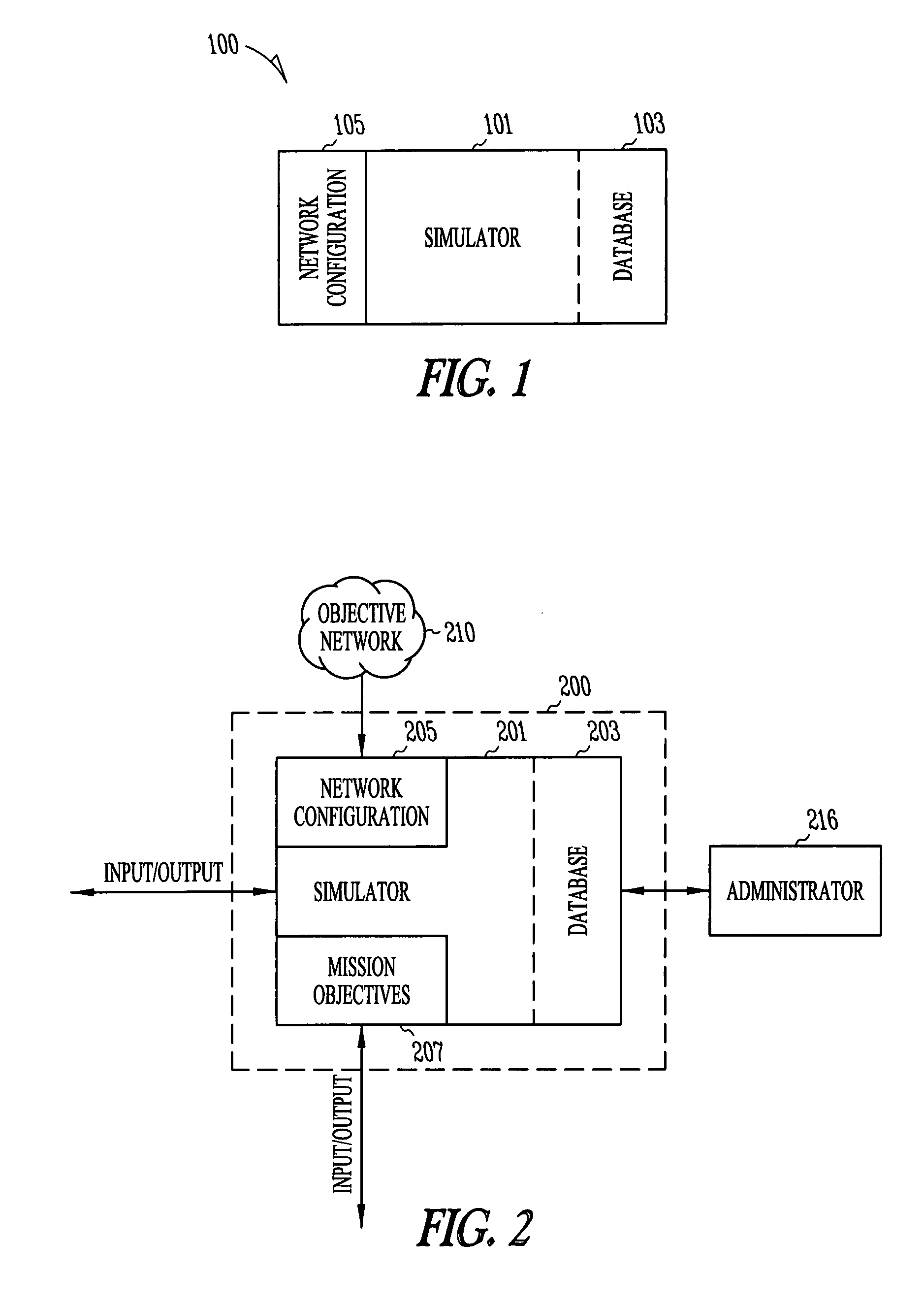
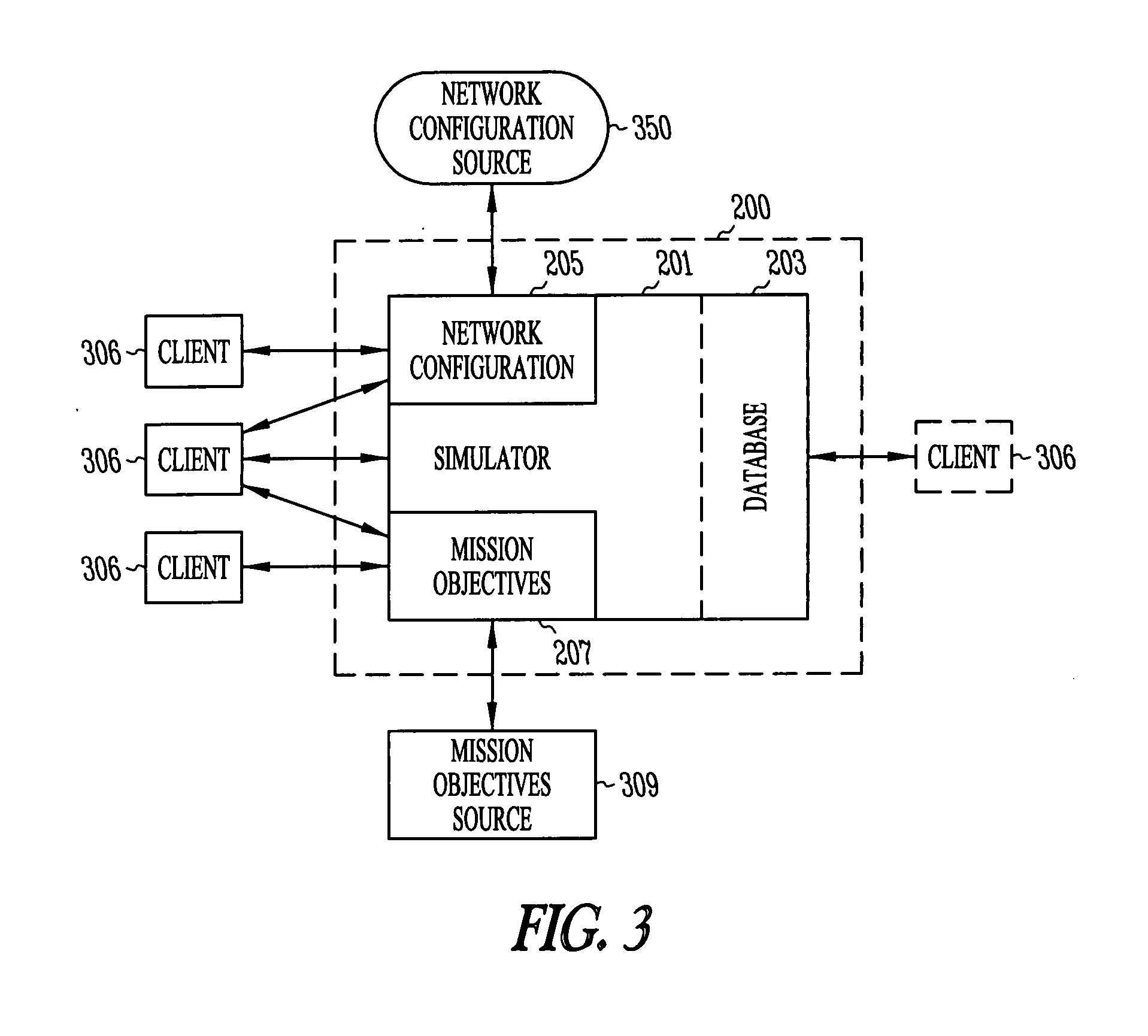
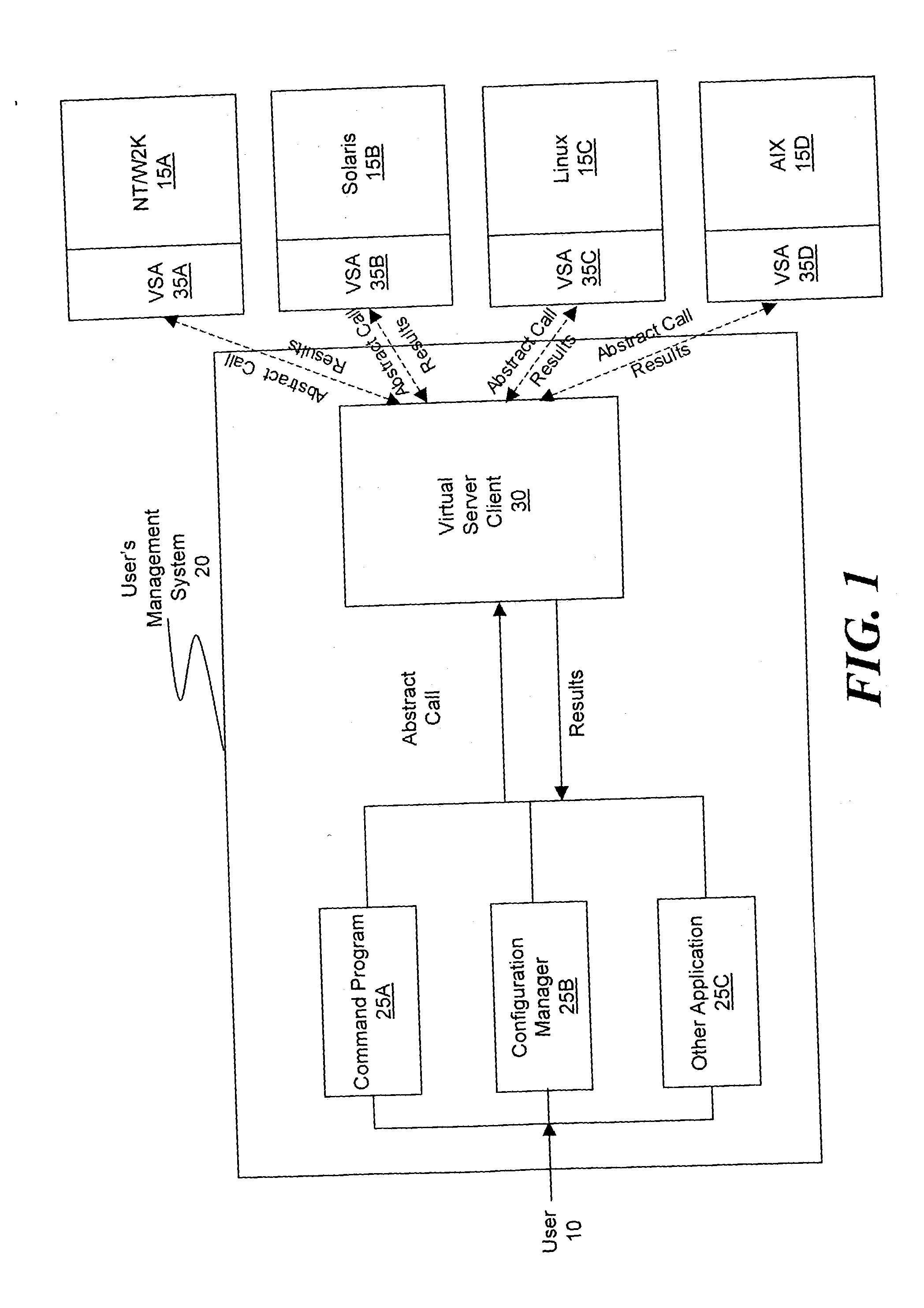
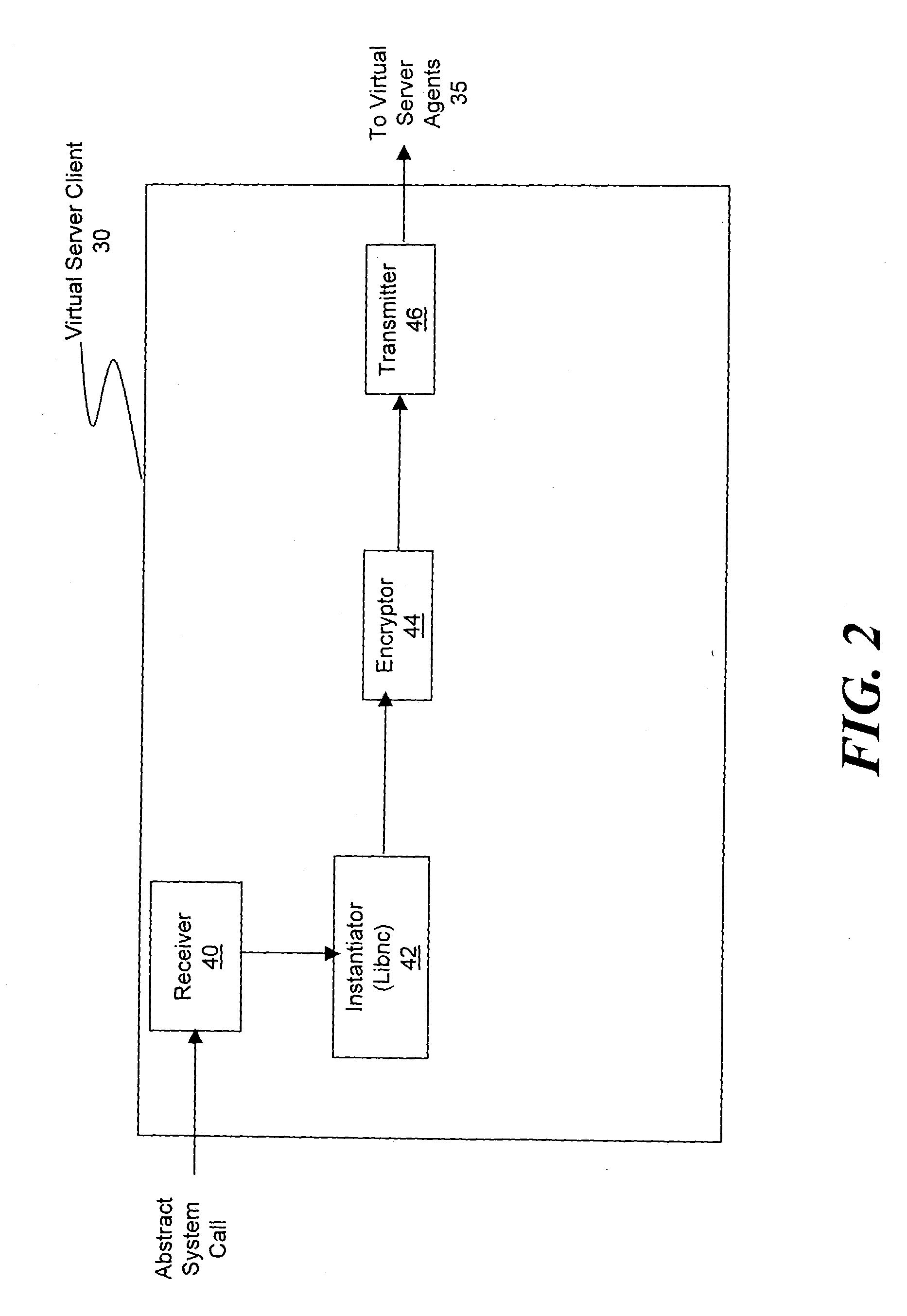
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4028 results about "Network configuration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
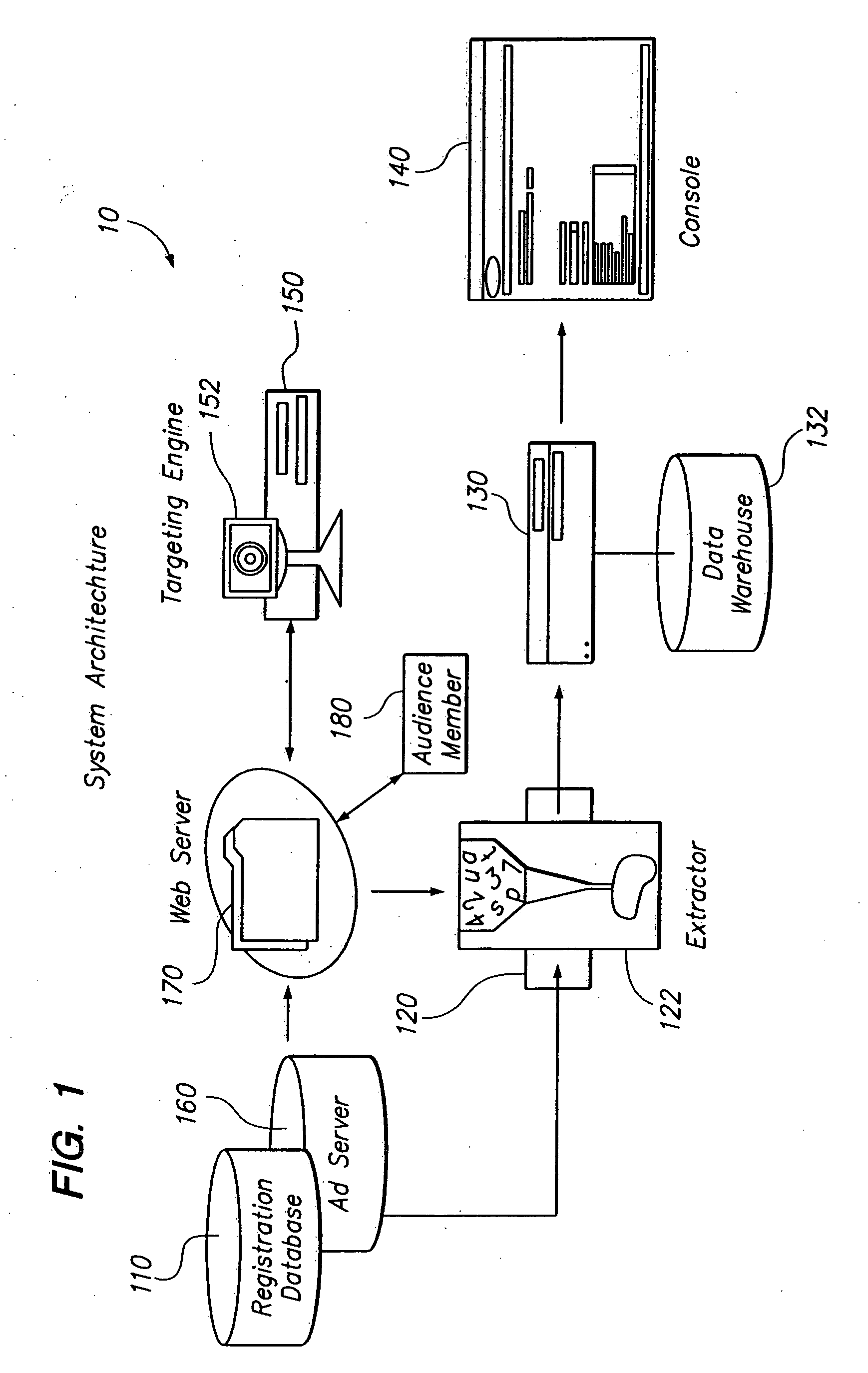
Network configuration and change management (NCCM) is a discipline in information technology. According to research from IDC and Gartner, NCCM is one of the fastest growing markets in the ITOM (IT Operations Management) market.
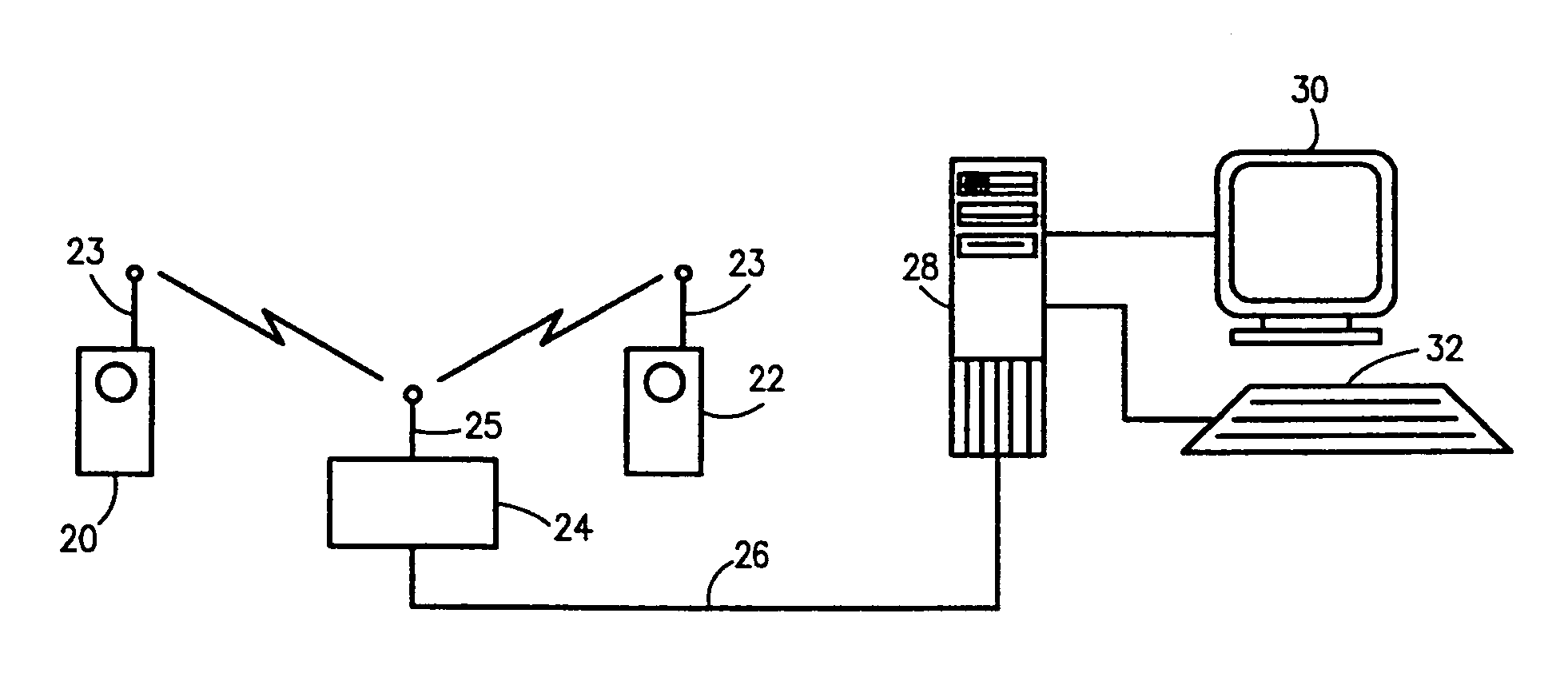
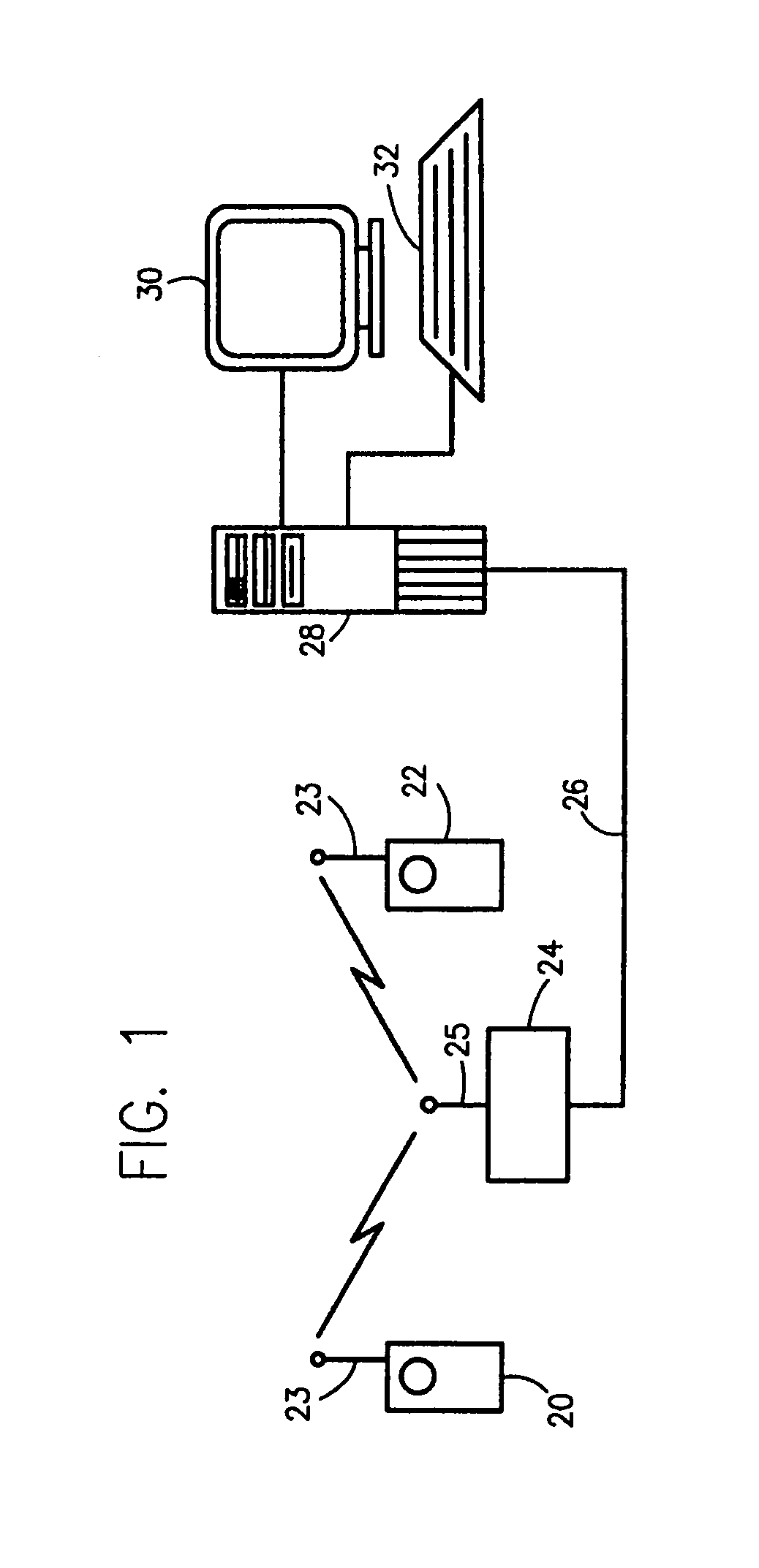
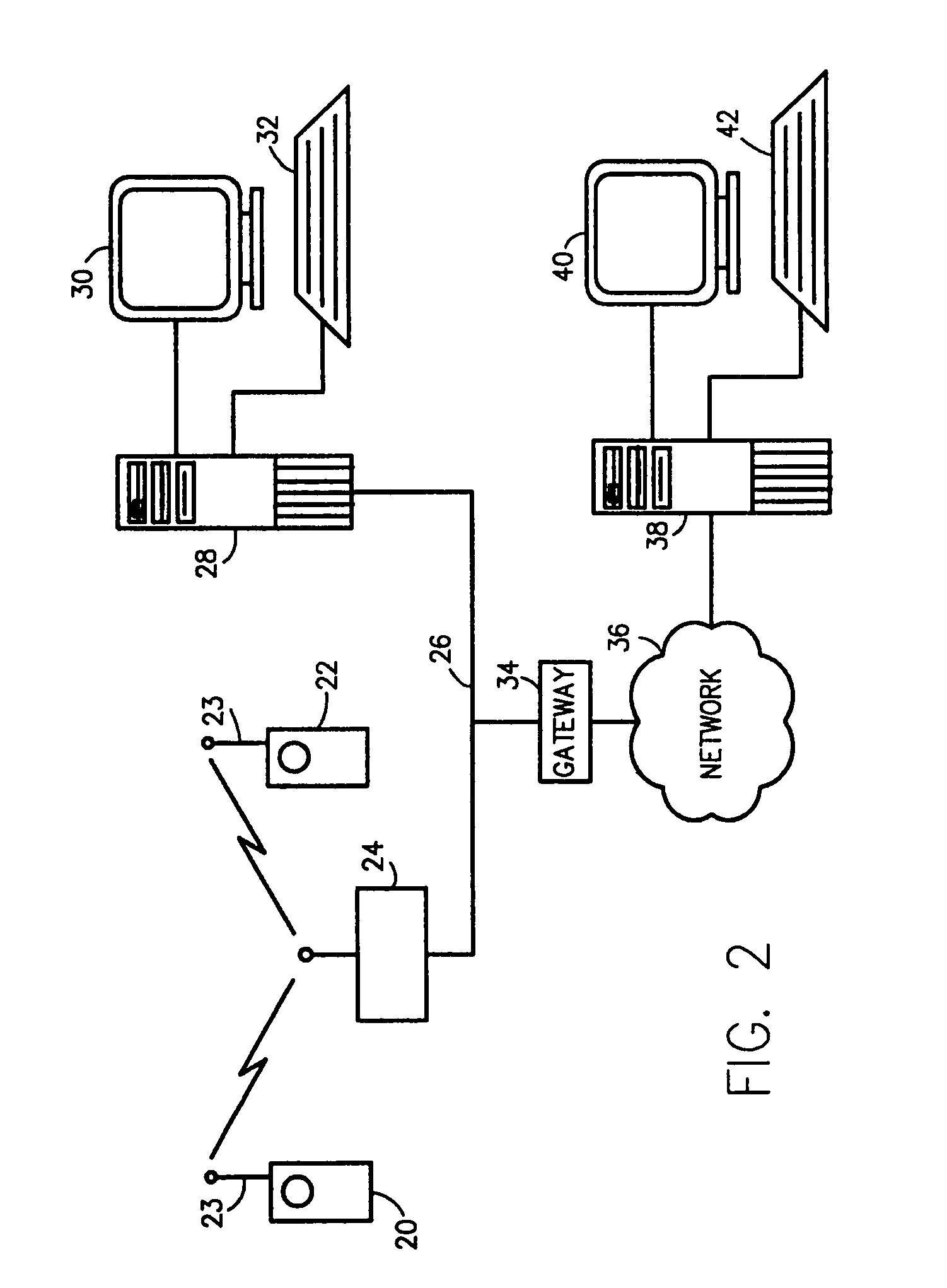
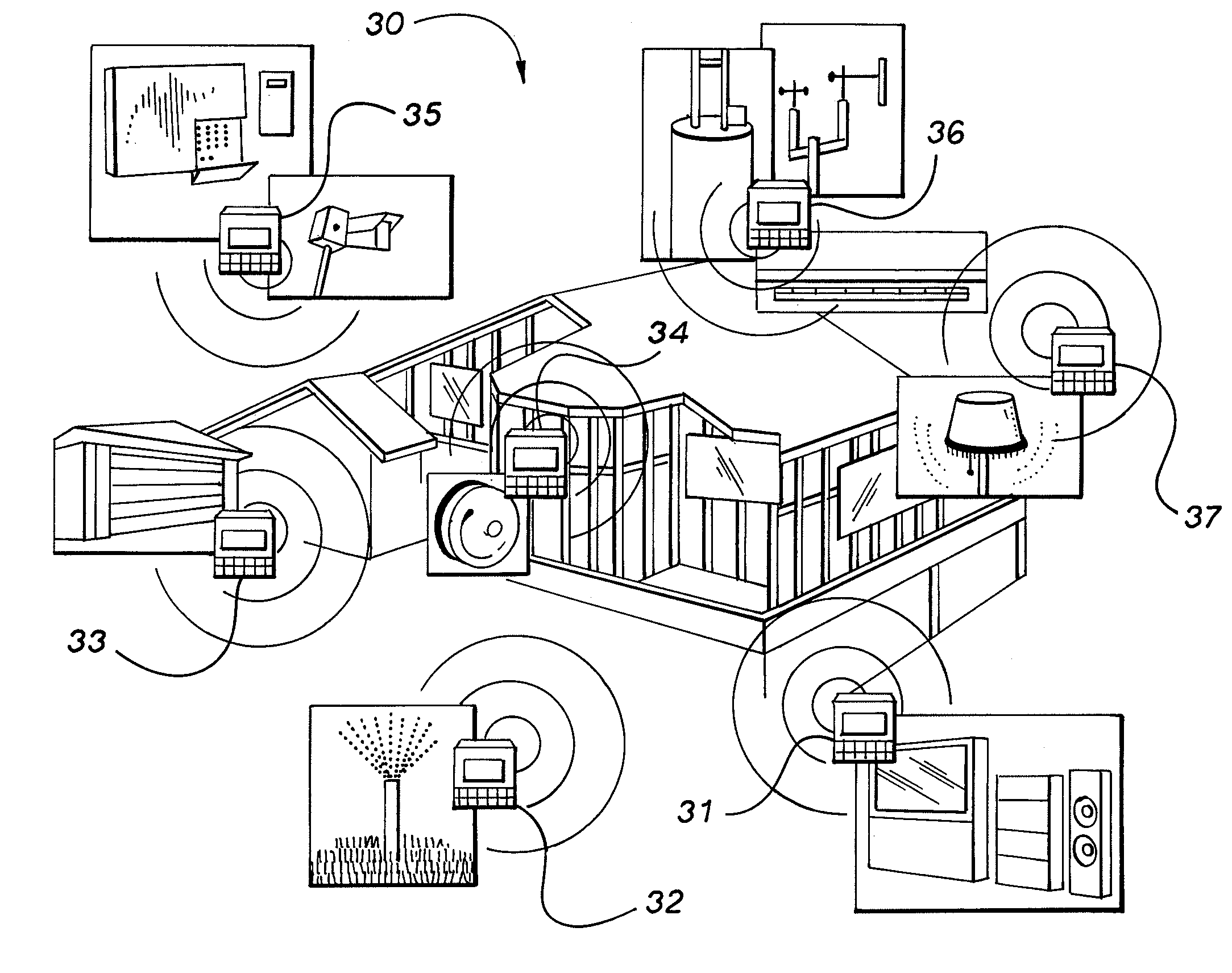
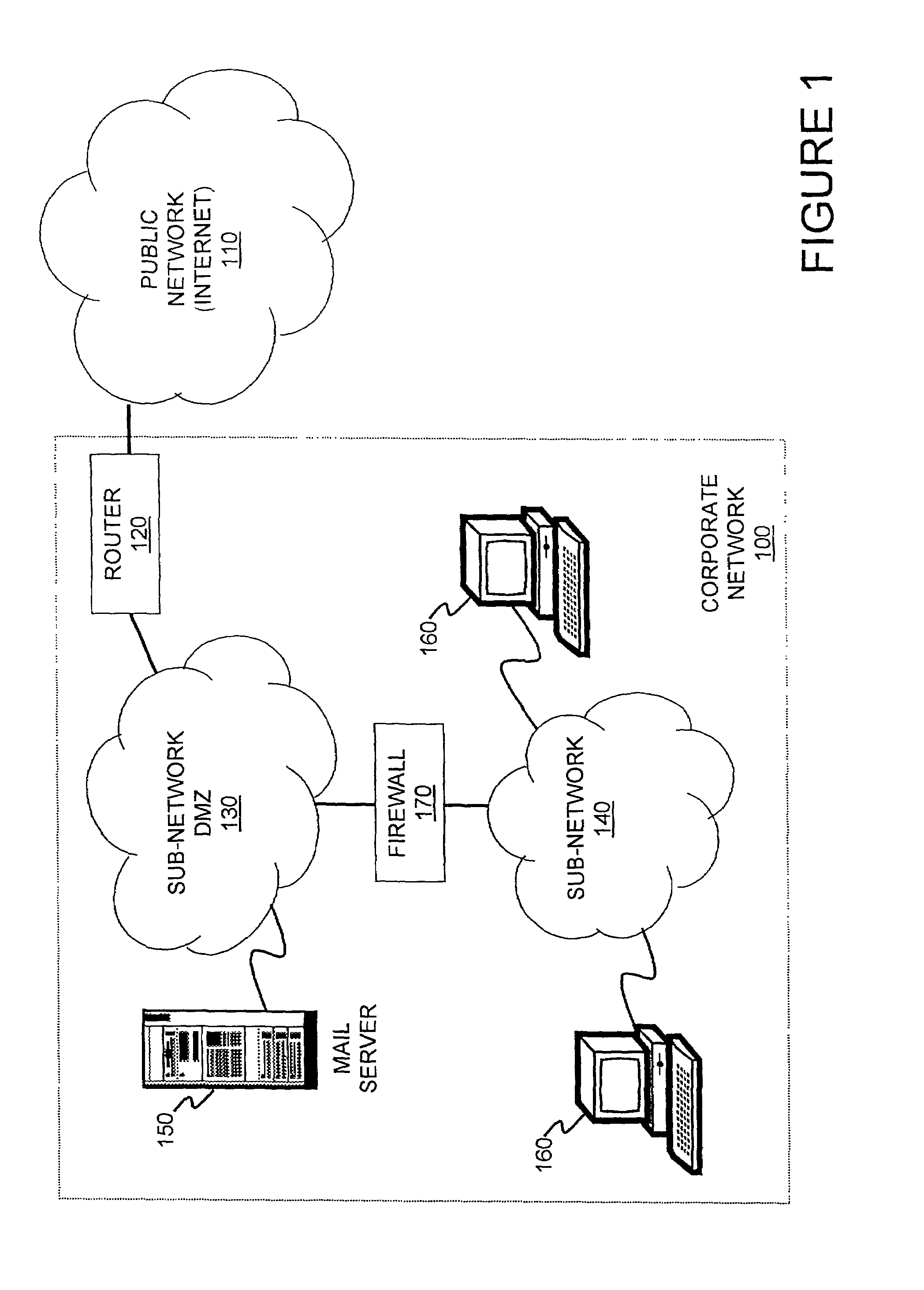
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
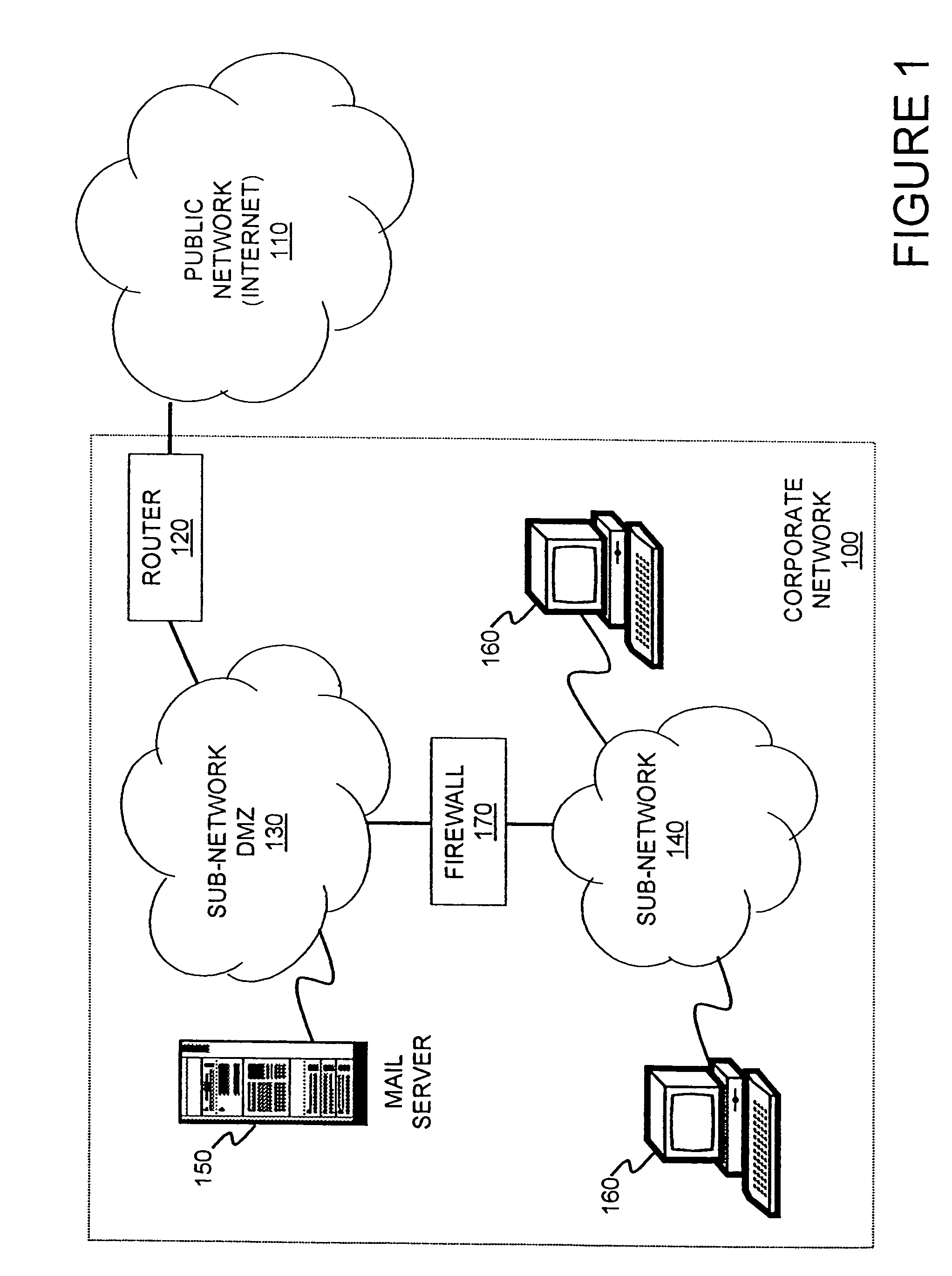
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
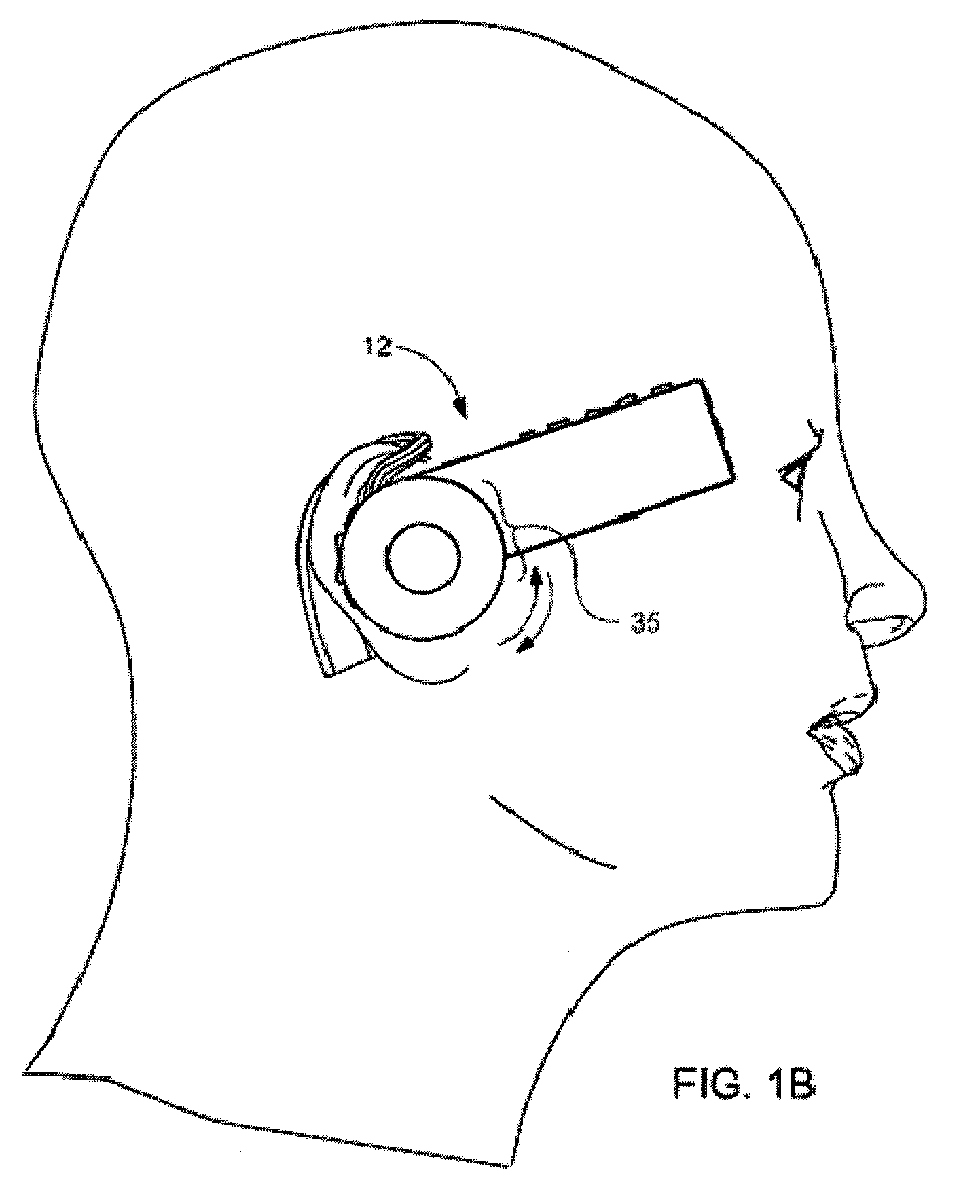
Headset-Based Telecommunications Platform
ActiveUS20100245585A1Extend battery lifeTelevision system detailsOptical rangefindersData streamPeer-to-peer
A hands-free wireless wearable GPS enabled video camera and audio-video communications headset, mobile phone and personal media player, capable of real-time two-way and multi-feed wireless voice, data and audio-video streaming, telecommunications, and teleconferencing, coordinated applications, and shared functionality between one or more wirelessly networked headsets or other paired or networked wired or wireless devices and optimized device and data management over multiple wired and wireless network connections. The headset can operate in concert with one or more wired or wireless devices as a paired accessory, as an autonomous hands-free wide area, metro or local area