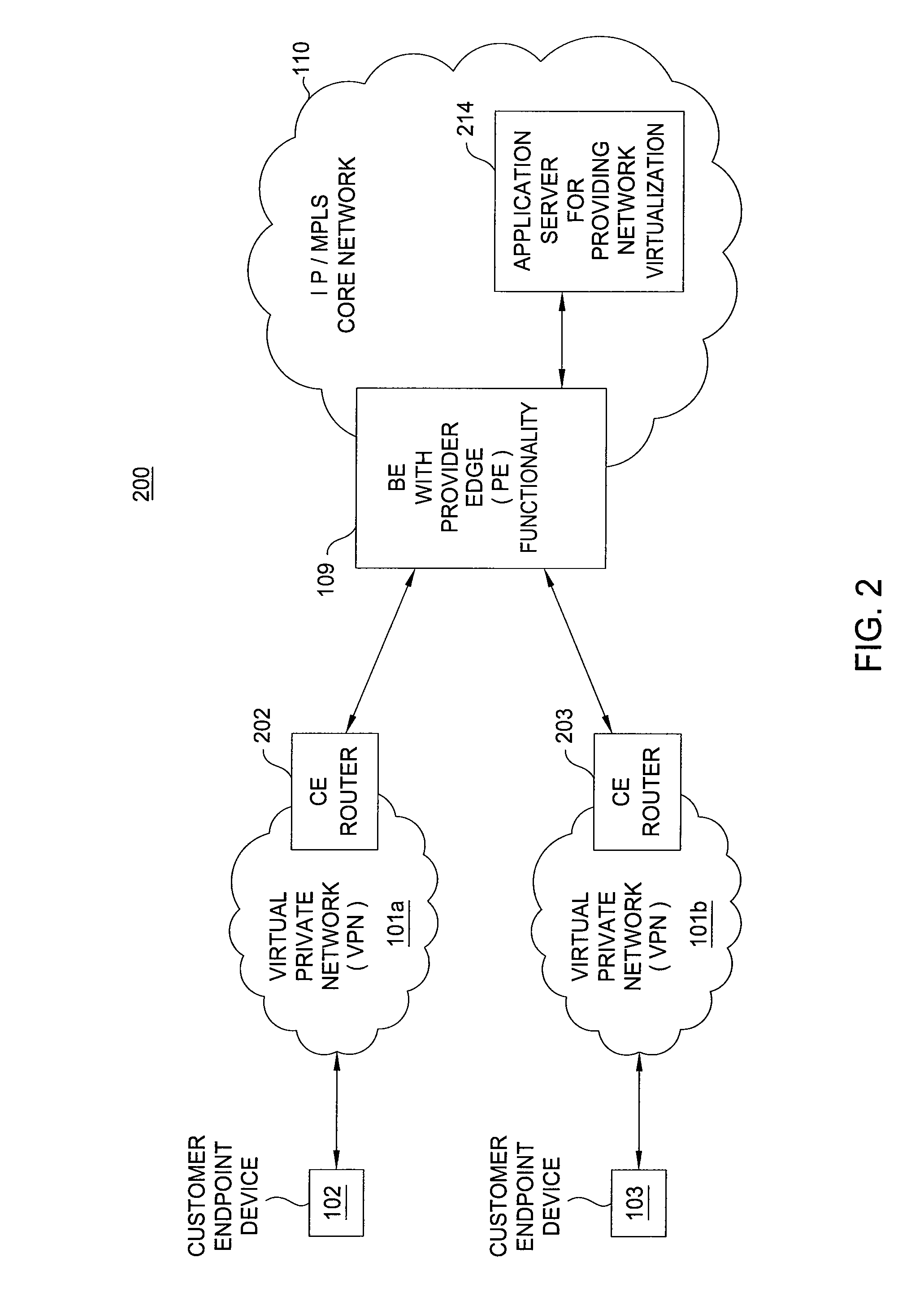
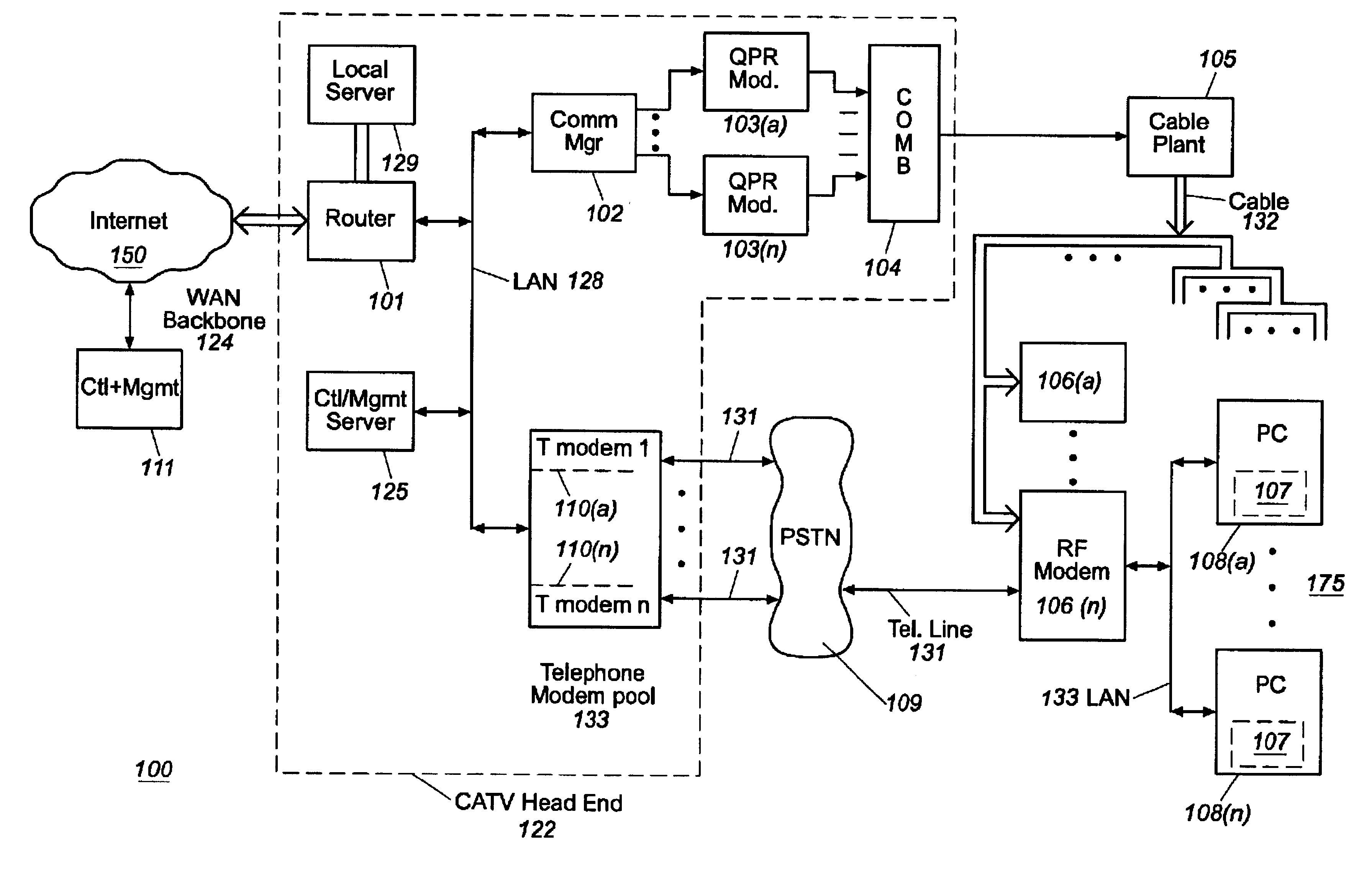
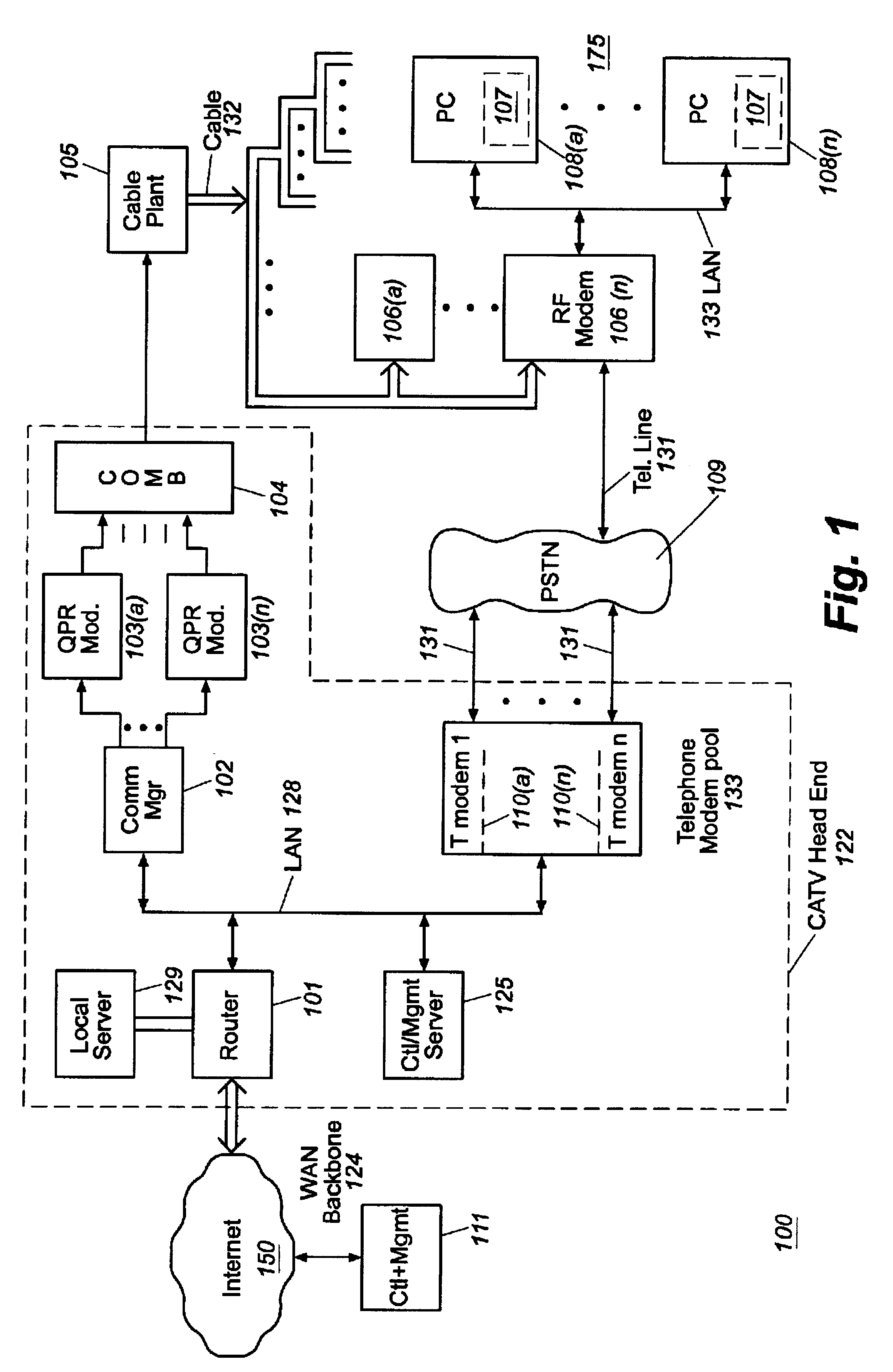
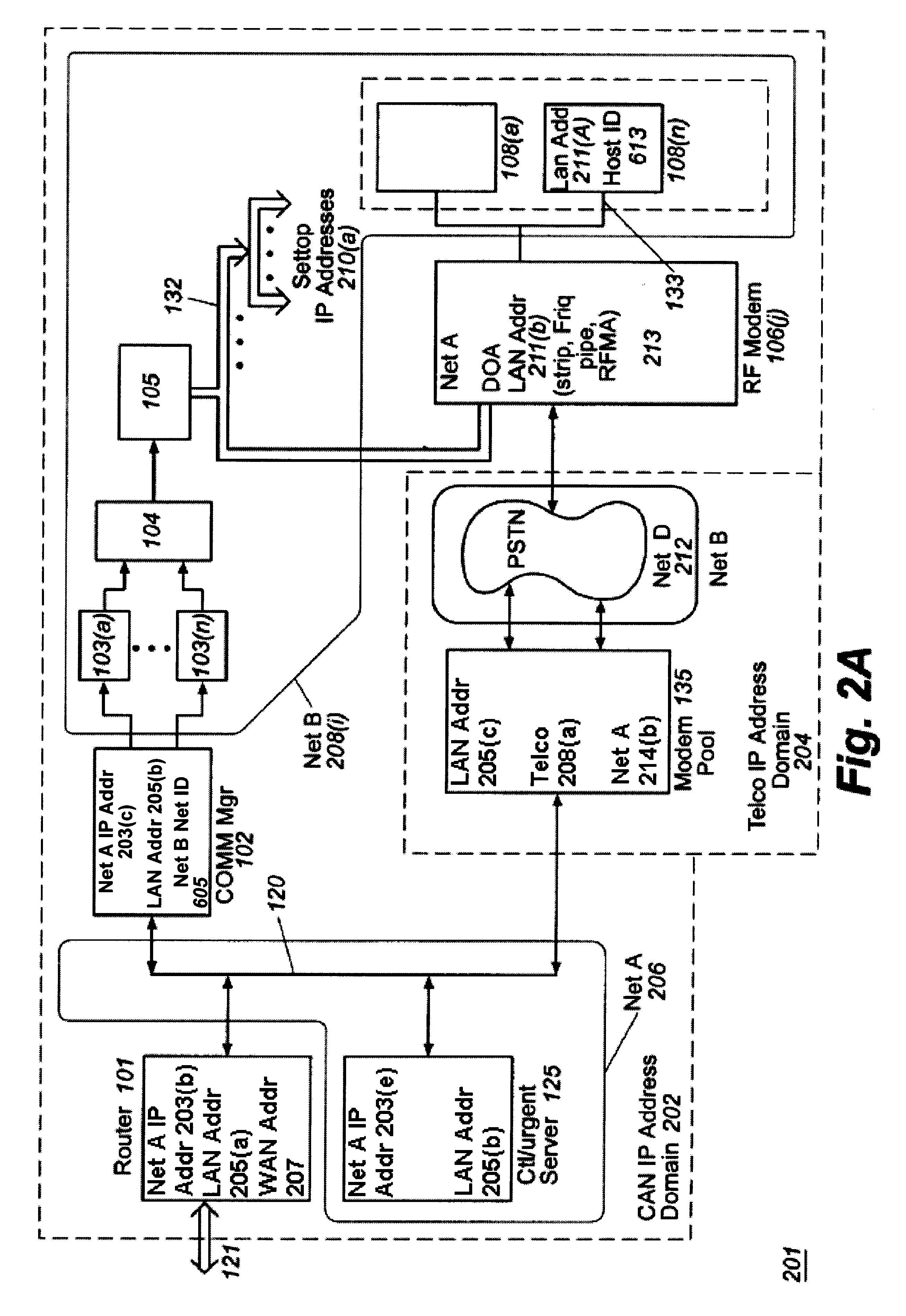
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1303 results about "Network component" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
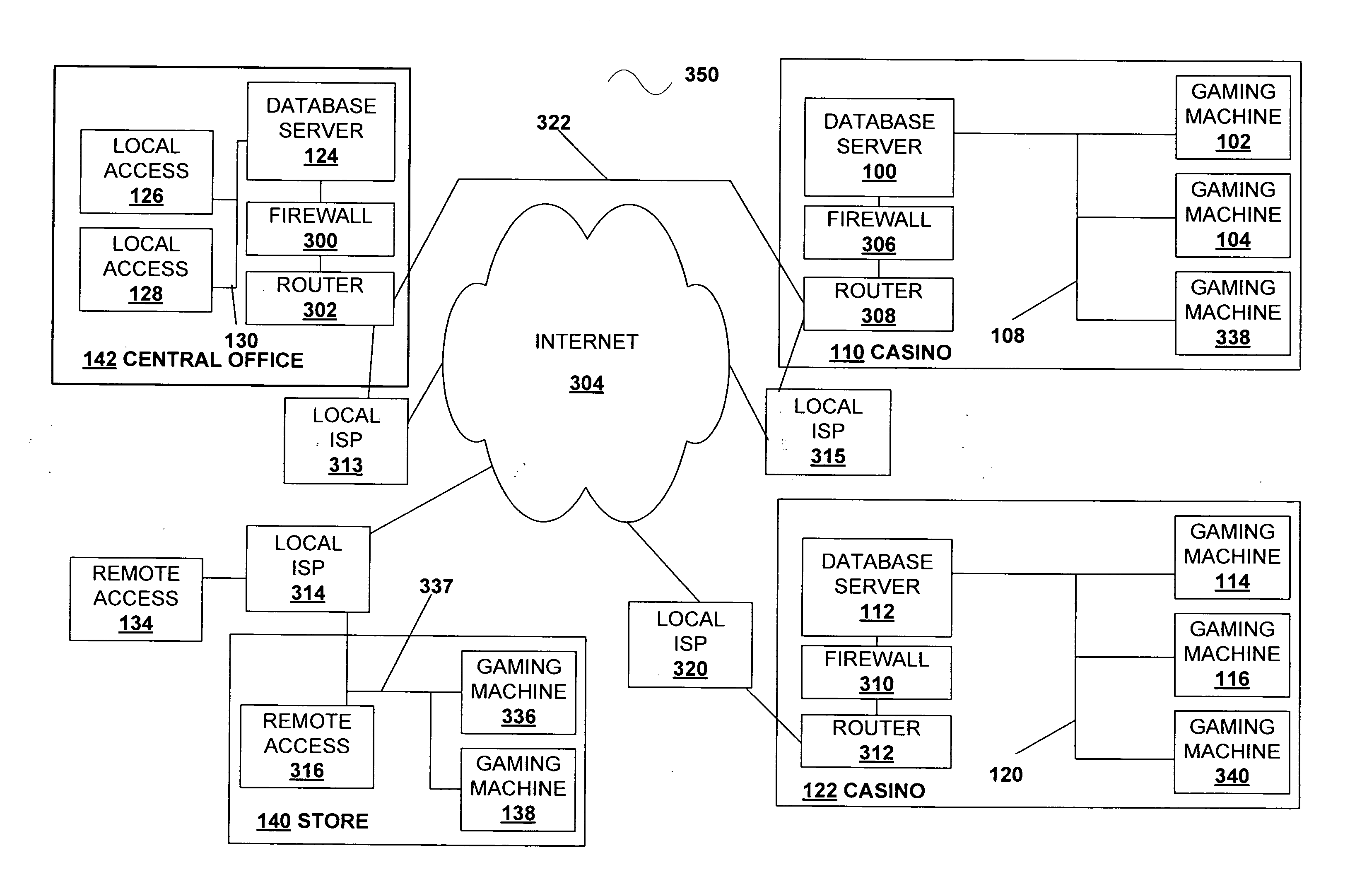
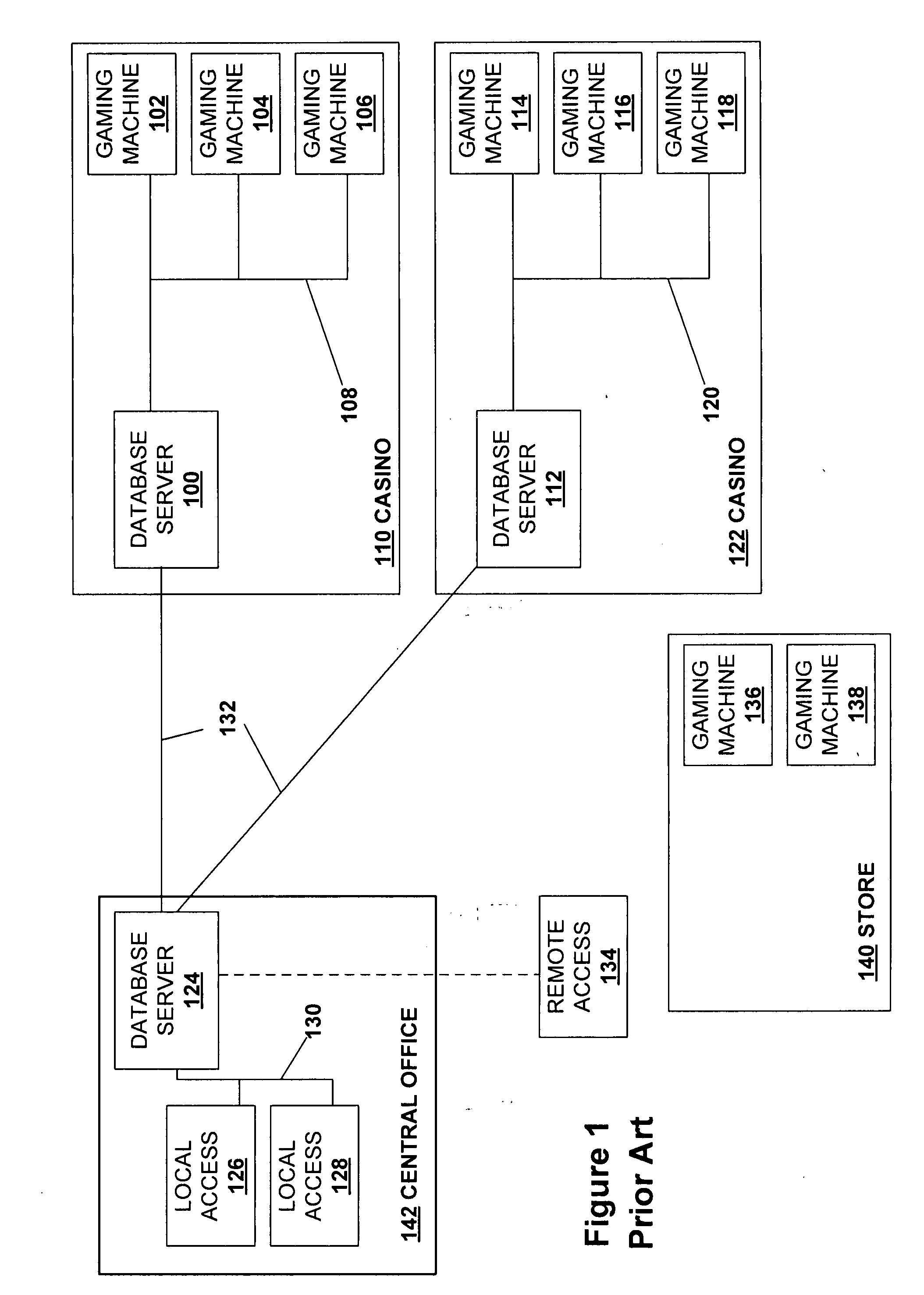
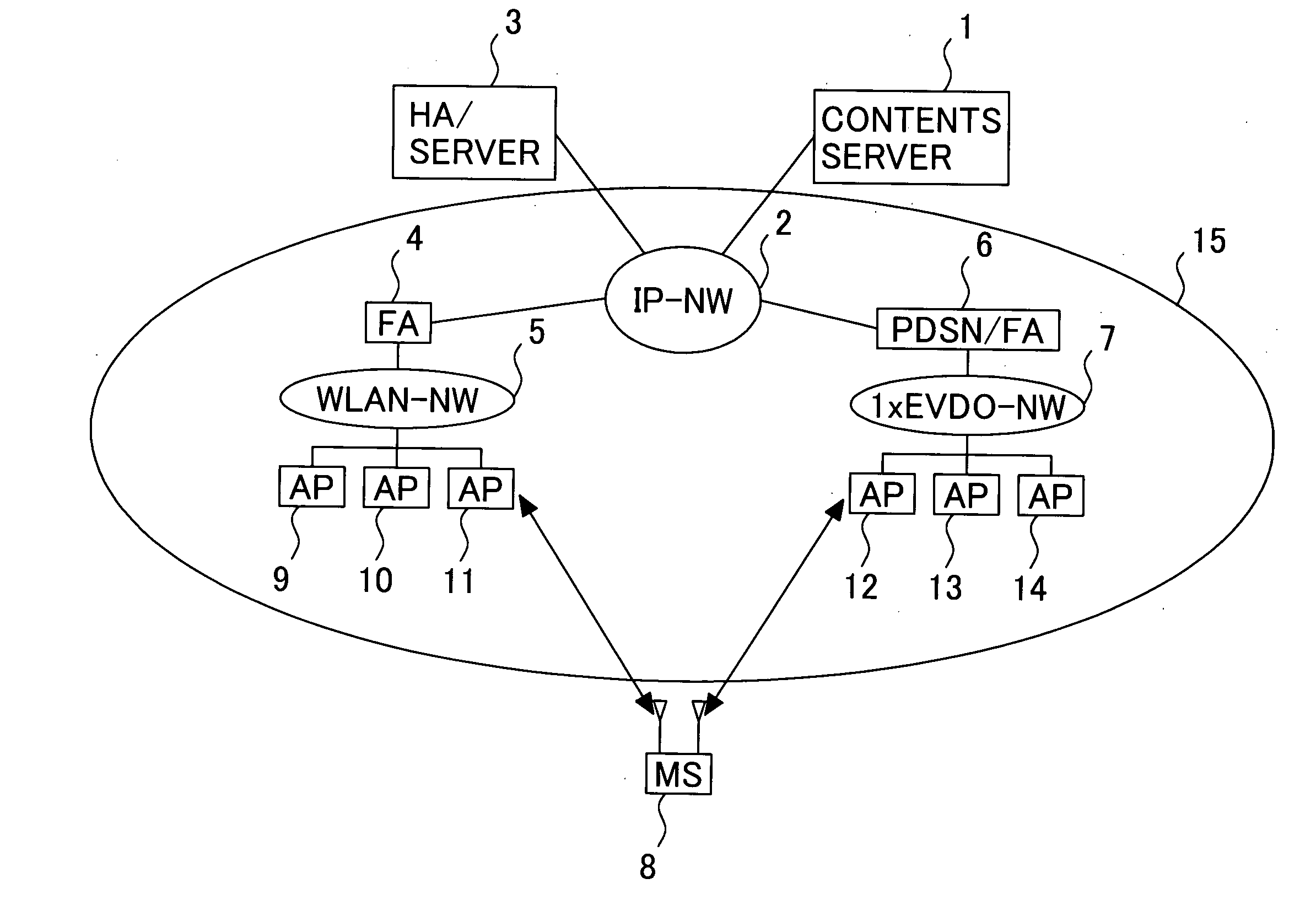
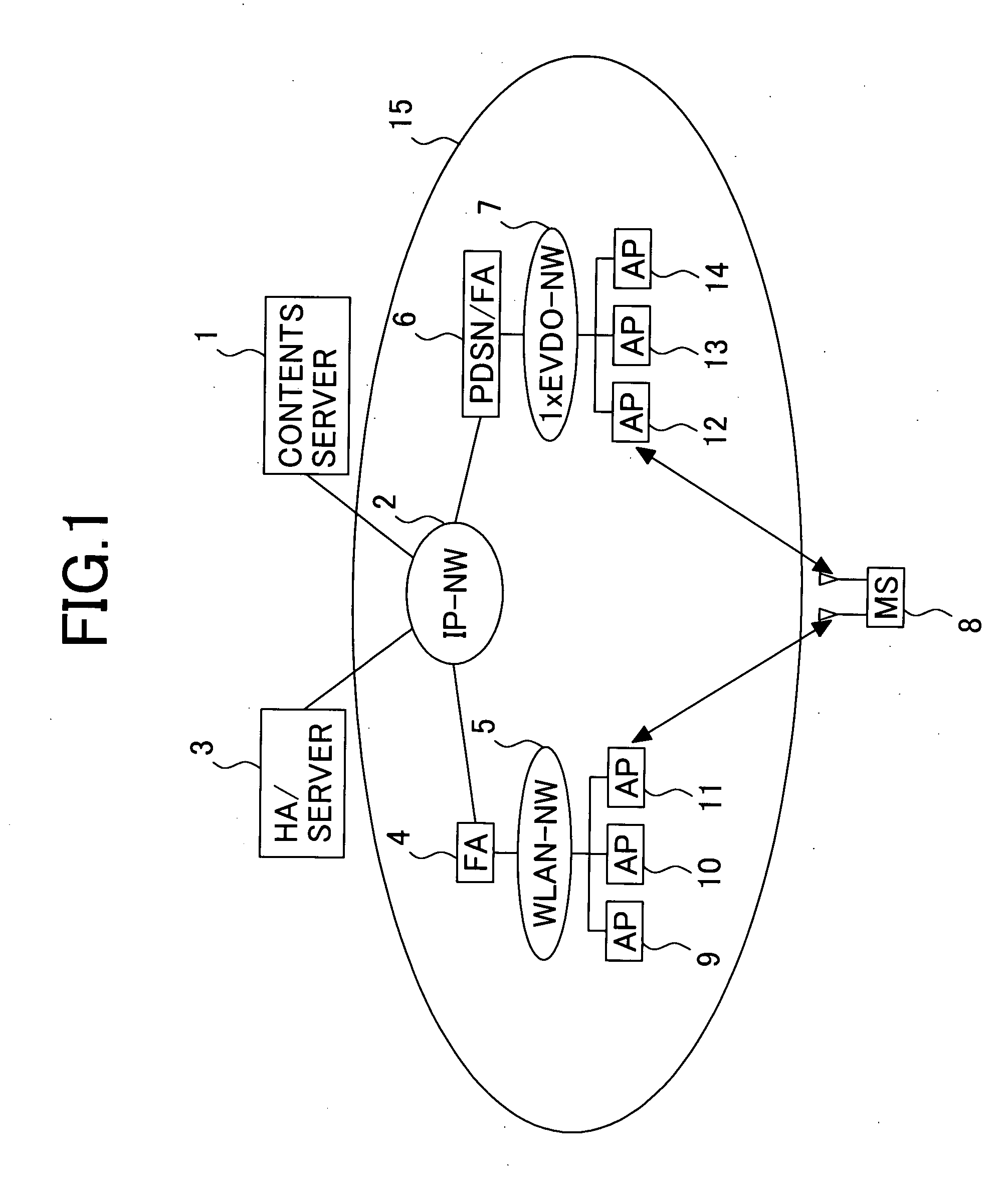
Computer network components Computer network components include the major parts that are needed to install a network both at the office and home level. These hardware components include cable, Hub, Switch, NIC (network interface card), modem and router.
