Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2569 results about "Executable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, executable code or an executable file or executable program, sometimes simply referred to as an executable, causes a computer "to perform indicated tasks according to encoded instructions", as opposed to a data file that must be parsed by a program to be meaningful.
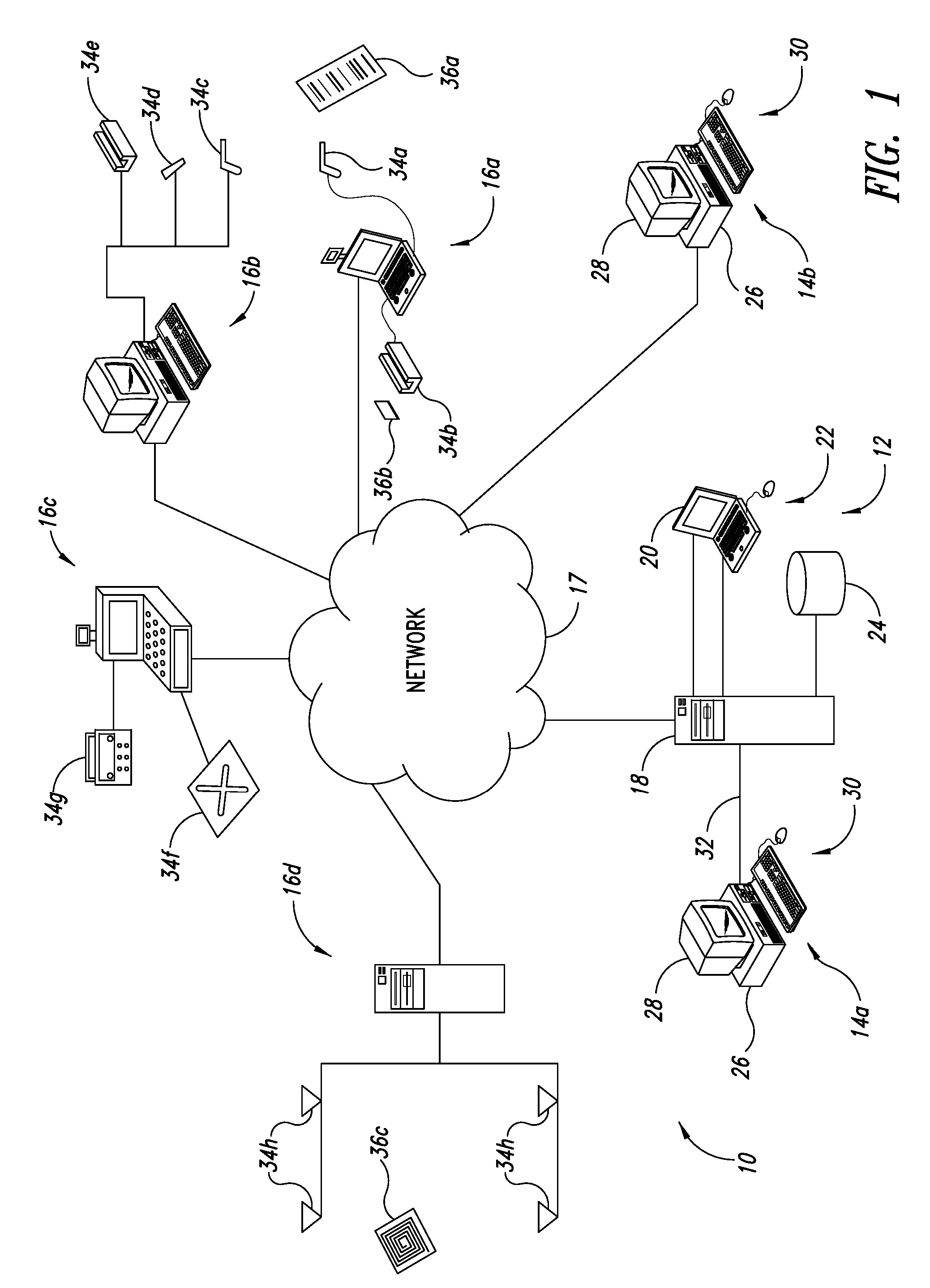
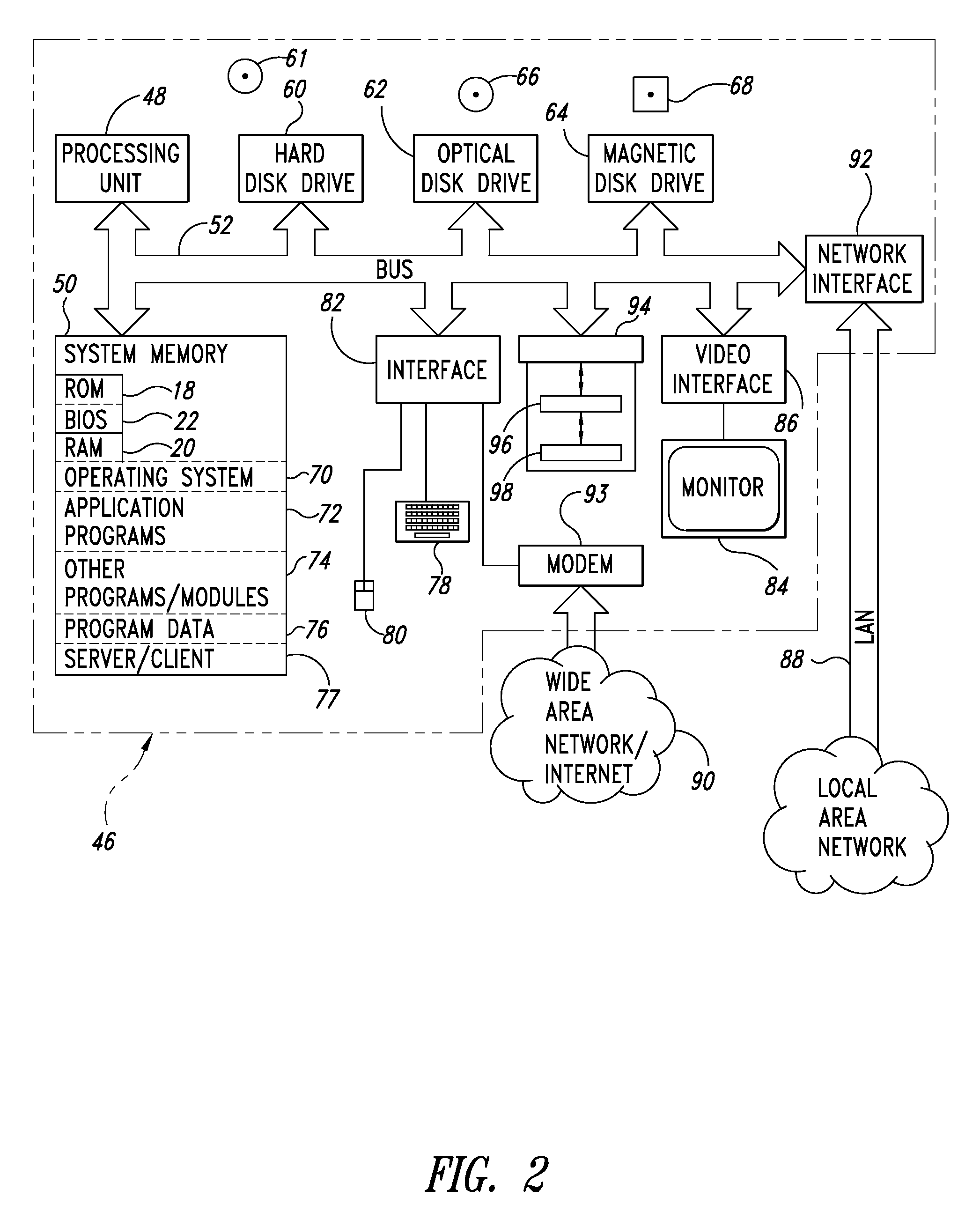
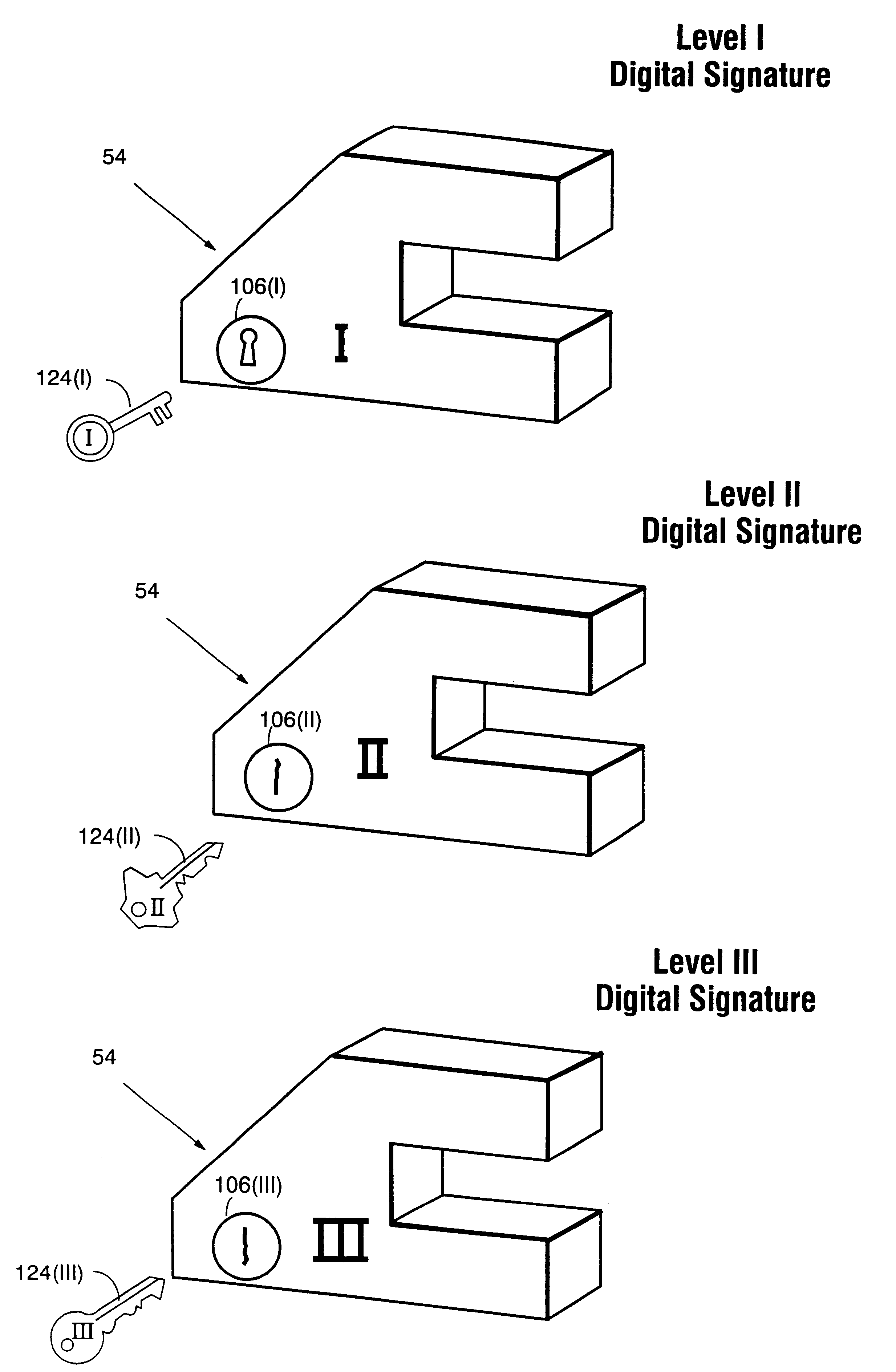
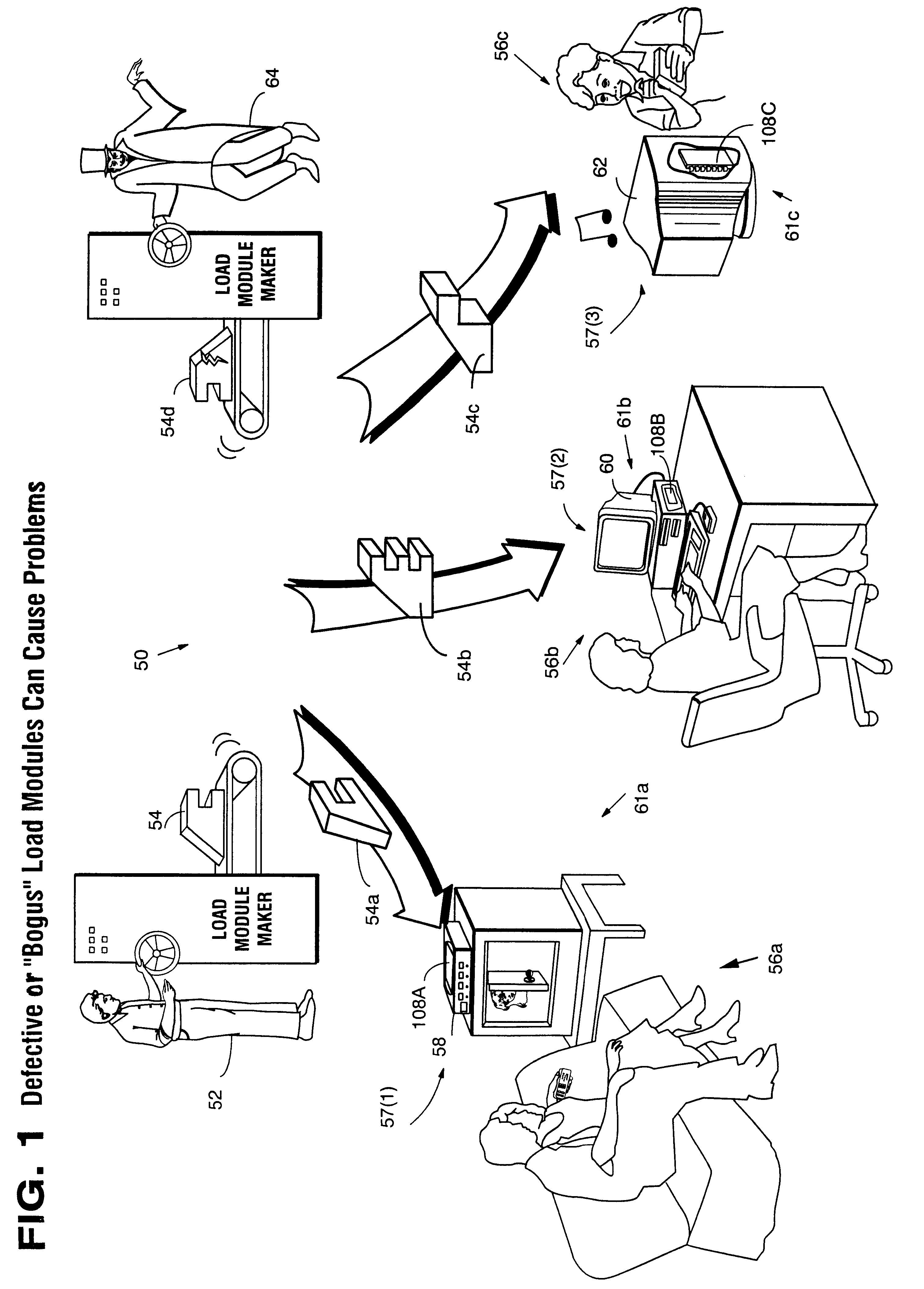
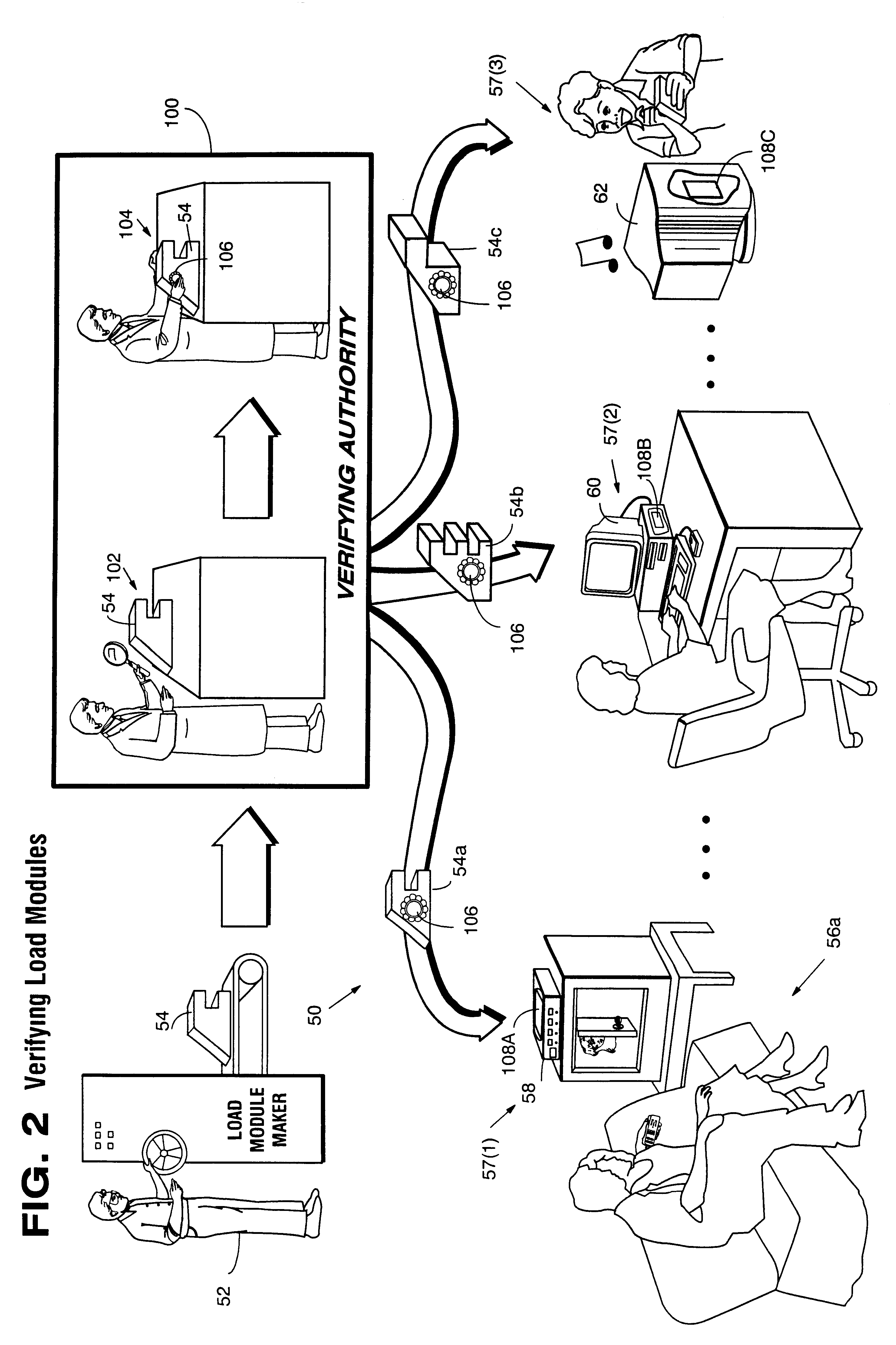
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
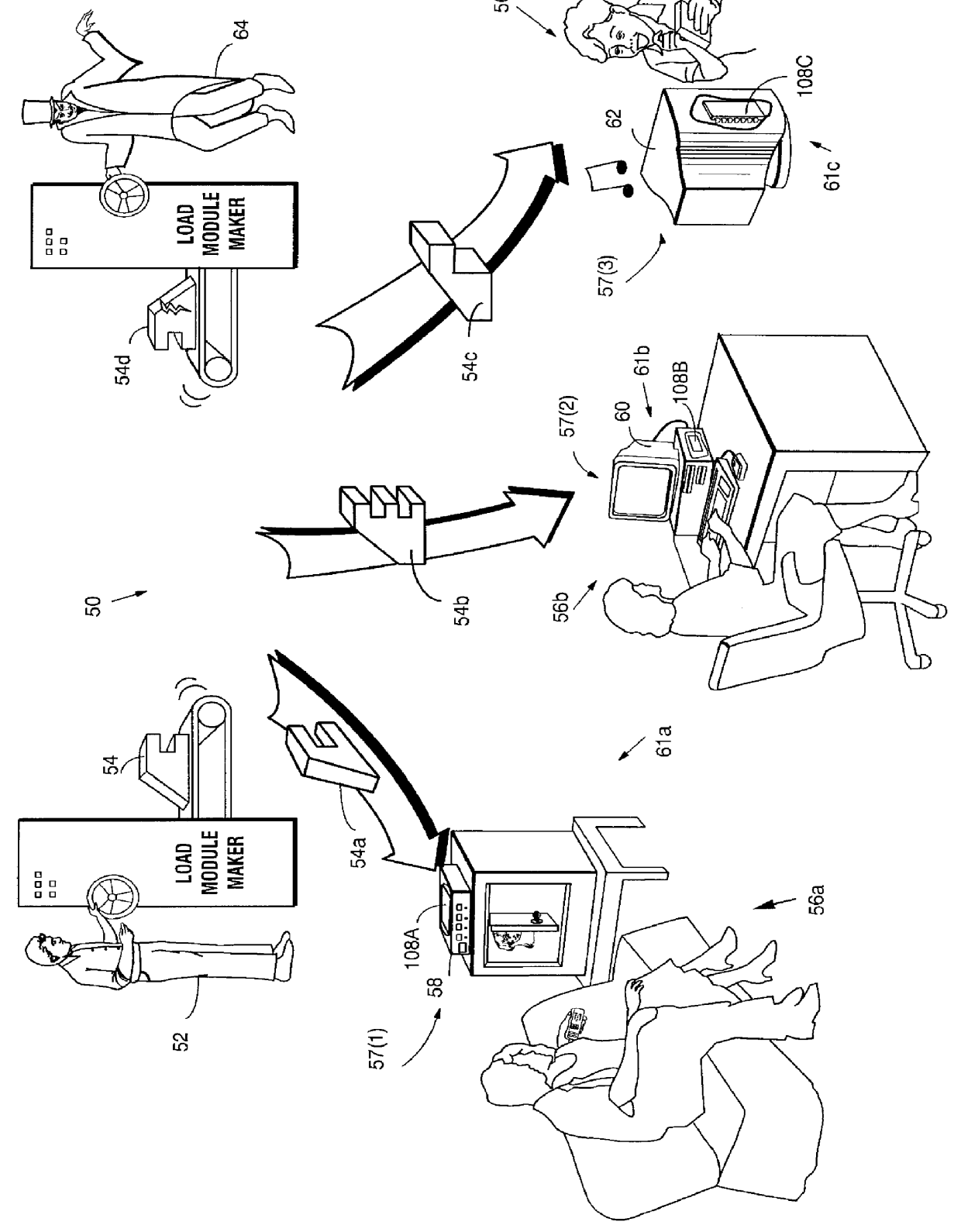
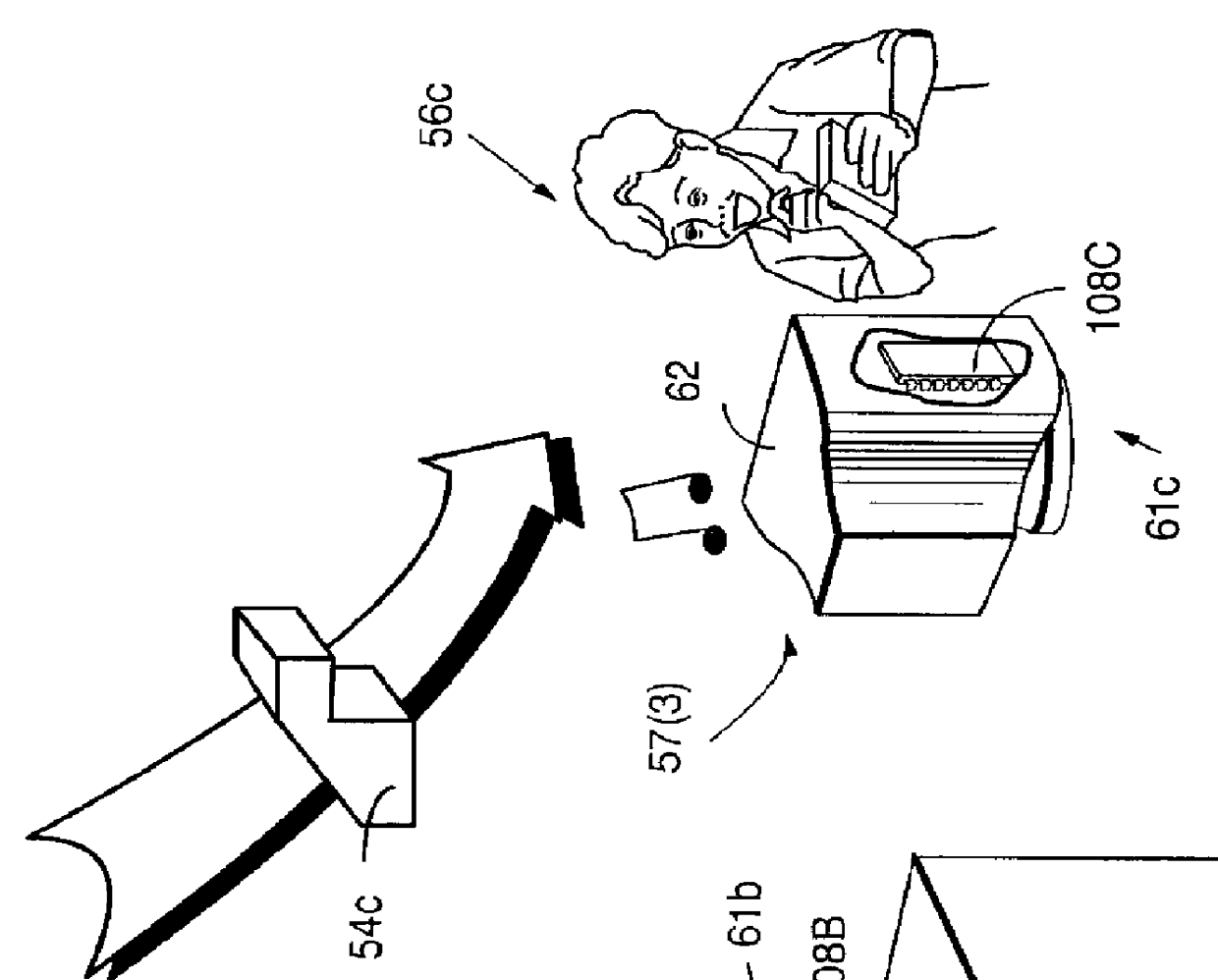
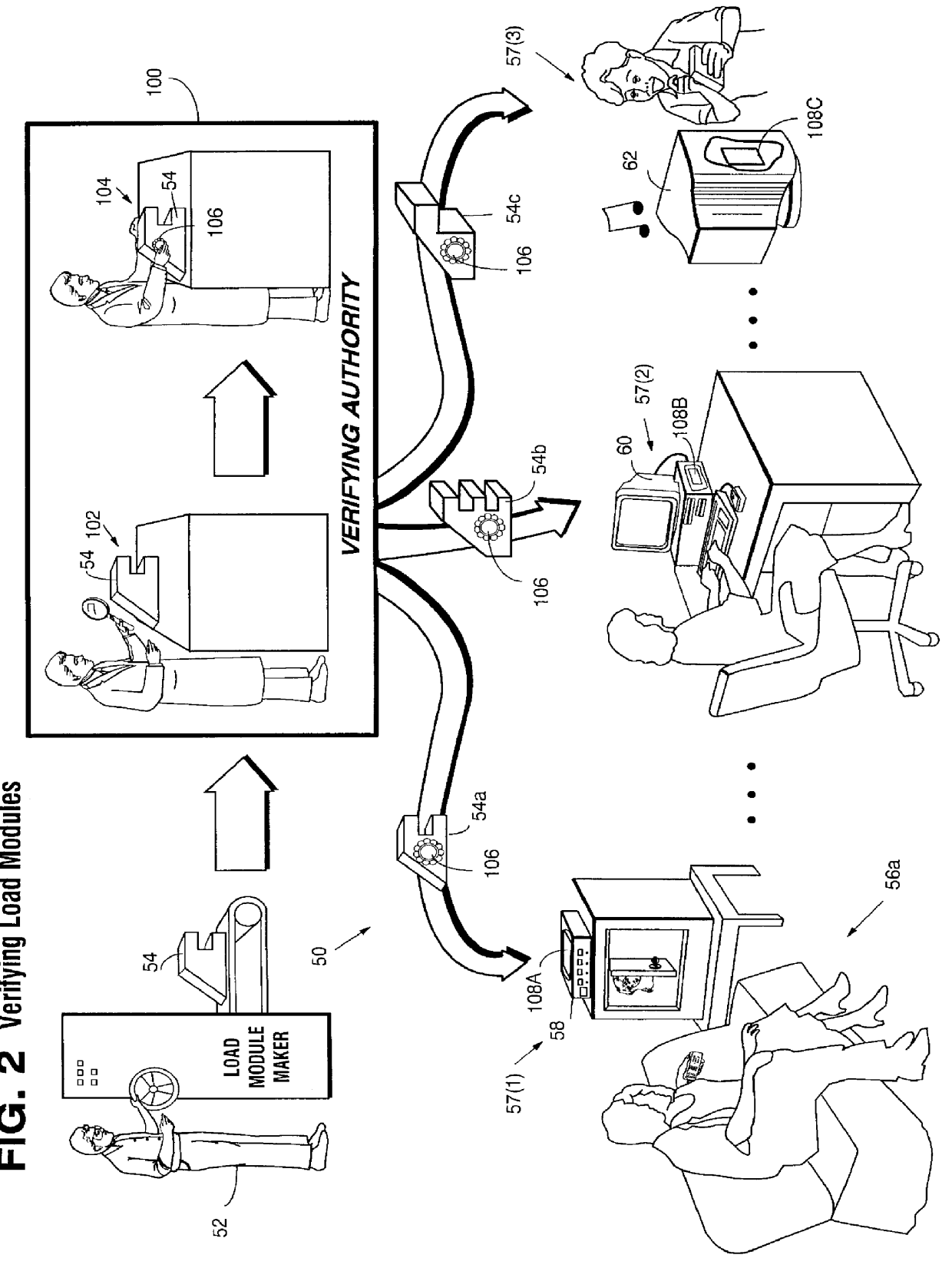
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Testing automatic data collection devices, such as barcode, RFID and/or magnetic stripe readers
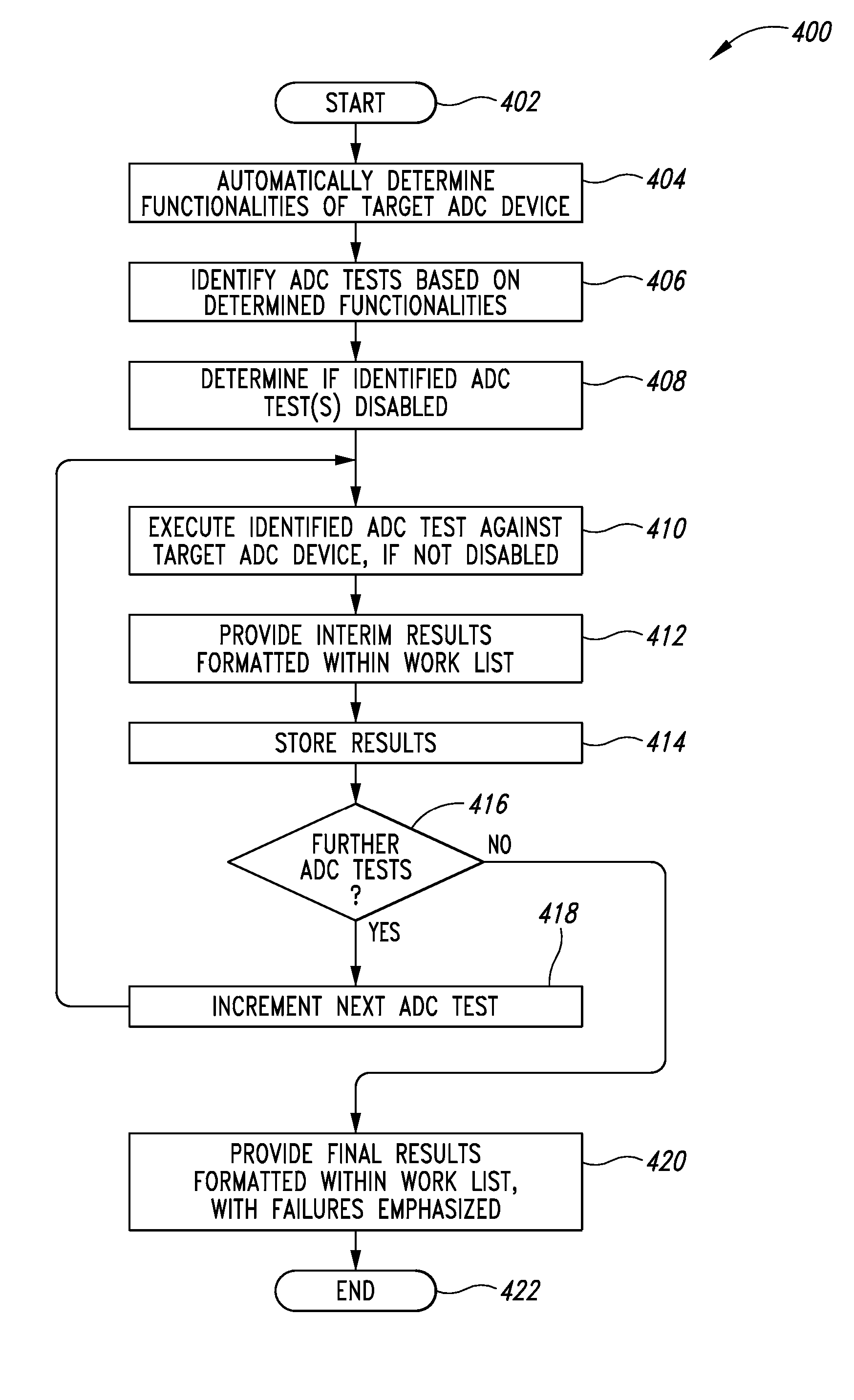
ActiveUS8944332B2Conveying record carriersTesting sensing arrangementsData acquisitionBarcode reader
Automatic data collection devices such as barcode readers, RFID readers, magnetic stripe readers and the like may be tested using ADC device test executables, modules or processes stored at a variety of network locations. One or more sets of tests or work lists may be defined to facilitate testing. Tests may be identified by name and / or keyword. Keywords may be indicative one or more functionalities tested by the respective ADC device test module.