and personal area wireless audio-video communications and multimedia device and / or as a wearable docking station, hot spot and wireless router supporting direct connect multi-device ad-hoc virtual private networking (VPN). The headset has built-in intelligence to choose amongst available network protocols while supporting a variety of onboard, and remote operational controls including a retractable monocular viewfinder display for real time hands-free viewing of captured or received video feed and a duplex data-streaming platform supporting multi-channel communications and optimized data management within the device, within a managed or autonomous federation of devices or other peer-to-peer network configuration.
Owner:EYECAM INC
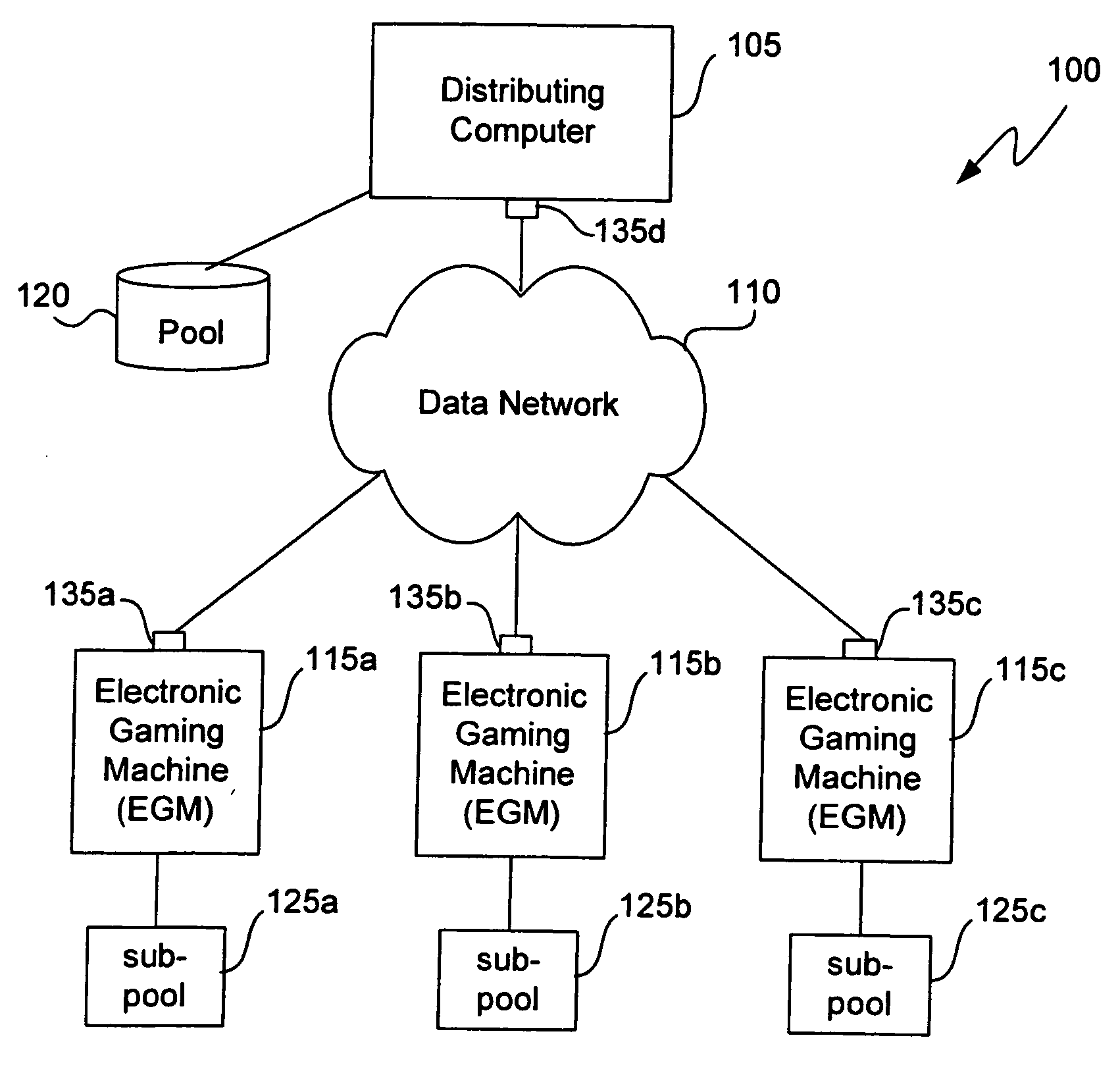
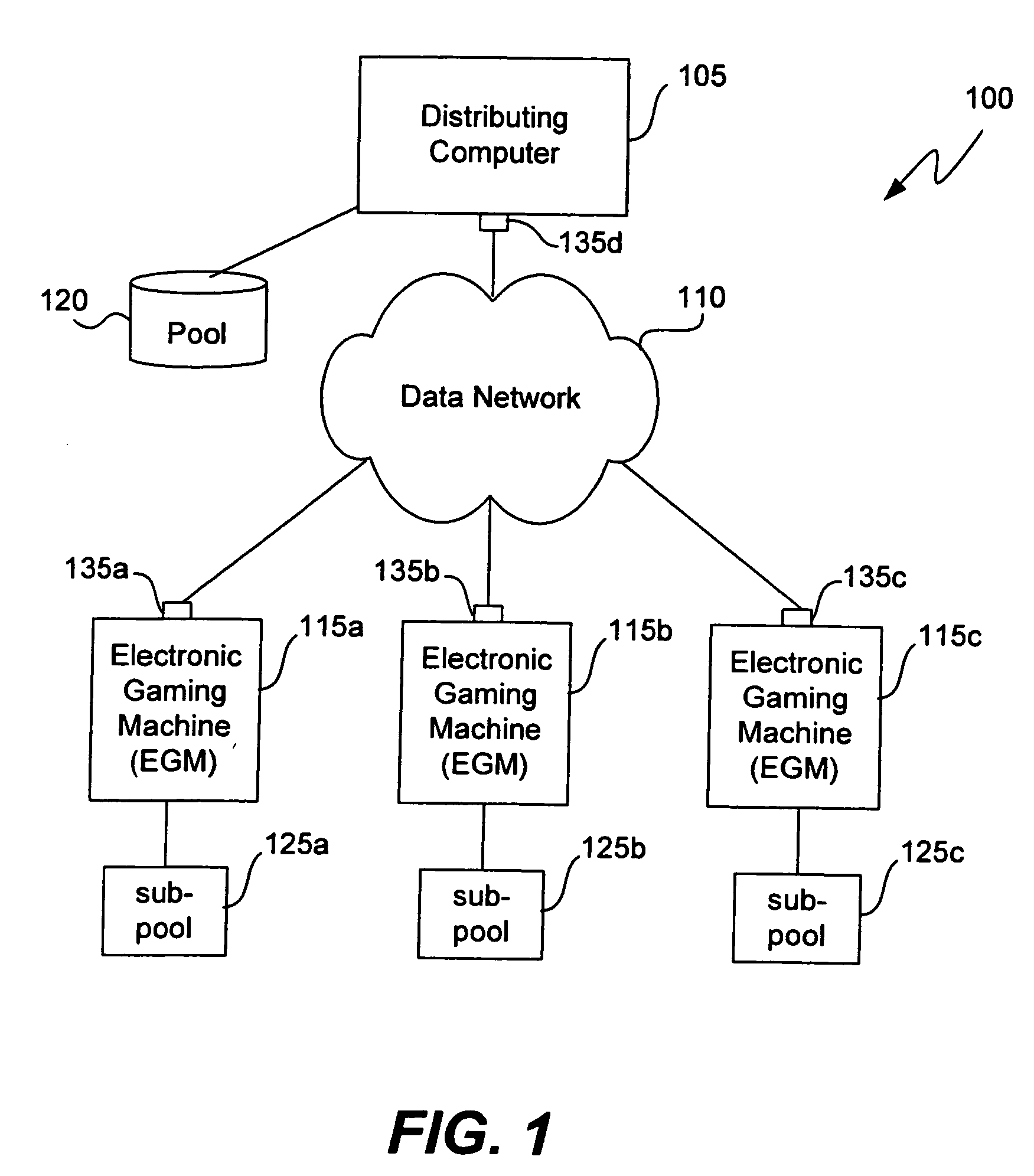
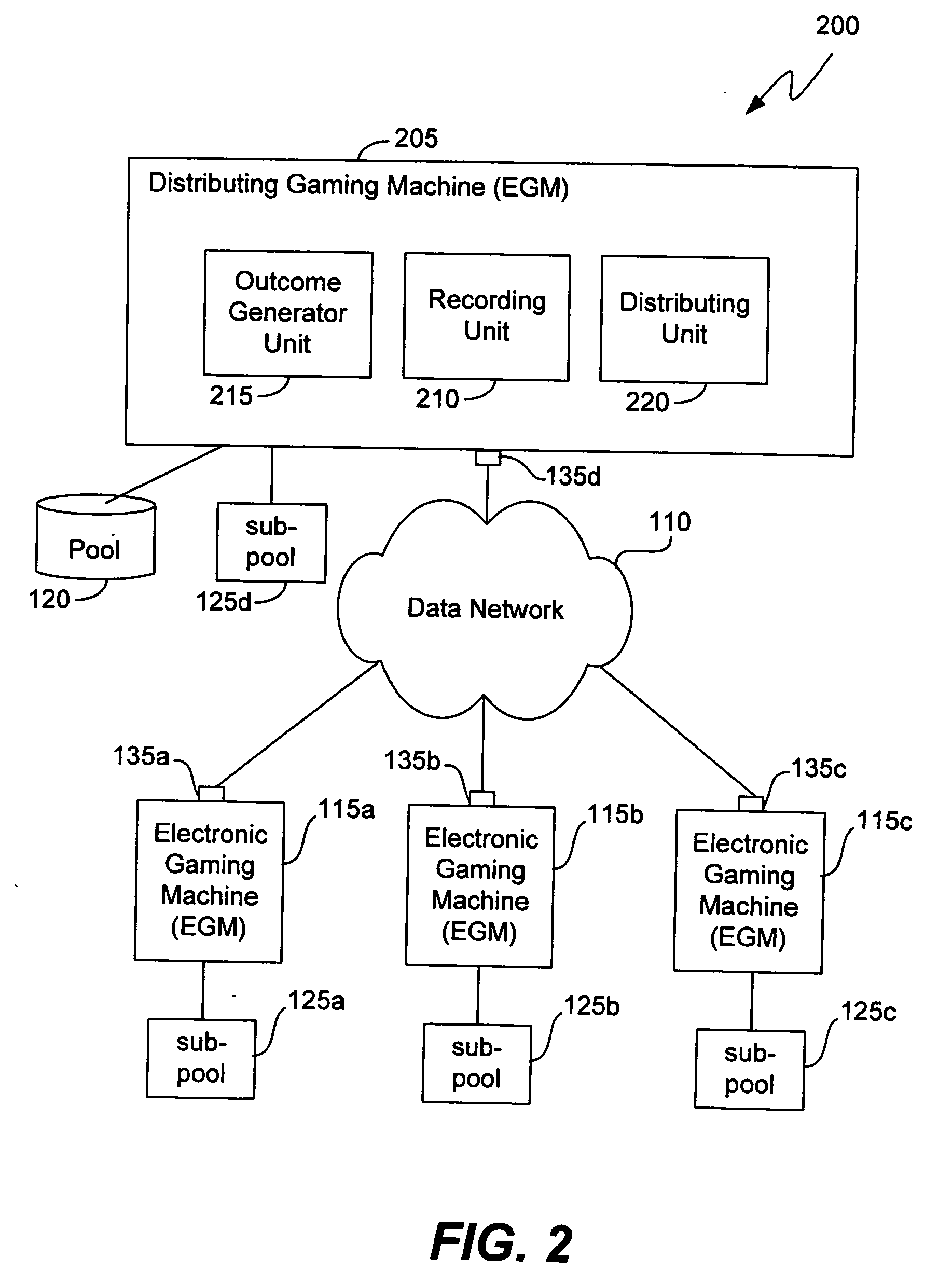
Gaming methods and systems
ActiveUS20060234791A1Apparatus for meter-controlled dispensingVideo gamesClass iiiHuman–computer interaction
Disclosed are central determination methods and systems in which pools and sub-pools of outcomes can be distributed among various units of the central determination system. The methods and systems are applicable to Class II and, in some implementations, Class III gaming configurations. The methods and systems disclosed herein can be implemented in a gaming machine network, wherein one of the gaming machines distributes game outcomes to other gaming machines in the network. The gaming machines can be oriented in a peer-to-peer configuration, a central storage medium configuration, a stand alone configuration, an autonomous gaming machine configuration, and other network configurations. Methods are disclosed for managing the distribution of outcomes among the gaming machines in the various networks.
