Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
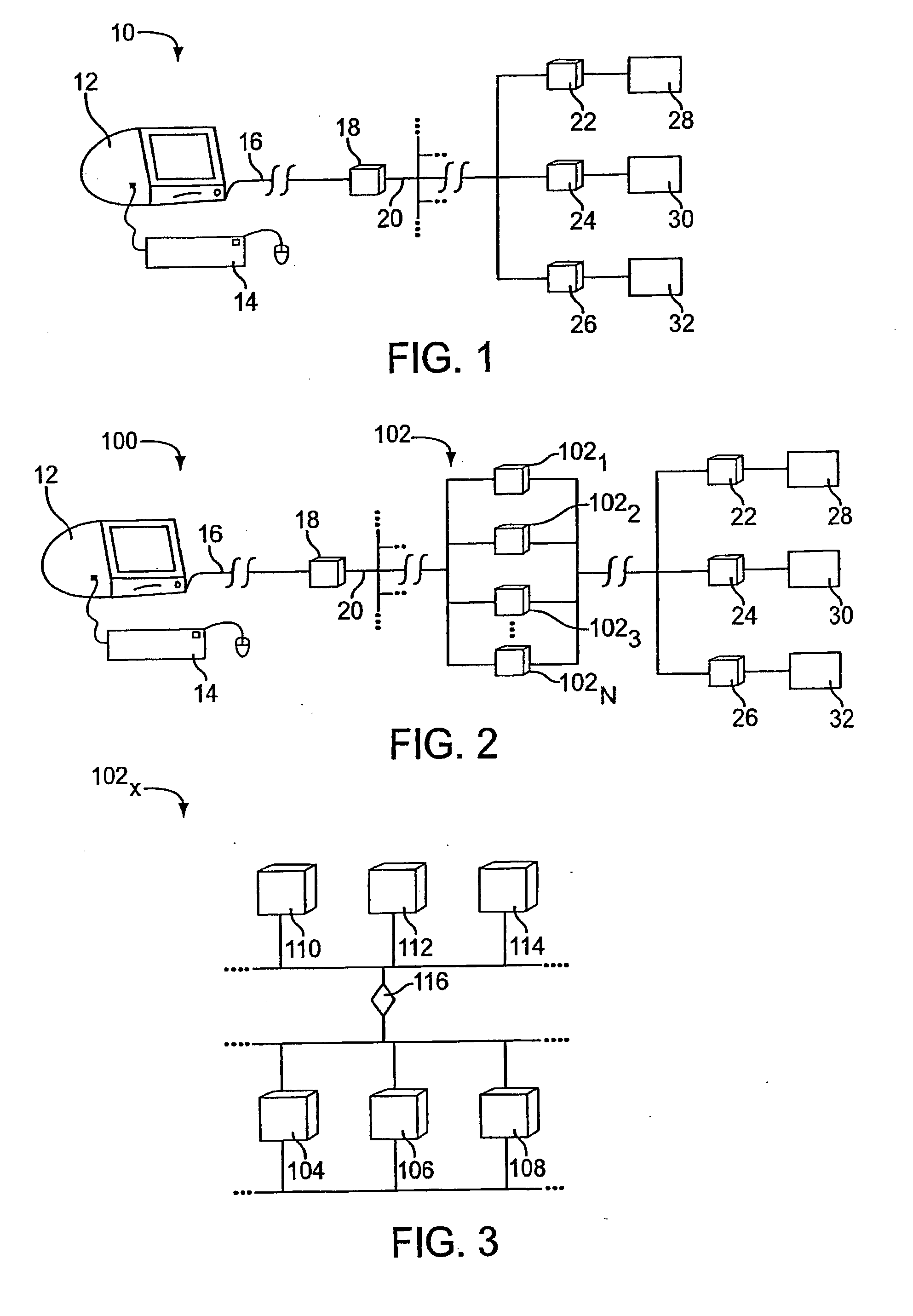
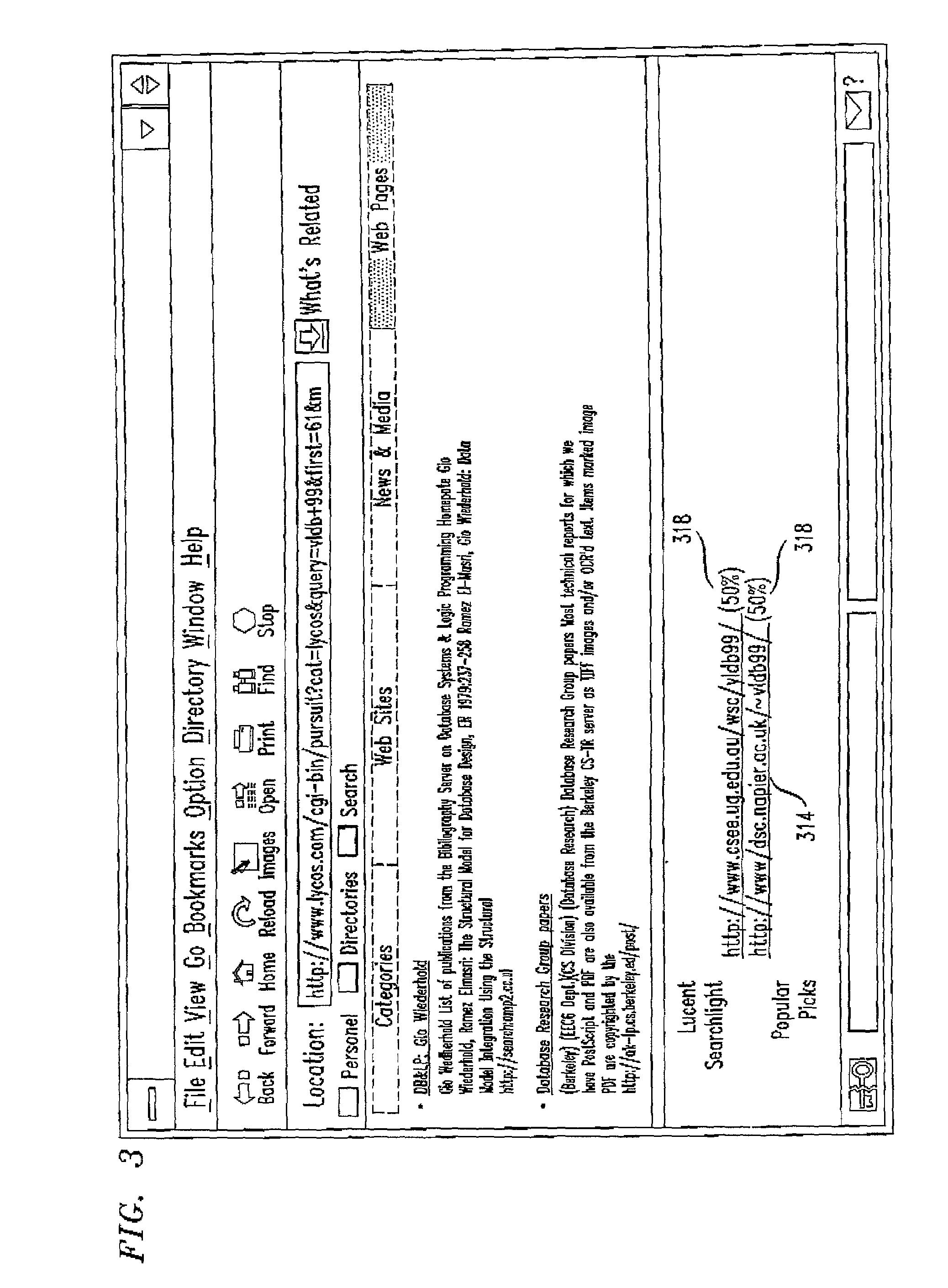
5150 results about "Proxy server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
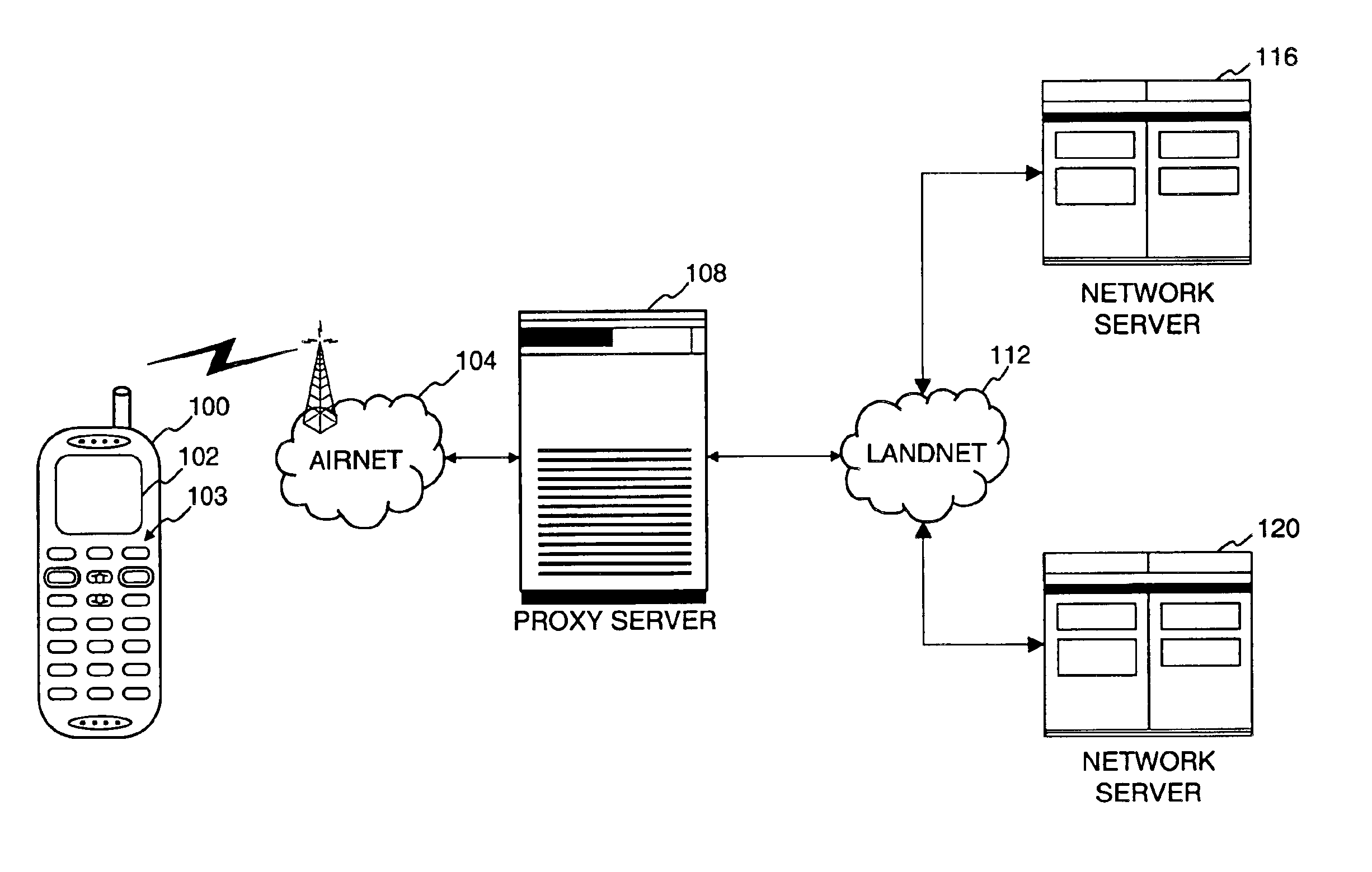
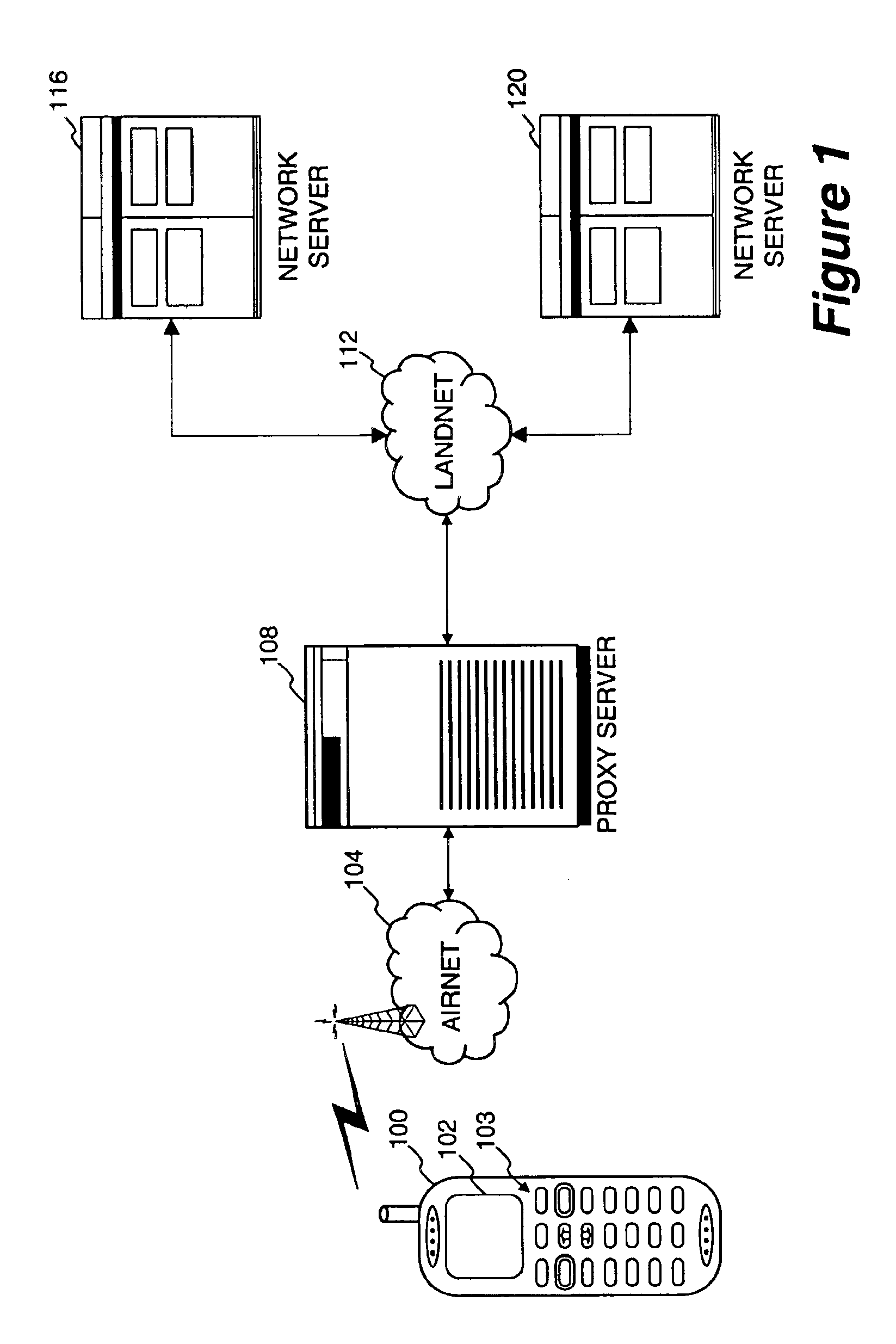
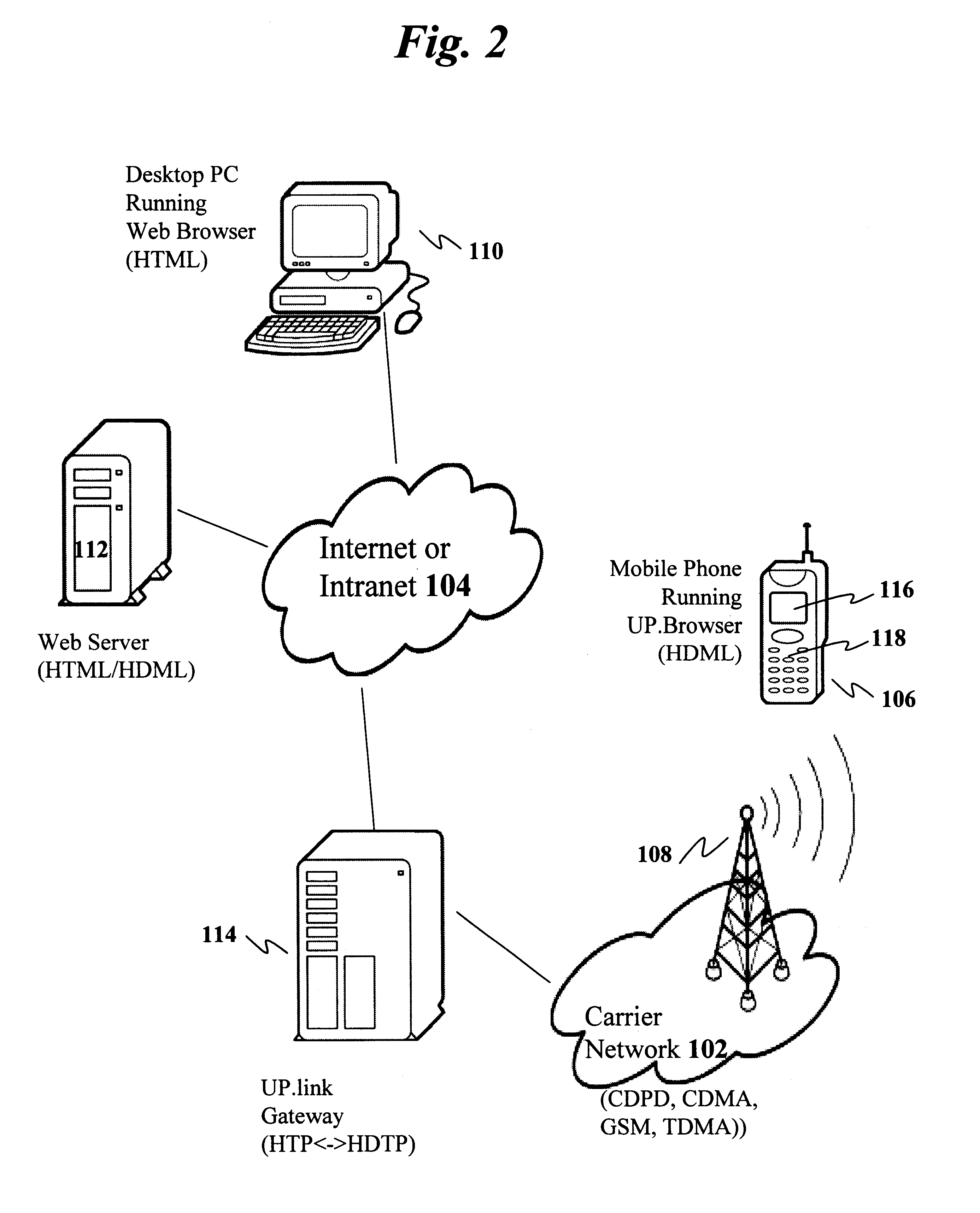
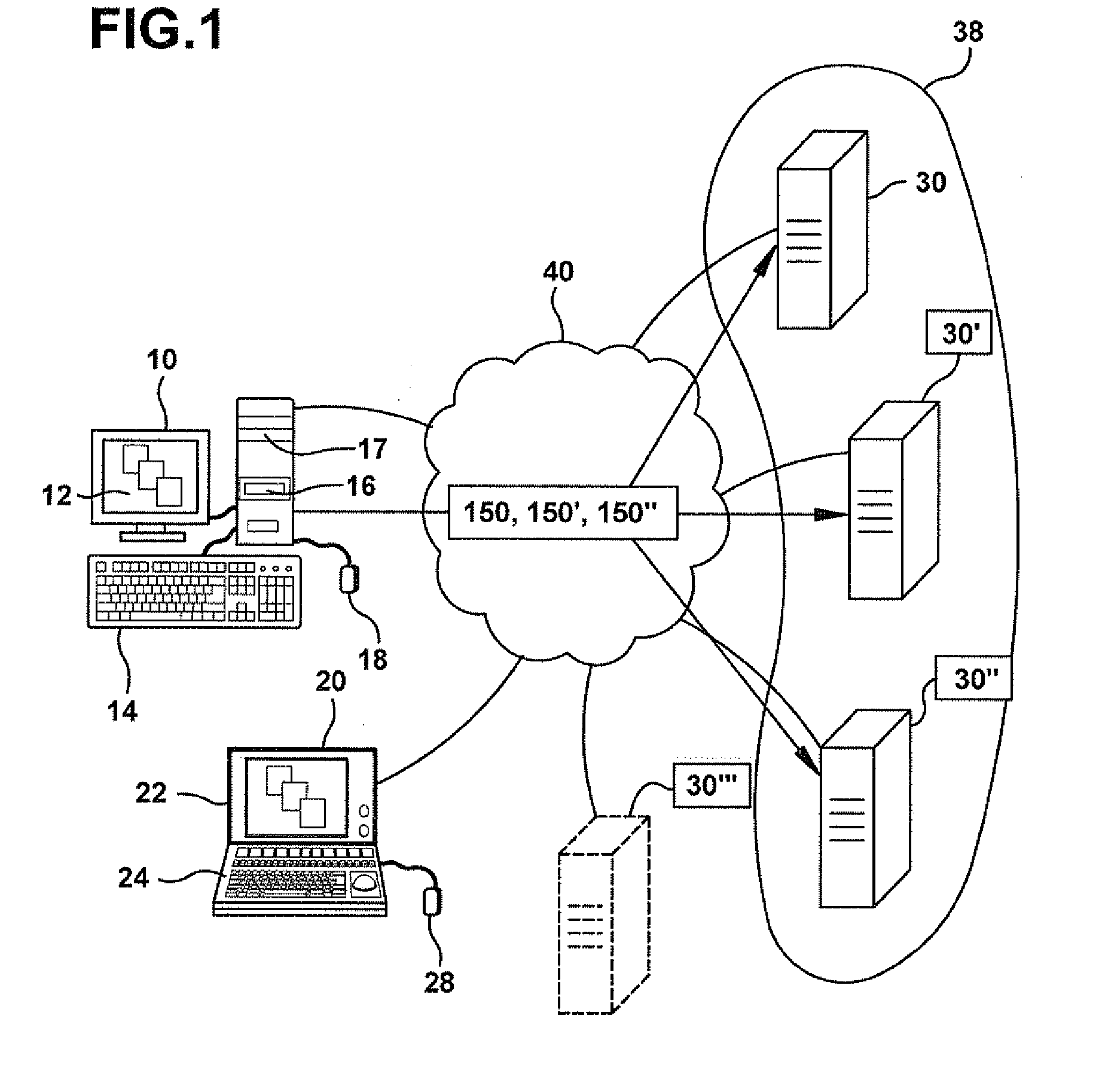
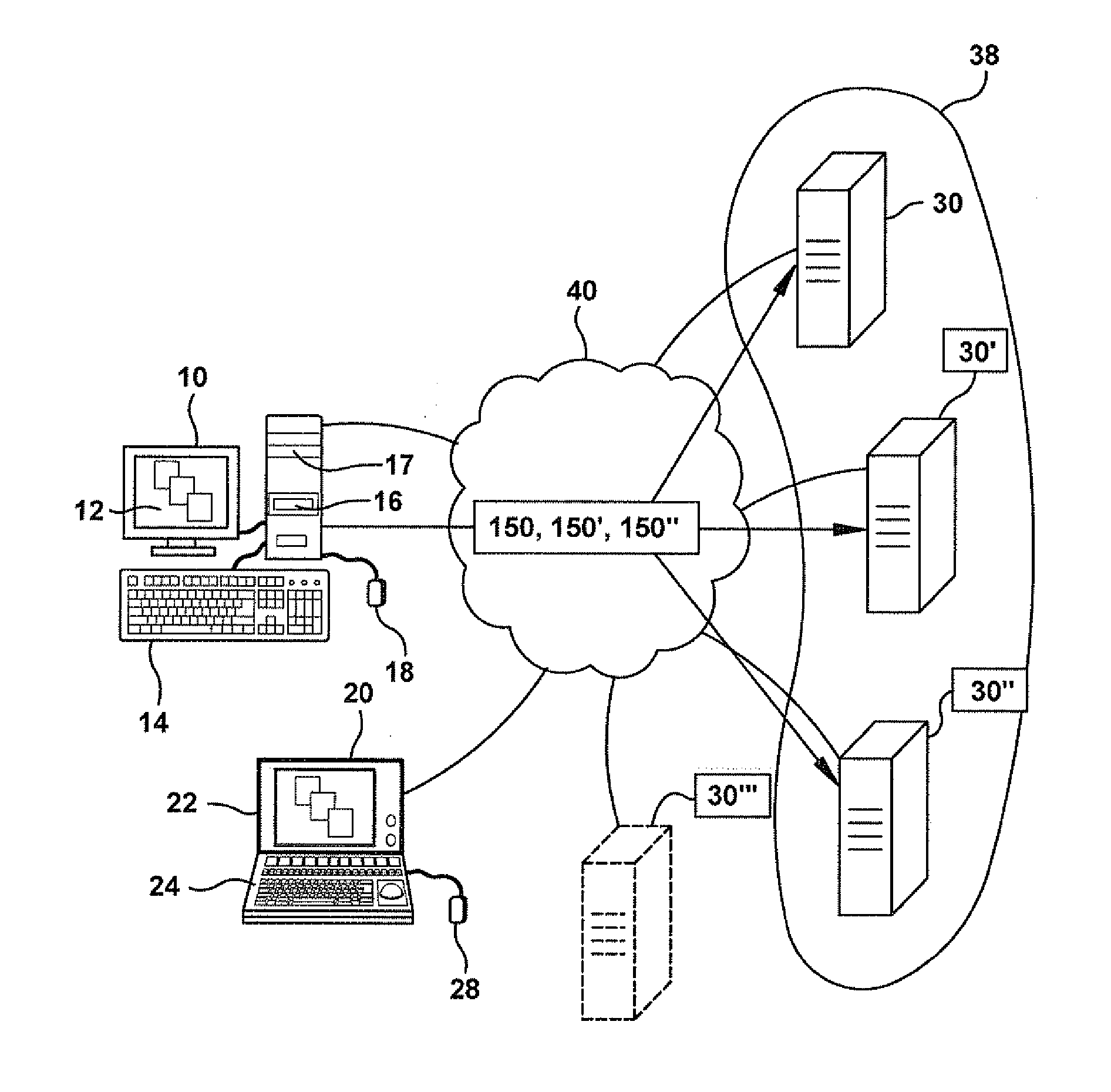
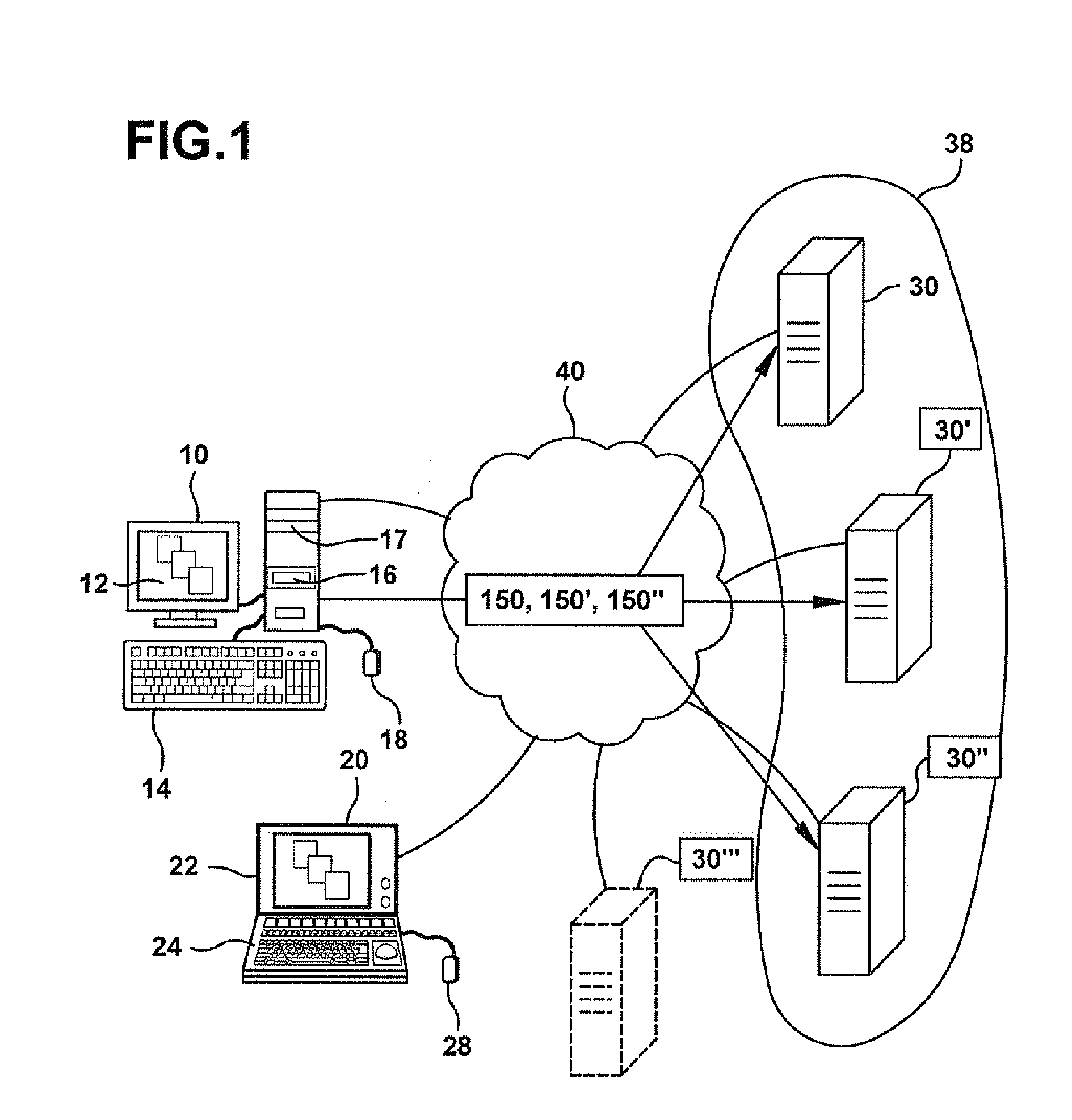
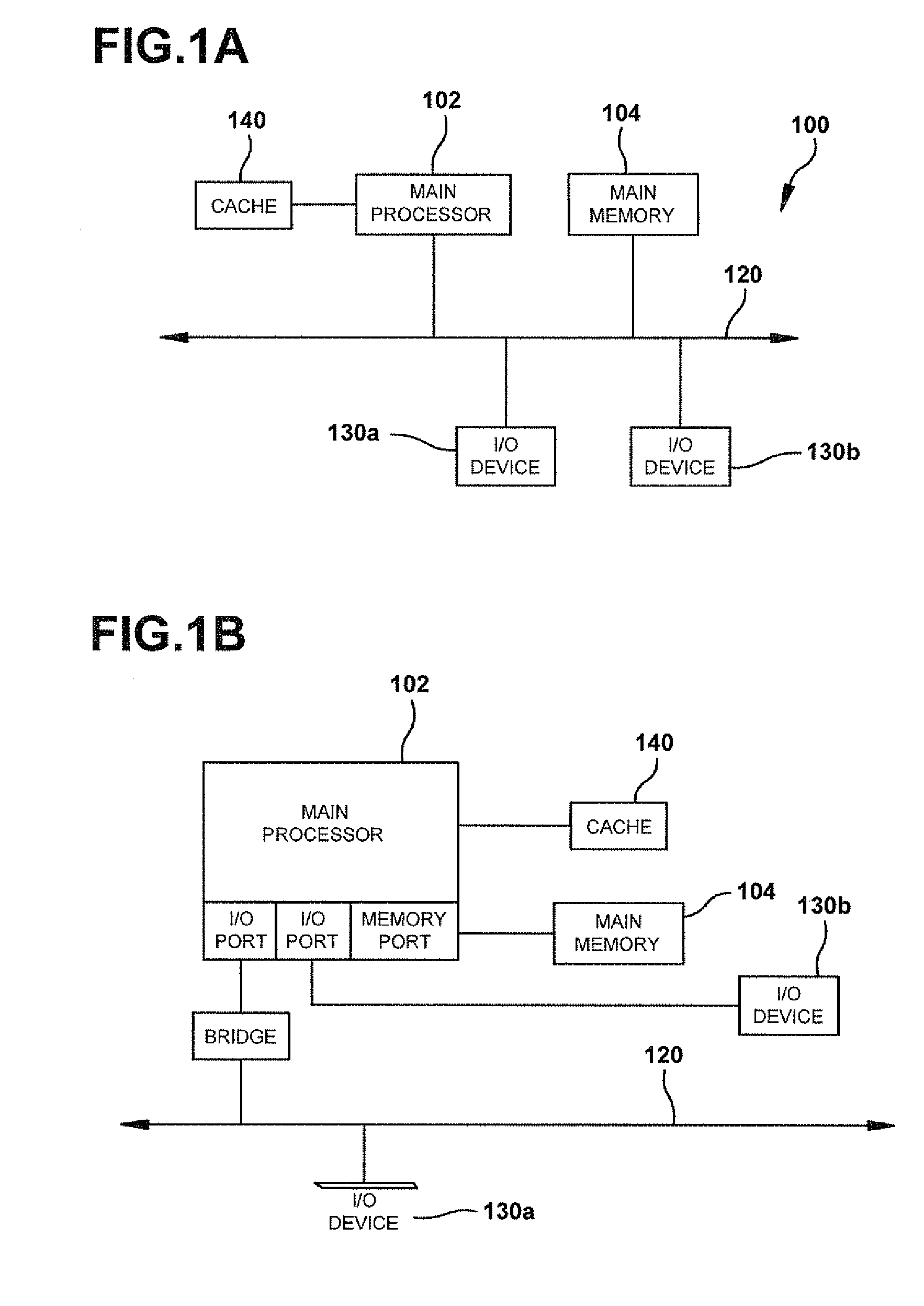
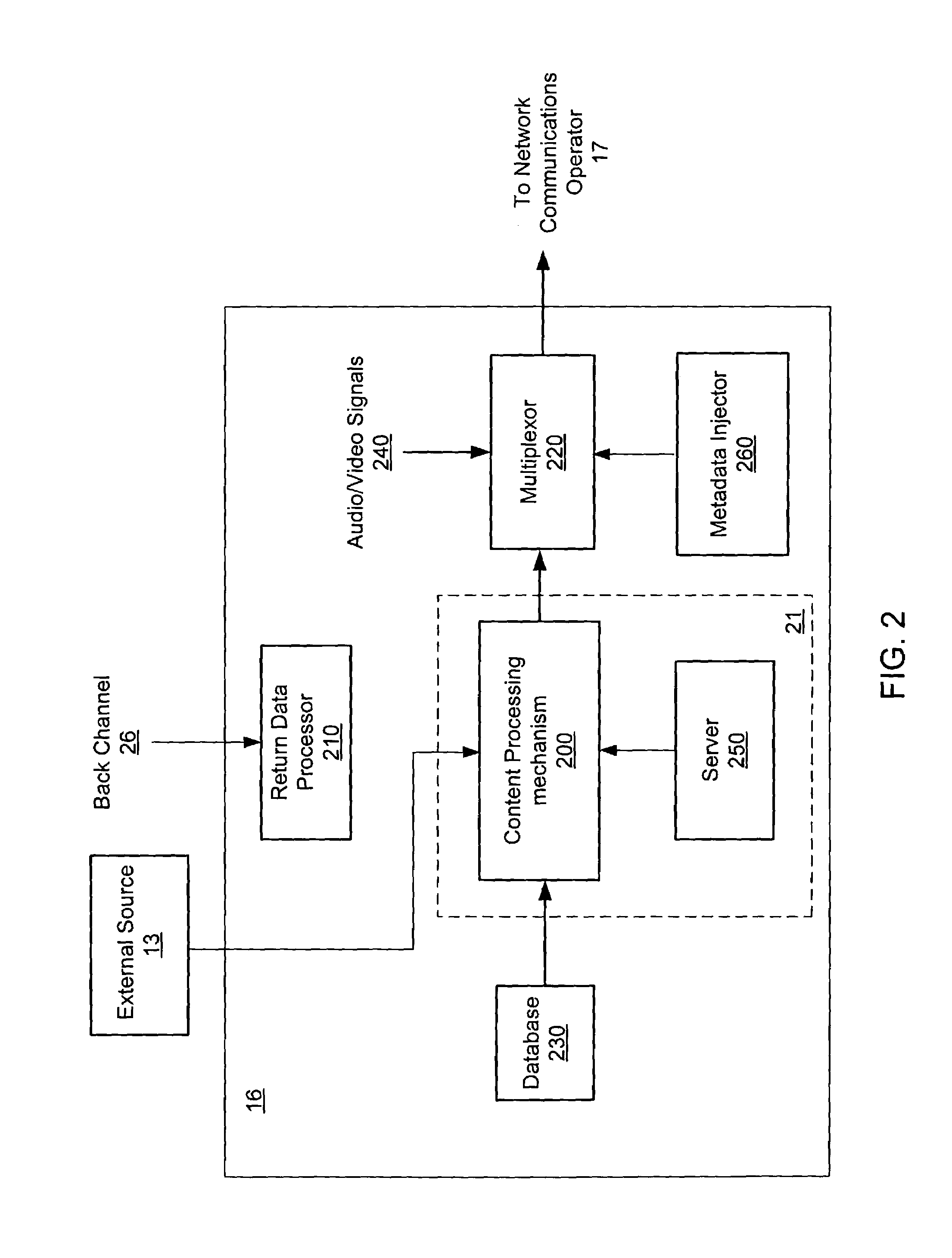
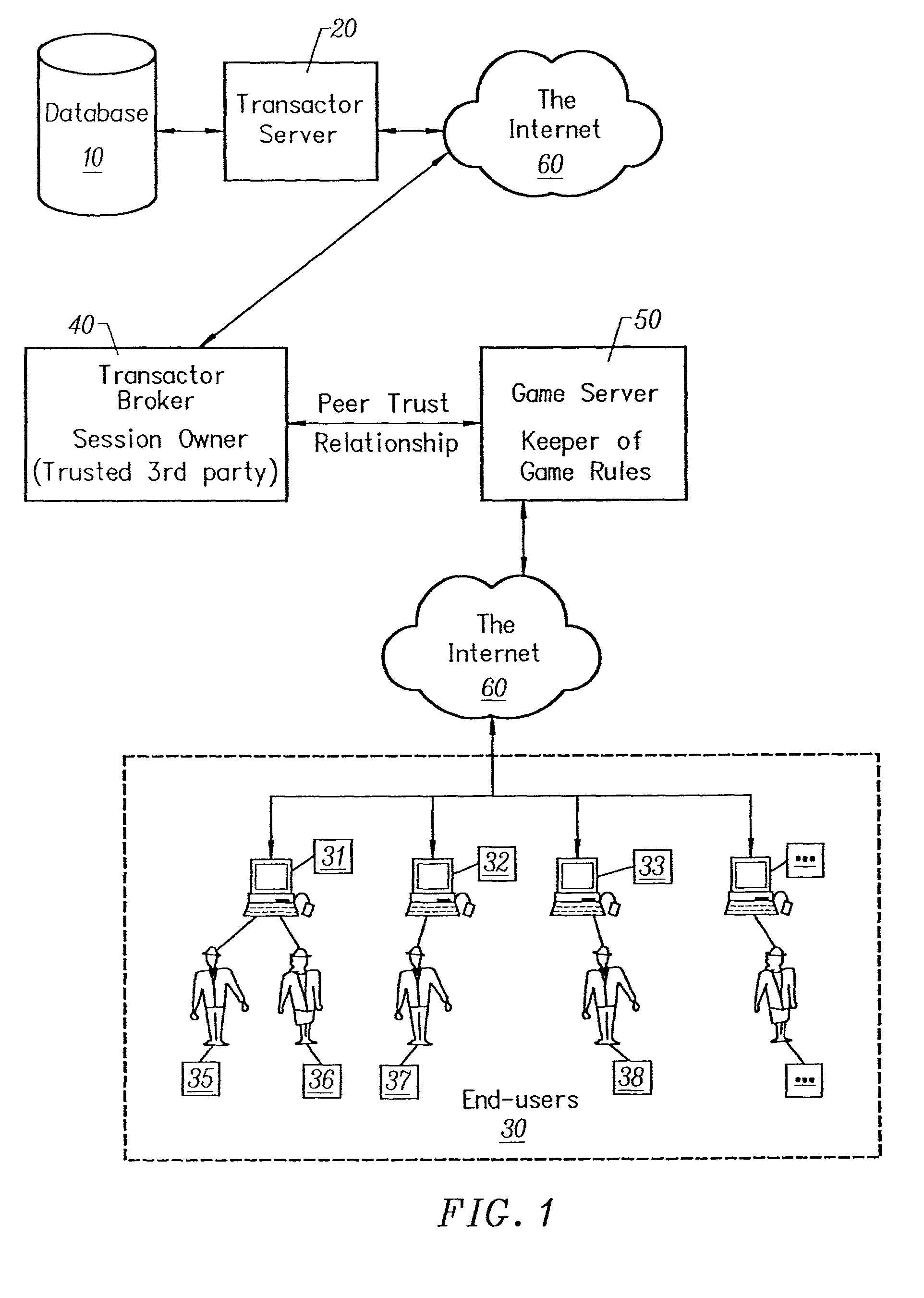
In computer networks, a proxy server is a server (a computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server and the proxy server evaluates the request as a way to simplify and control its complexity. Proxies were invented to add structure and encapsulation to distributed systems.
