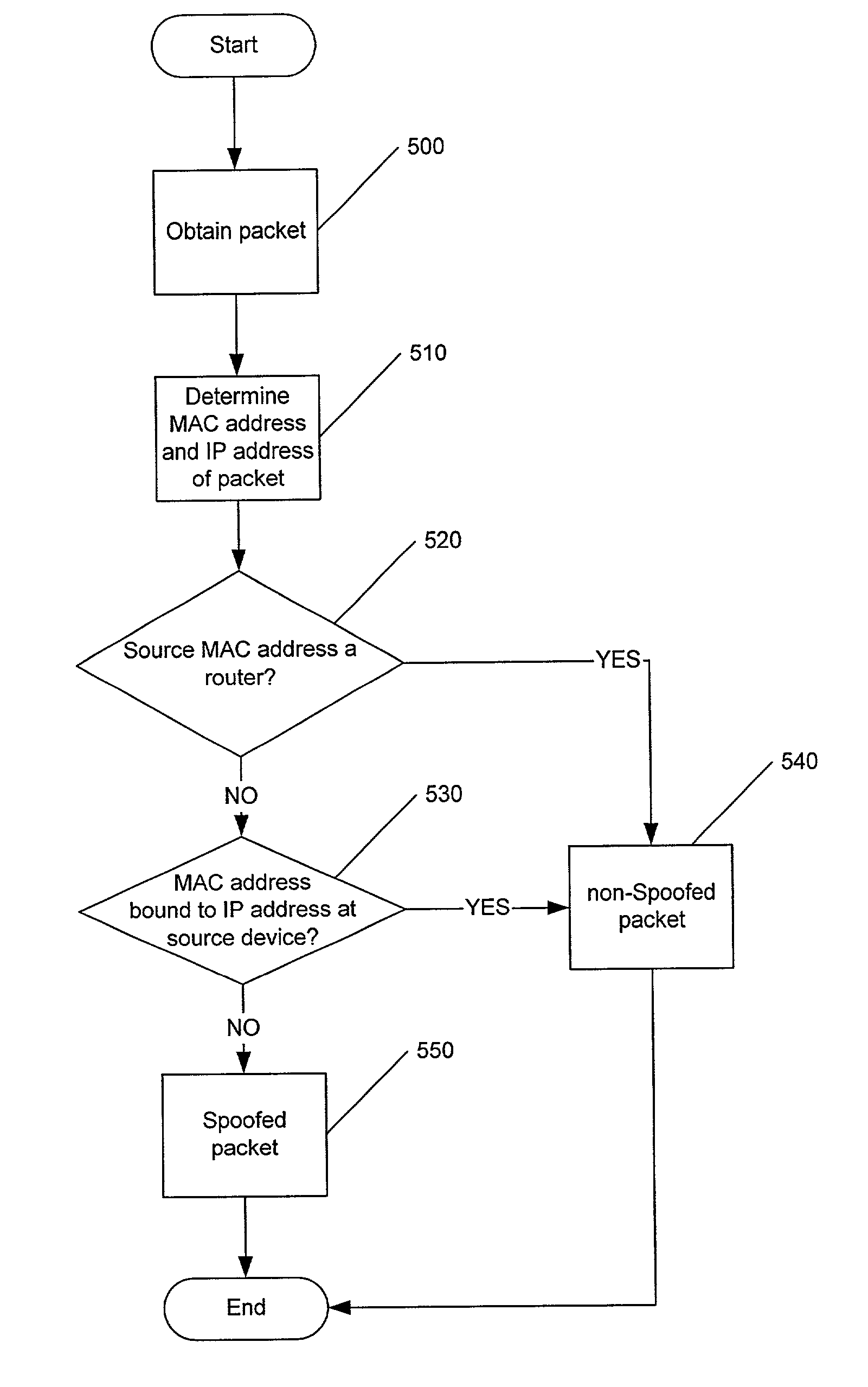
Methods, systems and computer program products for detecting a spoofed source address in IP datagrams
InactiveUS7134012B2Improve usabilityFrequency-division multiplexData switching by path configurationIp addressMedia access control
Methods, systems and computer program products are provided for determining if a packet has a spoofed source Internet Protocol (IP) address. A source media access control (MAC) address of the packet and the source IP address are evaluated to determine if the source IP address of the packet has been bound to the source MAC address at a source device of the packet. The packet is determined to have a spoofed source IP address if the evaluation indicates that the source IP address is not bound to the source MAC address. Such an evaluation may be made for packets having a subnet of the source IP address which matches a subnet from which the packet originated.
