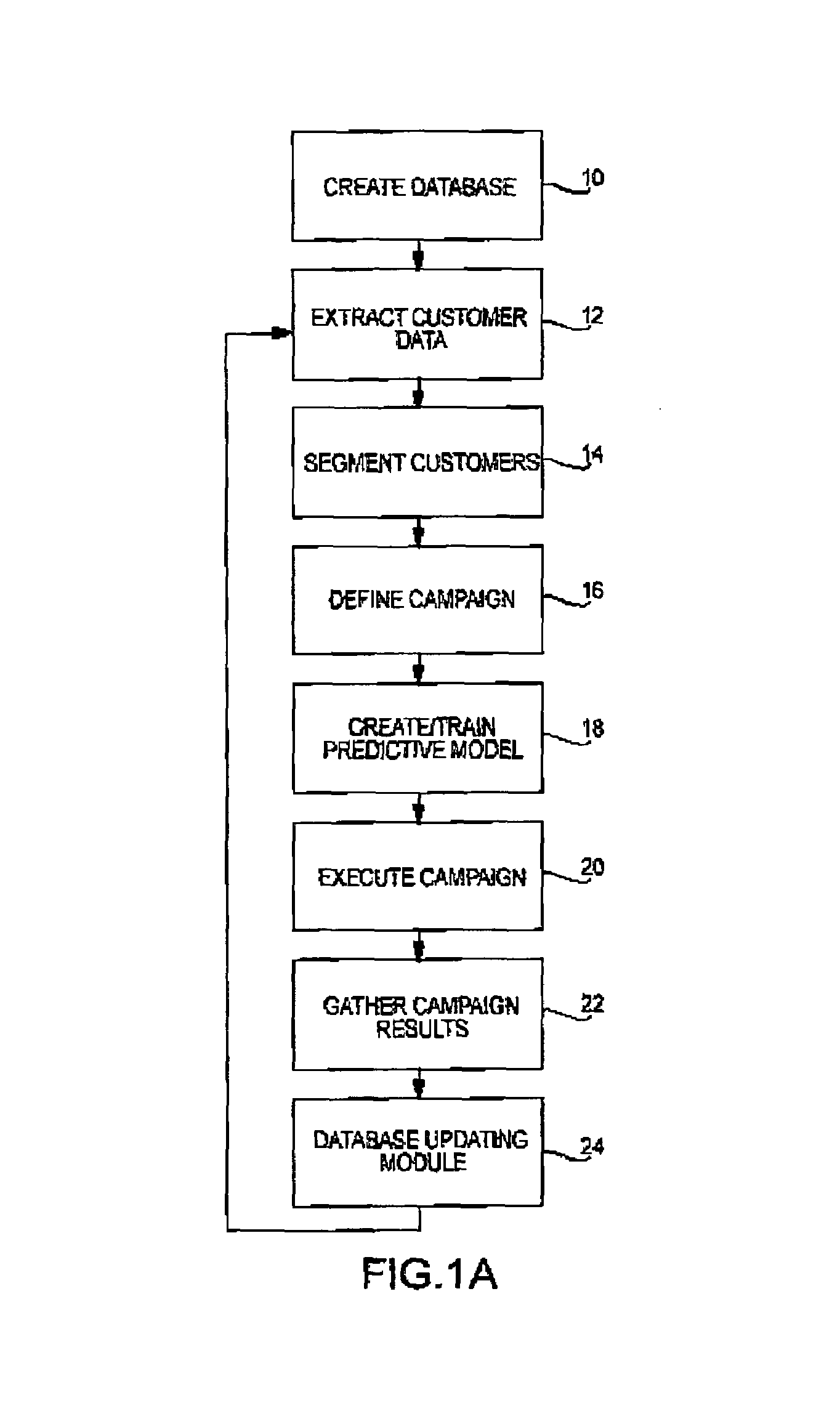
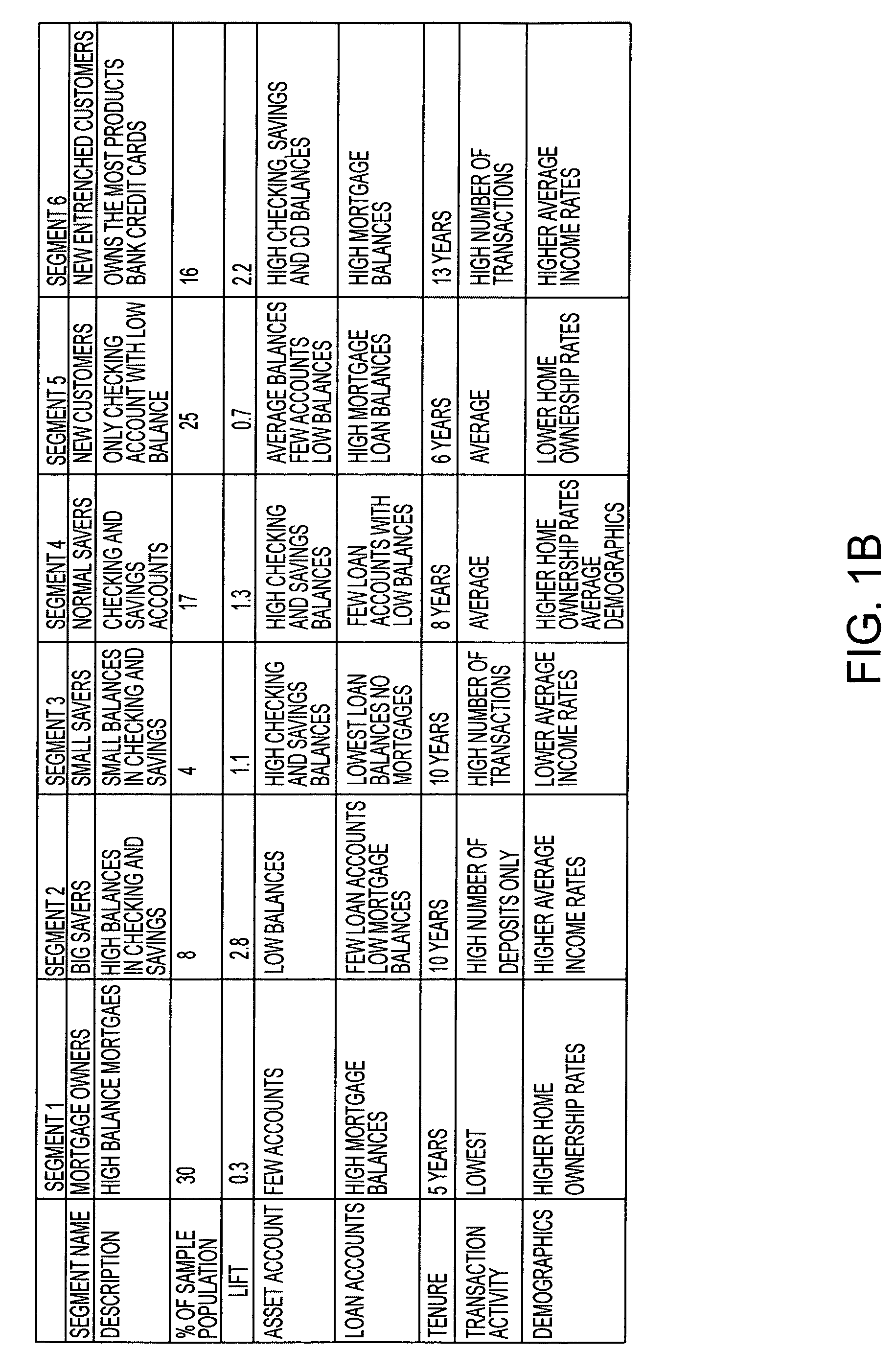
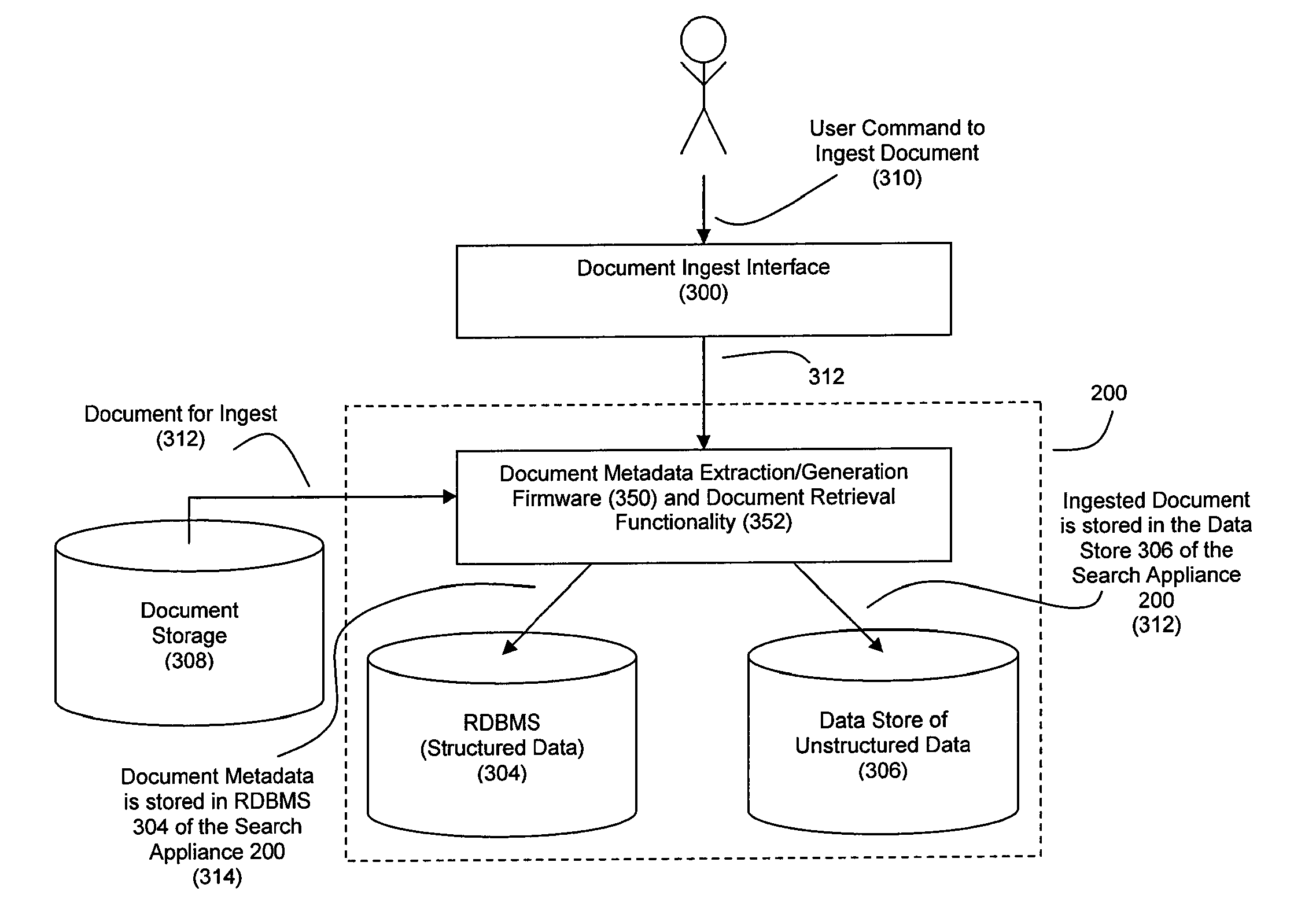
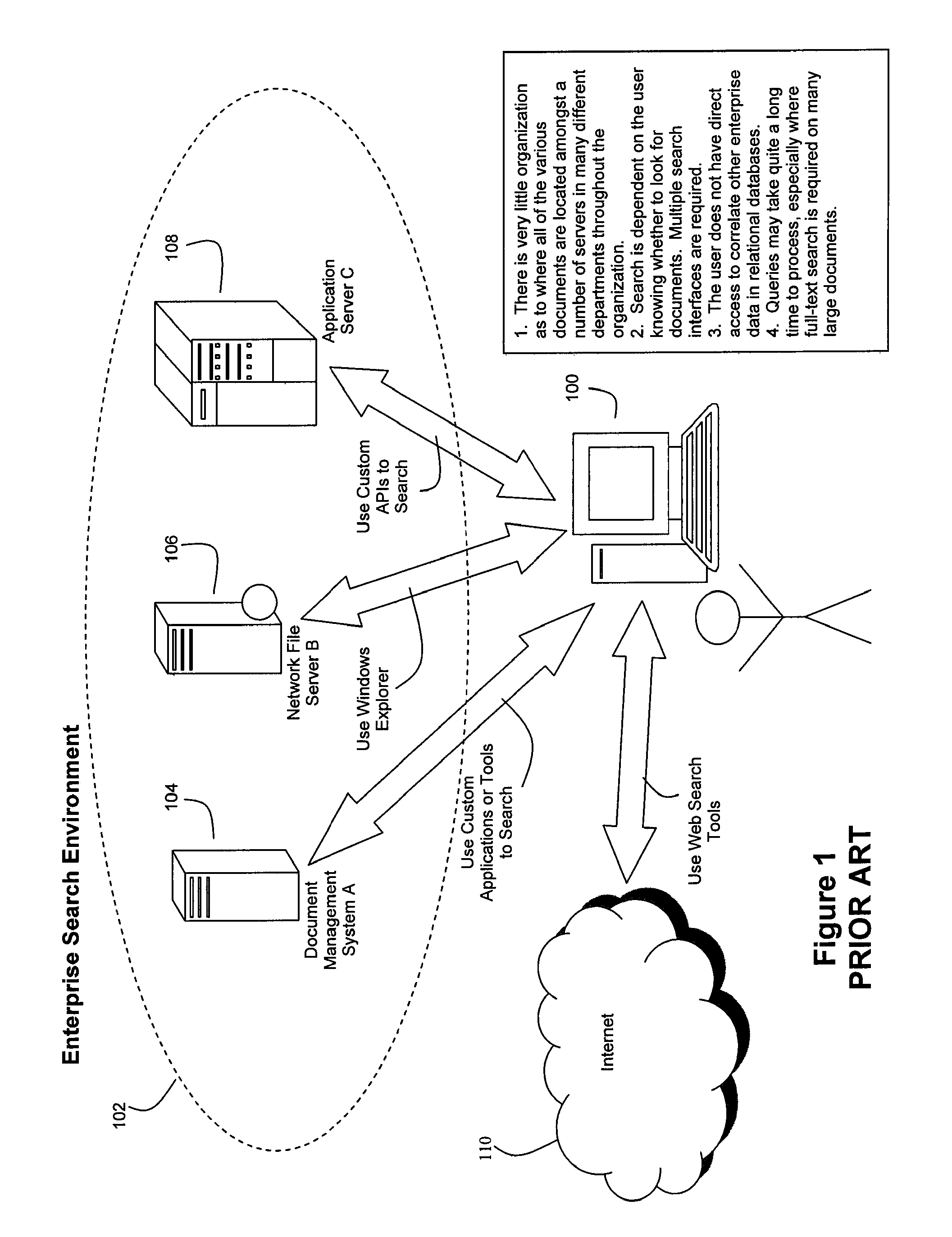
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4894 results about "SQL" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
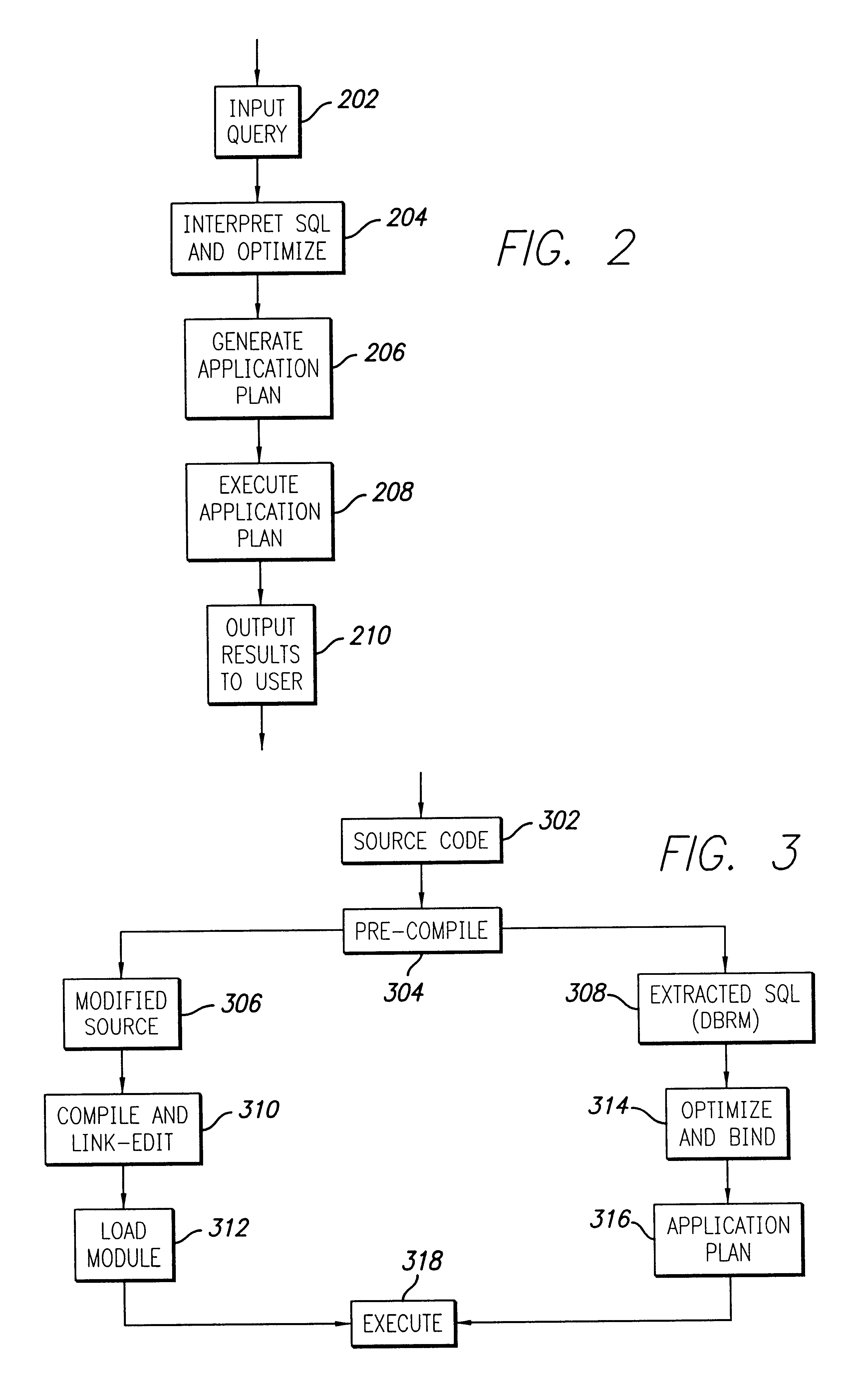
SQL (/ˌɛsˌkjuːˈɛl/ S-Q-L, /ˈsiːkwəl/ "sequel"; Structured Query Language) is a domain-specific language used in programming and designed for managing data held in a relational database management system (RDBMS), or for stream processing in a relational data stream management system (RDSMS). It is particularly useful in handling structured data, i.e. data incorporating relations among entities and variables.
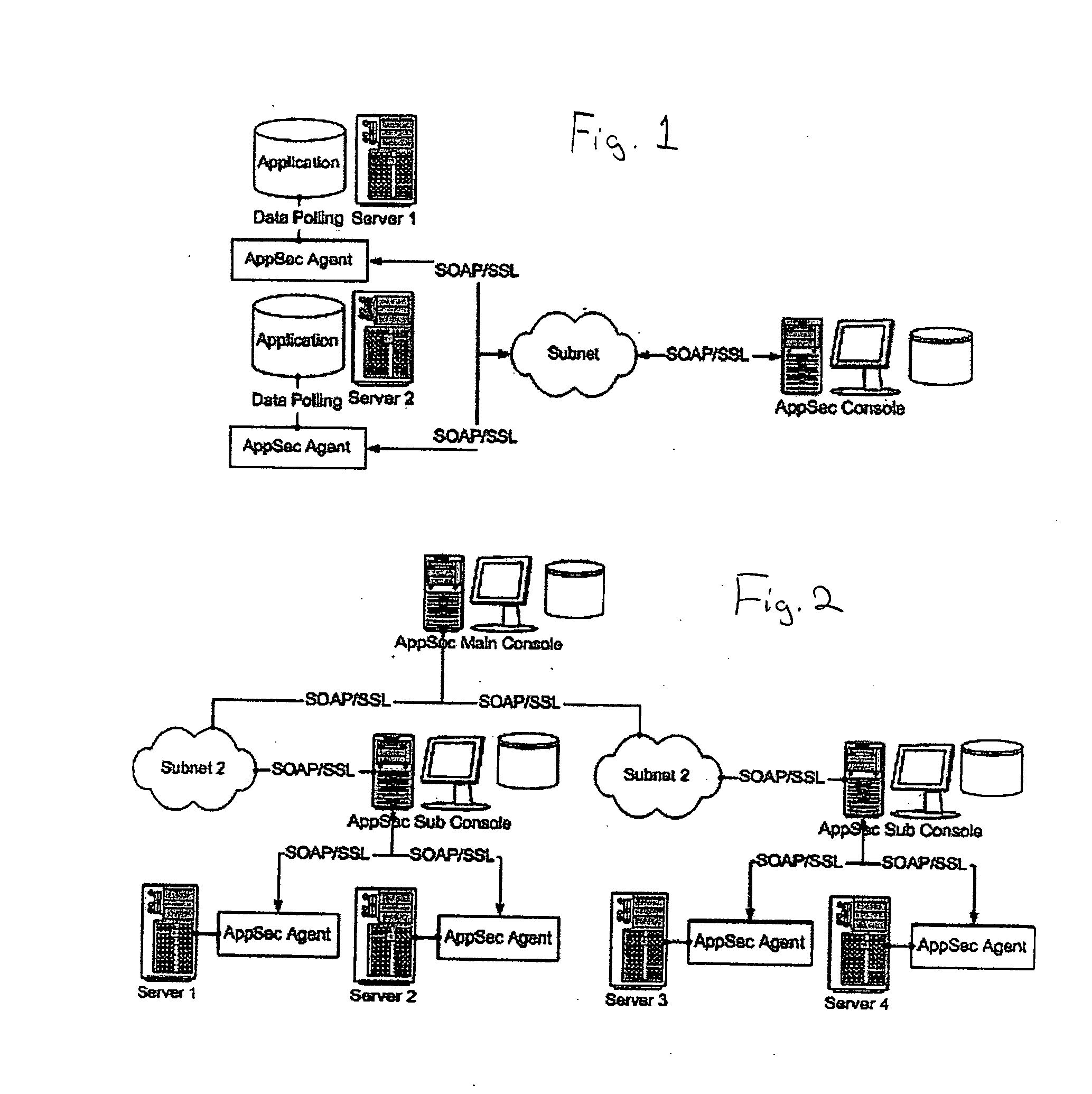
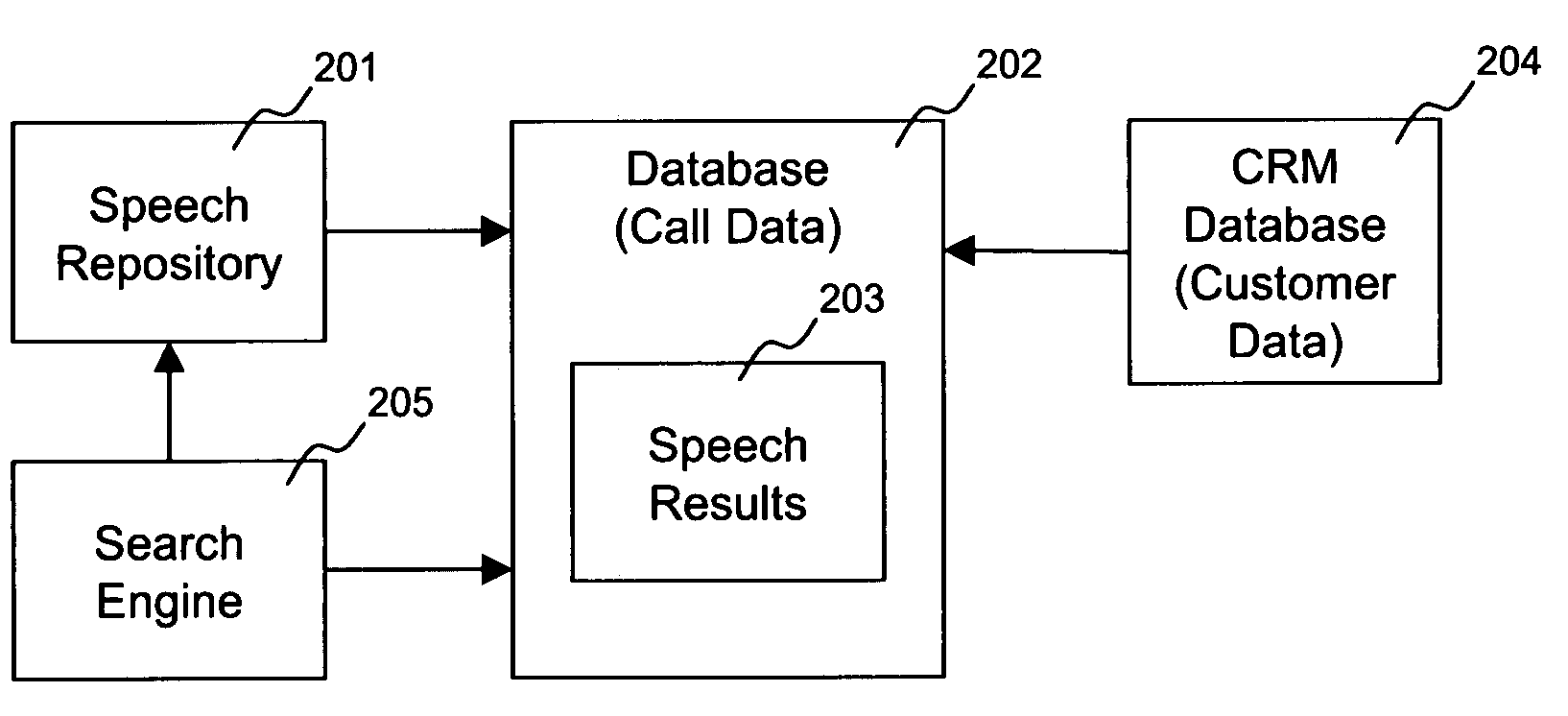
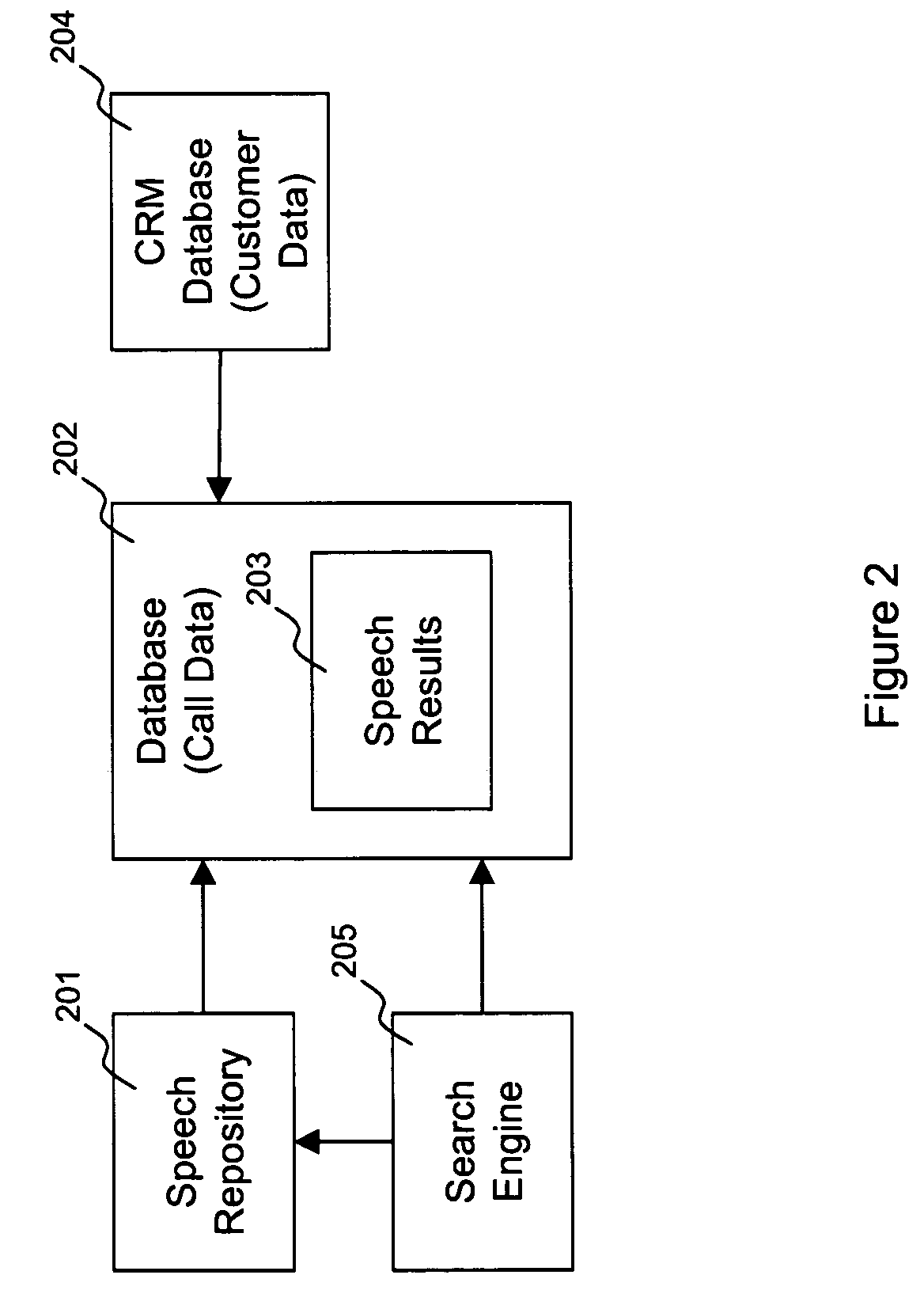
Distributed real time speech recognition system
InactiveUS20050080625A1Facilitates query recognitionAccurate best responseNatural language translationData processing applicationsFull text searchTime system
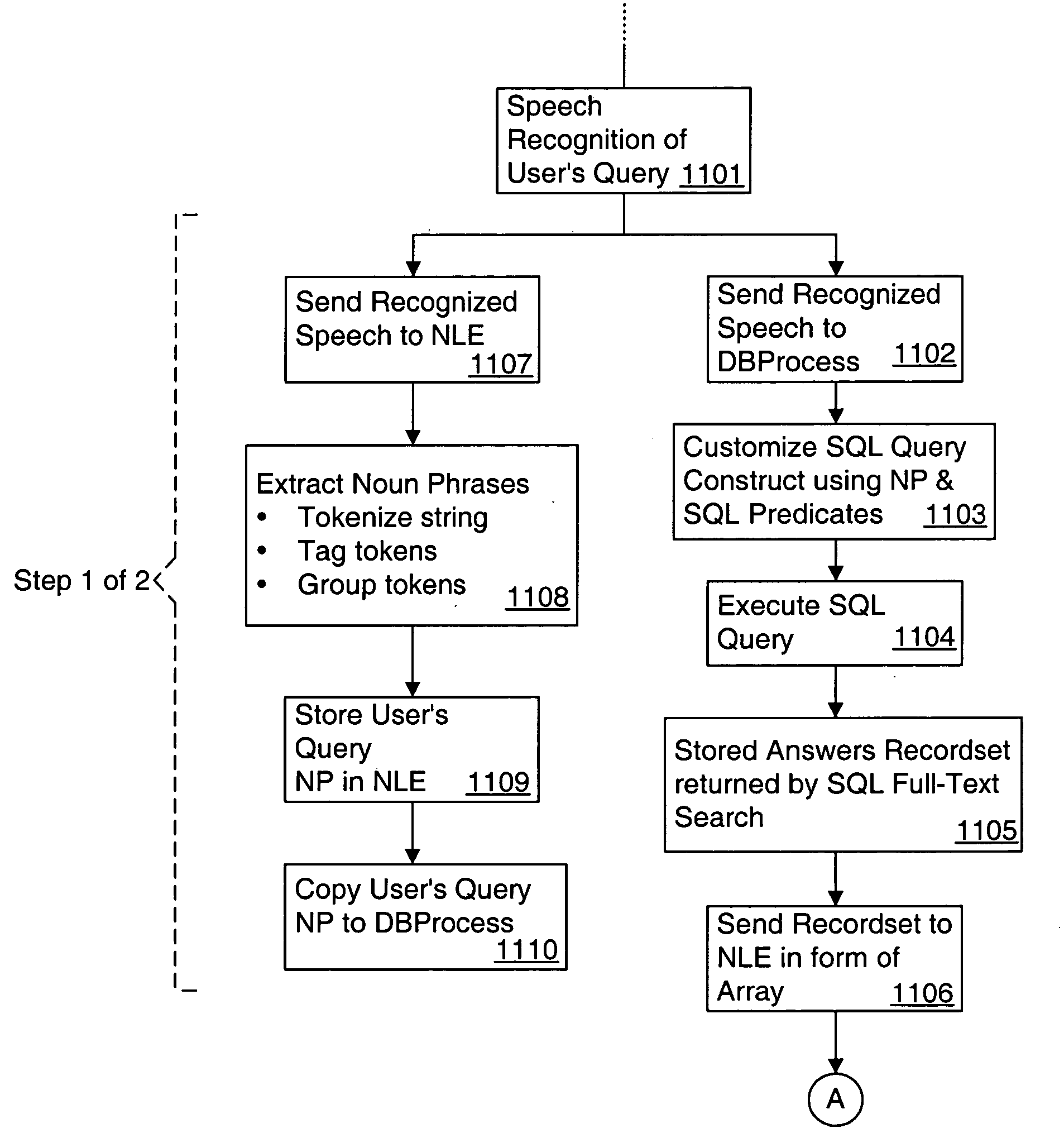
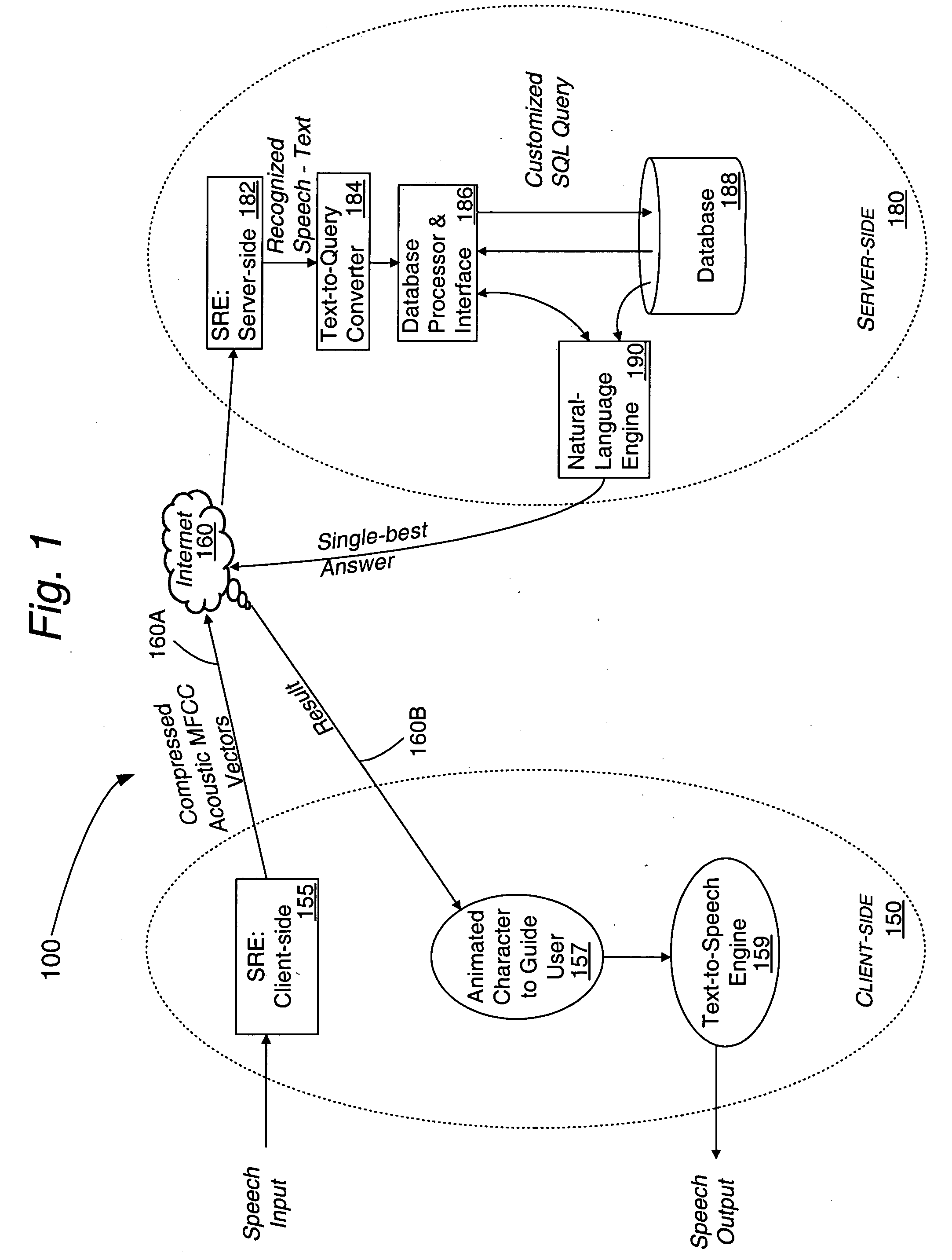
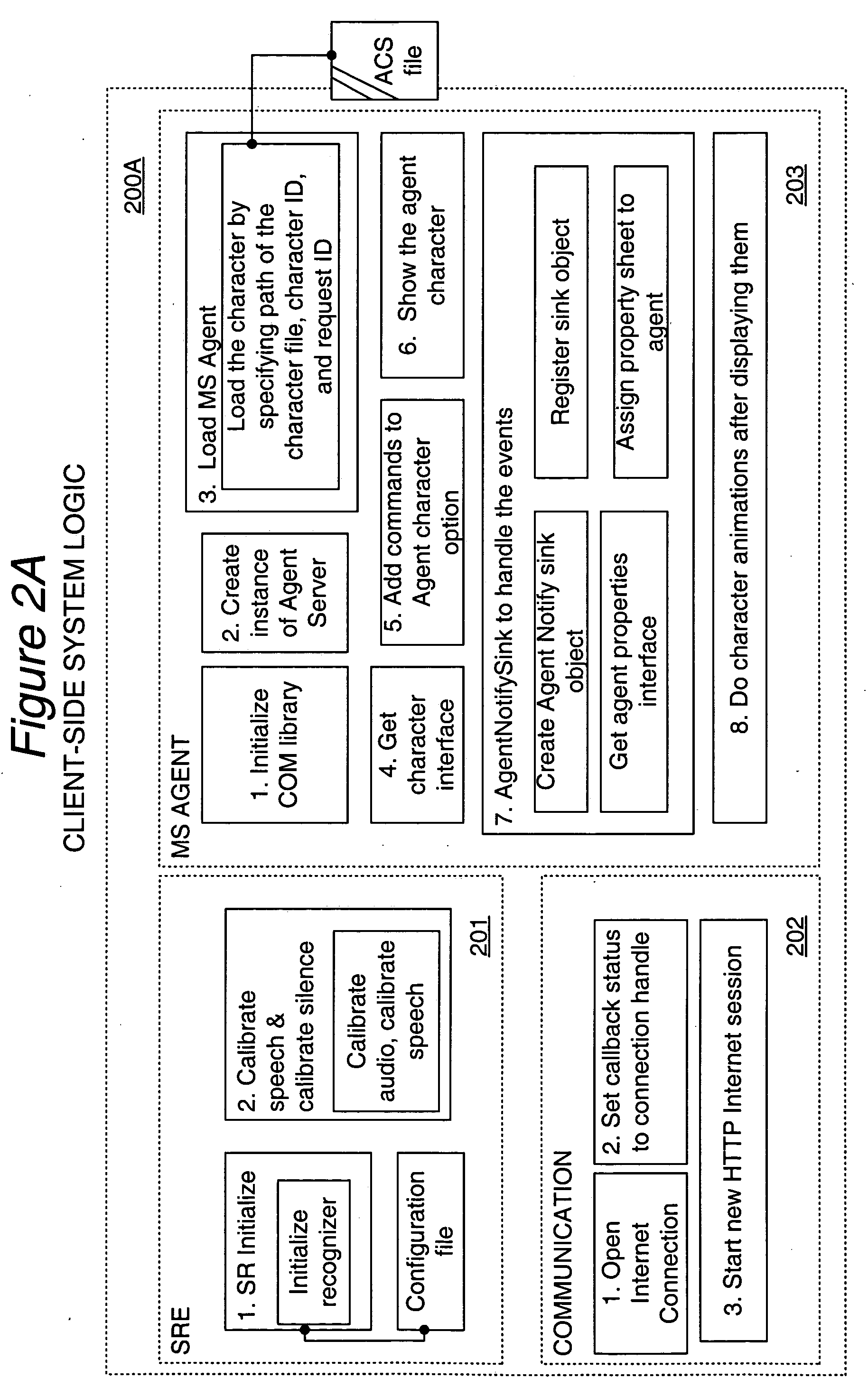
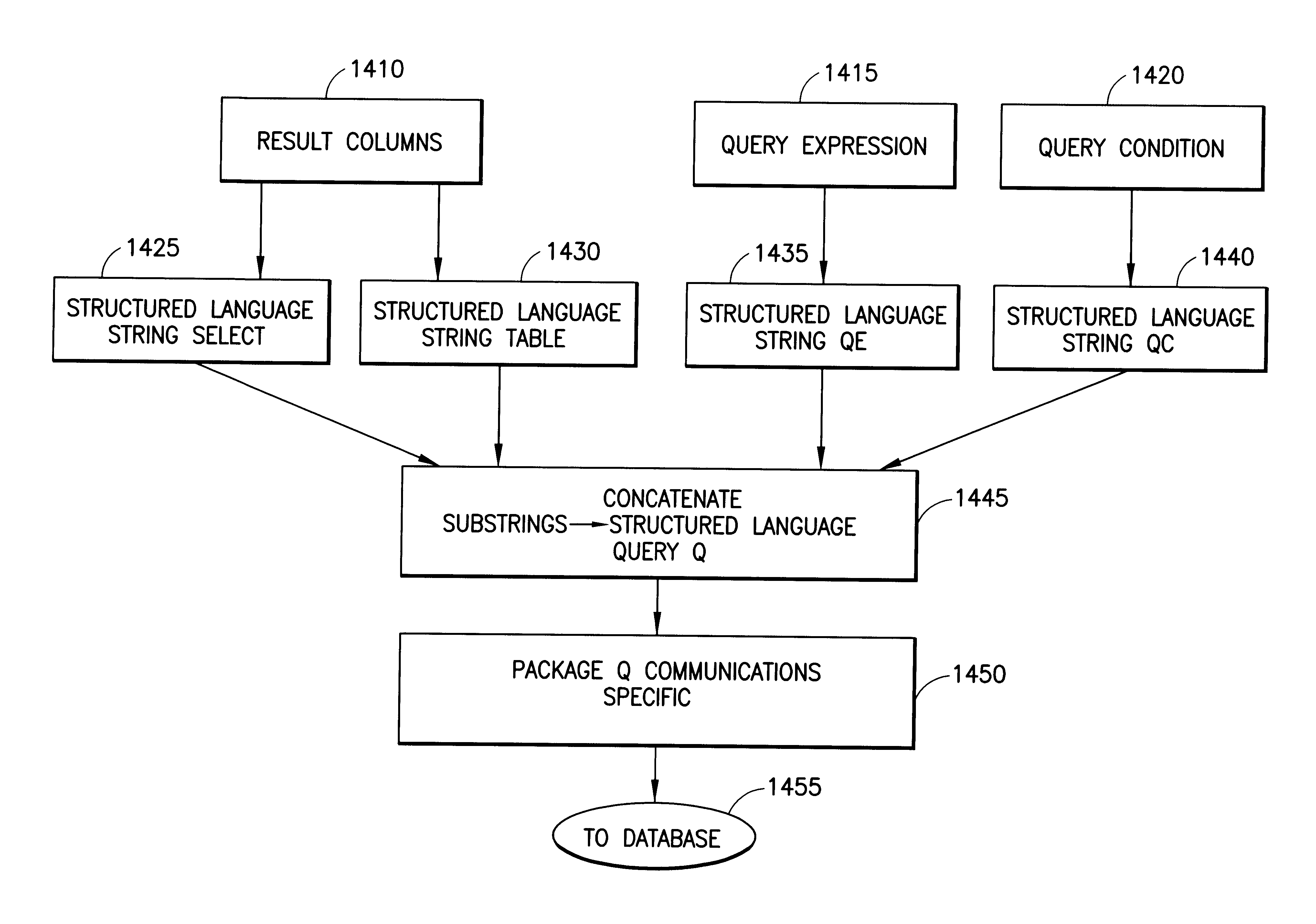
A real-time system incorporating speech recognition and linguistic processing for recognizing a spoken query by a user and distributed between client and server, is disclosed. The system accepts user's queries in the form of speech at the client where minimal processing extracts a sufficient number of acoustic speech vectors representing the utterance. These vectors are sent via a communications channel to the server where additional acoustic vectors are derived. Using Hidden Markov Models (HMMs), and appropriate grammars and dictionaries conditioned by the selections made by the user, the speech representing the user's query is fully decoded into text (or some other suitable form) at the server. This text corresponding to the user's query is then simultaneously sent to a natural language engine and a database processor where optimized SQL statements are constructed for a full-text search from a database for a recordset of several stored questions that best matches the user's query. Further processing in the natural language engine narrows the search to a single stored question. The answer corresponding to this single stored question is next retrieved from the file path and sent to the client in compressed form. At the client, the answer to the user's query is articulated to the user using a text-to-speech engine in his or her native natural language. The system requires no training and can operate in several natural languages.
