Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
948 results about "Schema for Object-Oriented XML" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
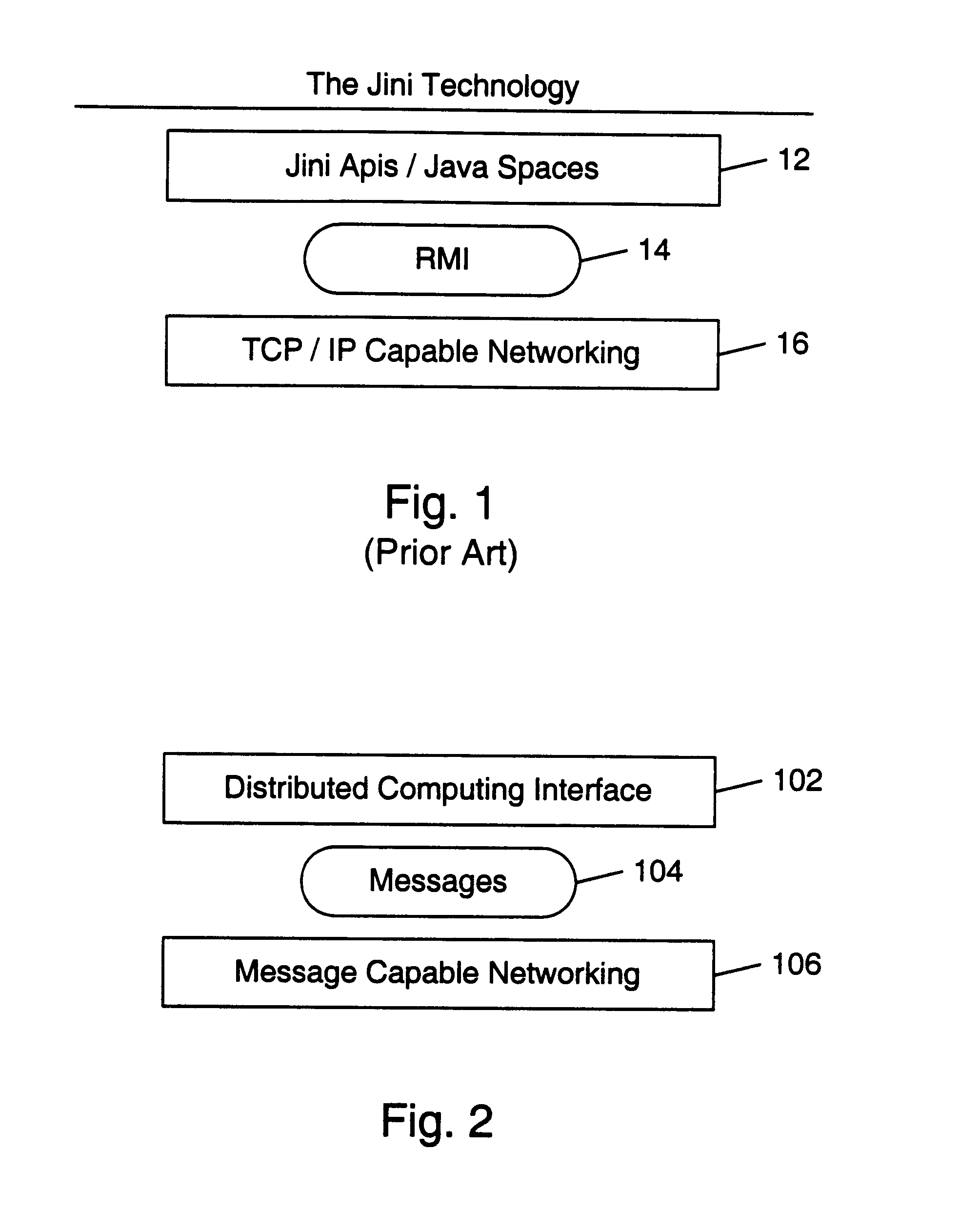
Schema for Object-Oriented XML, or SOX, is an XML schema language developed by Commerce One. In 1998 a SOX specification was submitted to the World Wide Web Consortium and published as a W3C Note. A revised version, SOX 2.0, was published as a W3C Note in 1999.
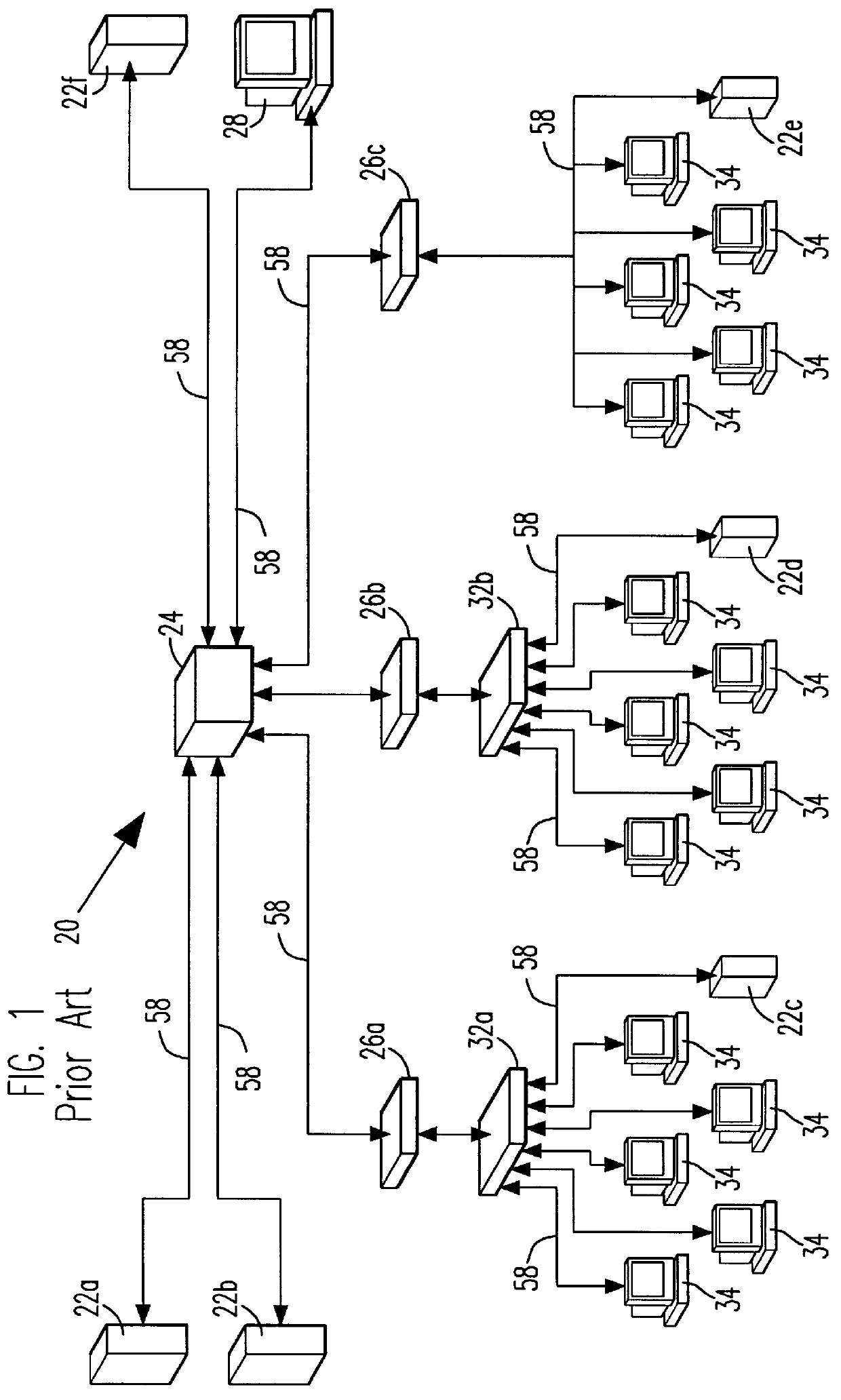
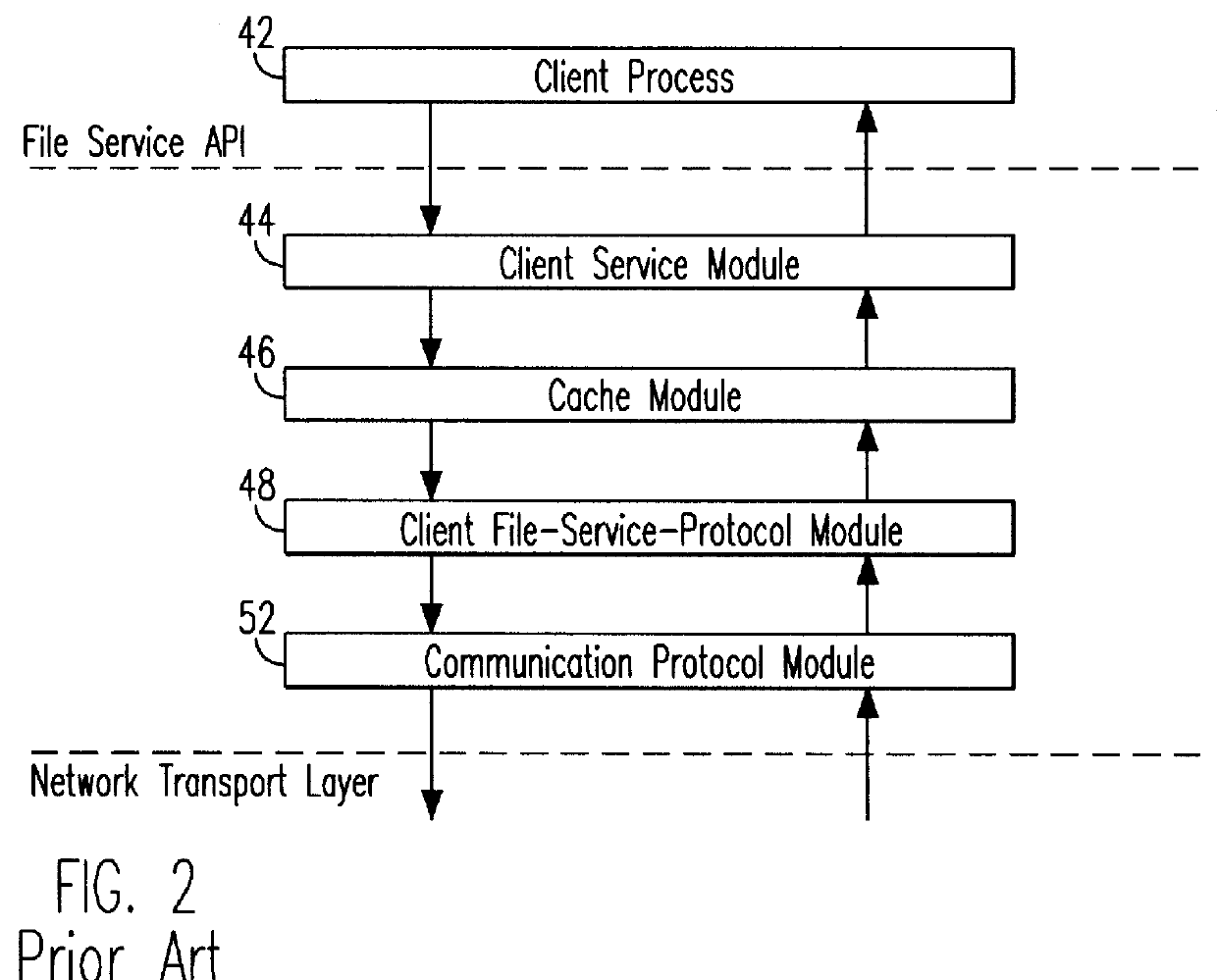
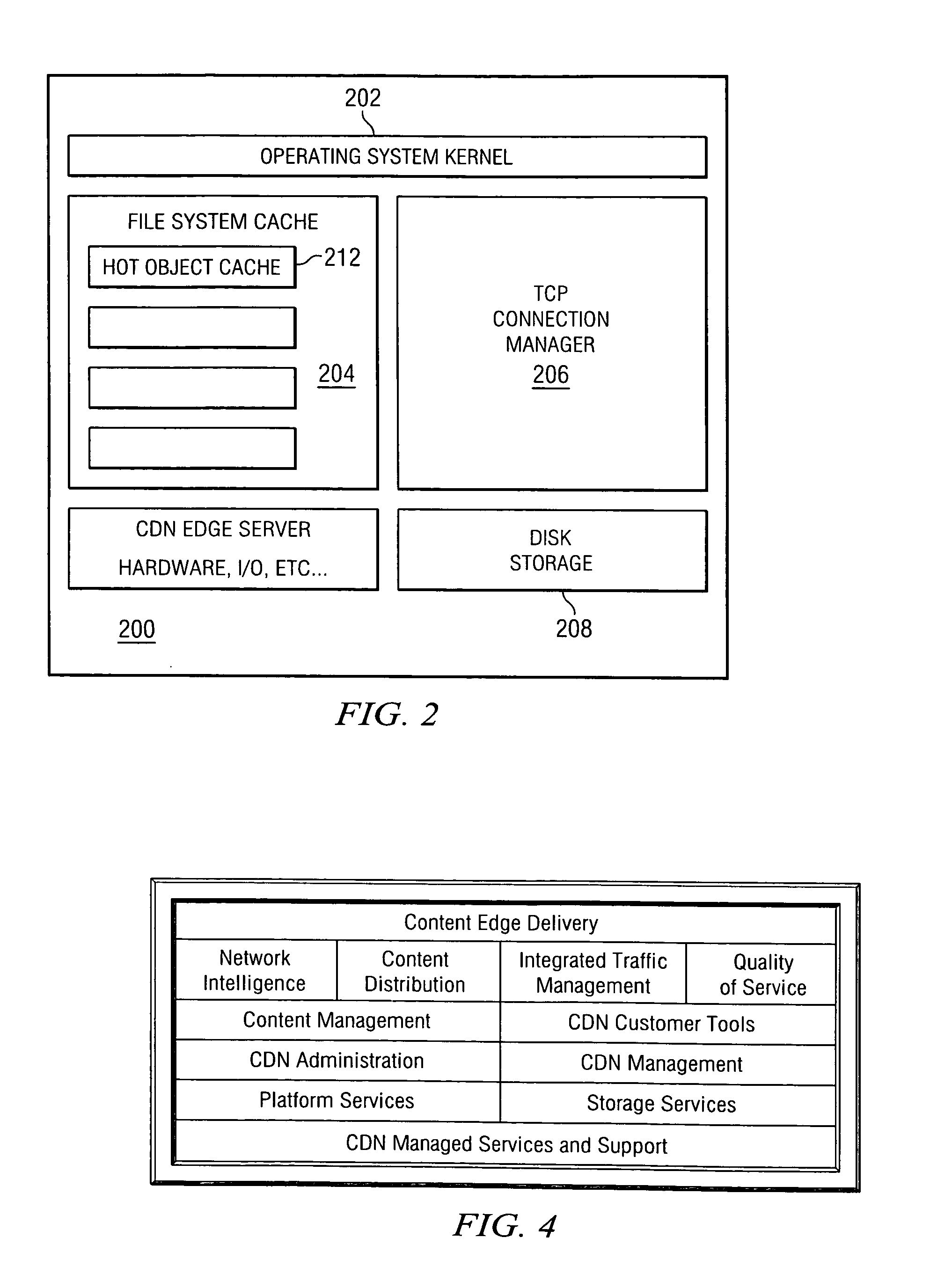
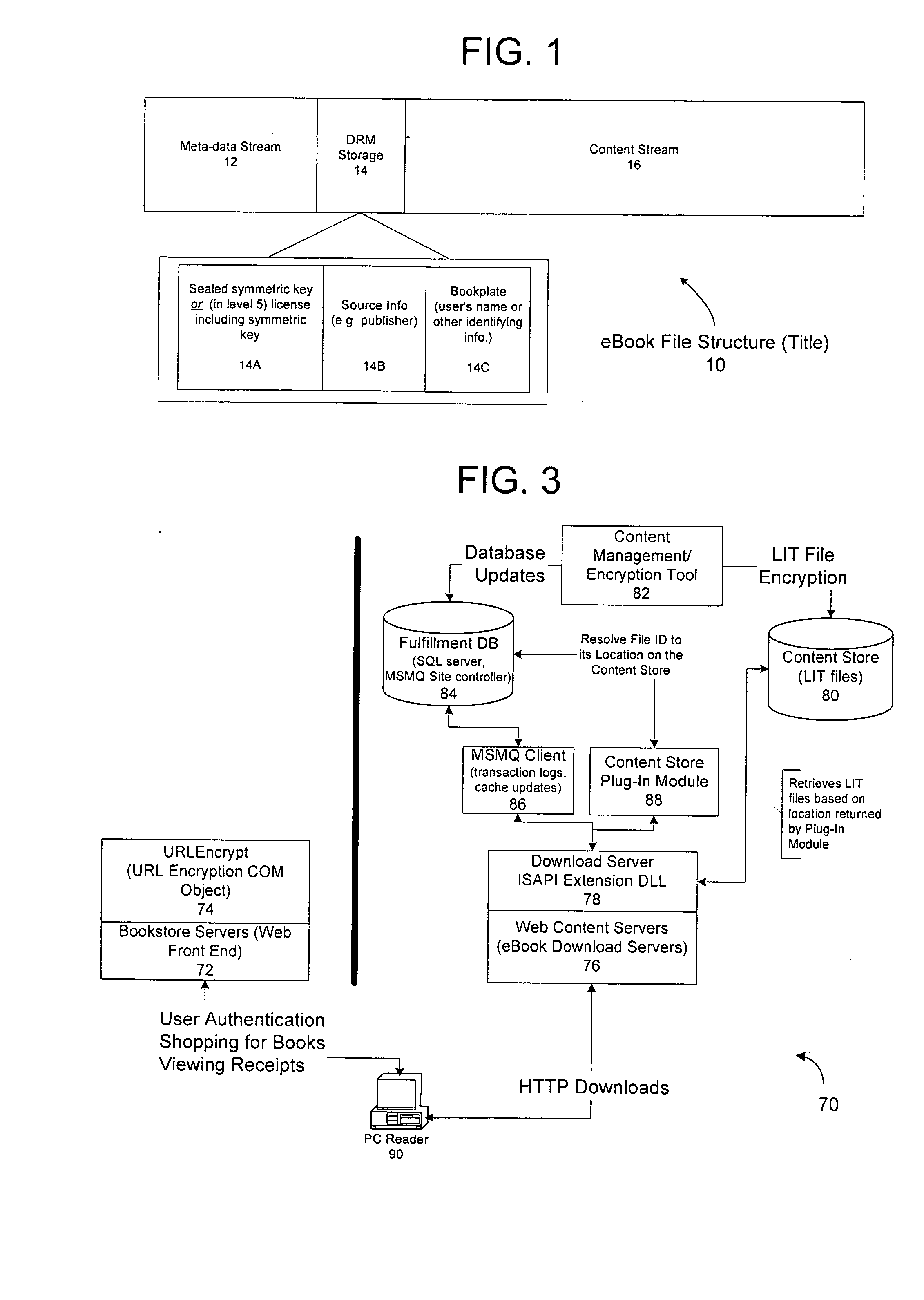
Remote file services network-infrastructure cache
InactiveUS6085234AMultiple digital computer combinationsMemory systemsService protocolSchema for Object-Oriented XML
A network-infrastructure cache ("NI Cache") transparently provides proxy file services to a plurality of client workstations concurrently requesting access to file data stored on a server. The NI Cache includes a network interface that connects to a digital computer network. A file-request service-module of the NI Cache receives and responds to network-file-services-protocol requests from workstations through the network interface. A cache, also included in the NI Cache, stores data that is transmitted back to the workstations. A file-request generation-module, also included in the NI Cache, transmits requests for data to the server, and receives responses from the server that include data missing from the cache.
Owner:MOSAID TECH +1
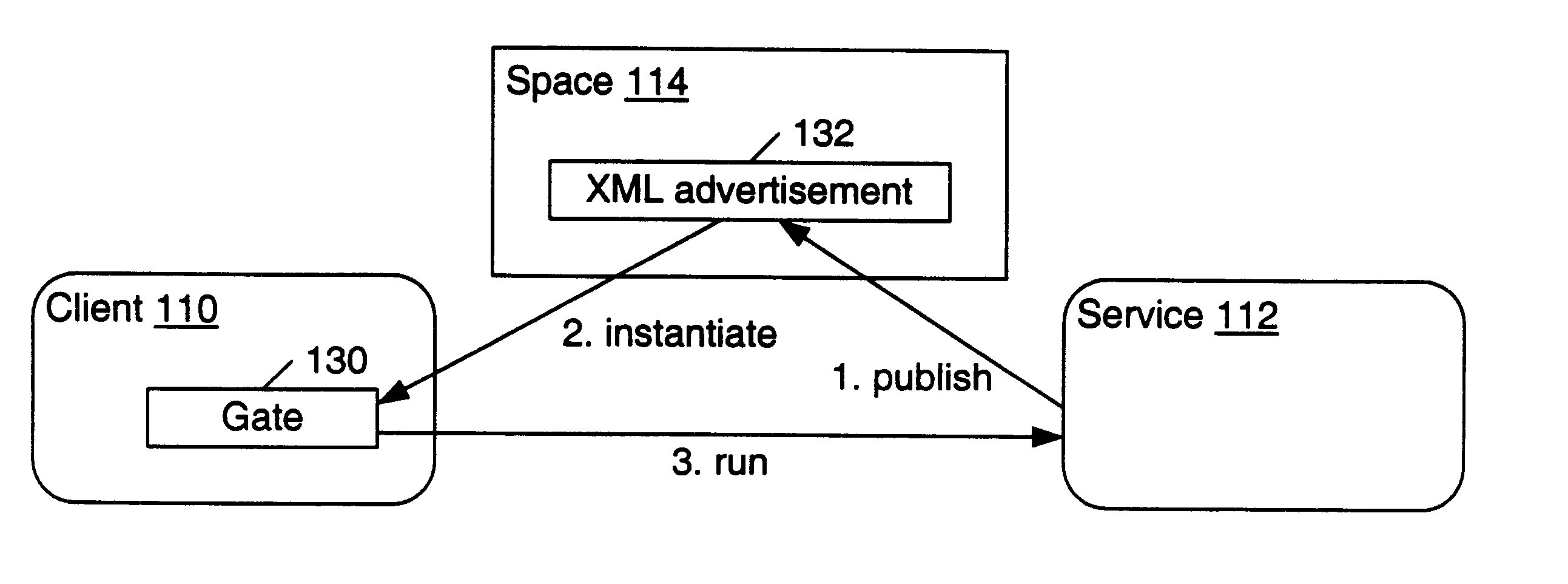
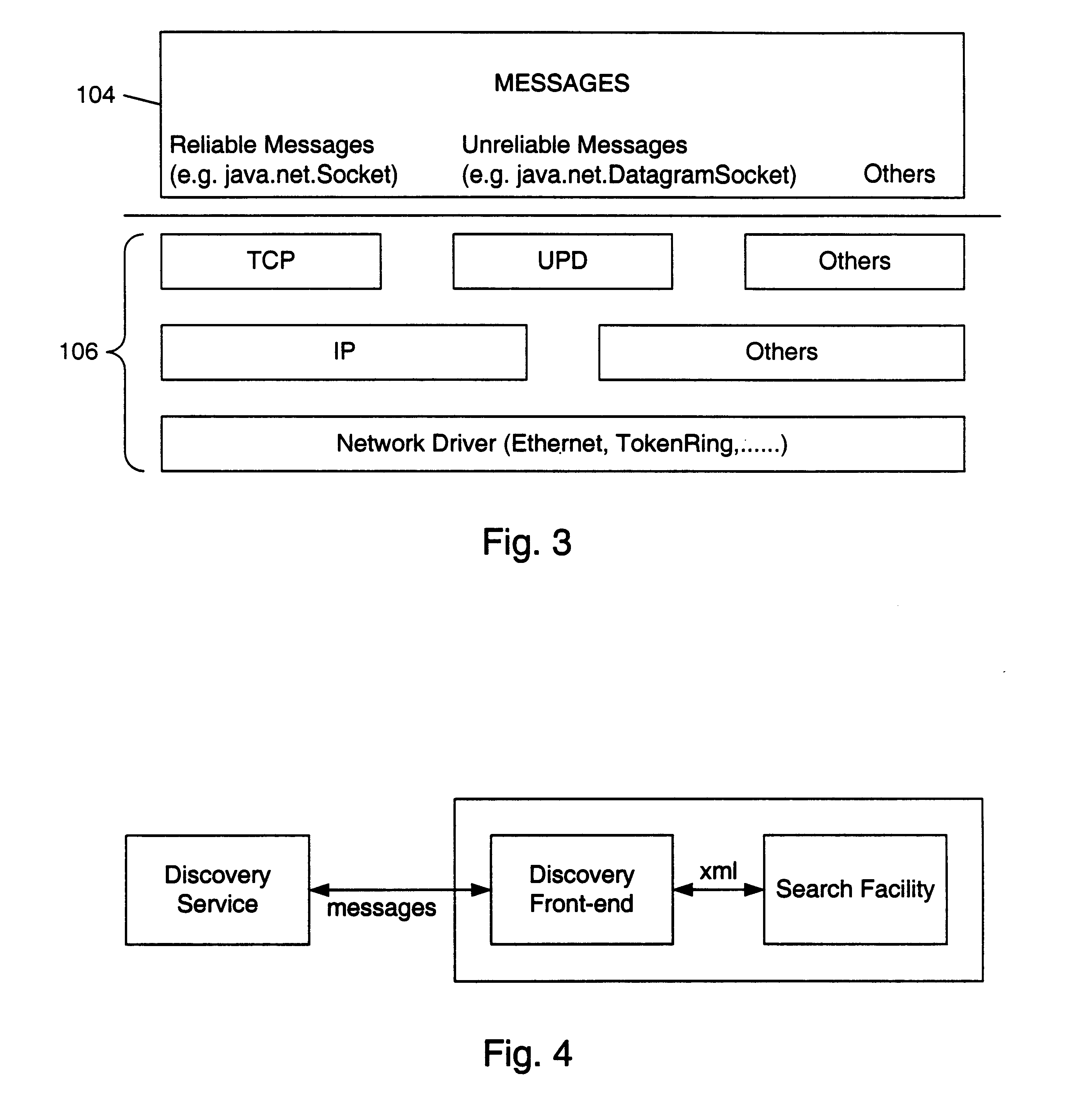
Mechanism and apparatus for using messages to look up documents stored in spaces in a distributed computing environment
InactiveUS6643650B1AdvertisementsMultiple digital computer combinationsXML schemaRepresentation language
A system and method for searching for documents within spaces in a distributed computing environment are provided. A client sends a lookup message to a space which stores documents. The lookup message may specify desired characteristics, such as a name or partial XML schema, of the stored documents. The documents may include XML service advertisements and XML device advertisements as well as general-purpose XML documents. A set of zero or more documents which match the lookup message are discovered. In one embodiment, the lookup message may include a desired name. If the lookup message includes both a desired name and a desired schema, the set of discovered documents may include both discovered documents having a name that matches the desired name and discovered documents having a schema that matches the desired schema. If the lookup message includes neither a desired name nor a desired schema, the set of discovered documents may include substantially all the documents stored in the space. After the matching documents are found, the space may send a lookup response message to the client. For each discovered document, the lookup response message may include a name and an advertisement. Each advertisement may include information which is usable by the client to obtain the respective discovered document or access the resource (e.g., a service) that the document advertises. The advertisements and messages may be expressed in a data representation language such as XML.
