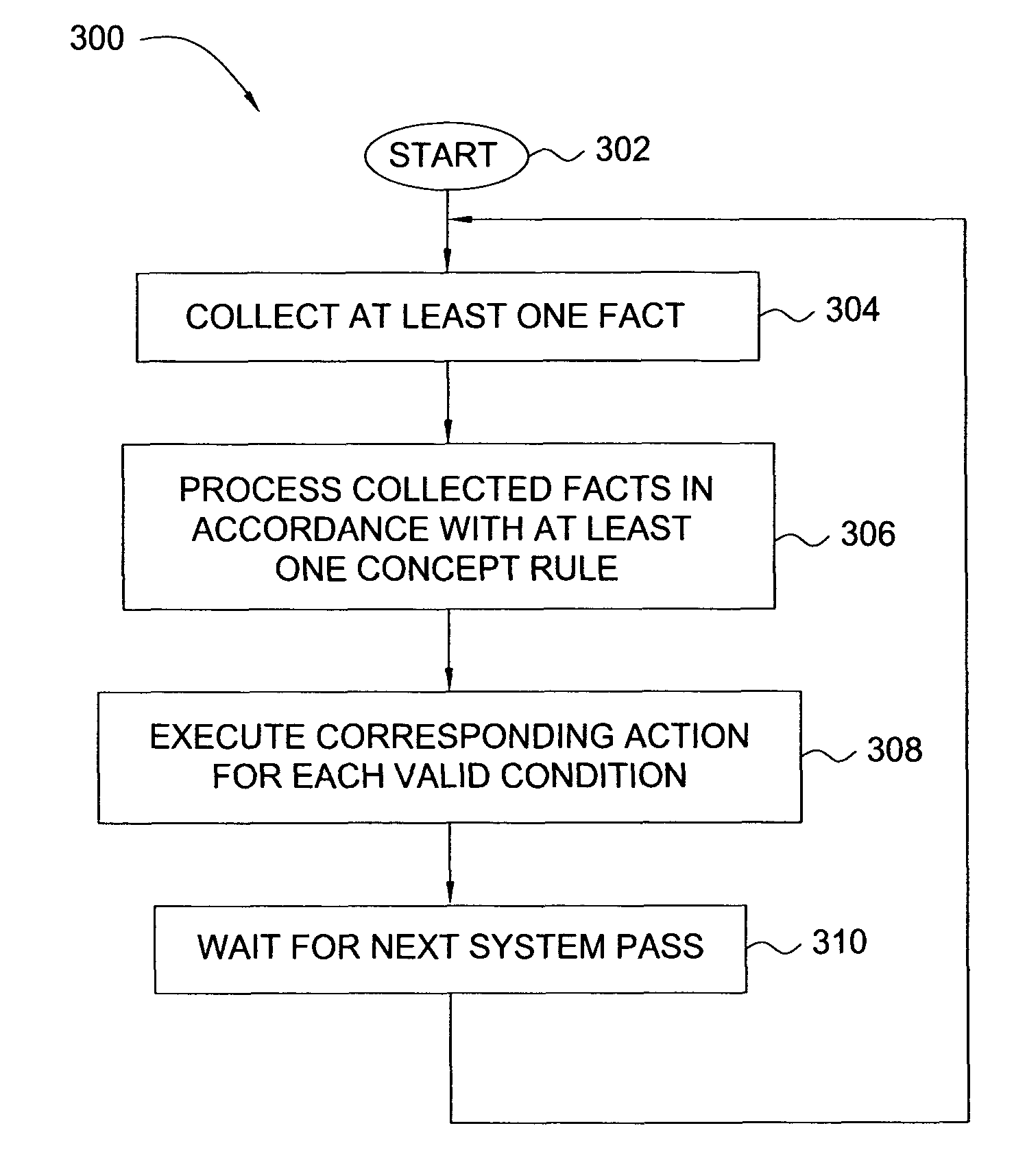
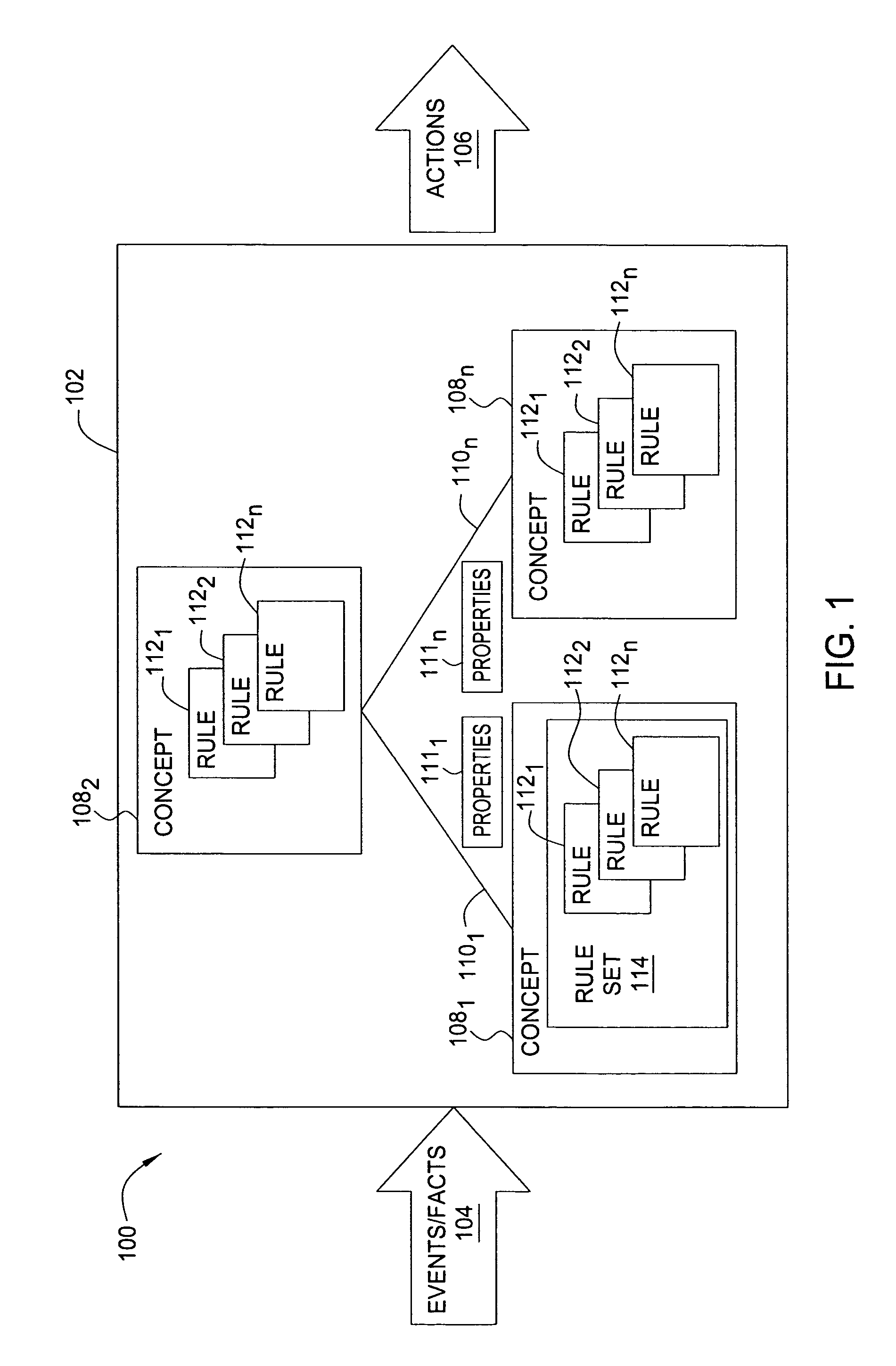
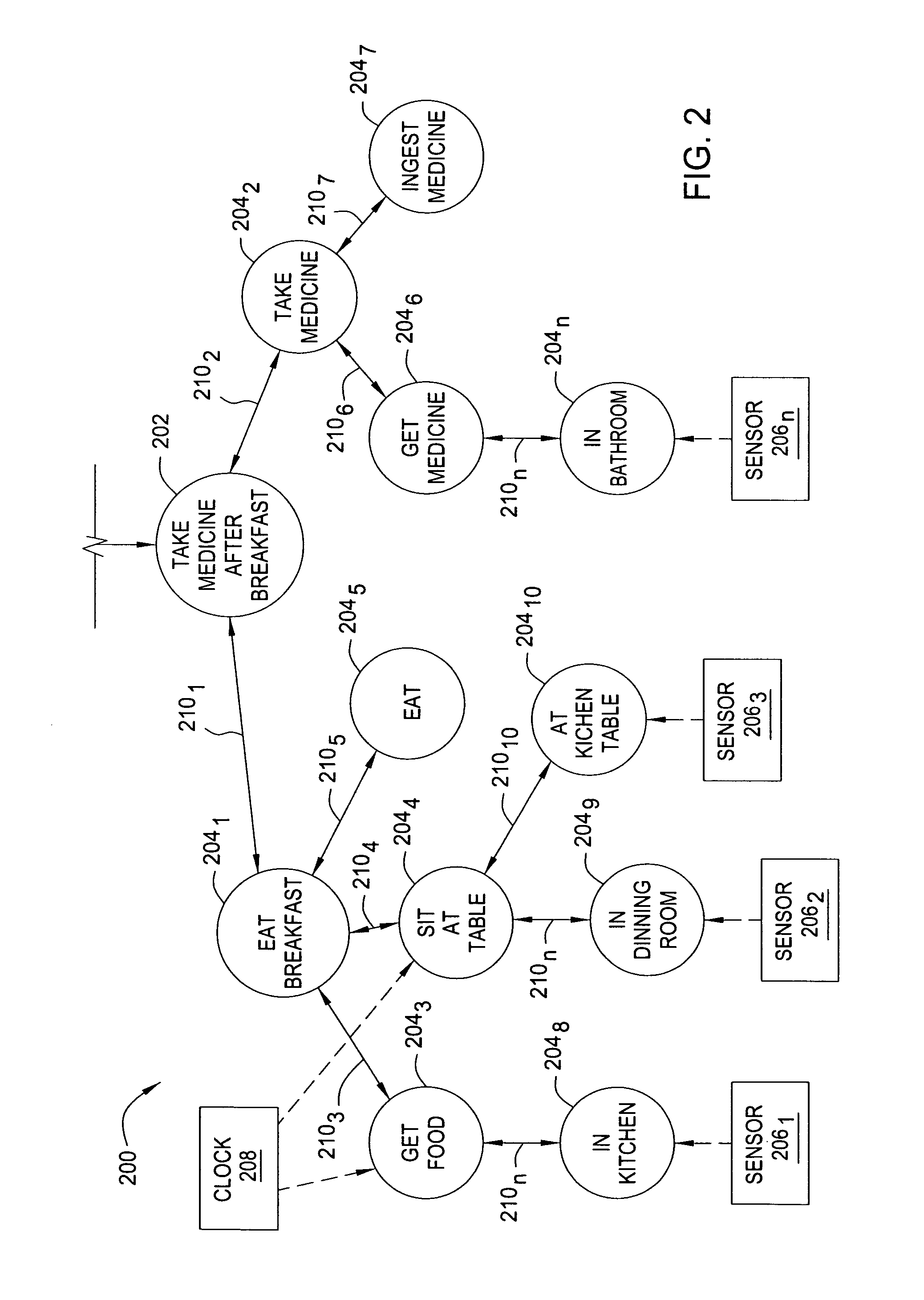
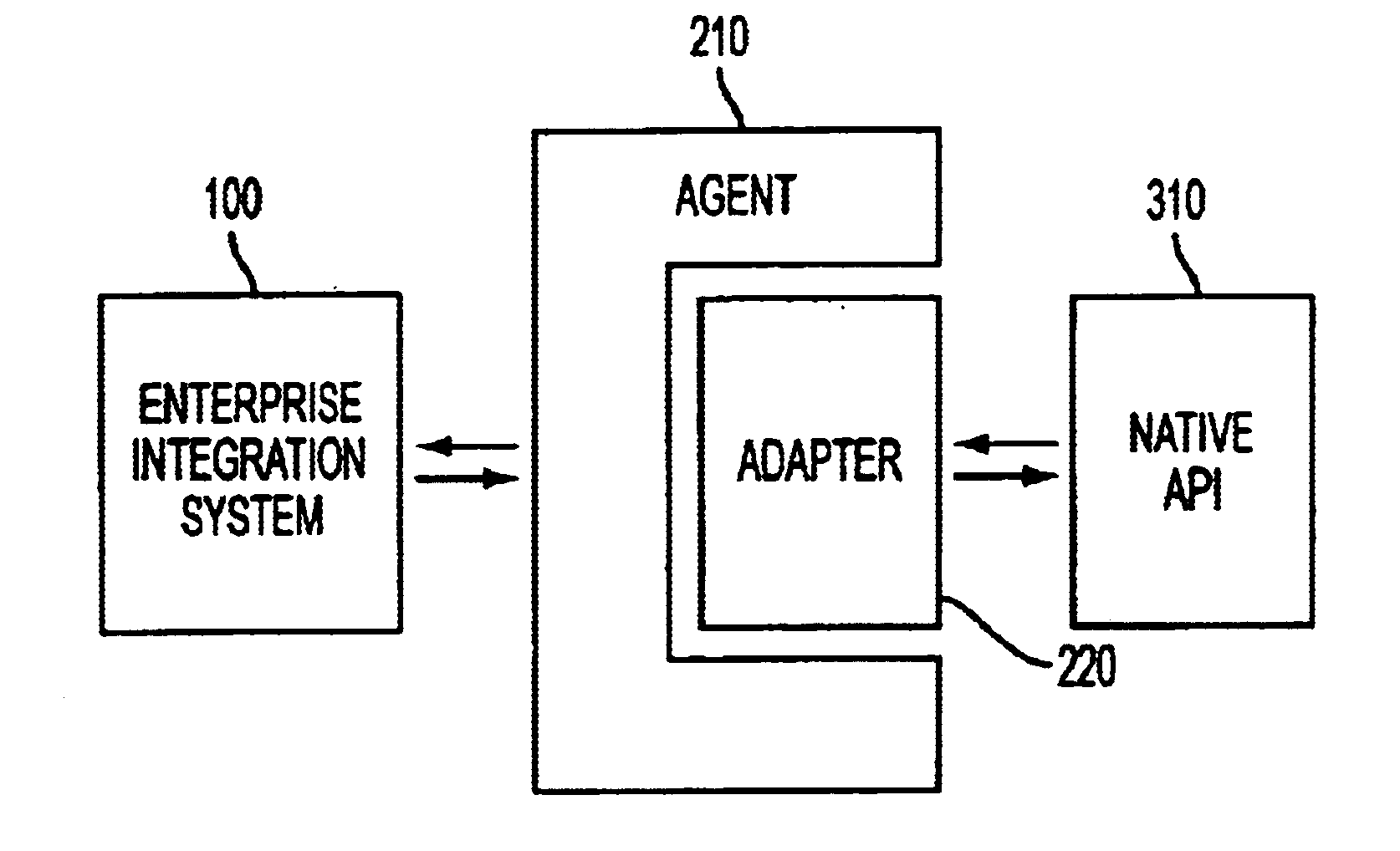
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
20407results about "Interprogram communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
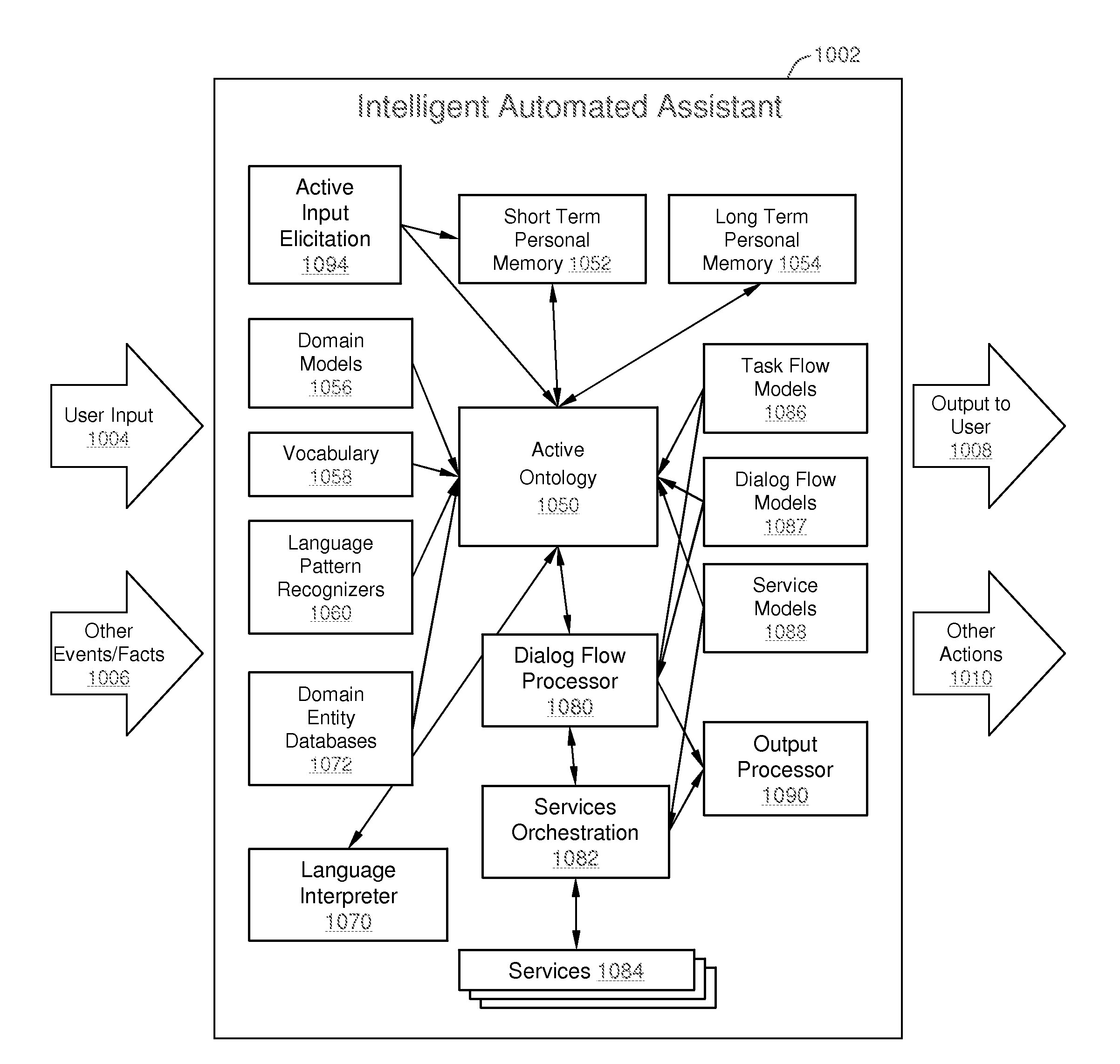
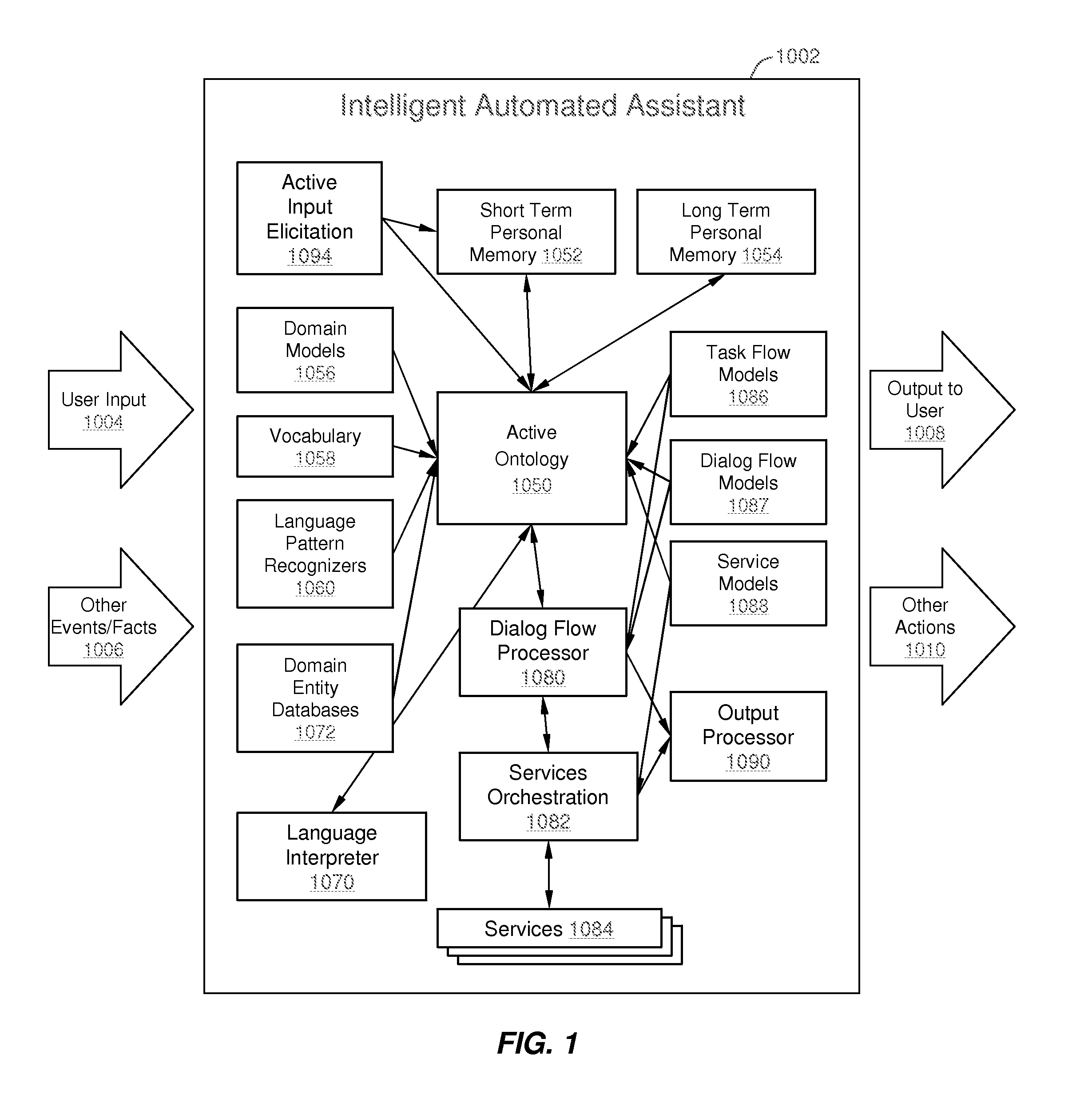
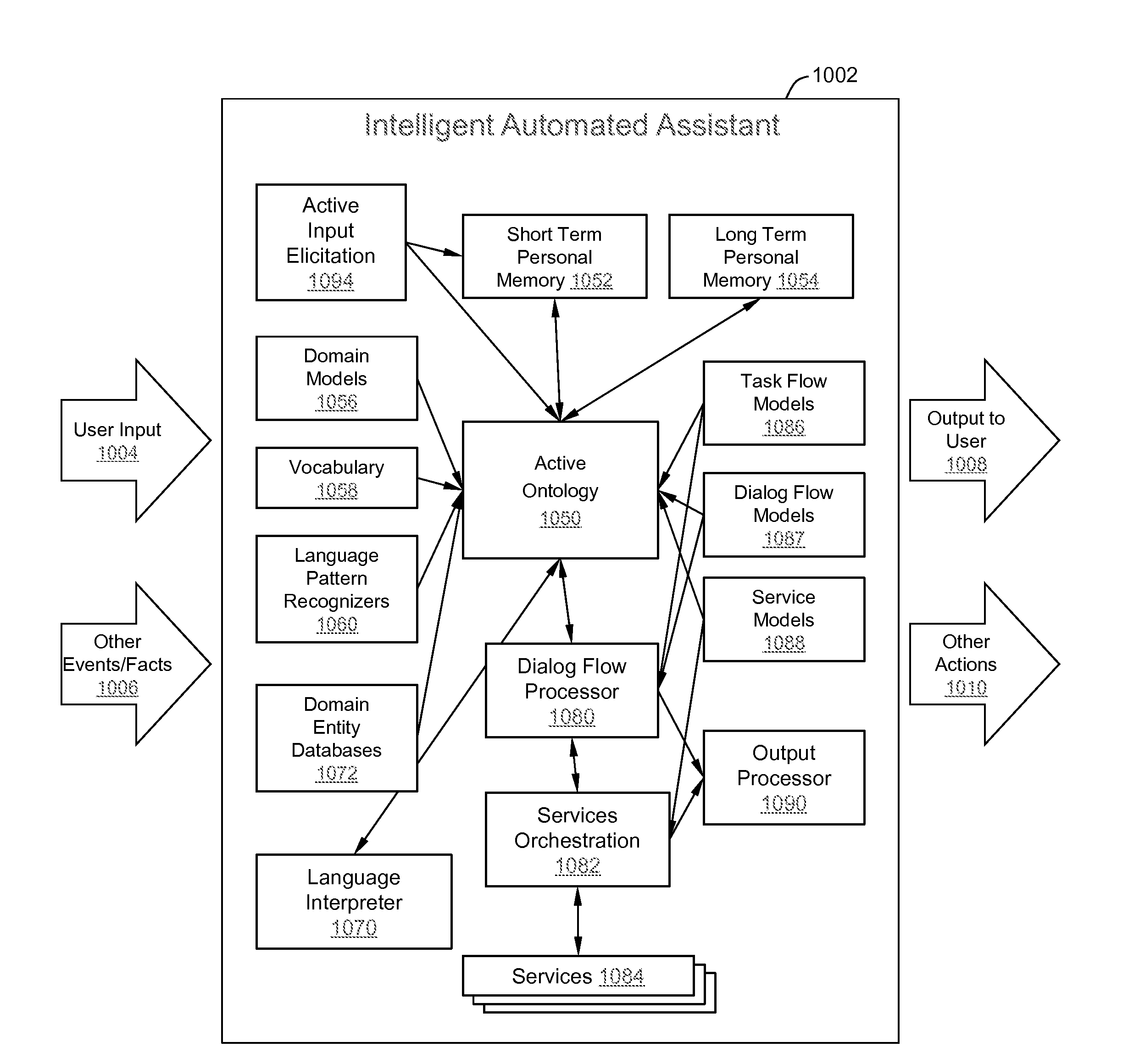
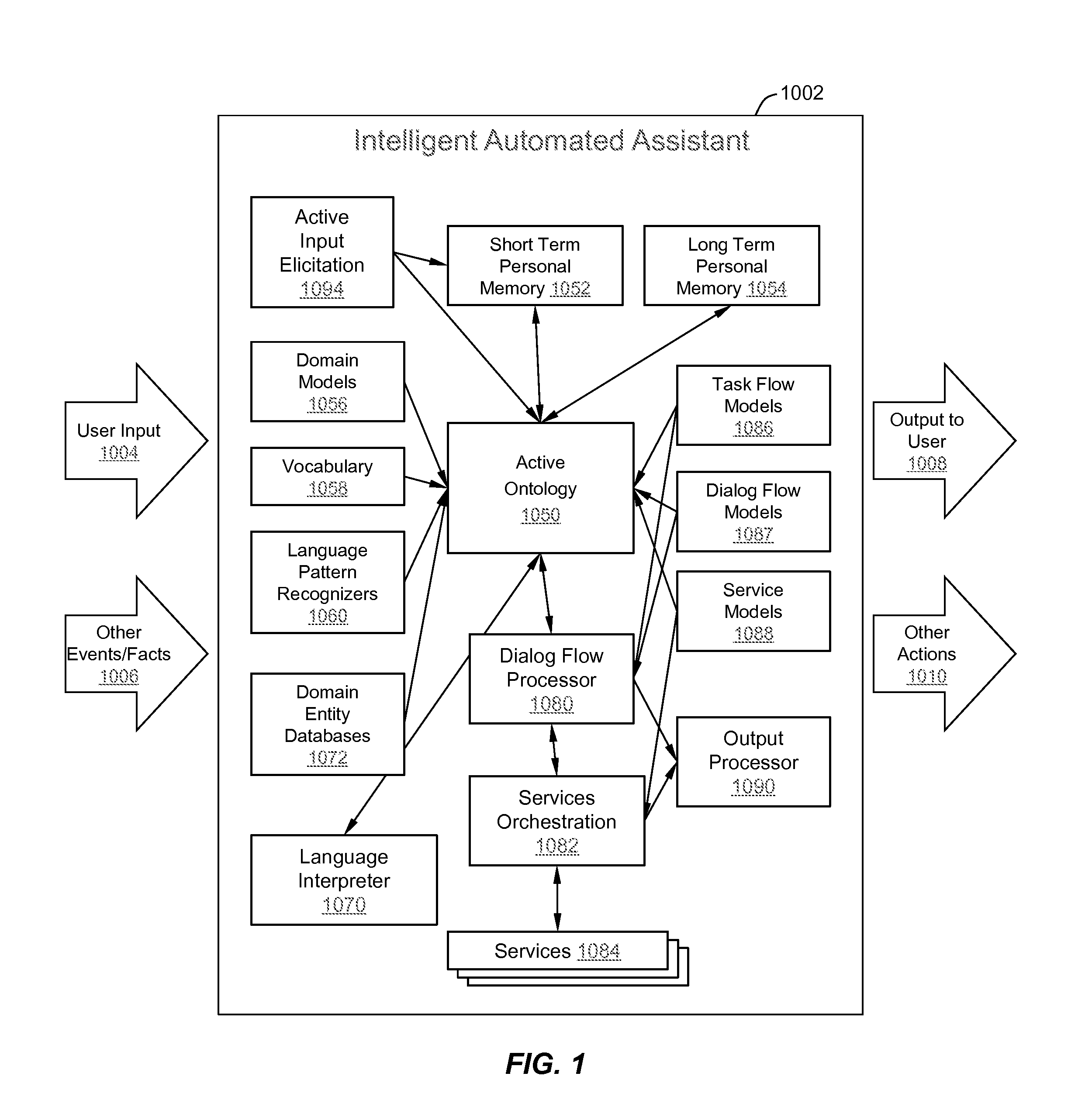
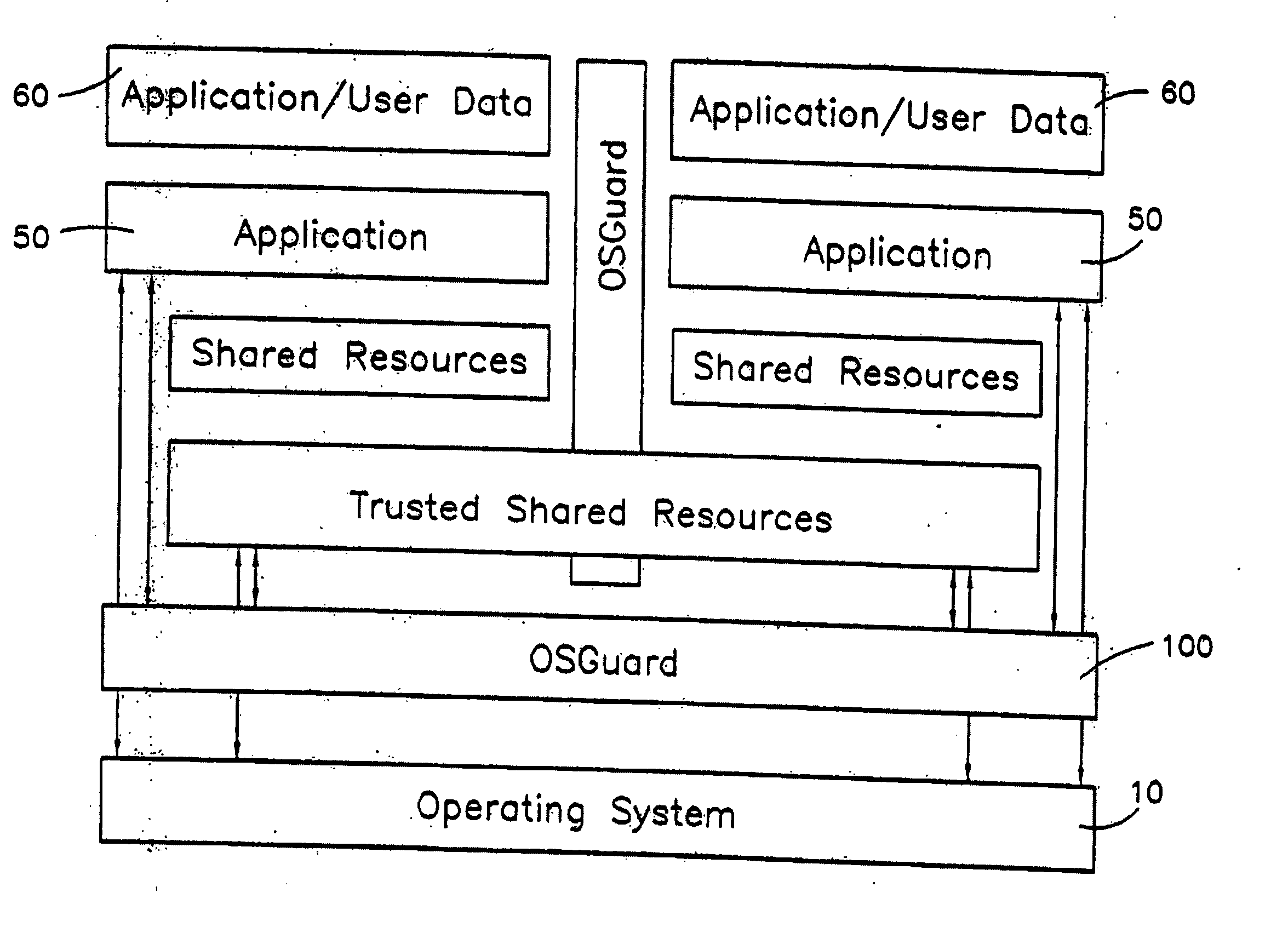
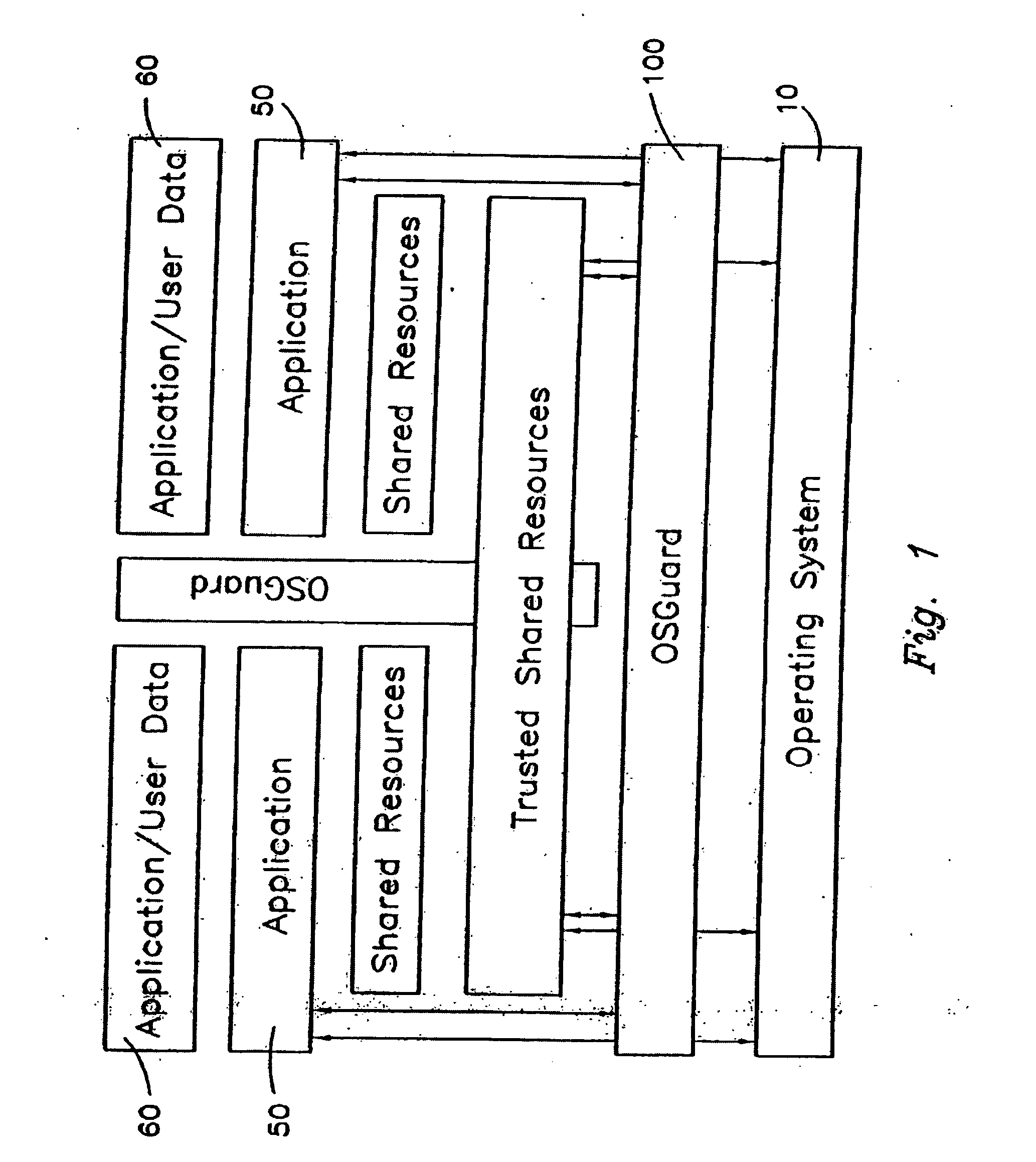
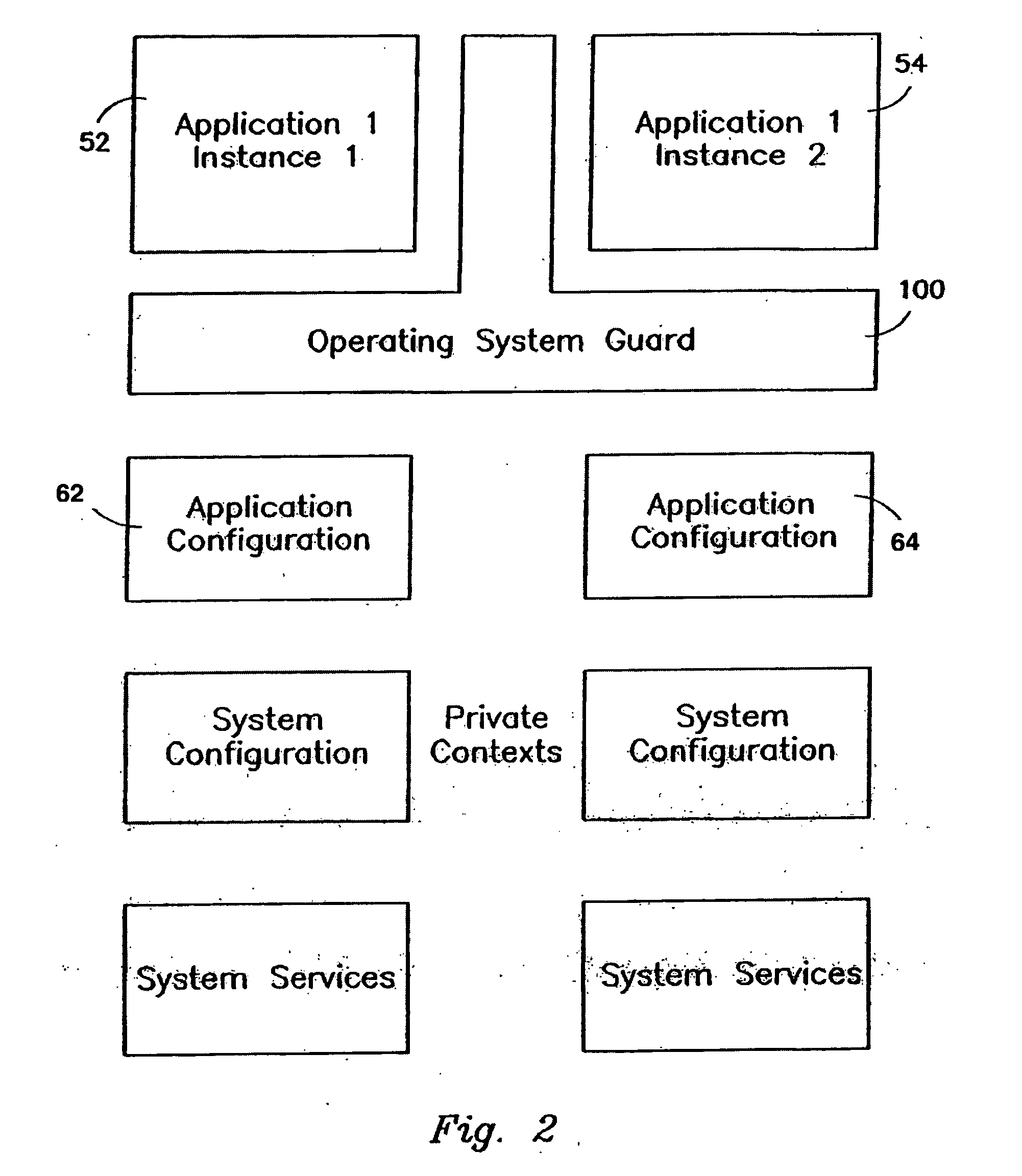
Intelligent Automated Assistant
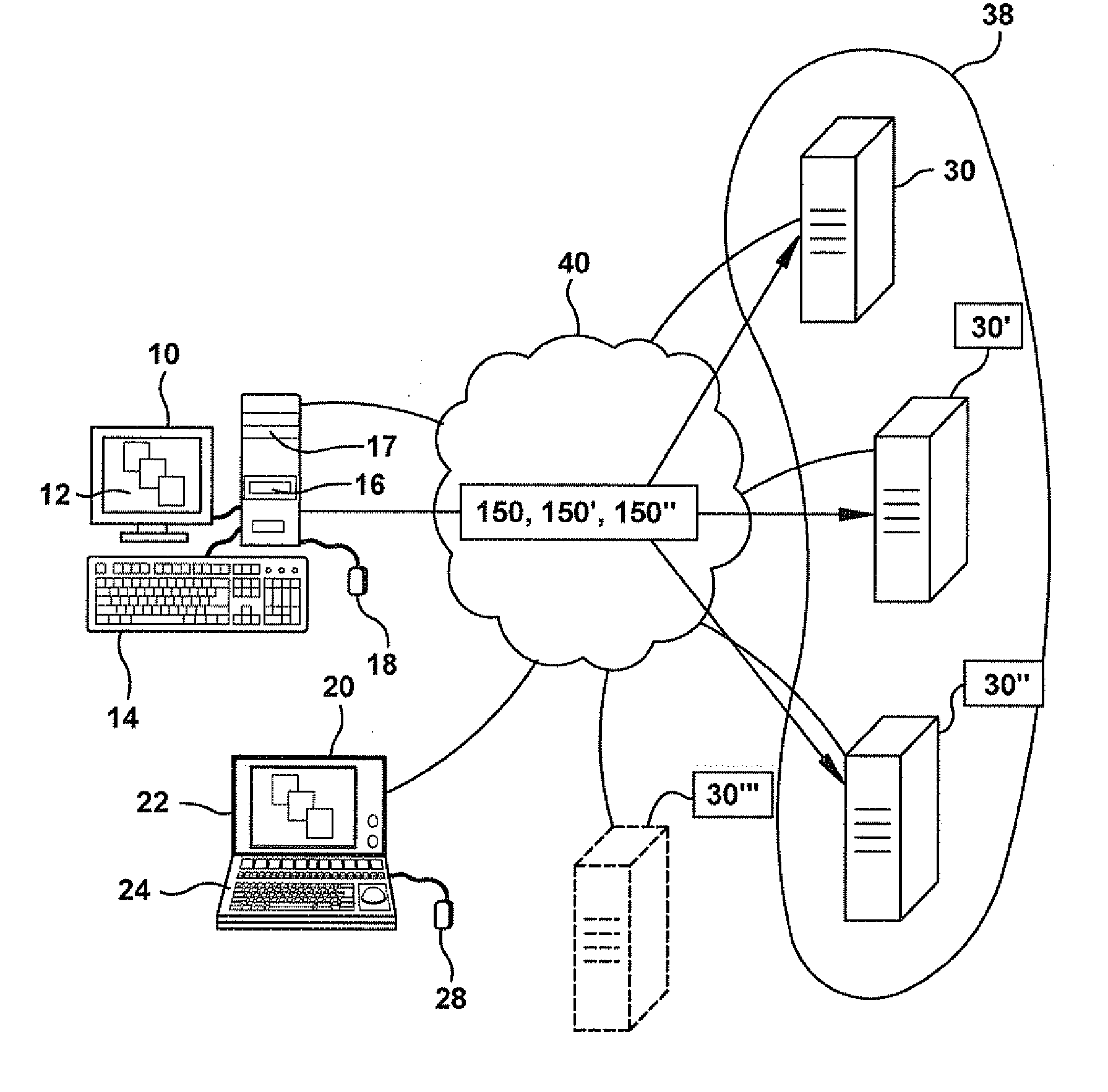
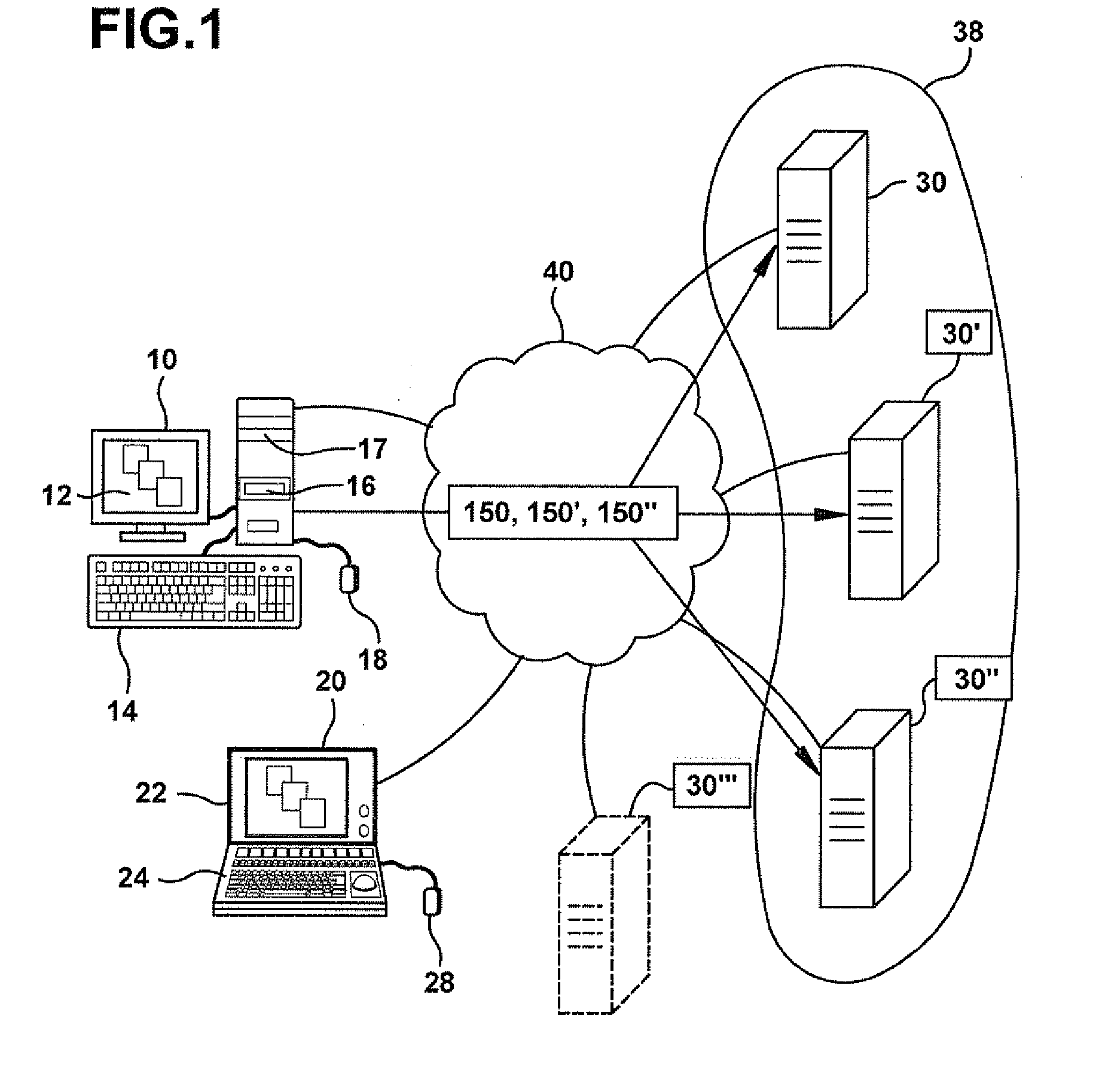
ActiveUS20120016678A1Improve user interactionPromote effective engagementNatural language translationSemantic analysisService provisionSystem usage
An intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
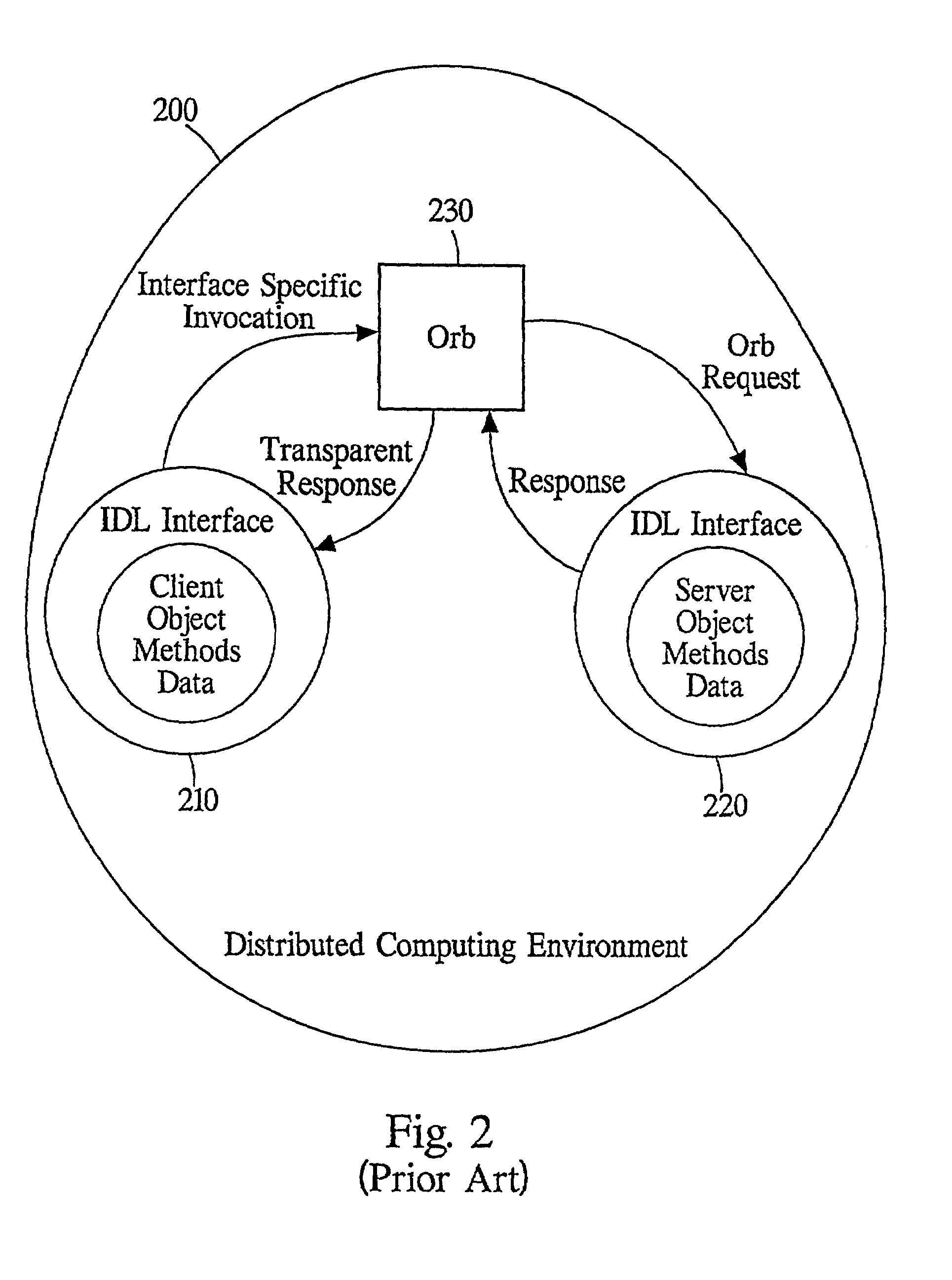
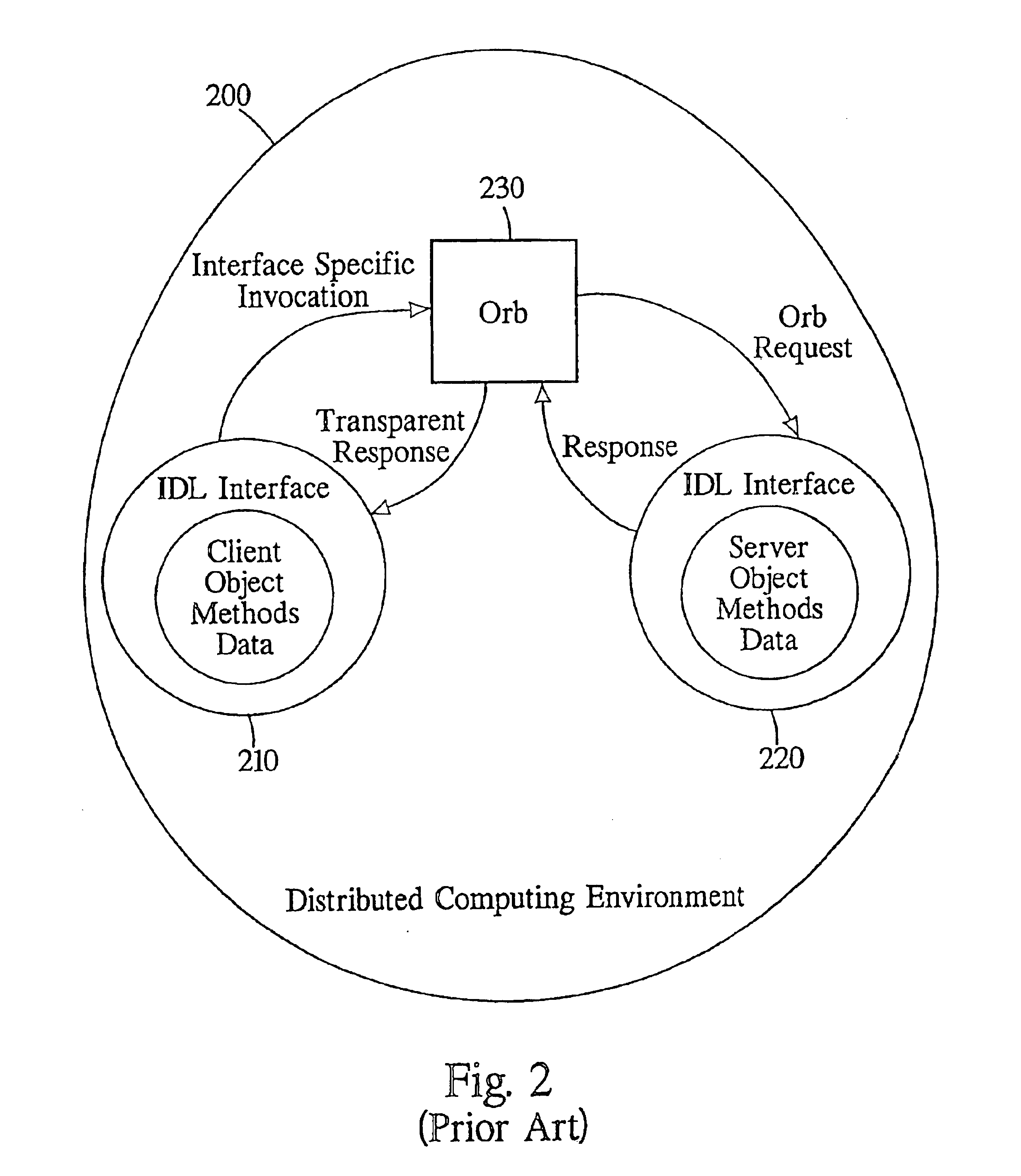
Self-described stream in a communication services patterns environment
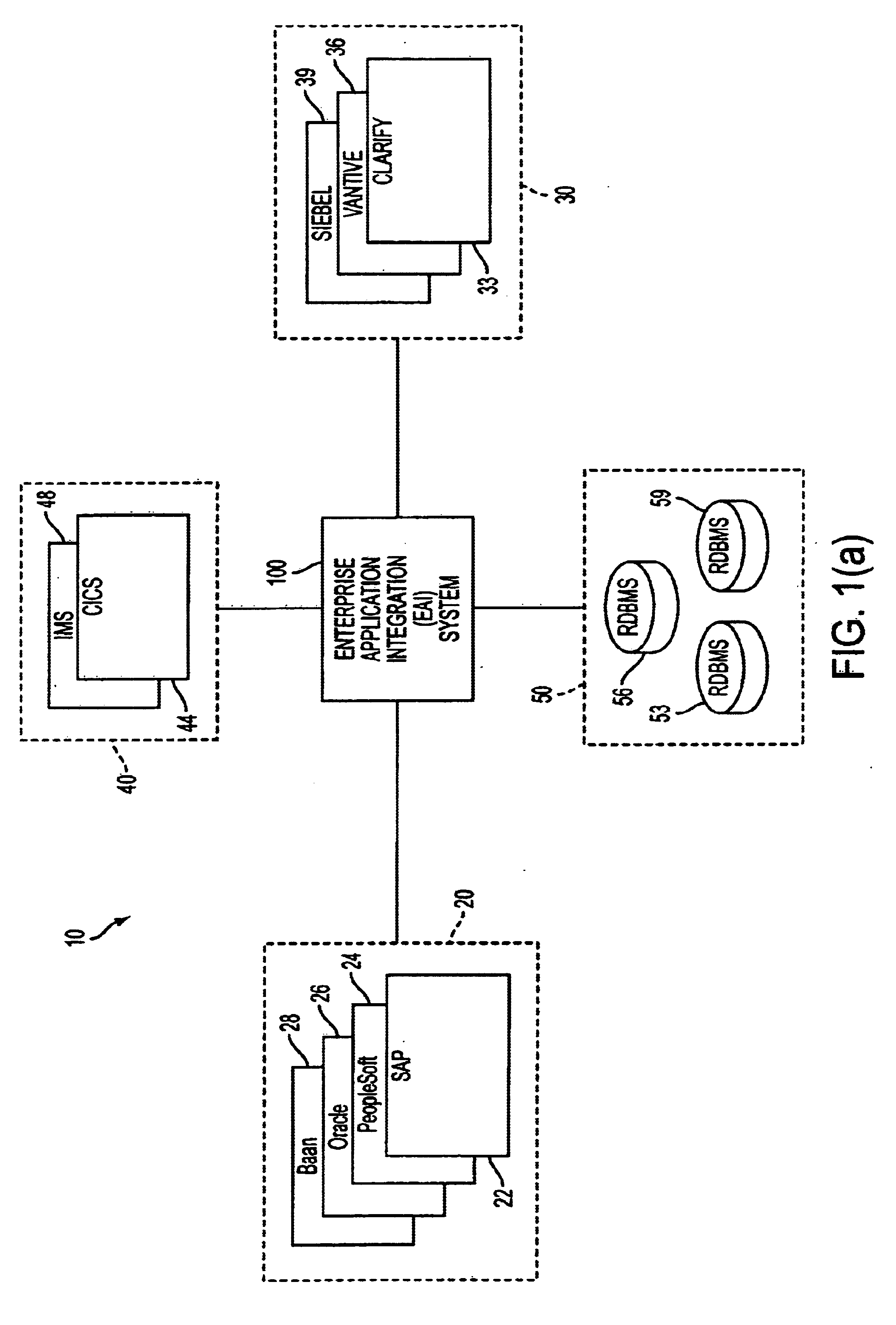
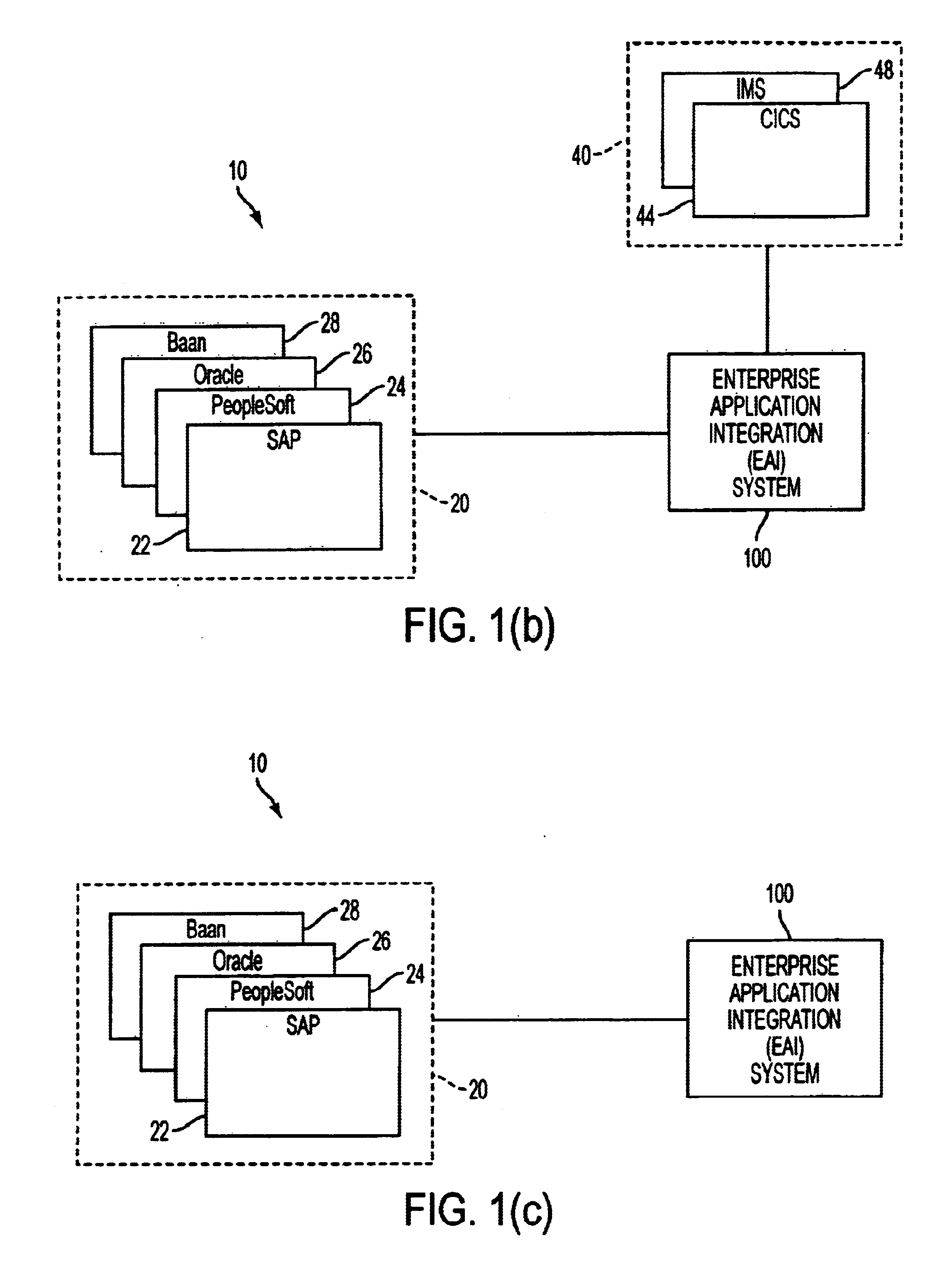
InactiveUS6477580B1Interprogram communicationMultiple digital computer combinationsCommunications systemDatabase
