Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10554 results about "Data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data security means protecting digital data, such as those in a database, from destructive forces and from the unwanted actions of unauthorized users, such as a cyberattack or a data breach.
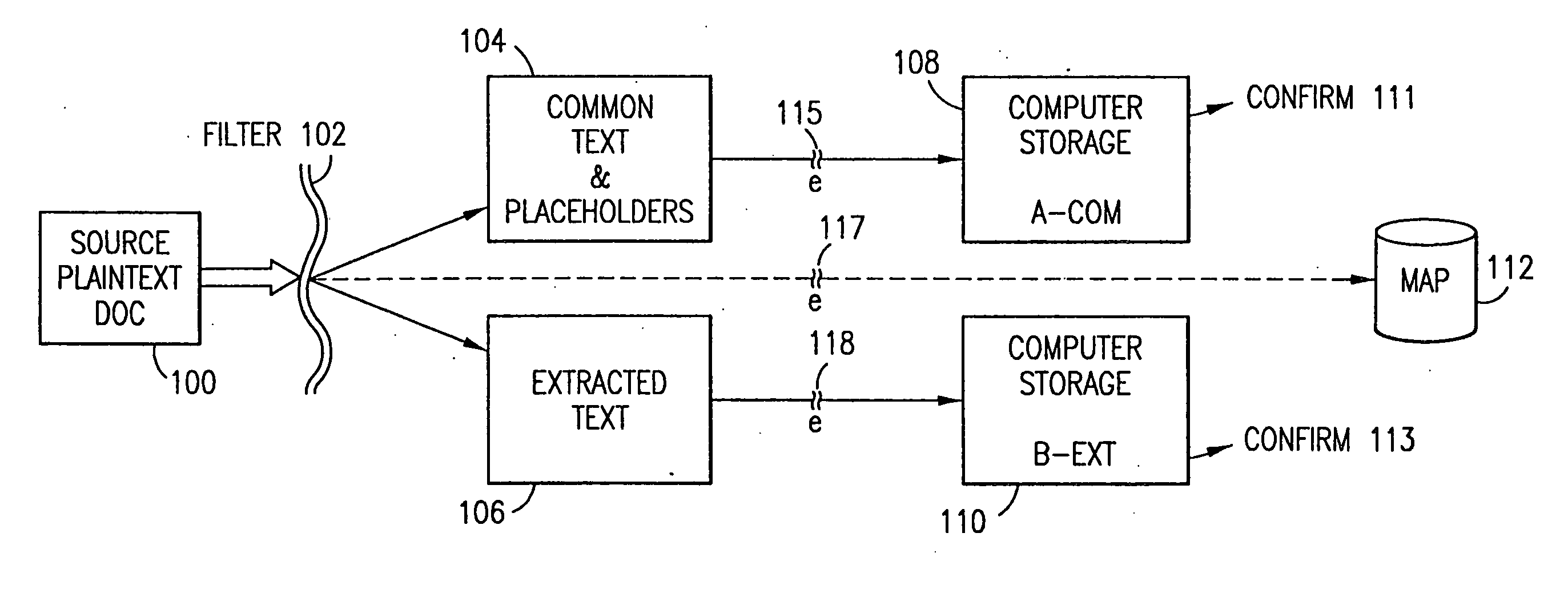
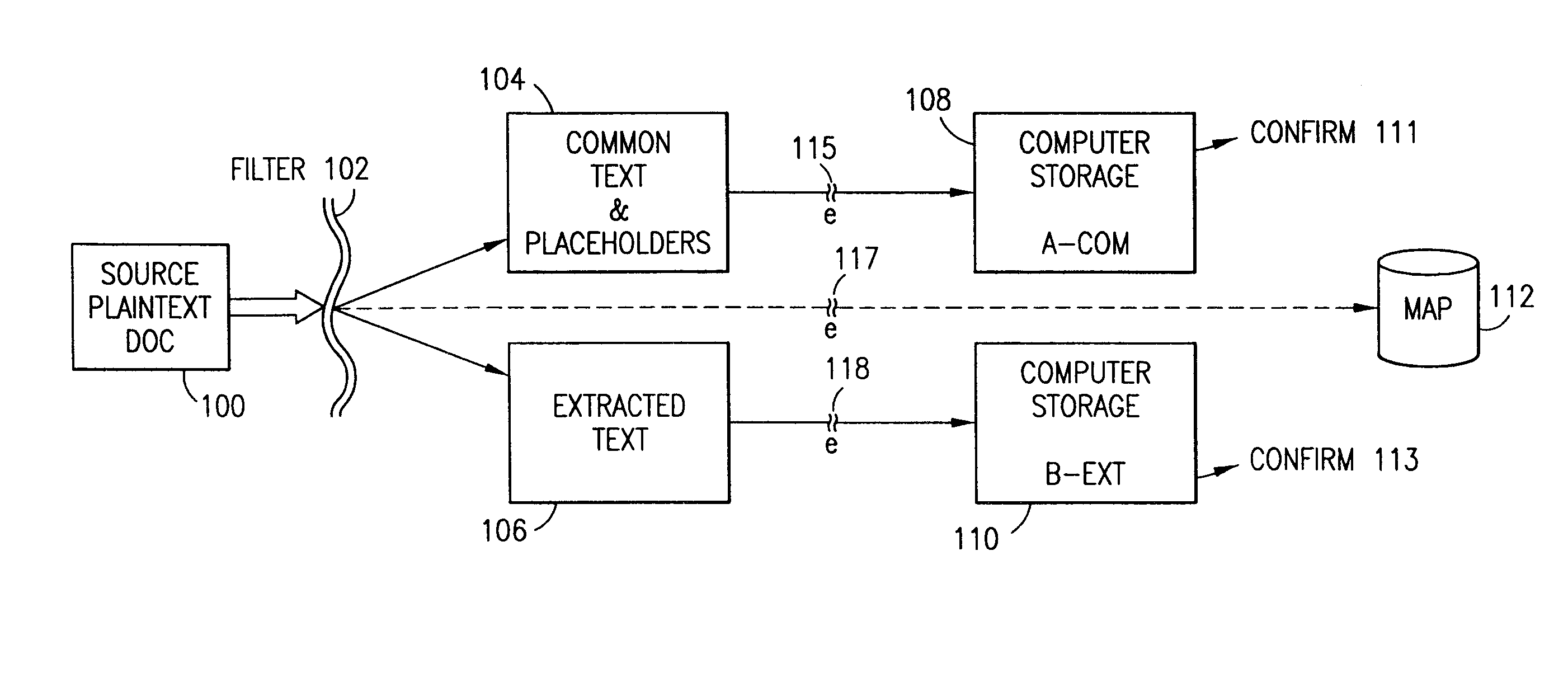
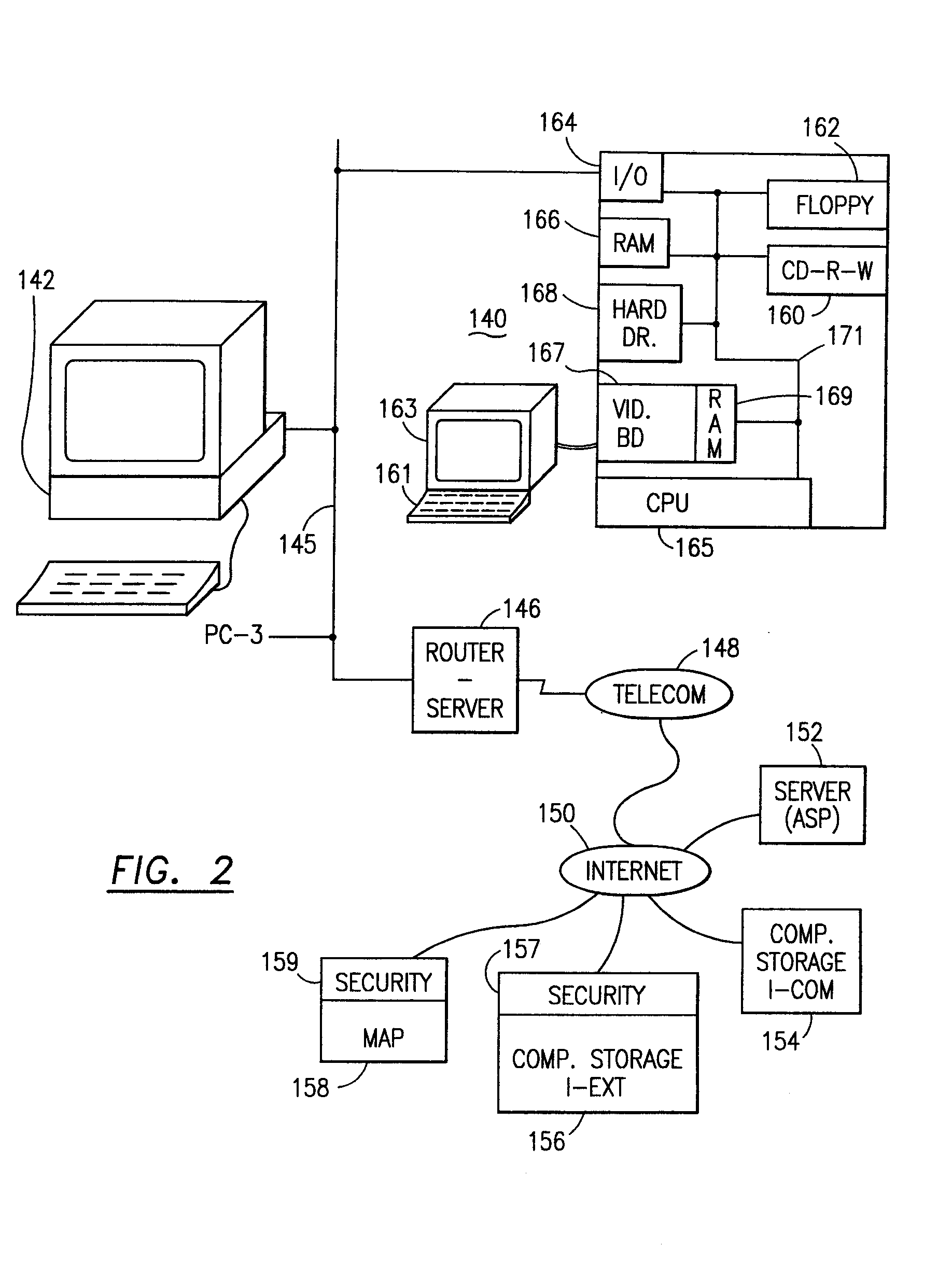
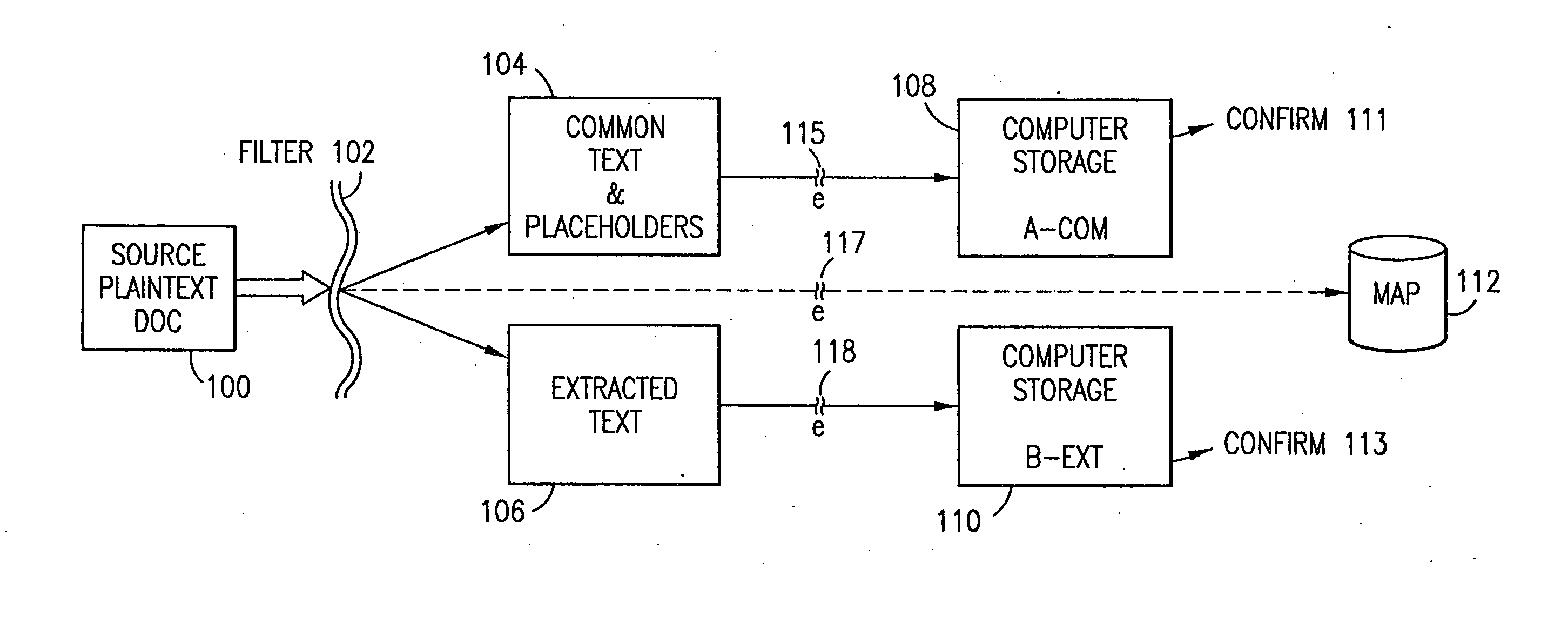
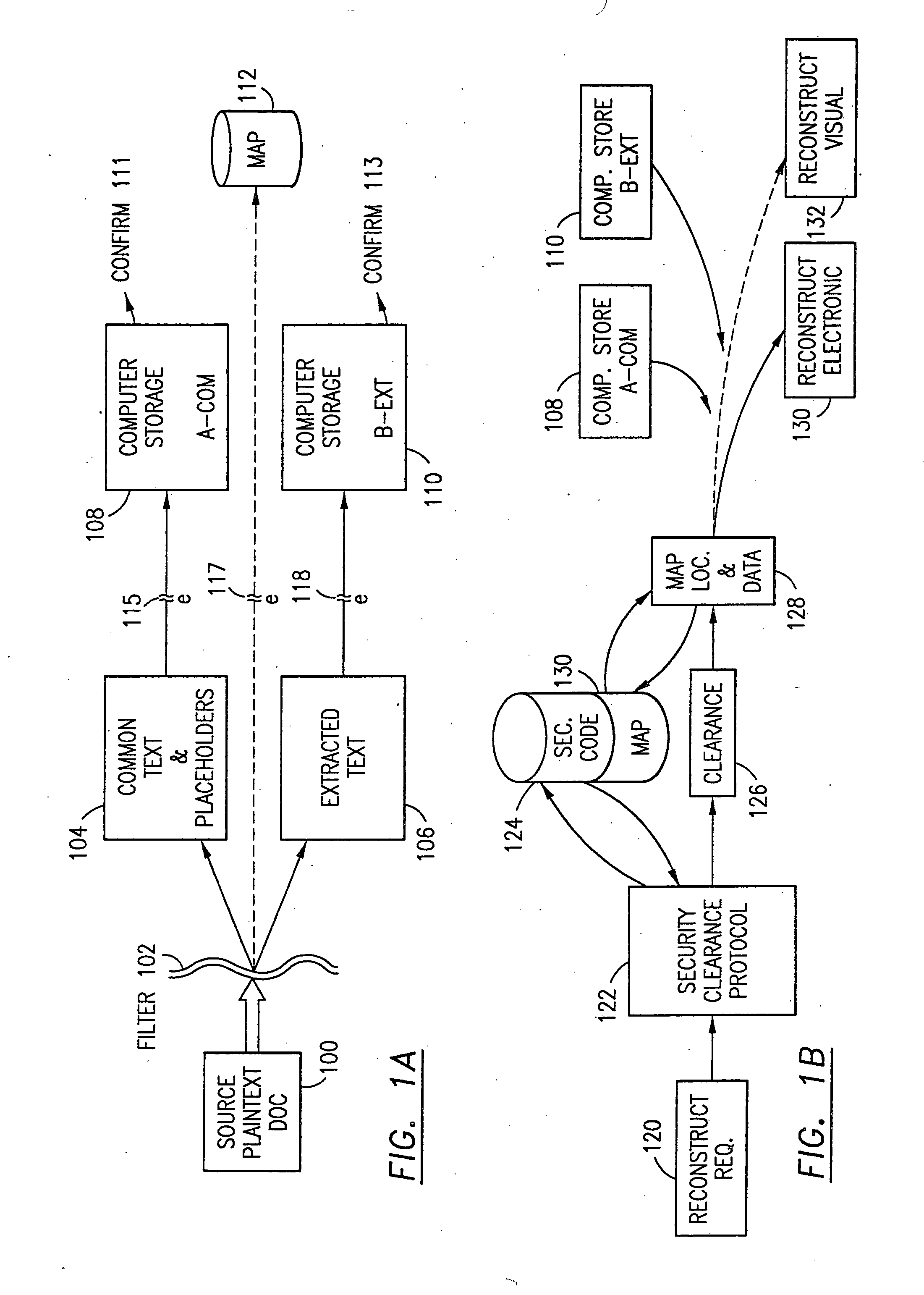
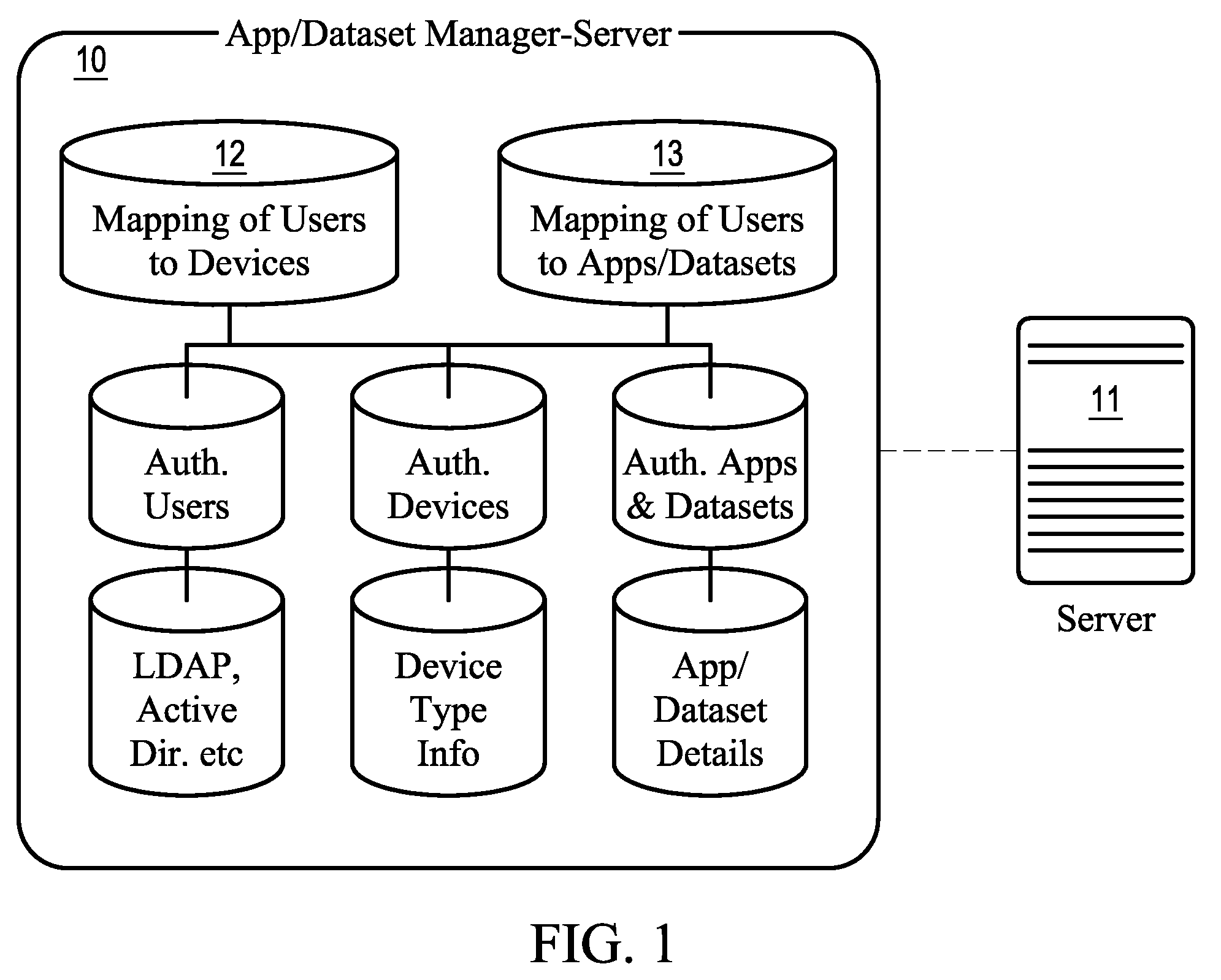
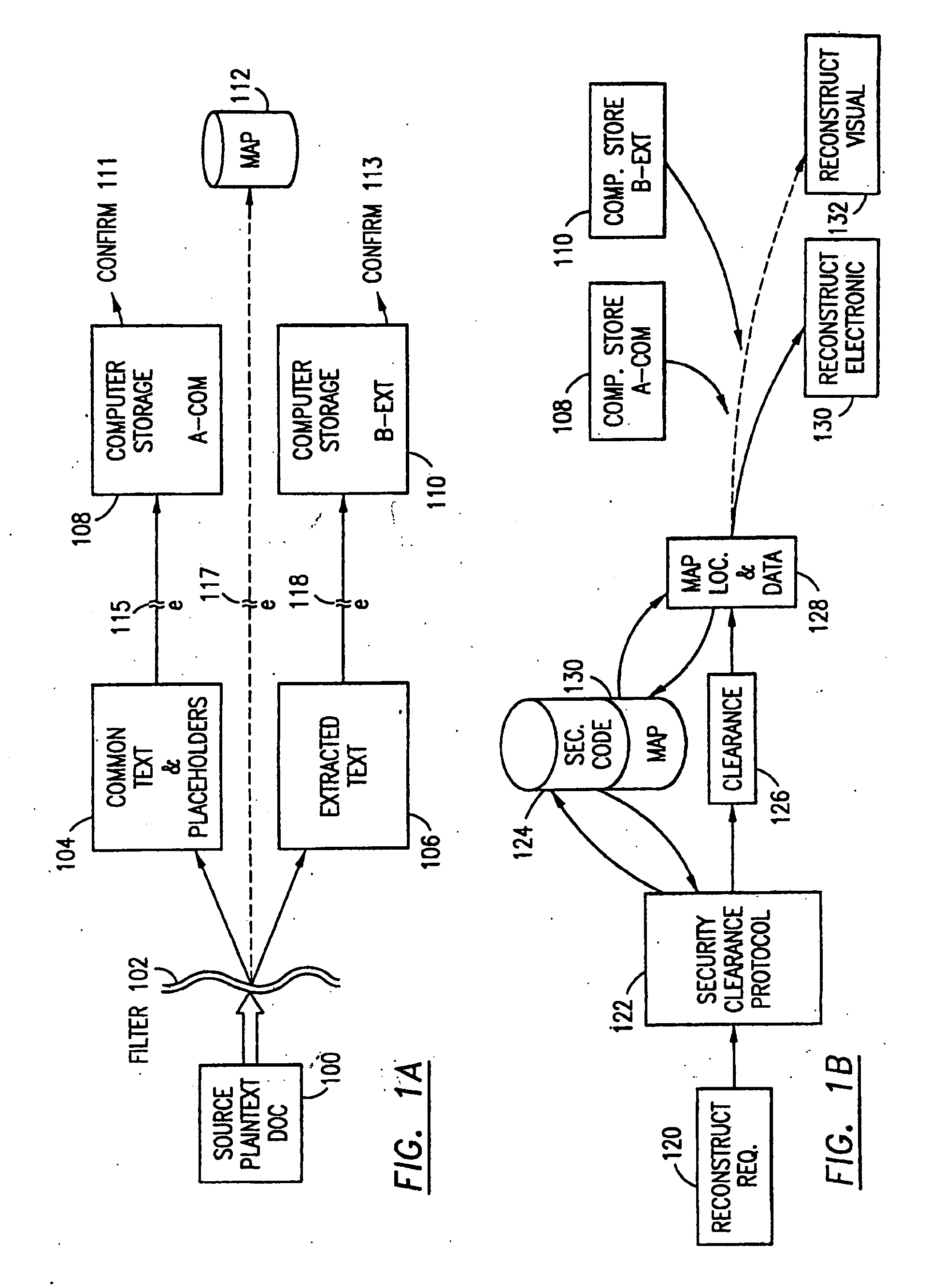
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
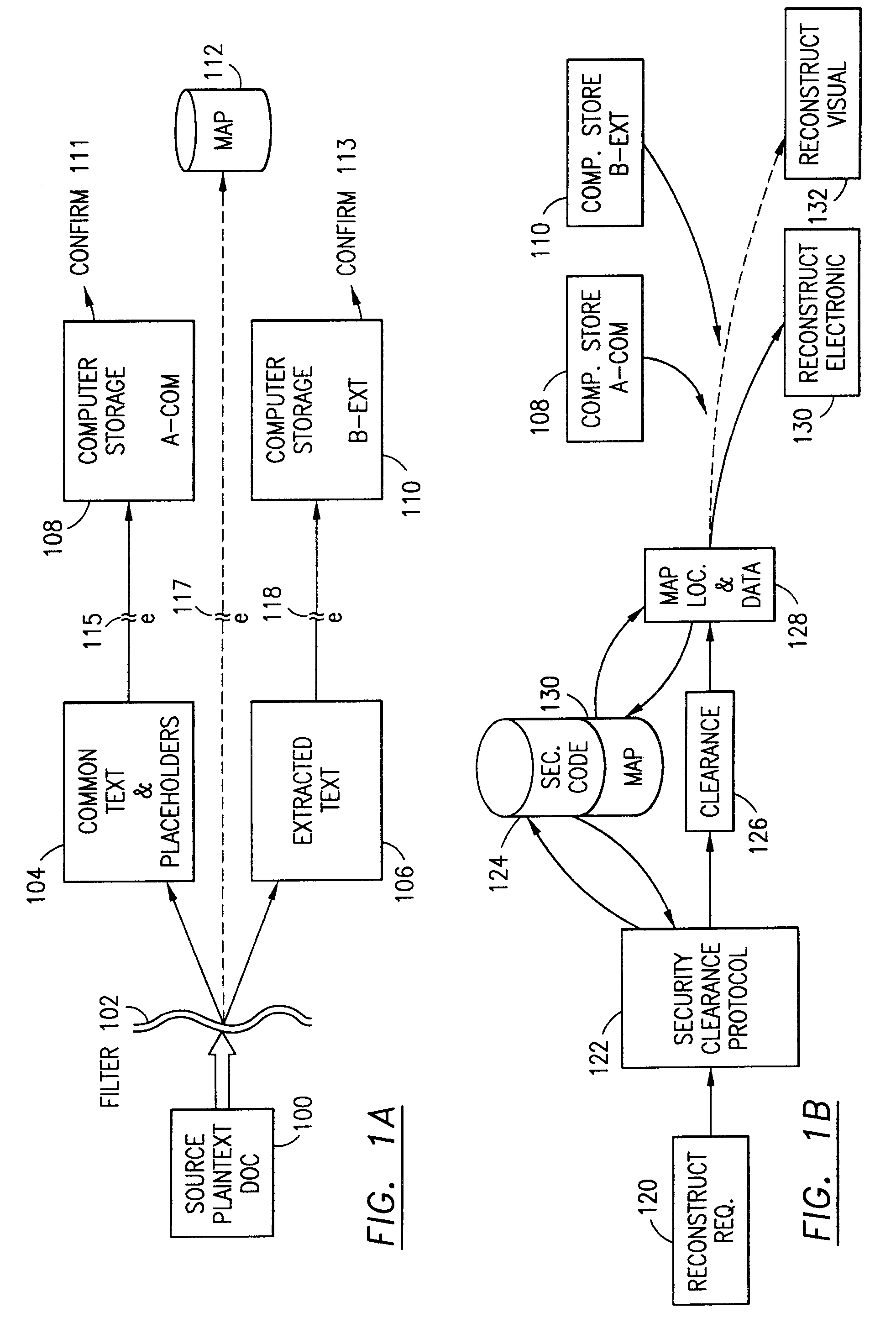
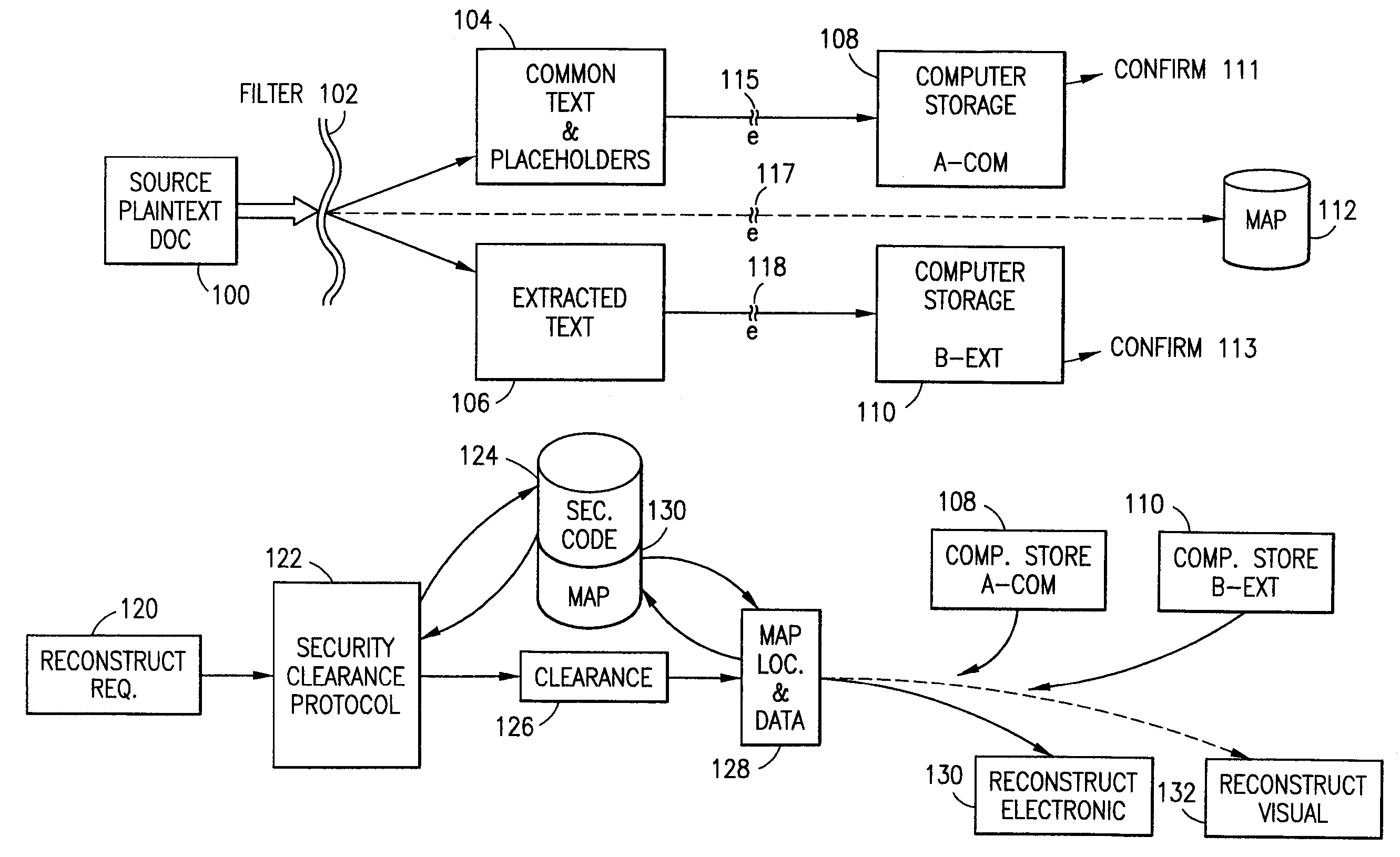
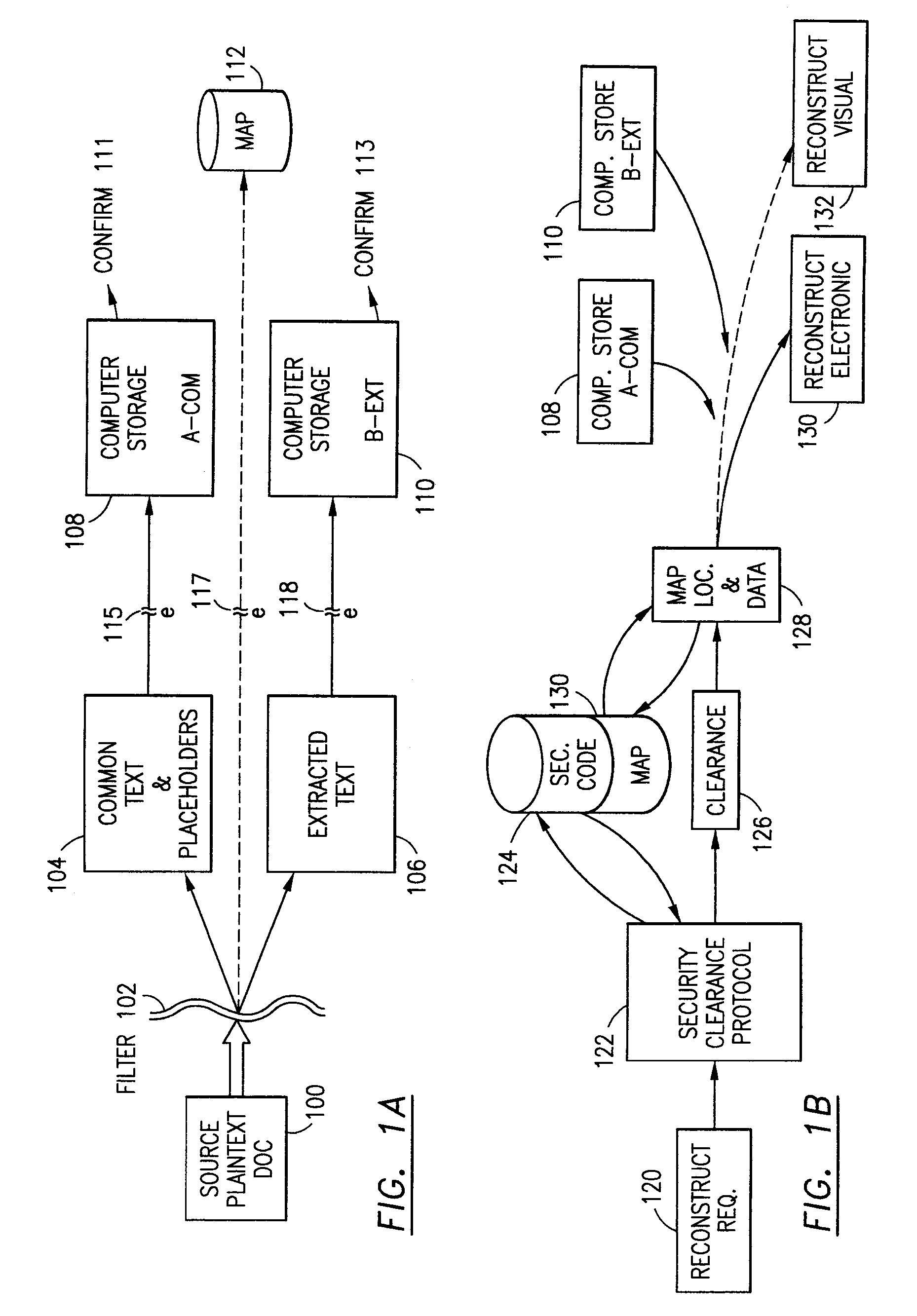