Owner:ORACLE INT CORP
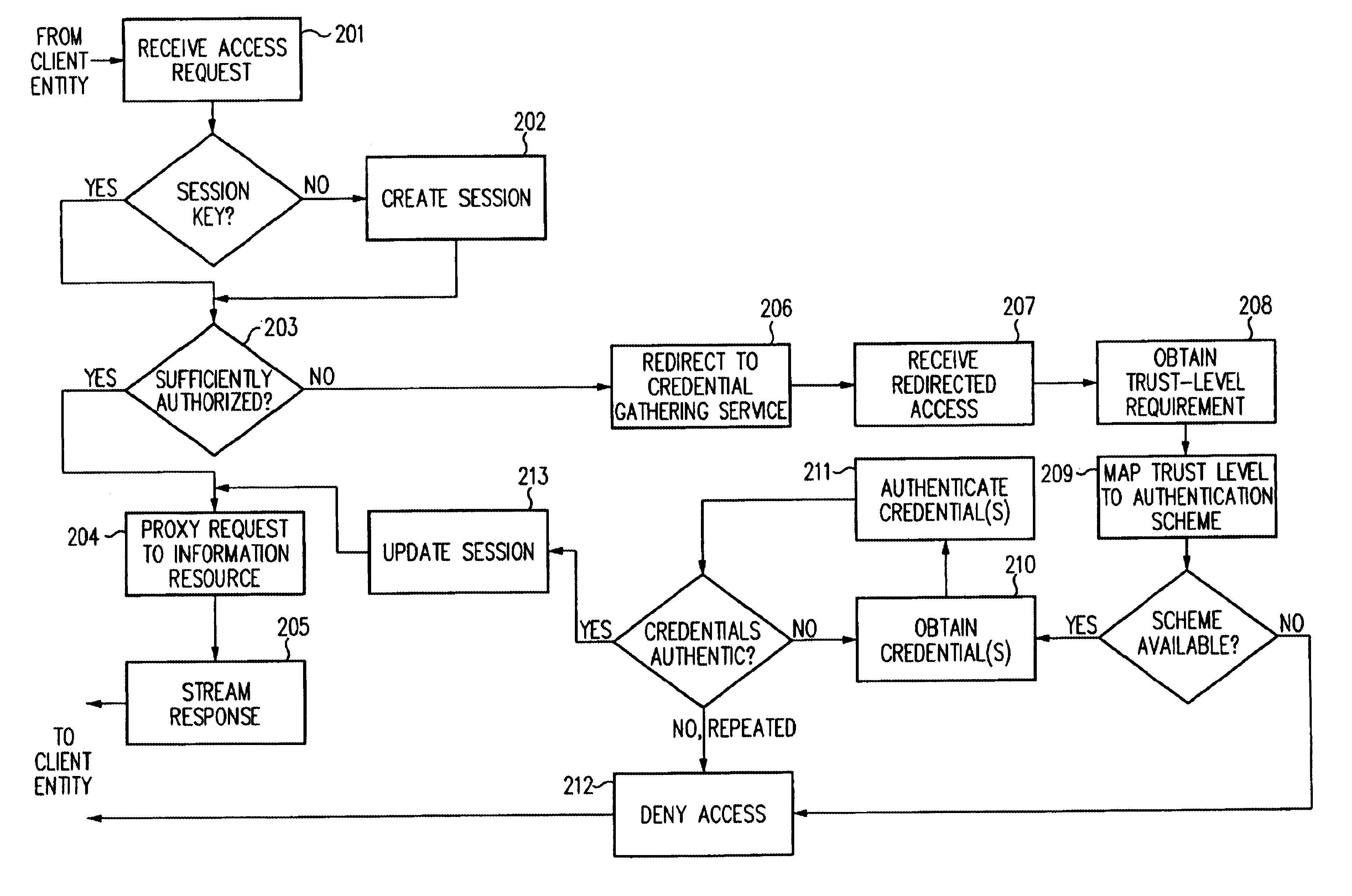
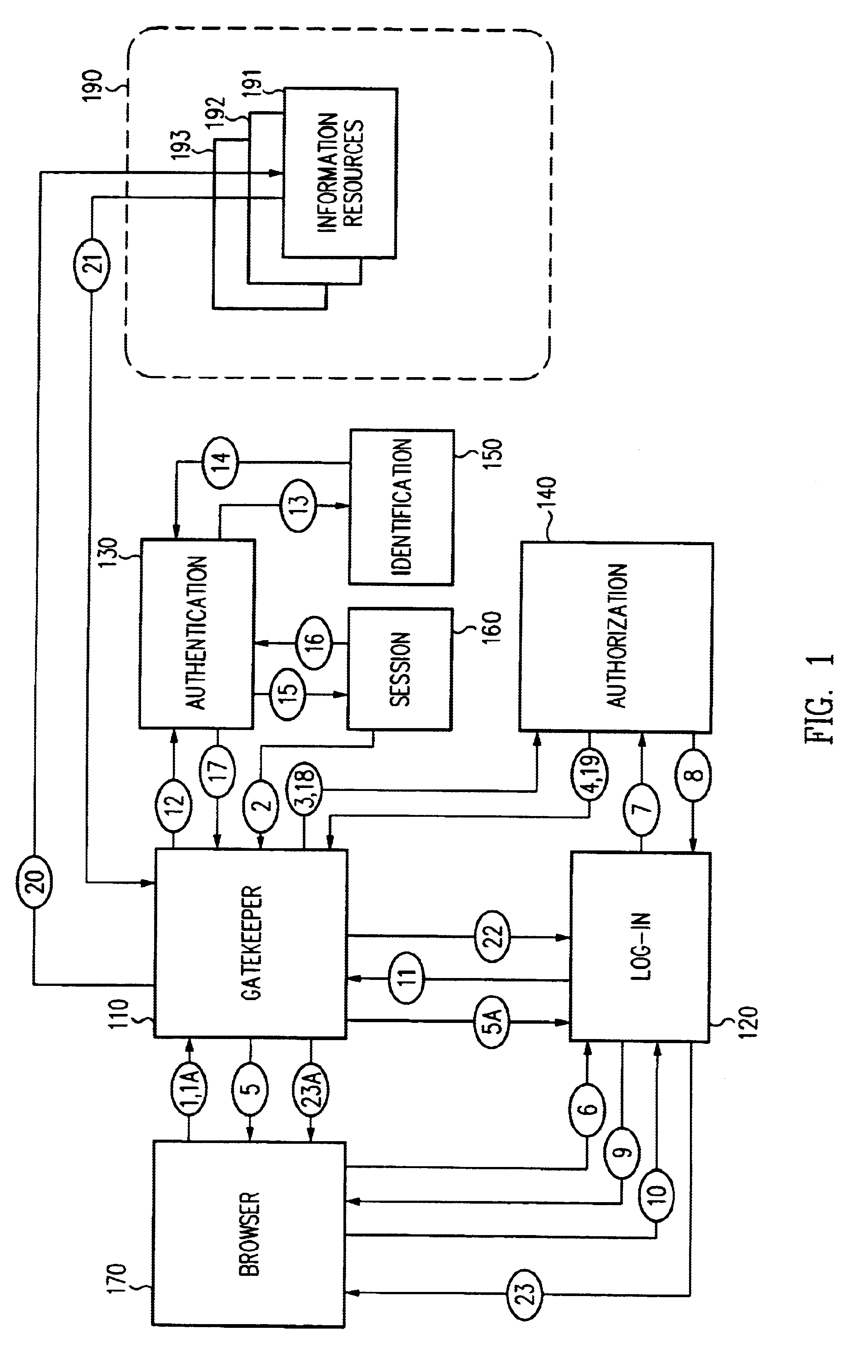
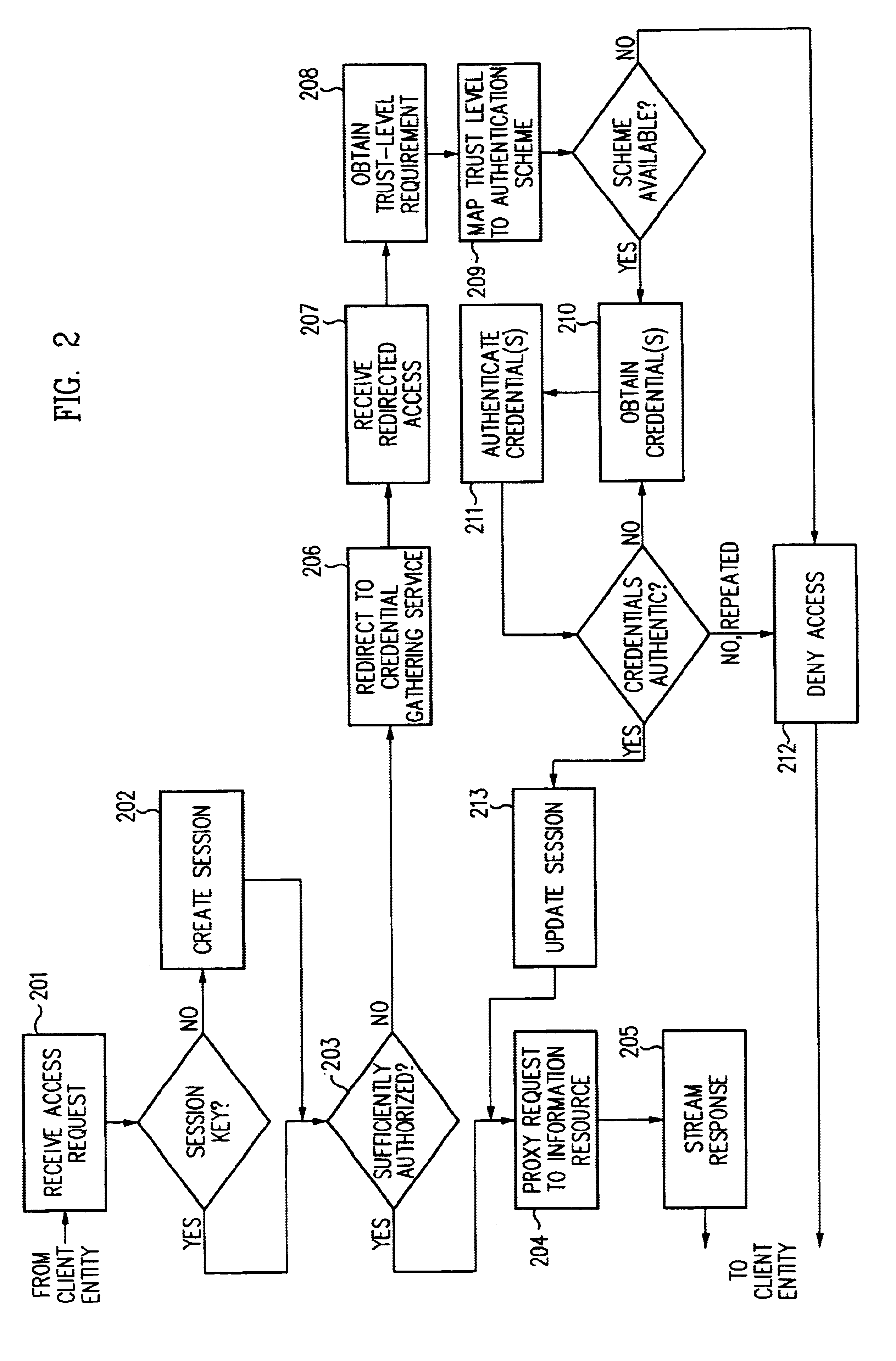
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
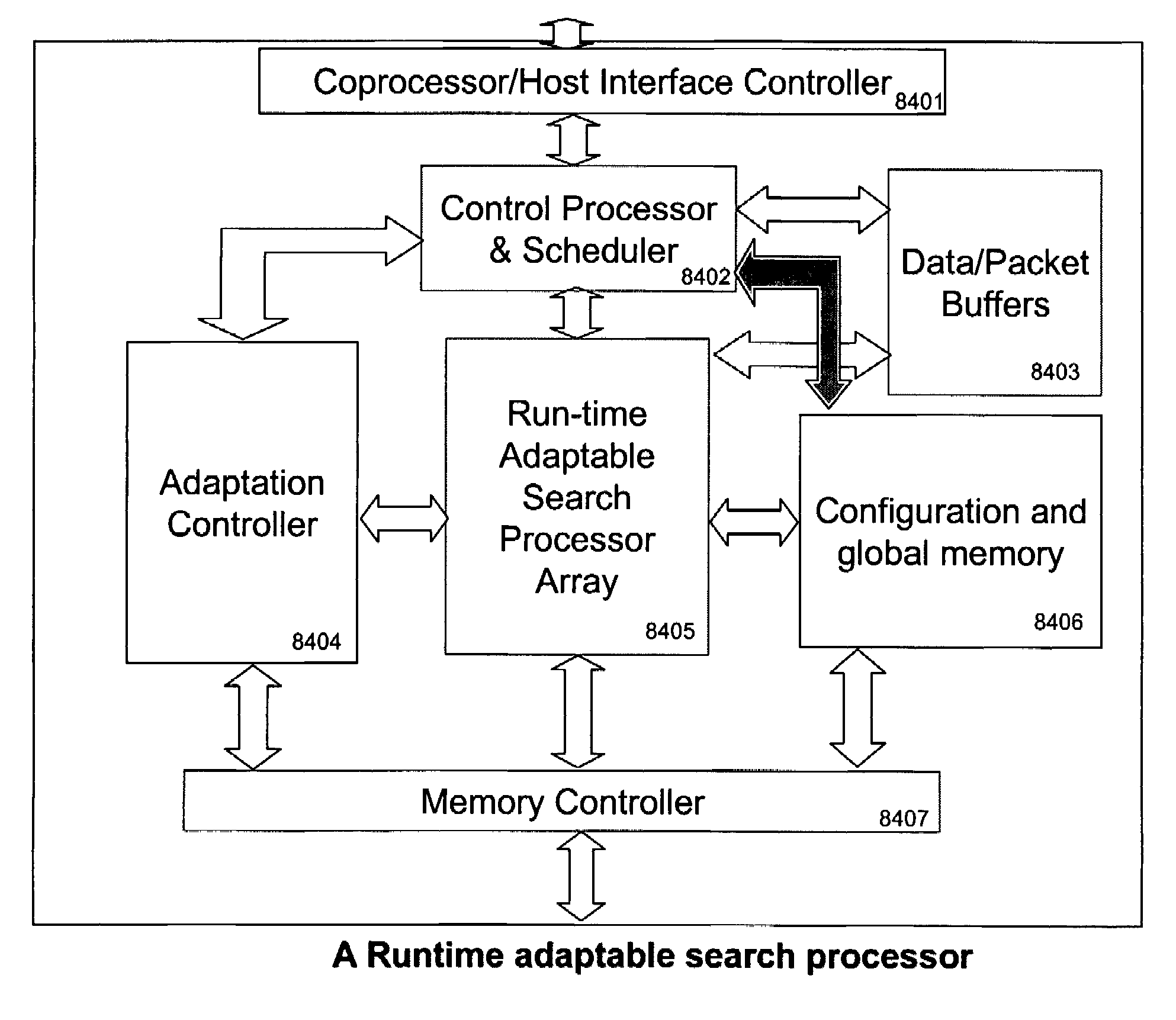
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
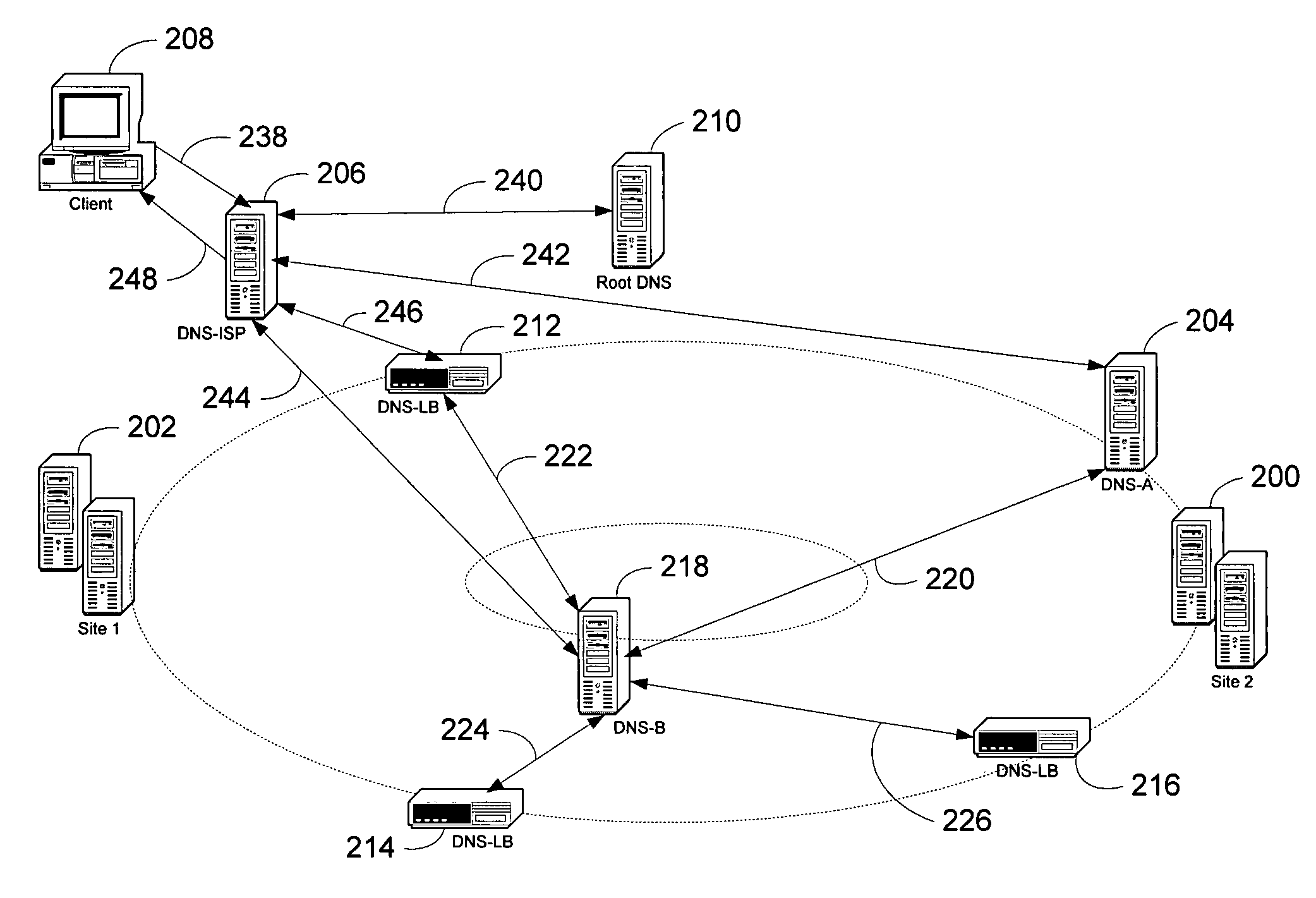
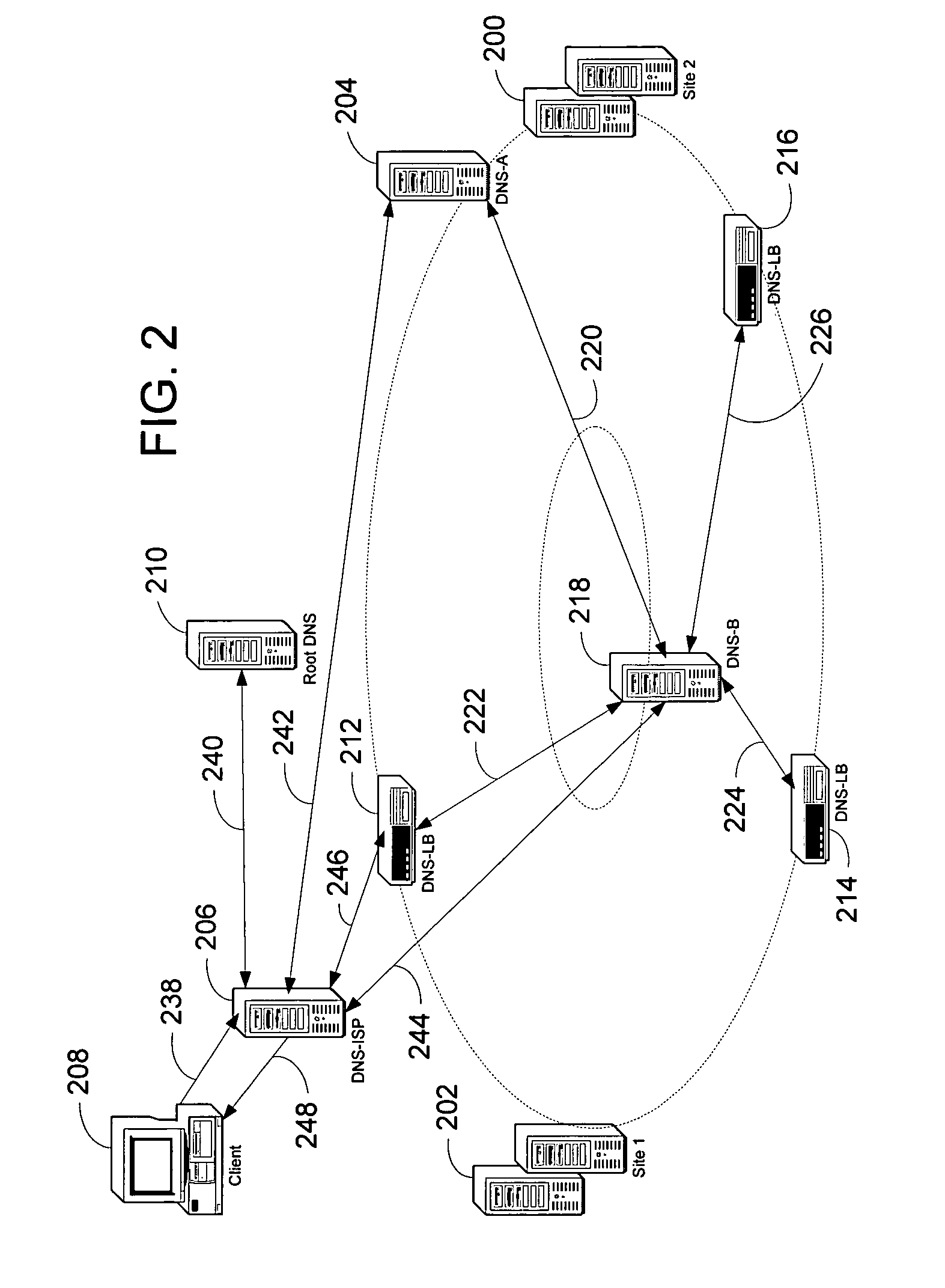
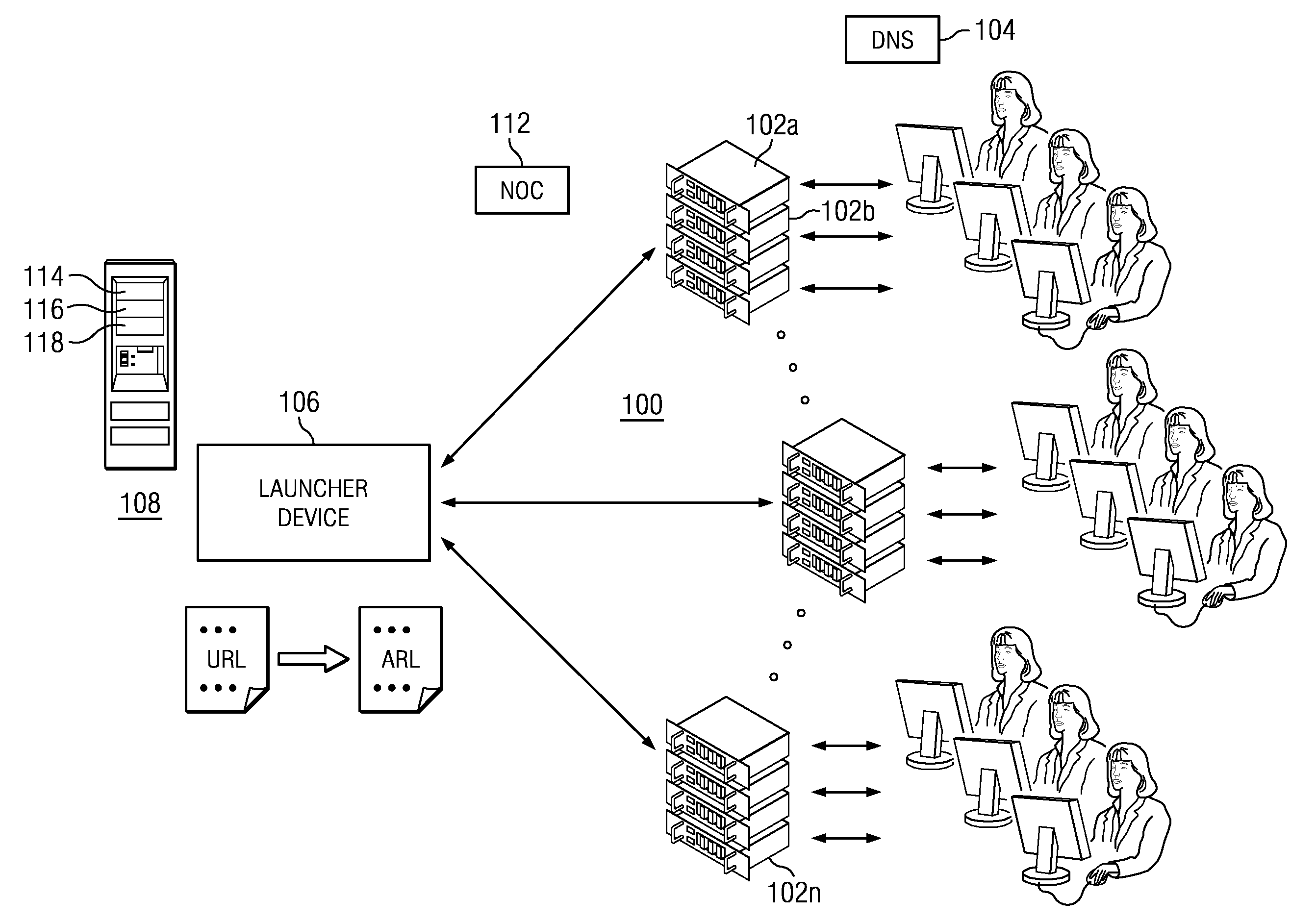
System and method for performing client-centric load balancing of multiple globally-dispersed servers
InactiveUS7653700B1Improve performanceLittle latencyMultiple digital computer combinationsData switching networksDomain nameIp address
Presented is a system and a method for load balancing multiple globally-dispersed servers based on client-centric performance criteria. The infrastructure of the system includes load balancing domain name servers (DNS-LBs) deployed in close physical proximity to the Internet service providers' points of presence. The DNS-LBs are then able to monitor the performance of the servers from a location close to the clients, which allows the DNS-LBs to select a server that will yield the best performance from that location for the client. A second level of the infrastructure utilizes domain name servers (DNS-Bs) that are deployed on the Internet backbones and regional provides. The authoritative domain name servers (DNS-As) for the servers to be load balanced refer all name queries to these DNS-Bs. The DNS-Bs then refer the queries to one of the DNS-LBs based on a mapping of the DNS-ISP address to its physically proximate DNS-LB. The DNS-LB then returns the IP address of the server that will provide the best performance from that location.
