However, the
receipt stage of the transaction where the buyer receives confirmation of a purchase is still rather primitive.
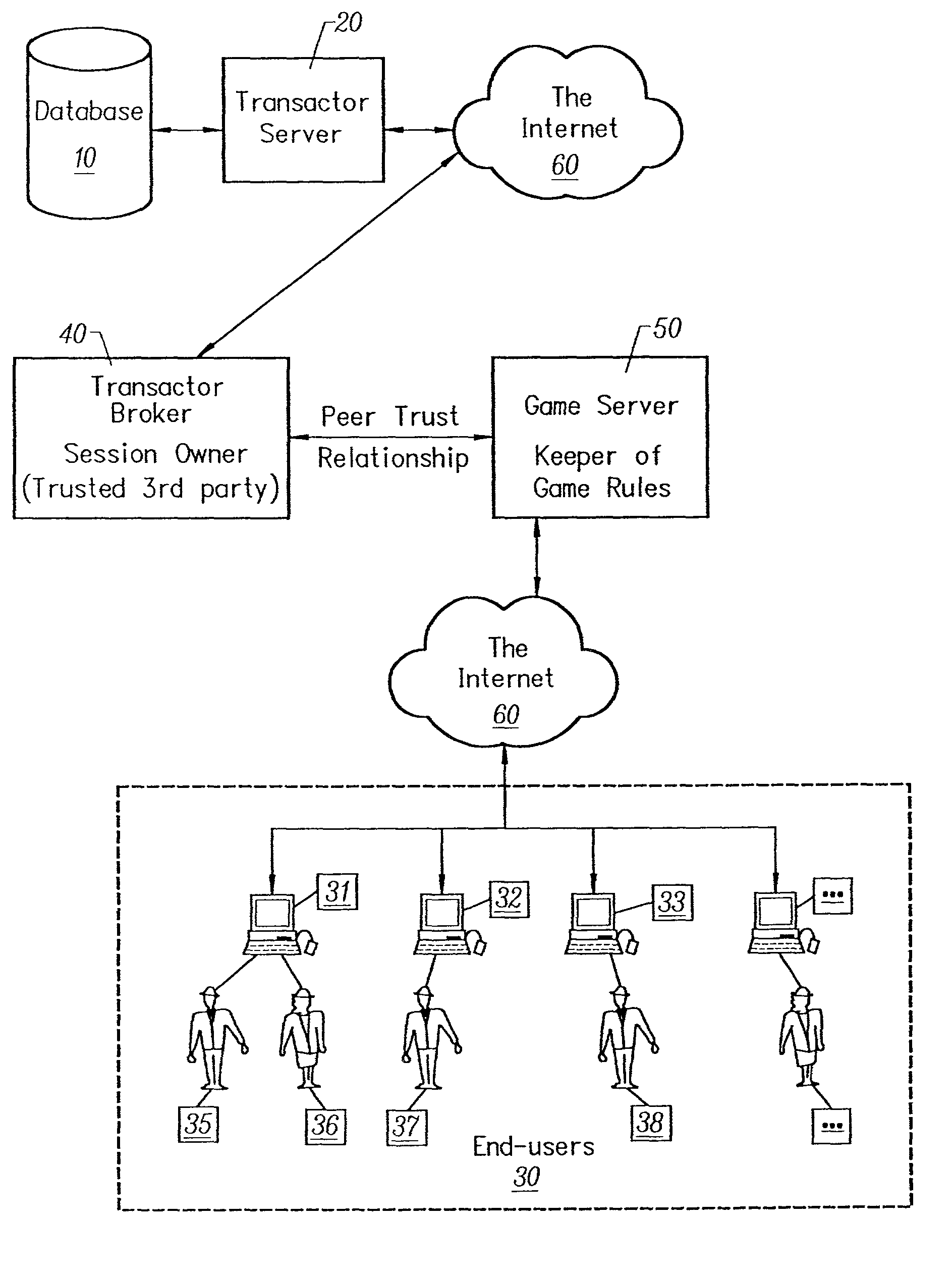
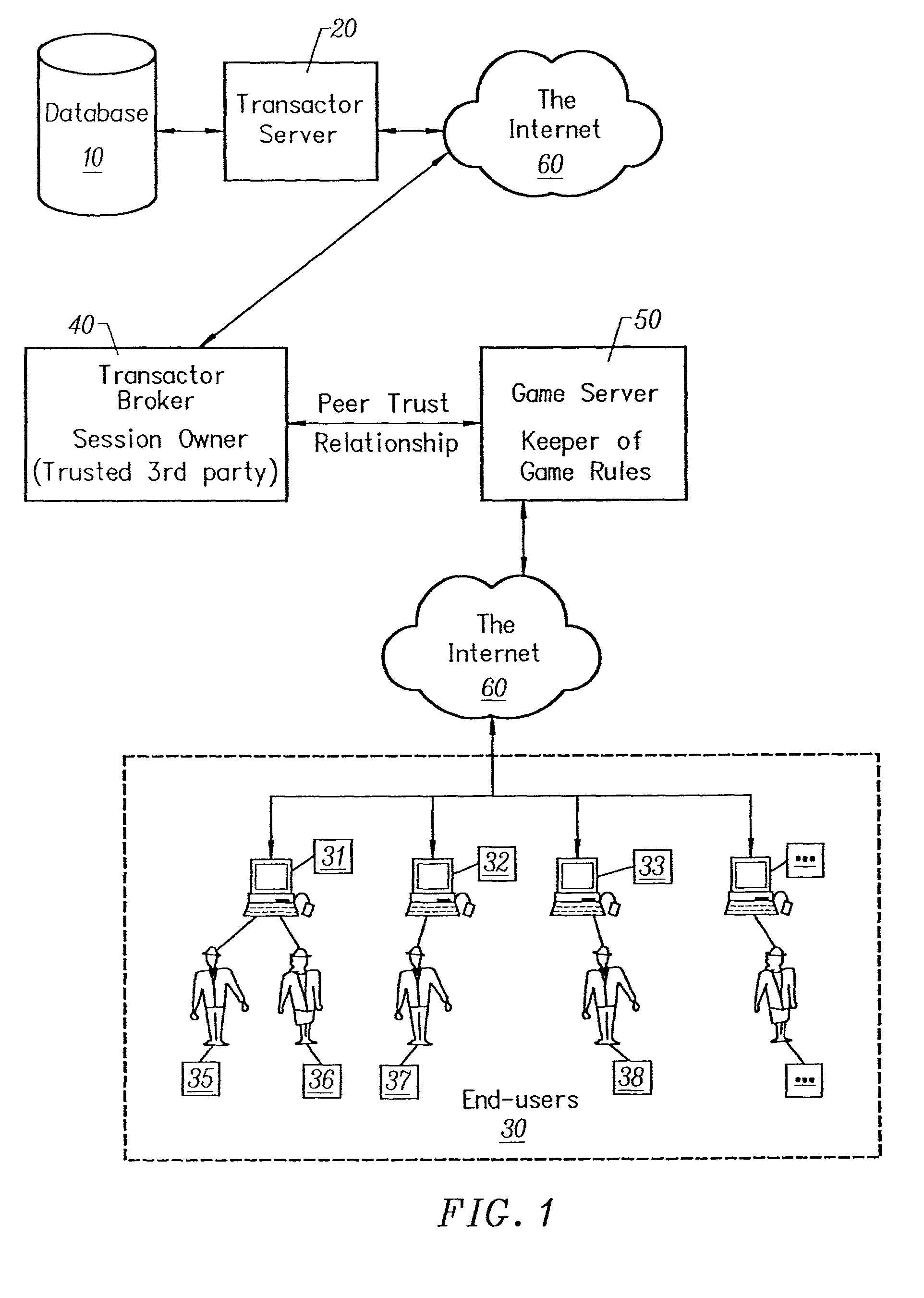
It can, however, detect certain kinds of
cheating that might occur in its conversations with those other Transactor servers.
Thus, they are limited to the core Transactor activities of creating objects, making transactions, and authenticating ownership and existence.
