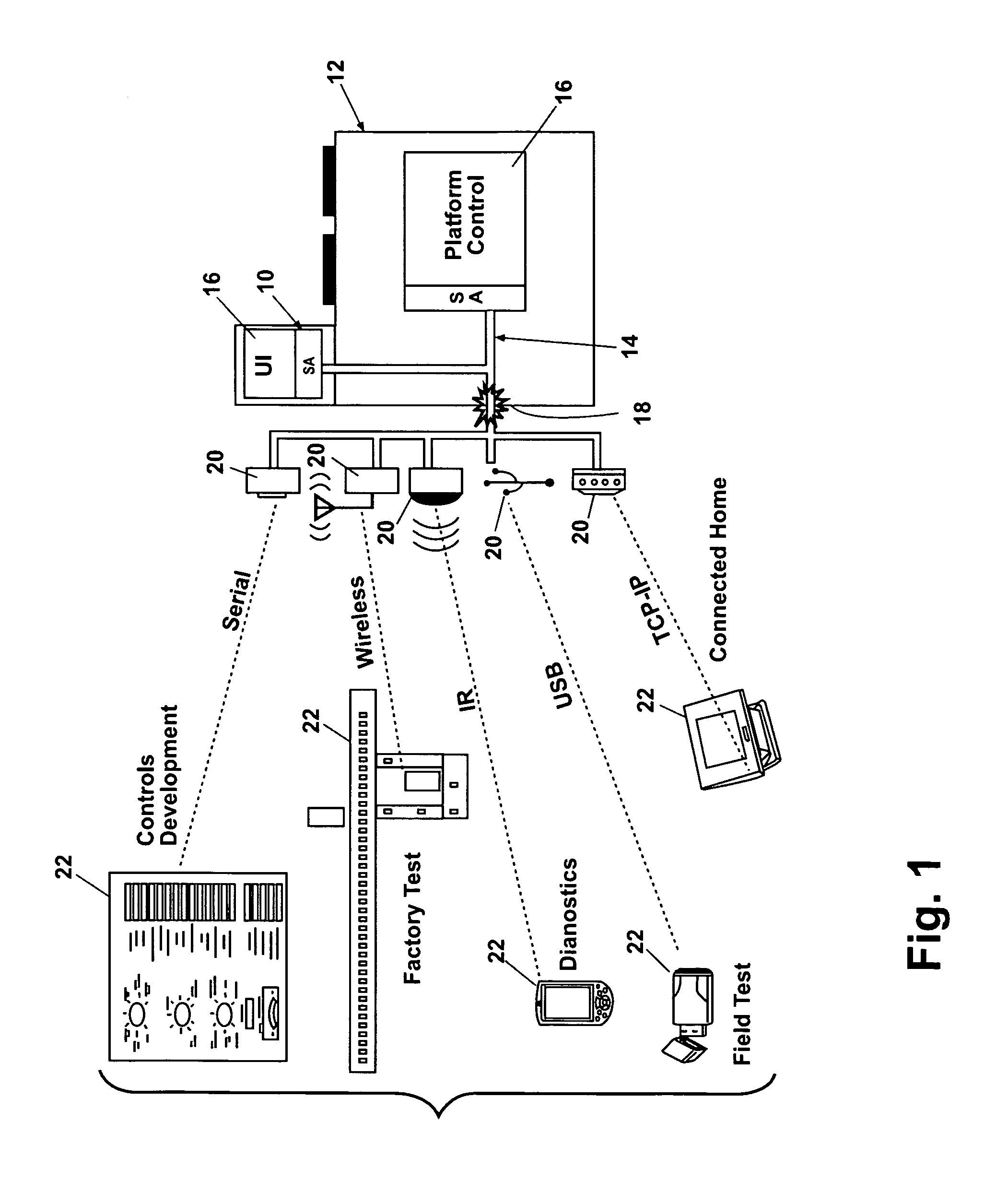
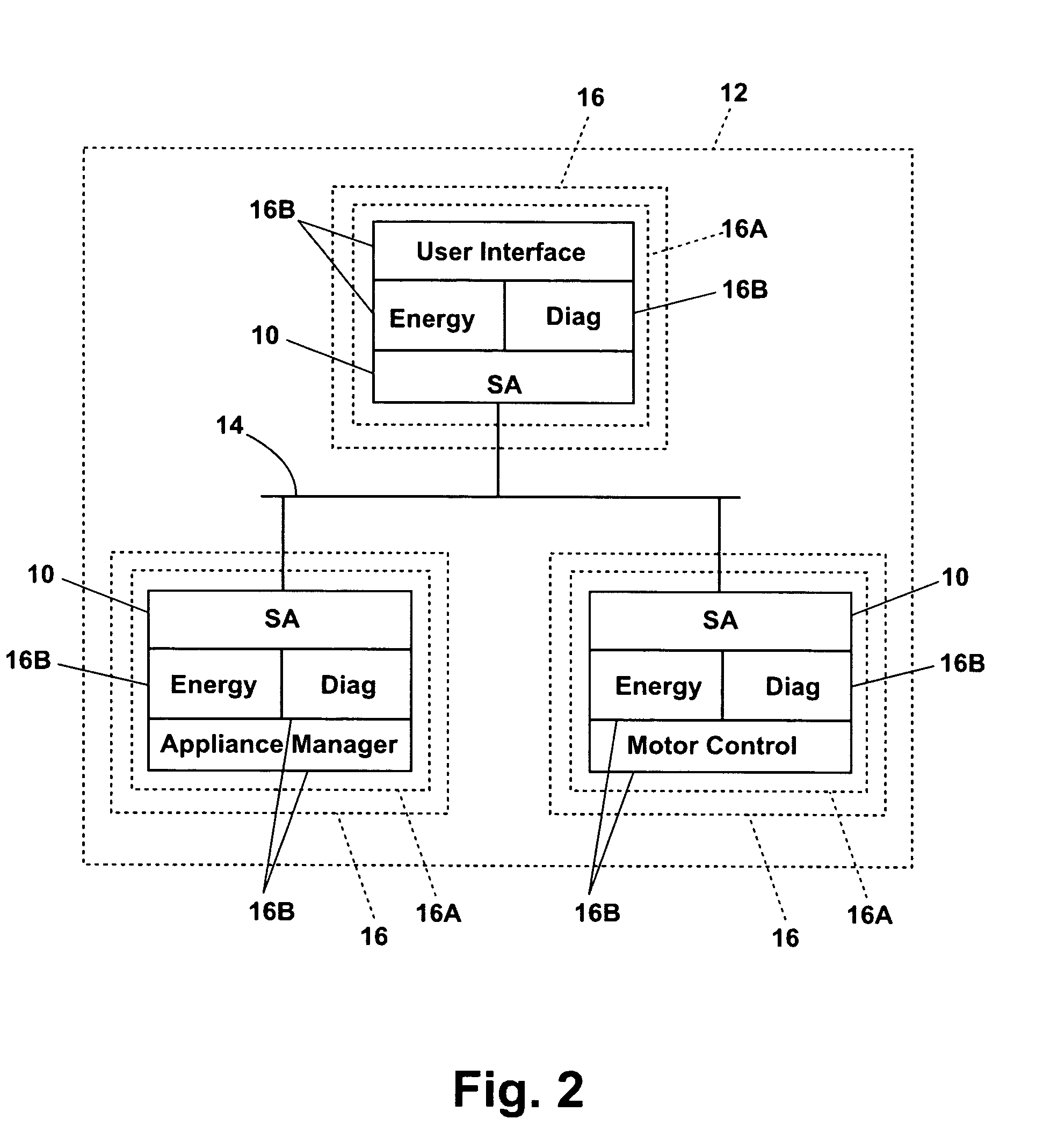
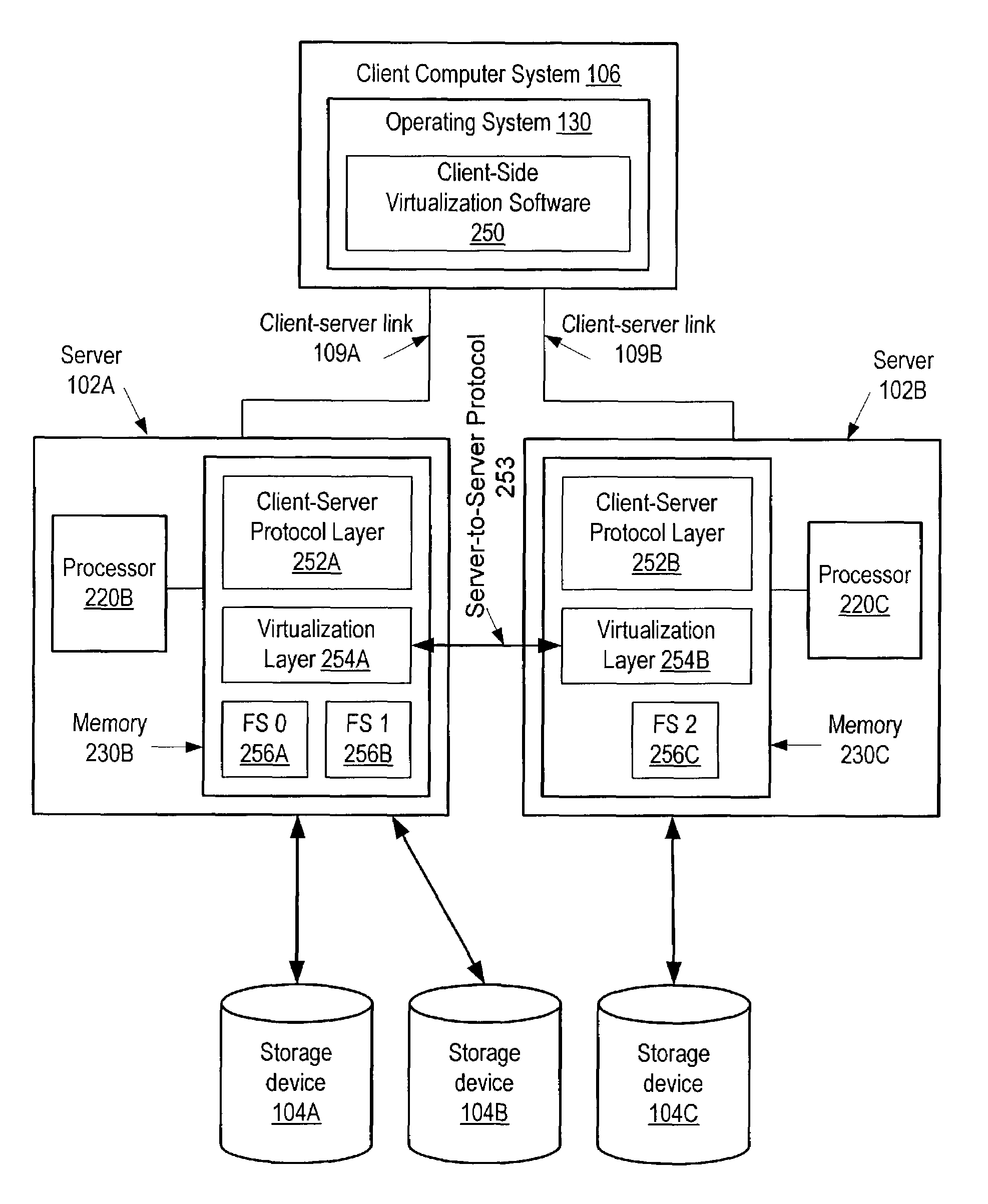
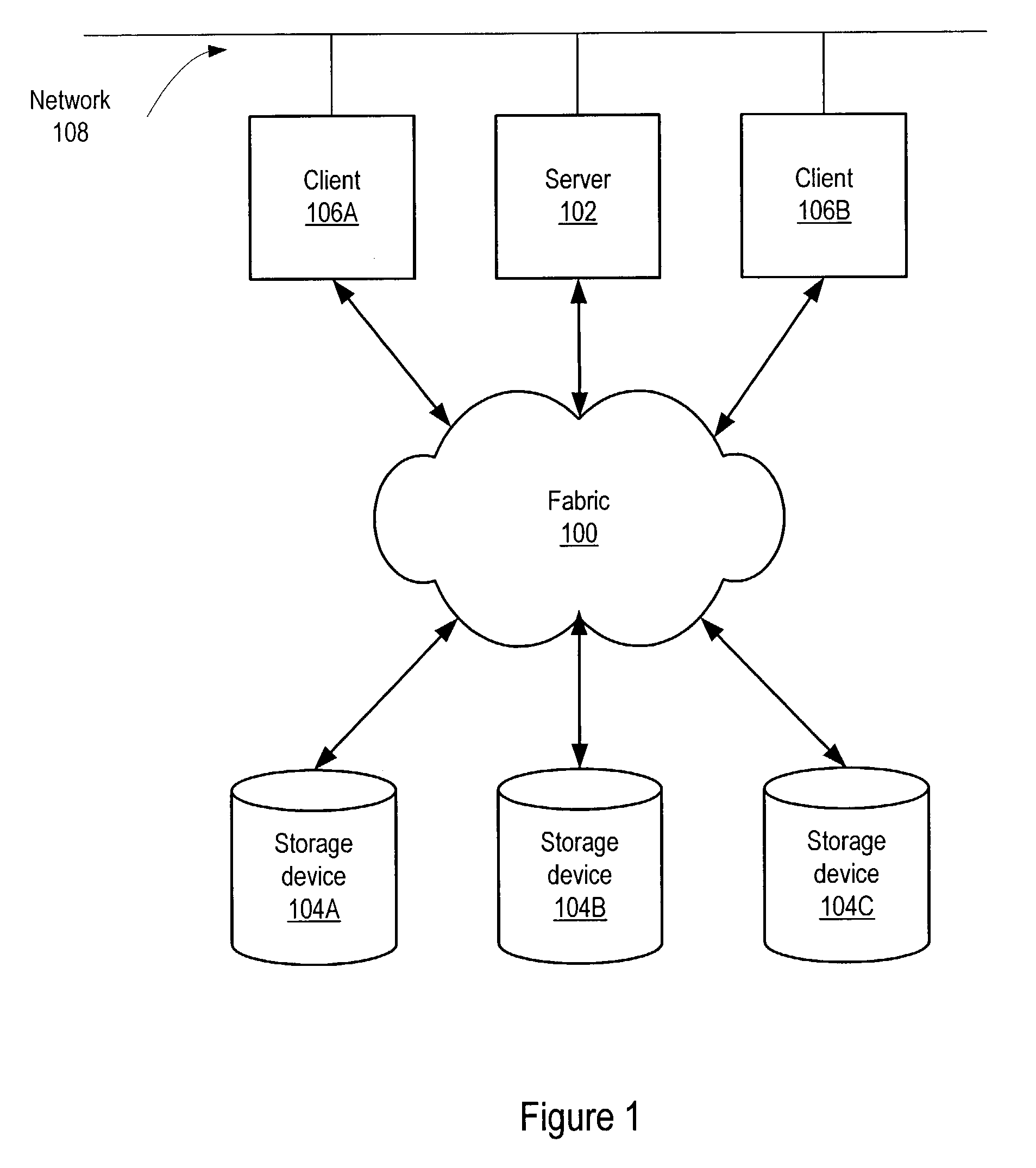
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1017 results about "Namespace" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a namespace is a set of symbols that are used to organize objects of various kinds, so that these objects may be referred to by name. A namespace ensures that all the identifiers within it have unique names so that they can be easily identified.
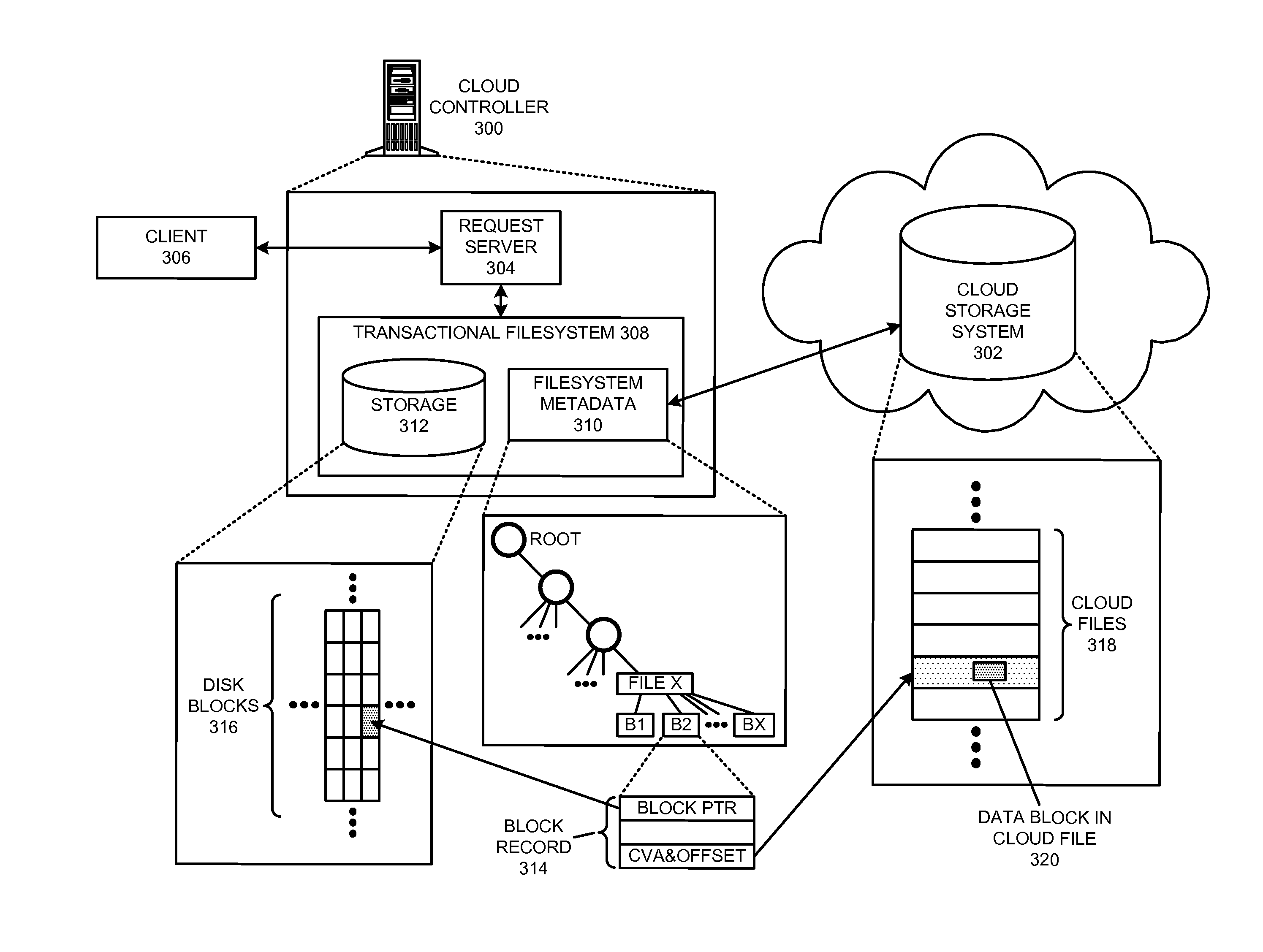
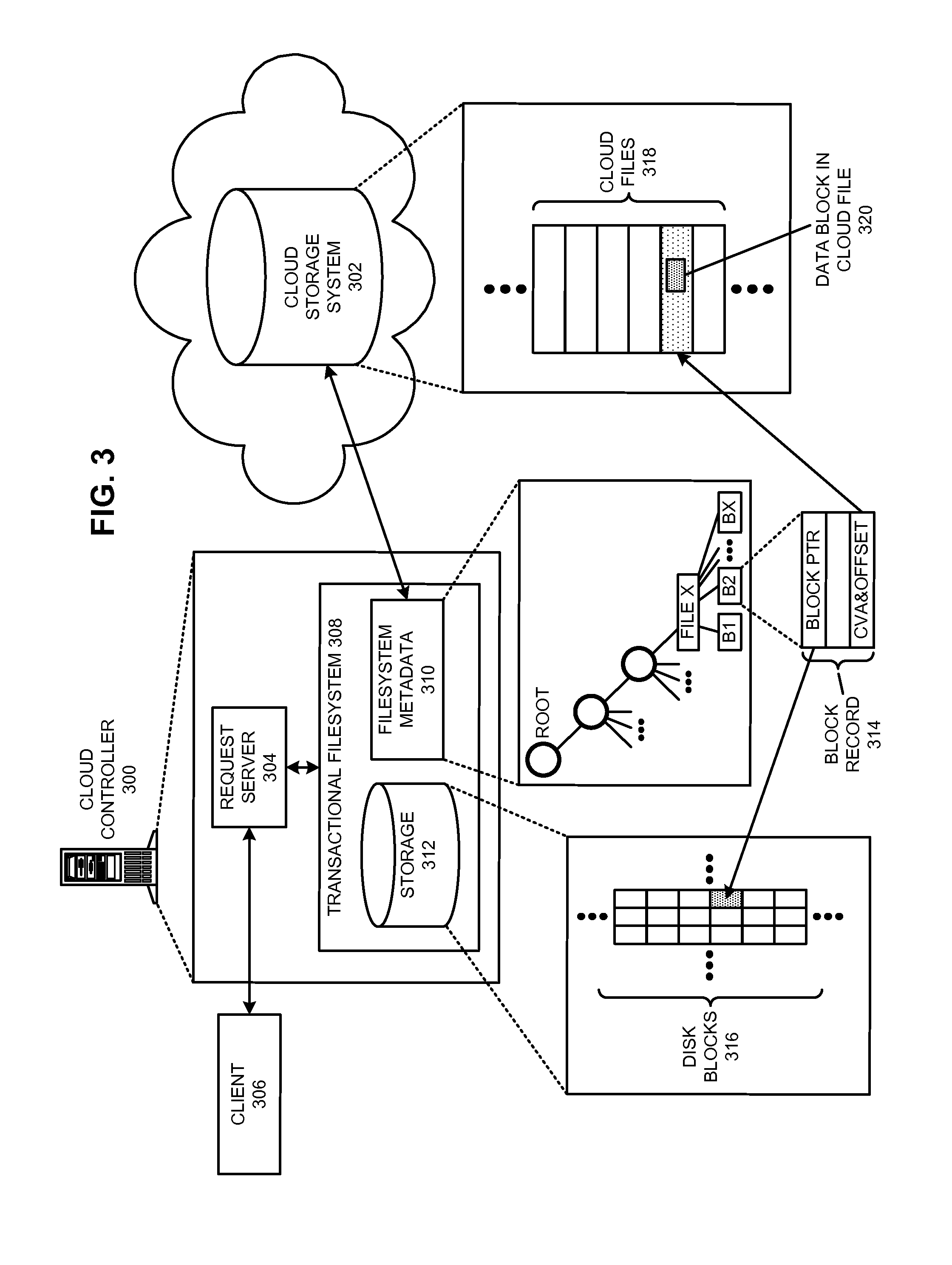
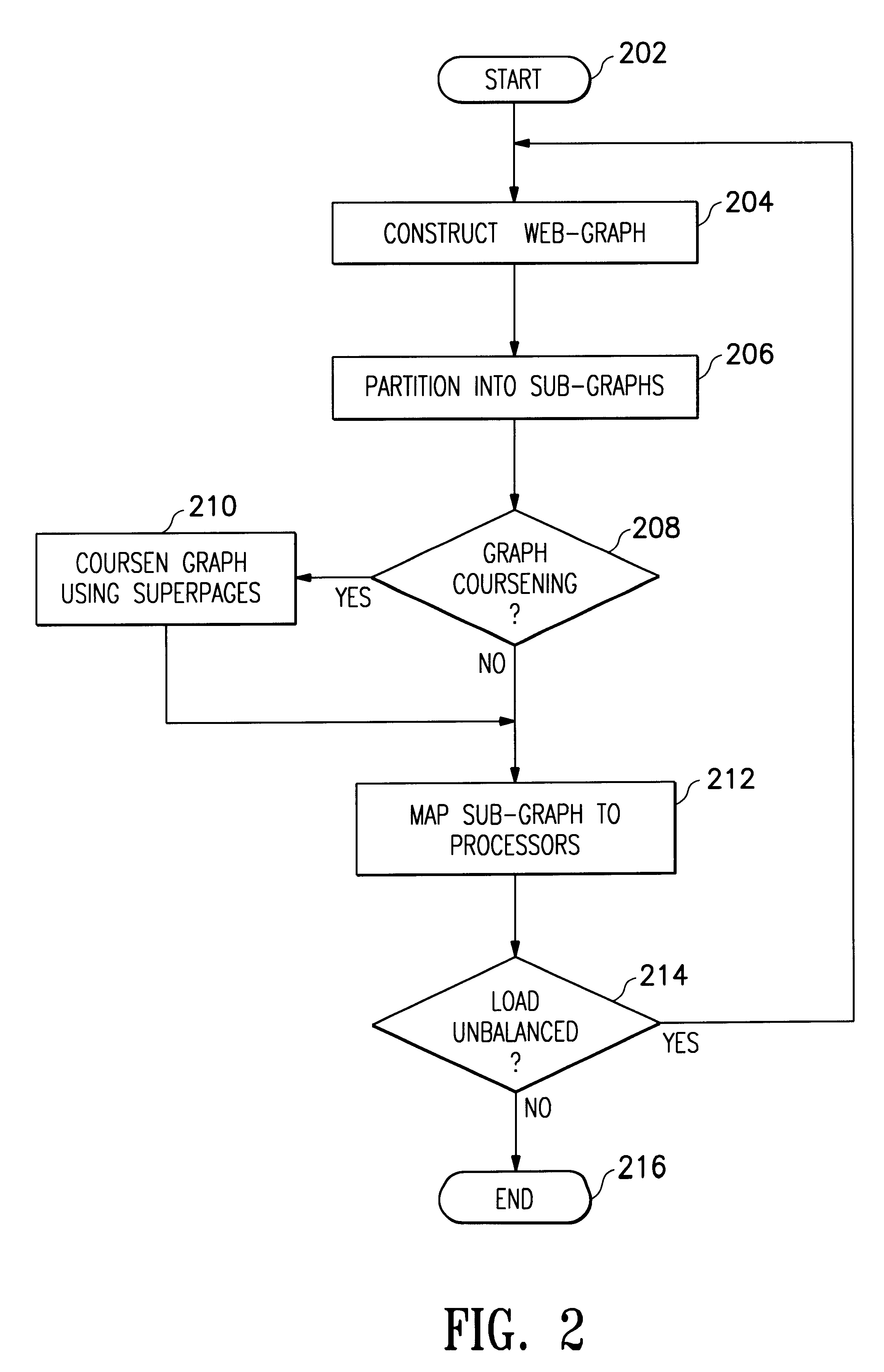
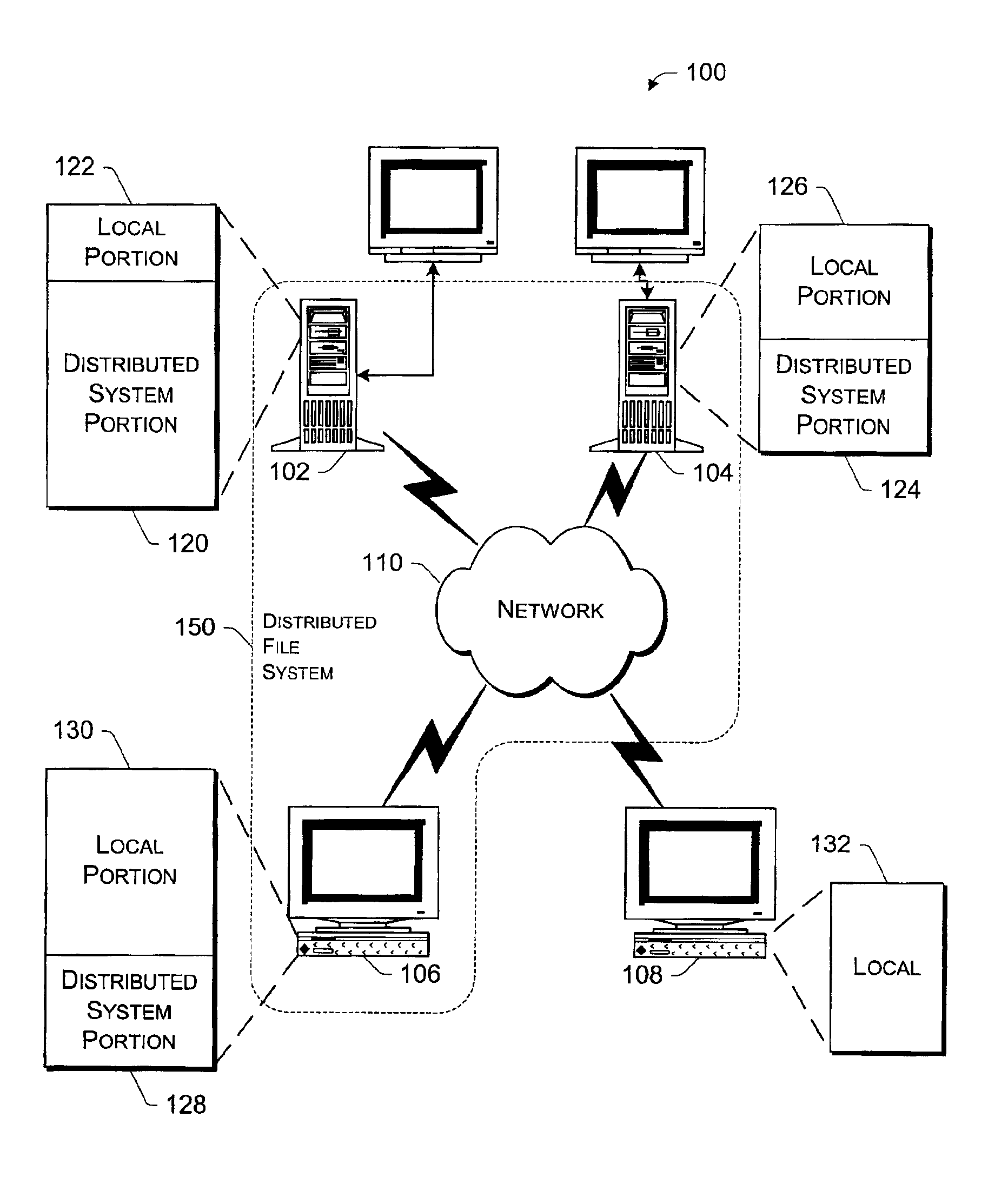
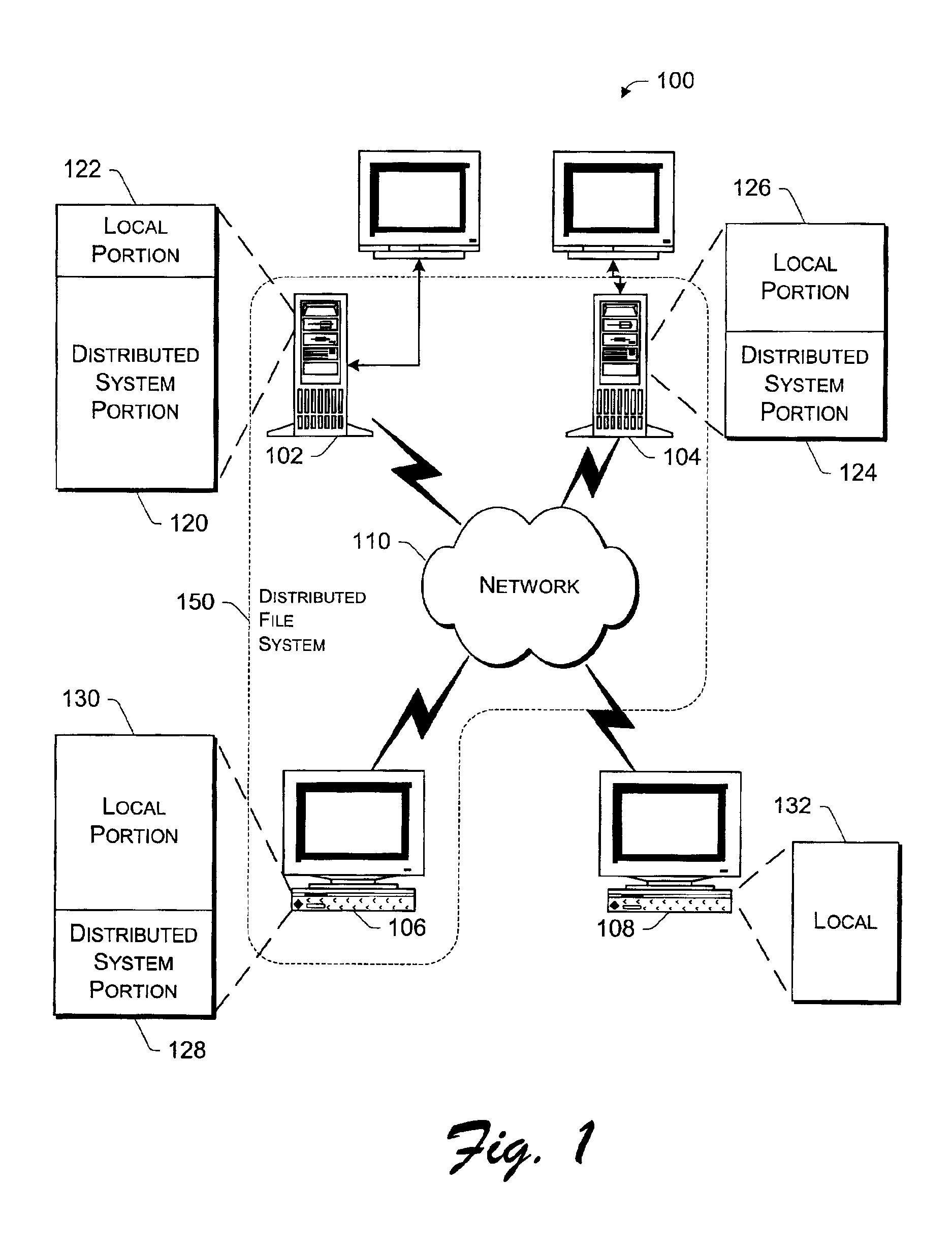
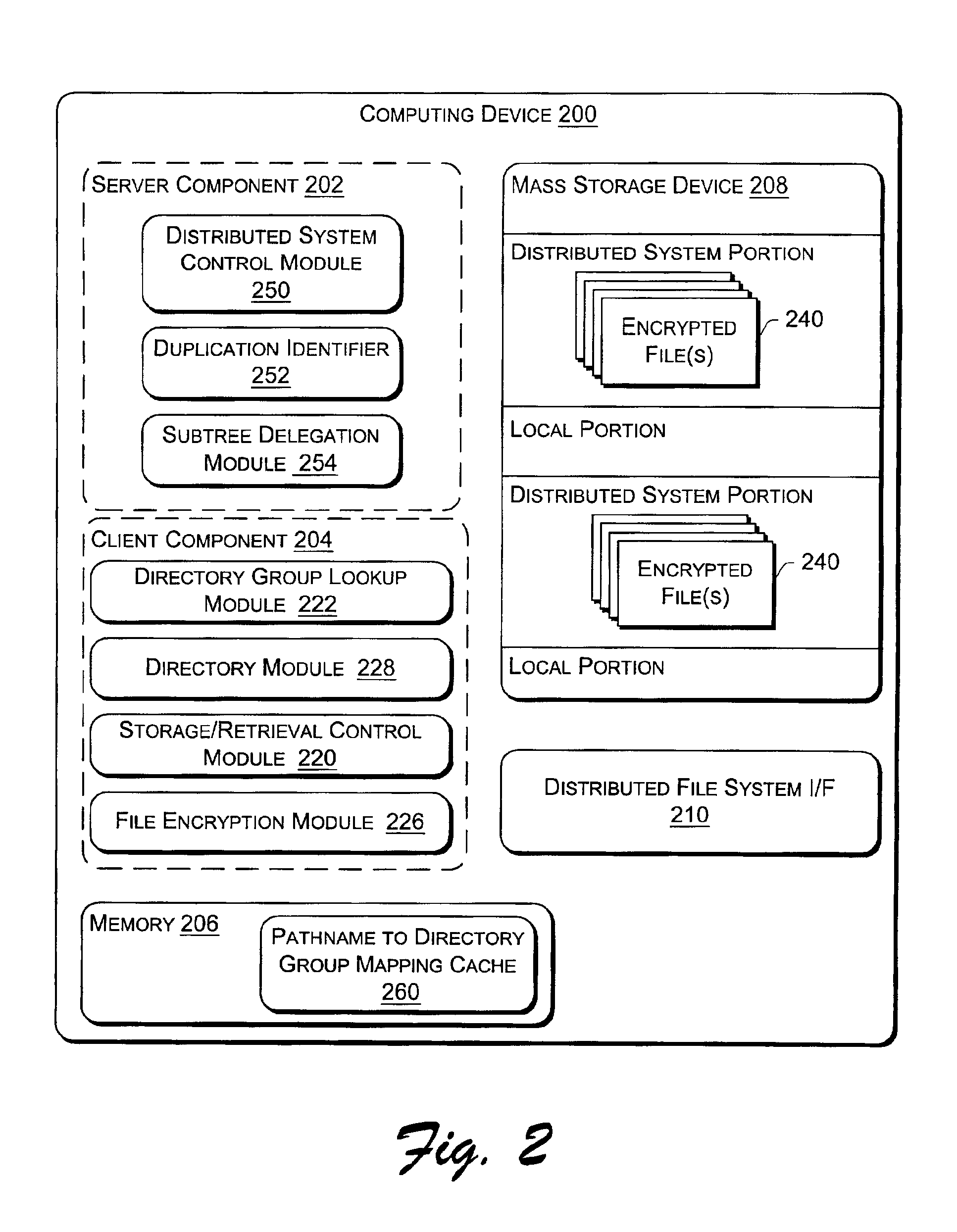
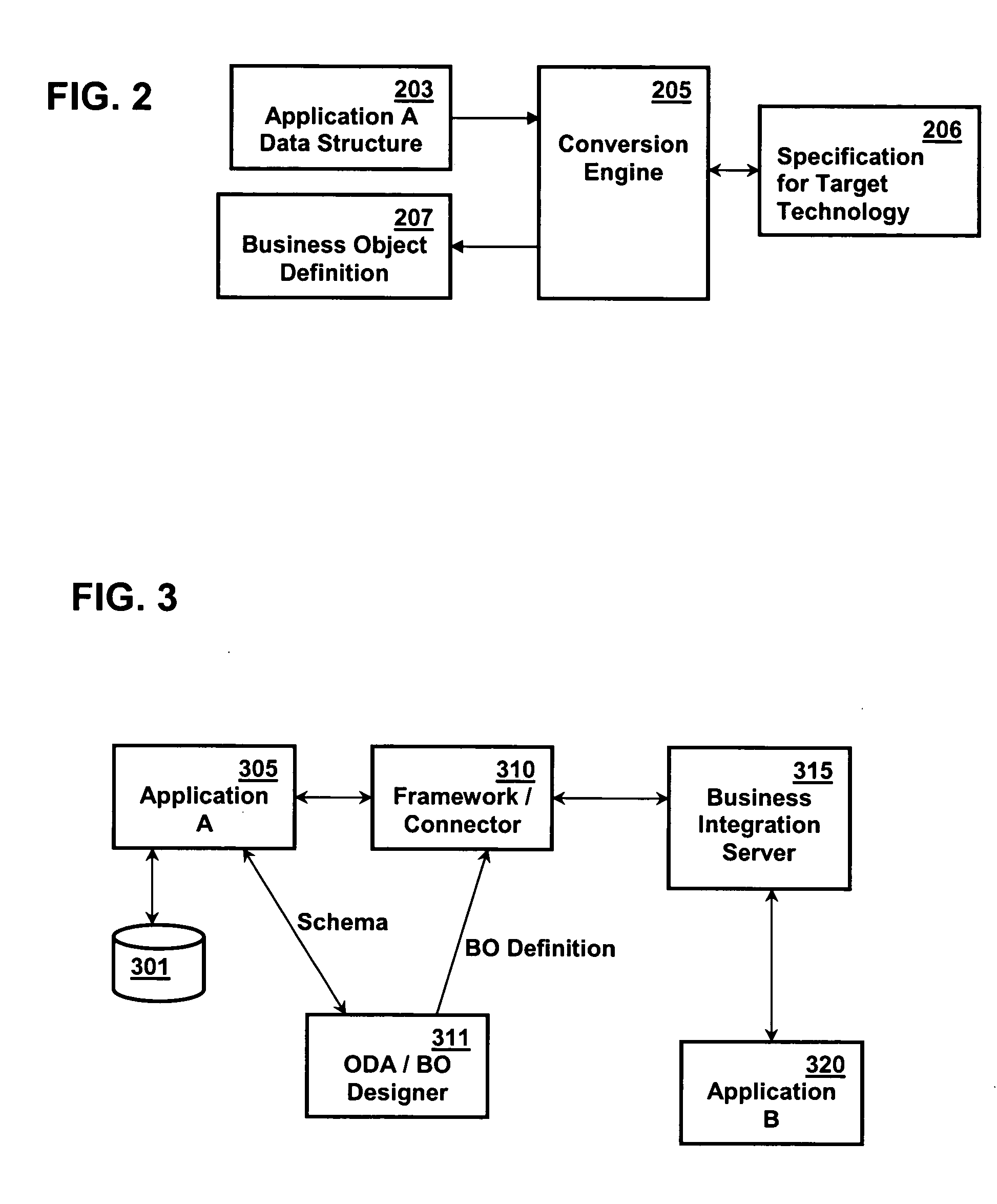
Managing a global namespace for a distributed filesystem
ActiveUS20140006465A1Outweigh additional overheadIncreasing file access performanceDigital data information retrievalSpecial data processing applicationsFile systemCloud storage system
The disclosed embodiments disclose techniques for managing a global namespace for a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in a cloud storage system; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. Furthermore, a global namespace for the distributed filesystem is also split across these cloud controllers, with each cloud controller “owning” (e.g., managing write accesses for) a distinct portion of the global namespace and maintaining a set of namespace mappings that indicate which portion of the namespace is assigned to each cloud controller. During operation, an initial cloud controller receives a request from a client system to access a target file in the distributed system. This initial cloud controller uses the namespace mappings for the global namespace to determine a preferred cloud controller that will handle the request.
Owner:PANZURA LLC
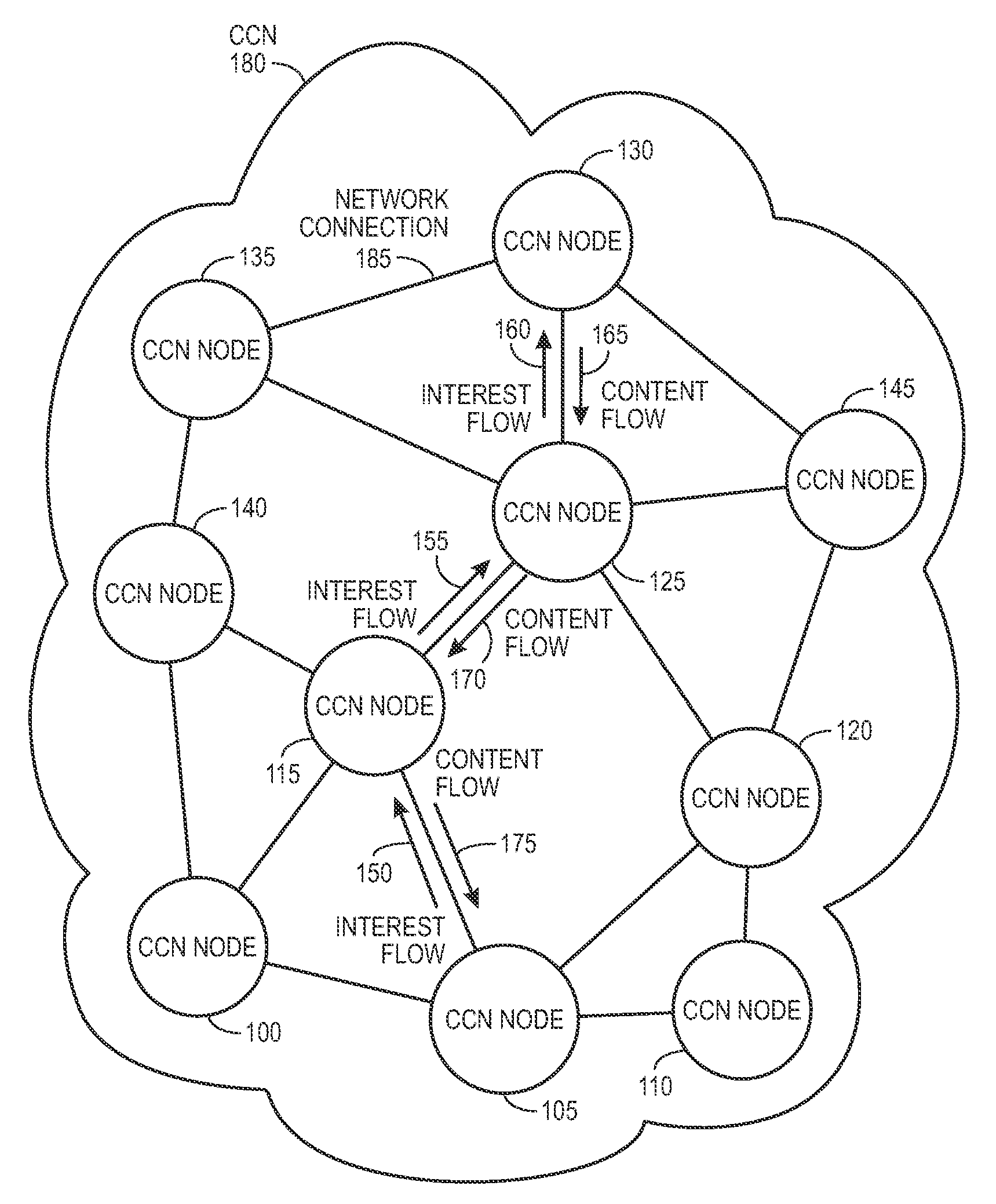
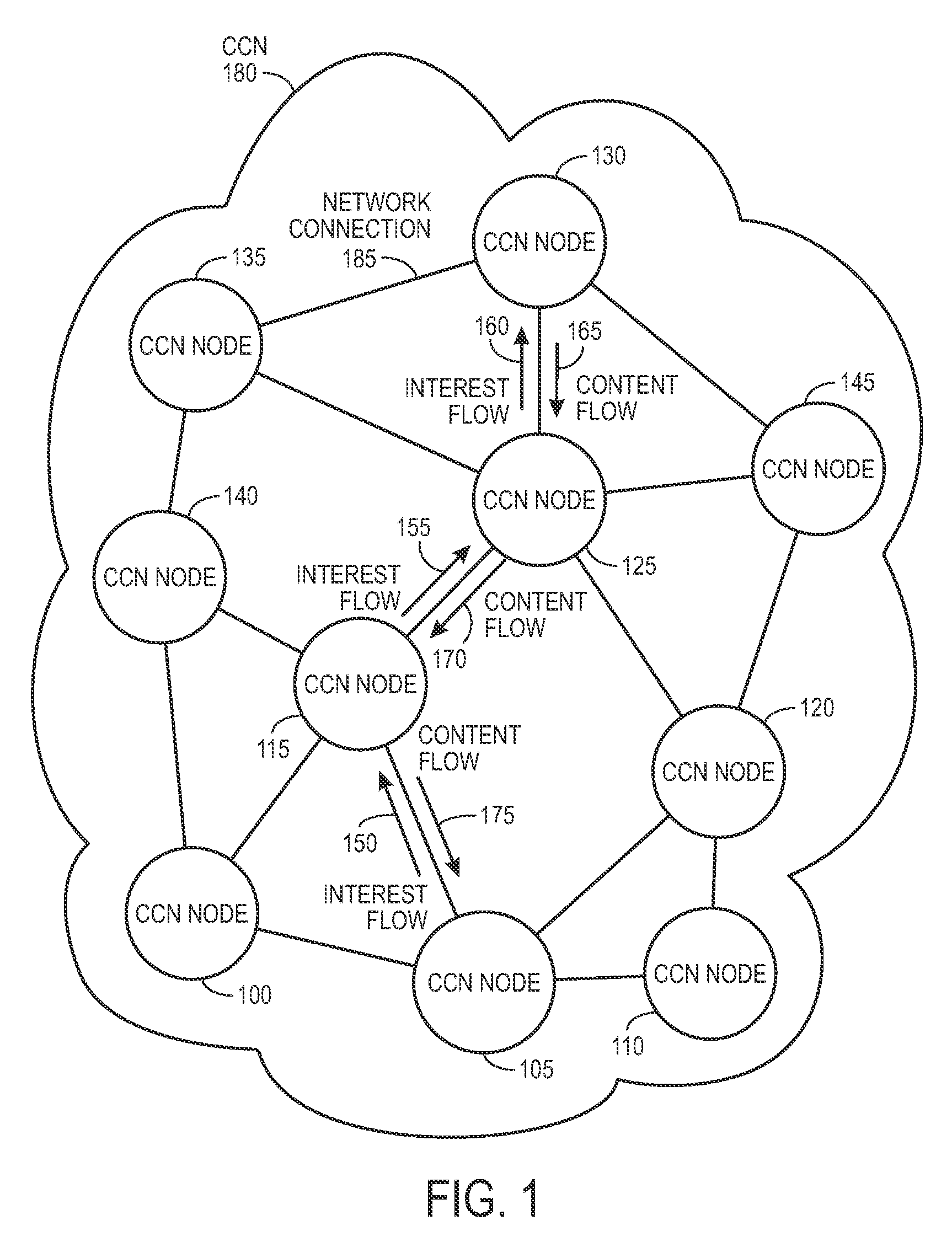
Controlling the spread of interests and content in a content centric network