Owner:INTERMEC IP CORP
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
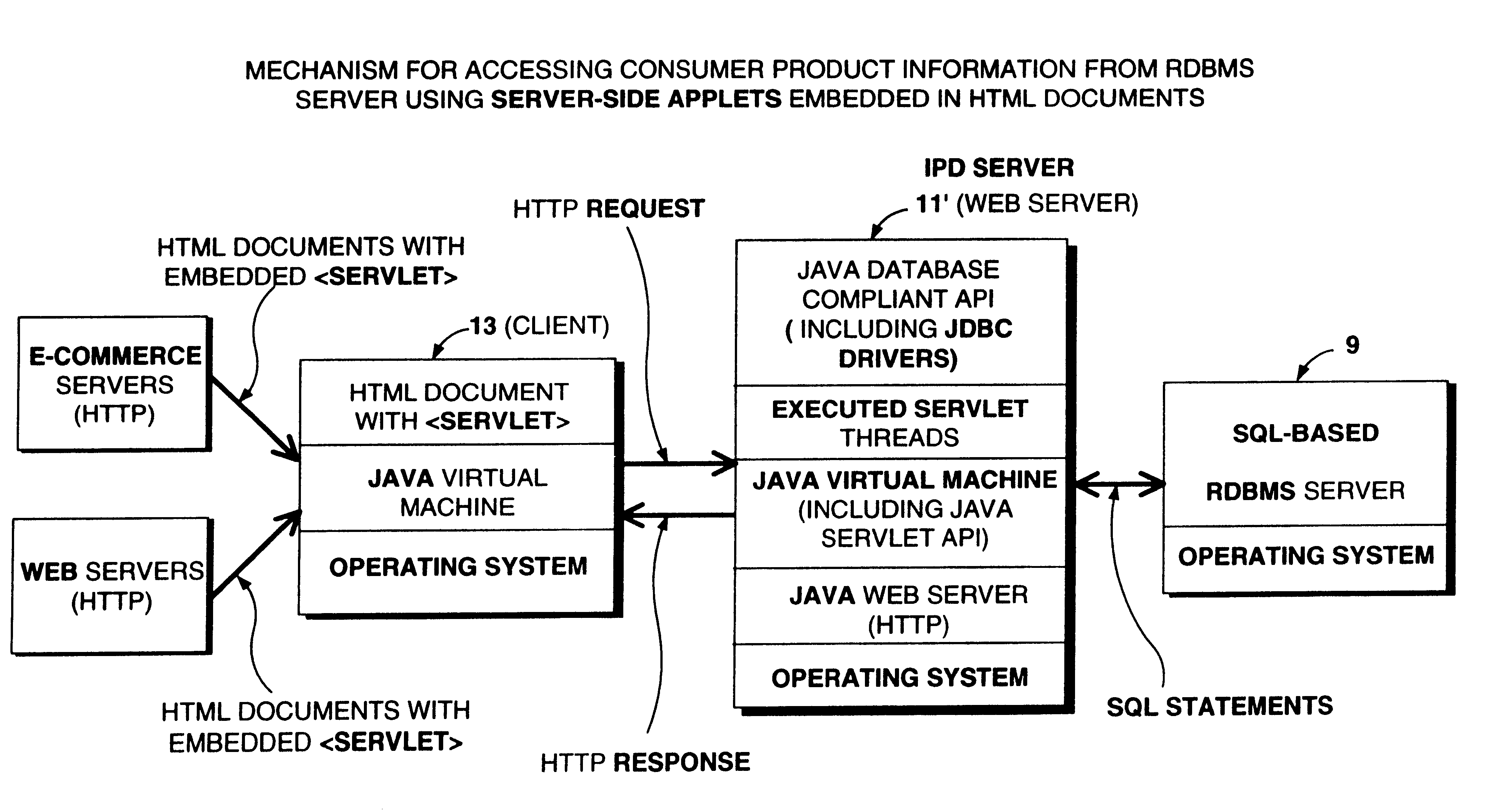
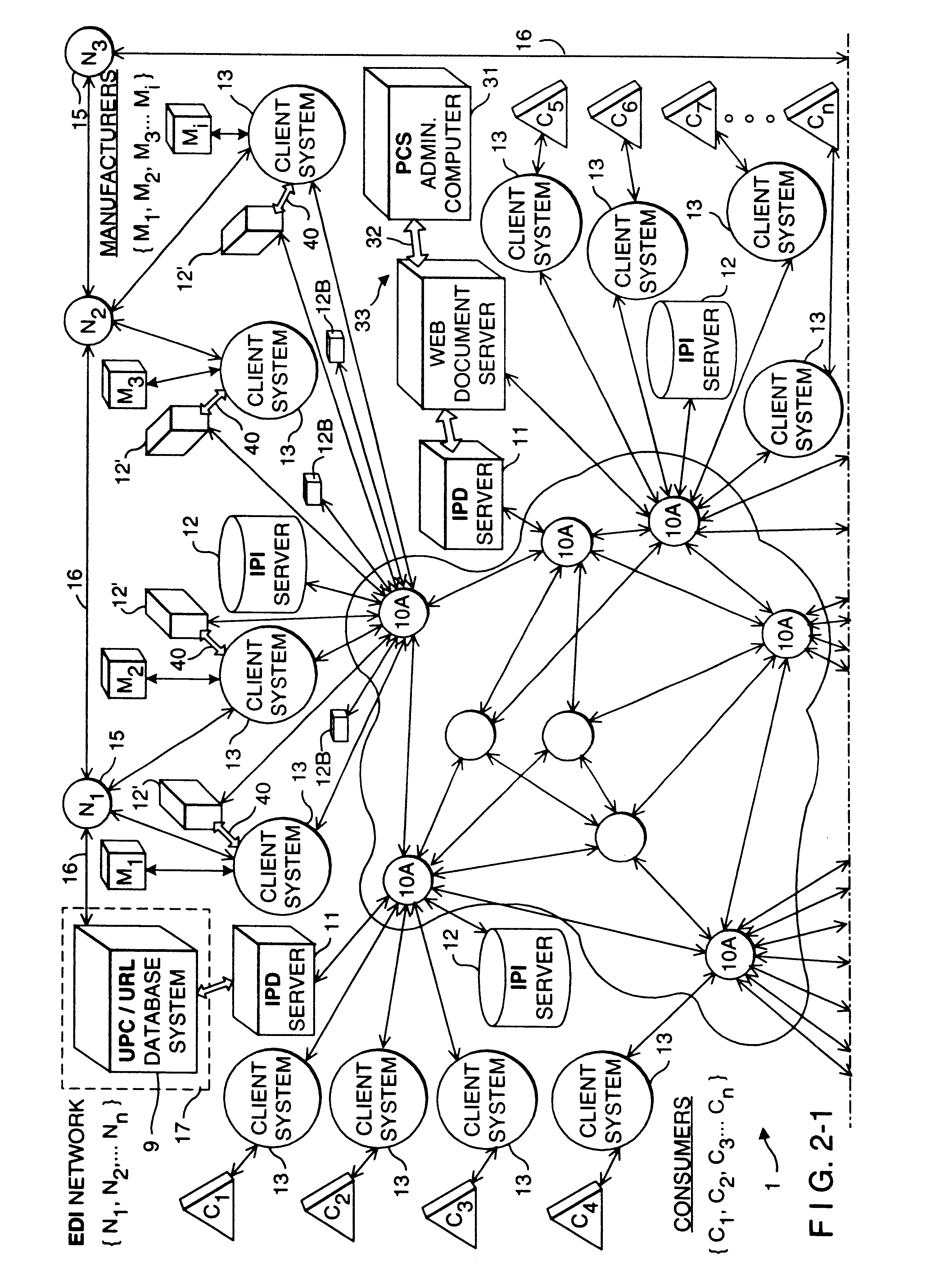
Method of and system for enabling the access of consumer product related information and the purchase of consumer products at points of consumer presence on the world wide web (WWW) at which consumer product information request (CPIR) enabling servlet tags are embedded within html-encoded documents
InactiveUS6625581B1Easy to readDigital data information retrievalAdvertisementsPoint of presenceAlternative technology
Method of and system for delivering consumer product related information to consumers over the Internet. The system and method involves creating an UPN-encoded Consumer Product Information (CPIR) enabling Applet for each consumer product registered within a manufacturer-managed UPN / URL database management system. Each CPIR-enabling Applet is encapsulated within an executable file and then stored in the UPN / URL database management system. Each CPIR-enabling Applet is searchable and downloadable by, for example, (1) retailers purchasing products from an electronic-commerce enabled product catalog, (2) advertisers desiring to link consumer product information to Web-based product advertisements, or (3) anyone having a legitimate purpose of disseminating such information within the stream of electronic commerce. After downloading and extraction from its encapsulating file, the CPIR-enabling Applet is embedded within an HTML-encoded document associated with, for example, an EC-enabled store, on-line auction site, product advertisement, Internet search engine or directory, and the like. Upon encountering such an Applet-encoded HTML document on the WWW, the consumer need only perform a single mouse-clicking operation to automatically execute the underlying CPIR-enabling Applet (on either the client or server side of the network), causing a UPN-directed search to be performed against the manufacturer-defined UPN / URL Database, and the results thereof displayed in an independent Java GUI, without disturbing the consumer's point of presence on the WWW. Preferably, the CPIR-enabling Applets are realized using Java(TM) technology, although it is understood that alternative technologies can be used to practice the system and methods of the present invention.
Owner:PERKOWSKI THOMAS J
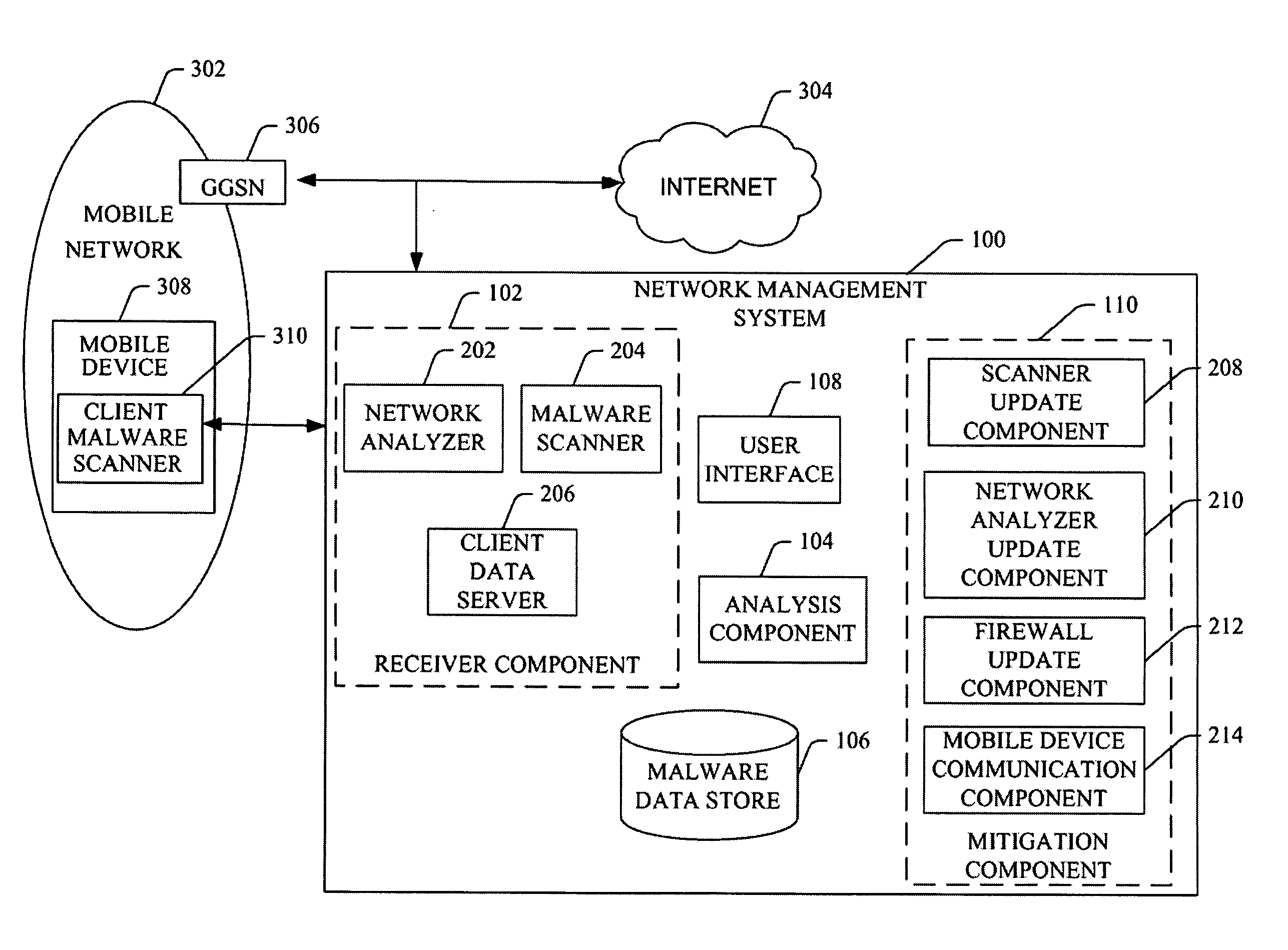
Malware Modeling Detection System And Method for Mobile Platforms
ActiveUS20070240217A1Suitable for useReliable detectionMemory loss protectionUser identity/authority verificationFeature setAlgorithm
A system and method for detecting malware by modeling the behavior of malware and comparing a suspect executable with the model. The system and method extracts feature elements from malware-infected applications, groups the feature elements into feature sets, and develops rules describing a malicious probability relationship between the feature elements. Using malware-free and malware-infected applications as training data, the system and method heuristically trains the rules and creates a probability model for identifying malware. To detect malware, the system and method scans the suspect executable for feature sets and applies the results to the probability model to determine the probability that the suspect executable is malware-infected.
Owner:PULSE SECURE
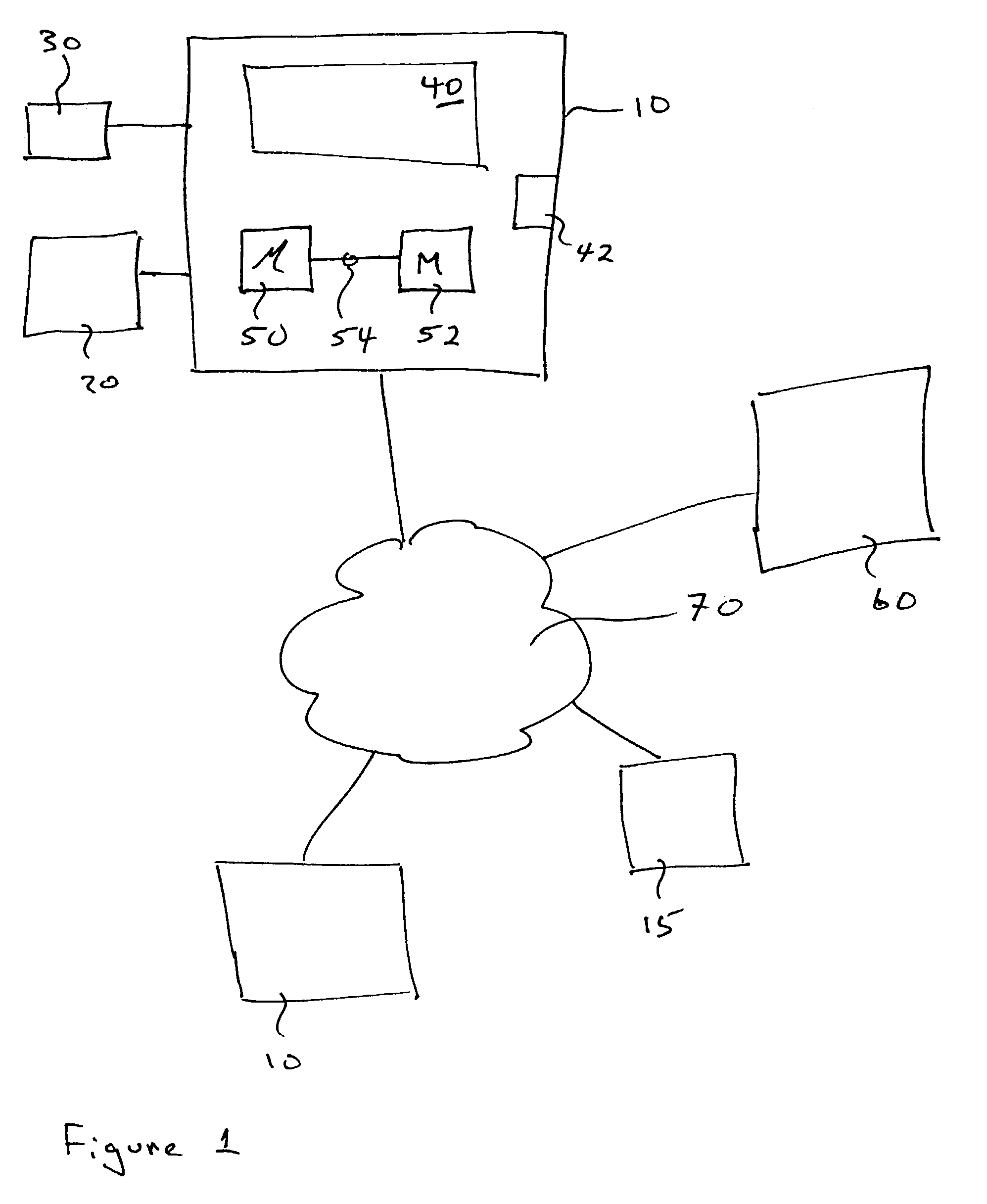
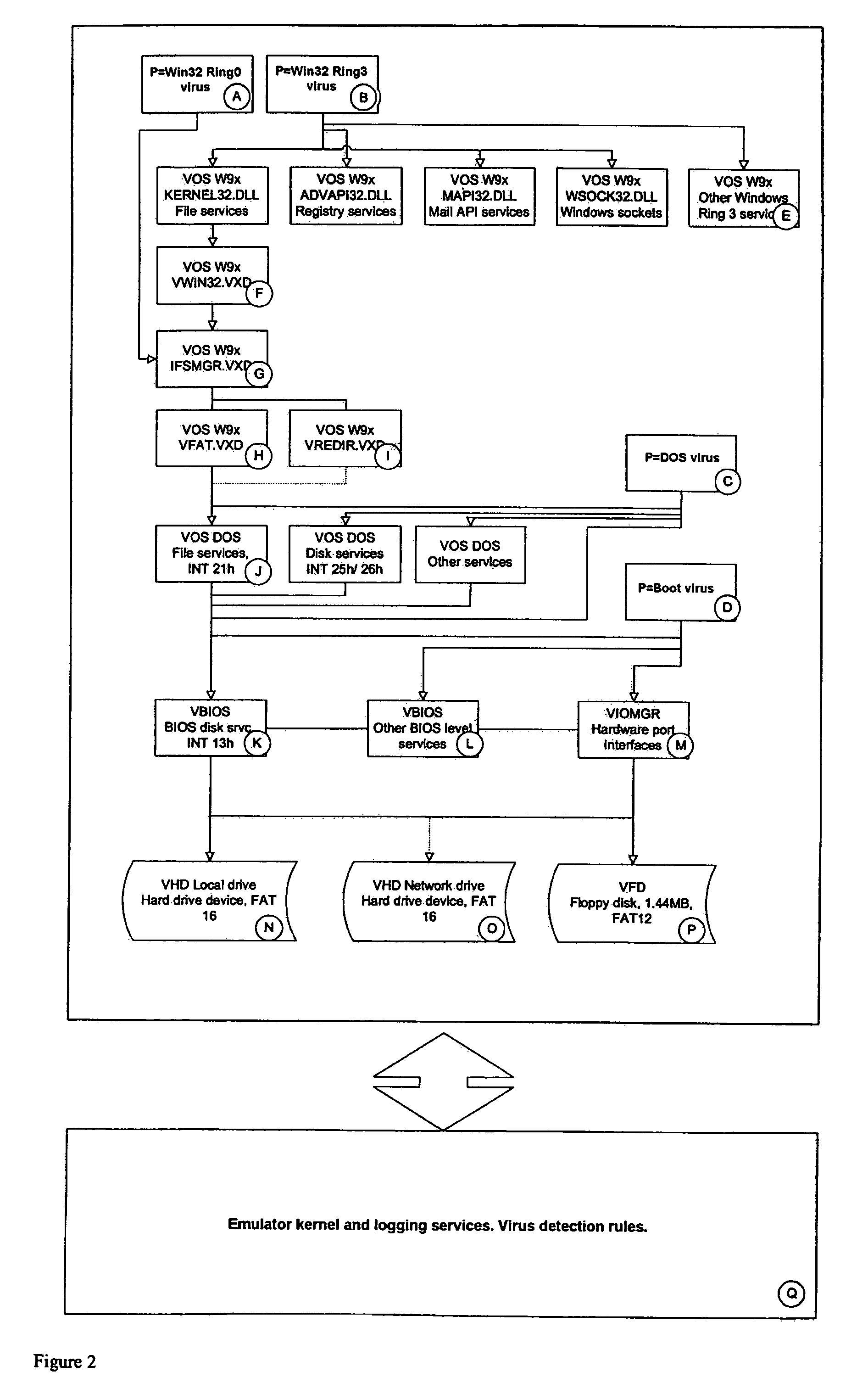
Simulated computer system for monitoring of software performance
InactiveUS7356736B2Reduce riskMemory loss protectionError detection/correctionVery low riskOperational system
A system S is defined which is capable of simulating a computer (virtual computer, VC) for the purpose of software performance monitoring. The system is implemented as a set of software modules (SM) that can be exchanged to change the behavior of the VC. The VC is driven by a CPU emulator, and can run any operating system (virtual operating system, VOS) that is supported by the available SM's. The system is designed to log accesses to system resources and the nature of these accesses. The system is particularly useful for determining whether an executable or file contains an unknown virus, with a very low risk of false positives. Detected viruses include encrypted, polymorphic, metamorphic and other virus types.
