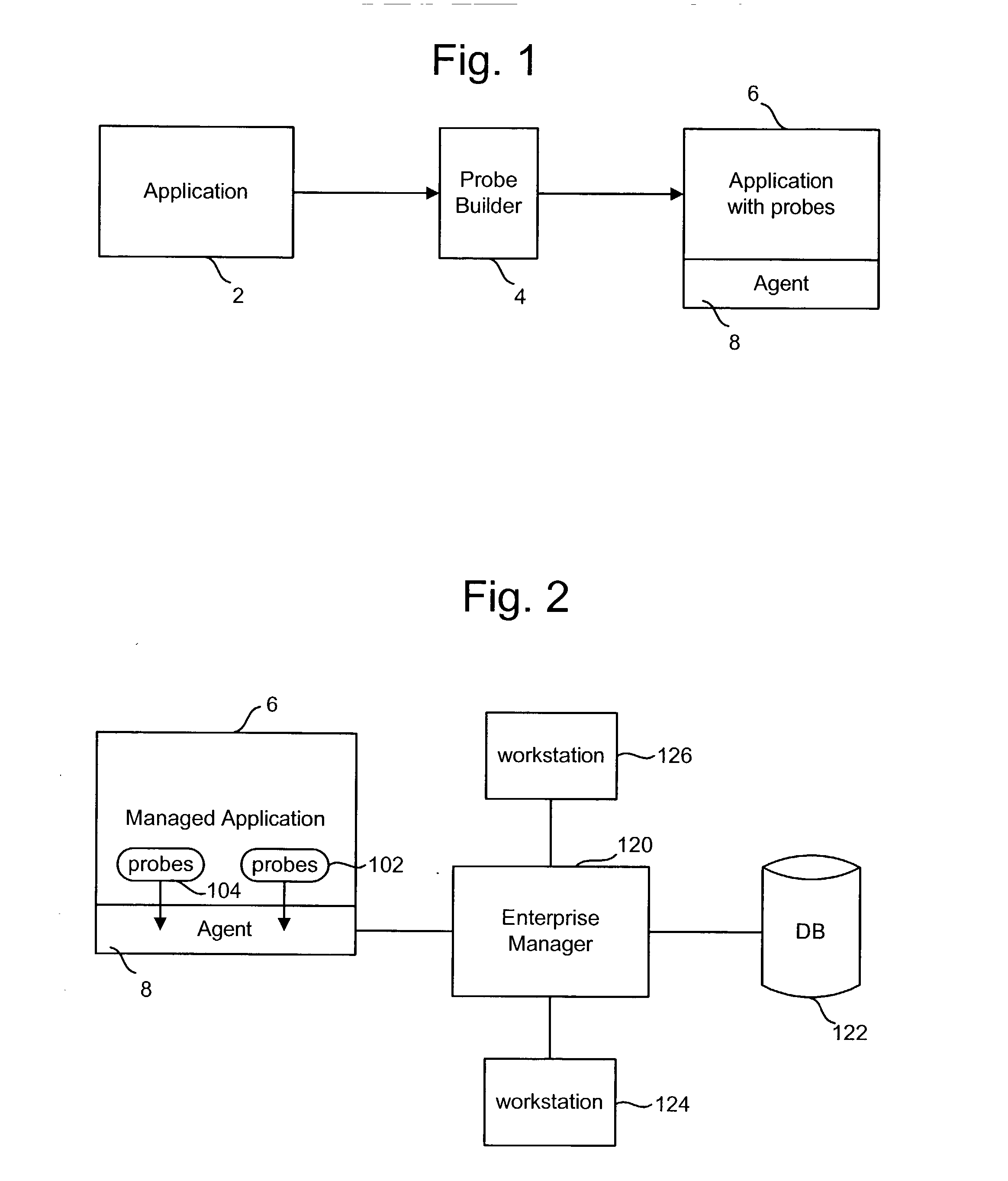
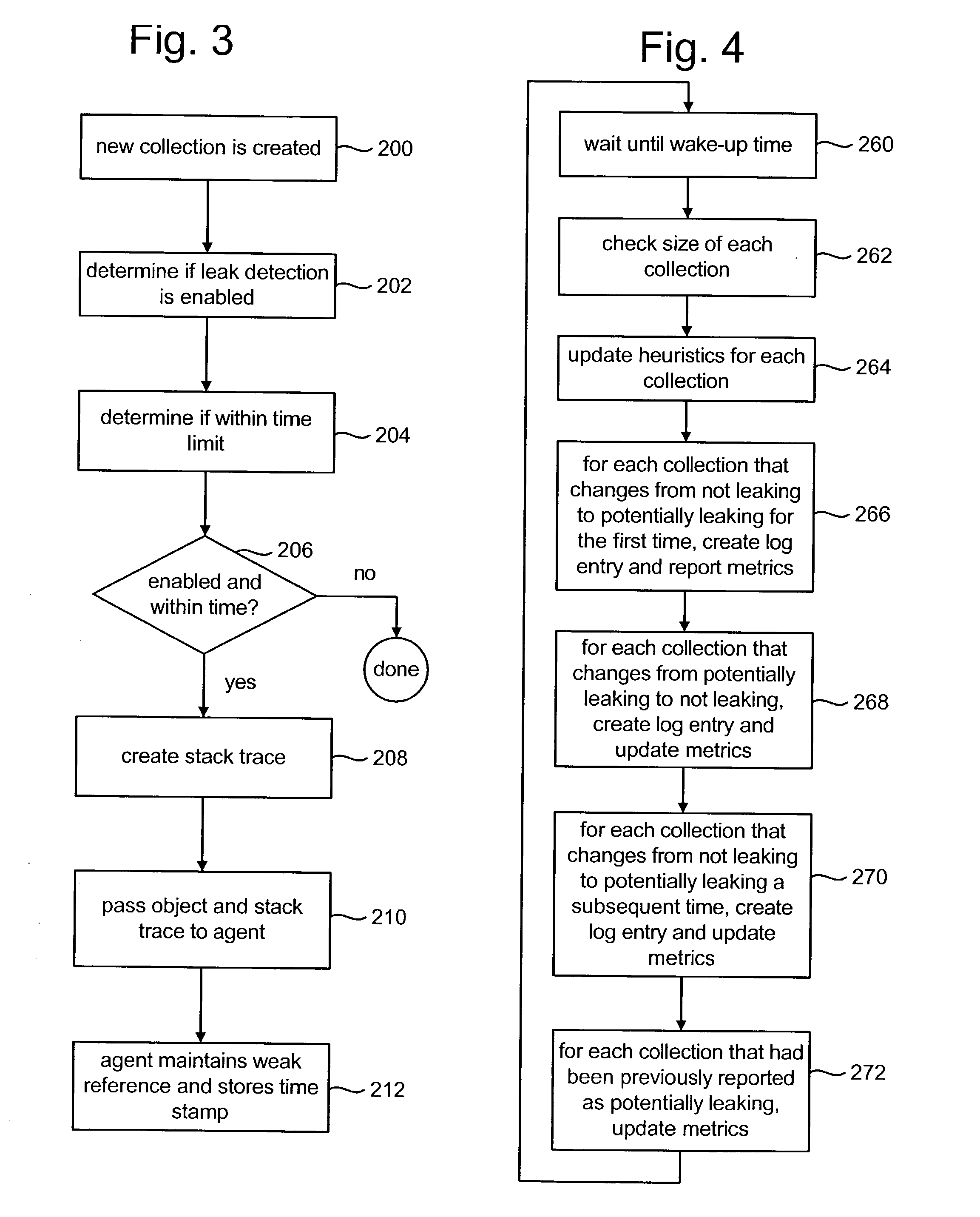
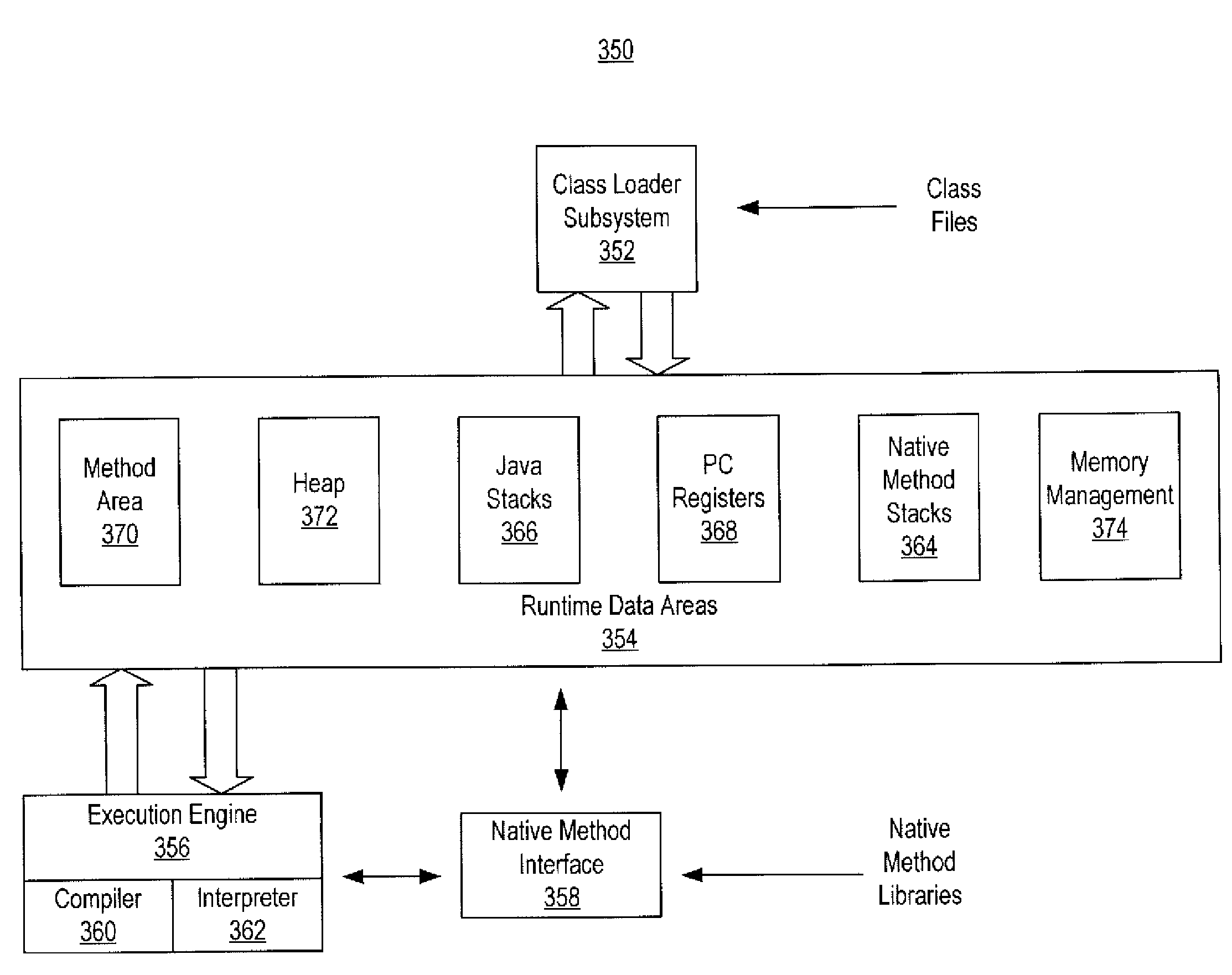
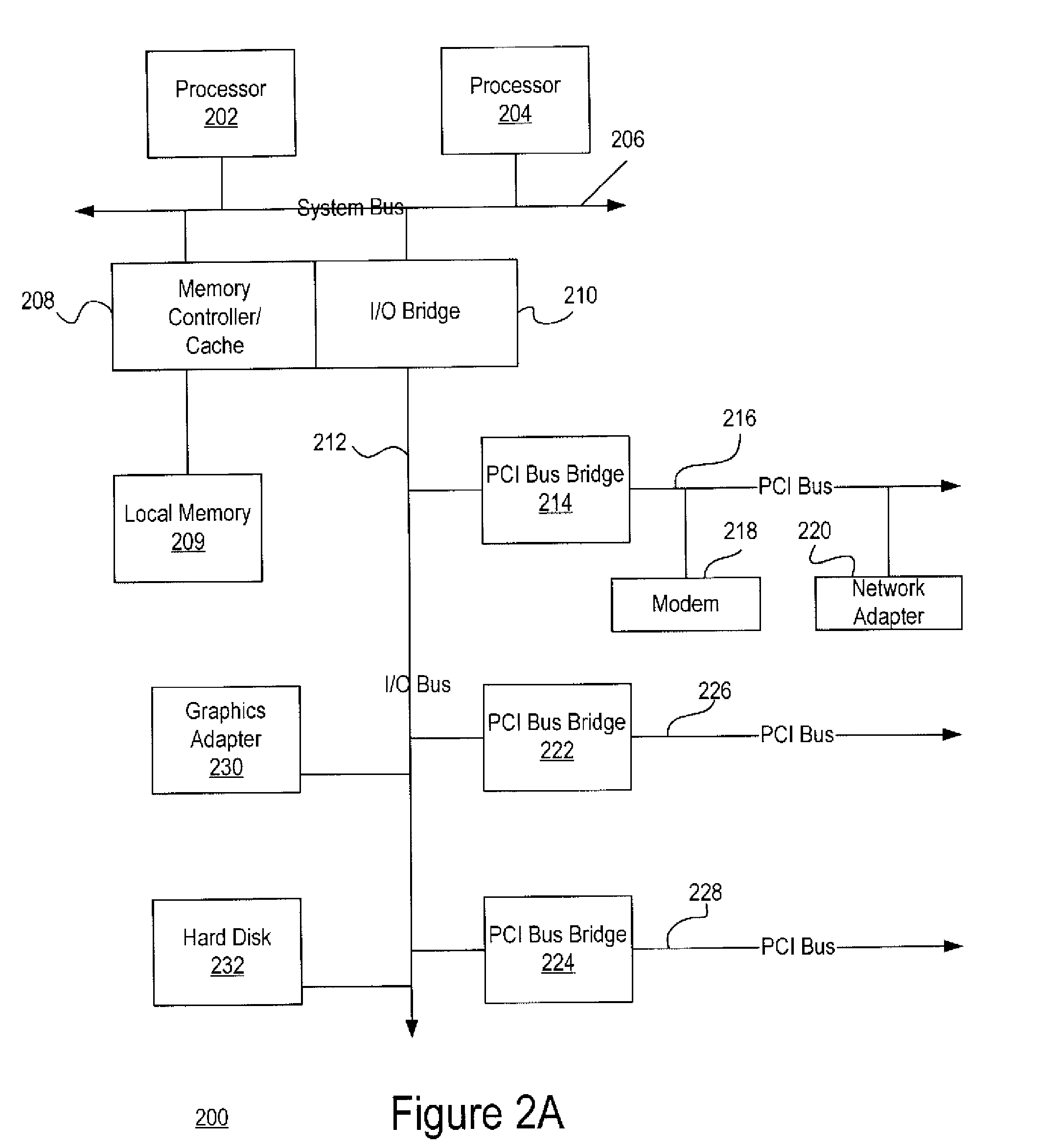
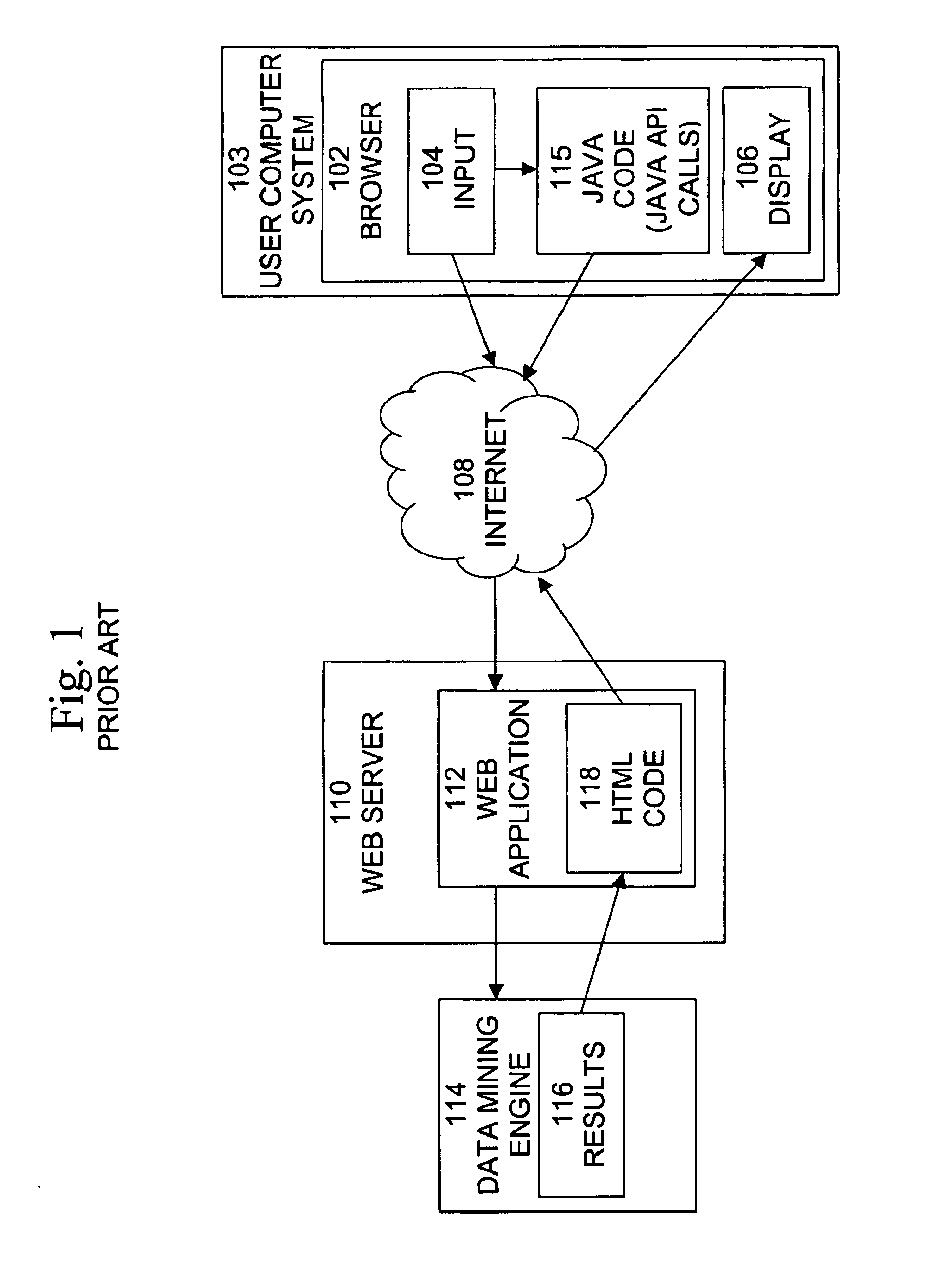
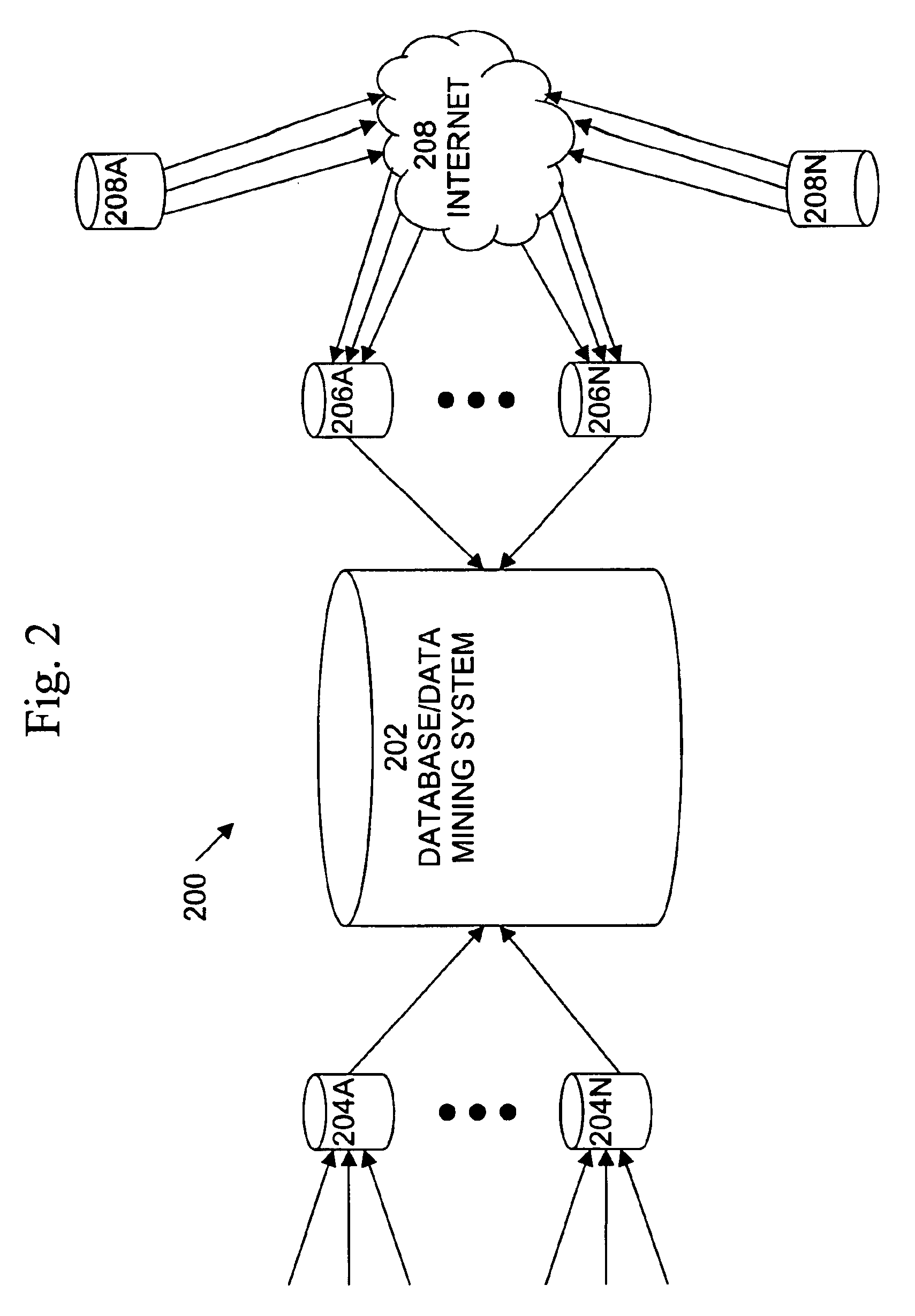
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1181 results about "Java" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Java is a general-purpose programming language that is class-based, object-oriented (although not a pure object-oriented language, as it contains primitive types), and designed to have as few implementation dependencies as possible. It is intended to let application developers write once, run anywhere (WORA), meaning that compiled Java code can run on all platforms that support Java without the need for recompilation. Java applications are typically compiled to bytecode that can run on any Java virtual machine (JVM) regardless of the underlying computer architecture. The syntax of Java is similar to C and C++, but it has fewer low-level facilities than either of them. As of 2019, Java was one of the most popular programming languages in use according to GitHub, particularly for client-server web applications, with a reported 9 million developers.
