Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
123045 results about "Server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
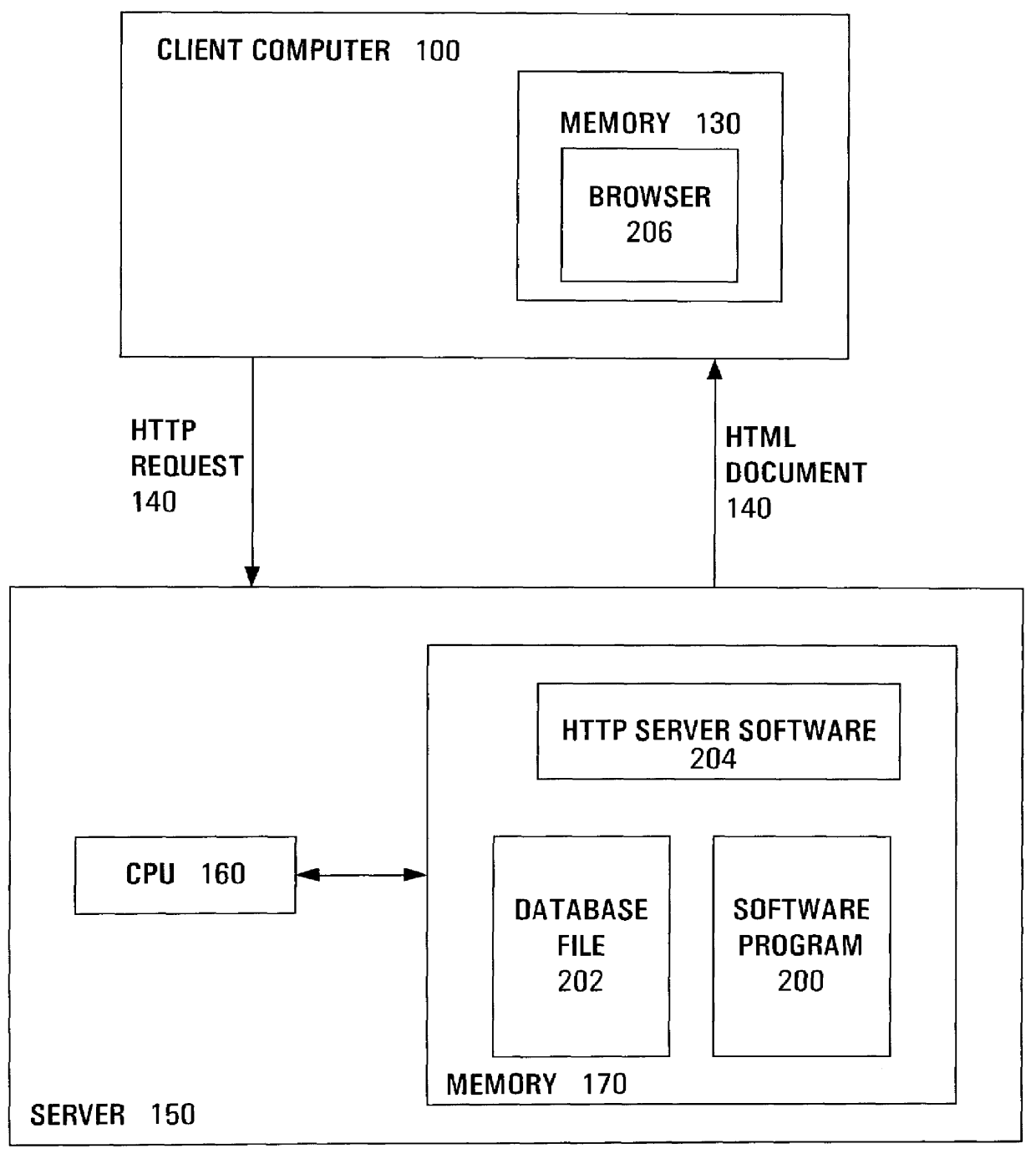
In computing, a server is a computer program or a device that provides functionality for other programs or devices, called "clients". This architecture is called the client–server model, and a single overall computation is distributed across multiple processes or devices. Servers can provide various functionalities, often called "services", such as sharing data or resources among multiple clients, or performing computation for a client. A single server can serve multiple clients, and a single client can use multiple servers. A client process may run on the same device or may connect over a network to a server on a different device. Typical servers are database servers, file servers, mail servers, print servers, web servers, game servers, and application servers.
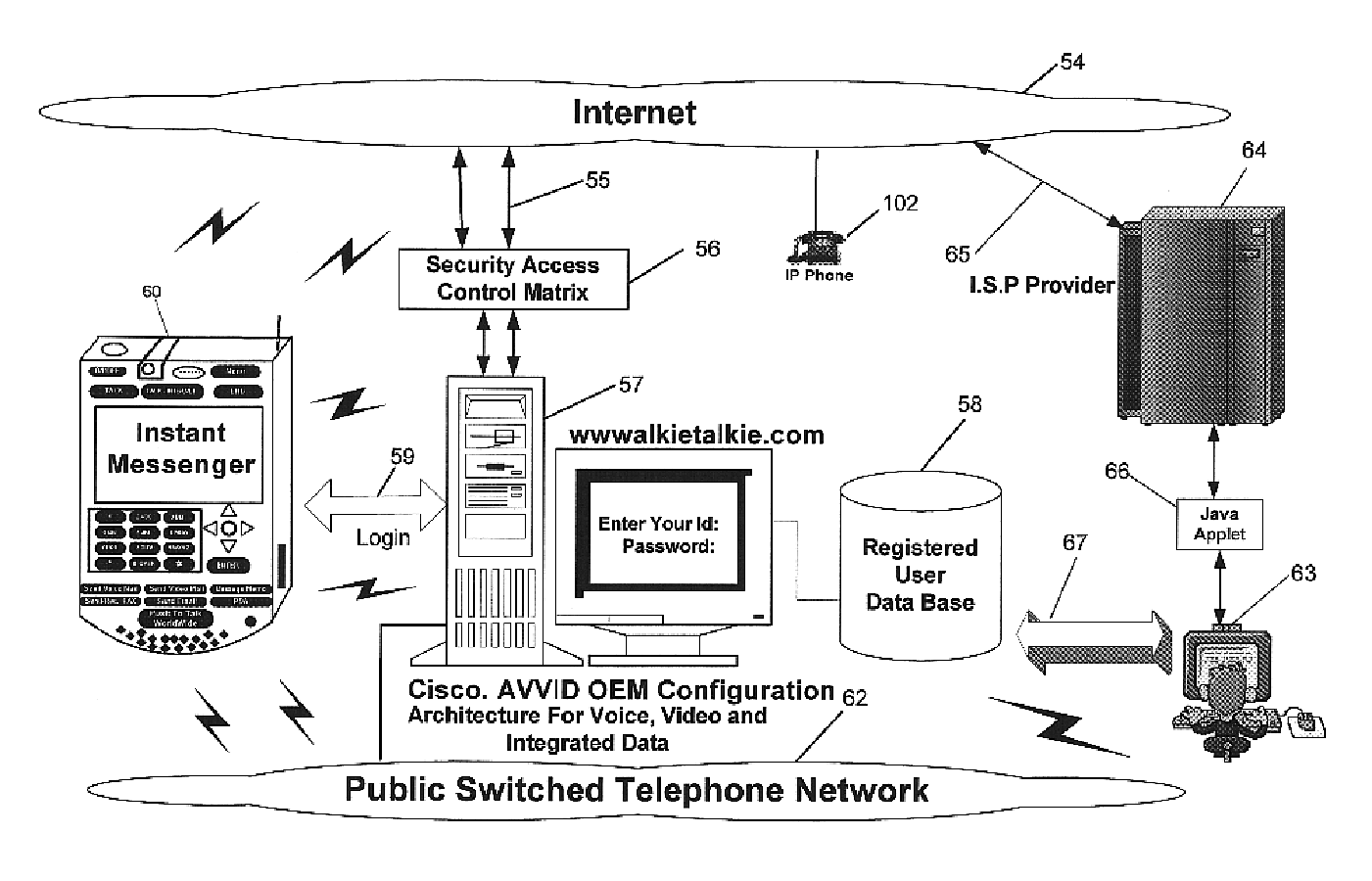
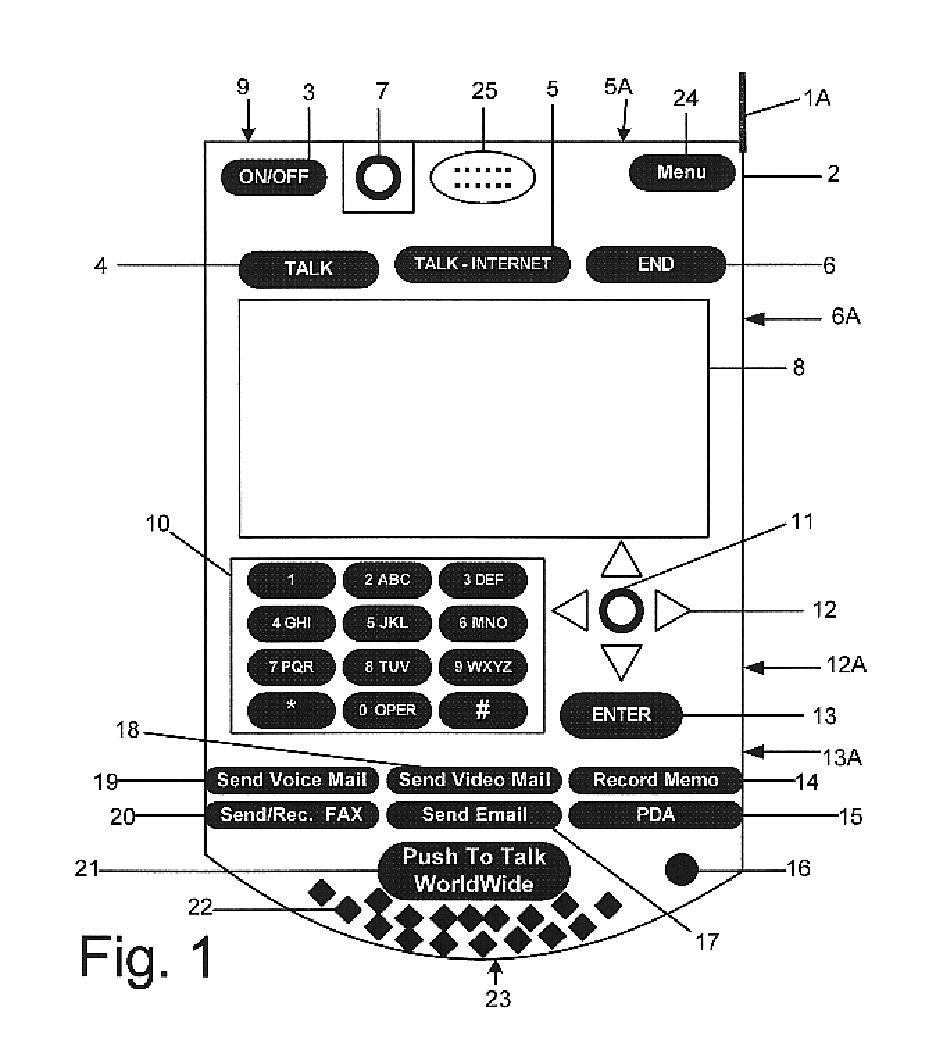
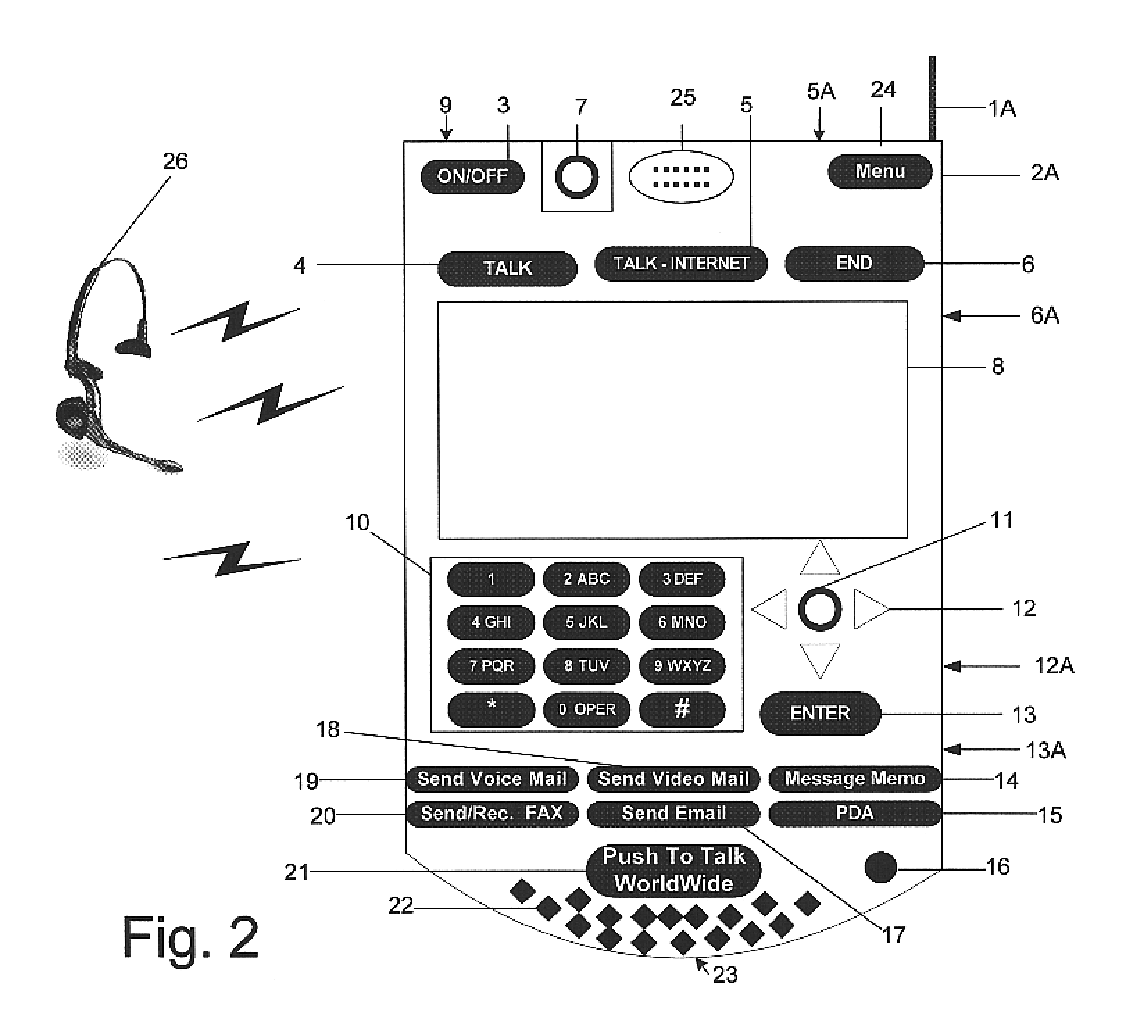
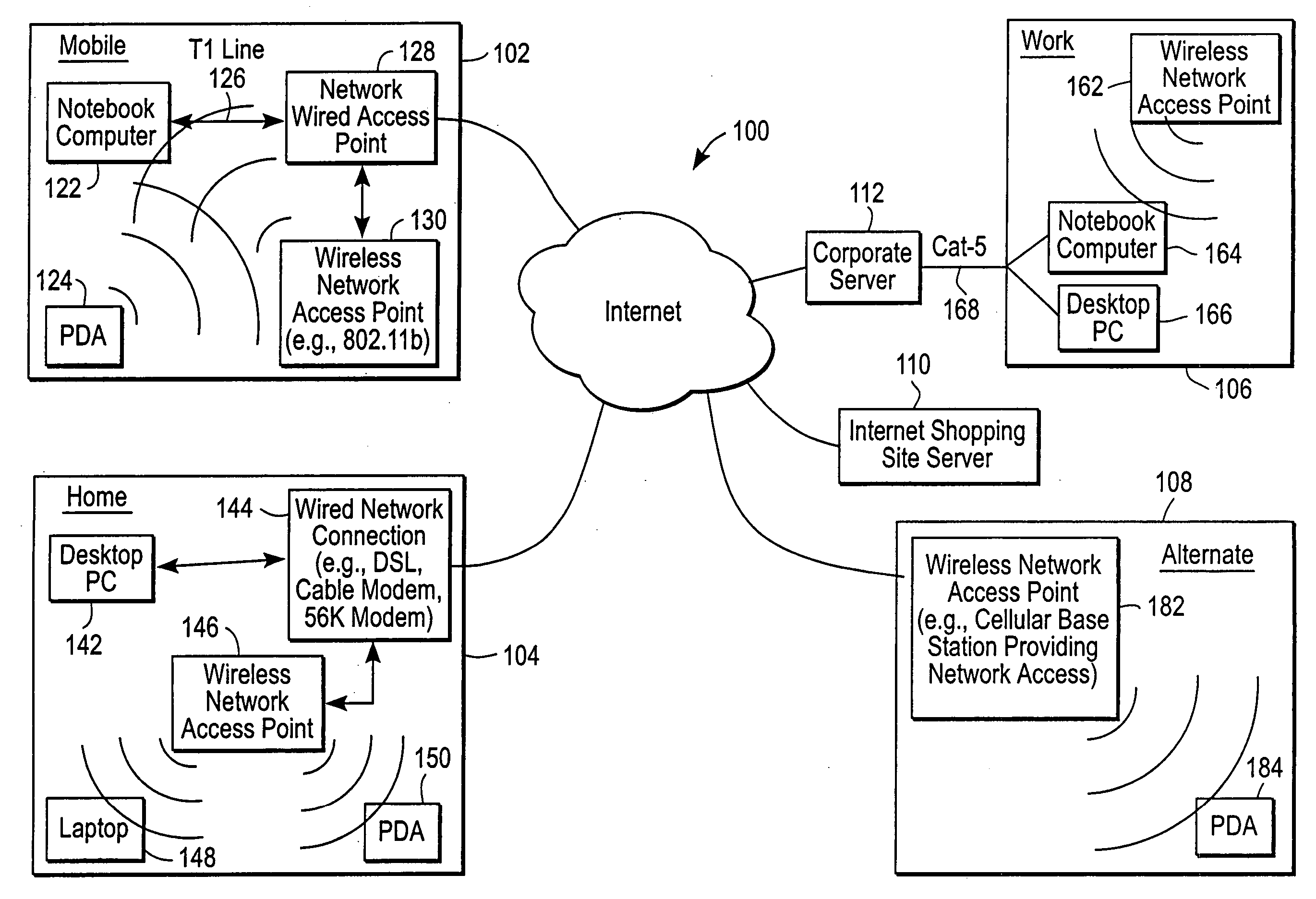
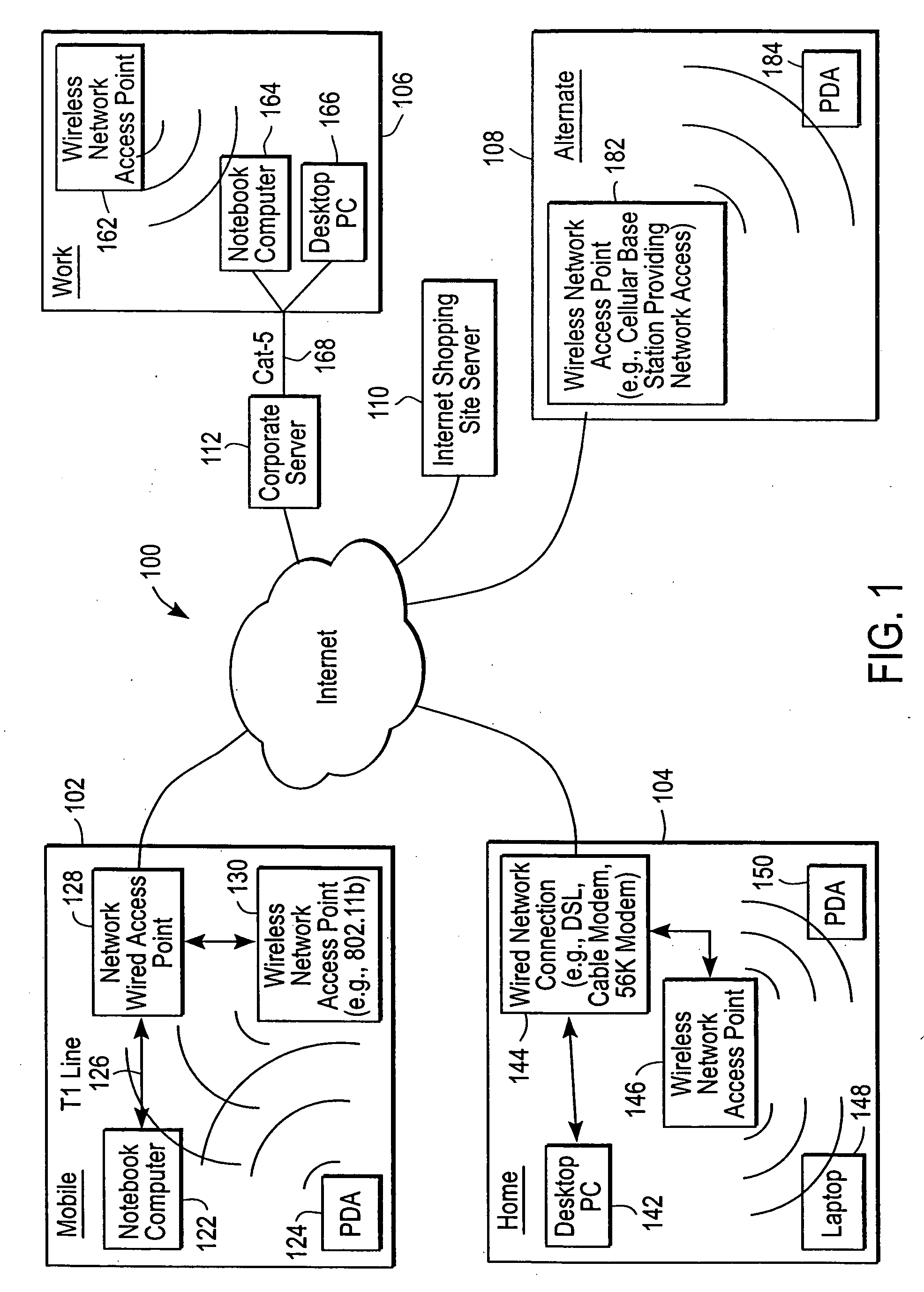
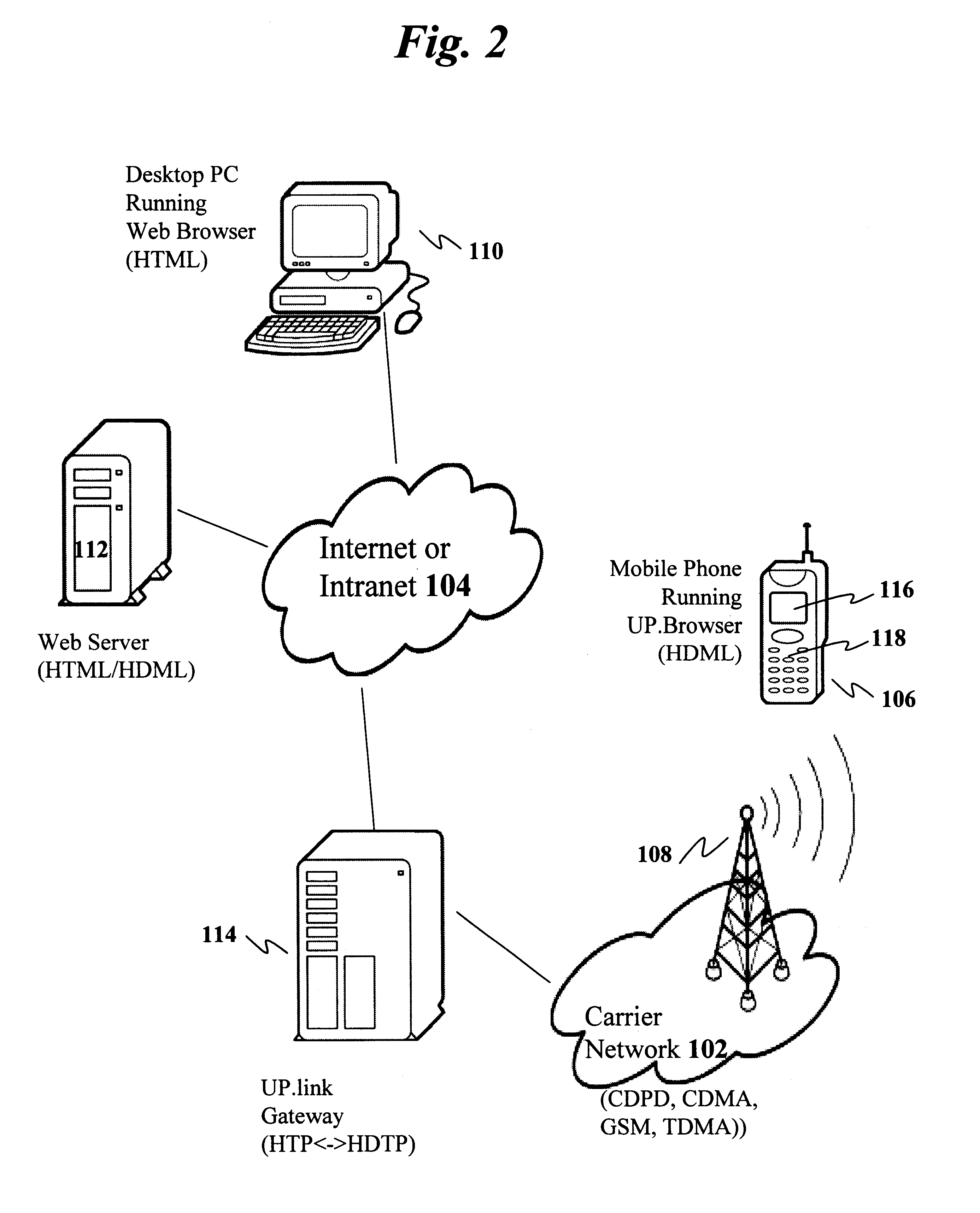
Multifunctional world wide walkie talkie, a tri-frequency cellular-satellite wireless instant messenger computer and network for establishing global wireless volp quality of service (QOS) communications, unified messaging, and video conferencing via the internet
InactiveUS6763226B1High quality voice and data communicationMinimal costCordless telephonesInterconnection arrangementsQuality of serviceMass storage
World-Wide-Walkie-Talkie, a high speed multifunction interstellar wireless computer / instant messenger communicator, Personal Digital Assistant (PDA), coupled with a resilient, robust, VoIP data network and internet server method, deploying multiple wireless networks and protocols such as Voice Over IP, GPRS, WAP, Bluetooth, PCS, I-Mode, comprising a high speed Intel Pentium 4 Mobile(TM) or compatible Processor, to formulate a internet gateway system (99) and network bridge (150) for establishing instant low cost, real time global communications to the Public Switched Telephone Network via the internet (54). A PUSH-TO-TALK-WORLDWIDE button (21) instantly initiates global bisynchronous communications, or videoconferencing sessions. Fax, VideoMail, and unified messaging services are immediately available. GPS and mass memory provides global navigational tracking and data storage. Internet users, telephones, and cellular / satellite phone users can intercommunicate with the invention via VoIP / IM services. The invention provides uniformed global wireless communications, eliminates traditional long distance costs, and operates anywhere on earth.
Owner:COMP SCI CENT
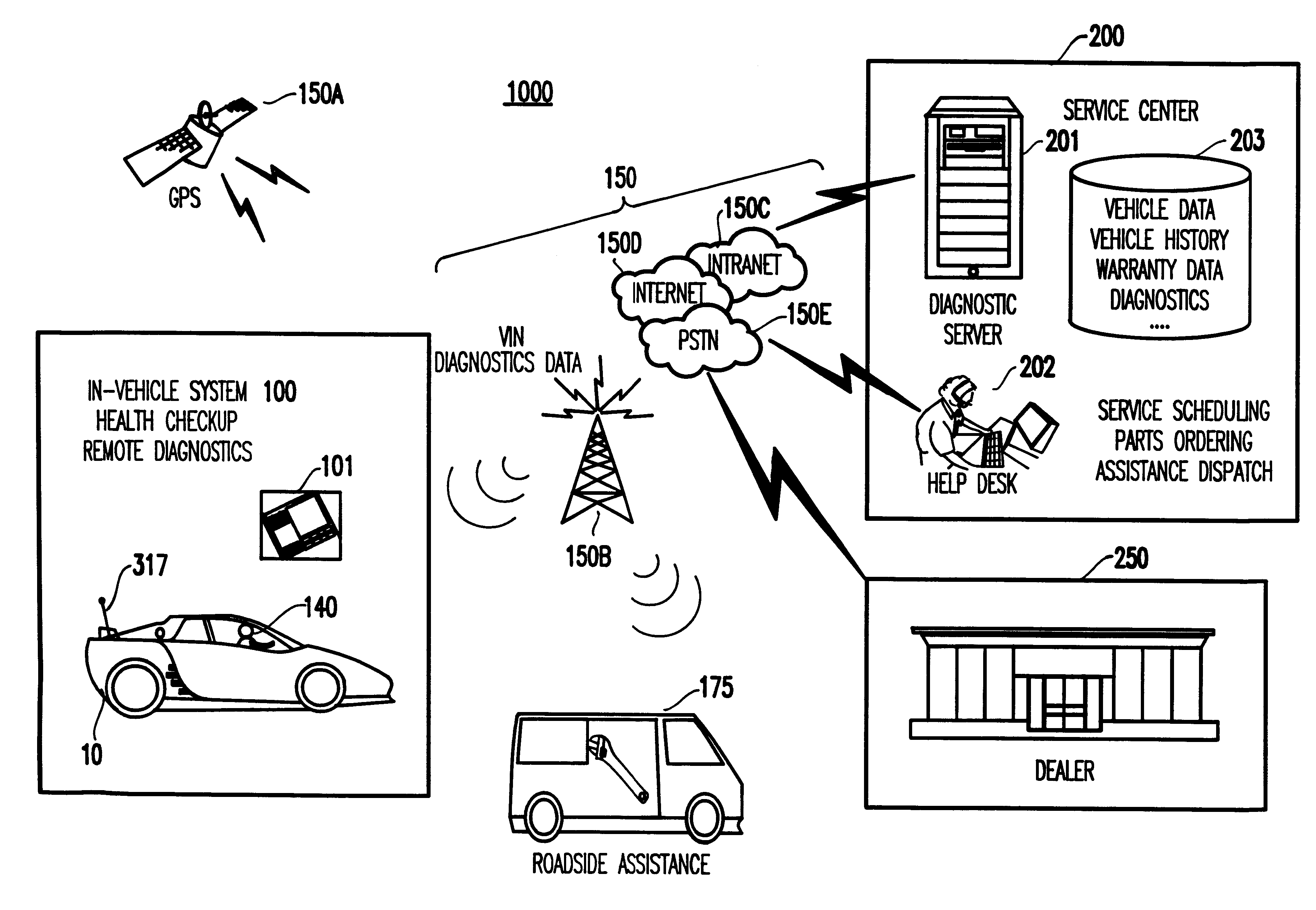
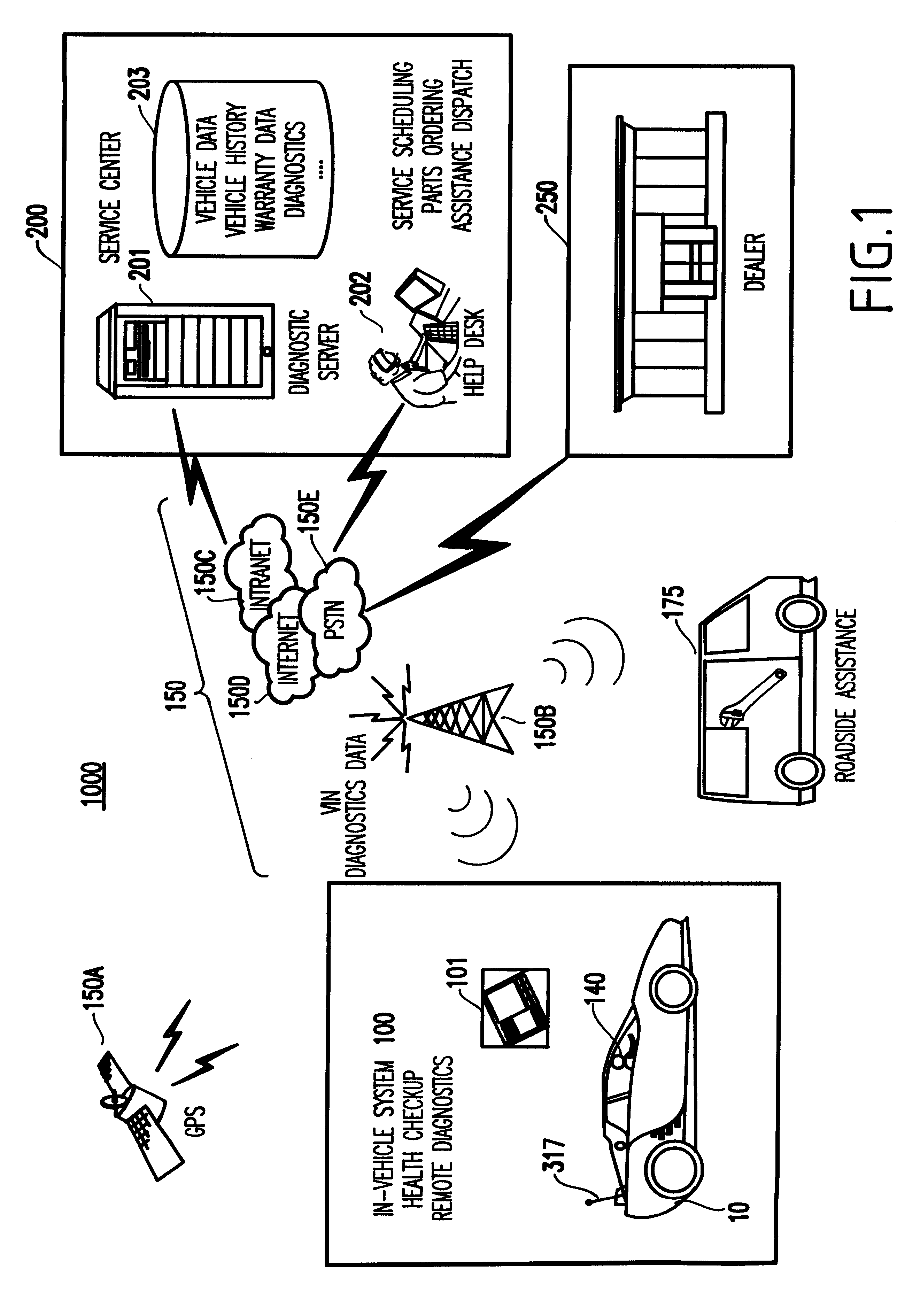
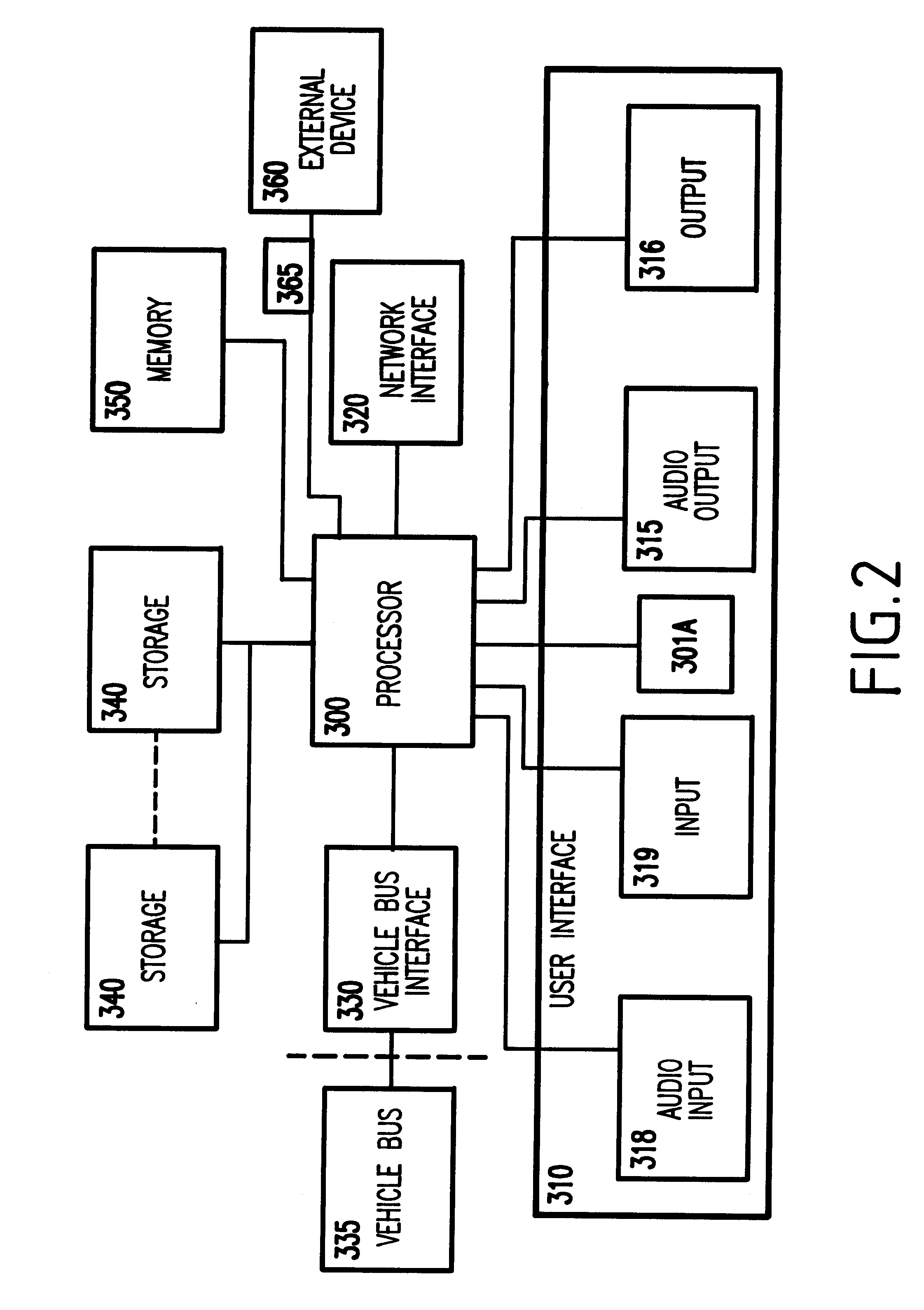
System and method for vehicle diagnostics and health monitoring
InactiveUS6330499B1Vehicle testingRegistering/indicating working of vehiclesSession managementCommunications system
A system and method for vehicle diagnostic and health monitoring includes a client computer device within the vehicle, coupled to the vehicle's monitoring systems, for data management, remote session management and user interaction, a communication system, coupled to the client computer device, for providing remote communication of data including data derived from internal monitoring systems of the vehicle, and a remote service center including a vehicle data store, a server computer, a diagnostic engine, and a communicator for communicating the results of analysis of vehicle information to the client computer device via the communication system.