Owner:NUANCE COMM INC
System and method for performance complex heterogeneous database queries using a single SQL expression
InactiveUS6341277B1Easy to implementEasy maintenanceDigital data information retrievalData processing applicationsDatabase queryClient-side
Query objects are created by a client process. The query objects have one or more sub-query objects and one or more execute methods that are capable of operating on their respective query object to produce one or more query expressions. All of the execute methods are capable of producing the respective query expression that is compatible with a structured query language. A compound query contains one or more boolean expressions of one or more of the query objects. The compound query has one or more compound execute methods which invoke one or more the execute methods of each of the query objects. Each of the execute methods returns their respective query expression and the compound execute method uses one or more common table expressions to combine the query expressions to form a single compound query expression that represents the boolean expression. This single expression can be execute against a database to return a result without executing any of the query expressions against the database individually.
Owner:IBM CORP
Method and apparatus for efficient SQL processing in an n-tier architecture
ActiveUS7580971B1Efficient processingFree of ChargeDigital data information retrievalMultiple digital computer combinationsData setCache server
A method and apparatus for efficiently processing data requests in a network oriented n-tier database environment is presented. According to one embodiment of the invention, certain or all data from the tables of a database server device can be maintained in tables on the client device in a client side database cache server system. This local cache allows the network oriented n-tier database system to eliminate the expense of repetitive network transmissions to respond to duplicate queries for the same information. Additionally, the local client device may also keep track of what data is cached on peer network nodes. This allows the client to request that data from a peer database cache server and off load that burden from the database server device. Moreover, the local client may also keep statistics regarding the frequency of requested data in order to optimize the data set maintained in the local database cache server.
Owner:ORACLE INT CORP
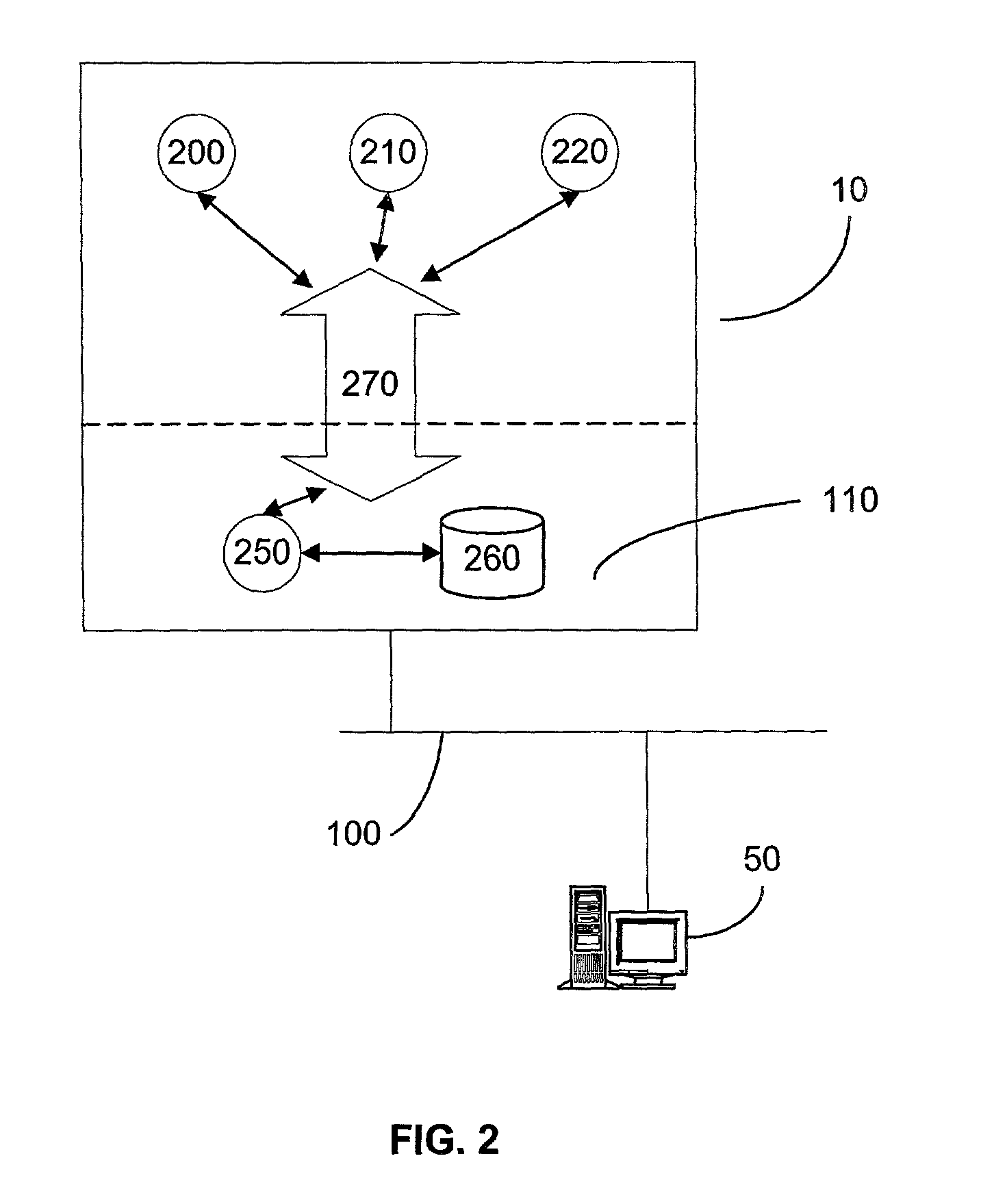
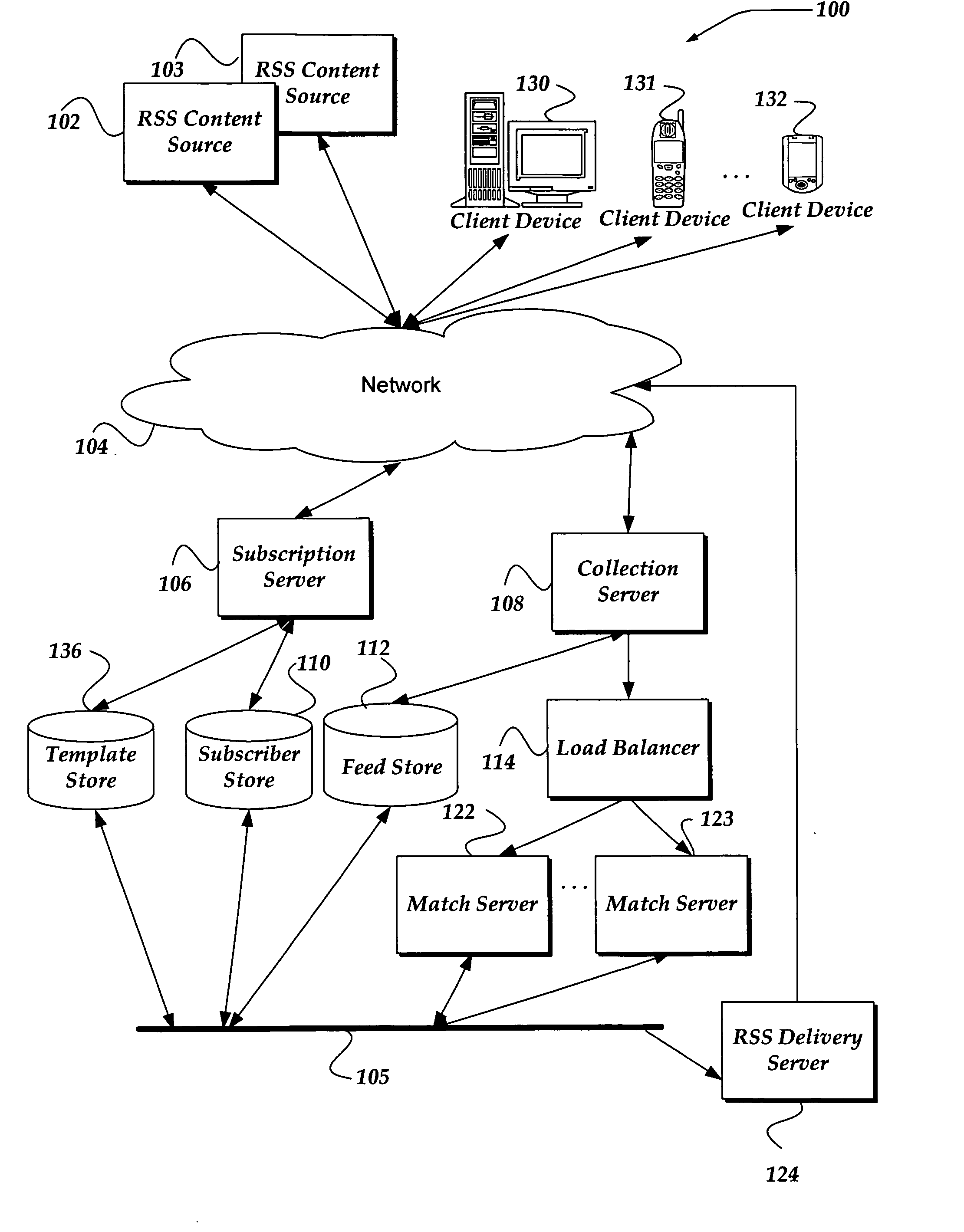
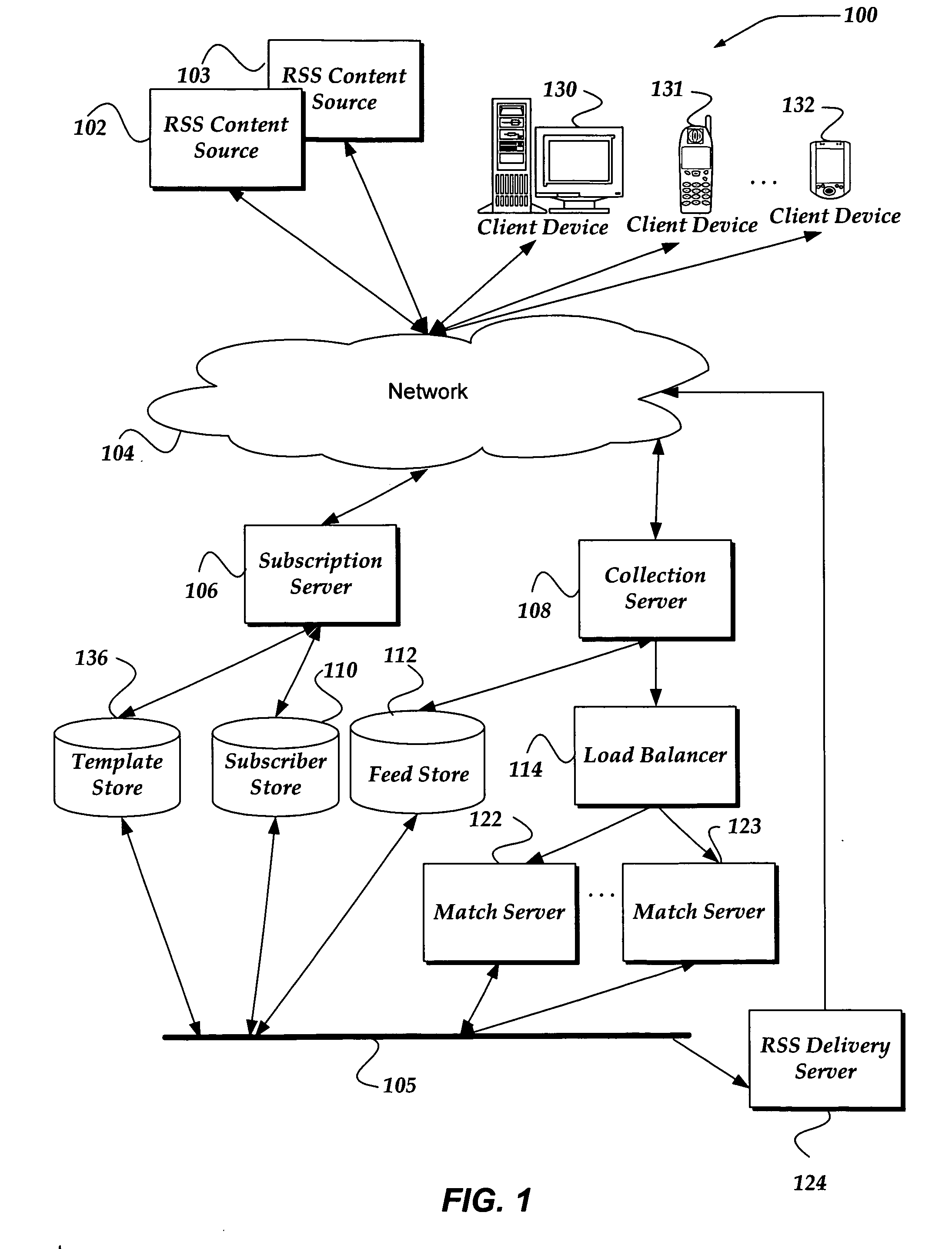
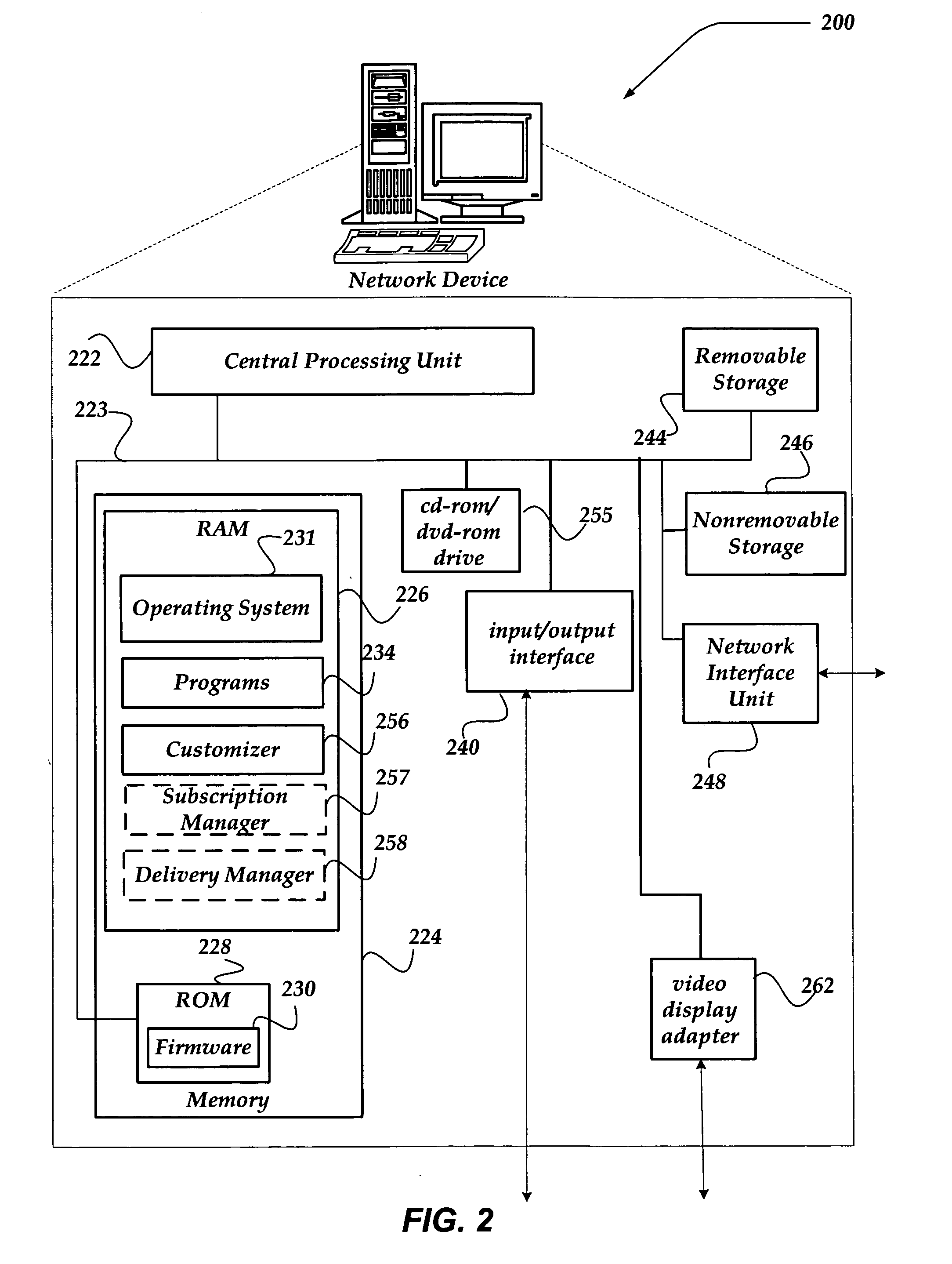
User interface for providing third party content as an RSS feed
A system, method, and apparatus are directed to managing a subscription to an RSS feed. A search component enables searching over a network for content associated with an RSS feed. In one embodiment, the search component receives a search query in the form of a structured query language (SQL), Boolean expression, or the like. The search component may search for content based on the search query and validate the RSS feed associated with the results from the search. A list of validated RSS feeds may be sent to the user. The user may then select from the list and subscribe to a validated RSS feed. In addition, the user may employ the search query as an RSS feed. Thus, the same search may be performed automatically and the results compared to the previous search results. If a change in the search results is detected, the user may be alerted.
Owner:OATH INC
Metamodel-based metadata change management
InactiveUS6839724B2Data processing applicationsDigital data processing detailsChange managementData warehouse
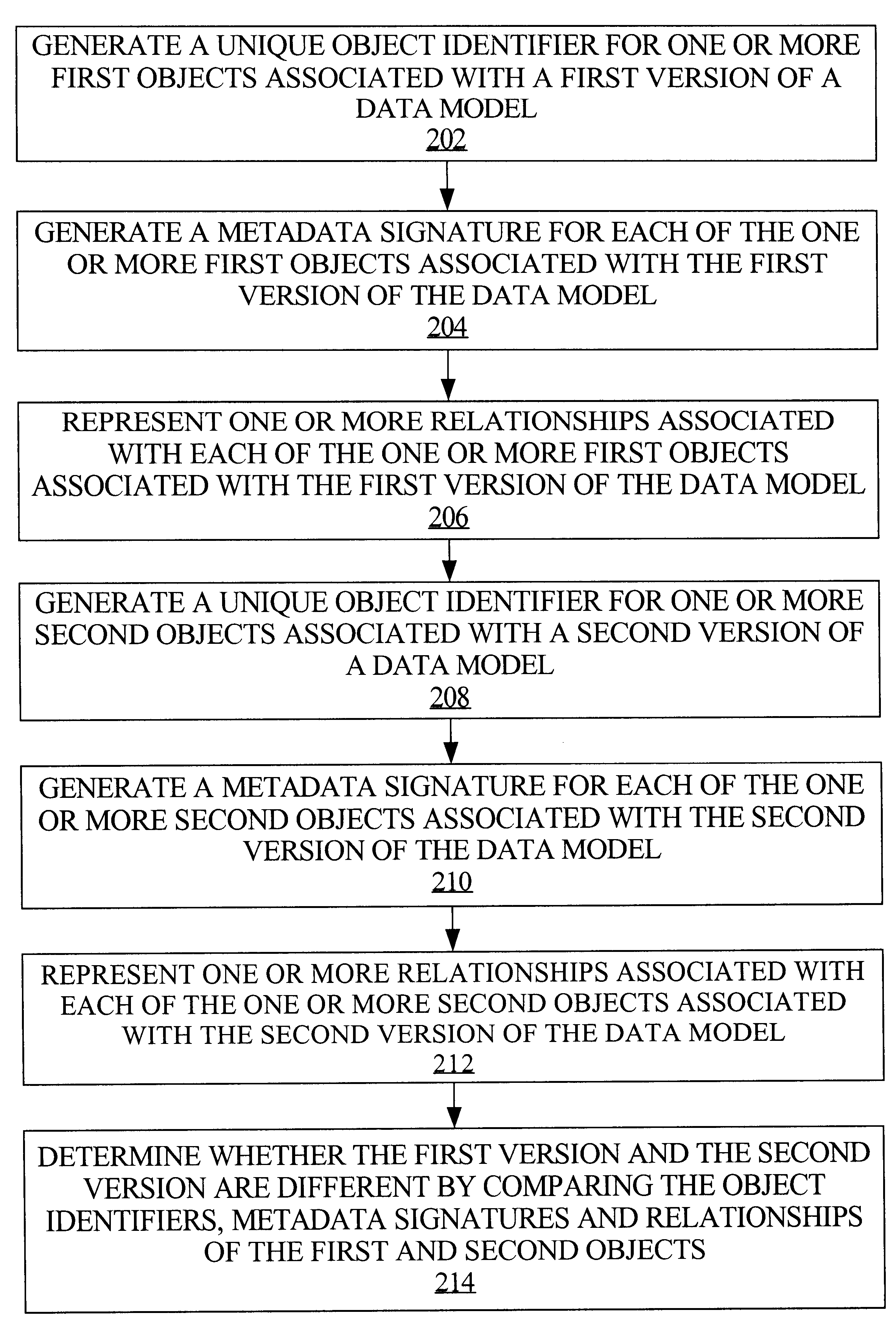
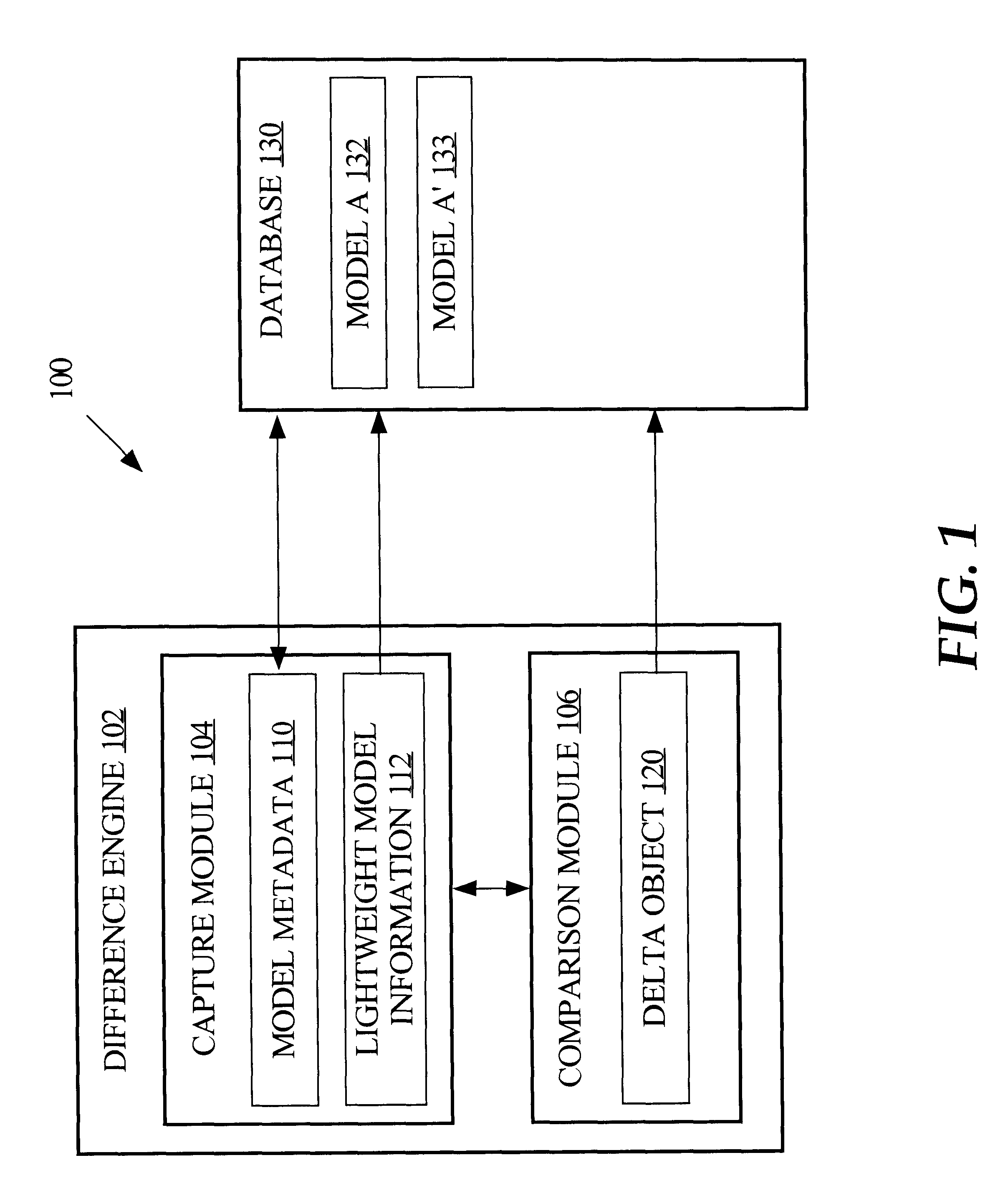
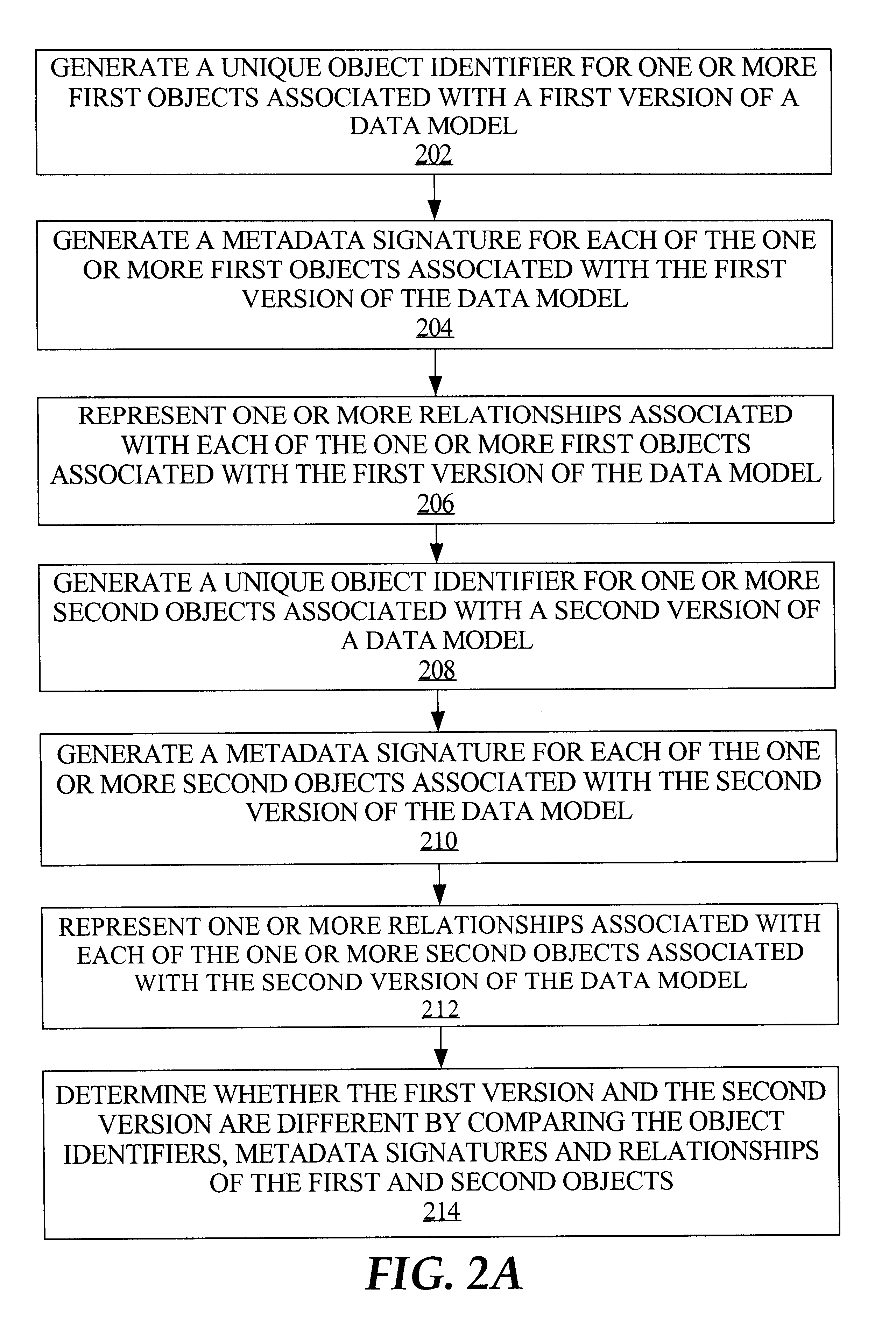
A framework is provided for management of models. Management of data models or other types of models includes model change comparison and change implementation. For example, in the context of data warehouse models, model components and their process interactions are captured in a form such that different versions of a model can be automatically compared and any changes between versions determined. The framework provides the capability of capturing a model definition down to the level of an individual object and the semantics and relationships of each object. A model is represented and stored as a set of (1) unique object identifiers, (2) object metadata signatures that represent the semantics of objects, and (3) object relationships. Such model information can be stored in a relational database, against which a query, such as an SQL (Structured Query Language) query, can be executed to determine whether two models differ.
