Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2183 results about "Resource based" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Resource based theory of the firm. a conceptual framework developed by business strategists which focuses on the key resources and capabilities possessed by a business which forms the basis of establishing a sustainable COMPETITIVE ADVANTAGE over rival suppliers.
Assignment manager
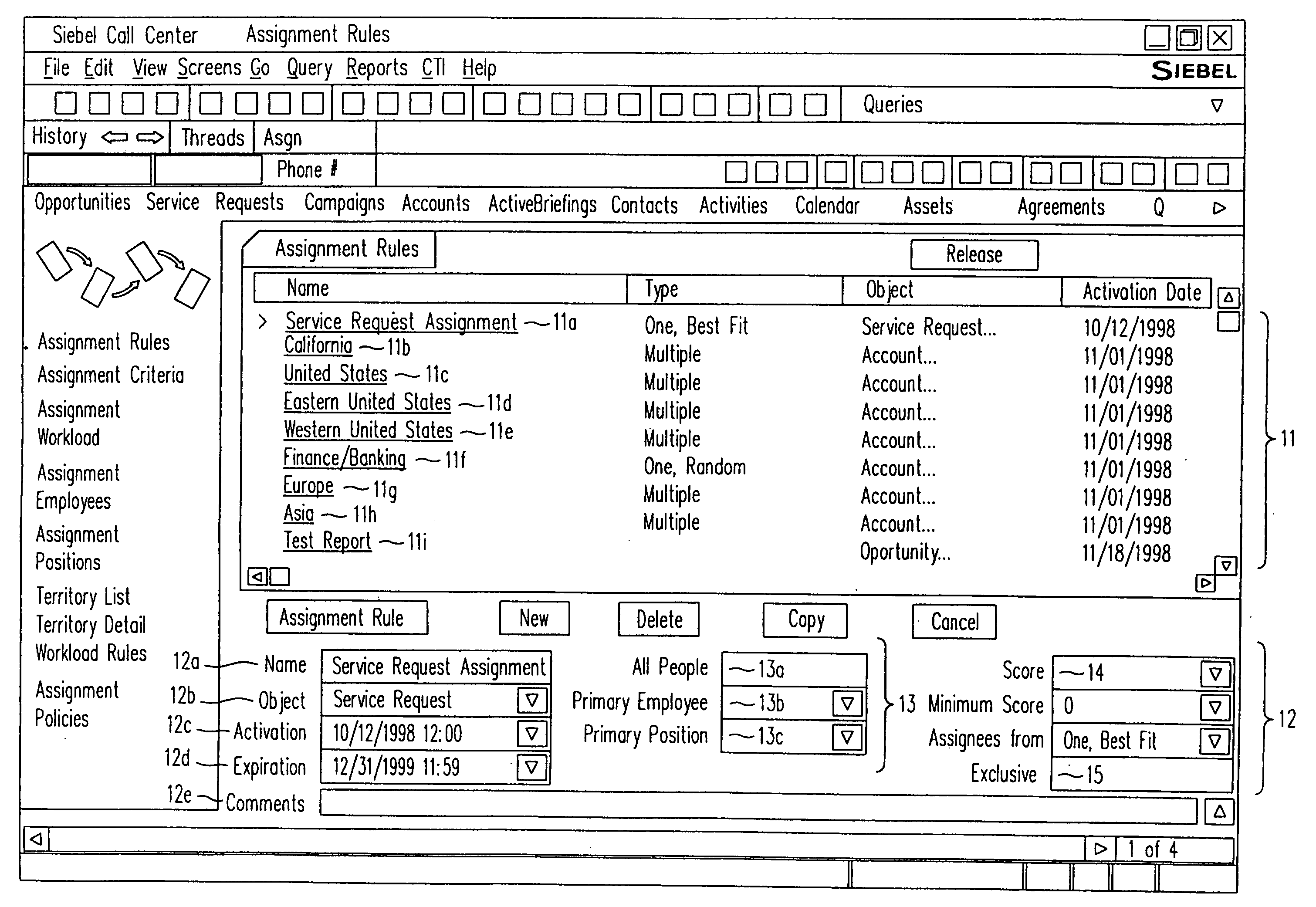
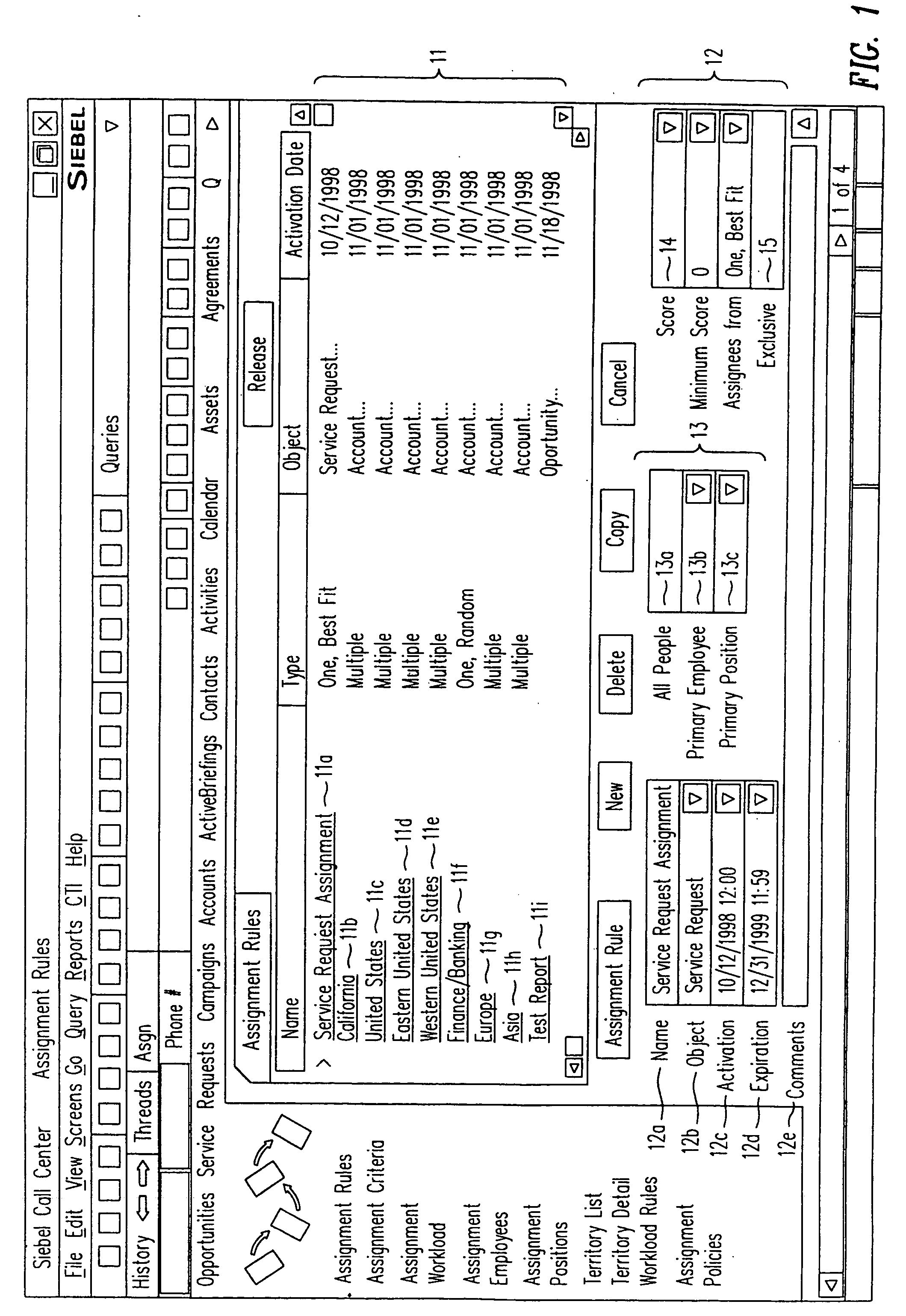
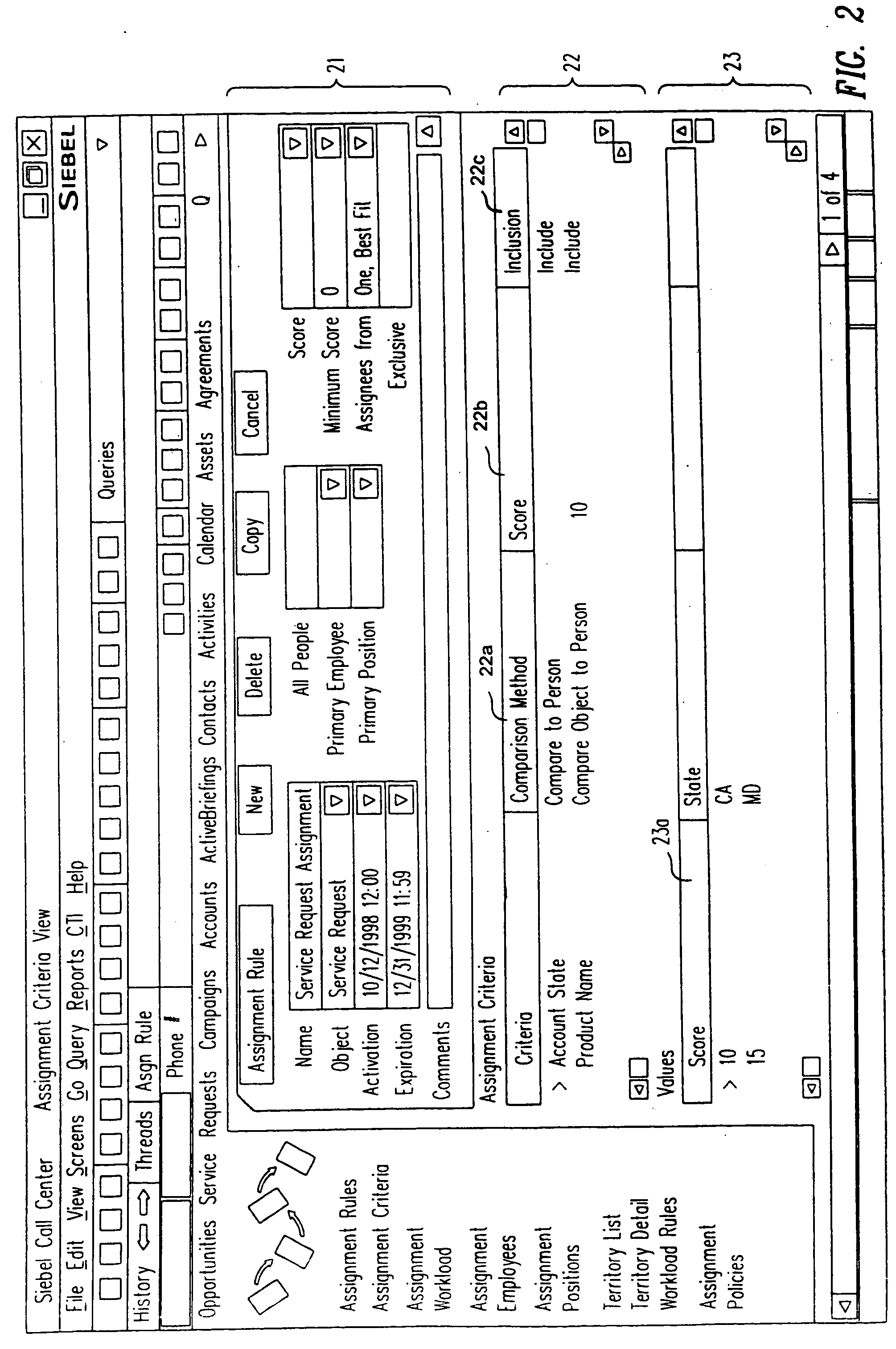
InactiveUS20050091098A1ResourcesSpecial data processing applicationsResource basedResource allocation
A method, a program product, and a system for assigning resources to tasks in a rule based, resource constrained system. This is done by receiving as inputs tasks and task attributes; resources and resource attributes; and assignment rules. These inputs are used to searching a database of tasks, task attributes, and assignment rules thereof, to search a database of resources including resource attributes thereof, and to retrieve resources based upon the resource attributes. Resources are assigned to tasks based upon matches and scores of the resource attributes, the task attributes, and the assignment rules.
Owner:SIEBEL SYST INC
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
Systems and Methods for Providing Levels of Access and Action Control Via an SSL VPN Appliance
ActiveUS20070245409A1Digital data processing detailsUser identity/authority verificationOrganizational controlInformation access
The present invention relates to systems and methods to identify a level of access for a resource being accessed via a secure socket layer virtual private network (SSL VPN) connection to a network, and to control the action on the resource based on the identified level of access. The appliance described herein provides intelligent secure access and action control to resources based on a sense and respond mechanism. When a user requests access to a resource via the SSL VPN connection of the appliance, the appliance obtains information about the client to determine the user access scenario—the location, device, connection and identify of the user or client. Based on the collected information, the appliance responds to the detected user scenario by identifying a level of access to the resource for the user / client, such as rights to view, print, edit or save a document, Based on the identified level of access, the appliance controls the actions performs on the resource by various techniques described herein so that the user can only perform the allowed action n accordance with the level of access. As such, the present invention allows organization to control and provide the appropriate level of access to valuable, confidential or business critical information accessed remotely or via a pubic network while protecting such information by controlling the types of actions performed or allowed to be performed remotely on the information.
Owner:CITRIX SYST INC
System and method for integrating search results from heterogeneous information resources
A system and method for relative ranking and contextual summarization of search hits from multiple distributed, heterogeneous information resources based upon the original content of each hit is disclosed. In particular, the system and method of the present invention improve upon metasearch engine techniques by downloading the original documents (text or multimedia) identified by standard search engines as relevant and using the original content of each "hit" to re-rank them relative to each other according to the original query pattern for the search, providing a uniform ranking methodology for the user. The present invention is also directed to an improved summarization process where the downloaded documents are re-summarized relative to each other according to the original query pattern for the search, providing a uniform summarization methodology for the user.
Owner:PEROT SYSTEMS
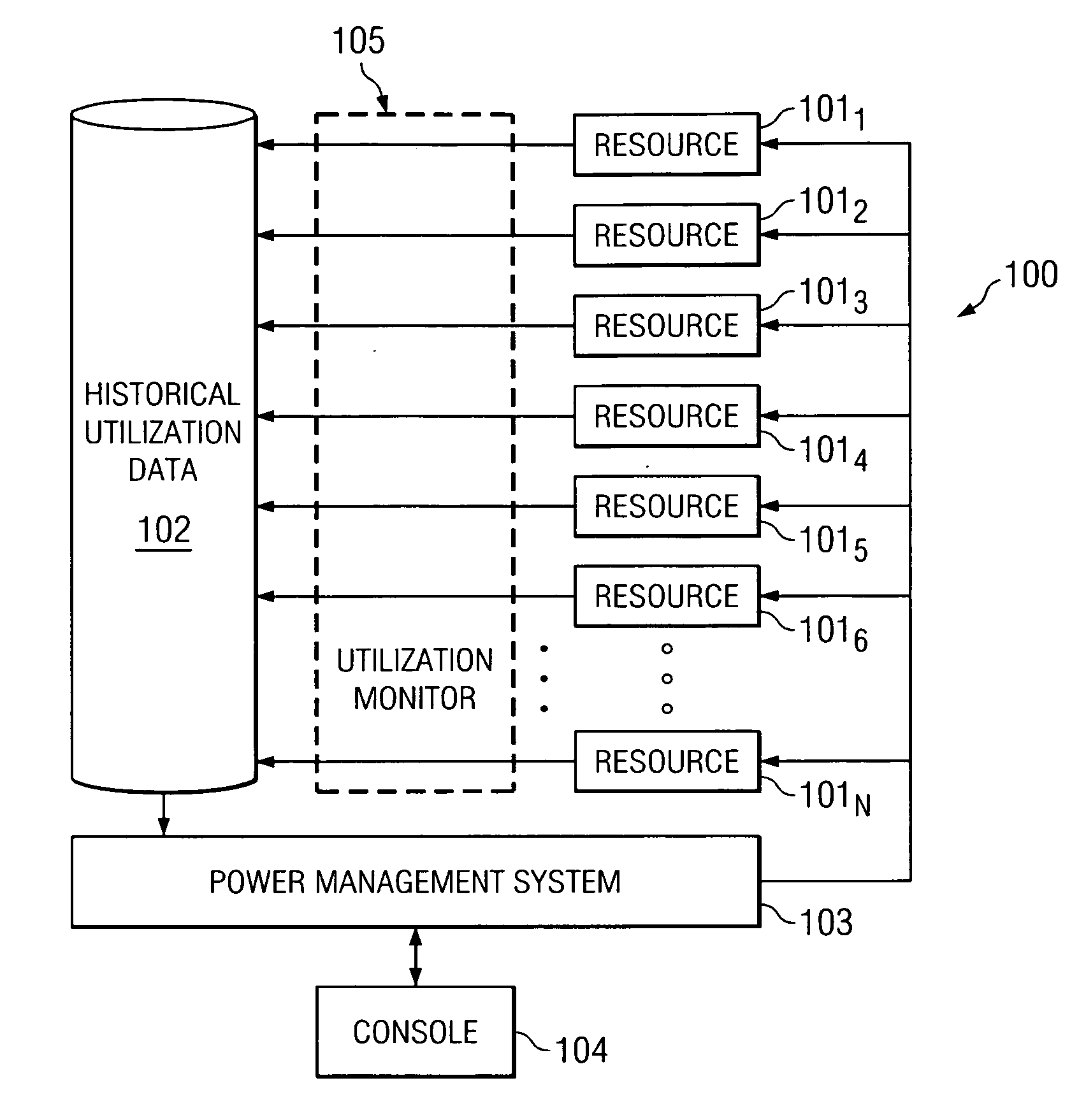
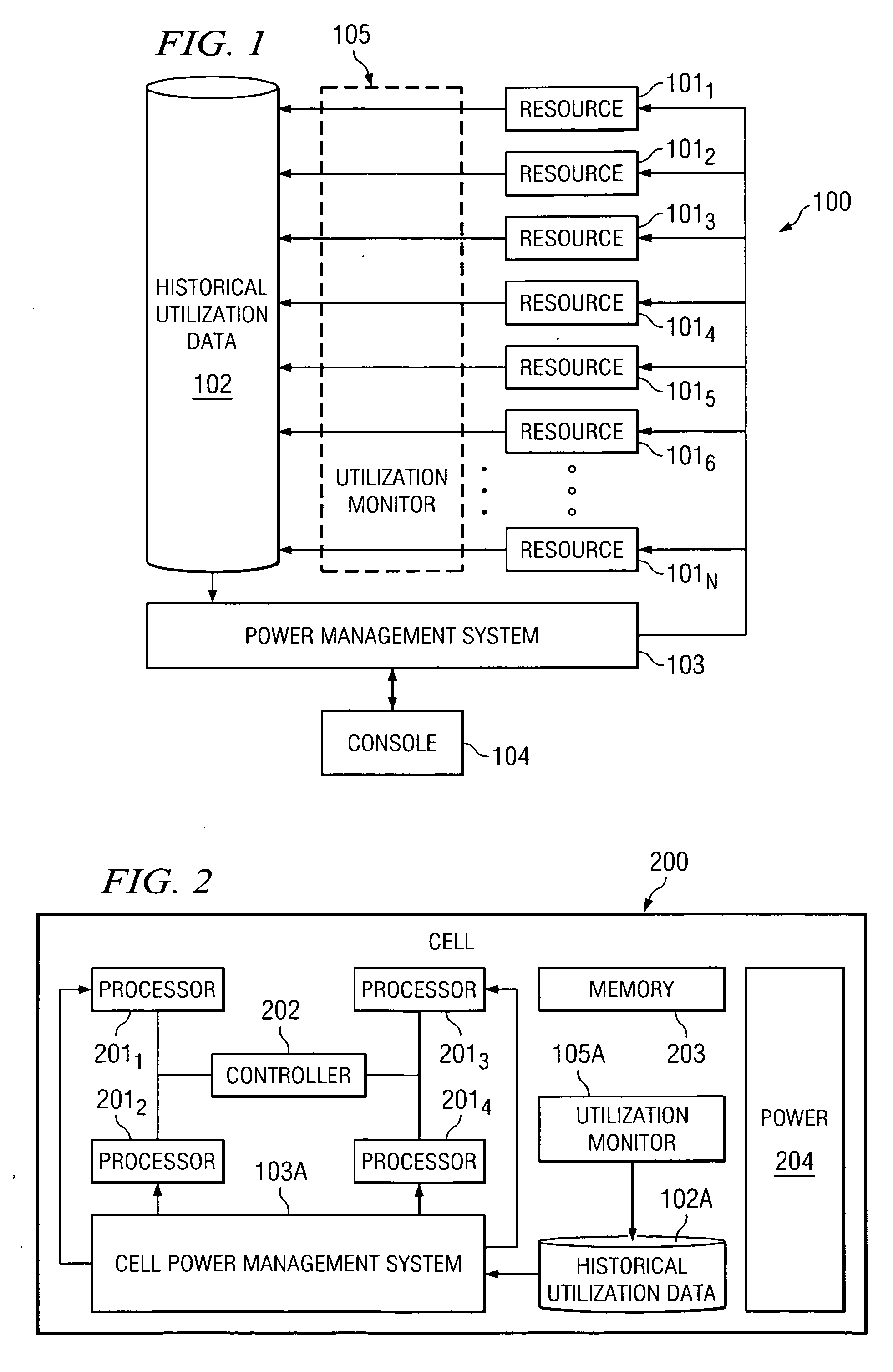
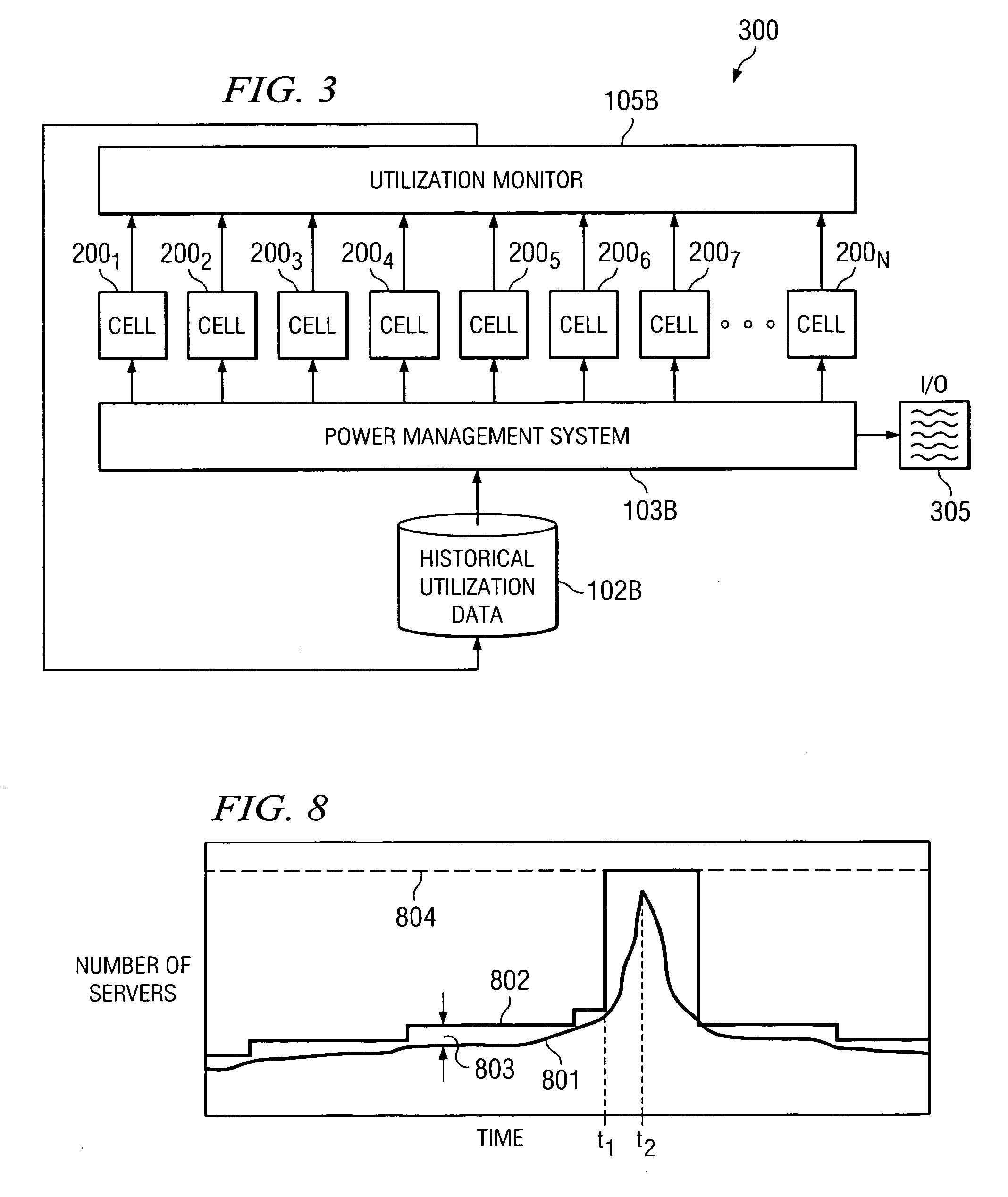
System and method for controlling power to resources based on historical utilization data
ActiveUS20060184287A1Energy efficient ICTMechanical power/torque controlResource basedSystem configuration
A method comprises collecting utilization data for a resource, and predicting by a power management system, based on the collected utilization data, future utilization of the resource. The method further comprises controlling, by the power management system, power to the resource, based at least in part on the predicted future utilization of the resource. In one embodiment, the utilization data is collected for a plurality of resources that are operable to perform tasks, and the method further comprises determining, by the power management system, how many of the resources are needed to provide a desired capacity for servicing the predicted future utilization of the resources for performing the tasks. The method further comprises configuring, by the power management system, ones of the resources exceeding the determined number of resources needed to provide the desired capacity in a reduced power-consumption mode.
