Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
429 results about "File allocation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
File allocation methods are basically ways in which any file is stored in the memory block of the system. A lot of useless information is given on GeeksforGeeks which is not relevant for placements. We have only covered what is necessary. In this method for any file in the memory block, it occupies a Contagious i.e. continuous set of memory blocks.
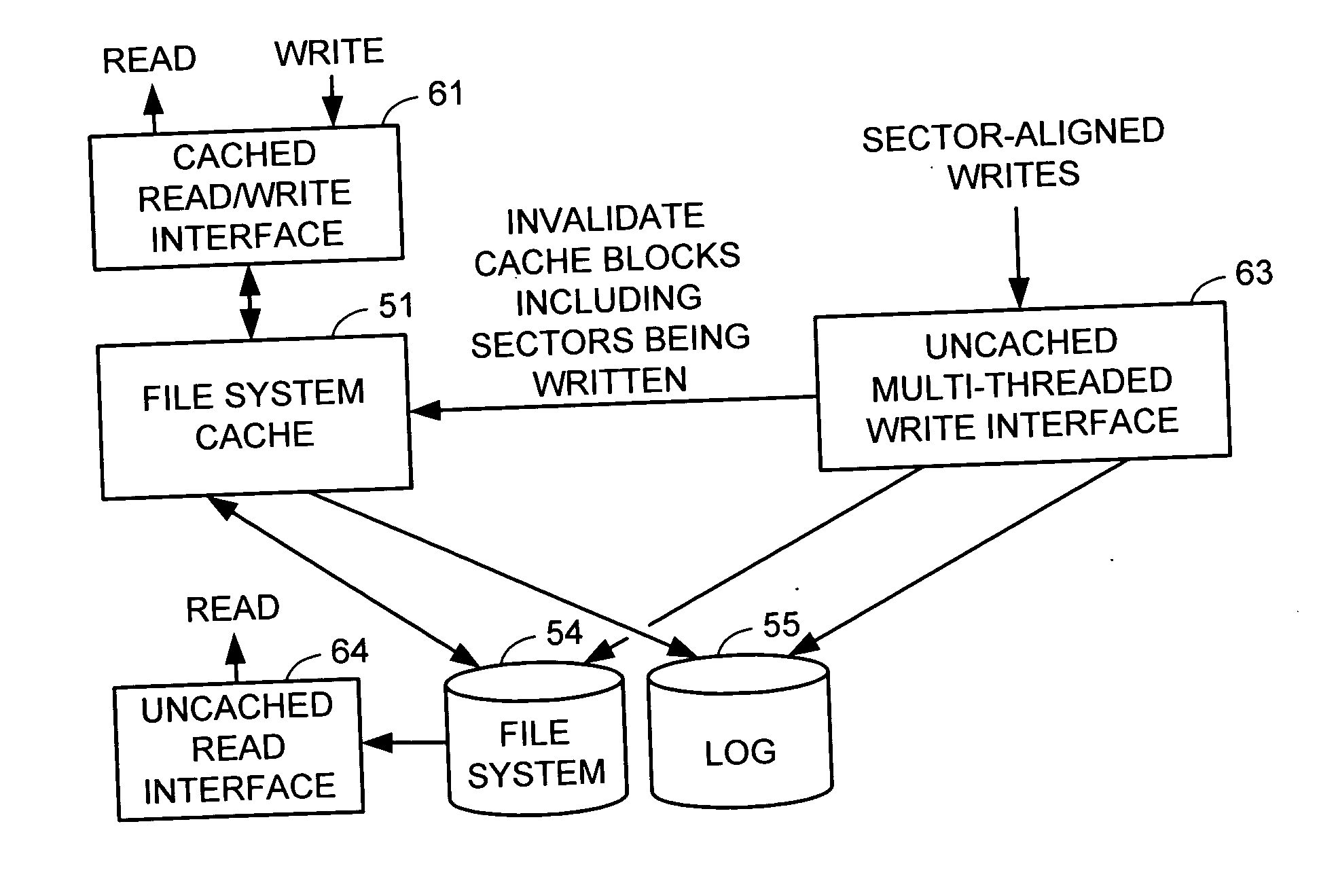
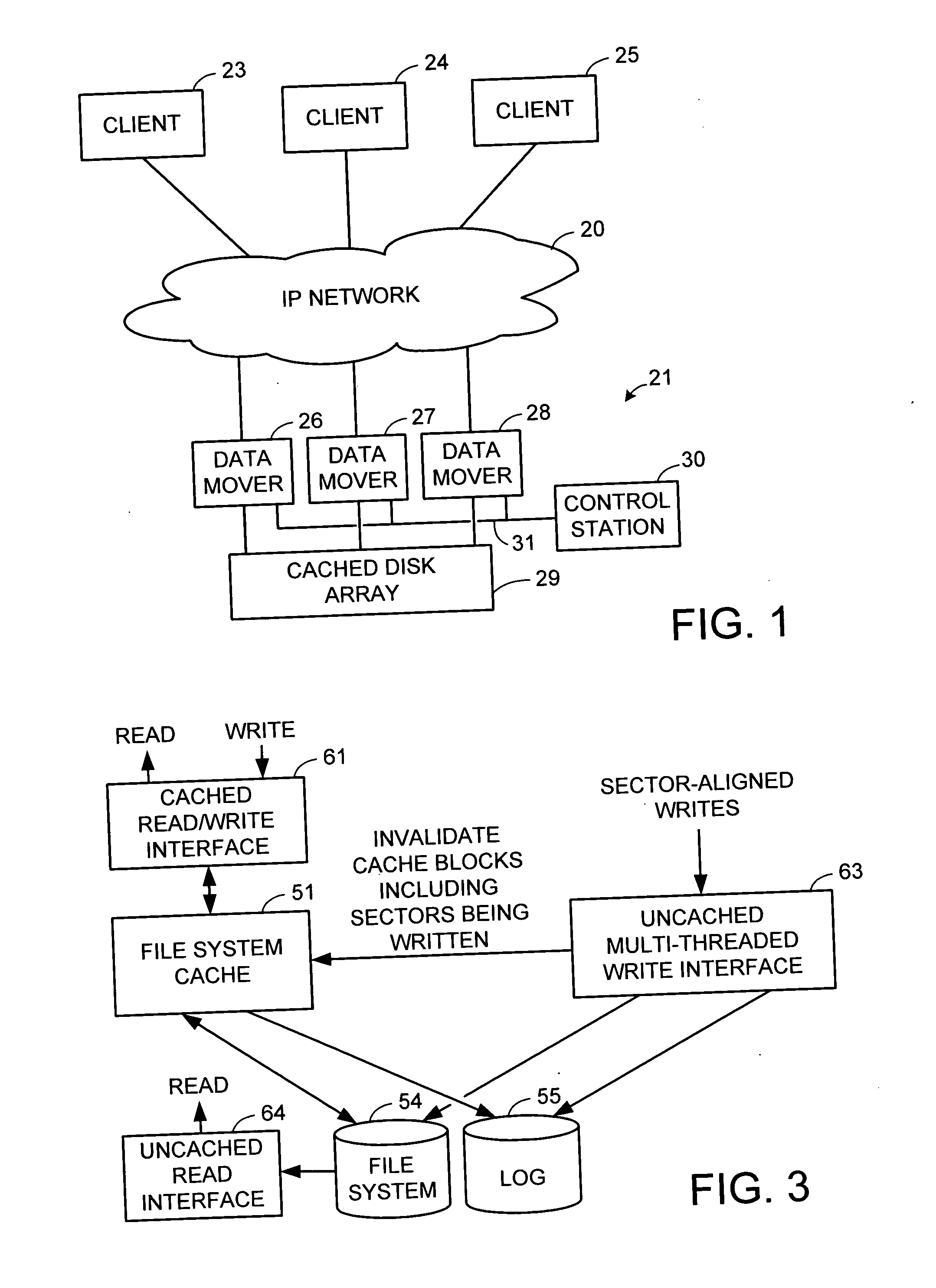
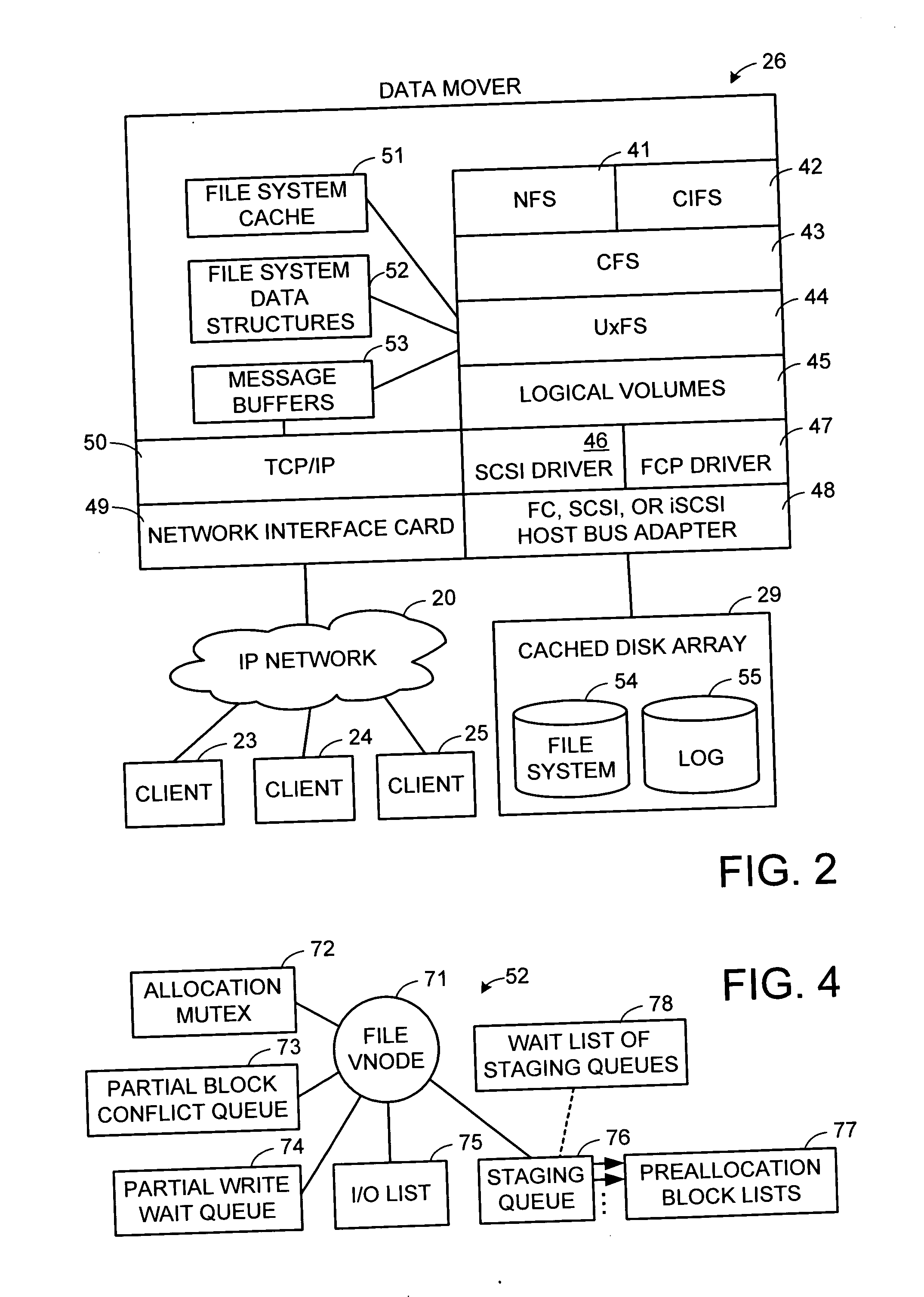
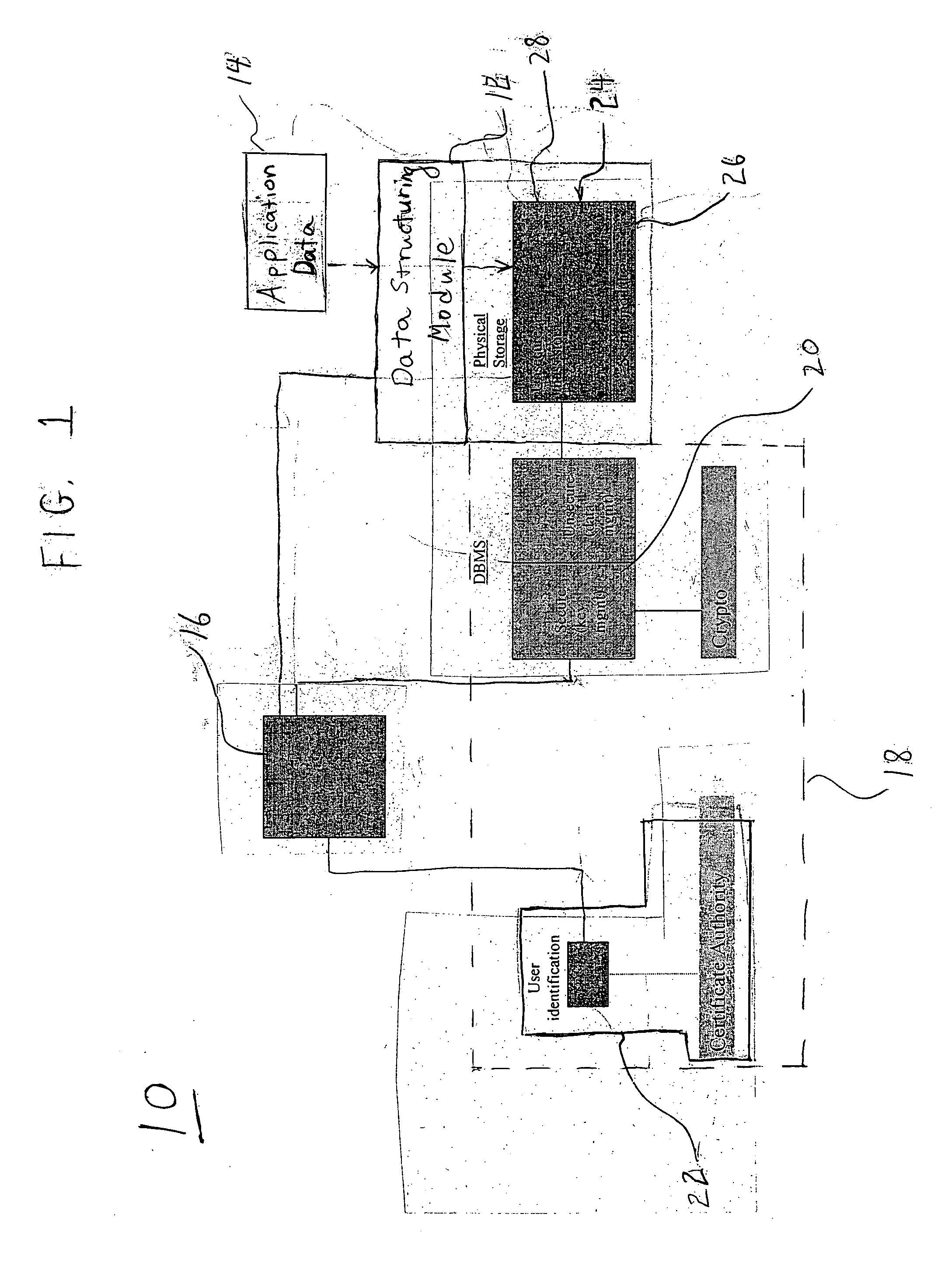
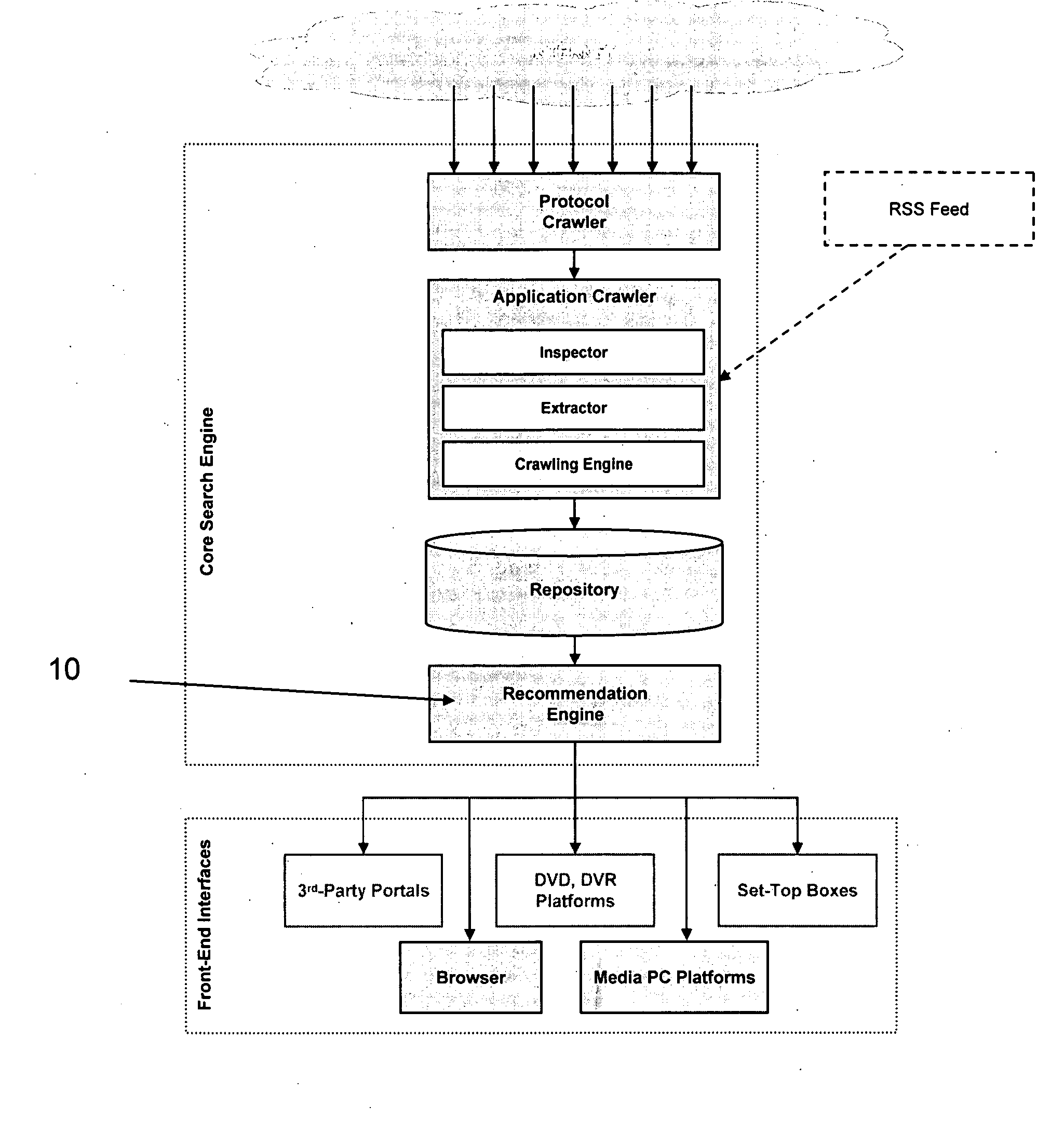
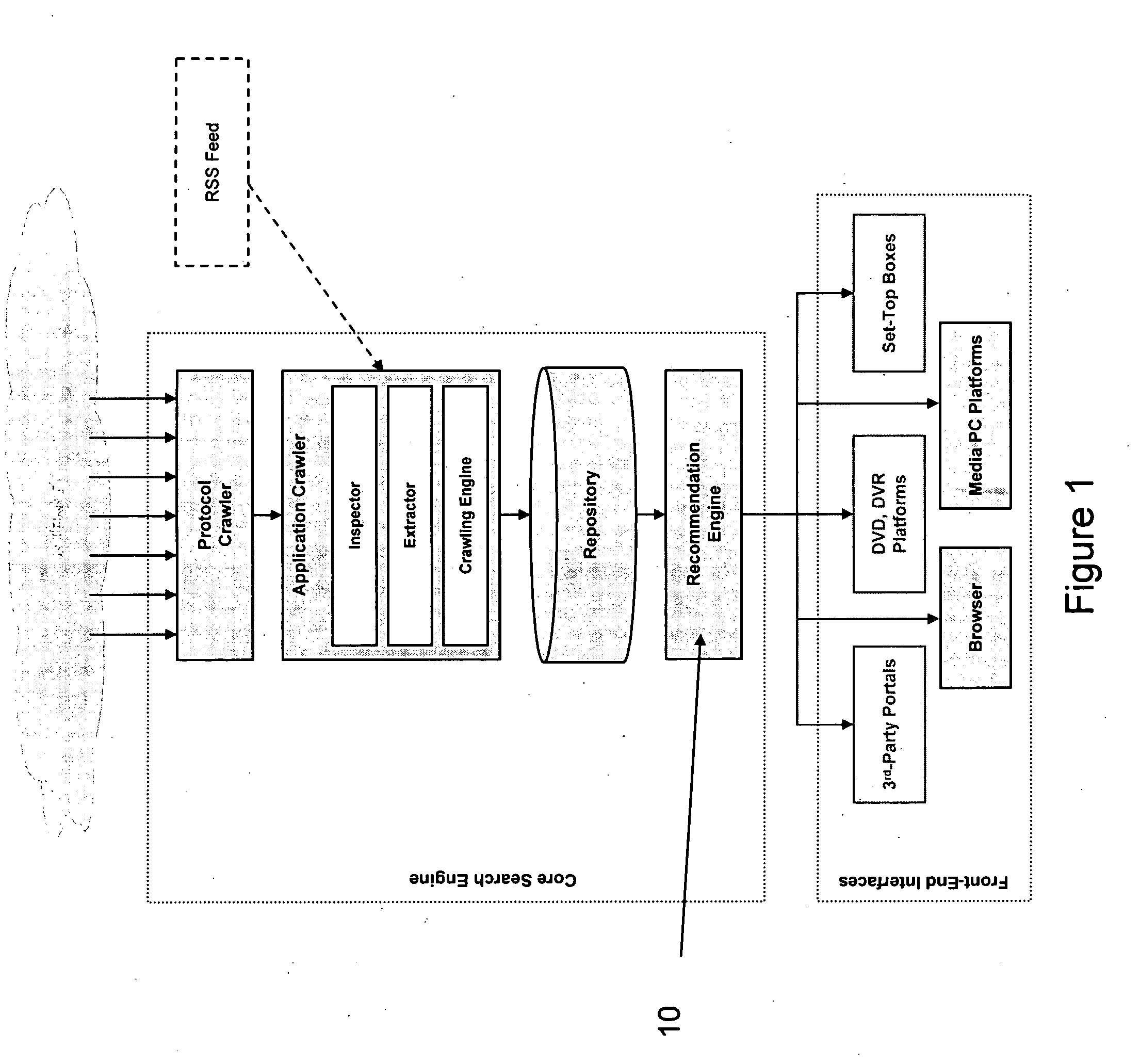
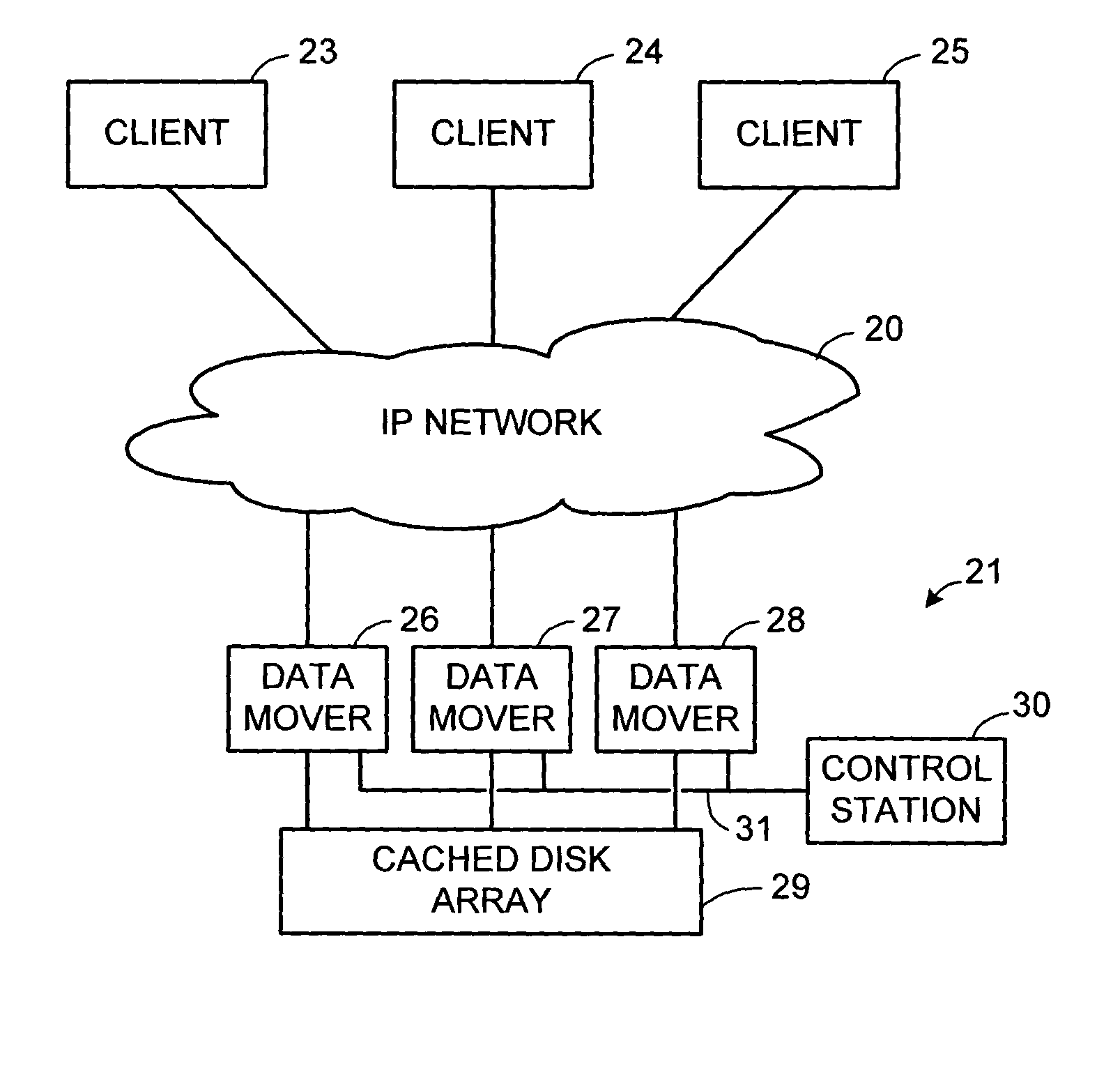
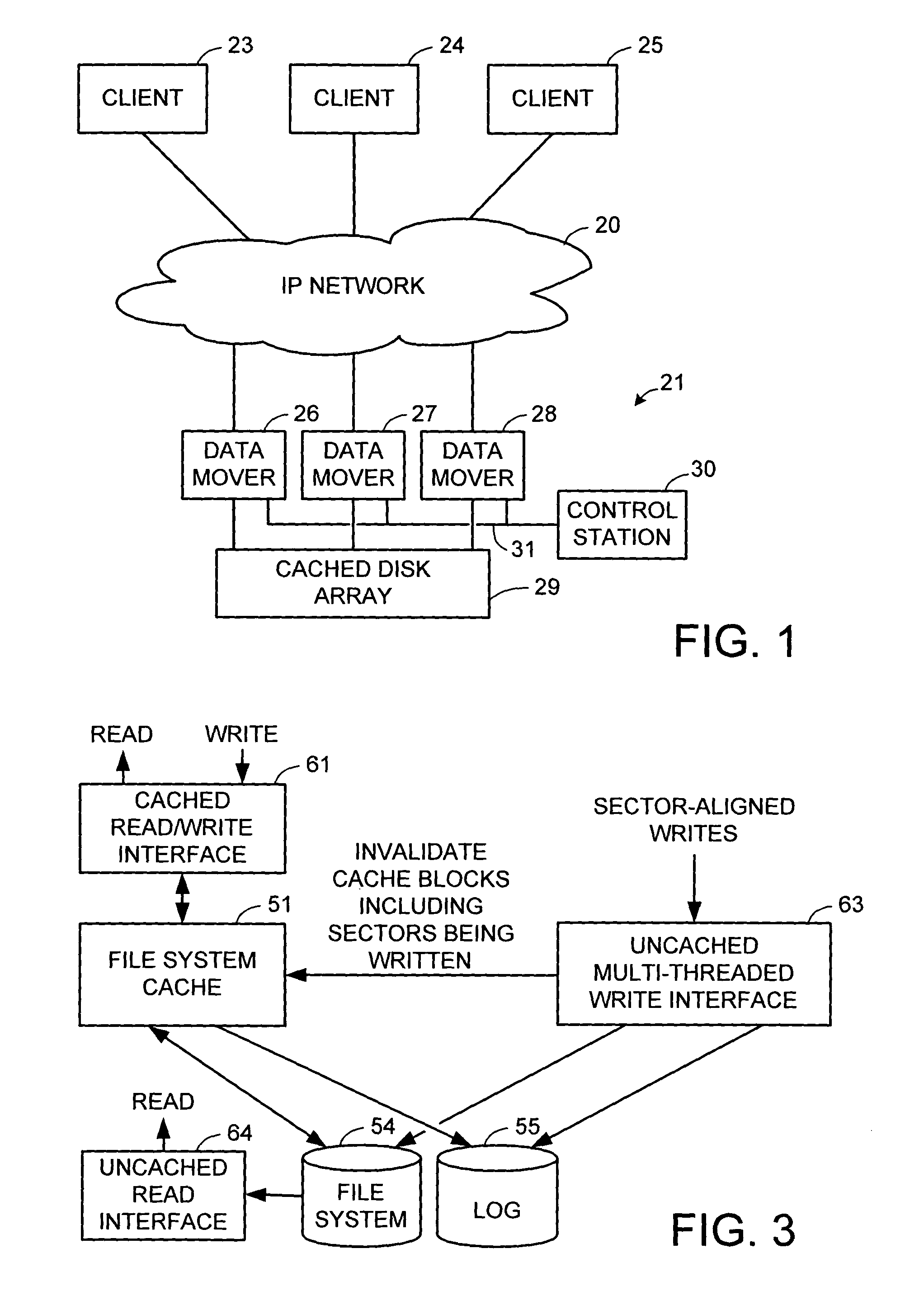
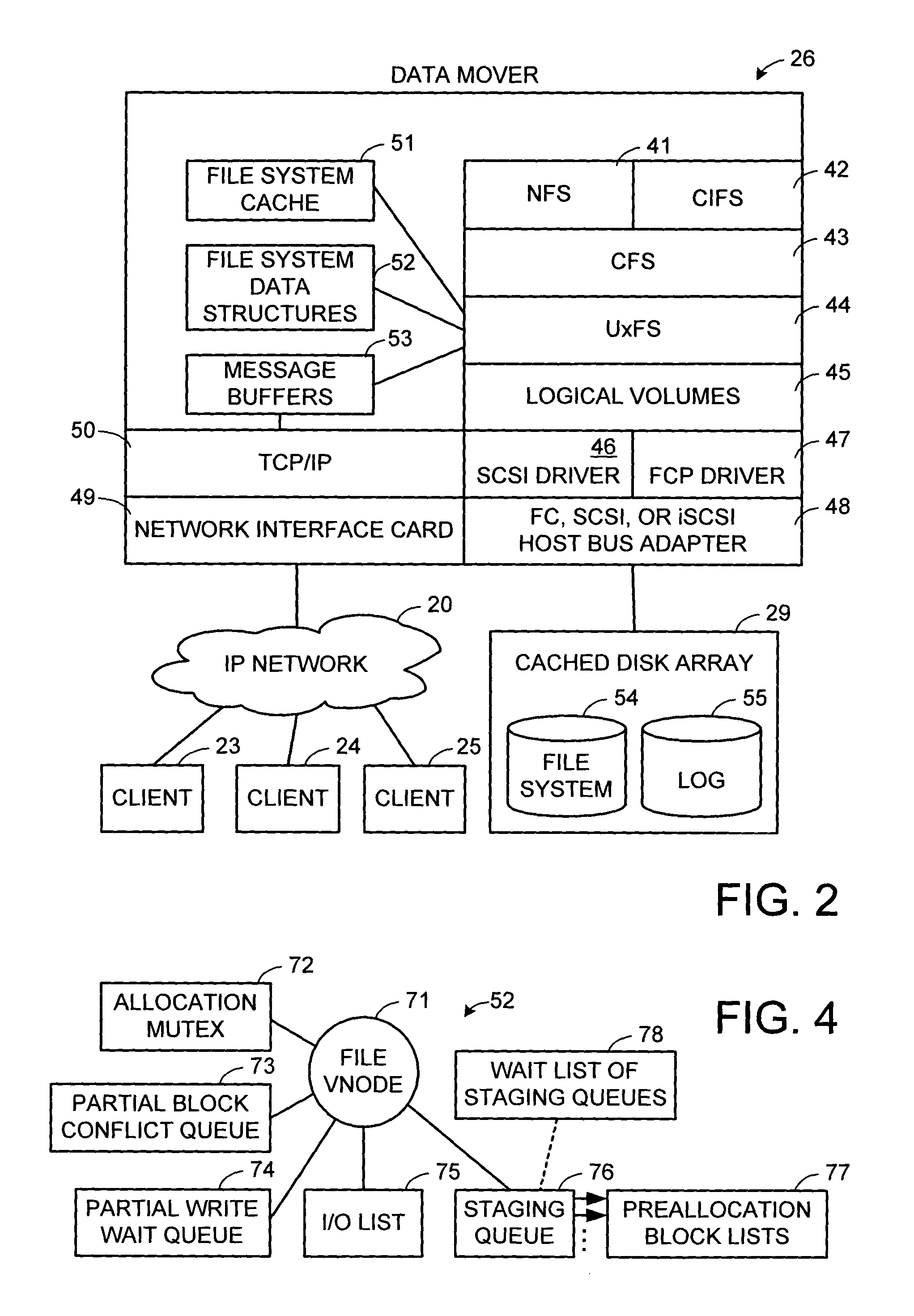
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS20050066095A1Digital data information retrievalDigital data processing detailsData integrityFile allocation
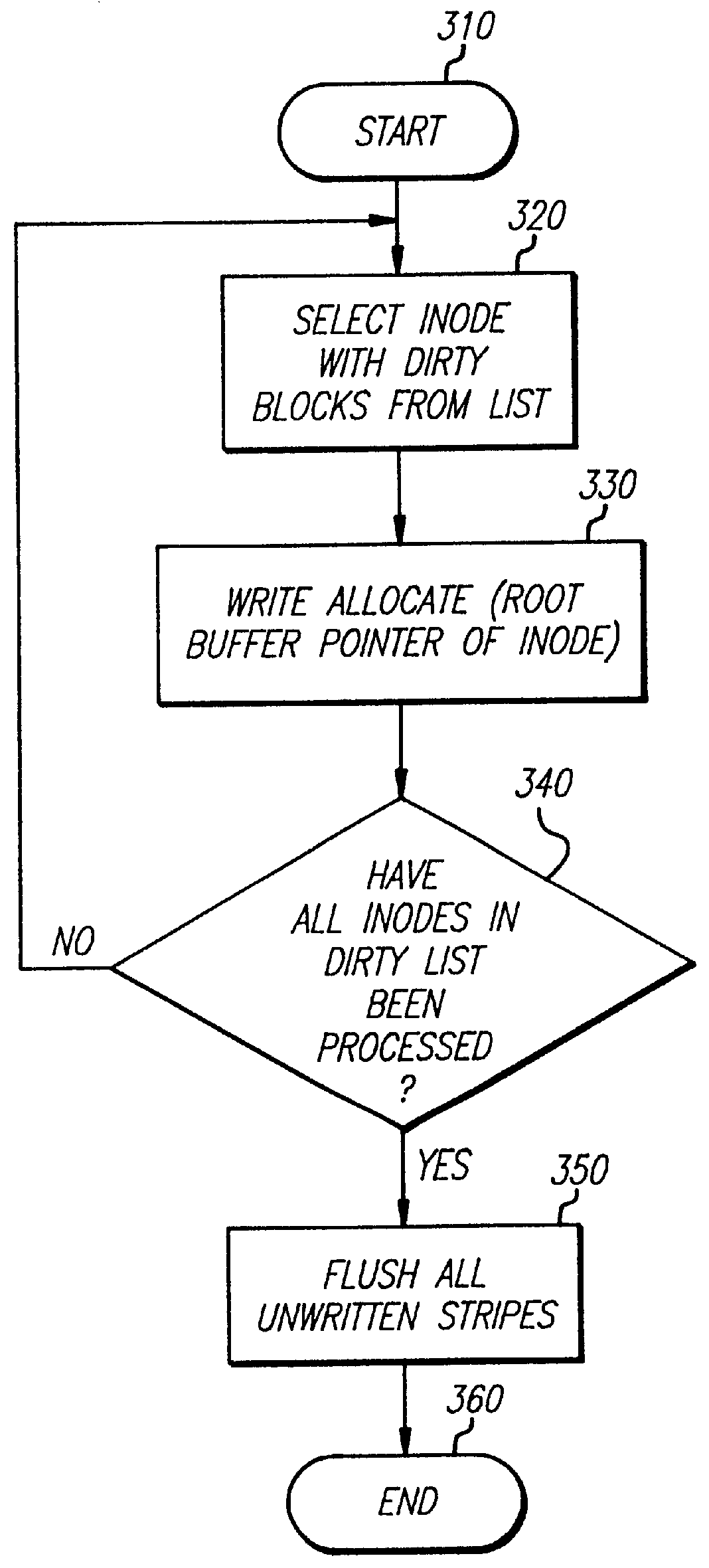
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
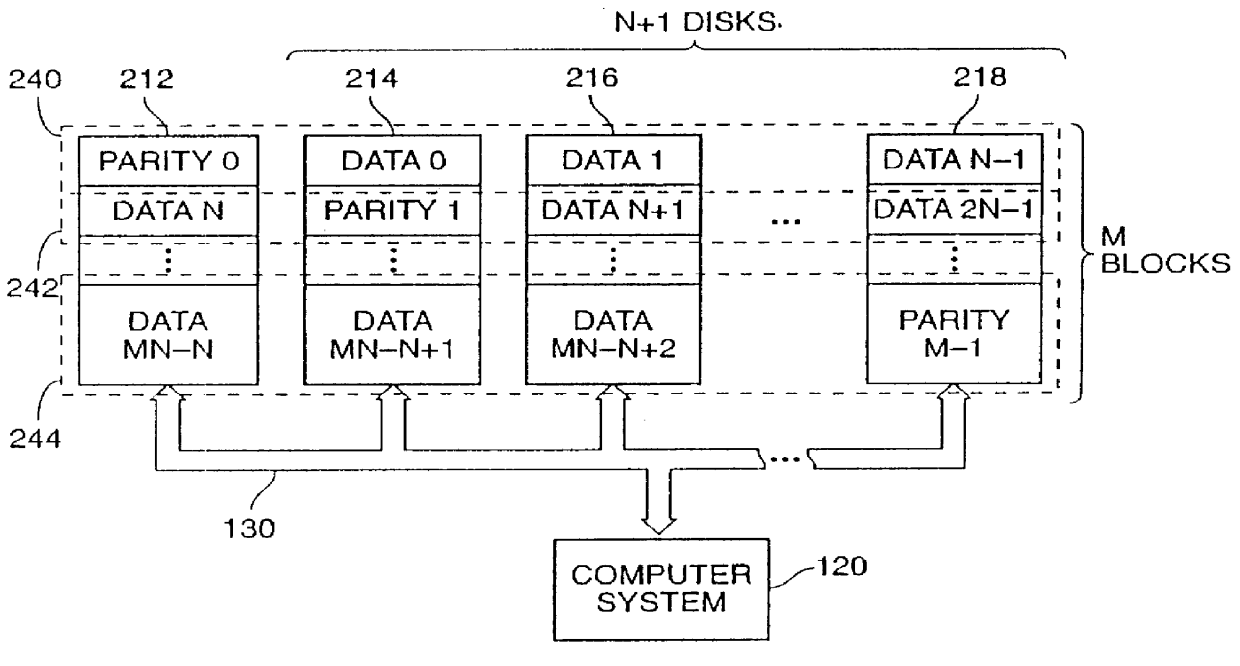
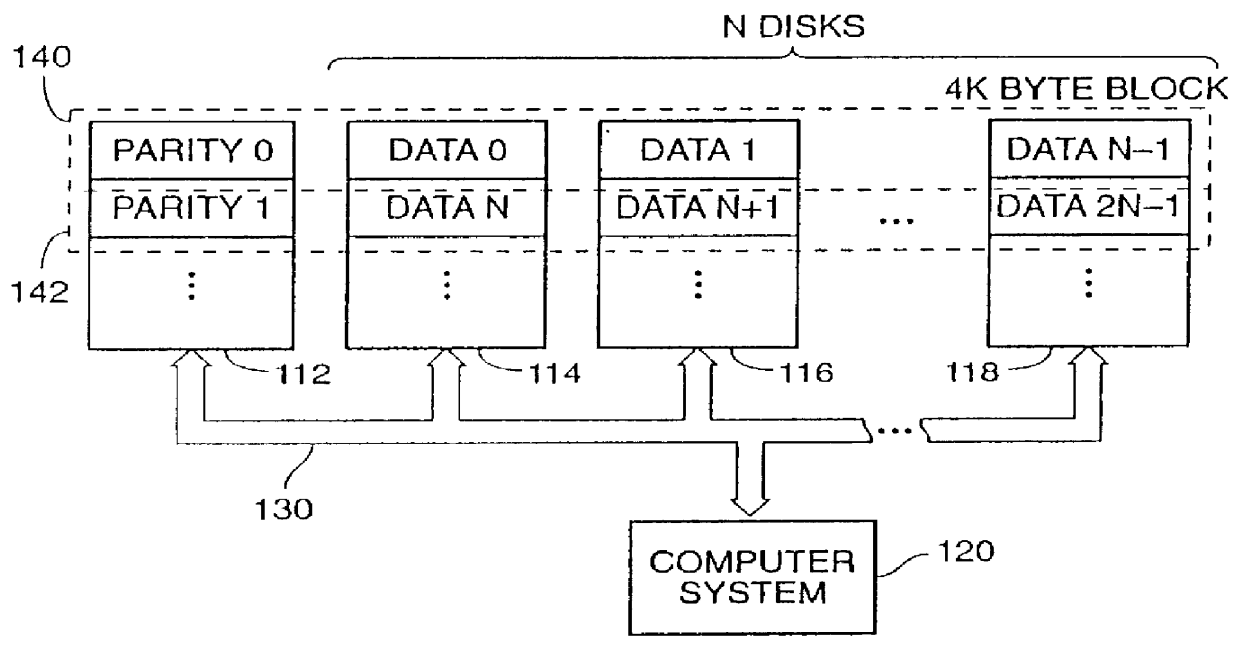
Method for allocating files in a file system integrated with a RAID disk sub-system
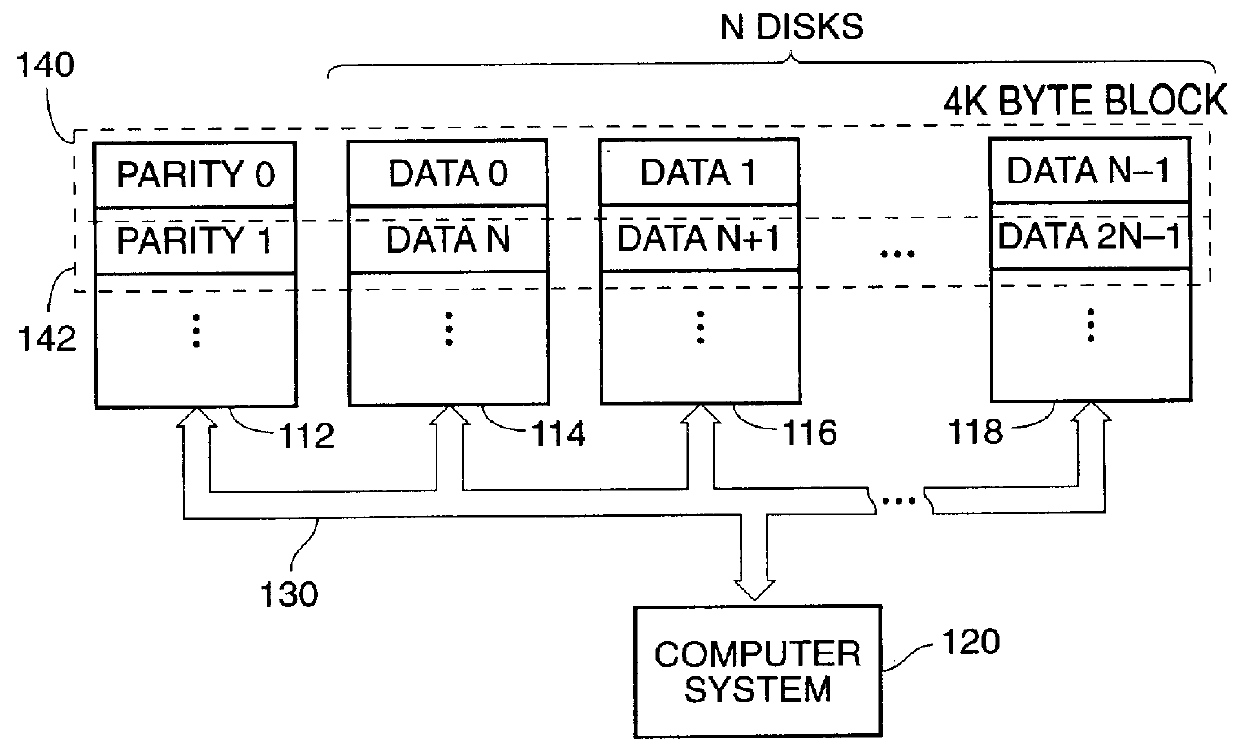
The present invention is a method for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The present invention uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The present invention satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disk is chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
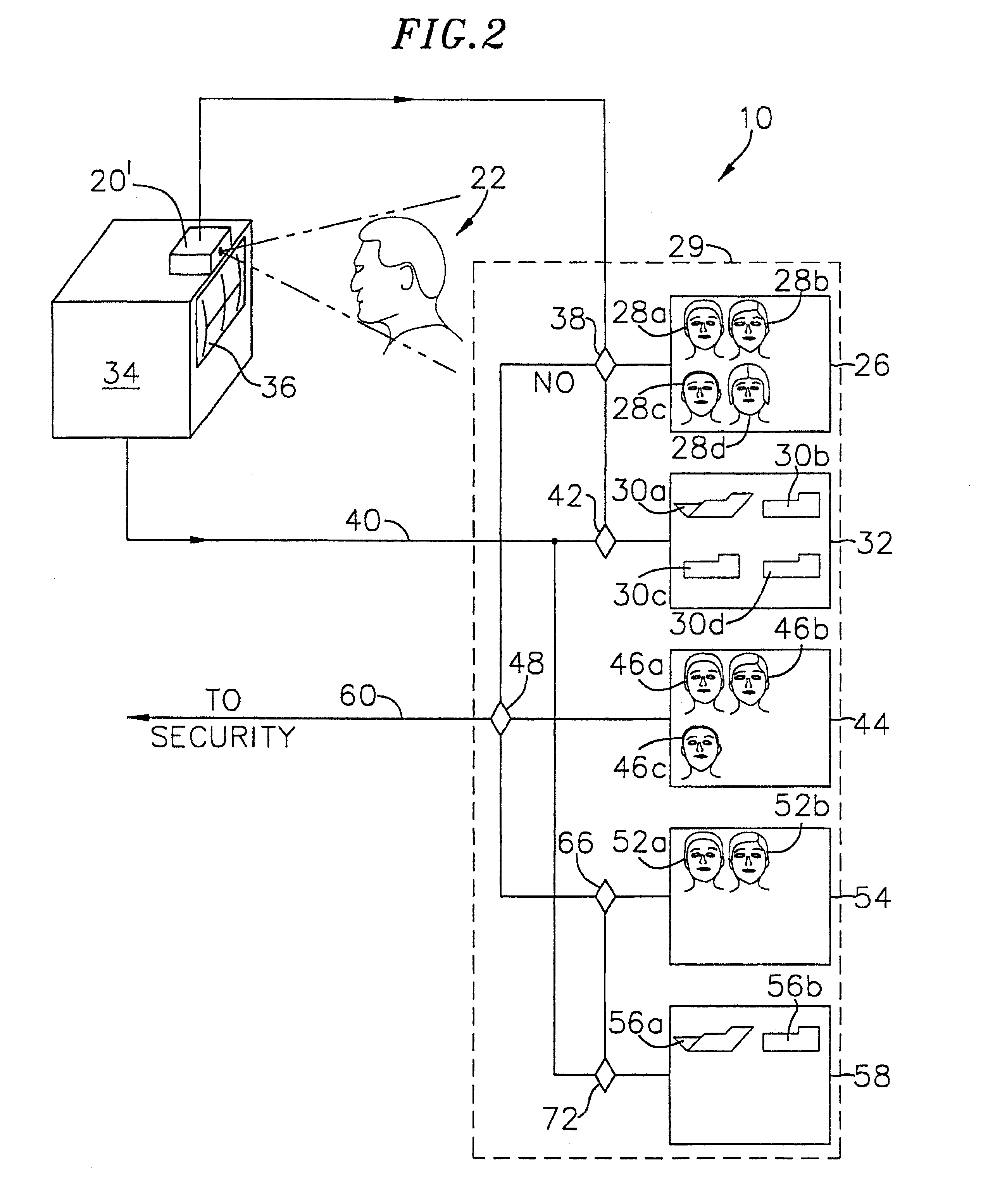
Passive biometric customer identification and tracking system
InactiveUS6554705B1Simplifies search techniqueMinimal useCharacter and pattern recognitionApparatus for meter-controlled dispensingBiometric dataFile allocation
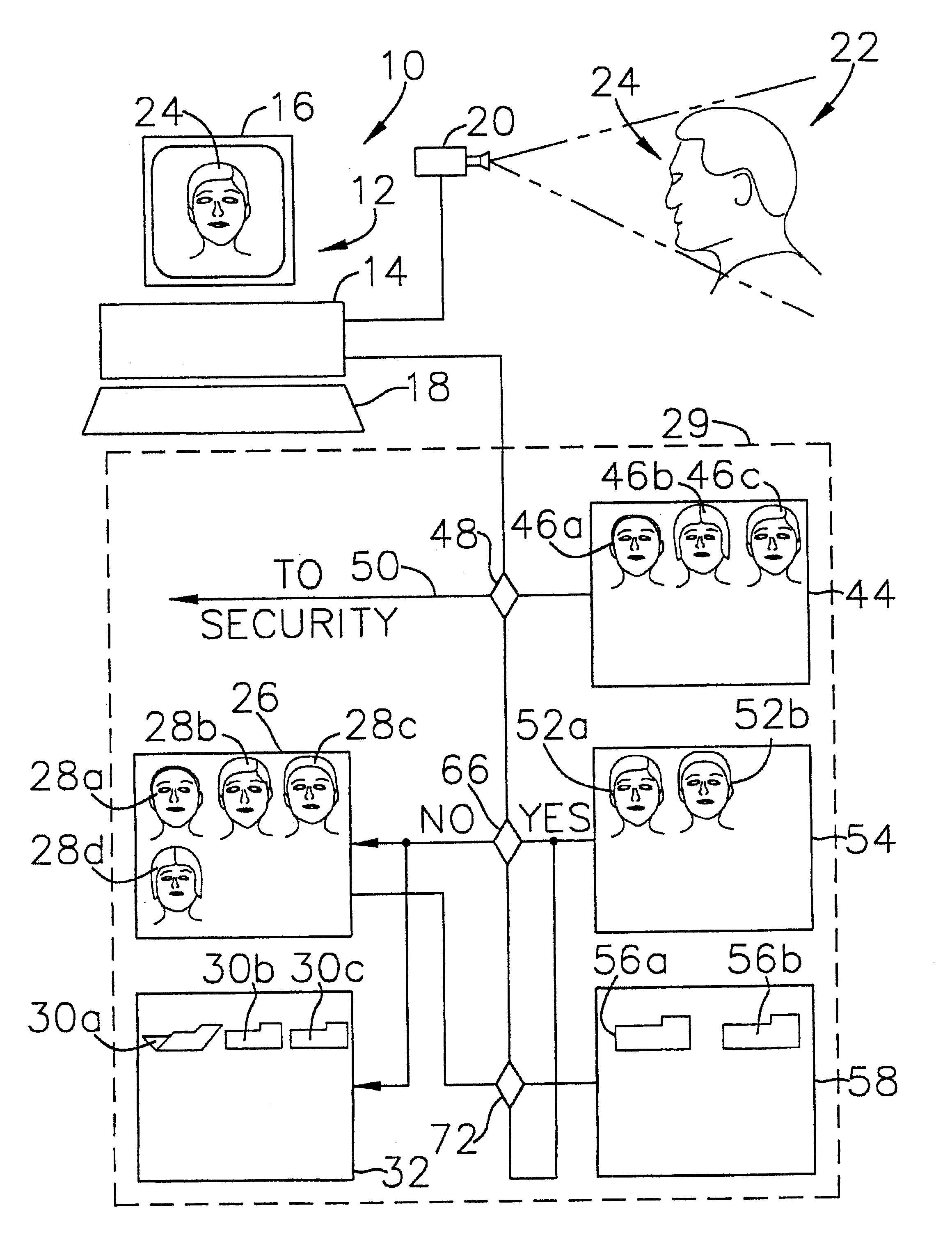
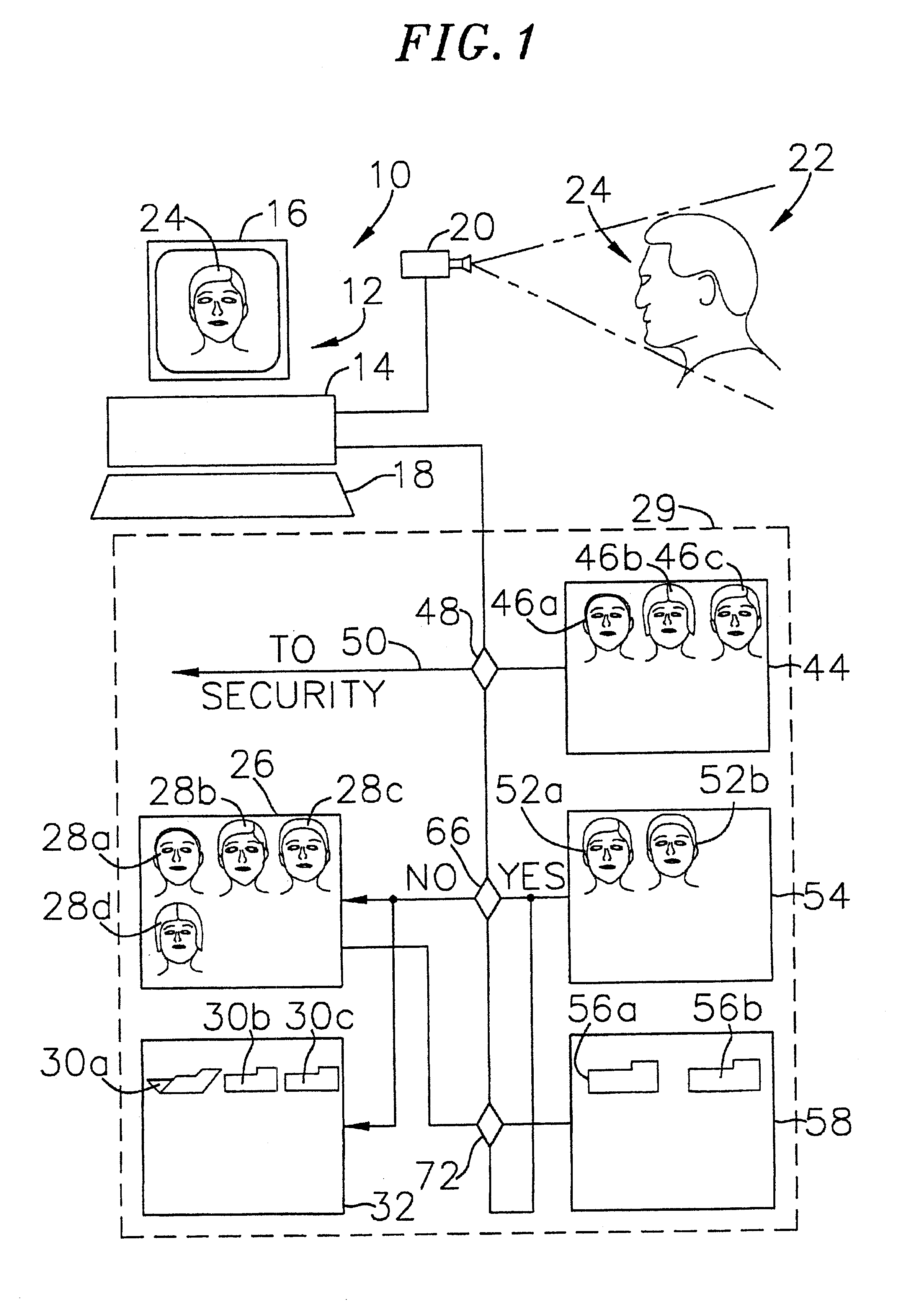
A computer-based customer tracking system uses a passive biometric identification for identifying customers. Neither the customer, nor any establishment personnel, are required to enter any informational data with respect to the customer; identification is done completely biometrically. Biometric identification information is sent to a central computer processor, which searches files in a library for matching biometric data. If no match is found, the processor opens a new file in the