Owner:ORACLE INT CORP
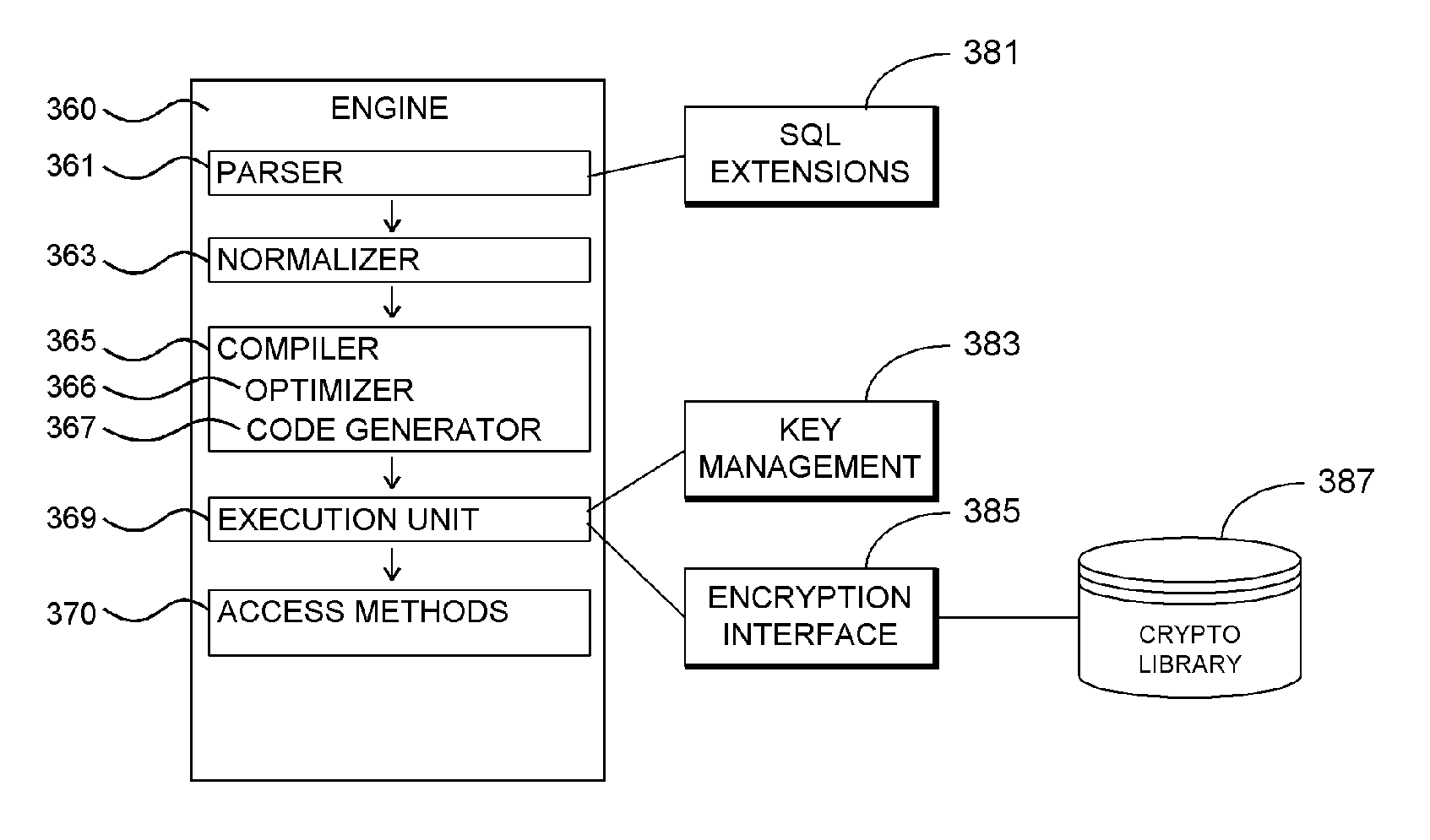
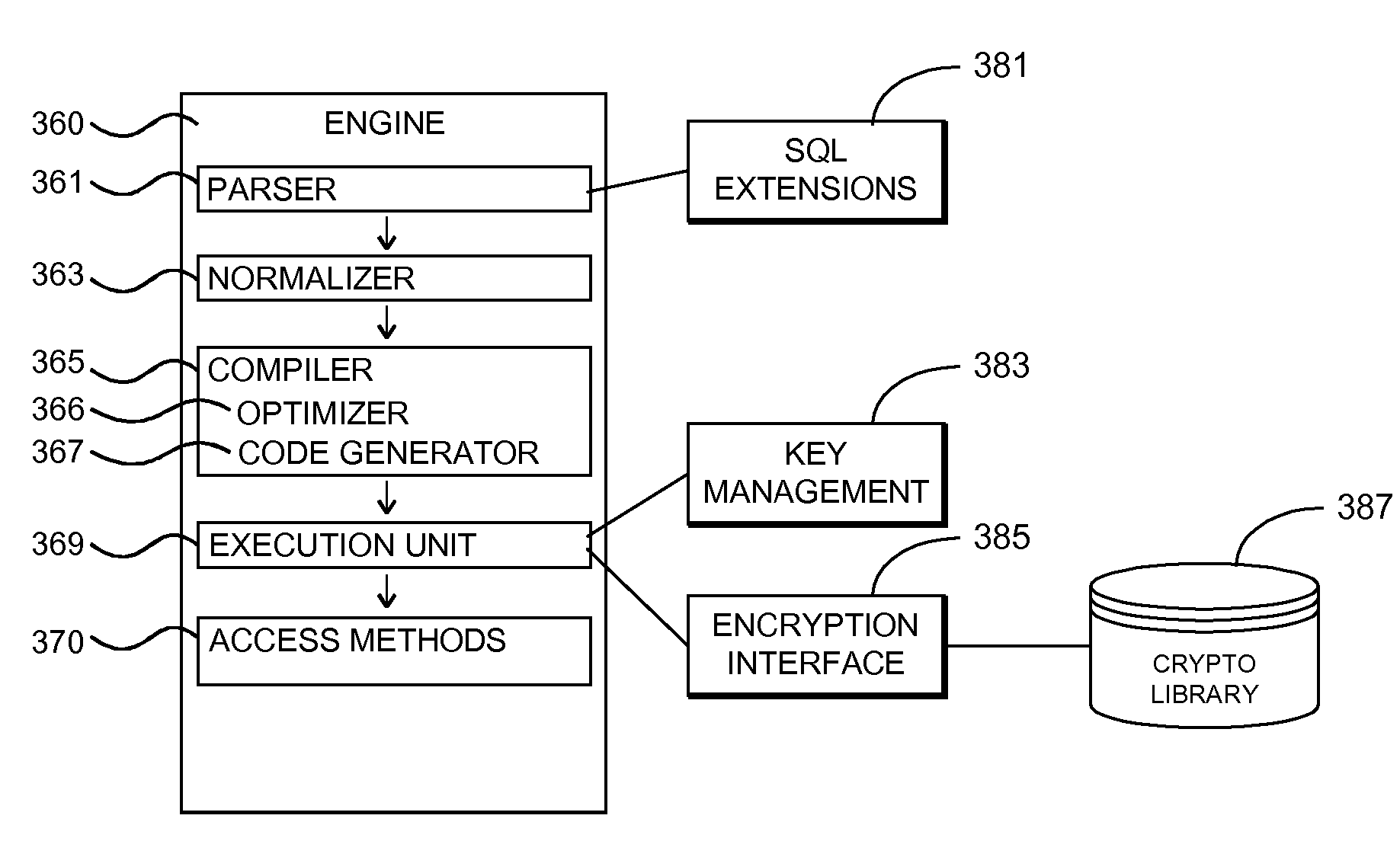
Database System Providing SQL Extensions for Automated Encryption and Decryption of Column Data
ActiveUS20060053112A1Data processing applicationsDigital data processing detailsQuery languageComputer science
A database system providing SQL extensions for automated encryption and decryption of column data is described. In one embodiment, for example, in a database system, a method is described for providing automated encryption support for column data, the method comprises steps of: defining Structured Query Language (SQL) extensions for creating and managing column encryption keys, and for creating and managing database tables with encrypted column data; receiving an SQL statement specifying creation of a particular column encryption key; receiving an SQL statement specifying creation of a database table having particular column data encrypted with the particular column encryption key; and in response to a subsequent database operation that requires the particular column data that has been encrypted, automatically decrypting the particular column data for use by the database operation.
Owner:SYBASE INC
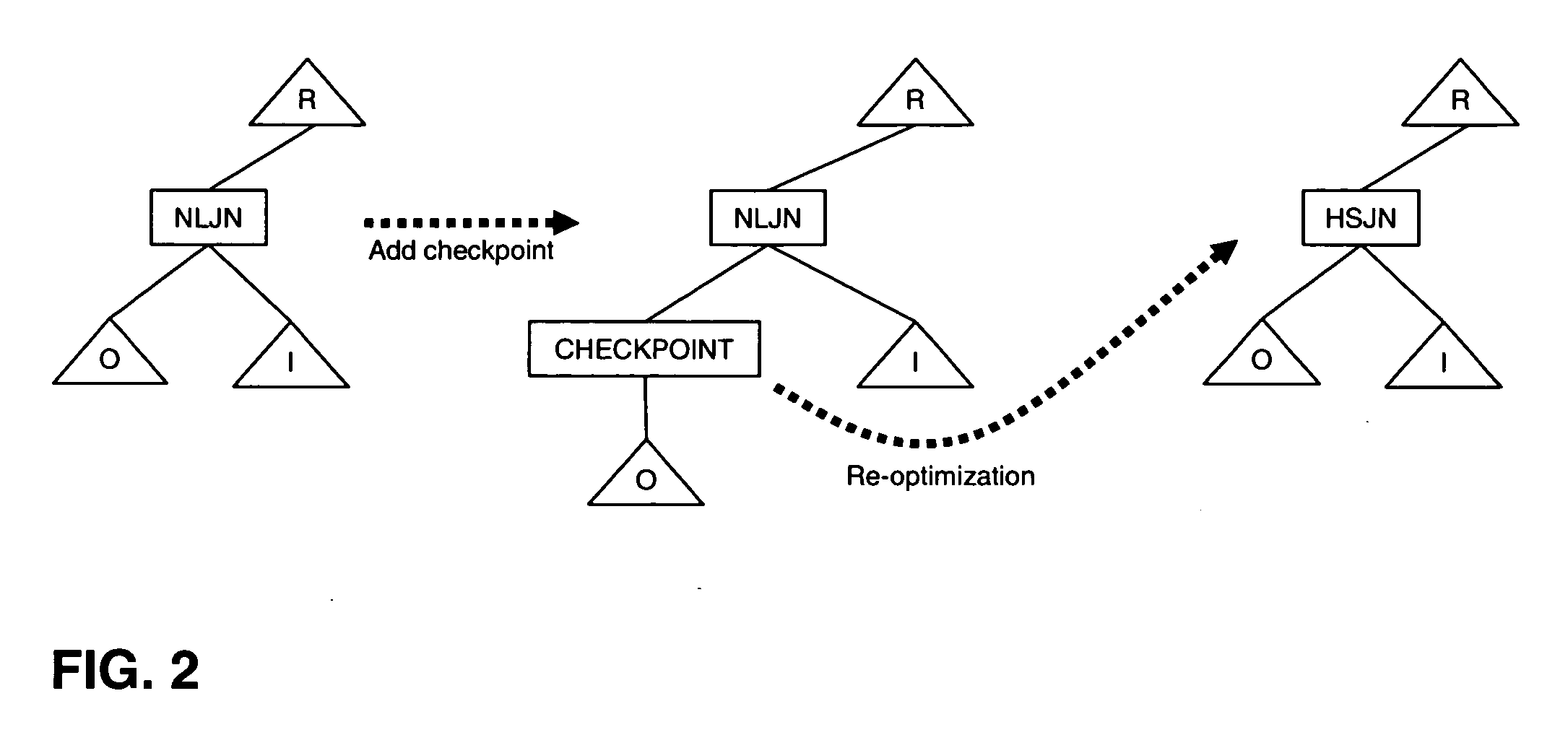
System, method, and computer program product for progressive query processing
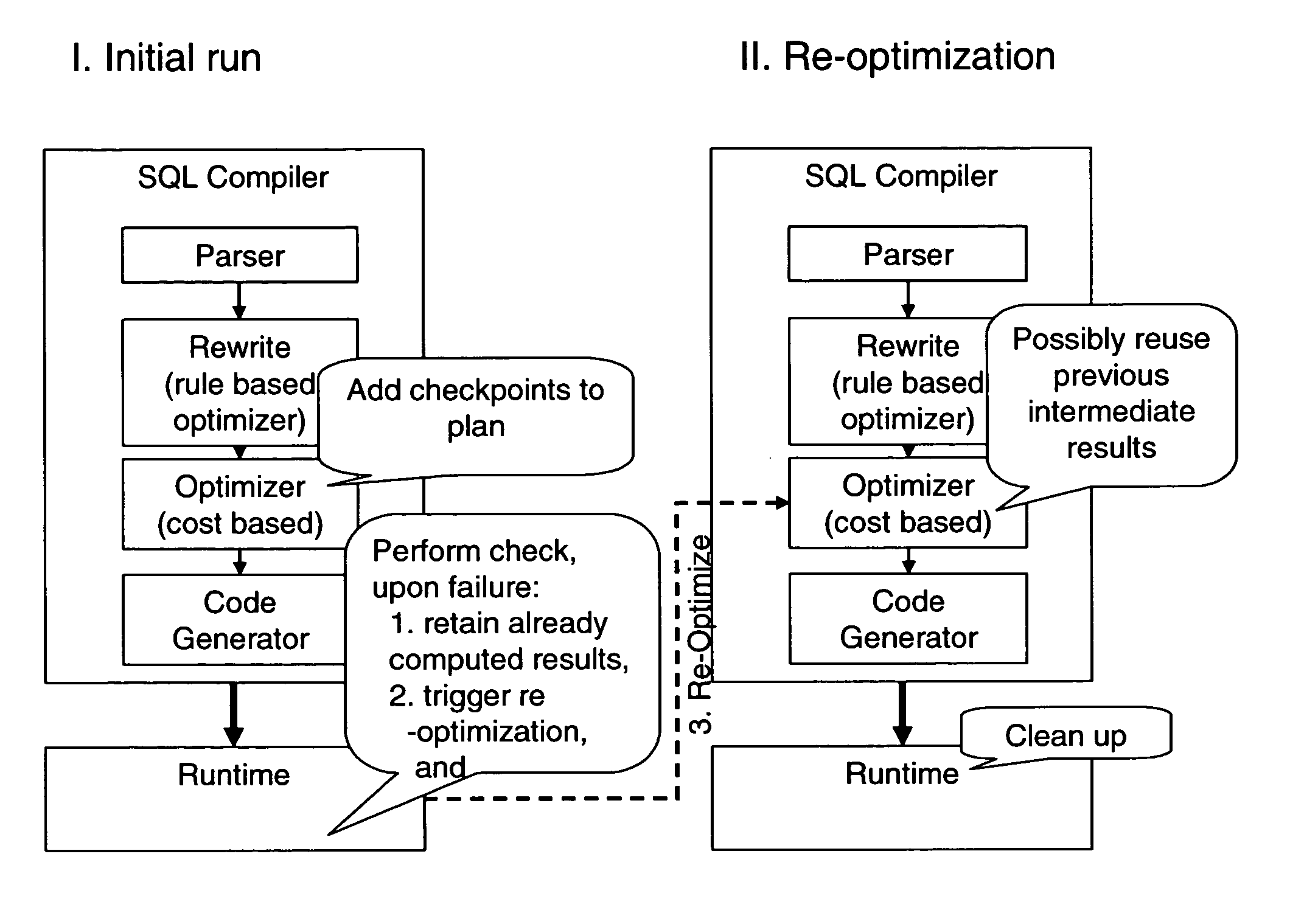
ActiveUS20050097078A1Reduce computing costEliminate duplicationData processing applicationsDigital data information retrievalExecution planView maintenance
A method, system, and computer program product to make query processing more robust in the face of optimization errors. The invention validates the statistics and assumptions used for compiling a query as the query is executed and, when necessary, progressively re-optimizes the query in mid-execution based on the knowledge learned during its partial execution. The invention selectively places a number of CHECK operators in a query execution plan to validate the optimizer's cardinality estimates against actual cardinalities. Errors beyond a threshold trigger re-optimization, and the optimizer decides whether the old plan is still optimal and whether to re-use previously computed results. The invention addresses arbitrary SQL queries whose plans can contain sub-queries, updates, trigger checking, and view maintenance operations. The invention can handle concurrent update transactions or updates of common sub-expressions in a query execution plan without compromising consistency and isolation as locking information is tied to the record ID.
Owner:HULU
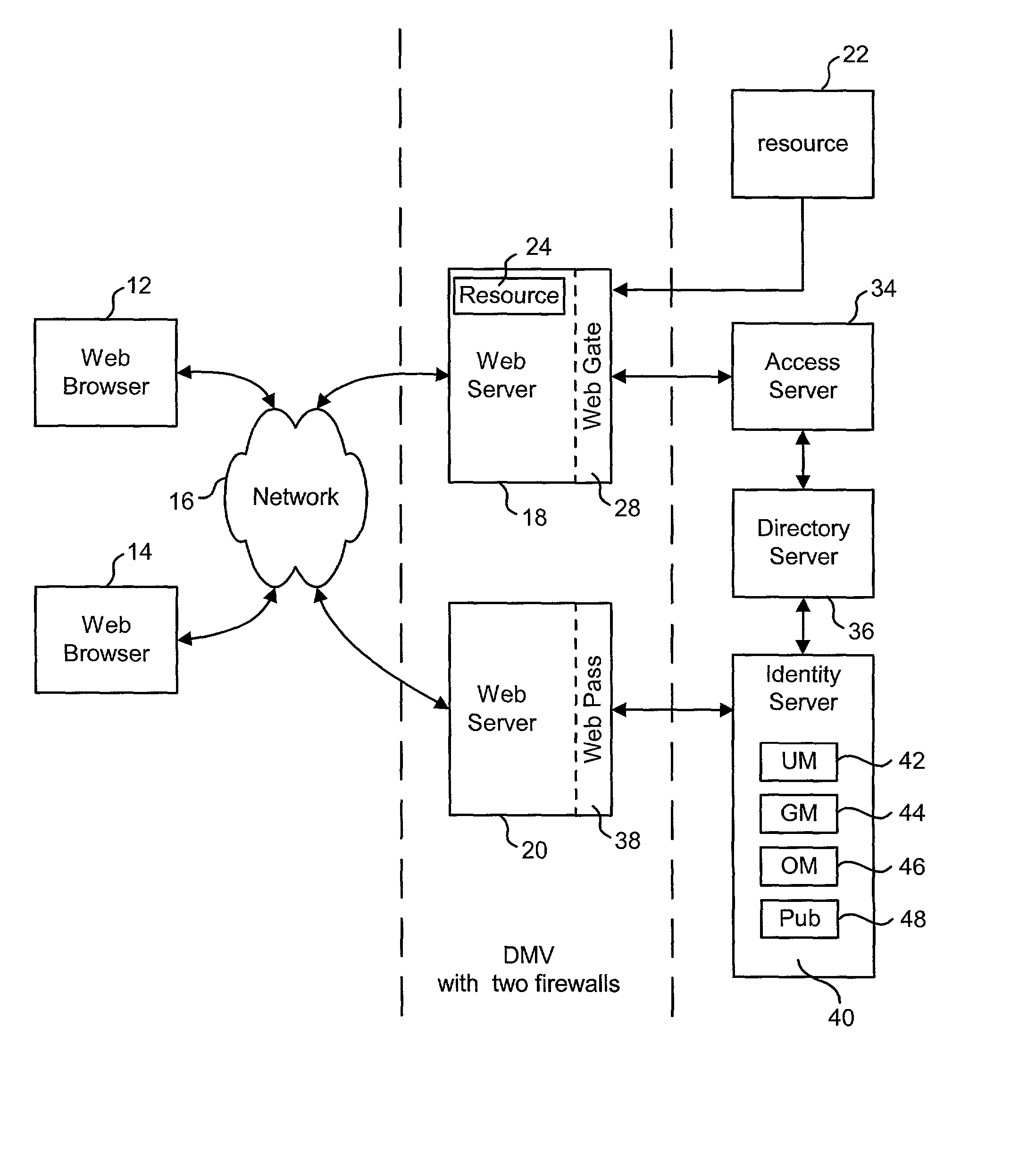
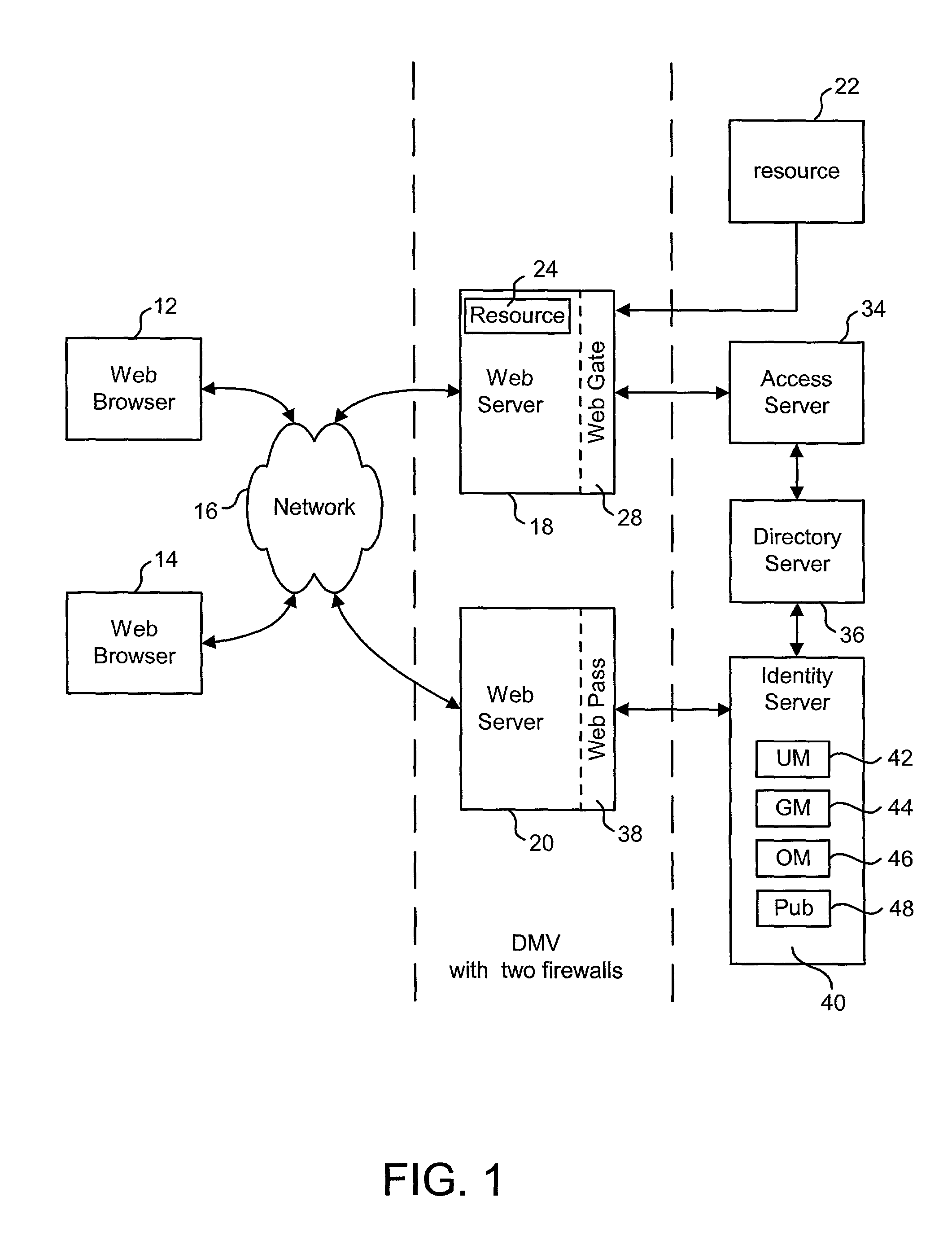
Support for multiple data stores
ActiveUS20020143943A1Complete banking machinesDigital data information retrievalData accessData storing
Technology is disclosed for supporting multiple data stores. The set of data stores can be of a uniform type, or the various data stores can be different types (e.g. LDAP, SQL, etc.). One implementation of the disclosed technology is with an Identity System. Another implementation is with an integrated Identity System and Access System. Various embodiments of the present invention utilize different means to separate the business logic of a system from the data access logic so that different types of data stores can be used without changing the business logic.
Owner:ORACLE INT CORP
Standardized customer application and record for inputting customer data into analytic models
InactiveUS7047251B2Special data processing applicationsMarketingAnalytic modelDocumentation procedure
A system and method for creating virtual “flat” customer records derived from database customer data that may be used as standardized input for analytical models. A Customer Analytic Record (“CAR”) application may be created as a database object to extract, transform, and format all of the customer data needed for customer segmentation and predictive modeling. The CAR may be a set of database “views” that are defined using virtual stored queries and enabled using capabilities of a data base management system and a structured query language. The CAR is preferably a virtual “flat” record of the customer data needed for customer analytics. The customer data may be extracted by running one or more SQL queries against the database view(s). The CAR application may dynamically calculate additional variables using predetermined transformations, including custom transformations of an underlying behavior. If additional variables are created, the CAR may be modified to include the additional variables. The CAR is preferably a dynamic view of the customer record that changes whenever any update is made to the database. The definition of the CAR provides documentation of each data element available for use in models and analytics.
Owner:ACCENTURE GLOBAL SERVICES LTD
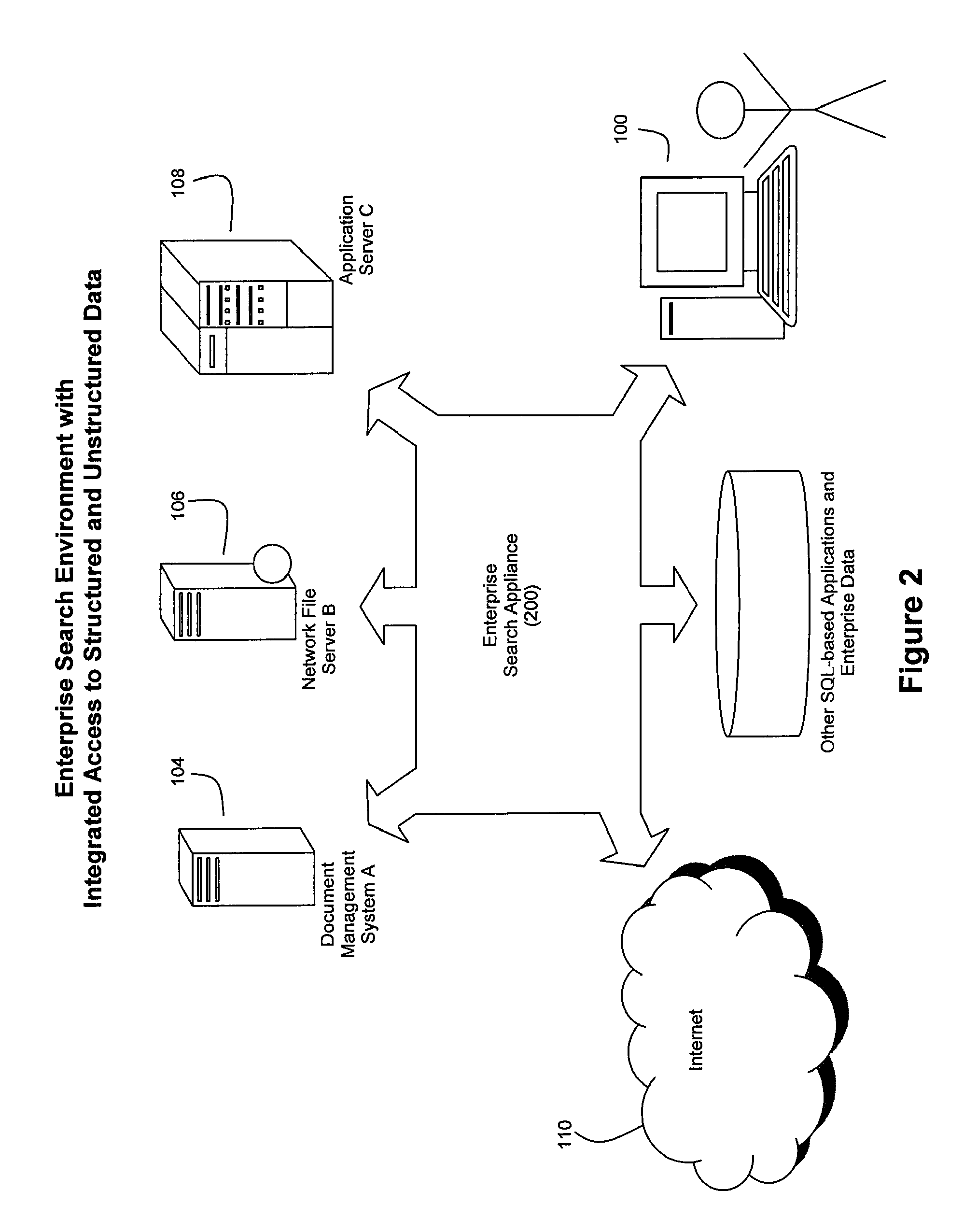
Method and System for High Performance Integration, Processing and Searching of Structured and Unstructured Data Using Coprocessors
ActiveUS20080114724A1Faster and more unified accessEffectively bifurcate query processingData processing applicationsDigital data processing detailsFull text searchRelational database
Disclosed herein is a method and system for integrating an enterprise's structured and unstructured data to provide users and enterprise applications with efficient and intelligent access to that data. Queries can be directed toward both an enterprise's structured and unstructured data using standardized database query formats such as SQL commands. A coprocessor can be used to hardware-accelerate data processing tasks (such as full-text searching) on unstructured data as necessary to handle a query. Furthermore, traditional relational database techniques can be used to access structured data stored by a relational database to determine which portions of the enterprise's unstructured data should be delivered to the coprocessor for hardware-accelerated data processing.
