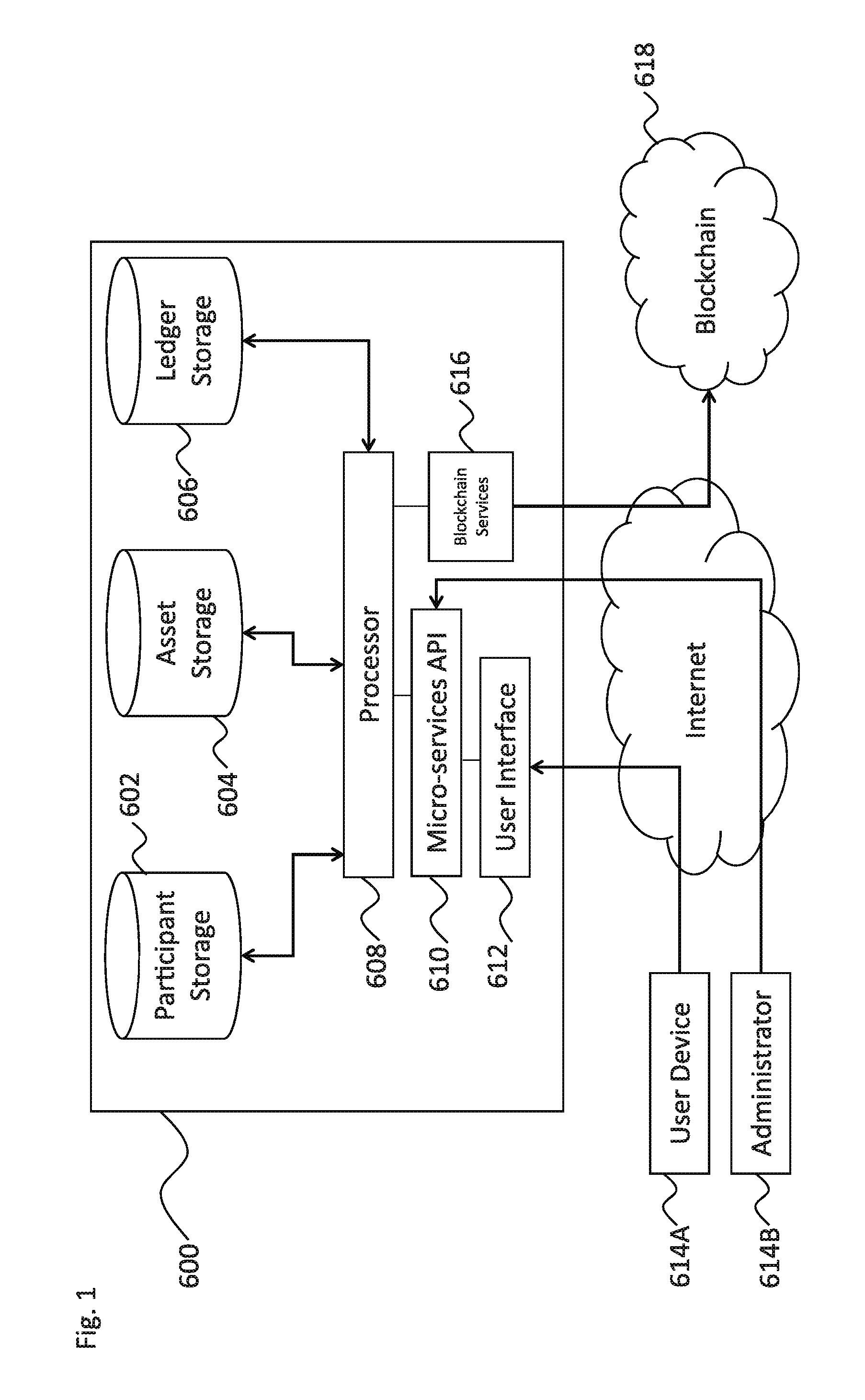
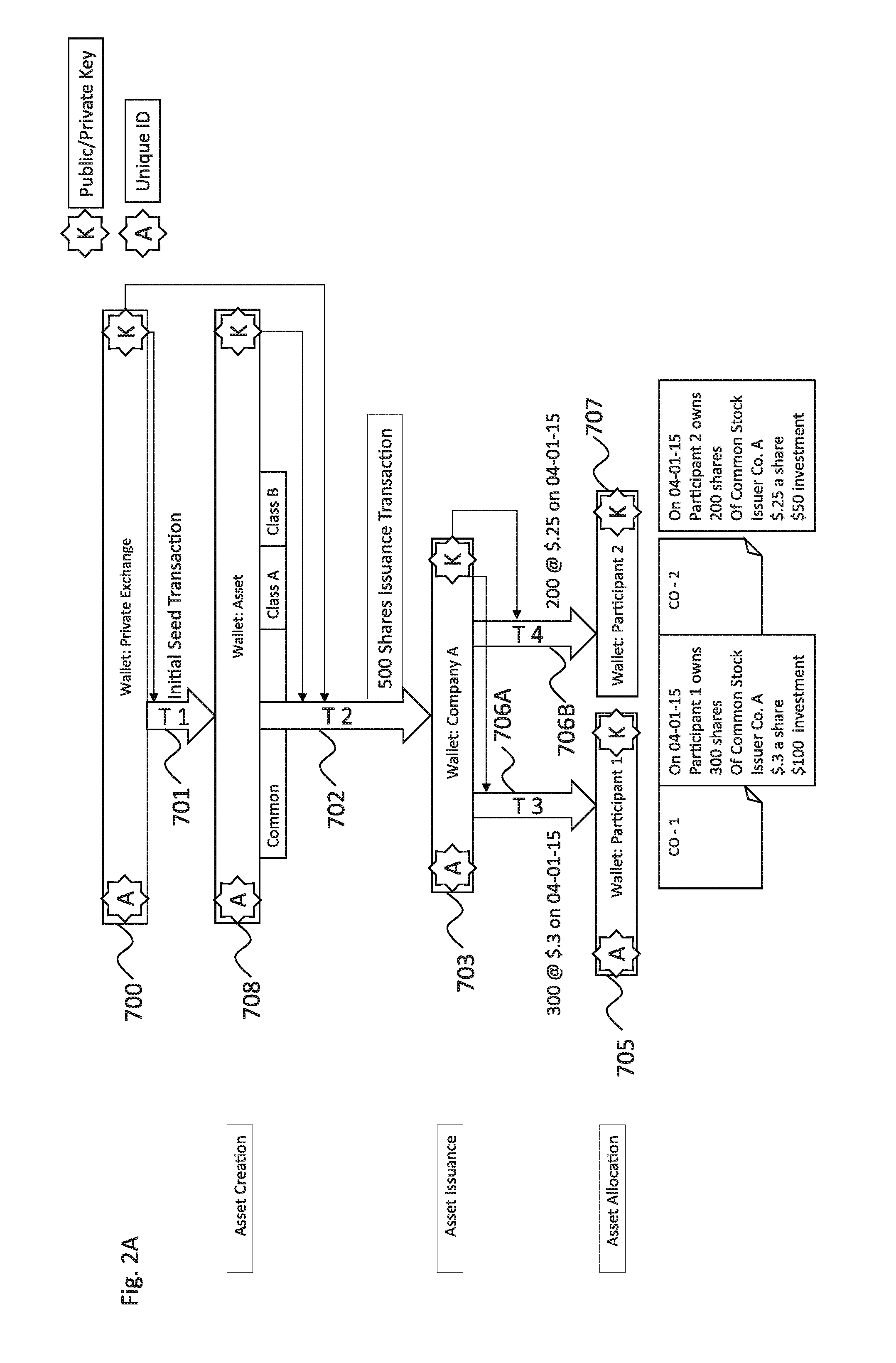
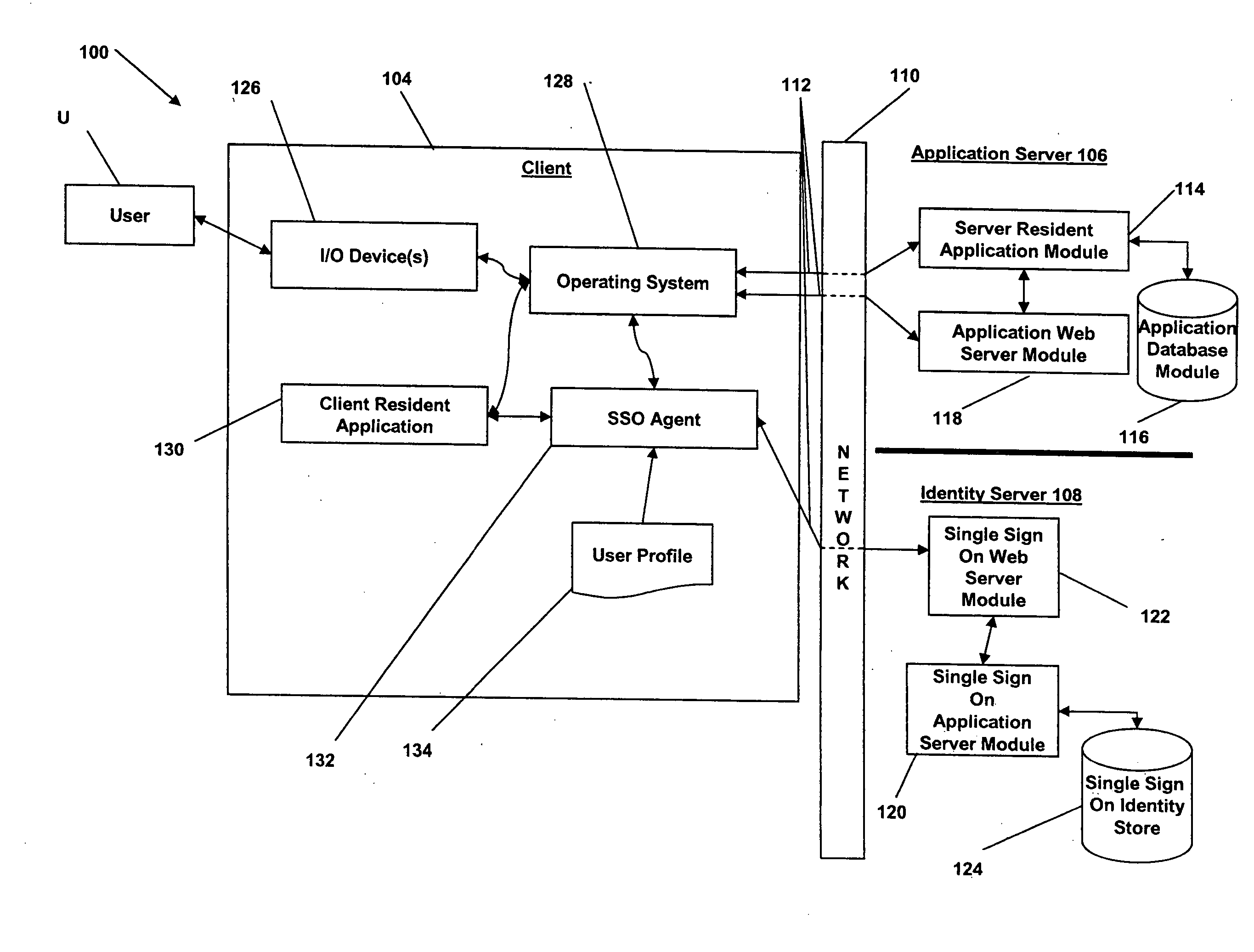
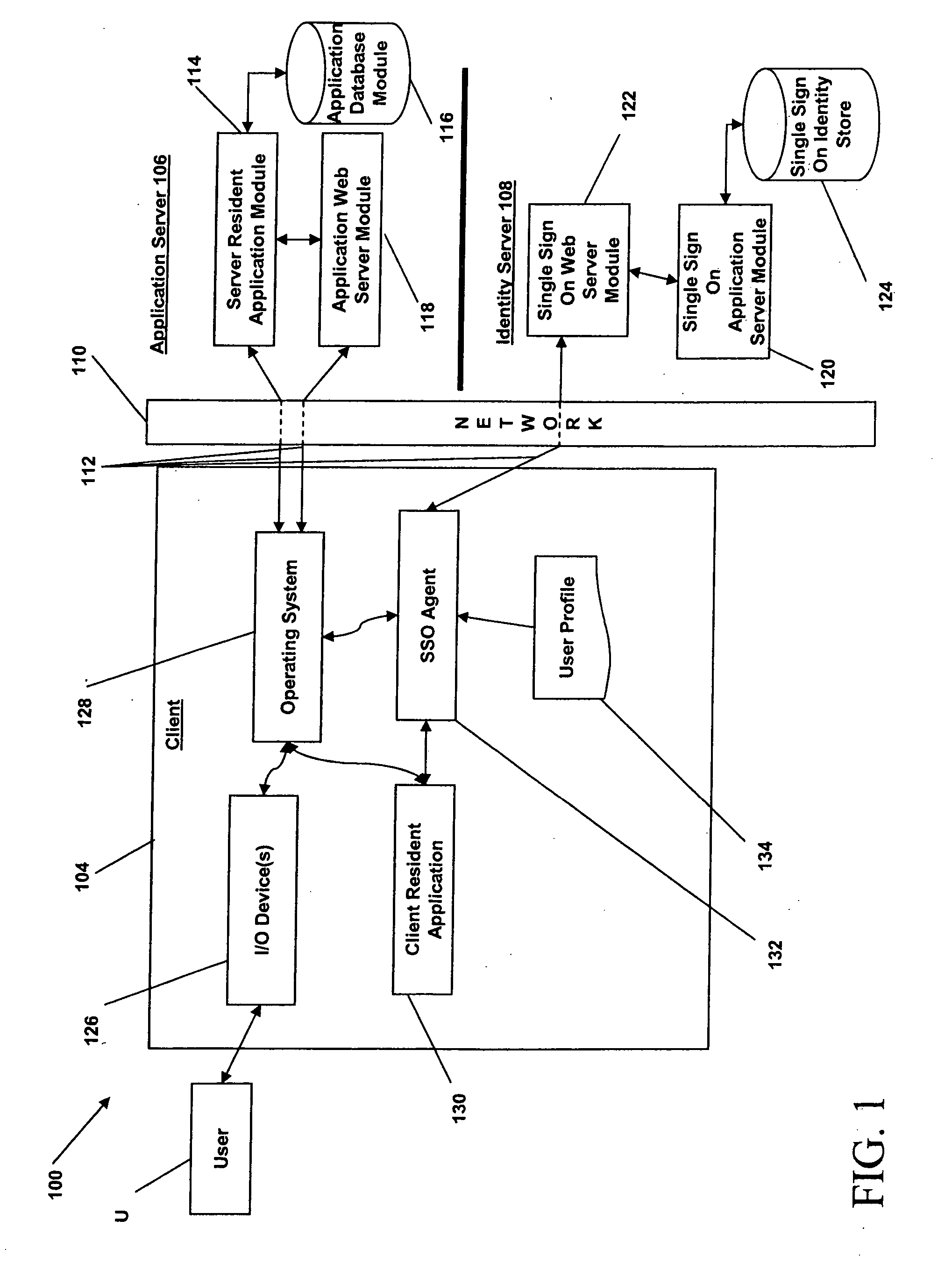
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
60432results about "User identity/authority verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
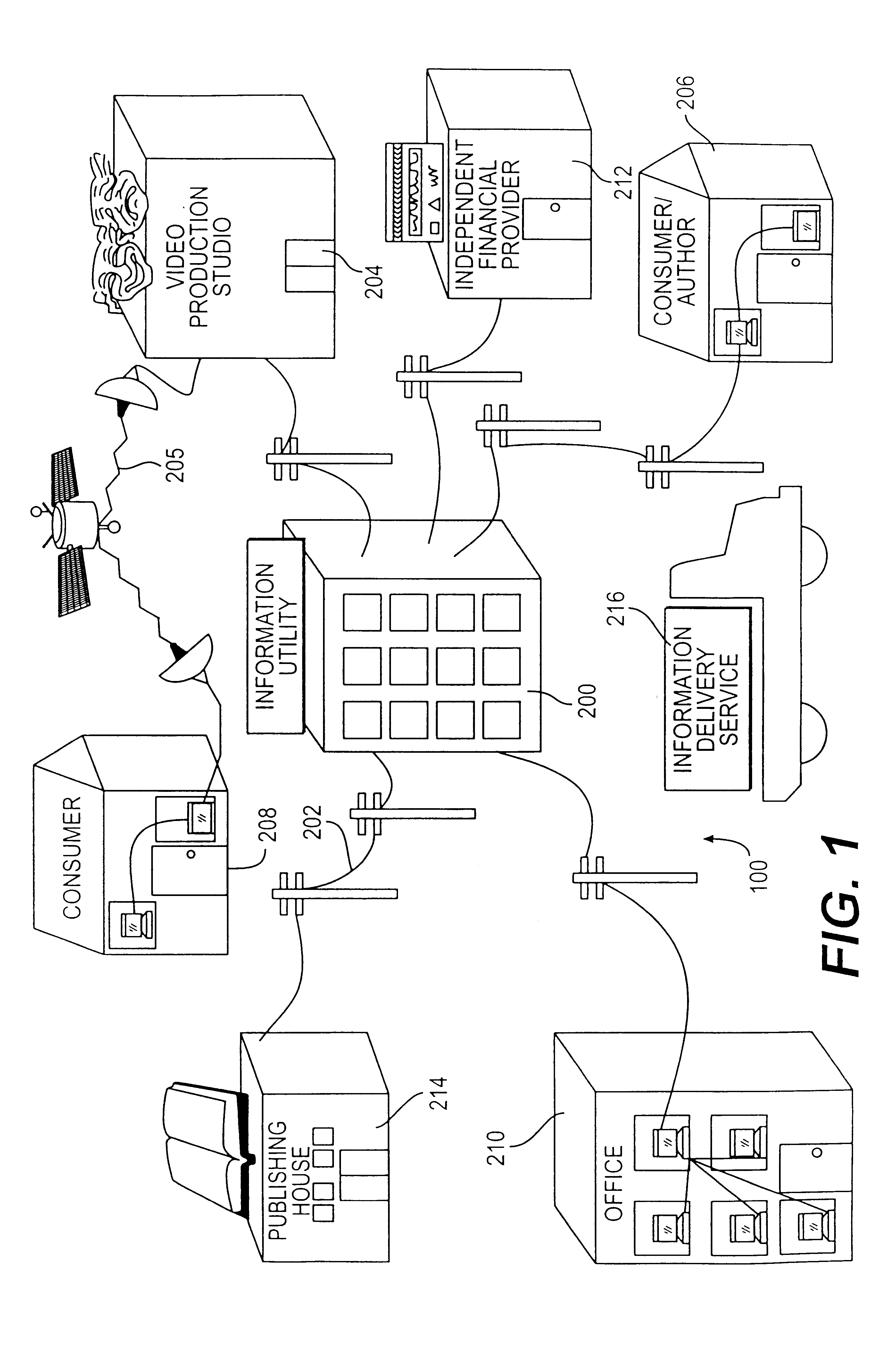
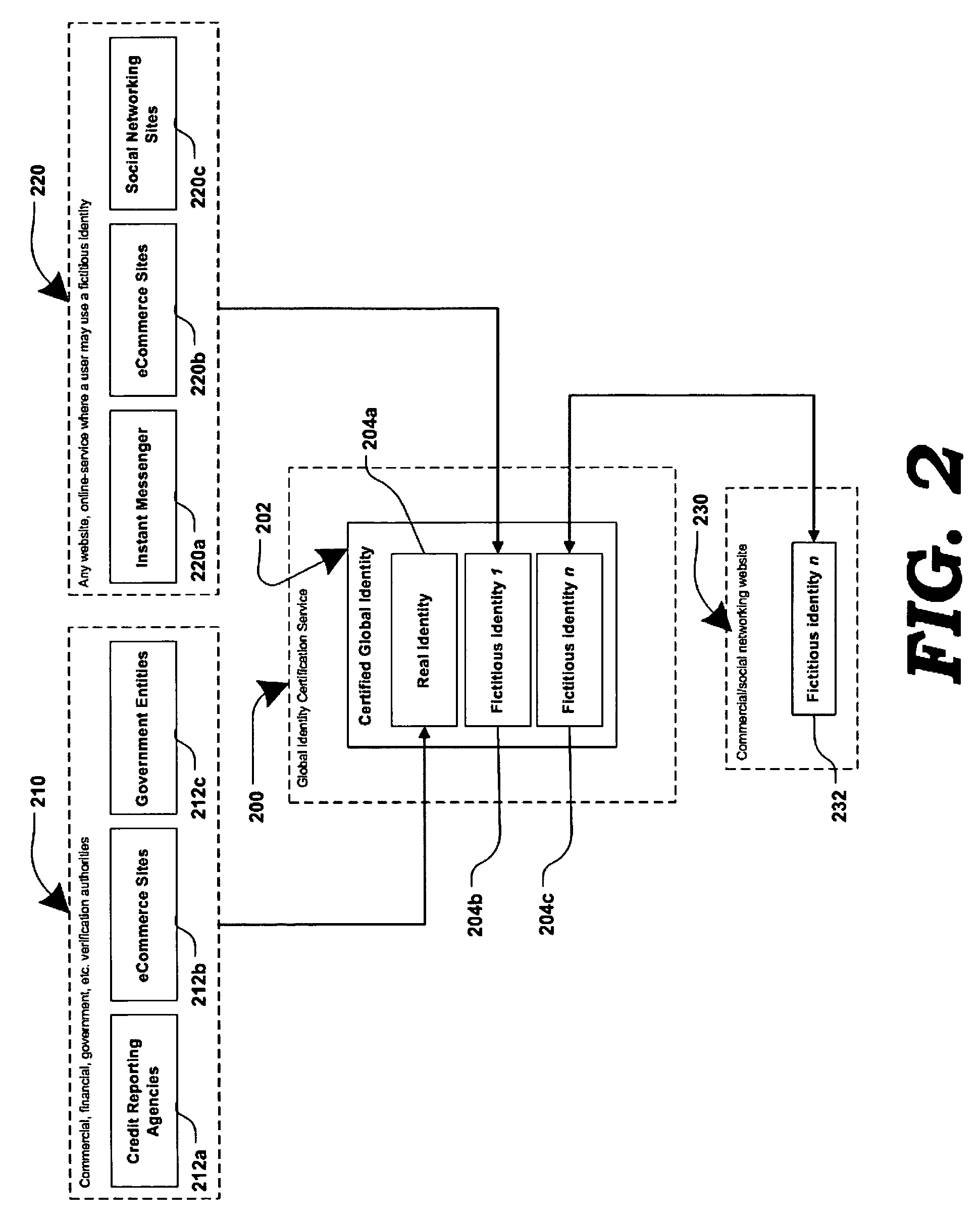
Systems and methods for matching, selecting, narrowcasting, and/or classifying based on rights management and/or other information
InactiveUS6112181AIncrease success rateCostly and inefficientUser identity/authority verificationSignalling system detailsRights managementUtility system
Rights management information is used at least in part in a matching, narrowcasting, classifying and / or selecting process. A matching and classification utility system comprising a kind of Commerce Utility System is used to perform the matching, narrowcasting, classifying and / or selecting. The matching and classification utility system may match, narrowcast, classify and / or select people and / or things, non-limiting examples of which include software objects. The Matching and Classification Utility system may use any pre-existing classification schemes, including at least some rights management information and / or other qualitative and / or parameter data indicating and / or defining classes, classification systems, class hierarchies, category schemes, class assignments, category assignments, and / or class membership. The Matching and Classification Utility may also use at least some rights management information together with any artificial intelligence, expert system, statistical, computational, manual, or any other means to define new classes, class hierarchies, classification systems, category schemes, and / or assign persons, things, and / or groups of persons and / or things to at least one class.