library, assigning a code or identification number to the file. Information with respect to the customer's biometric data, along with any transactional information, are stored in the file. If prior activity information stored in the file exceeds a predetermined level, information with respect to the customer's prior activity is retrieved from the file and sent to a terminal, preferably at the location of the transaction. Any new information from the transaction is then sent to the processor and stored for future access. The processor scans the files periodically, and deletes files for which the activity level in the file is below a certain predetermined level over a preselected time period. Deletion of inactive files precludes the processor memory from being overloaded with information which is not useful to the establishment, and also reduces the amount of time necessary for the processor to search library files for biometric matches.
Owner:BIOMETRIC RECOGNITION
Method for allocating files in a file system integrated with a raid disk sub-system
A method is disclosed for integrating a file system with a RAID array that exports precise information about the arrangement of data blocks in the RAID subsystem. The file system examines this information and uses it to optimize the location of blocks as they are written to the RAID system. Thus, the system uses explicit knowledge of the underlying RAID disk layout to schedule disk allocation. The method uses separate current-write location (CWL) pointers for each disk in the disk array where the pointers simply advance through the disks as writes occur. The algorithm used has two primary goals. The first goal is to keep the CWL pointers as close together as possible, thereby improving RAID efficiency by writing to multiple blocks in the stripe simultaneously. The second goal is to allocate adjacent blocks in a file on the same disk, thereby improving read back performance. The method satisfies the first goal by always writing on the disk with the lowest CWL pointer. For the second goal, a new disks chosen only when the algorithm starts allocating space for a new file, or when it has allocated N blocks on the same disk for a single file. A sufficient number of blocks is defined as all the buffers in a chunk of N sequential buffers in a file. The result is that CWL pointers are never more than N blocks apart on different disks, and large files have N consecutive blocks on the same disk.