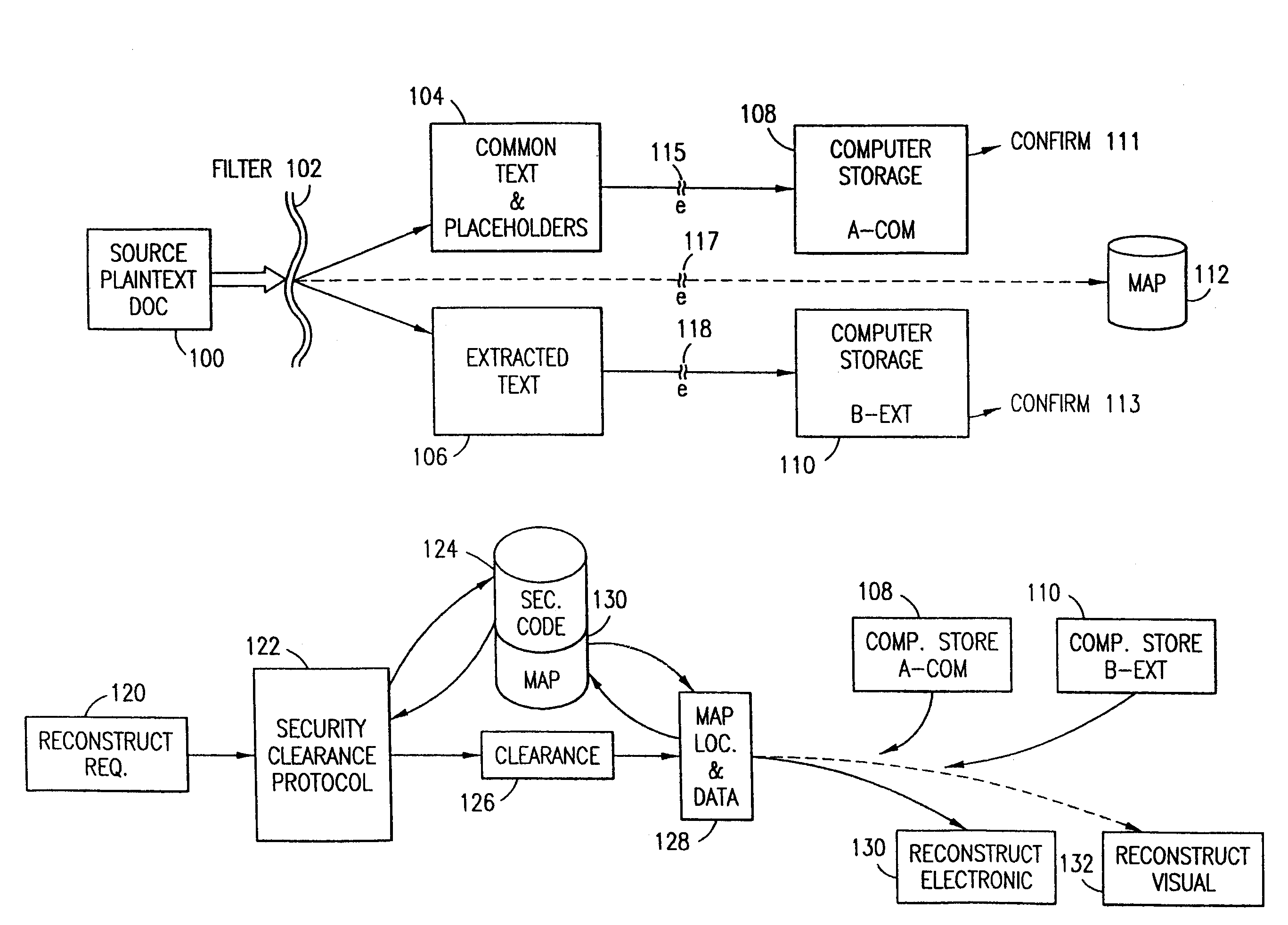
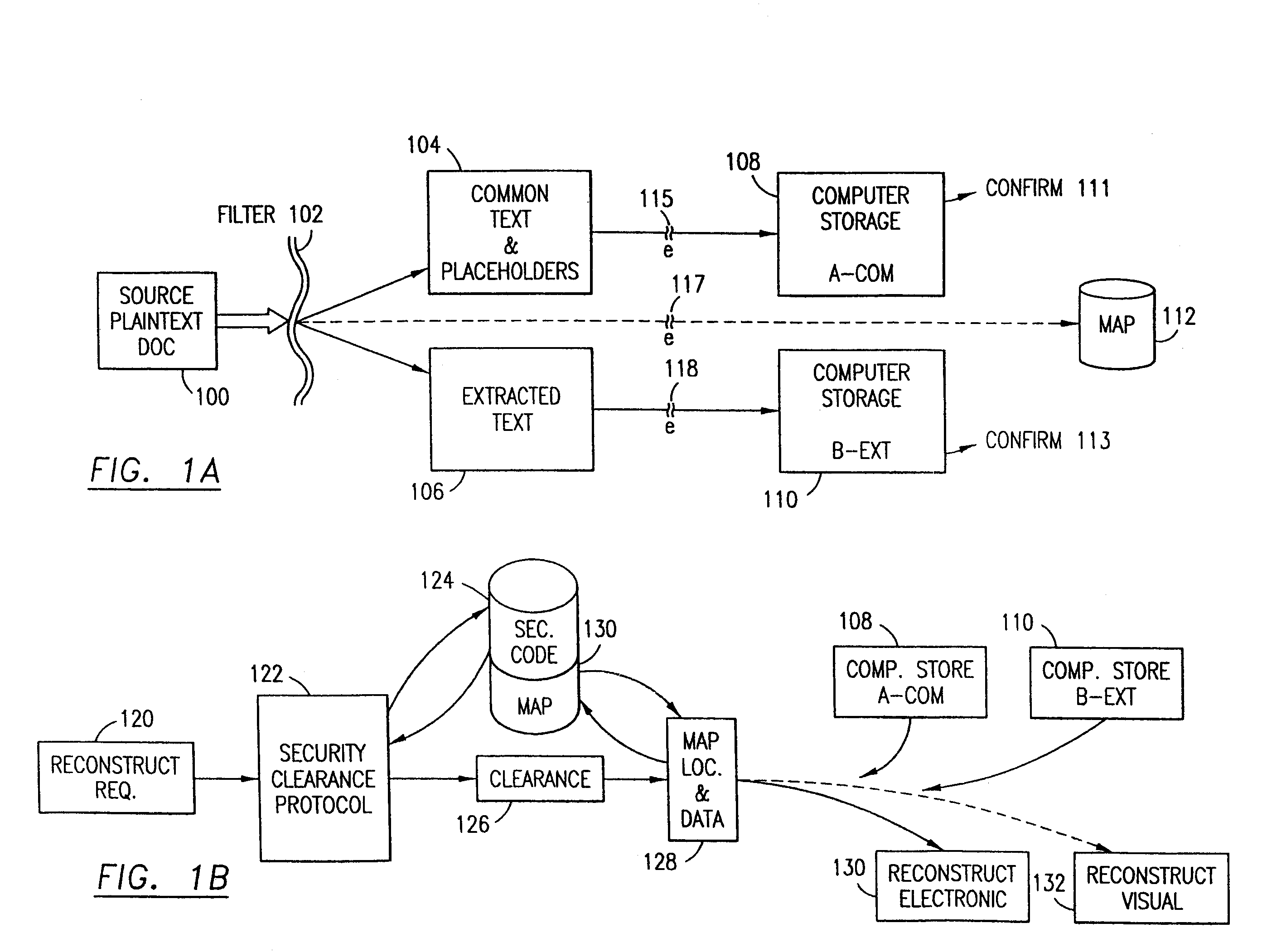
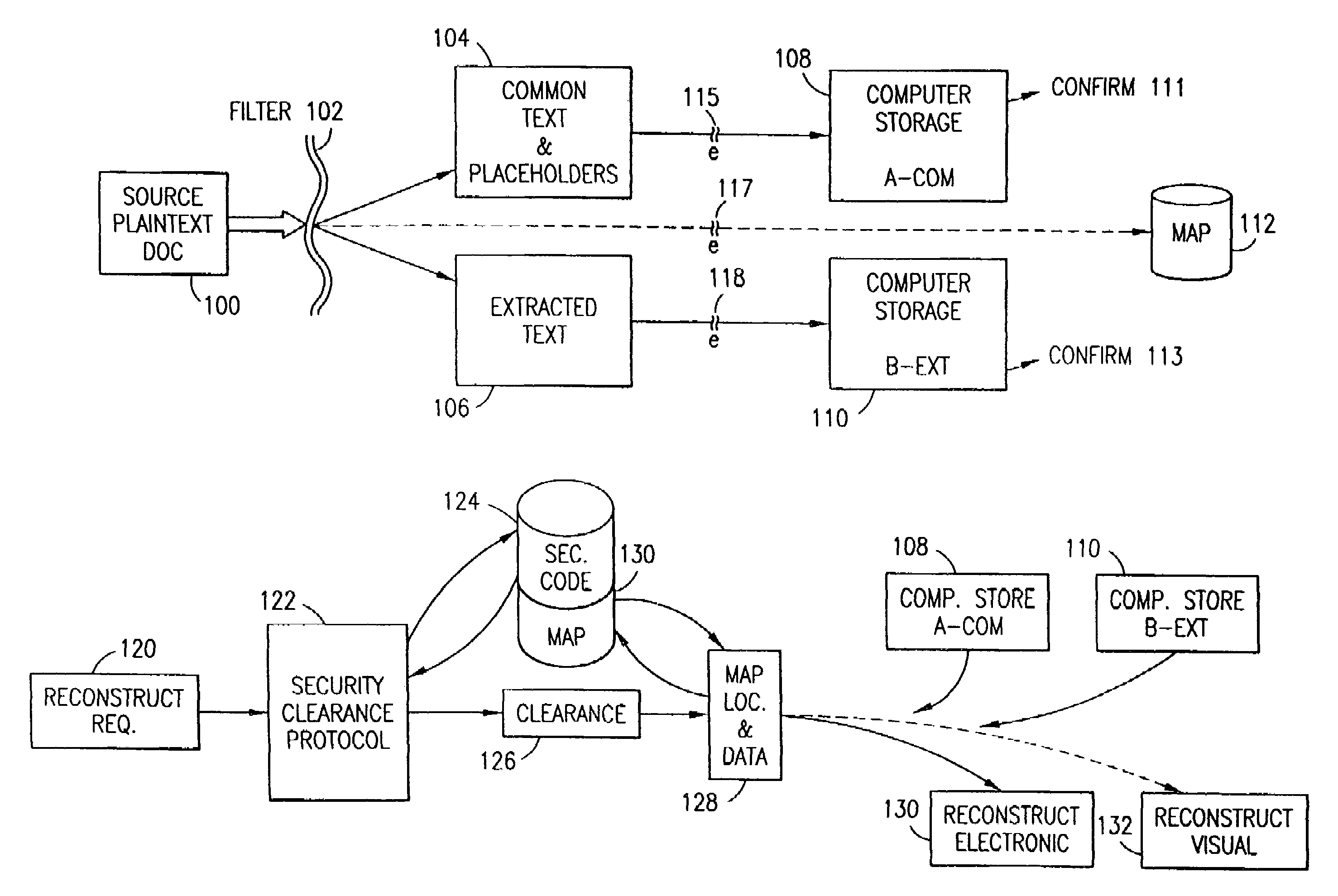
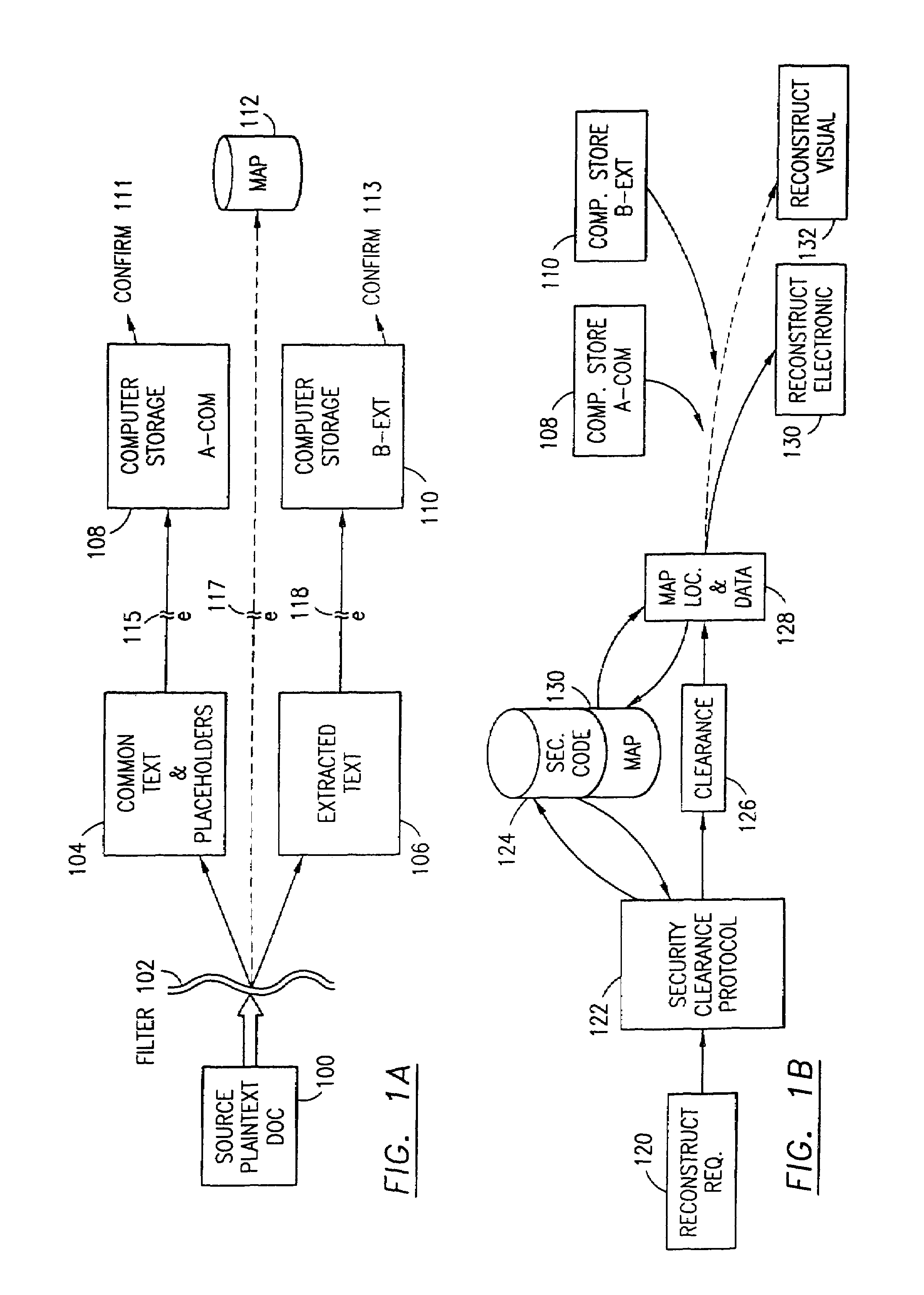
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
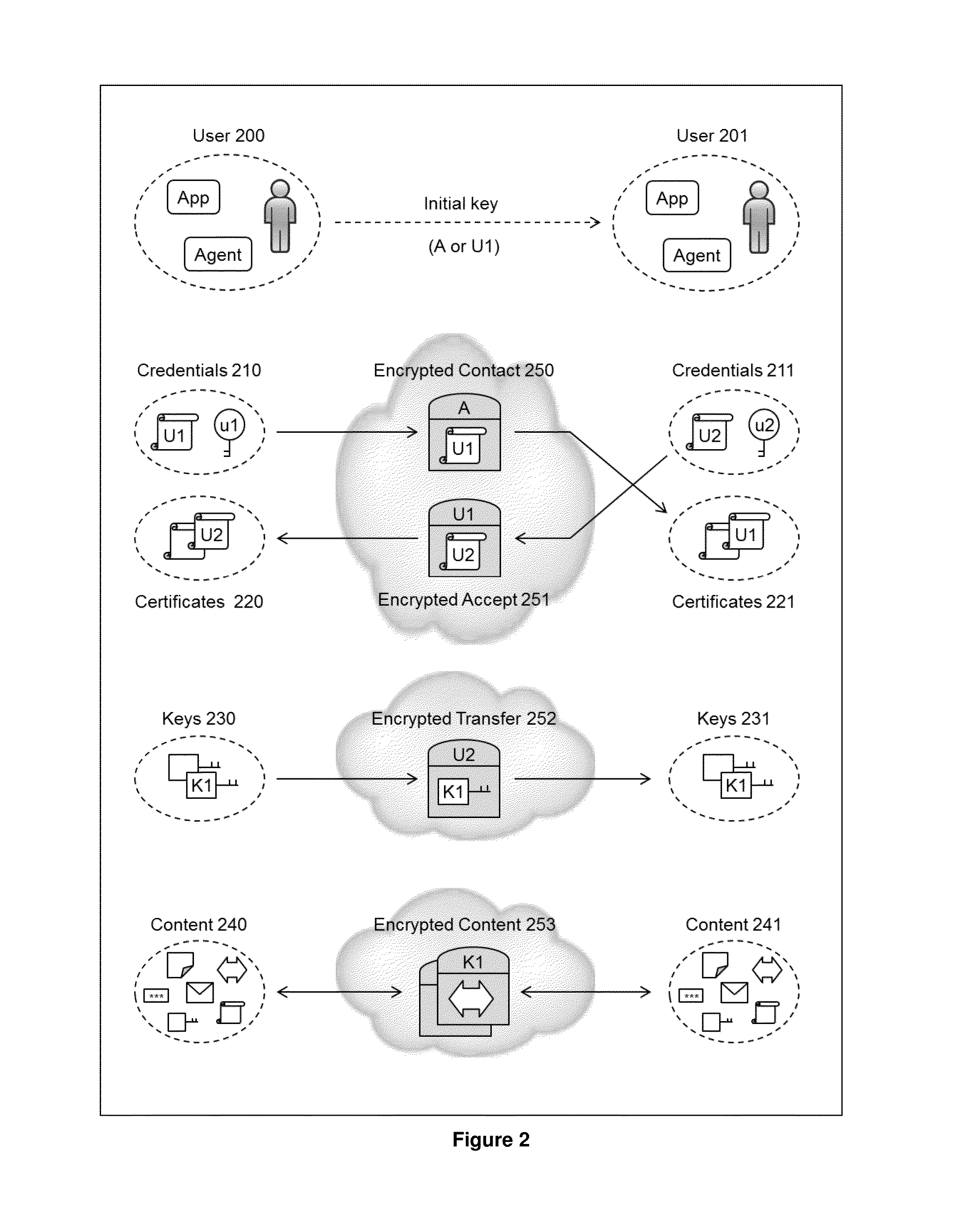
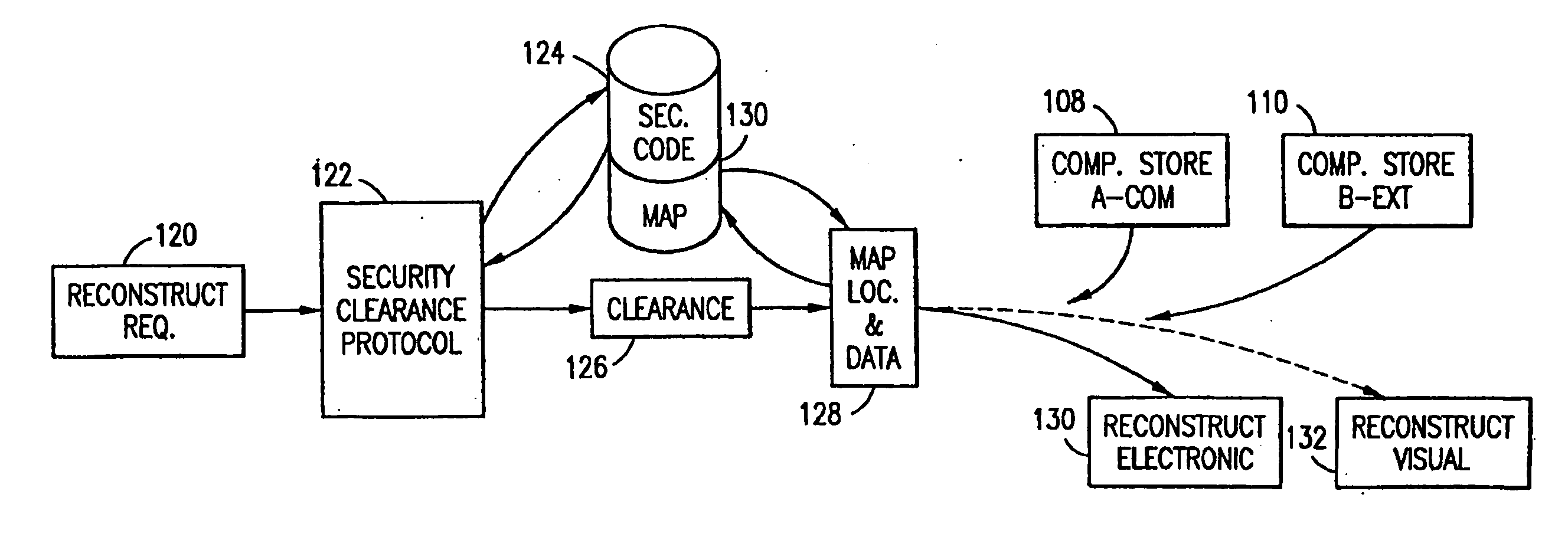
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
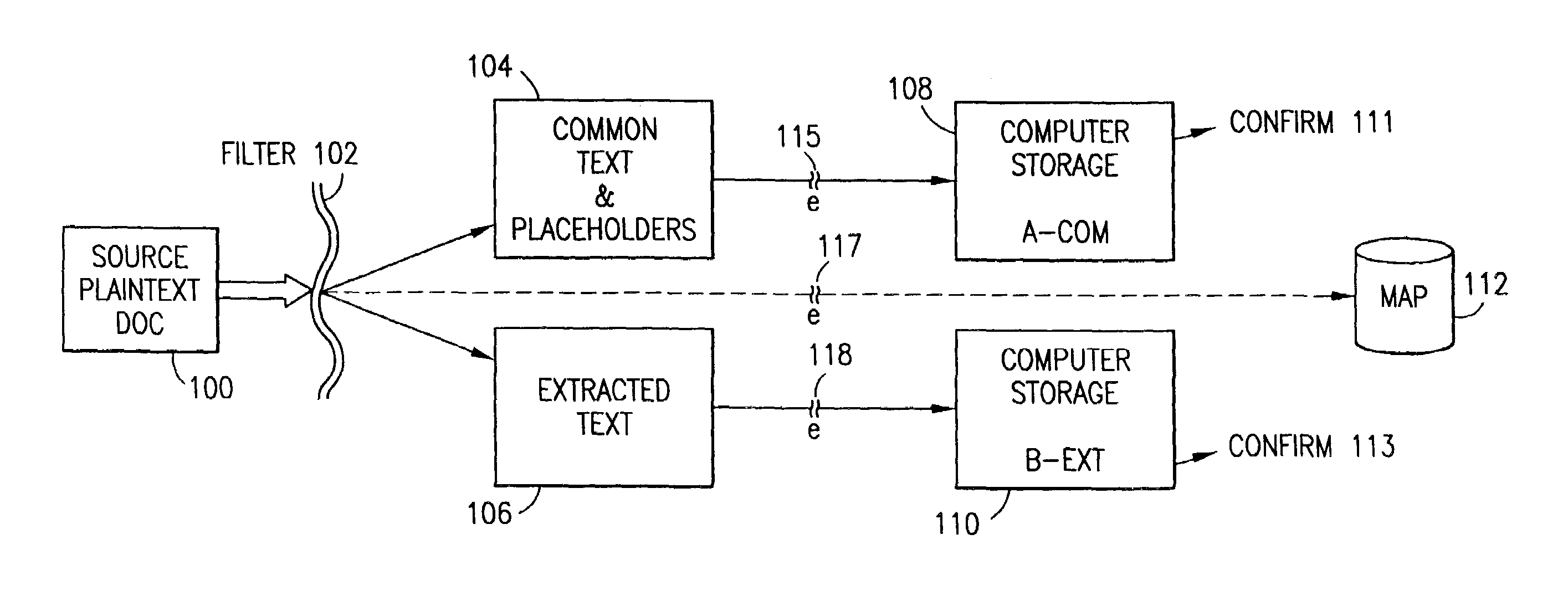
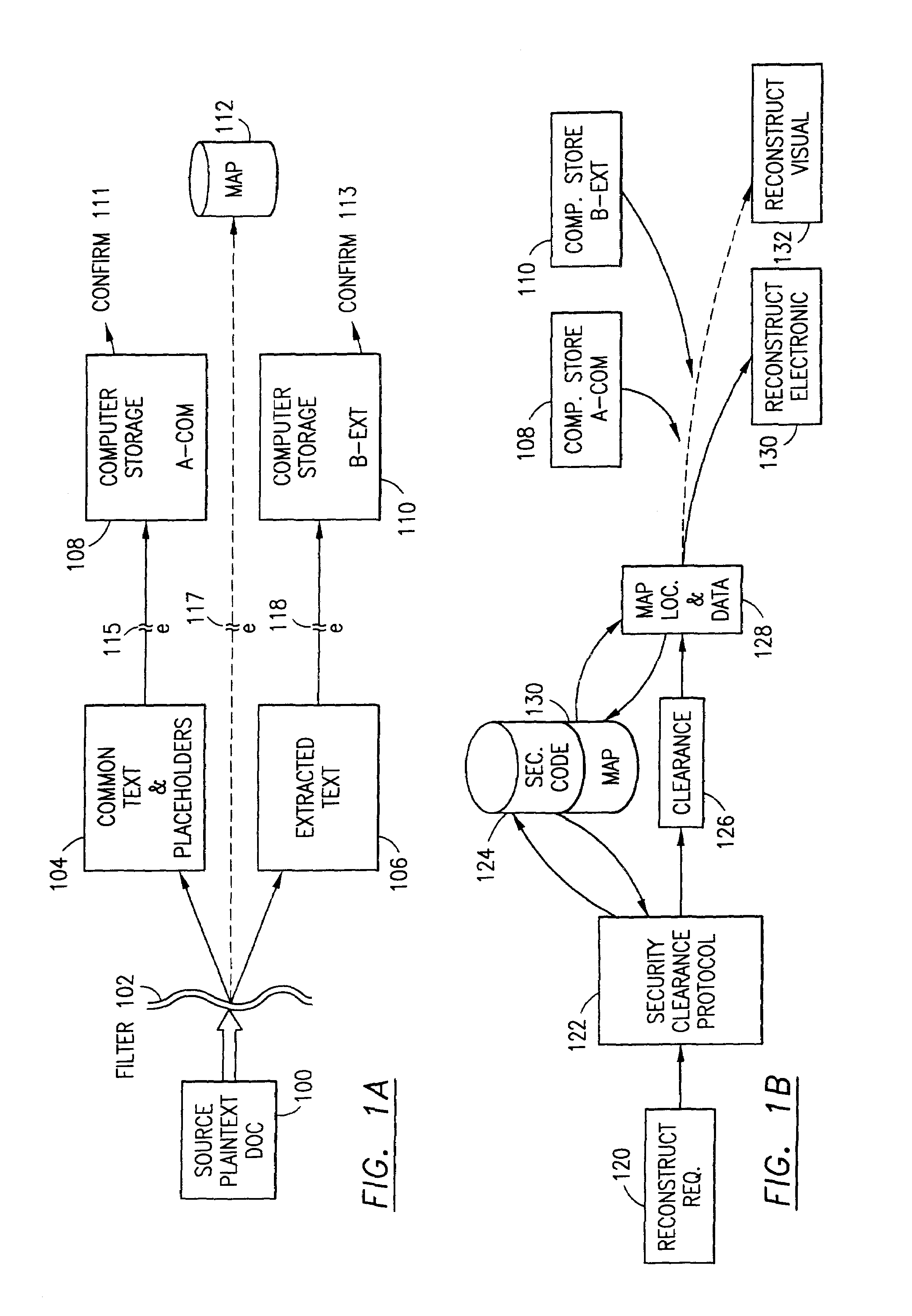
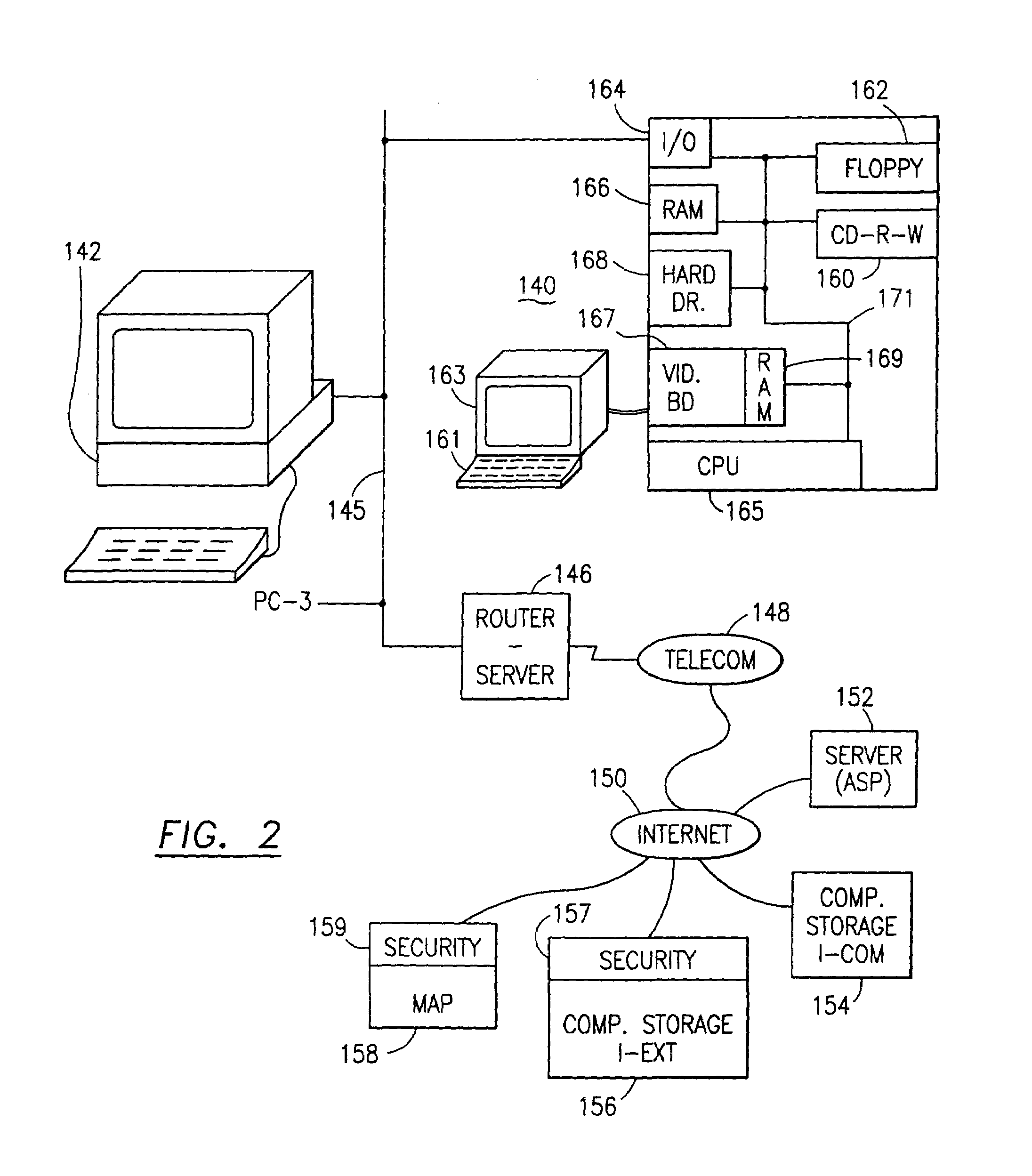
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
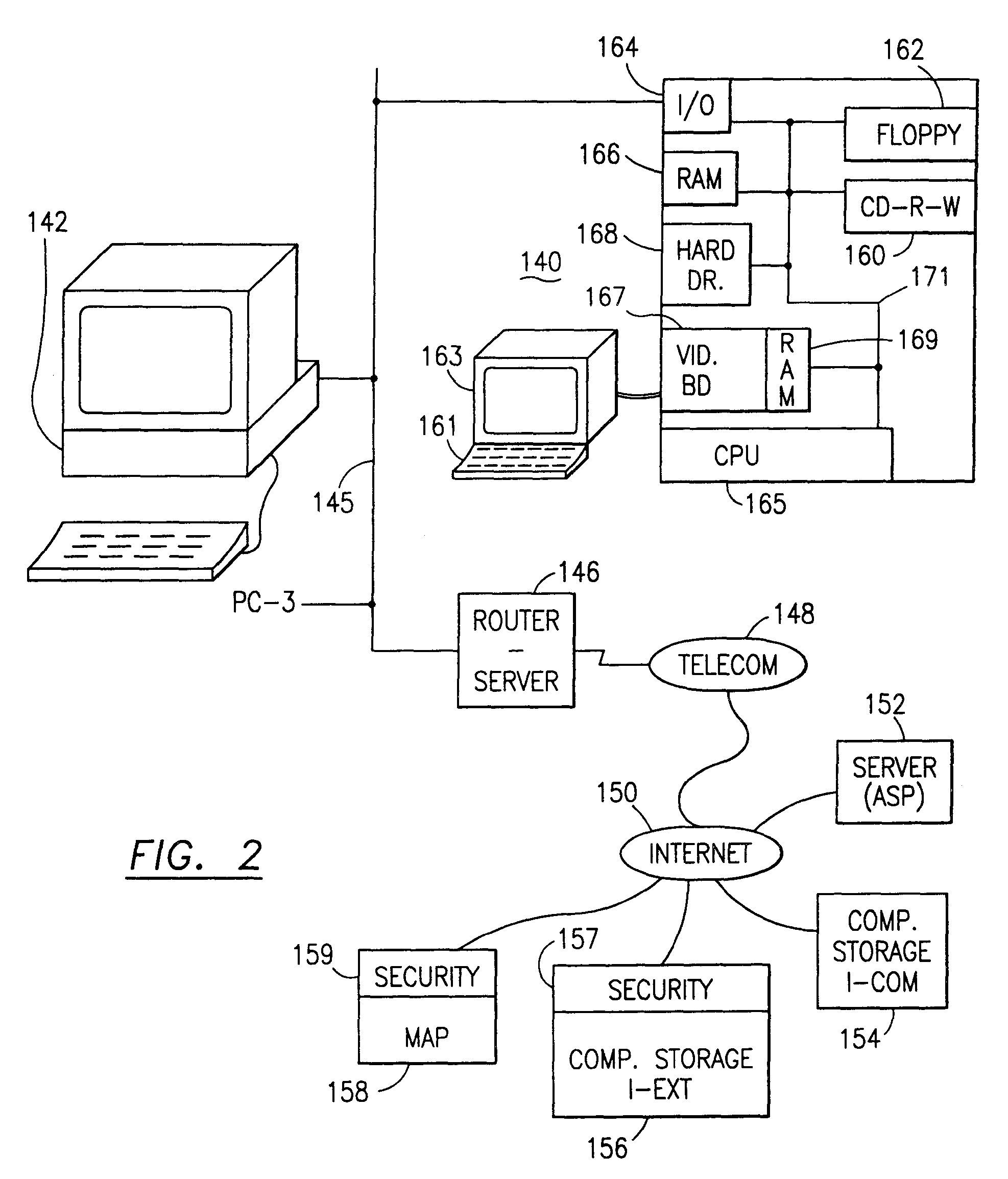
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
Methods and entities using IPSec ESP to support security functionality for UDP-based traffic
ActiveUS8639936B2Improve efficiencyOptimize procedureUser identity/authority verificationComputer security arrangementsTraffic capacityIPsec