Owner:MICROSOFT TECH LICENSING LLC
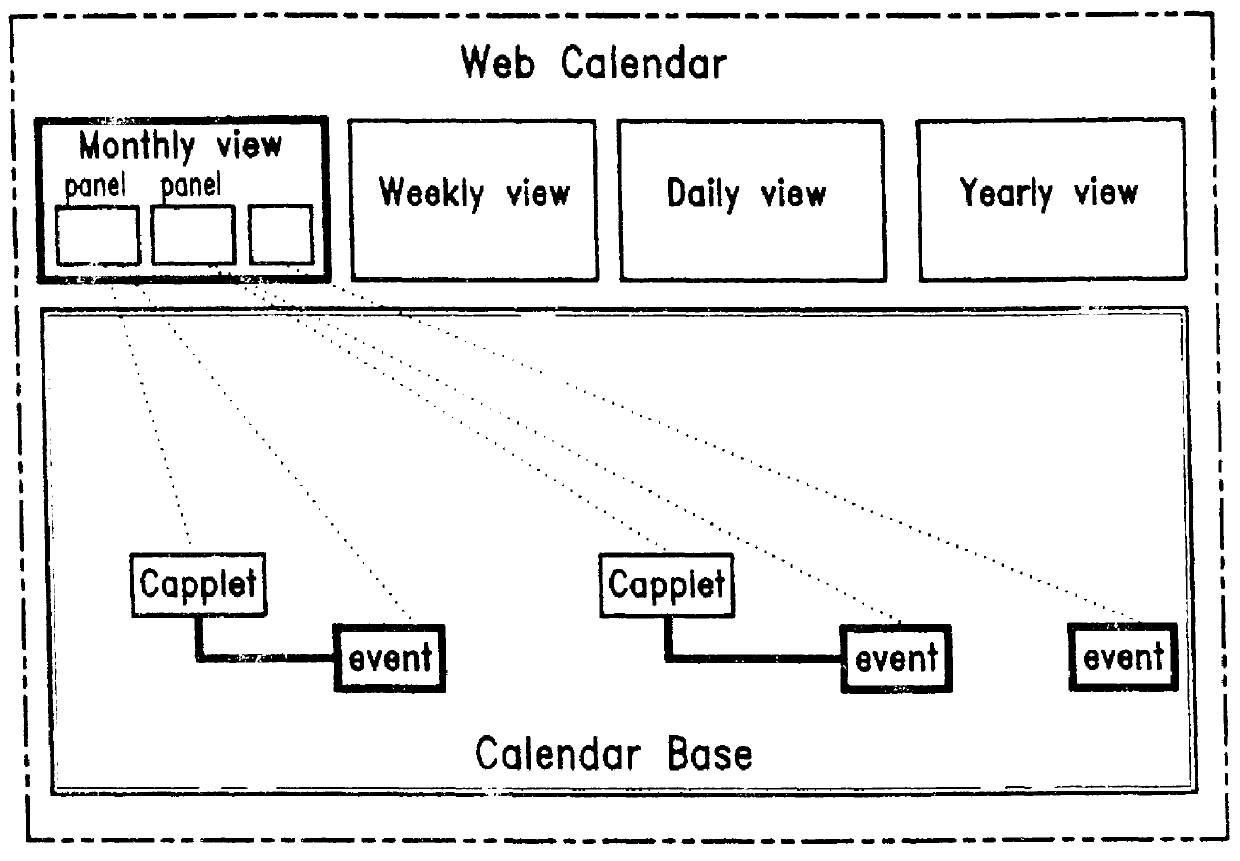
Web calendar architecture and uses thereof
InactiveUS6018343ADigital data processing detailsCathode-ray tube indicatorsInternet groupwarePersonal organizer
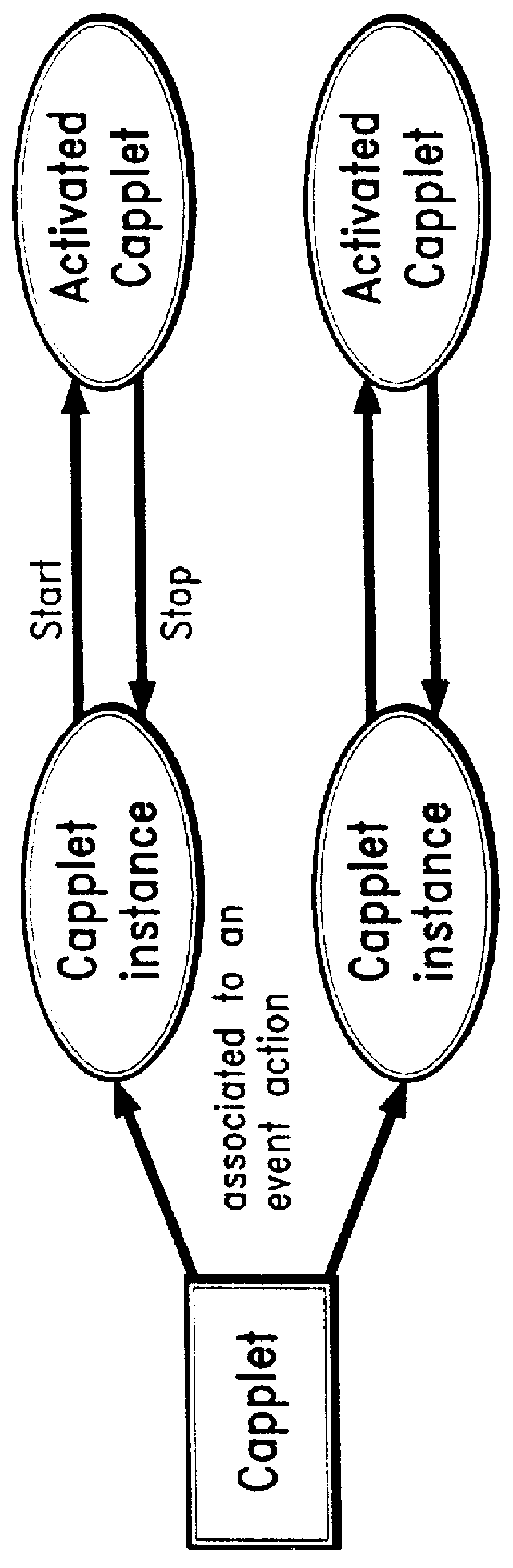
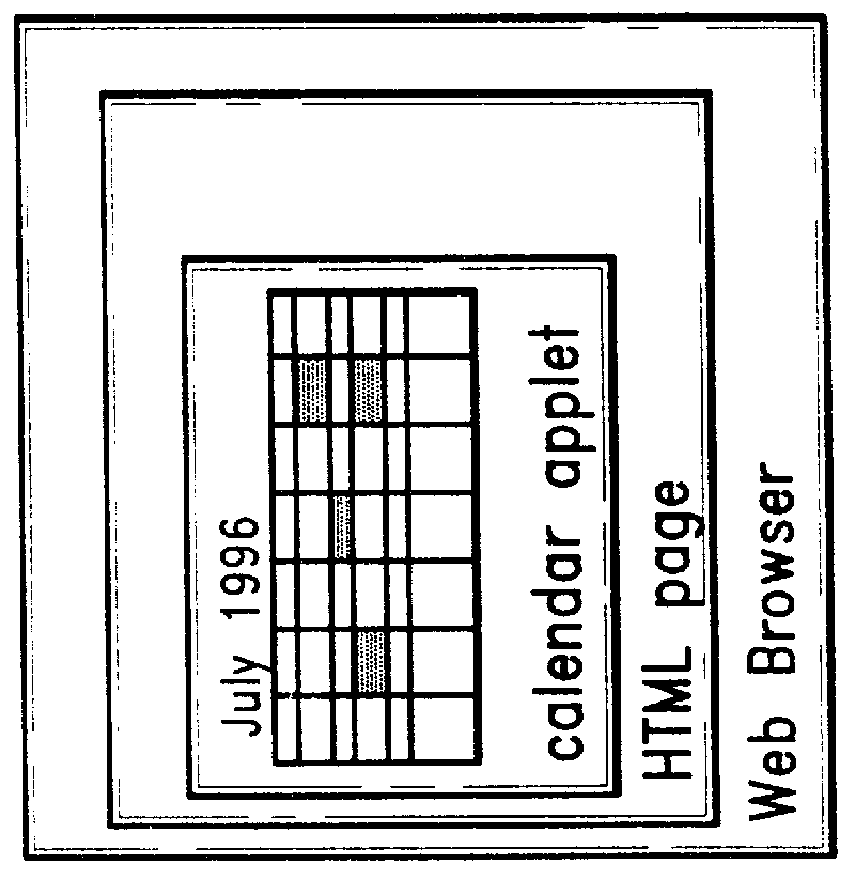
An architecture for facilitating Web-based client-side calendar event scheduling includes a Web Calendar scheduling tool which takes input via either a mouse and / or a keyboard to achieve a) an Internet personal organizer, b) multimedia effects associated with scheduled events, c) an Internet groupware that shares group members' individual schedules, d) an Internet transaction associated with scheduled events, and e) an open platform that supports any Java applet. Users of the Web Calendar can schedule events, associate a special purpose Capplet TM with scheduled events, and store them for future reference or public use. It features concurrent Capplet TM views running under one of four calendar grids: yearly, monthly, weekly, and daily. The architecture also supports multimedia animation in pop-up windows whose dimensions are defined dynamically by an invocation method. It is an open platform on which any user can create a special purpose applet and run it on the Web Calendar.
Owner:VIVINT INC
Content delivery network service provider (CDNSP)-managed content delivery network (CDN) for network service provider (NSP)
InactiveUS20070168517A1FinanceData switching by path configurationSchema for Object-Oriented XMLDistributed computing
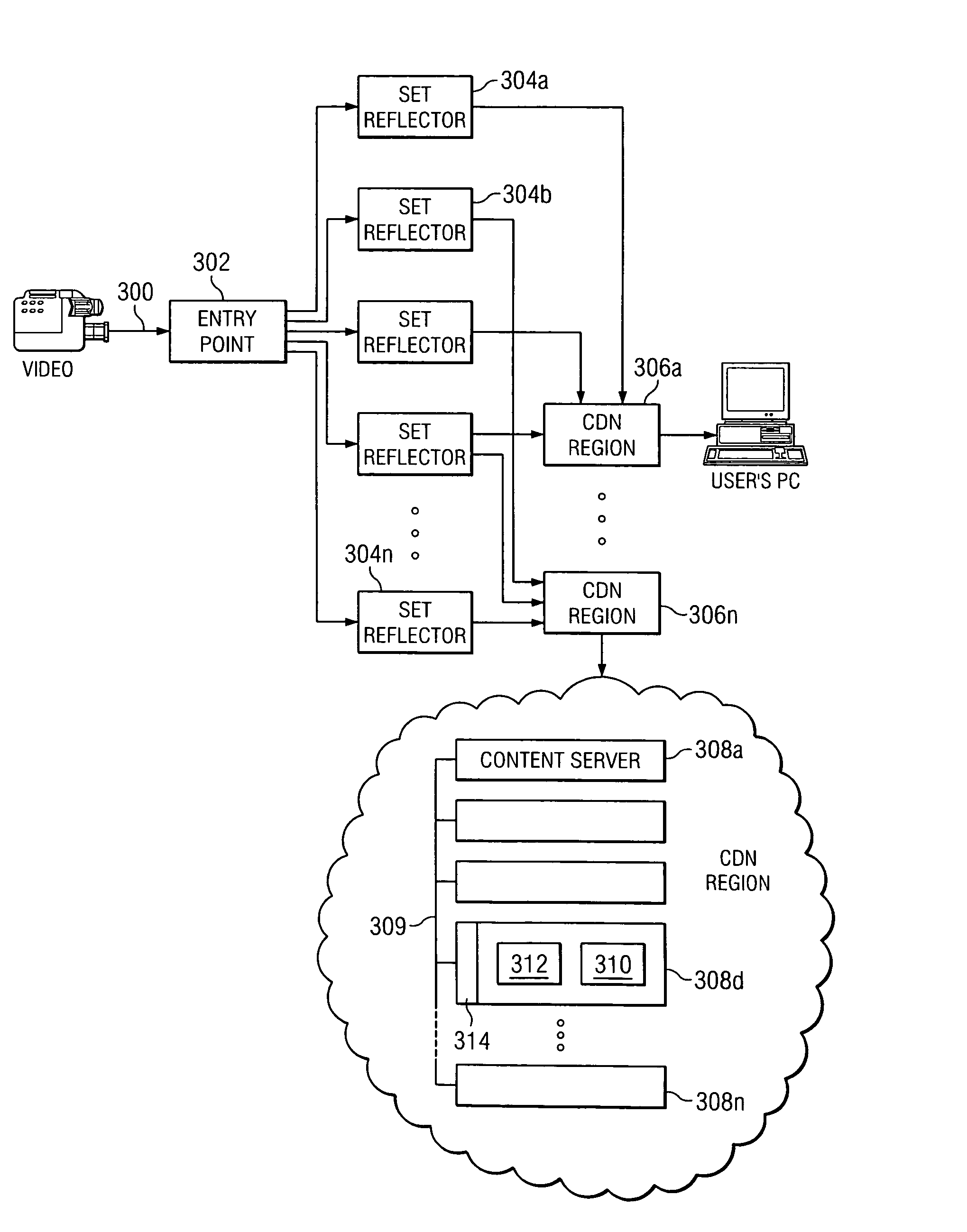
A CDN service provider shares its CDN infrastructure with a network to enable a network service provider (NSP) to offer a private-labeled network content delivery network (NCDN or “private CDN”) to participating content providers. The CDNSP preferably provides the hardware, software and services required to build, deploy, operate and manage the CDN for the NCDN customer. Thus, the NCDN customer has access to and can make available to participating content providers one or more of the content delivery services (e.g., HTTP delivery, streaming media delivery, application delivery, and the like) available from the global CDN without having to provide the large capital investment, R&D expense and labor necessary to successfully deploy and operate the network itself. Rather, the global CDN service provider simply operates the private CDN for the network as a managed service.
Owner:AKAMAI TECH INC
Network performance monitoring in a content delivery service
InactiveUS7716367B1Multiple digital computer combinationsLocation information based serviceContent distributionNetwork architecture
A network architecture or framework that supports hosting and content distribution on a truly global scale allows a Content Provider to replicate and serve its most popular content at an unlimited number of points throughout the world. The inventive framework comprises a set of servers operating in a distributed manner. The actual content to be served is preferably supported on a set of hosting servers (sometimes referred to as ghost servers). This content comprises HTML page objects that, conventionally, are served from a Content Provider site. A base HTML document portion of a Web page is served from the Content Provider's site while one or more embedded objects for the page are served from the hosting servers, preferably, those hosting servers near the client machine. By serving the base HTML document from the Content Provider's site, the Content Provider maintains control over the content.
Owner:AKAMAI TECH INC
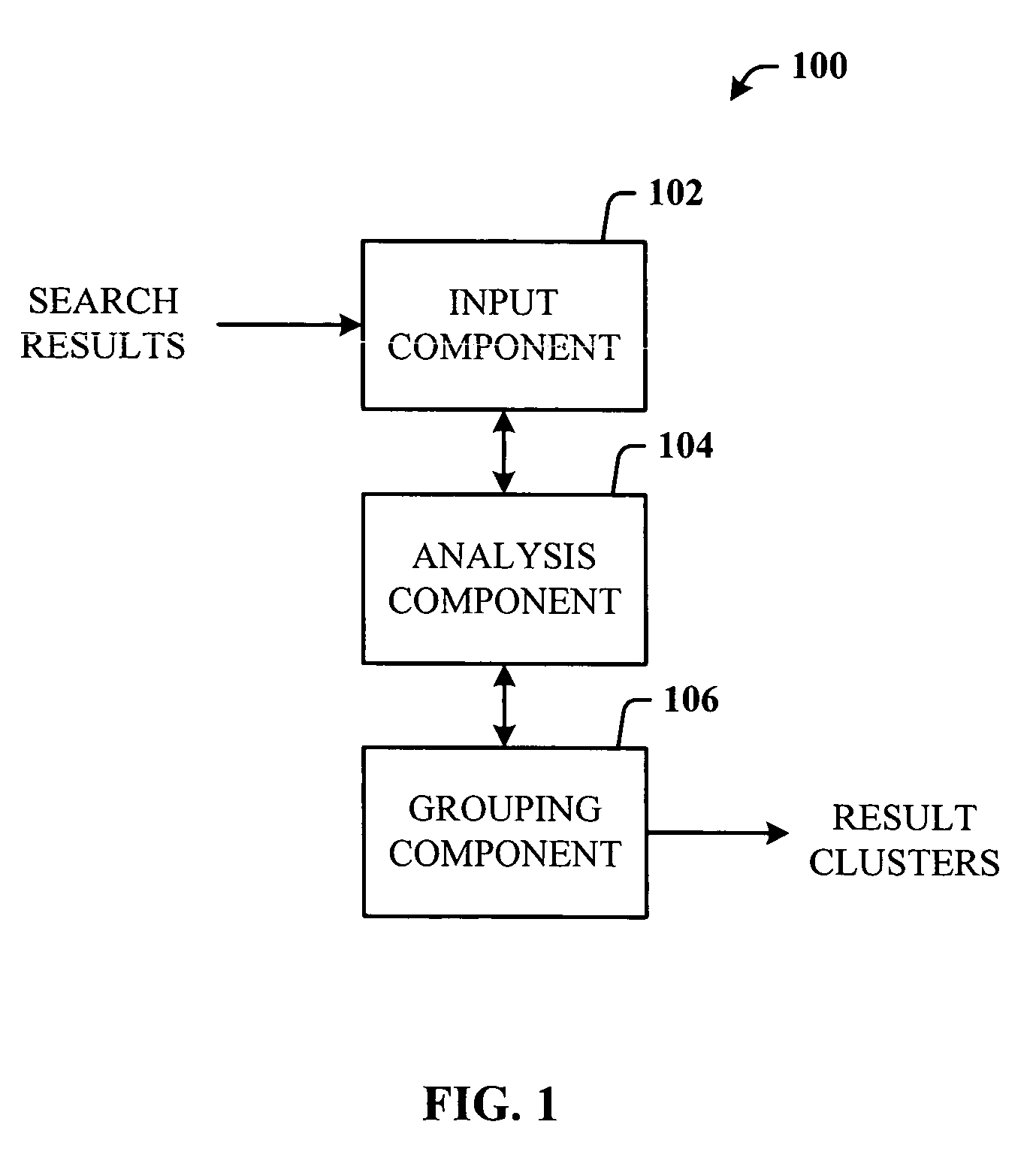
Query-based snippet clustering for search result grouping
InactiveUS20060026152A1Quick identificationEfficient identificationWeb data indexingSpecial data processing applicationsFeature vectorCo-occurrence
Owner:MICROSOFT TECH LICENSING LLC
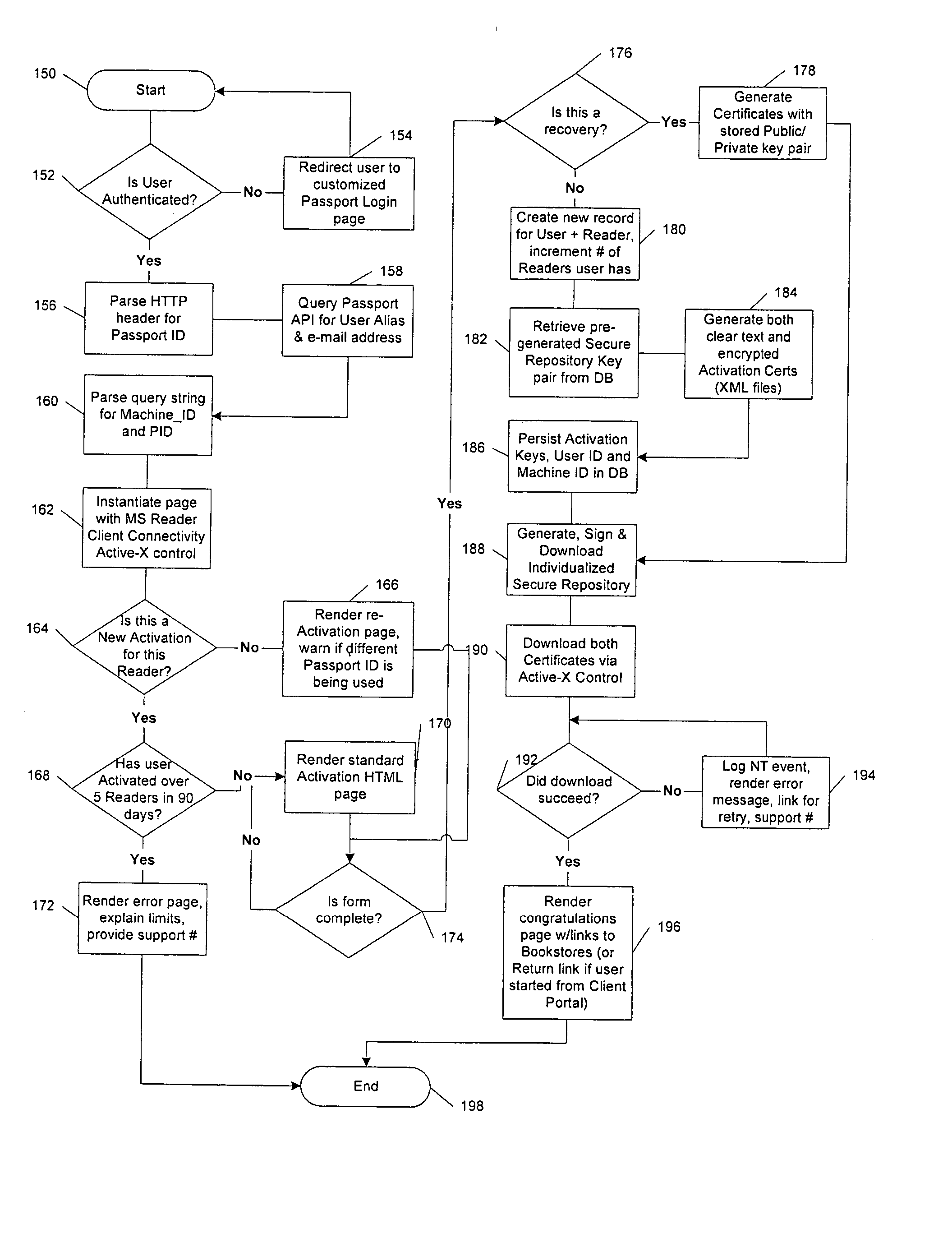
Method and system for limiting the use of user-specific software features
InactiveUS20050060266A1Preventing unchecked proliferationDigital data processing detailsUser identity/authority verificationSchema for Object-Oriented XMLUniform resource locator
A server architecture for a digital rights management system that distributes and protects rights in content. The server architecture includes a retail site which sells content items to consumers, a fulfillment site which provides to consumers the content items sold by the retail site, and an activation site which enables consumer reading devices to use content items having an enhanced level of copy protection. Each retail site is equipped with a URL encryption object, which encrypts, according to a secret symmetric key shared between the retail site and the fulfillment site, information that is needed by the fulfillment site to process an order for content sold by the retail site. Upon selling a content item, the retail site transmits to the purchaser a web page having a link to a URL comprising the address of the fulfillment site and a parameter having the encrypted information. Upon following the link, the fulfillment site downloads the ordered content to the consumer, preparing the content if necessary in accordance with the type of security to be carried with the content. The fulfillment site includes an asynchronous fulfillment pipeline which logs information about processed transactions using a store-and-forward messaging service. The fulfillment site may be implemented as several server devices, each having a cache which stores frequently downloaded content items, in which case the asynchronous fulfillment pipeline may also be used to invalidate the cache if a change is made at one server that affects the cached content items. An activation site provides an activation certificate and a secure repository executable to consumer content-rendering devices which enables those content rendering devices to render content having an enhanced level of copy-resistance. The activation site “activates” client-reading devices in a way that binds them to a persona, and limits the number of devices that may be activated for a particular persona, or the rate at which such devices may be activated for a particular persona.