ActiveUS20090288163A1Easy flow controlExpected levelMemory loss protectionMultiple keys/algorithms usageContent centricSystem maintenance
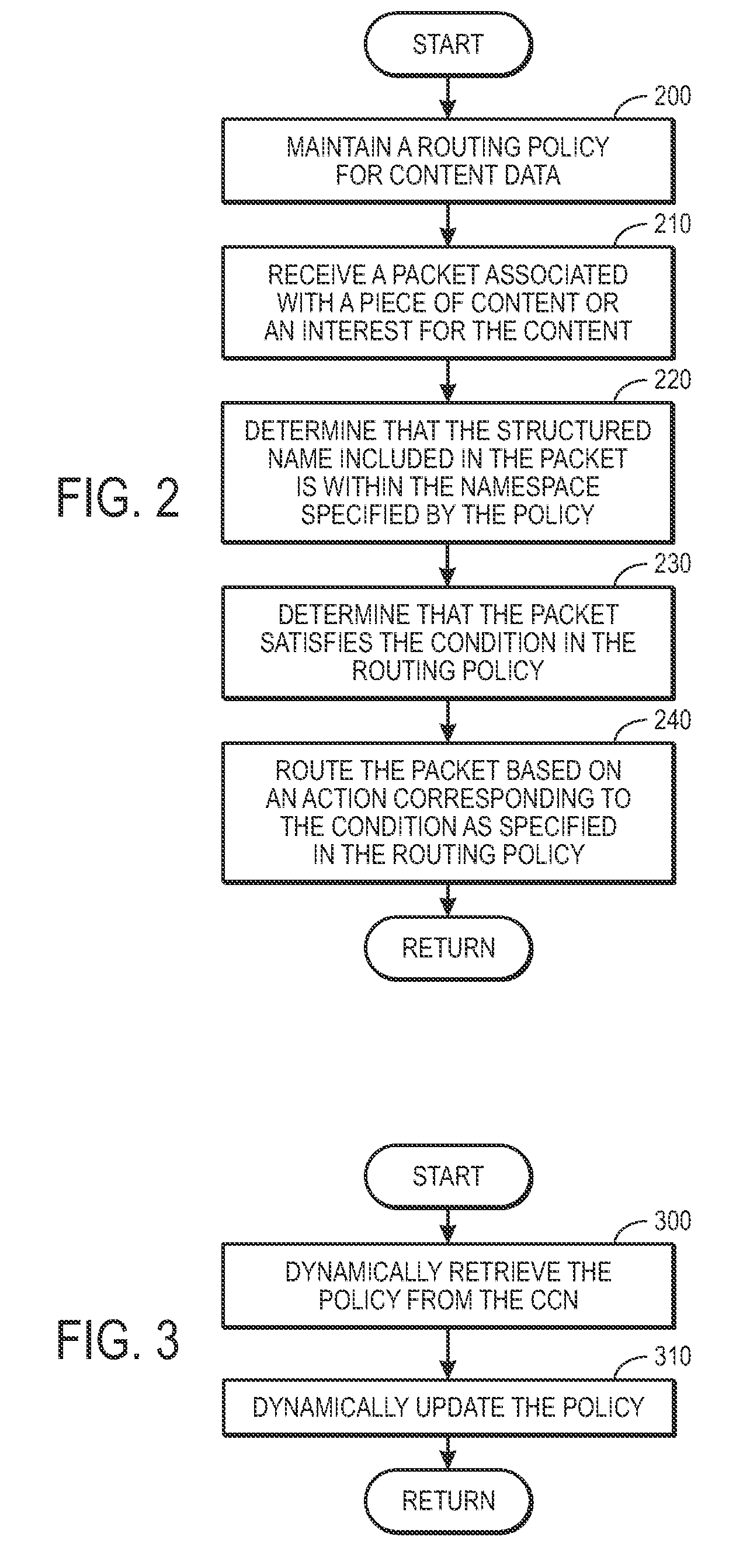
One embodiment of the present invention provides a system for controlling the spread of interests and content in a content centric network (CCN). During operation, the system maintains a routing policy for content data. The system also receives a packet associated with a piece of content or an interest for the content. Next, the system determines that the structured name included in the packet is within the namespace specified in the routing policy. The system further determines that the packet satisfies the condition in the routing policy. Subsequently, the system routes the packet based on in part the action corresponding to the condition as specified in the routing policy.
Owner:CISCO TECH INC
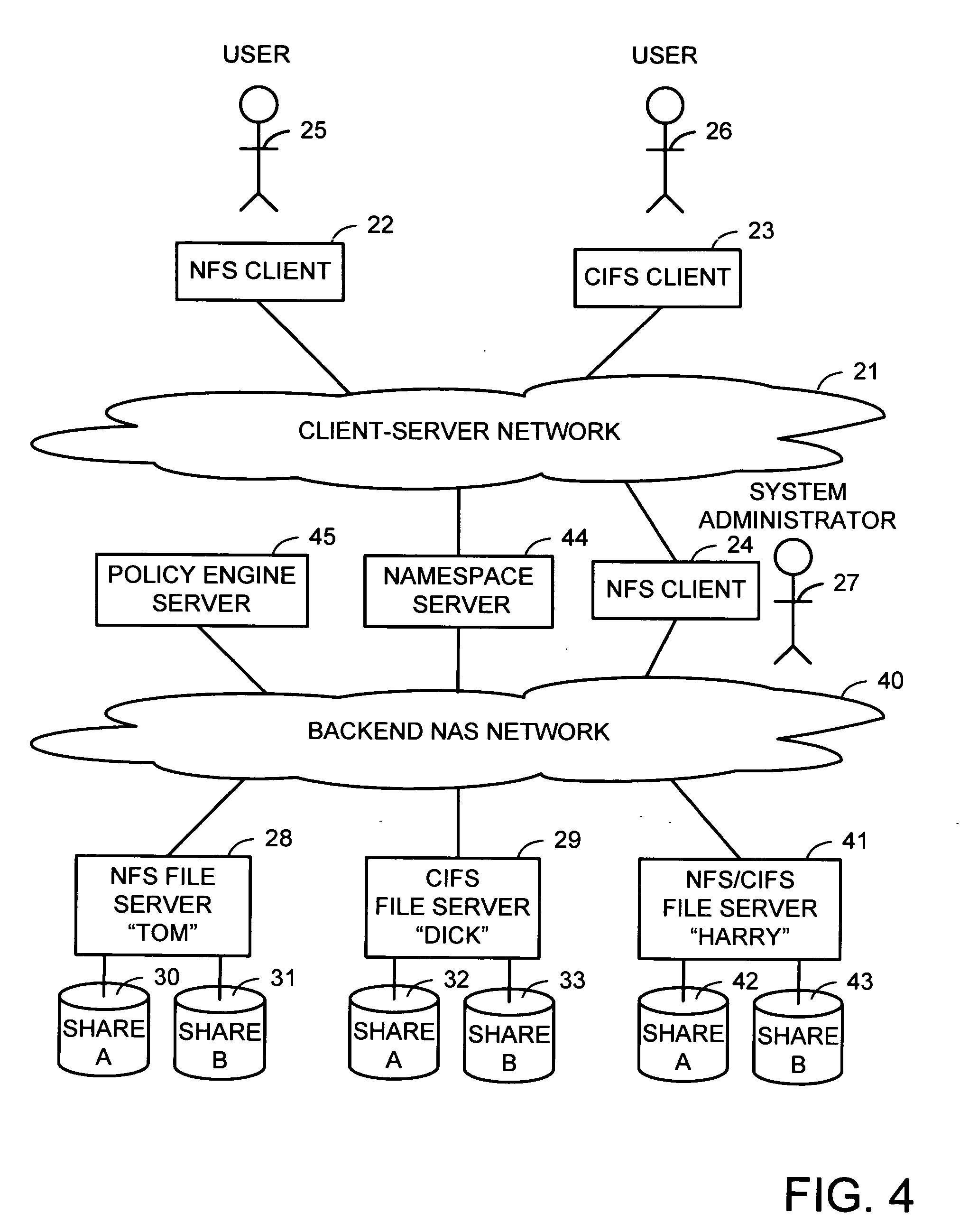
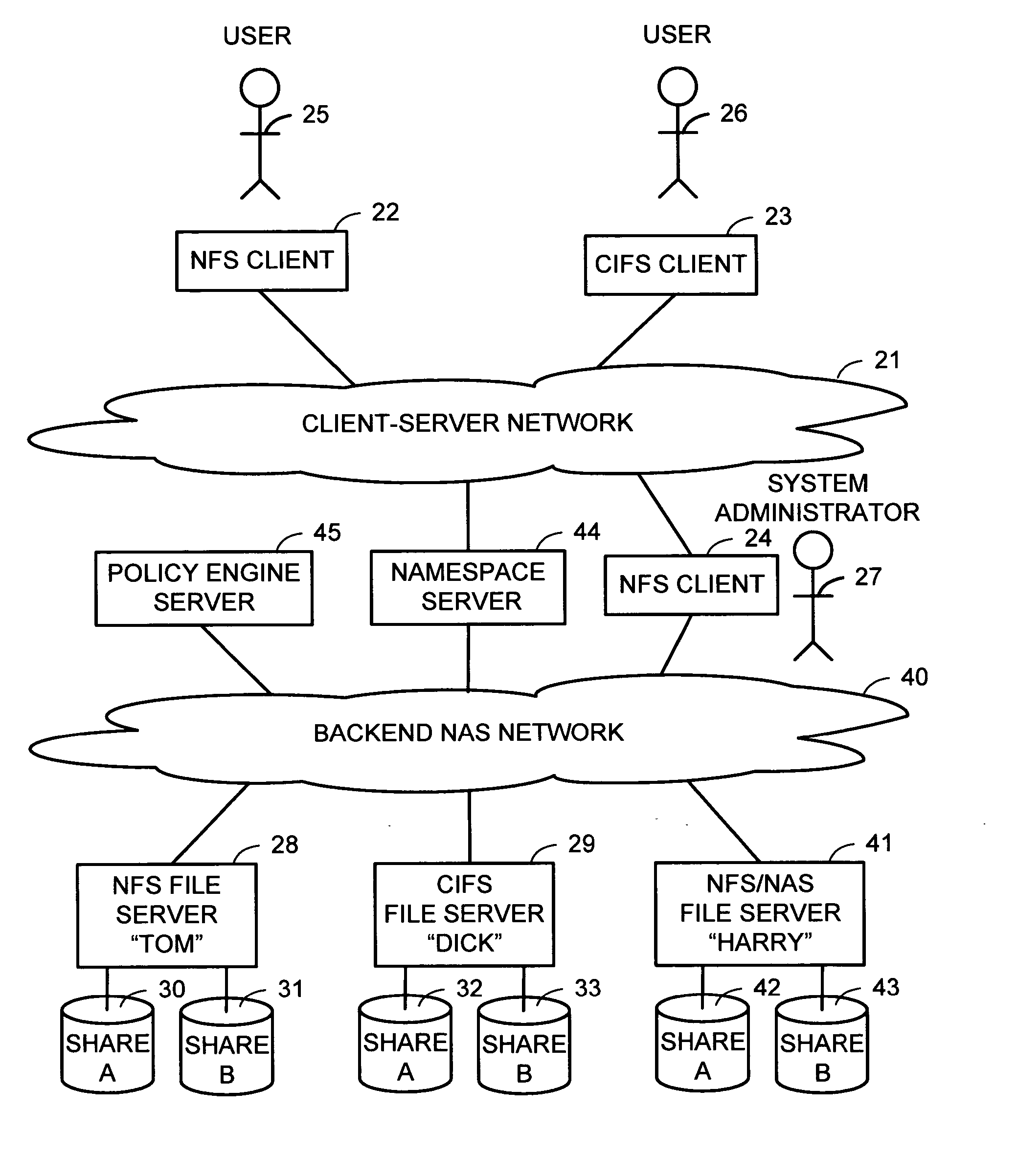
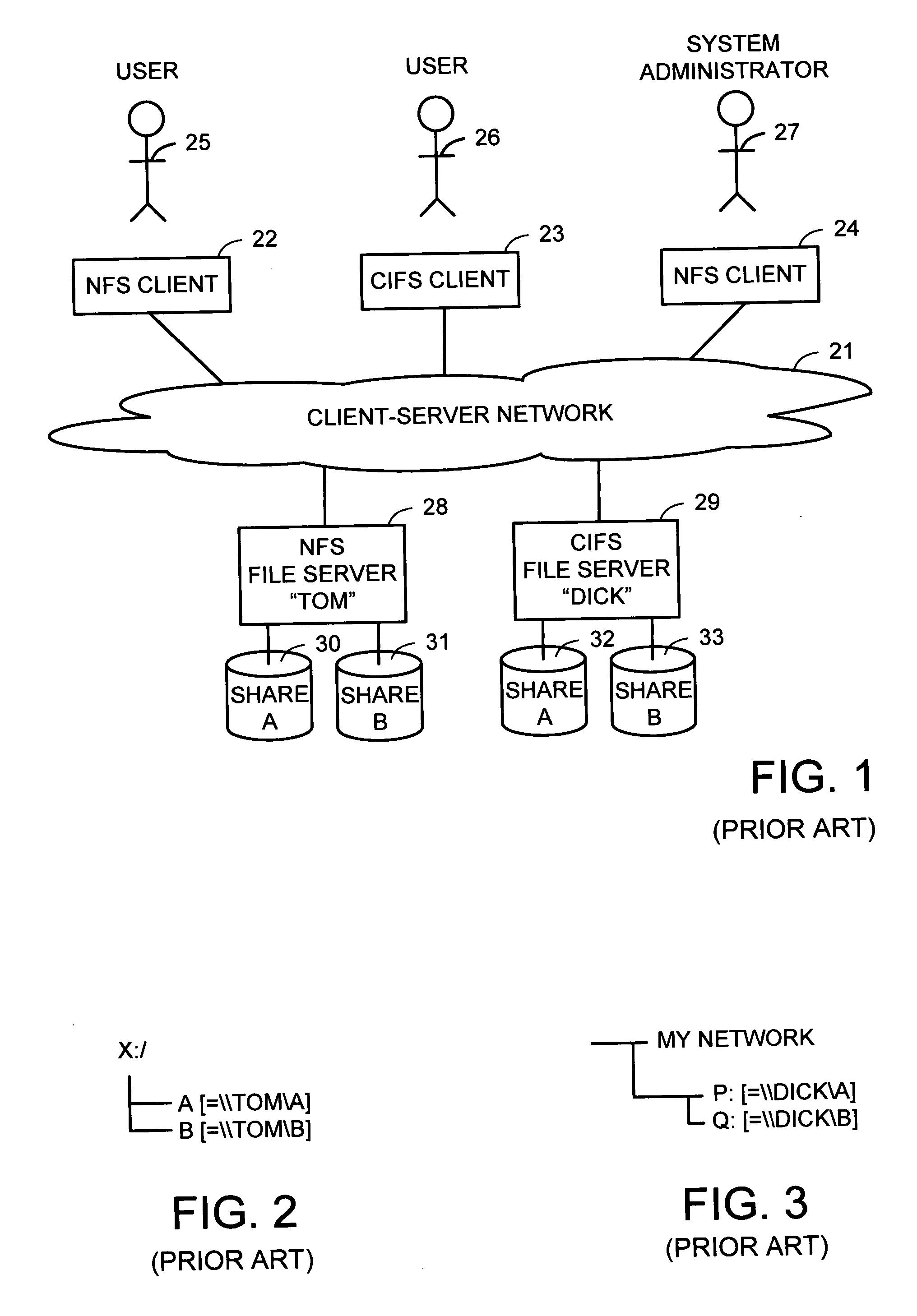
Intelligent network client for multi-protocol namespace redirection
InactiveUS20070088702A1Multiple digital computer combinationsTransmissionIntelligent NetworkEngineering
An intelligent network client has the capability of accessing a first network server in accordance with a first high-level file access protocol, and responding to a redirection reply from the first network server by accessing a second network server in accordance with a second high-level file access protocol. For example, the intelligent network client can be redirected from a CIFS / DFS server to a NFS server, and from an NFSv4 server to a CIFS server. Once redirected, the intelligent network client performs a directory mounting operation so that a subsequent client access to the same directory goes directly to the second network server. For example, the first network server is a namespace server for translating pathnames in a client-server network namespace into pathnames in a NAS network namespace, and the second network server is a file server in the NAS network namespace.