Owner:NETWORK APPLIANCE INC
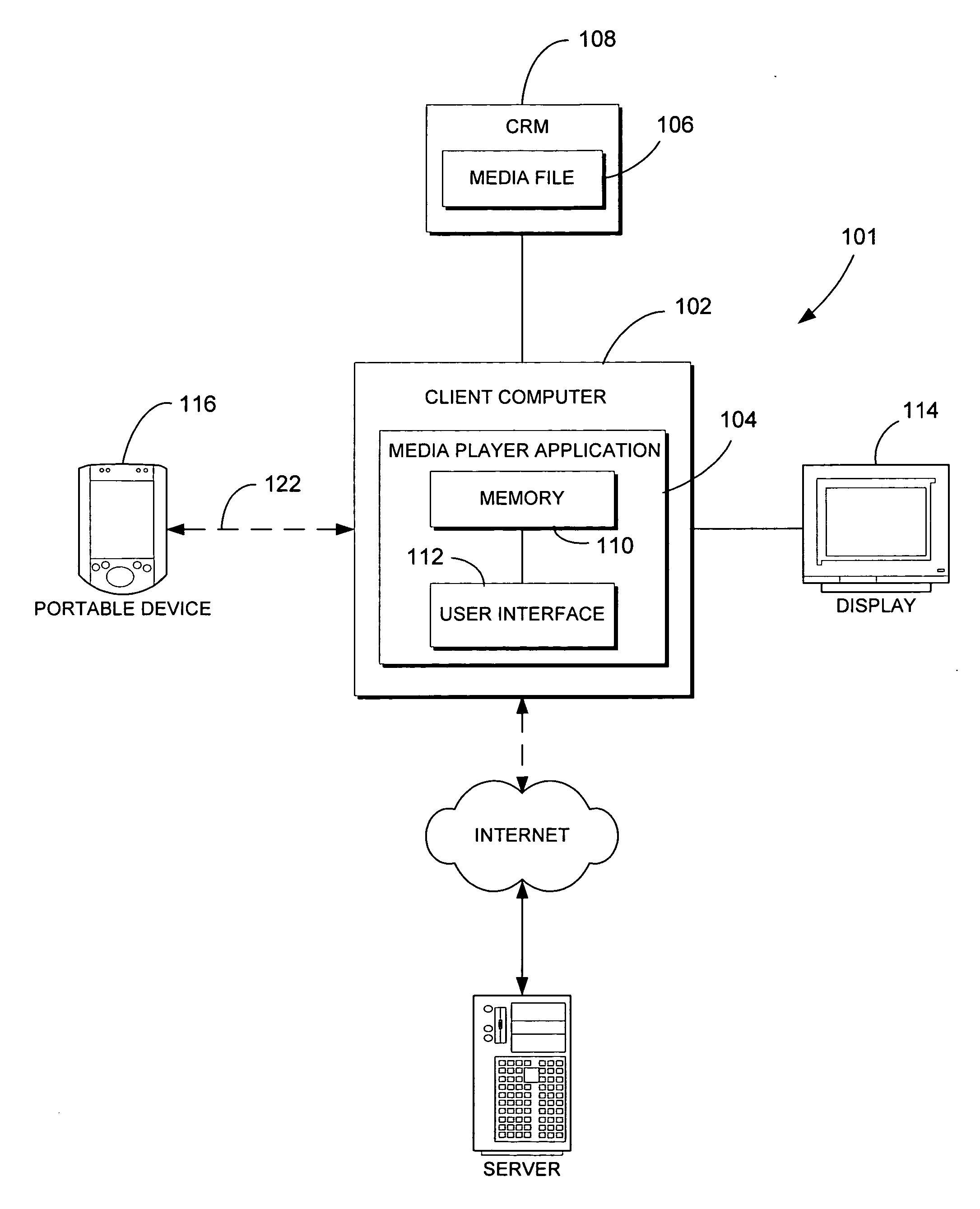
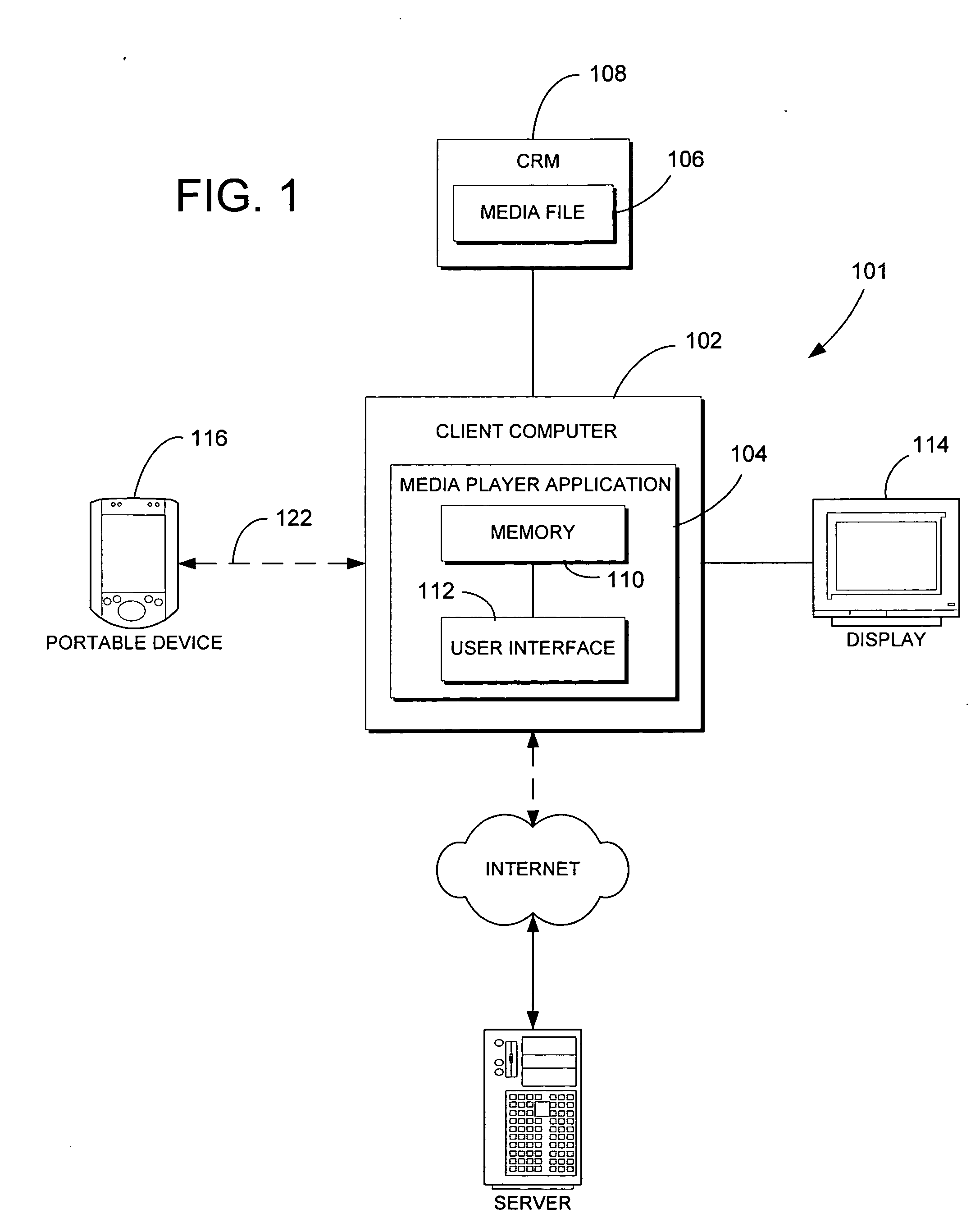
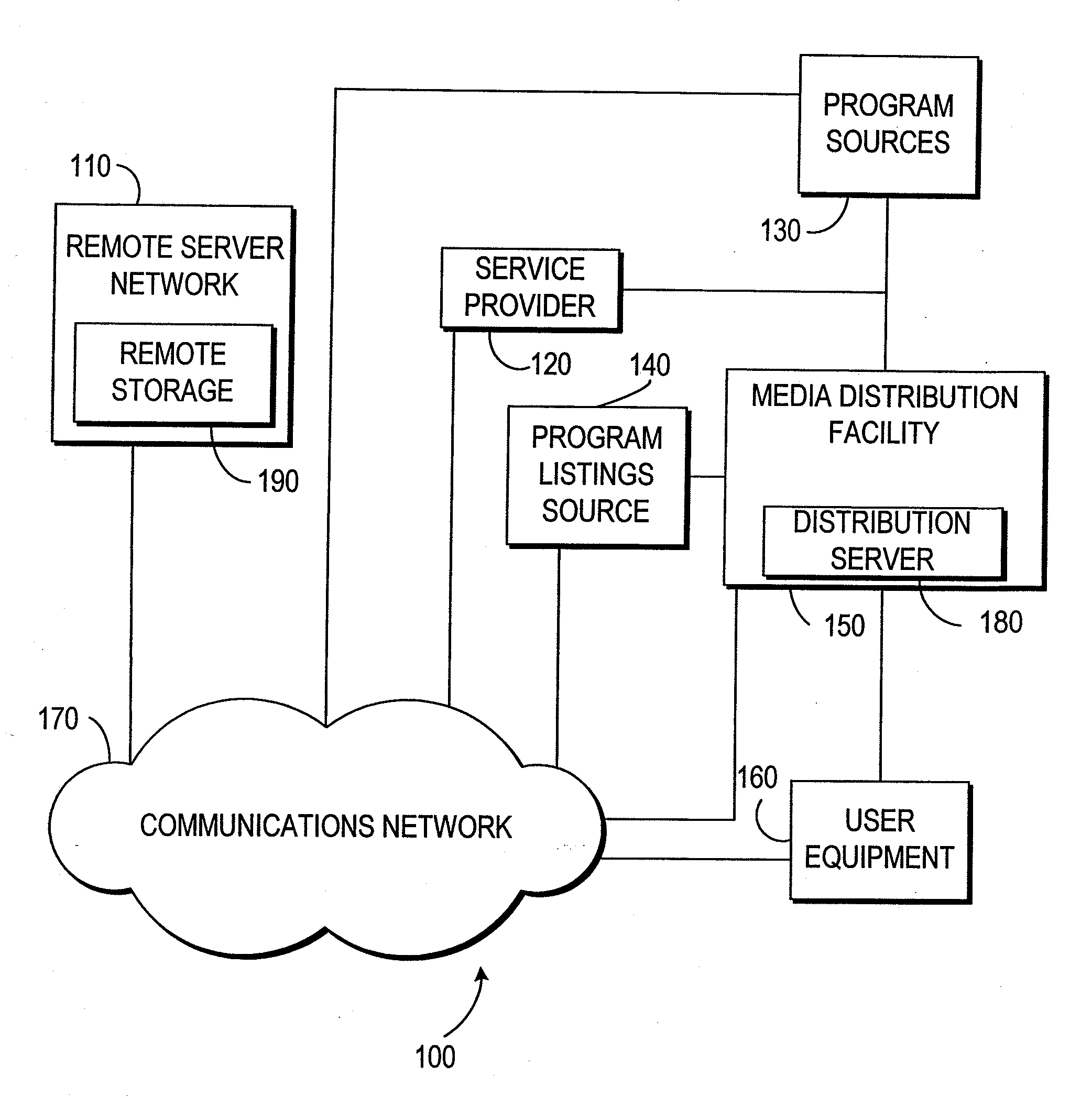
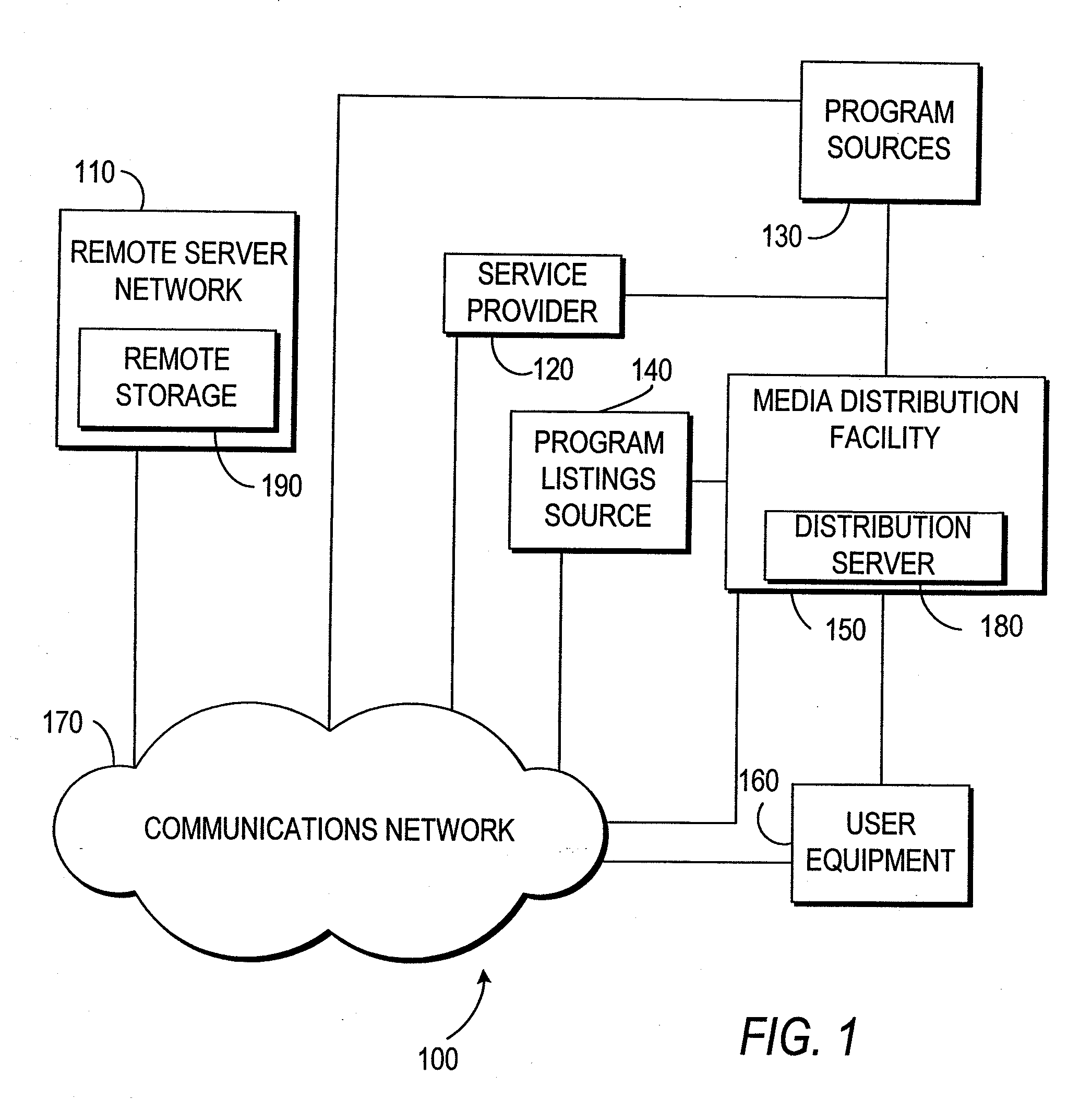
Systems and methods for providing storage of data on servers in an on-demand media delivery system
ActiveUS7650621B2Television system detailsAnalogue secracy/subscription systemsFile allocationData storing
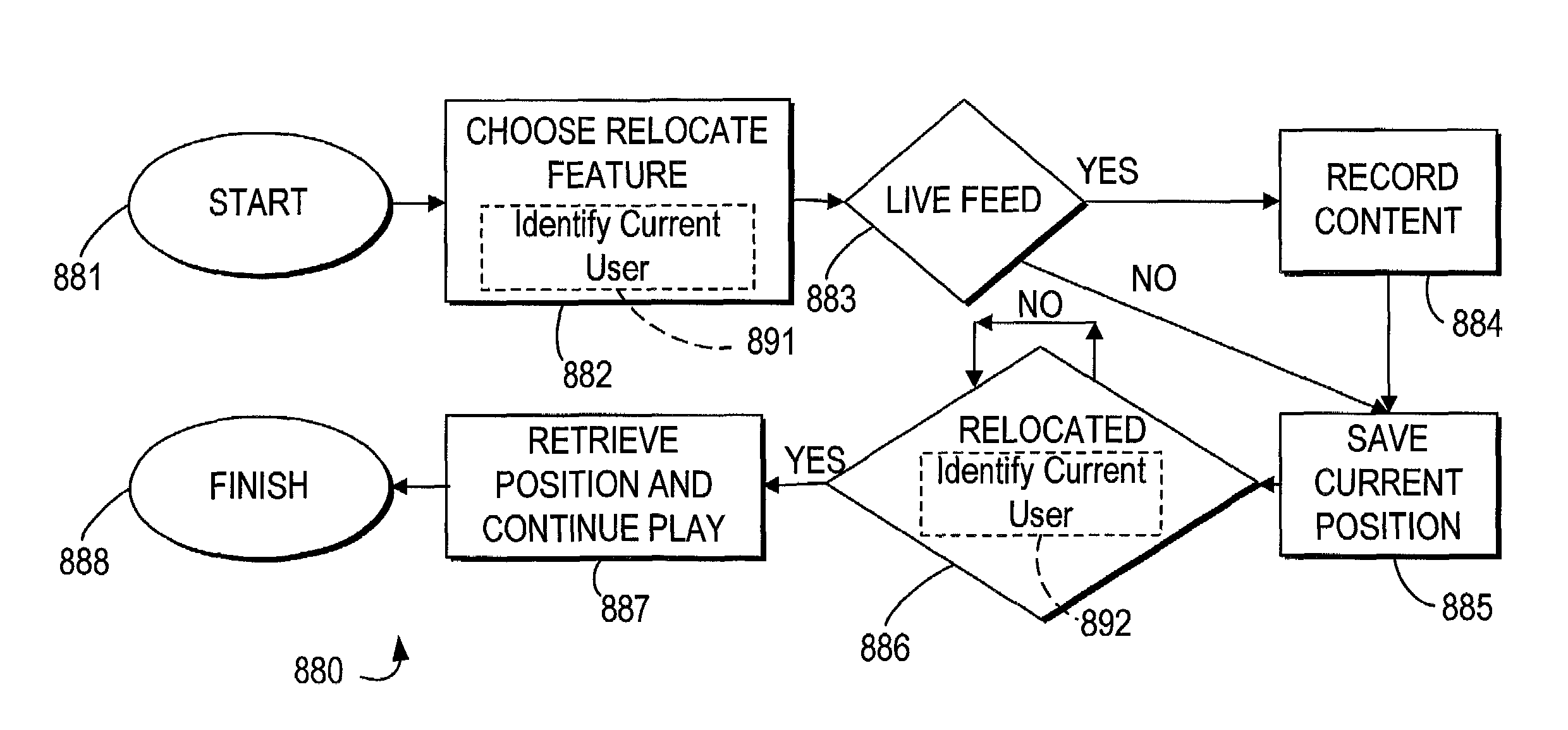
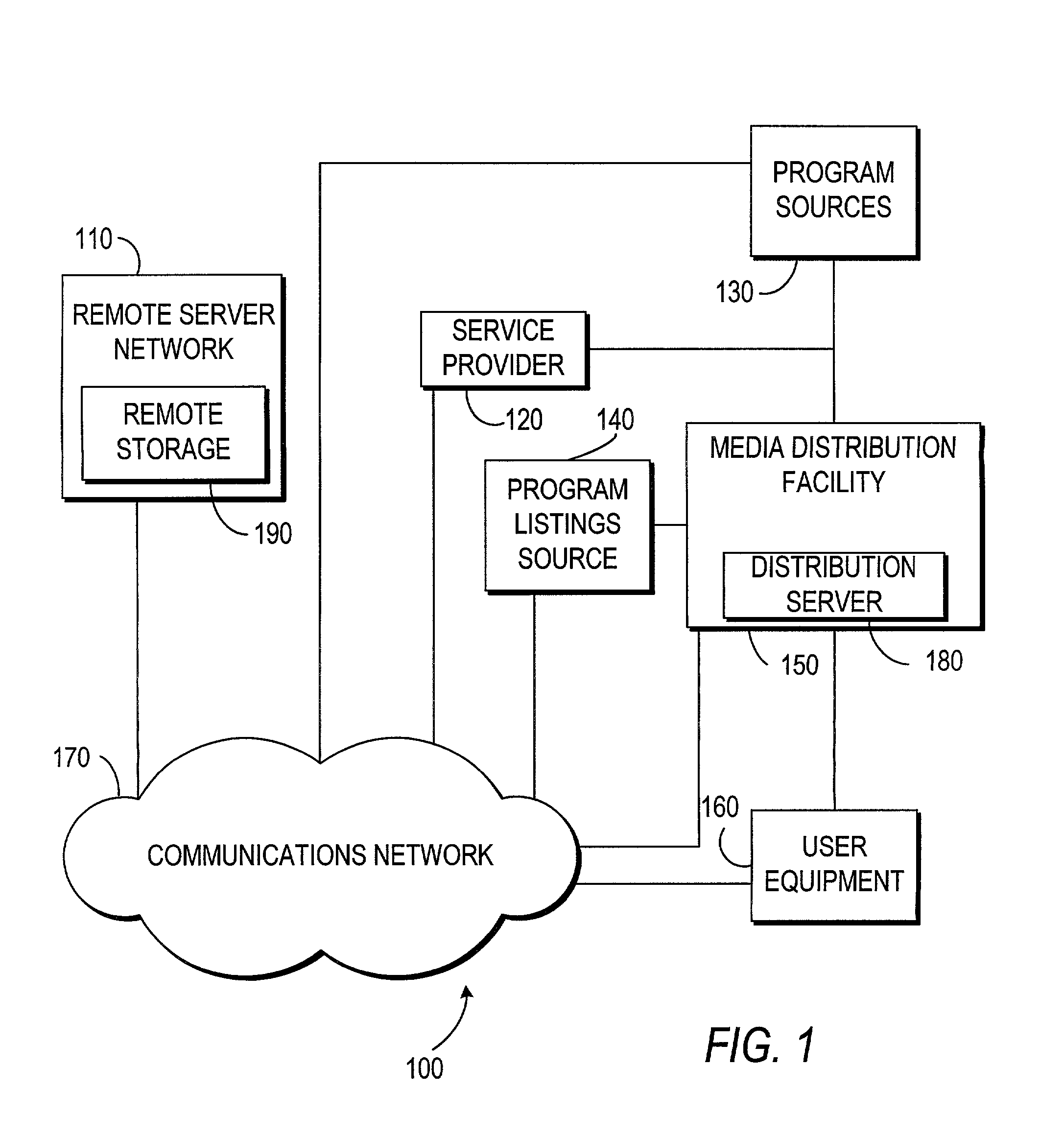
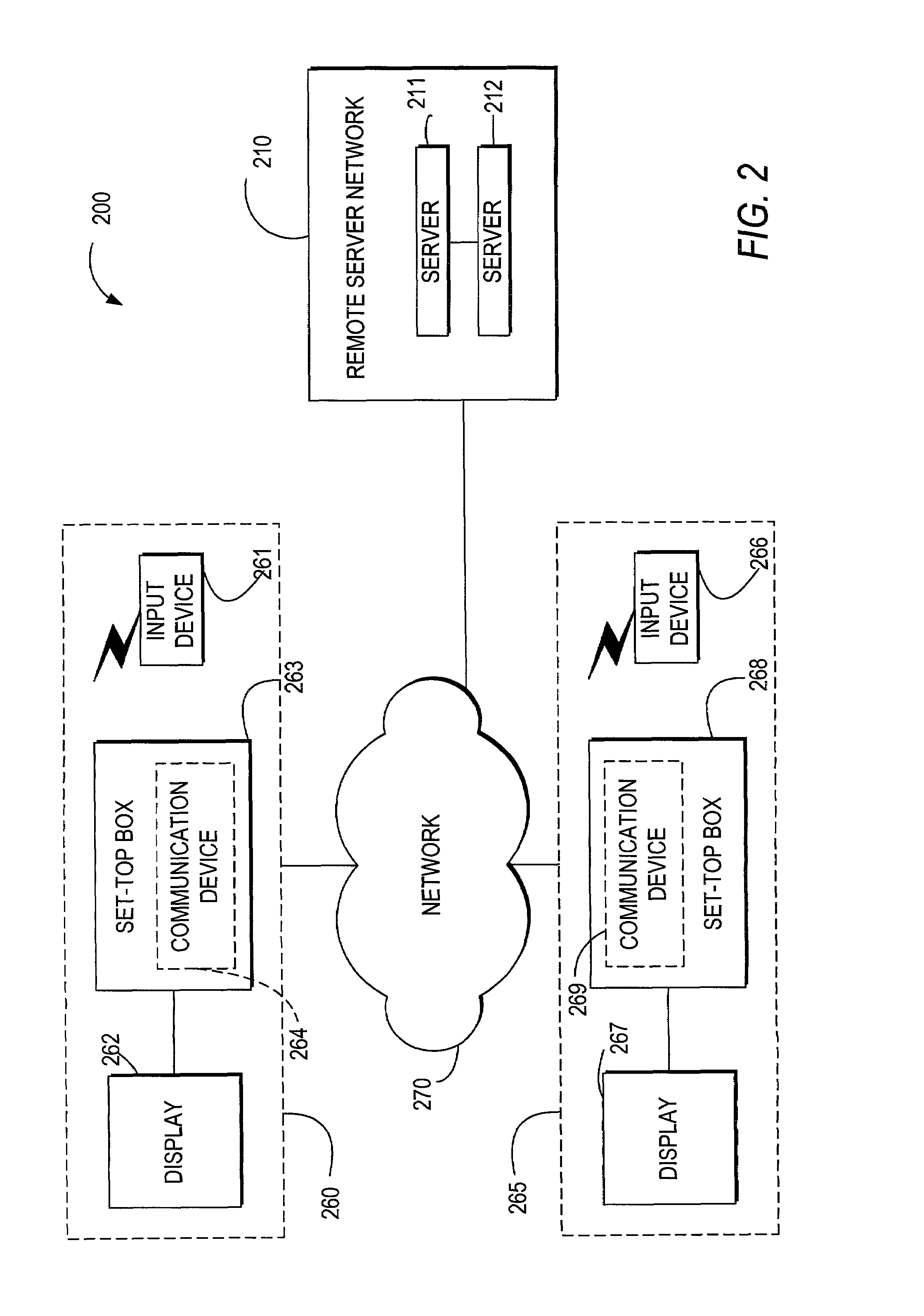
A system and method may be provided that allows users to store, retrieve, and manipulate on-demand media content and data stored on a remote server network in an on-demand media delivery system. More particularly, the system may allow a user to access his or her on-demand media account from user equipment in different locations as long as the current user equipment can communicate with a remote server that stores user-specific information. The system upon user selection may freeze the delivery of on-demand media at a particular point and allow the user to resume the media at a later time from some other network location in system. Users may upload personal images or files to an on-demand delivery server for later retrieval and display. Users may be permitted to assign access rights to the uploaded files.
Owner:ROVI GUIDES INC
Method and system for providing a secure multi-user portable database
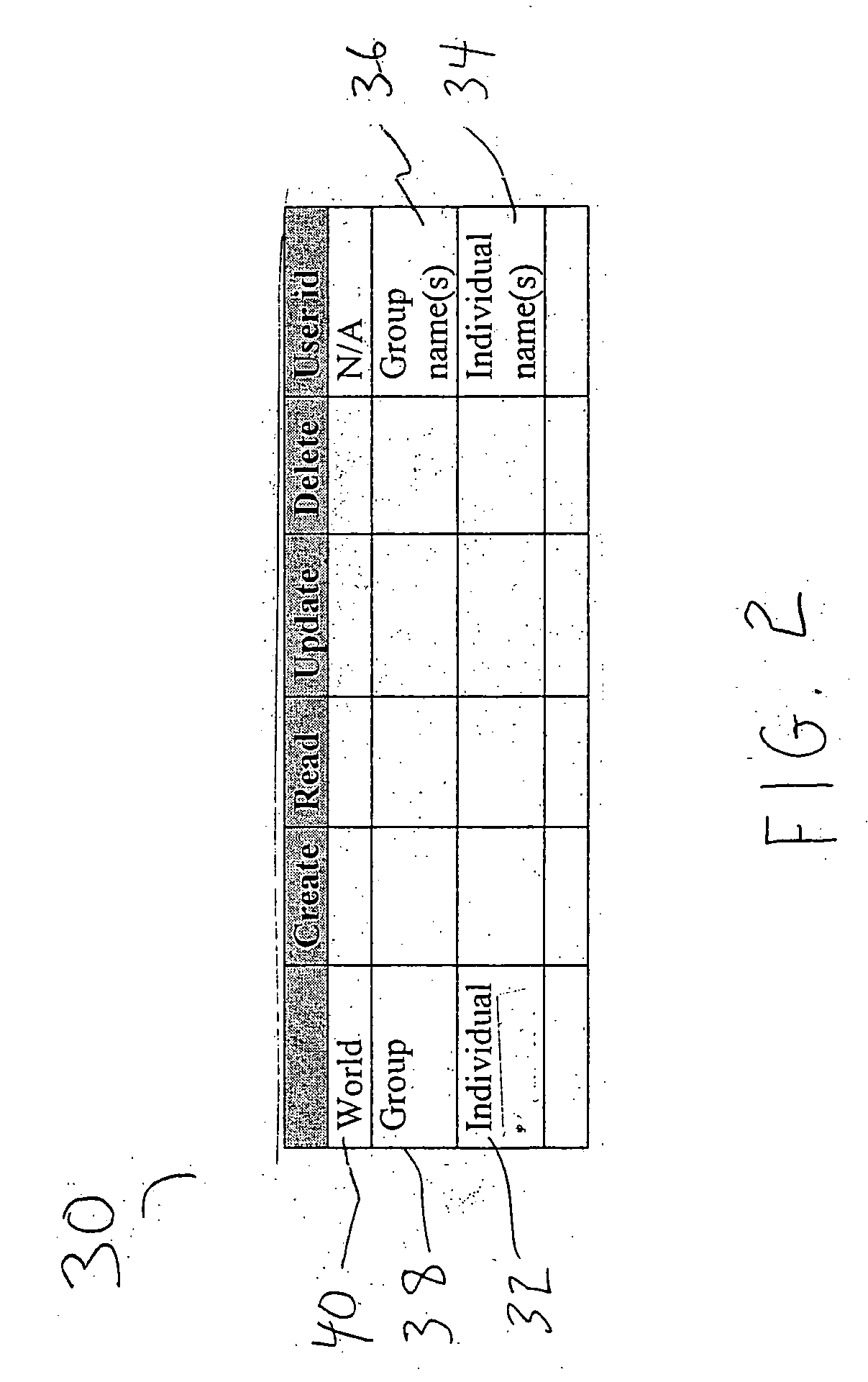
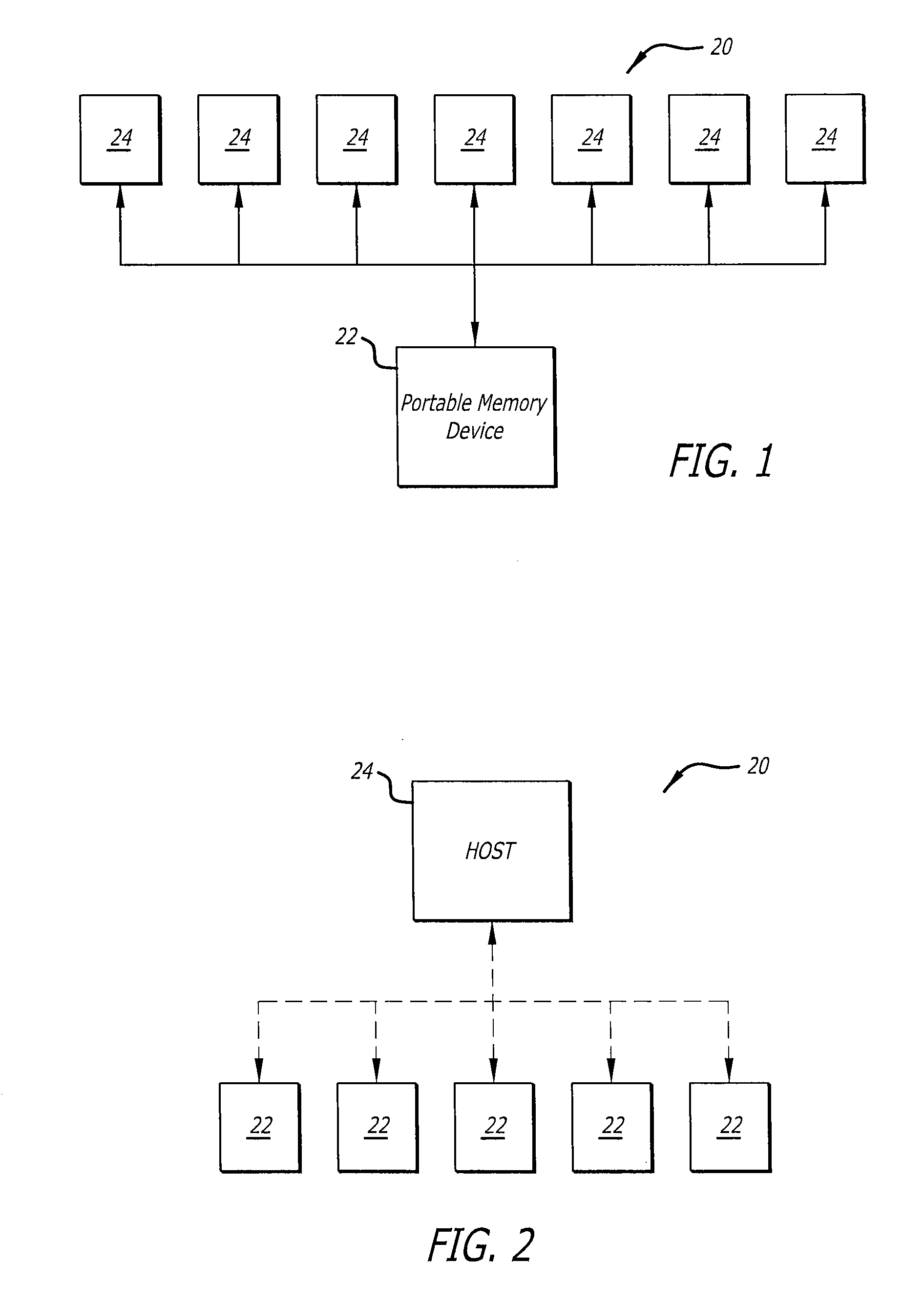
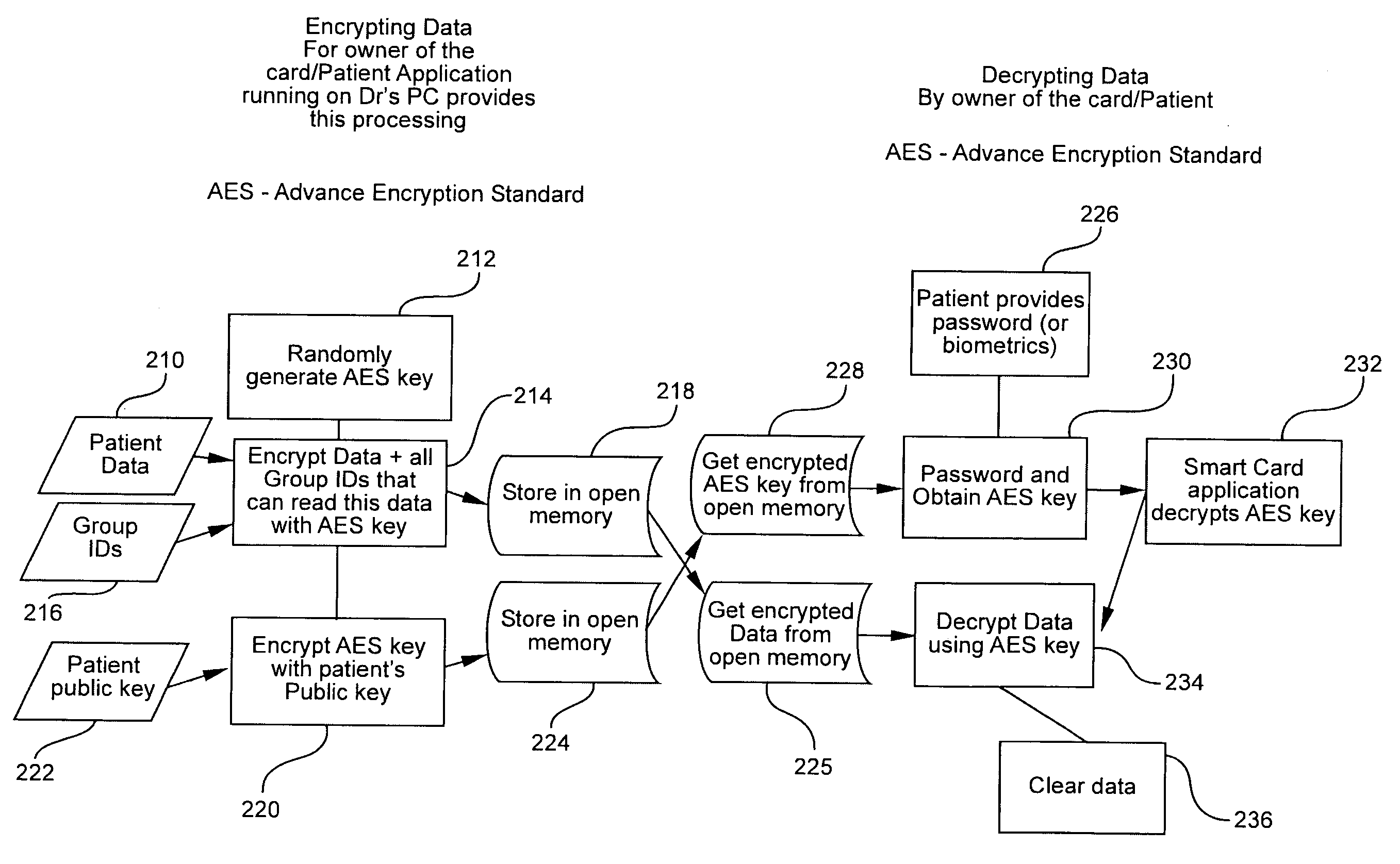
ActiveUS20070006322A1Easy to useLimited storage capabilityFinanceDigital data processing detailsMedical recordFile allocation
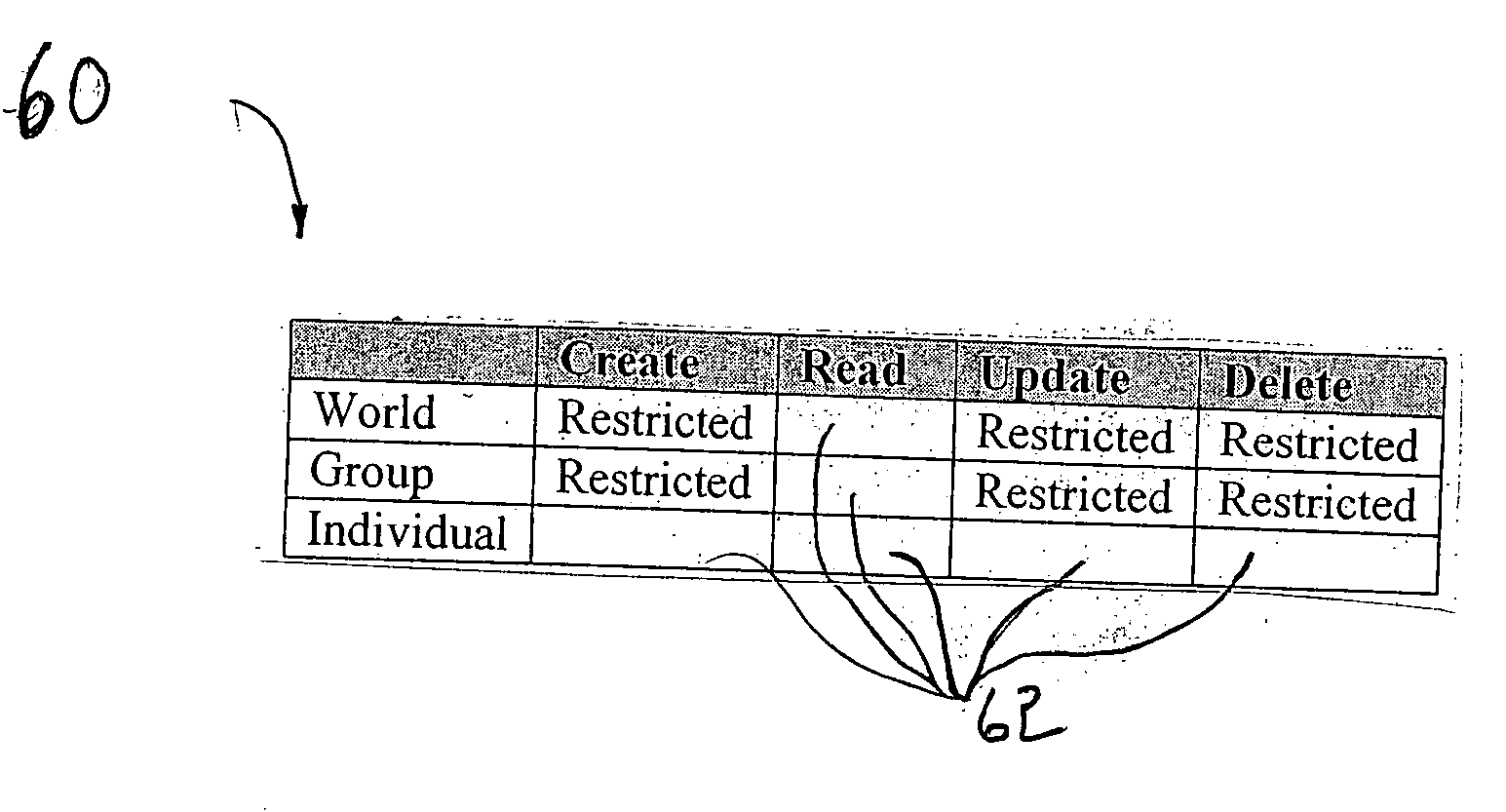
A system and method for providing, managing, and accessing a multi-user secure portable database using secure memory cards is provided. The database has a secure portion for storing security keys and a non-secure portion for encrypted data files. Access to the encrypted data files is controlled by assigning access rights through an access control matrix to each encrypted data file according to a hierarchical structure of users. A user requesting access is identified in the hierarchy, associated with a key for allowing the requested access, and the requested access allowed to a file in accordance with the rights allocated through the access control matrix. A patient can selectively grant access to encrypted medical records on his card to a physician. Authentication of the owner / patient is preferably required. Other records required by emergency medical personnel are readable from the same card without requiring permission from the patient.