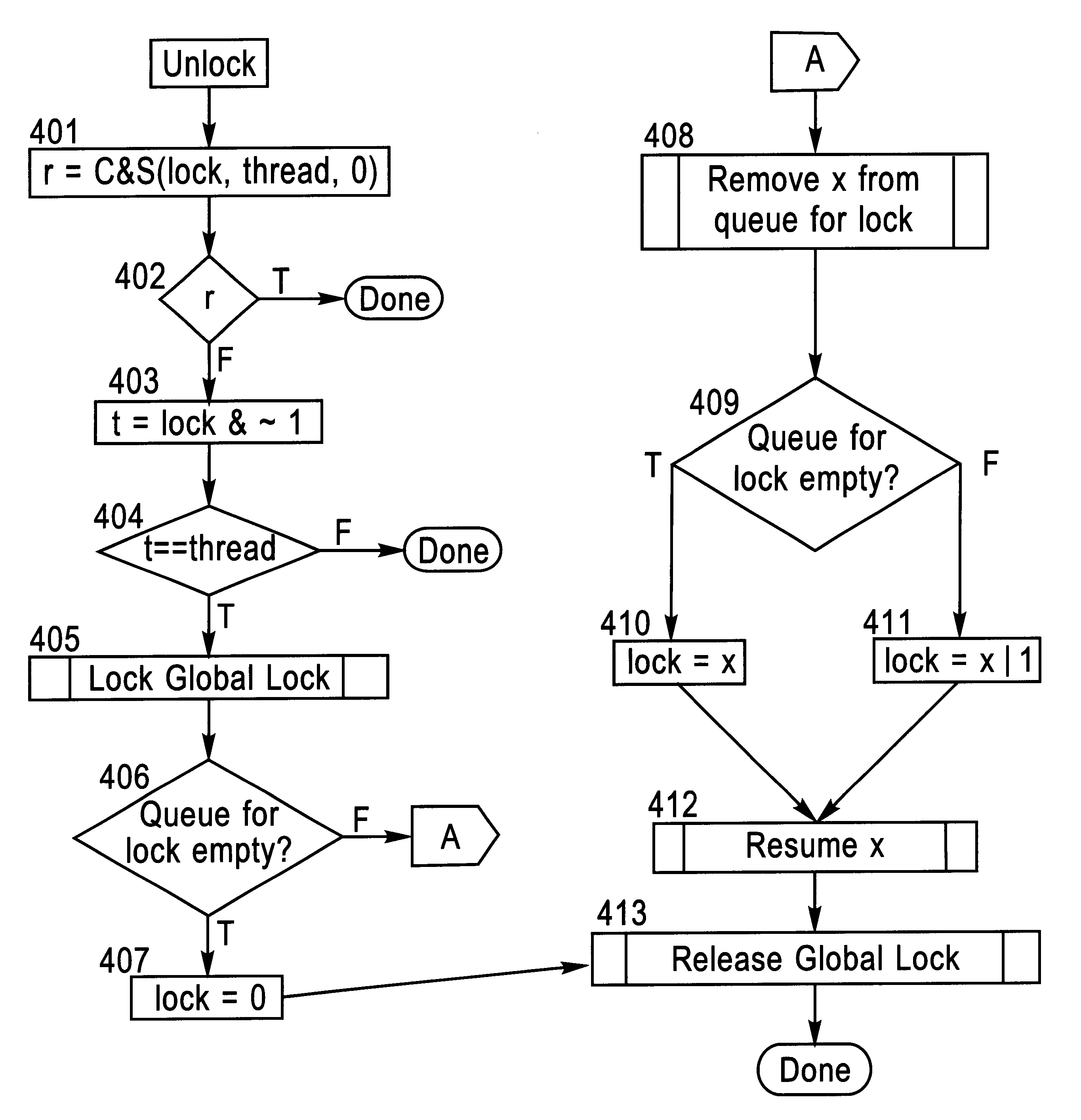
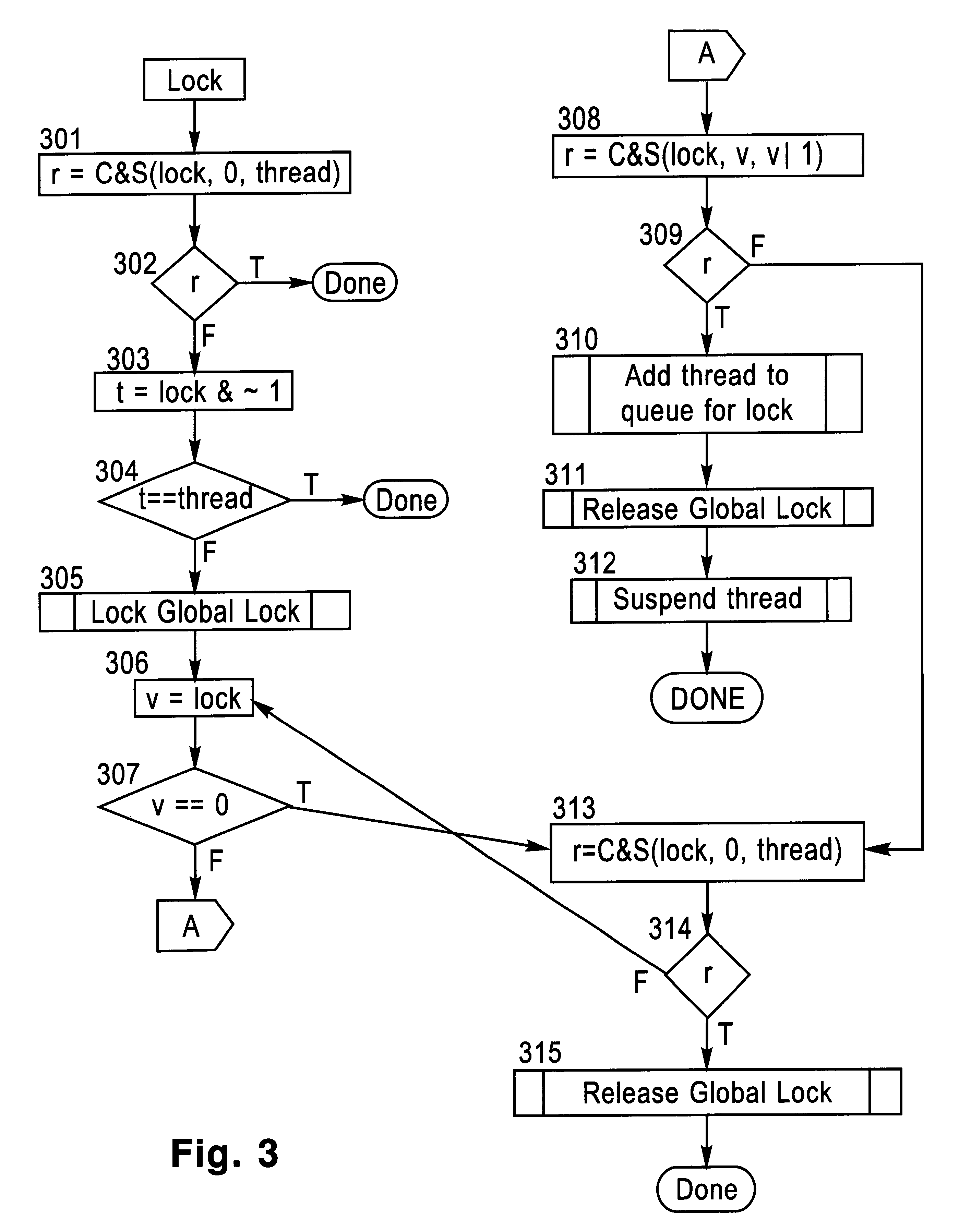
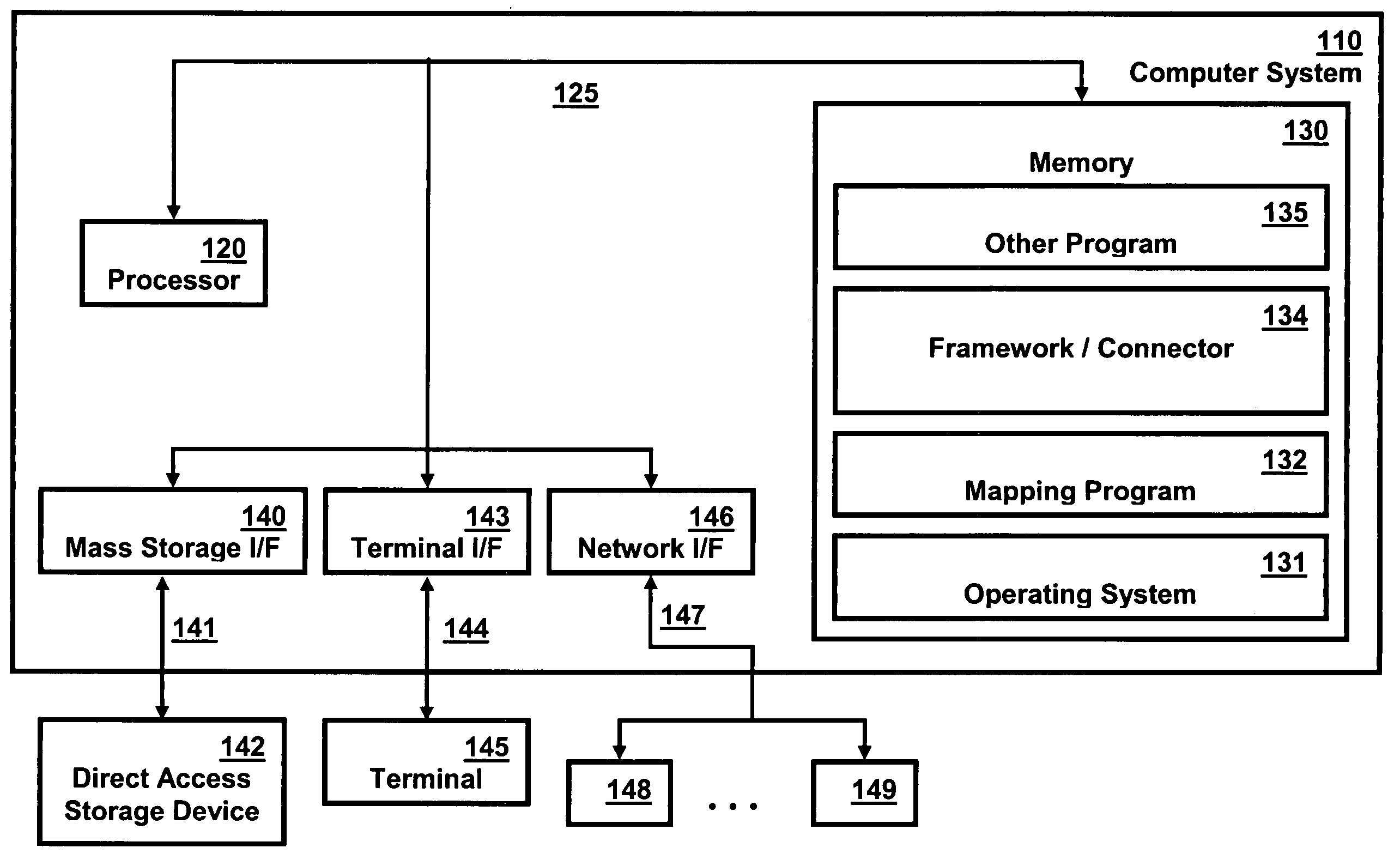
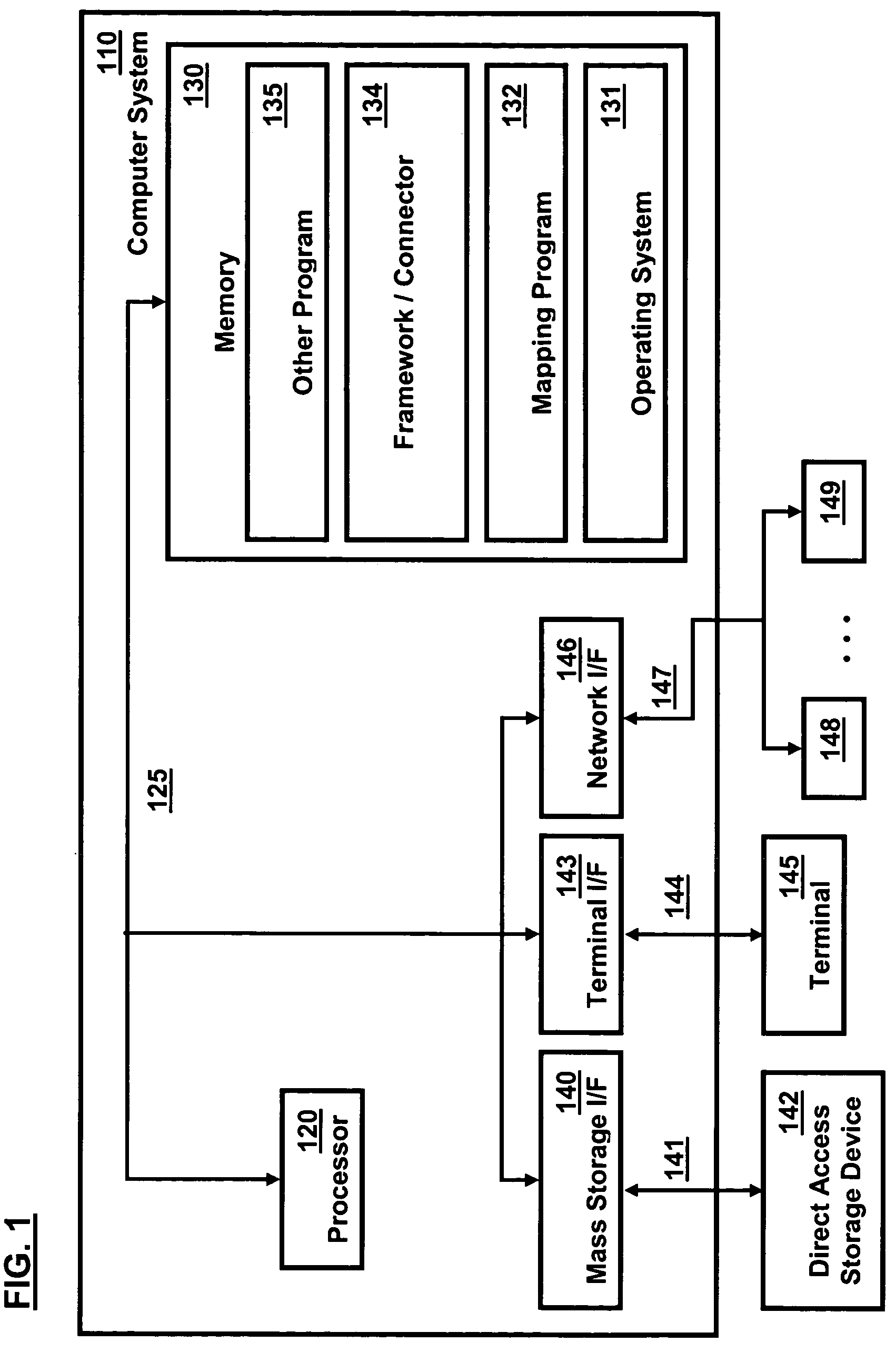
Locking and unlocking mechanism for controlling concurrent access to objects
InactiveUS6247025B1Data processing applicationsDigital data information retrievalNormal caseSpin locks
A lock / unlock mechanism to control concurrent access to objects in a multi-threaded computer processing system comprises two parts: a thread pointer (or thread identifier), and a one-bit flag called a "Bacon bit". Preferably, when an object is not locked (i.e., no thread has been granted access to the object), the thread identifier and Bacon bit are set to 0. When an object is locked by a particular thread (i.e., the thread has been granted access to the object), the thread identifier is set to a value that identifies the particular thread; if no other threads are waiting to lock the object, the Bacon bit is set to 0; however, if other threads are waiting to lock the object, the Bacon bit is set to "1', which indicates the there is a queue of waiting threads associated with the object. To lock an object, a single CompareAndSwap operation is preferably used, much like with spin-locks; if the lock is already held by another thread, enqueueing is handled in out-of-line code. To unlock an object, in the normal case, a single CompareAndSwap operation may be used. This single operation atomically tests that the current thread owns the lock, and that no other threads are waiting for the object (i.e., the Bacon bit is "0'). A global lock is preferably used to change the Bacon bit of the lock. This provides an lock / unlock mechanism which combines many of the desirable features of both spin locking and queued locking, and can be used as the basis for a very fast implementation of the synchronization facilities of the Java language.
Owner:IBM CORP
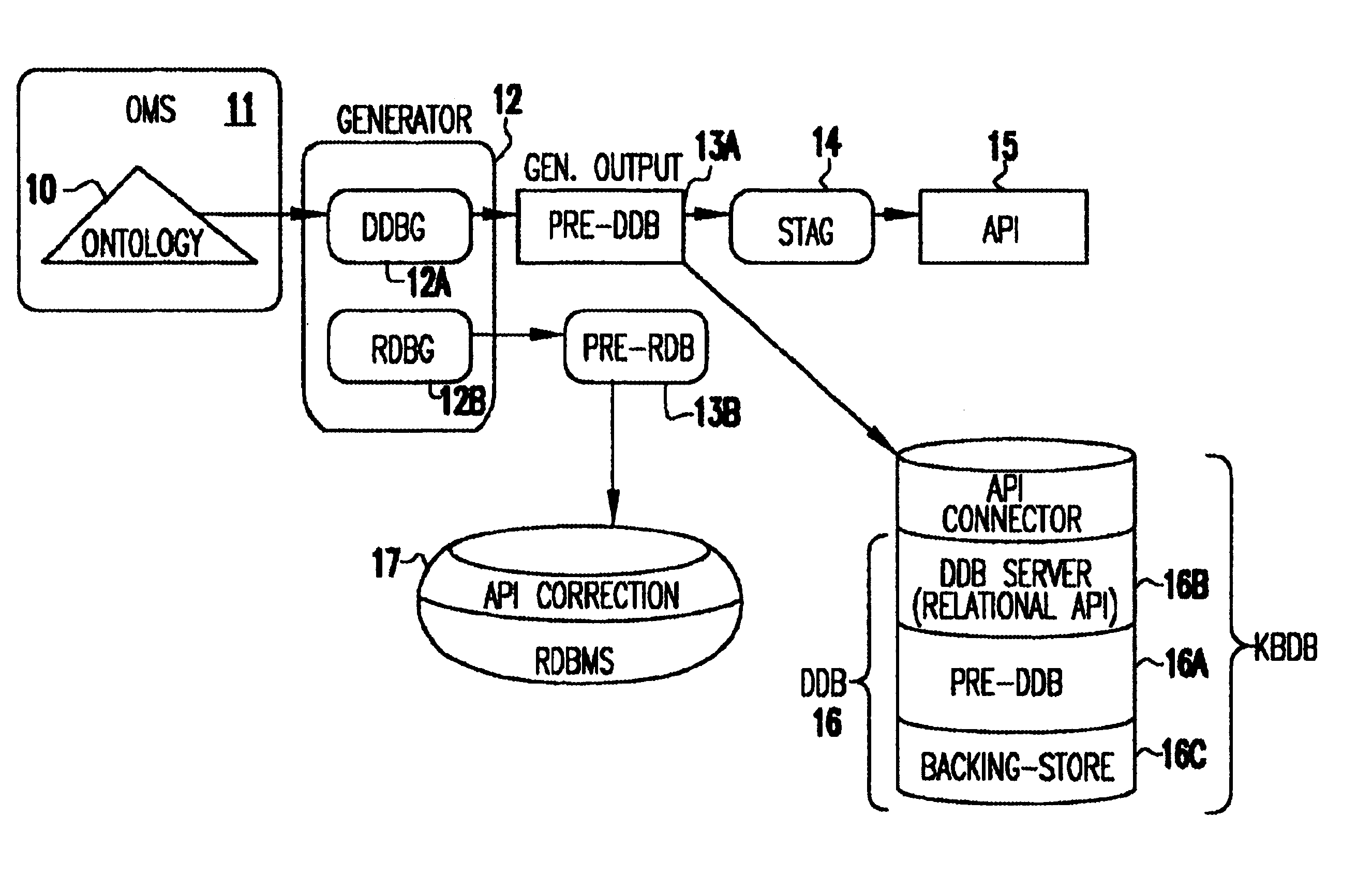
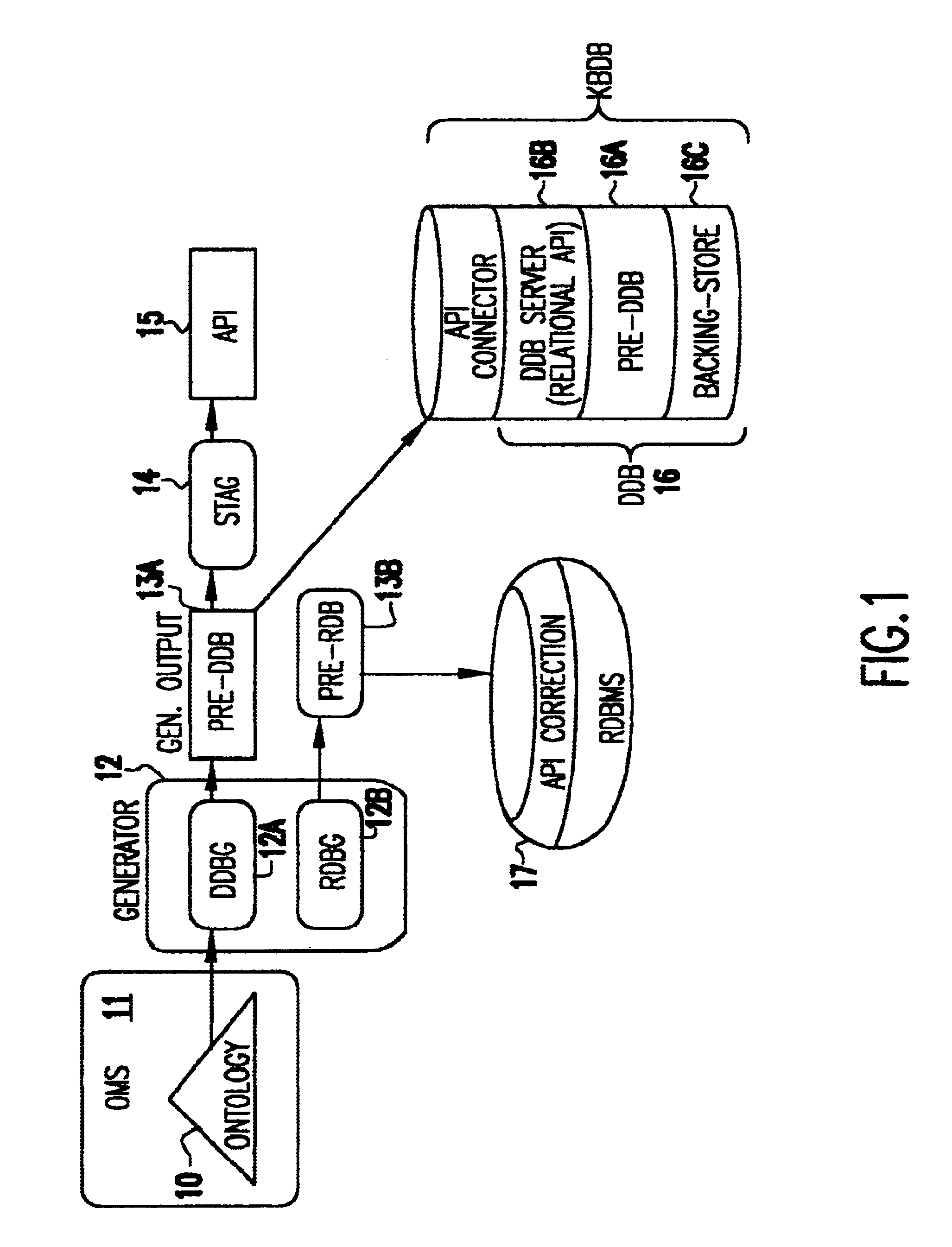
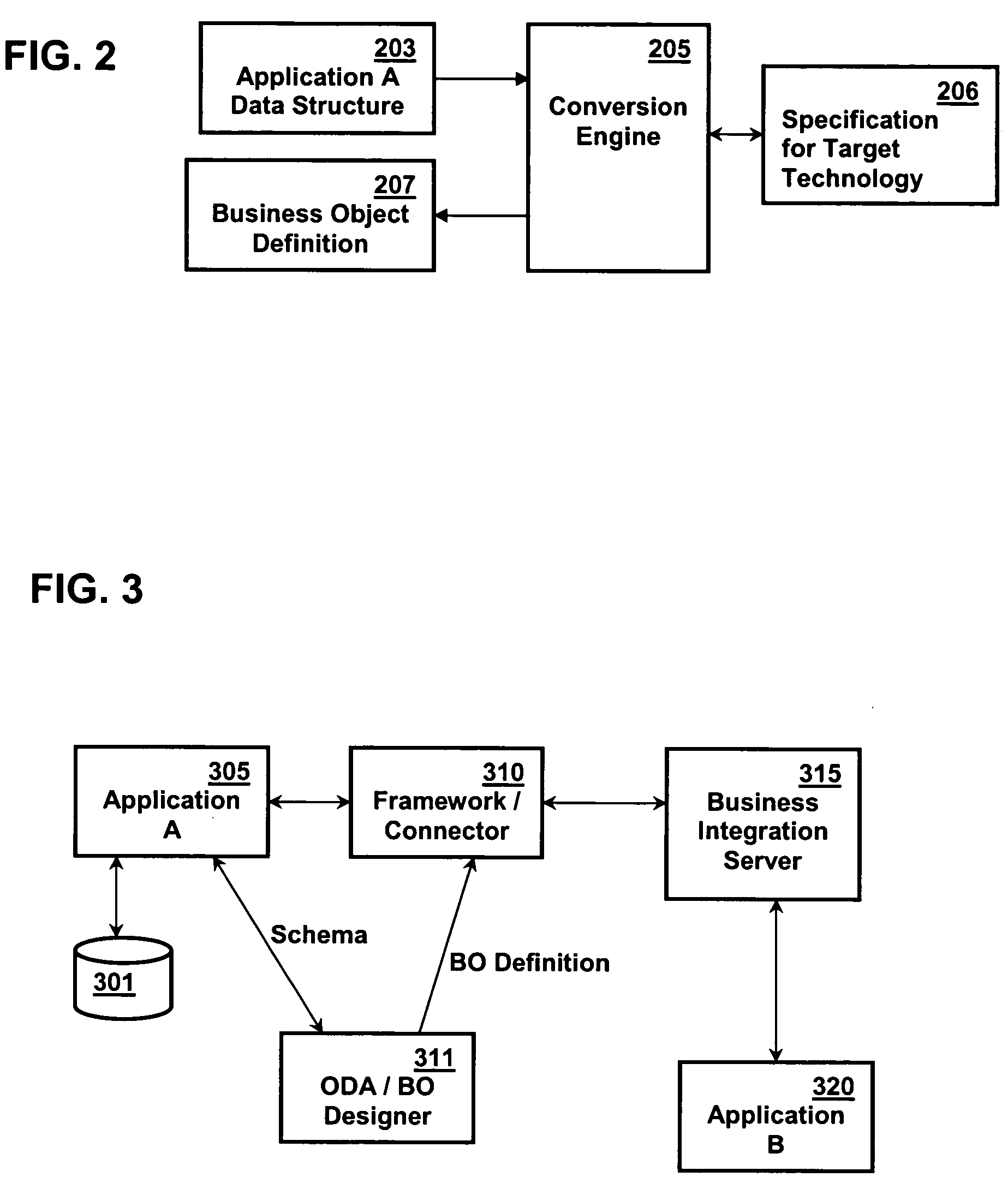
Ontology for database design and application development
InactiveUS6640231B1Improve fidelityImprove efficiencyData processing applicationsDigital data processing detailsEntity typeMaintainability
A system and method lets a user create or import ontologies and create databases and related application software. These databases can be specially tuned to suit a particular need, and each comes with the same error-detection rules to keep the data clean. Such databases may be searched based on meaning, rather than on words-that-begin-with-something. And multiple databases, if generated from the same basic ontology can communicate with each other without any additional effort. Ontology management and generation tools enable enterprises to create databases that use ontologies to improve data integration, maintainability, quality, and flexibility. Only the relevant aspects of the ontology are targeted, extracting out a sub-model that has the power of the full ontology restricted to objects of interest for the application domain. To increase performance and add desired database characteristics, this sub-model is translated into a database system. Java-based object-oriented and relational application program interfaces (APIs) are then generated from this translation, providing application developers with an API that exactly reflects the entity types and relations (classes and methods) that are represented by the database. This generation approach essentially turns the ontology into a set of integrated and efficient databases.
Owner:KYNDI
Recording medium, reproduction device, program, reproduction method, and recording method
ActiveUS20060143666A1Improve developmentIncrease added valueTelevision system detailsFilamentary/web record carriersComputer hardwareComputer graphics (images)
Recorded on the recording medium (BD-ROM) is an AV stream that is obtained by multiplexing a video stream and one or more audio streams. MOVIE objects are scenarios showing playback procedures of video data described using playback device-oriented commands. In addition to the MOVIE objects, enhanced-mode scenarios (Java and WebPage objects) are also recorded on the recording medium. These enhanced-mode scenarios, each of which is described in the Java language or a markup language, show control procedures with respect to playback devices. The Java and WebPage objects are capable of taking over register setting values set by MOVIE objects, and extracting parts of video data played by MOVIE objects.
Owner:PANASONIC CORP
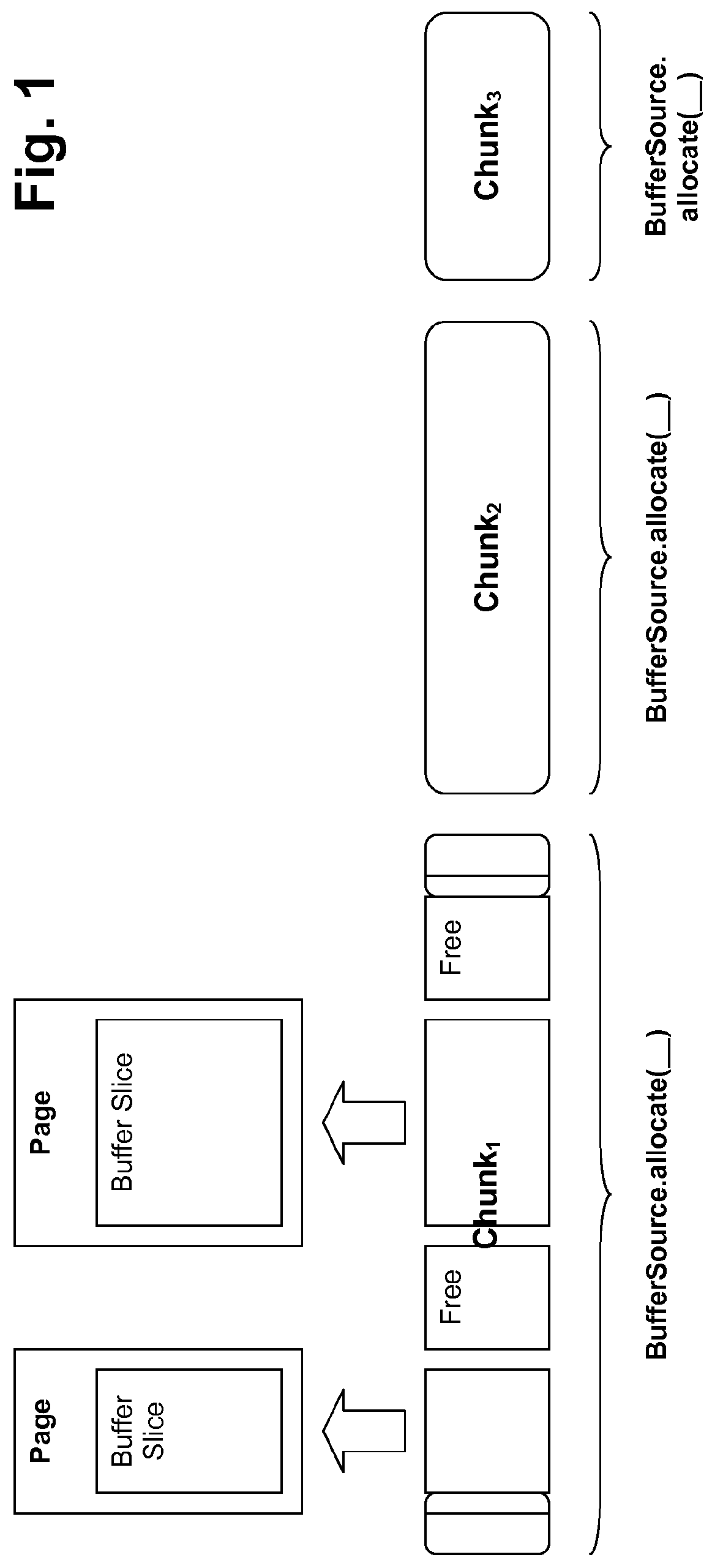
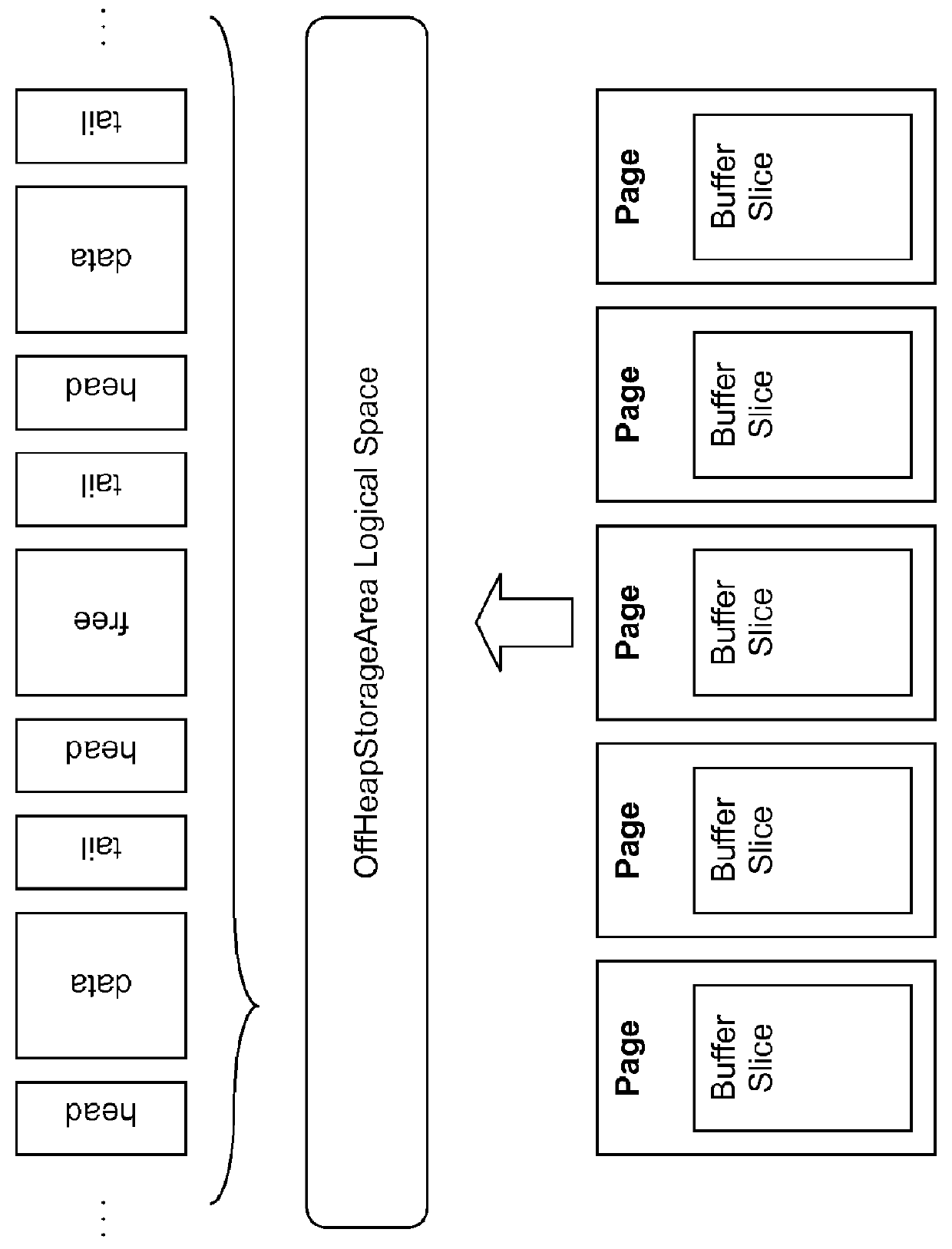
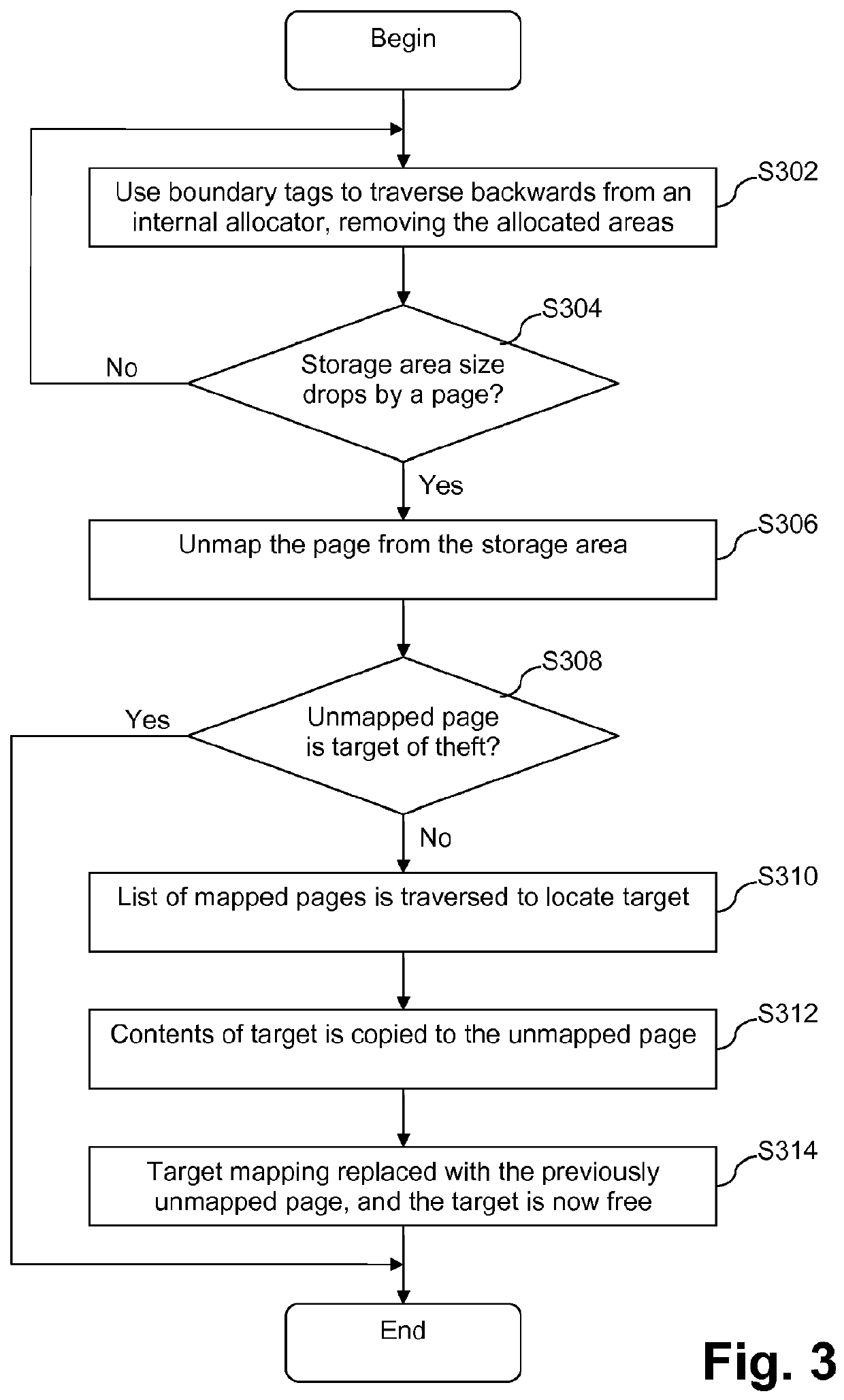
Off-heap direct-memory data stores, methods of creating and/or managing off-heap direct-memory data stores, and/or systems including off-heap direct-memory data store
ActiveUS20120222005A1Fast timeReduce the amount requiredMemory architecture accessing/allocationSpecific program execution arrangementsRefuse collectionJava
Certain example embodiments relate to a highly-concurrent, predictable, fast, self-managed, in-process space for storing data that is hidden away from the garbage collector and its related pauses. More particularly, certain example embodiments relate to improved memory management techniques for computer systems that leverage an off-heap direct-memory data store that is massively scalable and highly efficient. The off-heap store may be provided in connection with a Java-based environment, and garbage collection may be completely or nearly completely avoided for the off-heap store. The off-heap store may be integrated into a tiered storage solution in certain example embodiments.