Method and apparatus for automatic placement of advertising
InactiveUS7039599B2Efficient use ofPrevention of ad “burn out.AdvertisementsCash registersWeb siteComputerized system
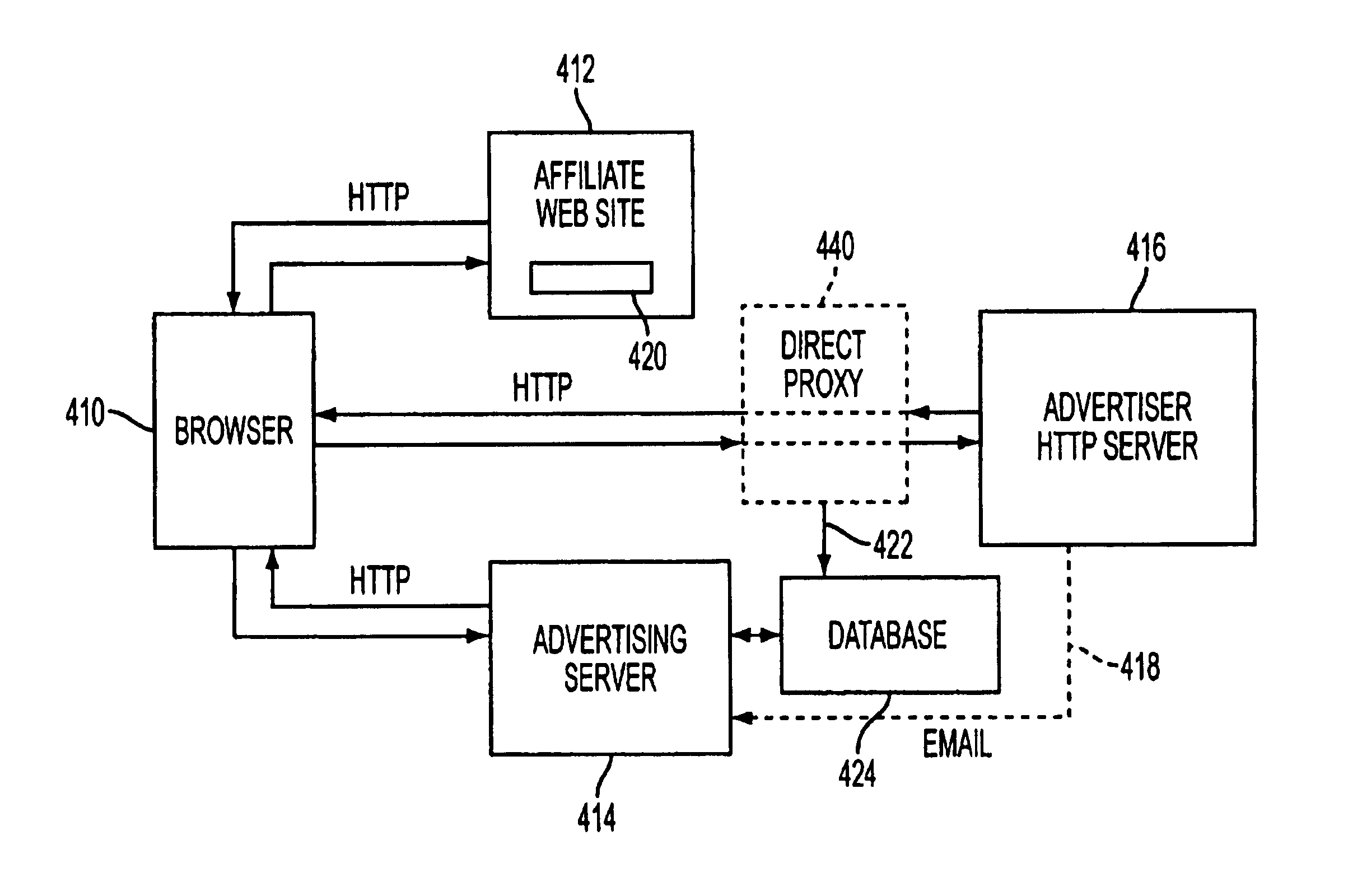
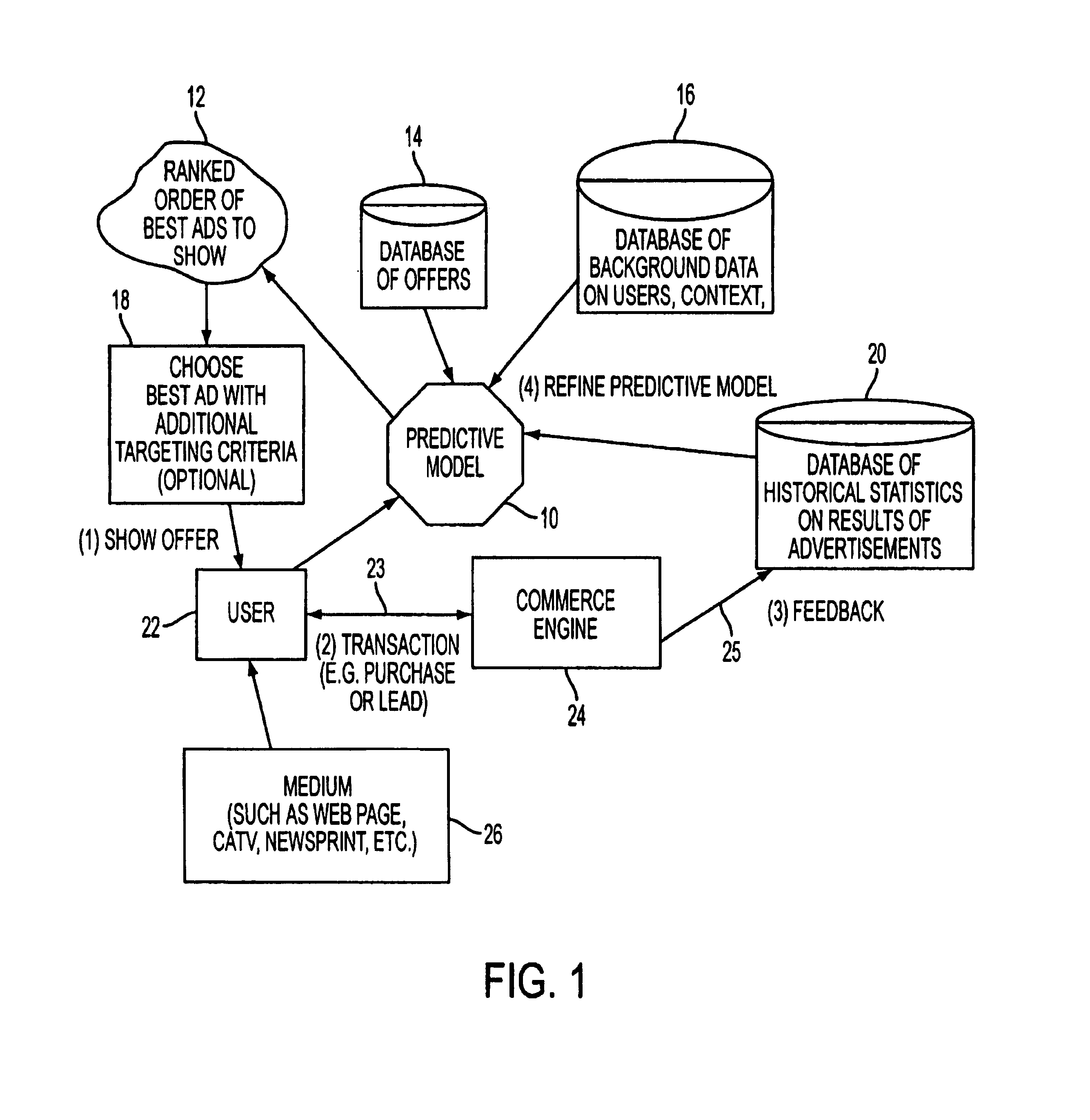
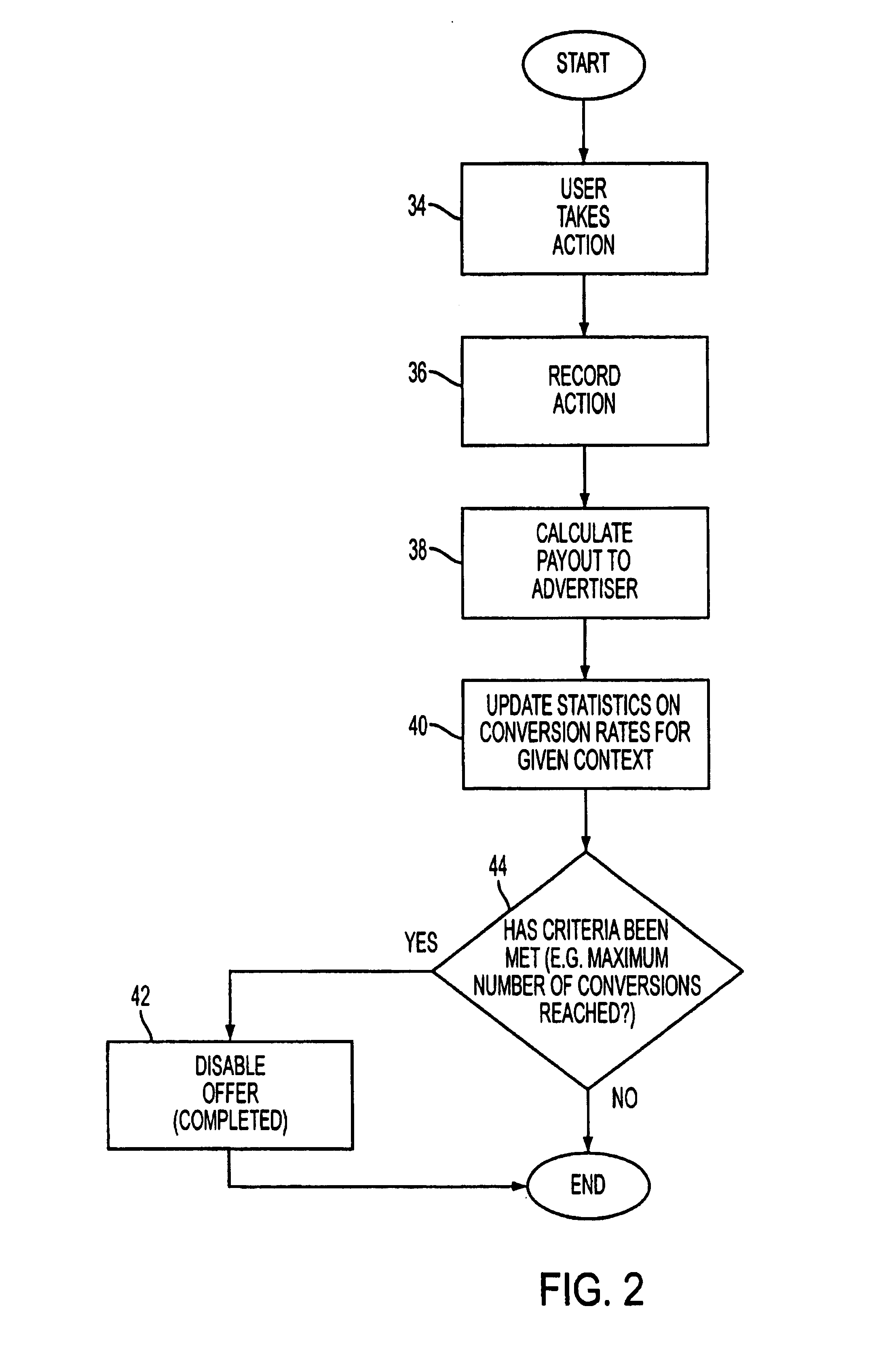
A computer system for automatic replacement of direct advertisements in scarce media includes an advertising server for selecting a direct advertisement based on certain criteria. Transaction results of the direct advertisement placement are reported back to the advertising server, and an associated accounting system. In one embodiment, the direct advertiser's server reports transactions back to the advertising server by email. In a second embodiment, a direct proxy server brokers the user's session (or interaction) with the direct advertiser's server, including transaction processing and the direct proxy server reports the results of transactions back to the advertising server and its associated accounting system. A direct proxy provides an independent audit of transactions at a remote direct advertiser's web site. The feedback of the results of direct advertisement transactions provides an efficient utilization of direct advertising space by way of an automated computer system with a predictive model for selection and distribution of direct advertising.
Owner:GOOGLE LLC
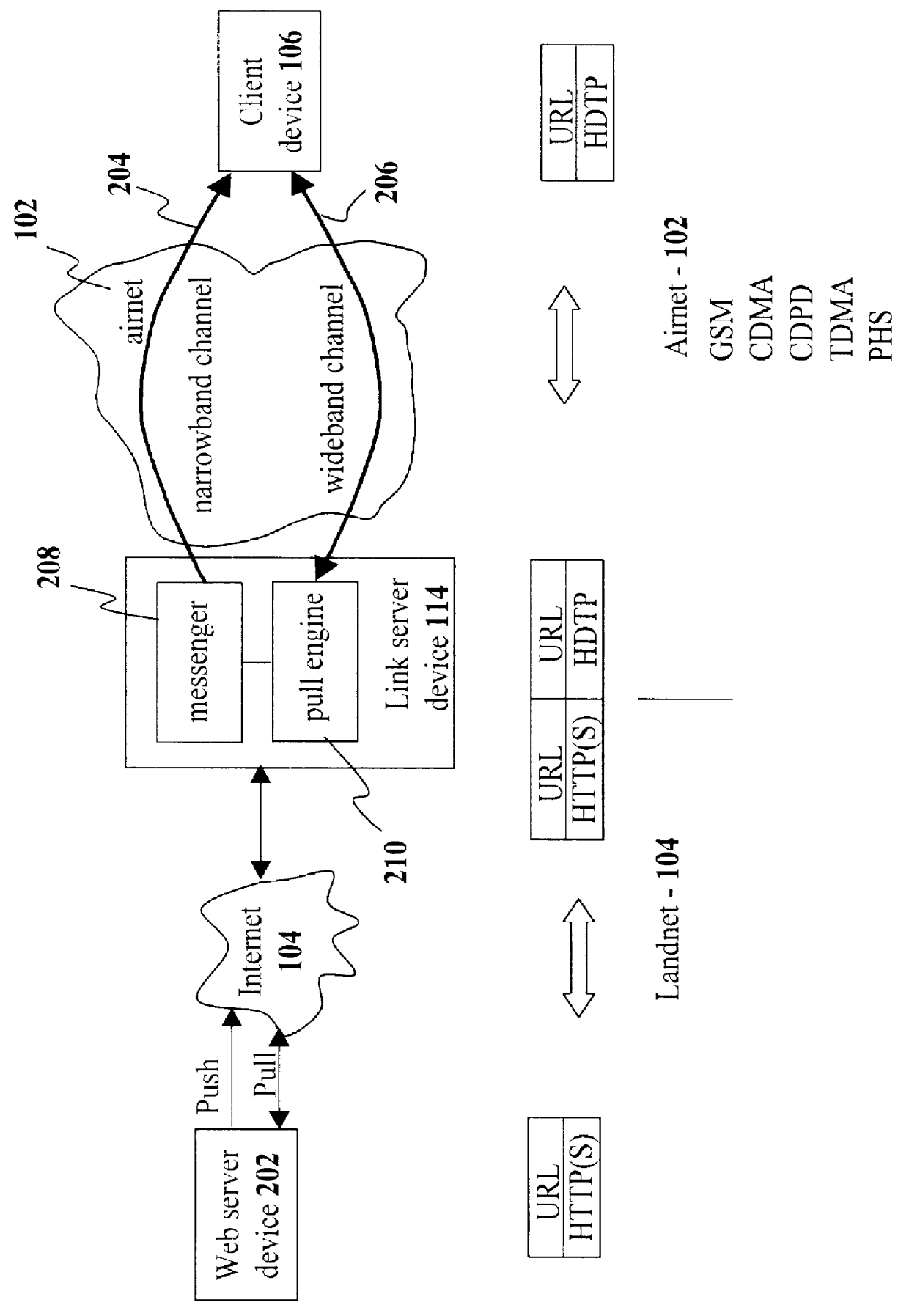
Method and system for pushing and pulling data using wideband and narrowband transport systems
InactiveUS6138158AWithout incurring uncontrollable costHigh trafficNetwork traffic/resource managementNetwork topologiesTransport systemThe Internet
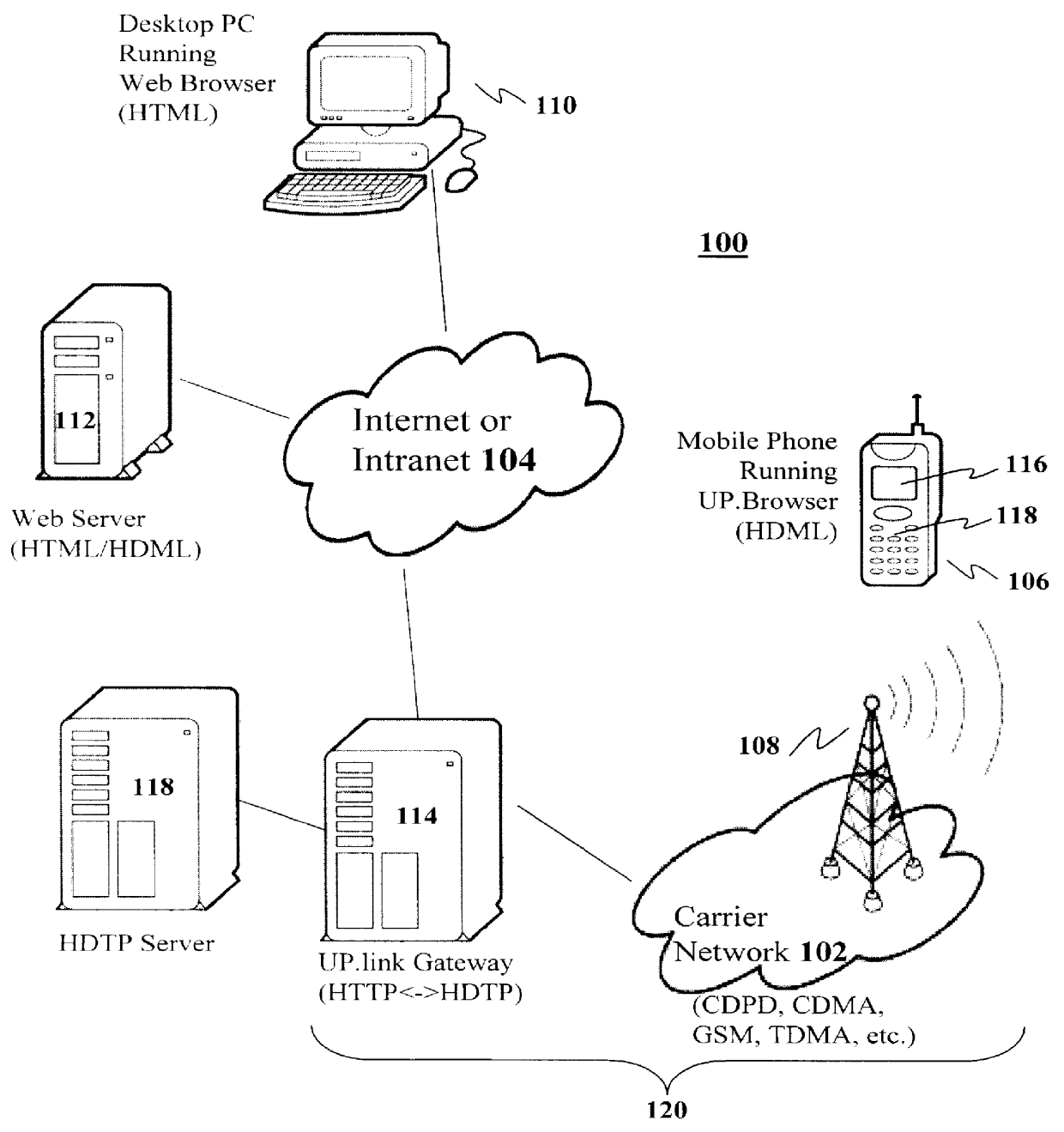
The present invention has particular applications to the navigation of Internet web pages using two-way interactive communication devices, such as a mobile device, a mobile phone, a landline telephone, and an Internet capable remote controller. According to one aspect of the present invention, each of the two-way interactive communication devices is a node in a distributed network, thus the devices can access hypermedia or hierarchic layers of information stored in server devices on the network. When one or more pages of information are updated, rather than sending the entire updated information to users of the devices subscribing to the updated information through the network, the present invention sends a notification to a proxy server that forwards the notification to the users using a messaging system via a low cost narrowband channel. Upon receiving the notification, the users can fetch the updates, when needed, through a wideband channel. Hence systemic solutions are provided in the present invention to integrate wideband and narrowband channels so as to keep the users informed of any updates to their desired information and meanwhile provide efficient means to the users for retrieving the latest updates without incurring uncontrollable costs and increasing unnecessary network traffics.
Owner:UNWIRED PLANET
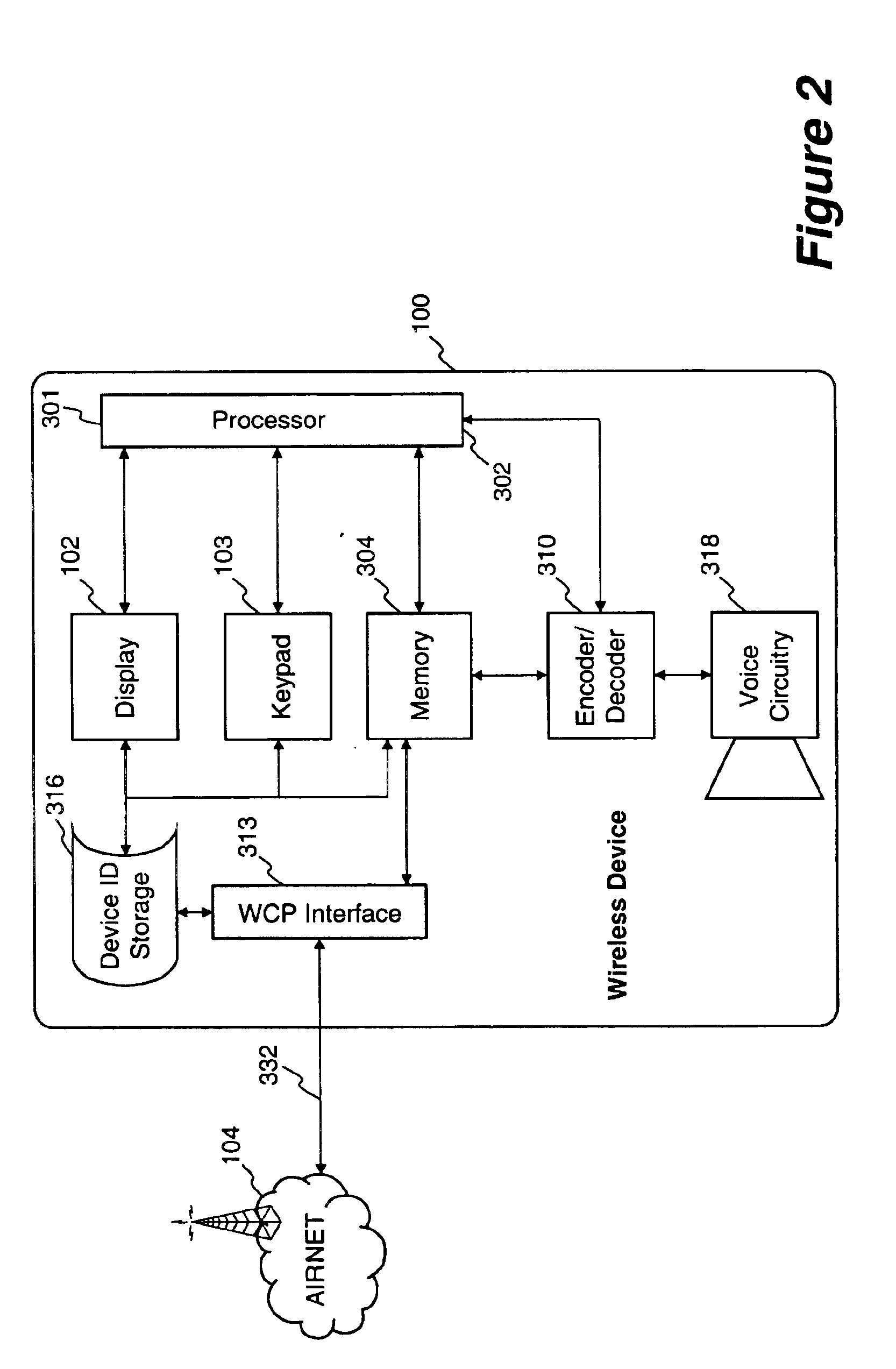
Method and apparatus for providing internet content to SMS-based wireless devices
A method and apparatus for providing hypermedia content maintained remotely on a network to a wireless device without a browser are described. A Short Message Service (SMS) request for Internet-based content is received from the wireless device at a proxy server, via an SMS Center (SMSC). The SMS request is transmitted to the SMSC on a wireless network. The proxy server transcodes the SMS request from a character set of the SMSC to a character set of an application and extracts a keyword from the trancoded request. The proxy server maintains a mapping of keywords to URLs. The proxy server looks up the extracted keyword in the keyword-to-URL mapping to identify the URL of an application associated with the keyword. The proxy server constructs an HTTP POST operation containing the keyword and the URL, and submits the HTTP POST operation to the application over a wireline network such as the Internet. Upon receiving an HTTP response containing the requested content from the application in response to the POST operation, the proxy server extracts the content from the HTTP response. The proxy server then translates the content from the content-type used by the application to the content-type used by the SMSC and transcodes the content from the character set used by the application to the character set used by the SMSC. The proxy server then sends the translated and transcoded content in an SMS response to the SMSC, for subsequent delivery to wireless device as an SMS message.