Owner:PRIVAMED
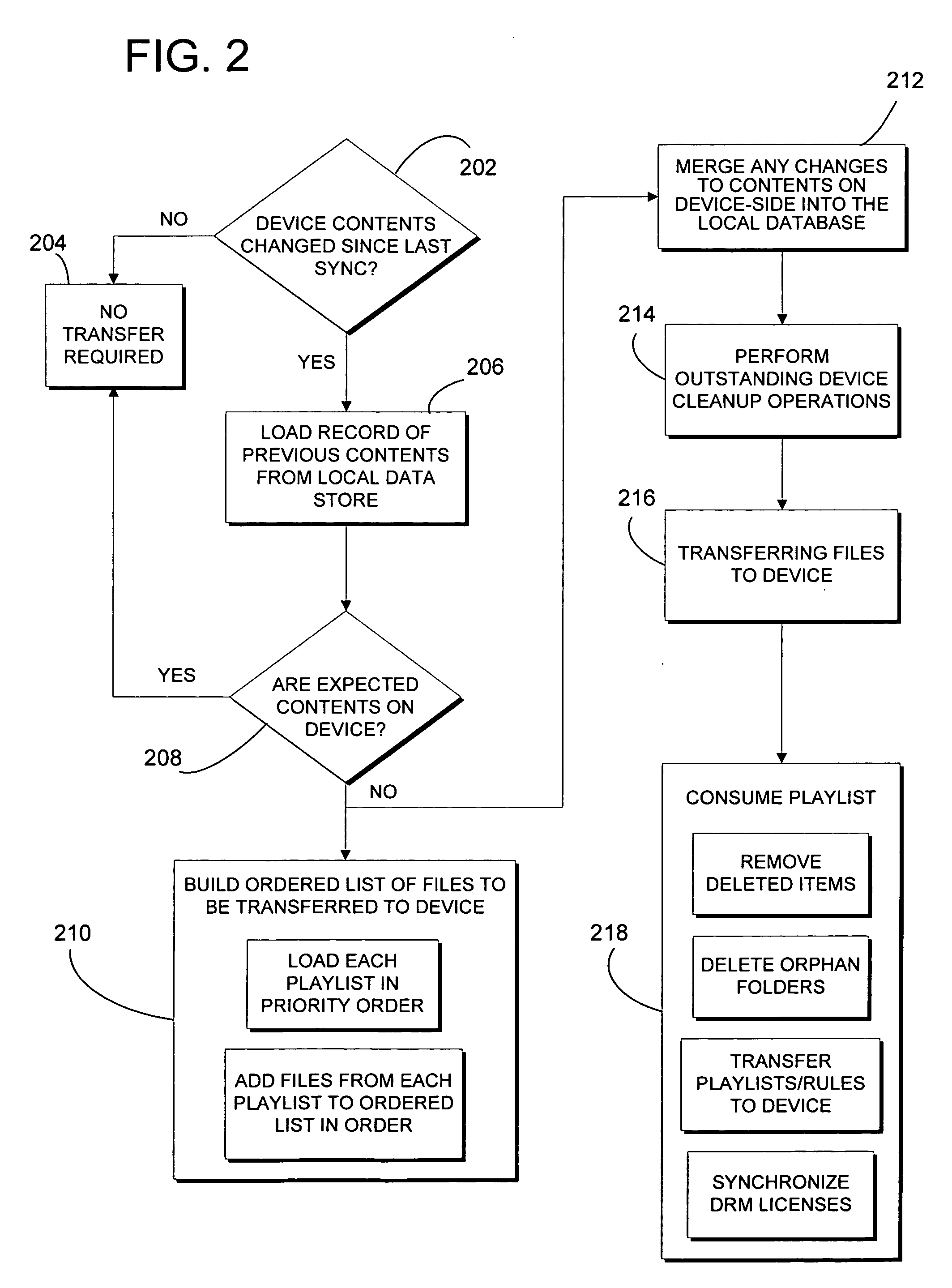
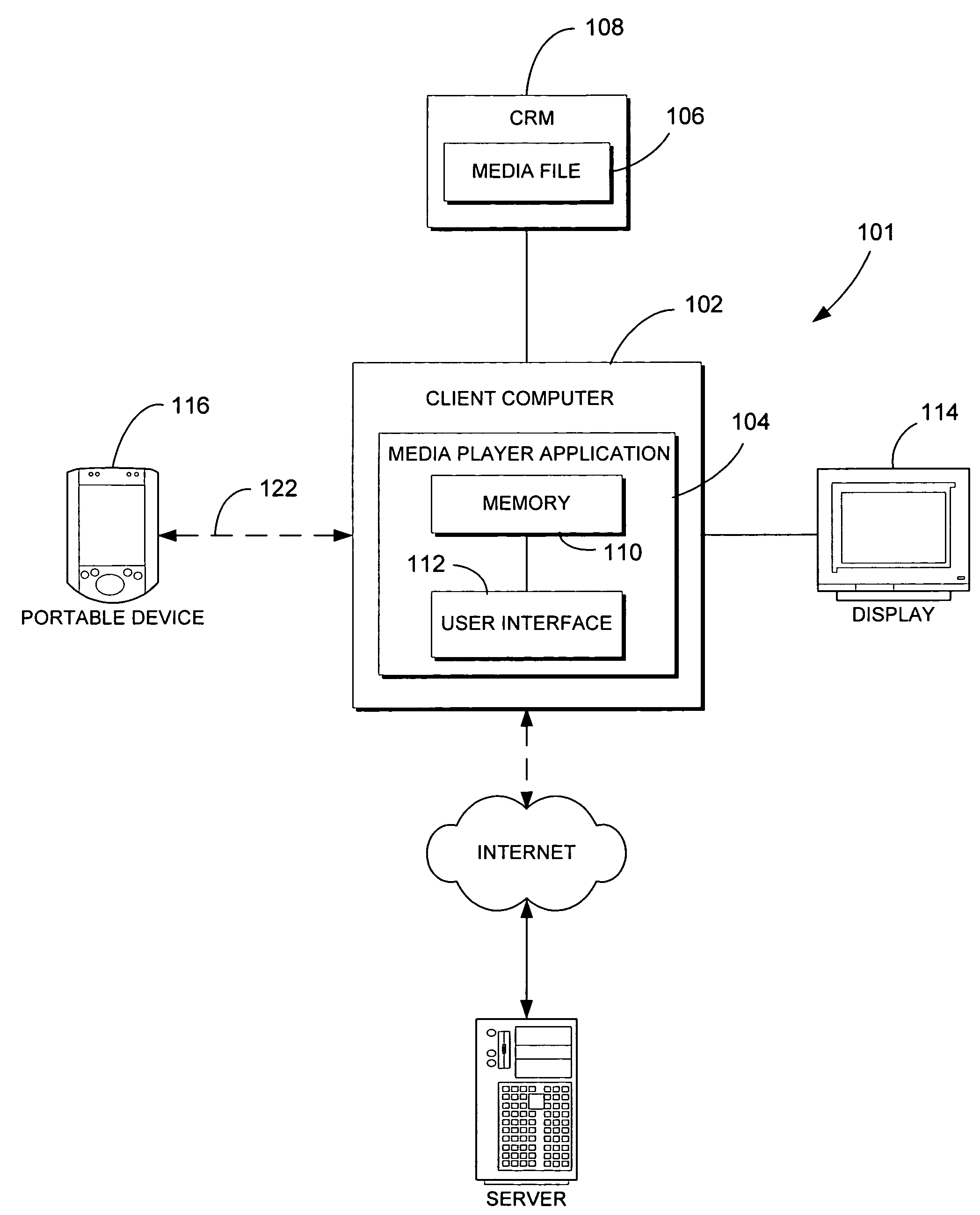
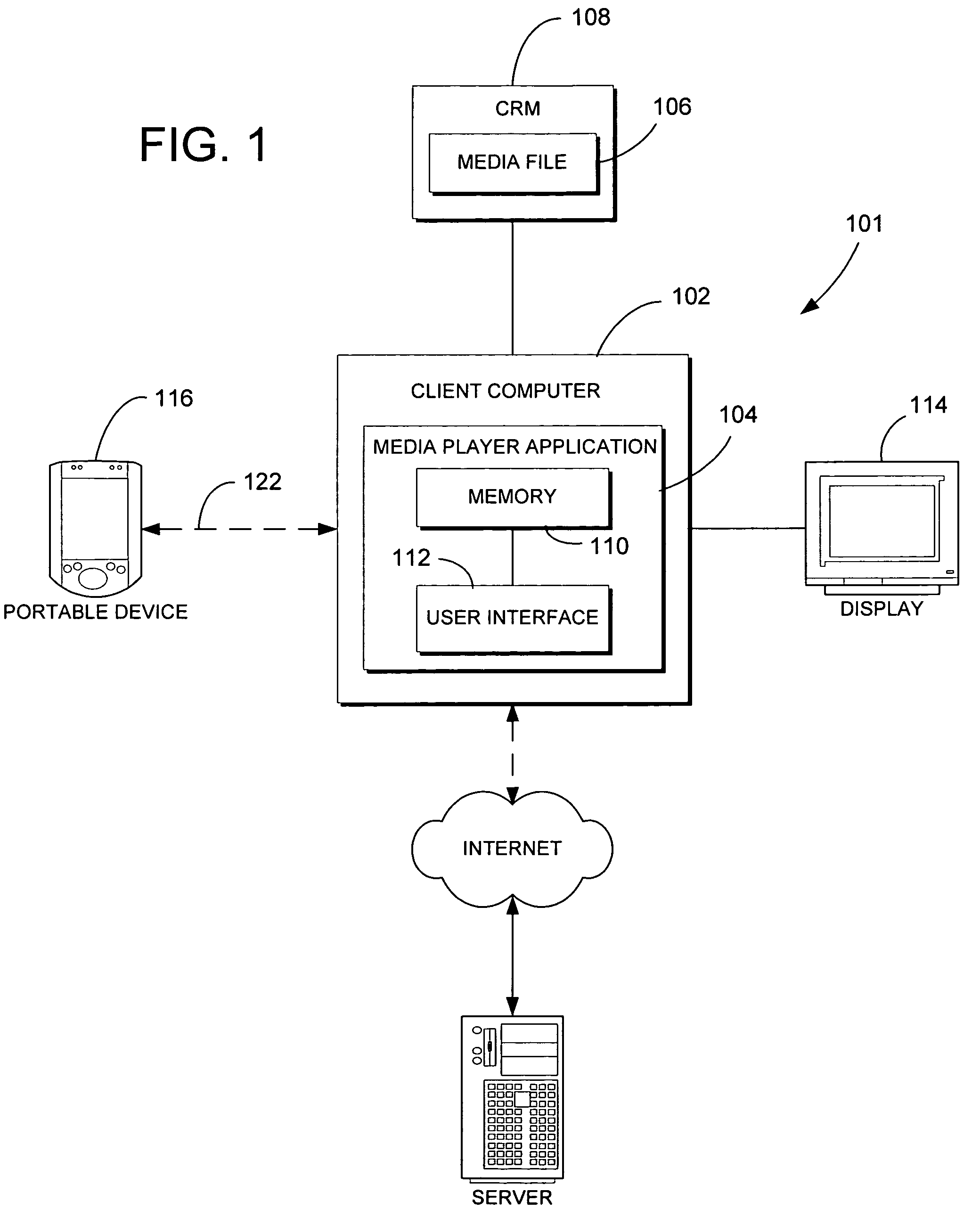
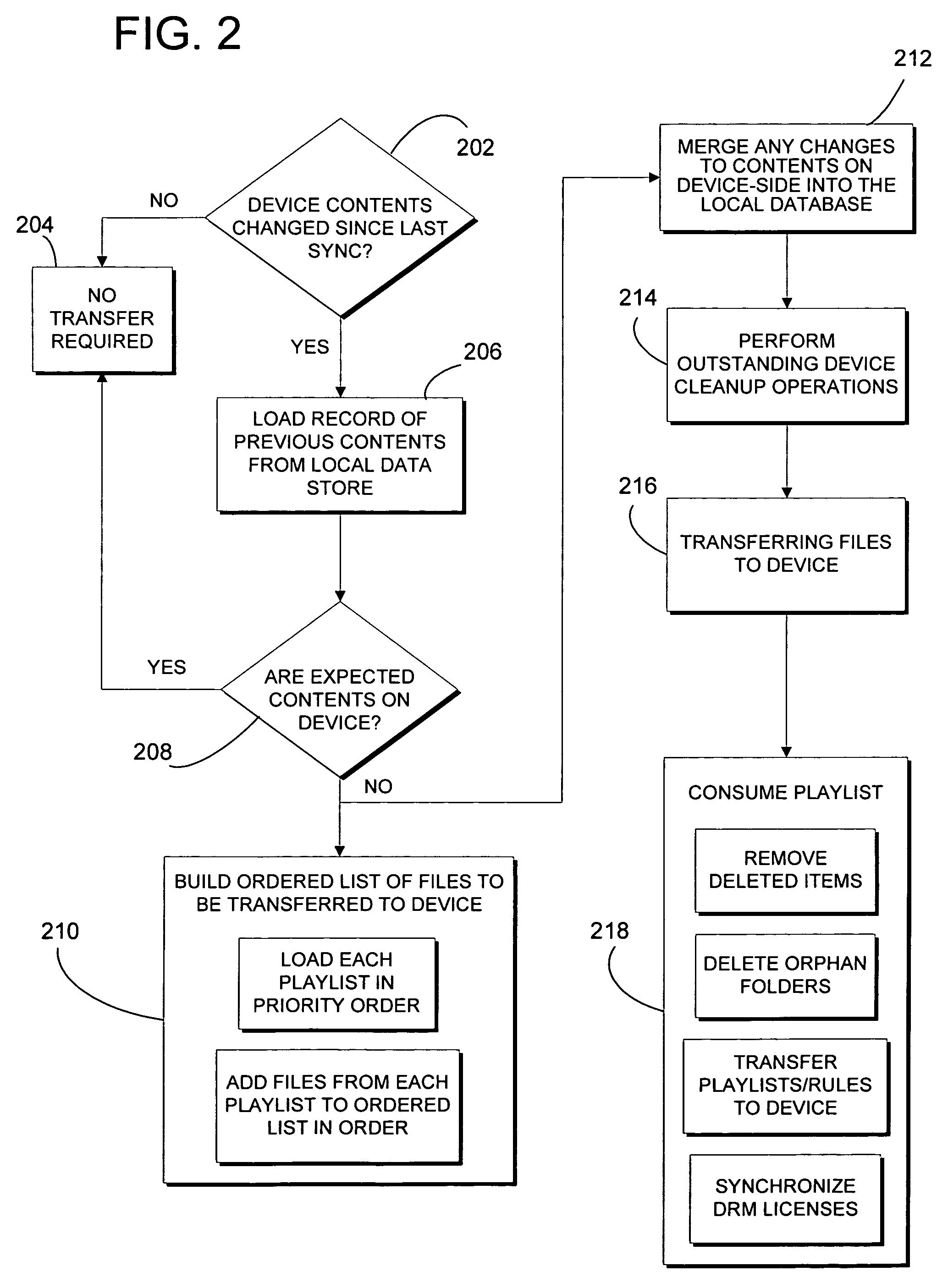
Automatic rules-based device synchronization
ActiveUS20060224620A1Enhances device synchronization experienceImprove experienceData processing applicationsDigital data information retrievalFile transmissionFile allocation
Automatic rules-based synchronization of digital files on a source device and a target device coupled to it. A source computer executes a synchronization engine for managing transfer of files from a source database to a target device coupled to the computer as a function of a defined storage capacity of the device. The synchronization engine is configured to receive user-defined rules for selecting which of the files are to be transferred to the device and assigning priorities to the files. The synchronization engine builds a designated list of the files to be transferred according to the priorities defined by the rules.
Owner:MICROSOFT TECH LICENSING LLC
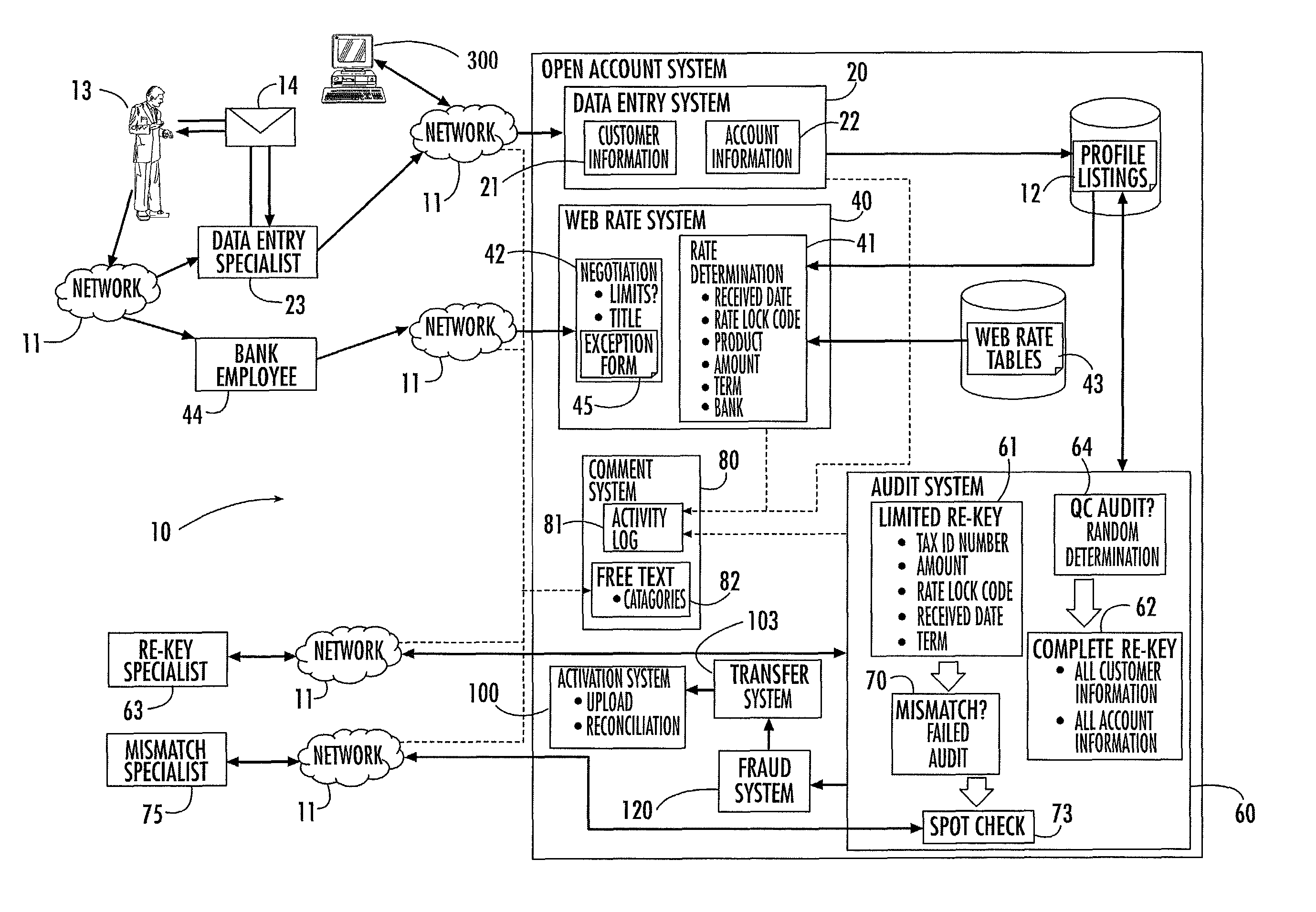
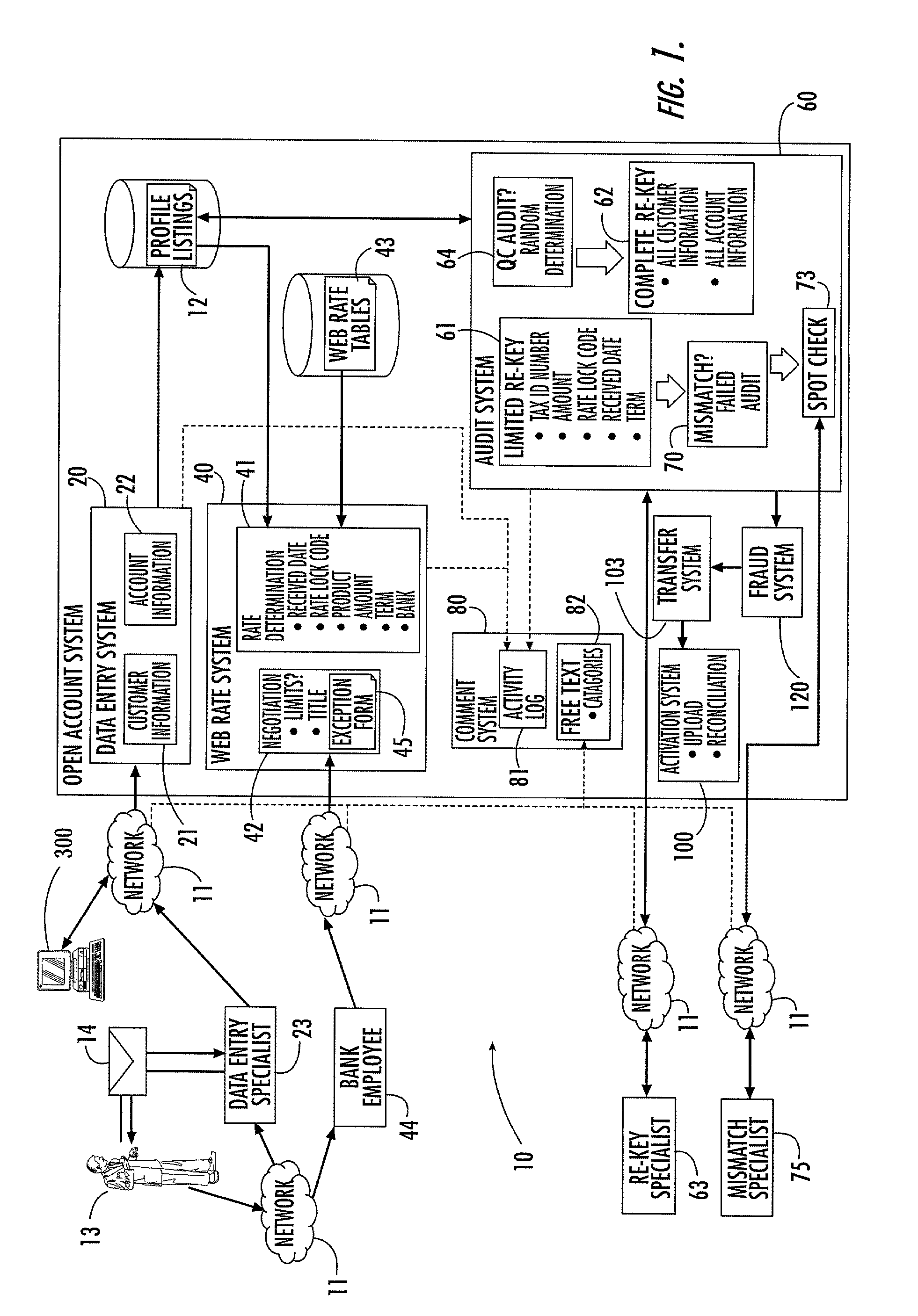
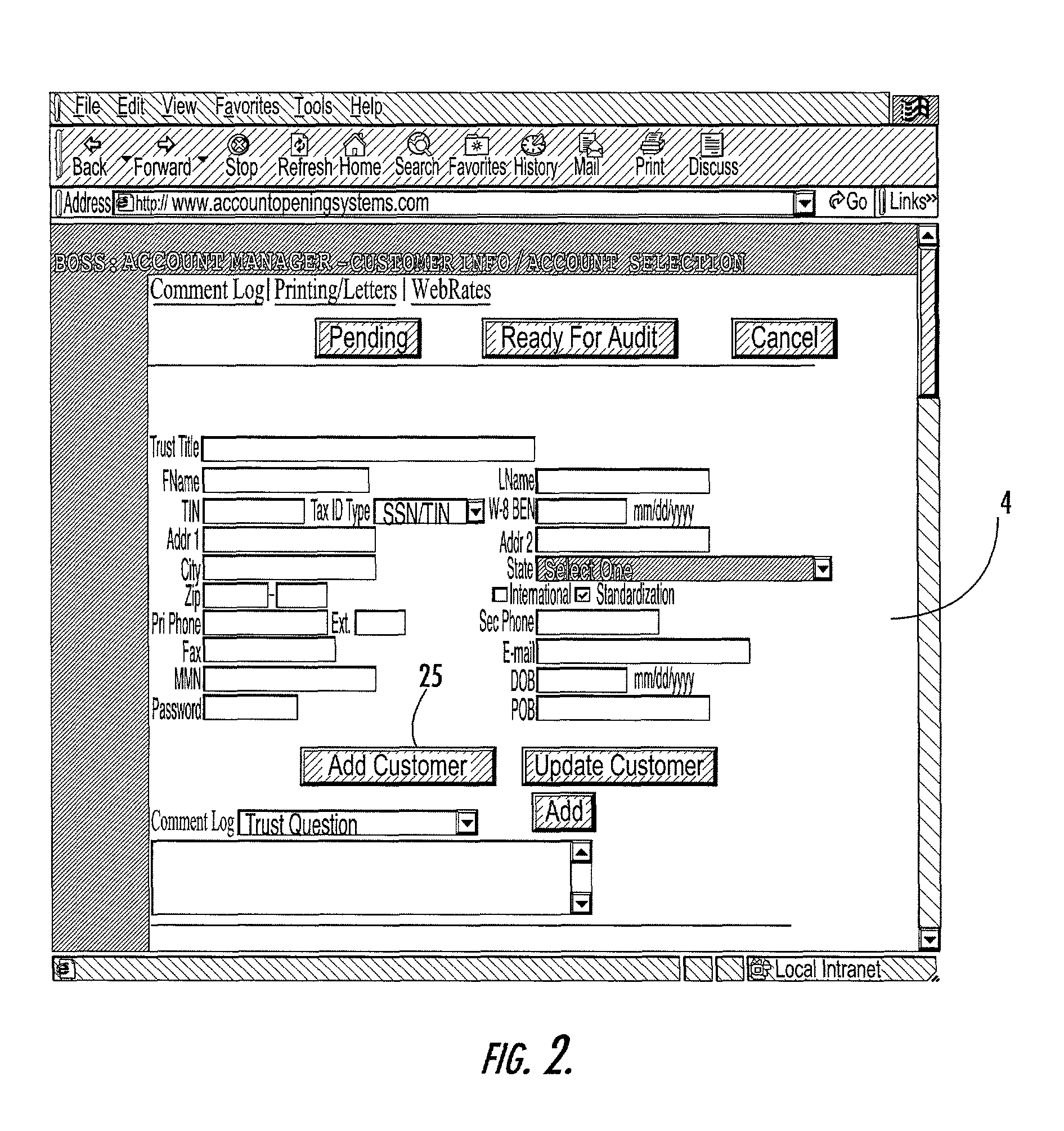
Account opening system, method and computer program product
ActiveUS8224723B2Improve accuracyImprove efficiencyFinancePayment architectureFile allocationBank account
A system that facilitates opening of a bank account by banking personnel for a customer. The account opening system includes an automatic rate determination feature that uses customer information, account information and other criteria to determine an account interest rate. The rate determination system may also mediate rate negotiation between a personal banker and the customer by limiting the increase in rate awarded by the personal banker. An auditing system assigns numbers to a series of profiles, each describing a request to open an account. Profiles to be audited are determined by generating random numbers that fall within the range of assigned profile numbers. Random number generation is repeated until a threshold percentage of profiles have been selected for auditing. The account opening system includes a system for tracking the progress of the account application and for organizing information recorded by the personal banker during interactions with the customer.
Owner:JPMORGAN CHASE BANK NA +1
Method and apparatus for a ranking engine
ActiveUS20060218141A1Highly targeted search resultImprove accuracyData processing applicationsWeb data indexingOrganizational documentFile allocation
A computer-implemented method is provided for ranking files from an Internet search. In one embodiment, the method comprises assigning a score to each file based on at least one of the following factors: recency, editorial popularity, clickthru popularity, favorites metadata, or favorites collaborative filtering. The files may be organized based on the assigned scores to provide users with more accurate search results.