A system, method, and article of manufacture are described for providing a self-describing stream-based communication system. Messages are sent which include data between a sending system and a receiving system. Meta-data is attached to the messages being sent between the sending system and the receiving system. The data of the messages sent from the sending system to the receiving system is translated based on the meta-data. The meta-data includes first and second sections. The first section identifies a type of object associated with the data and a number of attribute descriptors in the data. The second section includes a series of the attribute descriptors defining elements of the data.
Owner:ACCENTURE GLOBAL SERVICES LTD
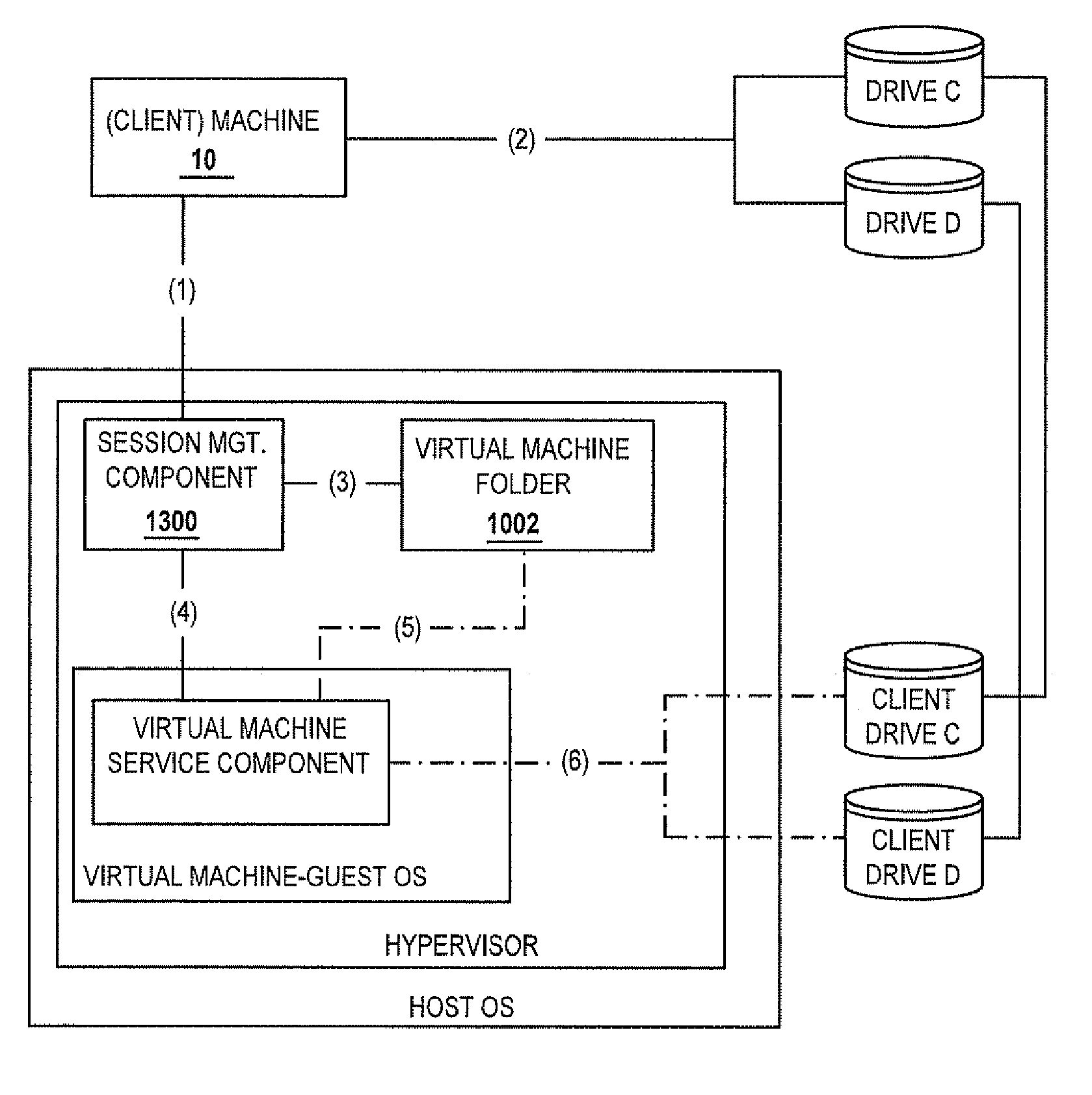
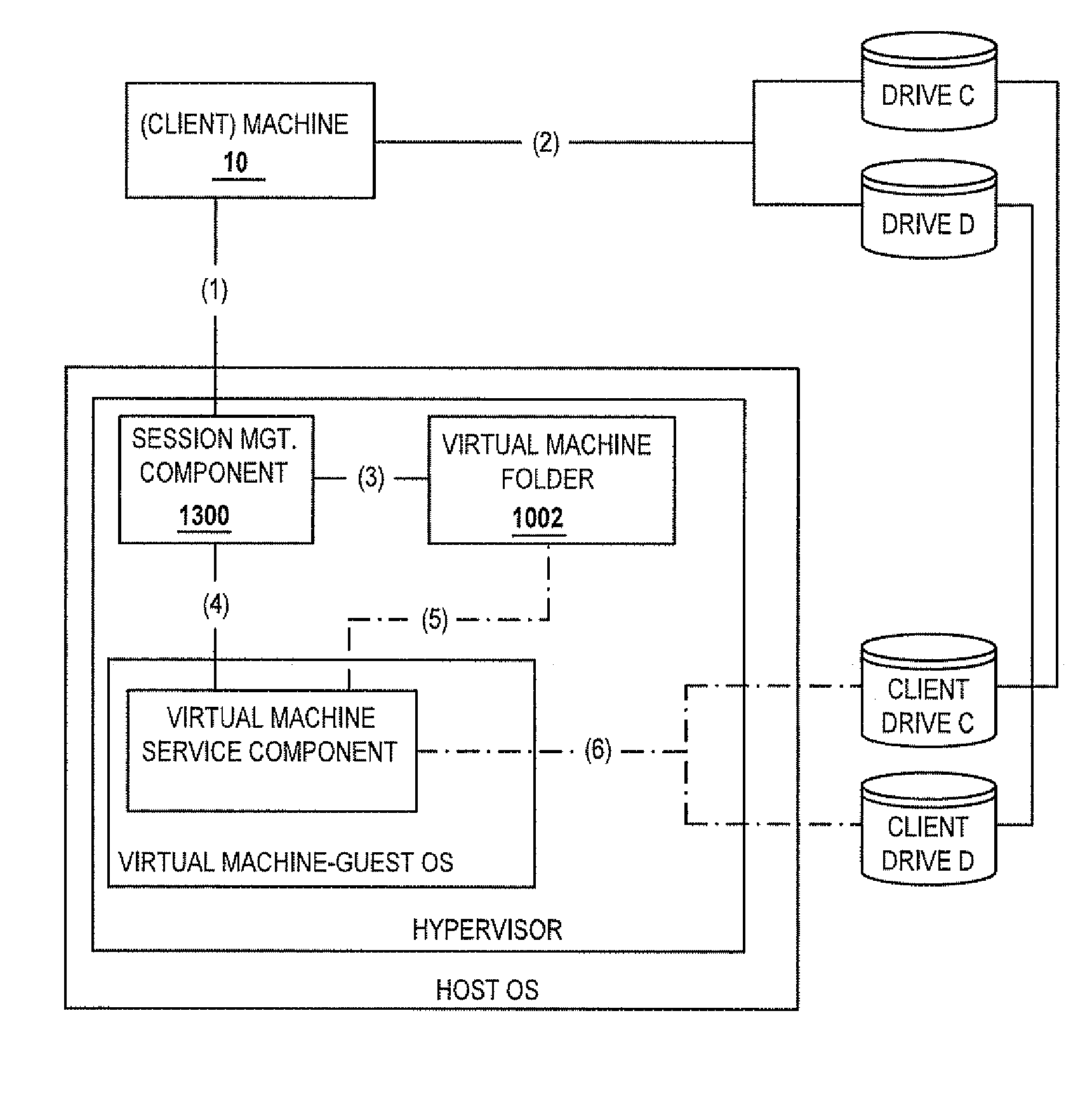
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
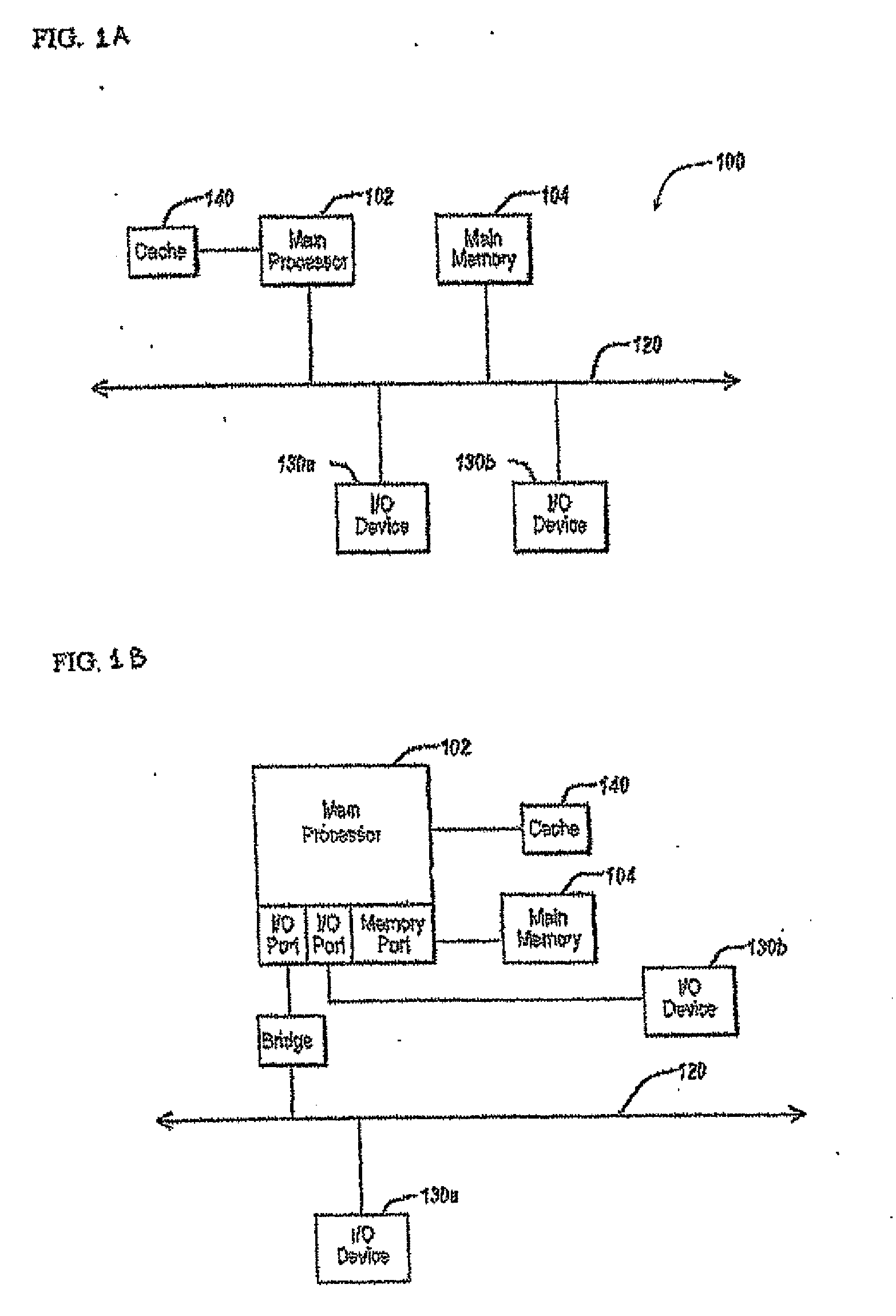
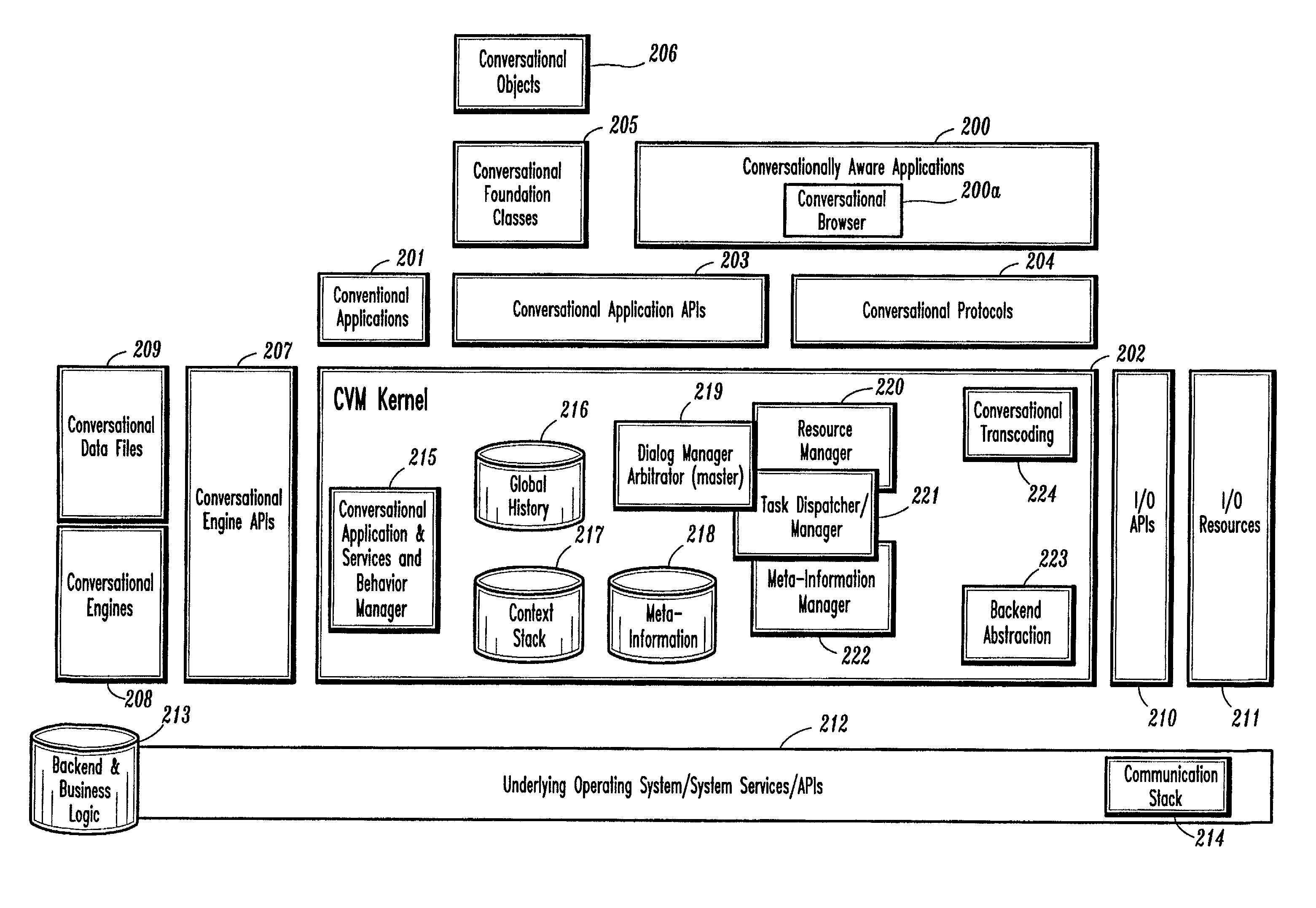
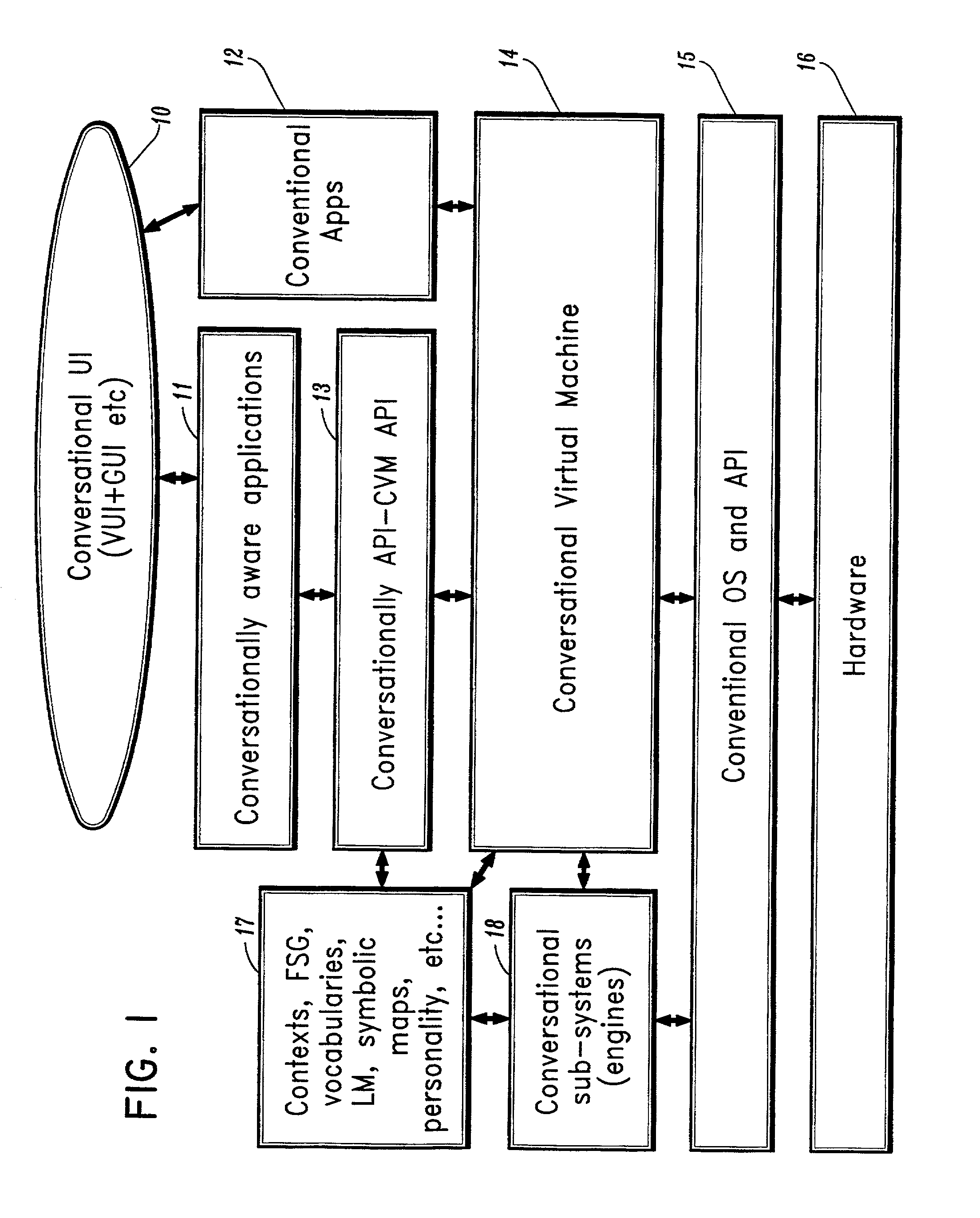
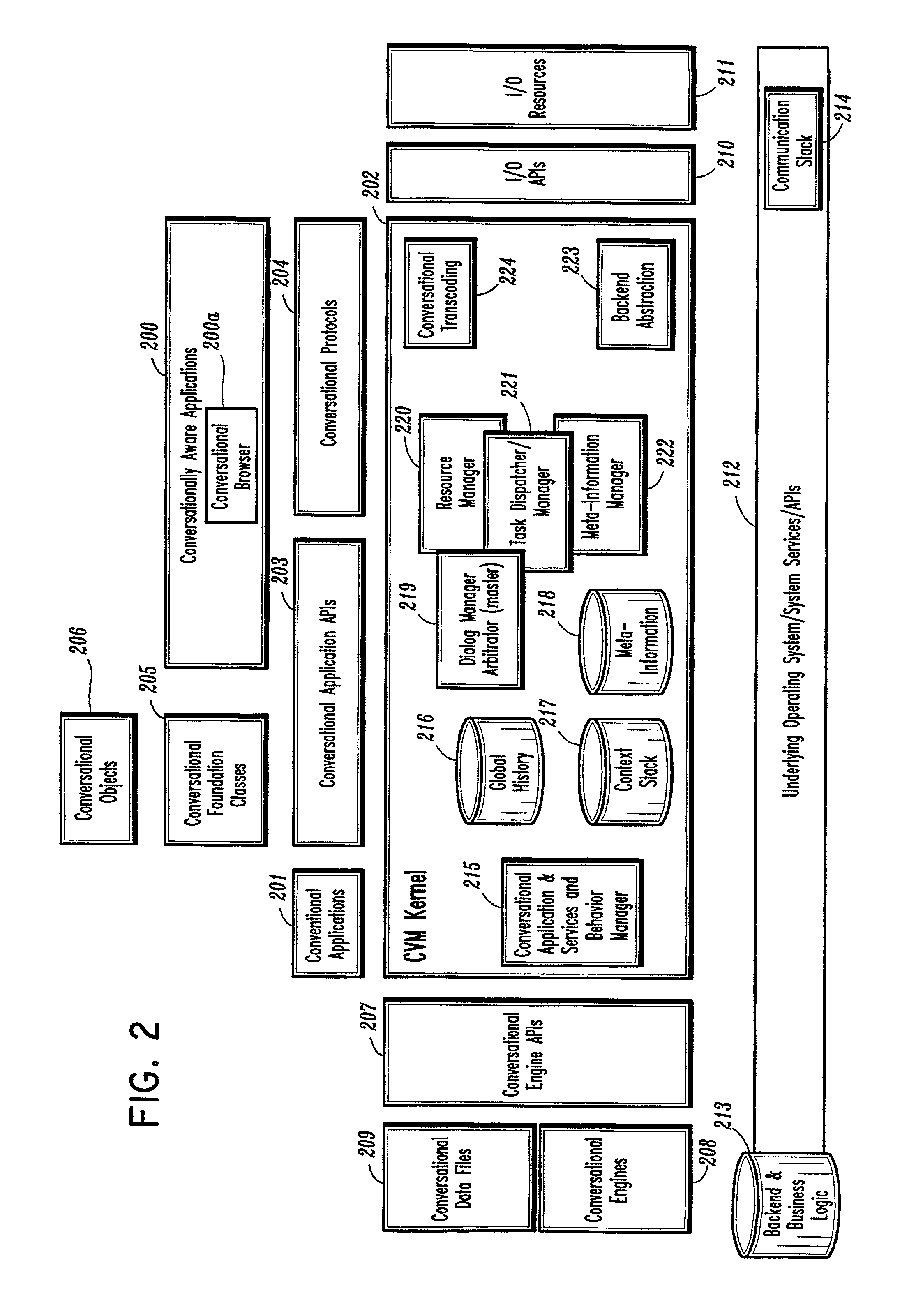
Conversational computing via conversational virtual machine
InactiveUS7137126B1Limitation for transferReduce degradationInterconnection arrangementsResource allocationConversational speechApplication software
A conversational computing system that provides a universal coordinated multi-modal conversational user interface (CUI) (10) across a plurality of conversationally aware applications (11) (i.e., applications that “speak” conversational protocols) and conventional applications (12). The conversationally aware maps, applications (11) communicate with a conversational kernel (14) via conversational application APIs (13). The conversational kernel (14) controls the dialog across applications and devices (local and networked) on the basis of their registered conversational capabilities and requirements and provides a unified conversational user interface and conversational services and behaviors. The conversational computing system may be built on top of a conventional operating system and APIs (15) and conventional device hardware (16). The conversational kernel (14) handles all I / O processing and controls conversational engines (18). The conversational kernel (14) converts voice requests into queries and converts outputs and results into spoken messages using conversational engines (18) and conversational arguments (17). The conversational application API (13) conveys all the information for the conversational kernel (14) to transform queries into application calls and conversely convert output into speech, appropriately sorted before being provided to the user.