Owner:IGT
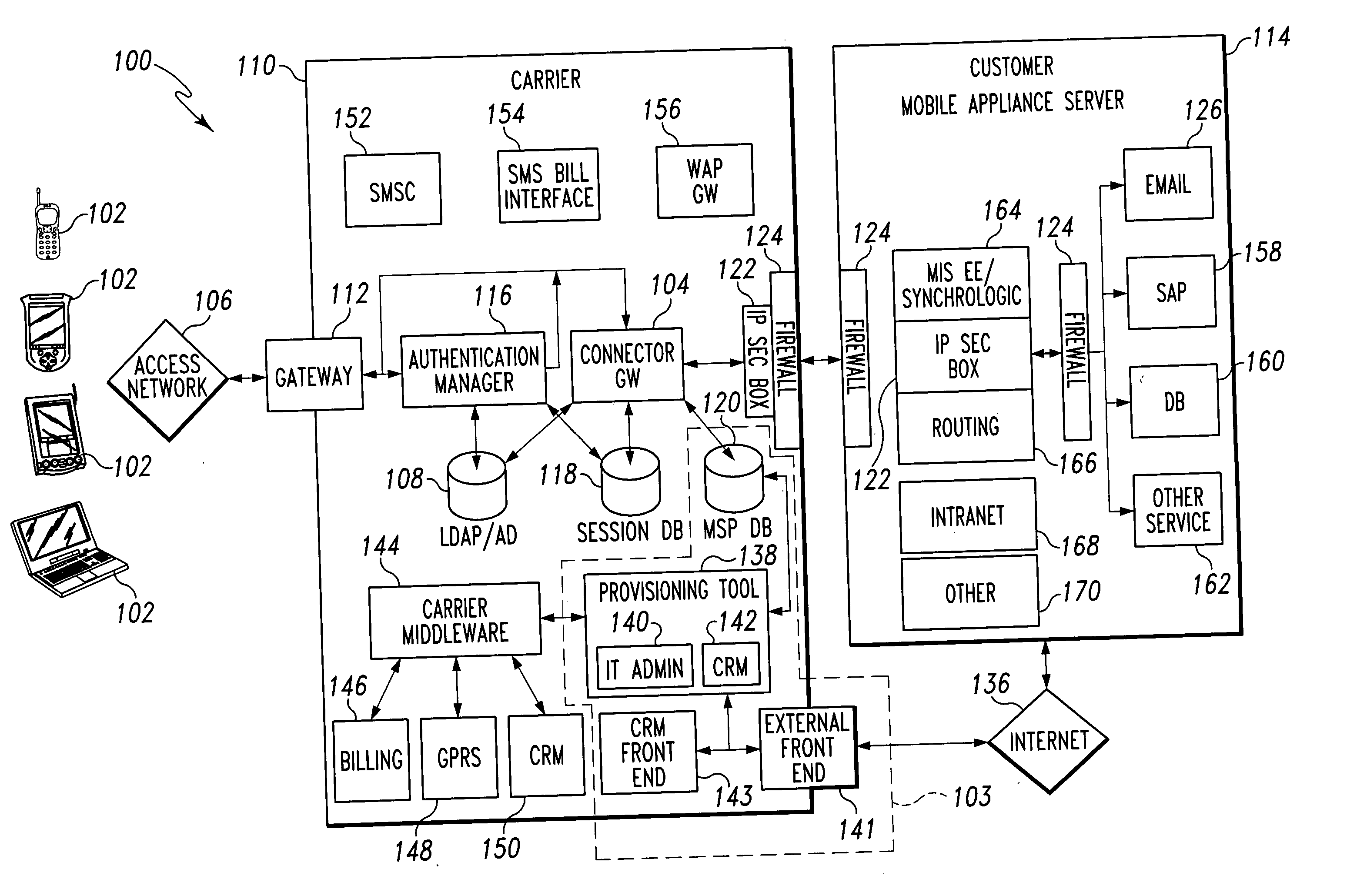
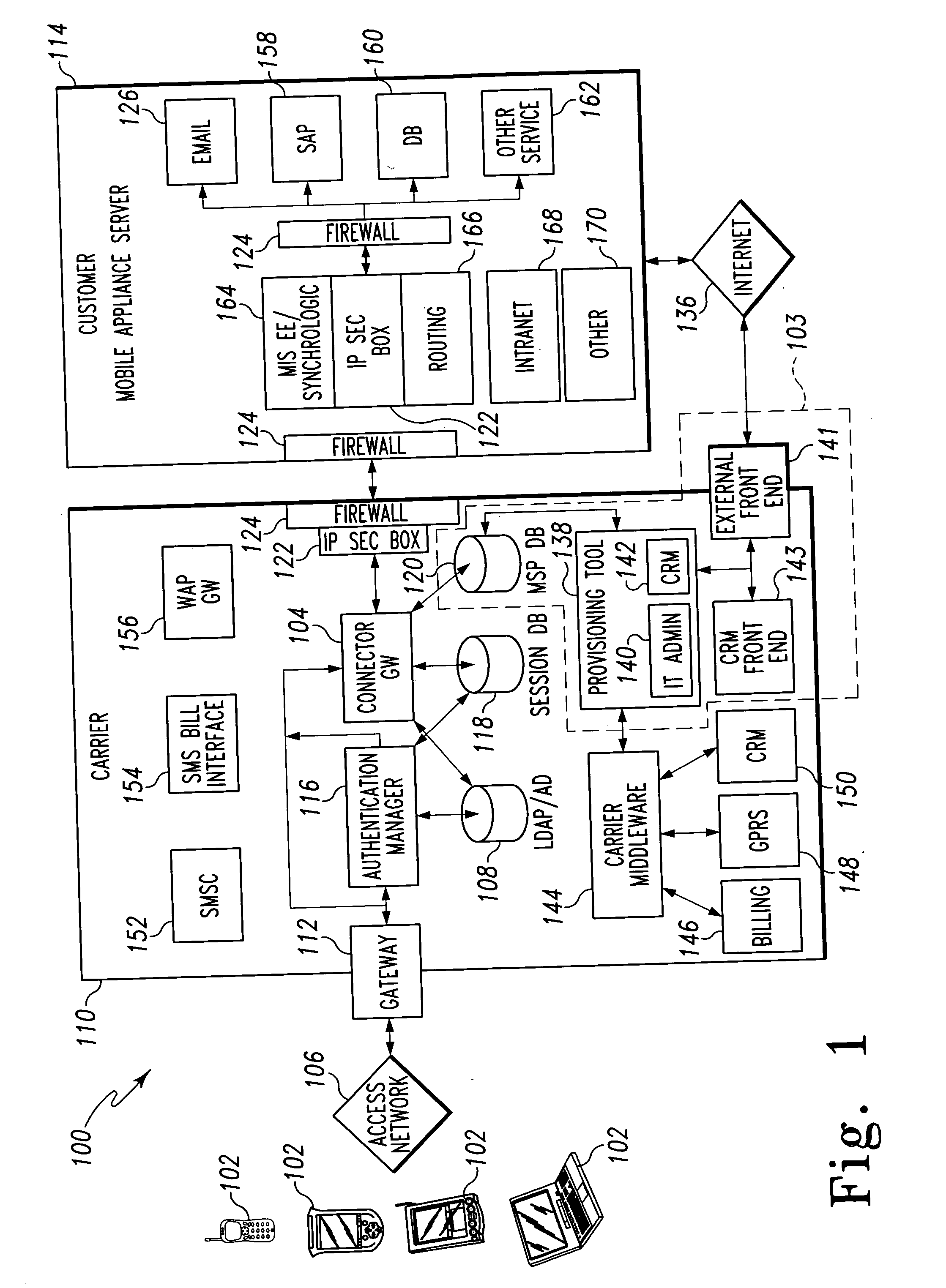
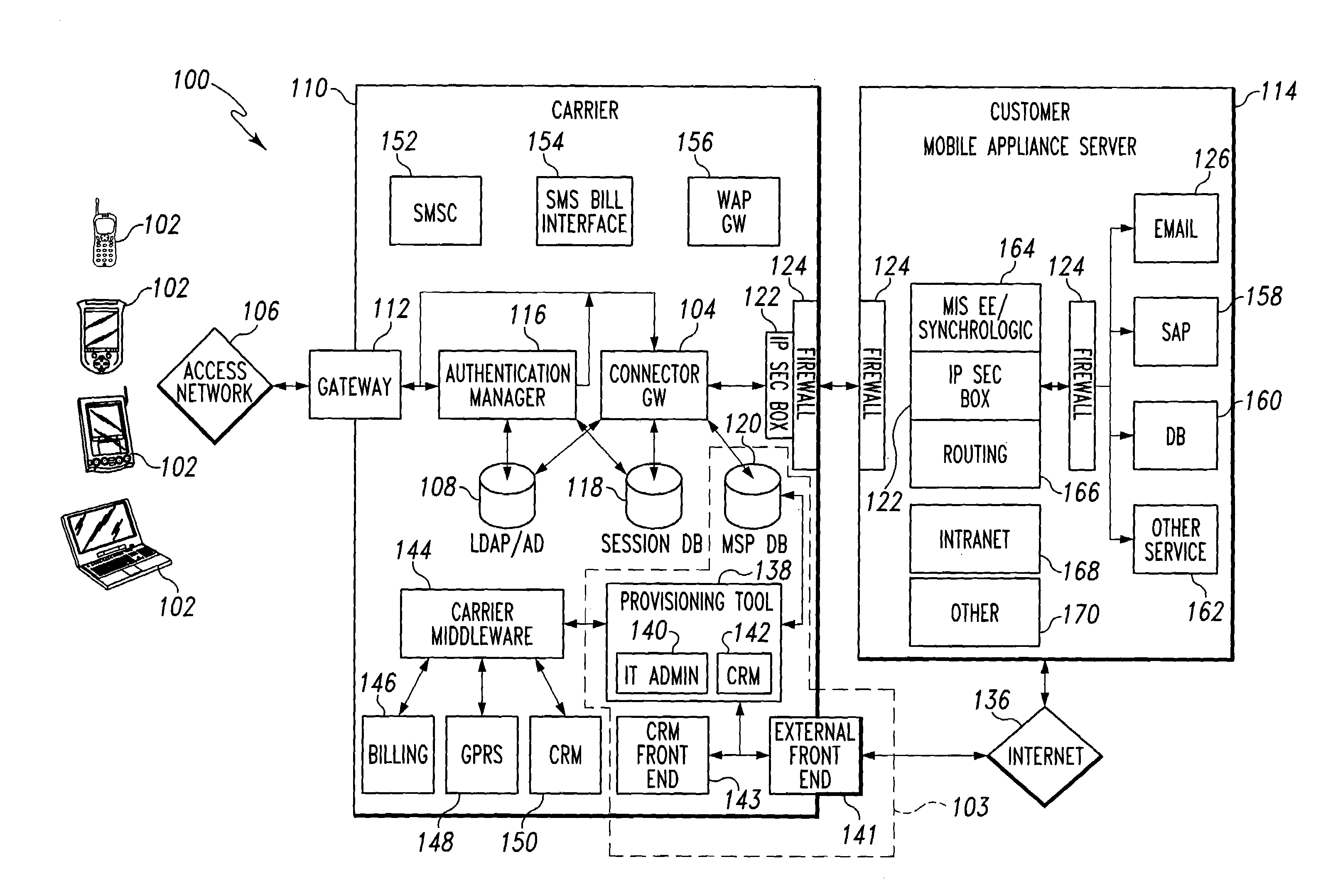
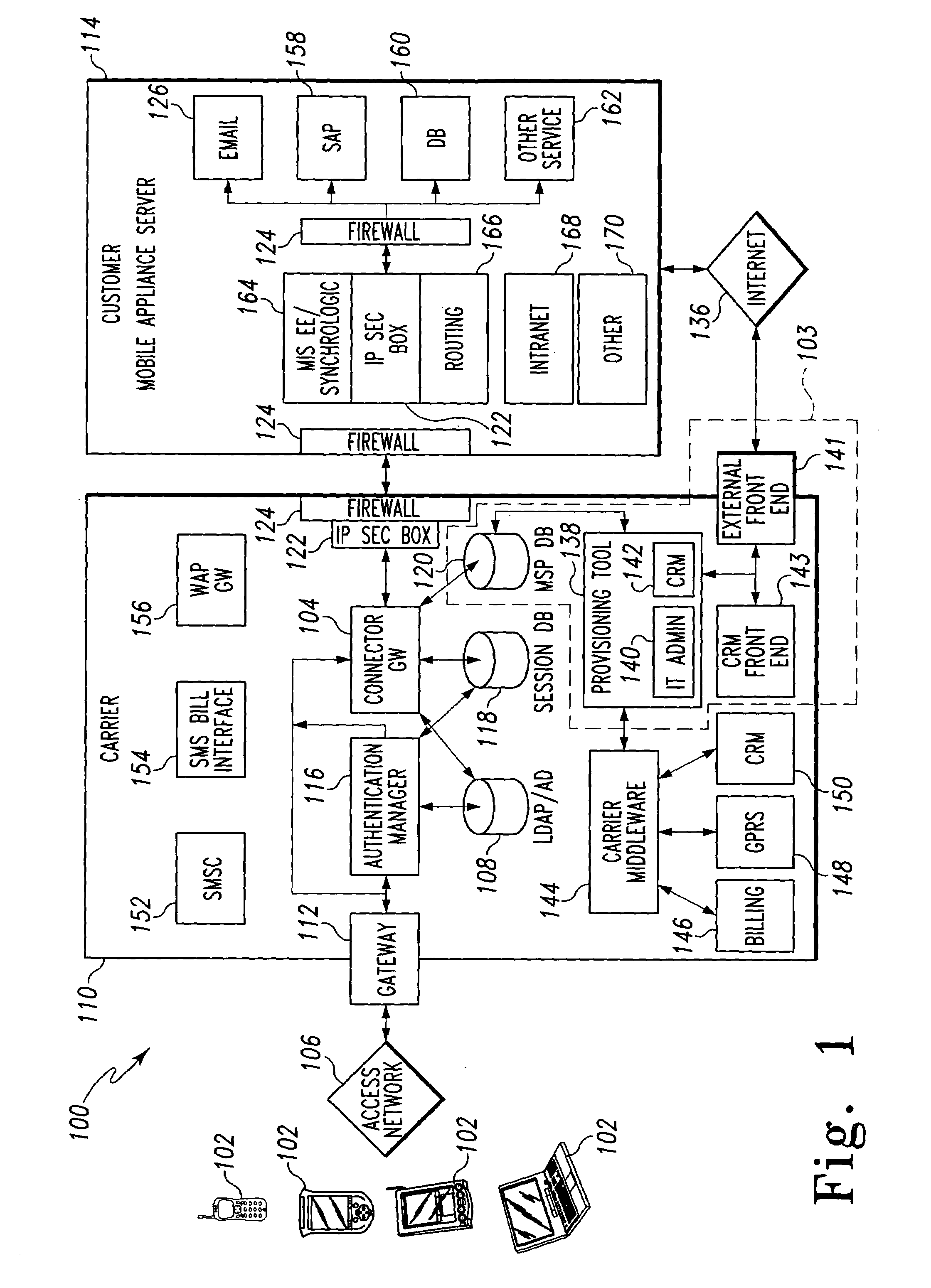
Mobile provisioning tool system
ActiveUS20050075115A1Simple processLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessWorkstation
A mobile provisioning tool system including a software provisioning tool application. The mobile provisioning tool system includes mobile devices capable of conducting wireless communication with wireless access points. A carrier network is connected with the wireless access points and a customer network that includes at least one business application. A provisioning tool application is located on a provisioning server. The provisioning tool application includes a CRM Rep component and an IT Admin component. A software provisioning tool application allows the provisioning workstation to automatically install mobile business services and configure network configuration settings on the mobile device.
Owner:ACCENTURE GLOBAL SERVICES LTD
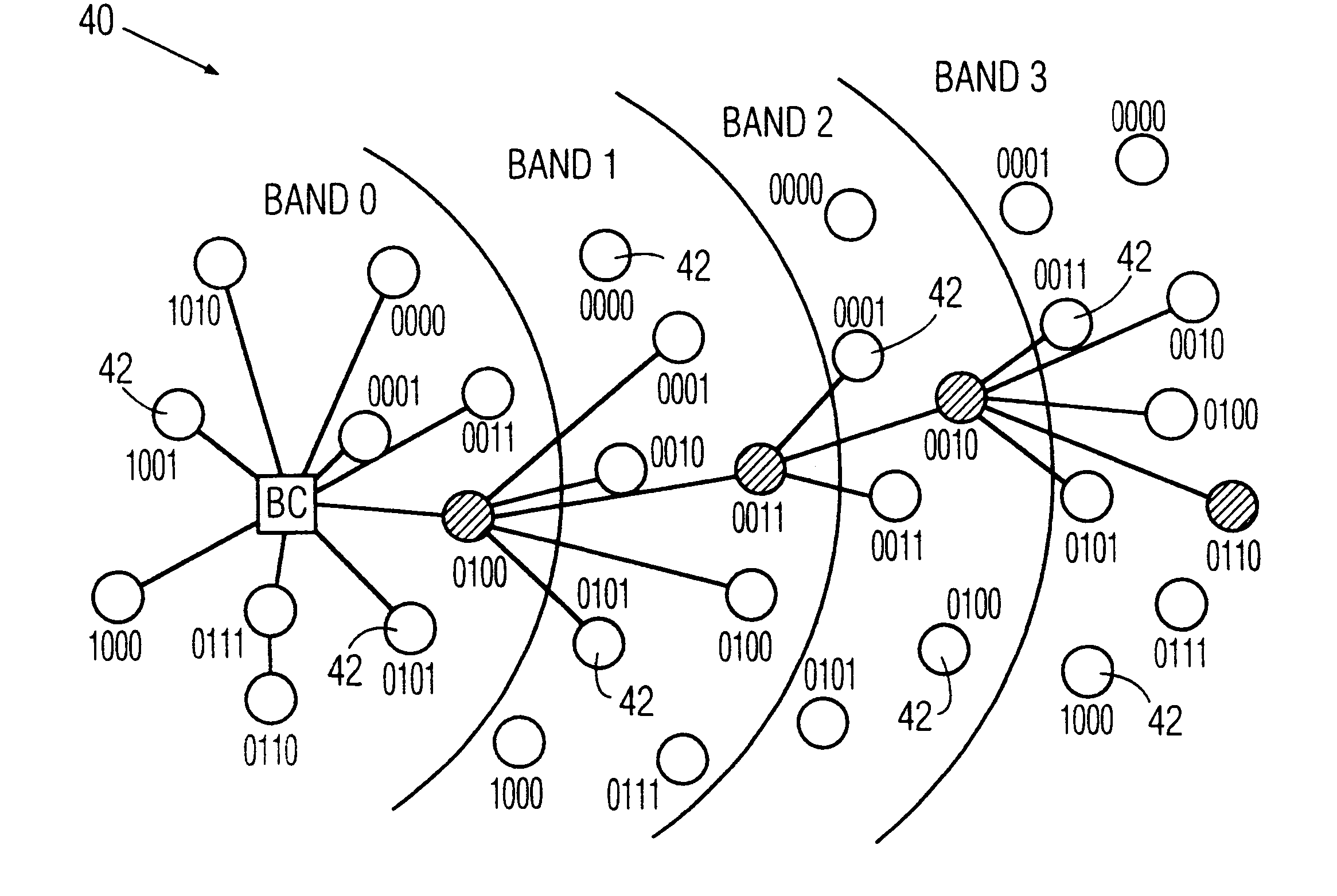
Method for configuring and routing data within a wireless multihop network and a wireless network for implementing the same
InactiveUS6842430B1Active radio relay systemsData switching by path configurationDistributed computingWireless network
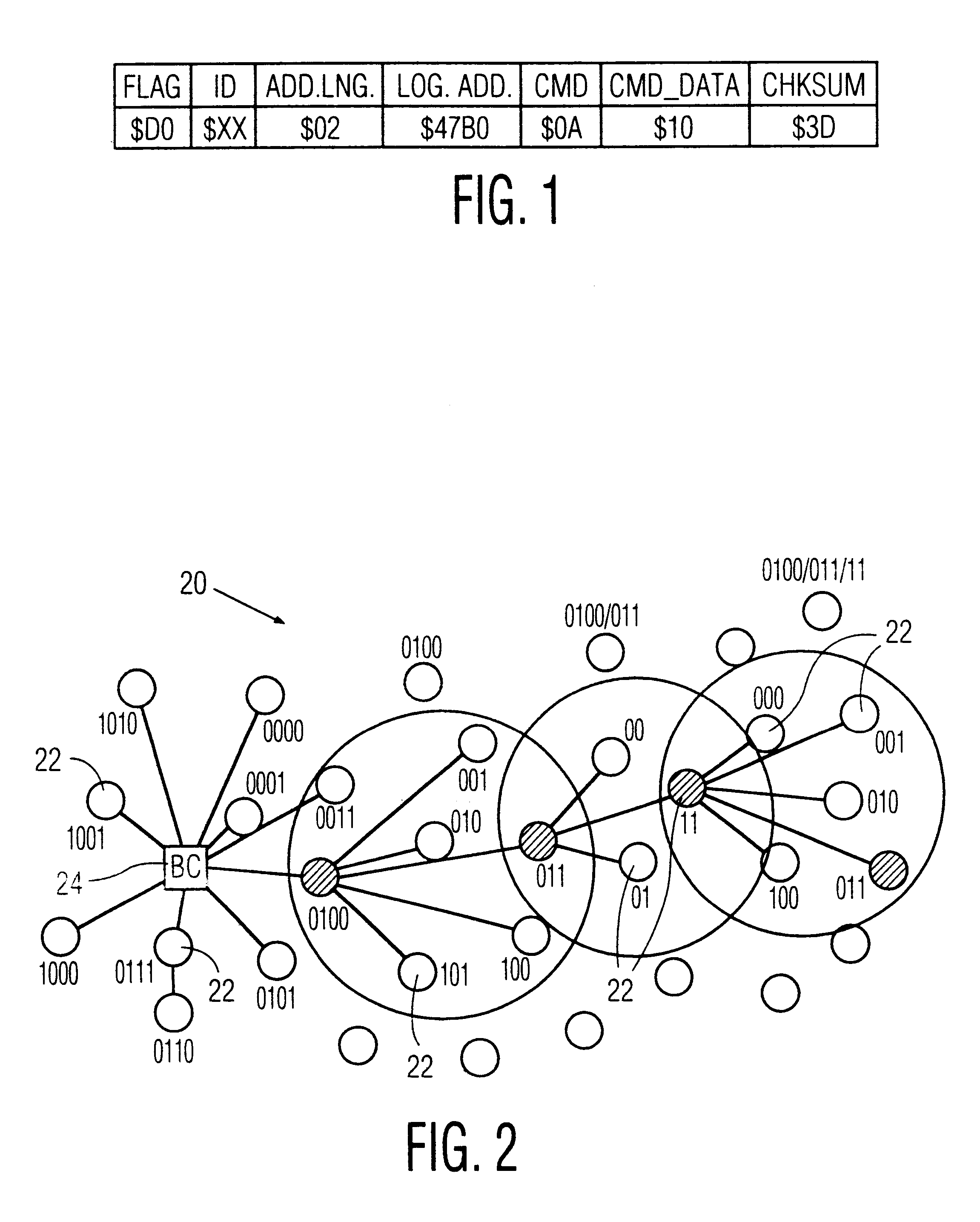
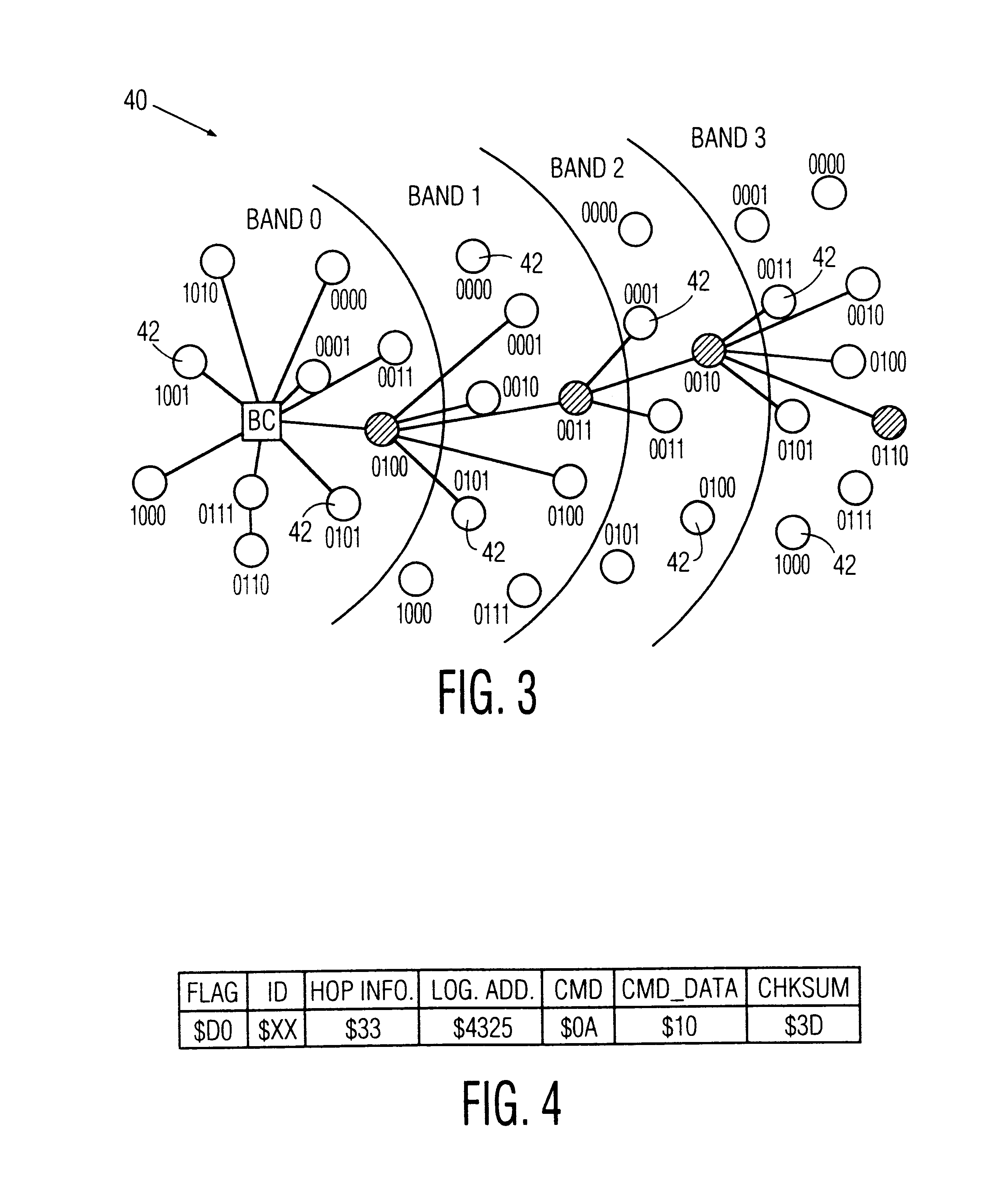
A method for configuring a wireless network comprised of a control node and a multiplicity of individual nodes includes the steps of logically organizing the network into a plurality of bands Bi, wherein each of the bands Bi includes a plurality of the individual nodes and is located a number i of hops away from the control node, where i=0 through N, and N≧1, and then assigning a logical address to each of the individual nodes, and storing the assigned logical addresses in the respective individual nodes. The assigned logical address for each individual node includes a first address portion which indicates the band Bi in which that individual node is located, and a second address portion that identifies that node relative to all other individual nodes located in the same band. The network is preferably a packet-hopping wireless network in which data is communicated by transferring data packets from node-to-node over a common RF channel. Each of the individual nodes is preferably programmed to perform the step of comparing its own logical address to a routing logical address contained in each packet which it receives, and to either discard, re-transmit, or process the packet based upon the results of the comparison. The routing logical address contained in a received packet contains the full routing information required to route the packet from a sending node to a destination node along a communication path prescribed by the routing logical address. The control node is programmed to control the routing of packets by inserting the routing logical address into each packet which it transmit, detecting any unsuccessfully transmitted packets, detecting a faulty node in the communication path prescribed by the routing logical address in response to detecting an unsuccessfully transmitted packet, and changing the routing logical address of the unsuccessfully transmitted packet to a new routing logical address which prescribes a new communication path which does not include the detected faulty node. Also disclosed are a wireless network and a network node which are designed to implement the foregoing network configuration and / or routing methods.
Owner:SIGNIFY HLDG BV
Method and apparatus for on demand multicast and unicast using controlled flood multicast communications
ActiveUS7184421B1Efficient routingEasy to collectSpecial service provision for substationData switching by path configurationFlexible MechanismsTraffic capacity
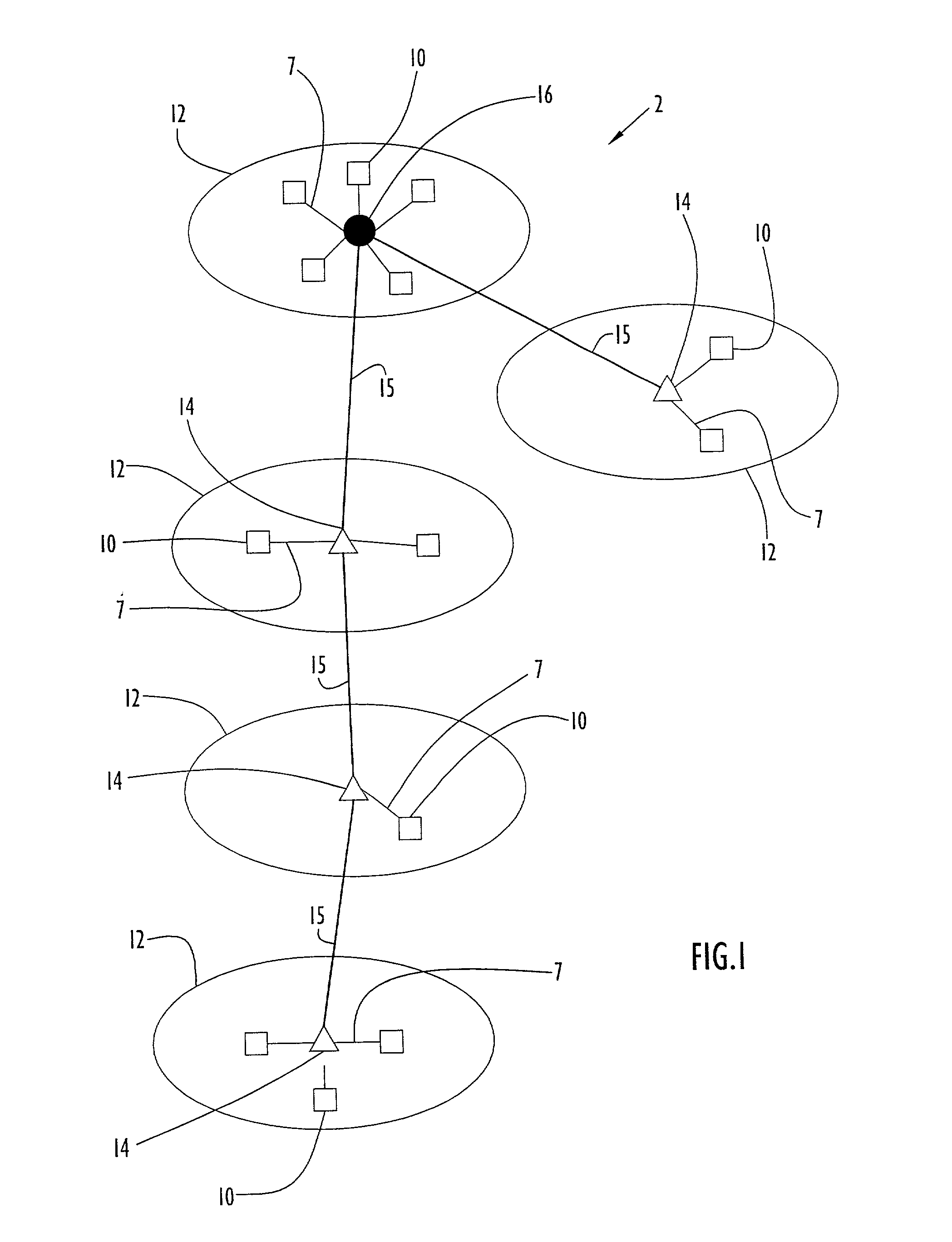
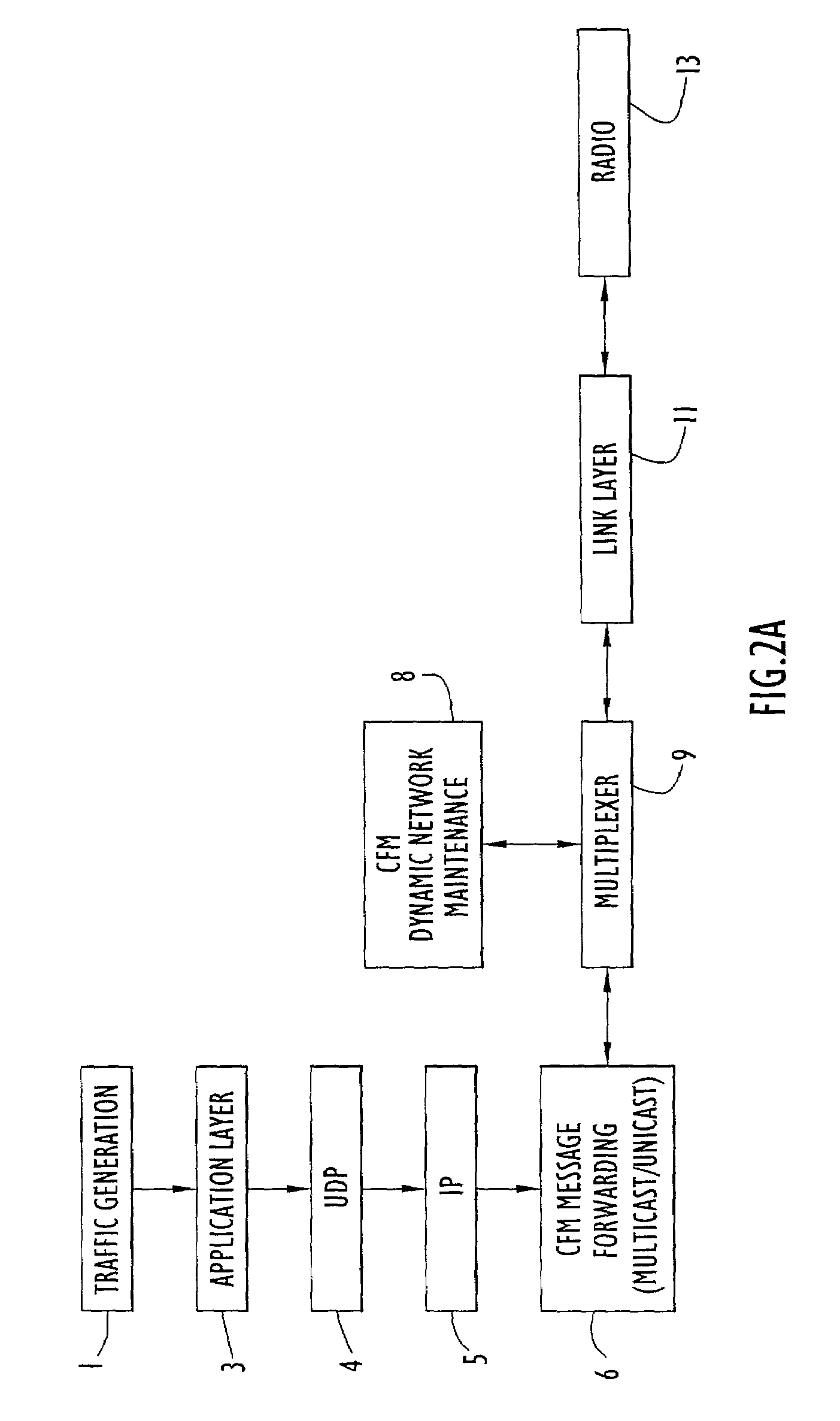
Network configuration hierarchy information is maintained using flexible mechanisms and methods for establishing routes and transferring information between nodes in ad-hoc data communication networks using on-demand multicast and unicast techniques. Communication nodes use network topology information to build and maintain a dynamically mobile, wireless, ad-hoc network capable of efficiently routing both unicast and multicast traffic. Network nodes that facilitate the collection and distribution of network topology and routing data are dynamically selected, configured, and maintained. Network traffic overhead necessary for maintaining and distributing network routing table information is held to a minimum and efficiently distributed across the network, thereby reducing the potential for network traffic bottlenecks due to network overhead processes.