Owner:INTERTRUST TECH CORP
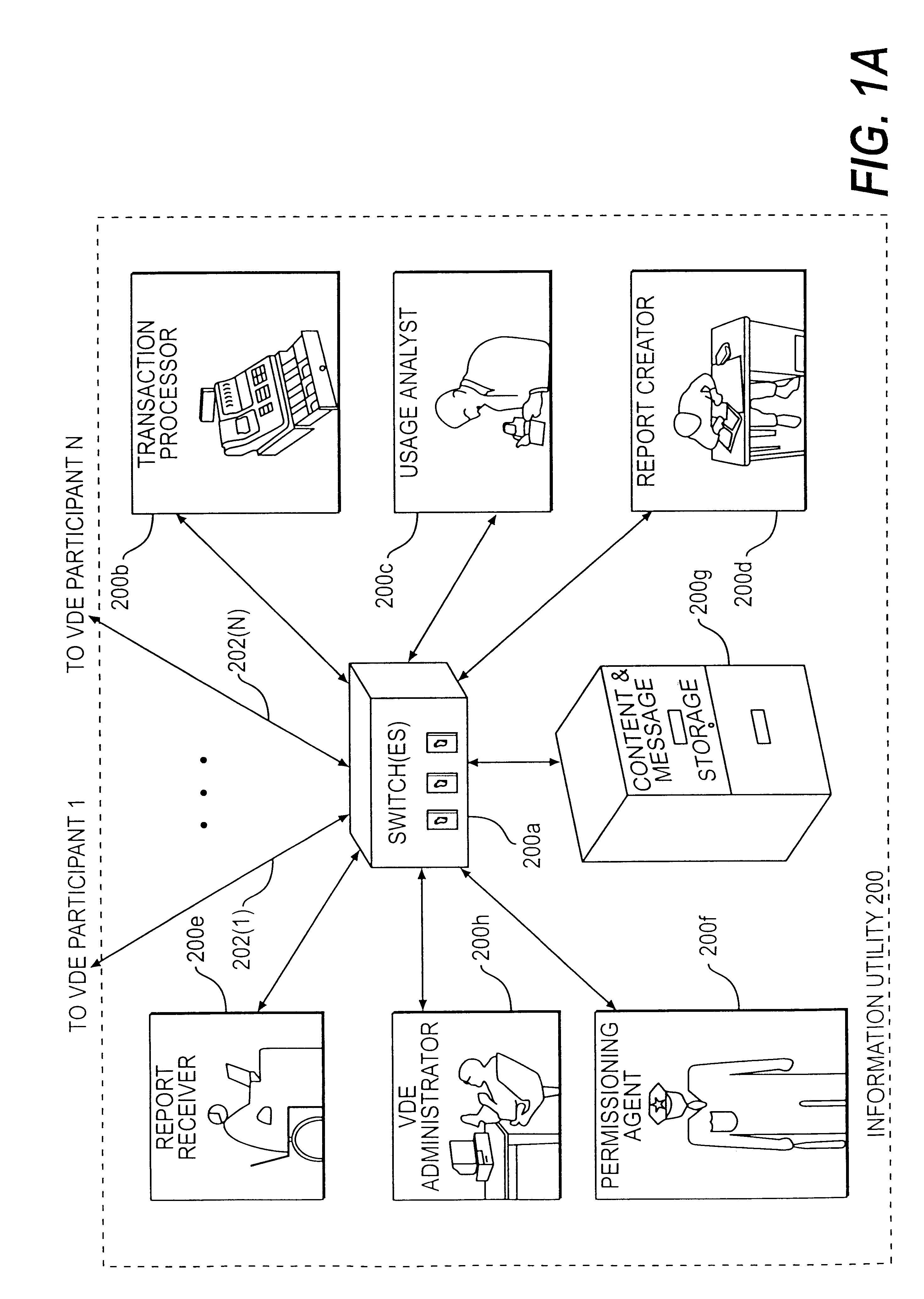
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
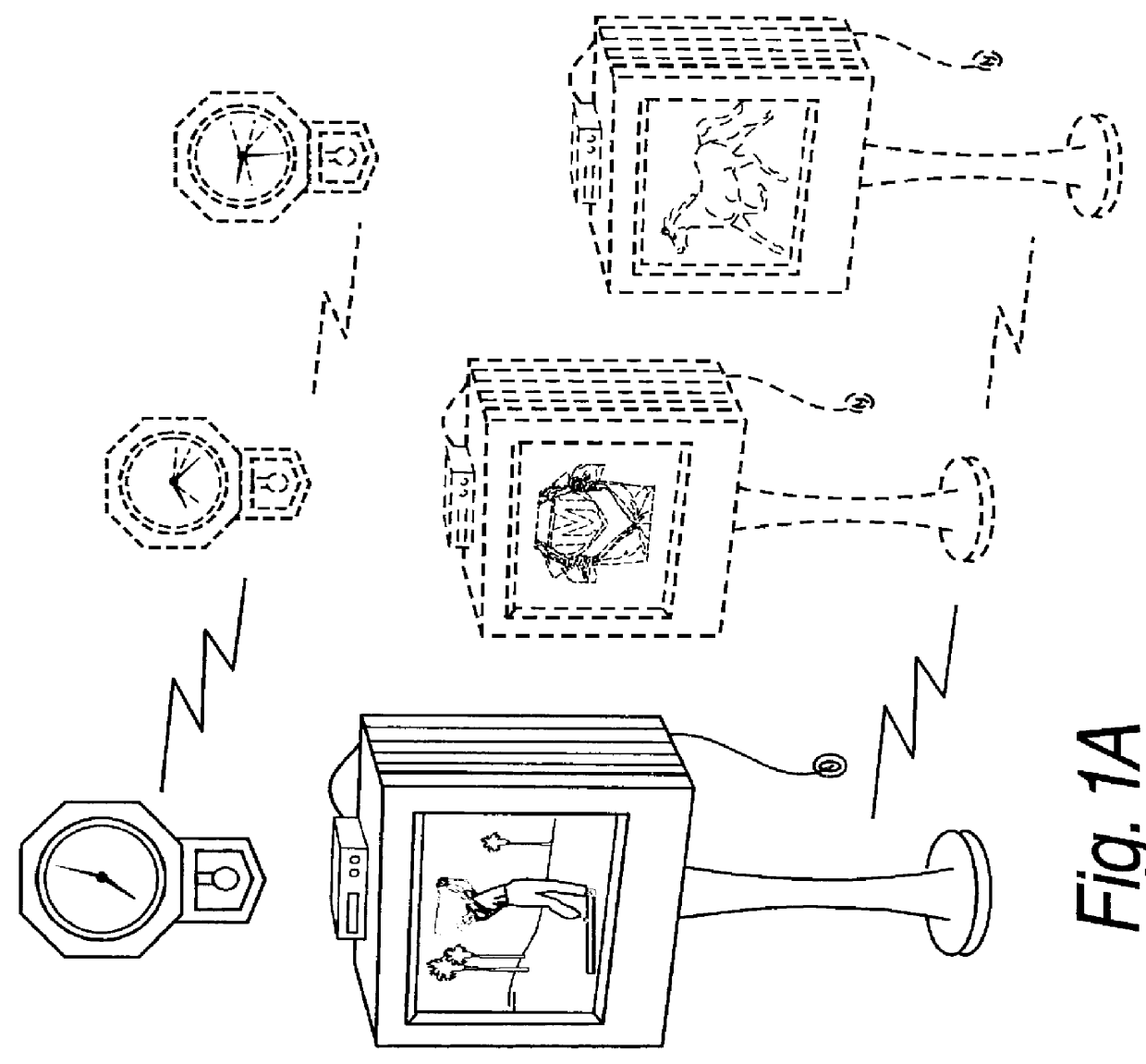
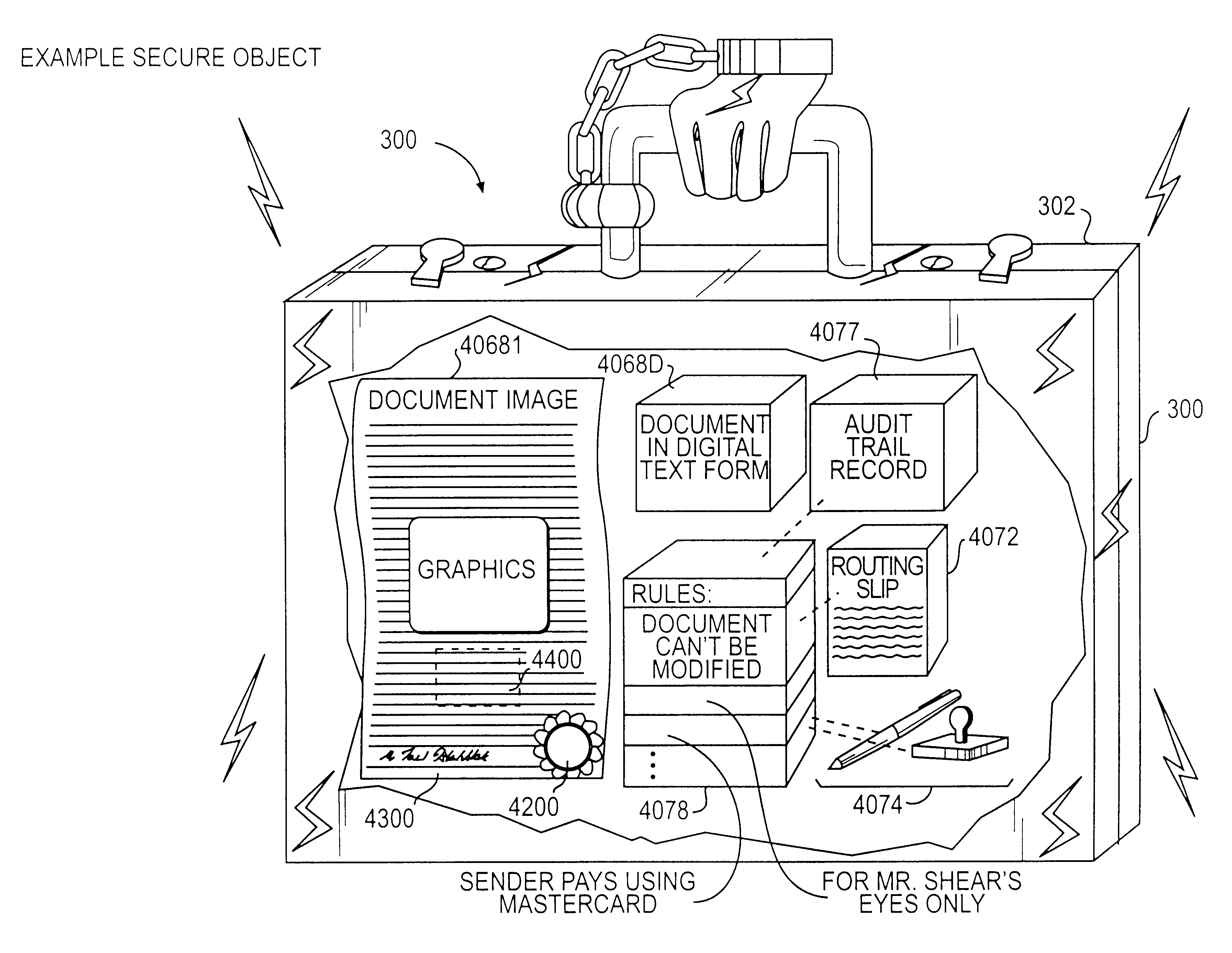
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
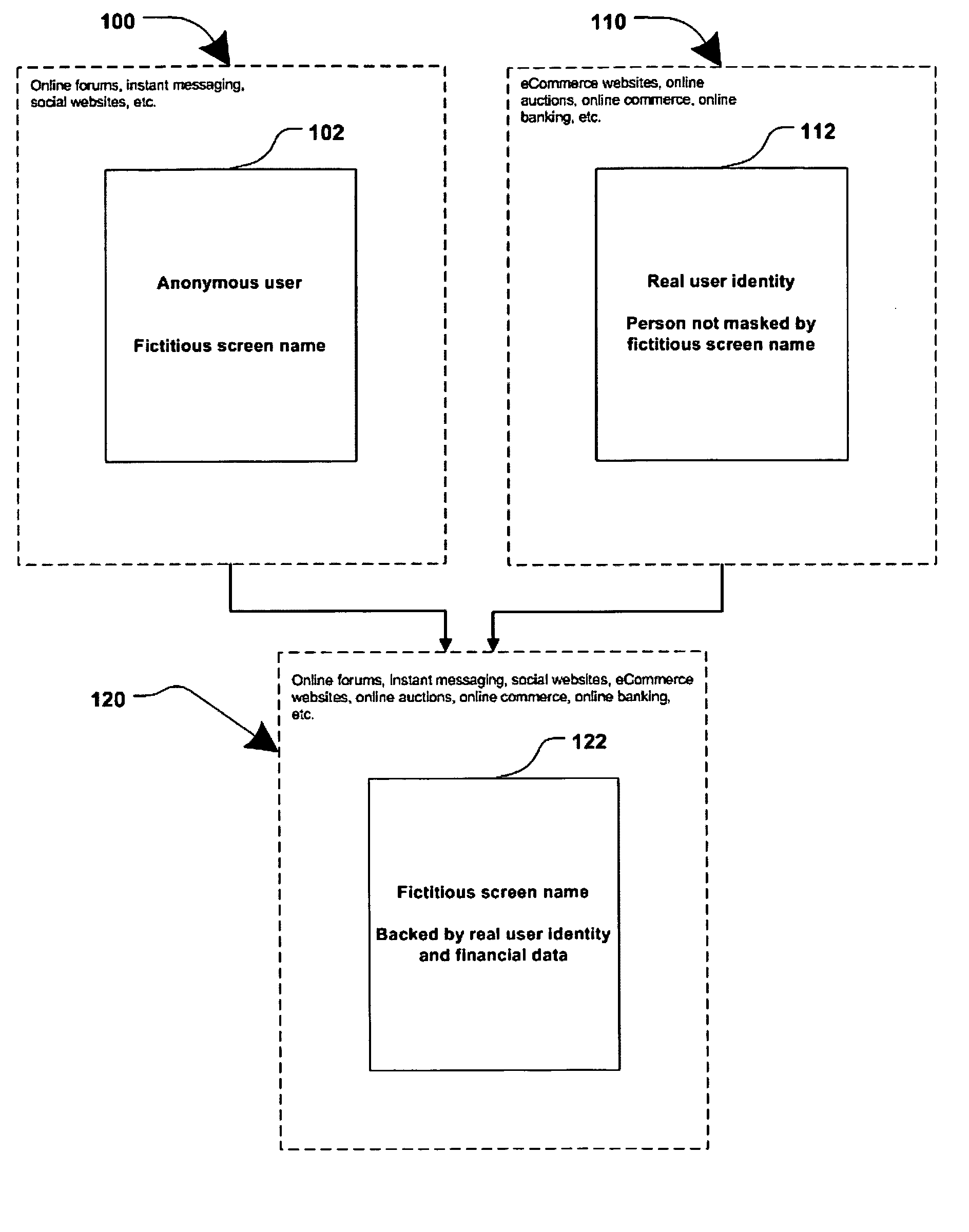
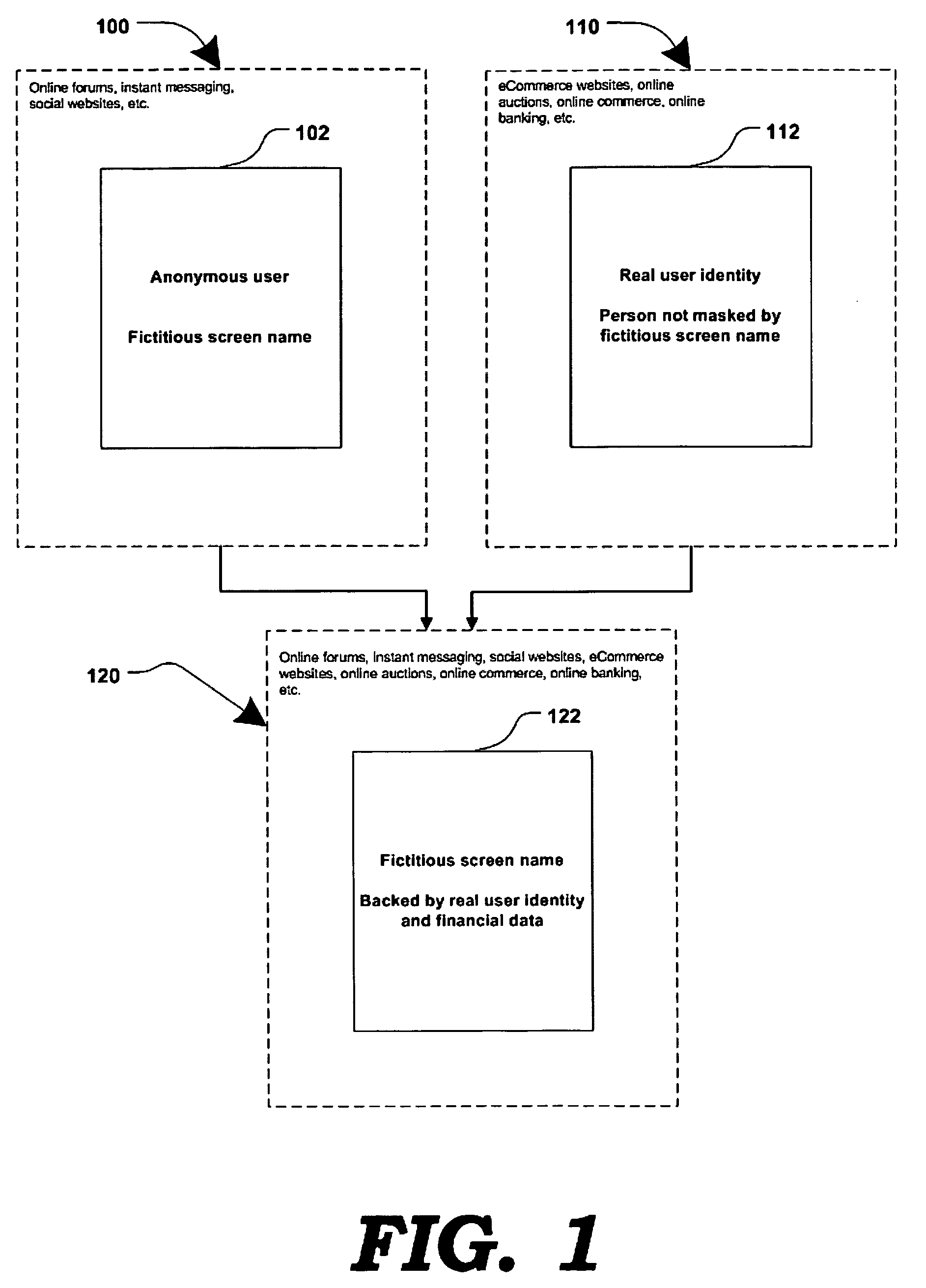
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
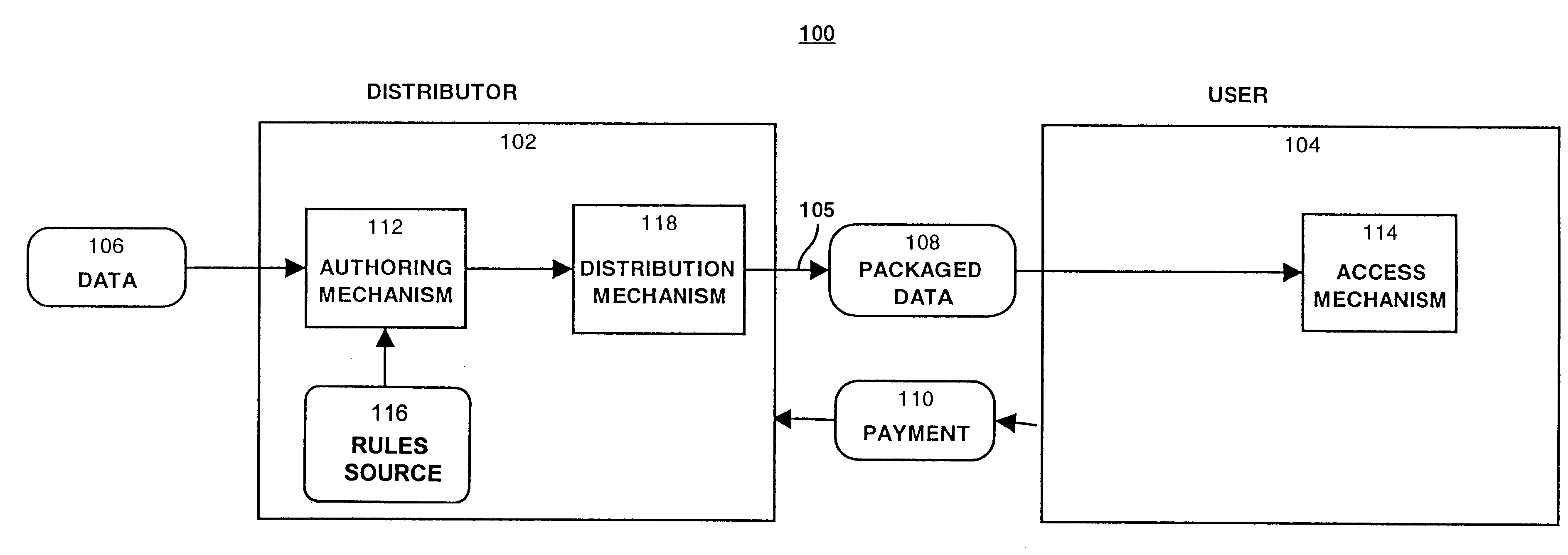
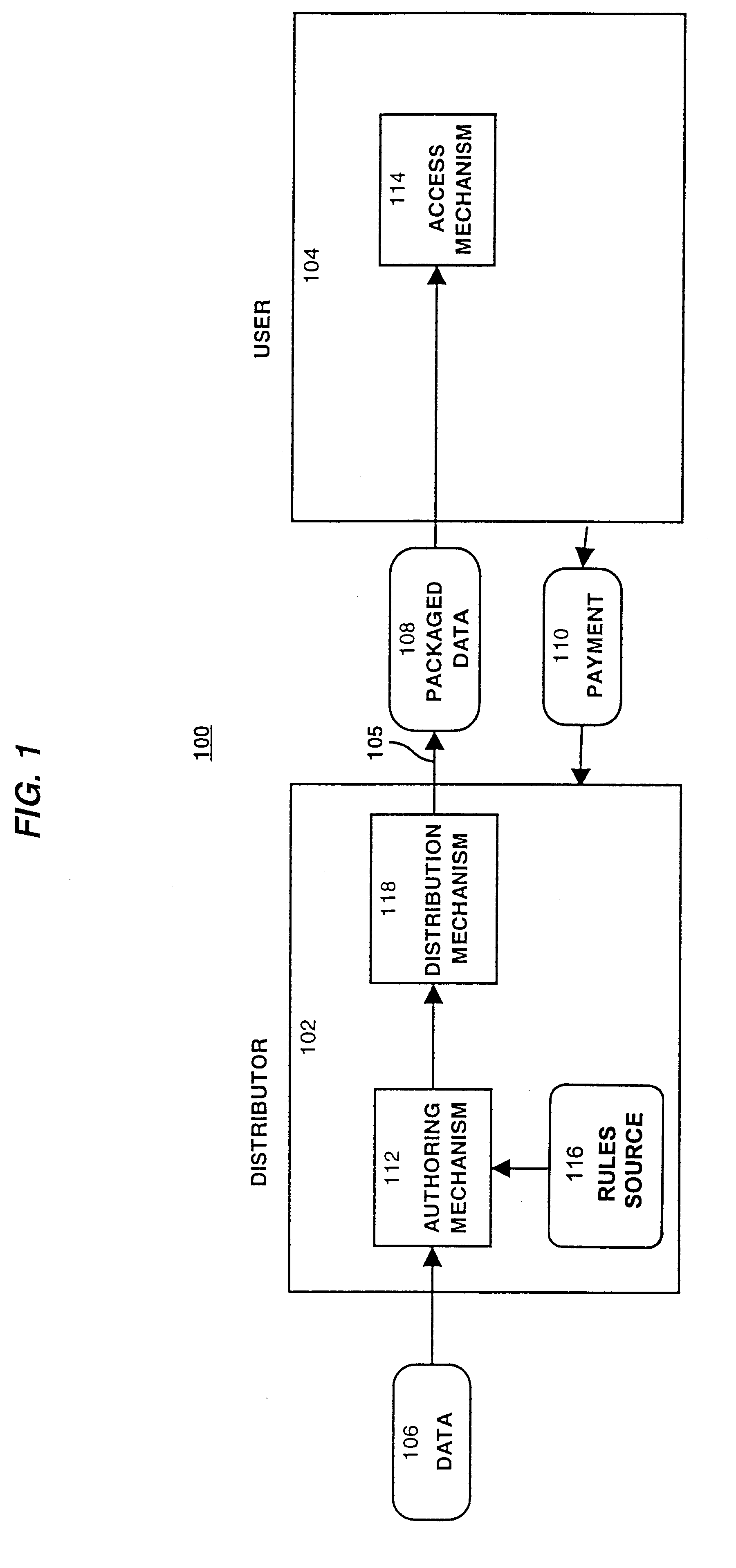
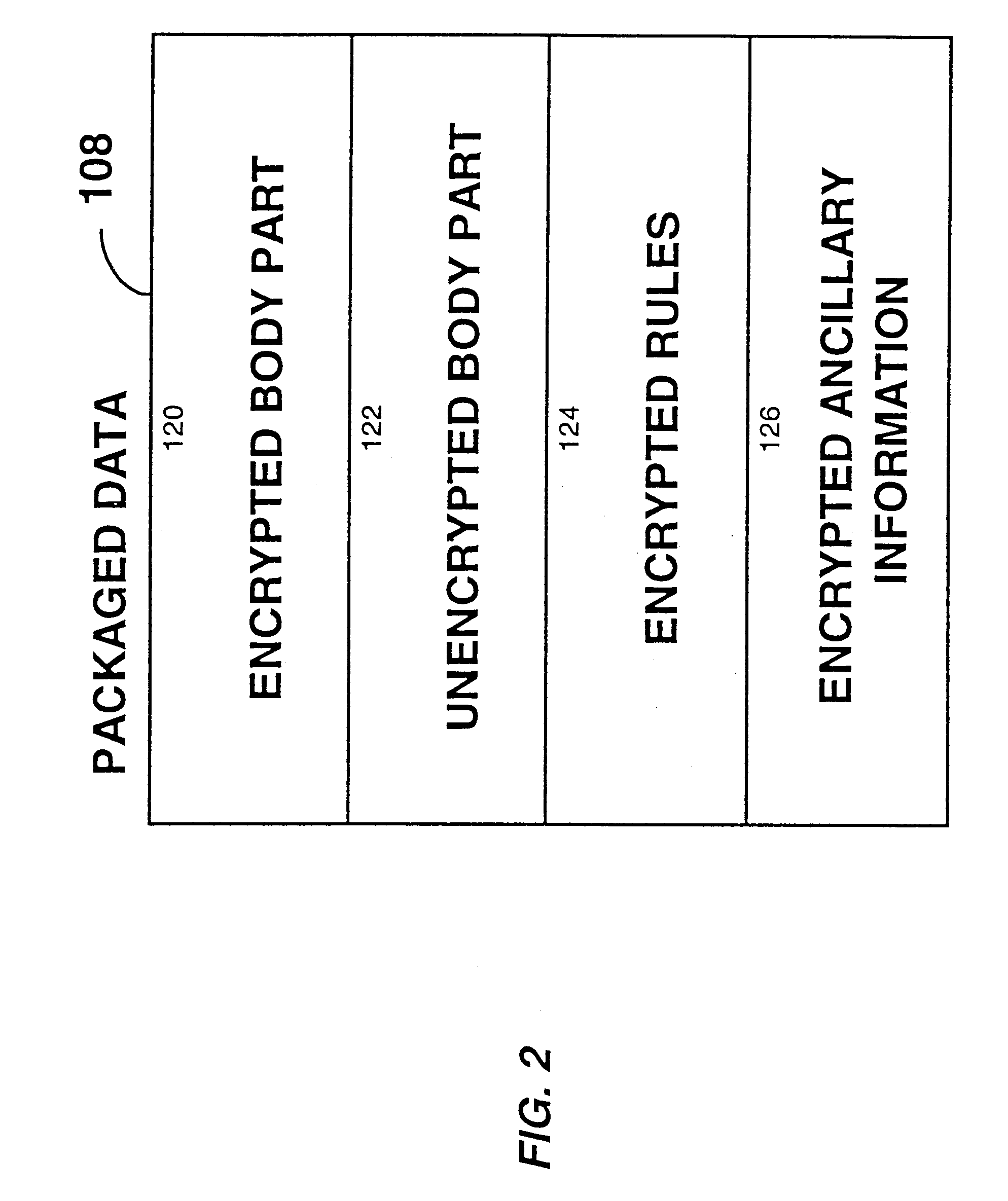
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
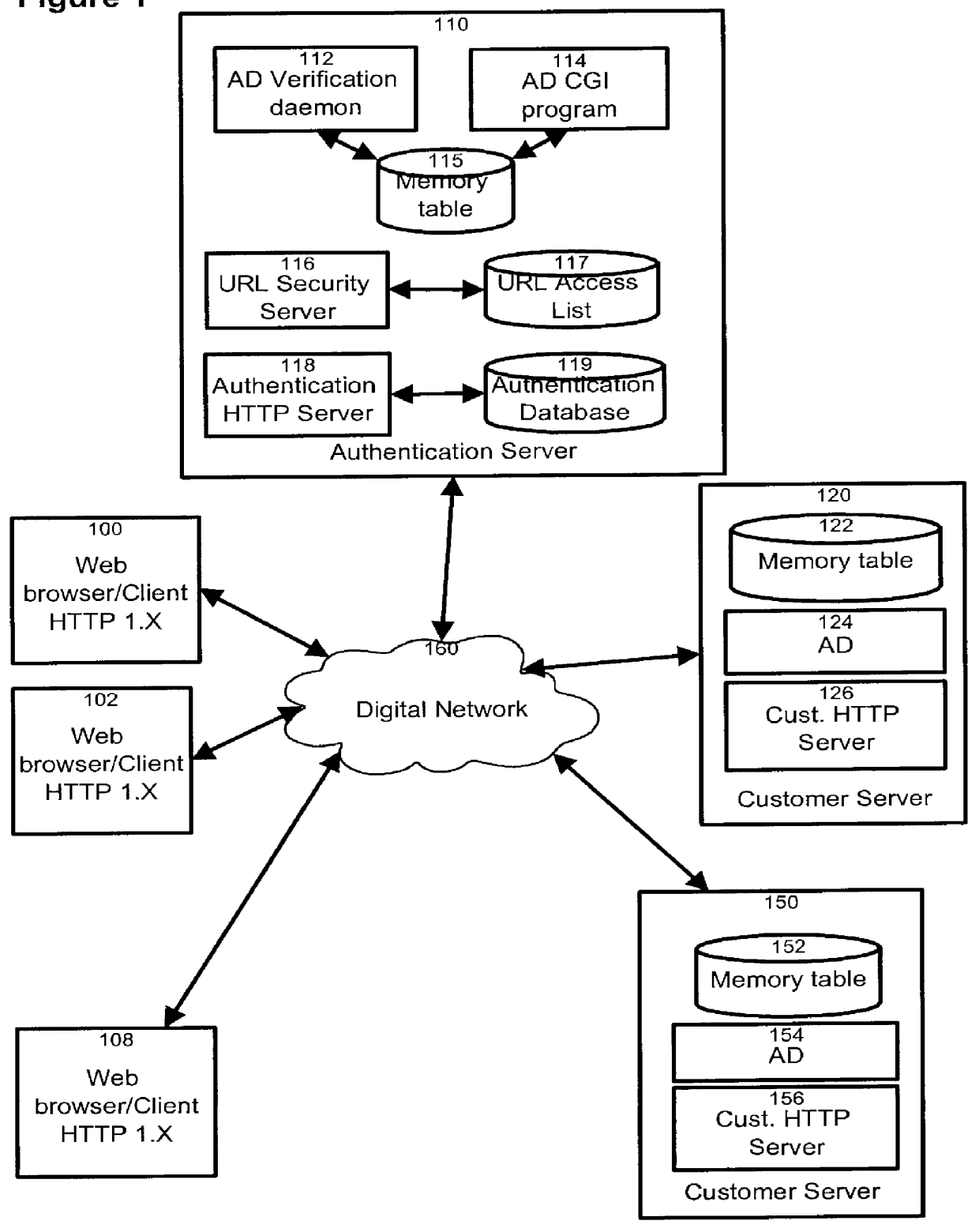
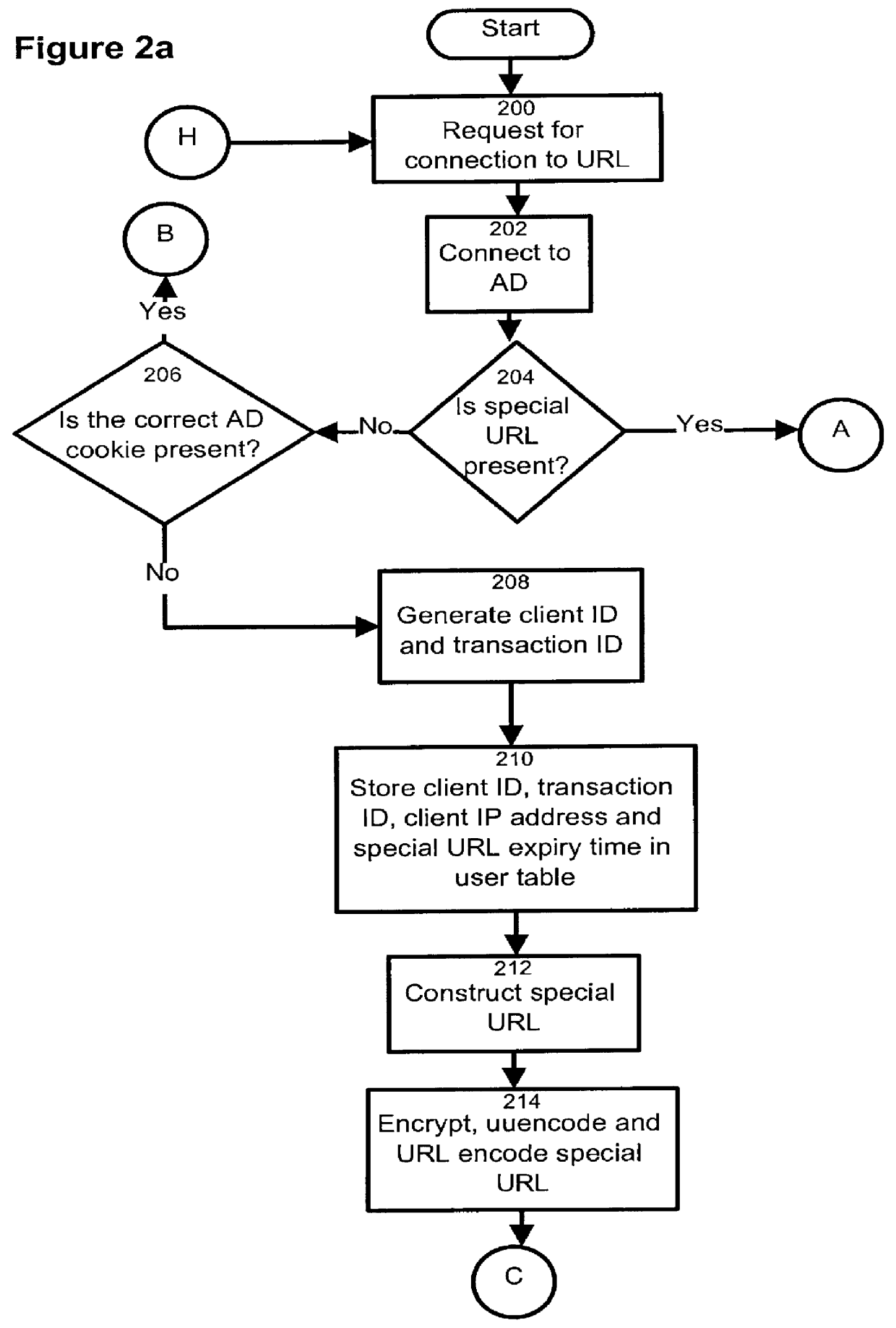
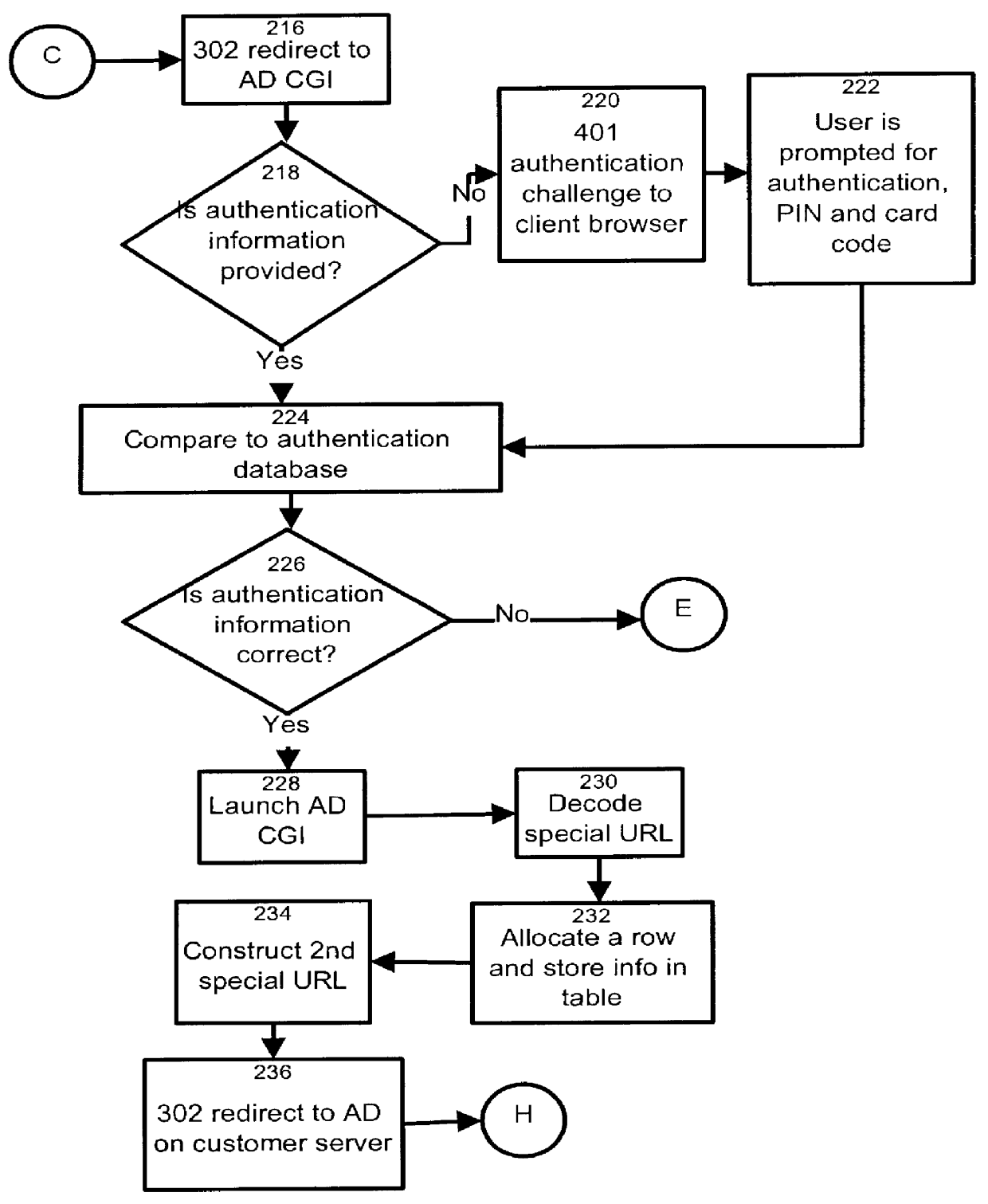
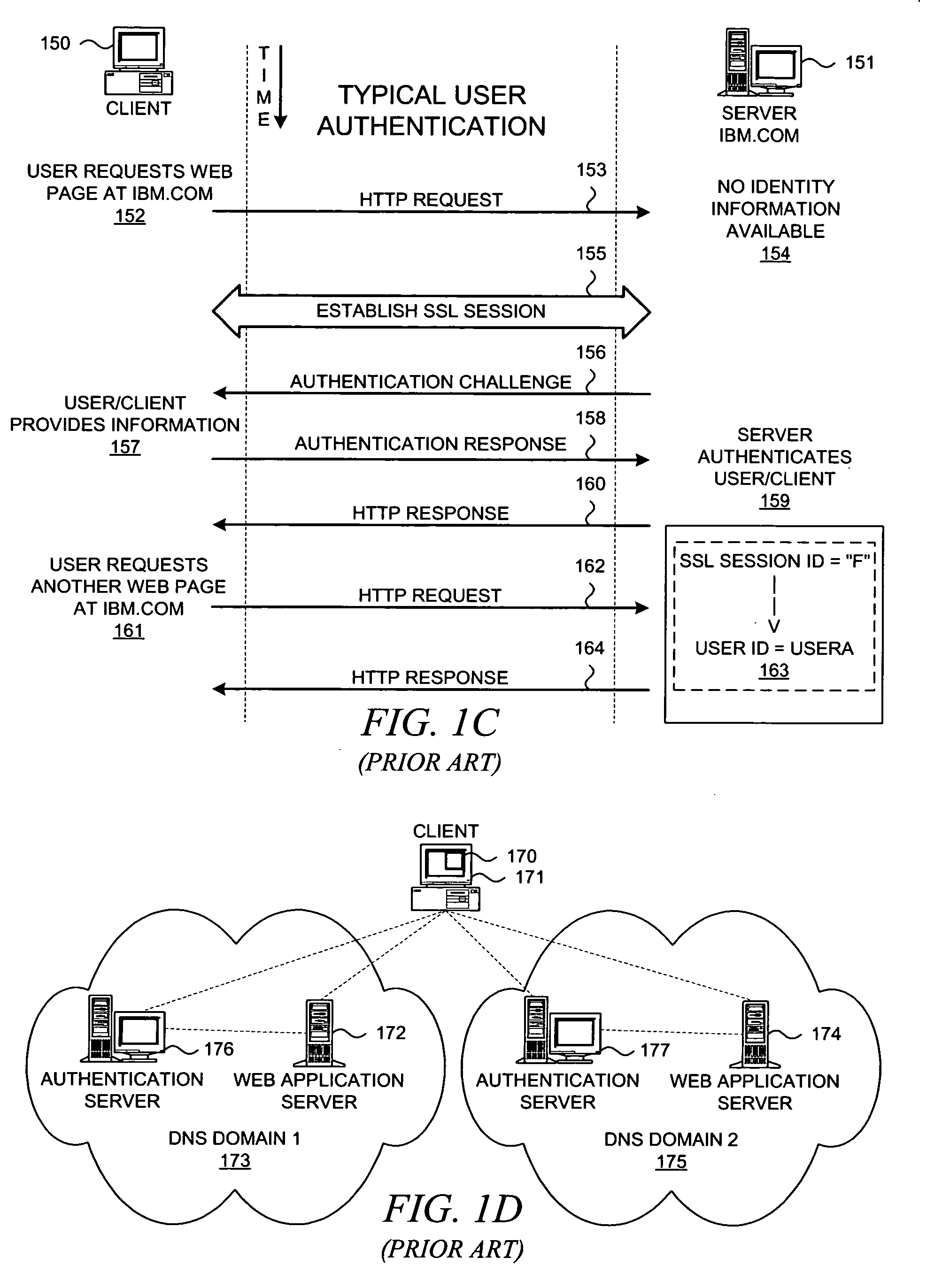
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
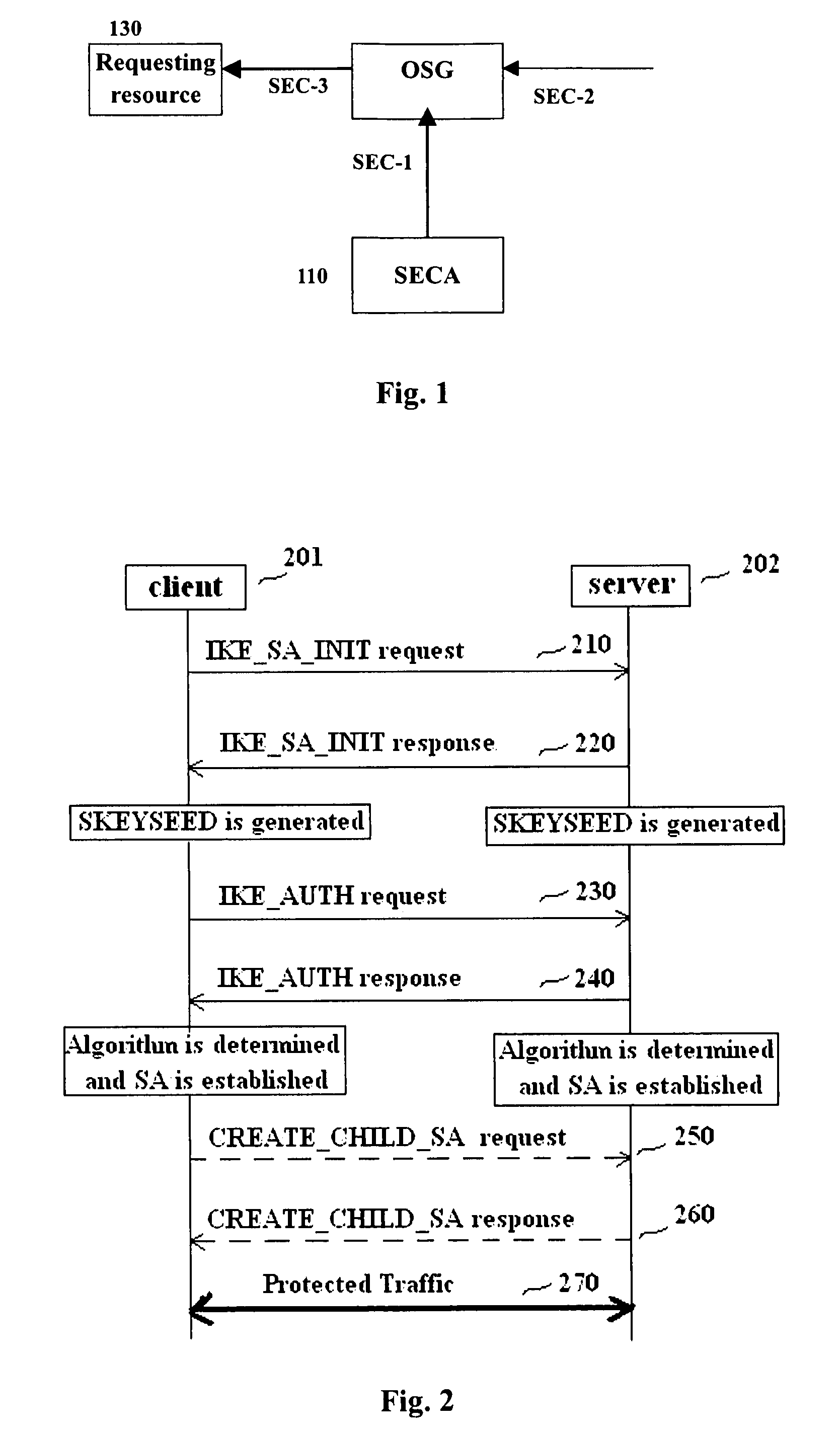
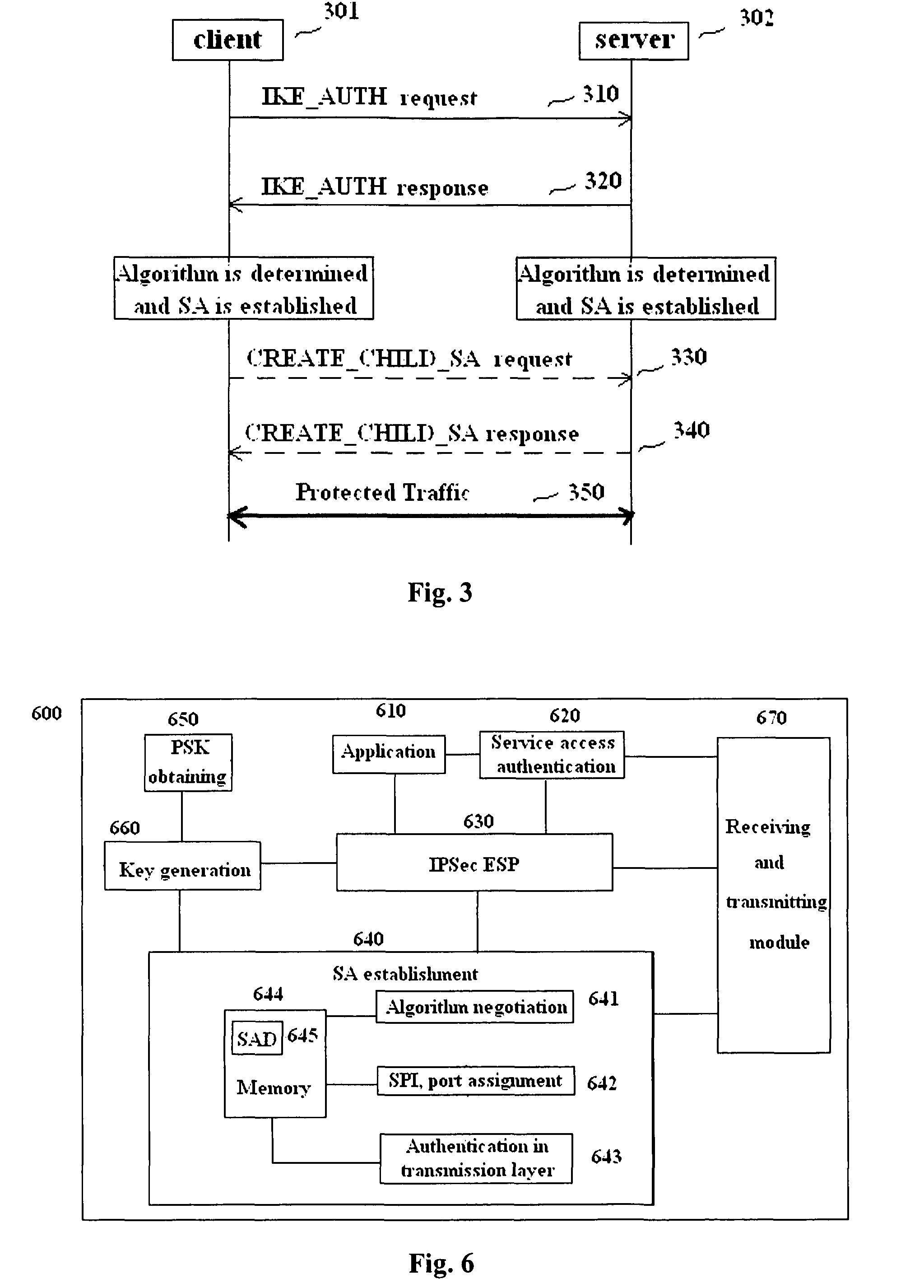
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
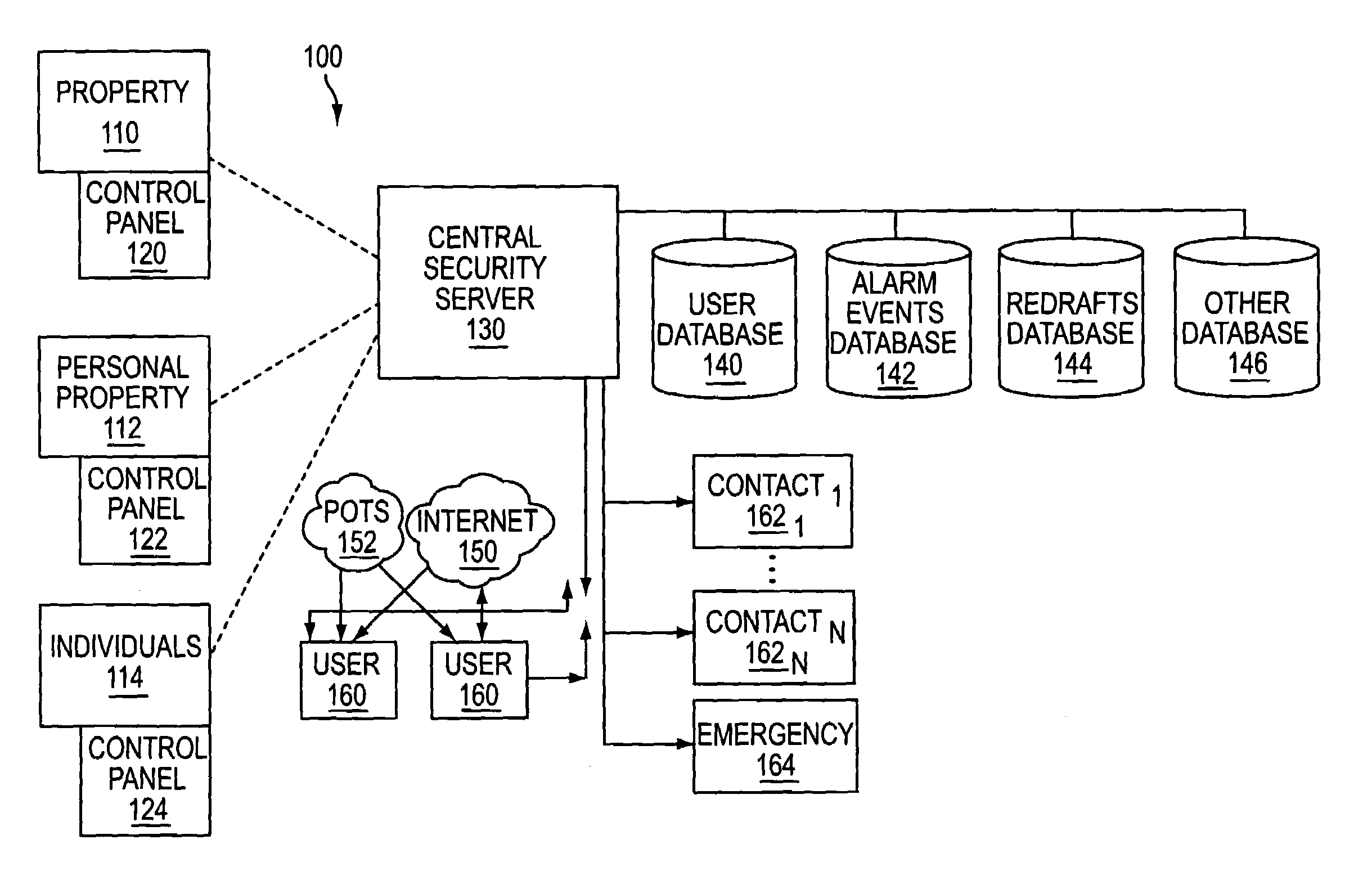
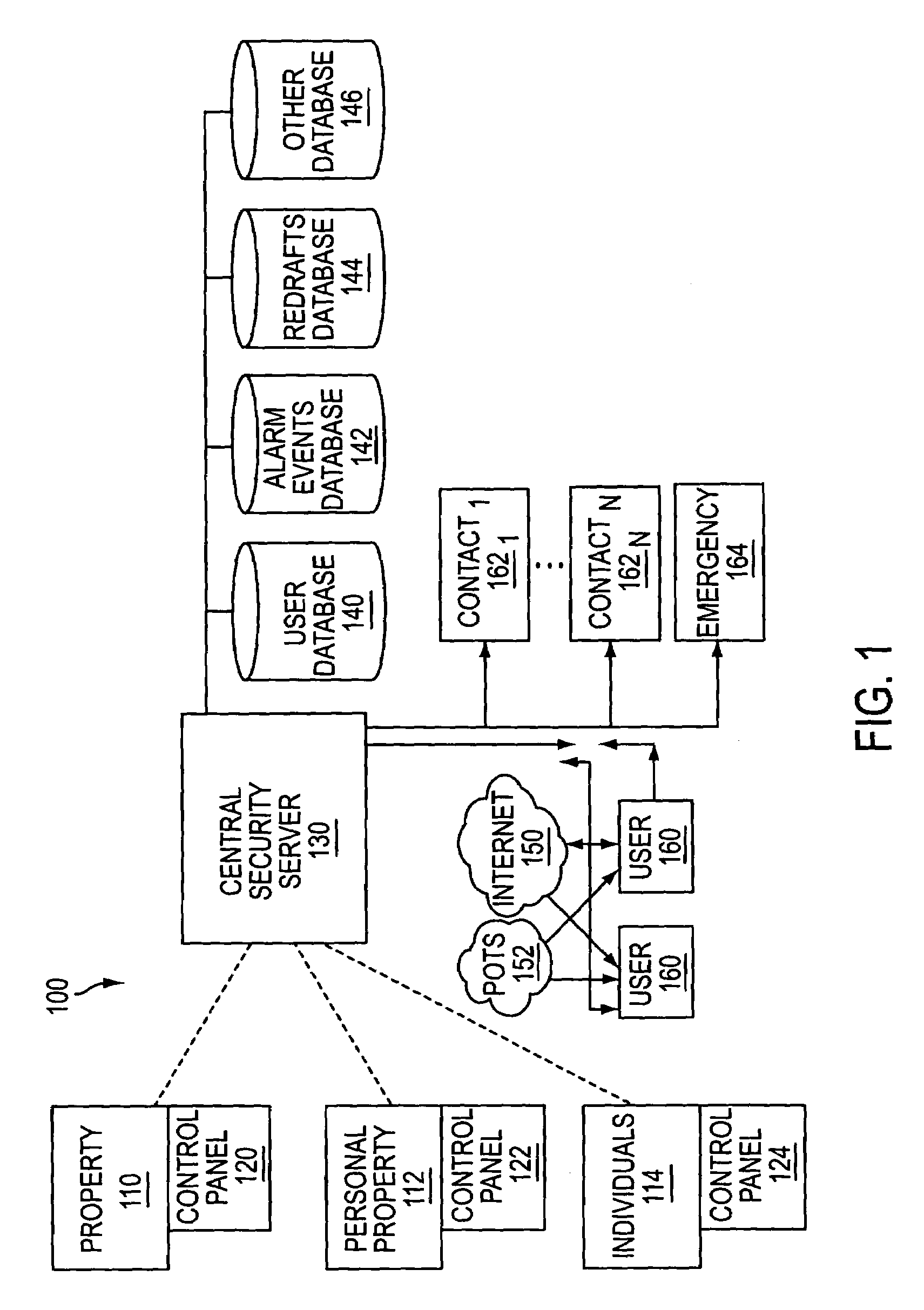
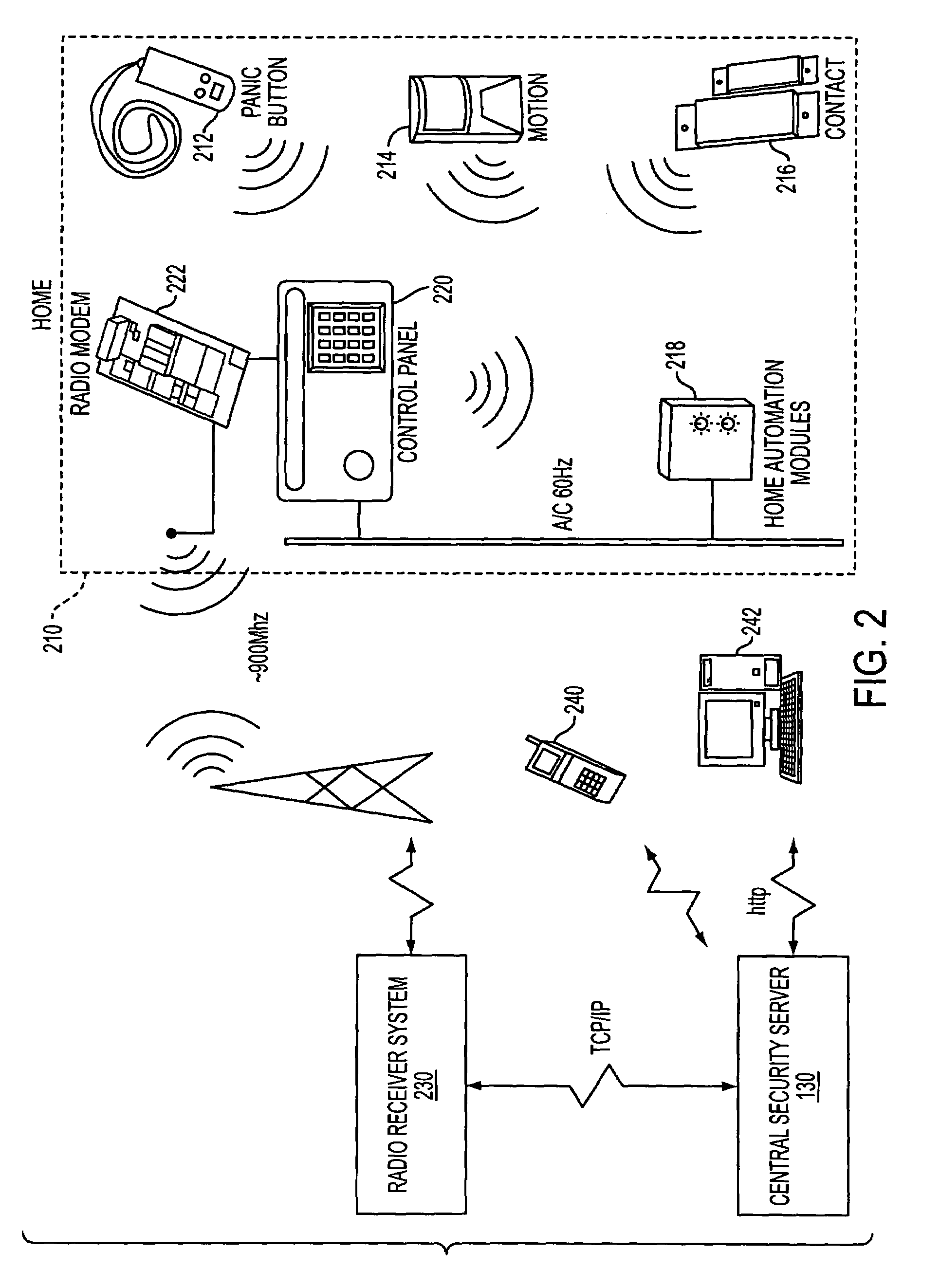
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
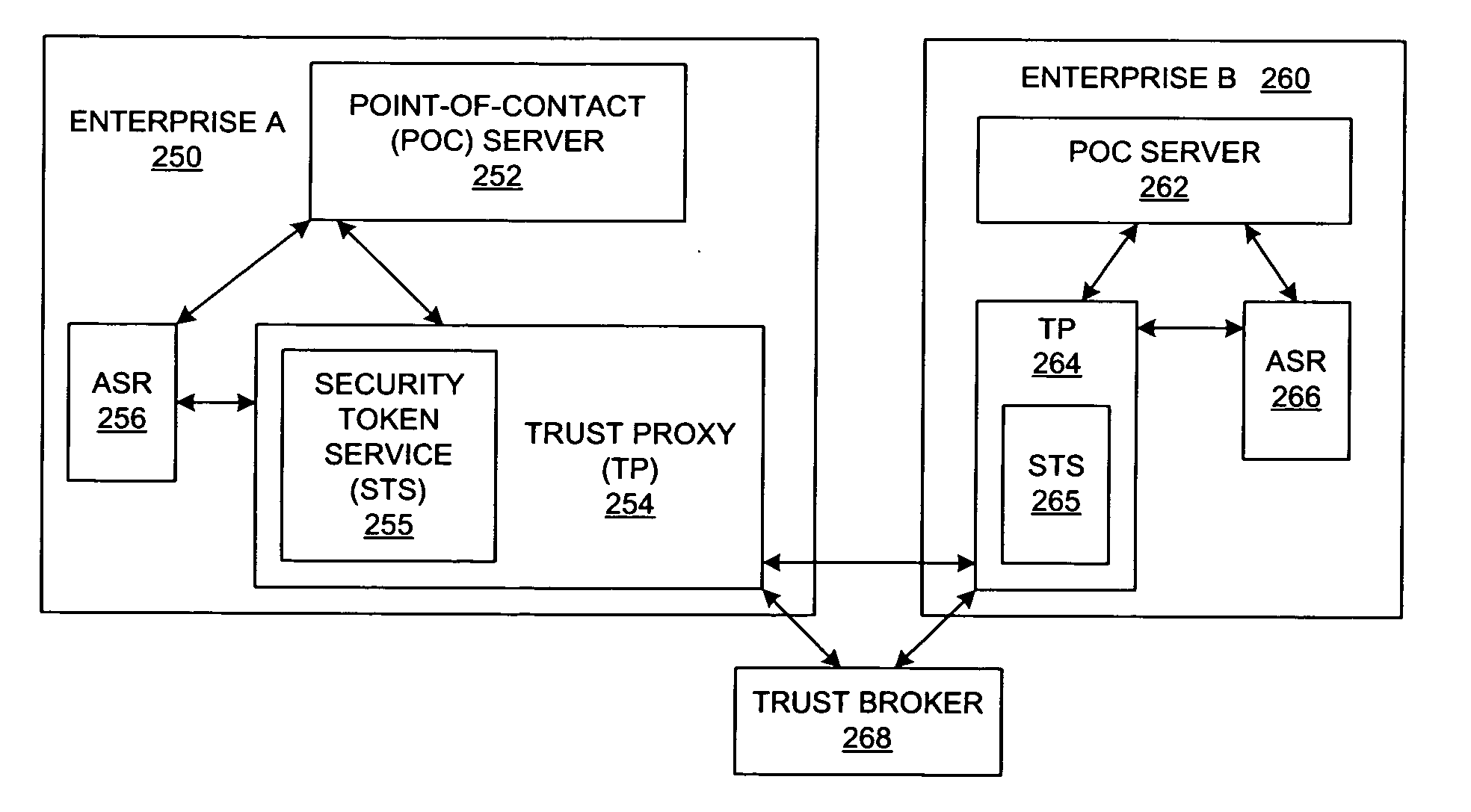
Method and system for federated provisioning
ActiveUS20060021019A1Digital data processing detailsUser identity/authority verificationInternet privacyTrust relationship
A method and a system are presented in which federated domains interact within a federated environment. Domains within a federation can initiate federated single-sign-on operations for a user at other federated domains. A point-of-contact server within a domain relies upon a trust proxy within the domain to manage trust relationships between the domain and the federation. Trust proxies interpret assertions from other federated domains as necessary. Trust proxies may have a trust relationship with one or more trust brokers, and a trust proxy may rely upon a trust broker for assistance in interpreting assertions. When a user is provisioned at a particular federated domain, the federated domain can provision the user to other federated domains within the federated environment. A provision operation may include creating or deleting an account for a user, pushing updated user account information including attributes, and requesting updates on account information including attributes.