Owner:UNWIRED PLANET
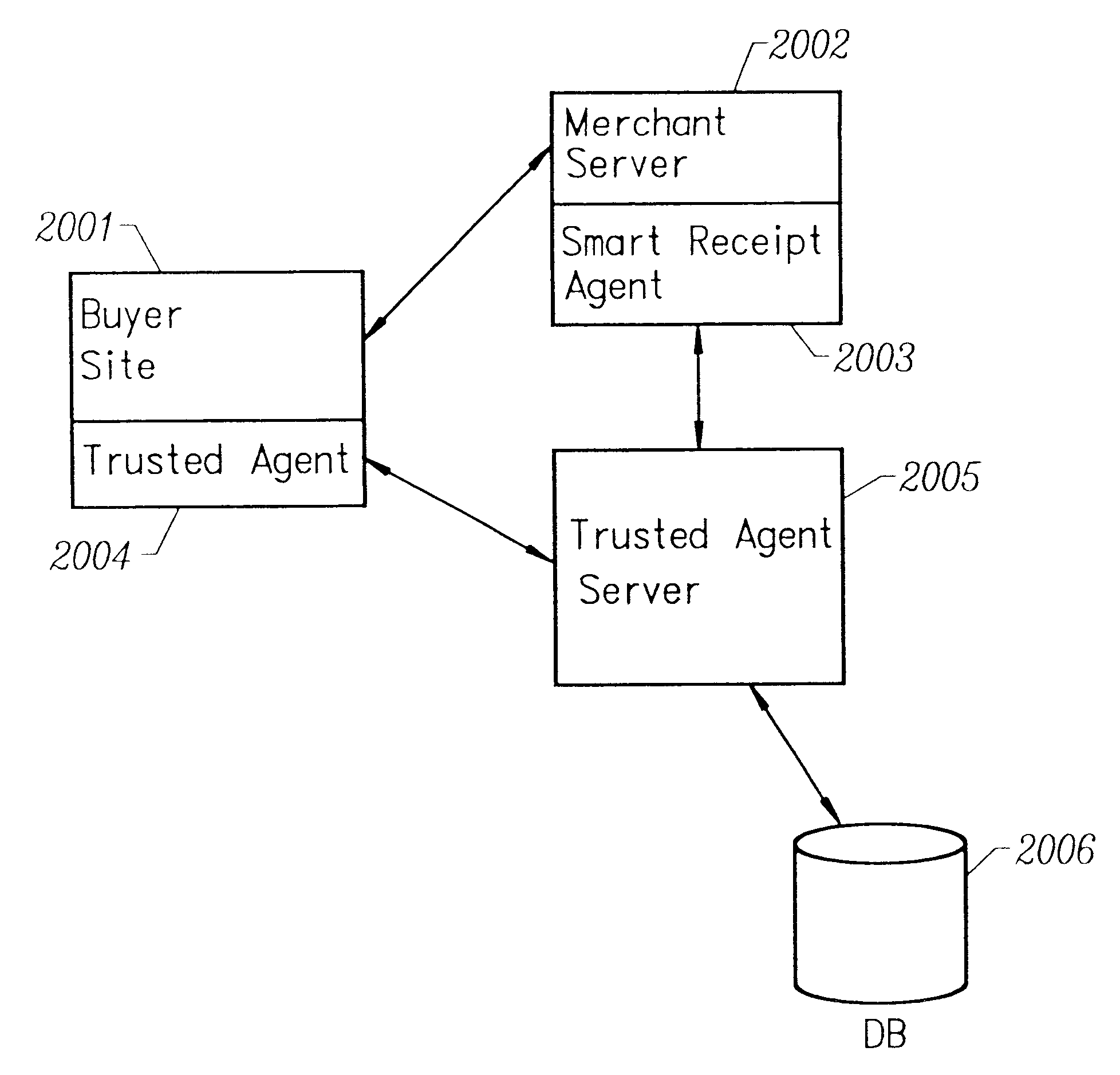
Smart electronic receipt system
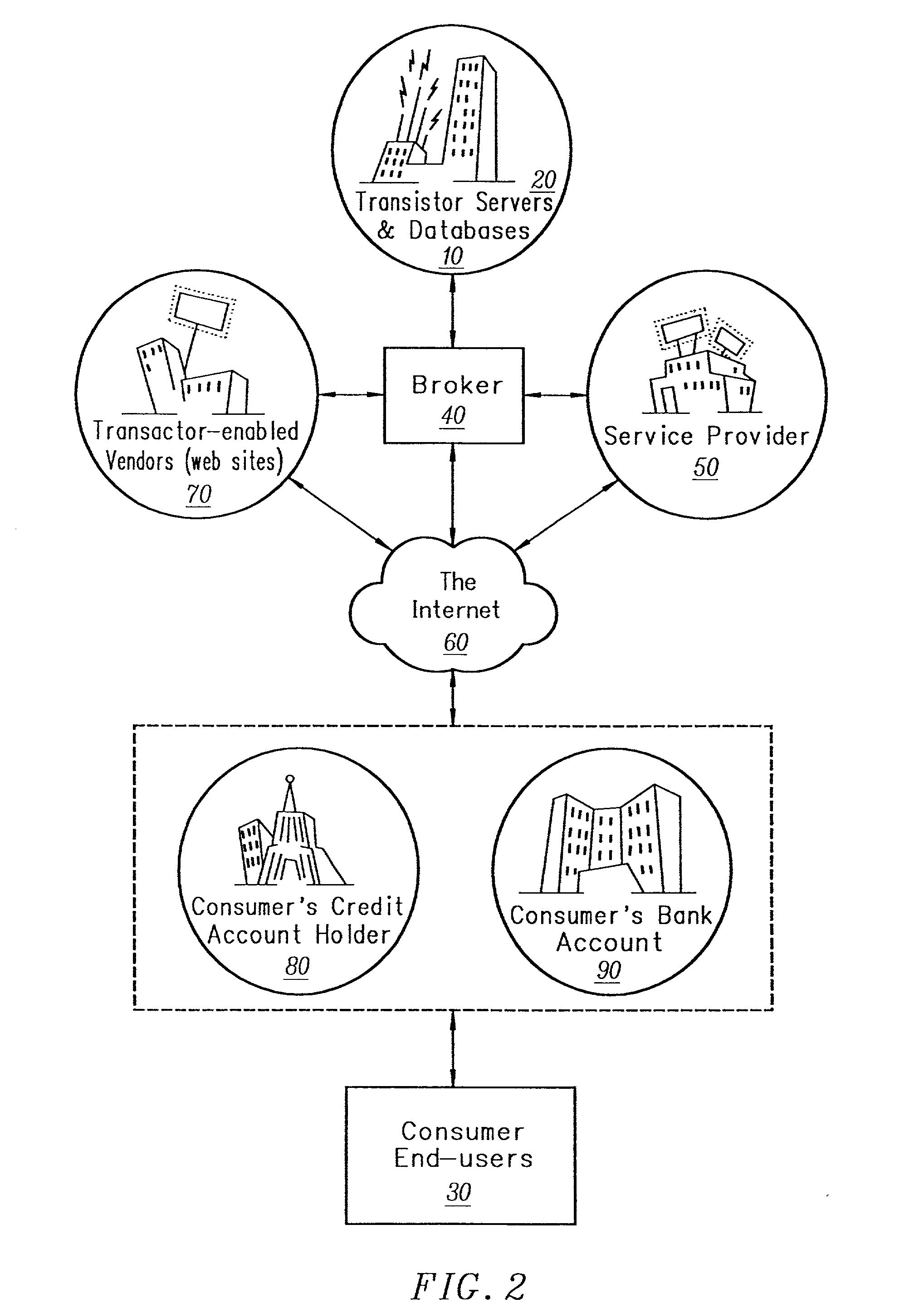
A smart electronic receipt system that provides intelligent receipts, called Smart Receipts, that electronically document a transaction between two parties and maintains a persistent connection between the two parties following a successful online transaction. A Trusted Agent on the Buyer's client system creates an order record which is stored in a database on a Trusted Agent Server and starts the transaction process with the merchant. A Smart Receipt is delivered by a Smart Receipt Agent over a secure connection from the merchant to the Trusted Agent Server upon successful completion of a purchase and reflects the details of the transaction. It is stored in a secure database on the Trusted Agent Server and is made available to the Buyer (user) through a Trusted Agent located on his machine. The Trusted Agent Server compares the order record Limited Edition Digital Objects (LEDOs) stored in database with the Smart Receipt's LEDO to find the corresponding order record. The Smart Receipt provides the customer with detailed information about an online purchase in a standardized format. Hyperlinks embedded in the Smart Receipt enable the customer to access customer service and order status. The merchant may also embed addition-al services within the Smart Receipt, including special offers for future purchases. Offers provided in a Smart Receipt can be personalized to a user's preferences which are stored on the Trusted Agent Server. Each Smart Receipt is comprised of a chain of LEDOs with each LEDO object having a unique owner. A Smart Receipt is a dynamic entity and is continuously updated until the Buyer deletes it from the Trusted Agent Server.
Owner:THE BRODIA GROUP
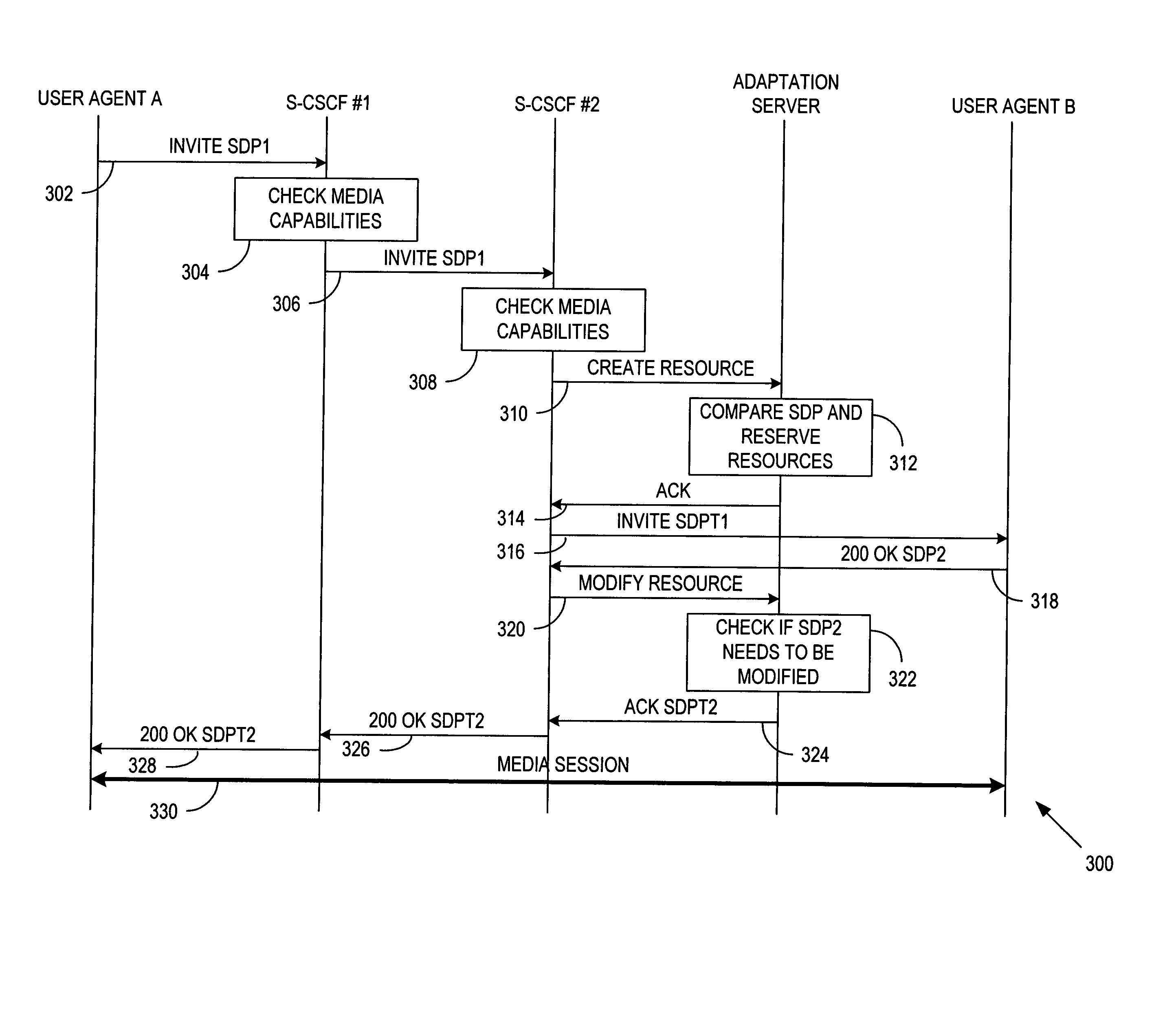
System and method for adaptation of peer-to-peer multimedia sessions
InactiveUS20050060411A1Multiple digital computer combinationsElectric digital data processingAdaptive servicesComputer compatibility
A system and method is provided that allows proxy servers to receive capability and preference information concerning user agents (502 and 510) desiring to establish a media session. The proxy server compares the capabilities of the user agents and determines whether an incompatibility exists between them. In the event that an incompatibility does exist, the proxy server may invoke the services of an adaptation server (508) to provide the necessary adaptation required to allow the media session to proceed. The adaptation system allows either the terminating or originating proxy server to make the adaptation determination to allow the adaptation server to modify the offered media session descriptions so that the media streams may be routed through the adaptation server to adapt between incompatible media parameters.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Network caching system for streamed applications
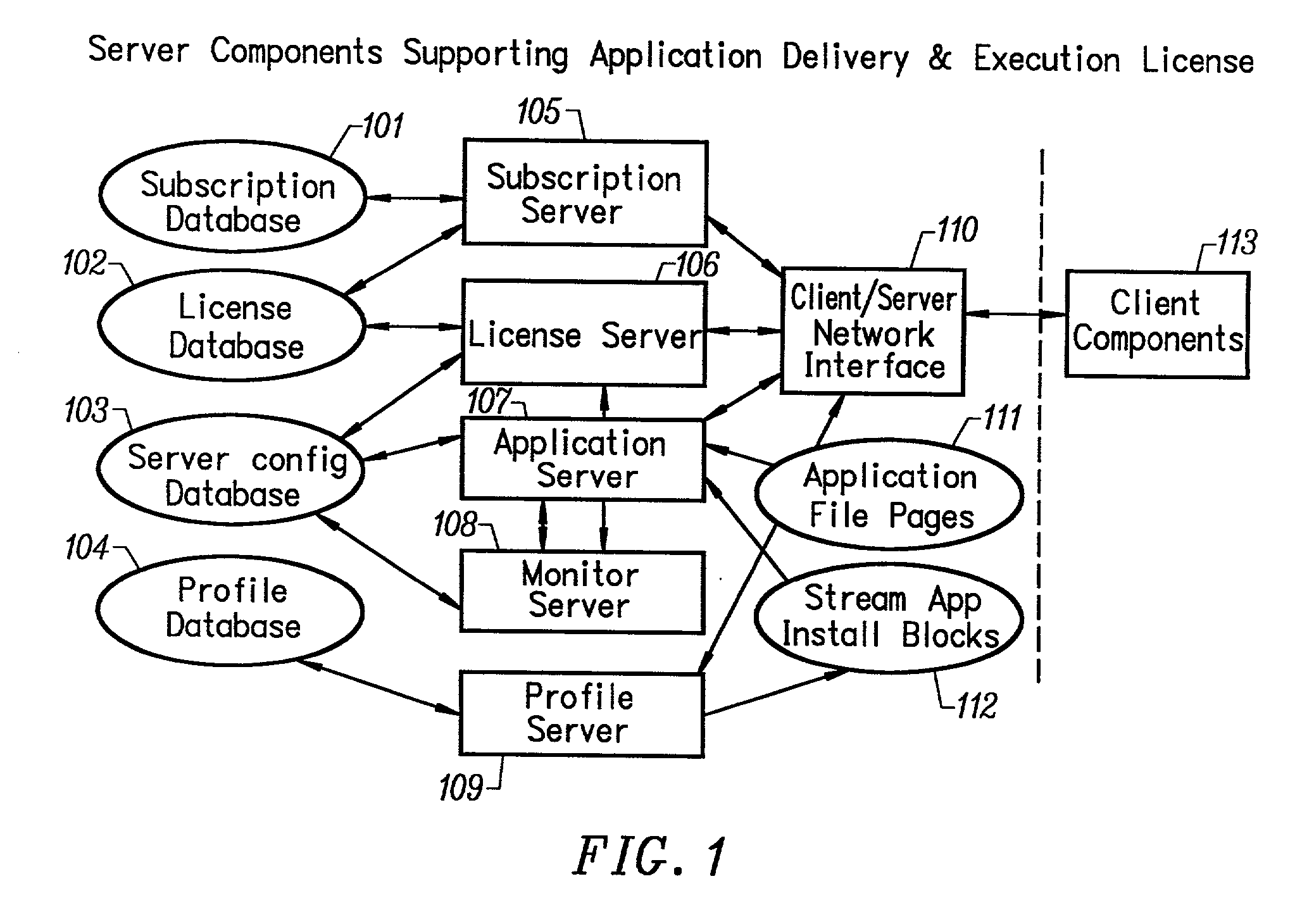
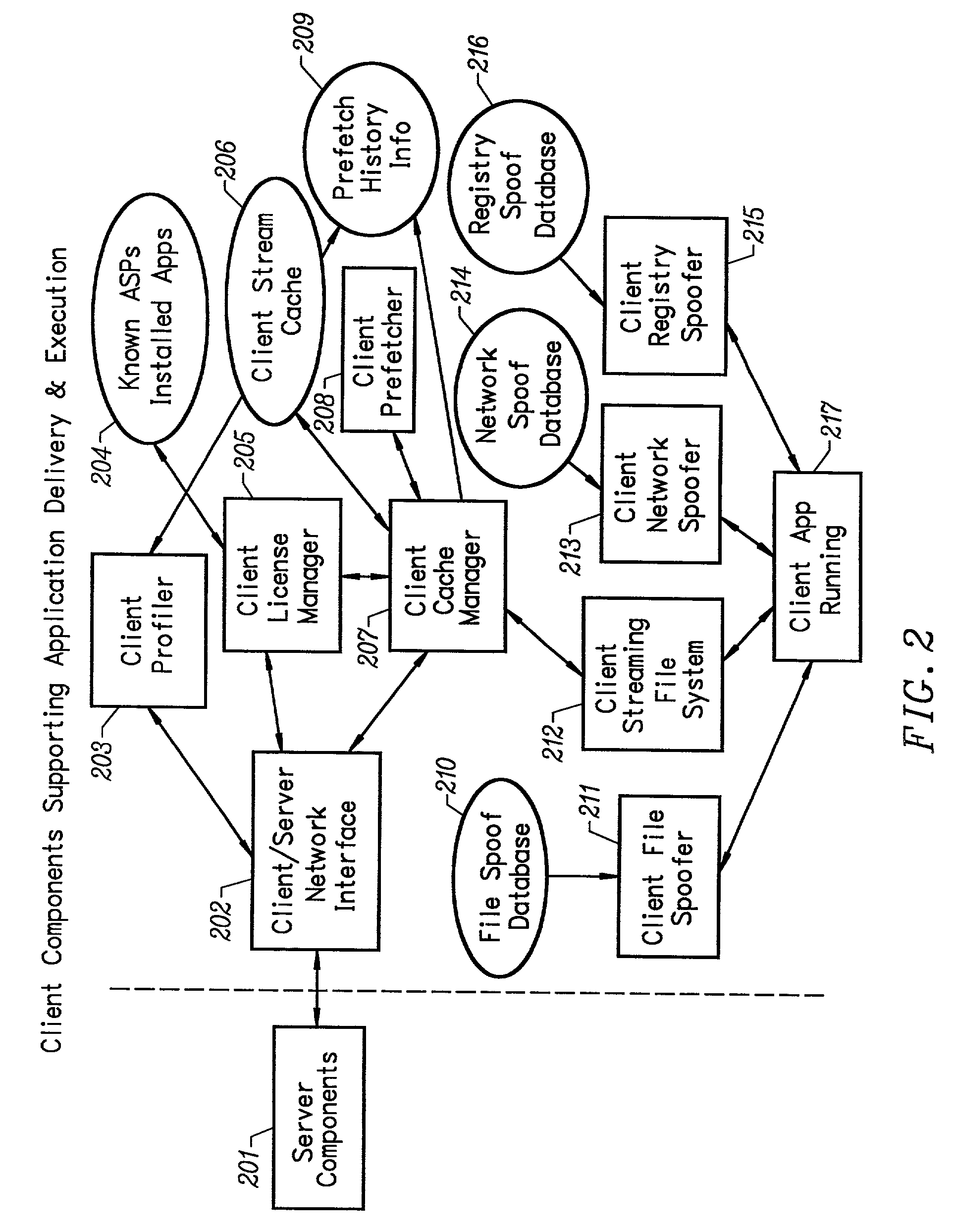
InactiveUS20030009538A1Data processing applicationsMultiple digital computer combinationsApplication serverNetwork packet
A network caching system for streamed applications provides for the caching of streamed applications within a computer network that are accessible by client systems within the network. Clients request streamed application file pages from other client systems, proxy servers, and application servers as each streamed application file is stored in a cache and used. Streamed application file page requests are broadcast to other clients using a multicast packet. Proxy servers are provided in the network that store a select set of streamed application file pages and respond to client requests by sending a response packet containing the requested streamed application file page if the streamed application file page is stored on the proxy server. Streamed application servers store all of the streamed application file pages. Clients try to send requests to streamed application servers as a last resort. Clients can concurrently send requests to other clients, to a proxy server, and to a streamed application server. Clients measure the response time to the clients requests placing a positive weighting on the more responsive request path and sending subsequent requests to the more positively weighted request path first.
Owner:NUMECENT HLDG
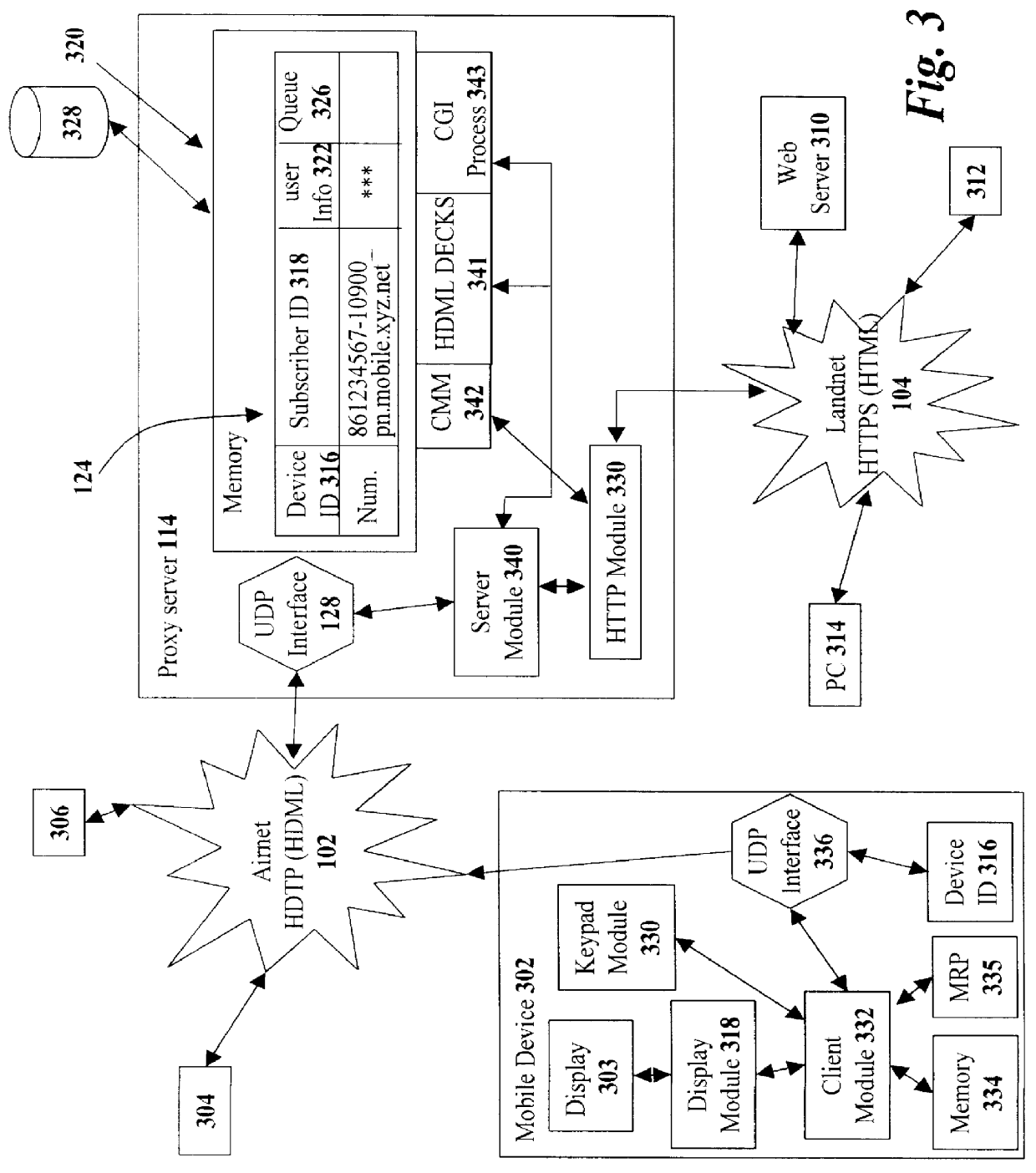