Owner:EMC CORP
Enterprise management system and method which includes a common enterprise-wide namespace and prototype-based hierarchical inheritance
InactiveUS6895586B1Multiple digital computer combinationsTransmissionBusiness managementEnterprise level
A system and method for providing an improved namespace and object description system for enterprise management are disclosed. The system and method employ a hierarchical namespace with objects including prototypes and instances where an instance inherits traits from a prototype, such as attribute values and / or child objects.
Owner:BMC SOFTWARE
System and method for controlling inter-application association through contextual policy control
ActiveUS20060036570A1Resource identifiedInterprogram communicationDigital data protectionContext managementNamespace
A method for controlling the interoperation of a plurality of software applications and resources includes intercepting communications from a first application to a second application or resource, directing the communication to a context management system, generating a candidate list of contexts for the communication, evaluating the candidate list according to at least one policy defined for these contexts to identify the resultant action and namespace for the communication, and performing the action as defined by the policies within the identified namespace. The method further includes tracking one or more versions of the second application, as well as tracking an evolution of application and / or resource names. The method further includes identifying one or more operations associated with a context on the candidate list, and executing the identified operations prior to a further communication.
Owner:MICROSOFT TECH LICENSING LLC
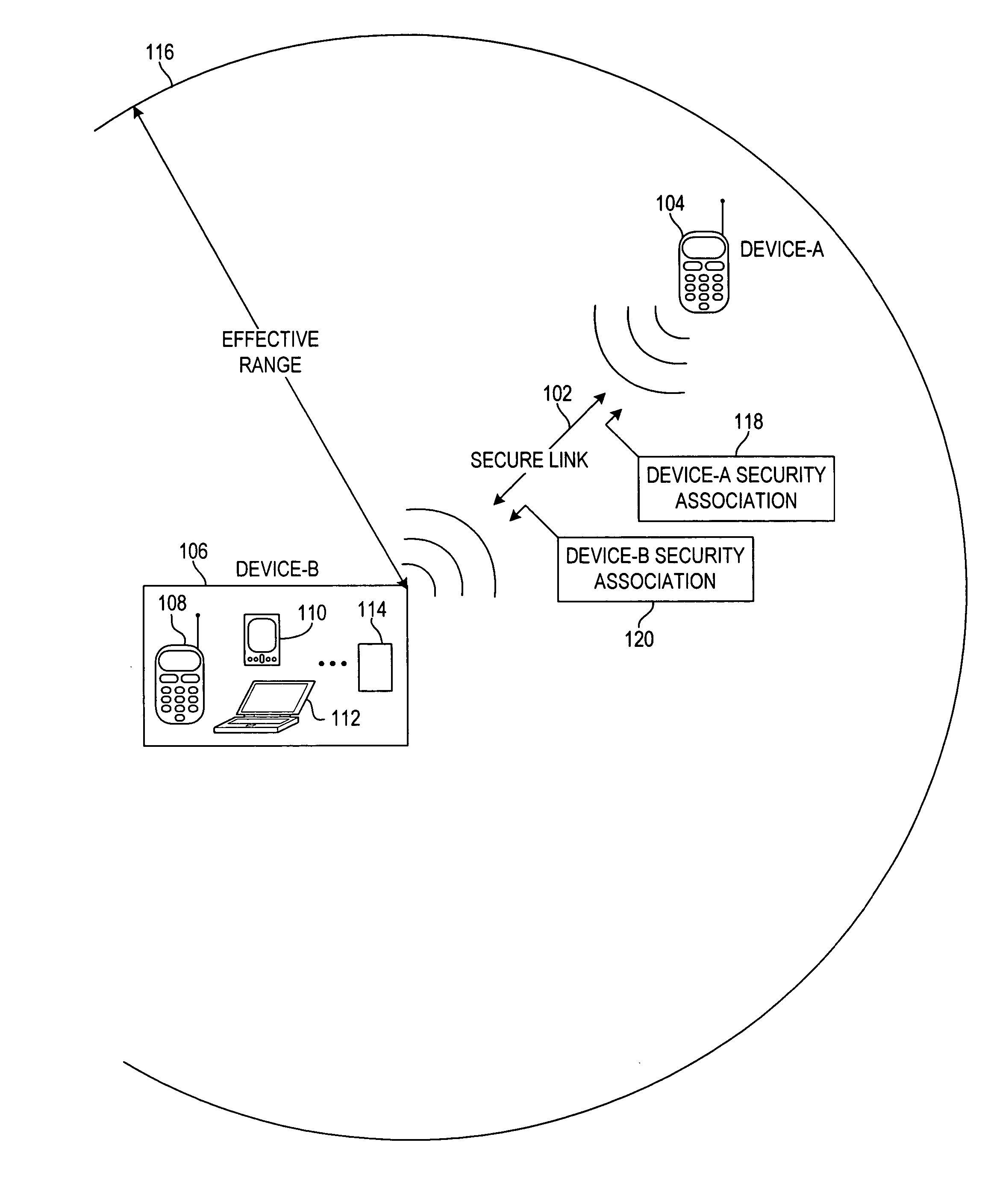
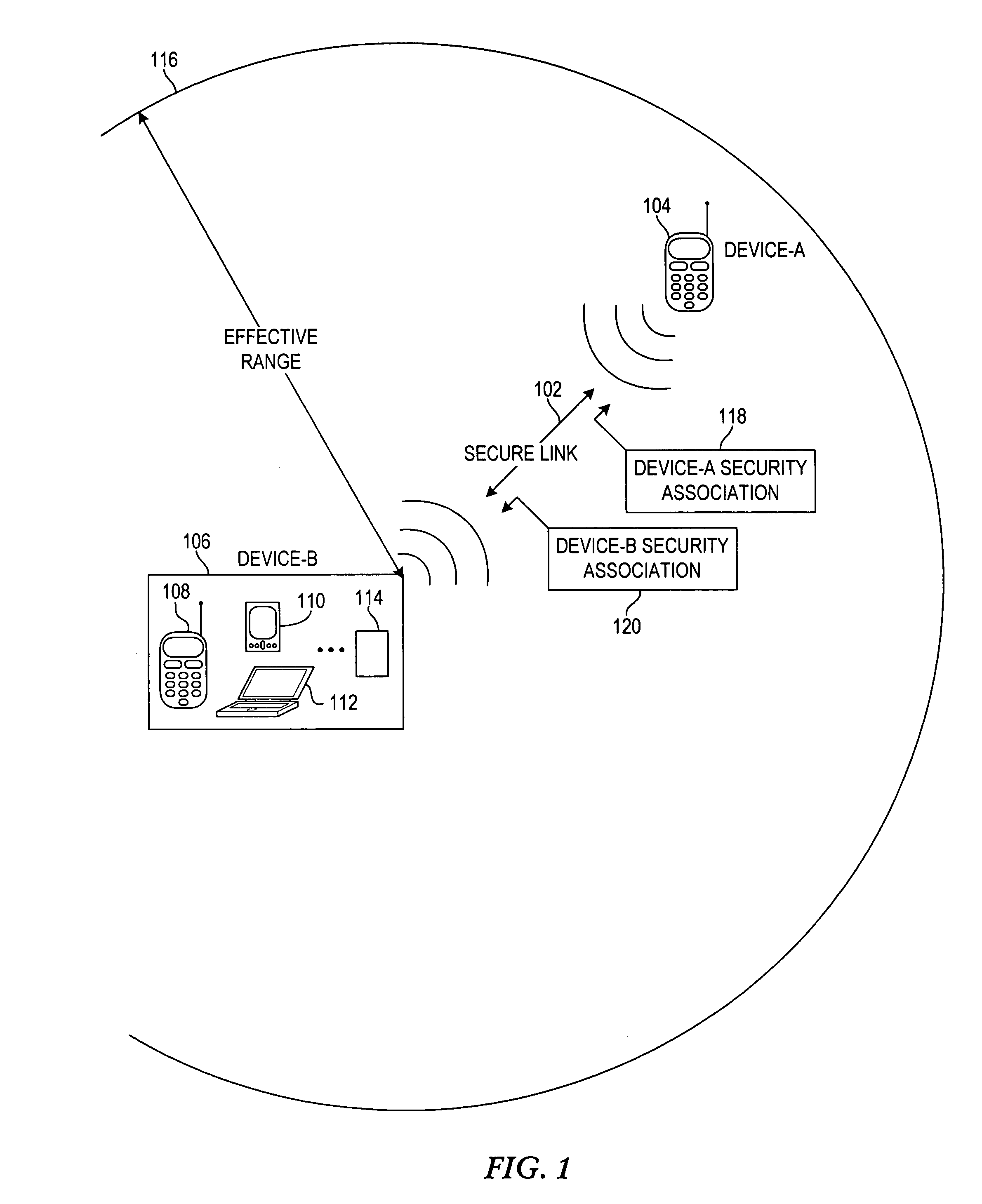
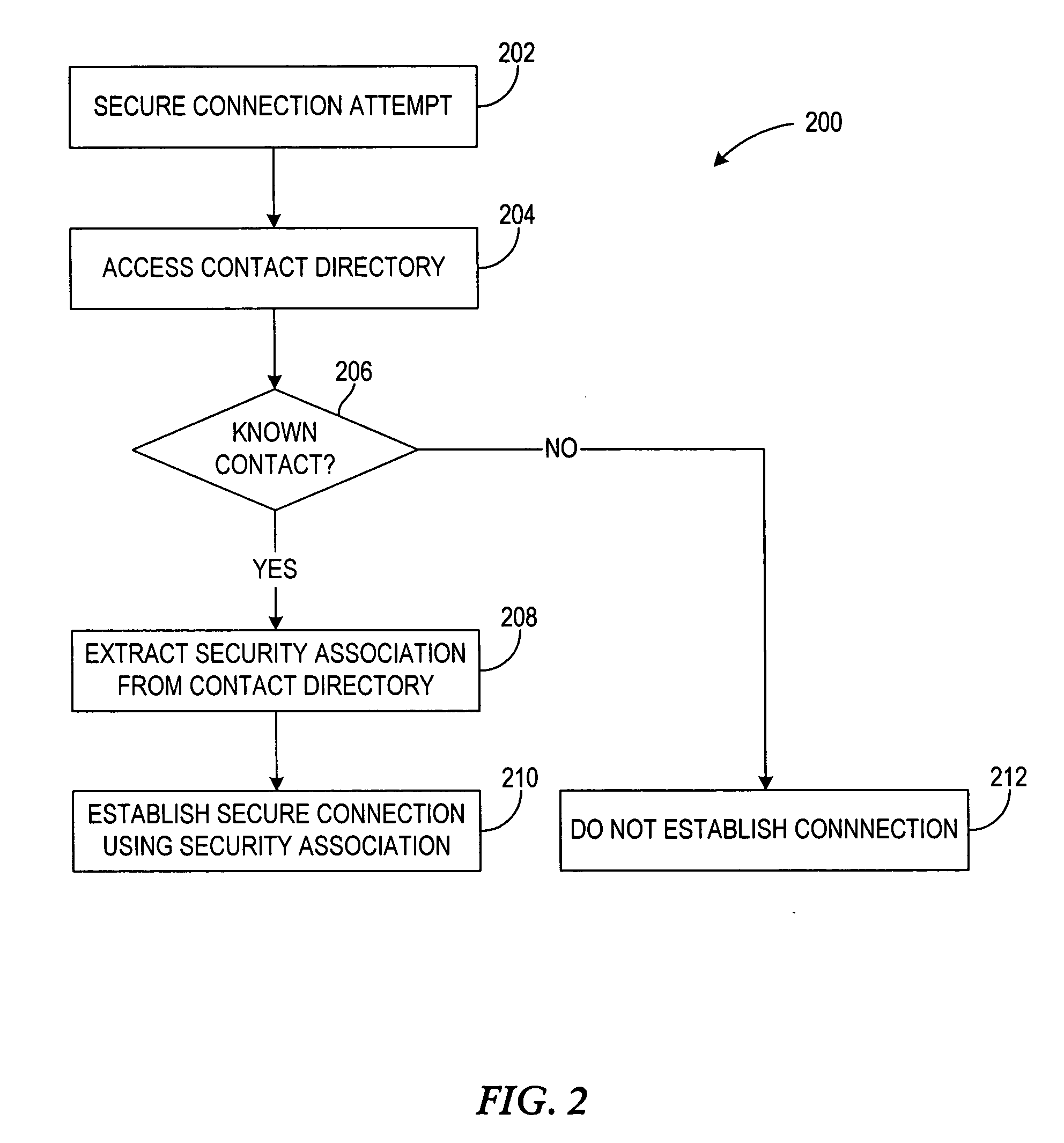
Linking security association to entries in a contact directory of a wireless device
InactiveUS20050266798A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecurity associationBluetooth
A system, apparatus and method for relating a security association to a contact in a namespace familiar to the user, and using this association to make access control decisions. An identifier of a first device is received at a second device. Using the identifier, the second device locates a contact entry corresponding to the identifier in a contact directory. A contact name associated with the identified contact entry is presented to the user of the second device to facilitate user authorization of the wireless proximity connection. An authorization identifier, e.g., a Bluetooth link key, is associated with the contact entry if authorized by the user of the second device. A wireless proximity connection, e.g., a Bluetooth connection, is established between the first and second devices in response to associating the authorization identifier with the entry. When subsequent wireless proximity connection are attempted between the first and second devices, the connection may be automatically established.
Owner:NOKIA SOLUTIONS & NETWORKS OY
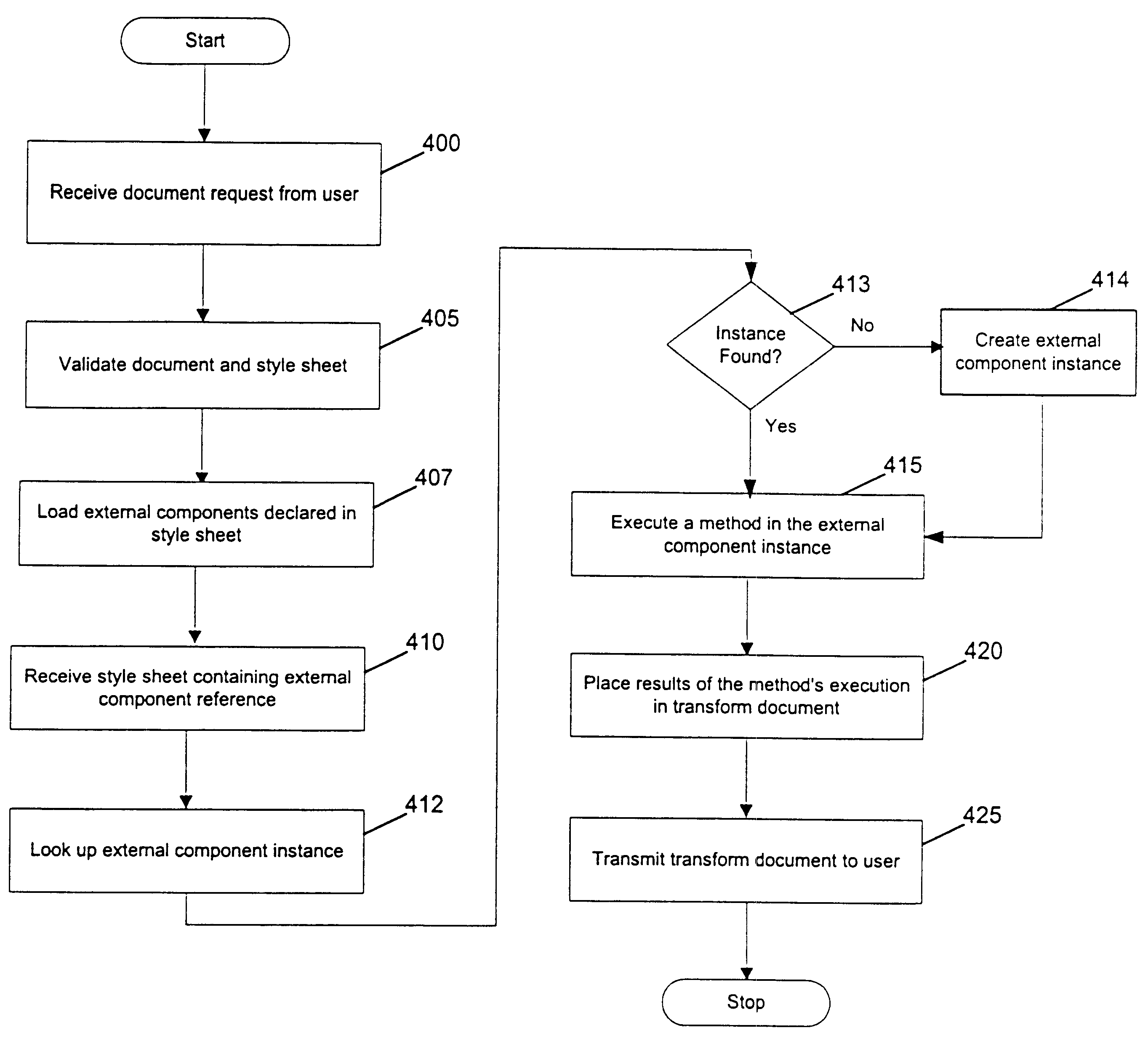
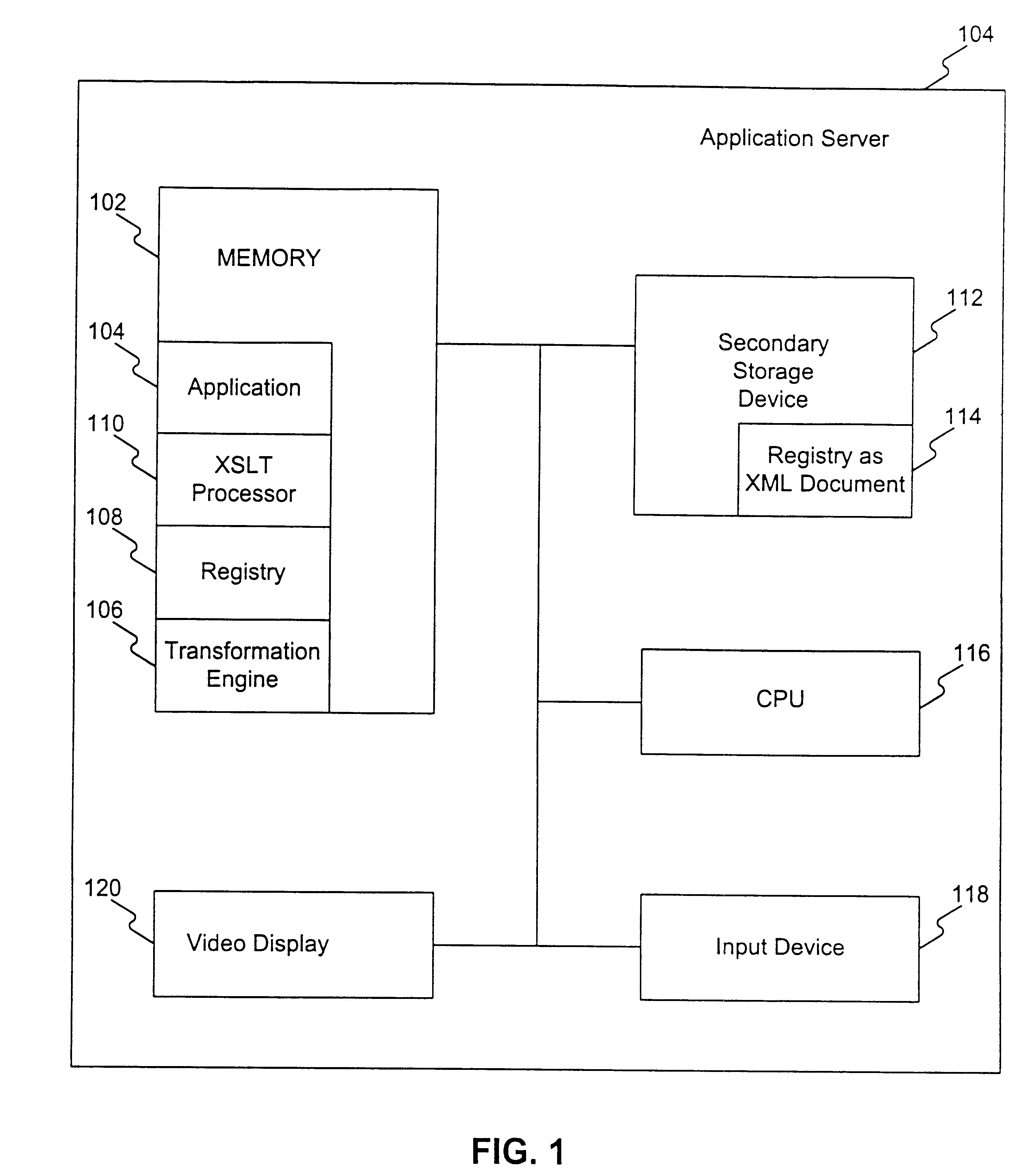
Extending the capabilities of an XSL style sheet to include components for content transformation
InactiveUS6507857B1Digital data information retrievalNatural language data processingXSLTDocumentation
Systems and methods consistent with the present invention use a Namespace paradigm to define an external component reference to a style sheet. When the style sheet processor processes the tags in the style sheet, it recognizes the external component declaration. The style sheet will contain a name of the external component instance and a definition of the method to execute associated with the external component instance, and may contain arguments for the method associated with the external component instance which is executing. The XSLT processor then relinquishes control to the external component to execute the method defined in the style sheet. The results of the method's execution may be placed in the transform document generated by processing the style sheet. However, this is not required and other results may be generated, including those not related to the transform document.
Owner:ORACLE INT CORP
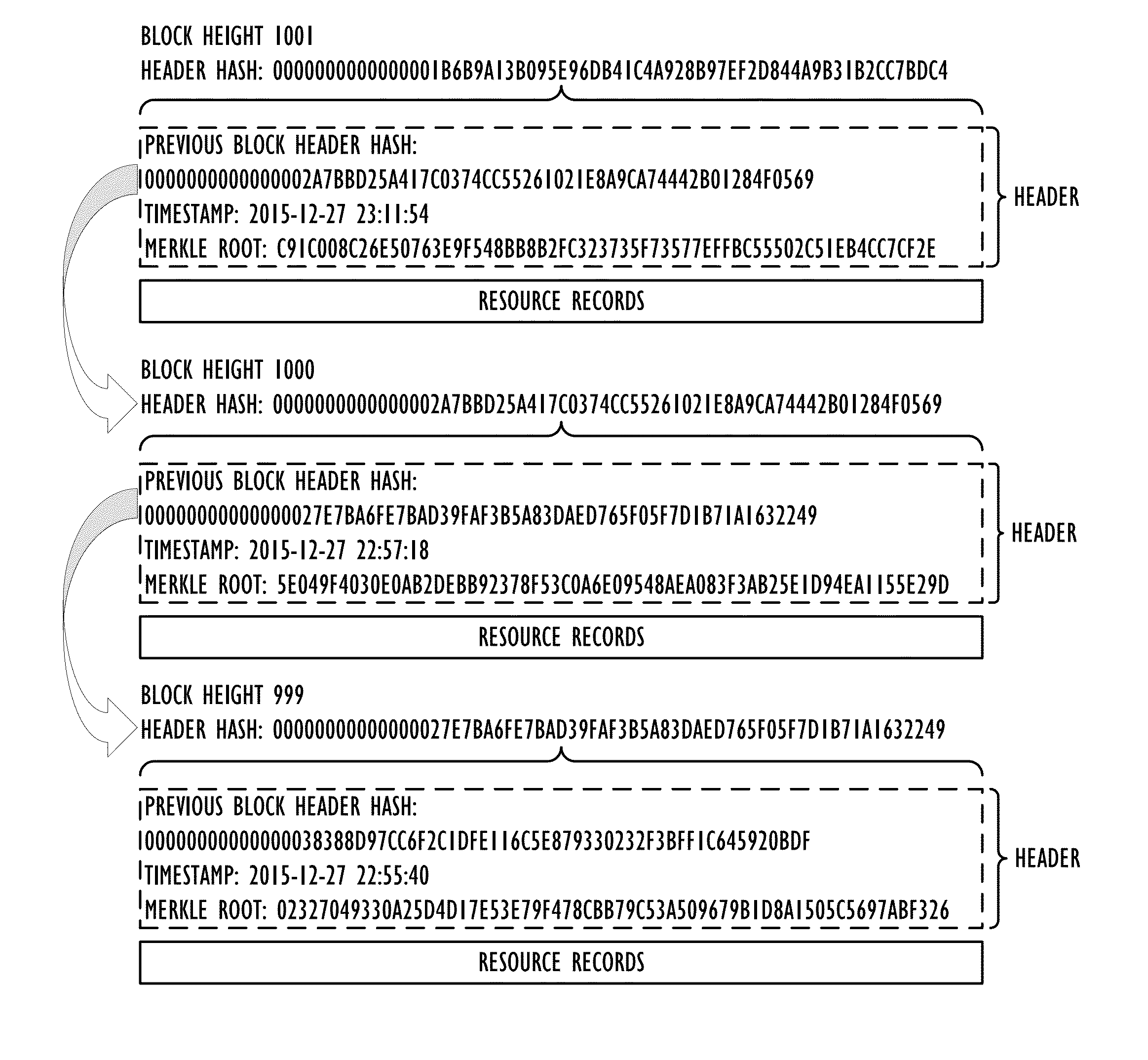
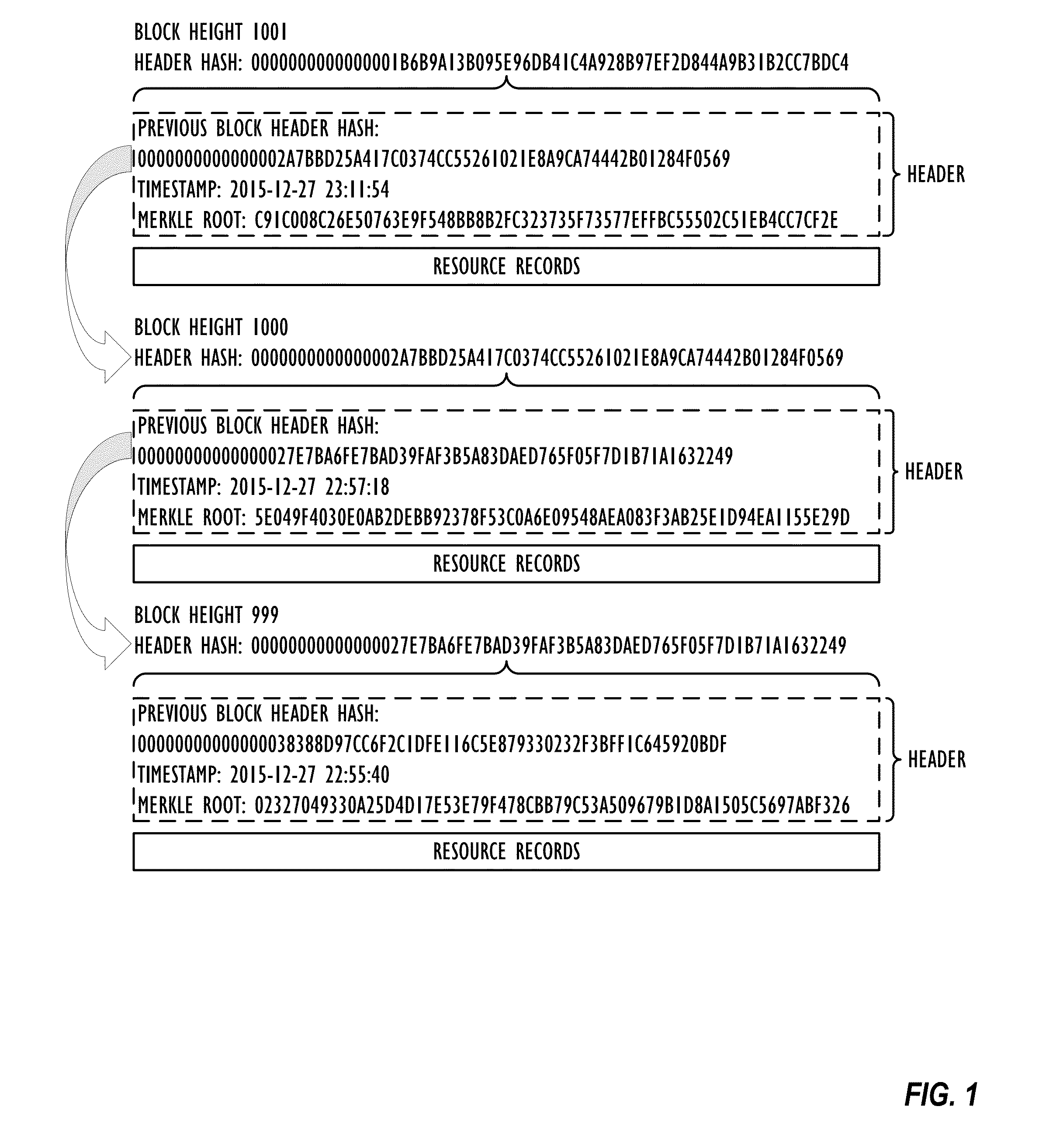
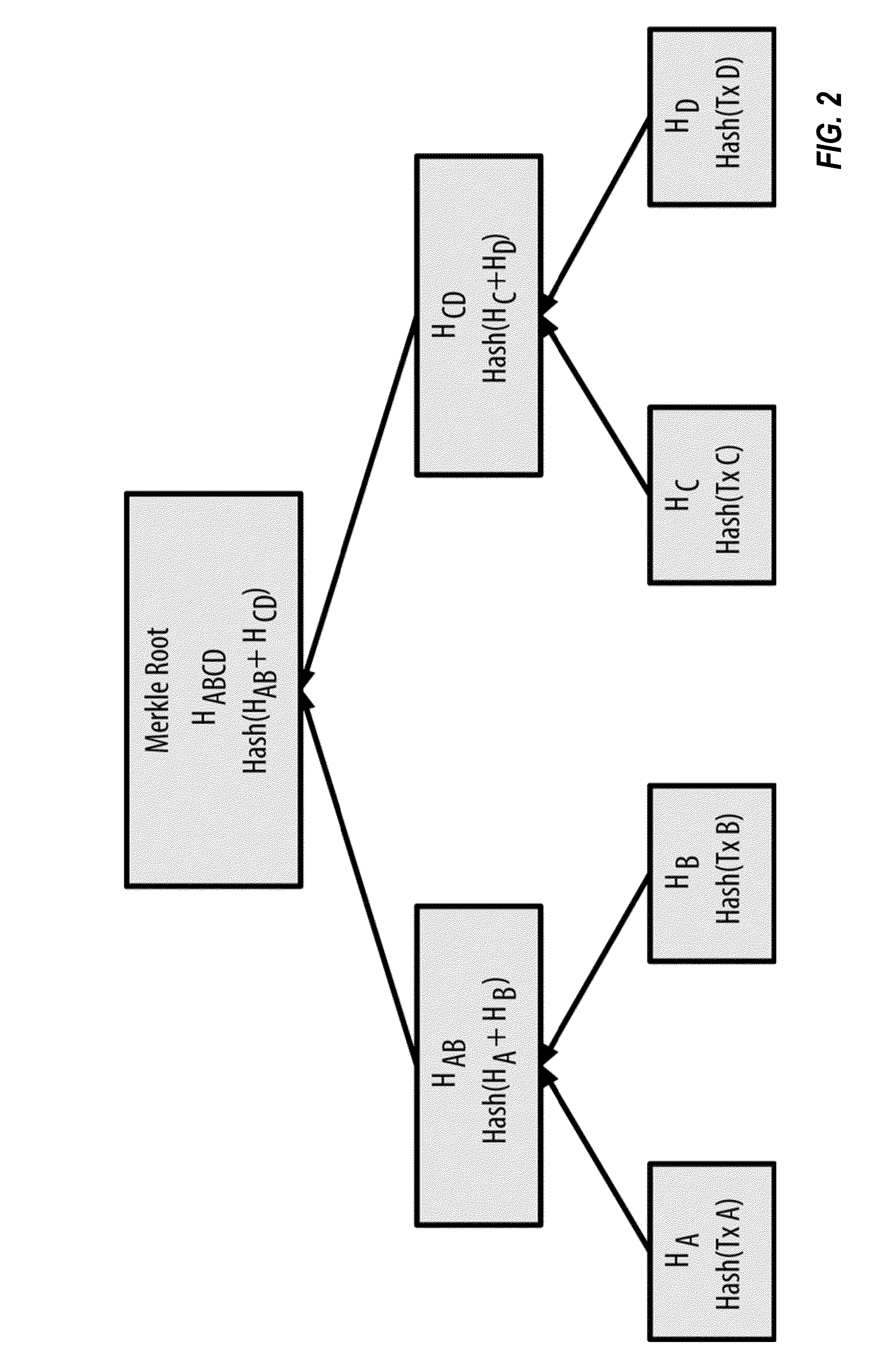
Out-of-band validation of domain name system records
An out-of-band Domain Name System (DNS) security technique uses a cryptographic blockchain for securing and validating DNS data in a chain of custody that exists outside the DNS namespace, allowing validated access to cached DNS information without requiring real-time access to root servers.