Owner:SERVICENOW INC
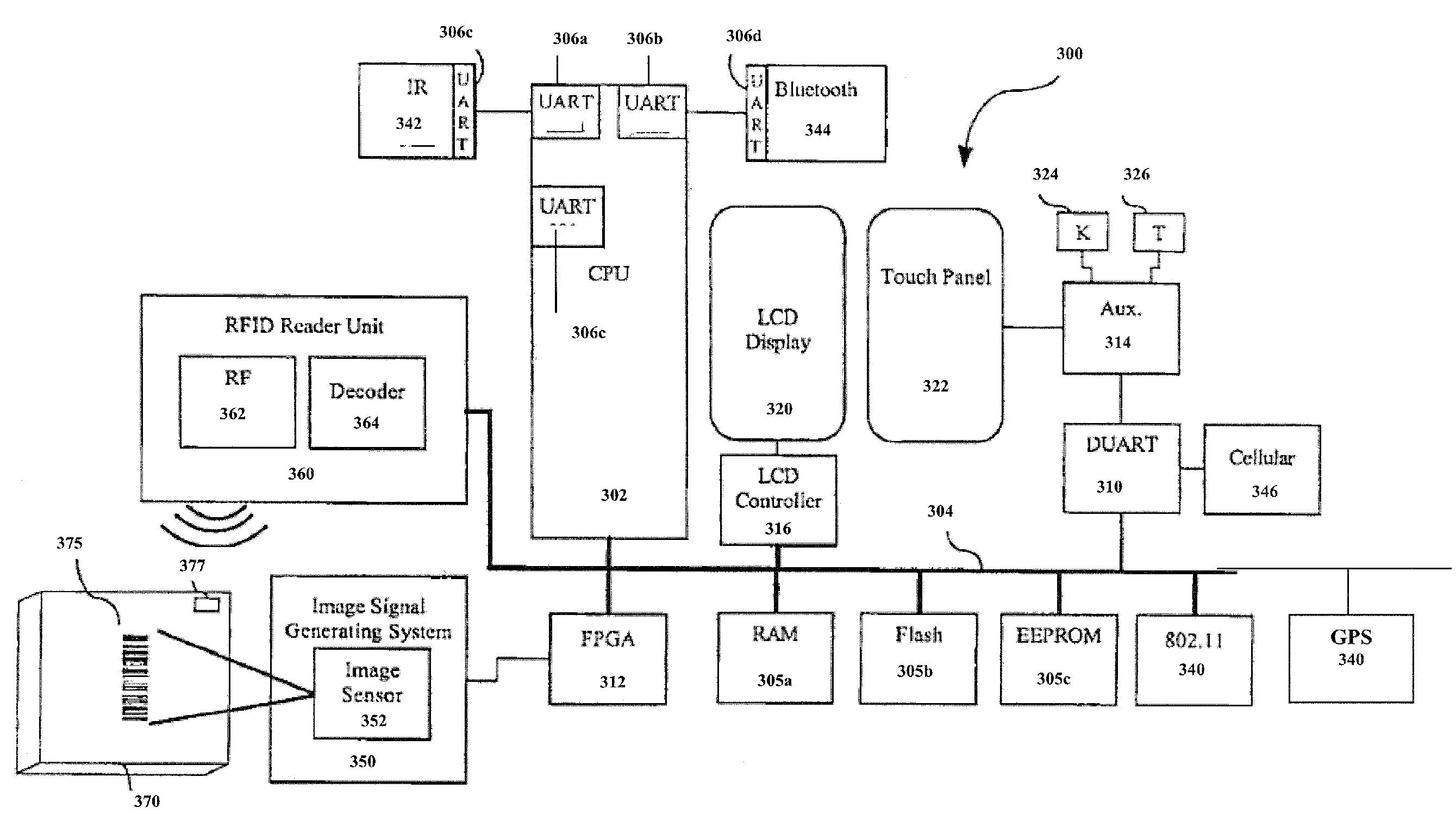
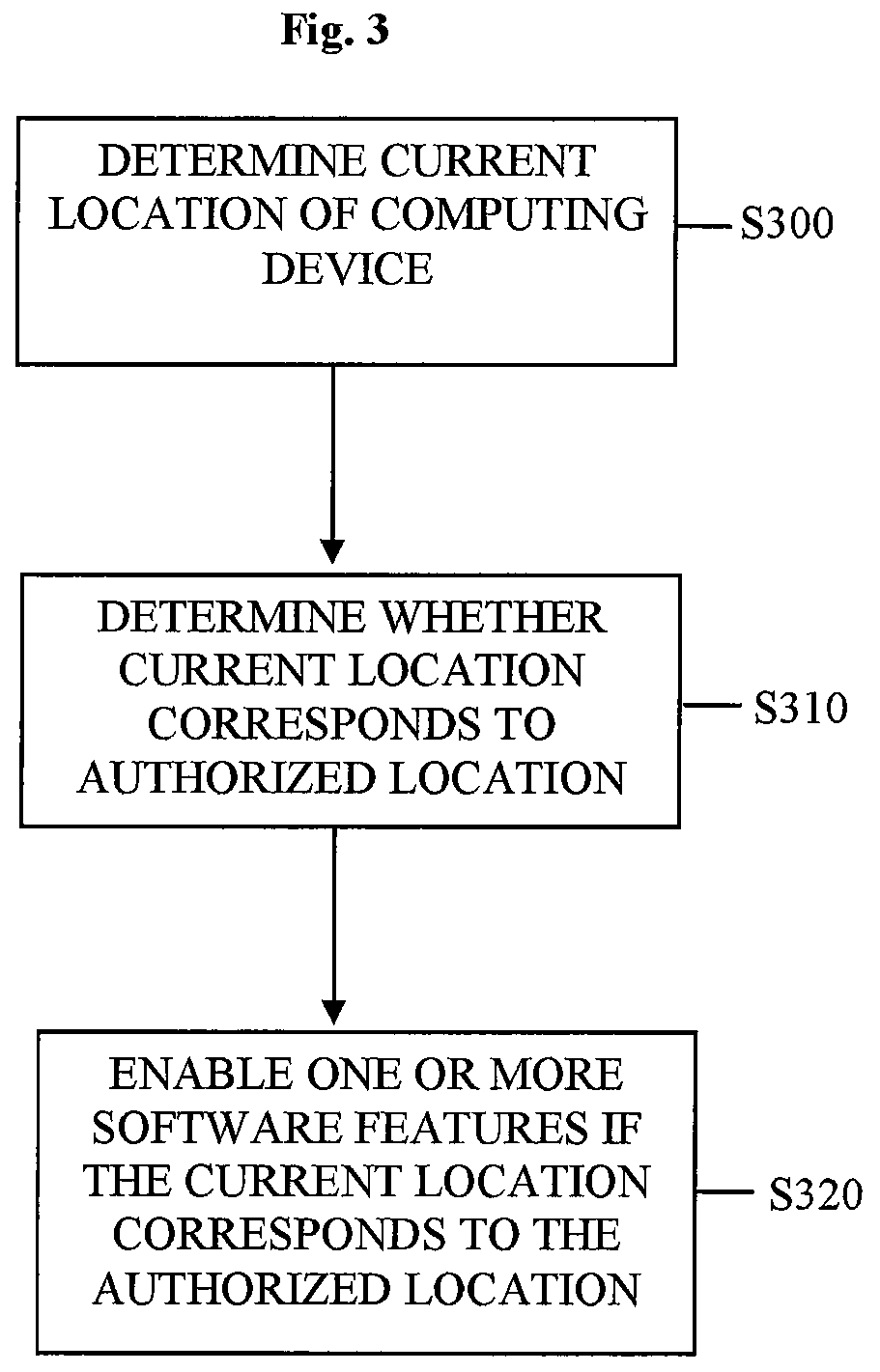
Location-based feature enablement for mobile terminals
ActiveUS8583924B2Digital data processing detailsUser identity/authority verificationComputer terminalComputer science
Owner:HAND HELD PRODS
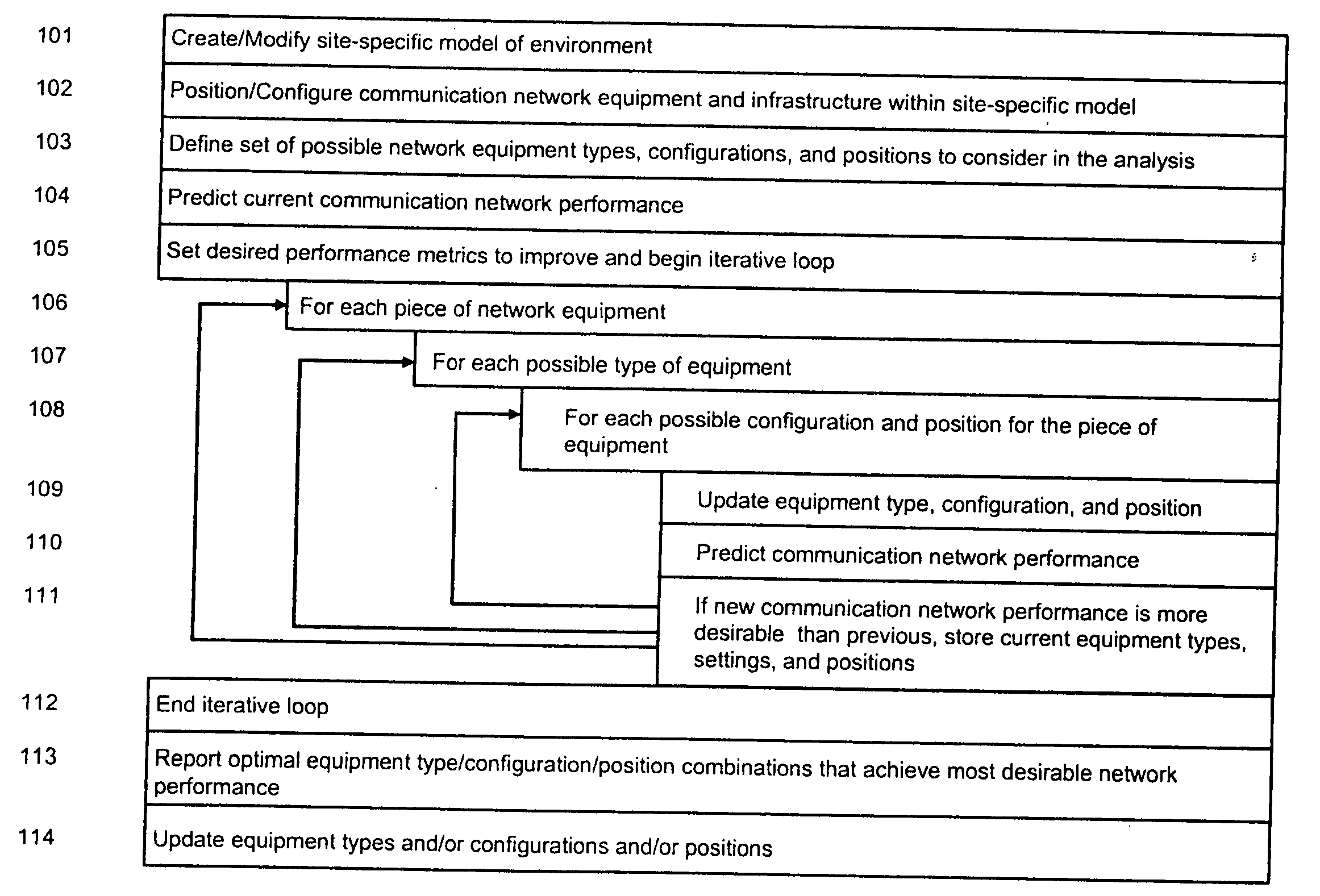
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
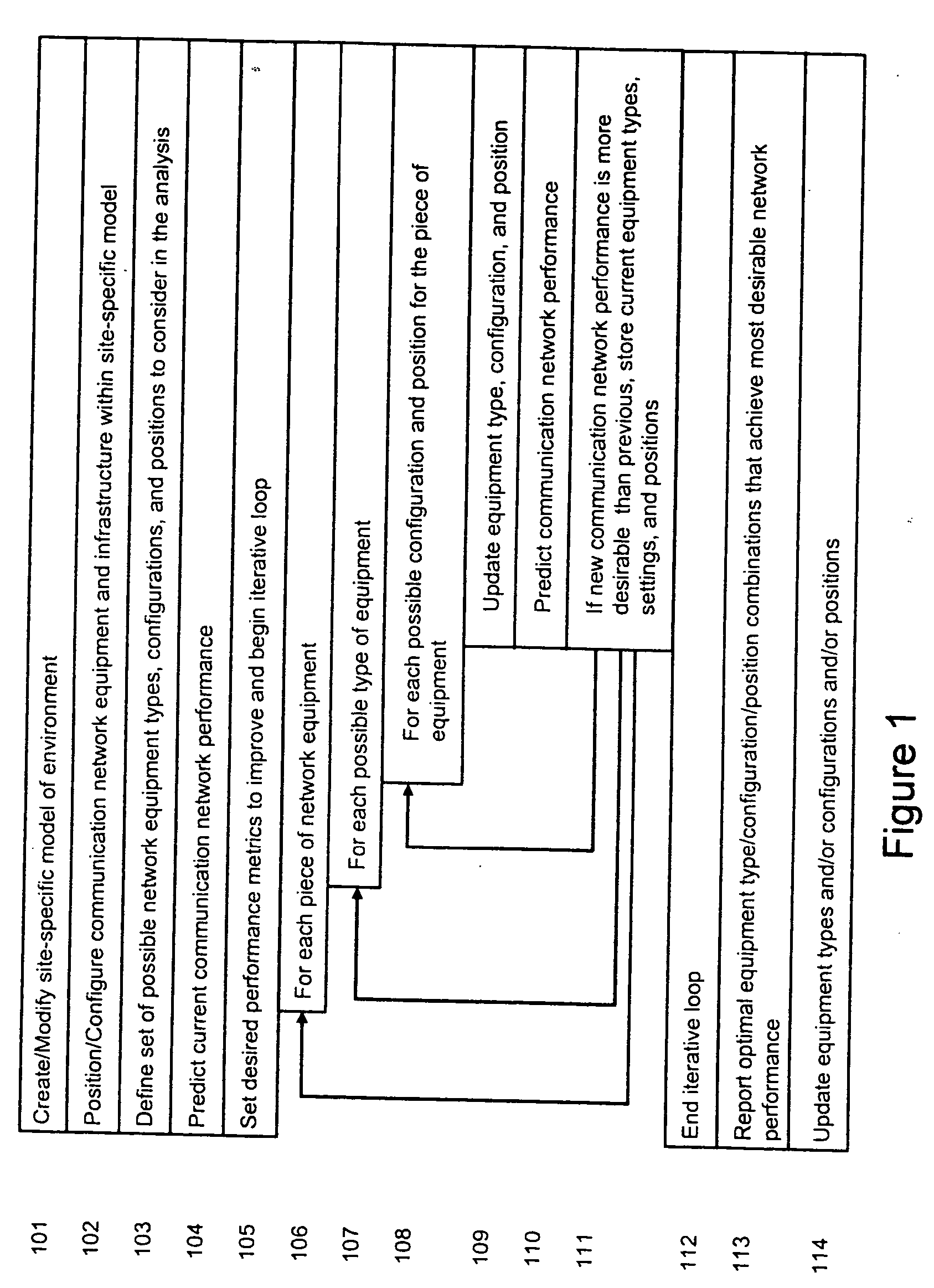
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
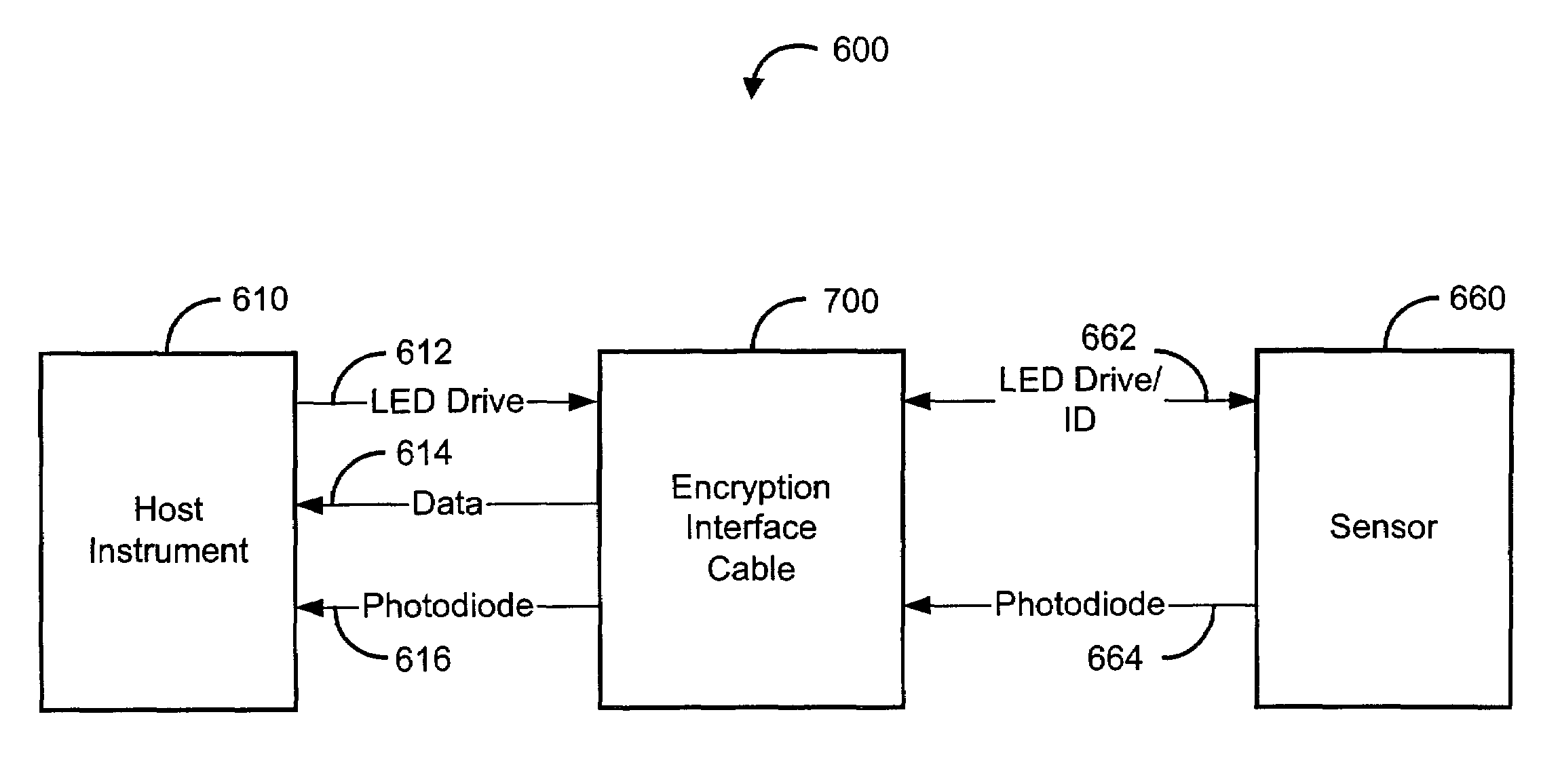
Interface cable
ActiveUS7509494B2Digital data processing detailsUser identity/authority verificationData signalEngineering
An interface cable is configured to connect a host instrument to a physiological sensor. The interface cable has an ID signal input from the sensor and a LED drive signal input from the host instrument sensor port. The interface cable also has a data signal output to the host instrument sensor port. The LED drive signal and the data signal provide an encrypted handshake to and from the host instrument. The handshake is responsive to the ID signal so as to enable normal operation of the host instrument and the sensor.
Owner:JPMORGAN CHASE BANK NA
Electronic menu document creator in a virtual financial environment
The disclosure provides for creating a finalized document relating to a transaction. A buyer selects documents associated with a proposed transaction and indicates trade terms of an agreement relating to the documents selected. The trade terms are presented to a seller on an electronic form via an electronic document platform. The electronic form includes a combined purchase order proforma invoice, a transportation document, and a shipping document. The seller can amend the trade terms on the form, and each amendment creates a new version of the form. Negotiations of the trade terms between the buyer and the seller are conducted electronically and the negotiated fonn detailing the negotiation of the trade terms is generated and displayed electronically, also. A compliance check is performed and is triggered in response to a digital signature of the form. Payment is initiated to the seller after a verification of credit of the buyer.
Owner:ACCENTURE GLOBAL SERVICES LTD
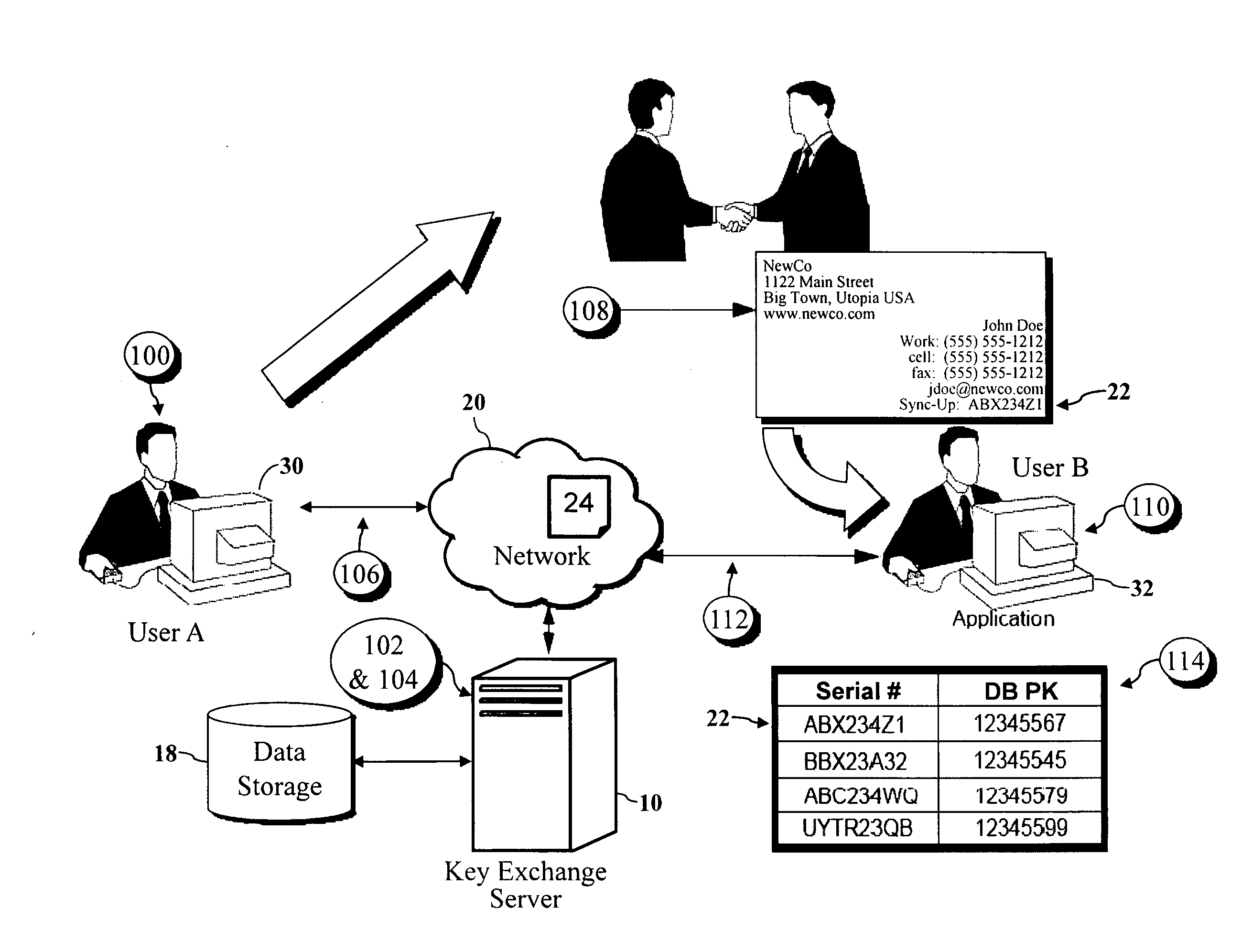
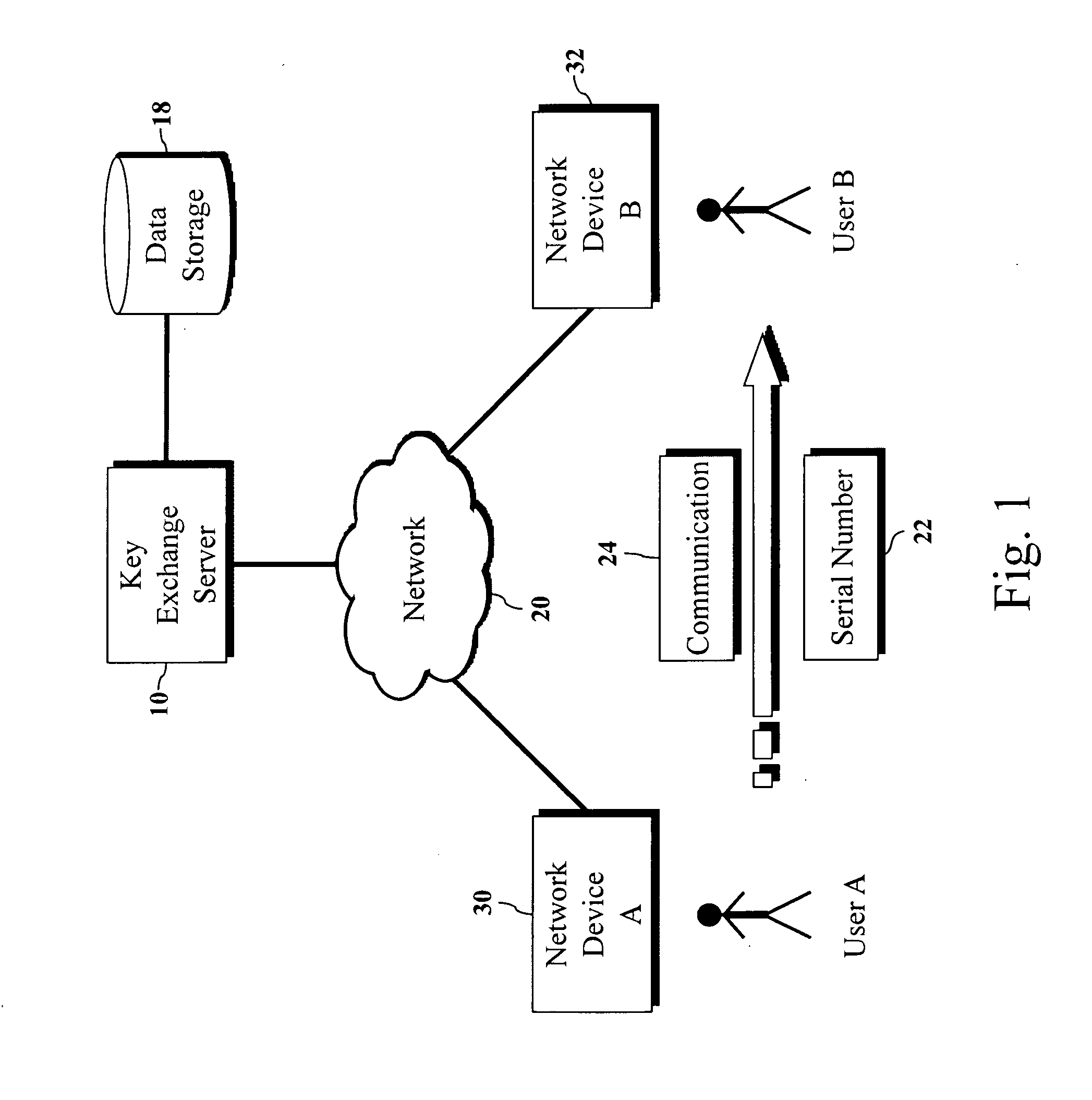
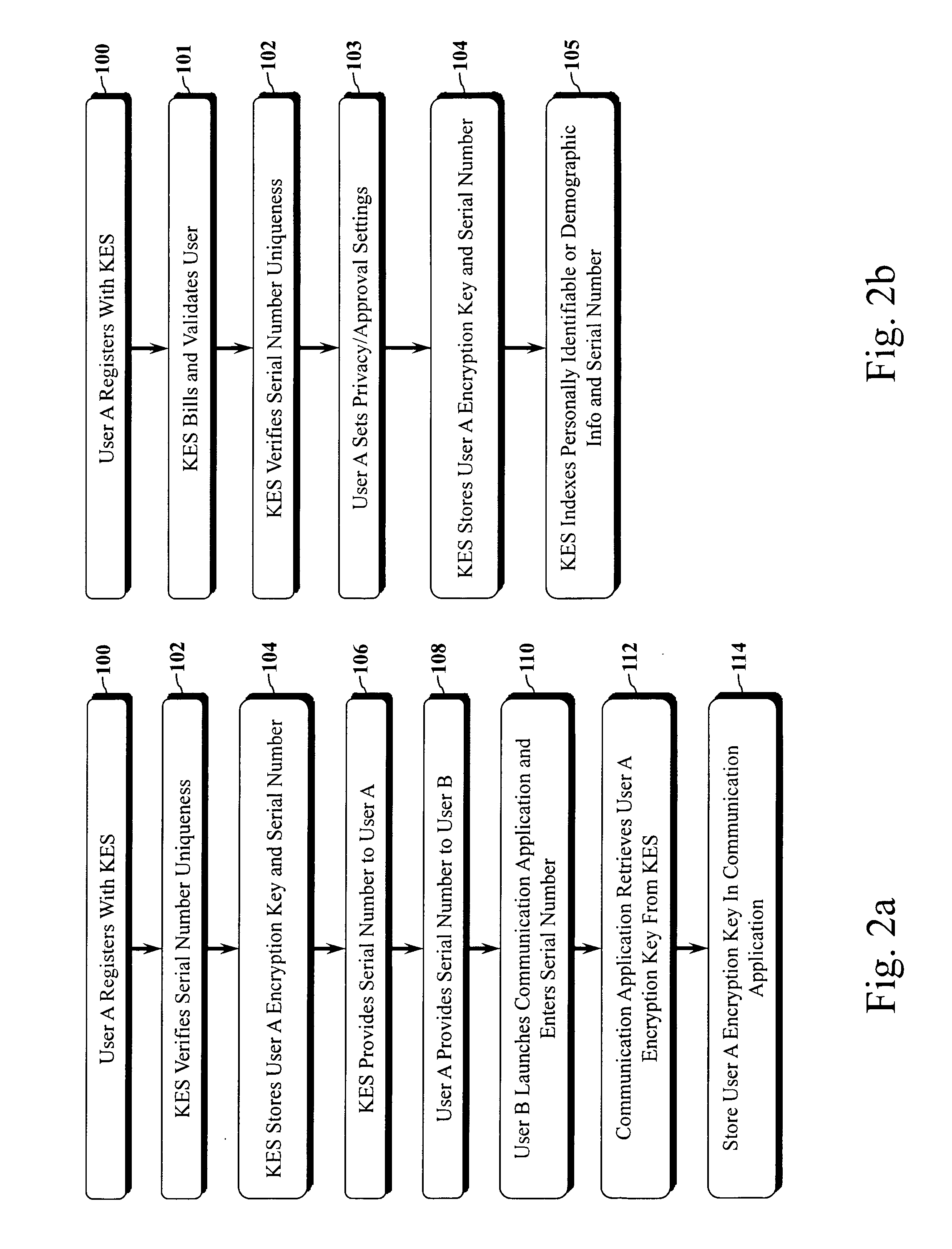
Encryption key exchange system and method
InactiveUS20120204032A1Improve usabilityUser identity/authority verificationPublic key infrastructure trust modelsUsabilityEncryption
The present invention is a computer-implemented key exchange system and methods for improving the usability of encryption technologies such as Public Key Infrastructure (PKI). One aspect of the present invention includes registering users, verifying user identity, and classifying users such that the users may send a communications such that communication recipients can verify the user identity and classification of the communication sender. Another aspect of the present invention includes users initiating relationships with other users, approving the establishment of relationships, and exchanging encryption keys between users after the establishment of a relationship.