Owner:IP RESERVOIR
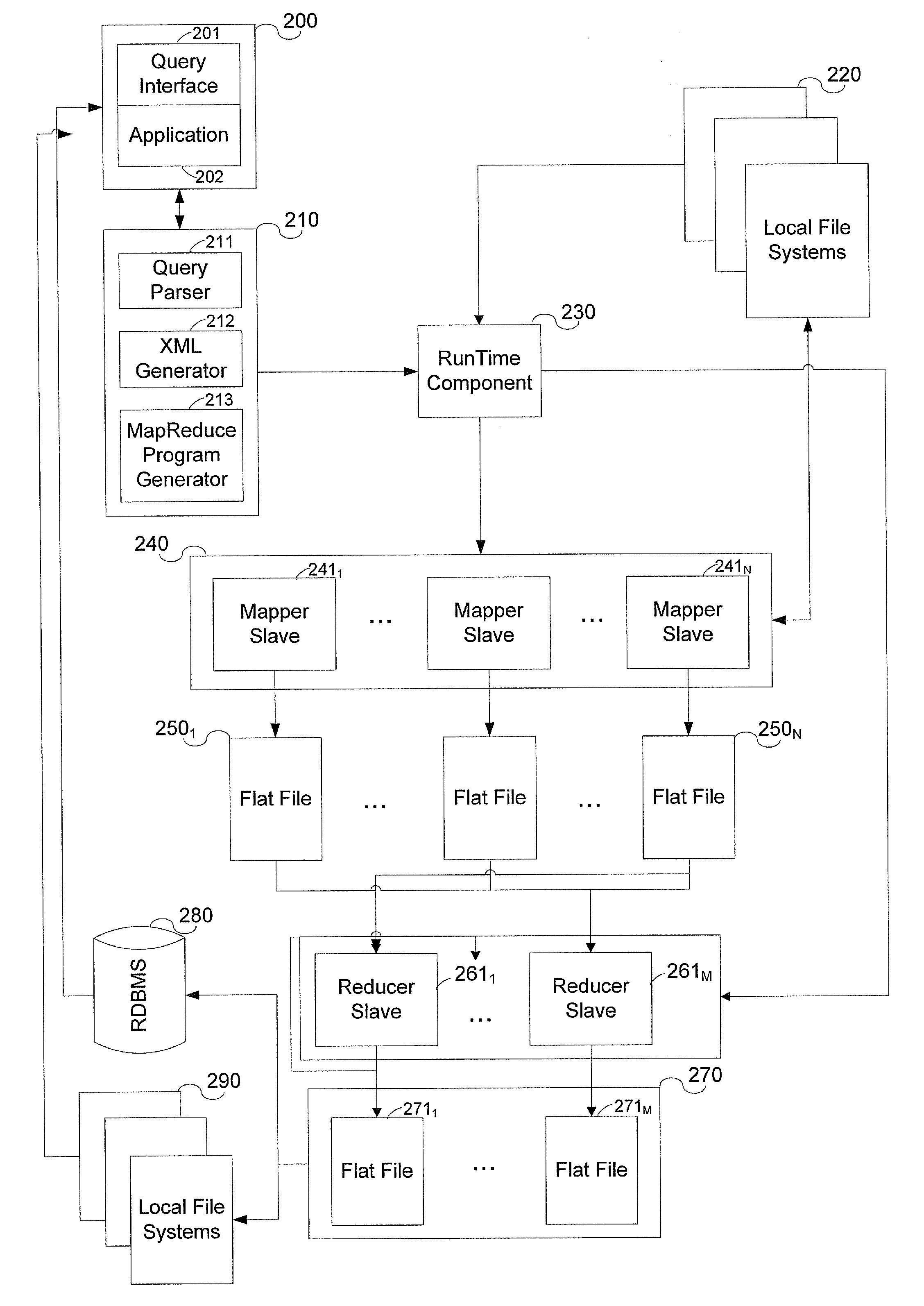
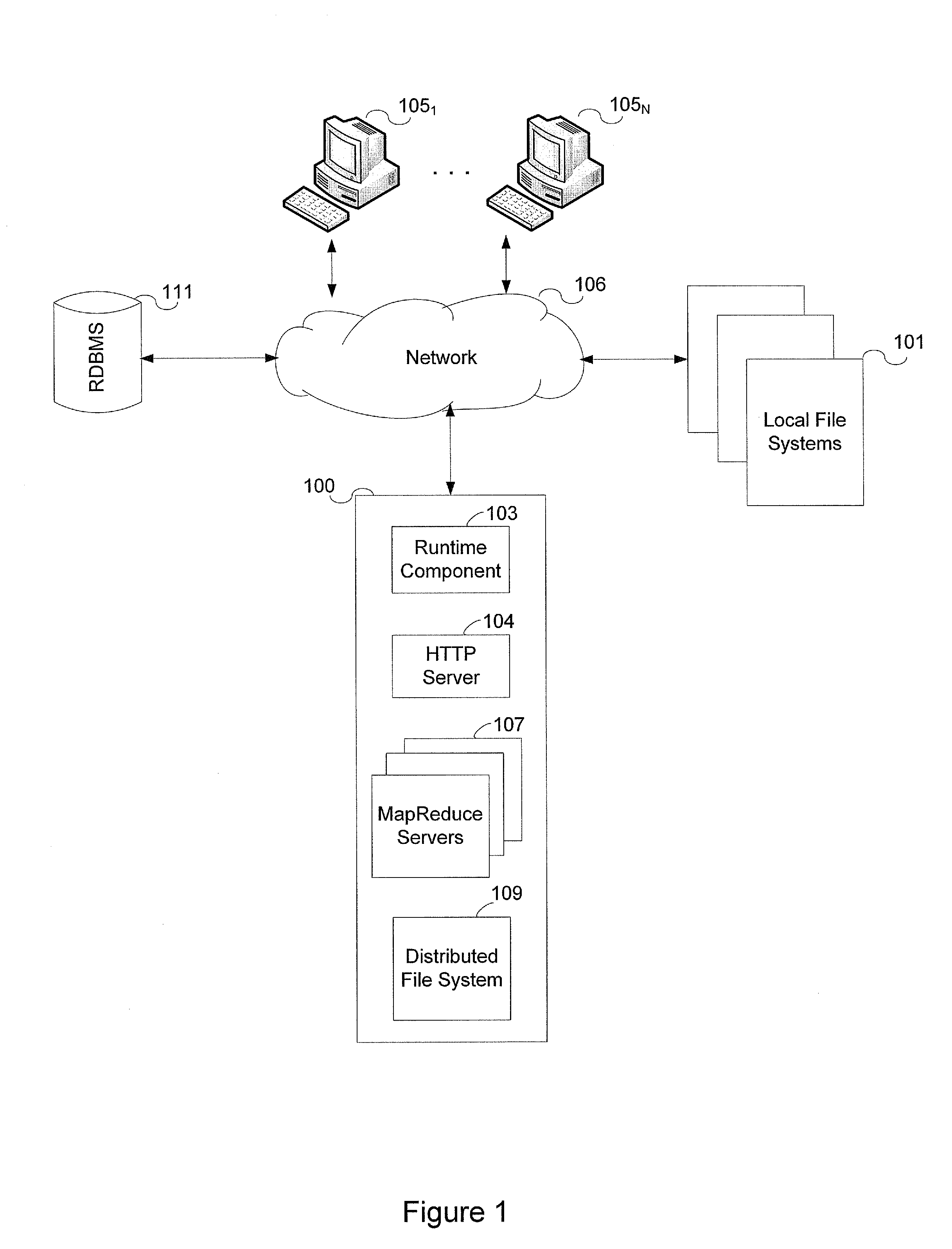
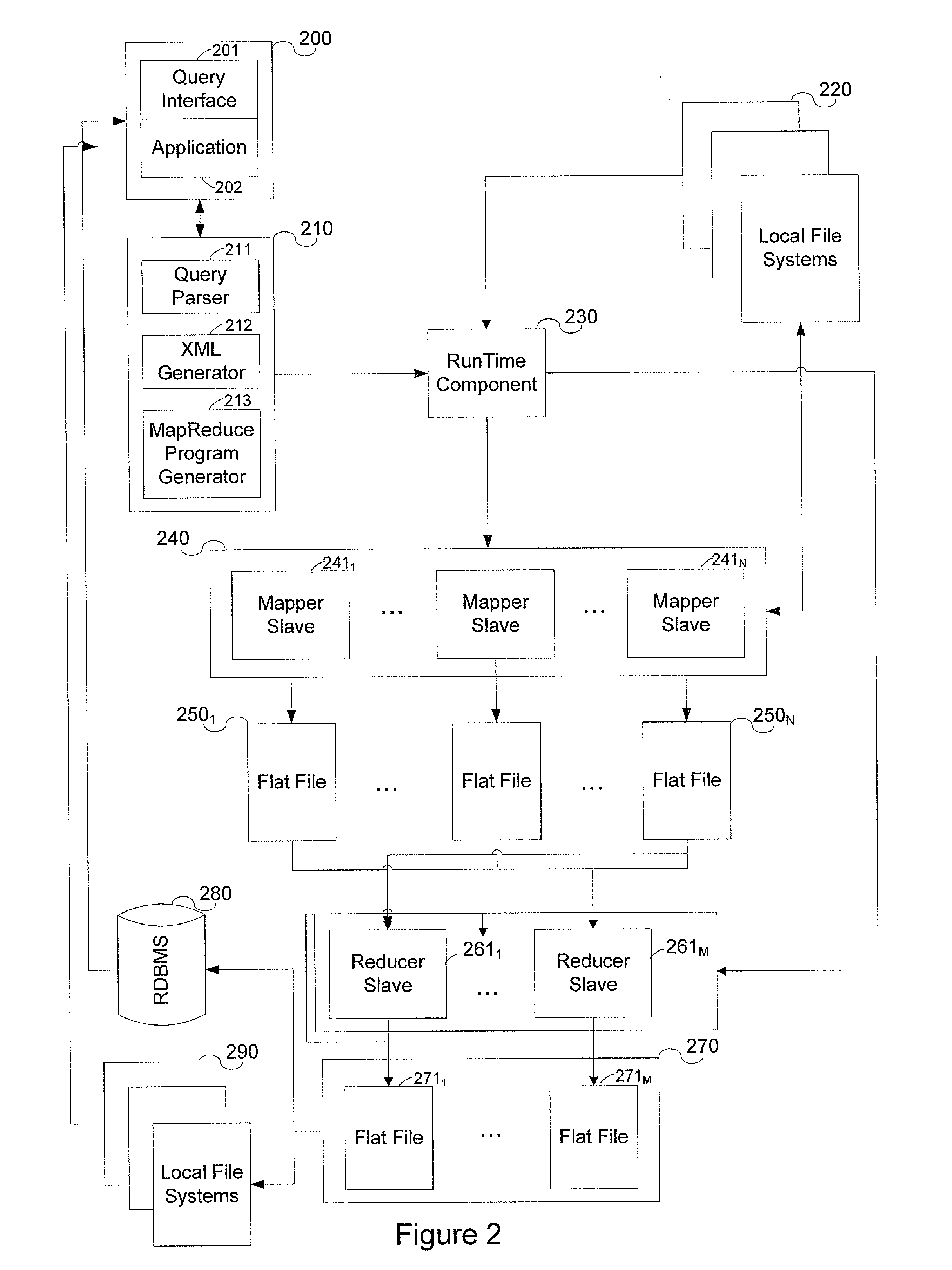
System and method for data warehousing and analytics on a distributed file system
ActiveUS20090055370A1Significant performance bottleneckProcess is time-consume and expensiveDigital data information retrievalDigital data processing detailsData warehouseMap reduce
A computer implemented method for executing an ANSI SQL expression belonging to the SELECT-WHERE-equi-JOIN class on data residing in a distributed file system, said method comprising the steps of entering the ANSI SQL expression into a user interface; converting the ANSI SQL expression into a map-reduce program; running the map-reduce program on the distributed file system; storing the result set of the program in the distributed file system; and presenting the result set through a user interface.
Owner:THRYV INC
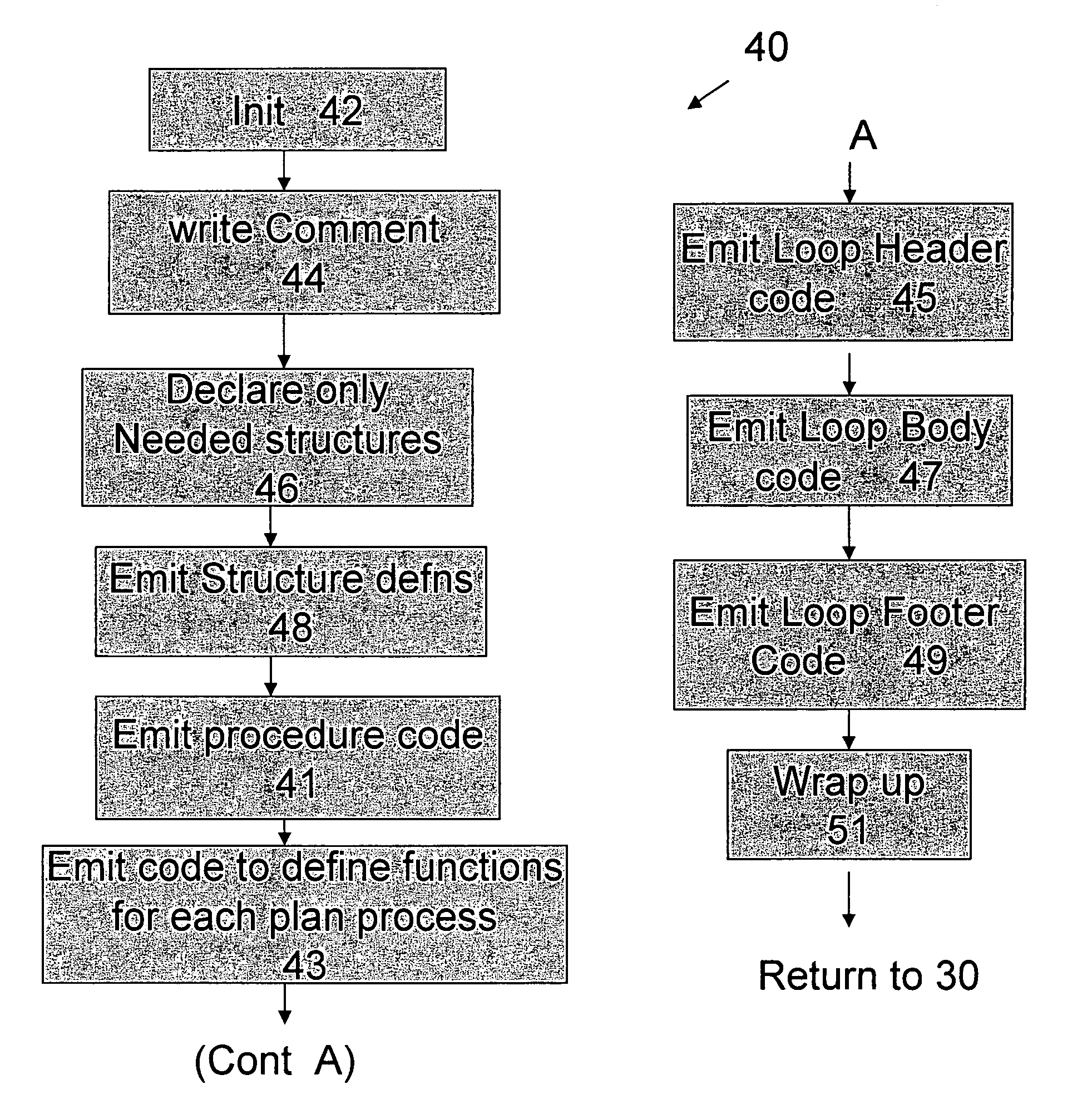
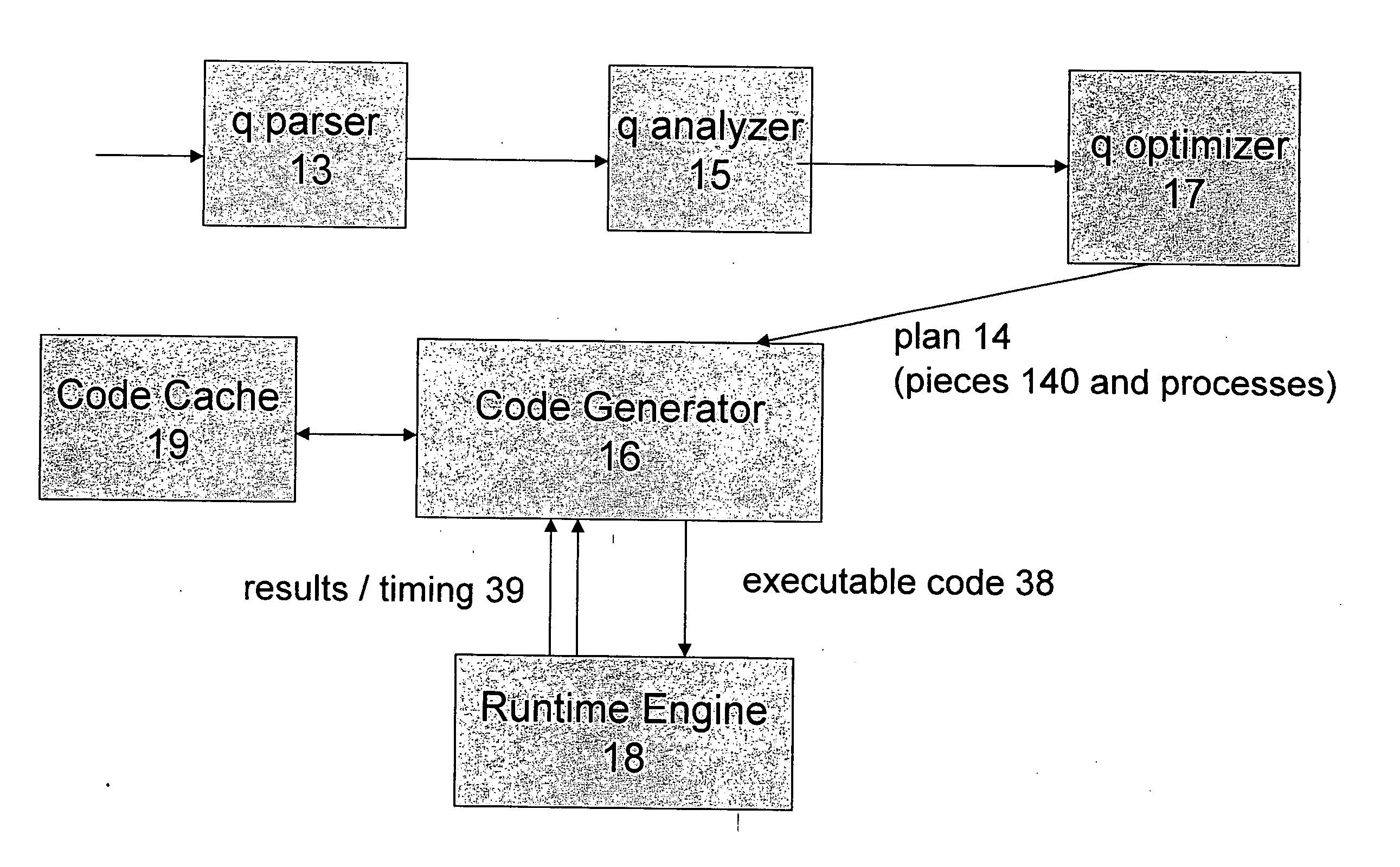
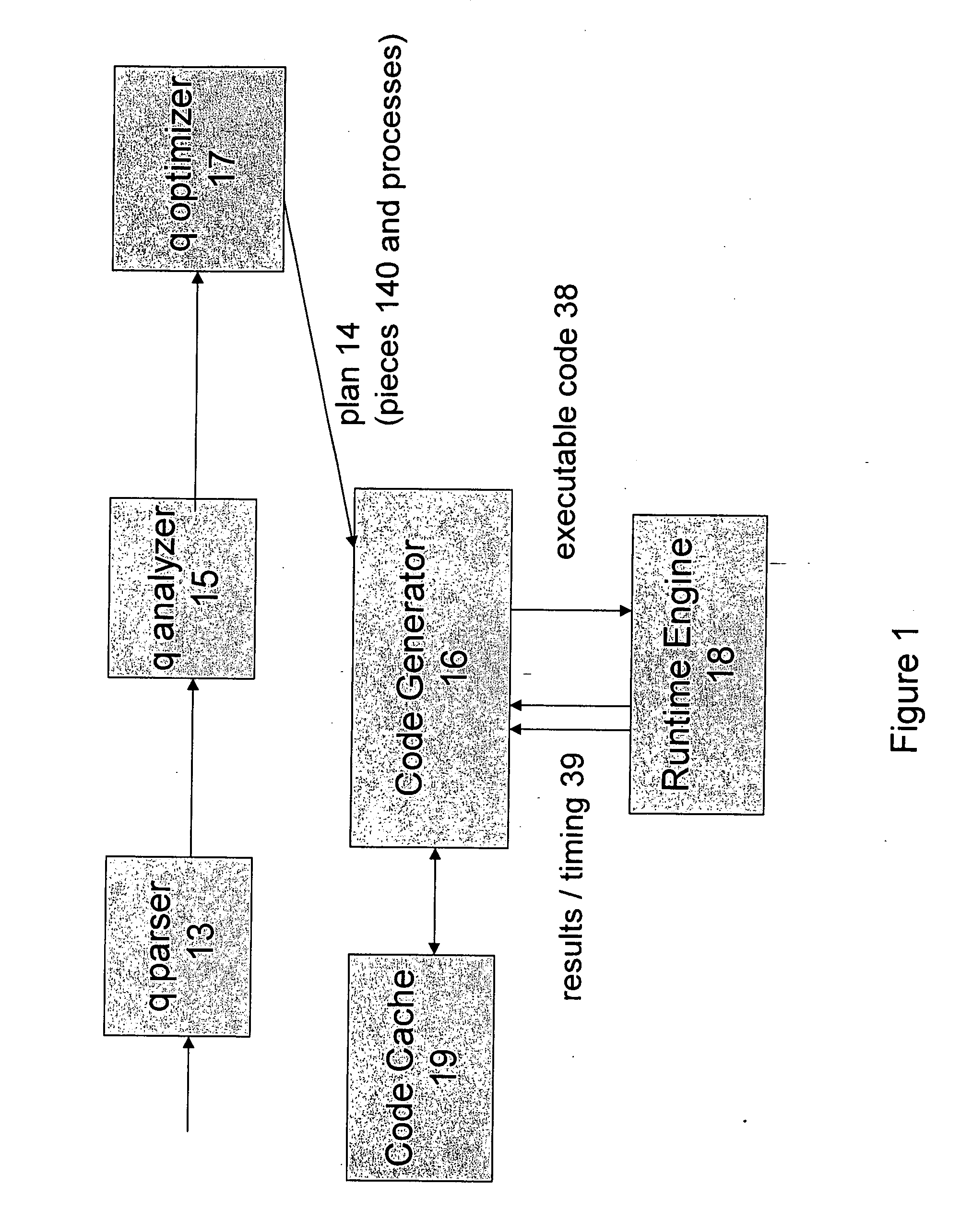
Optimized SQL code generation
ActiveUS7430549B2Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planCode generation
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:INT BUSINESS MASCH CORP
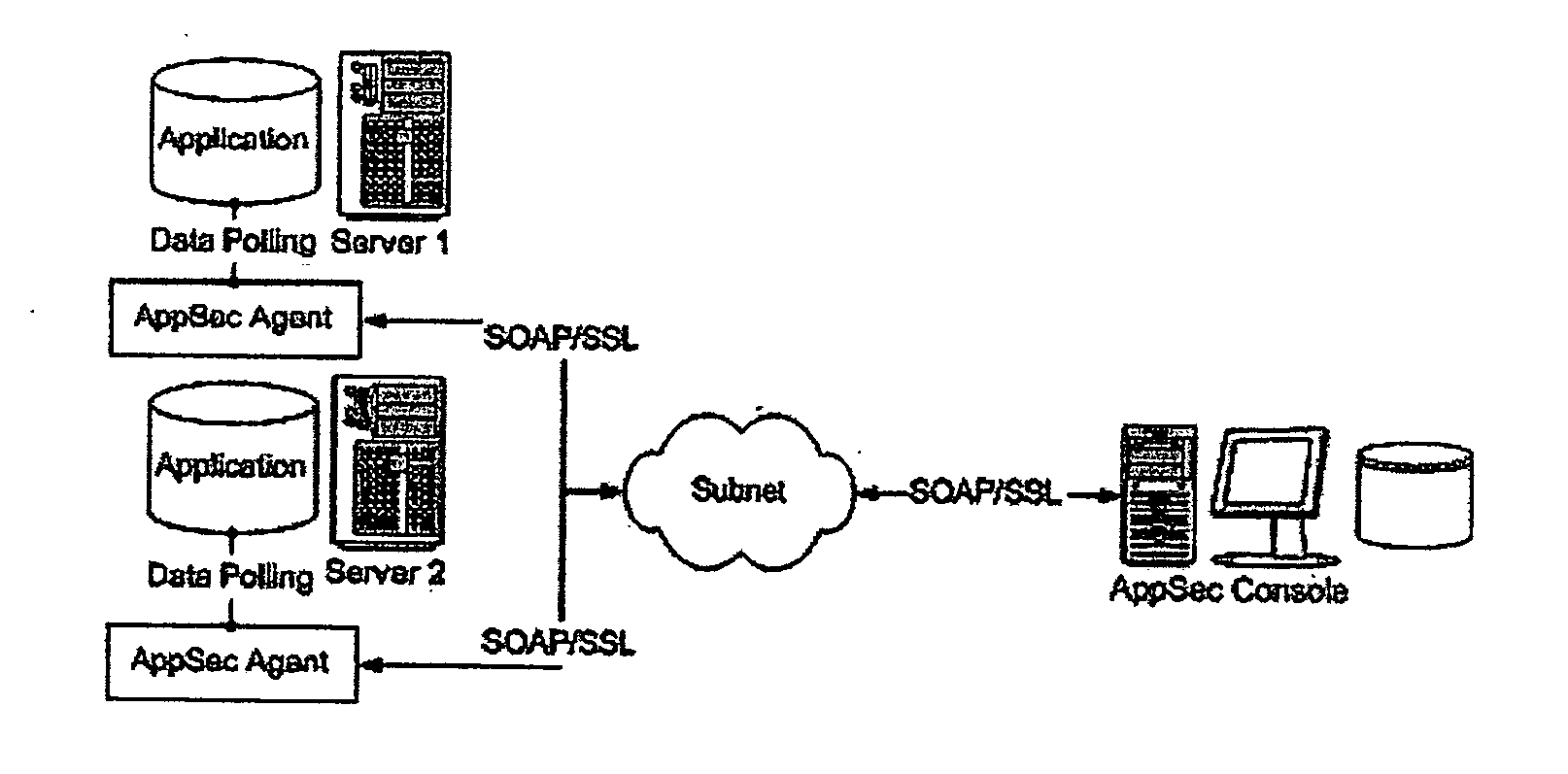
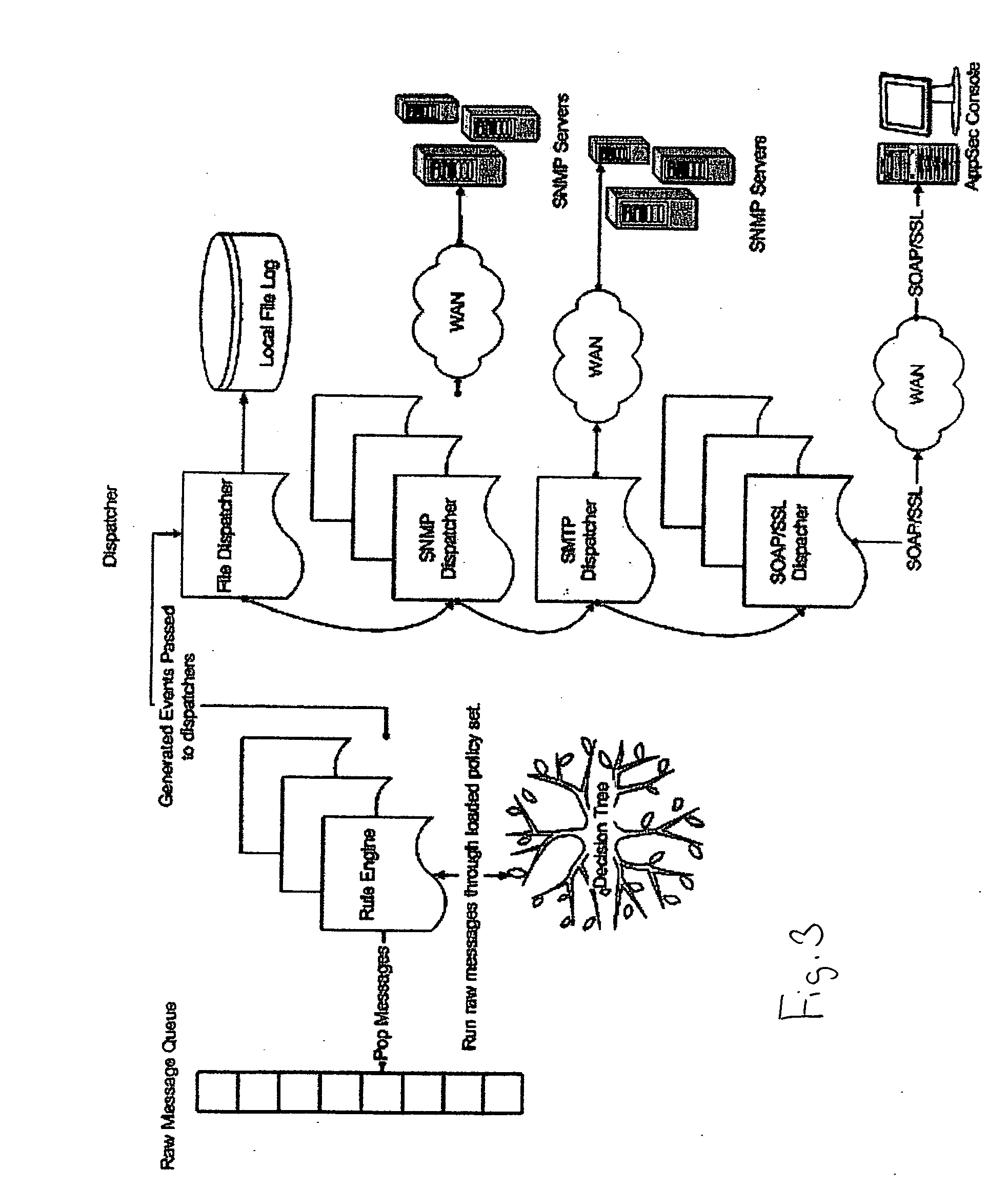
System for protecting database applications from unauthorized activity
InactiveUS20050203921A1Easy to configureEasy to monitorDigital data processing detailsPlatform integrity maintainanceDatabase applicationComputer science
A method for protecting database applications including analyzing the activity on the server, analyzing the response from the server, and blocking malicious or unauthorized activity. Commands are analyzed for suspicious or malicious SQL statements or access to unauthorized data. Server responses are monitored for suspicious results likely to have occurred from a successful attack or unauthorized access to data. When malicious or unauthorized activity occurs, activity by the source is blocked or an alert is issued.
Owner:NEWMAN AARON CHARLES +1
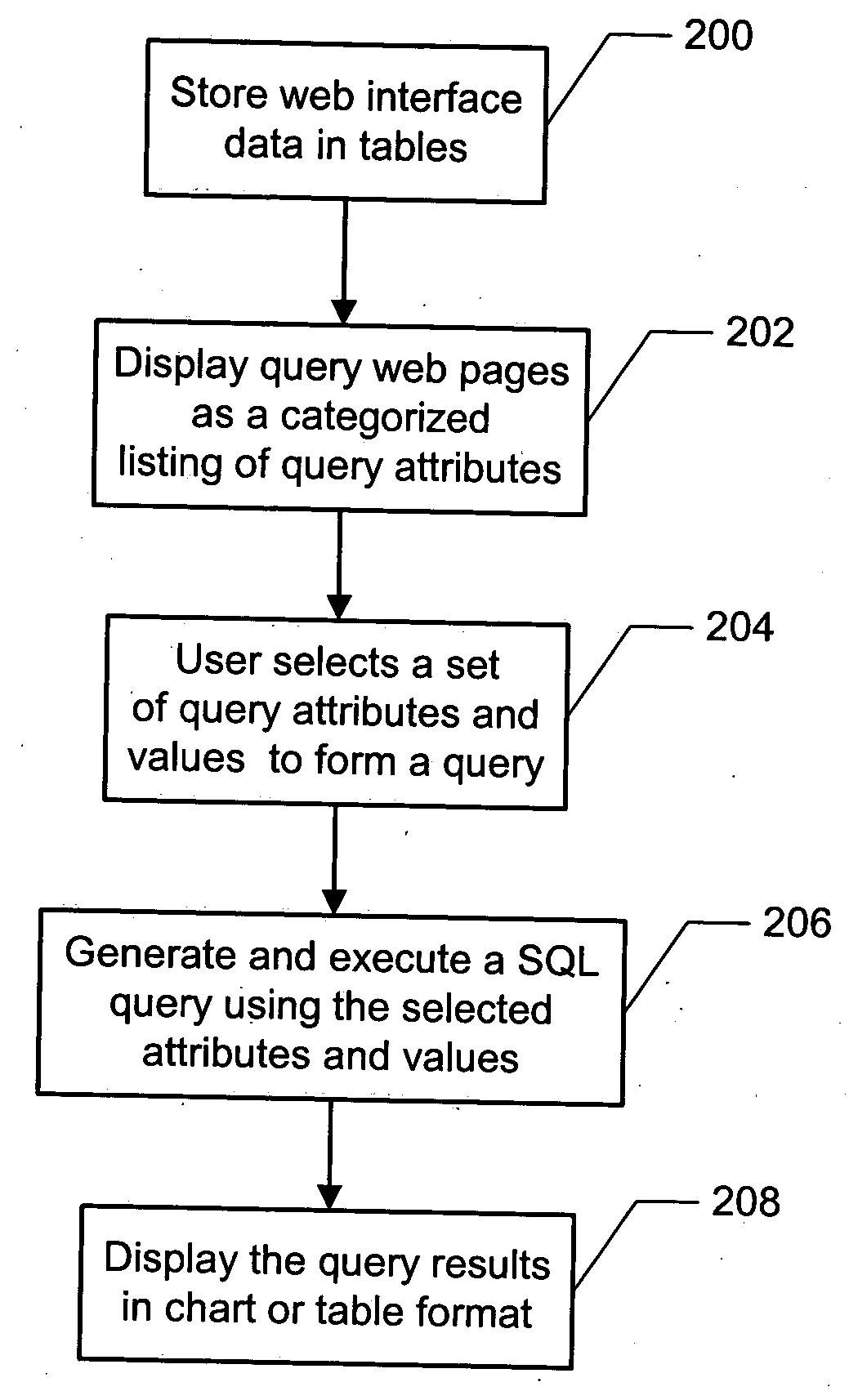
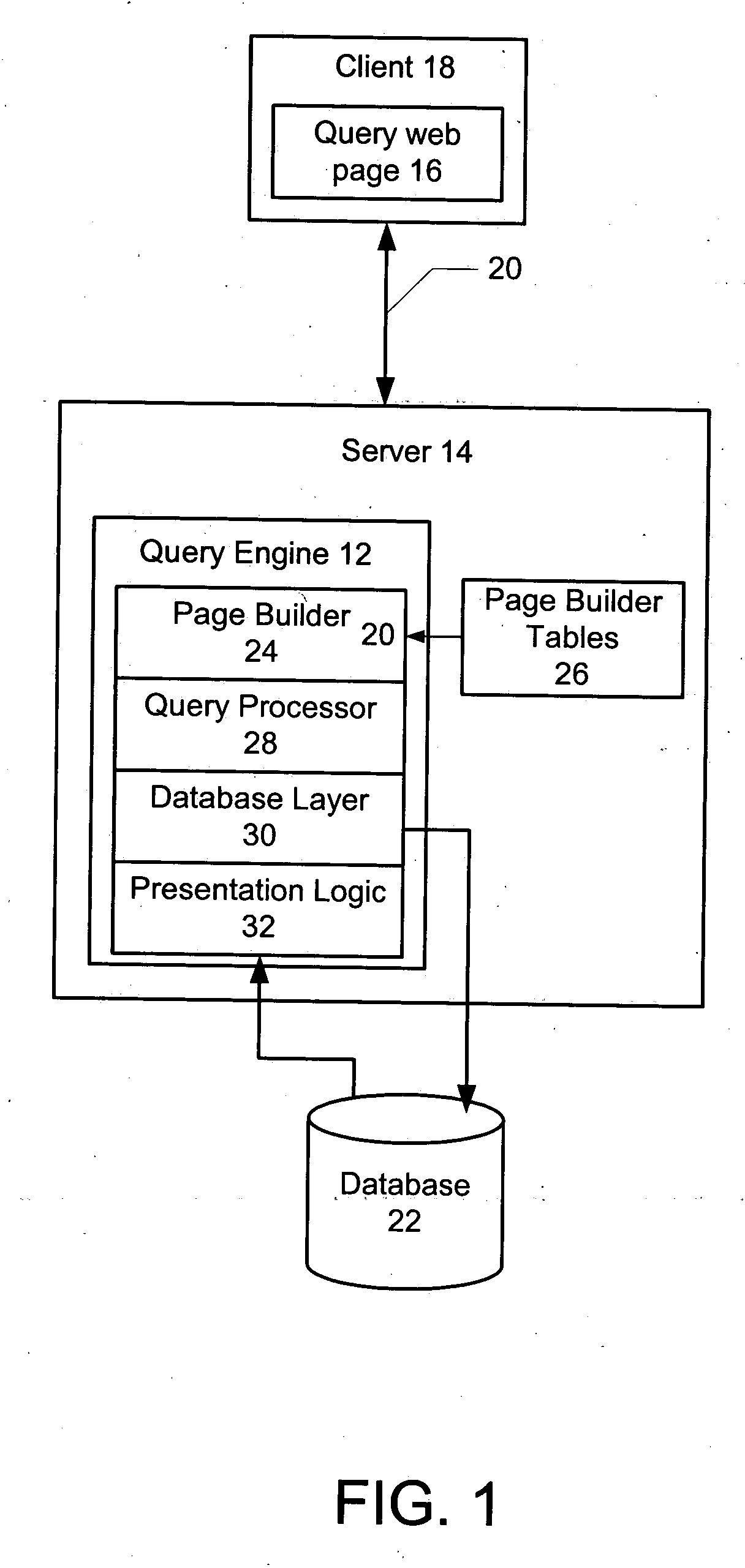
Dynamic graphical user interface and query logic SQL generator used for developing Web-based database applications
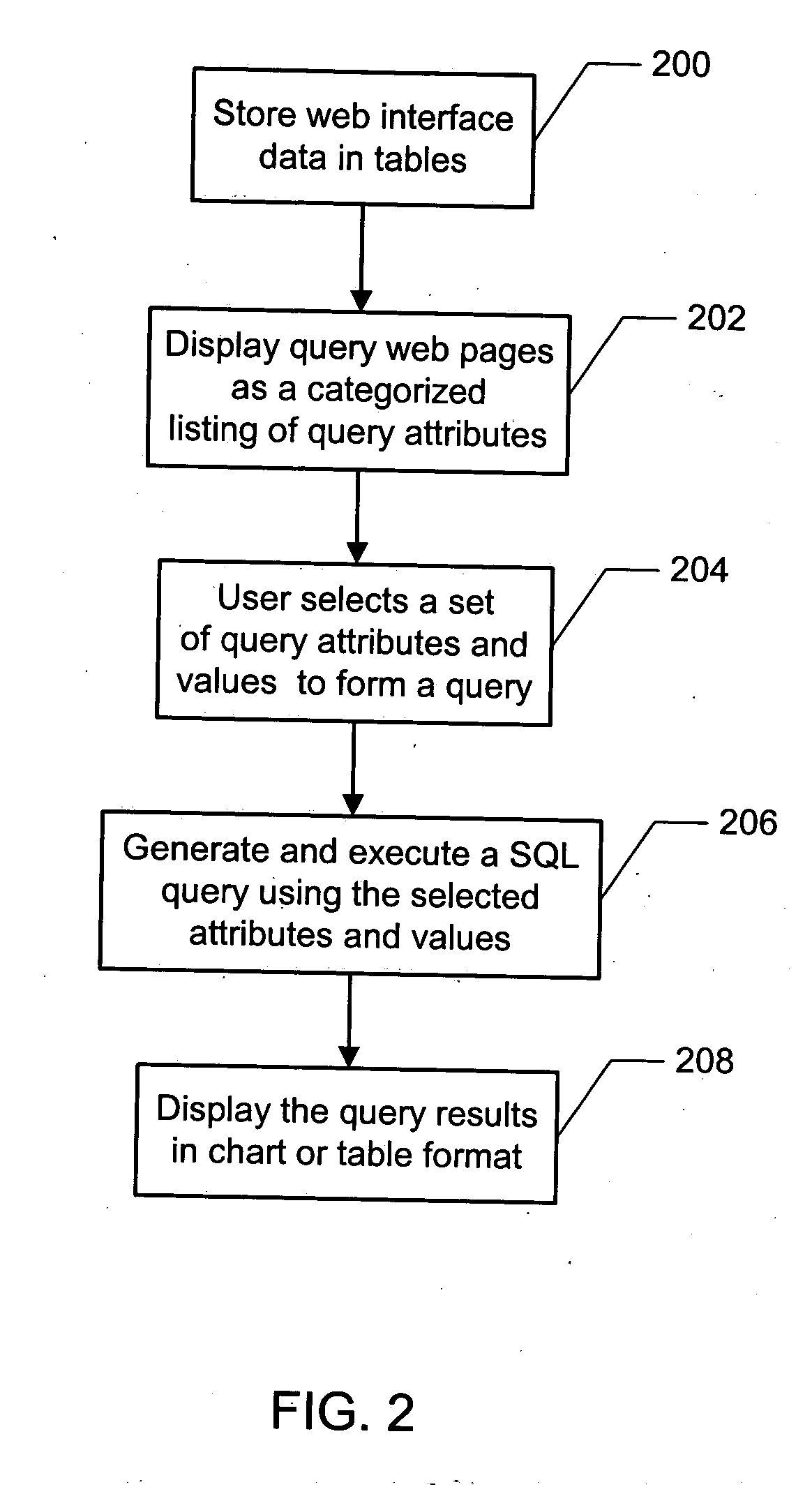
InactiveUS20050102284A1Improve scalabilityMinimal investmentDigital data information retrievalSpecial data processing applicationsGraphicsGraphical user interface
A method and system for dynamically generating database queries is disclosed. The method and system include storing web interface data, including query attributes for a database, in one more tables. The attributes are then retrieved from the tables and displayed in a graphical user interface web page for user selection. Based on the attributes selected by the user, a SQL query is dynamically generated. The method and system further include displaying results of the SQL query to the user in graphical format, thereby enabling dynamic generation of custom queries.