Owner:STINGRAY IP SOLUTIONS LLC
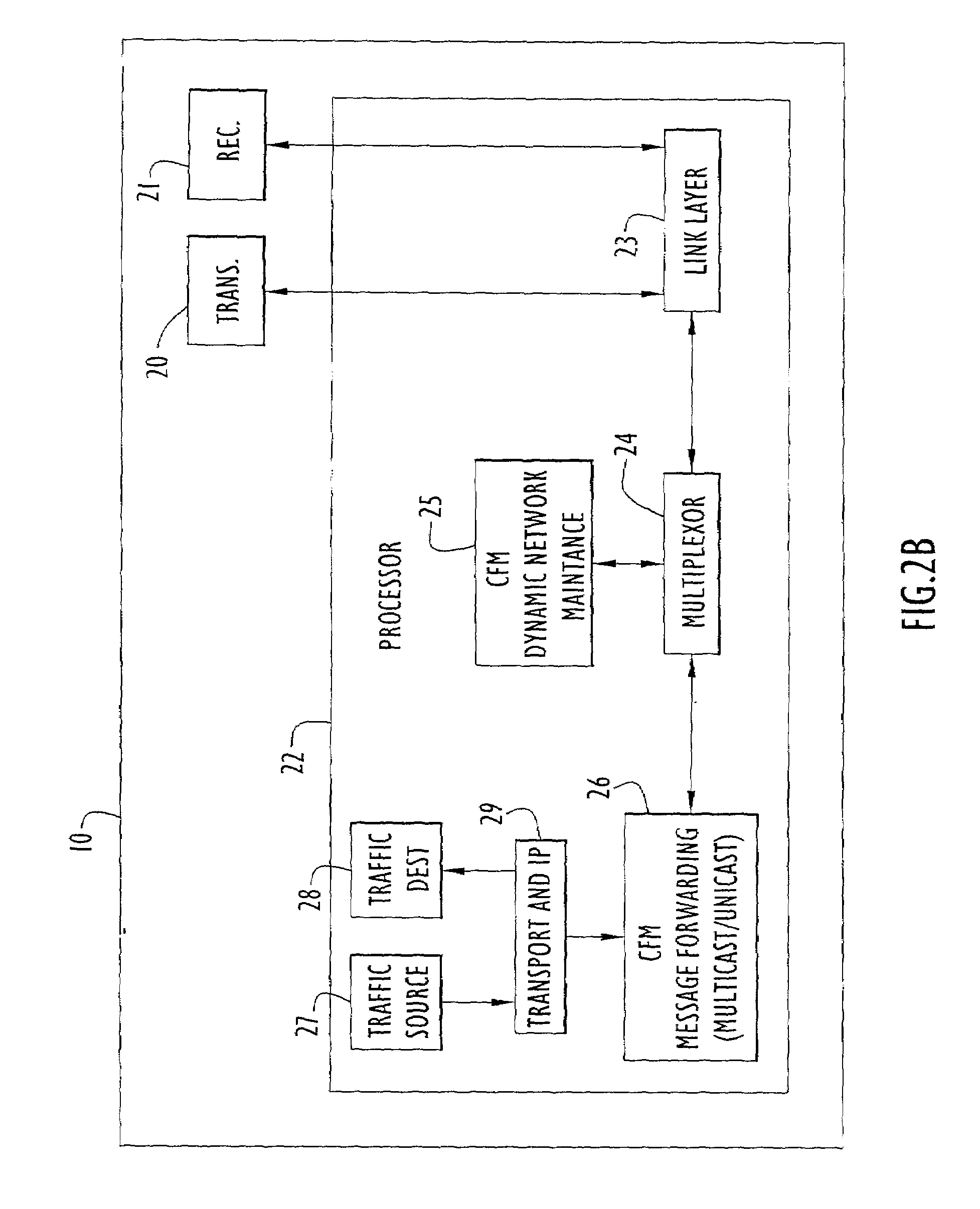
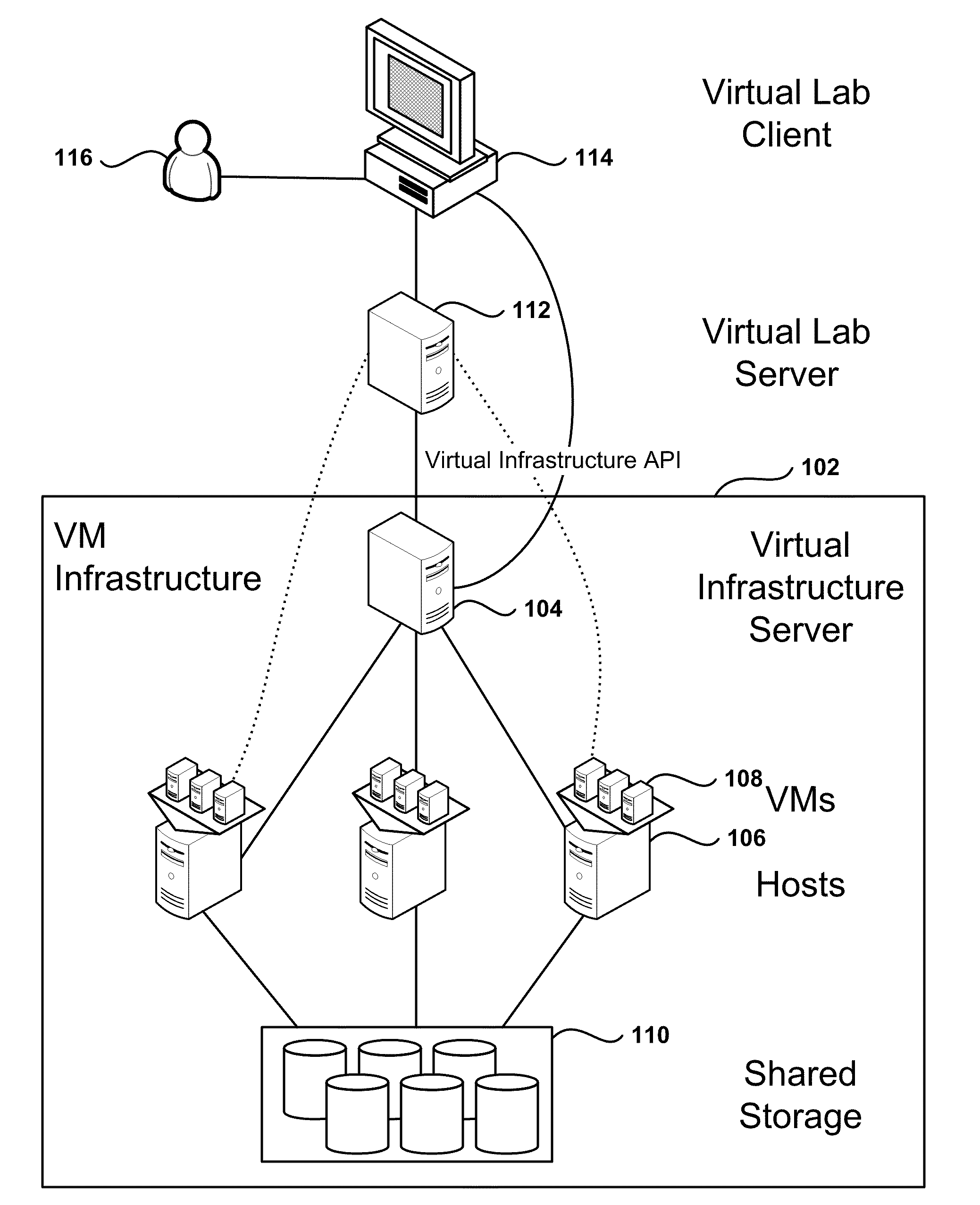
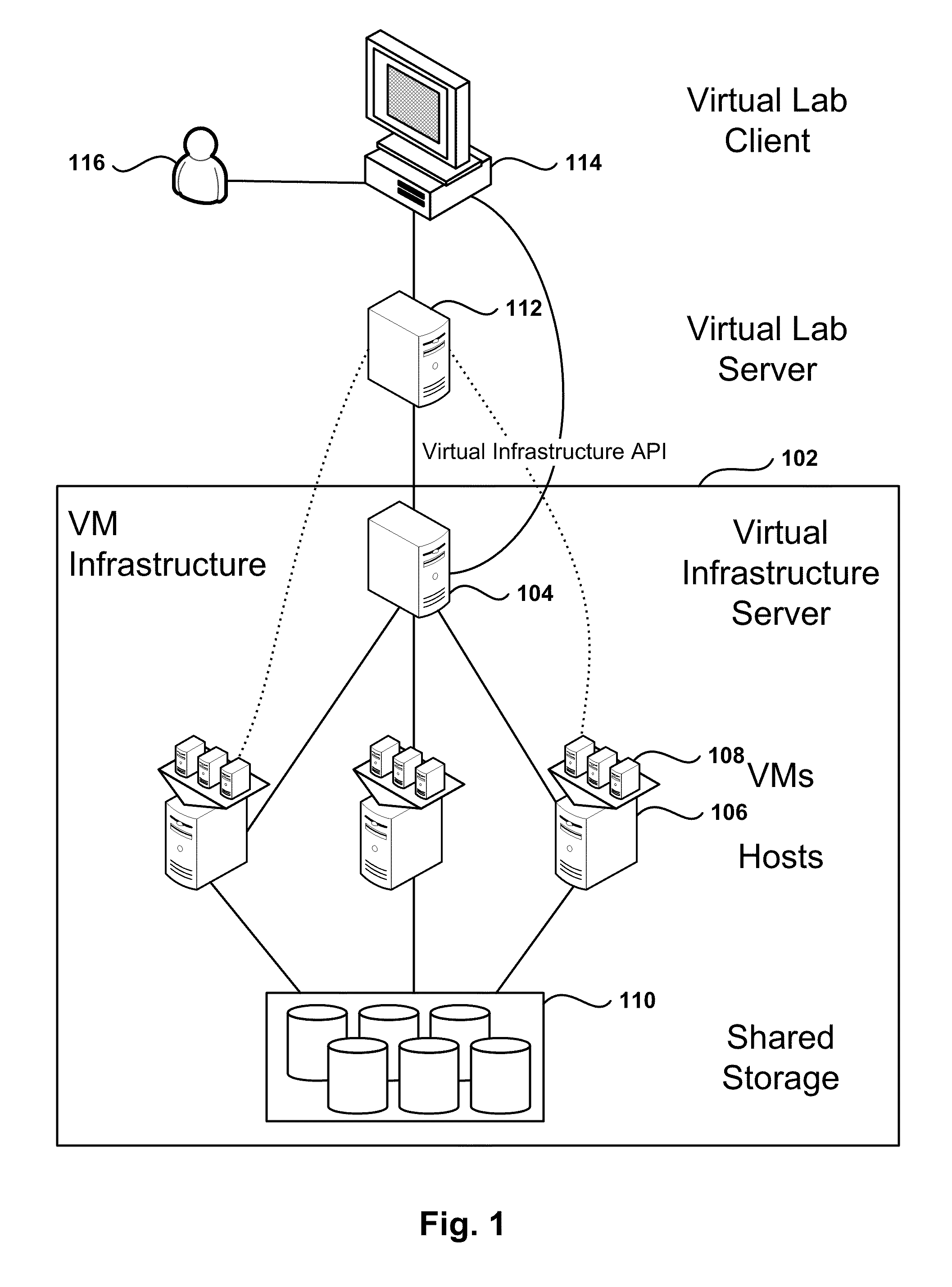
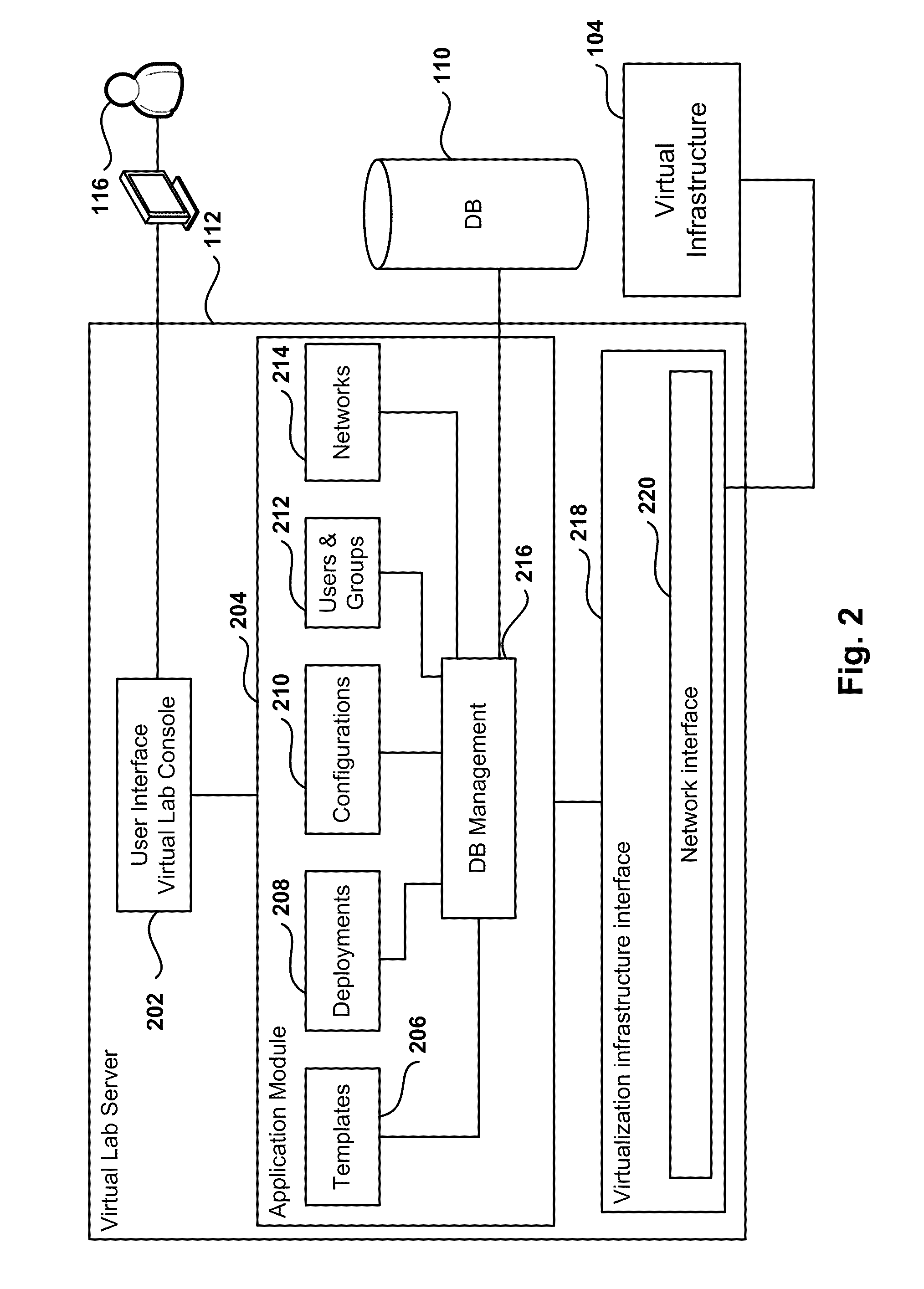
Automated Network Configuration of Virtual Machines in a Virtual Lab Environment
Methods, systems, and computer programs for creating virtual machines (VM) and associated networks in a virtual infrastructure are presented. The method defines virtual network templates in a database, where each virtual network template includes network specifications. A configuration of a virtual system is created, which includes VMs, virtual lab networks associated with virtual network templates, and connections from the VMs to the virtual lab networks. Further, the configuration is deployed in the virtual infrastructure resulting in a deployed configuration. The deployment of the configuration includes instantiating in the virtual infrastructure the VMs of the configuration, instantiating in the virtual infrastructure the virtual lab networks, retrieving information from the database, and creating and executing programming instructions for the VMs. The database information includes the network specifications from the virtual network templates associated with the virtual lab networks, and network resources for the virtual lab networks from a pool of available network resources. The programming instructions are created for the particular Guest Operating System (GOS) running in each VM based on the GOS and on the retrieved database information. When executed in the corresponding VM GOS, the programming instructions configure the VMs network interfaces with the corresponding network specifications.
Owner:NICIRA
Wager game license management in a peer gaming network
InactiveUS20070136817A1Digital data processing detailsAnalogue secracy/subscription systemsDistributed computingPeer-to-peer
Novel wager gaming systems and methods for wager game license management in a network utilizing peer networking technology are in the various embodiments. A network component, such as a server computer or a gaming machine, is deputized by a central licensing authority or other authorized license management component. The network component is deputized once it receives what may be referred to as a license deputizing certificate. Upon receiving this certificate or at some point thereafter, the deputized component is provided with various data relating to devices in the gaming network, wagering games available in the network, and network configuration data. The gaming network may have a primary network backbone and local peer gaming networks operating in conjunction with each other via the network backbone. A local peer gaming network may share wager game code, memory space, and other gaming-related resources. Once a network component is deputized to perform as an authorized license management component, it assumes the role of local licensing server for the gaming network or for a local peer gaming network. This component may be a gaming machine in a local peer network or an existing local license server which is now able to supply and manage the distribution of license tokens in a gaming network utilizing peer network technology.
Owner:IGT
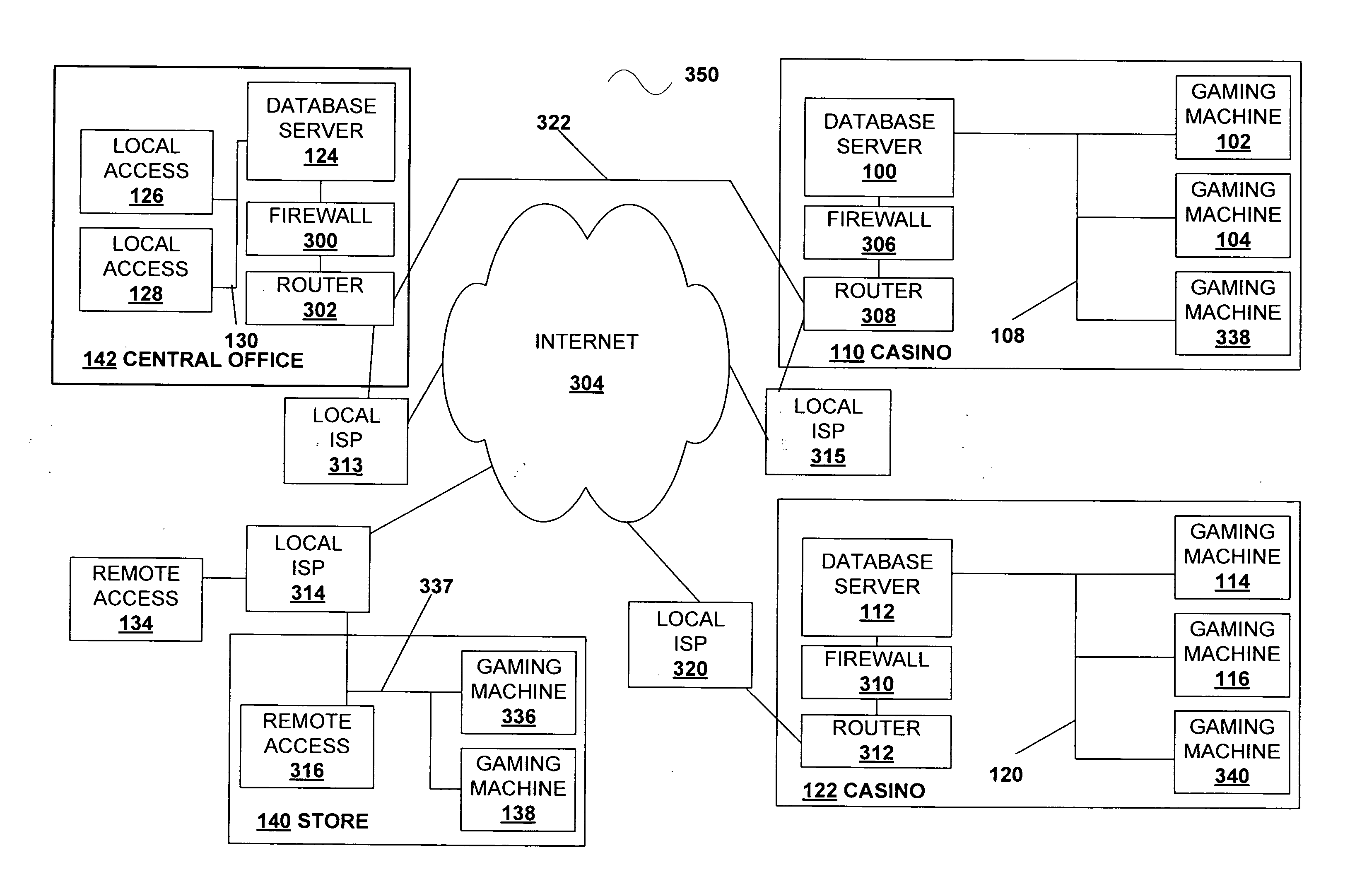
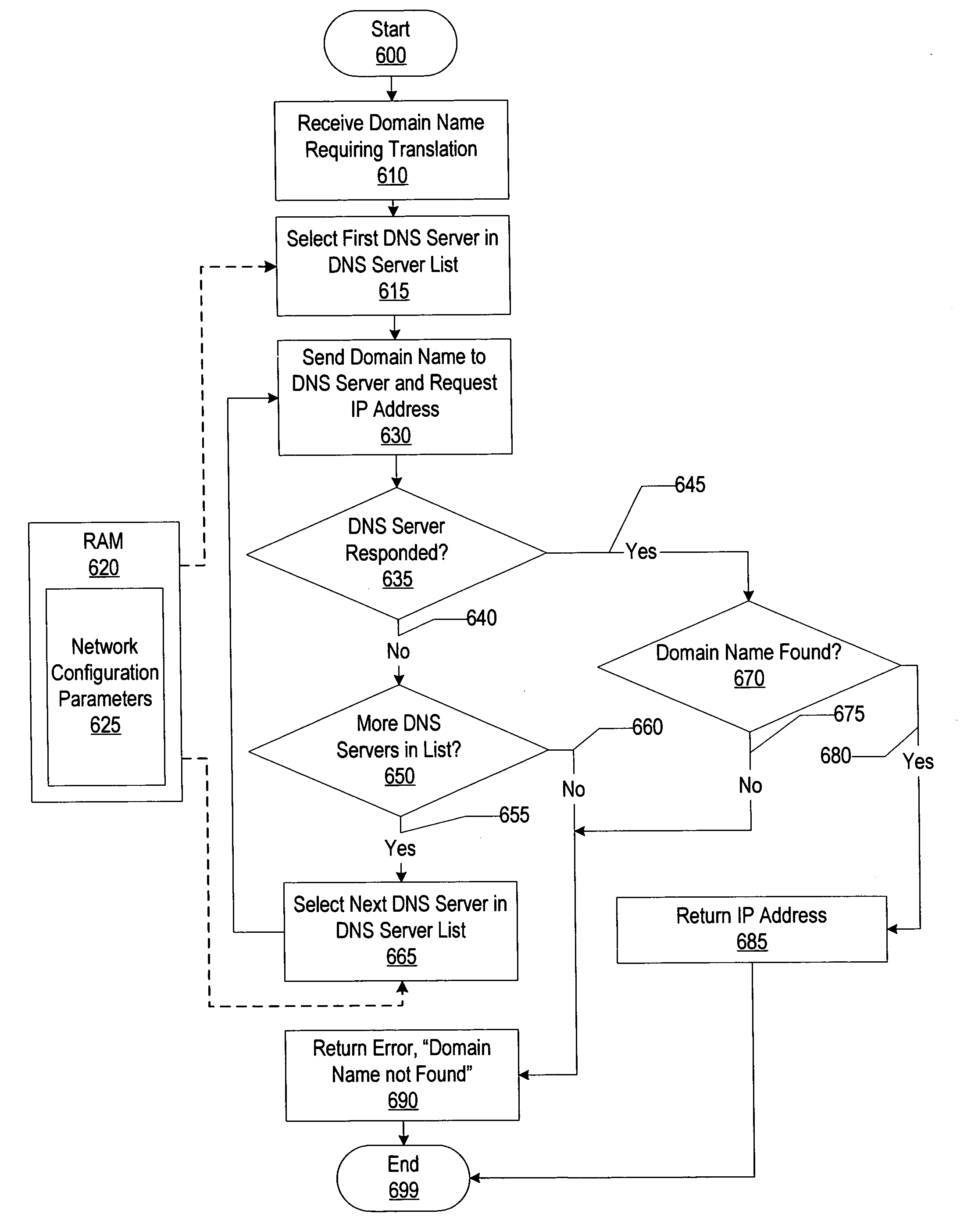
System and method for designating a priority access order of domain name service servers
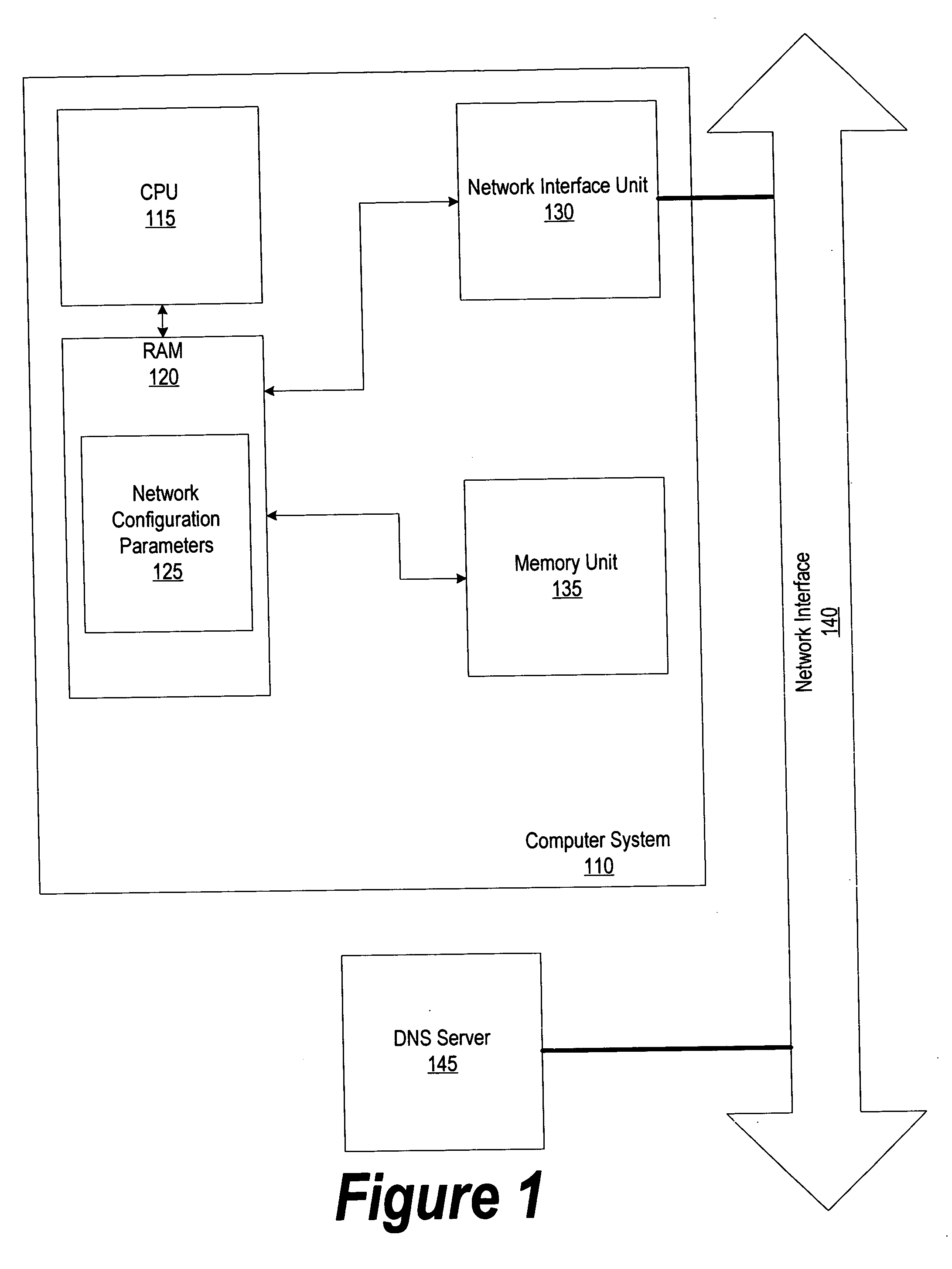
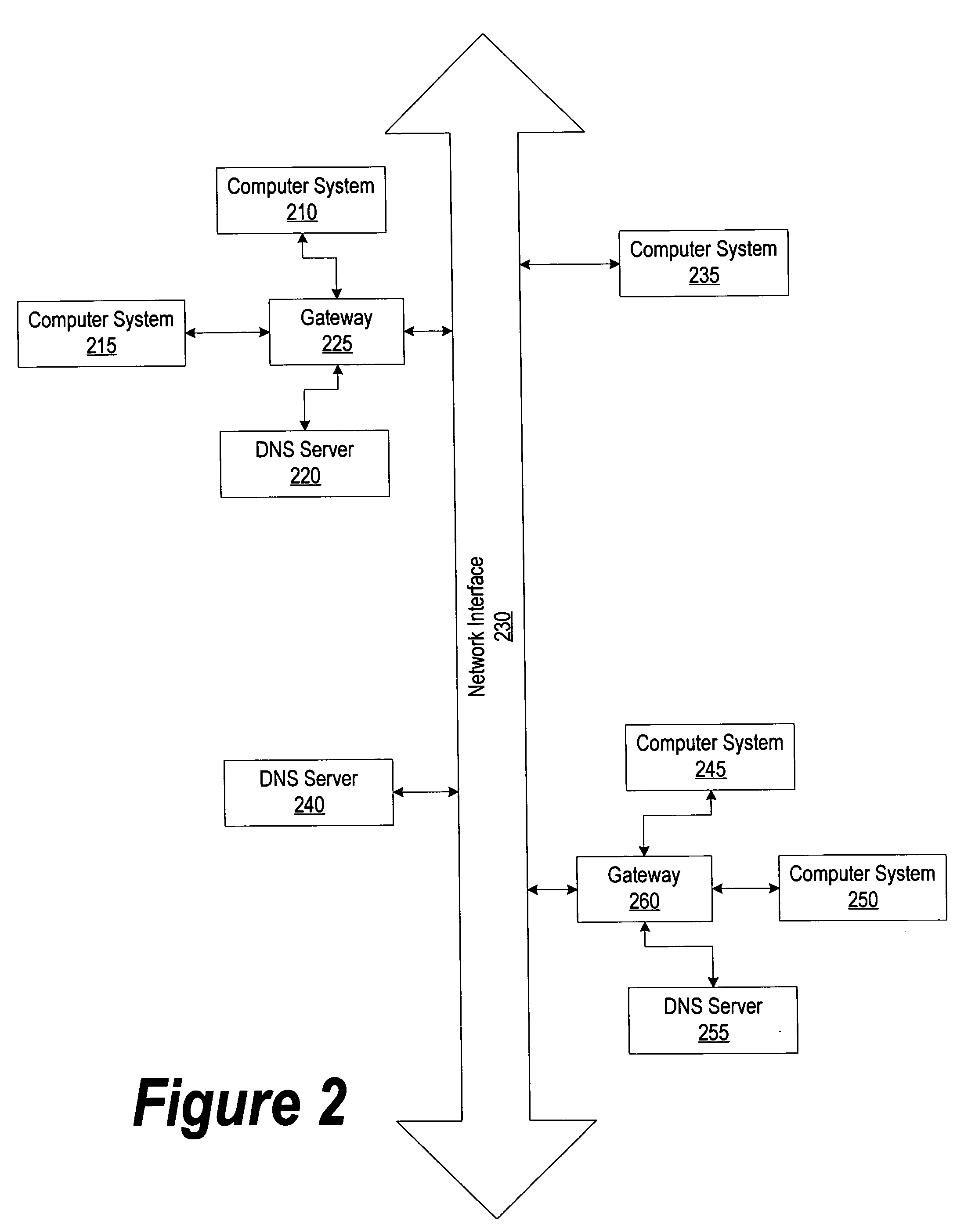
A method and a system for designating a priority access order of one or more DNS servers. DNS servers are accessed in the designated order until an IP address is found or until there are no more DNS servers to access. The DNS servers' IP addresses may be received from a network configuration server or the IP addresses may be entered by a user. The priority access order may be designated by a user or the order may be determined by examining a history of DNS server requests and a history of DNS server responses. After a translation of a domain name into an IP address is requested, the request is sent to one or more of the DNS servers in the designated access order. Alternatively, the DNS servers may be accessed in the order the servers are listed in the computer system's network configuration settings.