Owner:CARRUM TECH LLC
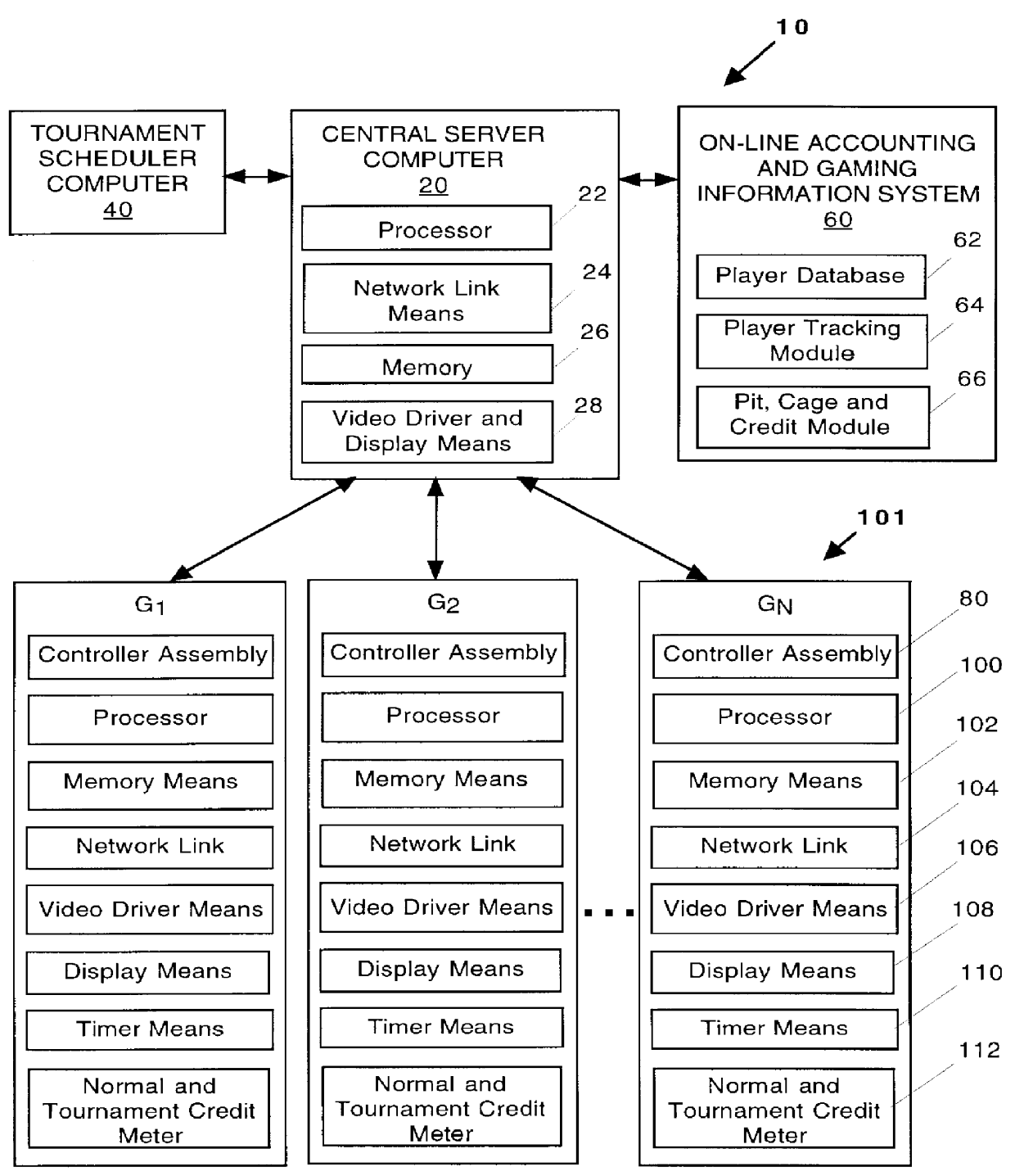
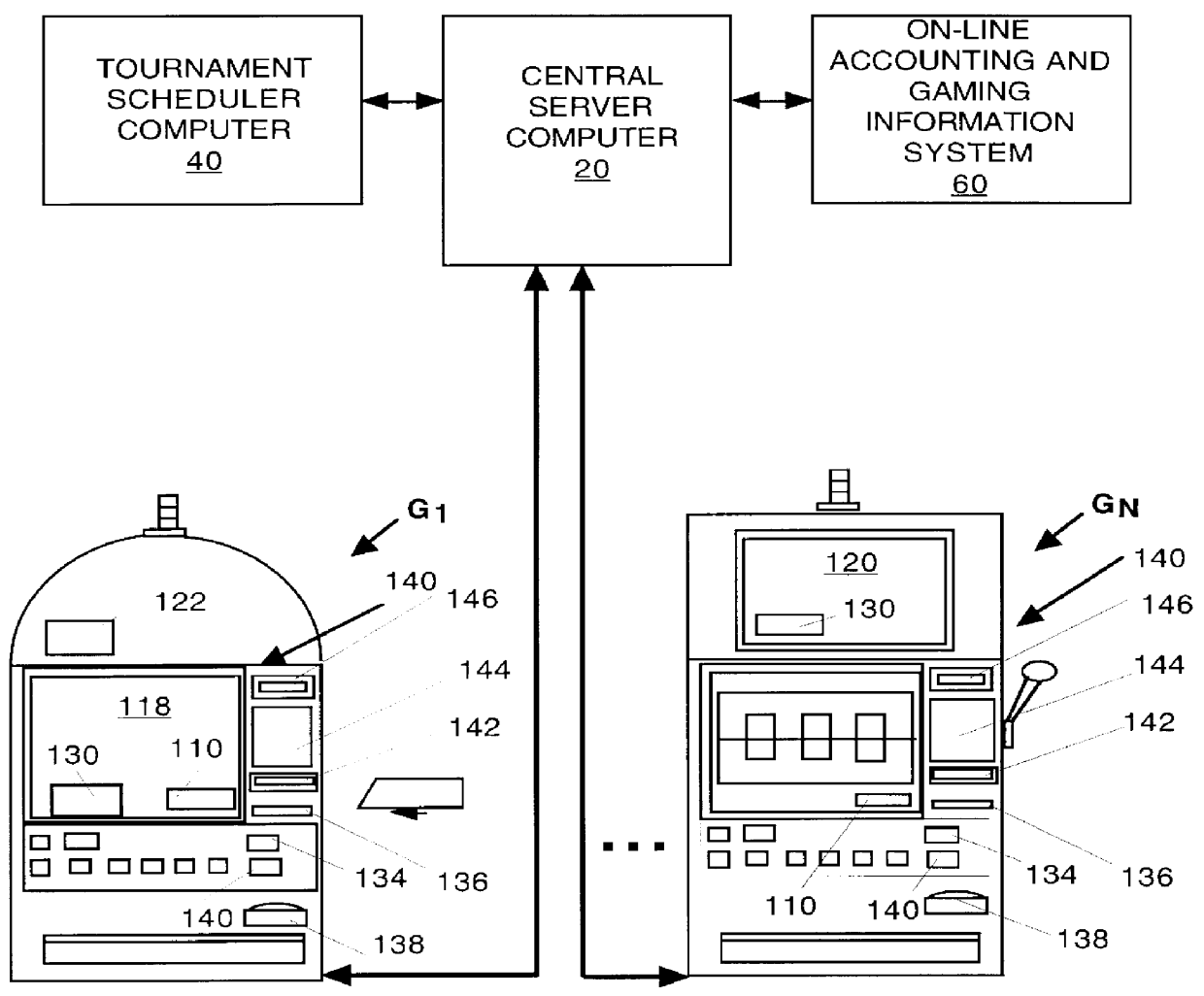
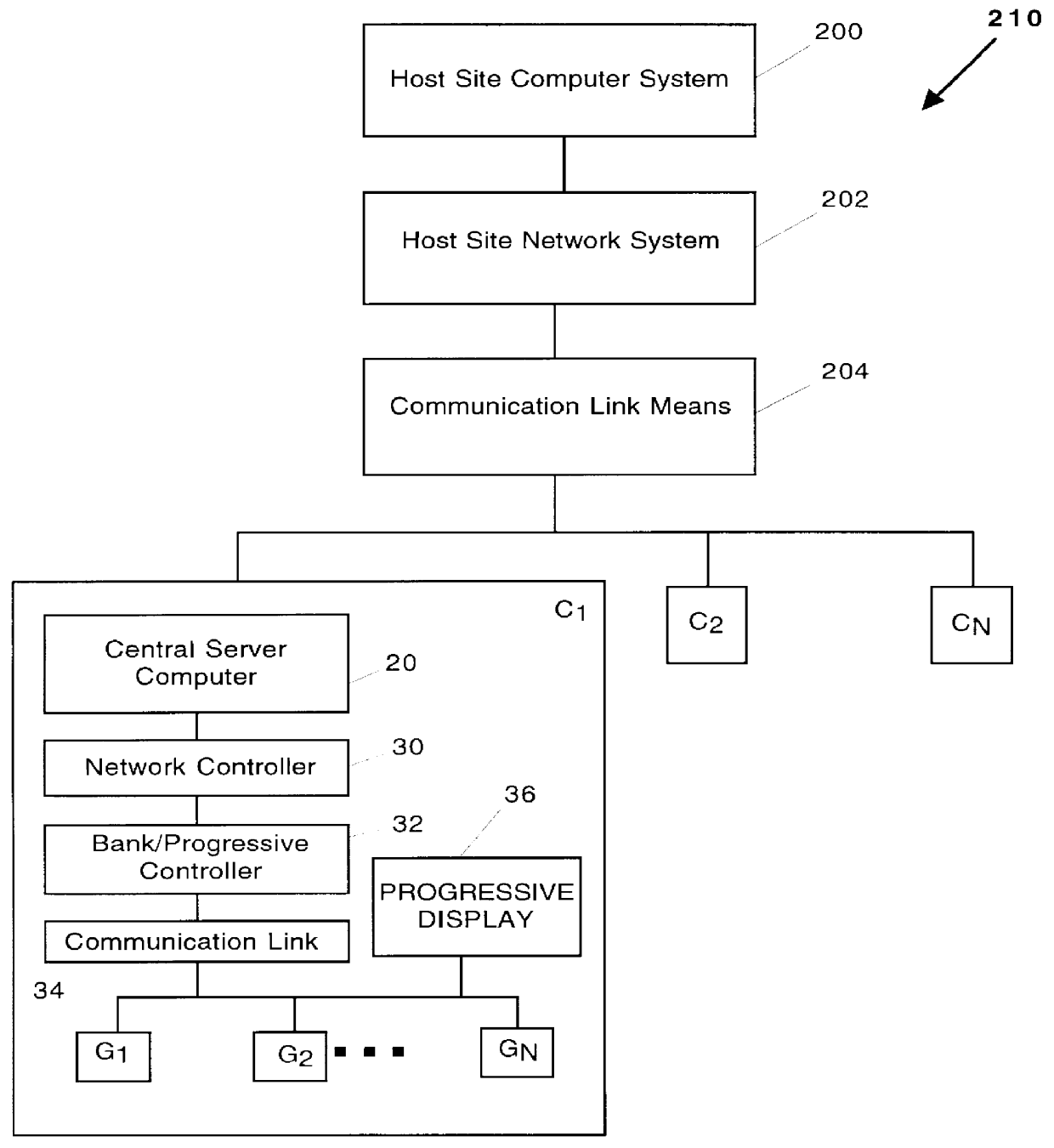
Automated tournament gaming system: apparatus and method
InactiveUS6039648AStimulate gaming experienceCard gamesApparatus for meter-controlled dispensingMulti siteHuman–computer interaction
An apparatus and method for an automated tournament gaming system (10) comprising a central server computer (20) operatively coupled to, inter alia, a plurality of gaming machine G1, G2 . . . GN for automatically harnessing any of the gaming machines for automatically inciting and running a tournament where a group of players are participating for a period after which prizes are awarded to the winning tournament play participants. In addition, the system (10) includes a host site computer (200) operatively coupled to a plurality of the central servers (20) at a variety of remote gaming sites C1, C2 . . . CN for providing a multi-site progressive automated tournament gaming system (210). The multi-site system (210) is integrated into the system (10) to increase the winnings, progressive amounts and the total buy-ins.
Owner:CASINO DATA SYST
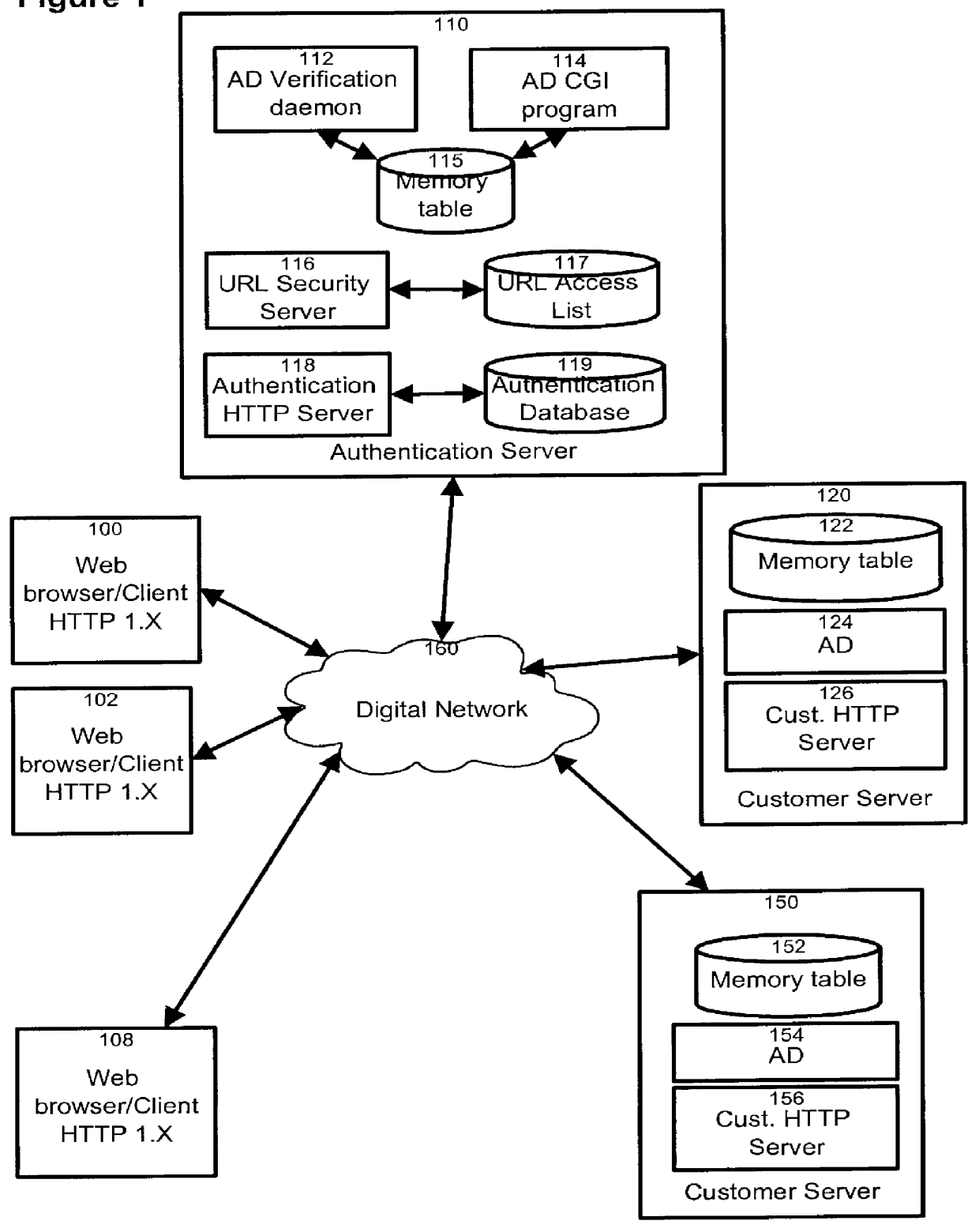
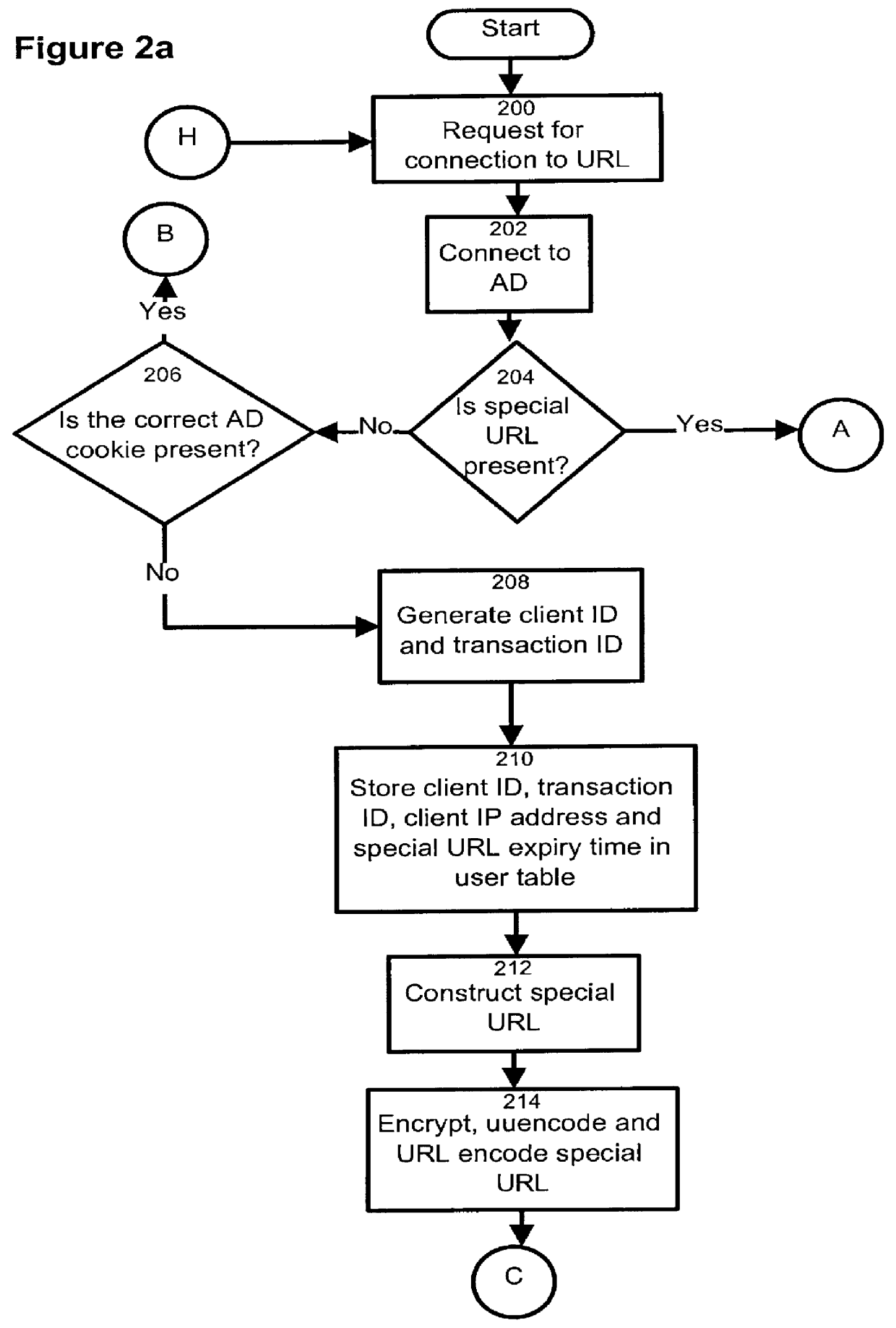
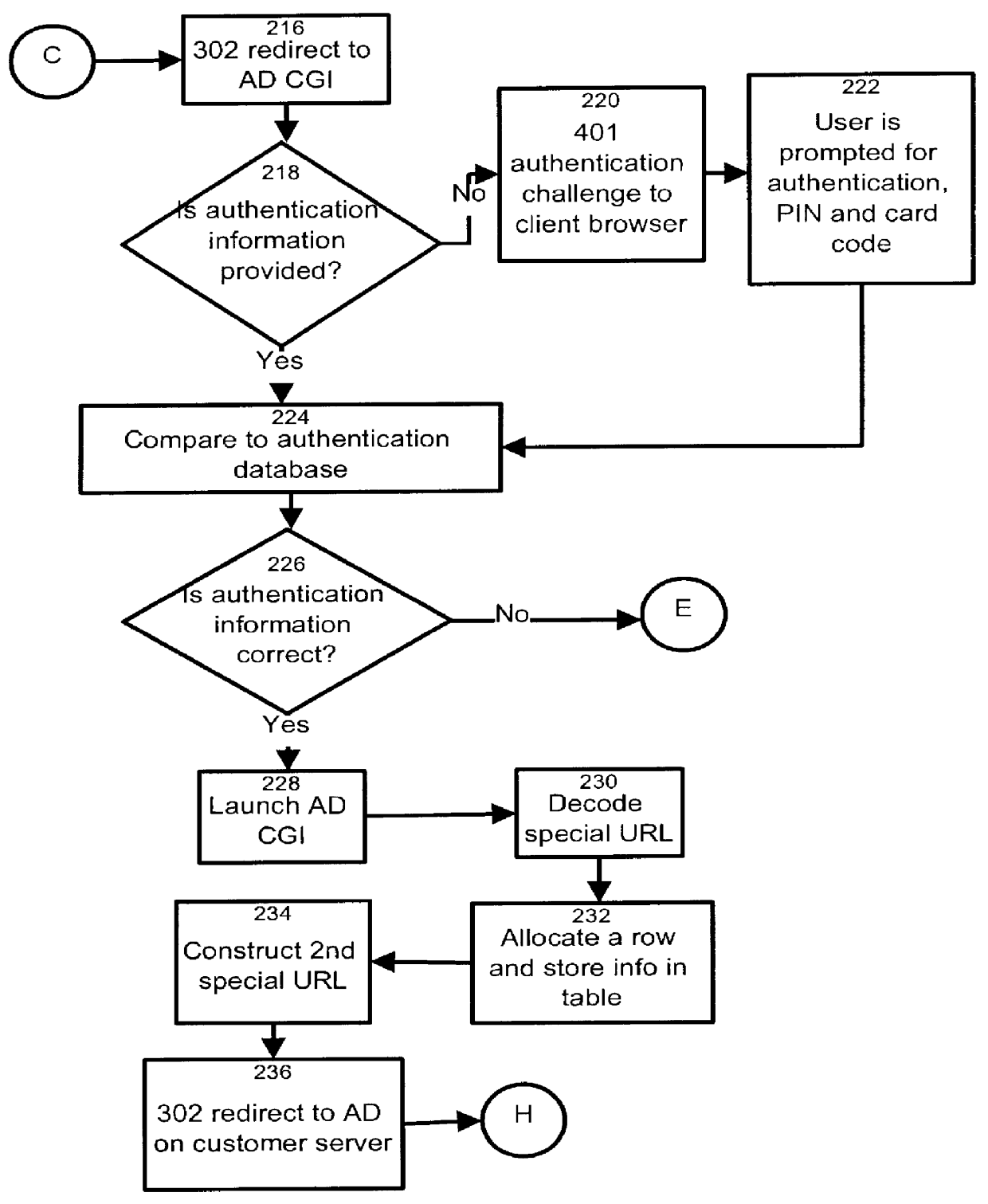
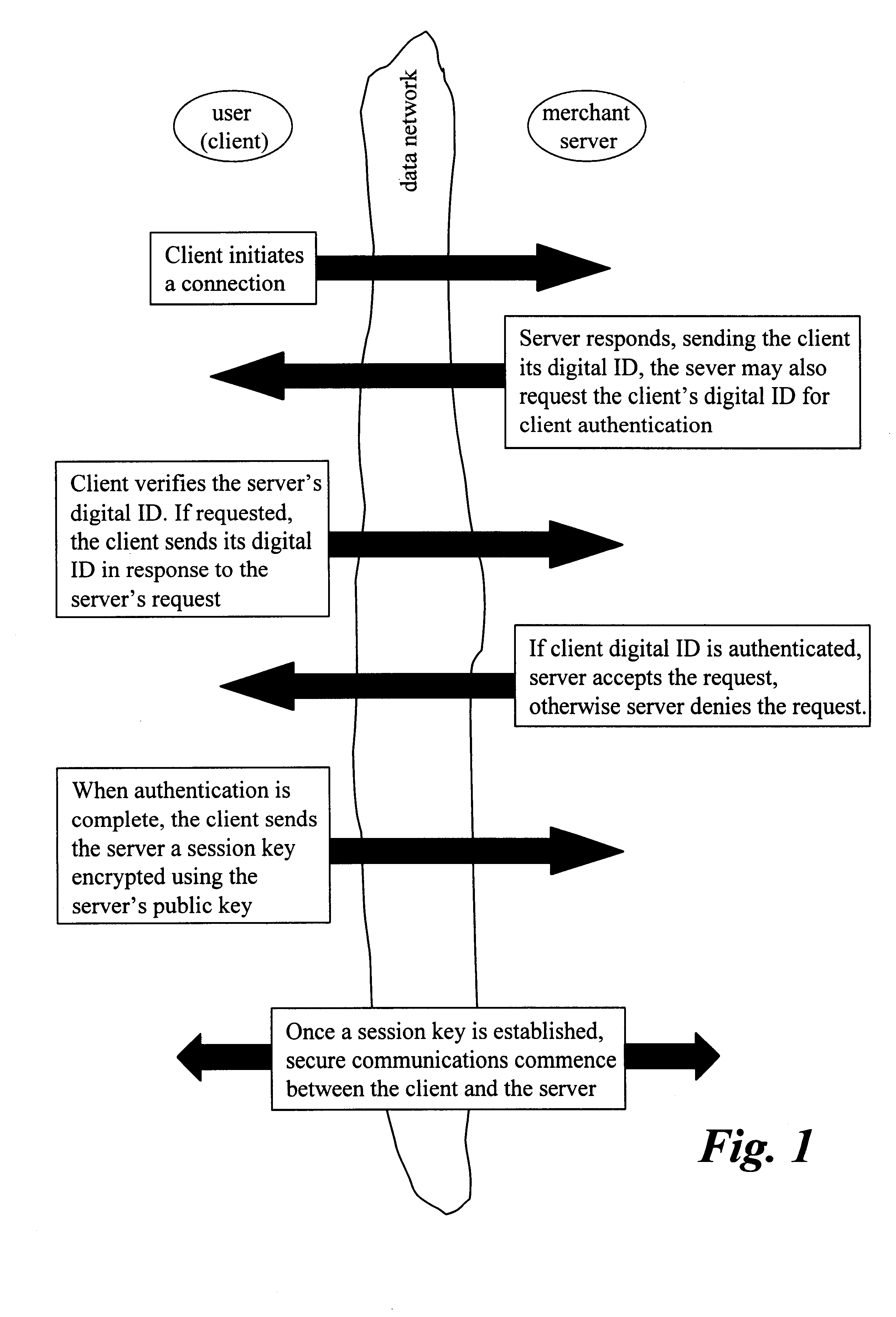
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
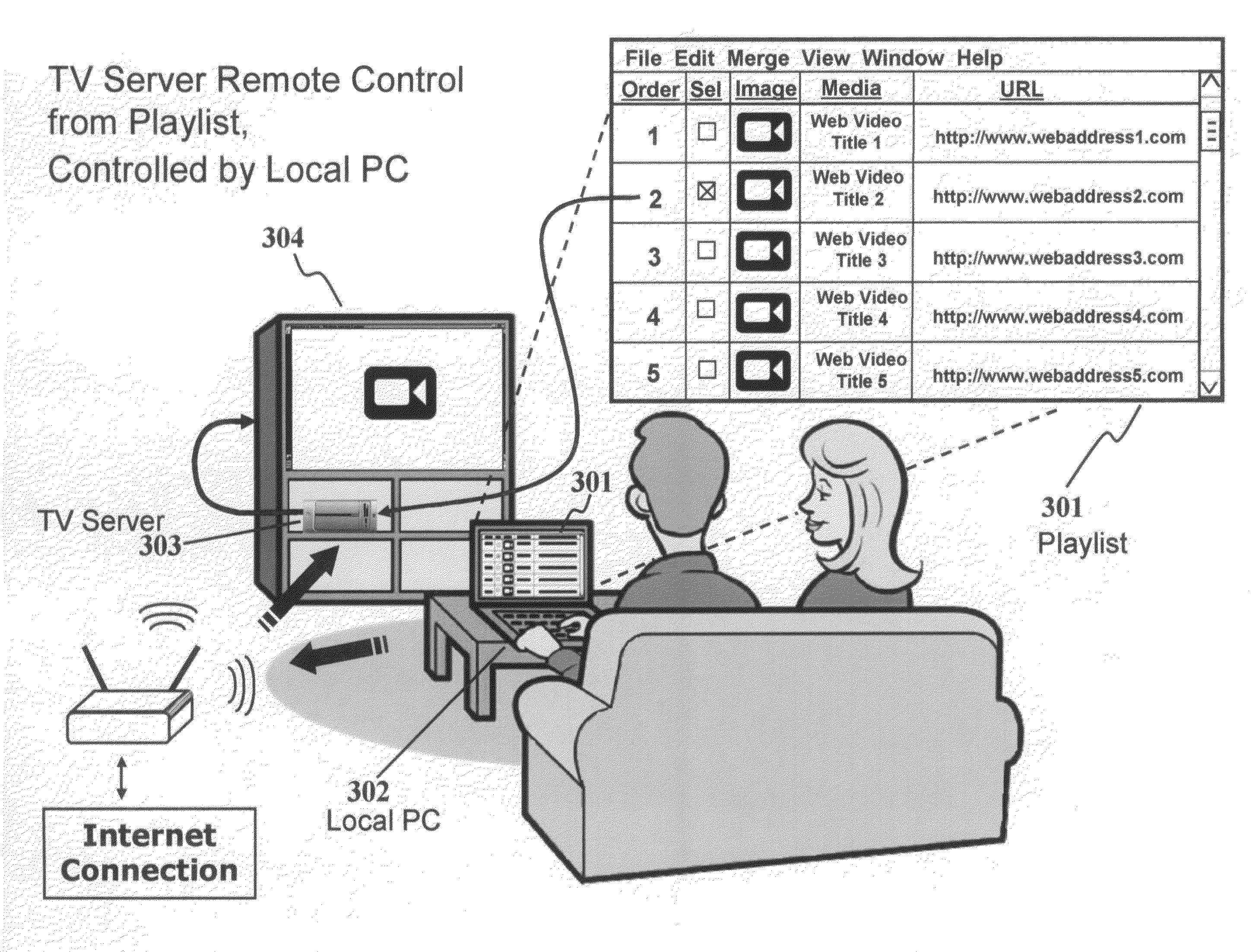
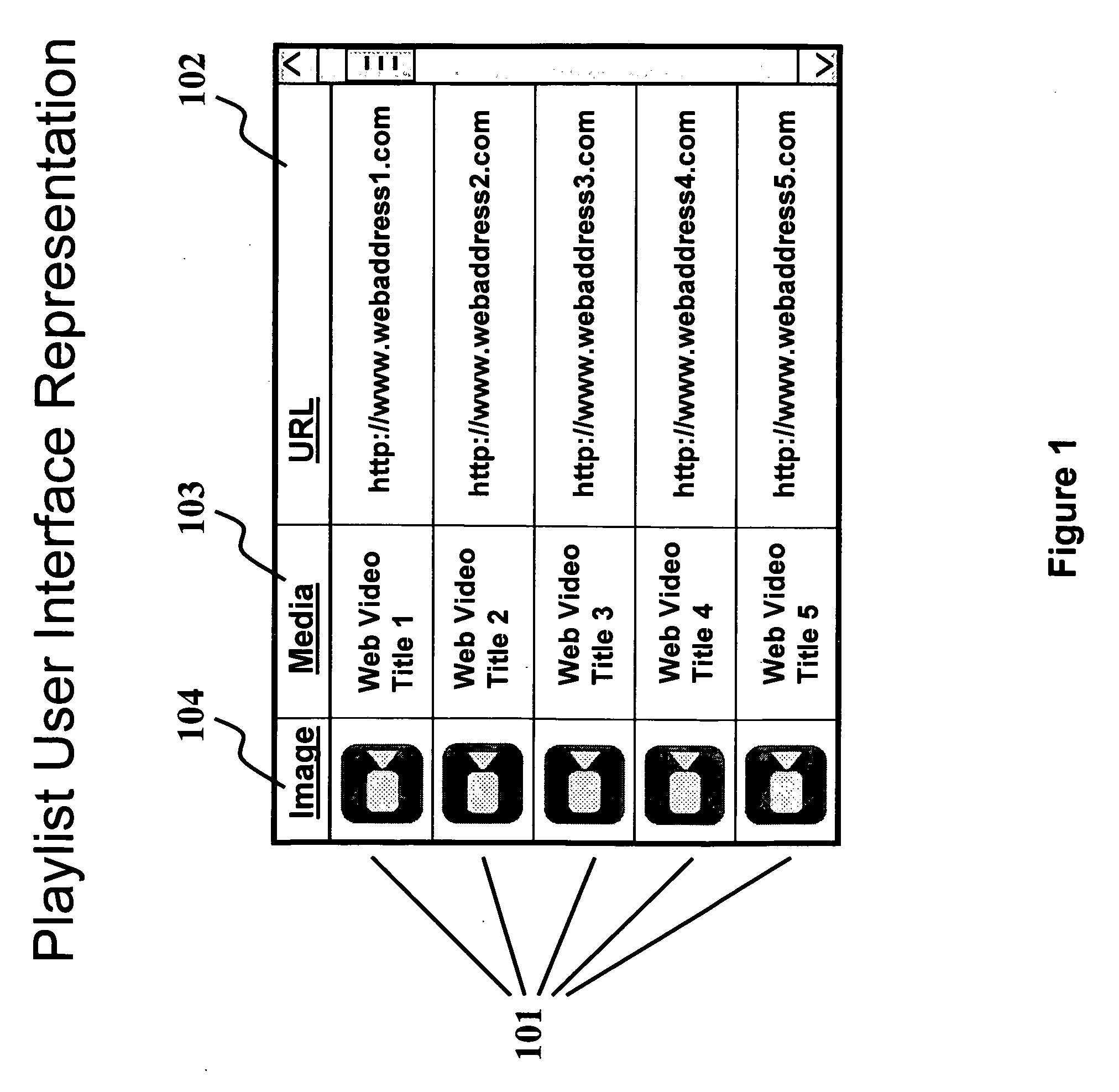
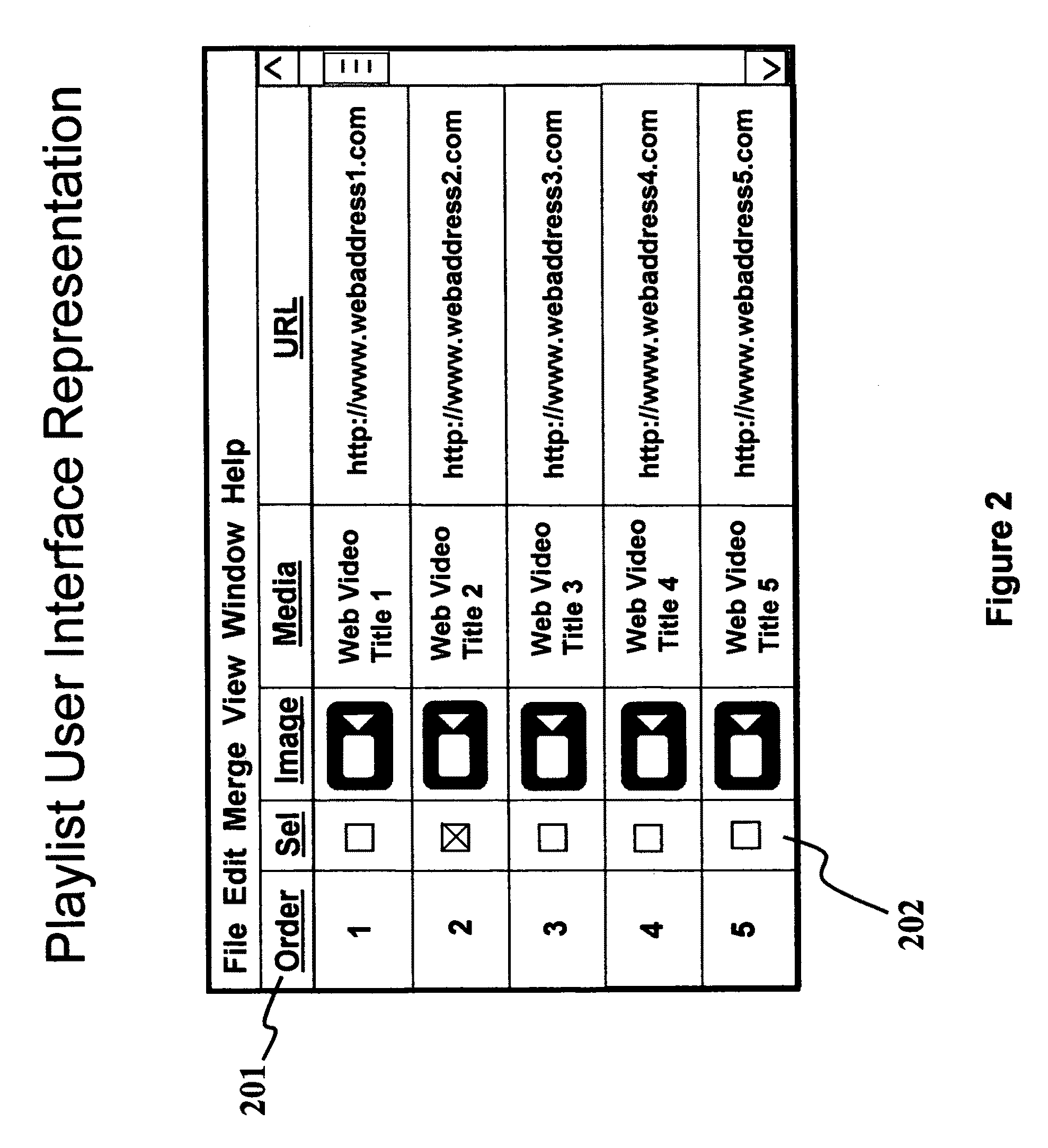
Media playlist management and viewing remote control
According to this invention, a user may capture a media link on any PC and perform this capture function at any physical location, then save the media link in a playlist, and subsequently play the media located at the media link on a TV server. The TV server may be controlled from a local device—typically a PC or a handheld remote control. Playlists may be maintained on a Web playlist function. Software on a local controller device can then select a media link from a Web playlist through the Internet, and the Web playlist function can then pass that link to a local TV server, thus avoiding the need for the controller device and the TV server to communicate through a LAN. Additionally, a playlist may include targeted advertisements shown physically adjacent to related playlist items.