Owner:SYNC UP TECH
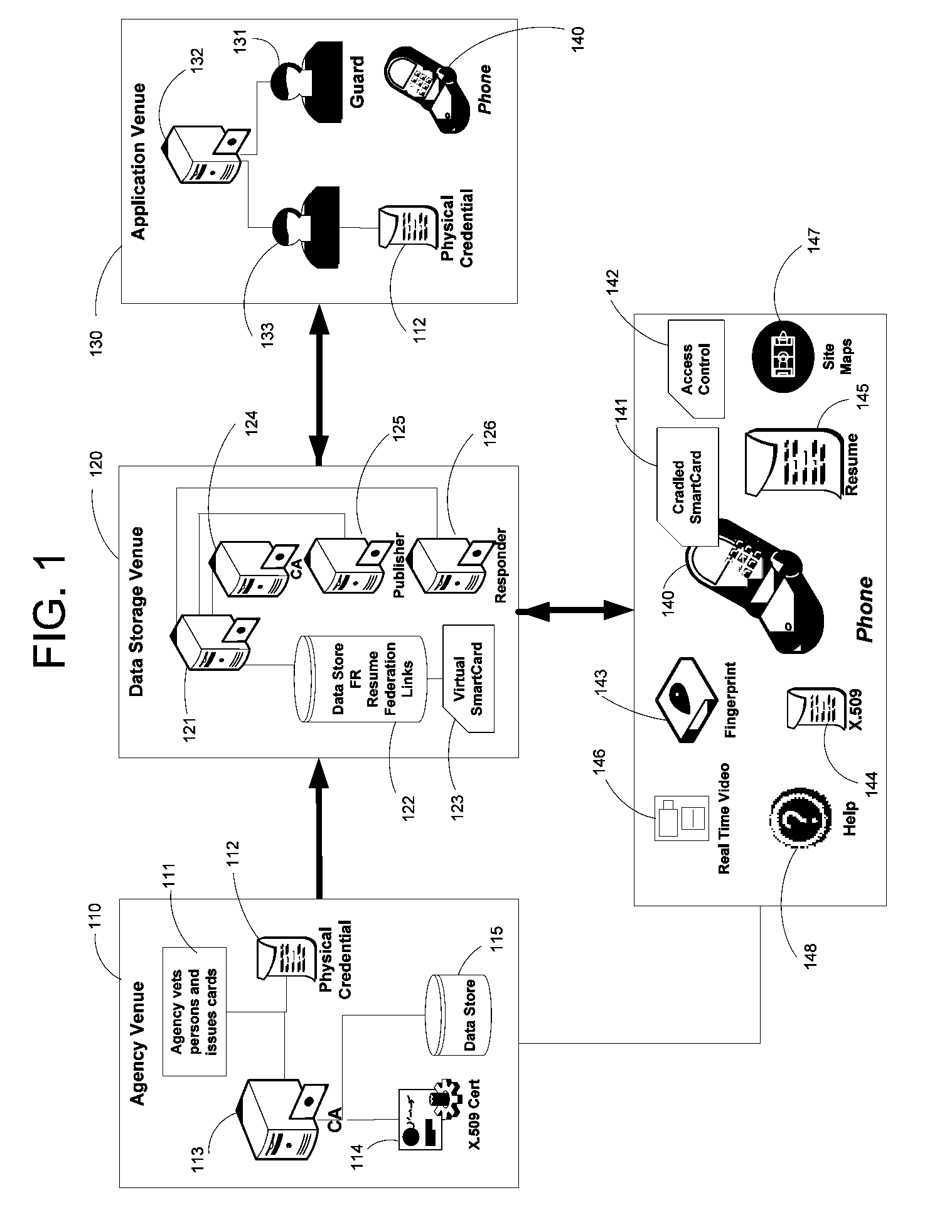
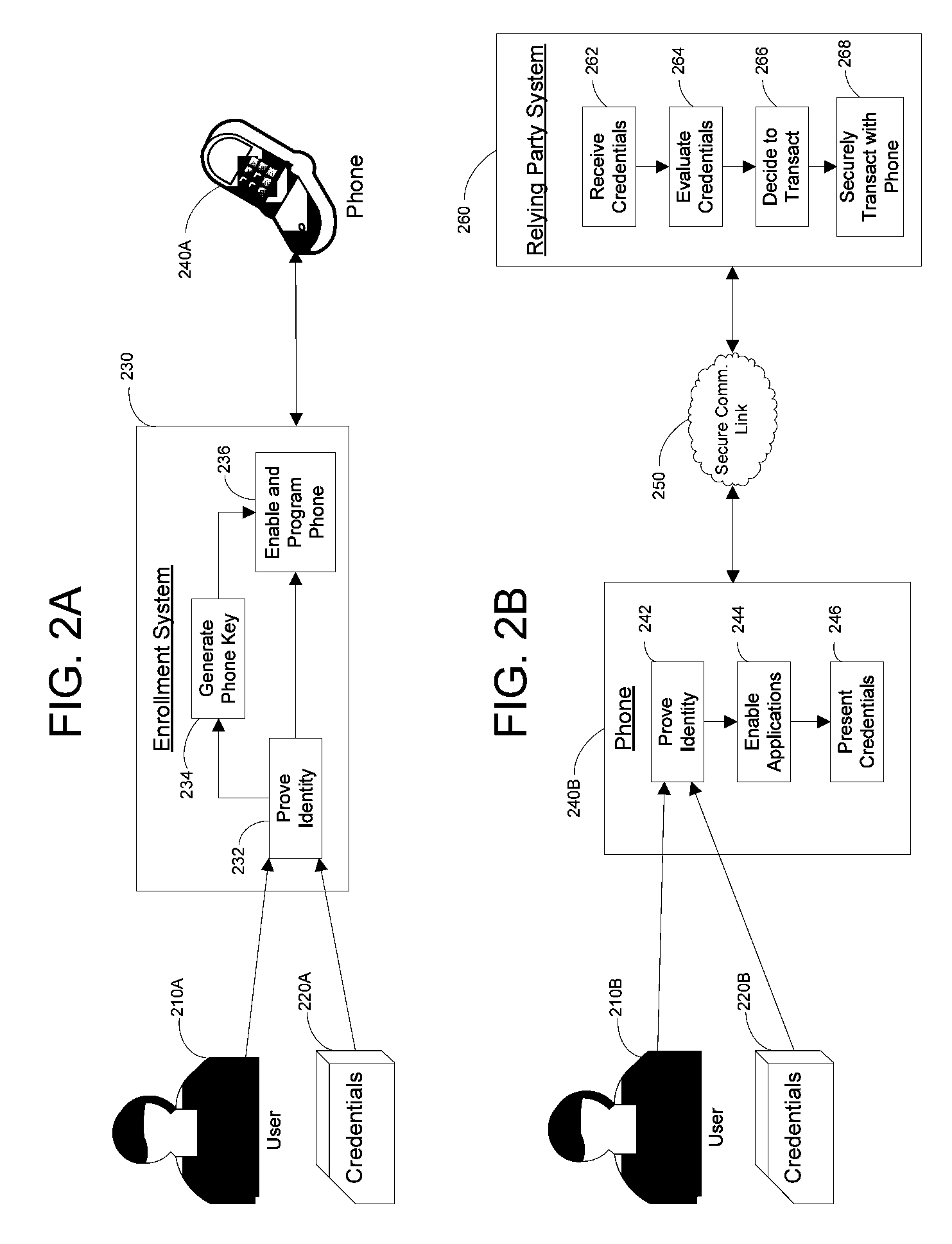
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
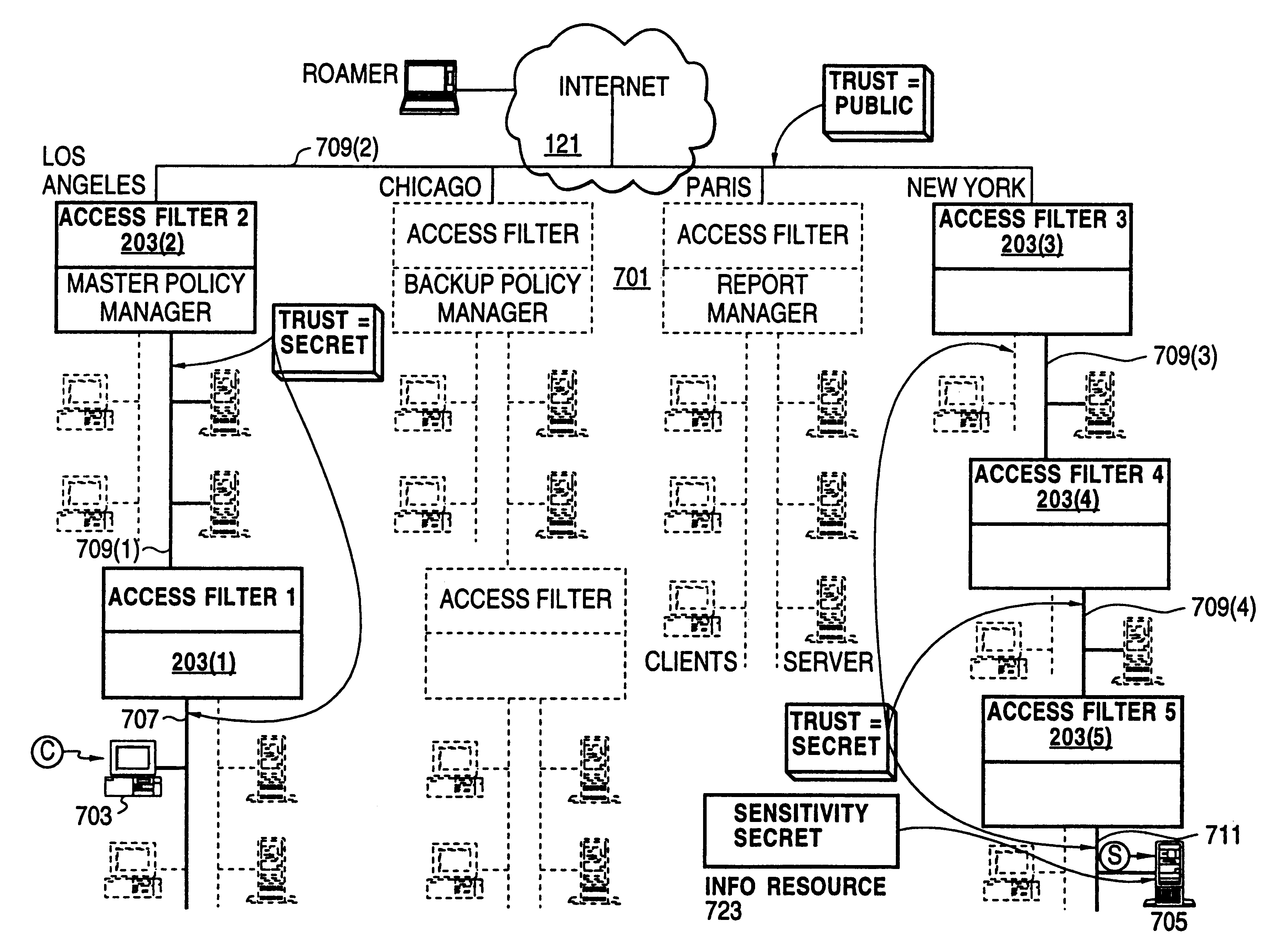
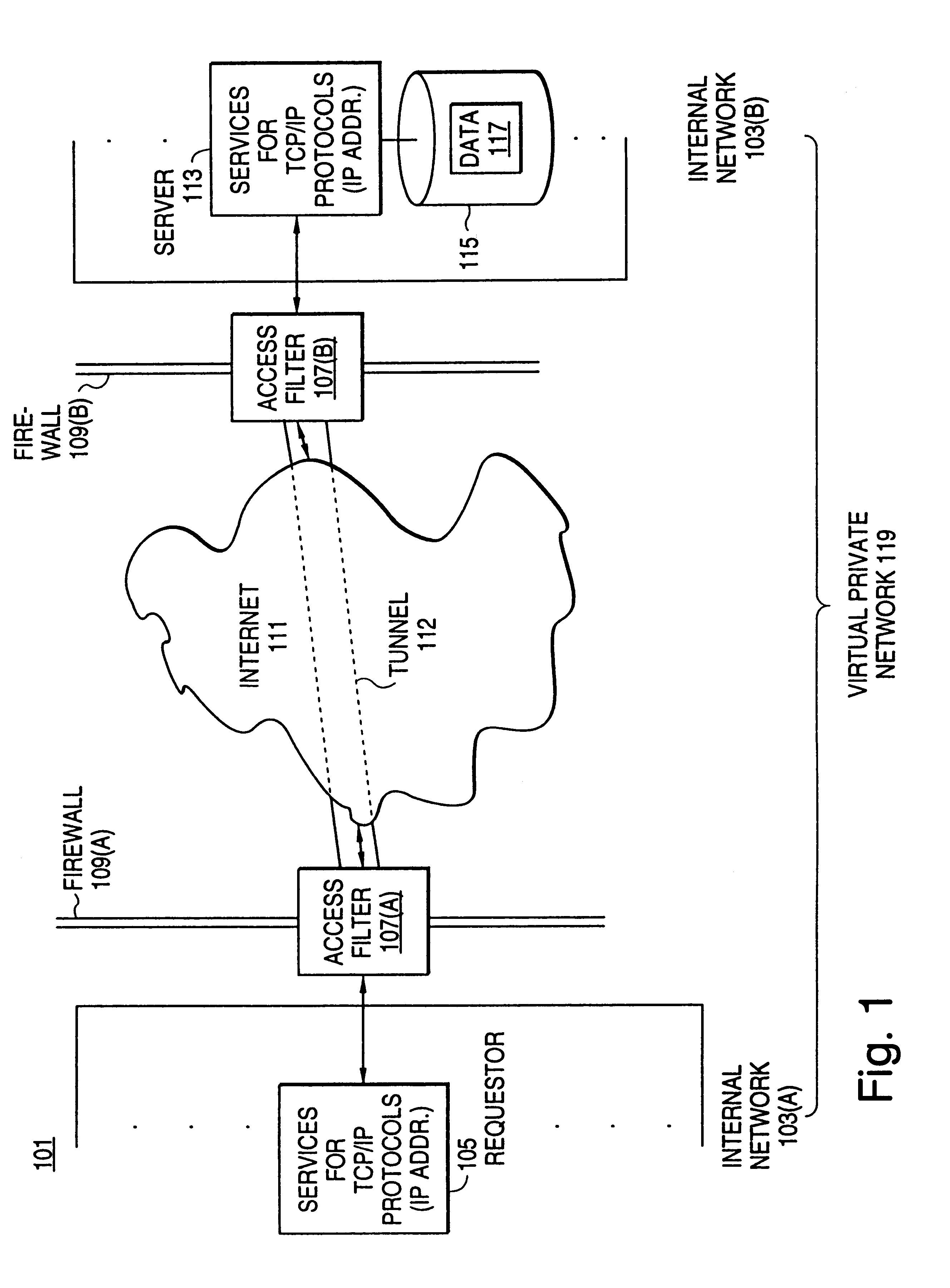
Secure delivery of information in a network
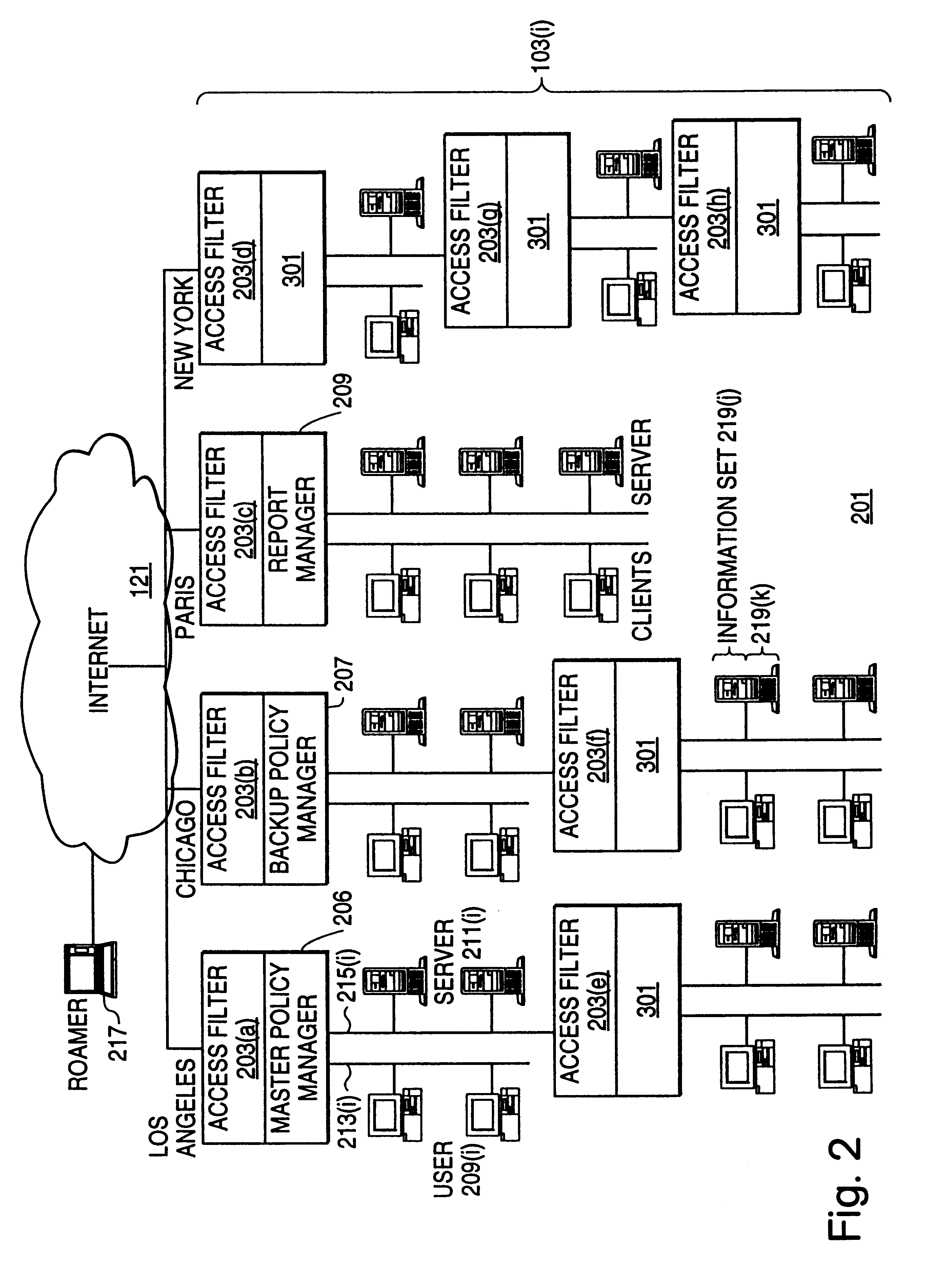
InactiveUS6178505B1User identity/authority verificationData switching networksPrivate networkInformation resource
A scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network. Each access filter use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to of access policies which define access in terms of the user groups and information sets. The rights of administrators are similarly determined by administrative policies. Access is further permitted only if the trust levels of a mode of identification of the user and of the path in the network by which the access is made are sufficient for the sensitivity level of the information resource. If necessary, the access filter automatically encrypts the request with an encryption method whose trust level is sufficient. The first access filter in the path performs the access check and encrypts and authenticates the request; the other access filters in the path do not repeat the access check.
Owner:DROPBOX
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
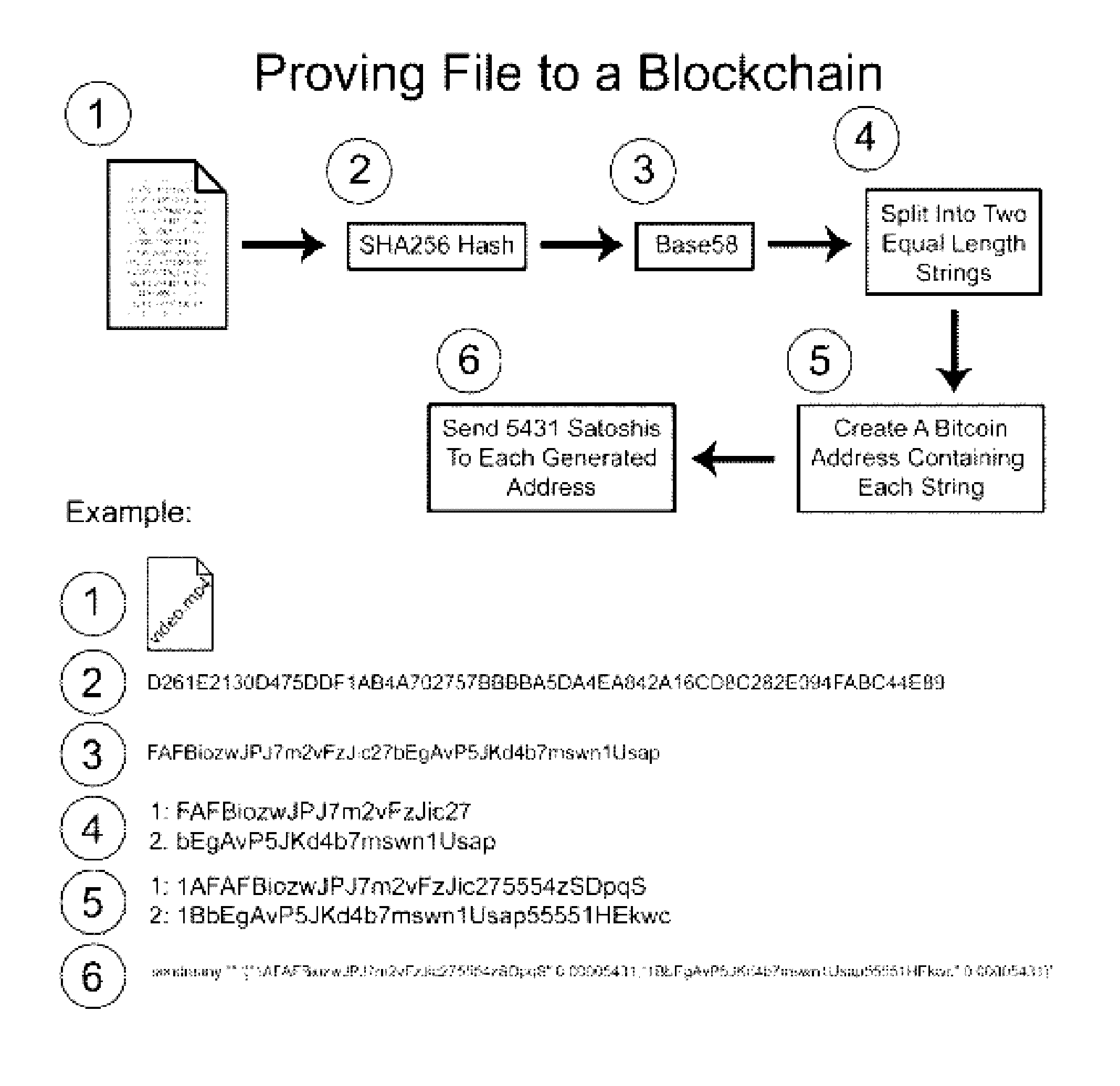
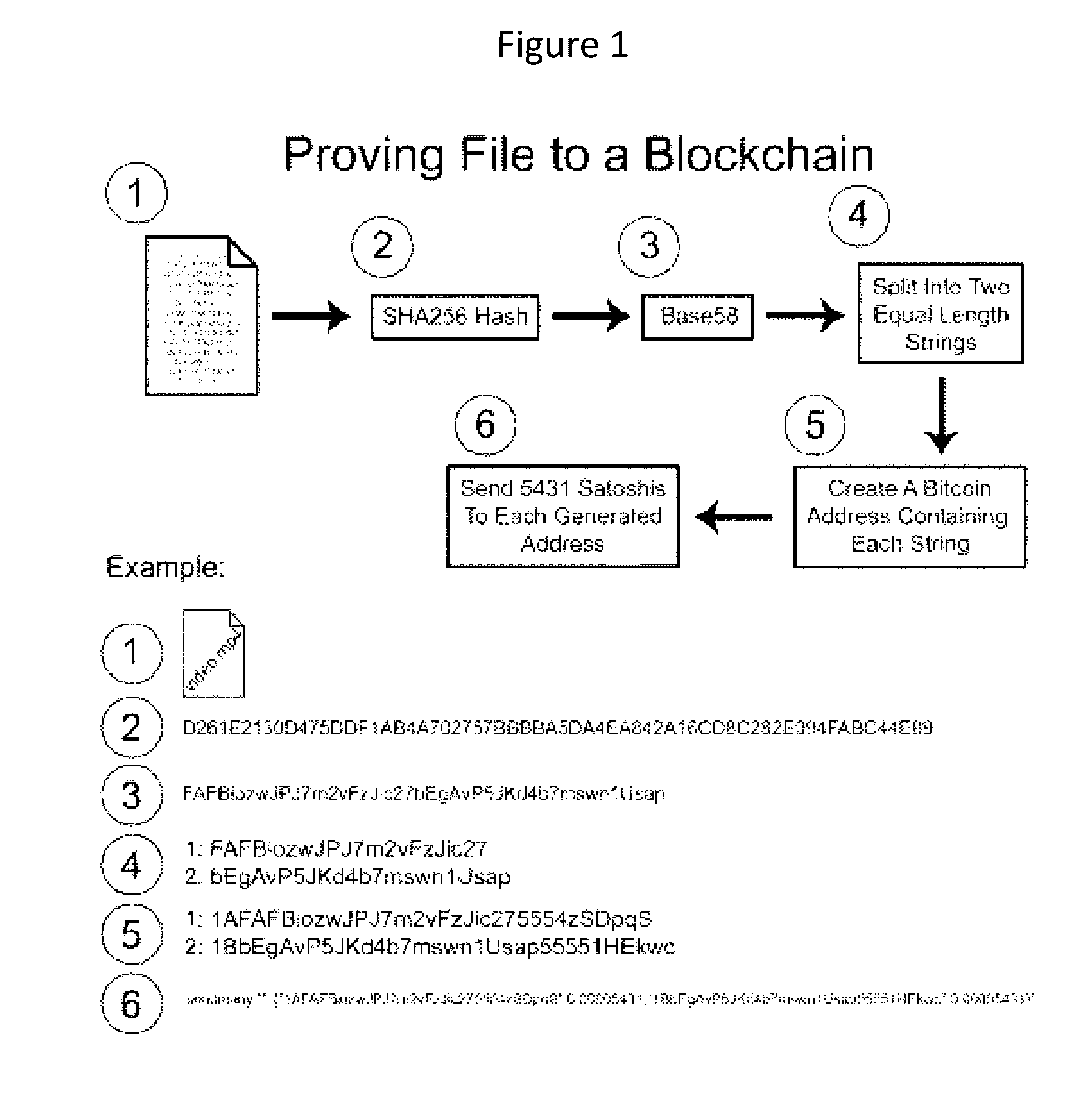
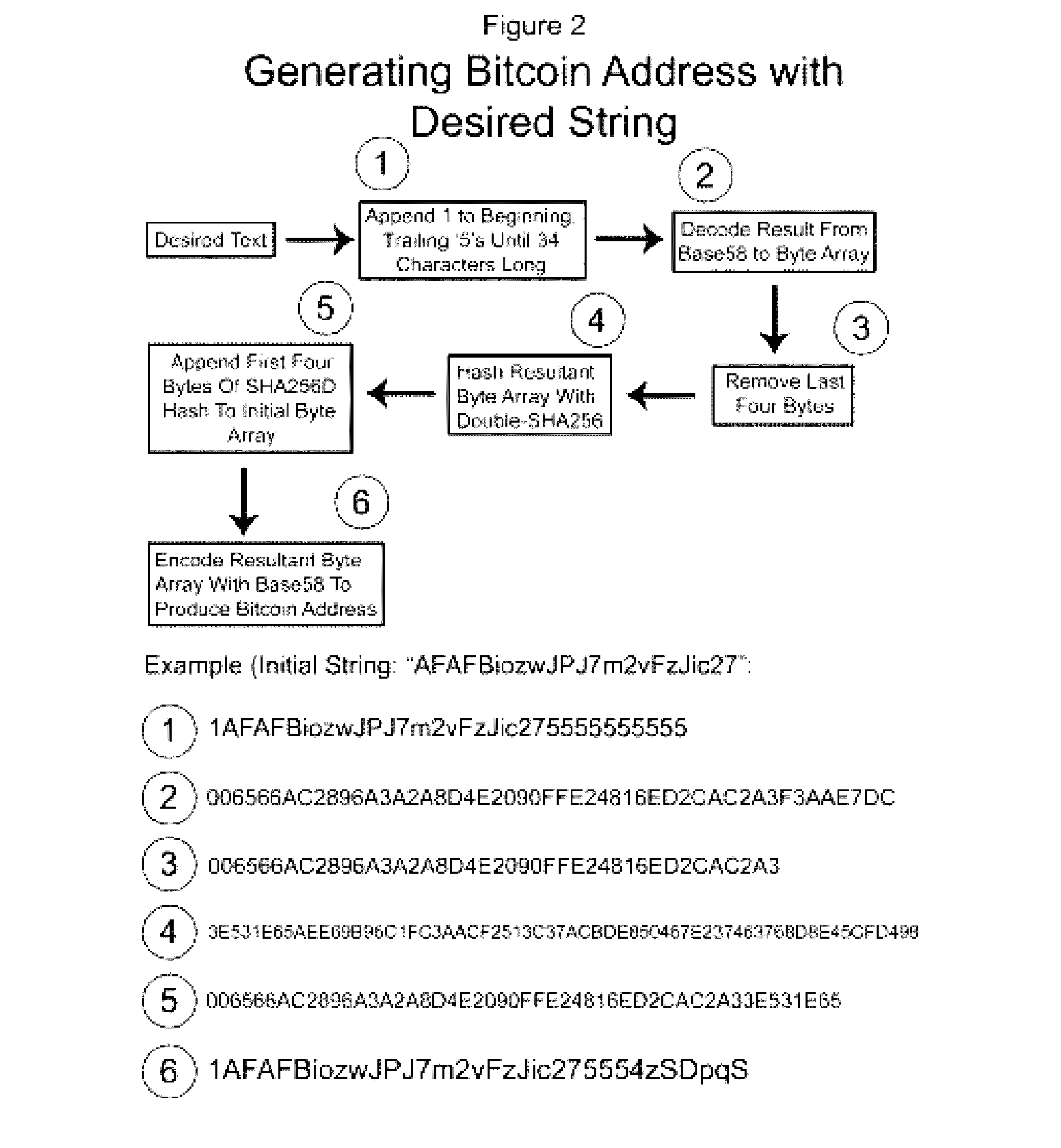
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Techniques for fraud monitoring and detection using application fingerprinting
ActiveUS20090089869A1Acutation objectsDigital data processing detailsMultiple contextApplication software
Techniques for fraud monitoring and detection using application fingerprinting. As used herein, an “application fingerprint” is a signature that uniquely identifies data submitted to a software application. In an embodiment, a plurality of historical application fingerprints are stored for data previously submitted to a software application. Each historical application fingerprint is associated with one or more contexts in which its corresponding data was submitted. When new (i.e., additional) data is subsequently submitted to the application, a new application fingerprint is generated based on the new data, and the new application fingerprint is associated with one or more contexts in which the new data was submitted. The new application fingerprint is then compared with one or more historical application fingerprints that share the same, or substantially similar, context(s). Based on this comparison, a risk score is generated indicating a likelihood that the new data was submitted for a fraudulent / malicious purpose.