Owner:IBM CORP
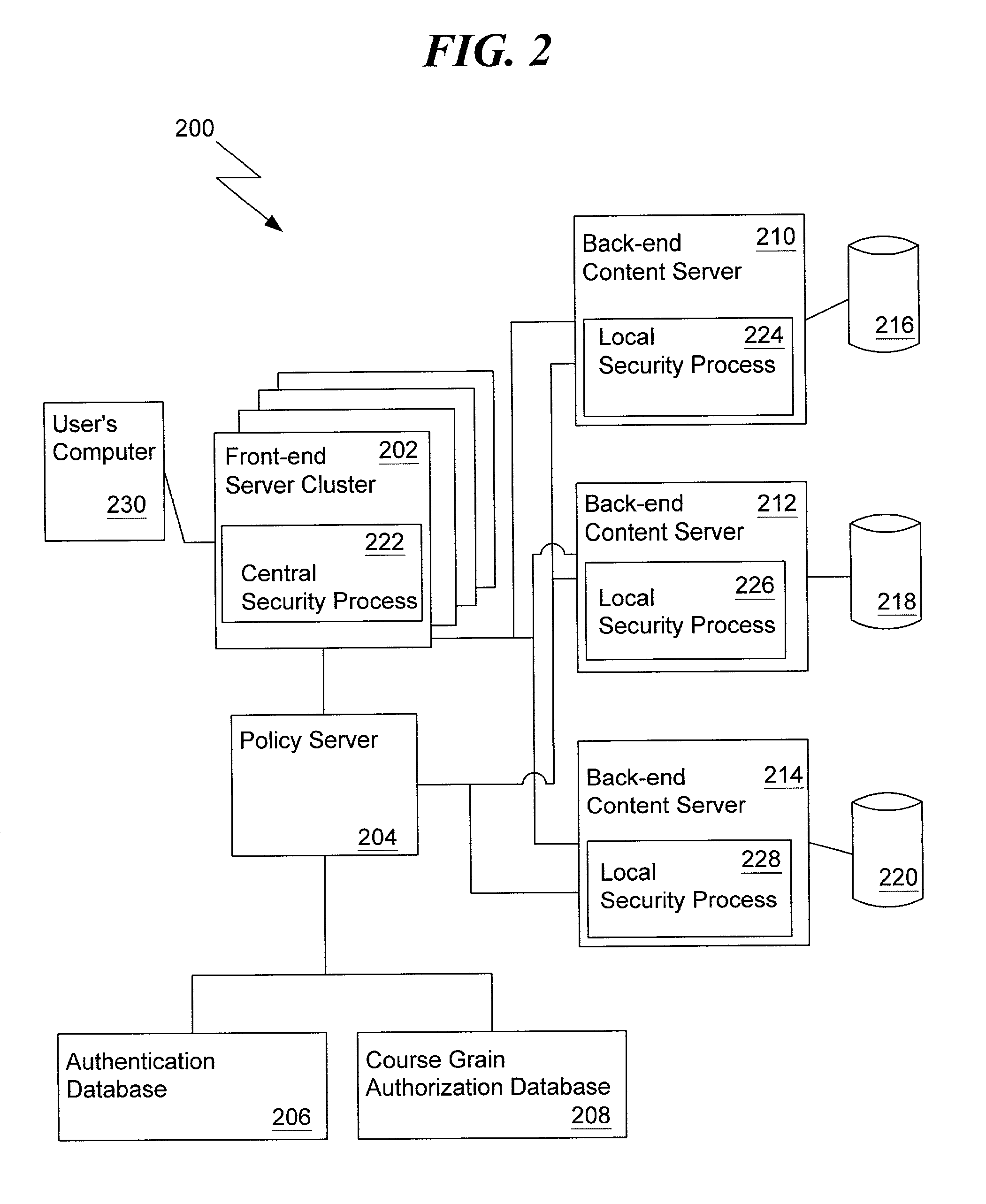
Authentication and authorization mapping for a computer network
ActiveUS7350229B1User identity/authority verificationComputer security arrangementsApplication softwareAuthorization
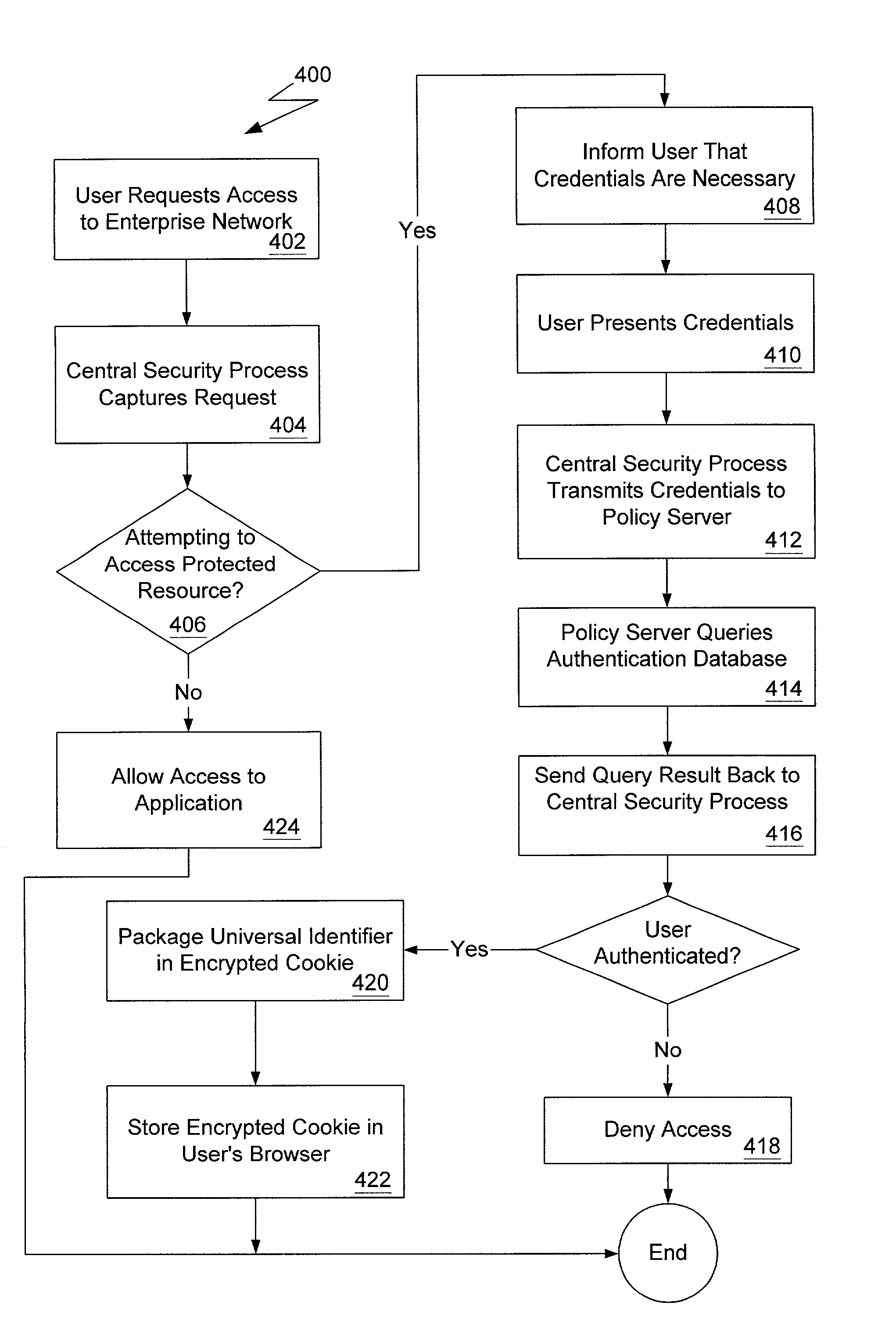
A method and apparatus for a network-wide authentication and authorization mapping system for a network is provided. The global authentication and authorization mapping system enables a seamless transition from one web-based application in the network configuration to another web-based application in the network configuration, including a single sign-on capability for users. There are no localized security enforcement processes required to further authenticate a user.
Owner:COMP ASSOC THINK INC
Systems and methods for device discovery
Systems and methods for enabling wireless devices to discover a number of other proximate wireless devices are disclosed. The discovery may include the discovery of network configuration parameters useful for establishing a connection between the wireless devices. The disclosed systems and methods for device discovery may operate in a number of different modes to timely discover wireless devices that receive communications continuously, as well as wireless devices that turn off their wireless receivers for intermittent periods of time. The wireless devices may, for example, communicate using the IEEE 802.11 protocol.
Owner:INTELLECTUAL VENTURES I LLC
Internet protocol-based computer network service
InactiveUS20020112076A1Existing technologyMetering/charging/biilling arrangementsSubstation remote connection/disconnectionClient-sideFile transfer
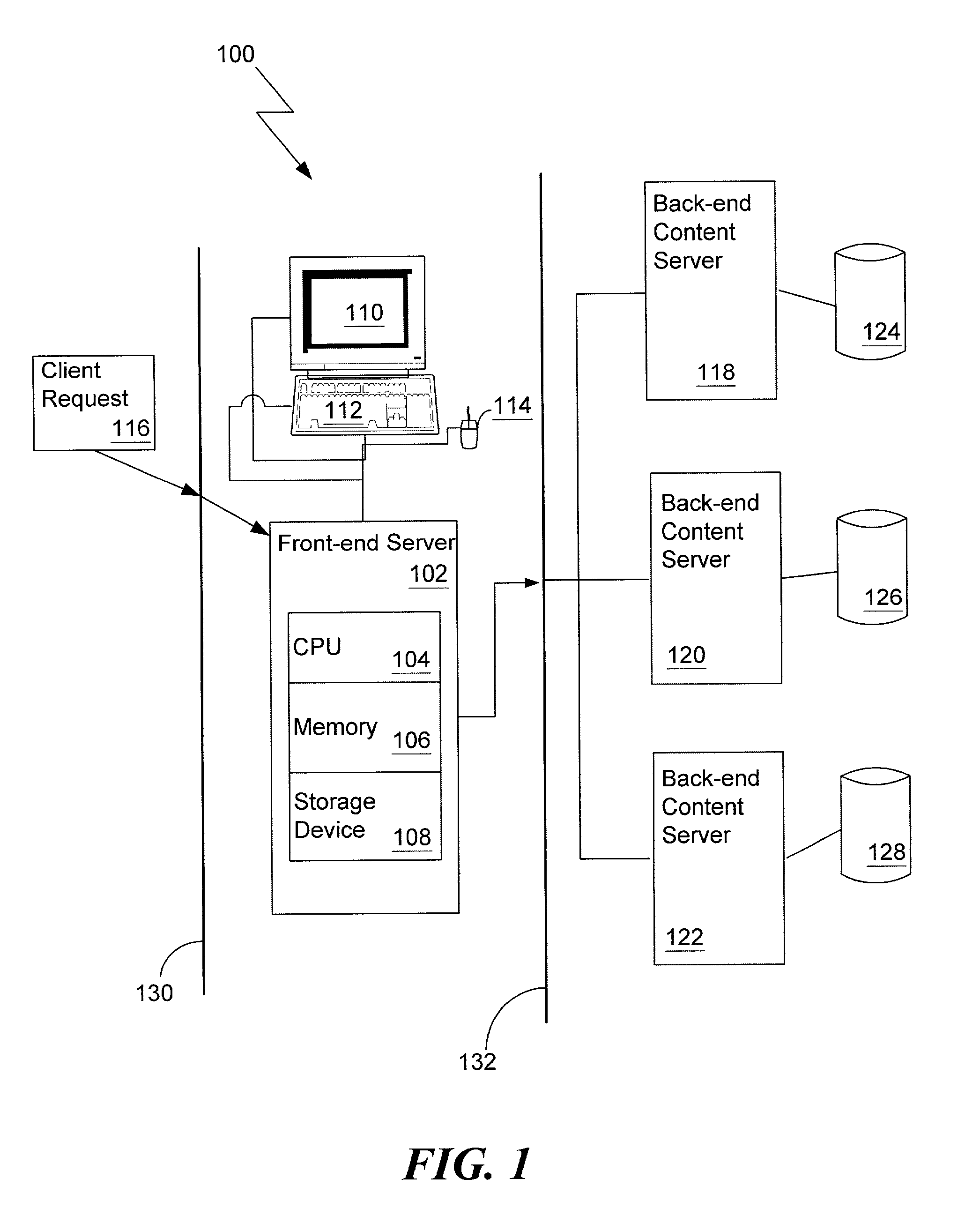
The system is an Internet Protocol-based computer network service that when installed, allows connected computers access Internet Protocol-based services if they are configured for any Internet Protocol-based network. This is different from a conventional Internet Protocol-based network in which connected computers must be configured specifically for that network to access Internet Protocol-based services or to have custom applications running on them to allow this access. These services include, but are not limited to, World-Wide-Web browsing, sending and / or receiving electronic mail, file transfer, and multimedia conferencing. The system supports any service that is Internet Protocol-based. The system is completely software-based. That is, it is a set of algorithms that are run on a computing platform. The platform that is executing the algorithms (the server) is a stand-alone system. No proprietary software is installed on the client.
Owner:TELECOMM RES LAB
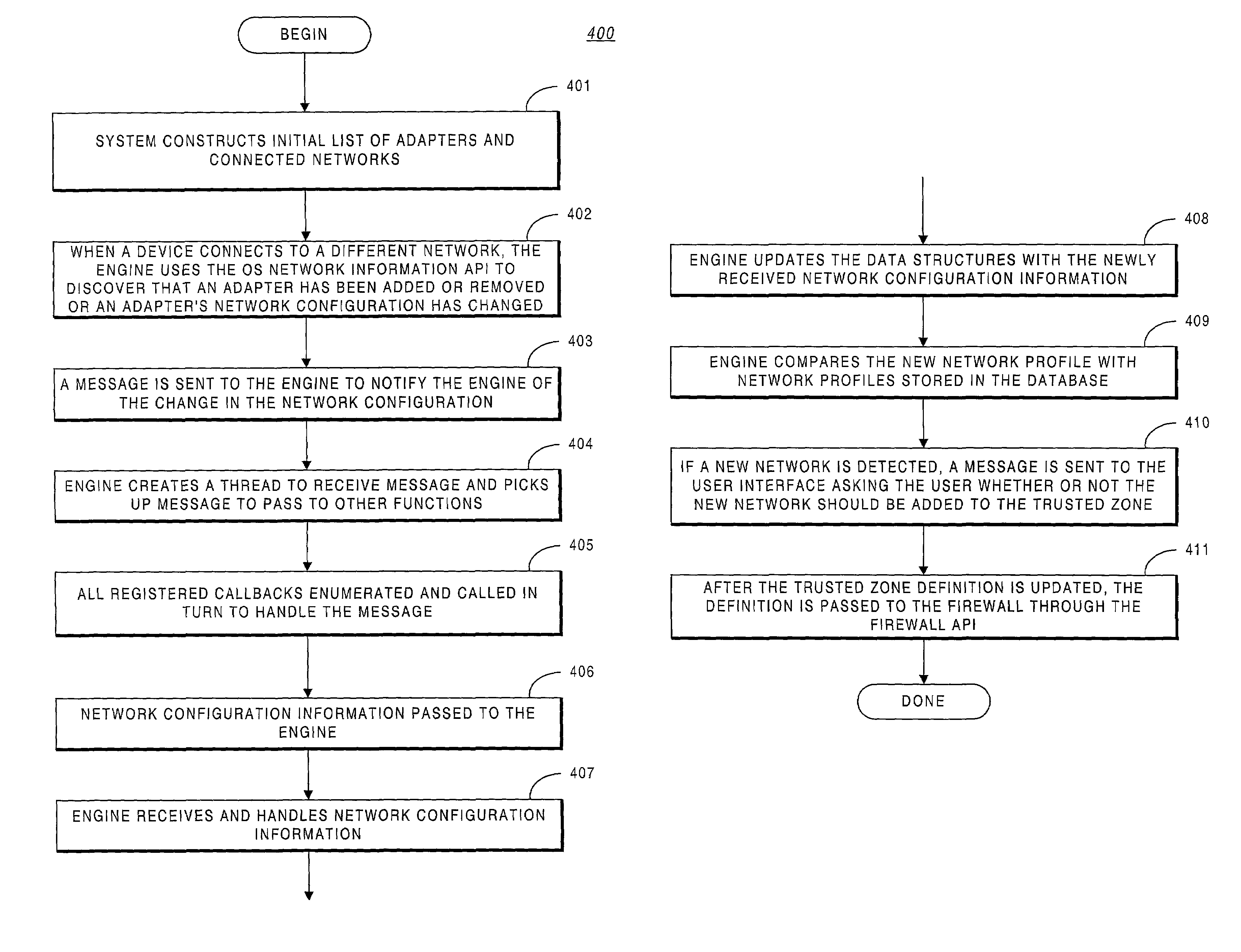