Owner:META PLATFORMS INC
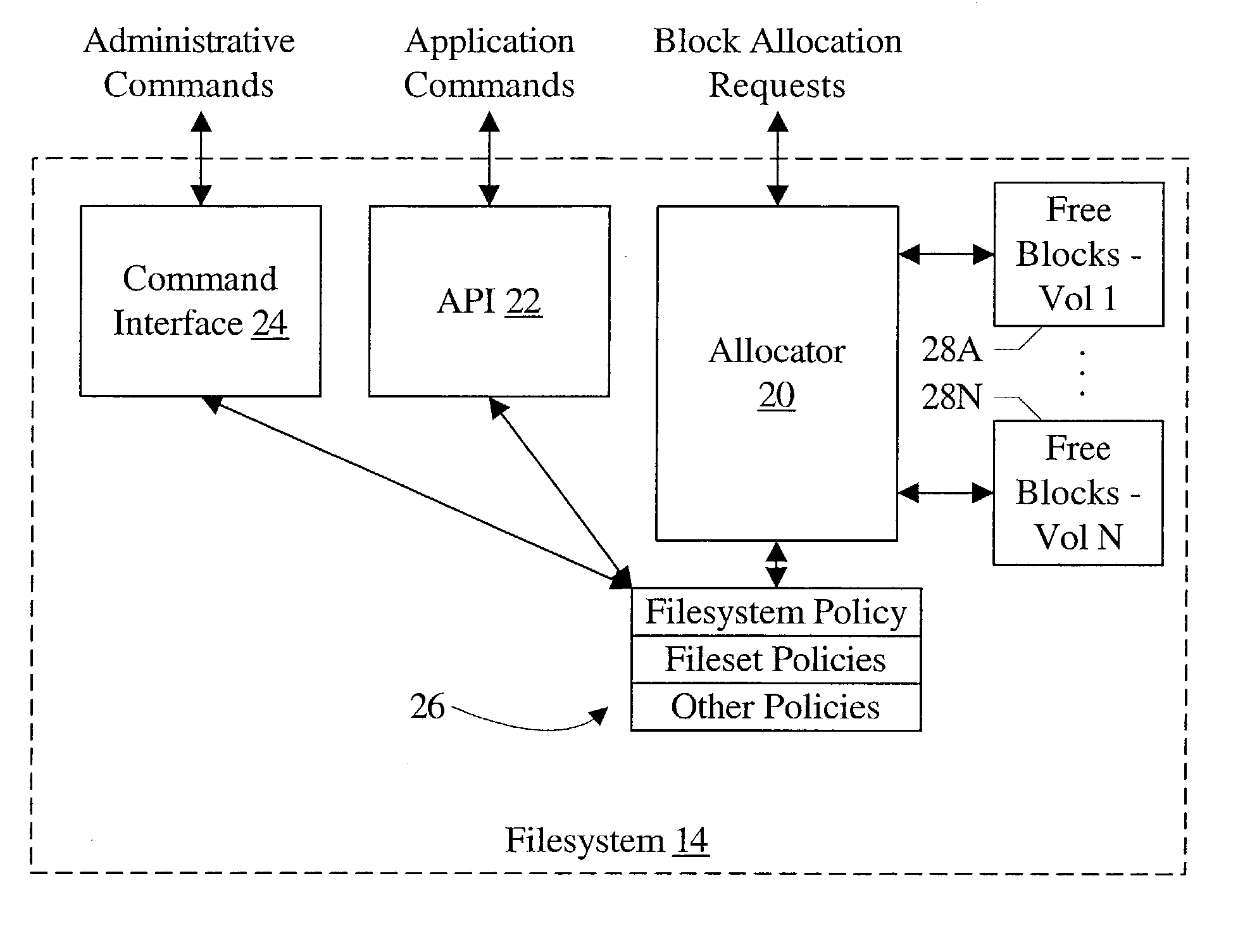
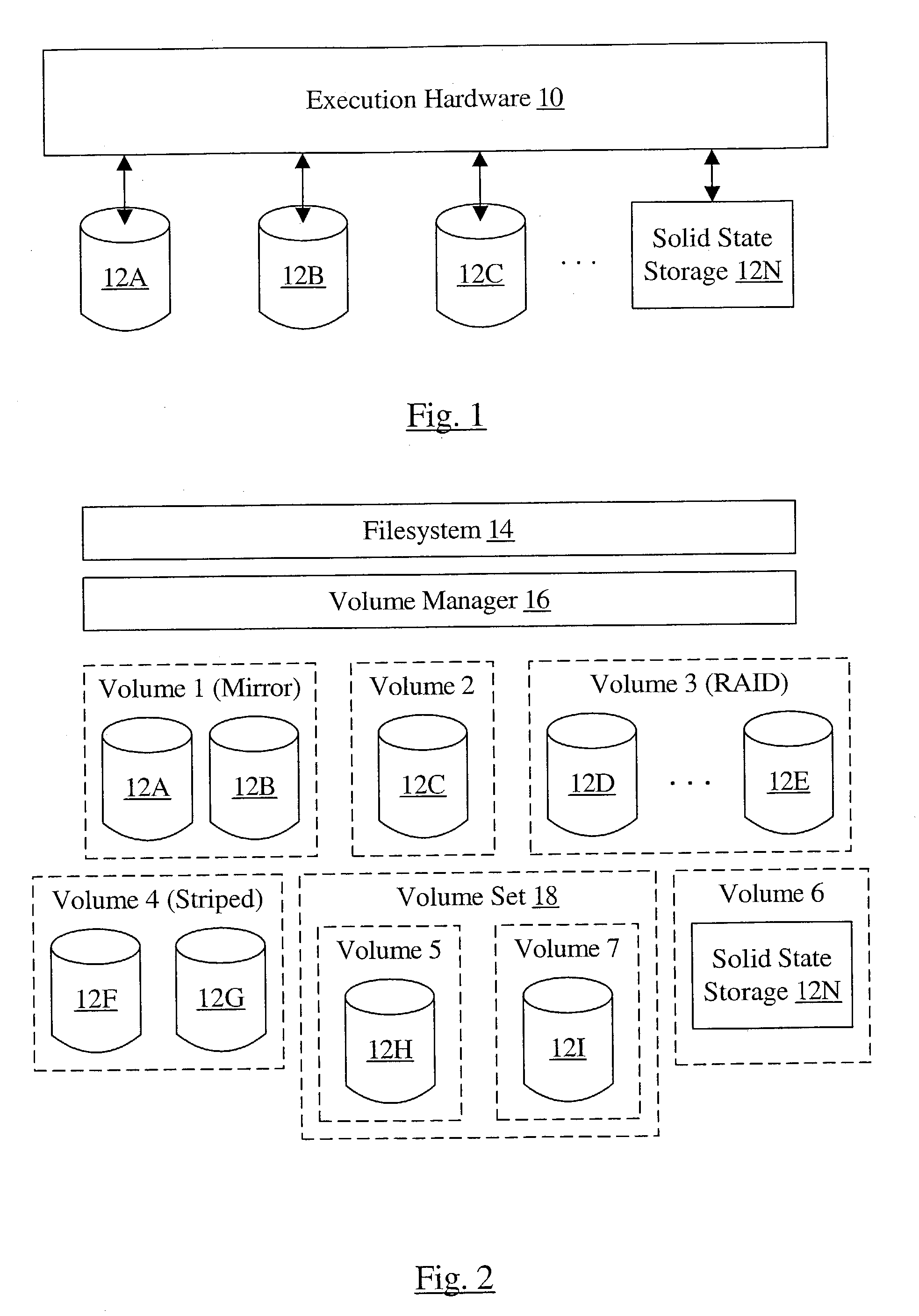
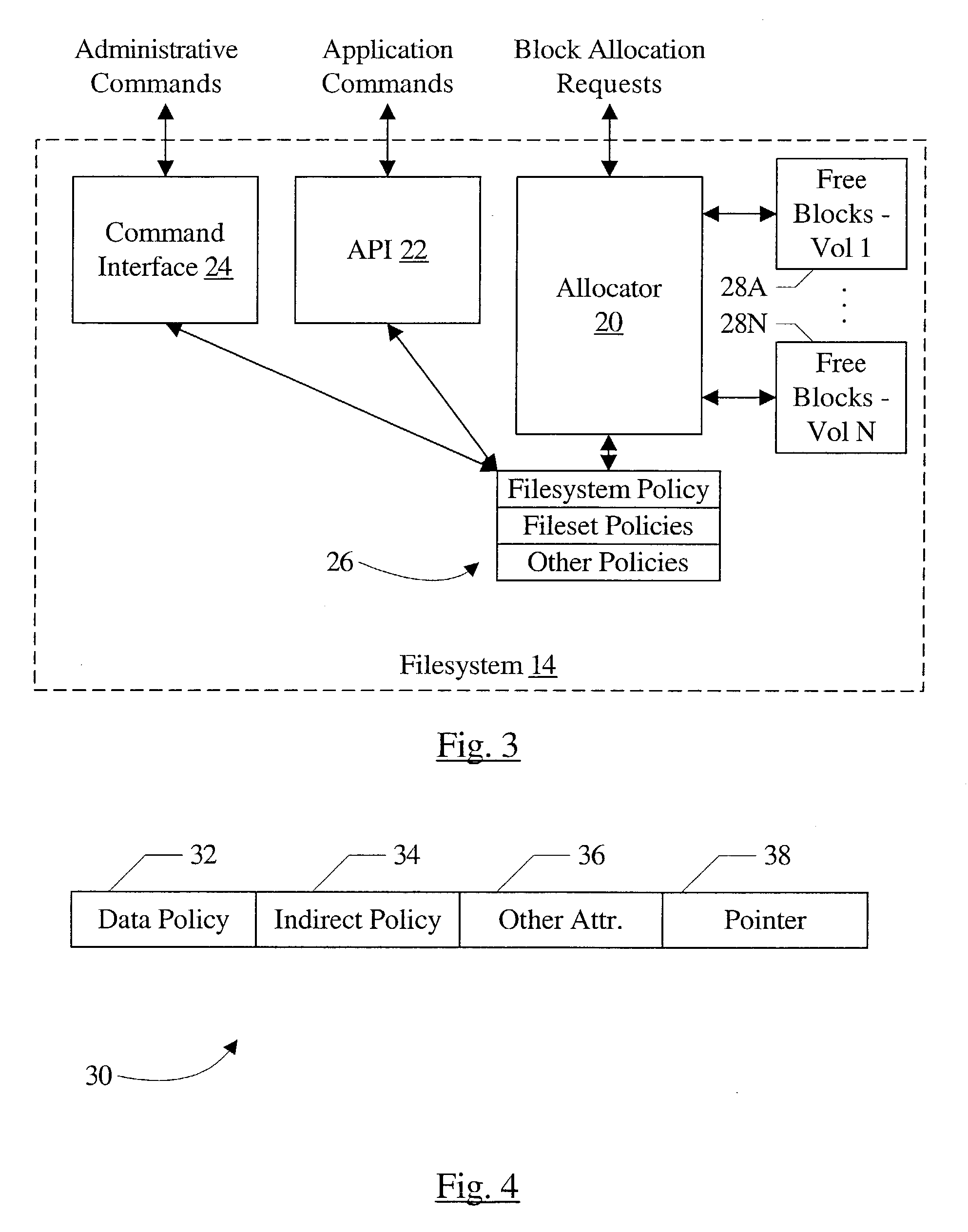
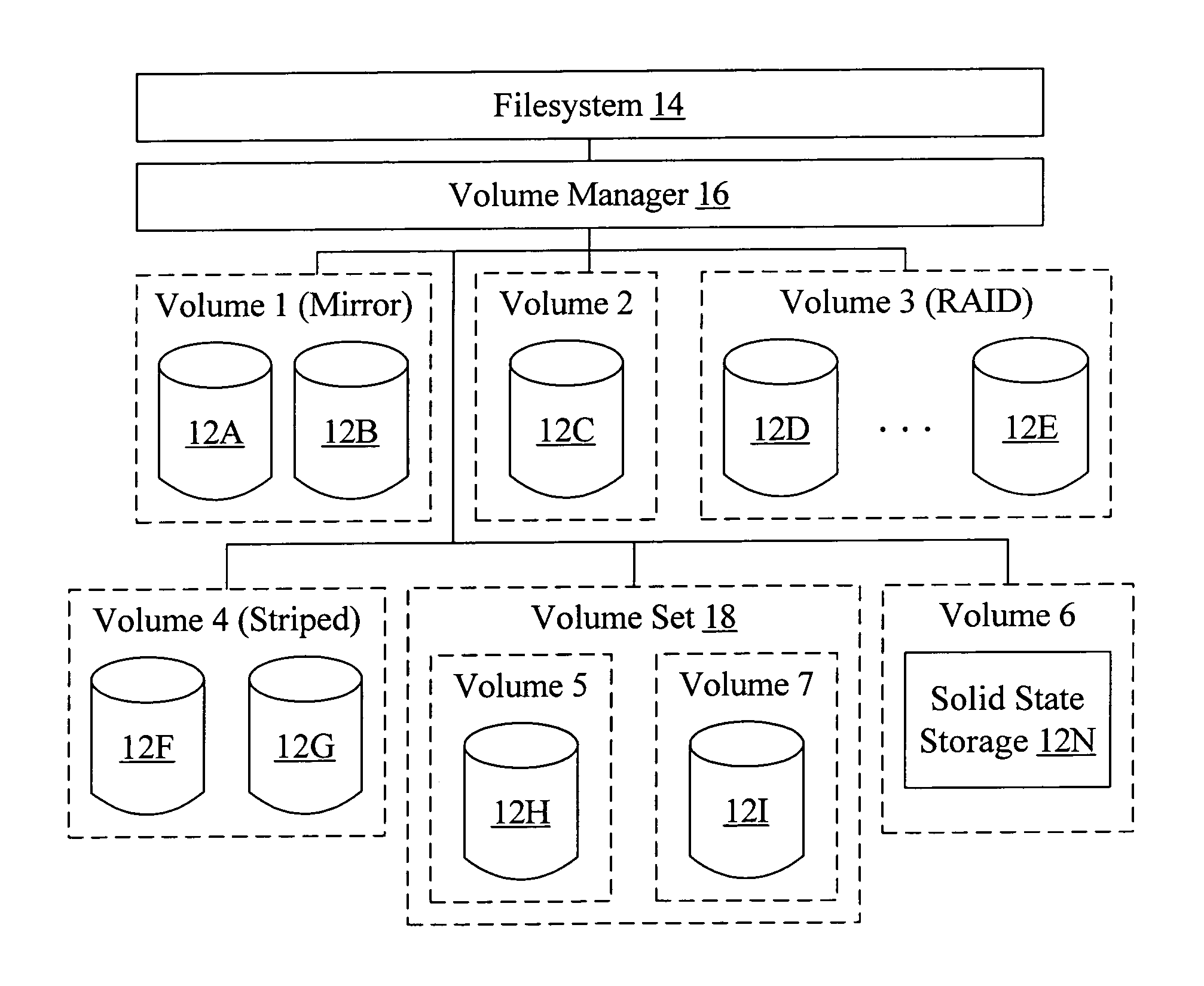
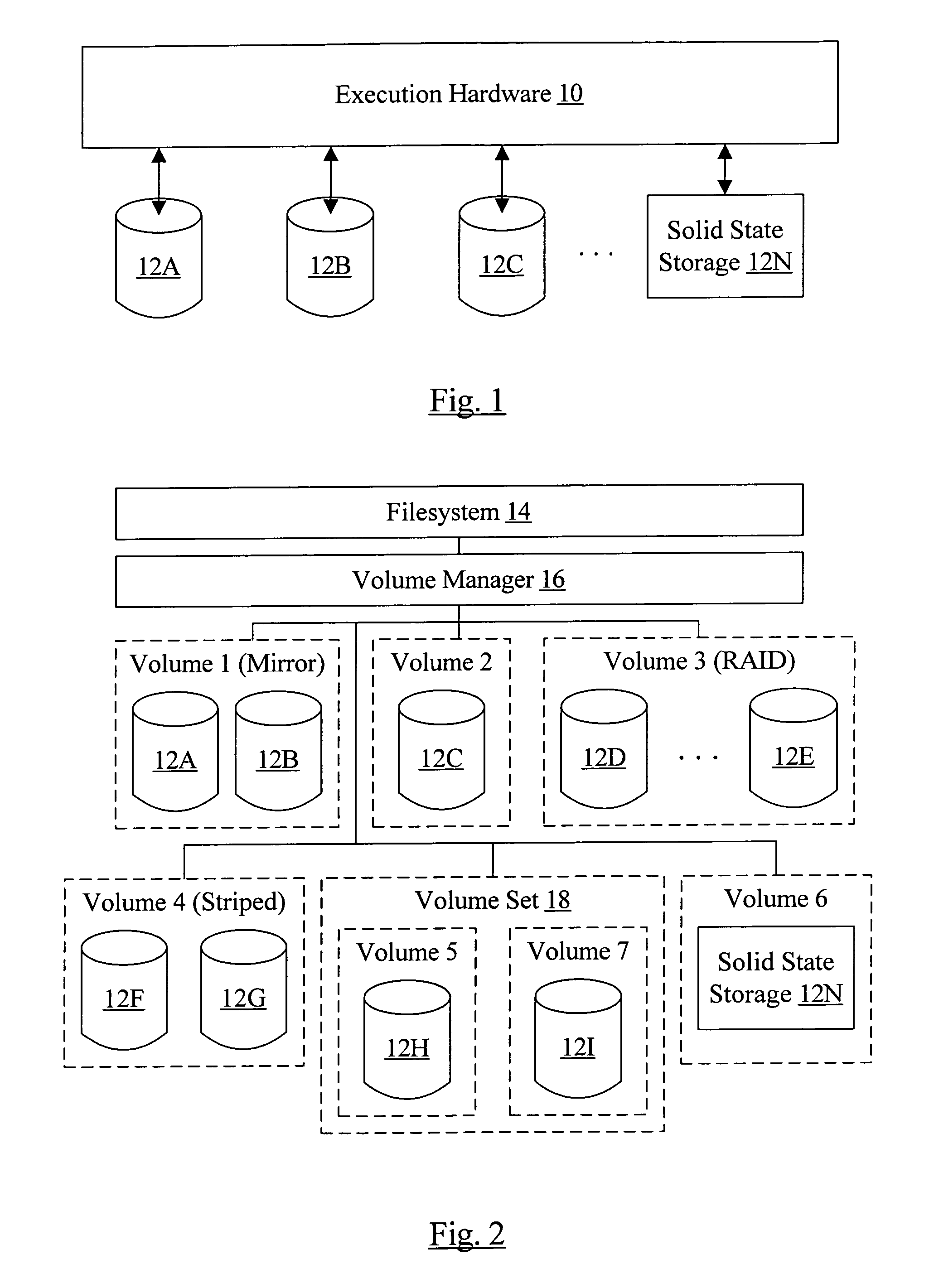
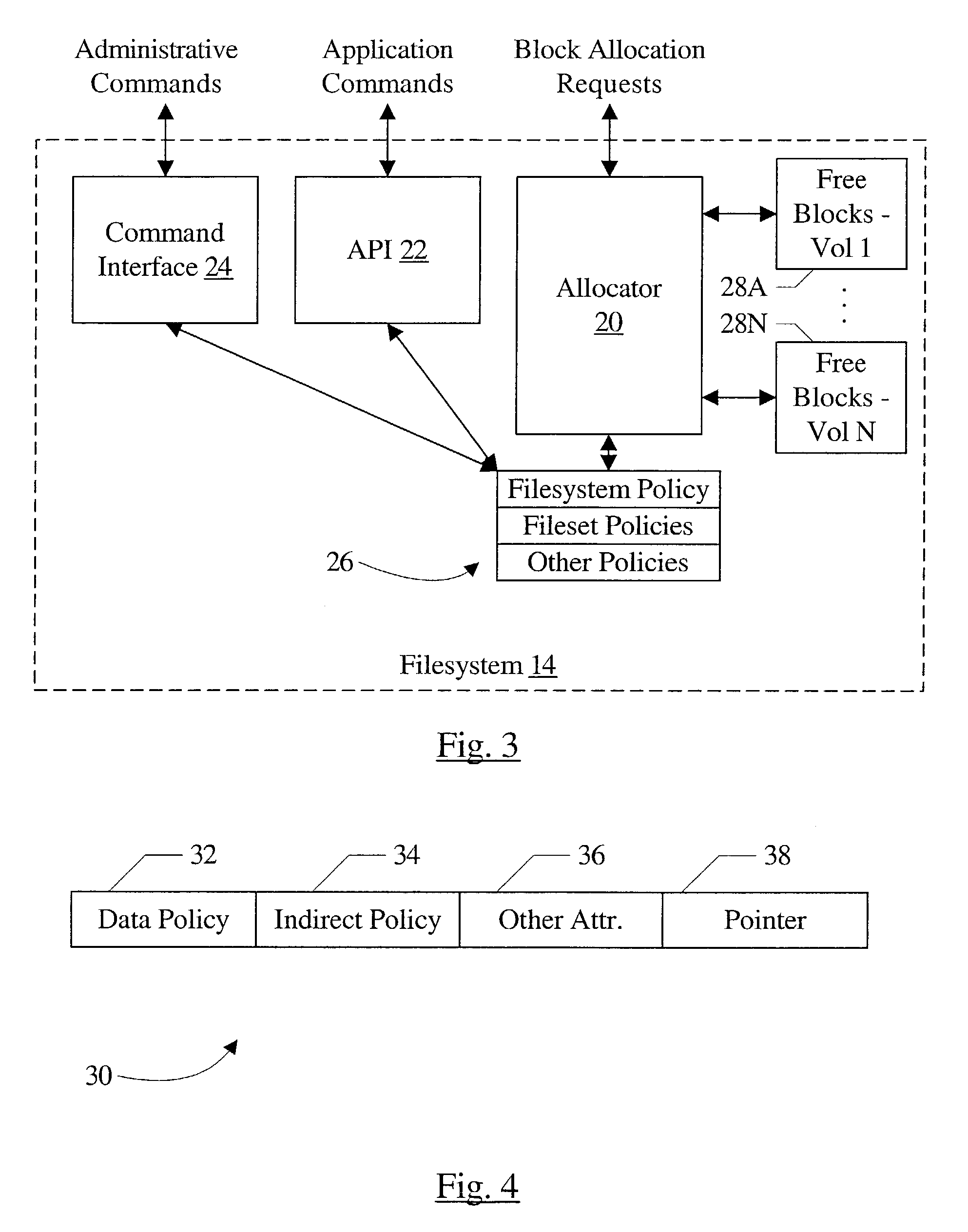
Multi-volume file support
ActiveUS20050010620A1Input/output to record carriersDigital data processing detailsFile allocationGranularity
A computer accessible medium comprises instructions which, when executed, receive a request to allocate one or more blocks for a file. At least one allocation policy is assigned to the file, wherein the allocation policy specifies one or more storage units on which the blocks are to be allocated. Additionally, if more than one storage unit is specified, the allocation policy includes a control indication indicating a mechanism for selecting among the storage units. The instructions, when executed, may also allocate blocks according to the allocation policy. In another implementation, a computer accessible medium comprises instructions which, when executed receive a request to allocate one or more blocks for a file in a filesystem and allocate blocks according to an allocation policy. Allocation policies are specifiable at two or more levels of granularity in the filesystem.
Owner:SYMANTEC OPERATING CORP
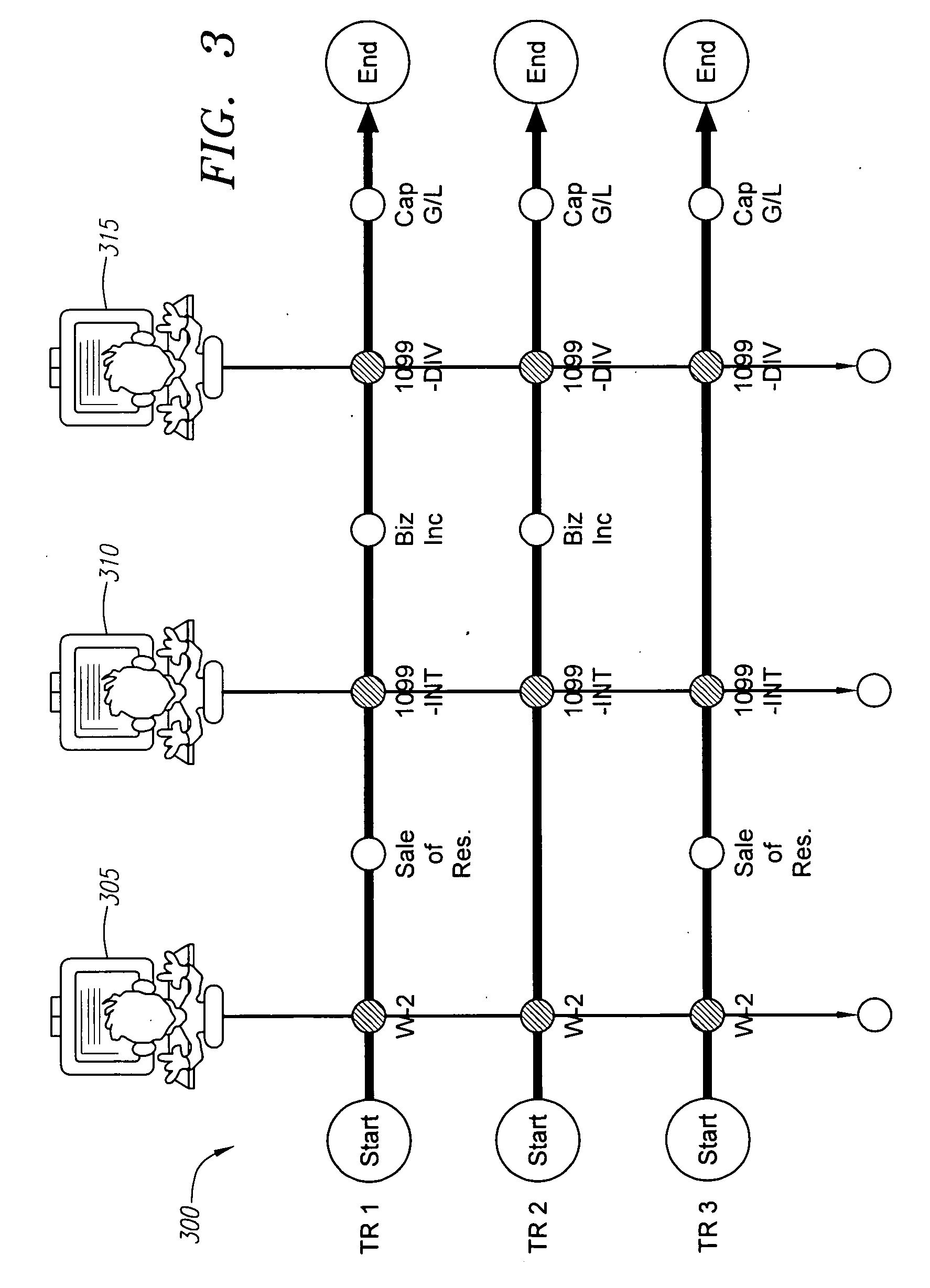
Efficient work flow system and method for preparing tax returns
ActiveUS20060155618A1Increase the number ofImprove productivityComplete banking machinesFinanceFile allocationService provision
A processor-based method for preparing a tax return using multiple service providers. The method includes receiving at a first service provider an image file that includes a plurality of data values and assigning at the first service provider the image file to a form having a plurality of predefined field names, wherein each of the plurality data values belong to one of the plurality of predefined field names. The method also includes receiving at a second service provider the image file and an input form having a plurality of input fields corresponding to the plurality of predefined field names and associating at the second service provider the plurality of data values from the image file with the plurality of input fields.
Owner:SUREPREP
System and method for viewing and editing multi-value properties
InactiveUS7188316B2Input/output for user-computer interactionDigital data information retrievalFile allocationVisual perception
In a display of properties (or metadata) for multiple selected files, properties may be aggregated. Visual differentiation may be used to associate displayed aggregated values with one or more selected files to which the values pertain. Multi-value properties may also be aggregated and differentiated and / or accentuated. When aggregating multiple multi-value properties, steps may be taken to carry relative priority or positioning assigned by each of the selected files to which the multi-value properties pertain. Aggregated multi-value properties may include prompt text informing them of editing options, and users may edit properties by editing the displayed aggregated properties. Changes to the aggregated properties may be applied to the properties of the various selected files.
Owner:MICROSOFT TECH LICENSING LLC
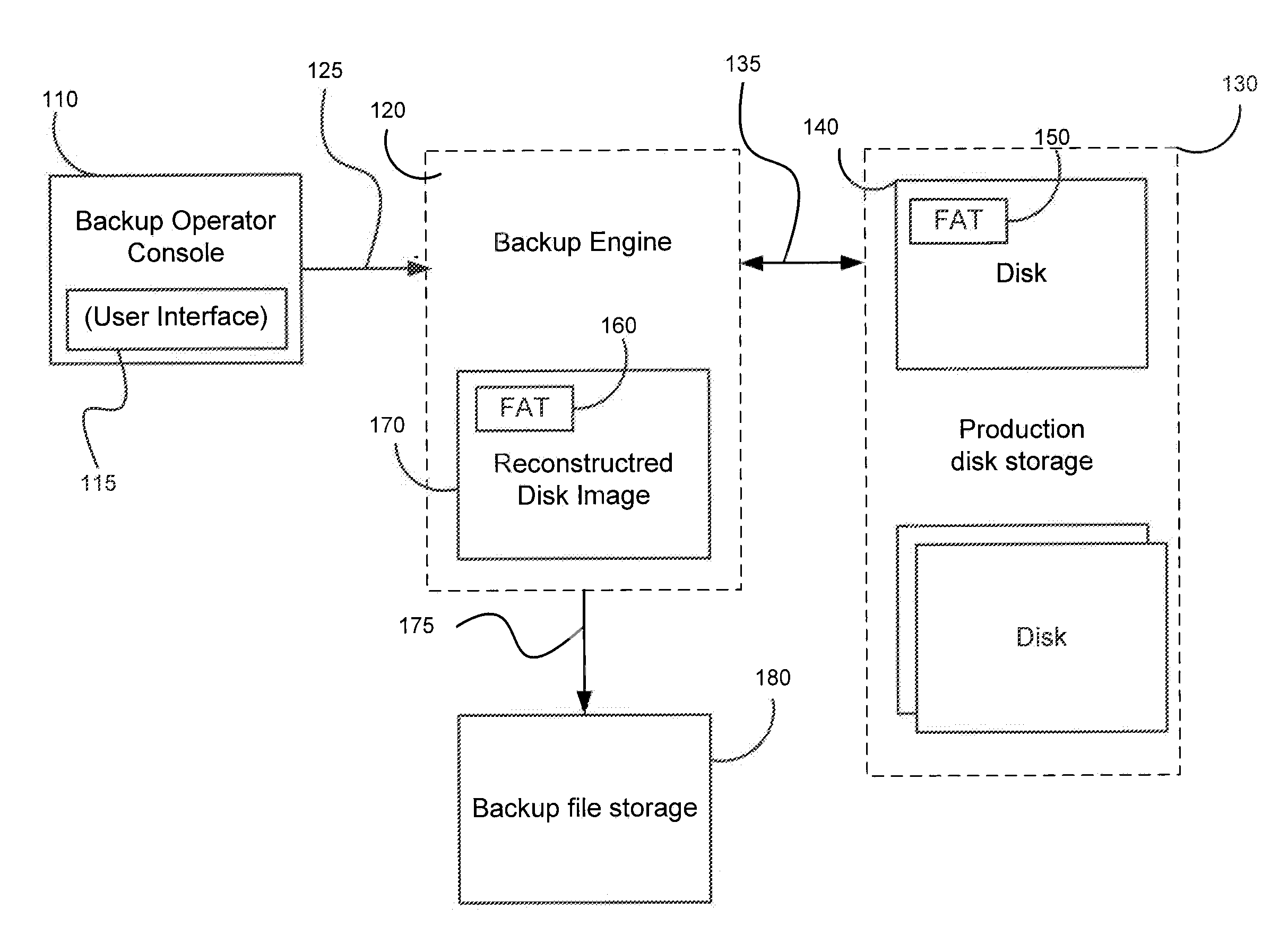
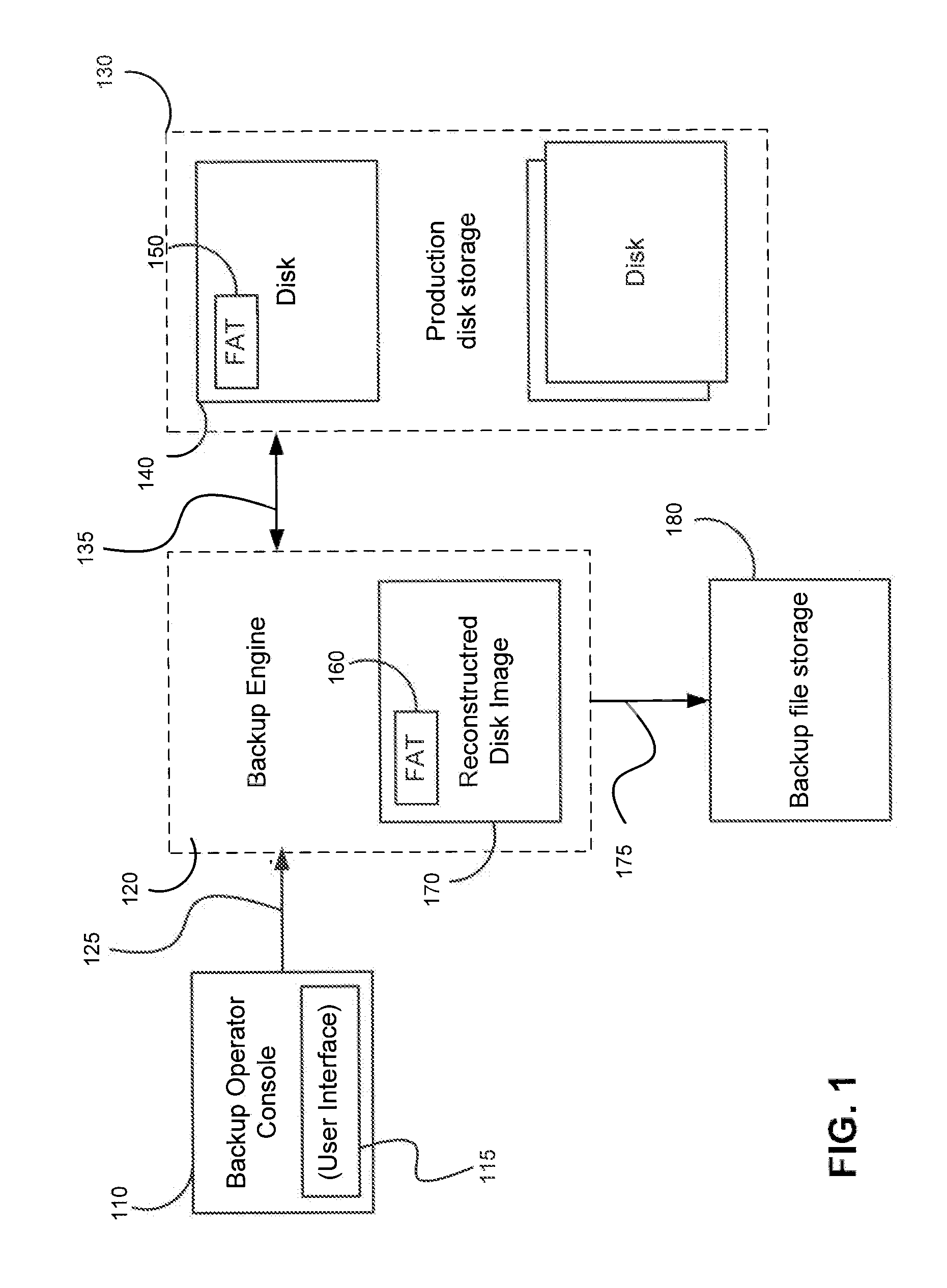
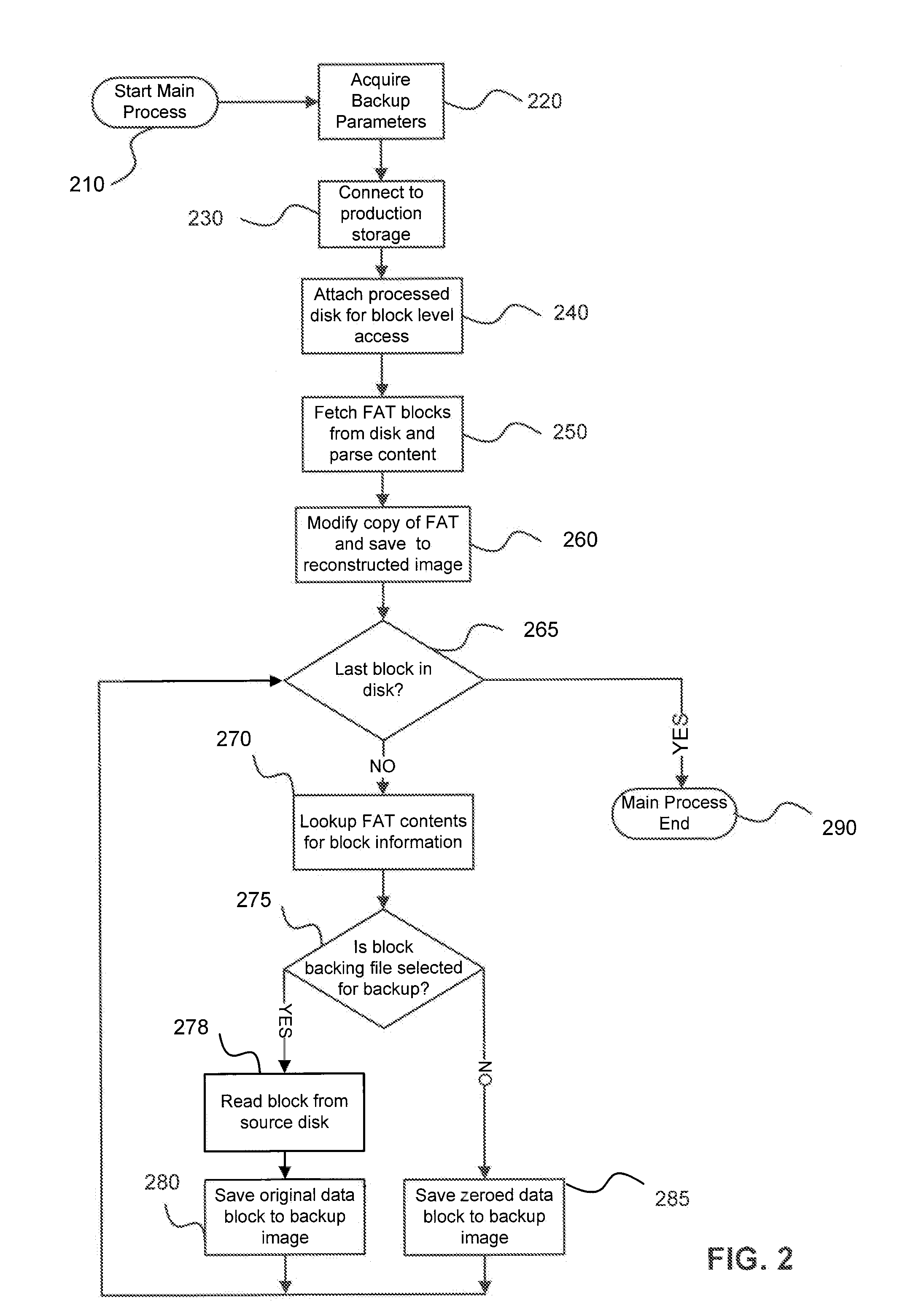
Selective Processing of File System Objects for Image Level Backups
ActiveUS20110307657A1Reduce the amount requiredReduce data volumeMemory loss protectionError detection/correctionFile allocationData storing
Systems, methods, and computer program products are provided for reducing the size of image level backups. An example method receives backup parameters identifying a physical or Virtual Machine (VM) to backup and at least one file system object to include in the backup. The method connects to production storage corresponding to the selected physical or virtual machine and obtains access to data stored in disk corresponding to the selected file system object(s). The method fetches file allocation table (FAT) blocks from the disk and parses contents of the FAT blocks to determine if the disk blocks correspond to the selected file system object(s). The method creates a backup disk image FAT comprising blocks corresponding to the selected file system object(s). The method creates a reconstructed disk image FAT blocks corresponding to the backup FAT and disk image data blocks belonging to the selected file system object(s) and all other disk image data blocks are saved as zero blocks. A reconstructed disc image is compressed and stored in a backup file on backup storage, or replicated (copied) to another storage intact.
Owner:VEEAM SOFTWARE GROUP GMBH
Systems and methods for providing storage of data on servers in an on-demand media delivery system
InactiveUS20090138922A1Television system detailsAnalogue secracy/subscription systemsFile allocationData storing
A system and method may be provided that allows users to store, retrieve, and manipulate on-demand media content and data stored on a remote server network in an on-demand media delivery system. More particularly, the system may allow a user to access his or her on-demand media account from user equipment in different locations as long as the current user equipment can communicate with a remote server that stores user-specific information. The system upon user selection may freeze the delivery of on-demand media at a particular point and allow the user to resume the media at a later time from some other network location in system. Users may upload personal images or files to an on-demand delivery server for later retrieval and display. Users may be permitted to assign access rights to the uploaded files.
Owner:ROVI GUIDES INC
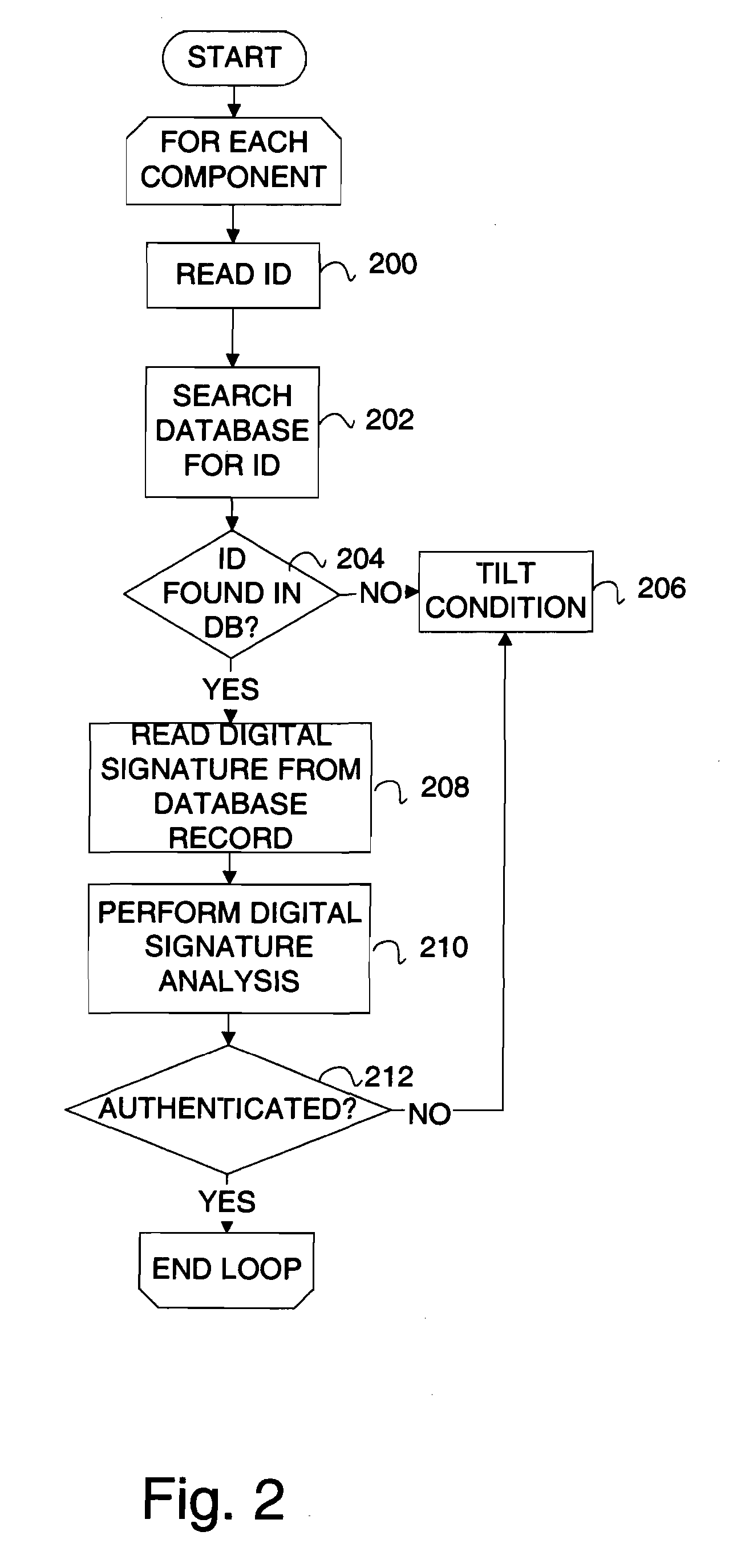
Device verification system and method
InactiveUS20070006329A1Little informationImprove securityDetecting faulty hardware by configuration testDetecting faulty hardware by remote testFile allocationOperational system
There is provided a method and system for verifying a device, having components. Identification numbers of the components are read and then verified. The process of verifying comprises matching each identification number in a database to determine whether each identification number is valid. In one embodiment, the database is remote from the device, wherein verification is performed over a network connecting a database server containing the database with the device. The device transmits the identification numbers for each of the components to the database server for verification. A file allocation structure reader may be located in a basic input / output system of the device for reading and verifying data files from a persistent storage media without loading an operating system. The device may comprise a gaming machine that contains a monitor for monitoring one or more system events being processed by the gaming machine. The monitor monitors routine and non-routine events. A detector is included for detecting selected system events so that they may be recorded.