Owner:ORACLE INT CORP
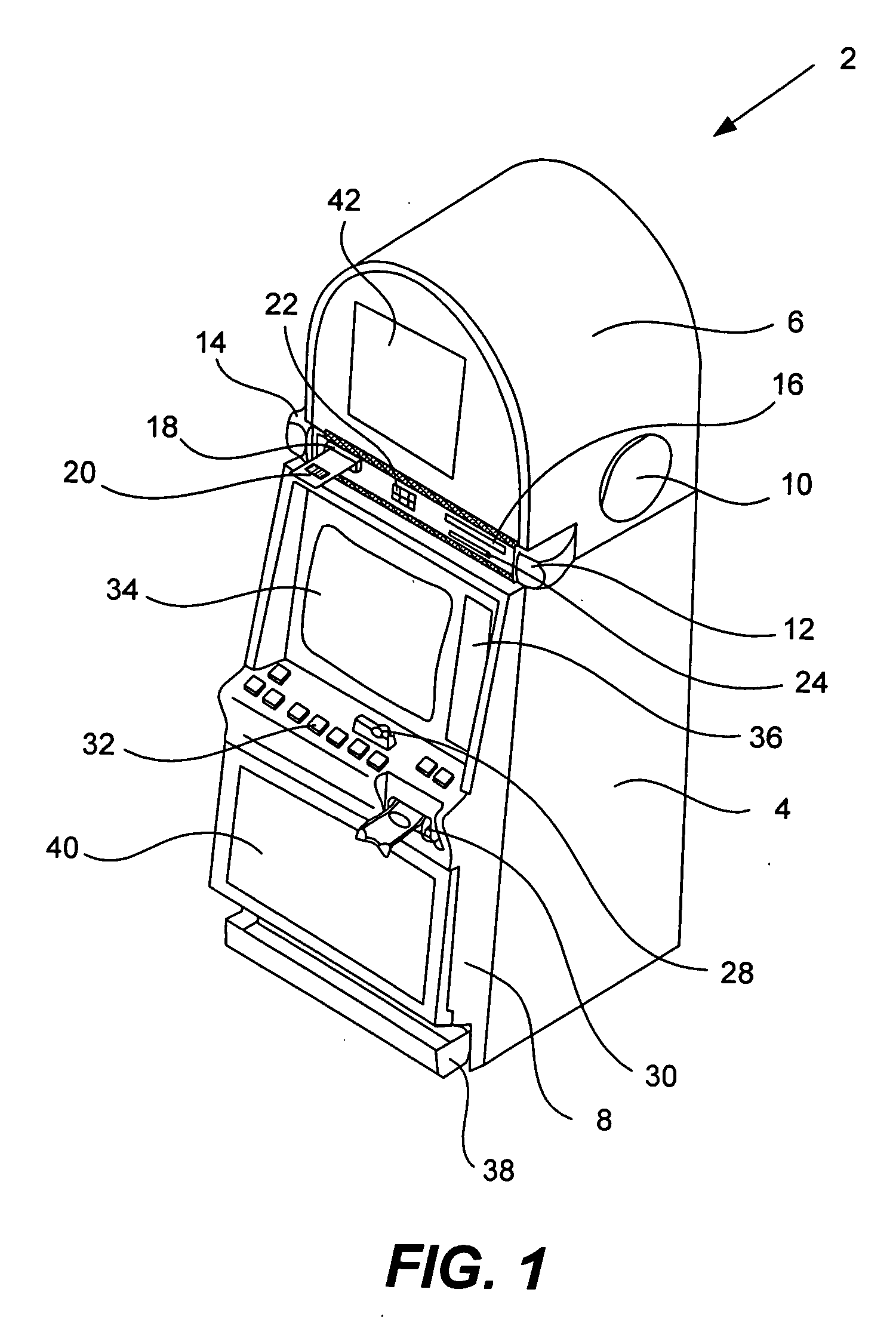
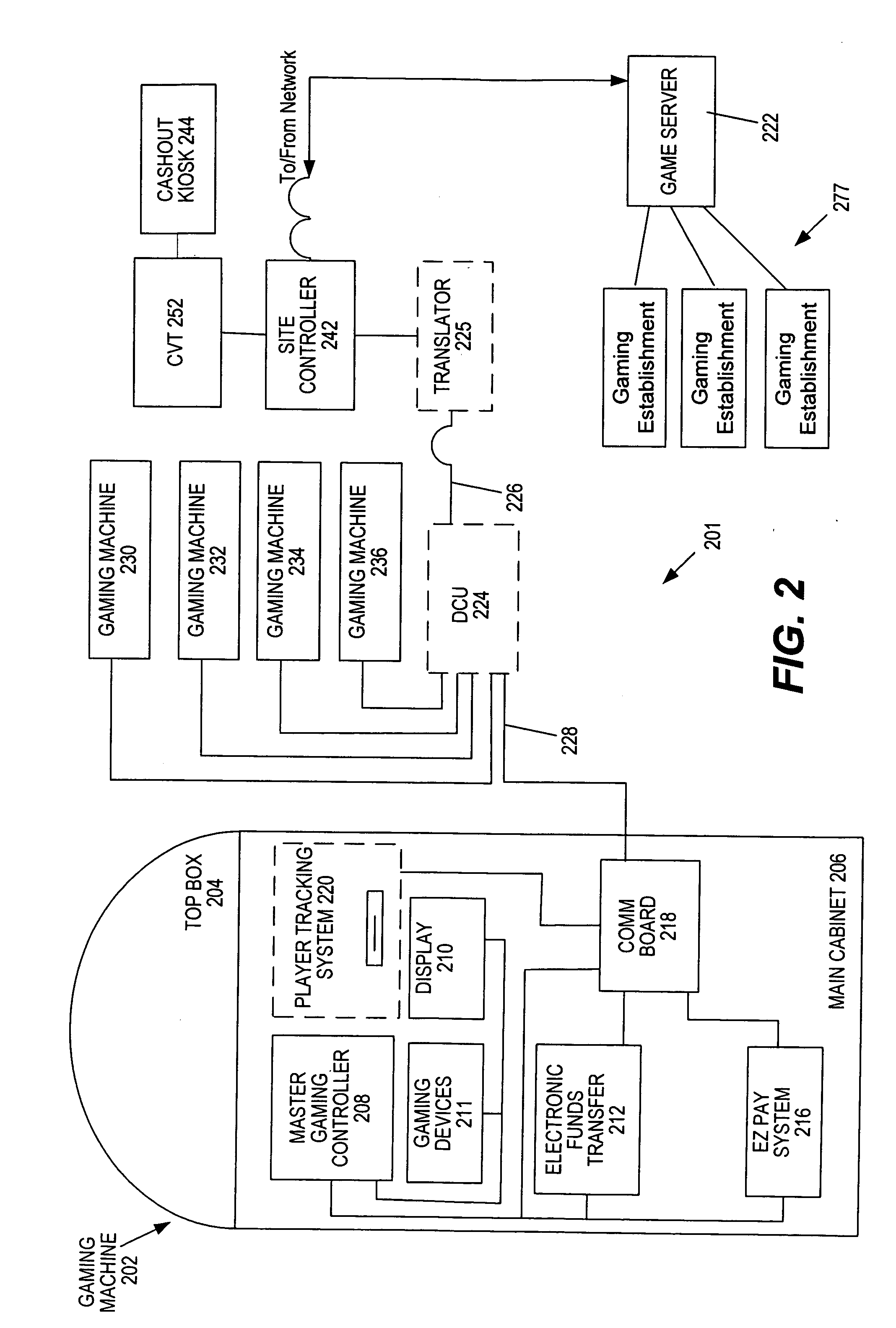
Method and apparatus for registering a mobile device with a gaming machine
InactiveUS20060189382A1User identity/authority verificationCard gamesComputer hardwareCommunications system
Disclosed are methods, apparatus, and systems, including computer program products, implementing techniques for securing a gaming machine for a player of the gaming machine using a mobile device such as a cell phone associated with the player. A player input requests securing of the gaming machine. Responsive to the player input, an access code and a security code are retrieved. The access code defines an access point of a communication system. The security code is specific to a game play session for the player at the gaming machine. The retrieved access code and security code are provided for the player. When the mobile device accesses the communications system and submits the security code, a secure signal is sent to the gaming machine, instructing the gaming machine to enter a remote game play state. The gaming machine can be released from the remote game play state responsive to a releasing event. In one implementation, a wireless interface enables communication between the mobile device and gaming machine according to a wireless protocol such as Bluetooth.
Owner:IGT
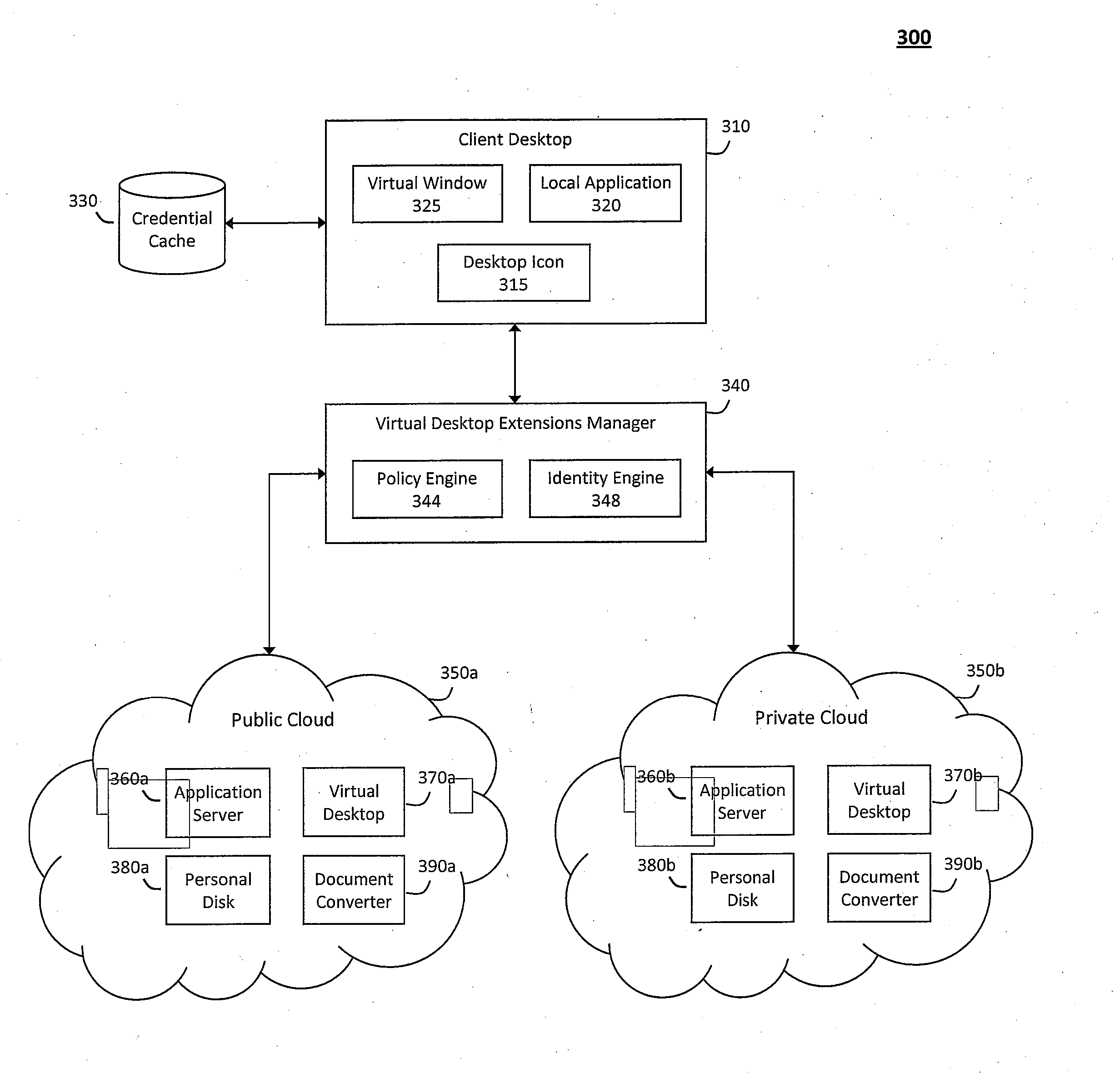
System and method for providing virtual desktop extensions on a client desktop
ActiveUS20110209064A1Simplify complexityProvide capabilityInput/output for user-computer interactionDigital data processing detailsClient-sideCloud computing
The system and method described herein may identify one or more virtual desktop extensions available in a cloud computing environment and launch virtual machine instances to host the available virtual desktop extensions in the cloud. For example, a virtual desktop extension manager may receive a virtual desktop extension request from a client desktop and determine whether authentication credentials for the client desktop indicate that the client desktop has access to the requested virtual desktop extension. In response to authenticating the client desktop, the virtual desktop extension manager may then launch a virtual machine instance to host the virtual desktop extension in the cloud and provide the client desktop with information for locally controlling the virtual desktop extension remotely hosted in the cloud.
Owner:MICRO FOCUS SOFTWARE INC
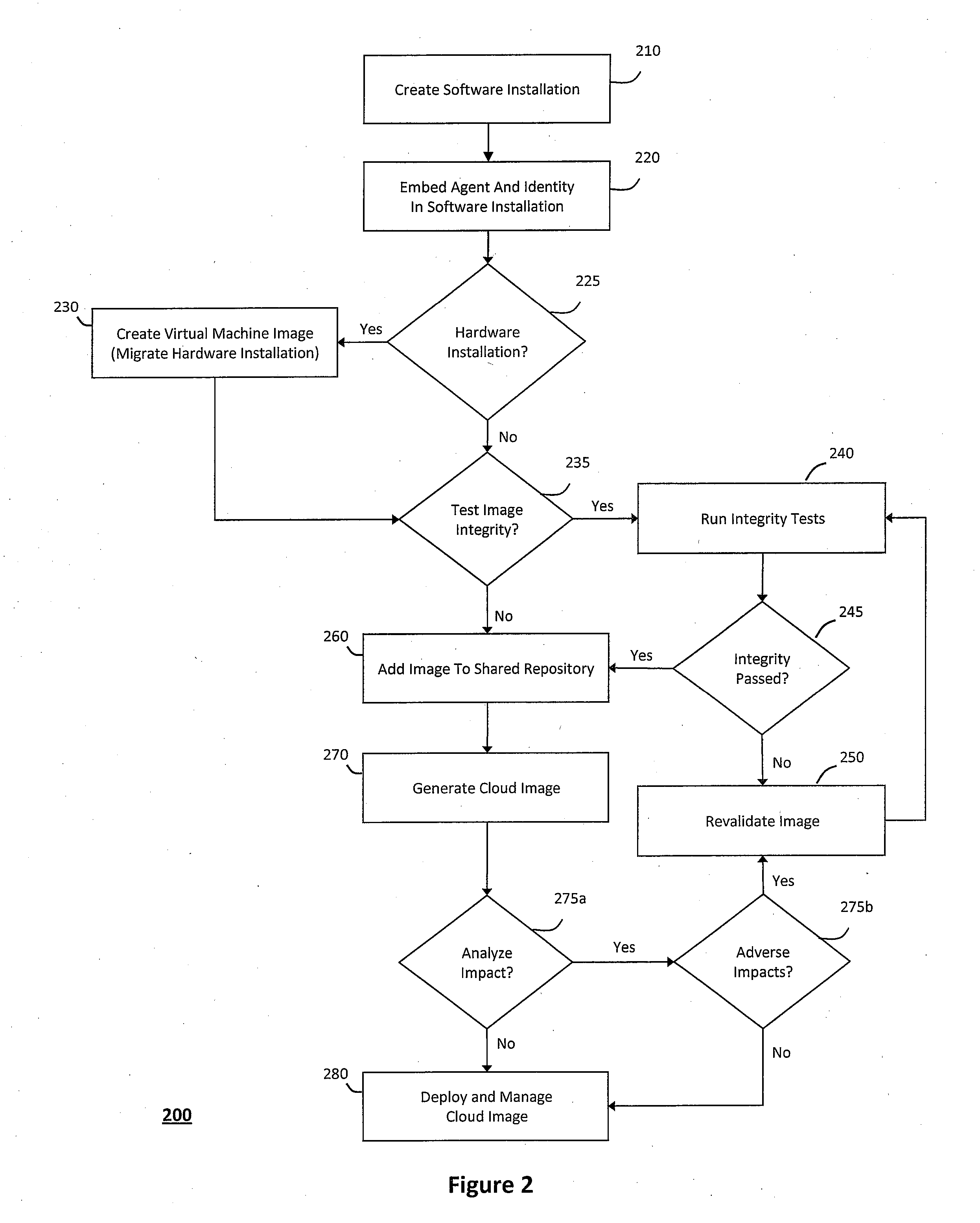
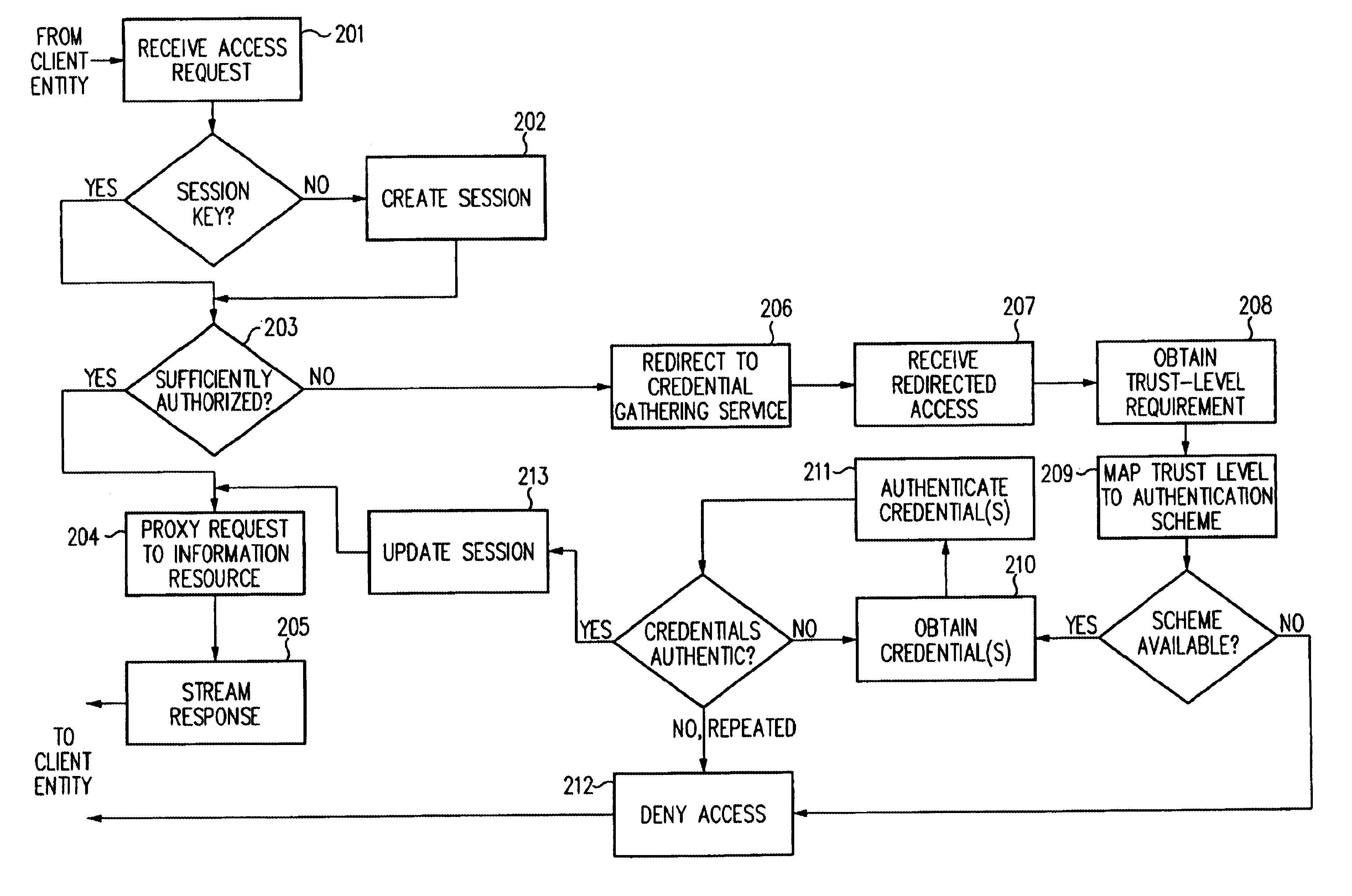
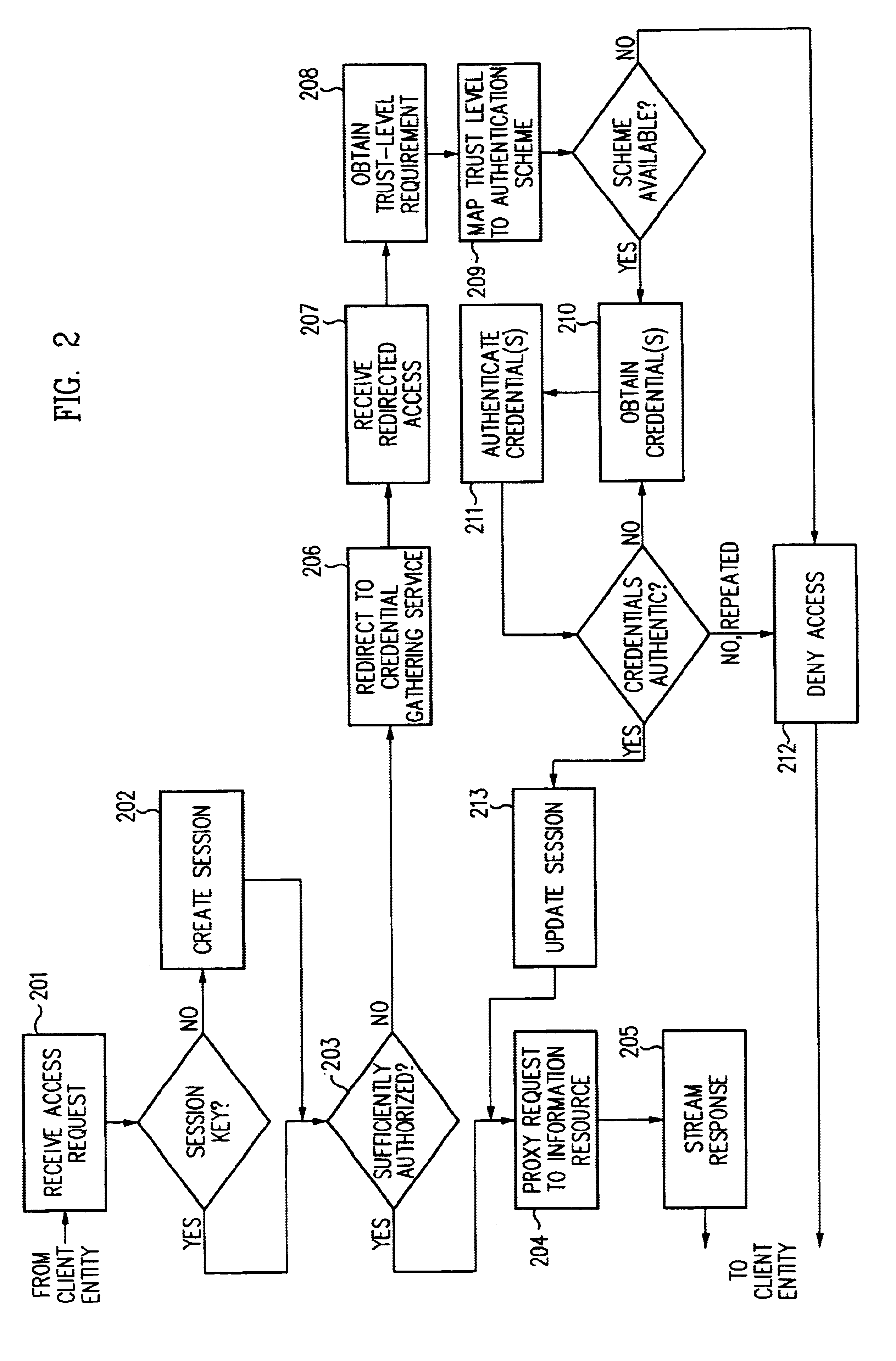
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
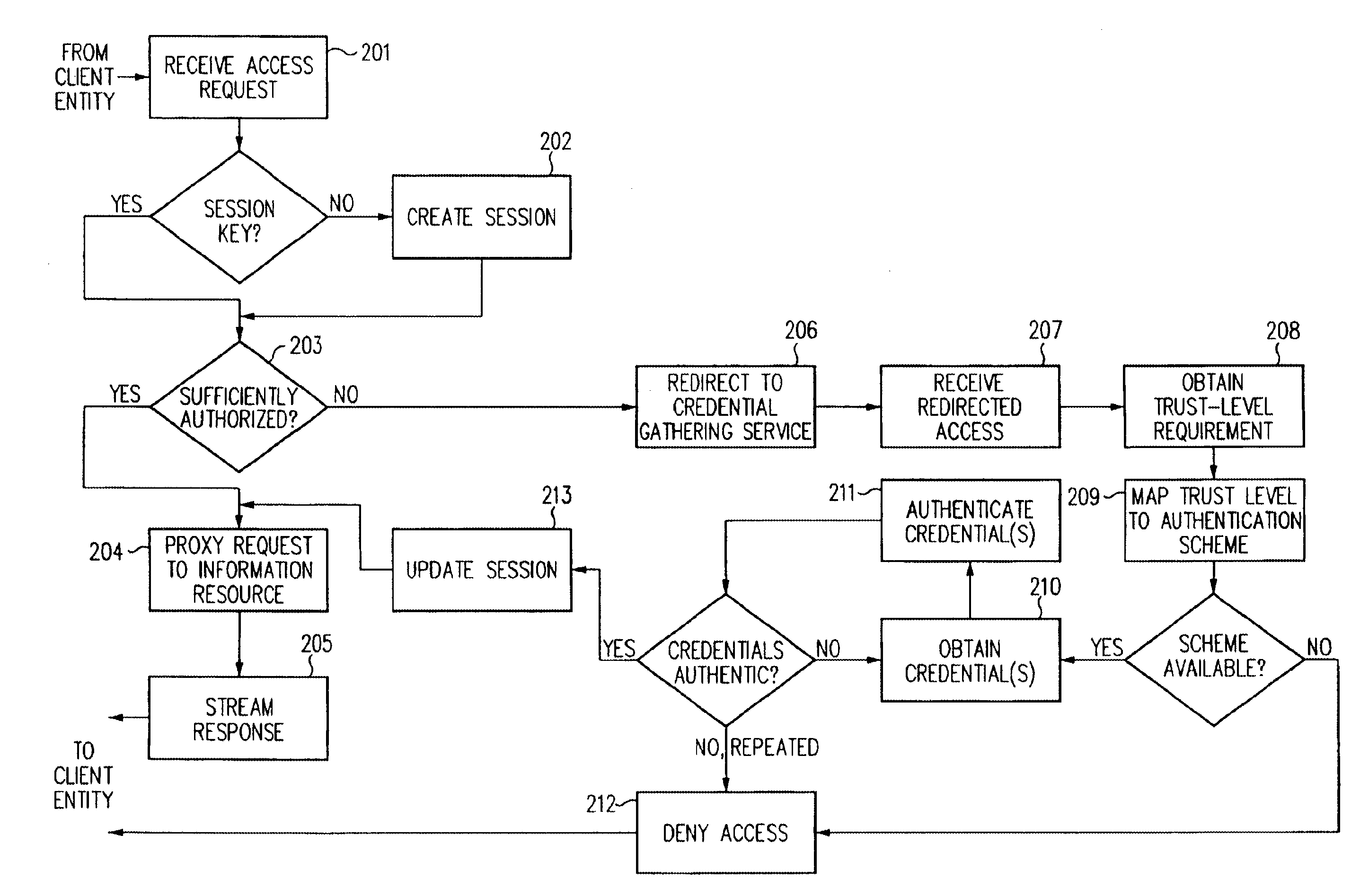
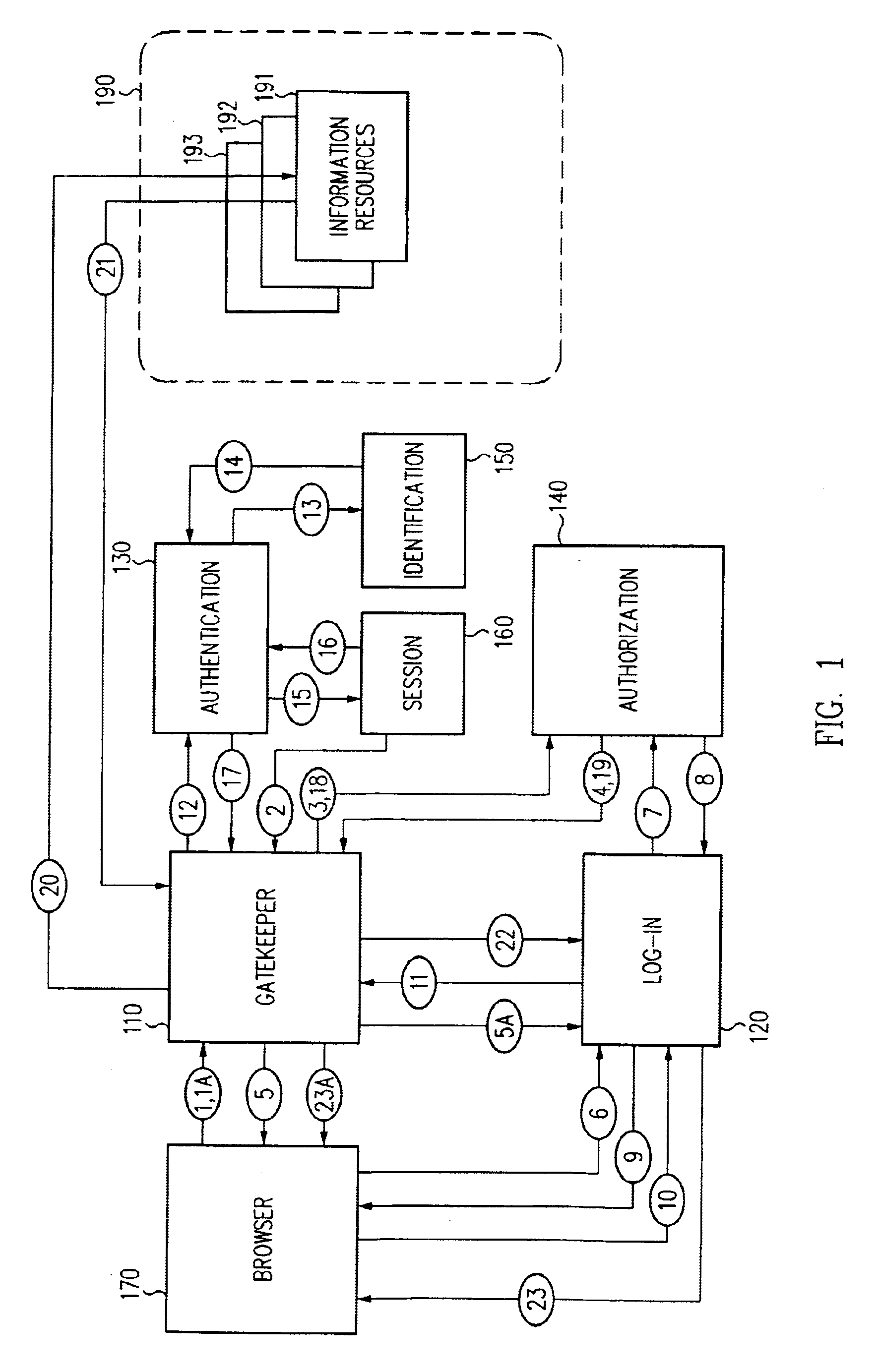
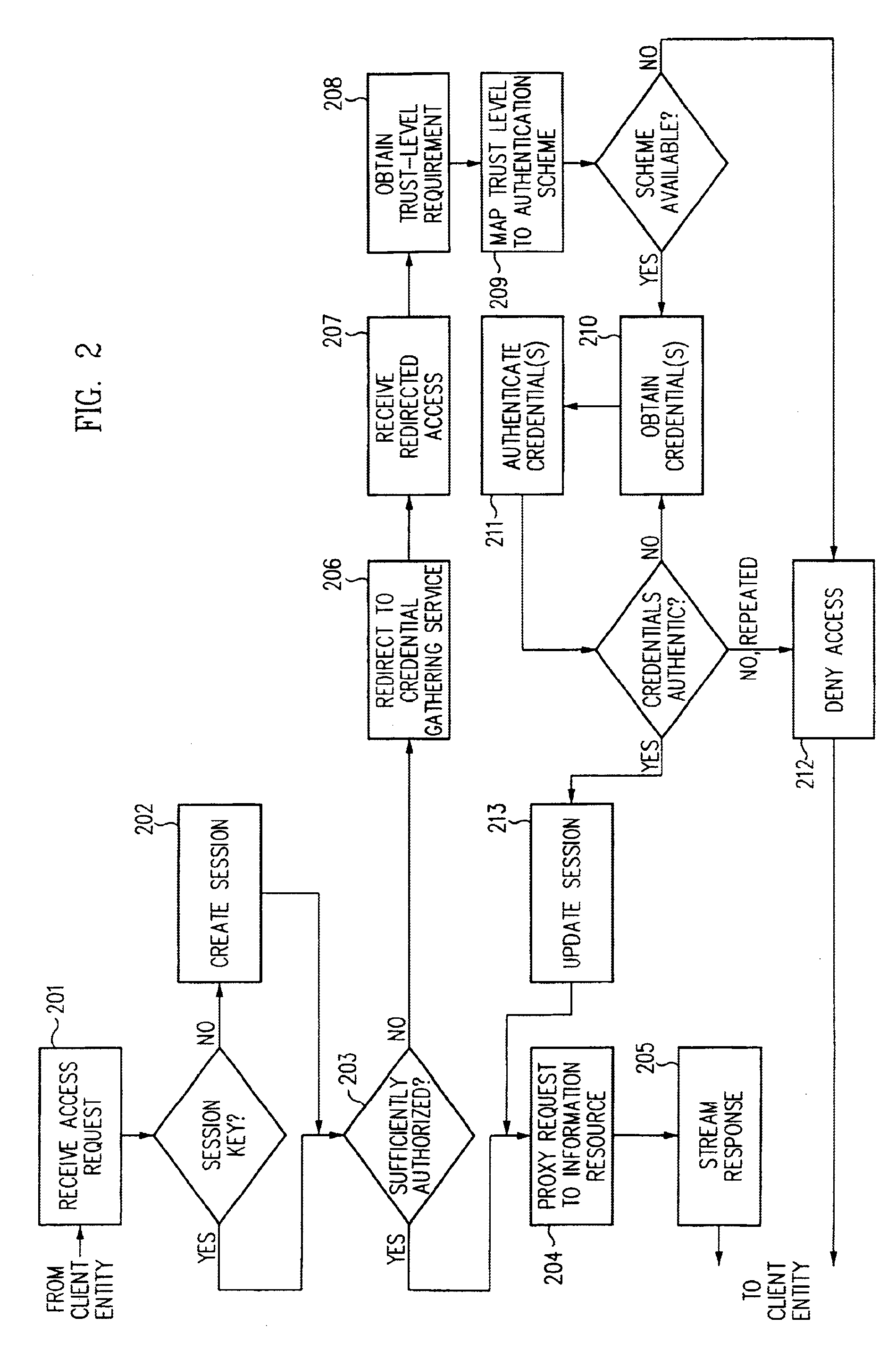
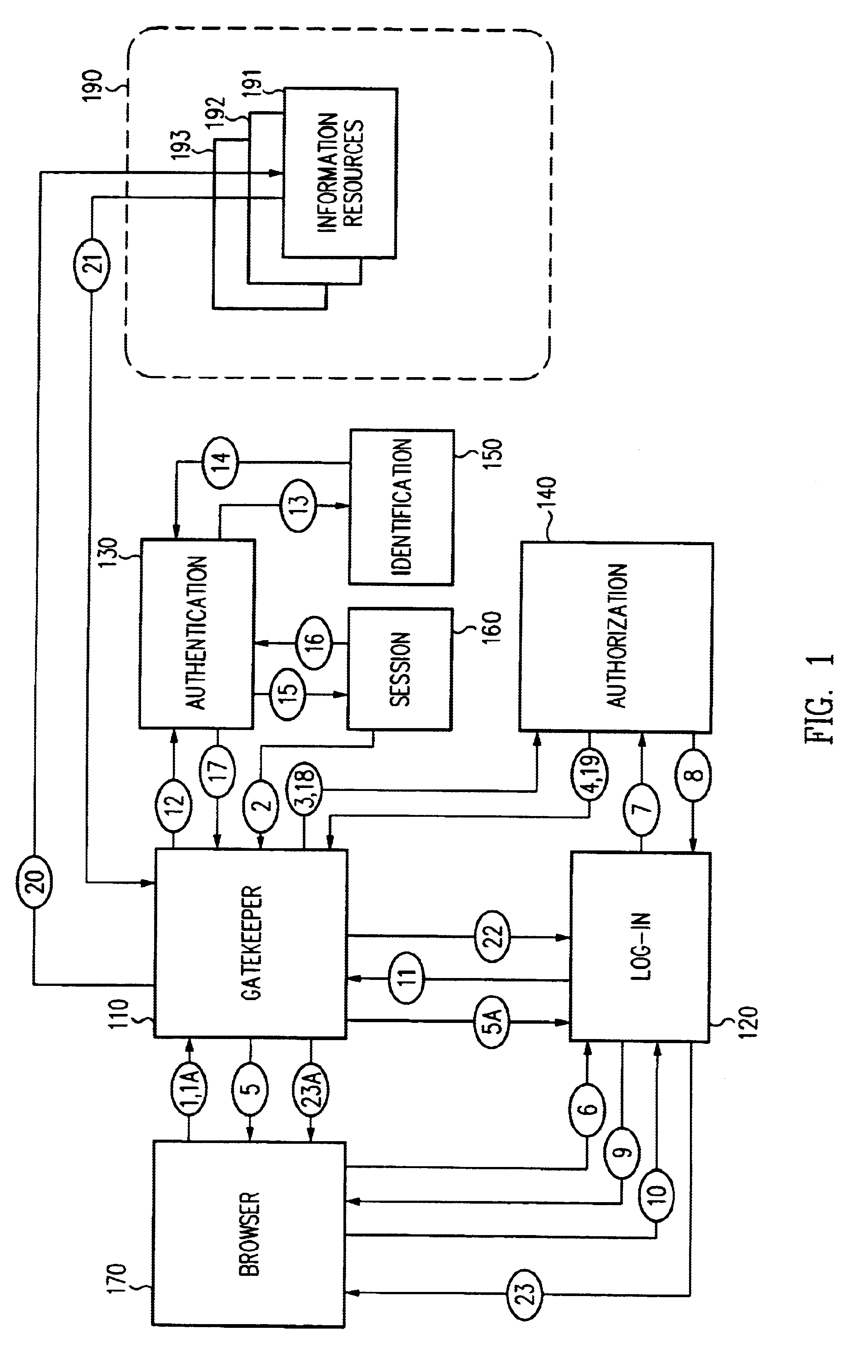
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
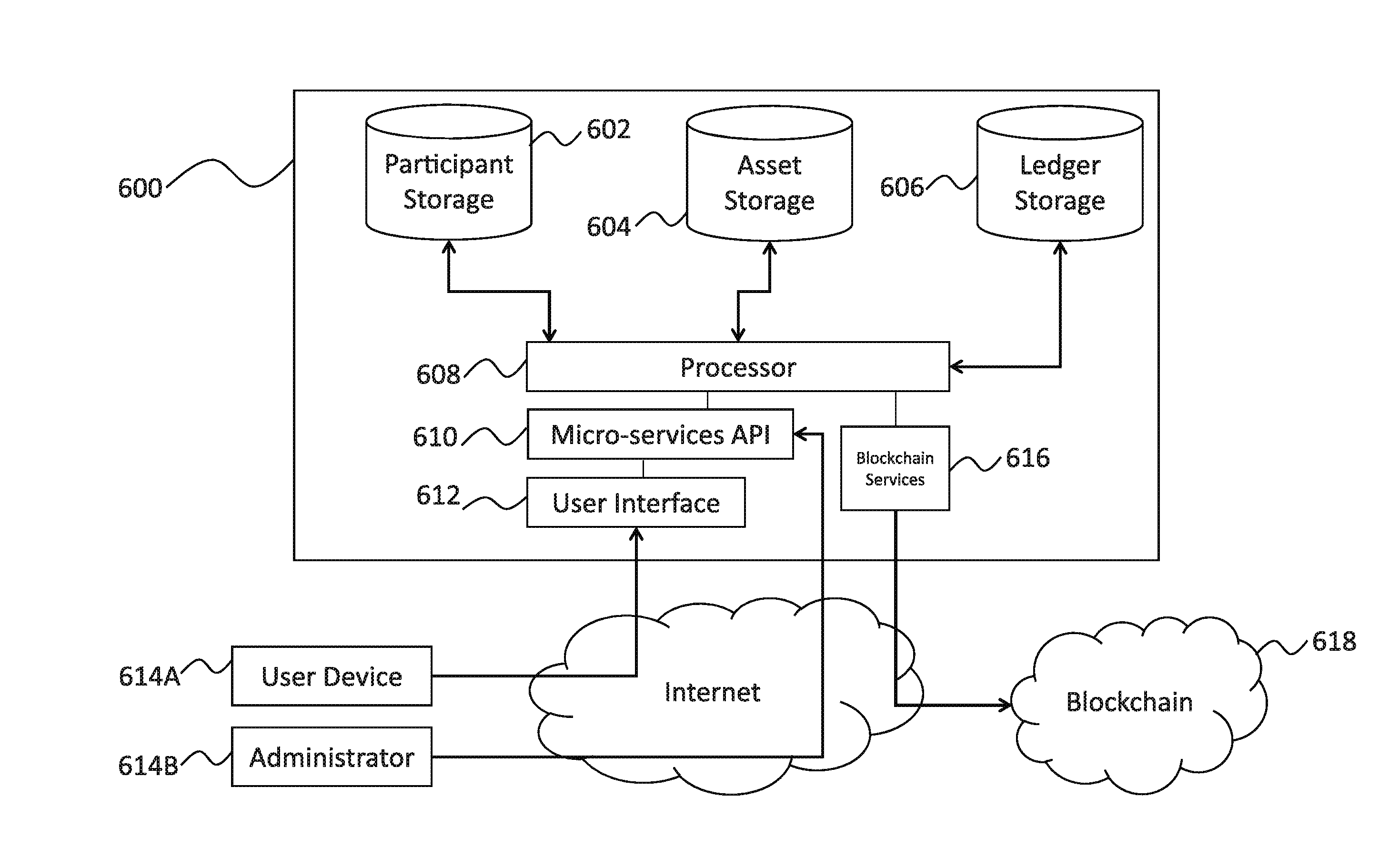
Systems and methods of secure provenance for distributed transaction databases
ActiveUS20170005804A1Direct accessImprove usabilityUser identity/authority verificationDigital data protectionFinancial transactionHandling system