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS7222359B2Easy to detectDigital data processing detailsMultiple digital computer combinationsNetwork generationUnique identifier
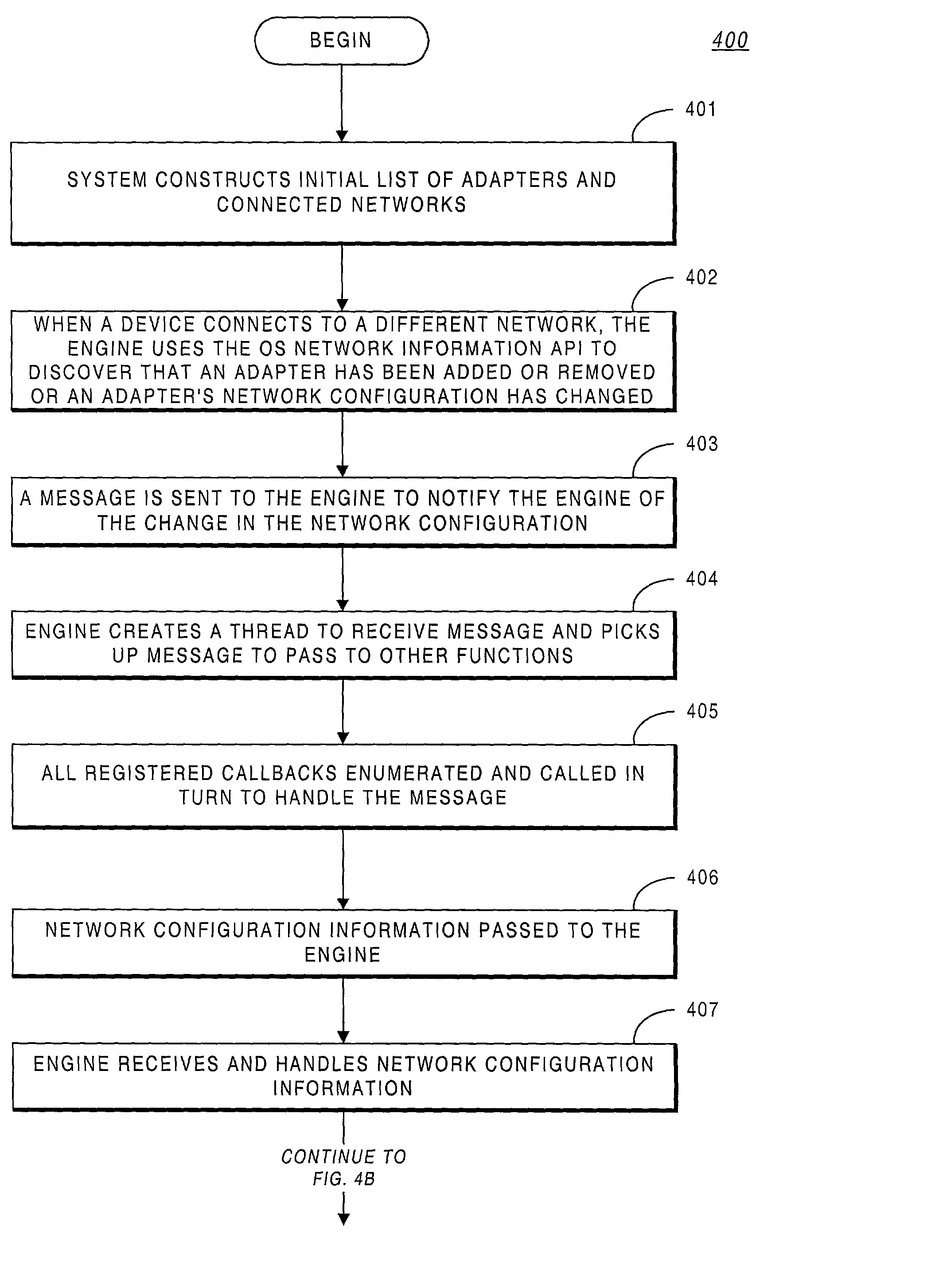
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
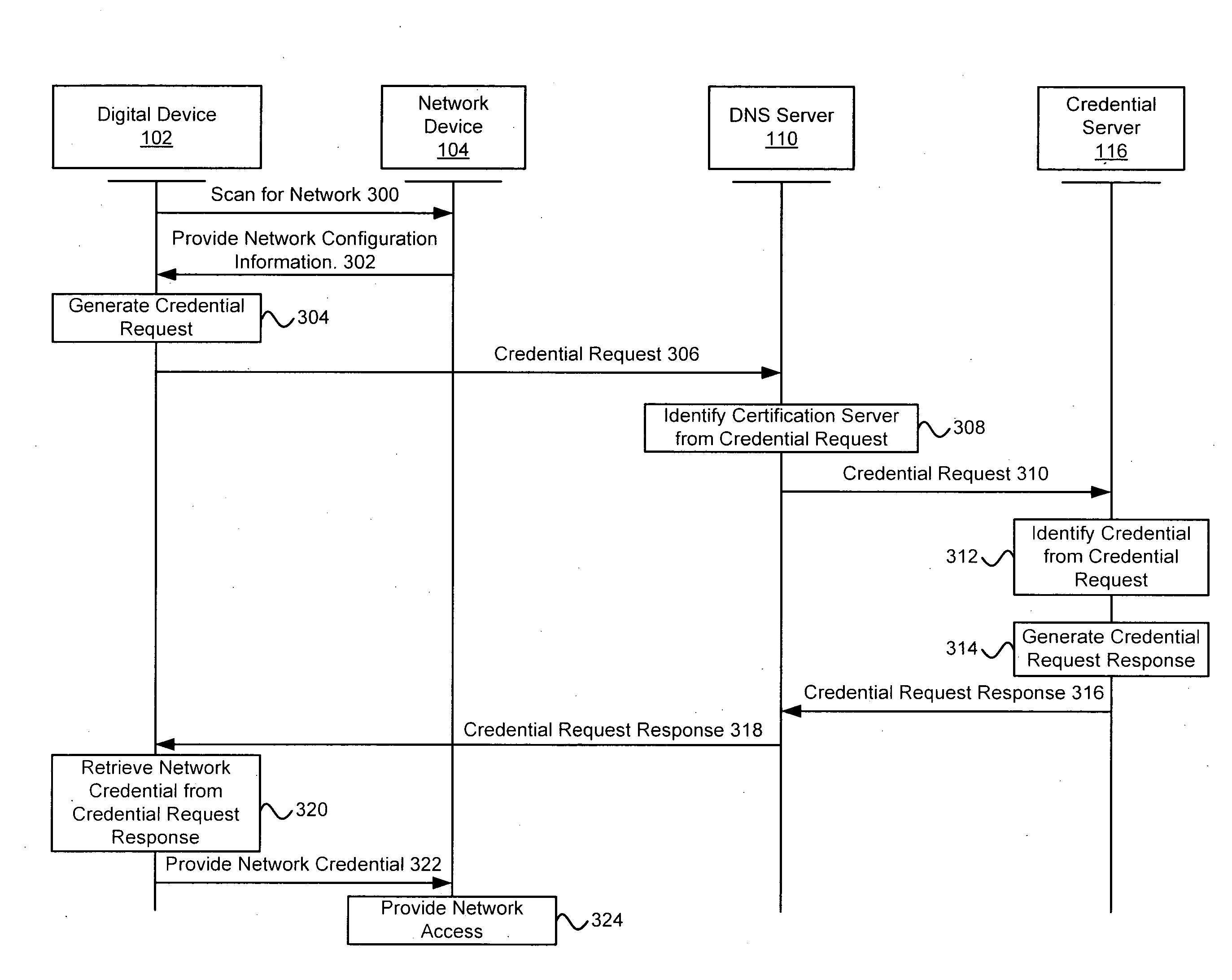
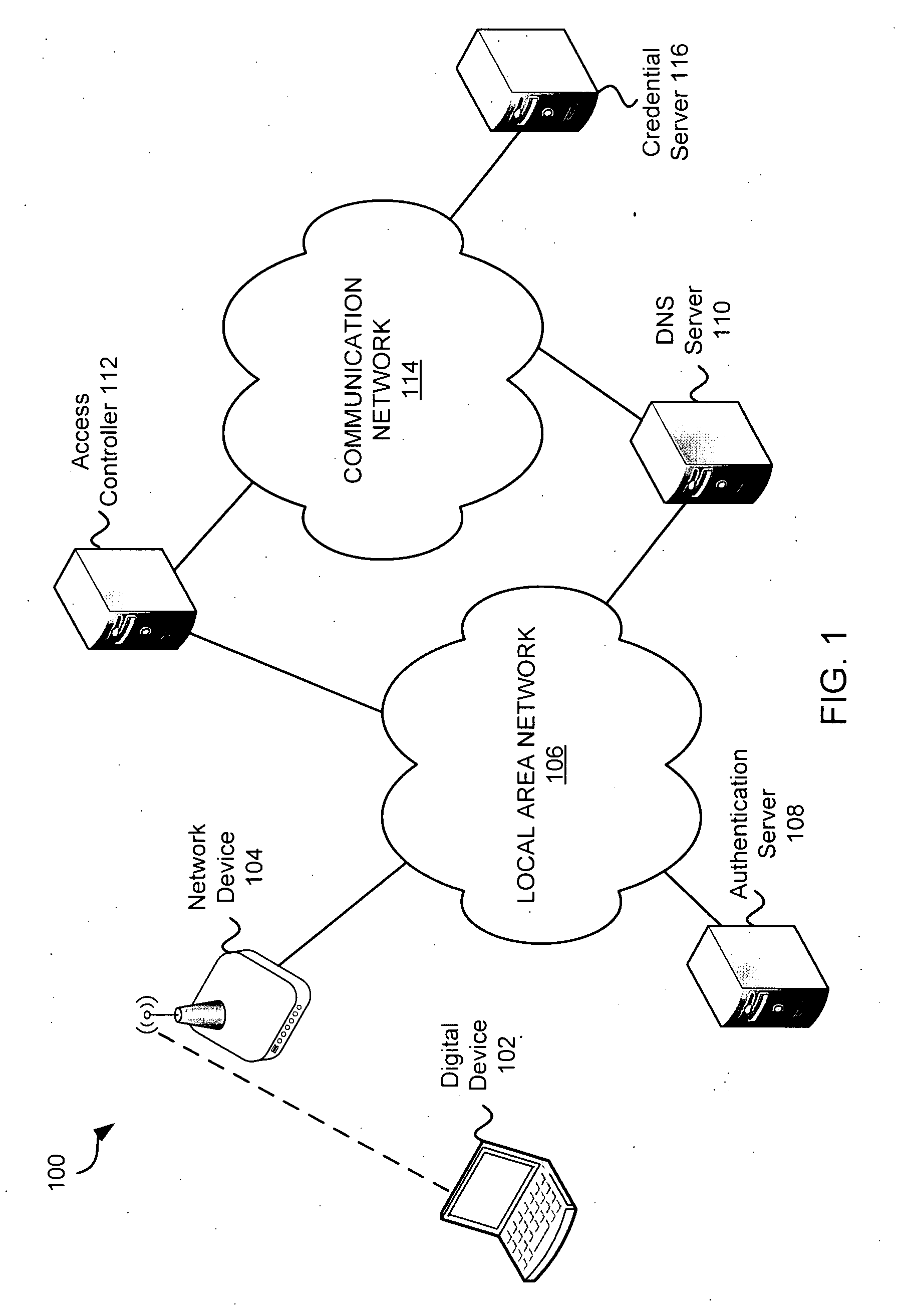
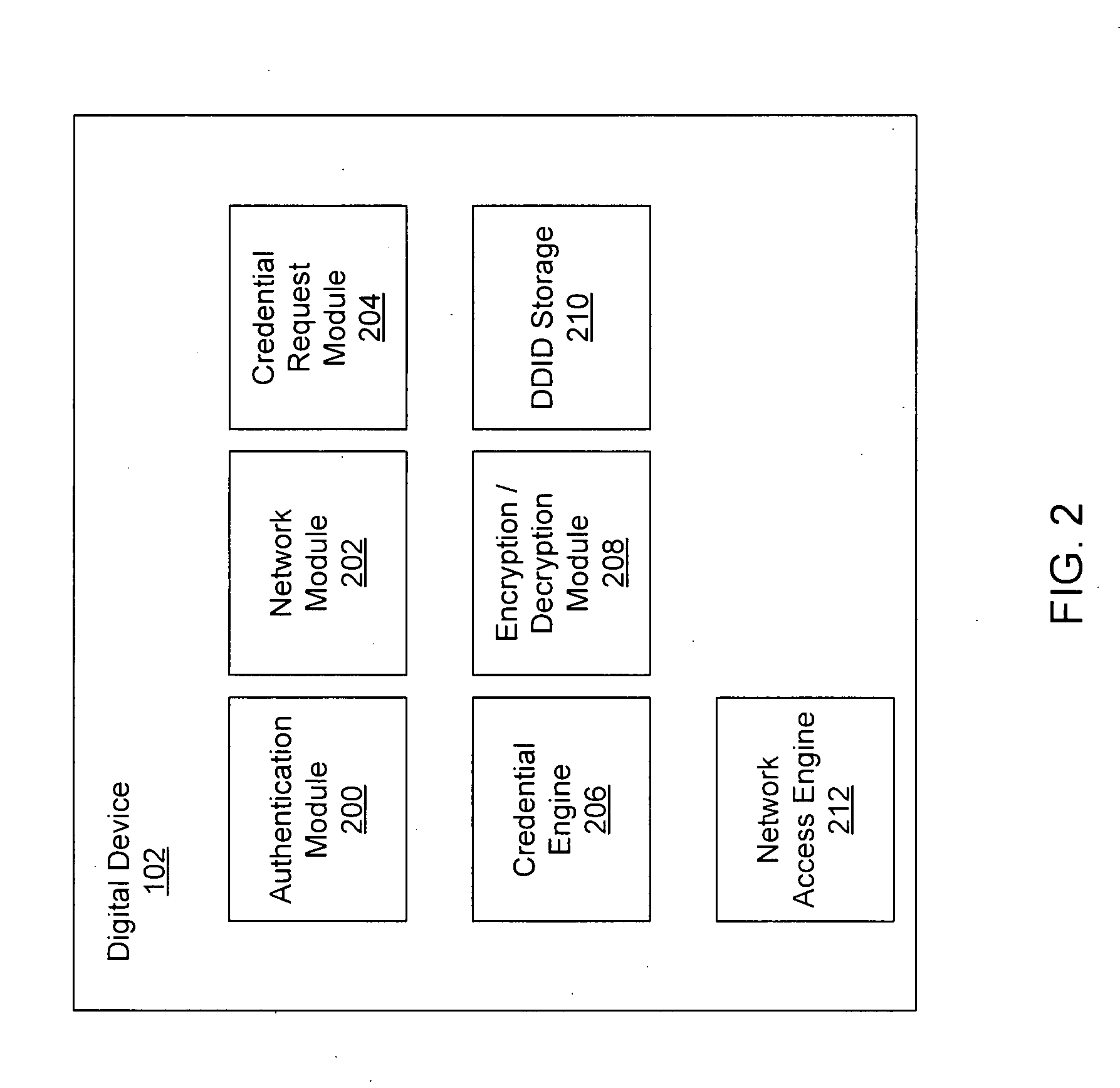
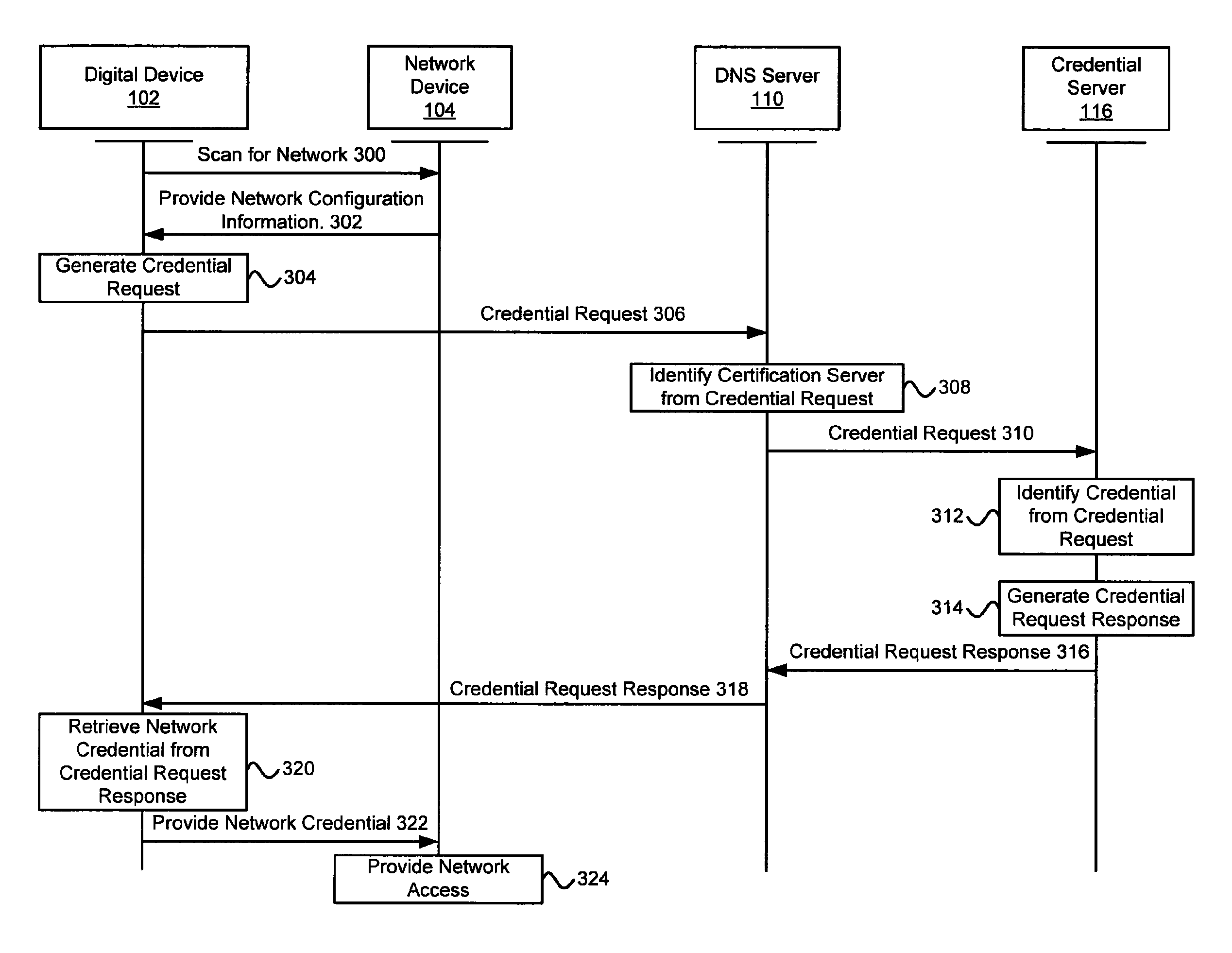
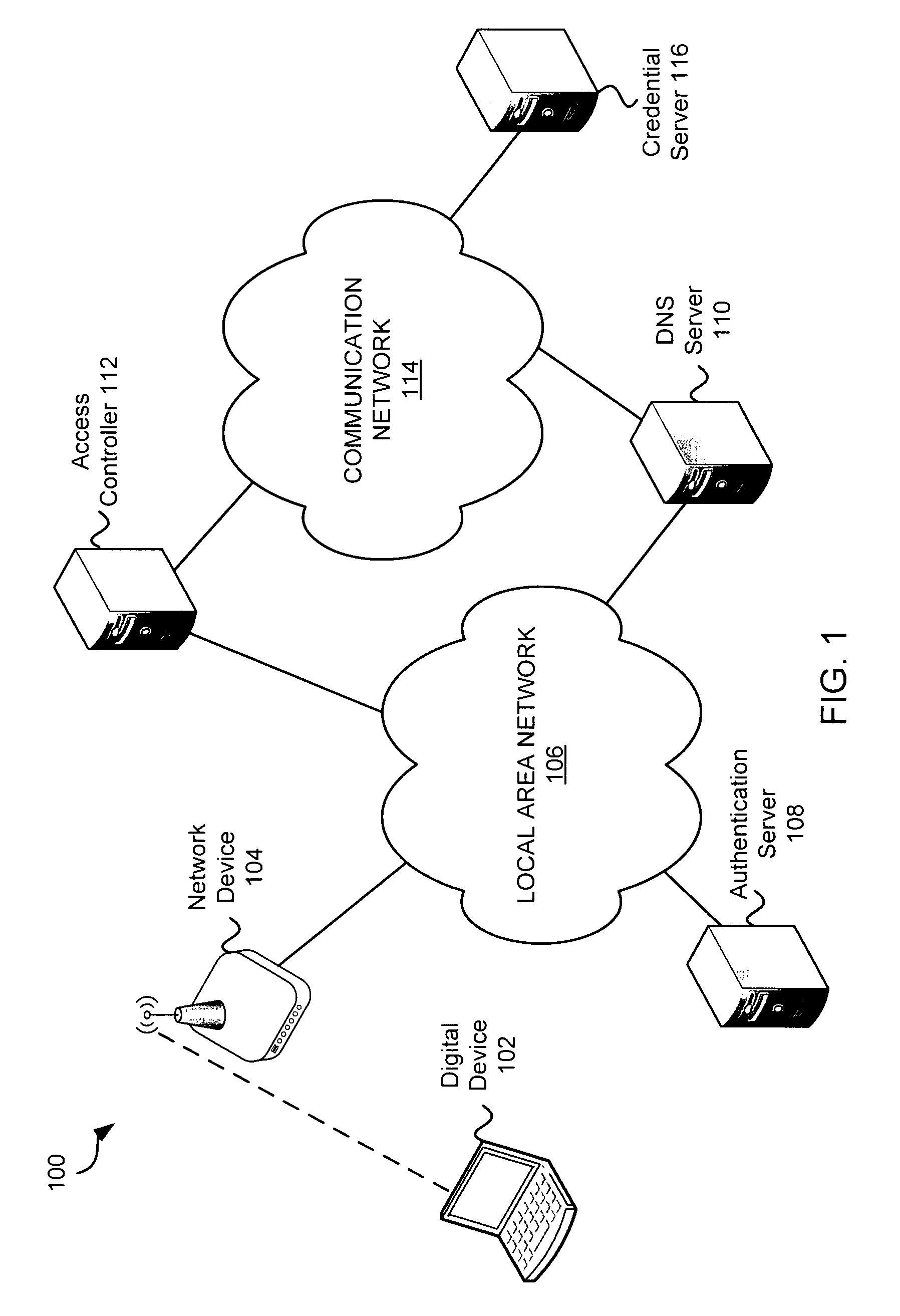
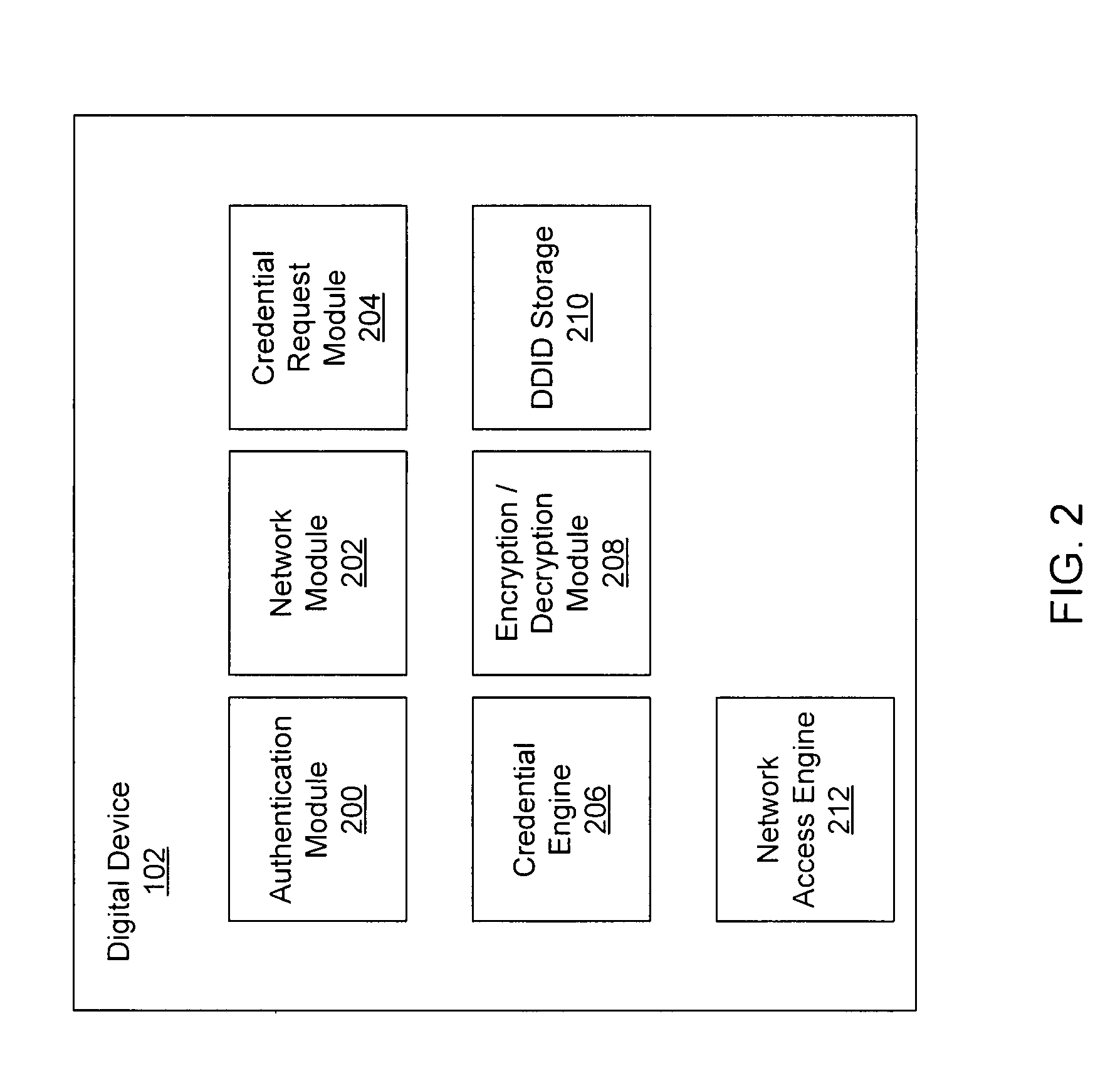
Systems and methods for acquiring network credentials
ActiveUS20080060066A1Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method comprises receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
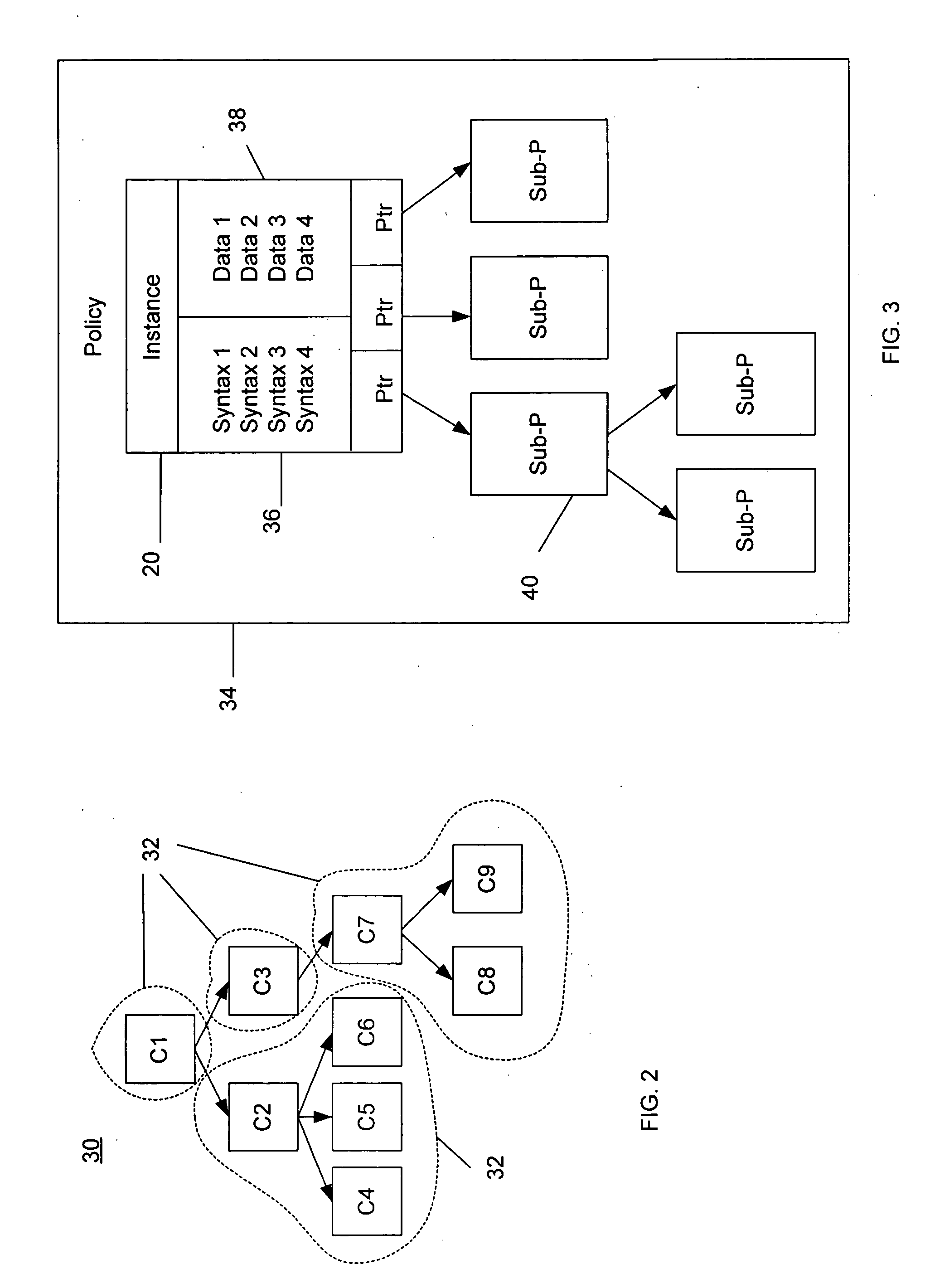
System and method for implementing logic control in programmable controllers in distributed control systems
ActiveUS7225037B2Easy to installEasy to modifyTemperatue controlStatic/dynamic balance measurementProgrammable logic controllerDistributed control system
The present invention provides a system and method for implementing logic control in programmable controllers in distributed control systems using a wired or wireless network. A software application is used to define the configuration of the network. Based on the network configuration, a compiler engine automatically assigns each statement of the control program to at least one programmable logic controller in the network. Each statement is then transmitted over a data transmission medium to the programmable logic controller assigned to the statement.
Owner:UNITRONICS 1989 RG
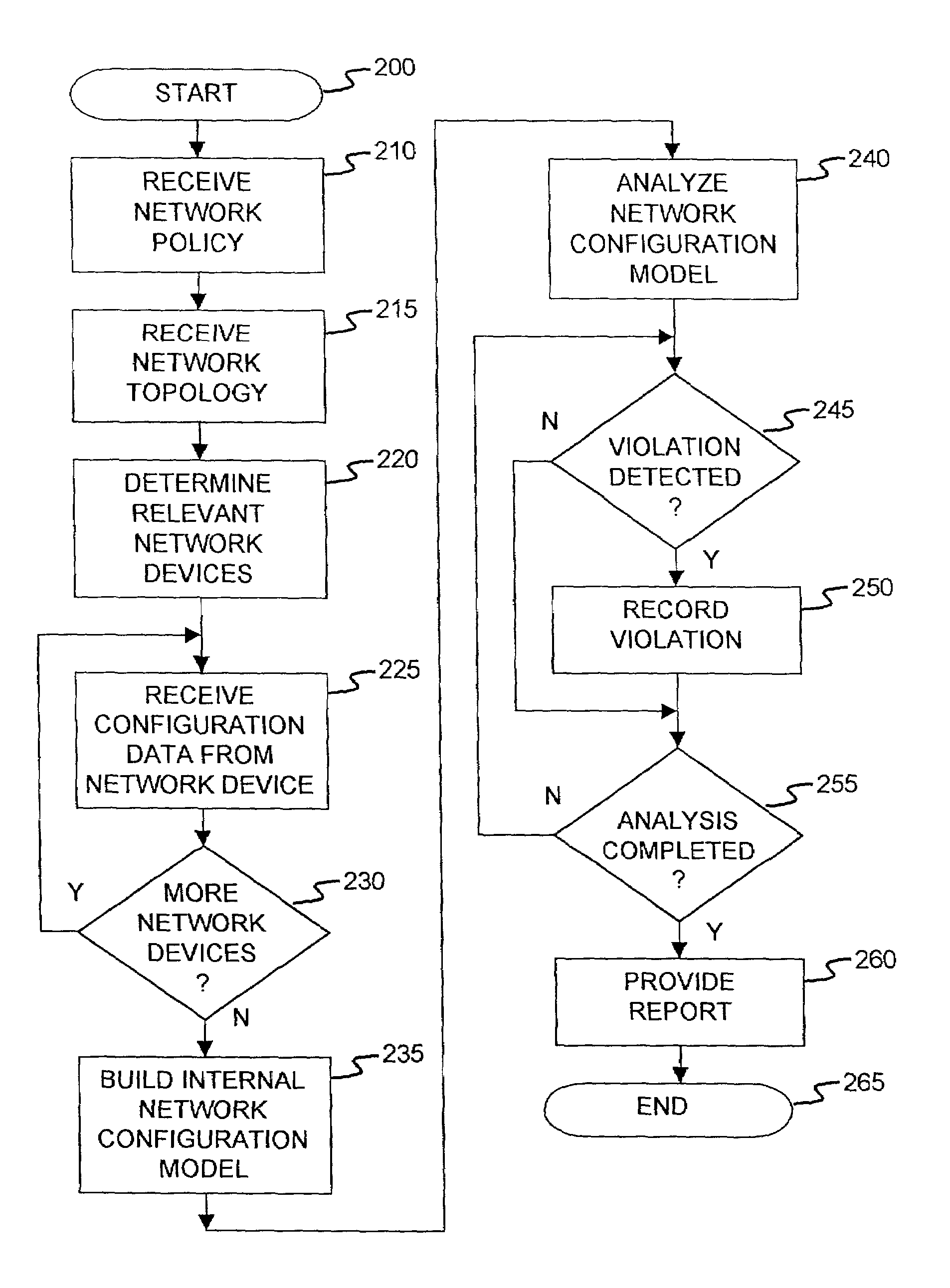
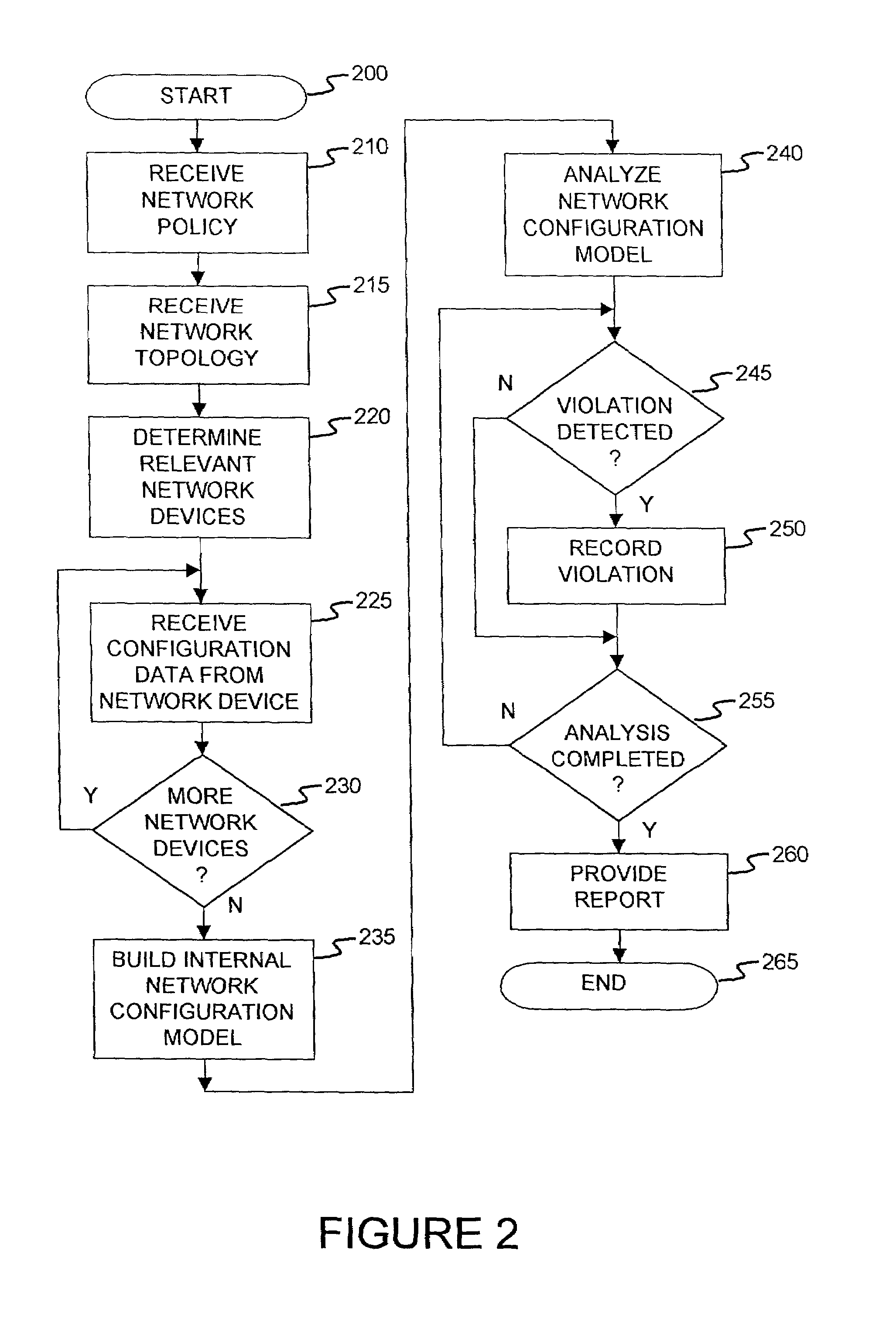
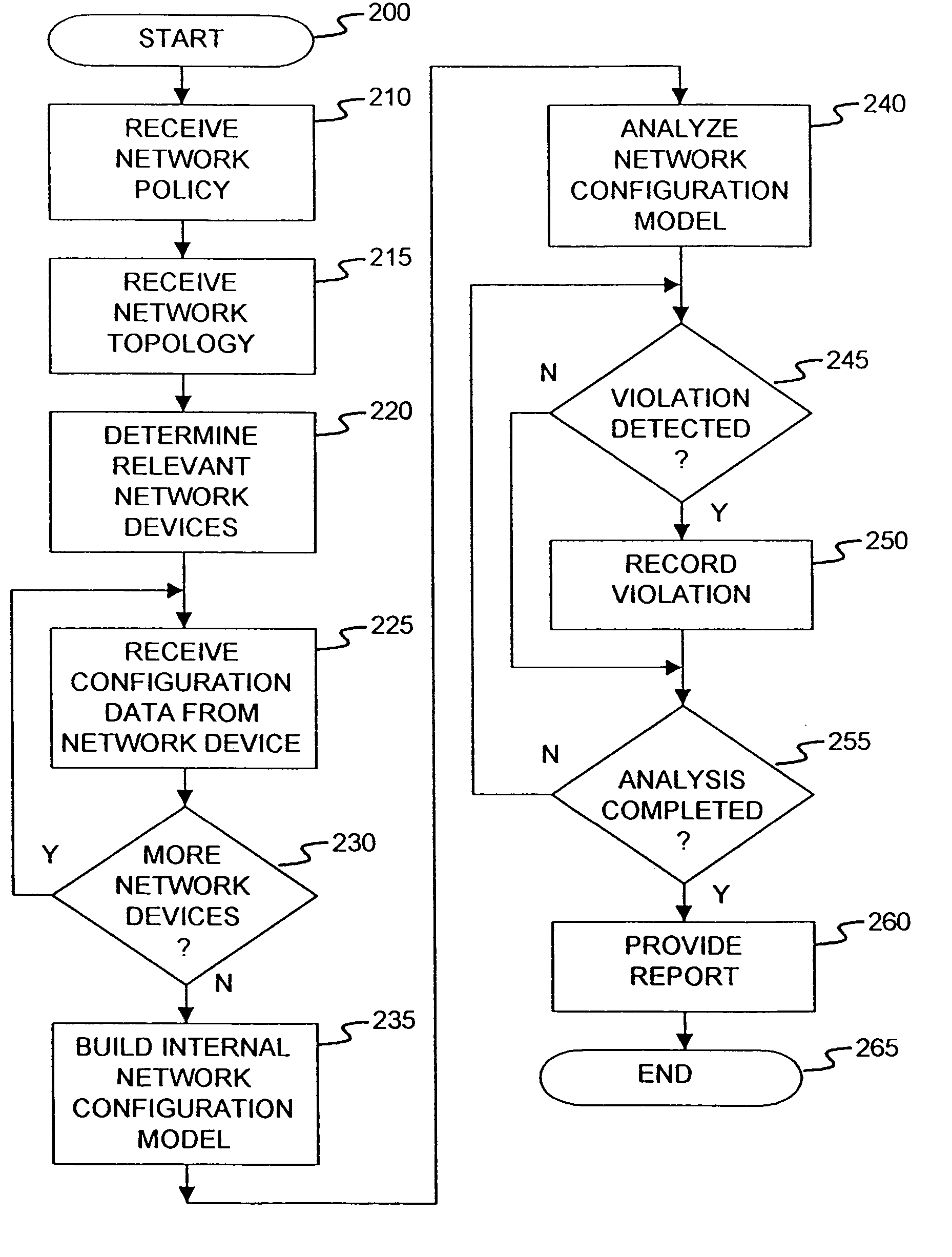
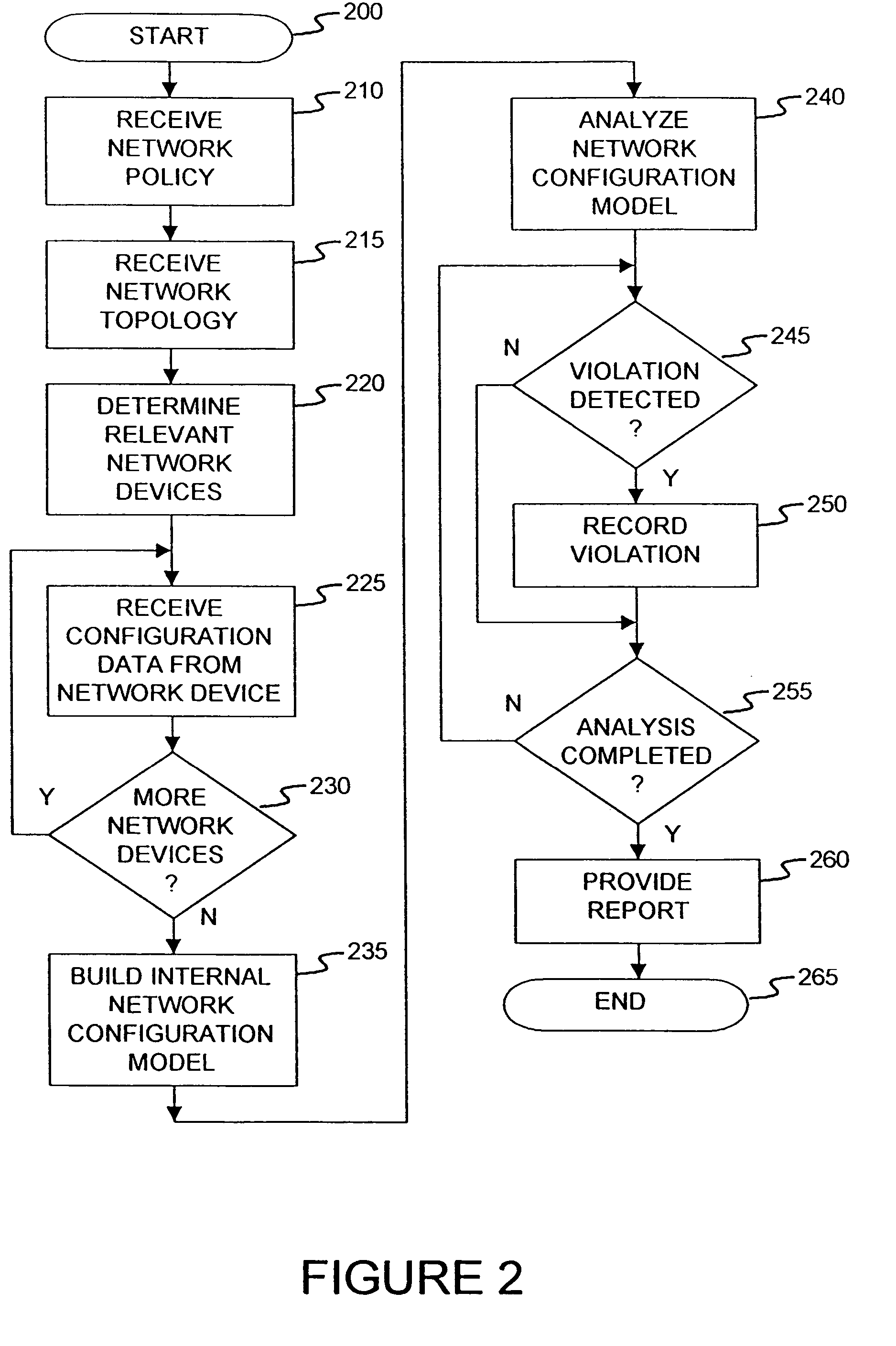
Method and apparatus for network wide policy-based analysis of configurations of devices
ActiveUS7003562B2Traffic controlDigital computer detailsData switching networksNetwork strategyNetwork topology
A method and an apparatus for analyzing a network configuration against a corporate network policy and determining violation(s) against the corporate network policy. A report indicating the violation(s) can be generated indicating instances of the violation(s). An analysis platform reads in a network policy. The analysis platform collects configuration files from the relevant network devices in the network and builds up an internal instance of a network configuration model based on the configuration files and the network topology. The analysis platform analyzes this network configuration model according to the network policy and adds an entry to its final report each time that it detects a violation against the network policy in the network configuration model. The data in the entries pinpoints the cause of the deviation(s) from the network policy.