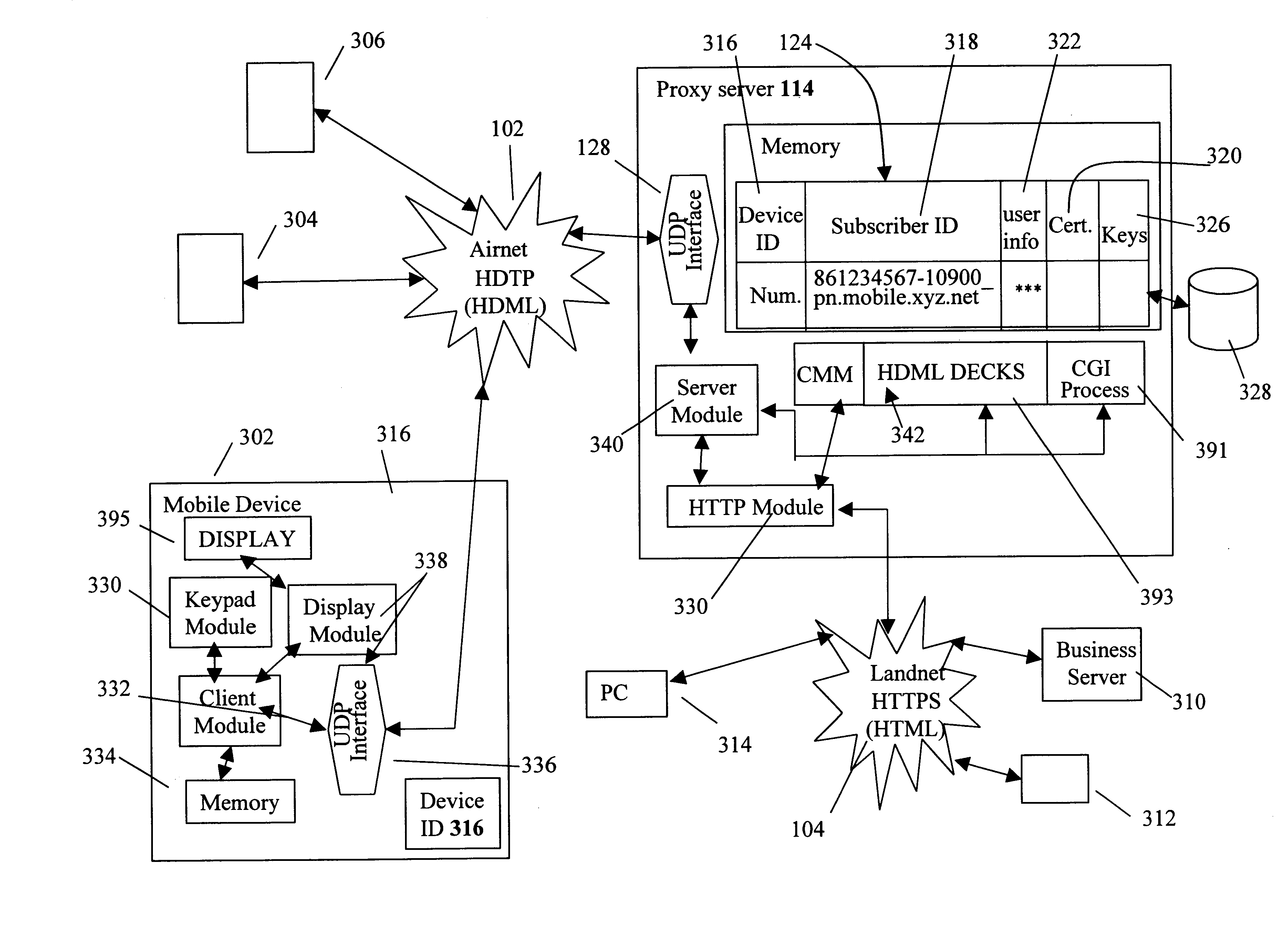
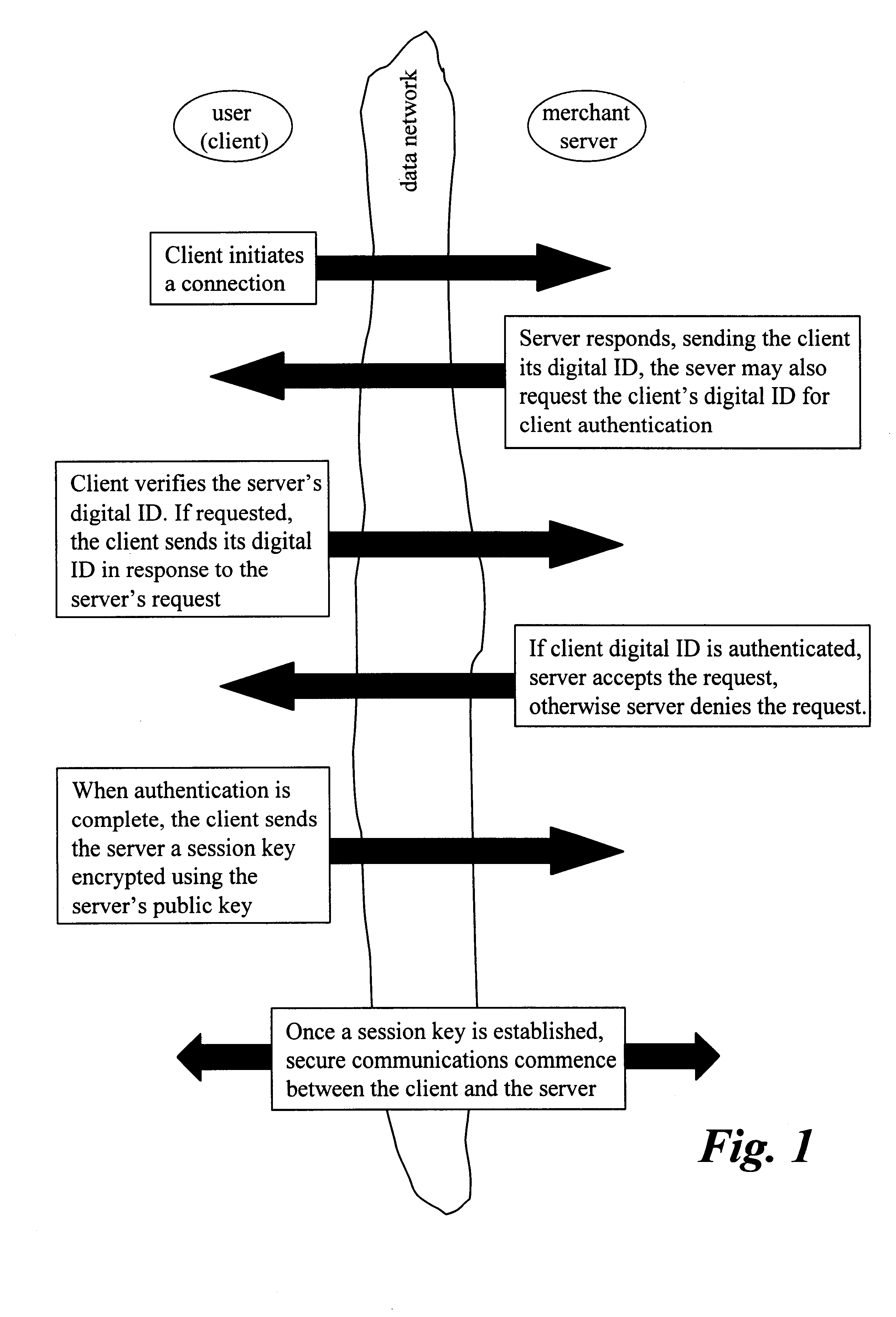
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
Dynamic file access control and management
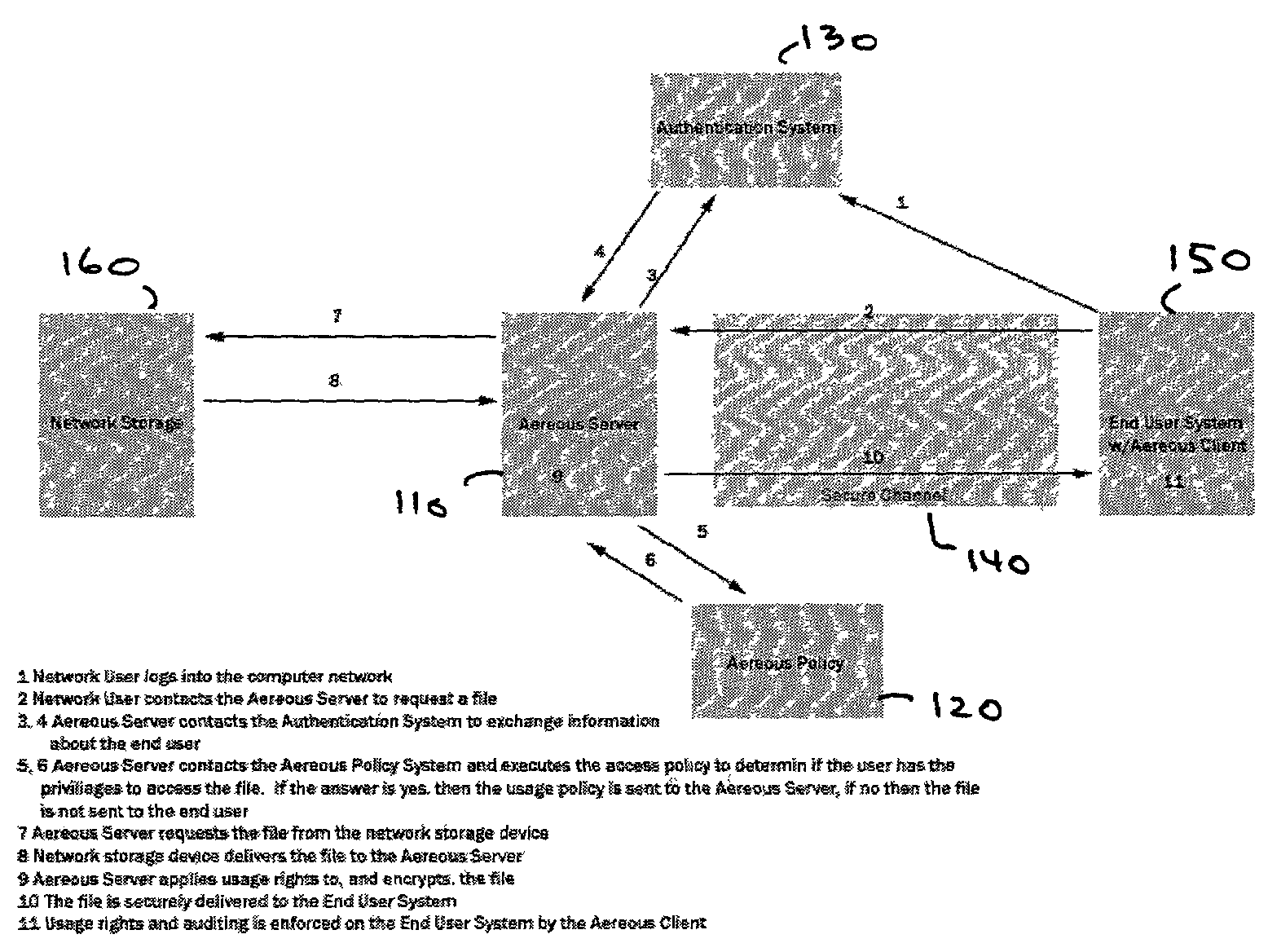
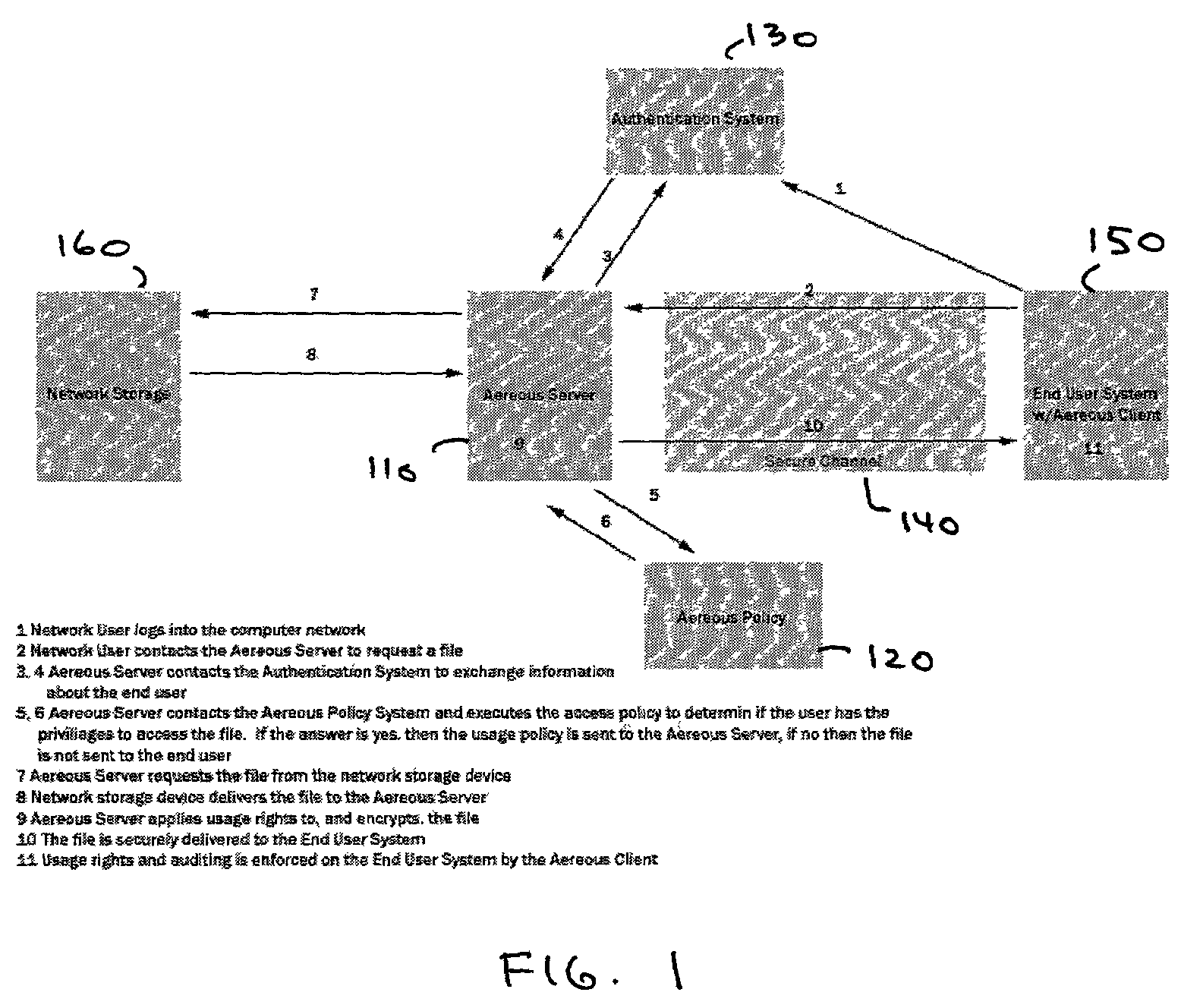
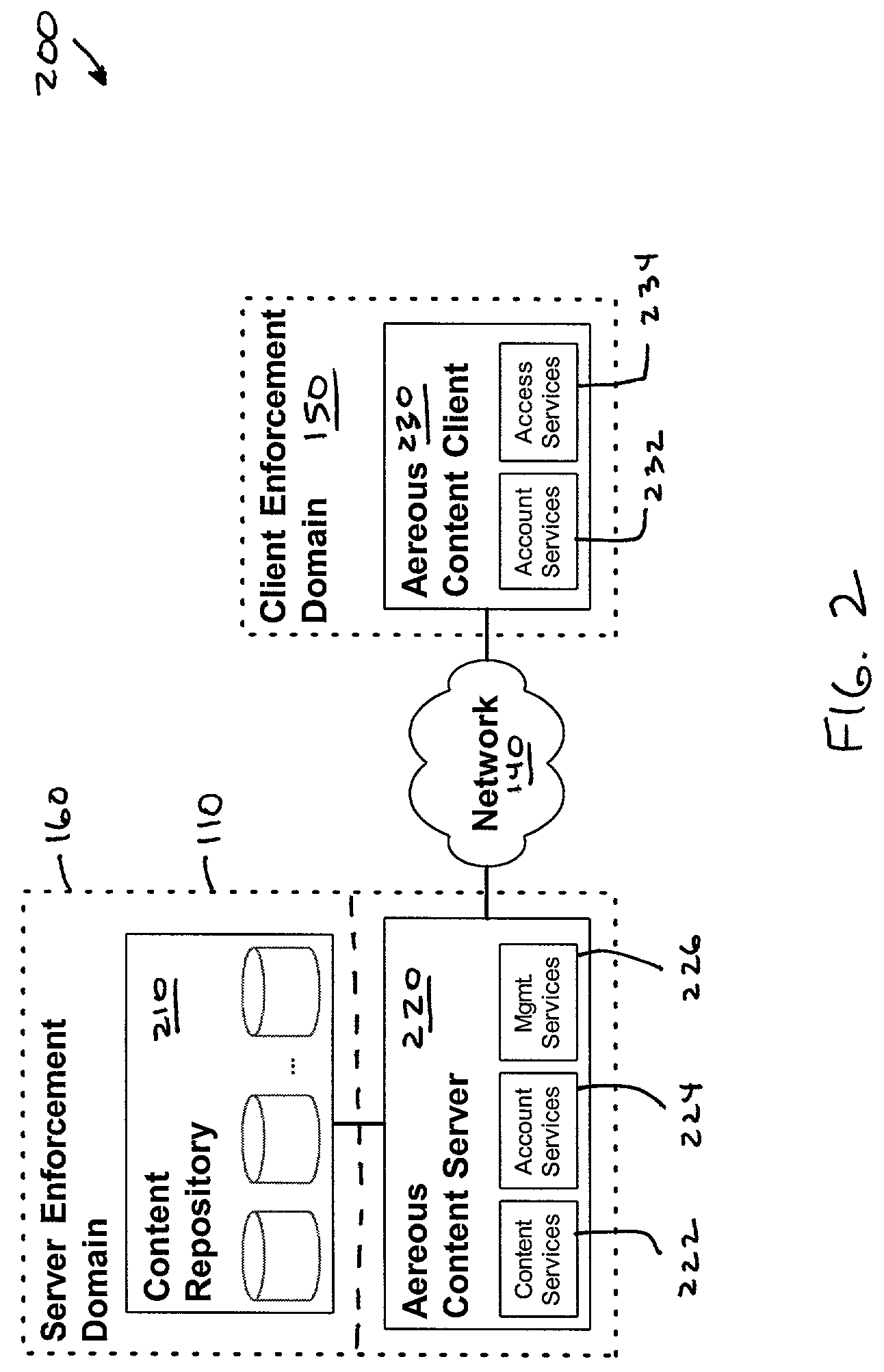
InactiveUS7660902B2Improve securitySelectively accessedComputer security arrangementsMultiple digital computer combinationsDistributed File SystemFile system
A dynamic file access control and management system and method in accordance with the present invention may be a proxy file management system that includes one or more file system proxy servers that provide selective access and usage management to files available from one or more file systems or sources. The present invention may embody a secure transport protocol that tunnels distributed file systems, application independent usage controls connected to files on end-user computers, dynamically merging secondary content to a requested file, and applying bandwidth management to any of the foregoing. Embodied in the various implementations of the present invention is enhanced file security. Preferably, the proxy file management system is transparent to an end-user. A dynamic content management system may also be included that selectively adds content to requested files.
Owner:EMC IP HLDG CO LLC
Scalable system for monitoring network system and components and methodology therefore
InactiveUS20020078382A1Memory loss protectionDigital computer detailsScalable systemSecurity software
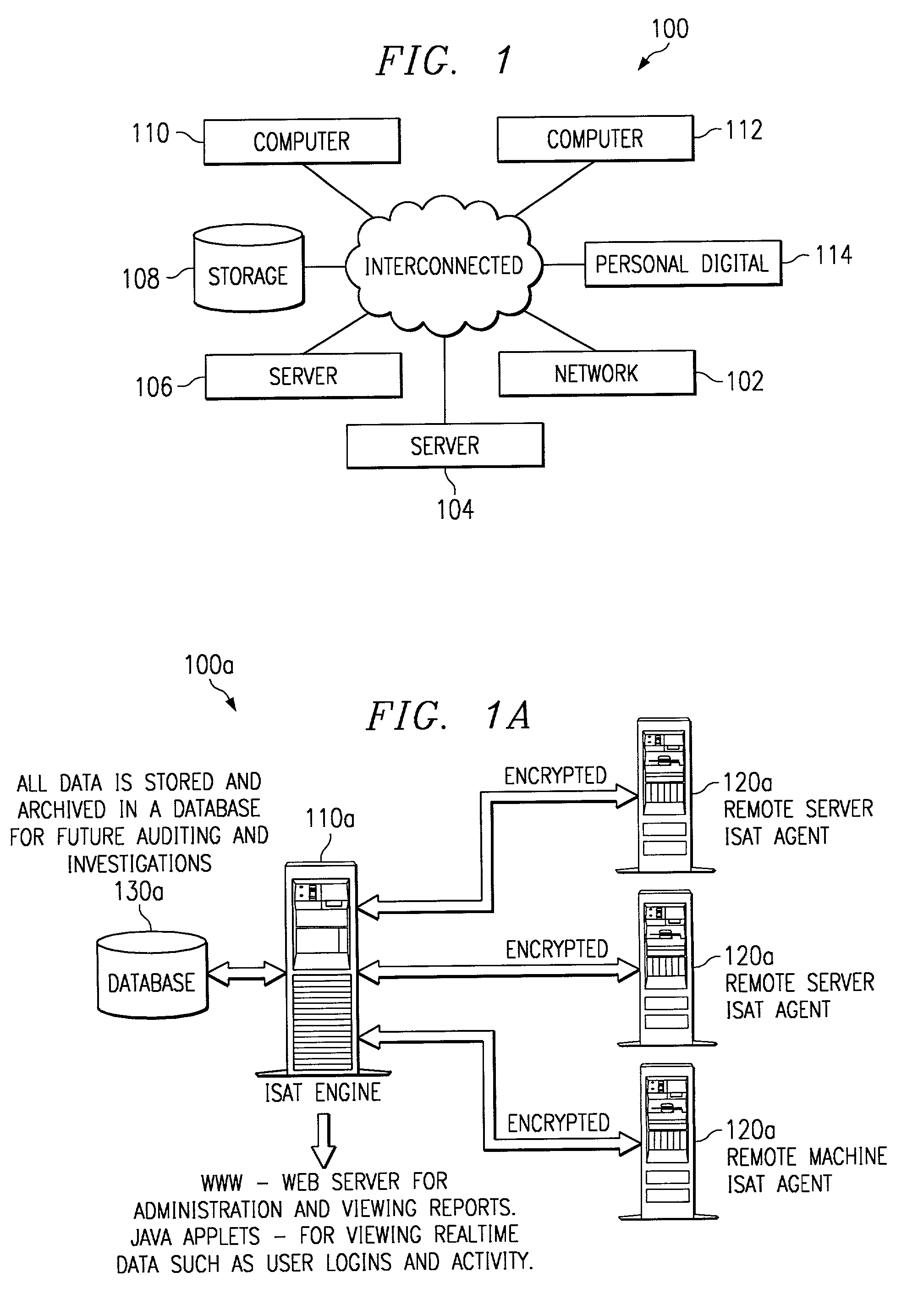
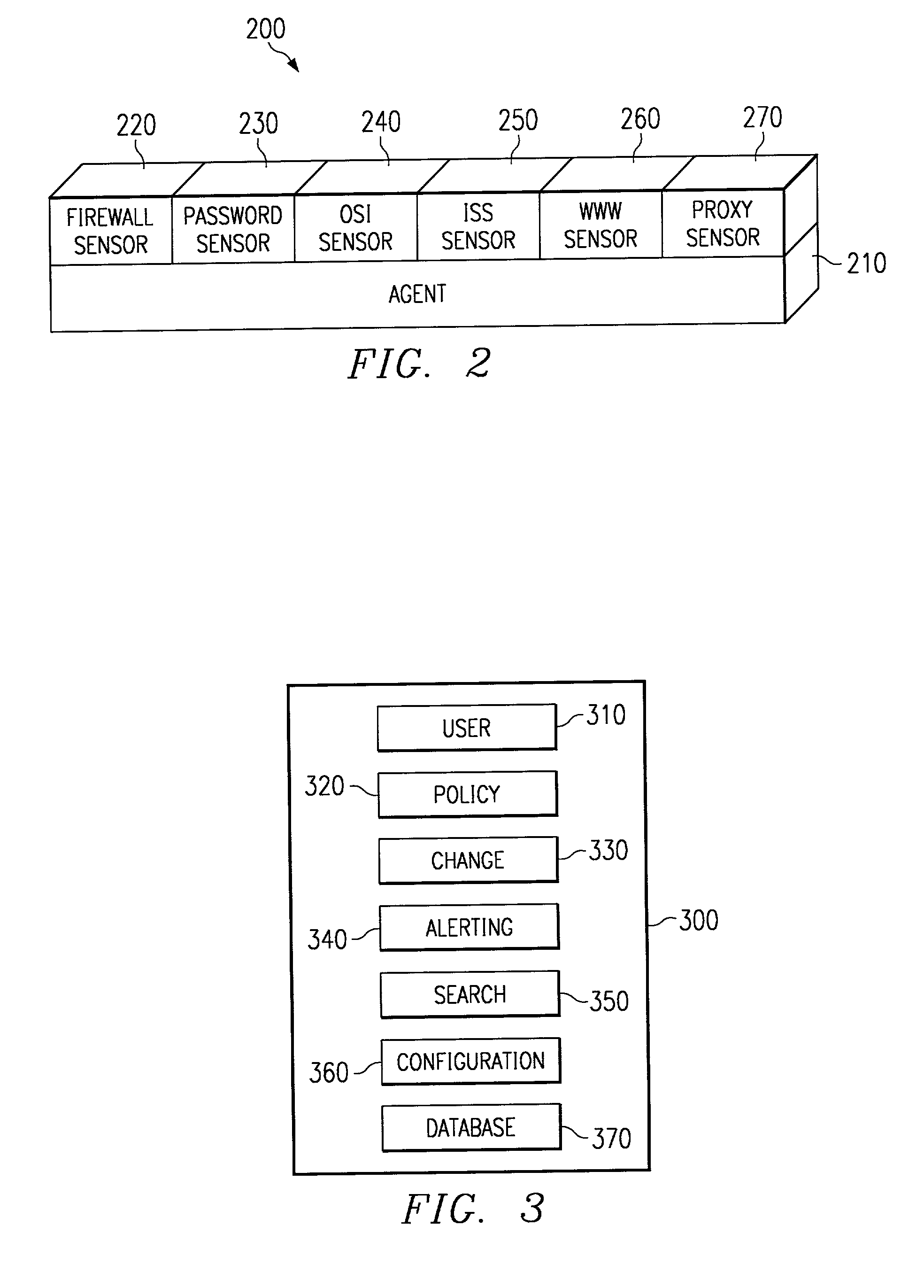
The present invention is a security software methodology and system that takes an internal approach to mitigating security risks from authorized and unauthorized users. The security software system uses the methodology of monitoring, in great detail, any configuration changes made to information systems within a network. These systems and applications include web servers, firewalls, proxy servers, log servers, intrusion detection software systems, routers and any other device or application which can be considered a part of the enterprise information system infrastructure.
Owner:SECURITY & INTRUSION DETECTION RES LABS
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
Methods and systems for assigning access control levels in providing access to resources via virtual machines
ActiveUS20070180493A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
Owner:CITRIX SYST INC
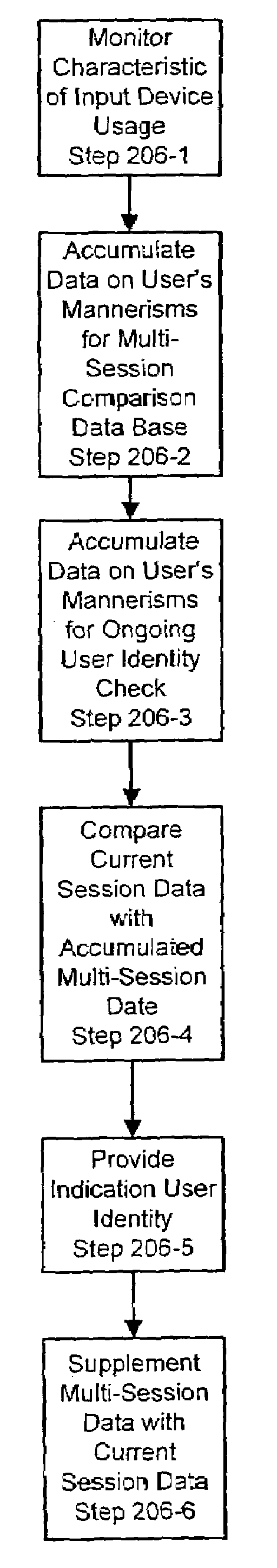
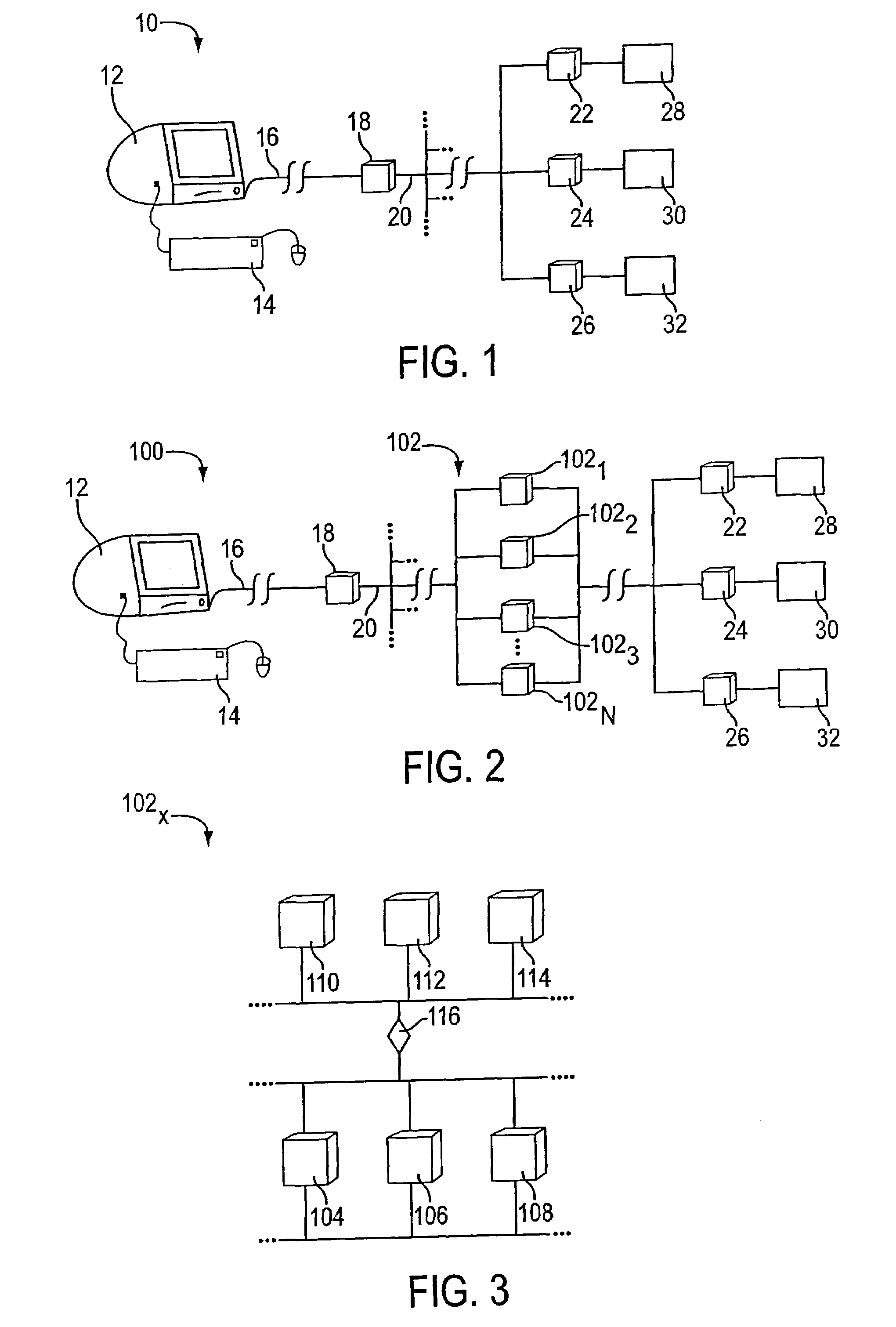
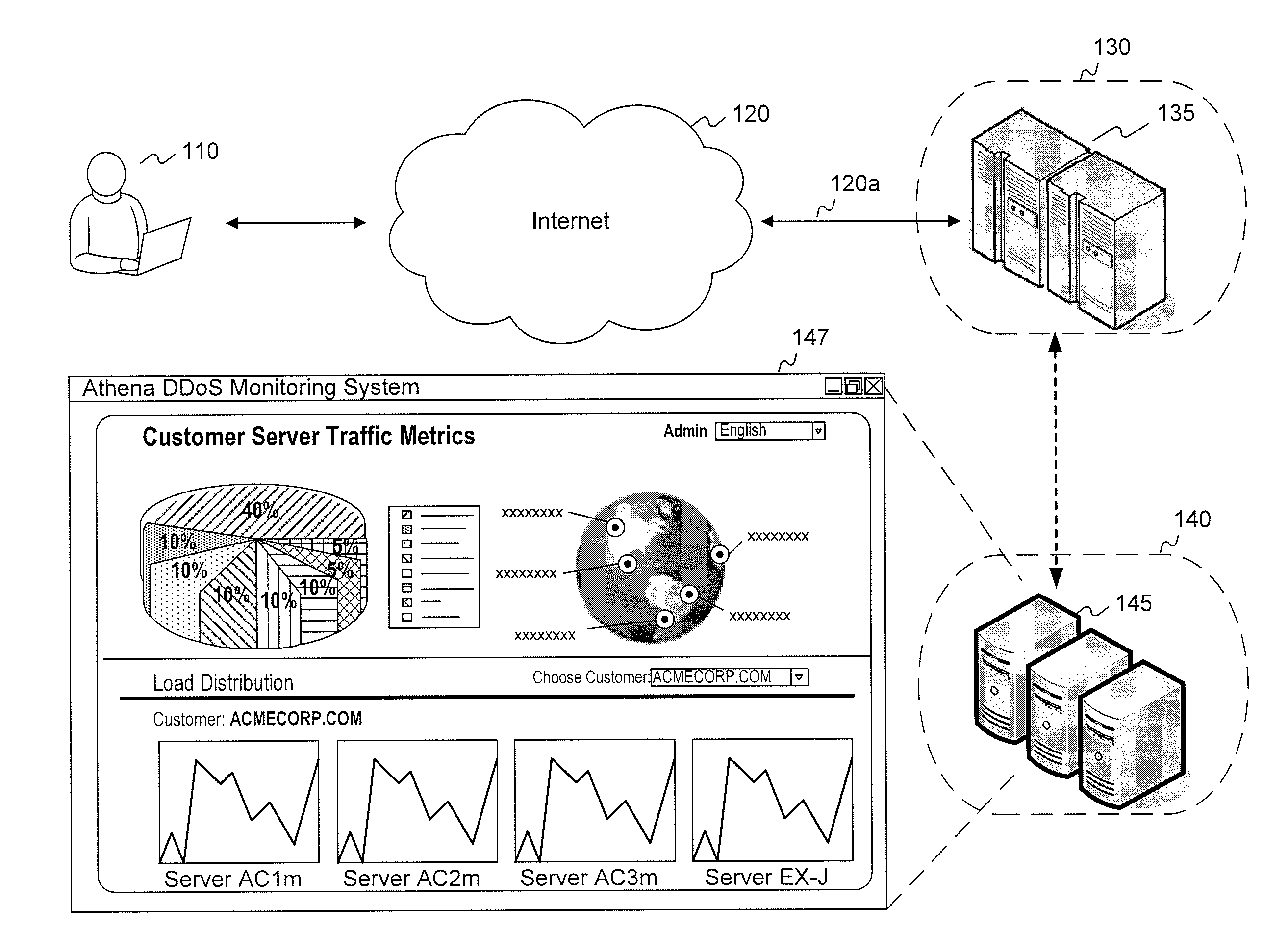
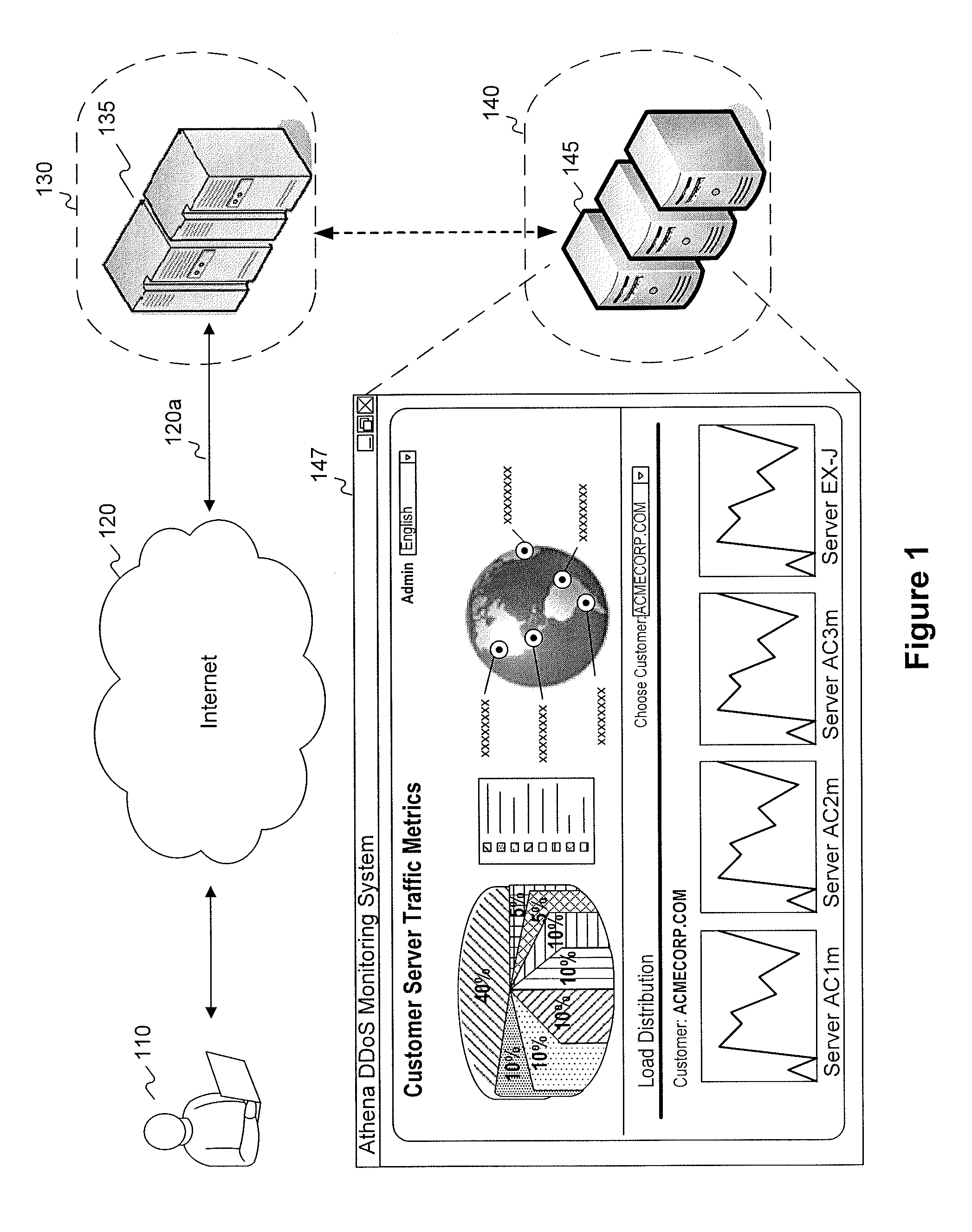
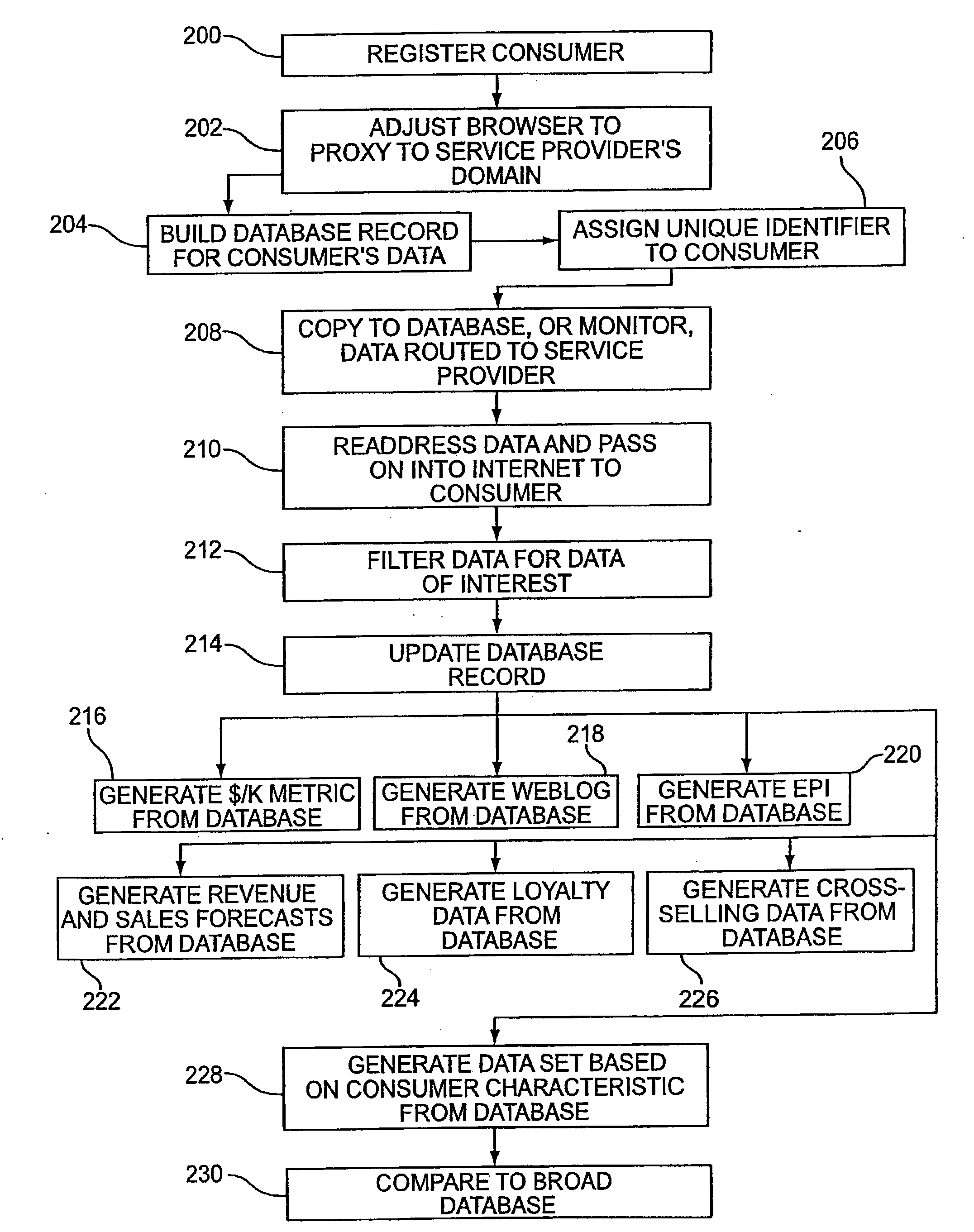
Systems and methods for user identification, user demographic reporting and collecting usage data usage biometrics
InactiveUS7260837B2Digital data information retrievalDigital data processing detailsData setDatabase server
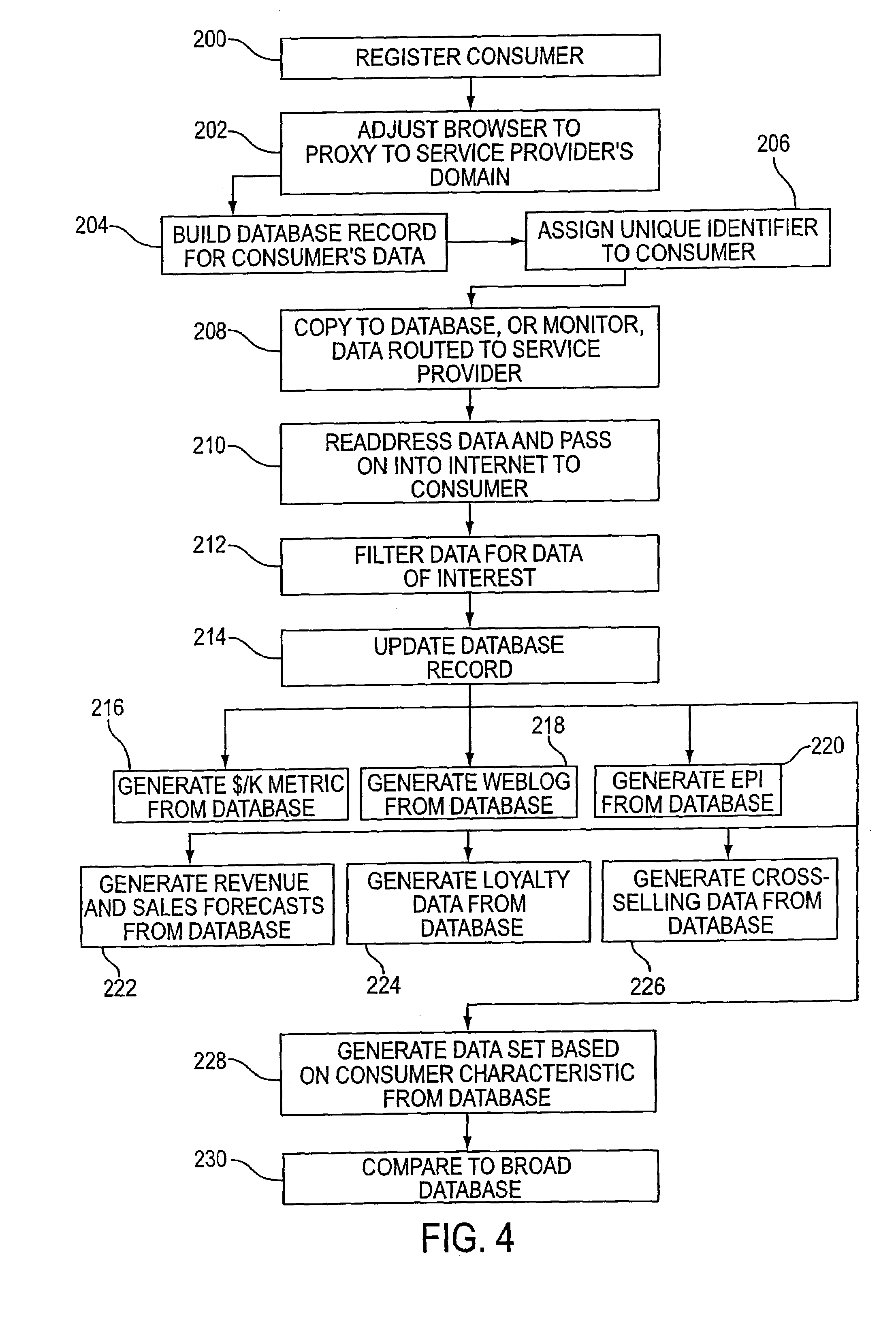
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
Method and system for web page personalization
InactiveUS20020138331A1Digital data information retrievalNatural language data processingPersonalizationWeb service
The invention includes a method and system for personalizing displays of published Web pages provided by Web content providers to meet the interests of Web users accessing the pages, based on profiles of the users. The system preferably provides to the requesting user, through a proxy server, an edited version of the HTML file for the original published Web page that is served by a host Web server. The system uses user profiles that may include demographic and psychographic data to edit the requested Web page. The content of a Web page as published by a host Web server may be coded to correlate components of the Web page with demographic and psychographic data. The user profiles may then be used to filter the content of a coded Web page for delivery to a requesting user. The system may rearrange content on a published Web page so that content determined to be of higher interest to a user is more prominently featured or more easily or quickly accessible. The system may also delete content on a published Web page that is determined to be of low interest to a user. In embodiments of the invention, a single proxy server or proxy server system personalizes Web pages from multiple Web servers, using a single user profile for a user.