Owner:ALCATEL LUCENT SAS
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
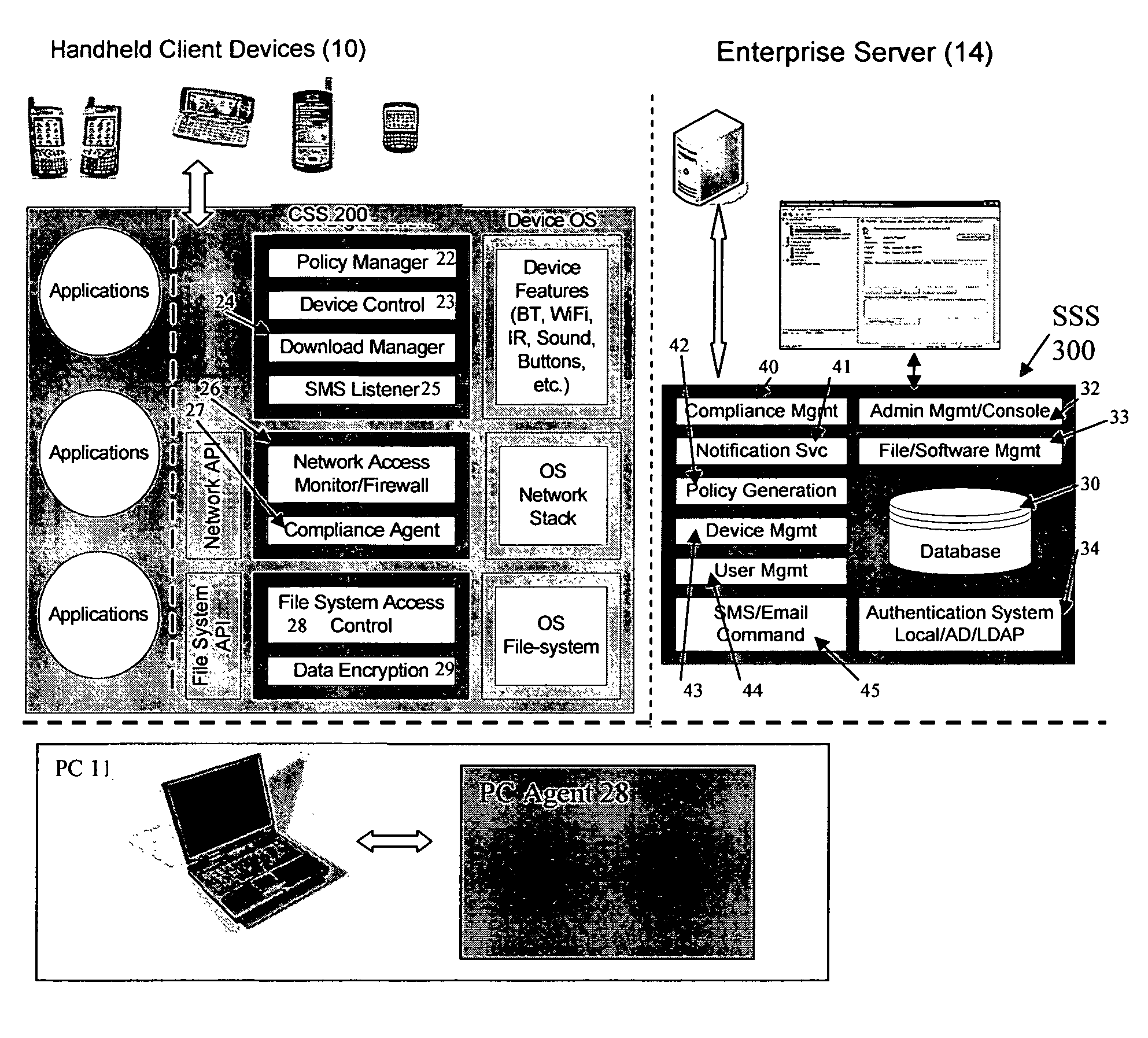
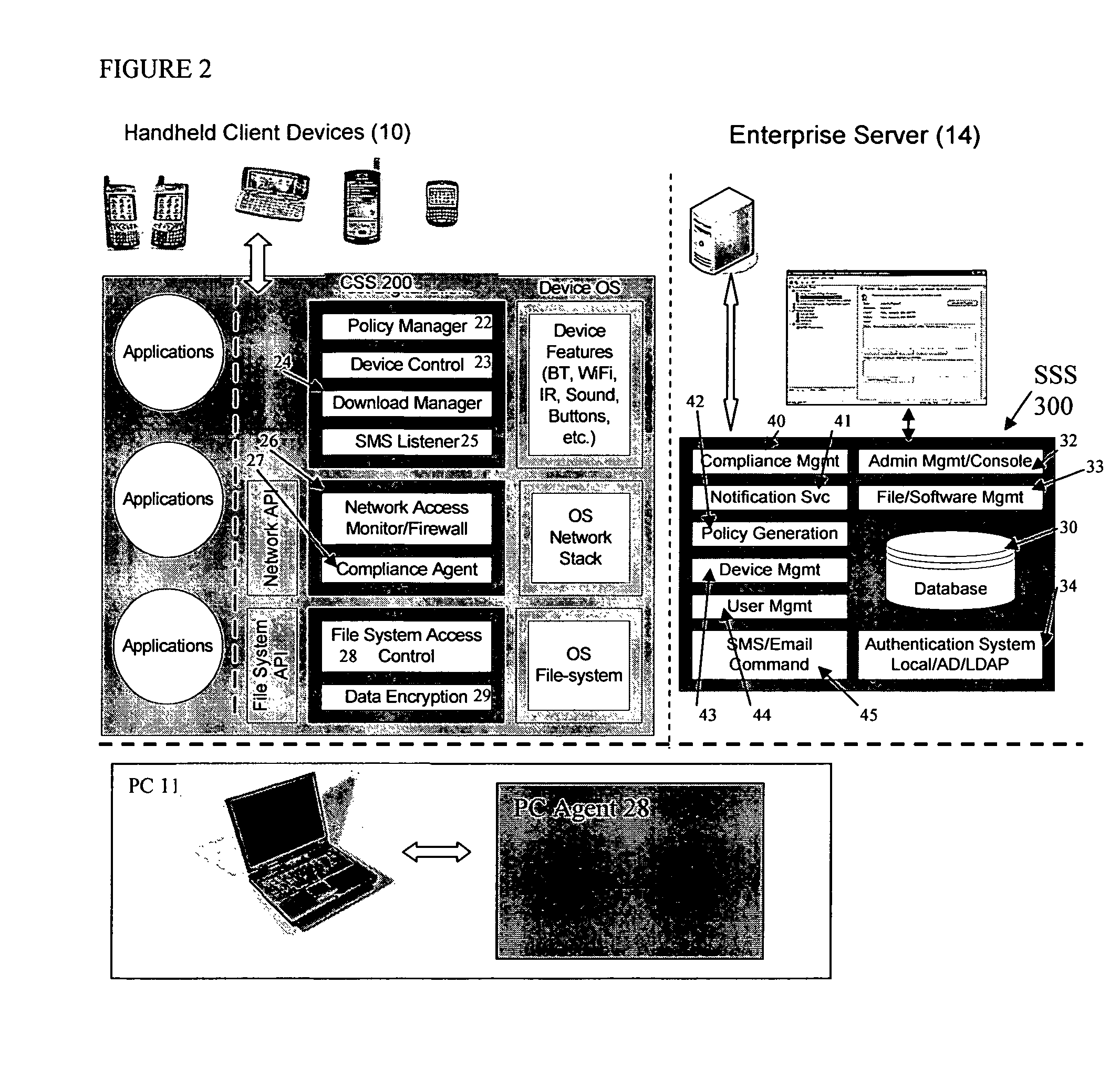
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
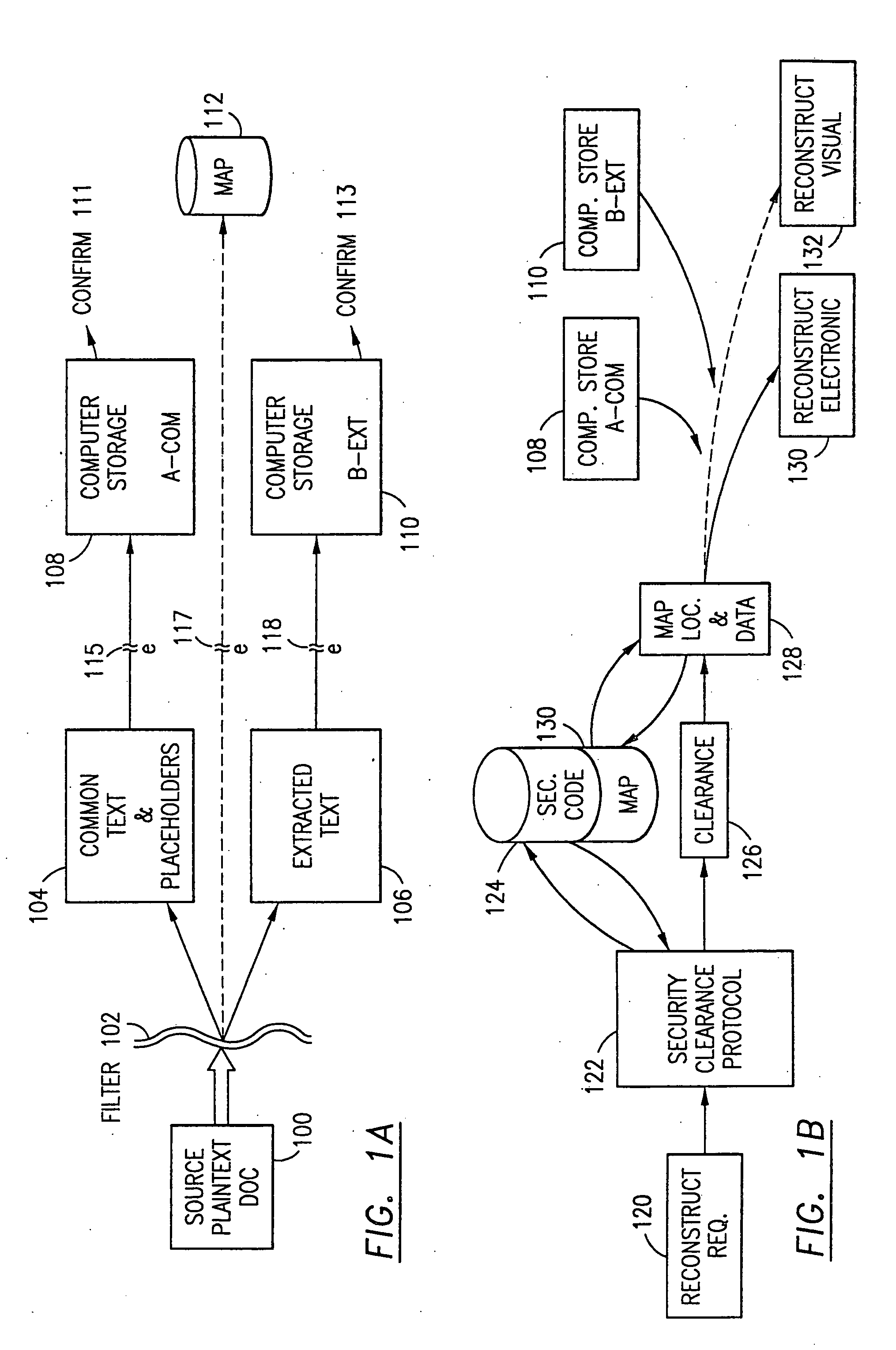
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
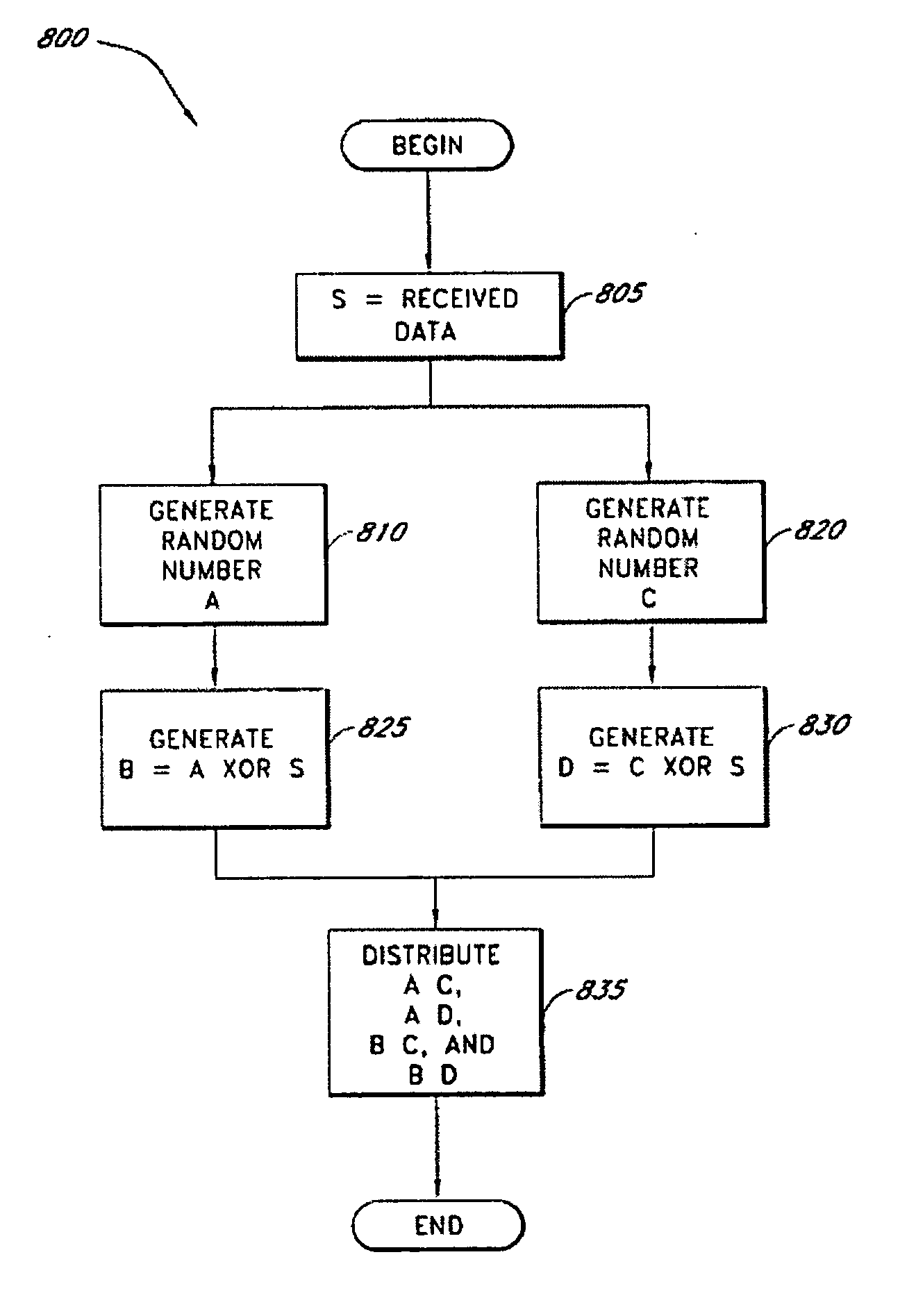
Secure data parser method and system
InactiveUS20060177061A1Minimal compute resourceAvoid the needKey distribution for secure communicationError detection/correctionOriginal dataEncryption
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths.
Owner:SECURITY FIRST INNOVATIONS LLC
Data storage safety indicator and expander
The safety of data stored across distributed storage resources may be dynamically monitored and indicated to the user. Monitoring may occur in real time and / or in response to changes in the stored data. The notification may be in the form of, e.g., a visual indicator that appears in the taskbar of a graphical user interface of an operating system. The indicator may be presented in a particular color or having some other visual property associated with the particular data safety state. In addition, the user may be provided with a convenient way of obtaining additional storage resources. Upon automatically detecting that storage is running low, the user may be presented with a user interface that offers the user a way to easily add to the existing storage. For example, the user may be directed to a predefined Internet web site that is known to offer such additional storage.