Owner:REDSEAL
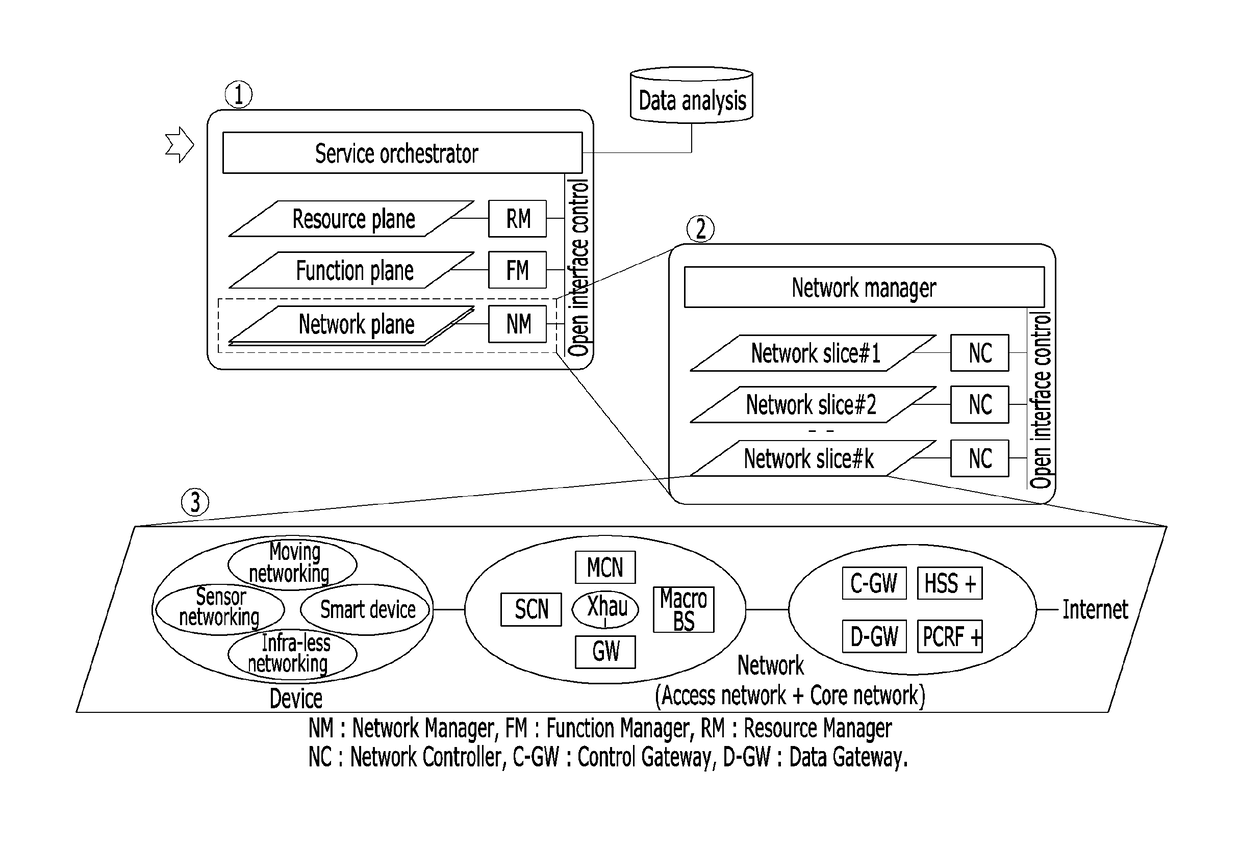
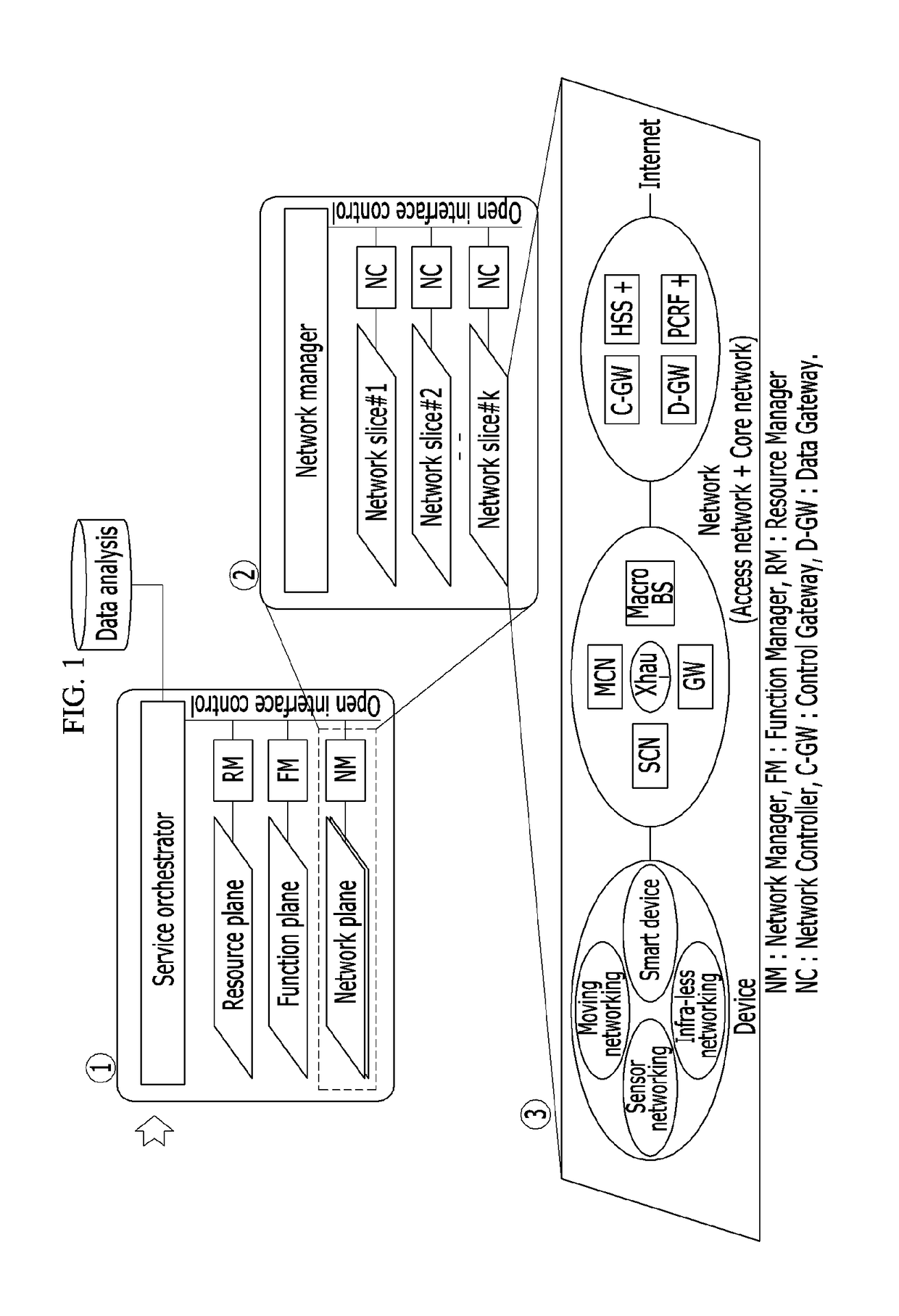
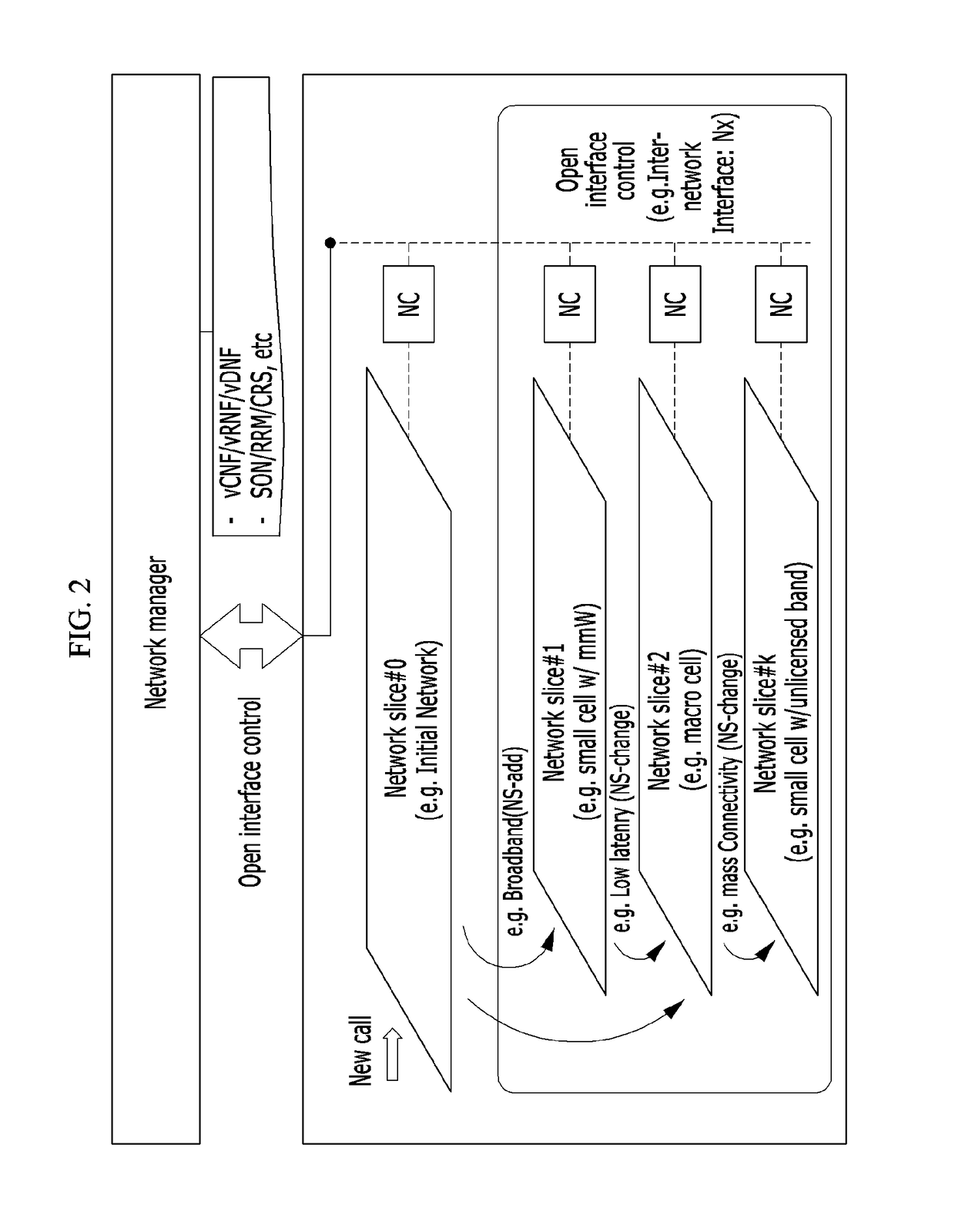
Mobile communication network system and method for composing network component configurations
ActiveUS20170070892A1Configuring networkAssess restrictionNetwork topologiesAccess networkNetworked system
Disclosed is a mobile communication network system and a network configuring method. The communication network system includes: a common control access network; at least one access network slice added according to a service type requested by a device; a common control core network; and at least one core network slice added according to a service type requested by the device. The access network slice and the core network slice are determined by the service type requested by the device.
Owner:ELECTRONICS & TELECOMM RES INST
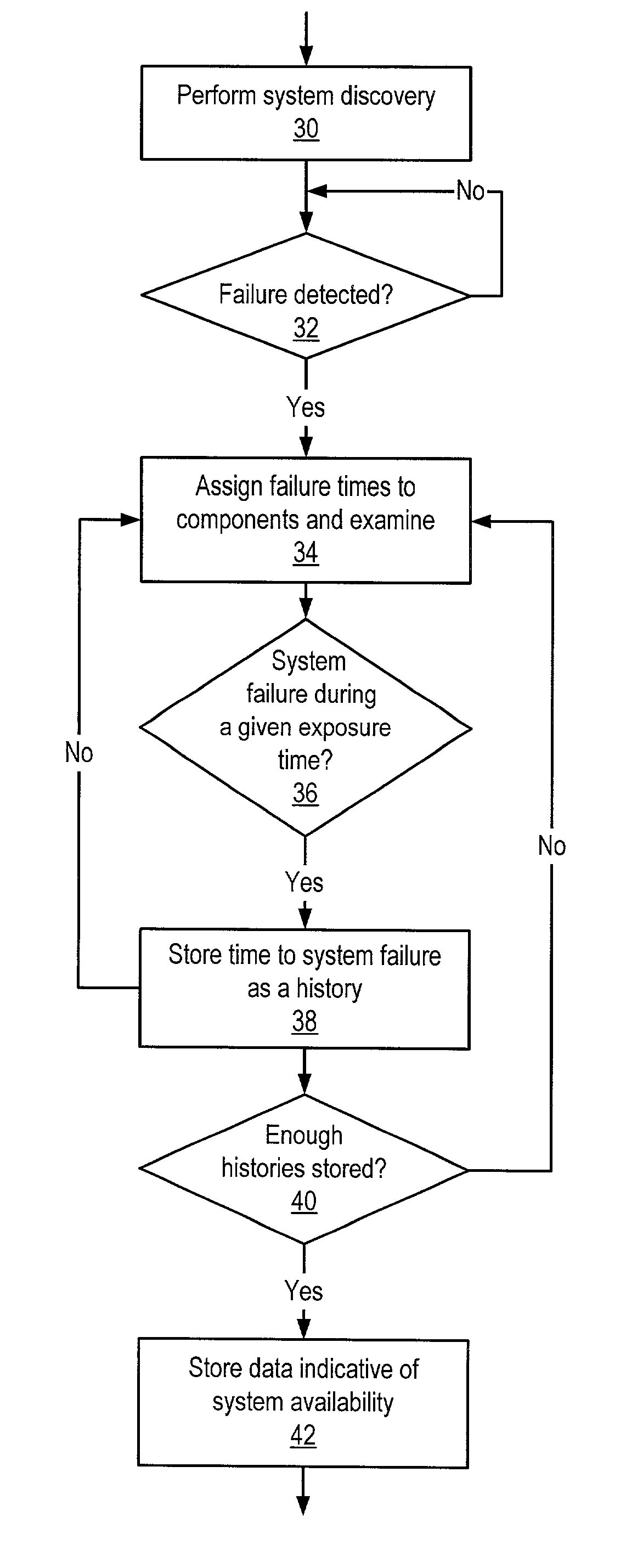
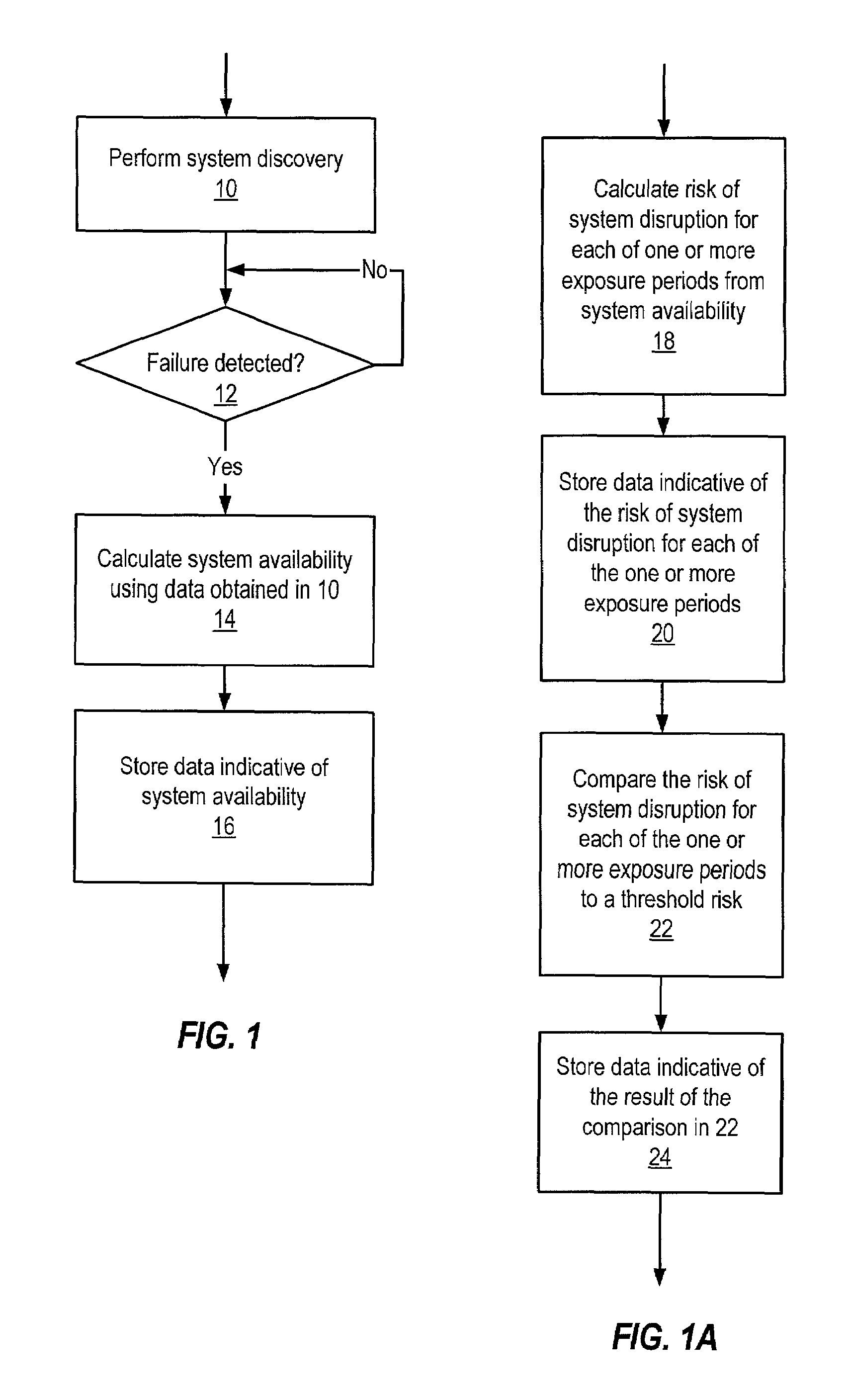
System and method for determining availability of an arbitrary network configuration
ActiveUS7426554B2Error detection/correctionDigital computer detailsNetworked systemReal-time computing
A method of operating a network system may involve receiving data indicating a configuration of components that are included in the network system, detecting a failure of one of the components, computing an availability (e.g., by calculating the instantaneous availability) of the network system from the data in response to detecting the failure, and storing data indicative of the availability of the network system.
Owner:ORACLE INT CORP
System and method for remote discovery and configuration of a network device
A technique for remotely configuring a computing device via a network. A device configuration system is provided to determine a network address of the computing device, to identify the computing device, and to facilitate network configuration of the computing device. The device configuration system also may include a remote interface and a remote device information system.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Mobile provisioning tool system
ActiveUS7239877B2Significant processingLimited accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile businessNetwork connection
Owner:ACCENTURE GLOBAL SERVICES LTD
Network security modeling system and method
InactiveUS7315801B1Analogue computers for electric apparatusDigital computer detailsNetwork security policyVulnerability
A network security modeling system which simulates a network and analyzes security vulnerabilities of the network. The system includes a simulator which includes a network vulnerabilities database and a network configuration module having network configuration data. The simulator determines vulnerabilities of the simulated network based on the network configuration data and the vulnerabilities database.
Owner:MCAFEE LLC
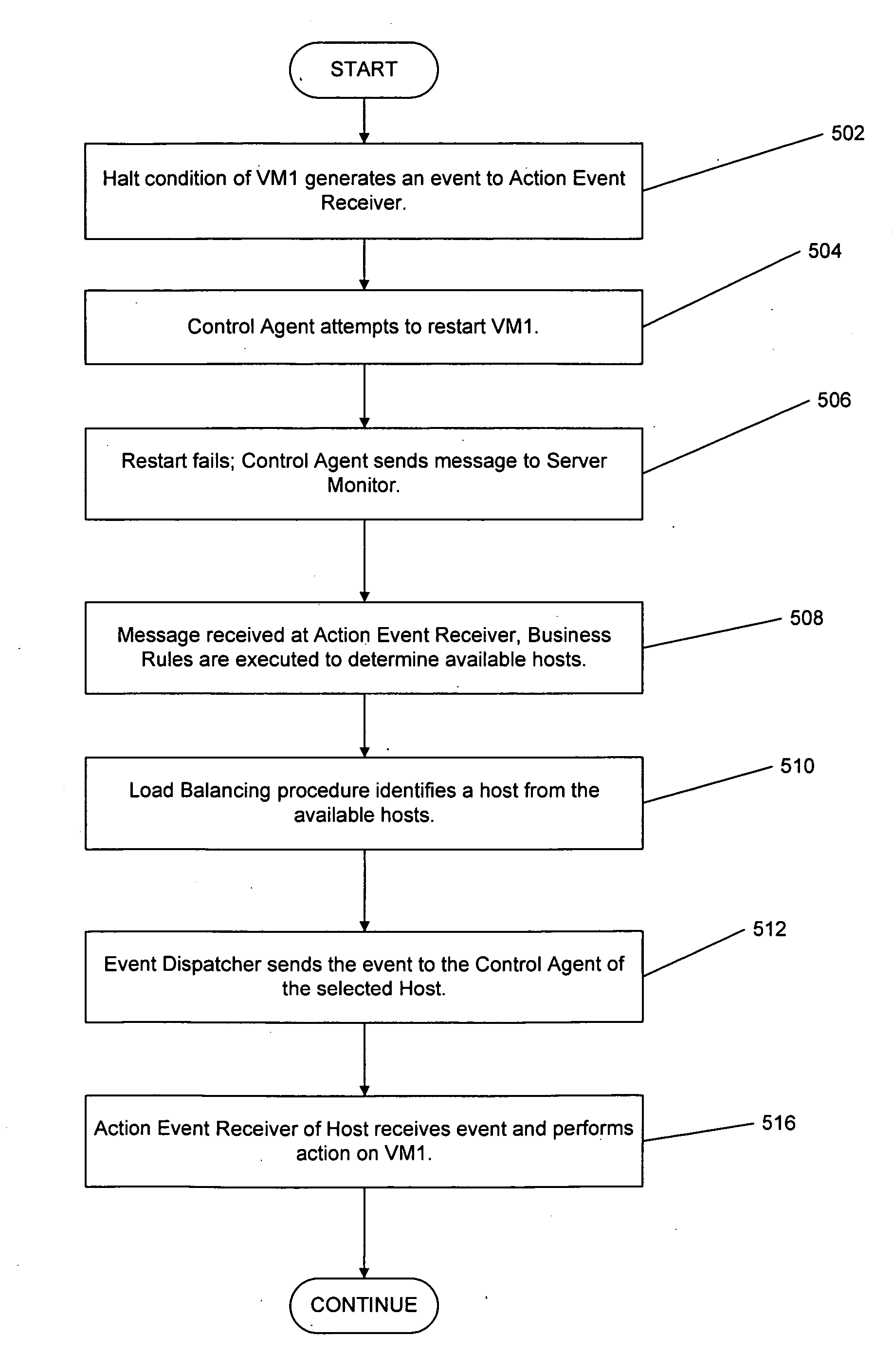
Method and system for model-based heterogeneous server configuration management
ActiveUS20030233431A1Error detection/correctionInterprogram communicationReference modelingReal time services
A method and system for configuring heterogeneous servers across a network through modules that can browse, snapshot, track changes, track compliance, correct server objects on each of the servers, and provision new servers is provided. In one embodiment, server objects on multiple servers can be browsed in real time. While browsing, a collection of server object identifiers can be selected and collected in a template. The values of the server objects identified in the template can be recorded for a "gold server" through a "snapshot" process, which collects the values and saves them in a reference model. By comparing other live servers to the reference model, discrepancies in configuration of the other live servers can be identified and corrected. The reference models can also be used to provision a new server. Alternative to the reference model, an arbitrary snapshot or scheduled snapshots of a server can be used to track change and compliance in that server.