Owner:MOSAID TECH
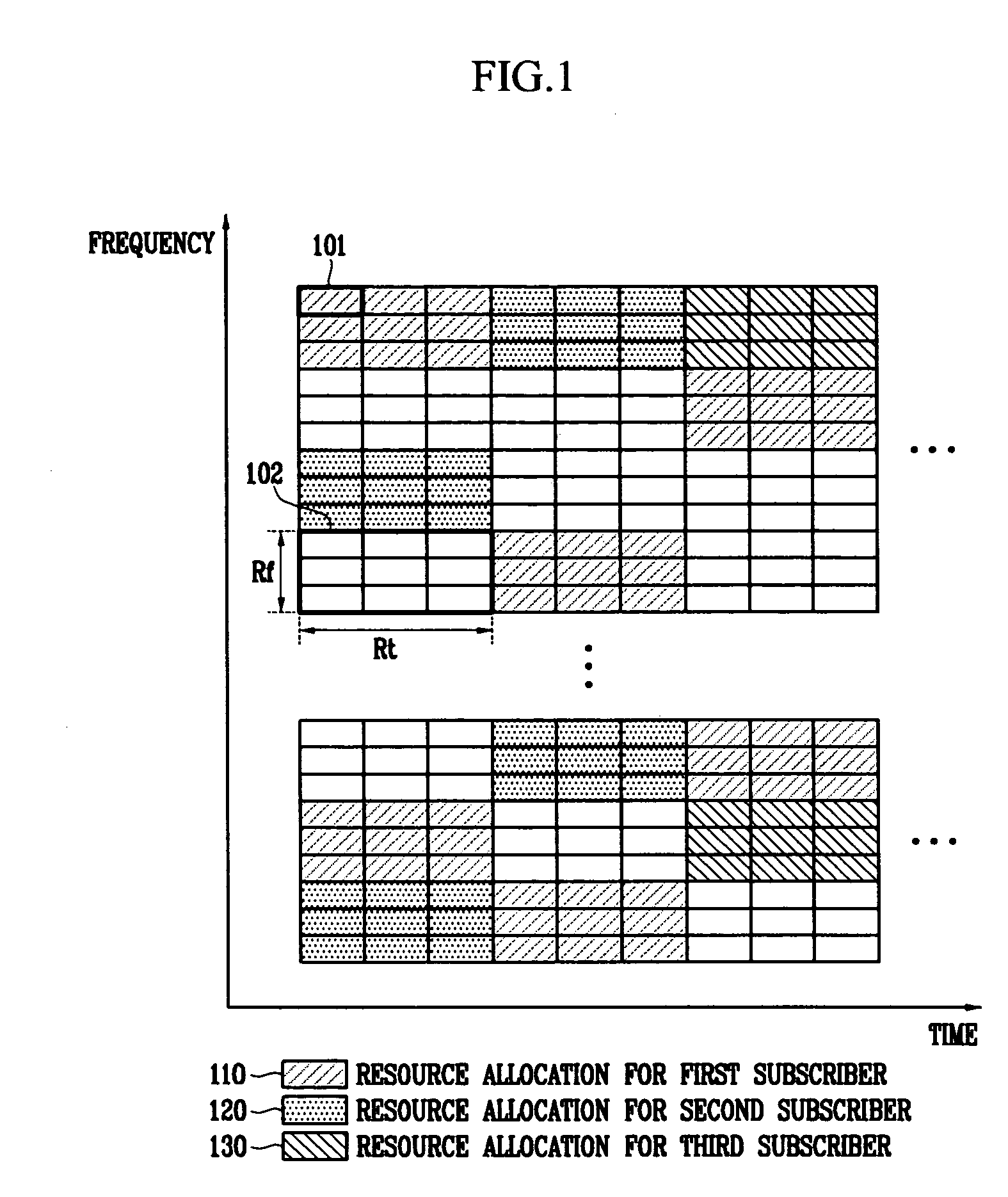
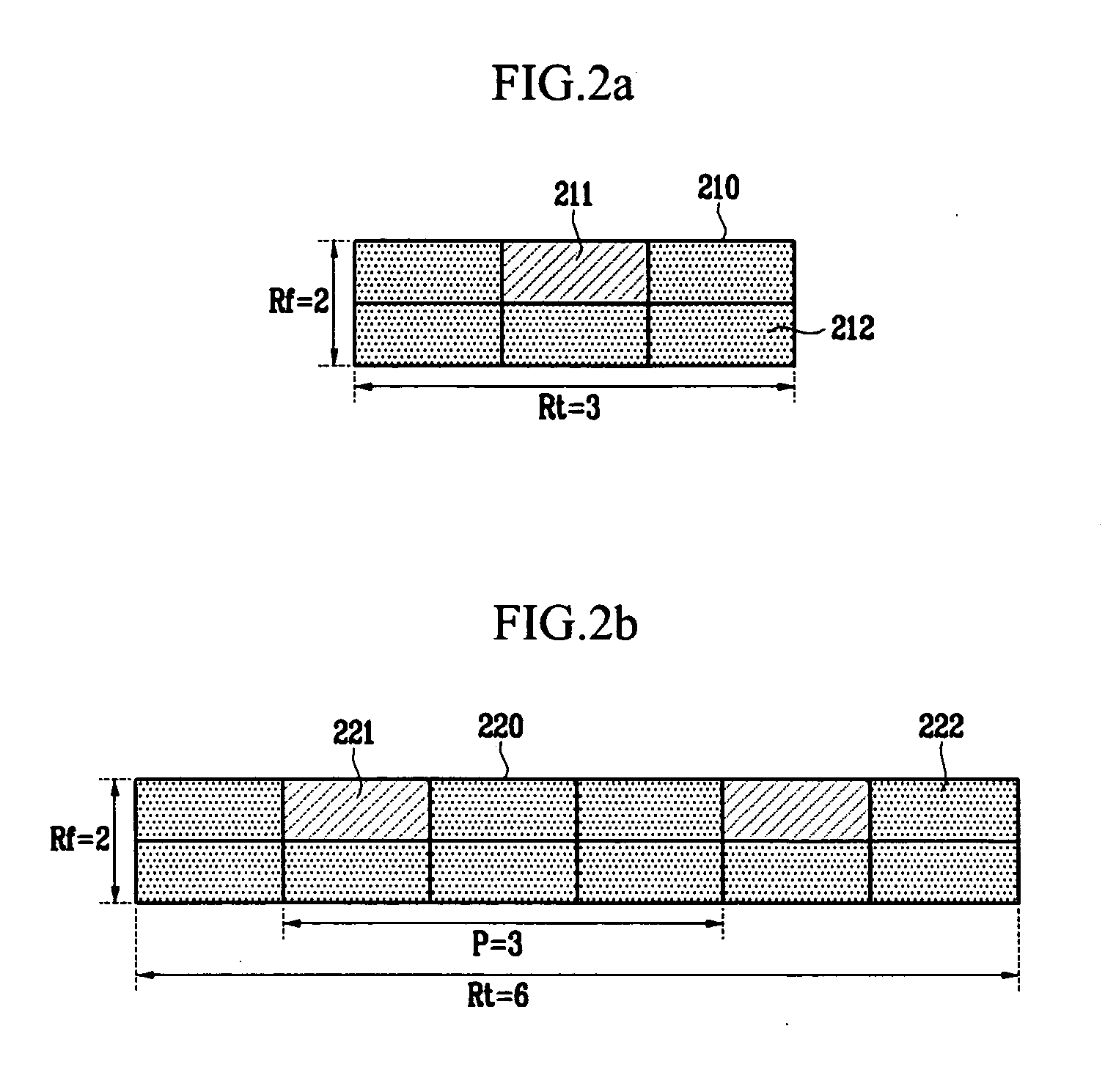
Apparatus for OFDMA transmission and reception for coherent detection in uplink of wireless communication system and method thereof
InactiveUS20050135324A1Improve channel estimation performanceFrequency-division multiplexSecret communicationCommunications systemResource block
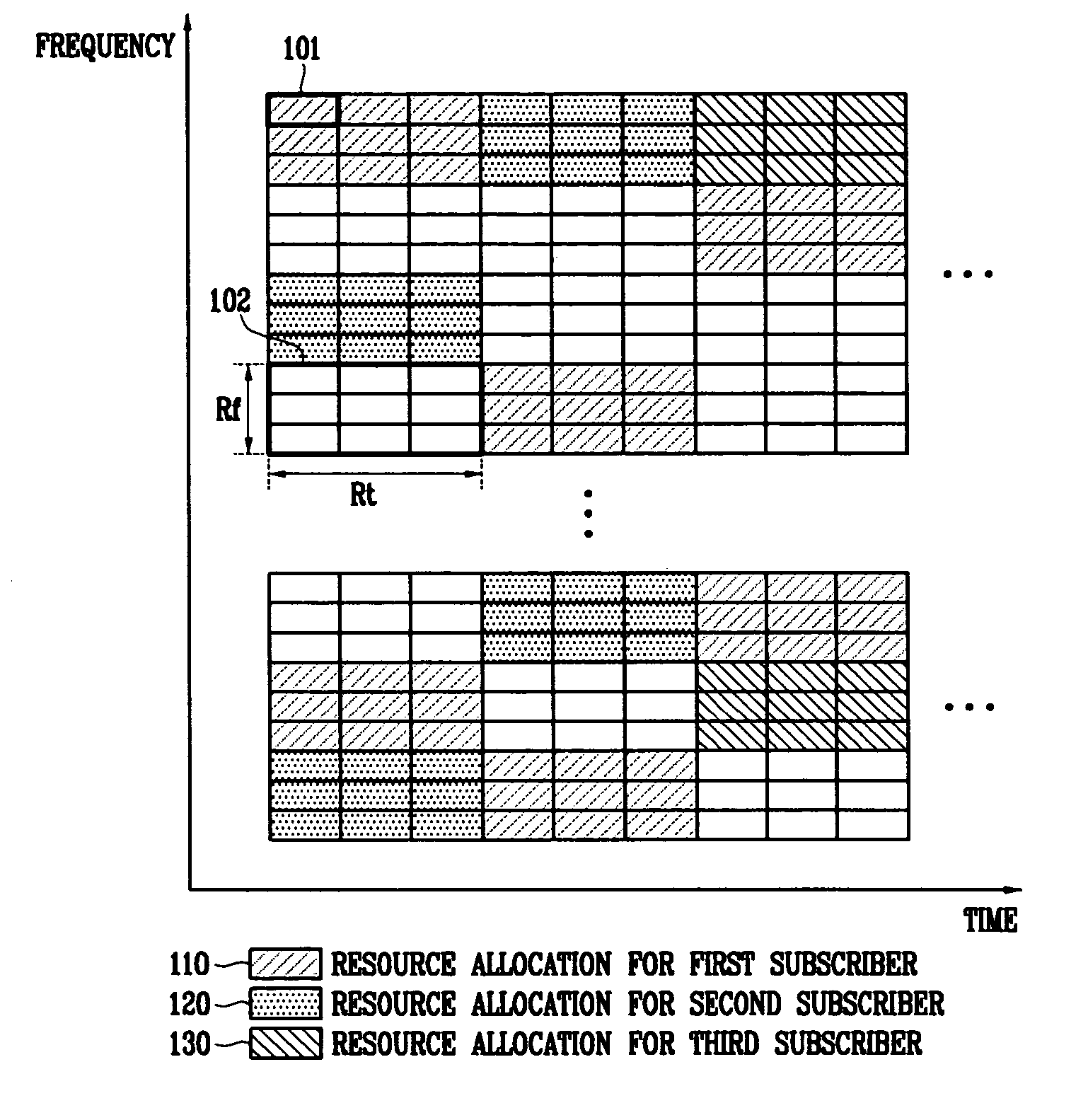
In the resource mapping method for data transmission, a time-frequency resource of a slot interval including OFDM symbols is divided into traffic channels and shared among the subscribers, the traffic channel including resource blocks uniformly distributed in the whole transmit frequency band, the resource block including consecutive subcarriers of consecutive received symbols having at least one inserted pilot symbol. The pilot symbols and the channel-encoded and modulated data symbols are processed by time-frequency mapping according to the resource-block-based mapping method to generate received symbols. The receiver separates the received symbols by subscribers according to the resource-block-based mapping method in a frequency domain, and performs iterative channel estimation, demodulation, and decoding by using the pilot and a data reference value after decoding for each traffic channel.
Owner:ELECTRONICS & TELECOMM RES INST
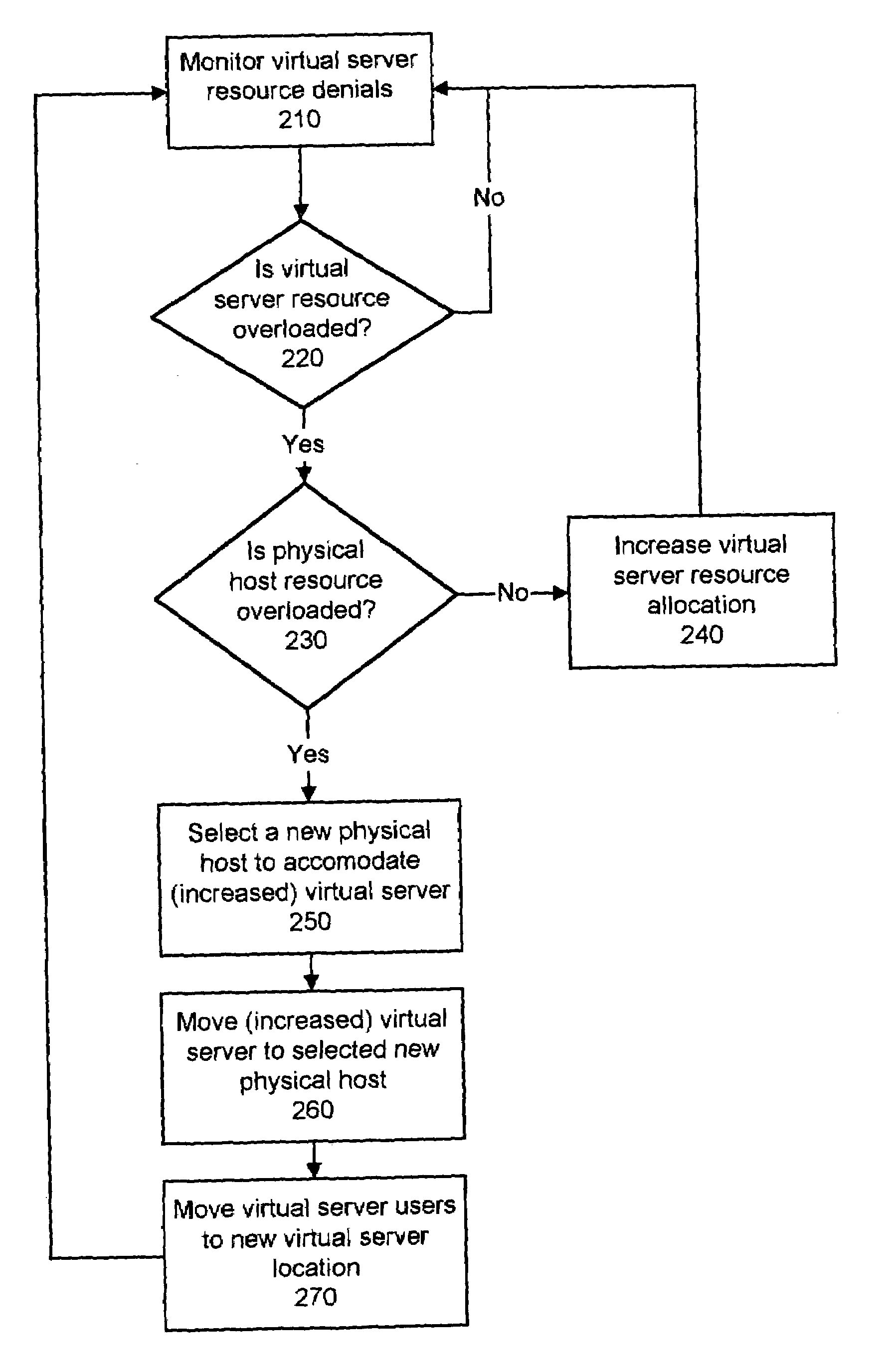
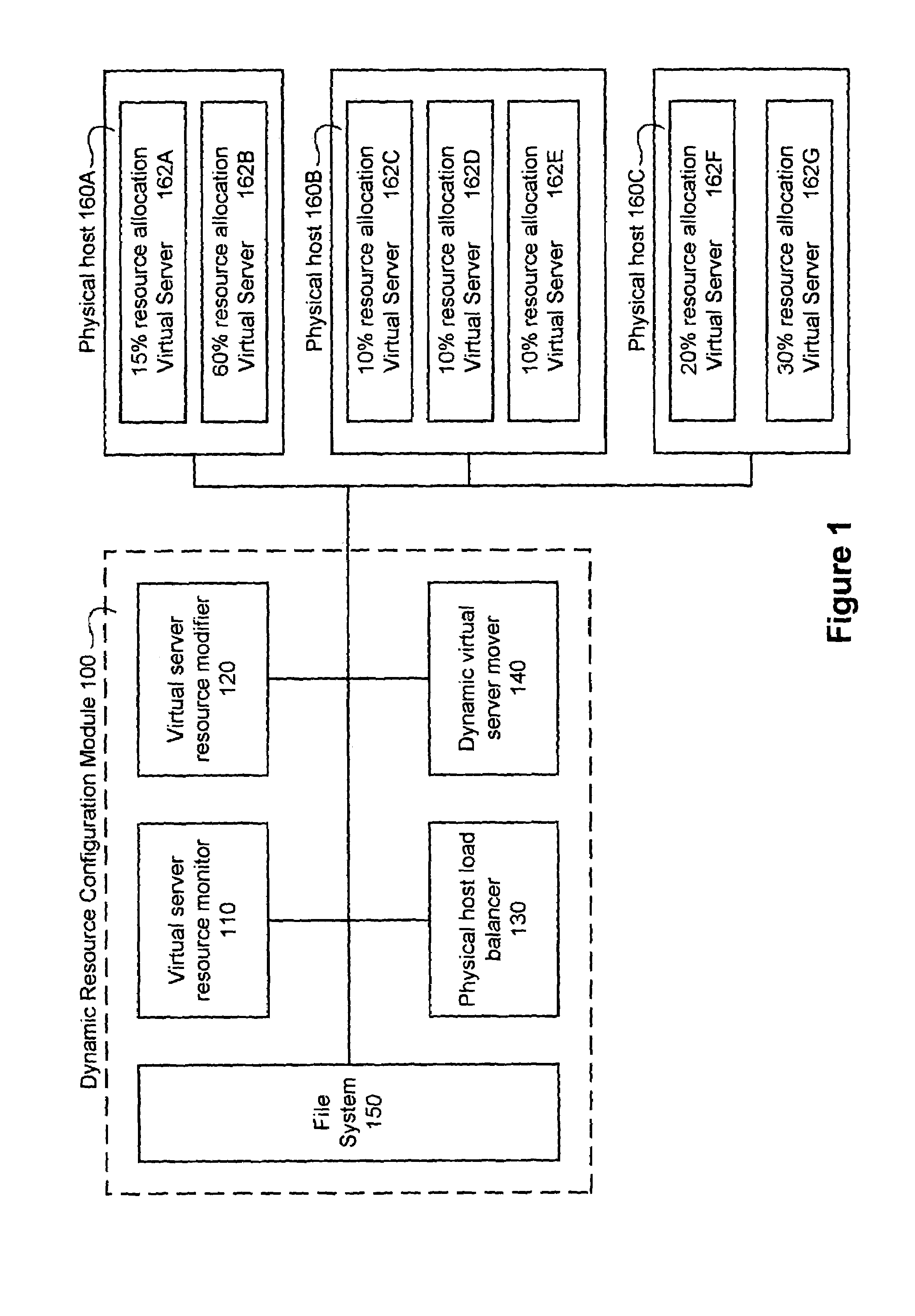
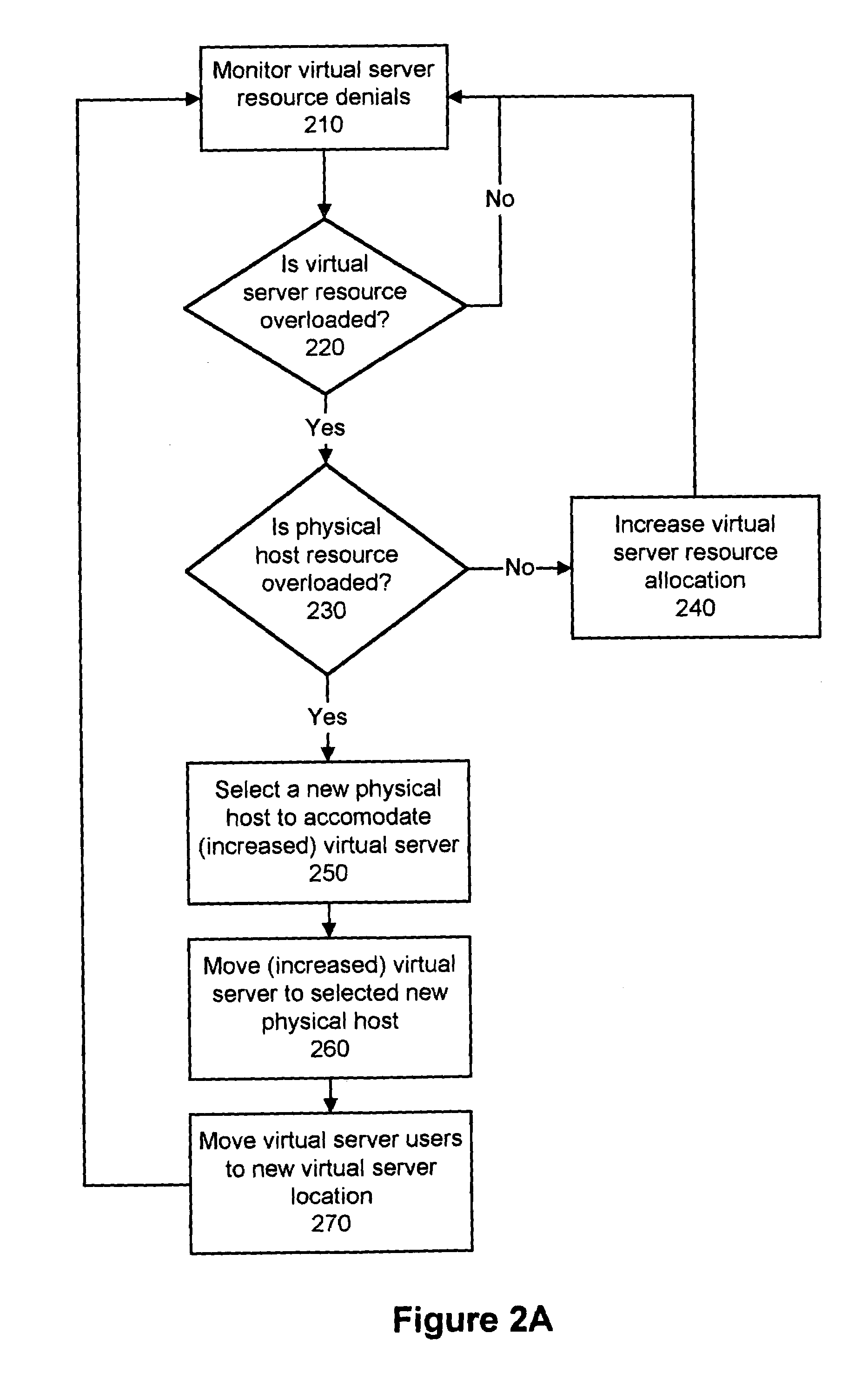
Dynamically modifying the resources of a virtual server
InactiveUS6985937B1Guaranteed service qualityError preventionFrequency-division multiplex detailsQuality of serviceResource based
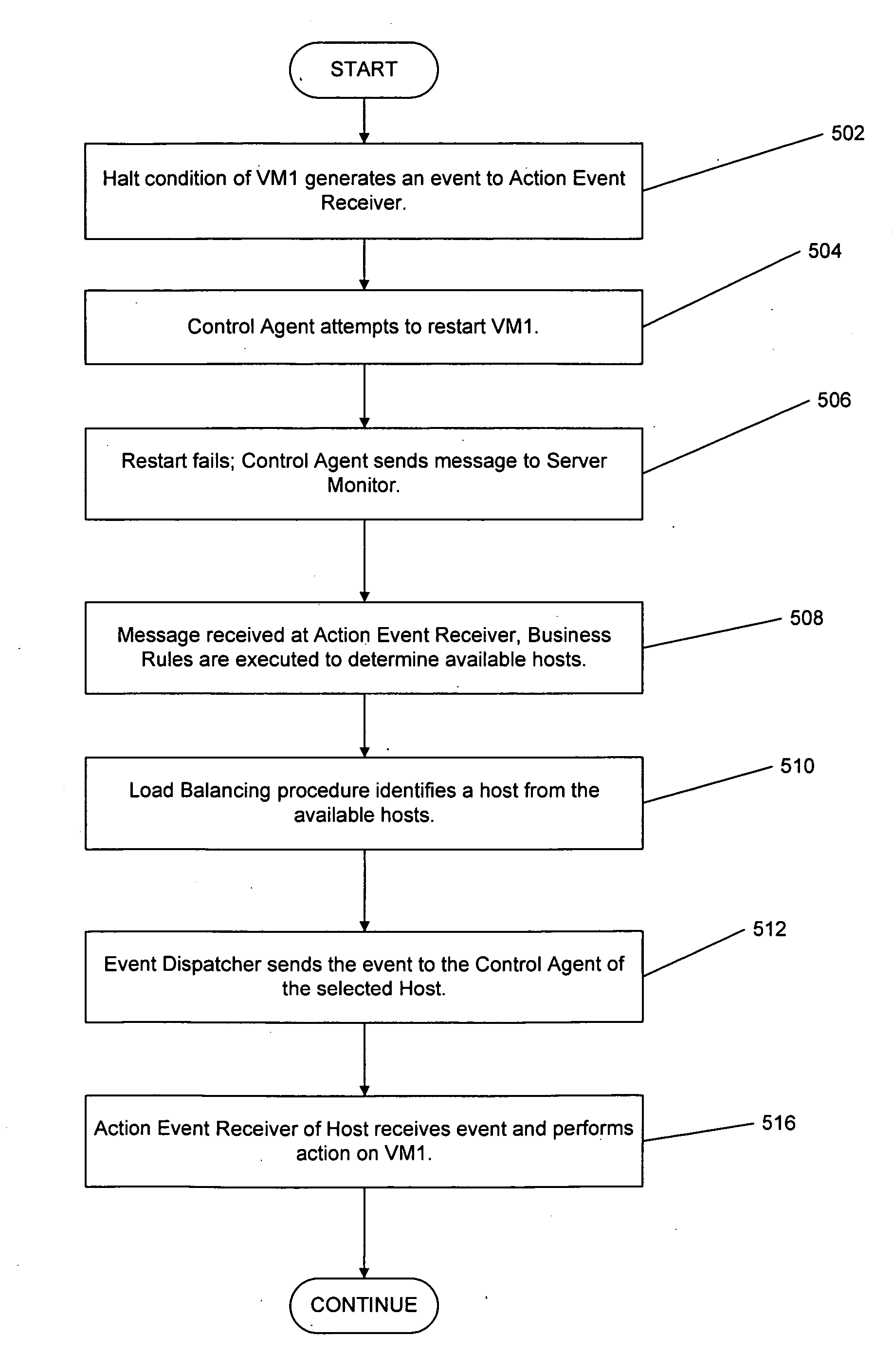
A system and a method dynamically adjusts the quality of service guarantees for virtual servers based upon the resource demands experienced by the virtual servers. Virtual server resource denials are monitored to determine if a virtual server is overloaded based upon the resource denials. Virtual server resources are modified dynamically to respond to the changing resource requirements of each virtual server. Occasionally, a physical host housing a virtual server may not have additional resources to allocate to a virtual server requiring increased resources. In this instance, a virtual server hosted by the overloaded physical host is transferred to another physical host with sufficient resources.