Owner:BALLY GAMING INC
Automatic rules-based device synchronization
ActiveUS7647346B2Improve experienceDigital data information retrievalData processing applicationsData synchronizationFile synchronization
Owner:MICROSOFT TECH LICENSING LLC
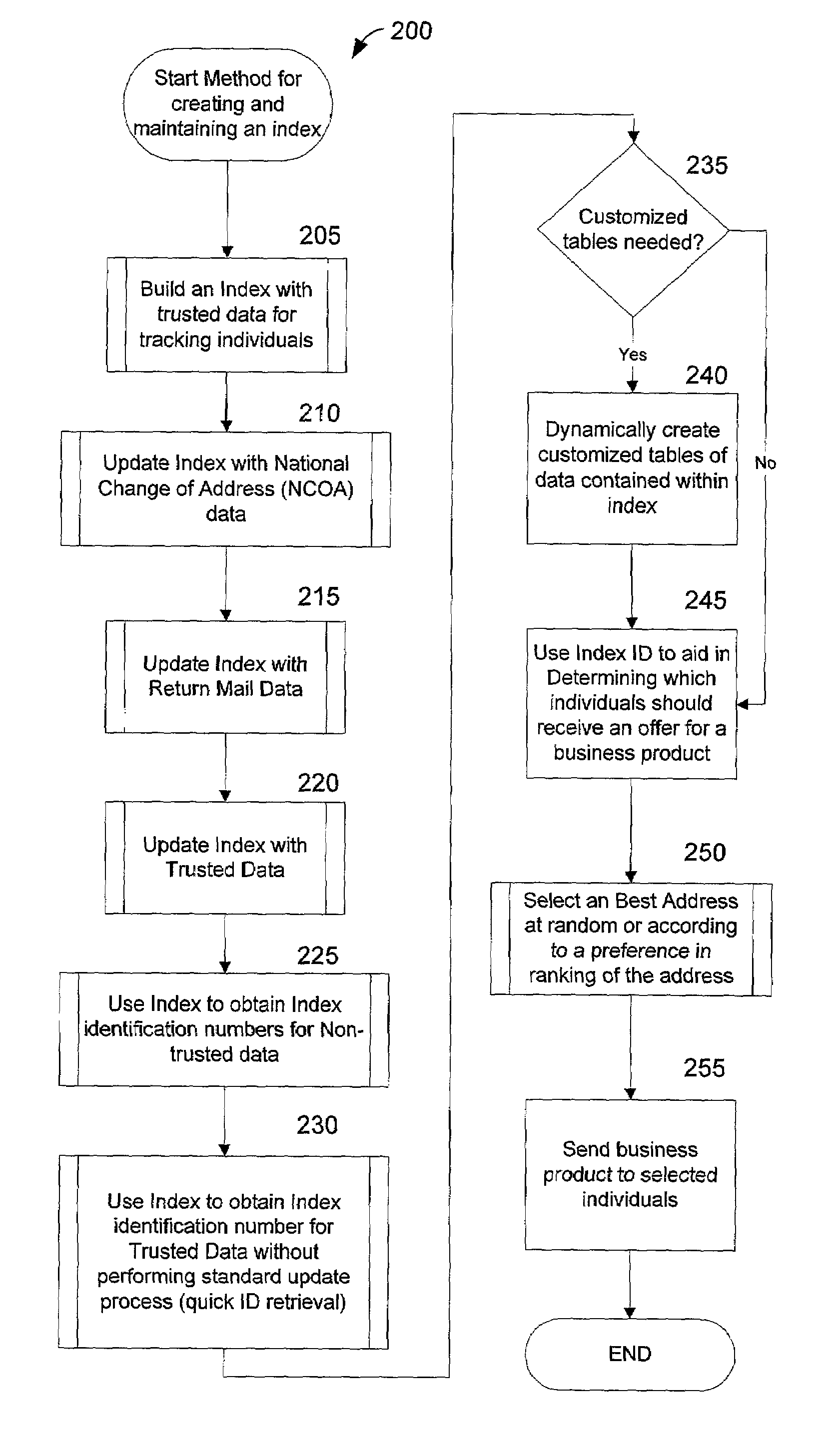
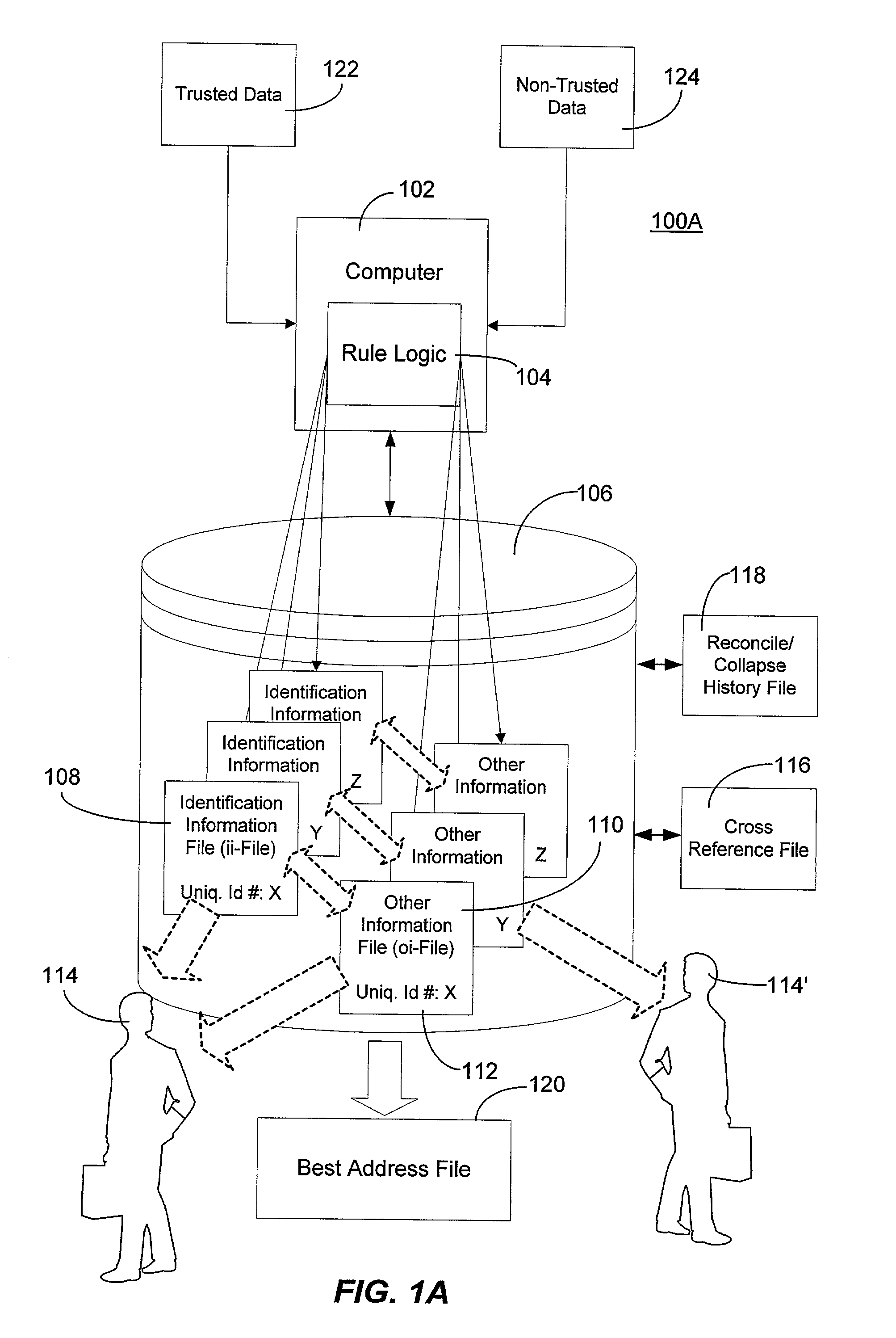
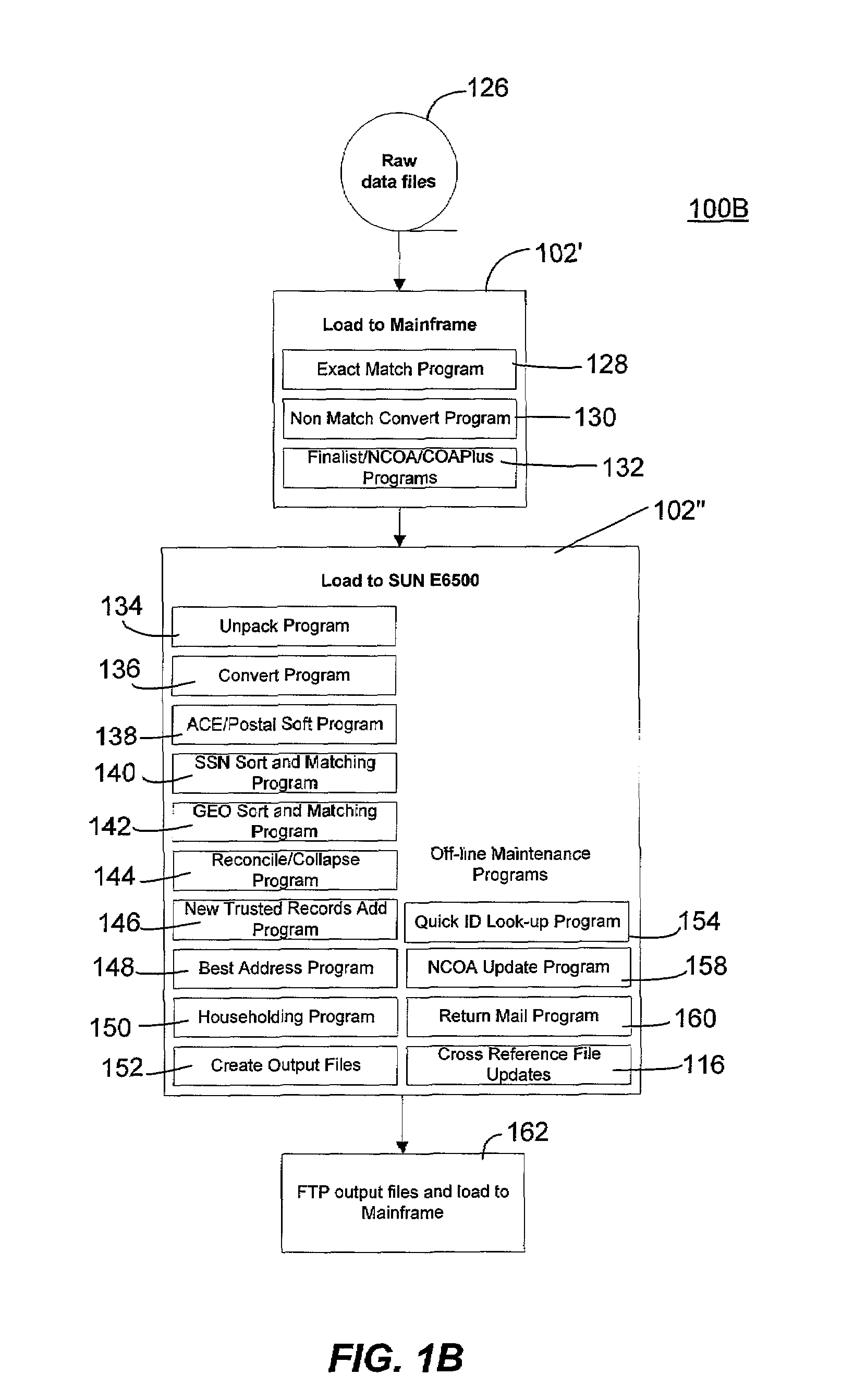
Method and system for creating and maintaining an index for tracking files relating to people
InactiveUS6968348B1Easy accessEasy to manufactureFinanceDigital data processing detailsFile allocationSocial Security number
A computer system creates and maintains an index for tracking information relating to individuals. Such information can include, but is not limited to, social security numbers, names, address information, credit bureau identification numbers, and credit history information on individuals. The invention employs logical rules to this information in order to create and maintain a set of files for each individual. The logical rules can include social security rules, geography rules, and address ranking rules. The invention is designed to evaluate slight variations in information very carefully in order to insure that appropriate files are assigned the same index identification number or that appropriate records are assigned separate and different index identification numbers as a situation warrants. The present invention is designed to maintain numerous files for each individual being tracked instead of merging and purging files as is done in the conventional art.
Owner:PROVIDIAN FINANCIAL CORP +1
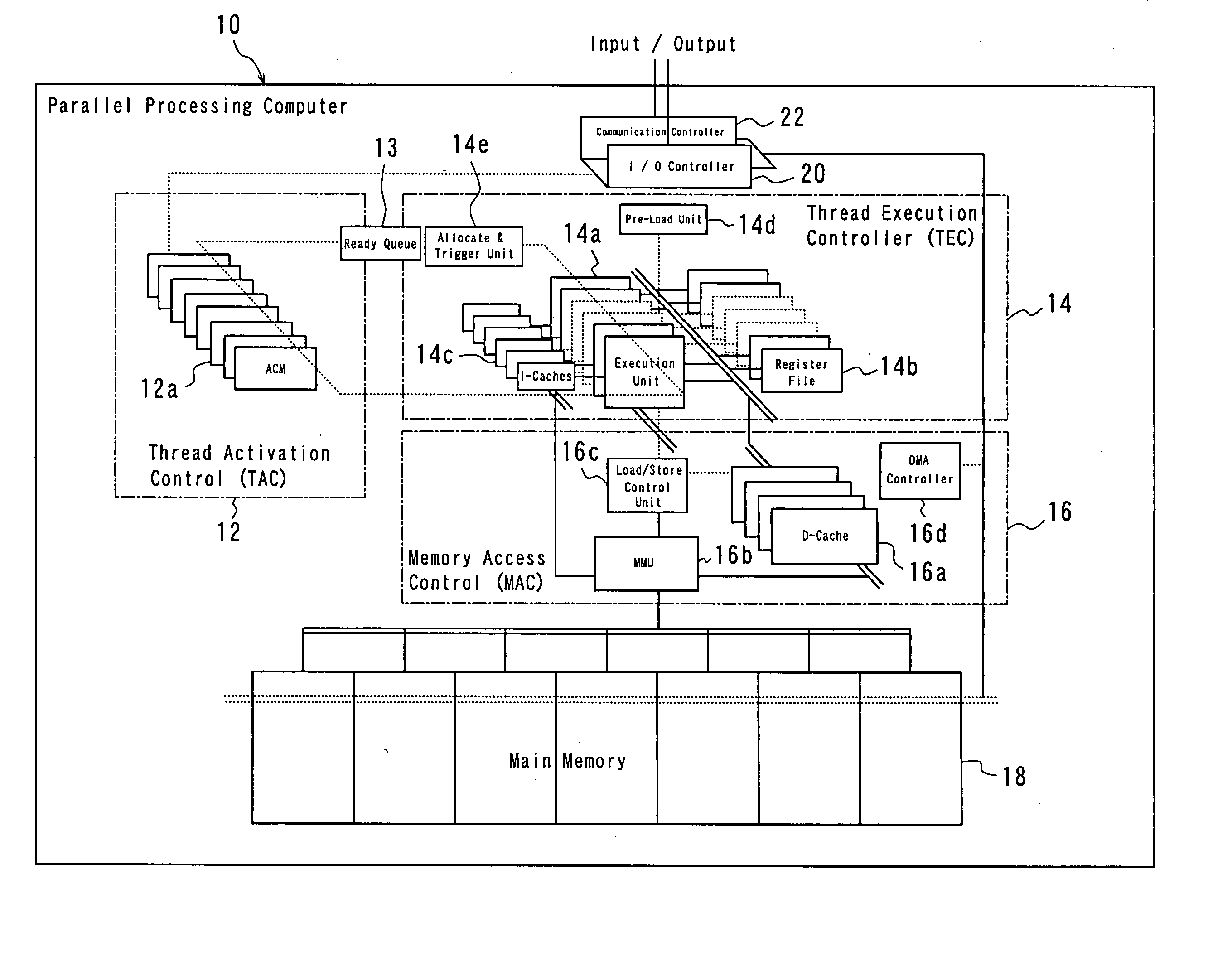
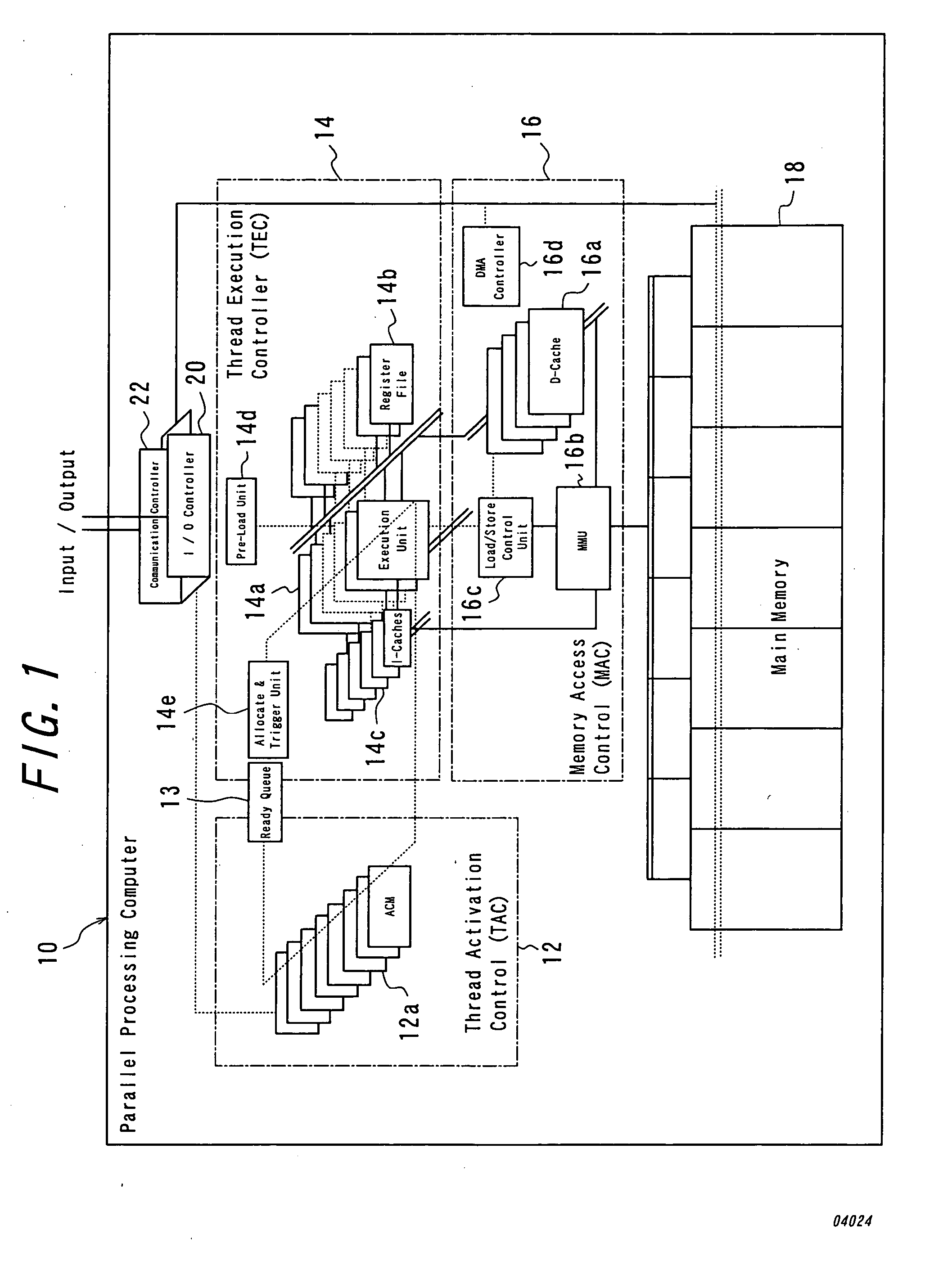
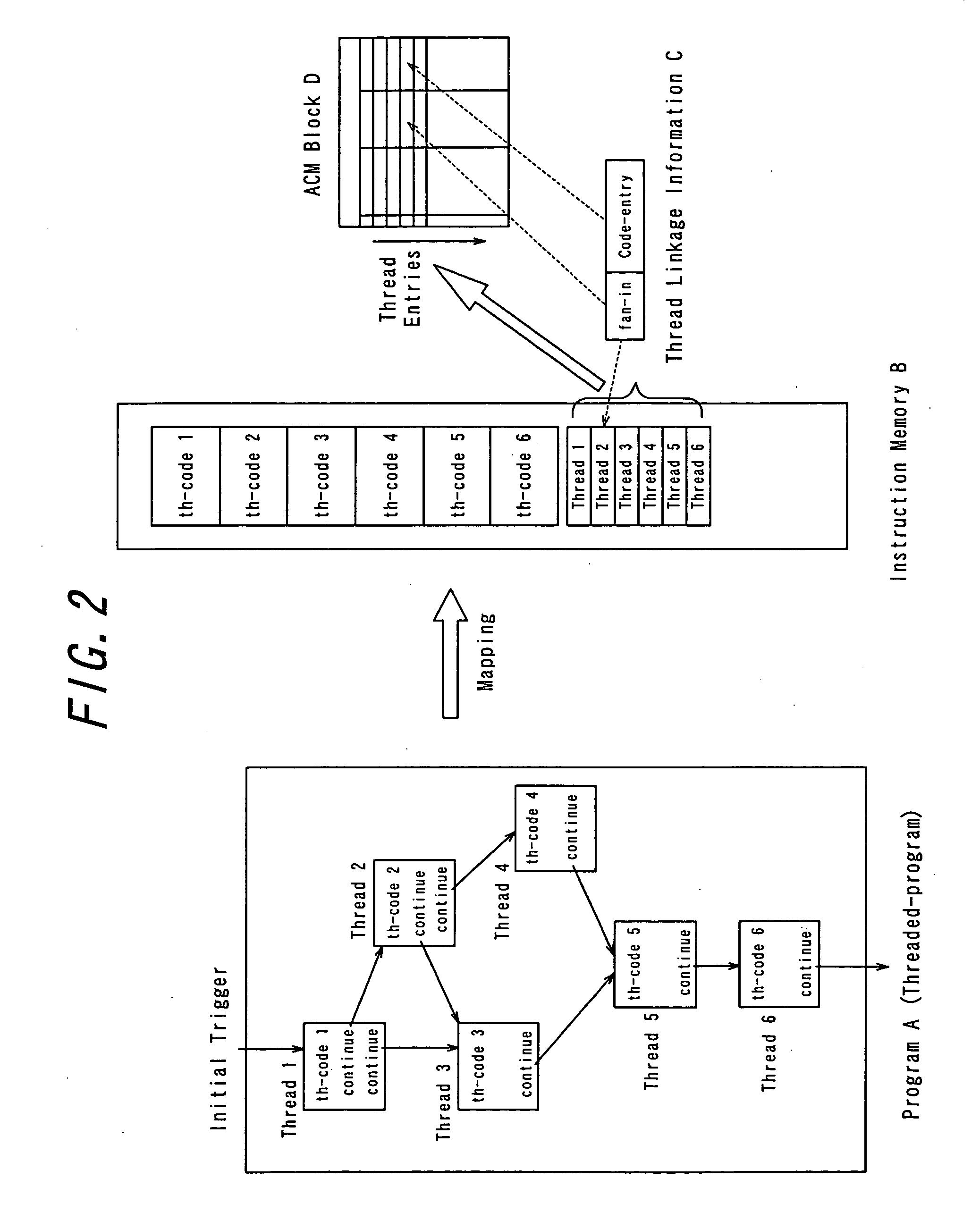
Parallel processing computer
InactiveUS20050240930A1Efficient executionImprove throughputProgram initiation/switchingRegister arrangementsProgram fragmentFile allocation
There is provided a parallel processing computer for executing a plurality of threads concurrently and in parallel. The computer includes: a thread activation controller for determining whether or not each of threads, which are exclusively executable program fragments, is ready-to-run, to put the thread determined ready-to-run into a ready thread queue as ready-to-run thread; and a thread execution controller having a pre-load unit, an EU allocation and trigger unit, a plurality of thread execution units and a plurality of register files including a plurality of registers, and the pre-load unit, prior to when each ready-to-run thread in the ready thread queue is executed, allocates a free register file of the plurality of register files to the each ready-to-run thread, to load initial data for the each ready-to-run thread into the allocated register file, and the EU allocation and trigger unit, when there is a thread execution unit in idle state of the plurality of thread execution unit, retrieves ready-to-run thread from the top of the ready thread queue, and to allocate the retrieved ready-to-run thread to the thread execution unit in idle state, and to couple the register file loaded the initial data for the ready-to-run thread with the allocated thread execution unit in idle state, and to trigger the ready-to-run thread. The plurality of thread execution units execute the triggered threads concurrently in parallel.
Owner:KYUSHU UNIV
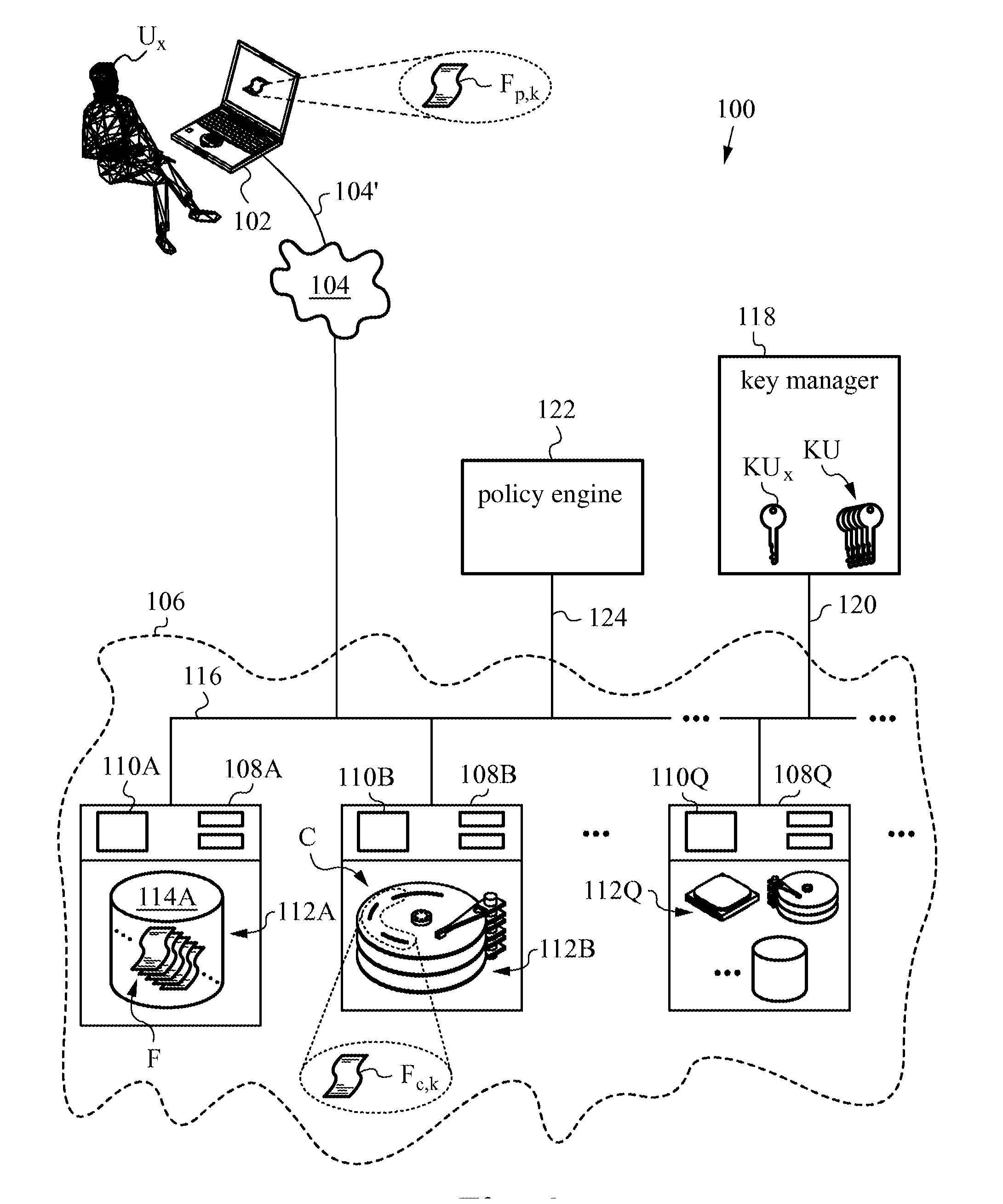
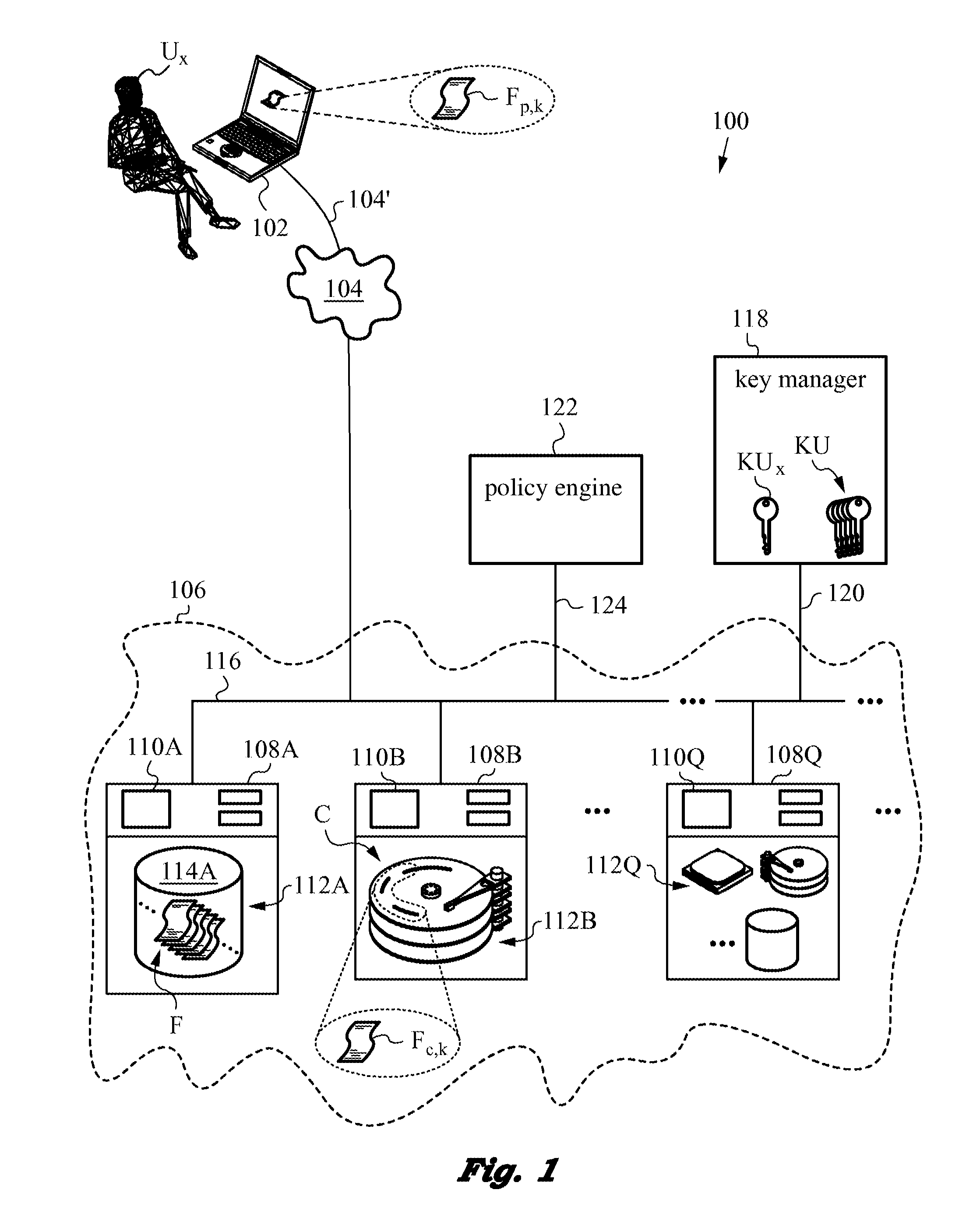
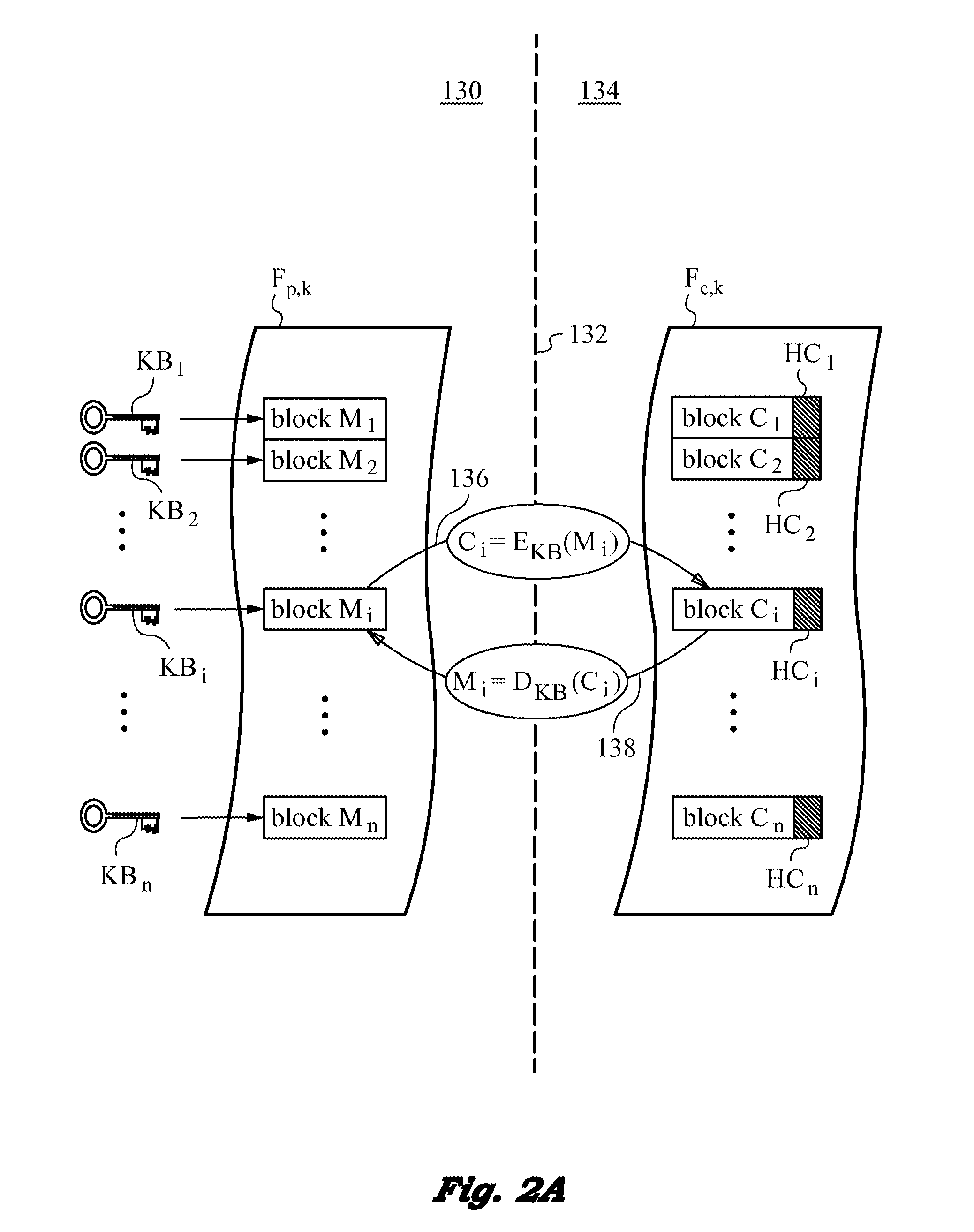
Securing files under the semi-trusted user threat model using per-file key encryption
ActiveUS20160277373A1Improve security levelEnsure integrityInterprogram communicationComputer security arrangementsFile allocationCiphertext
A computer system and methods for securing files in a file system with storage resources accessible to an authenticable user using an untrusted client device in a semi-trusted client threat model. Each file is secured in the file system in one or more ciphertext blocks along with the file metadata. Each file is assigned a unique file key FK to encrypt the file. A wrapping key WK assigned to the file is used for encrypting the file key FK to produce a wrapped file key WFK. The file is encrypted block by block to produce corresponding ciphertext blocks and corresponding authentication tags. The authentication tags are stored in the file metadata, along with an ID of the wrapping key WK, wrapped file key WFK, last key rotation time, an Access Control List (ACL), etc. The integrity of ciphertext blocks is ensured by authentication tags and the integrity of the metadata is ensured by a message authentication code (MAC).