Owner:MICROSOFT TECH LICENSING LLC
System for providing mobile data security
ActiveUS7917963B2Save bandwidthShorten the timeDigital data processing detailsAnalogue secracy/subscription systemsData setData security
Owner:VAULTUS MOBILE TECH
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
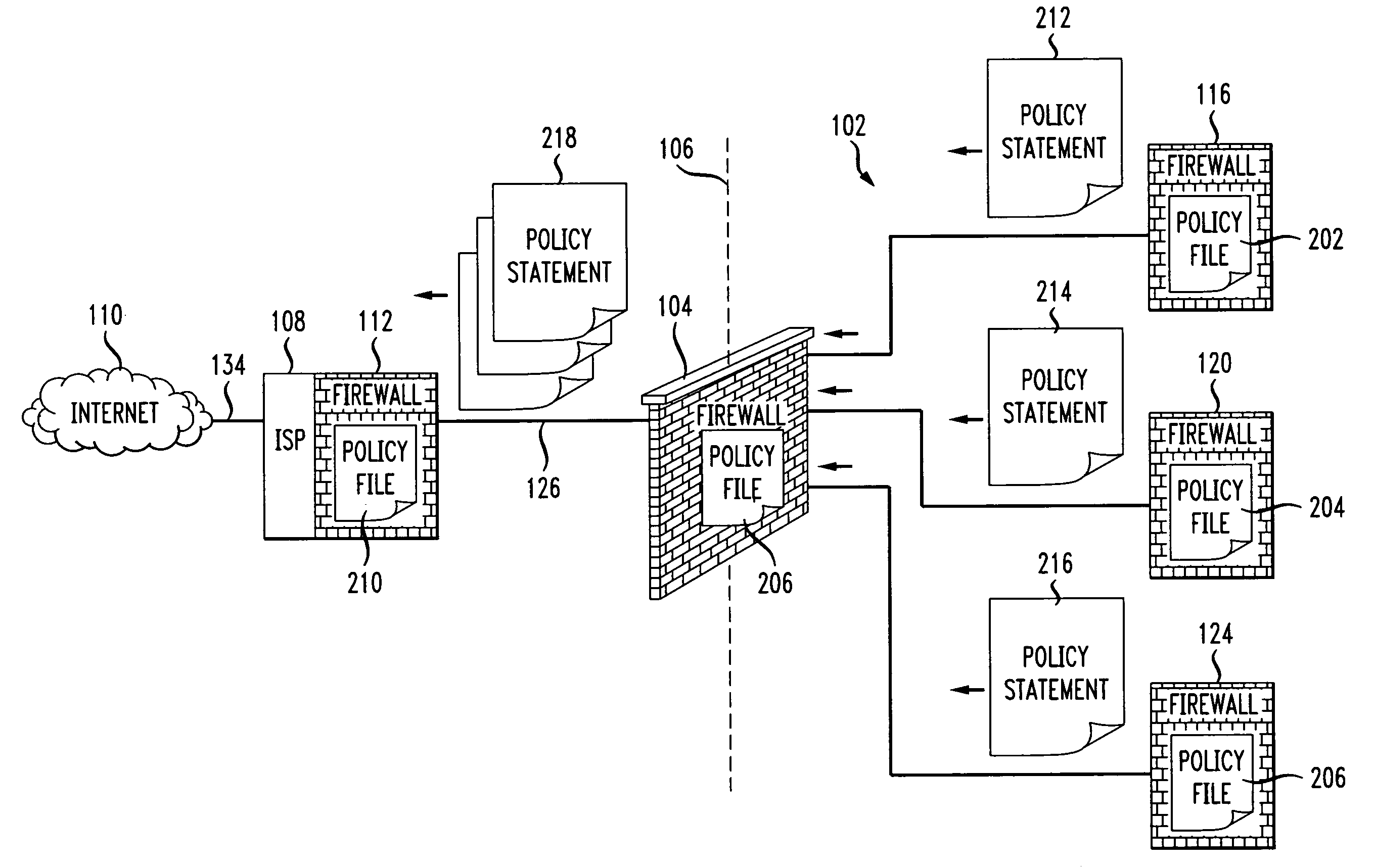
Firewall propagation
InactiveUS20080235755A1Unauthorized memory use protectionHardware monitoringSecurity ruleSecurity policy
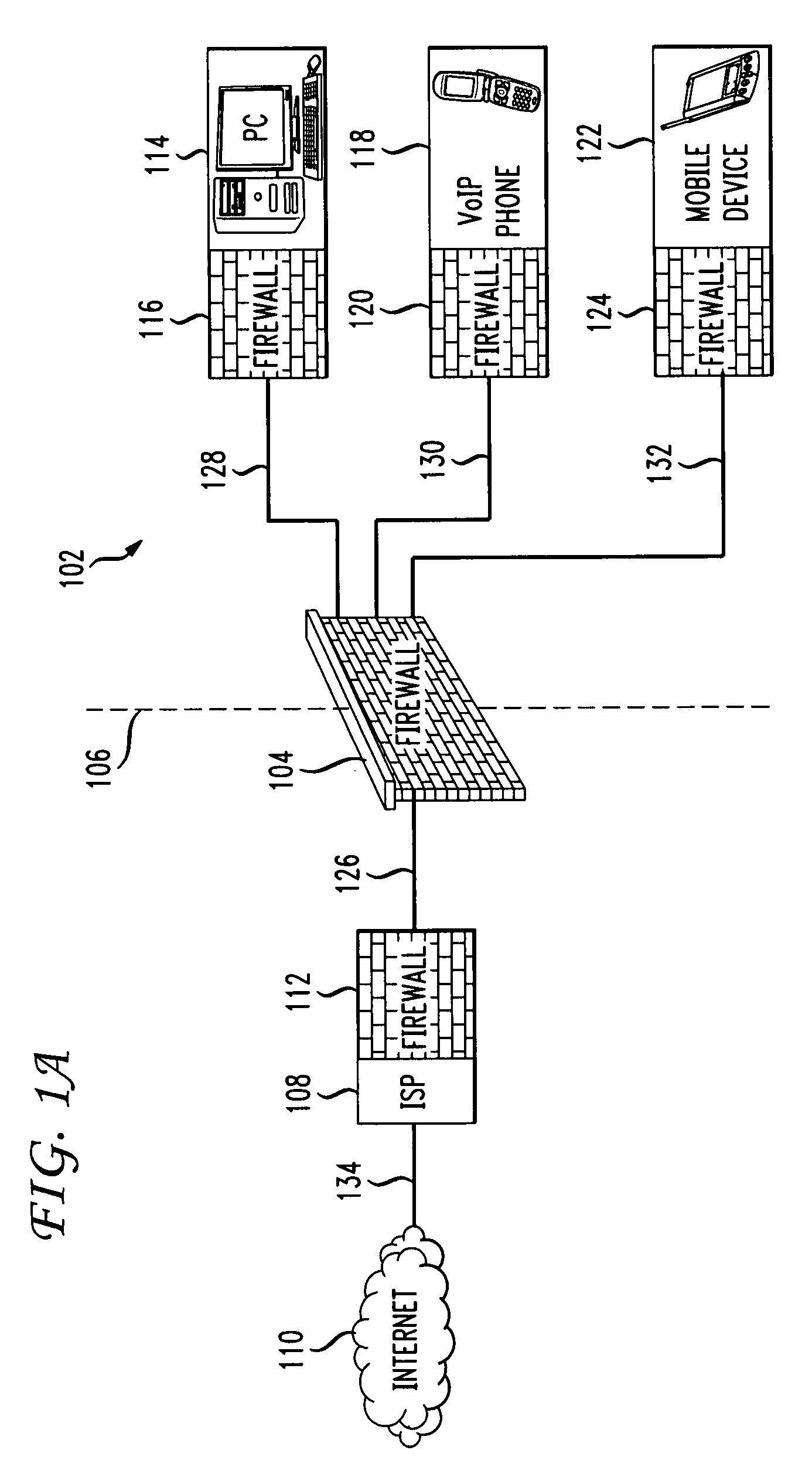
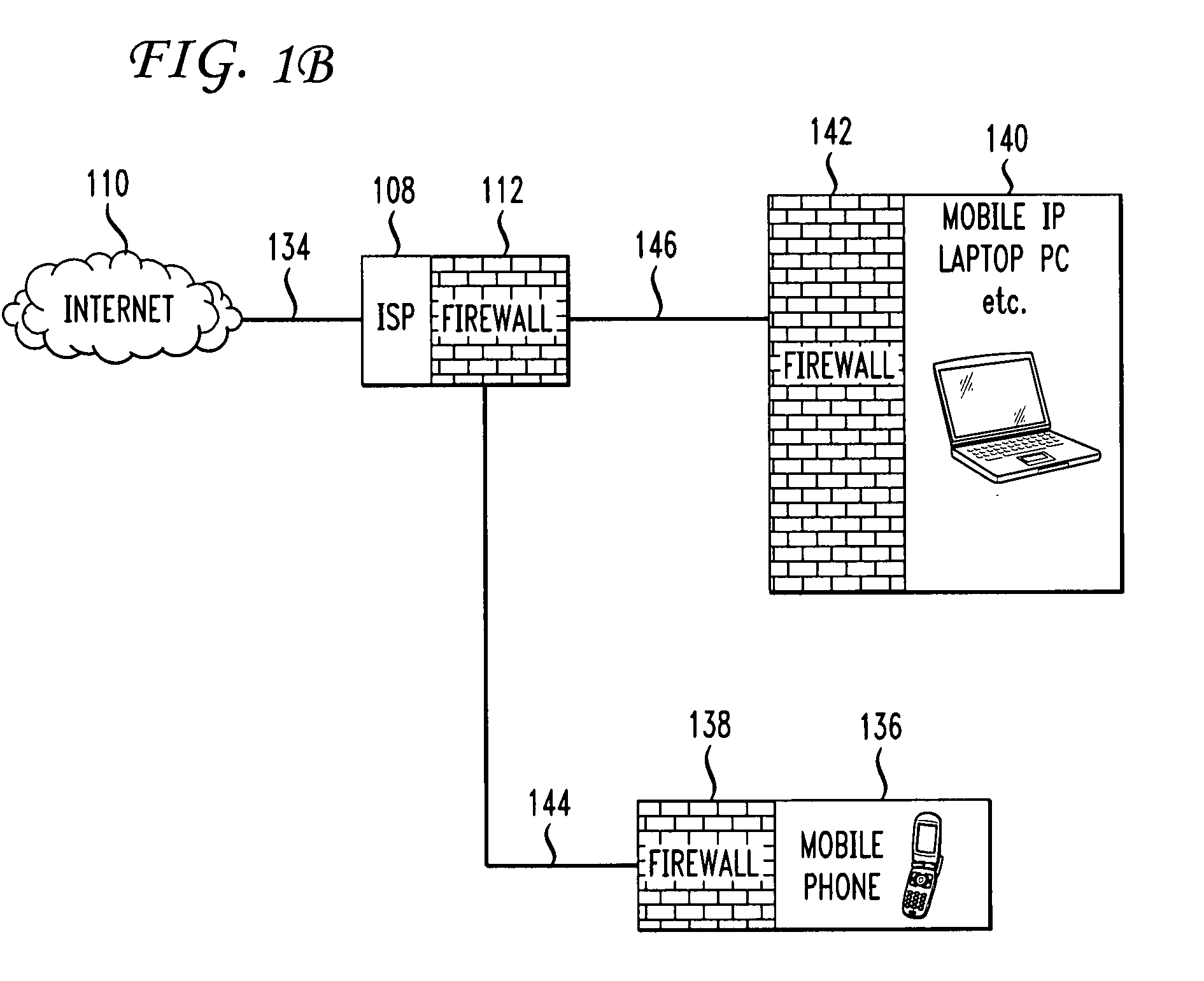
Methods and systems for propagating data security policies and rules up a chain of network components, for example, from an end-user device having a firewall, to a network component at the “edge” of the network, such as a so-called “edge” firewall server, from where a policy statement can be transmitted to a service provider, such as an ISP, are described. A device, such as a computer or mobile phone, has, as part of its firewall software, a policy propagation file, that communicates with pre-existing firewall software. The firewall software creates a policy statement upon detecting a triggering event, which is transmitted from the device to the next data security component up the chain, “upstream,” in the network. In some cases this device may be a firewall server or a firewall policy server. The firewall server may combine policy statements from numerous end-user type devices and transmit the policy statement to an external network component, such as an ISP firewall server or similar device. The ISP or other service provider may then use the policy statement to implement date security rules for the devices in the network. In this manner, the firewall operated by the ISP implements rules and policies of a network owner or the owner of a stand-alone device, thereby preventing unwanted traffic from entering the network.
Owner:DIGICERT
Cryptographic method and system
InactiveUS20140164776A1Easy to useImprove abilitiesKey distribution for secure communicationMultiple keys/algorithms usageInformation sharingInternet privacy
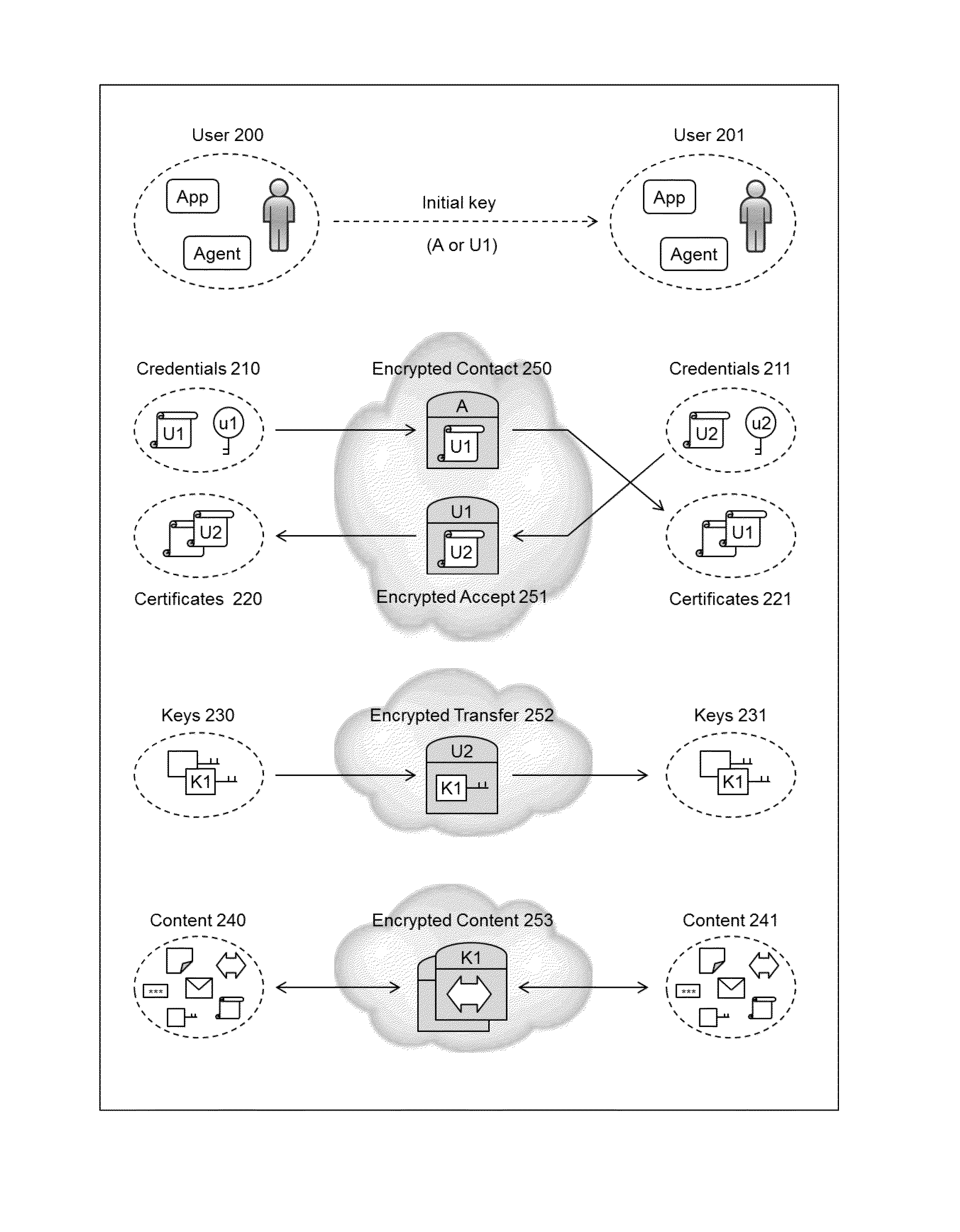
The present invention relates to the field of security of electronic data and / or communications. In one form, the invention relates to data security and / or privacy in a distributed and / or decentralised network environment. In another form, the invention relates to enabling private collaboration and / or information sharing between users, agents and / or applications. Embodiment(s) of the present invention enable the sharing of key(s) and / or content between a first user and / or agent and a second user and / or agent. Furthermore, embodiment(s) of the present invention have application in sharing encrypted information via information sharing services.A number of inventions, aspects and embodiments are disclosed herein.
Owner:LOCK BOX