Owner:SOFTWARE AG USA
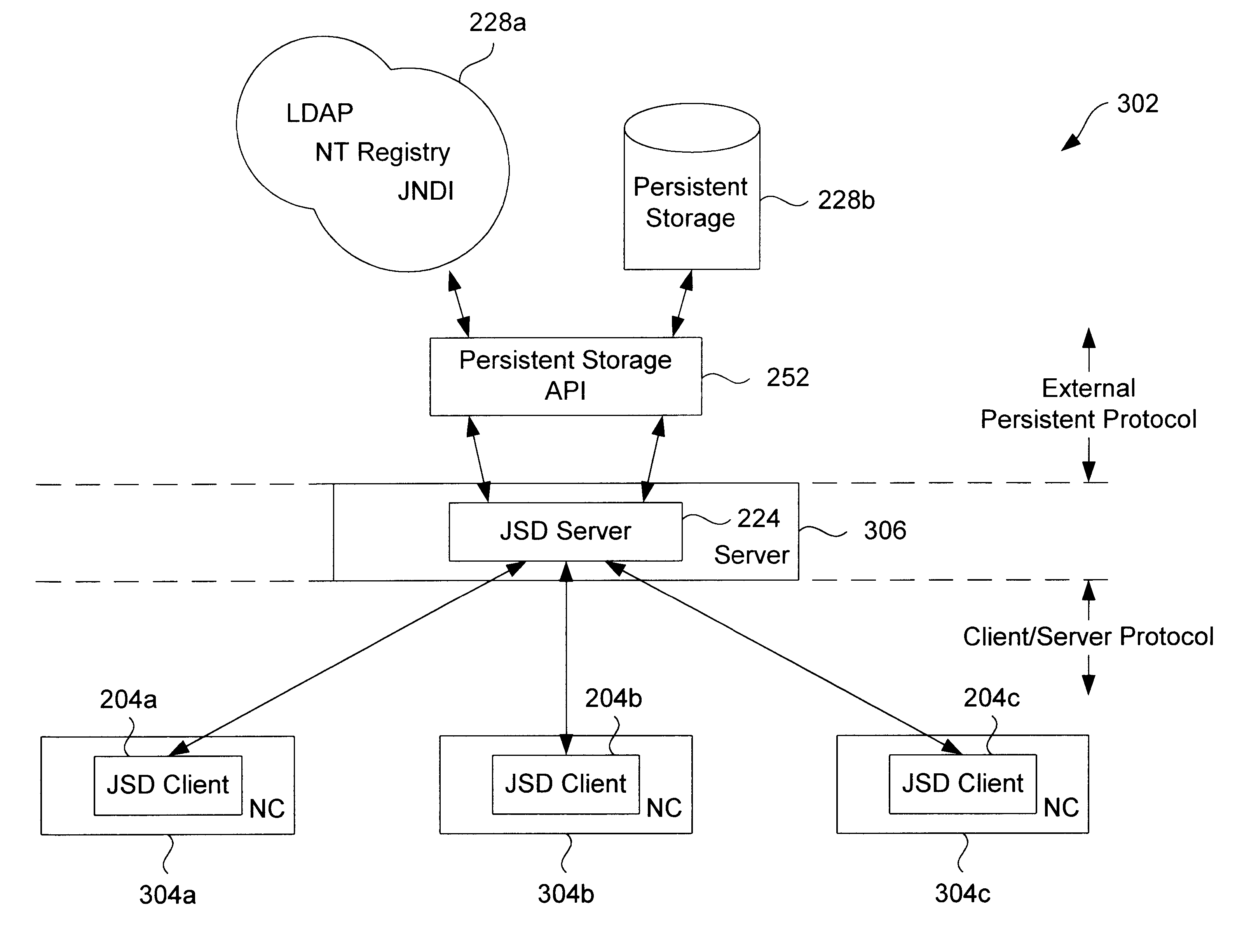
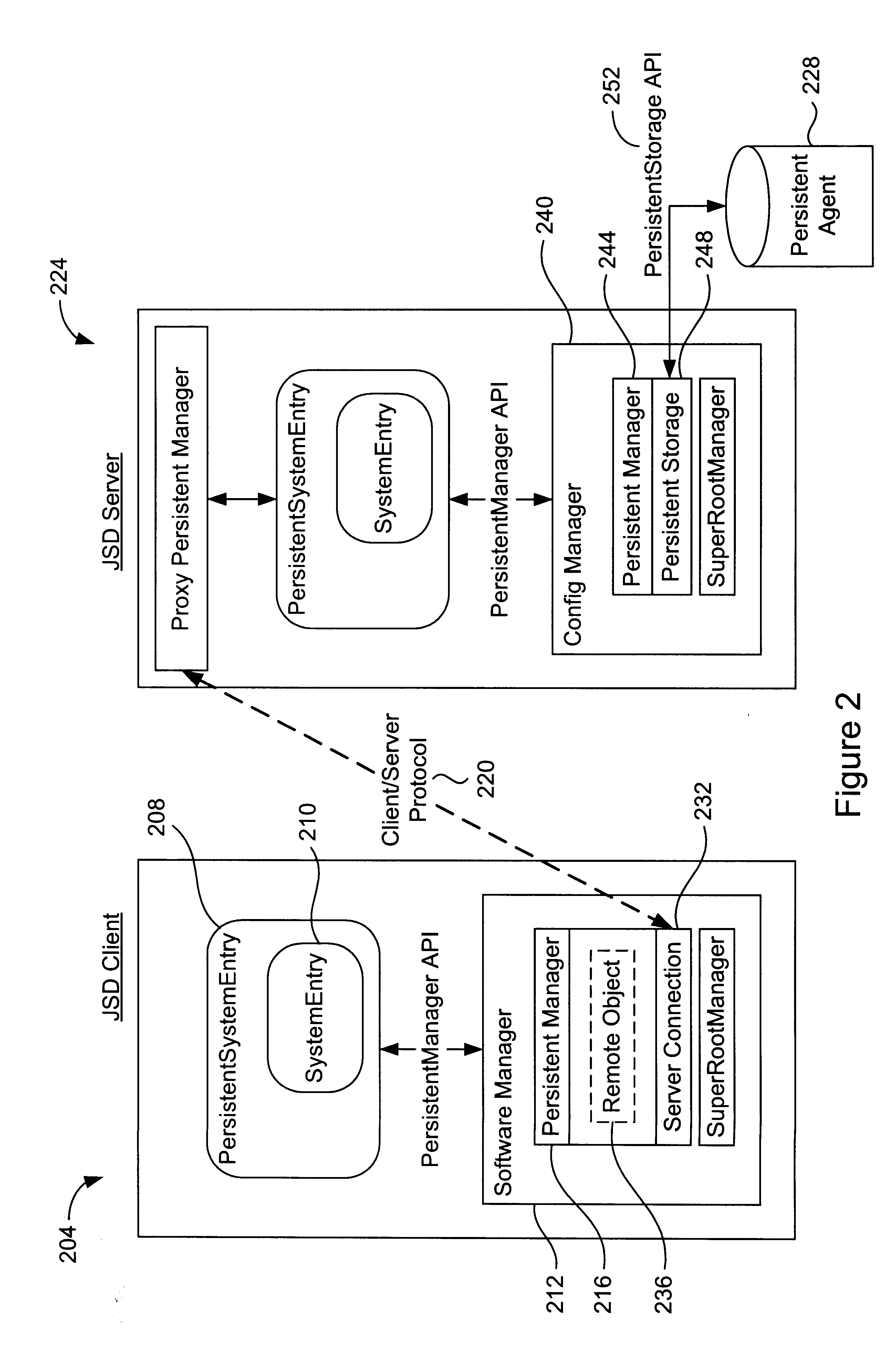
Persistent storage interface for a configuration object-based system
InactiveUS6233582B1Data processing applicationsMultiple digital computer combinationsObject basedApplication programming interface
Methods and apparatus for implementing a persistent storage interface that may be used to store entries into a variety of different storage subsystems are disclosed. According to one aspect of the present invention, an object-based system which is arranged to store and to retrieve configuration information includes a server and a client that is in communication with the server. The client communicates with the server using a client / server protocol. The system also includes at least one persistent agent that is arranged to store persistent entries, as well as a persistent storage application programming interface that allows the server to communicate with the at least one persistent agent. The persistent storage application programming interface is arranged to support multiple persistent agents such that different persistent agents may be used with respect to the system. In one embodiment, the object-based system is a Java System Database.
Owner:ORACLE INT CORP
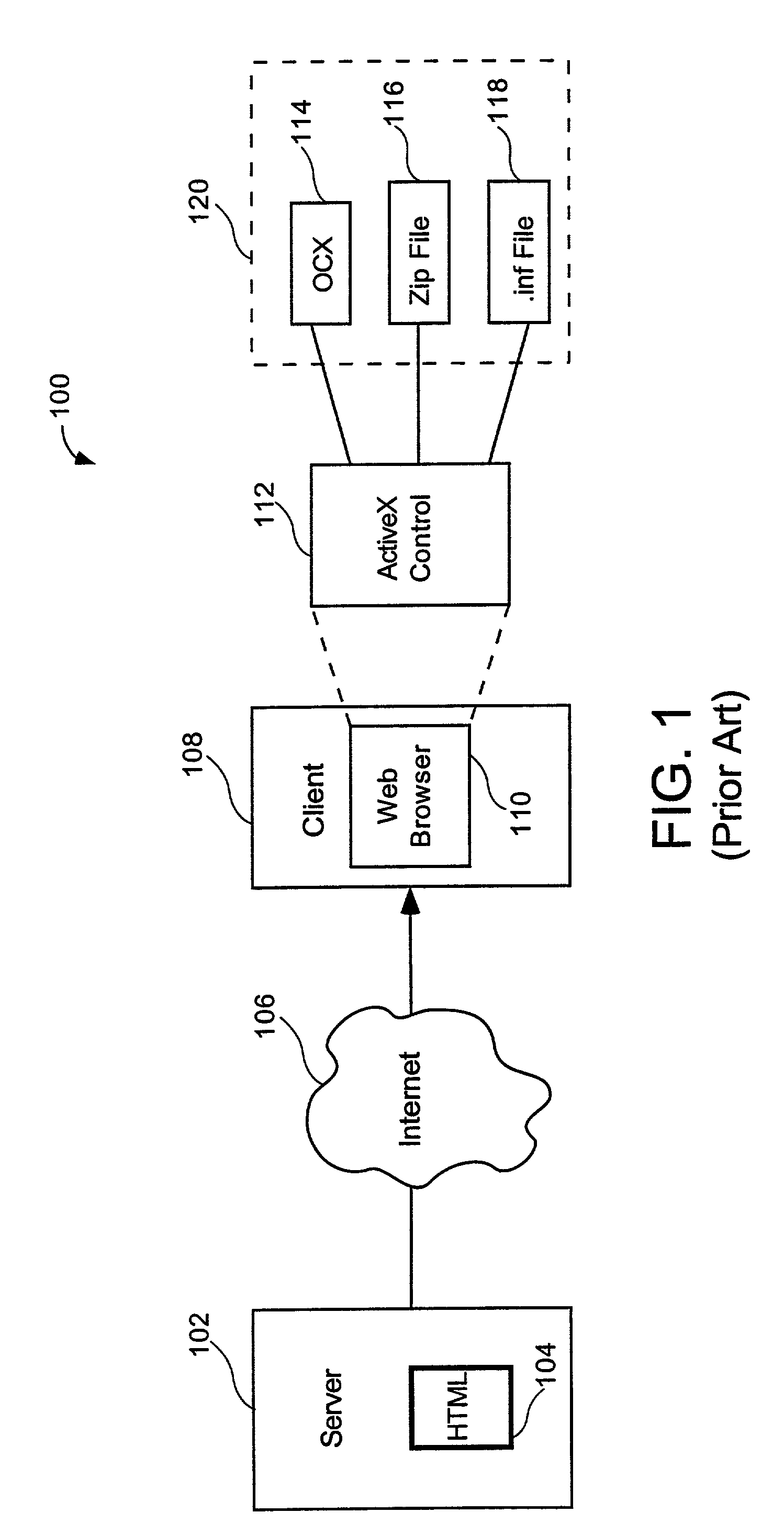
System and method for accessing internet-based information resources by scanning Java-Applet encoded bar code symbols
InactiveUS6338434B1Simple methodEasy accessCharacter and pattern recognitionSpecial data processing applicationsInformation resourceBarcode
A novel hand-supportable wireless Internet-enabled terminal is disclosed, wherein a transaction-enabling Java-Applet is embedded within 2-D bar code symbol. An HTML-encoded document and code associated with the transaction-enabling Java-Applet is created and stored in an HTTP server for use in enabling a predetermined information-related transaction. When a bar code symbol encoded with a transaction-enabling Java-Applet is read using the hand-supportable wireless Internet-enabled terminal, the corresponding code on the HTTP Server is automatically accessed and one or more HTML-encoded documents are displayed at the hand-supportable wireless Internet-enabled terminal, and the transaction-enabling Java-Applet initiated for execution so that the customer, consumer or client desiring the transaction can simply and conveniently conduct the information-related transaction over the Internet.
Owner:METROLOGIC INSTR
Fault tolerance software system with periodic external self-test failure detection
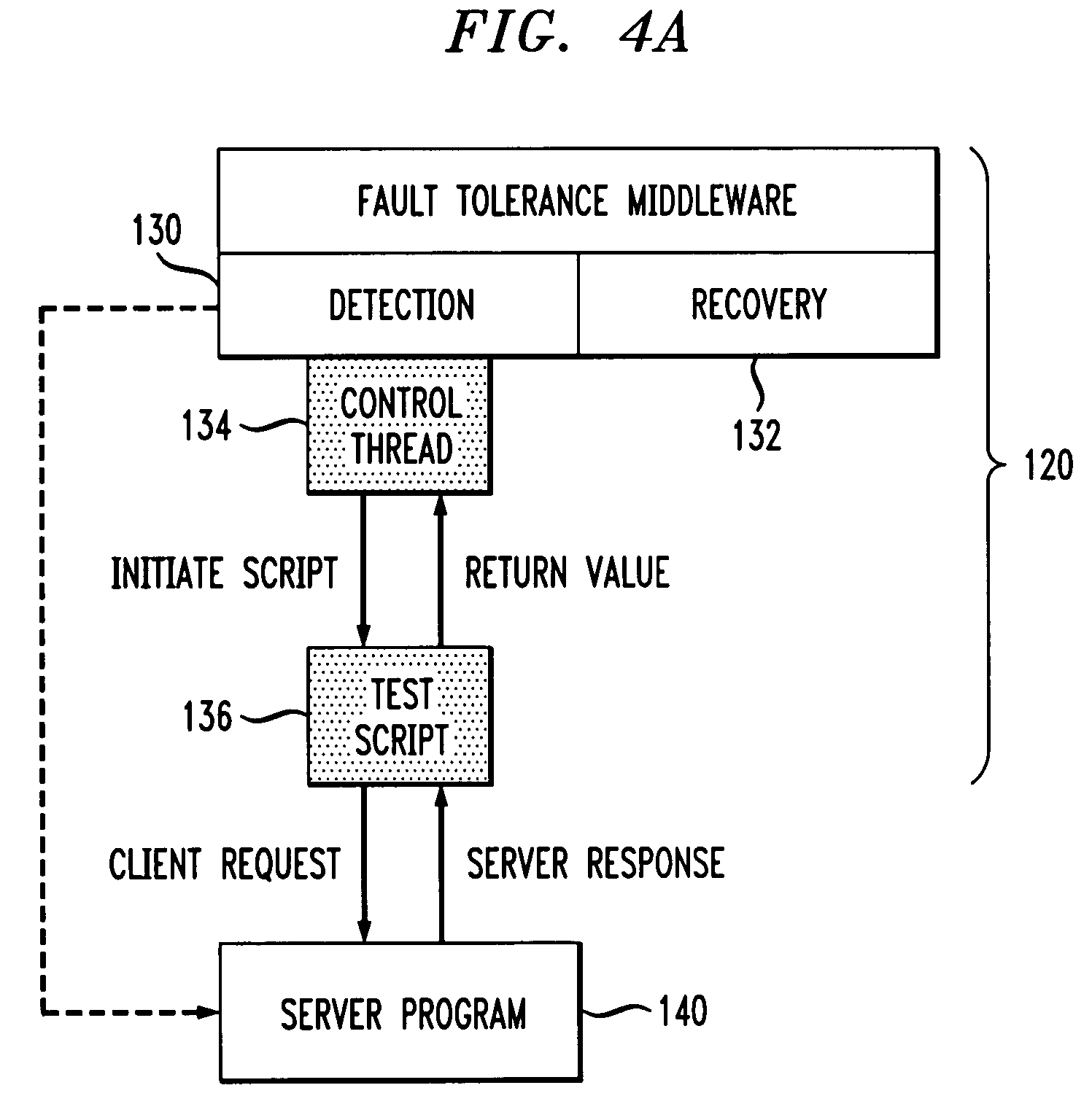
ActiveUS7096388B2Simple and rapid developmentImproved failure detectionSoftware testing/debuggingClient-sideMonitoring program
Fault tolerance is improved in a computing system which includes one or more computing machines by (i) executing a control thread or other control program in conjunction with a fault tolerance software system running on at least one of the machines, and (ii) initiating via the control program a test script program which sends one or more requests to a monitored program. The test script program also processes corresponding responses to the one or more requests, and generates a return value utilizable by the control program to indicate a failure condition in the monitored program. The computing system may be configured in accordance with a client-server architecture, with the fault tolerance software system and the monitored program both running on a server of the system. The test script program is preferably implemented in an object-oriented programming language such as Java, such that one or more components of the test script program comprise a base class from which one or more other components of the test script program are generatable for use with the monitored program.
Owner:AVAYA INC
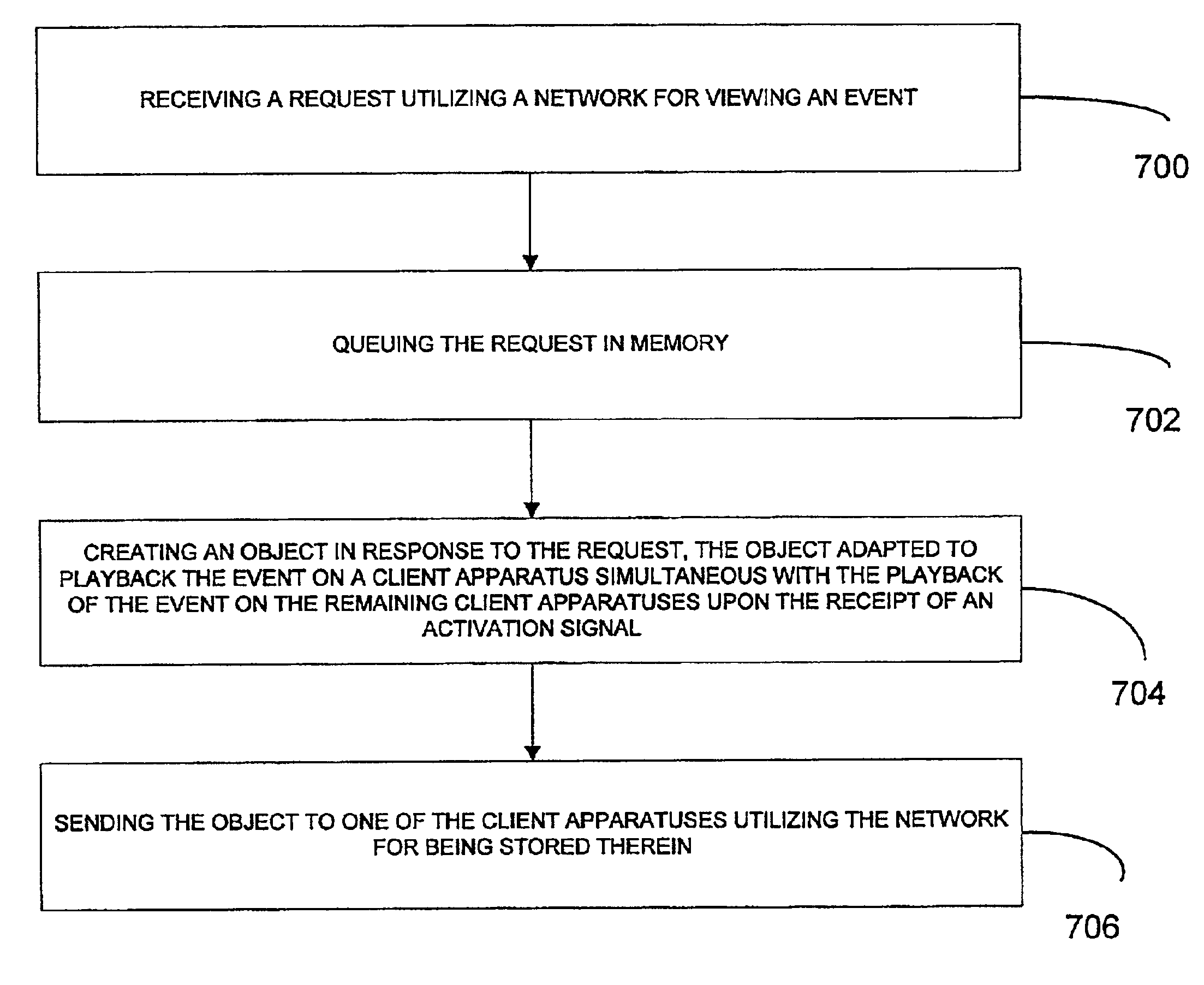
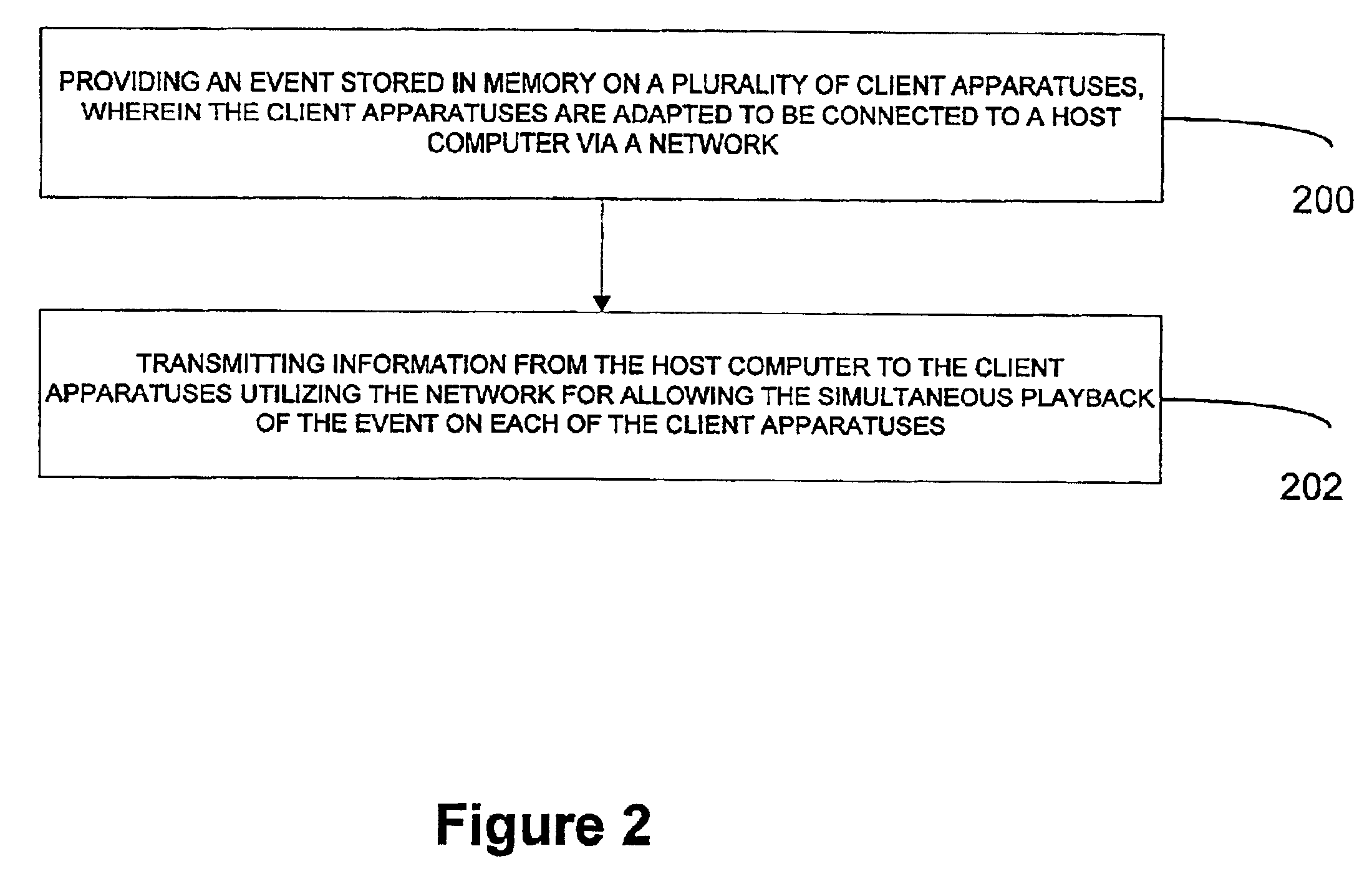
System, method and article of manufacture for java/javascript component in a multimedia synchronization framework
InactiveUS6941383B1Multiple digital computer combinationsTransmissionNetwork connectionApplication software
A system, method and article of manufacture are provided for synchronizing an event on a plurality of client apparatuses. First, a plurality of client apparatuses are connected via a network. Next, an application program is embedded on a site on the network. In use, information is requested from a server on the network utilizing the application program. Such information relates to an event to be played back simultaneously on the client apparatuses. In response to such request, a script is received for displaying the information.