Owner:CA TECH INC
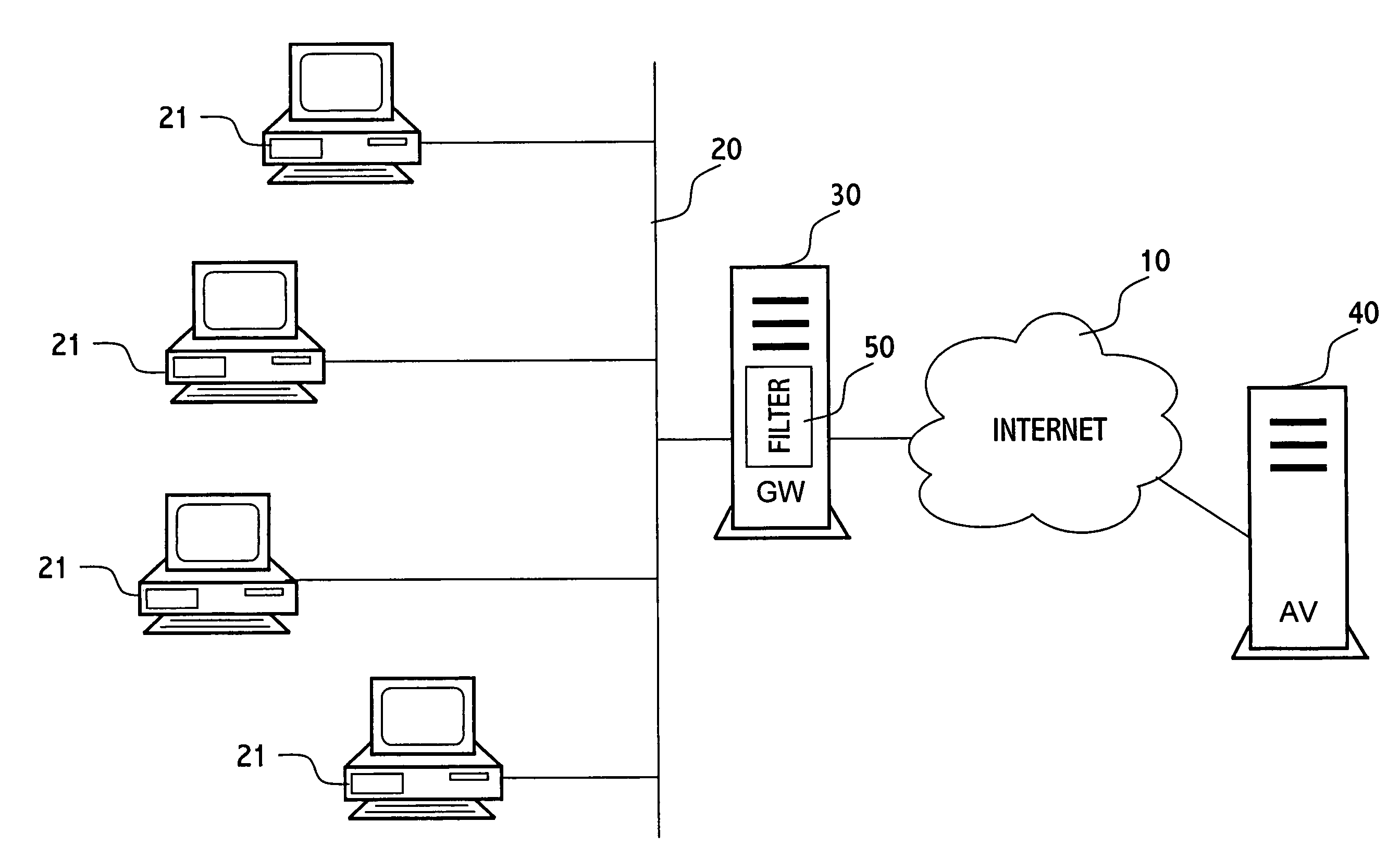
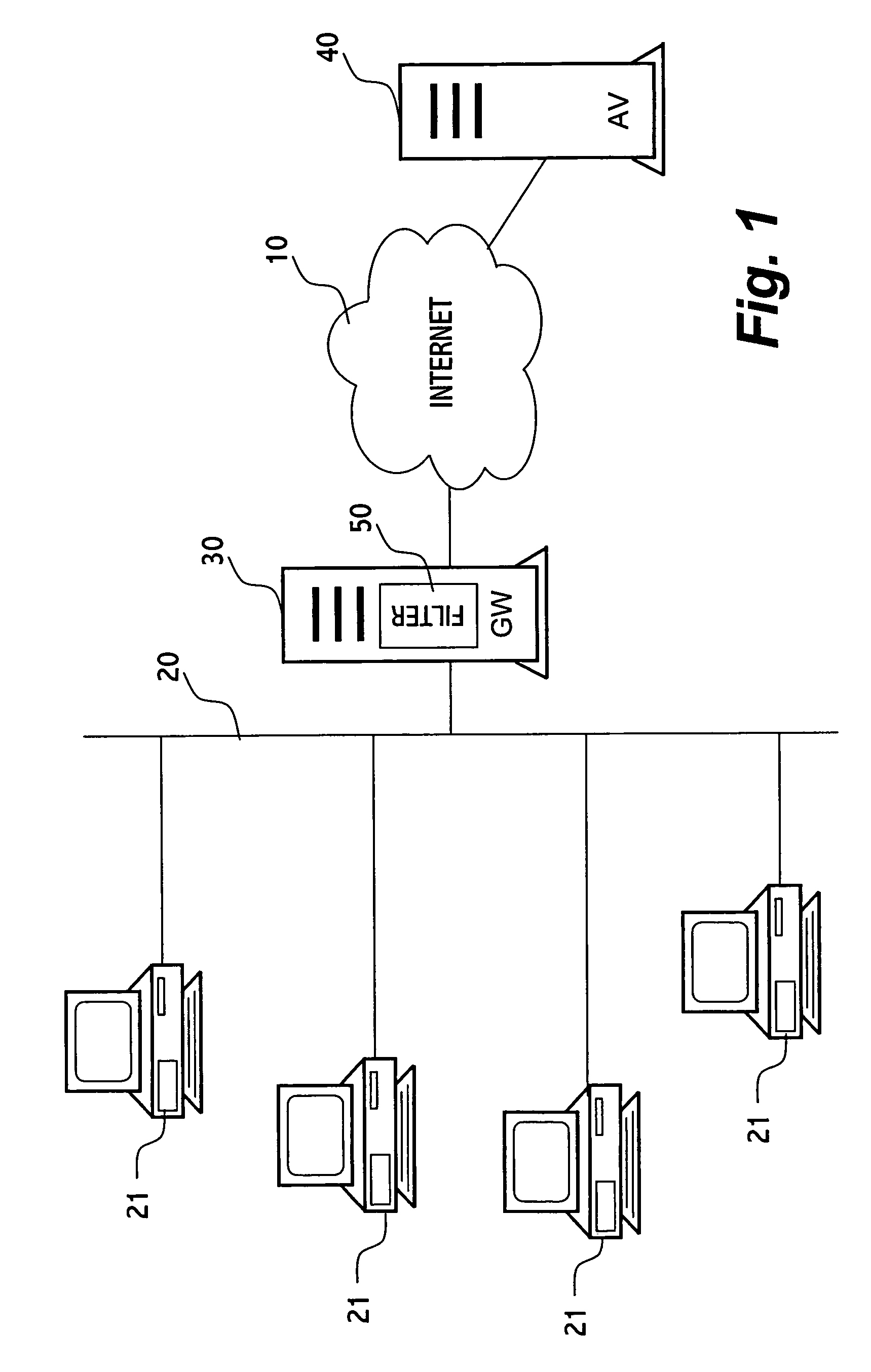
Method for protecting a computer from suspicious objects
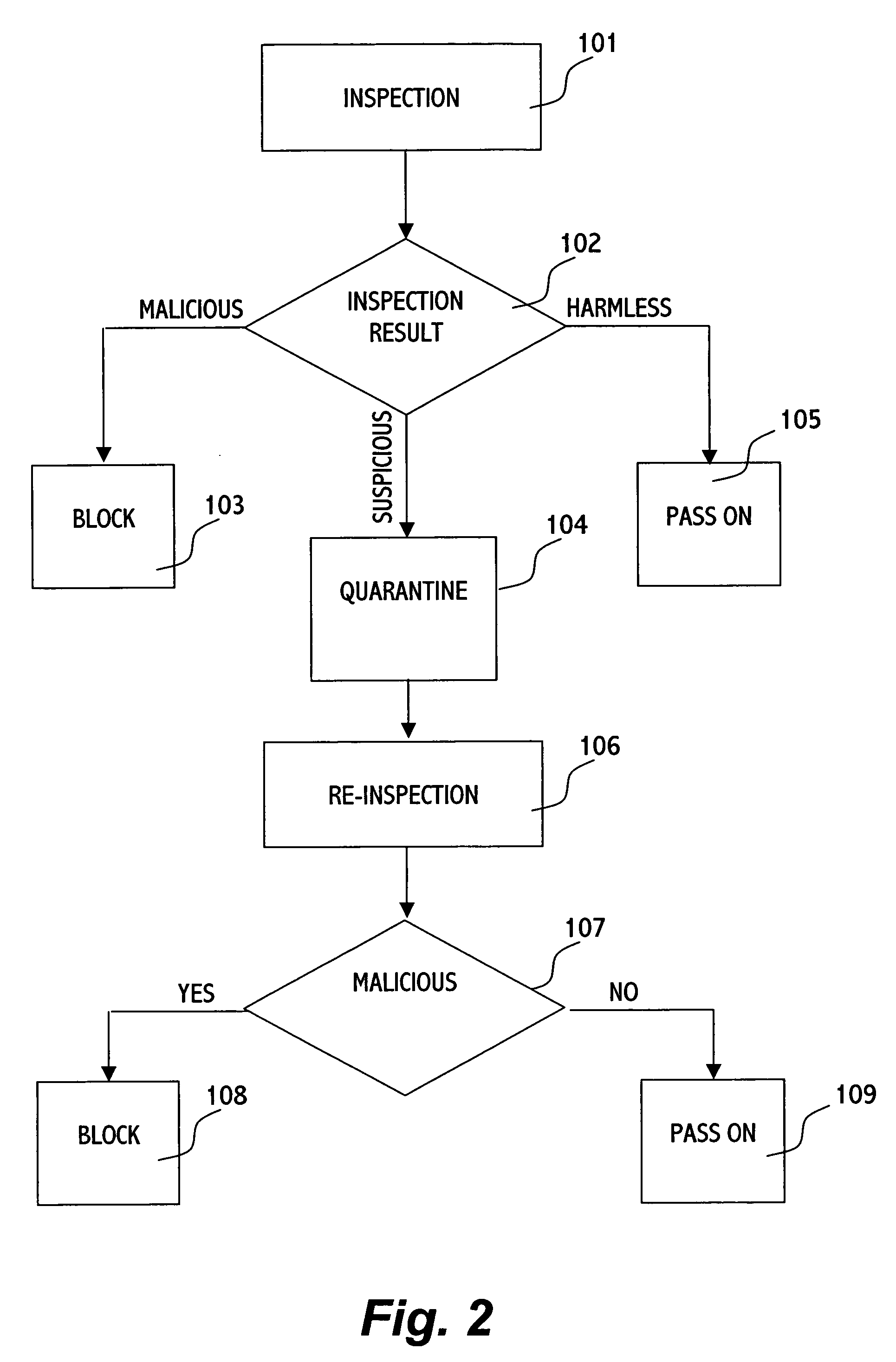
In an inspection facility (e.g. at a gateway server, at a proxy server, at a firewall to a network, at an entrance to a local area network or even at the user's computer) connected to an anti-virus center for updates, a method for protecting a computer from suspicious objects (e.g. a file, an executable, a Web page, an email message, etc.), the method comprising the steps of: inspecting an object; upon determining the object as suspicious, holding the object in quarantine (e.g. preventing from the object to be forwarded to its destination) for a time period, thereby enabling the inspection facility to be updated during the time period by the anti-virus center; upon ending of the time period, re-inspecting the object, thereby inspecting the object by updated inspection tests; and upon determining the object as malicious by the re-inspection, blocking the object, otherwise forwarding the object toward its destination.
Owner:ALADDIN KNOWLEDGE SYSTEMS
Data access, replication or communication system comprising a distributed software application
ActiveUS7912896B2Improve availabilityHigh bandwidthMultiple digital computer combinationsData switching networksCommunications systemData access
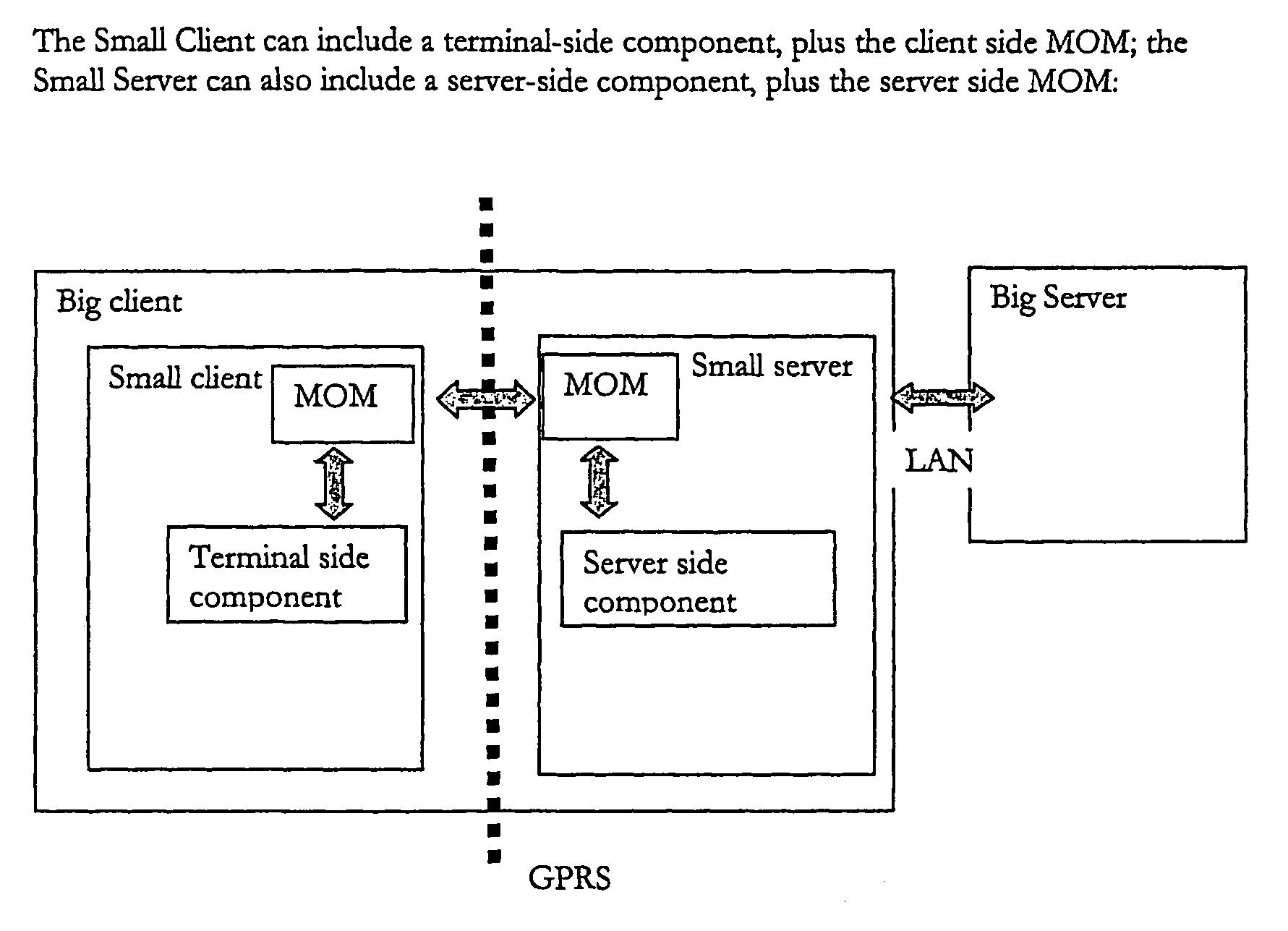
A data access, replication or communications system is distributed across a terminal-side executable running on a terminal and a server-side executable. Together the terminal-side executable and the server-side executable form a client to a larger server and collaborate by sending messages using a message queuing system over a network. The larger server can be, for example, a mail server. Splitting the client into a terminal-side executable and a server-side executable allows a terminal, such as mobile device with limited processing capacity, power, and connectivity, to enjoy the functionality of full-featured client access to a server environment using minimum resources on the mobile device by distributing some of the functionality normally associated with the client onto the server side executable, which is not so resource constrained.
Owner:MALIKIE INNOVATIONS LTD
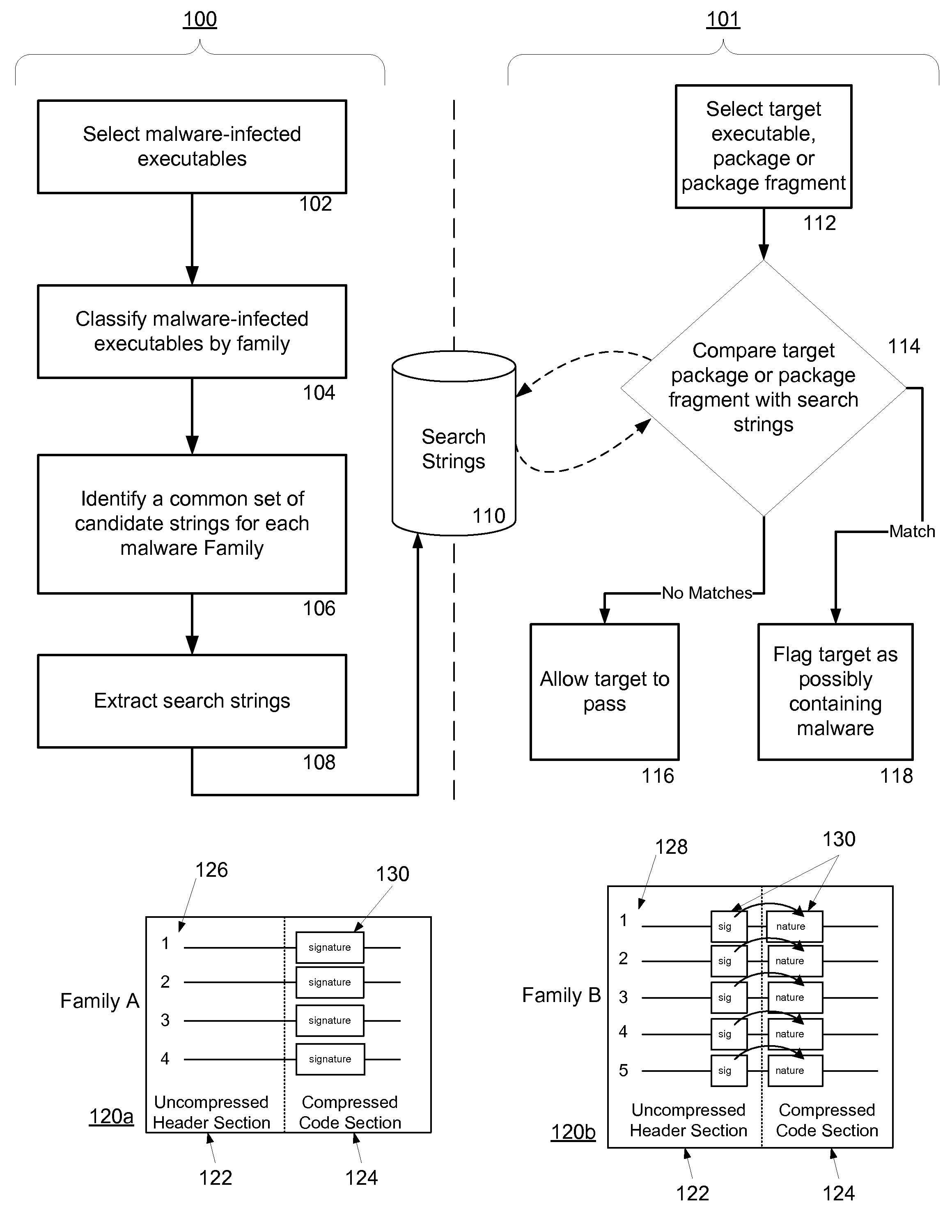
Methods for identifying malicious software
ActiveUS7644441B2Memory loss protectionEncryption apparatus with shift registers/memoriesGraphicsEncrypted function
Malicious software is identified in an executable file by identifying malicious structural features, decryption code, and cryptographic functions. A malicious structural feature is identified by comparing a known malicious structural feature to one or more instructions of the executable file. A malicious structural feature is also identified by graphically and statistically comparing windows of bytes or instructions in a section of the executable file. Cryptography is an indicator of malicious software. Decryption code is identified in an executable file by identifying a tight loop around a reversible instruction that writes to random access memory. Cryptographic functions are identified in an executable file be obtaining a known cryptographic function and performing a string comparison of the numeric constants of the known cryptographic function with the executable file.
Owner:SYNOPSYS INC
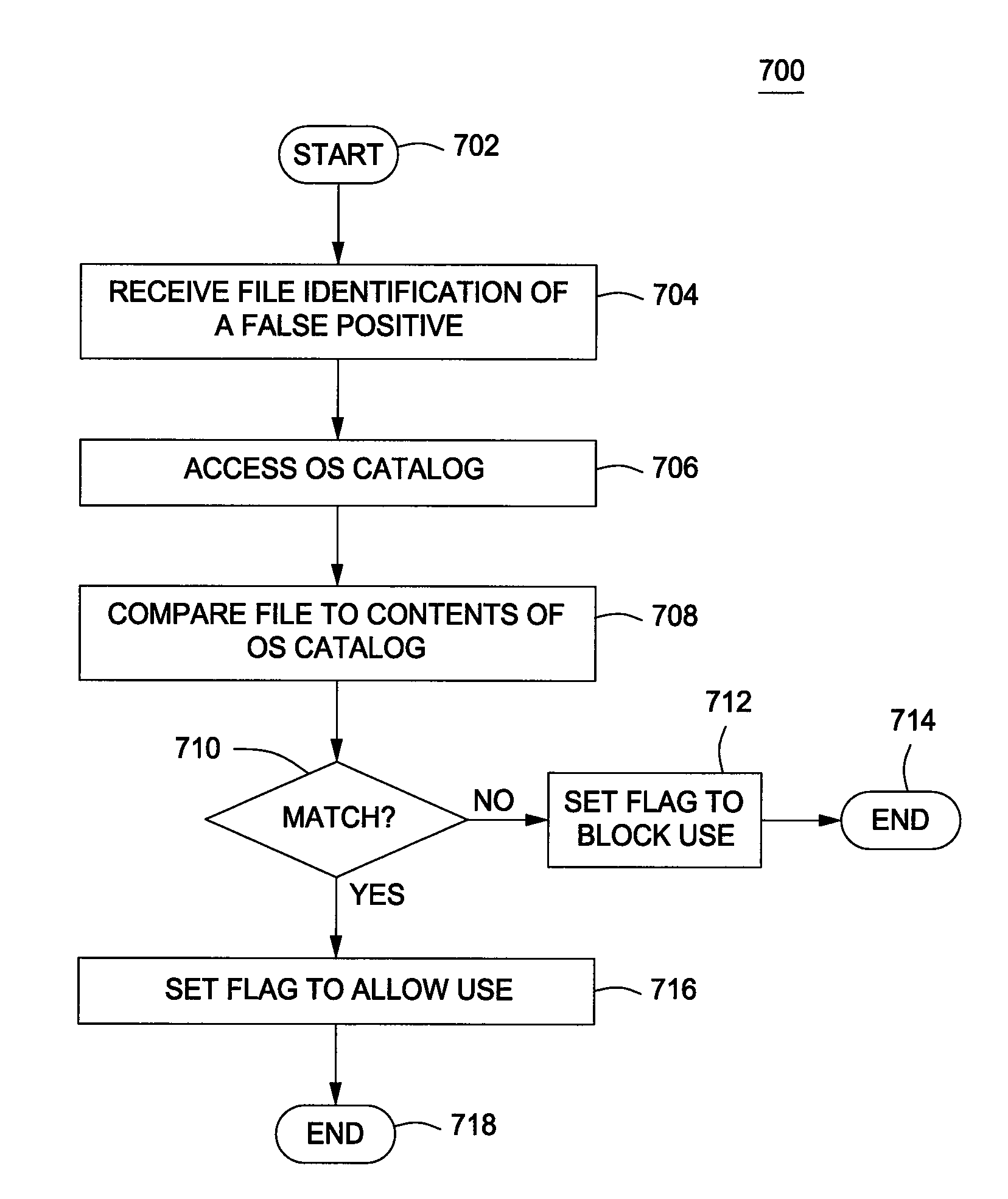
Method for mitigating false positive generation in antivirus software
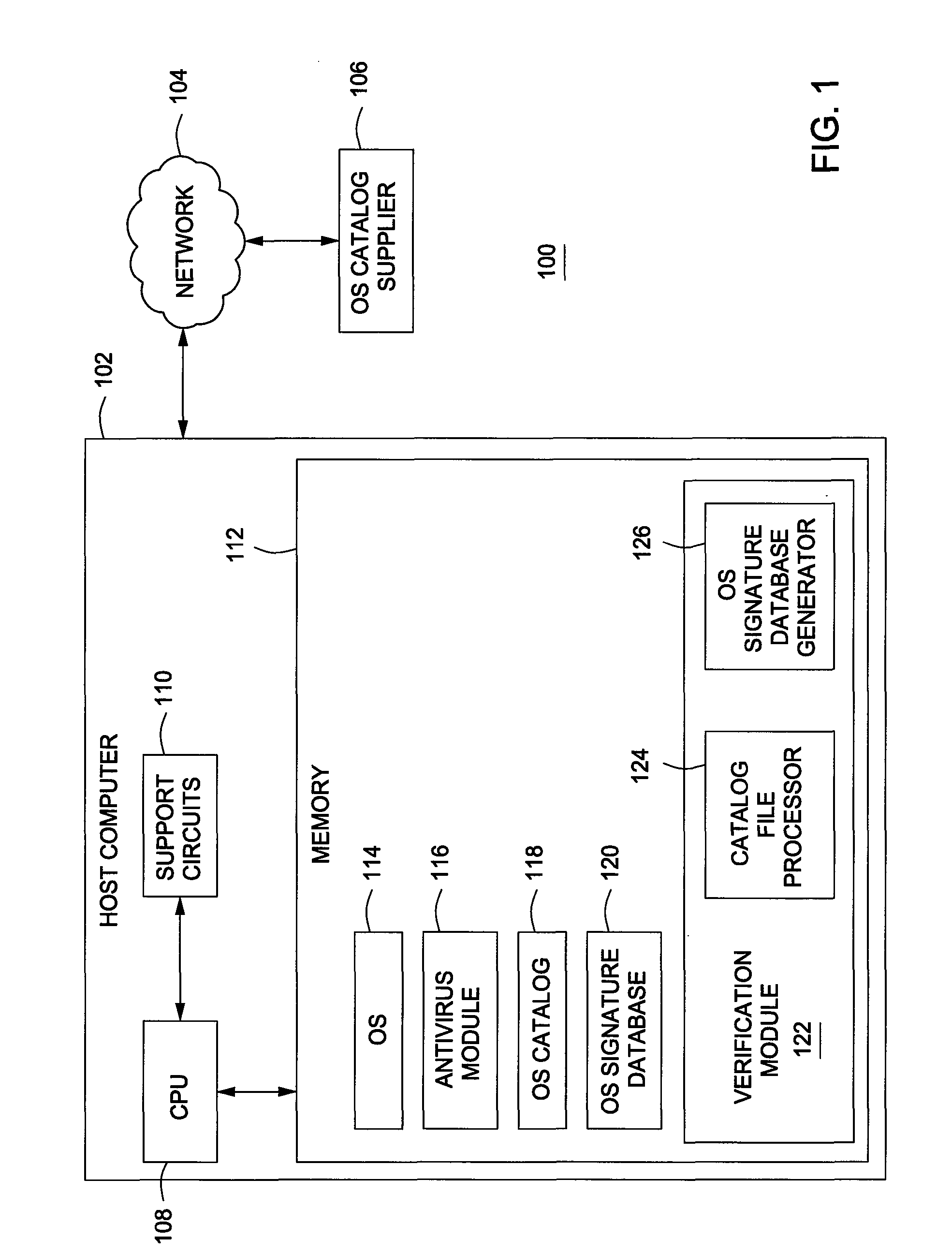
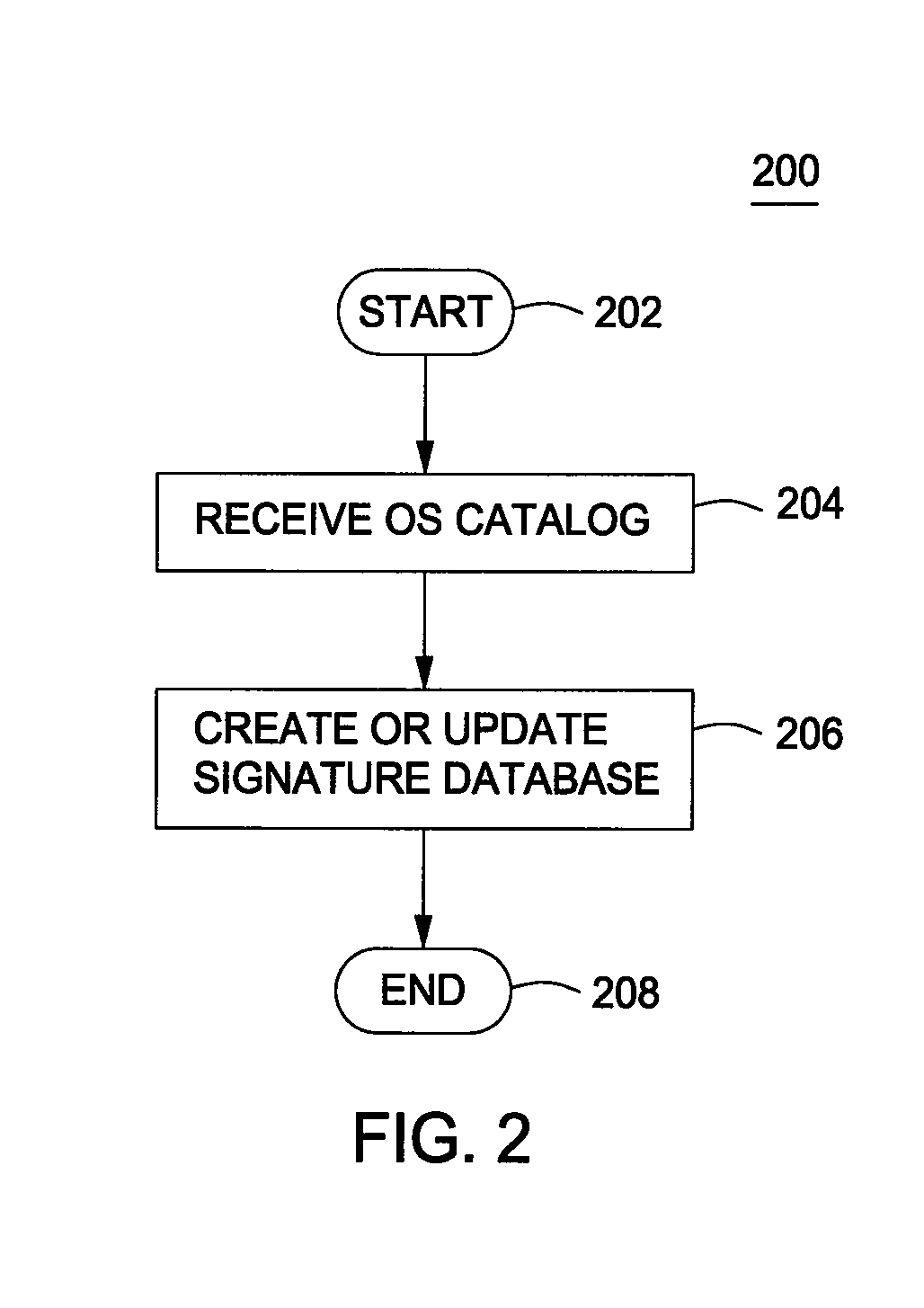
A method for mitigating false-positives as detected by antivirus software comprising accessing an operating system file that has been identified as malware; creating a signature for the operating system file; comparing the created signature to a signature database; and, if the created signature is not found in the signature database, defining the operating system file as malware. An operating system file, as used herein, is any file included as a part of the operating system binary executable file set, as well as any files added from third party vendors that integrate with or plug into the operating system.