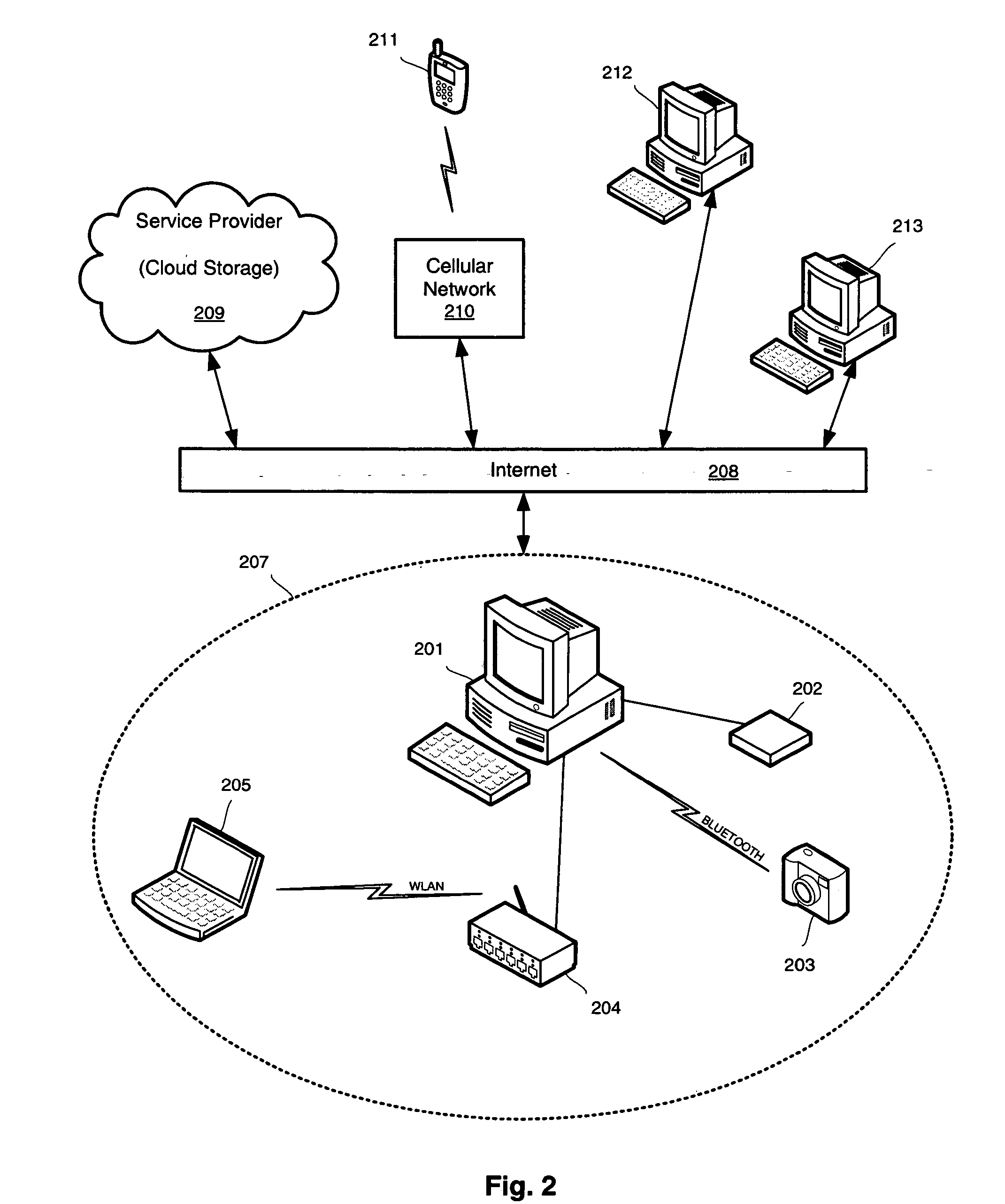
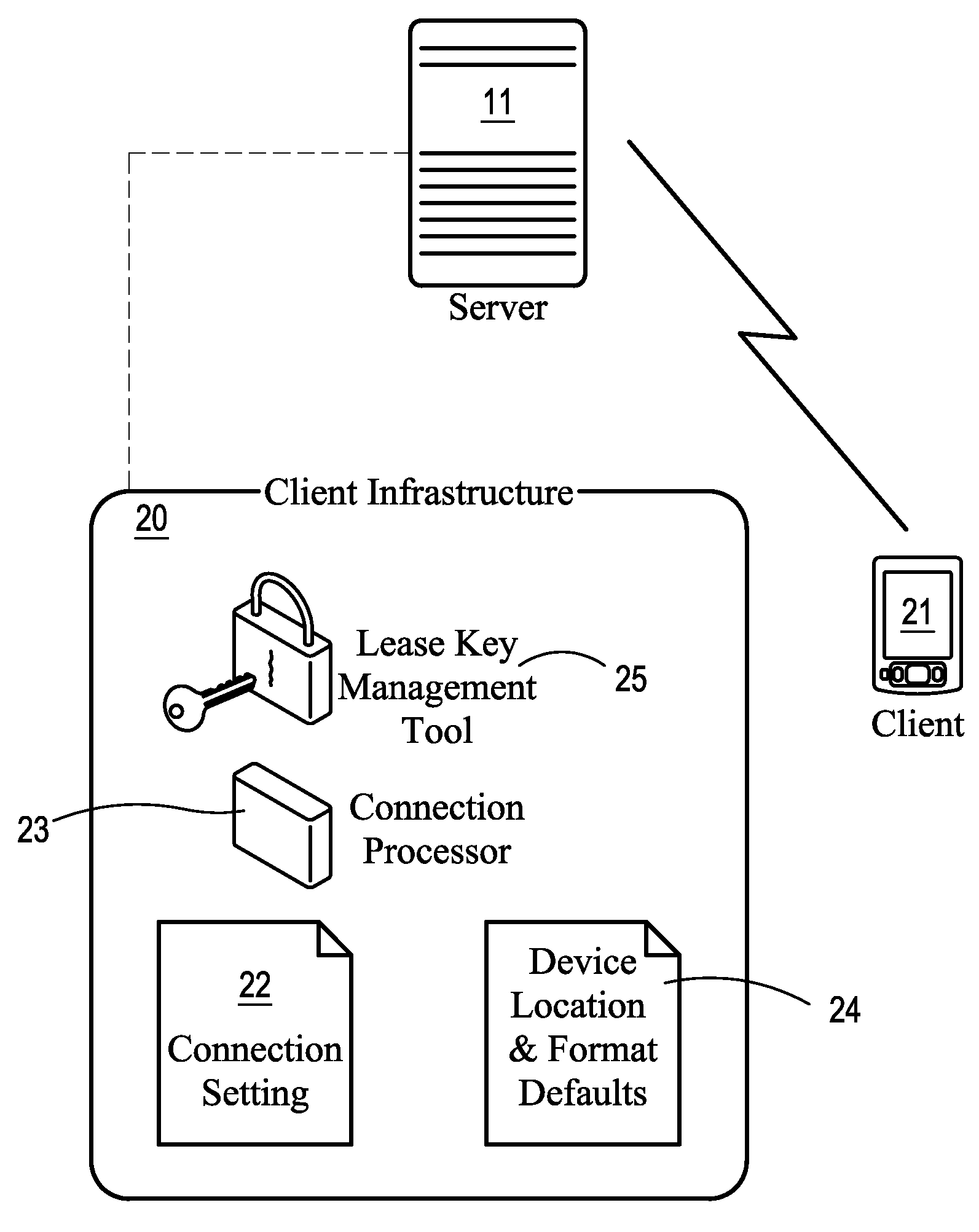
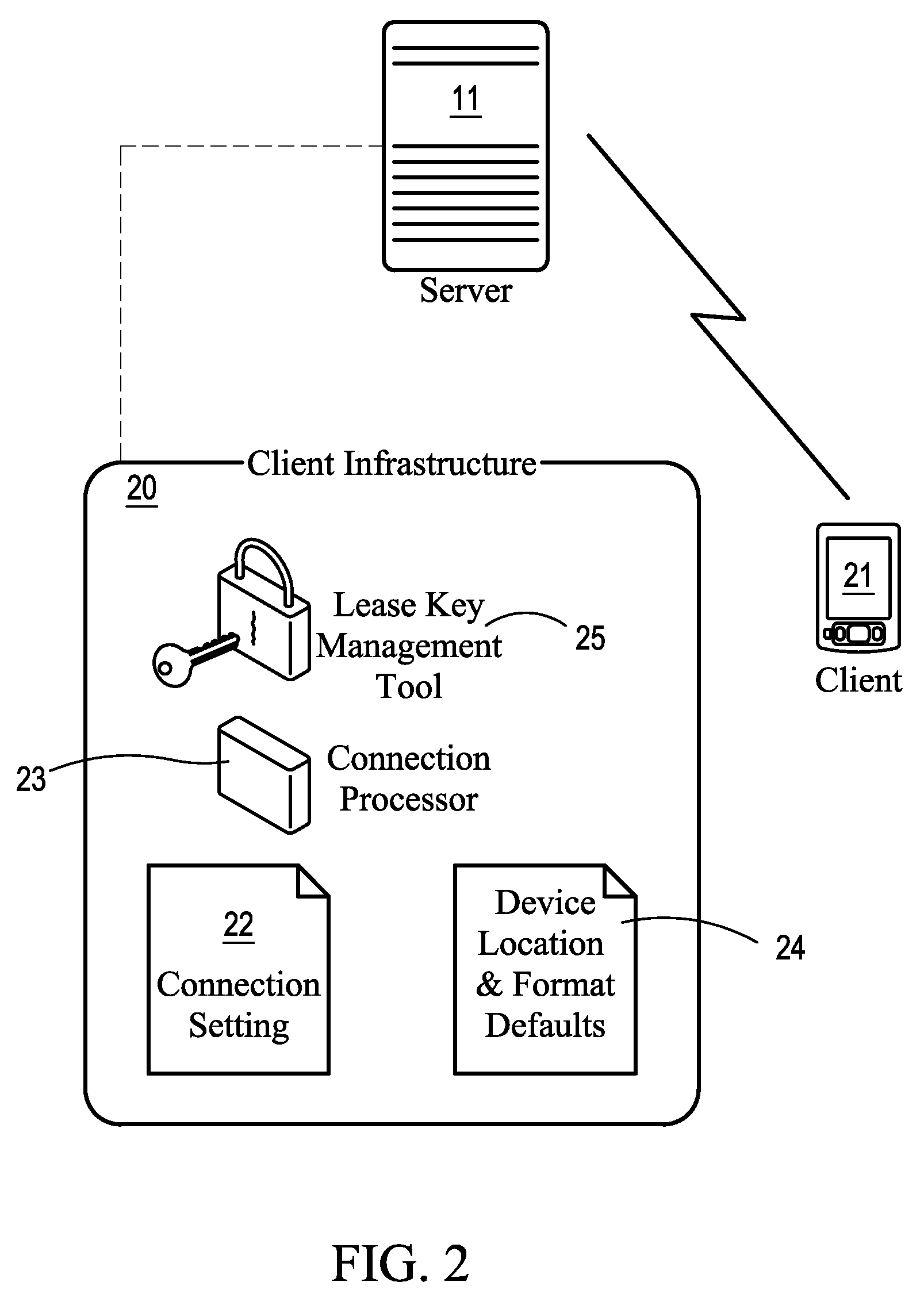
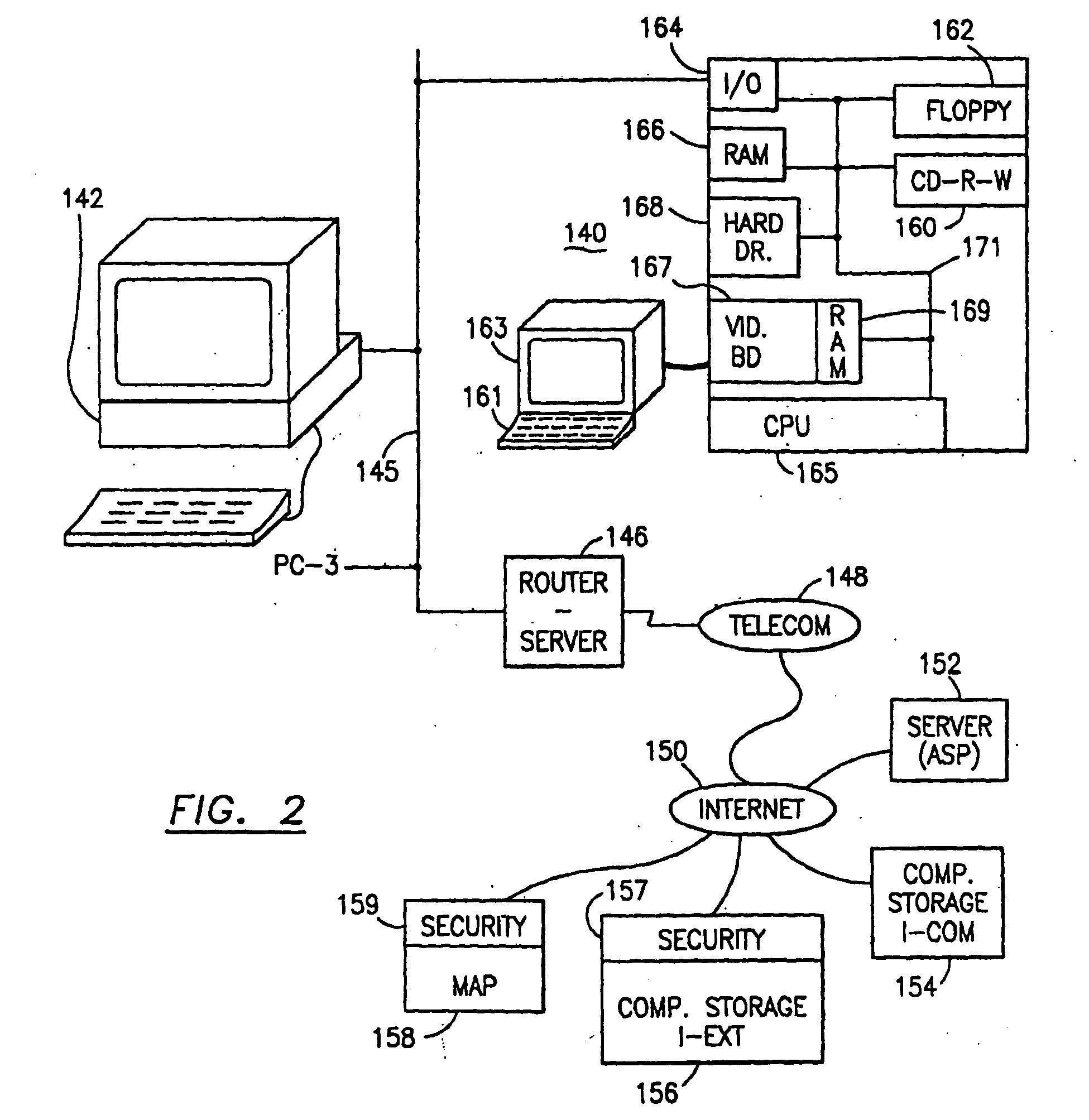
Data security system and method for portable device
ActiveUS7313825B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsDigital data processing detailsInformation processingEvent trigger
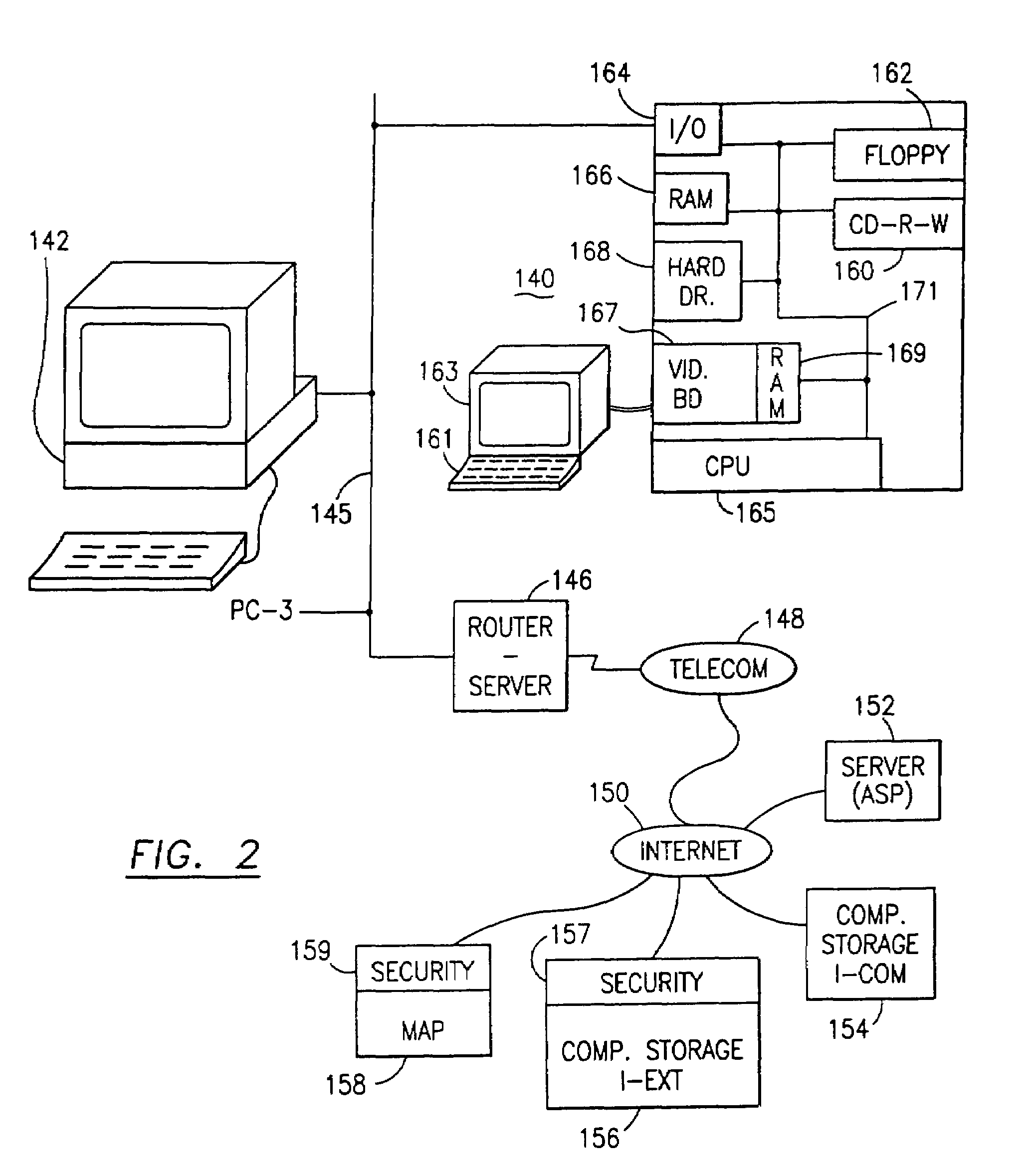
The method, used with a portable computing device, secures security sensitive words, icons, etc. by determining device location within or without a predetermined region and then extracting the security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only in the presence of a predetermined security clearance and within certain geographic territories. A computer readable medium containing programming instructions carrying out the methodology for securing data is also described herein. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
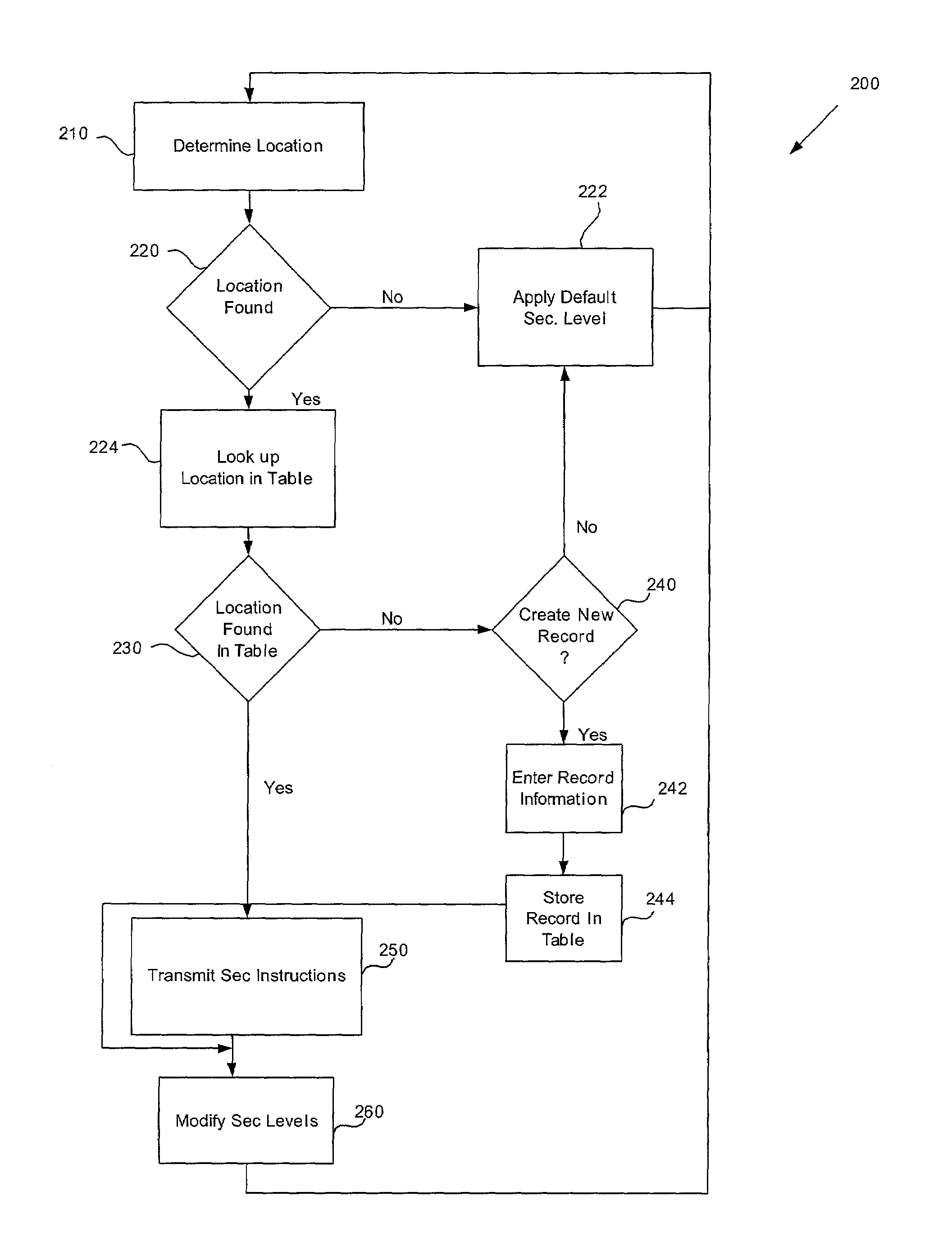
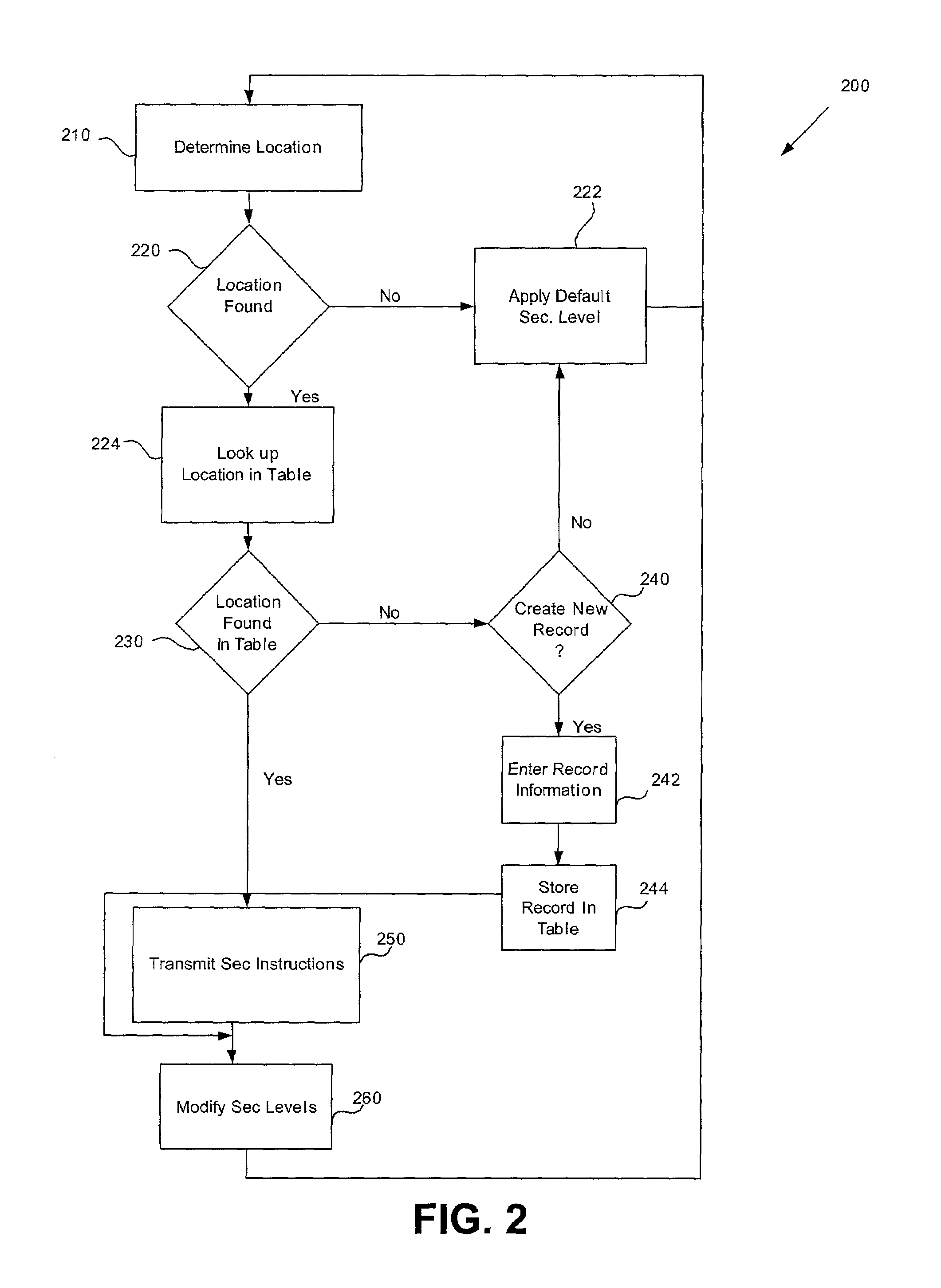
Location based security modification system and method
ActiveUS7591020B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSingle levelSecurity level
A method or system for providing a level of data security dependent on the location of the user of a wireless device is disclosed. One exemplary embodiment relates to a method of adjusting security for a network user node in communication with a network based upon the location of the node. The method is performed by determining the location of a network user node, selecting a single level of security from a group of more than two security levels based on the determined location, and modifying the security protection for the network user node based upon the selected level of security.
Owner:QUALCOMM INC
Data Security System and with territorial, geographic and triggering event protocol
ActiveUS20090178144A1Ease overhead performanceHigh overhead performanceDigital data processing detailsAnalogue secracy/subscription systemsInformation processingEvent trigger
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with territorial, geographic and triggering event protocols. The method and system determines device location within or without a predetermined region and then extracts security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only with security clearance and within certain geographic territories. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
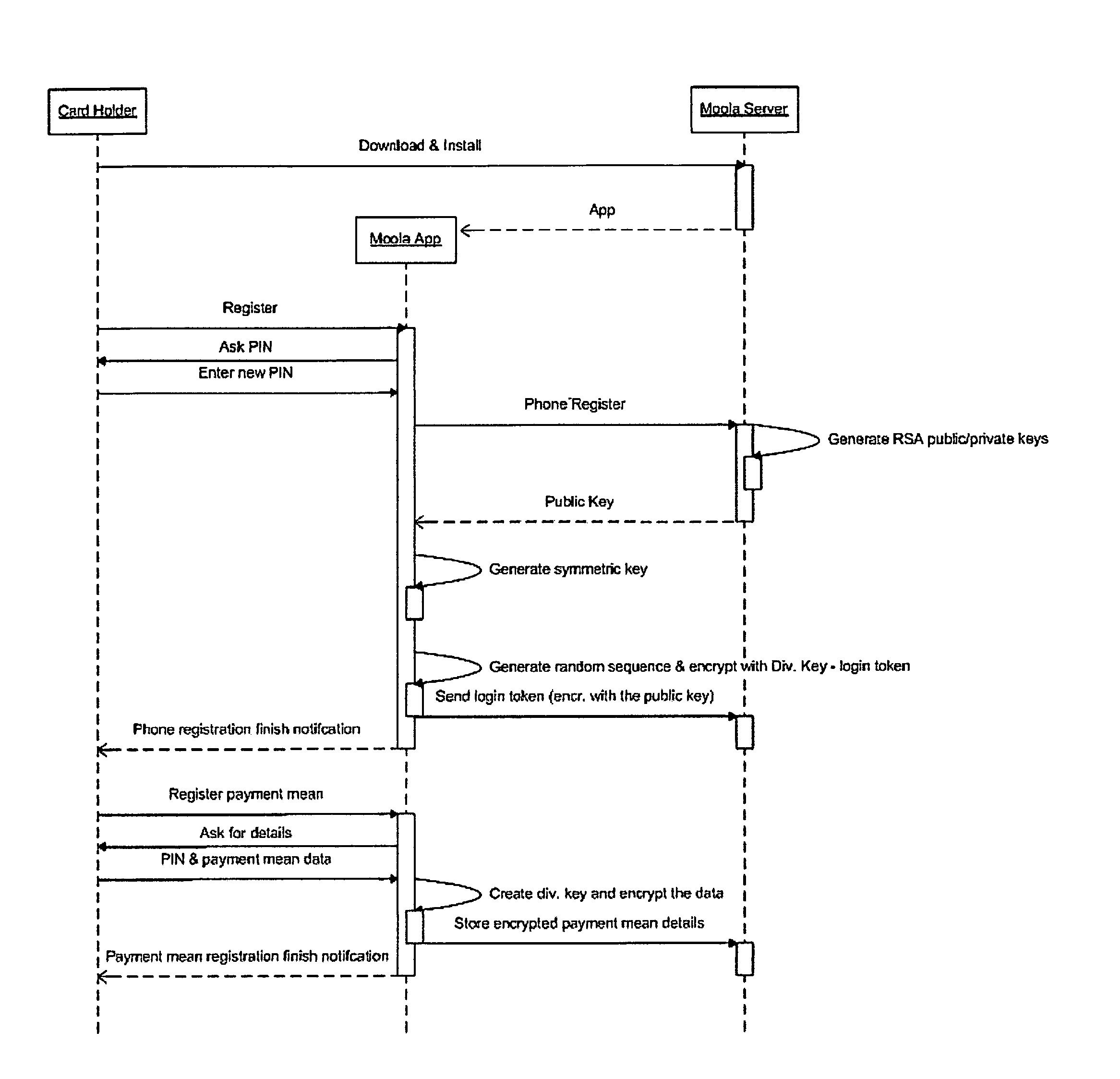
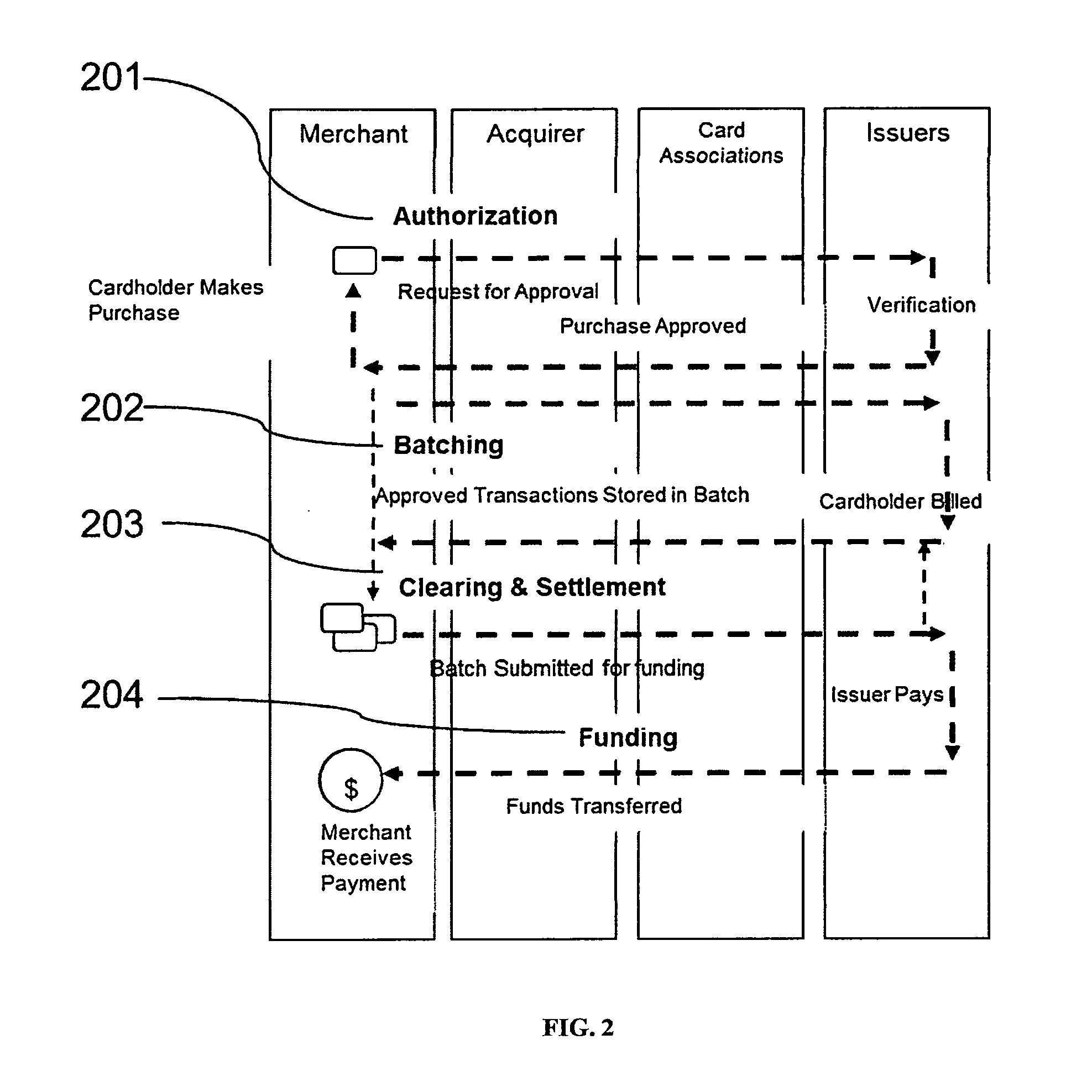
Mobile Device Based Financial Transaction System
A system and method for conducting financial transactions by means of a smartphone is disclosed. A barcode is printed on the invoice, which is scanned by the mobile device screen. The mobile device is used instead of a credit card or cash. Provisions for data security, transaction verification, and communications protocols are disclosed.