Owner:INTELLECTUAL VENTURES I LLC
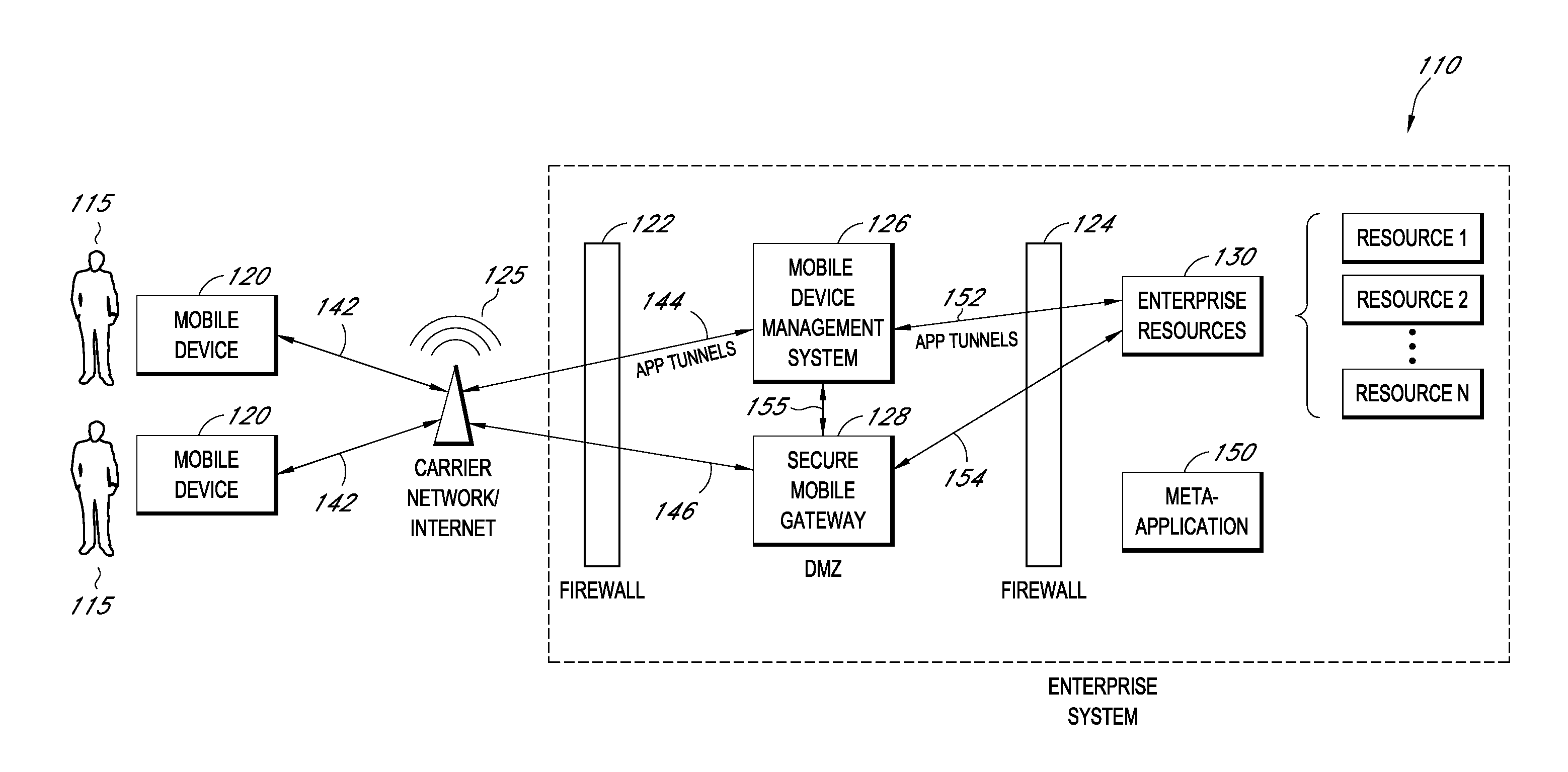
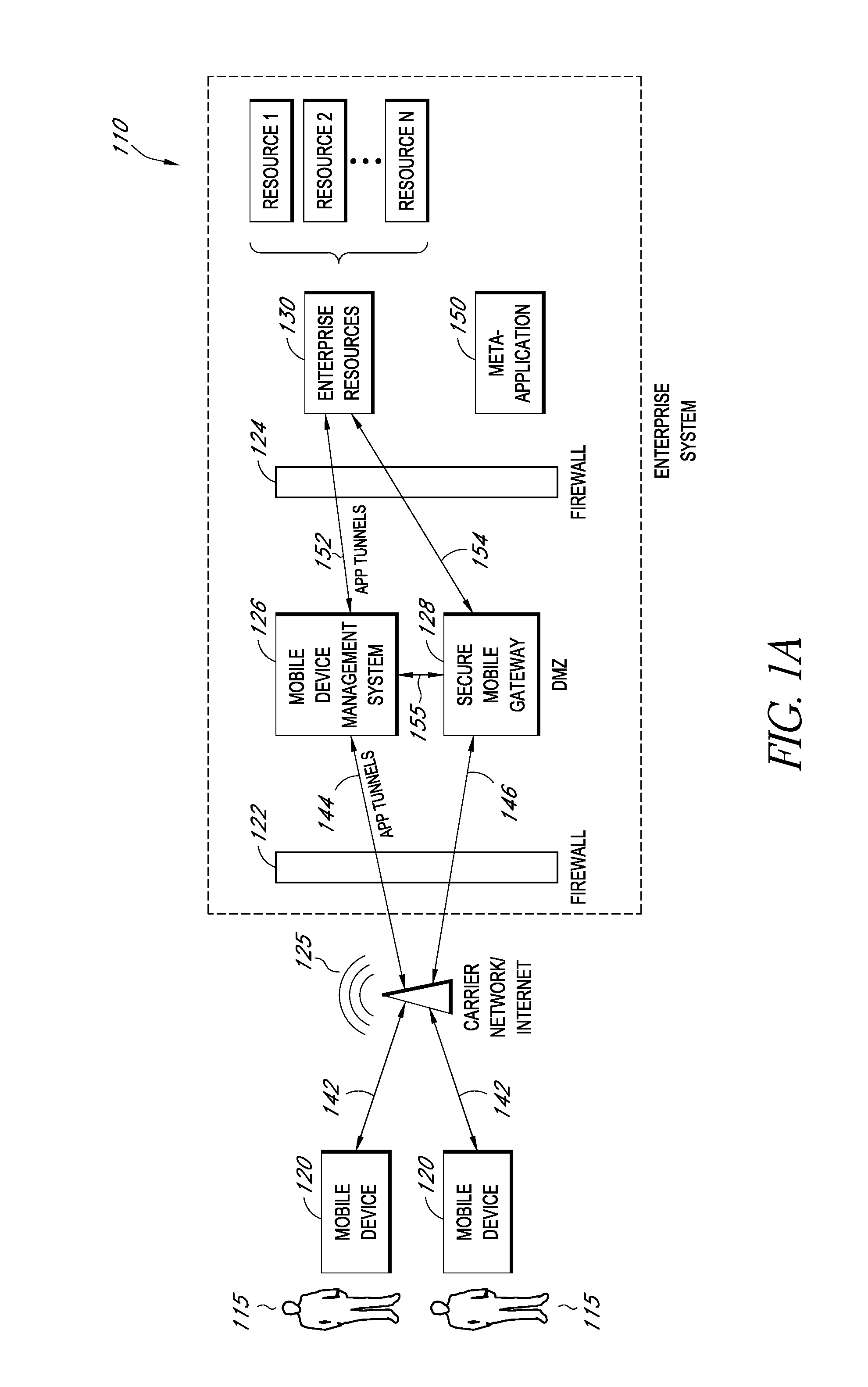
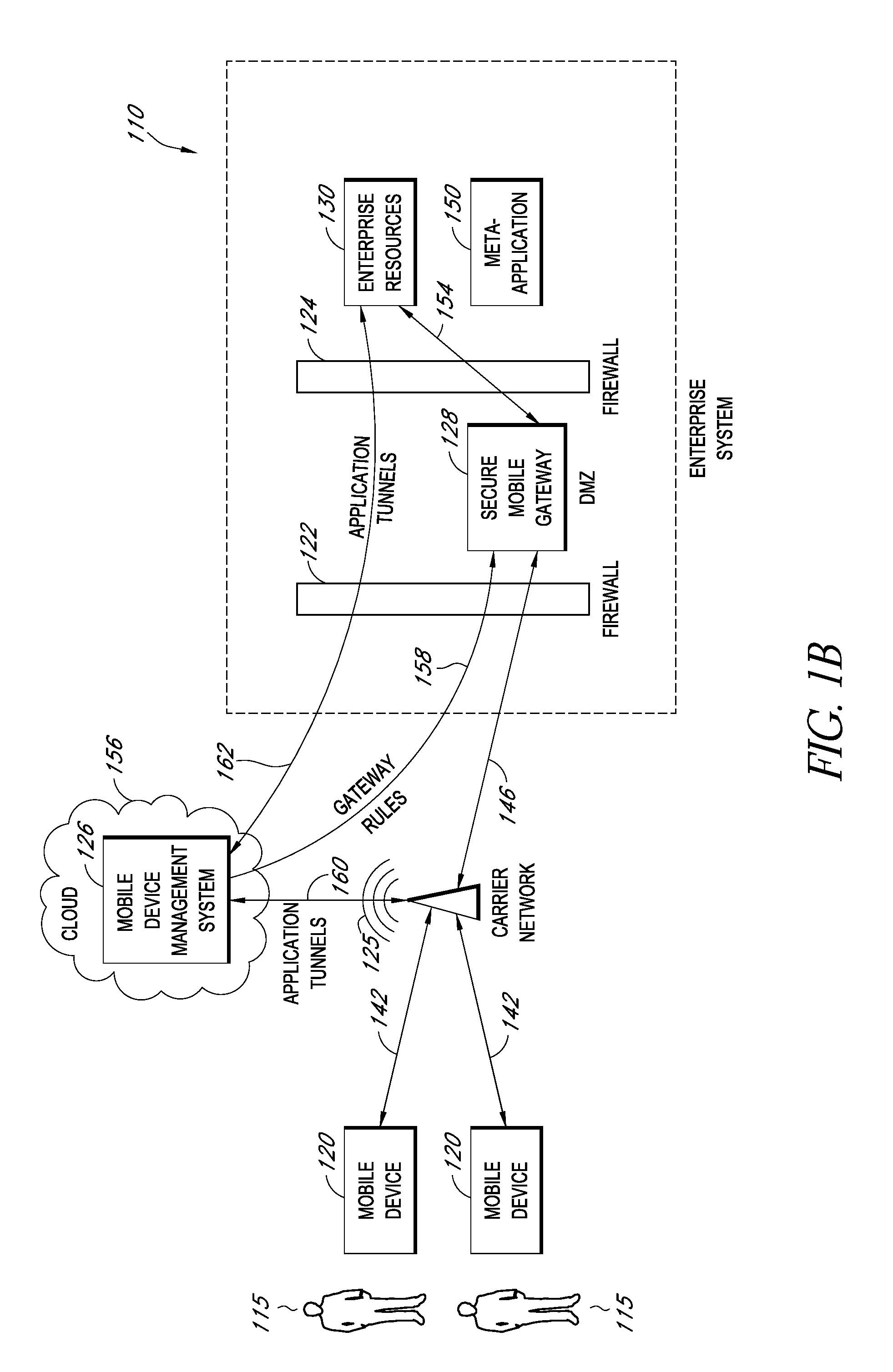
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Method for improving performance in a computer storage system by regulating resource requests from clients
InactiveUS7228354B2Improve performanceTotal system performance requirements can be achieved and guaranteedError detection/correctionMultiprogramming arrangementsResource basedClient-side
Owner:IBM CORP
Dynamic allocation of subframe scheduling for time divison duplex operation in a packet-based wireless communication system
ActiveUS20110211503A1Easy to useError preventionTransmission path divisionCommunications systemResource based
Systems and methods for enabling the dynamic allocation of certain sub frames as downlink or uplink resources in a time division duplexed over the air communications system. A base station or eNB may allocate certain subframes within a repeating radio frame of a TDD configuration as either DL or UL subframes for communicating to user equipment or UE devices to increase efficient use of system resources based on the data to be transmitted. Methods for determining the capabilities of a selected UE and based on the determining step, dynamically allocating certain subframes are disclosed. The methods and systems are compatible with user equipment that does not support the dynamic allocation of subframes.
Owner:NOKIA TECHNOLOGLES OY
Controlling resource access based on user gesturing in a 3D captured image stream of the user
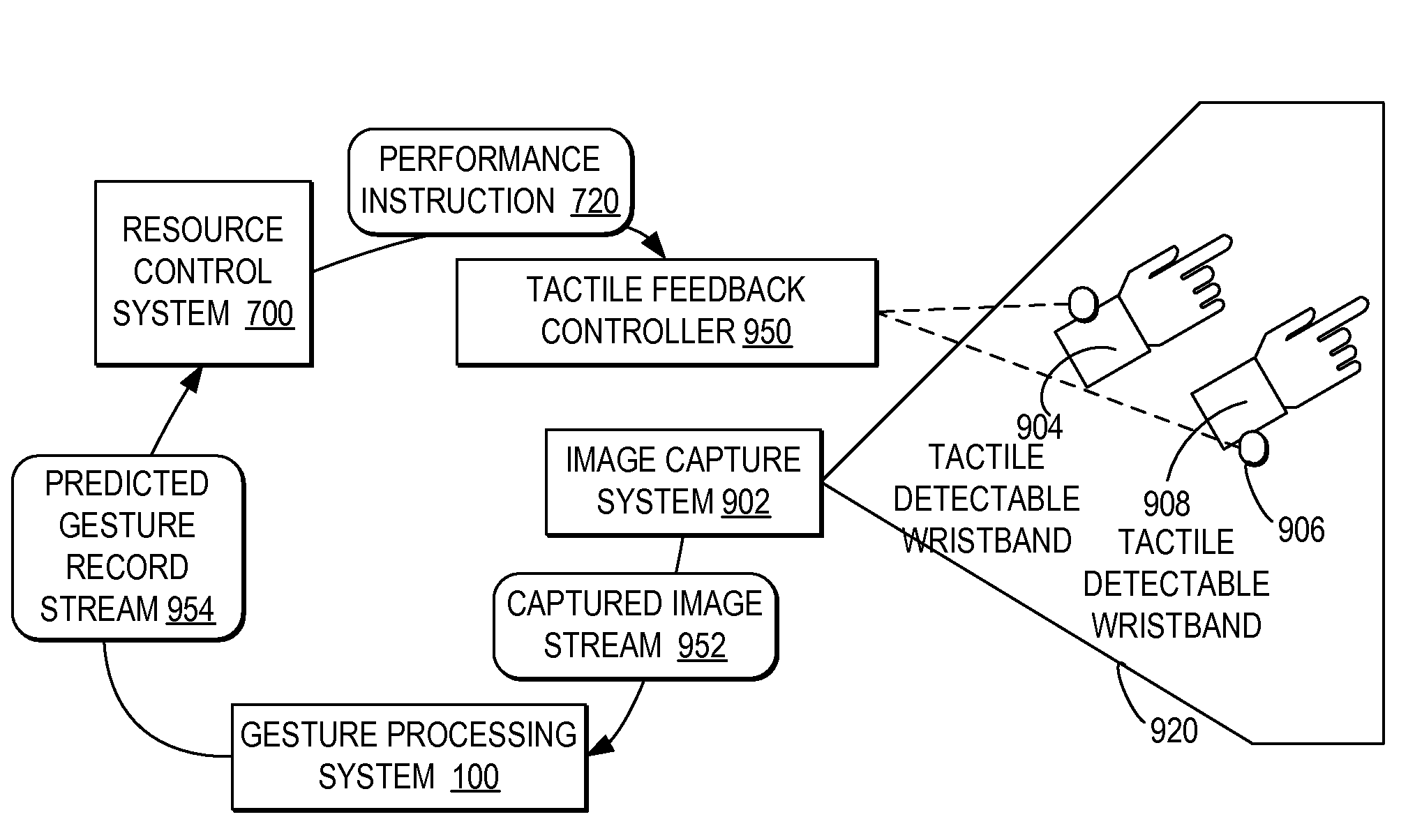
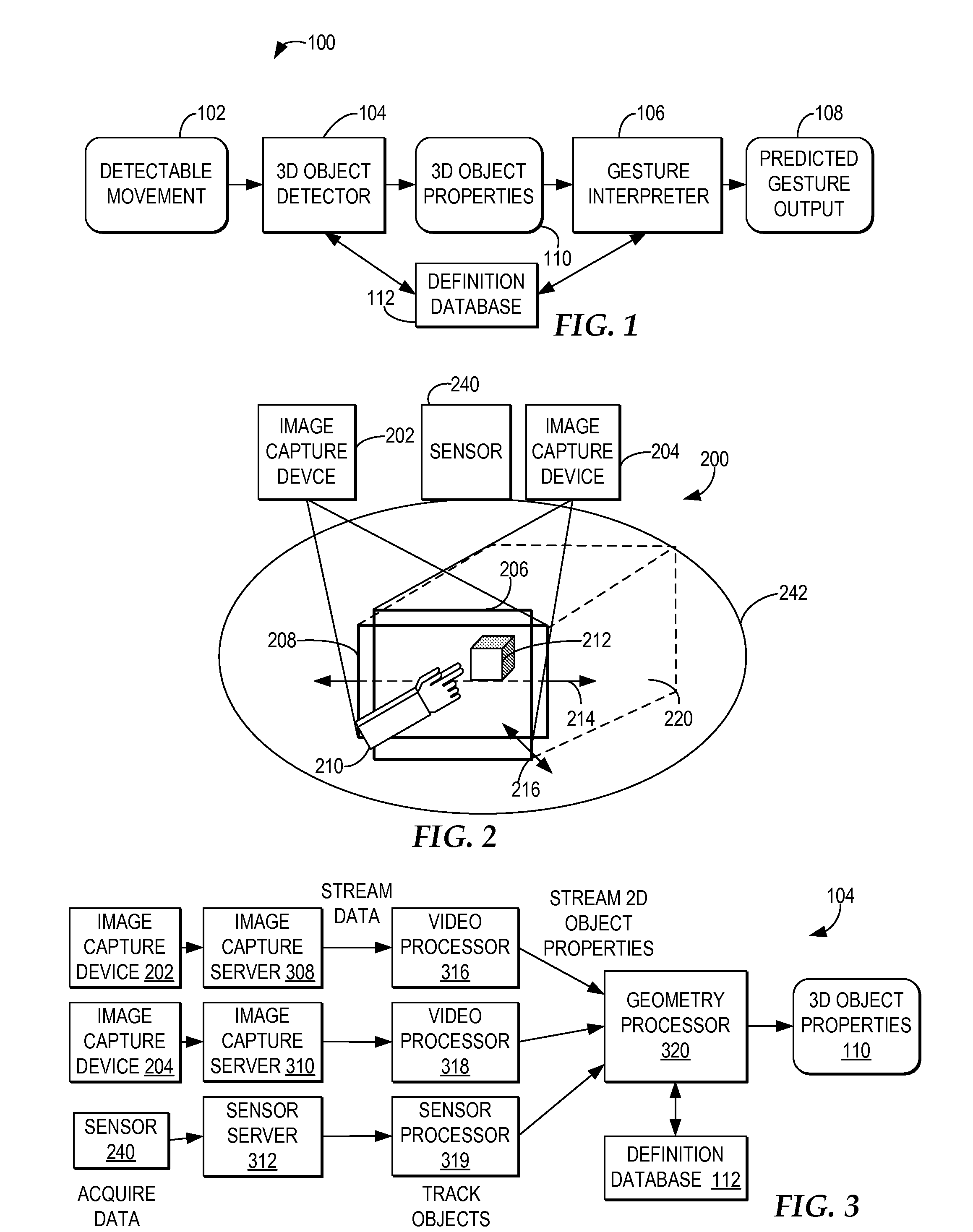
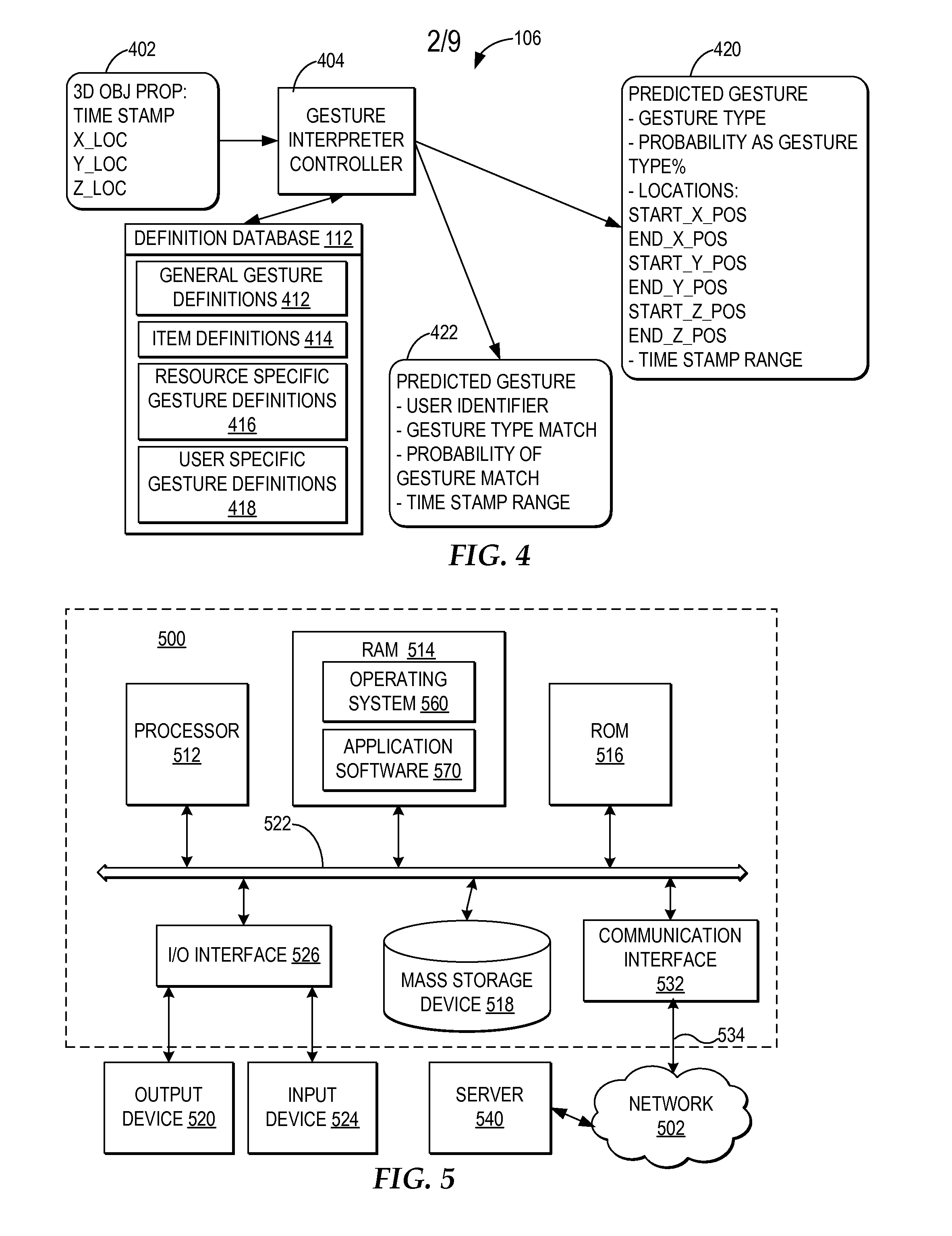
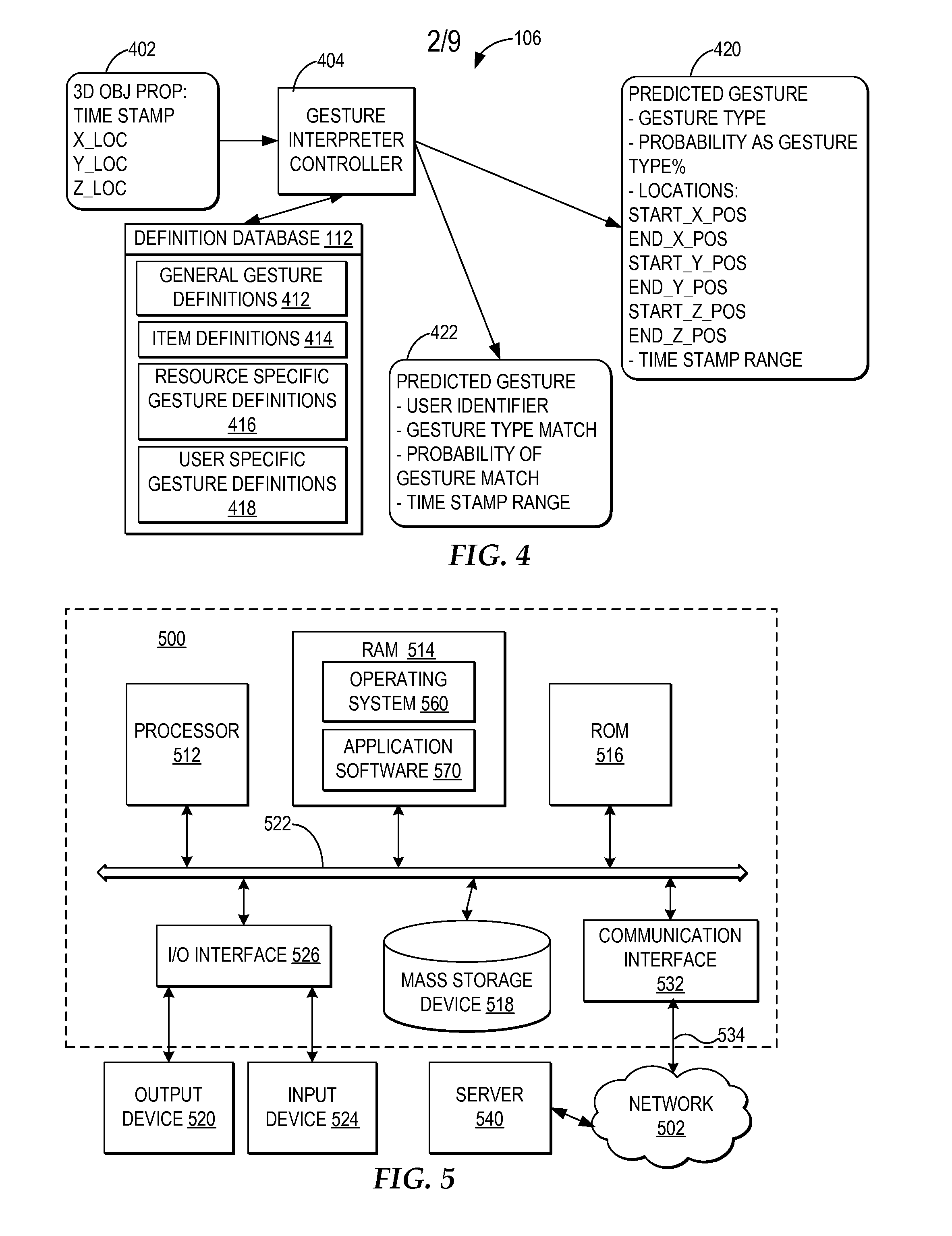
ActiveUS20080170776A1Improved resource securityIncrease resourcesCharacter and pattern recognitionMultiple digital computer combinationsControl systemResource based
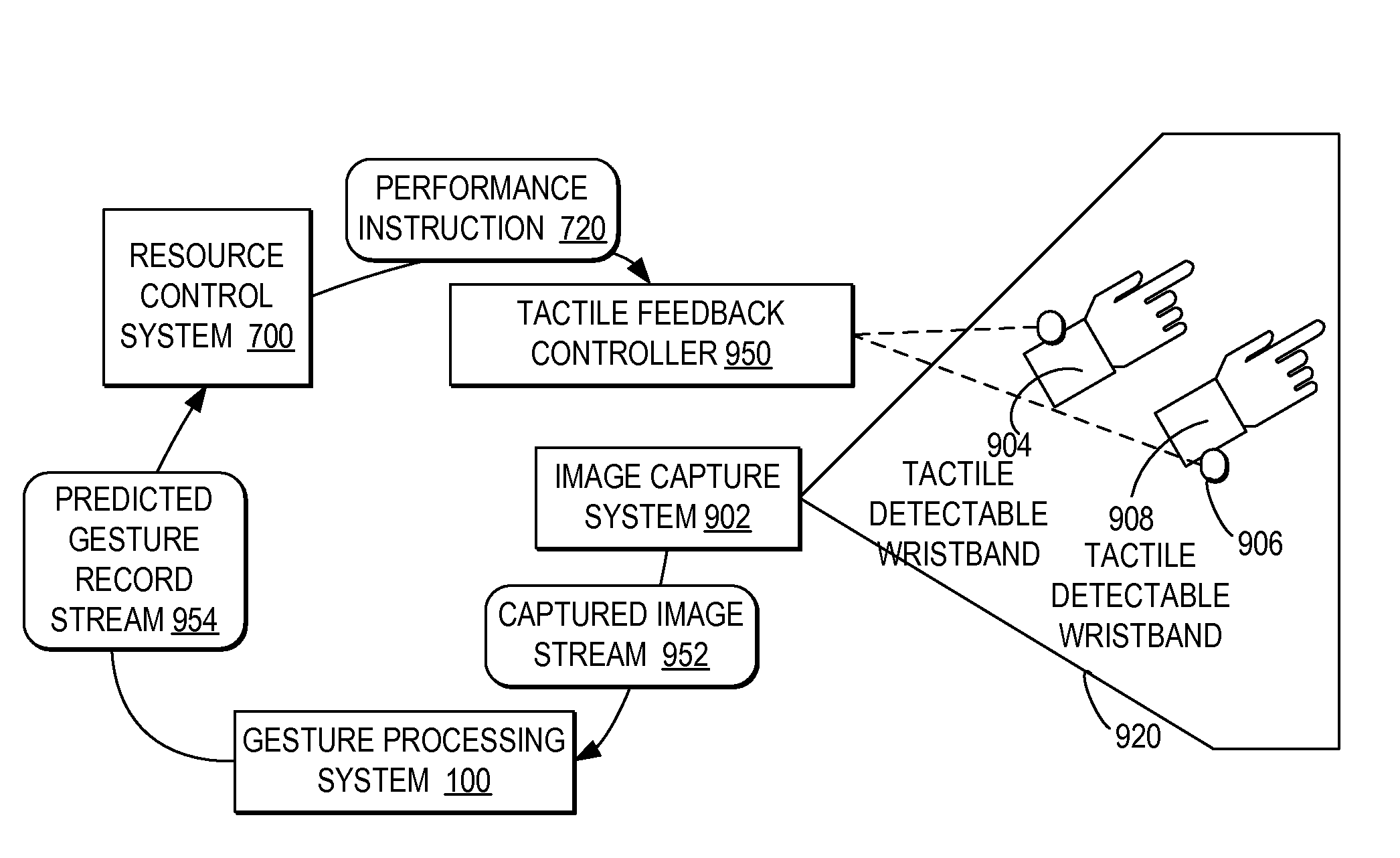
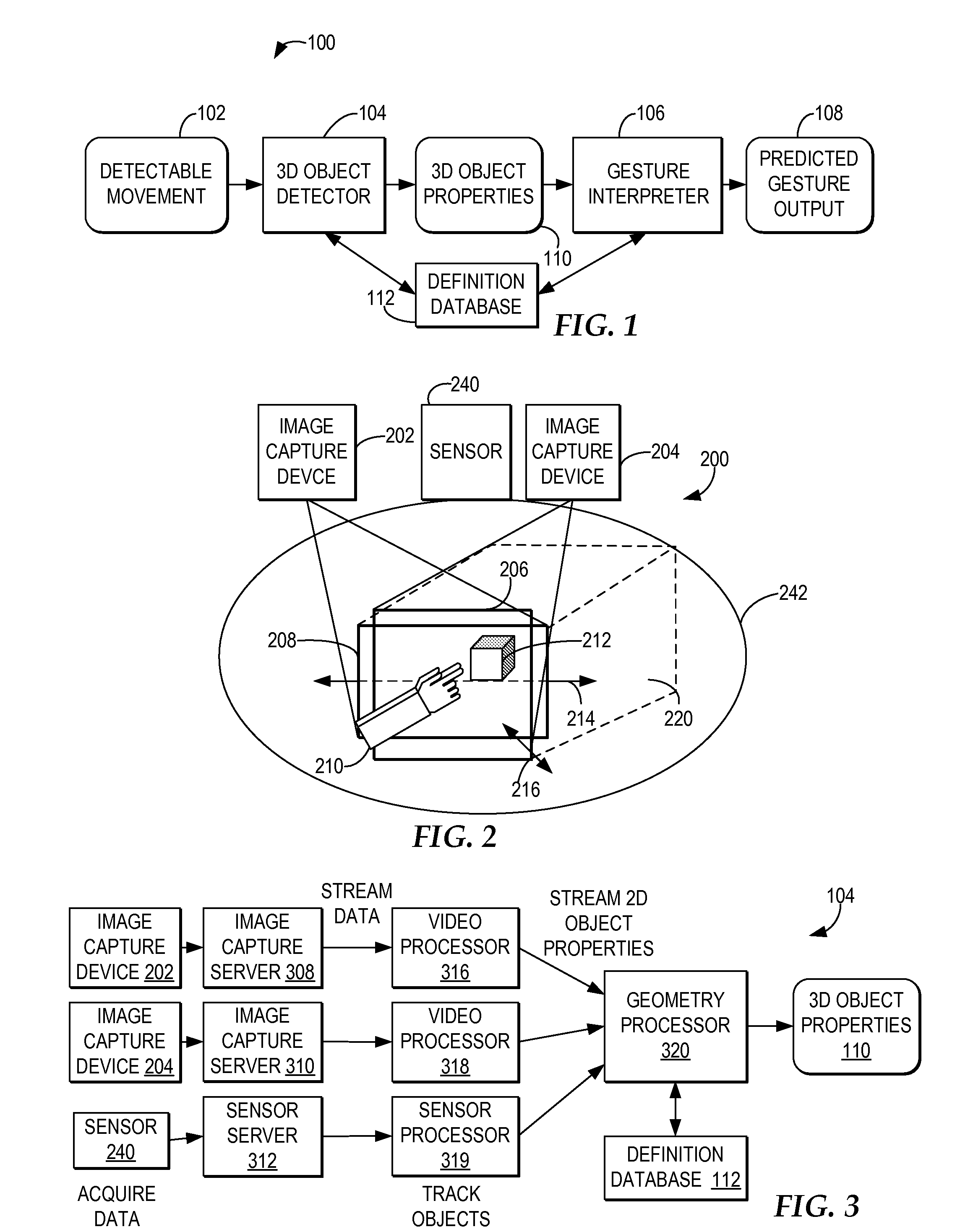
A computer-implemented method, system, and program product comprises a gesture processing system for capturing a three-dimensional movement of a user, wherein the three-dimensional movement is determined using at least one stereoscopic image device aimed at the user to identify and track at least one particular three-dimensional movement of the user. The gesture processing system predicts at least one defined movement within the captured three-dimensional movement matching at least one gesture definition of at least one gesture type from among a plurality of gesture definitions. A resource control system receives a request to access a resource based on the predicted at least one gesture type. The resource control system only allows user access to the resource by matching the predicted at least one gesture type with at least one required gesture type.