Owner:LSI CORPORATION
Database System Providing Encrypted Column Support for Applications
ActiveUS20080033960A1Data processing applicationsDigital data processing detailsApplication softwareQuery language
A database system providing encrypted column data support with decrypt default functionality. In a database system, a method providing automated encryption support for column data comprises steps of: defining Structured Query Language (SQL) extensions for creating and managing column encryption keys and database tables with encrypted column data; receiving an SQL statement specifying creation of a column encryption key; receiving an SQL statement specifying creation of a database table having particular column data encrypted with the column encryption key; receiving an SQL statement specifying a default value to be provided in response to requests for the column data without decrypt permission; in response to a subsequent database operation requesting encrypted column data from a user with decrypt permission, automatically decrypting the column data; and in response to a subsequent database operation requesting the encrypted column data from a user without decrypt permission, returning the default value.
Owner:SYBASE INC
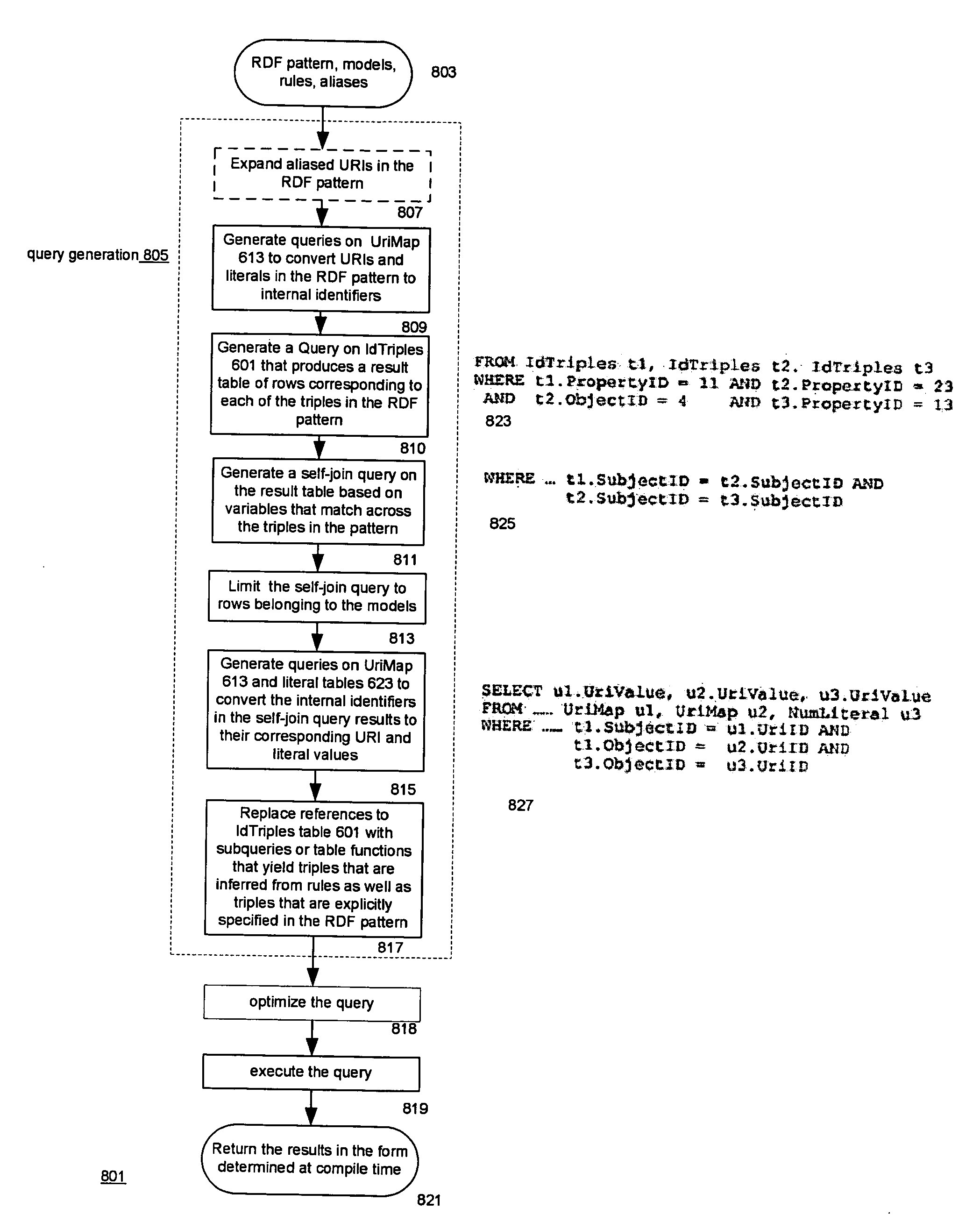
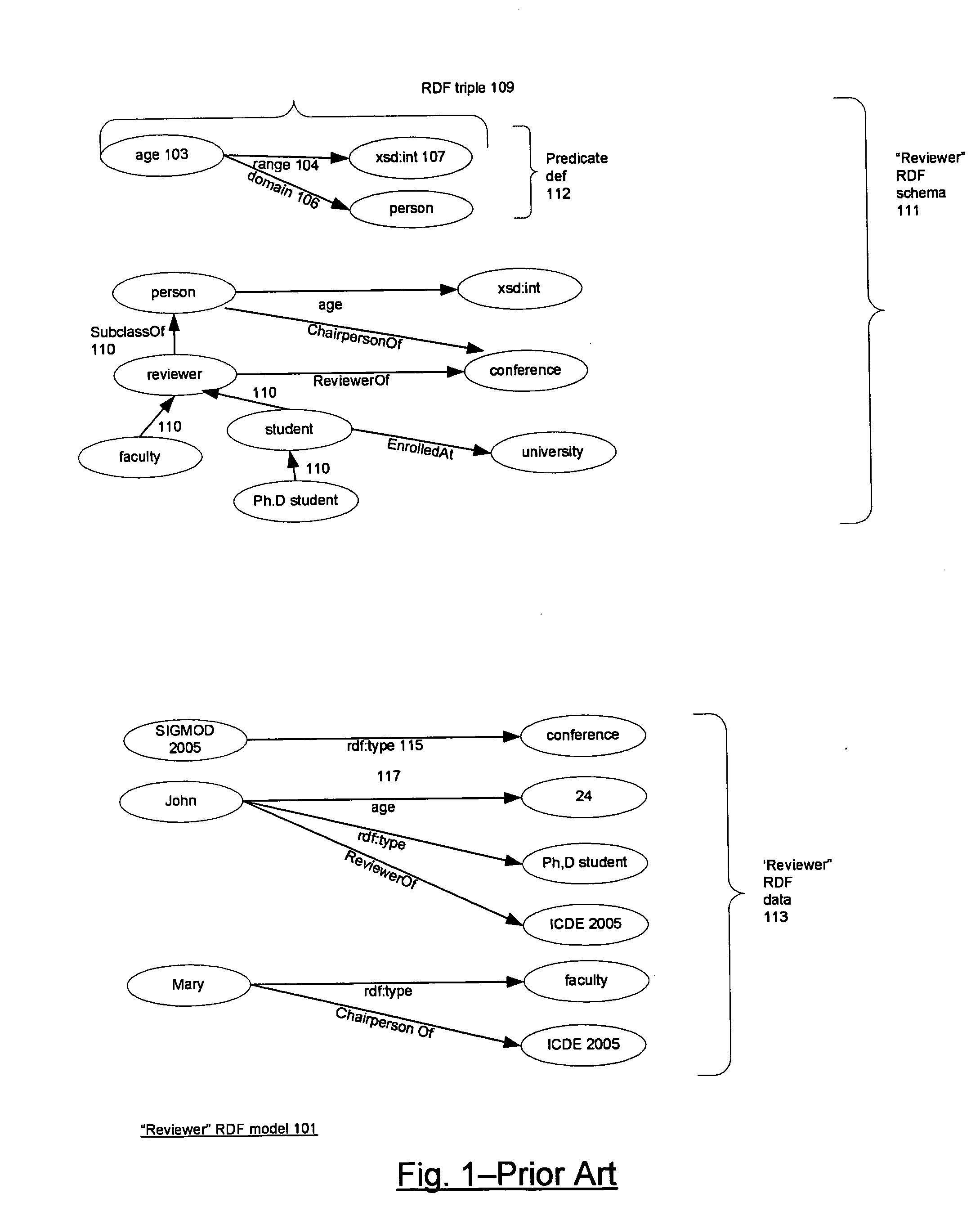
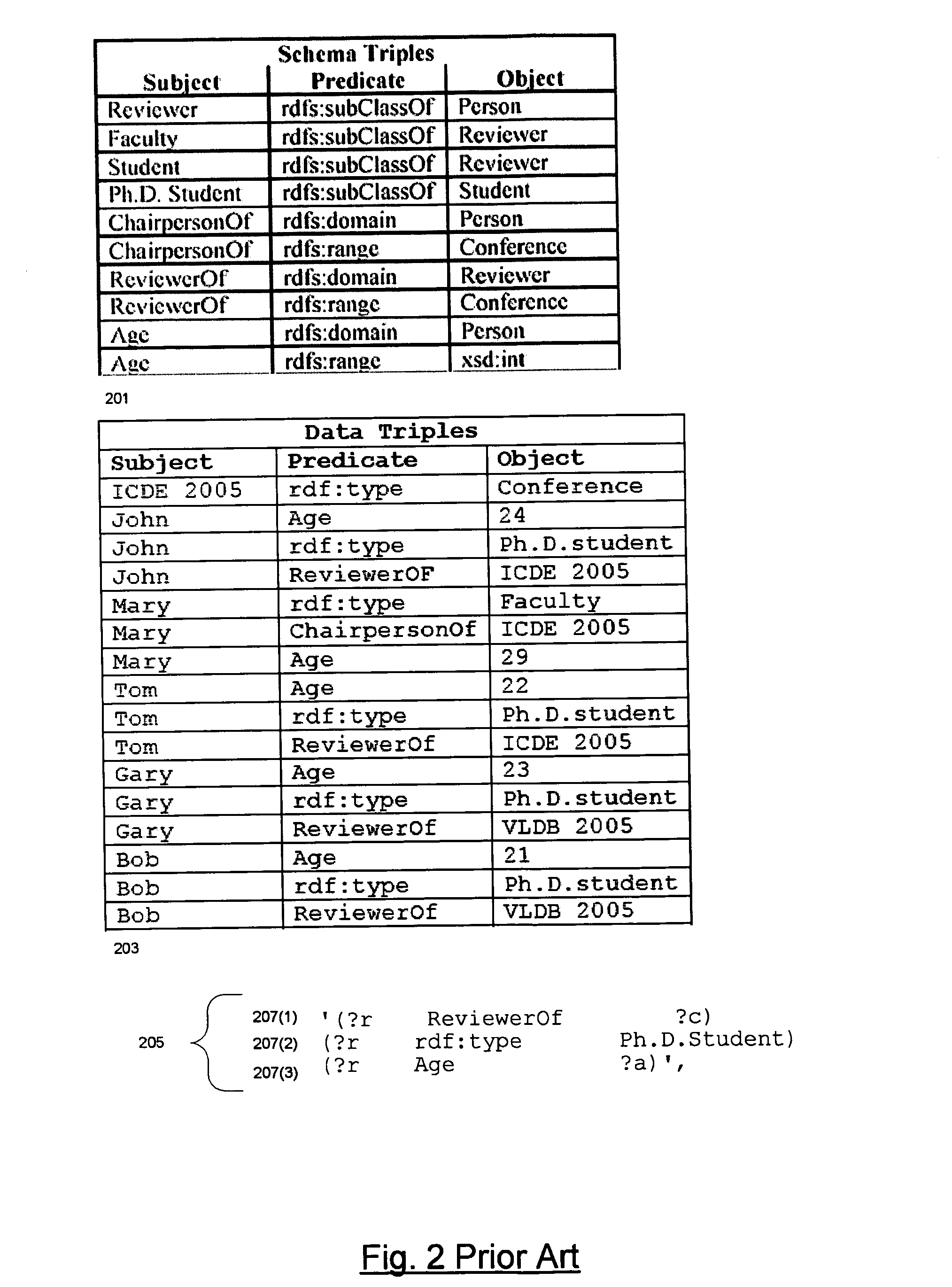
Rewriting table functions as SQL strings
ActiveUS20060235837A1Digital data information retrievalDigital data processing detailsSQLTheoretical computer science
The TABLE function mechanism available in a RDBMS is used to integrate RDF models into SQL queries. The table function invocation takes parameters including an RDF pattern, an RDF model, and an RDF rule base and returns result rows to the SQL query that contain RDF triples resulting from the application of the pattern to the triples of the model and the triples inferred by applying the rule base to the model. The RDBMS includes relational representations of the triples and the rules. Optimizations include indexes and materialized views of the representations of the triples, precomputed inferred triples, and a method associated with the TABLE function that rewrites the part of the SQL query that contains the TABLE function invocation as an equivalent SQL string. The latter technique is generally applicable to TABLE functions.
Owner:ORACLE INT CORP
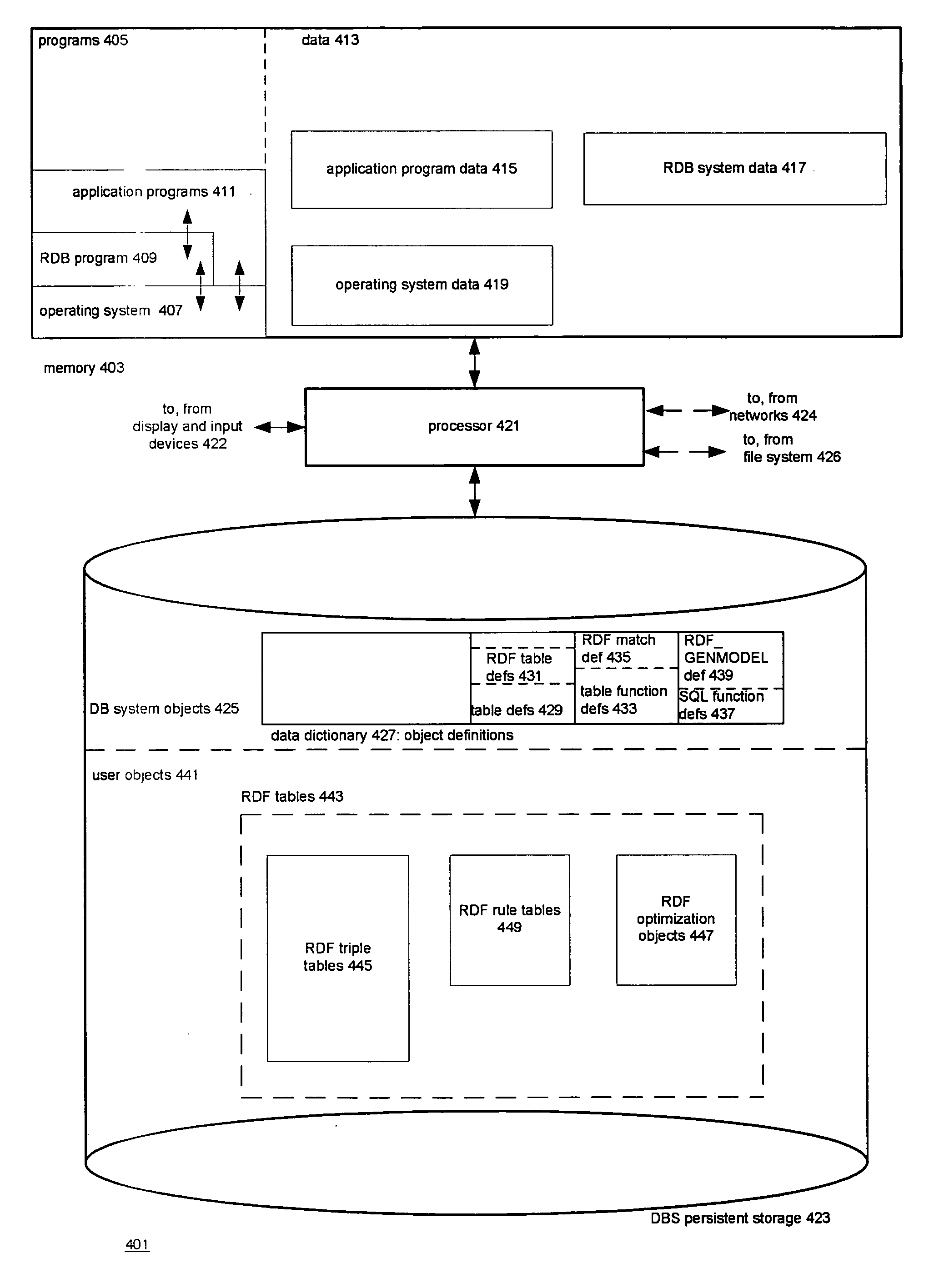
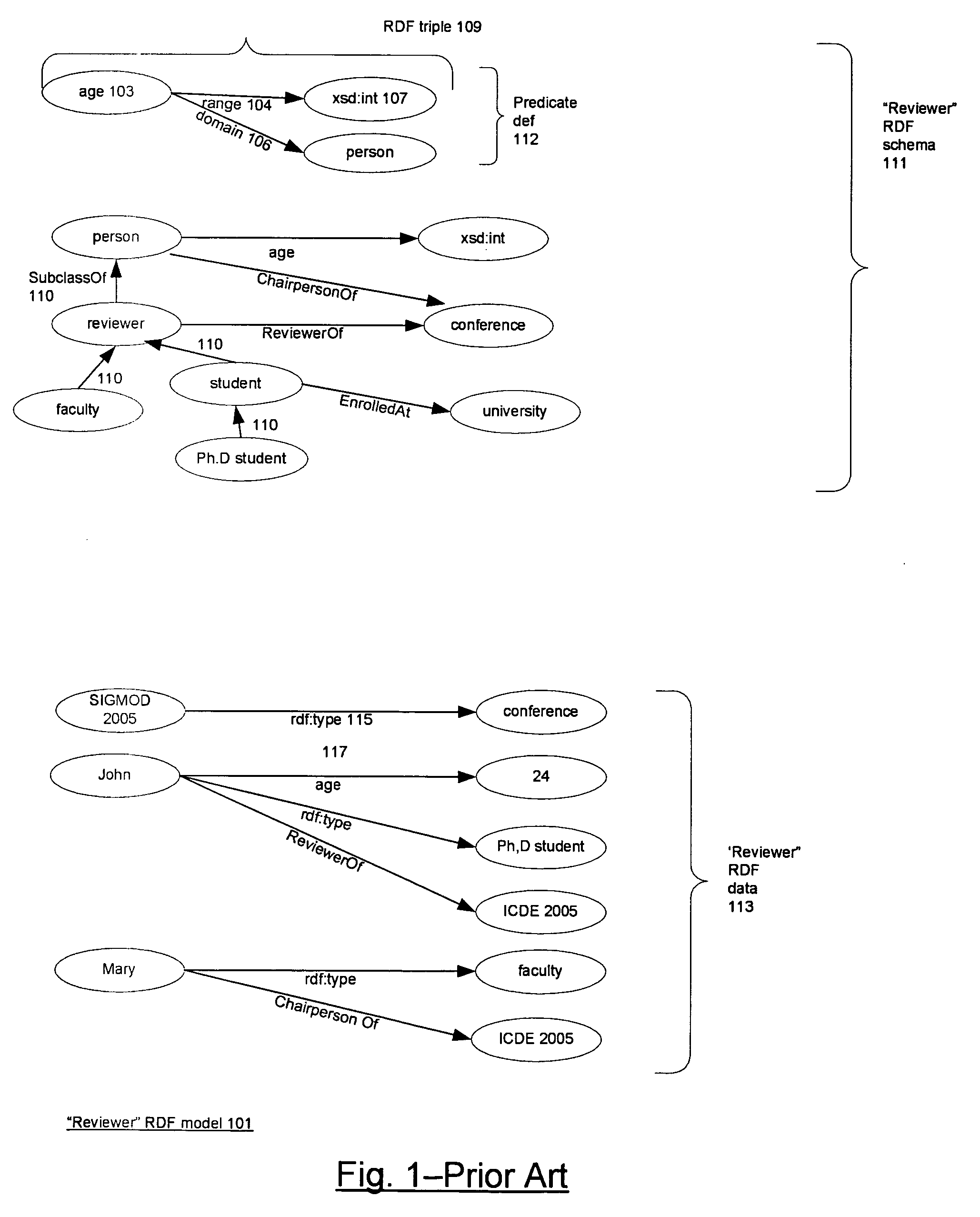
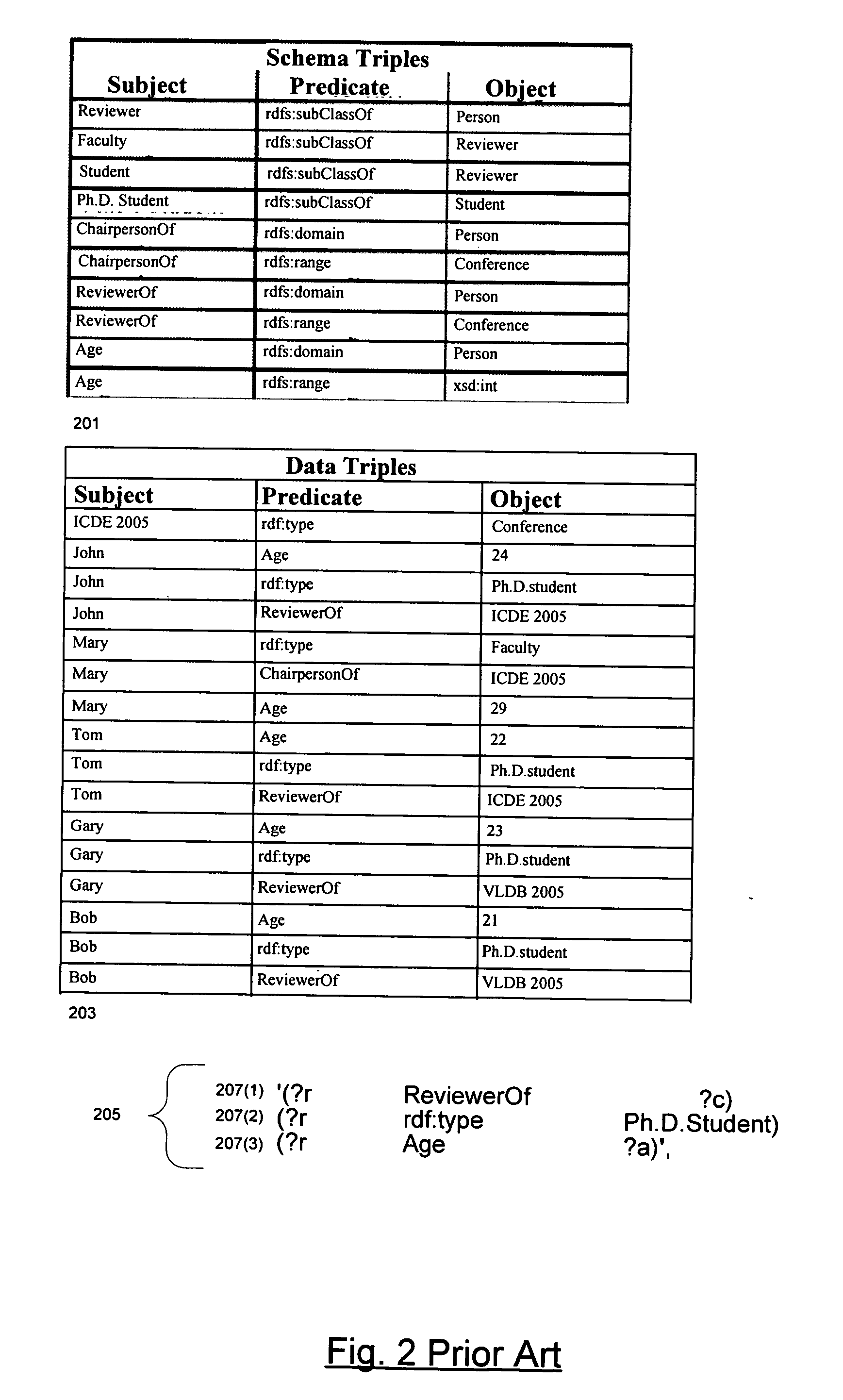
Integrating RDF data into a relational database system
ActiveUS20060235823A1Database management systemsSpecial data processing applicationsRDF SchemaRelational database
The TABLE function mechanism available in a RDBMS is used to integrate RDF models into SQL queries. The table function invocation takes parameters including an RDF pattern, an RDF model, and an RDF rule base and returns result rows to the SQL query that contain RDF triples resulting from the application of the pattern to the triples of the model and the triples inferred by applying the rule base to the model. The RDBMS includes relational representations of the triples and the rules. Optimizations include indexes and materialized views of the representations of the triples, precomputed inferred triples, and a method associated with the TABLE function that rewrites the part of the SQL query that contains the TABLE function invocation as an equivalent SQL string. The latter technique is generally applicable to TABLE functions.
Owner:ORACLE INT CORP
Set definition language for relational data
InactiveUS20050050030A1Facilitate query compositionEasy to buildRelational databasesSpecial data processing applicationsSyntaxSQL
The present invention relates to the usage pattern, commonly found in many software applications, of defining sets of objects based on object attributes. A specifically designed set definition language for defining sets, called SDL, is described and a software system that implements this language efficiently on top of a standard relational database management system (RDBMS) is presented. The unique features of the SDL language are the implicit constraints that are enforced on the relational data that belong to the objects. Unique to the SDL system is also the logical metadata of dimensions that enables the SDL system to enforce these constraints across relations. The SDL system utilizes several optimization techniques to enable efficient implementation on top of RDBMS. It is also shown how the SDL language and the SQL language can be merged with bidirectional inlining using syntactic gates. Query composition tools are also described that facilitate the creation of SDL expressions.