Owner:SINCAI DAN MOSHE
Secure enterprise network
ActiveUS8166554B2Digital data processing detailsDigital computer detailsUser authenticationApplication software
What is proposed is a method of implementing a security system (Packet Sentry) addressing the internal security problem of enterprises having a generalized approach for inferential determination and enforcement of network policy with directory service based group correlation with transparent authentication of the connected customer and the policy enforcement inside the network. The security system enables the network to analyze and enforce policy using any bit or bits in a stream or a packet, conduct Flow Vector analysis on the data traffic, provide Application Monitoring, Normalization and user authentication validation. The system enables the network to implement Group relationship Analysis and correlation using combination of Network inferences and Directory service data resulting in generation of Group norms using statistically significant relationships. These will provide a more secure enterprise environment where data security levels can be enforced and the usage monitored effectively in the infrastructure.
Owner:VMWARE INC
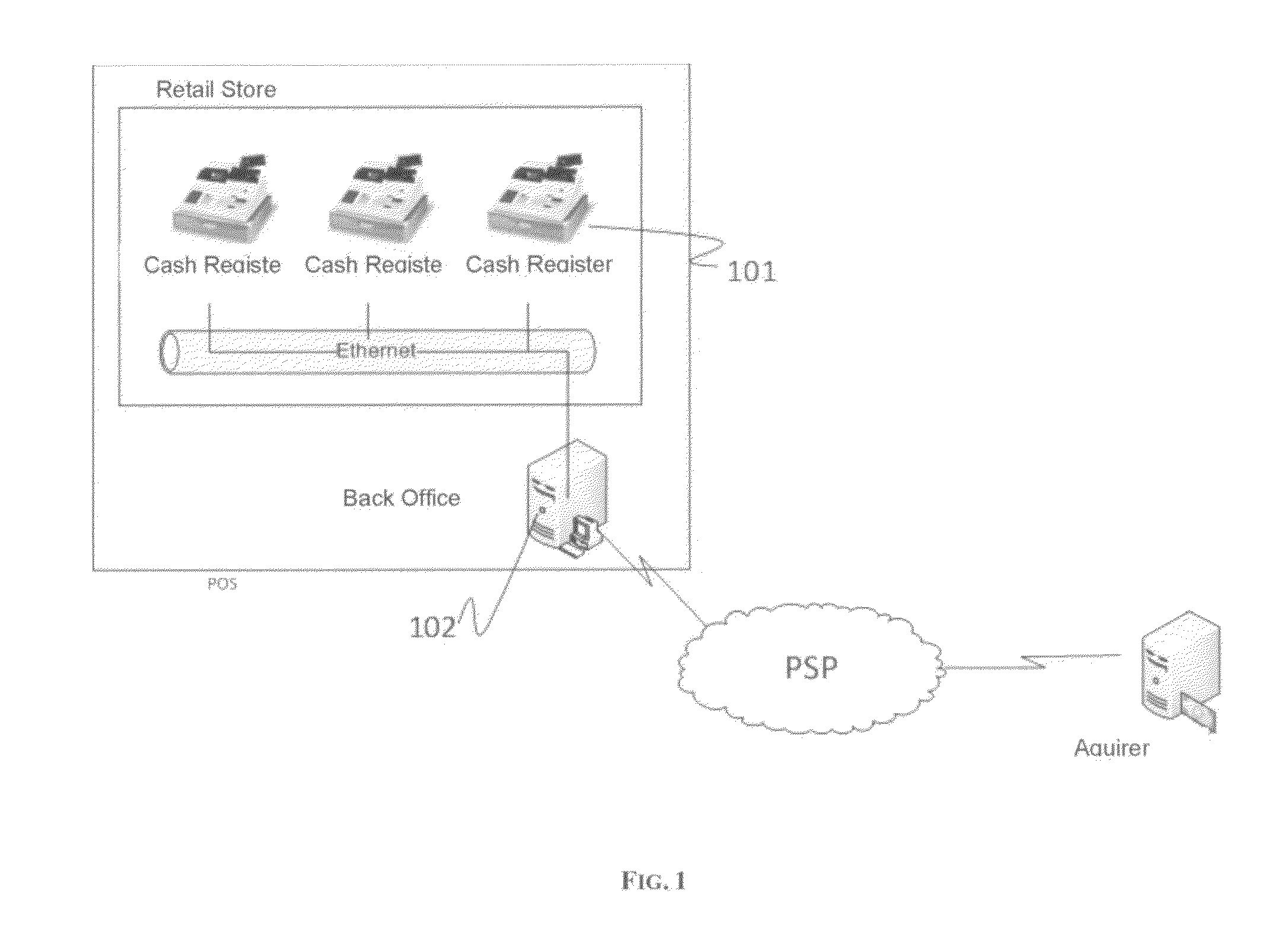
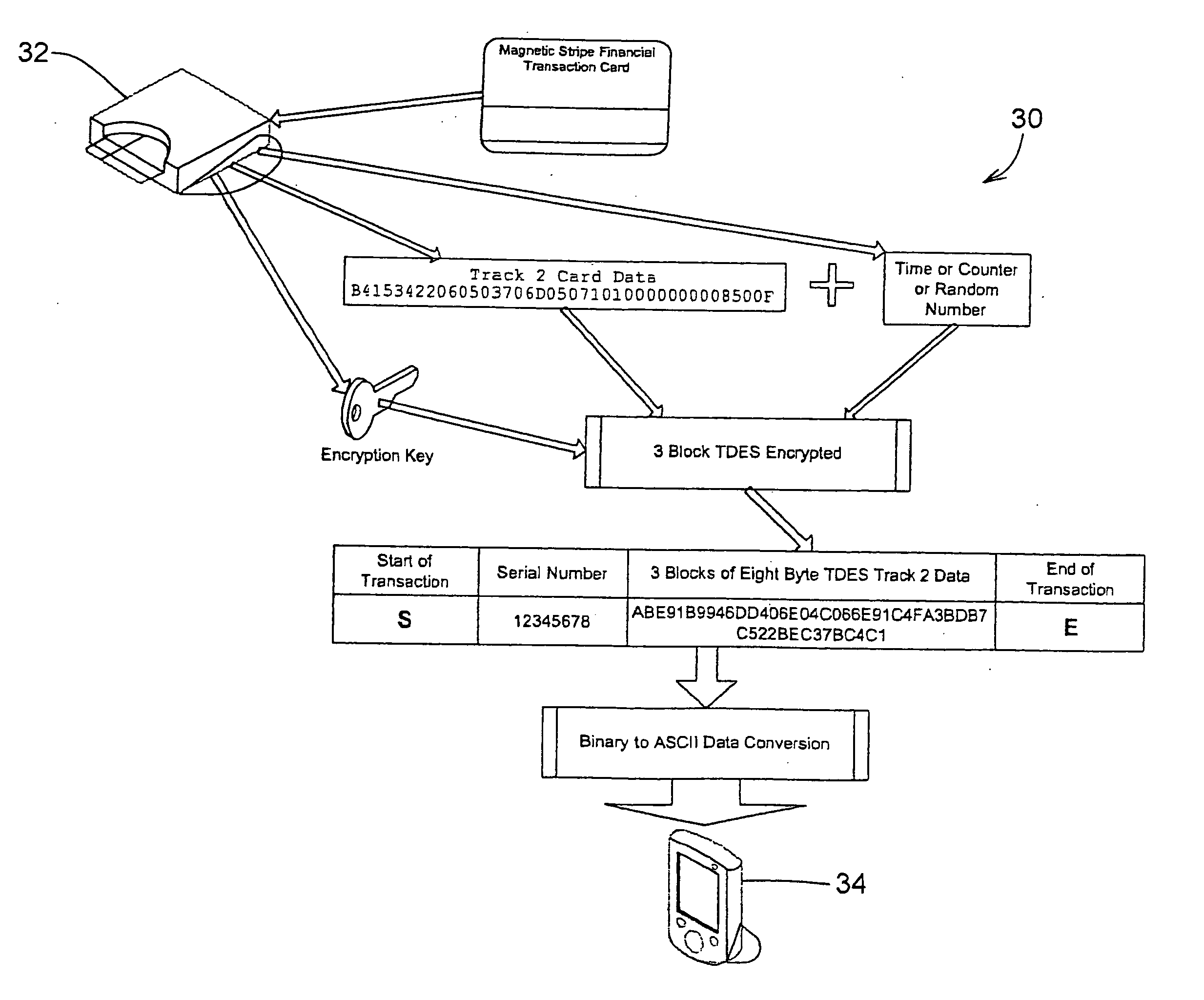
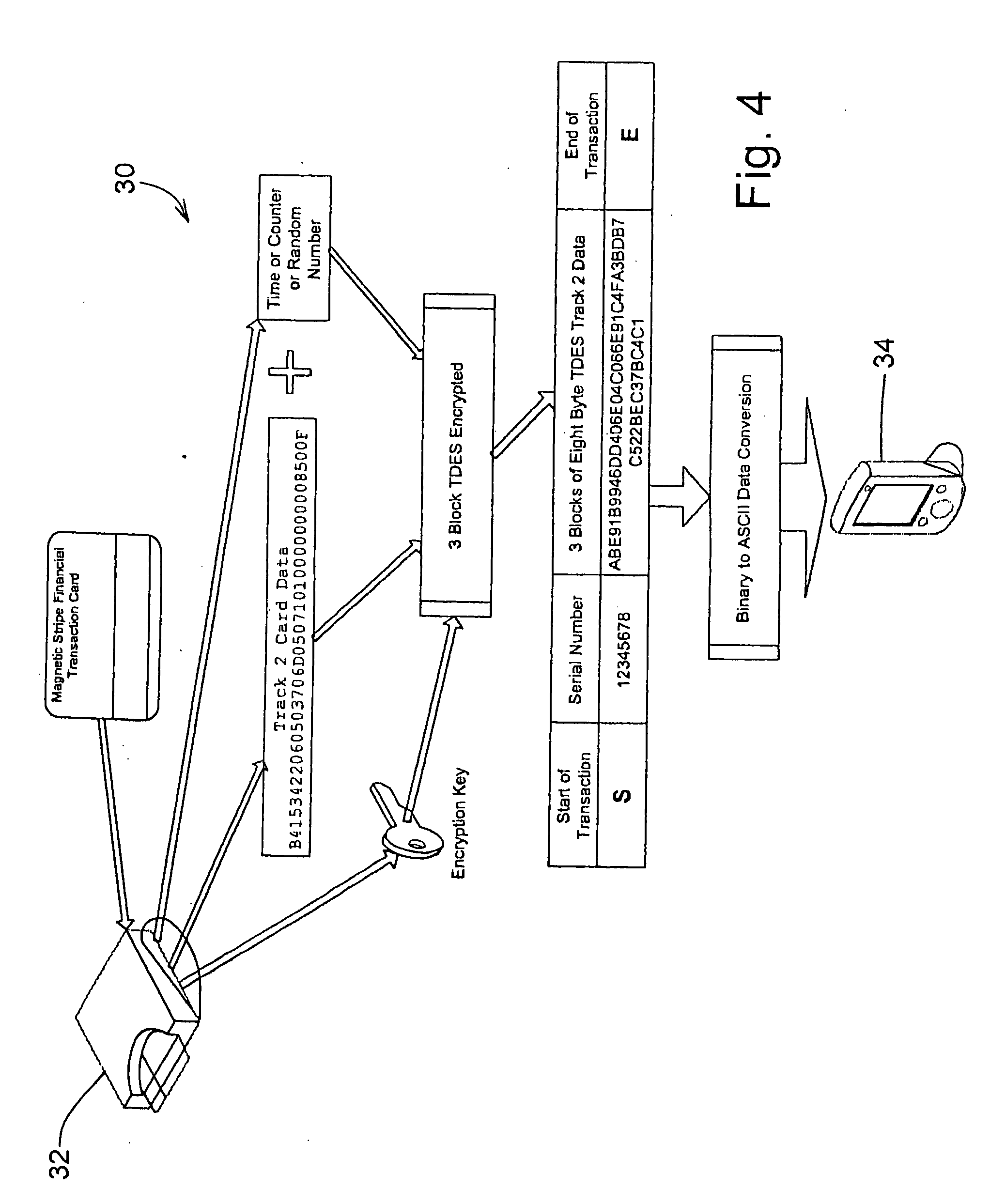
Transparently securing data for transmission on financial networks
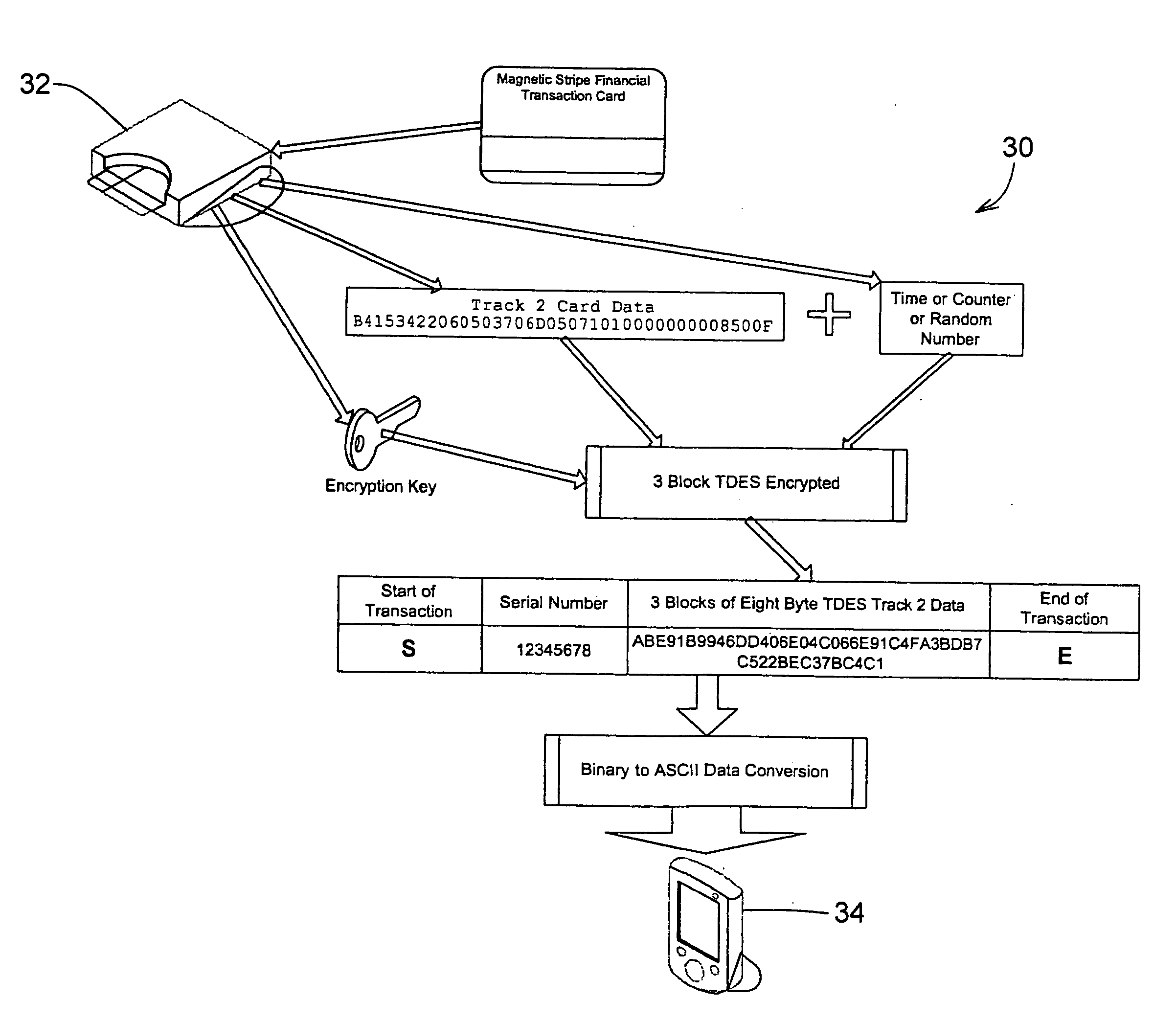
ActiveUS20060049256A1Easy to operateIncrease powerAcutation objectsFinanceInformation processingSoftware system
A secure magnetic stripe card stripe reader (MSR) module and software system capable of encrypting the magnetic stripe data to CPI, SDP and CISP standards for use in point of sale (POS) and other applications requiring data security using non secure networks and computing devices. Additionally, when incorporated within an attachment for conventional personal digital assistant (PDA) or cell phone or stationary terminal, provides encrypted data from the magnetic head assembly providing compliance with Federal Information Processing Standards Publication Series FIPS 140 covering security and tampering standards. Moreover, this module and software system includes the capability of providing secure POS transactions to legacy transaction processing systems and POS terminals transparently to the existing infrastructure. Furthermore, this module and software system includes the capability of transparently providing detection of fraudulently copied magnetic stripe cards.
Owner:VERIFONE INC
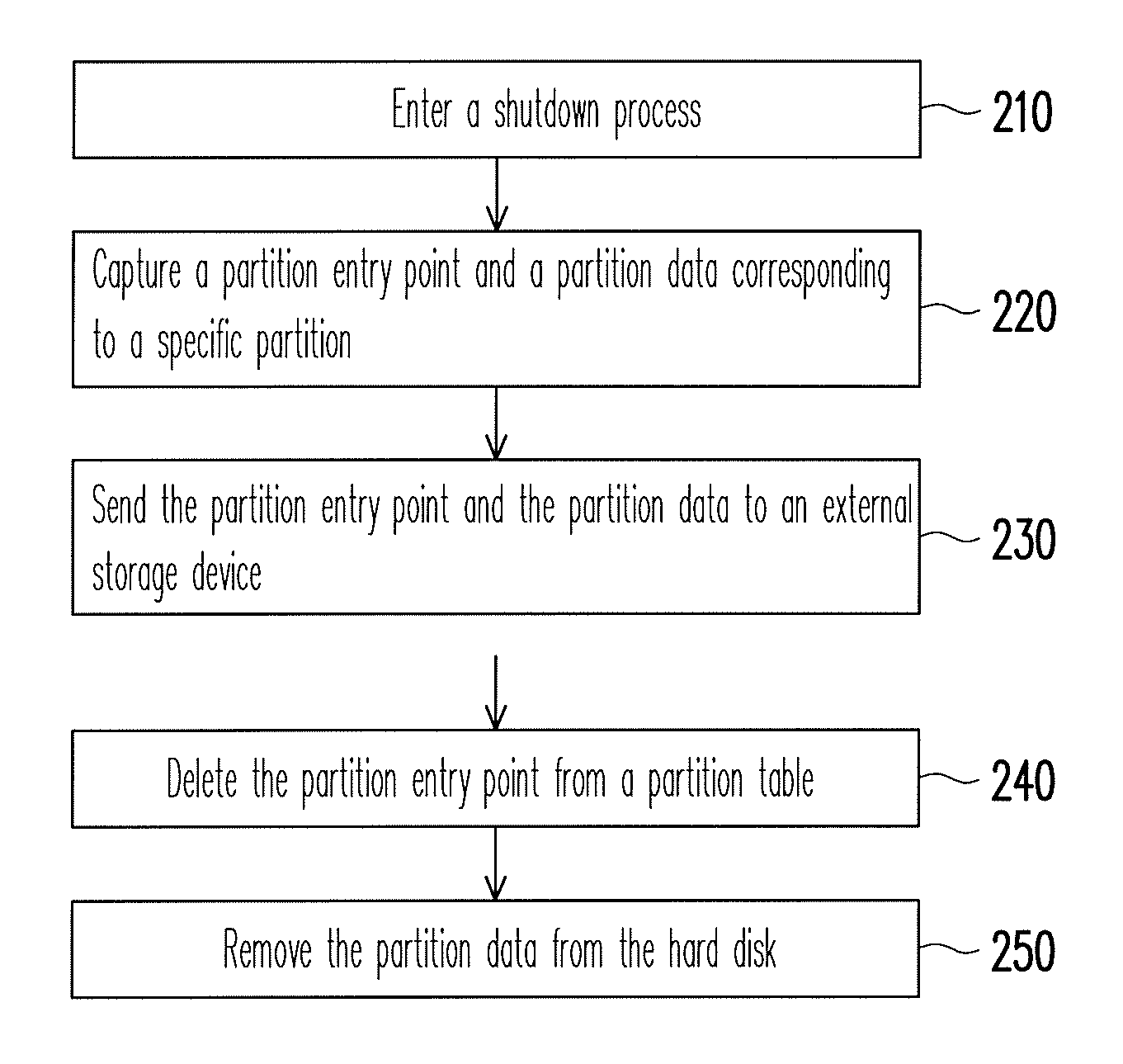
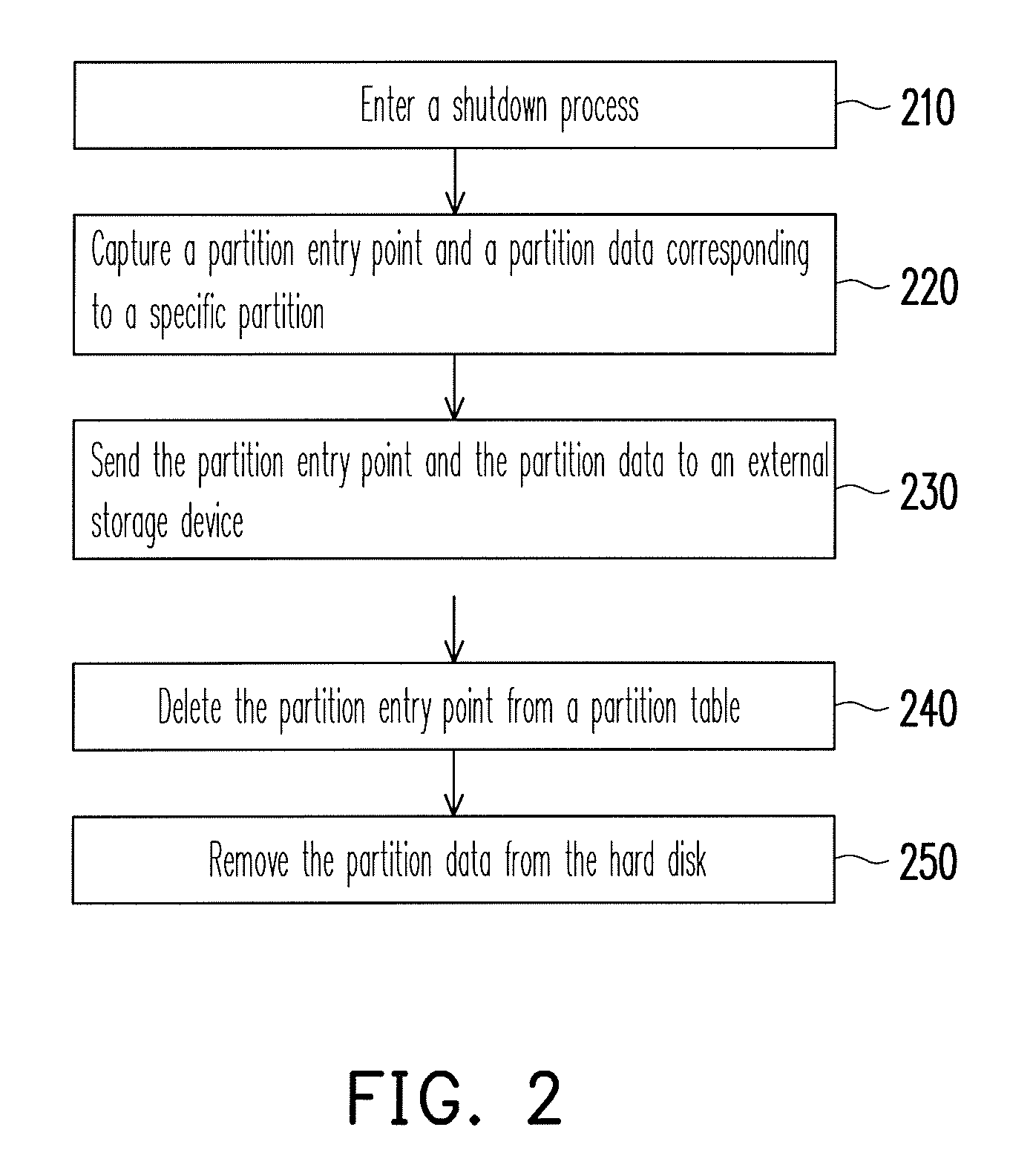
Data protection method
ActiveUS8041913B2Data SecurityEnsure safetyDigital data processing detailsUnauthorized memory use protectionExternal storageEntry point
A data protection method for an electronic device having a storage medium is provided, wherein the storage medium includes a plurality of partitions and a partition table. In the data protection method, a partition entry point and a partition data corresponding to the specific partition are captured and sent to an external storage device when the electronic device enters a shutdown process. Then, the partition entry point is deleted from the partition table and the partition data is removed from the storage medium. When the electronic device is turned on, a user has to provide the corresponding external storage device to restore the partition entry point and the partition data back to the storage medium. Thereby, personal data stored in the storage medium is protected and accordingly data security is ensured.