Owner:SNAP INC
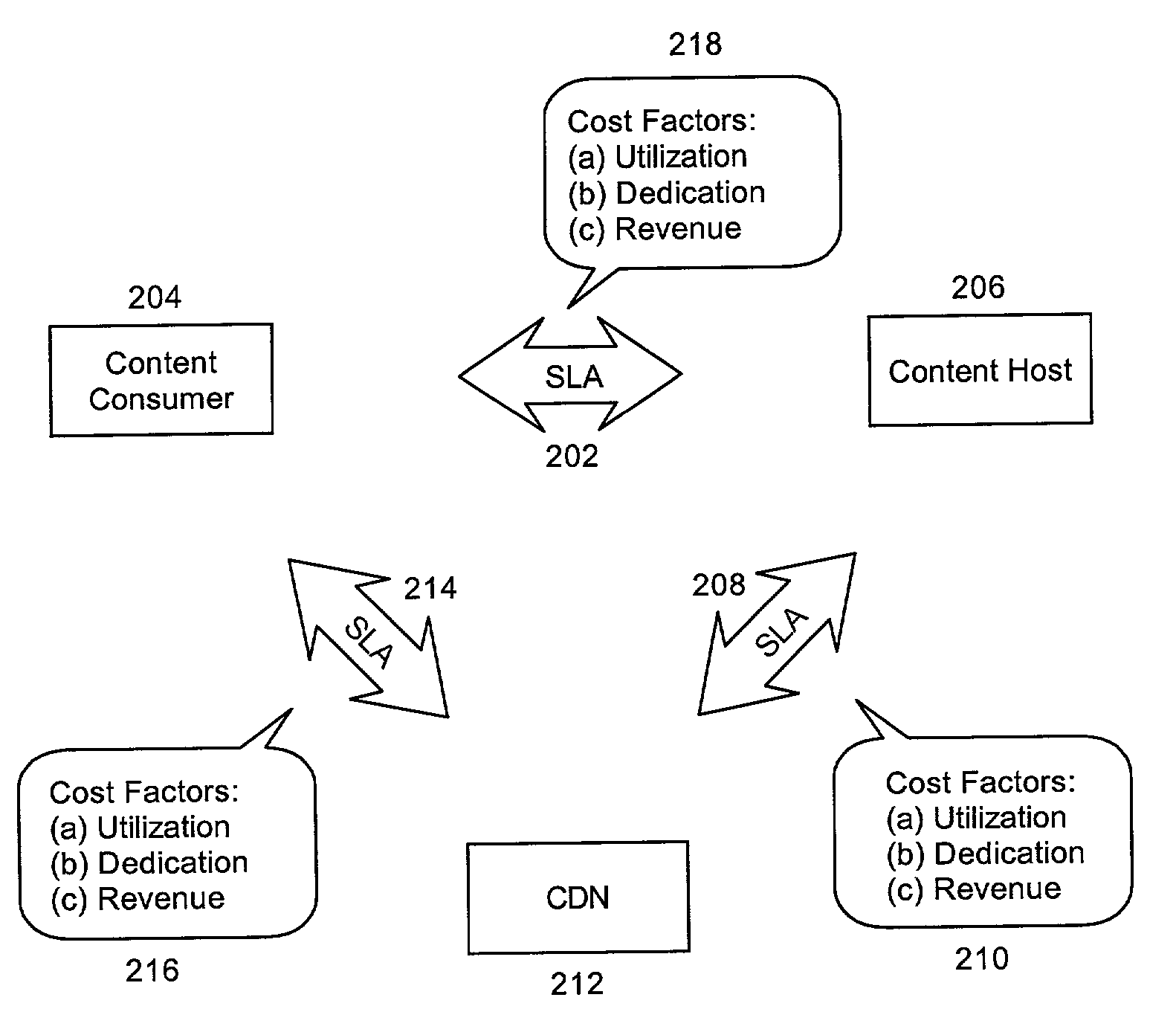
Multi-tier service level agreement method and system
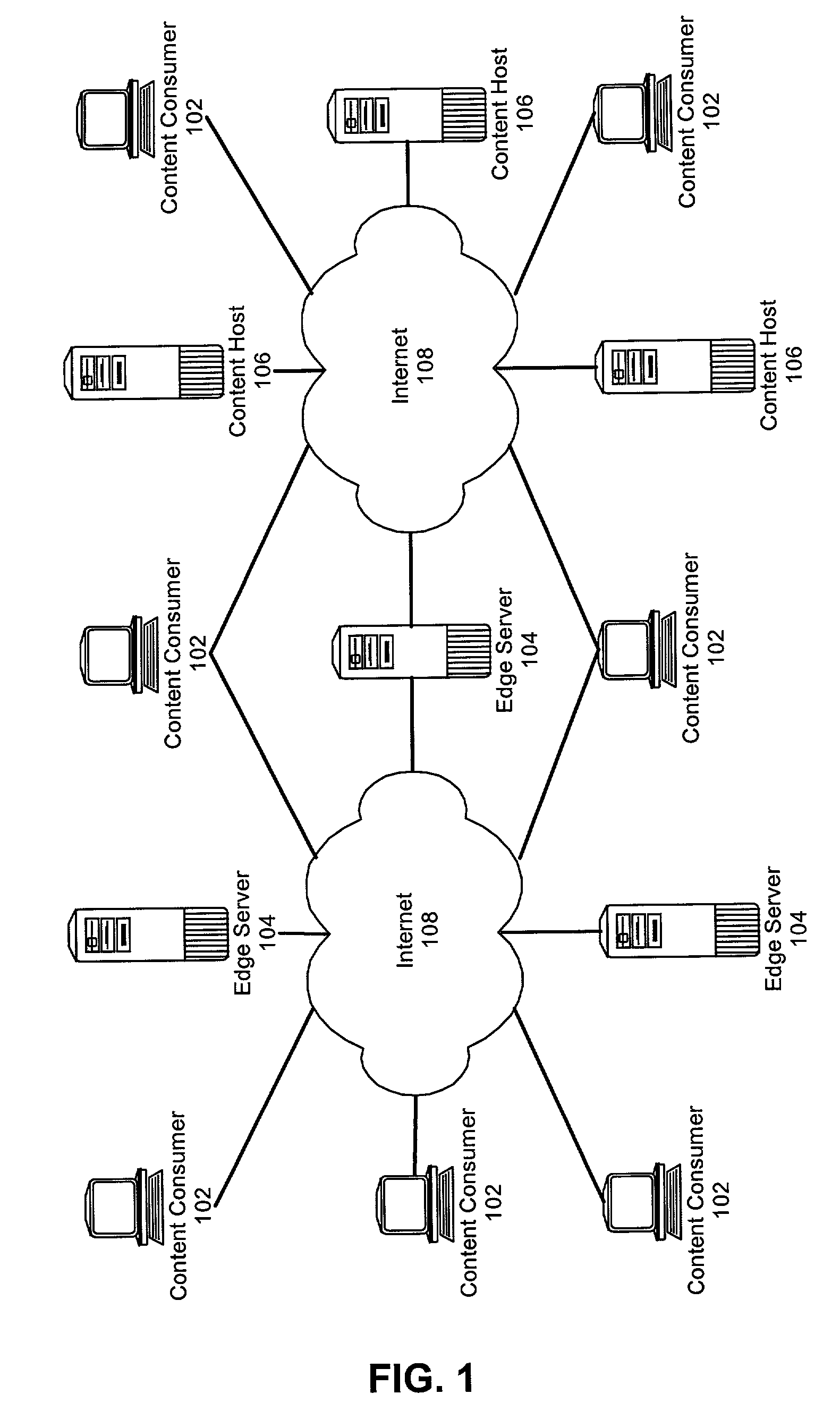
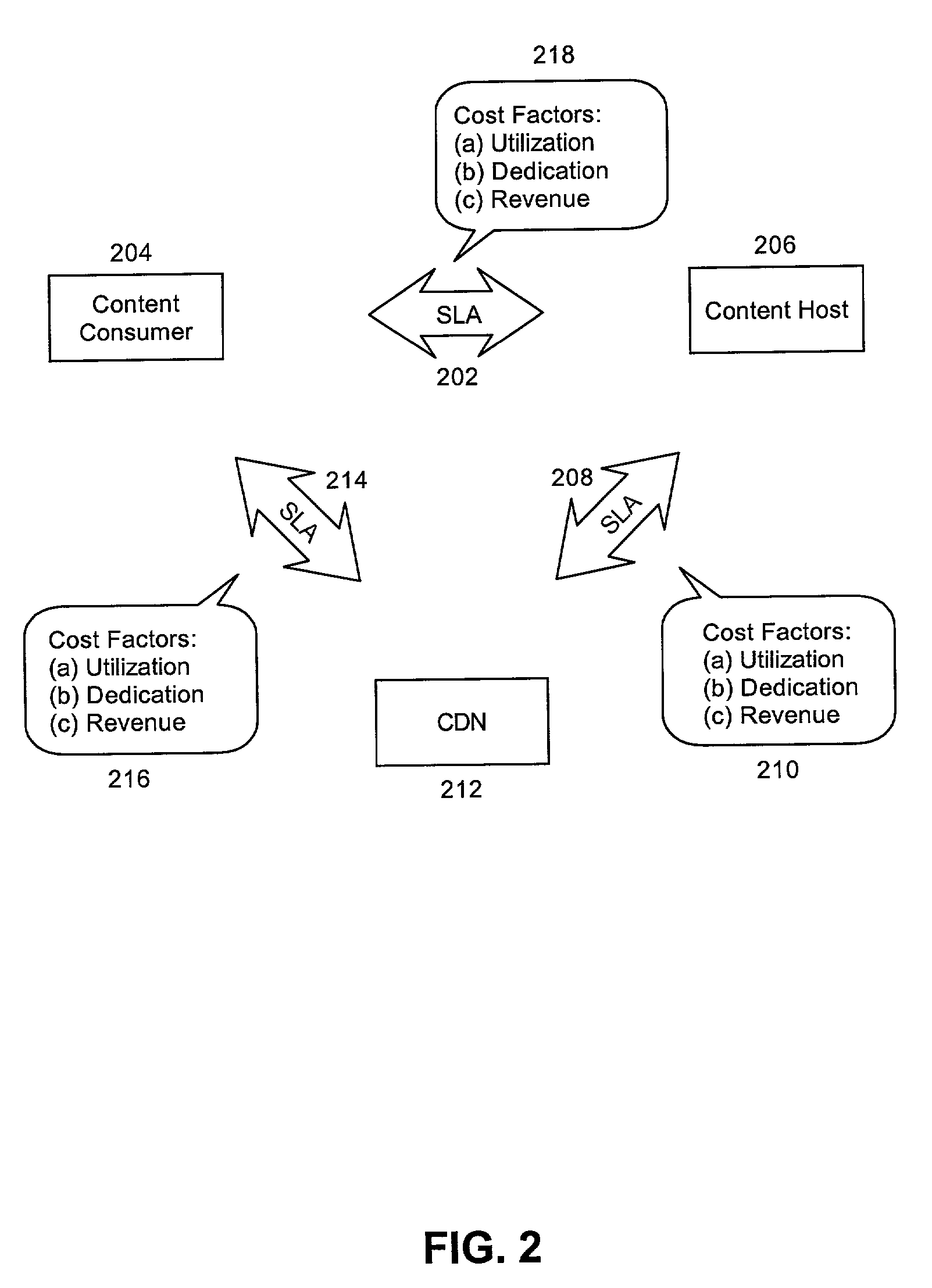
ActiveUS7099936B2Overcome limitationsMultiple digital computer combinationsResourcesService-level agreementEdge server
A method for managing multi-tier SLA relationships. The method can include first computing costs of utilizing edge server resources in a CDN, costs of dedicating content host resources in a content host in lieu of the utilization, and prospective revenues which can be generated by the content host providing services based on the resources to content consumers. Minimum QoS levels can be identified which must be maintained when providing the services to the content consumers according to QoS terms in established SLAs between the content host and individual ones of the content consumers. Finally, a new SLA can be established between the content host and the CDN. Importantly, the new SLA can include QoS terms for selectively allocating resources in the CDN. Moreover, the QoS terms can optimize revenues generated by the content host providing services based on the selective allocation of resources and the computed costs.
Owner:IBM CORP
Controlling resource access based on user gesturing in a 3D captured image stream of the user
ActiveUS7971156B2Increase resourcesCharacter and pattern recognitionMultiple digital computer combinationsControl systemResource based
A computer-implemented method, system, and program product comprises a gesture processing system for capturing a three-dimensional movement of a user, wherein the three-dimensional movement is determined using at least one stereoscopic image device aimed at the user to identify and track at least one particular three-dimensional movement of the user. The gesture processing system predicts at least one defined movement within the captured three-dimensional movement matching at least one gesture definition of at least one gesture type from among a plurality of gesture definitions. A resource control system receives a request to access a resource based on the predicted at least one gesture type. The resource control system only allows user access to the resource by matching the predicted at least one gesture type with at least one required gesture type.
Owner:SNAP INC
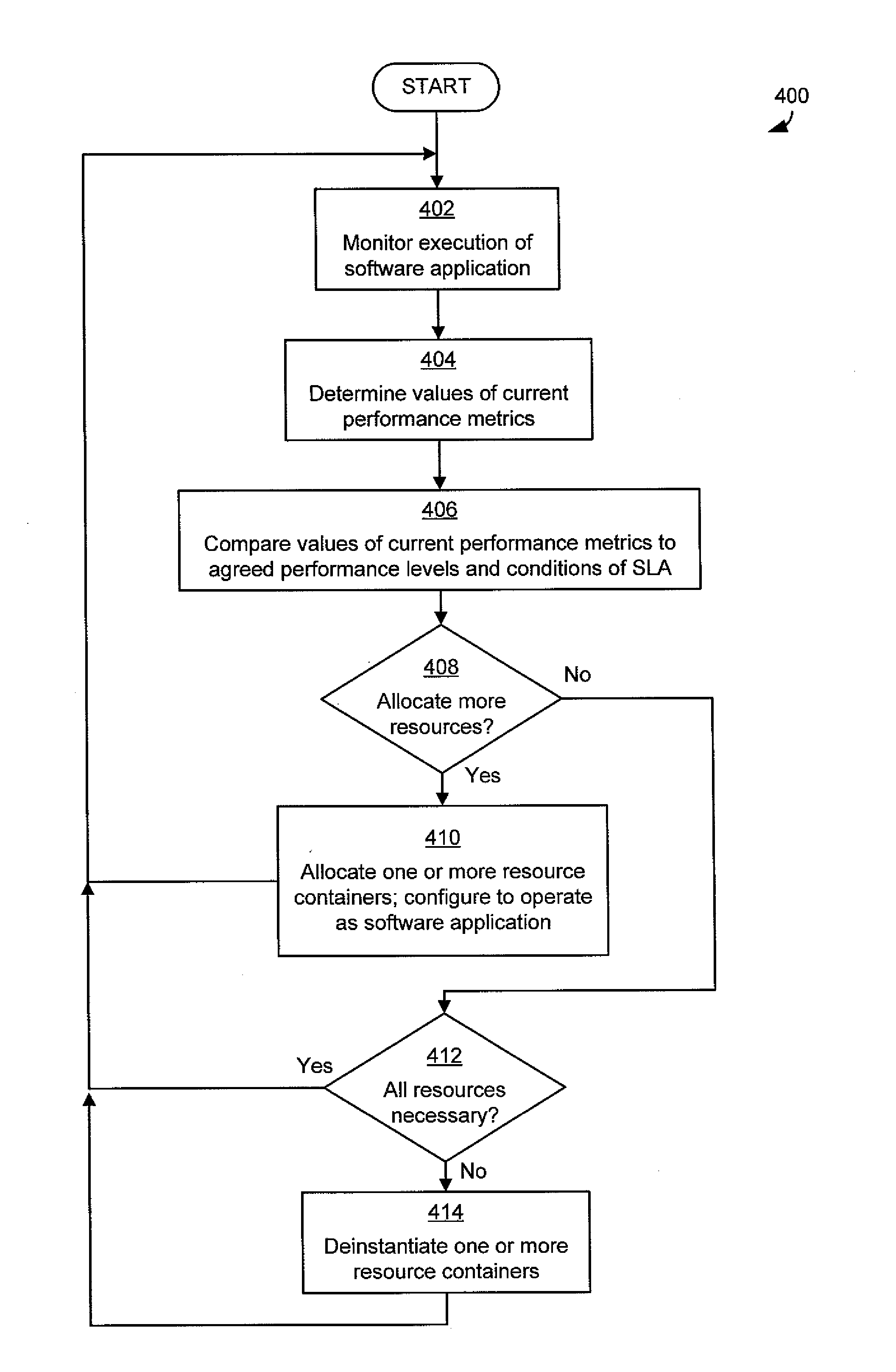
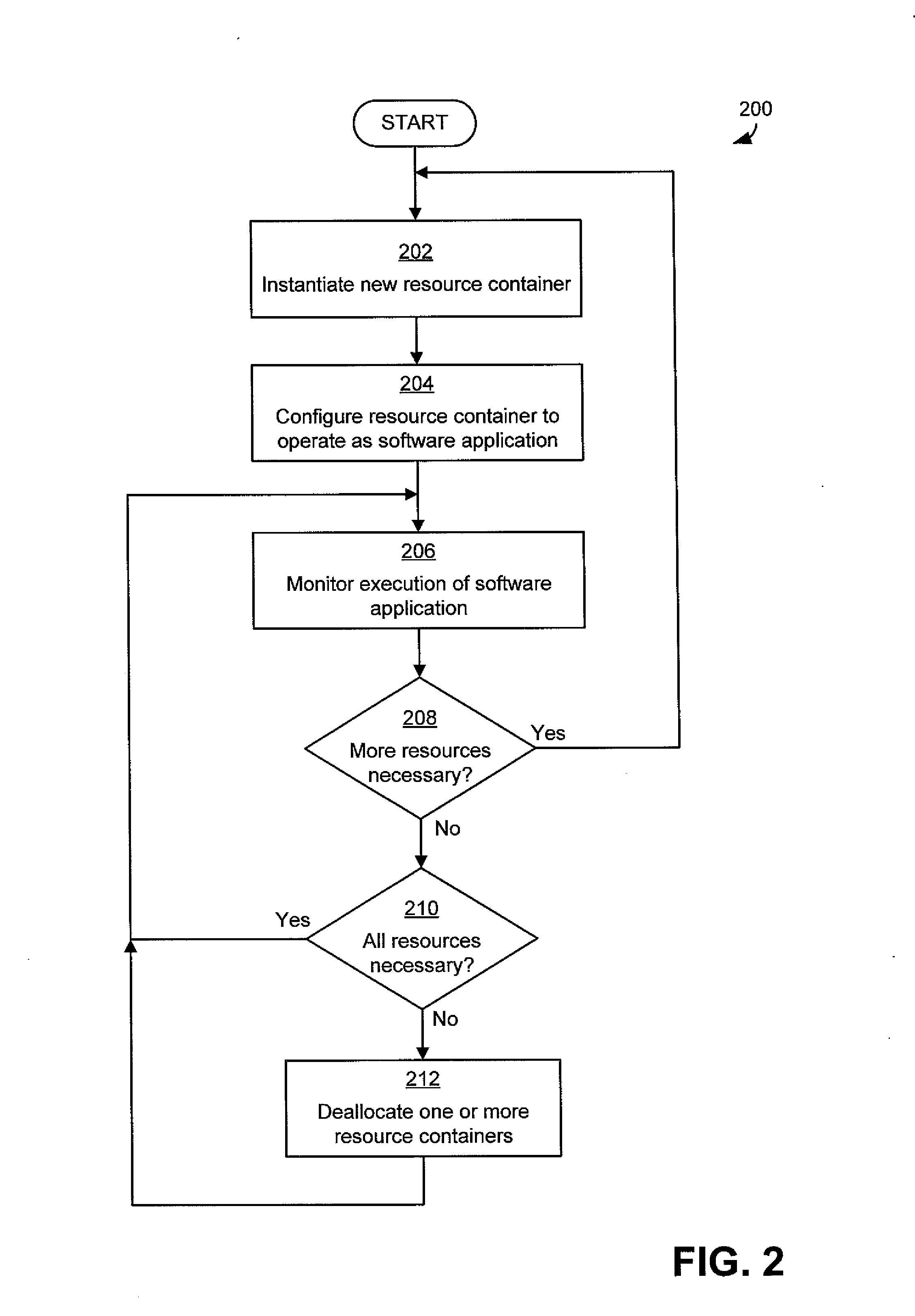
Resource management for cloud computing platforms
ActiveUS20120331113A1Reduce complexityGood flexibilityDigital computer detailsProgram controlService-level agreementService level requirement
A system for managing allocation of resources based on service level agreements between application owners and cloud operators. Under some service level agreements, the cloud operator may have responsibility for managing allocation of resources to the software application and may manage the allocation such that the software application executes within an agreed performance level. Operating a cloud computing platform according to such a service level agreement may alleviate for the application owners the complexities of managing allocation of resources and may provide greater flexibility to cloud operators in managing their cloud computing platforms.