An electronic resource tracking and storage computer system is provided that communicates with a distributed blockchain computing system that includes multiple computing nodes. The system includes a storage system, a transceiver, and a processing system. The storage system includes an resource repository and transaction repository that stores submitted blockchain transactions. A new resource issuance request is received, and a new resource is added to the resource repository in response. A new blockchain transaction is generated and published to the blockchain. In correspondence with publishing to the blockchain, the transaction storage is updated with information that makes up the blockchain transaction and some information that was not included as part of the blockchain transaction. The transaction storage is updated when the blockchain is determined to have validated the previously submitted blockchain transaction.
Owner:NASDAQ INC
Systems and methods for multi-factor authentication
ActiveUS20070186106A1User identity/authority verificationElectric digital data processingInternet privacyControl system
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems.
Owner:IMPRIVATA
Authentication services using mobile device
InactiveUS7606560B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet Authentication ServiceMobile device
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
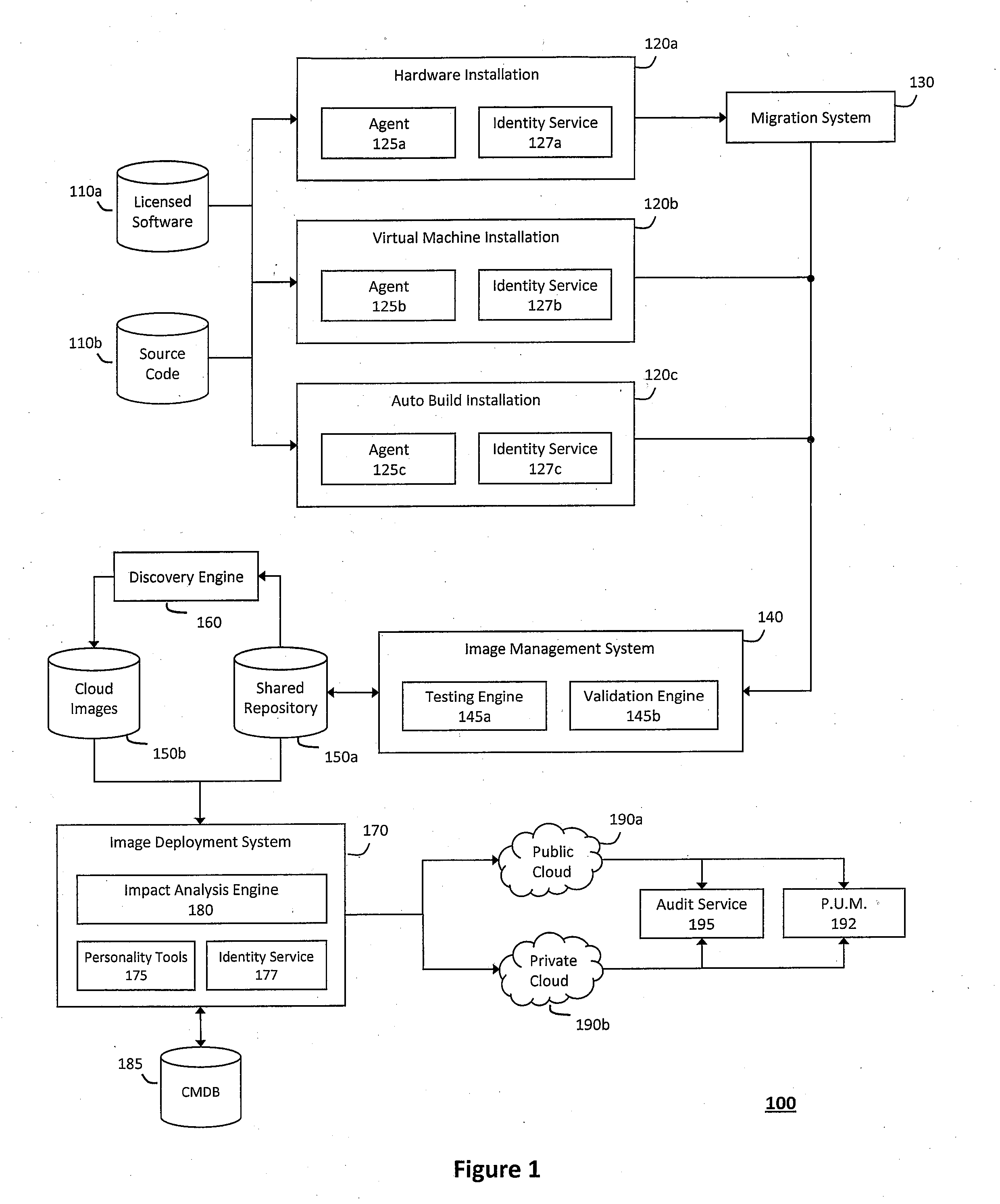
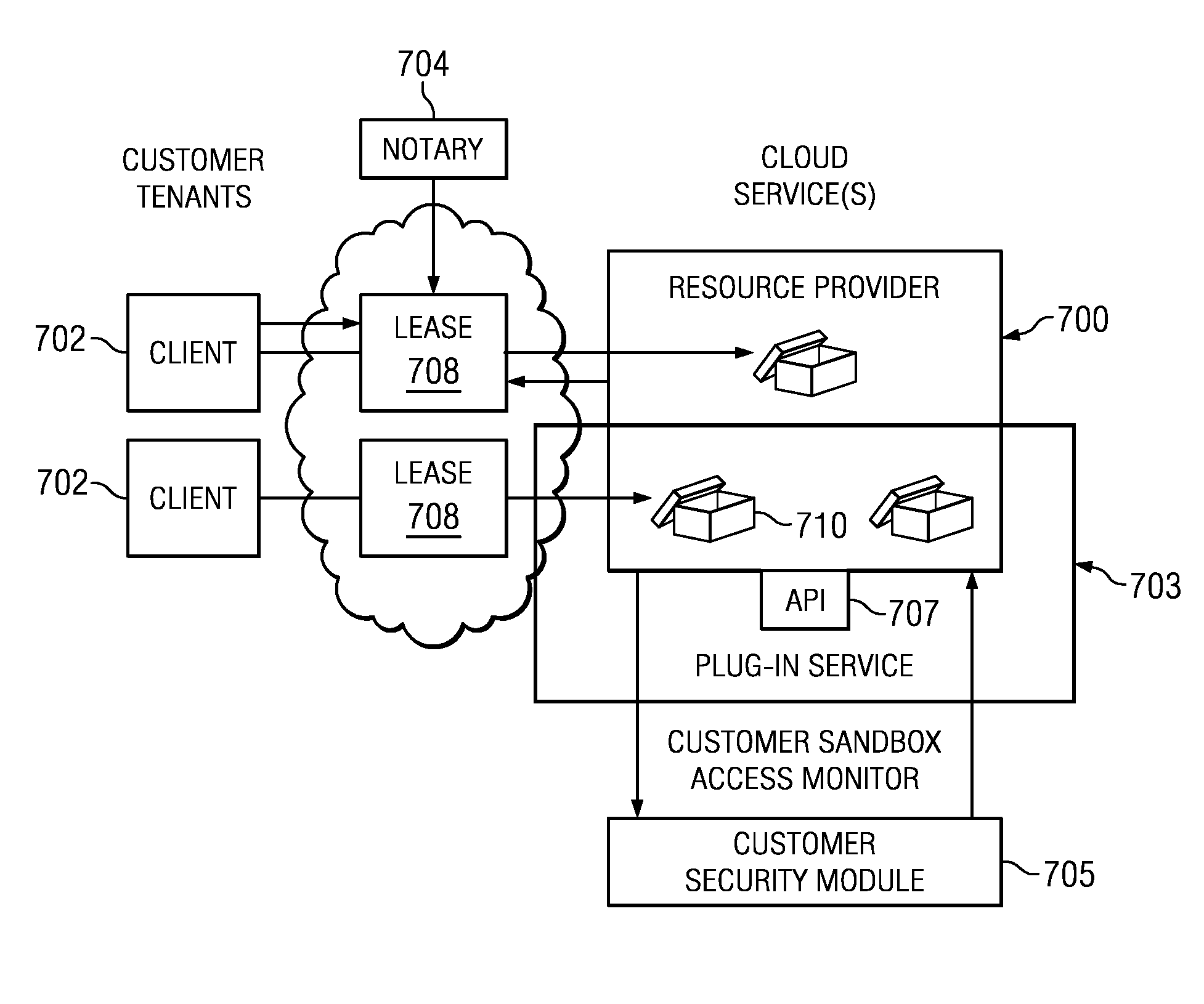
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
Customer-controlled instant-response anti-fraud/anti-identity theft devices (with true- personal identity verification), method and systems for secured global applications in personal/business e-banking, e-commerce, e-medical/health insurance checker, e-education/research/invention, e-disaster advisor, e-immigration, e-airport/aircraft security, e-military/e-law enforcement, with or without NFC component and system, with cellular/satellite phone/internet/multi-media functions
ActiveUS20140162598A1Prevent fraudulent multiple swipingDevices with card reading facilityUnauthorised/fraudulent call preventionChequeMessage passing
All-in-one wireless mobile telecommunication devices, methods and systems providing greater customer-control, instant-response anti-fraud / anti-identity theft protections with instant alarm, messaging and secured true-personal identity verifications for numerous registered customers / users, with biometrics and PIN security, operating with manual, touch-screen and / or voice-controlled commands, achieving secured rapid personal / business e-banking, e-commerce, accurate transactional monetary control and management, having interactive audio-visual alarm / reminder preventing fraudulent usage of legitimate physical and / or virtual credit / debit cards, with cheques anti-forgery means, curtailing medical / health / insurance frauds / identity thefts, having integrated cellular and / or satellite telephonic / internet and multi-media means, equipped with language translations, GPS navigation with transactions tagging, currency converters, with or without NFC components, minimizing potential airport risks / mishaps, providing instant aid against school bullying, kidnapping, car-napping and other crimes, applicable for secured military / immigration / law enforcements, providing guided warning / rescue during emergencies and disasters.