Owner:ZOTT JOSEPH A +2
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
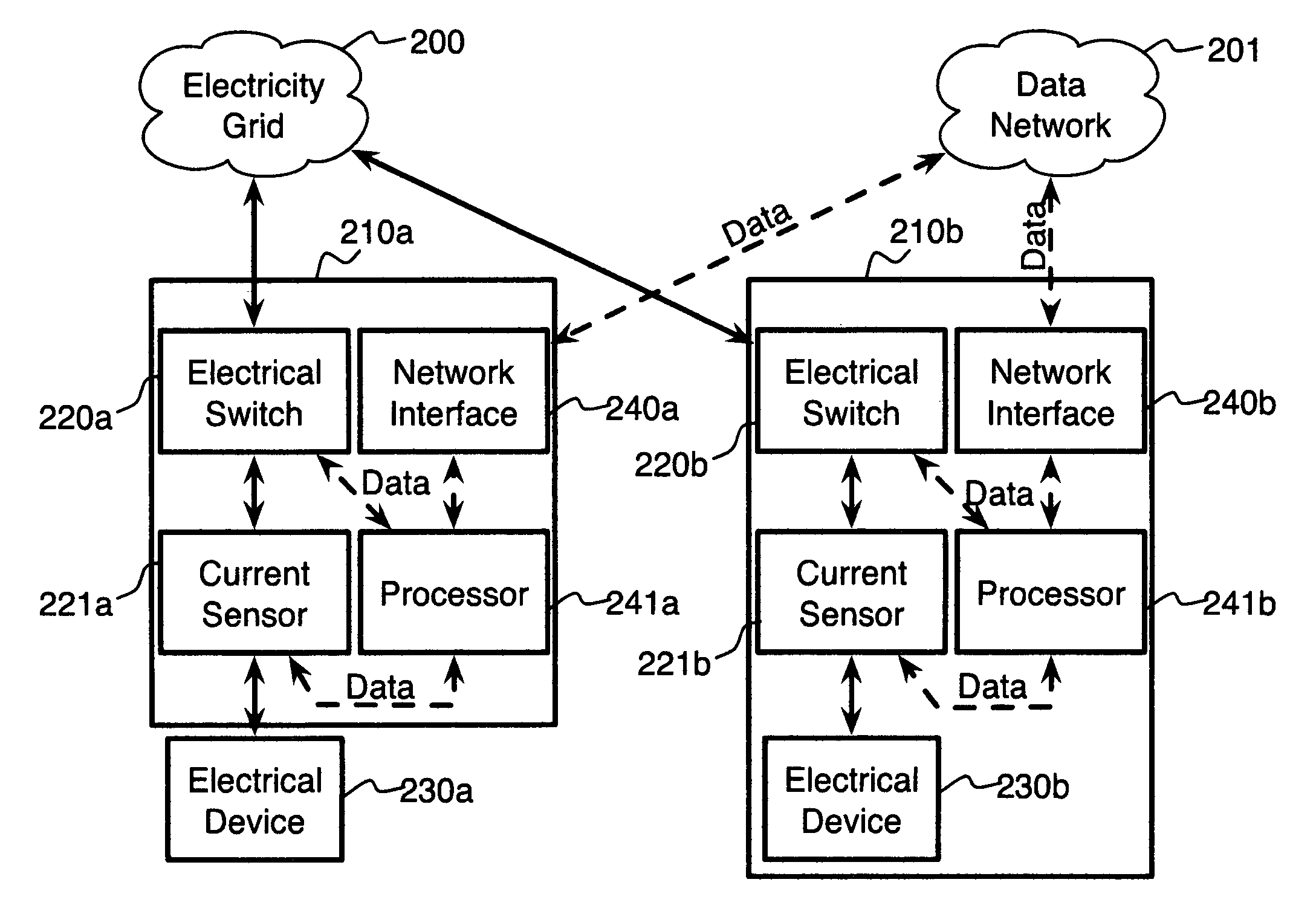
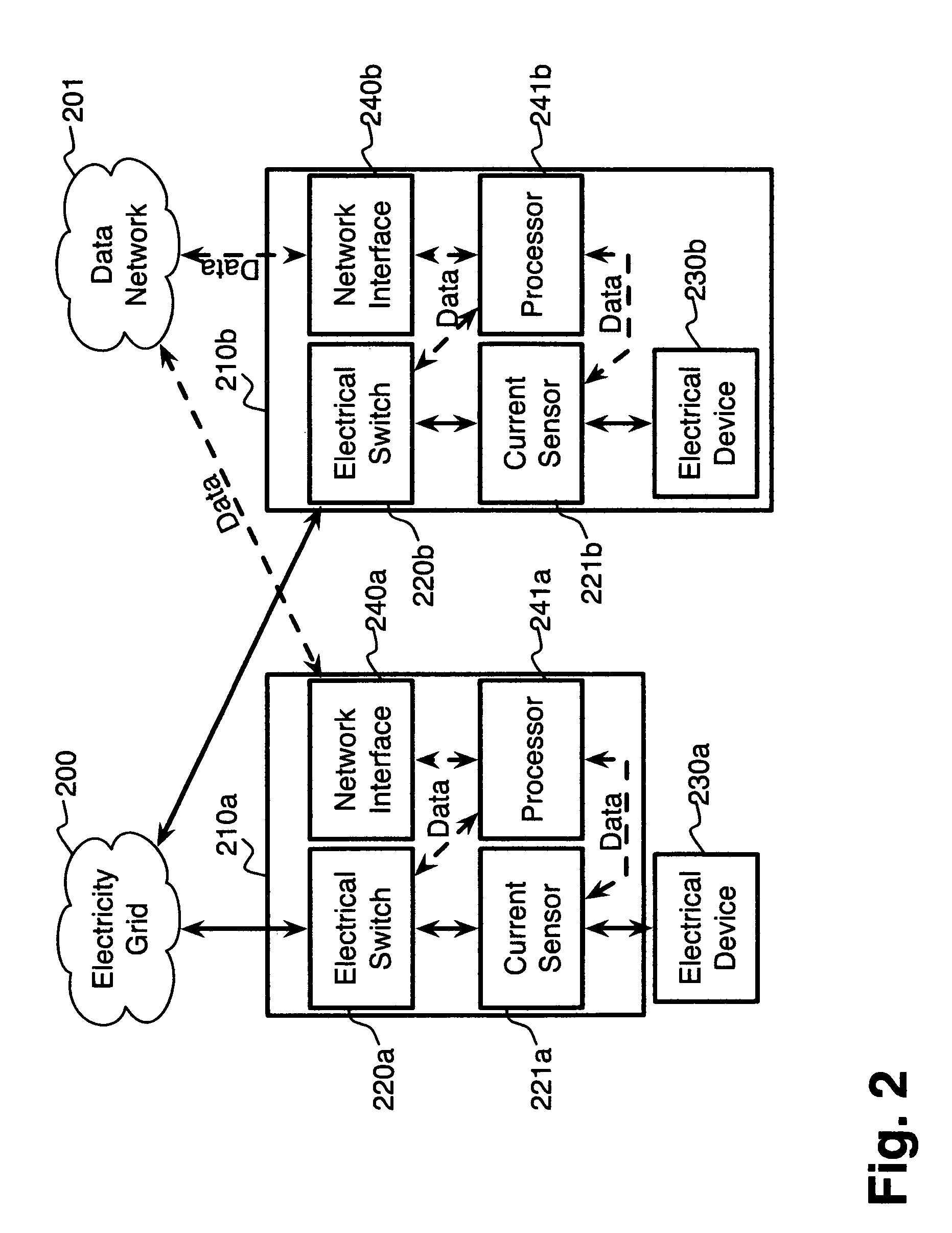
System and method for electric grid utilization and optimization
InactiveUS20100217550A1Selective ac load connection arrangementsElectric devicesSimulationTransmission loss
A system for electric grid utilization and optimization, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of iNodes, the plurality of iNodes comprising a source iNode, a sink iNode, and a plurality of transmission or distribution iNodes, an event database coupled to the communications interface and adapted to receive events from a plurality of iNodes via the communications interface, a modeling server coupled to the communications interface, and a statistics server coupled to the event database and the modeling server, wherein the modeling server, on receiving a request to establish an allocation of at least one of transmission losses, distribution losses, and ancillary services to a specific sink iNode, computes at least one virtual path for flow of electricity between a source iNode and the specific sink iNode and wherein the modeling server further computes, for each transmission or distribution iNode included in the computed virtual path, at least one energy loss and allocates a portion thereof to the specific sink iNode, is disclosed.
Owner:CRABTREE JASON +4
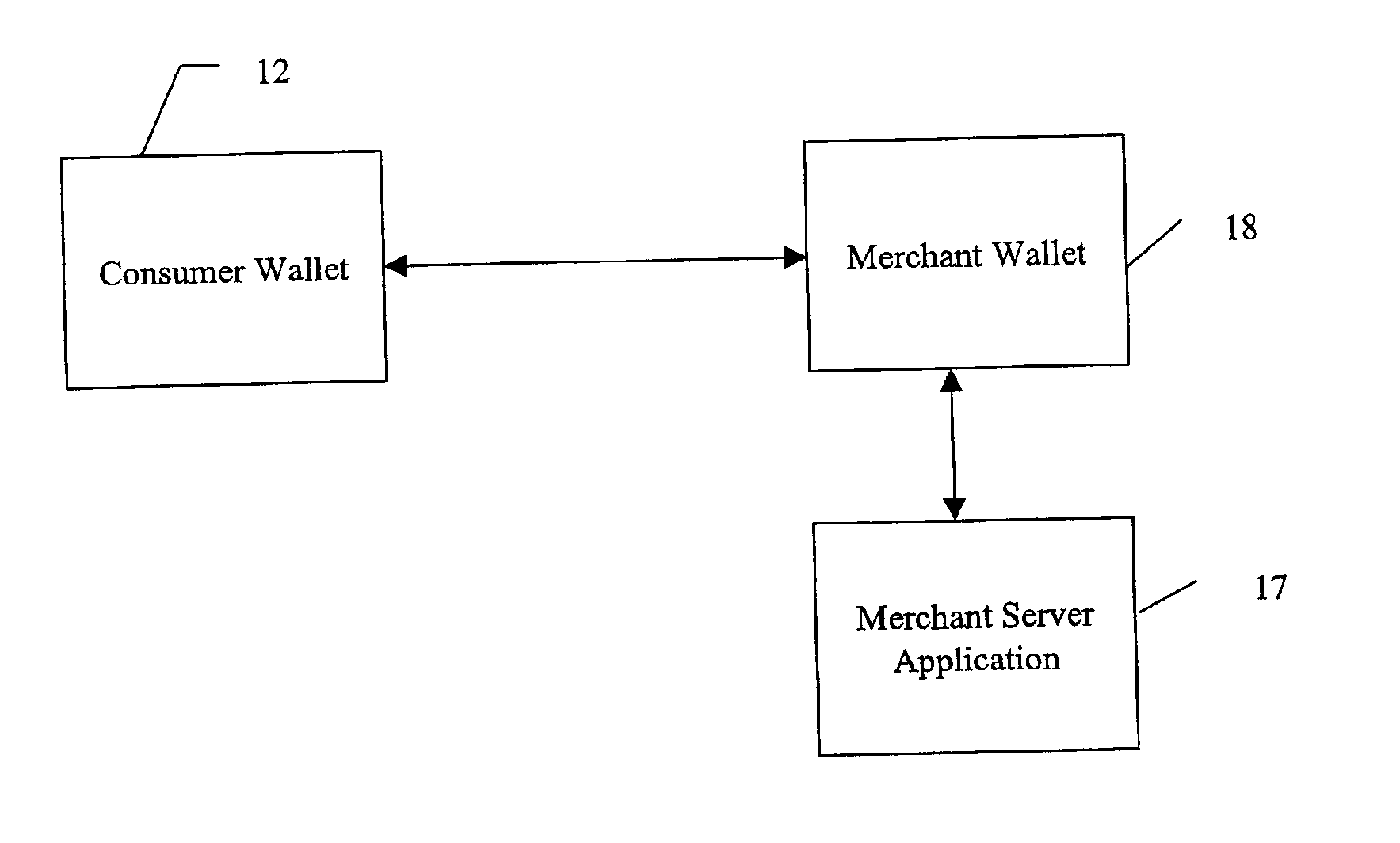
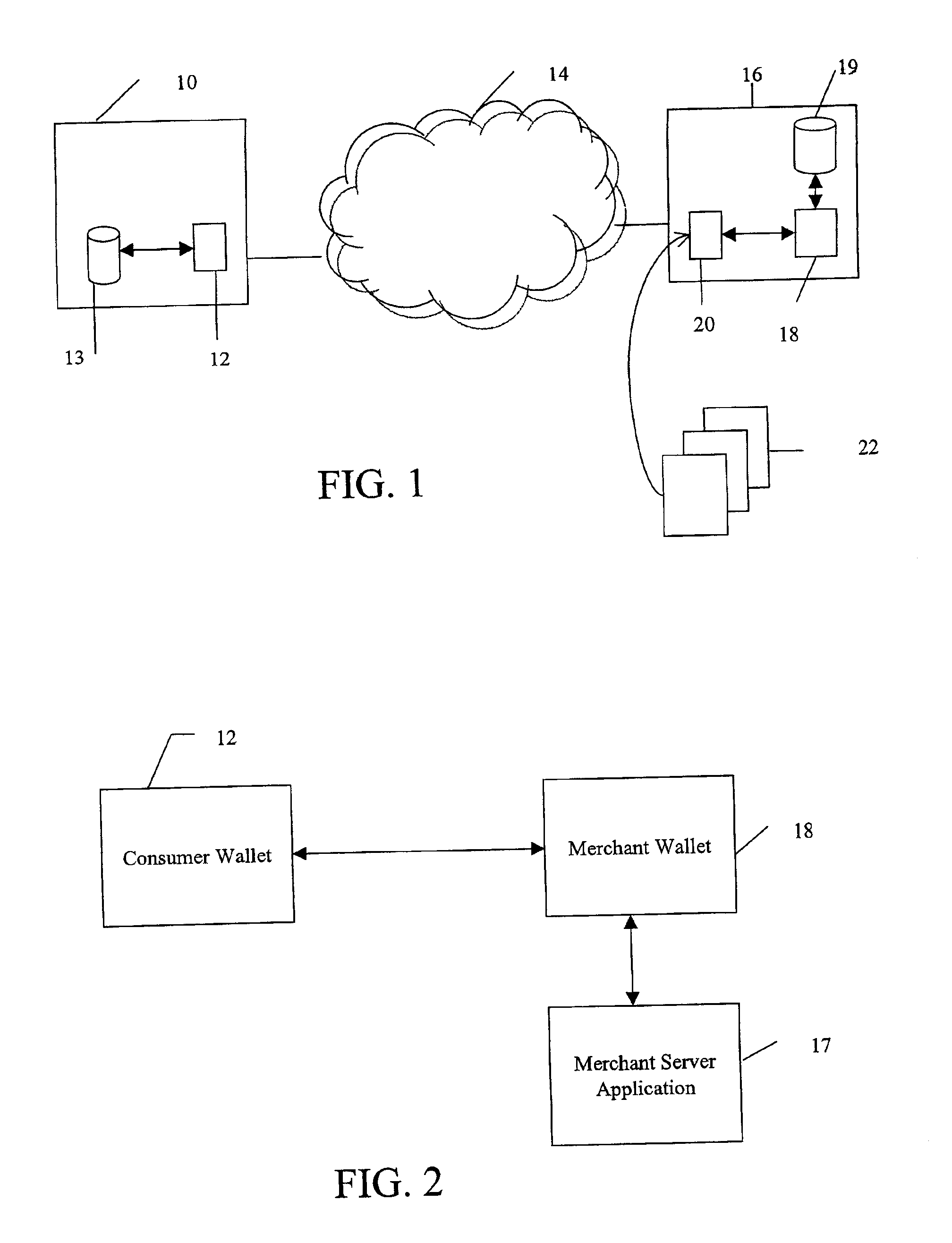
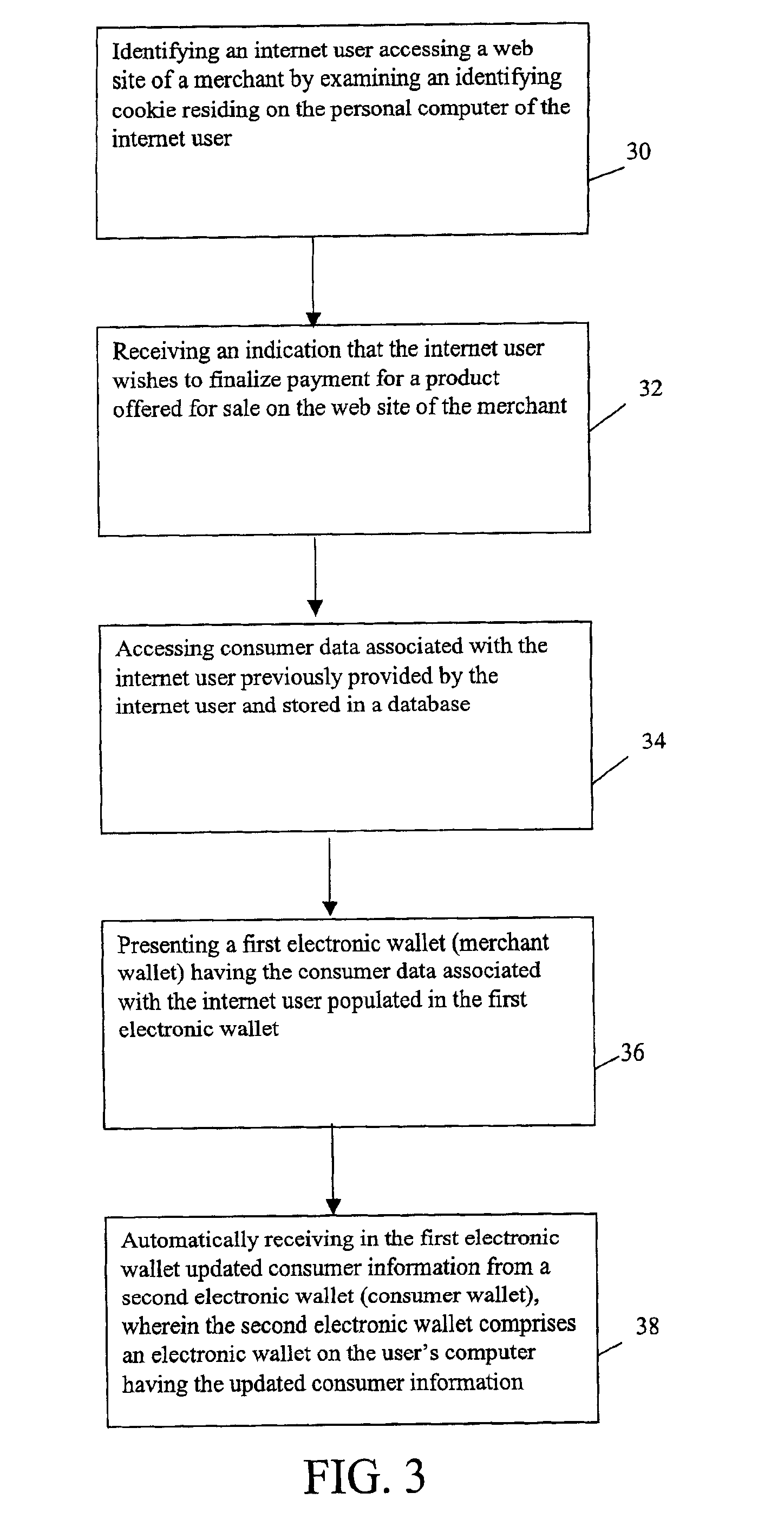
System and method for use of distributed electronic wallets
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
Method of creating and editing a web site in a client-server environment using customizable web site templates
InactiveUS6026433AEasily and efficiently creatingEasily and efficiently and editingUnauthorized memory use protectionNatural language data processingWeb siteClient-side
A method for creating and editing a Web site in a client-server computer network using customizable templates is provided. To create a Web site, the present embodiment first stores a plurality of templates in a storage device coupled to the client-server computer network. When a client computer generates a request to create a new Web site, the server computer transmits a list of templates to the client for display. The templates contain a multitude of editable objects or elements. A template is then selected upon which the new Web site will be based on. The new site is then customized according to a user's preference by editing the objects or elements. The customized site is then published as a new Web site. To edit a Web site, a client computer generates a request to edit a Web site and passes the request on to the server computer. The server computer transmits the Web site to the client for display. The Web site contains a multitude of editable objects or elements. The elements of the Web site are then customized according to a user's preference. The Web site with the customized elements is then published as a Web site.