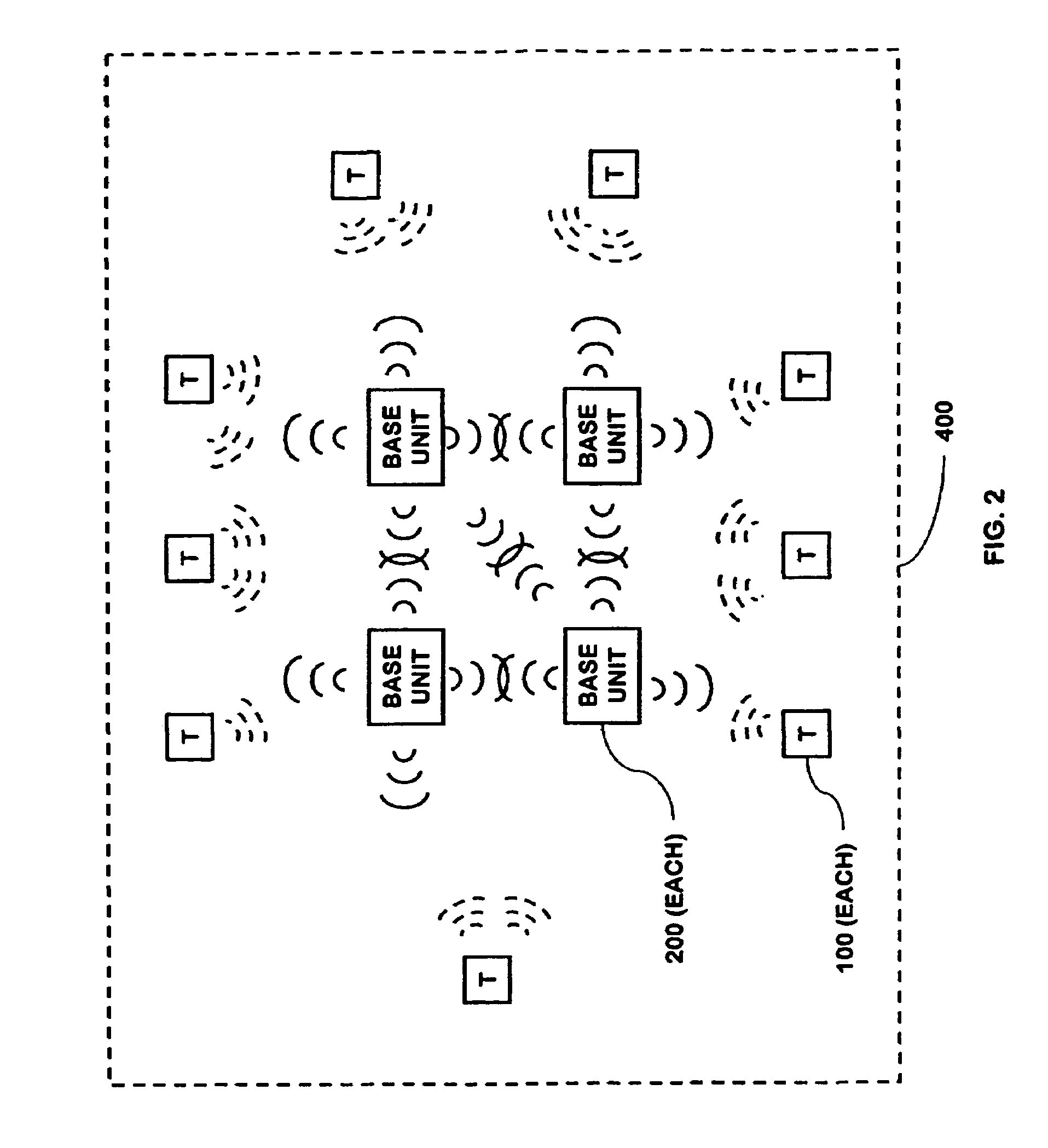
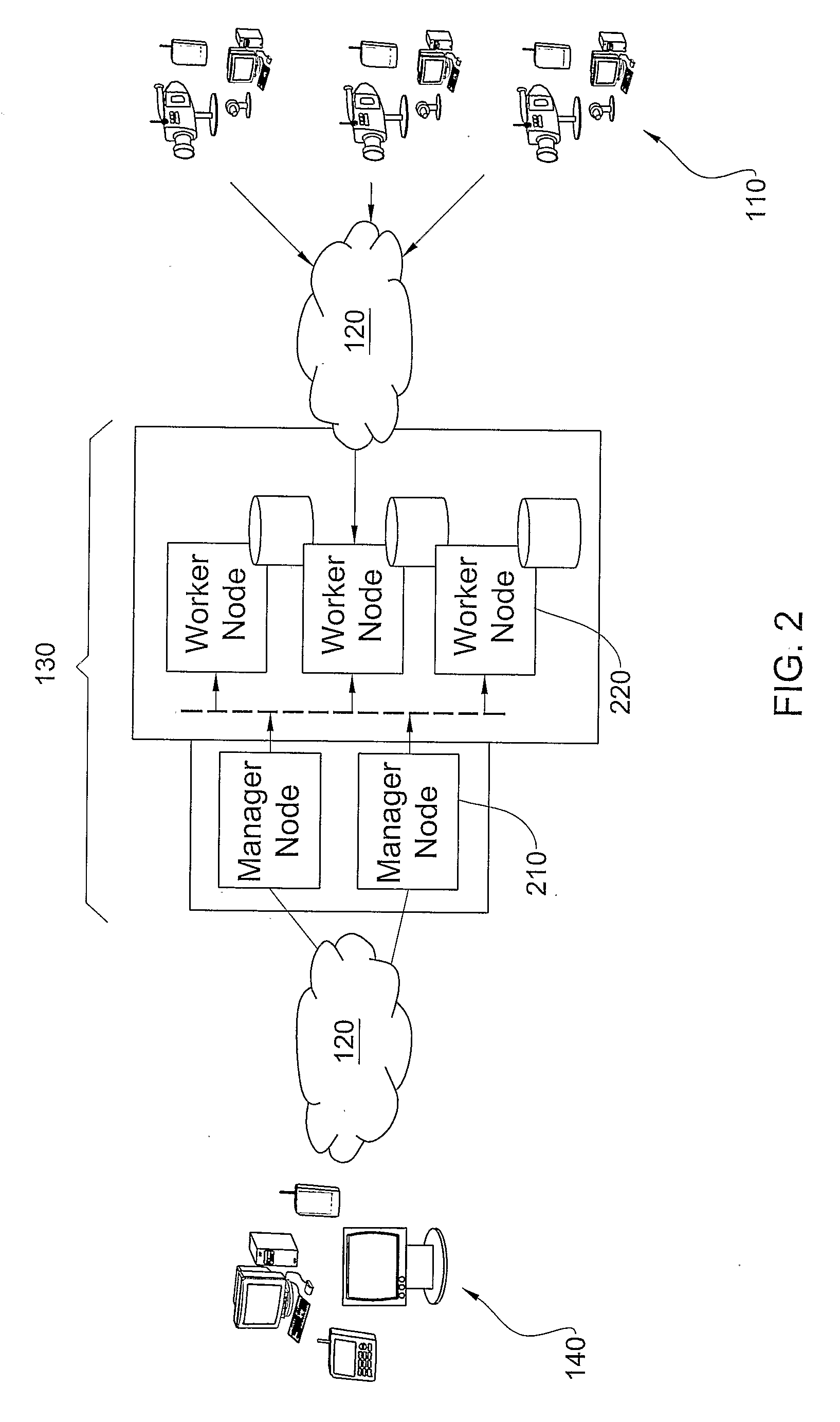
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
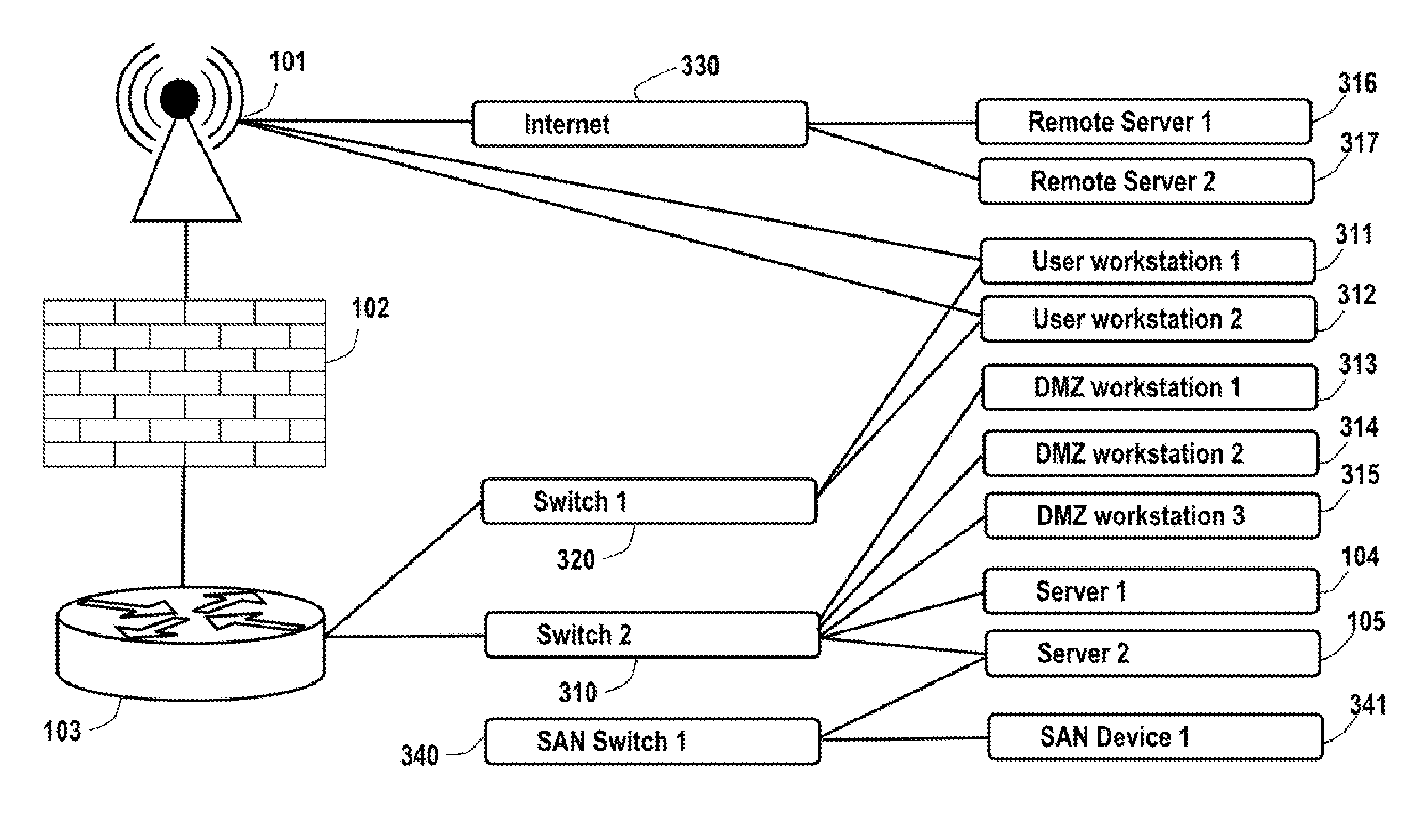
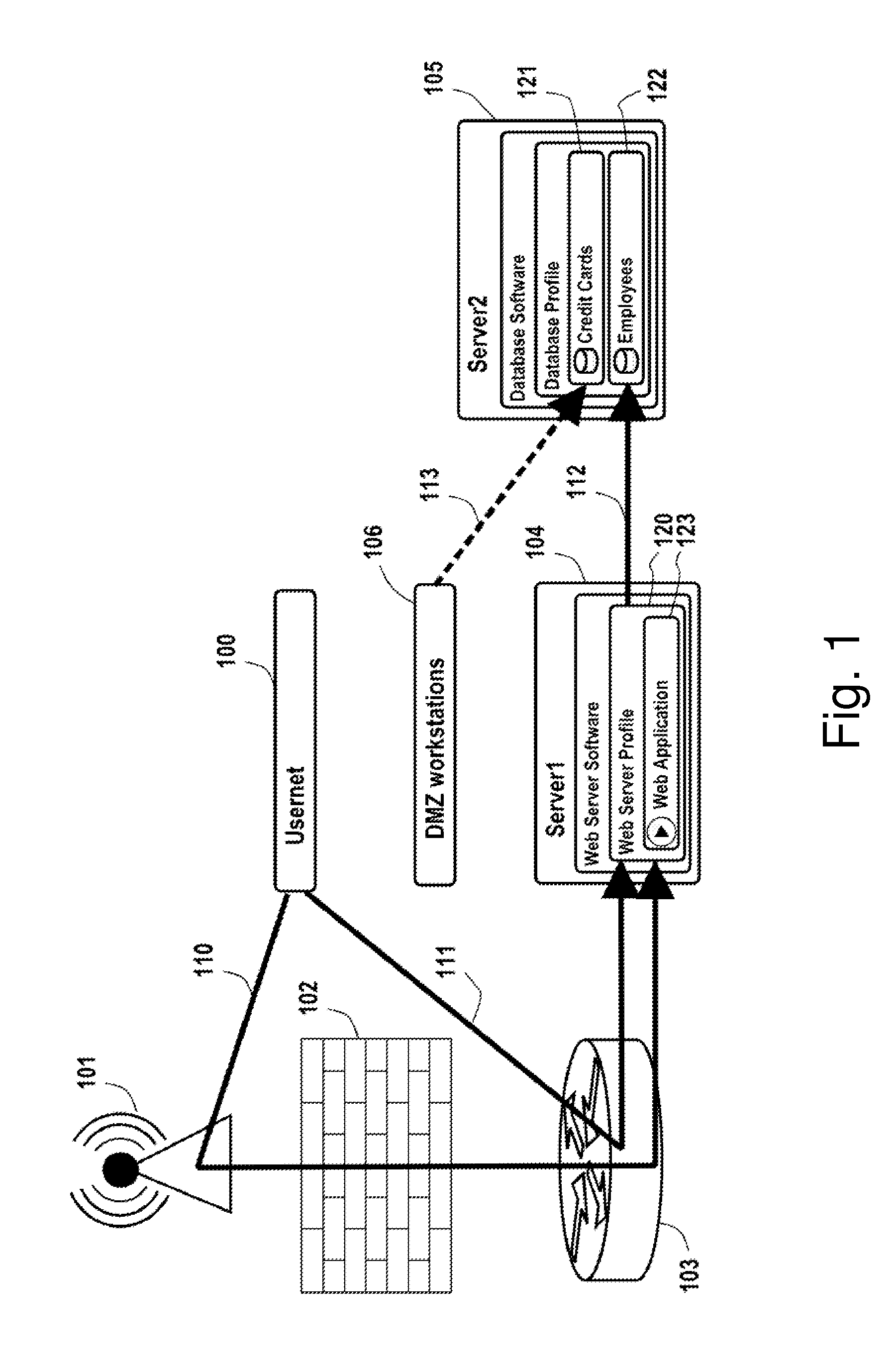
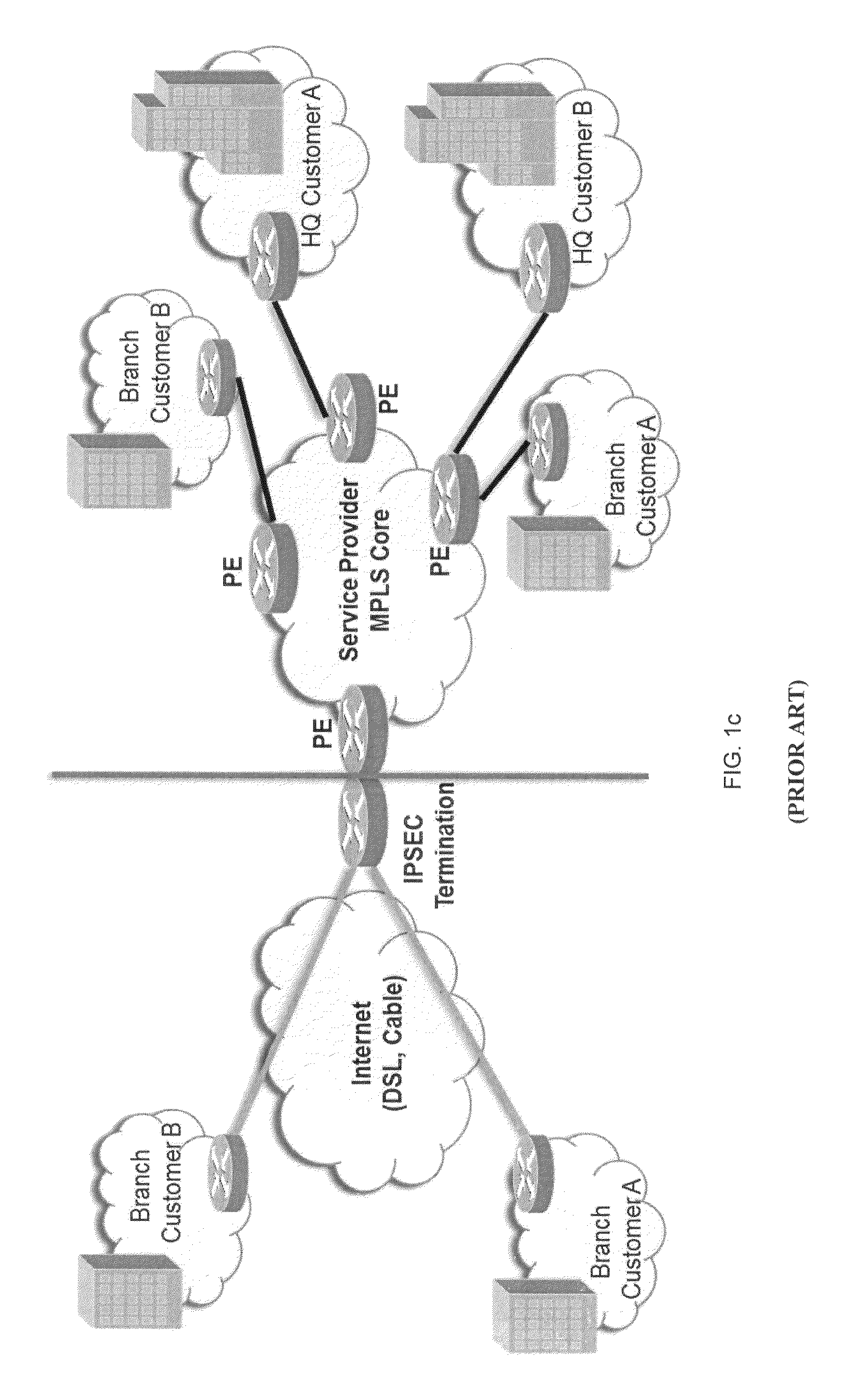
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
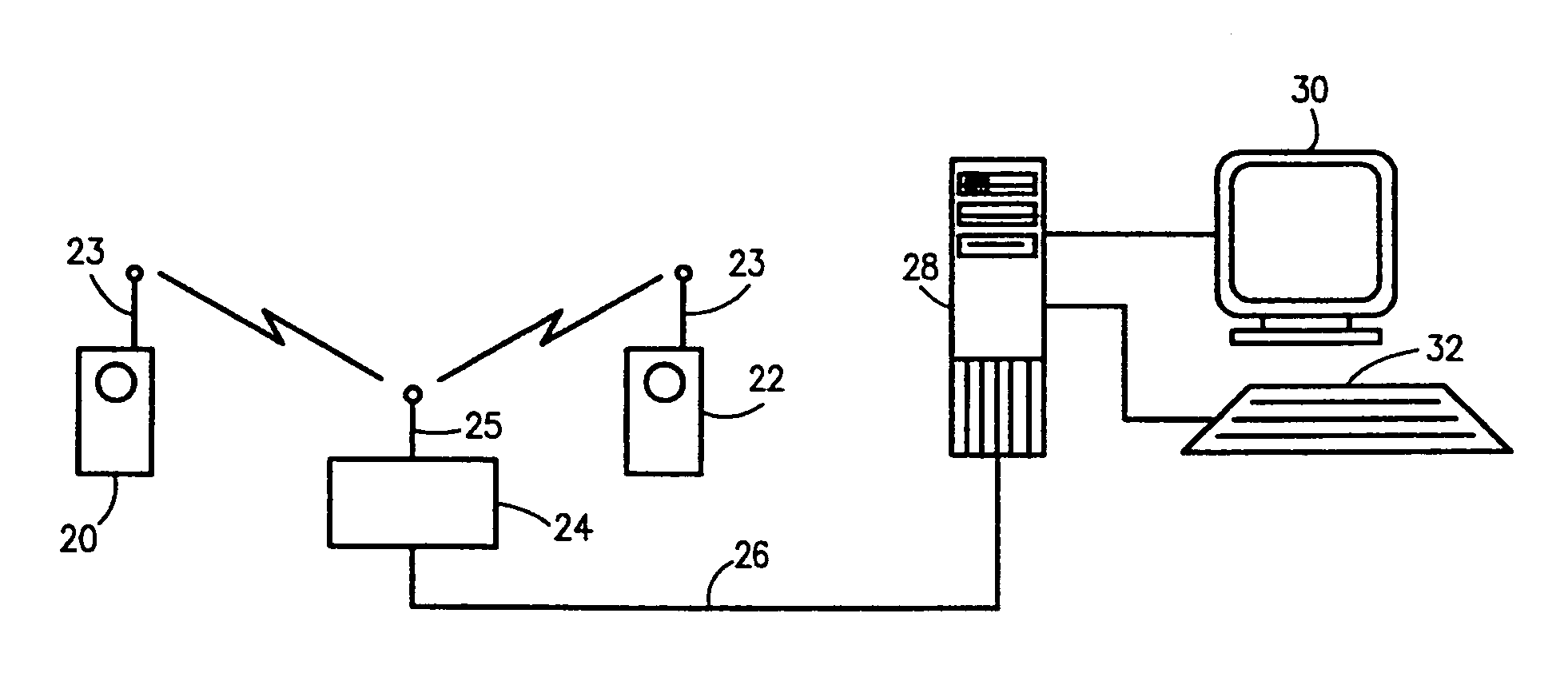
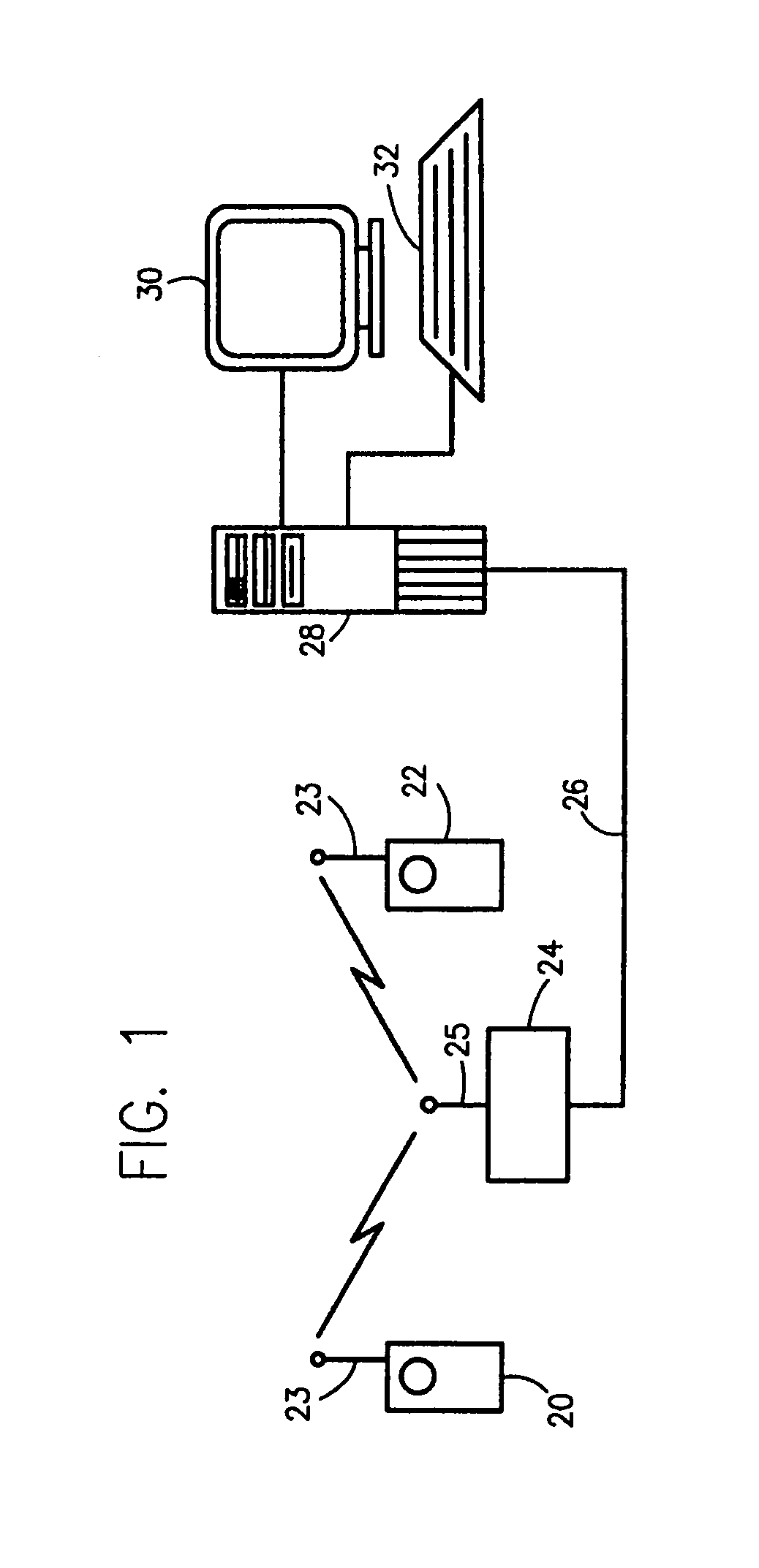
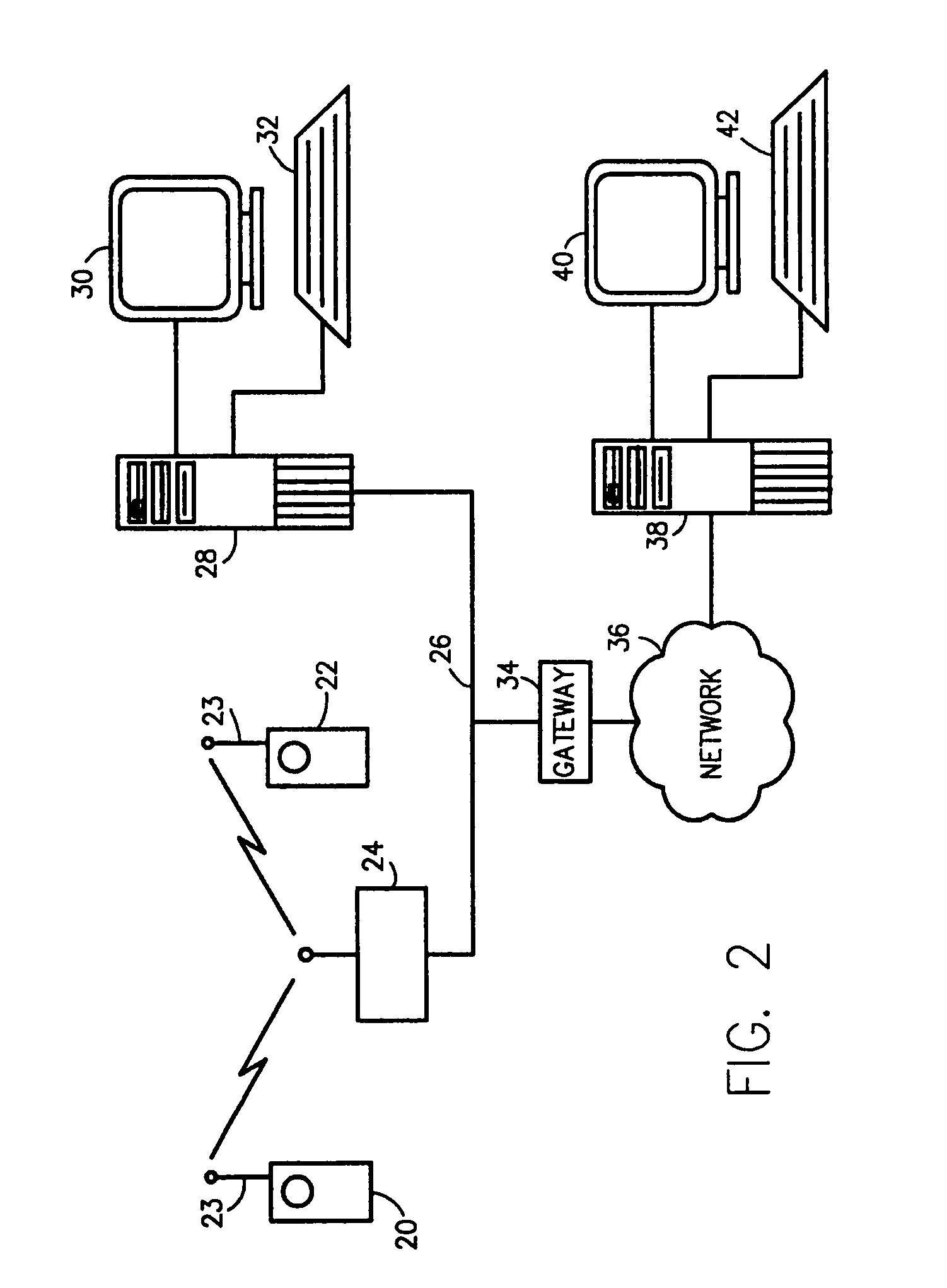
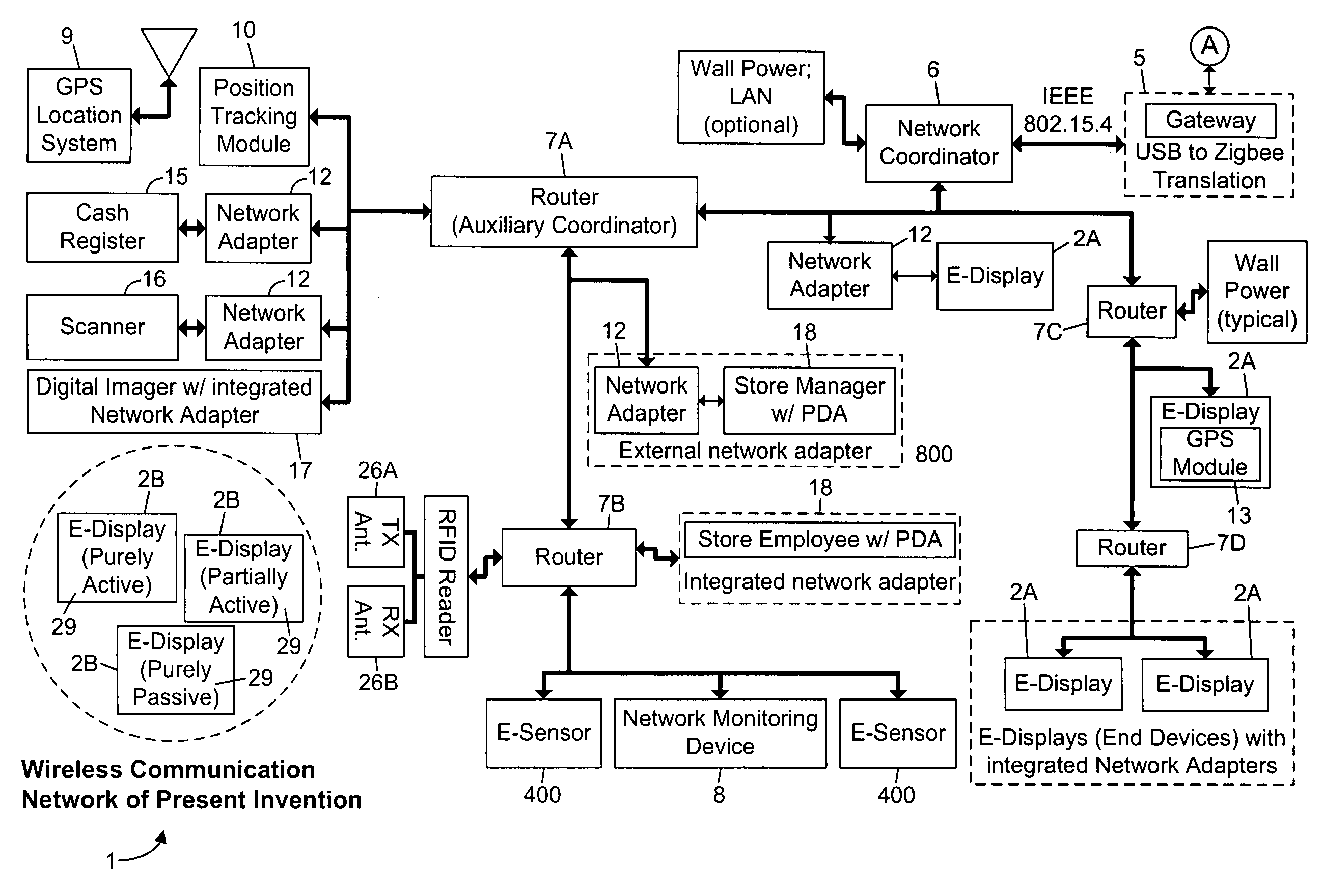
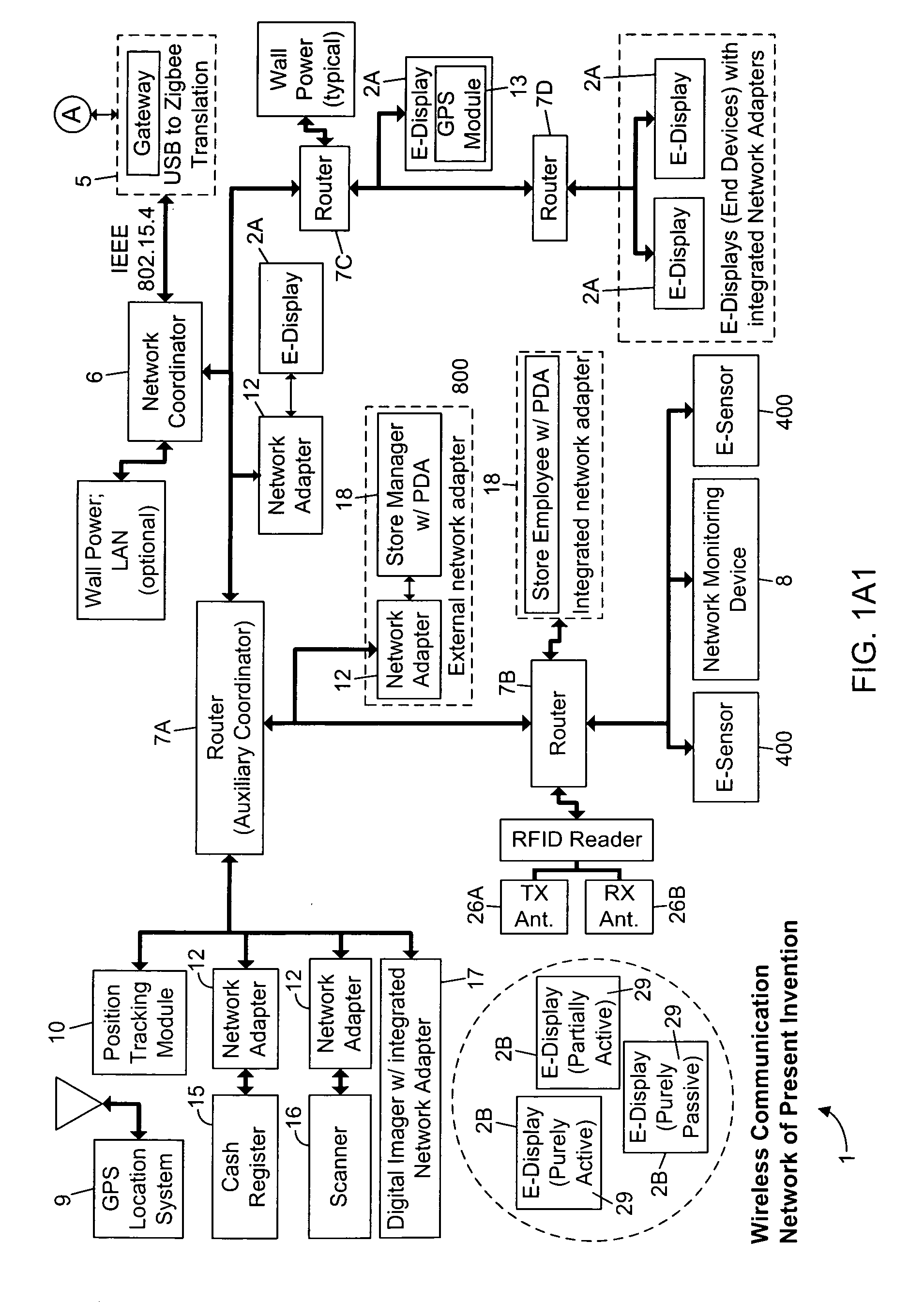
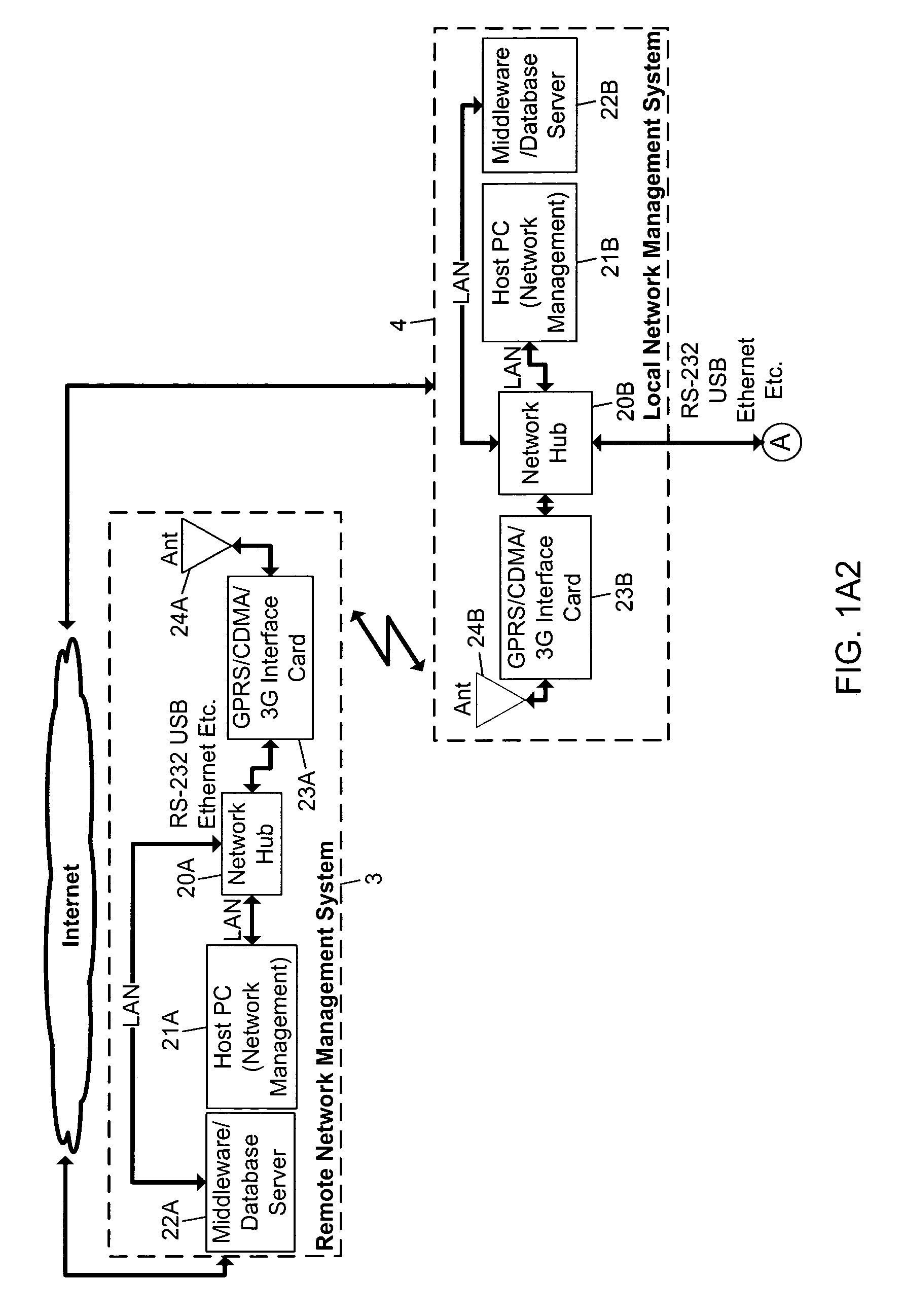
Methods of and apparatus for programming and managing diverse network components, including electronic-ink based display devices, in a mesh-type wireless communication network
InactiveUS20100177749A1Static indicating devicesDigital data processing detailsLogistics managementDisplay device
A wireless communication network for programming and monitoring a plurality of network-managed devices, including electronic-ink based display devices, comprising a network management computer system, a network gateway device, one or more wireless network routers, a plurality of network-managed devices, and a network coordinator. The wireless communication network of the present invention bridges the gap between wireless display networks, wireless sensor networks, and the worlds of passive, active and partially-active RFID and real-time locating systems. The wireless communication network of the present invention allows conventional communication network protocols to operate in more flexible ways in dynamic, diverse, and heterogeneous application environments, in fields including retail, healthcare, transport, logistics, manufacturing, education, etc. At the same time, the wireless communication network of the present invention is preferably based on the IEEE 802.15.4 network layer standard, which offers low-cost wireless network communication between a large number of wireless network end-devices.