Owner:MICROSOFT TECH LICENSING LLC
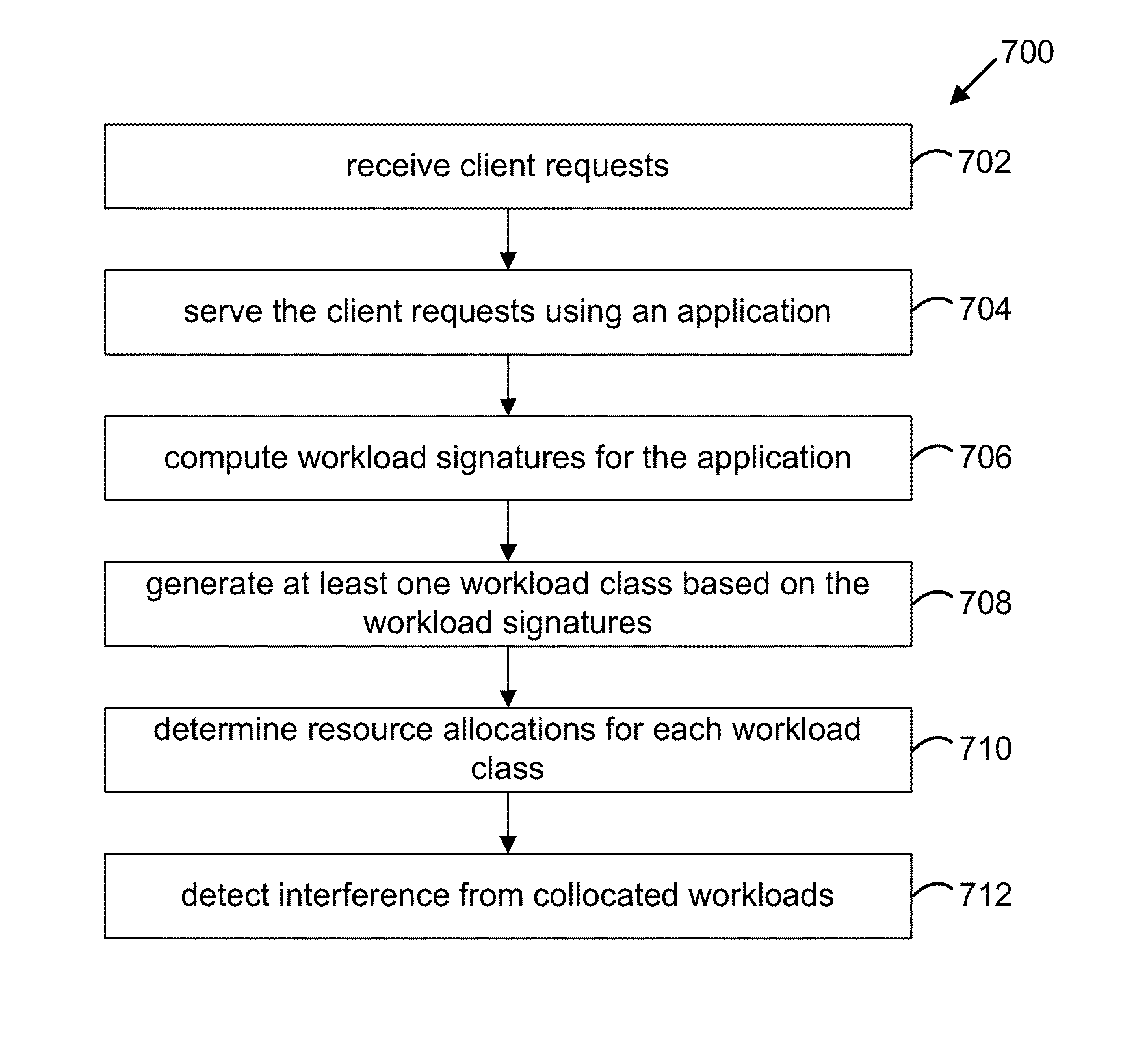
Accelerating resource allocation in virtualized environments using workload classes and/or workload signatures
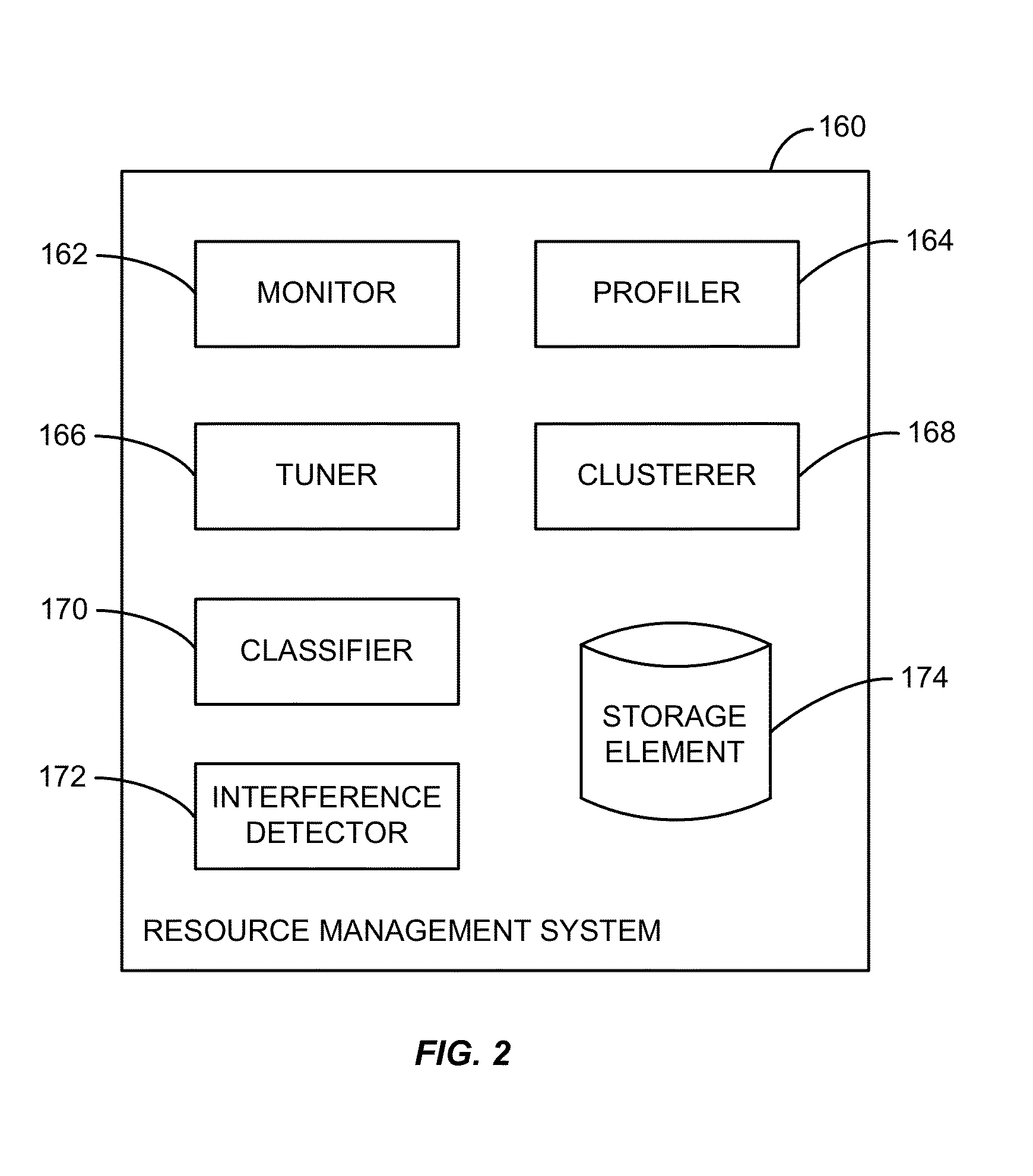
Systems, methods, and apparatus for managing resources assigned to an application or service. A resource manager maintains a set of workload classes and classifies workloads using workload signatures. In specific embodiments, the resource manager minimizes or reduces resource management costs by identifying a relatively small set of workload classes during a learning phase, determining preferred resource allocations for each workload class, and then during a monitoring phase, classifying workloads and allocating resources based on the preferred resource allocation for the classified workload. In some embodiments, interference is accounted for by estimating and using an “interference index”.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL) +1
Method, apparatus and system for a location-based uniform resource locator
An aspect of the present invention is a method for routing content information to a mobile user or client application. The method preferably comprises re-directing a user request to one or more gateway servers provided via an overlay network. In another aspect, the present invention is an apparatus that includes a proxy service that intercepts content information requests to the Internet and re-directs the content requests to an overlay. Another aspect of the present invention comprises a location-based Uniform Resource Locator that includes a protocol semantic portion and a location-based resolver address portion that identifies one or more resources on a network based on the geographical location of the resources.
Owner:TELCORDIA TECHNOLOGIES INC +1
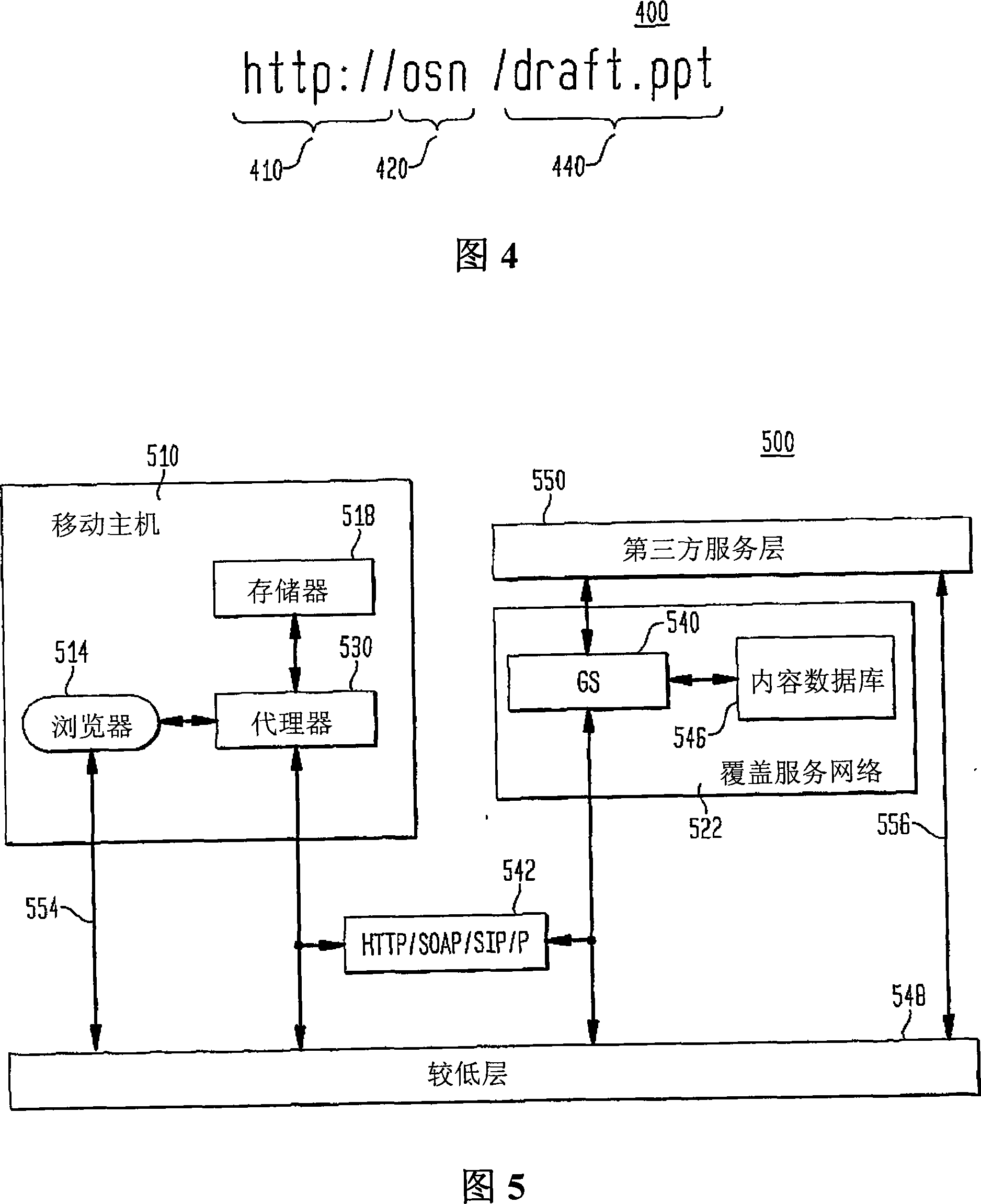
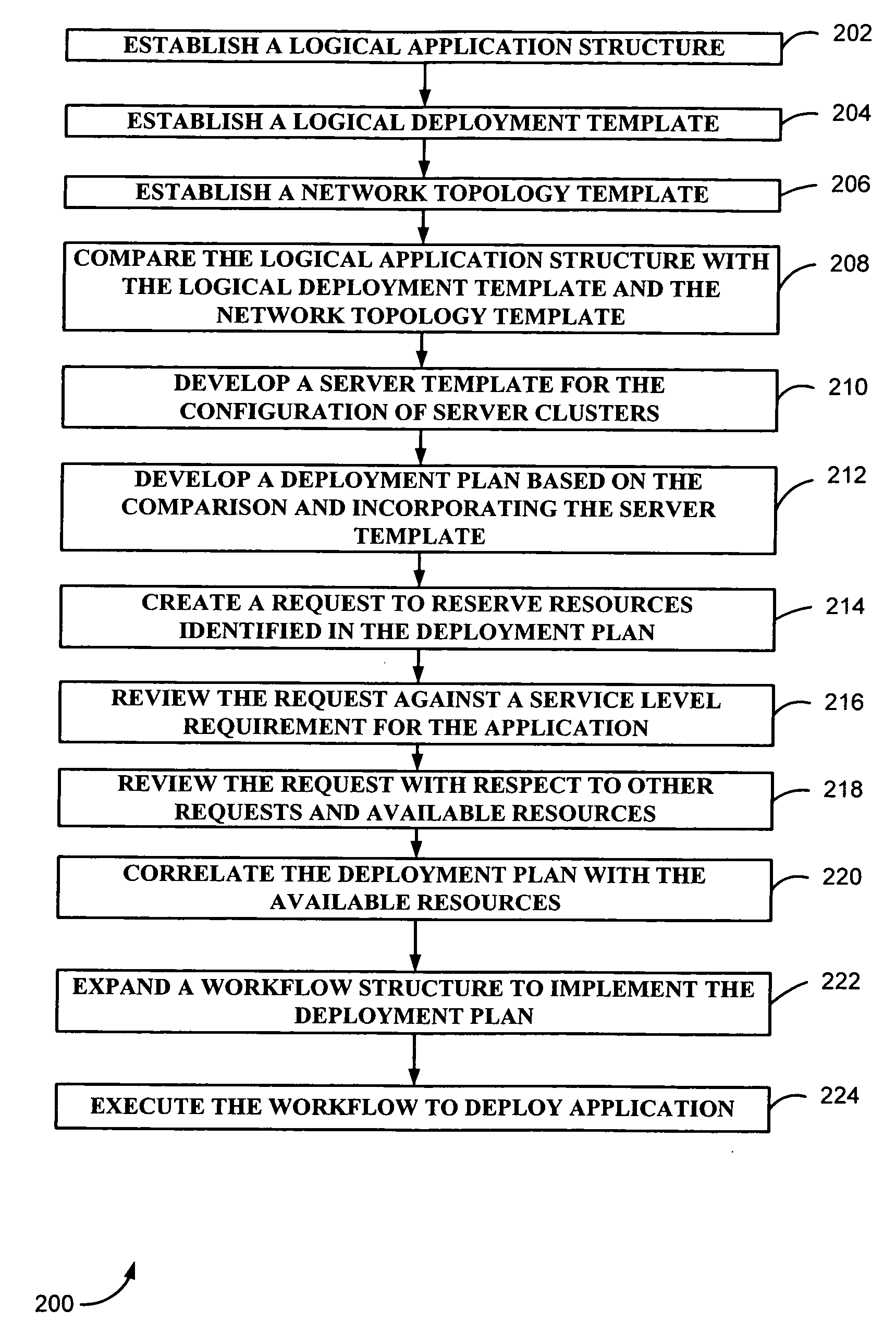
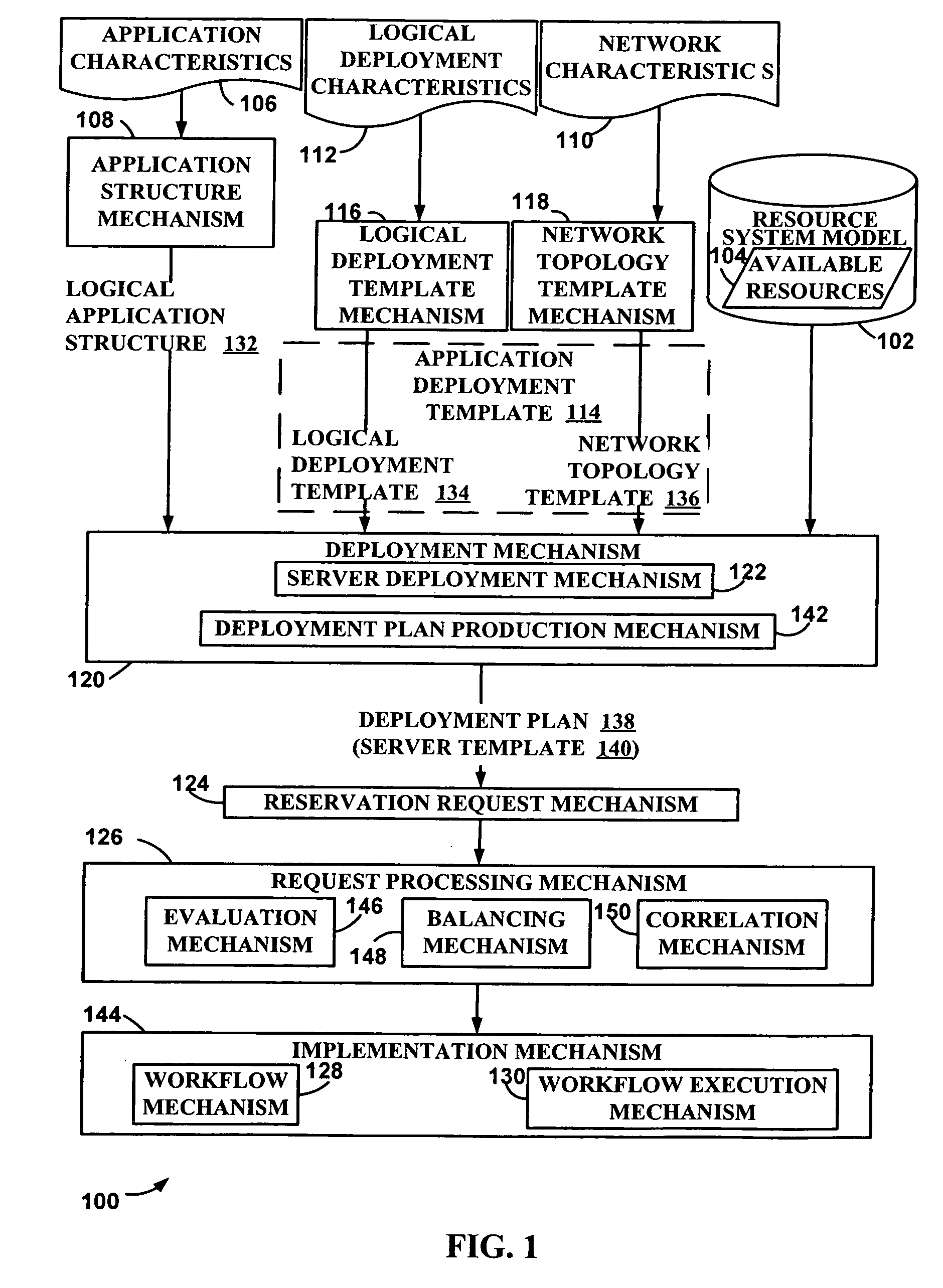
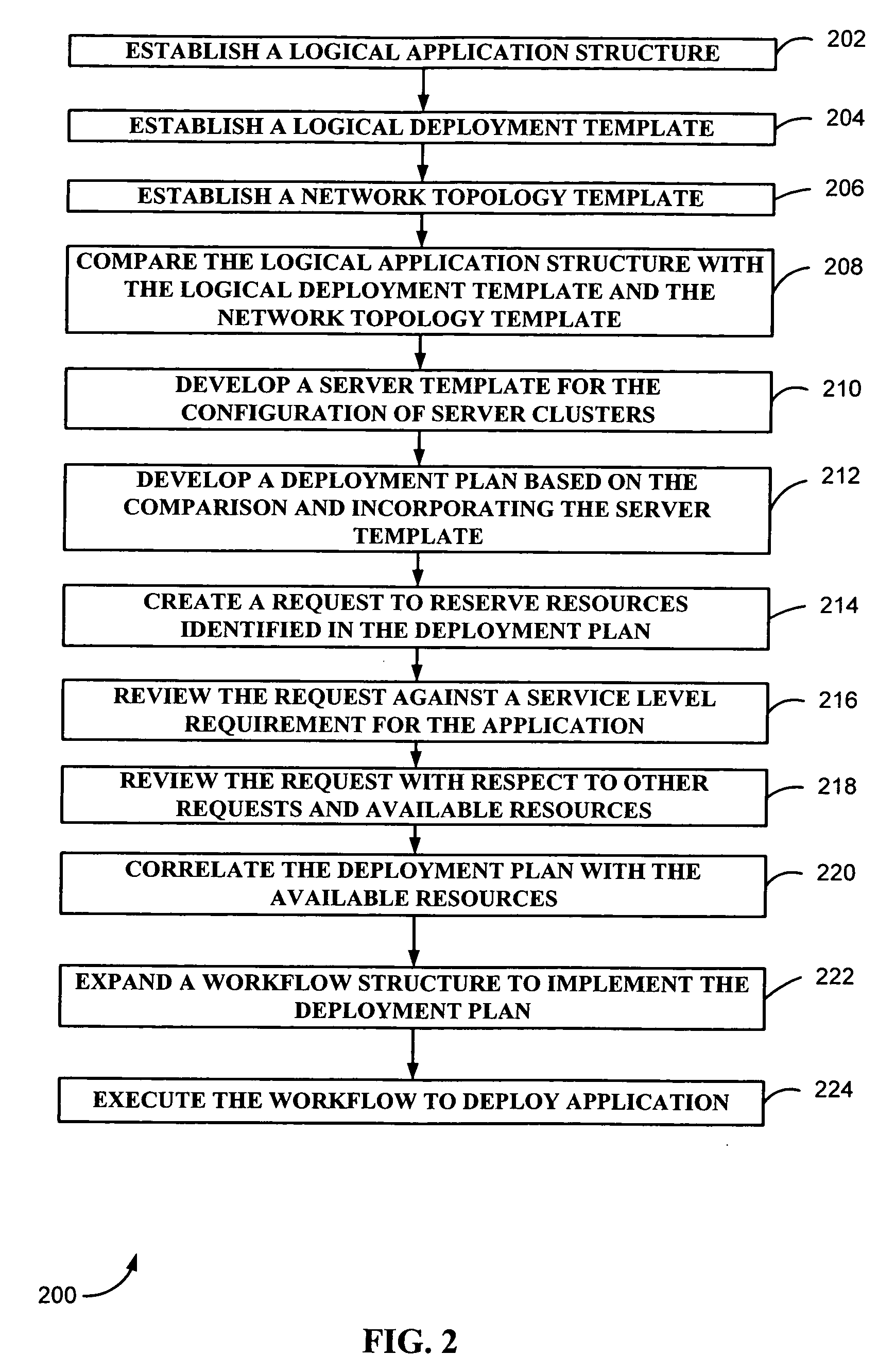
Method and system for managing application deployment
Deployment of an application is managed using available resources from a resource system. A resource dependency characterization of the application is established to enable deployment of the application. A logical characterization and a network characterization of a desired deployment are also established. A deployment plan containing an outline for resources and configurations used for deployment is developed based on the resource dependency characterization, the logical characterization and the network characterization. The deployment plan is processed for correlation with the available resources. The processed deployment plan is then implemented.
Owner:HULU
Resource management utilizing quantified resource attributes
InactiveUS6978006B1Effective serviceData processing applicationsManual exchangesHuman resource managementSkill sets
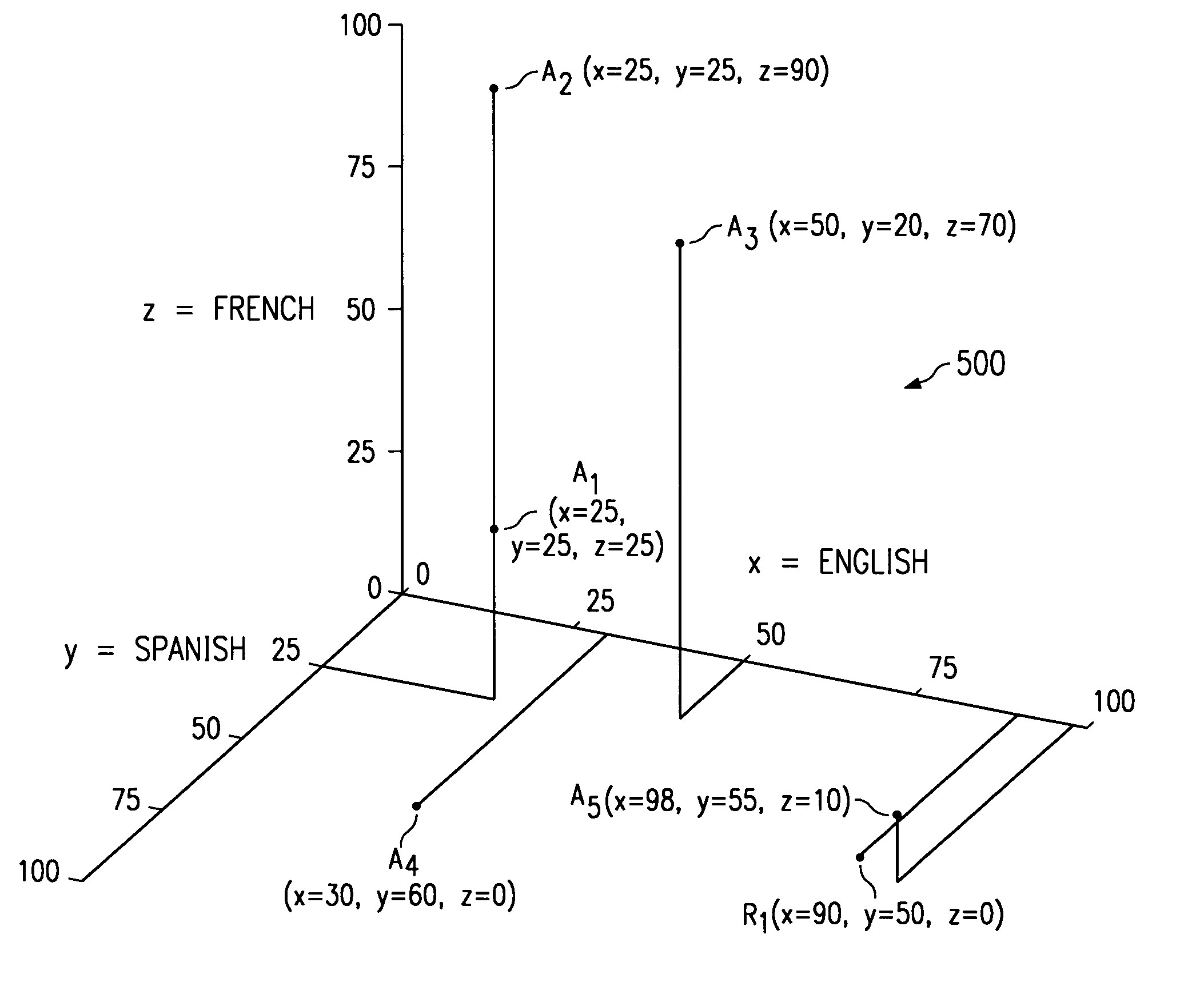
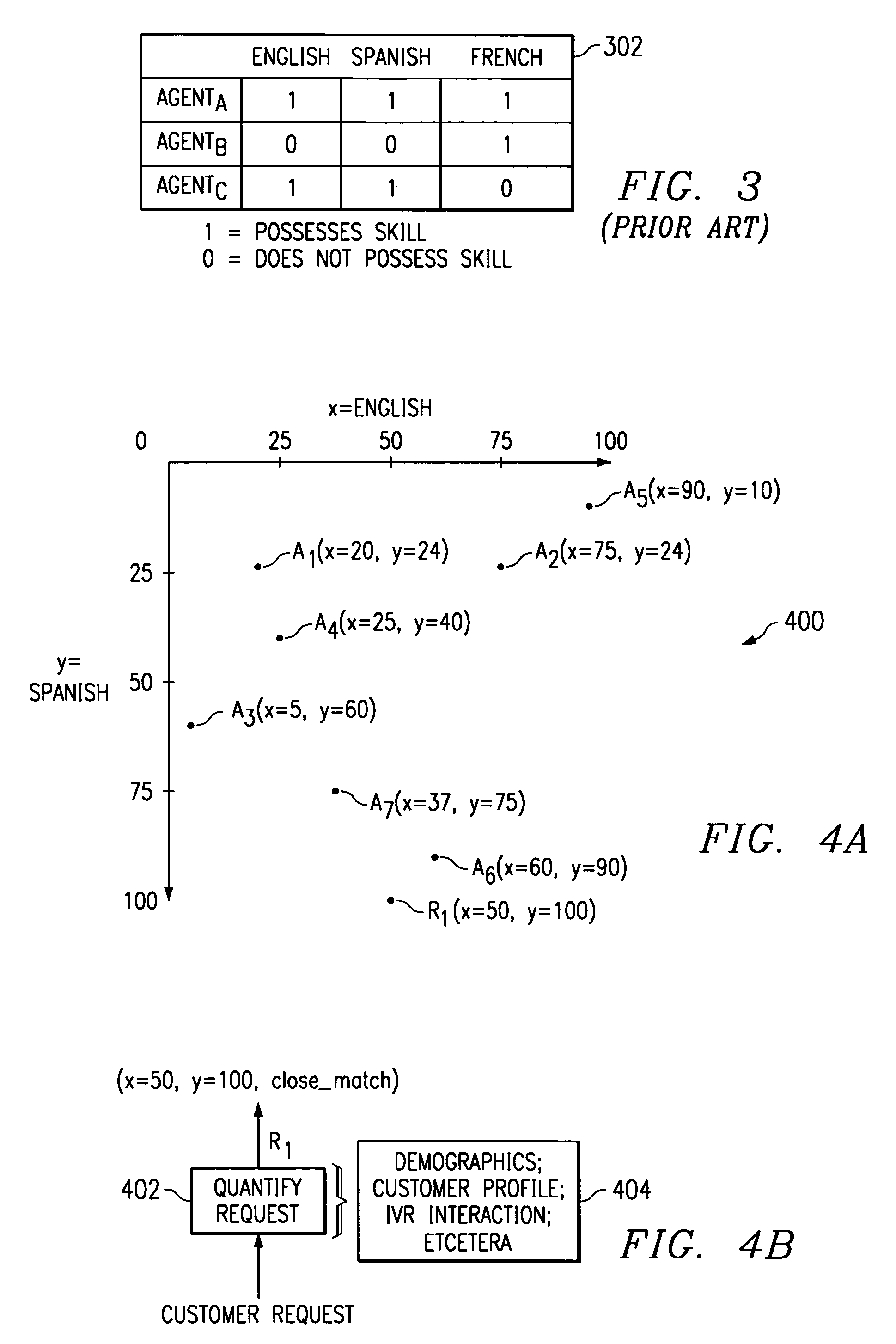
A system and method are disclosed which quantify one or more attributes of a finite number of resources for effective management of such resources. Quantifiable attributes possessed by a resource may include skills or functional capabilities possessed by the resources, as examples. A request for service by one or more of the resources is received, and at least one attribute desired by the request is quantified. Based at least in part on the quantified attributes of the resources and the quantified attributes desired by the request, at least one suitable resource for servicing the received request is determined. Most preferably, attributes of resources may be quantified along a scale, such as a scale of 0 to 100. For example, within a telephony call center, attributes possessed by agents, such as language skills or product knowledge may be quantified along such a scale. A request for service may be received, and the attributes of a resource desired by the request are quantified along such a scale. Suitable resources for servicing a request may be determined by evaluating the quantified attributes possessed by the resources and the quantified attributes desired by the request. Thus, “N” number of resource attributes may be quantified and plotted within an N-dimensional space. Additionally, attributes desired by a received request may be quantified and plotted within such N-dimensional space. The distance between the plotted resource attributes and the plotted requests may be calculated to determine at least one suitable resource for servicing the request.