Owner:RED HAT
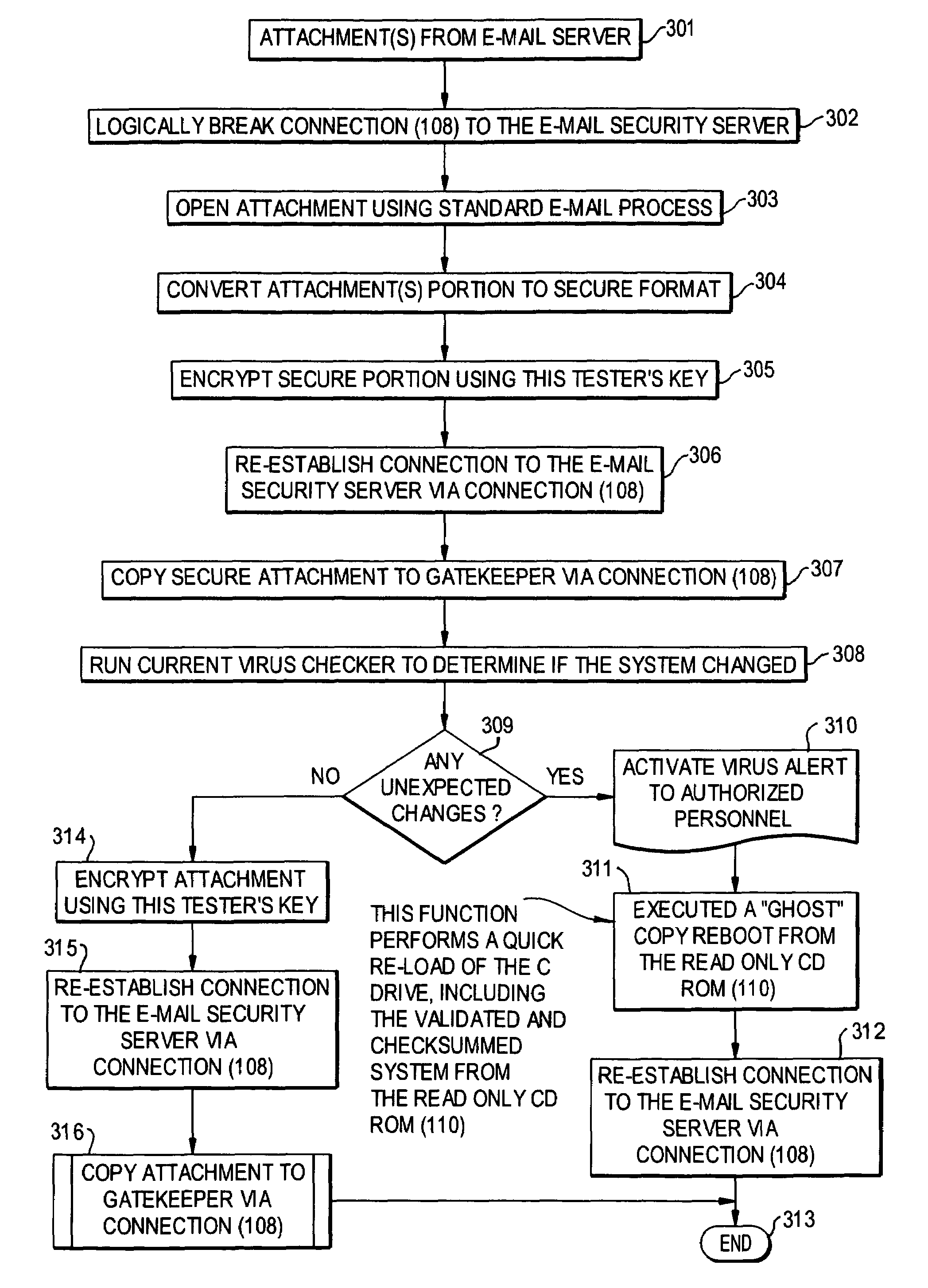
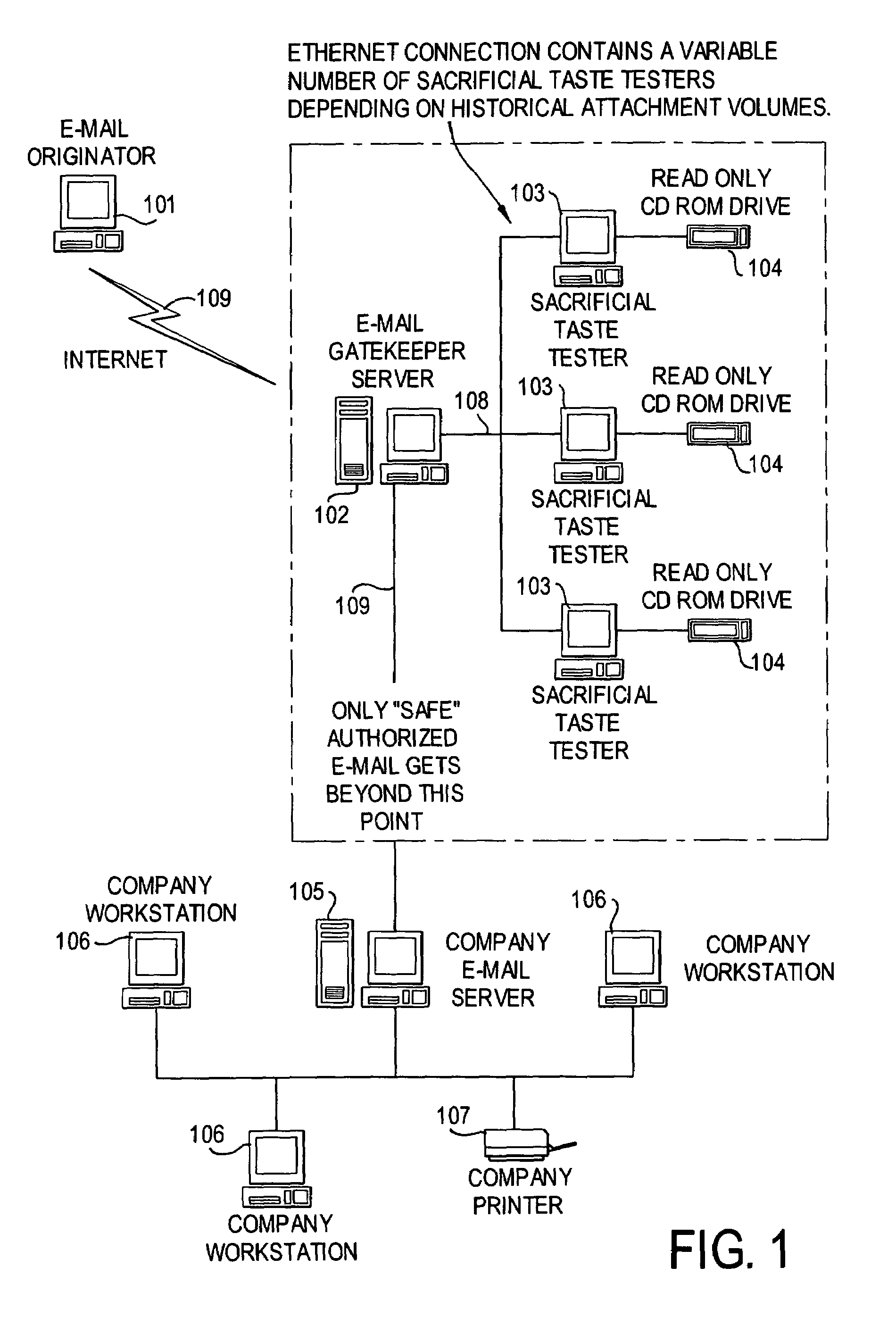
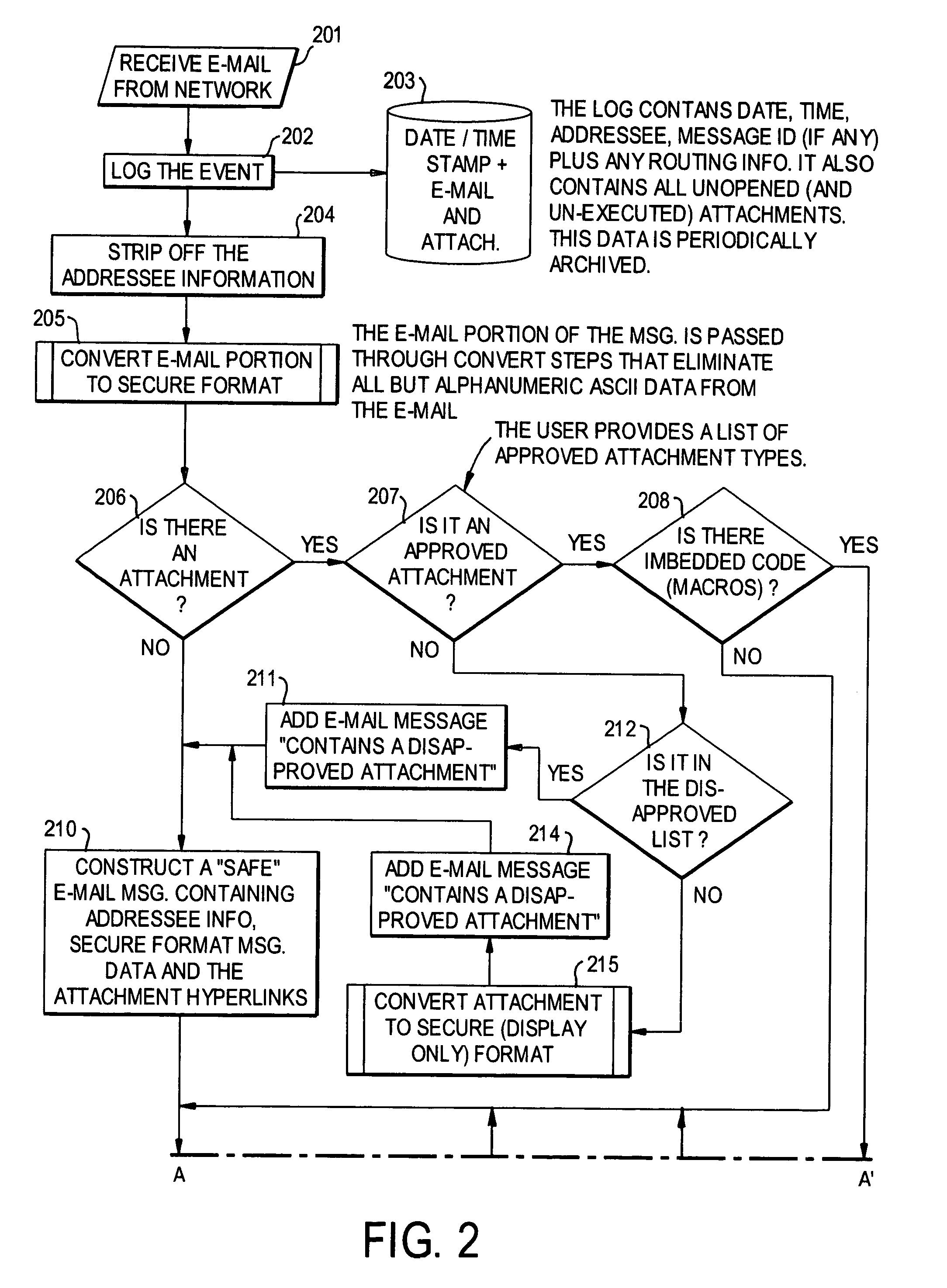
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
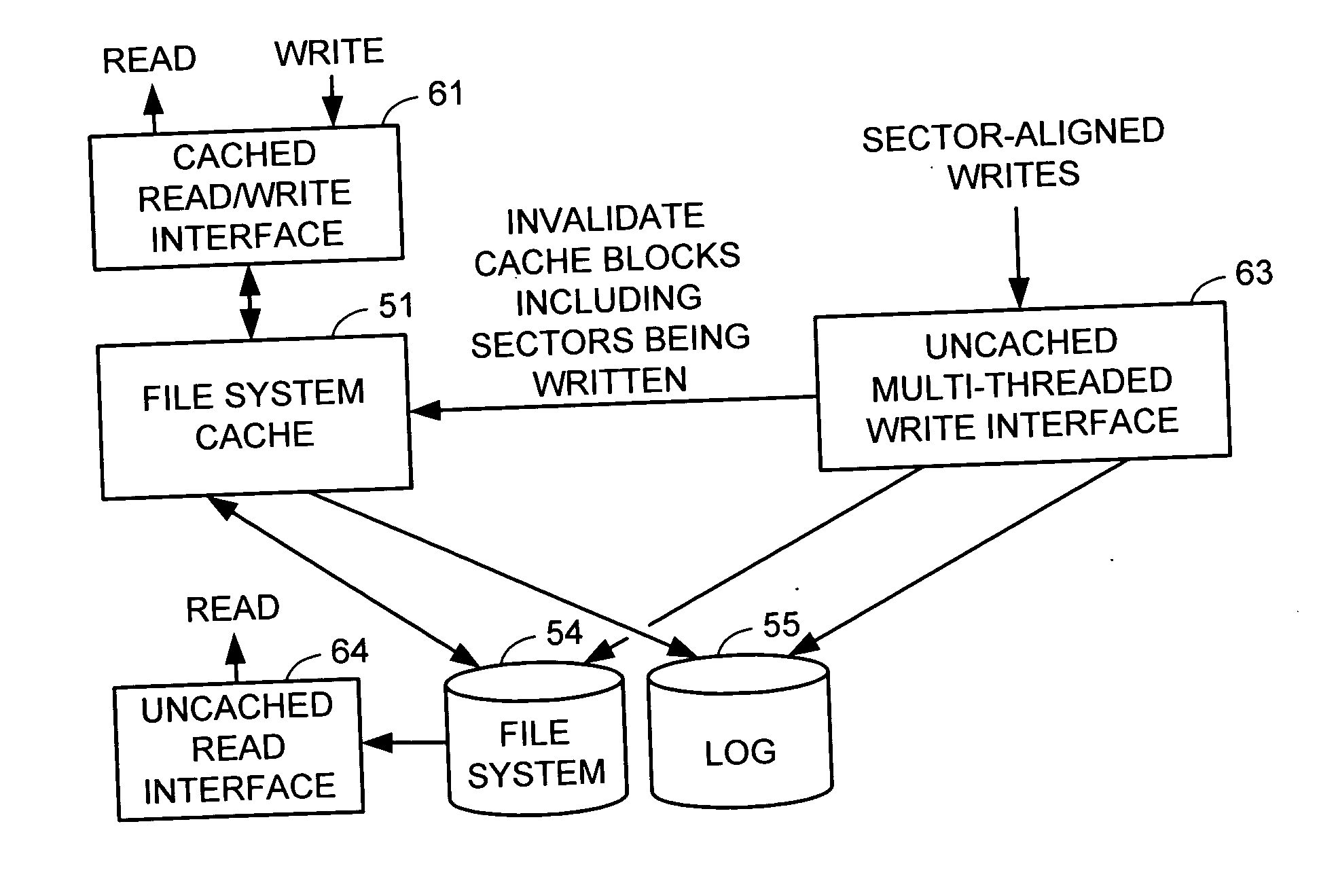
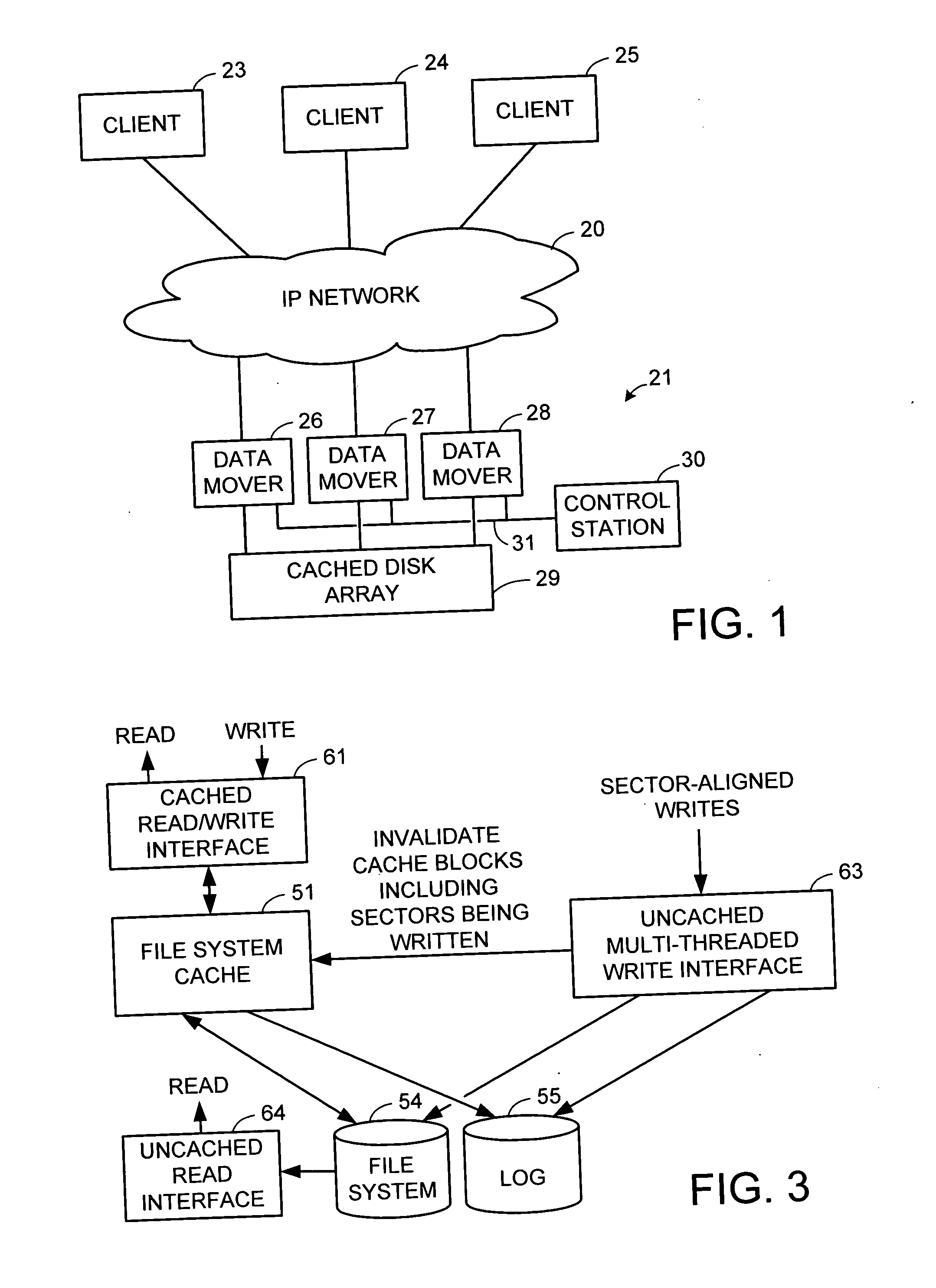
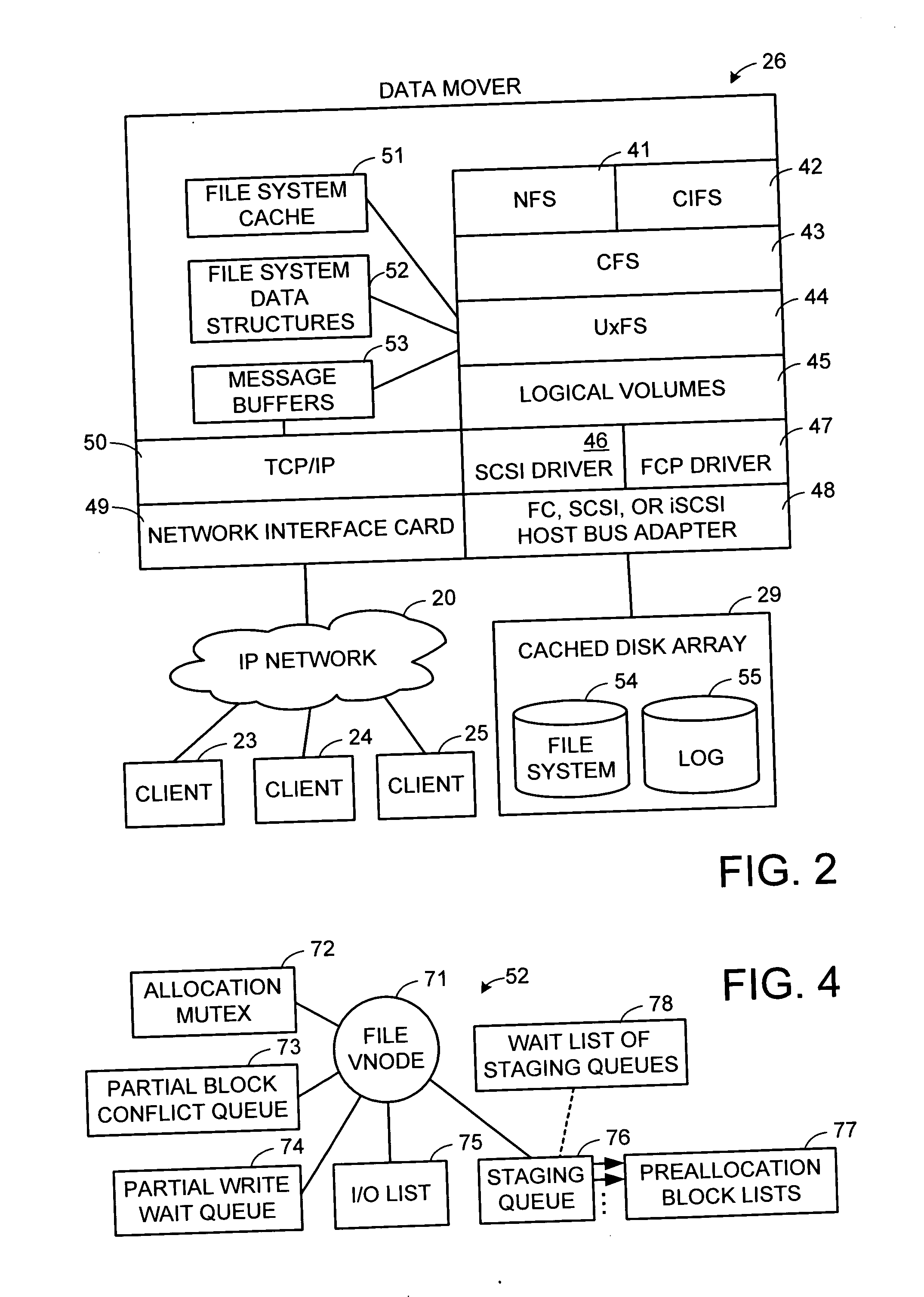
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS20050066095A1Digital data information retrievalDigital data processing detailsData integrityFile allocation
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
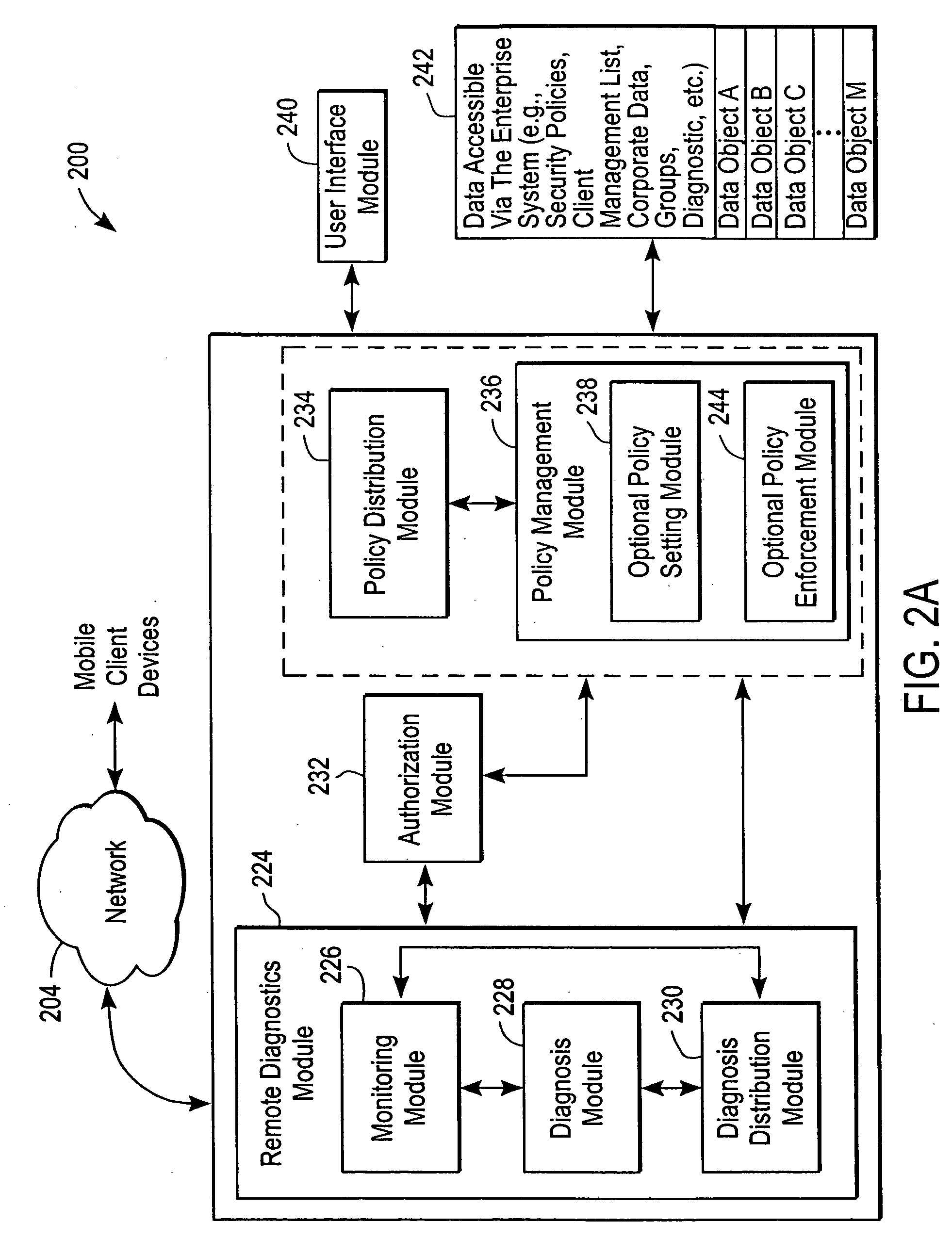
Administration of protection of data accessible by a mobile device
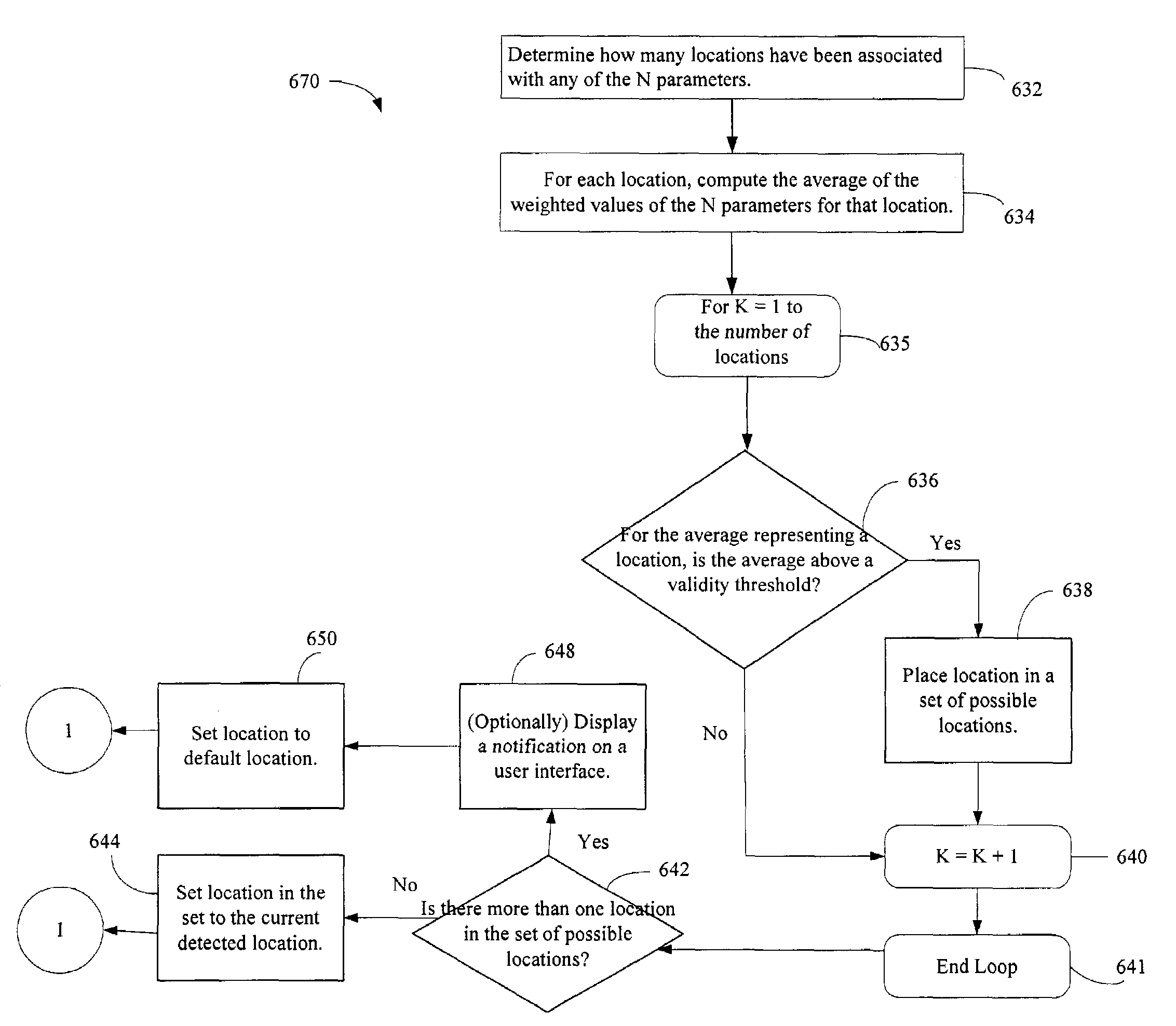
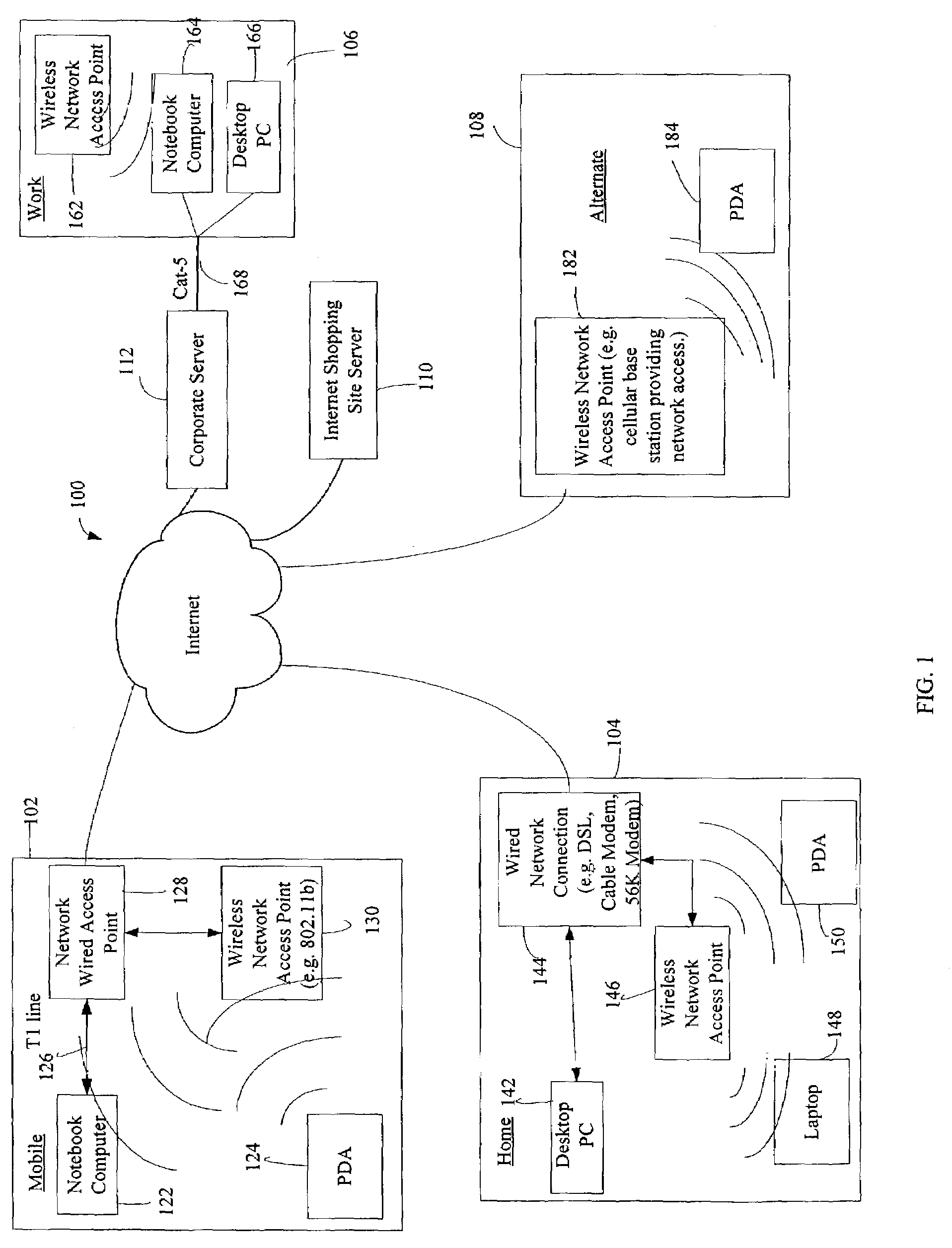
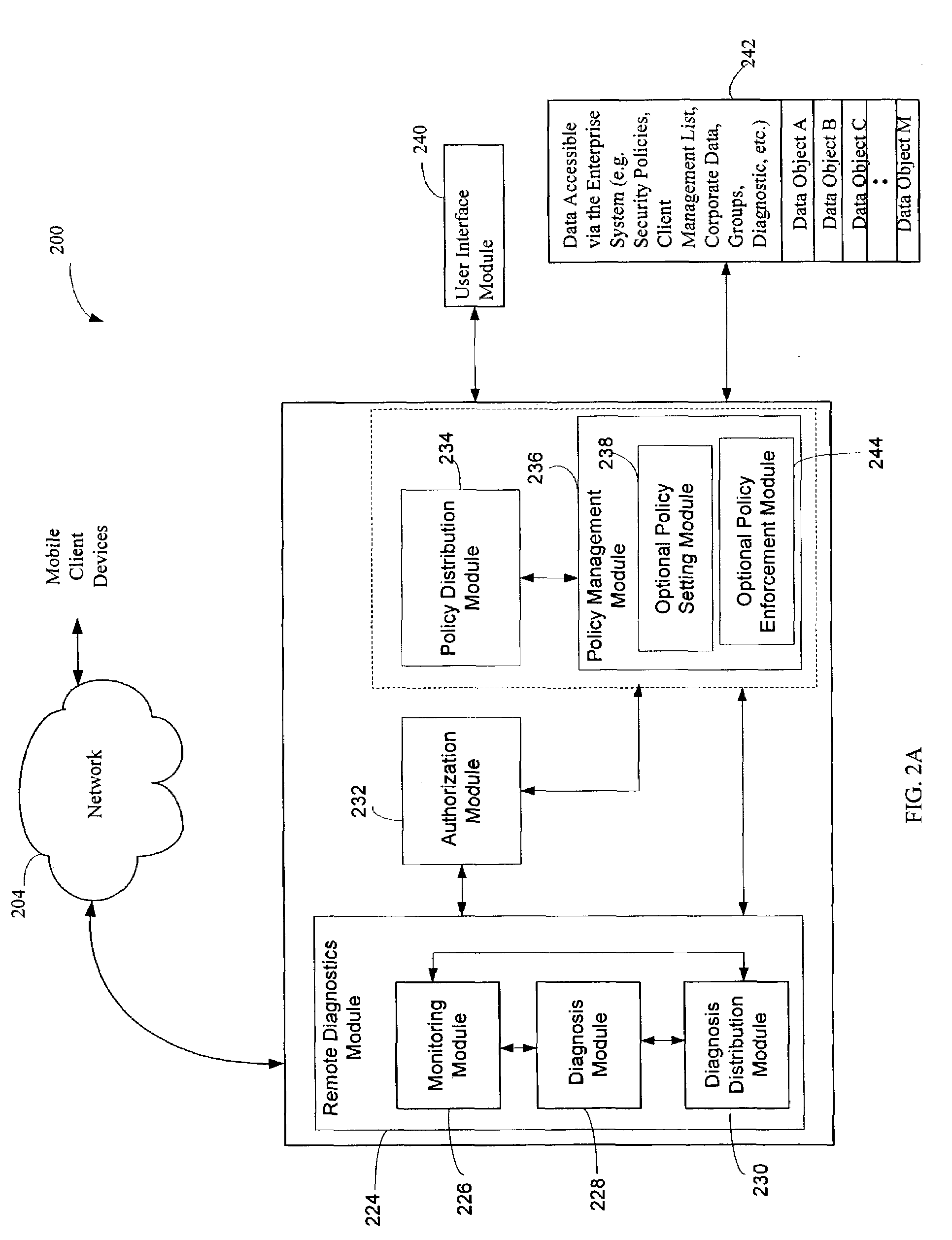
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
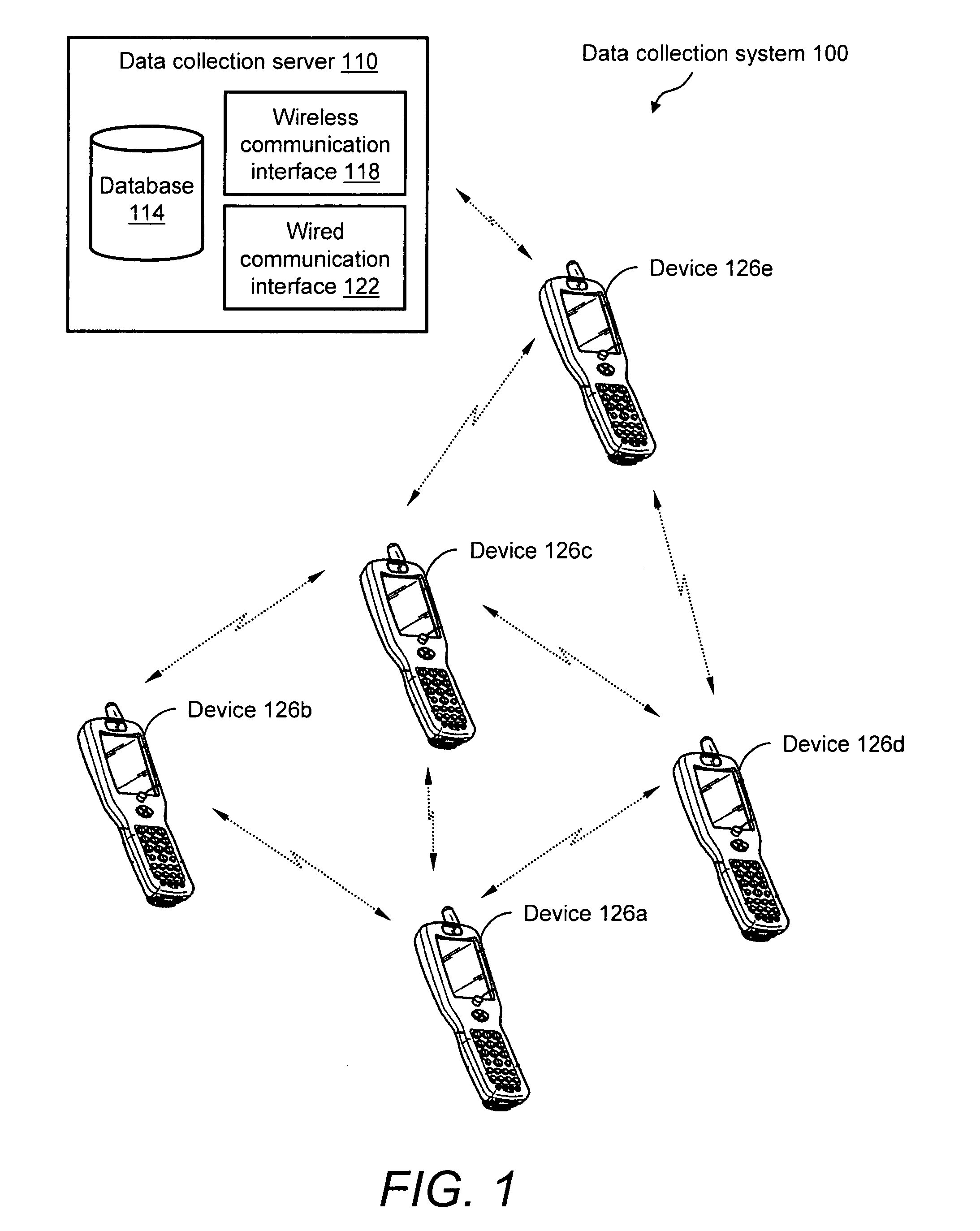
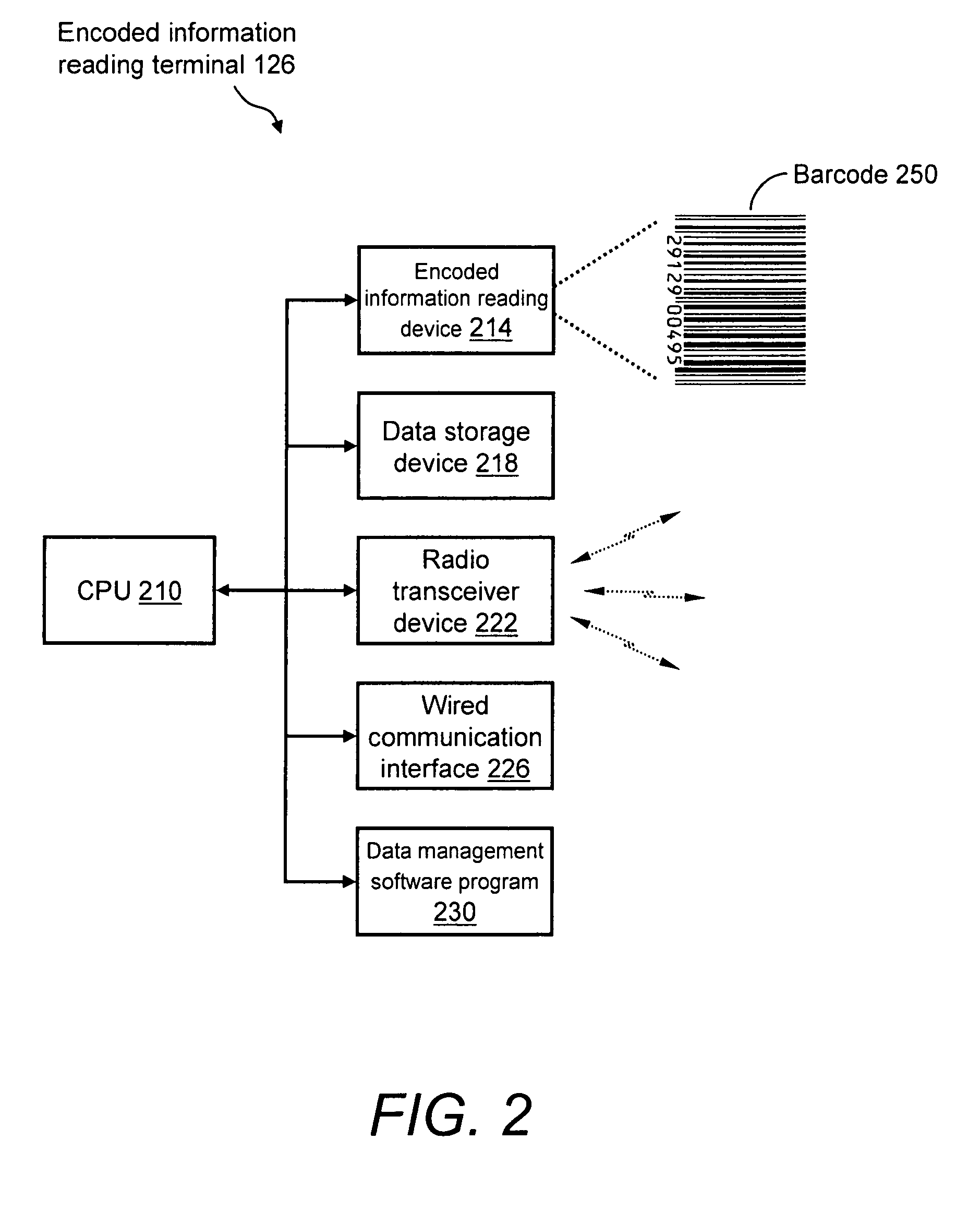
System and method for reliable store-and-forward data handling by encoded information reading terminals
InactiveUS8971346B2Error preventionFrequency-division multiplex detailsStore and forwardComputer terminal
A data collection system for, and methods of, providing reliable store-and-forward data handling by encoded information reading terminals can utilize ad-hoc peer-to-peer (i.e., terminal-to-terminal) connections in order to store data that is normally stored on a single terminal only, in a redundant manner on two or more terminals. Each portable encoded information reading terminal can be configured so that when it captures data, a software application causes the terminal to search out nearby peer terminals that can store and / or forward the data to other peer terminals or to a data collection server, resulting in the data having been stored by one or more peer terminals that are immediately or not immediately accessible by the data-originating terminal.