Owner:UNILOC 2017 LLC
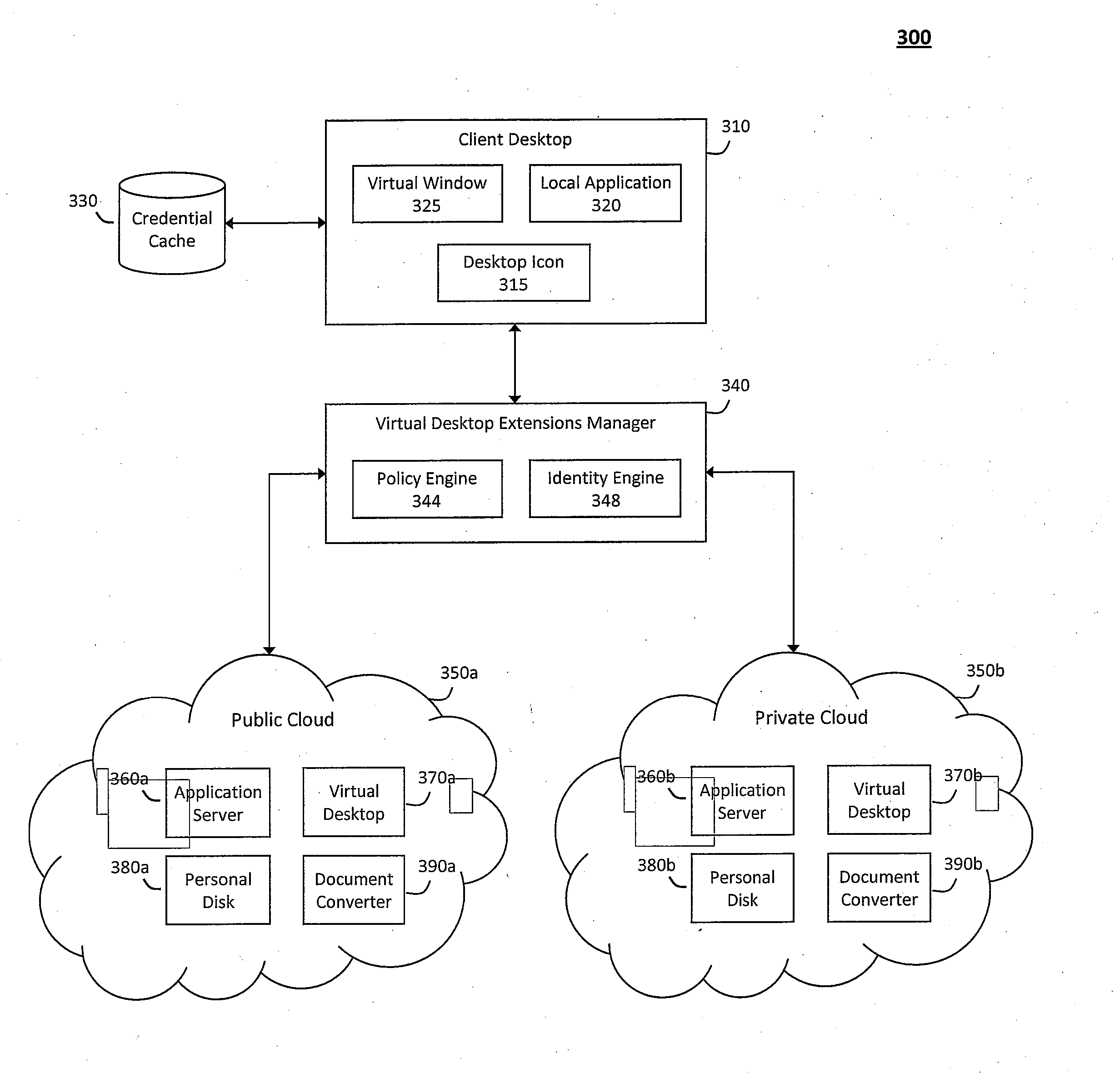
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
Intelligent Automated Assistant
ActiveUS20120245944A1Improve user interactionEffectively engageNatural language translationSemantic analysisService provisionComputer science
The intelligent automated assistant system engages with the user in an integrated, conversational manner using natural language dialog, and invokes external services when appropriate to obtain information or perform various actions. The system can be implemented using any of a number of different platforms, such as the web, email, smartphone, and the like, or any combination thereof. In one embodiment, the system is based on sets of interrelated domains and tasks, and employs additional functionally powered by external services with which the system can interact.
Owner:APPLE INC
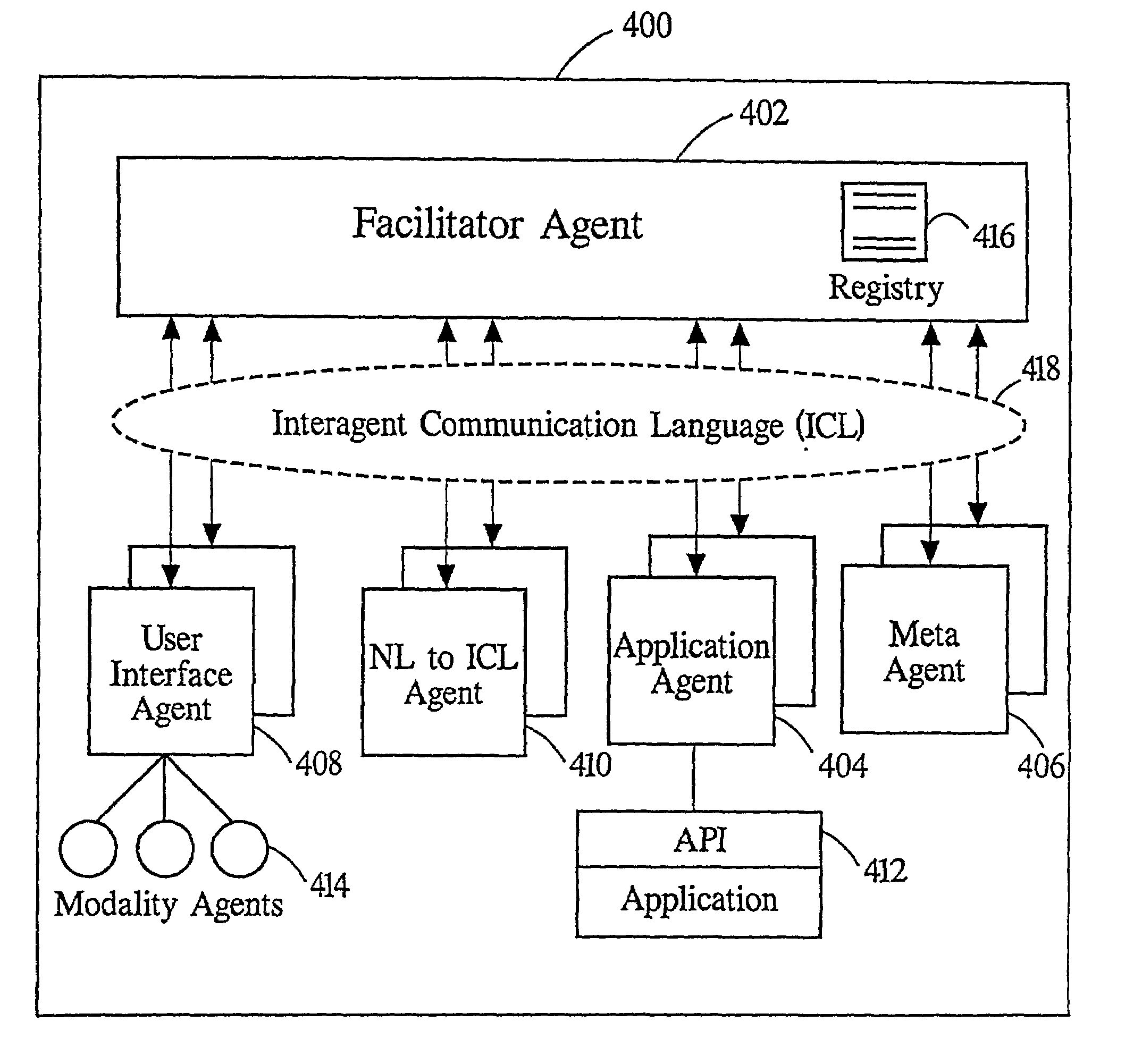
Using a community of distributed electronic agents to support a highly mobile, ambient computing environment
InactiveUS7036128B1Minimize dependenciesIncreased leverageDigital data information retrievalInterprogram communicationJet aeroplaneApplication software
A highly mobile, ambient computing environment is disclosed for serving a knowledge worker away from the their desk. The present invention allows a knowledge worker to get increased leverage from personal, networked, and interactive computing devices while in their car, airplane seat, or in a conference room with others. An Open Agent Architecture is used to incorporate elements such as GPS agents, speech recognition, and opportunistic connectivity among meeting participants. Communication and cooperation between agents are brokered by one or more facilitators, which are responsible for matching requests, from users and agents, with descriptions of the capabilities of other agents. It is not generally required that a user or agent know the identities, locations, or number of other agents involved in satisfying a request, and relatively minimal effort is involved in incorporating new agents and “wrapping” legacy applications. Extreme flexibility is achieved through an architecture organized around the declaration of capabilities by service-providing agents, the construction of arbitrarily complex goals by users and service-requesting agents, and the role of facilitators in delegating and coordinating the satisfaction of these goals, subject to advice and constraints that may accompany them.
Owner:IPA TECH INC
Extensible software-based architecture for communication and cooperation within and between communities of distributed agents and distributed objects
InactiveUS6859931B1Minimal effortIncrease flexibilityDigital data information retrievalInterprogram communicationIntelligent planningDistributed object systems
A distributed agent community is able to dynamically interact with alternative sofware technologies that manage distributed objects. The leveraging of capabilities of distributed object systems greatly expands the flexibility and capabilites of the distributed agent community. Through access to distributed object systems, the distributed agent community can draw on the capabilites of all the objects managed by the distributed object systems. The access to distributed systems by the distributed agent community allows for collaboration and intelligent planning that the distributed object systems do not themsleves provide.
Owner:IPA TECH INC
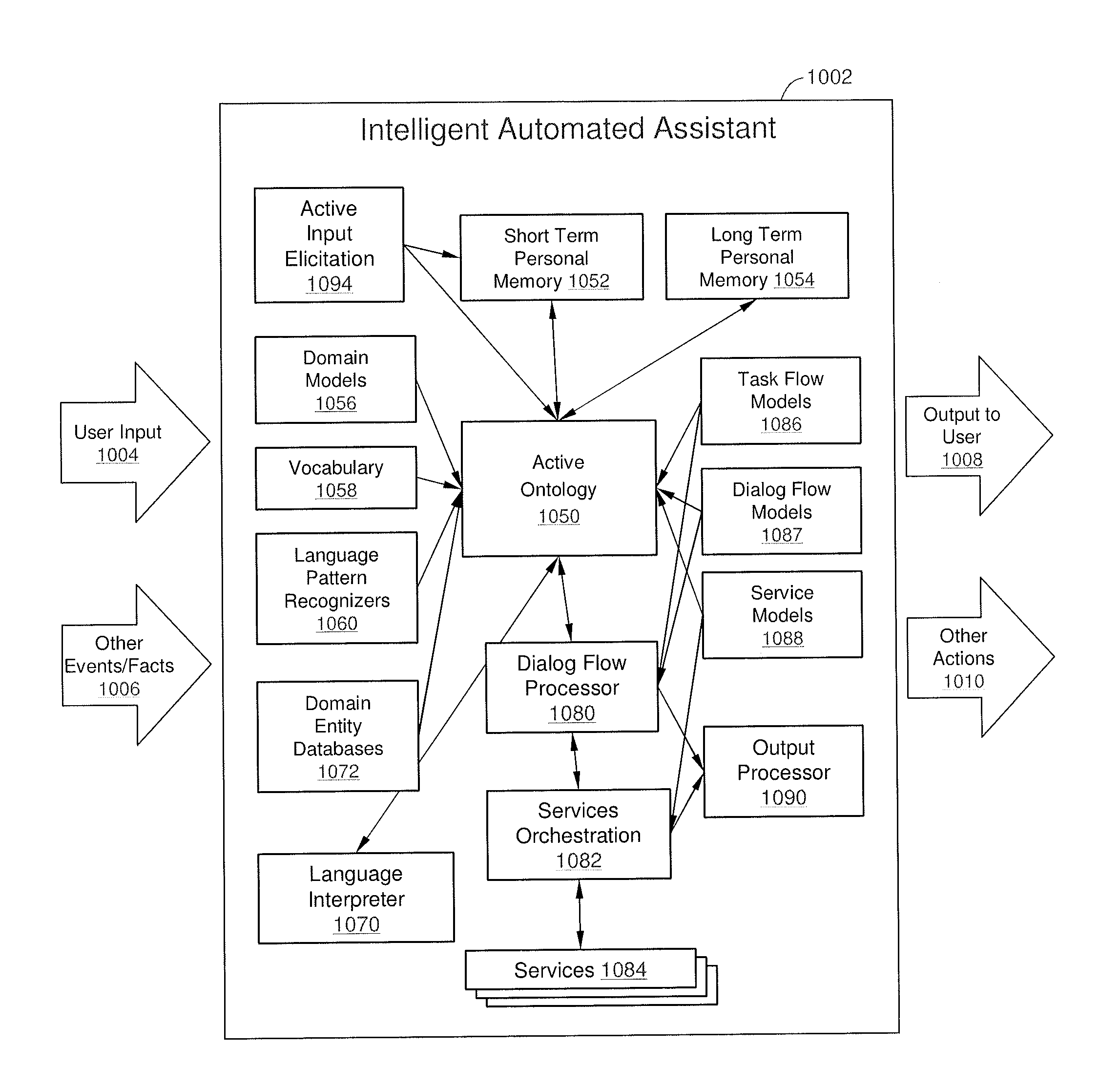
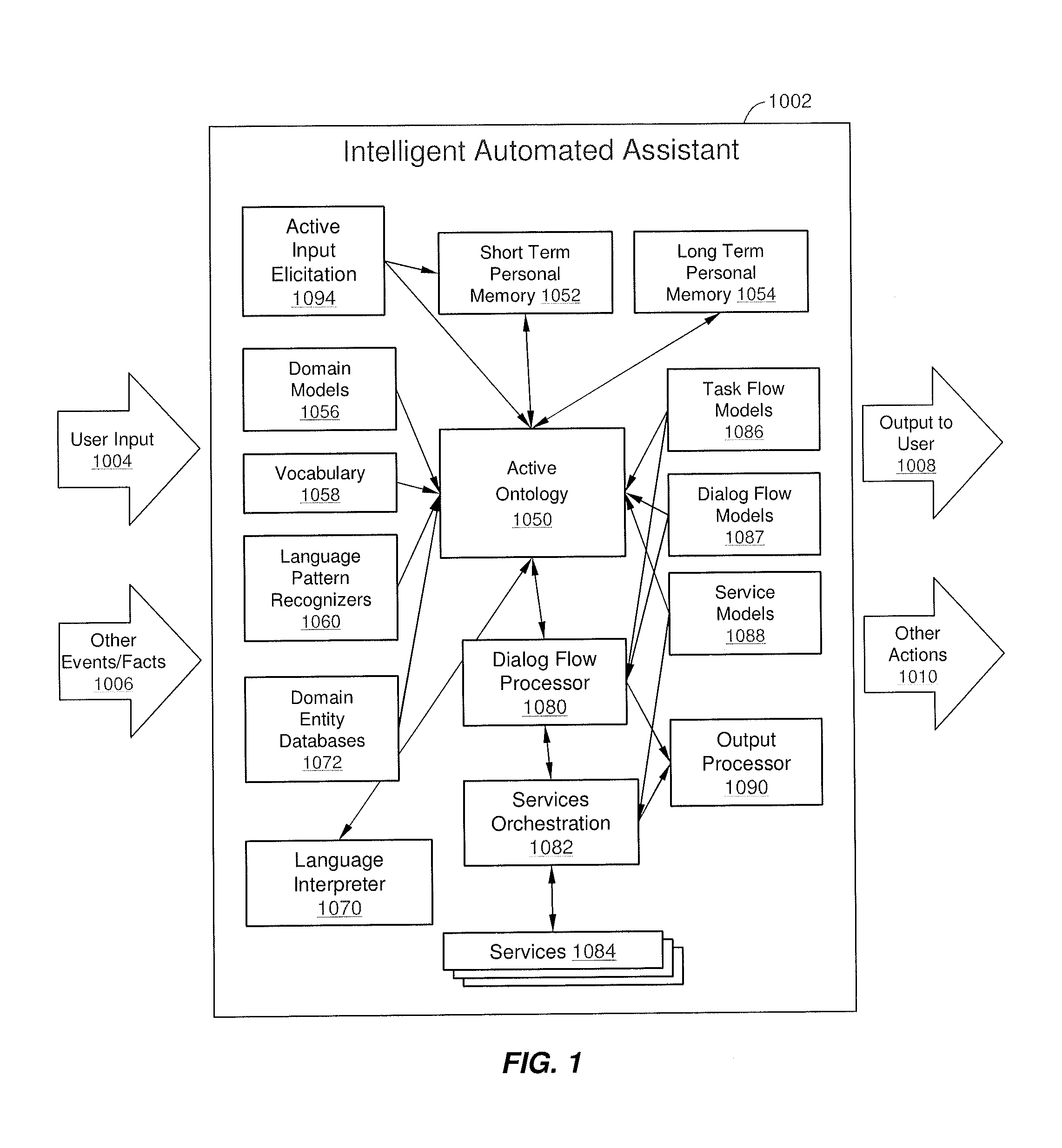
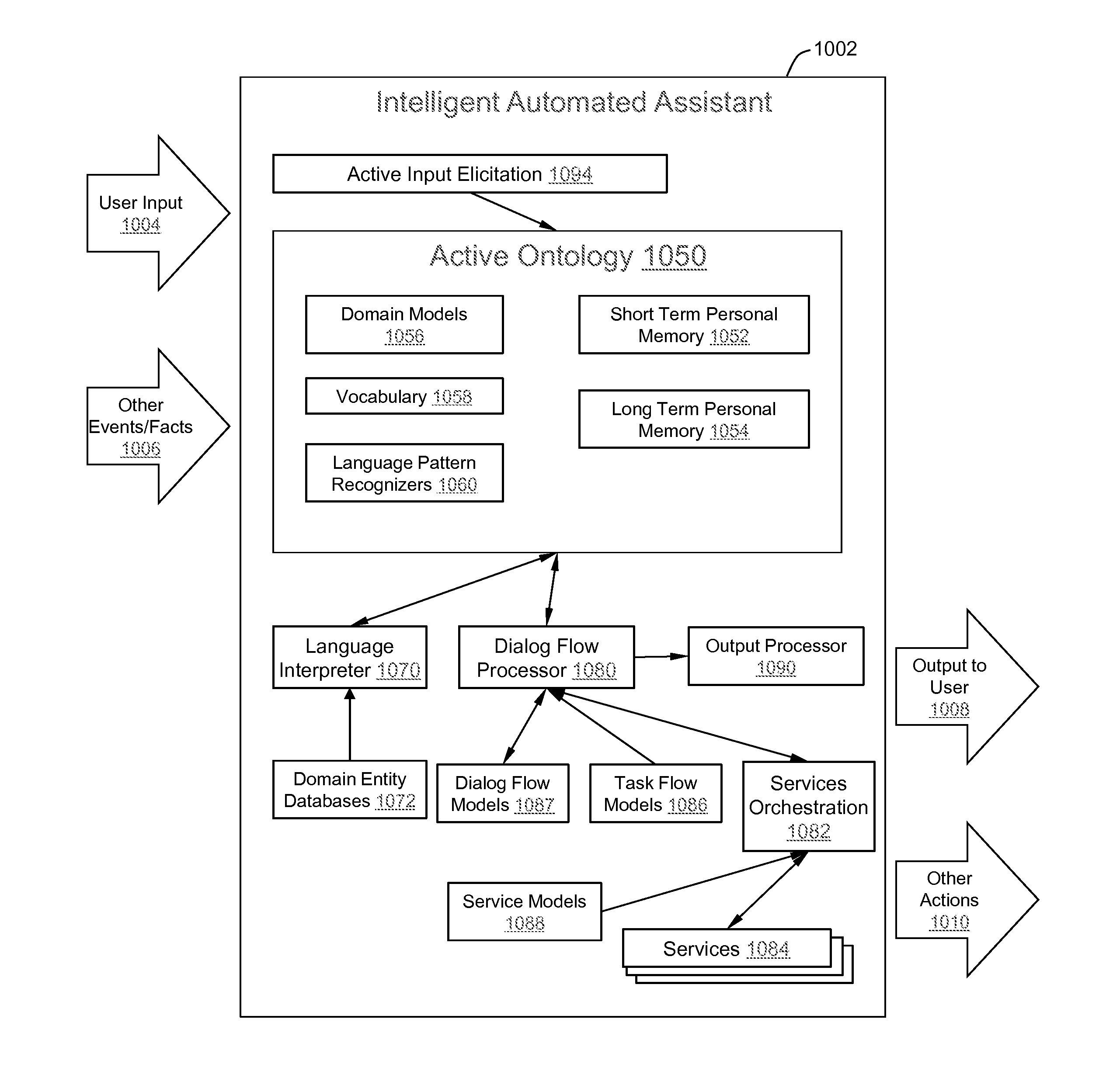
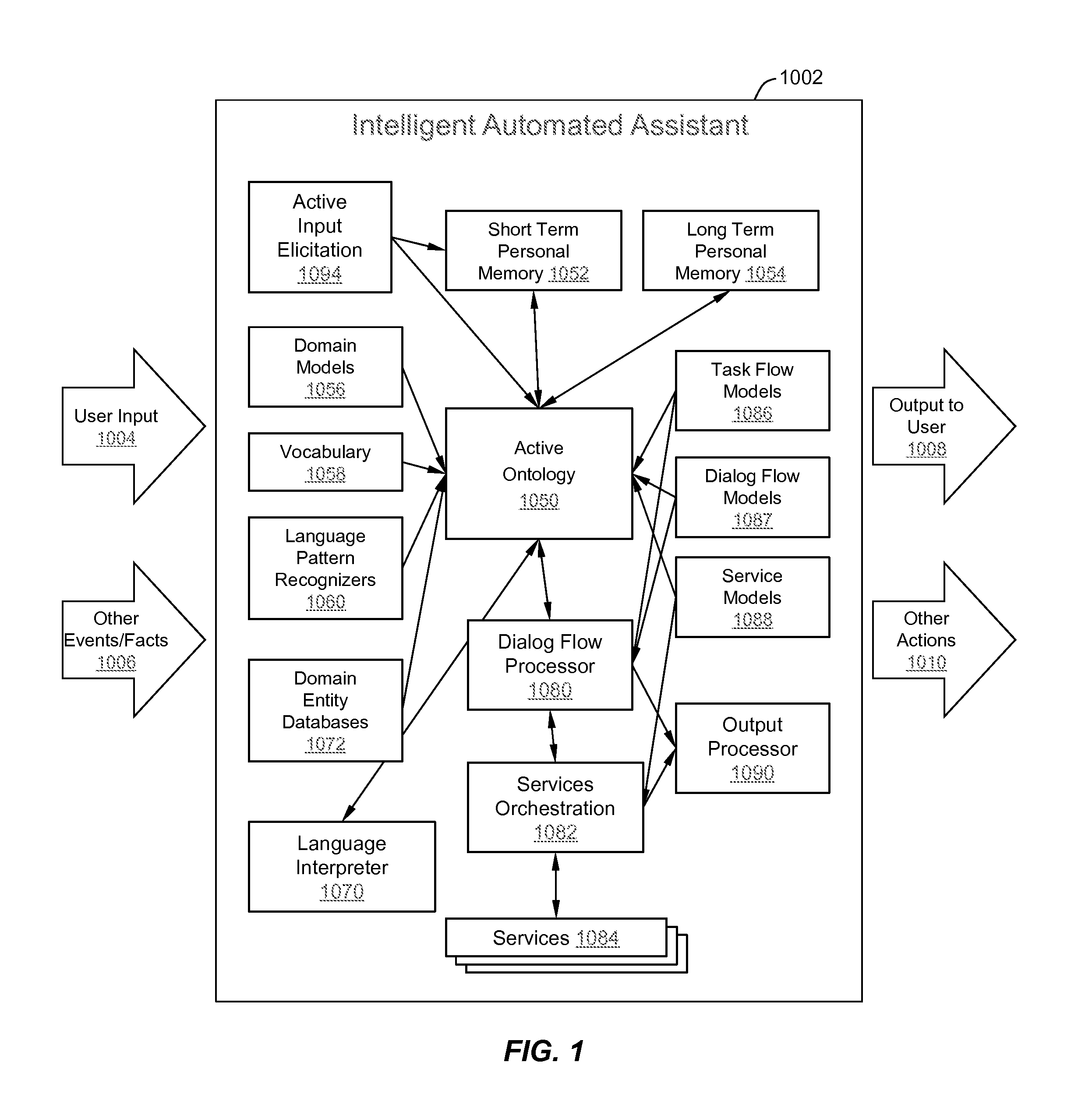
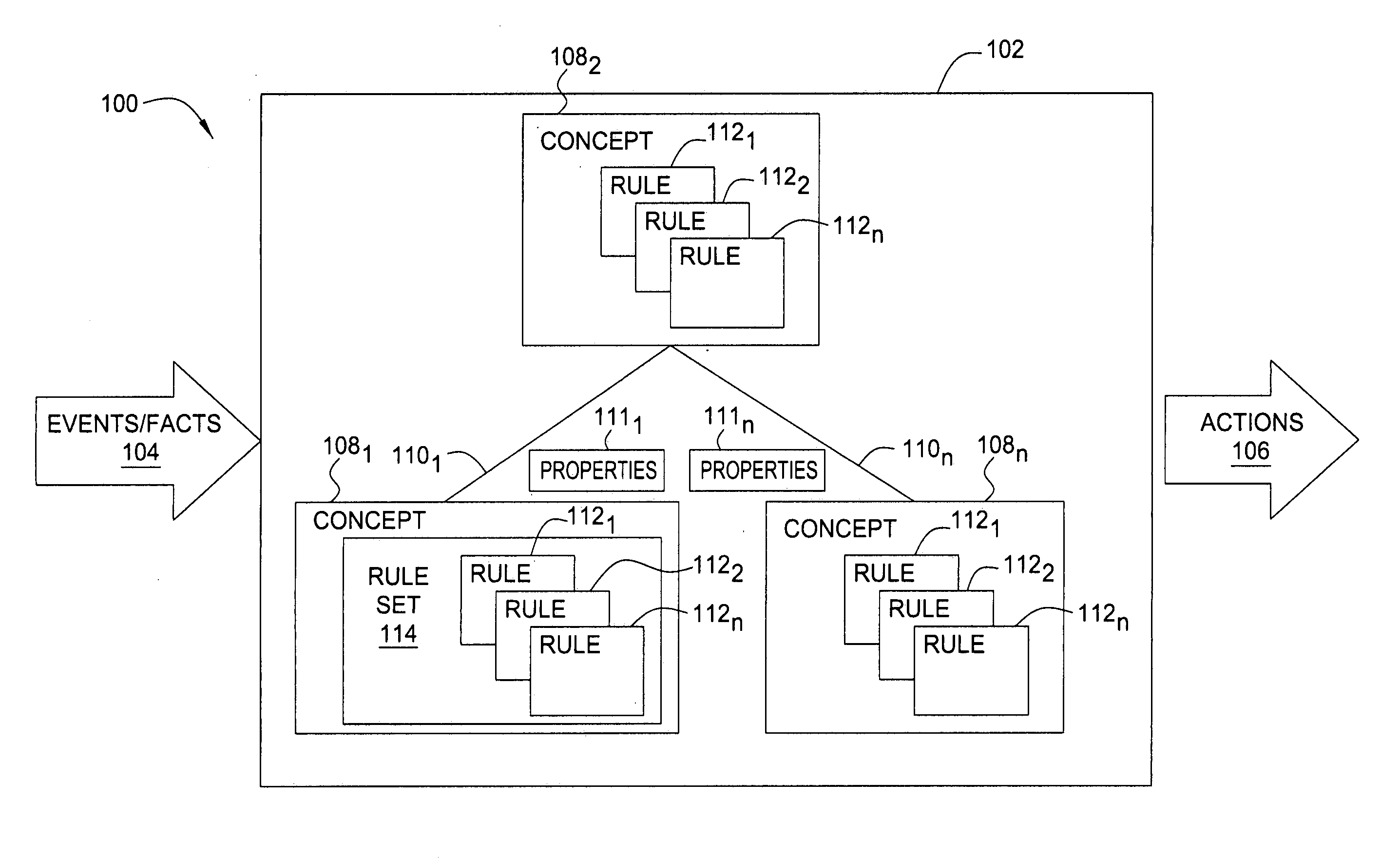
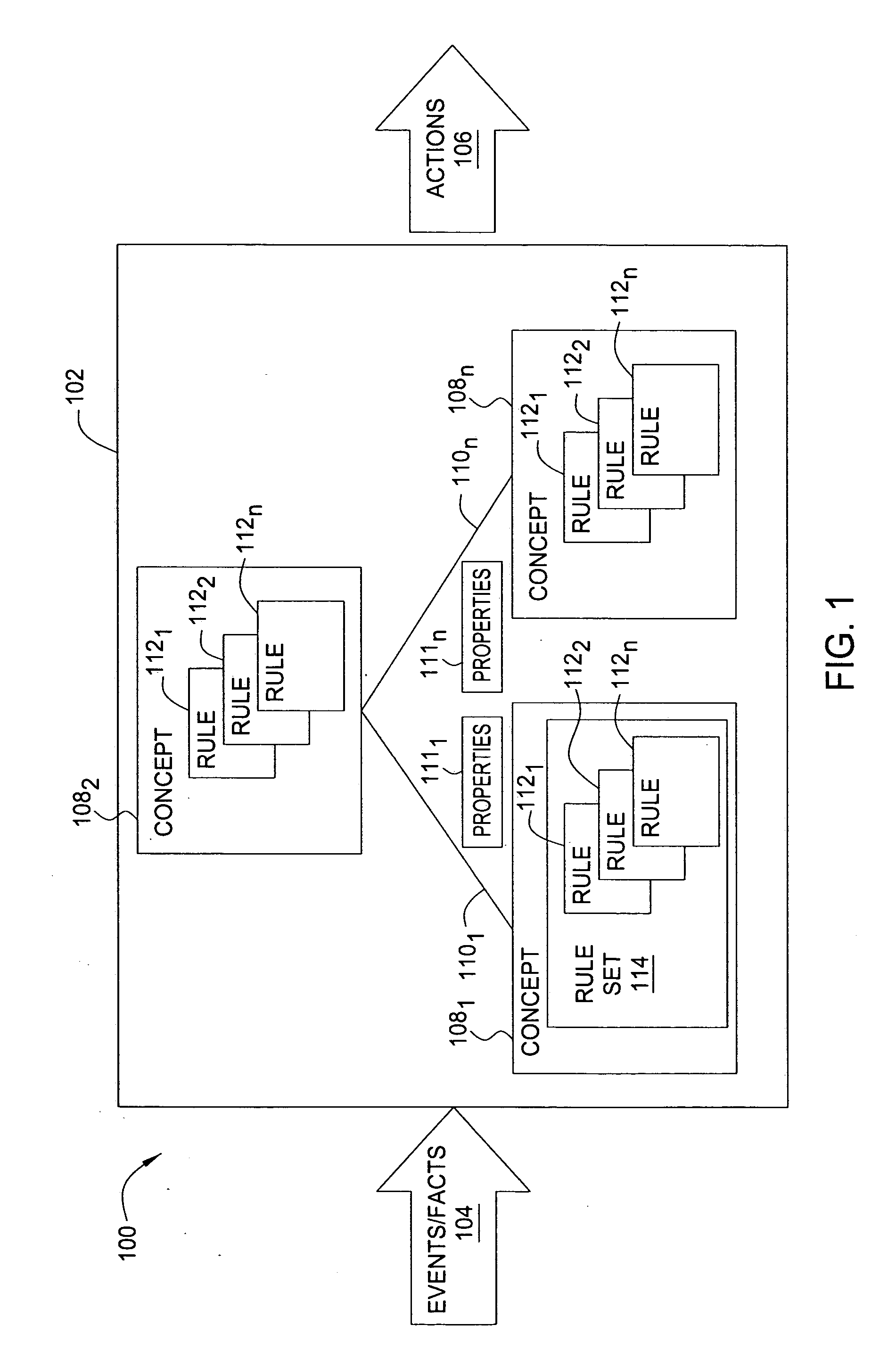
Method and apparatus for building an intelligent automated assistant
A method and apparatus are provided for building an intelligent automated assistant. Embodiments of the present invention rely on the concept of “active ontologies” (e.g., execution environments constructed in an ontology-like manner) to build and run applications for use by intelligent automated assistants. In one specific embodiment, a method for building an automated assistant includes interfacing a service-oriented architecture that includes a plurality of remote services to an active ontology, where the active ontology includes at least one active processing element that models a domain. At least one of the remote services is then registered for use in the domain.
Owner:APPLE INC
Extensible distributed enterprise application integration system
InactiveUS6738975B1Improve securityImprove the environmentInterprogram communicationMultiple digital computer combinationsTransaction serviceInteroperability