Owner:METROLOGIC INSTR
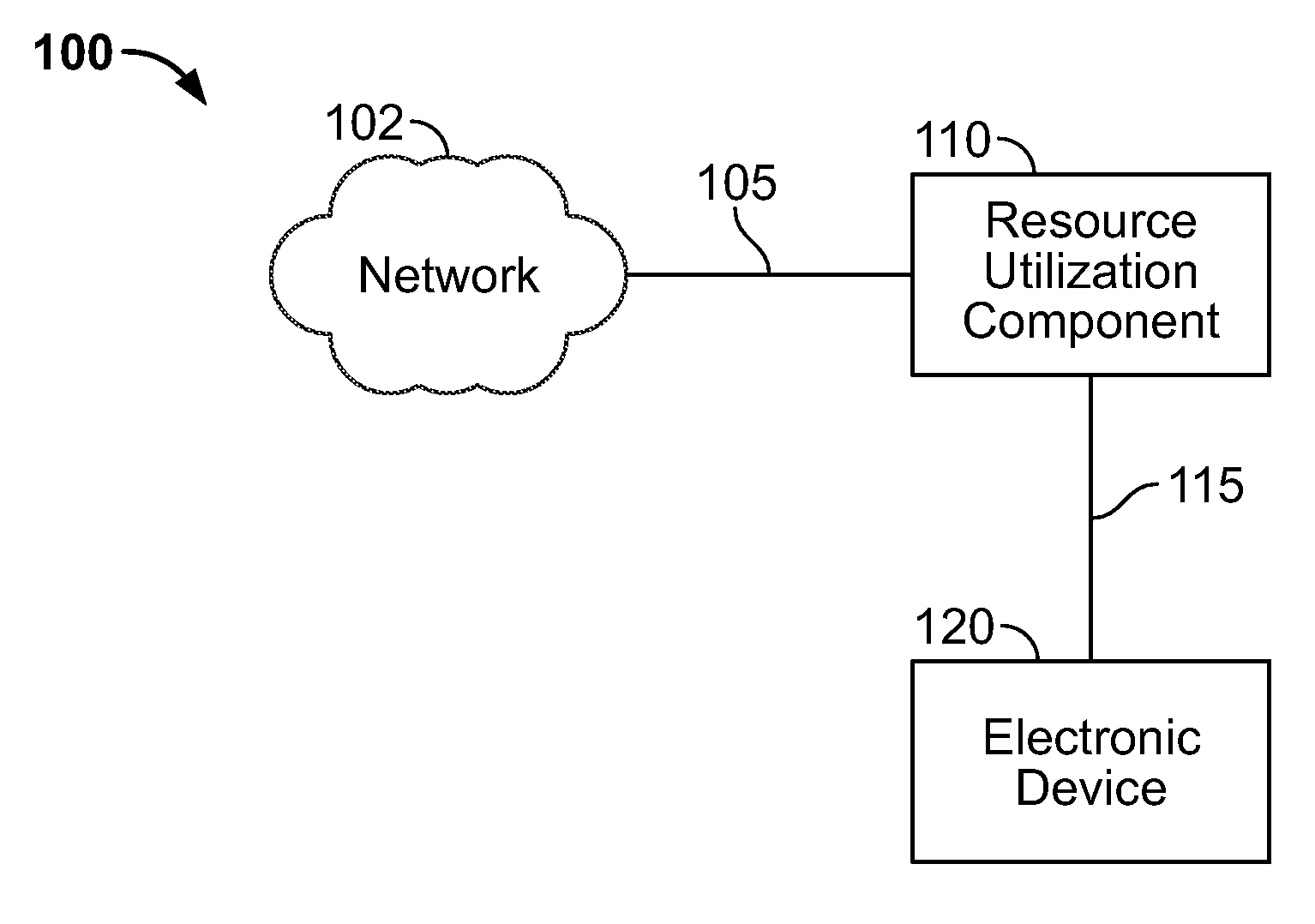
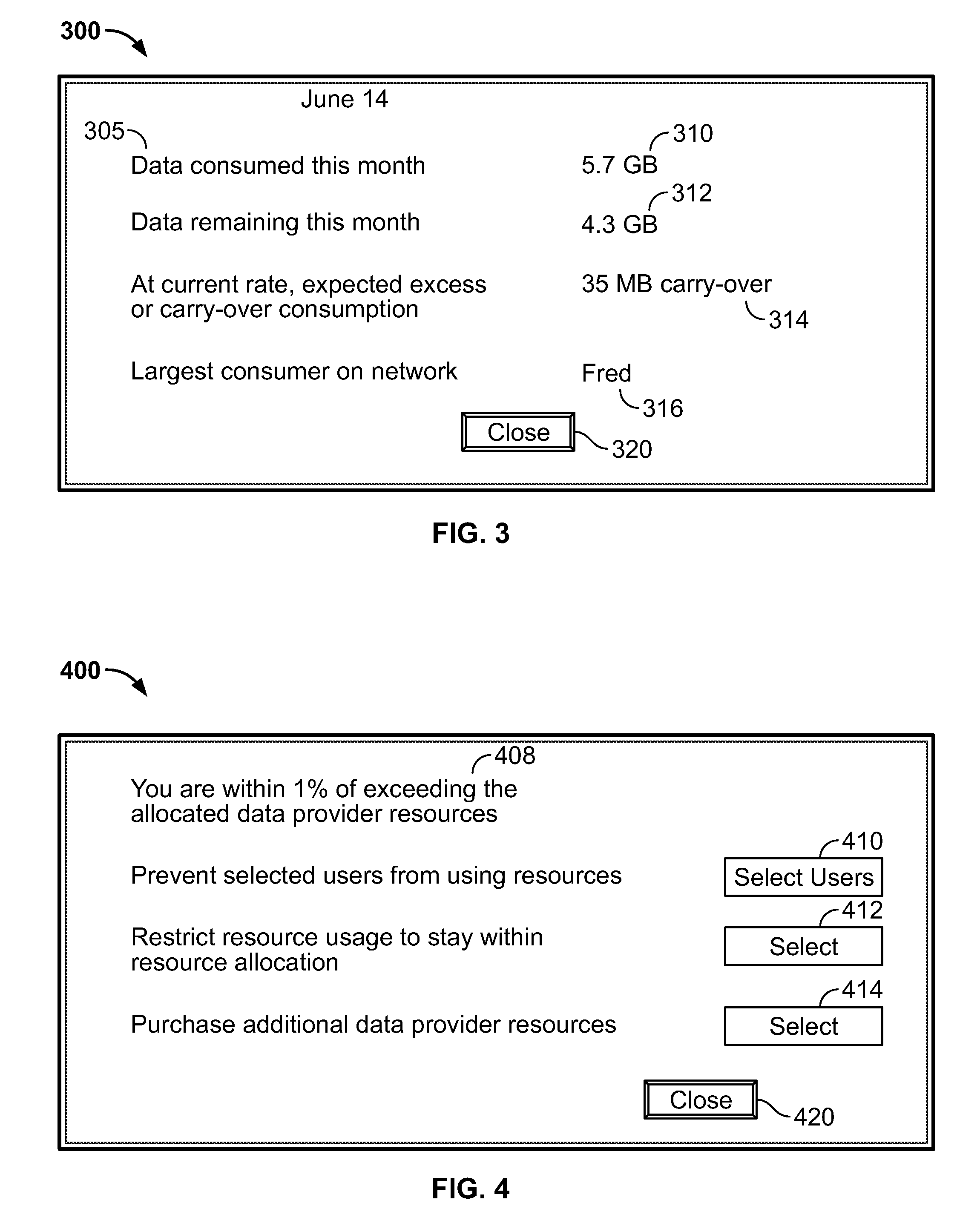
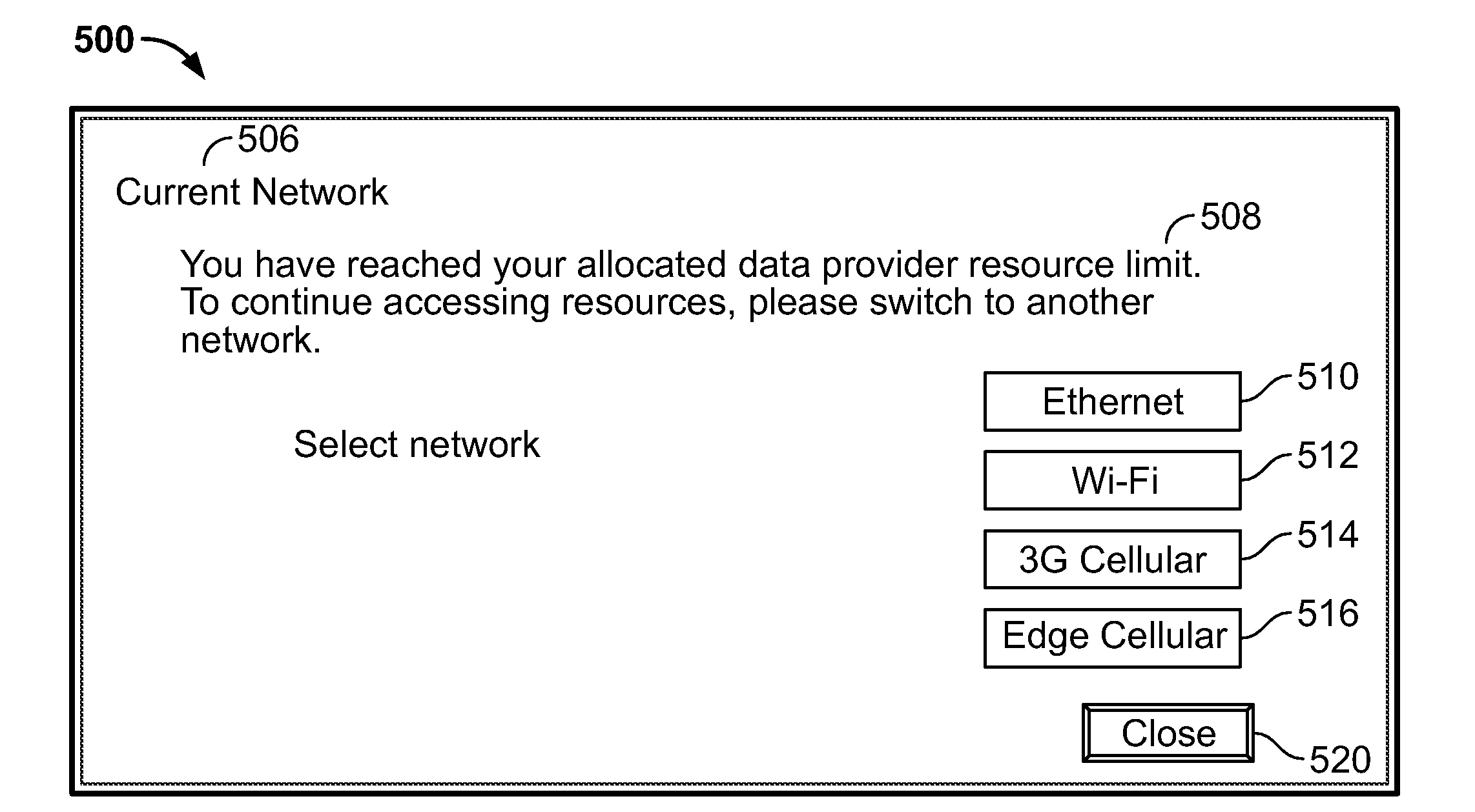
Systems and methods for monitoring data and bandwidth usage
ActiveUS20100017506A1Assess restrictionMultiple digital computer combinationsResource consumptionResource utilization
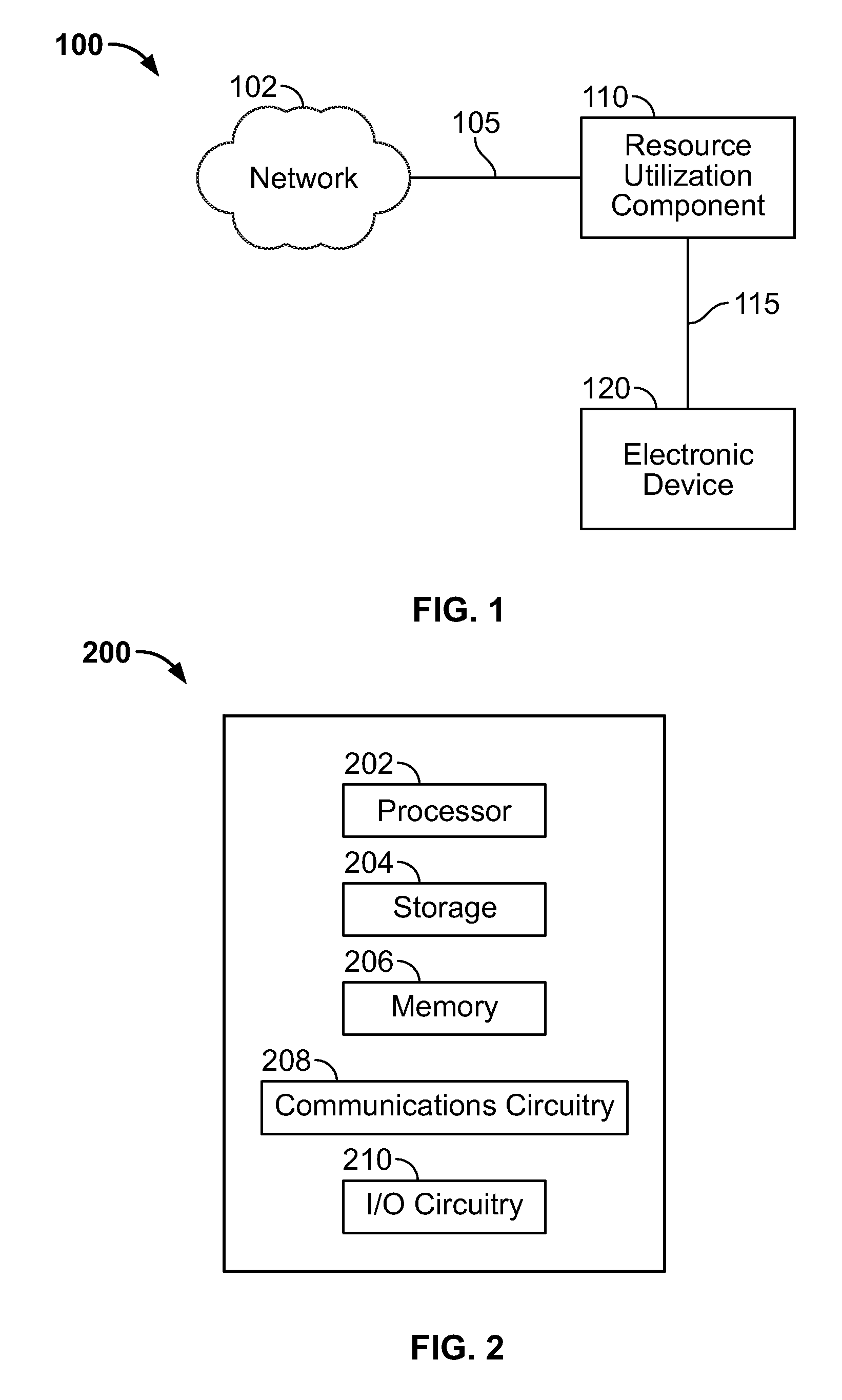
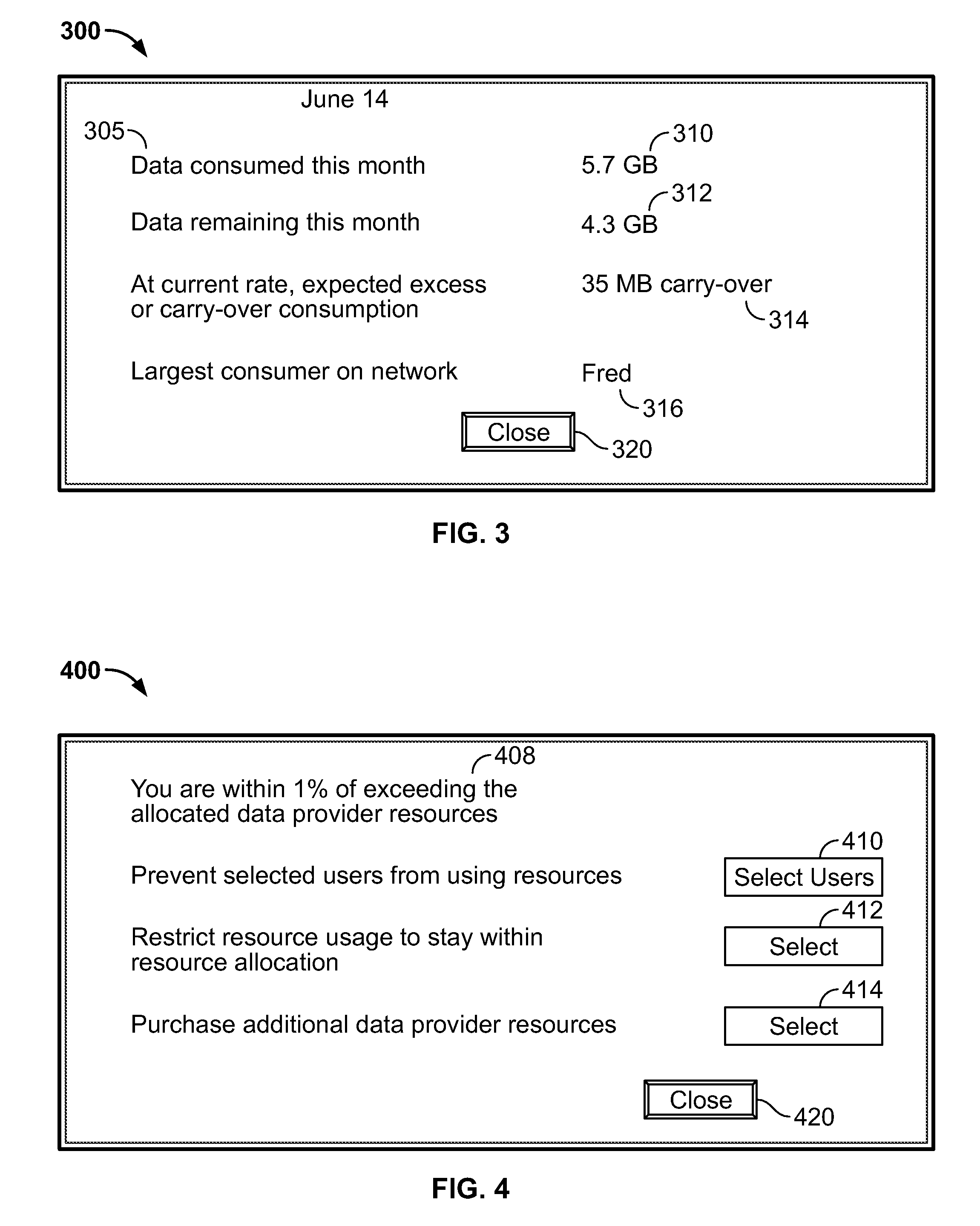
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
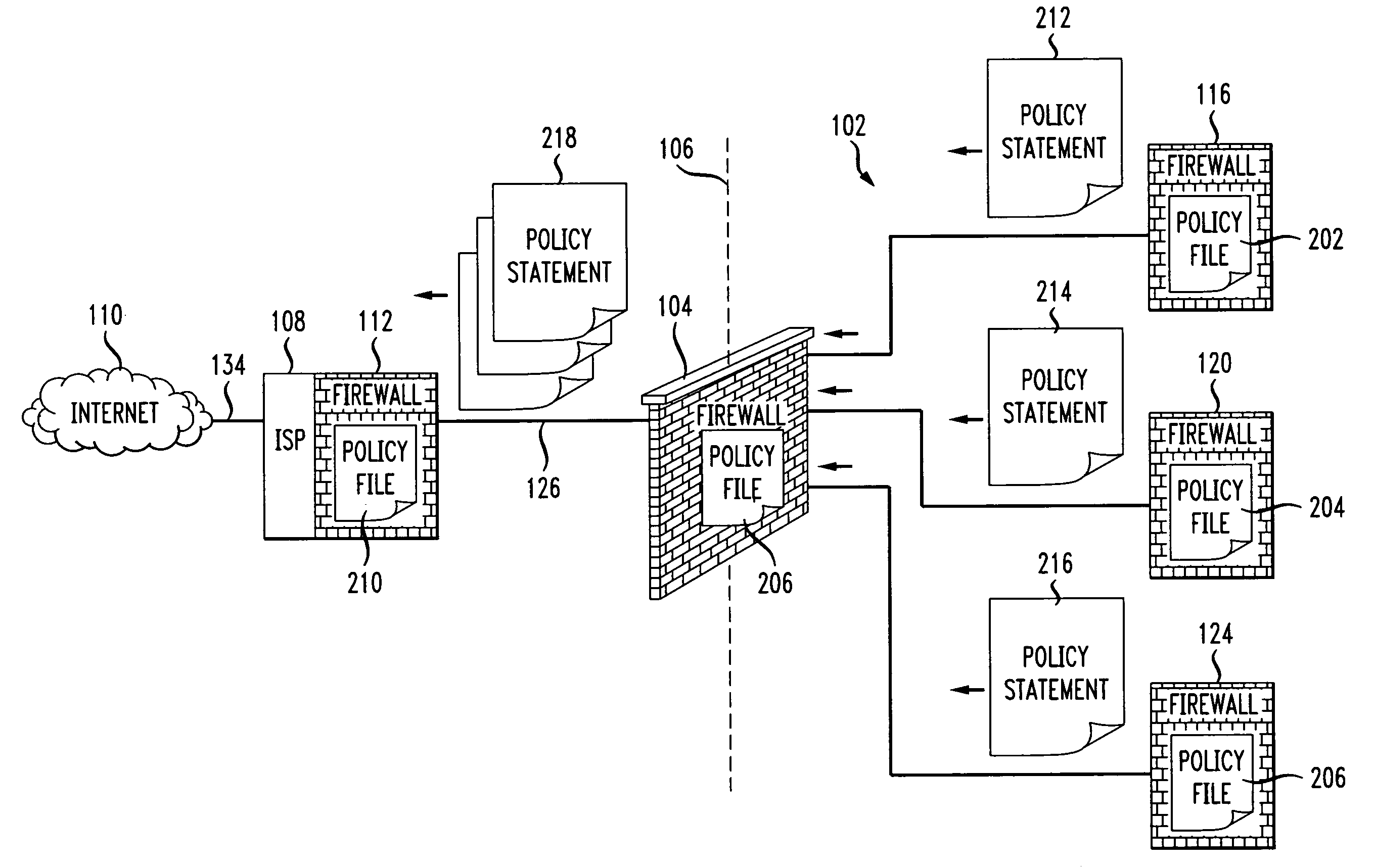
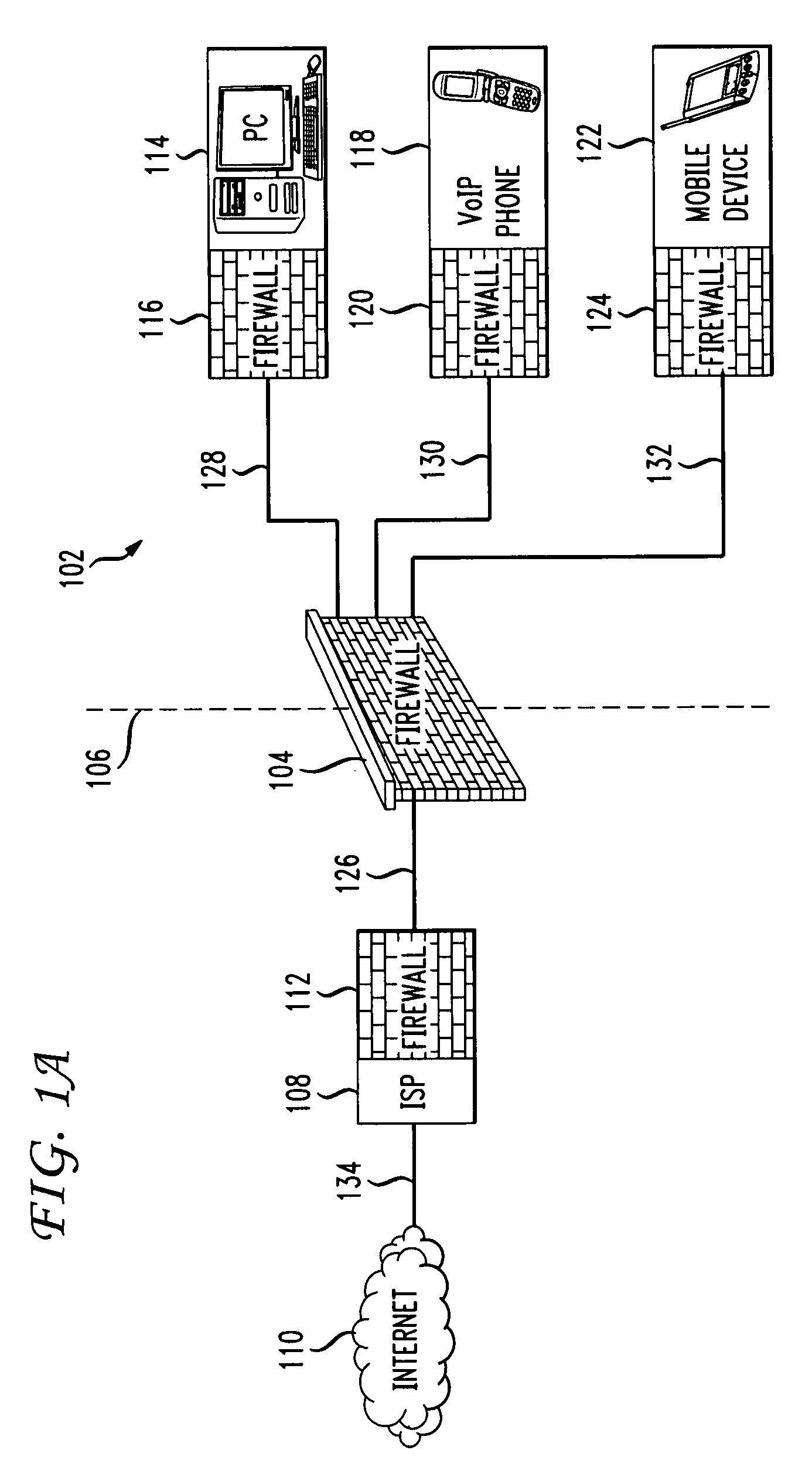
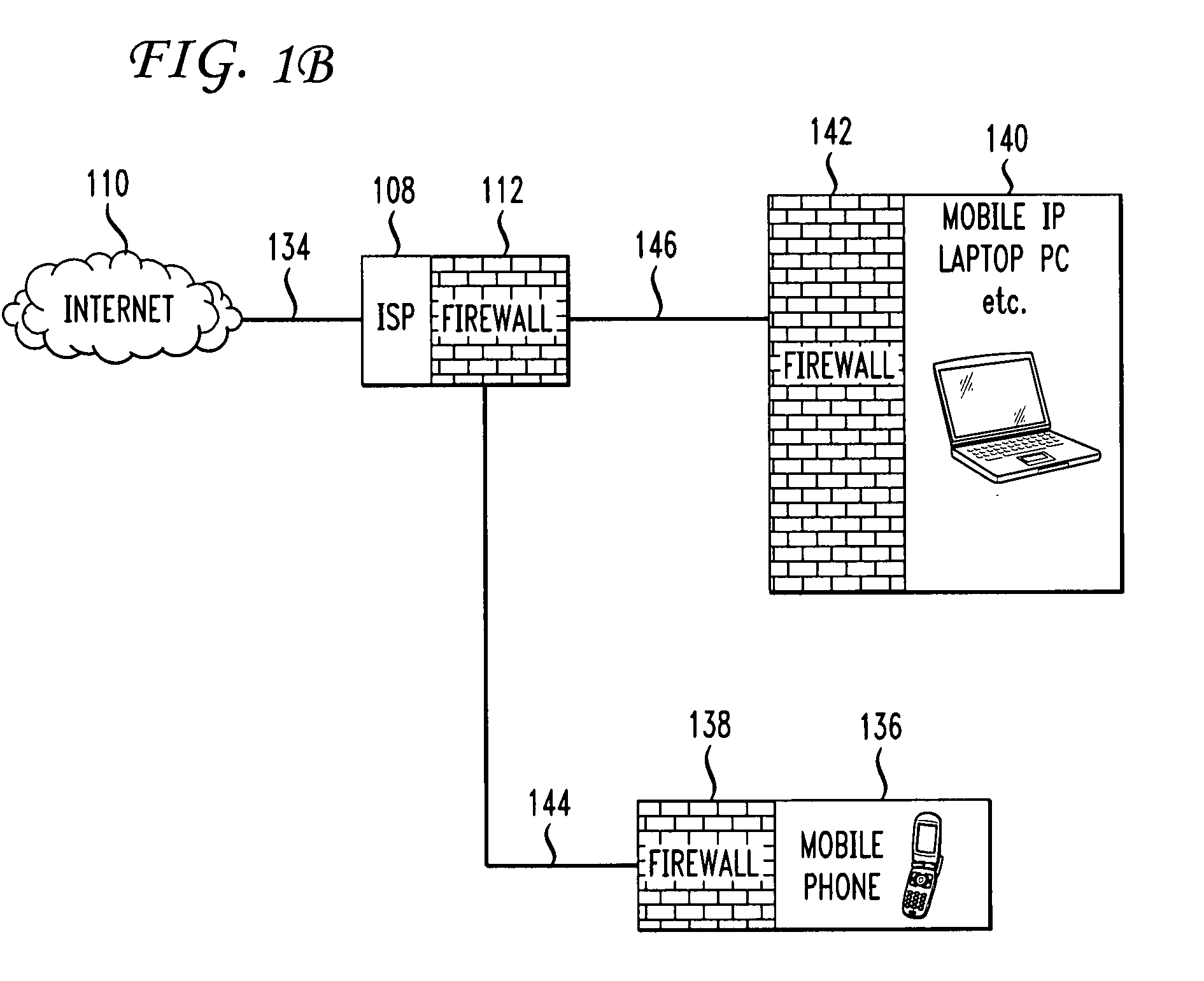
Firewall propagation
InactiveUS20080235755A1Unauthorized memory use protectionHardware monitoringSecurity ruleSecurity policy
Methods and systems for propagating data security policies and rules up a chain of network components, for example, from an end-user device having a firewall, to a network component at the “edge” of the network, such as a so-called “edge” firewall server, from where a policy statement can be transmitted to a service provider, such as an ISP, are described. A device, such as a computer or mobile phone, has, as part of its firewall software, a policy propagation file, that communicates with pre-existing firewall software. The firewall software creates a policy statement upon detecting a triggering event, which is transmitted from the device to the next data security component up the chain, “upstream,” in the network. In some cases this device may be a firewall server or a firewall policy server. The firewall server may combine policy statements from numerous end-user type devices and transmit the policy statement to an external network component, such as an ISP firewall server or similar device. The ISP or other service provider may then use the policy statement to implement date security rules for the devices in the network. In this manner, the firewall operated by the ISP implements rules and policies of a network owner or the owner of a stand-alone device, thereby preventing unwanted traffic from entering the network.
Owner:DIGICERT
Wager game license management in a peer gaming network
InactiveUS20070136817A1Digital data processing detailsAnalogue secracy/subscription systemsDistributed computingPeer-to-peer
Novel wager gaming systems and methods for wager game license management in a network utilizing peer networking technology are in the various embodiments. A network component, such as a server computer or a gaming machine, is deputized by a central licensing authority or other authorized license management component. The network component is deputized once it receives what may be referred to as a license deputizing certificate. Upon receiving this certificate or at some point thereafter, the deputized component is provided with various data relating to devices in the gaming network, wagering games available in the network, and network configuration data. The gaming network may have a primary network backbone and local peer gaming networks operating in conjunction with each other via the network backbone. A local peer gaming network may share wager game code, memory space, and other gaming-related resources. Once a network component is deputized to perform as an authorized license management component, it assumes the role of local licensing server for the gaming network or for a local peer gaming network. This component may be a gaming machine in a local peer network or an existing local license server which is now able to supply and manage the distribution of license tokens in a gaming network utilizing peer network technology.