Owner:HAND HELD PRODS
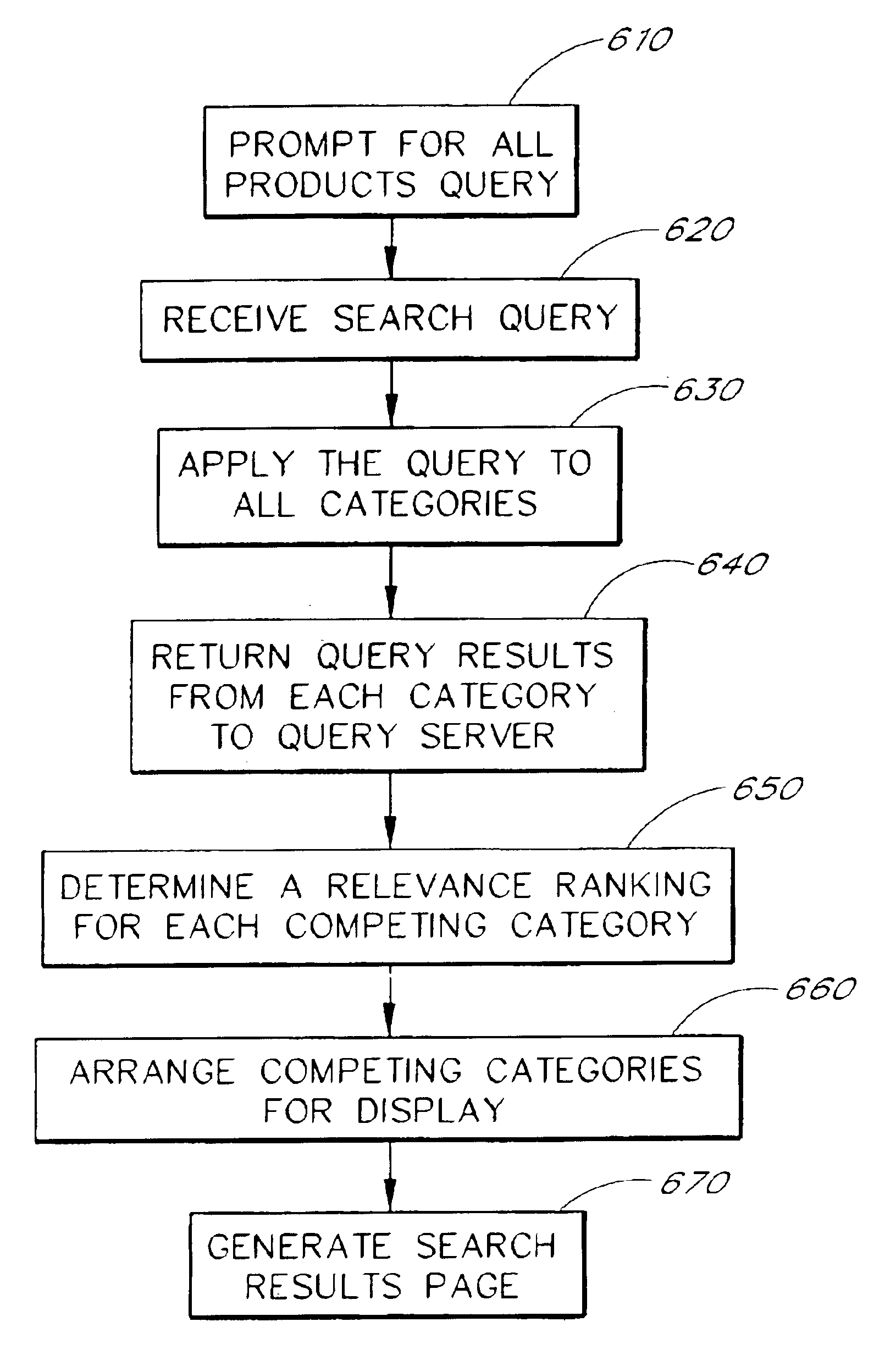
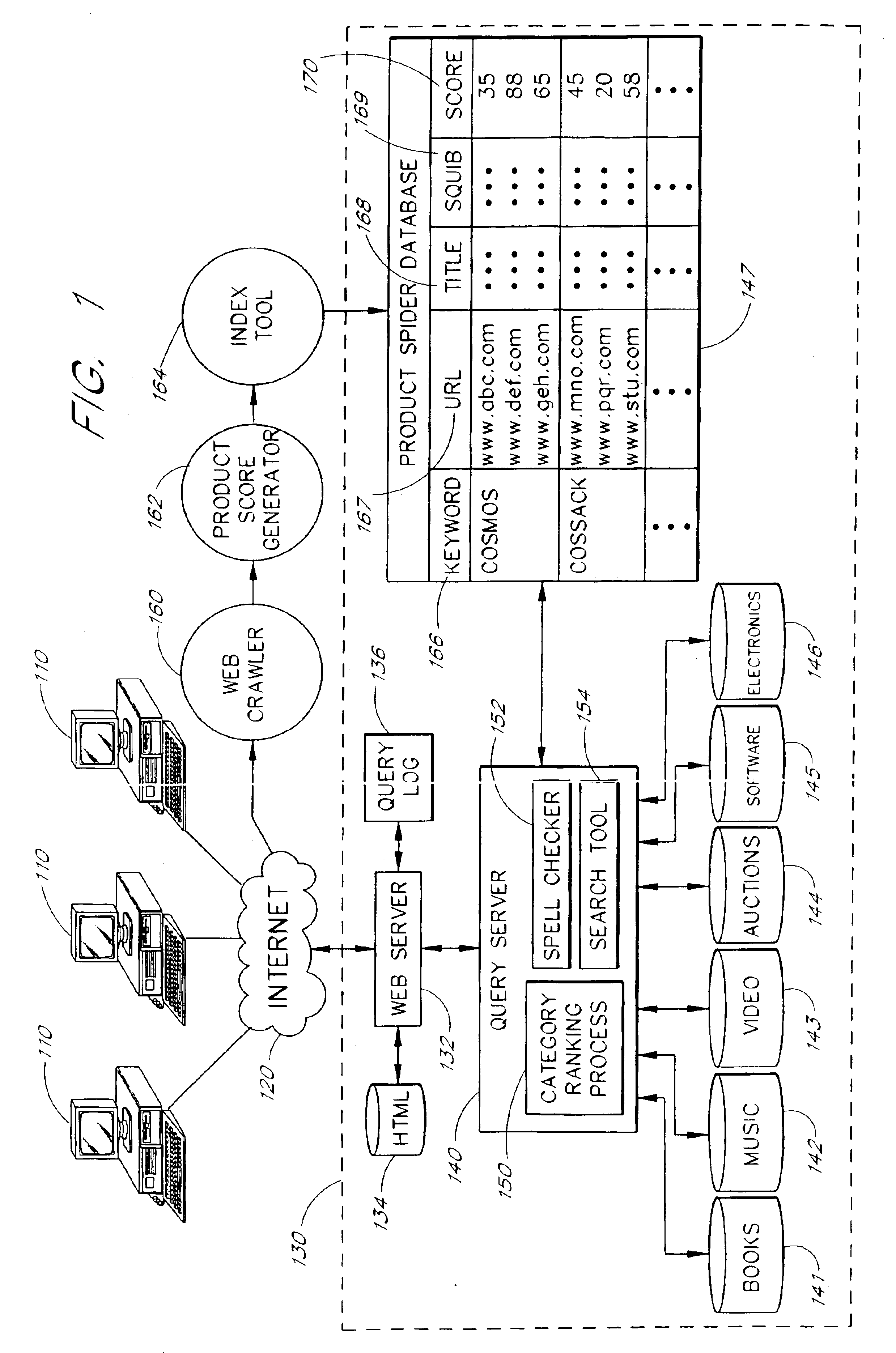
Search query processing to provide category-ranked presentation of search results
InactiveUS6963867B2View effectivelyRaise the possibilityWeb data indexingDigital data processing detailsLevels significanceMultiple category
A search engine system displays the results of a multiple-category search according to levels of relevance of the categories to a user's search query. A query server receives a search query from a user and identifies, within each of multiple item categories, a set of items that satisfy the query. The sets of items are used to generate, for each of the multiple categories, a score that reflects a level significance or relevance of the category to the search. The scores may be based, for example, on the number of hits within each category relative to the total number of items in that category, the popularity levels of items that satisfy the query, a personal profile of the user, or a combination thereof. The categories are then presented to the user, together with the most relevant items within each category, in the order of highest to lowest category relevance.
Owner:A9 COM INC
Method and apparatus for operating networked gaming devices
InactiveUSRE37885E1Coin countersApparatus for meter-controlled dispensingComputer moduleComputer terminal
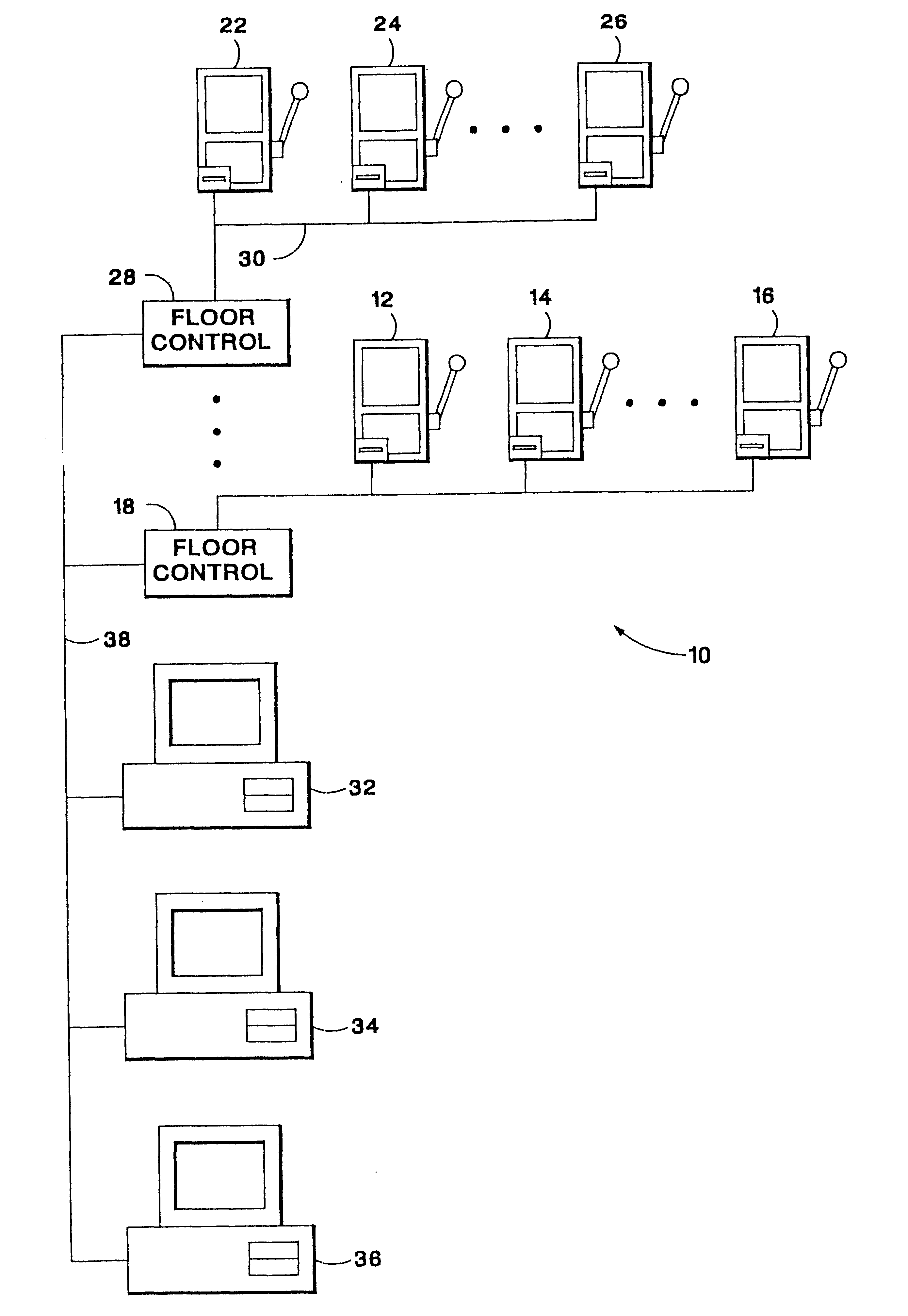
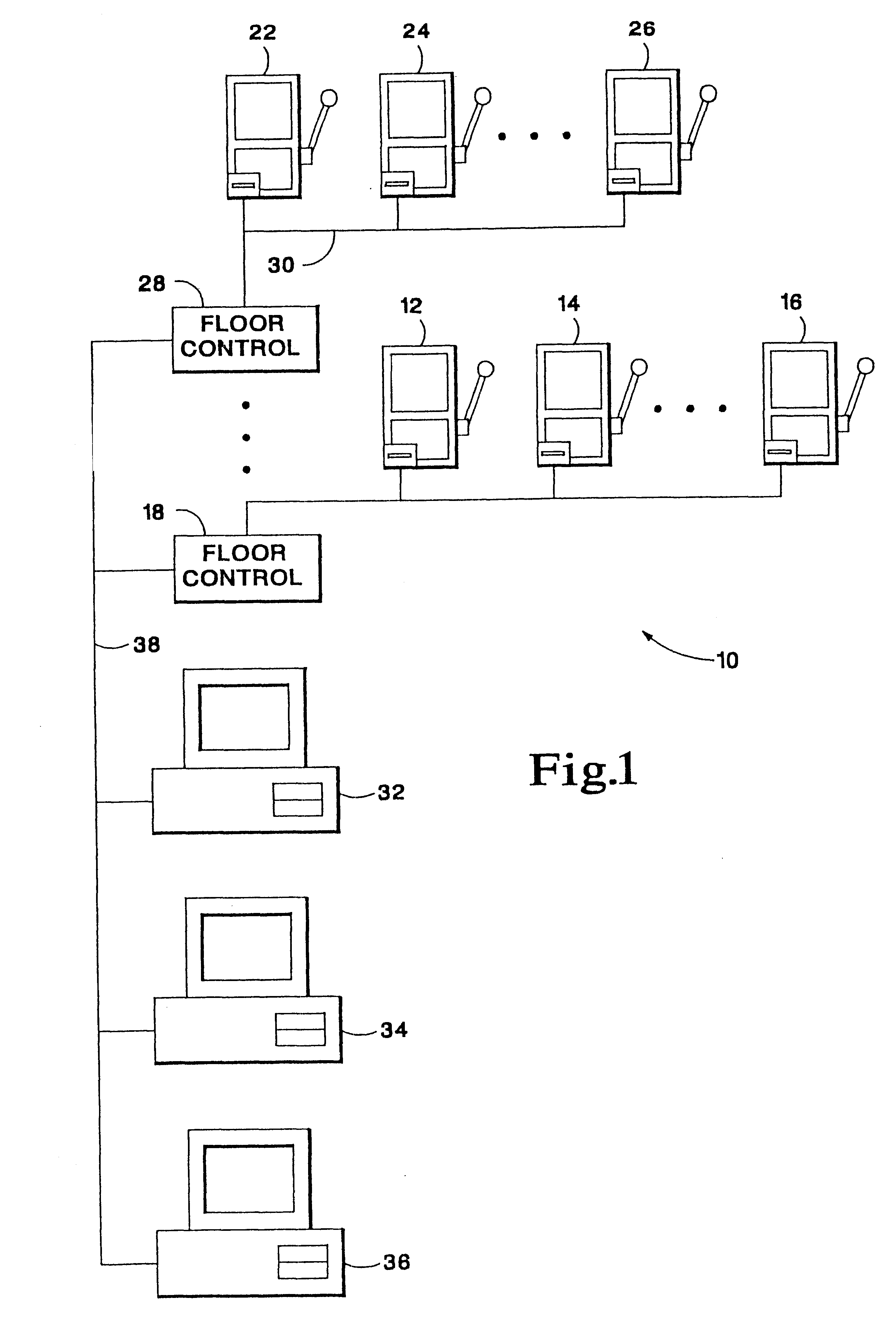
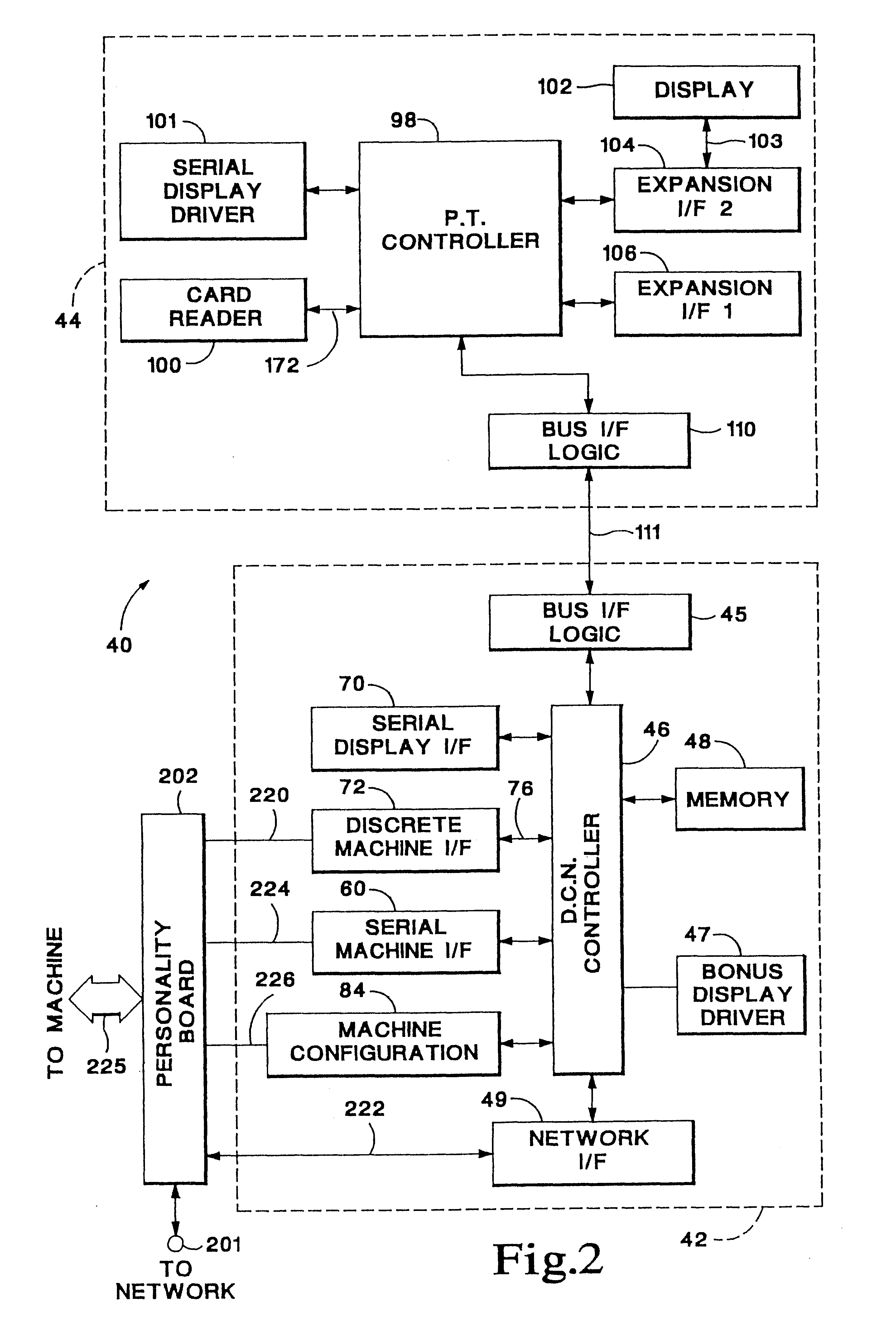
A system for monitoring and configuring gaming devices interconnected over a high-speed network is disclosed. The system can support a file server, one or more floor controllers, one or more pit terminals, and other terminals all interconnected over the network. Each gaming device includes an electronic module which allows the gaming device to communicate with a floor controller over a current loop network. The electronic module includes a player tracking module and a data communication node. The player tracking module includes a card reader for detecting a player tracking card inserted therein which identifies the player. The data communication node communicates with both the floor controller and the gaming device. The data communication node communicates with the gaming device over a serial interface through which the data communication node transmits reconfiguration commands. The gaming device reconfigures its payout schedule responsive to the reconfiguration commands to provide a variety of promotional bonuses such as multiple jackpot bonuses, mystery jackpot bonuses, progressive jackpot bonuses, or player specific bonuses.