Owner:MICROSOFT TECH LICENSING LLC
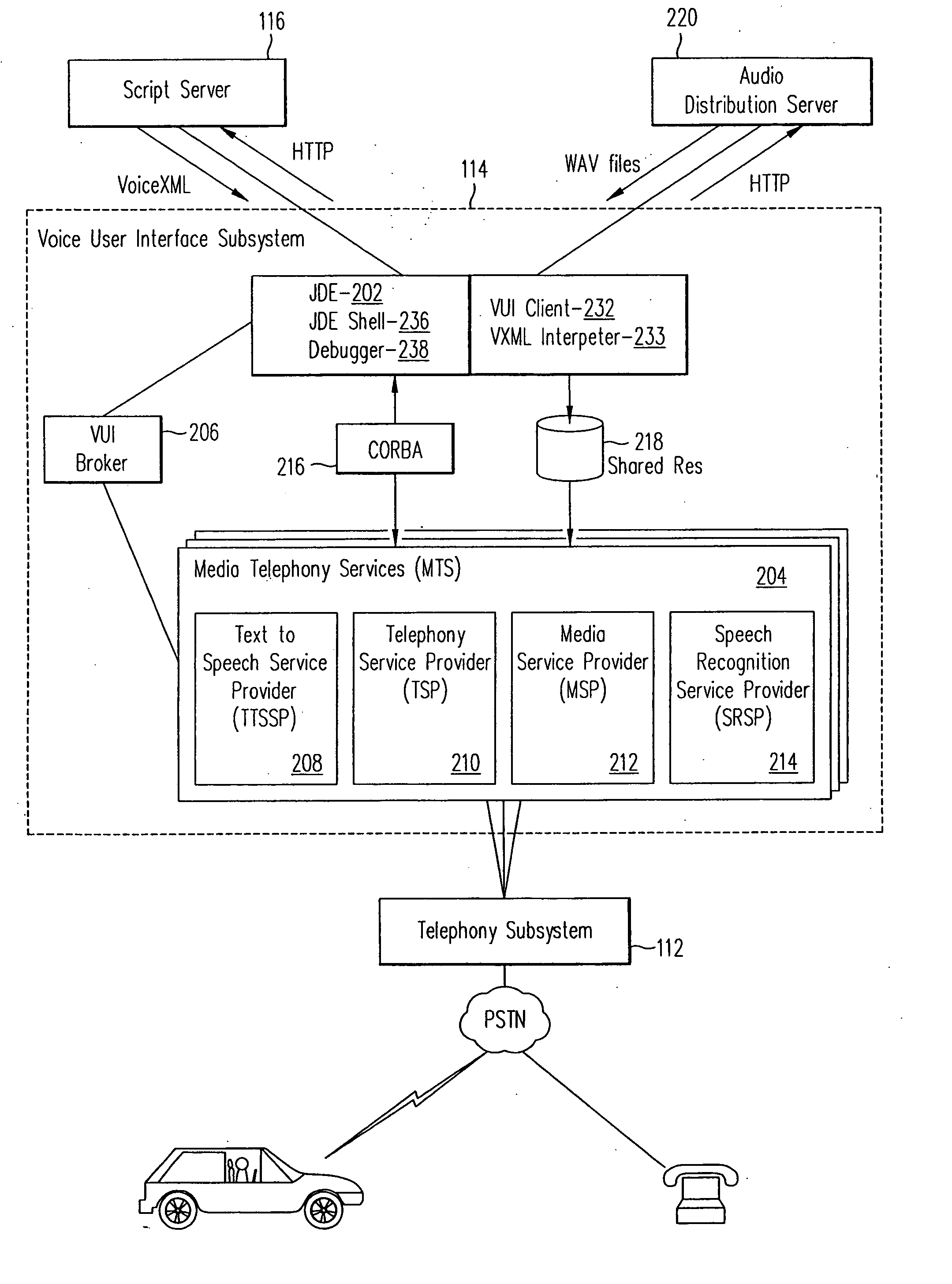
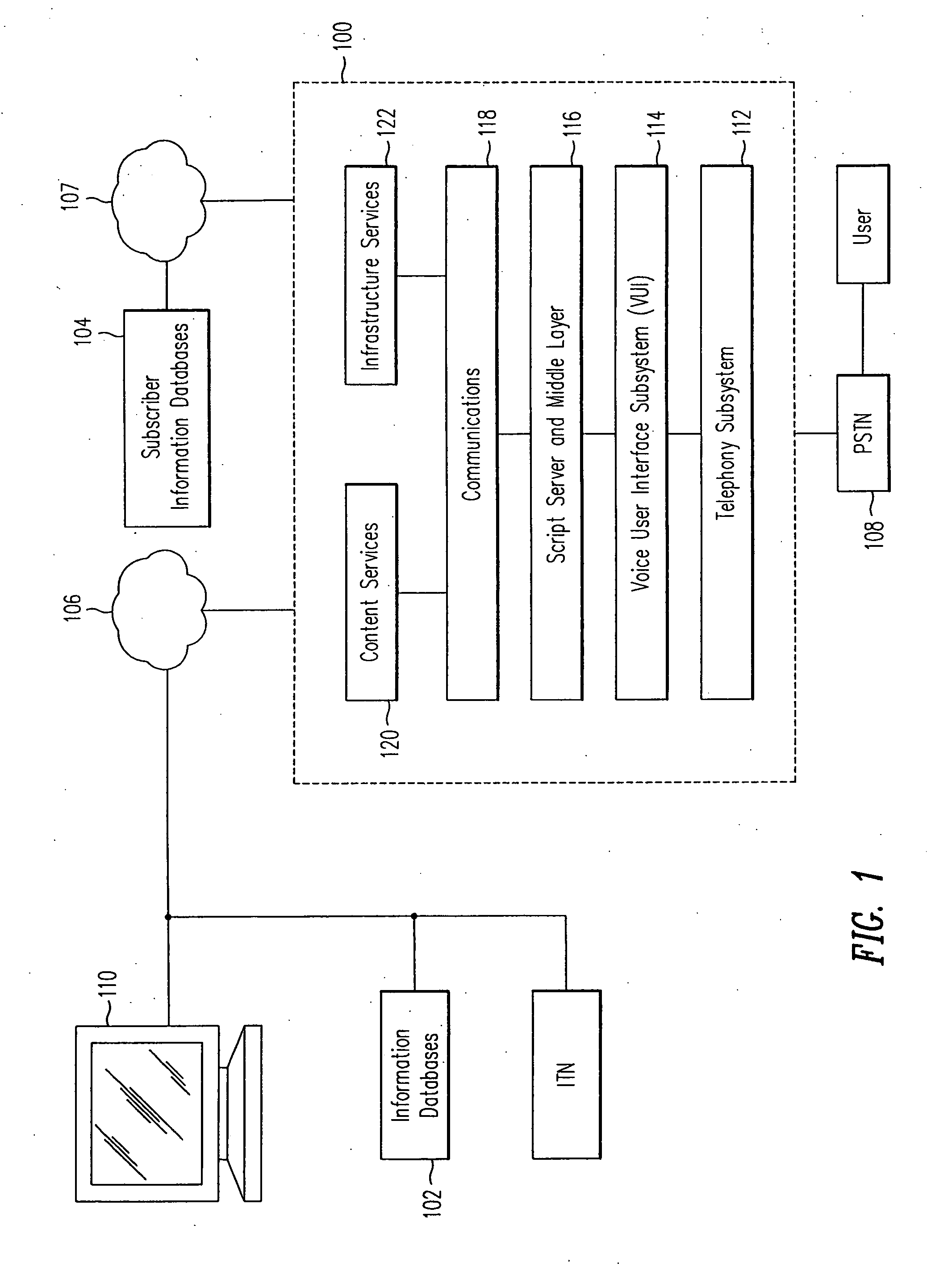
Open architecture for a voice user interface
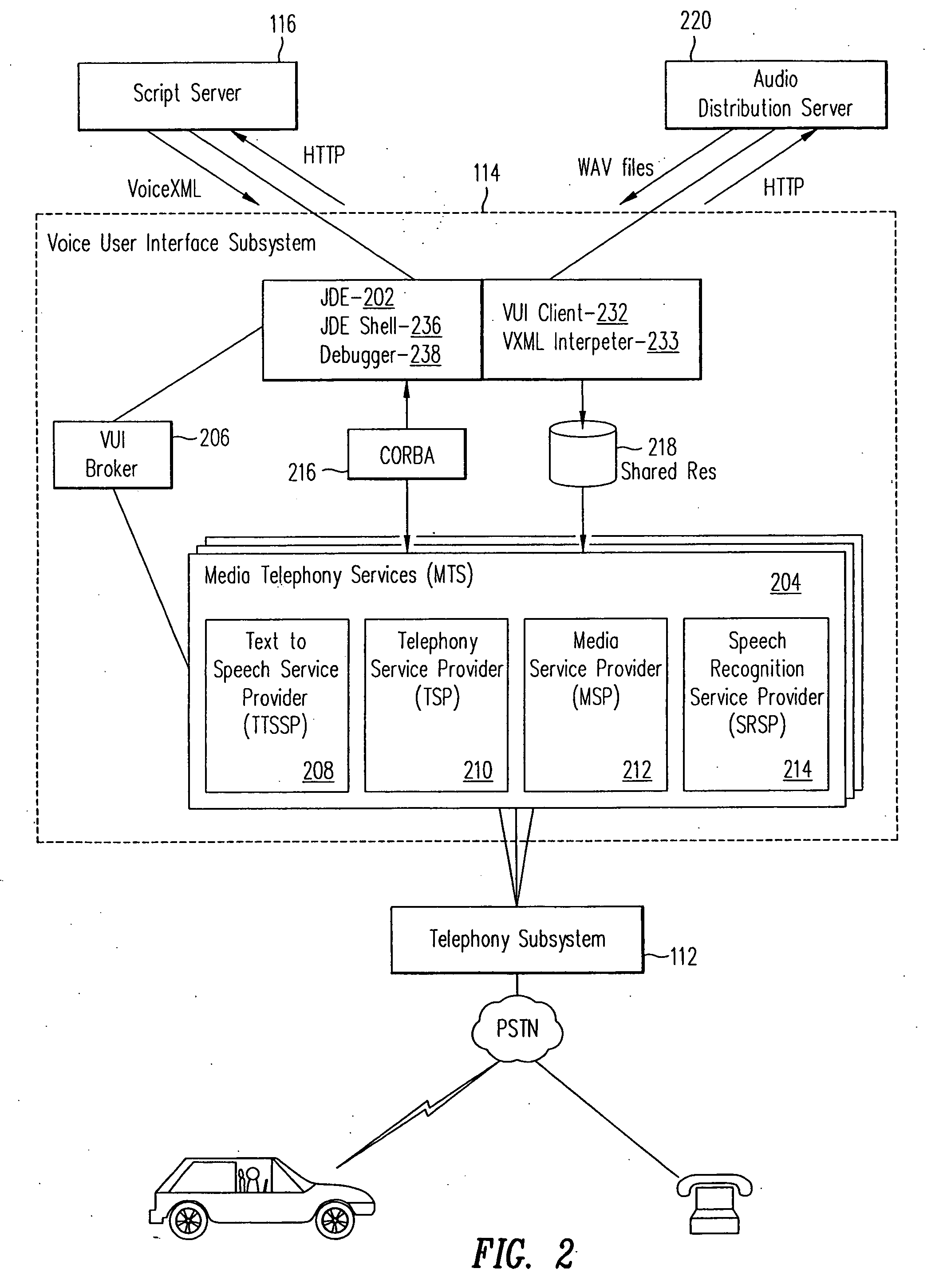
InactiveUS20060190269A1Automatic call-answering/message-recording/conversation-recordingSpeech recognitionUser inputSchema for Object-Oriented XML
A system and method for processing voice requests from a user for accessing information on a computerized network and delivering information from a script server and an audio server in the network in audio format. A voice user interface subsystem includes: a dialog engine that is operable to interpret requests from users from the user input, communicate the requests to the script server and the audio server, and receive information from the script server and the audio server; a media telephony services (MTS) server, wherein the MTS server is operable to receive user input via a telephony system, and to transfer the user input to the dialog engine; and a broker coupled between the dialog engine and the MTS server. The broker establishes a session between the MTS server and the dialog engine and controls telephony functions with the telephony system.
Owner:INTELLECTUAL VENTURES I LLC
Method and apparatus for providing content access controls to access the internet
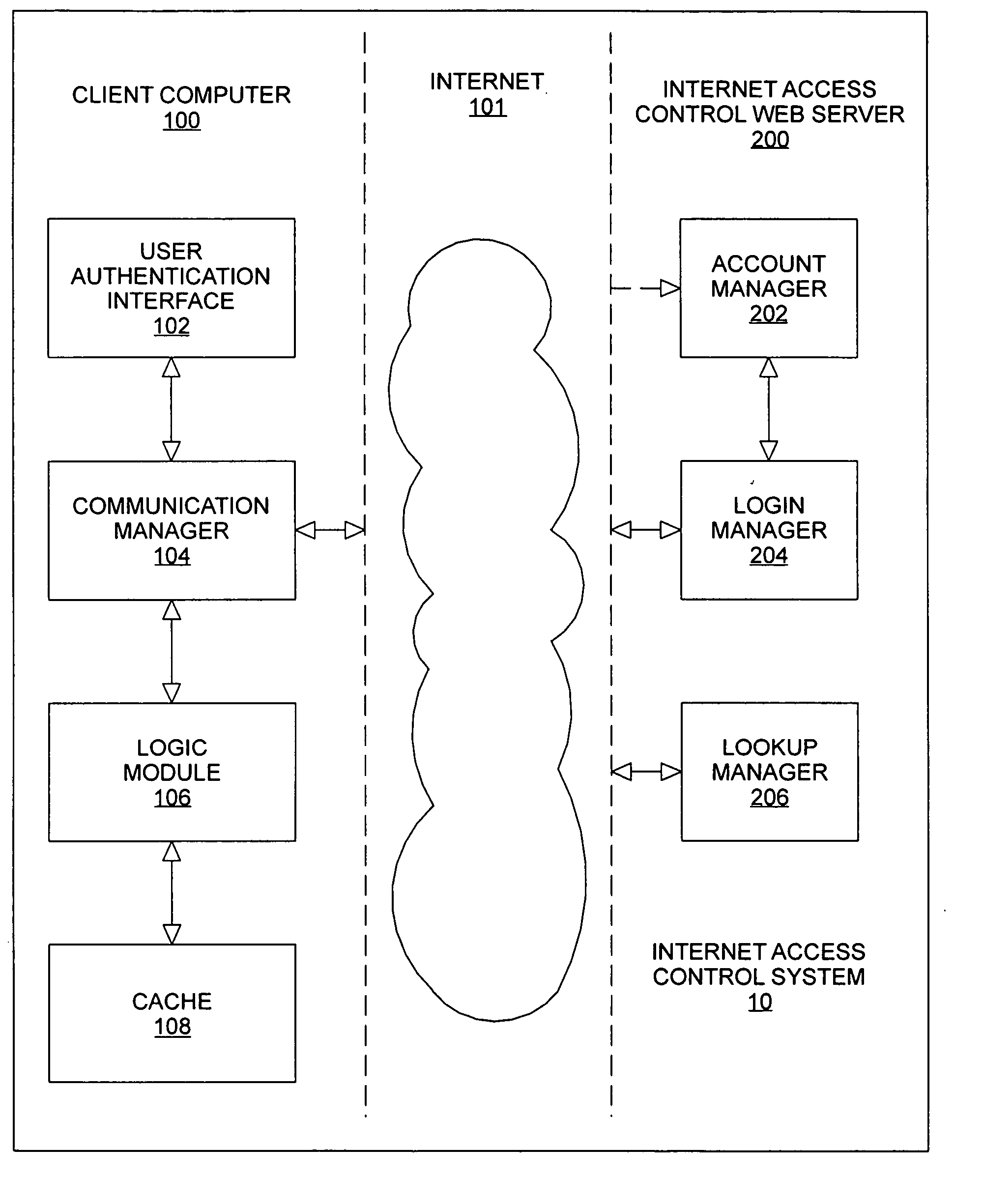
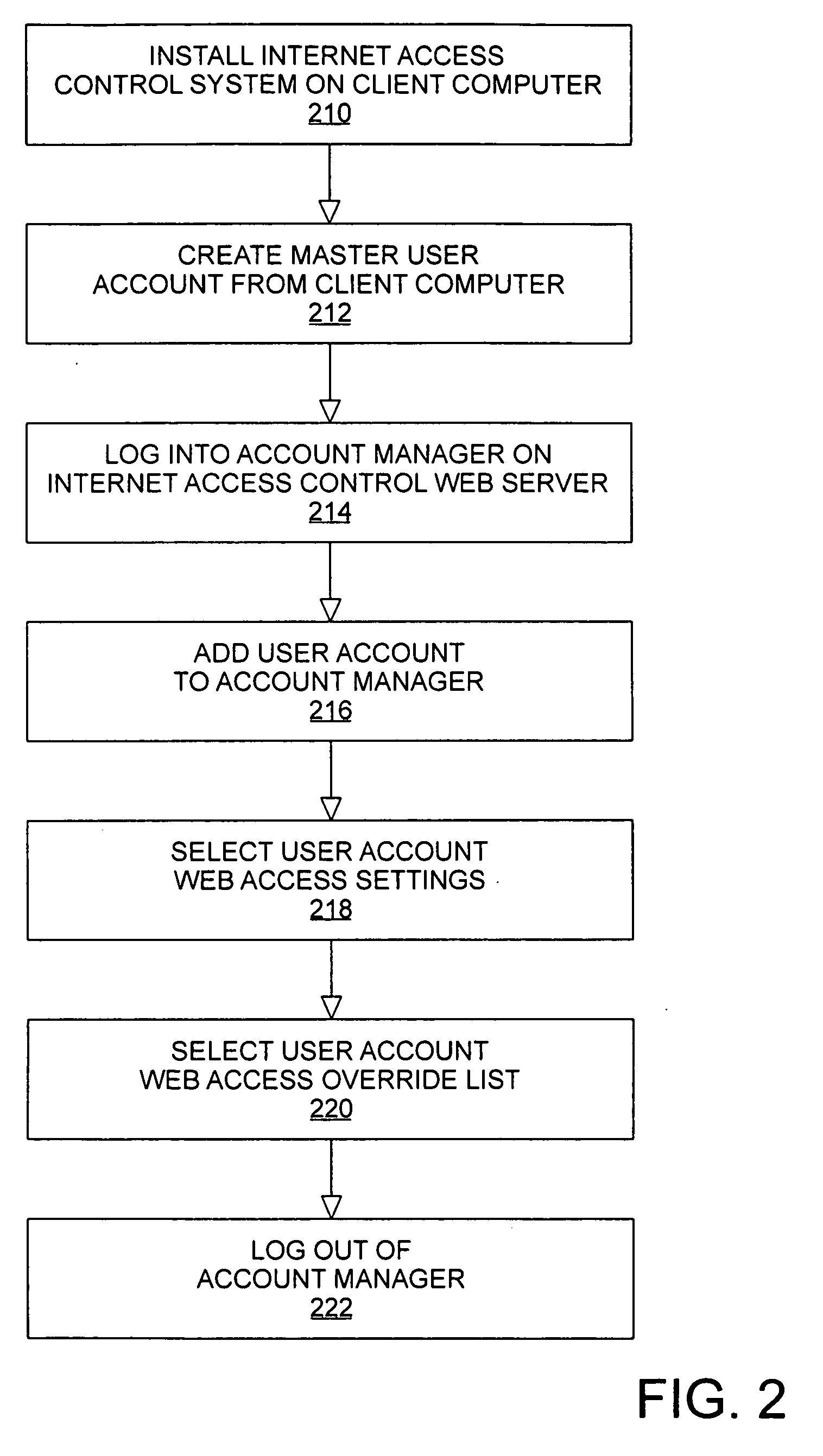
InactiveUS20050144297A1Multiple digital computer combinationsTransmissionInformation transmissionControl system
An Internet access control system is defined using a client-server architecture. The computer program installed on the client computer validates / identifies the user and user specific information is passed to the client computer. All user requests to access the Internet are intercepted by an application executing on the client computer. The URL extracted from the internet access request is sent to the Internet access control web server to determine if the URL is in a master list of previously evaluated websites. If the URL is found, the website ratings and subject matter categories are sent to the client computer for determination of whether or not the website contains information appropriate for the user attempting to access the Internet using web access settings defined by, for example, a parent or employer. If the URL is determined to be appropriate, the Internet access request is sent to the computer networking layer to which the request was originally routed; otherwise, the Internet access request is edited and is sent to the computer networking layer to which the request was originally routed for redirection of the transmission request.
Owner:KIDSNET
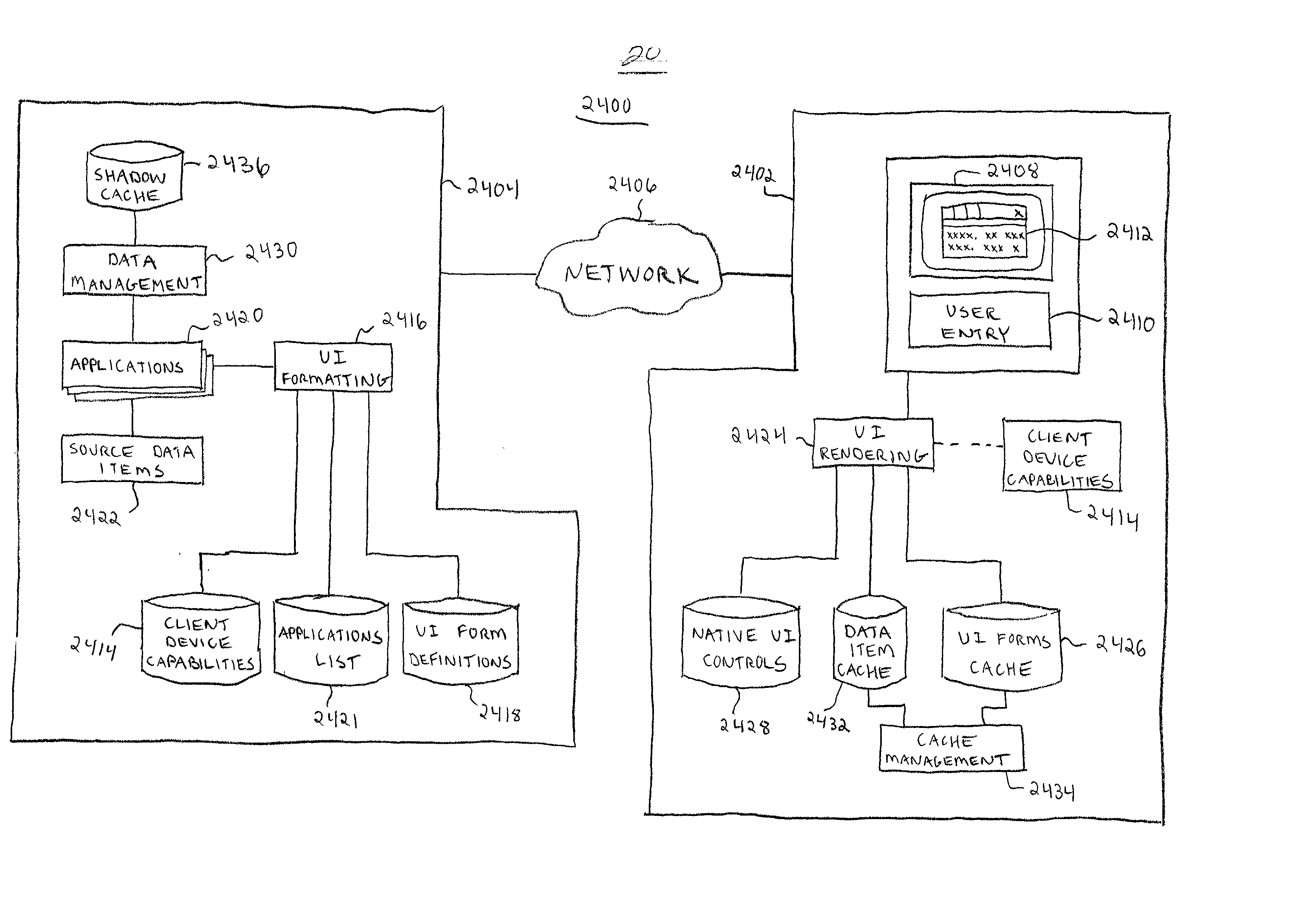
Platform-independent distributed user interface client architecture
InactiveUS20020129096A1Reduce demandLower-bandwidthCathode-ray tube indicatorsMultiple digital computer combinationsDistributed user interfaceThe Internet
A distributed user interface (UI) system includes a client device configured to render a UI for a server-based application. The client device communicates with a UI server over a network such as the Internet. The UI server performs formatting for the UI, which preferably utilizes a number of native UI controls that are available locally at the client device. In this manner, the client device need only be responsible for the actual rendering of the UI. The source data items are downloaded from the UI server to the client device when necessary, and the client device populates the UI with the downloaded source data items. The client device employs a cache to store the source data items locally for easy retrieval.
Owner:SPROQIT TECHNOLGIES
Triggering applications based on a captured text in a mixed media environment
ActiveUS20070050360A1Easy to optimizeFacilitate methodMultimedia data indexingSpecial data processing applicationsInformation retrievalApplication software
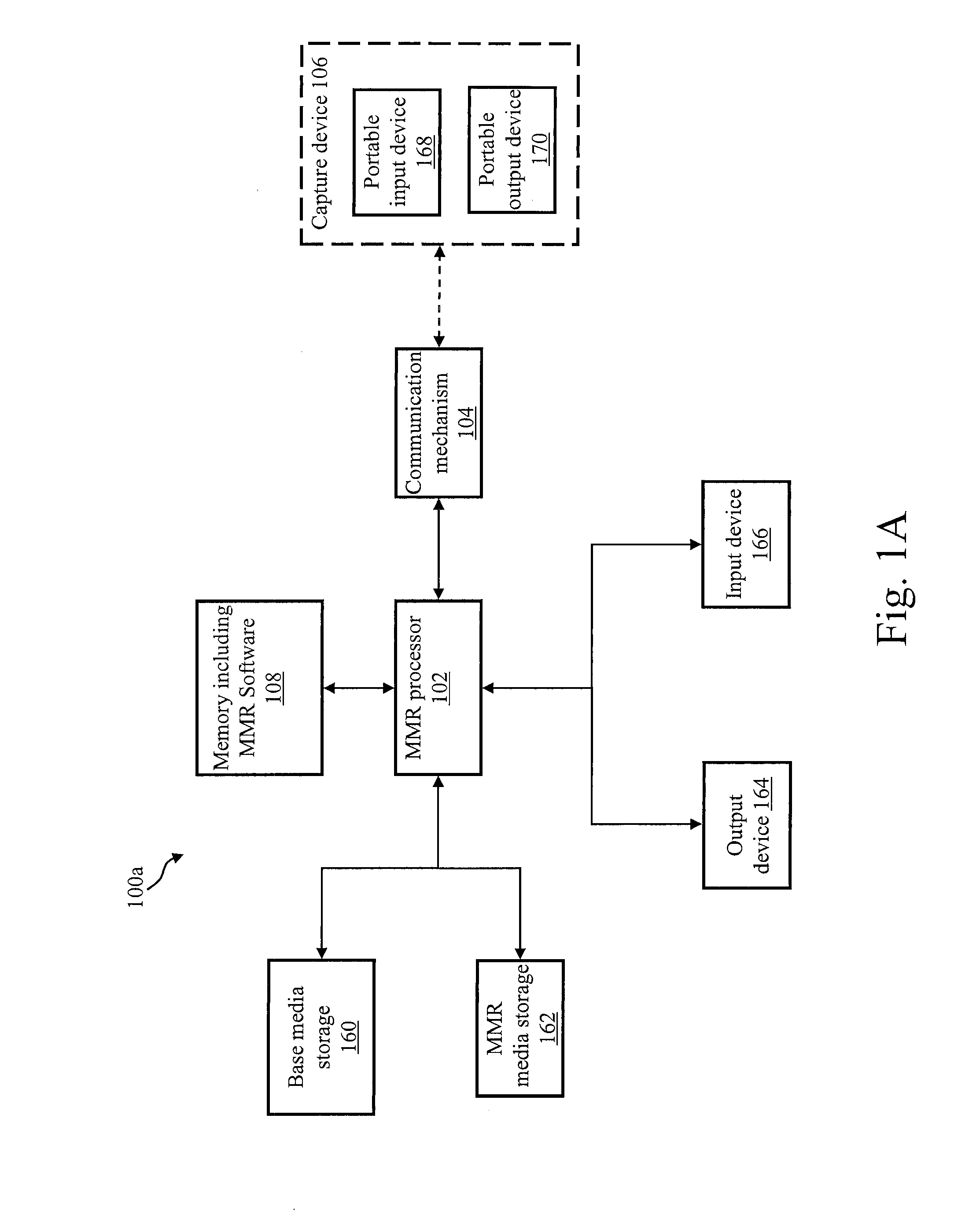
A Mixed Media Reality (MMR) system and associated techniques are disclosed. The MMR system provides mechanisms for forming a mixed media document that includes media of at least two types (e.g., printed paper as a first medium and digital content and / or web link as a second medium). In one particular embodiment, the MMR system includes an action processor and method, and MMR documents with an associated action. The MMR document structure is particularly advantageous because the ability to specify different actions for different MMR documents, combined with the ability to create any number of MMR documents for a particular location on any media, allows the MMR architecture to serve as a universal trigger or initiator for additional processing. In other words, addition processing or actions can be triggered or initiated based on MMR recognition. The action processor receives the output of the MMR recognition process which yields an MMR document including at least one action. The action processor executes that action which includes various commands to the MMR system or other systems coupled to the MMR system. The MMR system architecture is advantageous because an action can be executed by pointing the capture device at a block of text, and the action is performed. Example actions include retrieving the text in electronic form to the capture device, retrieving the specification for the action, inserting data to a MMR document, transferring data between documents, purchasing items, authoring actions or reviewing historical information about actions. The MMR system includes a variety of user applications (one or more actions) initiated by the MMR recognition of a text patch such as information retrieval for a travel guide book, stock listings or advertisements; information capture such as recording content from a conference, recording and storing multimedia associated with the document, capturing information for a calendar and on the fly authoring; purchasing media files for storage on any part of an MMR document.