Owner:INTERVOICE PARTNERSHIP
System and method for provisioning resources to users based on policies, roles, organizational information, and attributes
InactiveUS6947989B2Reducing and minimizing numberDigital data processing detailsSpecial service for subscribersResource basedApplication software
A method for provisioning users with resources is disclosed. The method includes the steps of establishing a set of attributes, organizational information, and user roles, and defining a plurality of resource provisioning policies based on selected attributes and user roles. The method also includes the steps of receiving attribute information, organizational information, and user role information for a particular user or resource, determining which resource access policies are applicable to the user based on the received user role information and attribute information, and provisioning the user with resources based on the applicable resource access policies. The resources to be provisioned include “hard” resources, such as telephones, computers, personal digital assistants, desks, chairs and the like, as well as “soft” resources. such as e-mail and voice mail accounts, application programs, databases, files, folders, the like.
Owner:IBM CORP
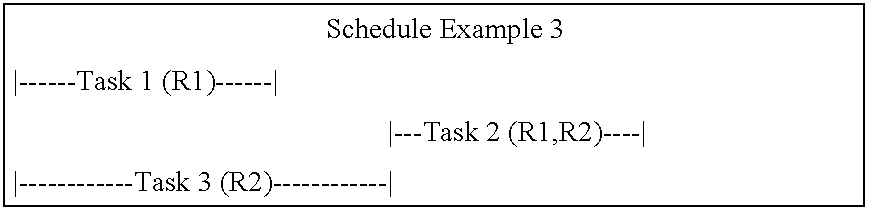
System and method for generating a schedule based on resource assignments
A system for generating a schedule by generating assignments for the tasks of a project and sequentially scheduling the individual assignments to available resources. First, input information is received which includes a resource calendar and a task list. A resource calendar identifies the resources available to work on a project and any constraints that are associated with the resources. A task list identifies the tasks that must be performed and any constraints that are associated with the tasks. At a minimum, the constraints associated with the tasks must identify each of the resources assigned to the task, and the work-amount that each resource must perform. Next, assignments are generated for each of the tasks. Each of the assignments identifies a specific resource and the work-amount required by the specific resource. Finally, each of the assignments are scheduled in accordance with the provided resource constraints identified in the resource calendar. The resulting schedule maximizes the utilization of the resources by scheduling on an assignment basis. The assignments are individually scheduled into the next available time-slot of the resources, thus, eliminating idle time where a resource is under-utilized.
Owner:MICROSOFT TECH LICENSING LLC
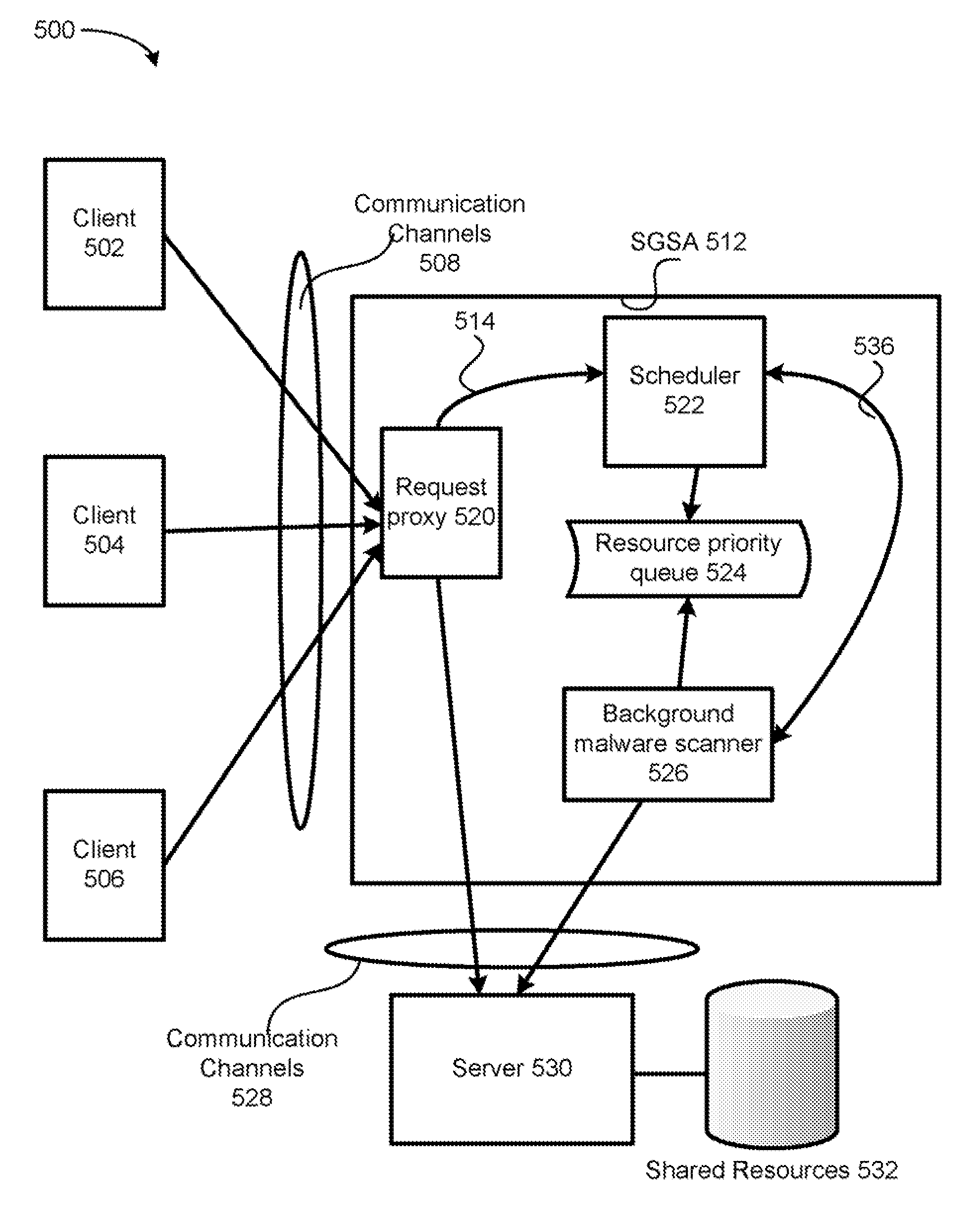
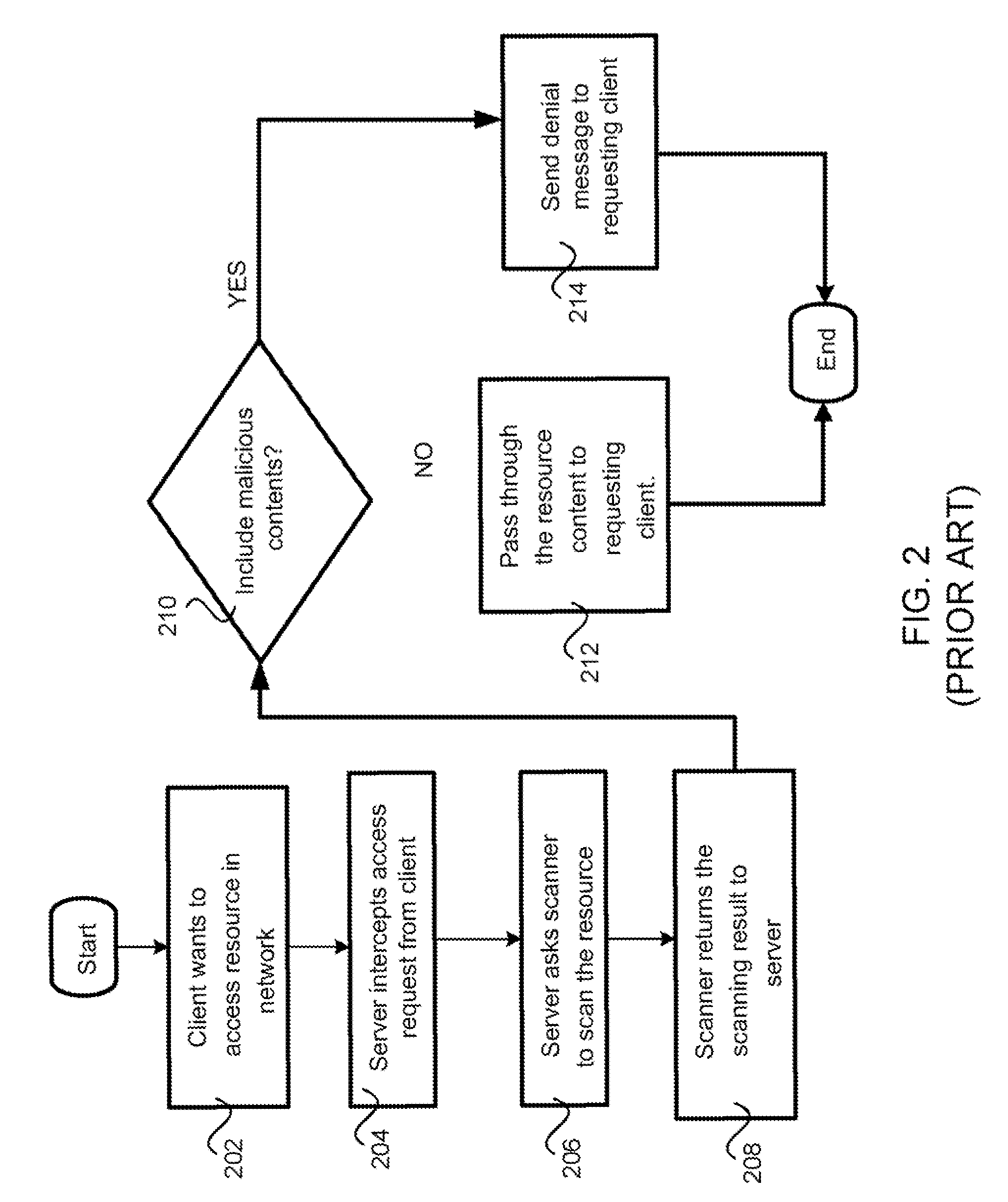
Scheduled gateway scanning arrangement and methods thereof
InactiveUS7836502B1Raise priorityMemory loss protectionError detection/correctionResource basedComputer science
A method for performing content analysis of a plurality of resources is provided. The method includes performing background content scanning on the plurality of resources based on a resource priority queue. The method also includes storing already scanned resources of the plurality of resources in a scan result database. The method further includes receiving a first access request asynchronously with the scanning and the storing. The method yet also includes, if the first access request pertains to a given resource not contemporaneously designated as a satisfactory scan result according to the scan result database, granting the given resource a higher priority in the resource priority queue than resources remaining to be scanned in the plurality of resources, thereby enabling the given resource to be scanned ahead of the resources remaining to be scanned.
Owner:TREND MICRO INC
Proximity detection using wireless signal strengths
InactiveUS7509131B2Multiple digital computer combinationsSatellite radio beaconingWi-FiResource based
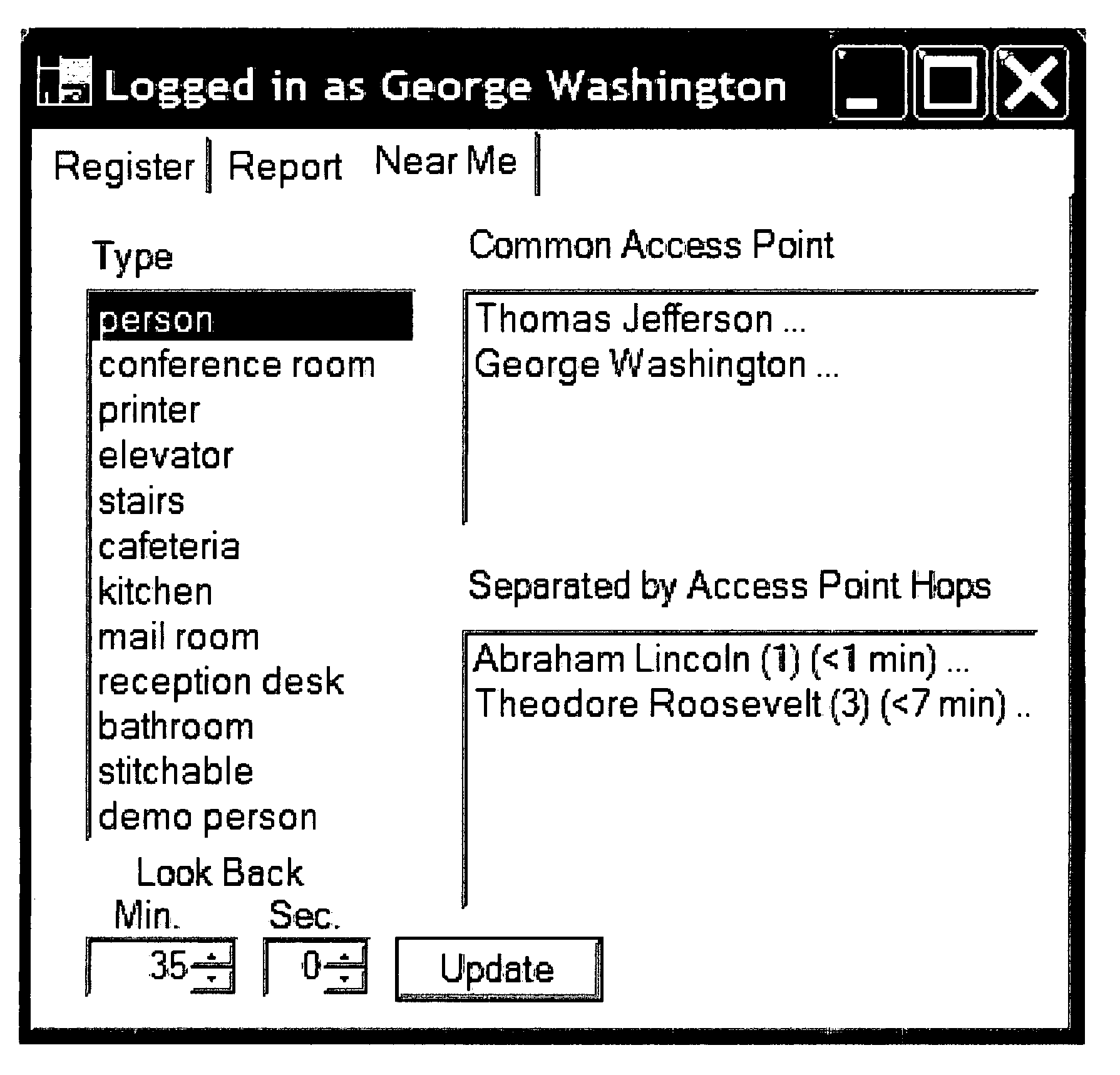
Described is a system and method in a wireless (Wi-Fi) network comprising a server, clients and various mechanisms that compute lists of other clients and resources that are physically nearby. Clients report Wi-Fi access points' signal strengths to a server, which uses that data to compute the proximity of resources to one another, including an estimate the distance between resources. The data may be returned to the client as a list of resources within short range proximity, or resources within long-range proximity, with an approximate time to that resource based on previous clients' reporting. Because proximity is used rather than absolute location, only minimal setup is needed. As the number of clients and resources that use the system increases, the server knowledge also increases with respect to the number of resources that can be found and in the physical range over which other people and places can be found.
Owner:MICROSOFT TECH LICENSING LLC
Methods, systems, and media to expand resources available to a logical partition
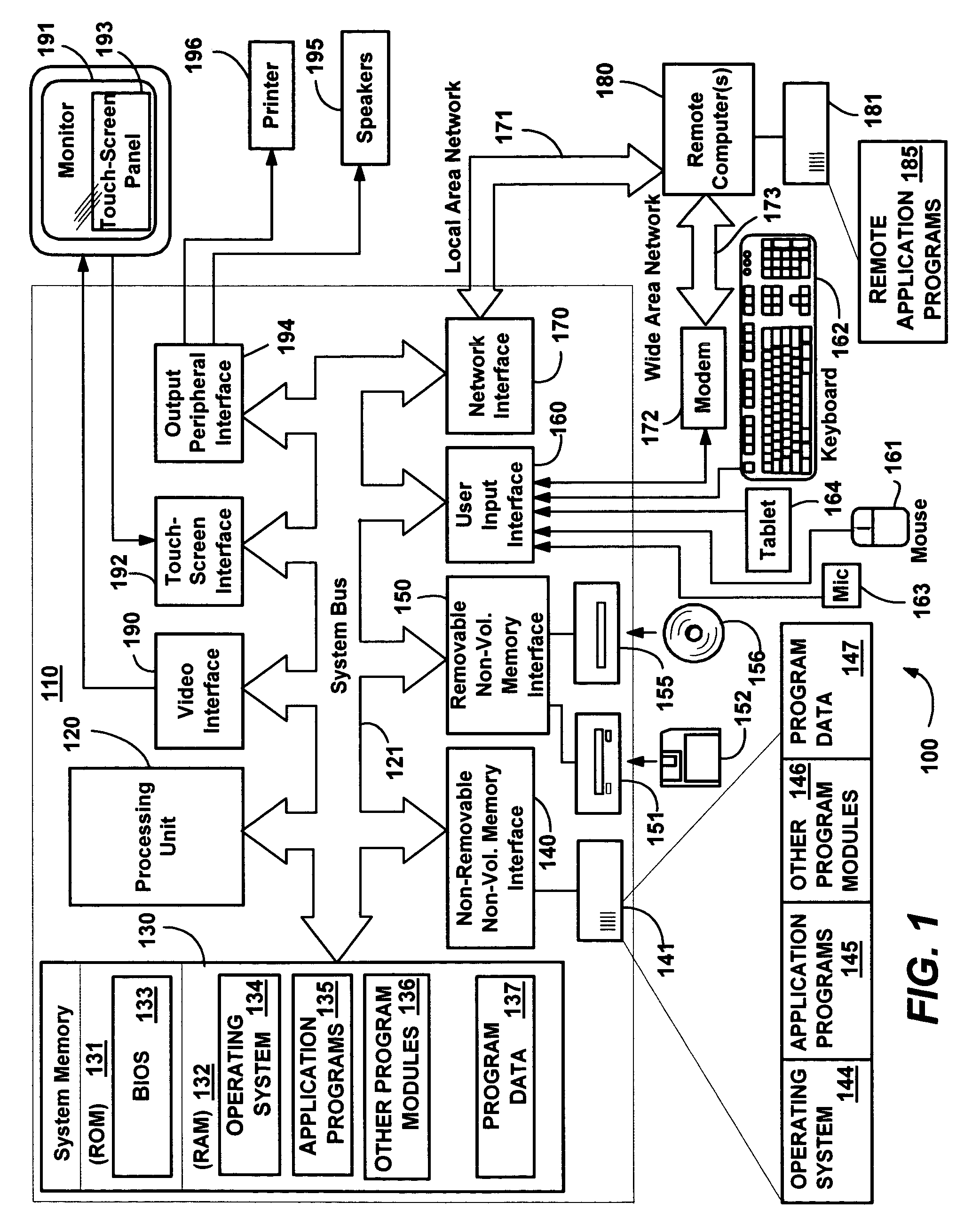
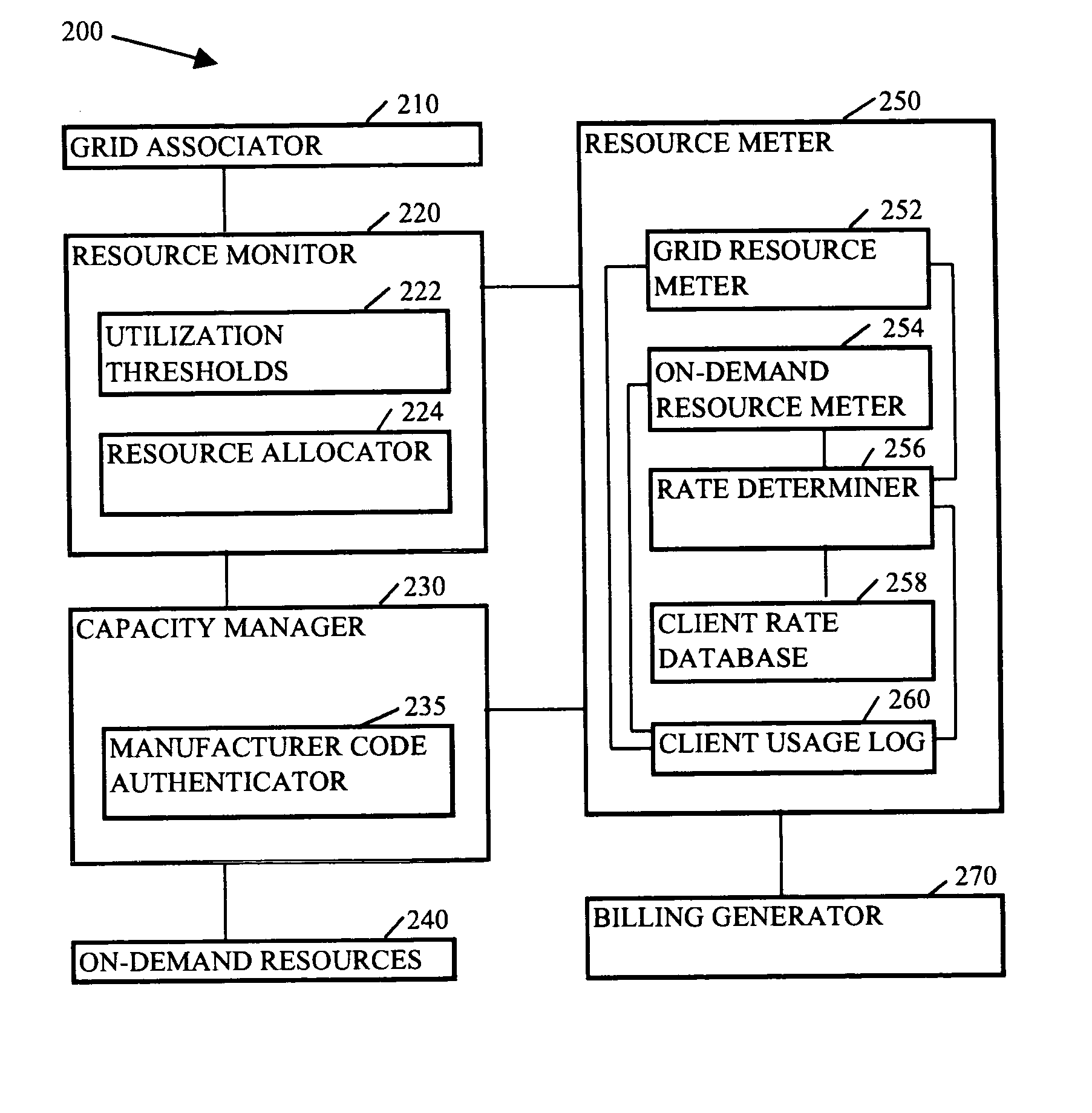
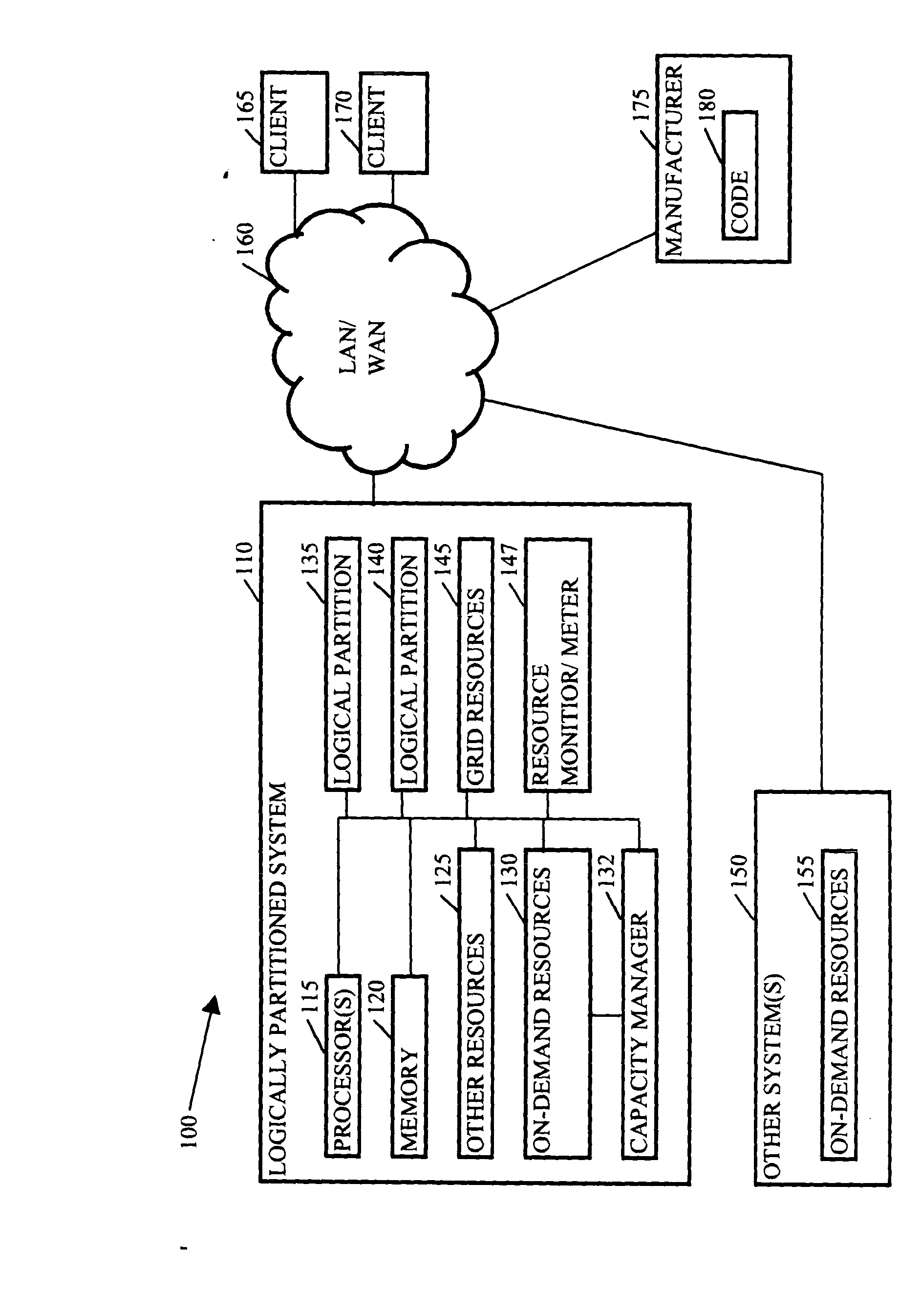
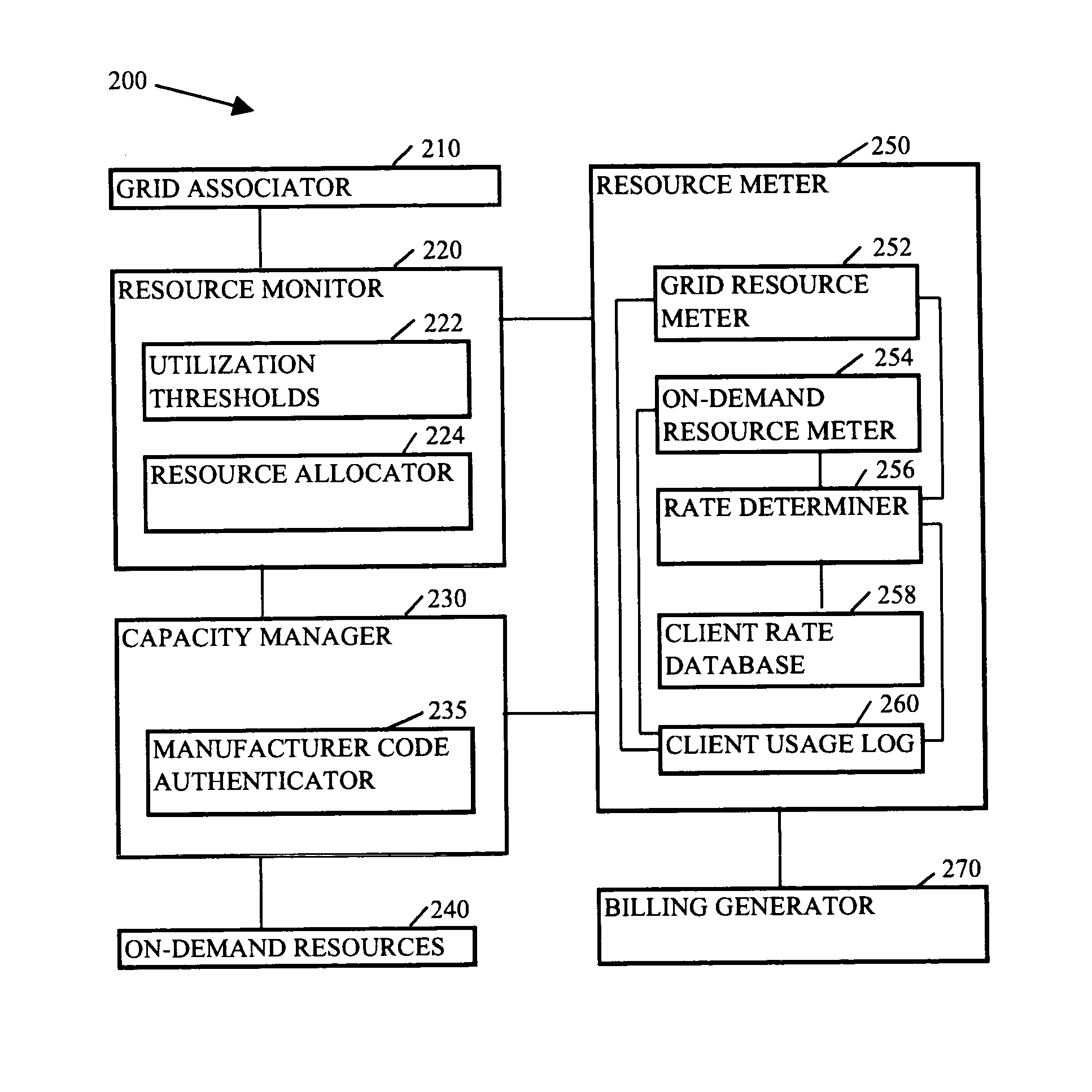
InactiveUS20050044228A1Digital computer detailsMultiprogramming arrangementsGrid resourcesService provision
Methods, systems, and media to expand resources available to logical partition associated with a client are contemplated. Embodiments may associate the logical partition with a grid that retains a list of resources, referred to as grid resources, available for allocation to logical partitions. The grid resources may include resources from, e.g., other logical partitions within the logically partitioned system, logical partitions from other logically partitioned systems, another type of system, a cluster, and the like. Further, one or more of the systems associated with the grid may include on-demand resources that are also available to supplement resources based upon the demands of the client. Embodiments may also monitor resource usage by the client and meter billable usage of the grid resources and / or on-demand resources based upon agreements between service providers and clients.