Owner:SYMANTEC CORP
Integrity verifying and correcting software
InactiveUS6023586AEfficiently provideData processing applicationsDigital computer detailsSelf-healingApplication software
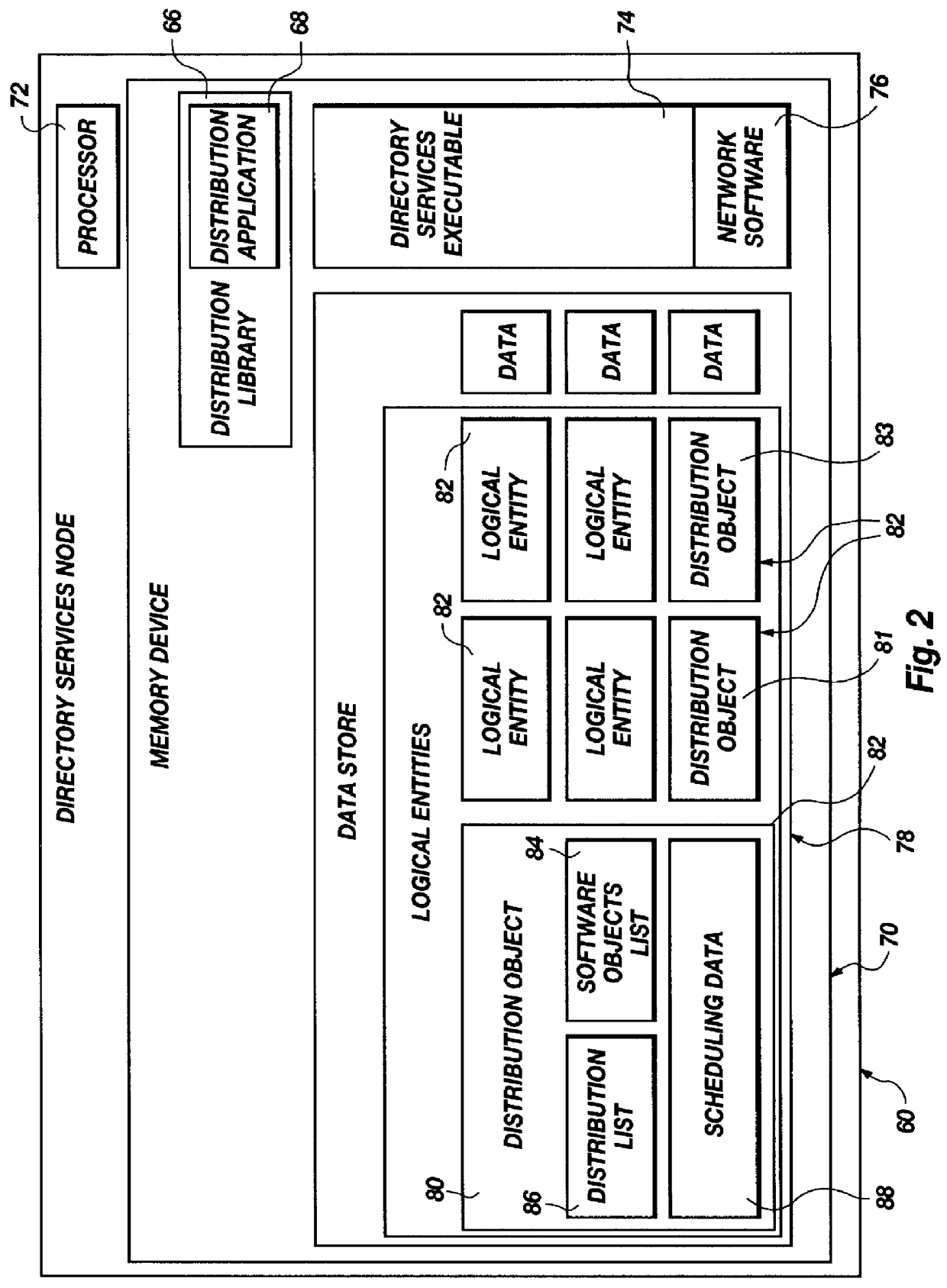
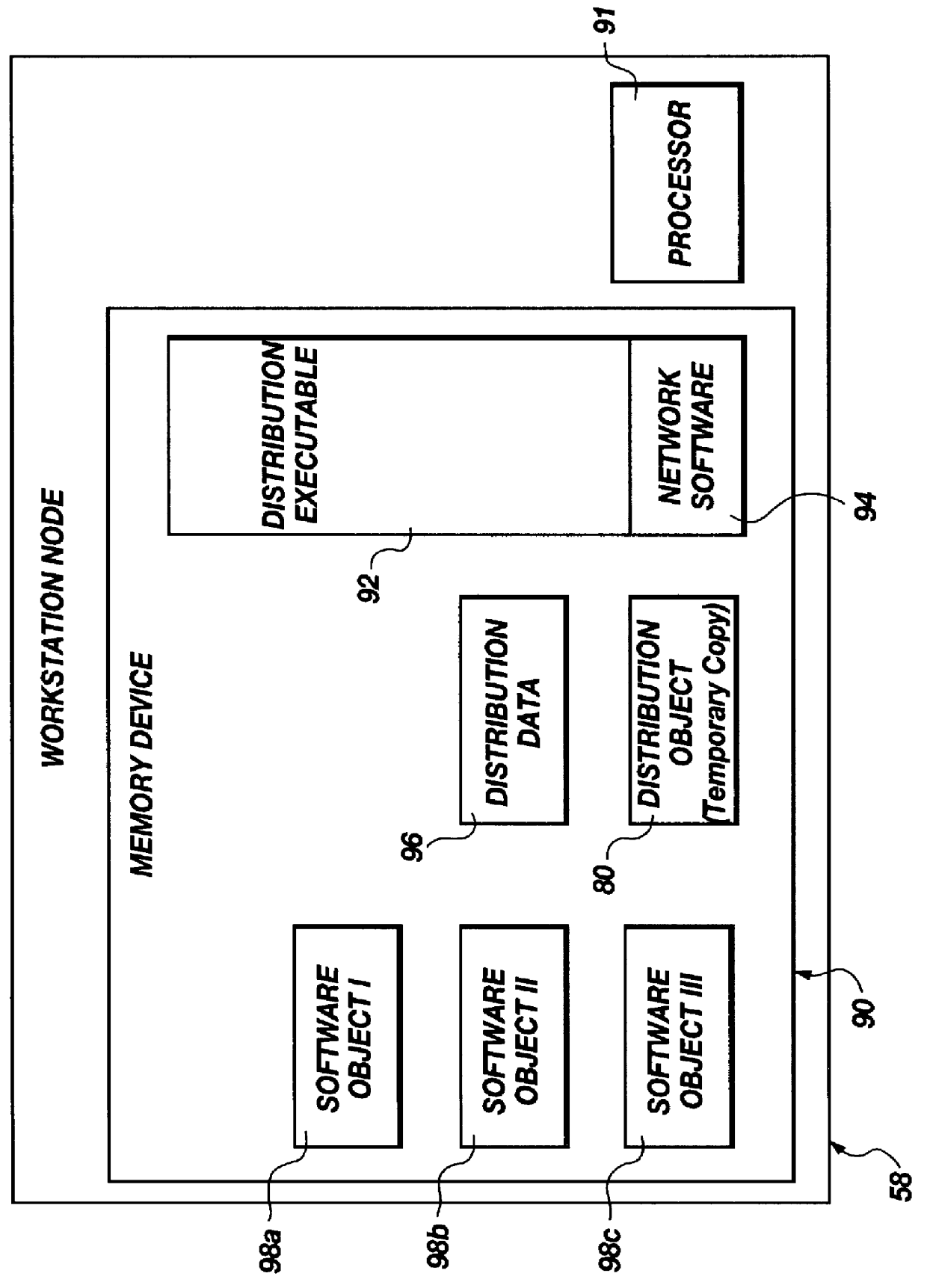
An apparatus and method for self-healing of software may rely on a distribution object in a directory services of a network to provide data for controlling distribution of software and installation of files associated therewith. A software object may represent a software product, system, data structure, application, or the like, from a single byte, to a complex program. A directory services system is responsible for maintaining a data store of inter-related logical entities (directory services objects), including software objects and a distribution object containing all distribution information associated with certain distribution processes. Maintenance methods may be programmed into a directory services object or some other executable to verify the existence of files required for particular software. Verification may be completed in association with a launch request, by explicit request, or in an ongoing maintenance procedure. Maintenance may include executables and data to control, complete, and record integrity of distributed files as a distinct activity or as an ongoing, routine, periodic process of verification and appropriate re-installation of files, operating transparently to a user.
Owner:RPX CORP
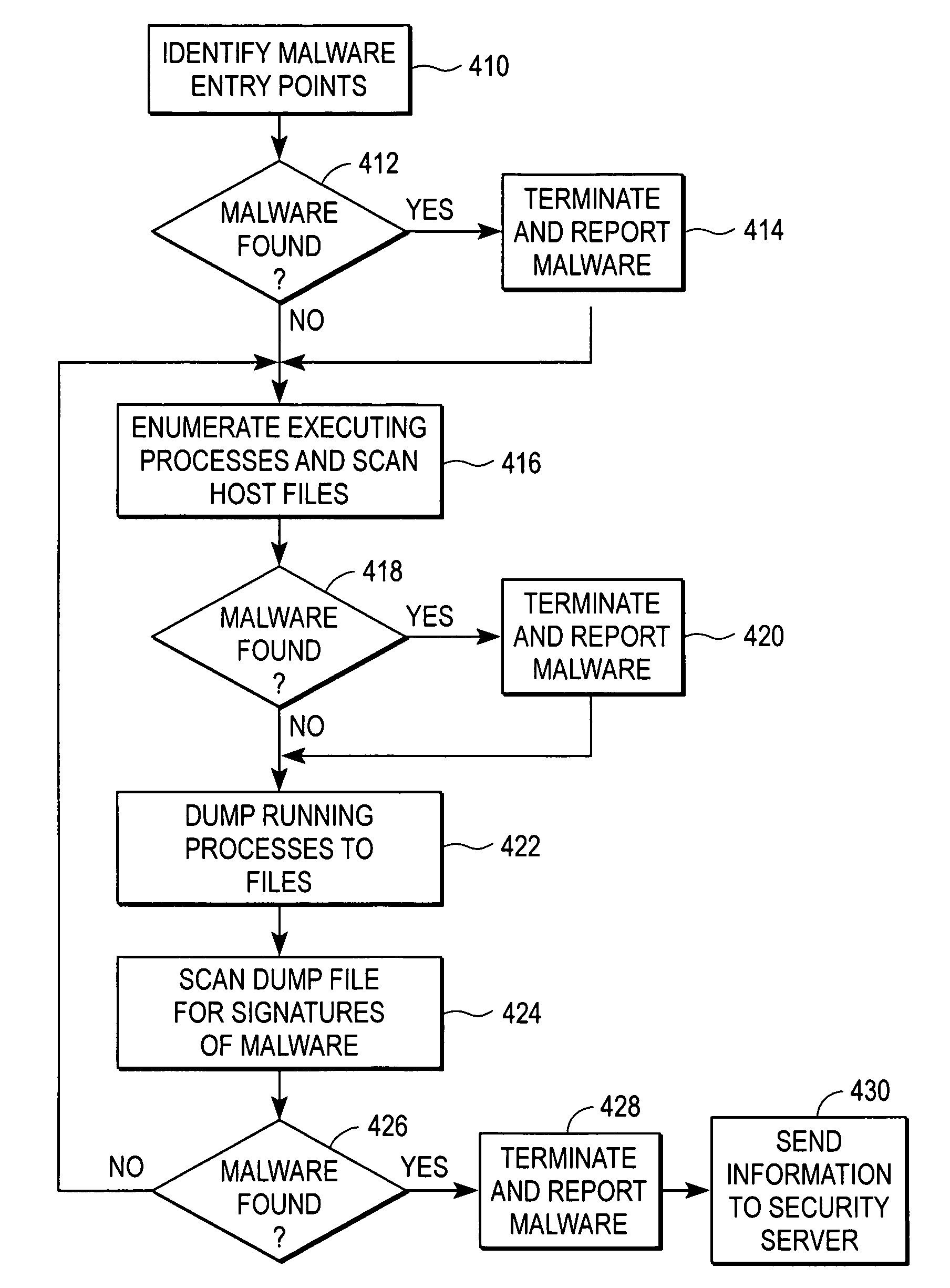
Detecting malicious software through process dump scanning
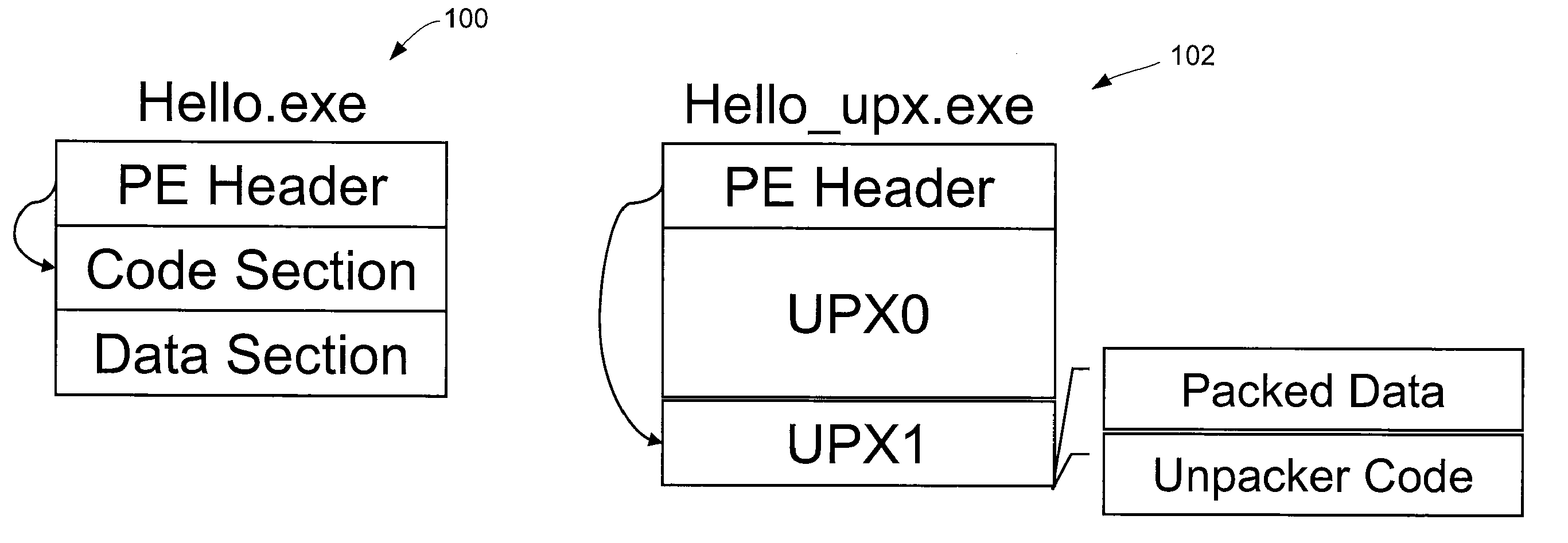
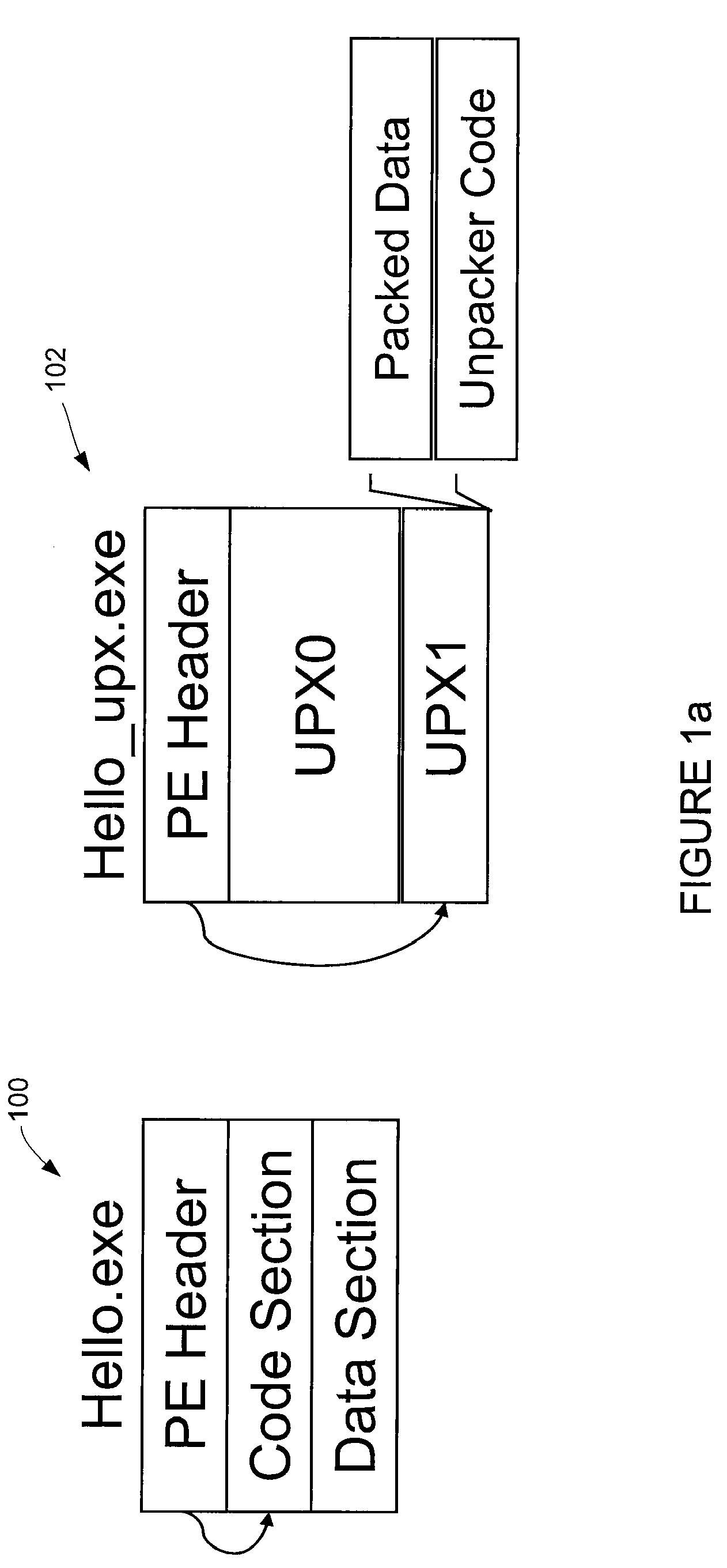
An executable file containing malicious software can be packed using a packer to make the software difficult to detect. The executable file is loaded into the computer's memory and executed as a process. A memory dump module analyzes the address space for the process and identifies an executable file image within it. The memory dump module creates a memory dump file on the computer's storage device containing the file image and modifies the file to make it resemble a normal executable file. A signature scanning module scans the memory dump file for signatures of malicious software. If a signature is found in the file, a reporting module sends the host file for the process and the memory dump file to a security server for analysis.
Owner:CA TECH INC
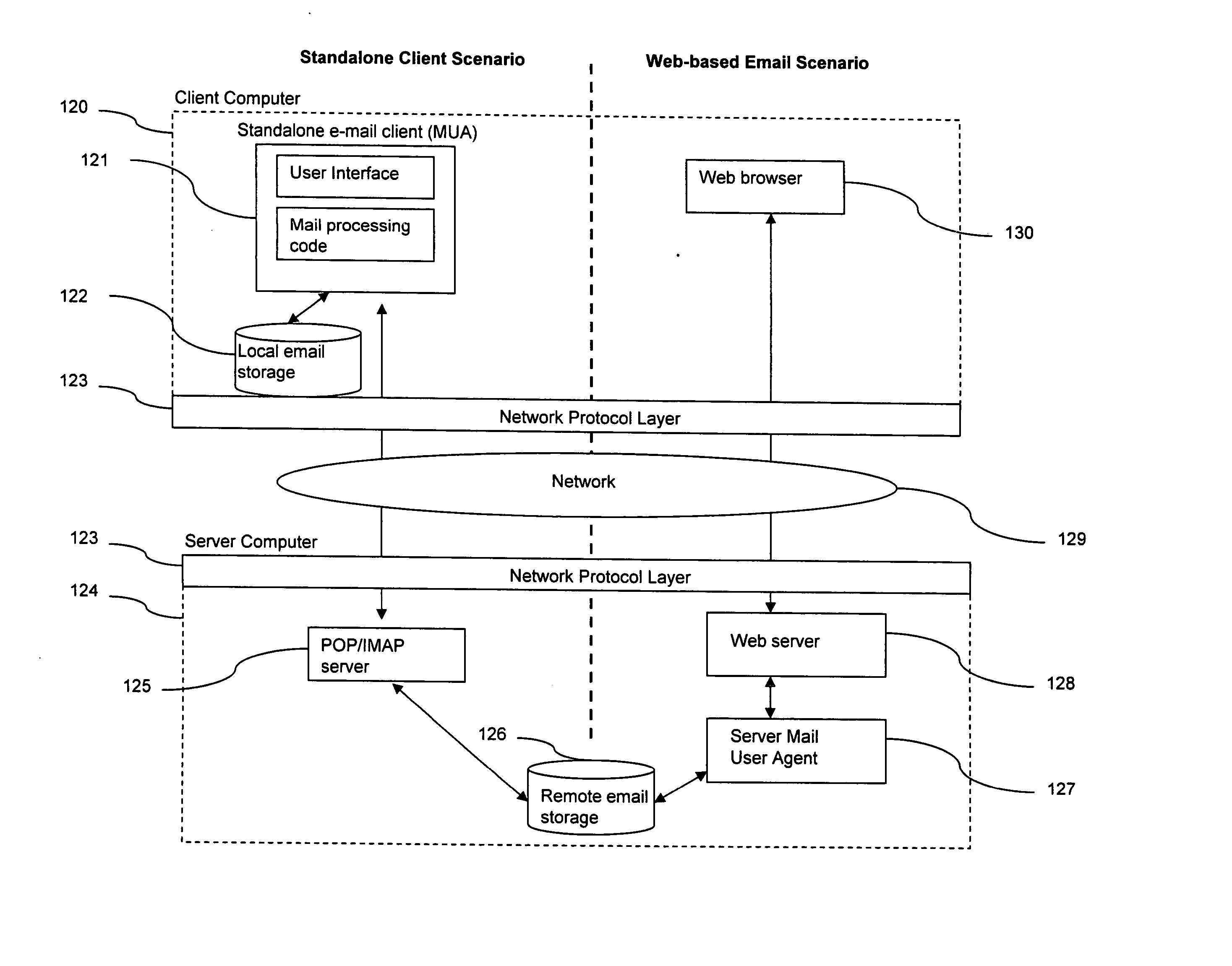
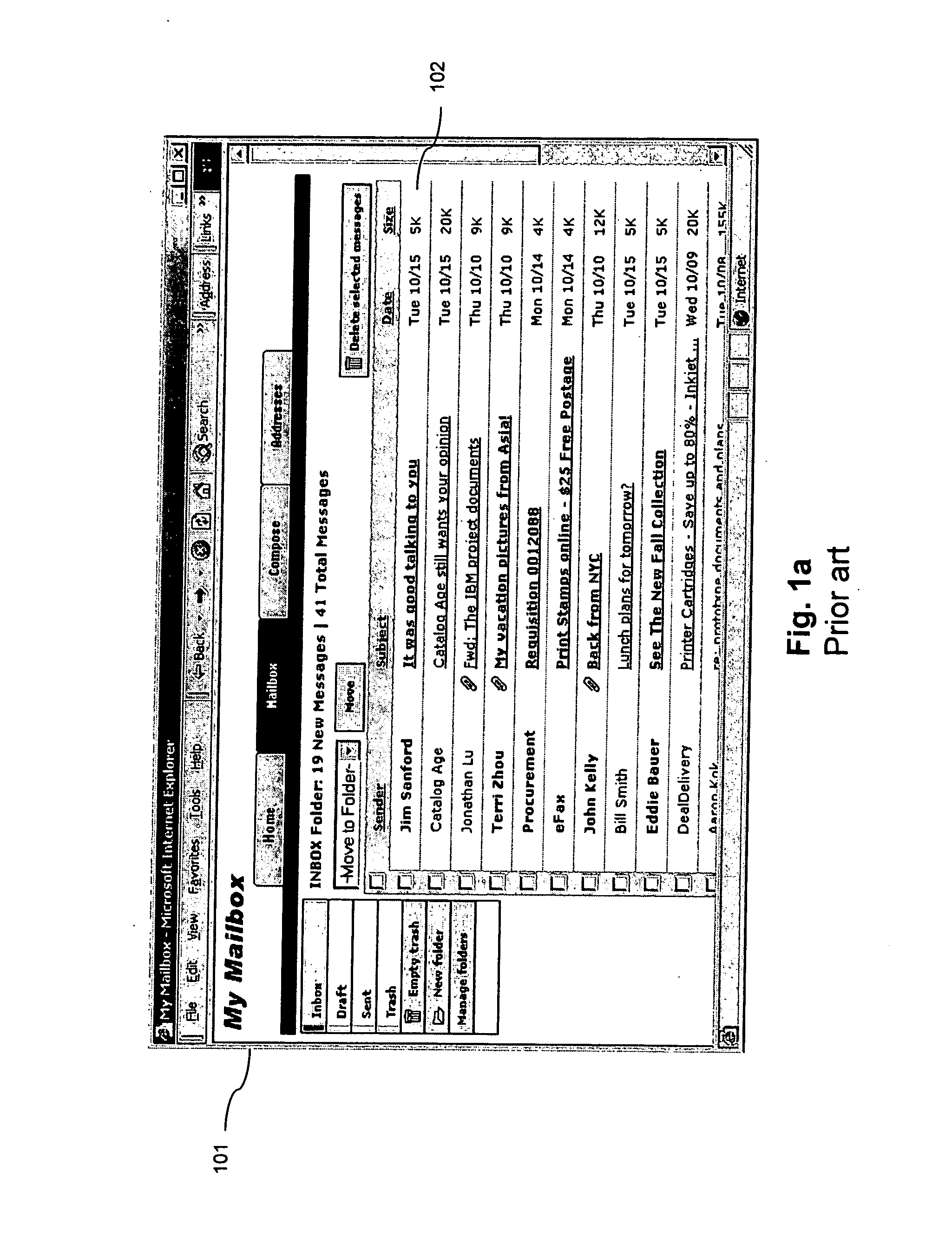
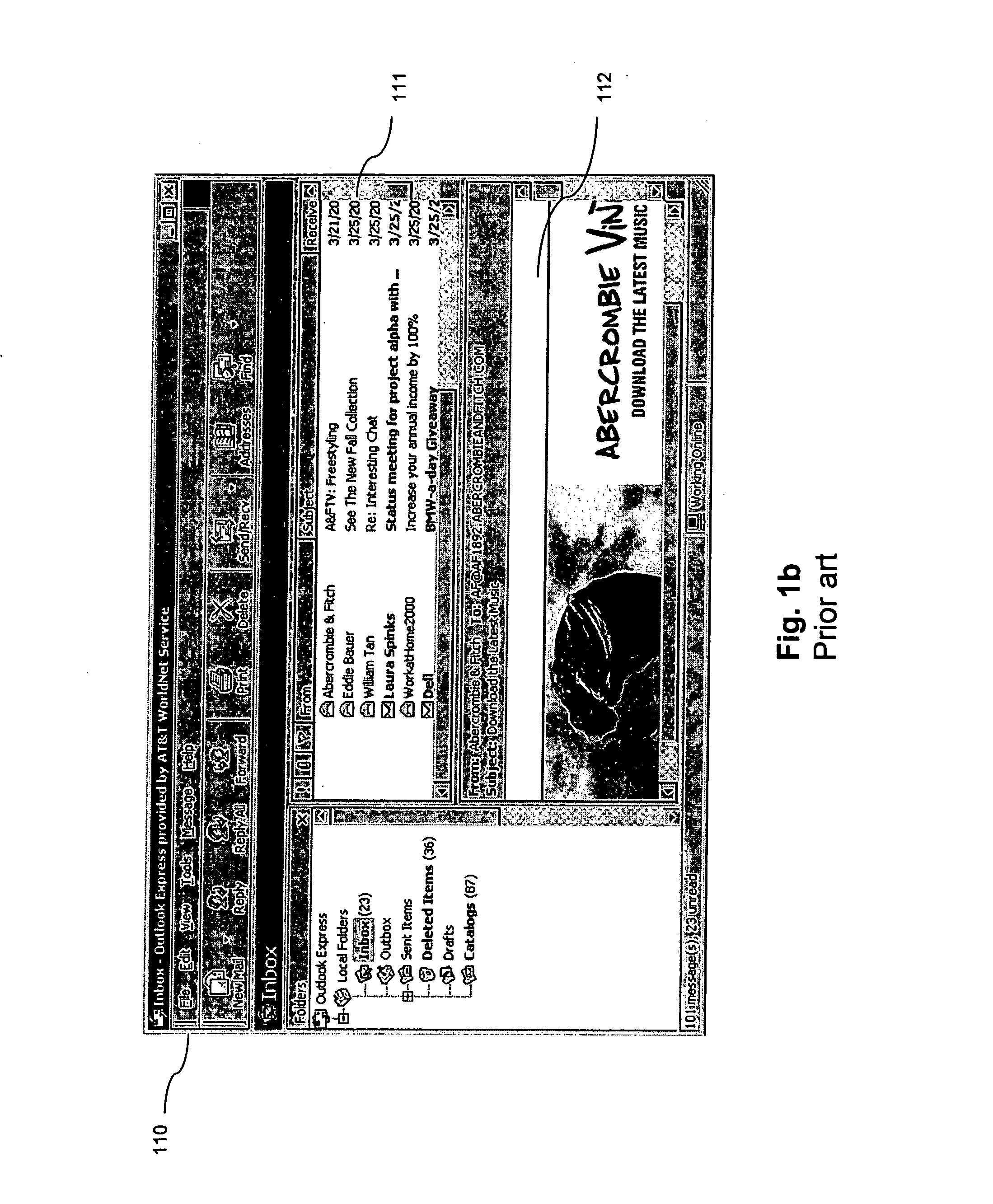
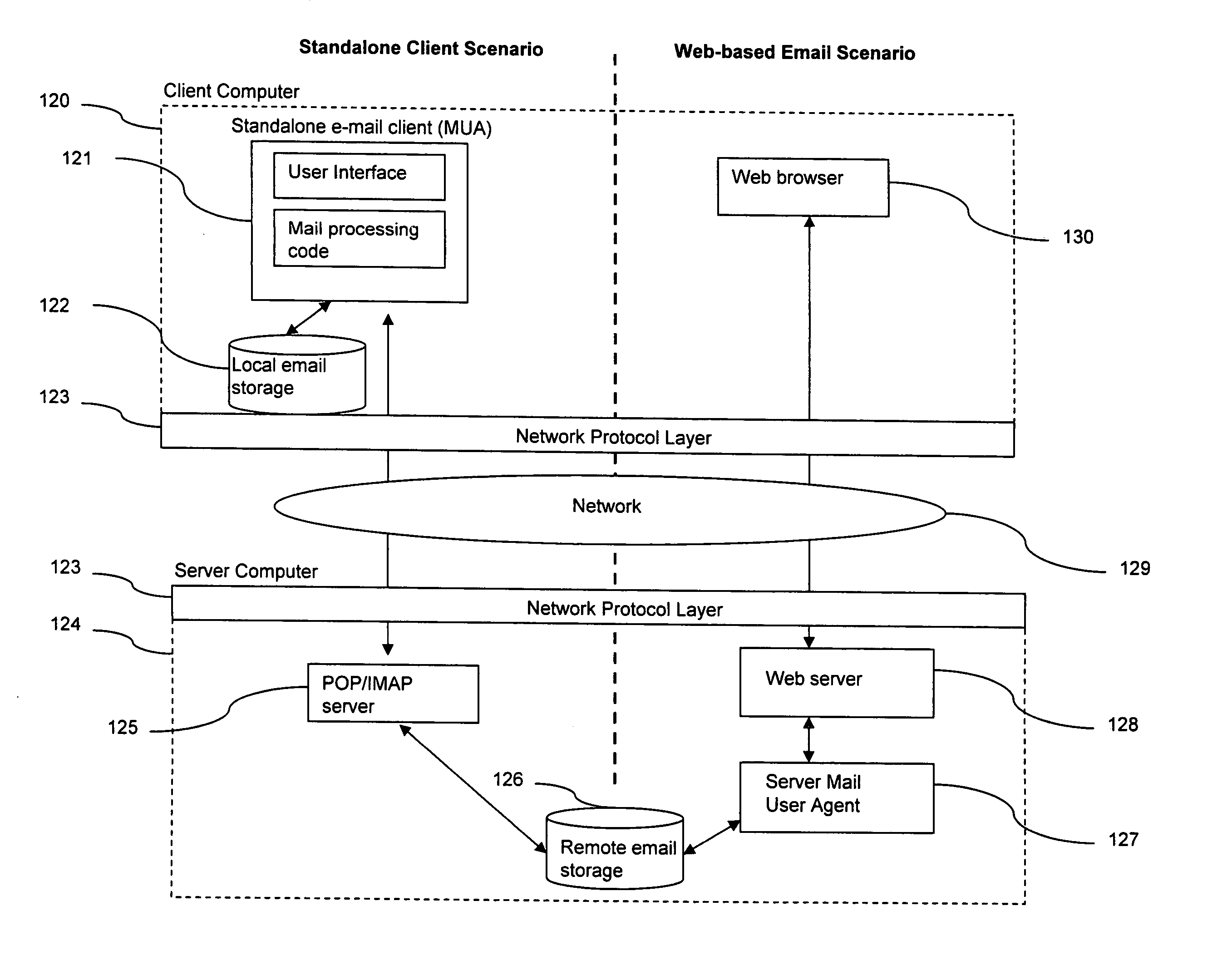
Enhancement of e-mail client user interfaces and e-mail message formats
ActiveUS20080005247A9Good user interfaceMultiple digital computer combinationsTransmissionClient-sideElectronic mail
An enhancement to e-mail user interfaces and message formats includes a dynamic preview window to view and retrieve attachments and summaries of e-mail messages directly in the e-mail list view or inbox view without opening an e-mail message. The efficient viewing mechanism further allows previews without cluttering the listing of the e-mails in the inbox by allowing the client to detect special preview instructions within an e-mail and run executables within the preview window. The enhancement is applicable to standalone e-mail clients (POP or IMAP based) and to web-based e-mail systems.