Owner:IGT
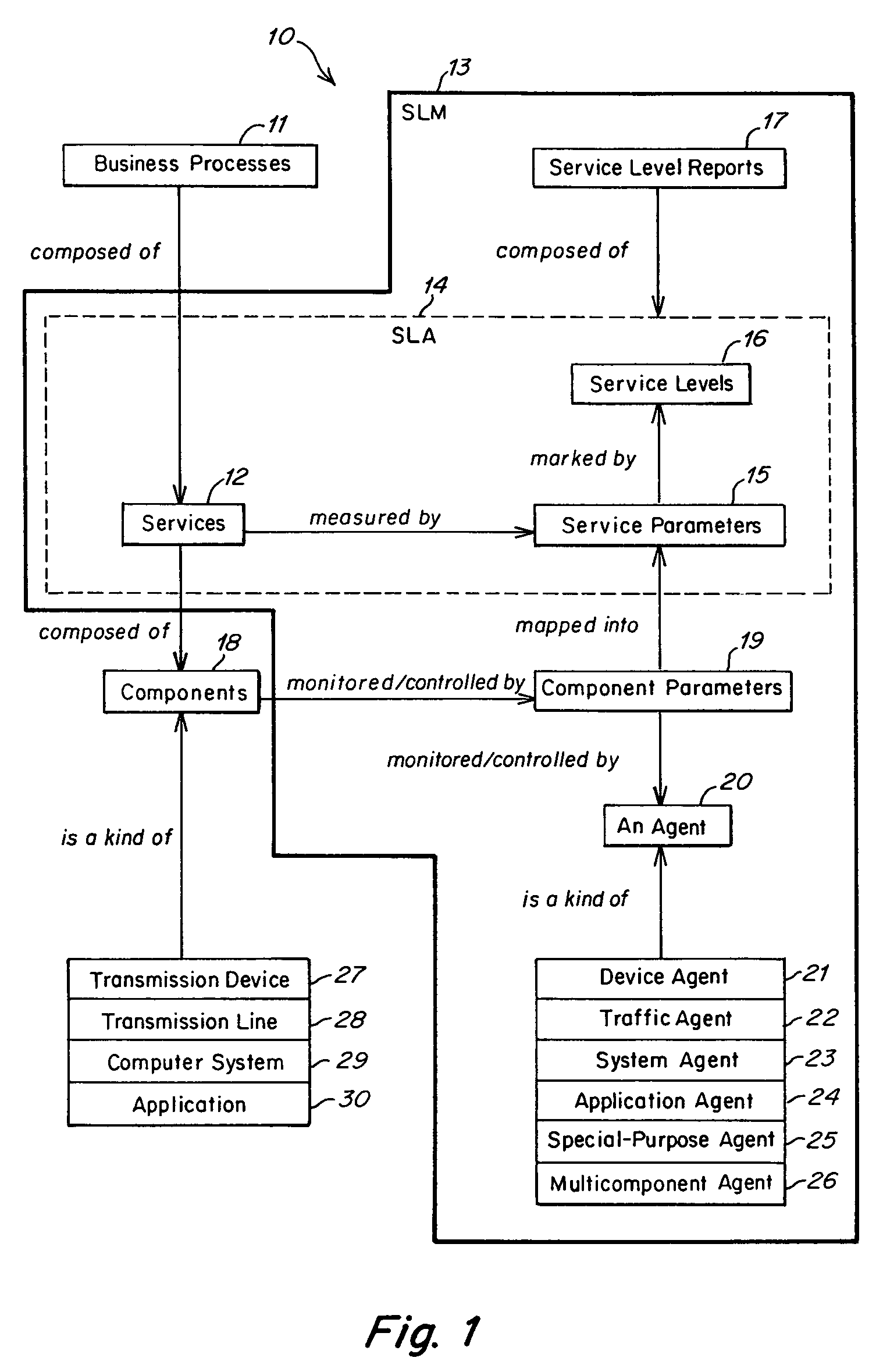
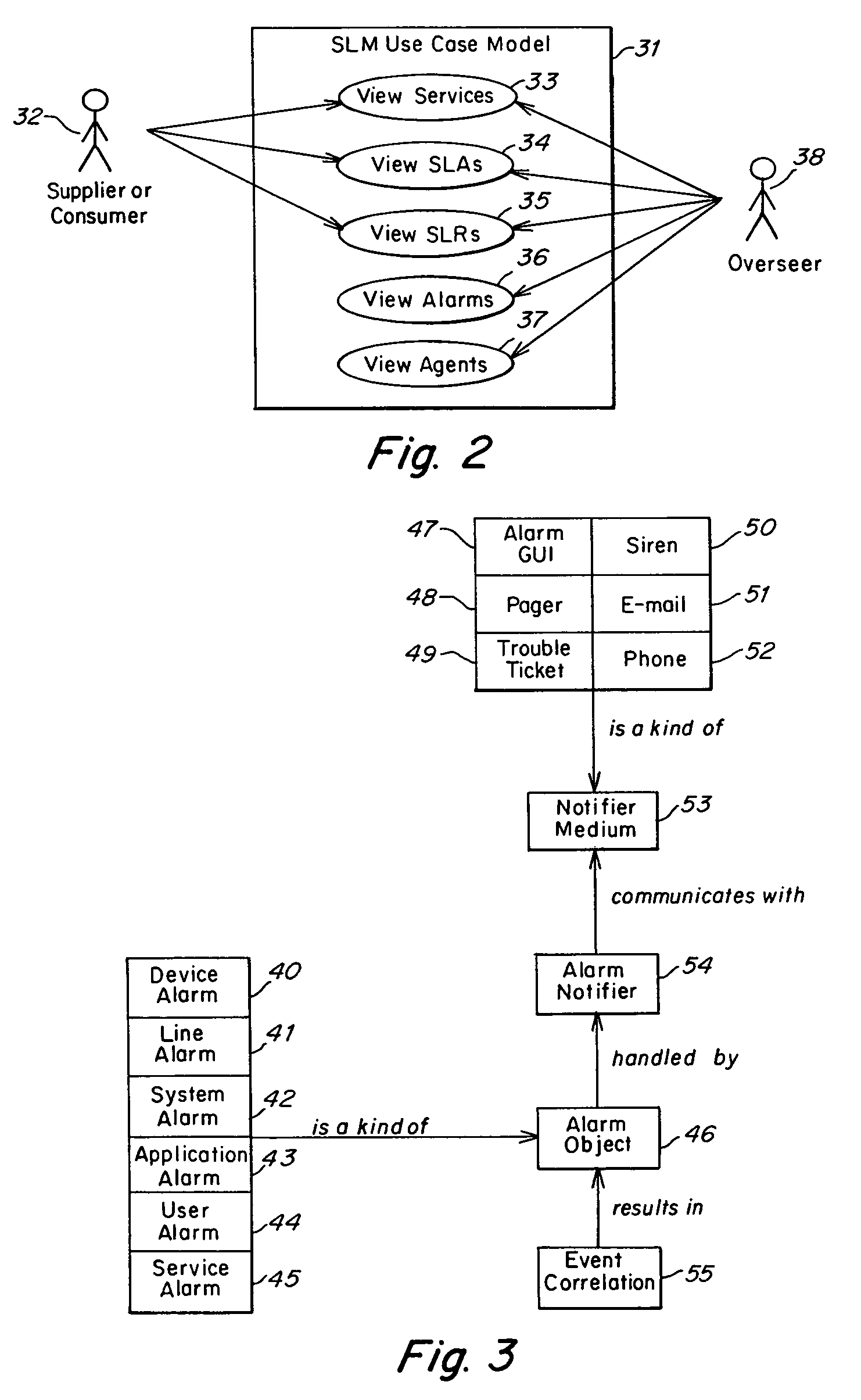
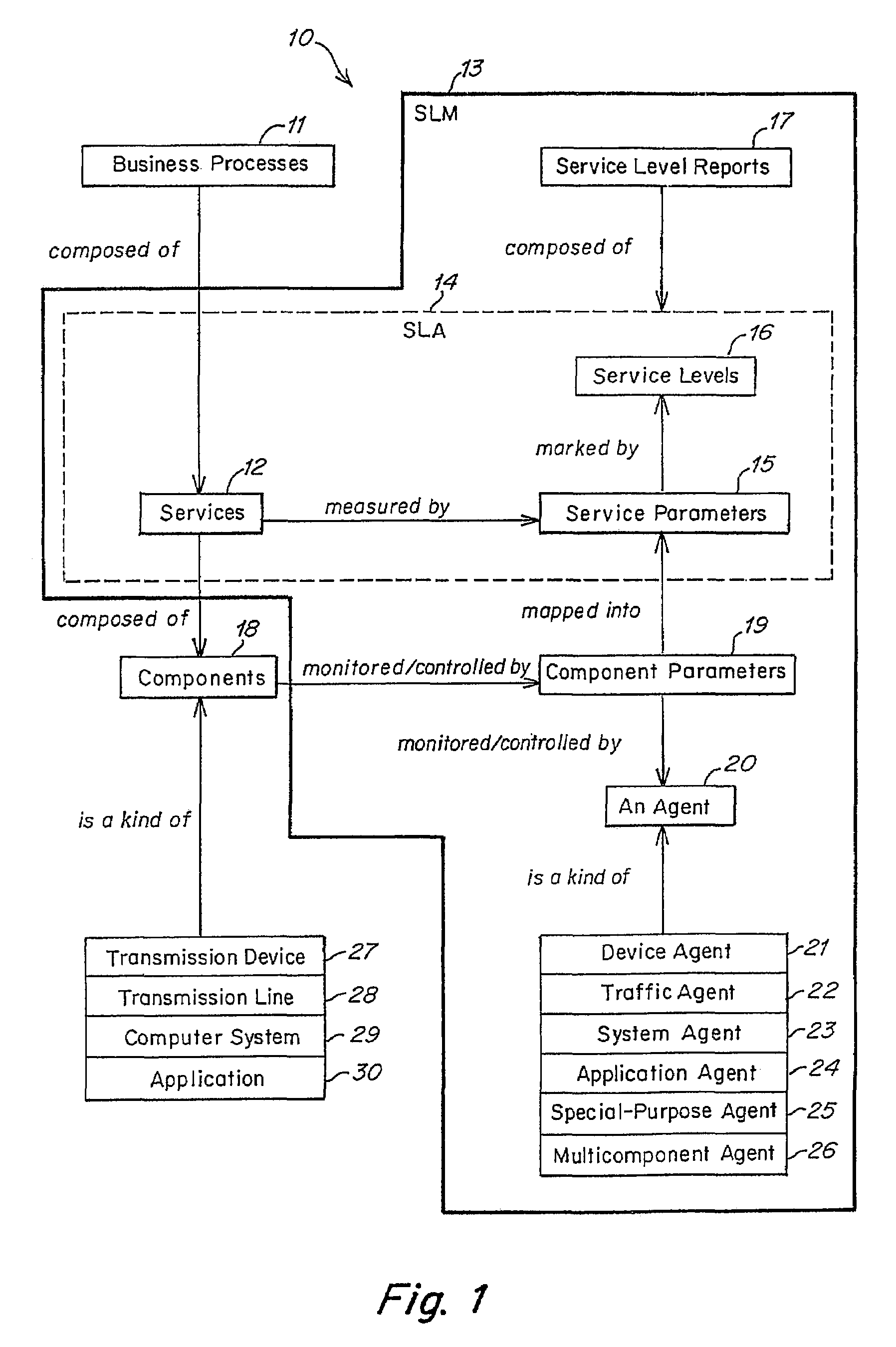
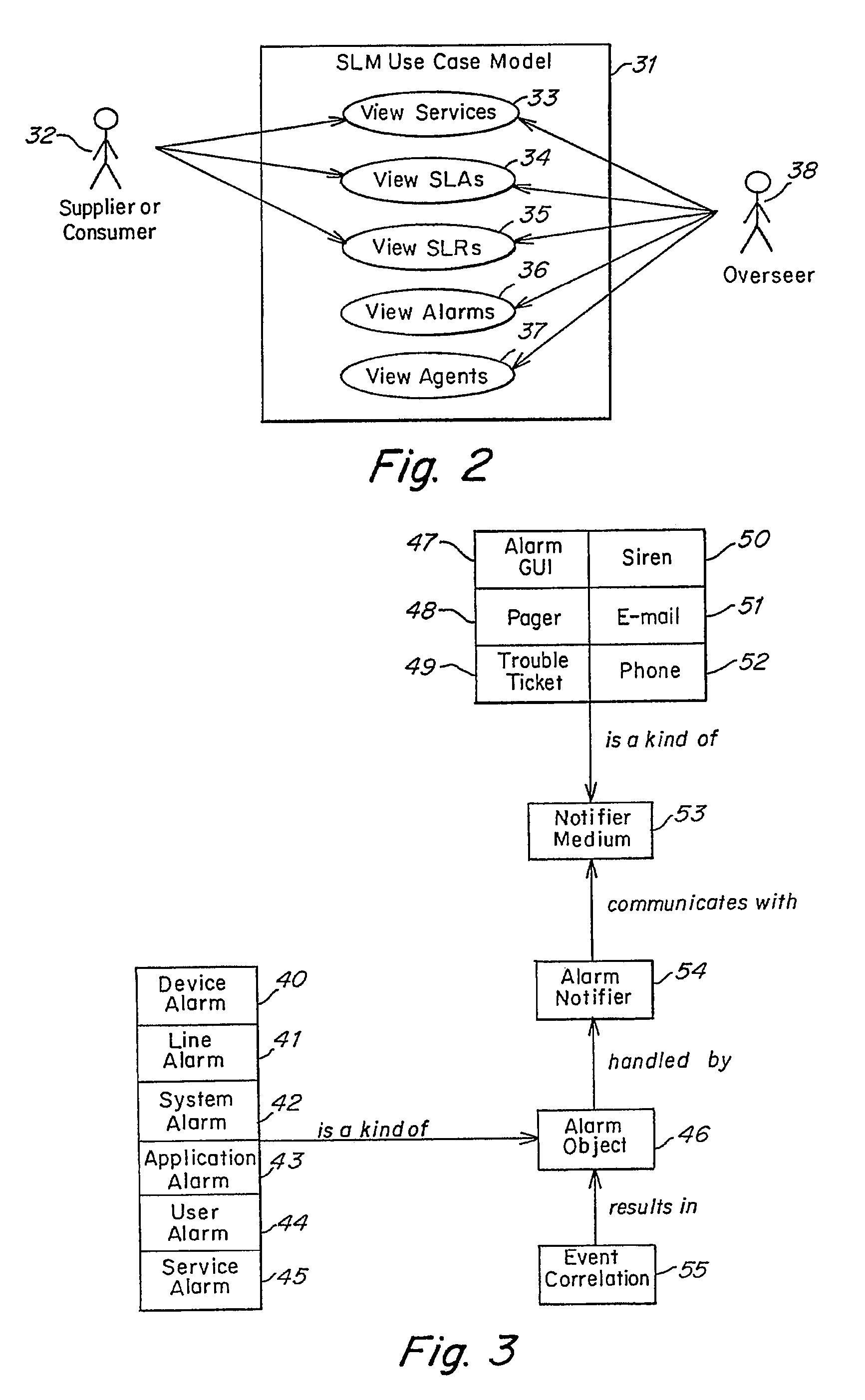
Method and apparatus for component to service mapping in service level management (SLM)
Owner:COMP ASSOC THINK INC
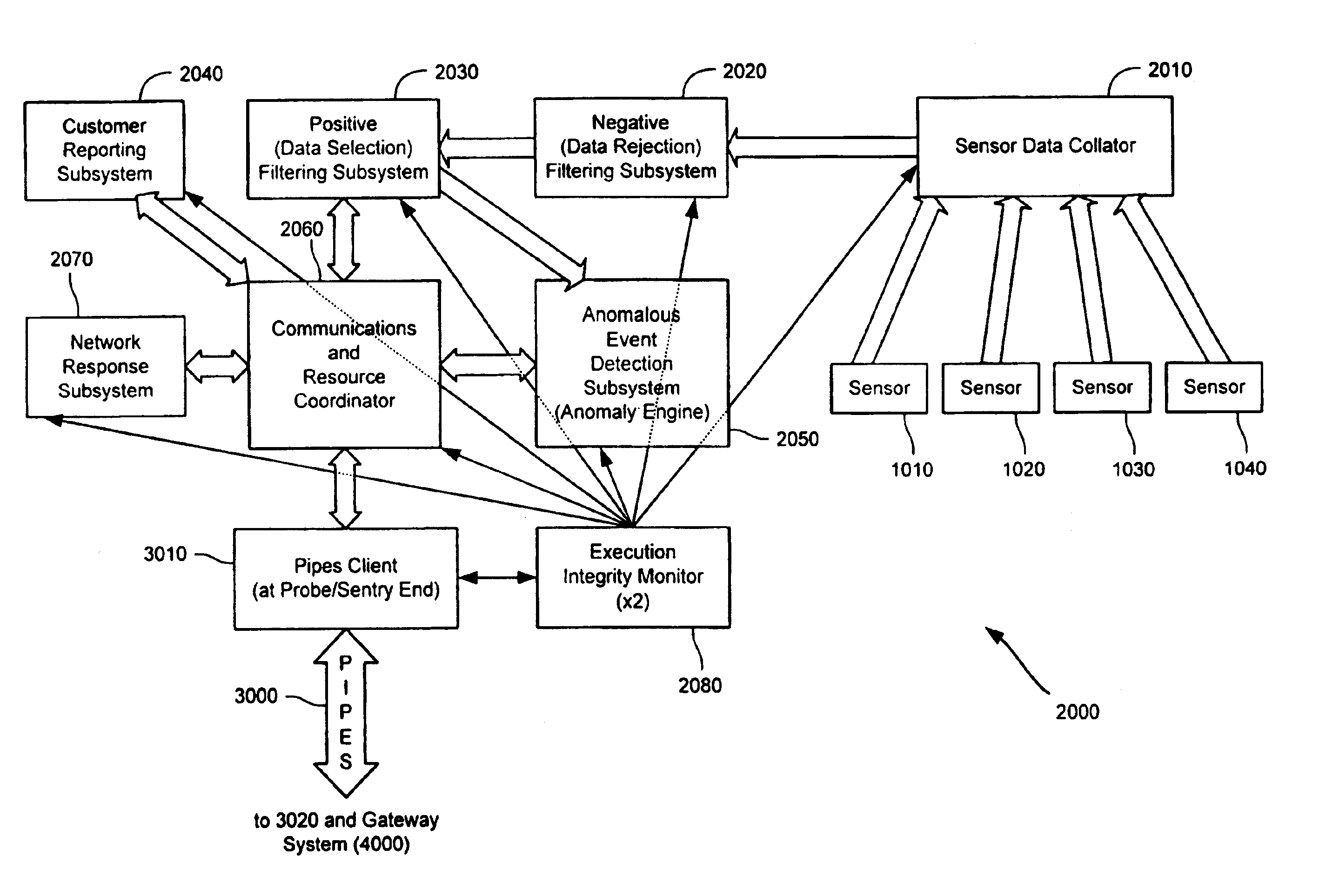
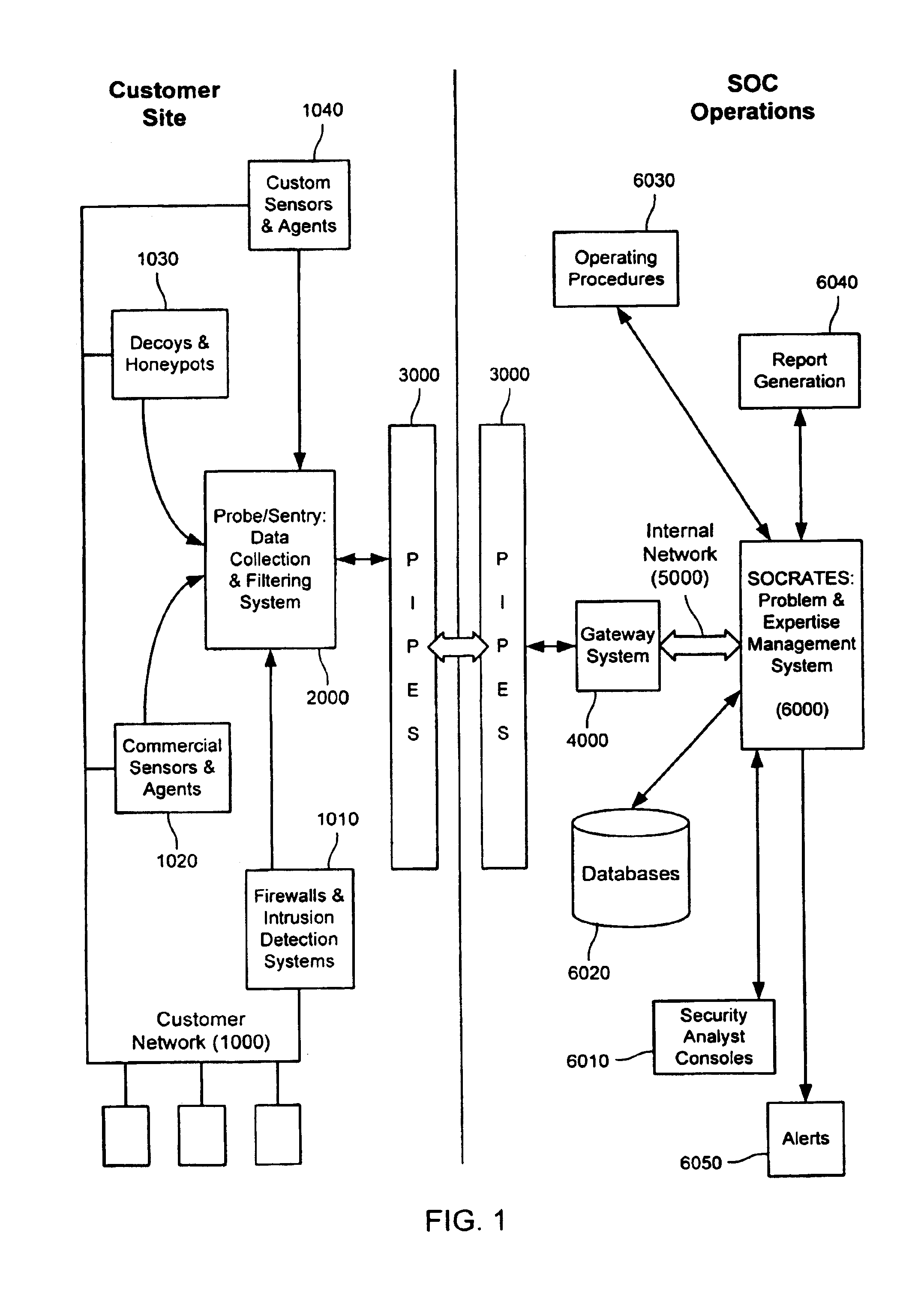
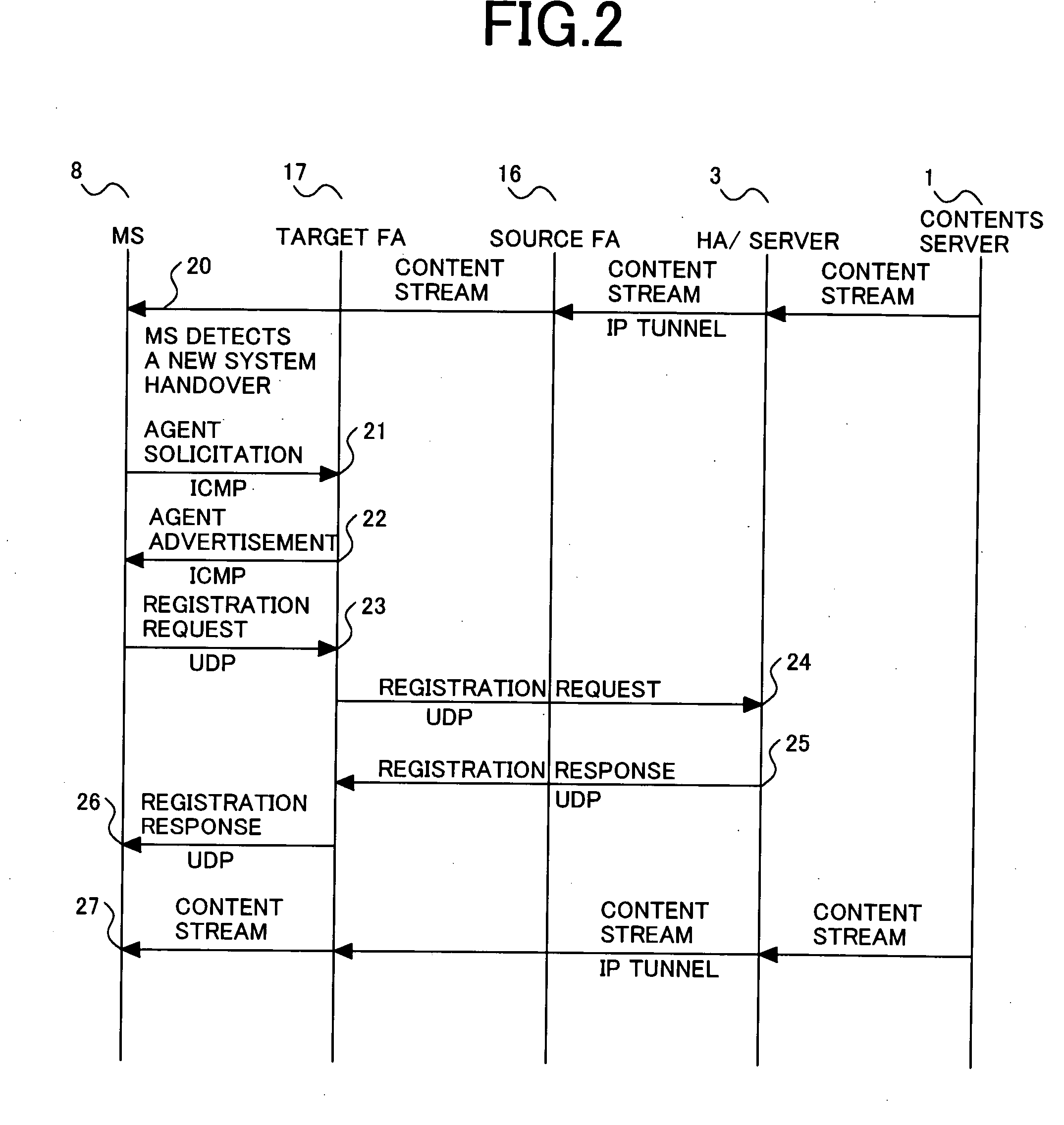
Method and system for dynamic network intrusion monitoring, detection and response
InactiveUS7159237B2Eliminate false positivesIncrease in sizeMemory loss protectionDigital data processing detailsProblem resolutionVulnerability
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
Analysis of data flows in complex enterprise it environments
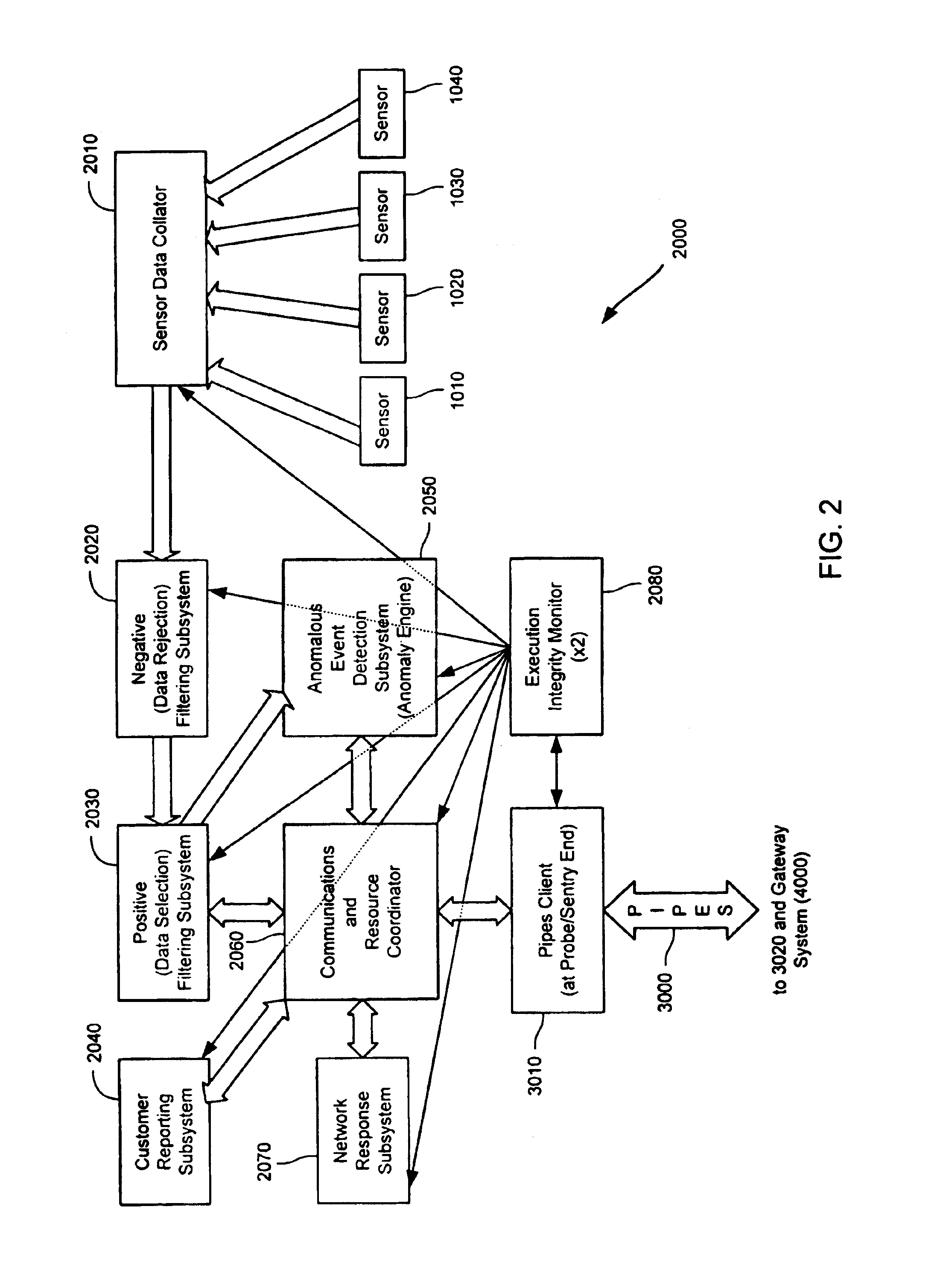
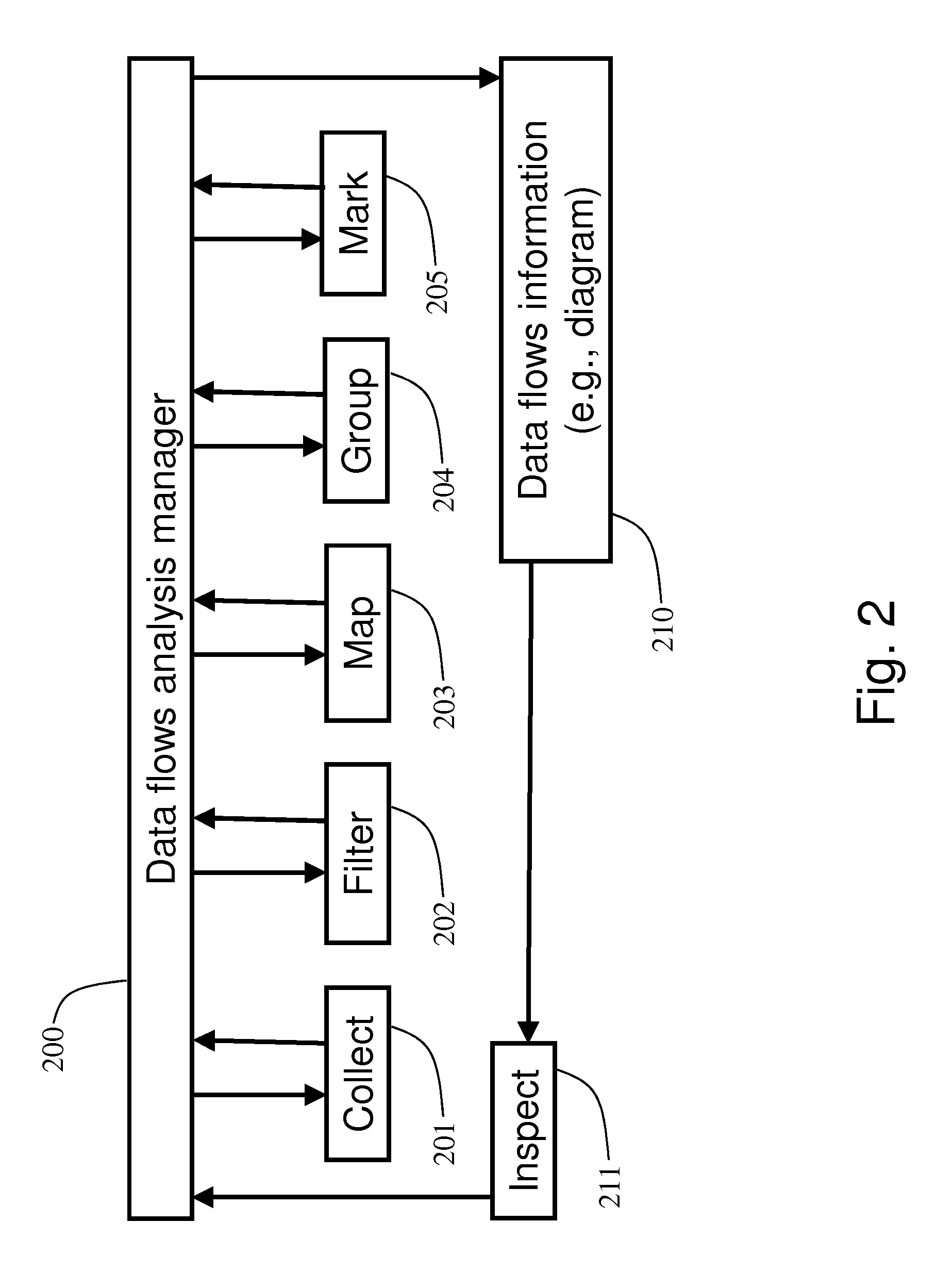
The present technology enables identification, visualization, and analysis of data flows via network components in complex enterprise IT environments including but not limited to servers, workstations, switches, routers, wireless access points, traffic shapers, firewalls, storage systems and SAN systems. The technology is based on a combination of information collection, information filtering, mapping, grouping, marking, report generation, and verification.
Owner:MODELIZEIT INC
Methods and systems for hierarchical management of distributed data
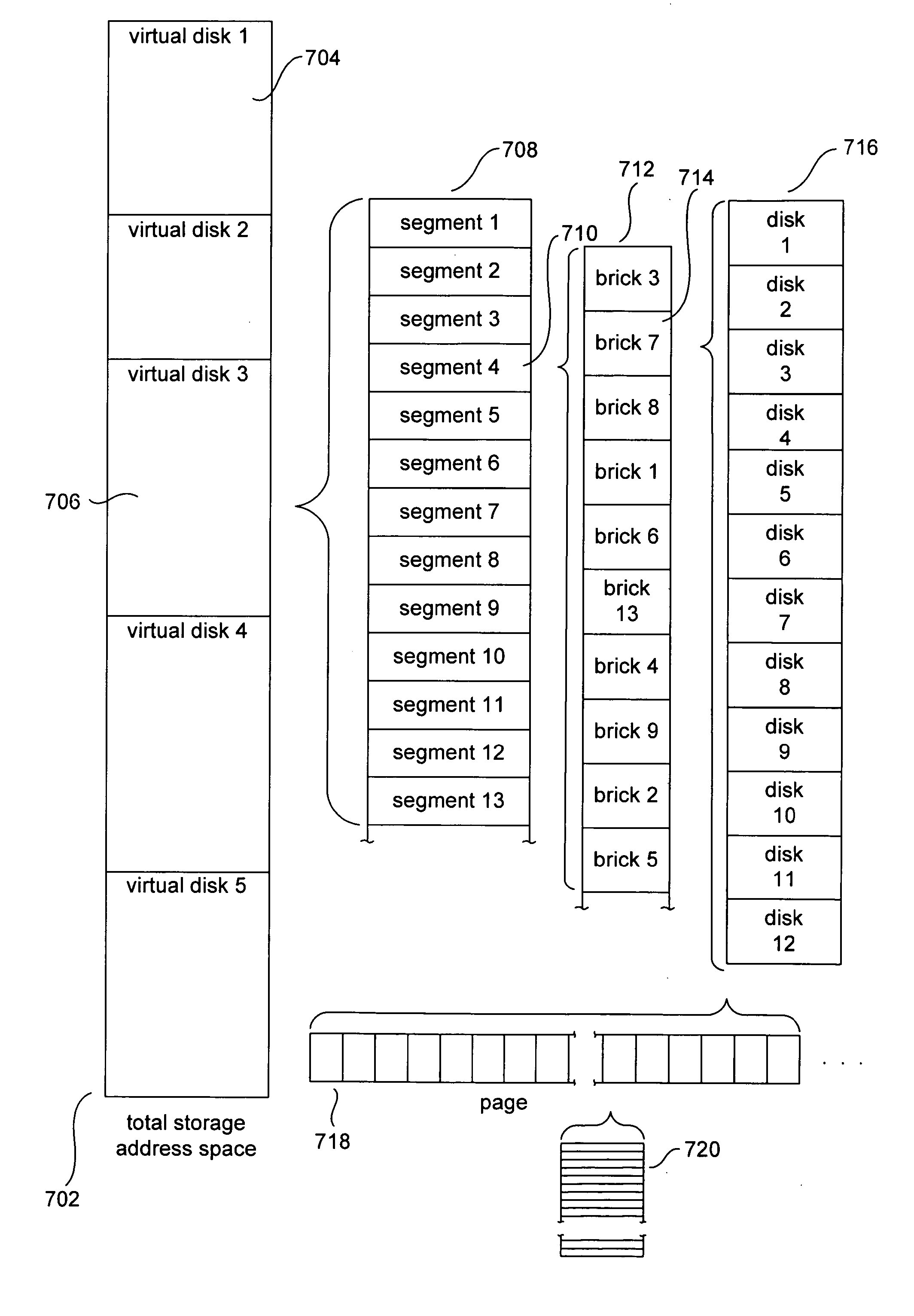
Various method and system embodiments of the present invention are directed to hierarchical control logic within each component data-storage system of a distributed data-storage system composed of networked component data-storage systems over which virtual disks, optionally replicated as virtual-disk images, composed of data segments in turn composed of data blocks, are distributed at the granularity of segments. Each data segment is distributed according to a configuration. The hierarchical control logic includes, in one embodiment of the present invention, a top-level coordinator, a virtual-disk-image-level coordinator, a segment-configuration-node-level coordinator, a configuration-group-level coordinator, and a configuration-level coordinator.