Owner:IBM CORP
Method and Apparatus for Managing Device-to-Device Interference
ActiveUS20120051315A1Control overheadImprove performanceNetwork topologiesWireless commuication servicesTelecommunicationsResource block
Various methods for managing device-to-device interference are provided. One example method includes receiving an expected interference level for a resource block, where the expected interference level is represented by data indicative of interference associated with the resource block due to device-to-device communications using the resource block. The example method further includes selecting the resource block for a device-to-device communications session based at least in part on the expected interference level for the resource block. Similar and related example methods and example apparatuses are also provided.
Owner:NOKIA TECHNOLOGLES OY
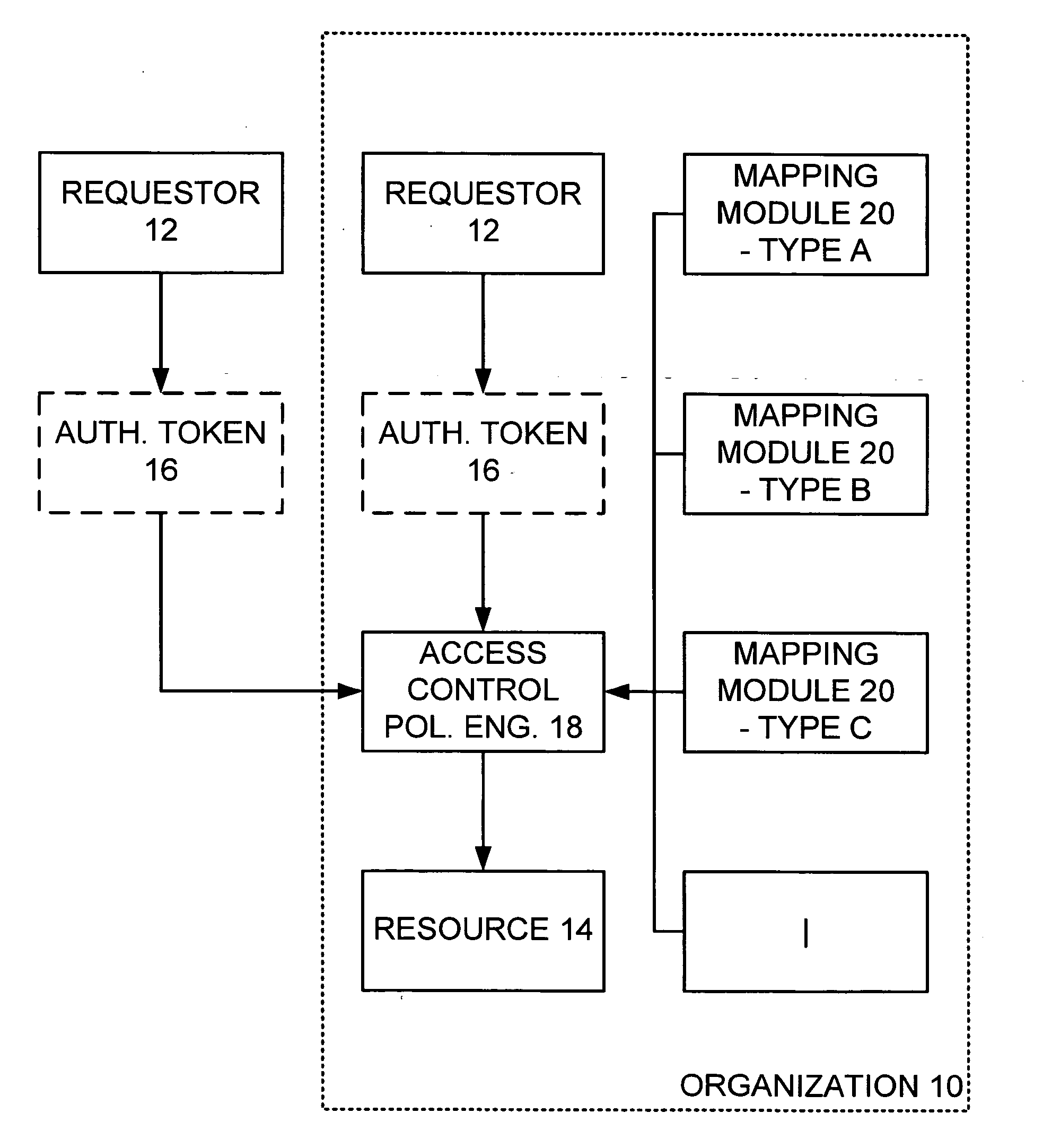
Access control policy engine controlling access to resource based on any of multiple received types of security tokens
ActiveUS20060206931A1Satisfies needDigital data processing detailsUser identity/authority verificationResource basedAccess control
An access control policy engine associated with a resource determines whether to allow a request to access same. The engine receives the request with an security token, retrieves the token determines a type thereof, and maps access decision information in the token to a common format as at least one security claim setting forth adequate information to determine a right of the requestor. Thereafter, the engine retrieves a set of rules for accessing the resource, applies the rules to the security claims to determine whether to allow the request from the requestor, and if the request is to be allowed, provides the requestor access to the resource in accordance with the request and the rights of the requestor as determined based on the security claims.
Owner:MICROSOFT TECH LICENSING LLC
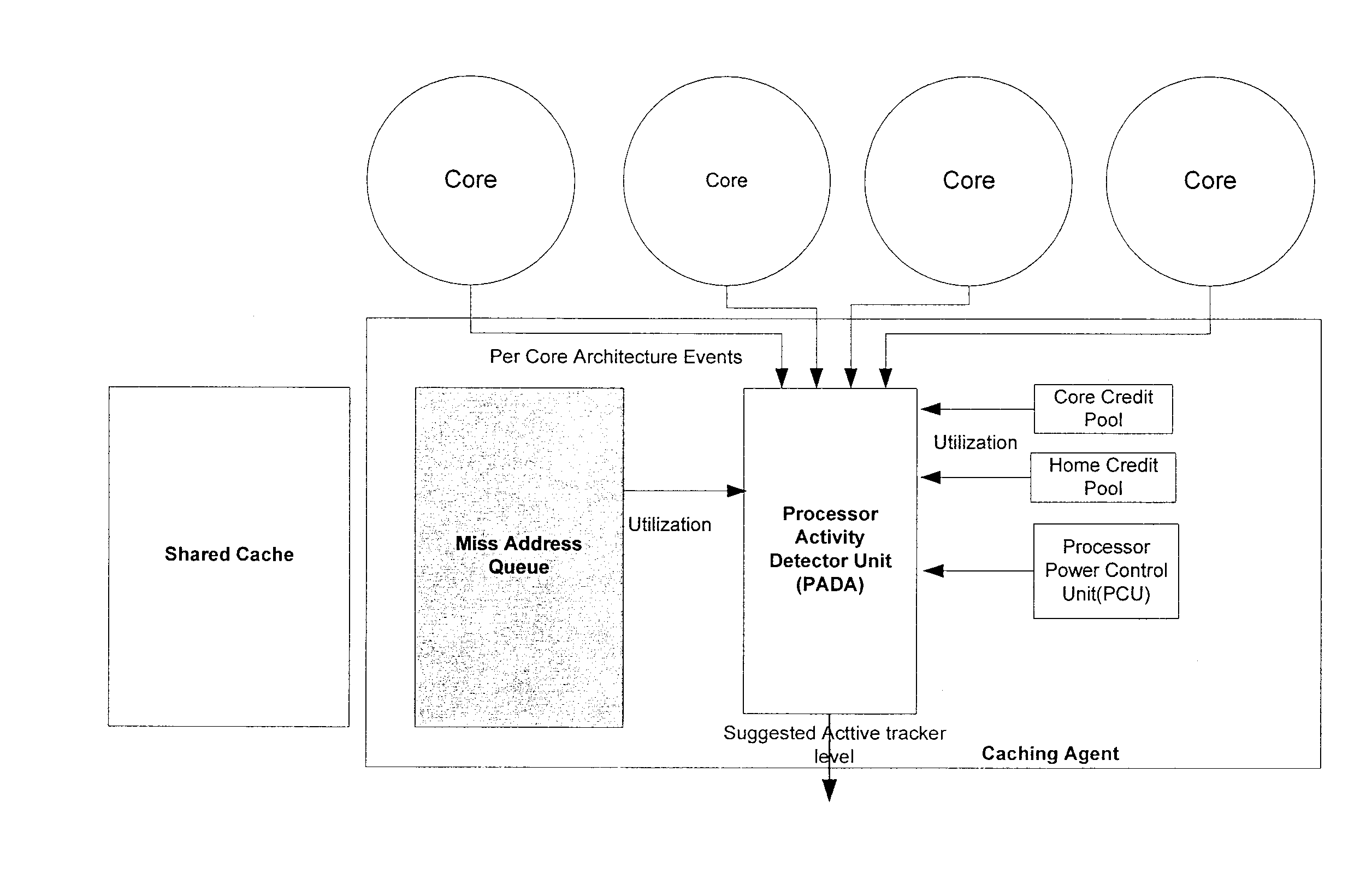
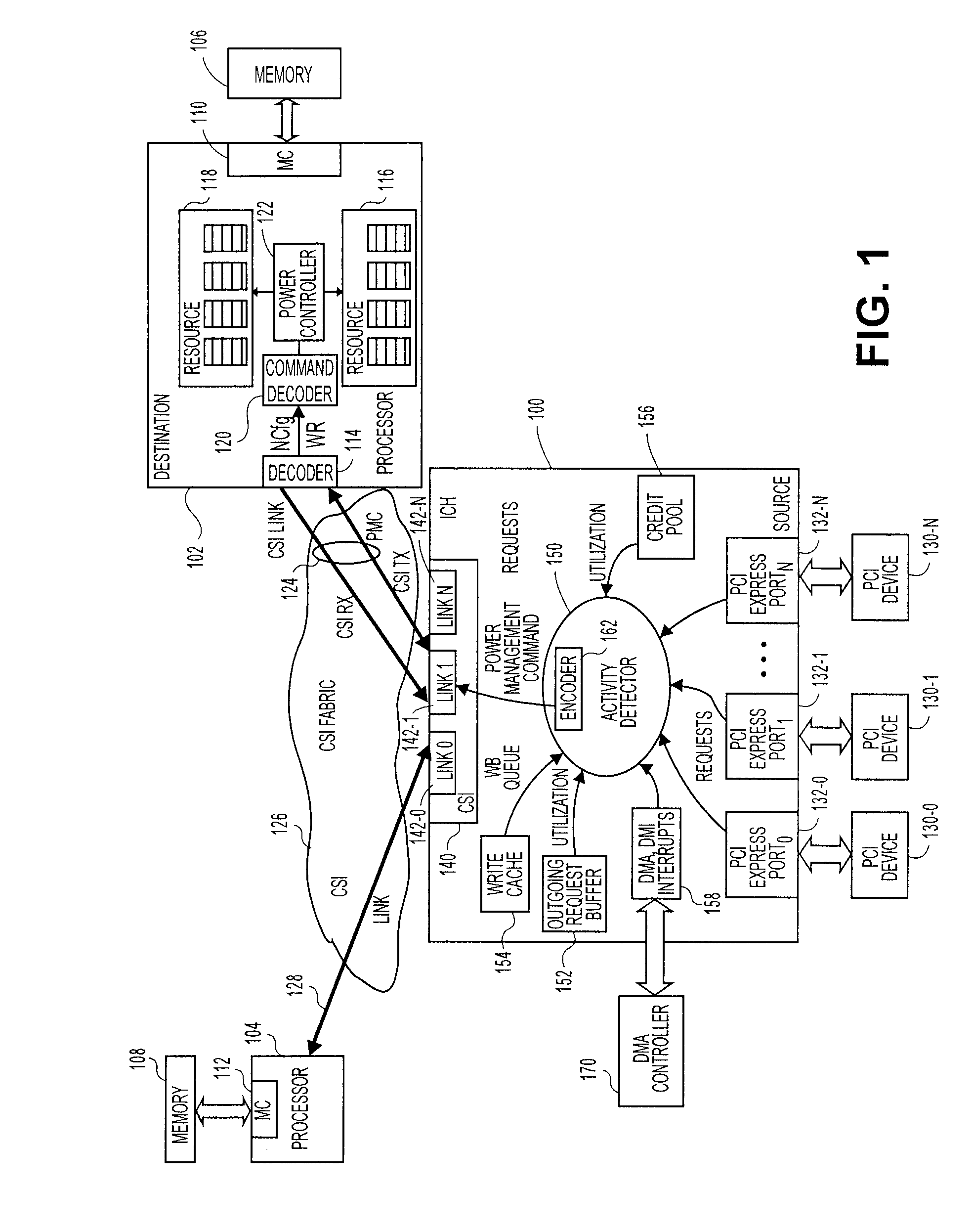
Method, system, and apparatus for a core activity detector to facilitate dynamic power management in a distributed system
A system and method to provide source controlled dynamic power management. An activity detector in a source determines expected future resource usage. Based on that expected usage, the source generates a power management command and sends that command to a destination. The destination then adjusts the power level of the resource based in the command.
Owner:INTEL CORP
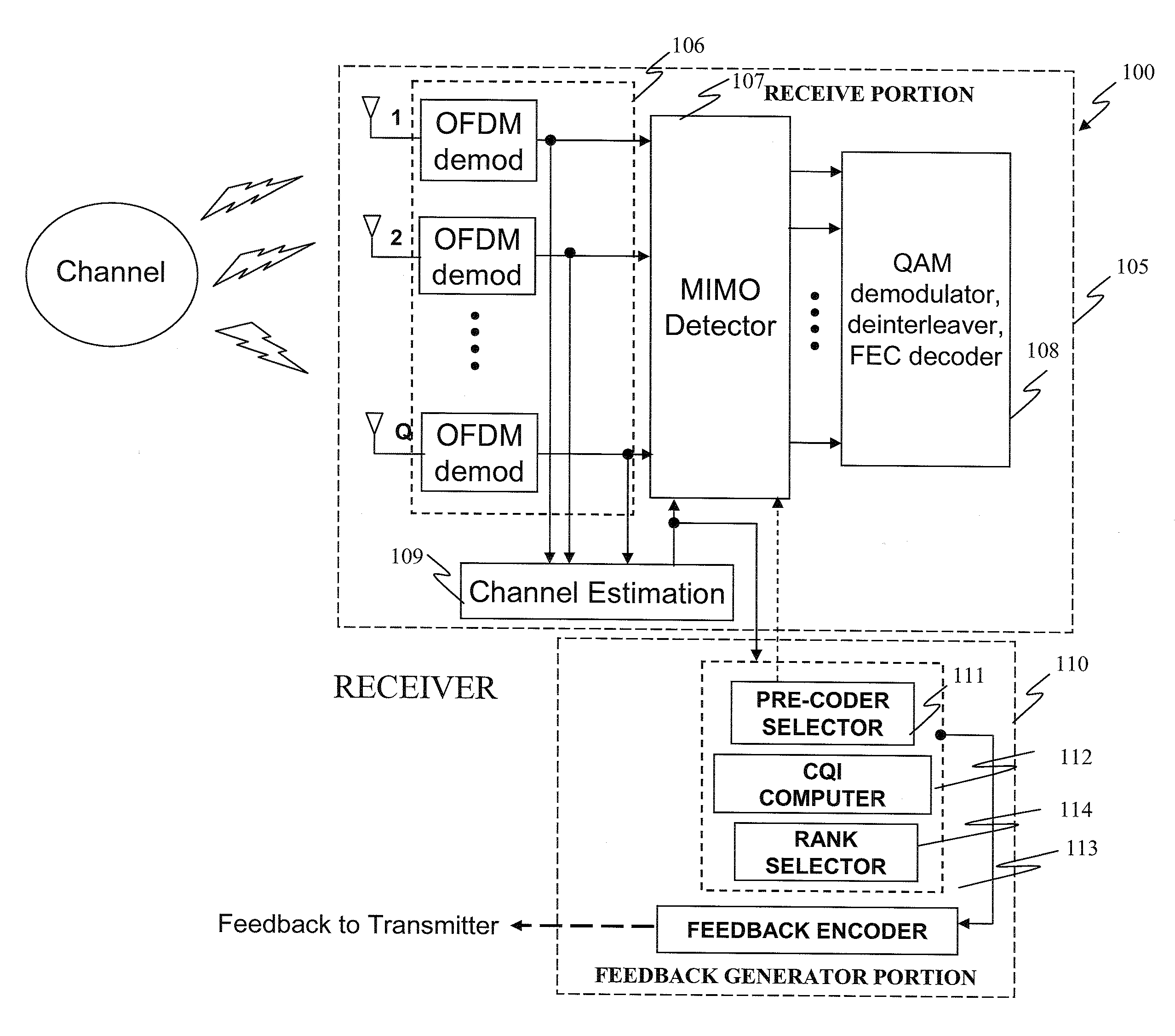
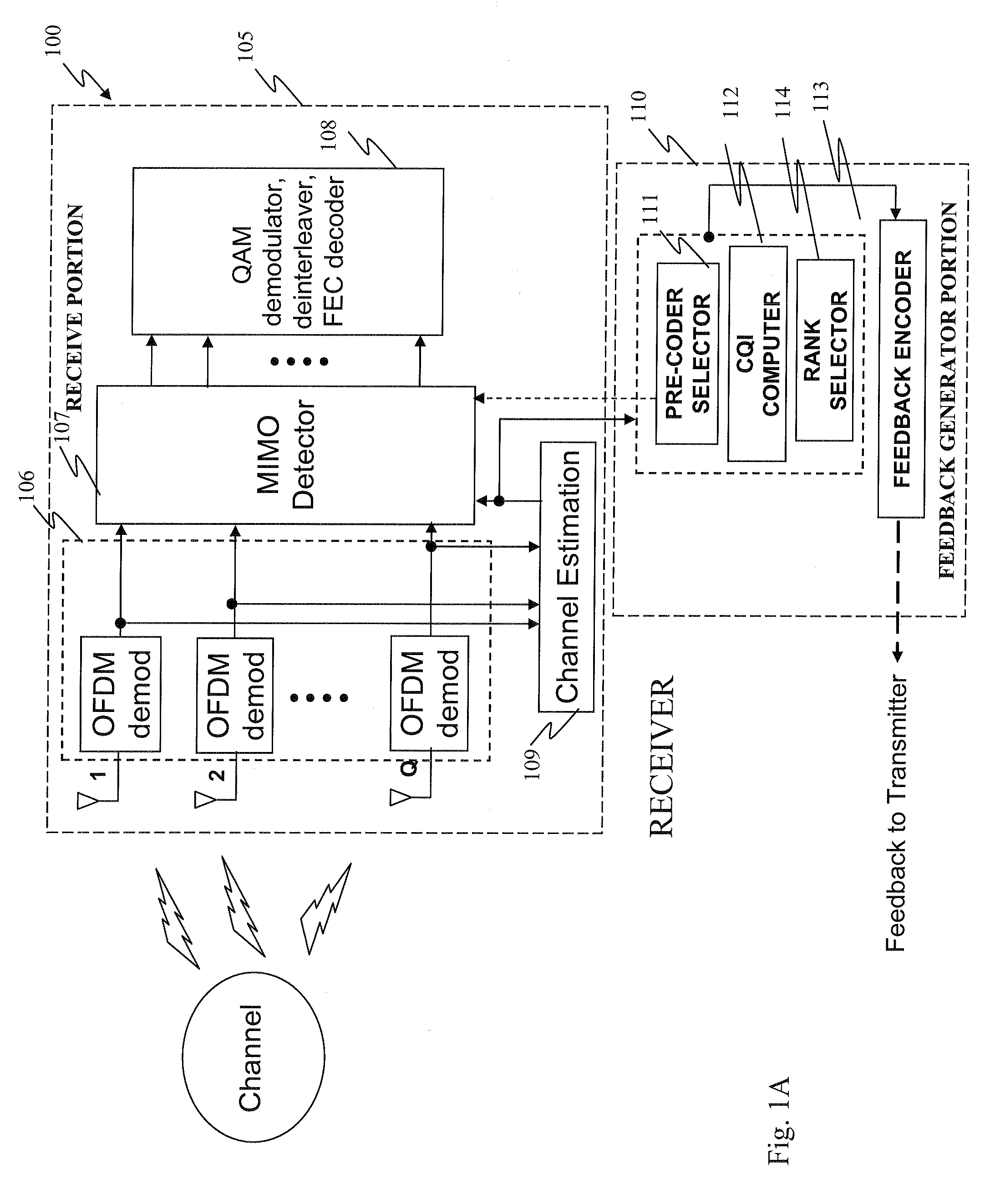
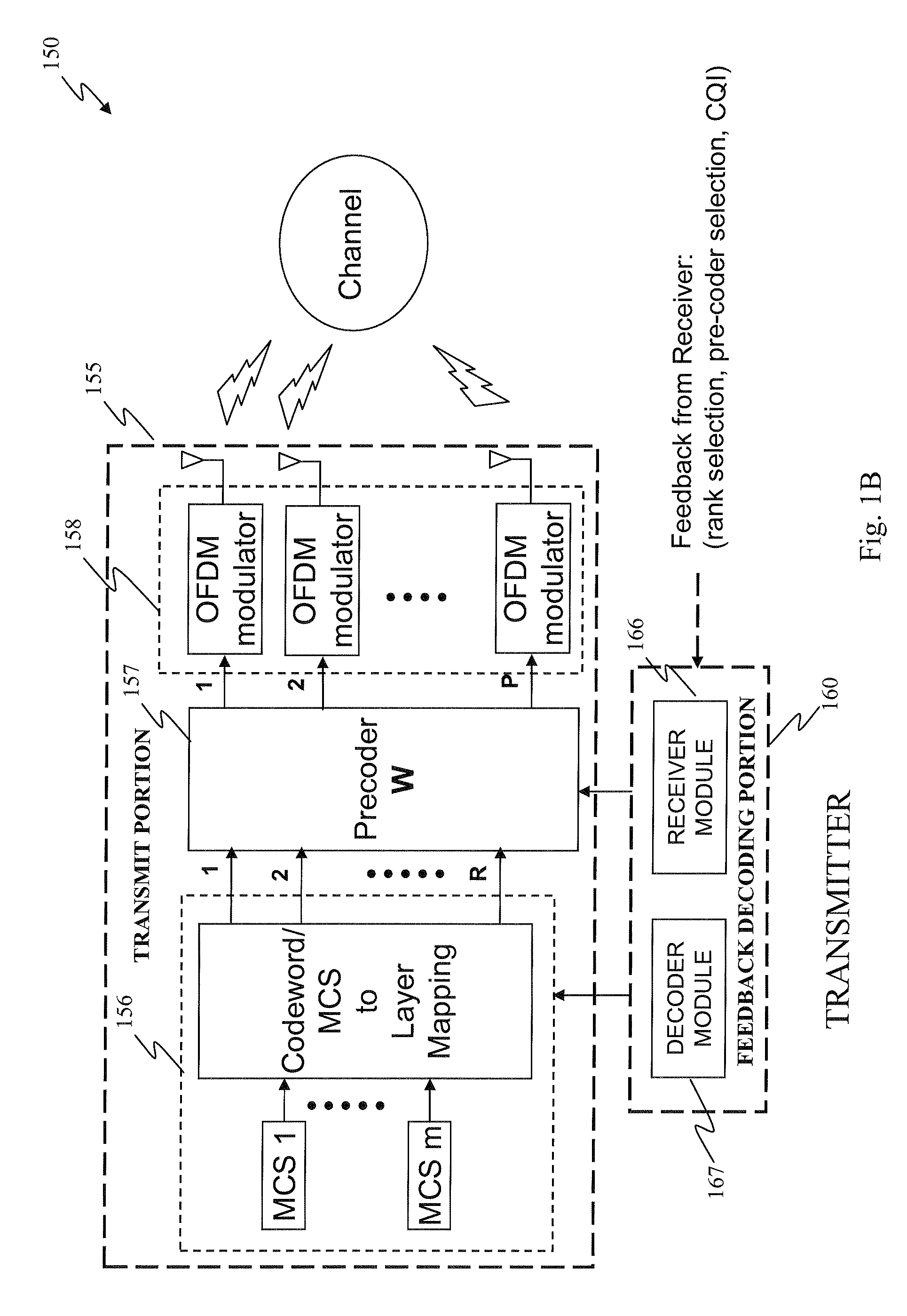
Pre-coder selection based on resource block grouping
The present invention provides a receiver. In one embodiment, the receiver includes a receive portion employing transmission signals from a transmitter having multiple antennas and capable of providing channel estimates. The receiver also includes a feedback generator portion configured to provide to the transmitter a pre-coder selection for data transmission that is based on the channel estimates, wherein the pre-coder selection corresponds to a grouping of frequency-domain resource blocks. The present invention also provides a transmitter having multiple antennas. In one embodiment, the transmitter includes a transmit portion coupled to the multiple antennas and capable of applying pre-coding to a data transmission for a receiver. The transmitter also includes a feedback decoding portion configured to decode a pre-coder selection for the data transmission that is fed back from the receiver, wherein the pre-coder selection corresponds to a grouping of frequency-domain resource blocks.