Owner:BLADELOGIC
System methodology for automatic local network discovery and firewall reconfiguration for mobile computing devices
ActiveUS20030167405A1Easy to detectDigital data processing detailsHardware monitoringNetwork generationUnique identifier
A system providing methodologies for automatically detecting when a computing device is plugged into a new network is described. The system includes methods for detecting a connection to a new network by receiving notice of, and evaluating, changes to an existing network configuration. The system profiles and generates an identity for the new network. This includes collecting information about the network to uniquely identify it and generating a unique identifier for the network. Once a network has been profiled, a user may decide whether or not to include it as part of a trusted zone. Alternatively, this decision may be guided by policy established by a system administrator or user. The system automatically reconfigures a firewall to include or exclude the network from the trusted zone based upon this decision. The profile of each network is stored so that the next time the device is connected to the same network it remembers the network and applies the same security settings previously adopted. The stored profile also facilitates the detection of changes to the network configuration or the connection to a new network.
Owner:CHECK POINT SOFTWARE TECH INC
Network for matching an audience with deliverable content
ActiveUS20050166233A1Television system detailsBroadcast systems characterised by addressed receiversDistributed computingNetwork segment
Owner:YAHOO AD TECH LLC
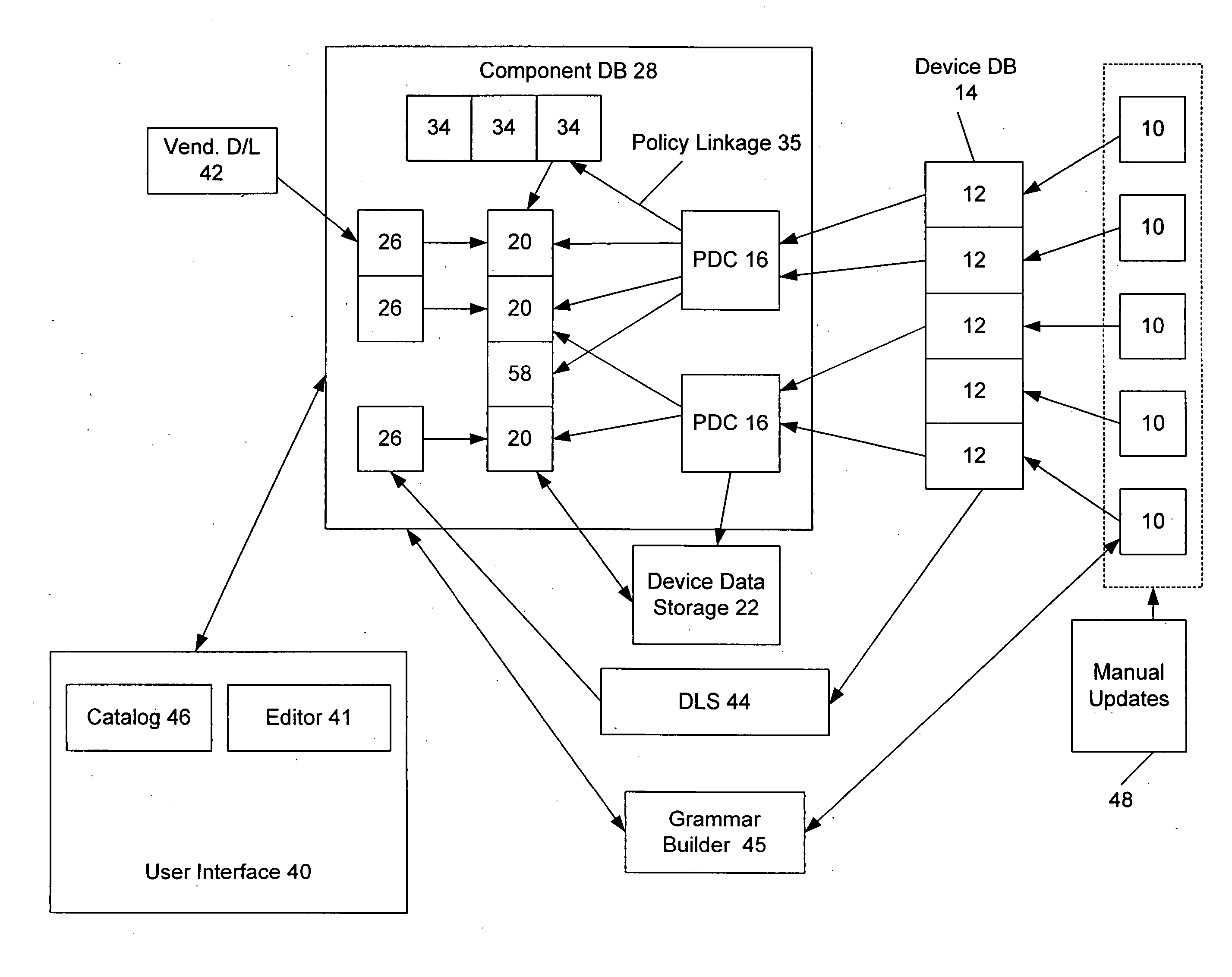
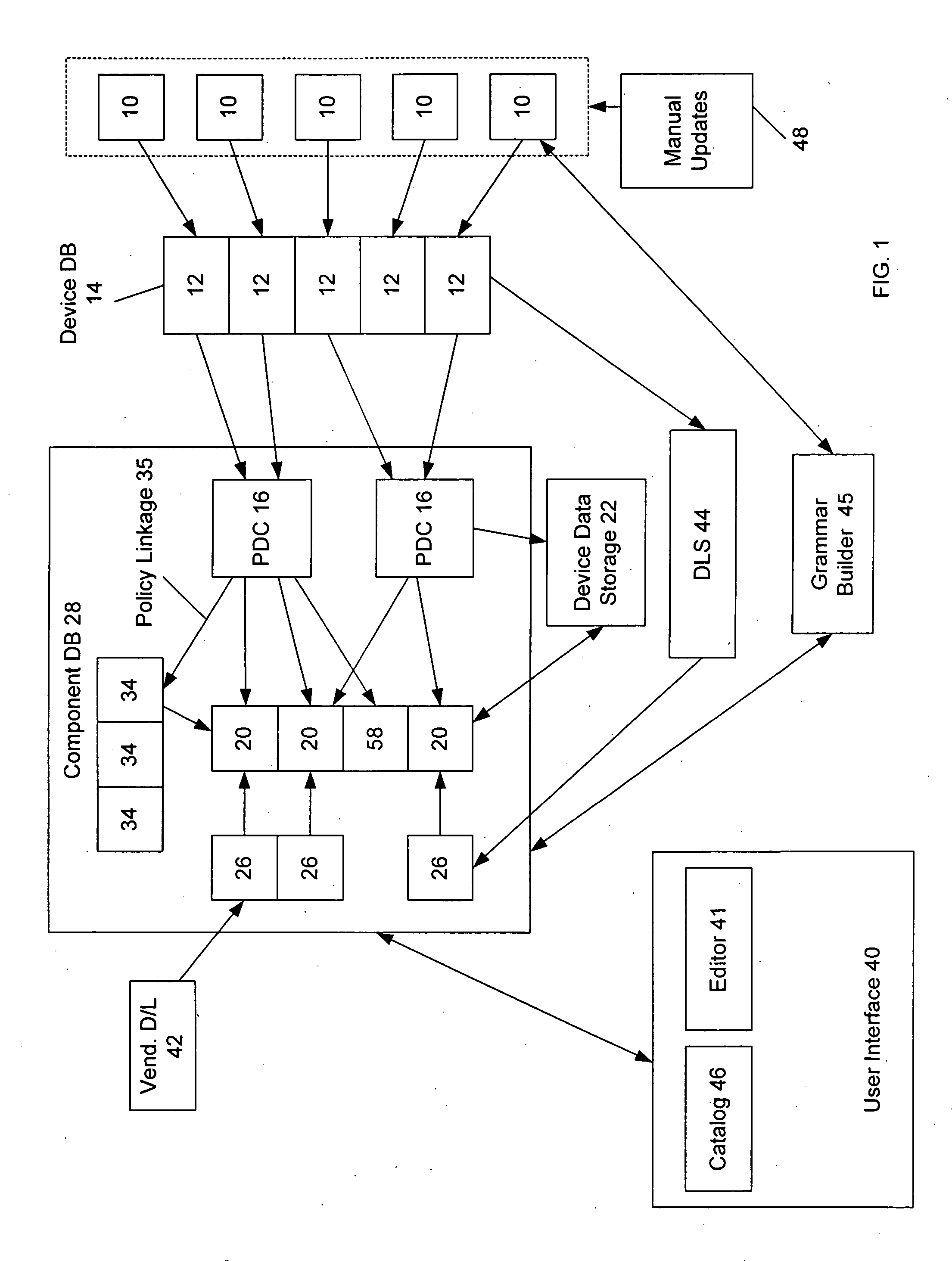
Methods and systems for controlling network infrastructure devices
InactiveUS20050004942A1Easy to createBridging the gapDigital data processing detailsData switching networksNetwork managementDistributed computing
A network management system is provided that allows a user to configure multiple devices according to a consistent set of policies. The system includes a device learning module that can read configuration data from a network device and automatically match that configuration data to existing policies and components of policies within the system. The device learning module also identifies unknown configuration data, which does not match any existing policy. The system further includes a grammar builder that can parse the unknown configuration data and construct a component or policy from the unknown data, by matching the unknown data to a grammar of configuration commands for the network device. The system also provided auditing capabilities, where policies are compared to running network configurations, and differences are identified.
Owner:NETWORK CLARITY
System and method for implementing logic control in programmable controllers in distributed control systems
ActiveUS20050085928A1EliminateAchieve modularityTemperatue controlStatic/dynamic balance measurementProgrammable logic controllerDistributed control system
Owner:UNITRONICS 1989 RG
Method and apparatus for network wide policy-based analysis of configurations of devices
InactiveUS8135815B2Easy to determineAvoid problemsMultiple digital computer combinationsData switching networksApplication serverInternet traffic
A method for a computer system includes determining network devices within a network topology, wherein the network devices includes a first application server hosting a first application, receiving a policy for the network comprising requirements of a first application server including a description of a set of required network traffic, receiving a plurality of configuration files associated with the plurality of network devices, determining a network configuration model in response to the plurality of configuration files, computing network traffic on all network paths to and from the first application server to determine a plurality of computed paths, determining if the network traffic includes at least the set of required network traffic associated with the first server, and generating a report indicating whether the network traffic includes at least the set of required network traffic.
Owner:REDSEAL
Systems and methods for acquiring network credentials
ActiveUS8191124B2Digital data processing detailsAnalogue secracy/subscription systemsRequest–responseNetwork Access Device
Exemplary methods and systems for acquiring network credentials for network access are described. The exemplary method includes receiving network configuration information from a network device on a communication network, generating a credential request, transmitting the credential request to a credential server over a standard protocol of the network device, receiving the credential request response, and providing a network credential from the credential request response to the network device to access the communication network.
Owner:CHANNEL IP BV
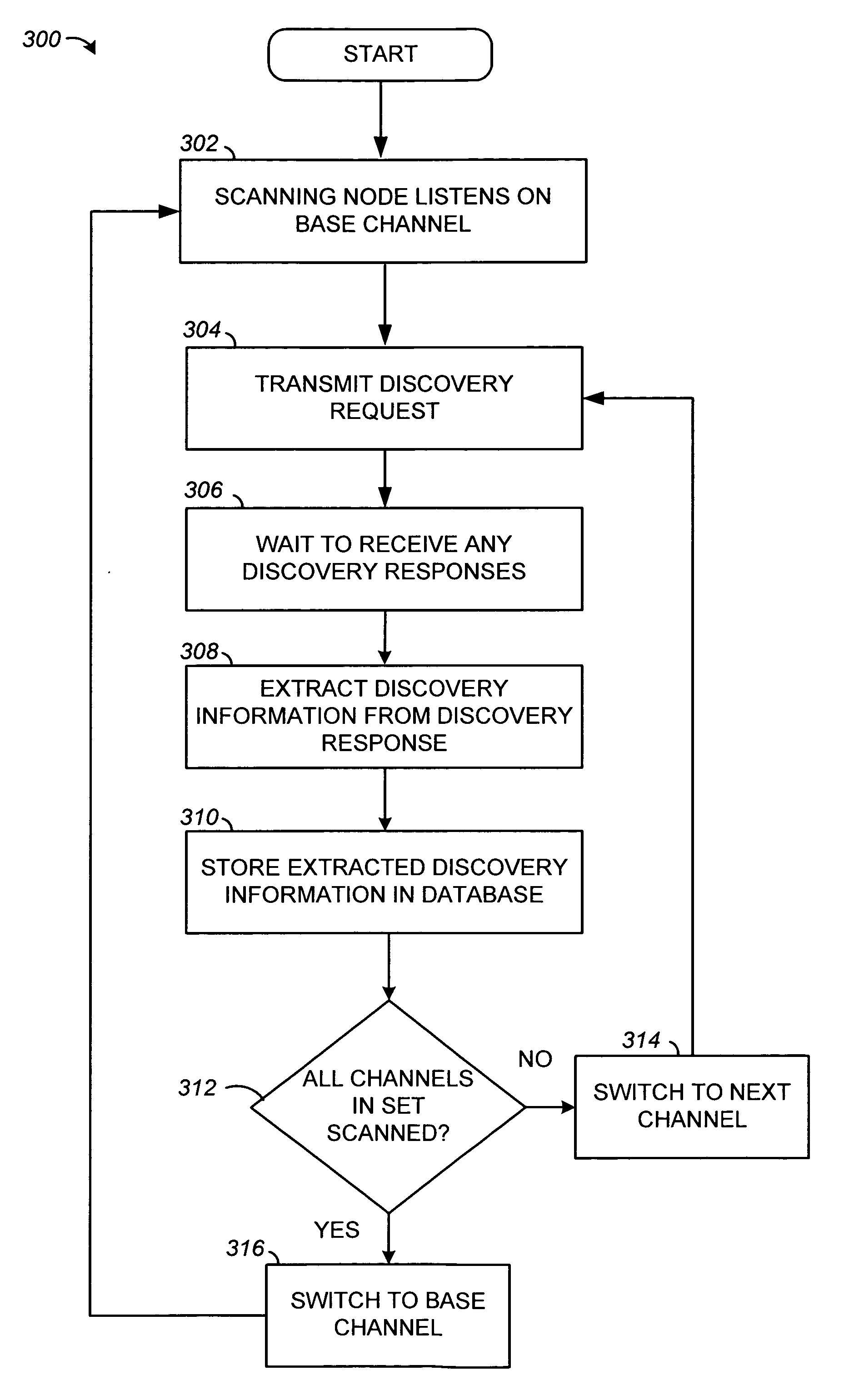
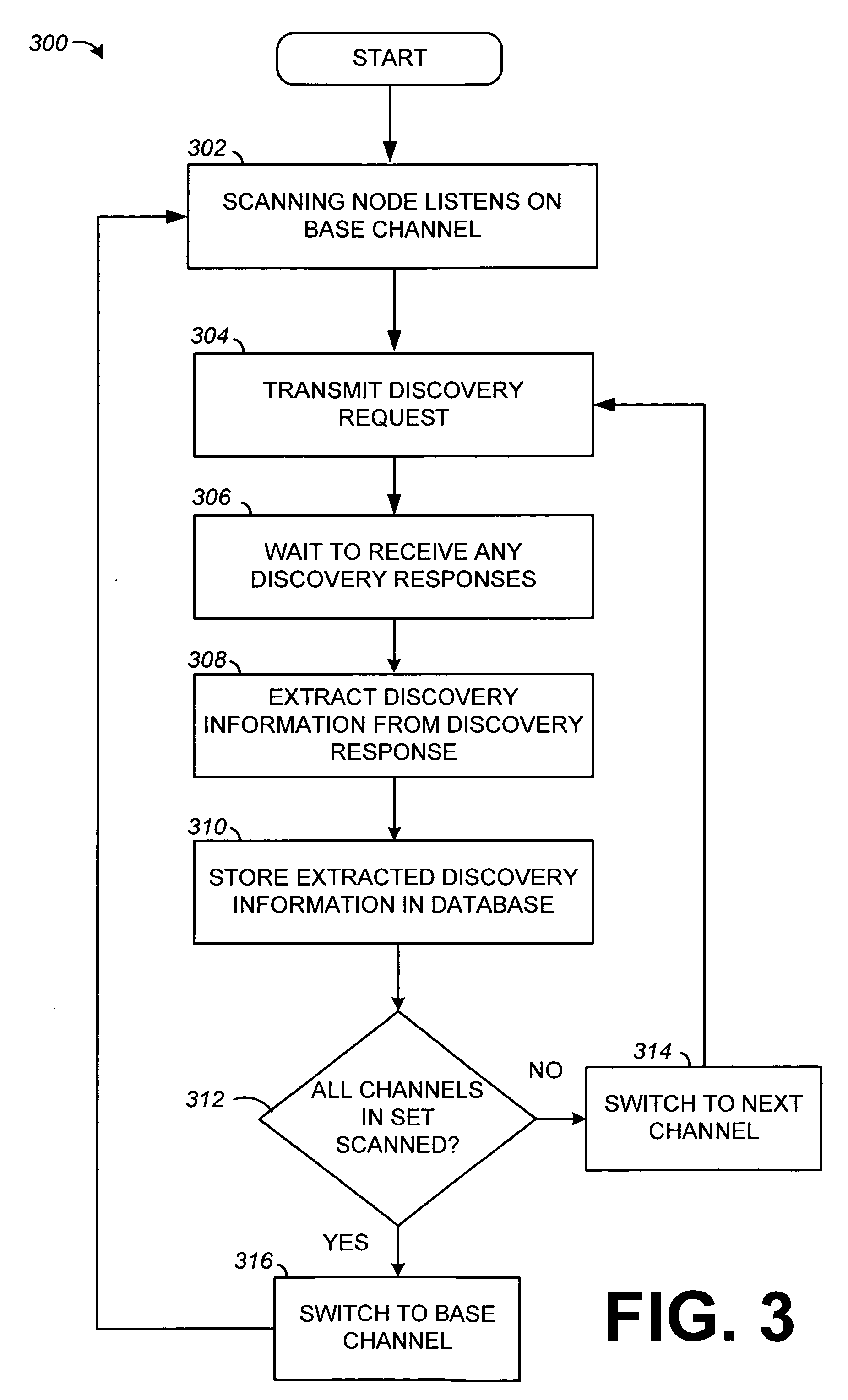
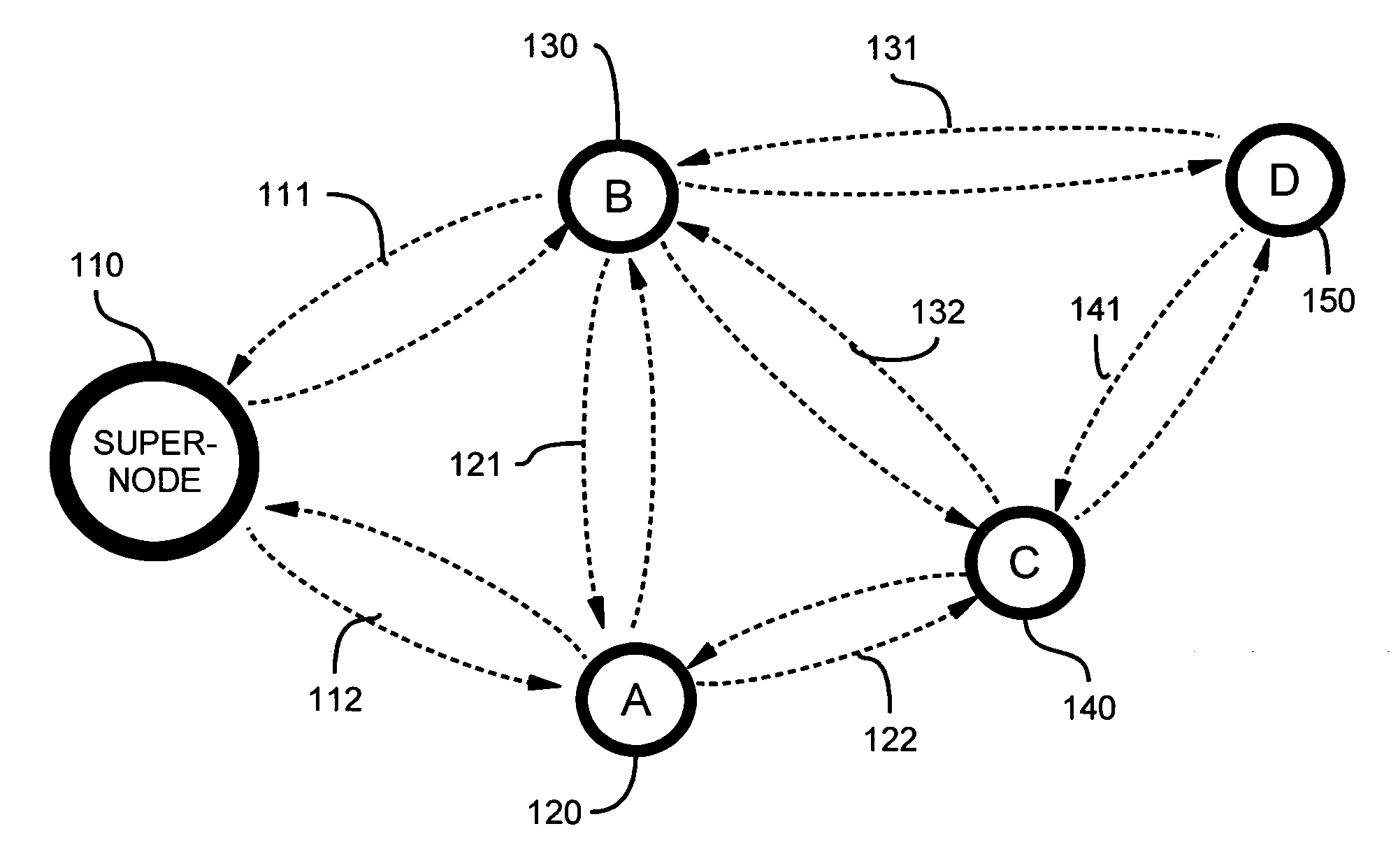
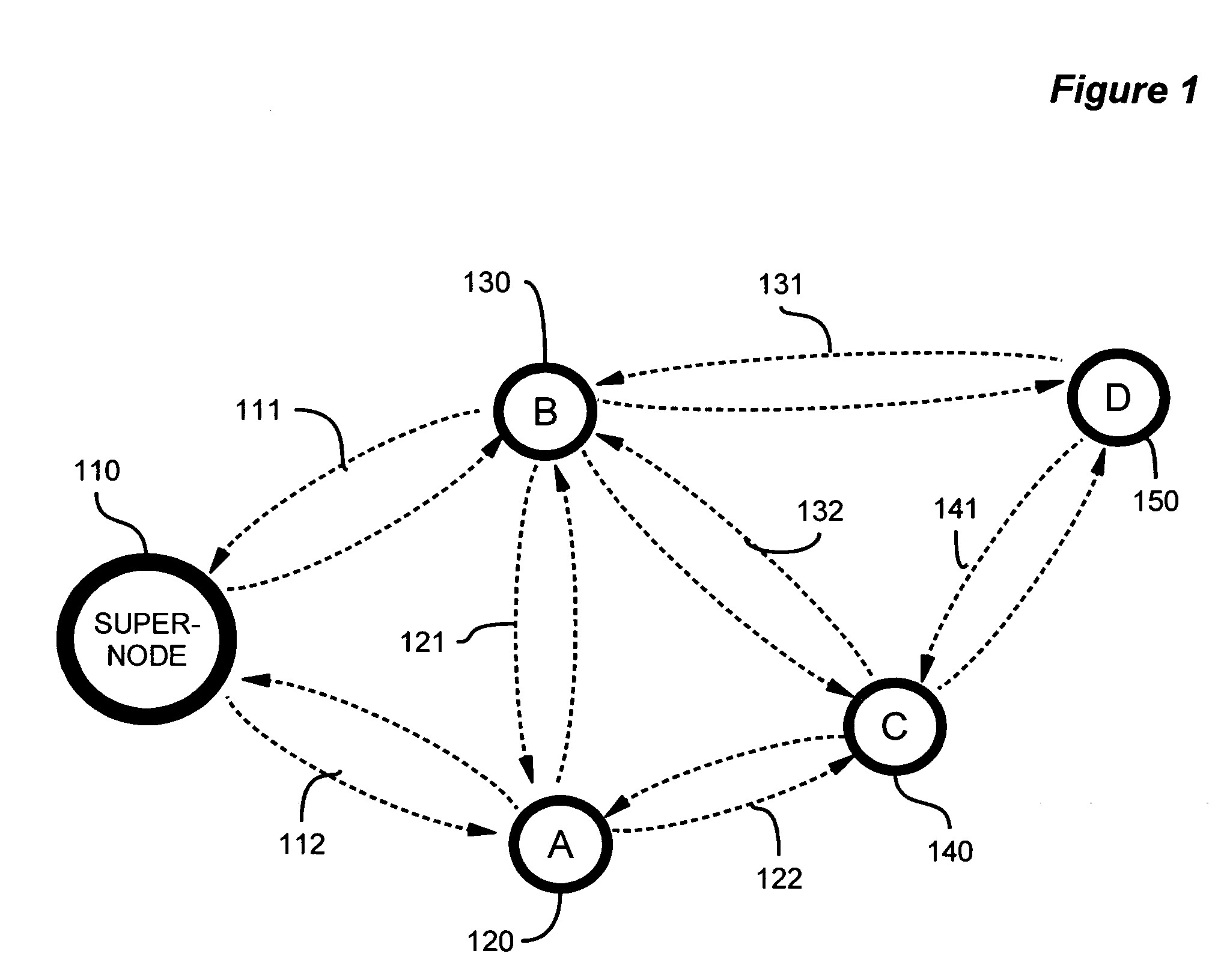
Device discovery and channel selection in a wireless networking environment
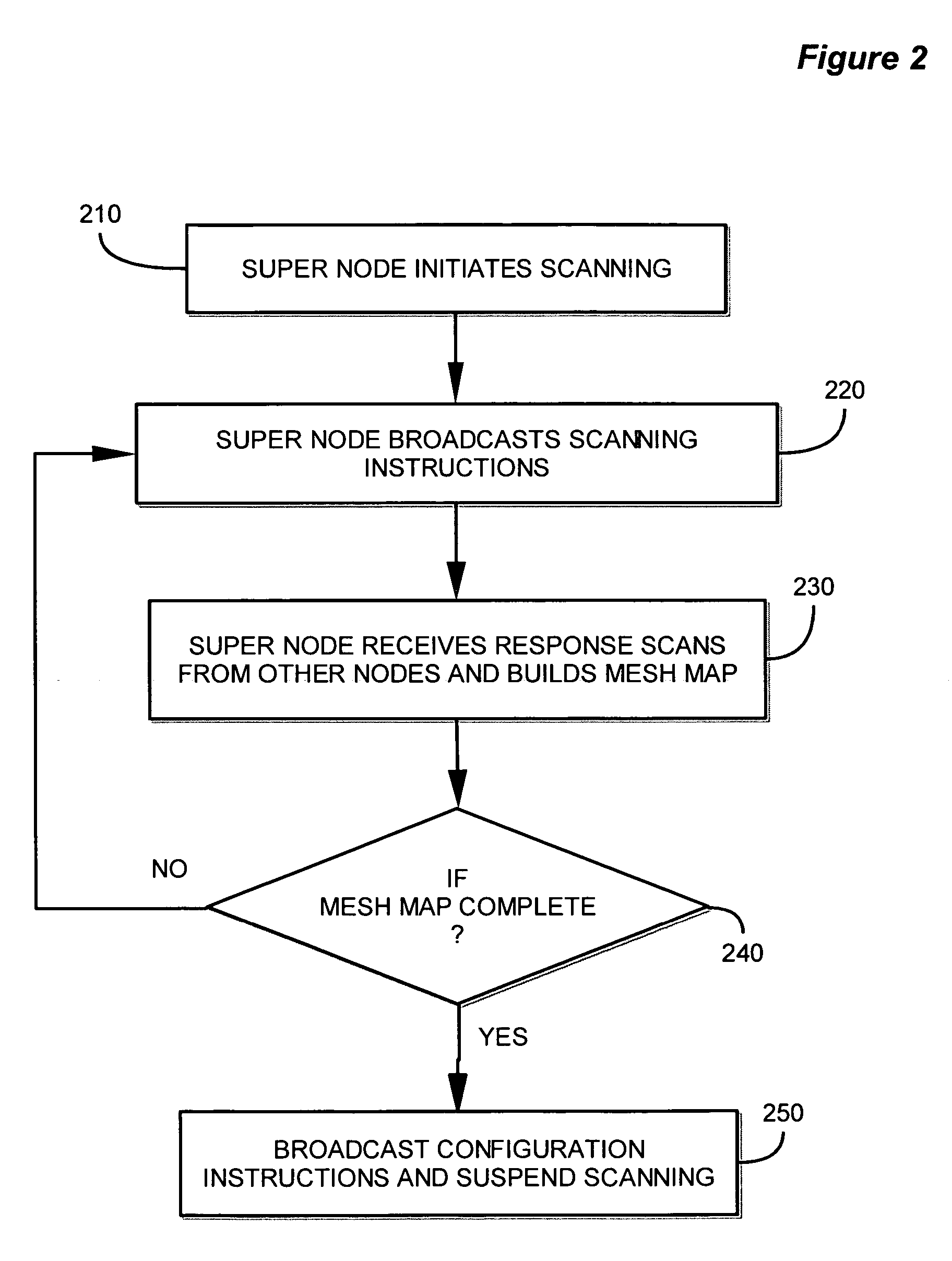
ActiveUS20060171332A1Multiplex system selection arrangementsAssess restrictionBroadcastingSwitching time
A method and apparatus for device discovery and channel selection in a wireless networking environment are described. As part of an automatic network configuration process, a super node sequentially traverses the available channels, broadcasting discovery messages including the channel switching schedule. Wireless nodes that receive those broadcast messages switch channels in lock step with the super node, sending discovery replies on those channels over which the broadcast discovery messages are successfully received. An association is generated identifying accessible nodes and the channels through which those nodes may be accessed. An optimum channel may then be selected based on this association information. Sub-nodes may repeat the broadcast discovery messages, and relay any discovery replies to the super node. The super node may then identify sub-nodes that may be used as proxies to access nodes that would otherwise be inaccessible.
Owner:SNAP ONE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com