Owner:ZETTASET
Multi-volume file support
ActiveUS7814128B2Input/output to record carriersDigital data processing detailsFile allocationGranularity
A computer accessible medium comprises instructions which, when executed, receive a request to allocate one or more blocks for a file. At least one allocation policy is assigned to the file, wherein the allocation policy specifies one or more storage units on which the blocks are to be allocated. Additionally, if more than one storage unit is specified, the allocation policy includes a control indication indicating a mechanism for selecting among the storage units. The instructions, when executed, may also allocate blocks according to the allocation policy. In another implementation, a computer accessible medium comprises instructions which, when executed receive a request to allocate one or more blocks for a file in a filesystem and allocate blocks according to an allocation policy. Allocation policies are specifiable at two or more levels of granularity in the filesystem.
Owner:SYMANTEC OPERATING CORP
Object file organization method based on object storage device
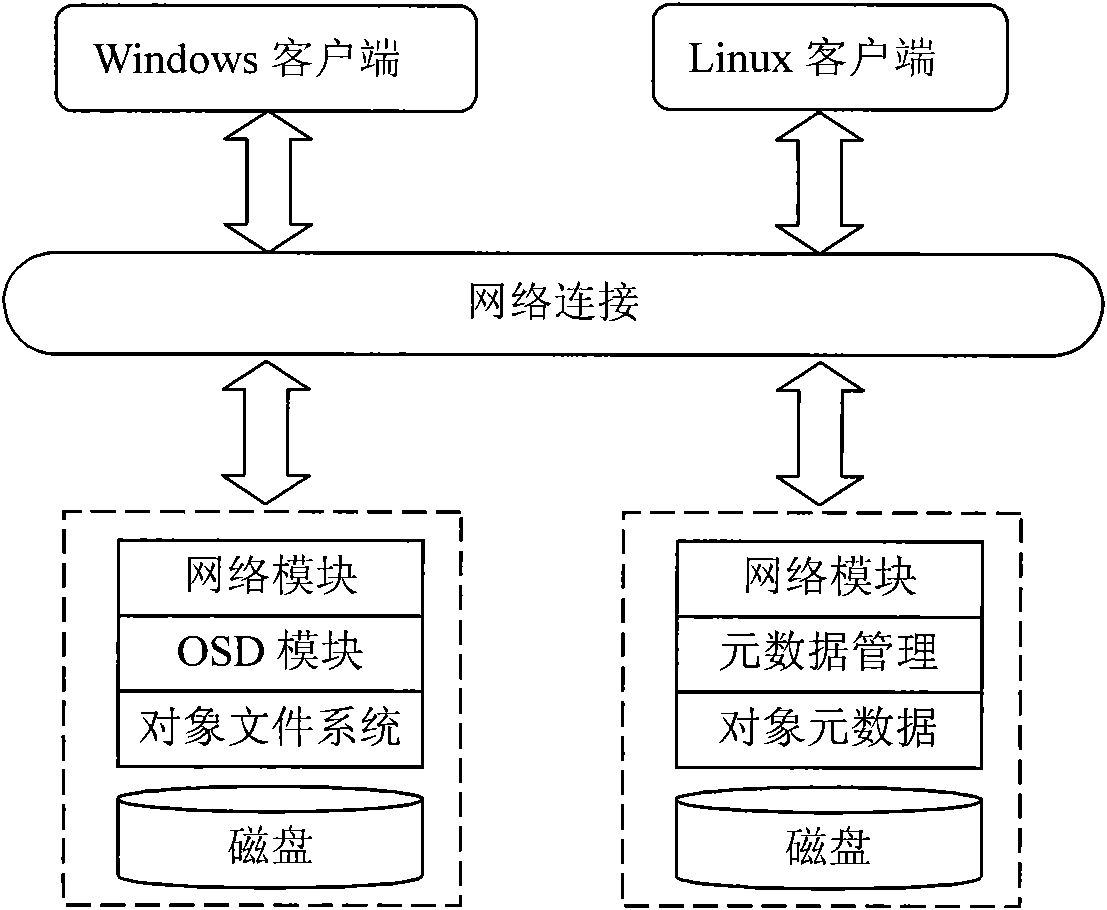
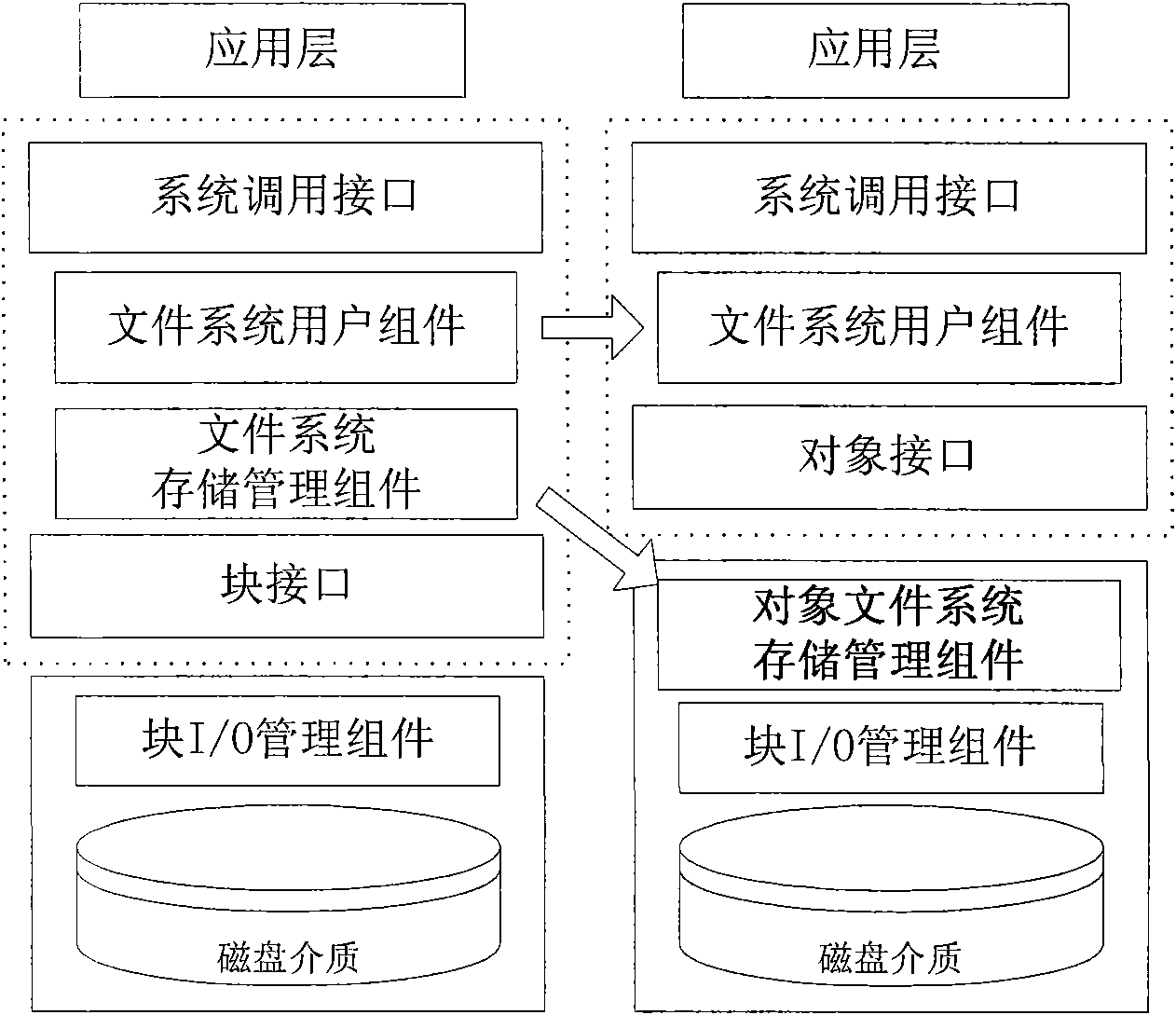
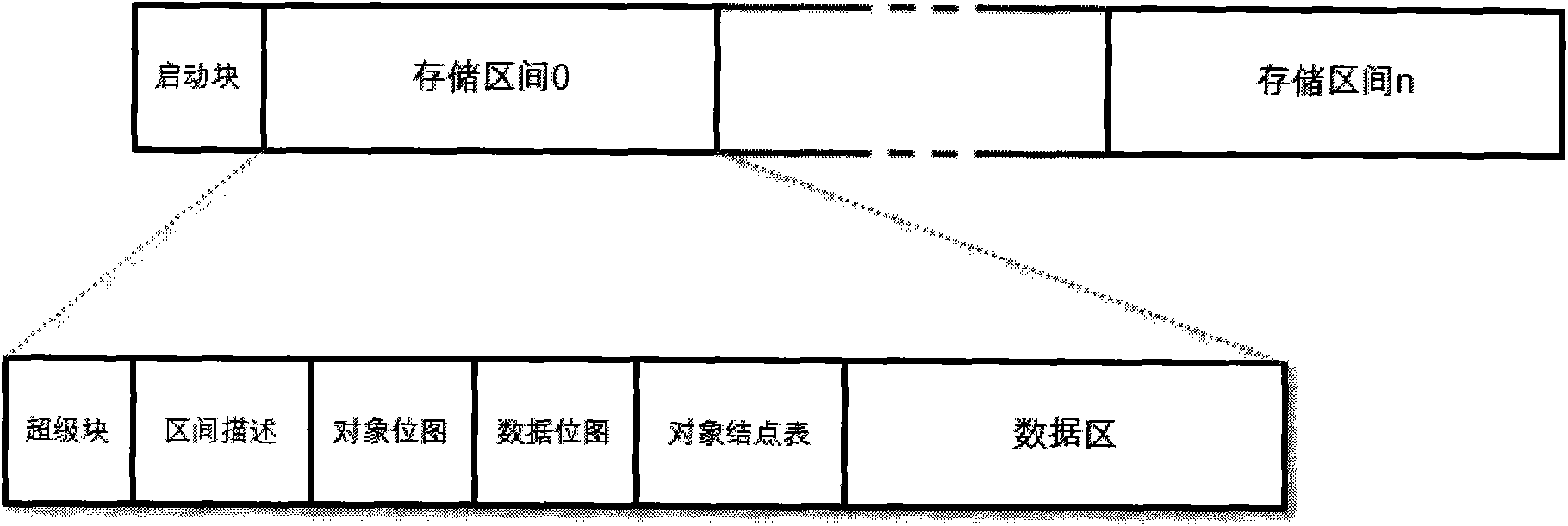
InactiveCN101556557AEfficiencyImprove reliabilityMemory adressing/allocation/relocationSpecial data processing applicationsObject basedFile allocation
The invention relates to an object file organization method based on an object storage device, comprising the following steps of: establishing the layout of an object file system in a disk, loading information including object description, object bitmap and the like in a memory; detecting the size of the object file by a space allocator before allocating the space; if the size of the object file is acquired, adopting a pre-allocating method to allocate space for the object file on the disk; if the size of the object file can not be acquired, firstly writing part data of the object file into a buffer zone; detecting whether the buffer zone is fully filled or whether the client needs to release the caching data, allocating space for the data in the buffer zone on the disk, and writing the data into the disk; and when the data in the buffer zone is far larger than size of the logic data sub-block, allocating storage space for the data by the space allocator. The invention adopts the method of continuously allocating a plurality of data blocks, thus reducing the time for searching and allocating free blocks, and making up the limitation and disadvantage of object file system disk space allocation in the current distribution-type file system.
Owner:ZHEJIANG UNIV
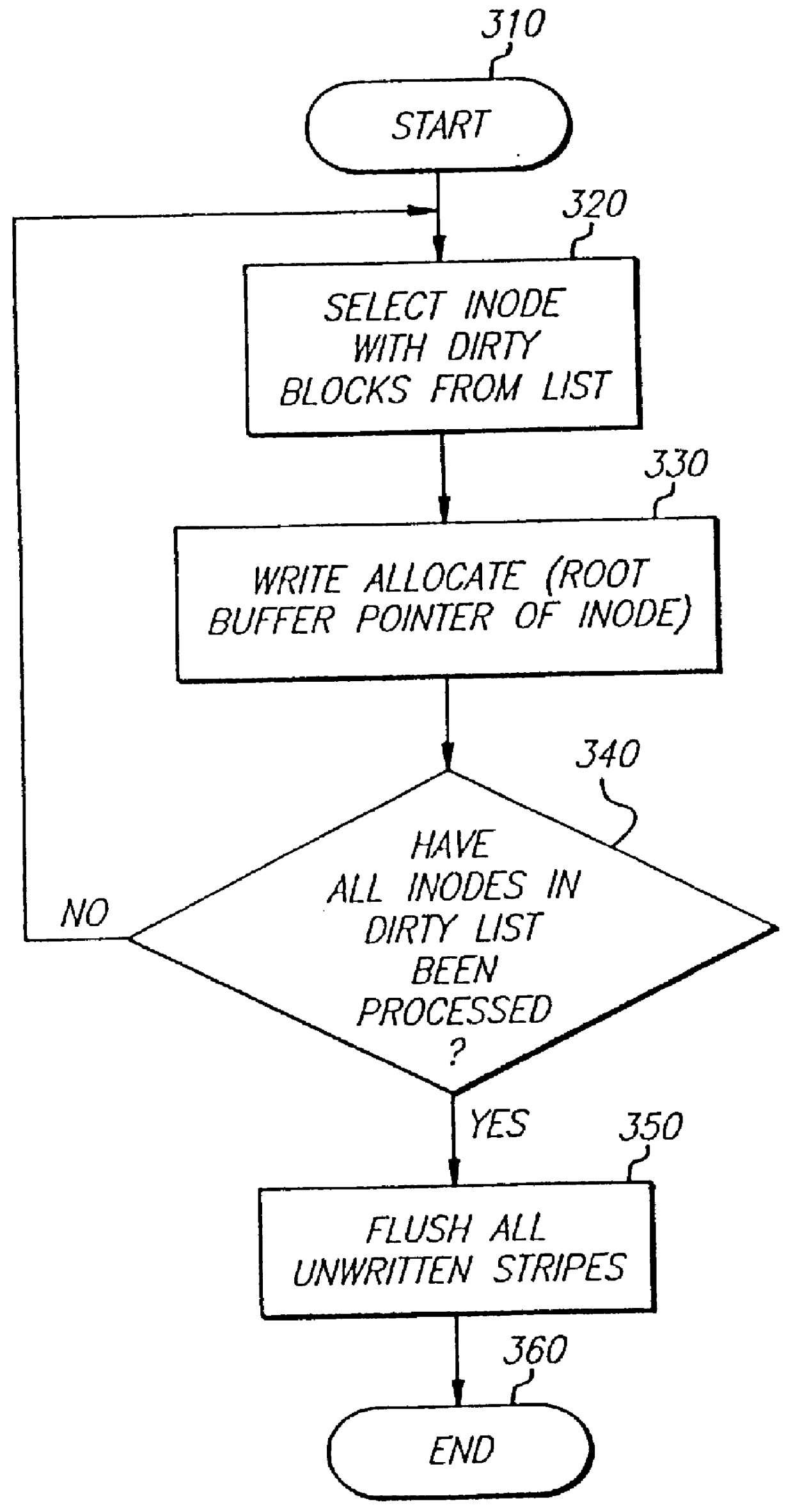
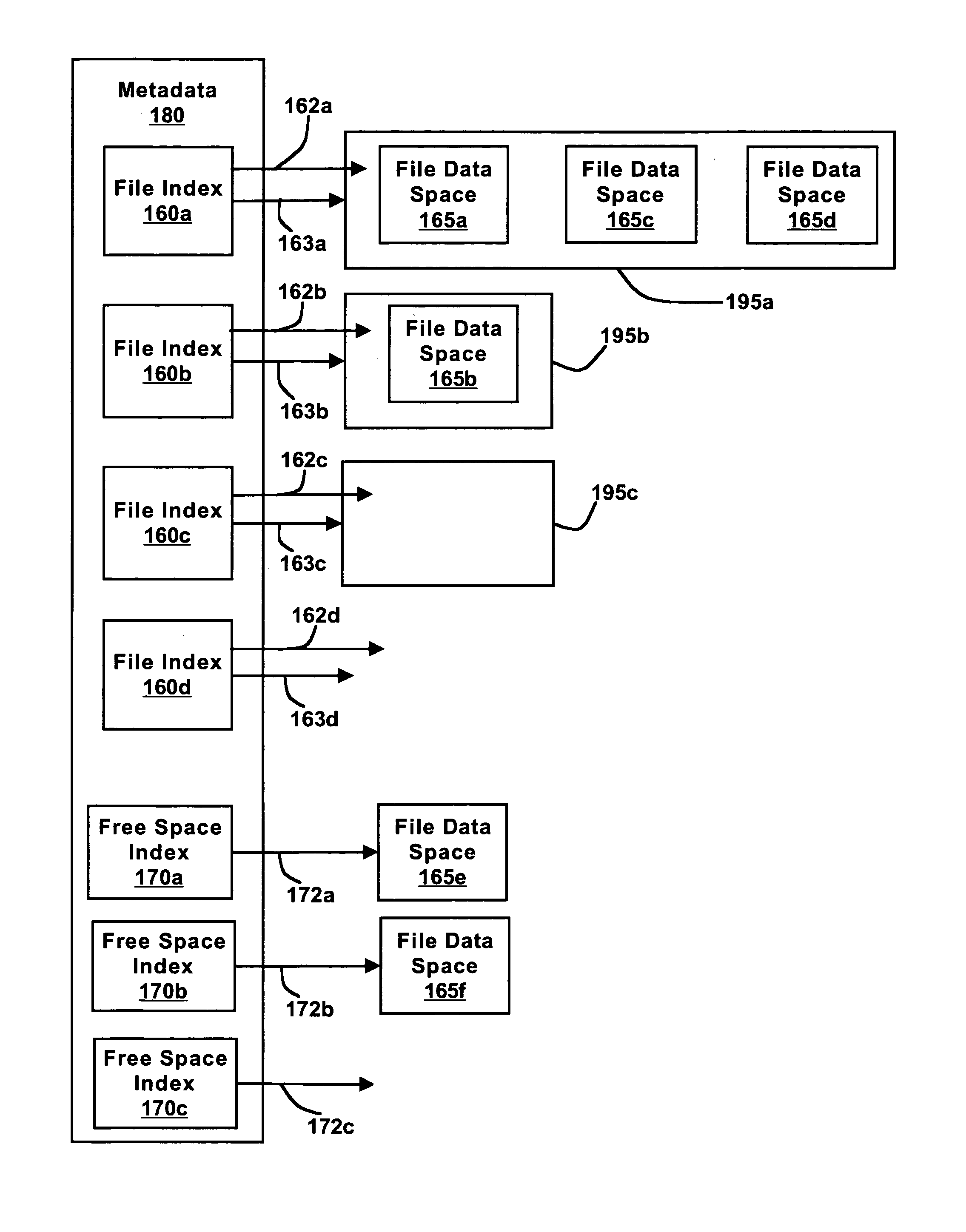
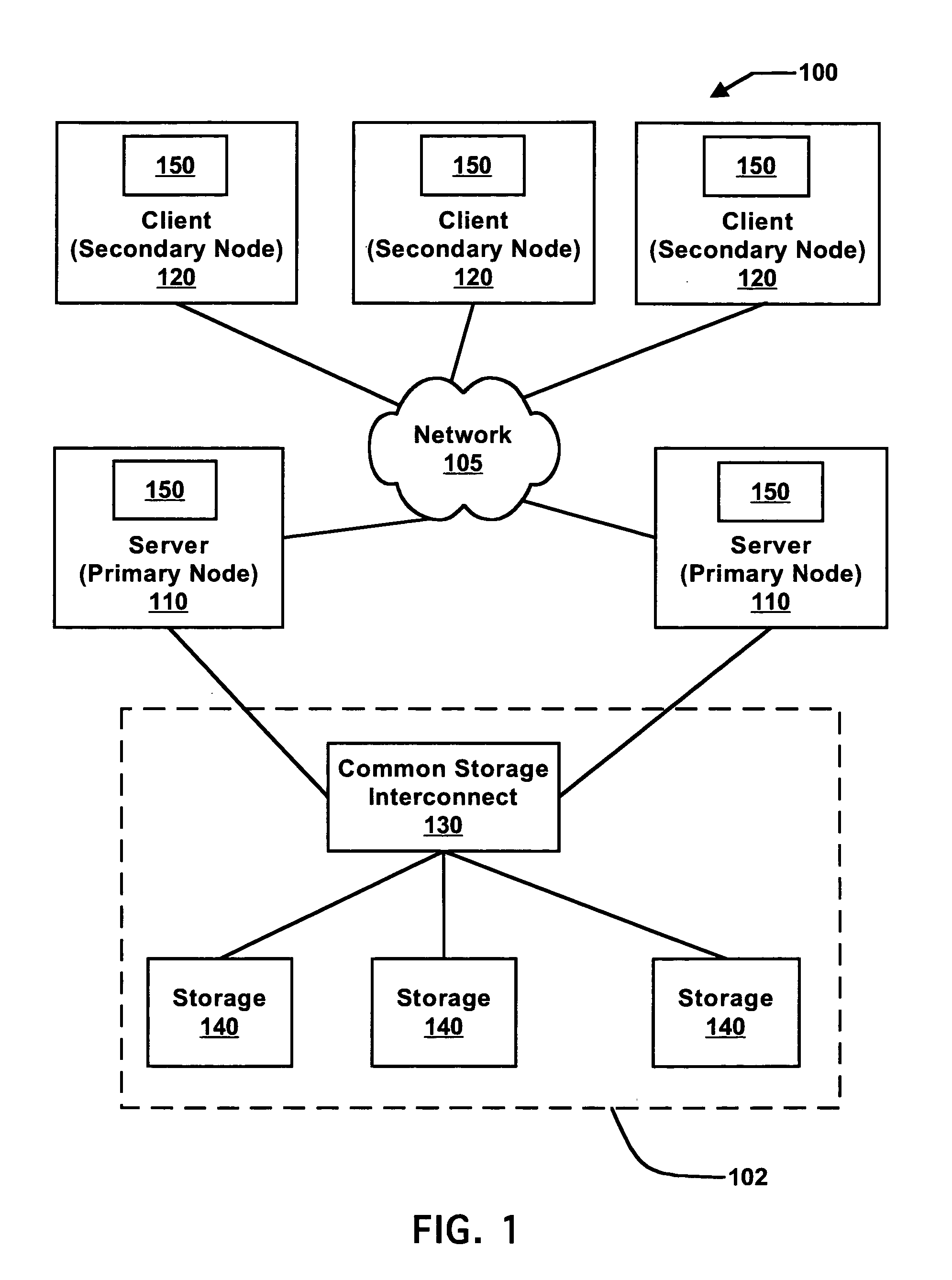
File system and methods for performing file create and open operations with efficient storage allocation
A client computer system of a cluster may send a request to create a file in a cluster file system. A server may create a file in response to the information and allocate space in a storage to the file. If a request to write to the file is received within a predetermined amount of time, the write may complete without requiring that additional operations be performed to allocate space to the file. If a write to the file is not received within the predetermined amount of time, the space allocated to the file when it was created may be de-allocated. The file system may additionally or alternatively perform a method for opening a file while delaying an associated truncation of space allocated to the file. If a request to write to the file is received within a predetermined amount of time, the write may be performed in the space already allocated to the file.
Owner:SYMANTEC OPERATING CORP
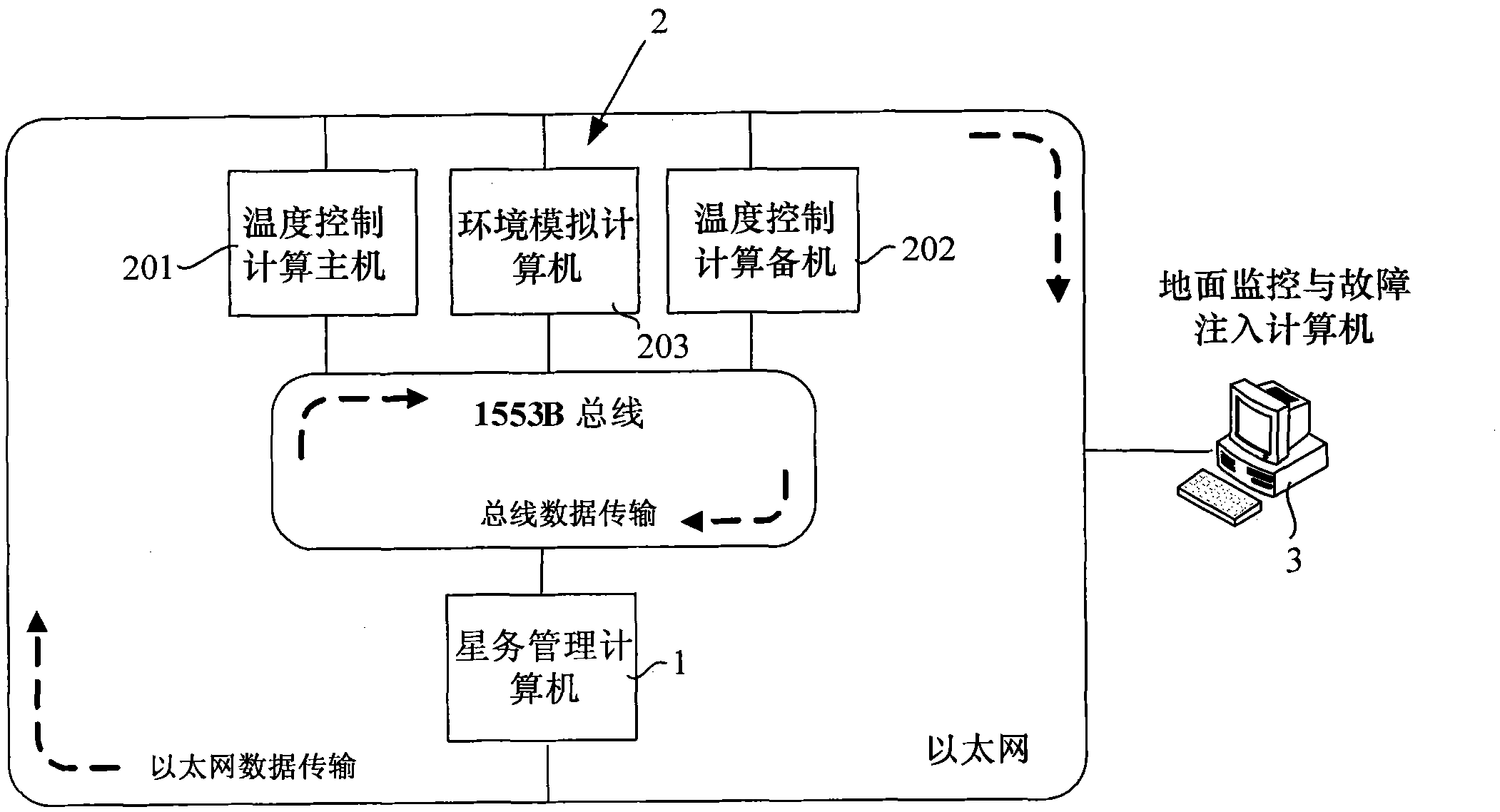
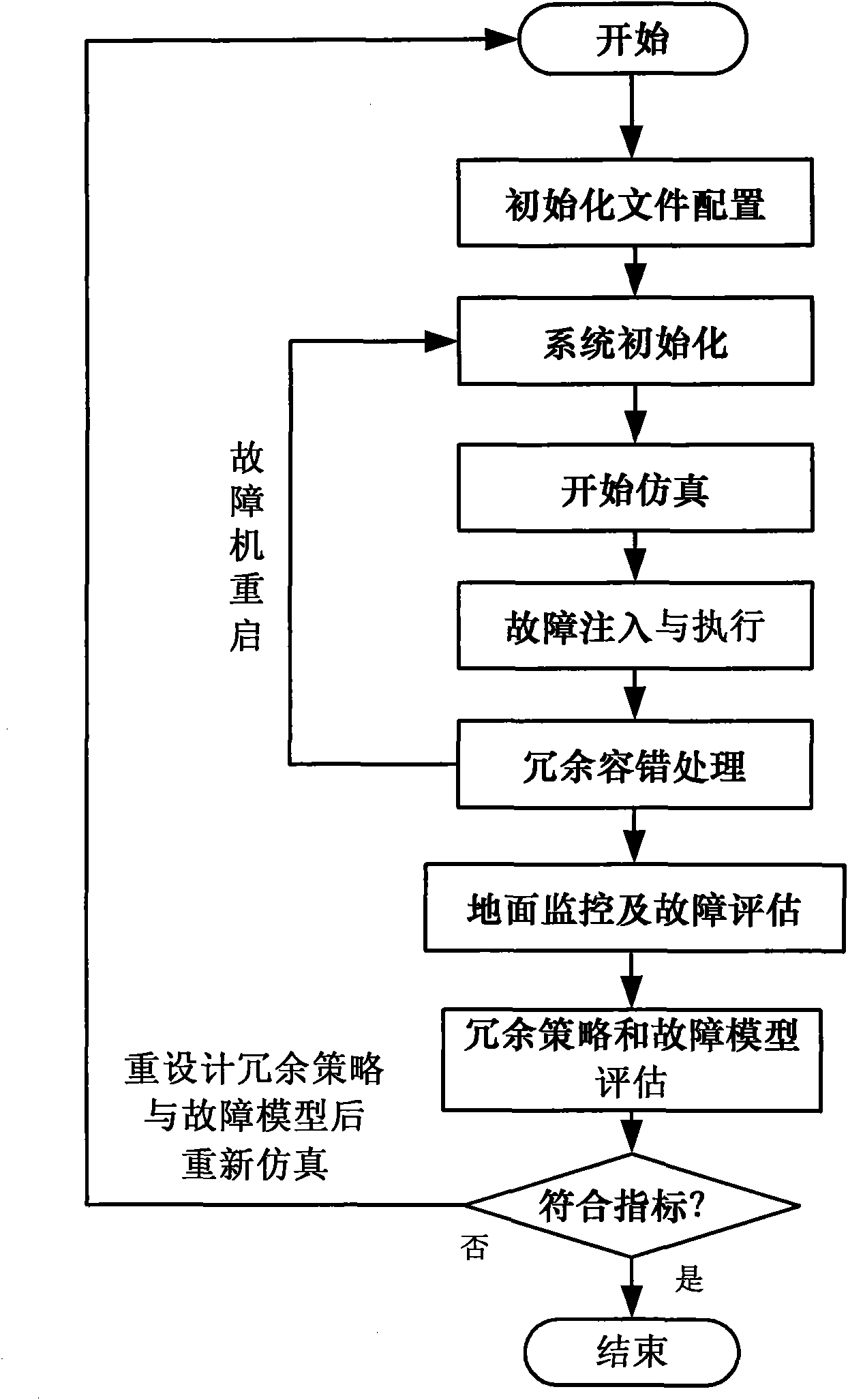
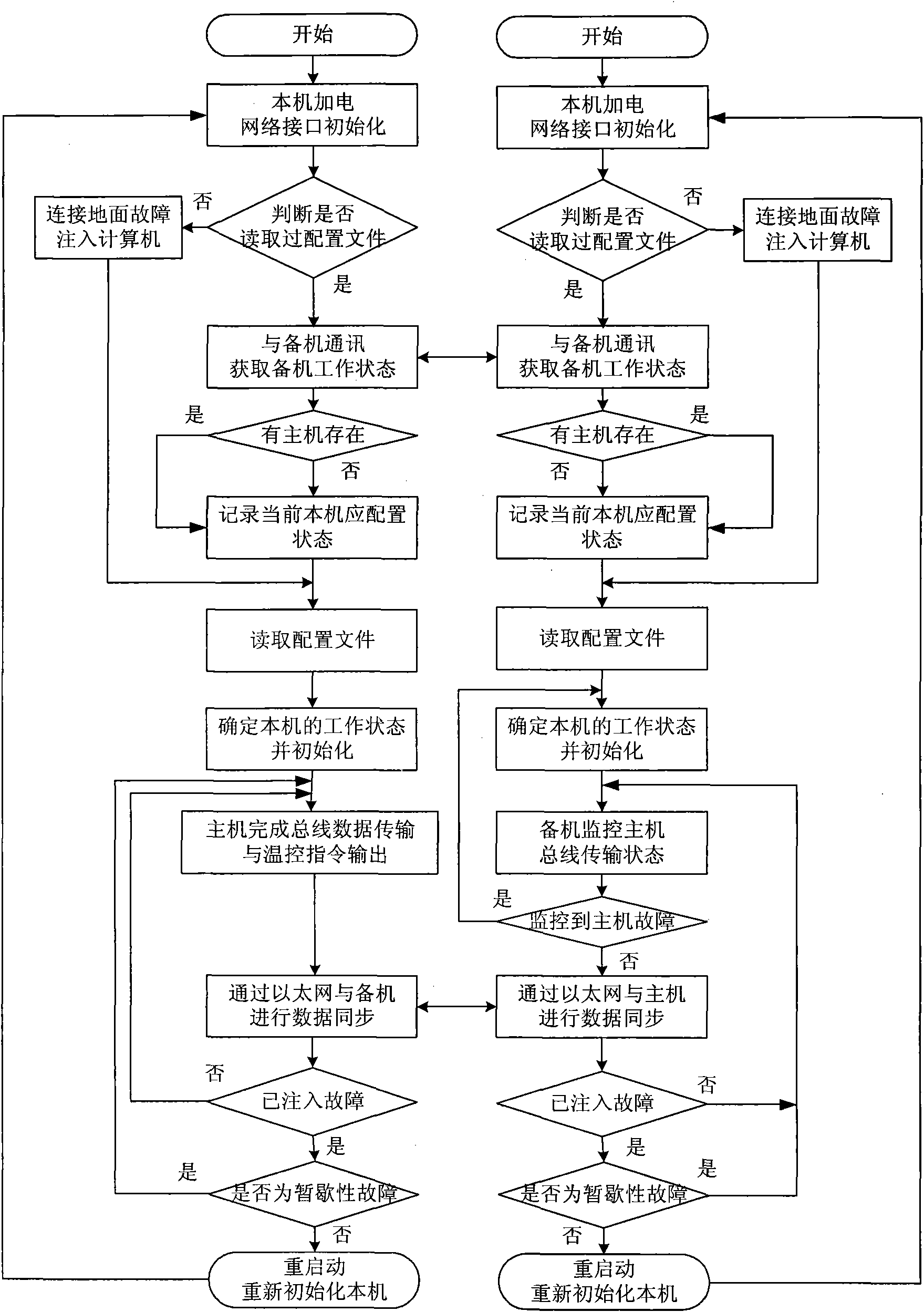
Embedded satellite-borne fault-tolerant temperature control system and verification method thereof
InactiveCN101819445AIn line with the development trendWith real development prospectsTemperatue controlError detection/correctionFault toleranceTemperature control
The invention discloses an embedded satellite-borne fault-tolerant temperature control system and a verification method thereof. The system comprises a satellite management computer, an on-satellite temperature control system and a ground monitoring and fault injection computer; the on-satellite temperature control system comprises a temperature control calculation host machine, a temperature control calculation standby machine and an environmental simulation computer; and the temperature control calculation host machine and the temperature control calculation standby machine are temperature control computers. The verification method comprises the following steps of: 1, initializing a file allocation; 2, initializing the system; 3, beginning simulation; 4, injecting and executing a fault; 5, processing redundant fault tolerance; 6, monitoring the ground and evaluating the fault; and 7, evaluating a fault model and a redundancy strategy of the temperature control system. The fault injection and the verification process of the whole running stage of the real satellite-borne temperature control system are completely realized; and the method is simple, convenient and reliable, and greatly reduces the test time and expense for the practical system.