Owner:TEXAS INSTR INC
Semiconductor device for controlling access right to resource based on pairing technique and method thereof
A method of operating a hub includes the hub receiving a pairing request from an Internet of Things (IoT) device, the hub performing pairing with the IoT device using one authentication technique from among a plurality of predetermined pairing authentication techniques, and the hub assigning an access right to a resource to the IoT device. The access right is determined according to the one authentication technique.
Owner:SAMSUNG ELECTRONICS CO LTD
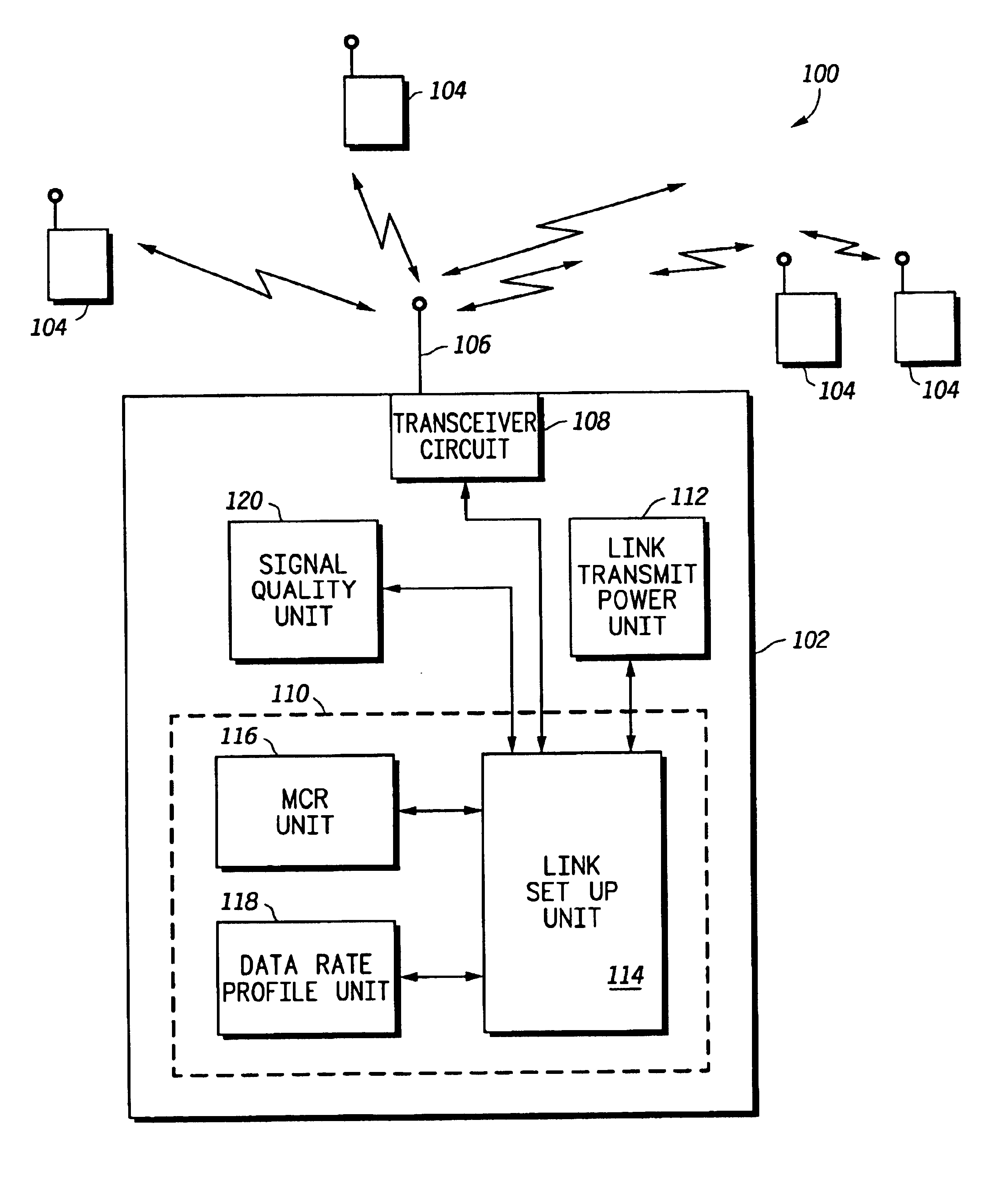
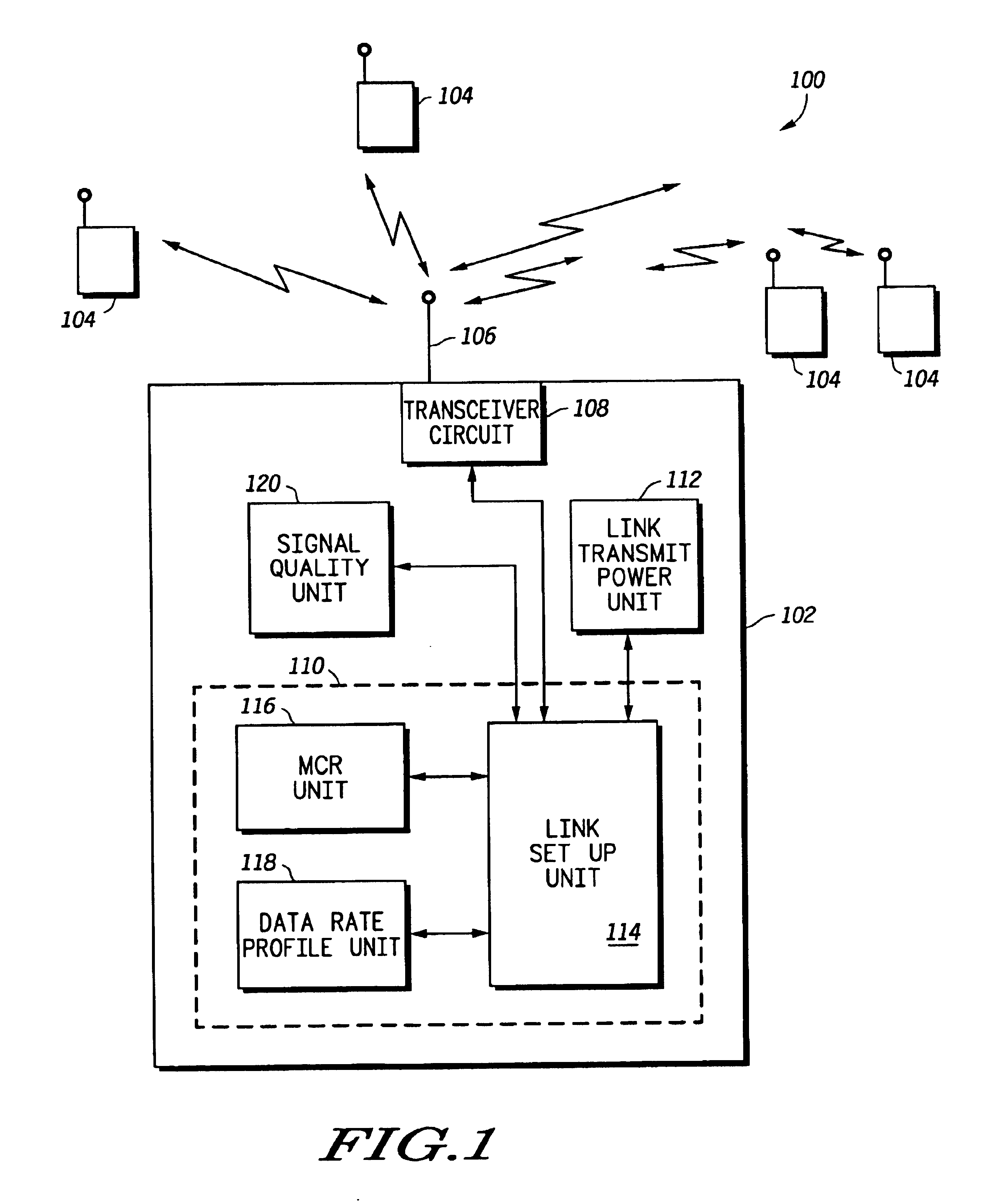
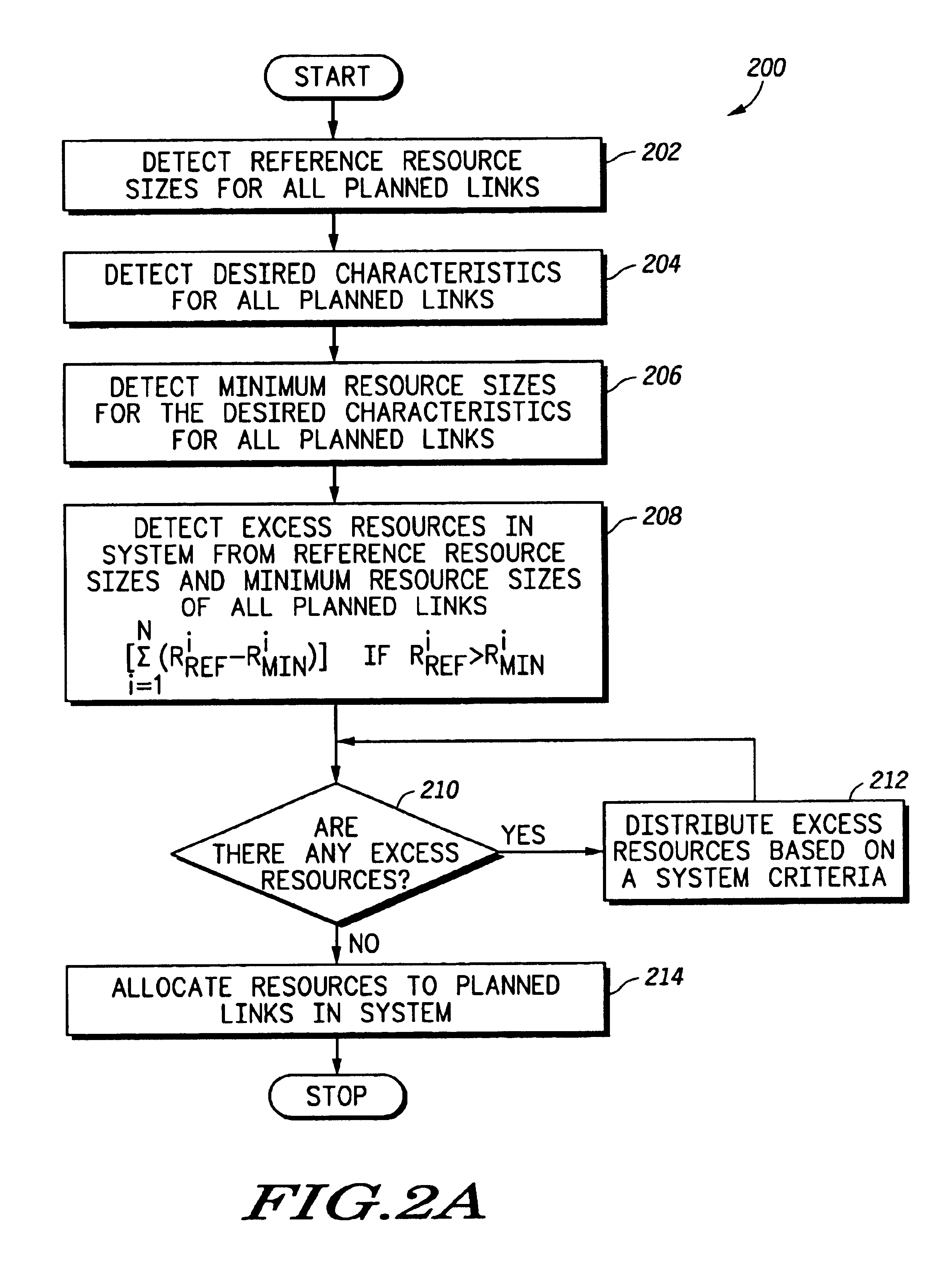
Method and system for excess resource distribution in a communication system
InactiveUS6865393B1Network traffic/resource managementRadio/inductive link selection arrangementsSystem capacityCommunications system
A method and system (102) provide adaptive modulation / coding with distribution of excess resources based on one or more system criteria. The system (102) may be any system with more than one modulation rate or more than one coding rate and may be a wireless communication system using CDMA, TDMA, OFDM or any other signal formats. Generally, the method determines excess resources of the system based on desired characteristics of links supported by the system. The excess resources may be any number of system resources, such as transmit power. These excess resources are then distributed to the links based on various system criteria, such as to increase system coverage, to increase system capacity, to modify a data rate profile of the system or to reduce interference in the system. Methods for providing such distribution of the excess resources are also provided for equal data rate systems.
Owner:MOTOROLA SOLUTIONS INC
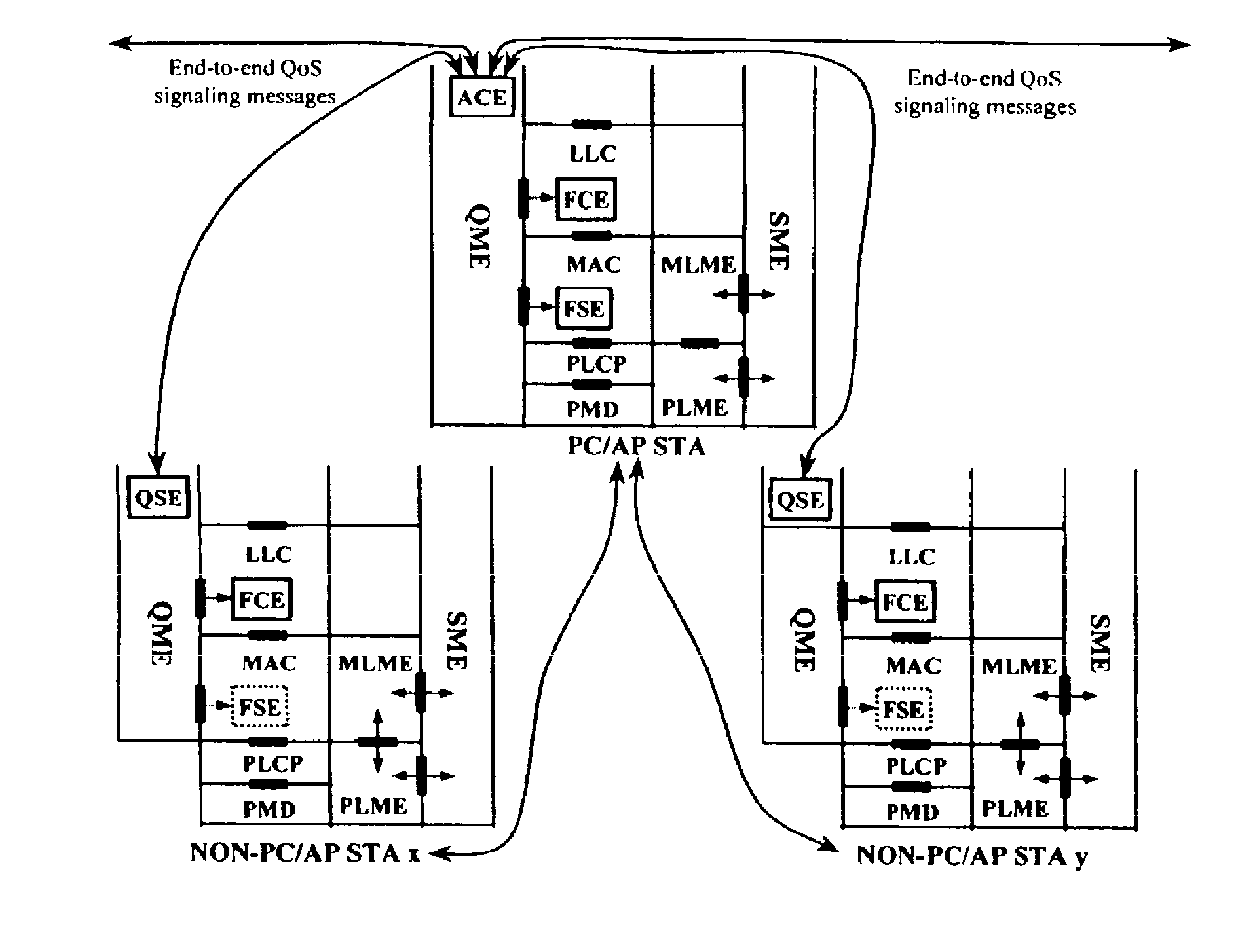
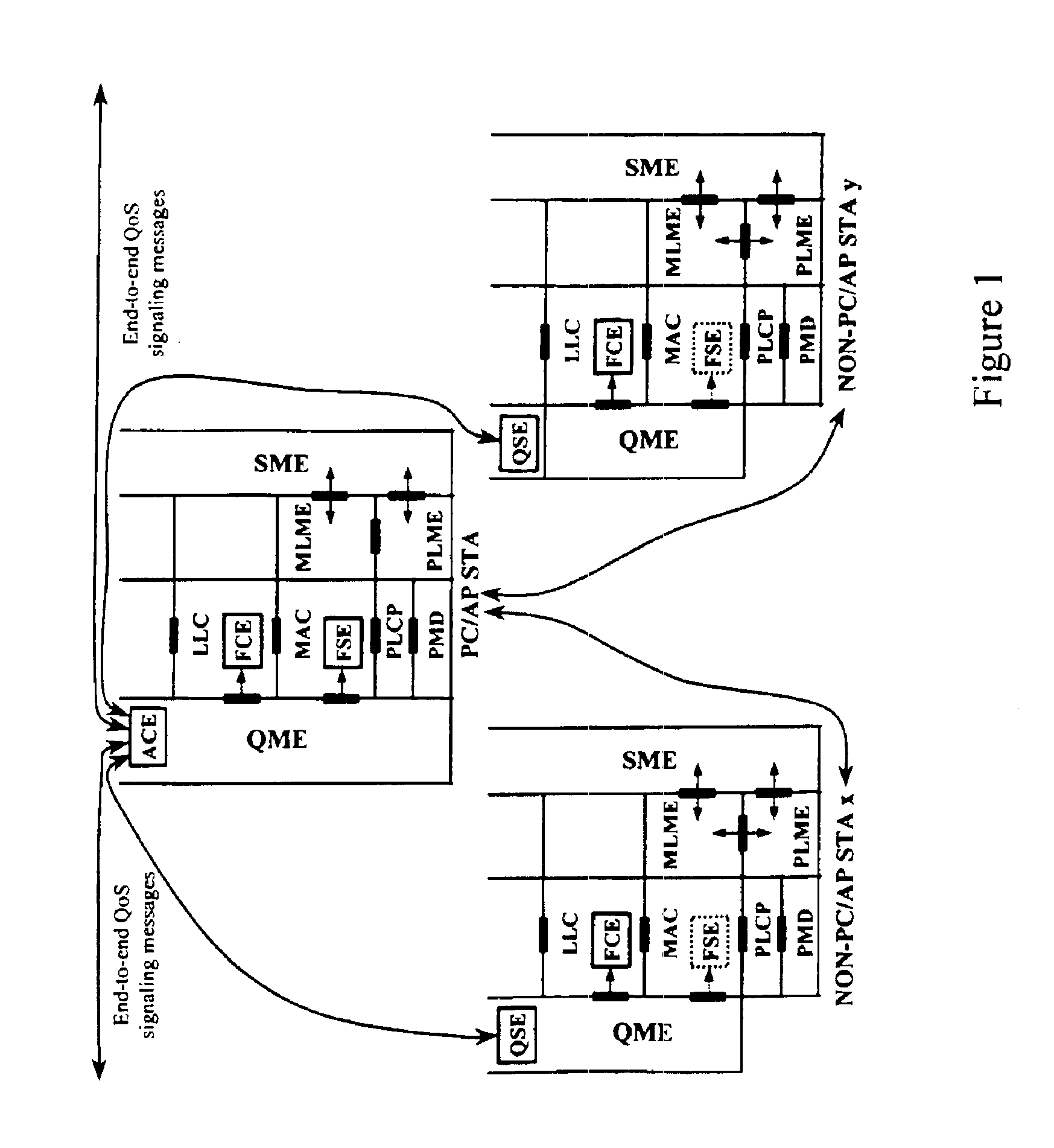
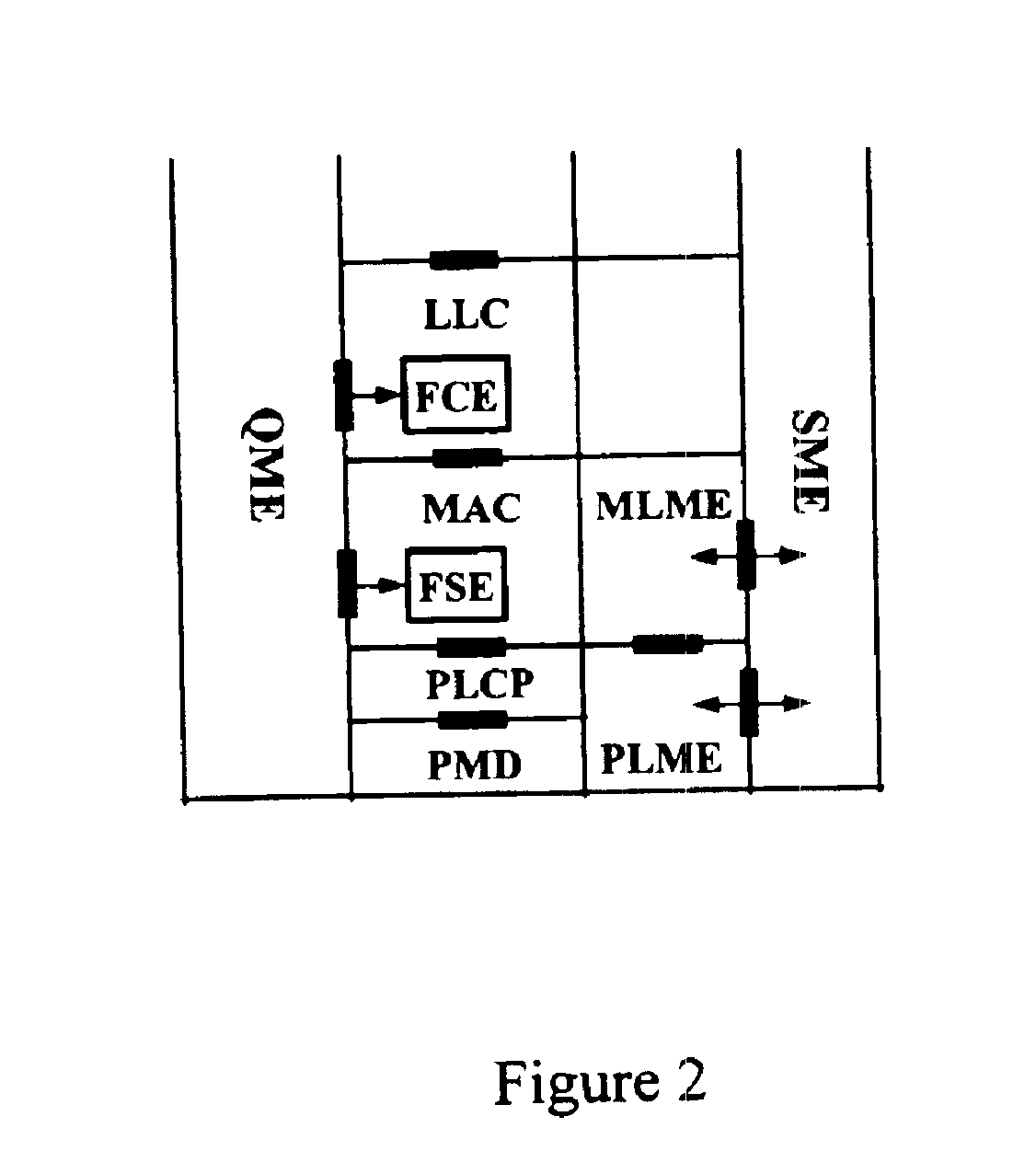
Architectural reference model for QoS-driven wireless LANs
InactiveUS6862270B1Enhanced channel accessImprove bandwidth utilizationNetwork traffic/resource managementNetwork topologiesOpen Systems InterconnectionEnd to end qos
A quality of service (QoS) station is disclosed containing a point coordinator (PC) for a basic service set (BSS) in a wireless LAN. The PC station includes a QoS management entity (QME) and an admission control entity (ACE). The QME receives at least one end-to-end QoS message that characterizes a user application, such as a voice call, a video call, a data call and a multimedia call. The at least one end-to-end QoS message includes at least one QoS parameter set that is expressed at layer 3 and higher of an ISO / IEC basic reference model of Open Systems interconnection (OSI) (ISO / IEC 7498-1) and is to be passed down to layer 2 of the PC-station for enabling QoS traffic transport of the application. The ACE performs an admission control decision relating to the application based on the at least one end-to-end QoS message characterizing the application. The ACE reserves a resource based on a QoS parameter set contained in the end-to-end QoS message. The ACE can be part of the QME and can include a resource control module that performs at least one admission control decision based on resource permission, and a policy control module that performs at least one admission control decision based on policy permission.
Owner:AT&T INTPROP I L P
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com