Owner:SEDNA PATENT SERVICES
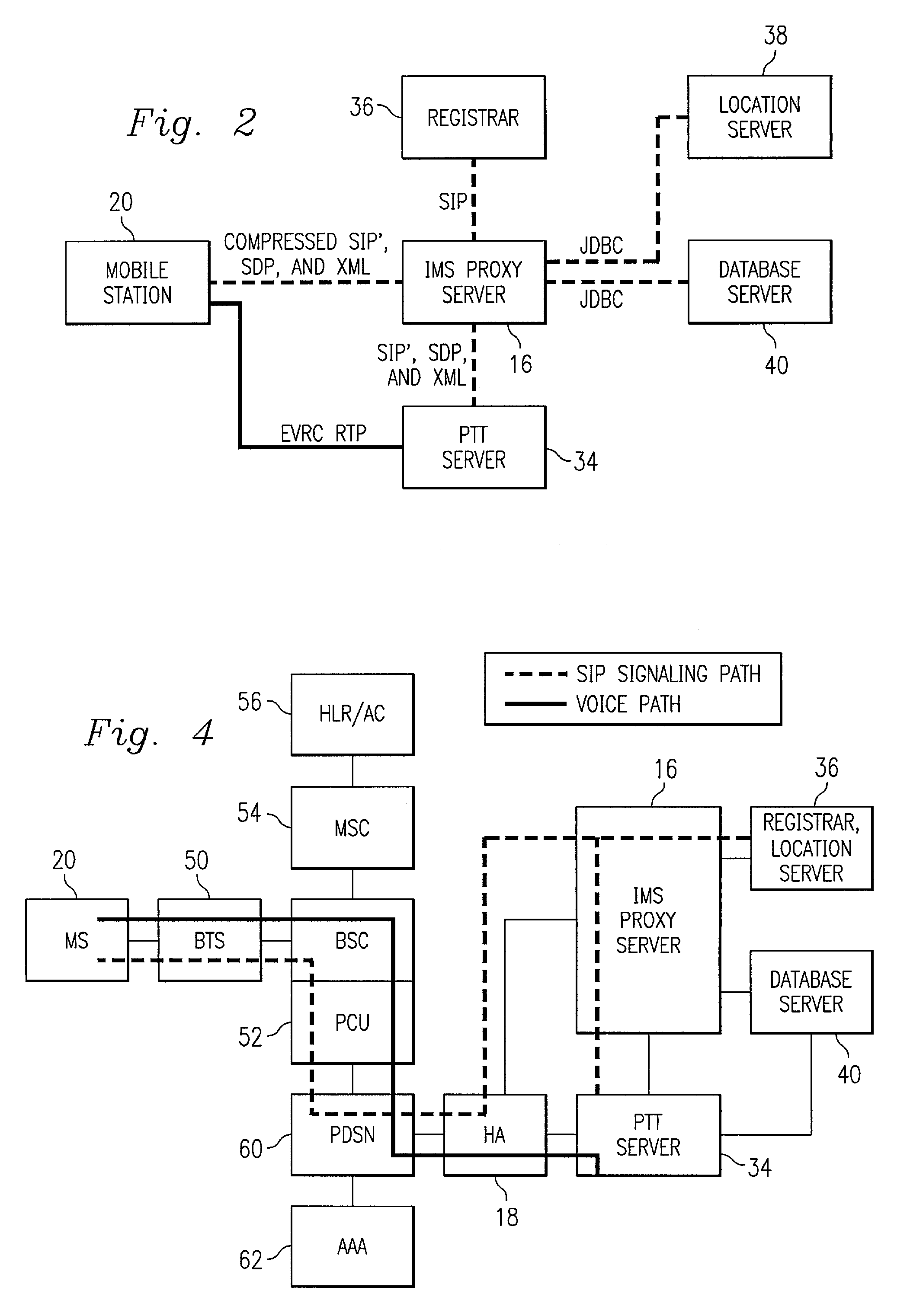
Push-to-talk wireless telecommunications system utilizing a voice-over-IP network
ActiveUS7170863B1Multiplex system selection arrangementsSpecial service provision for substationSession Initiation ProtocolTelecommunications network
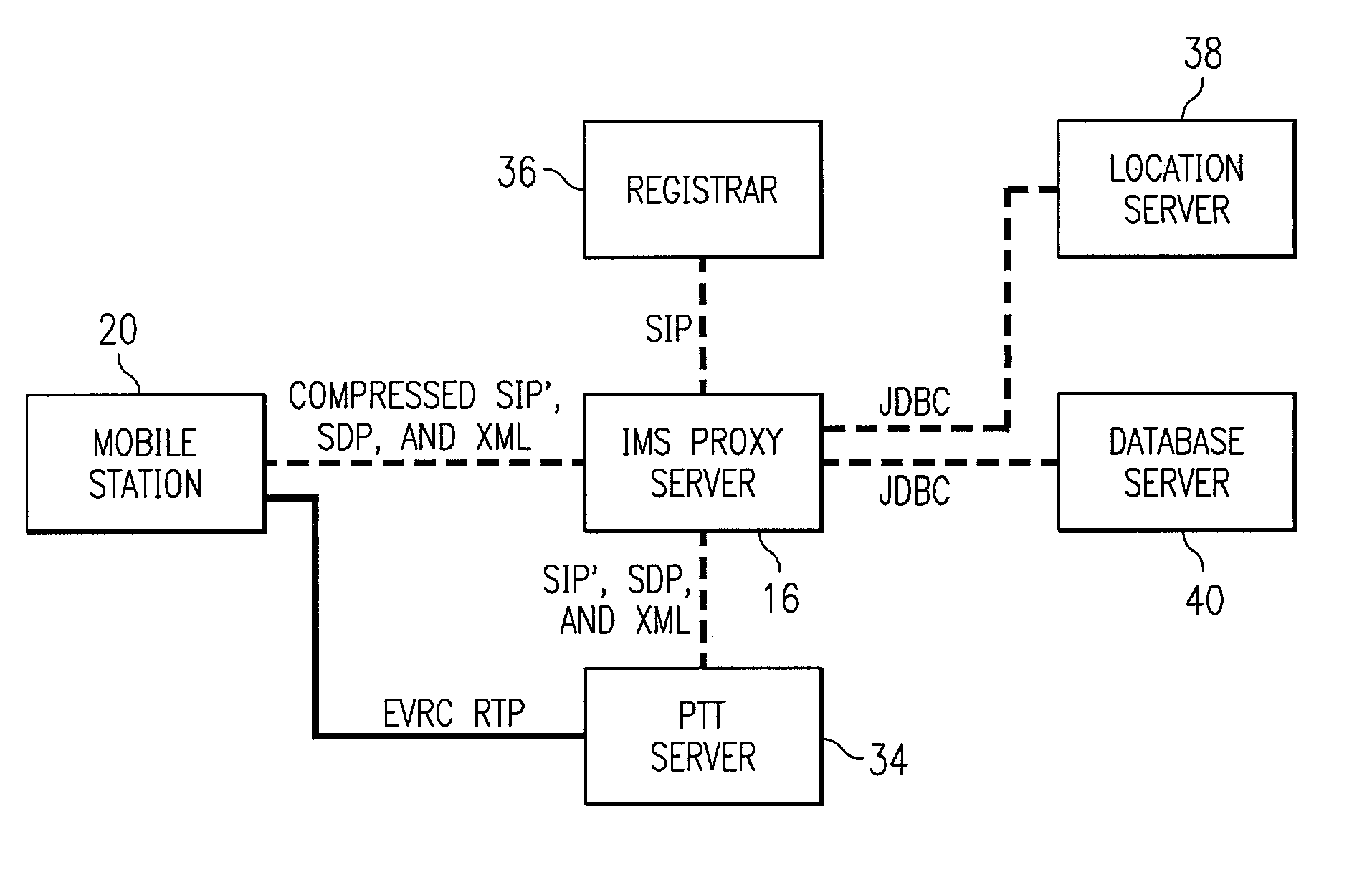
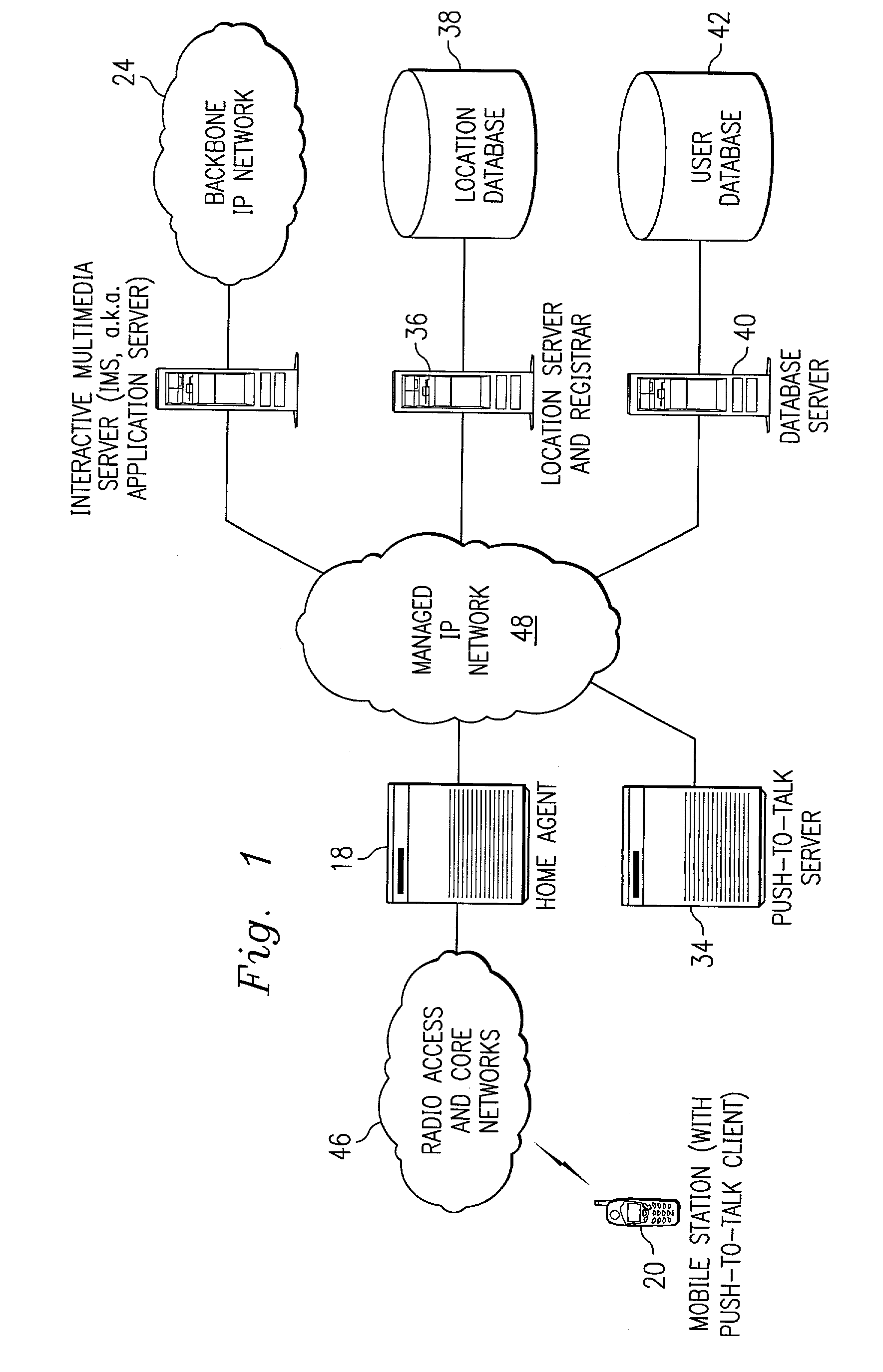
A method and system to provide push-to-talk from one user to another in a wireless packet data telecommunications network is described. The system may include: a wireless communication network including push-to-talk (PTT) functionality, with a Session Initiation Protocol (SIP) Proxy Server; a SIP Registrar and Location Server operable to store contact addresses of active mobile devices; a Realtime Transport Protocol (RTP) Media Gateway (PTT Server) operable to function as a call endpoint for each of a plurality of mobile devices wherein the plurality of mobile devices are segmented into membership groups, the PTT Server further operable to multicast a communication from one member of the group to the other members of the group; and an Internet Protocol (IP) network interconnecting the SIP Proxy server, the SIP Registrar and Location Server, and the PTT Server.
Owner:APPLE INC
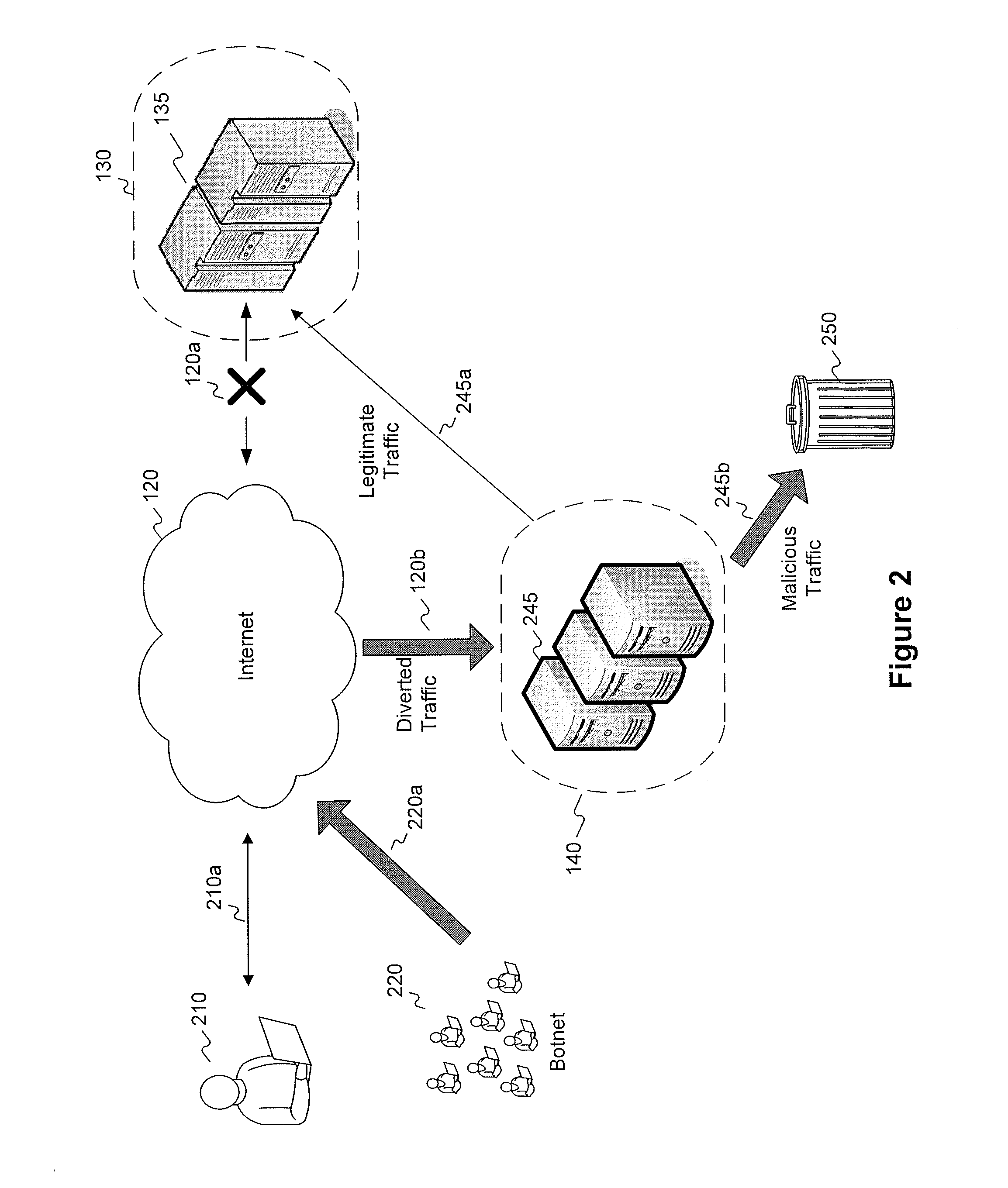
Active validation for ddos and ssl ddos attacks
InactiveUS20120174196A1Memory loss protectionError detection/correctionApplication serverClient-side
Methods and systems for detecting and responding to Denial of Service (“DoS”) attacks comprise: detecting a DoS attack or potential DoS attack against a first server system comprising one or more servers; receiving, at a second server system comprising one or more servers, network traffic directed to the first server system; subjecting requesting clients to one or more challenge mechanisms, the challenge mechanisms including one or more of challenging requesting clients to follow through HTTP redirect responses, challenging requesting clients to request Secure Sockets Layer (SSL) session resumption, or challenging requesting clients to store and transmit HTTP cookies; identifying one or more non-suspect clients, the one or more suspect clients corresponding to requesting clients that successfully complete the one or more challenge mechanisms; identifying one or more suspect clients, the one or more suspect clients corresponding to requesting clients that do not successfully complete the one or more challenge mechanisms; and forwarding, by the second server system, traffic corresponding to the one or more non-suspect clients to the first server system. Once a client has been validated, clients may communicate directly with application servers in a secure manner by transparently passing through one or more intermediary proxy servers.
Owner:VERISIGN
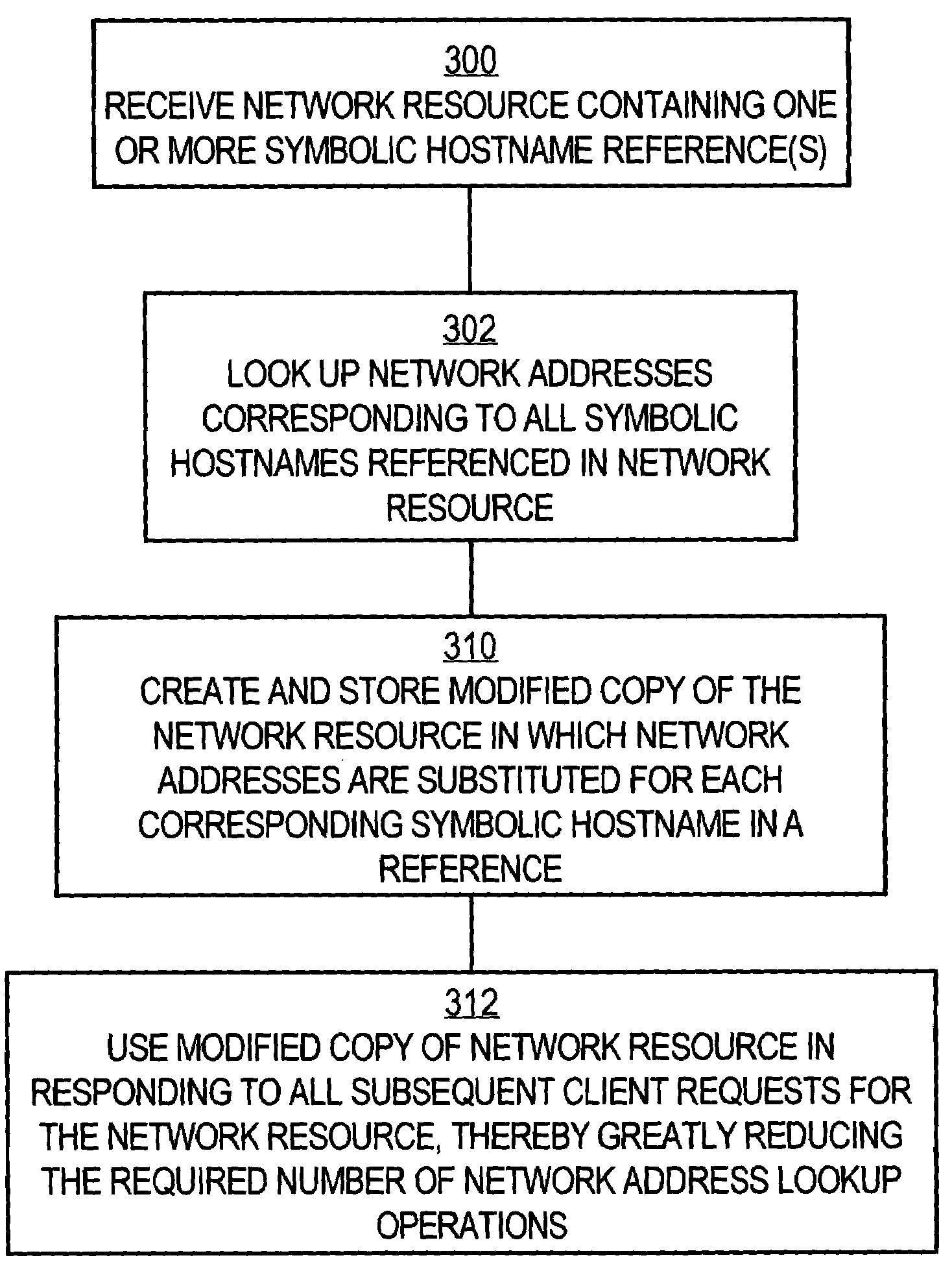
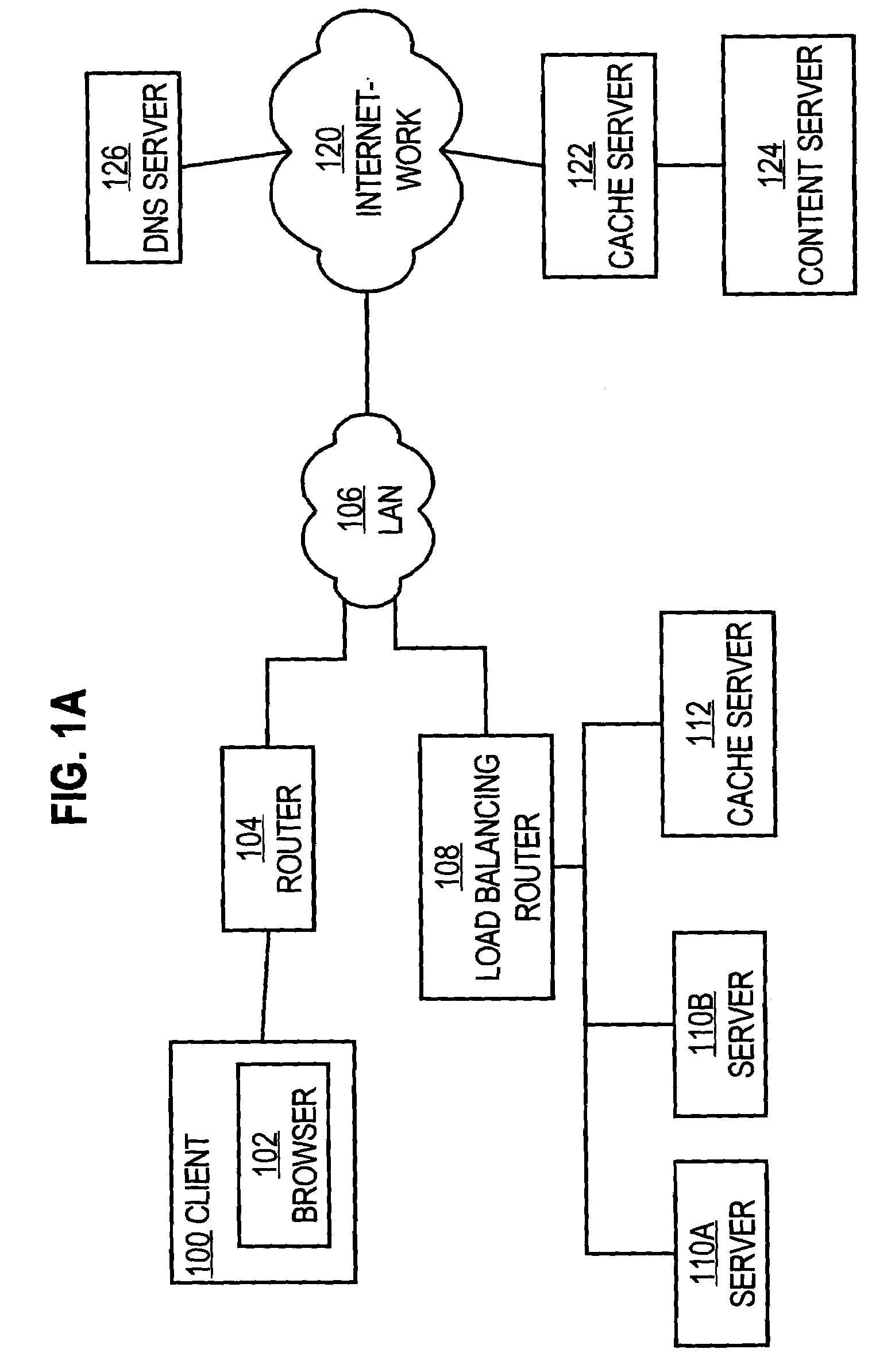
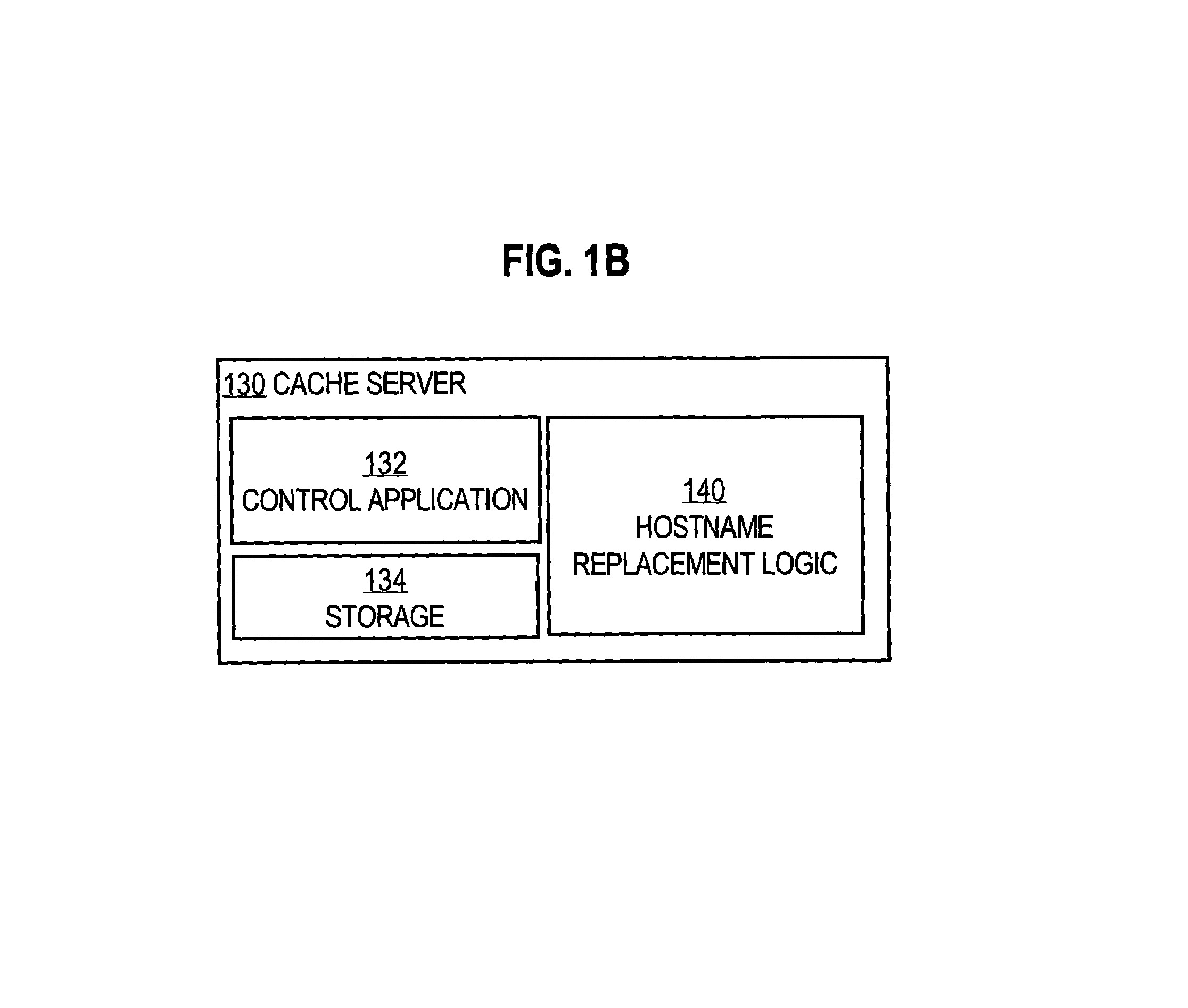
System and method of optimizing retrieval of network resources by identifying and substituting embedded symbolic host name references with network addresses in accordance with substitution policies
InactiveUS7082476B1Reduce in quantityEasy accessMultiple digital computer combinationsTransmissionCache serverNetwork addressing
A method and apparatus are provided for optimizing retrieval of network resources. In one embodiment, a method of optimizing access to a network resource is implemented in a computer program executed by a router, cache server, or proxy server. A network resource that contains one or more embedded symbolic host name references is received. A network address corresponding to each of the embedded symbolic host name references is determined. A modified copy of the network resource is created and stored; in the modified copy, a network address is substituted for each corresponding embedded symbolic host name reference. Thereafter, the modified copy of the network resource in responding to all subsequent client requests for the network resource, thereby greatly reducing the required number of network address lookup operations. In one specific embodiment, IP addresses are determined using DNS queries for the hostname portion of all URLs that are embedded in a Web page using image, applet, object, or embed tags. The IP addresses are stored in place of the hostname portions in a modified copy of the Web page, typically in a cache. As a result, when the modified page is subsequently served to clients, the clients need not carry out DNS resolution of all the embedded URLs, resulting in reduced network message traffic and more rapid page display.