Owner:MANNING WILLIAM
Transactional file system
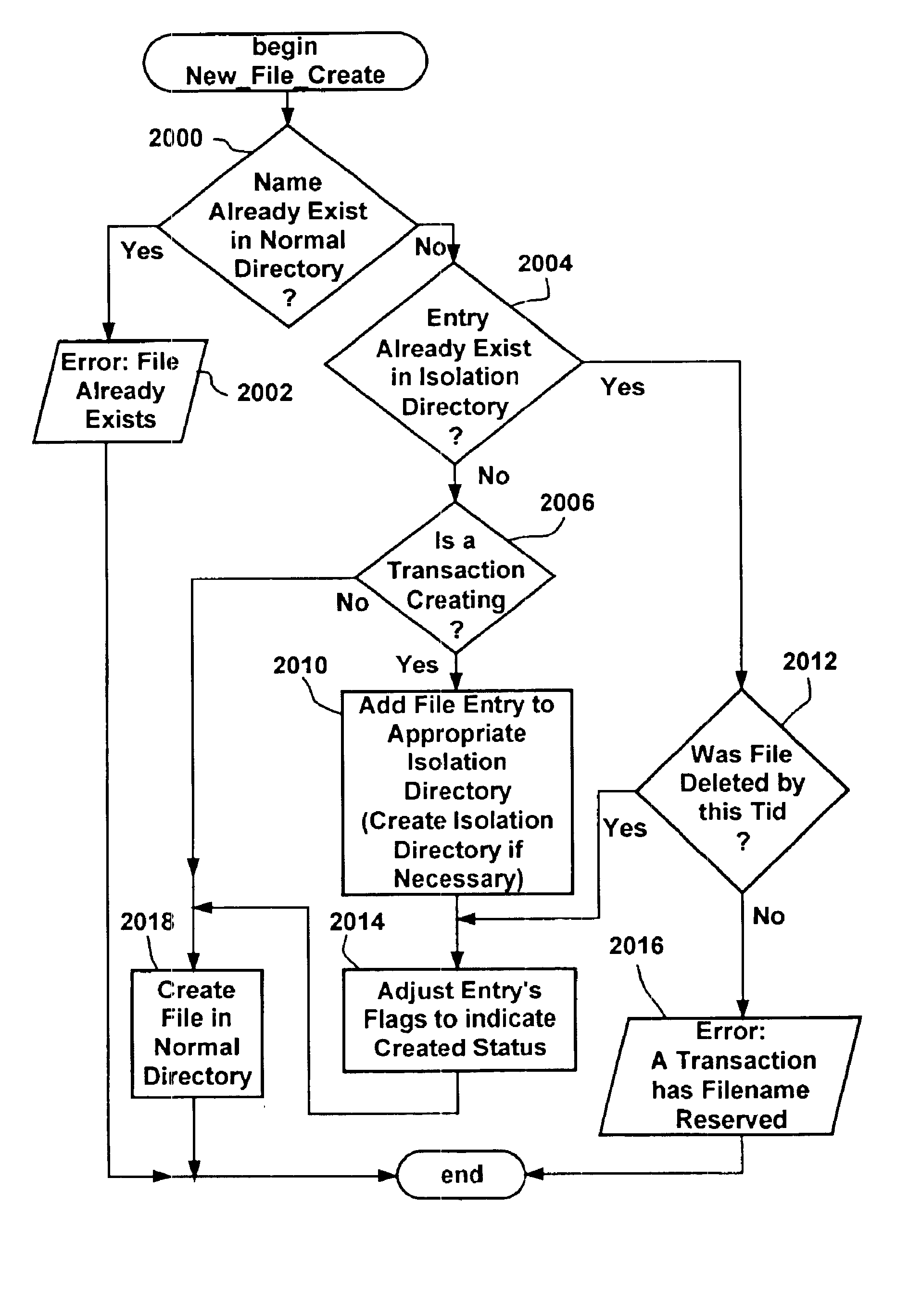
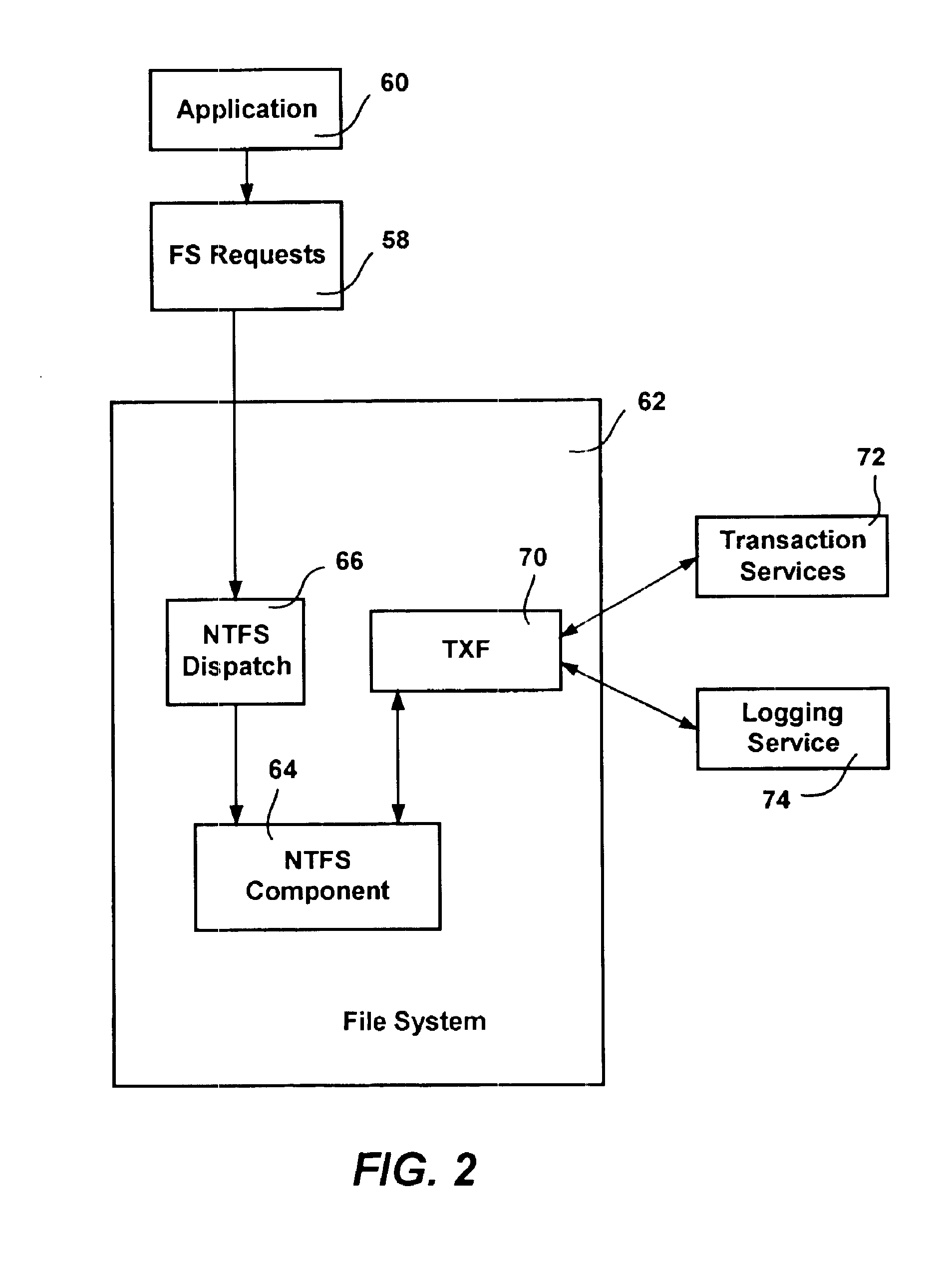
InactiveUS6856993B1Easy to implementMultiple operationData processing applicationsDigital data information retrievalFile systemApplication software
A transactional file system wherein multiple file system operations may be performed as transaction. An application specifies that file system-related operations should be handled in a transaction, and is given a file handle associated with a transaction context. For file system requests associated with a transaction context, a file system component manages operations consistent with transactional behavior. The component provides data isolation by providing multiple file versions such that transactional readers do not receive changes until after the transaction commits and the reader reopens the file. The component handles namespace logging operations in a multiple-level log that facilitates logging and recovery. Page data is logged separate from the main log, with signatures establishing whether pages were fully flushed to disk. Namespace isolation via isolation directories allows a transaction to see its operational effects but not effects of other uncommitted transactions. Transactions over a network are facilitated.
Owner:MICROSOFT TECH LICENSING LLC
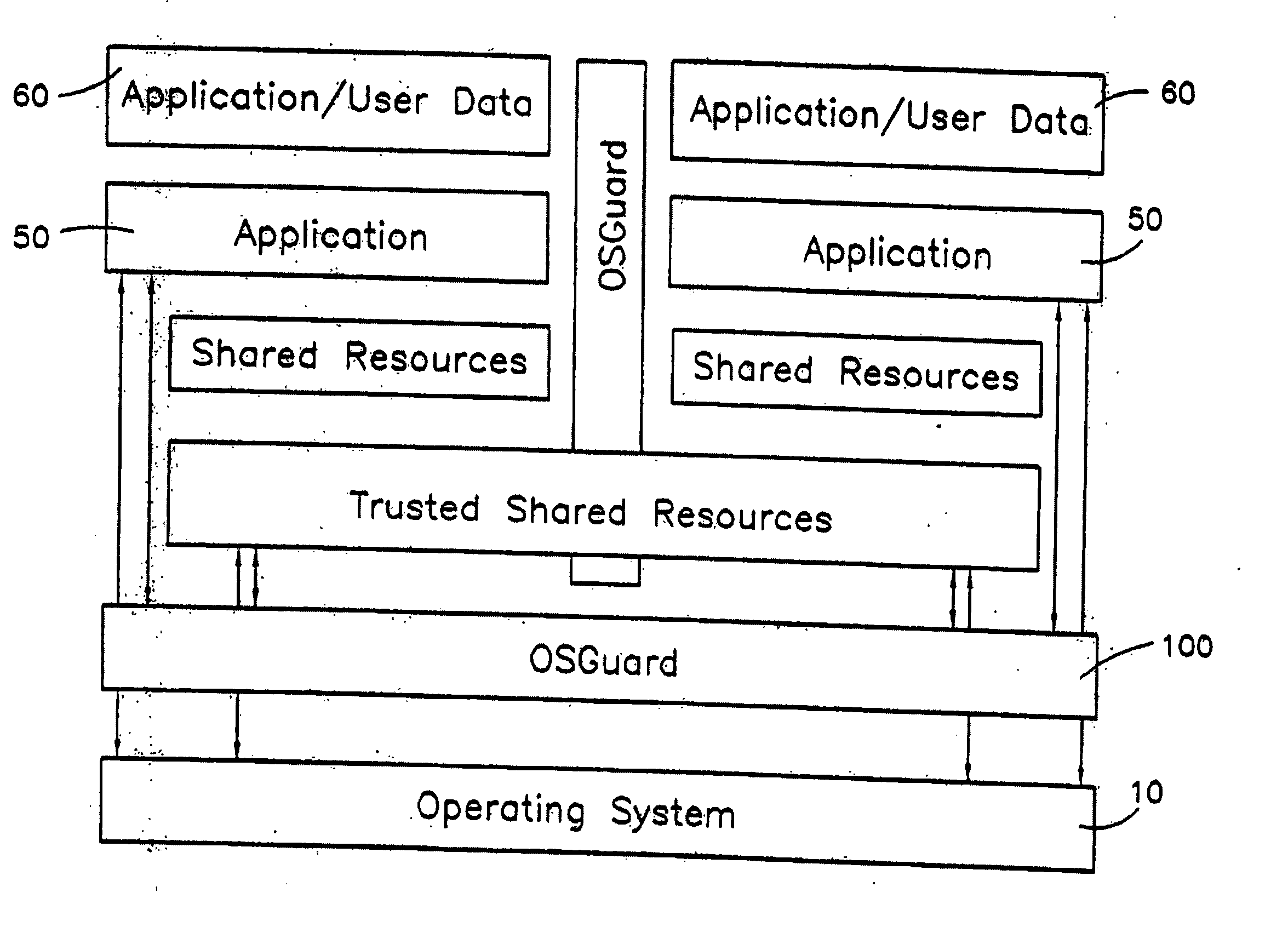
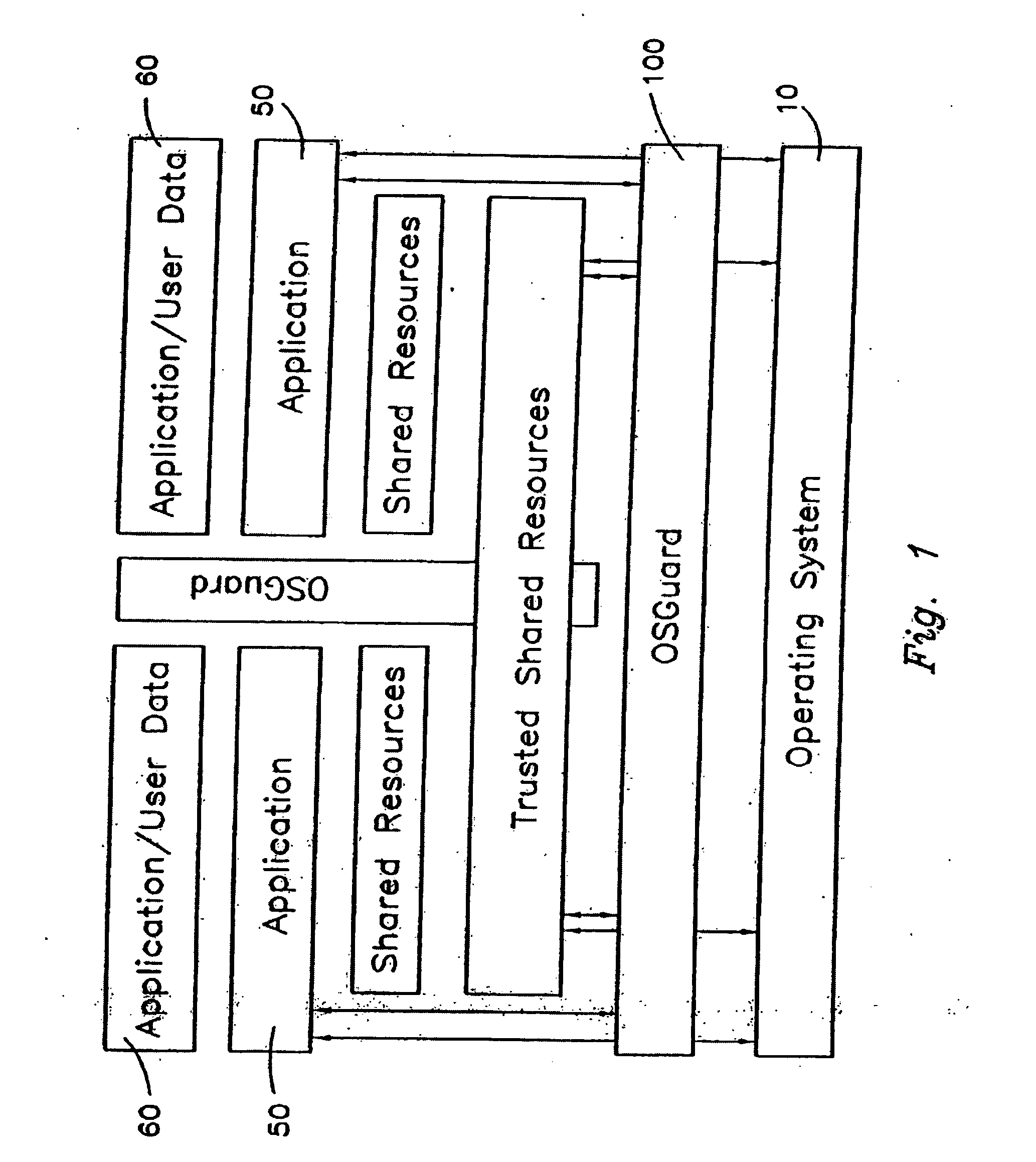
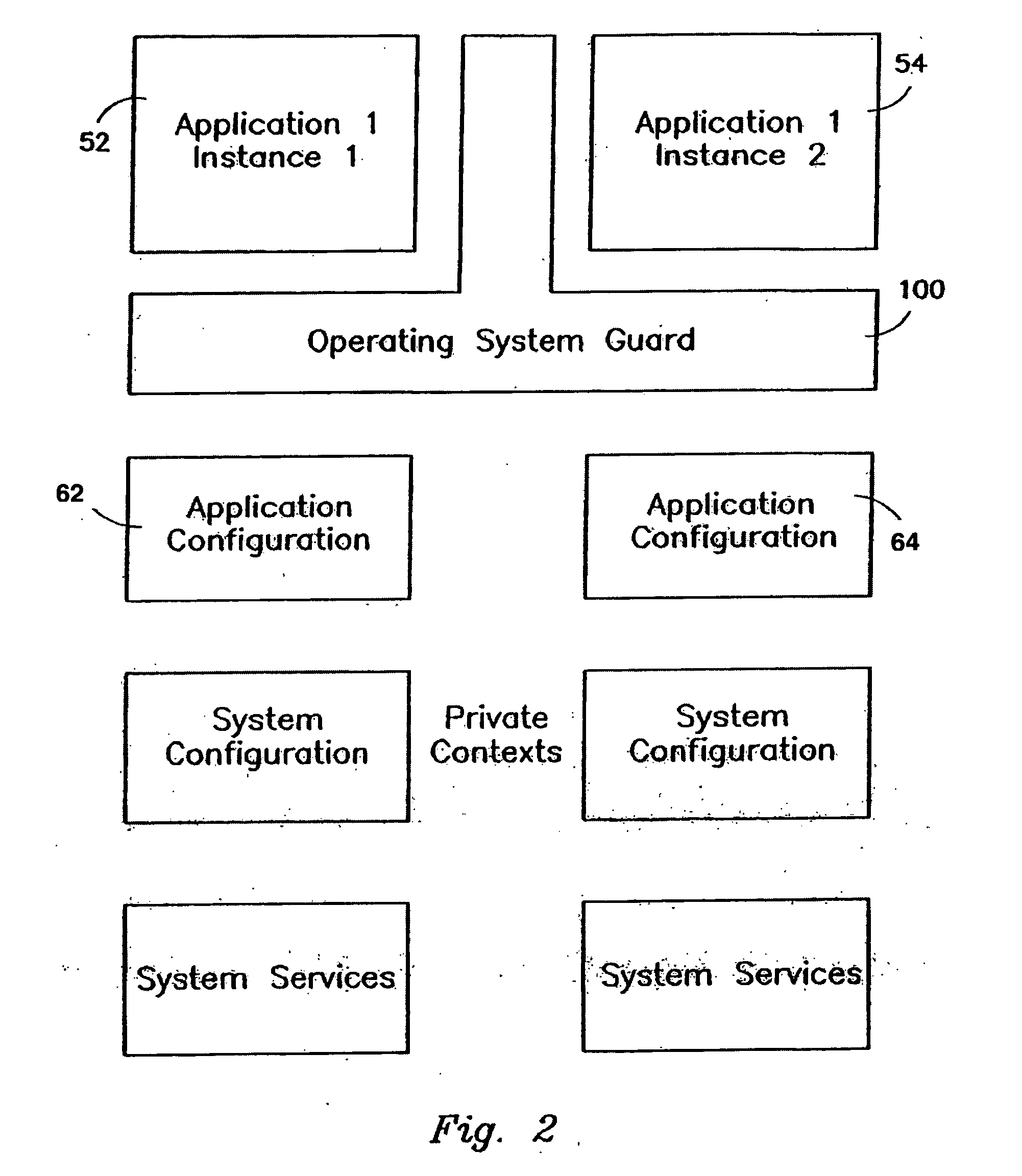
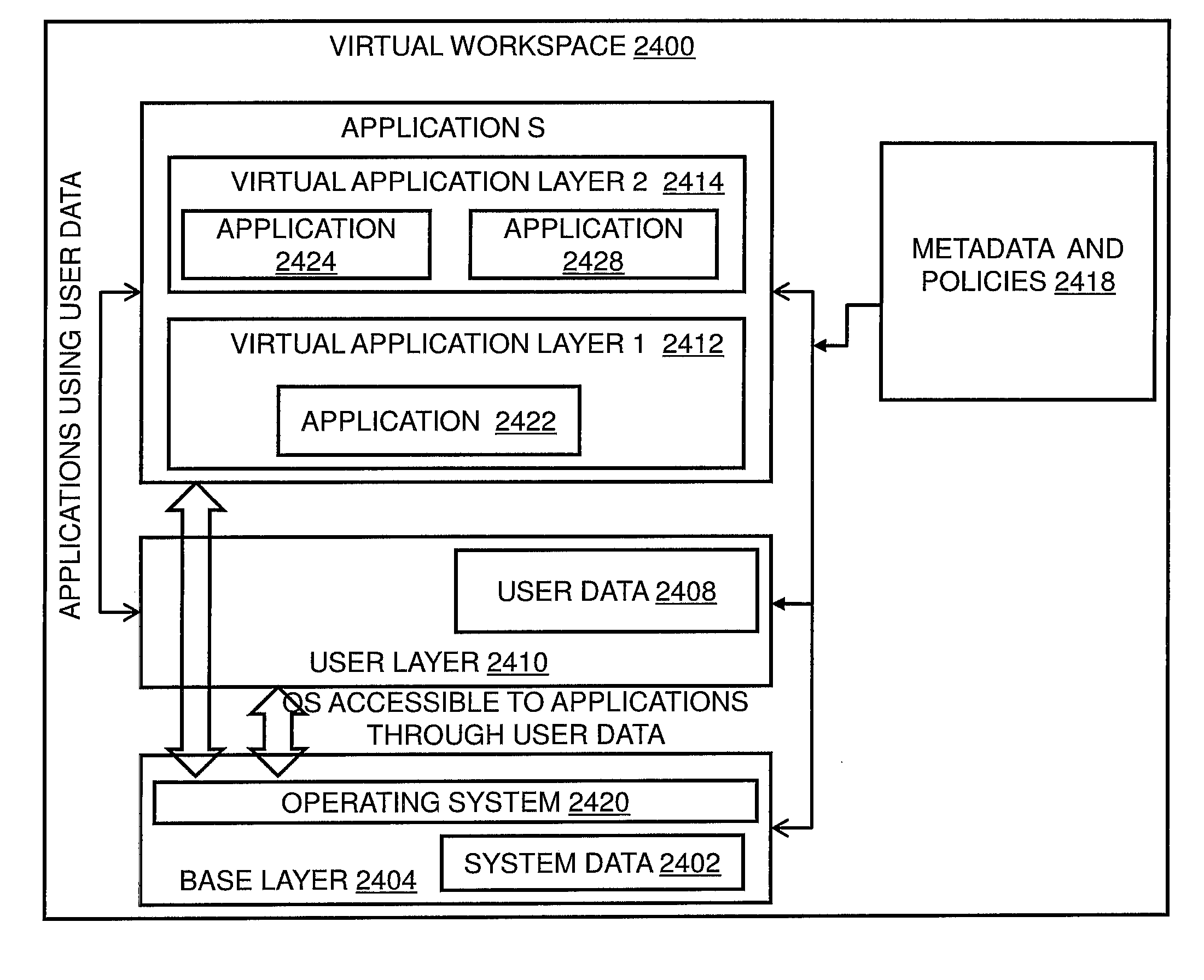
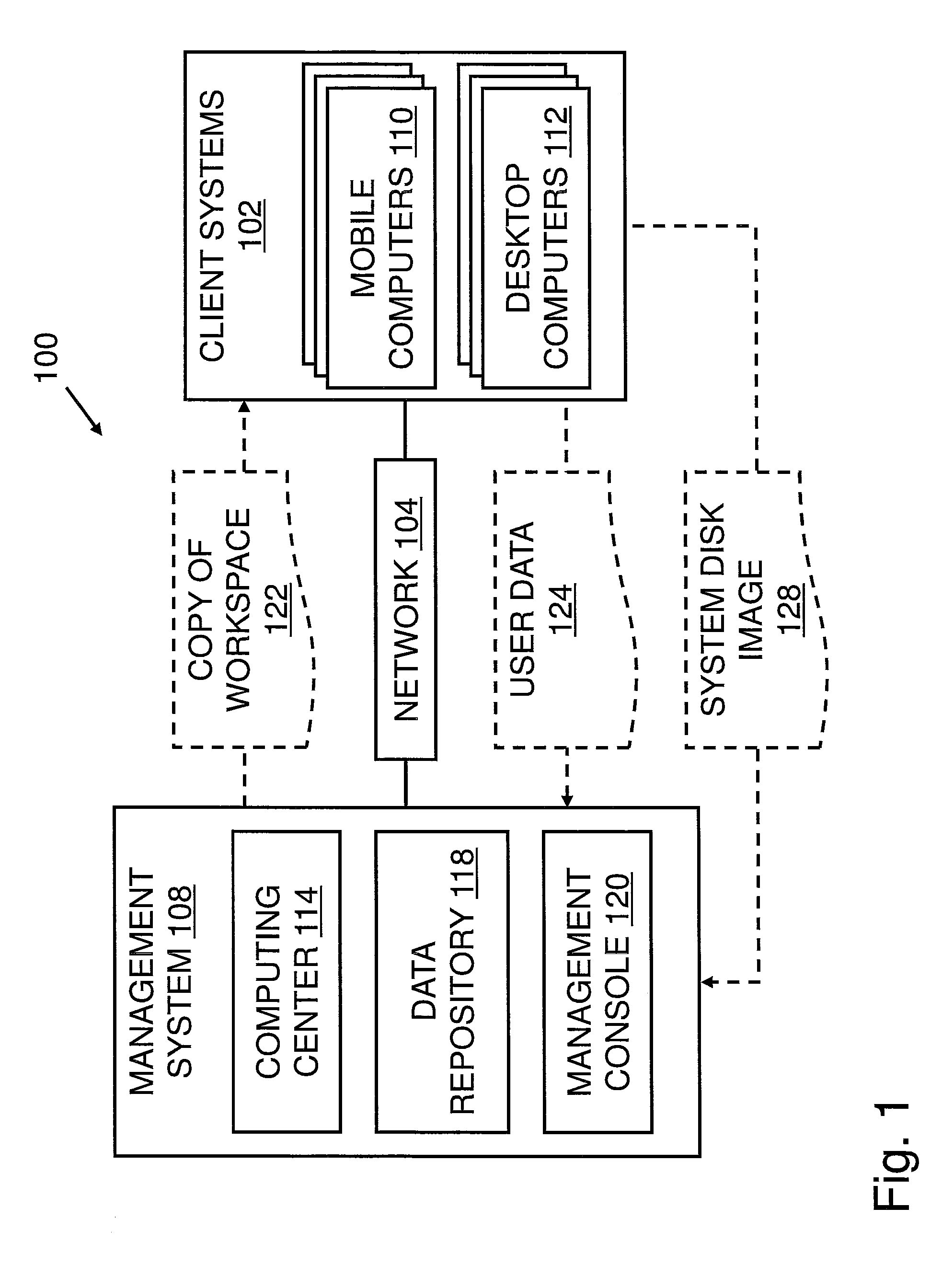
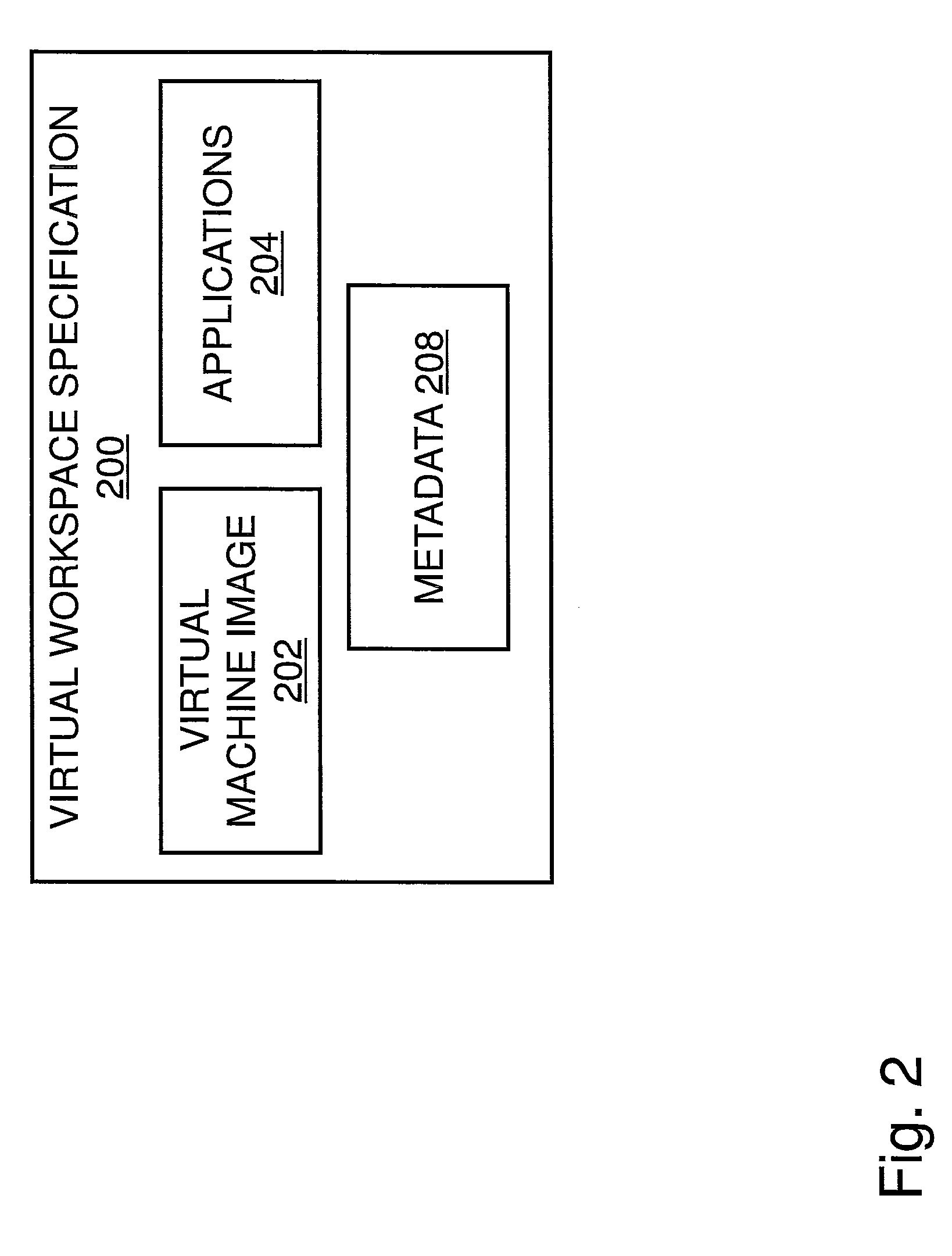
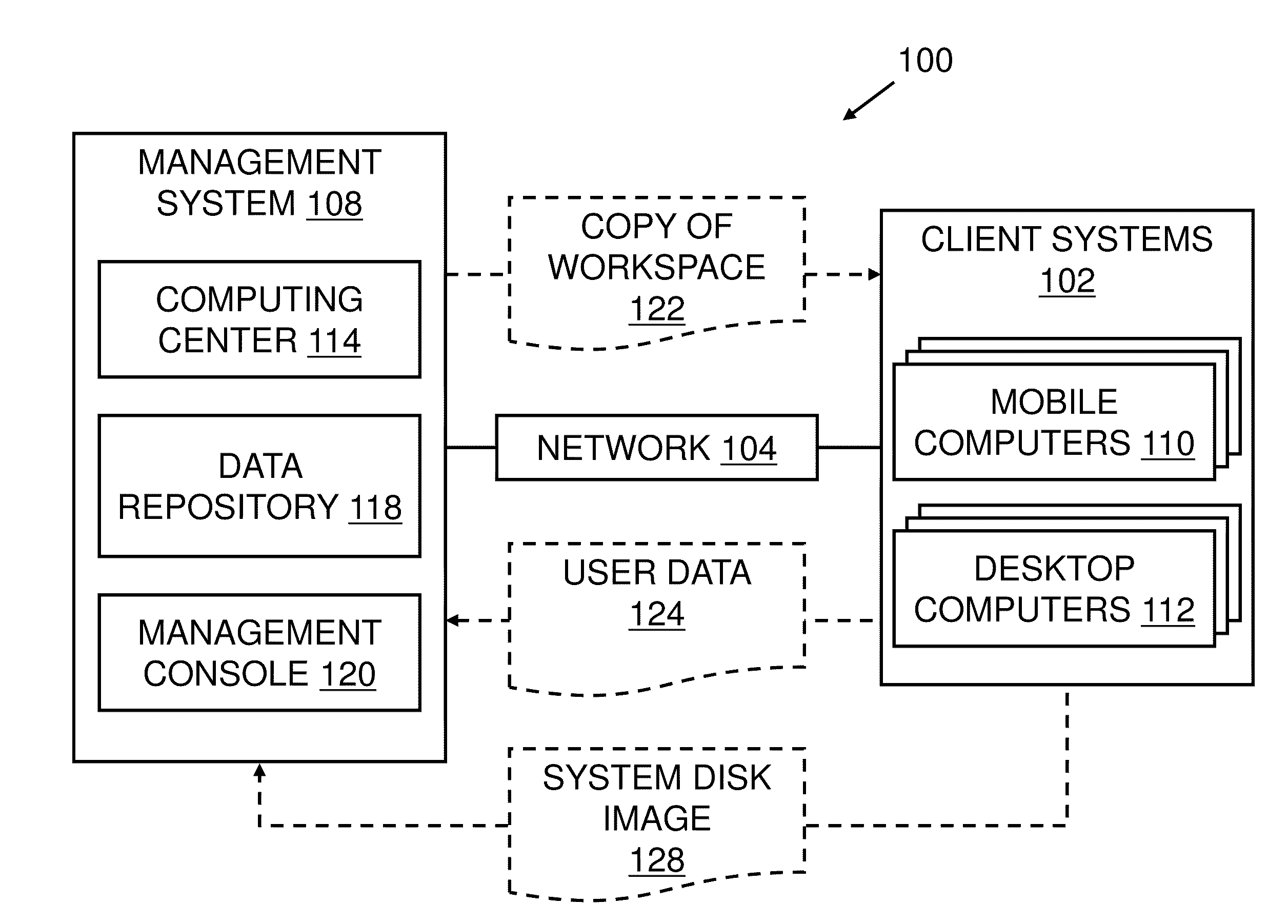
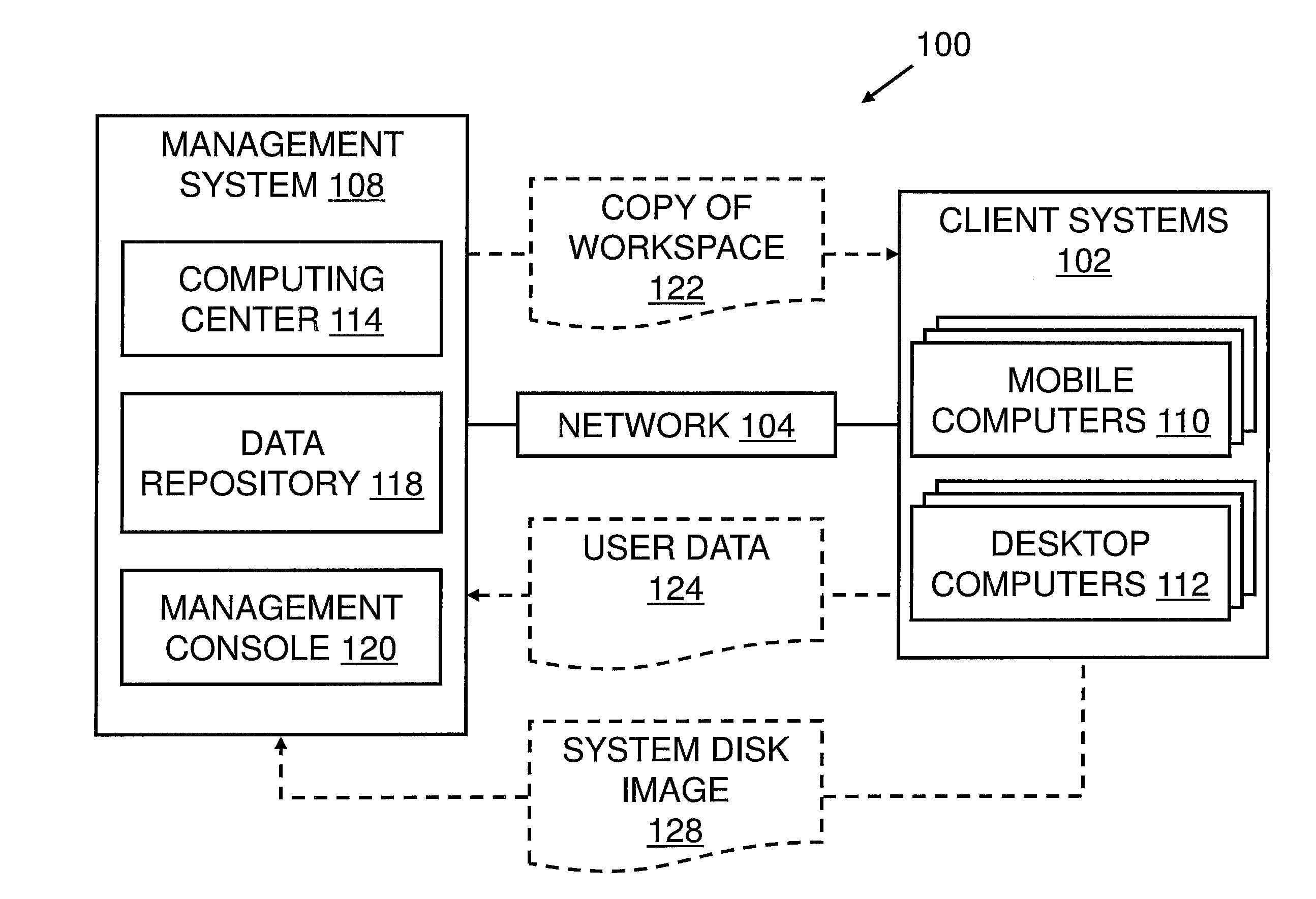
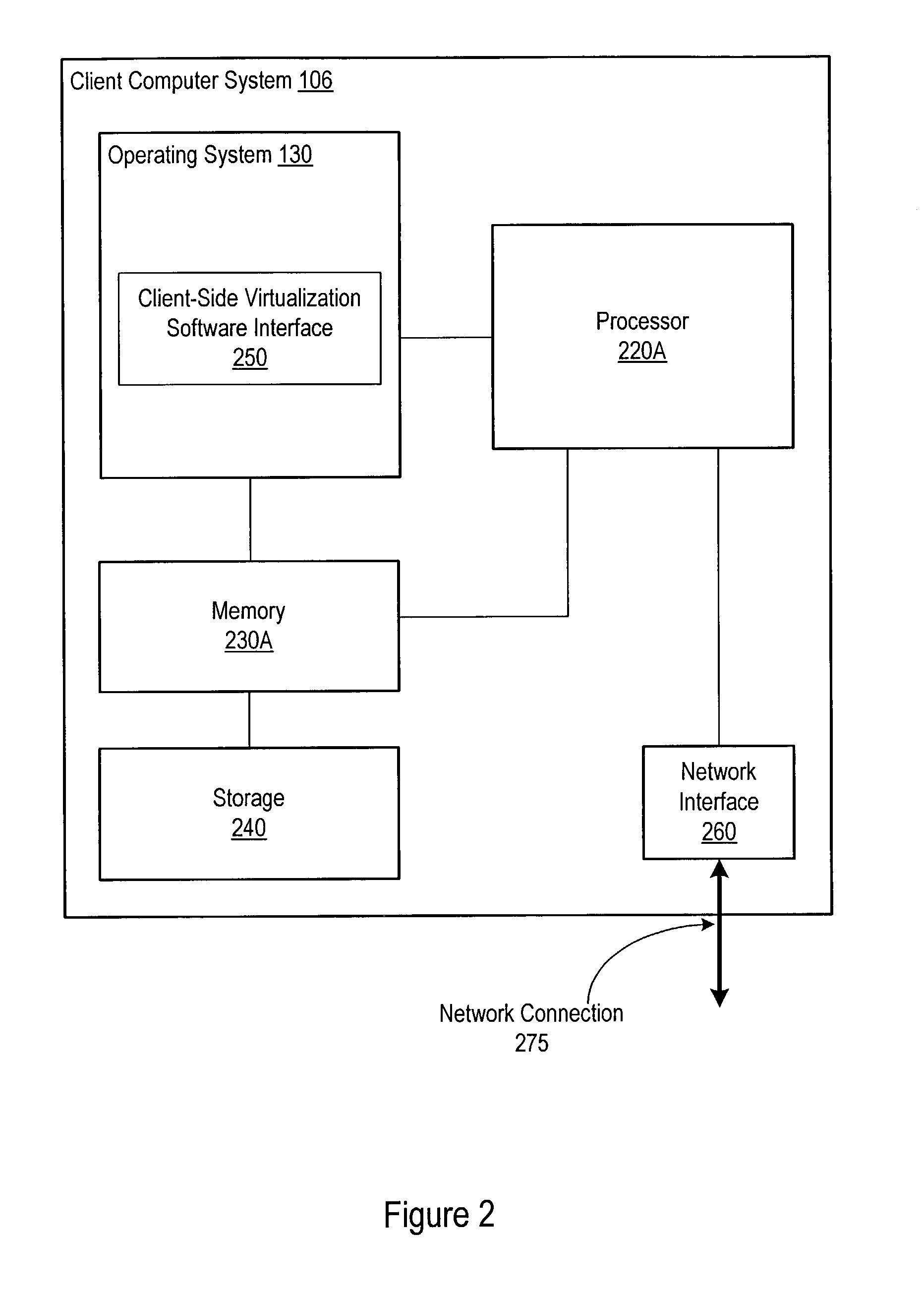
Operating Systems in a Layerd Virtual Workspace
InactiveUS20110061045A1Easy to manageImprove usabilitySoftware simulation/interpretation/emulationMemory systemsVirtualizationVirtual file system
A virtual workspace can include an active instance of a layered virtual file system namespace. A layered virtual file system namespace is referred to by the virtual workspace and includes a collection of system data (e.g. layered virtual file system base layer), user data (e.g. layered virtual file system user layer), and virtualized applications (e.g. virtual app layer), metadata and policies (e.g. layered virtual file system layer scope). Because a virtual workspace can include software such as an operating system and one or more applications in addition to user data, a virtual workspace can be aligned with a namespace so that an operating system of the virtual workspace may be located at a “base layer”, one or more applications executing on the operating system may be located at an upper “virtual app” layer, and user data in a virtual workspace may be found at any layer at or above the user layer.
Owner:VIRTUAL COMP
Layered Virtual File System
InactiveUS20110040812A1Improves lifecycle managementEasy to manageProgram controlSpecial data processing applicationsVirtualizationVirtual file system
A virtual workspace can include an active instance of a layered virtual file system namespace. A layered virtual file system namespace is referred to by the virtual workspace and includes a collection of system data (e.g. layered virtual file system base layer), user data (e.g. layered virtual file system user layer), and virtualized applications (e.g. virtual app layer), metadata and policies (e.g. layered virtual file system layer scope). Because a virtual workspace can include software such as an operating system and one or more applications in addition to user data, a virtual workspace can be aligned with a namespace so that an operating system of the virtual workspace may be located at a “base layer”, one or more applications executing on the operating system may be located at an upper “virtual app” layer, and user data in a virtual workspace may be found at any layer at or above the user layer.