Owner:IBM CORP
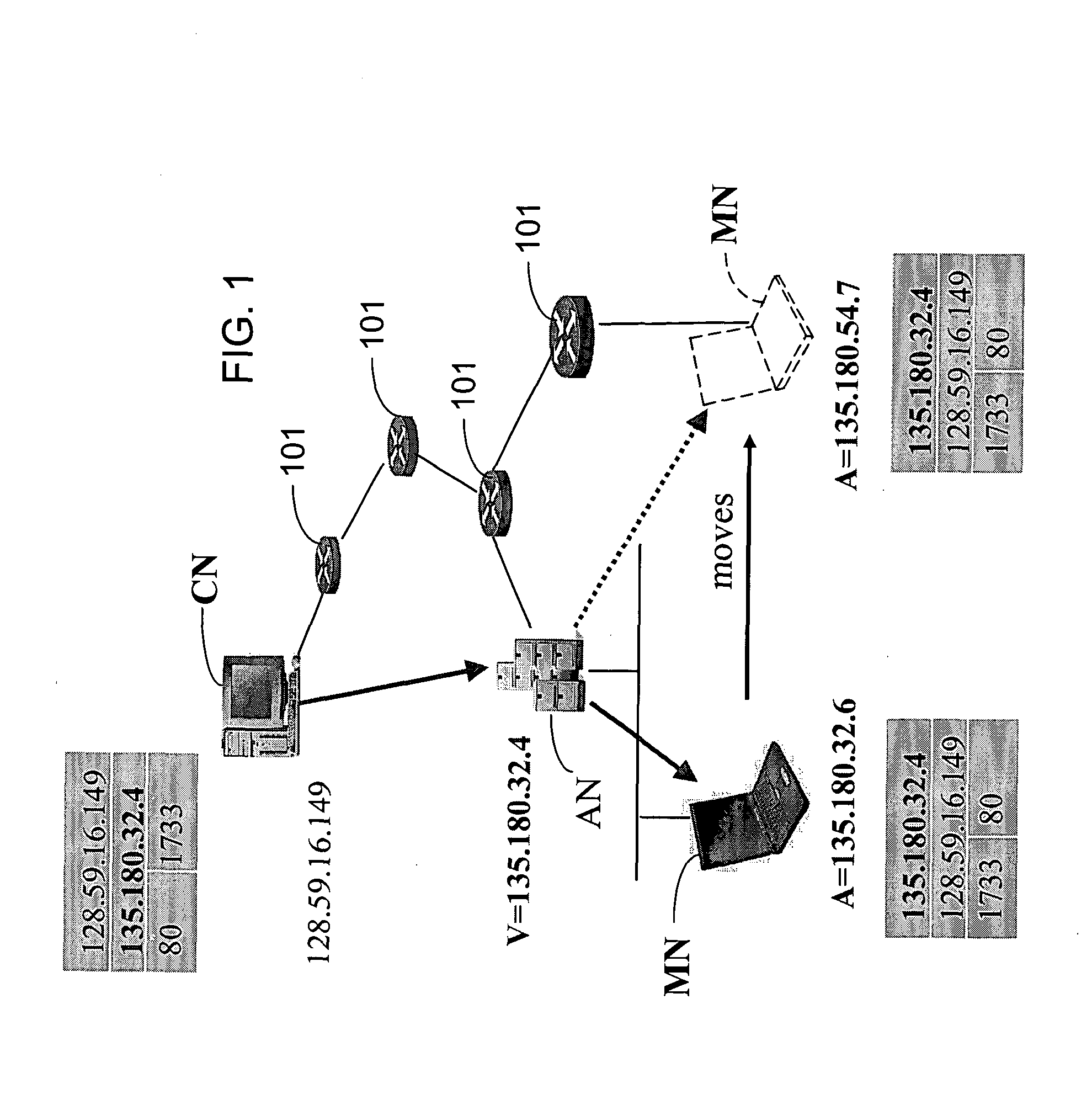
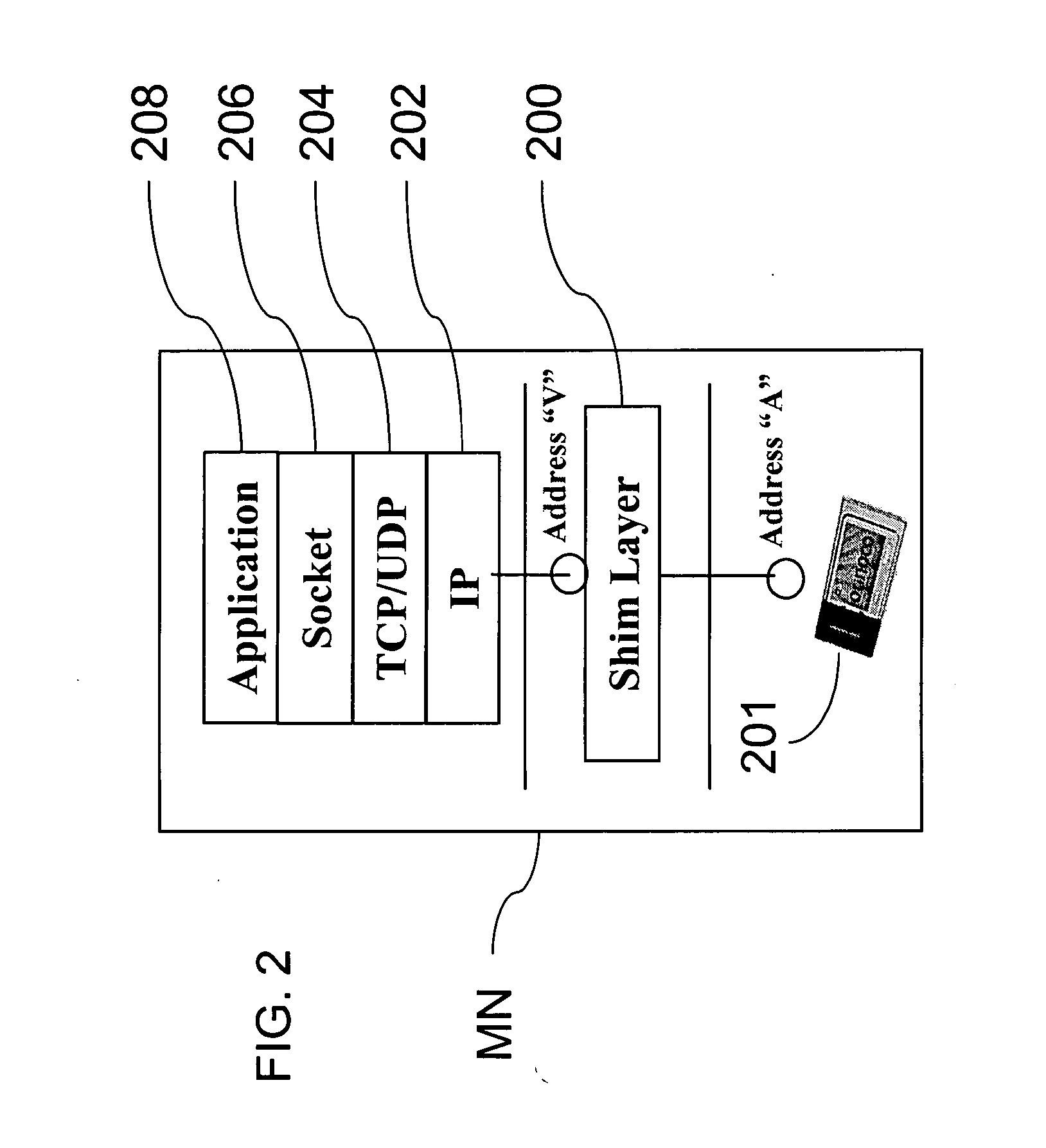
Method and system for mobility across heterogeneous address spaces
ActiveUS20050013280A1Time-division multiplexData switching by path configurationAddress spaceInternet Protocol
A mobile node includes a processor, a network interface, and a storage device having computer program code for execution by the processor. The computer program code includes a network layer for transmitting and receiving packets and an intermediate driver that transmits packets to the network layer and receives packets from the network layer using a virtual internet protocol (IP) address to identify the mobile node. The intermediate driver transmits packets to the network interface and receives packets from the network interface using a routable actual IP address to identify the mobile node. The intermediate driver permits the actual IP address to change when the mobile node moves from a first subnet to a second subnet without a corresponding change in the virtual IP address. A corresponding NAT associates the virtual IP address with a second actual IP address when the NAT is notified that the mobile node is in the second subnet.
Owner:ALCATEL LUCENT SAS
Methods and apparatus for routing a content request
ActiveUS7315541B1Digital computer detailsData switching by path configurationNetwork address translationCommunication device
Mechanisms and techniques provide a method for routing a packet that includes a content request and an Internet Protocol address and port number that identify a source transmitting the packet. The method relates to selecting a routing policy to forward the packet, based upon at least a portion of content request. The method includes a data communications device receiving a packet having a content request and an Internet Protocol address and port number that identify a source transmitting the packet. The device performs a network address translation, based upon at least a portion of the content request, to translate the Internet Protocol address and port number of the packet to a respective communications device Internet Protocol address and communications device port number. The device then selects a routing policy based upon the communications device Internet Protocol address and routes the packet to a destination according to the routing policy.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com