Owner:ROVI TECH CORP
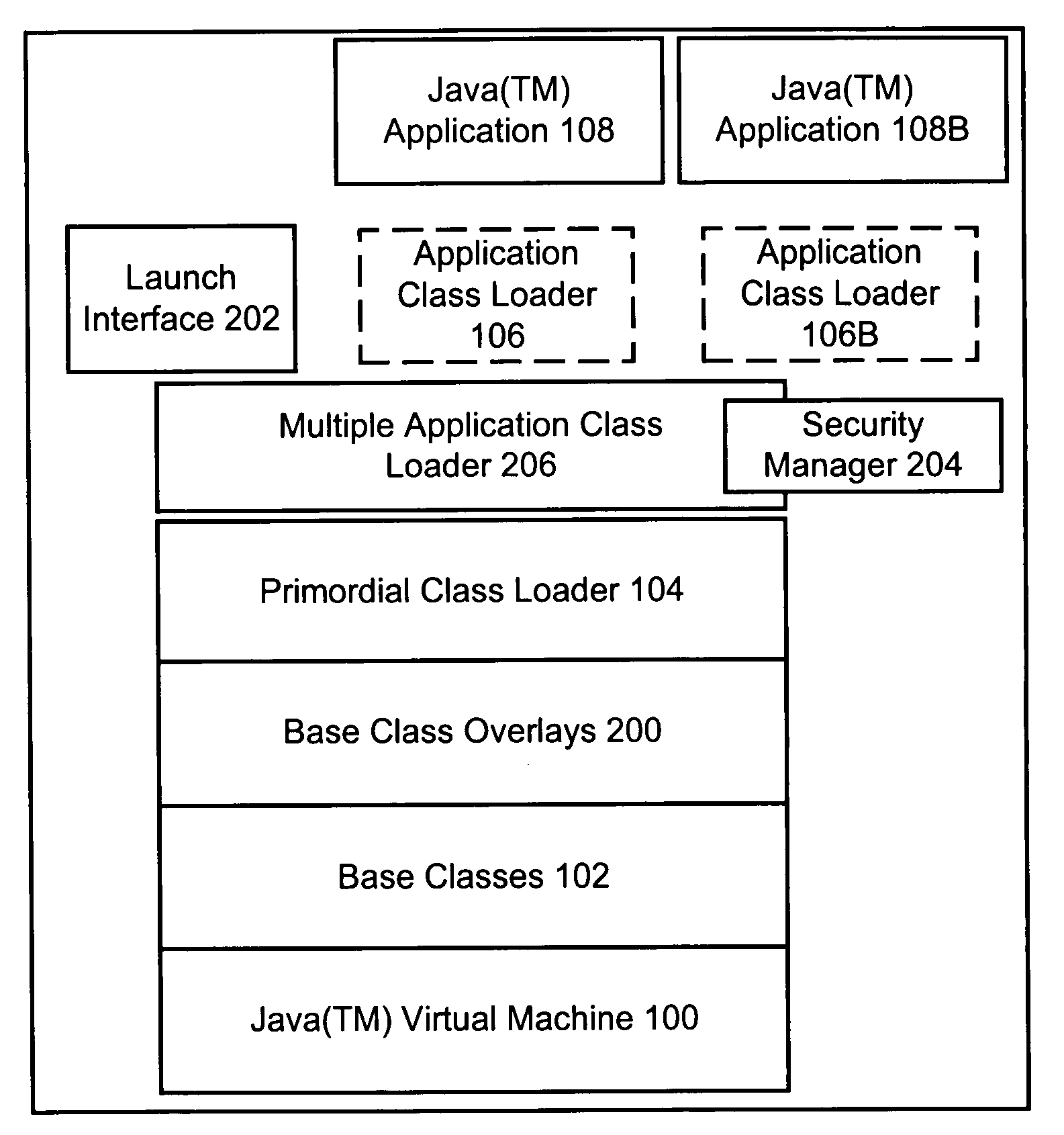
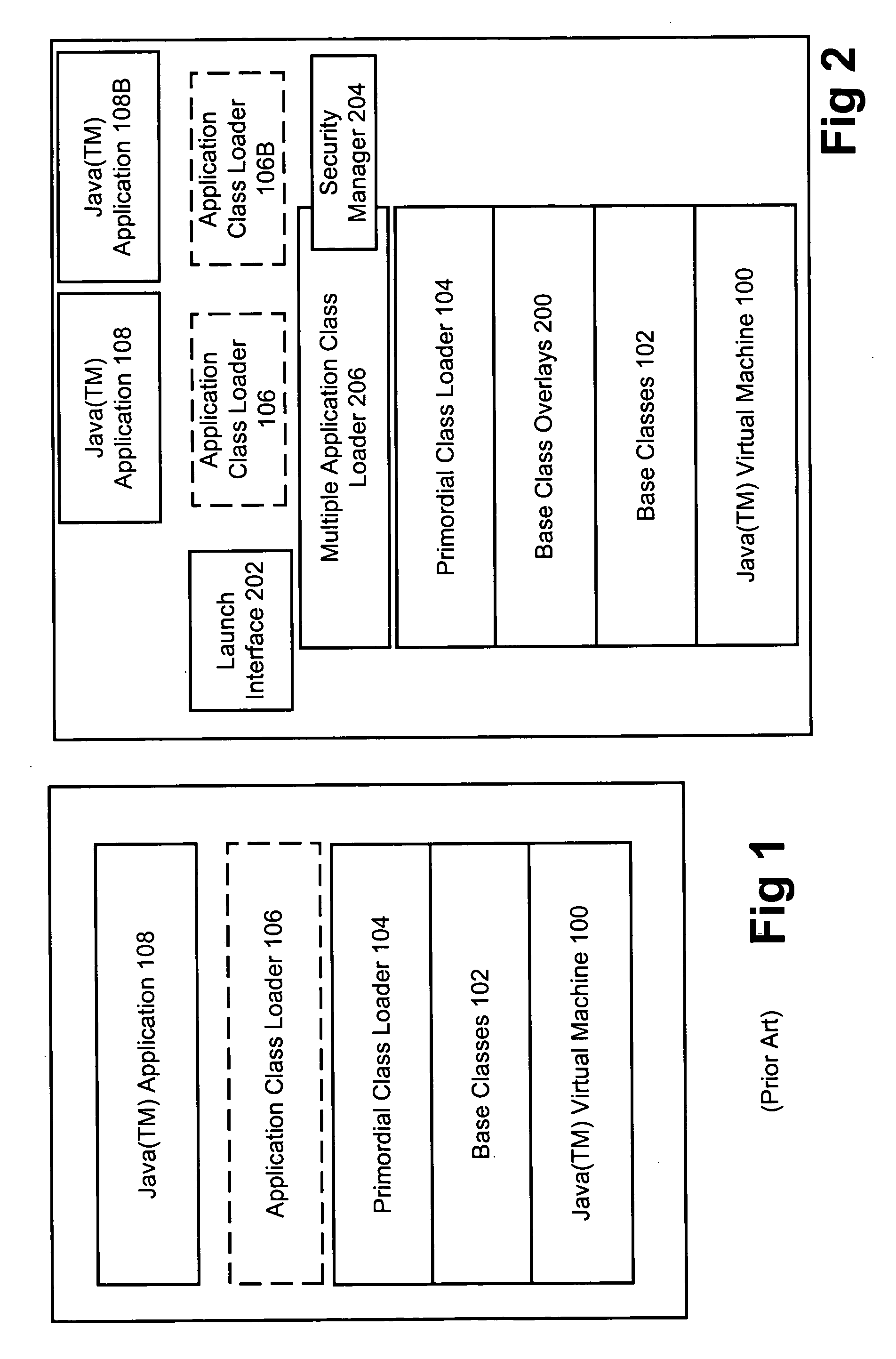
Method and apparatus for executing multiple JAVA((TM)) applications on a single JAVA((TM)) virtual machine
InactiveUS6931544B1Big memorySignificant performance improvementProgram loading/initiatingSoftware simulation/interpretation/emulationOverlayUser Privilege
A modified JAVA(™) execution environment is described. The modified environment supports multiple JAVA(™) applications on a single JAVA(™) virtual machine (JVM). This modified environment provides significant memory and performance improvements when running multiple applications on a single computer system. Notably, no changes are needed to the source code of an application to take advantage of the modified environment. Further, embodiments of the invention may support shared access to base classes through the use of overlays. Additionally, system resource permissions can be enforced based upon the user permissions associated with a running application. Notably, embodiments of the invention allow multiple applications to share the abstract window toolkit (AWT) on a per display basis. Since only a single garbage collection routine is necessary, applications see improved performance relative to running in different JVMs. Further, the shared base classes eliminate significant memory overhead.
Owner:APPLE INC
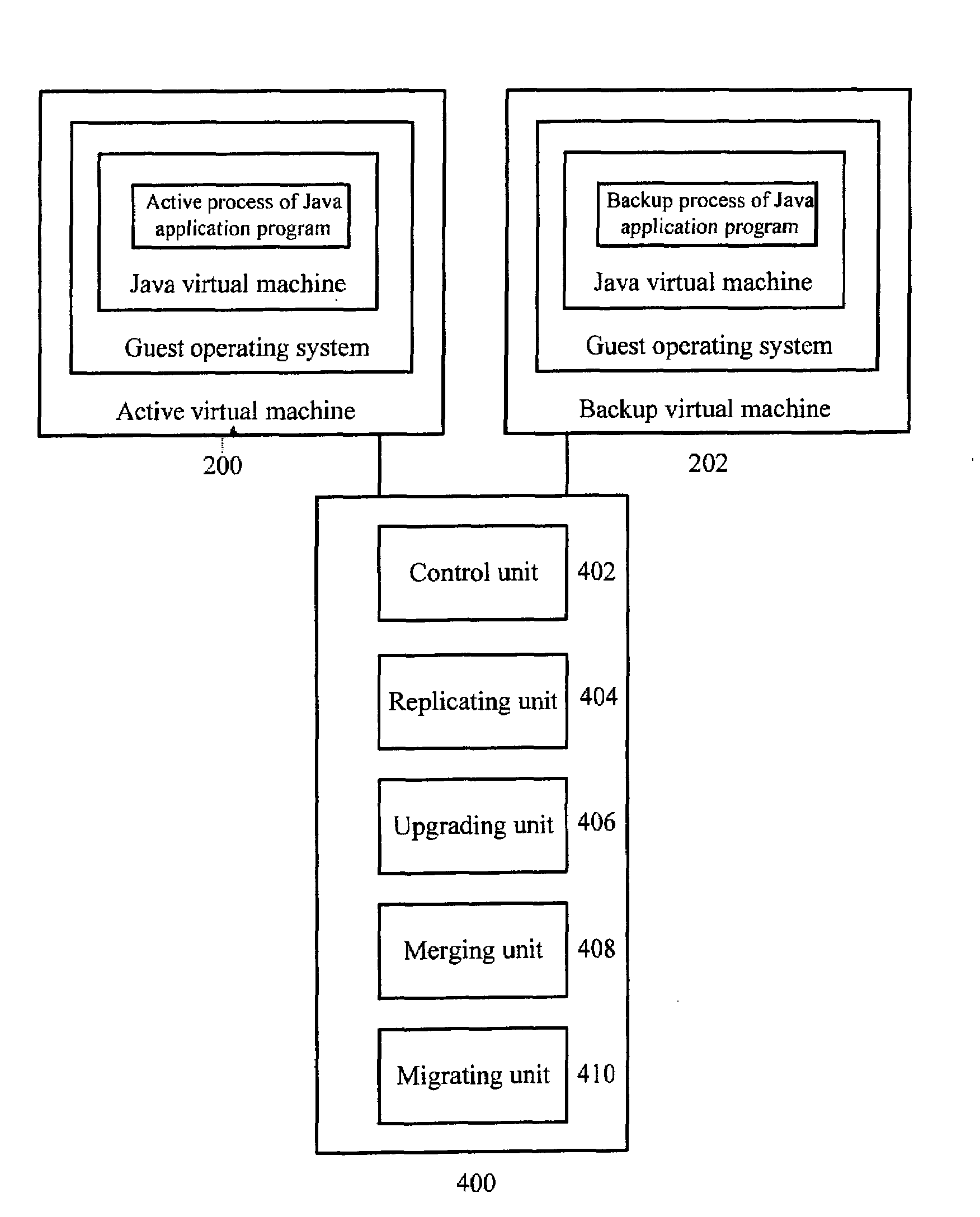
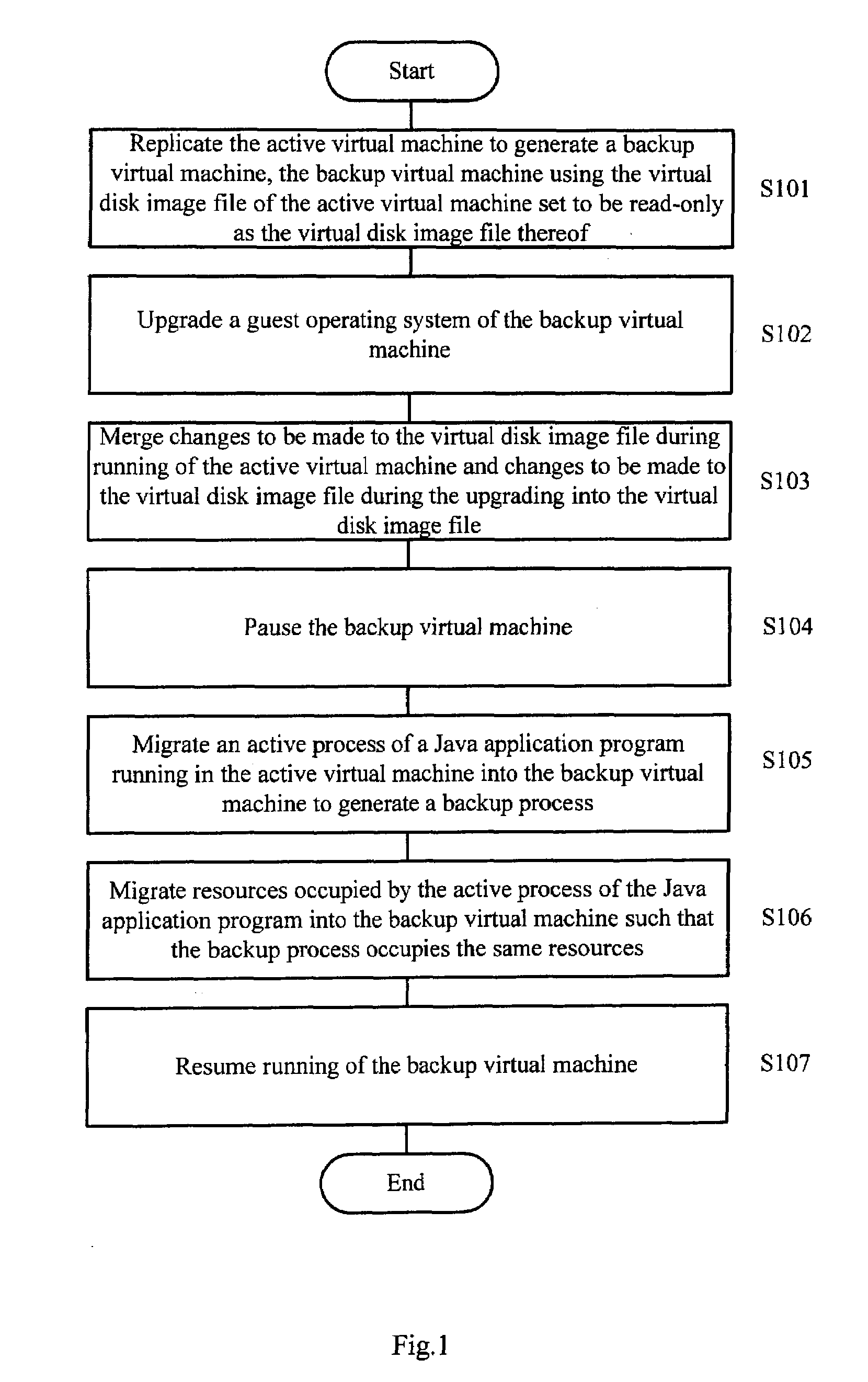
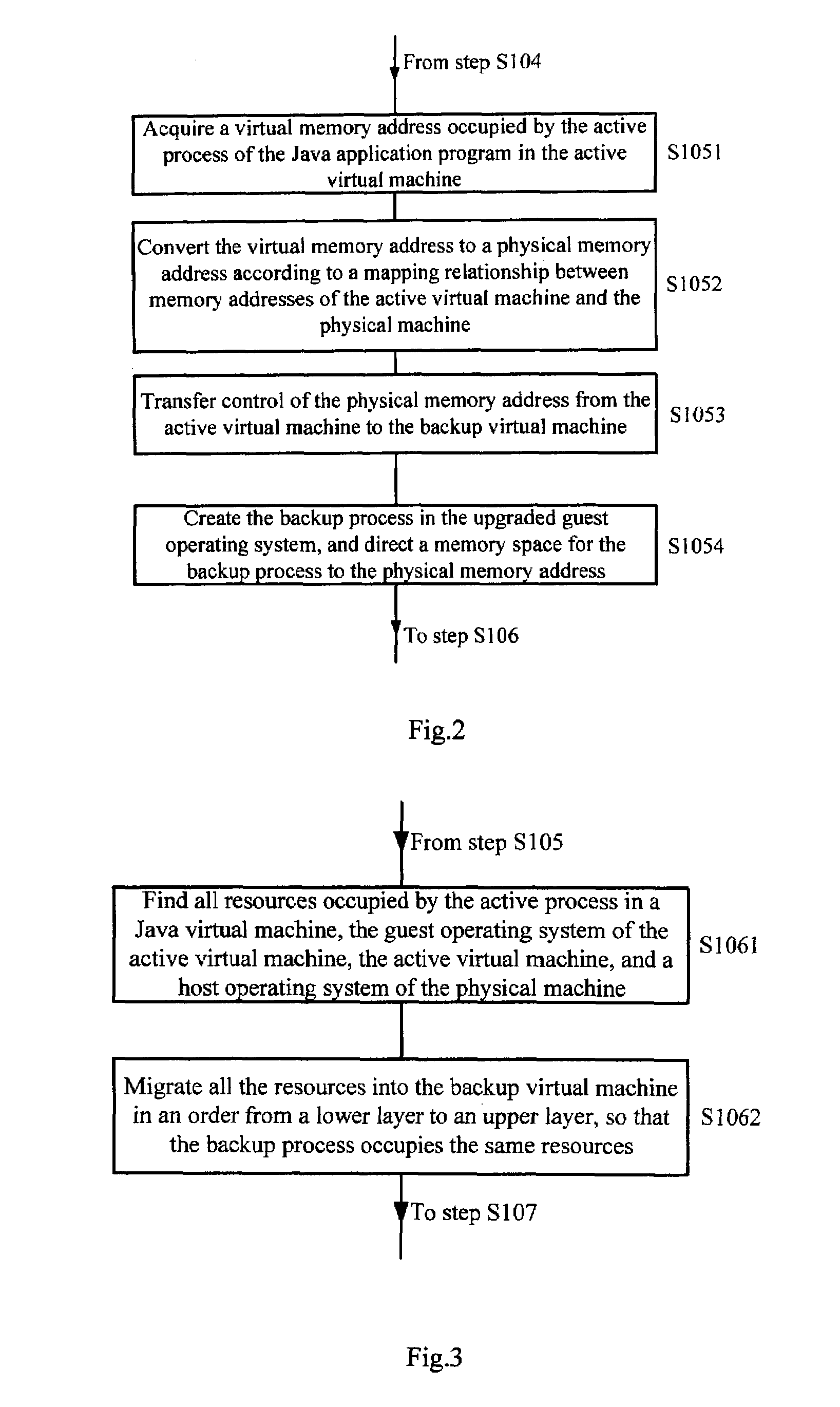
Method and Device for Upgrading a Guest Operating System of an Active Virtual Machine
InactiveUS20100106885A1Improve usabilityMemory loss protectionComputer security arrangementsOperational systemApplication software
A method and device for upgrading a guest operating system (OS) of an active Virtual Machine (VM). The method includes: replicating the active VM to generate a backup VM; upgrading a guest OS of the backup VM; merging changes to be made to a virtual disk image file during running of the active VM and changes to be made to the virtual disk image file during the upgrading; pausing the backup VM; migrating an active process of a Java application program running in the active VM into the backup VM to generate a backup process; migrating resources occupied by the active process of the Java application program into the backup VM such that the backup process occupies the same resources; and resuming running of the backup VM. The device includes: a replicating unit; an upgrading unit; a merging unit; a migrating unit; and a control unit.
Owner:IBM CORP
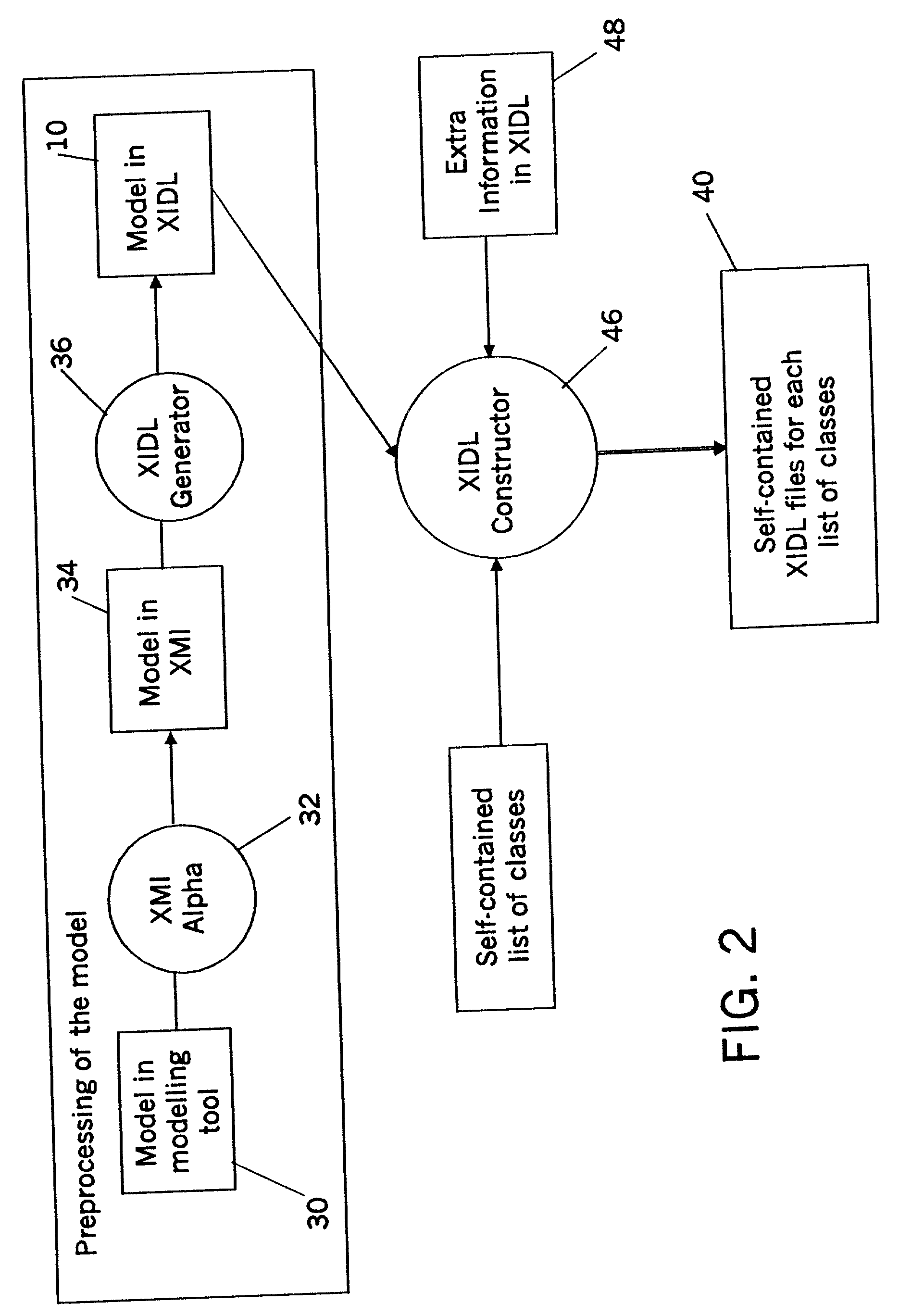
Method and apparatus for generating serialization code for representing a model in different type systems
In order to use object-oriented models over the Internet for applications in different type systems it is necessary to marshal and unmarshal objects between Java, SQL and XML. Hand-writing specific code to do this is difficult. A computer-implemented method of generating serialization code for representing a model in a plurality of type systems is disclosed, the method comprising the steps of: i) producing an input file from the model for a given set of objects; and ii) providing a code generator for acting on the input file to generate the serialization code.
Owner:IBM CORP
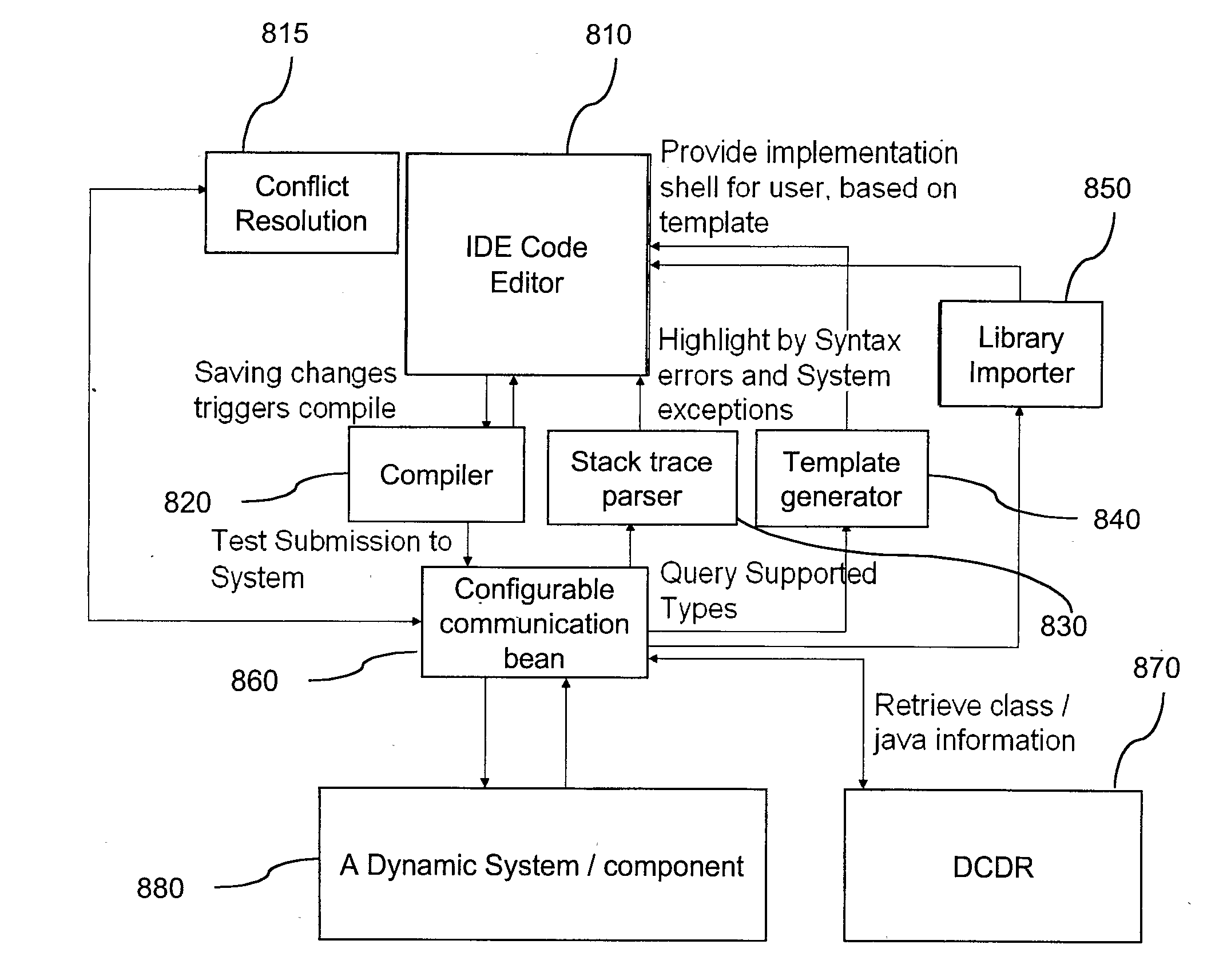
Interactive development tool and debugger for web services
InactiveUS20090172636A1Error detection/correctionMultiprogramming arrangementsText editingApplication software
A development environment, comprising: text editing means (810); an interface (860) for passing amended code to a live running application (880) on a Java EE platform, and for receiving an exception in the event that said exception is generated by the application; means (830) for parsing said received exception in order to identify an associated portion of the amended code as identified in the exception; and means (810) for identifying the associated line of the class within the text editing means (810).
Owner:BRITISH TELECOMM PLC
Mapping XML schema components to qualified java components
InactiveUS7194485B2Data processing applicationsSemi-structured data mapping/conversionXML schemaComputer science
The present invention provides a method, apparatus, and computer instructions for mapping and labeling XML schema elements and types. In an exemplary embodiment, each XML schema element and type is uniquely labeled, using distinguishing parameters such as namespace to create name parts like a Hashing code and suffixes in order to achieve unique mapping. The parameters selected are predetermined in order to achieve naming that remains distinct across successive consumptions of a schema. The selection disclosed accomplishes unique labeling, while also permitting one to still adhere to the strict naming standards of the target language (e.g., Java). As a result, schema components belonging to multiple namespaces can be mapped to Java components belonging to a single package.