In general, in one aspect, the invention provides a modular application collaborator for providing inter-operability between applications including a plurality of connectors for communicating with a like plurality of applications and an interchange server. The interchange server includes an application collaboration module and service module. The service module transfers messages between connectors and the application collaboration module. The application collaboration defines the inter-operability between two or more applications. The interchange server service module includes a transaction service and an error service. Transactions are executed in the application collaboration module and the transaction service records each action and a compensating action for undoing an associated action. An error service monitors for errors in the interchange server, and, upon detection of an error, stops the execution of a transaction and initiates the execution of any required compensating actions to undo the interrupted transaction. The compensating transactions may be executed at the connectors and are not required to be overseen by the interchange server.
Owner:SAGA SOFTWARE
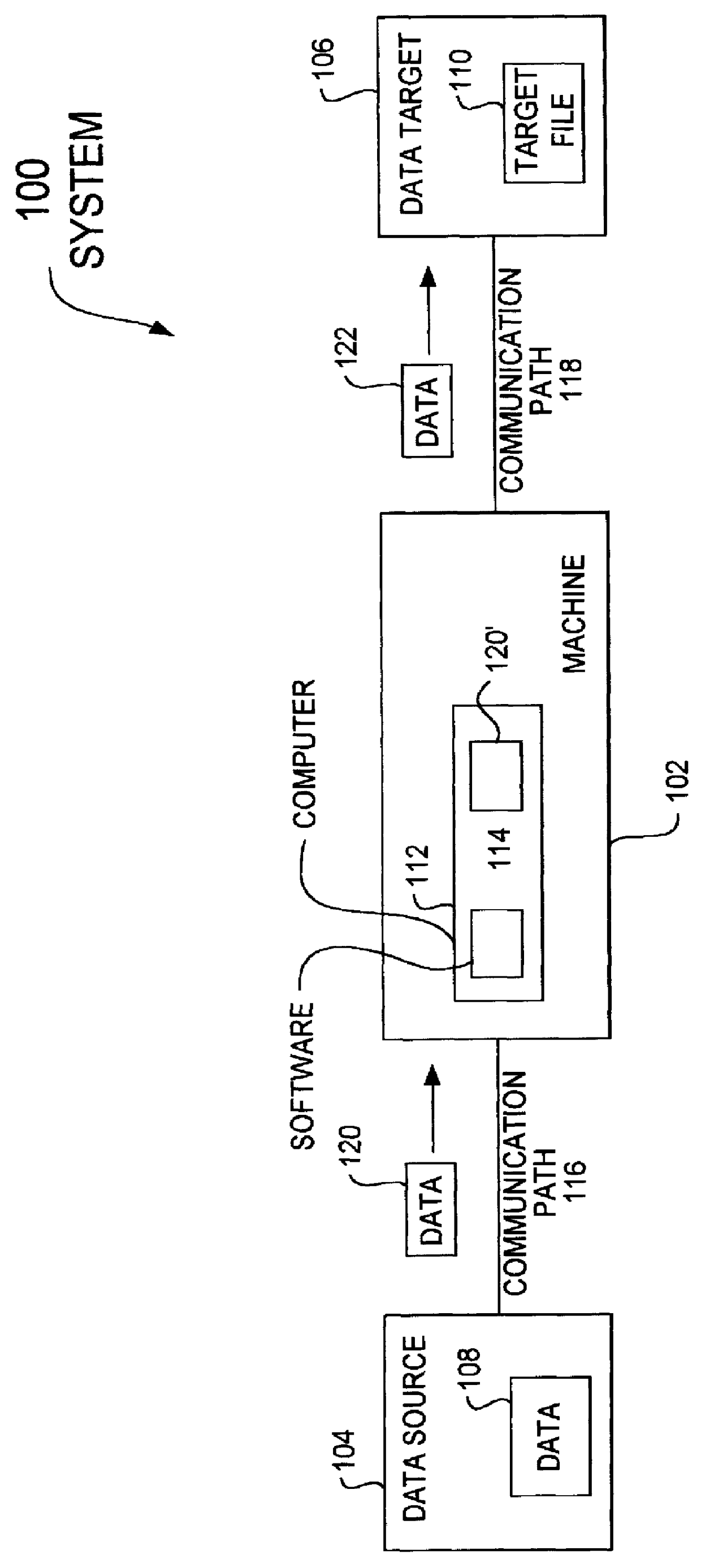
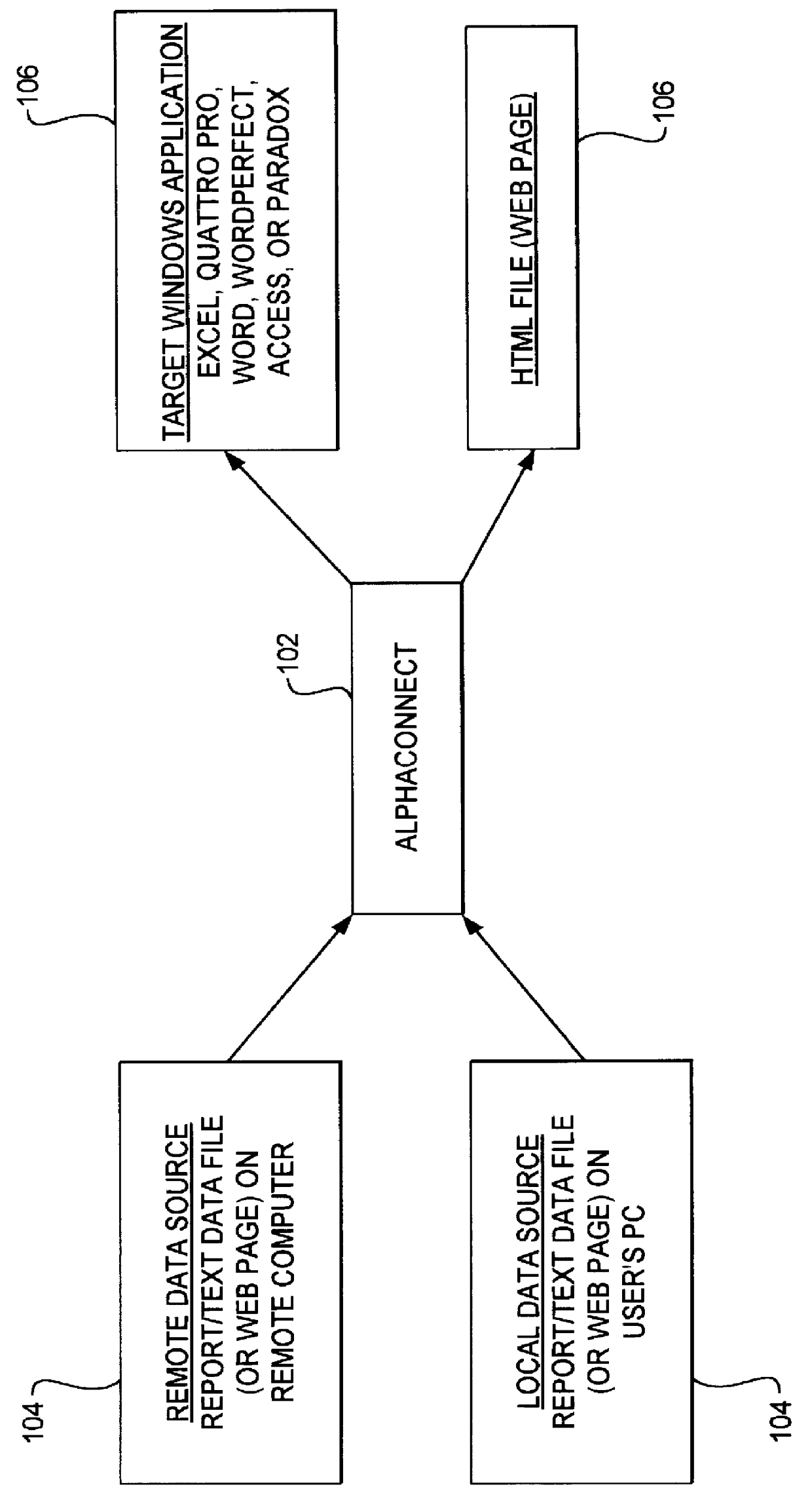
Method and apparatus for data communication
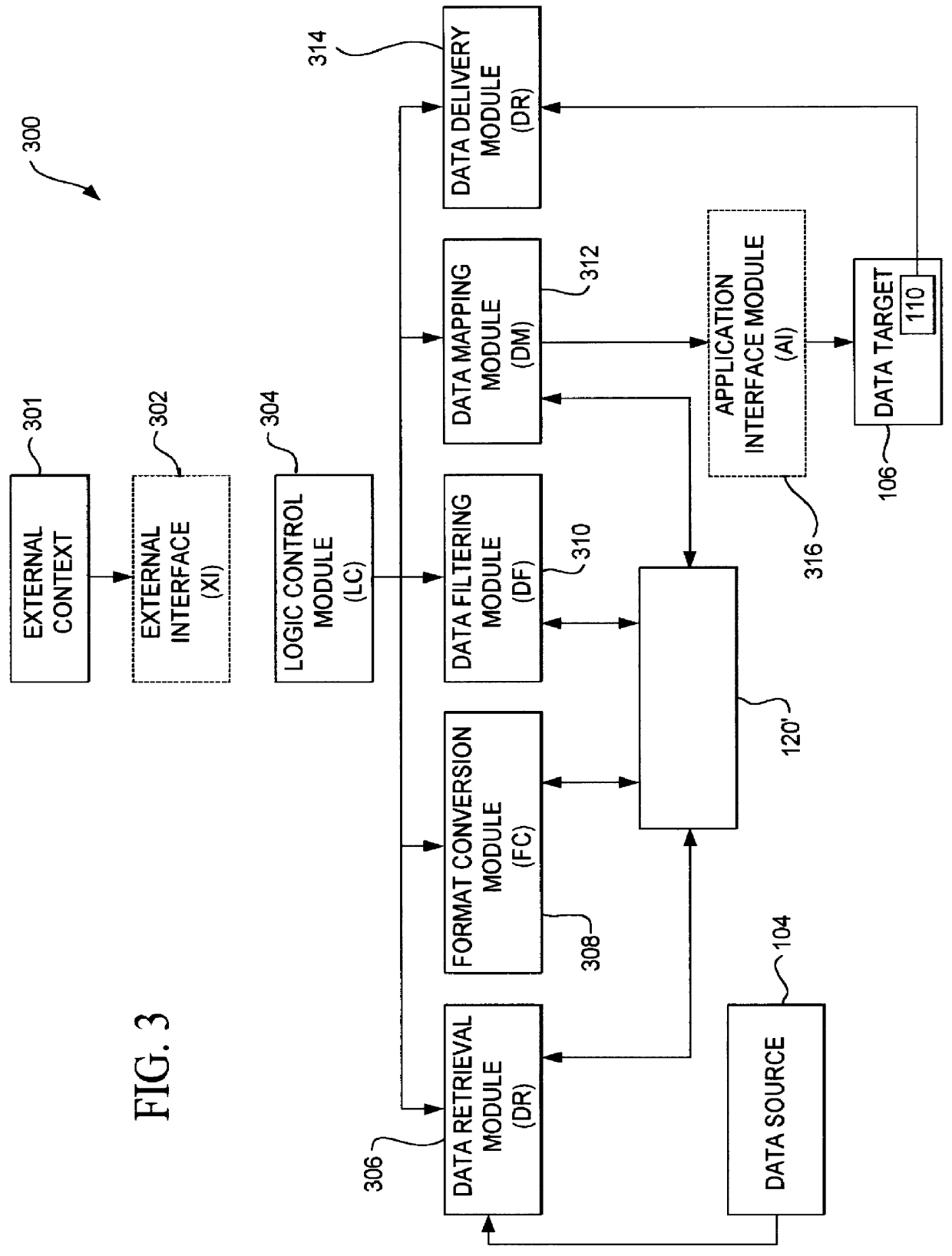
InactiveUS6094684AInterprogram communicationMultiple digital computer combinationsGraphicsGraphical user interface
A data acquisition and delivery system for performing data delivery tasks is disclosed. This system uses a computer running software to acquire source data from a selected data source, to process (e.g. filter, format convert) the data, if desired, and to deliver the resulting delivered data to a data target. The system is designed to access remote and / or local data sources and to deliver data to remote and / or local data targets. The data target might be an application program that delivers the data to a file or the data target may simply be a file, for example. To obtain the delivered data, the software performs processing of the source data as appropriate for the particular type of data being retrieved, for the particular data target and as specified by a user, for example. The system can communicate directly with a target application program, telling the target application to place the delivered data in a particular location in a particular file. The system provides an external interface to an external context. If the external context is a human, the external interface may be a graphical user interface, for example. If the external context is another software application, the external interface may be an OLE interface, for example. Using the external interface, the external context is able to vary a variety of parameters to define data delivery tasks as desired. The system uses a unique notation that includes a plurality of predefined parameters to define the data delivery tasks and to communicate them to the software.
Owner:E BOTZ COM INC A DELAWARE +2
Methods and servers for establishing a connection between a client system and a virtual machine hosting a requested computing environment
InactiveUS20070174429A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient system
A method for providing access to a computing environment includes the step of receiving a request from a client system for an enumeration of available computing environments. Collected data regarding available computing environments are accessed. Accessed data are transmitted to a client system, the accessed data indicating to the client system each computing environment available to a user of the client system. A request is received from the client system to access one of the computing environments. A connection is established between the client system and a virtual machine hosting the requested computing environment.
Owner:CITRIX SYST INC
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
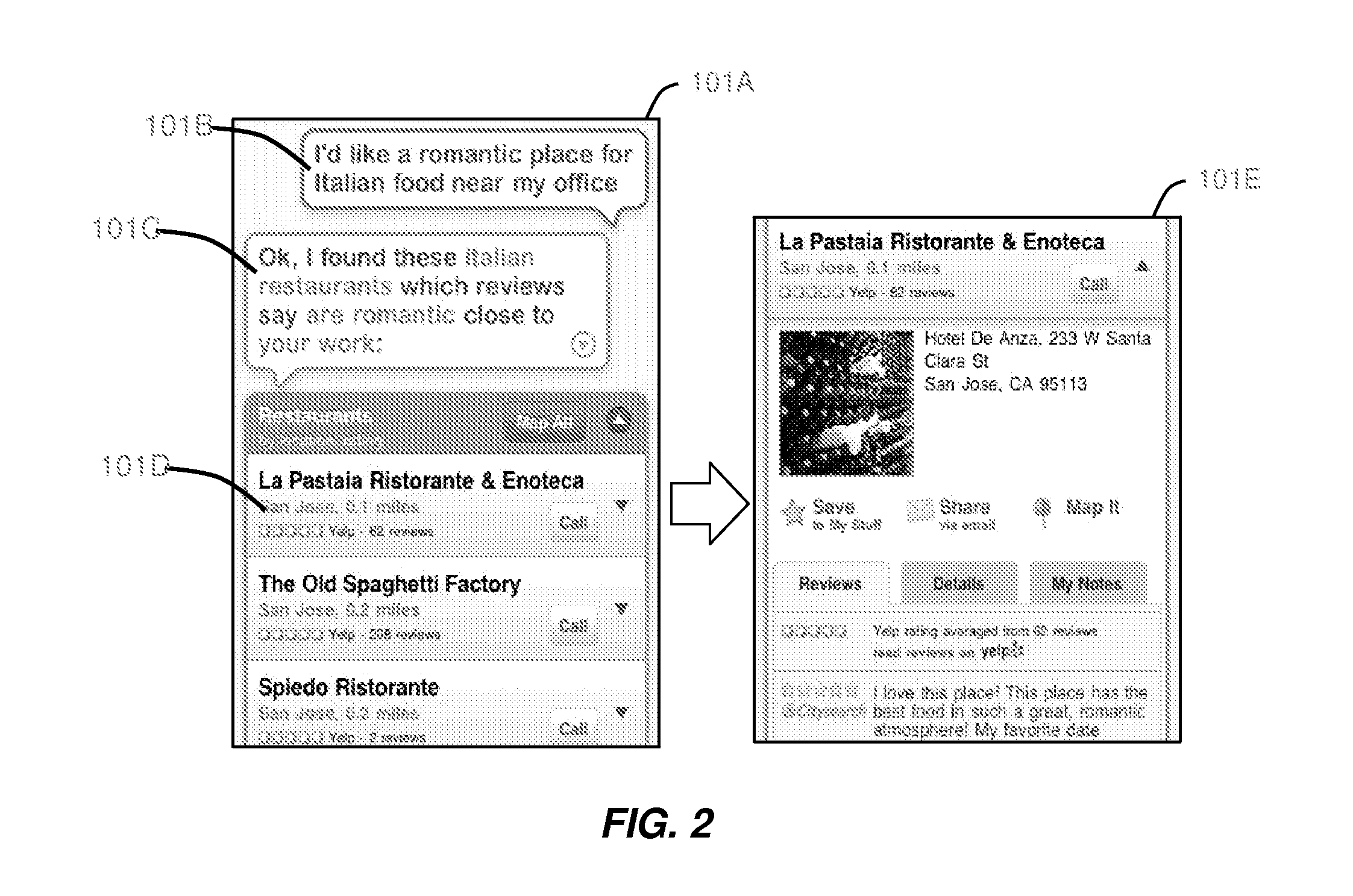
Prioritizing Selection Criteria by Automated Assistant
ActiveUS20130111348A1Improve user interactionEffectively engageNatural language translationSemantic analysisSelection criterionSpeech input
Methods, systems, and computer readable storage medium related to operating an intelligent digital assistant are disclosed. A user request is received, the user request including at least a speech input received from a user. The user request including the speech input is processed to obtain a representation of user intent for identifying items of a selection domain based on at least one selection criterion. A prompt is provided to the user, the prompt presenting two or more properties relevant to items of the selection domain and requesting the user to specify relative importance between the two or more properties. A listing of search results is provided to the user, where the listing of search results has been obtained based on the at least one selection criterion and the relative importance provided by the user.