That is, if the originally registered game object was flawed or illegal for the game
universe, it will be "correct" as far as the Transactor Server is concerned, but will be "incorrect" when the
game server tries to use it.
Game servers that do not play a fair game are unlikely to be successful in the game market, but there is no final Transactor
arbiter of what constitutes a "fair game."
A typical problem involving a game, game-players, and ownership transfer is first presented.
The basic problem is how a
game server or anyone else in the above
scenario can truly enforce transferring ownership involuntarily; that is, without the active assent of the object's original owner.
Even if the game-
client software running on the player's
machine automatically responded to a
game server request to transfer ownership, the user could have hacked the
software to not permit ownership transfers.
Thus, in conventional circumstances, the game
server would have no way to enforce ownership transfer to the object's new owner.
This approach appears simple, but would require greater underlying complexity in the overall Transactor system.
This arrangement would also require that Transactor servers trust all game servers, thus opening up potential holes in the overall system security model and greatly expanding the required trust relationships in the overall system.
But that asynchronicity can propagate to any depth, since objects may rapidly change owners again before a prior ownership transfer has completed.
This quickly leads to a large "roll-back" problem that a game
server must
handle on its own.
If a player's connection goes out, the game
server maintains the "designated owner" tags, subject to plundering by other players within the game context.
One downside to this arrangement is that, if a game is played and no objects change "true" owners, there is an initial ownership transfer from the players to the game server, plus a closing transfer back to the original owner.
In embodiments employing this "simple solution," there is no way to avoid this, because without it the game server has no enforceable authority to transfer objects that are in play.
Fortunately, this activity is largely confined to game startings and endings.
Normally Transactor objects are useless to those who would simply take them (i e. copy the file), because the object itself is encrypted under the owner'
s key, and because a Transactor server would disallow the object's use except by the owner.
It does not validate objects or ownership, only the identity of users.
These values are essentially impossible to
forge or fake, nor do they allow an altered or forged object or user to be improperly recognized as valid.
The fact that objects are, in this sense, immutable once registered does not prevent time-varying properties from accruing to the object.
This makes such objects recognizable but unusable.
But even the owner can't do everything.
There are advantages and disadvantages to any particular Financial Module design, anywhere along the continuum between the two possible methods presented above.
Note that even rejected transactions are logged, since they indicate some kind of problem (
data loss, theft attempt, etc.).
If rejected, there is no ownership transfer, but the Bookkeeper retains the record so it can detect patterns of fraud or other difficulties.
Without the expiration-time X, this would be a security flaw, since Sellers are not required to trust Buyers.
If either one detects
cheating or improper data using its own knowledge, it can simply refuse to sign the transaction record.
Some reasons may be embarrassing for either Buyer or Seller, such as "insufficient funds", so not all reasons for rejection are sent to the clients, only some.
Thus, the main reason for using a message-digest would be lost.
Rejection may mean any error.
Rejection may mean any error.
Transient objects cannot be stored in a user's inventory, and they automatically disappear when the connection with their originator is broken.
This transient object has no value, is unusable in play, and cannot be traded or retained in the user's inventory.
A membership card also identifies the holder as a member of the issuing organization, but this is primarily for use by other organizations, since in an electronic world an organization may be presumed to have an available database of members, making membership cards superfluous.
But perhaps the best-known example is S&H green stamps--they are fungible and valuable, but have no actual cash value.
Typically, the problem is in getting a sufficiently random
initial seed.
It suffers from the problems that it may be hard to find a trusted server
machine which has the computational ability and bandwidth to and from each player's machine to do this effectively.
Presenting users with signed versions of their ownership certificates is unimportant, as is verifying those signatures; instead, the server keeps track of everything.
However, if the Proxy is dishonest, then its dishonesty (at least in changing around object ownerships) should be easily detected.
This document will get larger for each transfer, which will leak information about this object's past.
If he doesn't want to allow the transfer, he can send any message that isn't the expected response, and the transfer will fail.
This makes the protocols much harder to make resistant to various kinds of
cheating.