Owner:HEWLETT PACKARD DEV CO LP
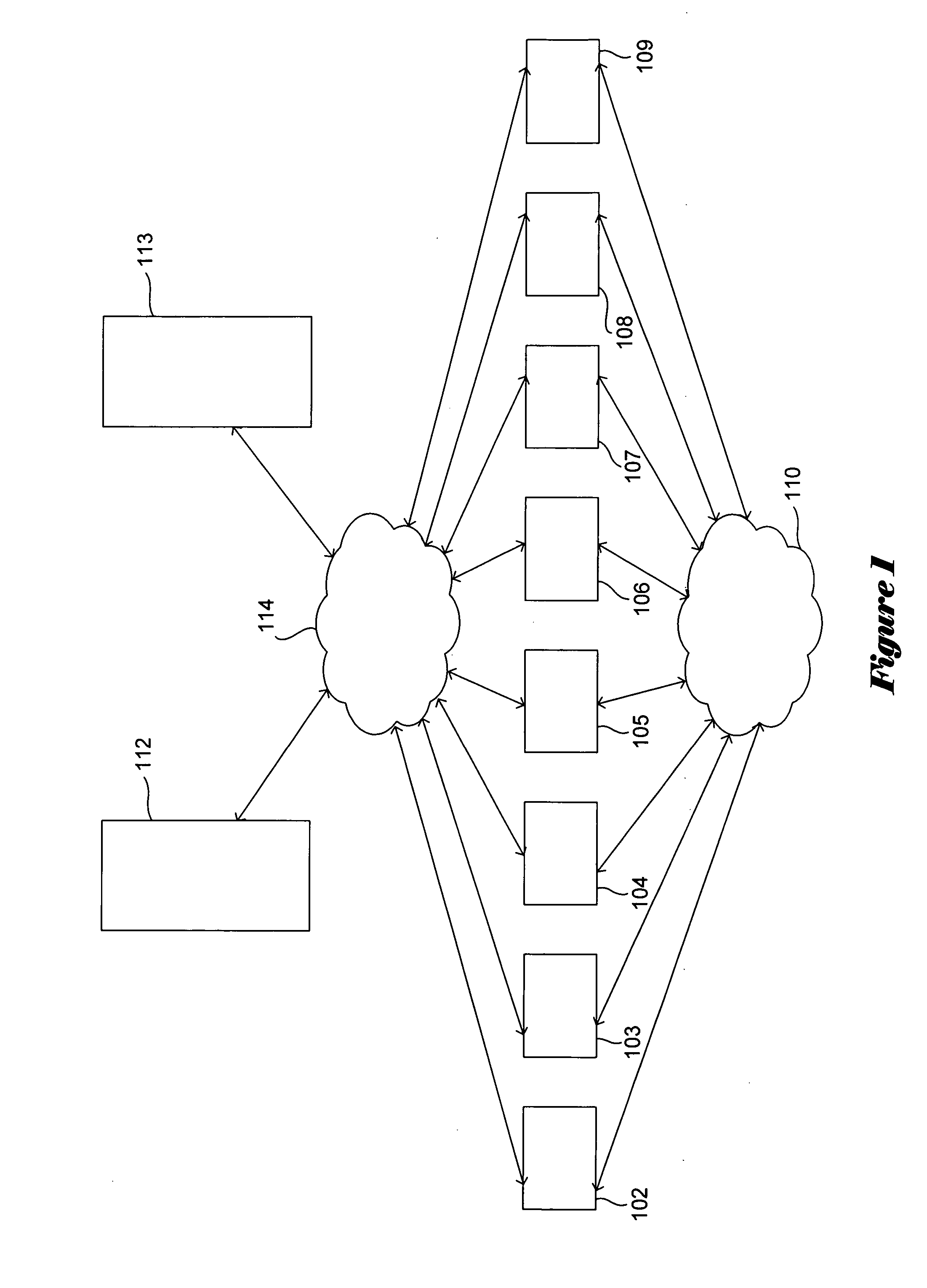
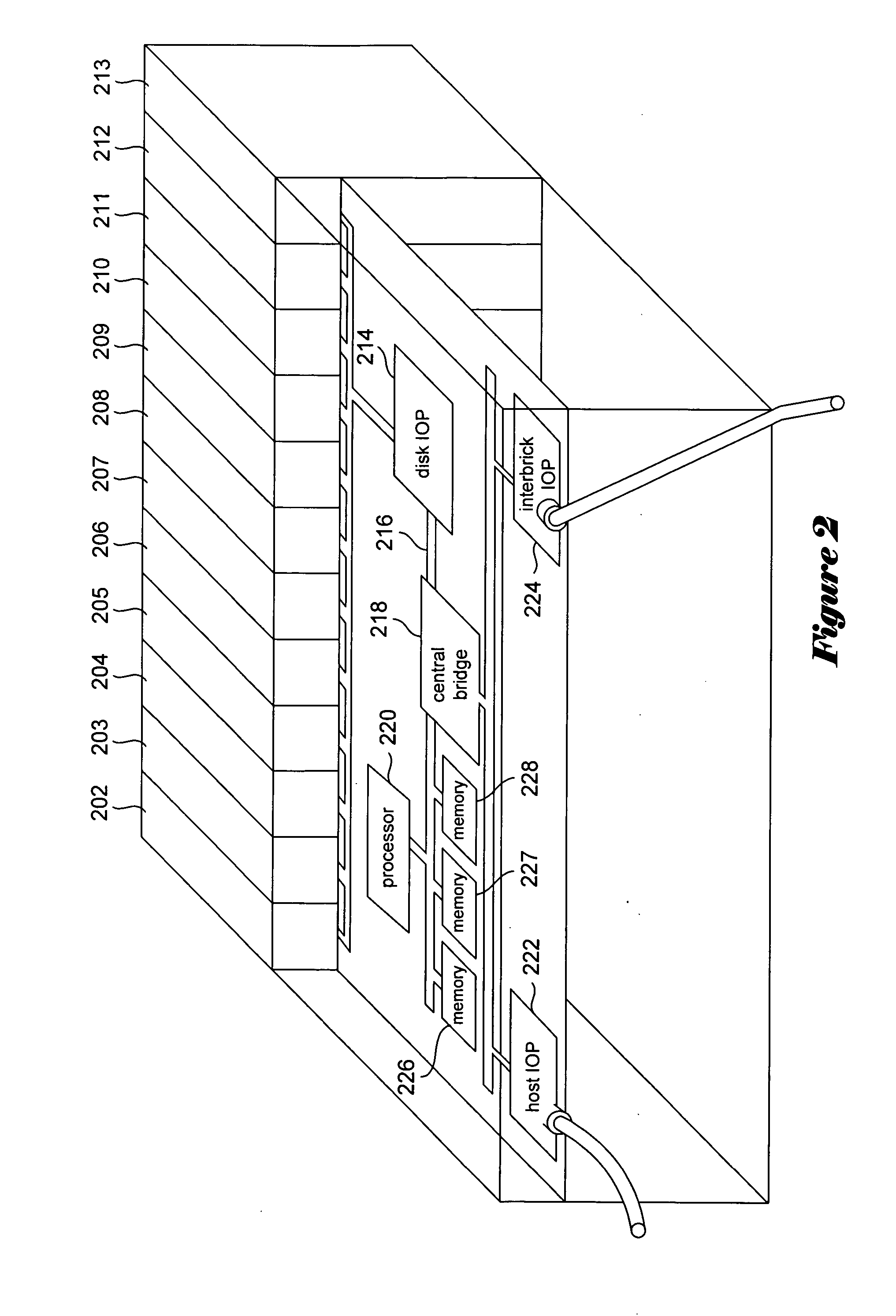
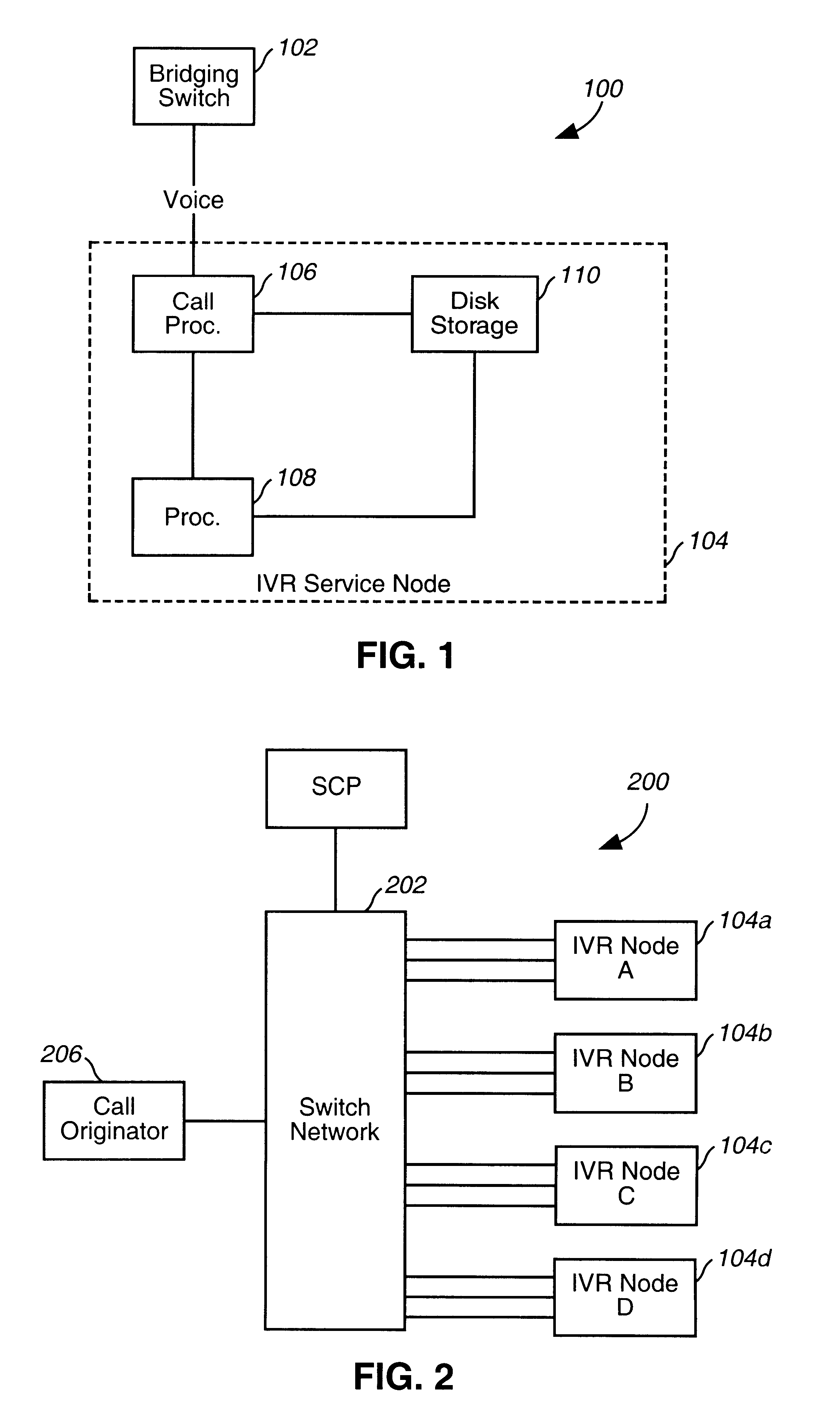
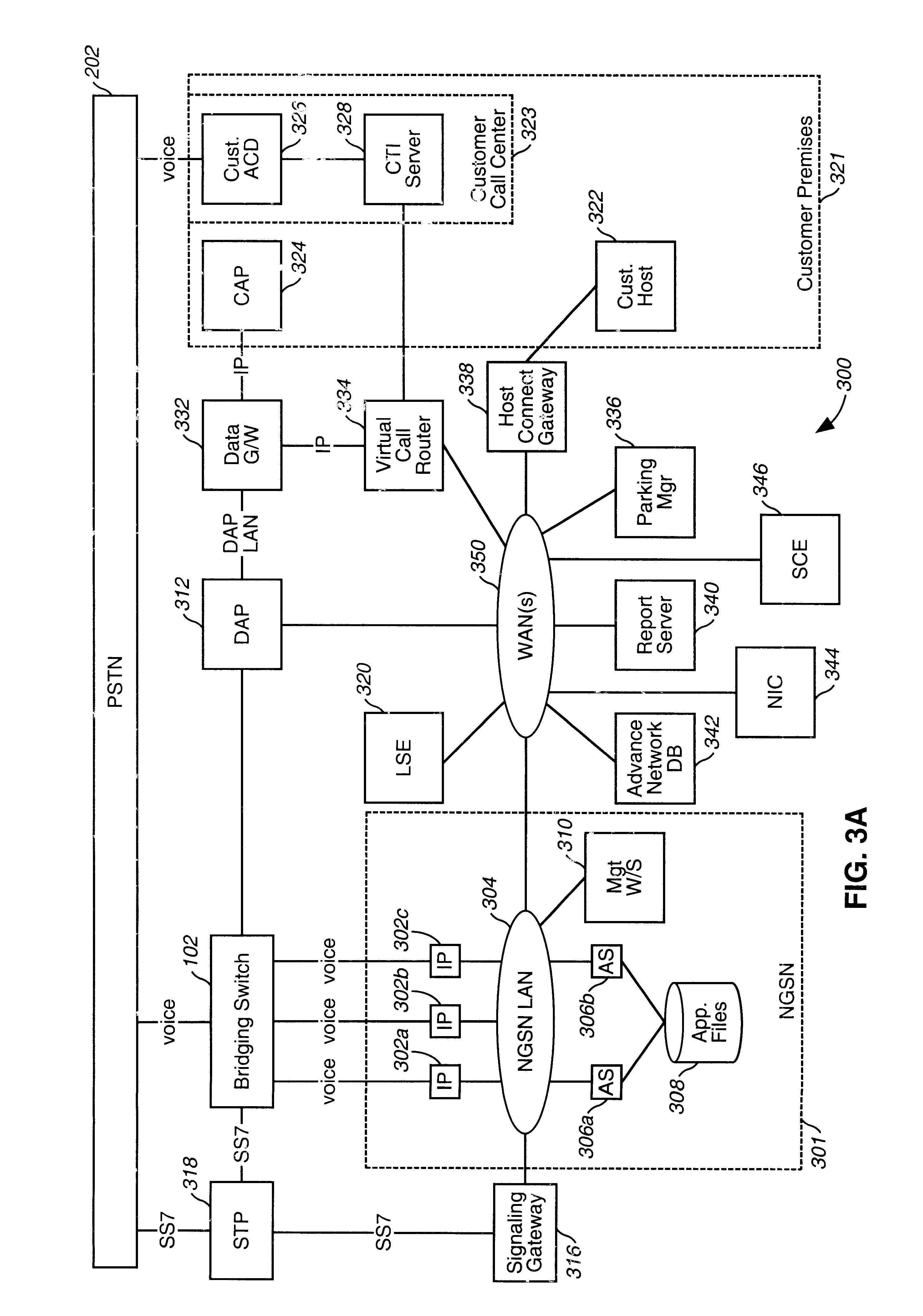
Telecommunications architecture for call center services using advanced interactive voice responsive service node
InactiveUS6366658B1Intelligent networksInterconnection arrangementsTelecommunications linkTelecommunications network
A telecommunications network that handles call center calls by providing advanced interactive voice response (IVR) services using a next generation service node (NGSN). The NGSN nodes combine with several other interacting network components to provide a scaleable architecture which allows several different, customized and flexible call center services to be performed for telecommunications service provider customers. In addition the network includes virtual call routers, parking managers, host connect gateways, report servers, advanced network databases, data access points, and data gateways to deliver calls to customer call centers with various features enabled.
Owner:VERIZON PATENT & LICENSING INC
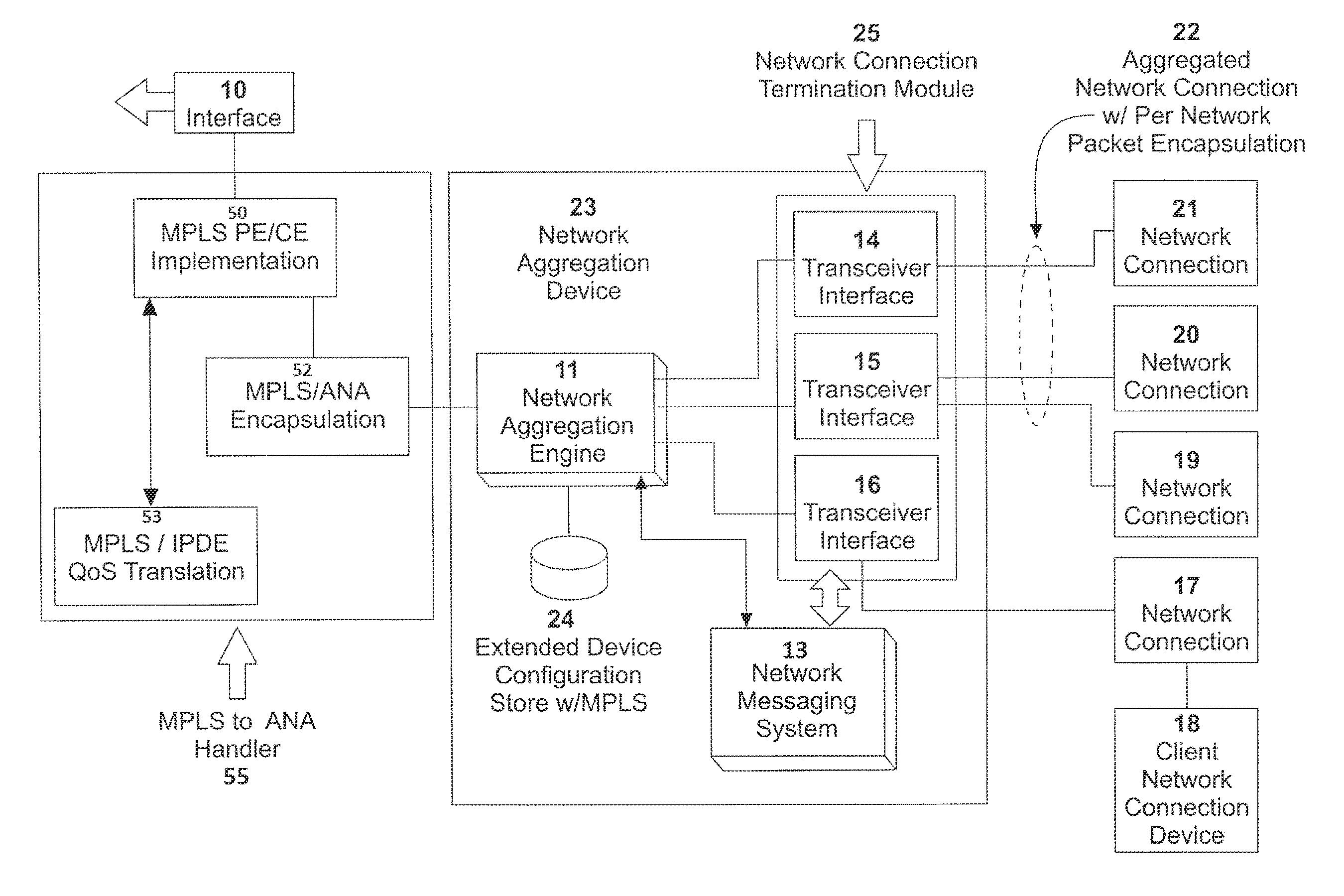
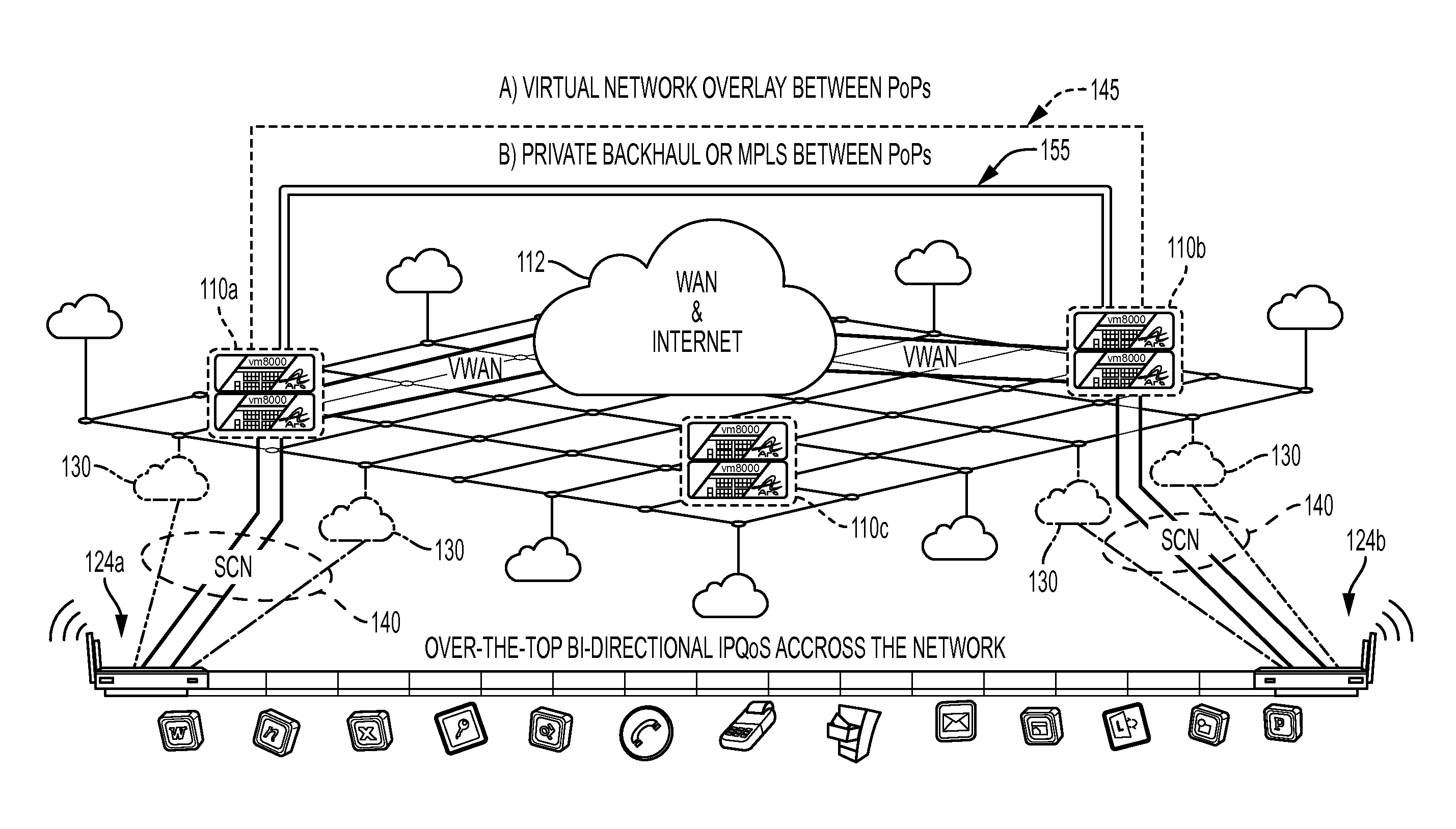
System, apparatus and method for providing a virtual network edge and overlay with virtual control plane
ActiveUS20160072669A1Improve communication performanceImprove throughputDigital computer detailsNetworks interconnectionTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site. A client site network component is implemented at least at the first client site, the client site network component aggregating one or more diverse network connections so as to configure an aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the aggregated connection between the client site network component and the network server component. The network server component includes a virtual control plane interface configured to establish a unicast path between the network server component and each of a plurality of remote network server components.
Owner:ADAPTIV NETWORKS INC
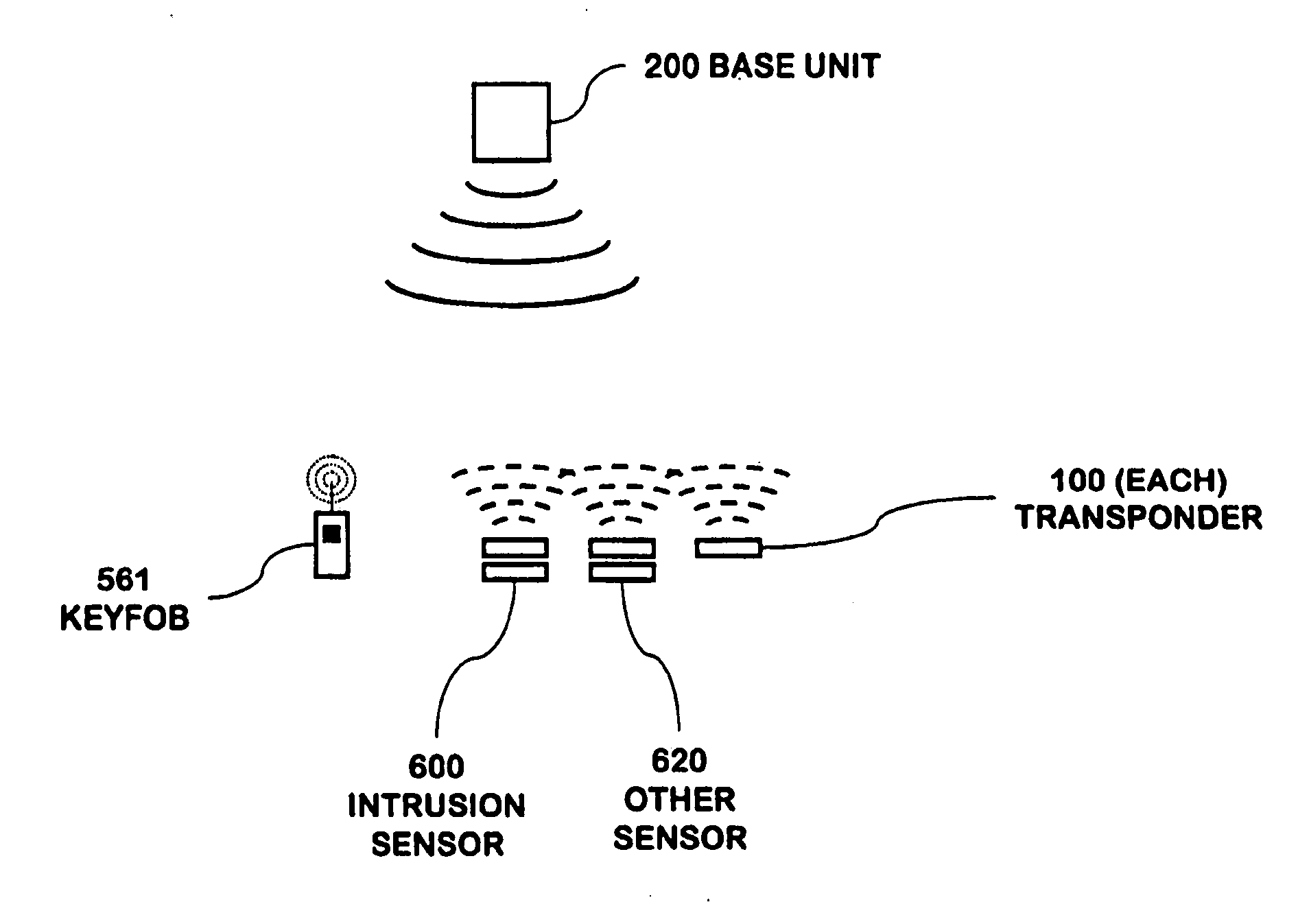
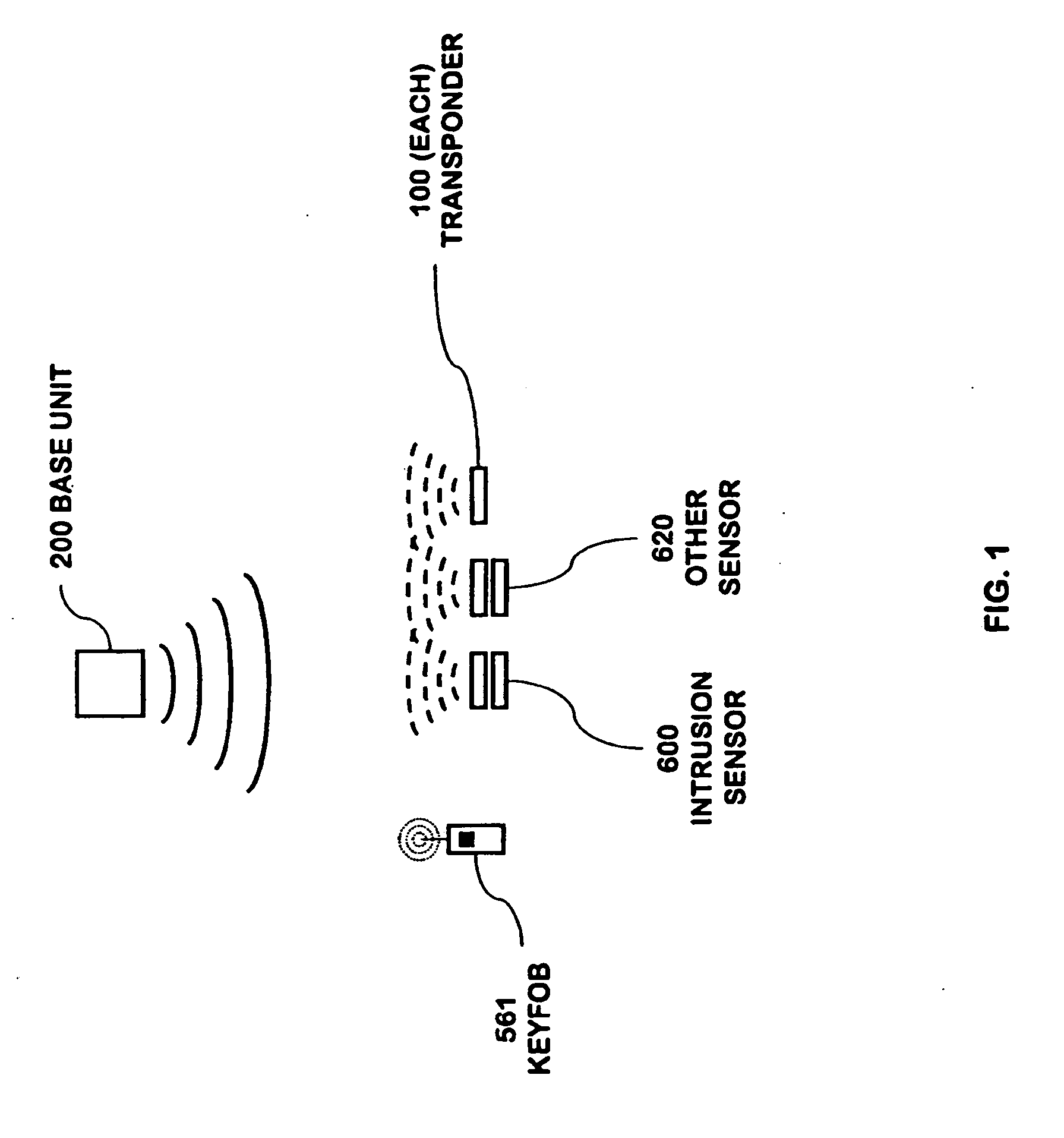
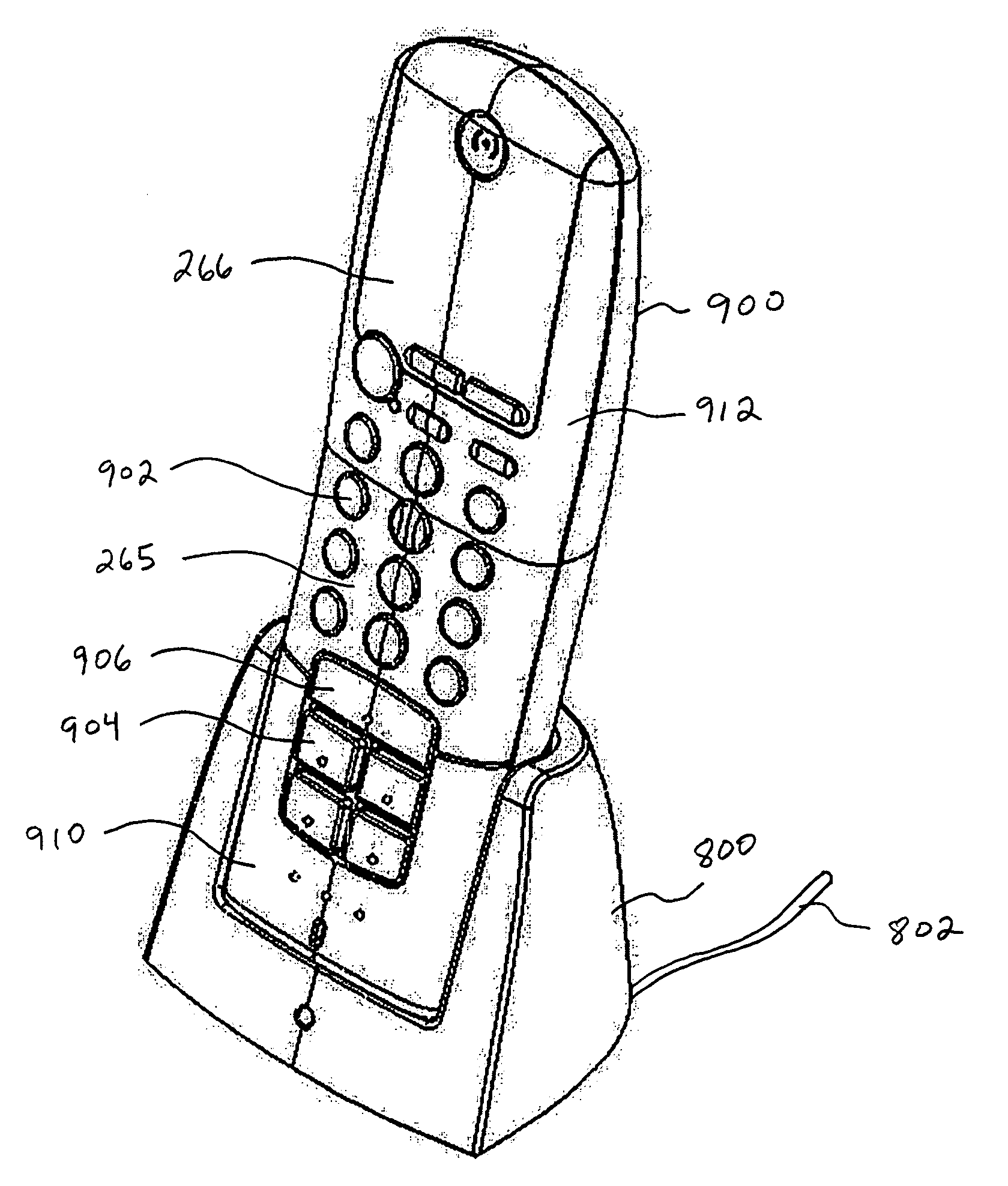
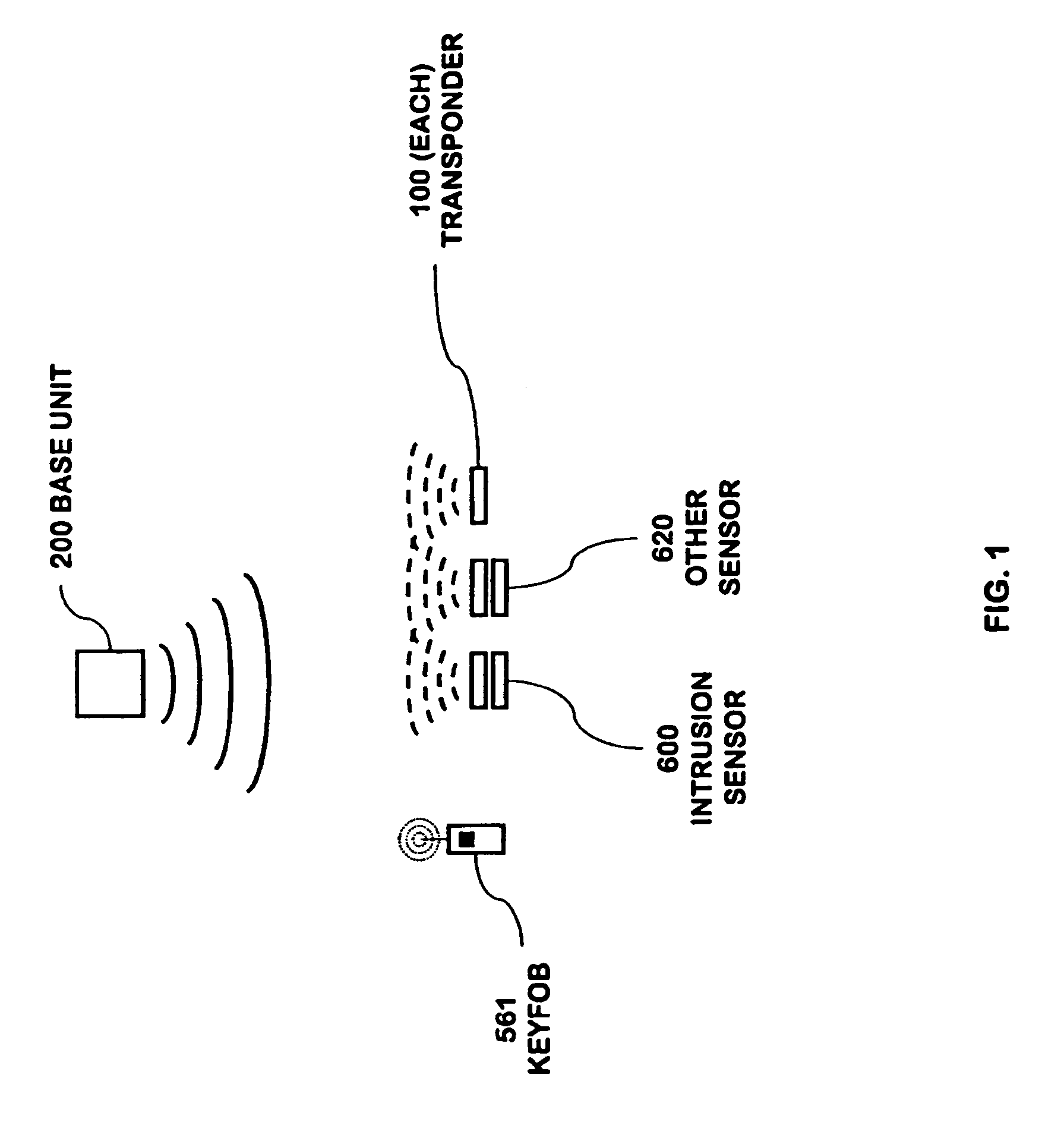
Portable telephone in a security network
InactiveUS20080001734A1Improve reliabilityLow costSafety arrangmentsComputer controlKey pressingNetwork communication
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
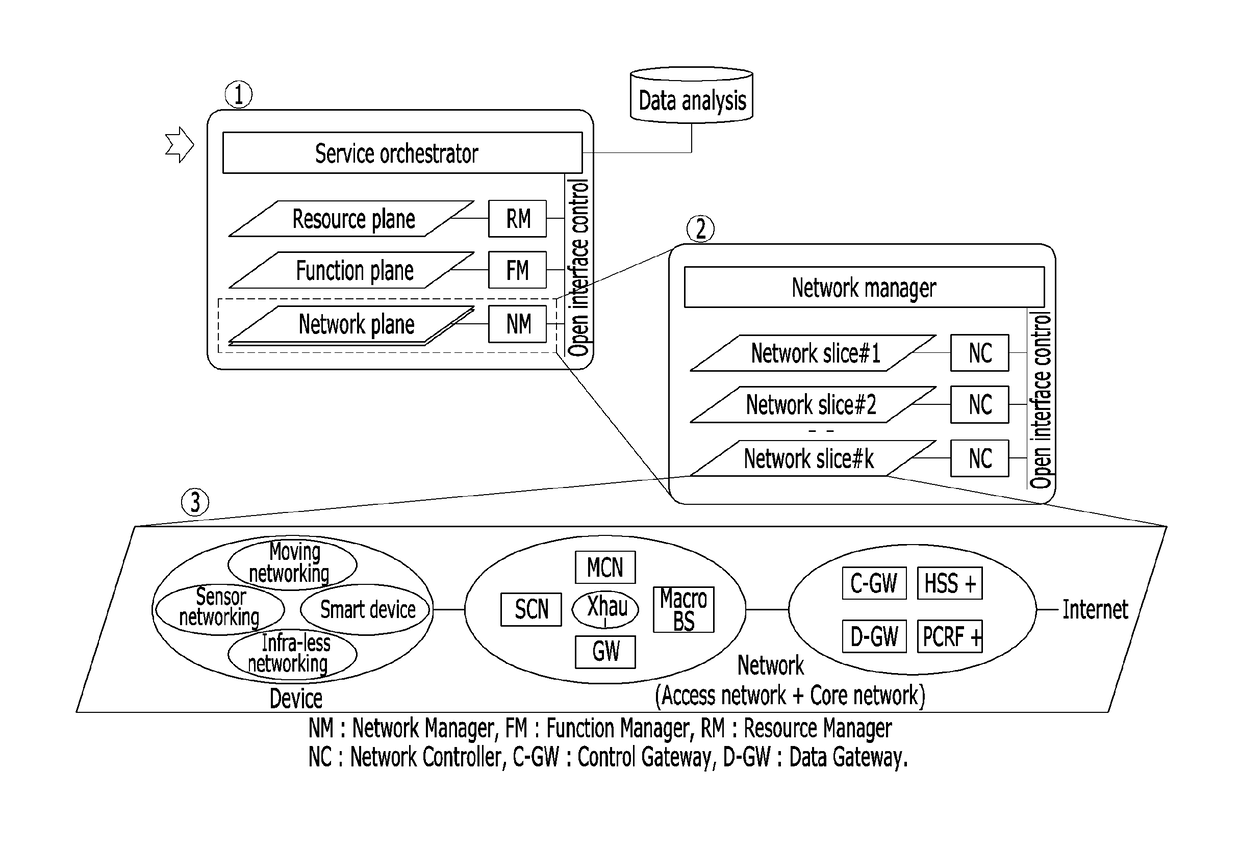
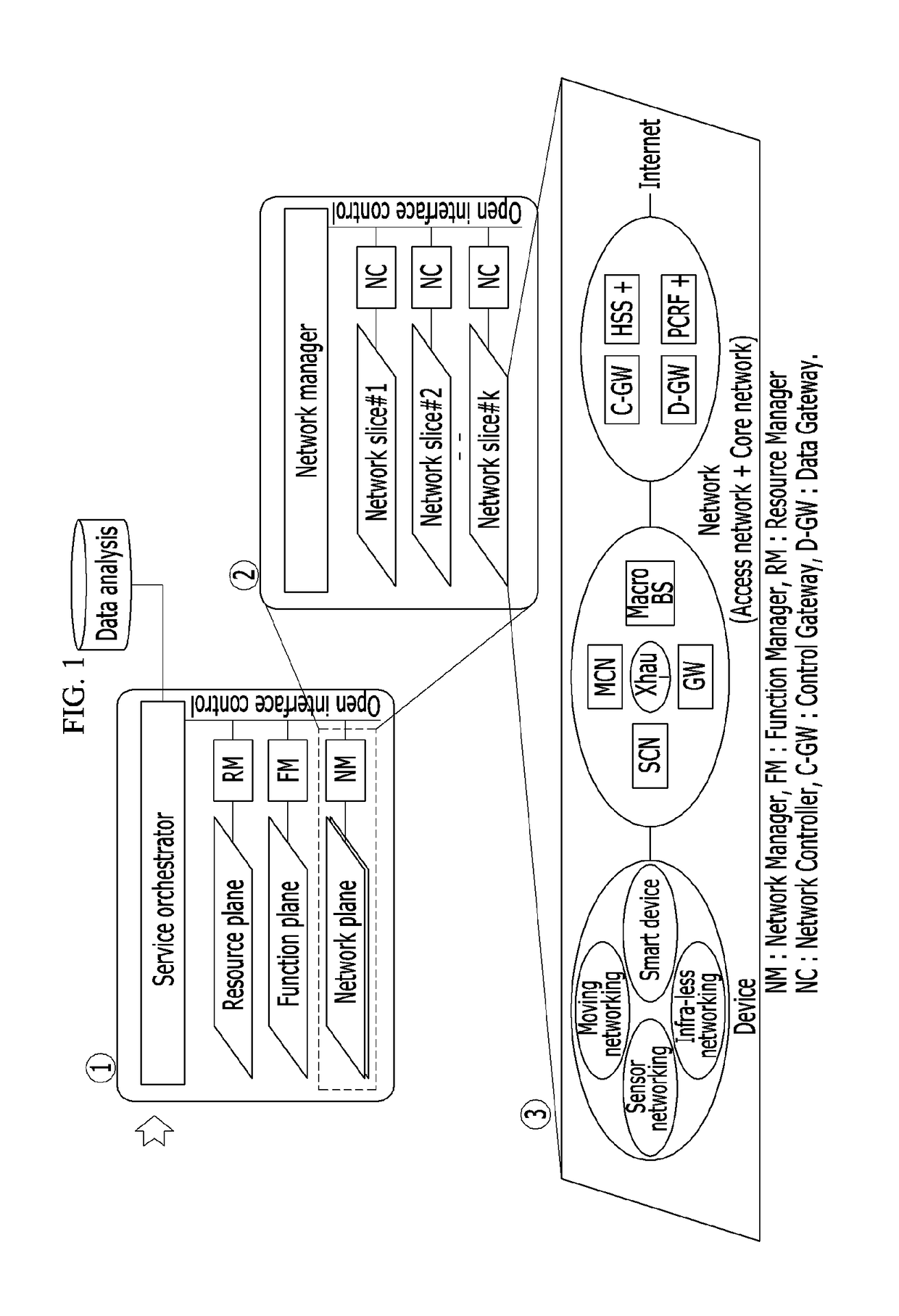
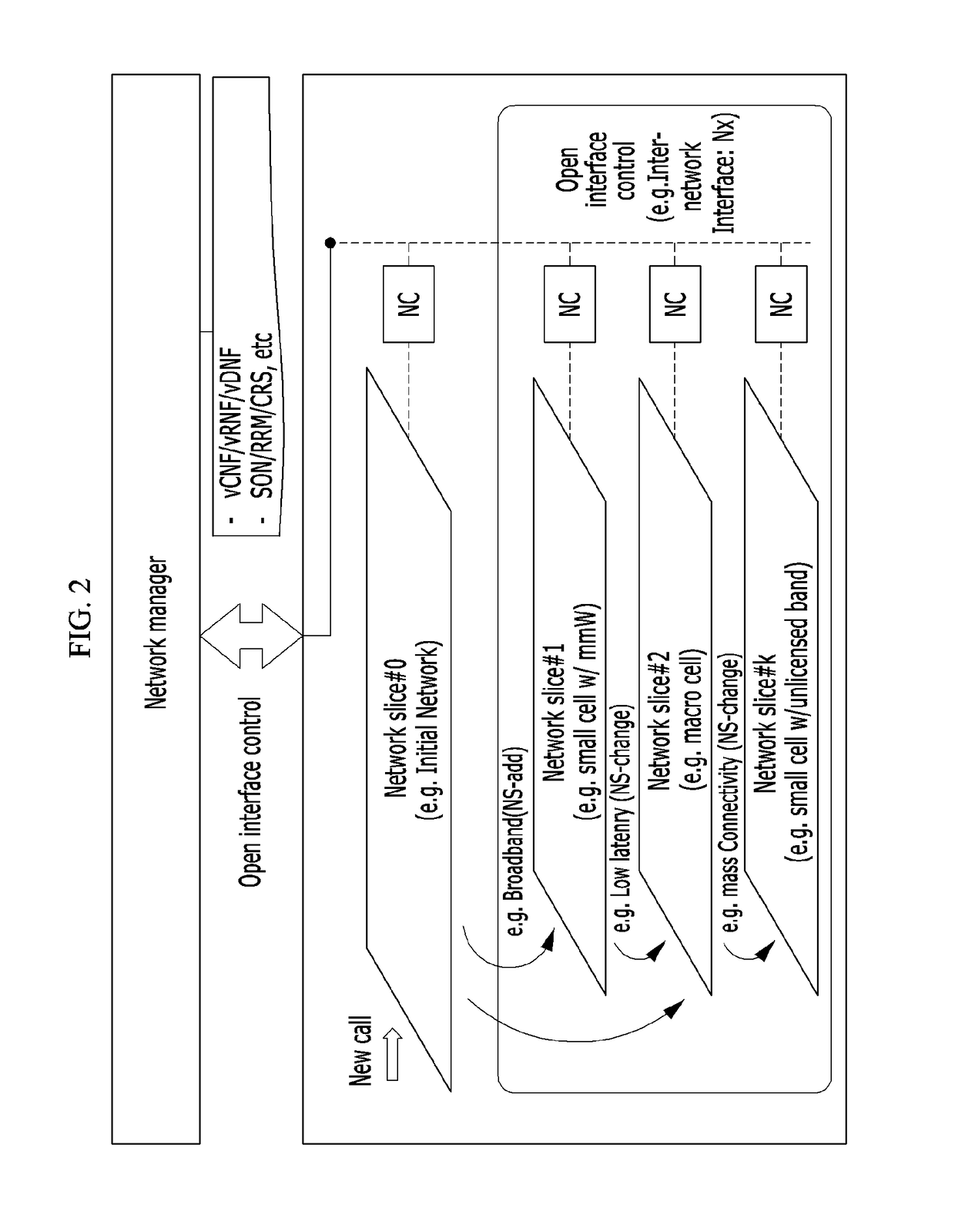
Mobile communication network system and method for composing network component configurations
ActiveUS20170070892A1Configuring networkAssess restrictionNetwork topologiesAccess networkNetworked system
Disclosed is a mobile communication network system and a network configuring method. The communication network system includes: a common control access network; at least one access network slice added according to a service type requested by a device; a common control core network; and at least one core network slice added according to a service type requested by the device. The access network slice and the core network slice are determined by the service type requested by the device.
Owner:ELECTRONICS & TELECOMM RES INST
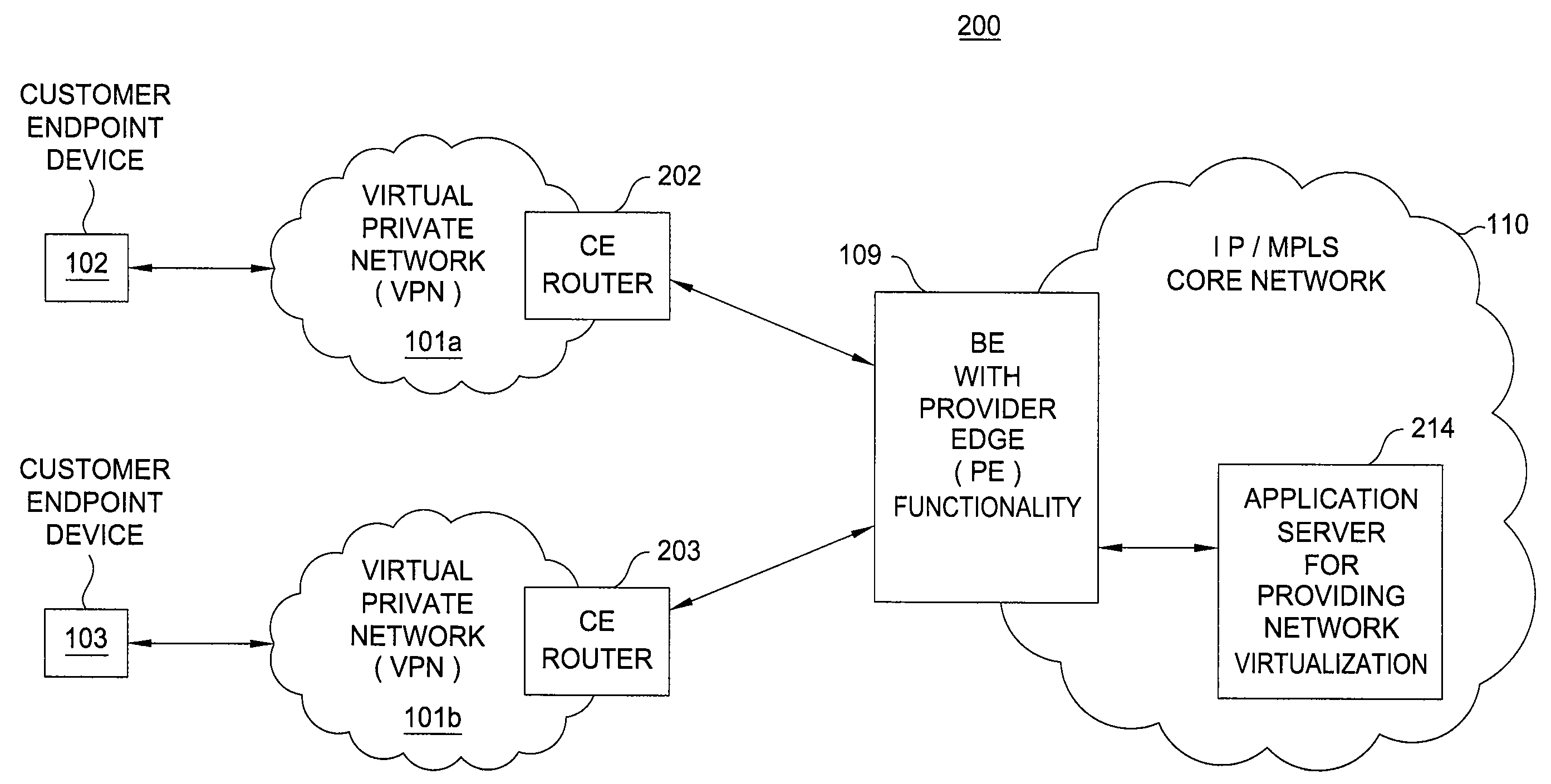