Owner:VIRTUAL COMP
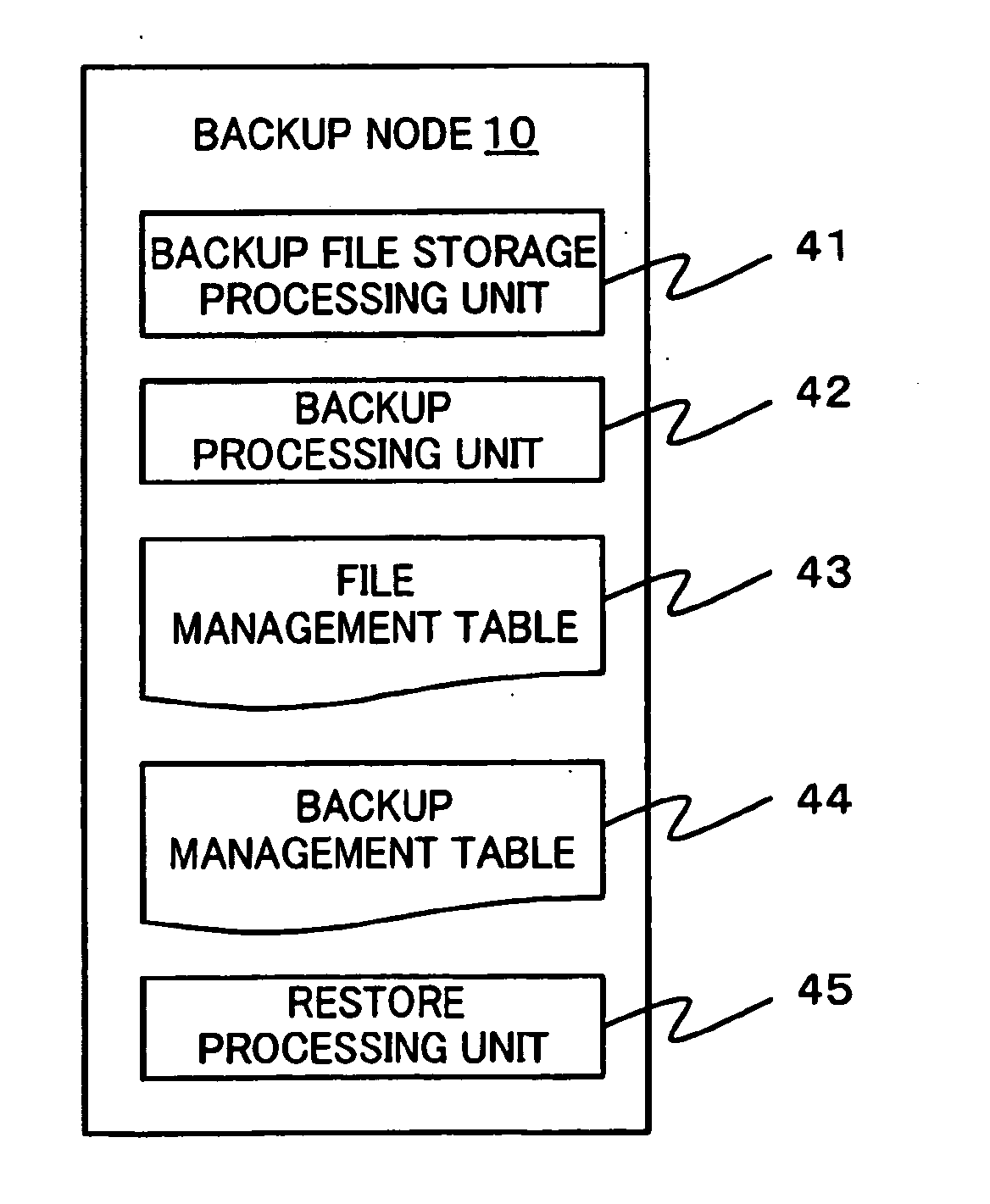
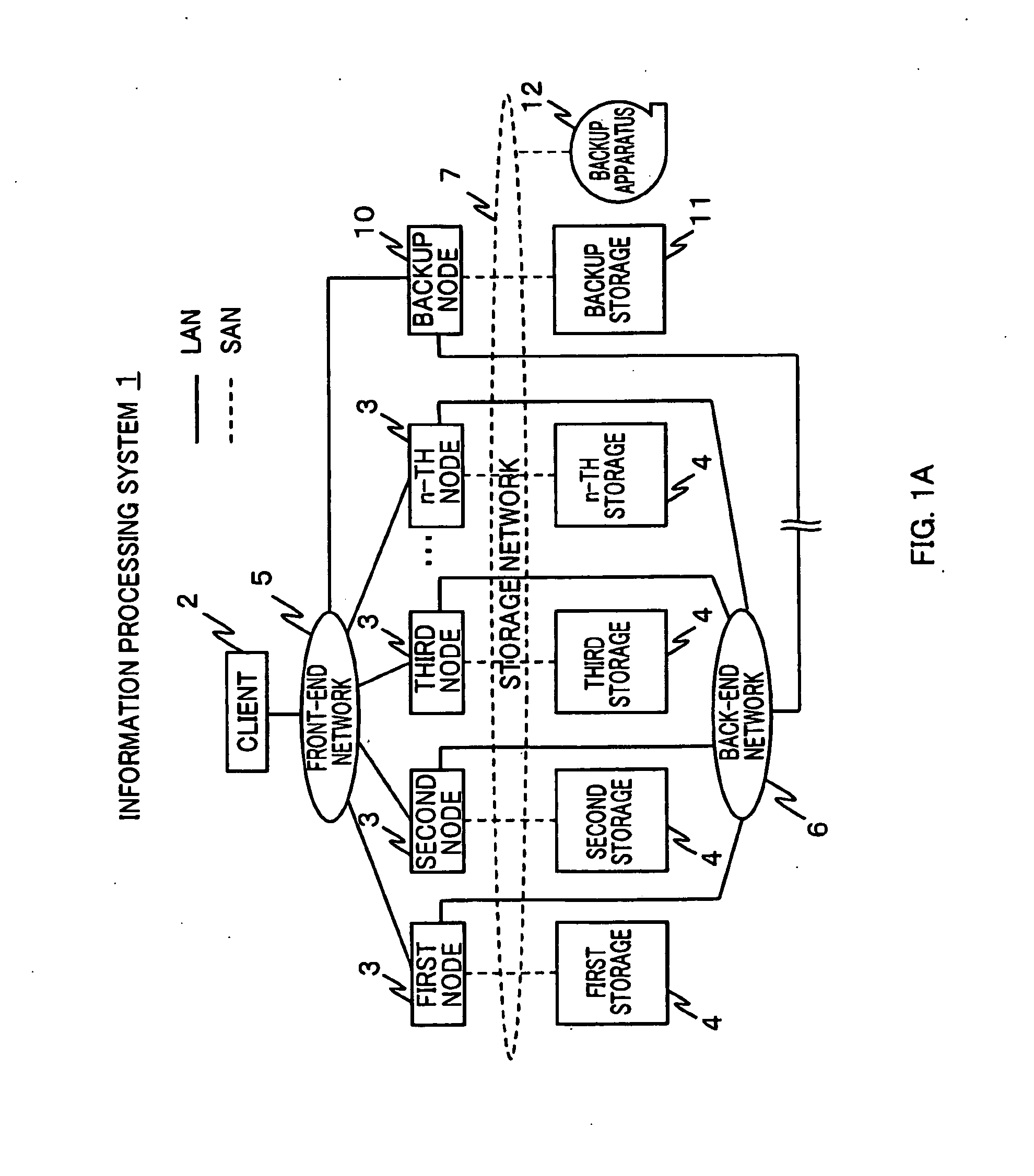
Information processing system and method of acquiring backup in an information processing system
InactiveUS20110238625A1Backup fileCreate efficientlyError detection/correctionDigital data processing detailsInformation processingVirtual file system
Provided is an information processing system including a plurality of nodes 3 and a plurality of storages 4 coupled subordinately to each of the nodes 3, each of the nodes 3 functioning as a virtual file system that provides a client 2 with storage regions of each of the storages 4 as a single namespace. This information processing system is further provided with a backup node 10 and a backup storage 11 coupled subordinately to the backup node 10. The backup node 10 synchronizes and holds location information (file management table 33) held by each of the nodes 3. Then, the backup node 10 creates a backup file, and stores the backup file in the backup storage 11 by accessing a location identified by the location information (file management table 43) synchronized and held by the backup node 10 itself to acquire a file.
Owner:HITACHI LTD
System and method for proxying network management protocol commands to enable cluster wide management of data backups
Owner:NETWORK APPLIANCE INC
Installing Software Applications in a Layered Virtual Workspace
InactiveUS20110061046A1Easy to manageImprove usabilityProgram loading/initiatingMemory systemsVirtualizationVirtual file system
A virtual workspace can include an active instance of a layered virtual file system namespace. A layered virtual file system namespace is referred to by the virtual workspace and includes a collection of system data (e.g. layered virtual file system base layer), user data (e.g. layered virtual file system user layer), and virtualized applications (e.g. virtual app layer), metadata and policies (e.g. layered virtual file system layer scope). Because a virtual workspace can include software such as an operating system and one or more applications in addition to user data, a virtual workspace can be aligned with a namespace so that an operating system of the virtual workspace may be located at a “base layer”, one or more applications executing on the operating system may be located at an upper “virtual app” layer, and user data in a virtual workspace may be found at any layer at or above the user layer.
Owner:VIRTUAL COMP
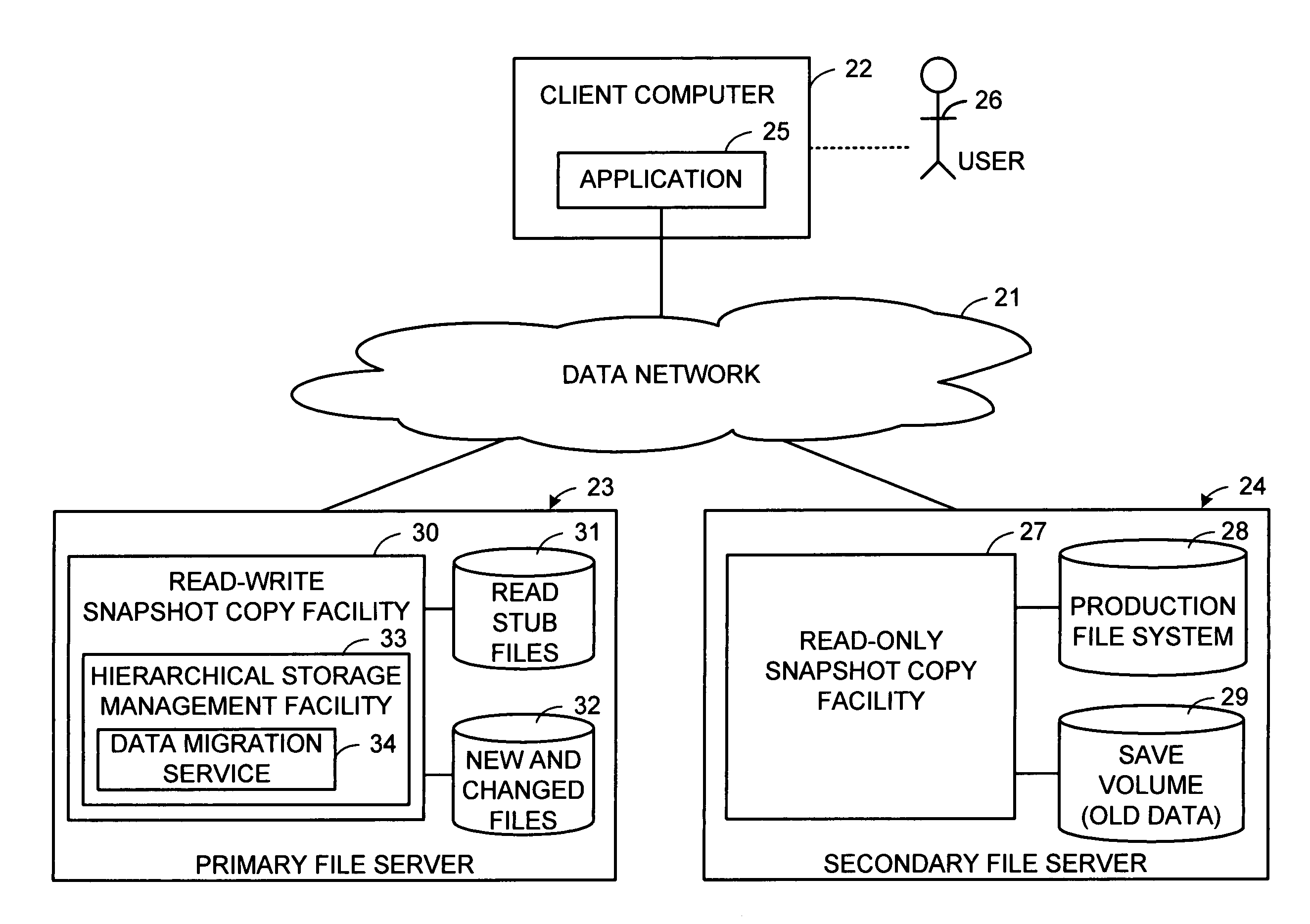
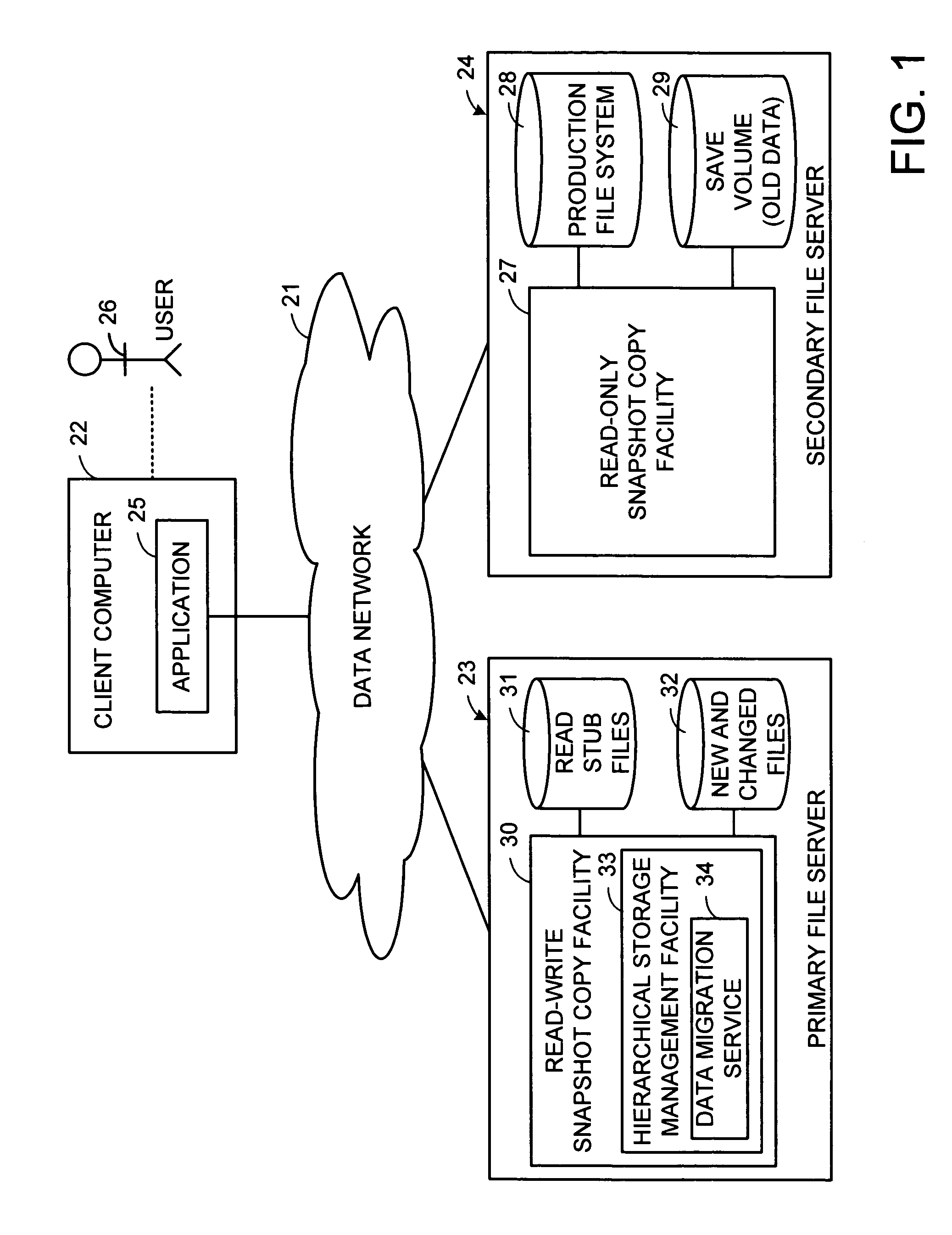
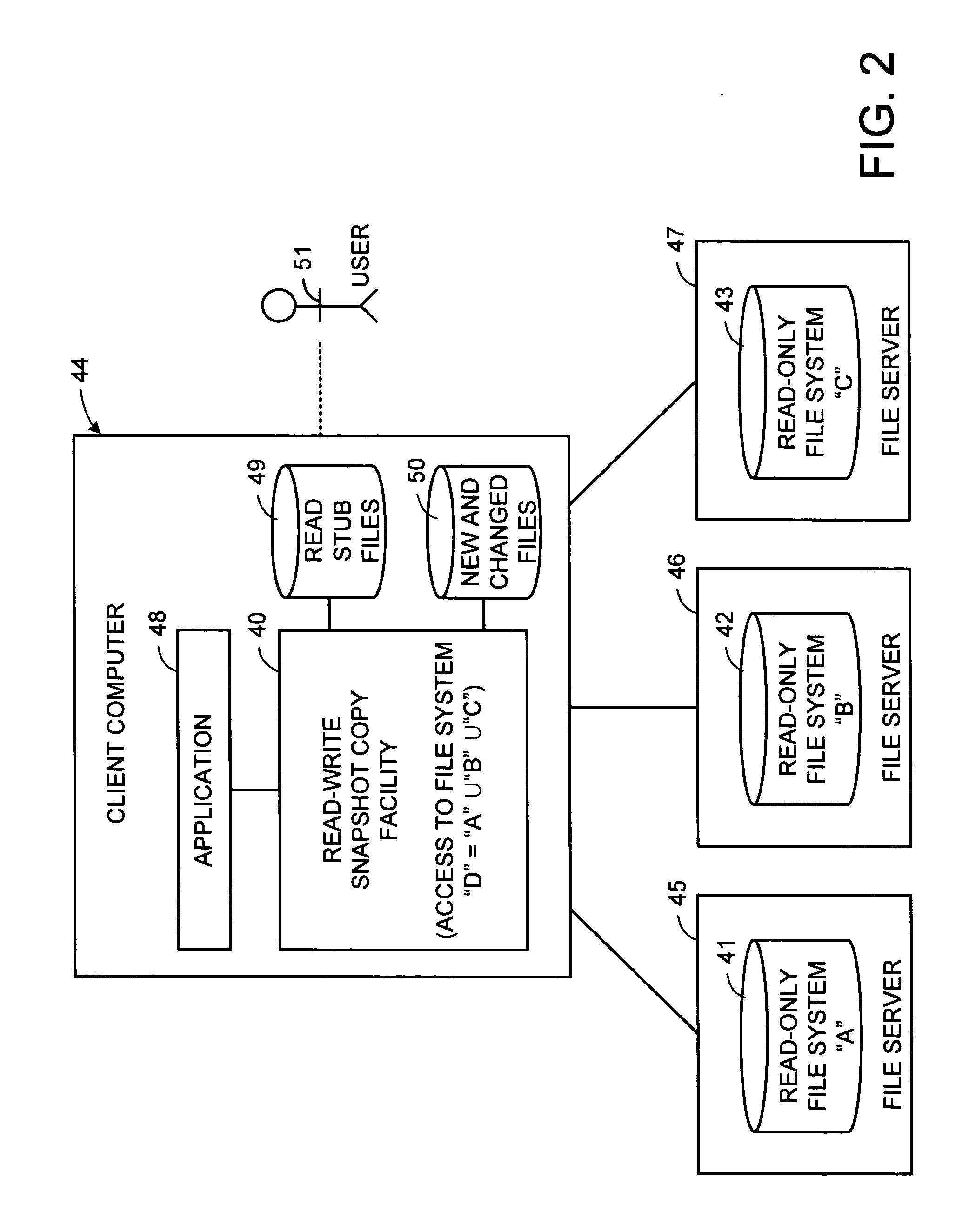
Distributed open writable snapshot copy facility using file migration policies
ActiveUS20060212481A1Data processing applicationsDigital data processing detailsFile systemHeterogeneous network
A read-write snapshot copy facility is constructed from a hierarchical storage management facility. The read-write snapshot copy file system initially comprises stub files pointing to the files in a read-only snapshot copy file system. When an application writes to a file in the read-write snapshot copy, the read-write snapshot copy facility migrates a copy of the file to replace the stub file, and then writes to the migrated file. Because the read-write snapshot copy facility references the files in the read-only snapshot file system in a network namespace using standard protocols such as NFS or CIFS, the read-write snapshot copy facility permits referencing of distributed read-only snapshot file systems in an open (heterogeneous) network environment, and the read-write snapshot copy is scalable by linking the read-write snapshot copy facility to multiple file servers containing read-only snapshot file systems.