Owner:RICOH KK
Systems and methods for direction of communication traffic
InactiveUS20050105513A1Avoid problemsServices signallingMultiple digital computer combinationsWeb browserIp address
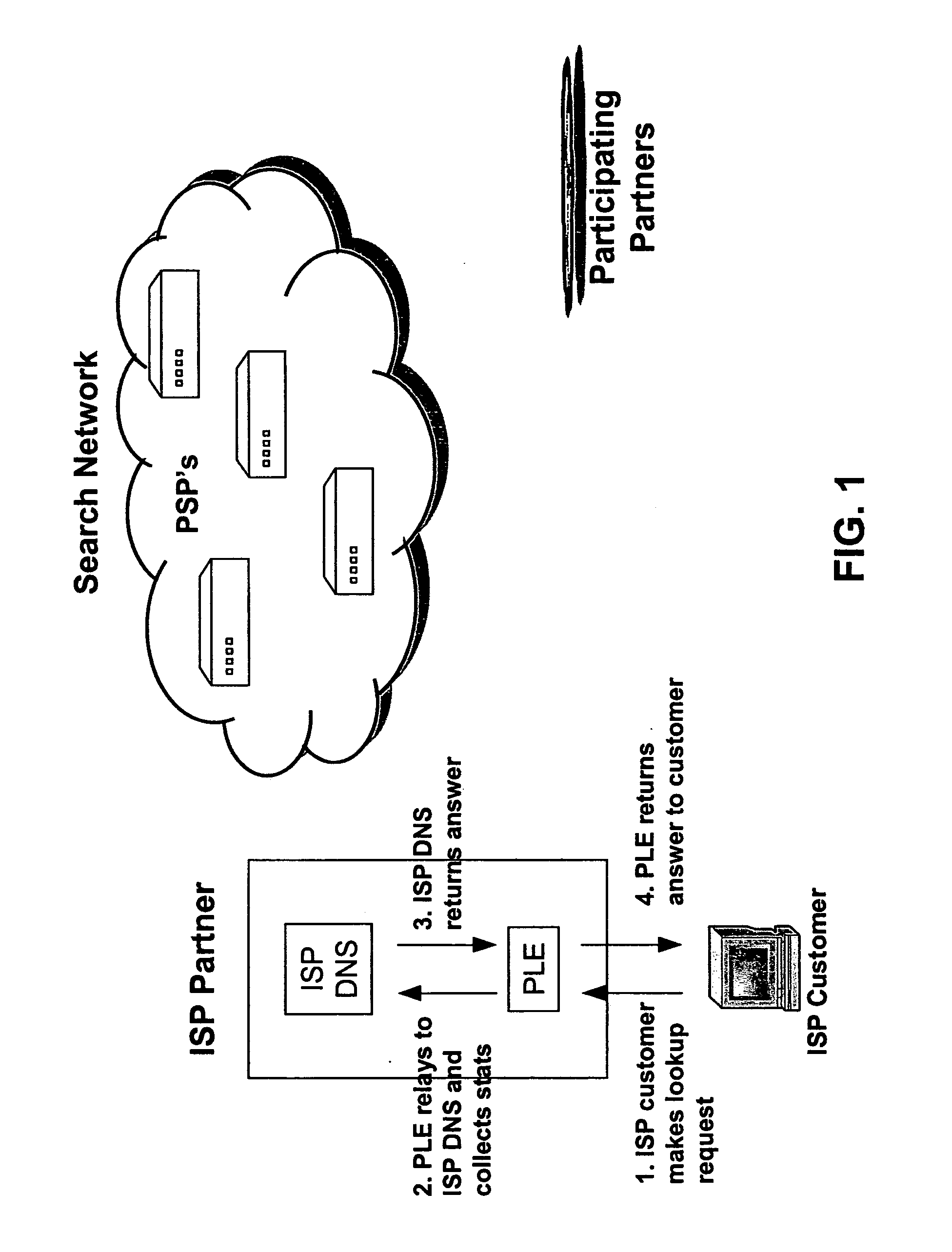
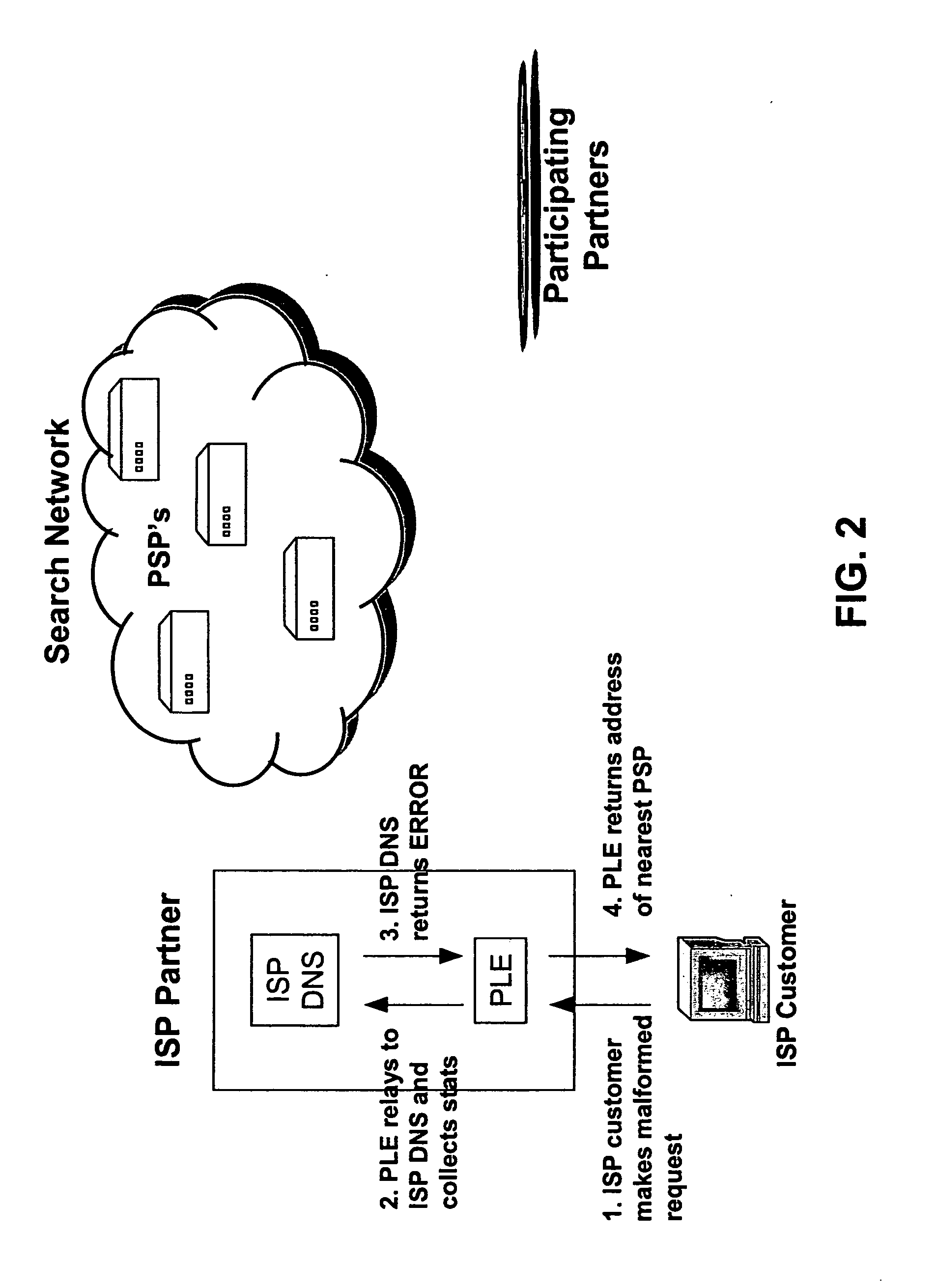
An internet traffic redirection architecture is disclosed that allows for directing of various traffic to specified sites. The system and method allow a controller, such as an ISP, to benefit from unresolved IP Address requests and keyword and hotword queries by capturing this traffic and directing it to participating partners who provide content relevant and / or geographically relevant results. The system and method can decrease lost traffic, irrelevant keyword and hotword search results, and irrelevant redirection by web browsers resident on user's personal computers.
Owner:PAXFIRE
Virtual file system
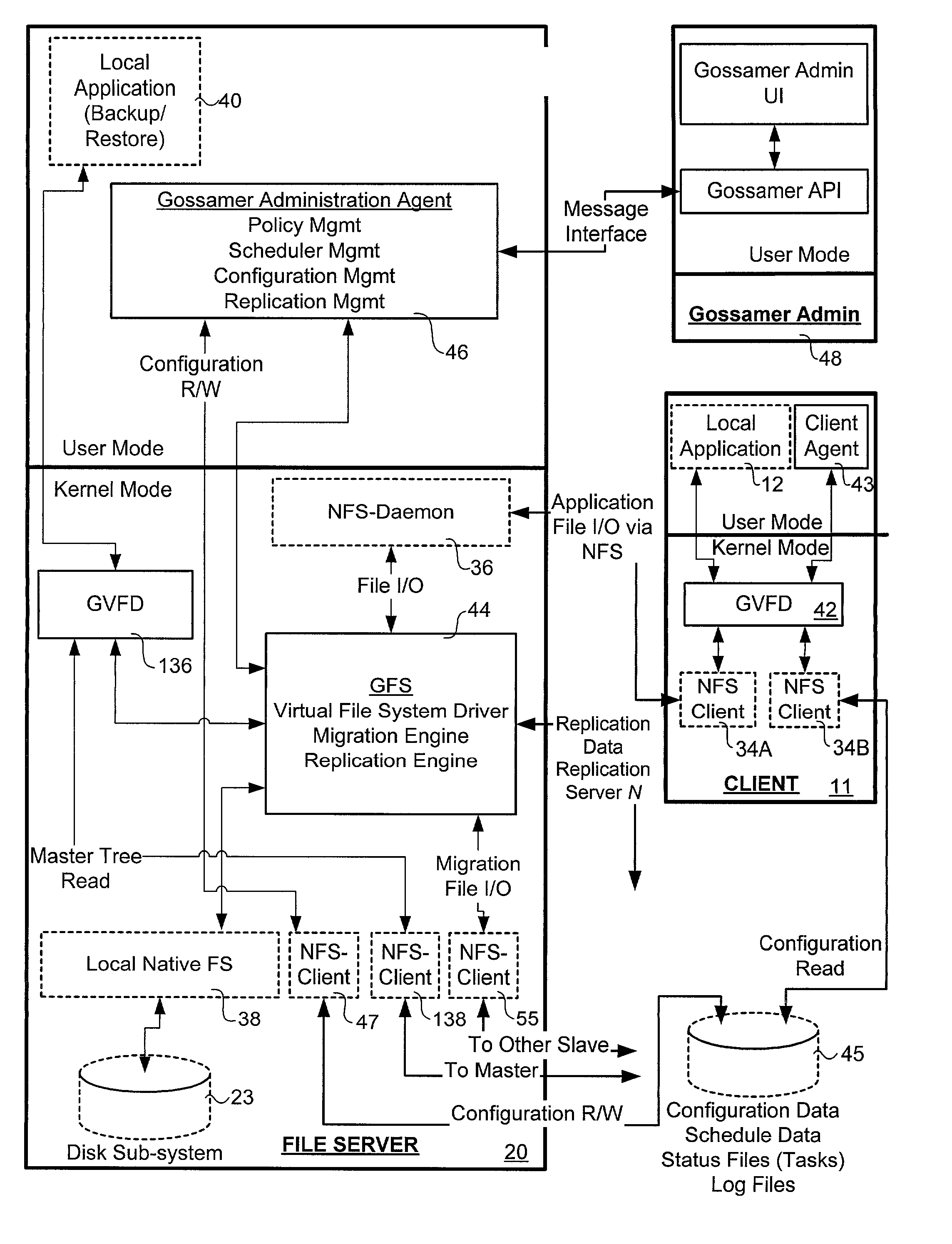
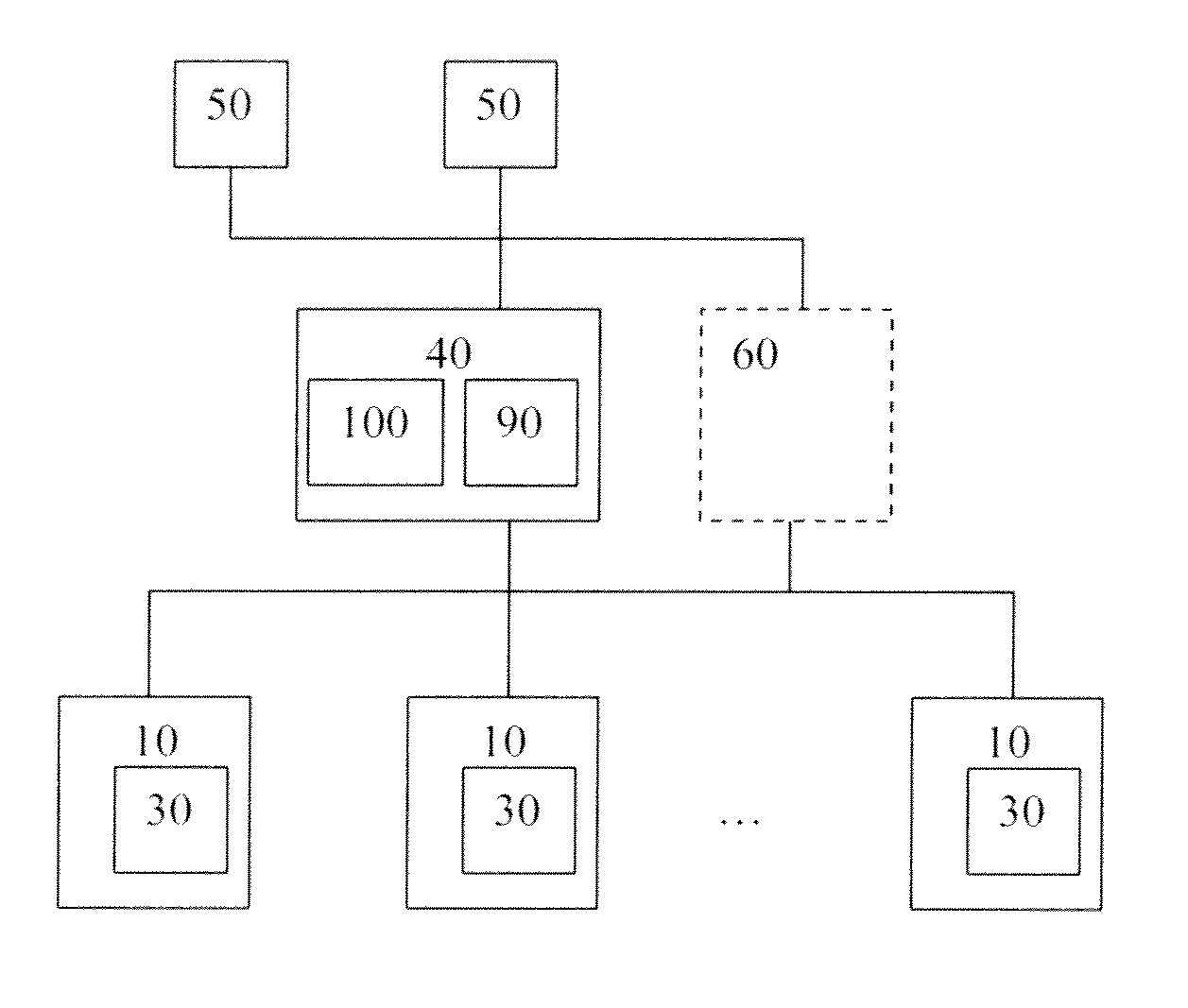
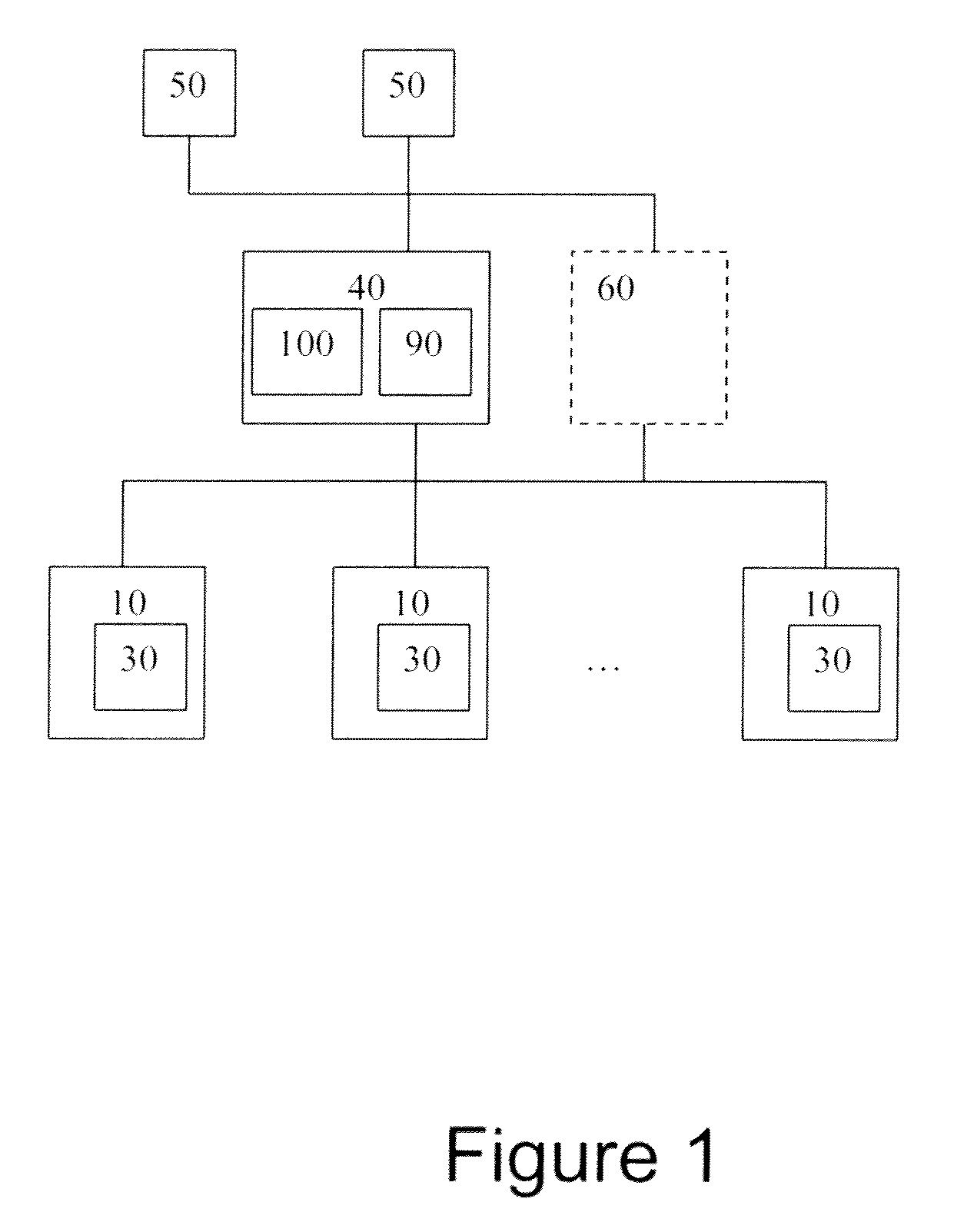
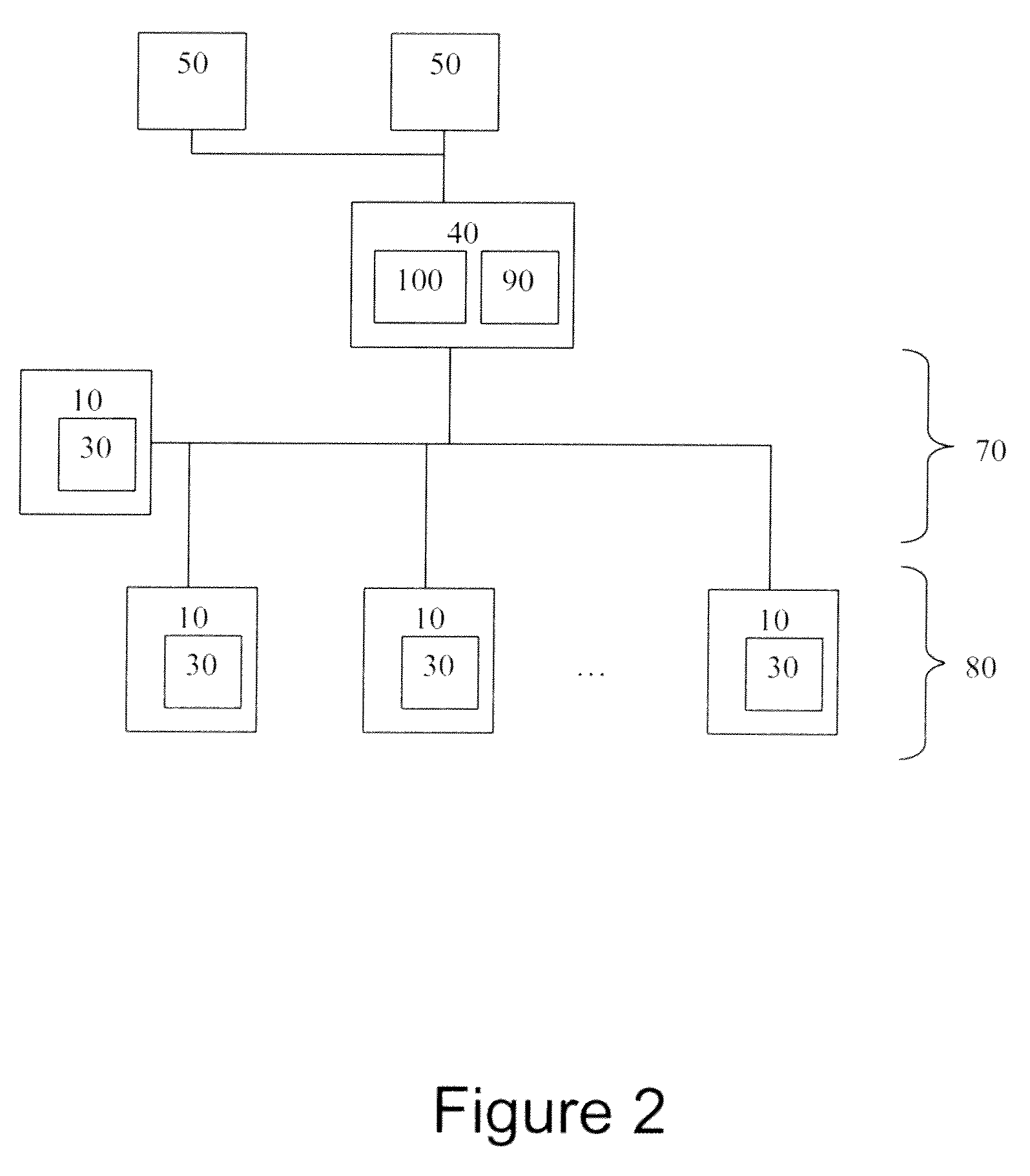
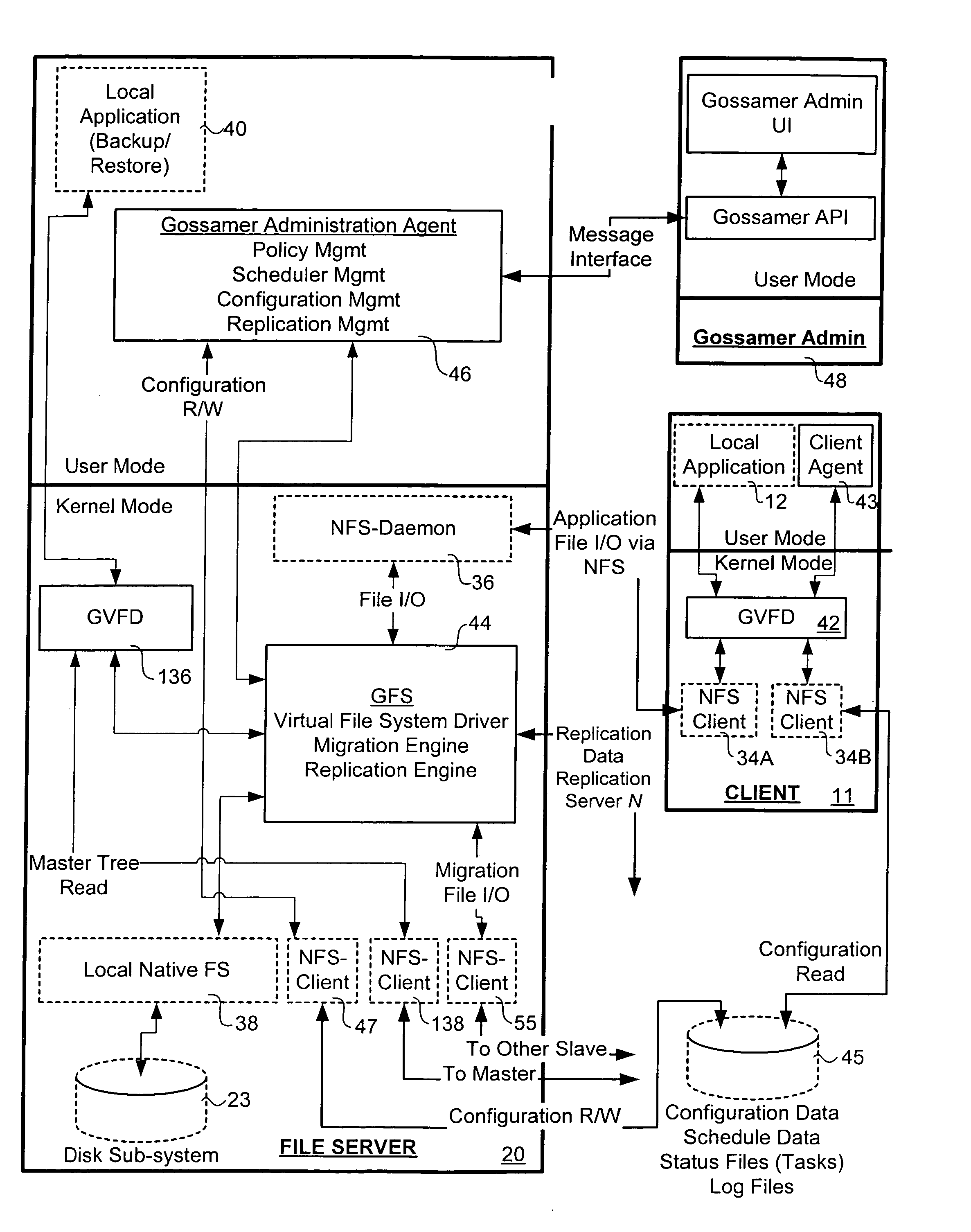
InactiveUS7024427B2Function increaseDigital data information retrievalInput/output to record carriersGlobal file systemData file
A virtual file system and method. The system architecture enables a plurality of underlying file systems running on various file servers to be “virtualized” into one or more “virtual volumes” that appear as a local file system to clients that access the virtual volumes. The system also enables the storage spaces of the underlying file systems to be aggregated into a single virtual storage space, which can be dynamically scaled by adding or removing file servers without taking any of the file systems offline and in a manner transparent to the clients. This functionality is enabled through a software “virtualization” filter on the client that intercepts file system requests and a virtual file system driver on each file server. The system also provides for load balancing file accesses by distributing files across the various file servers in the system, through migration of data files between servers.