Owner:INT BUSINESS MASCH CORP
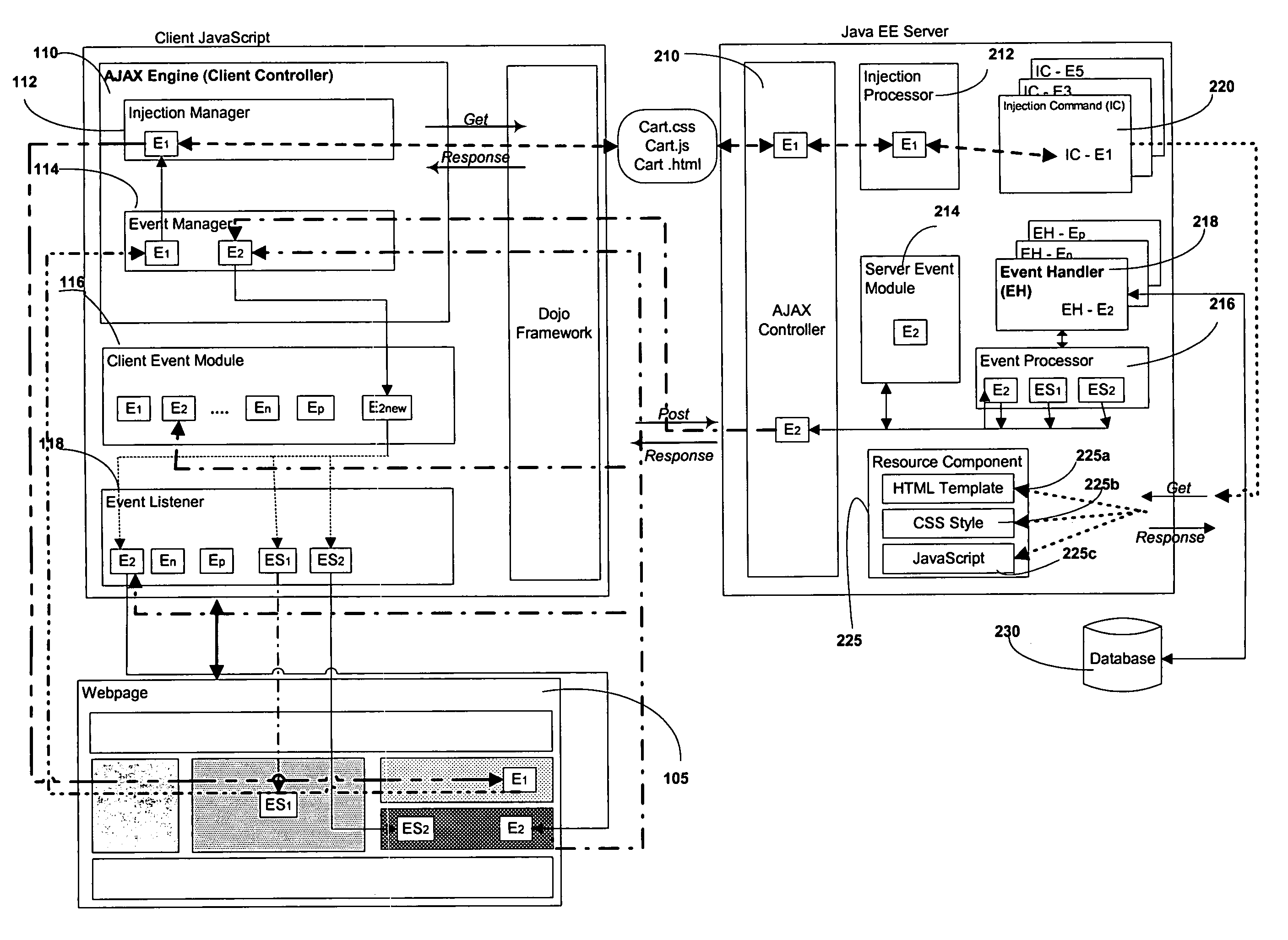
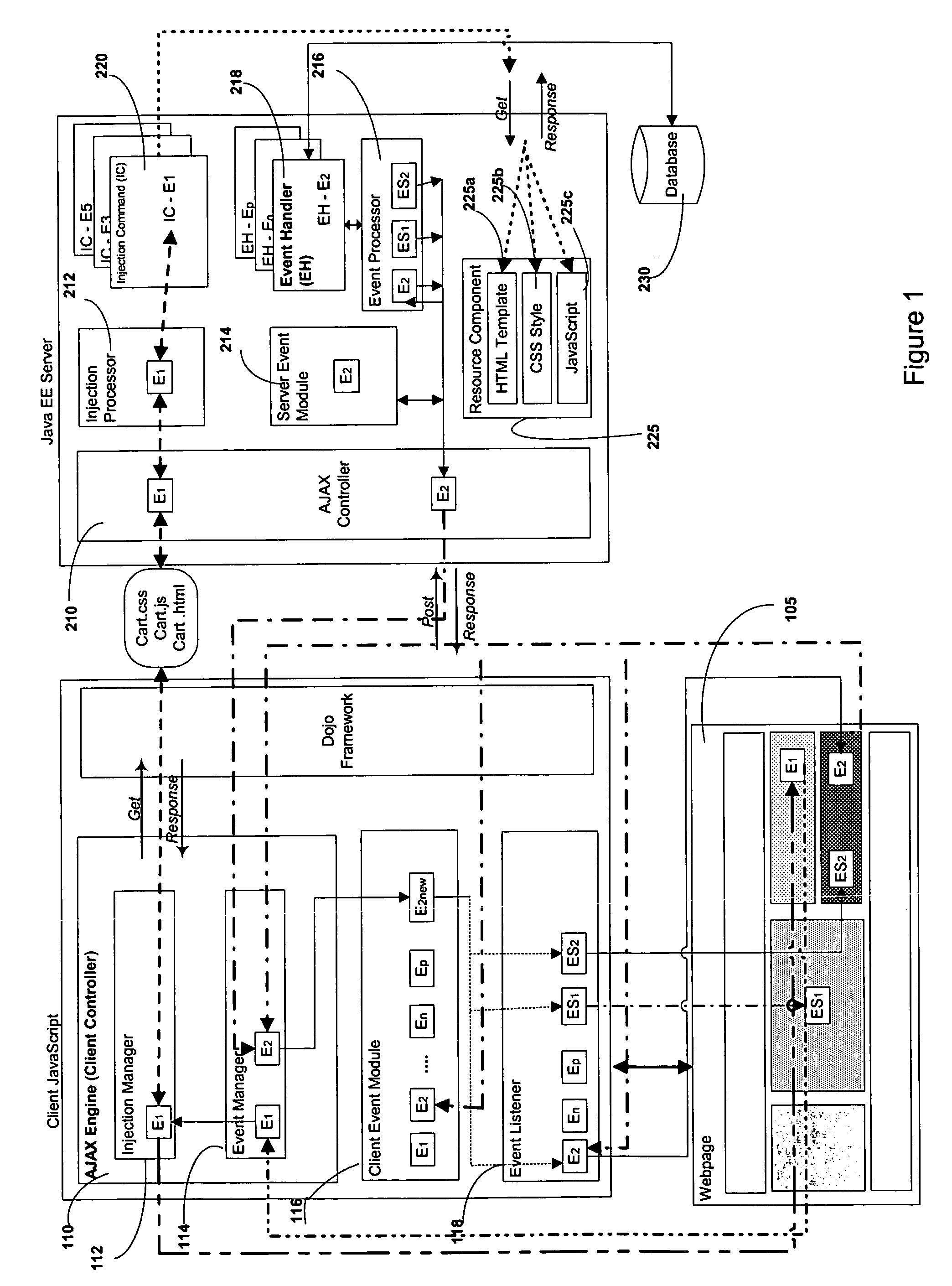
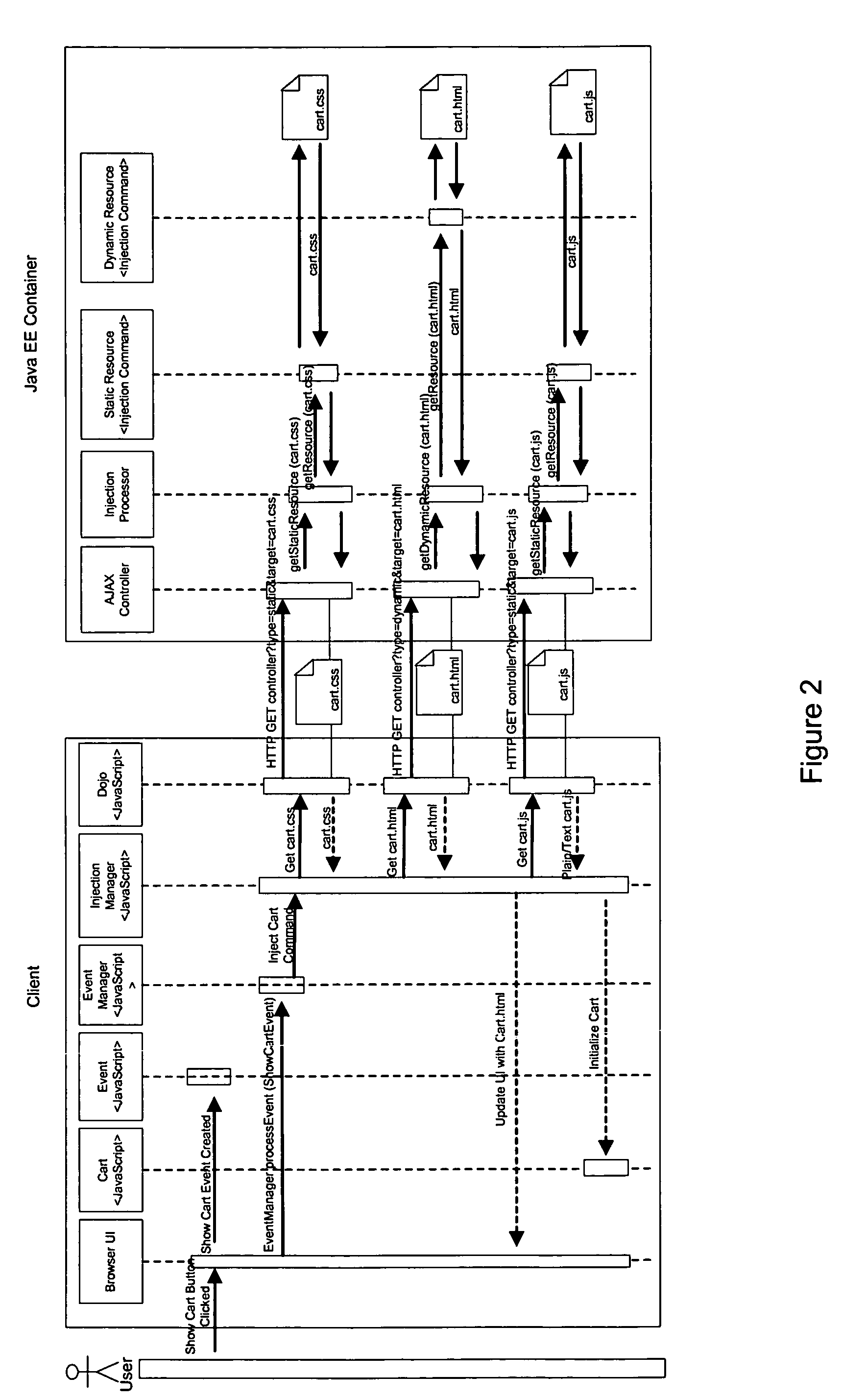
Method and system for providing framework for Java based AJAX web applications
ActiveUS7487201B1Multiple digital computer combinationsWebsite content managementAsynchronous communicationWeb application
A method and system for managing events associated with either the client or the server using a controller framework includes initiating a request at a client. The request triggers an event that is processed using a client controller on the client. The client controller registers the event on the client, forwards the event to a server controller on a server, polls the server controller on the server periodically for information related to the event and retrieves notifications in response to the request or upon a poll. The client controller communicates with the server controller using asynchronous communication. The response retrieved by the client controller is loaded onto the browser of the client dynamically and rendered at the client as and when notifications are received from the server.
Owner:ORACLE INT CORP
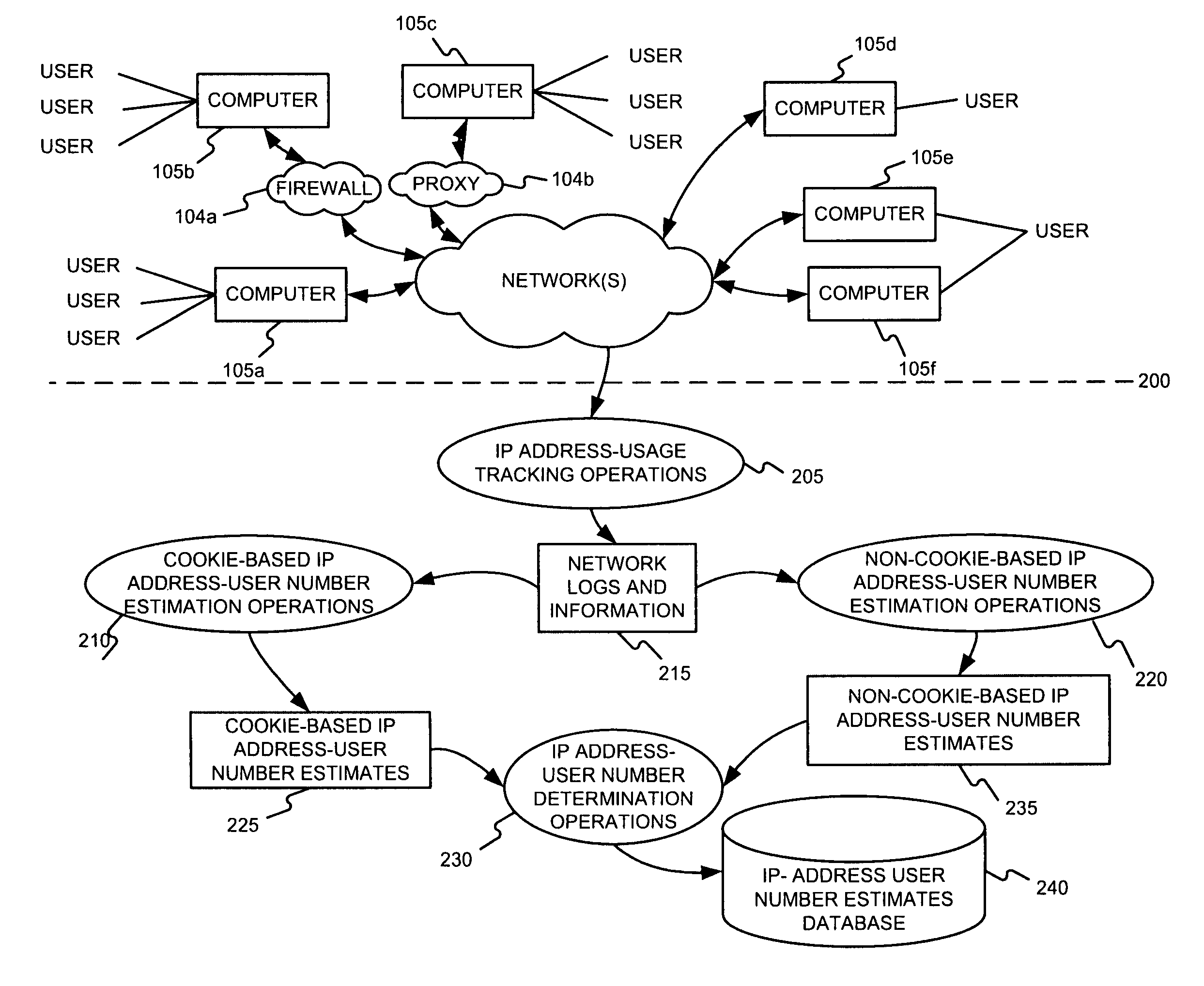
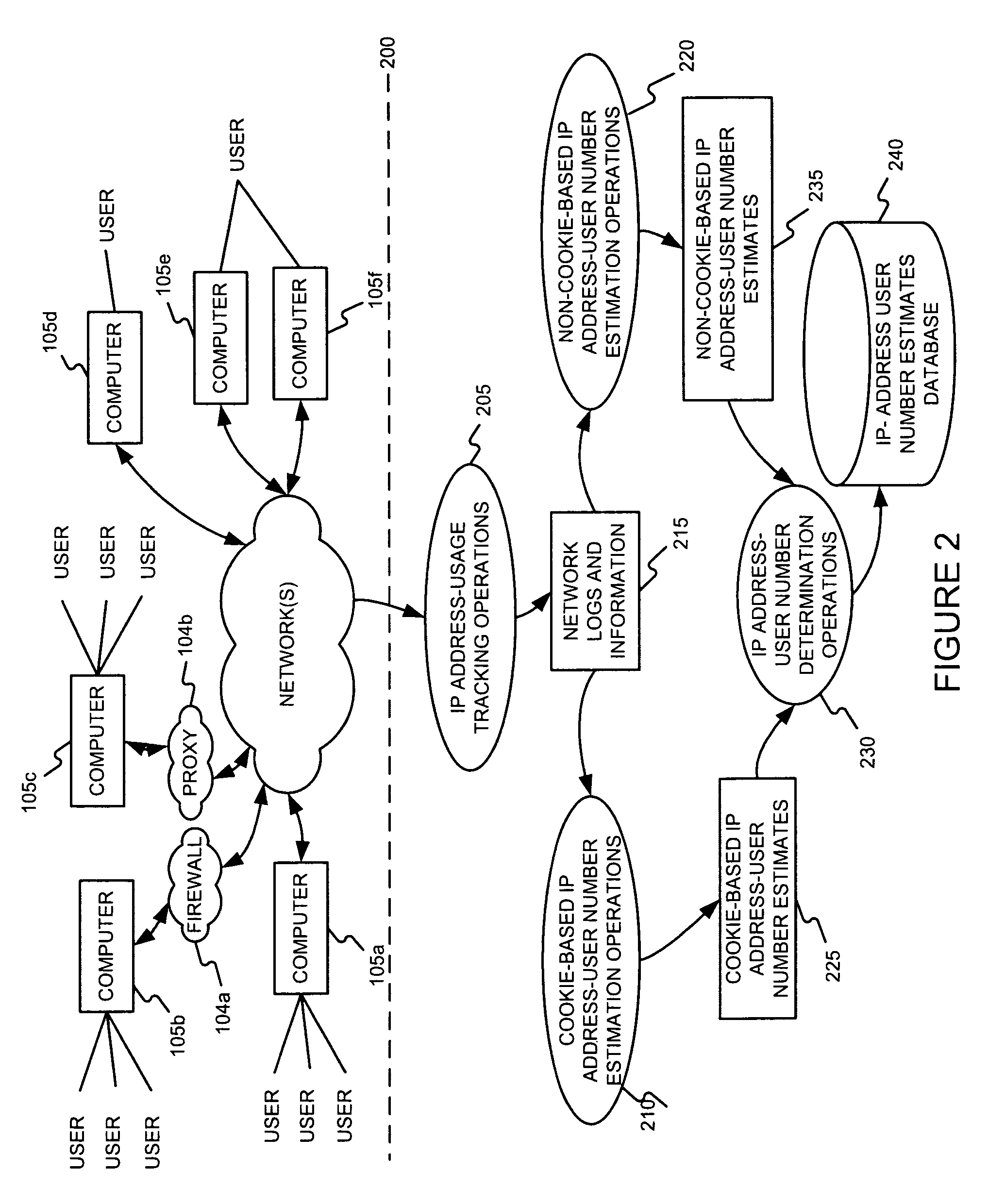
Determining a number of users behind a set of one or more internet protocol (IP) addresses
IP address-user number estimates may be determined by accepting IP address usage information associating various IP addresses with various client identifiers, and generating an estimate of a number of users for at least one of the IP addresses using the IP address usage information. If the client identifiers include cookies, the estimate of a number of users for at least one of the IP address might be generated, in part, by determining a number of cookies for the at least one IP address for a given period of time, and multiplying the first ratio by a second, predetermined, ratio of a number of users per cookie for the given time period. If the client identifiers are user-agent parameters and / or browser parameters (e.g., screen setting information, time zone, history length, whether or not Java enabled, number of plug-ins, mime types, etc.), the estimate of a number of users per IP address might be generated, in part, by determining a ratio of unique sets of user agent and / or browser parameters for an IP address.
Owner:GOOGLE LLC
Mobile internet solution using java application combined with local wireless interface
InactiveUS20030114106A1Near-field transmissionUnauthorised/fraudulent call preventionBluetoothApplication software
A telecommunications system and method for downloading application software to a local communications network via an external communications network. The local communications network comprises a plurality of devices including an interface device. The interface device includes an interface for interfacing with the external communications network for downloading an application software from an application software source to the interface device via the external communications network. The local communications network preferably comprises a local wireless network, such as a Bluetooth wireless network, and the external communications network preferably comprises a mobile communications network for downloading application software to a mobile phone of the local wireless network.
Owner:TELEFON AB LM ERICSSON (PUBL)
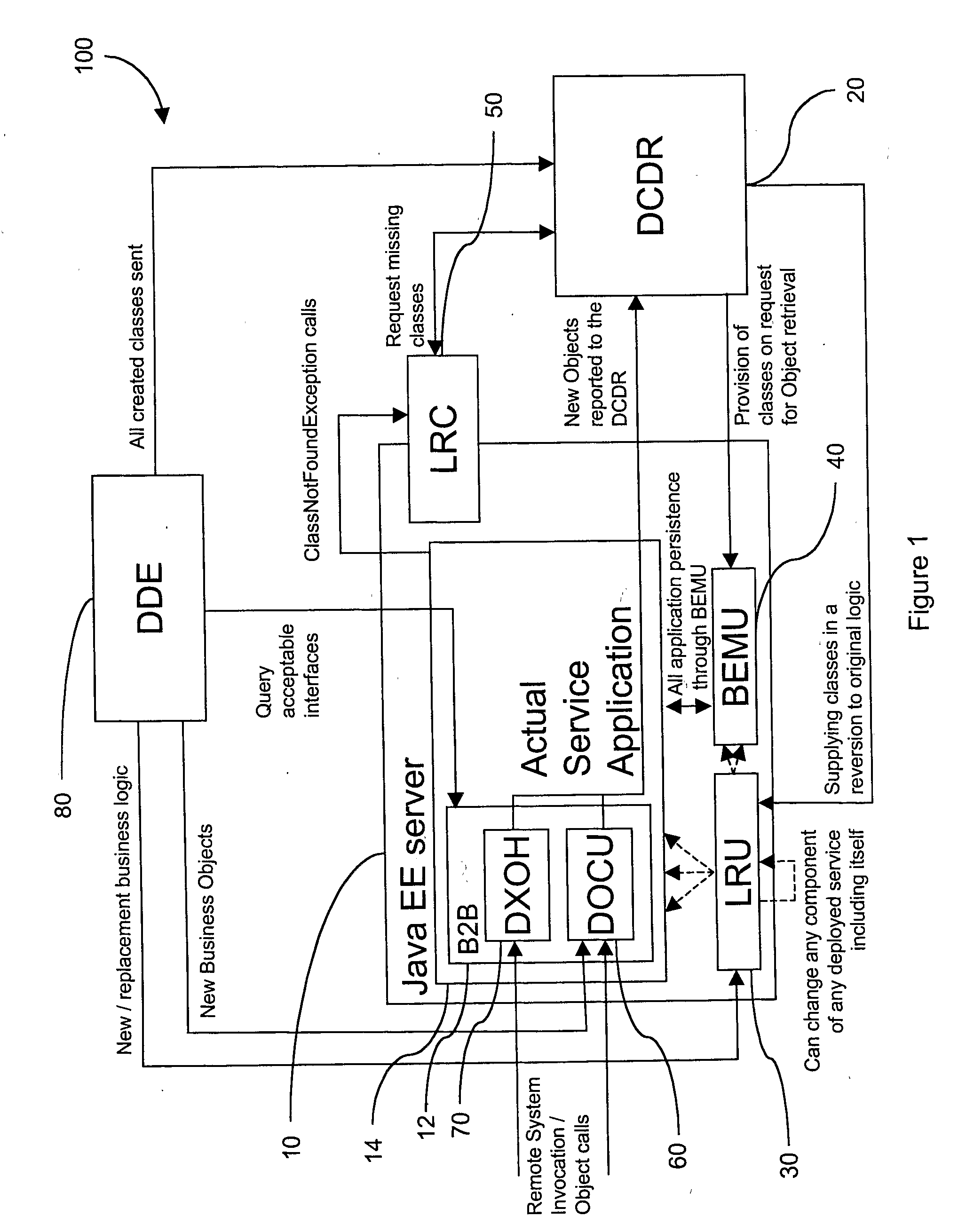
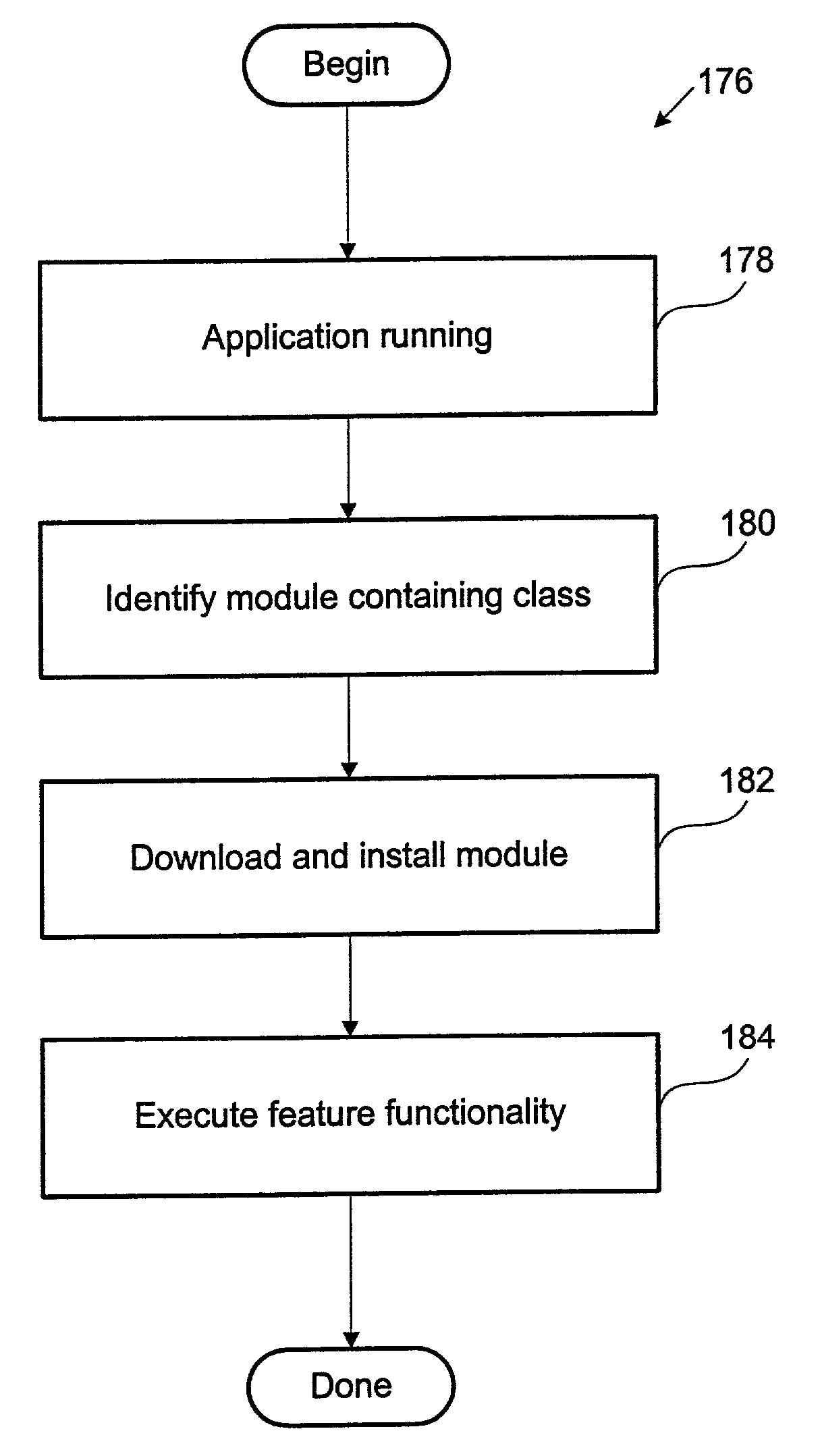
Dynamic java class loading for application execution
InactiveUS7028295B2Efficient downloadAvoid excessive delayInterprogram communicationDigital computer detailsGeneral purpose computerJava classes
Methods and an apparatus for downloading an application over a distributed network are provided. One exemplary method includes a computer implemented method executed by a general purpose computer, where the computer implemented method is capable of downloading an executable program from a networked storage to the general purpose computer. The method initiates with downloading a core module where the core module includes classes necessary to run an engine of the executable program. Then, the core module is installed which in turn module provides instant user functionality. The installed core module includes code for, requesting a class not associated with the core module, searching non-core modules of the executable program for the requested class, and downloading to the general purpose computer a non-core module containing the requested class while the executable program provides the user functionality.