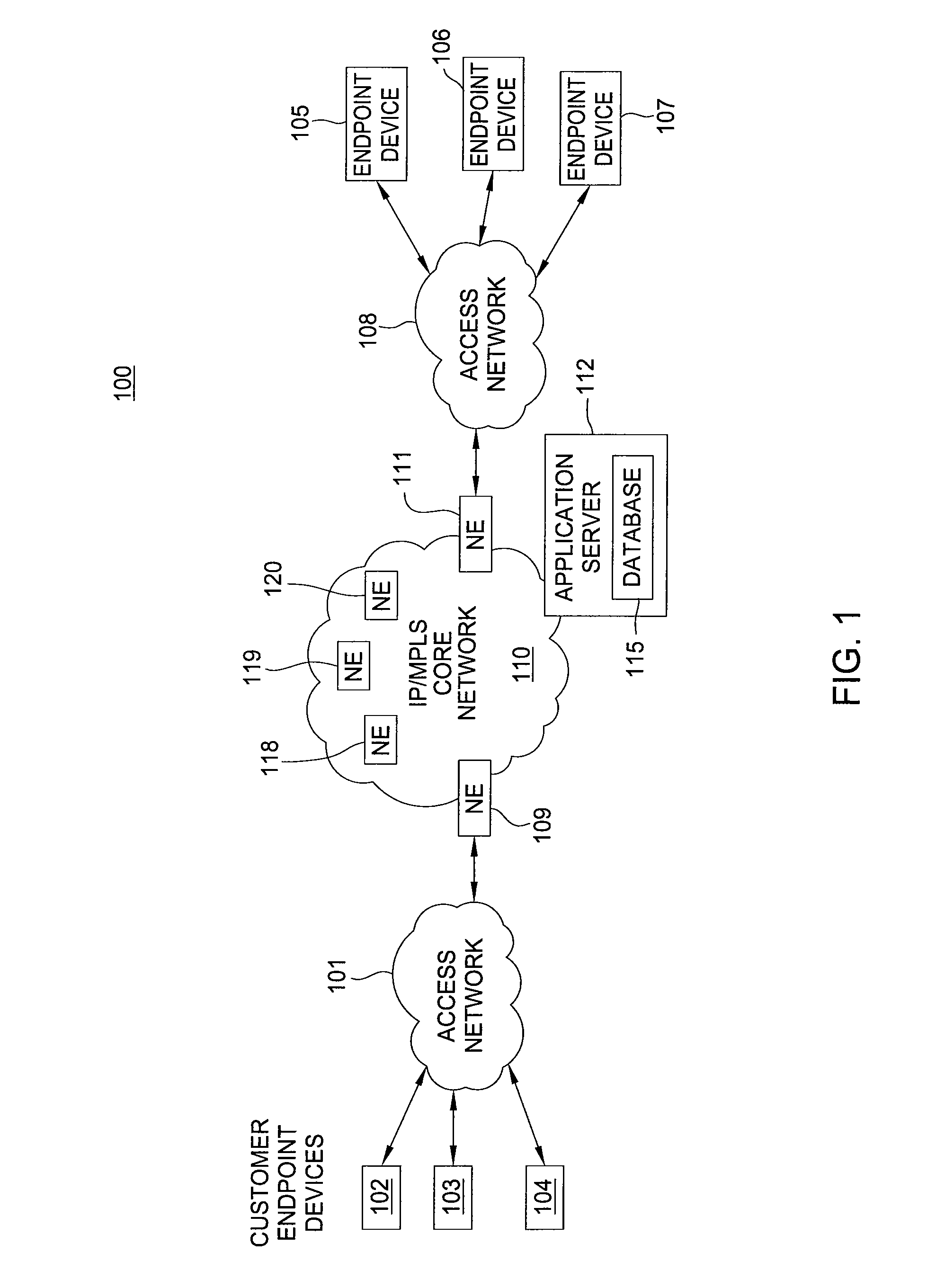
Method and apparatus for providing network virtualization
A method and apparatus for providing network virtualization on a packet network are disclosed. For example, the method receives a request from a user, wherein the request comprises at least one of: a feature of a network component or a network component for a virtual network. The method determines if the request can be instantiated over one or more real network resources, and then instantiates the request via the one or more real network resources, if it is determined that the request can be instantiated.
Owner:RAKUTEN GRP INC
Usage statistics collection for a cable data delivery system
InactiveUS6308328B1Broadband local area networksBroadcast transmission systemsData connectionNetwork management
Apparatus for recording and collecting usage and other statistical data from components of a cable data network comprises a network manager for maintaining and collecting the statistics. Internet protocol addresses are associated with components of the network. The component maintains a software agent that manages a statistics database. Responsive to a manager request generated at a service provider defined time interval, the component software agent provides the usage statistics to the network manager in real-time during an Internet session with a host. When the host to Internet or other data connection is torn down due to failure, disconnect or inactivity time-out, remaining usage statistics data is collected and the session duration updated with the time of tear down. Usage statistics collected include the amount of data transferred to / from a host, the amount of data that is discarded due to insufficient resource capacity and amount of data that cannot be corrected despite forward error correction used in a downstream high capacity channel to the host. Data traps may be defined and downloaded to components of the network for implementation. As a result, billing of users of the cable data network can be usage sensitive and determined based on actual data transferred (including credit given for errored data) and / or time sensitive based on session duration.
Owner:CISCO TECH INC
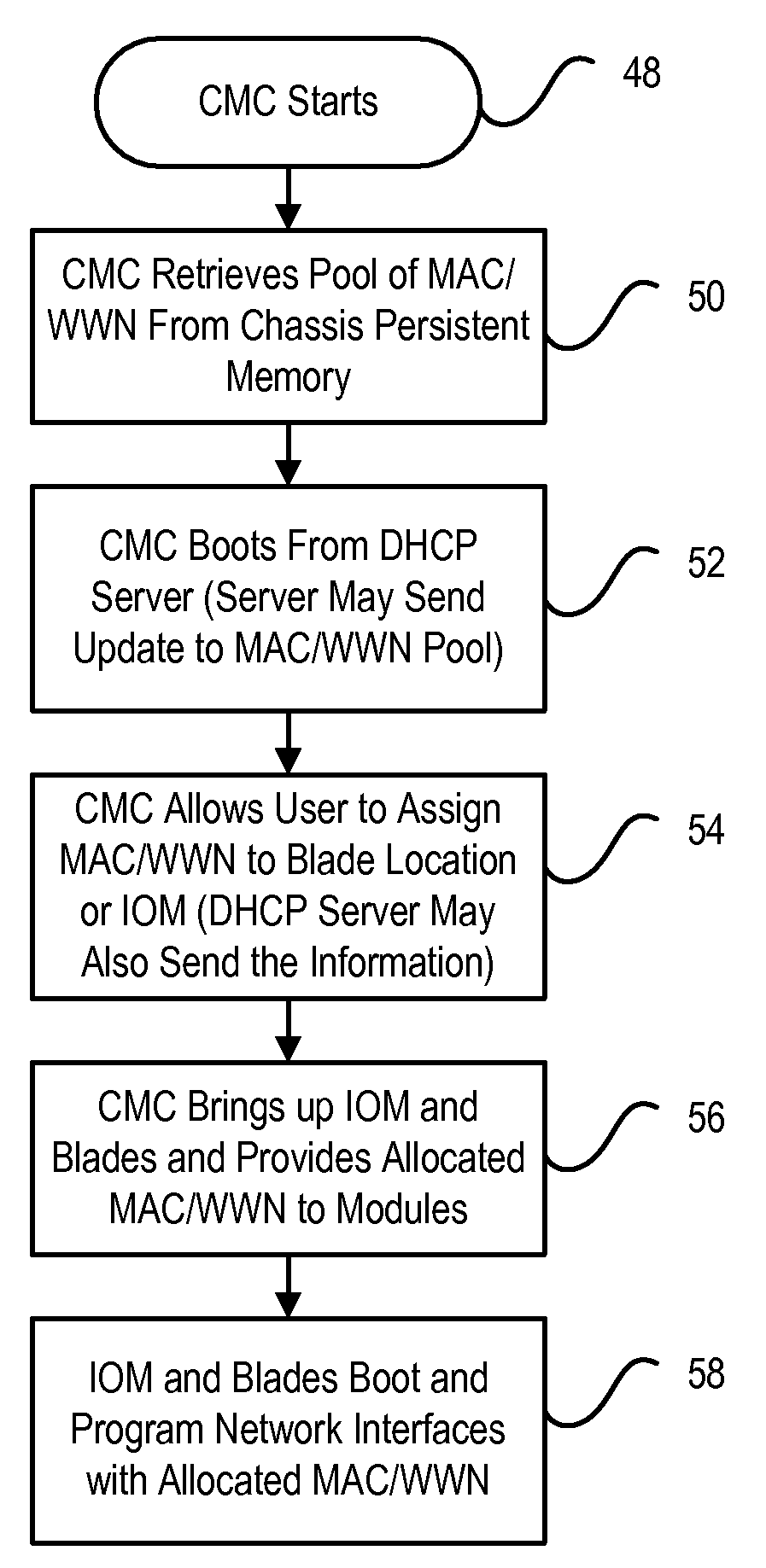
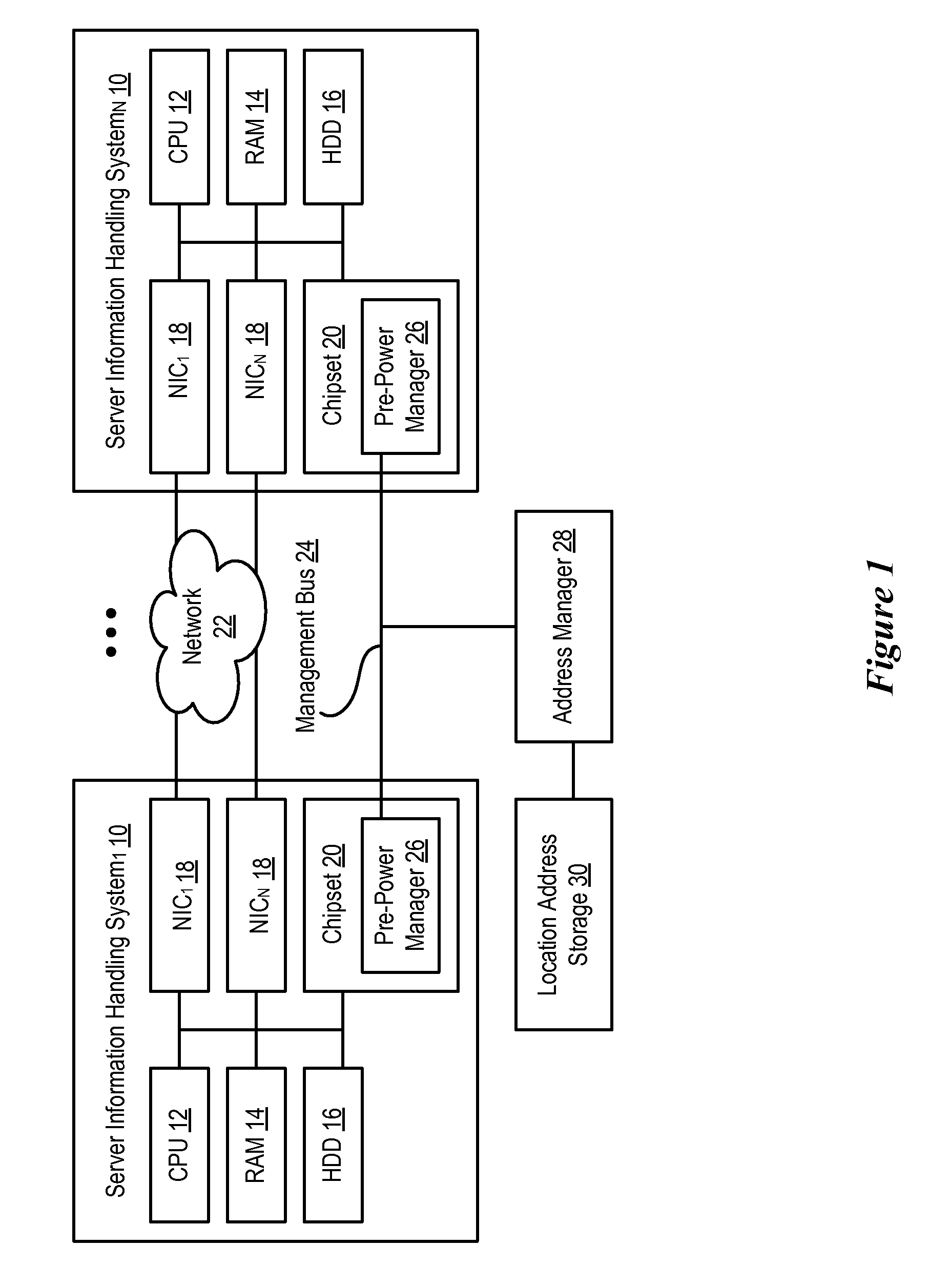
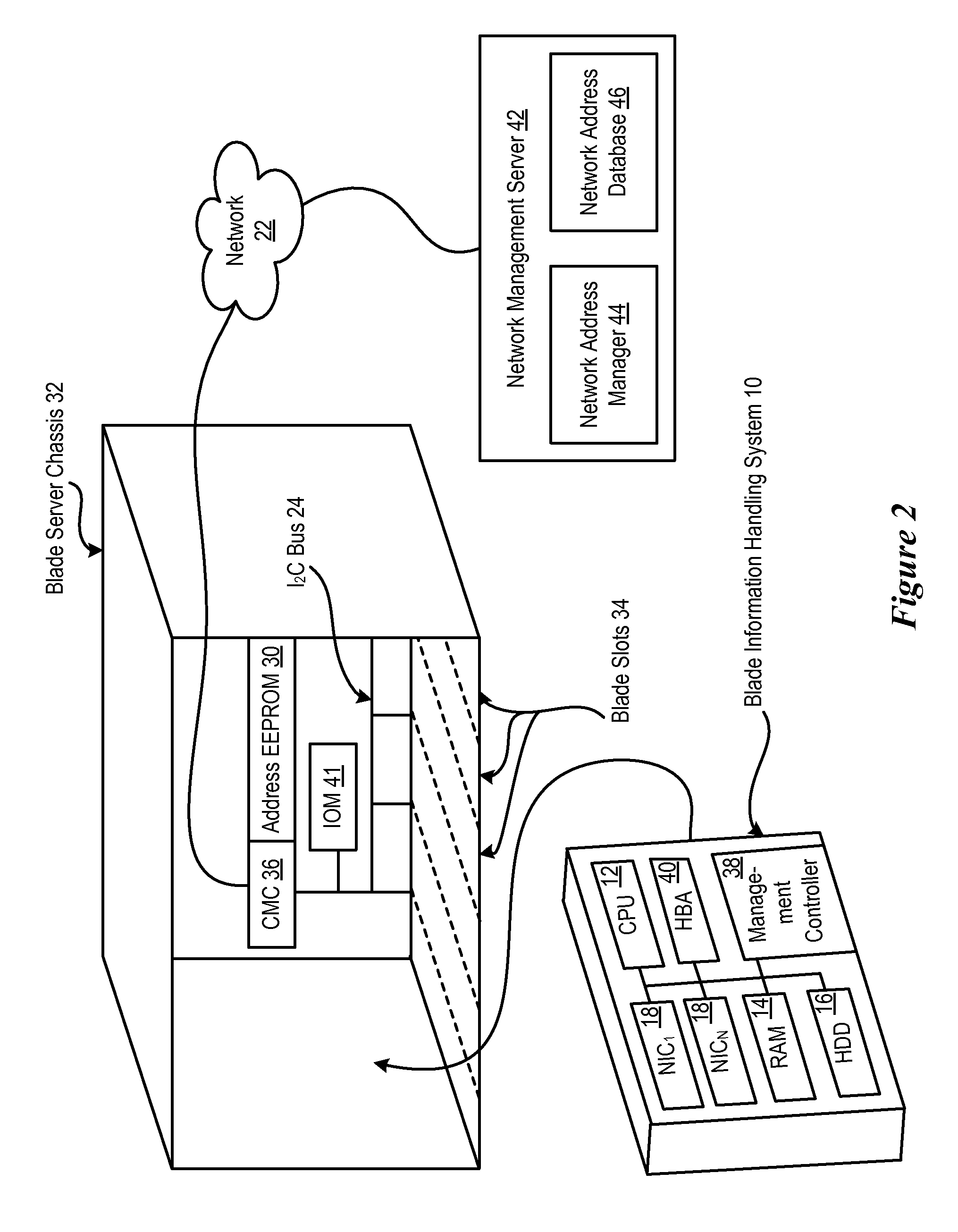
System And Method For Assigning Addresses To Information Handling Systems
ActiveUS20090077208A1Inadvertent duplication is preventedReduce disadvantagesError preventionFrequency-division multiplex detailsNetwork addressingNetwork communication
Information handling system network addresses are managed to support a consistent MAC address for iSCSI and fibre channel host bus adapter. For example, a management controller retrieves a MAC address from persistent memory, such as a network location, and assigns the MAC address to a non-persistent memory of a predetermined information handling system network component so that the MAC address remains consistent even if the network component is replaced. For example, an offload engine that supports network communications with iSCSI receives a MAC address from a network location and applies the MAC address for use by a host bus adapter. Alternatively, an offload engine supports Fibre Channel with World Wide Name or World Wide Identifier address assignments.