Owner:EMC IP HLDG CO LLC
Collaborative team crawling:Large scale information gathering over the internet
InactiveUS6182085B1Reduce processing overheadEfficient accessDrawing from basic elementsData processing applicationsTree (data structure)Workload
A distributed collection of web-crawlers to gather information over a large portion of the cyberspace. These crawlers share the overall crawling through a cyberspace partition scheme. They also collaborate with each other through load balancing to maximally utilize the computing resources of each of the crawlers. The invention takes advantage of the hierarchical nature of the cyberspace namespace and uses the syntactic components of the URL structure as the main vehicle for dividing and assigning crawling workload to individual crawler. The partition scheme is completely distributed in which each crawler makes the partitioning decision based on its own crawling status and a globally replicated partition tree data structure.
Owner:IBM CORP
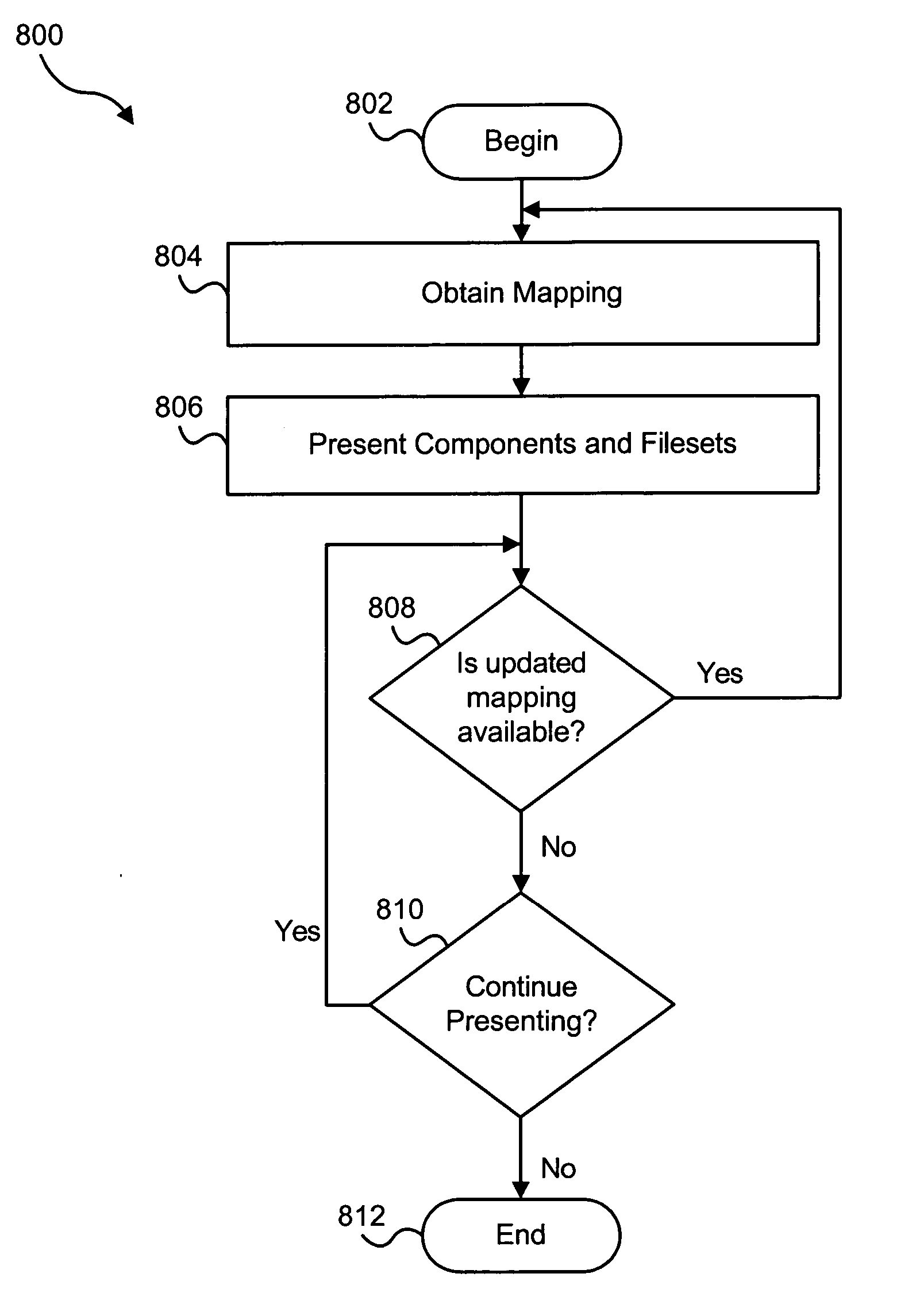
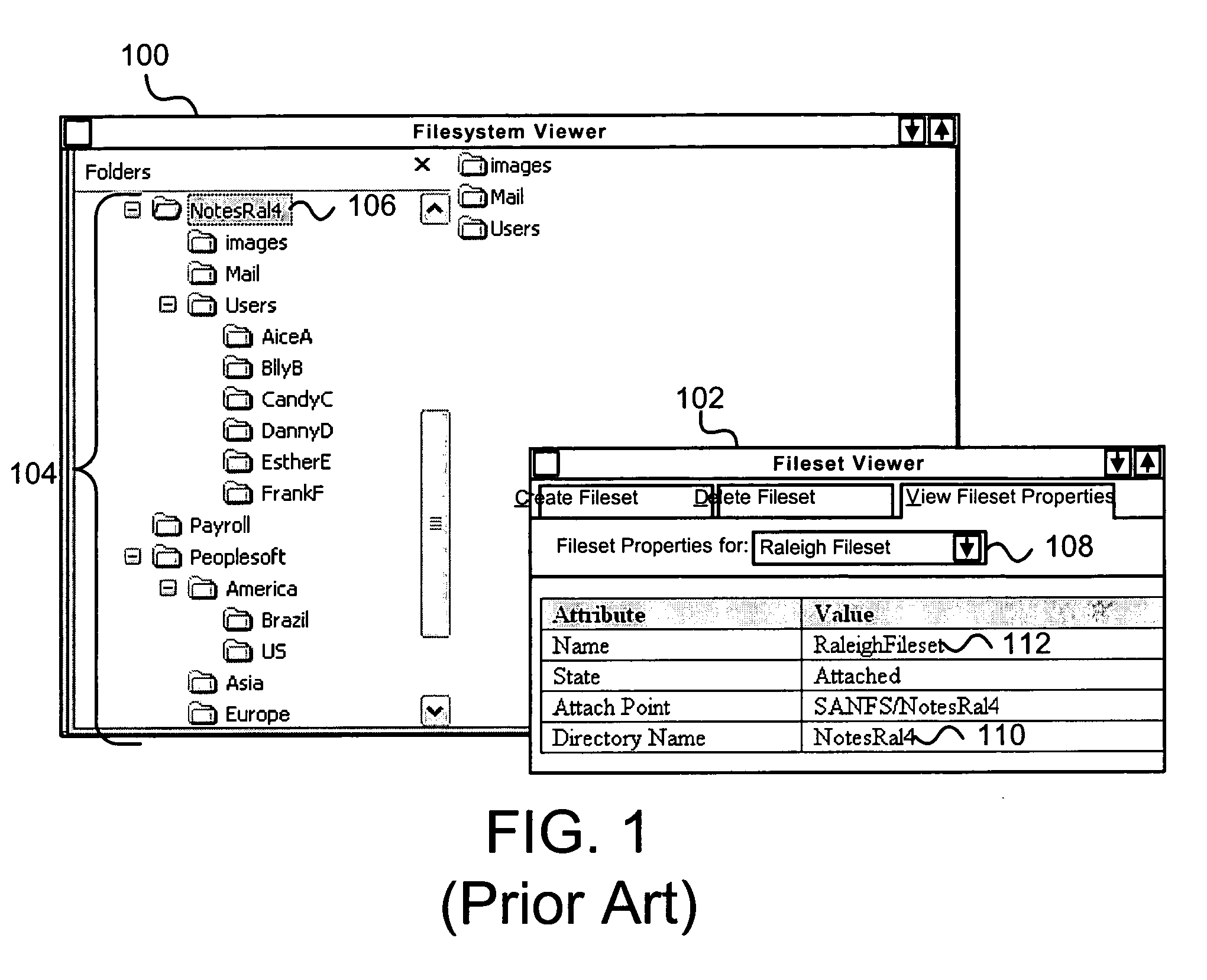
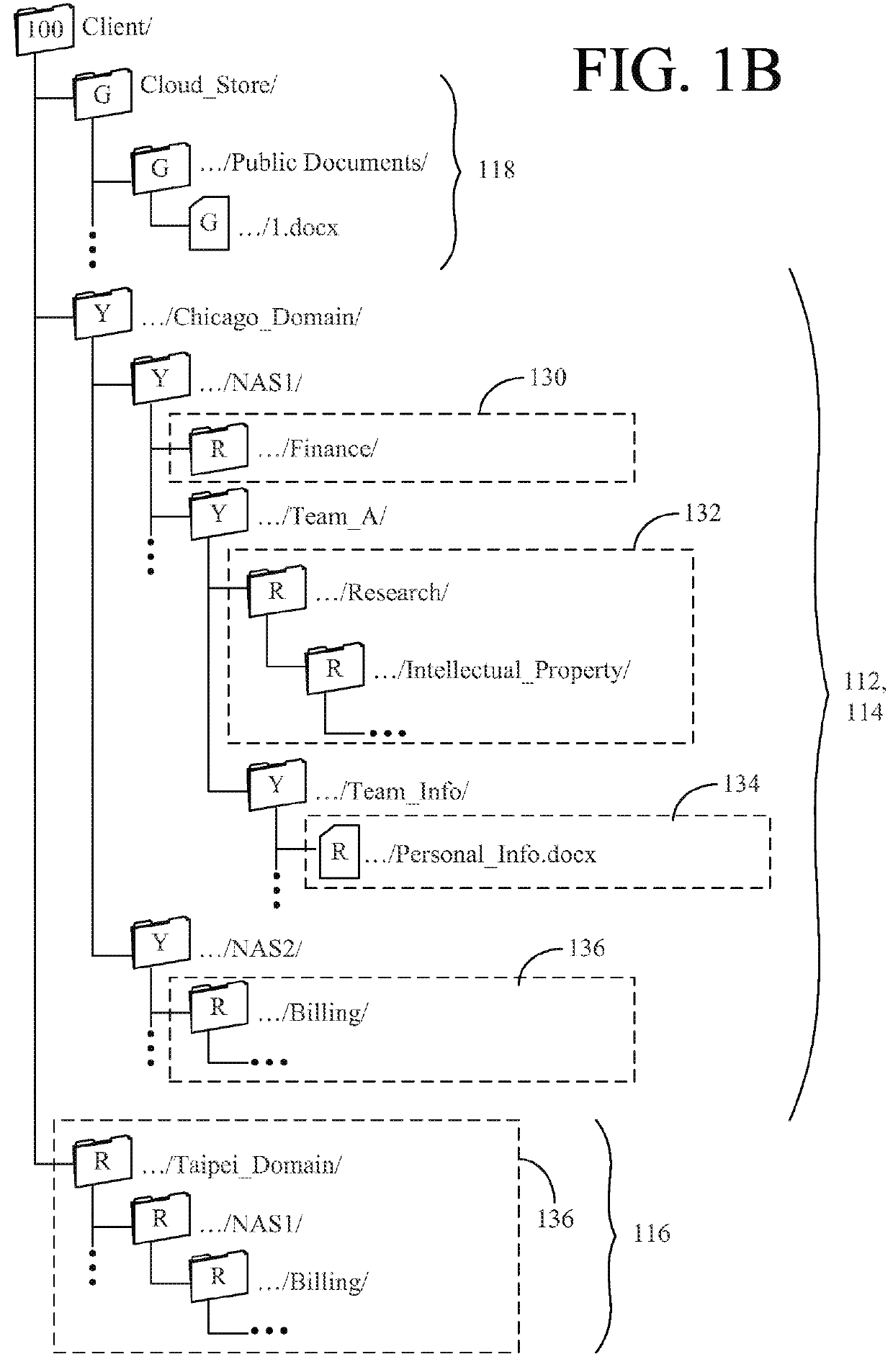
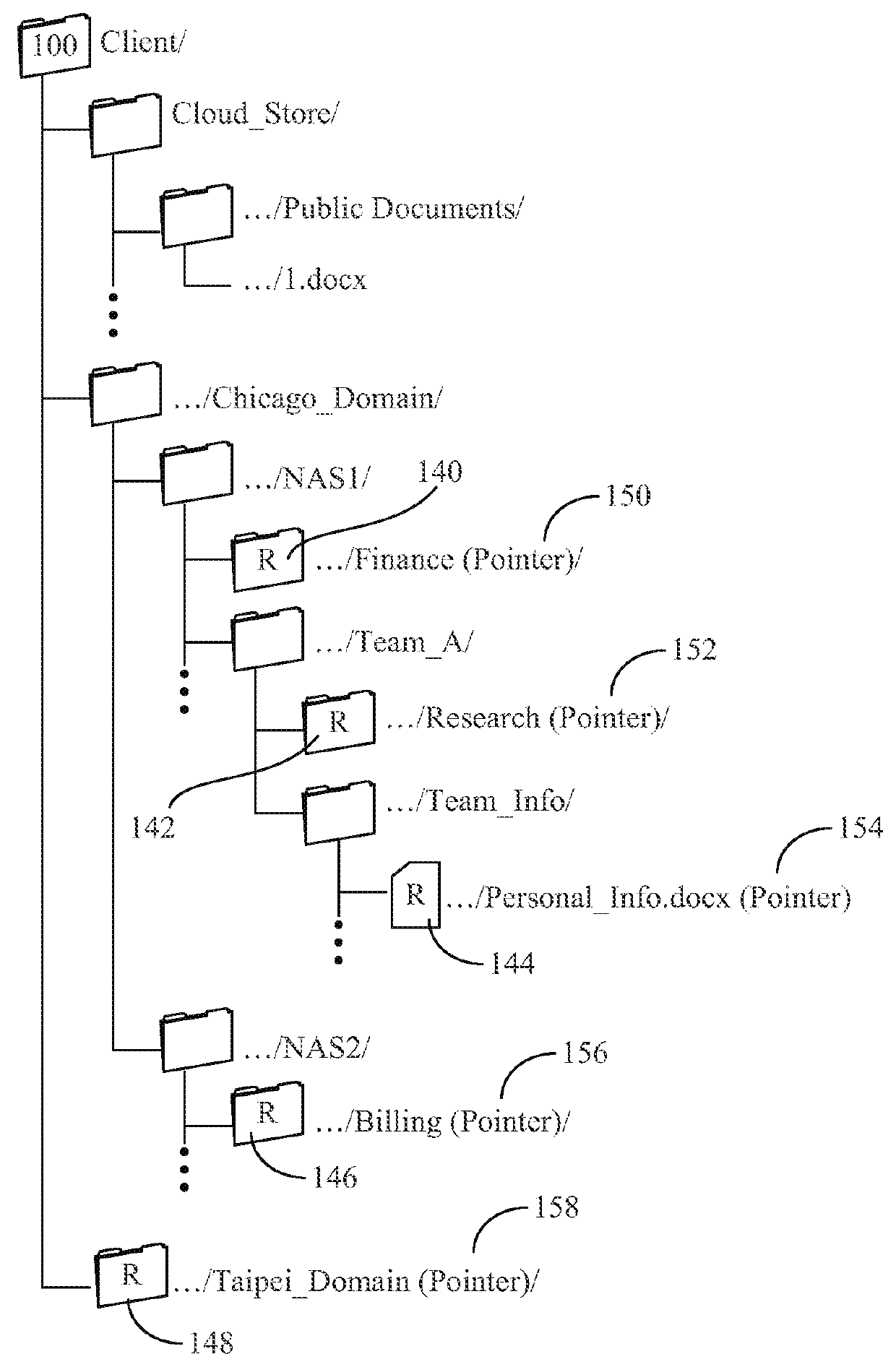
Apparatus, system, and method for presenting a mapping between a namespace and a set of computing resources
InactiveUS20060080465A1Digital data processing detailsMultiple digital computer combinationsGraphicsGraphical user interface
An apparatus, graphical user interface, system, and method are provided for presenting a mapping between a namespace and a set of computing resources. The apparatus includes an input module, a format module, and an output module. The input module obtains a mapping between namespace identifiers and a set of computing resources. The format module associates a namespace identifier and a computing resource according to the mapping. The output module provides the namespace identifiers and the associated computing resource corresponding to each namespace identifier. A graphical user interface includes a window with a file system pane and a fileset pane. The file system pane includes a first tree control that displays the components of the file system. The fileset pane includes a second tree control that displays the filesets. The tree controls are updated in response to user input in either the file system pane or the fileset pane.
Owner:IBM CORP
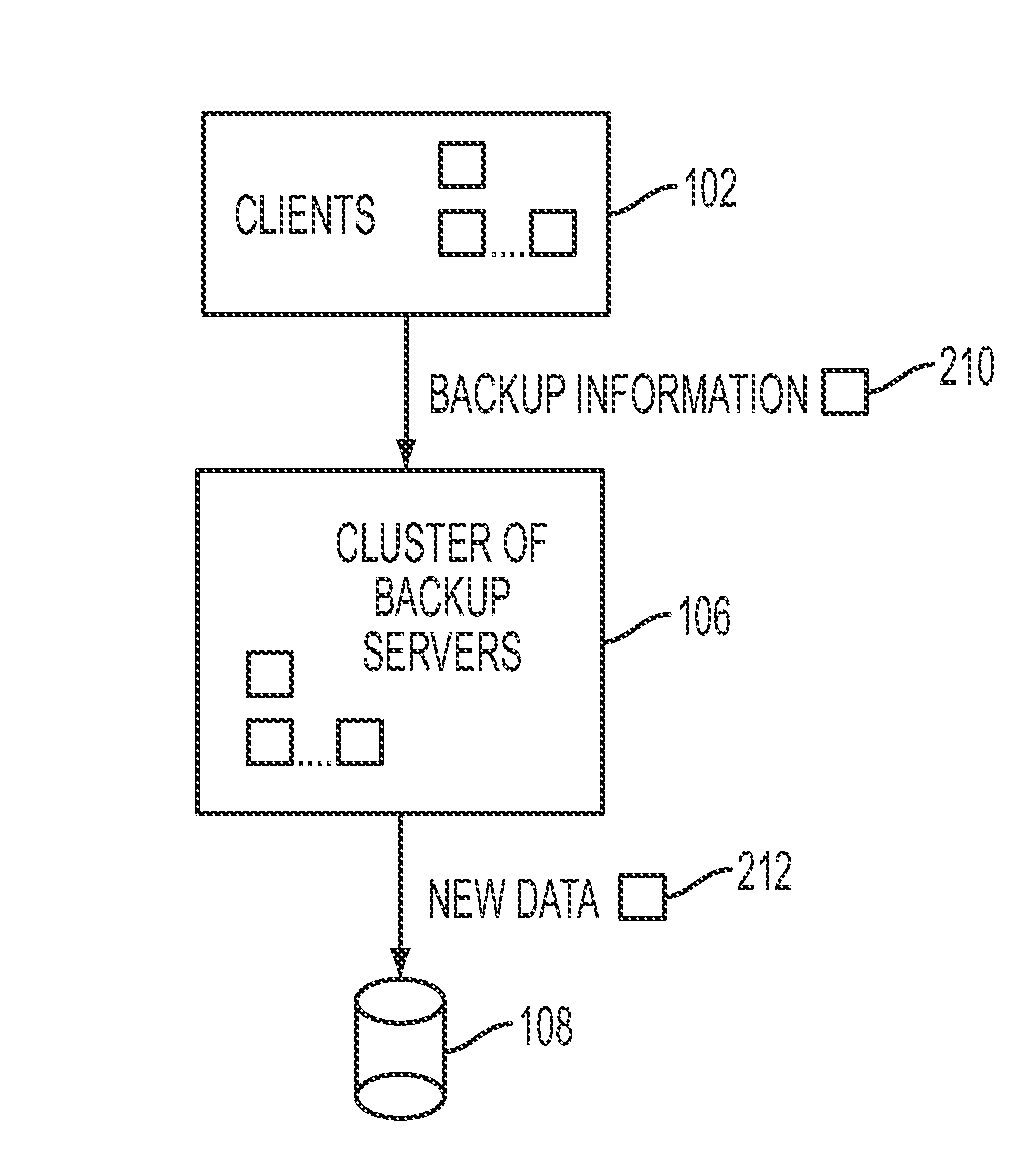
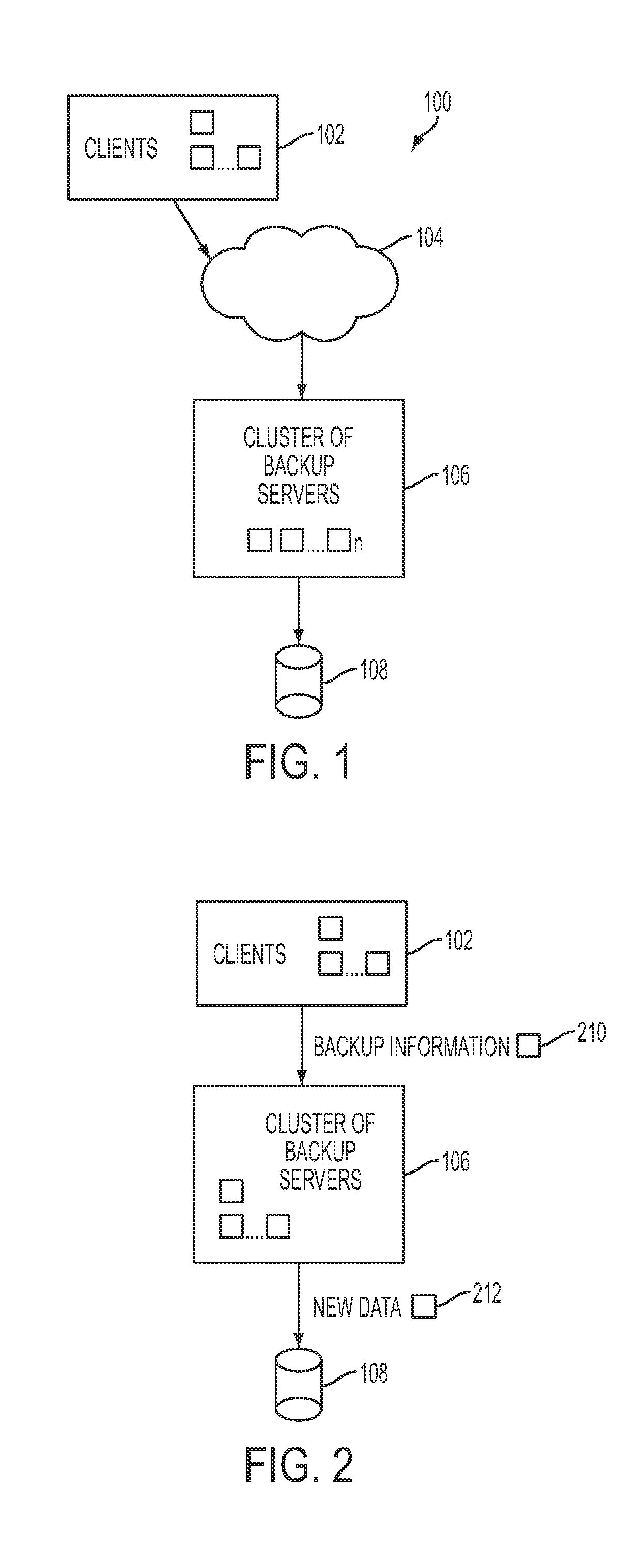
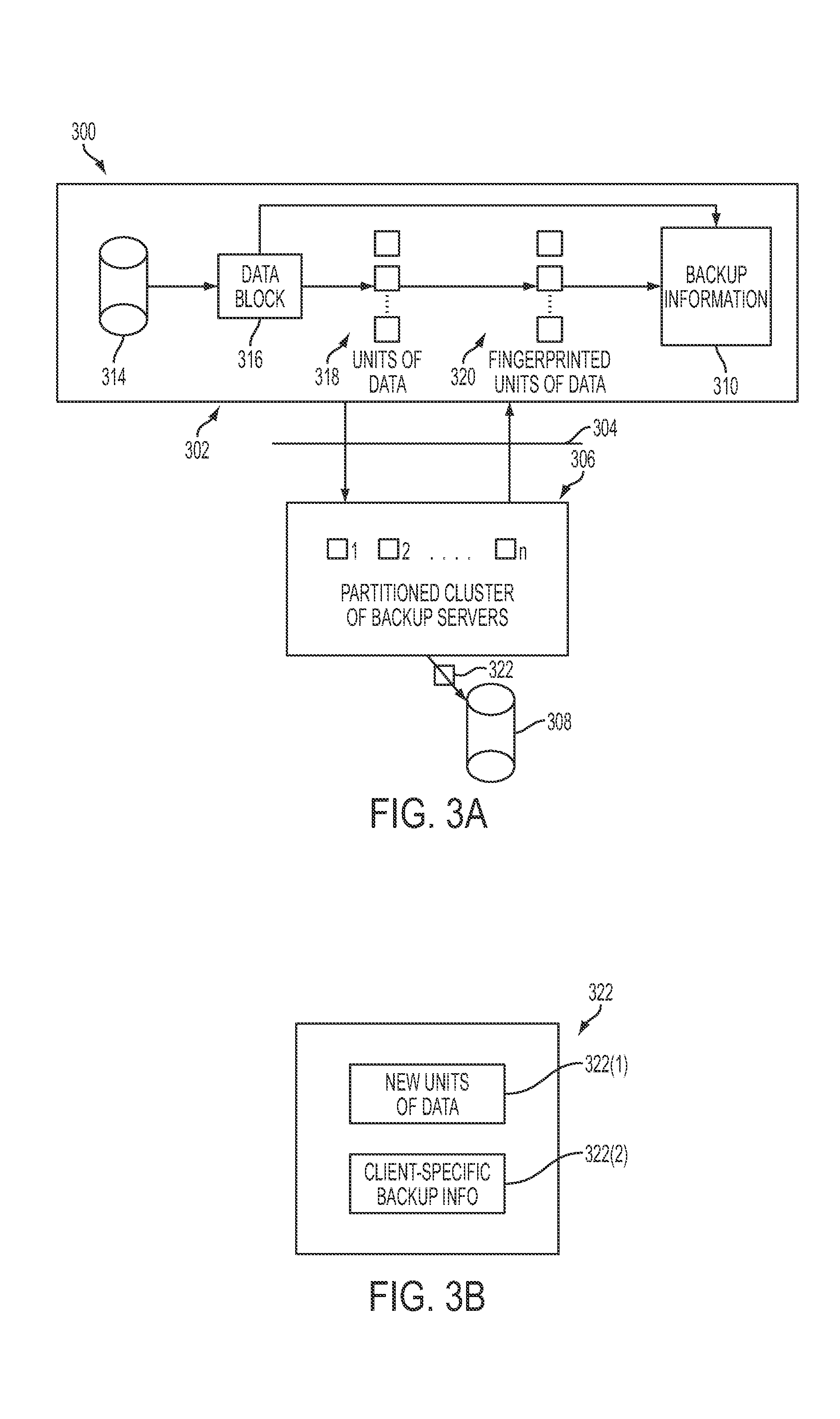
Remote backup and restore
ActiveUS20100106691A1Memory loss protectionDigital data processing detailsNamespaceData deduplication
In one embodiment of the present invention, a data-backup method includes partitioning a fingerprint namespace among a cluster of backup servers, the fingerprint namespace comprising fingerprints for representing units of data, each backup server of the cluster of backup servers managing units of data having fingerprints corresponding to an assigned partition of the fingerprint namespace. The method further includes receiving backup information from a client computing device for a block of data comprising units of data, the backup information including at least a fingerprint for each of the units of data and client-specific backup information. In addition, the method includes, utilizing the fingerprint for each of the units of data, deduplicating the units of data in parallel at the cluster of backup servers in accordance with the partitioning step, the deduplicating step comprising identifying ones of the units data already stored by the cluster of backup servers.
Owner:QUEST SOFTWARE INC
Systems and methods for facilitating access to private files using a cloud storage system
ActiveUS9251114B1Facilitates accessing fileOvercome problemsDatabase distribution/replicationDigital data protectionFile systemObject store
A method for providing access to objects associated with a particular client in a cloud storage system is disclosed. The method includes the steps of establishing a connection with a user, providing a client namespace associated with the client to the user, where the client namespace represents objects stored on the cloud storage system and objects stored on a private storage system apart from the cloud storage system, receiving a request from the user to access an object stored on the private storage system, and providing information to the user to facilitate access to the object stored on the private storage system by said user. Other systems and methods are also disclosed. Important advantages of the present invention are facilitated by separating the logic for user access (control plane) from the actual storage (Storage plane). Private file system access can still be managed from the cloud, while keeping the client data private.