Owner:SEIKO EPSON CORP
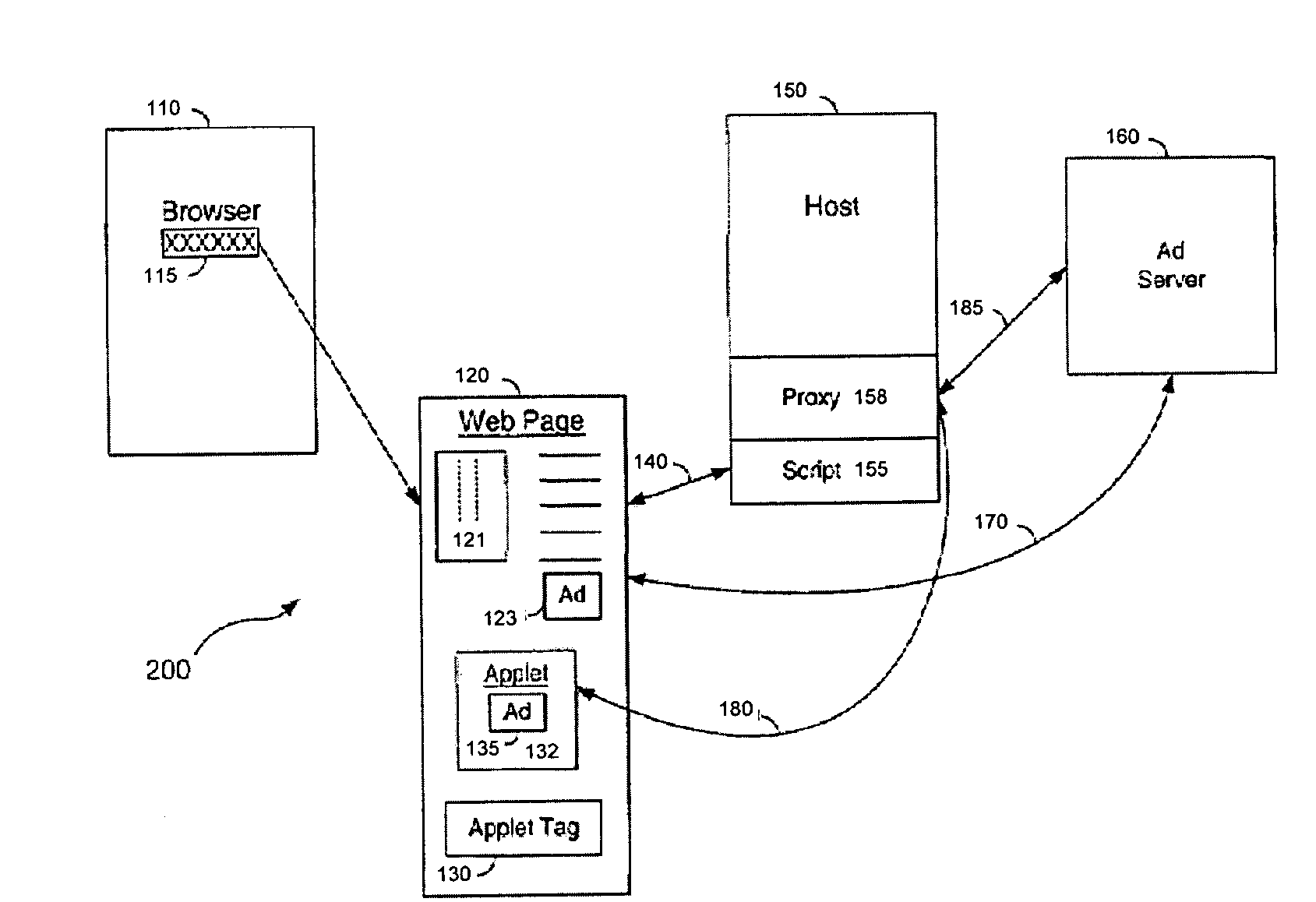
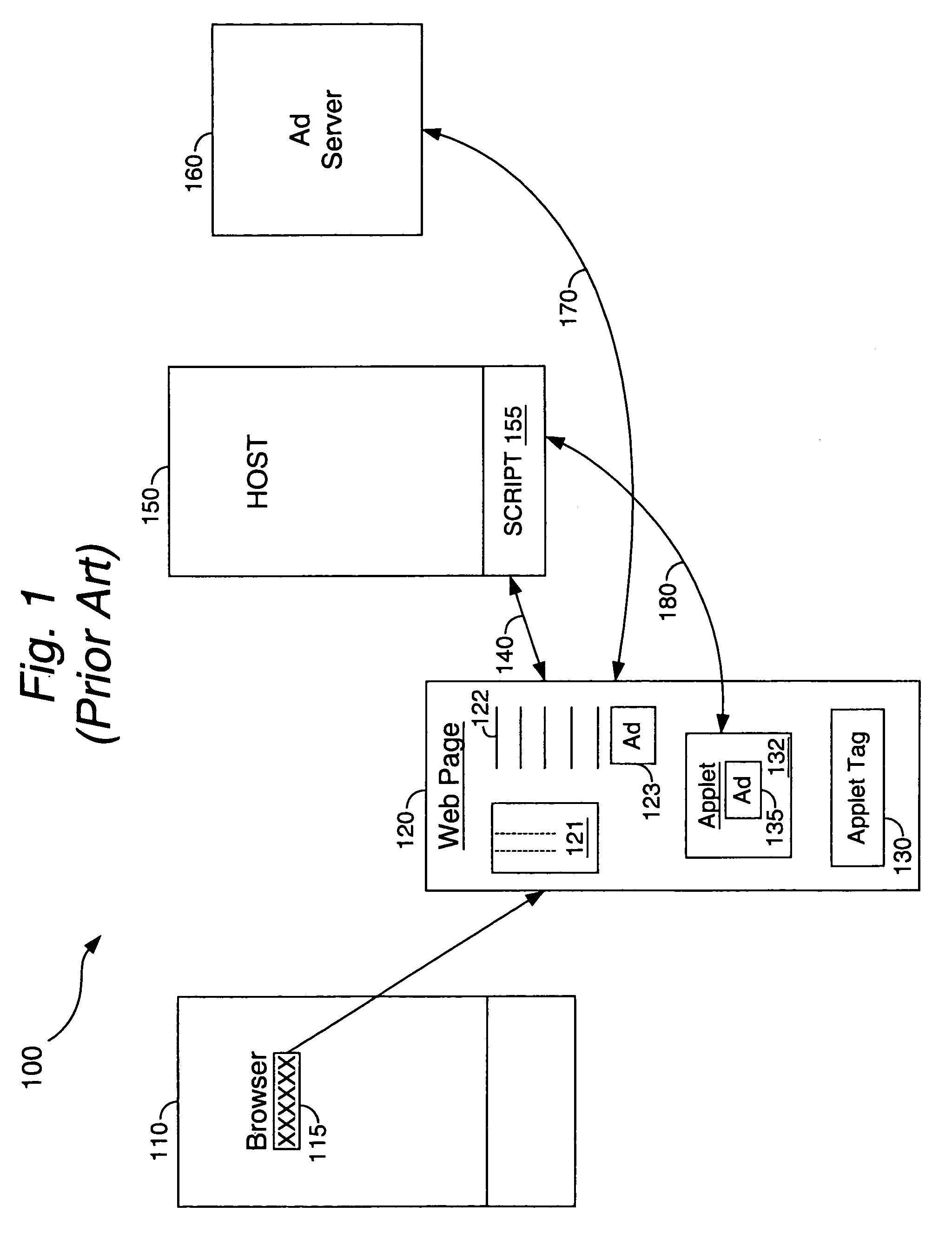
System and method for implementing click-through for browser executed software including ad proxy and proxy cookie caching
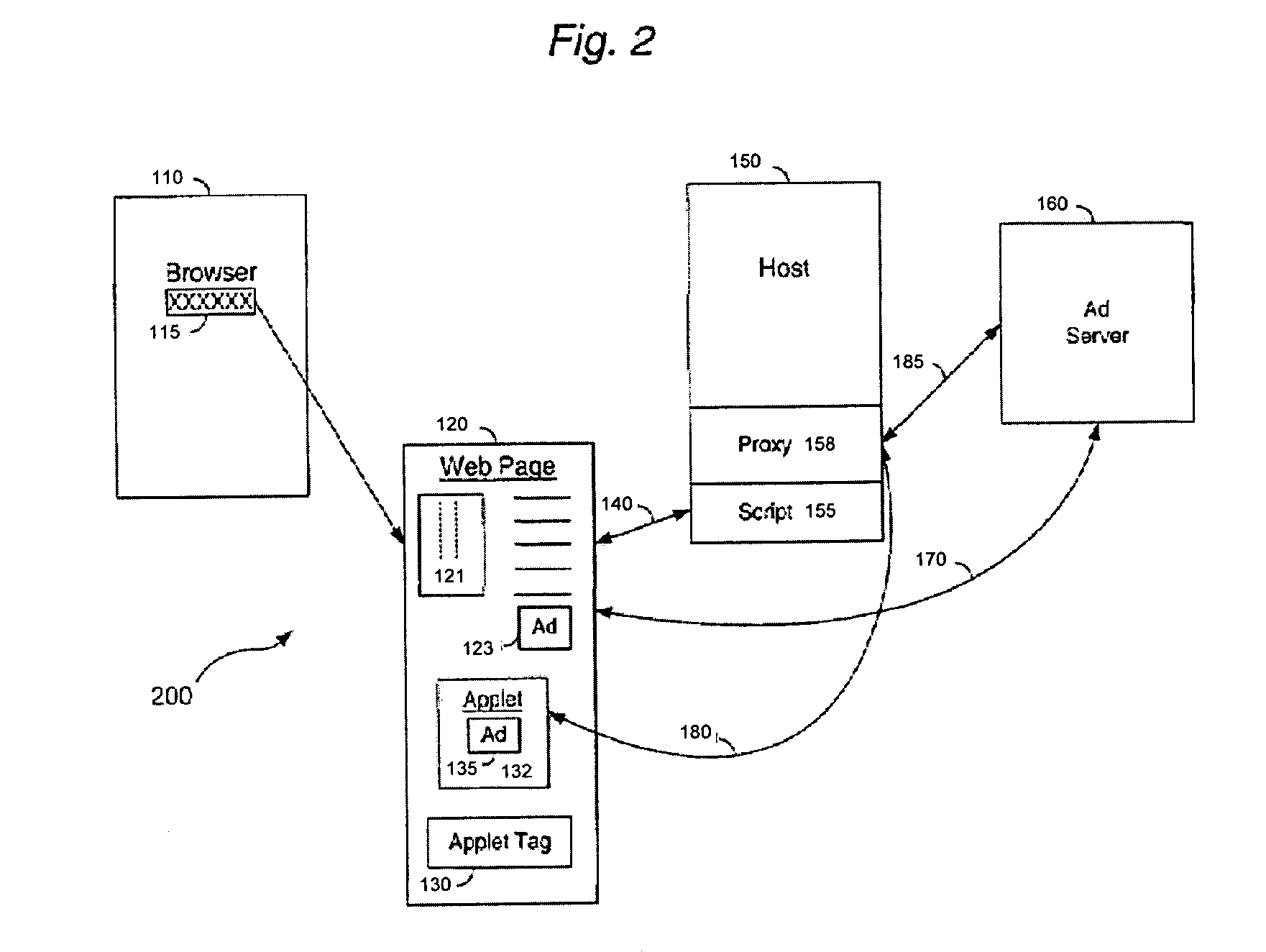
ActiveUS7475404B2Inability to overcomeExpanded advertisingDigital data information retrievalAdvertisementsThird partyIp address
An improved proxy is disclosed for allowing click-through on an ad URL delivered on a web page within a Java® applet executing on a client machine. The proxy caches cookie information for the browser, to support java applications that do not allow for planting of cookies directly. When the user clicks on the ad URL, the proxy retrieves the relevant cookie and link information from a host side database, and uses the same to help the browser open the correct URL associated with the ad. Additional controls are provided for the proxy including the ability to filter ads in an appropriate fashion for the applet, to cache ads from third party servers, to monitor applet behavior, to cache / pass on client IP address information, and to perform administrative tasks for the applet within the browser to enhance and facilitate ad delivery between advertisers and their intended audiences. The proxy thus acts to extend the reach and access of a conventional applet beyond the resources of a download host associated with such applet. In another embodiment, the applet controls a hidden frame within the browser, which hidden frame, unlike the applet frame, is able to download and plant a cookie from an ad server within the browser. When the user clicks on the ad URL, the browser uses the cooked from the hidden frame and passes it on to the Ad Server along with the URL, so that the user experiences a seamless and smooth transfer as would occur from a conventional HTML tag within the page.
Owner:RATEZE REMOTE MGMT LLC
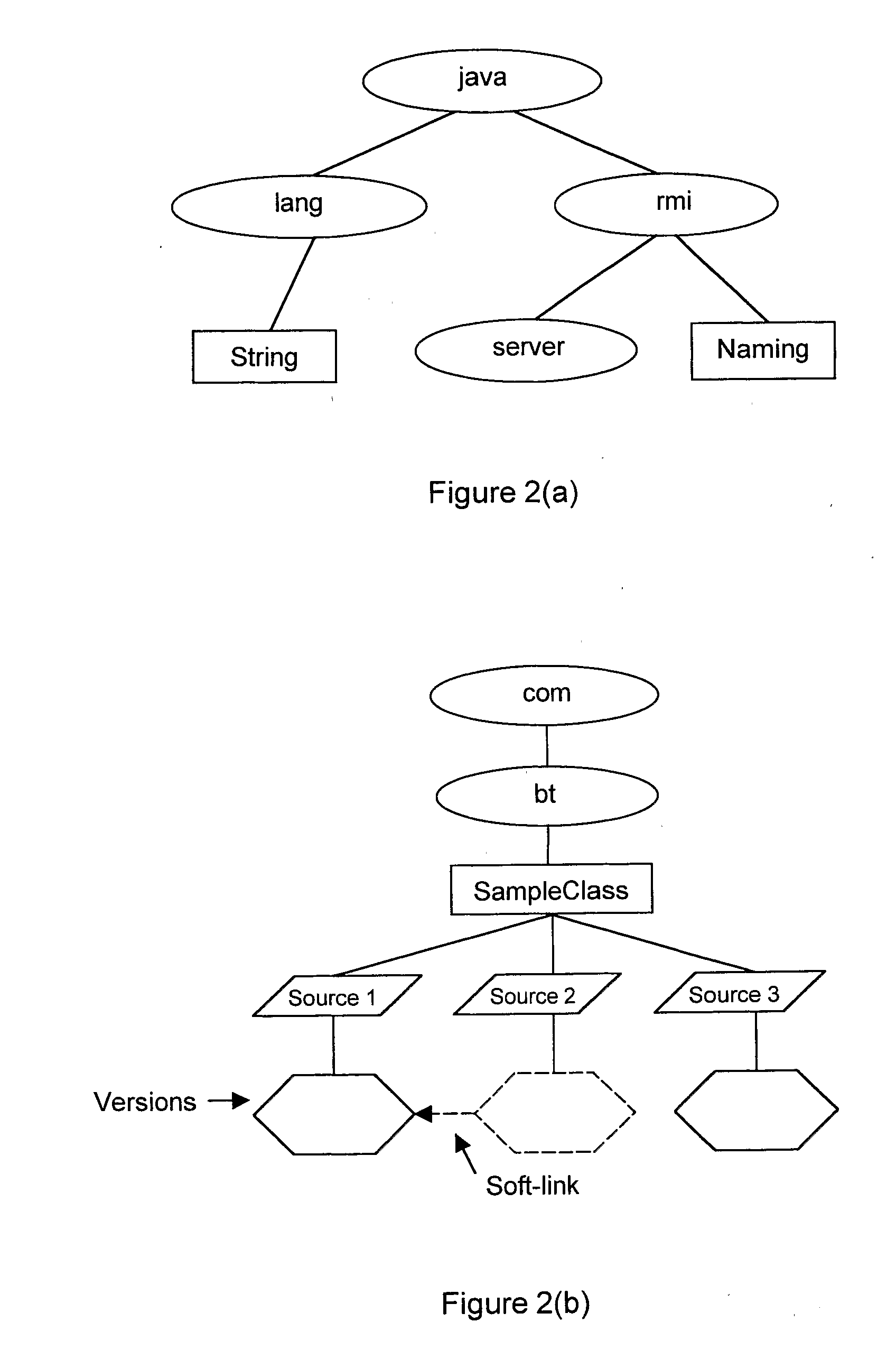
Object model for Java TM
The mechanism includes three data structures: object data associated with each object O1, O2, O3 ... of a program, a class descriptor associated with the classes to which the objects O1, O2, O3 ... belong, and interface references. For each class Ci, the class descriptor corresponding to the class Ci includes: i) a class method table comprising one or more entries, wherein each entry identifies an implementation of a method inherited or defined by the class Ci; and ii) for each interface implemented by the class Ci, an interface method table comprising one or more entries, wherein each entry identifies an implementation of a method declared by the particular interface or an implementation of a method declared by an interface extended by the particular interface. An interface reference for an interface declaration ID associated with a given object OI, wherein the object OI implements methods that are declared by an interface declaration ID includes a pointer to the interface method table corresponding to the interface declaration ID within the class descriptor corresponding to the object OI. An efficient mechanism for method invocations is provided by generating an index that identifies the entry corresponding to the appropriate method in the interface method table pointed to by the pointer of the interface reference, reading the data stored by the entry identified by the index, and controlling the computer processing apparatus to jump to the address identified by the data.
Owner:IBM CORP
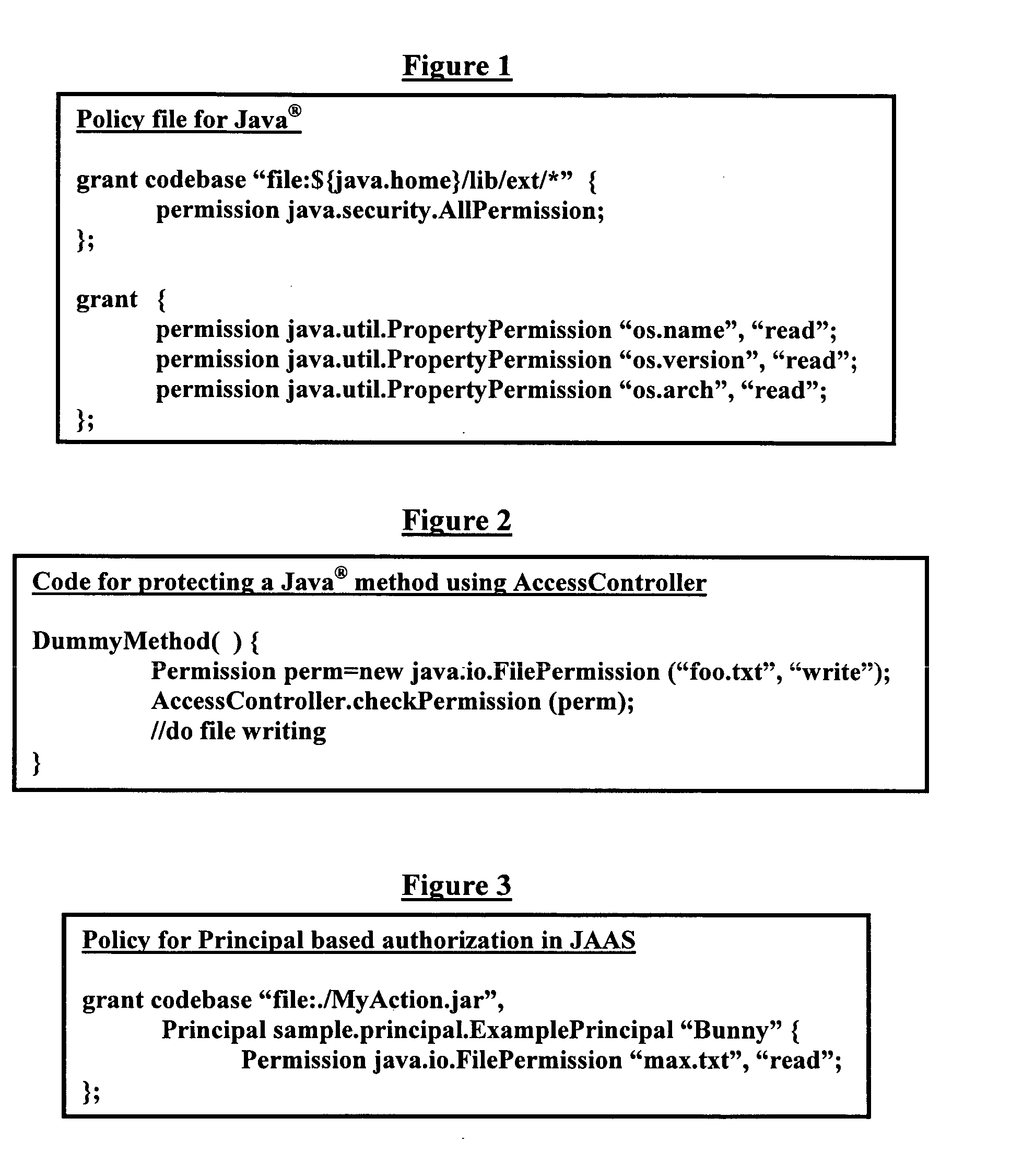
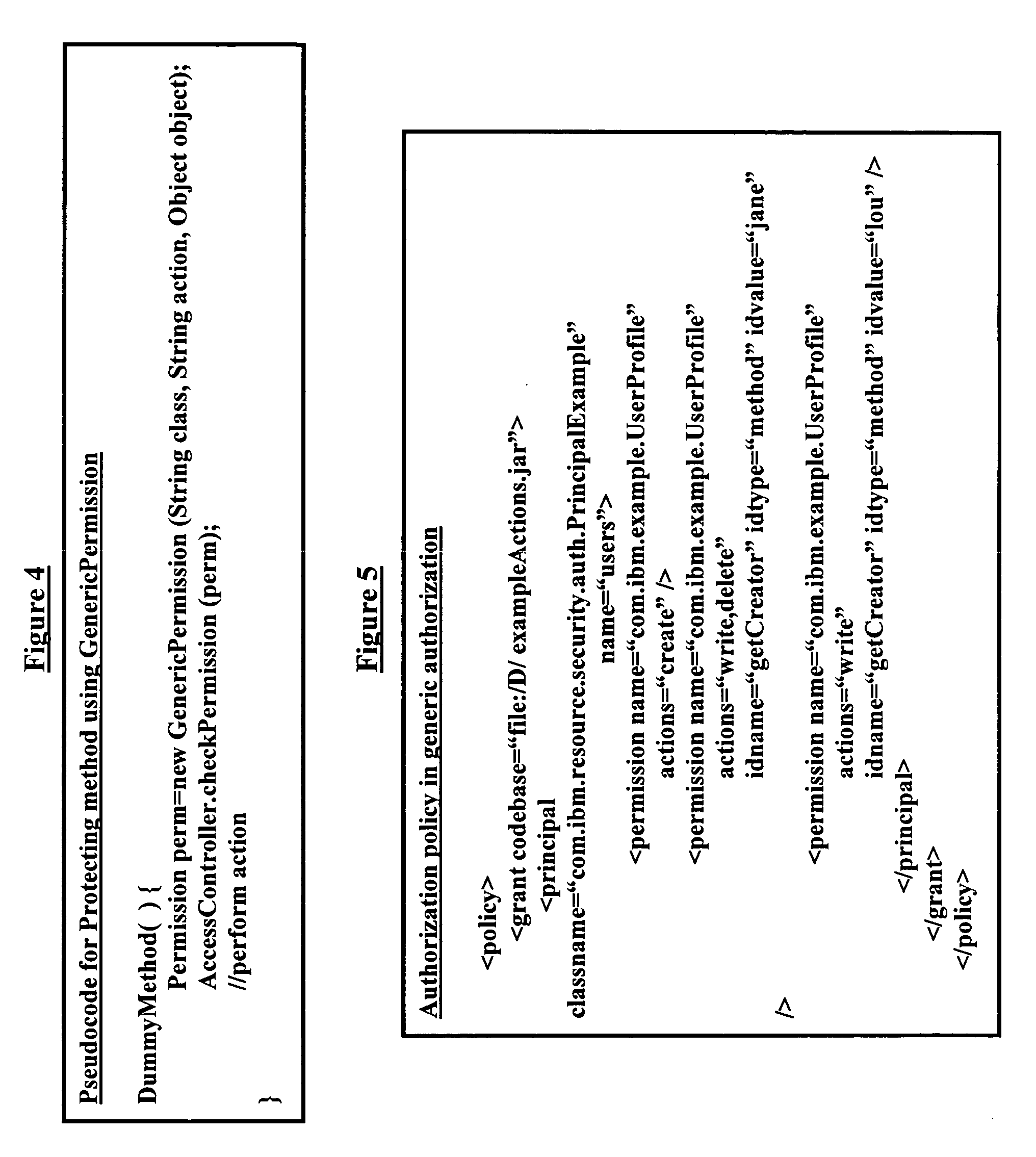
Generic declarative authorization scheme for Java
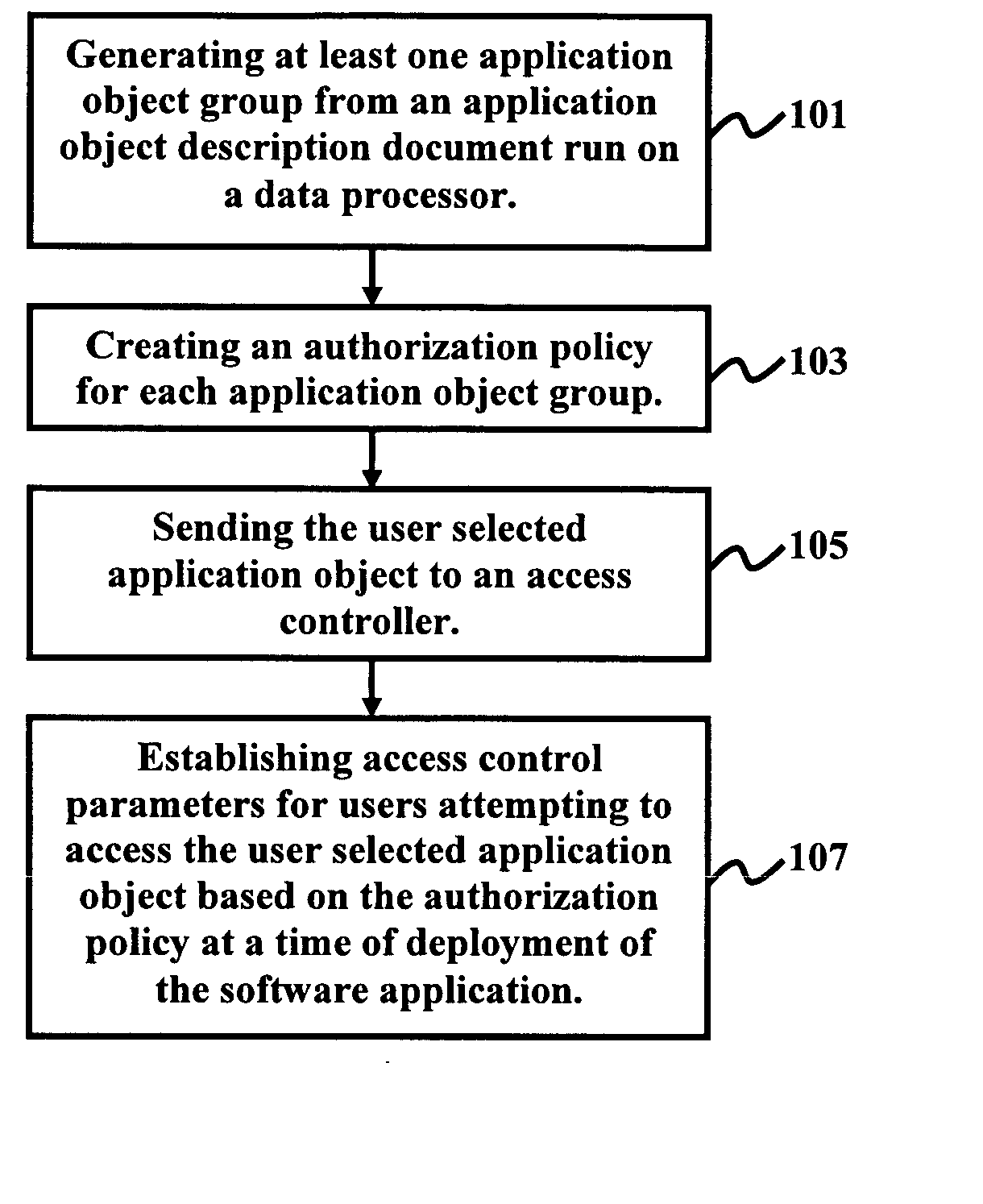
InactiveUS20060026667A1Digital data protectionProgram/content distribution protectionPaper documentDocument preparation
A method, system, and program storage device for establishing security and authorization policies for users accessing a software application, wherein the method comprises generating at least one application object group from an application object description document comprising an XML format run on a data processor; creating an authorization policy for each application object; sending a selected application object group to an access controller; and establishing access control parameters at a time of deployment of the software application for users attempting to access the selected application object group based on the authorization policy. The method further comprises specifying environmental variables for the authorization policy; changing the authorization policy by modifying a declarative specification of the environmental variables and modifying constraints defined on attributes of an application object; implementing varied classes of authorization policies using a same authorization policy classifier; and specifying the application object group using grouping parameters.
Owner:IBM CORP
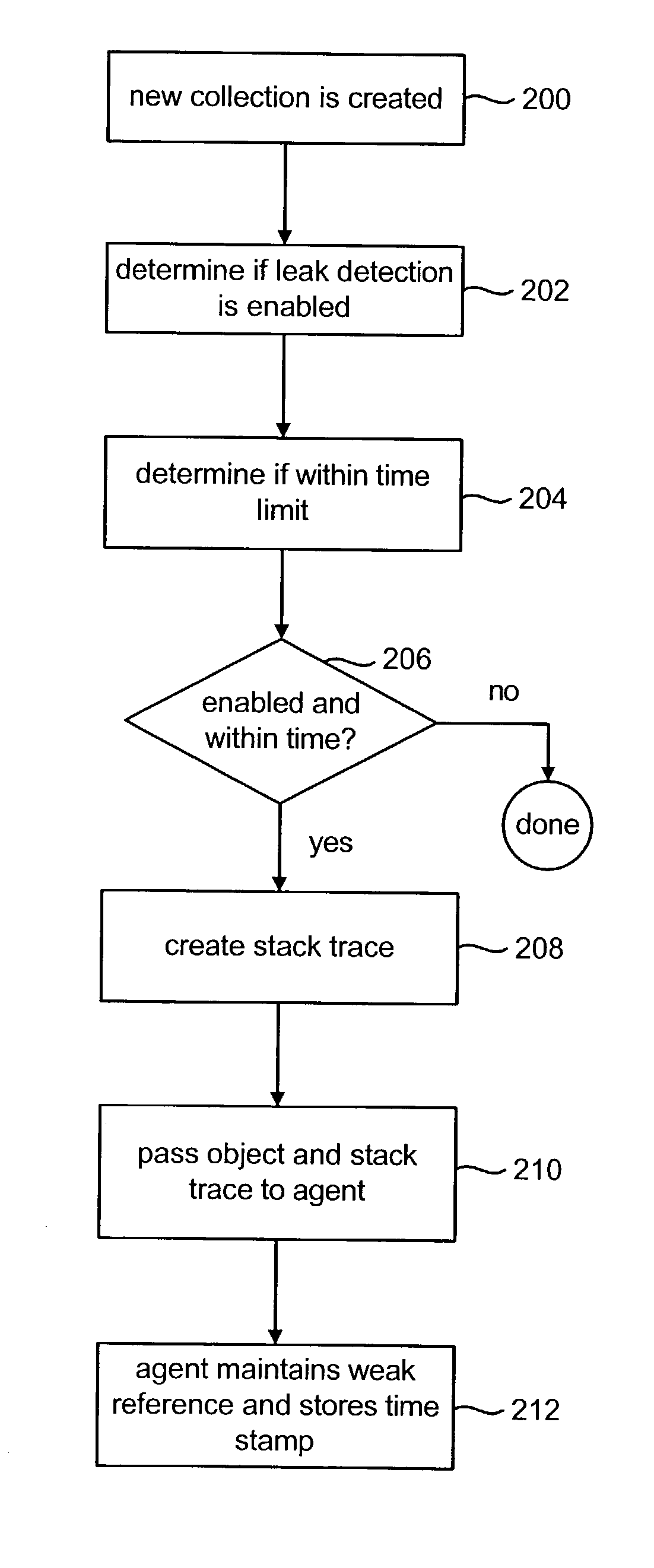
Locating potential sources of memory leaks
ActiveUS20040078540A1Error detection/correctionSpecific program execution arrangementsMemory leakOperating system
Potential sources of memory leaks are identified by tracking the size of groups of stored items and determining based on the growth pattern of the groups whether the groups of stored items are potential sources of memory leaks. An example of a group of stored items is an instance of a Java collection. If the growth pattern of a particular group of stored items indicates that it may be the source of a memory leak, that group is reported to a user and will continue to be tracked.
Owner:CA TECH INC
Method and System for Tracing Profiling Information Using Per Thread Metric Variables with Reused Kernel Threads
InactiveUS20090007075A1Error detection/correctionSpecific program execution arrangementsOperational systemOperating system
A method and system for tracing profiling information using per thread metric variables with reused kernel threads is disclosed. In one embodiment kernel thread level metrics are stored by the operating system kernel. A profiler request metric information for the operating system kernel in response to an event. After the kernel thread level metrics are read by the operating system for a profiler, their values are reset to zero by the operating system kernel. The profiler then applies the metric values to base metric values to appropriate Java threads that are stored in nodes in a tree structure base on the type of event and whether or not the kernel thread has been reused. In another embodiment non-zero values of thread level metrics are entered on a liked list. In response to a request from a profiler, the operating system kernel reads each kernel thread's entry in the linked list and zeros each entry. The profiler can then update the intermediate full tree snapshots of profiling information with the collection of non-zero metric variables.