Owner:CISCO TECH INC
User identification in the header of data packets
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE NETWORKS
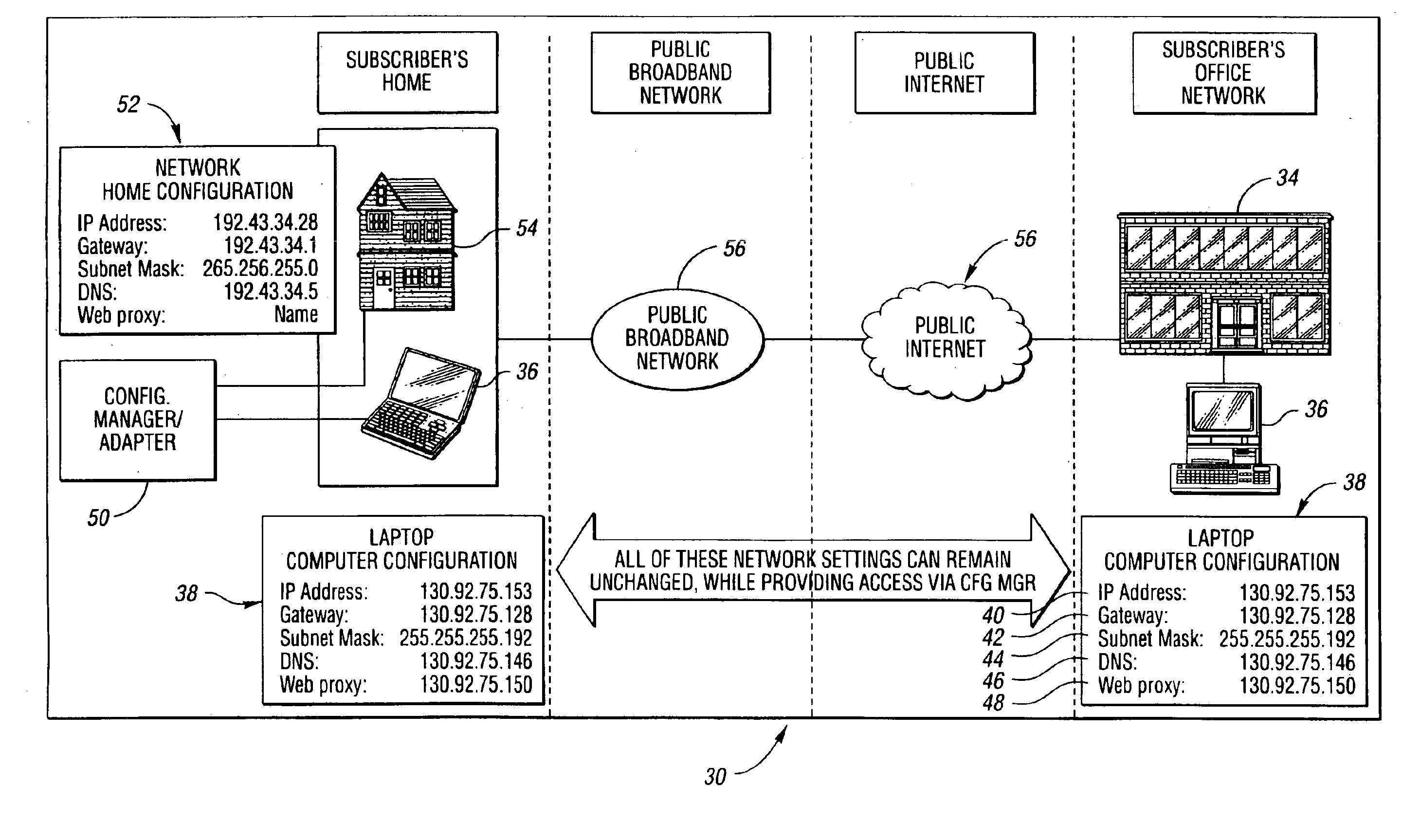
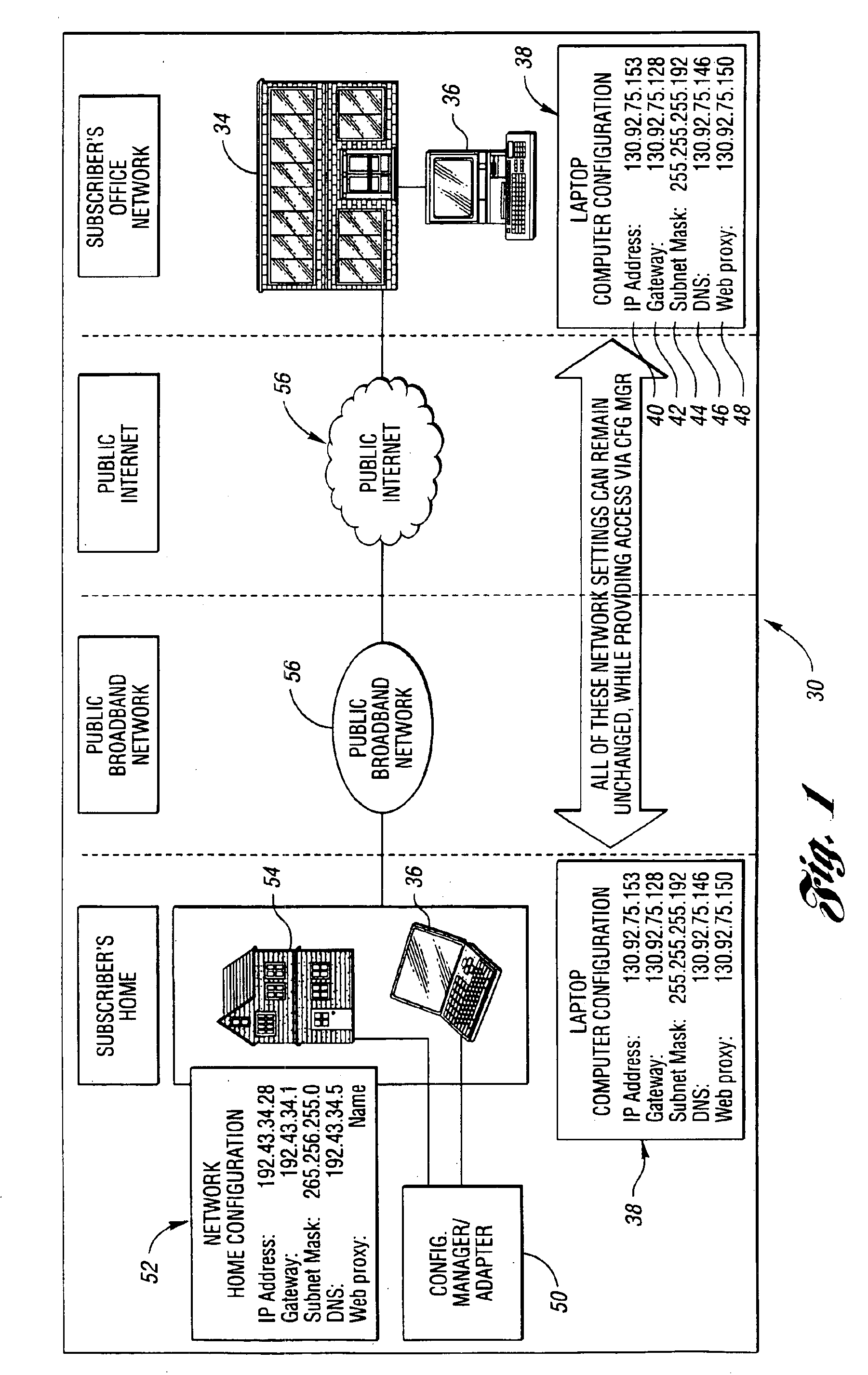
System and method for network access without reconfiguration
InactiveUS6857009B1Easy to addEasy to deleteTime-division multiplexData switching by path configurationDomain nameComputer compatibility
A system and method for providing connectivity to a foreign network for a device configured for communication over a home network without reconfiguring the device include intercepting packets transmitted by the device, selectively modifying intercepted packets which are incompatible with the foreign network to be compatible with network settings of the foreign network, and selectively providing network services for the device corresponding to network services available on the home network to reduce the delay associated with accessing the network services from the foreign network, or to provide network services otherwise inaccessible from the foreign network. Network services are provided by or through a configuration adapter connected to the device or to the foreign network. The configuration adapter accommodates incompatibilities resulting from proxy server requests, domain name server requests, and / or outgoing email service requests to provide transparent network access for mobile users without reconfiguration of the users computing device.
Owner:NOMADIX INC
Method for protecting a computer from suspicious objects
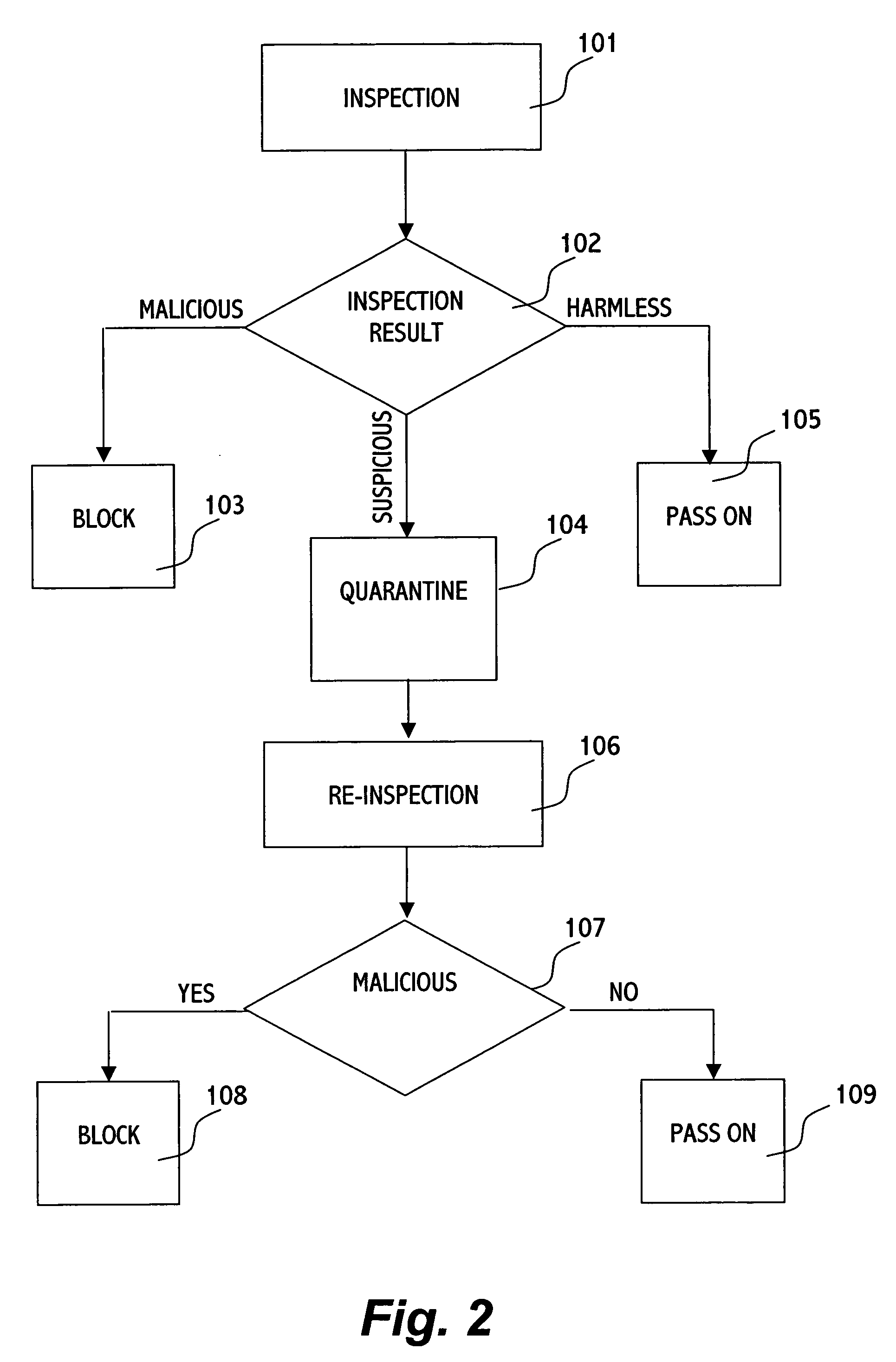
In an inspection facility (e.g. at a gateway server, at a proxy server, at a firewall to a network, at an entrance to a local area network or even at the user's computer) connected to an anti-virus center for updates, a method for protecting a computer from suspicious objects (e.g. a file, an executable, a Web page, an email message, etc.), the method comprising the steps of: inspecting an object; upon determining the object as suspicious, holding the object in quarantine (e.g. preventing from the object to be forwarded to its destination) for a time period, thereby enabling the inspection facility to be updated during the time period by the anti-virus center; upon ending of the time period, re-inspecting the object, thereby inspecting the object by updated inspection tests; and upon determining the object as malicious by the re-inspection, blocking the object, otherwise forwarding the object toward its destination.
Owner:ALADDIN KNOWLEDGE SYSTEMS
Method and apparatus for caching for streaming data
InactiveUS7028096B1Reduction of peak transmission bit rateReduce the transmission bit rateAnalogue secracy/subscription systemsMultiple digital computer combinationsStreaming dataHigh bandwidth
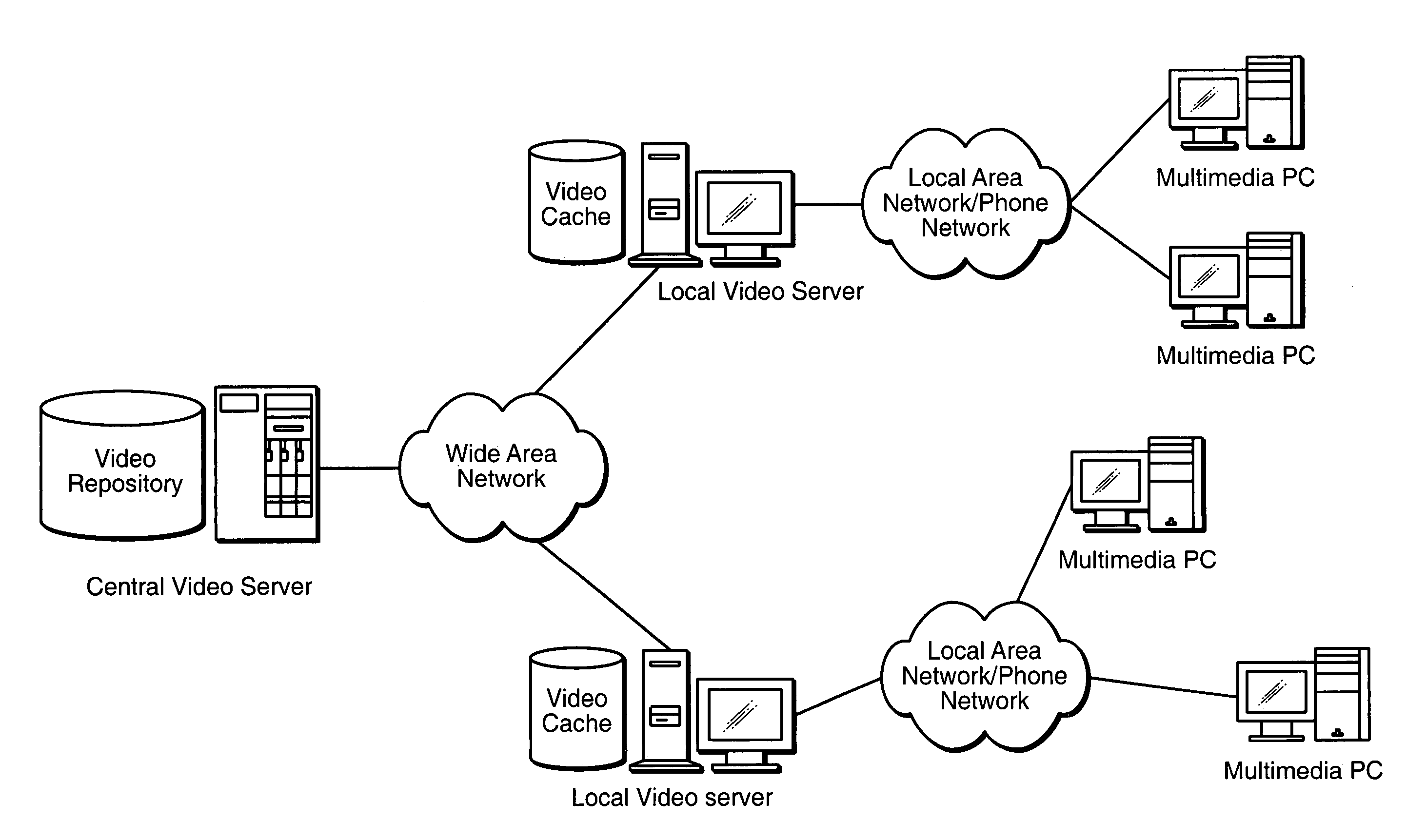
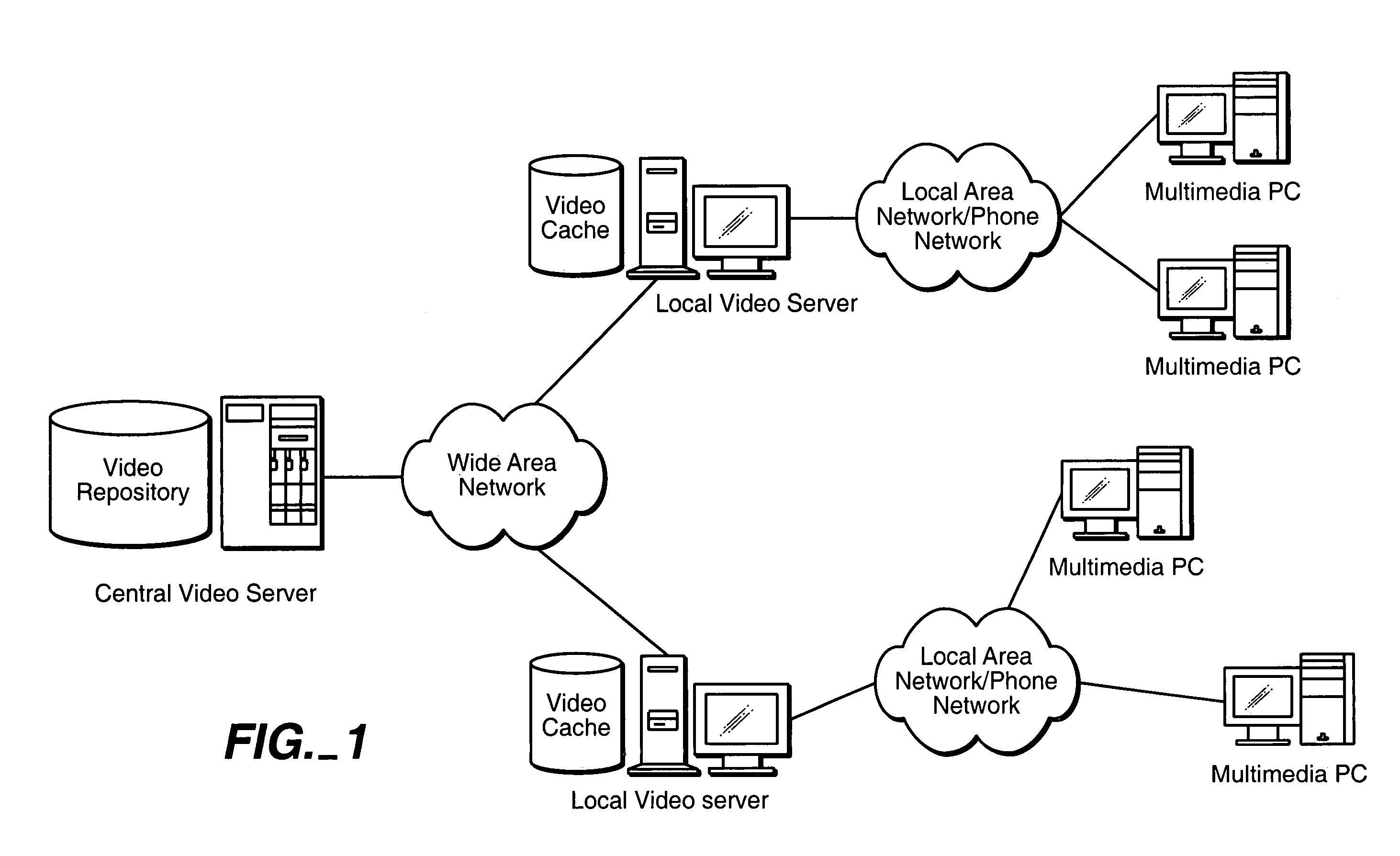
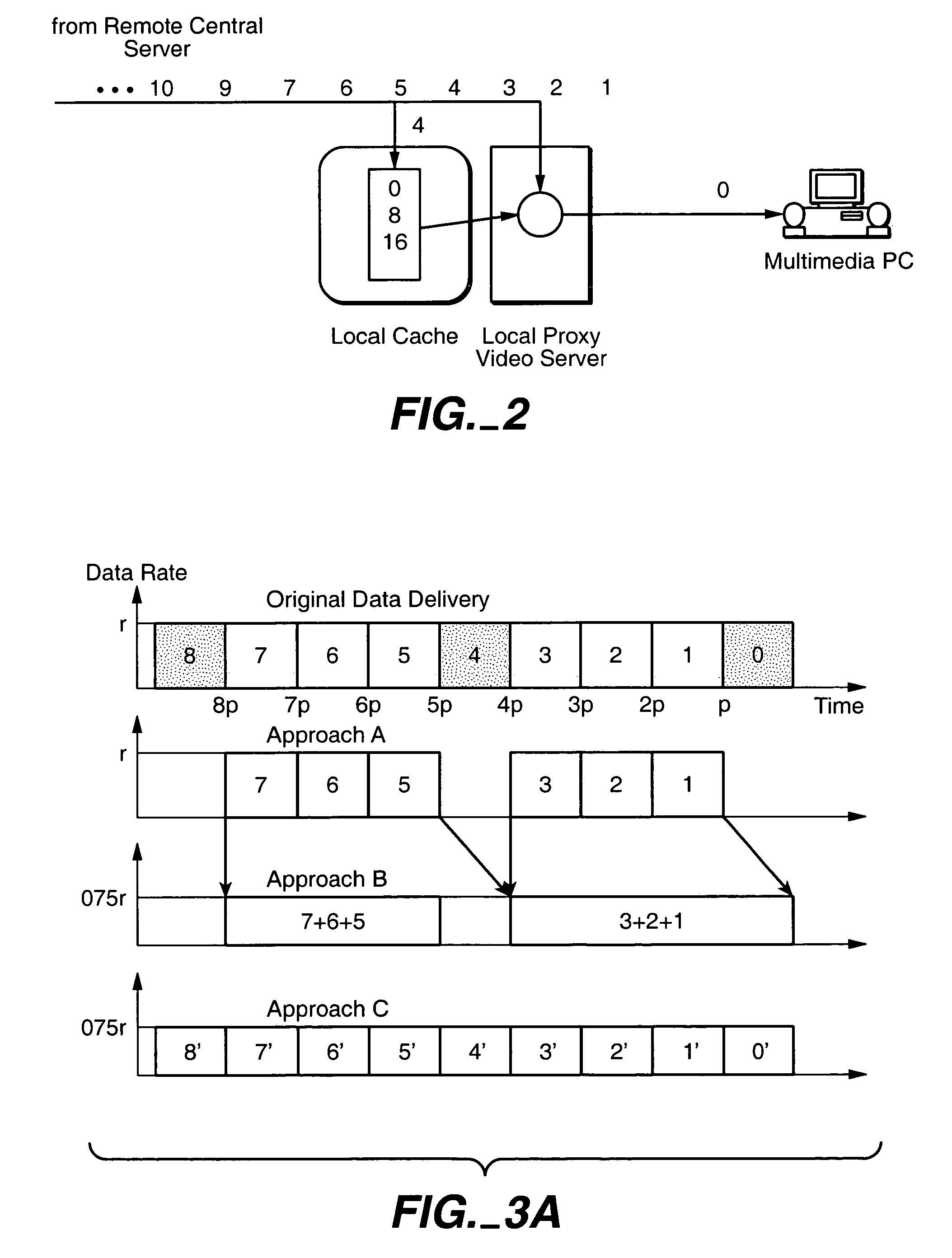
Streaming video data from the video title is delivered to a client from a central server and a proxy server. To reduce the backbone bandwidth required, a portion of the video title is cached at the proxy server where the portion cached is distributed over the video title so as to reduce the peak bit rate required for the central server to send the remaining portion of the video title. The amount cached at the proxy server may be adjusted in accordance with access profile of video titles to improve caching efficiency. The portion cached may be the basic layer in a scalable multilayer approach where only the basic layer may be sent to a client who has limited bandwidth while clients with higher bandwidth capability may also receive the enhancement layer(s) for improved video reception.