Owner:APPLE INC
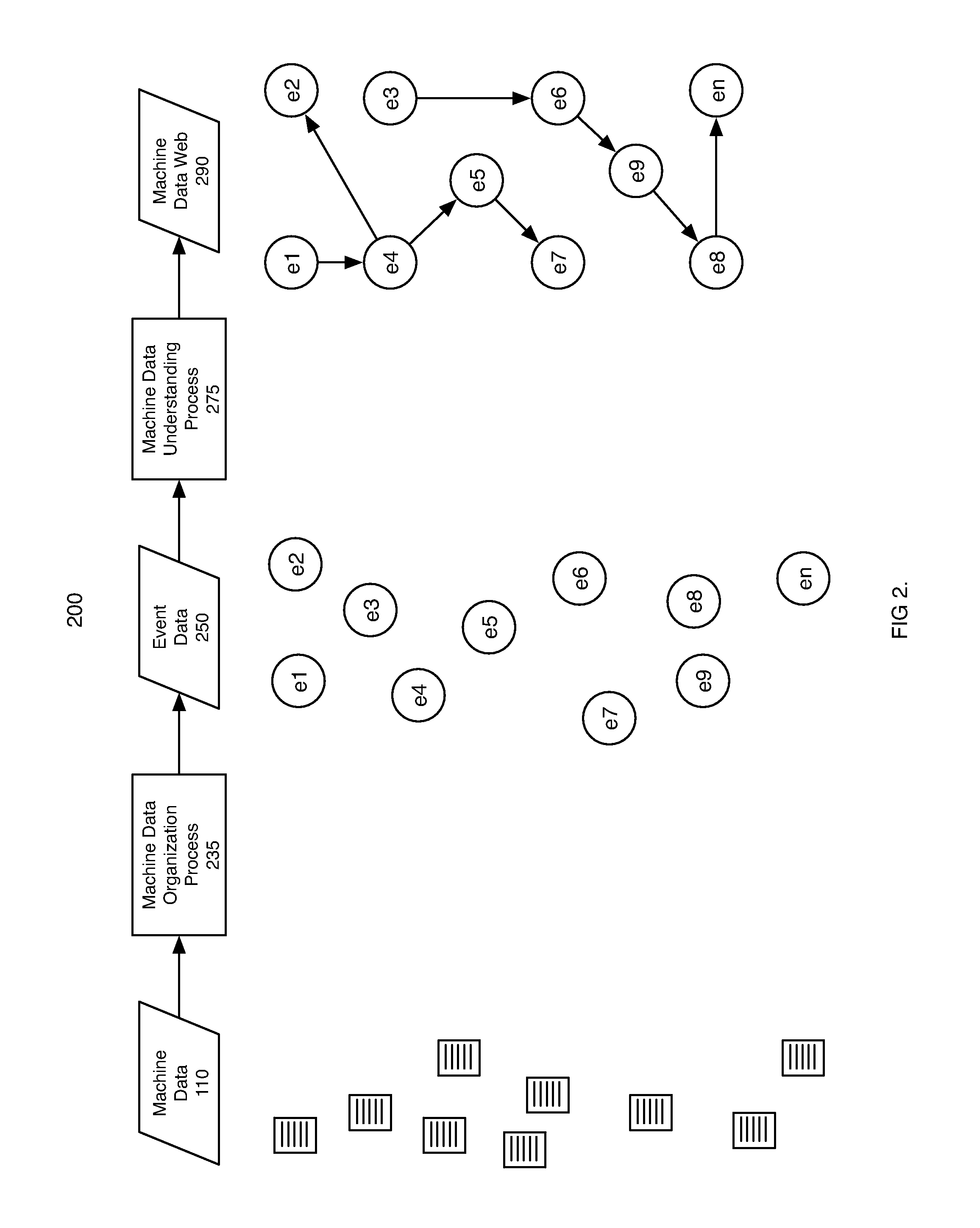
Machine data web
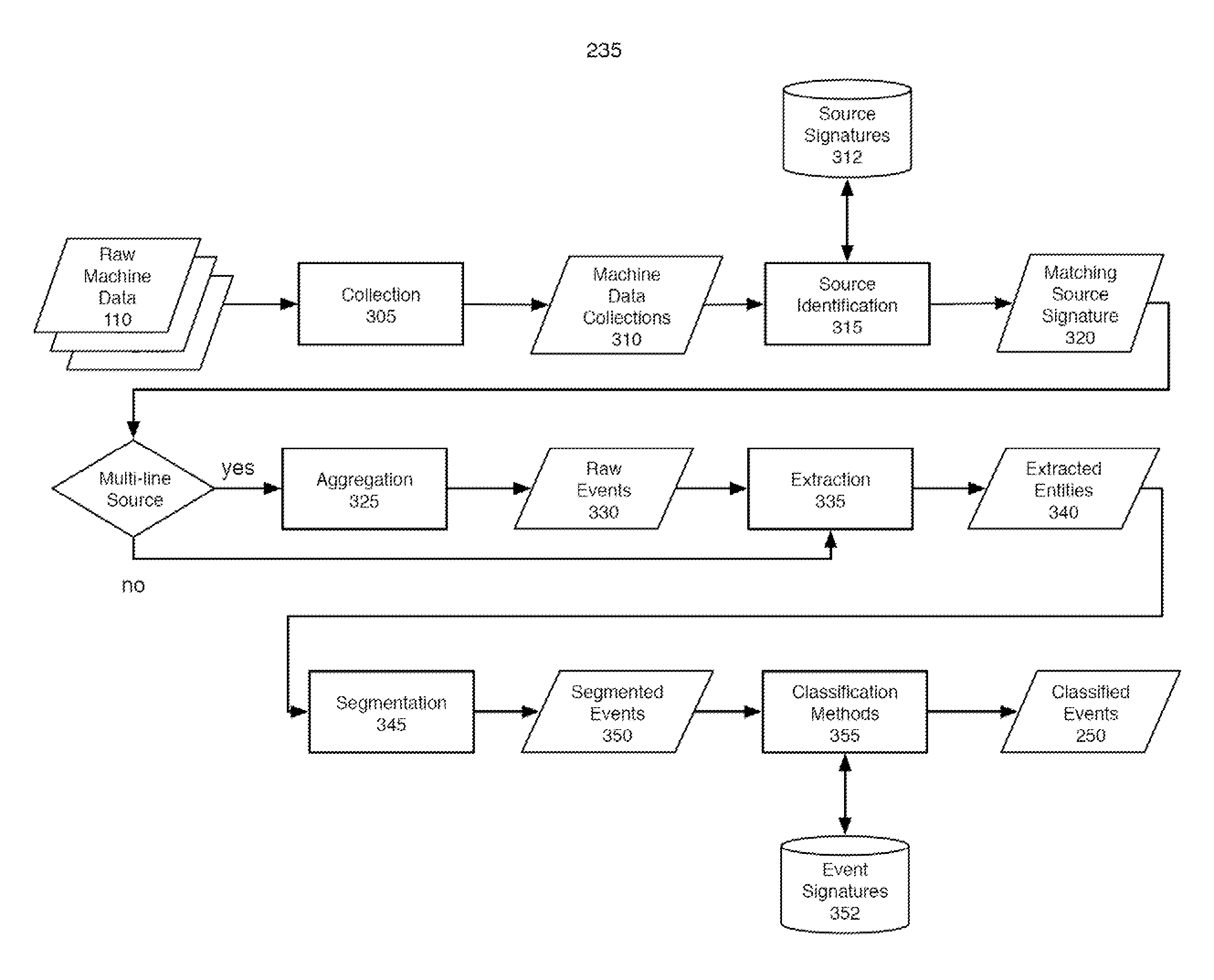
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
Methods and systems for assigning access control levels in providing access to resources via virtual machines
ActiveUS20070180493A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
Owner:CITRIX SYST INC
Method and apparatus for building an intelligent automated assistant
A method and apparatus are provided for building an intelligent automated assistant. Embodiments of the present invention rely on the concept of “active ontologies” (e.g., execution environments constructed in an ontology-like manner) to build and run applications for use by intelligent automated assistants. In one specific embodiment, a method for building an automated assistant includes interfacing a service-oriented architecture that includes a plurality of remote services to an active ontology, where the active ontology includes at least one active processing element that models a domain. At least one of the remote services is then registered for use in the domain.
Owner:APPLE INC
Disambiguation Based on Active Input Elicitation by Intelligent Automated Assistant
ActiveUS20130110515A1Improve user interactionEffectively engageNatural language translationSemantic analysisUser inputSpeech input
Owner:APPLE INC
Methods and systems for selecting a method for execution, by a virtual machine, of an application program
ActiveUS20070180450A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideClient machine
A method for selecting a method of execution for an application includes the step of receiving credentials. A plurality of applications available to a client machine is enumerated responsive to the received credentials. A request to execute an enumerated application is received. One of a predetermined number of methods for executing the requested application is selected responsive to a policy, the predetermined number of methods including a method for executing the requested application in a computing environment provided by a virtual machine.
Owner:CITRIX SYST INC
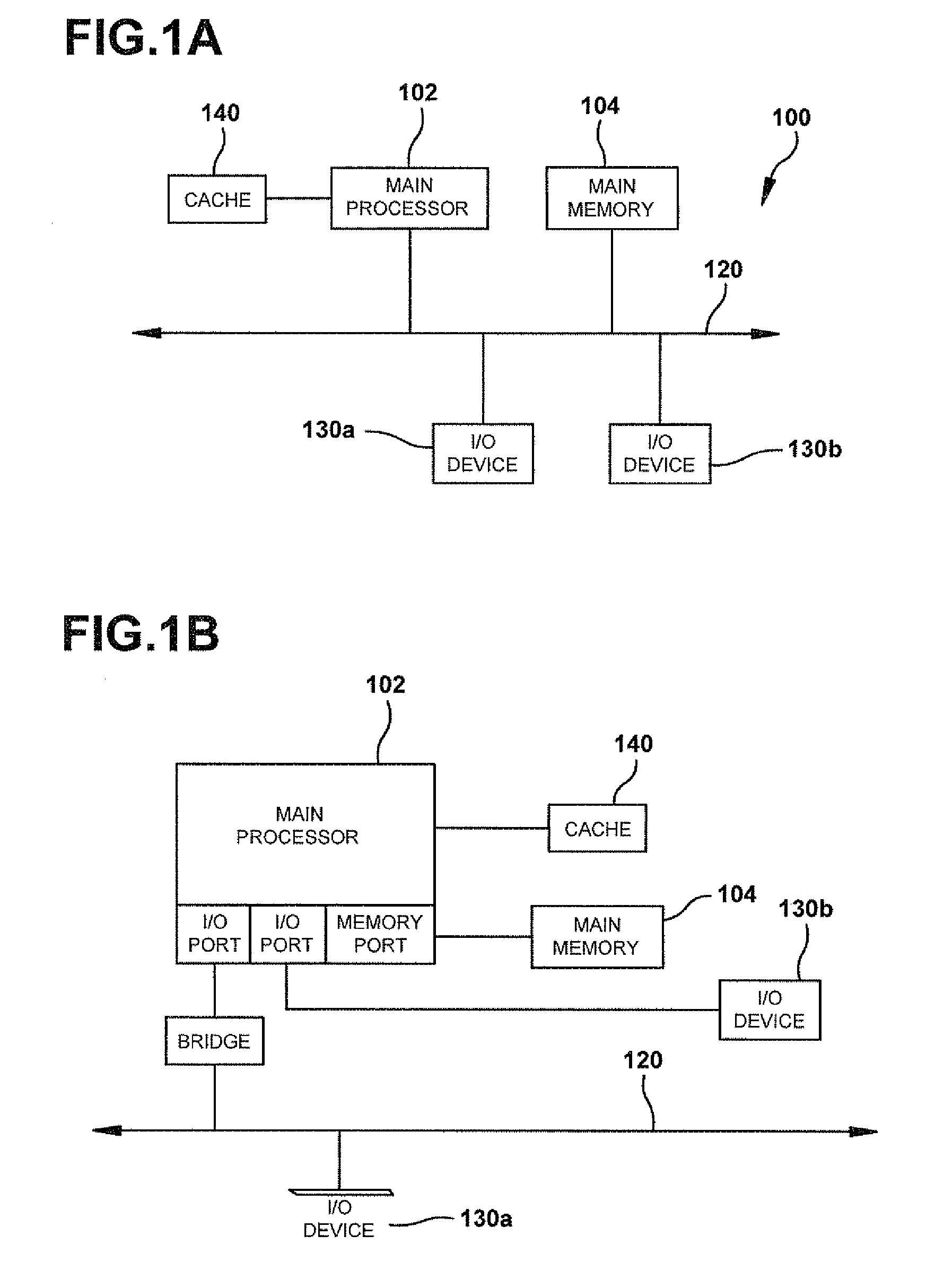
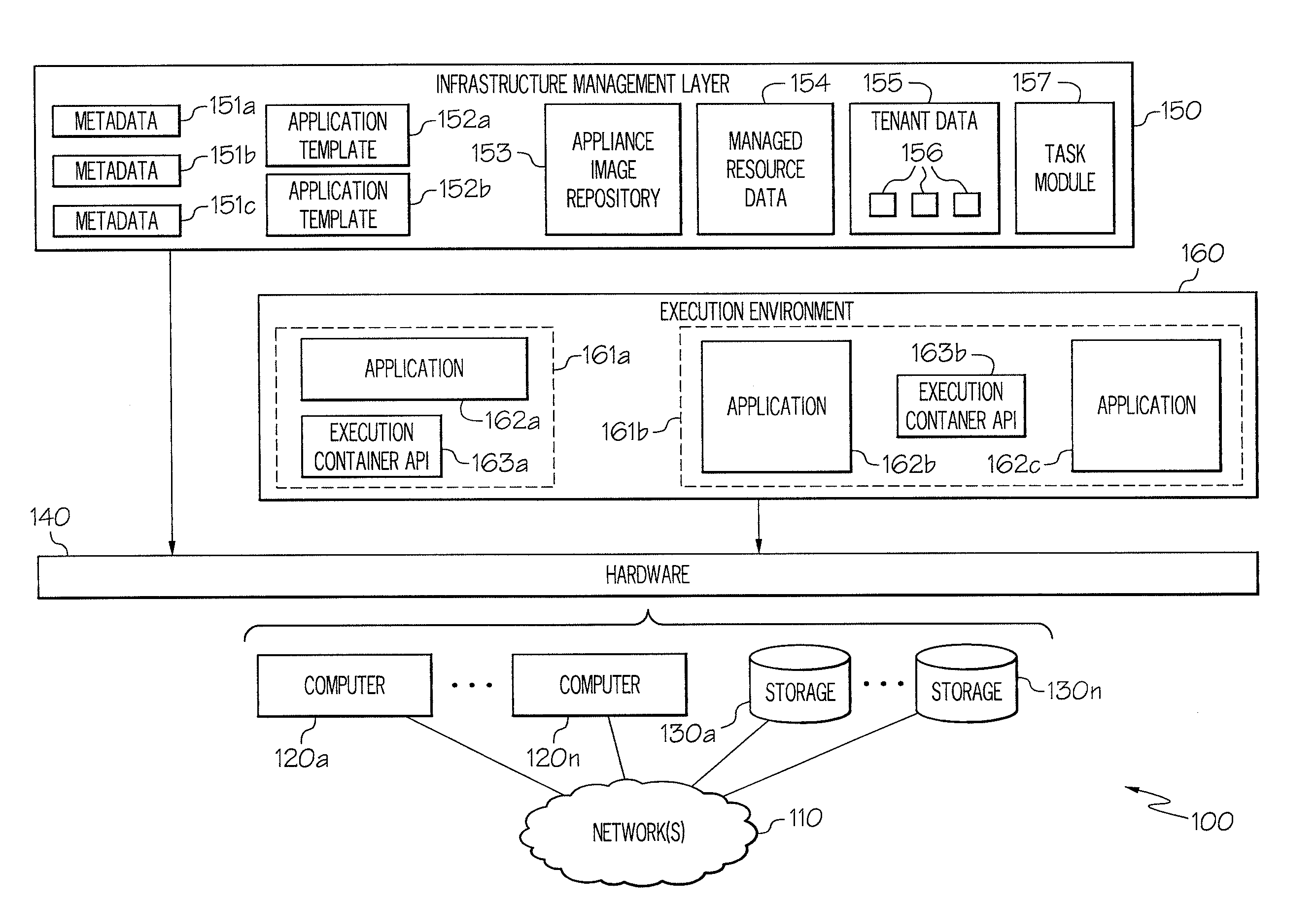
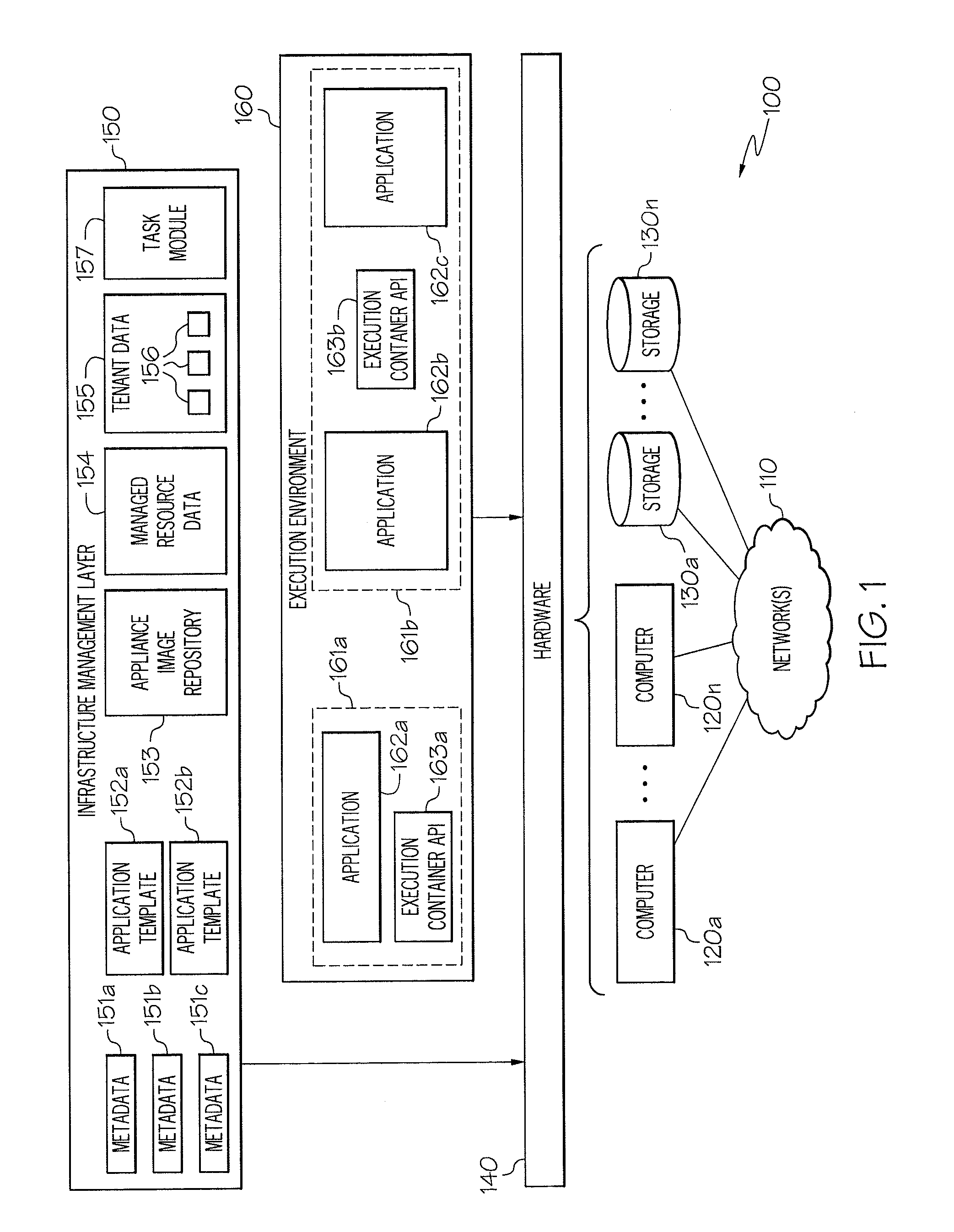
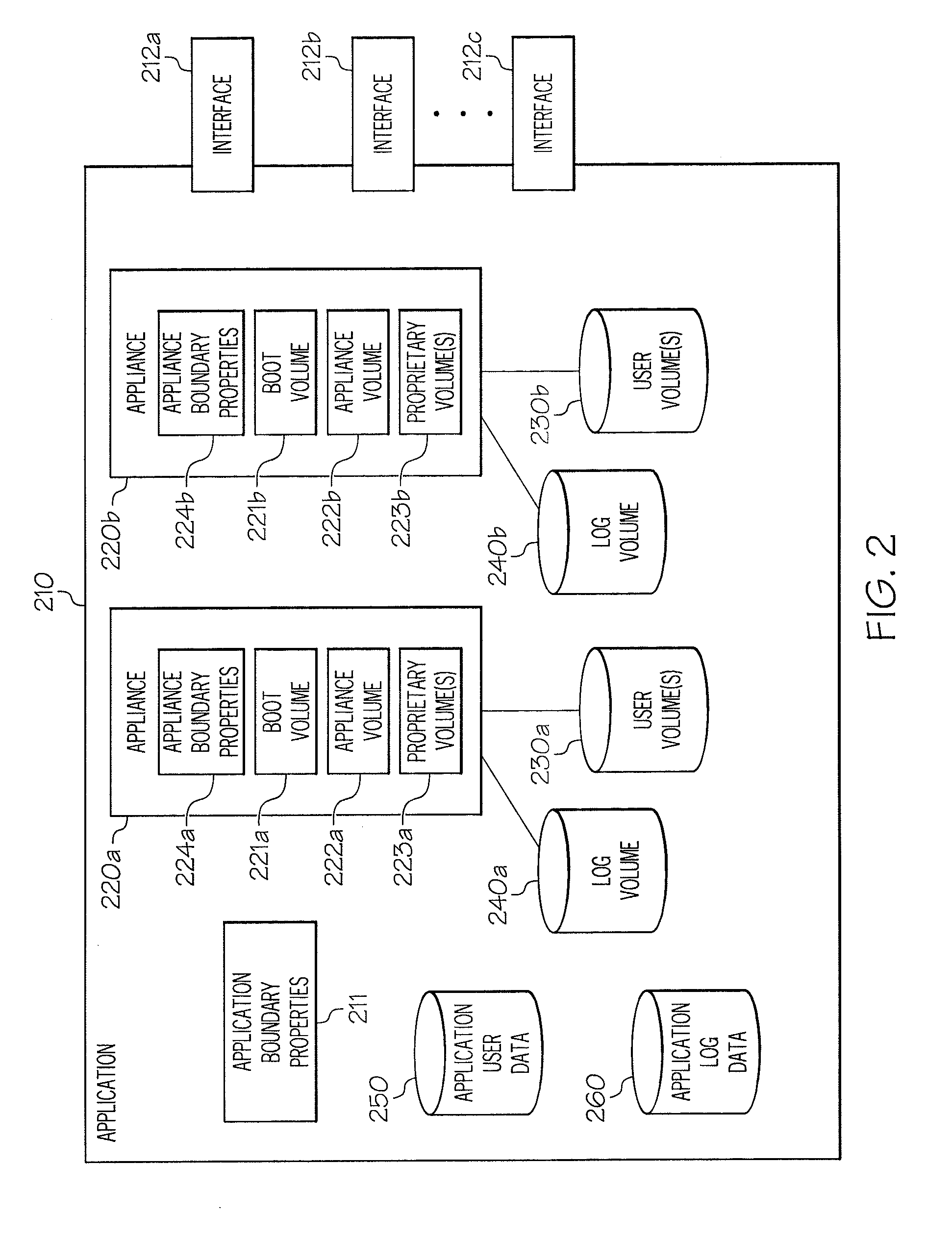
Enhanced Software Application Platform
A system includes information for generating a first appliance based on first appliance information, information for generating a second appliance based on second appliance information, and information for configuring communication between the first appliance and the second appliance. The system further includes at least one processor configured to generate a first volume by copying the first appliance information using a first set of parameters associated with an environment in which the first volume is situated, and generate a second volume by copying the second appliance information using a second set of parameters associated with an environment in which the second volume is situated. The system also includes at least one processor configured to initiate a first appliance instance by executing code from the first volume using information in the third volume, and initiate a second appliance instance by executing code in the second volume using information in a fourth volume.
Owner:CA TECH INC
Methods and systems for providing access to a computing environment
ActiveUS20070186212A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient-sideClient machine
A method for providing access to a computing environment includes the step of receiving, by a broker machine, a request from a client machine for access to a computing environment, the request including an identification of a user of the client machine. One of a plurality of virtual machines is identified, the identified virtual machine providing the requested computing environment. One of a plurality of execution machines is identified, the identified execution machine executing a hypervisor providing access to hardware resources required by the identified virtual machine. A connection is established between the client machine and the identified virtual machine.
Owner:CITRIX SYST INC
System and method for controlling inter-application association through contextual policy control
ActiveUS20060036570A1Resource identifiedInterprogram communicationDigital data protectionContext managementNamespace
A method for controlling the interoperation of a plurality of software applications and resources includes intercepting communications from a first application to a second application or resource, directing the communication to a context management system, generating a candidate list of contexts for the communication, evaluating the candidate list according to at least one policy defined for these contexts to identify the resultant action and namespace for the communication, and performing the action as defined by the policies within the identified namespace. The method further includes tracking one or more versions of the second application, as well as tracking an evolution of application and / or resource names. The method further includes identifying one or more operations associated with a context on the candidate list, and executing the identified operations prior to a further communication.