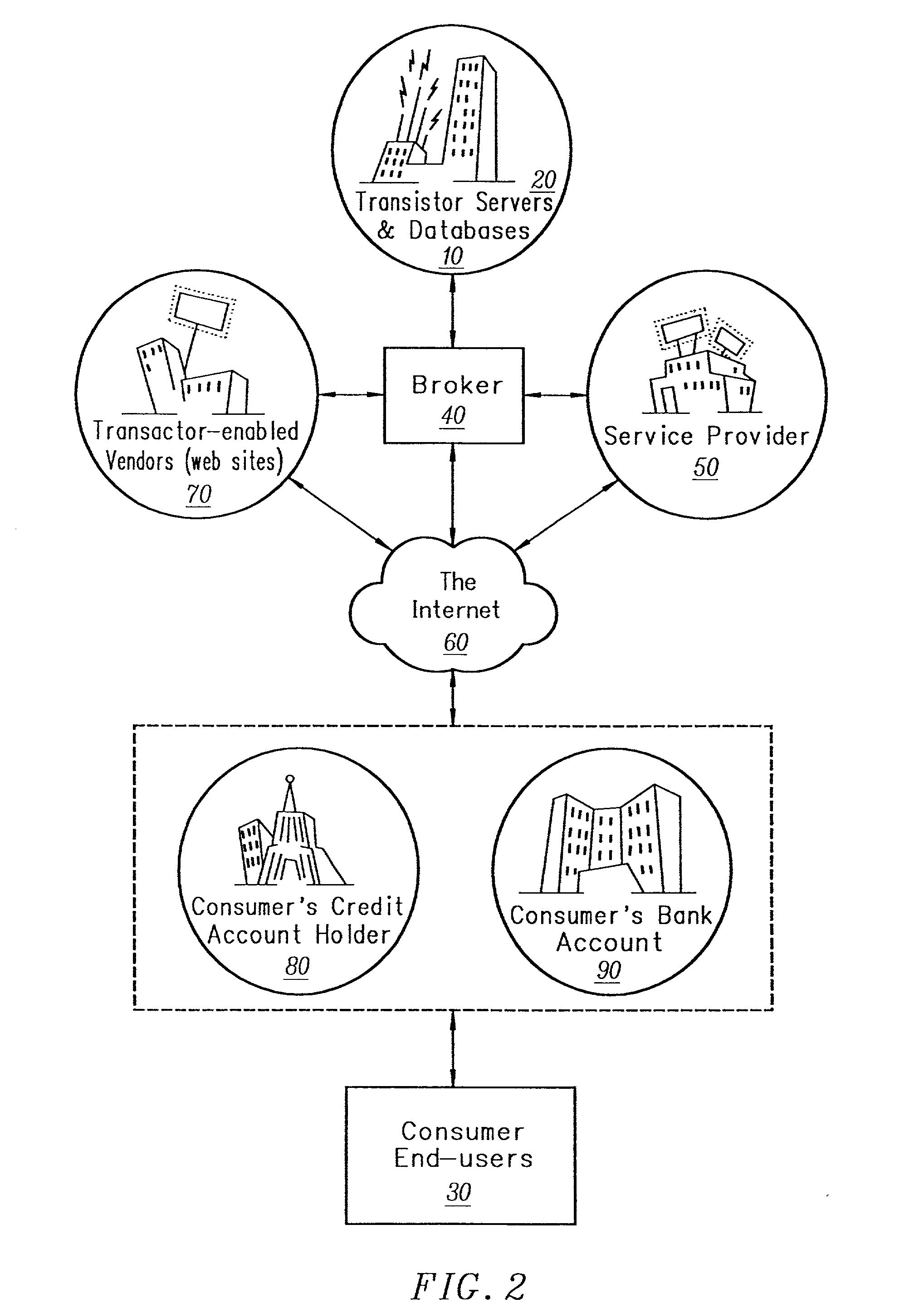
Businesses of type 1 are legacy businesses that are not yet enabled with the more modern direct techniques.
However, other, less efficient techniques may be applied to manage the instrument's business affairs.
The standard export-approved browser has only 40 bit bulk
encryption and 512 bit RSA, accordingly such
certificate provides much less security.
 Login to View More
Login to View More  Login to View More
Login to View More