Owner:DELL PROD LP
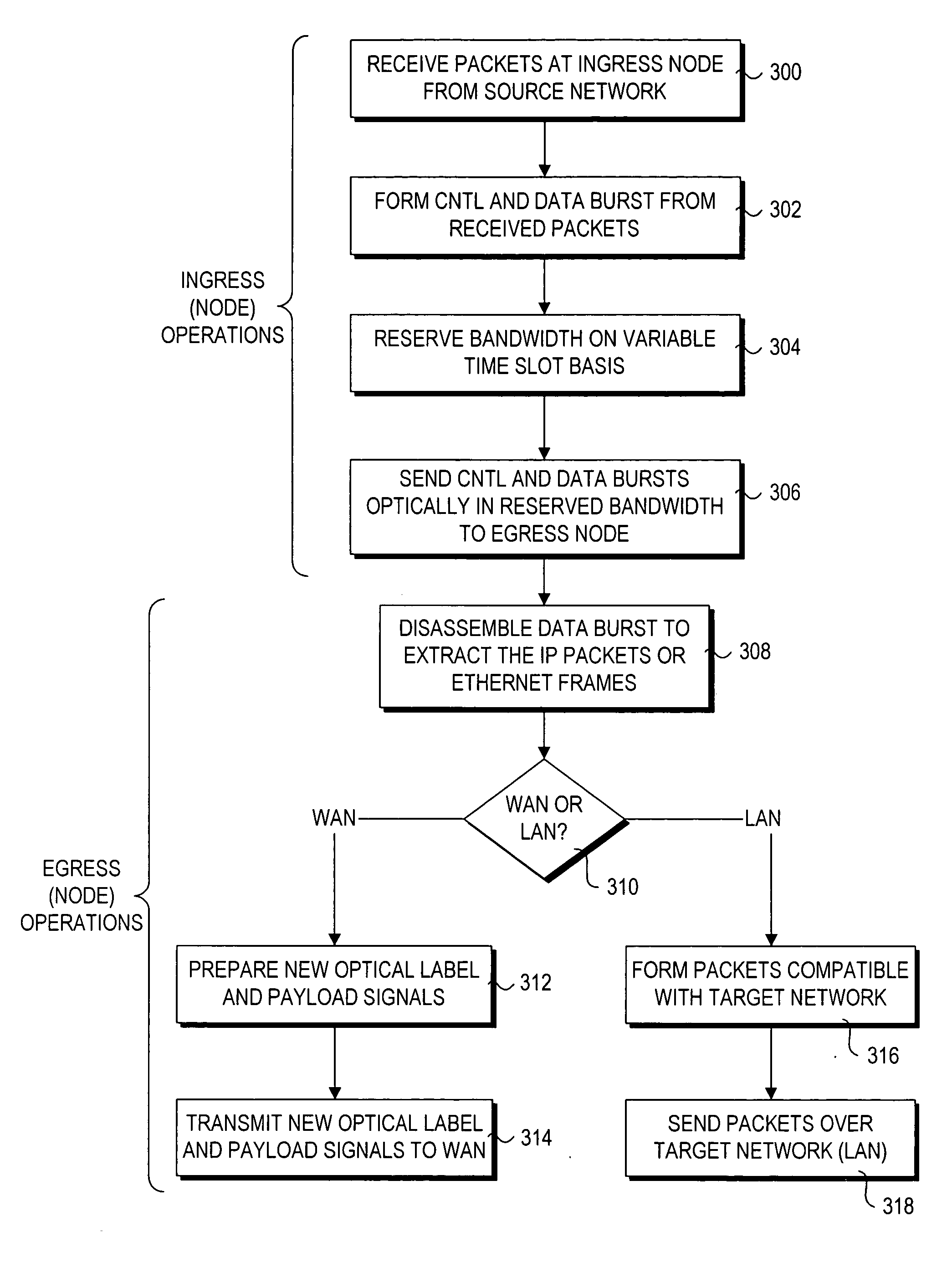
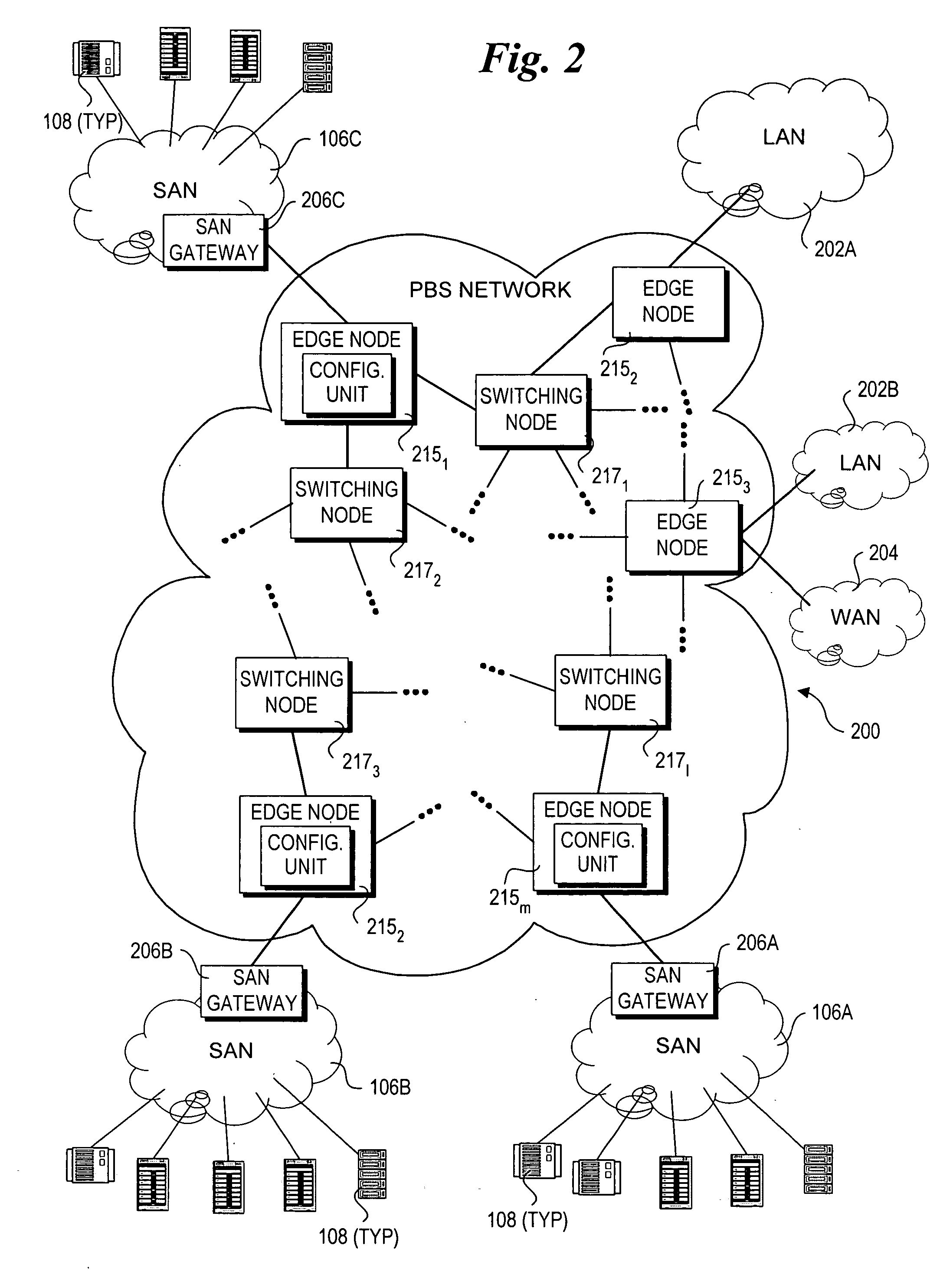
Method and architecture for optical networking between server and storage area networks
InactiveUS20050175341A1Multiplex system selection arrangementsMultiple digital computer combinationsArea networkStorage area network
A method and system for routing high-speed data to and from SANs (Storage Area Networks and Server Area Networks) via optical burst-switched (OBS) networks. OBS network components, including edge nodes and switching nodes, are coupled between SAN islands. In one embodiment, the OBS network comprises a photonic burst-switched (PBS) network. Under one scheme, a PBS edge node and SAN gateway are co-located at the interface to the SAN, while a plurality of PBS switching nodes are deployed between the PBS edge nodes. Under another scheme, PBS switching / edge nodes are co-located at respective SANs. This scheme employs an external gateway protocol (EGP) for routing data via selected route segments. Data going to and received from a SAN is packaged as Fibre Channel Frames. Data transmitted via the PBS network is converted into PBS frames having encapsulated Fibre Channel Frames. The schemes also support interfaces with legacy networks, such as LANs and WANs.
Owner:INTEL CORP
Portable telephone in a security network
InactiveUS7511614B2Improve reliabilityLow costSafety arrangmentsComputer controlCard readerProgram code
A security network for use in a building with an opening to be monitored for possible intrusion. The network includes an intrusion sensor monitoring the opening; an RFID transponder associated with the sensor; an RFID reader in wireless communication with the transponder; and a portable telephone handset having first keys activating conventional telephone capability and second keys activating interaction with the other security network components. The handset wirelessly communicates with the reader. The reader may take the form of a security cradle for the handset. Alternatively, the reader may take the form of a telephone console. The console has keys enabling a user to dial remote telephone numbers; circuitry adapted to receive wireless communications from the transponder; circuitry in wireless communication with the handset; circuitry in communication with an external network; and a processor executing program code enabling the handset to communicate with the external network via the telephone console.
Owner:ADT US HLDG INC
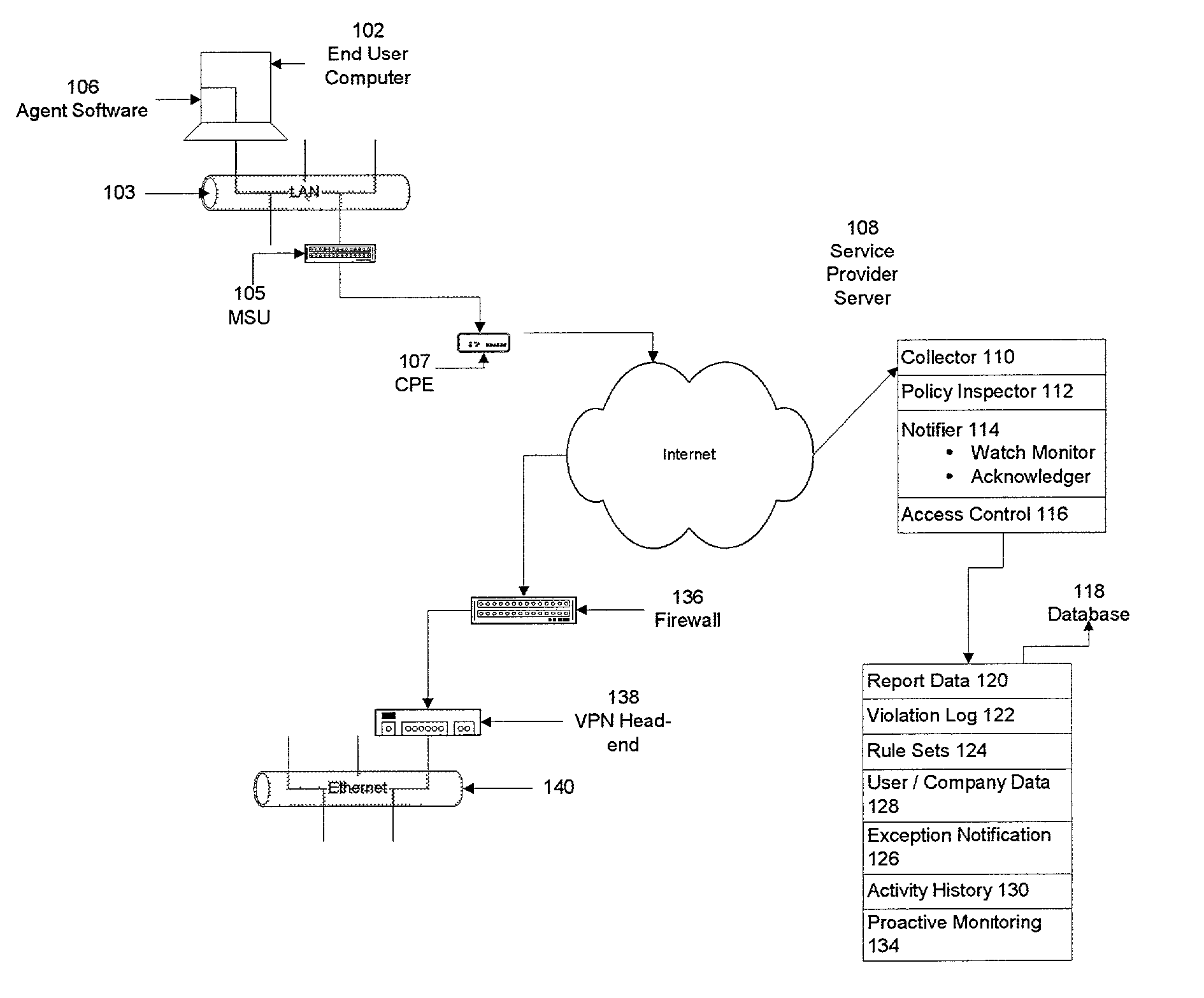
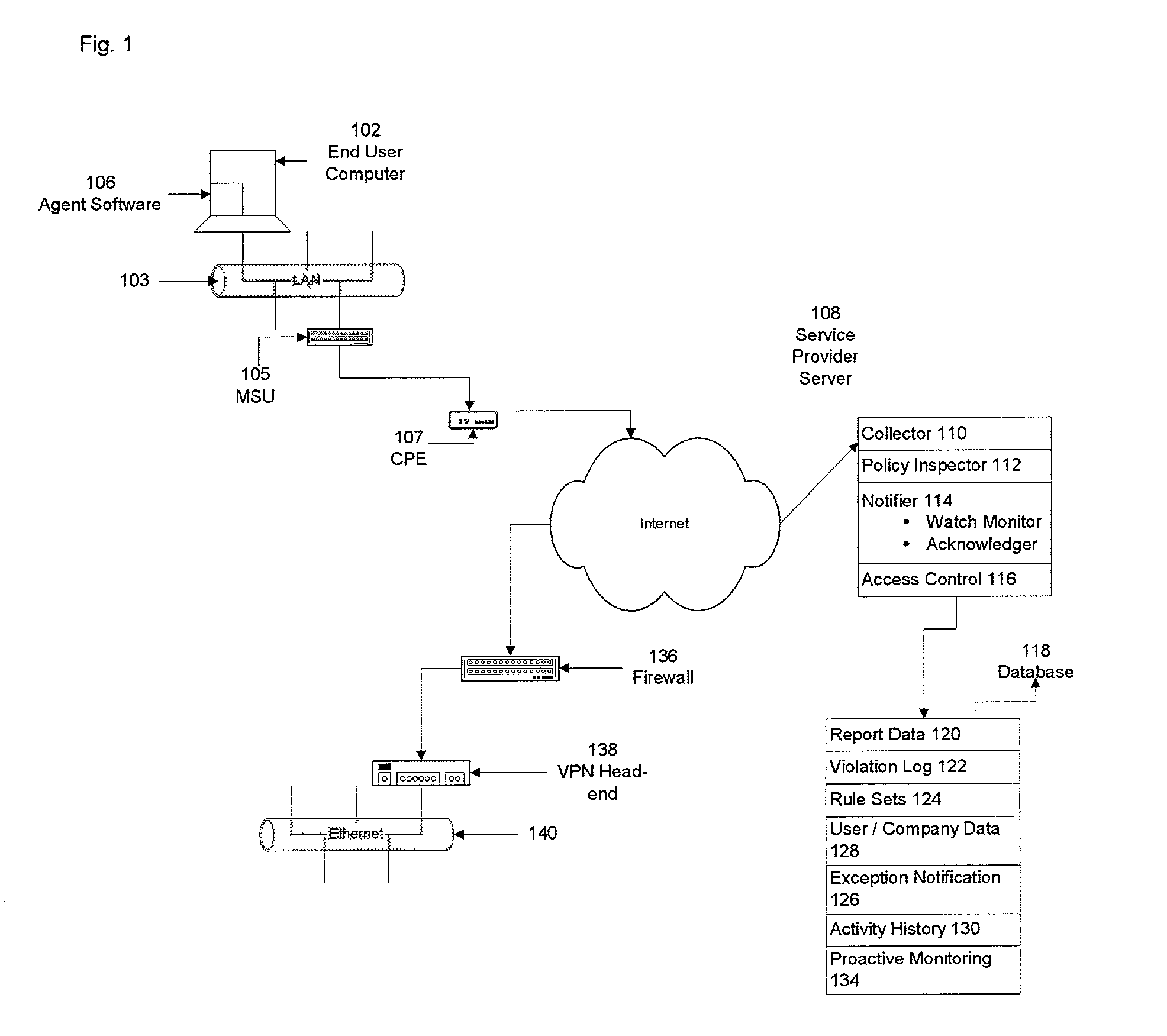
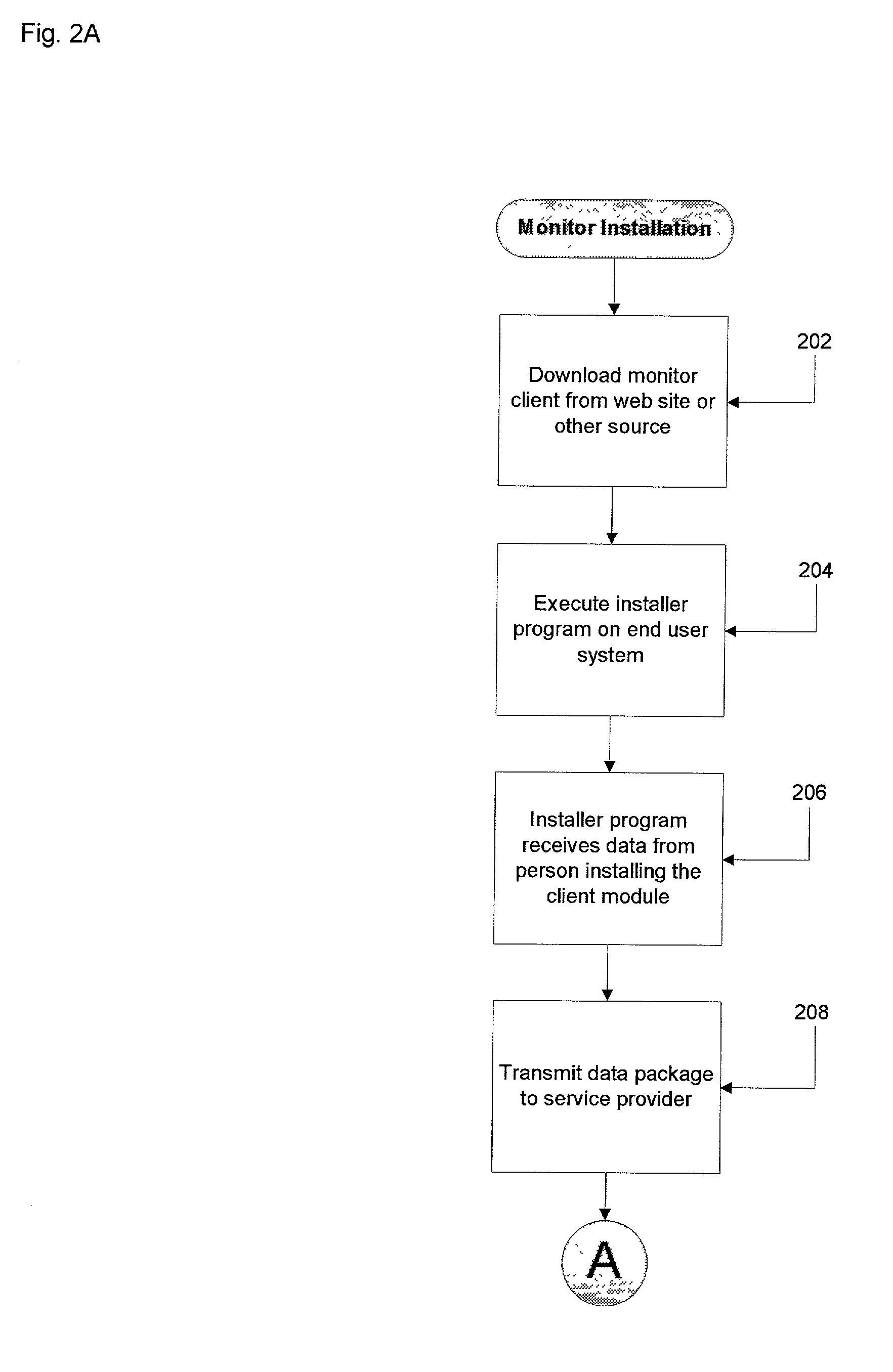
Method and apparatus for monitoring computer network security enforcement
ActiveUS20030229808A1Memory loss protectionUnauthorized memory use protectionThird partyPrivate network
Methods and systems are disclosed for monitoring activity of a user on a network component, such as an end user computer, in a virtual private network for adherence to a security enforcement provision or policy utilized in the virtual private network. A method of determining whether a security provision in a computer network has been violated is described. It is determined whether the network component has violated, modified or circumvented a security enforcement provision of the computer network. If the detection is affirmative, the network component, such as an end user system, is modified in a manner in which the computer network operates at a level appropriate to the degree of the violation, modification, or circumvention of the security enforcement provision. If instructed to do so, a third party operating the virtual private network is notified of the violation and access to the network by the network component is restricted or terminated. A security enforcement distributed system consists of an agent module on the end user computer and a collector module for receiving data from the agent on a security server computer coupled to a data repository. Also on the security serer are a policy inspector for checking compliance with a security provision and a notifier and access control module for informing the network operator of a violation and restricting access by the end user system to the security server.
Owner:CHANNEL IP BV
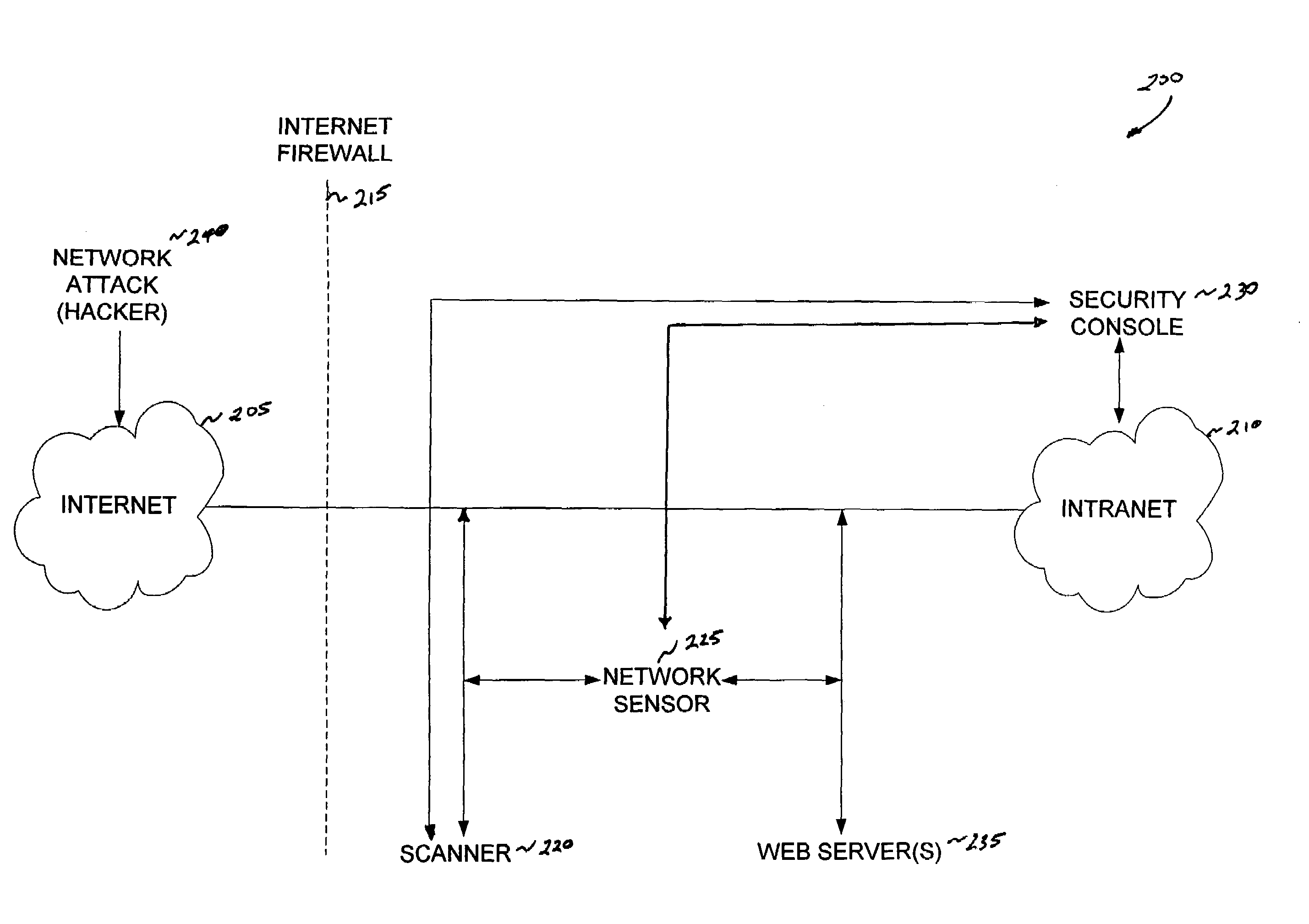
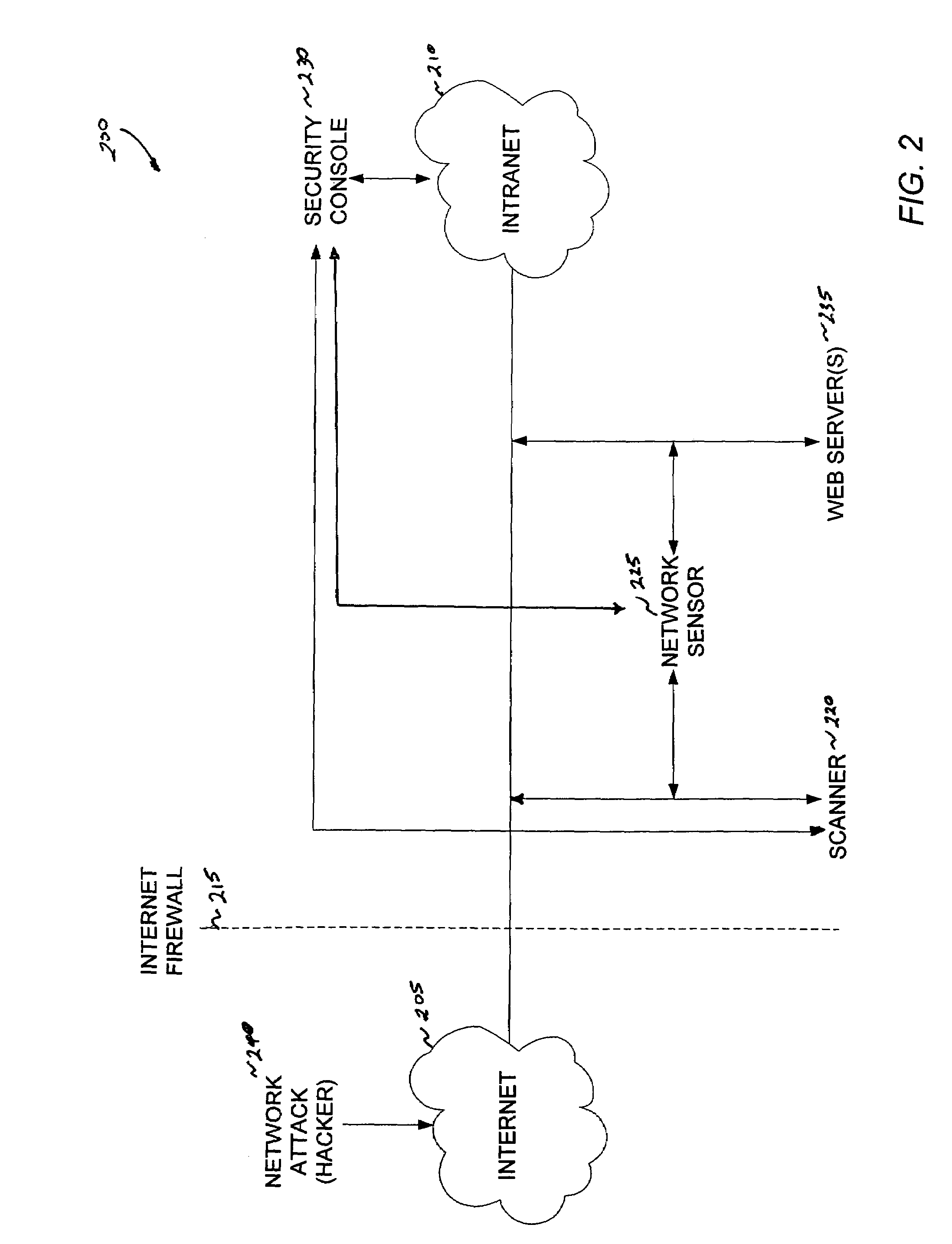
Method and system for intrusion detection in a computer network
InactiveUS7574740B1Memory loss protectionError detection/correctionDatabase intrusion detectionVulnerability
An intrusion detection system for detecting intrusion events in a computer network and assessing the vulnerability of the network components to the detected events. The intrusion detection system comprises a scanner, one or more sensors and a security console for operation within a networked computing environment. A sensor of the inventive intrusion detection system can monitor the networked computing environment for possible intrusion events representing an unauthorized access or use of the network resources. In response to detecting an intrusion event, the sensor can generate a scan request for handling by a scanner. This request initiates a scan of the target computer by the scanner to determine the vulnerability of the target to the attack. Based on this vulnerability analysis, the inventive intrusion detection system can evaluate the severity of the detected intrusion event and issue an alert having a priority corresponding to the severity of the intrusion.
Owner:IBM CORP
Systems and methods for monitoring data and bandwidth usage
ActiveUS8706863B2Assess restrictionData switching by path configurationResource utilizationData provider
Access to a communications network may be provided via a data provider that may charge for access. In some cases, the access fee may be related to the amount of network resources consumed (e.g., amount of data downloaded or bandwidth used). In some cases, a user may have access to a particular amount of data provider resources and be required to pay an additional fee for using resources in excess of the particular amount. To assist the user in managing his data resource consumption, a resource utilization component may provide different alerts and notices informing the user of current consumption, expected future consumption, and recommendations for reducing data provider resources consumed (e.g., stopping particular processes or data provider requests, such as downloading media). If several electronic devices in a network are connected to the same data provider resources, a network component may manage the data provider resource use among the several electronic devices (e.g., allow only particular users or devices access).
Owner:APPLE INC
System, method and apparatus for network service load and reliability management
InactiveUS20040210670A1Digital computer detailsSecuring communicationNetwork serviceDistributed computing
A method and system that enables a network and components of the network to be aware of the services existing at the edges of the network and to route connection requests for these services to appropriate servers within the network based on a variety of criteria. By making the network and network components service-aware, routing functions can be implemented in a more scalable and efficient way.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
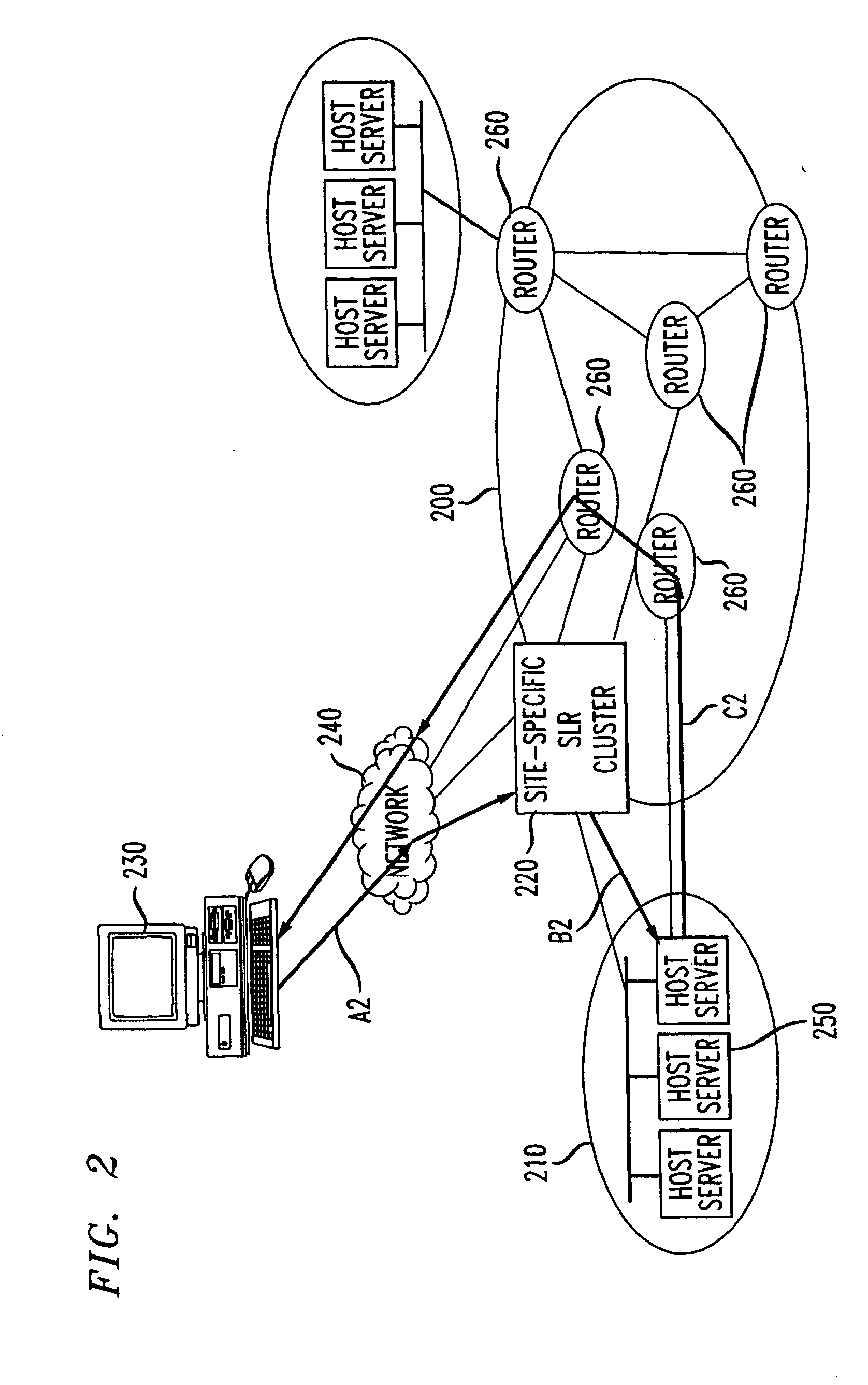
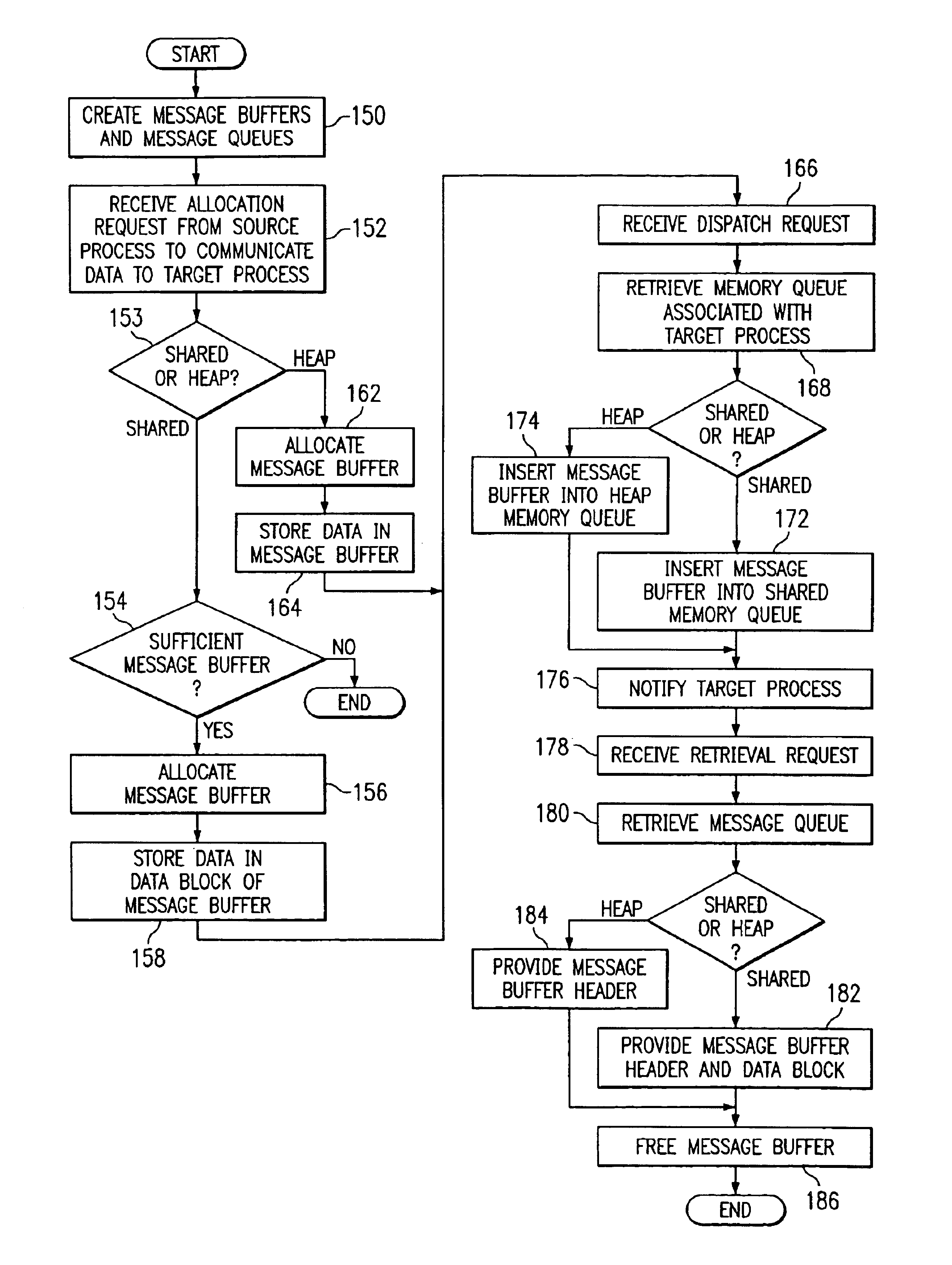
Data communication among processes of a network component
InactiveUS6847991B1Disadvantages and reduced eliminatedEasy to handleMultiple digital computer combinationsProgram controlMessage queueComputer module
A method for communicating data among processes of a network component is disclosed. A process communication module receives a request from a first process of a network component. The request requests a message buffer operable to store data associated with the first process. A message buffer is allocated to the first process in response to the request, and the data is stored in the message buffer. The message buffer is inserted into a message queue corresponding to a second process of the network component. The second process is provided access to the message buffer to read the data.