Owner:STREAMING21
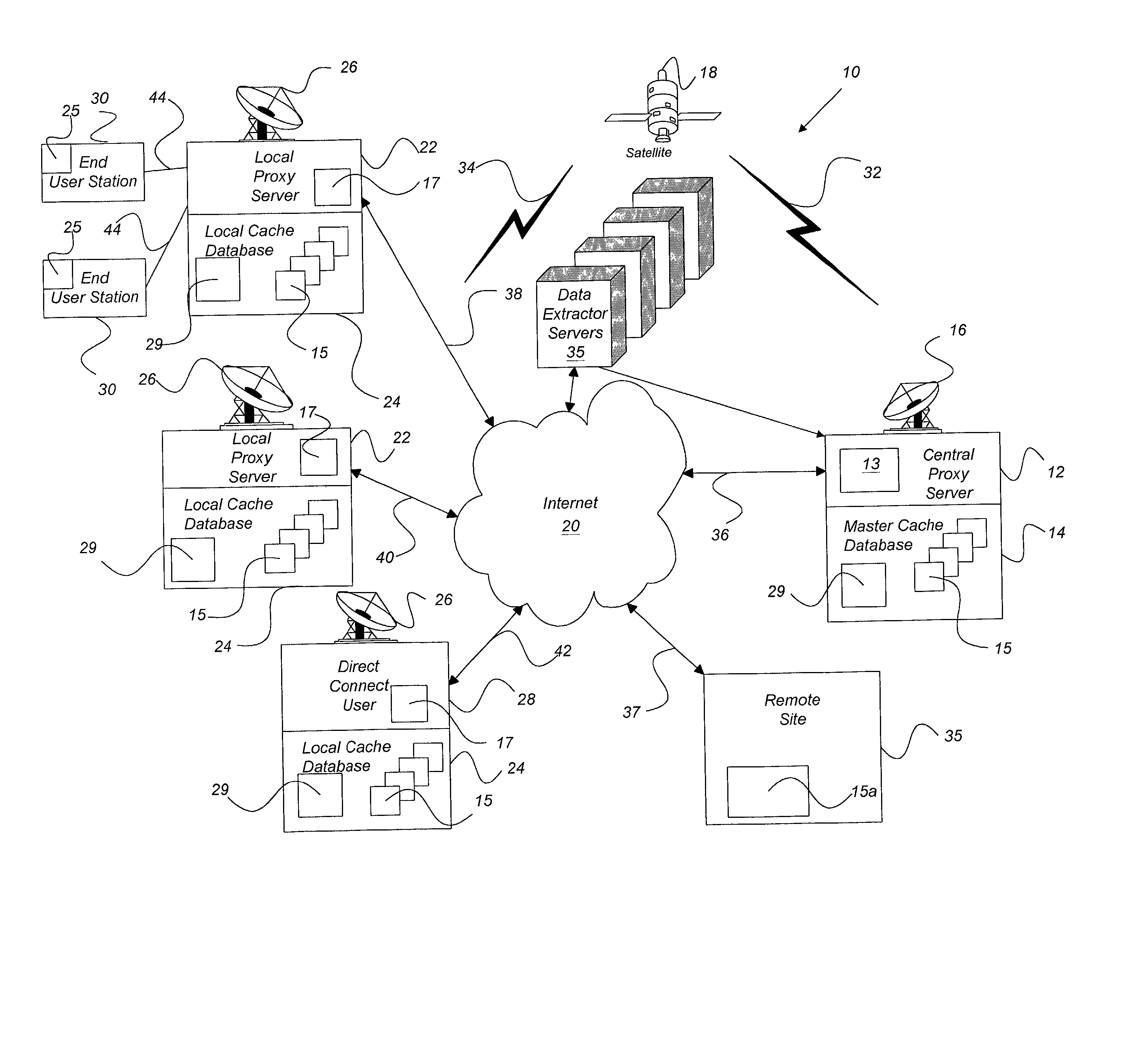
Internet content delivery acceleration system employing a hybrid content selection scheme
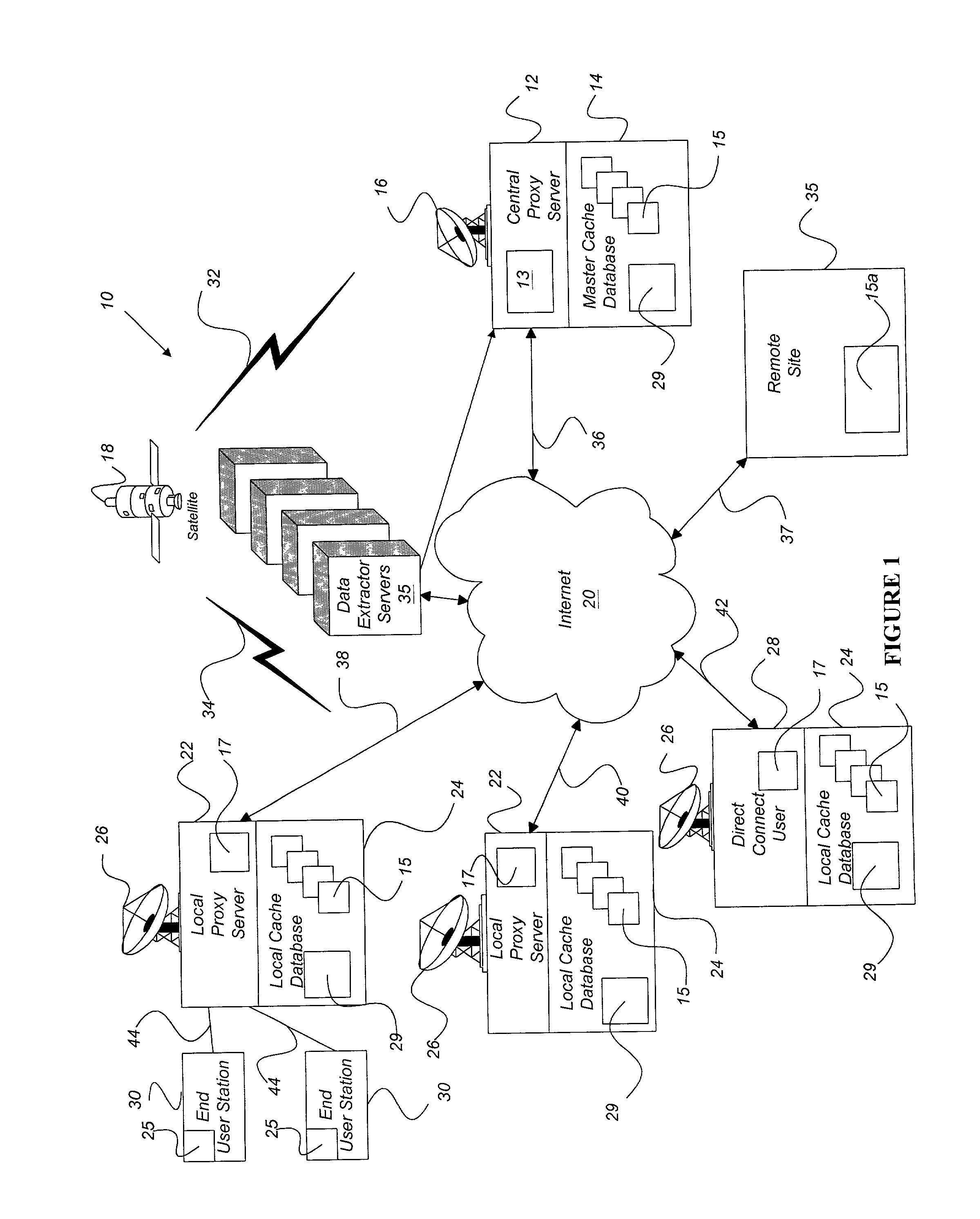
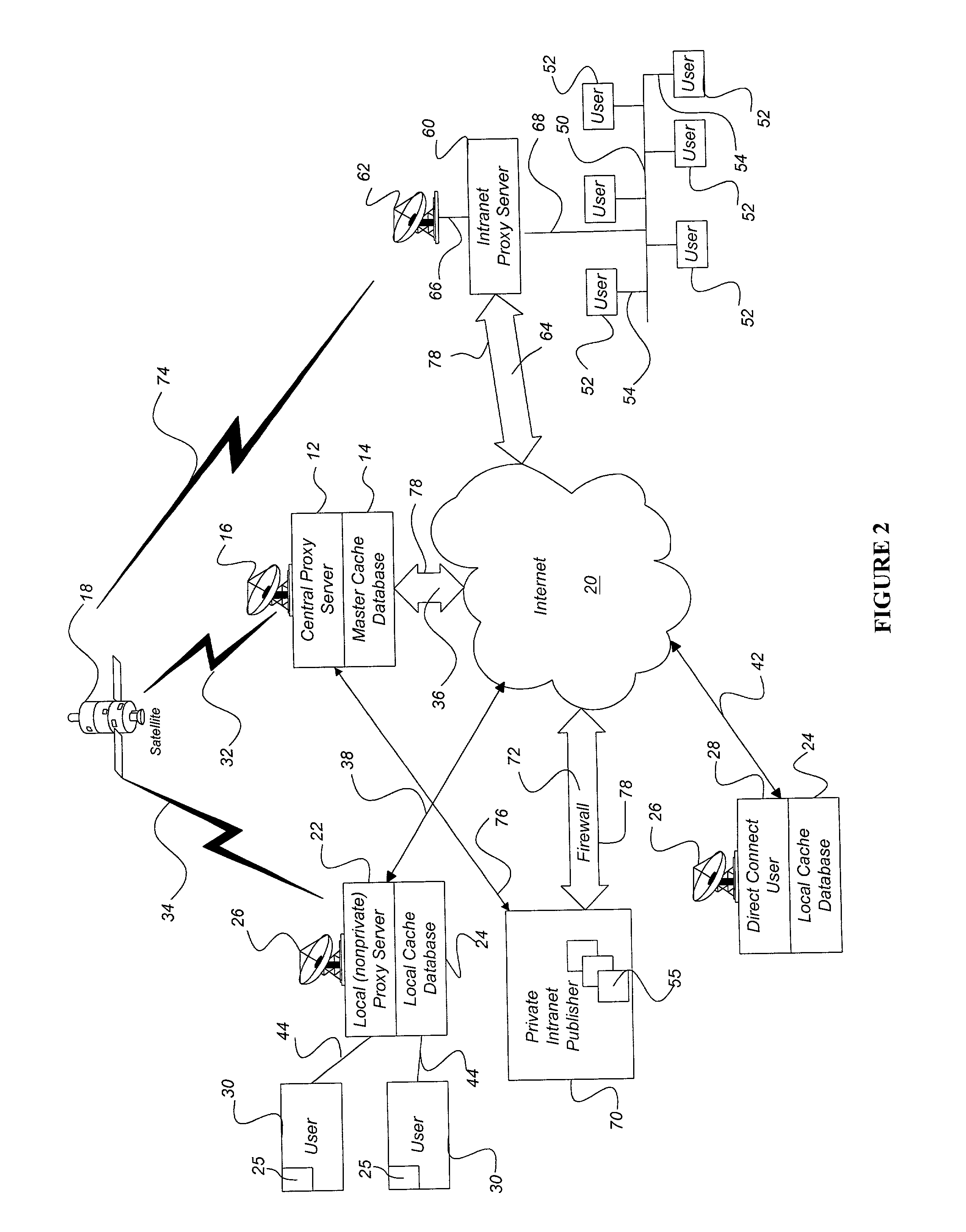
InactiveUS20020073167A1Facilitates very efficient reportingMultiple digital computer combinationsRadio transmissionInternet contentHigh rate
A system and method accelerates the distribution of digital content of a global communications network such as the Internet. A central proxy server selects popular digital objects for transmission over a communication medium to provide content filling of cache databases attendant to local proxy servers. The communication medium may comprise satellite transmission using an IP multicast protocol. The local proxy servers concurrently receive the digital objects at a high rate of speed and store the digital objects in the attendant local cache databases. The local proxy servers may utilize a localized priority determination scheme to determine whether to keep or discard the transmitted digital objects. The priority determination scheme may utilize global demand data and / or local demand data. The demand data may include hits and / or misses on digital objects and may also include quantitative data about the digital objects. The priority determination scheme may be driven by feedback regarding the needs and interests of subscribing users of the local cache database. Consequently, the priority determination scheme and ultimately, the contents of a local cache database, may be unique to that local cache database.
Owner:EDGIX CORP
Method for organizing records of database search activity by topical relevance
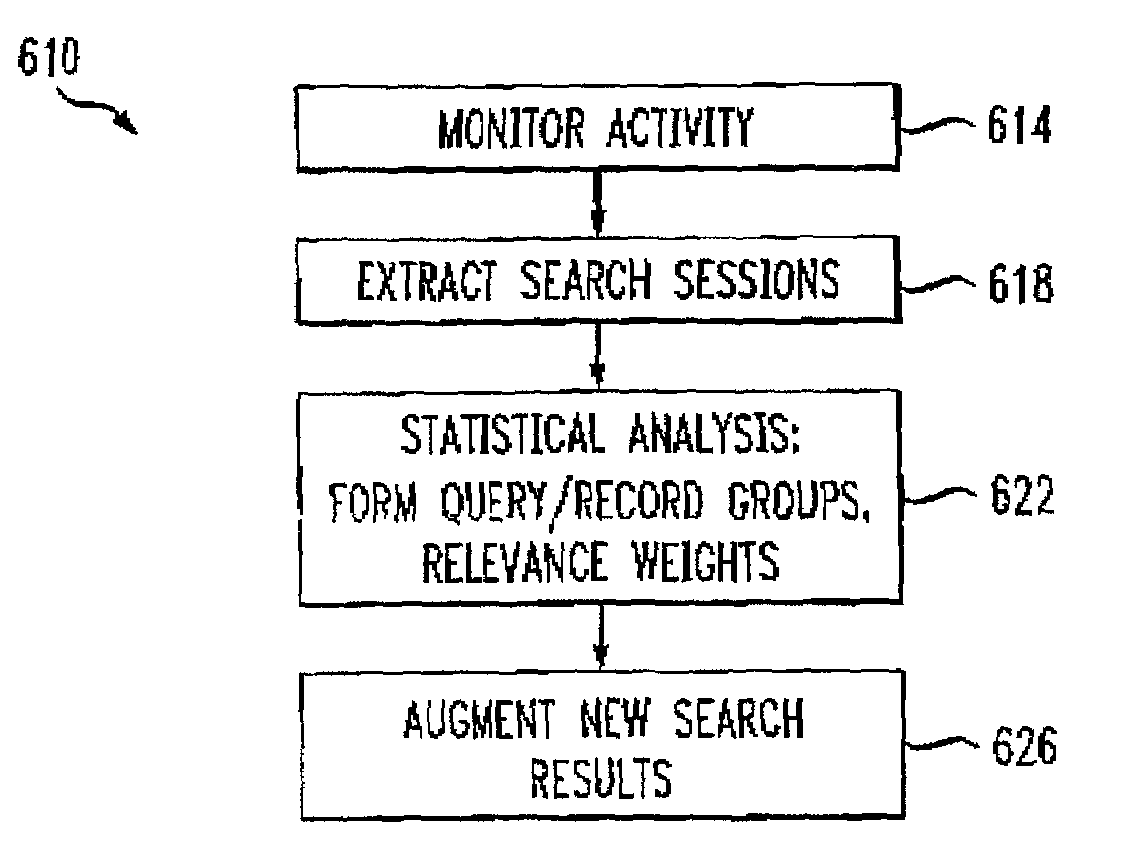
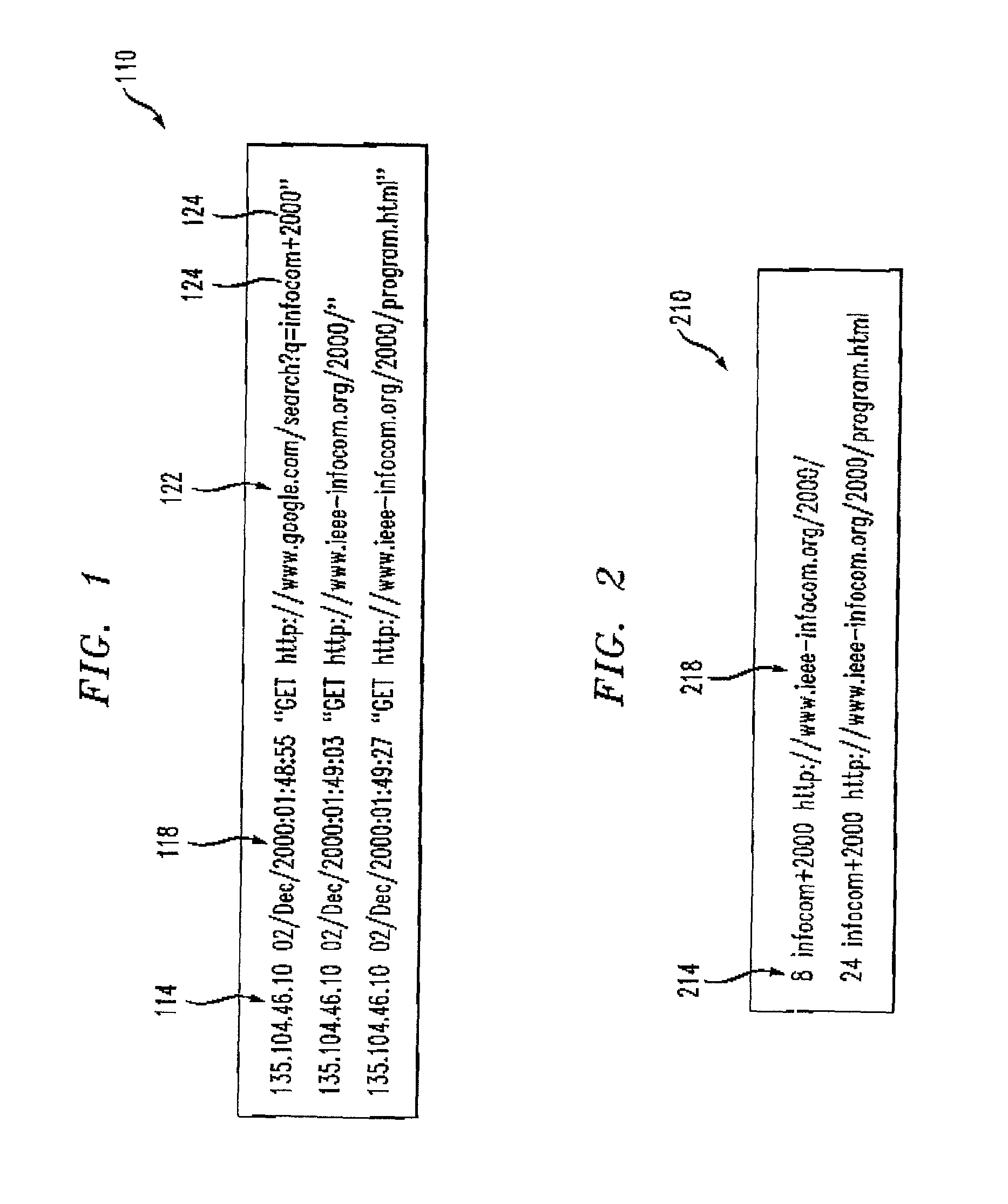
InactiveUS7194454B2Speed up searchData processing applicationsWeb data indexingOpen sourceThe Internet
A method for organizing records of a database by topical relevance generates statistics on relevance by monitoring search terms used and search paths traversed by a database user community. Records reviewed most often in relation to a given search term are assumed to be most relevant to that search term in the eyes of members of the user community. Additionally, a record reviewed in relation to a plurality of search terms is determined to be related by topical relevance to other records reviewed in relation to that plurality of search terms. Again, a probability is calculated, based on a frequency of record review and search terms used, as a measure of this record topical relevance. An embodiment directed toward Internet searches provides for seeding the probability calculations with information from labeled data available from open source Internet directories. The activities of the user community are monitored, for example, at a proxy server, or by reviewing proxy server logs. Other monitoring points are contemplated.
Owner:SOUND VIEW INNOVATIONS
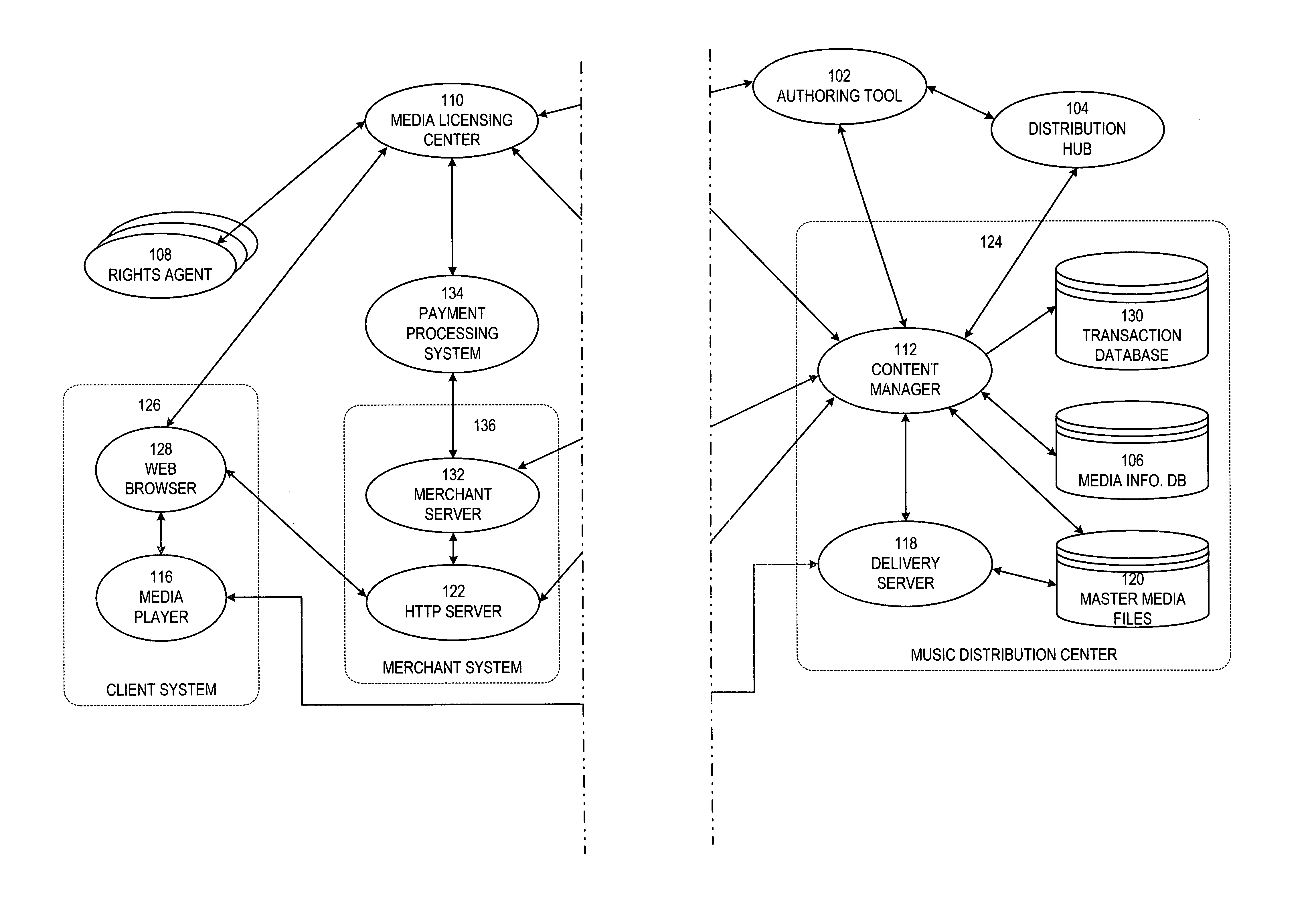
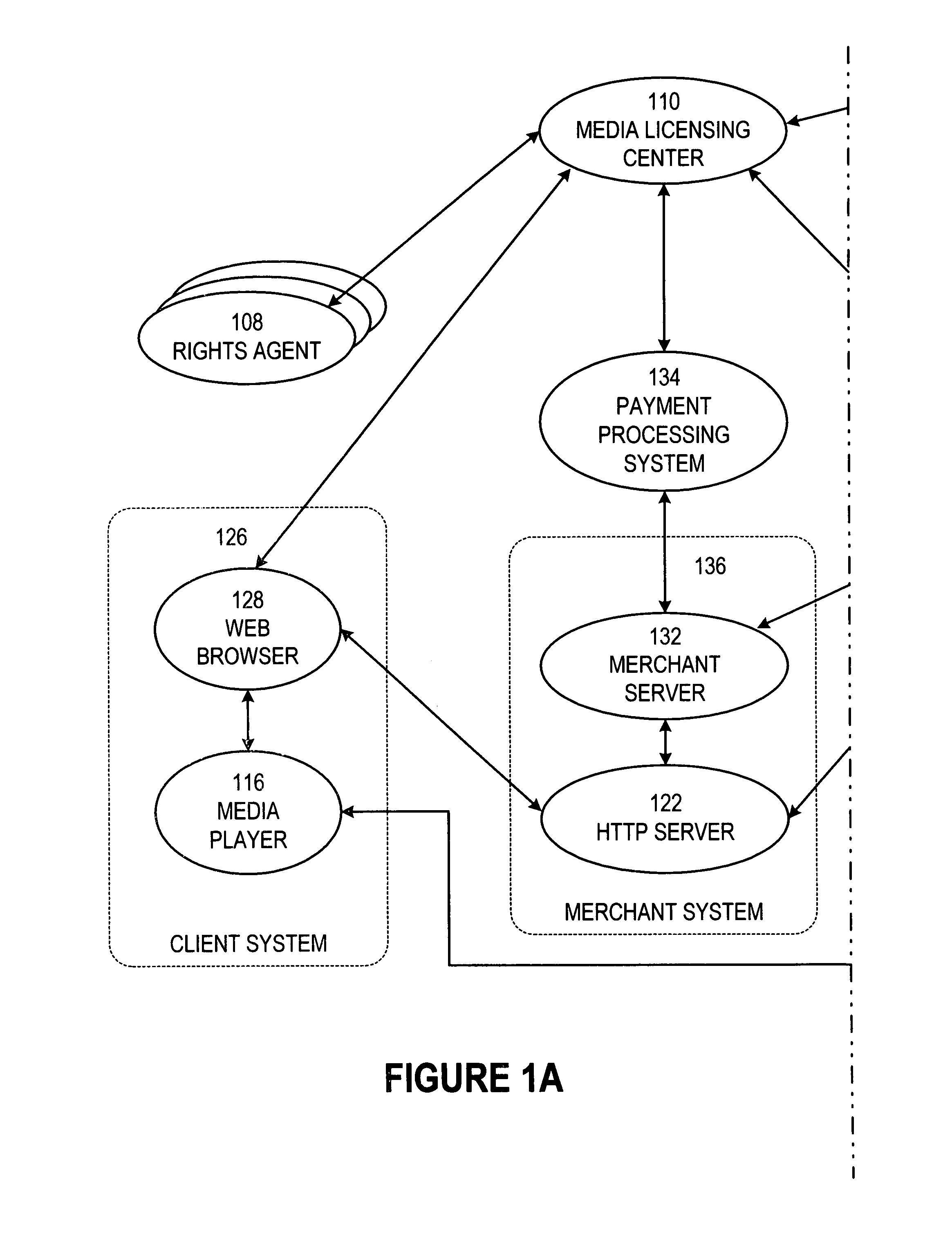
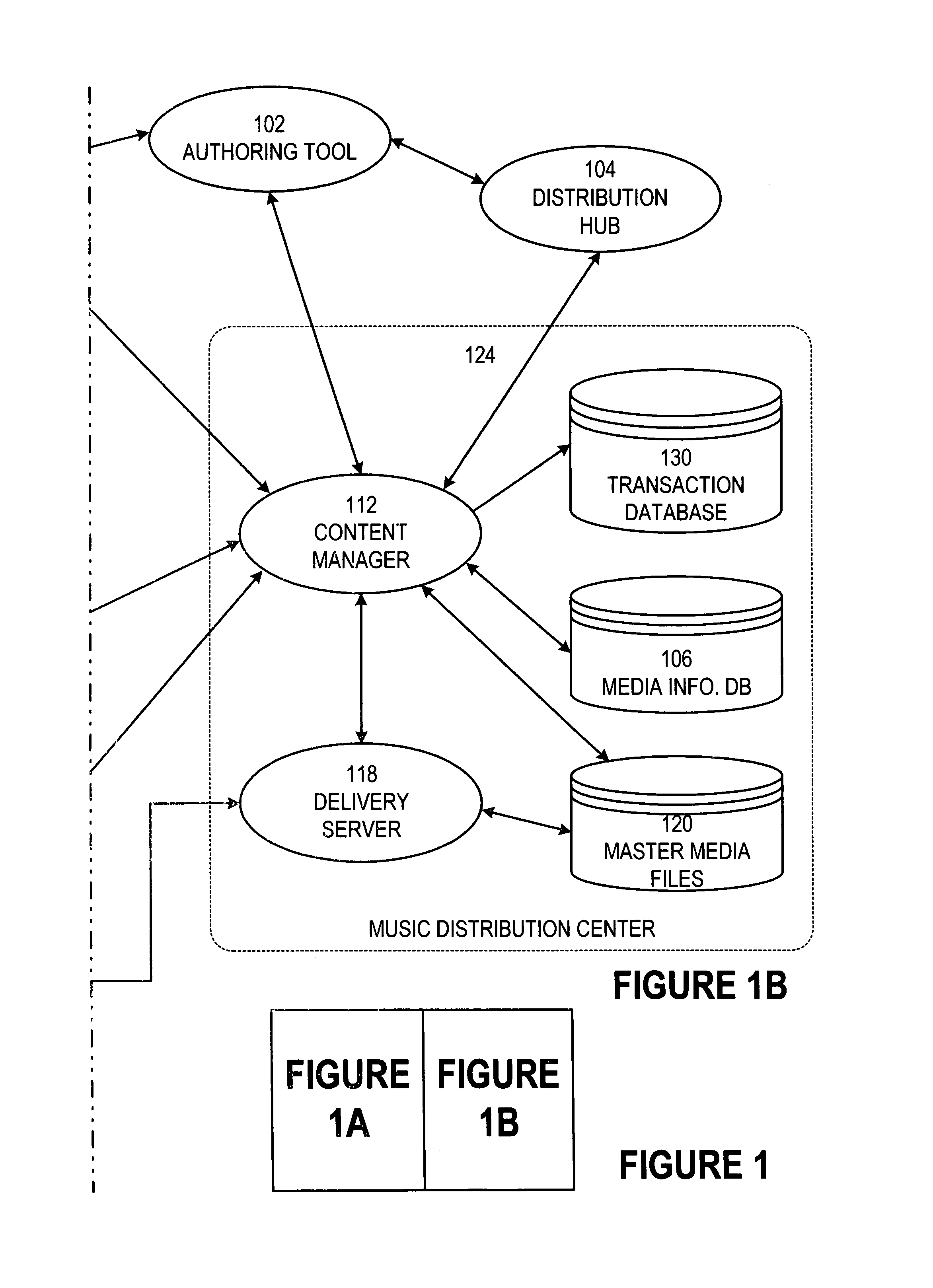
Secure online music distribution system
InactiveUS7263497B1Flexibility and ease of useGood flexibilityComputer security arrangementsPayment architectureContent managementInformation data
A secure music distribution system securely distributes digital products such as music, video, and / or computer software along with related media over a public telecommunications network, such as the Internet, employing a client-server architecture. The digital products are stored and controlled by a content manager computer system and are sold by separate merchant computer systems. The secure music distribution system includes a music distribution center which operates with any number of client systems and with any number of merchant systems. The music distribution center includes a content manager and at least one delivery server. The content manager maintains a media information database, a master media file system, and a transaction database. In addition, the music distribution center interfaces with a media licensing center, which in turn communicates with one or more distributed rights agent servers and the merchant servers. The merchant server executes in a merchant computer system, which also includes an HTTP (HyperText Transfer Protocol) server. The merchant servers interface with various payment processing systems. The client systems include a media player and a Web browser. Additional delivery servers and media licensing centers operate independently and externally to the music distribution center and interface with the music distribution center.
Owner:MICROSOFT TECH LICENSING LLC
Uniform power save method for 802.11e stations
ActiveUS20050018624A1Delay minimizationFast sampling rateEnergy efficient ICTPower managementAccess methodClient-side
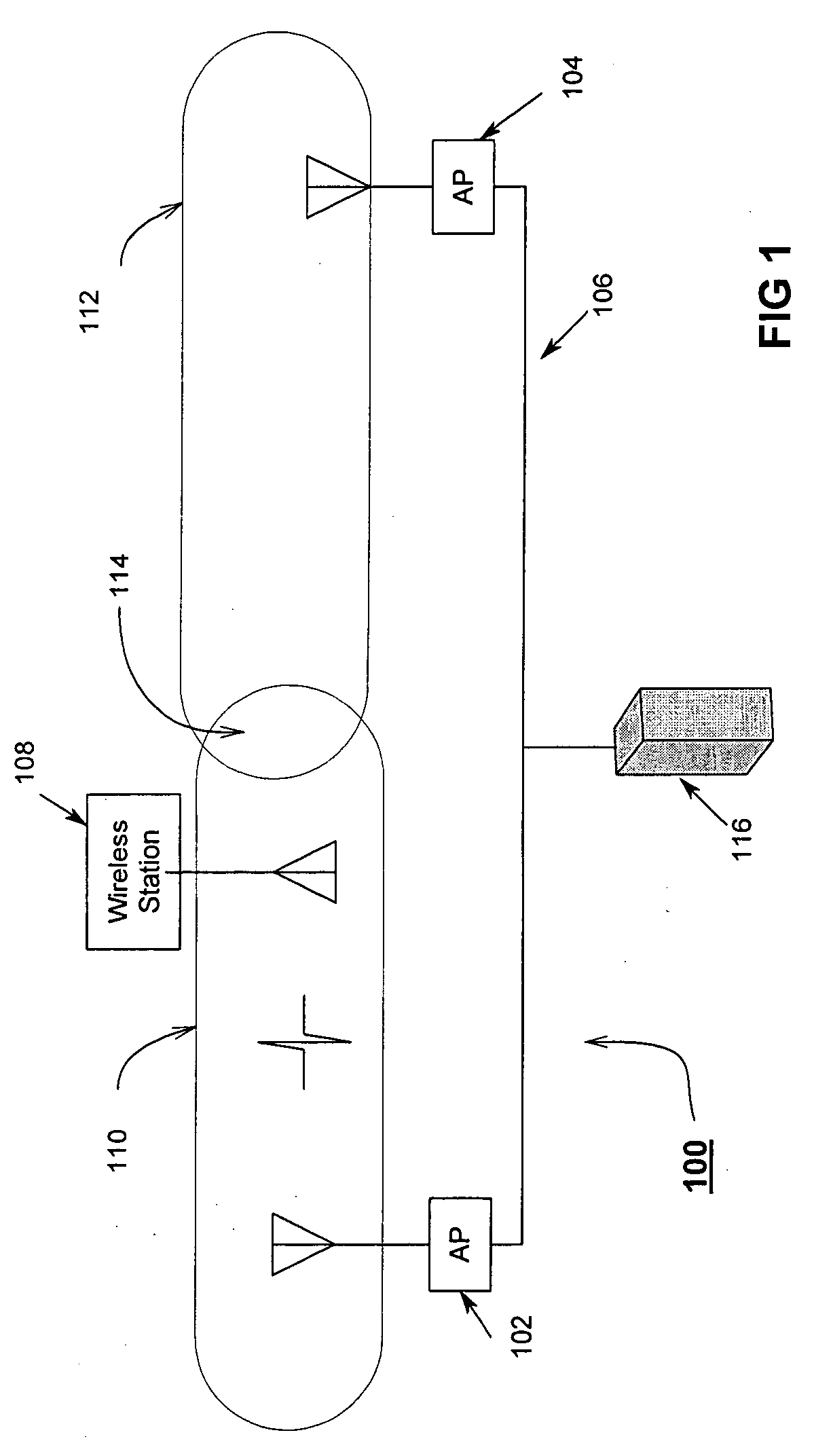
A power-save QSTA notifies an Access Point (AP) that its operating in a automatic power-save delivery (APSD) mode and negotiates a periodic wakeup schedule and a scheduled startup time with the AP. Wakeup times are synchronized with the 802.11 Timer Synchronization Function (TSF). The AP automatically sends frames to the QSTA when it determines the QSTA is in an awake state, otherwise downlink frames are buffered. The AP uses a combination poll+EDCF access method wherein at the start of each wakeup period the AP sends a poll to the QSTA, the poll having a flag that indicates to the QSTA if the AP has a downlink fame buffered for the QSTA. In addition, a Proxy ARP Server in an AP maintains IP / MAC bindings for associated clients so that when the AP receives a proxy ARP request for a client, the AP may respond for the client.
Owner:CISCO TECH INC
Supporting common interactive television functionality through presentation engine syntax
InactiveUS7055169B2Analogue secracy/subscription systemsTwo-way working systemsScripting languageInteractive television
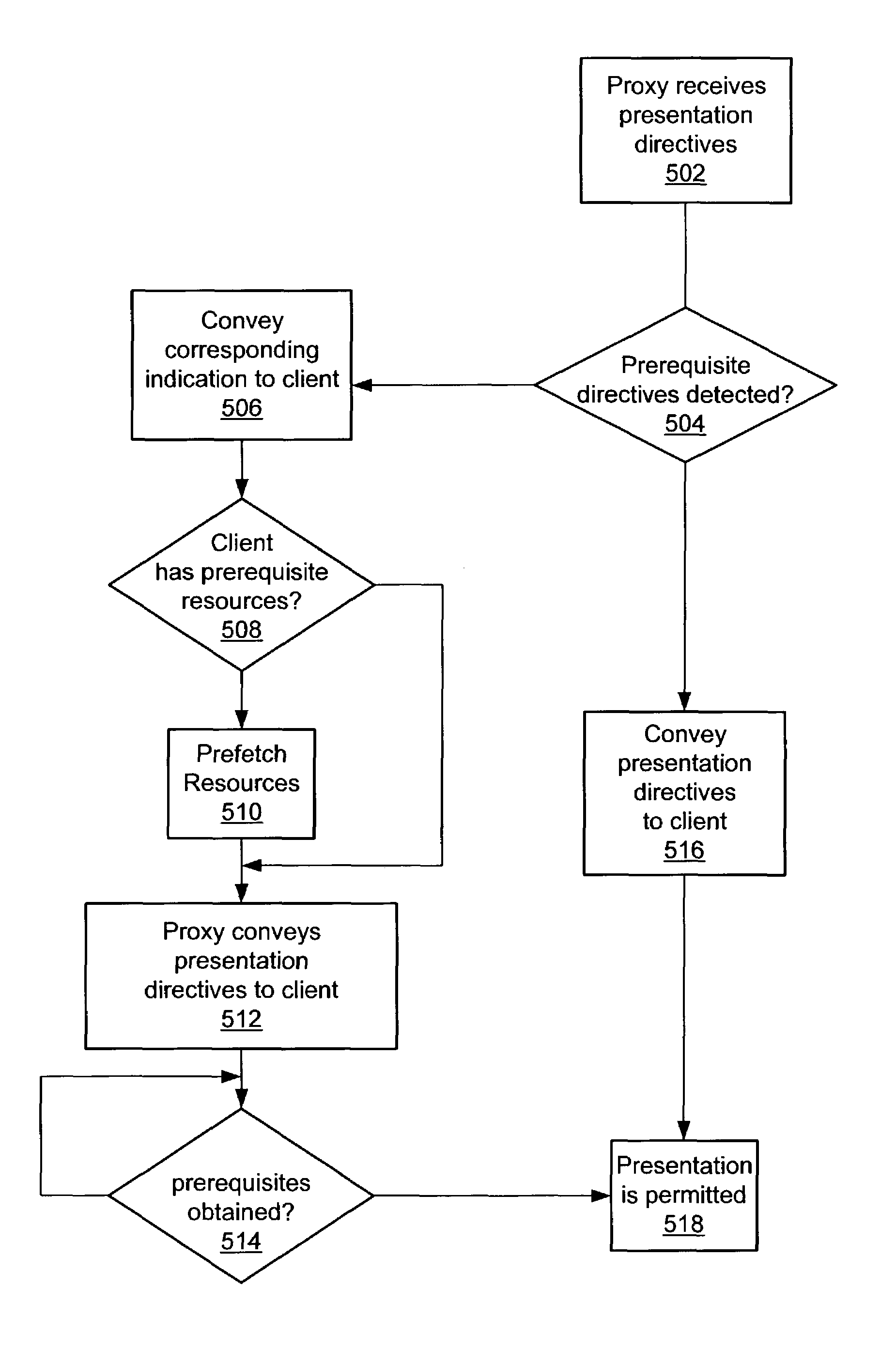
A method and mechanism for enabling the creation and / or control of interactive television content using declarative-like directives such as HTML, scripting languages, or other languages. A a centrally located proxy server is configured to receive, transcode and convey transcoded web based content to client devices. Upon detecting directives which indicate particular resources required for a presentation are prerequisites, the proxy server conveys signals to a client device that these particular resources are prerequisites. In response to receiving the conveyed signals, the client device may take actions to prefetch these resources. The client device is further configured to prohibit initiation of the presentation until the prerequisite resources are acquired.