Owner:EGNYTE
Internal object protection from application programs
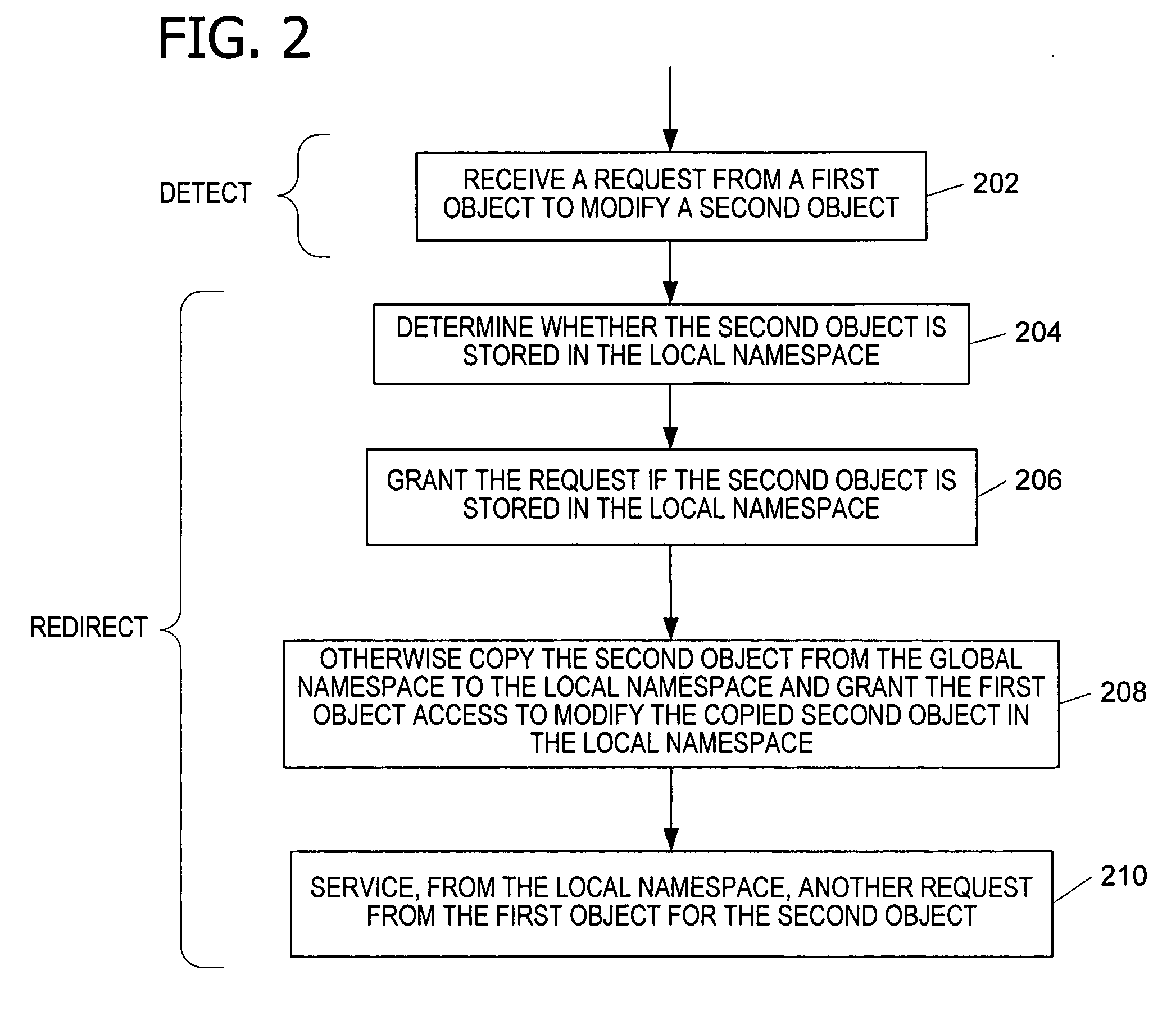
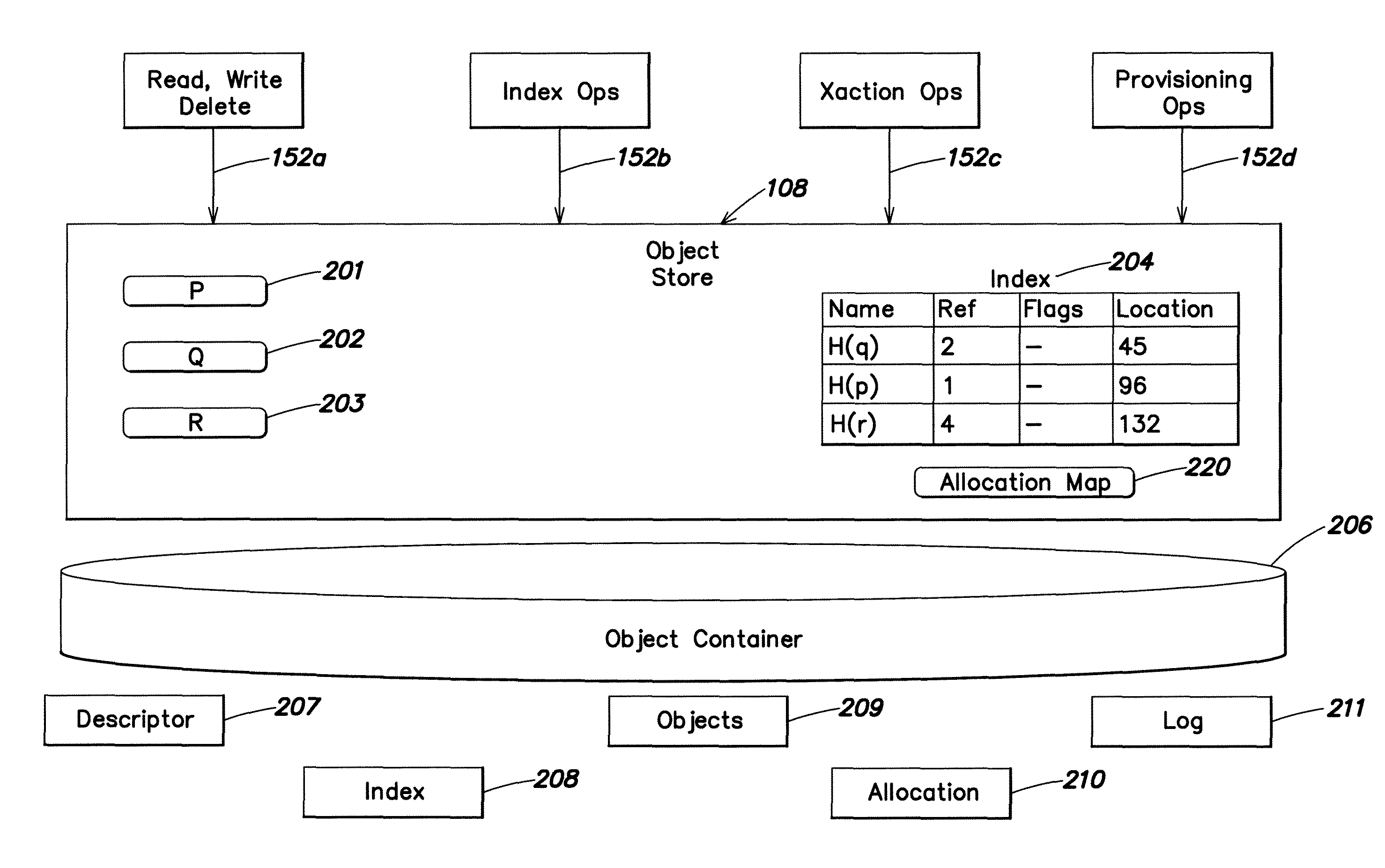
InactiveUS20050091214A1Reduce the possibilityResource allocationDigital data processing detailsOperational systemObject store
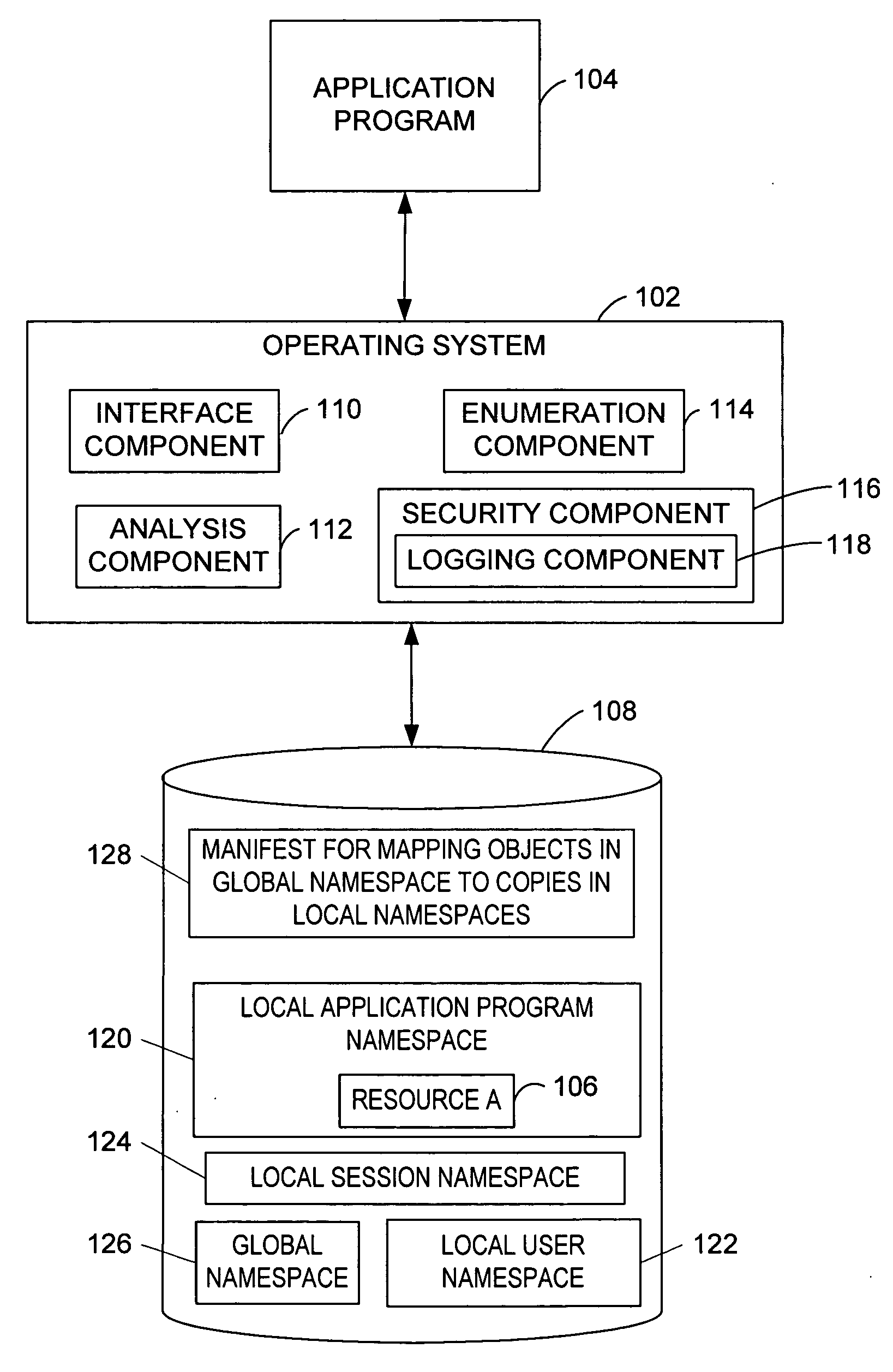
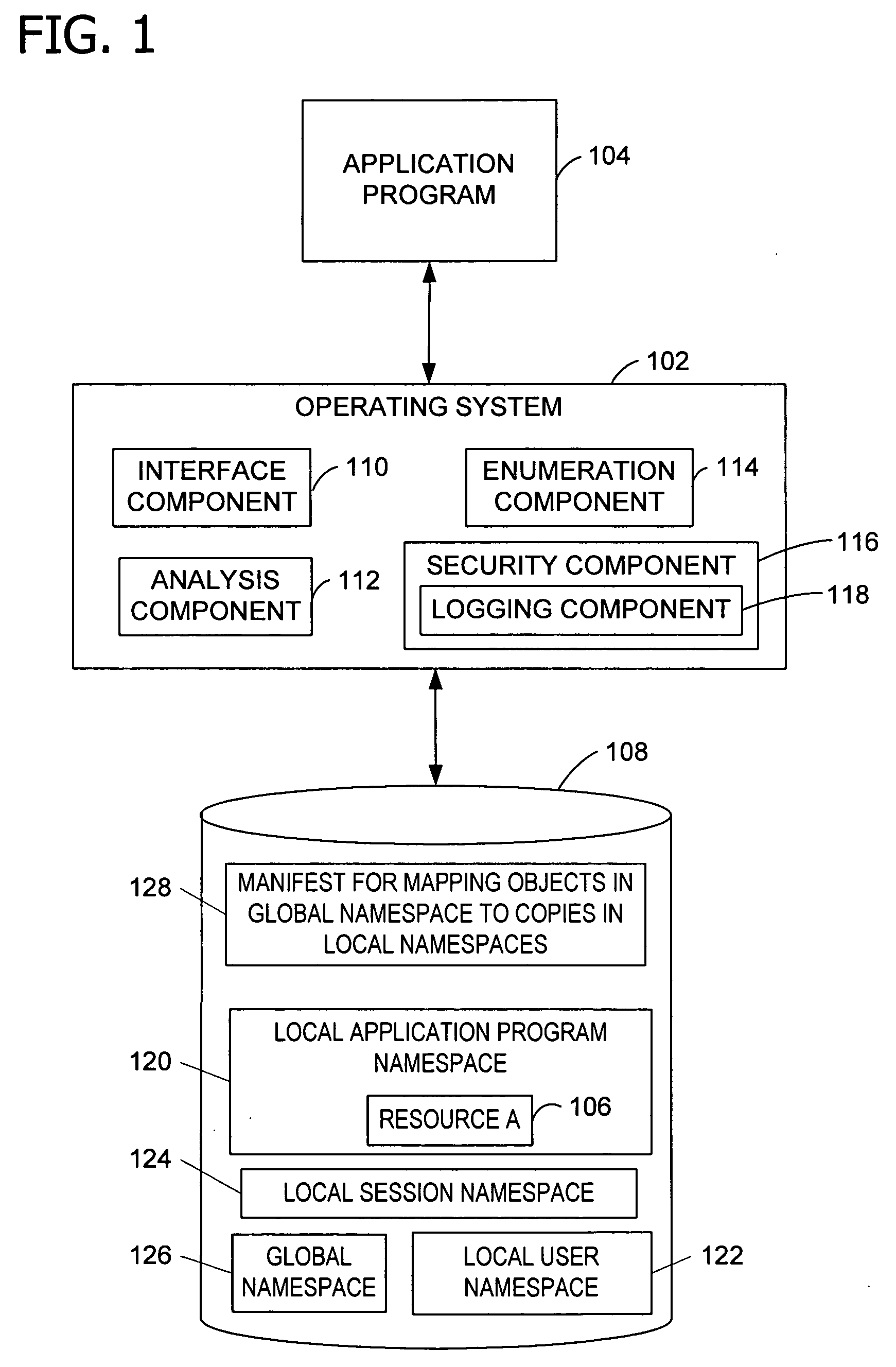
Granting an executable object (e.g., an application program, thread, or process) access to a namespace object (e.g., a named object, resource, file, or folder). A request by the executable object for the namespace object is intercepted and processed to determine whether a local namespace associated with the executable object, user, or session stores a copy of the requested namespace object. If the copy exists in one of the local namespaces, the request is granted and allowed to operate on that local namespace. If the requested namespace object exists only in a global namespace, the namespace object is copied to a local namespace. The request is then granted and allowed to operate on the copy of the namespace object in the local namespace. Protecting the namespace objects stored in the global namespace from modification improves the stability of the application program and operating system.
Owner:MICROSOFT TECH LICENSING LLC
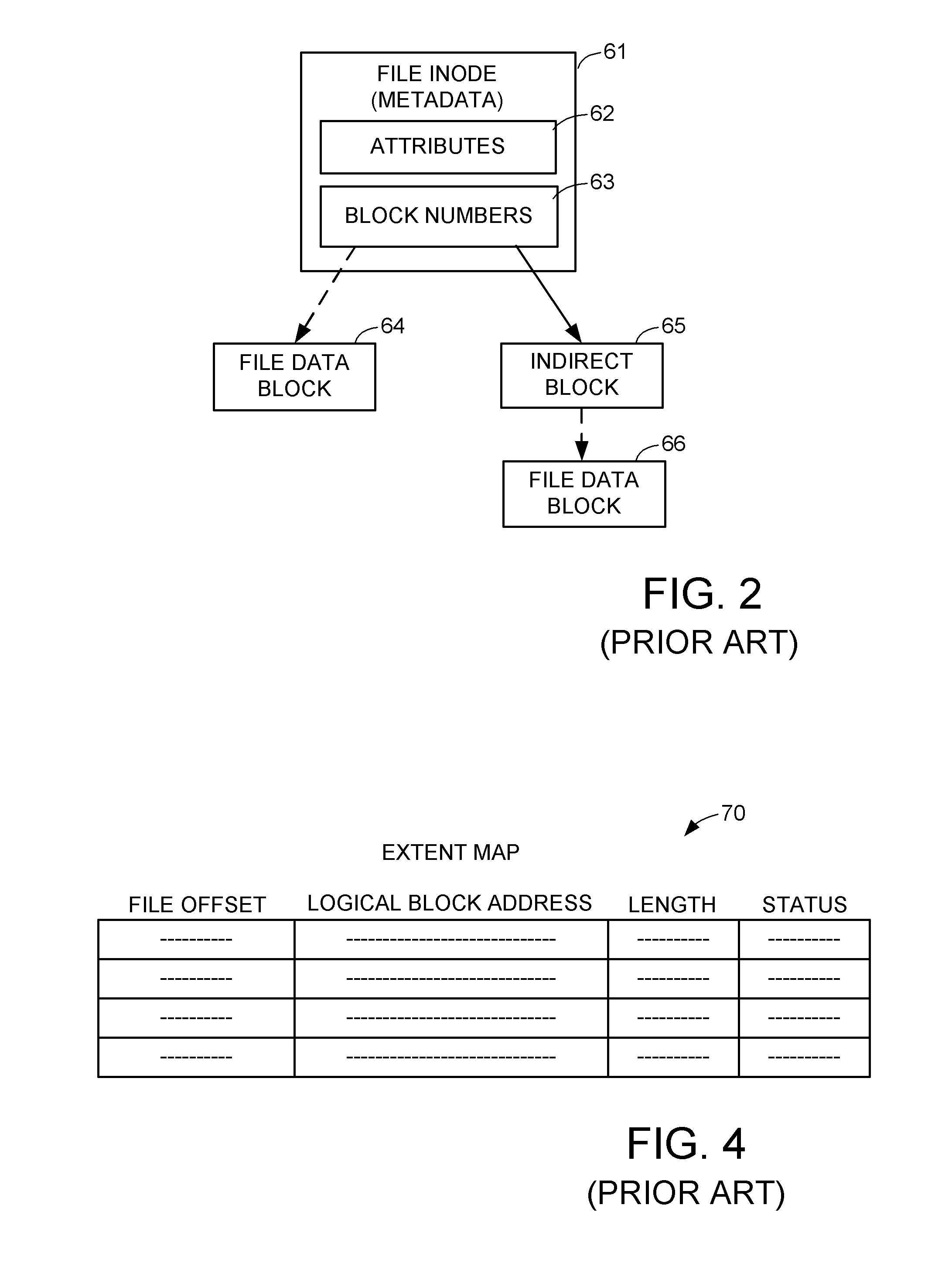
Serverless distributed file system
InactiveUS7062490B2Improve performanceData processing applicationsDigital data processing detailsByzantine fault toleranceDistributed File System
A serverless distributed file system manages the storage of files and directories using one or more directory groups. The directories may be managed using Byzantine-fault-tolerant groups, whereas files are managed without using Byzantine-fault-tolerant groups. Additionally, the file system may employ a hierarchical namespace to store files. Furthermore, the directory group may employ a plurality of locks to control access to objects (e.g., files and directories) in each directory.
Owner:MICROSOFT TECH LICENSING LLC
Distributed object-oriented appliance control system
InactiveUS20080188963A1Error detection/correctionInterprogram communicationDistributed objectControl system
The invention relates to an object-oriented control system for an appliance, configurable by a configuration mechanism in selective operable communication with a plurality of object oriented control systems using a packet protocol for constructing messages comprising identifiers from a plurality of namespaces associated with the building blocks of object-oriented systems. The meaning of each unique identifier within class library namespace is uniquely meaningful throughout a universe of appliances.
Owner:WHIRLPOOL CORP
System and method for partitioning a file system for enhanced availability and scalability
ActiveUS7653699B1Digital computer detailsSpecial data processing applicationsVirtual file systemFile system
A method and system are provided for partitioning a file system. The system may include one or more server computer systems and a plurality of physical file systems. The physical file systems may be hosted by the one or more server computer systems. The physical file systems may be accessible to clients through a virtual file system having a single namespace. The virtual file system may include metadata which are partitioned across the plurality of physical file systems. The server computer systems may be configured to independently perform file system consistency checks on each of the physical file systems, in order to independently validate each partition of the metadata.
Owner:SYMANTEC OPERATING CORP
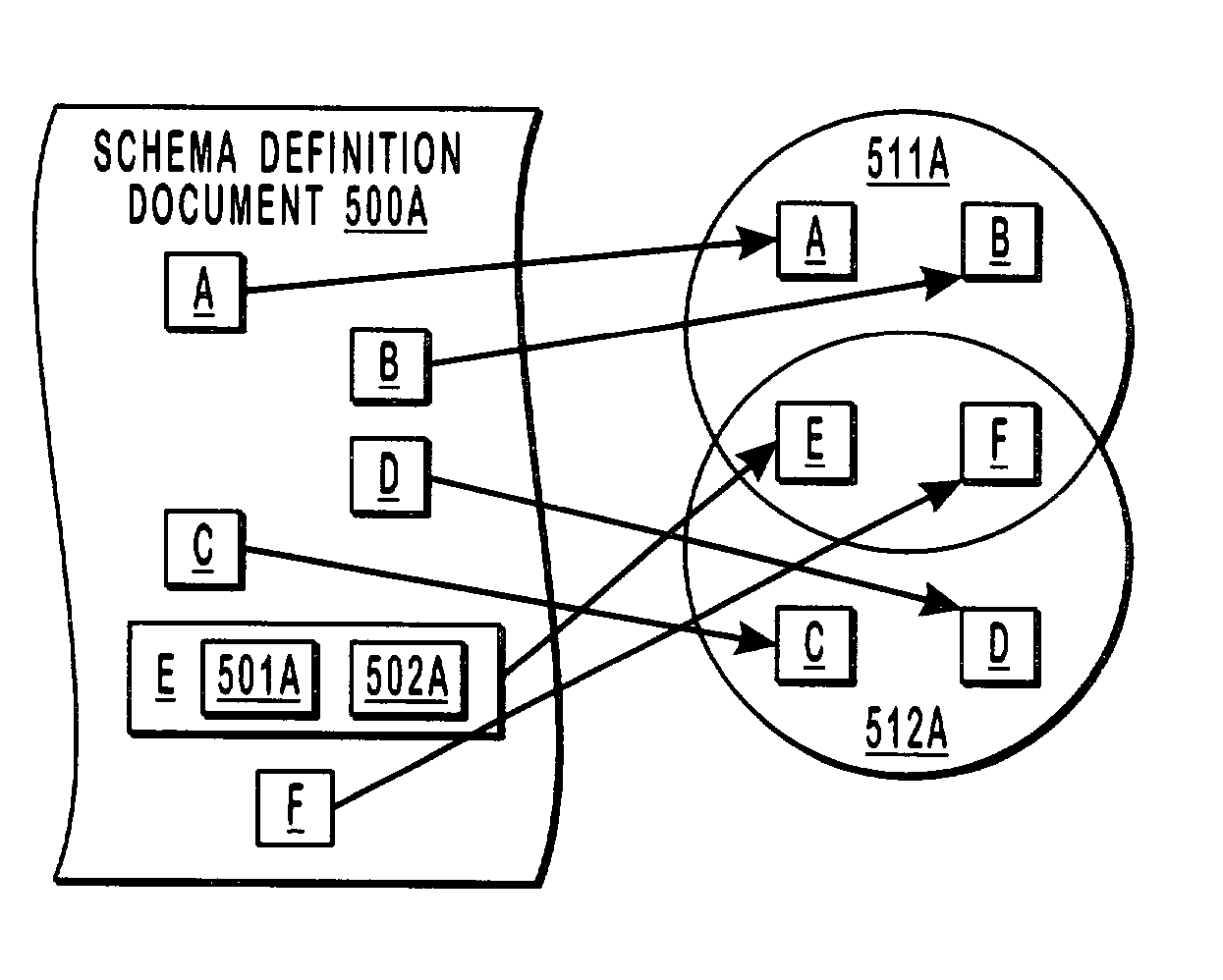
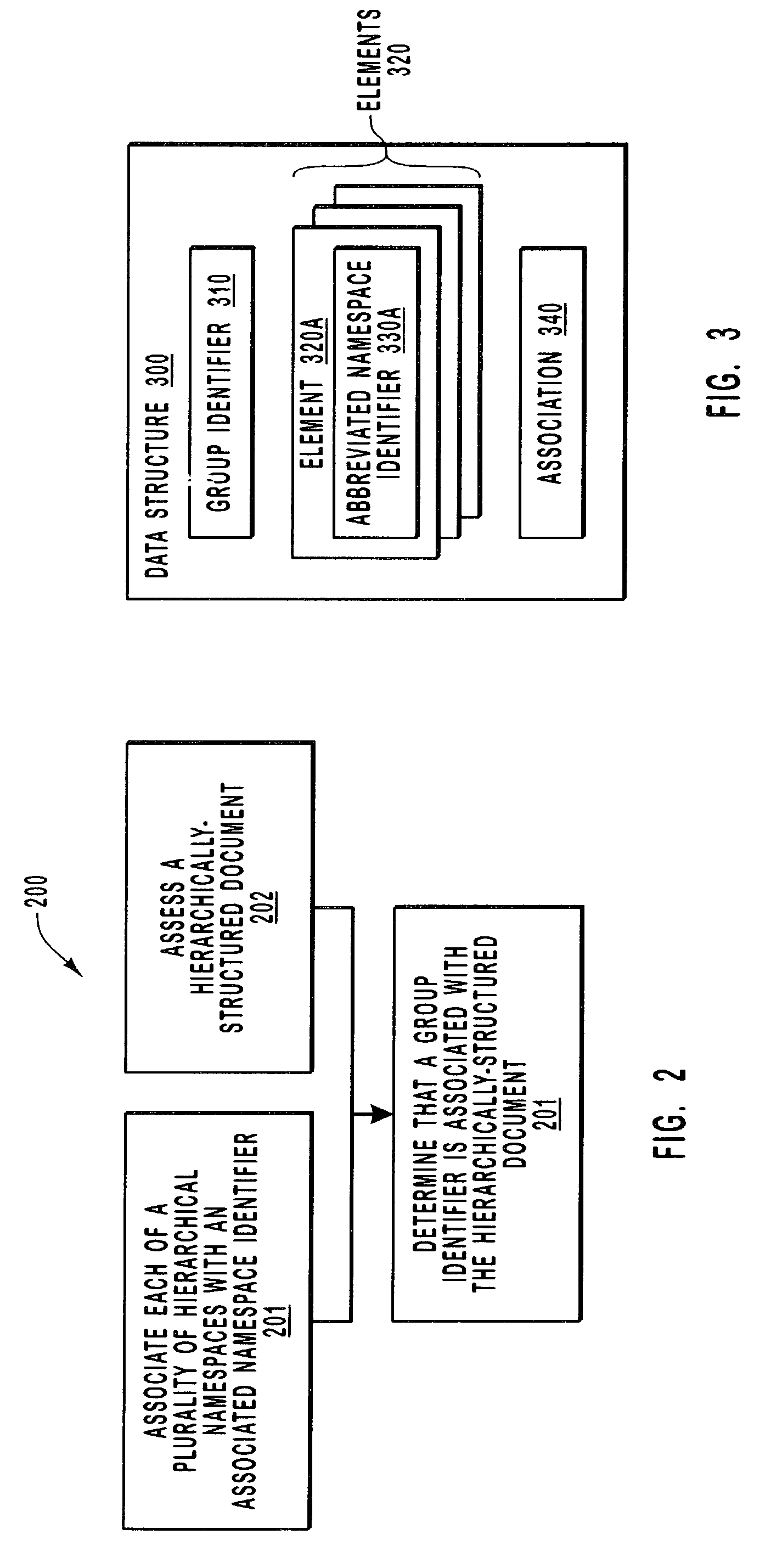
Grouping and nesting hierarchical namespaces
InactiveUS6993714B2Reduce sizeDigital data information retrievalDigital computer detailsXML namespaceIdenticon
A group identifier represents an association between each of a number of different abbreviated namespace identifiers with a corresponding hierarchical namespace (e.g., an XML namespace). A hierarchically-structured document (e.g., an XML document) is accessed by a computing system that determines that the group identifier is associated with the hierarchically-structured document. Hence, when using the abbreviated namespace identifiers in the hierarchically-structured document, the computing system knows that the corresponding namespace is associated with the designated portions of the hierarchically-structured document. Also, a schema description language document (e.g., an XSD document) may specify multiple target namespaces for a single element. Accordingly, groupings of elements may be included in different namespaces to creating overlapping or even nested namespaces.
Owner:MICROSOFT TECH LICENSING LLC
Object storage system with local transaction logs, a distributed namespace, and optimized support for user directories
ActiveUS9710535B2Maintain efficiencyProvide benefitsDigital data information retrievalUser identity/authority verificationTransaction logObject storage
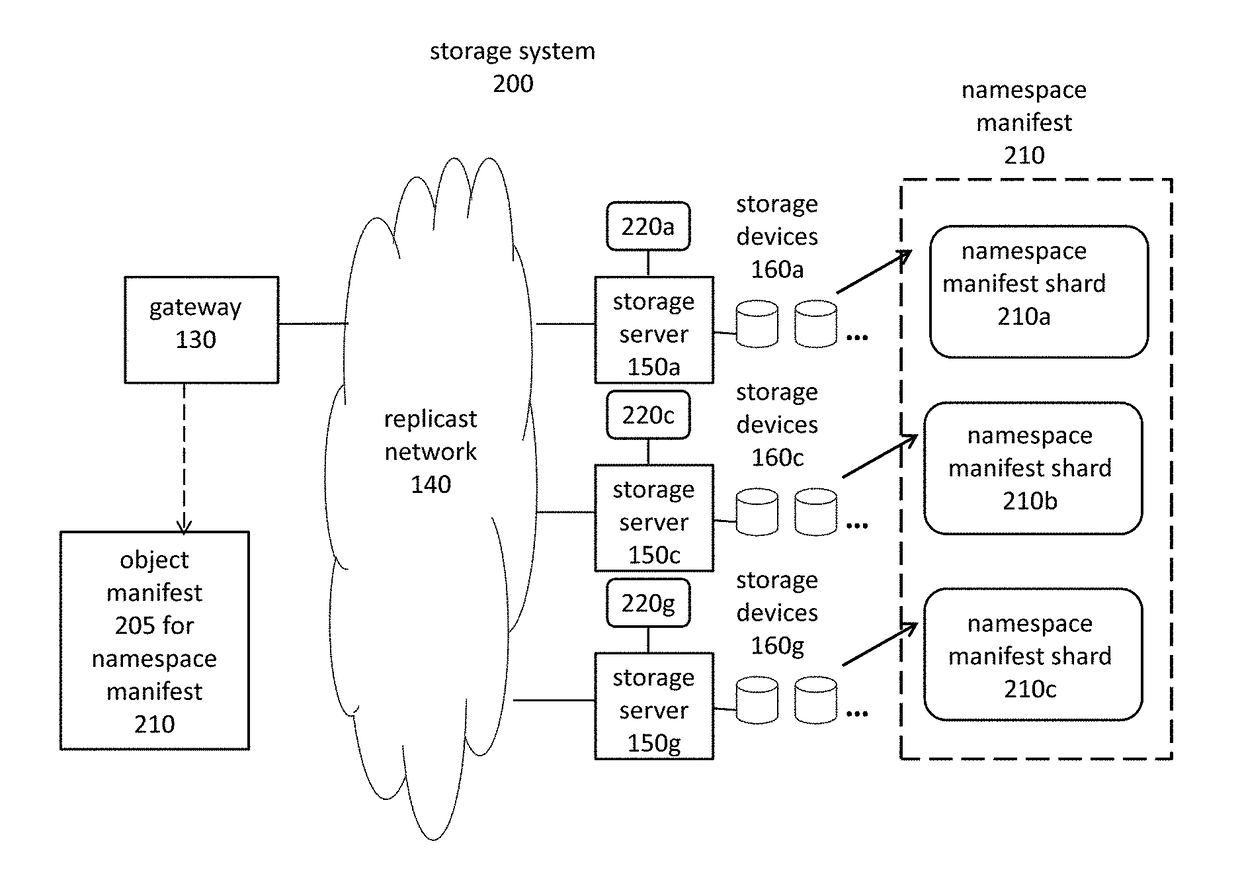
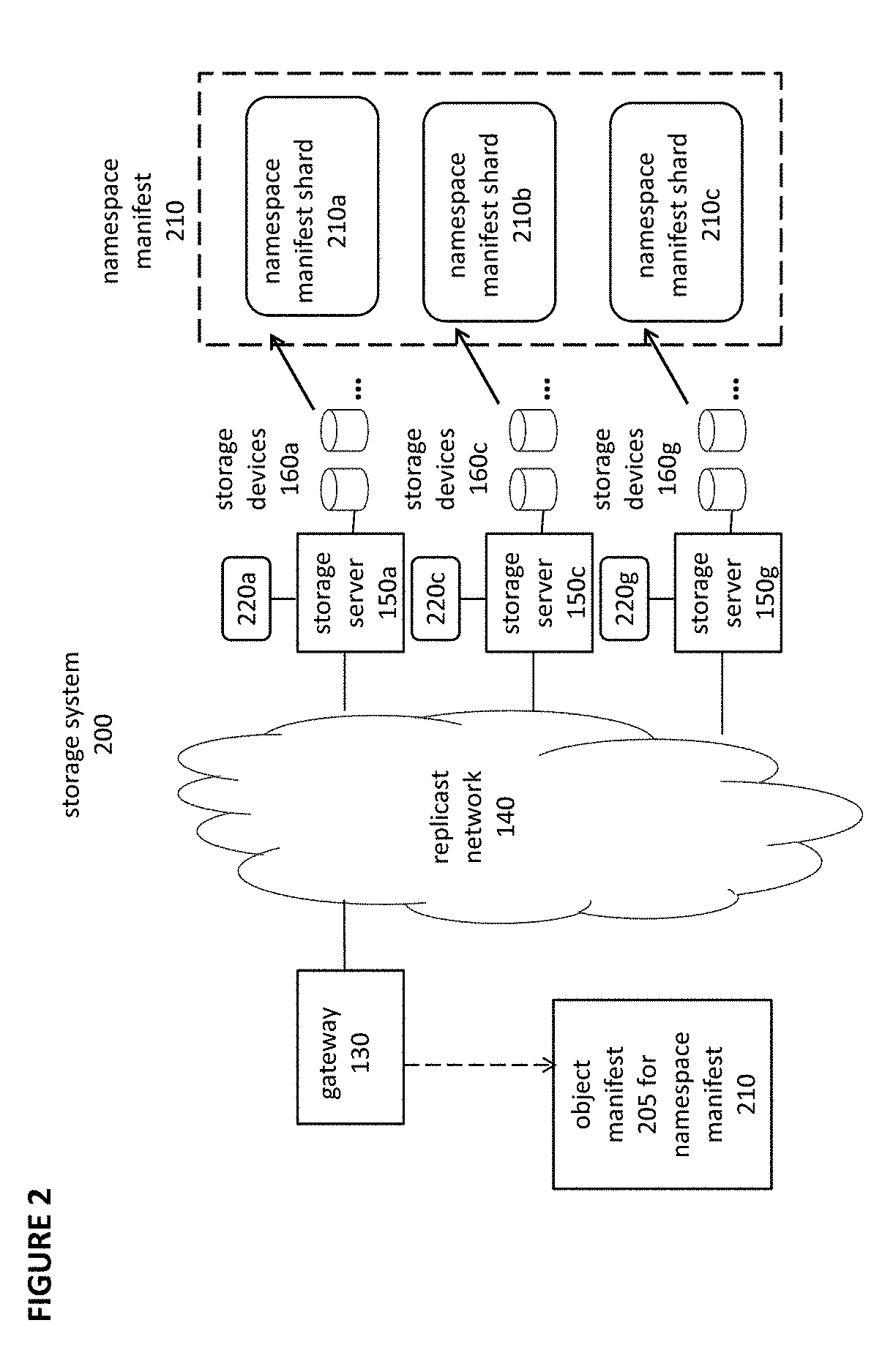
The present invention relates to object storage systems that support hierarchical directories within a namespace manifest stored as an object. The namespace manifest is stored as namespace manifest shards that are determined based on a partial key derived from the full name of the referenced version manifest in each directory entry. Each storage server maintains a local transaction log that keeps track of changes to the namespace manifest in response to put transactions. The namespace manifest can be updated after each put transaction is acknowledged, which minimizes the number of write operations required for a put transaction. Updates to the namespace manifest are batched, distributed, and processed concurrently and in parallel by the storage servers that store the corresponding shards. This reduces the latency that would otherwise exist in the object storage cluster as a result of a put transaction. Updates to namespace manifest shards optionally occur in a batch process using MapReduce techniques.