Owner:DECODE GENETICS EHF
Query interface to policy server
InactiveUS7580919B1Data processing applicationsDigital data information retrievalInformation resourcePrivate network
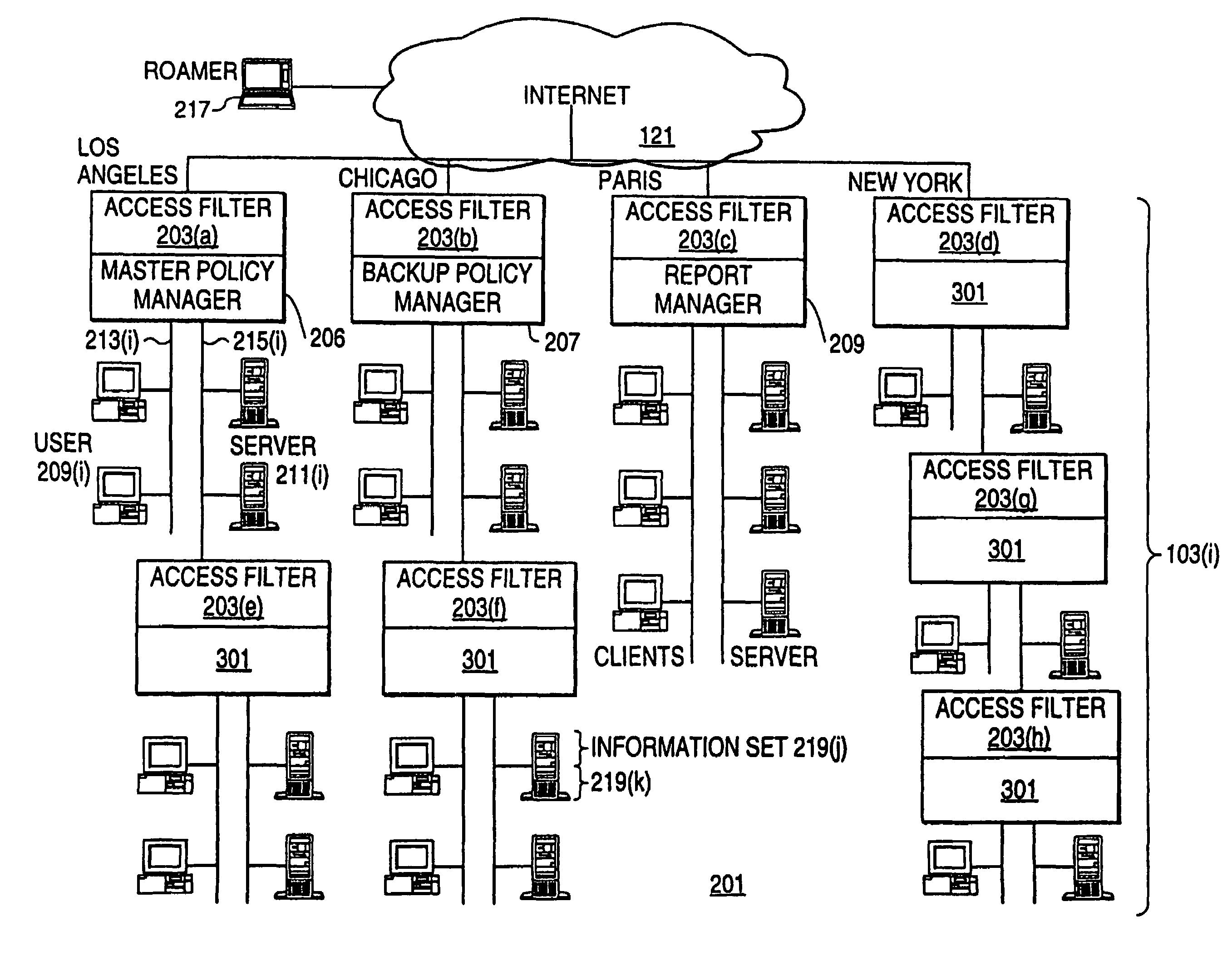
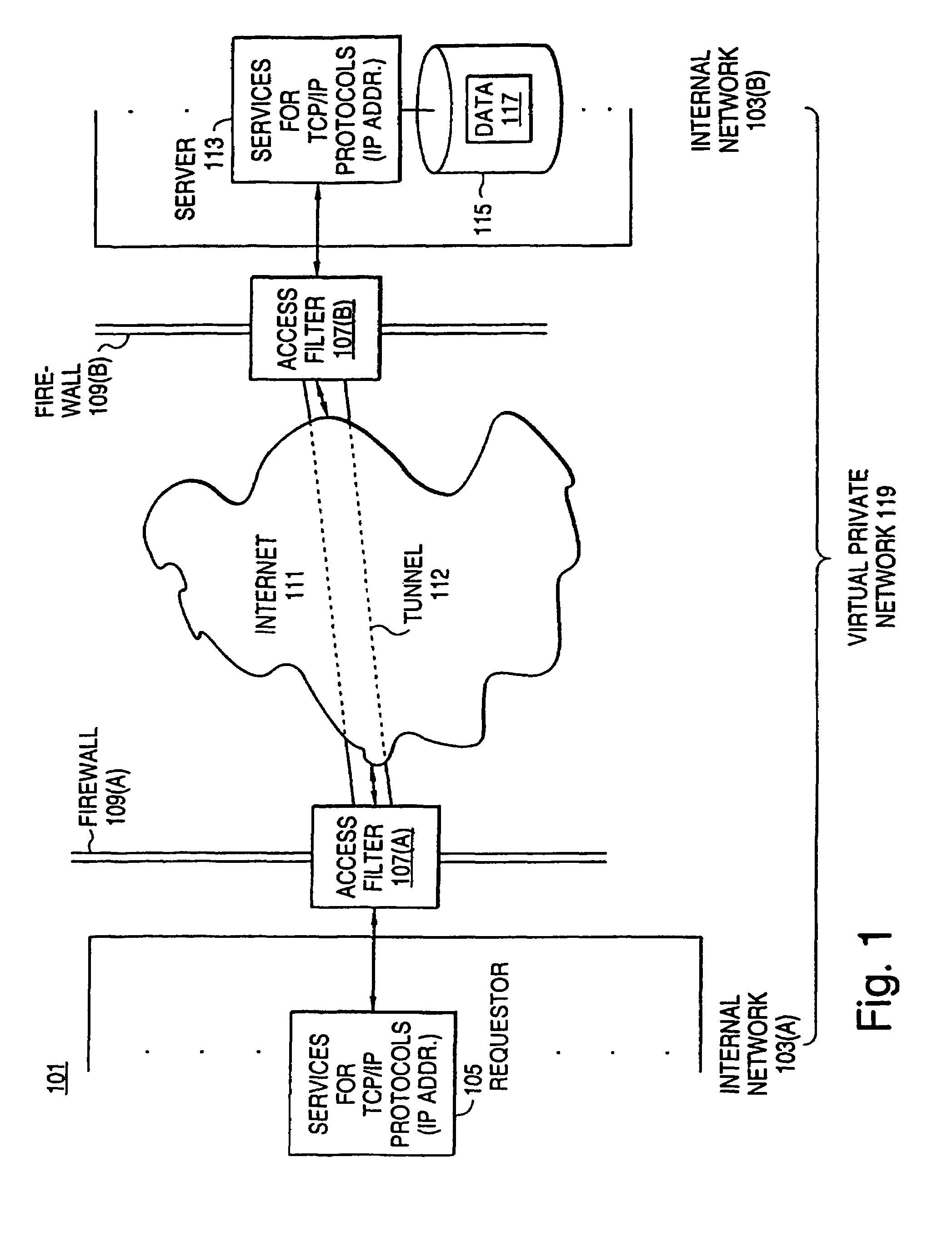
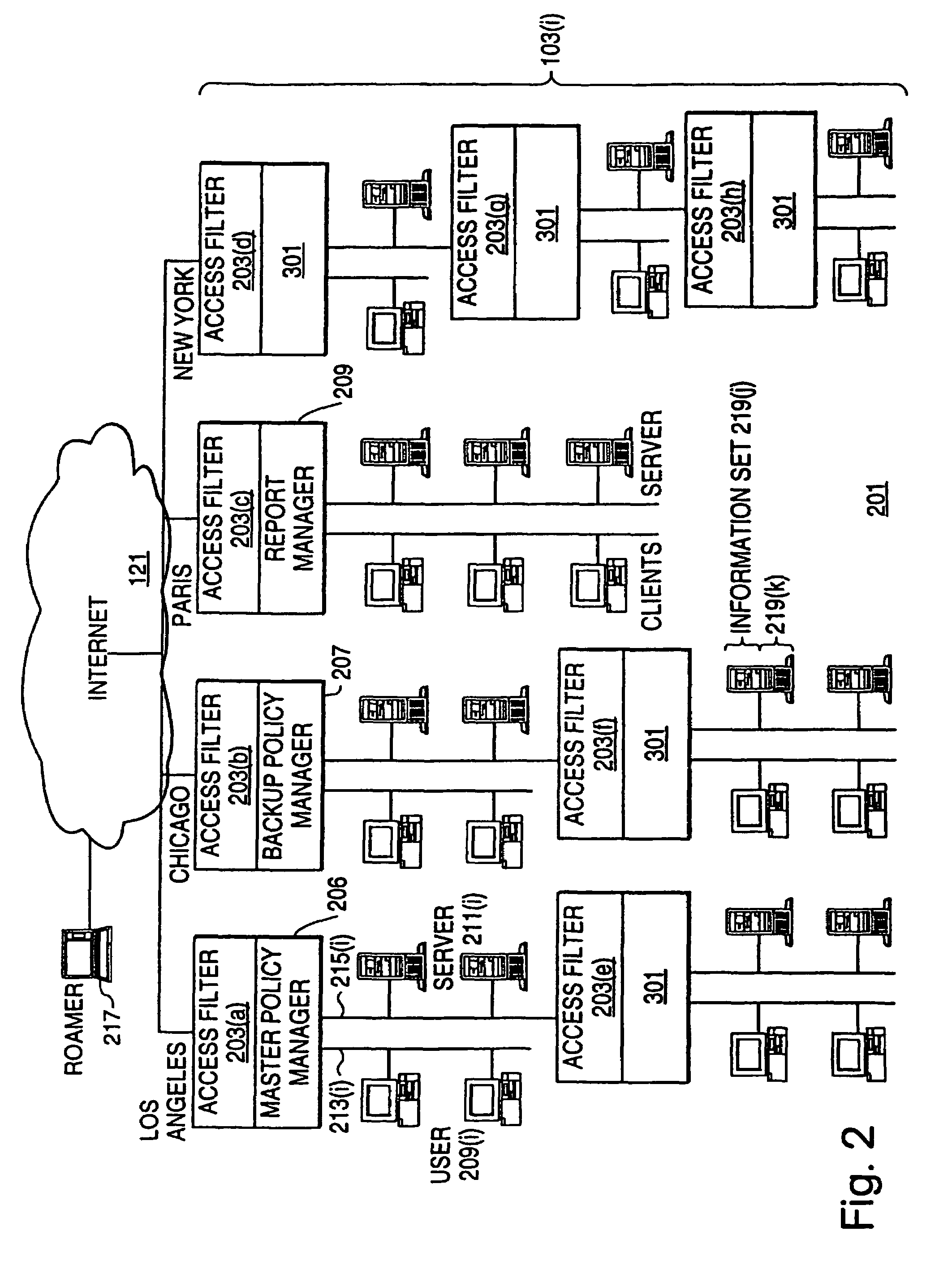
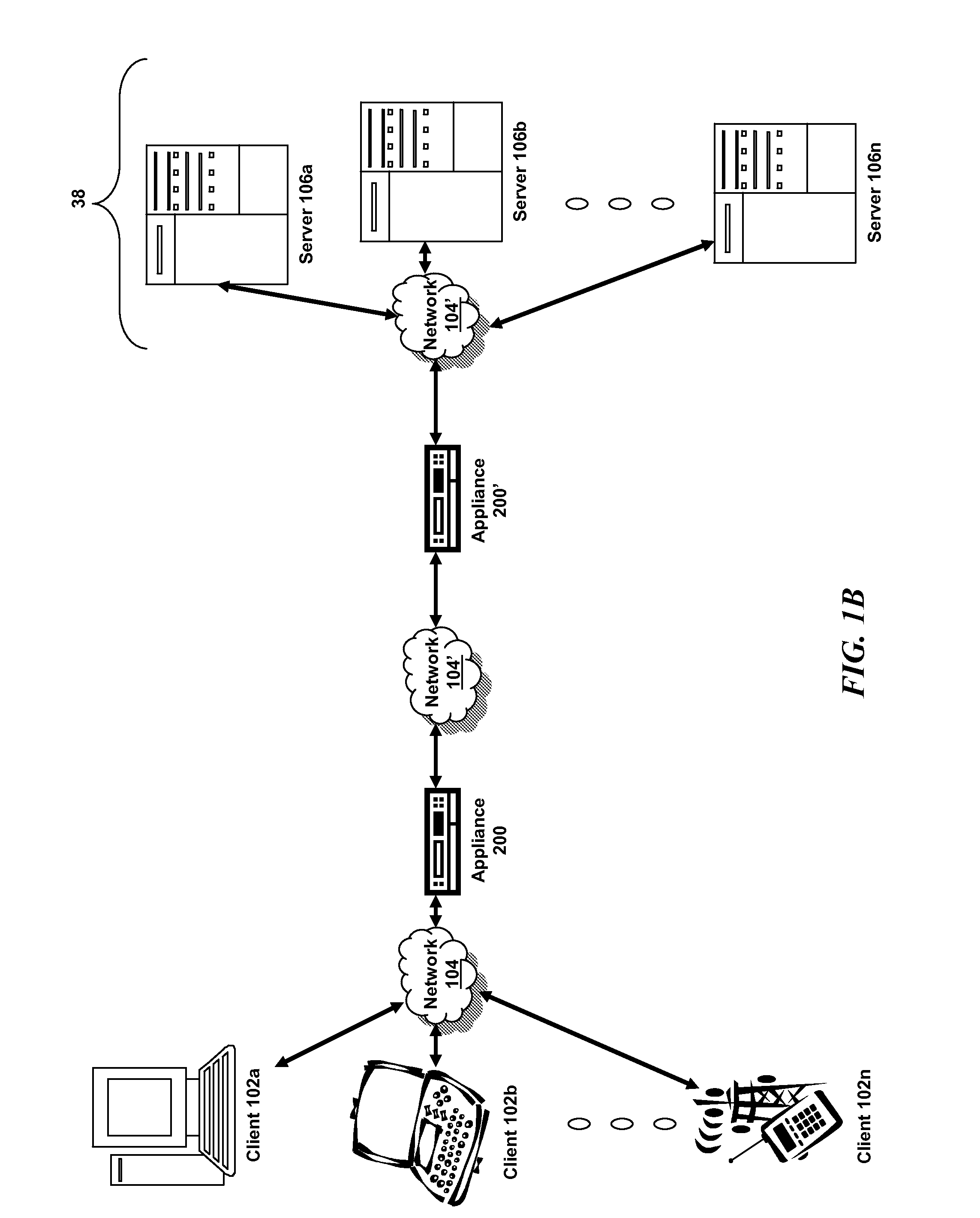
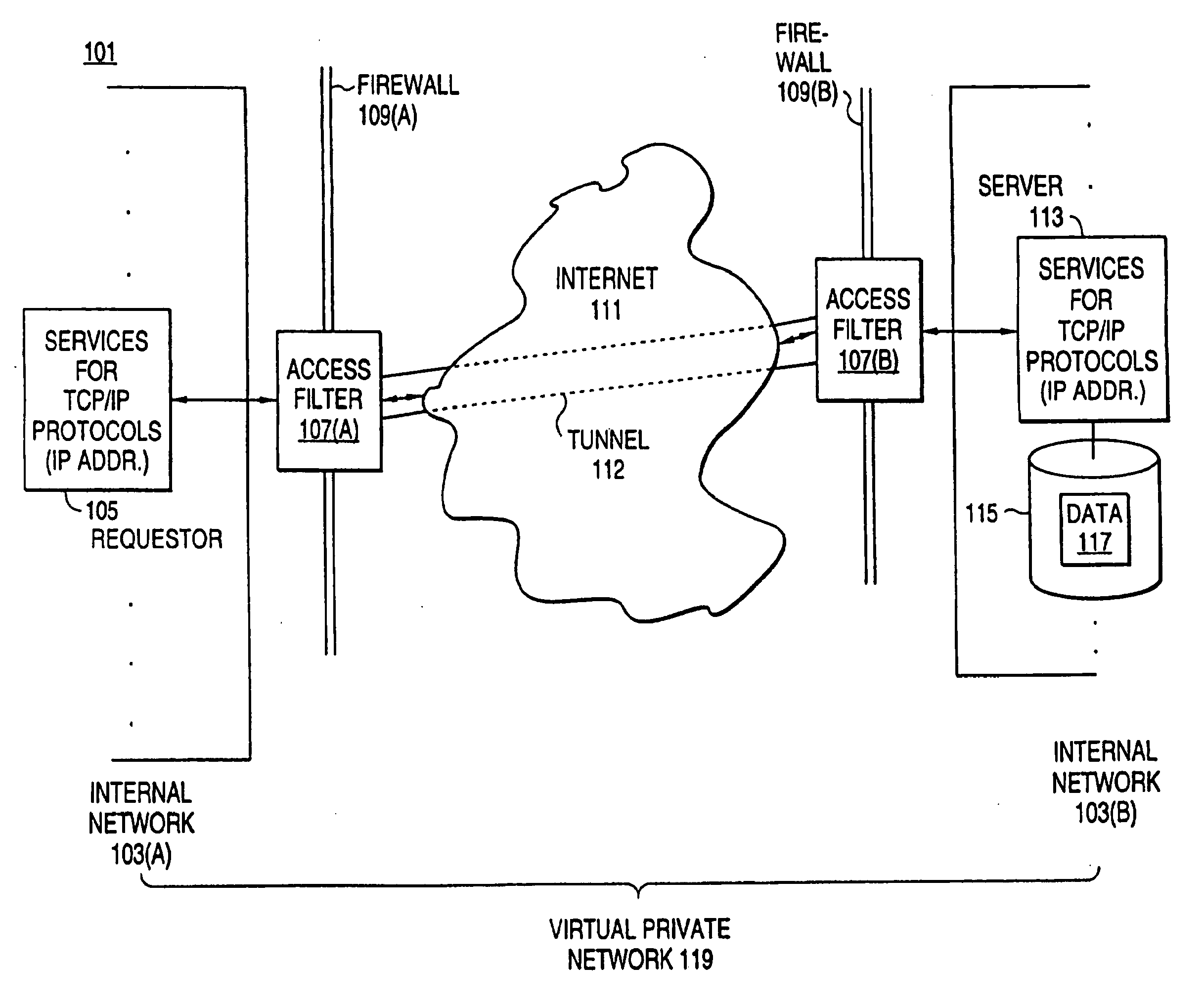
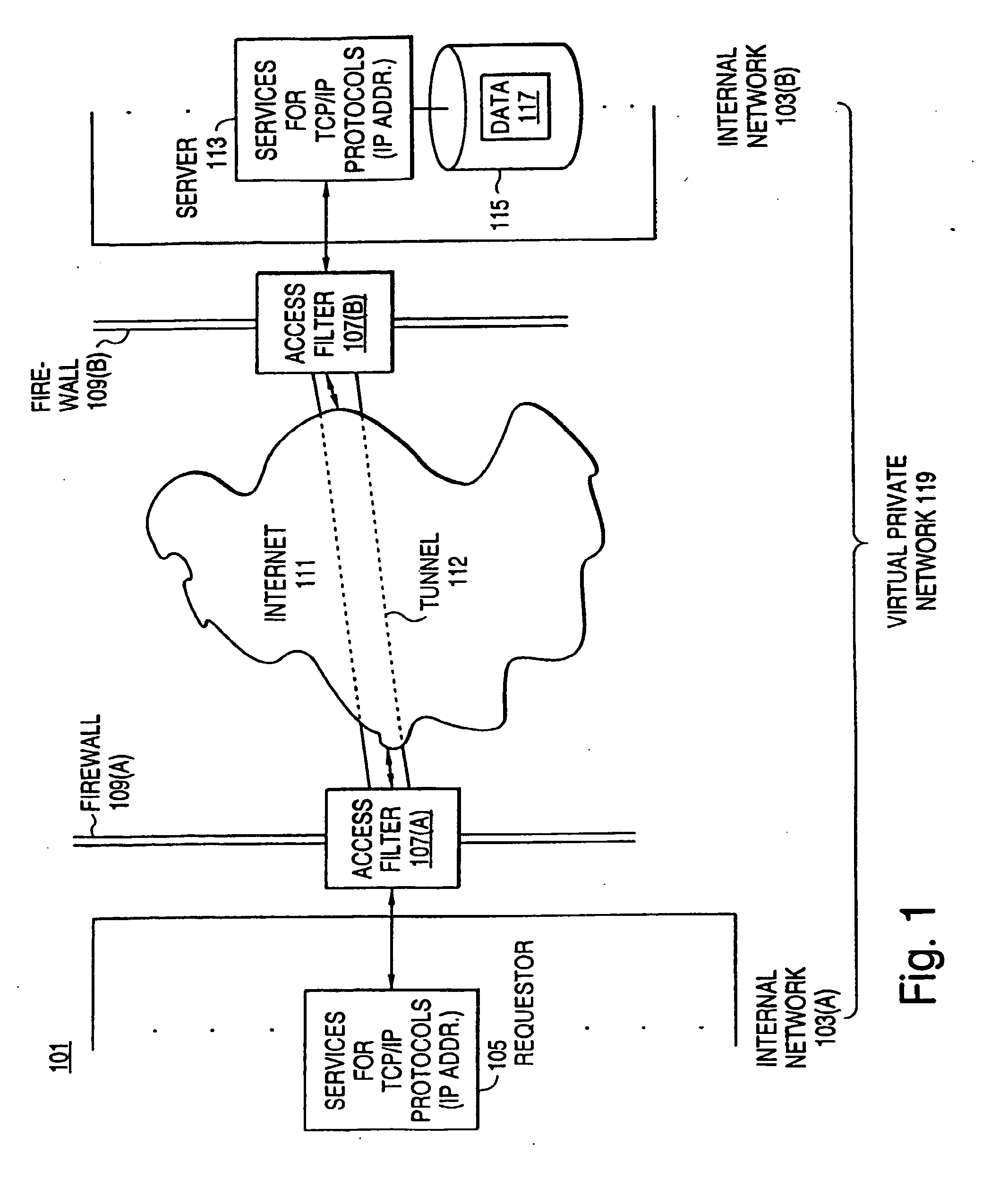
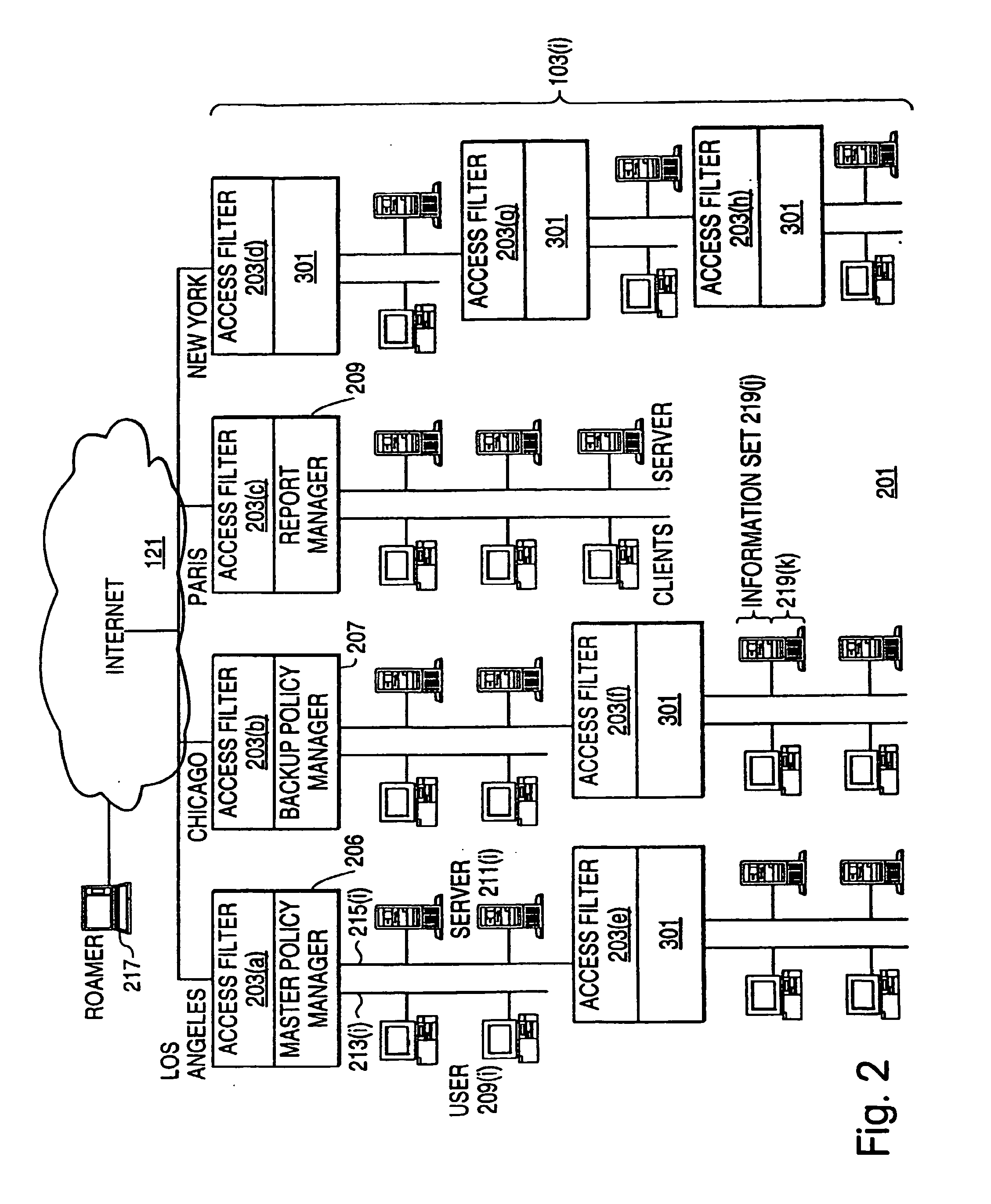
An exemplary scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network is disclosed. Each access filter uses a local copy of an access control data base (3845) to determine whether an access request is made by a user. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to access policies, which define access in terms of the user groups and information sets. The first access filter in the path performs the access check, encrypts and authenticates the request; the other access filters in the path do not repeat the access check. The interface used by applications to determine whether a user has access to an entity is now an SQL query. The policy server (3811) assembles the information needed for the response to the query from various information sources, including source external to the policy server.
Owner:MARSHMAN RES +1
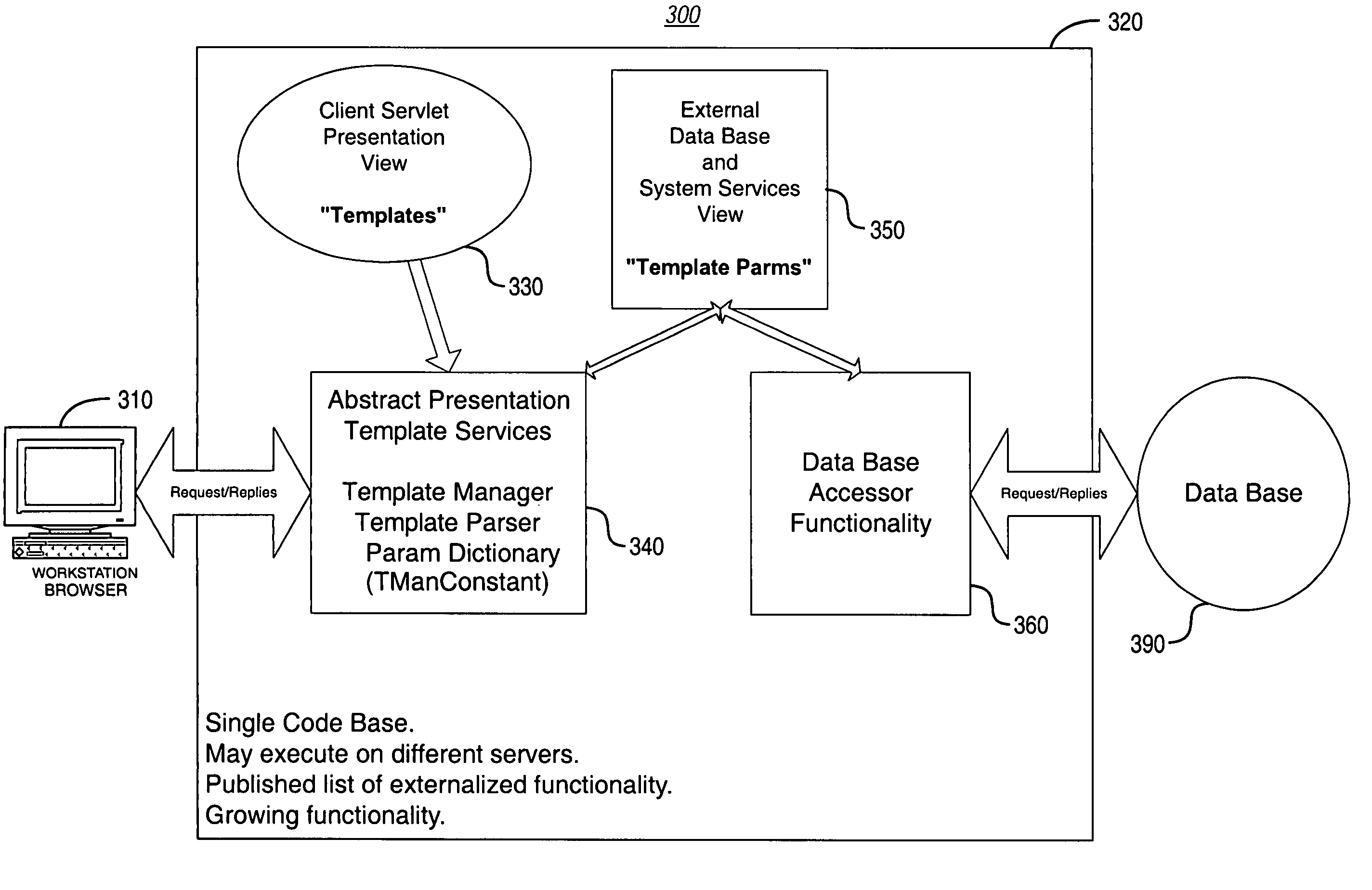
System and methodology for dynamic application environment employing runtime execution templates
InactiveUS7111231B1Digital data information retrievalSpecial data processing applicationsThe InternetApplication software
A dynamic application environment or system is described that includes a client, a run-time system, and a back-end database. The client comprises a workstation or desktop PC running browser software, such as Microsoft Internet Explorer or Netscape Navigator. The back-end database comprises a back-end (e.g., server-based) database system, such as an SQL-based database system. The run-time system includes a collection or repository module for storing “presentation templates,” a Template Services Module or engine, a Template Parameters Module, and a Database Accessor Module. The presentation templates are employed for presentation of the application to the user interface (at the client). At application run-time, the templates are provided to the Template Services Module, which includes a Template Manager and a Template Parser. These provide generic processing of the templates, which may be assembled to complete a finished product (i.e., run-time application). For instance, the Template Services Module knows how to load and parse a template and then look up its parameters, regardless of the application-specific details (e.g., user interface implementation) embodied by the template. In use, the system is deployed with presentation templates that represent the various client views of the target application, for the various platforms that the application is deployed to. In this manner, when new functionality needs to be added to the system, it may simply be added by expanding the run-time library portion of the system.
Owner:INTELLISYNC CORP
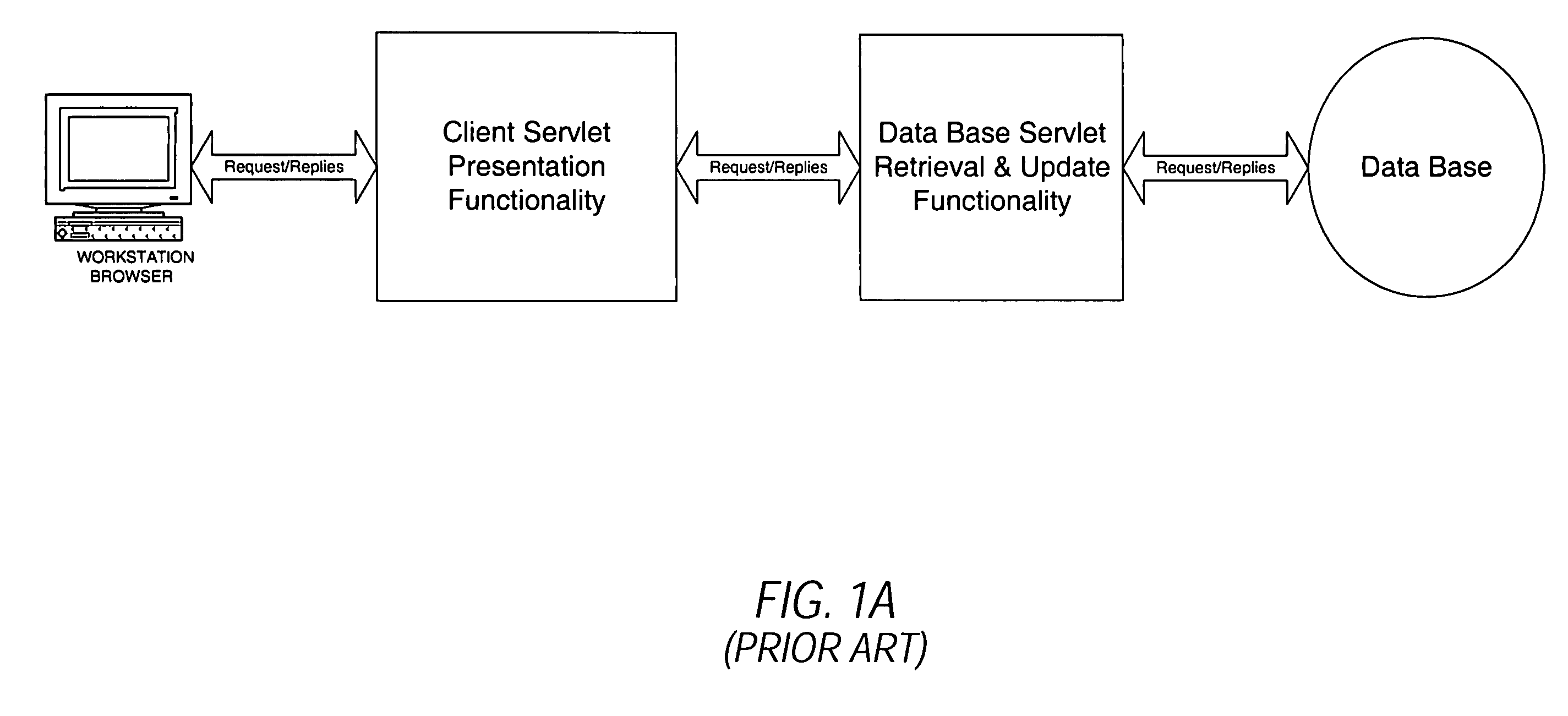
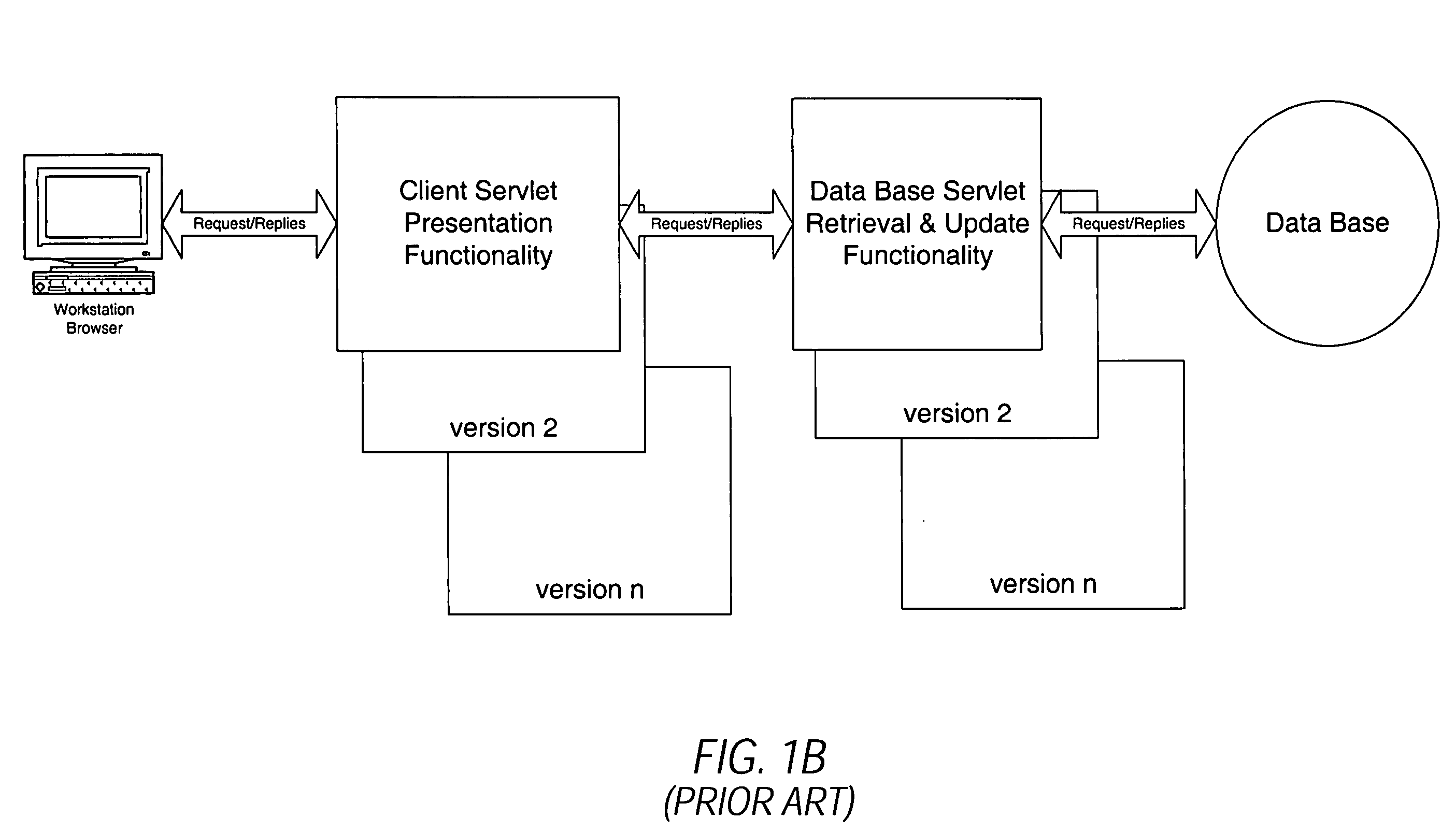
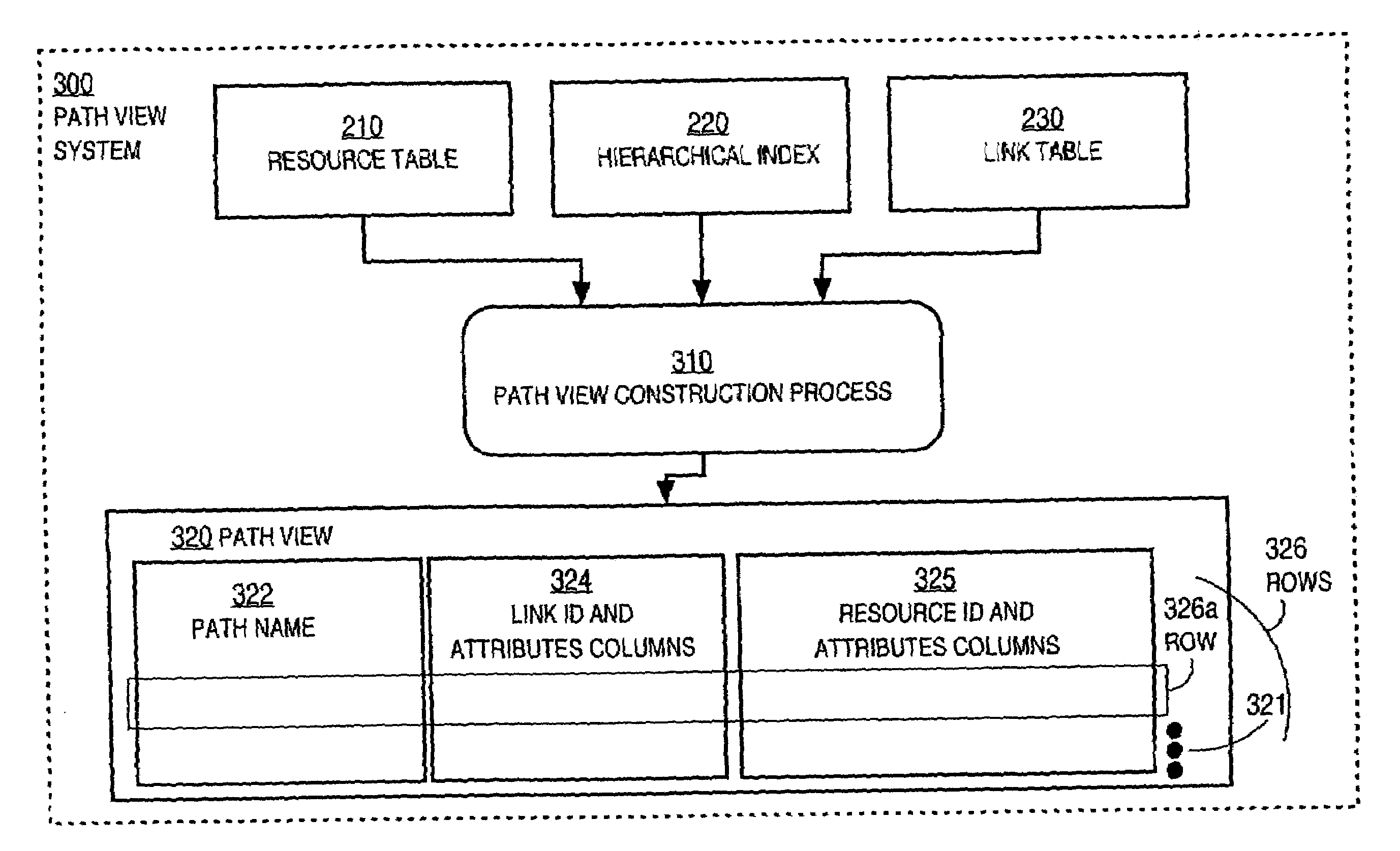
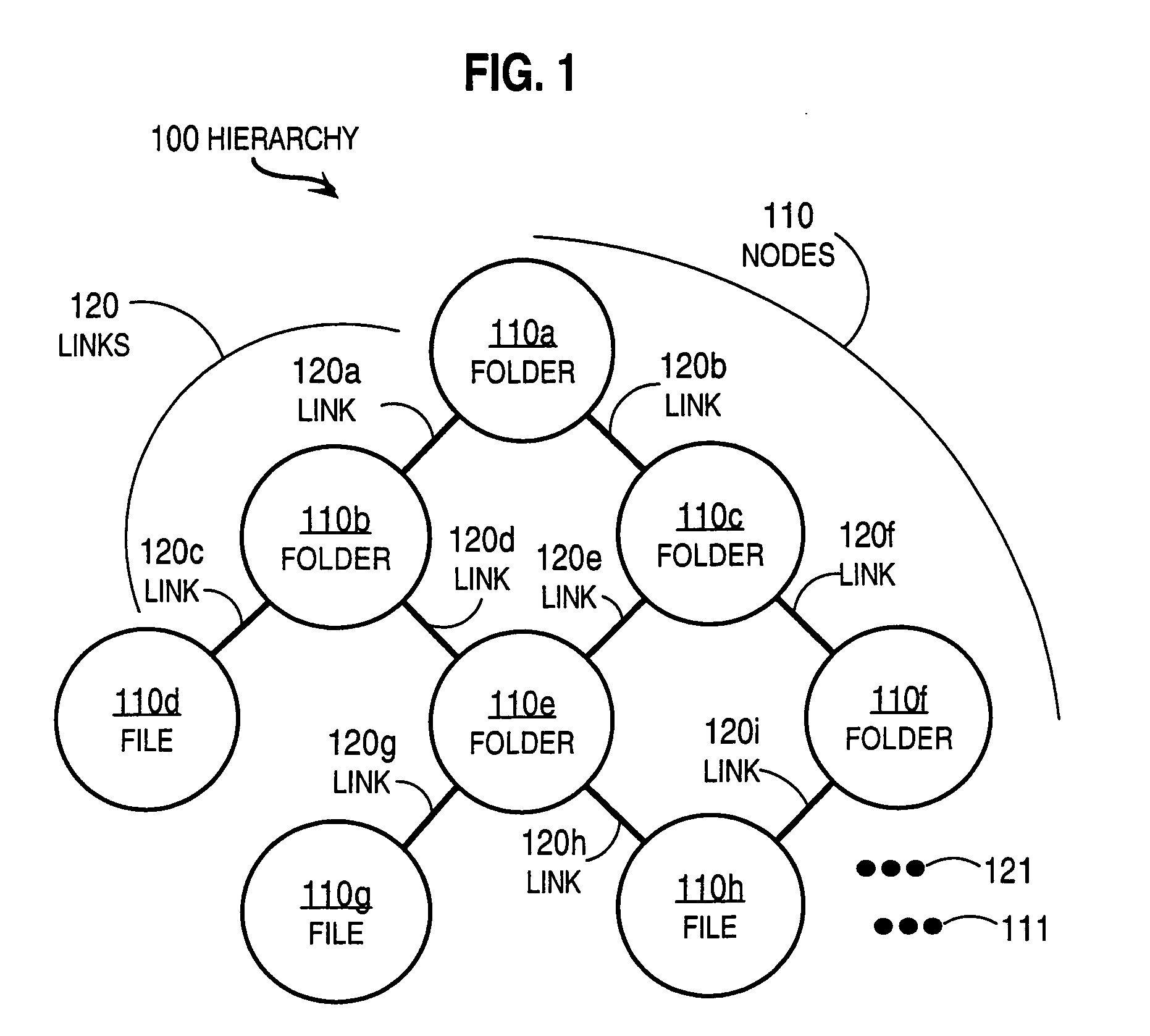
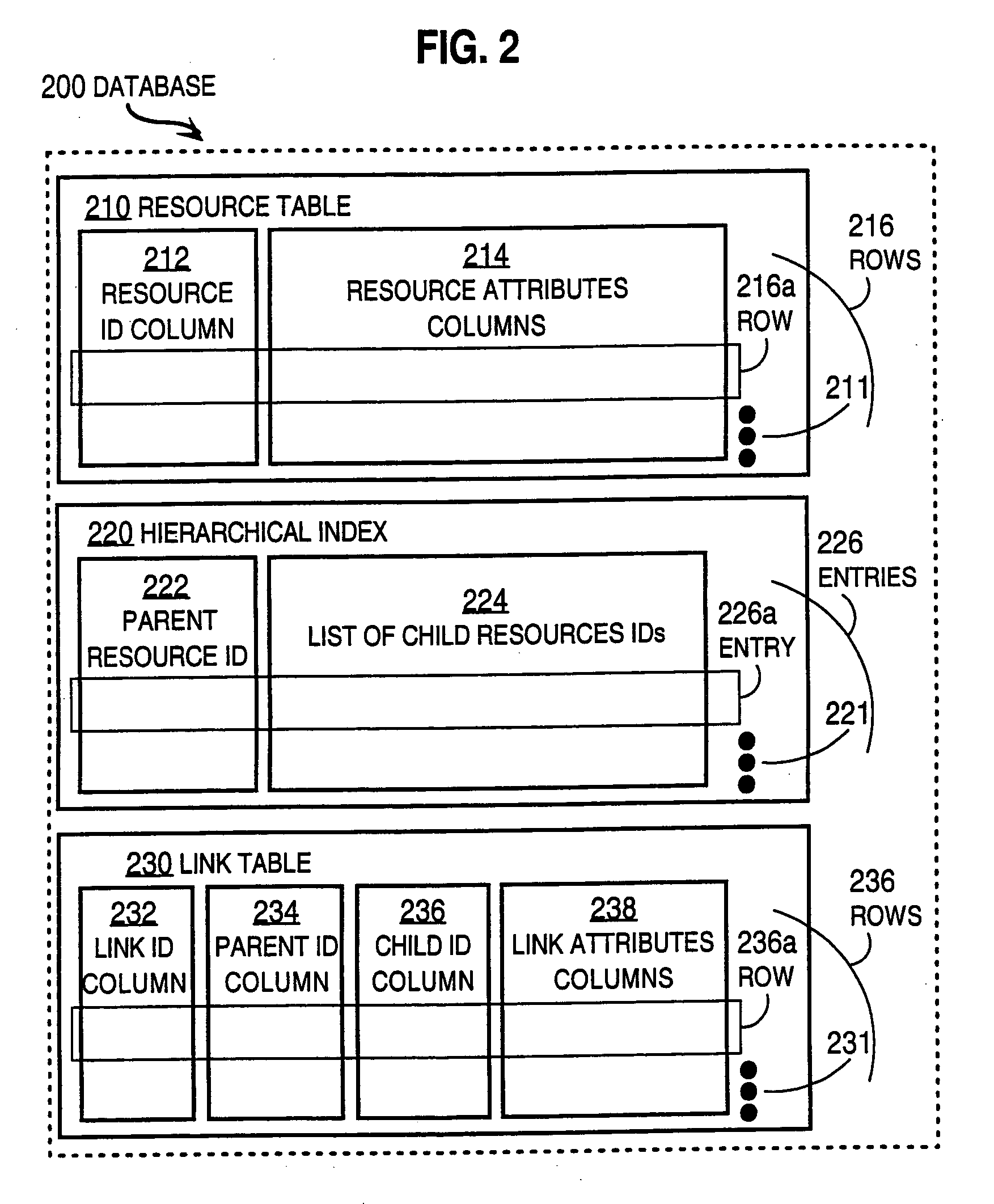
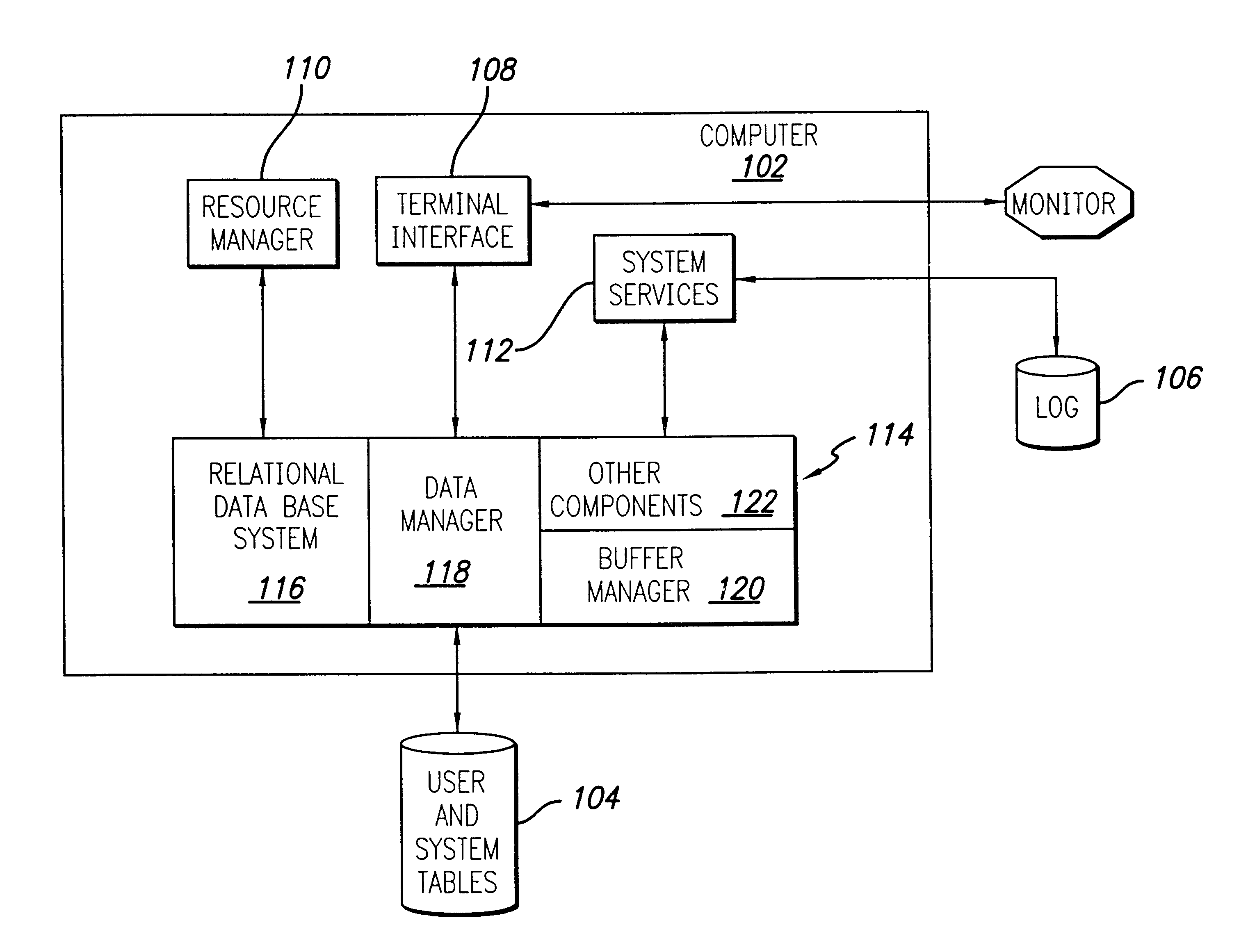
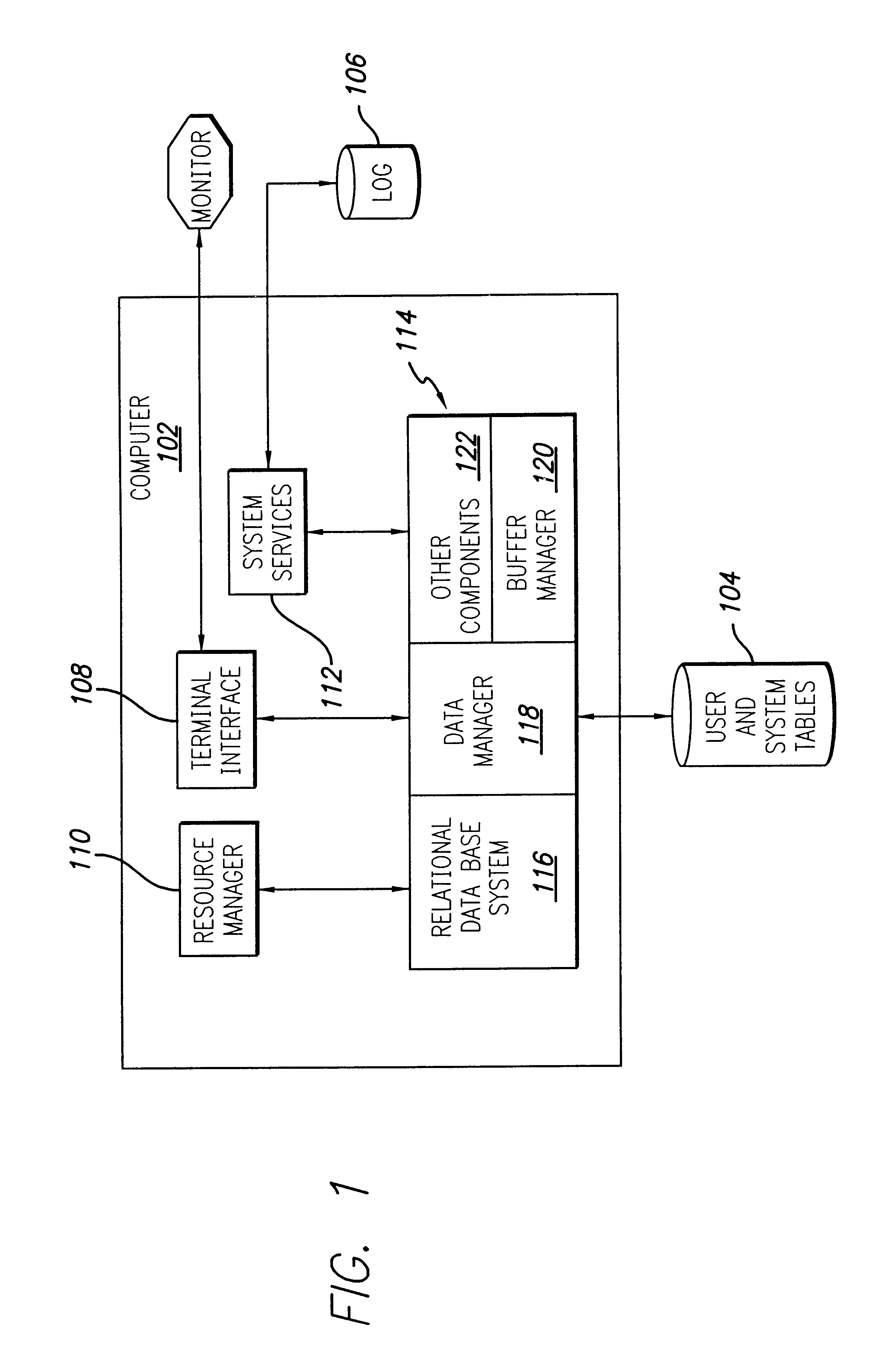
Techniques for managing hierarchical data with link attributes in a relational database