Owner:ADVENIX CORP CORP
Method and apparatus for delivering managed applications to remote locations
ActiveUS7774323B2Digital data processing detailsMultiple digital computer combinationsApplication softwareComputer science
Owner:SERVICENOW INC
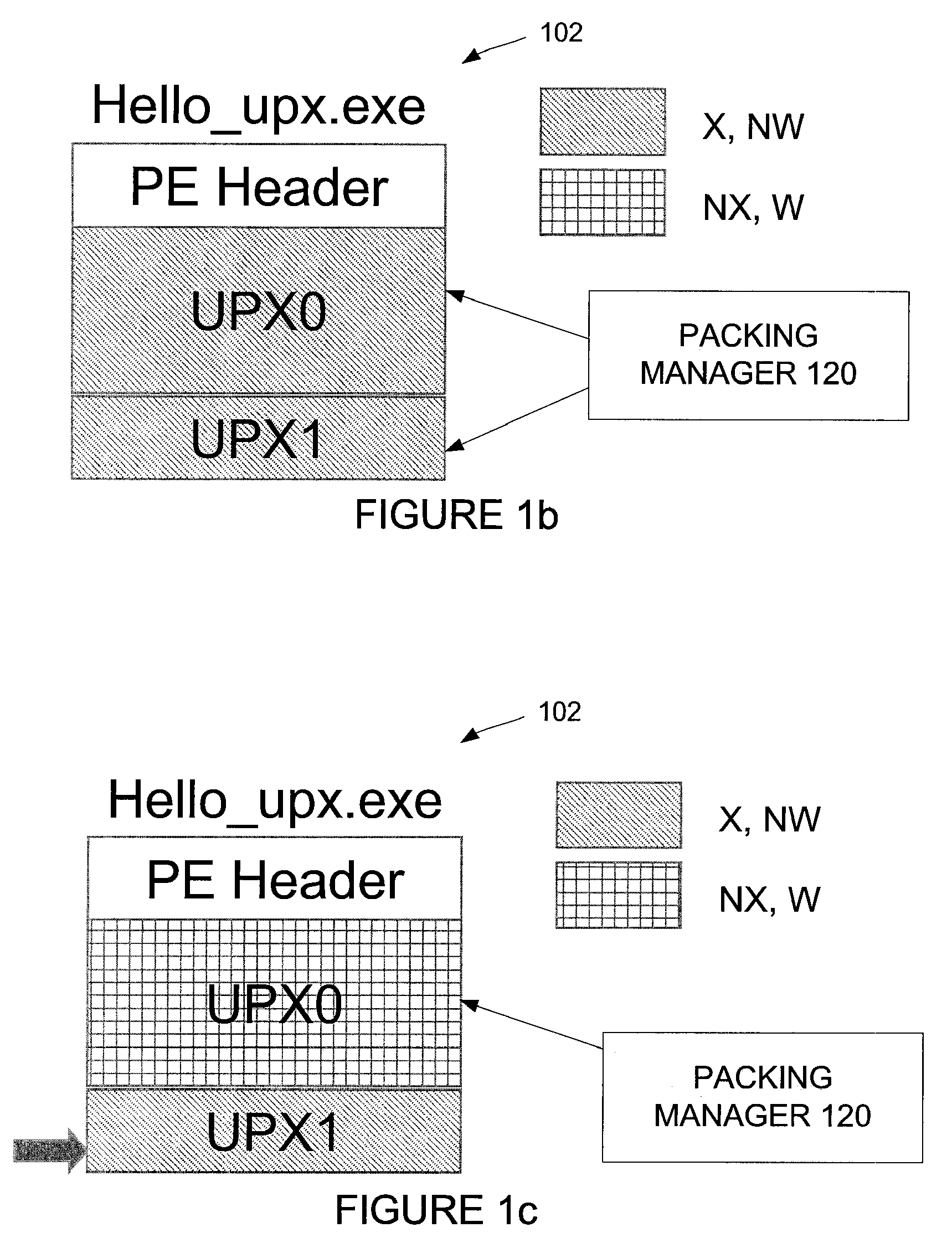
Automated unpacking of executables packed by multiple layers of arbitrary packers
The packing manager provides an automated method that allows existing AV scanning technology to be applied to detect known malware samples packed by one or more packers that are potentially proprietary. The packing manager tracks the memory areas to which an executable binary writes and executes, and so can unpack programs packed by multiple arbitrary packers without requiring reverse-engineering of the packers or any human intervention. By tracking page modification and execution of an executable binary at run time, the packing control module can detect the instant at which the program's control is first transferred to a page whose content is dynamically generated, so AV scanning can then be invoked. Thus, code cannot be executed under the packing control manager without being scanned by an AV scanner first.
Owner:NORTONLIFELOCK INC
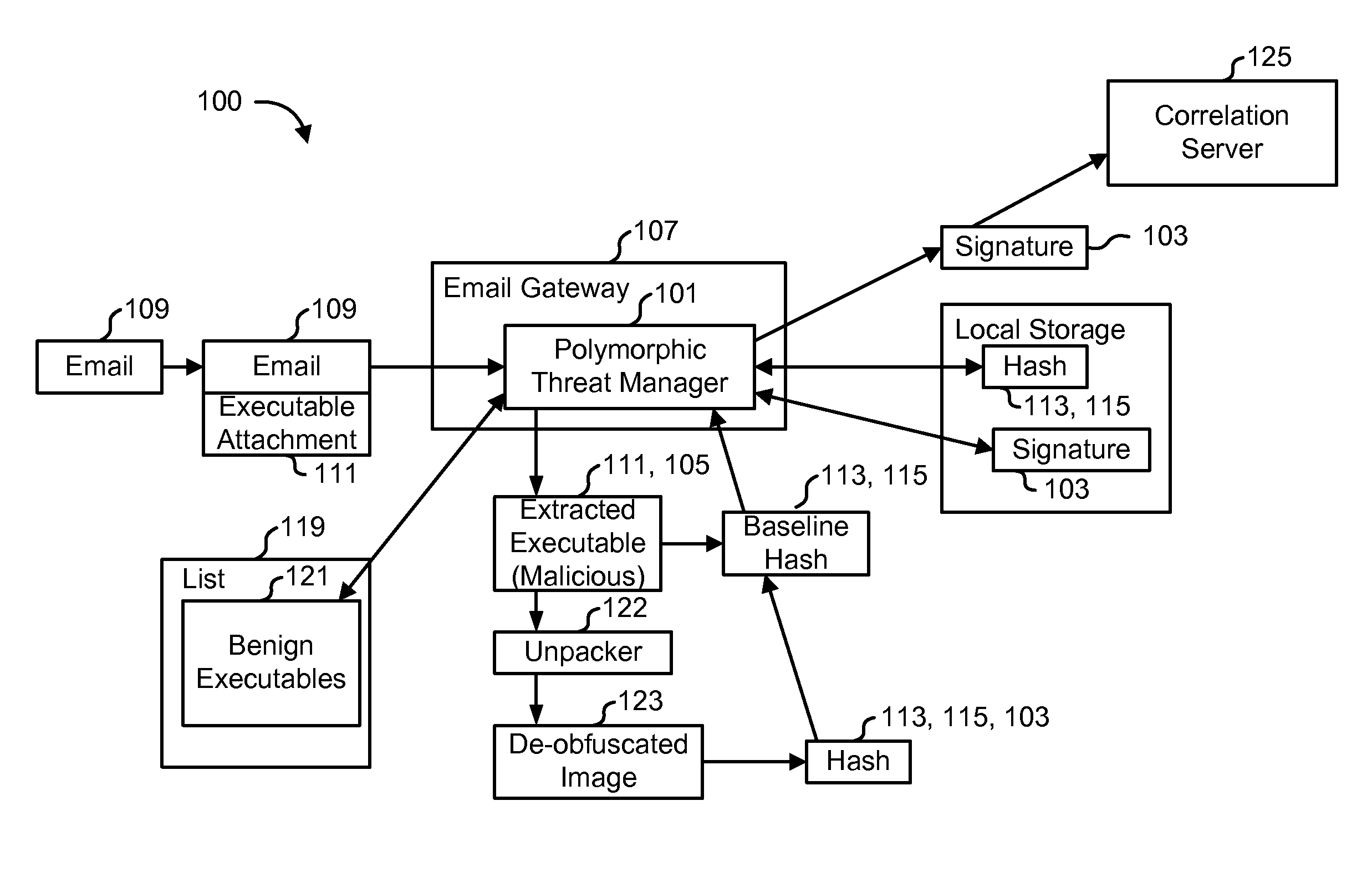
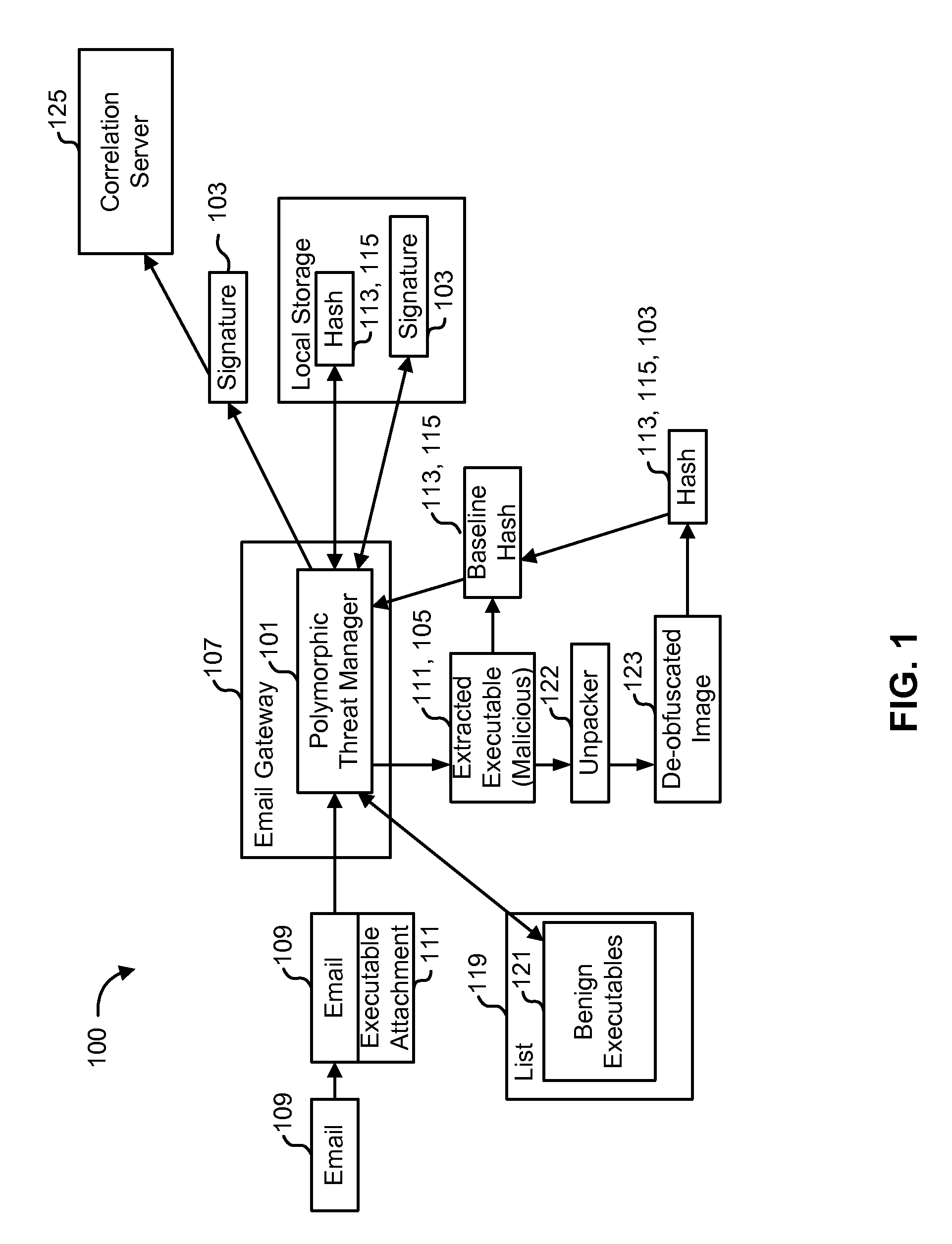
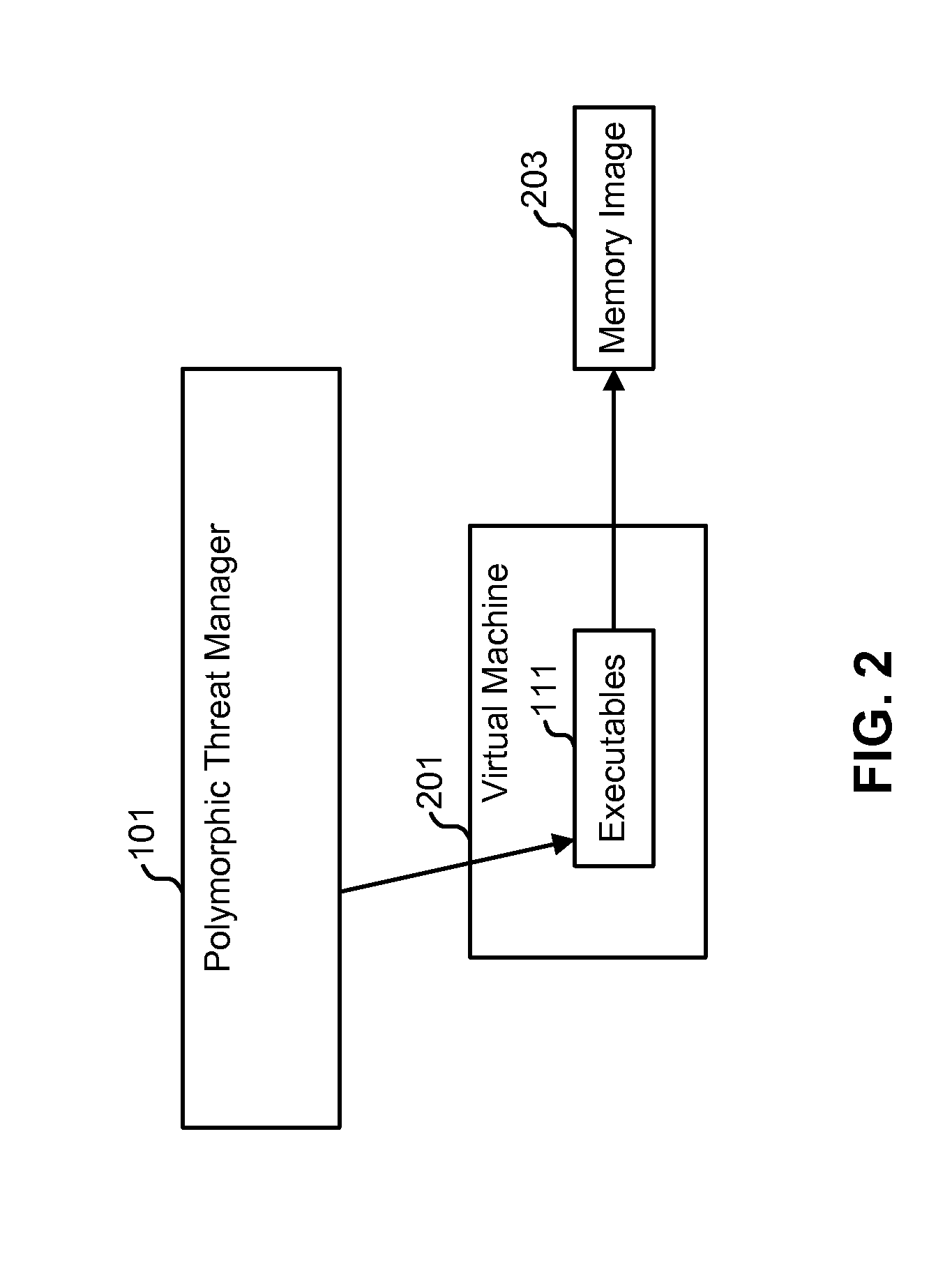
Detecting polymorphic threats
InactiveUS7739740B1Reduce loadMemory loss protectionUnauthorized memory use protectionObfuscationInternet privacy
A polymorphic threat manager monitors an incoming email stream, and identifies incoming email messages to which executable files are attached. The polymorphic threat manager characterizes incoming executable files according to at least one metric. For example, the polymorphic threat manager can decompose an executable file into fragments, hash some or all of these, and use the hashes as characterization metrics. The polymorphic threat manager subsequently de-obfuscates executable files, and creates corresponding characterization metrics for the de-obfuscated images. The characterizations of executable files before and after de-obfuscation are compared, and if they differ sufficiently, the polymorphic threat manager determines that the file in question is polymorphic. The characterization metrics of such an executable file after de-obfuscation can be used as a signature for that file.
Owner:CA TECH INC
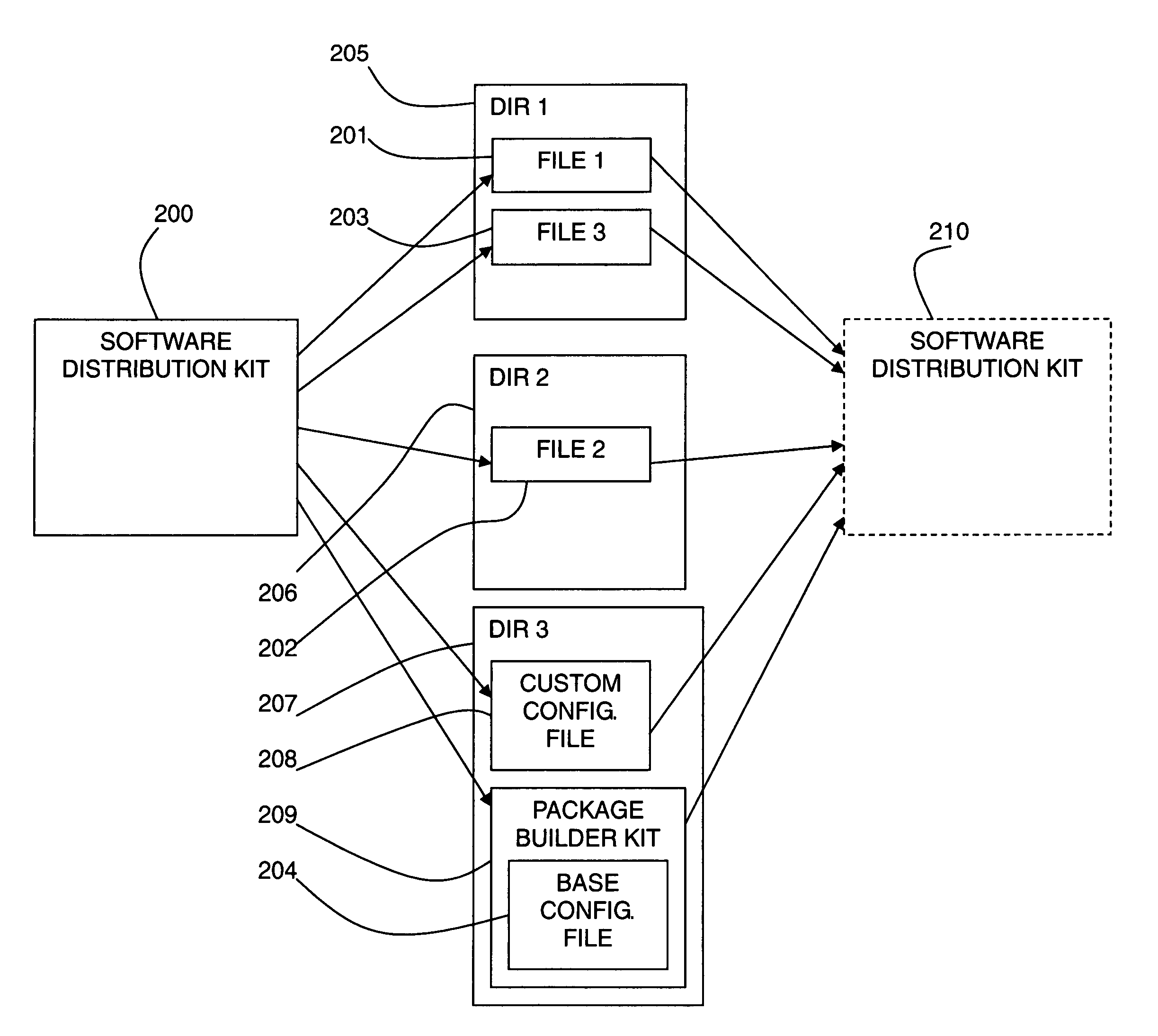
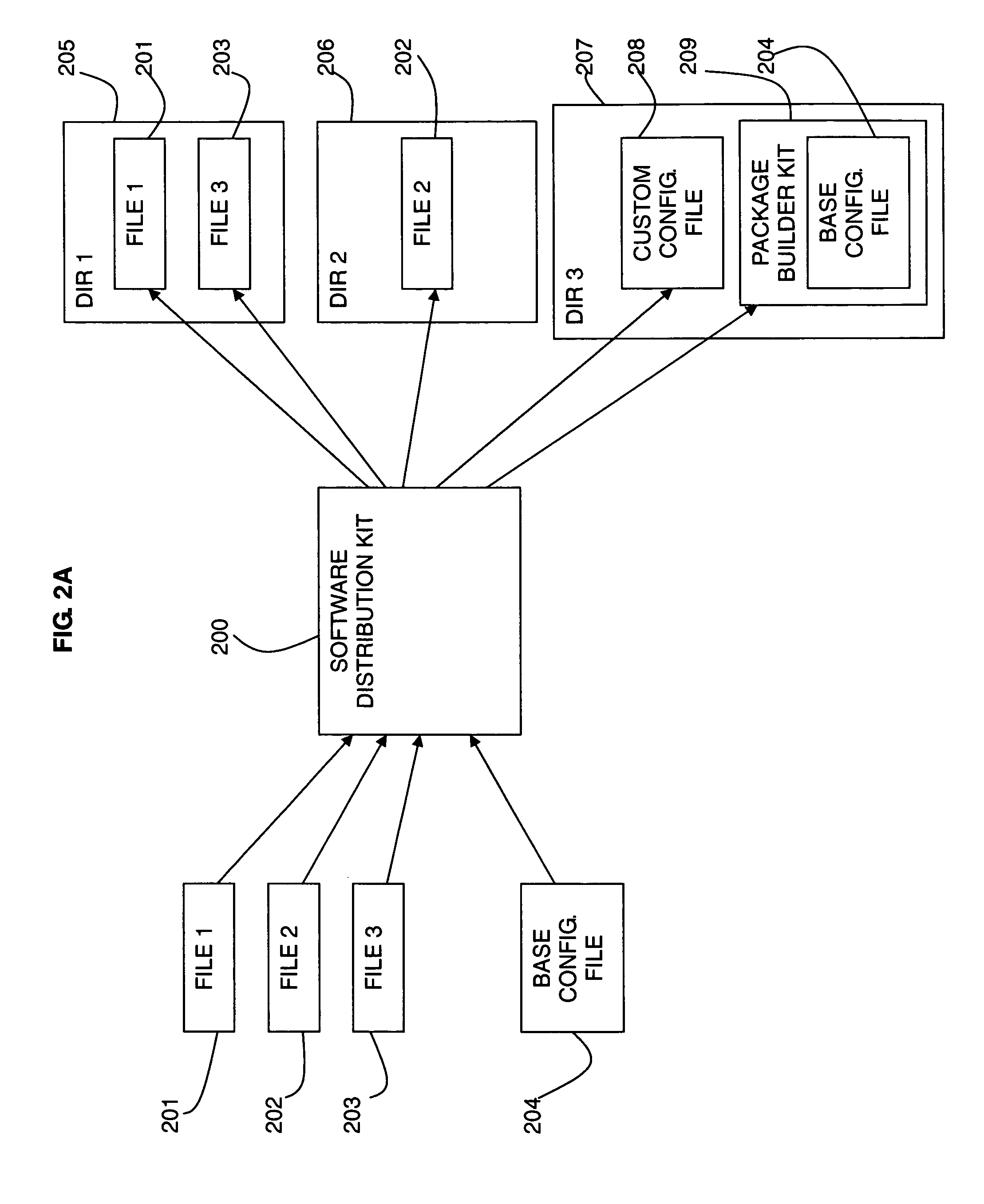
Method and system for peer-to-peer software distribution with a package builder
A method and system for software and data distribution are described in which an original software and / or data package is provided to a first device. The first device installs the original software package, which includes installing a package builder kit. The package builder kit allows a software distribution kit to be built by the first device. The software distribution kit can be transmitted from the first device to a second device for installation on the second device. The package builder kit includes a copy of an original configuration file from the original software package, details as to the installed files, addresses of the installed files on the first device, details of the internal structure of the original software package, and provides an executable program to build the software distribution kit.