Owner:CISCO TECH INC
Wireless communication system, server and mobile station therefor
InactiveUS20050119001A1Shorter to authenticateShorten handover timeAssess restrictionNetwork topologiesCommunications systemNetworked system
This invention provides a wireless communication system wherein a network to which a mobile station should be handed over can be selected, using parametric data collected from network components other than the mobile station. Time taken for a handover between different types of network systems is reduced. The wireless communication system of the present invention comprises a mobile station equipped with multiple wireless interfaces, a server connected to a fixed network, and multiple access points. The mobile station determines available wireless interfaces and sends notification of the available interfaces' identifiers to the server. The server collects managerial data from network components and selects a wireless interface, based on the notification from the mobile station and the managerial data. The mobile station registers its locations in visiting networks corresponding to multiple available wireless interfaces with the server. The server retains the registrations of mobile station locations for the above wireless interfaces.
Owner:HITACHI LTD
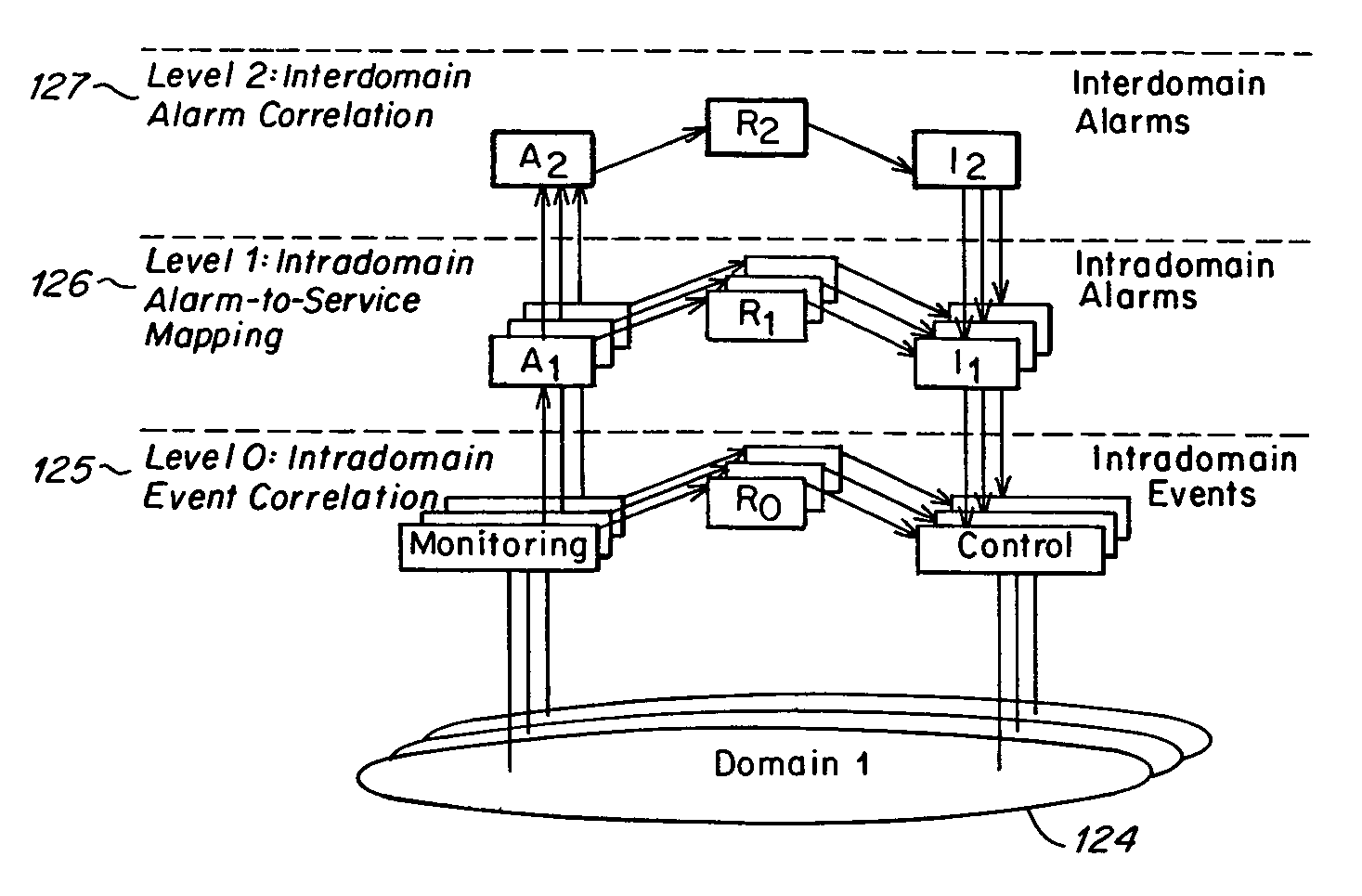
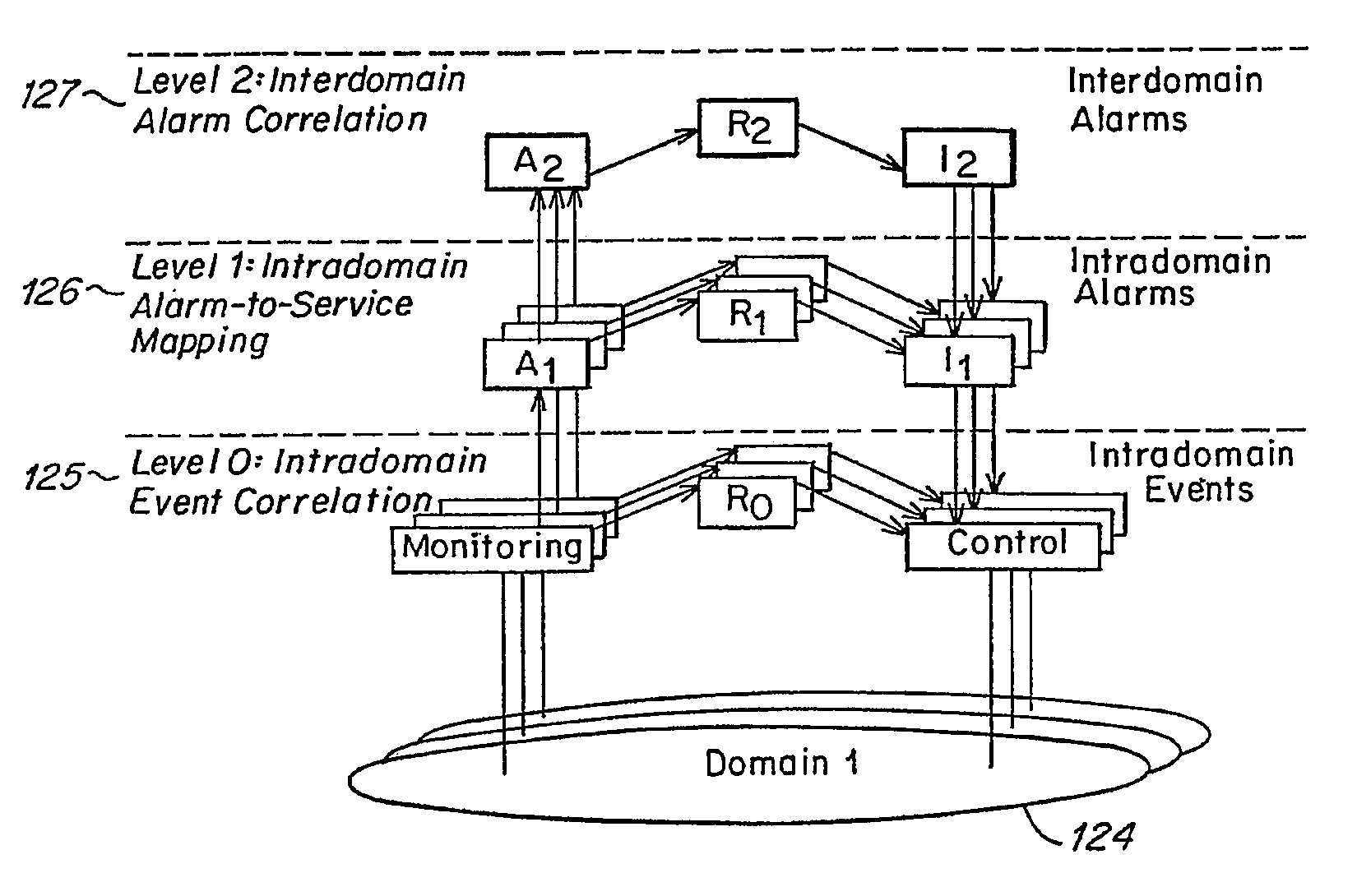
Method and apparatus for event correlation in service level management (SLM)
Method and apparatus for service level management, wherein business processes are composed of services. A state of the service is defined by one or more service parameters, and the service parameters depend upon performance of network components that support the service, e.g., component parameters. The state of the service may depend, for example, on a collection of service parameter values for availability, reliability, security, integrity and response time. A service level agreement is a contract between a supplier and a customer that identifies services supported by a network, service parameters for the services, and service levels (e.g., acceptable levels) for each service parameter.
Owner:COMP ASSOC THINK INC
System, apparatus and method for providing a virtual network edge and overlay
ActiveUS20160006672A1Improve communication performanceImprove throughputData switching by path configurationHigh level techniquesTraffic capacityNetwork connection
A network system is provided between at least a first client site and a second client site, the first and the second client site are at a distance from one another. A client site network component is implemented at least at the first client site, the client site network component bonding or aggregating one or more diverse network connections so as to configure a bonded / aggregated connection that has increased throughput. At least one network server component may be configured to connect to the client site network component using the bonded / aggregated connection. A cloud network controller may be configured to manage the data traffic and a virtual edge providing transparent lower-link encryption for the bonded / aggregated connection between the client site network component and the network server component.
Owner:ADAPTIV NETWORKS INC
Method and system for securing a computer network and personal identification device used therein for controlling access to network components
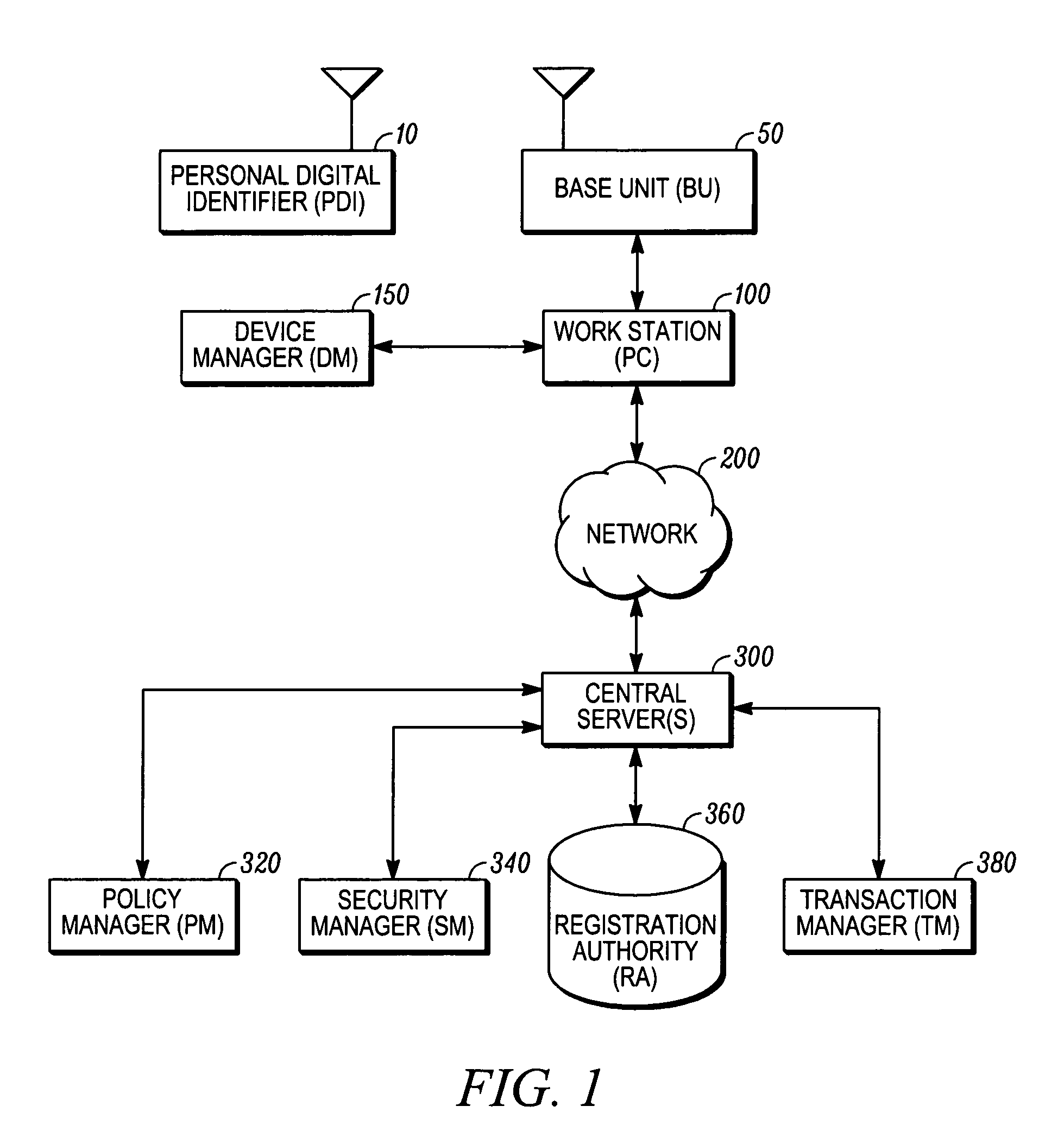
InactiveUS7310734B2Real-time authenticationDigital data processing detailsUser identity/authority verificationDigital signatureIdentification device
An improved computer network security system and a personal identifier device used for controlling network with real time authentication of both a person's identity and presence at a computer workstation is provided. A new user is registered to a portable personal digital identifier device and, within the portable personal digital identifier device, an input biometric of the user is received and a master template is derived therefrom and securely maintained in storage. A private key and public key encryption system is utilized to authenticate a user registered to the portable personal digital identifier device. The personal digital identifier device verifies the origin of a digitally signed challenge message from the network security manager component. A digitally and biometrically signed challenge response message is produced and transmitted by the personal digital identifier device in response to the verified challenge message.
Owner:3M INNOVATIVE PROPERTIES CO
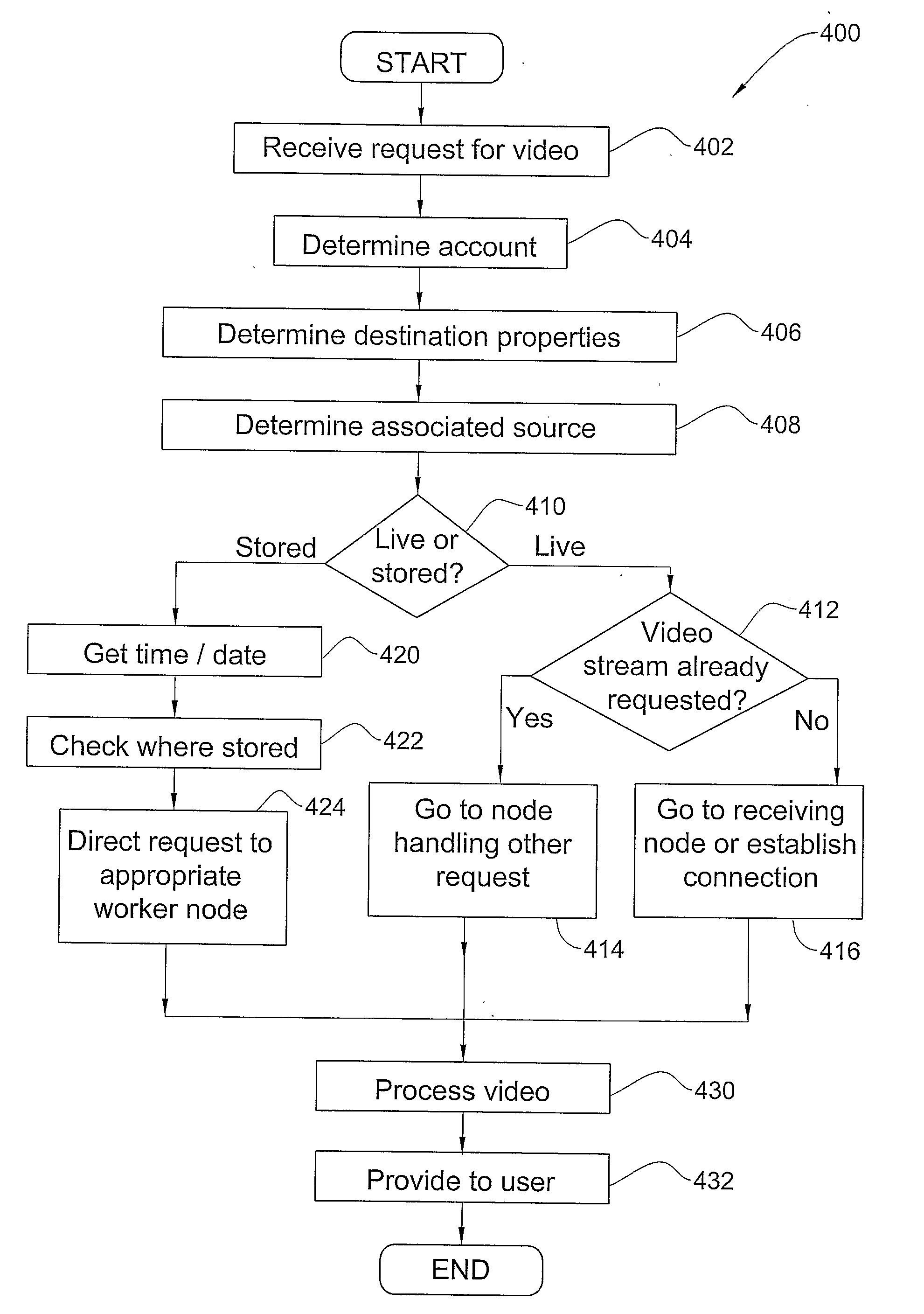
Method for a clustered centralized streaming system
InactiveUS20090254960A1Multiple digital computer combinationsTwo-way working systemsDistributed computingNetwork component
Owner:VIDEOCELLS
Patch panel with a motherboard for connecting communication jacks
InactiveUS7207846B2Two-part coupling devicesContact members penetrating/cutting insulation/cable strandsElectricityPatch panel
Owner:PANDUIT
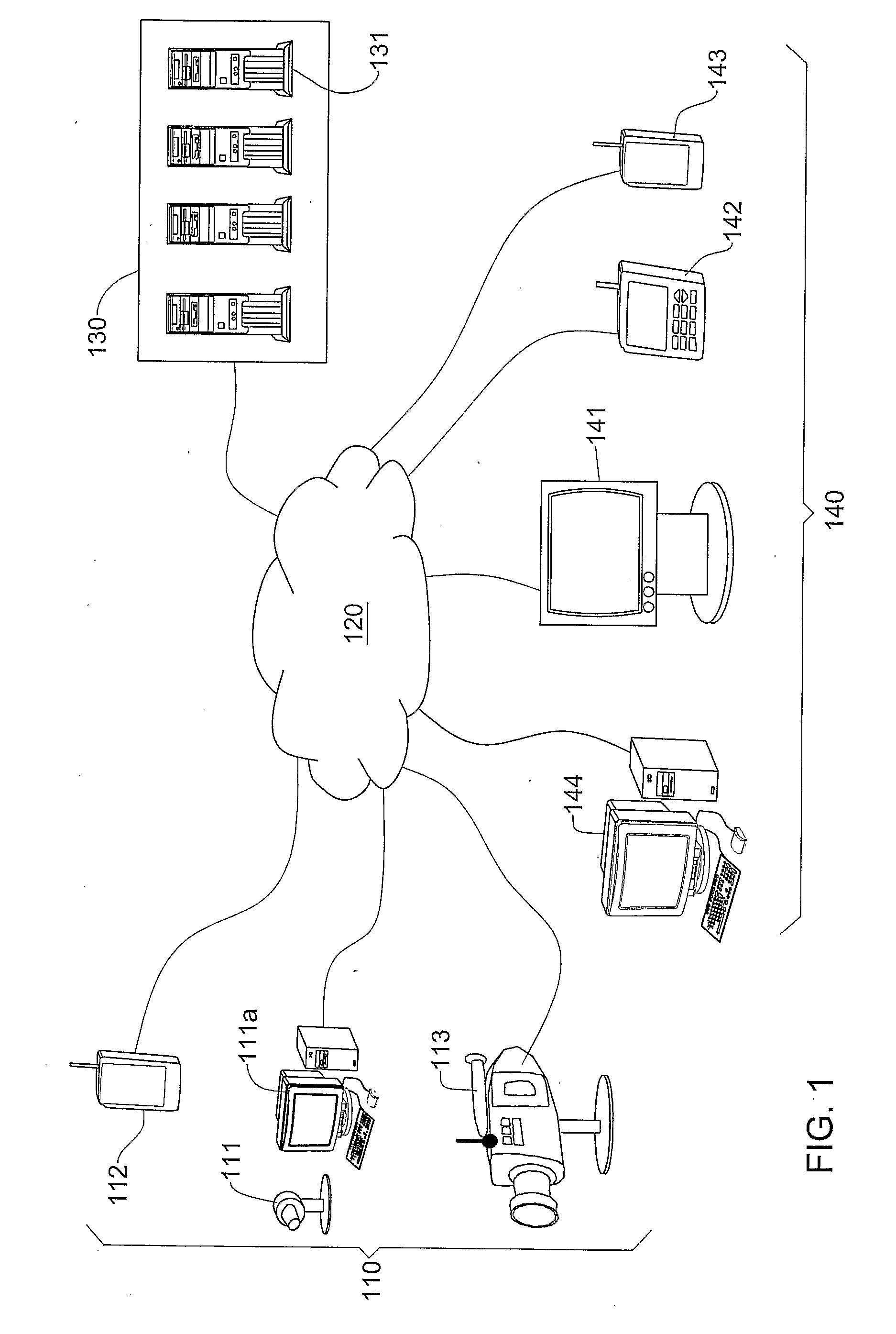
Wireless sensor system for monitoring skin condition using the body as communication conduit
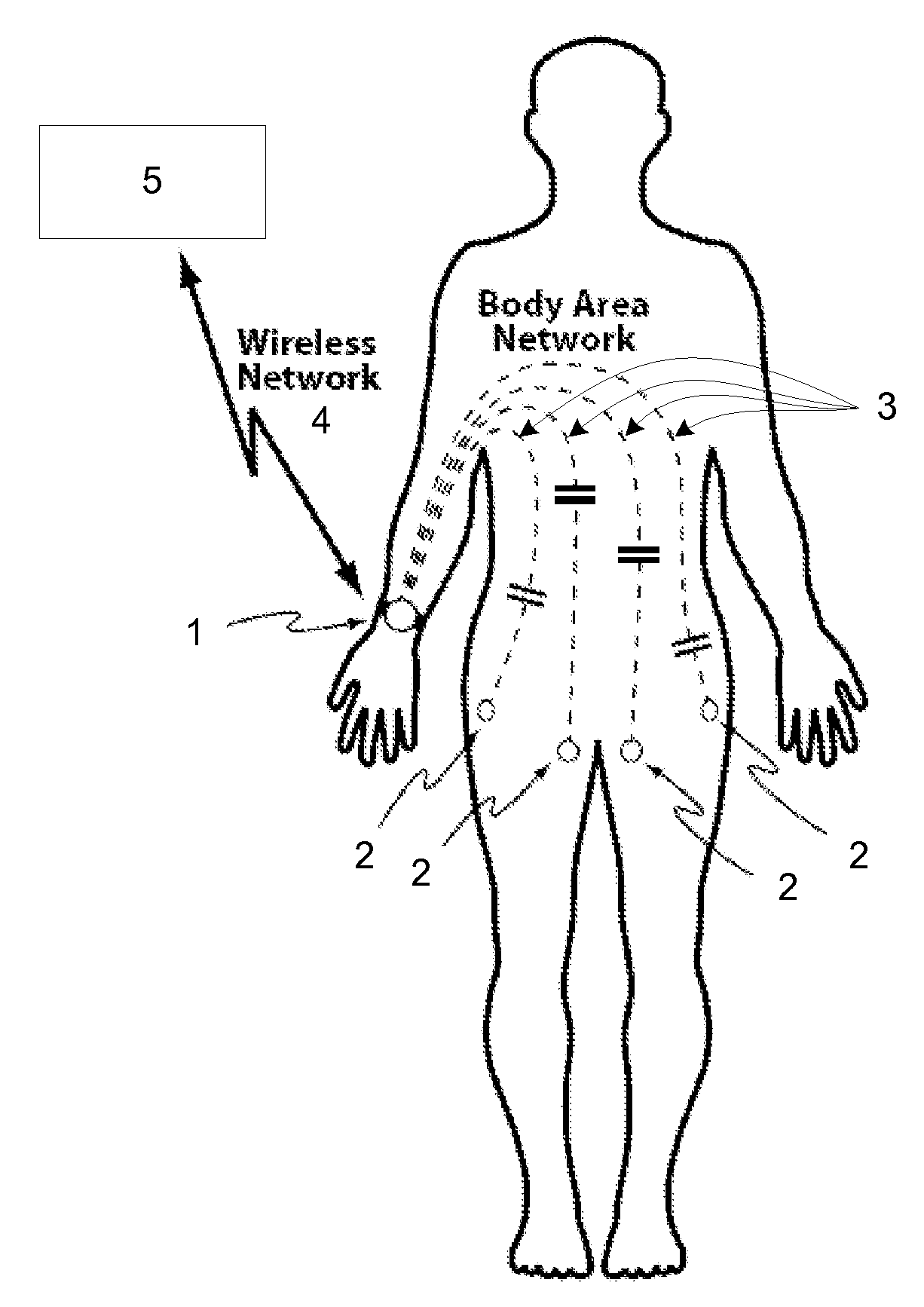
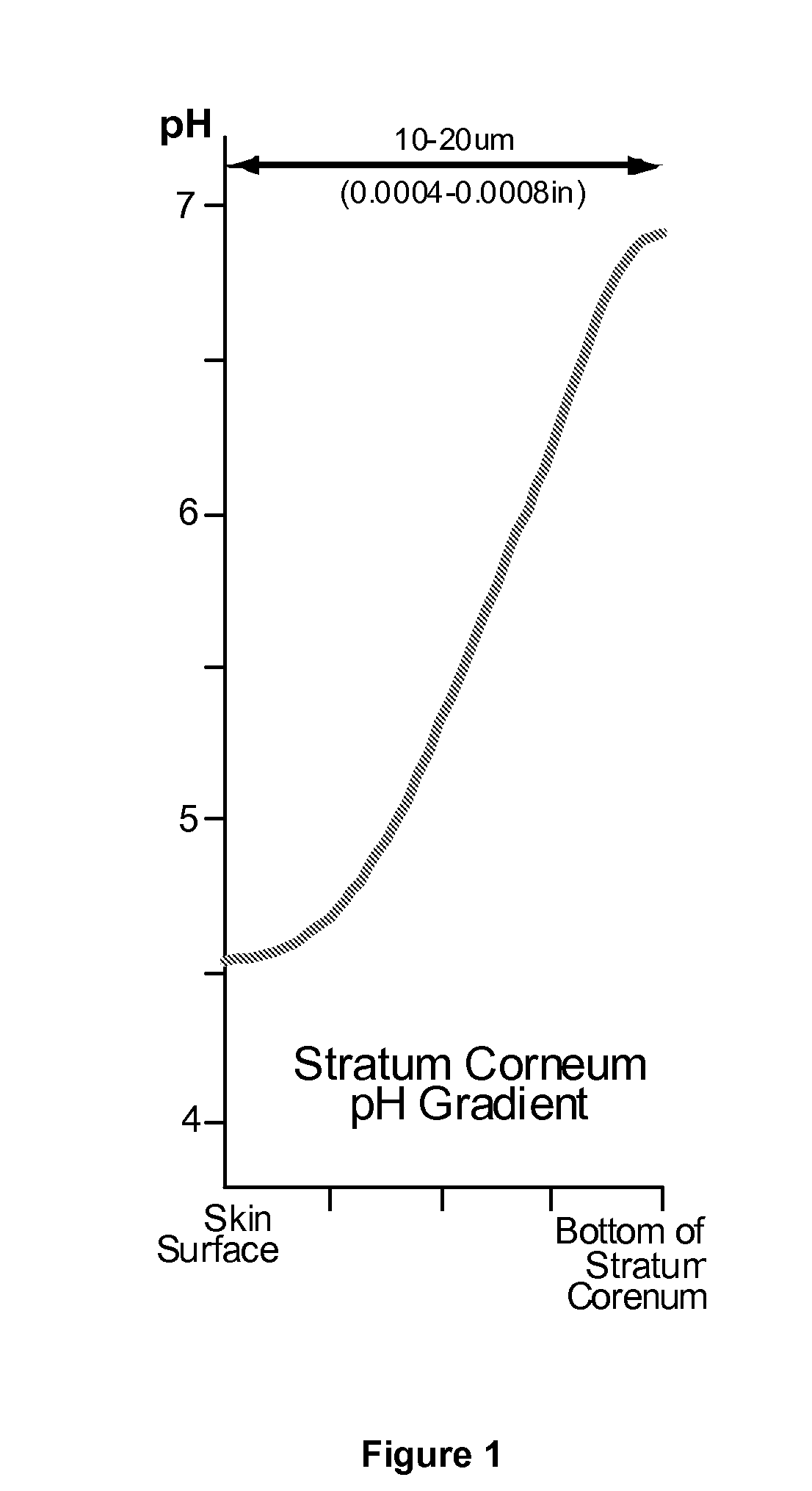
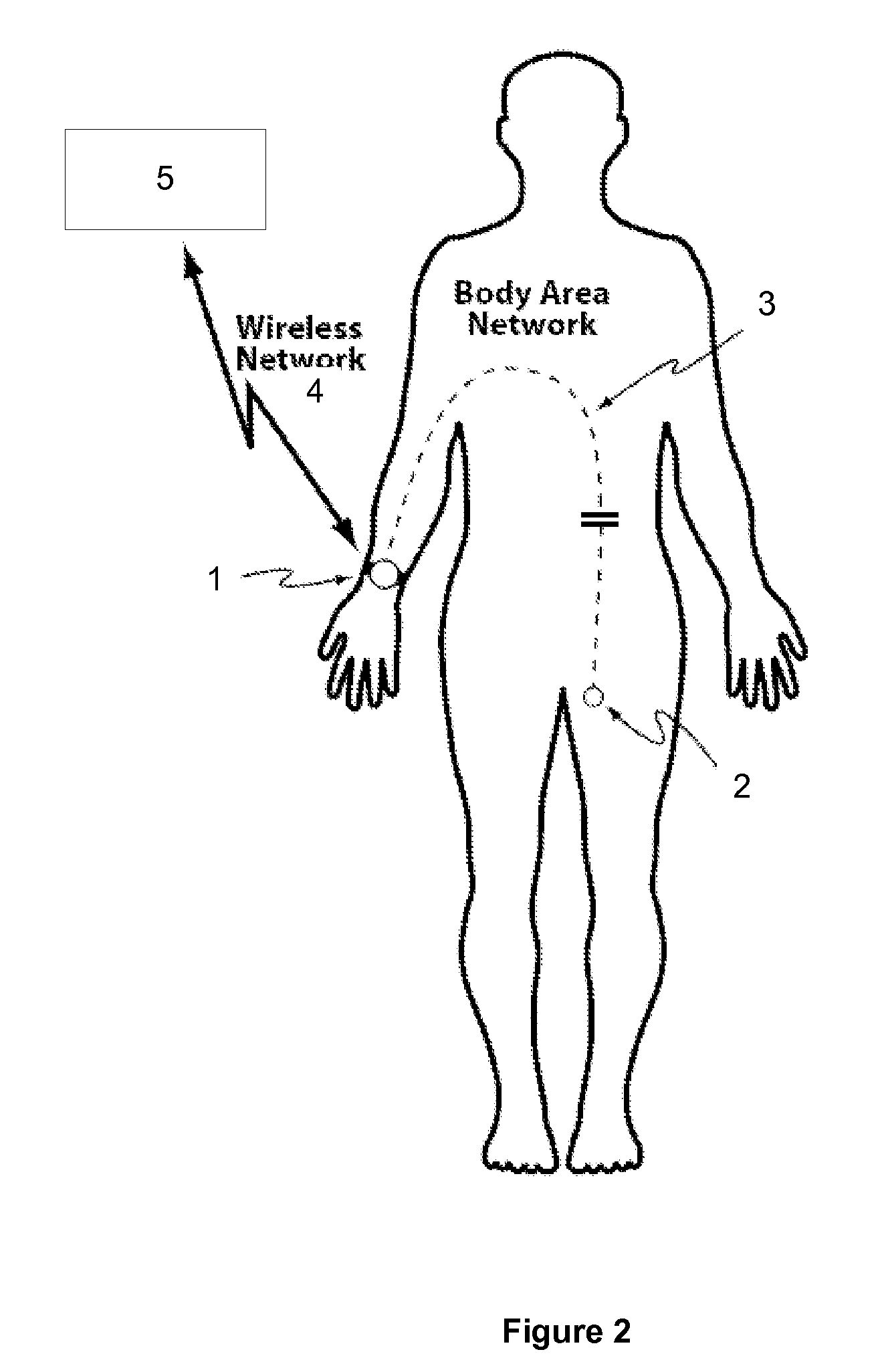
Devices and methods for measuring a local skin parameter or the presence or concentration of an analyte present in a biological medium are disclosed. A monitoring system comprising disposable sensor components and a network component for the collection of sensor information and for relaying this information for remote access and analysis is disclosed, where the sensor components and the network component communicate using the wearer as a signal propagation medium.
Owner:PROACTIVE HEALTH DEVICES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com