Techniques for managing hierarchical data include managing a link table in a relational database. The hierarchical data includes data about a hierarchy of nodes related by multiple links. The link table includes first information, second information and link information, for each link. First information indicates a first node in the hierarchical data. Second information indicates a second node that is associated with the first node by the link. Link information indicates values for link attributes of the link between the first node and the second node, and does not indicate a value for any attribute of the first node alone or any attribute of the second node alone. The techniques support directing a single SQL statement to a path database object, constructed based on the link table, in order to obtain paths that satisfy a search on link attributes.
Owner:ORACLE INT CORP
Improving performance of database queries
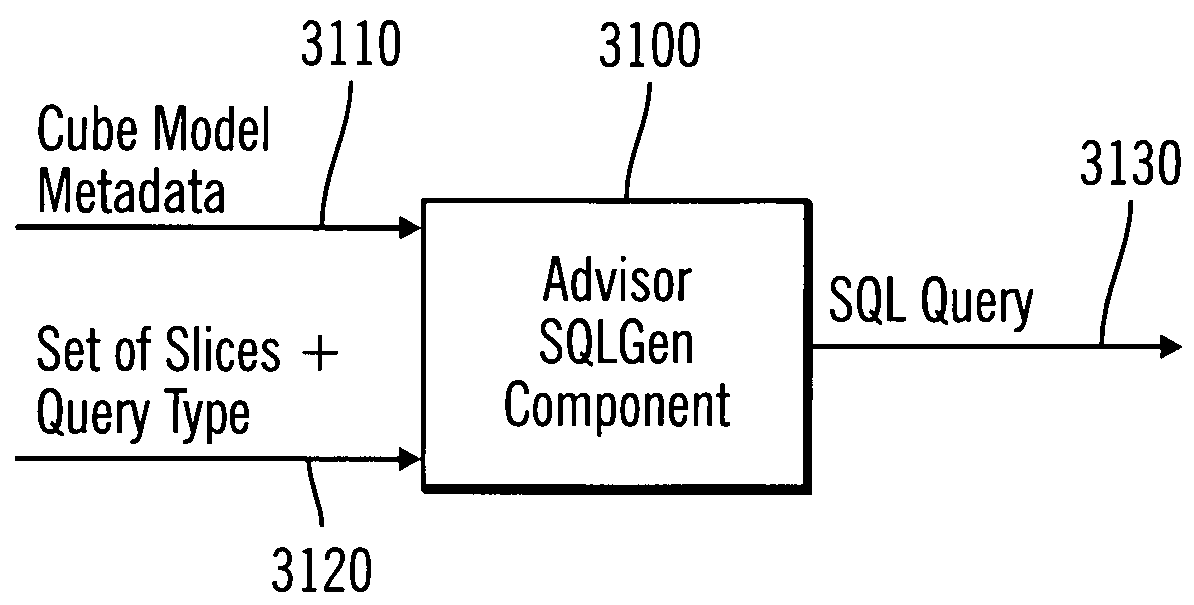
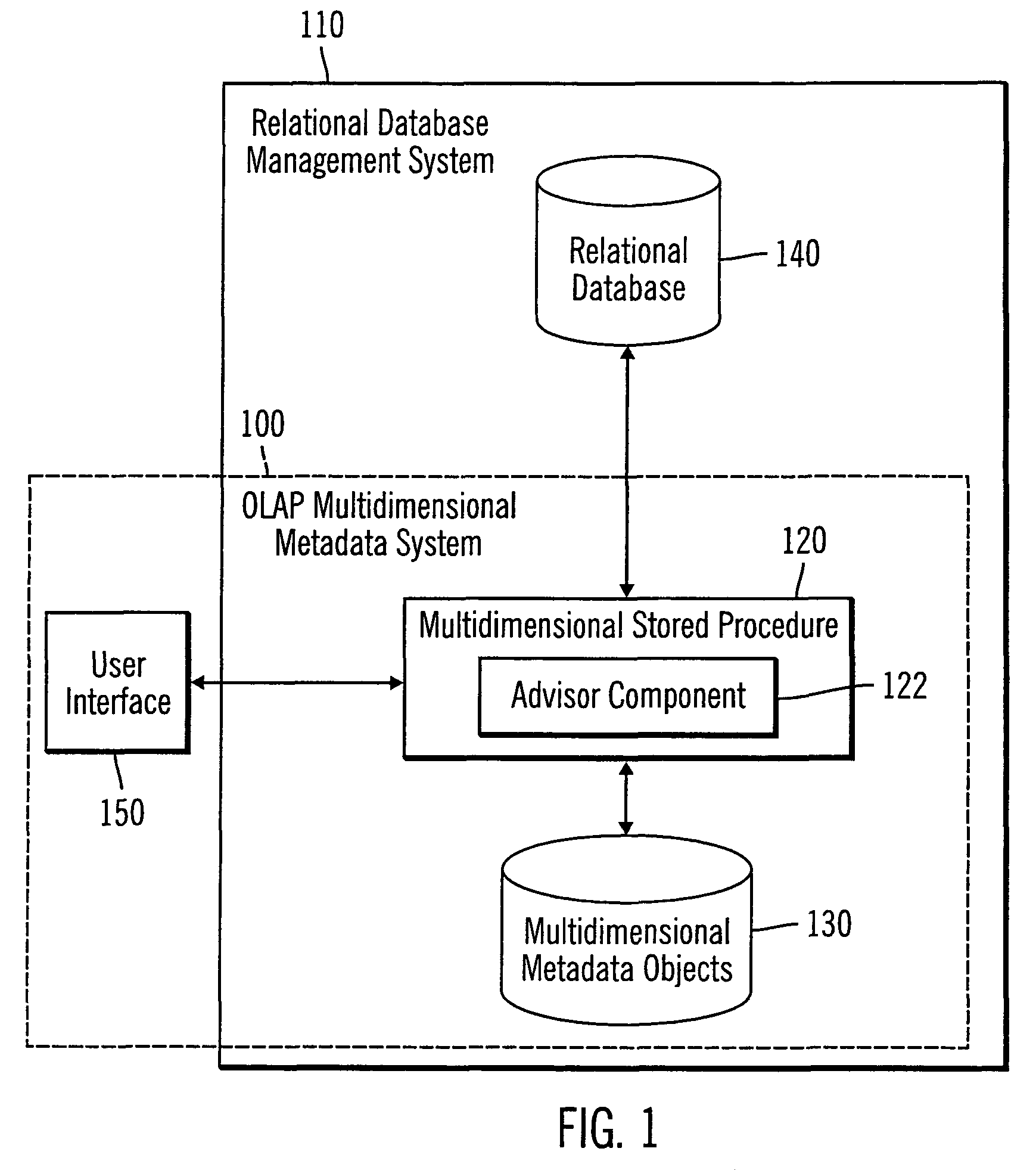
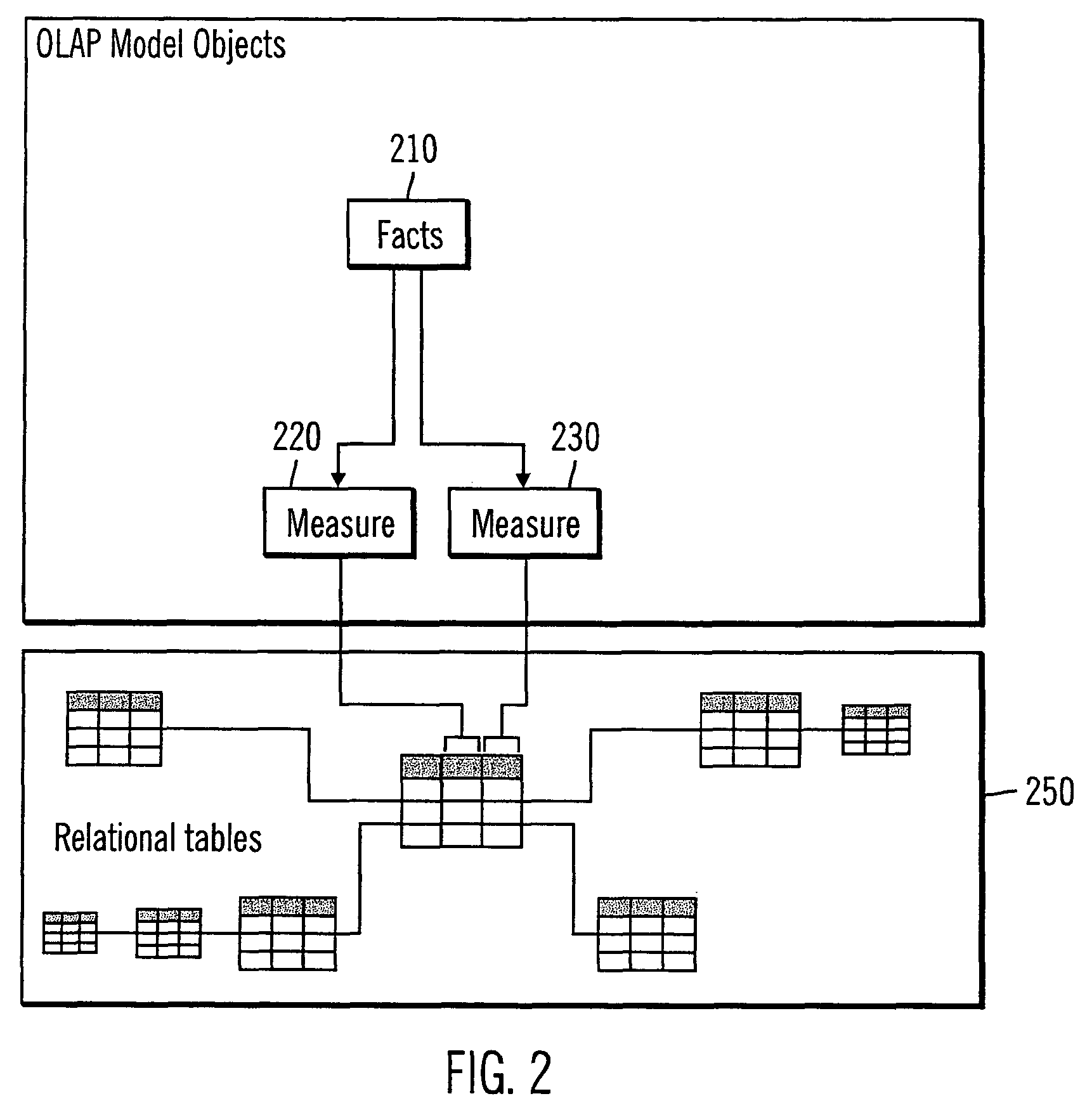
InactiveUS7895191B2Improve performanceDigital data processing detailsMulti-dimensional databasesSQLMetadata
A system, method, and program for improving the performance for SQL queries. Multidimensional metadata associated with a cube model metadata object is obtained. One or more summary tables to be built are automatically identified based on the obtained multidimensional metadata. One or more indexes to create are automatically identified based on the obtained multidimensional metadata.
Owner:IBM CORP
Methods and apparatus for audio data analysis and data mining using speech recognition
ActiveUS7133828B2Simplify the search processDigital data information retrievalAutomatic call-answering/message-recording/conversation-recordingSpoken languageSpeech identification
The present invention provides an audio analysis intelligence tool that provides ad-hoc search capabilities using spoken words as an organized data form. The present invention provides an SQL like interface to process and search audio data and combine it with other traditional data forms.
Owner:RINGCENTRAL INC
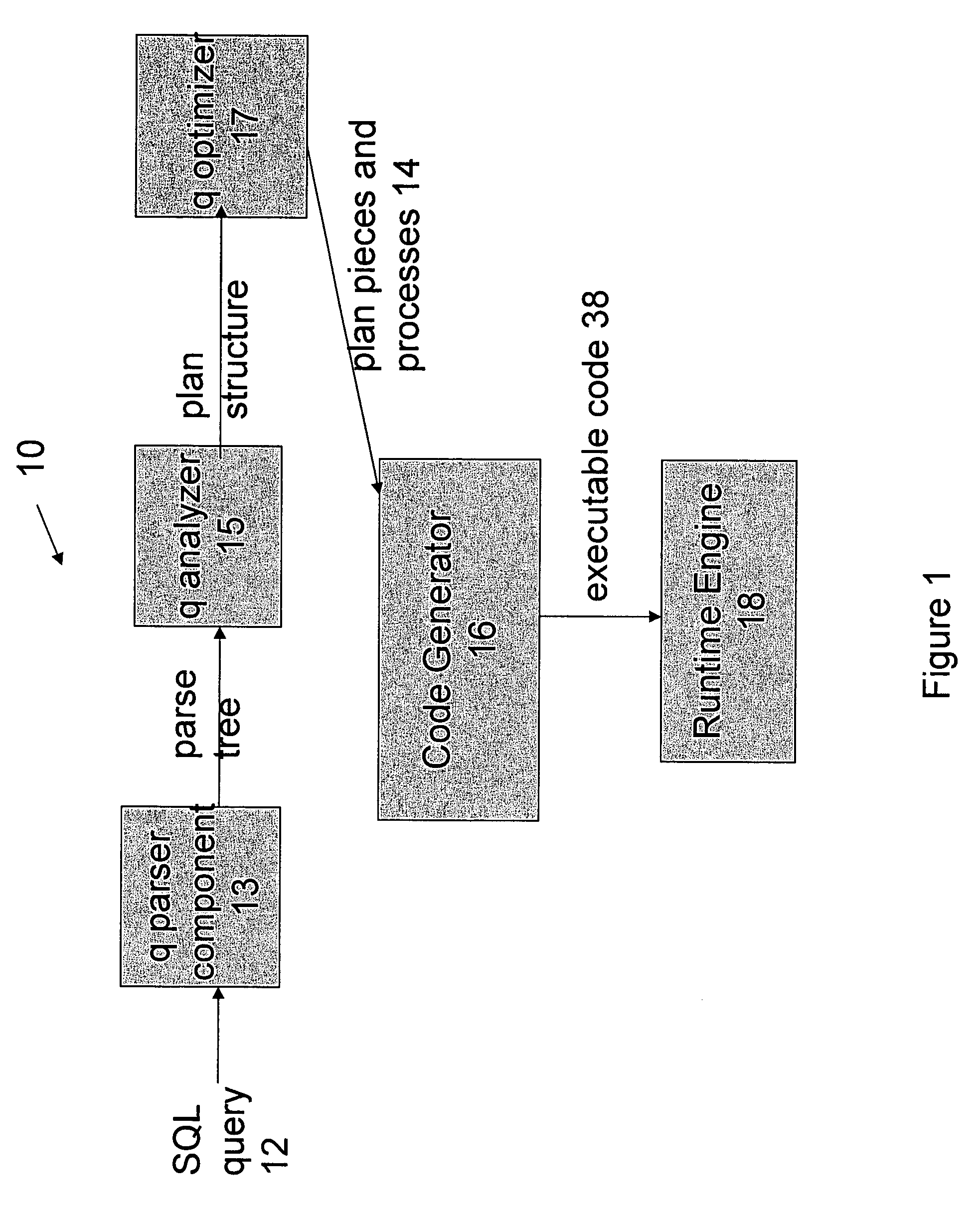
SQL code generation for heterogeneous environment
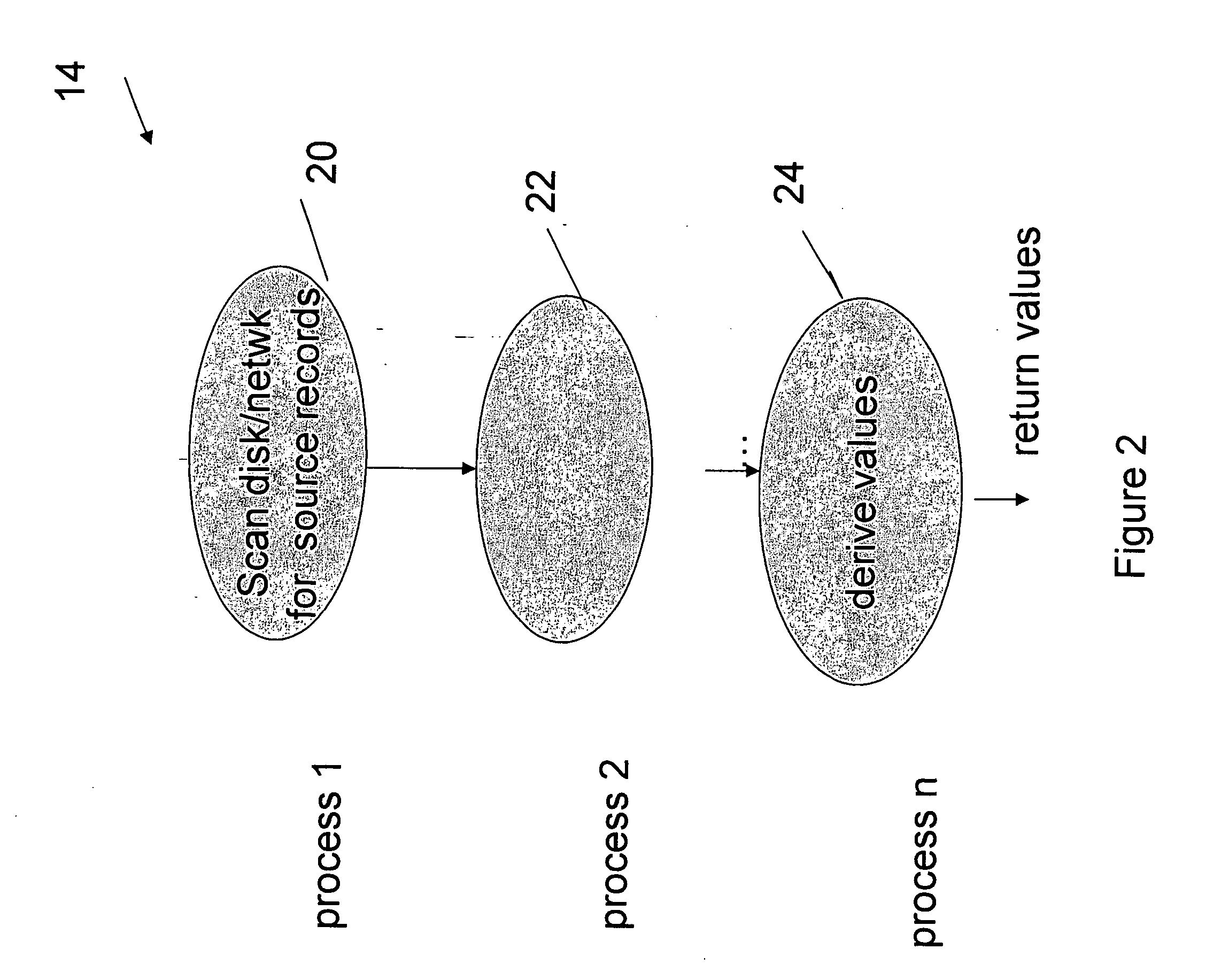
ActiveUS20050028134A1Avoiding runtime interpretationAnalysis latencyData processing applicationsDigital data information retrievalDatabase queryExecution plan
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. In one preferred embodiment, the method begins by receiving a subject query, and then forming an execution plan corresponding to the subject query. The execution plan will typically have a sequence of component snippets or pieces and corresponding processes for implementing the pieces. For at least one piece in the plan, the process then (a) generates source code using different code generation techniques as a function of expected runtime processing machine types; and then (b) compiles the generated source code to form machine executable code for implementing the subject query. As a result, the query executed directly as machine executable code thereby avoiding runtime interpretation of the pieces in the execution plan.
Owner:IBM CORP
Systems and Methods for Database Proxy Request Switching
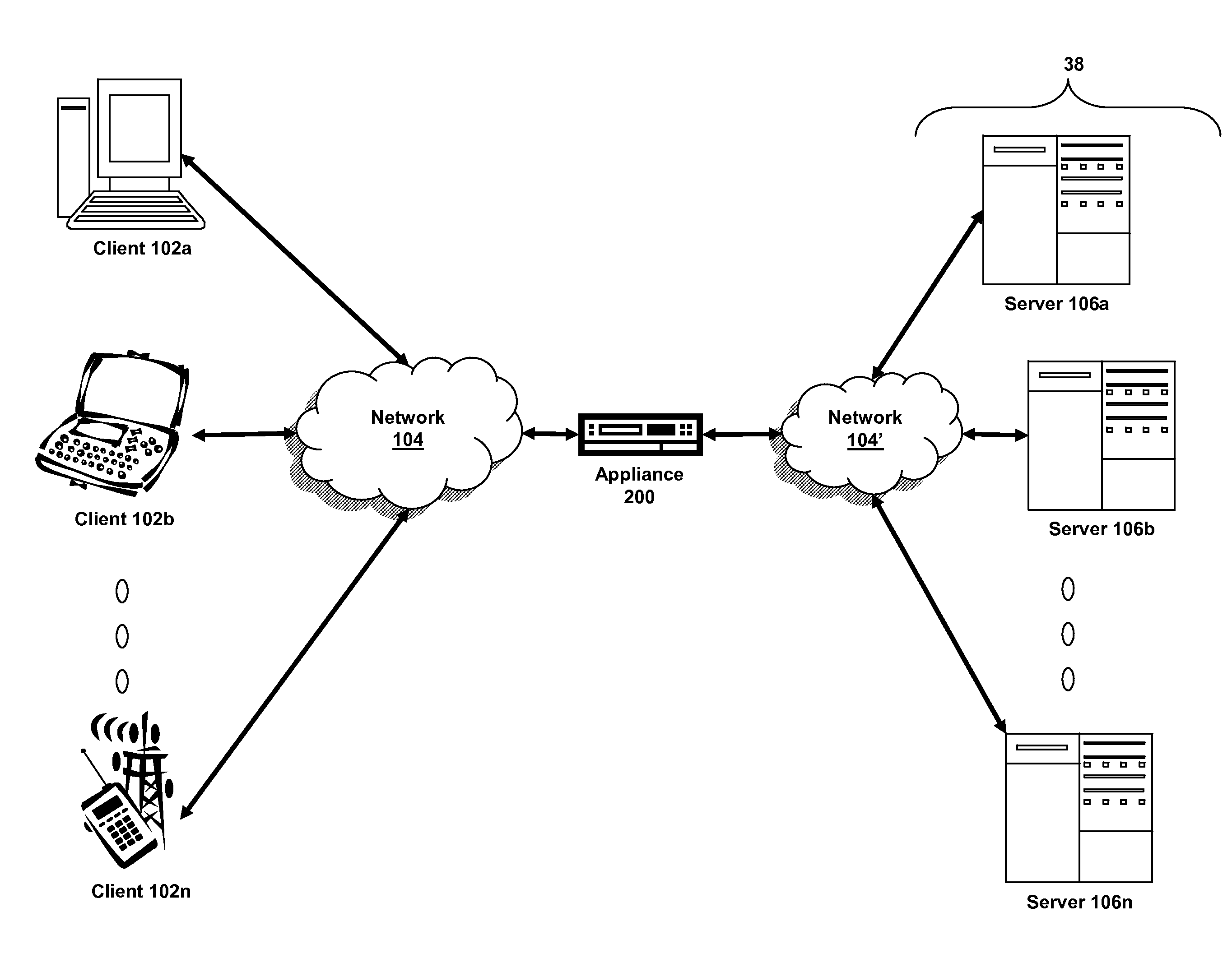
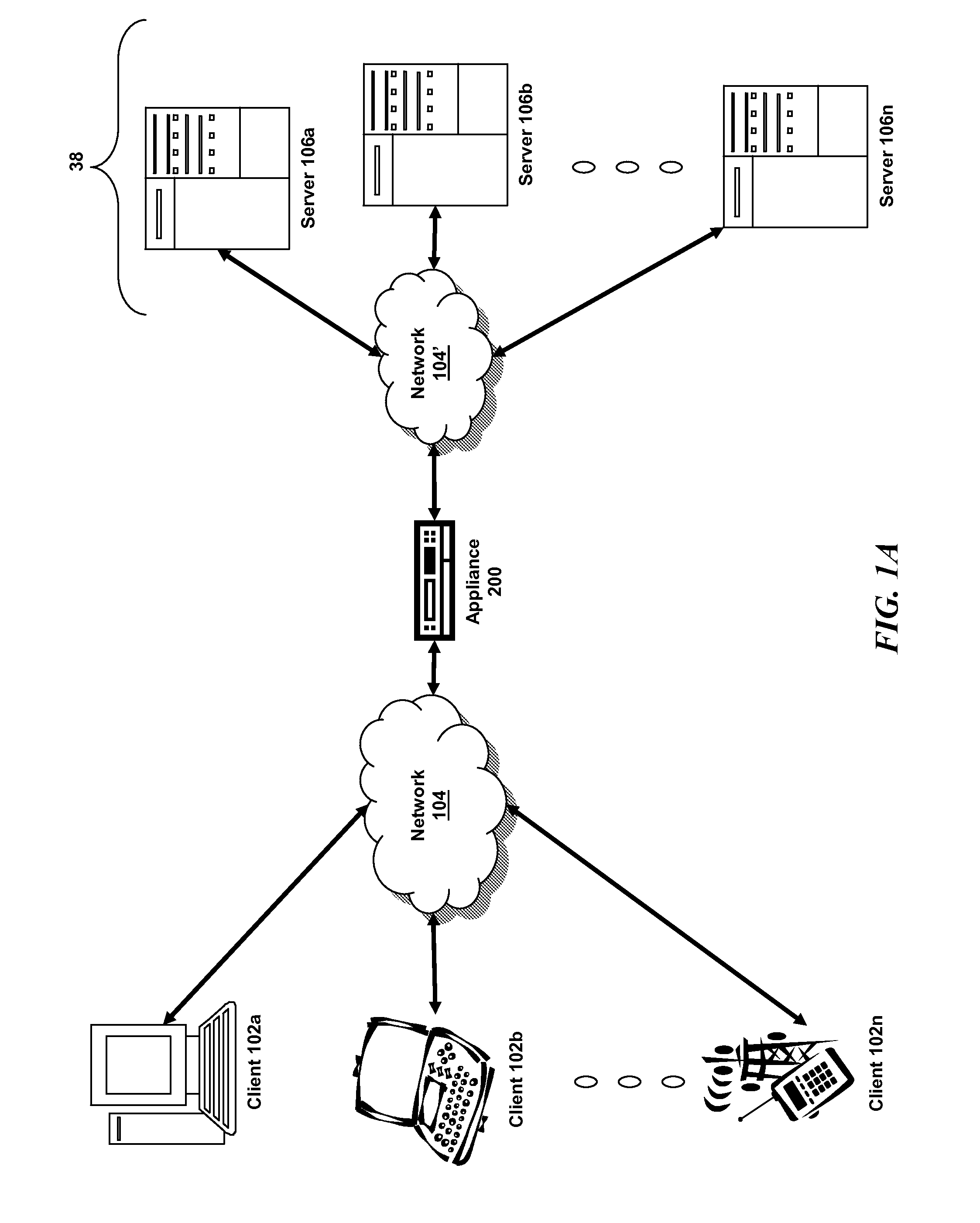
ActiveUS20120166483A1Digital data information retrievalDigital data processing detailsClient-sideSQL
The present application is directed towards systems and methods for selecting a database from a plurality of databases to forward a SQL query request based on a property of the SQL request. A device intermediary to a plurality of clients and databases may establish a plurality of connections to the plurality of databases. The device may receive, from a client of the plurality of clients, a request to execute a SQL query. The device may evaluate one or more properties of the request to execute the SQL query responsive to a policy. The device may select a database from the plurality of databases based on a result of evaluation of the one or more properties of the request to execute the SQL query. The device may forward the request to execute the SQL query to the selected database via a connection of the plurality of connections.