Owner:EMC IP HLDG CO LLC
Networked computer telephony system driven by web-based applications
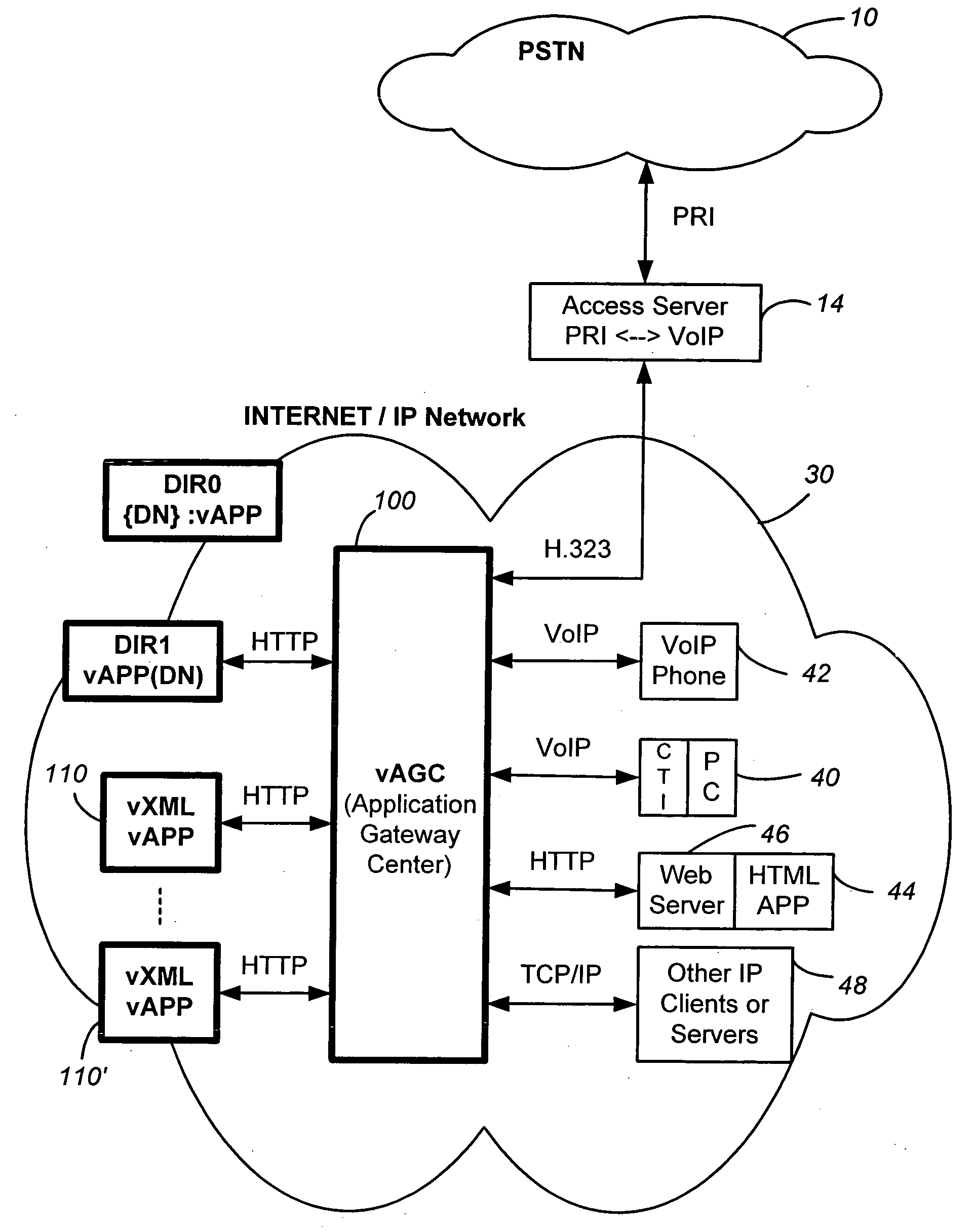
InactiveUS20050240659A1Easy development and deploymentLow costSpecial service for subscribersData switching by path configurationQuality of serviceWeb browser
A networked telephony system and method allow users to deploy on the Internet computer telephony applications associated with designated telephone numbers. The telephony application is easily created by a user in XML (Extensible Markup Language) with predefined telephony XML tags and easily deployed on a website. The telephony XML tags include those for call control and media manipulation. A call to anyone of these designated telephone numbers may originate from anyone of the networked telephone system such as the PSTN (Public Switched Telephone System), a wireless network, or the Internet. The call is received by an application gateway center (AGC) installed on the Internet. Analogous to a web browser, the AGC provides facility for retrieving the associated XML application from its website and processing the call accordingly. The architecture and design of the system allow for reliability, high quality-of-service, easy scalability and the ability to incorporate additional telephony hardware and software and protocols.
Owner:ALVARIA INC
Existent Domain Name DNS Traffic Capture and Analysis
ActiveUS20100257266A1Accurate ratingAccurate pictureAdvertisementsMultiple digital computer combinationsDomain nameTraffic capacity
Systems and methods for scoring a domain web traffic based on DNS traffic requests received at an authoritative name server to resolve the domain name. A request to resolve the domain name is received at an authoritative name server. A counter, such as a server counter or a hit counter, for the domain name is incremented based on the received request. A score, such as a domain traffic score or a domain rank, is calculated based upon a count of the counter. Calculating the score may also include applying a weighting factor to the counters based on information about a requesting set of resolvers and other domains / websites that may be linking and driving traffic to the domain whose traffic score is being calculated. Examples of relevant set of resolvers information may include location, traffic levels, traffic type and architecture of the set of resolvers.
Owner:VERISIGN
Automated method for identifying and repairing logical data discrepancies between database replicas in a database cluster
InactiveUS8126848B2Digital data processing detailsDatabase distribution/replicationData differencingTransaction log
A method and system for monitoring and maintaining the consistency of replicated databases in a shared-nothing database cluster architecture is presented. The method involves the continuous monitoring of the database transaction logs that are maintained by the autonomous database managers that manage the individual database replicas in the cluster. In the event that data discrepancies are detected via the comparison of the transaction logs of the individual database replicas, remedial action is carried out according to configured rules in the main cluster controller. These remedial actions may include, but are not limited to, making a database node inactive within the cluster, or automatically repairing any data discrepancies that are detected among the database replicas in the cluster.
Owner:WAGNER ROBERT EDWARD
Virtual file system
InactiveUS20060123062A1Input/output to record carriersDigital data information retrievalVirtualizationVirtual file system
A virtual file system and method. The system architecture enables a plurality of underlying file systems running on various file servers to be “virtualized” into one or more “virtual volumes” that appear as a local file system to clients that access the virtual volumes. The system also enables the storage spaces of the underlying file systems to be aggregated into a single virtual storage space, which can be dynamically scaled by adding or removing file servers without taking any of the file systems offline and in a manner transparent to the clients. This functionality is enabled through a software “virtualization” filter on the client that intercepts file system requests and a virtual file system driver on each file server. The system also provides for load balancing file accesses by distributing files across the various file servers in the system, through migration of data files between servers.
Owner:EMC CORP
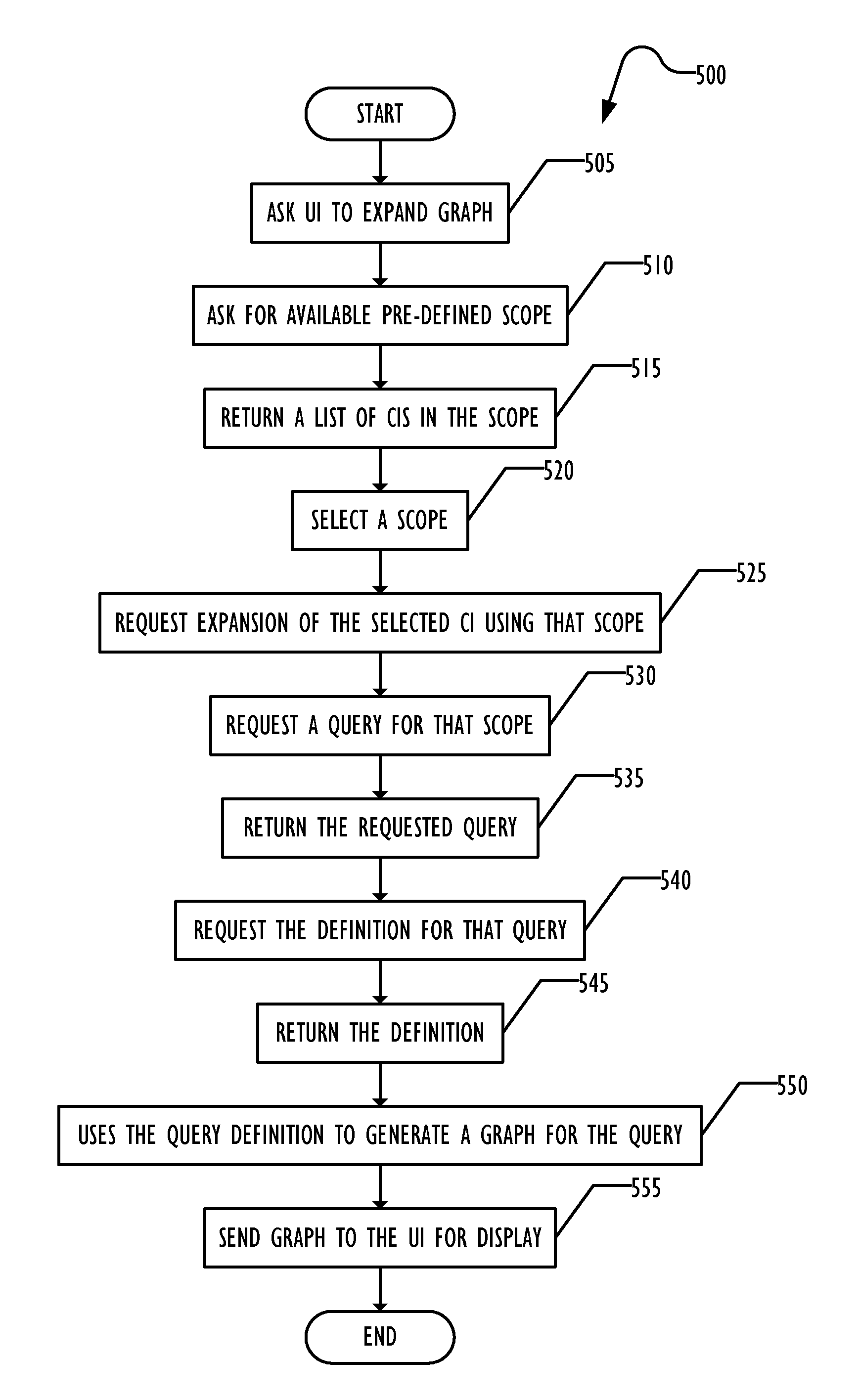
Mechanism to display graphical IT infrastructure using configurable smart navigation
ActiveUS9467344B2Digital data information retrievalDigital data processing detailsVisibilityGraphics
A system allows pre-defining CI scope definitions for use by users of a CMDB system. The pre-defined CI scope definitions may be used to expand a starting CI in a graph displaying a portion of the CMDB according to the types of CIs and relationships between CIs defined in the scope definition. The scope definition is converted into one or more CMDB queries that are restricted to a chain of CIs related to the starting CI. The system restricts the visibility of scope definitions to only those applicable to the starting CI.
Owner:BMC SOFTWARE
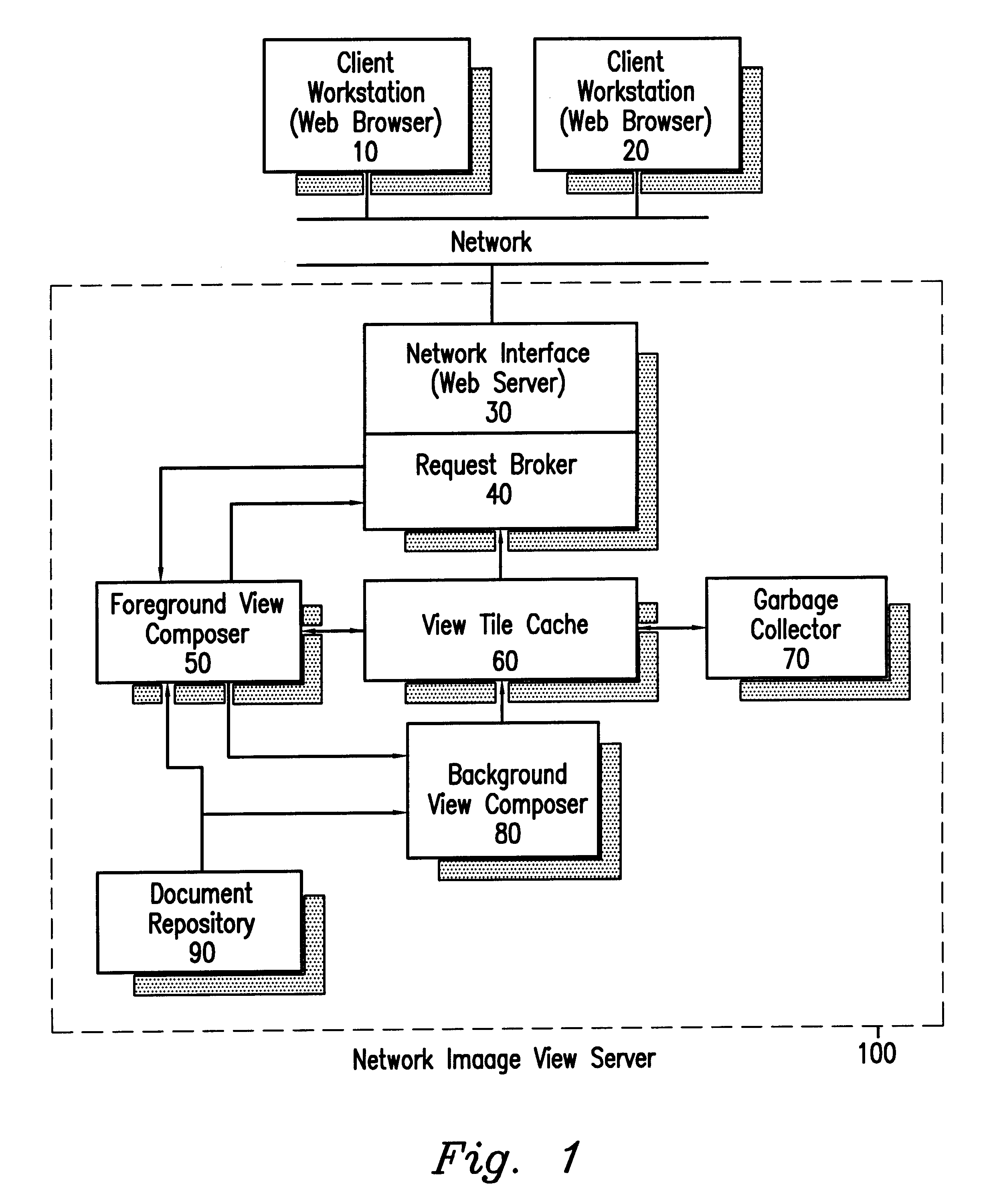
Network image view server using efficient client-server tiling and caching architecture
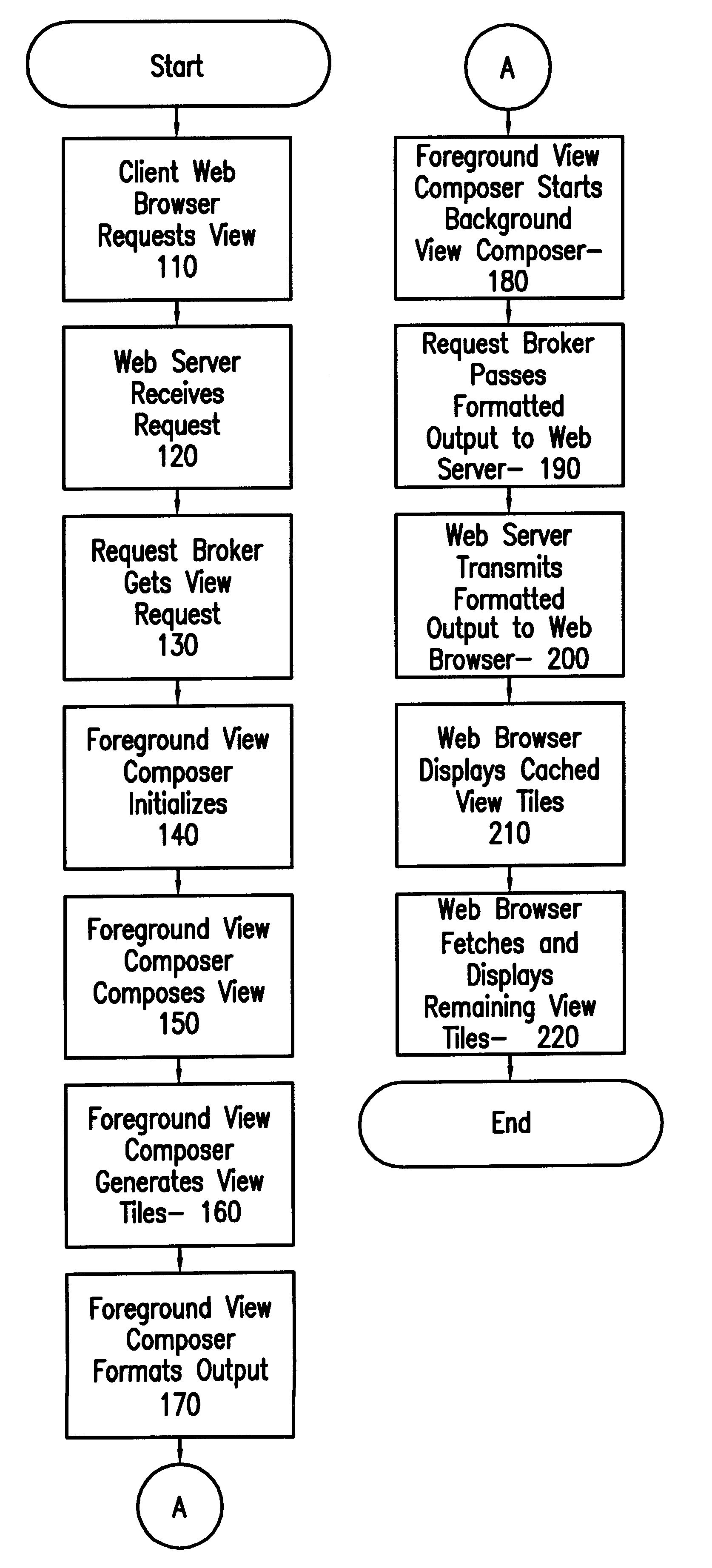
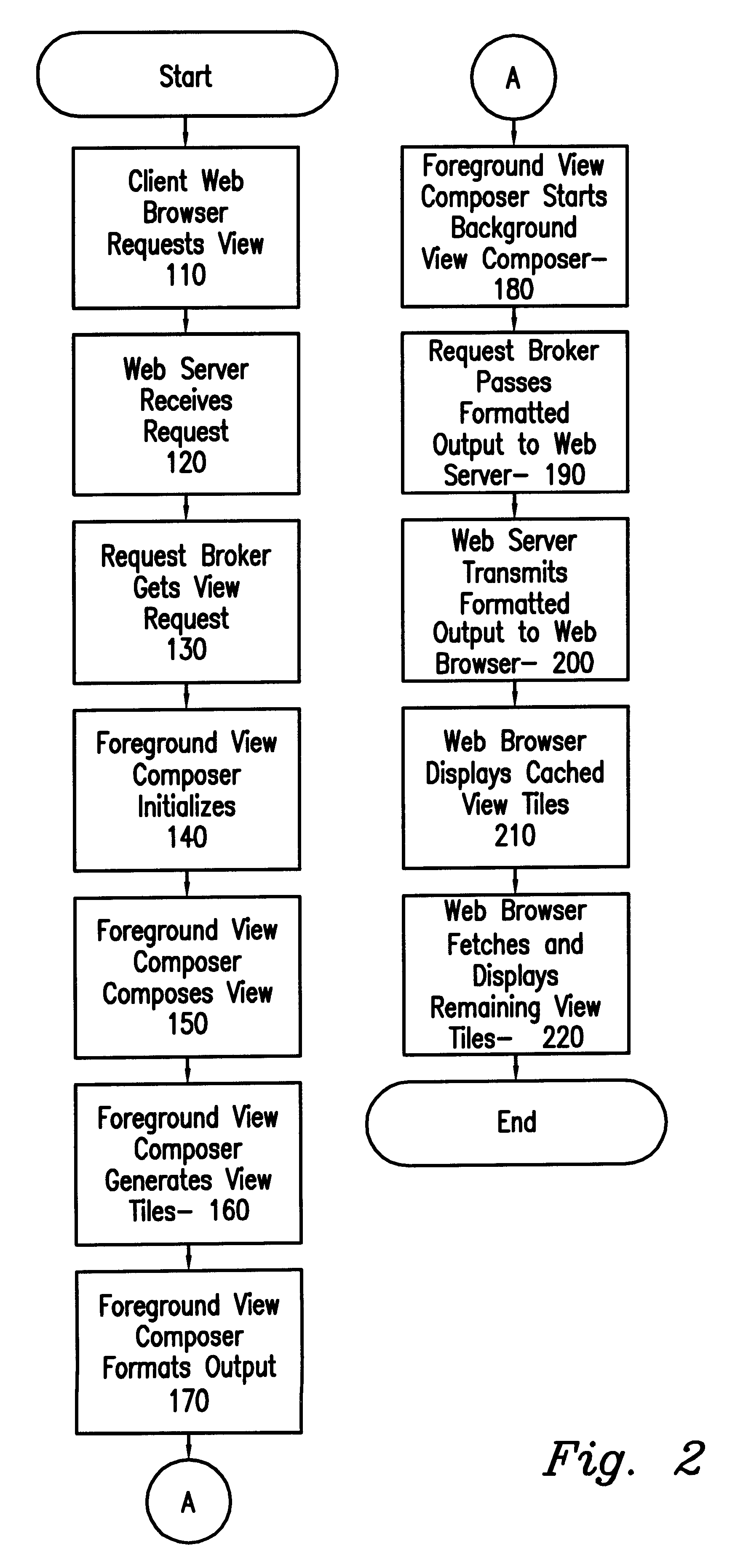
InactiveUS6182127B1Easy to useIncrease speedData processing applicationsDigital data information retrievalData displayComputer network server
A computer network server using HTTP (Web) server software combined with foreground view composer software, background view composer software, a view tile cache, view tile cache garbage collector software, and image files provides image view data to client workstations using graphical Web browsers to display the view of an image from the server. Problems with specialized client workstation image view software are eliminated by using the Internet and industry standards-based graphical Web browsers for the client software. Network and system performance problems that previously existed when accessing large image files from a network file server are eliminated by tiling the image view so that computation and transmission of the view data can be done in an incremental fashion. The view tiles are cached on the client workstation to further reduce network traffic. View tiles are cached on the server to reduce the amount of view tile computation and to increase responsiveness of the image view server.