Owner:INT BUSINESS MASCH CORP
Monitoring performance of applications in a distributed environment
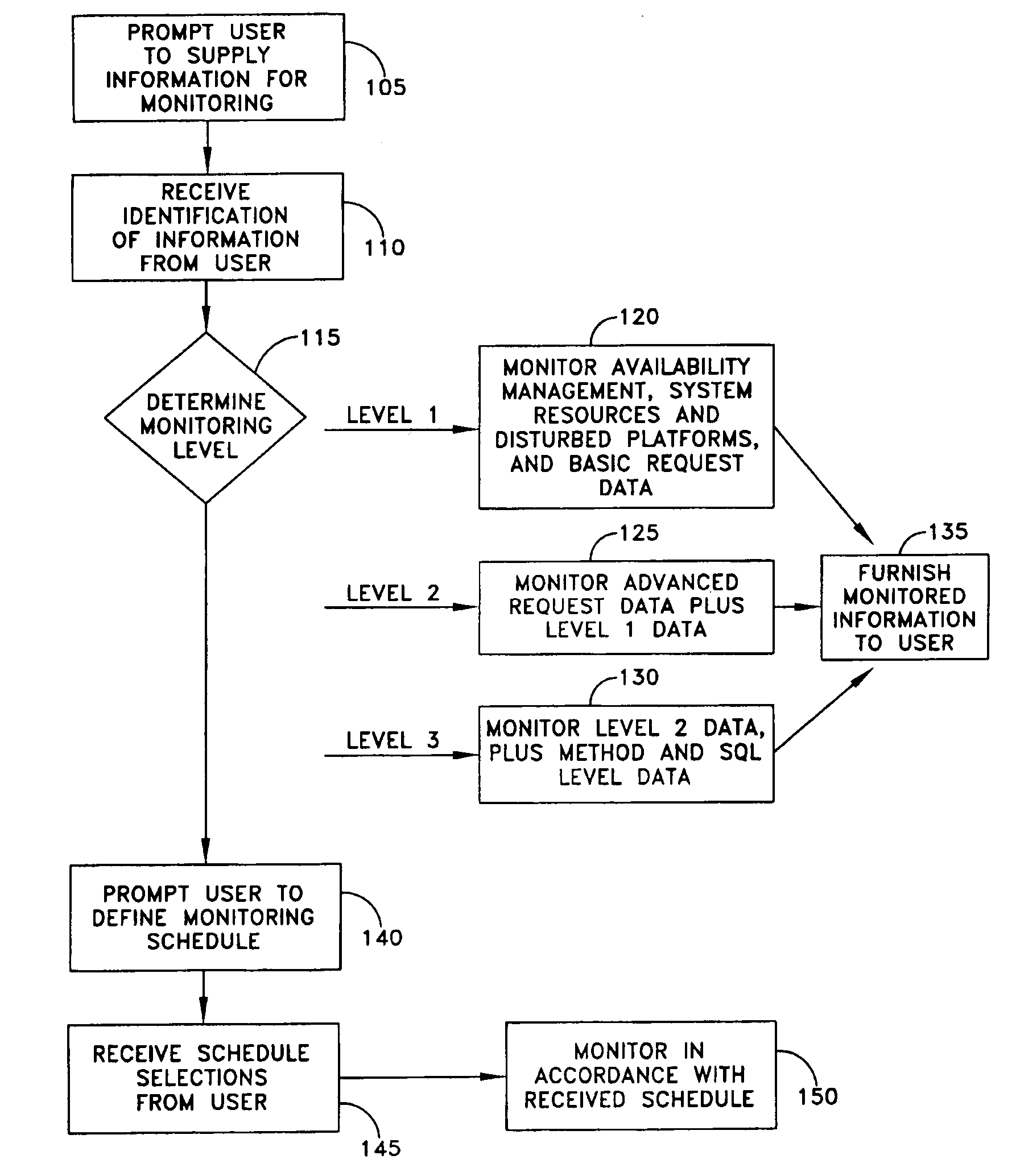
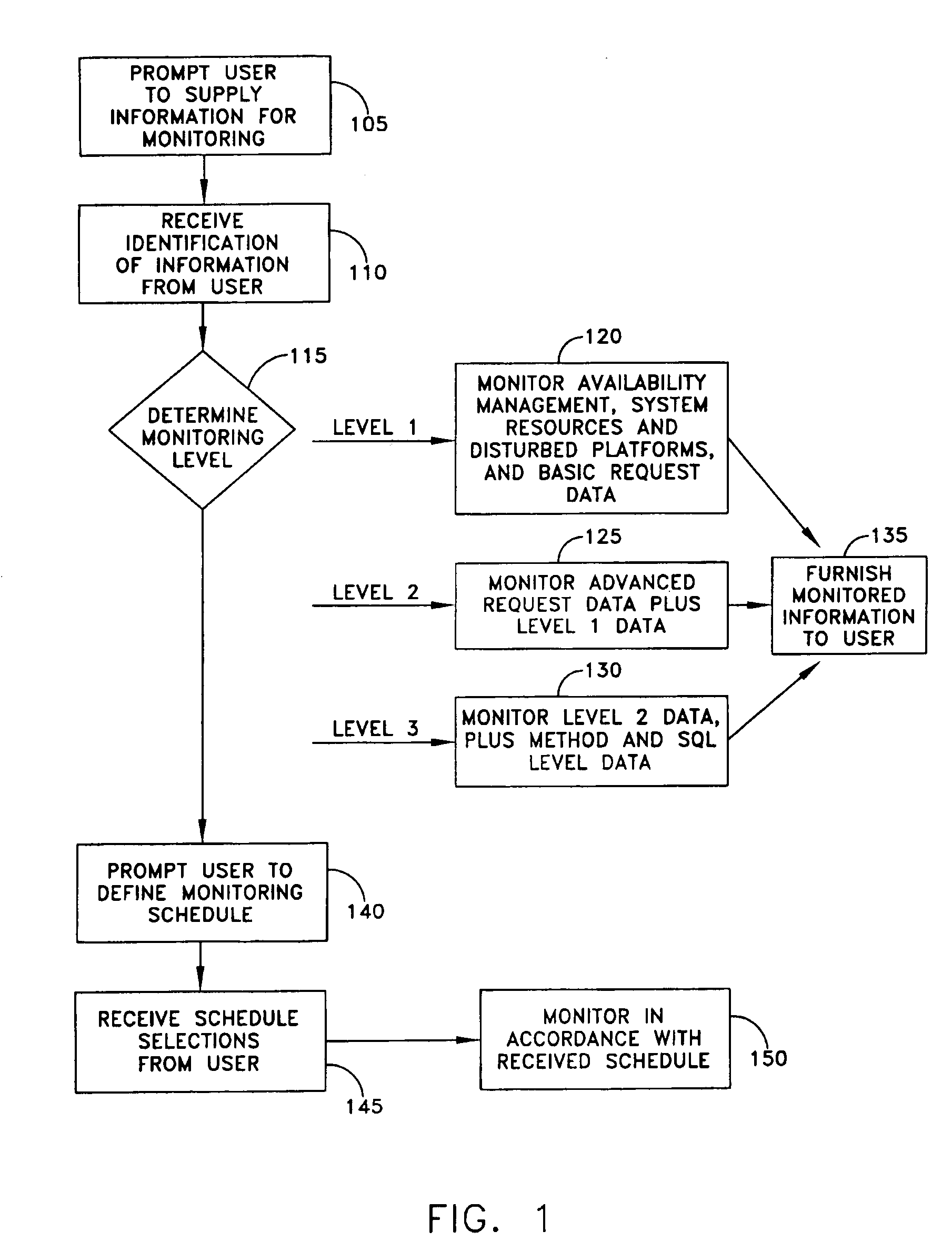
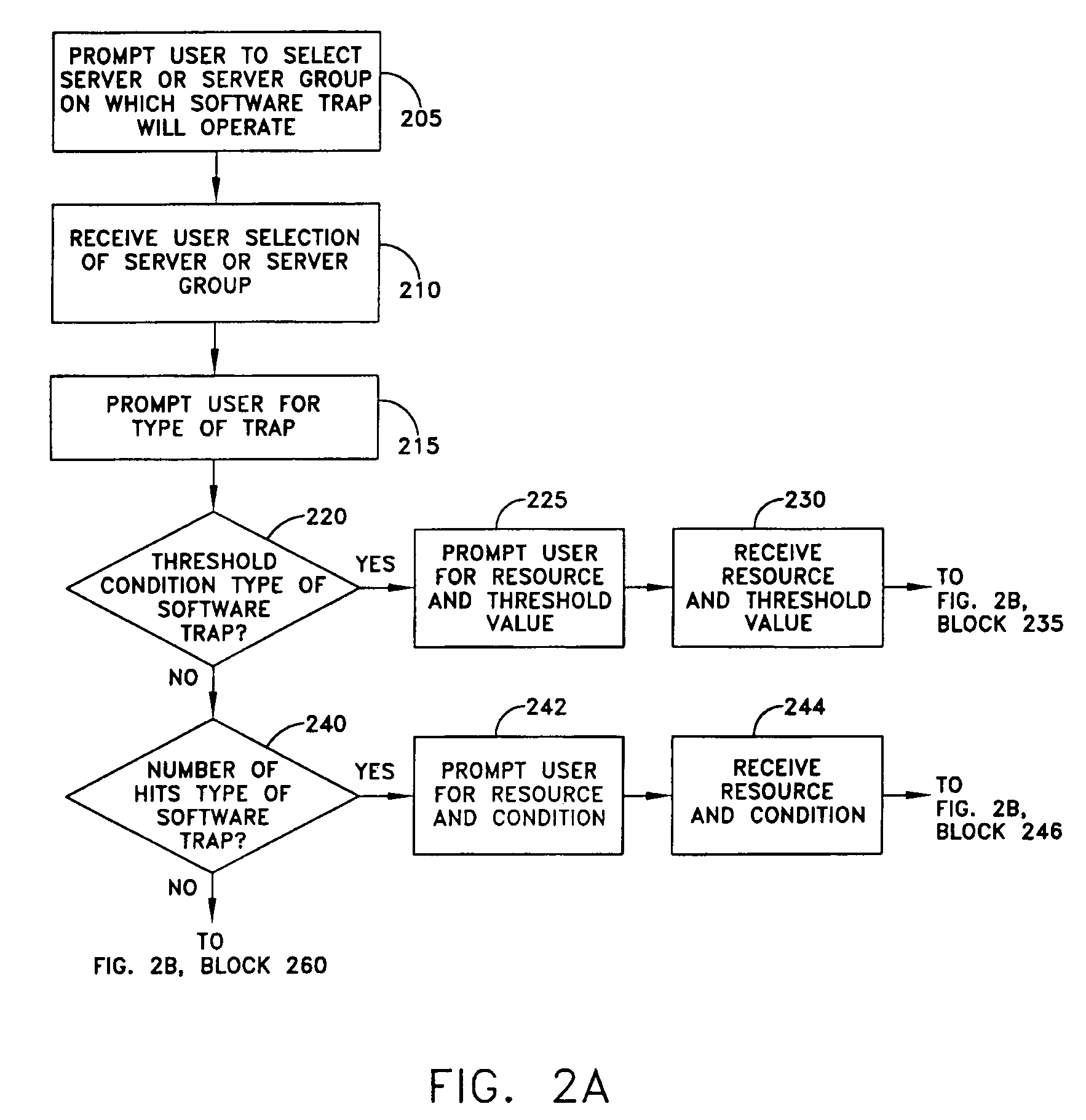
A method for management of performance of computer systems and applications includes prompting the user to select information for monitoring, monitoring the performance of applications running on servers, displaying data, and prompting users to input performance adjustments. A user is prompted to select a server or server group, a resource, and a threshold or condition for notification, and in response a system compares the value or quality of the parameter to the threshold or condition, and provides a notification to the user in the event that the parameter reaches the threshold or condition. A method includes the steps of providing the user with performance information, receiving from the user a request for more specific performance information, and providing more detailed performance information. A method according to the invention includes the steps of receiving from the user an identification of a server as an authoritative server, another server as a comparison server, comparing runtime environment data in the form of one or more of CPU data, server data and Java data between the selected servers, and displaying differences to a user. A method of the invention includes the steps of receiving from the user an identification of a server as an authoritative server, and another server as a comparison server, and providing a list of matching and differing file names. The method may further include the step of receiving from the user a selection of a file, conducting a comparison of the files, and providing a result to the user. A method of the invention includes the steps of assigning a role to each user, and mapping between access to functions and each user role by an access control list, whereby access to functions is limited depending on the assigned role of the user.
Owner:INT BUSINESS MASCH CORP
Data mining recommendation web beans and JSP tag libraries
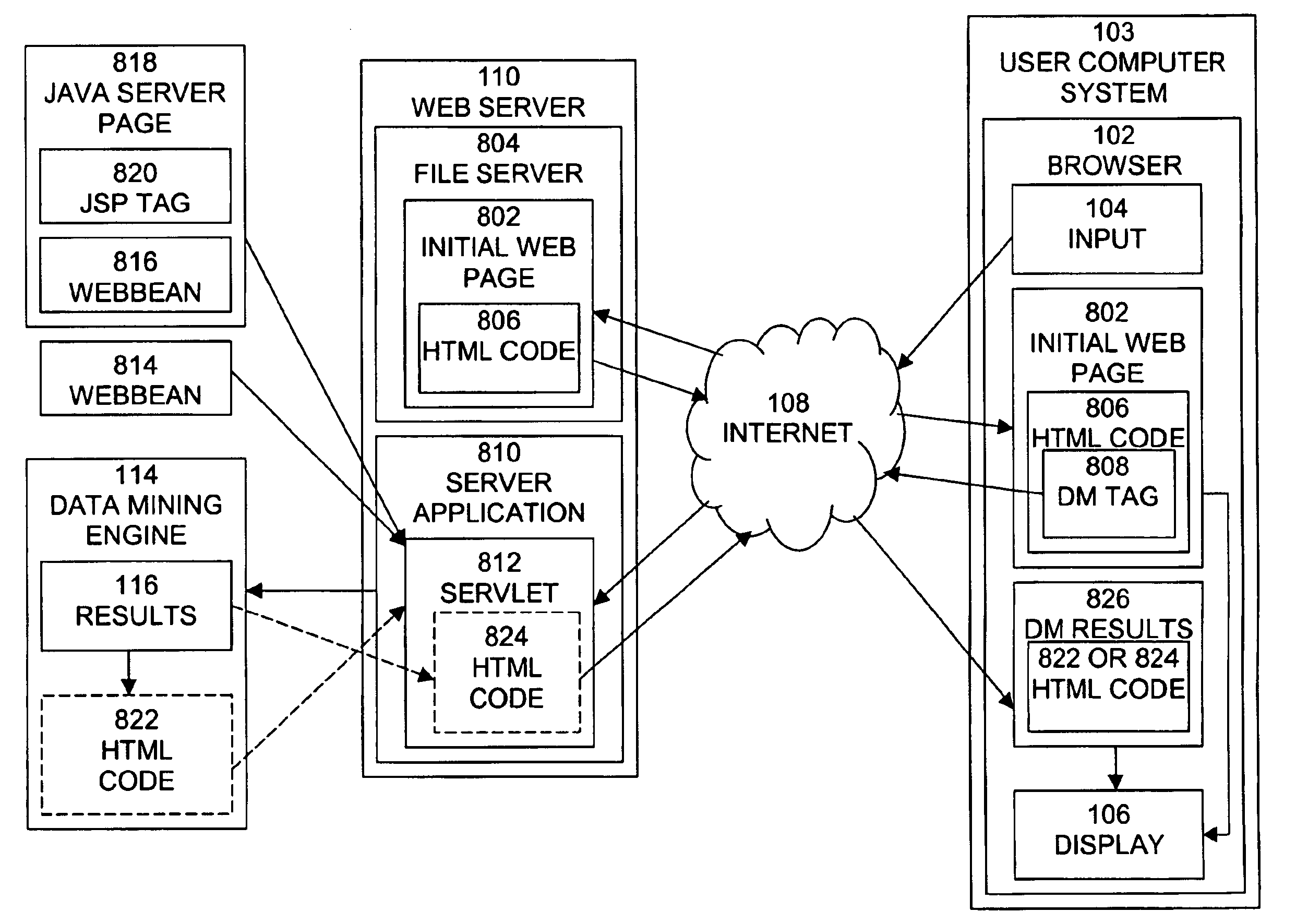
InactiveUS6873984B1Improve usabilityData processing applicationsWeb data indexingReusable softwareApplication software
A method, system, and computer program product for providing data mining functionality into Web page design that provides improved ease of design without the need for extensive custom programming. The method comprises the steps of: transmitting to a browser operated by a user a Web page for display to the user, the Web page including a control for activating a data mining function, launching a servlet in response to an indication that the control has been activated, transmitting a request for data mining processing from the servlet to a data mining engine, receiving a result of the data mining processing from the data mining engine, and transmitting the result to the browser. The servlet may be a reusable software component. The servlet may be a JavaBean. The JavaBean may comprise a call to a Java Application Program Interface. Activation of the control may activate a Hypertext Markup Language tag. The result of the data mining processing may comprise hypertext markup language code generated by the data mining engine. The method may further comprise the step of generating Hypertext Markup Language code based on the received result of the data mining processing.
Owner:ORACLE INT CORP
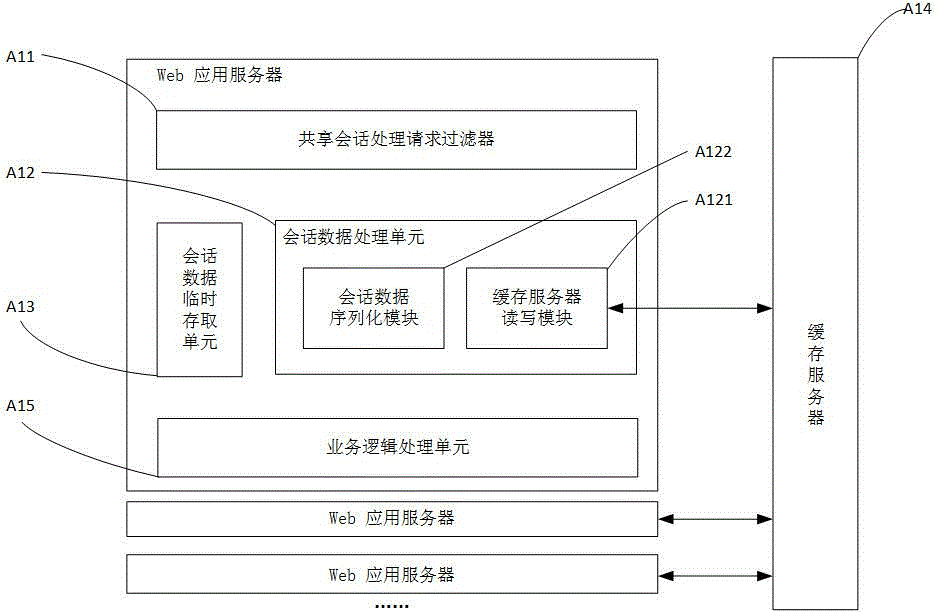
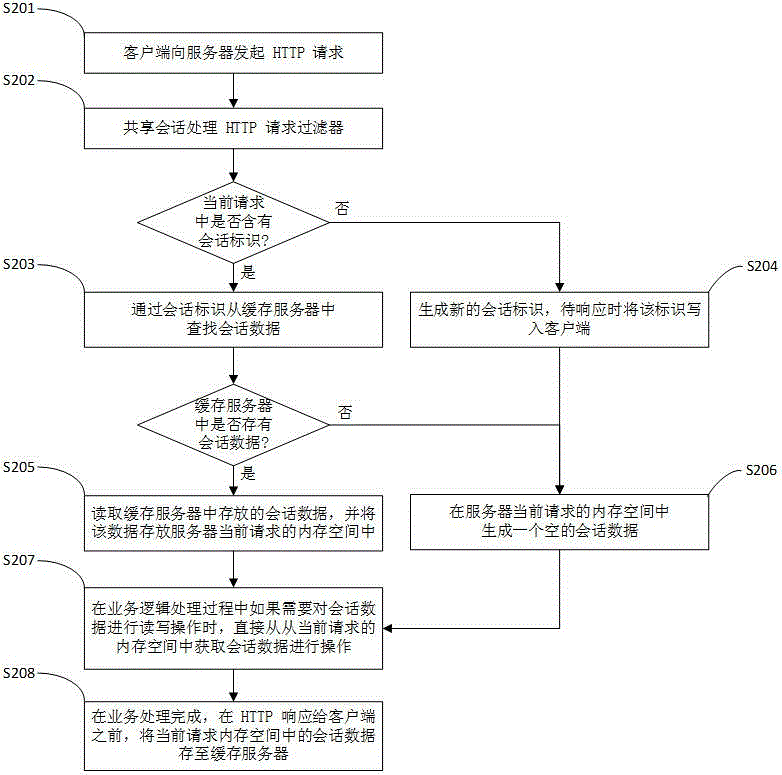
Session data sharing system and method
The invention belongs to the technical field of computer application and particularly provides a session data sharing system and method. The system comprises at least one Web application server and a cache server; the Web application servers are used for processing HTTP requests of client-sides and completing requested service logic, and each Web application server is a Servlet container based on Java and is composed of a session sharing processing request filter, a session data processing unit, a session data temporary storage unit and a service logic processing unit; the cache server is used for storing session data. According to the session data sharing system and method, the session data are stored into the cache server and can be shared by the Web application servers, so that memory occupation of the Web application servers is reduced; loss of the session data on the Web application servers can be avoided, the problems of loss of network performance and inconsistency of the session data caused by session data replication between cluster nodes can be avoided, the session data access speed is increased, and the session data processing performance is improved.
Owner:SHANGHAI HANDPAL INFORMATION TECH SERVICE
Program monitoring method and defending method thereof, as well as relevant device
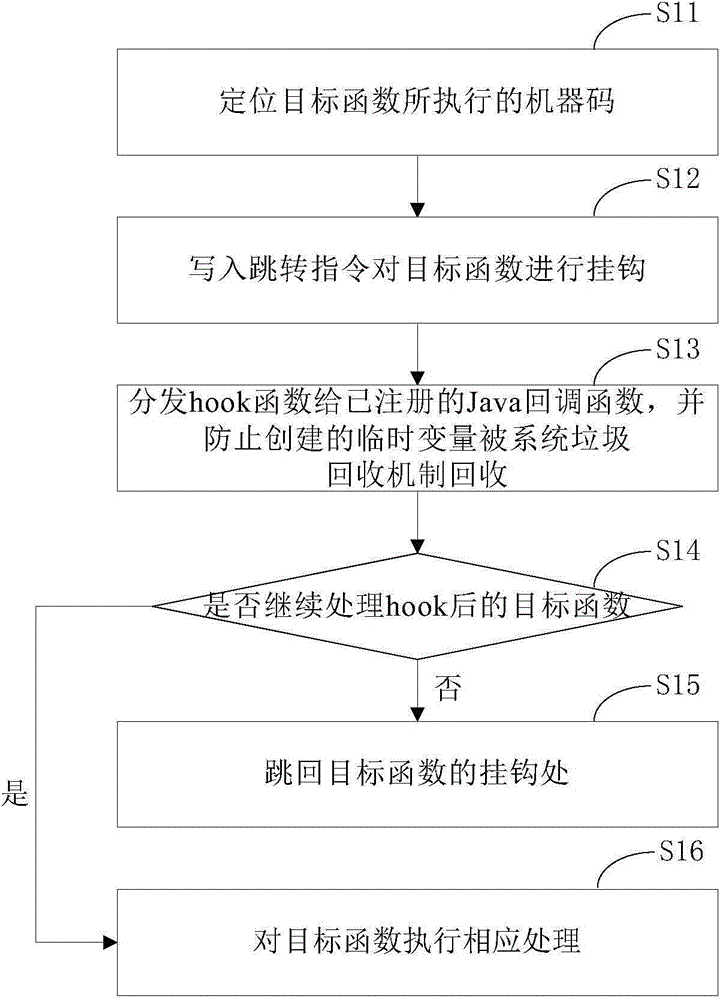
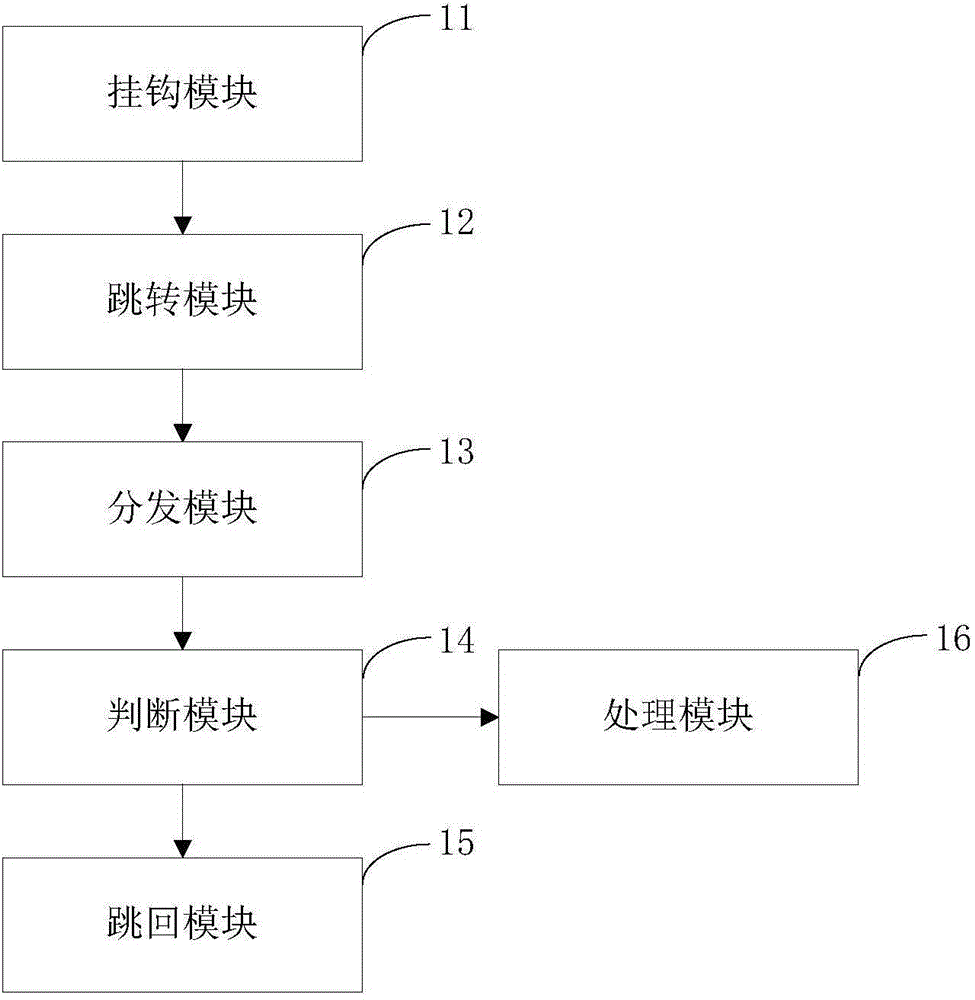
ActiveCN104598809AHook implementationAvoid markingPlatform integrity maintainanceTemporary variableProgram monitoring
The invention provides a program monitoring method and device. The program monitoring method comprises the following steps: writing in a skip instruction for positioned objective functions so as to perform a hook operation; distributing hook functions to registered Java callback functions, and preventing created temporary variables from being collected by a garbage collection mechanism of a system; enabling the objective functions which are not processed to skip back to hook positions, or else, continuing to process the objective functions. Through the adoption of the program monitoring method disclosed by the invention, any Java function of an Android system under an ART mode can be monitored without destroying the stack of the objective functions, so that the garbage collection mechanism of the ART can perform normal memory collection. The invention further provides a program defending method and device, which realize a defending mechanism of the Android system under the ART mode by adopting the program monitoring method disclosed by the invention.
Owner:BEIJING QIHOO TECH CO LTD
Portable terminal, methods, programs and storage media for managing application start
InactiveUS20060129628A1Information security is assuredSpecific access rightsProgram initiation/switchingComputer networkEmail address
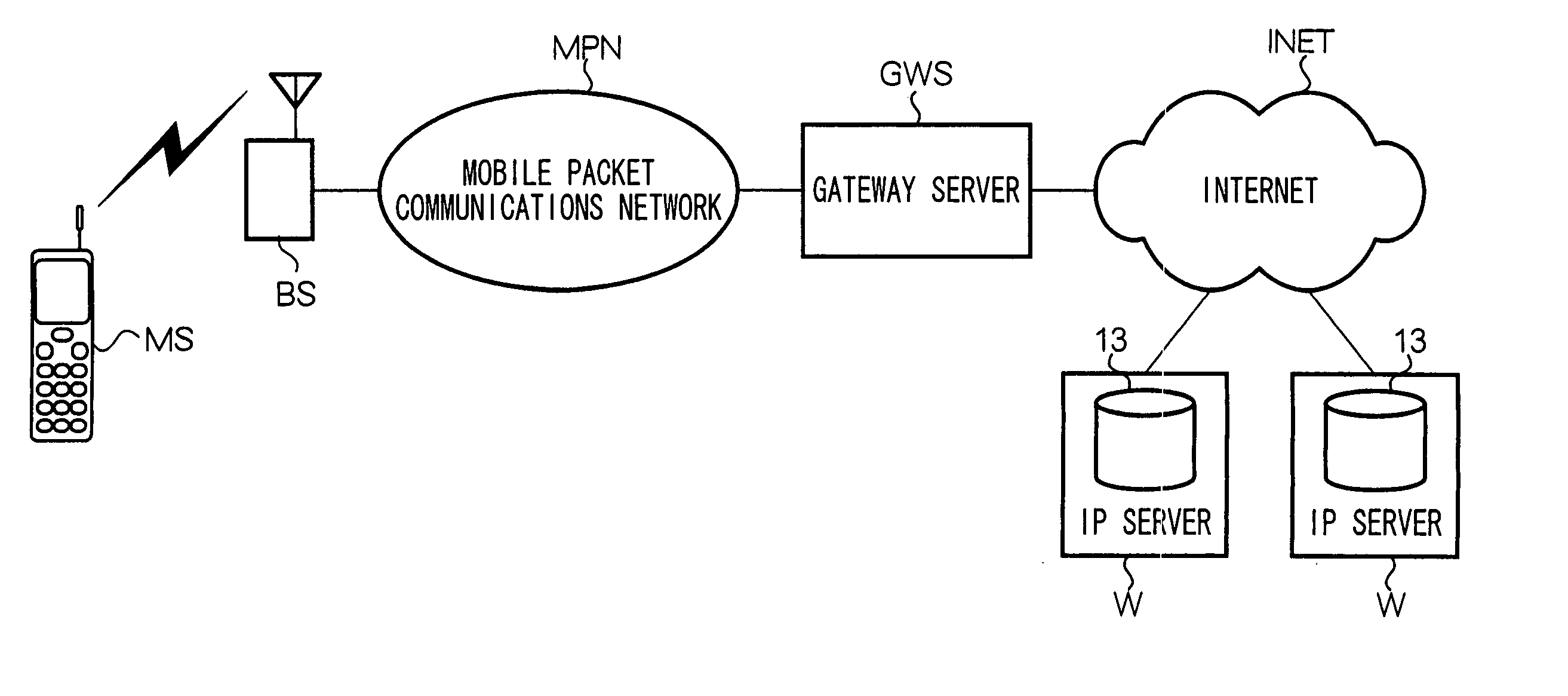
An IP server sends e-mail to a mobile device MS. This e-mail includes an application specifier that specifies startup of a Java application stored in mobile device MS. On the other hand, the ADF for the Java application stored in mobile device MS includes trusted source data containing a plurality of e-mail addresses that indicate trusted origins. Mobile device MS compares the e-mail transmission origin address with the trusted source data. Mobile device MS, only in the case where the transmission origin address of the received e-mail is included in the trusted source data, starts up a Java application based on an application specifier included in said e-mail.