Owner:CITRIX SYST INC
Query interface to policy server
InactiveUS20110231443A1Digital data processing detailsComputer security arrangementsInformation resourcePrivate network
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter uses a local copy of an access control data base to determine whether an access request is made by a user. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to access policies which define access in terms of the user groups and information sets. The first access filter in the path performs the access check, encrypts and authenticates the request; the other access filters in the path do not repeat the access check. The interface used by applications to determine whether a user has access to an entity is now an SQL entity. The policy server assembles the information needed for the response to the query from various information sources, including source external to the policy server.
Owner:QUEST SOFTWARE INC +1
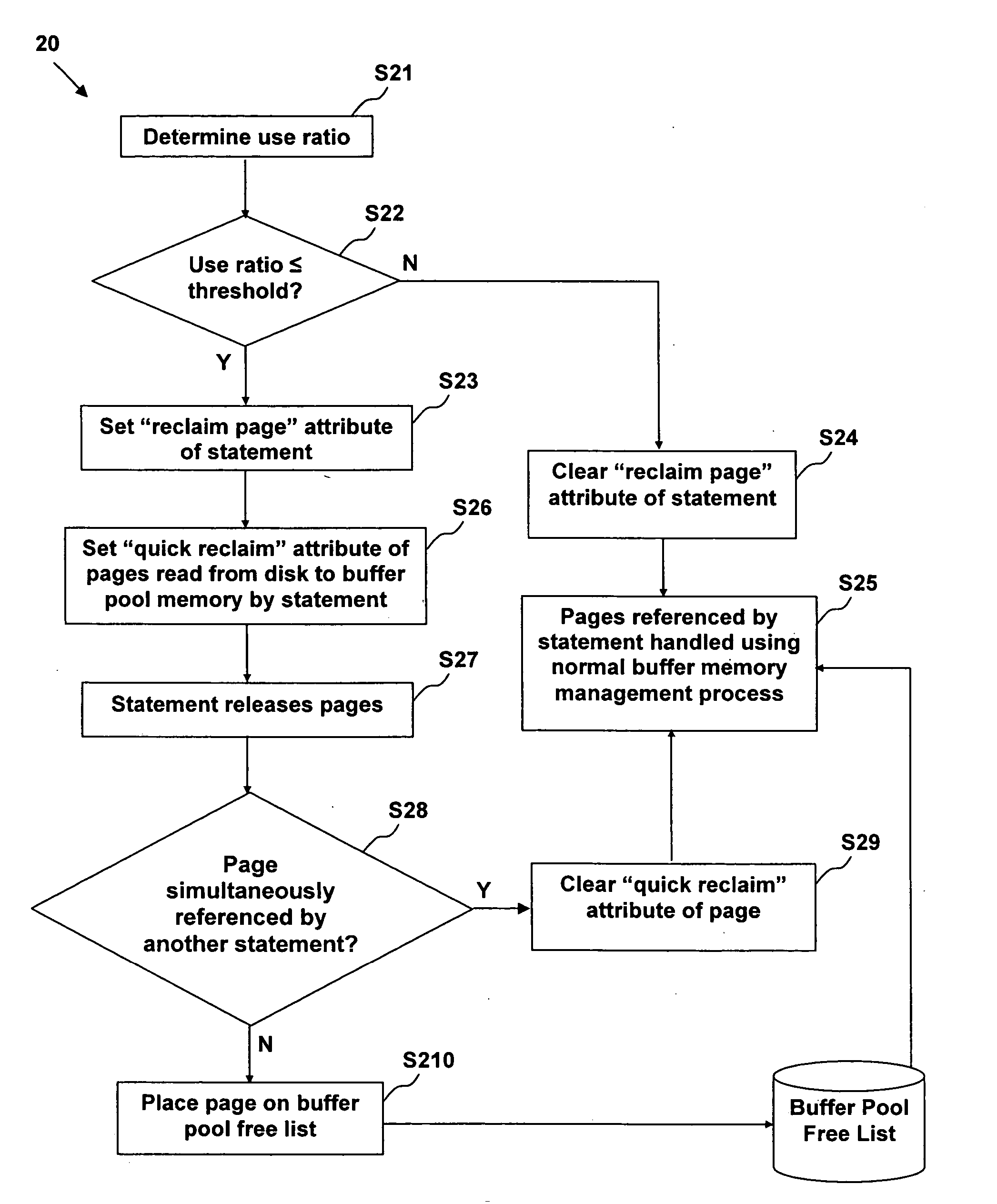
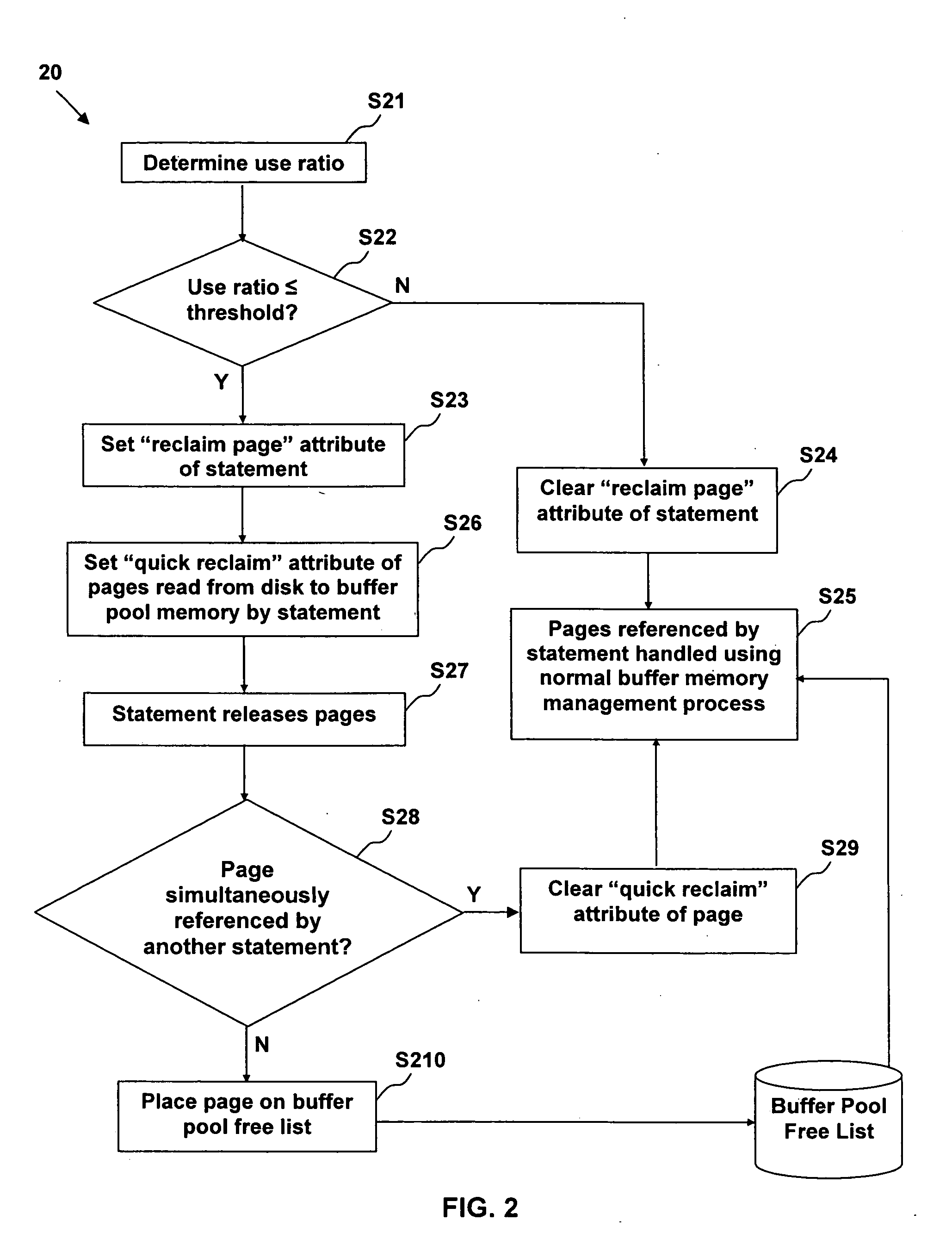
Adaptive database buffer memory management using dynamic SQL statement cache statistics
InactiveUS20060074872A1Speed up the processDigital data information retrievalSpecial data processing applicationsTerm memoryQuery language
The present invention provides a method, system, and computer program product for adaptive database buffer memory management using dynamic Structured Query Language (SQL) statement cache statistics. The method comprises: using SQL statement cache statistics to infer page re-use. The method further comprises: determining a use ratio of an SQL statement; comparing the use ratio of the statement to a threshold value; if the use ratio is less than the threshold value, setting a reclaim page attribute of the statement indicating a low likelihood of page re-use of pages referenced by the statement; and, if the reclaim page attribute of the statement is set: setting a quick reclaim attribute of each page read from disk by the statement; and after each page is released by the statement, placing the page in a buffer pool free list, wherein a memory location of the page in a buffer pool memory is immediately available for re-use.
Owner:IBM CORP
Database querying system and method
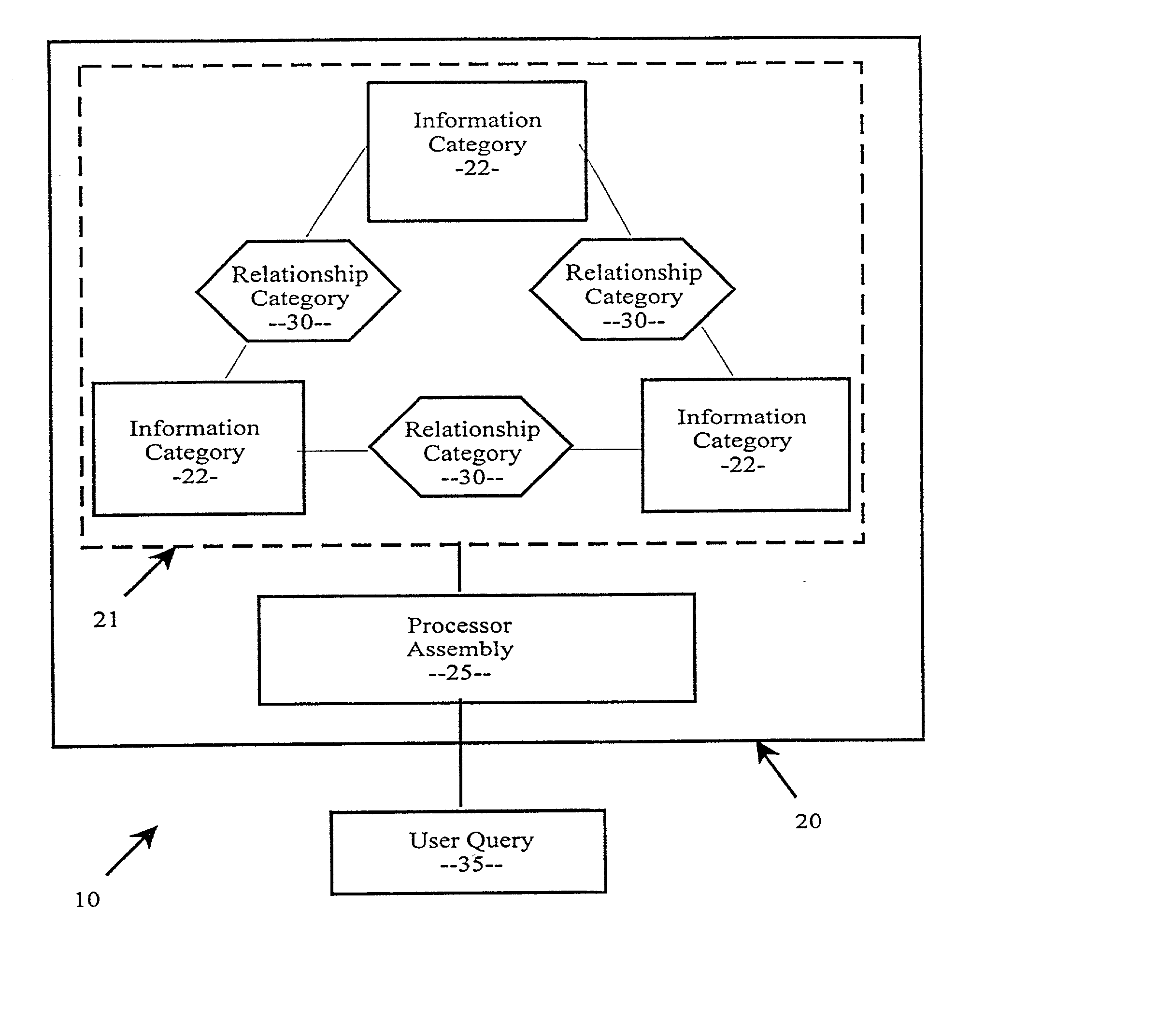
InactiveUS20020107840A1Data processing applicationsObject oriented databasesTable (database)Relation (database)
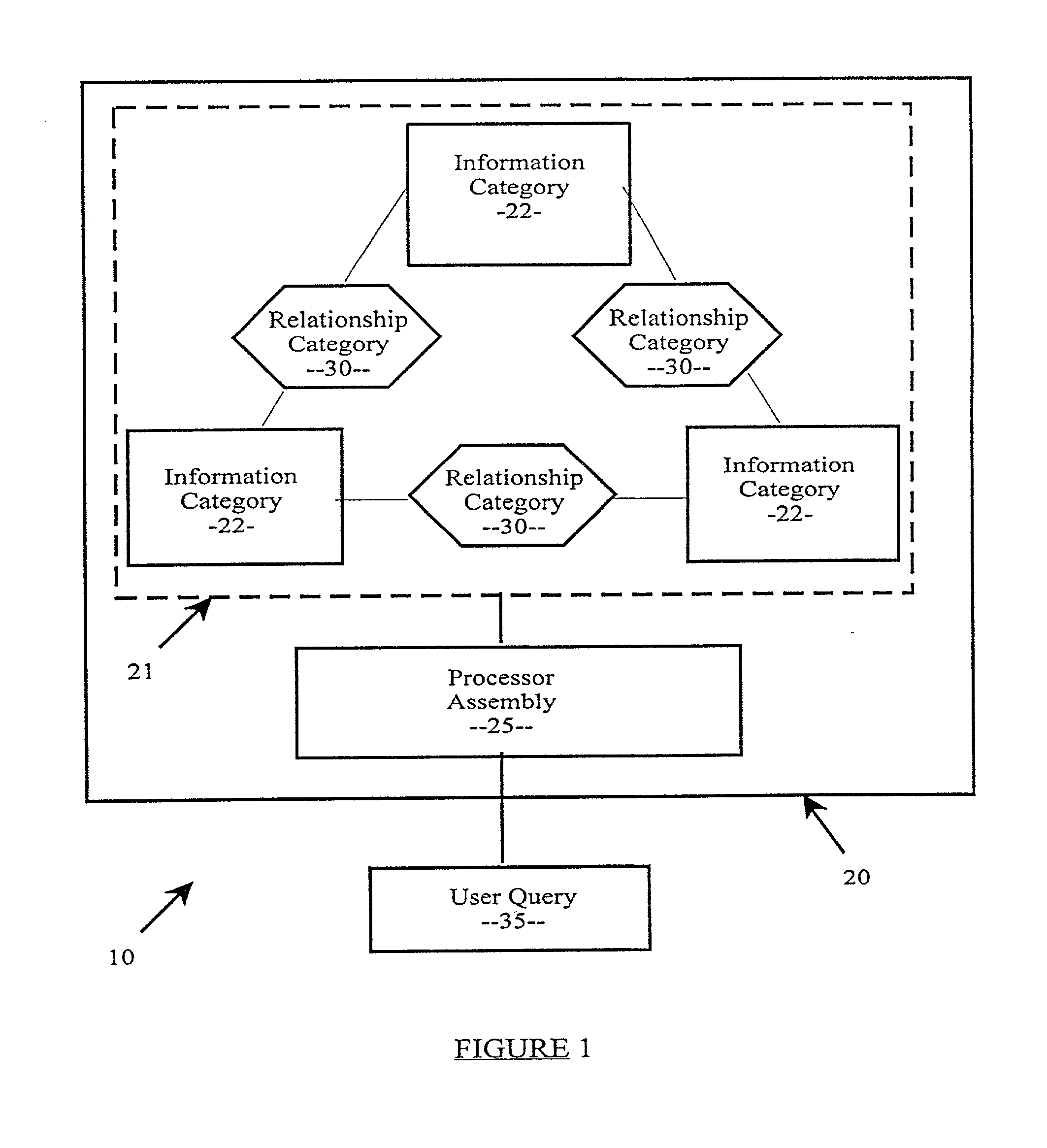
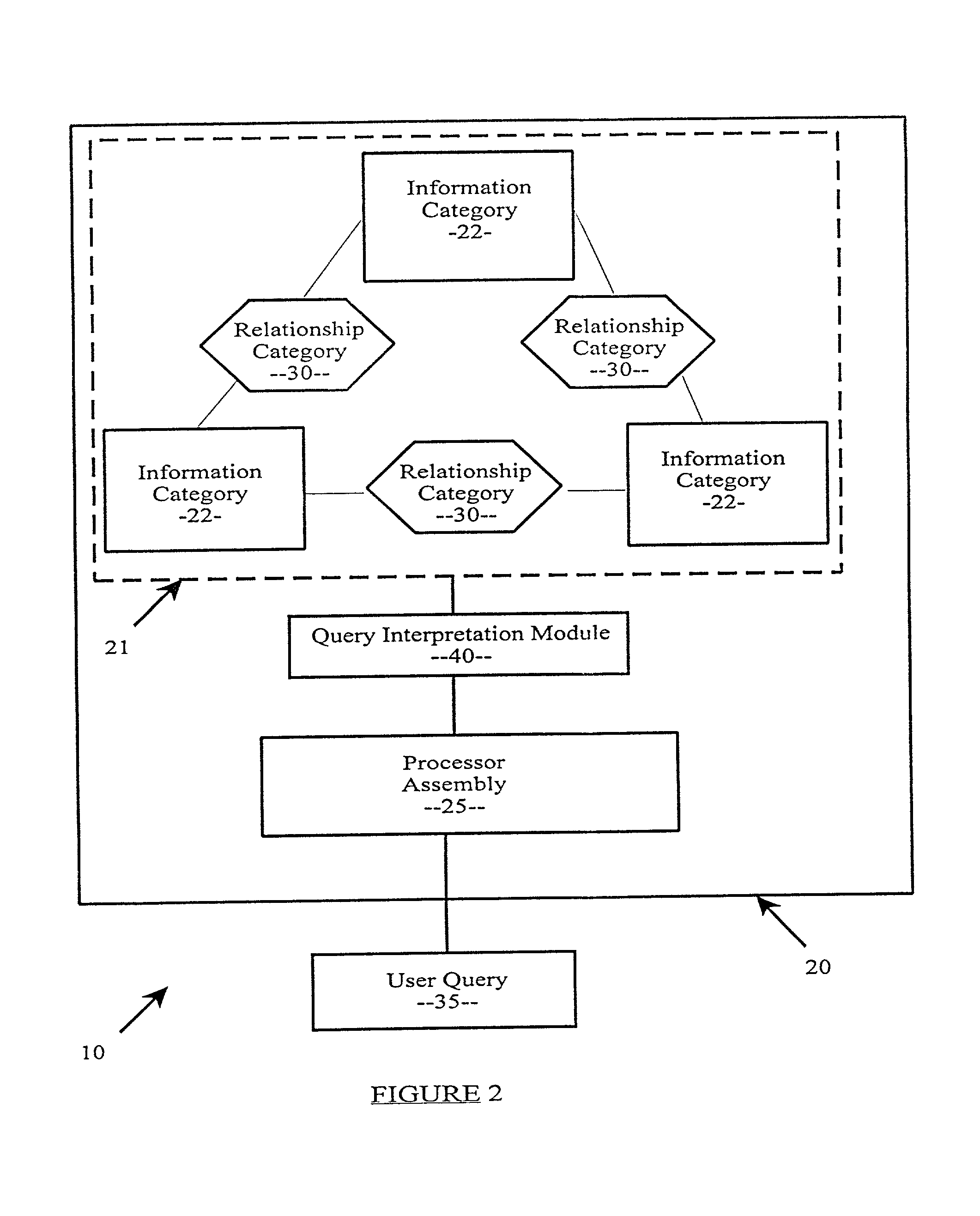
A database querying system to facilitate the retrieval of desired data from a database including information categories, the system including a plurality of object data items categorized in one information category and a plurality of object data items categorized in another information category. A processor assembly responsive to a user query is also provided and is structured to identify the desired data from the user query. A relationship category defined by relationships between the object data items of the information categories is further provided, the user query including a relationship identifier corresponding the relationship category so as to simplify syntax of the user query. Interpretation of relational-database query and data manipulation languages against non-relational schemas, including conceptual, semantic, object-relational, or object-oriented database schemas, by regarding the schemas as representing virtual relational databases with every class replaced by a virtual table comprised of all the attributes reachable from the class by a chain of relations. The interpretation allows concise and simple querying of non-relational and relational databases in a languages originally intended only for relational databases. The system further provides for wrapping of a relational database into a semantic conceptual schema so as to allow formulation of queries in SQL against the wrapping schema, reducing the size of SQL queries.
Owner:GULA CONSULTING LLC
Method of optimizing SQL queries where a predicate matches nullable operands
InactiveUS6996557B1Digital data information retrievalData processing applicationsRelational databaseTheoretical computer science
An optimization technique for SQL queries, a program storage device storing the optimization program, and an apparatus for optimizing a query is provided. A query is analyzed to determine whether it includes a predicate for matching nullable operands and, if so, it is transformed to return TRUE when all operands are NULLs. If the DBMS supports this new function, the predicate is marked. If not, the predicate is re-written into a CASE expression having two SELECT clauses. The query is then executed in the computer to efficiently retrieve data from the relational database.
Owner:TWITTER INC
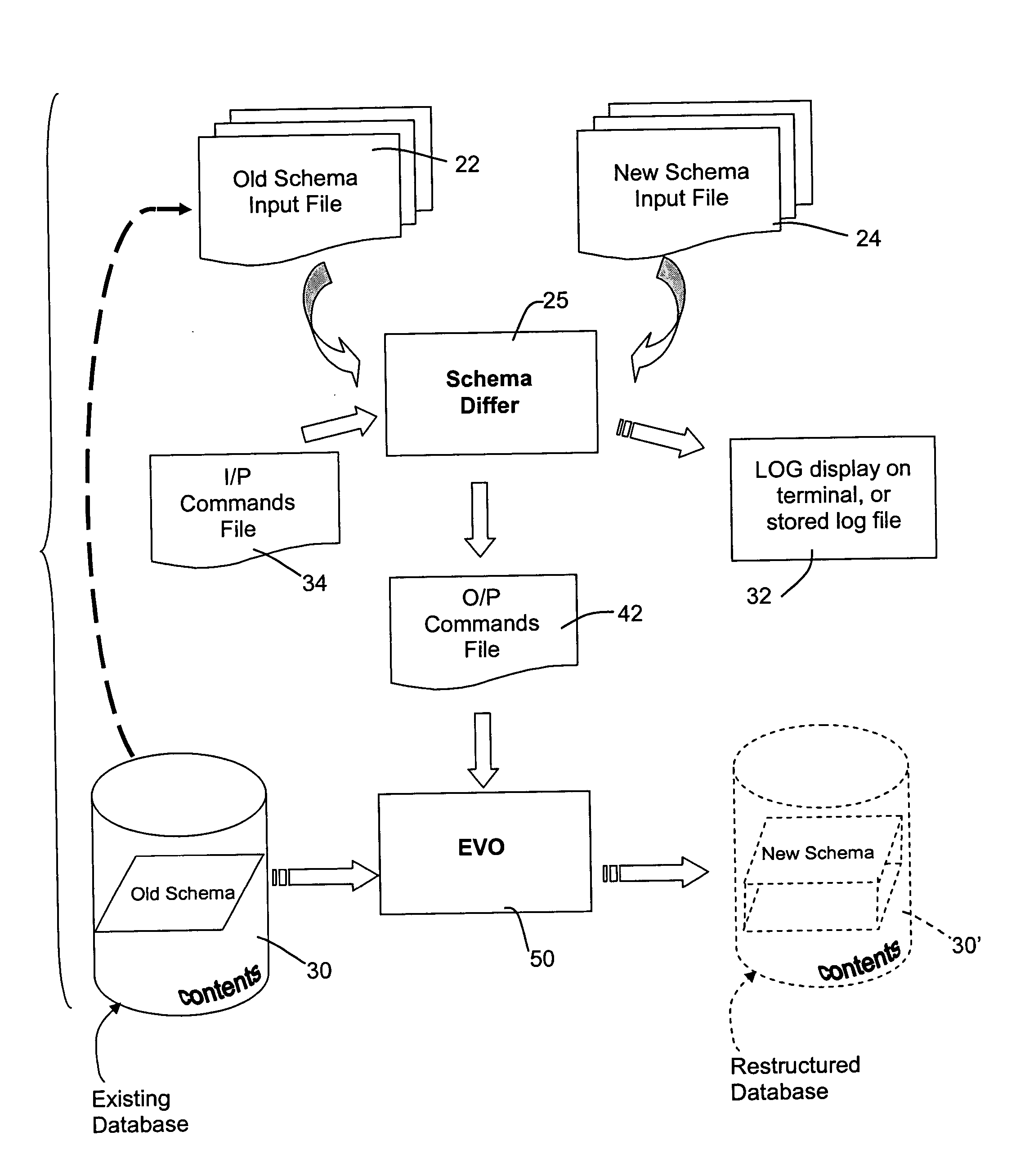
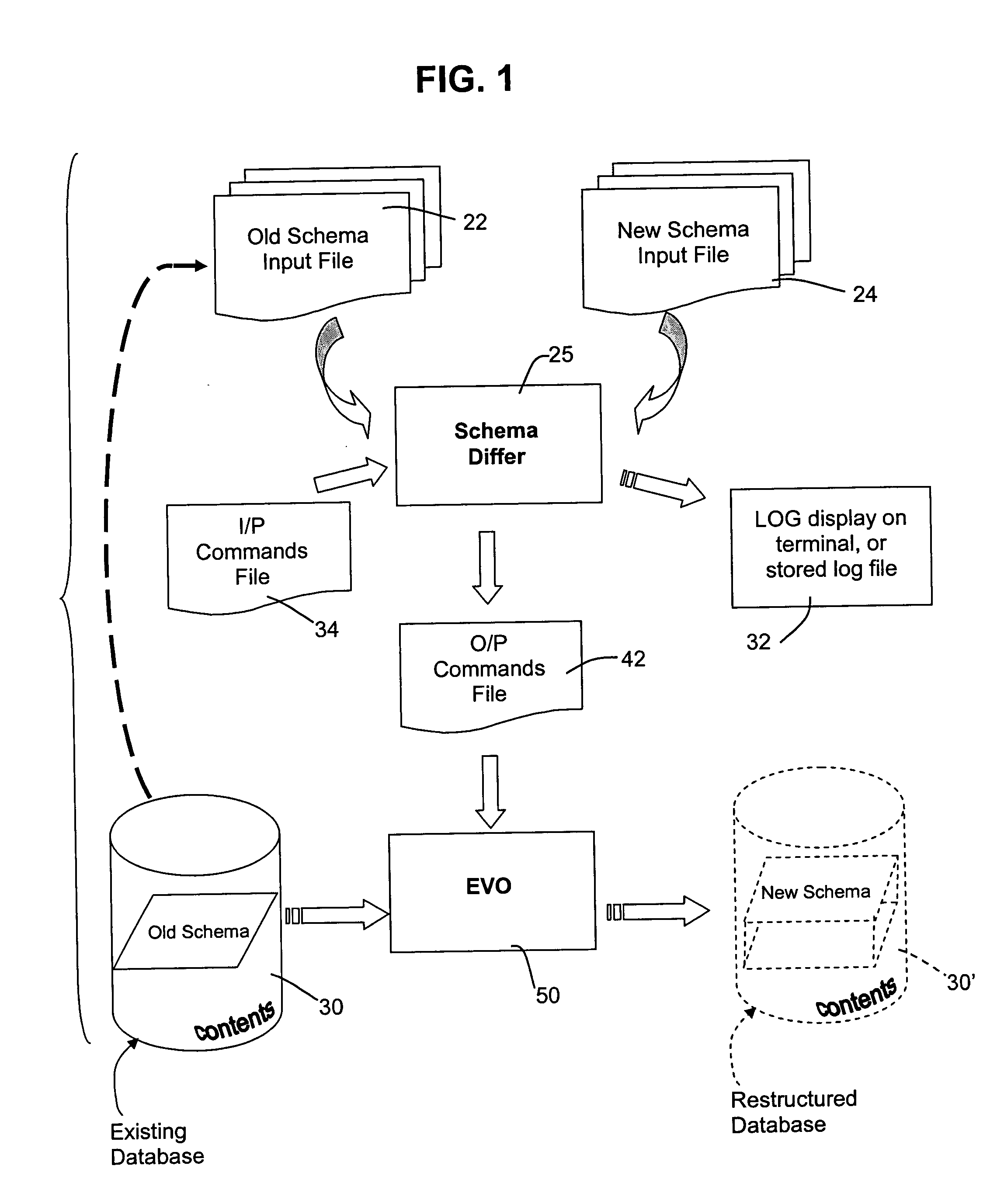
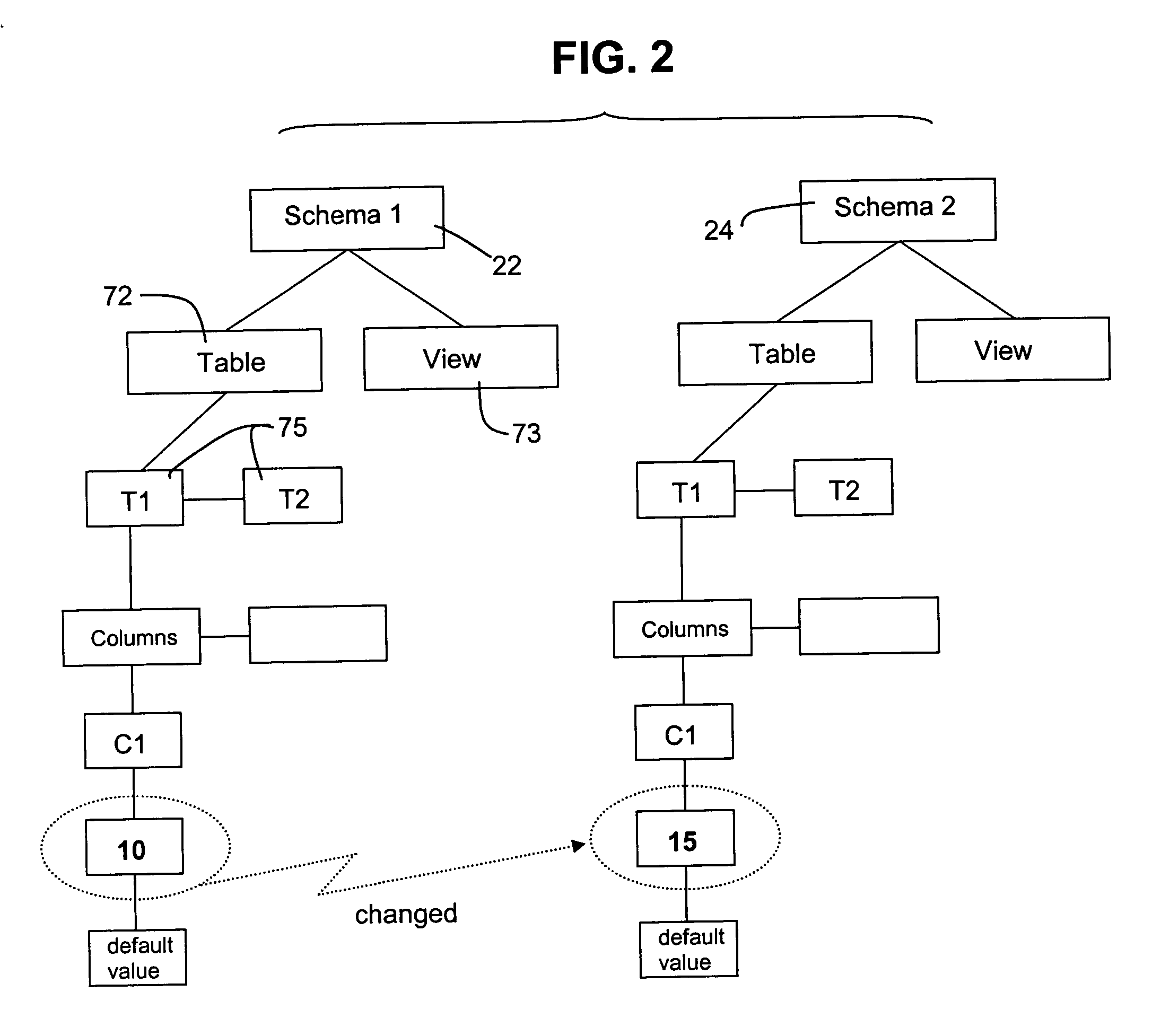
Method for automated database schema evolution
InactiveUS20050071359A1Easy to changeMinimal impactDigital data information retrievalSpecial data processing applicationsSchema for Object-Oriented XMLAutomated database
A database structure of a sort defined by an access and query language that defines tables of variables having labels and field characteristics, such as ANSI structured query language (SQL), is modified by determining the structural differences between an existing schema and a new schema, independent of database contents. The differences are processed to generate commands that are then applied to evolve an existing database from the old schema or structure to the new one. This avoids the need to dump and restructure the contents of the old database for reload into an empty new database that has been prepared to meet the new schema.
Owner:LUCENT TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com