Owner:BEIHANG UNIV
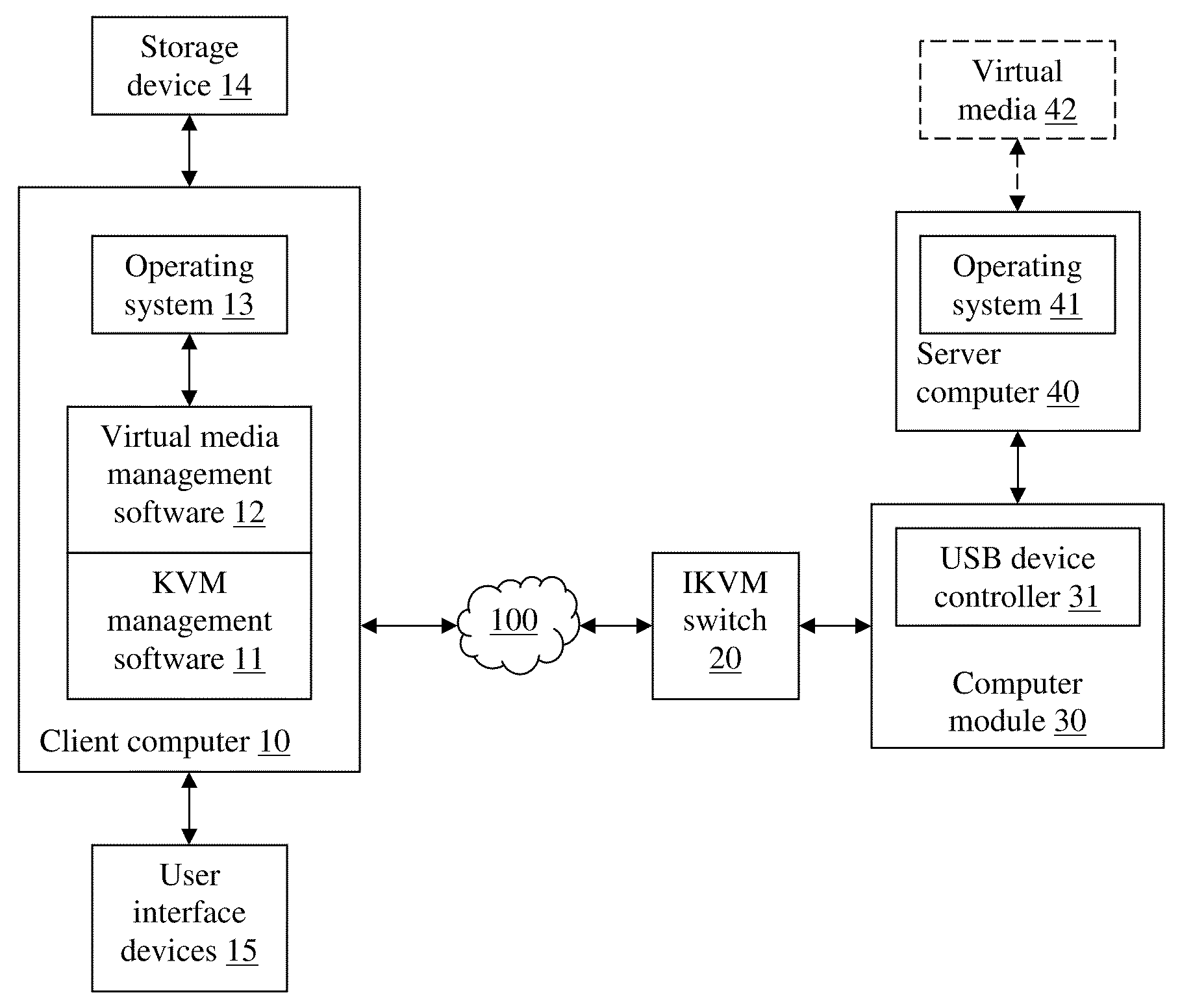
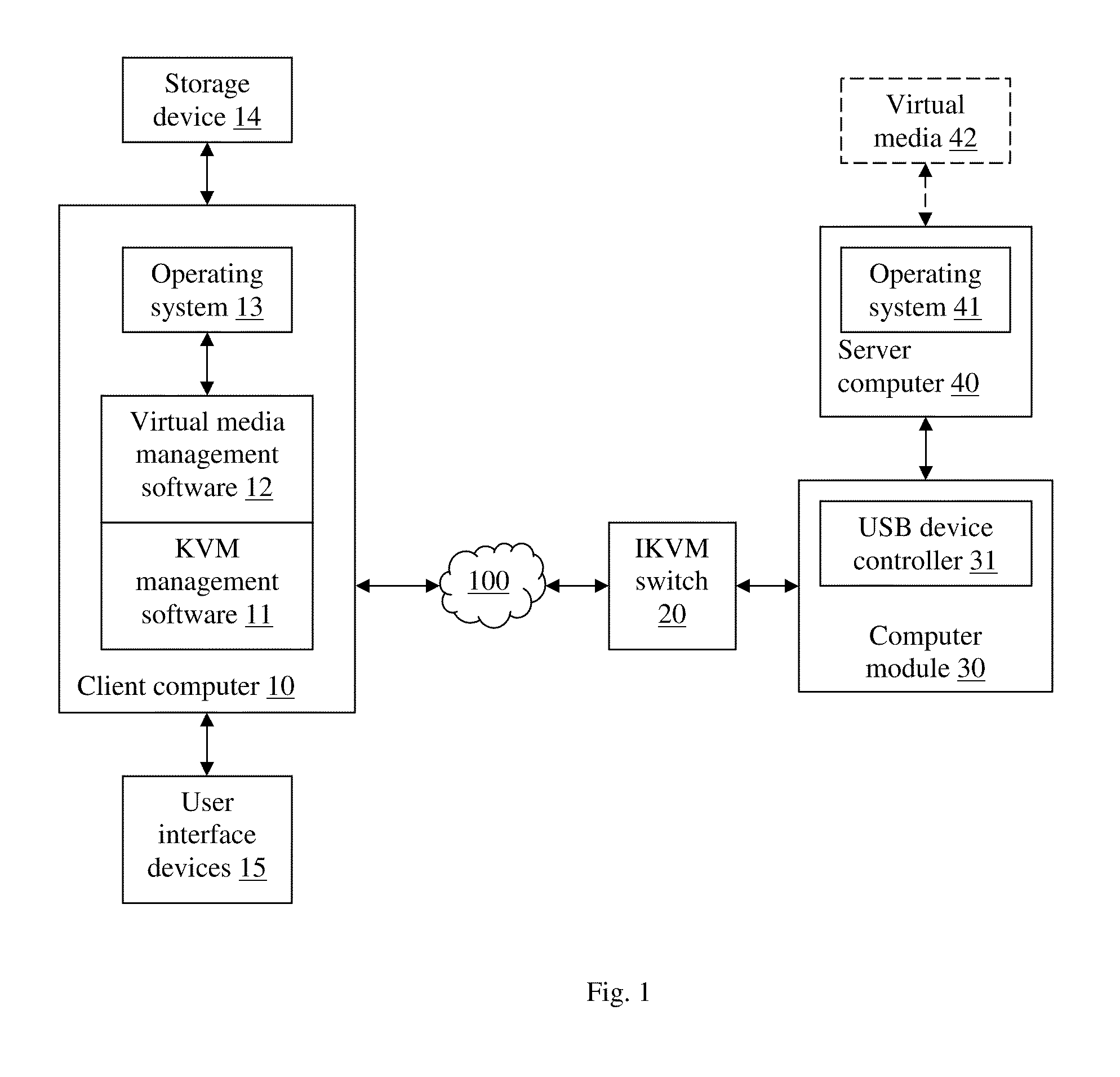
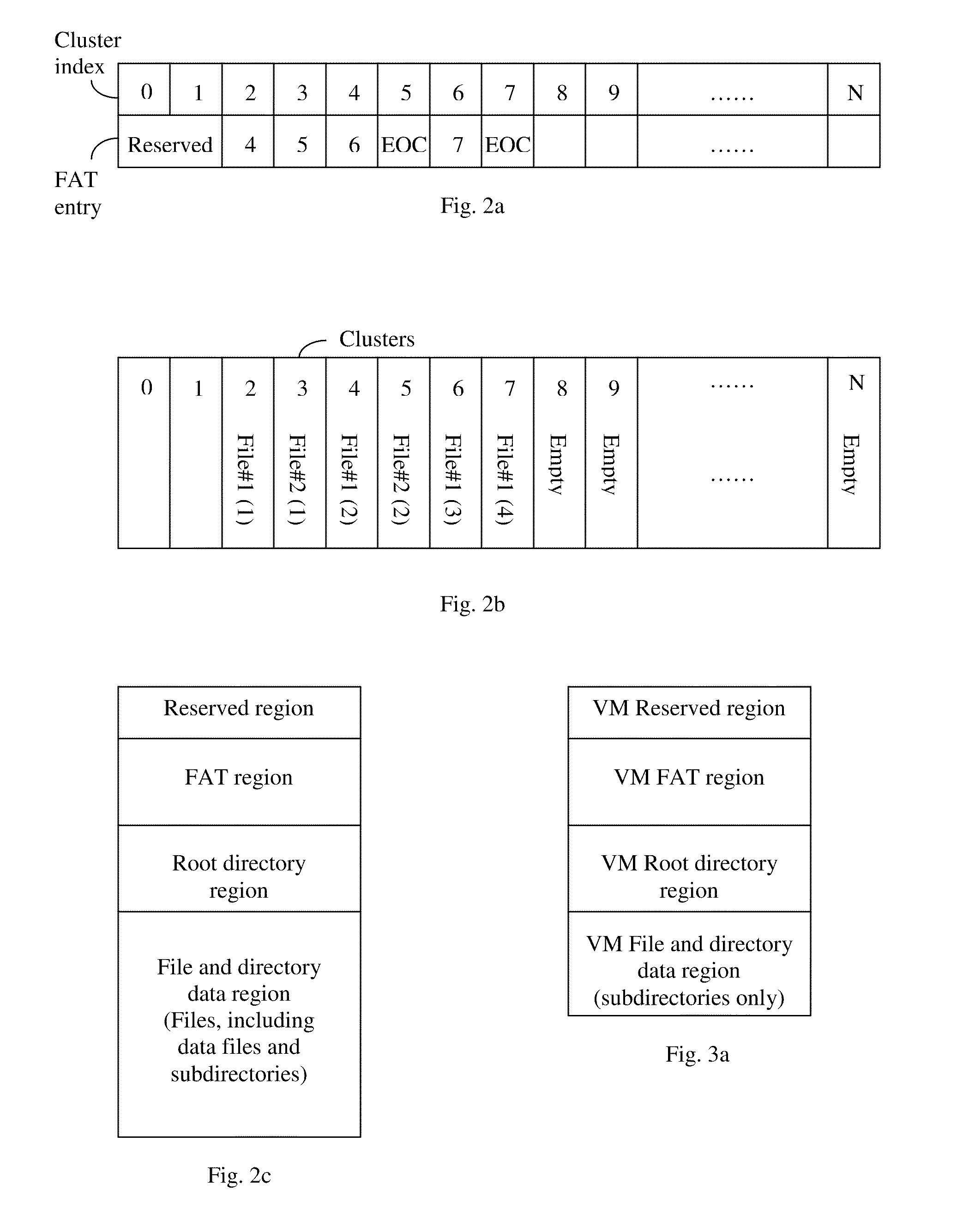
Virtual media with folder-mount function
ActiveUS20110016466A1Eliminate the problemMultiple digital computer combinationsSoftware simulation/interpretation/emulationFile allocationFile system
A virtual media (VM) method for mounting a folder stored in a storage device of a client for accessed by a server as a virtual drive. The client assigns virtual cluster indices to each file in the folder, and creates a file-cluster index table to store the assigned virtual cluster indices. The client also creates a VM file system complying with the FAT file system standard except that only subdirectories and no data files are stored in the VM FAT file system. The VM FAT table uses virtual cluster indices rather than actual cluster indices. Data written by the server are stored in a temporary data area without modifying the actual file system of the storage device. The virtual sectors requested to be written are “dirty”, and the dirty sector numbers and corresponding temporary sector numbers are stored in a dirty sector index table for use in a write-back step.
Owner:ATEN INT CO
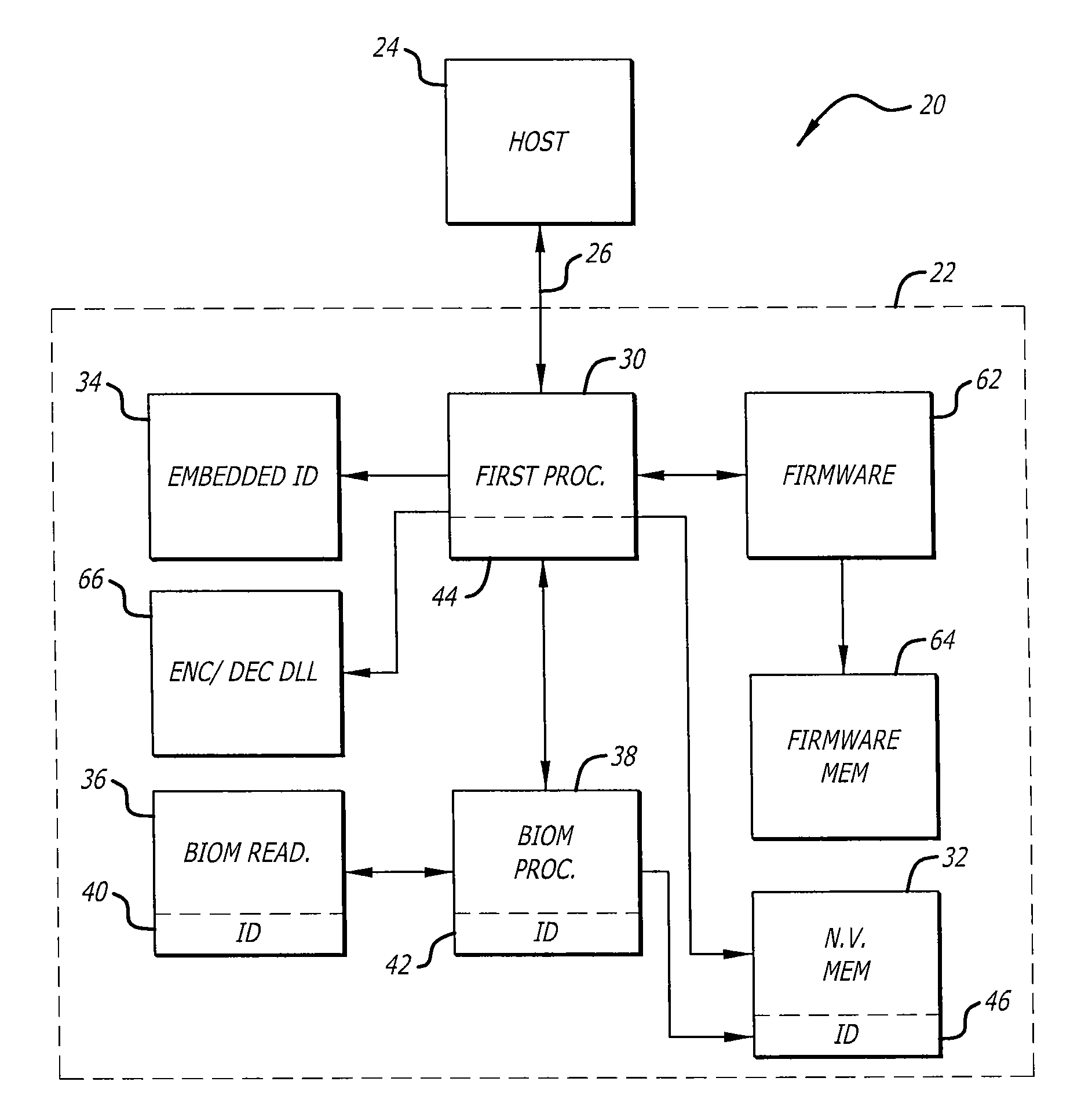
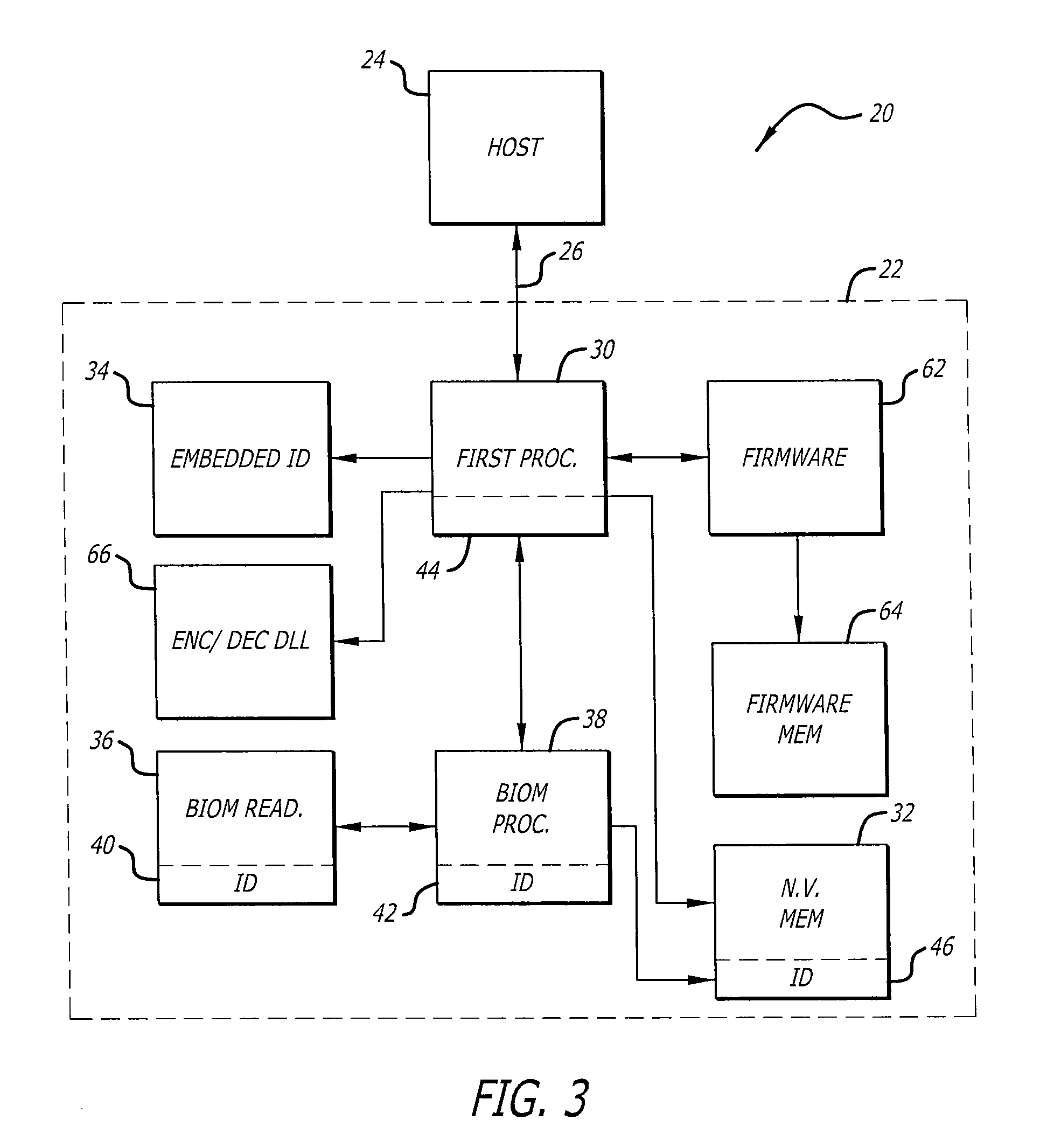
Secure portable data transport & storage system
InactiveUS20090327743A1Digital data processing detailsUnauthorized memory use protectionFile allocationHash function
A portable data transport device that provides security to data stored therein, and is configured to communicate data with a host computer for securing and transporting data. The portable data transport device includes a first processor and a biometric identification system. Upon successful biometric identification of an enrolled user, the first processor permits mounting of the data transport device to a host computer. However, prior to the commencement of read / write operations, cross-checking of stored identification codes of components of the portable data transport device occurs, including the use of a hash function. If any identifier does not match, no read / write data operations are permitted. The portable data transport device includes a file security program that includes a DLL encryption / decryption program having a self-check feature. Upon self check, if any changes were made to the encryption / decryption program, no read / write operations are permitted. The portable data transport device permits the selection of multiple files for encryption together into a single data container pack file and to store that data container pack file. The file security program permits an enrolled user at a host computer to assign only a password to a data container pack file. If a user at a host computer enters an incorrect password a predetermined number of times, portable data transport device processor will erase all data in any volatile memory it is using and will lock itself in a non-operational configuration.
Owner:PHOTONIC DATA SECURITY
Method and system for providing a secure multi-user portable database
A system and method for providing, managing, and accessing a multi-user secure portable database using secure memory cards is provided. The database has a secure portion for storing security keys and a non-secure portion for encrypted data files. Access to the encrypted data files is controlled by assigning access rights through an access control matrix to each encrypted data file according to a hierarchical structure of users. A user requesting access is identified in the hierarchy, associated with a key for allowing the requested access, and the requested access allowed to a file in accordance with the rights allocated through the access control matrix. A patient can selectively grant access to encrypted medical records on his card to a physician. Authentication of the owner / patient is preferably required. Other records required by emergency medical personnel are readable from the same card without requiring permission from the patient.
Owner:PRIVAMED
Cloud synchronized method of files and cloud storage server
InactiveCN102857570ASimple structureRelieve pressureTransmissionSpecial data processing applicationsFile synchronizationFile allocation
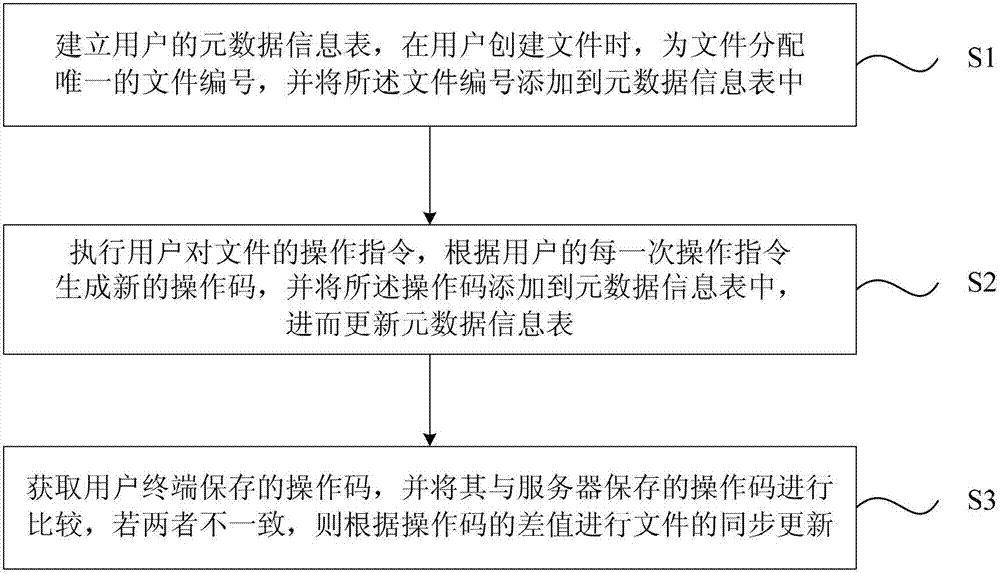
The invention discloses a cloud synchronized method of files and a cloud storage server. The cloud synchronized method comprises the following steps: a metadata information table of a user is established, a unique file number is allocated to a file when the file is established for the user, and the file number is added in the metadata information table; an operating command of the user on the file is carried out, a new operation code is generated according to the operation command of each time of the user, and the operation code is added to the metadata information table so as to update the metadata information table; an operation code stored by a user terminal is acquired and compared with the operation code stored by a server, and if the two operation codes are not consistent, the file is synchronously updated according to the difference of the operation codes. The cloud storage server comprises a control module, an updating module and a synchronizing module. According to the technical scheme provided by the invention, a mechanism which is simple, high effective, convenient in management and easy in expansion is realized on a cloud storage platform, and the file synchronization among different terminals is effectively realized.
Owner:TSINGHUA UNIV
System and method for evaluating information aggregates by generation of knowledge capital
Information in a database collection of knowledge resources is evaluated by collecting a plurality of documents having non-unique values on a shared attribute into an information aggregate; assigning to each document an usefulness value; and calculating and visualizing the knowledge capital of the aggregate as a sum of the usefulness values for all documents in the aggregate.
Owner:IBM CORP
Distributed pairing between different terminals
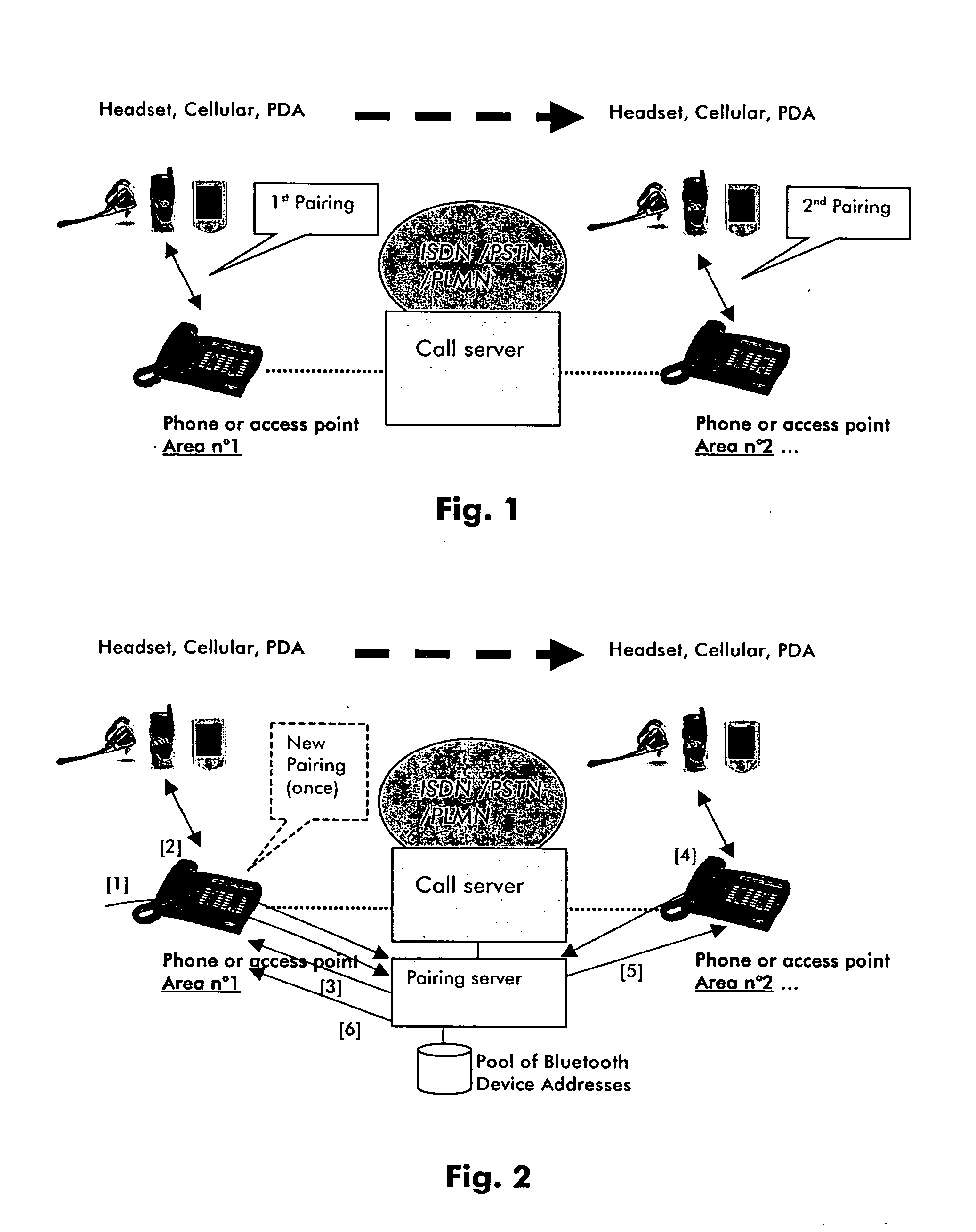
InactiveUS20050048919A1Avoid confictNetwork topologiesDevices with wireless LAN interfacePersonalizationNetwork termination
It is proposed a solution enabling the use of a personal portable device over a network comprising terminals allowing a wireless communication with that device without implying each time a new awkward pairing with the terminals. This is achieved by allocating an unique address to a personalized profile. Said unique address will be used for a pairing procedure between a terminal of the network and a personal portable device. After a successful pairing, such initialization will be affected to said personalized profile. Latter will be used for future wireless communication between said personal portable device and a terminal. Advantageously, a pairing procedure will not be anymore necessary after performing once such initialization since for a set up of a wireless communication some parameters affected to the called personal profile will be used. Among other, the unique address allocated to said personalized profile will be assigned to said terminal.
Owner:ALCATEL LUCENT SAS
Multi-threaded write interface and methods for increasing the single file read and write throughput of a file server
ActiveUS7865485B2Digital data information retrievalDigital data processing detailsFile allocationData integrity
A write interface in a file server provides permission management for concurrent access to data blocks of a file, ensures correct use and update of indirect blocks in a tree of the file, preallocates file blocks when the file is extended, solves access conflicts for concurrent reads and writes to the same block, and permits the use of pipelined processors. For example, a write operation includes obtaining a per file allocation mutex (mutually exclusive lock), preallocating a metadata block, releasing the allocation mutex, issuing an asynchronous write request for writing to the file, waiting for the asynchronous write request to complete, obtaining the allocation mutex, committing the preallocated metadata block, and releasing the allocation mutex. Since no locks are held during the writing of data to the on-disk storage and this data write takes the majority of the time, the method enhances concurrency while maintaining data integrity.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com