Owner:NEXENTA BY DDN INC
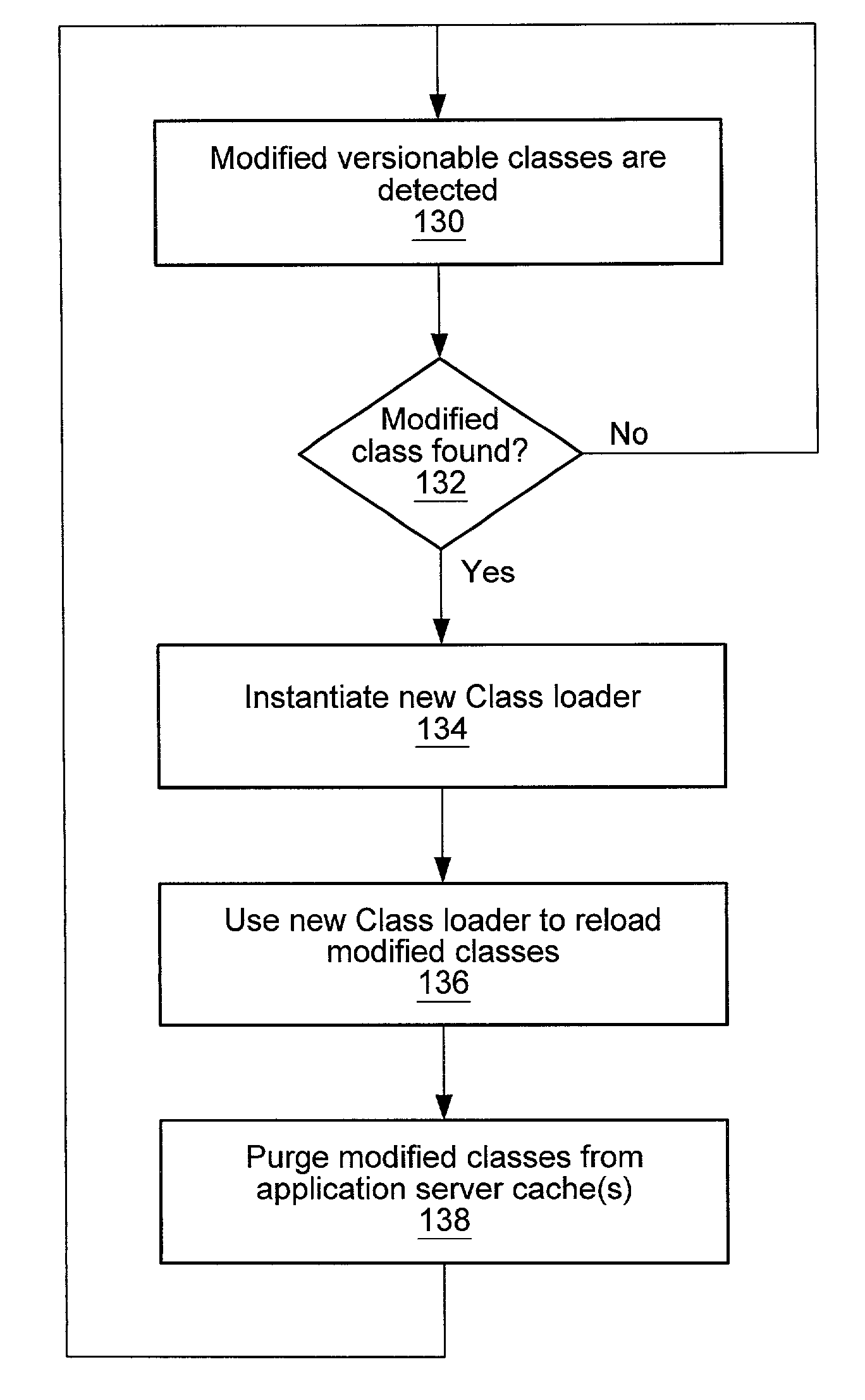
Class dependency graph-based class loading and reloading
Embodiments of a system and method for providing class dependency graph-based class loading and reloading may be used to segregate namespaces in a graph-centric way, and may provide a set of normalized topologies that may be used to efficiently support hot-swapping of programmatic logic such as classes, applets, and beans, among other applications. Embodiments may provide a domain-independent, flexible and robust namespace segregation technique that is based on the dependency between the various classes and not on details like the roles the classes play. The problem of segregating namespaces is formulated as a graph theory problem, and a solution is sought through graph techniques. The graph may be normalized by identifying and grouping interdependent classes and non-interdependent classes in separate groups. A directed dependency relationship of the groups may be determined using the relationships between the member classes of the groups.
Owner:ORACLE INT CORP
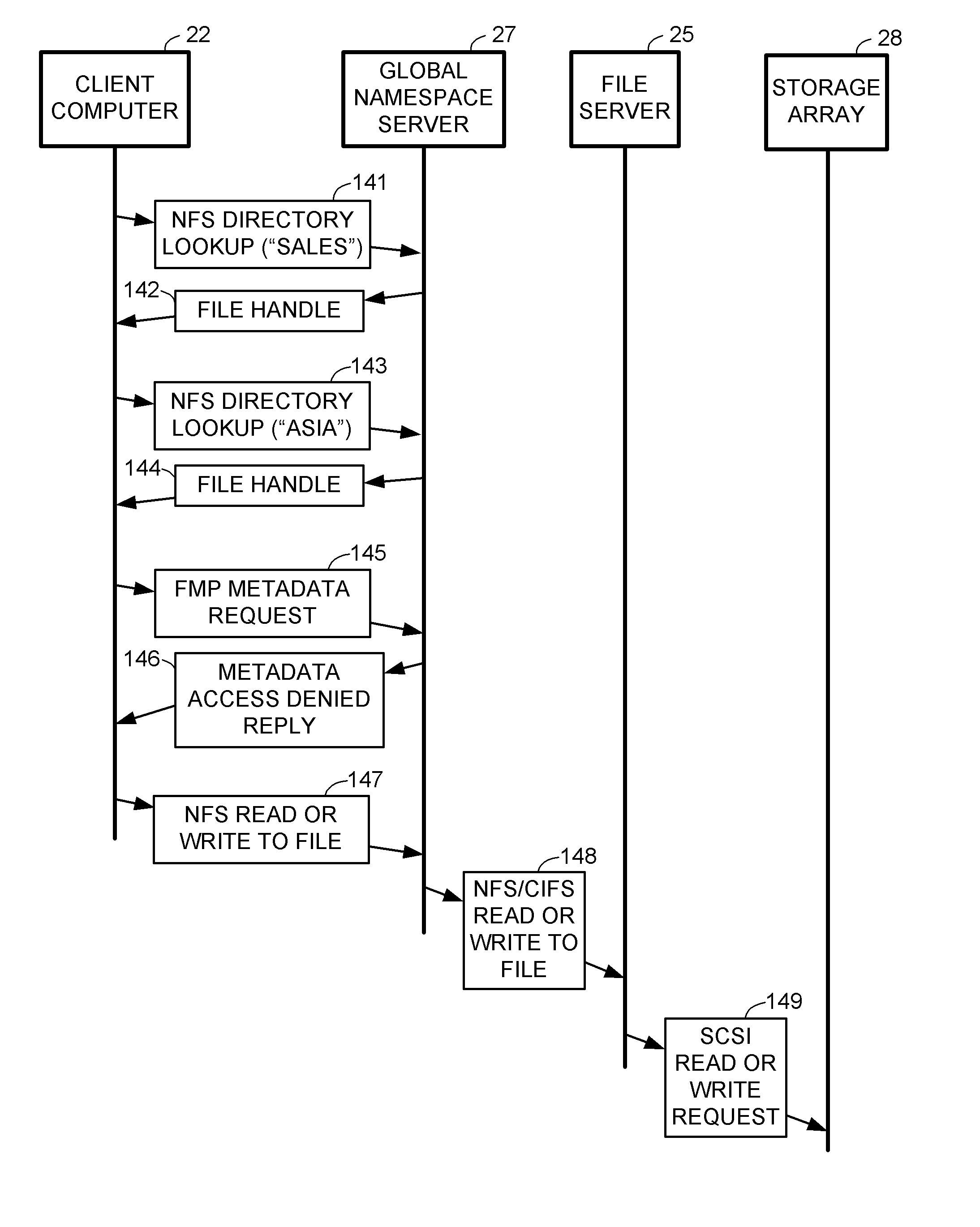
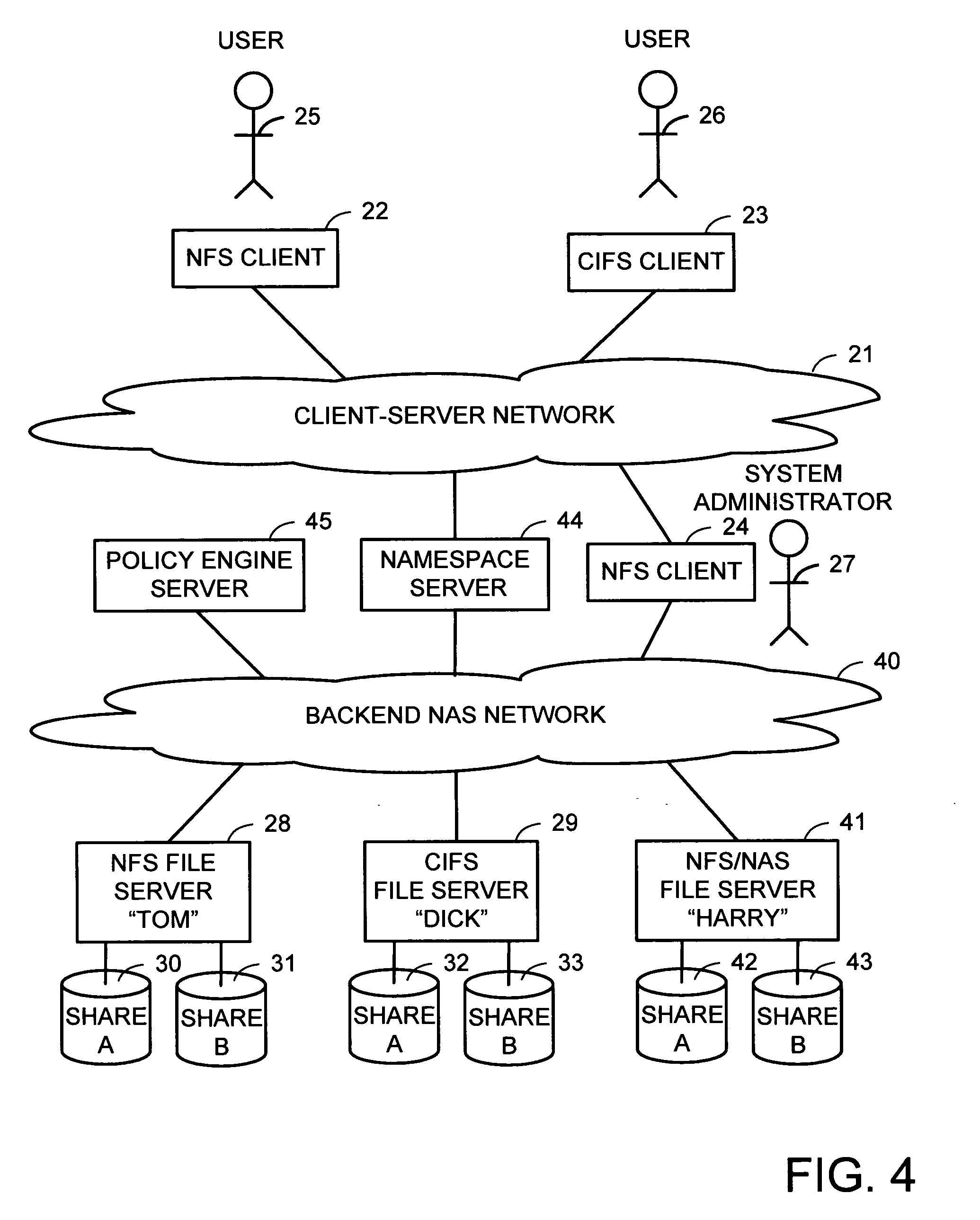
Scalable global namespace through referral redirection at the mapping layer
ActiveUS7937453B1Increase speedDigital data information retrievalDigital data processing detailsVirtual file systemStorage area network
Client computers, a namespace server, and file servers are linked in a data network so that the namespace server provides the clients with NFS or CIFS access to a virtual file system including files stored in the file servers, and also provides migration of files between the file servers in a fashion transparent to the client access using NFS or CIFS. The client computers and storage arrays storing the file data are also linked in a storage area network so that the clients have high speed block access to the file data using a file mapping protocol. The namespace server redirects a metadata access request in the file mapping protocol from a client to the appropriate file server when the file is not being migrated, and otherwise denies the metadata access request when the file is being migrated so that the client reverts to NFS or CIFS access.
Owner:EMC IP HLDG CO LLC
Mapping XML schema components to qualified Java components
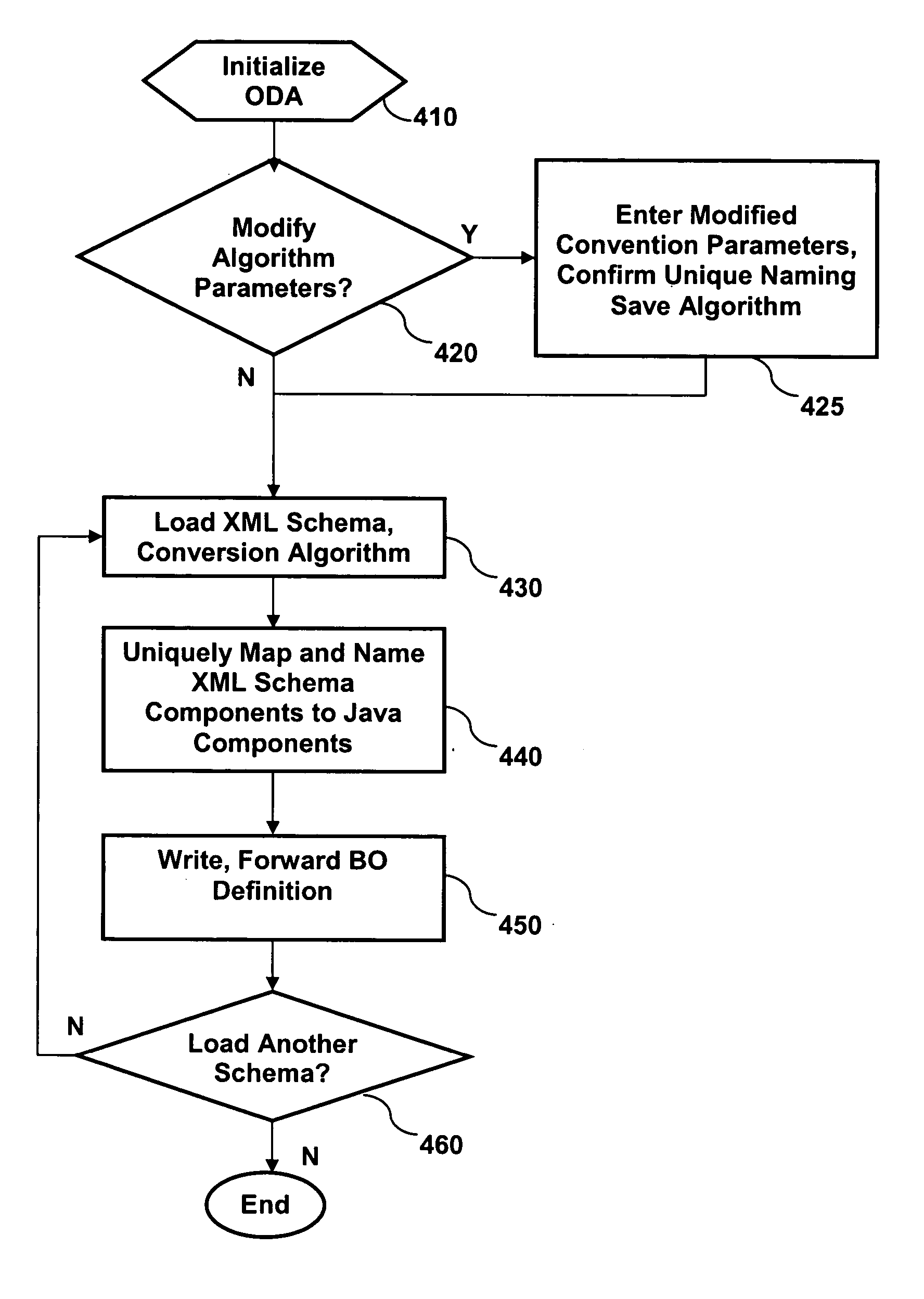
InactiveUS20050114394A1Data processing applicationsSemi-structured data mapping/conversionXML schemaNamespace
The present invention provides a method, apparatus, and computer instructions for mapping and labeling XML schema elements and types. In an exemplary embodiment, each XML schema element and type is uniquely labeled, using distinguishing parameters such as namespace to create name parts like a Hashing code and suffixes in order to achieve unique mapping. The parameters selected are predetermined in order to achieve naming that remains distinct across successive consumptions of a schema. The selection disclosed accomplishes unique labeling, while also permitting one to still adhere to the strict naming standards of the target language (e.g., Java). As a result, schema components belonging to multiple namespaces can be mapped to Java components belonging to a single package.
Owner:IBM CORP
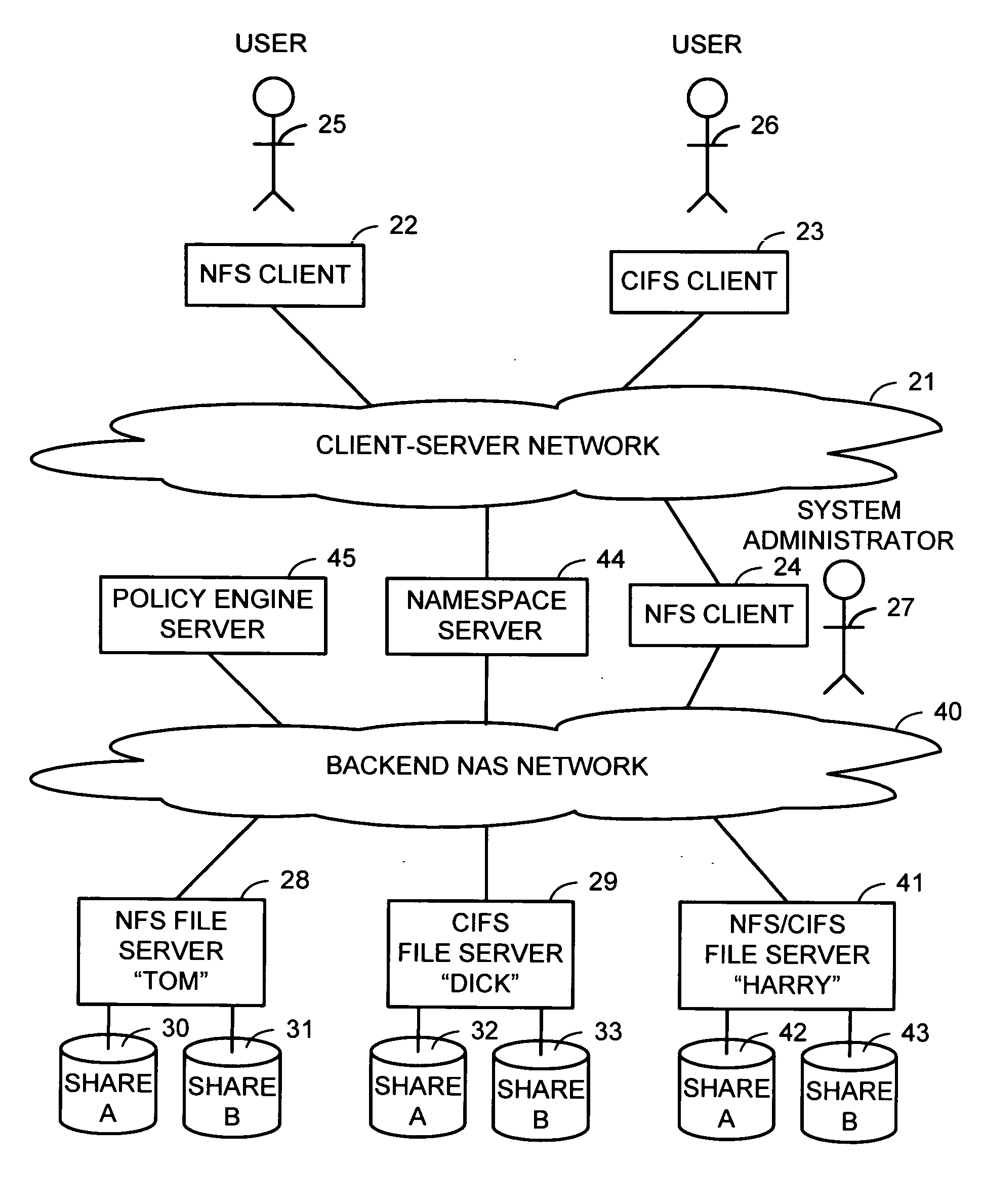
Multi-protocol namespace server
InactiveUS20070038697A1Digital data information retrievalMultiple digital computer combinationsVirtual file systemMulti protocol
A namespace server translates client requests for access to files referenced by pathnames in a client-server namespace into requests for access to files referenced by pathnames in a backend NAS network namespace. The namespace server also translates between different file access protocols. The namespace server may change the translation of a client-server network pathname from an old backend NAS network pathname to a new backend NAS network pathname for file migration without disruption to client access during file migration for load balancing or for a more appropriate service level. Client access can also be routed automatically and transparently to replicas in case of server or site failures. The namespace server may create the appearance of a virtual file system that contains multiple physical servers, a virtual share that contains physical shares from different servers, directories that contain files on different servers, and files that contain data from files on different servers.
Owner:EMC CORP
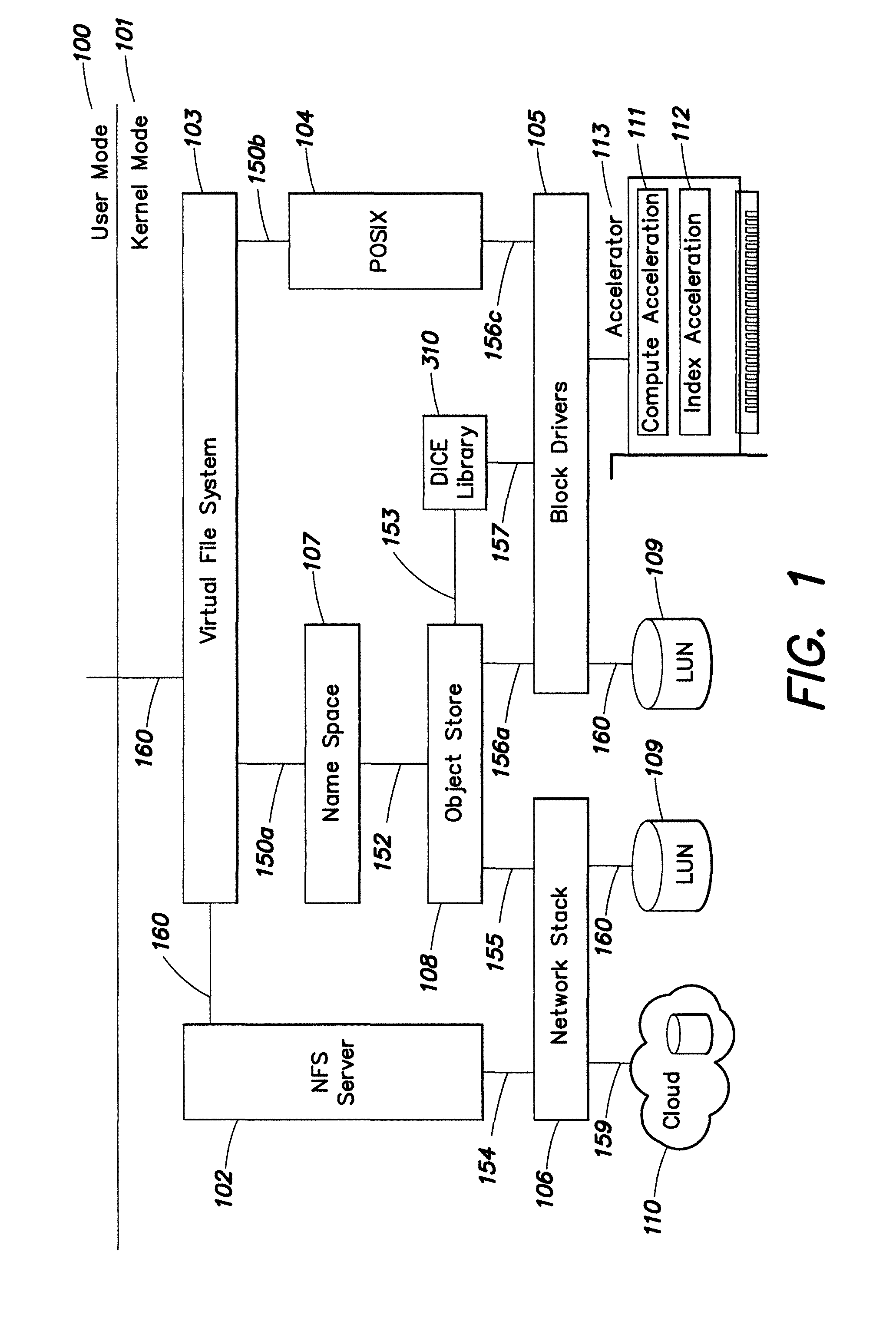
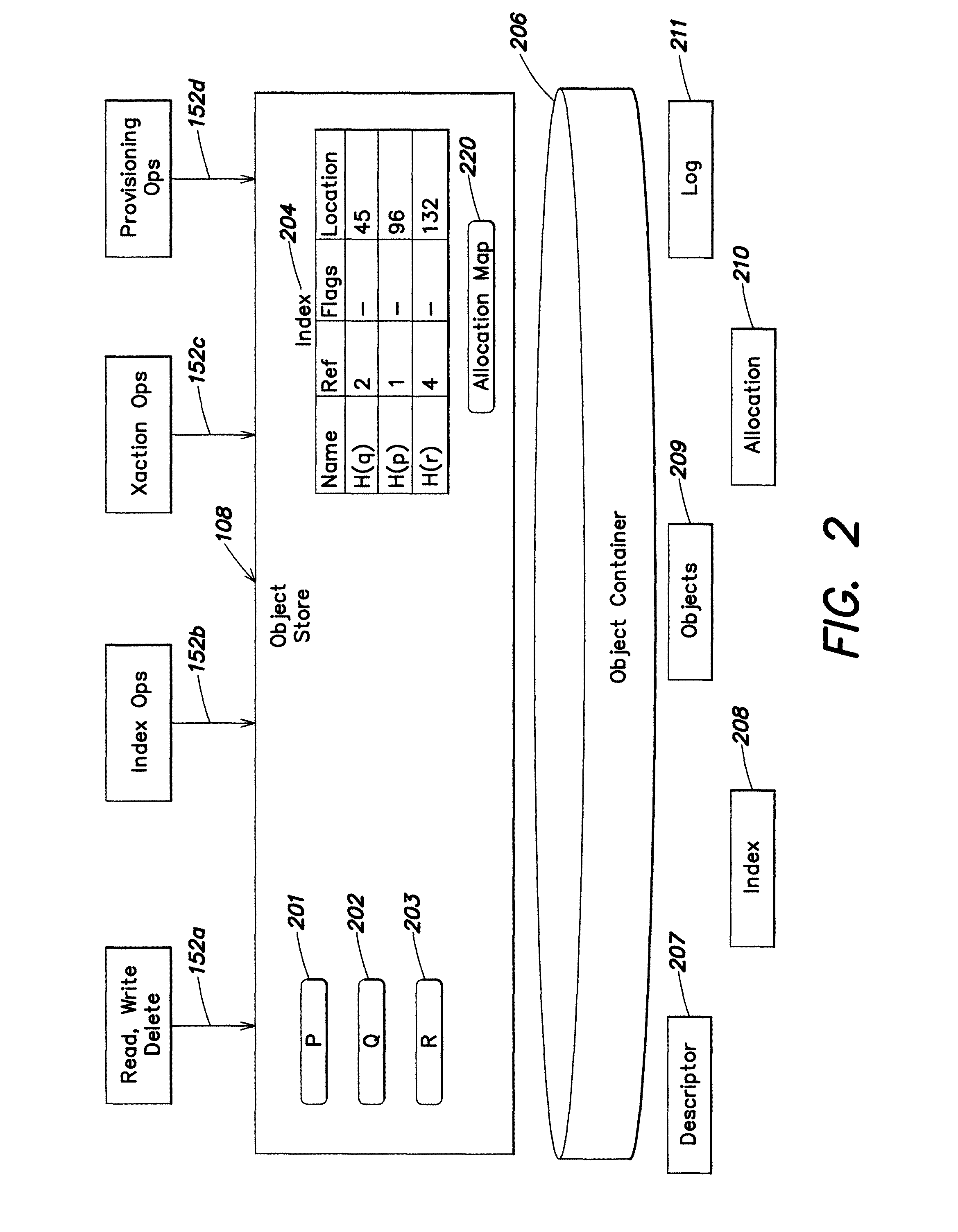
Namespace file system accessing an object store
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com