Owner:VILLA REAL ANTONY EUCLID C
Secure interactive electronic account statement delivery system
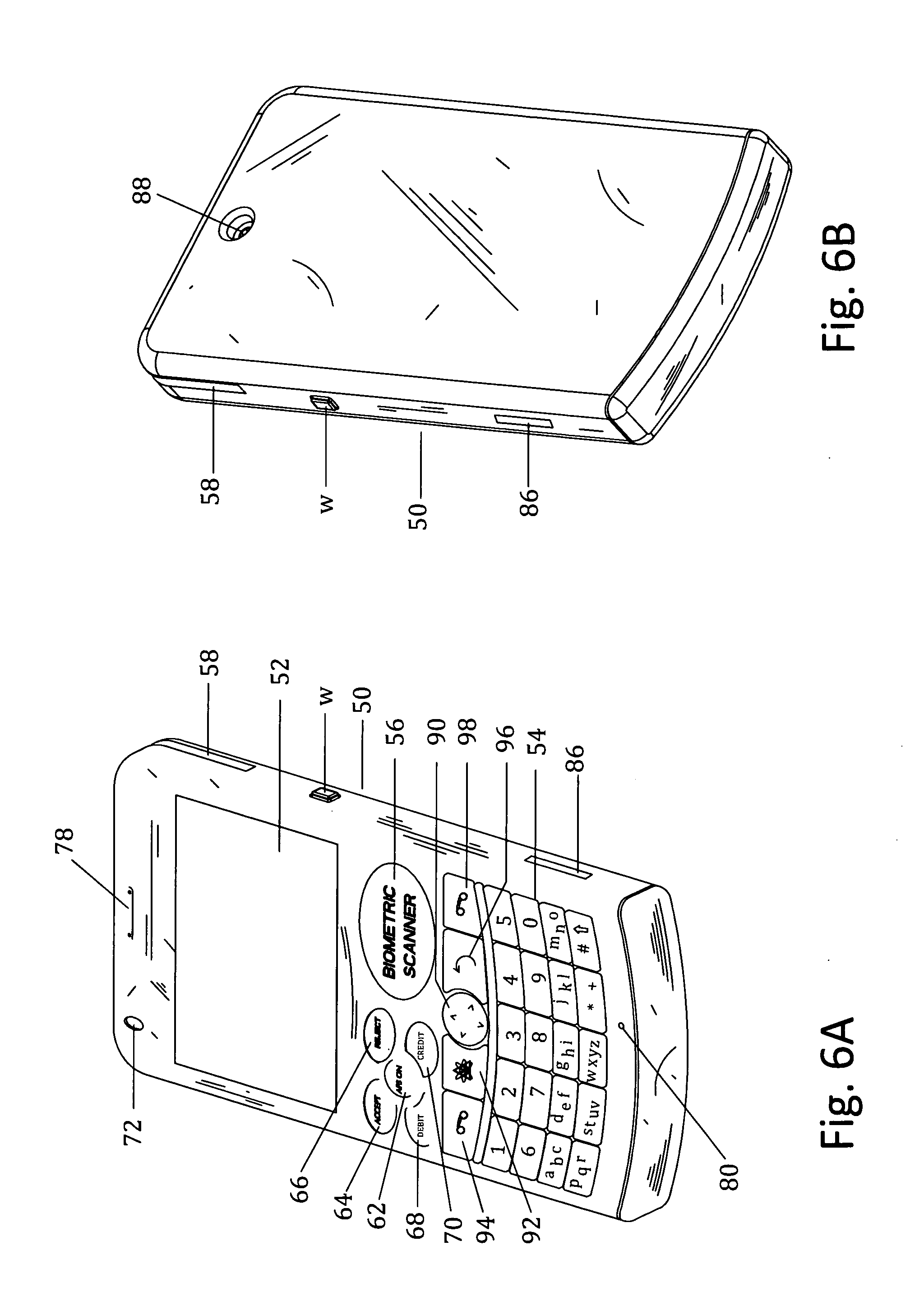
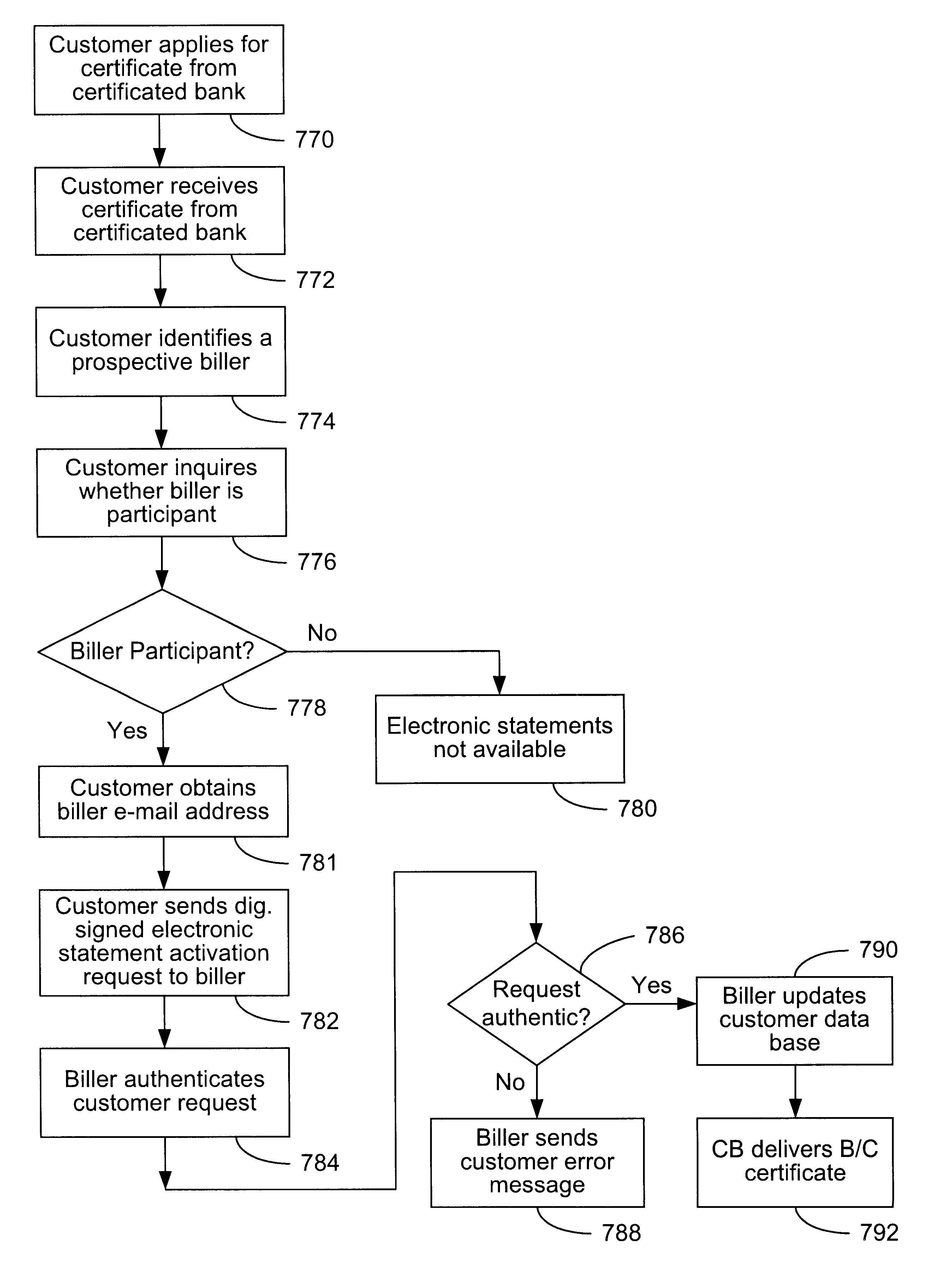
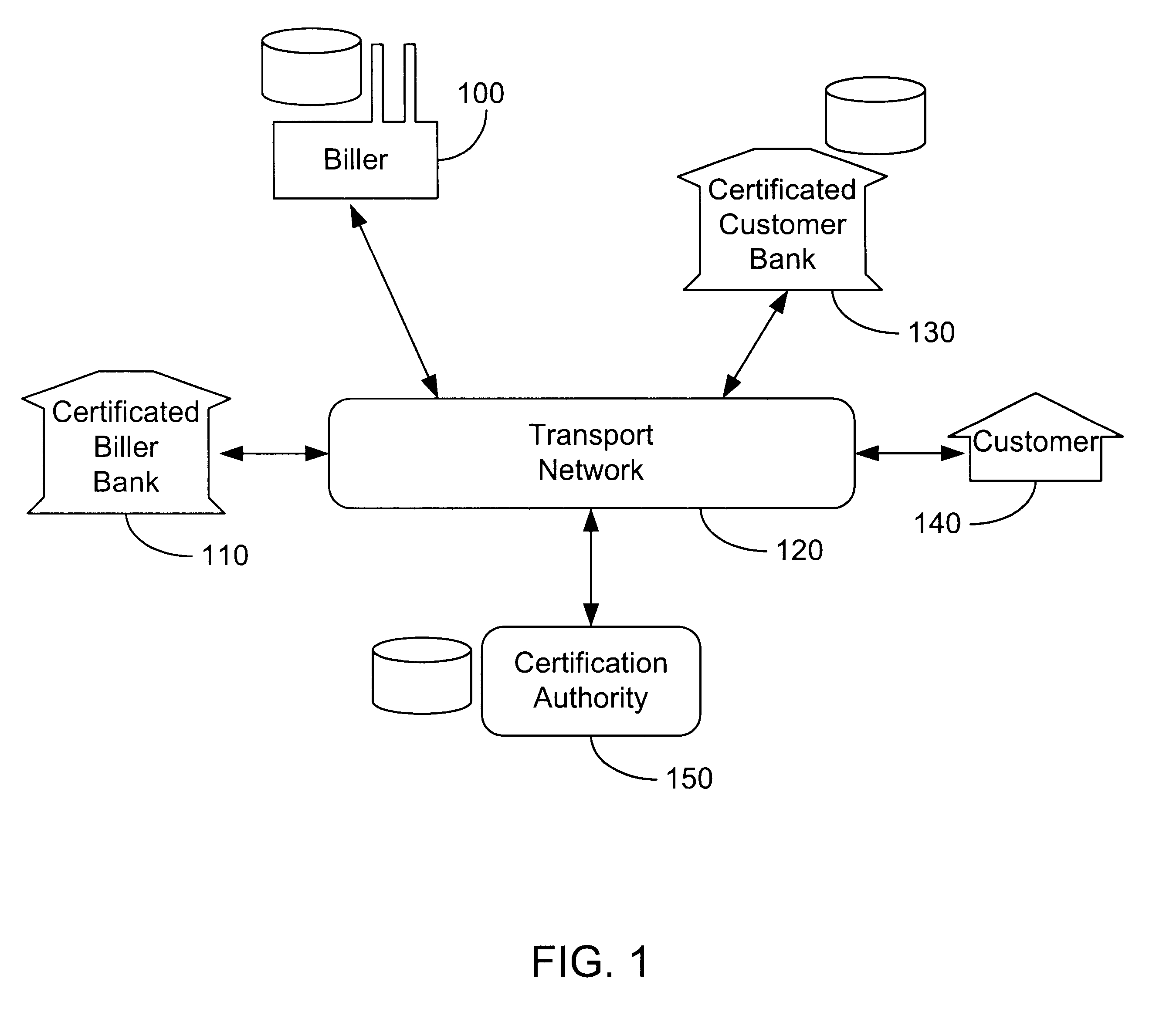
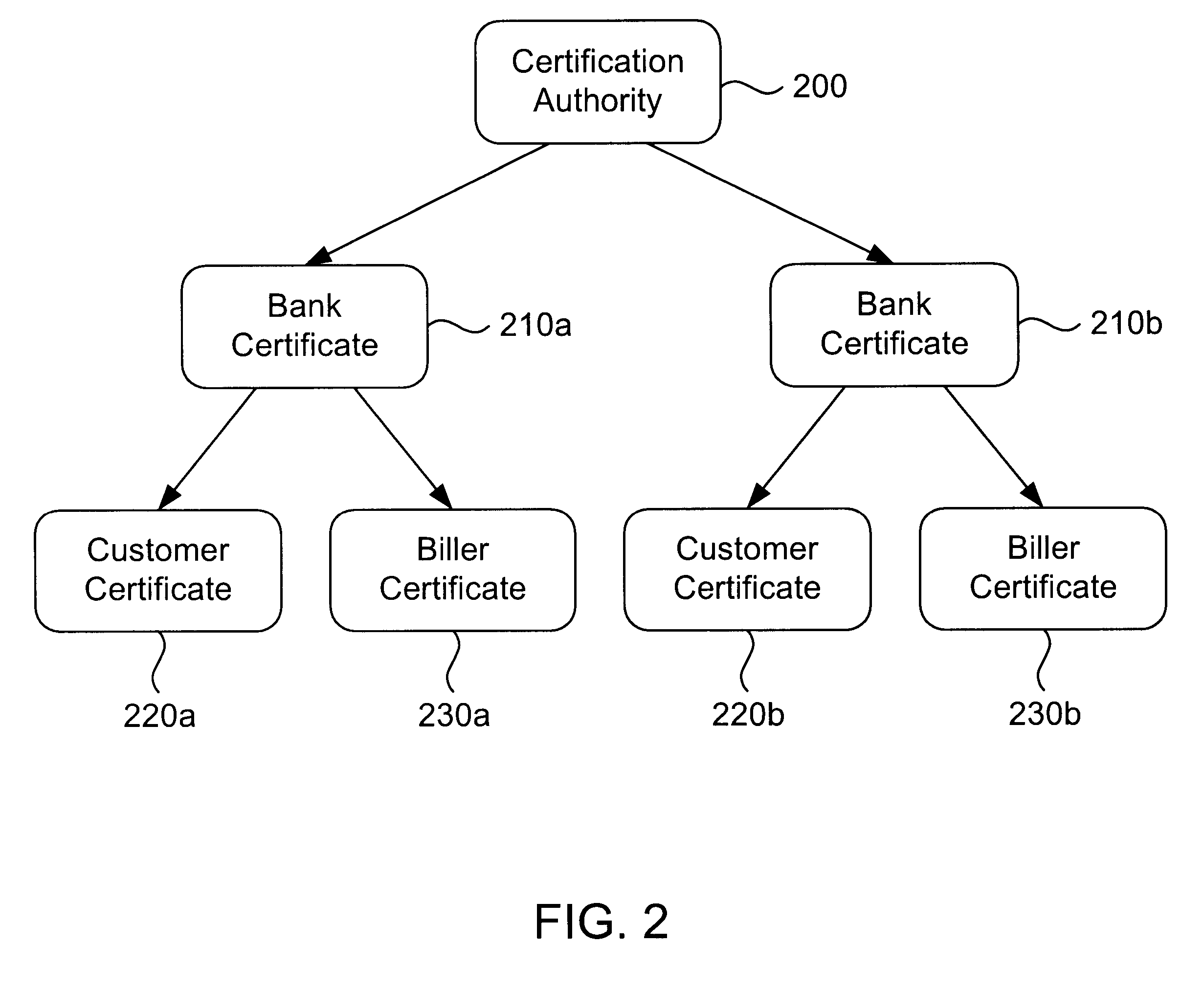
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
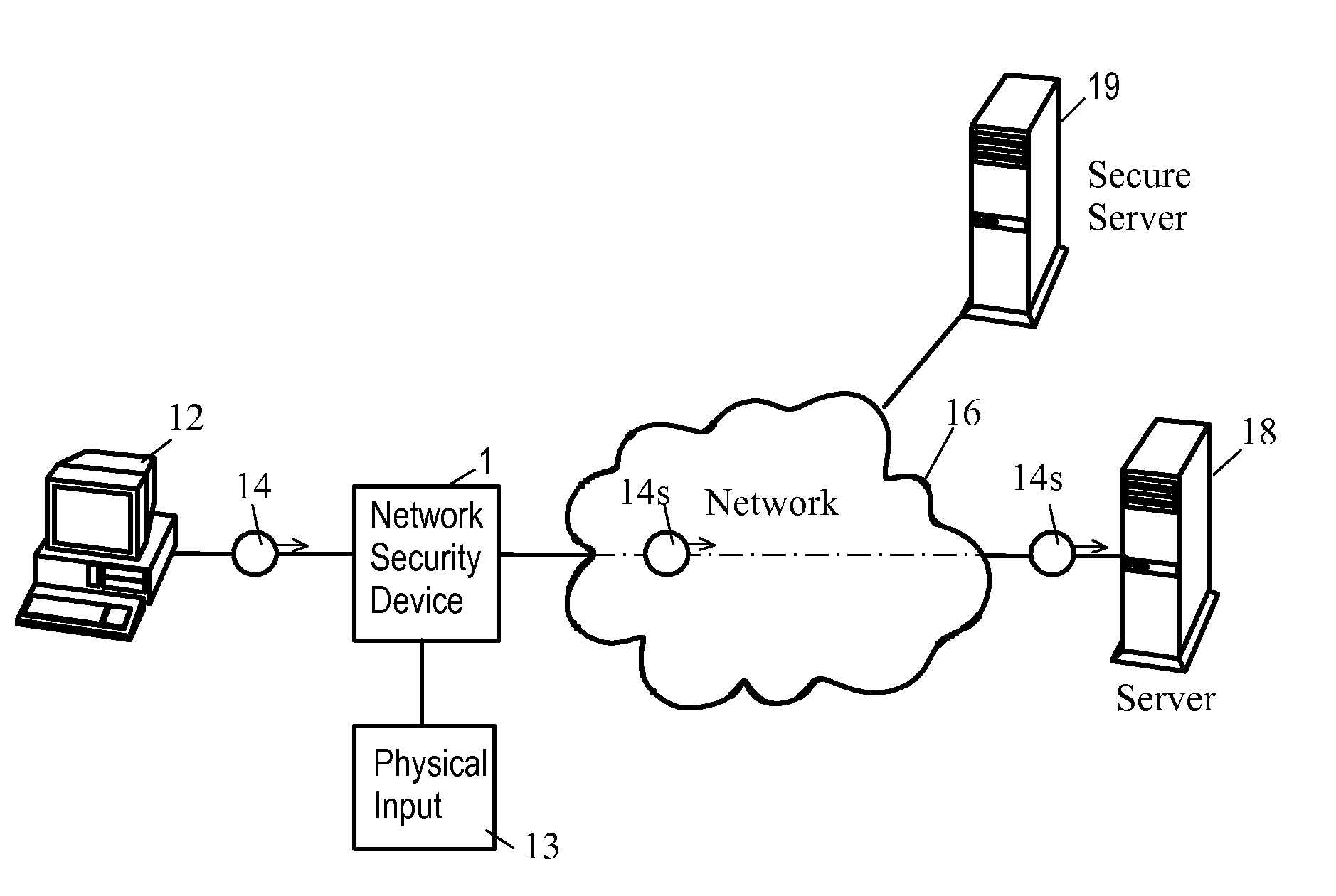
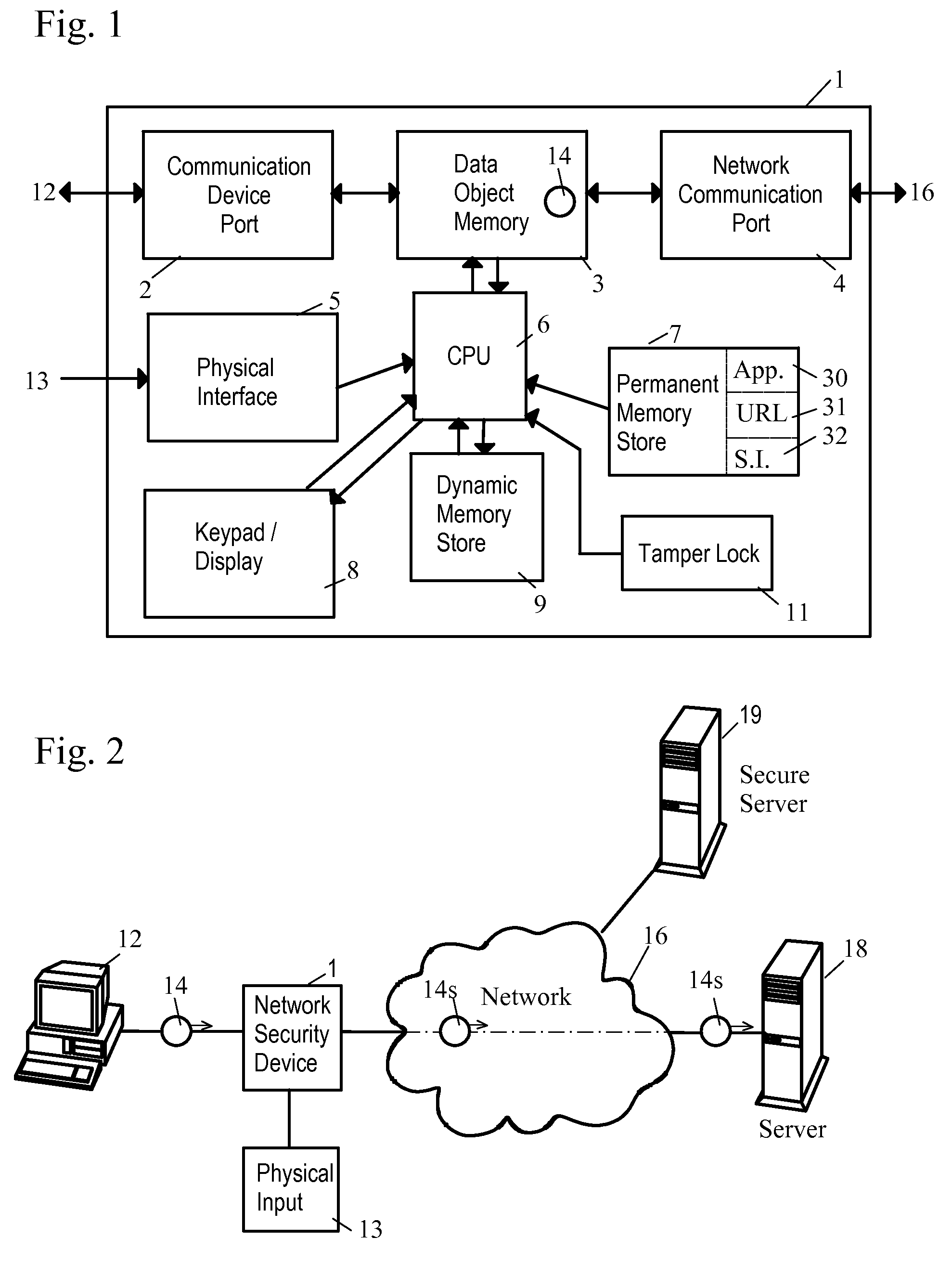
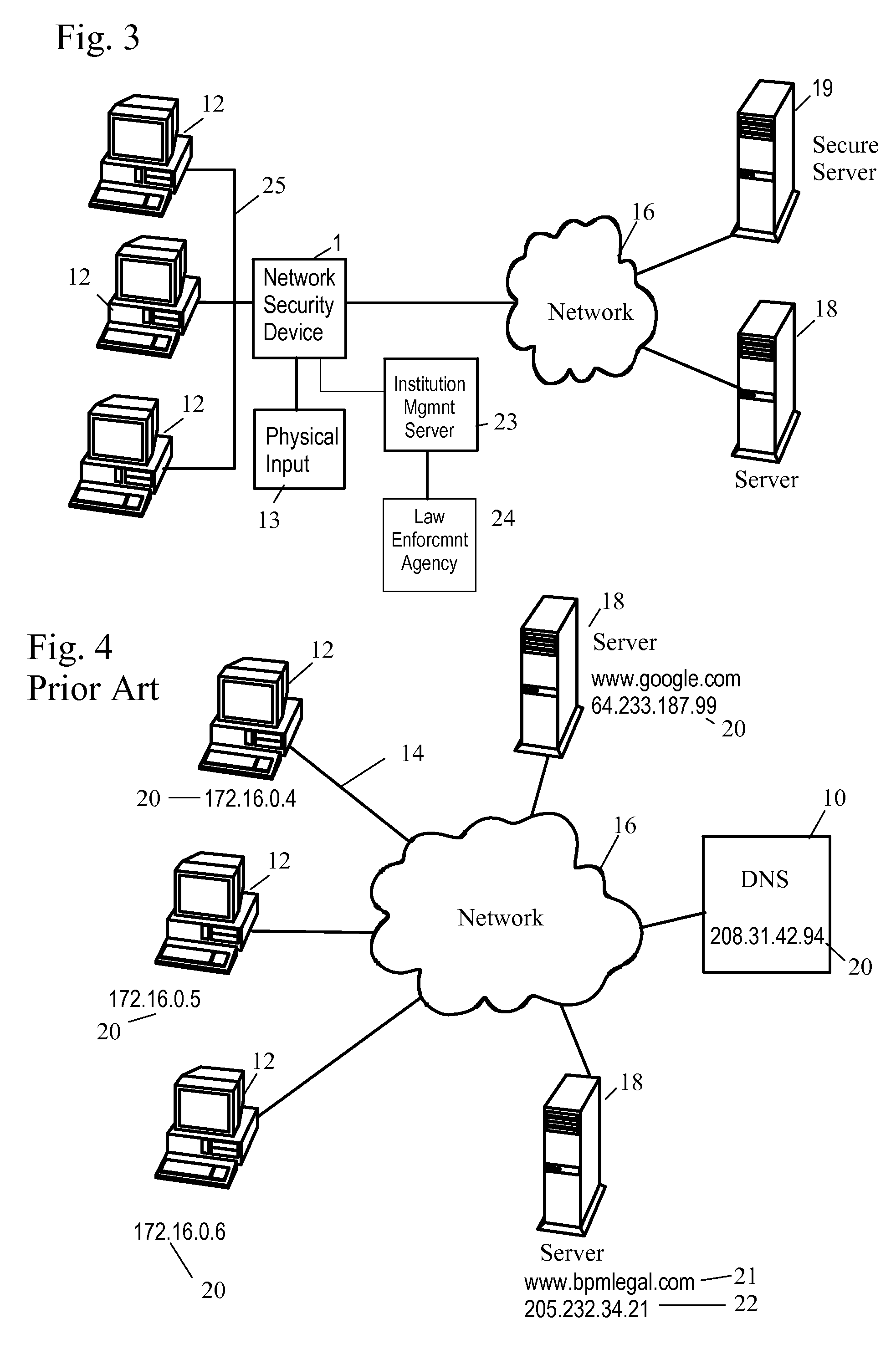
Network Security Device
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
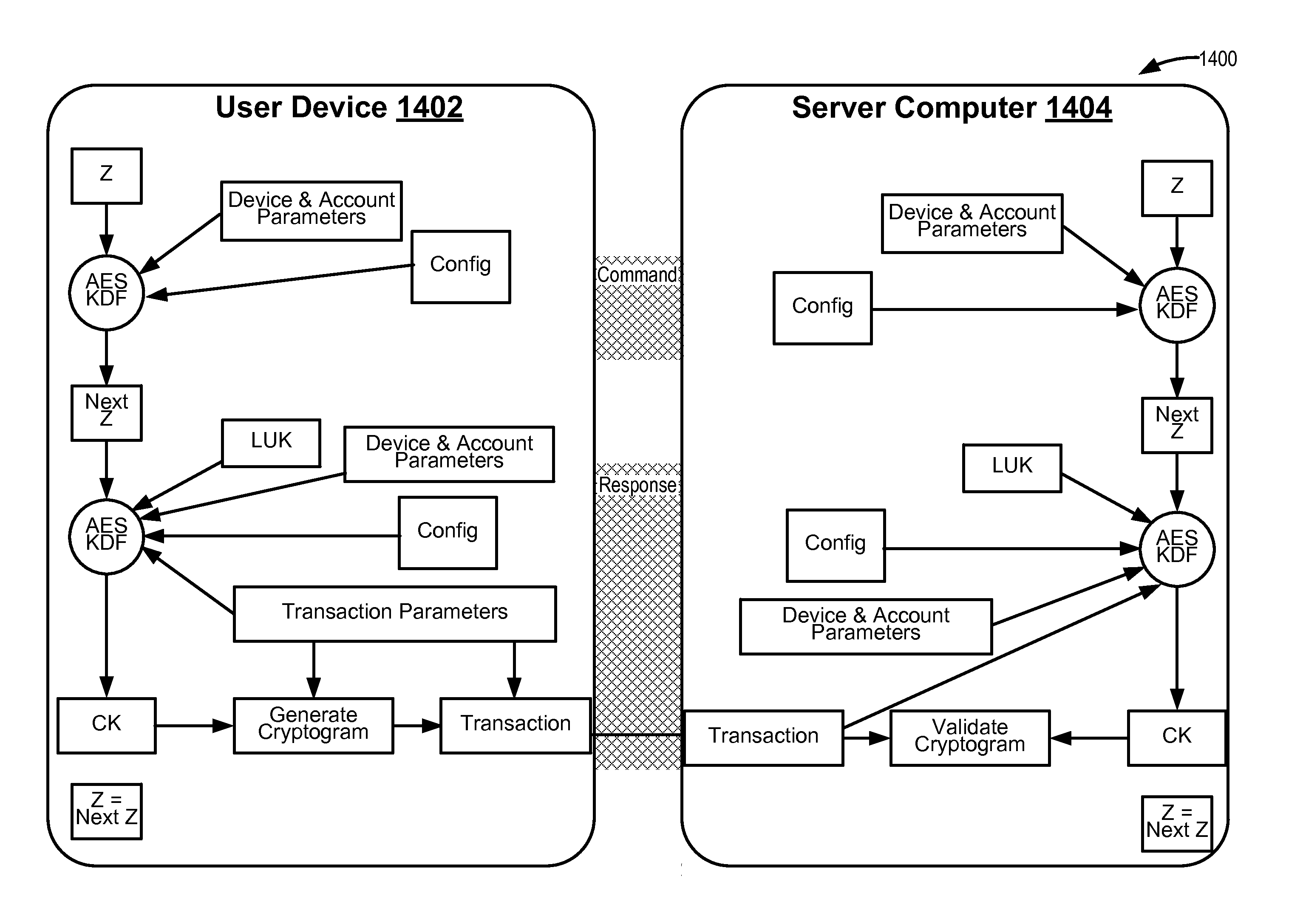
Methods for secure cryptogram generation
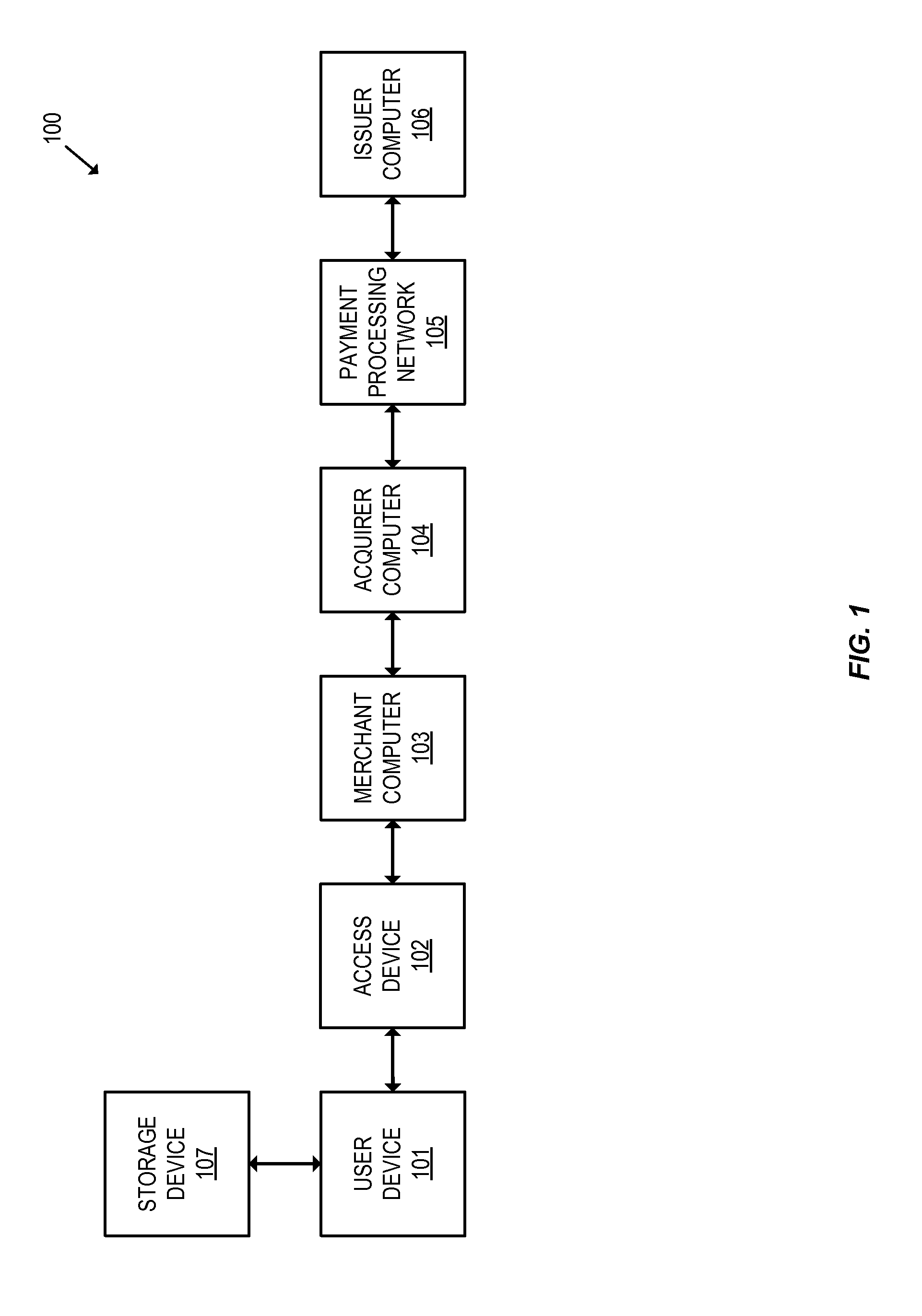
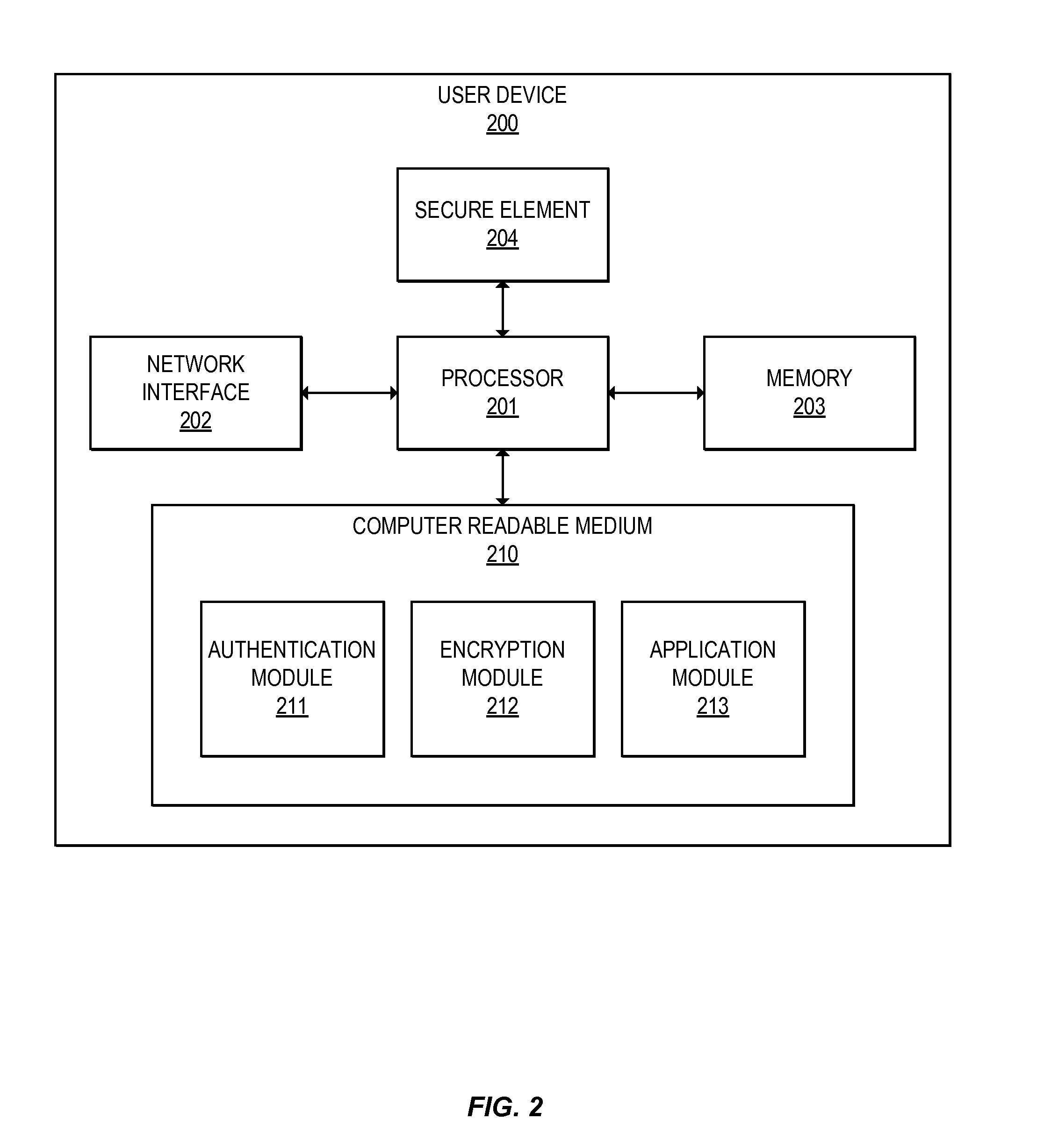
ActiveUS20160065370A1Avoid attackKey distribution for secure communicationMultiple keys/algorithms usageSecure communicationUser device
Embodiments of the invention introduce efficient methods for securely generating a cryptogram by a user device, and validating the cryptogram by a server computer. In some embodiments, a secure communication can be conducted whereby a user device provides a cryptogram without requiring the user device to persistently store an encryption key or other sensitive data used to generate the cryptogram. For example, the user device and server computer can mutually authenticate and establish a shared secret. Using the shared secret, the server computer can derive a session key and transmit key derivation parameters encrypted using the session key to the user device. The user device can also derive the session key using the shared secret, decrypt the encrypted key derivation parameters, and store the key derivation parameters. Key derivation parameters and the shared secret can be used to generate a single use cryptogram key. The cryptogram key can be used to generate a cryptogram for conducting secure communications.
Owner:VISA INT SERVICE ASSOC
Popular searches
Electric/electromagnetic visible signalling Digital data authentication Buying/selling/leasing transactions Program/content distribution protection Special data processing applications Market data gathering Advertisements Analogue secracy/subscription systems Color television details Internal/peripheral component protection
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com