Owner:IGT
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
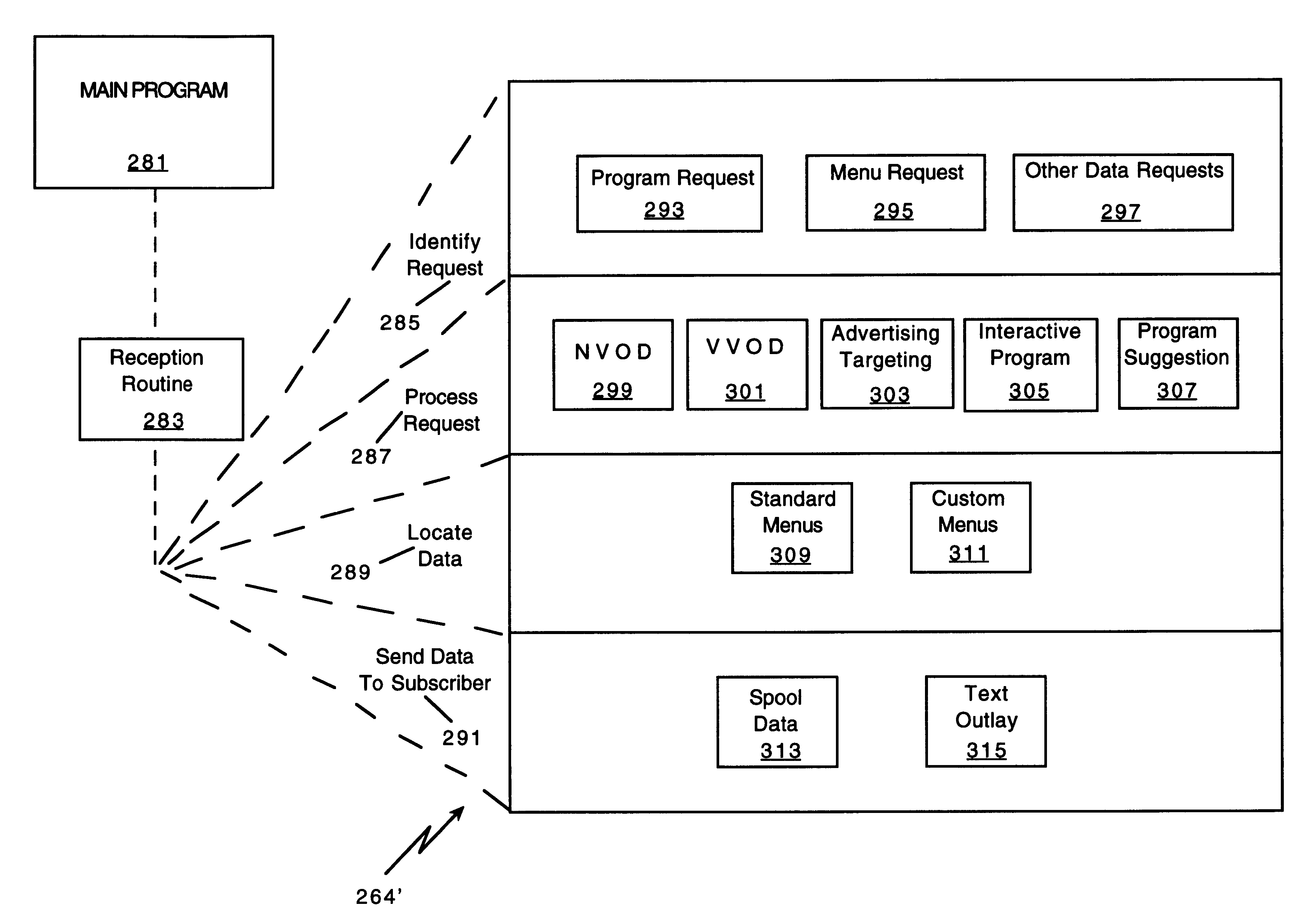
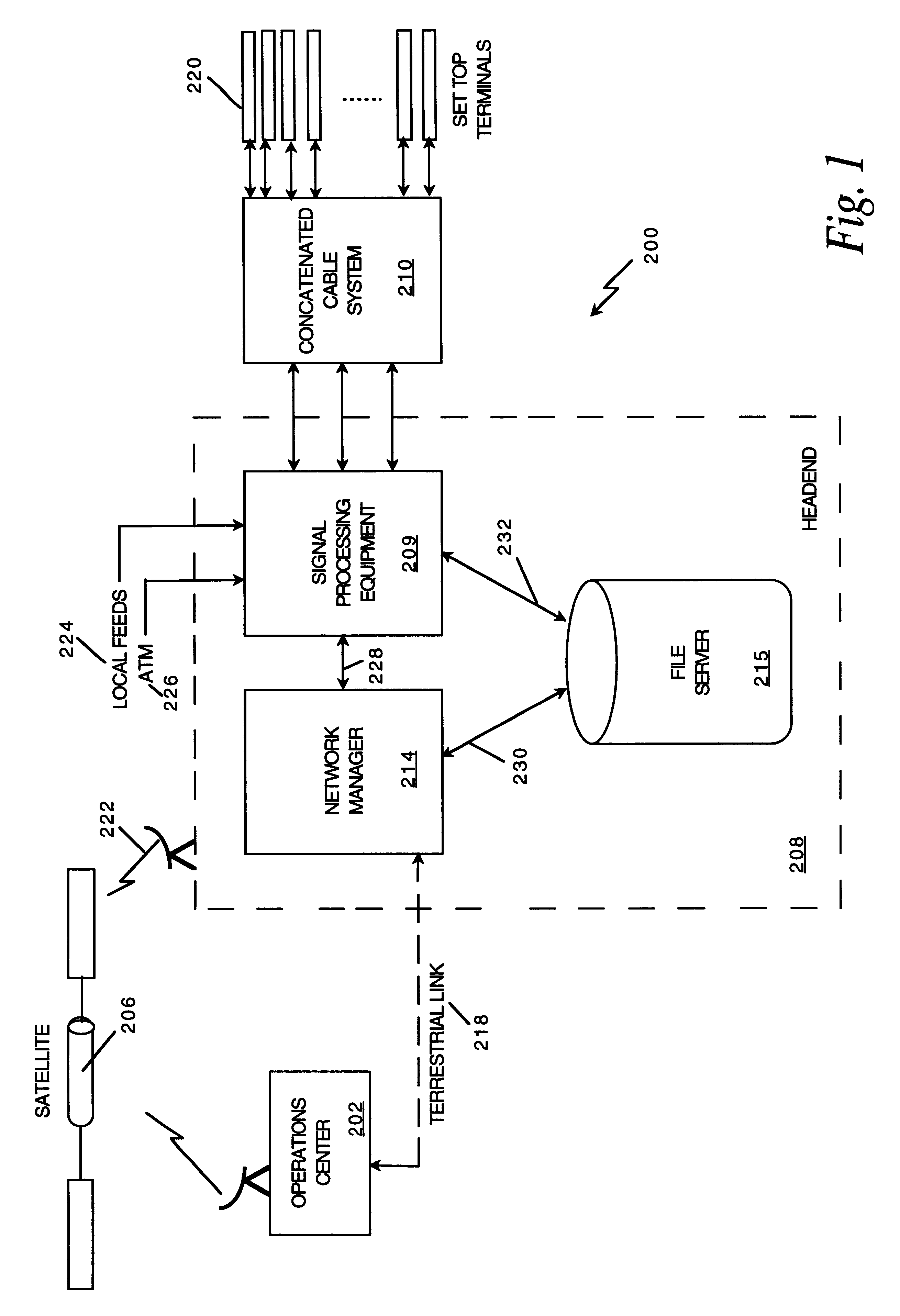
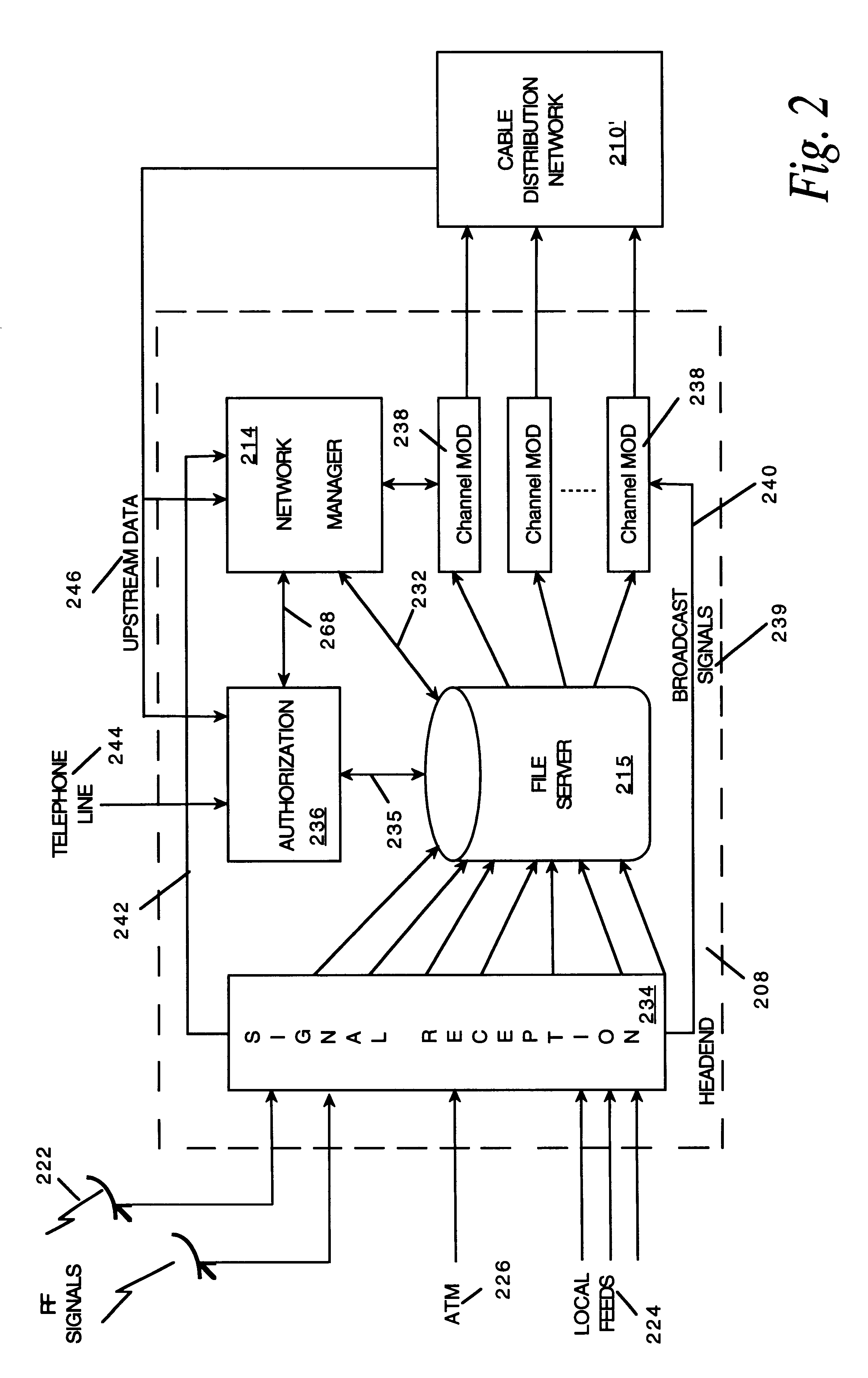
Network manager for cable television system headends
InactiveUS6201536B1Increase flexibilityImprove rendering capabilitiesTelevision system detailsPulse modulation television signal transmissionInformation processingInstruction memory
A novel network manager for use with a cable television system headend capable of monitoring and managing headend components and set top terminals in a television delivery system is described. The invention relates to methods and apparatus that manage and coordinate the reception of various programming and control signals at a headend. The invention manages and coordinates the storage of such signals for intelligent selection and distribution to set top terminals. The invention makes use of a receiver or set of receivers, a work station, a program control information processing component, a network management CPU, databases, control software and an instruction memory. The invention uses these components to manage and monitor certain headend components, such as signal reception equipment, an authorization component, a file server, MPEG decoders, a digital buffer with frame repeat and channel modulators. The invention is particularly useful in processing and responding to upstream information and subscriber communications received from set top terminals. In so doing, the invention accommodates various system services, including (1) near video on demand (NVOD), (2) virtual video on demand (VVOD), (3) video on demand (VOD), (4) interactive program services, (5) program suggestion features, (6) advertisement targeting, (7) generation of standard and custom menus, and (8) data spooling and text overlaying.
Owner:COMCAST IP HLDG I
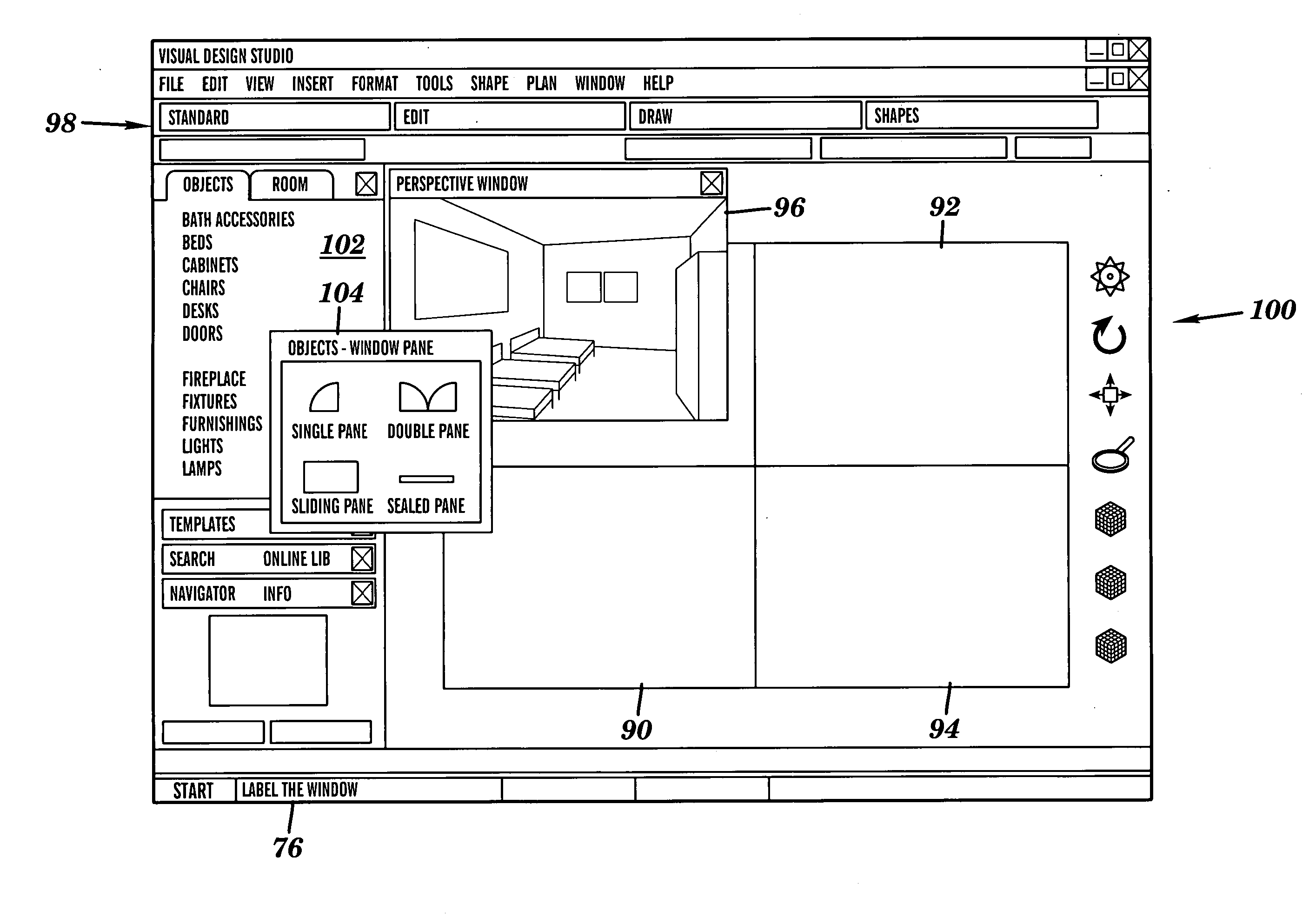
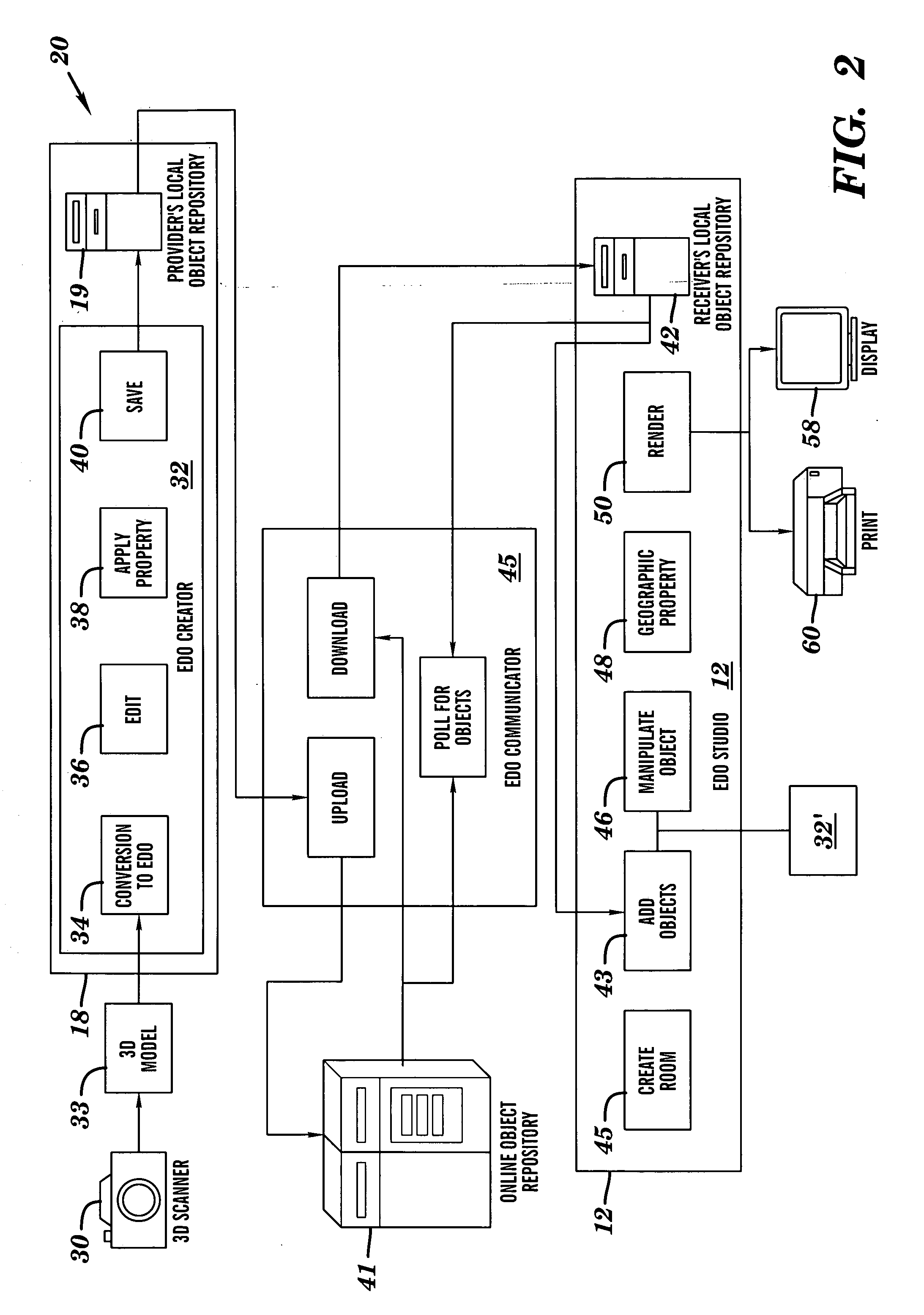
Three-dimensional interior design system
A system and method in a client-server computing environment is provided for generating and rendering a photorealistic three-dimensional (3D) perspective view of a 3D object selectively positioned within a 3D scene. A client is configured for communicably accessing a server, and includes a client application configured for scene editing and rendering, using a graphical user interface (GUI). The 3D scene may be selectively displayed in a plurality of views, and a 3D object may be retrieved from the server and imported into the 3D scene to generate a composite. The 3D object may also be manipulated within the composite for placement and orientation. A 3D image of the composite may then be rendered at the client and selectively reconfigured in real time. Luminosity characteristics may be applied to the 3D image; followed by rendering a photorealistic 3D view of the composite image.
Owner:AR DESIGN INNOVATIONS LLC
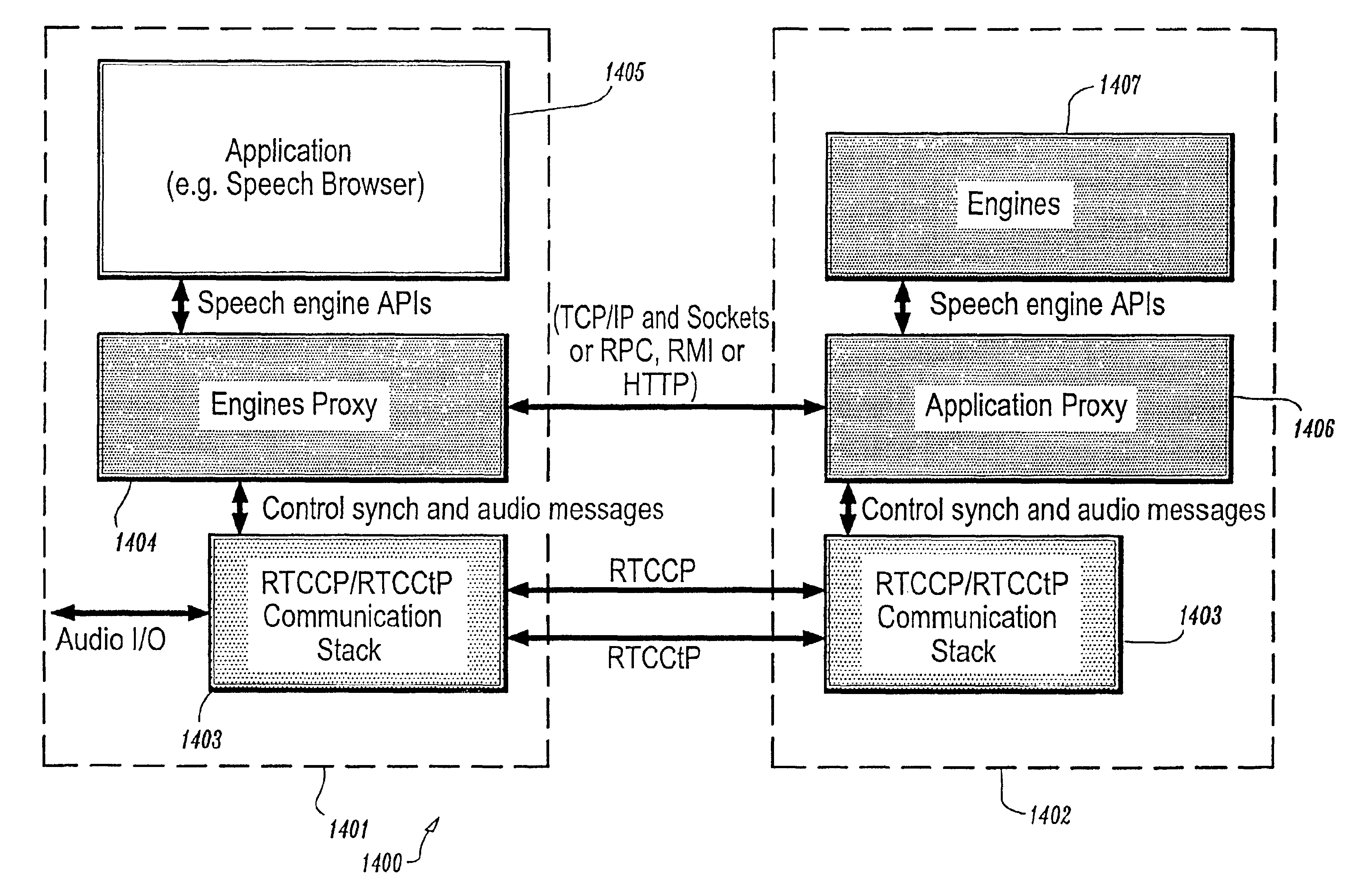
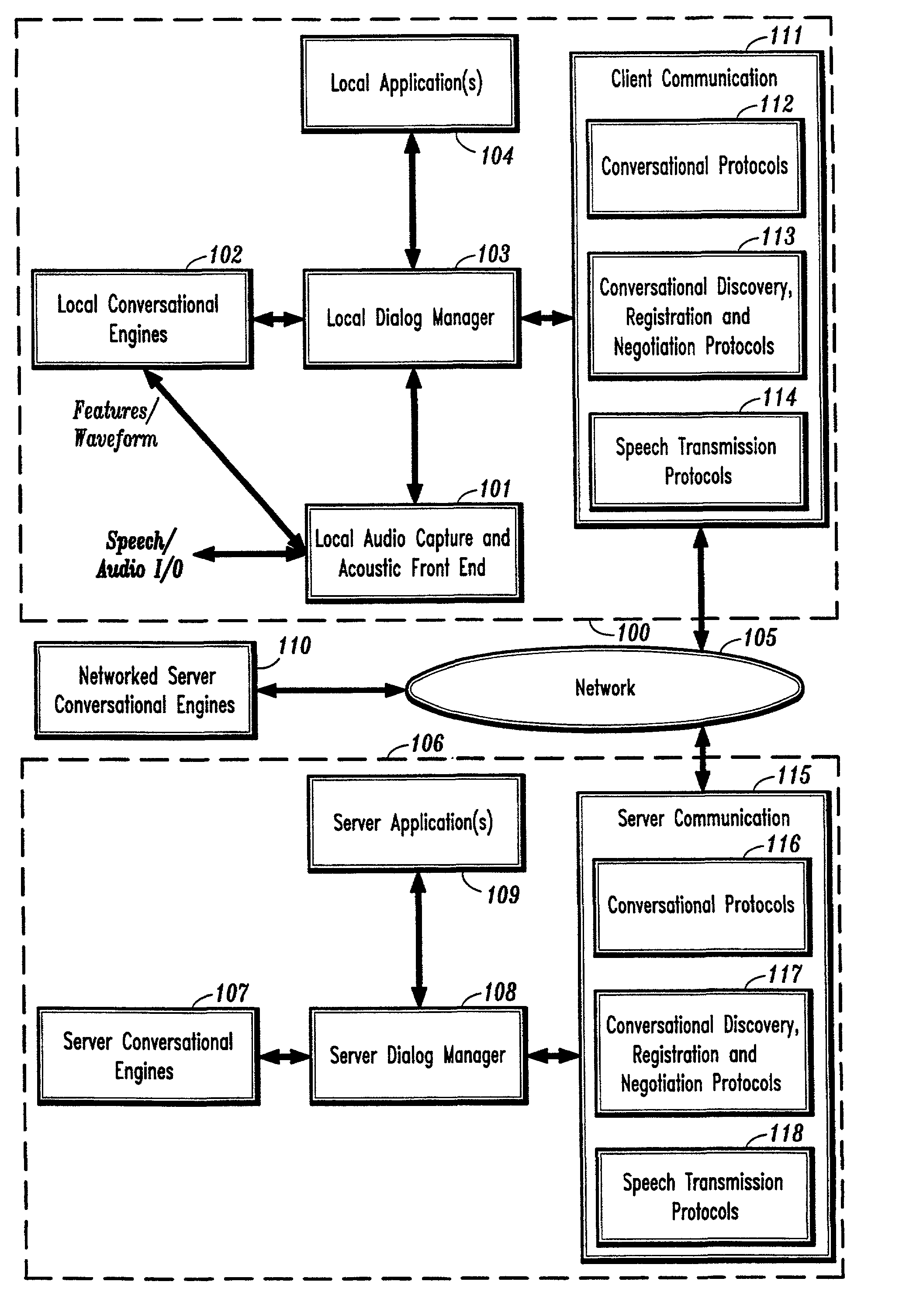
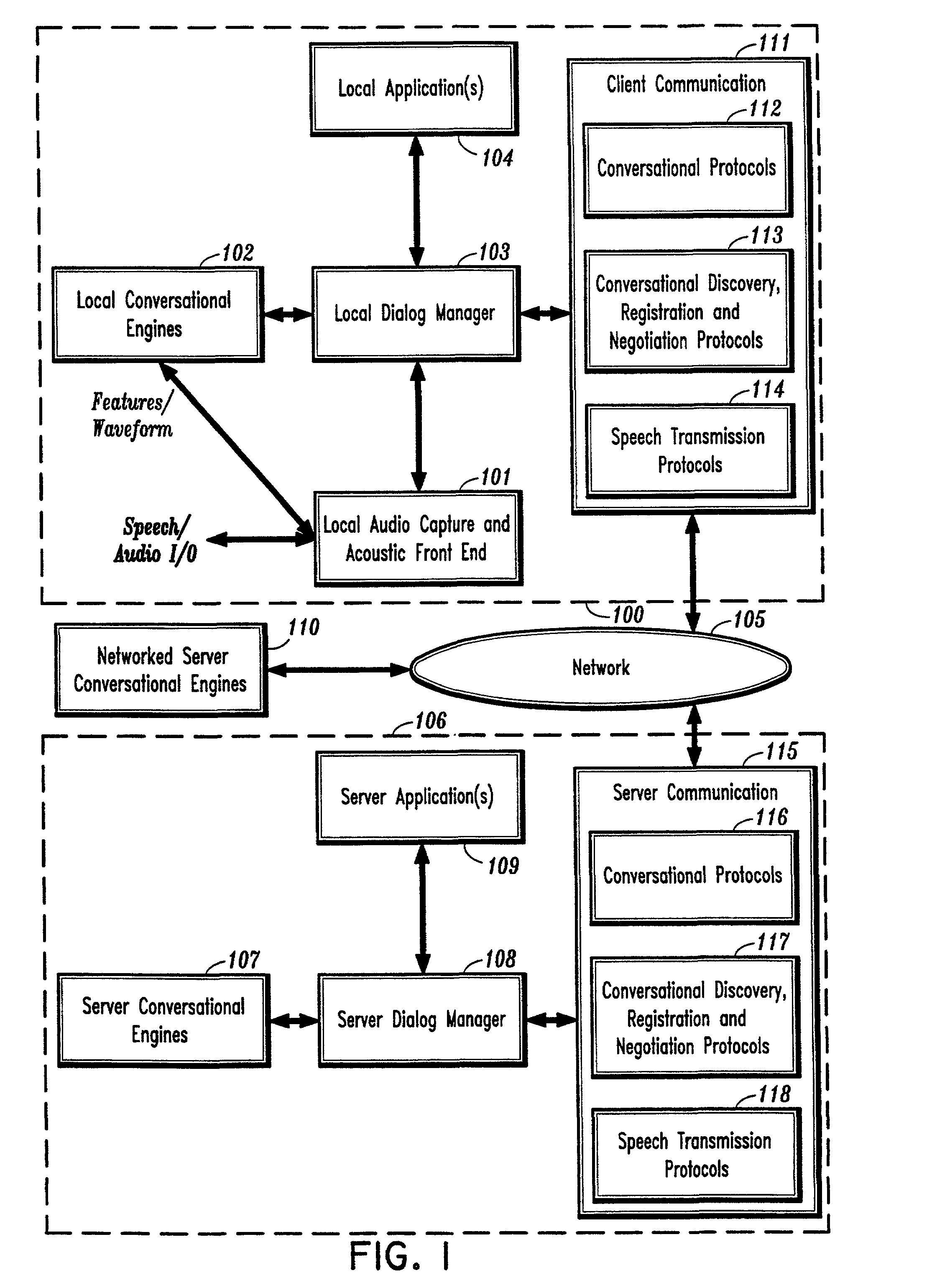
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
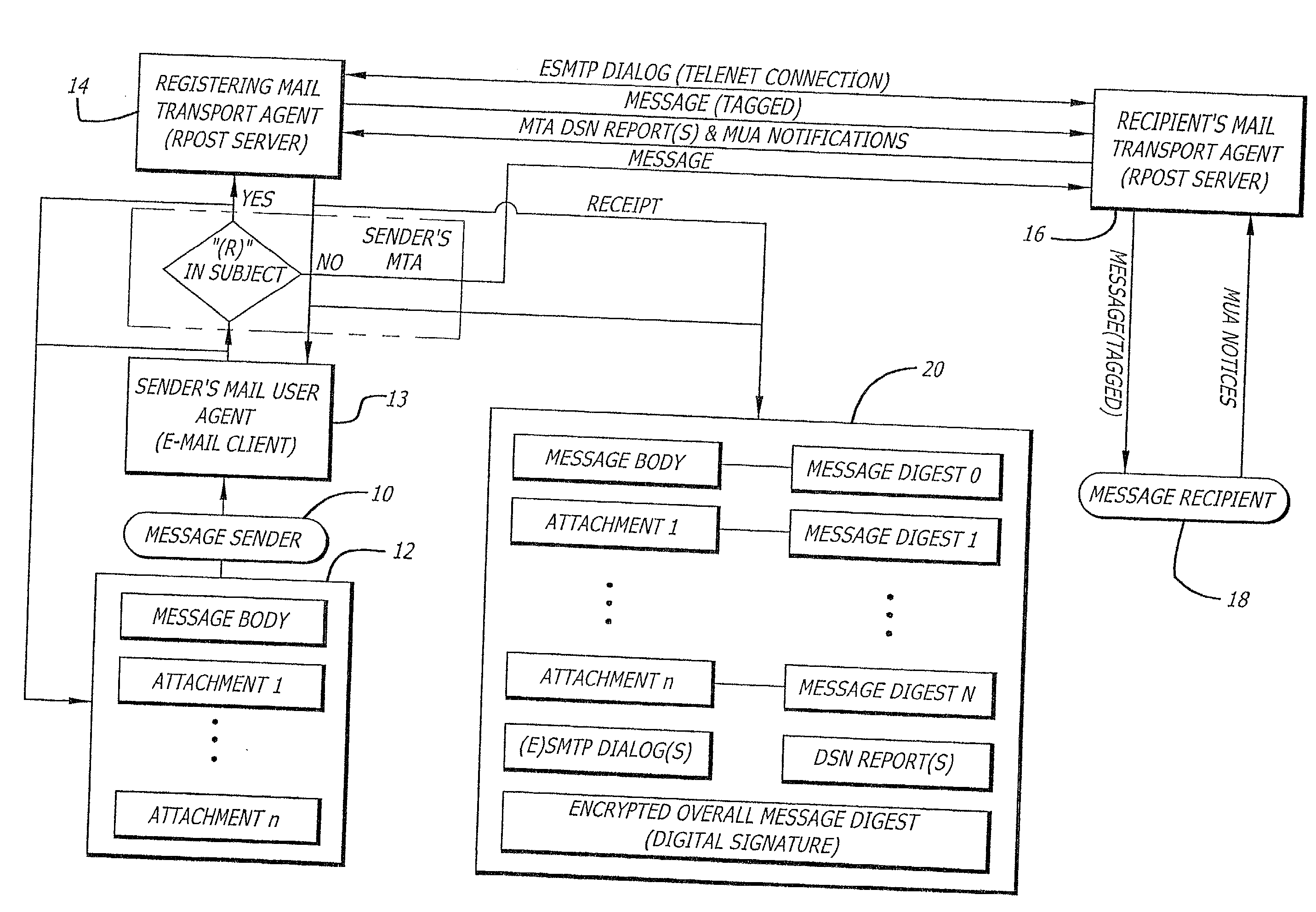
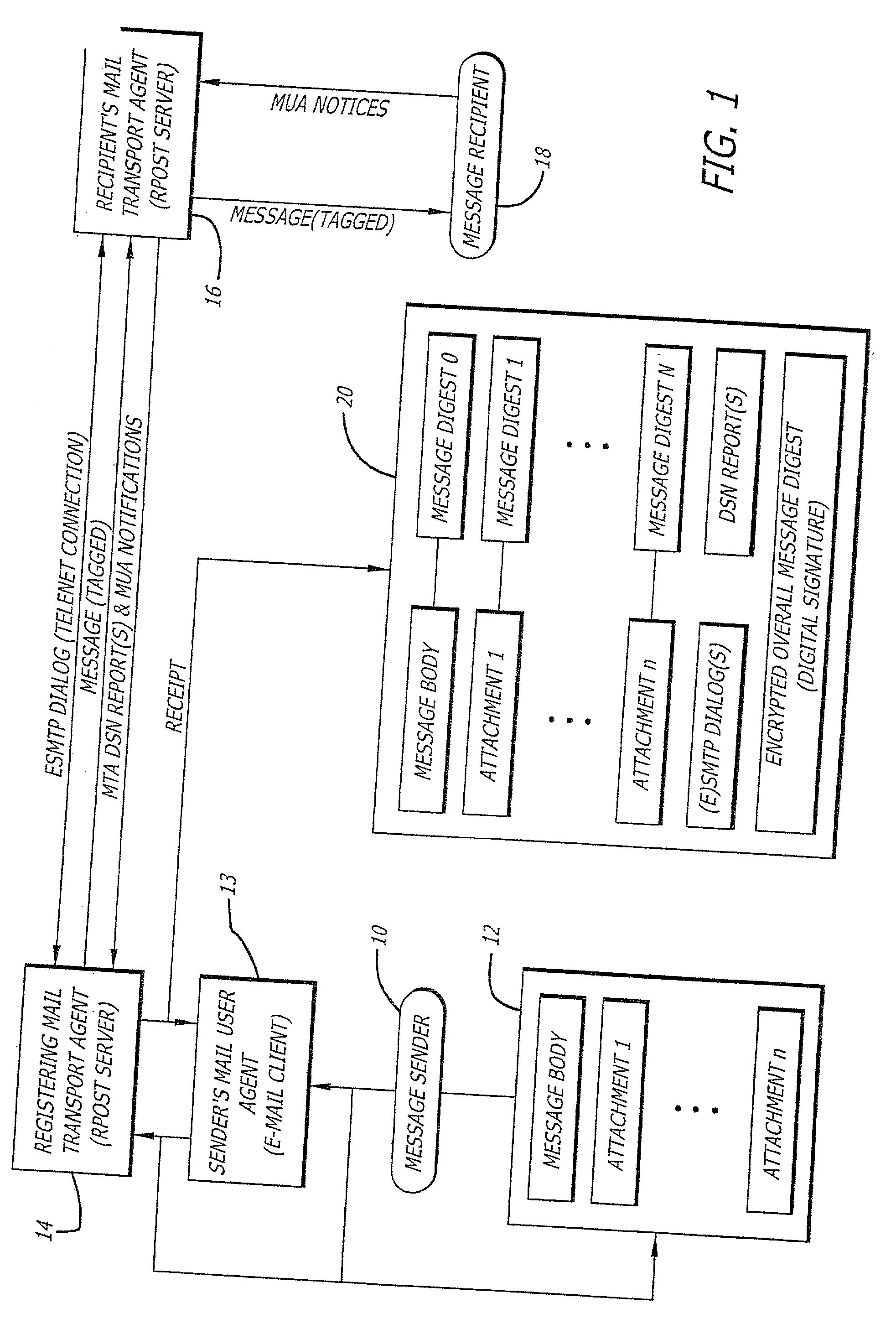
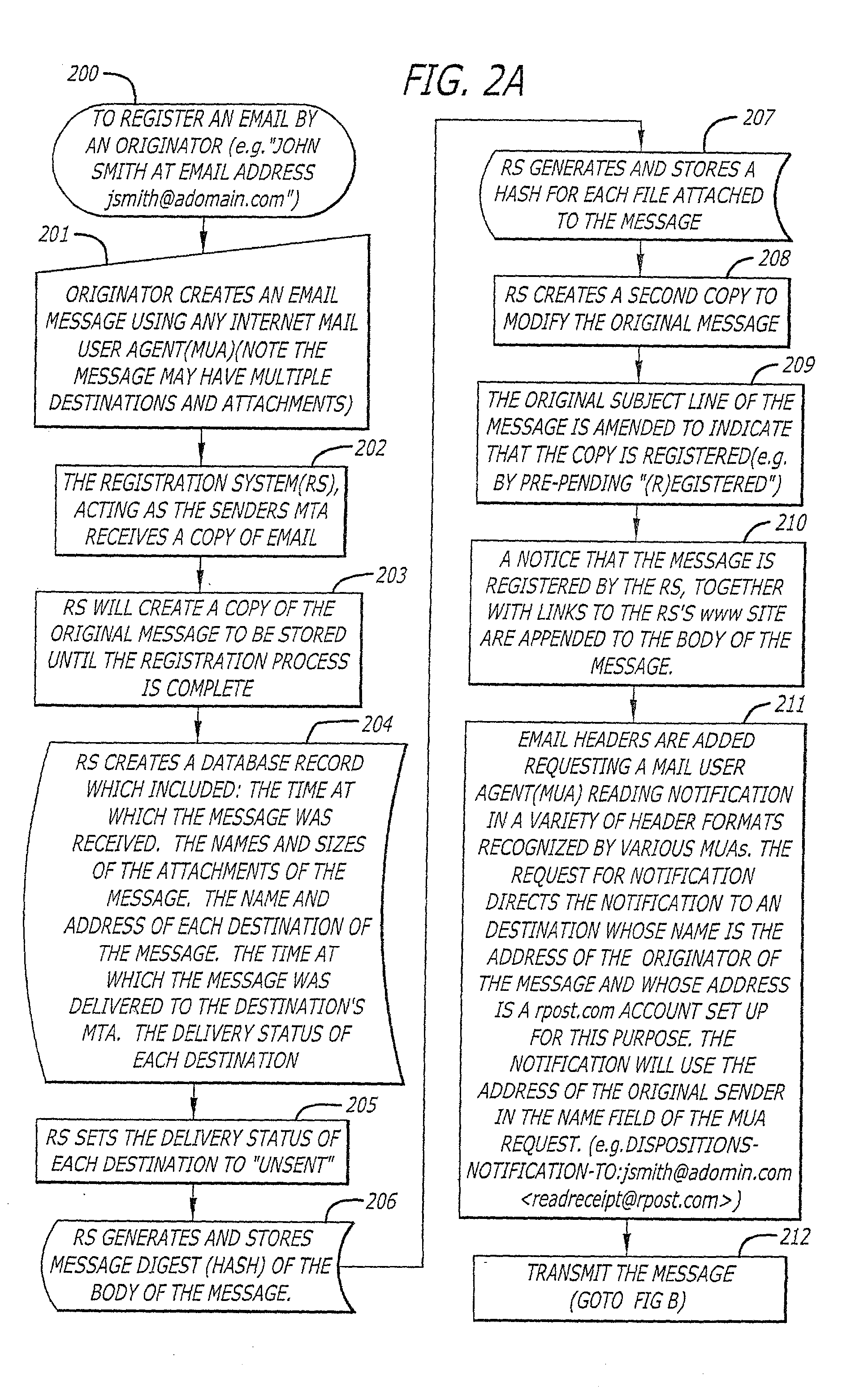