Owner:OPEN TV INC
Virtual private network having automatic reachability updating
InactiveUS20050138204A1Easy to createCommunication securityEnergy efficient ICTDigital data protectionPrivate networkReachability
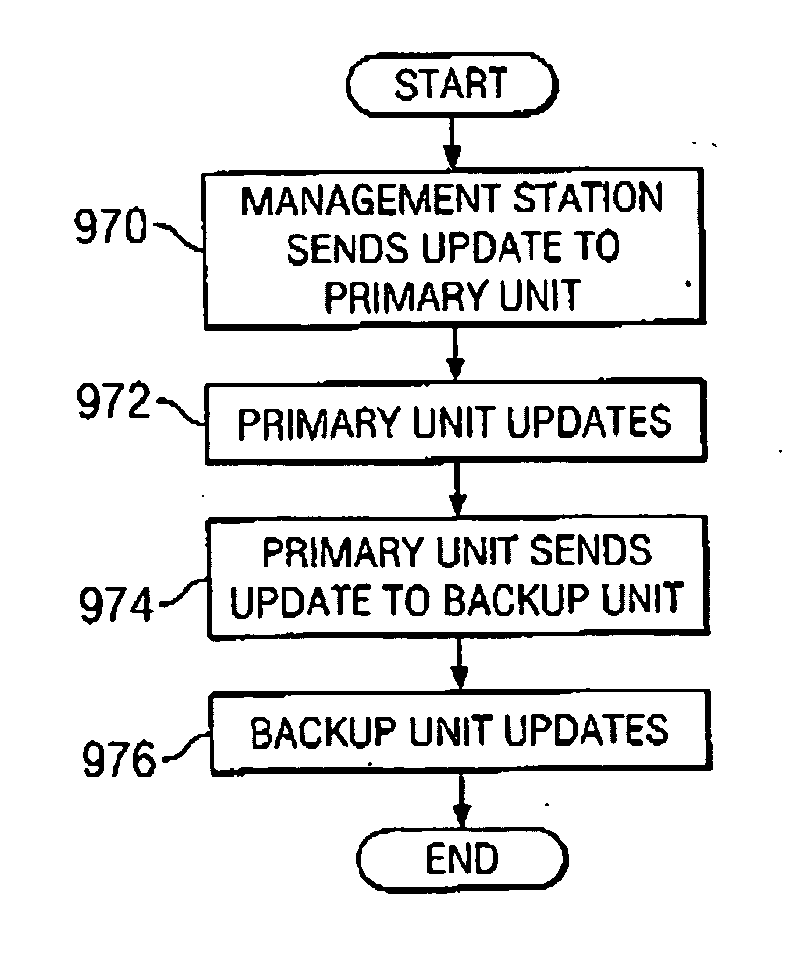
A unified policy management system for an organization including a central policy server and remotely situated policy enforcers. A central database and policy enforcer databases storing policy settings are configured as LDAP databases adhering to a hierarchical object oriented structure. Such structure allows the policy settings to be defined in an intuitive and extensible fashion. Changes in the policy settings made at the central policy server are automatically transferred to the policy enforcers for updating their respective databases. Each policy enforcer collects and transmits health and status information in a predefined log format and transmits it to the policy server for efficient monitoring by the policy server. For further efficiencies, the policy enforcement functionalities of the policy enforcers are effectively partitioned so as to be readily implemented in hardware. The system also provides for dynamically routed VPNs where VPN membership lists are automatically created and shared with the member policy enforcers. Updates to such membership lists are also automatically transferred to remote VPN clients. The system further provides for fine grain access control of the traffic in the VPN by allowing definition of firewall rules within the VPN. In addition, policy server and policy enforcers may be configured for high availability by maintaining a backup unit in addition to a primary unit. The backup unit become active upon failure of the primary unit.
Owner:IYER SHANKER V +3
Method for network-aware clustering of clients in a network
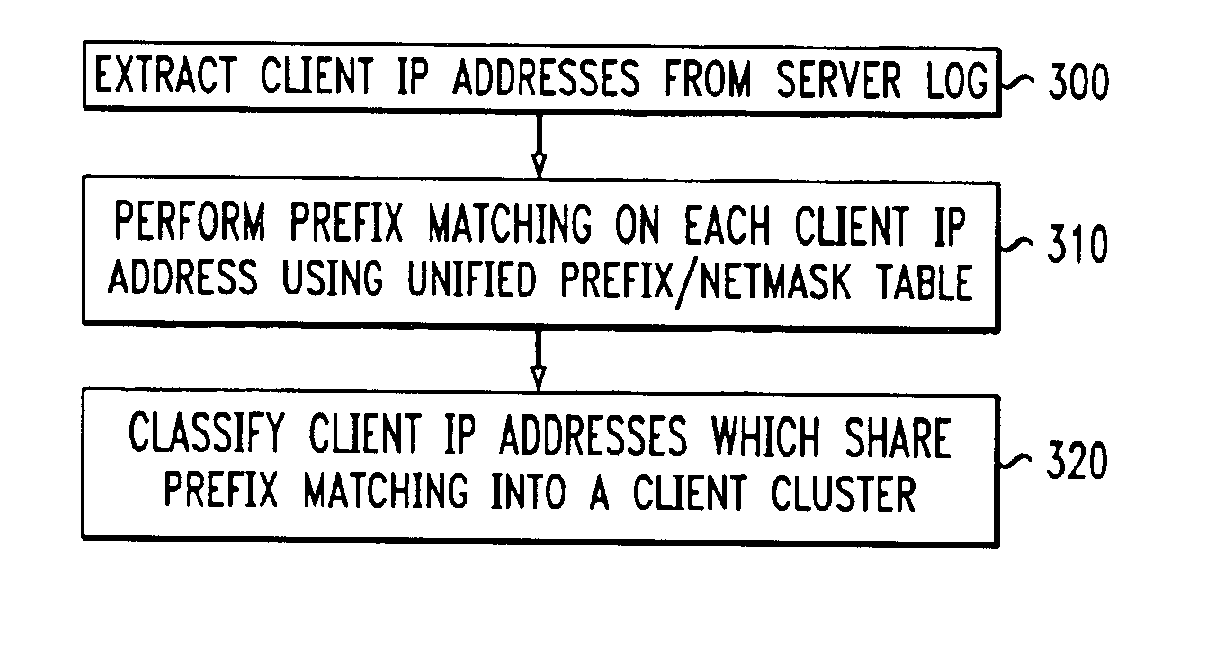
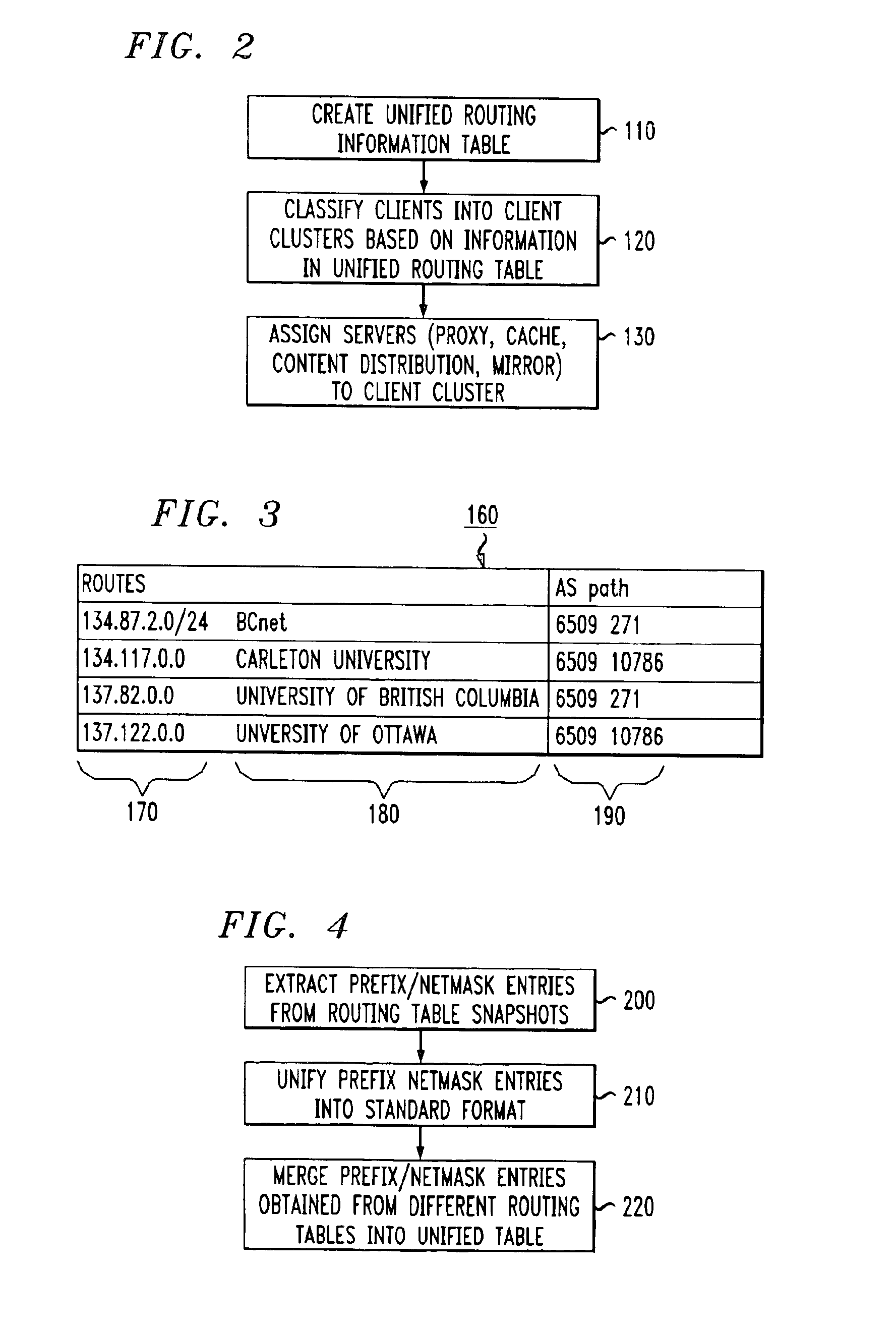
InactiveUS6928485B1Relational databasesMultiple digital computer combinationsServer logContent distribution
A method for clustering together network clients for guiding of placement of network servers is disclosed. A number of routing table prefix / netmask entries are aggregated and unified into a tubular format. The routing table entries may be converted into a singular format. A network server log is used to extract a number of client IP addresses which are compared to the entries within the unified routing table. A common prefix shared by a number of the client IP addresses and an entry in the unified routing table is determined and used to cluster the clients together in a client cluster. Network servers, such as proxy server, cache servers, content distribution servers and mirror server may be placed in the network according to the client clusters.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Smart electronic receipt system
InactiveUS20020073043A1Apparatus for meter-controlled dispensingSecret communicationPersonalizationHyperlink
A smart electronic receipt system that provides intelligent receipts, called Smart Receipts, that electronically document a transaction between two parties and maintains a persistent connection between the two parties following a successful online transaction. A Trusted Agent on the Buyer's client system creates an order record which is stored in a database on a Trusted Agent Server and starts the transaction process with the merchant. A Smart Receipt is delivered by a Smart Receipt Agent over a secure connection from the merchant to the Trusted Agent Server upon successful completion of a purchase and reflects the details of the transaction. It is stored in a secure database on the Trusted Agent Server and is made available to the Buyer (user) through a Trusted Agent located on his machine. The Trusted Agent Server compares the order record Limited Edition Digital Objects (LEDOs) stored in database with the Smart Receipt's LEDO to find the corresponding order record. The Smart Receipt provides the customer with detailed information about an online purchase in a standardized format. Hyperlinks embedded in the Smart Receipt enable the customer to access customer service and order status. The merchant may also embed additional services within the Smart Receipt, including special offers for future purchases. Offers provided in a Smart Receipt can be personalized to a user's preferences which are stored on the Trusted Agent Server. Each Smart Receipt is comprised of a chain of LEDOs with each LEDO object having a unique owner. A Smart Receipt is a dynamic entity and is continuously updated until the Buyer deletes it from the Trusted Agent Server.
Owner:HERMAN GARY +2
System and Method for Server-Based Antivirus Scan of Data Downloaded From a Network
ActiveUS20120110667A1Accurate and fast determinationFast and accurate selectionMemory loss protectionError detection/correctionWorkstationMalware
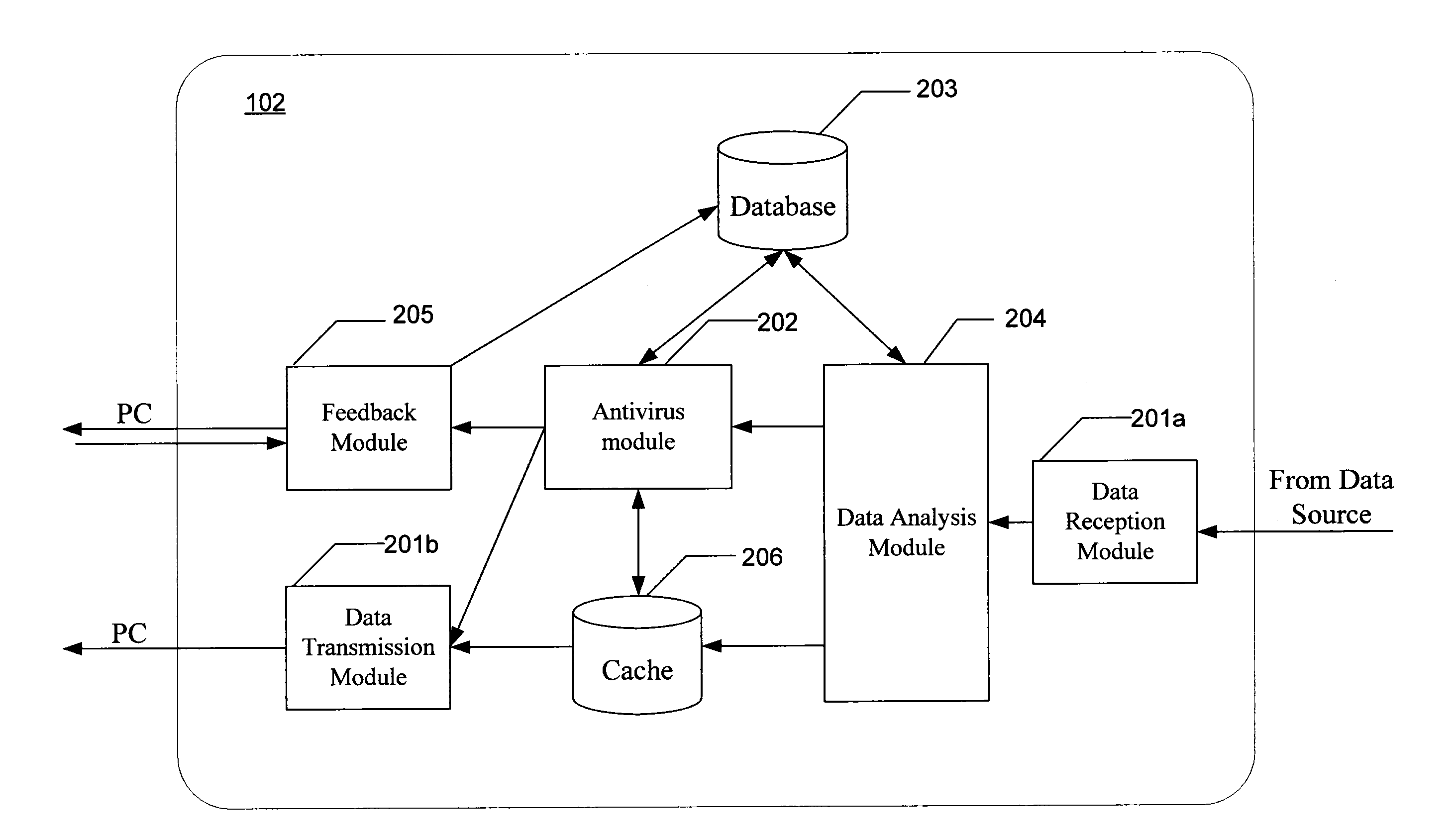
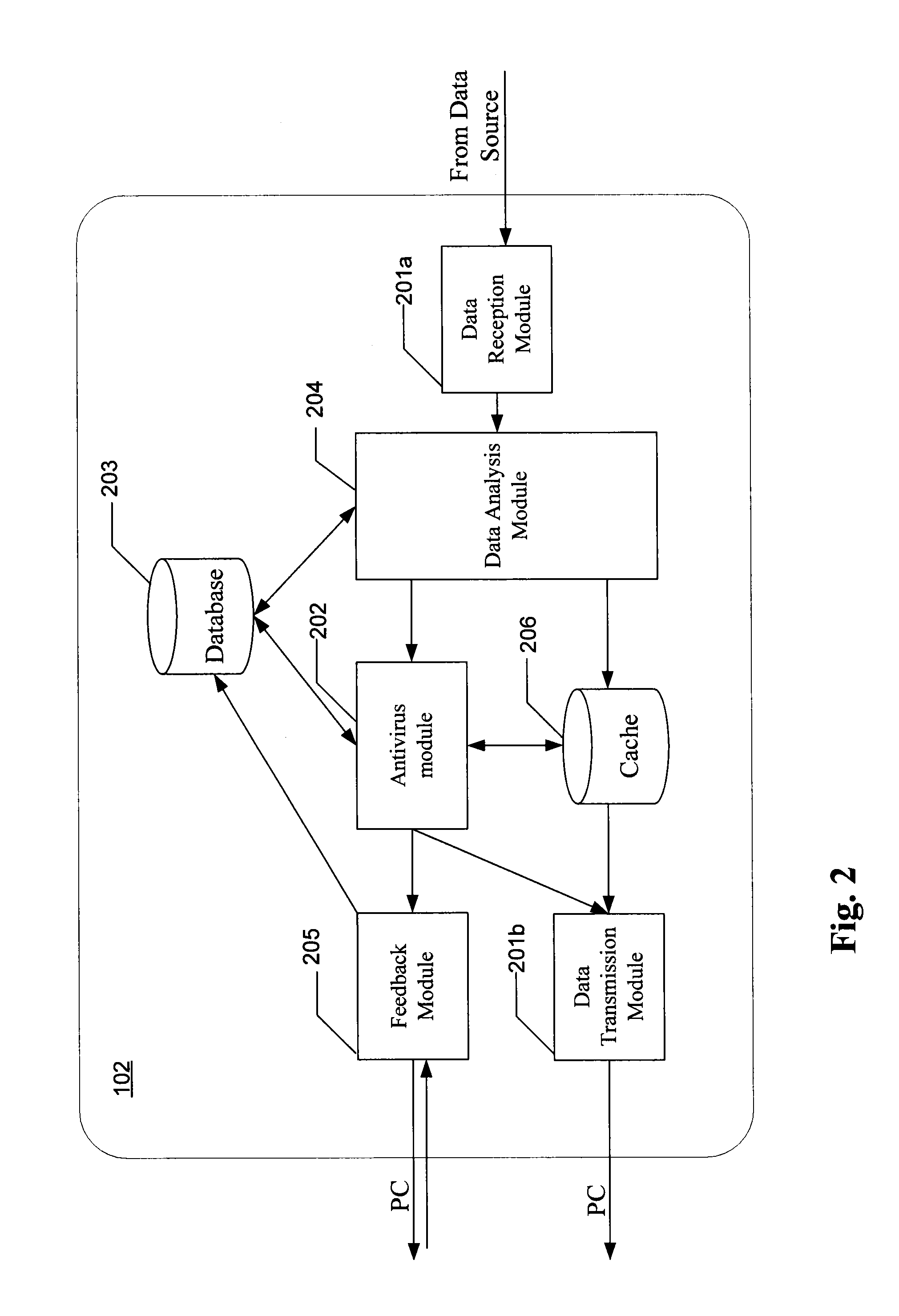
Aspect of the invention are directed to antivirus scanning, by a proxy server, of data downloaded from the network onto a PC workstation. The antivirus scanning is optimized for each scan by selecting an algorithm for that scan based on a determined overall likelihood that the downloaded data contains malicious code. Determination of the overall likelihood is augmented by the strength, or confidence, of statistical data relating to malware screening of results of previous downloads having similar parameters to the instant download.
Owner:AO KASPERSKY LAB
Enabling incoming VoIP calls behind a network firewall
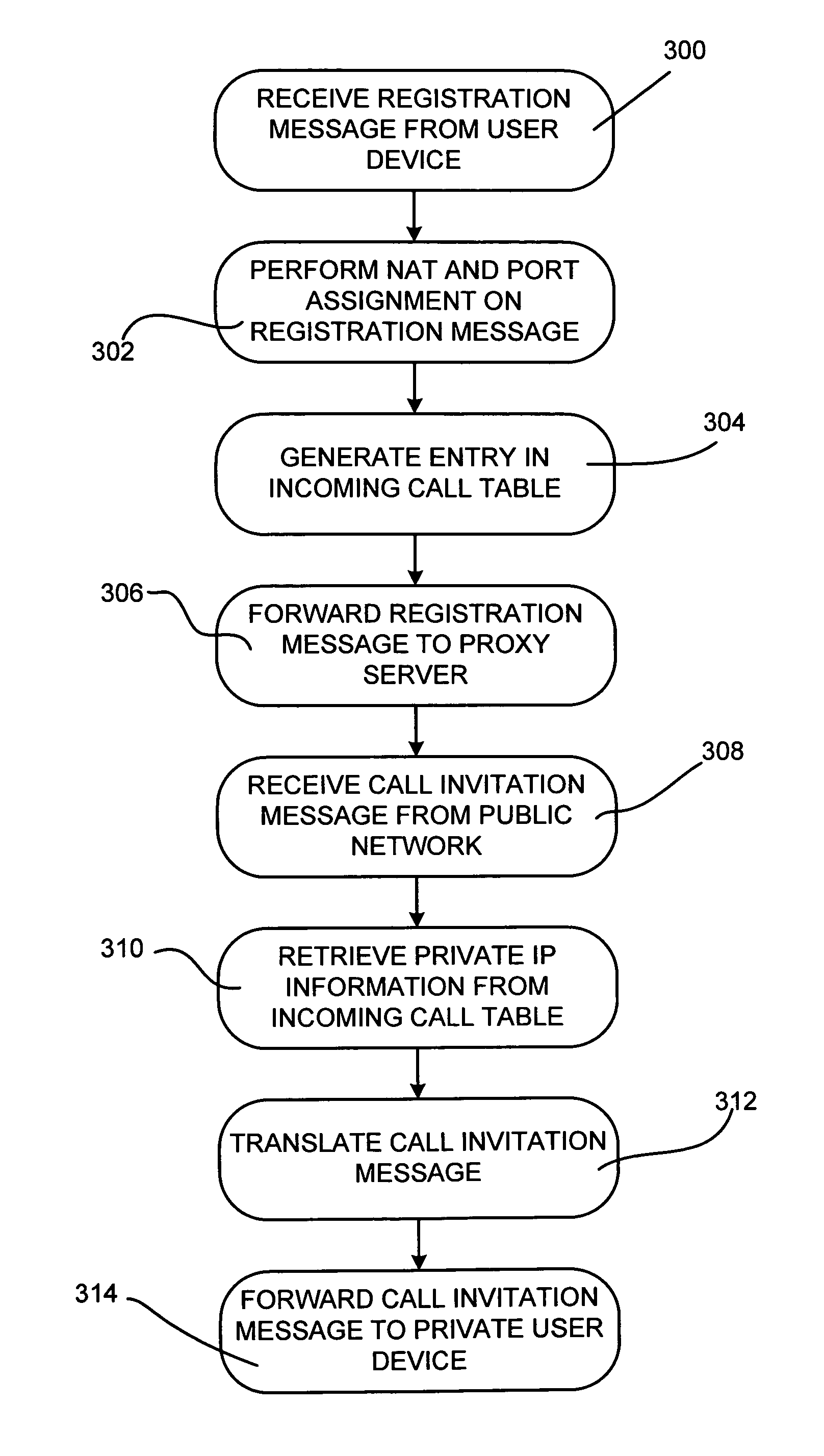
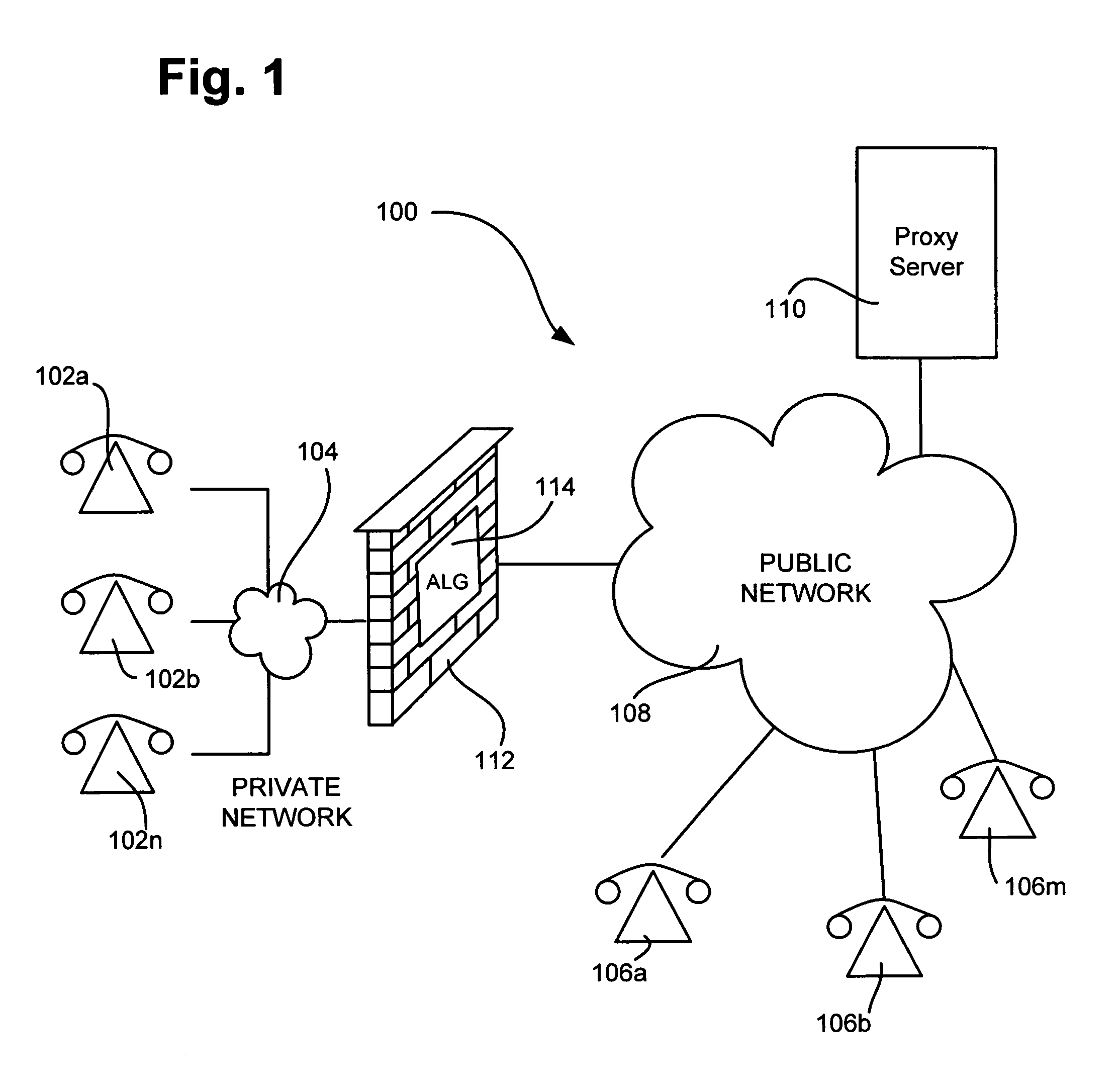
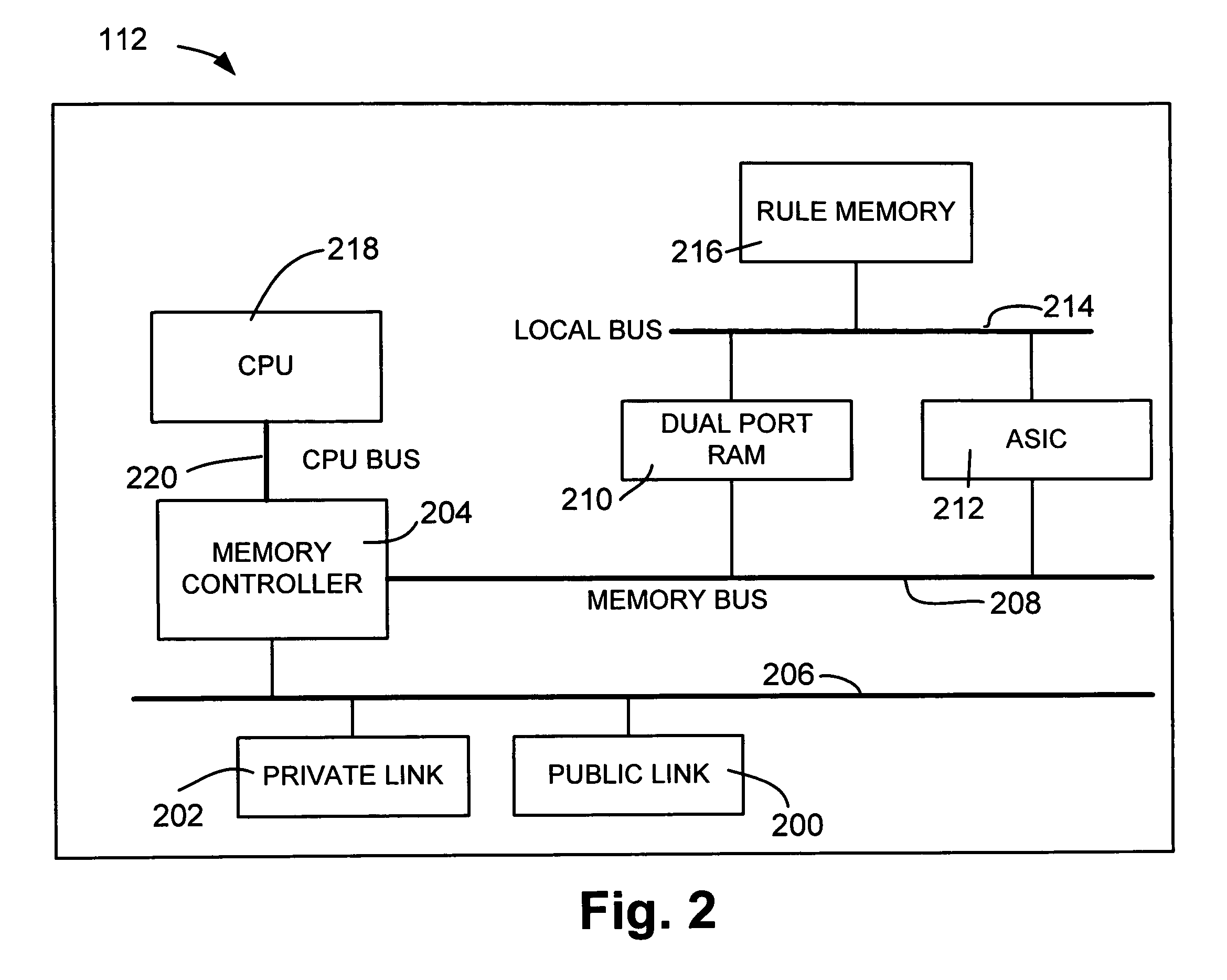
A network device is configured to receive a registration message from a private user device including a private internet protocol (IP) address associated with the private user device. A public IP address and discrete port number are assigned to the private user device and private IP address and stored in an incoming call table. The registration message is translated to include the public IP address and discrete port number. The registration message is forwarded to a proxy server for registration. An incoming call invitation message is received from a public user device, where the call invitation message is directed to the public IP address and discrete port number associated with the private user device. The call invitation message is translated to include the private IP address associated with the private user device based on the received public IP address and discrete port number and the incoming call table. The call invitation message is forwarded to the private user device.
Owner:JUMIPER NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com