Owner:EPLUS CAPITAL
Personalized marketing architecture
ActiveUS7925549B2Buying/selling/leasing transactionsSpecial data processing applicationsPersonalizationReal-time data
Owner:ACCENTURE GLOBAL SERVICES LTD
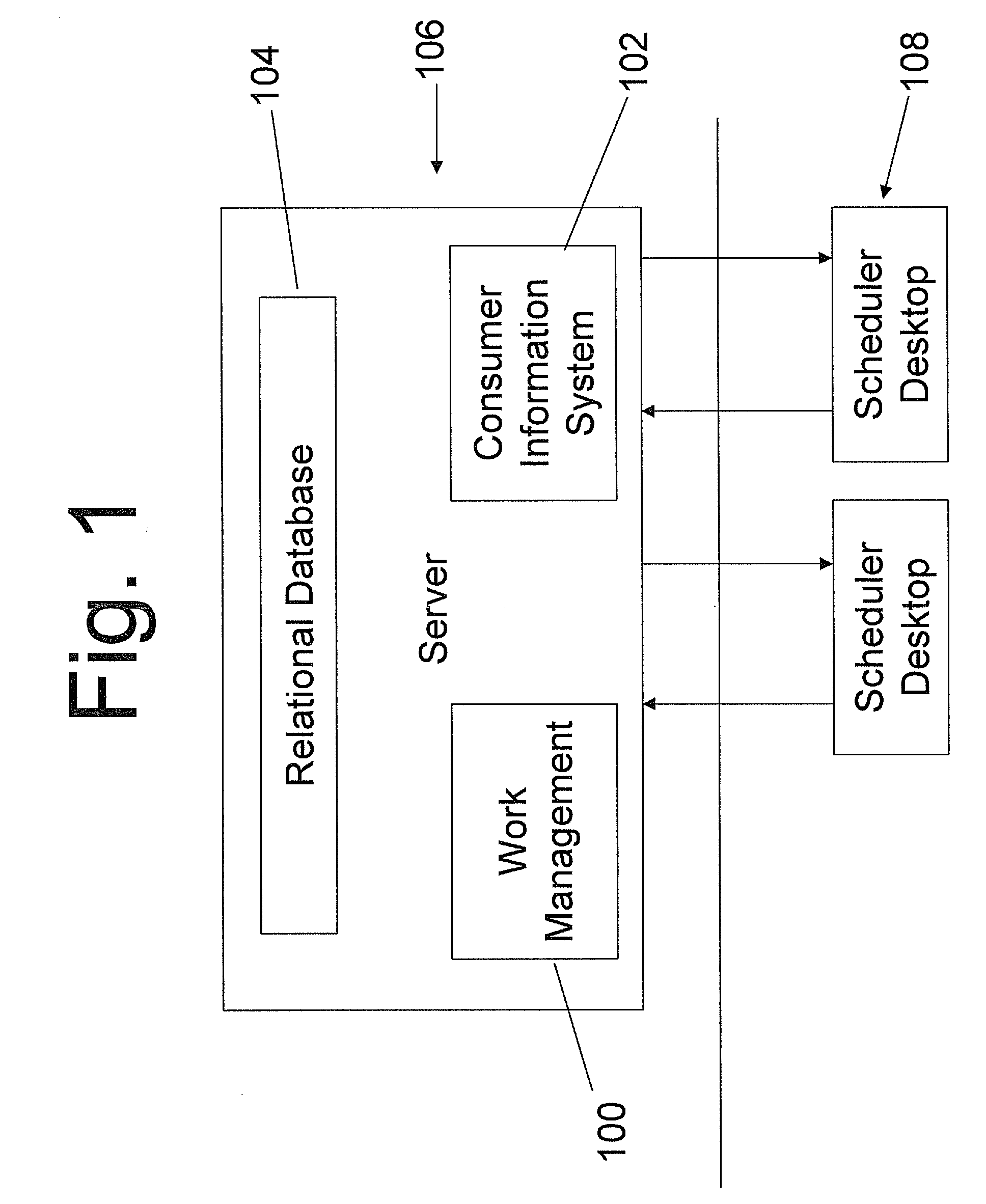
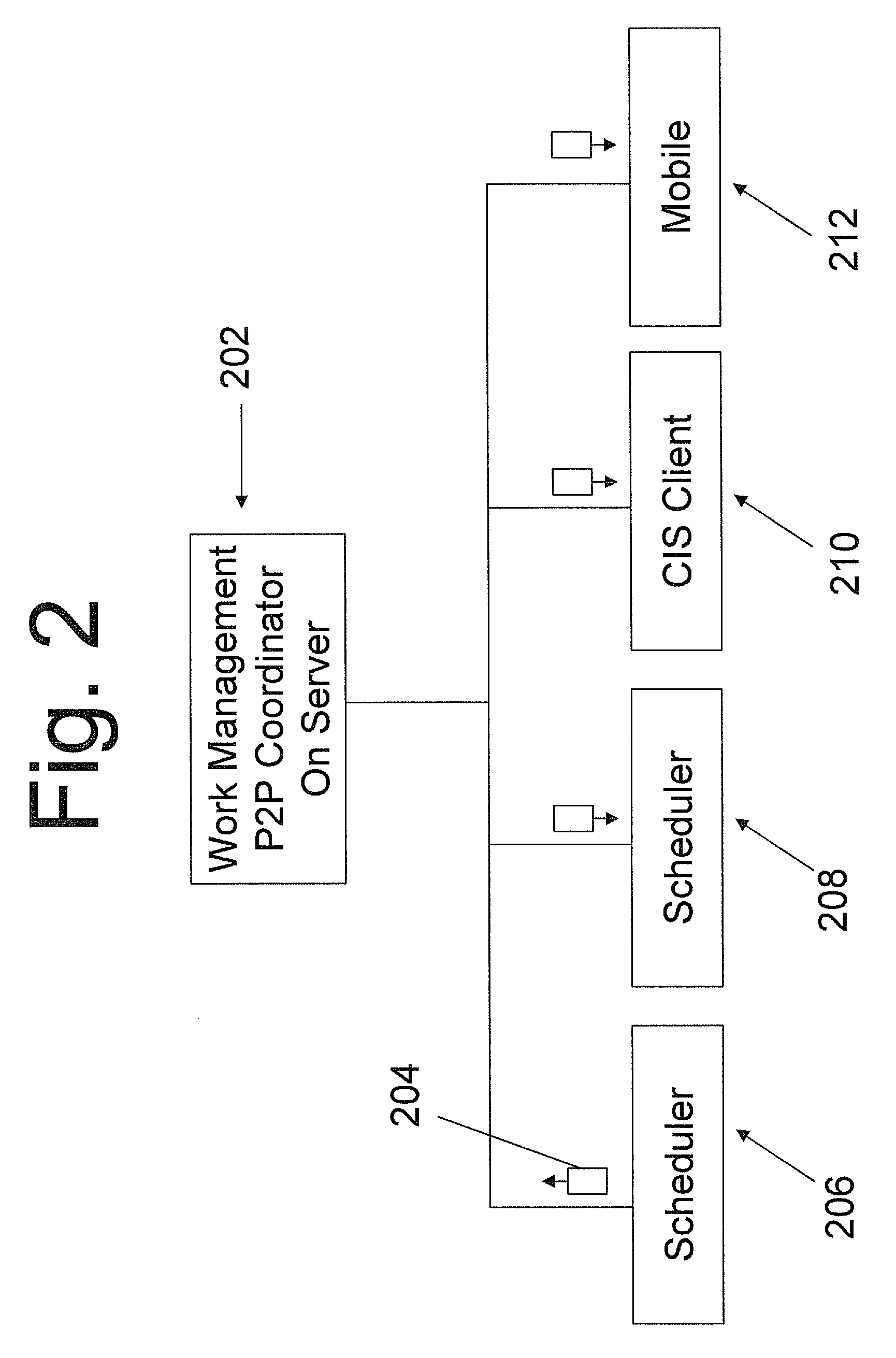
Graphical client interface resource and work management scheduler
InactiveUS20100257015A1Utilize bandwidthEasy to calculateResourcesSpecial data processing applicationsGraphicsProgram planning
A computer implemented system and method that ties in complex calendar event relationships, which provides the user with a context as to how the task needs to be completed and how it relates to larger initiatives. The system and method supports next to real time notification methods using a peer-to-peer (p2p) messaging architecture. As Calendar Events or Tasks are manipulated in the Work Management System, all scheduling clients can automatically adjust their events to reflect the changes. The present invention can also implement an Urgency Factor for tasks which can help visualize to the user which tasks need more immediate action from Work Management. The present invention can also provide a First Available function that not only finds the first available date that a task can be worked but also takes into consideration the resource's work hours, workdays and skill set via the work group that they have been assigned.
Owner:NAT INFORMATION SOLUTIONS COOP
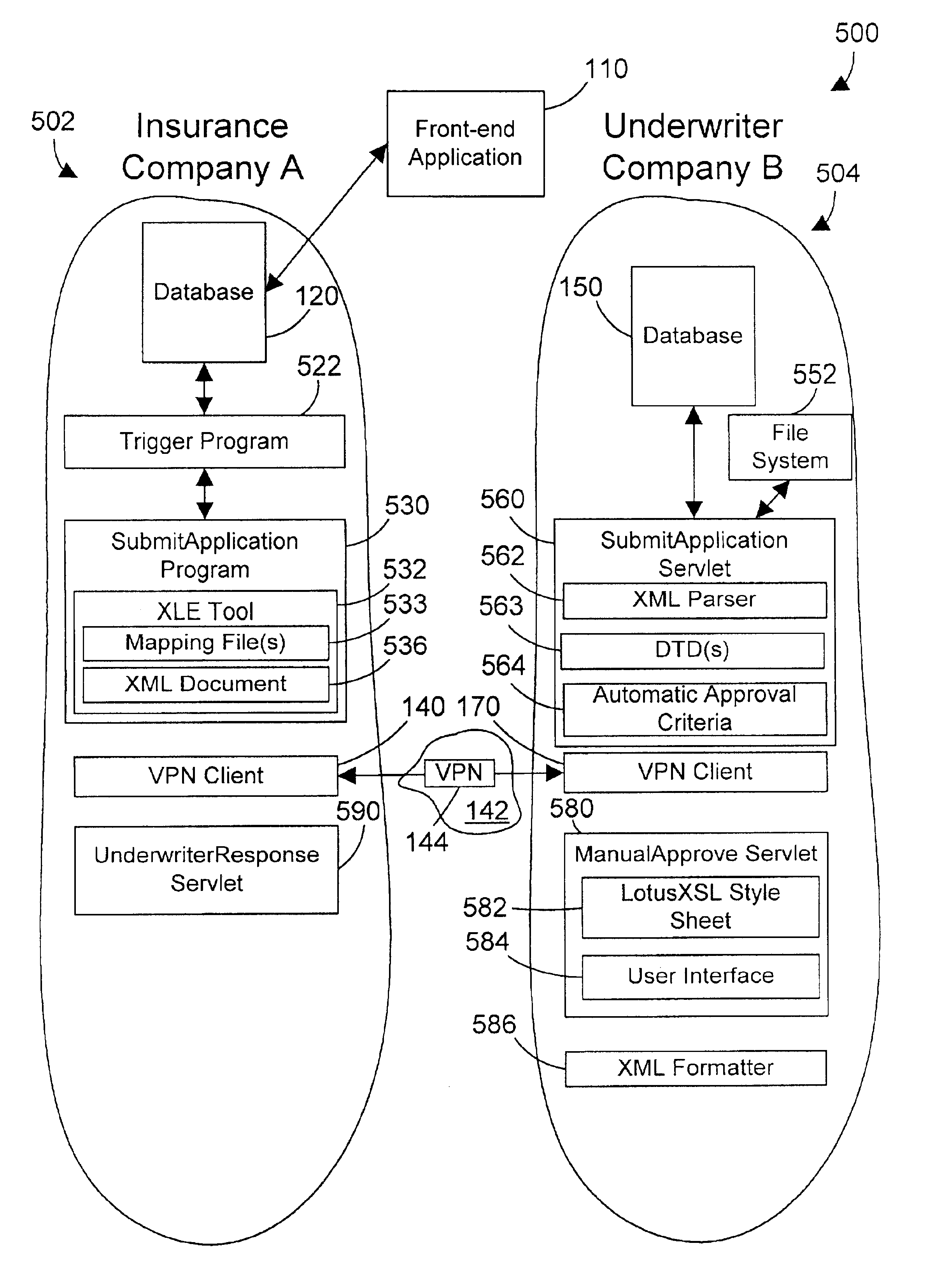
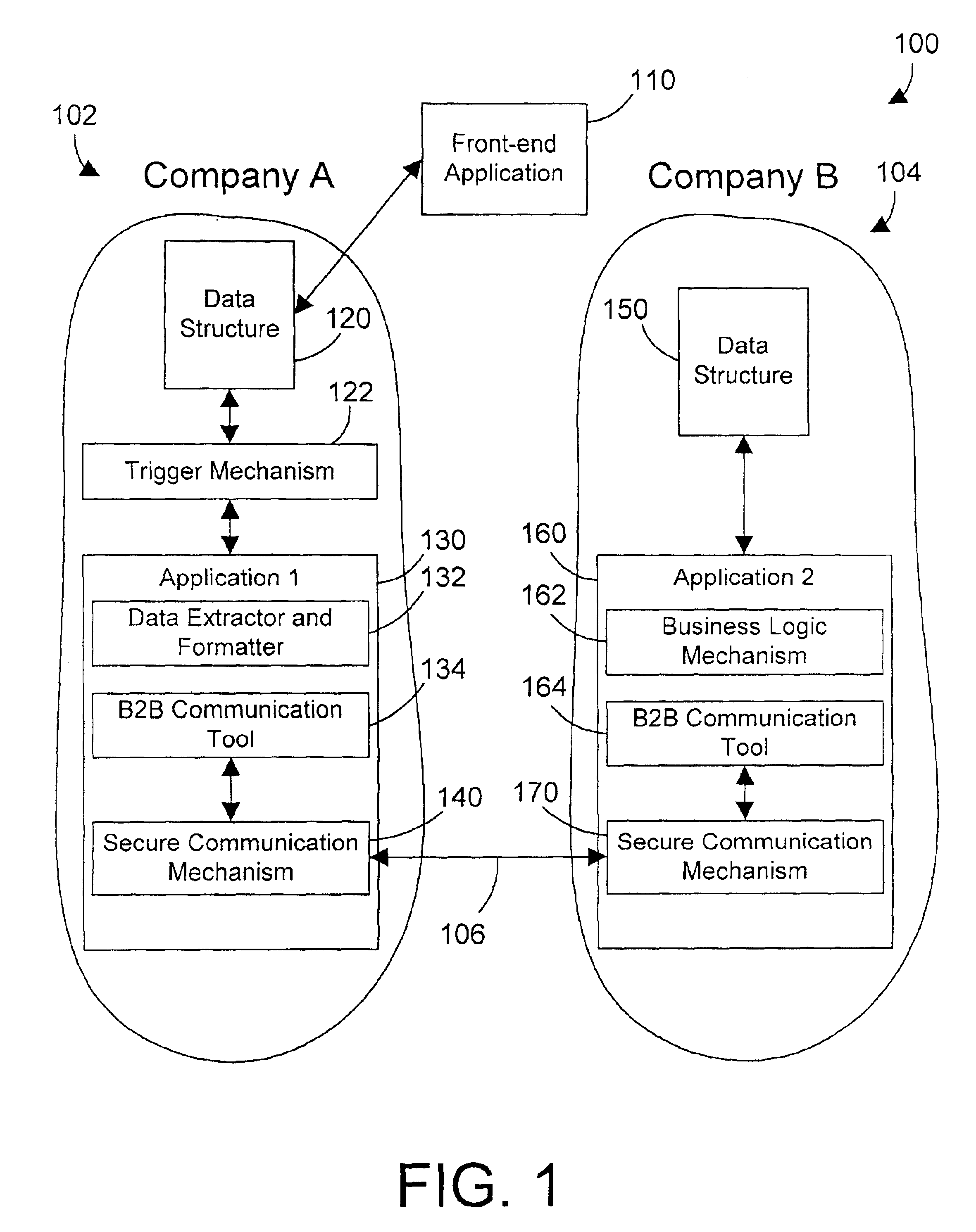
Computer system, method, and business method for automating business-to-business communications
InactiveUS6928487B2Database distribution/replicationMultiple digital computer combinationsSecure communicationPrivate network
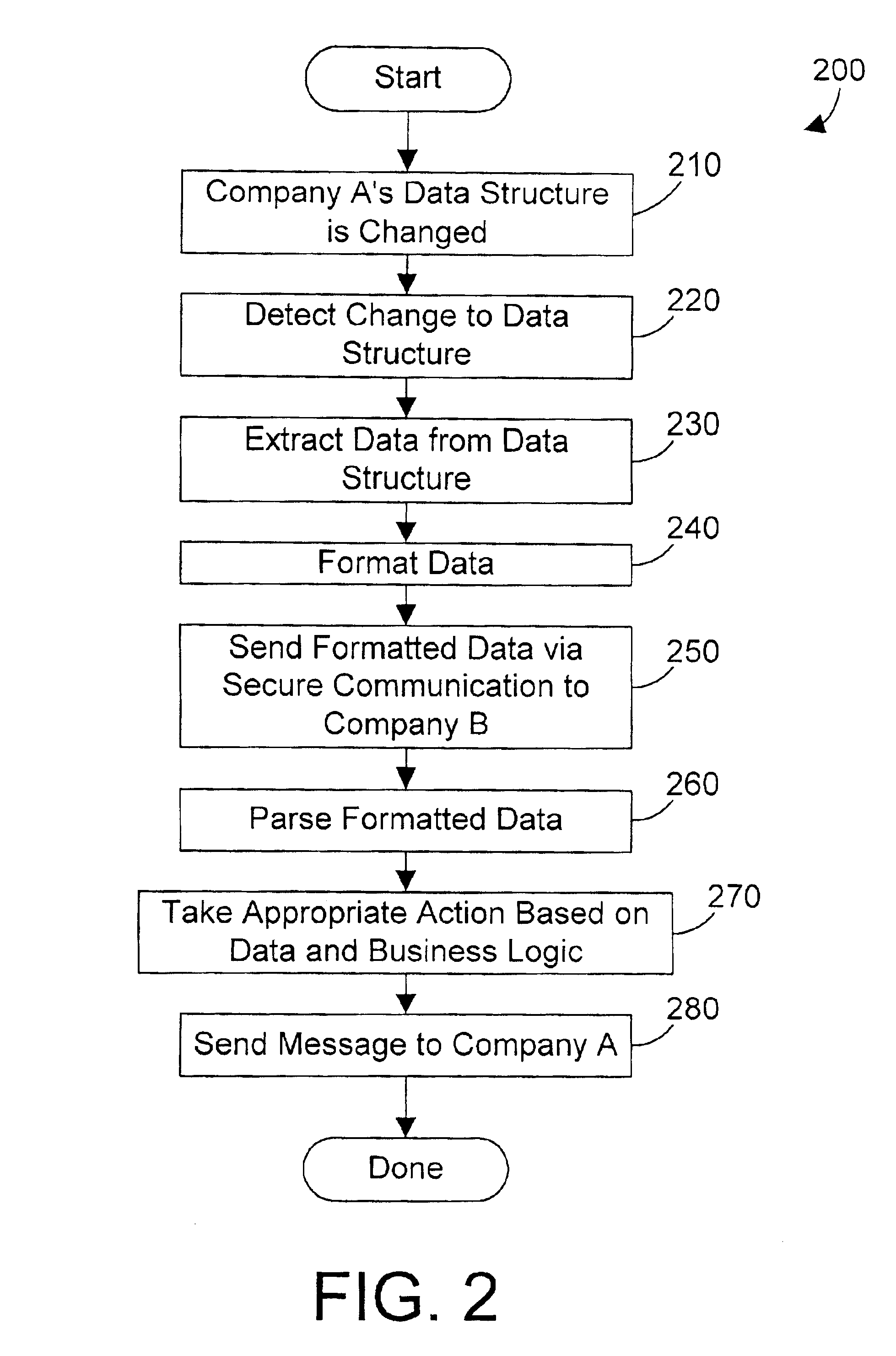
An apparatus, method, and method for doing business allows two business partners to communicate with each other in an architected manner. A first company monitors for changes to its internal data structure that indicate that communication with a second company may be required. A trigger mechanism monitors the data structure for changes, and invokes a software application when the data structure is changed in a defined manner. The software application extracts the new or changed data from the data structure, formats the data into an XML document, and sends the XML document to the second company via a secure communication mechanism, such as a virtual private network (VPN). The second computer system receives the information from the first computer system, parses the information, and processes the information. The second computer system then generates an appropriate response to the first computer system. In this manner, the first and second computer systems can communicate in an architected manner using XML documents, thereby allowing automation of processes between the two companies.
Owner:IBM CORP
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS6778498B2Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
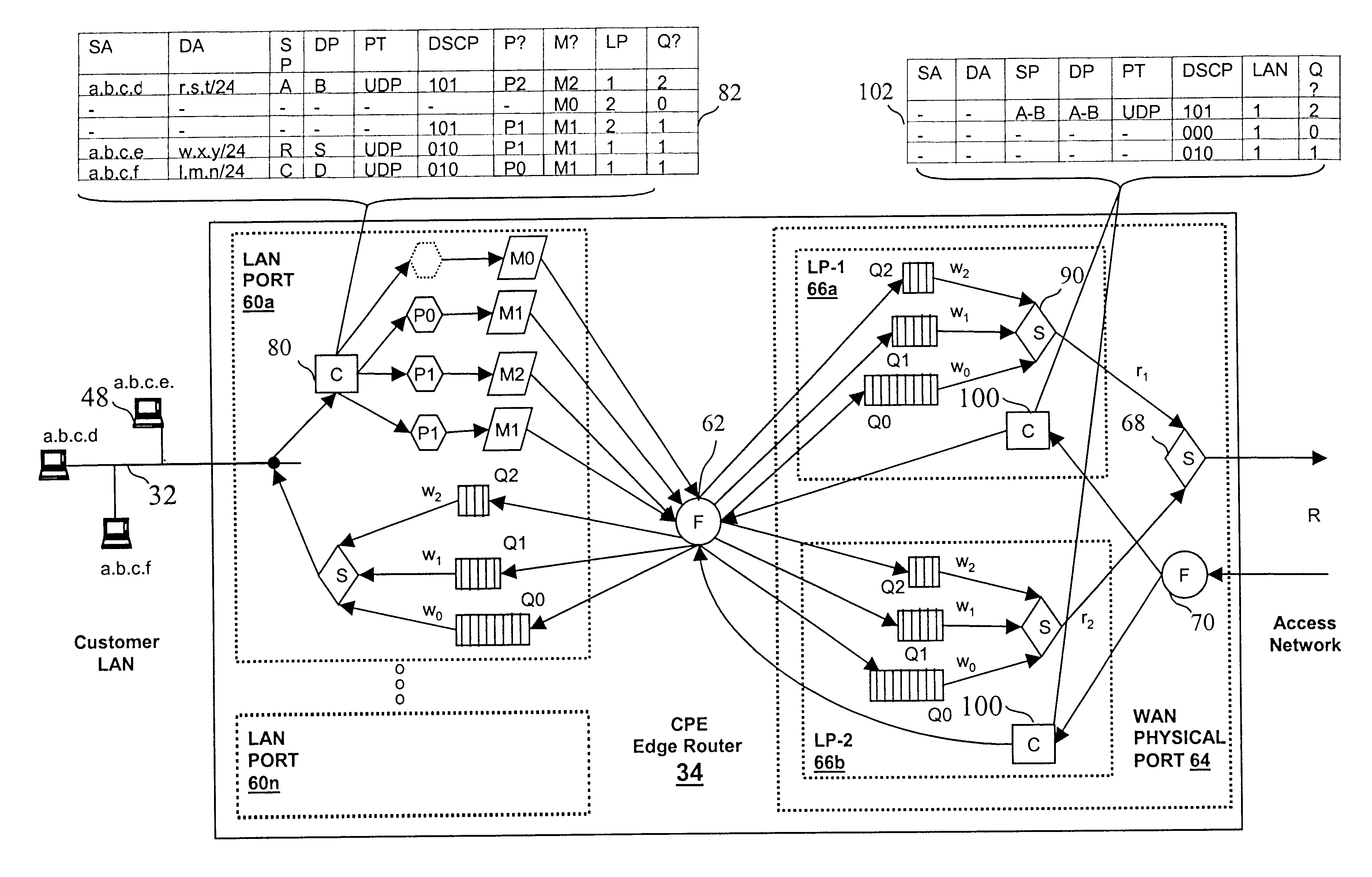
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Wide Area Networked File System
InactiveUS20070162462A1Eliminate overheadAlleviates the bottleneck at the central serverSpecial data processing applicationsMemory systemsWide areaRandomized algorithm
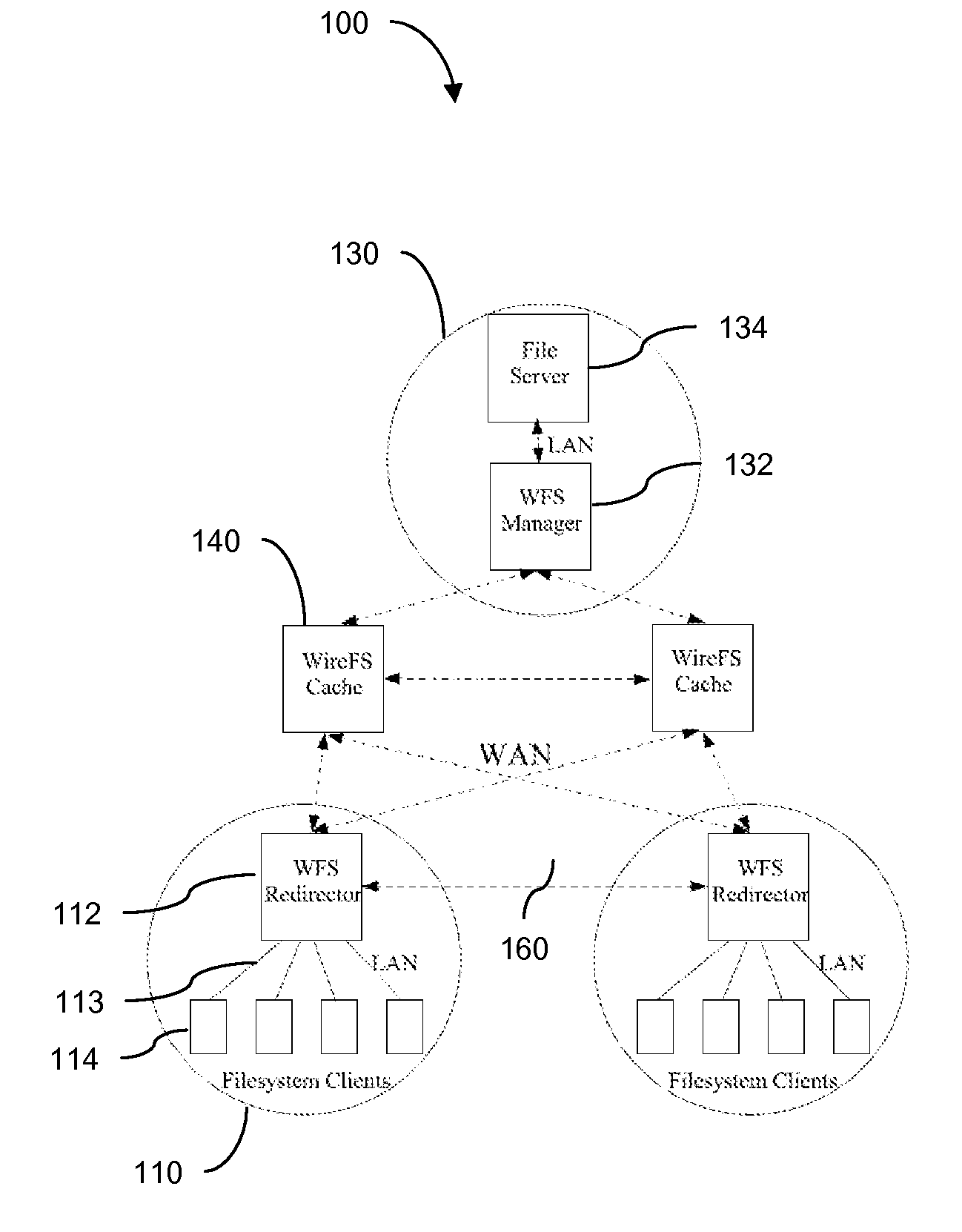
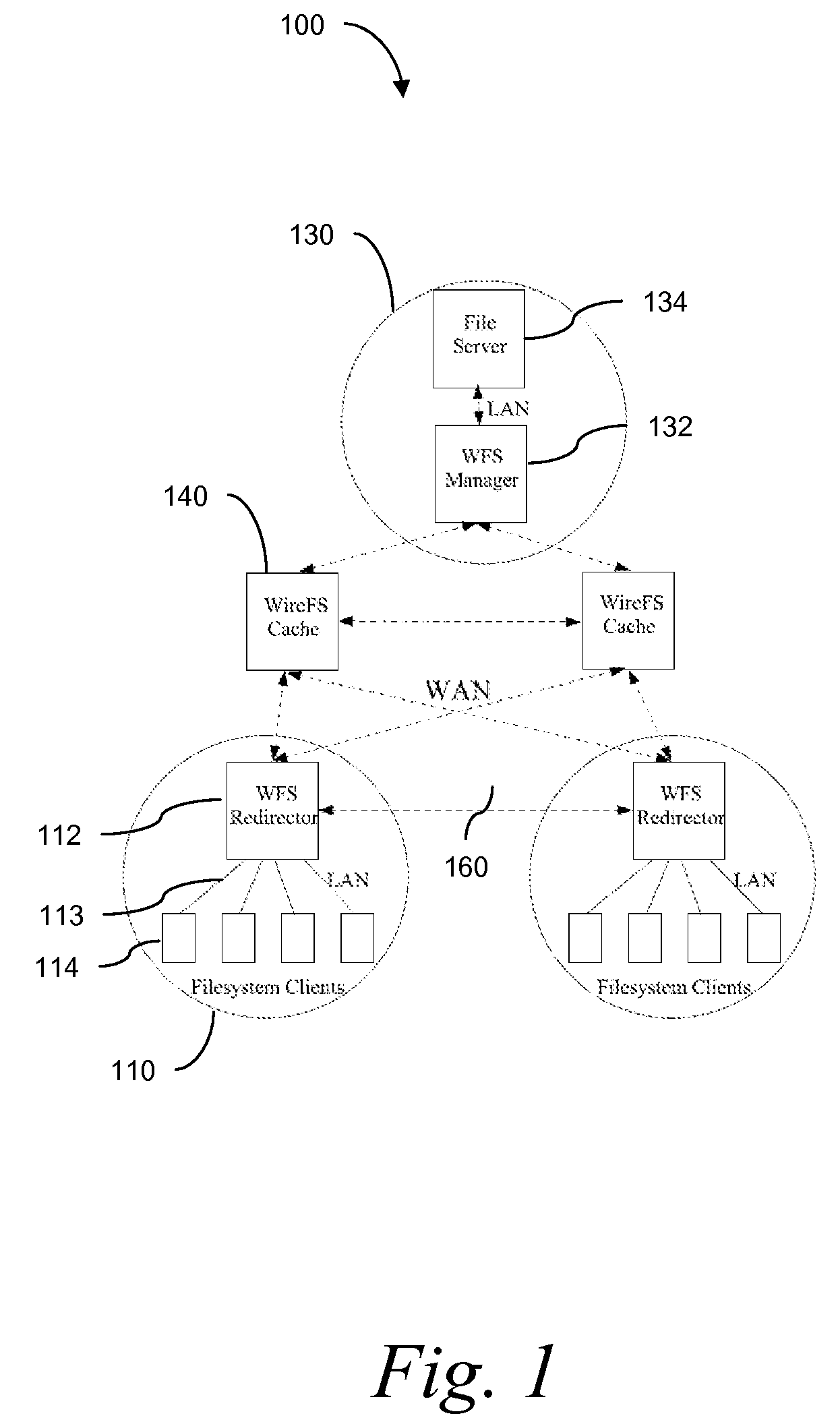
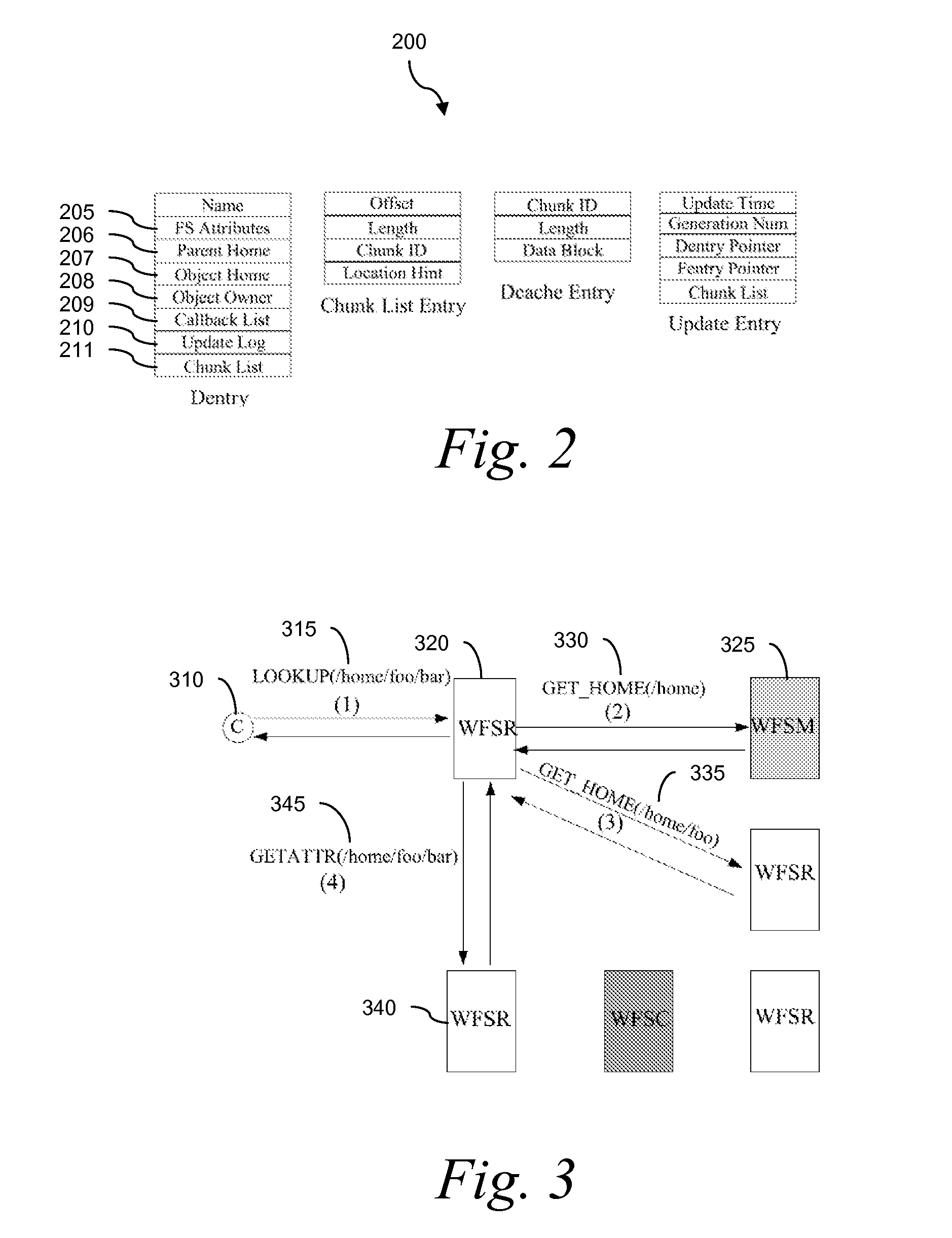
Traditional networked file systems like NFS do not extend to wide-area due to network latency and dynamics introduced in the WAN environment. To address that problem, a wide-area networked file system is based on a traditional networked file system (NFS / CIFS) and extends to the WAN environment by introducing a file redirector infrastructure residing between the central file server and clients. The file redirector infrastructure is invisible to both the central server and clients so that the change to NFS is minimal. That minimizes the interruption to the existing file service when deploying WireFS on top of NFS. The system includes an architecture for an enterprise-wide read / write wide area network file system, protocols and data structures for metadata and data management in this system, algorithms for history based prefetching for access latency minimization in metadata operations, and a distributed randomized algorithm for the implementation of global LRU cache replacement scheme.