Owner:MICROSOFT TECH LICENSING LLC
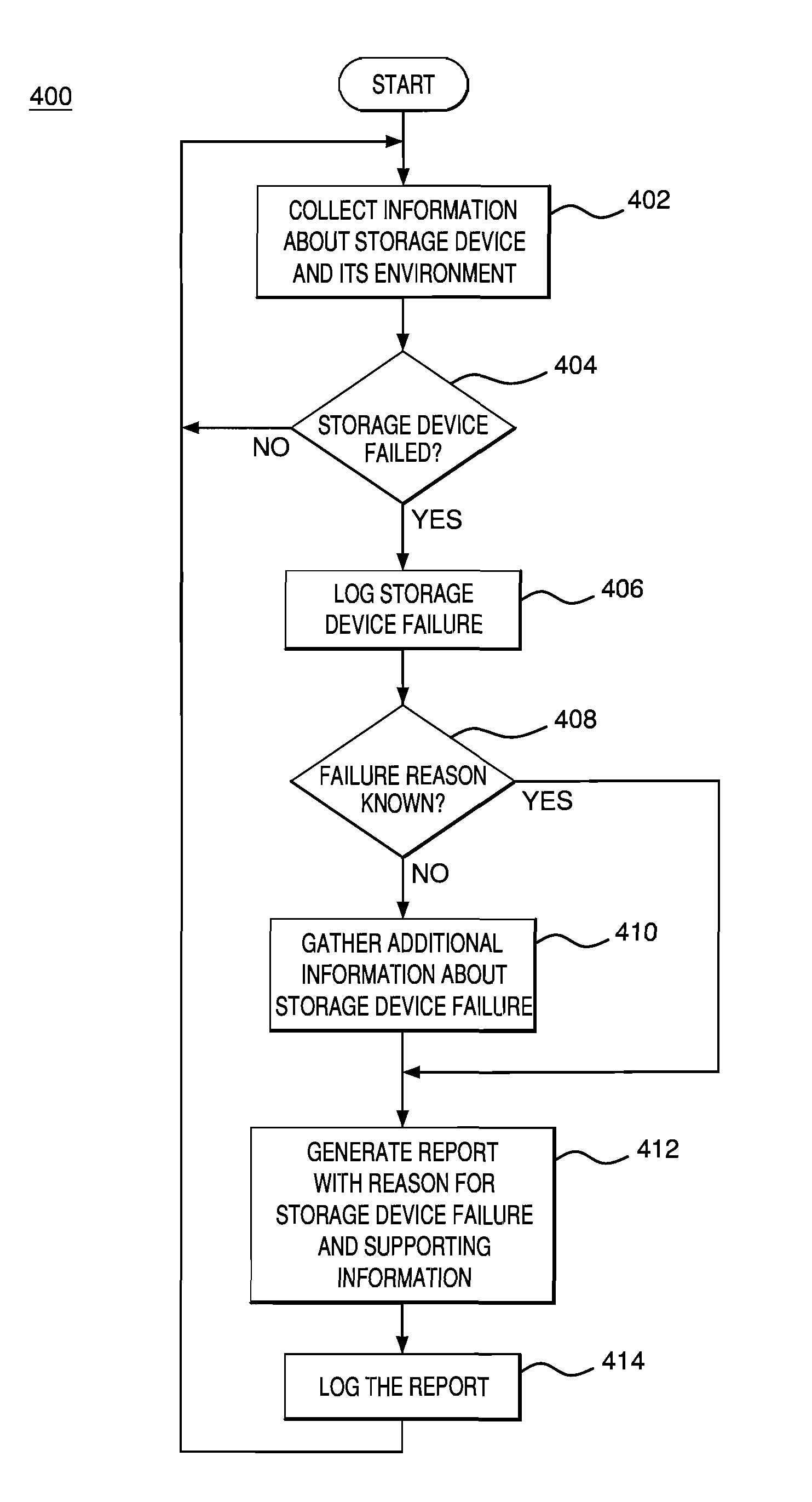
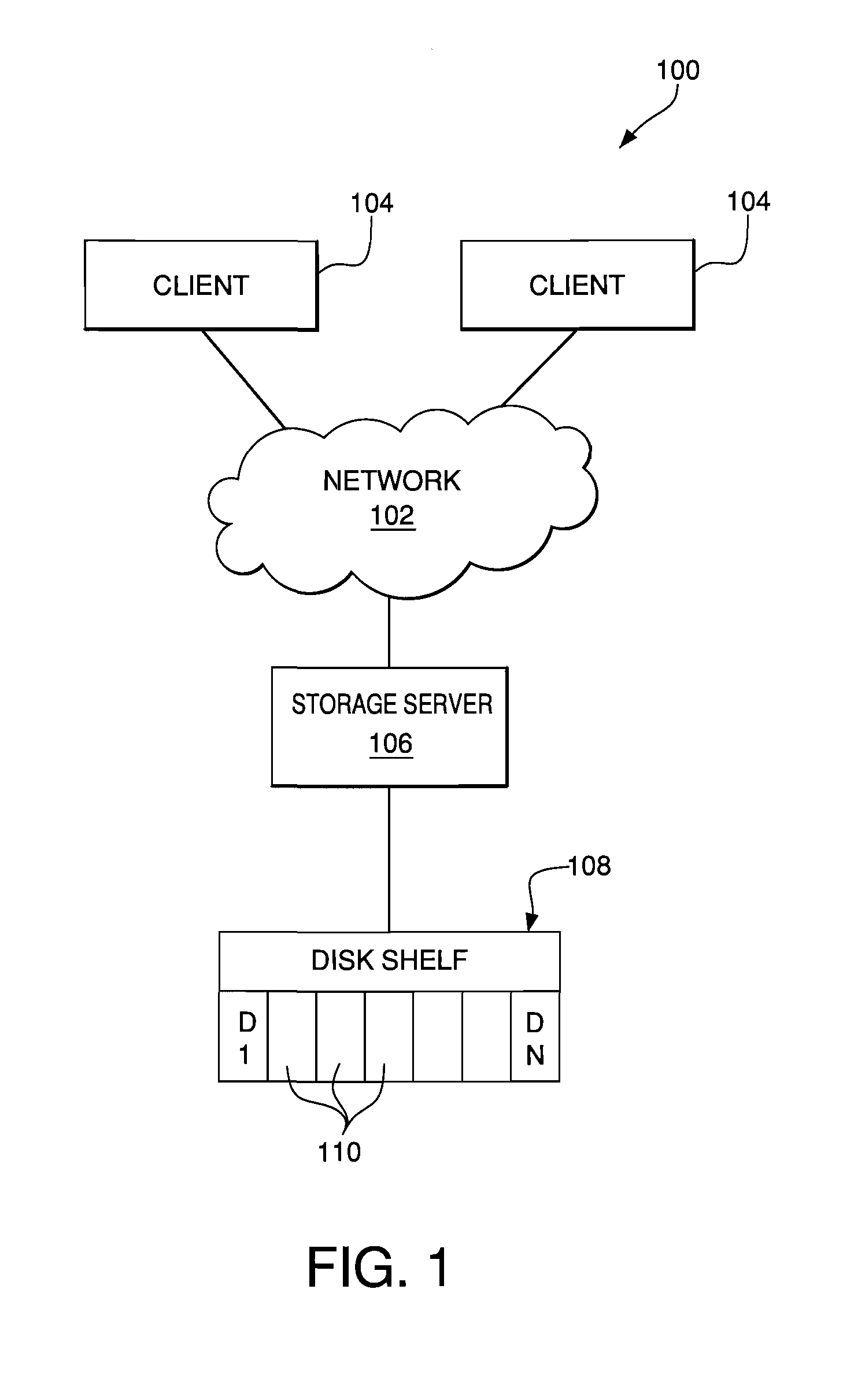
Creating environmental snapshots of storage device failure events
InactiveUS8949863B1Interprogram communicationNon-redundant fault processingRelevant informationDevice failure
A storage device failure in a computer storage system can be analyzed by the storage system by examining relevant information about the storage device and its environment. Information about the storage device is collected in real-time and stored; this is an on-going process such that some information is continuously available. The information can include information relating to the storage device, such as input / output related information, and information relating to a storage shelf where the storage device is located, such as a status of adjacent storage devices on the shelf. All of the relevant information is analyzed to determine a reason for the storage device failure. Optionally, additional information may be collected and analyzed by the storage system to help determine the reason for the storage device failure. The analysis and supporting information can be stored in a log and / or presented to a storage system administrator to view.
Owner:NETWORK APPLIANCE INC
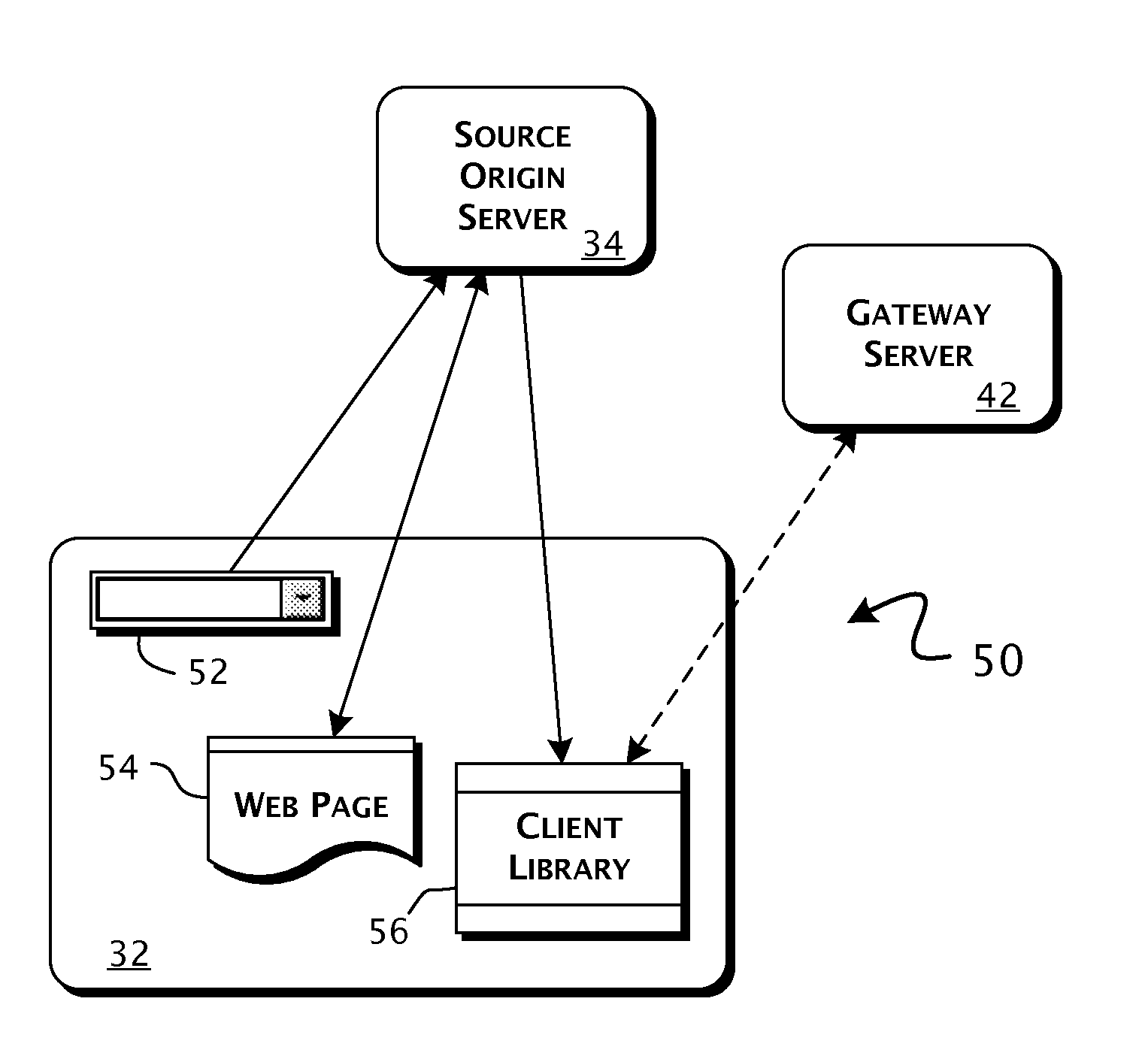
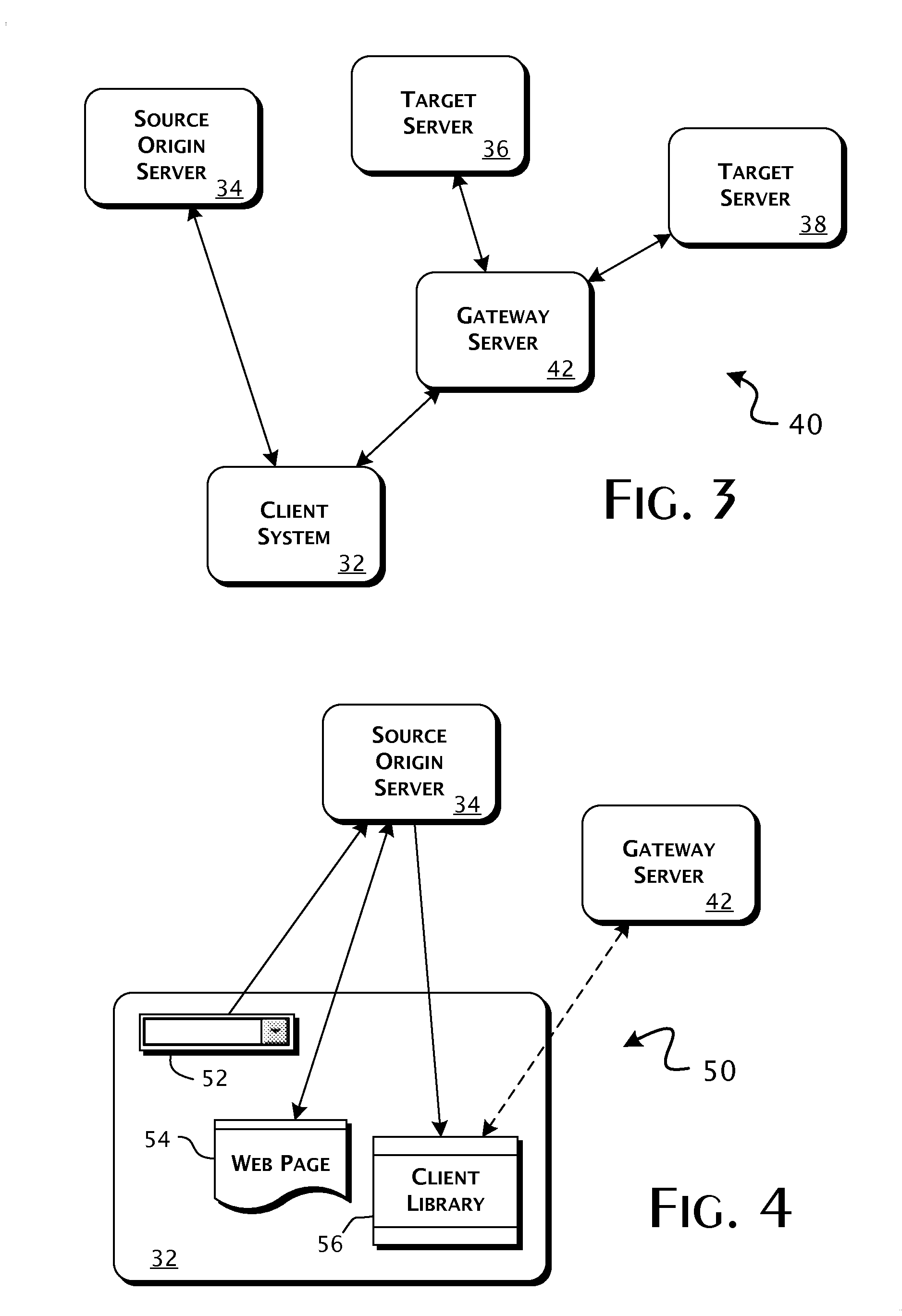
Enterprise client-server system and methods of providing web application support through distributed emulation of websocket communications
ActiveUS20100281107A1Appropriate deliveryEffective supportInterprogram communicationMultiple digital computer combinationsSecure communicationClient-side
A system enabling service communications in distributed Web applications between servers otherwise inaccessible due to cross-origin security restrictions in pre-HTML5 compliant Web-browser clients. A Web-browser client executes a client-side Web application received from a source origin server having a defined source origin and requests connections to request identified Web-application services. Execution of an emulation client library establishes a bidirectional capable HTTP-based communications connection between the Web-browser client and a gateway server, having a target origin outside the scope of the source origin, providing access to the request identified Web-application service. The bidirectional capable HTTP-based communications connection includes a cross-origin communications bridge providing a secure communications path between the source and target origins. The gateway server can establish an HTML5 compliant connection to a target defined service, provided by a target server, having a predefined relation to the request identified Web-application service.
Owner:KAAZING CORP
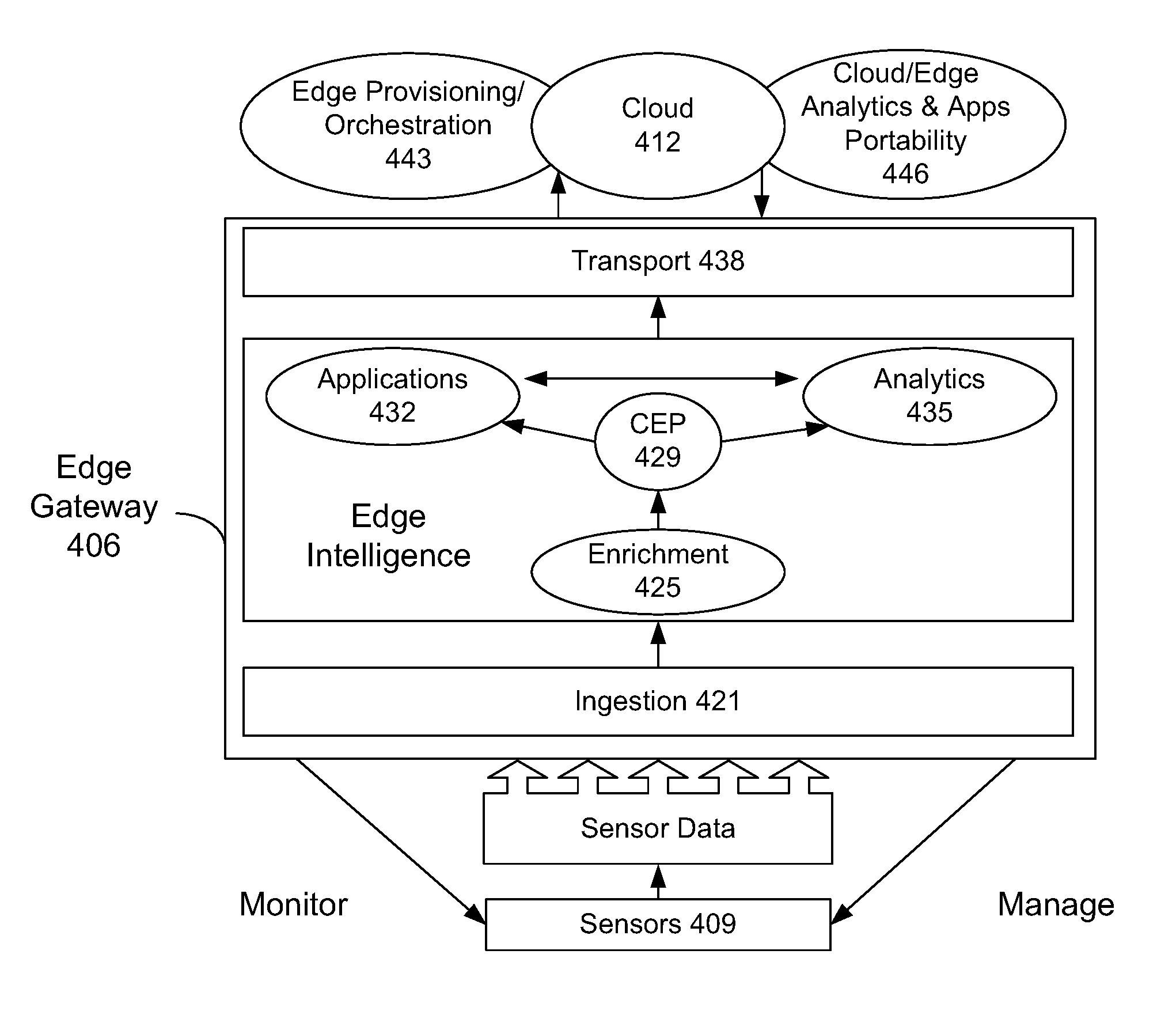
Edge Intelligence Platform, and Internet of Things Sensor Streams System
ActiveUS20170060574A1Delay minimizationMaximum performanceDigital data information retrievalParticular environment based servicesAnalytical expressionsApplication software
A method for enabling intelligence at the edge. Features include: triggering by sensor data in a software layer hosted on either a gateway device or an embedded system. Software layer is connected to a local-area network. A repository of services, applications, and data processing engines is made accessible by the software layer. Matching the sensor data with semantic descriptions of occurrence of specific conditions through an expression language made available by the software layer. Automatic discovery of pattern events by continuously executing expressions. Intelligently composing services and applications across the gateway device and embedded systems across the network managed by the software layer for chaining applications and analytics expressions. Optimizing the layout of the applications and analytics based on resource availability. Monitoring the health of the software layer. Storing of raw sensor data or results of expressions in a local time-series database or cloud storage. Services and components can be containerized to ensure smooth running in any gateway environment.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Methods and systems for providing access to a computing environment provided by a virtual machine executing in a hypervisor executing in a terminal services session
ActiveUS20070180448A1Low costReduce difficultyDigital data information retrievalInterprogram communicationSession managementClient-side
A method for providing access to a computing environment includes the step of receiving, by a broker machine, a request from a client machine for access to a computing environment, the request including an identification of a user of the client machine. One of a plurality of virtual machines is identified by a session management component, the identified virtual machine providing the requested computing environment. One of a plurality of execution machines is identified, the identified execution machine providing a terminal services session in which a hypervisor executes to provide access to hardware resources required by the identified virtual machine. The hypervisor launches the identified virtual machine. A connection is established between the client machine and the identified virtual machine, via the terminal services session.
Owner:CITRIX SYST INC
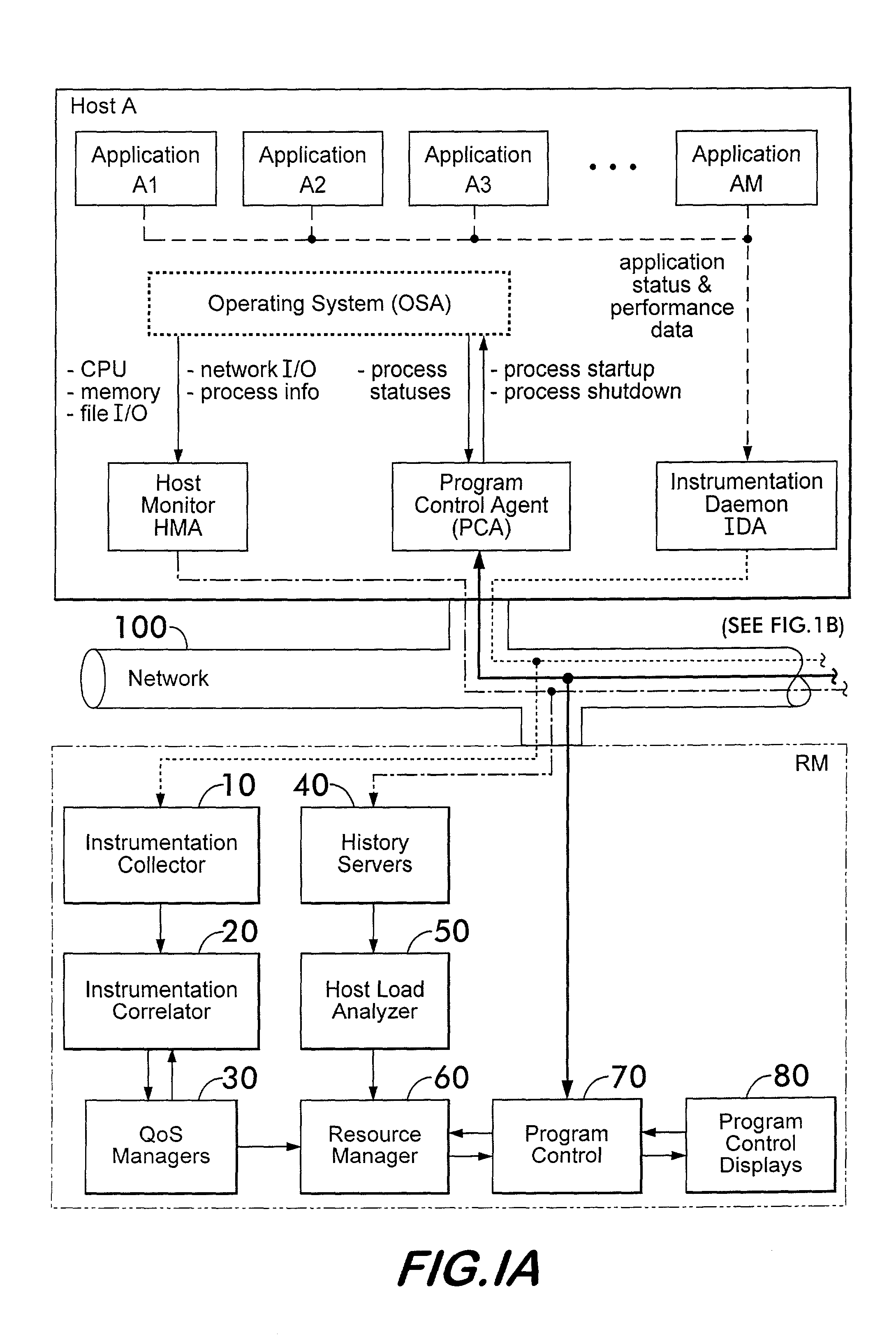
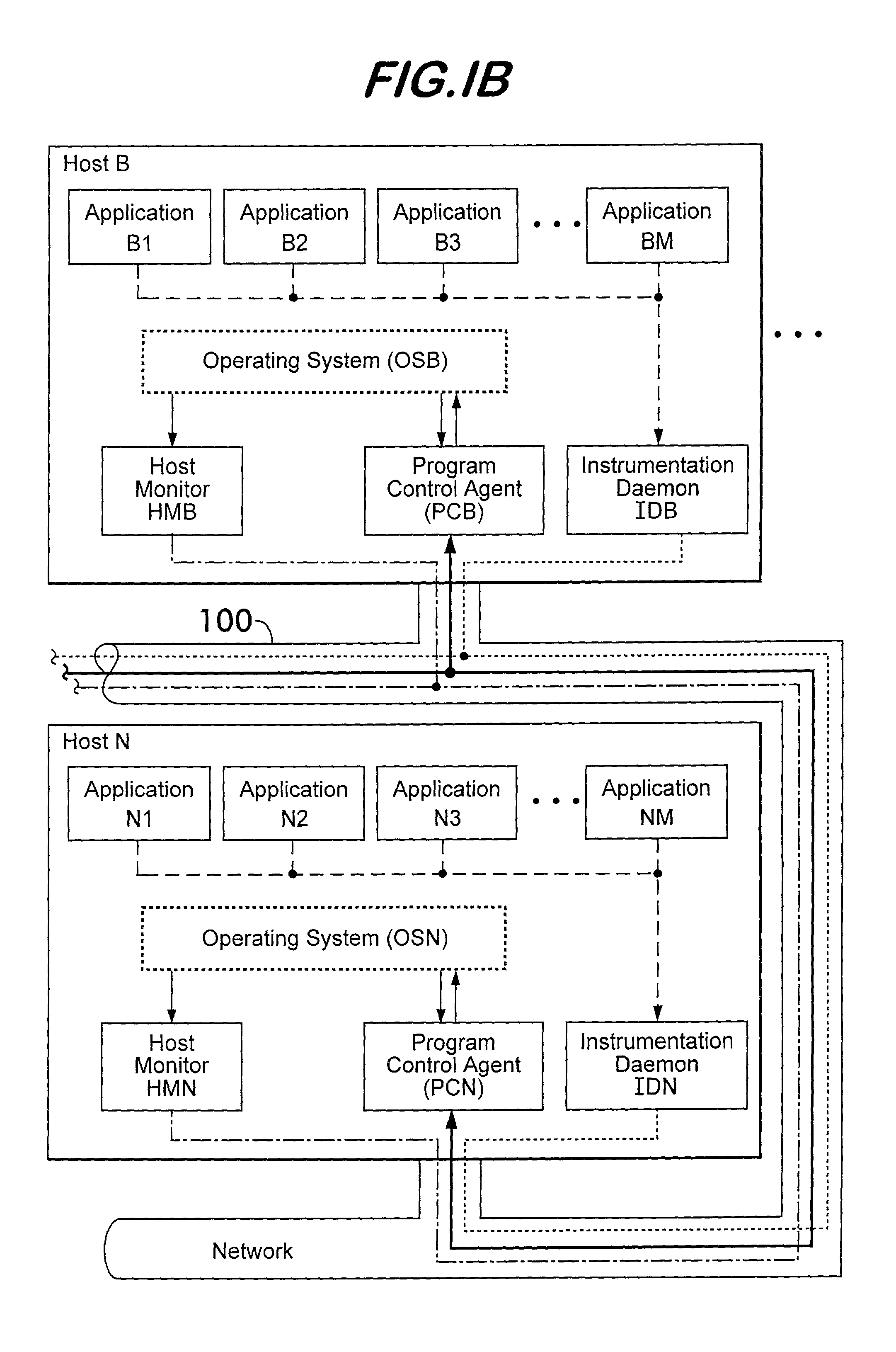
System for monitoring and reporting performance of hosts and applications and selectively configuring applications in a resource managed system
ActiveUS7051098B2Program initiation/switchingResource allocationResource Management SystemMonitoring system
A monitoring system for a distributed environment including a plurality of hosts capable of executing multiple copies of a scalable application includes a first device for generating first data corresponding to performance of all copies of the scalable application; a second device for generating second data corresponding to performance of all host in the distributed environment; and a third device for generating performance metrics based on the first and second data.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
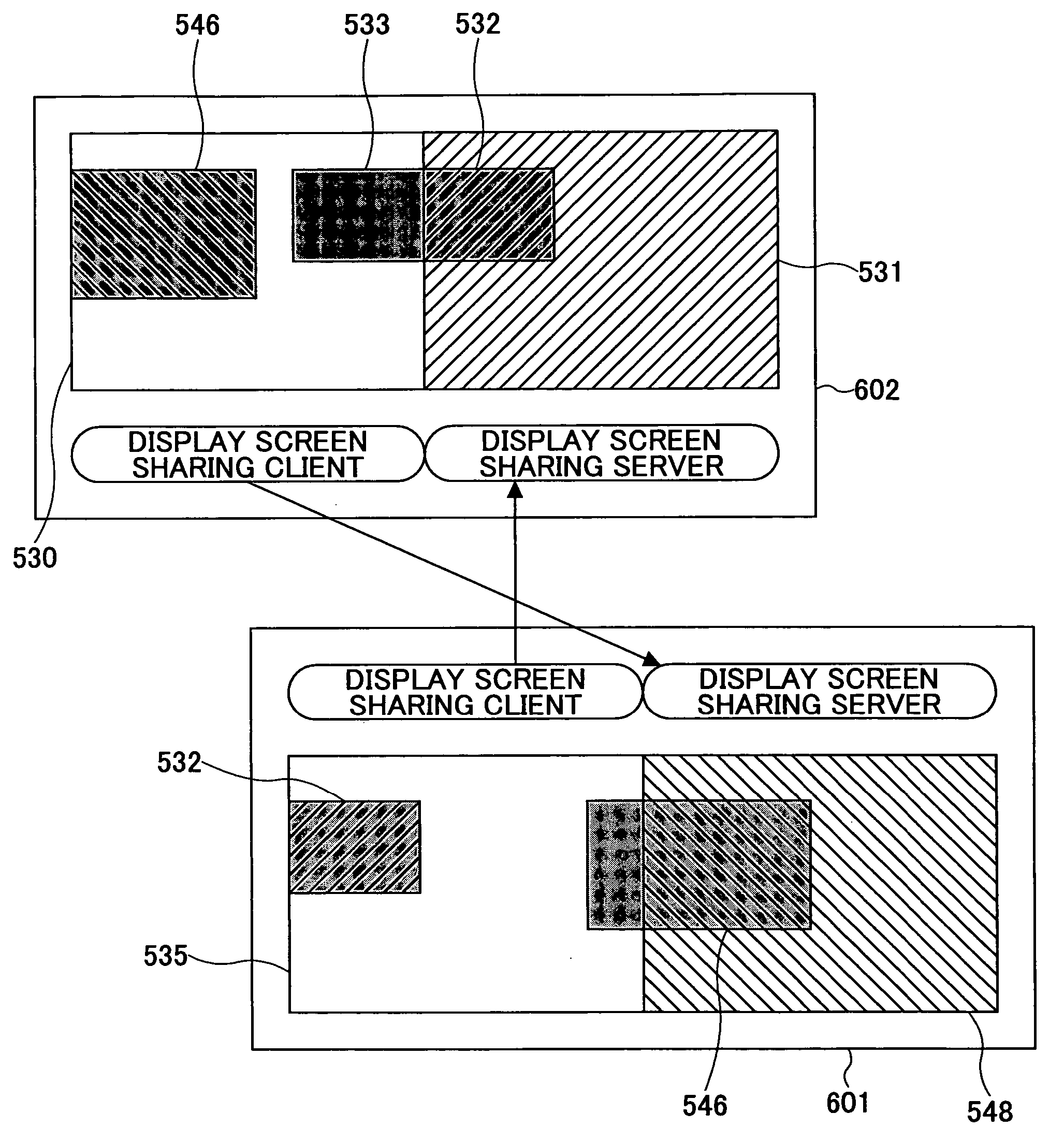
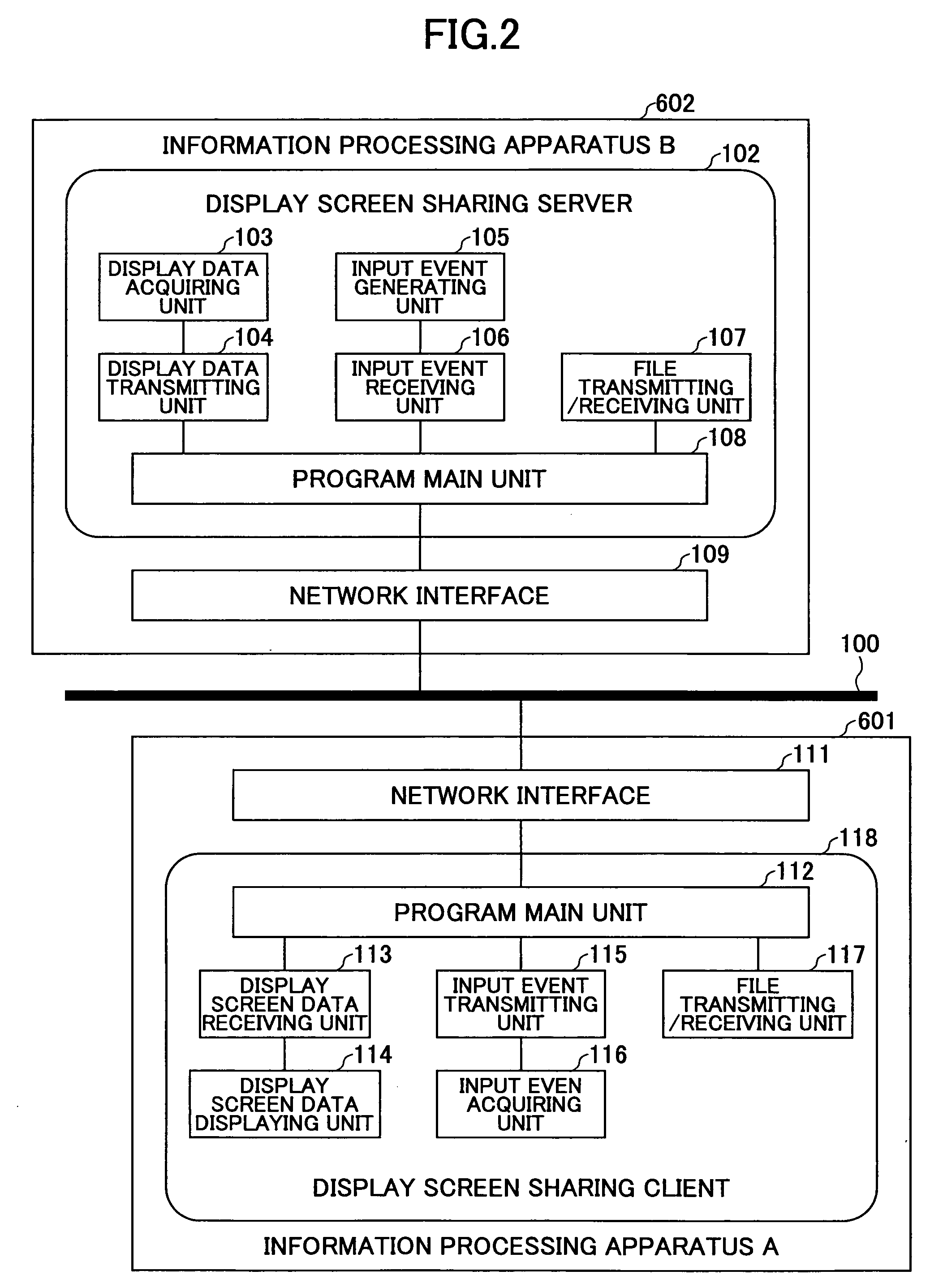
System and method for sharing display screen between information processing apparatuses
InactiveUS20060136828A1Interprogram communicationMemory systemsComputer hardwareInformation processing
A system includes a server information processing apparatus having a server function to provide a shared display screen to another information processing apparatus, and a client information processing apparatus having a client function to become a client of the server function, wherein the server function includes a virtual display screen generating unit configured to generate a virtual display screen for accommodating the shared display screen, and a shared display screen acquiring unit configured to acquires image data of at least a portion of the shared display screen displayed on the virtual display screen, and wherein the client function includes a shared display screen receiving unit configured to receive the image data from the server function, and a shared display screen displaying unit configured to display at least a portion of the shared display screen on a shared display screen presenting area in response to the received image data.