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
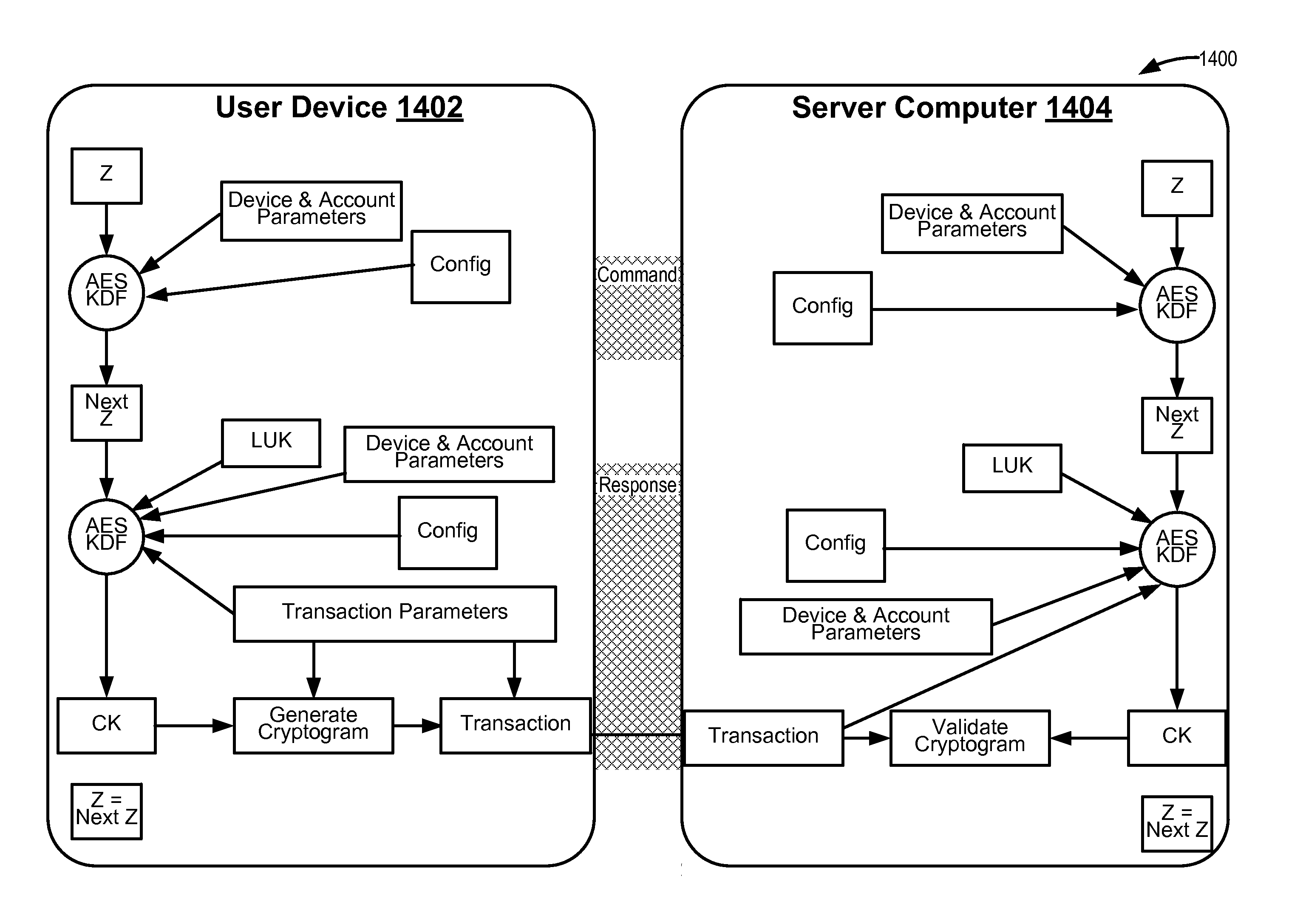
Methods for secure cryptogram generation
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
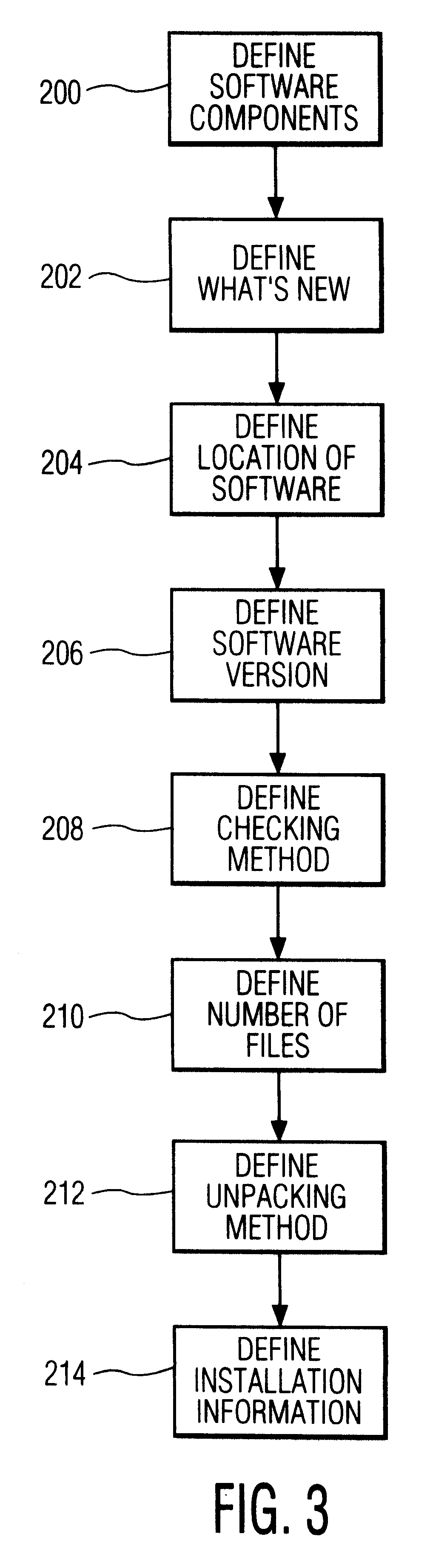
Software update manager
A method and apparatus for checking / updating existing software on a user's computer utilizes a graphical user interface (GUI). The GUI enables the user, without knowing what software exists on the computer, to download a text file from a remote server and check whether the software on the remote server is contained on the user's computer. The user can also download and automatically install a new or updated program via the GUI.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
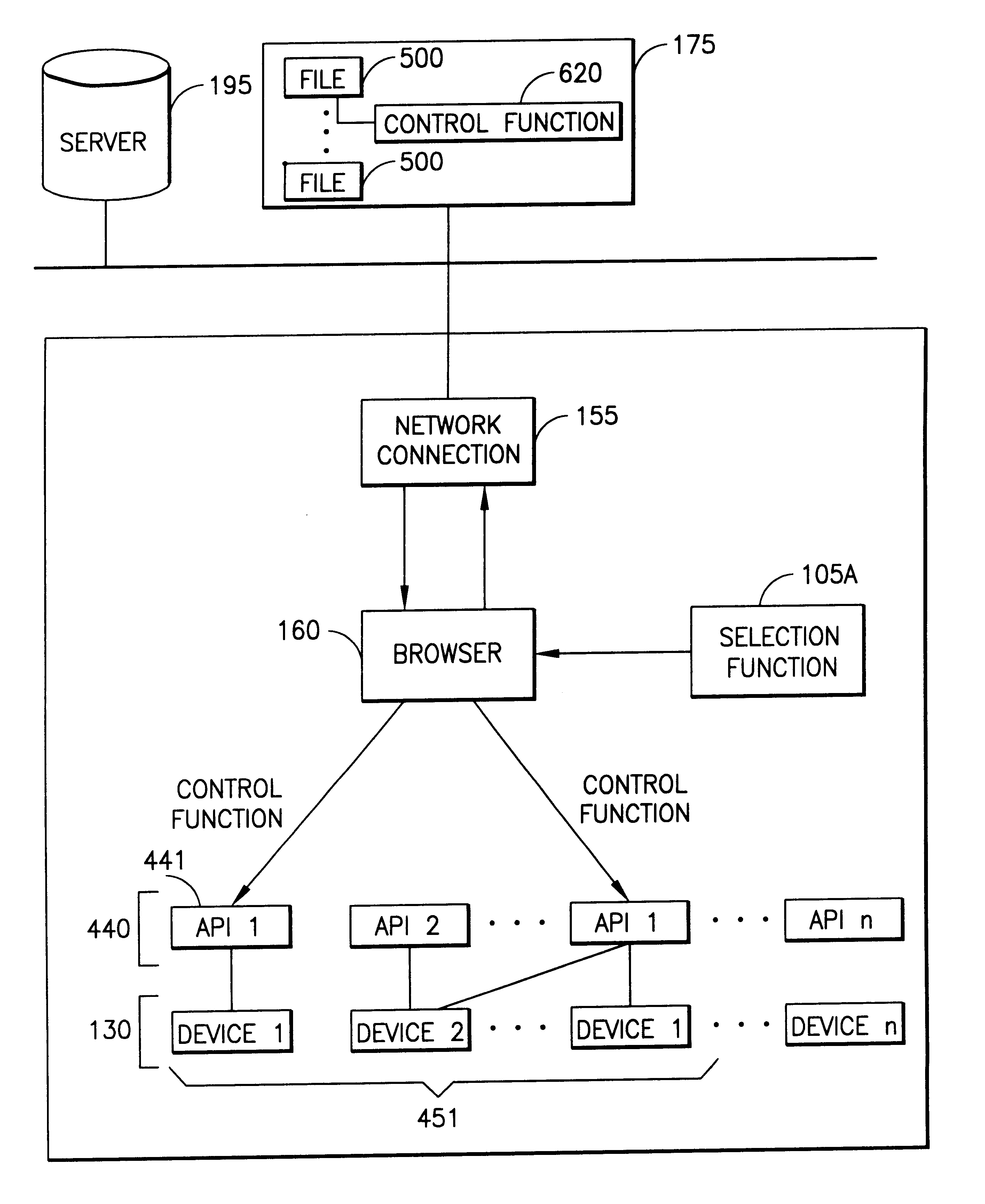
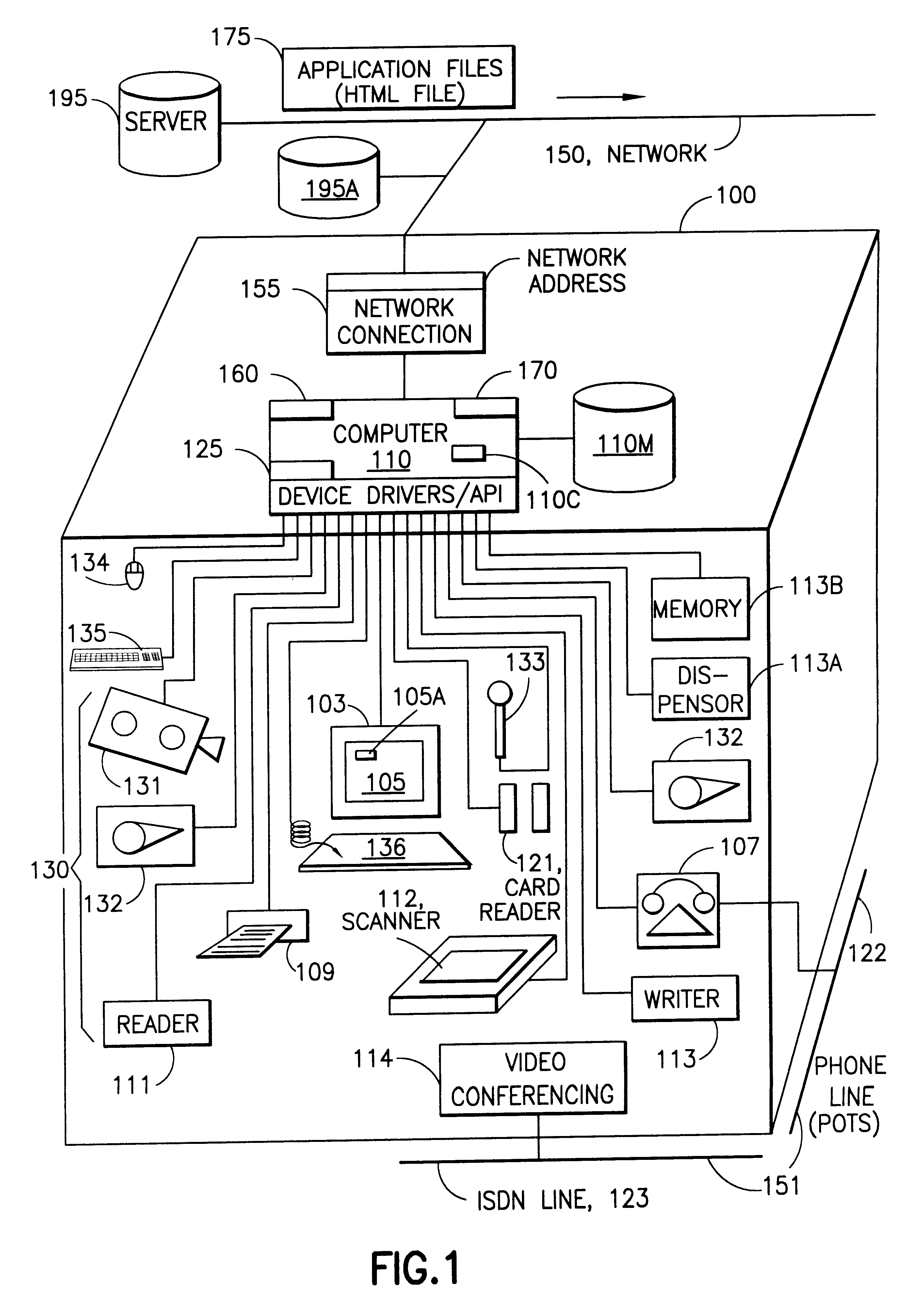
Server for reconfiguring control of a subset of devices on one or more kiosks
InactiveUS6195694B1Faster and reliable accessLow costAcutation objectsData switching by path configurationM-governmentComputer terminal
A server system that is connected to one or more networks, e.g., the Internet, corporate or government intranets, extranets, etc. The server has one or more application files or configuration sets that the server serves to from one or more kiosks on the network. The configuration sets are application specific. (An application is a use for which the kiosks are configured or reconfigured.) One or more of the files in the configuration sets include one or more embedded (control) programs that are used to control the local APIs of one or more of the devices on the kiosk. In this way, the devices are controlled to configure the kiosk to perform the application.
Owner:IBM CORP
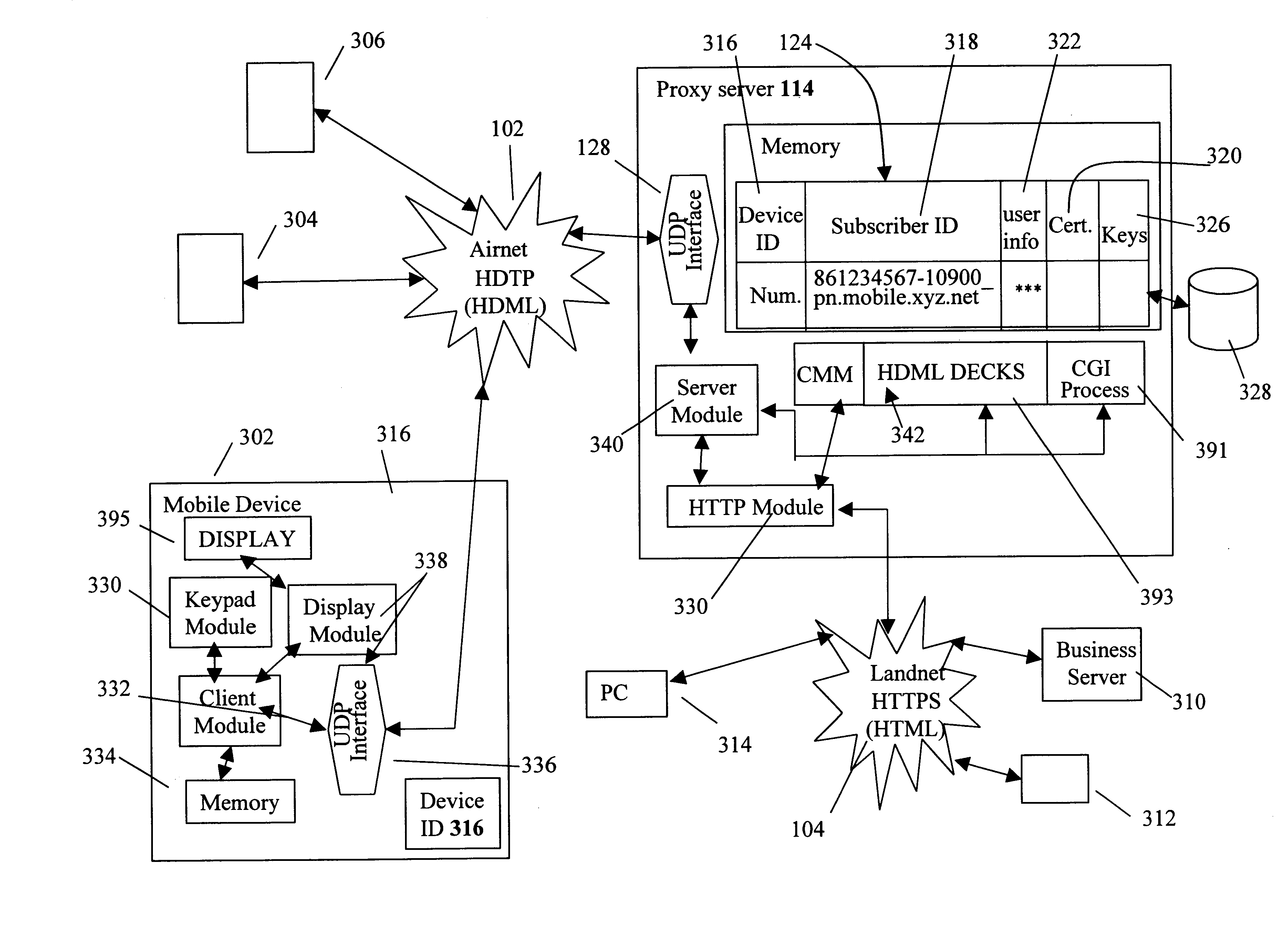
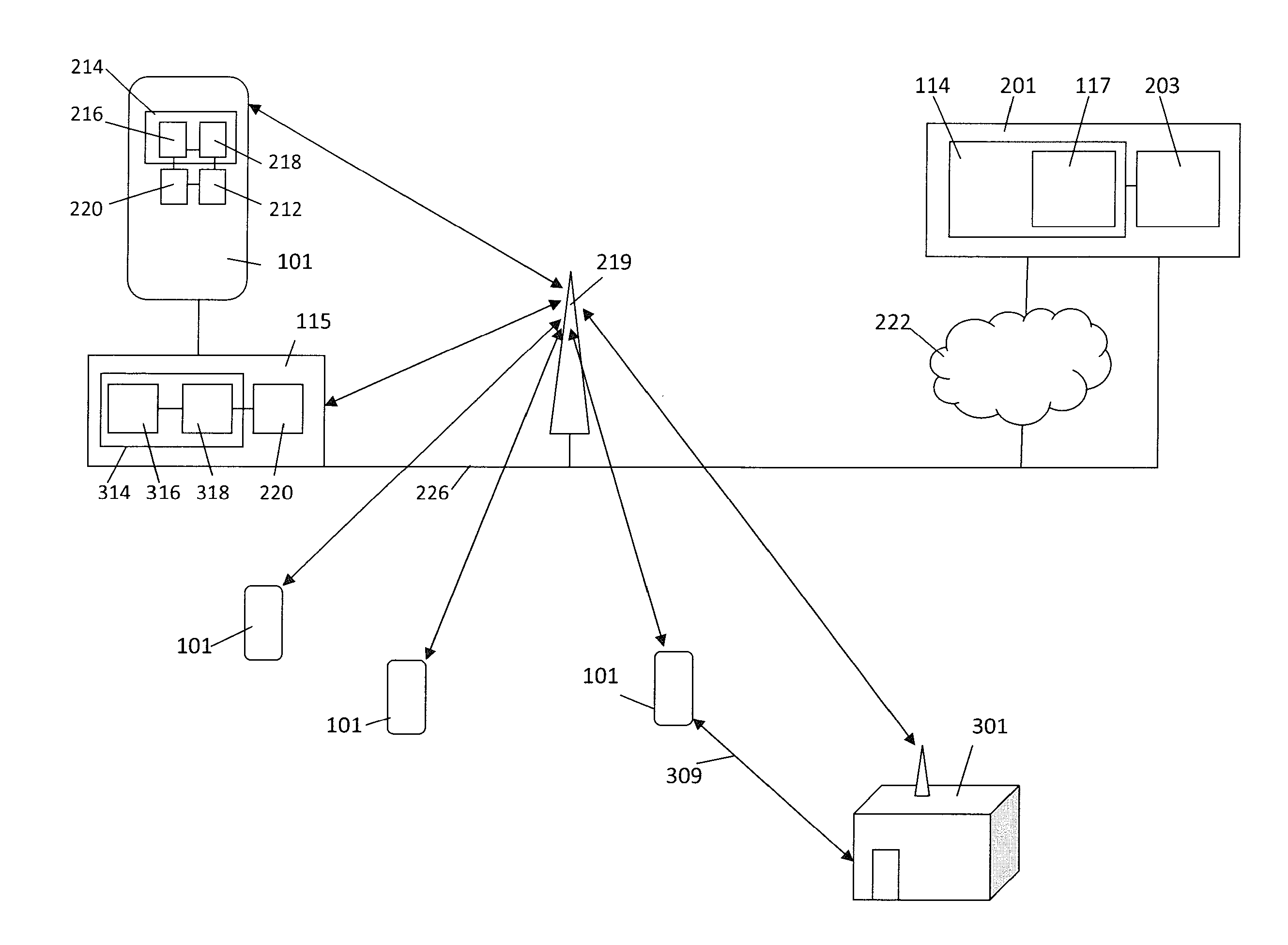
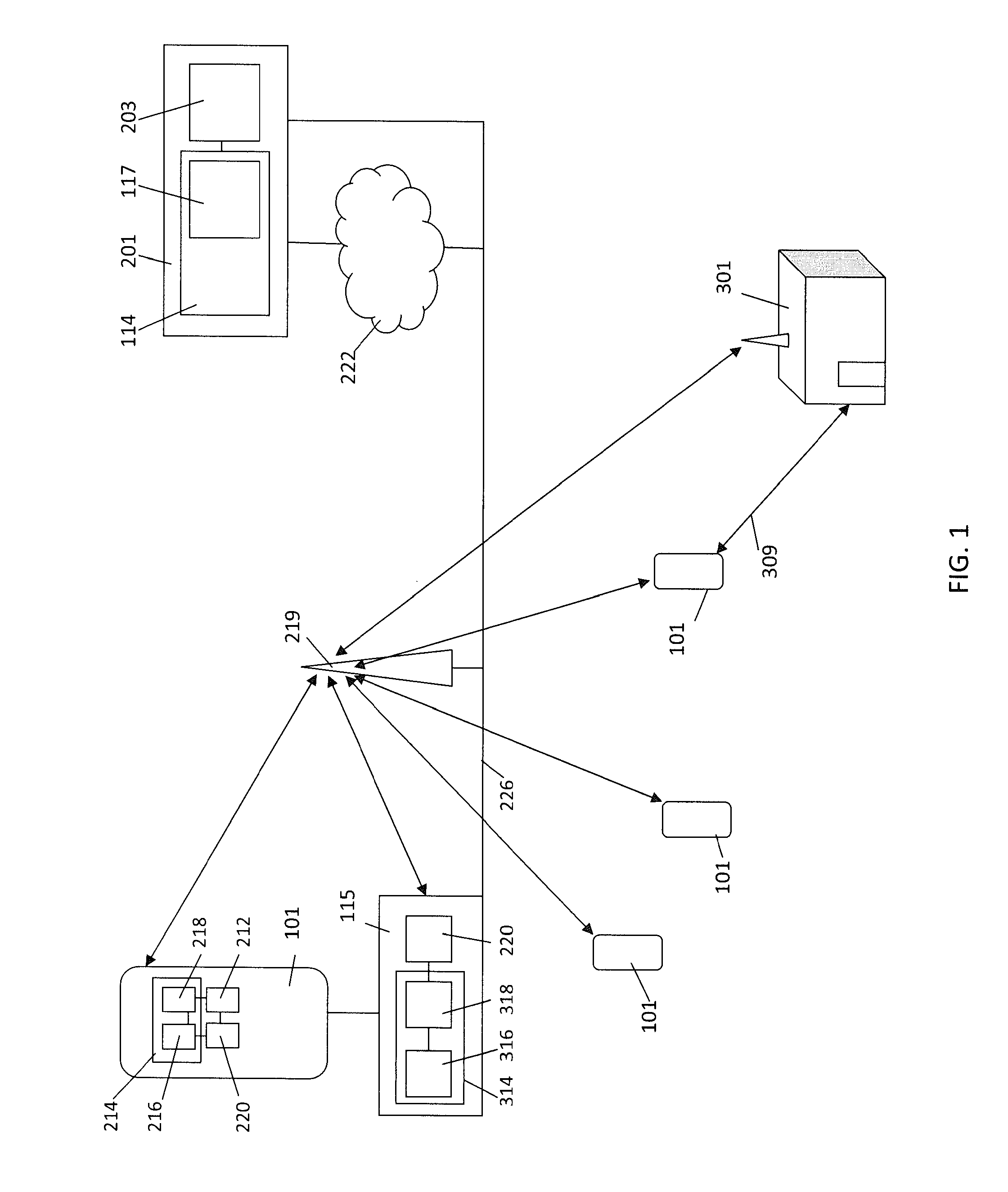
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
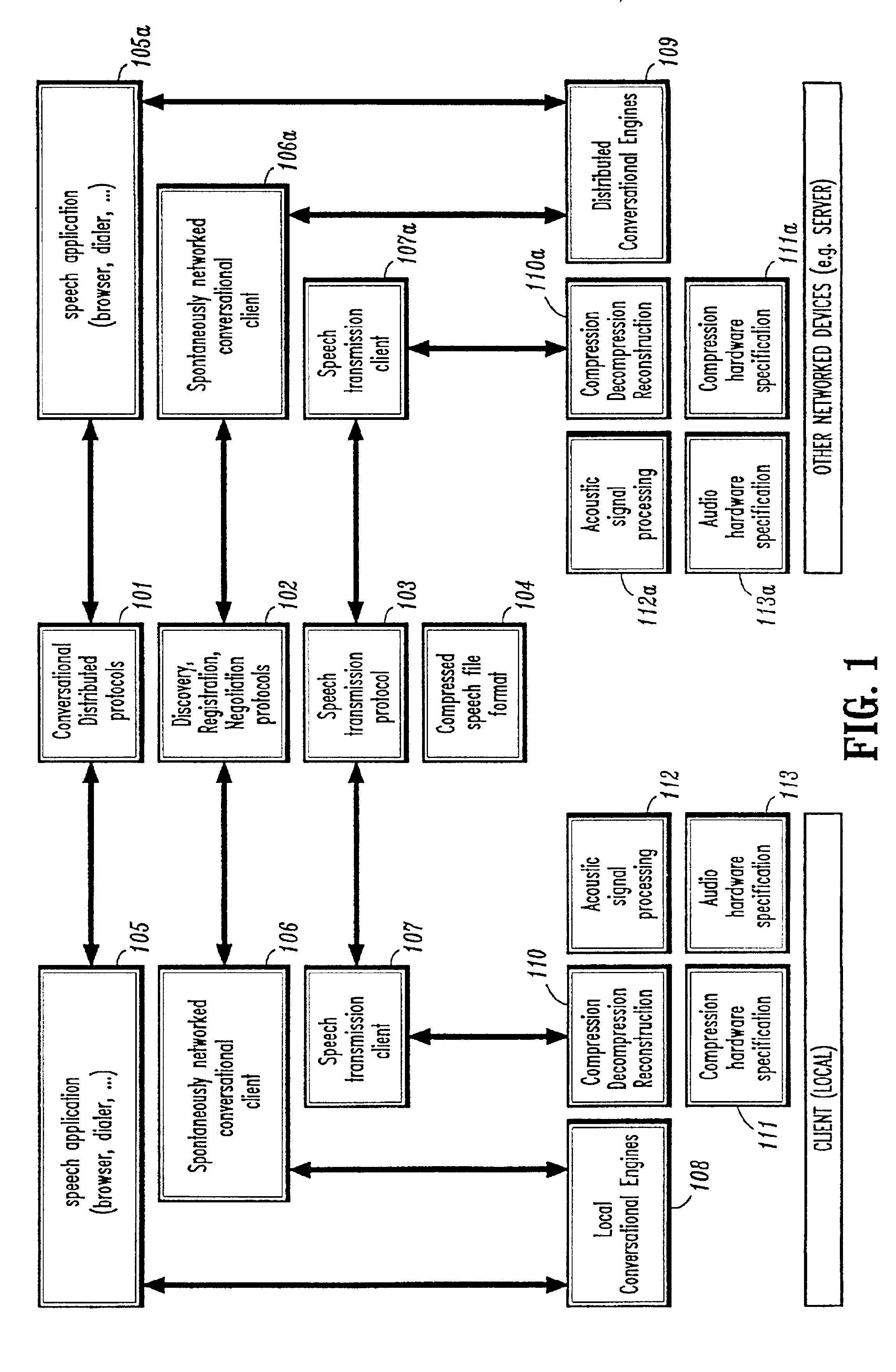
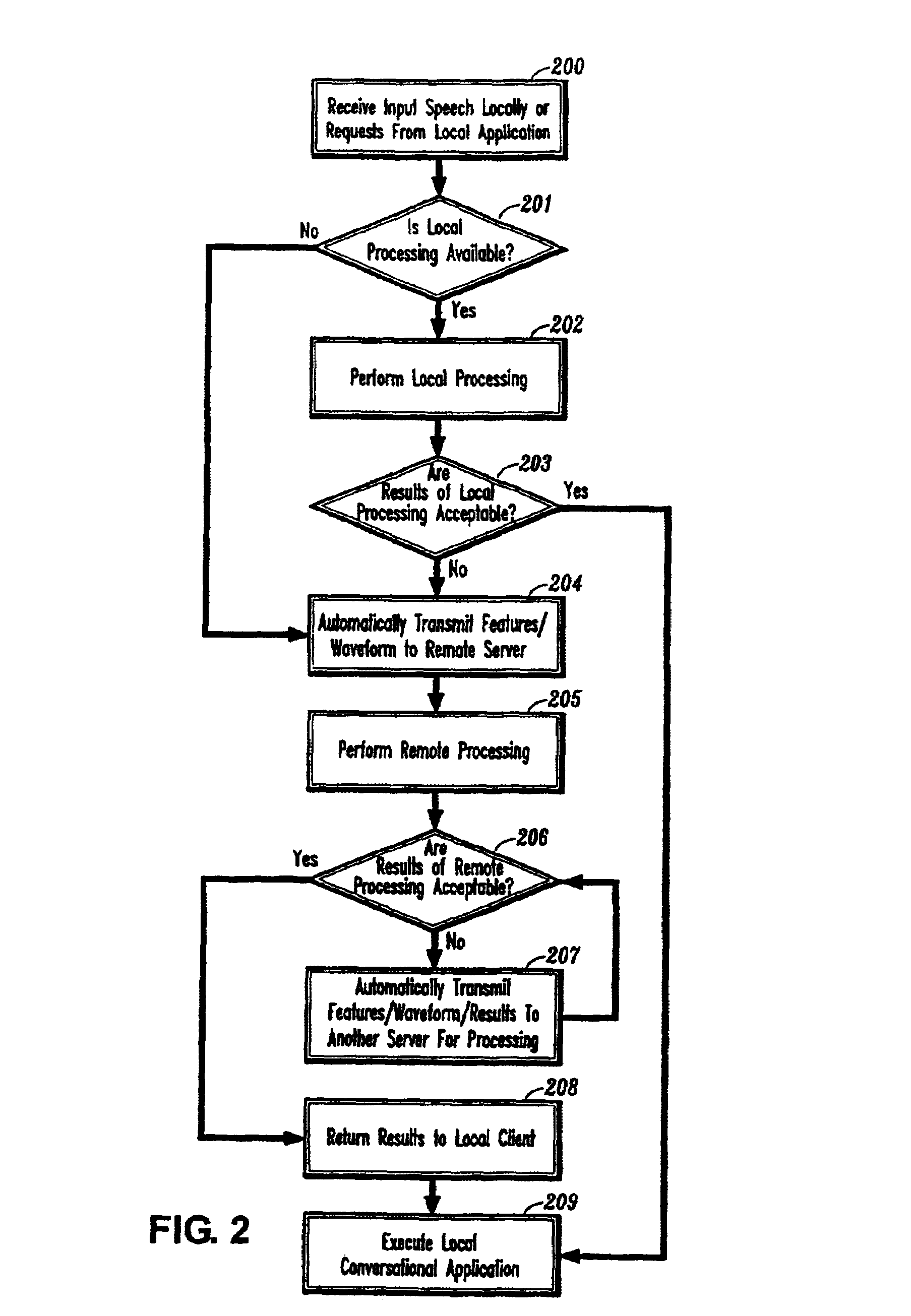
System and method for providing network coordinated conversational services
InactiveUS7003463B1Complex capabilitySimplifies taskMultiple digital computer combinationsSpeech recognitionApplication softwareDistributed computing
A system and method for providing automatic and coordinated sharing of conversational resources, e.g., functions and arguments, between network-connected servers and devices and their corresponding applications. In one aspect, a system for providing automatic and coordinated sharing of conversational resources inlcudes a network having a first and second network device, the first and second network device each comprising a set of conversational resources, a dialog manager for managing a conversation and executing calls requesting a conversational service, and a communication stack for communicating messages over the network using conversational protocols, wherein the conversational protocols establish coordinated network communication between the dialog managers of the first and second network device to automatically share the set of conversational resources of the first and second network device, when necessary, to perform their respective requested conversational service.