Owner:KYNDRYL INC
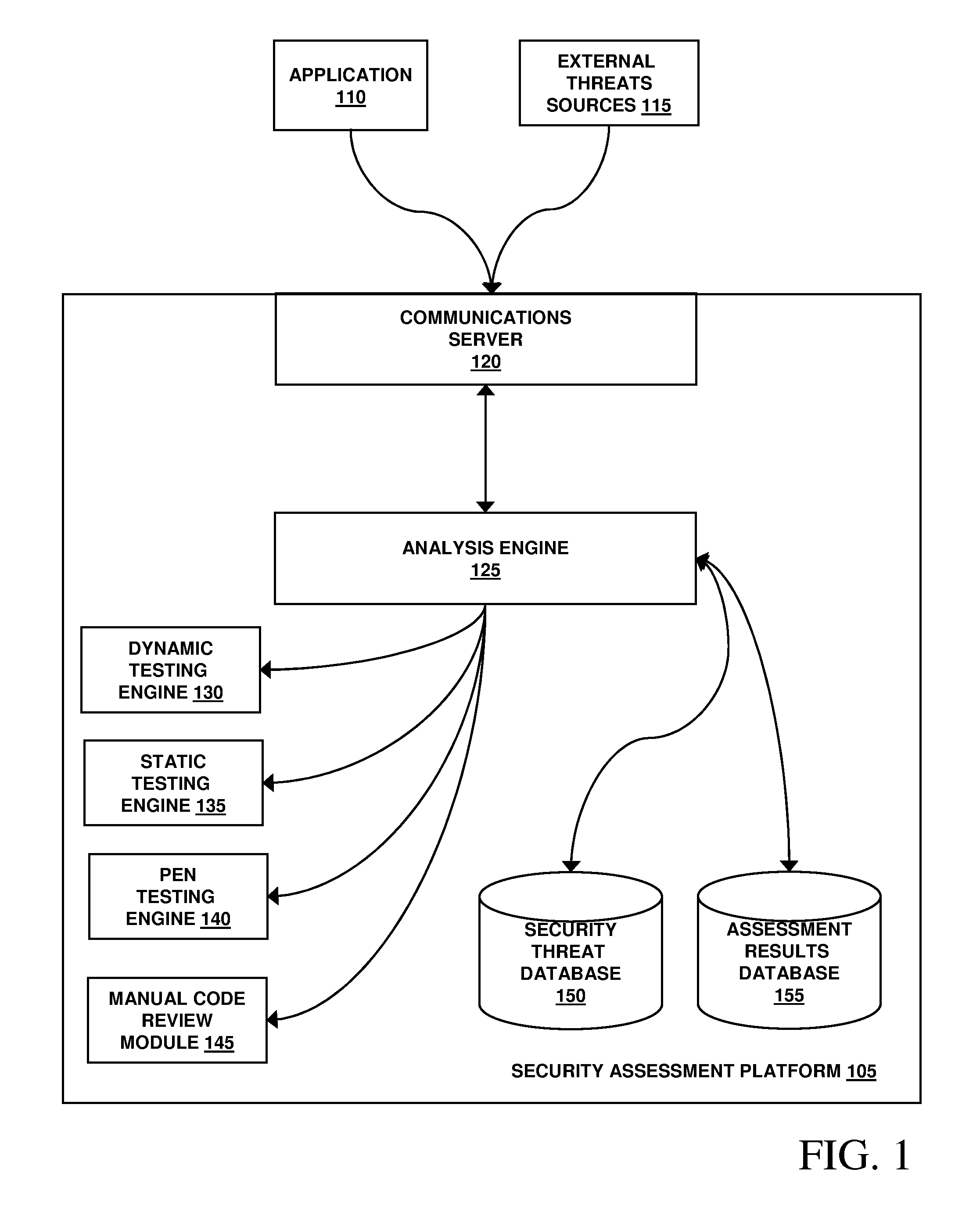
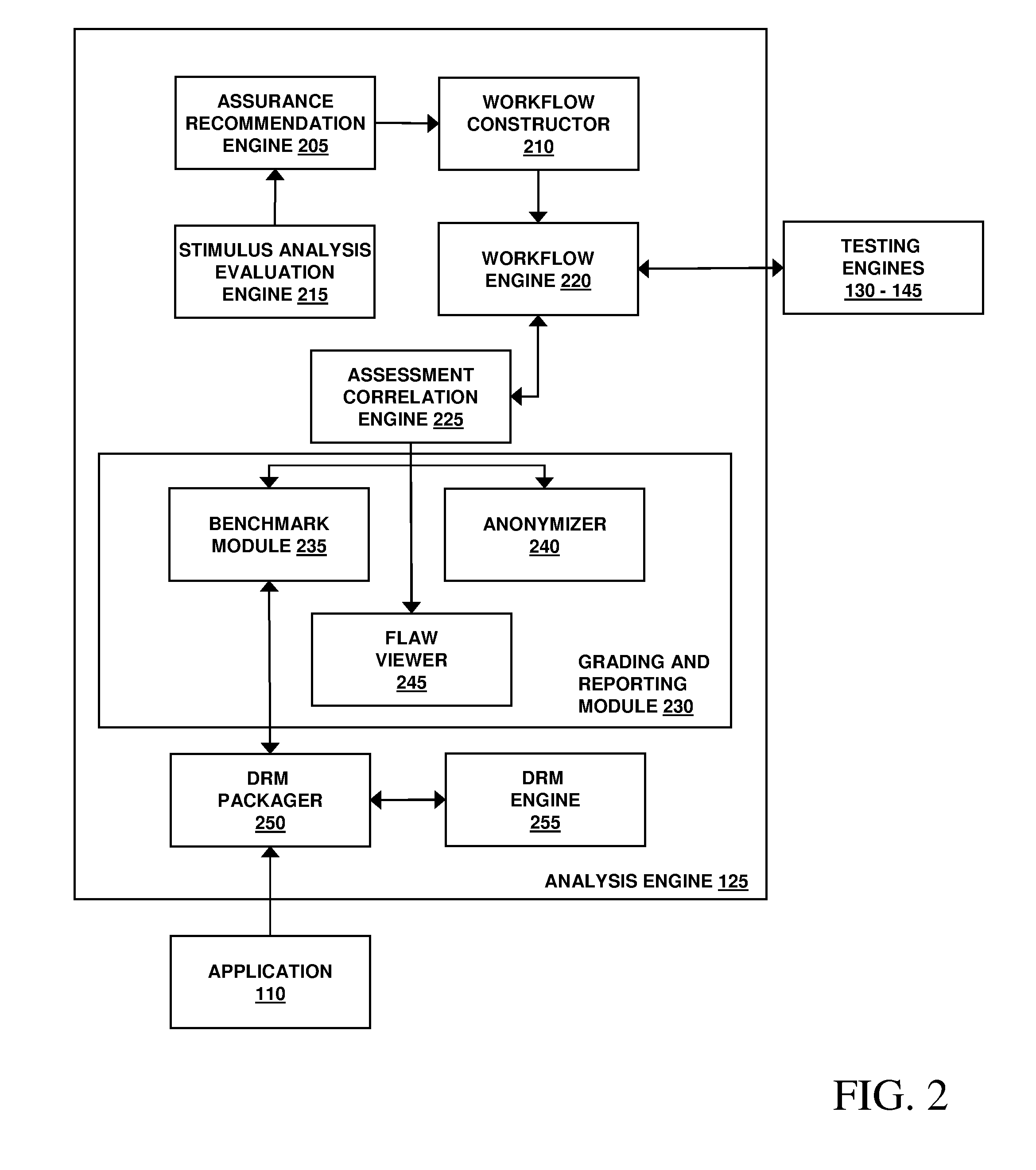
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Enhancement of e-mail client user interfaces and e-mail message formats
ActiveUS20070011258A1Good user interfaceMultiple digital computer combinationsTransmissionClient-sideElectronic mail
An enhancement to e-mail user interfaces and message formats includes a dynamic preview window to view and retrieve attachments and summaries of e-mail messages directly in the e-mail list view or inbox view without opening an e-mail message. The efficient viewing mechanism further allows previews without cluttering the listing of the e-mails in the inbox by allowing the client to detect special preview instructions within an e-mail and run executables within the preview window. The enhancement is applicable to standalone e-mail clients (POP or IMAP based) and to web-based e-mail systems.
Owner:ADVENIX CORP CORP
System and method of malware sample collection on mobile networks
ActiveUS20080086776A1Raise the possibilityMemory loss protectionError detection/correctionNetworking protocolProxify
A collection agent monitors a mobile network for data samples containing executable code. The collection agent accepts executables and forwards them to a sample collection center for further analysis, reporting, or in some instances initiating one or more mitigating actions. Depending on the network protocol being monitored, the collection agent responds to connection attempts from nearby mobile devices.
Owner:PULSE SECURE
Non-Signature Malware Detection System and Method for Mobile Platforms
ActiveUS20070240221A1Suitable for useReliable detectionMemory loss protectionError detection/correctionEntry pointChecksum
A system and method for detecting malware on a mobile platform in a mobile network. The system and method verifies that an executable is malware-free by computing the checksum of the executable and comparing that checksum with a checksum obtained from a malware-free copy of the executable. The checksum is a sum of all 32-bit values in a code section and an import section of said executable, a byte sequence at an entry point in said executable, a size descriptor of an import table, a size descriptor of said import section, a cyclic redundancy check of said executable, or a combination thereof.
Owner:PULSE SECURE
System and method for conditional tracing of computer programs
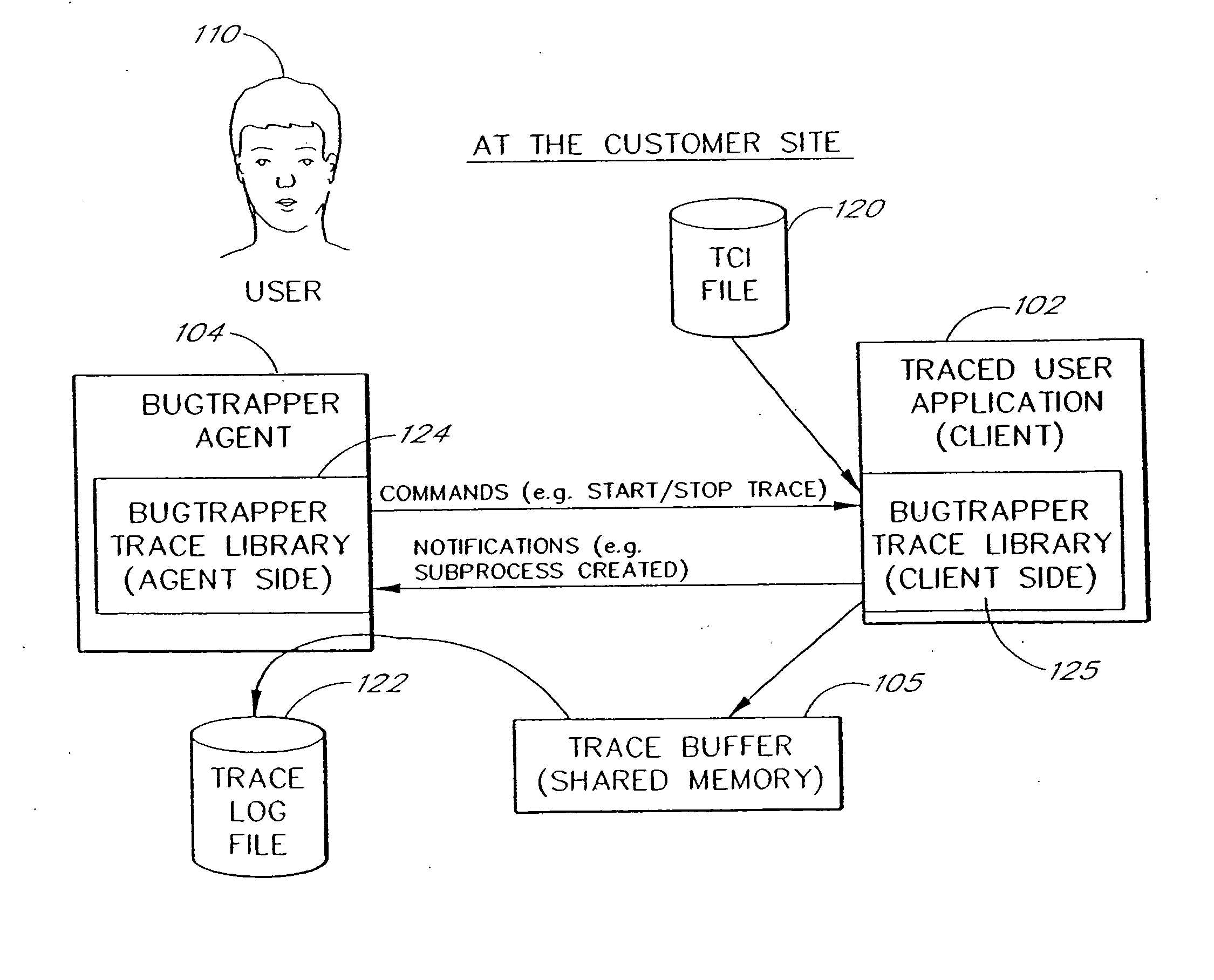
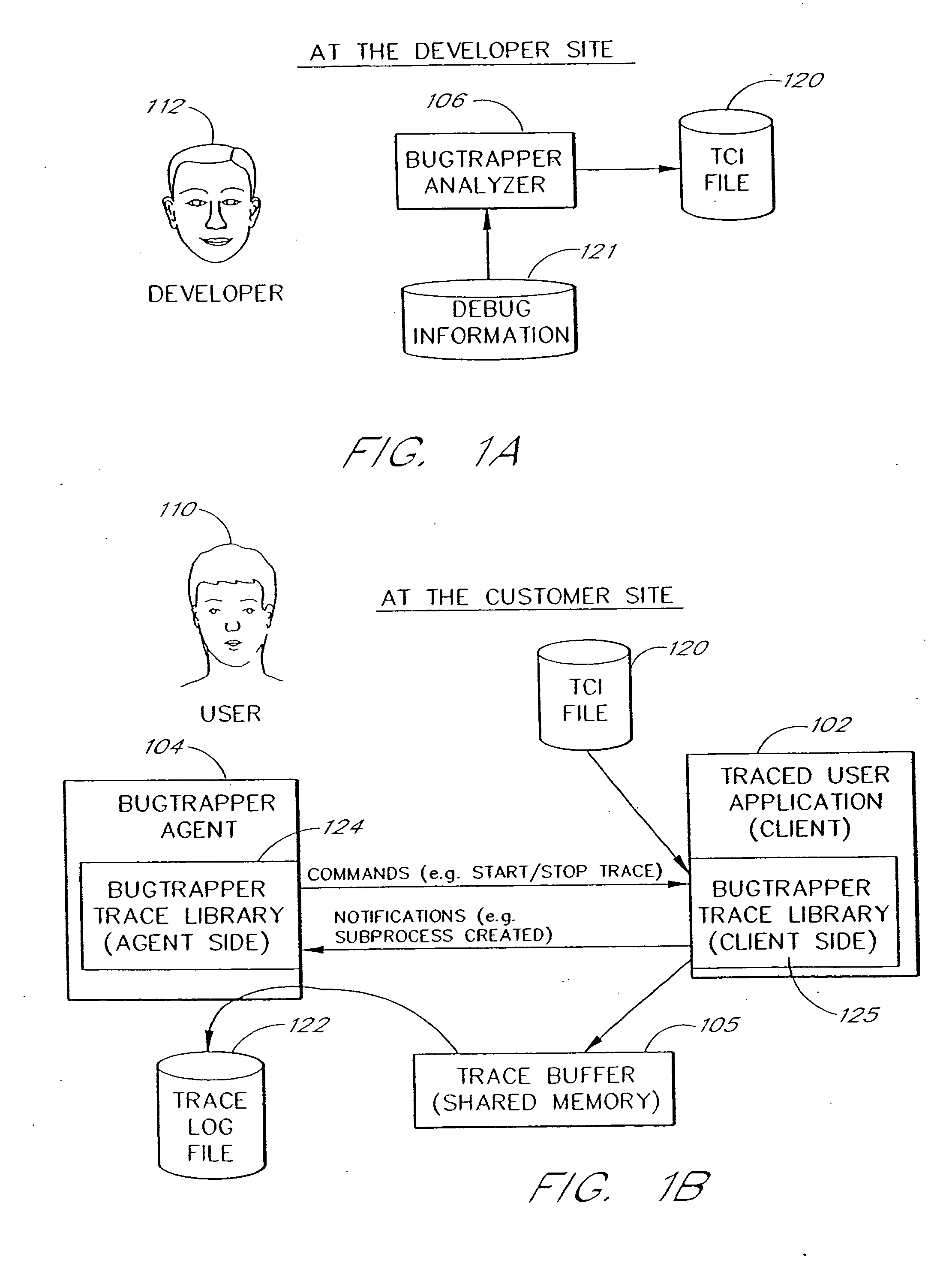
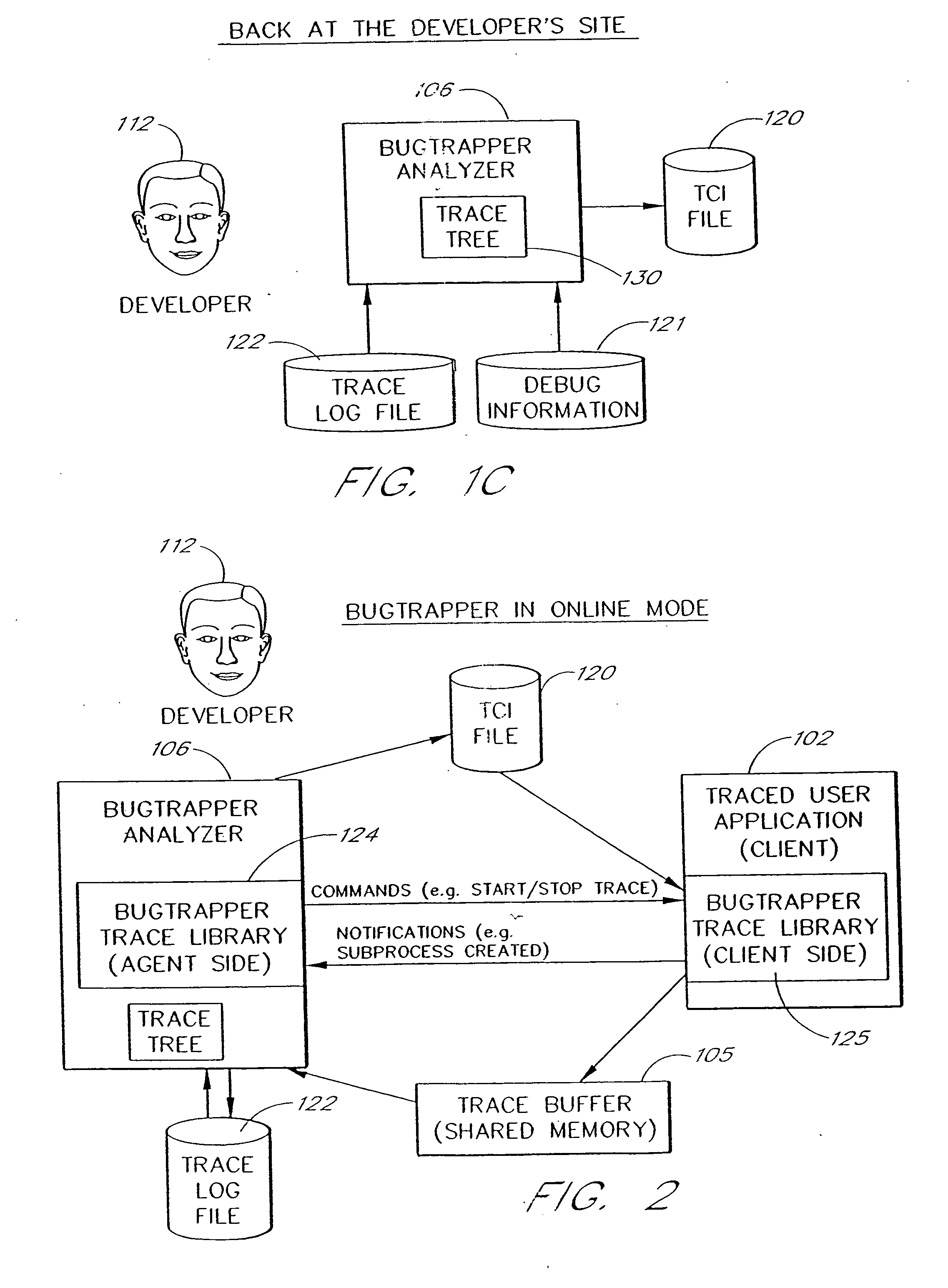
ActiveUS20060242627A1Small sizeRaise the possibilityError detection/correctionSpecific program execution arrangementsSource code fileTrace file
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
System And Method for High Performance Enterprise Data Protection
ActiveUS20100077160A1Improve performanceEliminate redundancyMemory loss protectionError detection/correctionOperational systemFile system
High performance, enterprise-level data protection system and method provides efficient block-level incremental snapshots of primary storage devices, and instant availability of such snapshots in immediately mountable form that can be directly used in place of the primary storage device. Related systems and applications are described, including an “Enterprise Image Destination” (EID) for backup images; a mirroring technique whereby a replacement physical primary facility may be created while working with a second storage unit as the primary source file system; and a technique for eliminating redundant data in backup images when multiple systems with partially common contents (e.g., operating system files, common databases, application executables, etc.) are being backed up. A number of examples showing “Fast Application Restore” (FAR) with the use of the invention are also provided.
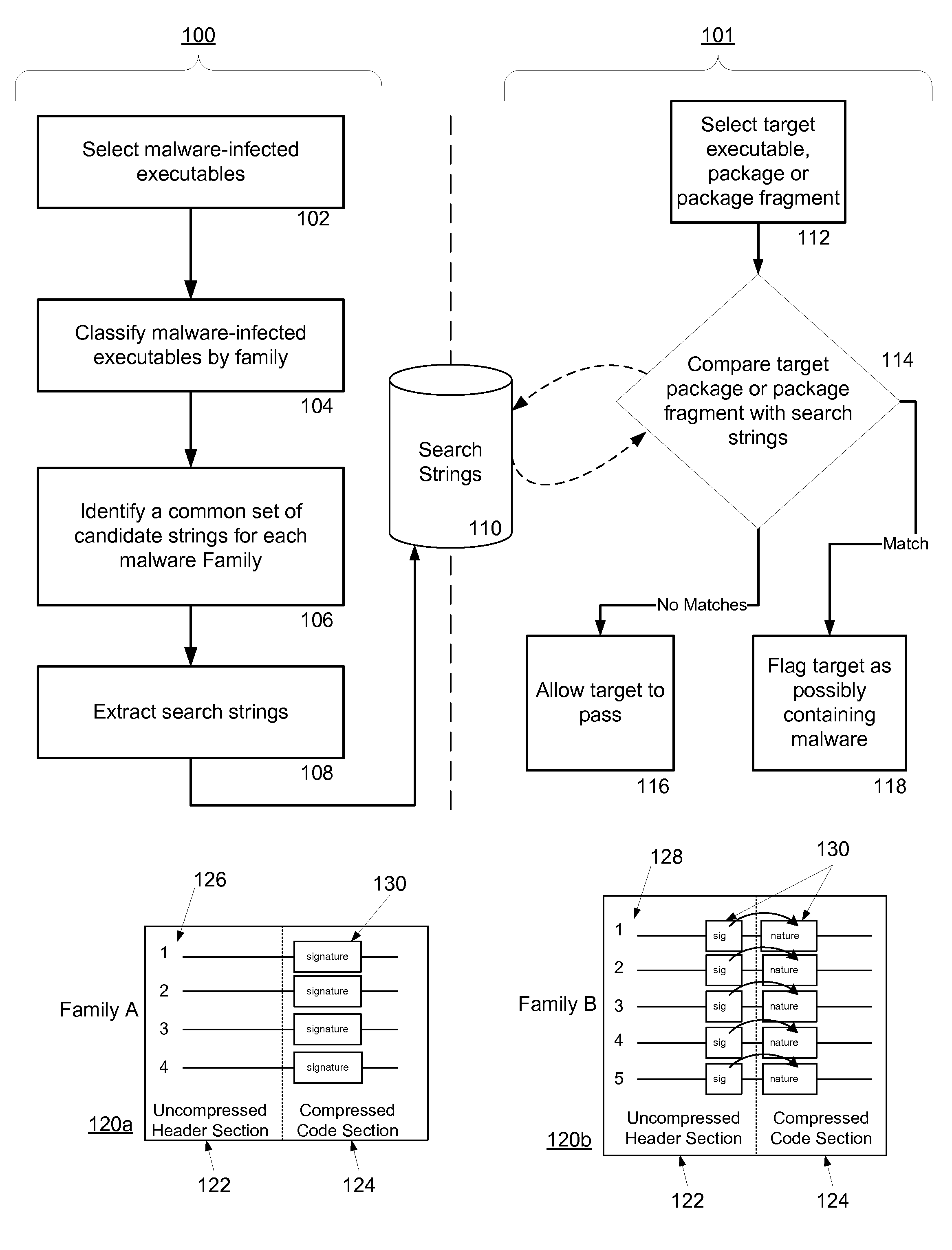
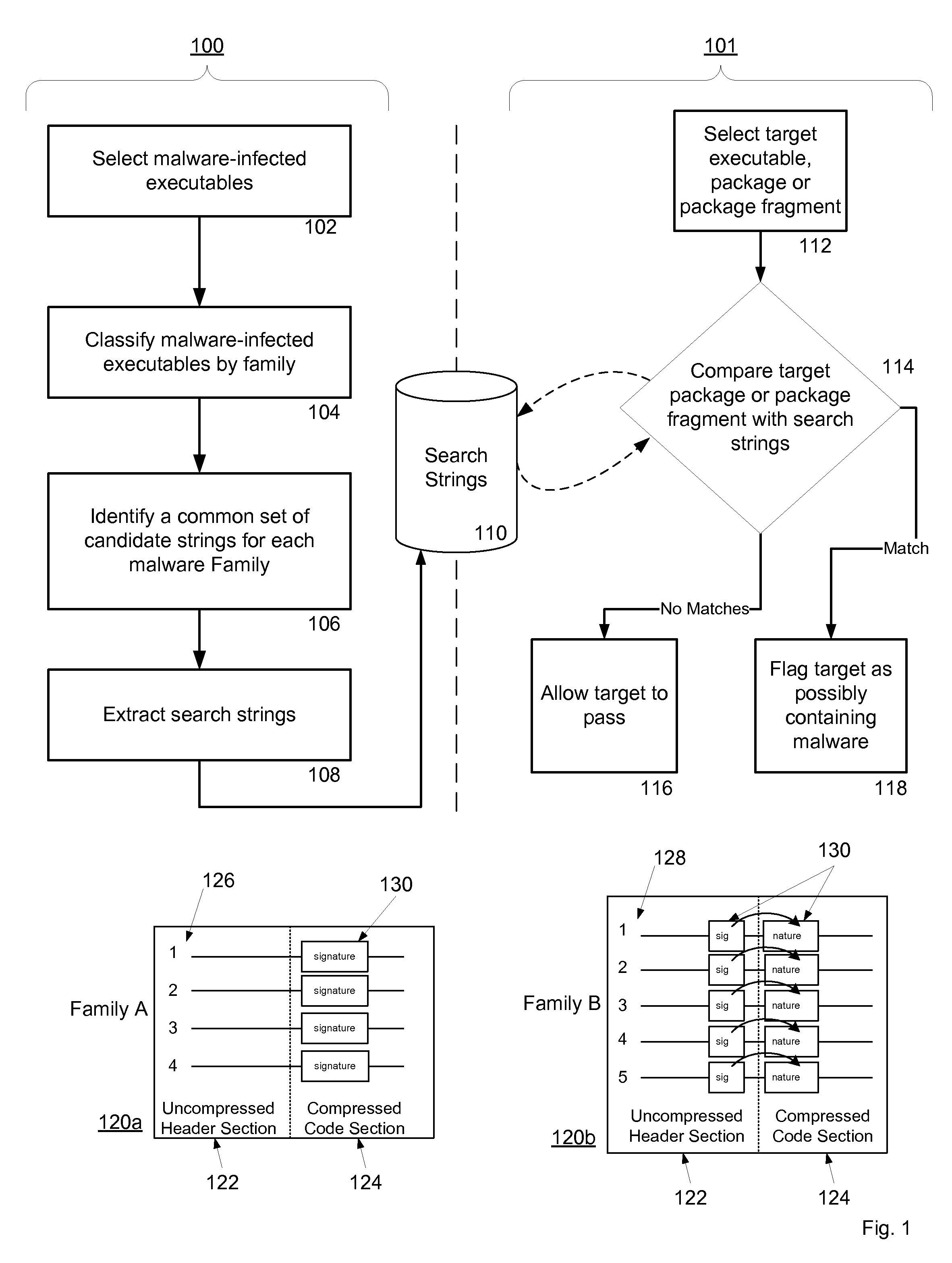
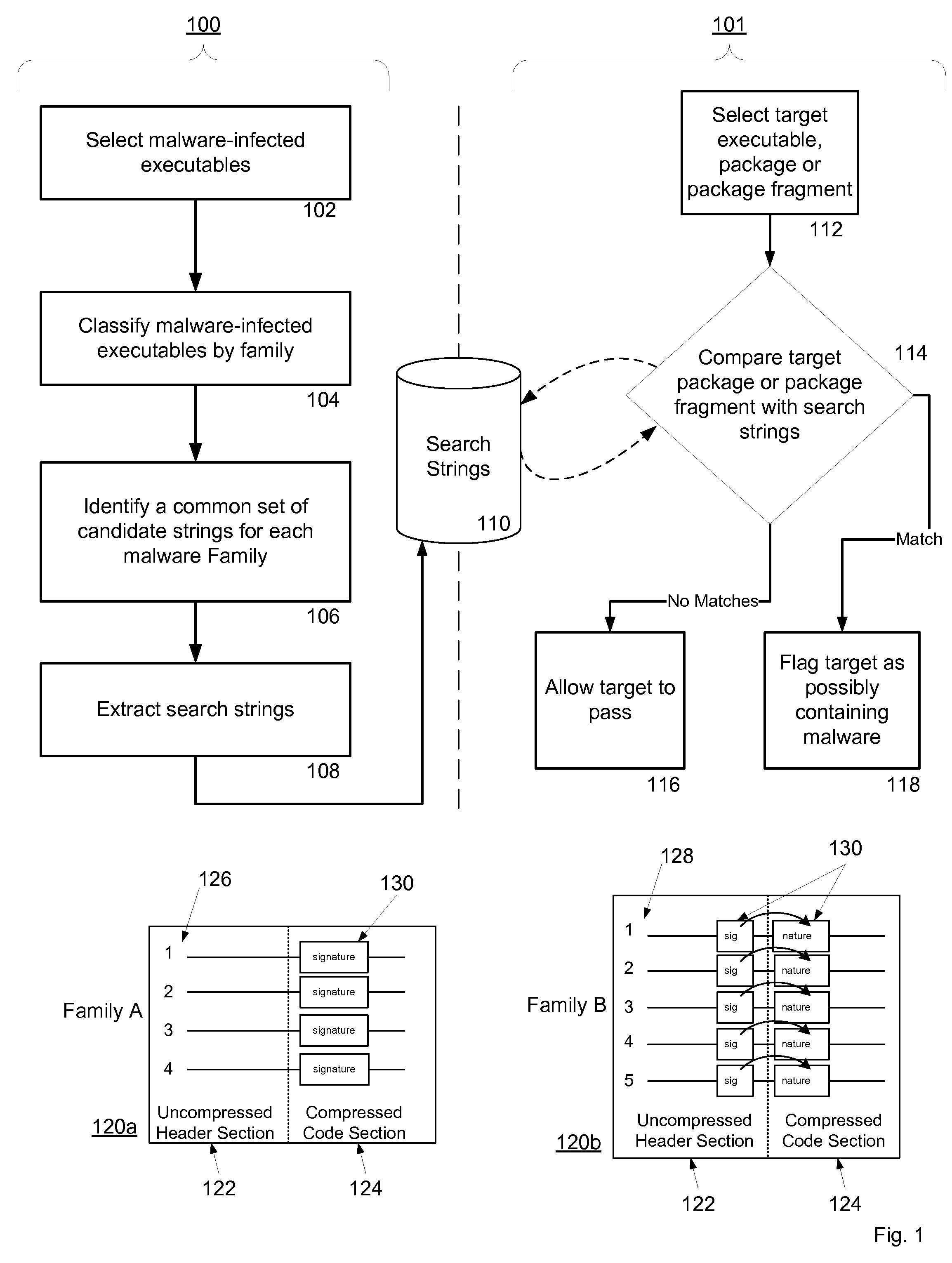
Owner:CATALOGIC SOFTWARE
Scheme of sending email to mobile devices
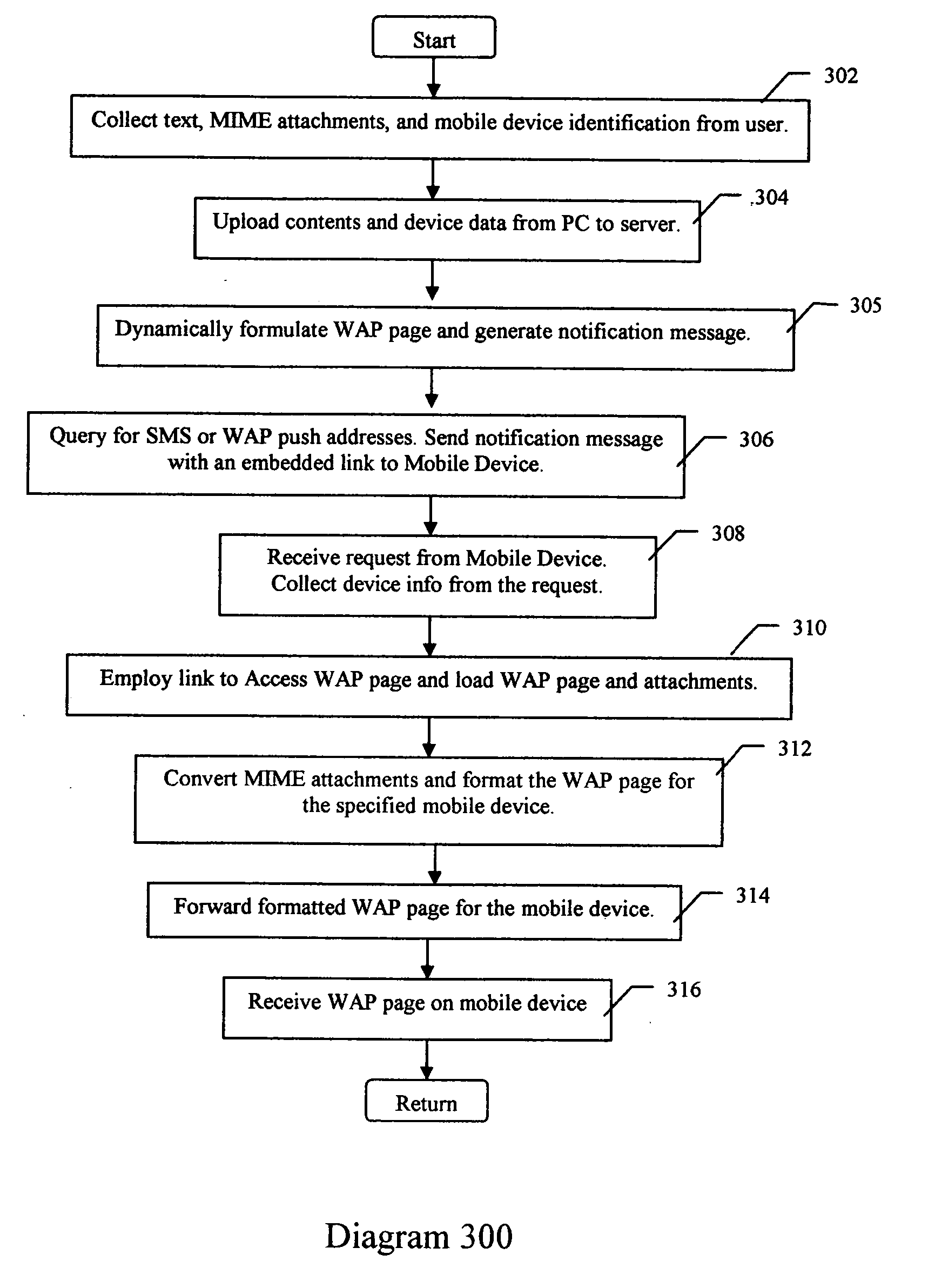
InactiveUS20060218234A1Multiple digital computer combinationsMessaging/mailboxes/announcementsMessage lengthRouting table
A method, apparatus, client and server are directed at providing a simplified scheme to deliver email messages that include text message body, and / or MIME attachments from desktop computing devices to messaging (such as SMS) and wireless internet capable phones. A web form is provided for users to compose messages and / or adding MIME attachments from their PC. Also provided in the form are input fields for users to enter device numbers for recipients. Upon submitting the form, message body and MIME attachments are uploaded and stored on the server. An email WAP page that contains the message body and the links to all the MIME attachments is created dynamically and stored on the server. The server then queries a service database and looks up a domain routing table to build the email like messaging addresses for recipients. The server sends a notification message with an embedded link to the email like messaging addresses. The link, such as a URL, a script, an executable, a program, and the like, pointing to the email WAP page, can be invoked from mobile devices. When the link is invoked on the mobile device, it sends a request to the server for the email WAP page. Upon receiving the request from the mobile device, the server collects the information about the mobile device; queries a device database for formats, display and capabilities; locates and loads the email WAP page; converts the MIME attachments to the formats supported by the mobile device; formats the email WAP page for display on the mobile device; delivers the formatted email WAP page to the mobile device. The email WAP page can be viewed, downloaded, and played on the mobile device. The scheme of the present invention supports a device number based authentication. The scheme of the present invention can also be implemented to deliver email messages to multiple mobile devices. The scheme of the present invention can expand the PC to SMS capabilities by enabling text messaging with arbitrary message length.