Owner:RICOH KK
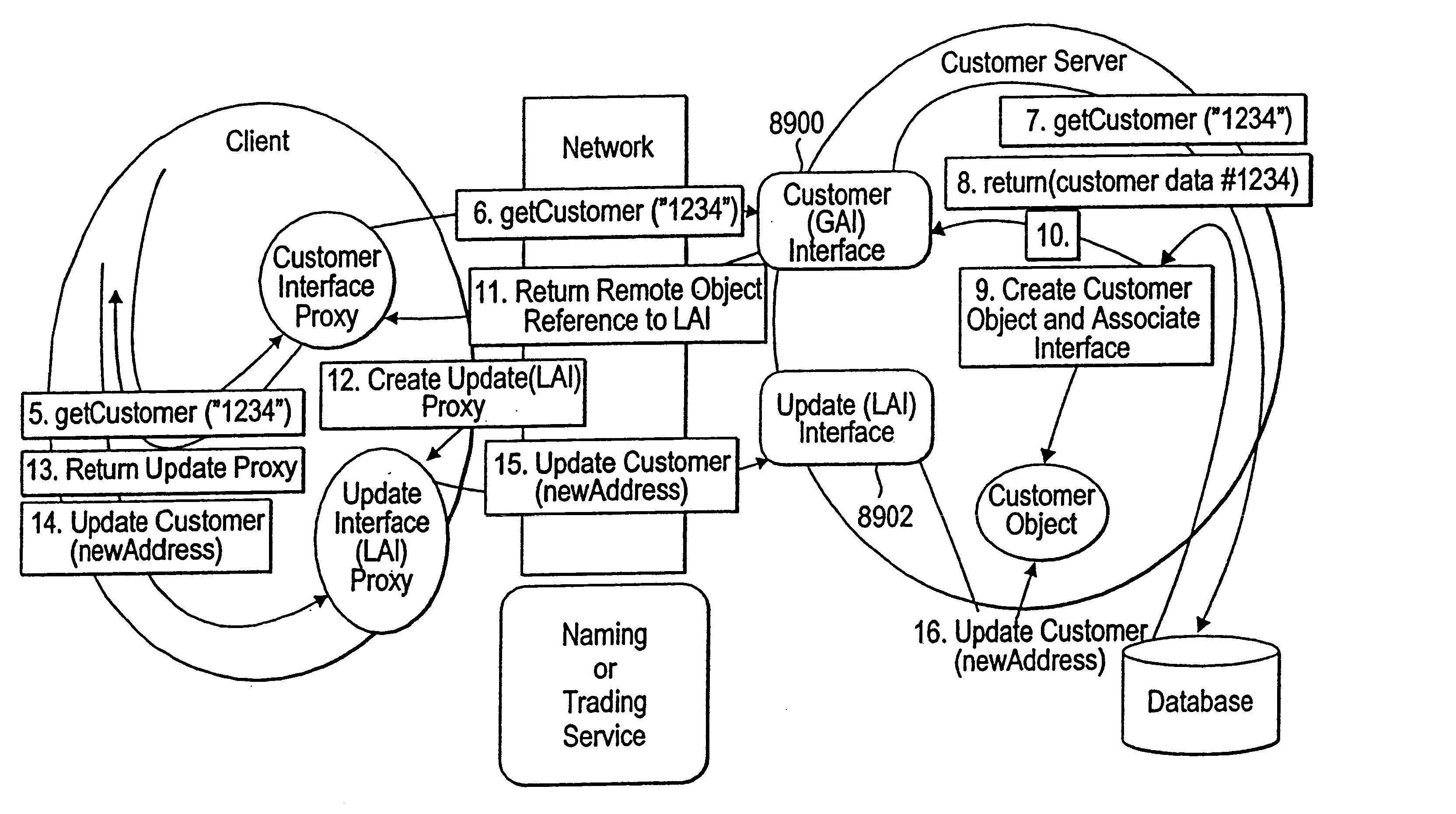
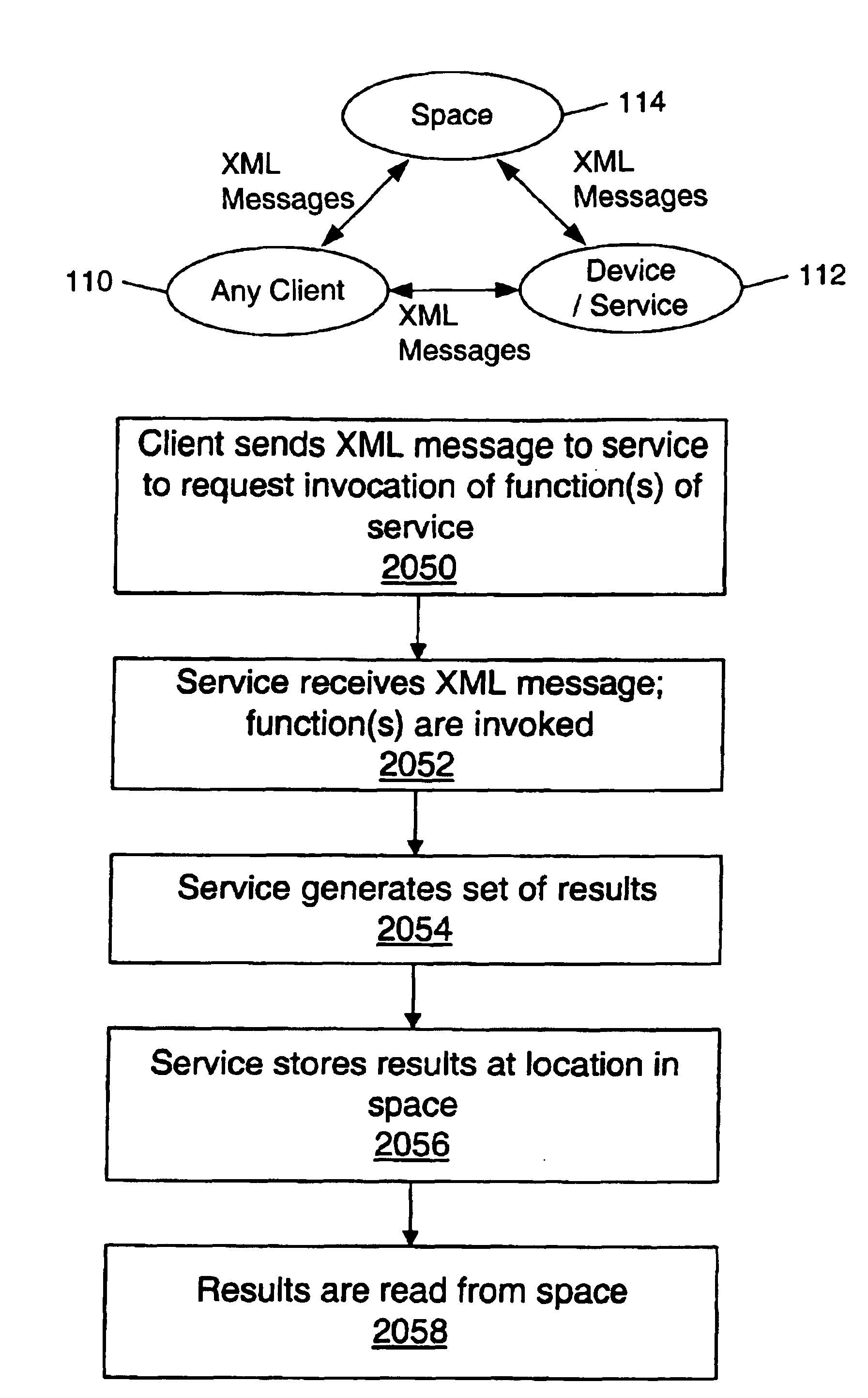
Mechanism and apparatus for returning results of services in a distributed computing environment
InactiveUS6868447B1Easy to storeSimple methodInterprogram communicationDigital computer detailsRepresentation languageDistributed Computing Environment
Systems and methods for returning results of services within a distributed computing environment are provided. After a client invokes one or more functions of a service, results of the function(s) may be returned to the client in a plurality of ways: for example, in a message, in a space (e.g., a network-addressable storage location), in a space wherein the client is notified via an event, using an advertisement returned in a message, using an advertisement returned in a space, and using an advertisement returned in a space wherein the client is notified via an event. The advertisement may include the information necessary to access and read the results in a storage location such as a space. A schema for the service may specify a plurality of messages which are usable to invoke the function(s) of the service. The messages, results, and advertisements may be expressed in a platform-independent and / or programming-language-independent data representation language such as XML. The availability of these plurality of methods may enhance the flexibility and adaptability of the distributed computing environment for a variety of situations, such as for clients having differing capabilities. For additional flexibility, results may also be efficiently passed to another service.
Owner:ORACLE INT CORP
Method and apparatus for providing plug in media decoders
InactiveUS6216152B1Data processing applicationsInterprogram communicationObject basedApplication software
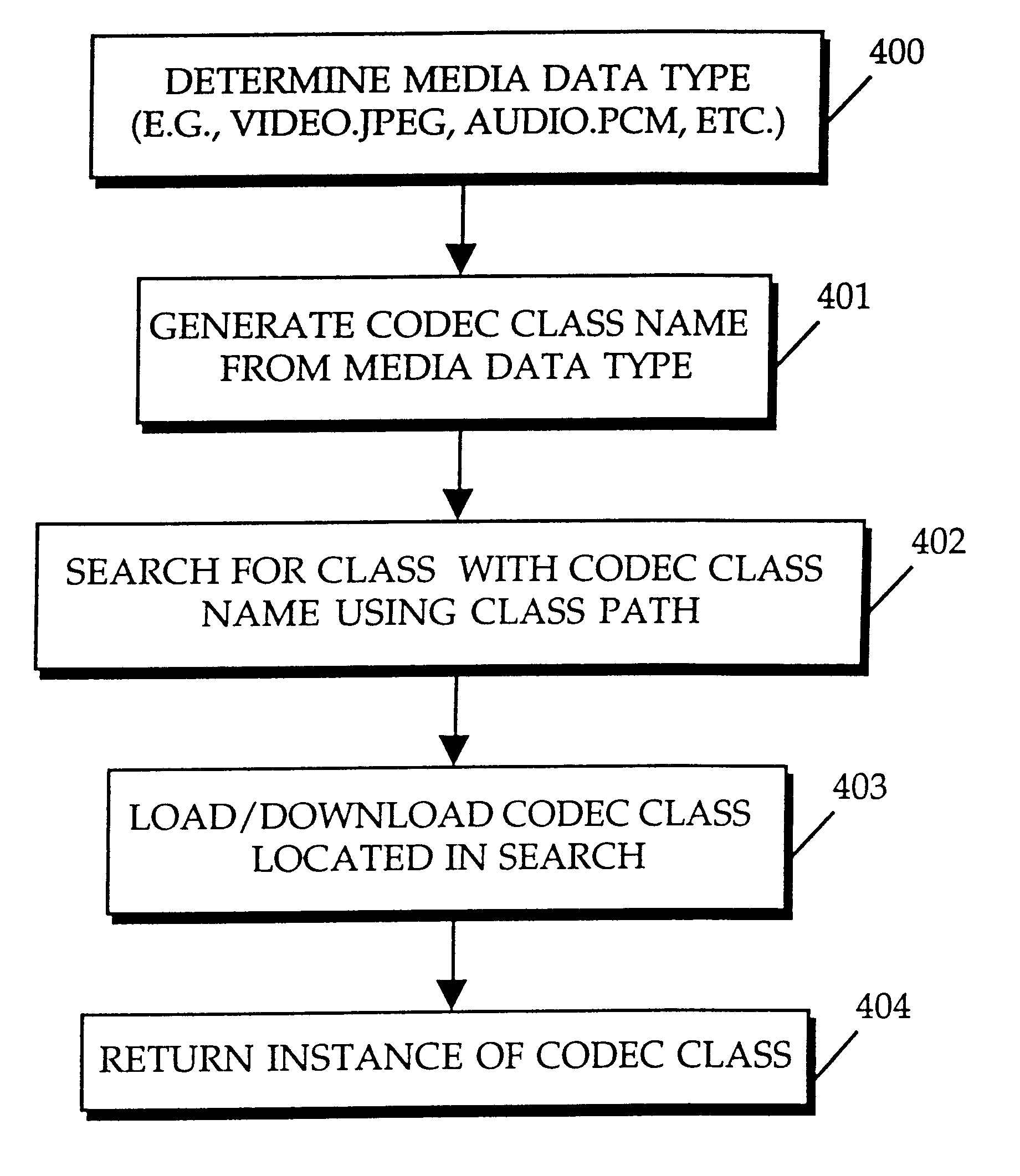
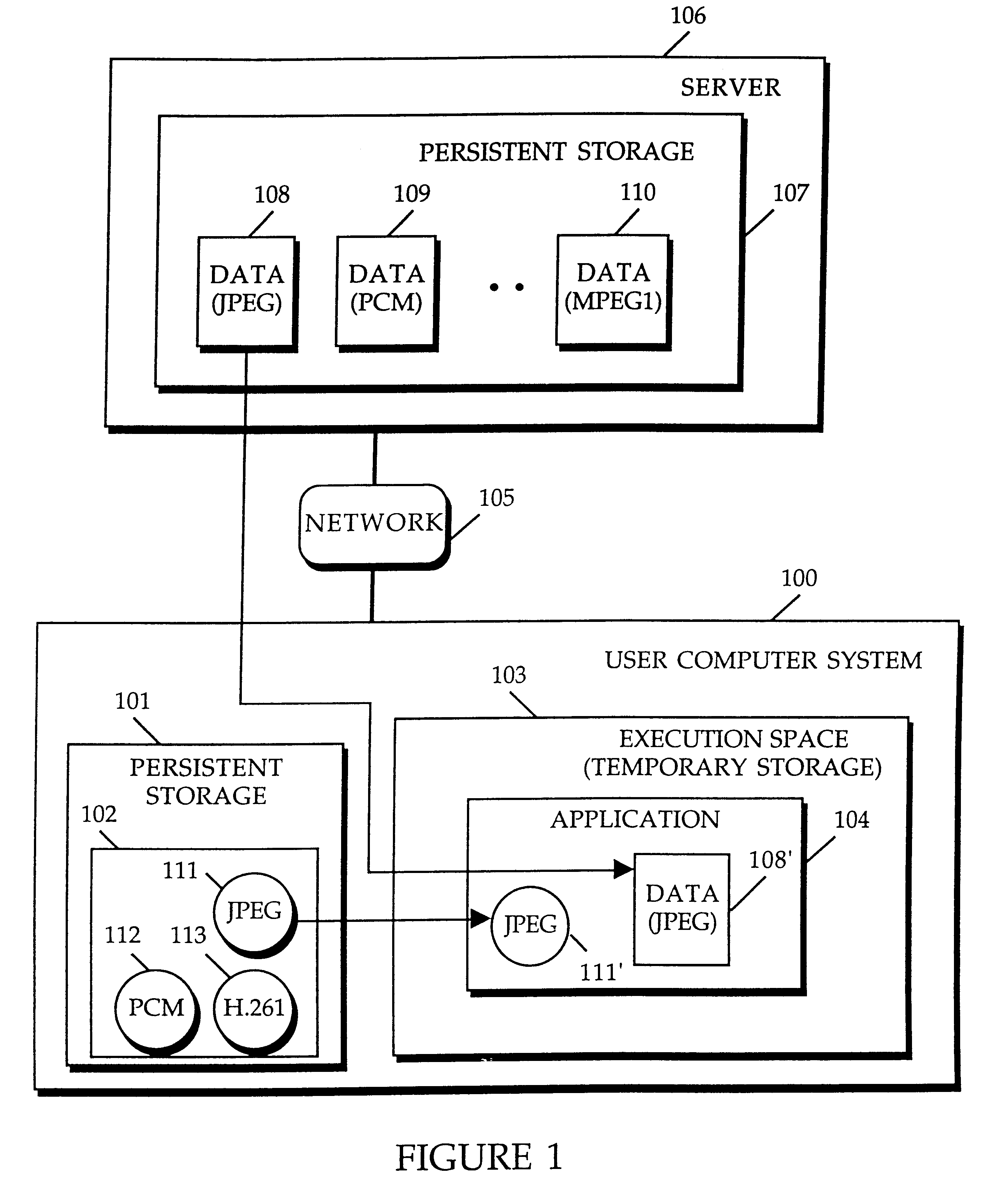
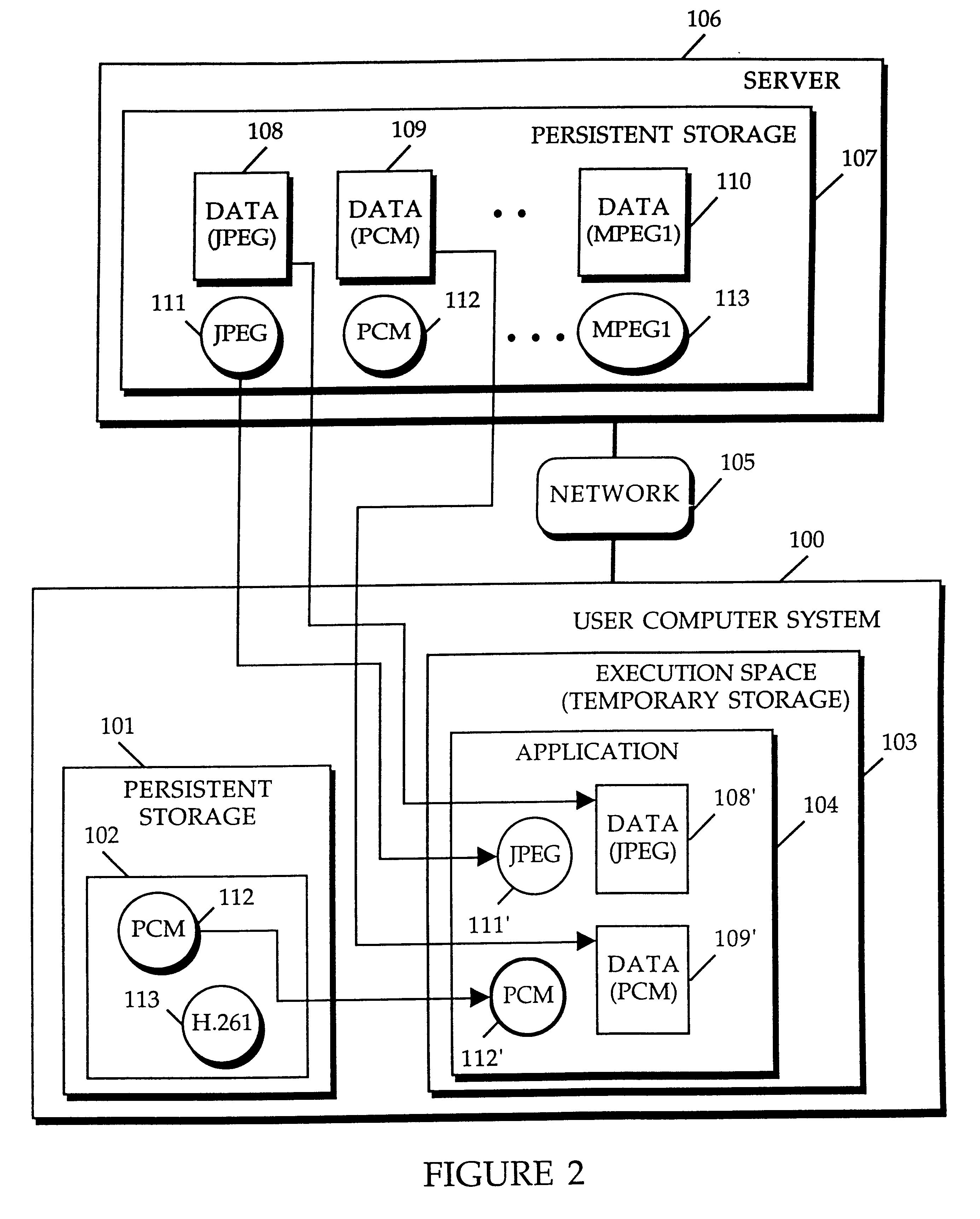
A method and apparatus for providing plug-in media decoders. Embodiments provide a "plug-in" decoder architecture that allows software decoders to be transparently downloaded, along with media data. User applications are able to support new media types as long as the corresponding plug-in decoder is available with the media data. Persistent storage requirements are decreased because the downloaded decoder is transient, existing in application memory for the duration of execution of the user application. The architecture also supports use of plug-in decoders already installed in the user computer. One embodiment is implemented with object-based class files executed in a virtual machine to form a media application. A media data type is determined from incoming media data, and used to generate a class name for a corresponding codec (coder-decoder) object. A class path vector is searched, including the source location of the incoming media data, to determine the location of the codec class file for the given class name. When the desired codec class file is located, the virtual machine's class loader loads the class file for integration into the media application. If the codec class file is located across the network at the source location of the media data, the class loader downloads the codec class file from the network. Once the class file is loaded into the virtual machine, an instance of the codec class is created within the media application to decode / decompress the media data as appropriate for the media data type.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com