Owner:NUANCE COMM INC
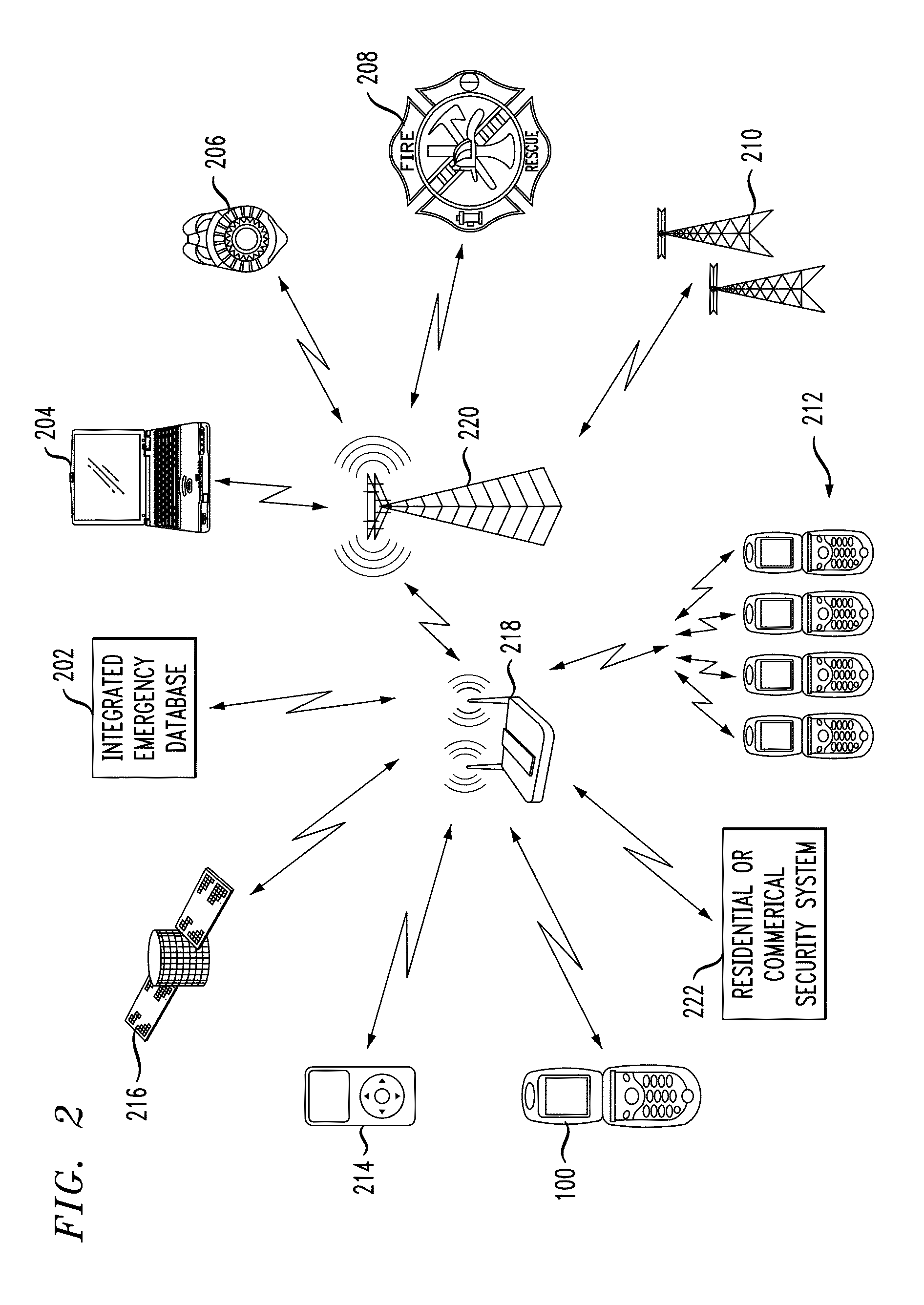
Personal safety mobile notification system
ActiveUS20130183924A1Well formedBiocideHydroxy compound active ingredientsGlobal Positioning SystemMobile device
In described embodiments, a system establishes a perimeter around an area, and mobile devices within the established perimeter communicate with a server that provides and collects personal and asset safety information. The provided information might enable users associated with the mobile devices to plan actions or take routes based on a given criteria, such as a safest route, through display on the mobile device. The collected information from the mobile device might be location, emergency event, environmental factors, sensor information and the like, which might then be communicated to users and / or administrators of the system. Location information, such as through global positioning system (GPS), might provide tracking of mobile devices and users or assets associated with each mobile device. GPS functionality associates latitude, longitude and elevation (X-Y-Z coordinate axis) data with the collected and provided information.
Owner:LIQUID RARITY EXCHANGE LLC
Method and system for location-triggered rewards
ActiveUS20110028160A1Improve consumer experienceImprove efficiencyDiscounts/incentivesSonic/ultrasonic/infrasonic transmissionServerMobile telephony
In some embodiments, techniques for rewarding presence include detecting a presence of a mobile phone within an enclosed space, transmitting information relating to the presence of the mobile phone within the enclosed space to a server computer, wherein the server computer processes an award for the presence of the mobile phone within the enclosed space, wherein the award is associated with a user account associated with the mobile phone; and receiving from the server computer information relating to the award.
Owner:SHOPKICK
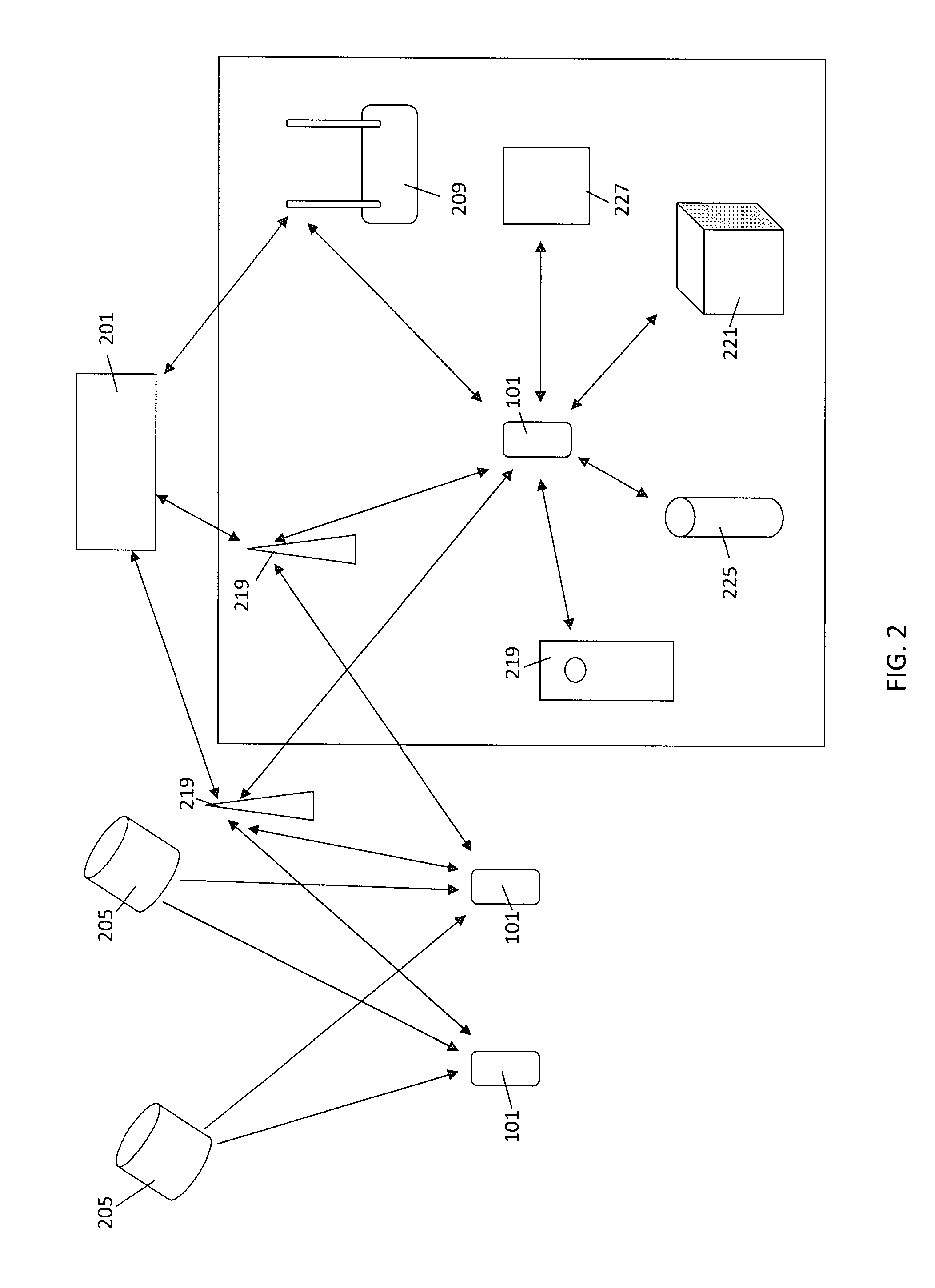
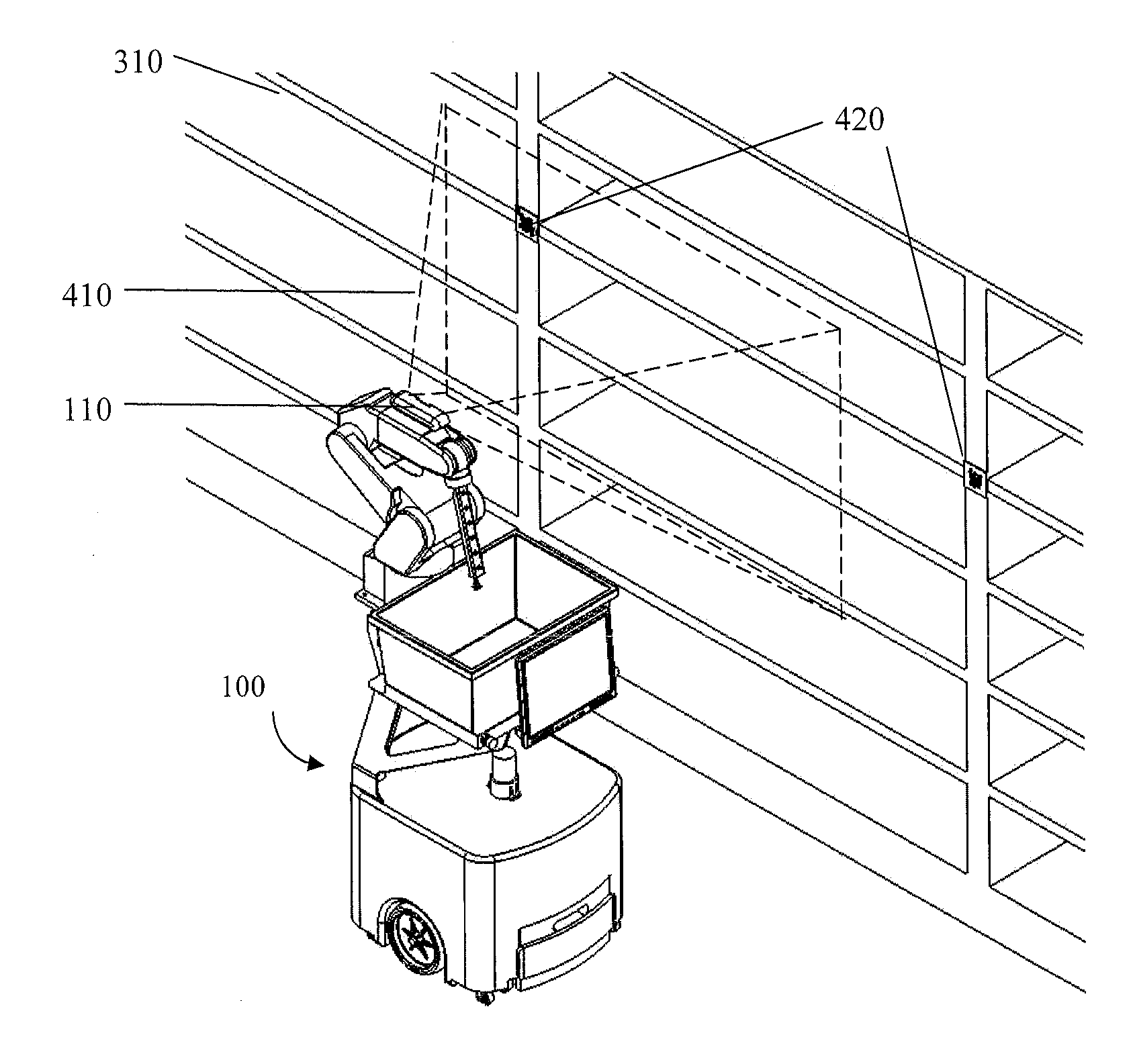
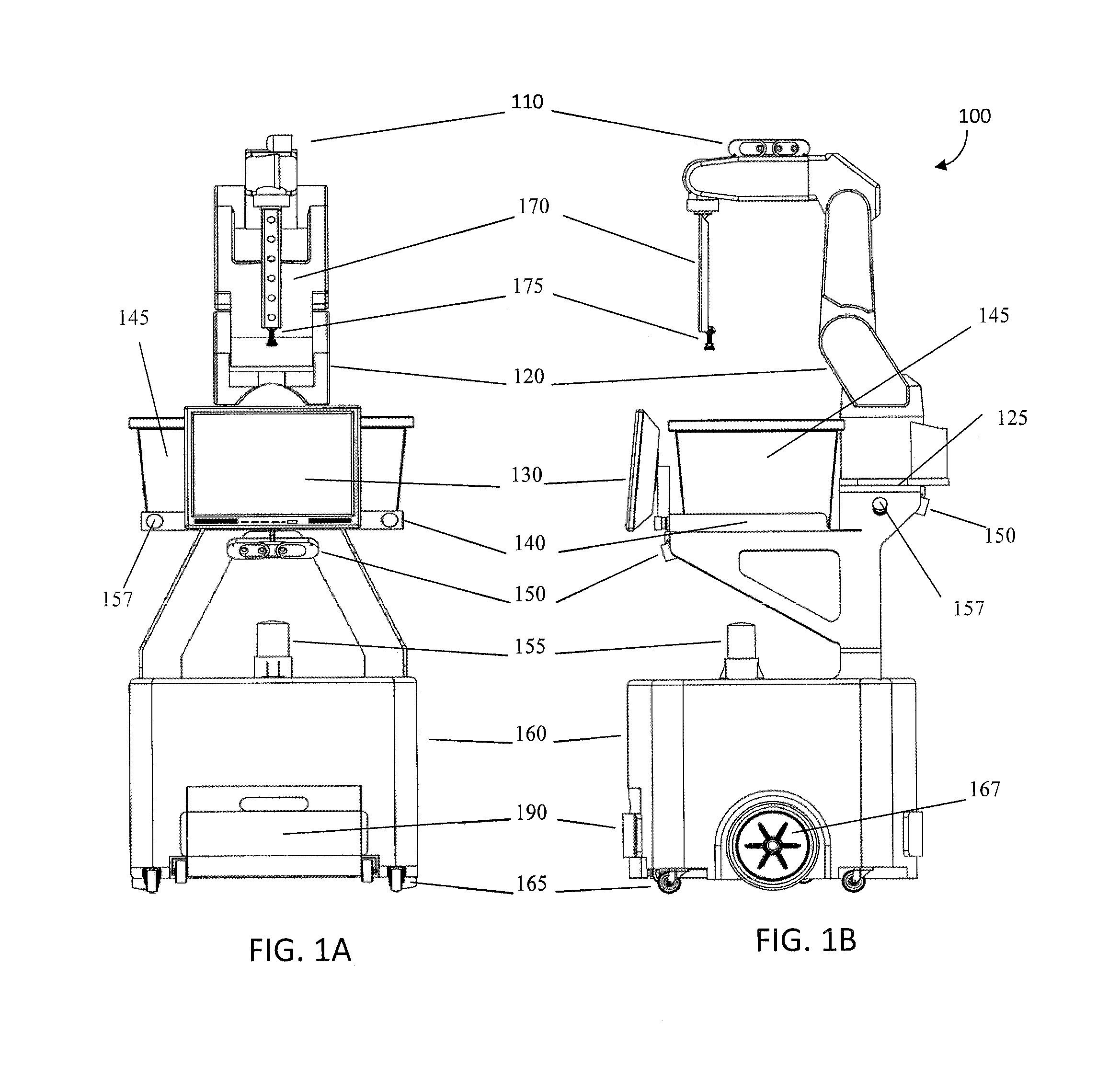
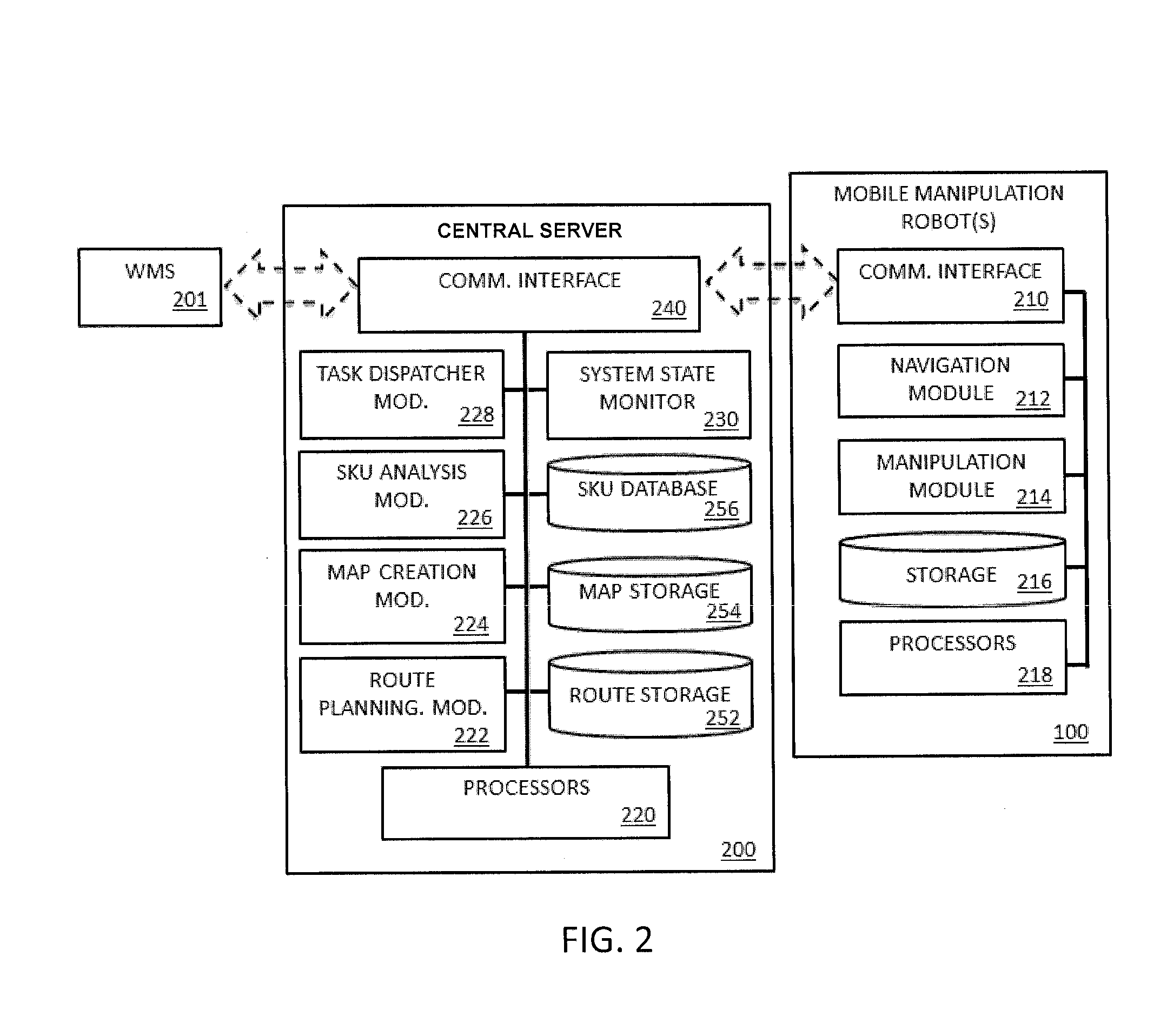
System and method for piece-picking or put-away with a mobile manipulation robot
ActiveUS20150032252A1Overcomes shortcomingReduce complexity and costProgramme-controlled manipulatorAutonomous decision making processLogistics managementPosition dependent
A method and system for piece-picking or piece put-away within a logistics facility. The system includes a central server and at least one mobile manipulation robot. The central server is configured to communicate with the robots to send and receive piece-picking data which includes a unique identification for each piece to be picked, a location within the logistics facility of the pieces to be picked, and a route for the robot to take within the logistics facility. The robots can then autonomously navigate and position themselves within the logistics facility by recognition of landmarks by at least one of a plurality of sensors. The sensors also provide signals related to detection, identification, and location of a piece to be picked or put-away, and processors on the robots analyze the sensor information to generate movements of a unique articulated arm and end effector on the robot to pick or put-away the piece.
Owner:IAM ROBOTICS
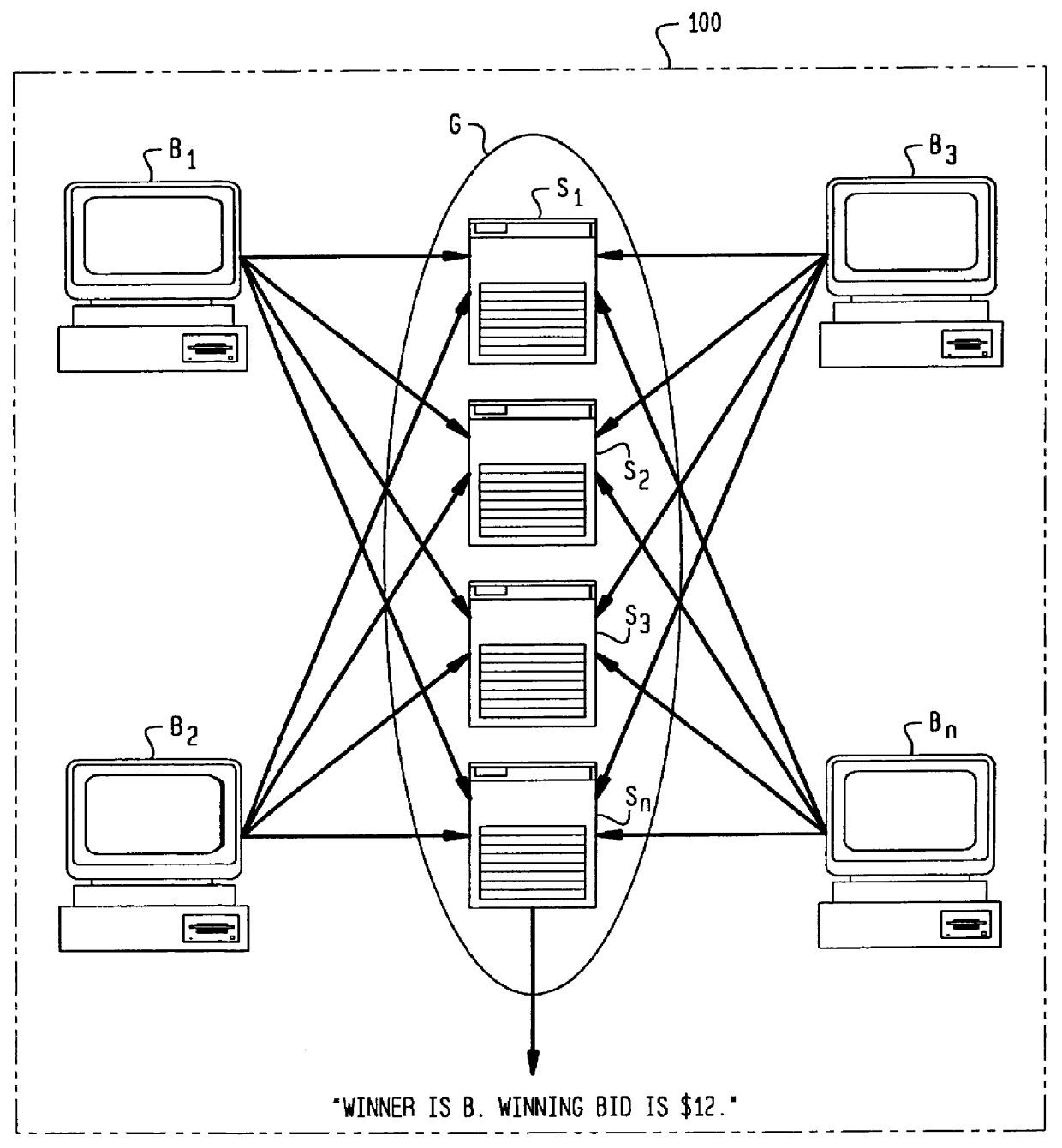
Secure auction systems
InactiveUS6055518AEasy to rebuildFinanceUser identity/authority verificationFinancial transactionMonetary value
The apparatus and method of the present invention provide secure auction service for use in a network having servers and bidding terminals. The auction service makes transactions among servers and bidding terminals subject to a distributed protocol. The distributed protocol distributes submitted bids among the multiple servers, closes a bidding period, verifies validity of monetary value of each submitted bid by utilizing said distributed protocol and determines a winning bidder.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
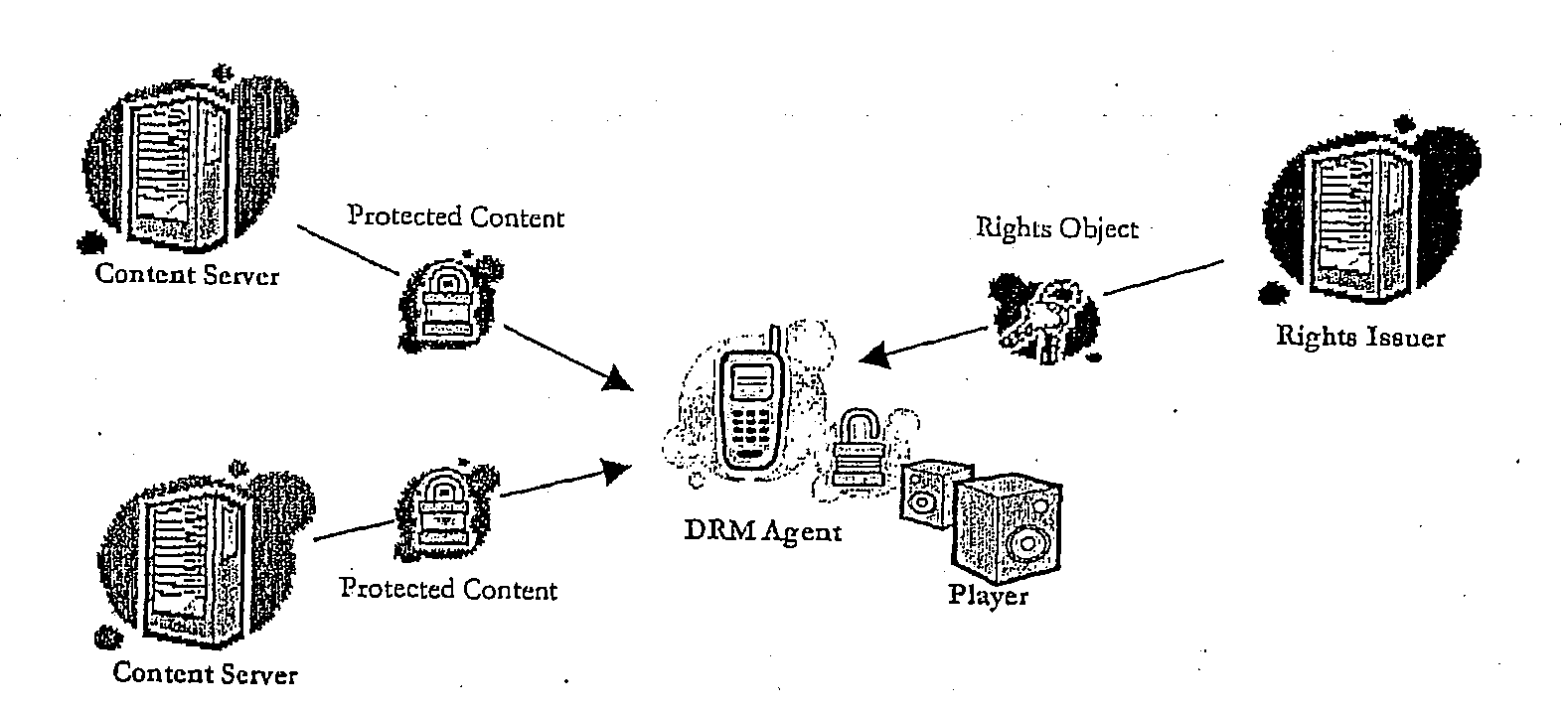
Method of Providing Digital Rights Management for Music Content by Means of a Flat-Rate Subscription
ActiveUS20100031366A1Reliable and goodEasy to manageMetering/charging/biilling arrangementsDigital data processing detailsOperational systemComputer network
The invention enables digital music content to be downloaded to and used on a portable wireless computing device. An application running on the wireless device has been automatically adapted to parameters associated with the wireless device without end-user input (e.g. the application has been configured in dependence on the device OS and firmware, related bugs, screen size, pixel number, security models, connection handling, memory etc. This application enables an end-user to browse and search music content on a remote server using a wireless network; to download music content from that remote server using the wireless network and to playback and manage that downloaded music content. The application also includes a digital rights management system that enables unlimited legal downloads of different music tracks to the device and also enables any of those tracks stored on the device to be played so long as a subscription service has not terminated.
Owner:TIKTOK PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com