Owner:NEC CORP
Flexible Authentication Framework
ActiveUS20070208744A1Limited lifetimeImprove performanceWeb data indexingDigital data authenticationThe InternetExtensible architecture
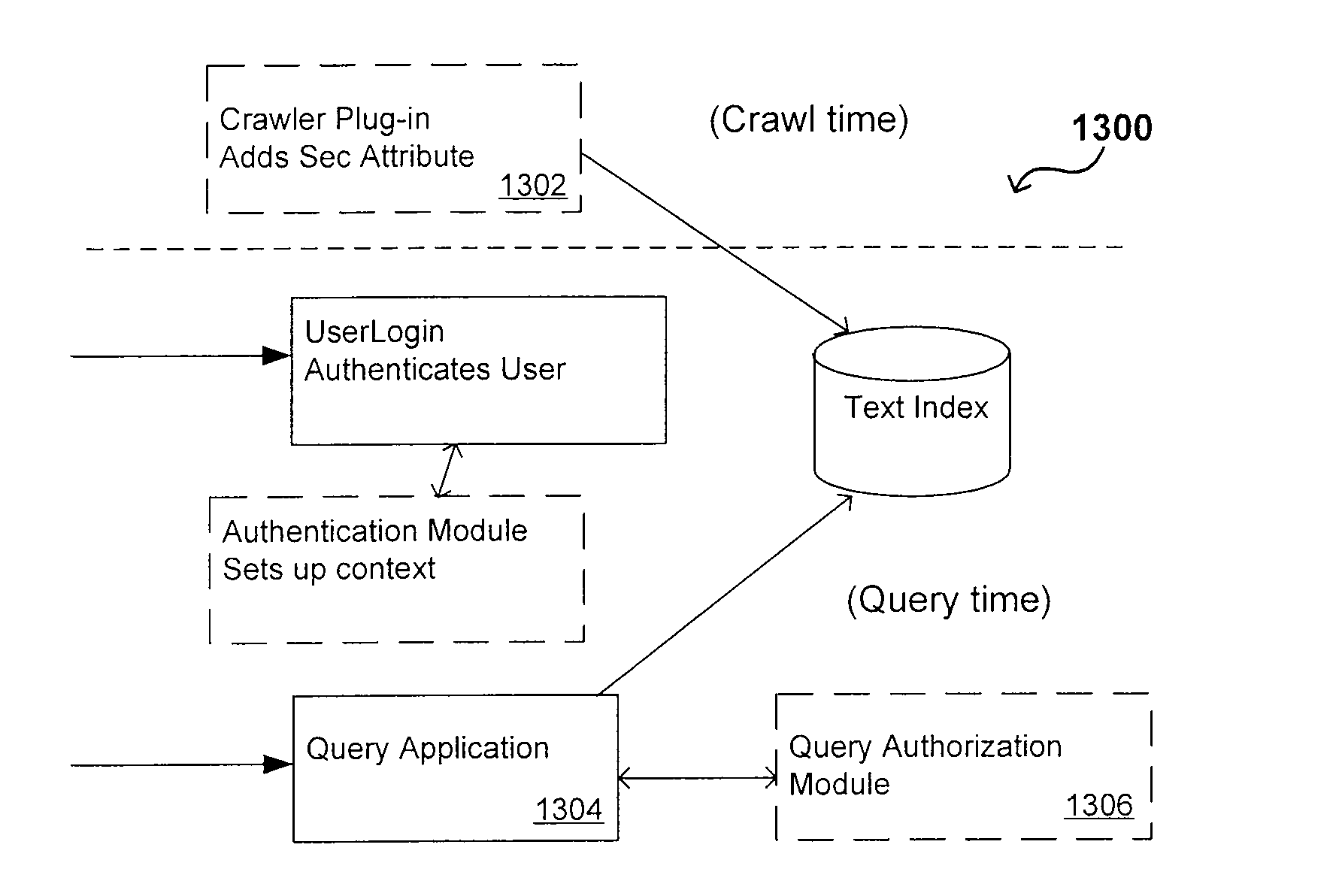
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
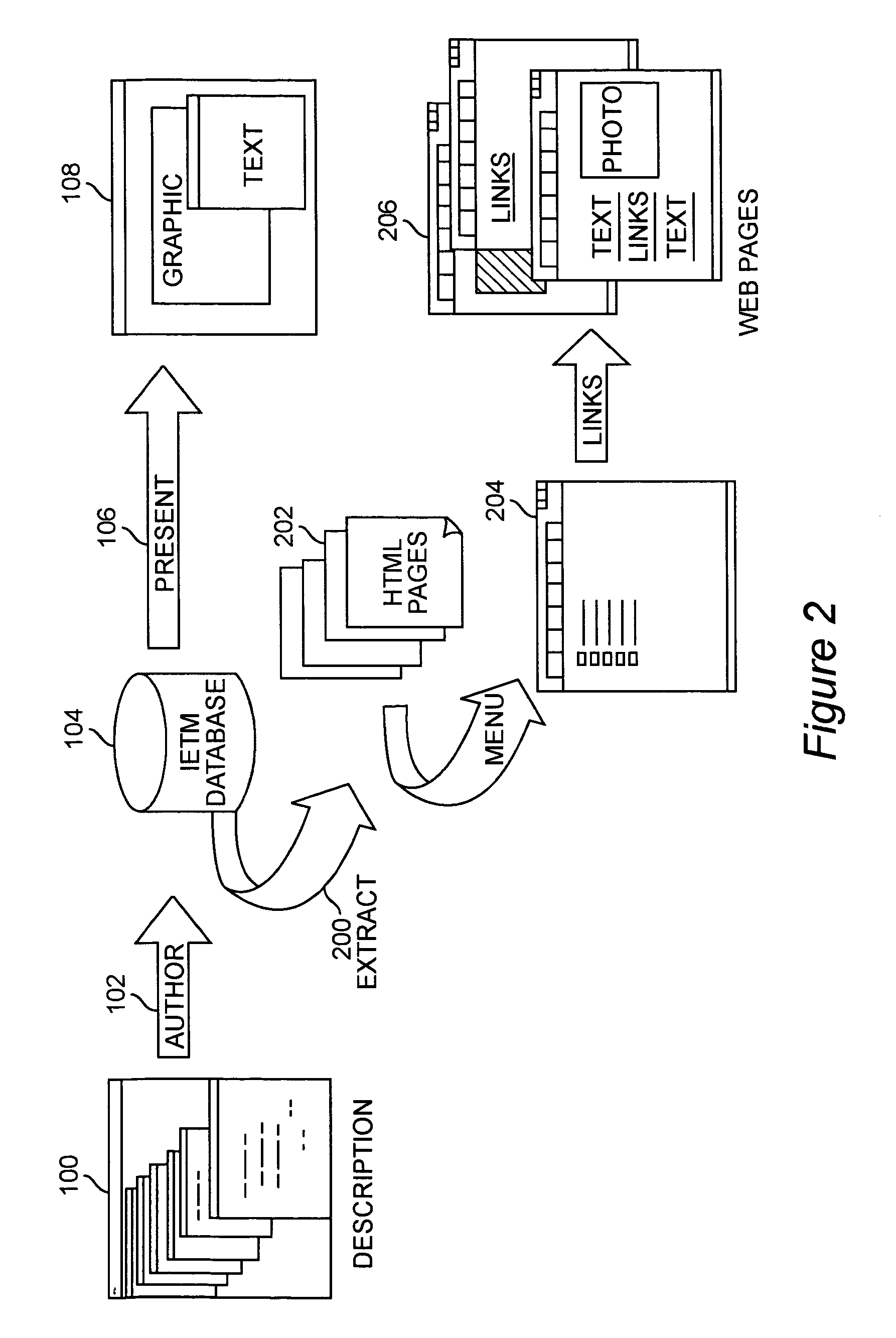
System and method for interactive electronic media extraction for web page generation
InactiveUS6961897B1Efficient updateExtend the life cycleDigital computer detailsNatural language data processingData warehouseRelational database
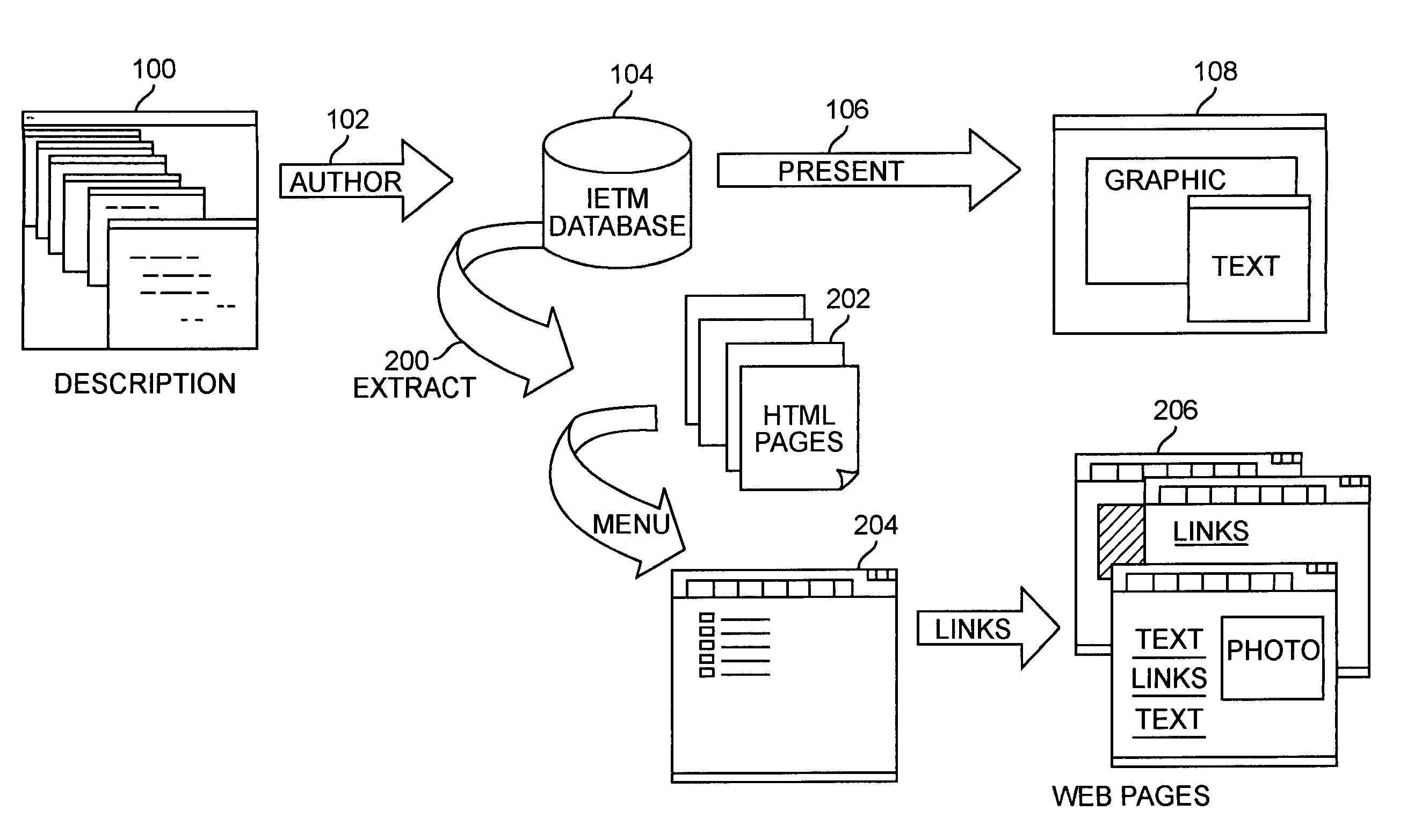
A system and method for parsing an electronic media database structure to produce tagged data that preserves the content, links, and electronic media structure. In particular, HyperText Markup Language (HTML) data is generated as an Interactive Electronic Technical Manual (IETM) (home page) linked into a relative structure of Web pages to support IETM deployment. An extraction process assesses the functionality associated with each node designated for presentation and builds a virtual Web, based on attributes stored in the IETM database. A series of Web pages with links that hierarchically presents IETM data at run time is produced. The method supports a data warehousing strategy that converts any data type eligible within the relational database. This expands support across multiple types of technical and engineering data. The preferred implementation utilizes a relative addressed pure HTML solution viewable in standard Web browsers. This open system implementation is cross platform and infrastructure independent, requiring no special server software. Retaining the hierarchical structure dictated by the relational database in HTML output enhances the supportability and maintainability of the Web implementation. Updates to this Web implementation can be incrementally applied within the hierarchy (small sections of data) or the entire logical sections of Web data.
Owner:LOCKHEED MARTIN CORP
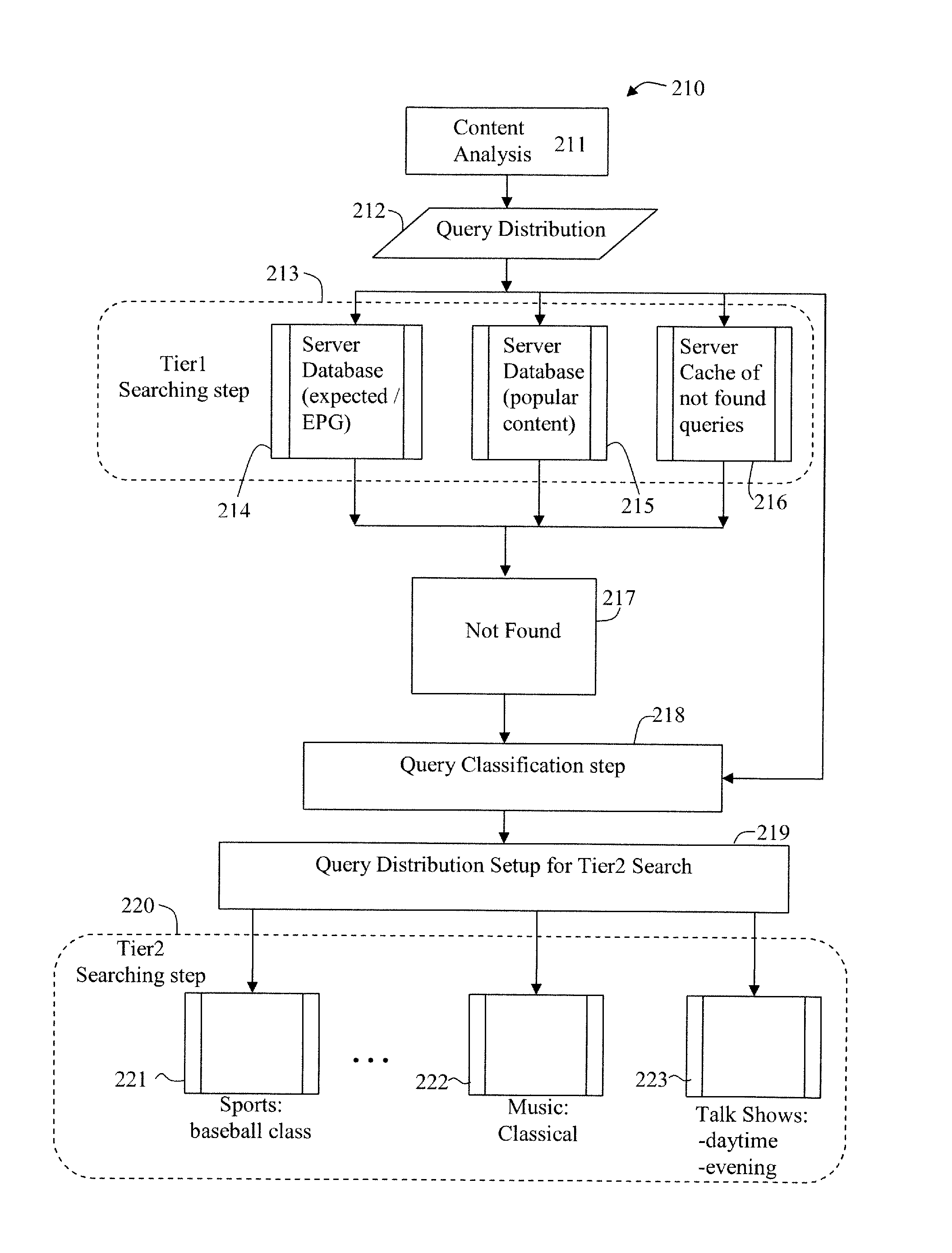
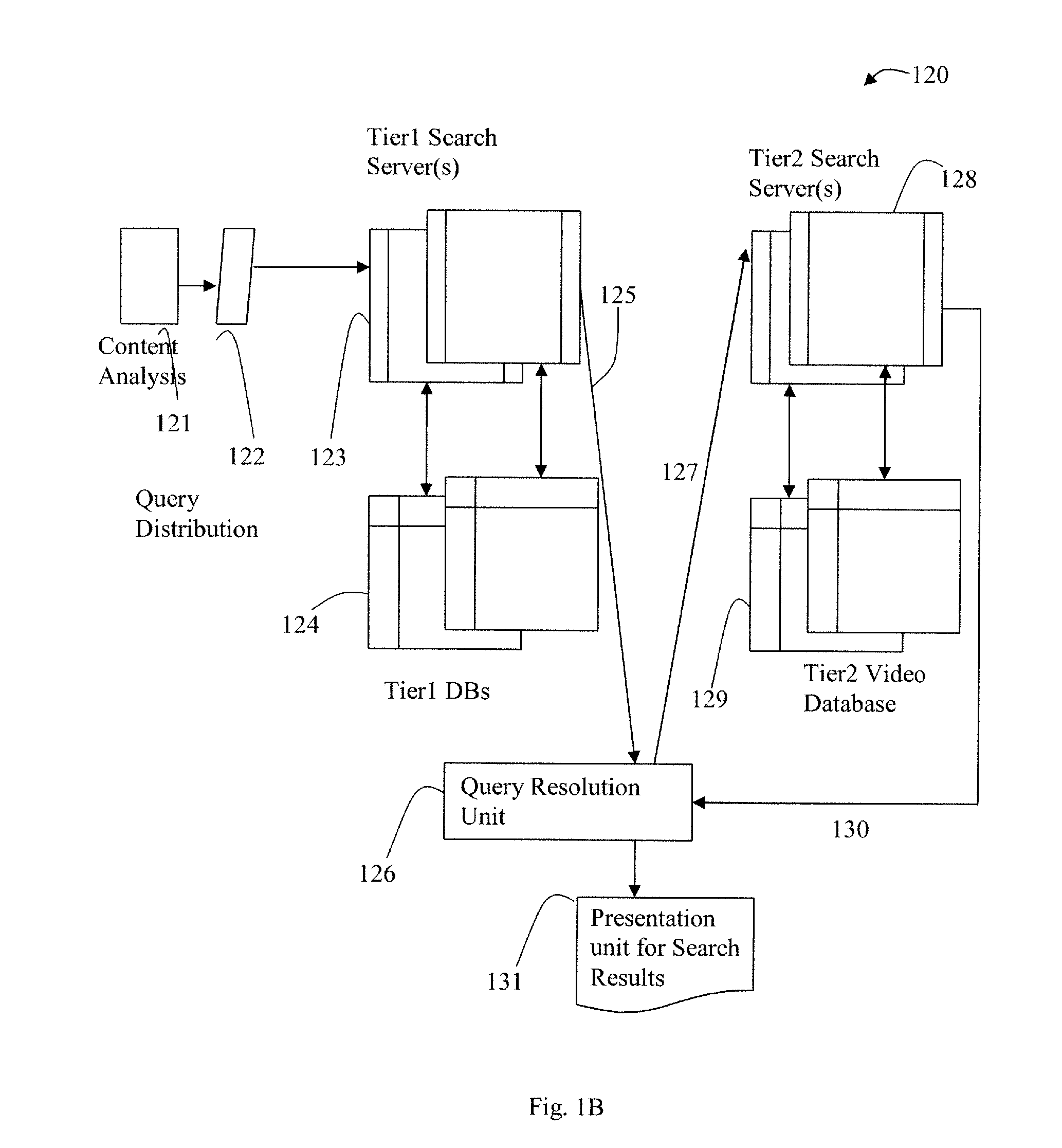
Distributed and Tiered Architecture for Content Search and Content Monitoring
ActiveUS20120095958A1Multimedia data indexingDigital data processing detailsTime segmentSchema for Object-Oriented XML
An efficient large scale search system for video and multi-media content using a distributed database and search, and tiered search servers is described. Selected content is stored at the distributed local database and tier1 search server(s). Content matching frequent queries, and frequent unidentified queries are cached at various levels in the search system. Content is classified using feature descriptors and geographical aspects, at feature level and in time segments. Queries not identified at clients and tier1 search server(s) are queried against tier2 or lower search server(s). Search servers use classification and geographical partitioning to reduce search cost. Methods for content tracking and local content searching are executed on clients. The client performs local search, monitoring and / or tracking of the query content with the reference content and local search with a database of reference fingerprints. This shifts the content search workload from central servers to the distributed monitoring clients.
Owner:ROKU INCORPORATED
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com