Owner:DENG LI +1
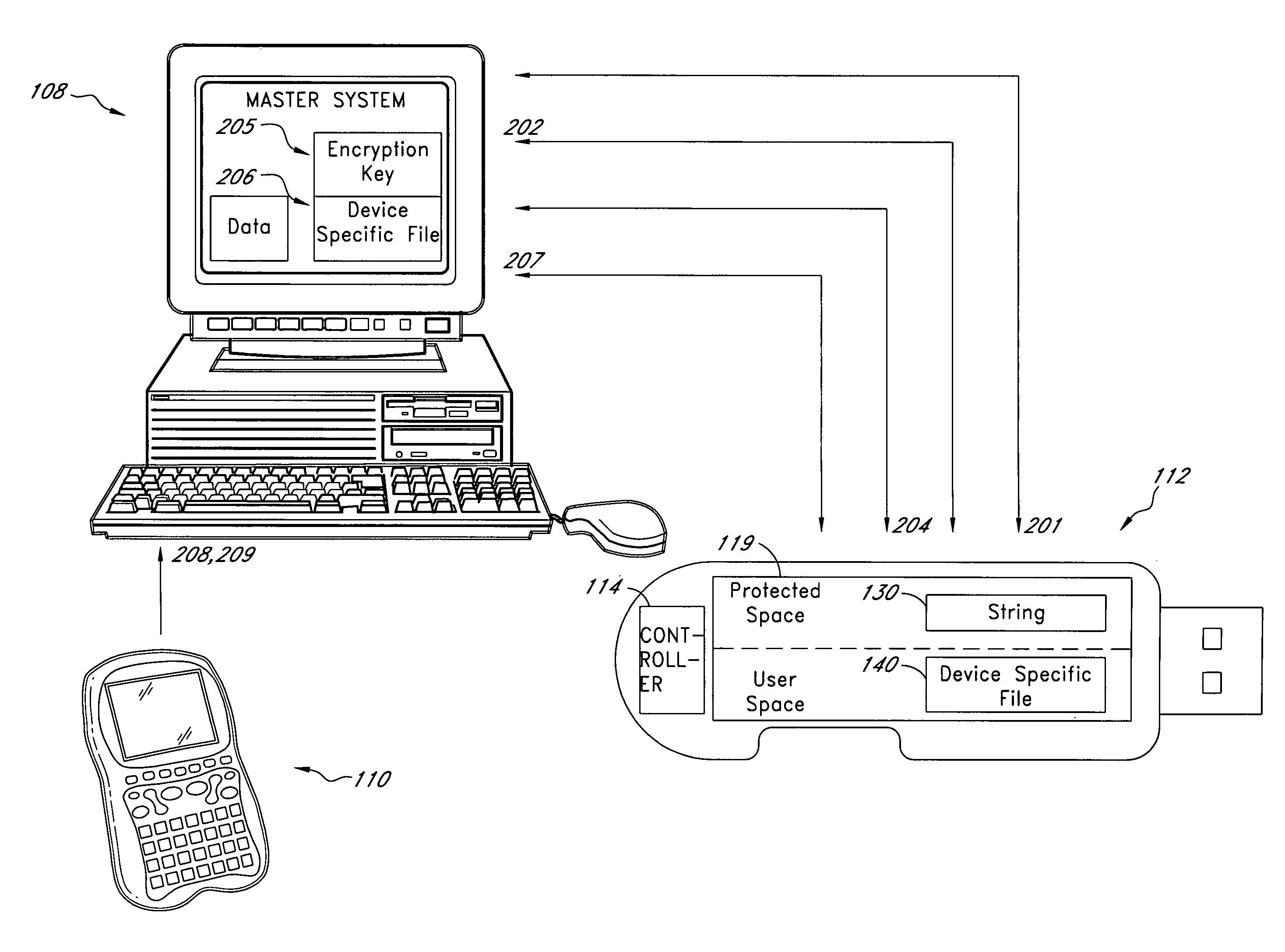
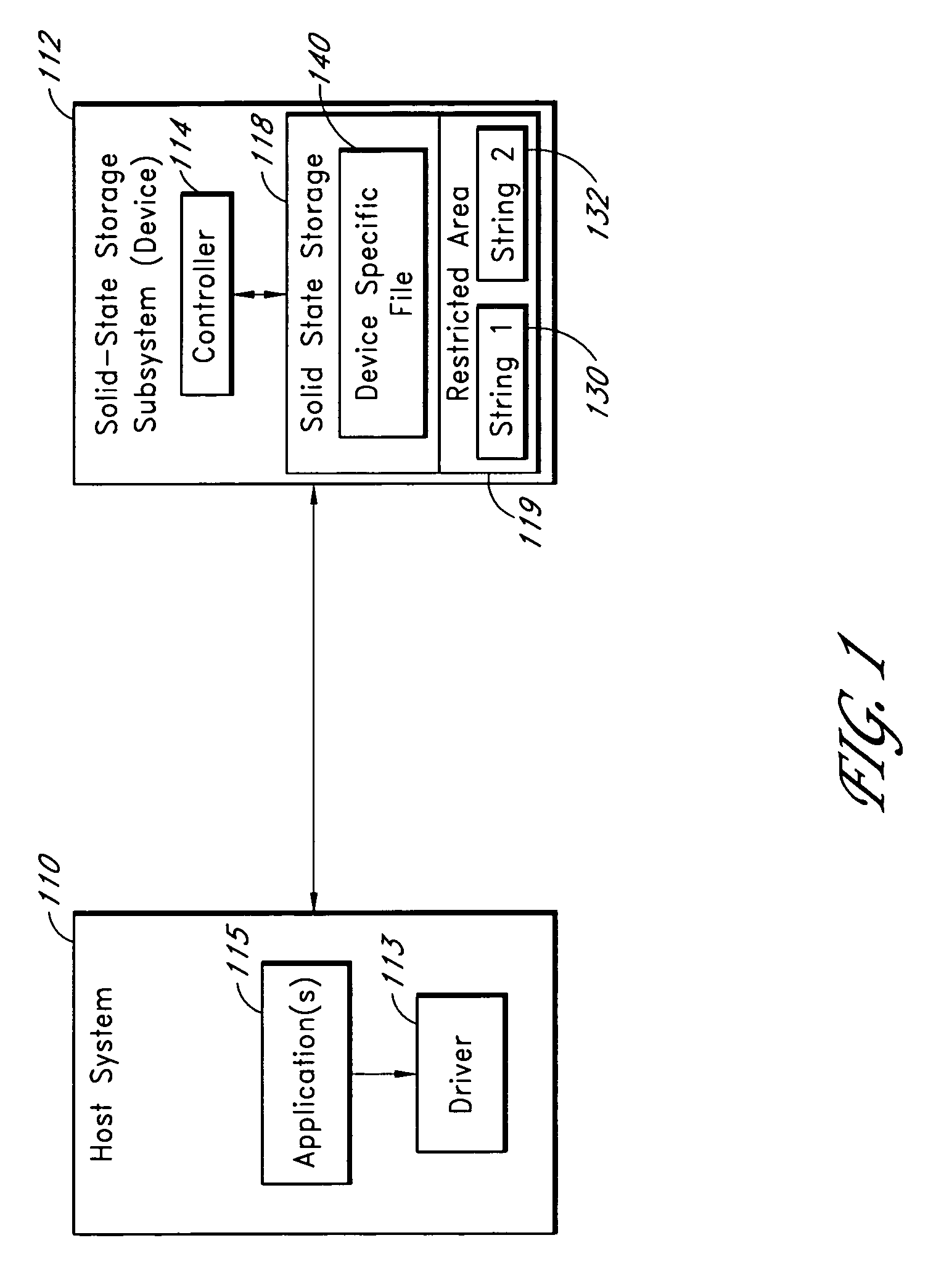
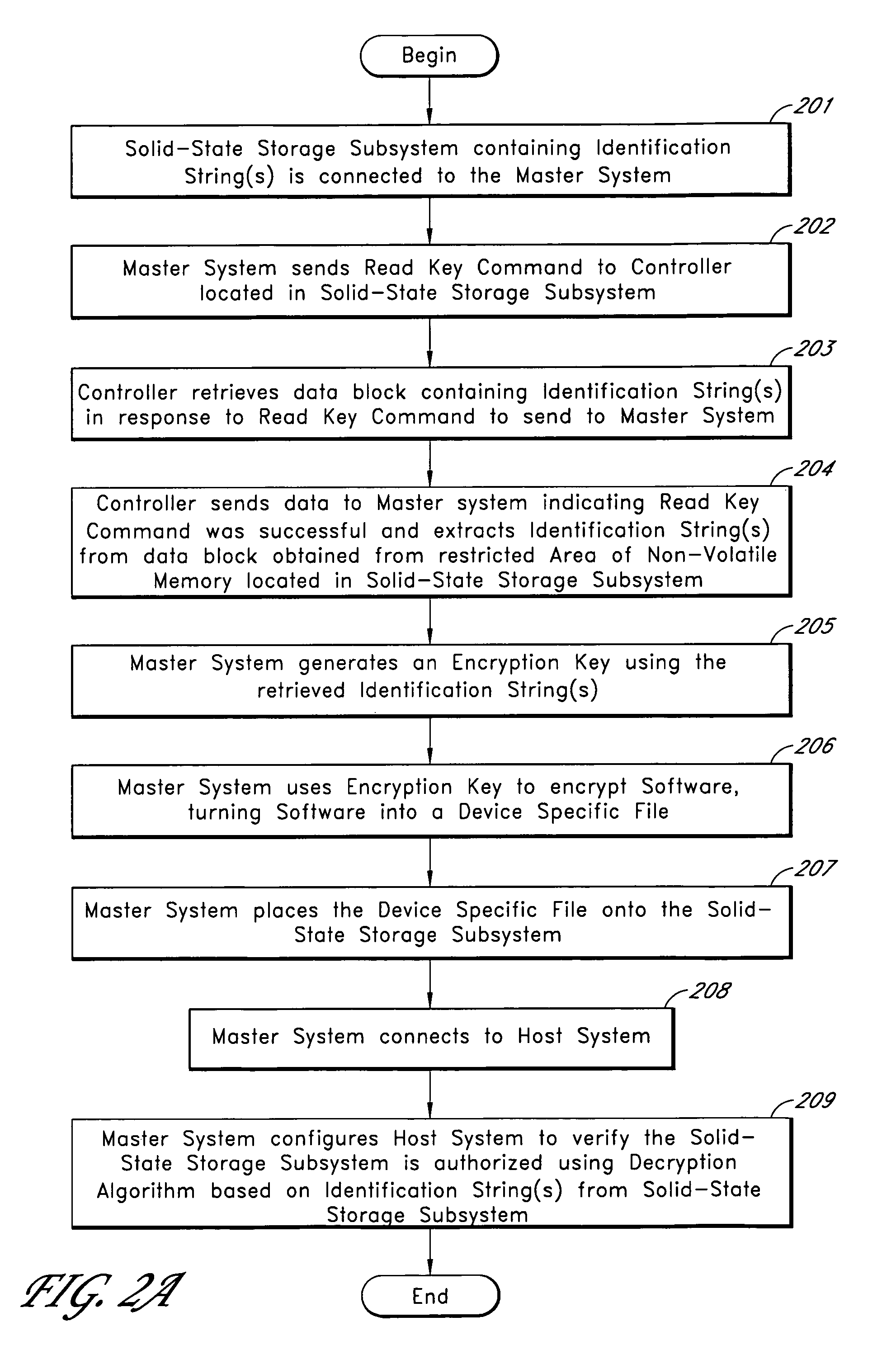
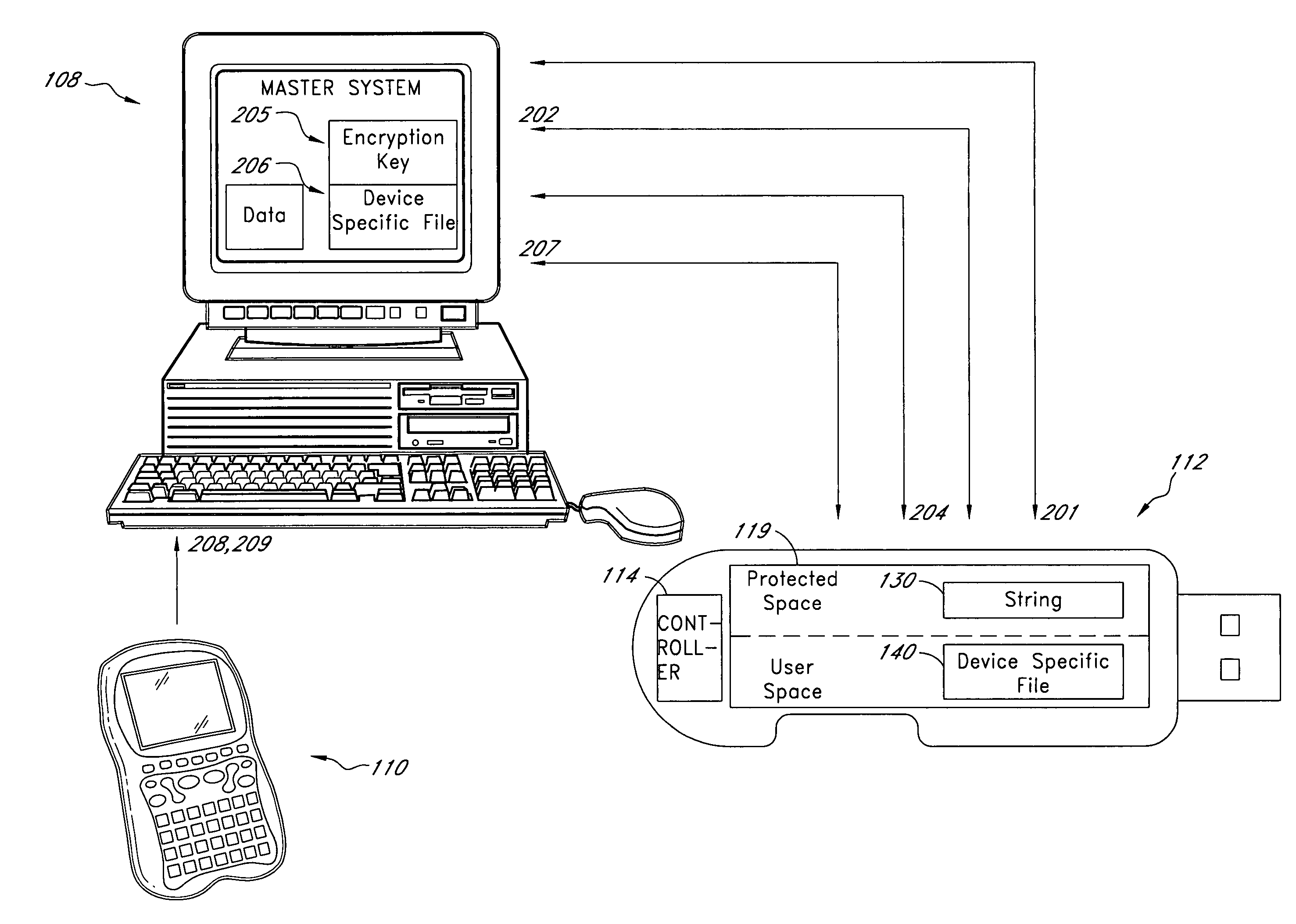
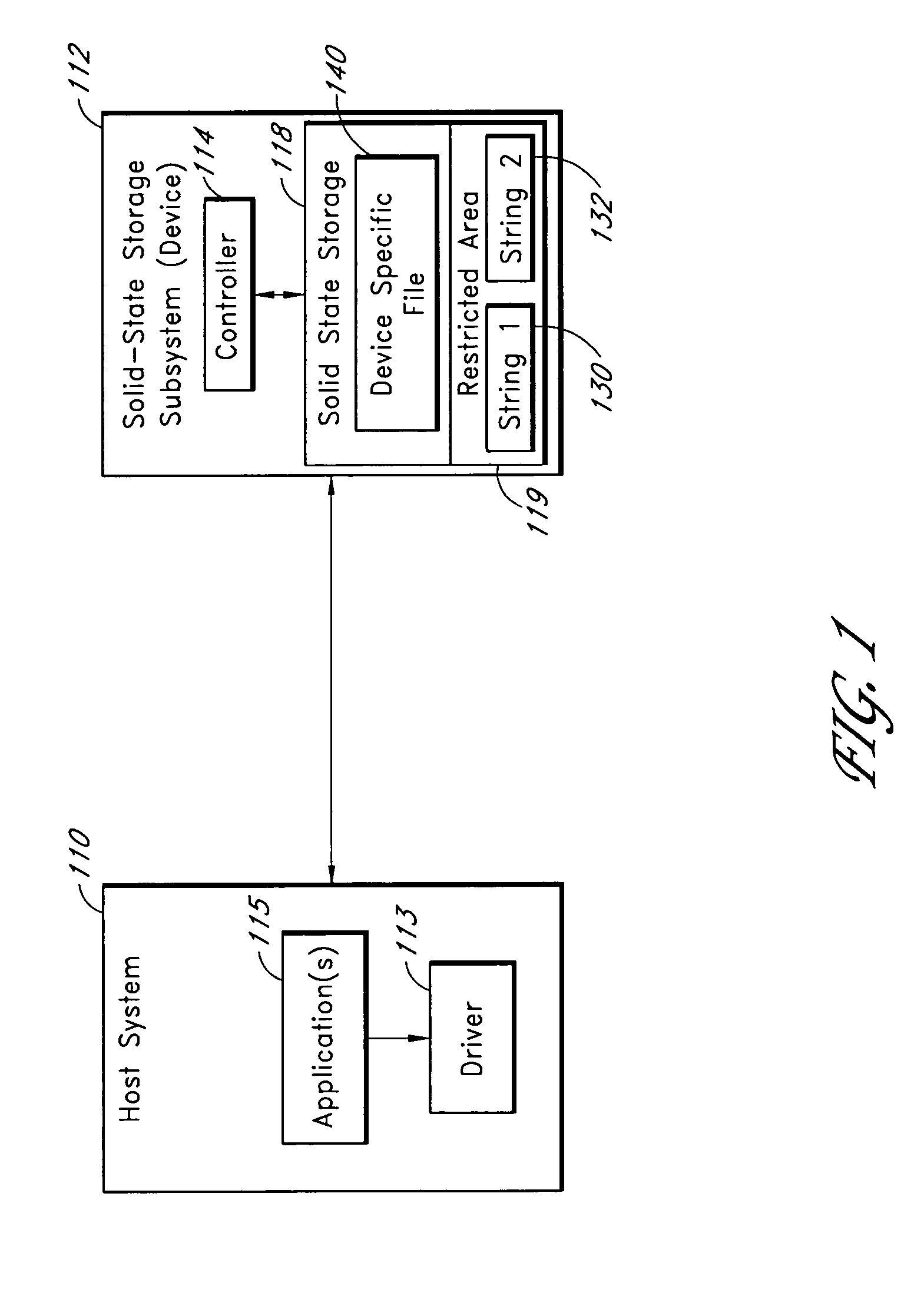
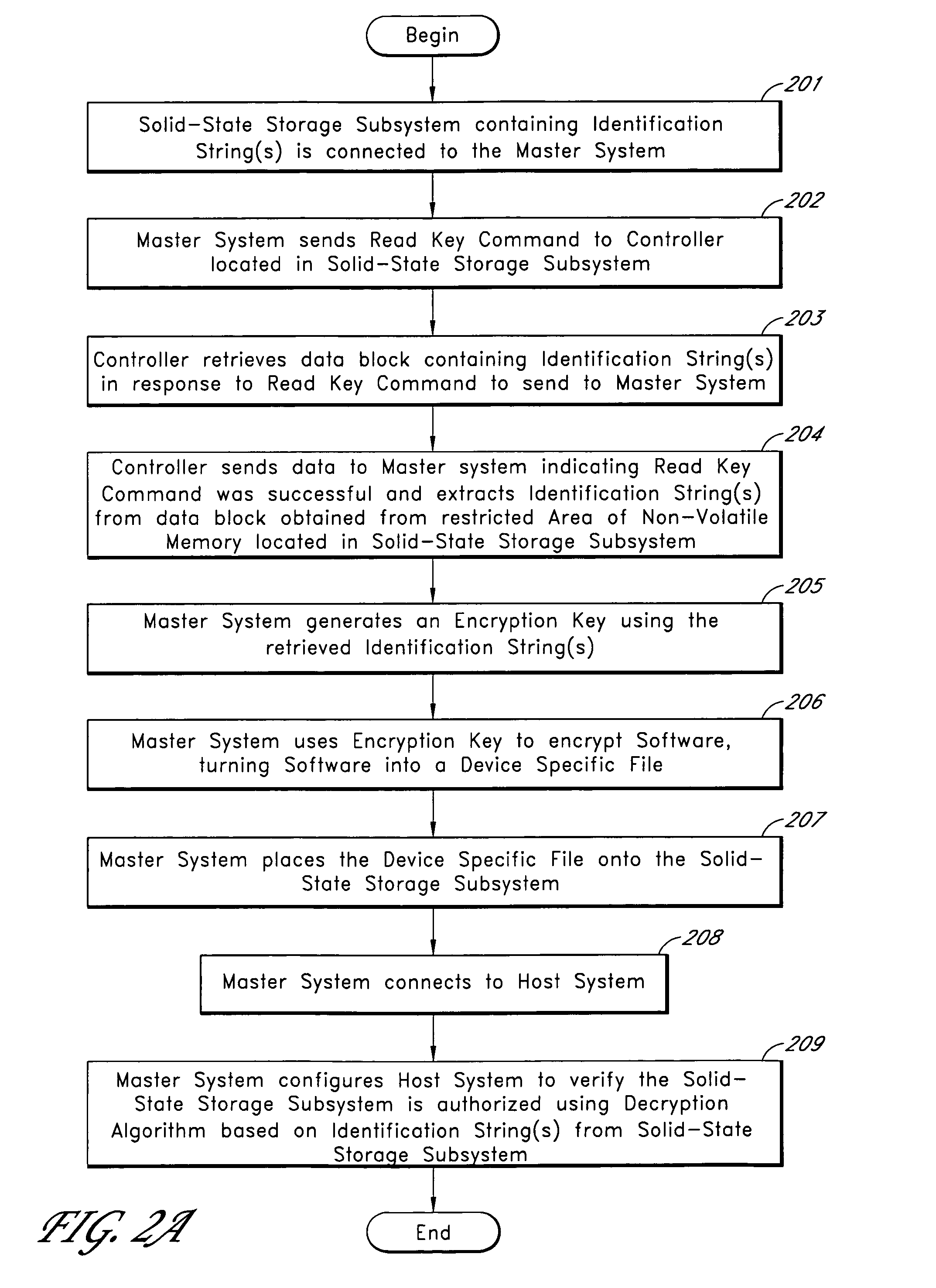
System for controlling use of a solid-state storage subsystem
ActiveUS7765373B1Digital data processing detailsUnauthorized memory use protectionSolid-state storageData file
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
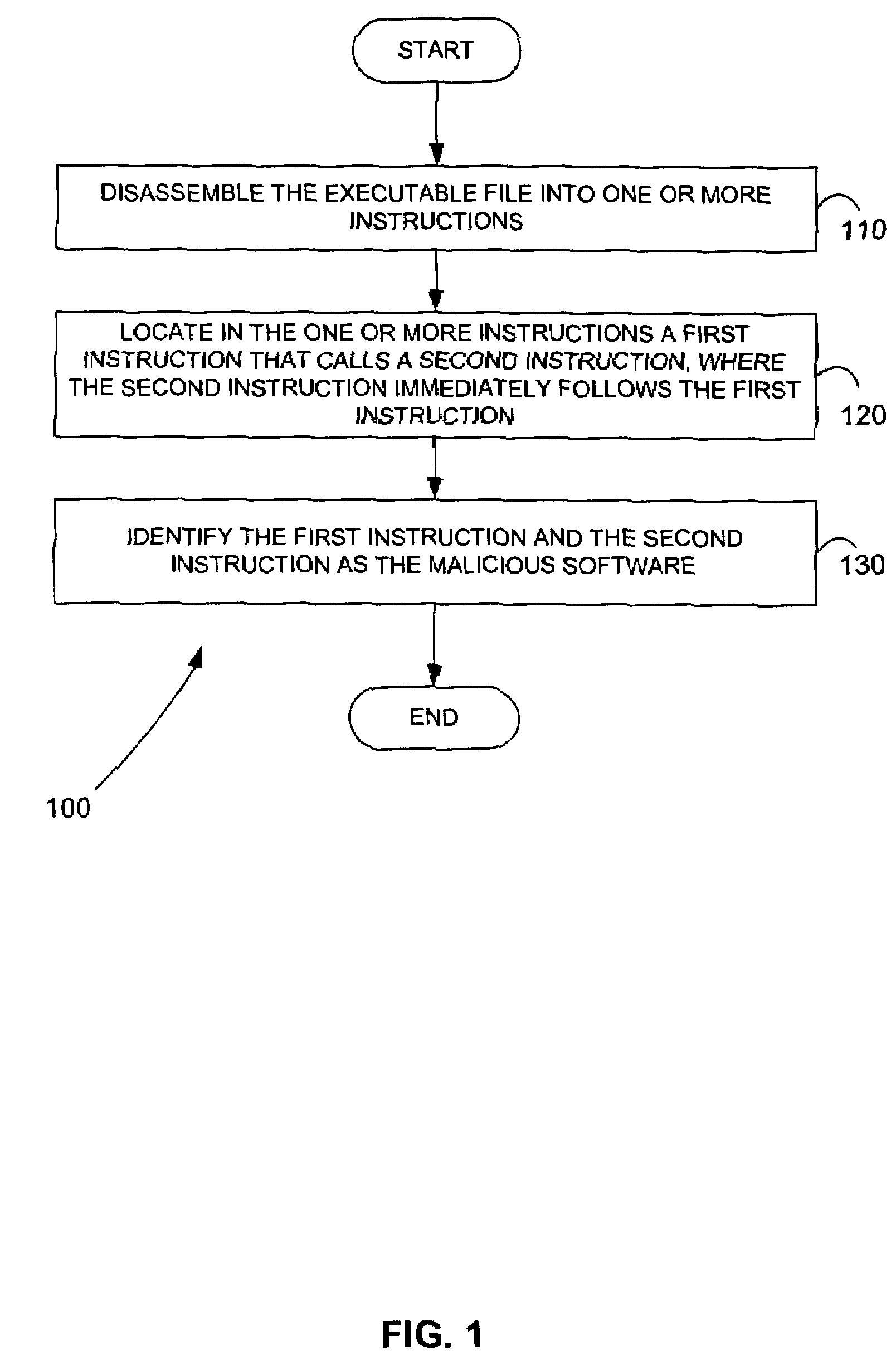
Owner:WESTERN DIGITAL TECH INC
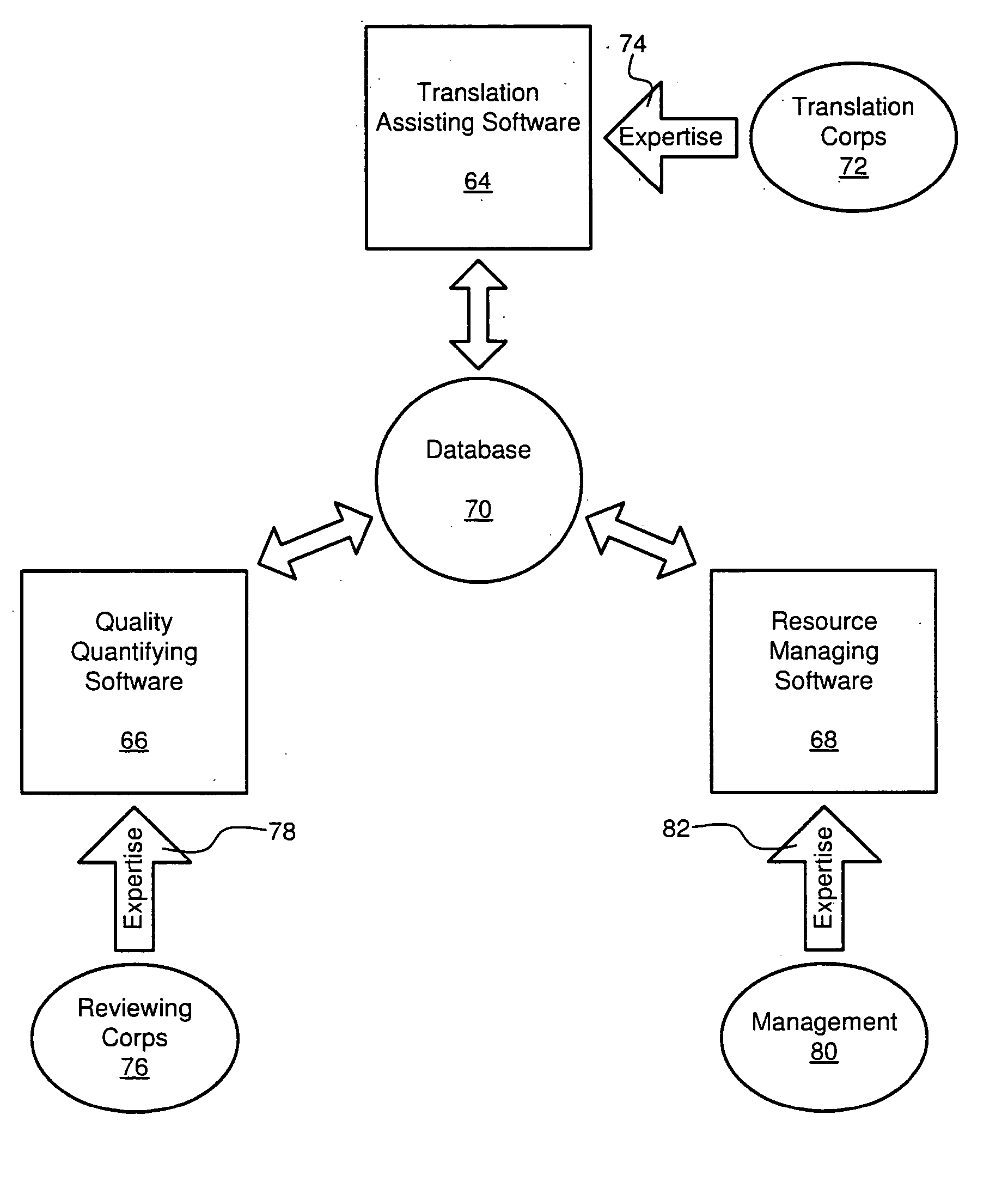
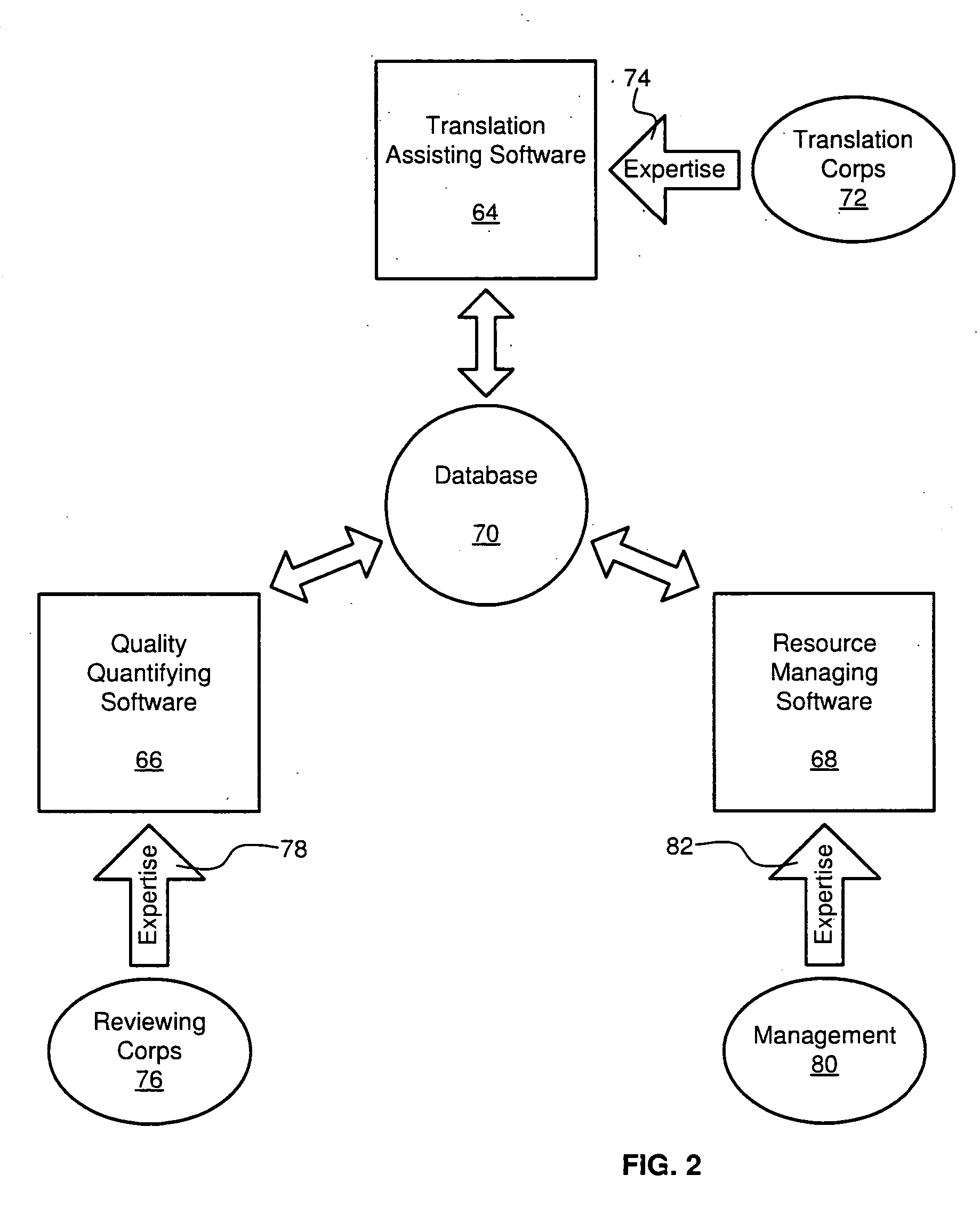
Translation quality quantifying apparatus and method
ActiveUS20070050182A1Effectively and predictably translateEfficiently determinedNatural language translationSpeech analysisTest sampleQuality assessment
A system for automating the quality evaluation of a translation. The system may include a computer having a processor and memory device operably connected to one another. A source text in a first language may be stored within the memory device. A target text comprising a translation of the source text into a second language may also be stored within the memory device. Additionally, a plurality of executables may be stored on the memory device and be configured to, when executed by the processor, independently identify a test sample comprising one or more blocks, each comprising a matched set having a source portion selected from the source text and a corresponding target portion selected from the target text.
Owner:MULTILING CORP
3D Image Generation and Display System
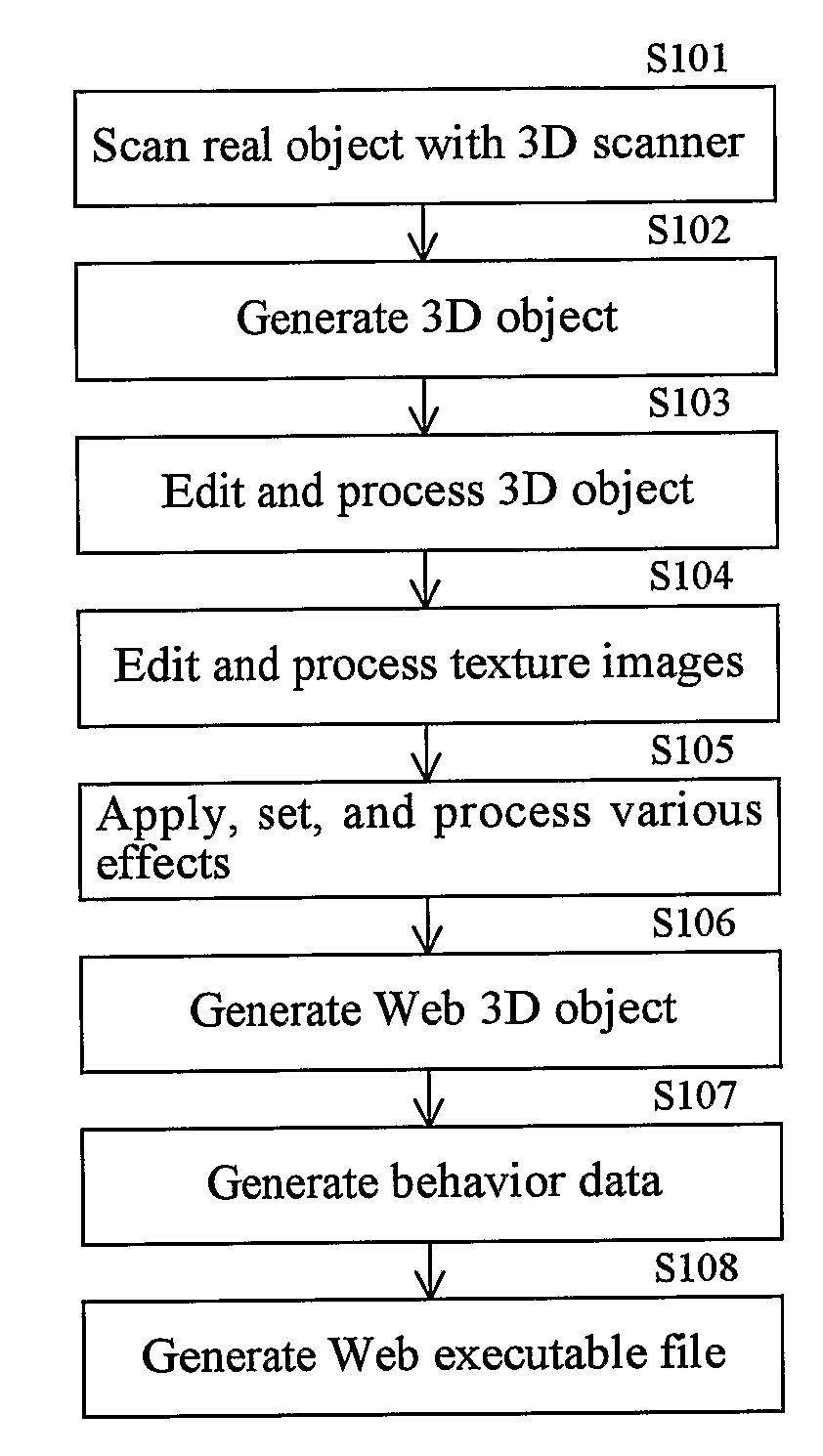
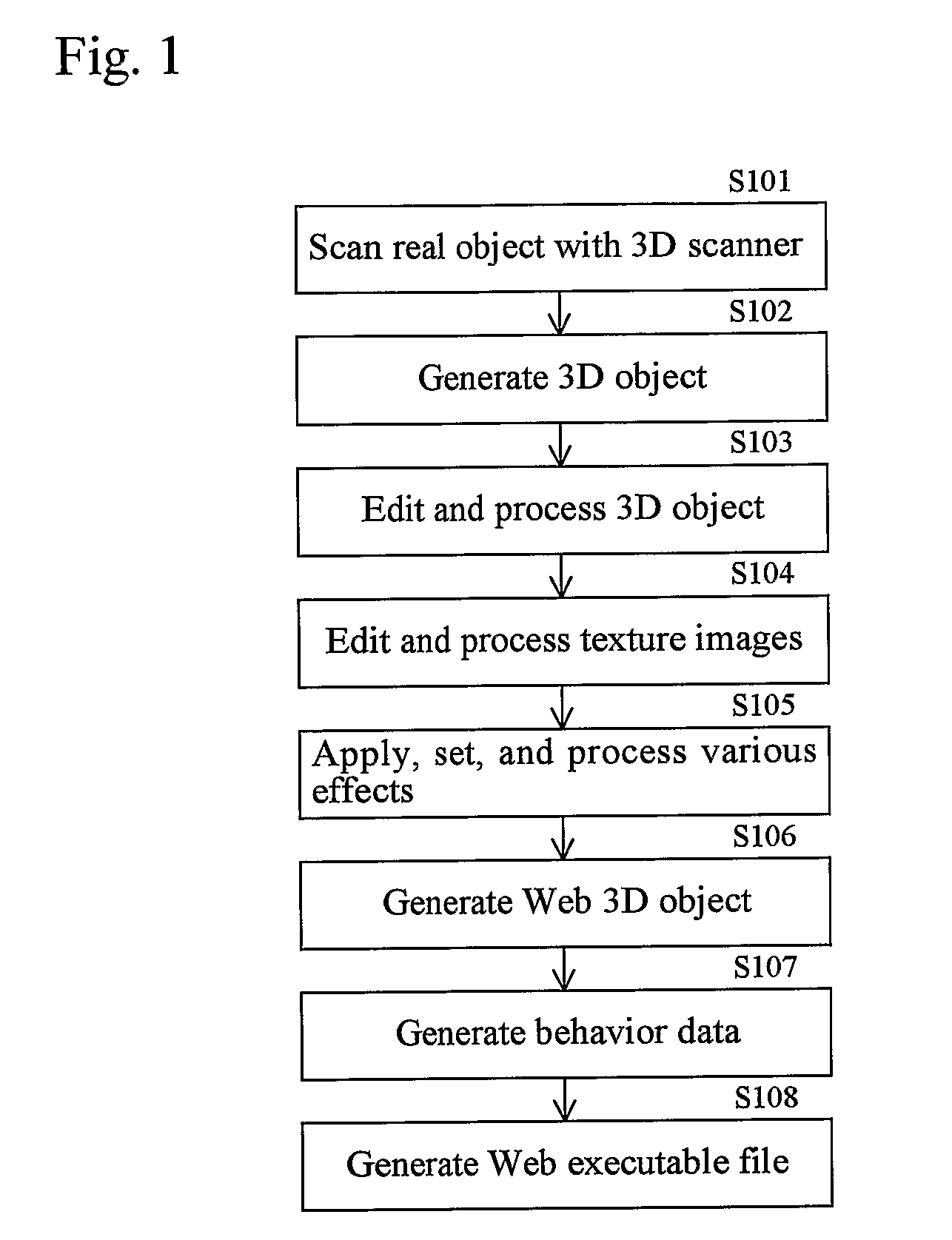
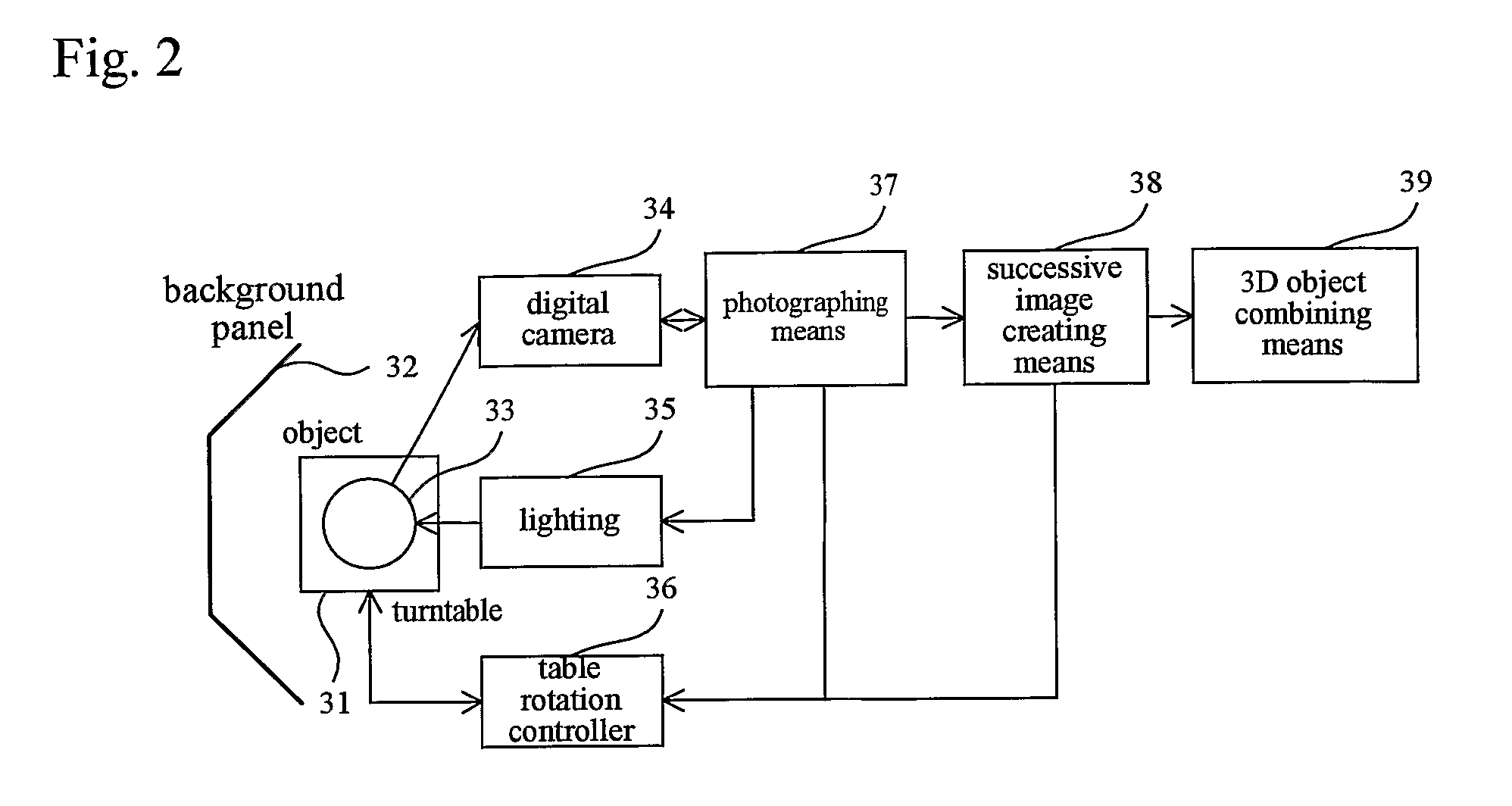
InactiveUS20080246757A1Easy constructionPromote generationSteroscopic systems3D-image renderingGraphicsWeb browser
A 3D image generation and display system facilitating the display of high-quality images in a Web browser comprises means for creating 3D images from a plurality of different images and computer graphics modeling and generating a 3D object from these images that has texture and attribute data; means for converting and outputting the 3D object as a 3D description file in a 3D graphics descriptive language; means for extracting a 3D object and textures from the 3D description file, setting various attribute data, and editing and processing the 3D object to introduce animation or the like and assigning various effects; means for generating various Web-based 3D objects from the 3D data files produced above that are compressed to be displayed in a Web browser and generating behavior data to display 3D scenes in a Web browser with animation; and means for generating an executable file comprising a Web page and Web-based programs such as scripts, plug-ins, and applets for drawing and displaying 3D scenes in a Web browser.