Owner:NTT DOCOMO INC
Communication device, control method of communication device, program and communication method
ActiveUS7421577B2Preventing executionSecure executionProgram initiation/switchingRandom number generatorsTelecommunicationsMobile station
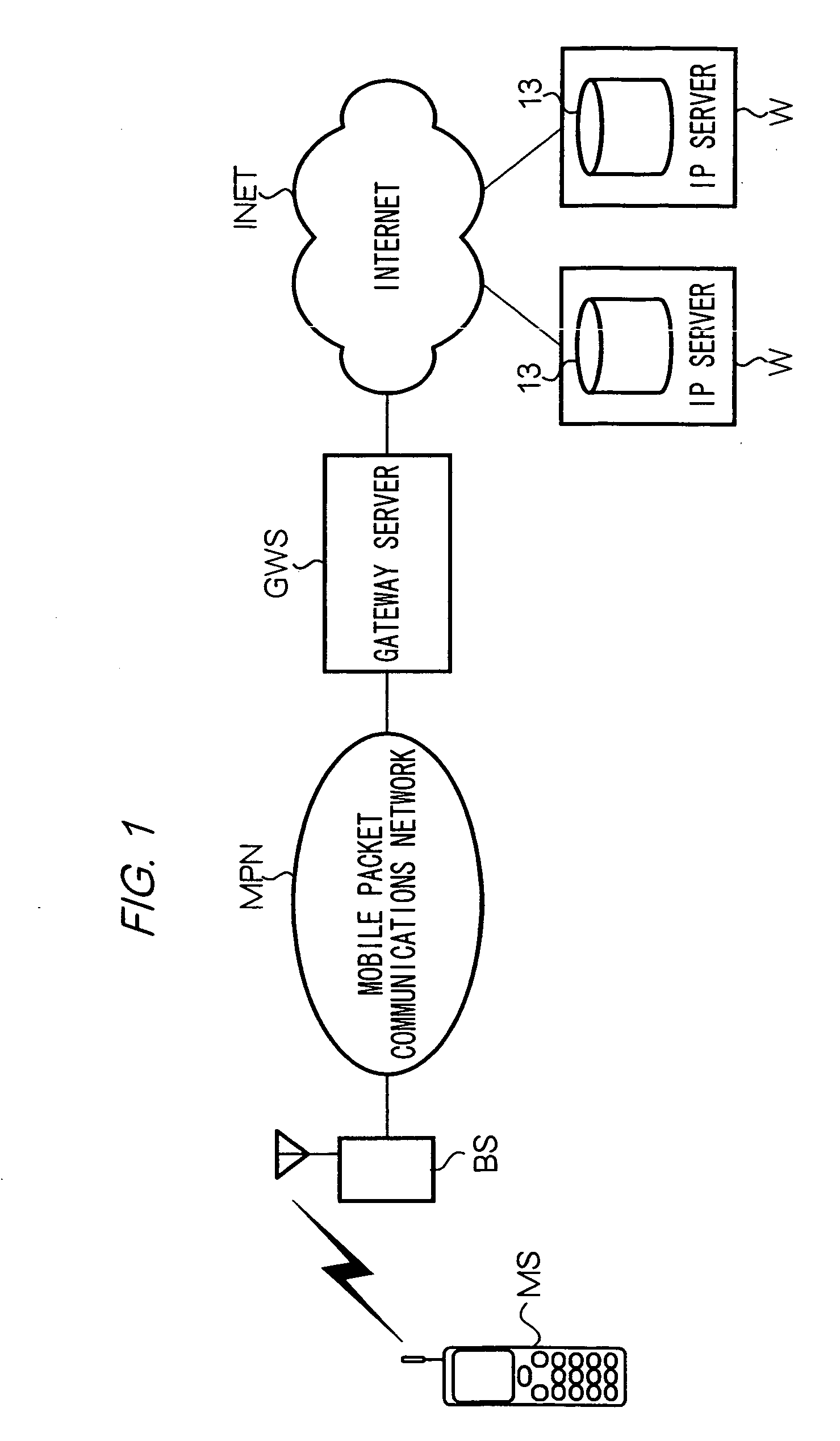
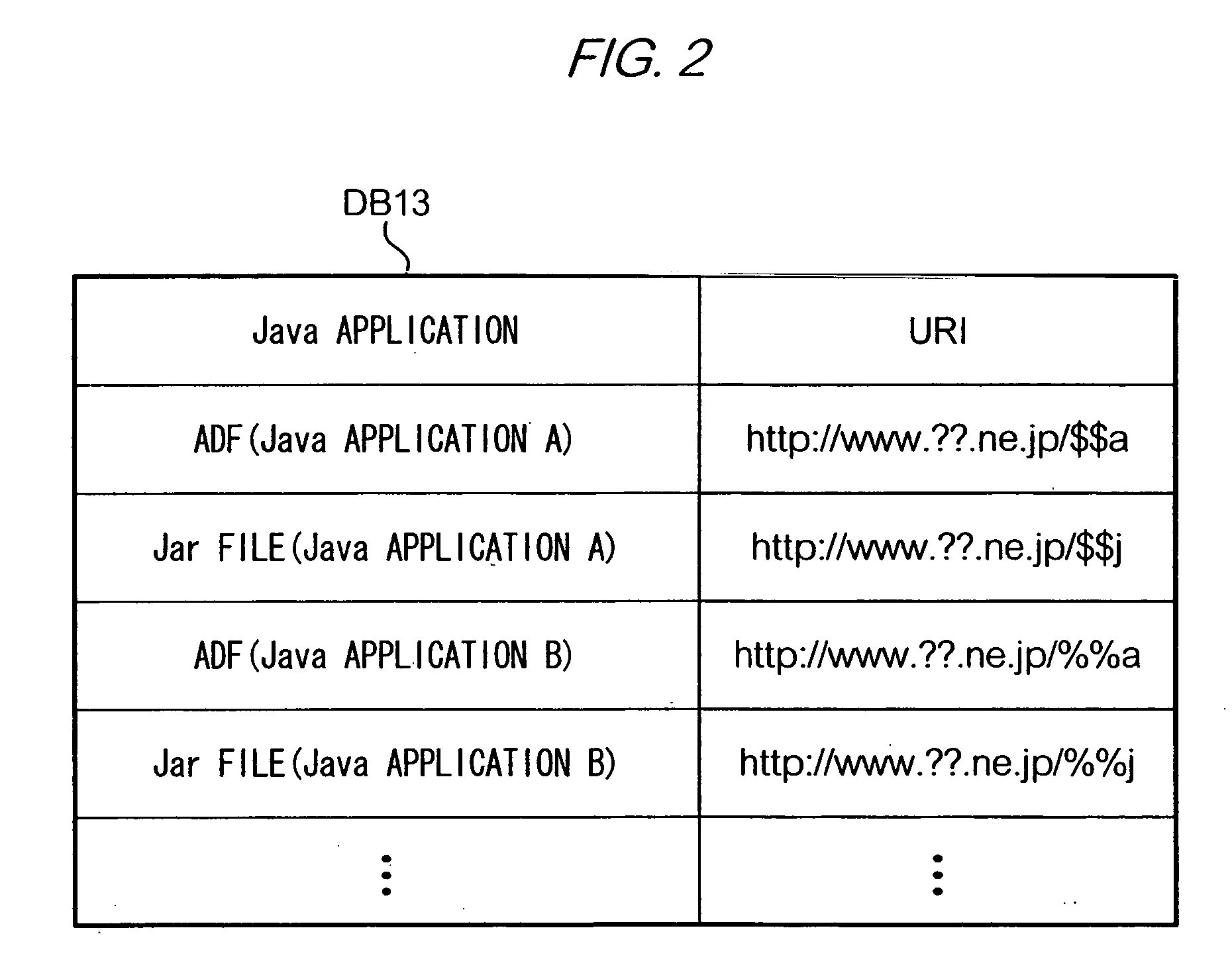
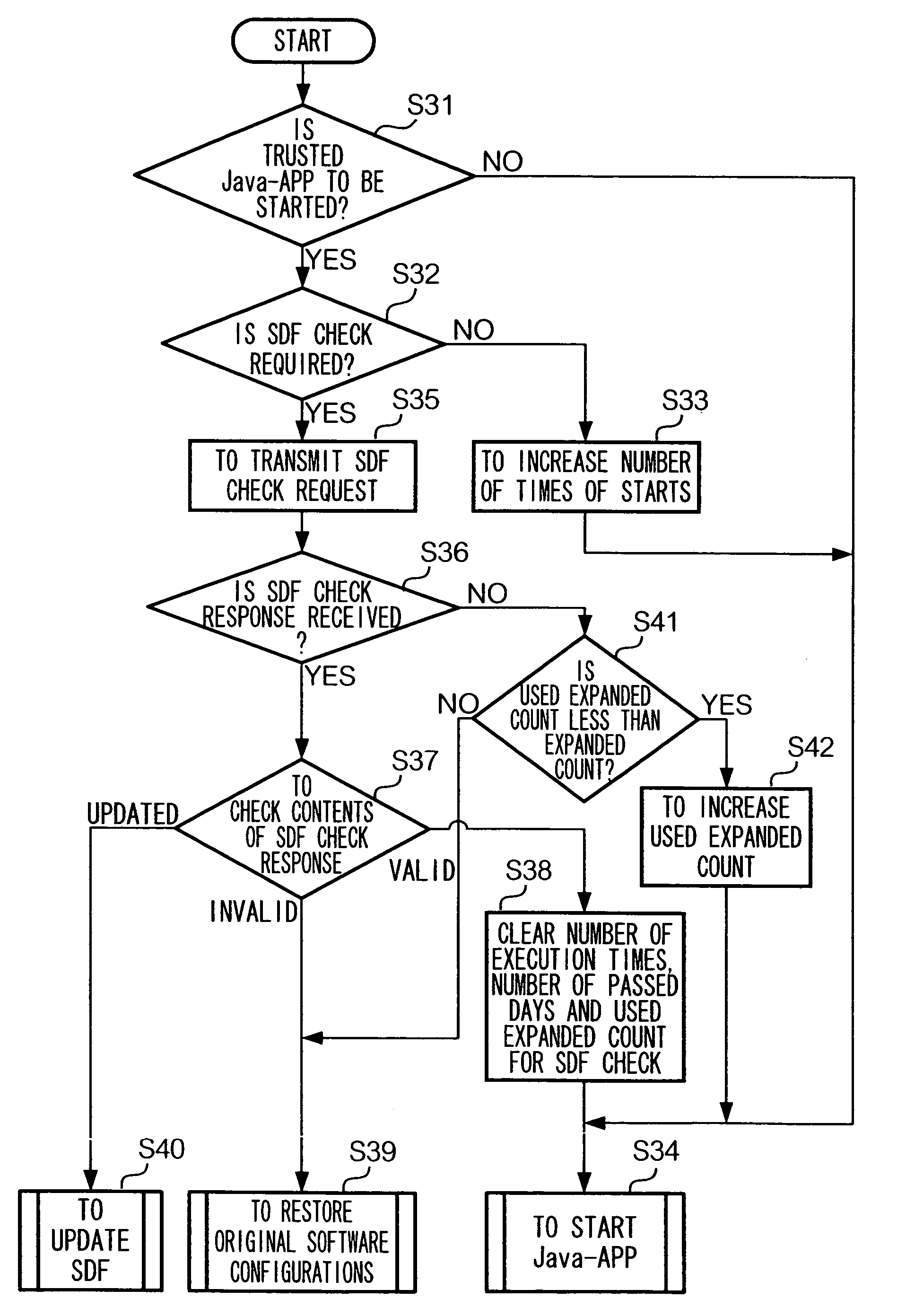
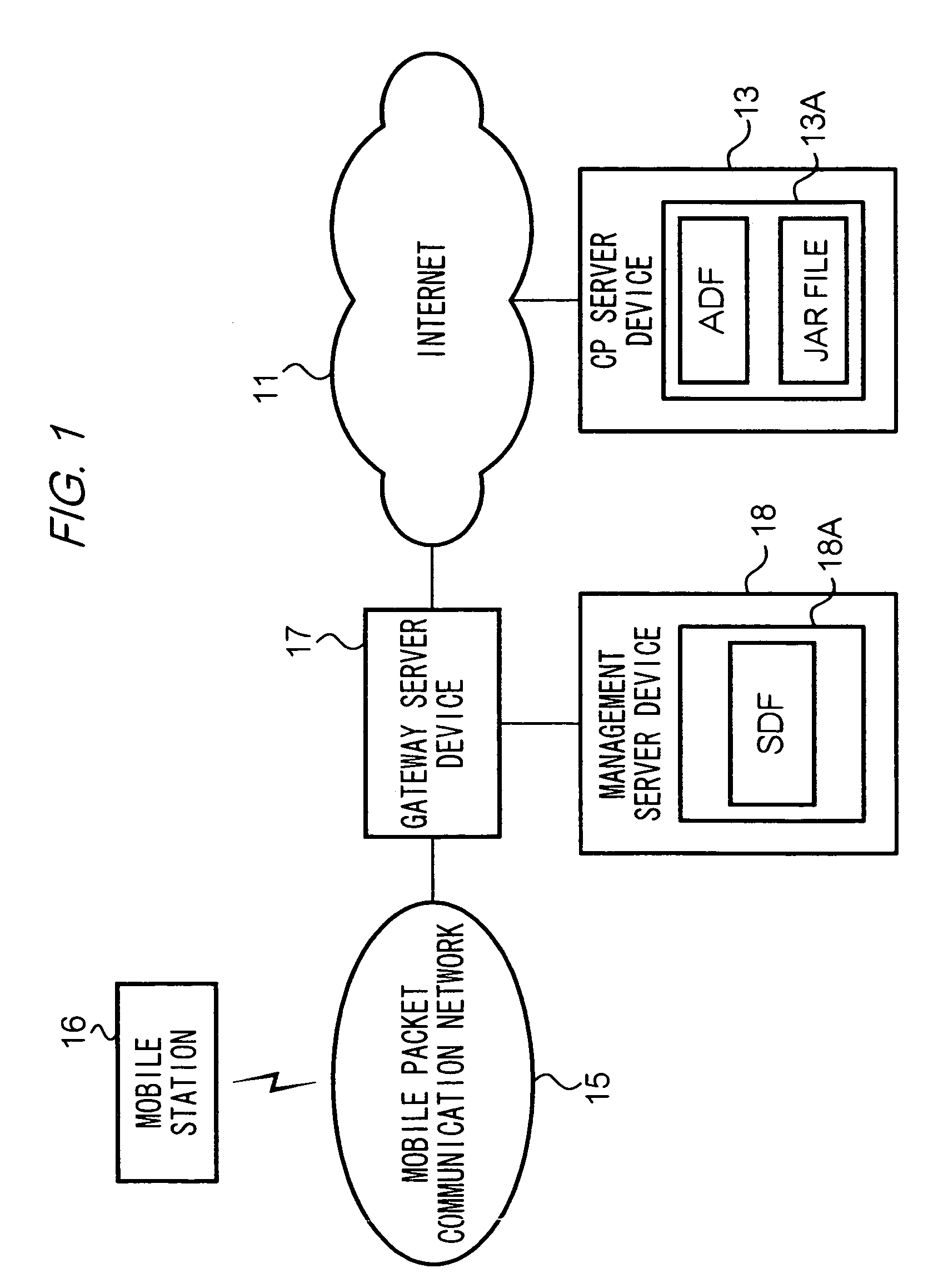
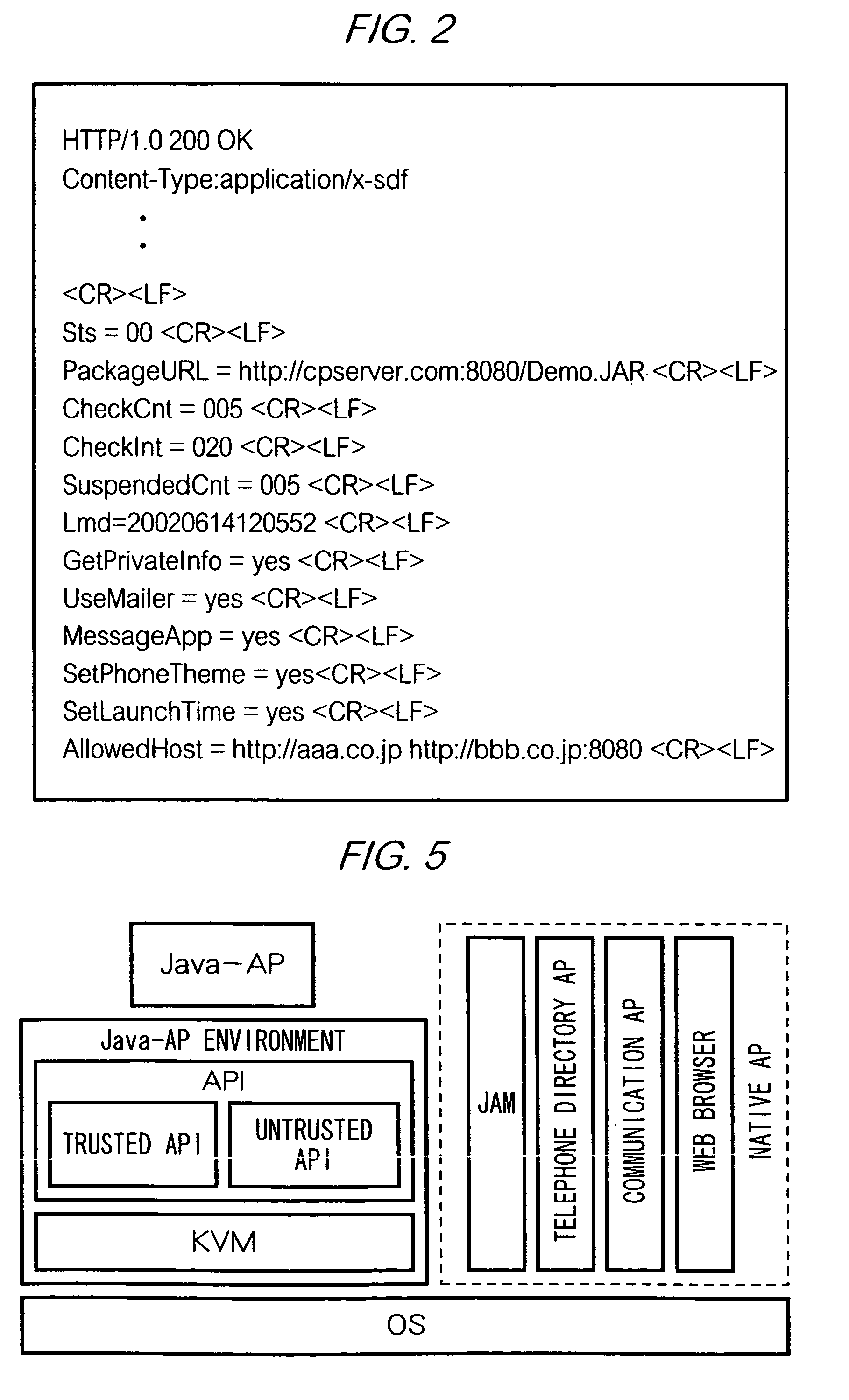
The present invention provides a means for reflecting modifications made in a server to data with regard to a scope of rights, which are granted to an application program operable in a communication device such as a mobile station, on data stored in the communication device. To achieve the aim, in a system according to the present invention, Java-AP software is provided to a mobile station by transmitting an ADF, a SDF and a JAR file from servers to the mobile station in that order. The SDF is a file containing data indicating restrictions of behavior of a Java-AP in a mobile station. The SDF also contains data indicating a validity state of the SDF, namely ‘valid’ or ‘invalid’, which is managed by management server device 18. Before a mobile station runs a Java-APP which is installed in the mobile station, the mobile station accesses management server device 18 and checks whether a SDF corresponding to the Java-APP is valid. When the SDF is valid, the mobile station runs the Java-APP following the restrictions indicated in the SDF.
Owner:NTT DOCOMO INC
Malicious mobile code runtime monitoring system and methods
InactiveUS20060026677A1Minimizing serverMinimizing client resource requirementMemory loss protectionError detection/correctionVisual BasicMonitoring system
Protection systems and methods provide for protecting one or more personal computers (“PCs”) and / or other intermittently or persistently network accessible devices or processes from undesirable or otherwise malicious operations of Java™ applets, ActiveX™ controls, JavaScript™ scripts, Visual Basic scripts, add-ins, downloaded / uploaded programs or other “Downloadables” or “mobile code” in whole or part. A protection engine embodiment provides, within a server, firewall or other suitable “re-communicator,” for monitoring information received by the communicator, determining whether received information does or is likely to include executable code, and if so, causes mobile protection code (MPC) to be transferred to and rendered operable within a destination device of the received information, more suitably by forming a protection agent including the MPC, protection policies and a detected-Downloadable. An MPC embodiment further provides, within a Downloadable-destination, for initiating the Downloadable, enabling malicious Downloadable operation attempts to be received by the MPC, and causing (predetermined) corresponding operations to be executed in response to the attempts, more suitably in conjunction with protection policies.
Owner:FINJAN LLC
System and method of generating applications for mobile devices
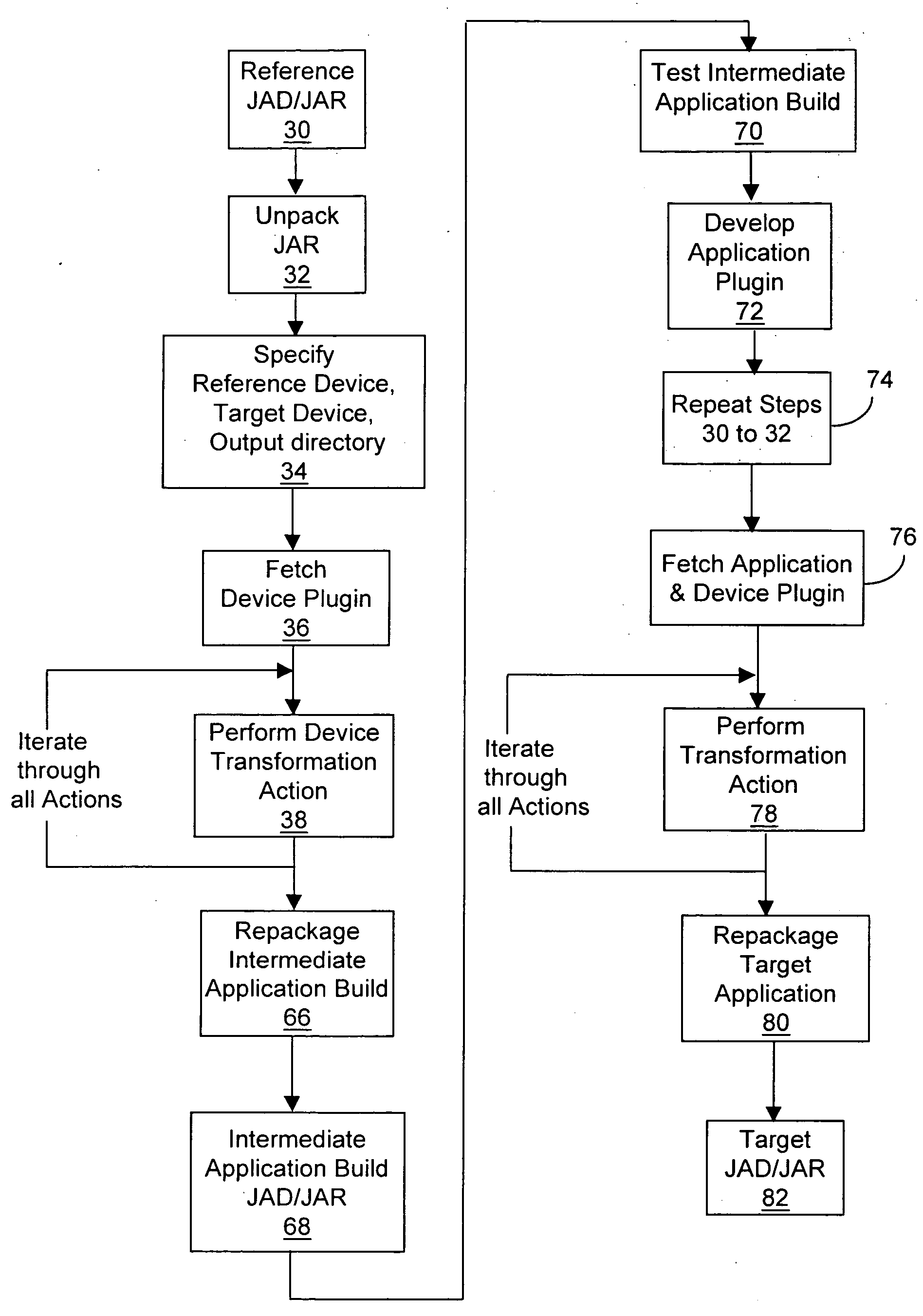
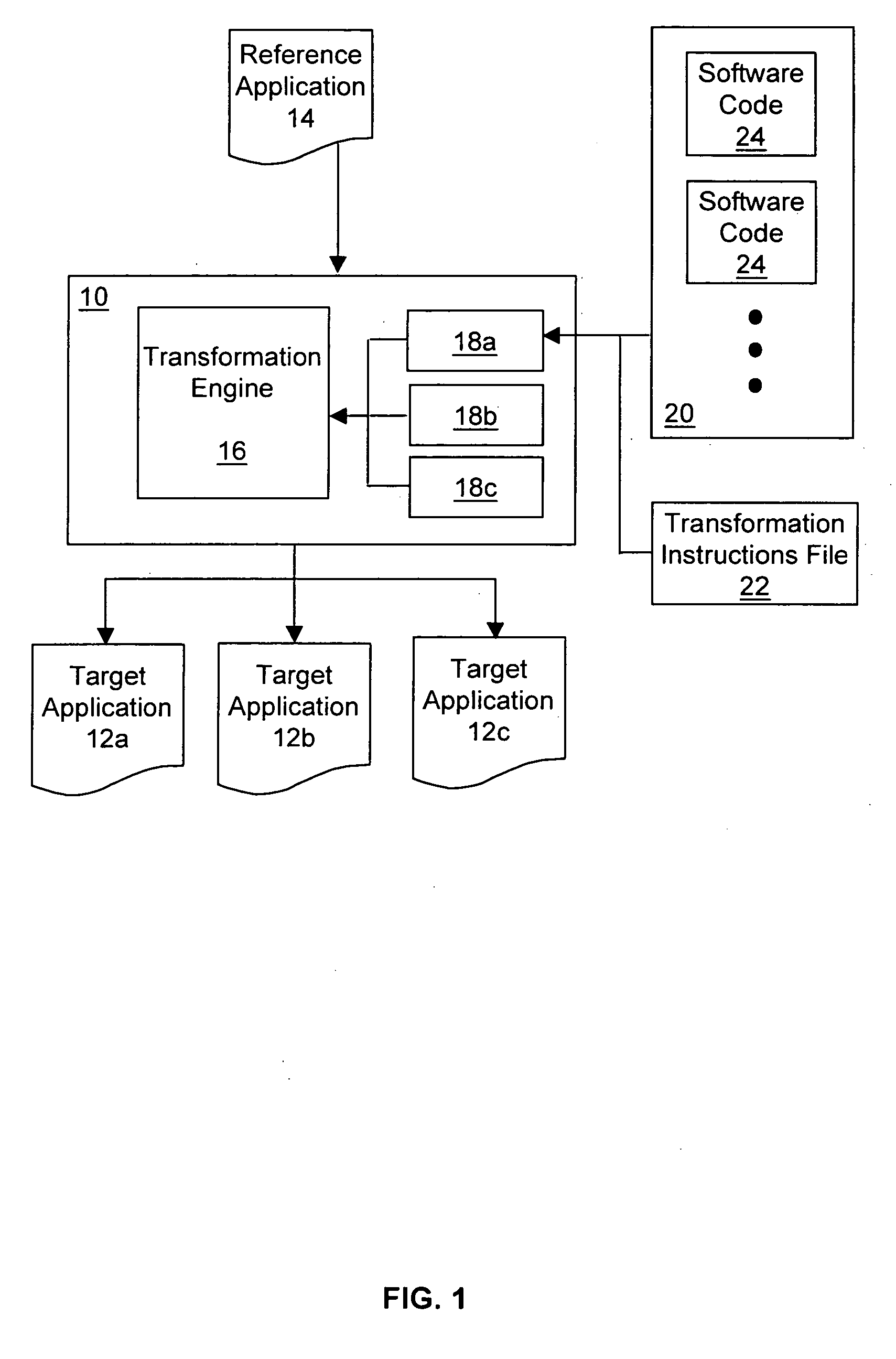
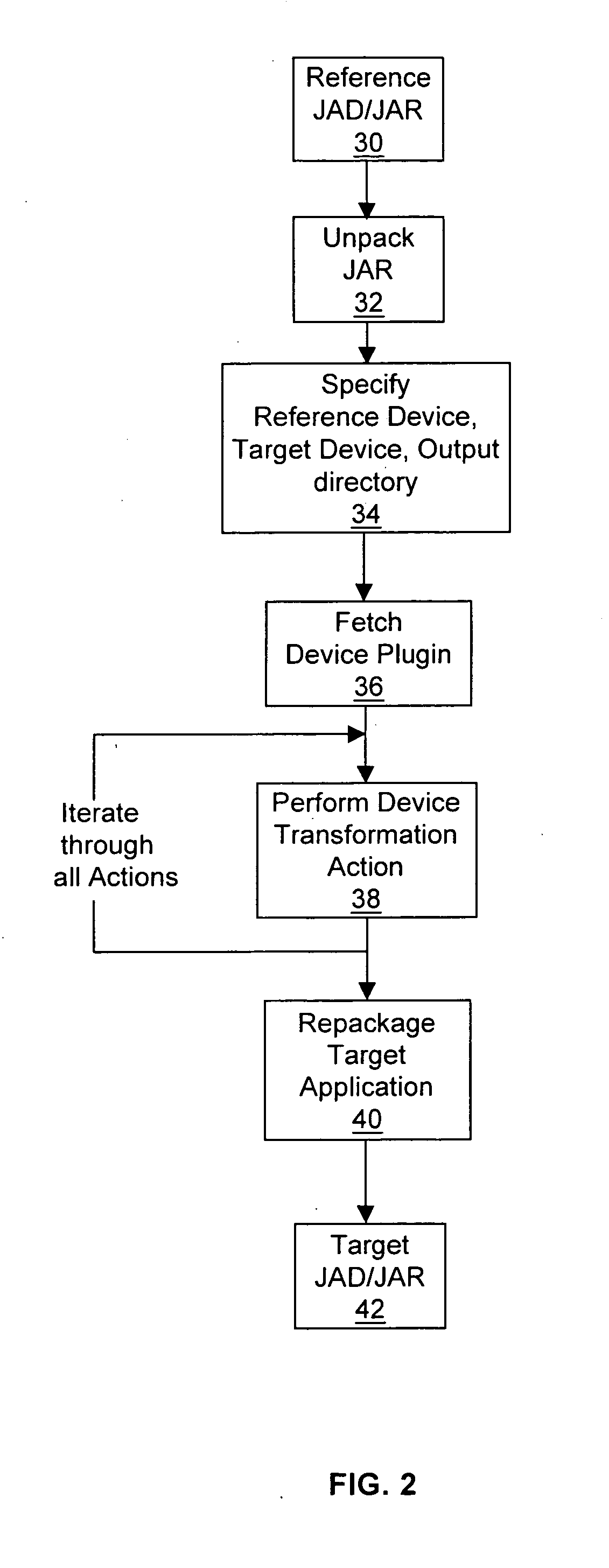
InactiveUS20050108692A1Shorten development timeReduce expensesBinary to binarySpecial service provision for substationJavaSoftware engineering
A method and system of generating target applications from Java reference applications for a particular combination of mobile devices is provided. The method includes the steps of: a) unpacking the reference application into a number of class files; and b) transforming the reference application into the target application by a device plug-in. The device plug-in is capable of transforming different reference applications into corresponding target applications for a particular combination of the reference mobile device and the target mobile device. The system includes a transformation engine and a device plug-in corresponding to the reference / target mobile device combination. The device plug-in includes an XML file and pieces of software code to modify corresponding portions of the reference application not supported by the target mobile device. The XML file directs the transformation engine to identify the unsupported portion of the reference application and to modify the portion with the selected software code.
Owner:TIRA WIRELESS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com