Owner:YAPPA CORP
Peripheral device, information processing method, and control program
ActiveUS20060026105A1Data processing applicationsDigital data processing detailsInformation processingComputer science
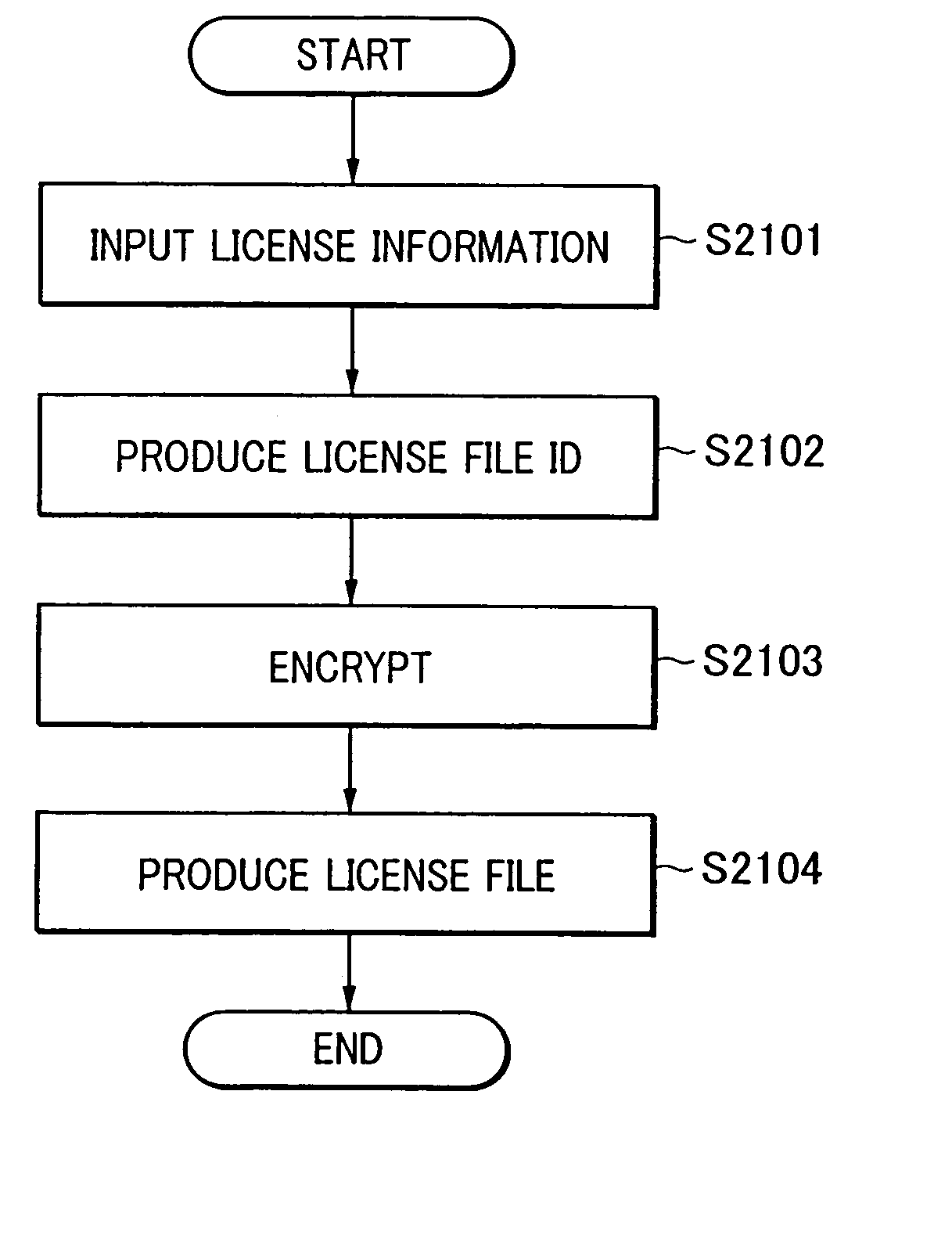
A management method is disclosed for managing license information indicating an allowed amount of usage of a program executable on a peripheral device or a function provided by the peripheral device. The method includes the steps of acquiring, from the outside, license identification information for identifying license information, and license information indicating an amount of a change in right of usage of the program, managing license identification information corresponding to license information that has already been installed, determining whether license identification information corresponding to license information is included in license identification information managed in the management step, and performing operation such that if it is determined in the determination step that the license identification information corresponding to the license information is included in the license identification information managed in the management step, changing the value of the already installed right of usage of the program by an amount equal to a change in the right of usage of the program.
Owner:CANON KK
System and method for providing a user interface with search query broadening
A system and method for providing a user interface with search query broadening is described. A query defining a search executable on potentially retrievable information is accepted. The query is parsed. A broadened query is provided. At least one of the broadened query and results of a search executed on the broadened query is presented.
Owner:GOOGLE LLC
Solid-state storage subsystem security solution
ActiveUS8108692B1Unauthorized memory use protectionHardware monitoringSolid-state storageSecurity solution
A solid-state storage subsystem, such as a non-volatile memory card or drive, includes a main memory area that is accessible via standard memory access commands (such as ATA commands), and a restricted memory area that is accessible only via one or more non-standard commands. The restricted memory area stores information used to control access to, and / or use of, information stored in the main memory area. As one example, the restricted area may store one or more identifiers, such as a unique subsystem identifier, needed to decrypt an executable or data file stored in the main memory area. A host software component is configured to retrieve the information from the subsystem's restricted memory area, and to use the information to control access to and / or use of the information in the main memory area.
Owner:WESTERN DIGITAL TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com