Owner:ASUSTEK COMPUTER INC
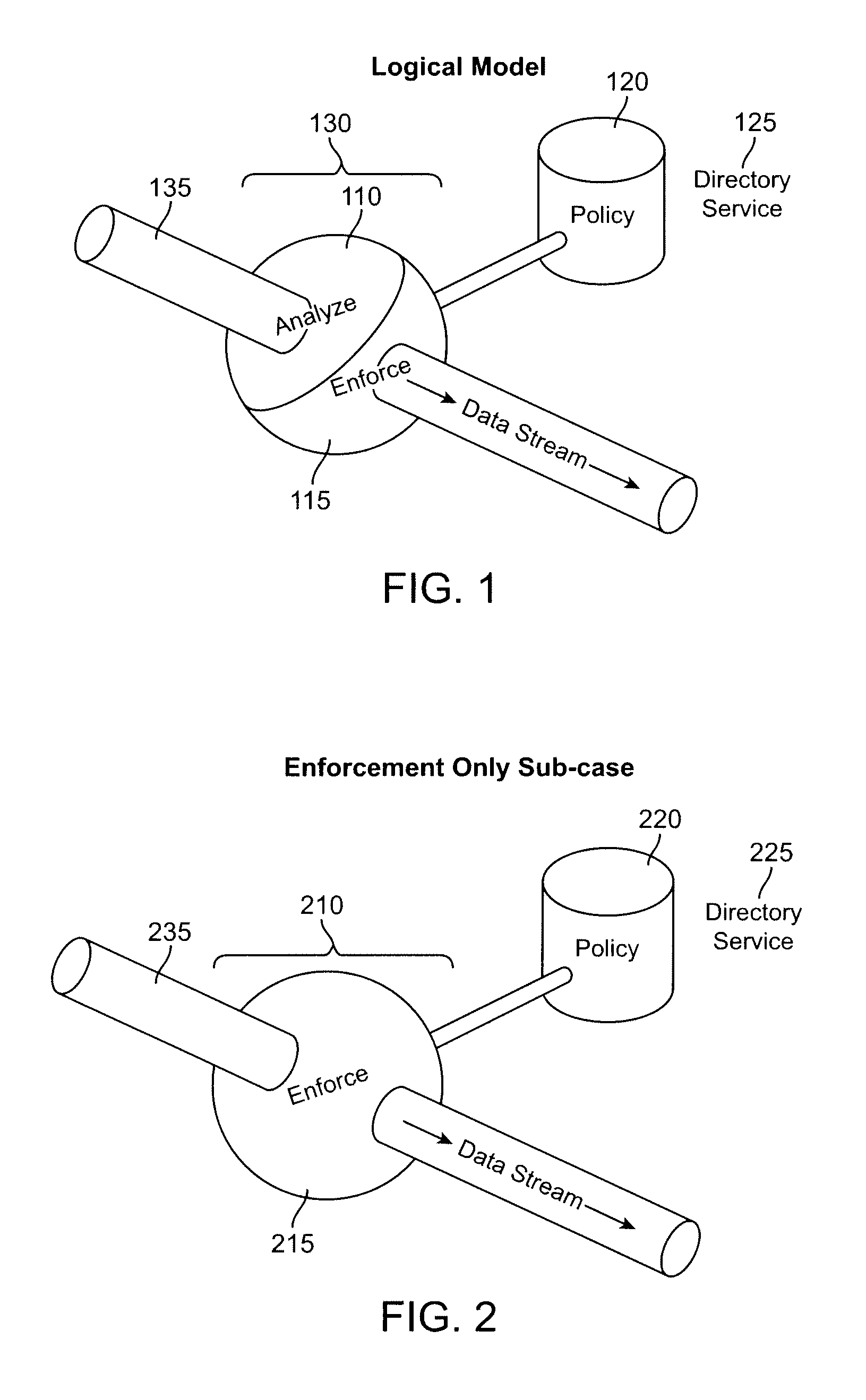
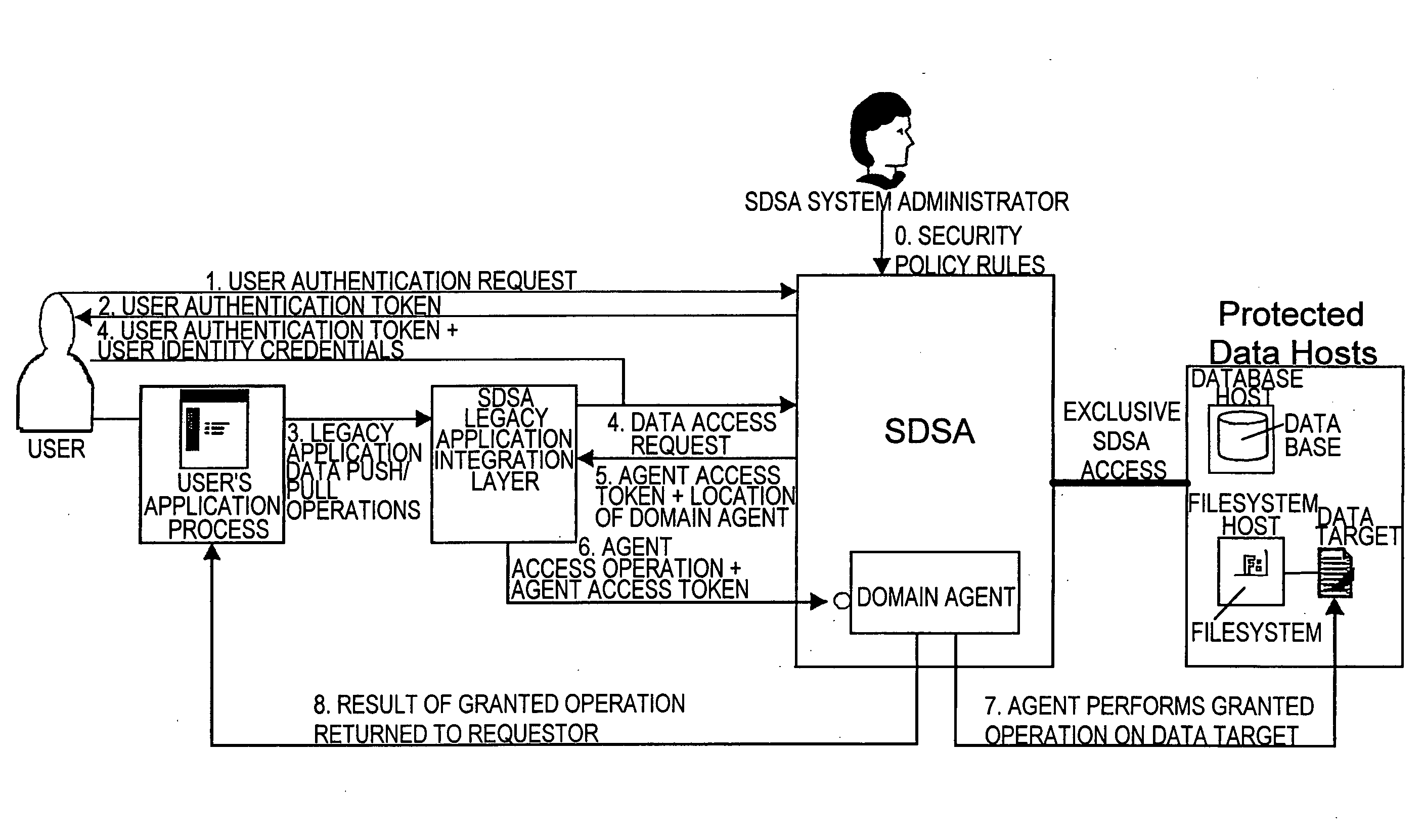
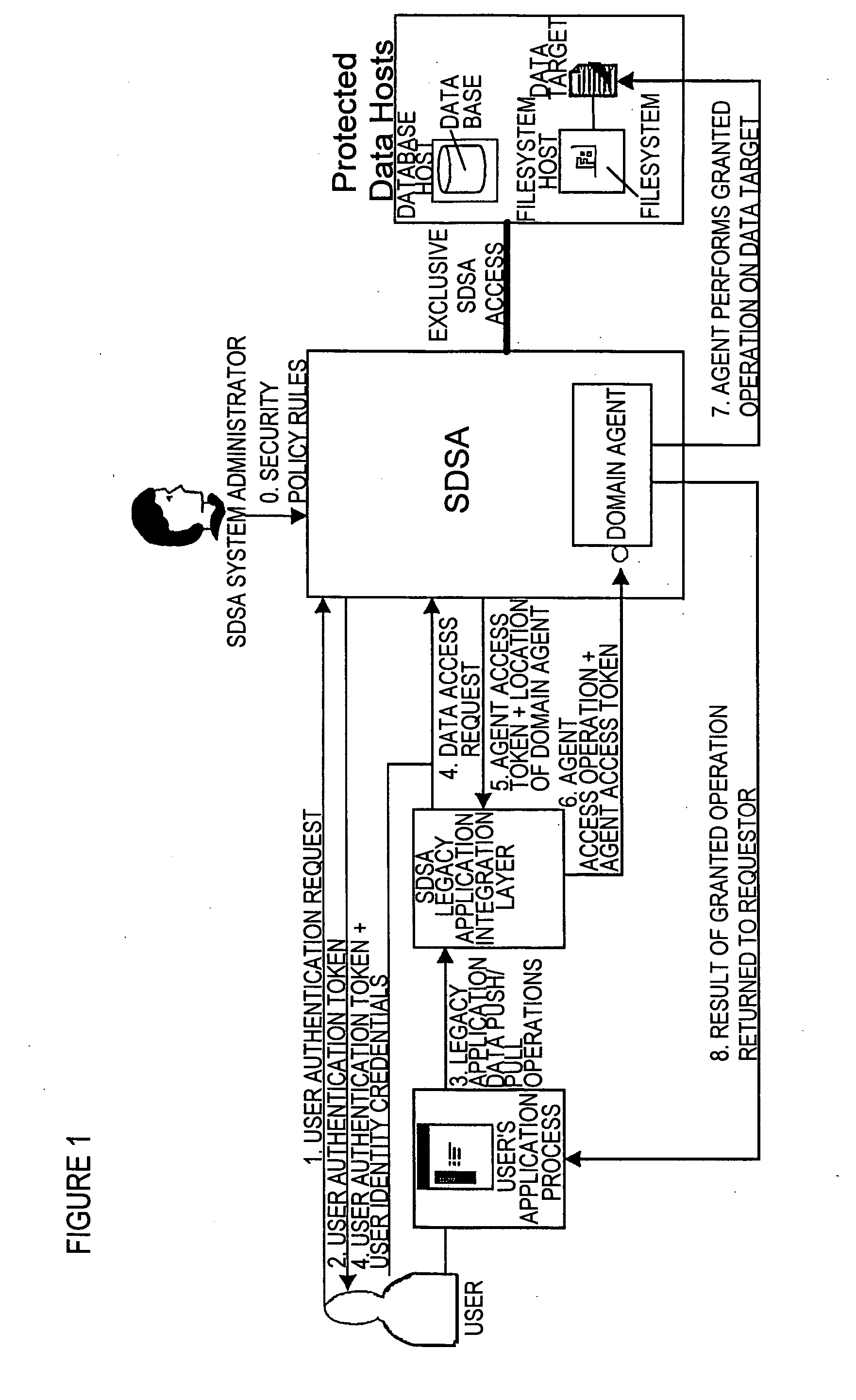
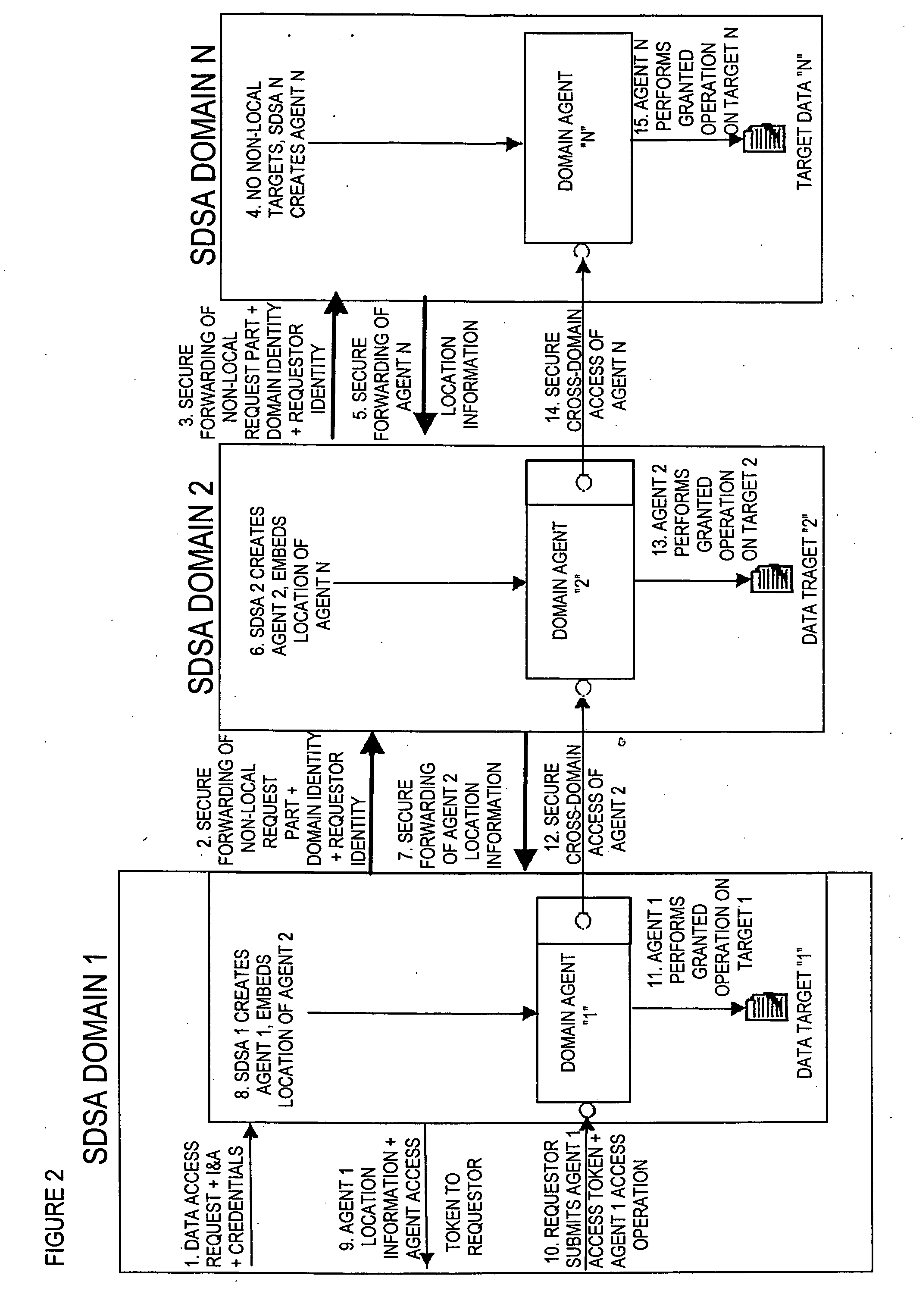
Method and apparatus for providing secure access control for protected information
InactiveUS20070136603A1Quick fixComputer security arrangementsSecuring communicationInternet privacyHigh assurance
There are provided methods and apparatuses for processing requests from requestors, methods and apparatuses for transmitting indicia representative of information from a first domain to a second domain, methods comprising, and apparatuses for, determining whether a requestor is authorized to perform a desired operation on a target comprising at least one element which comprises an information set of indicia and arrangements of stored data, as well as computer-readable media having computer-executable commands for performing the same. In some aspects of the present invention, there are provided high-assurance data security apparatuses and methods, in particular, user data protection via enforcement of policy-based access control.
Owner:SENSIS CORPORATION
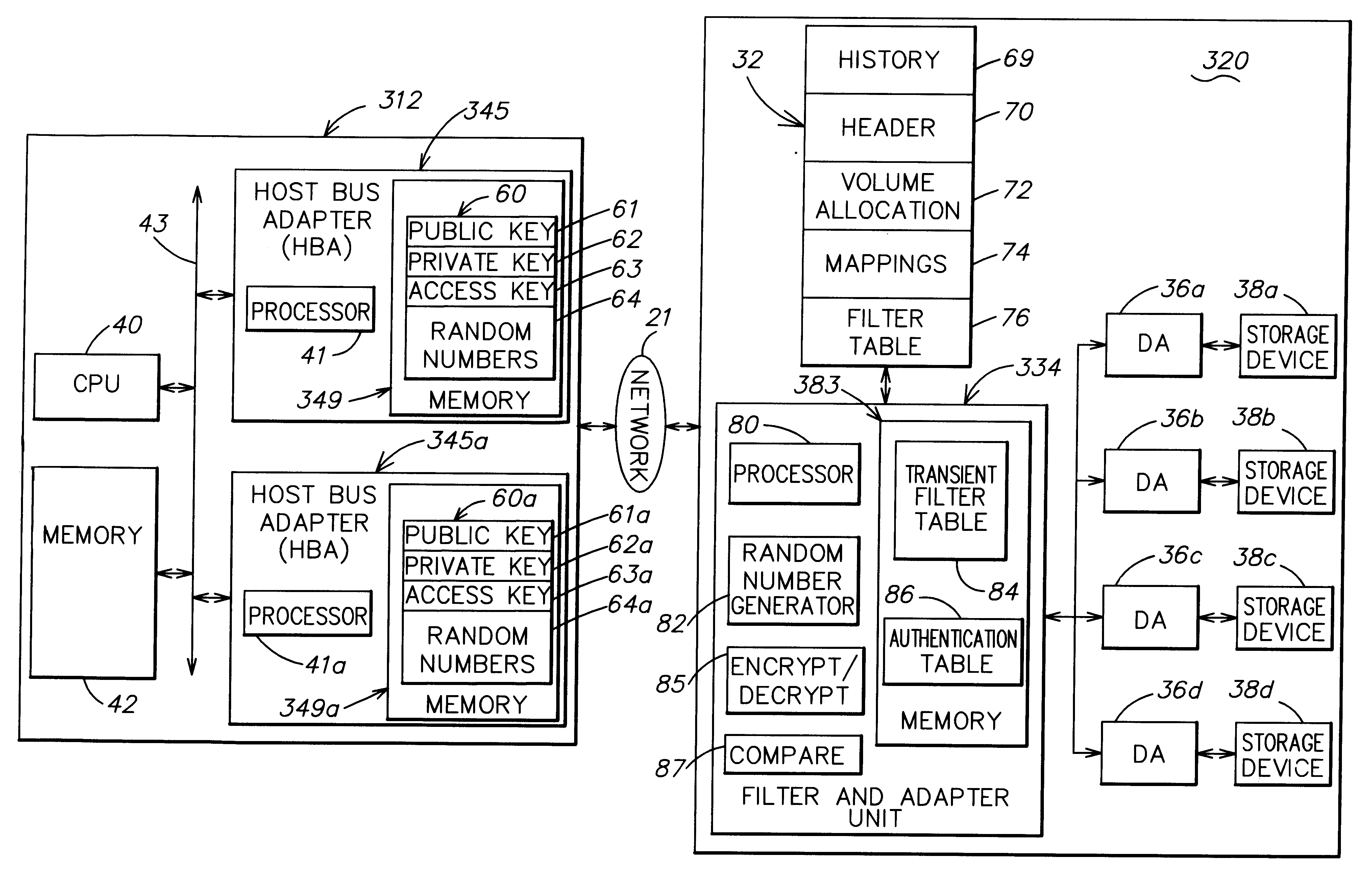
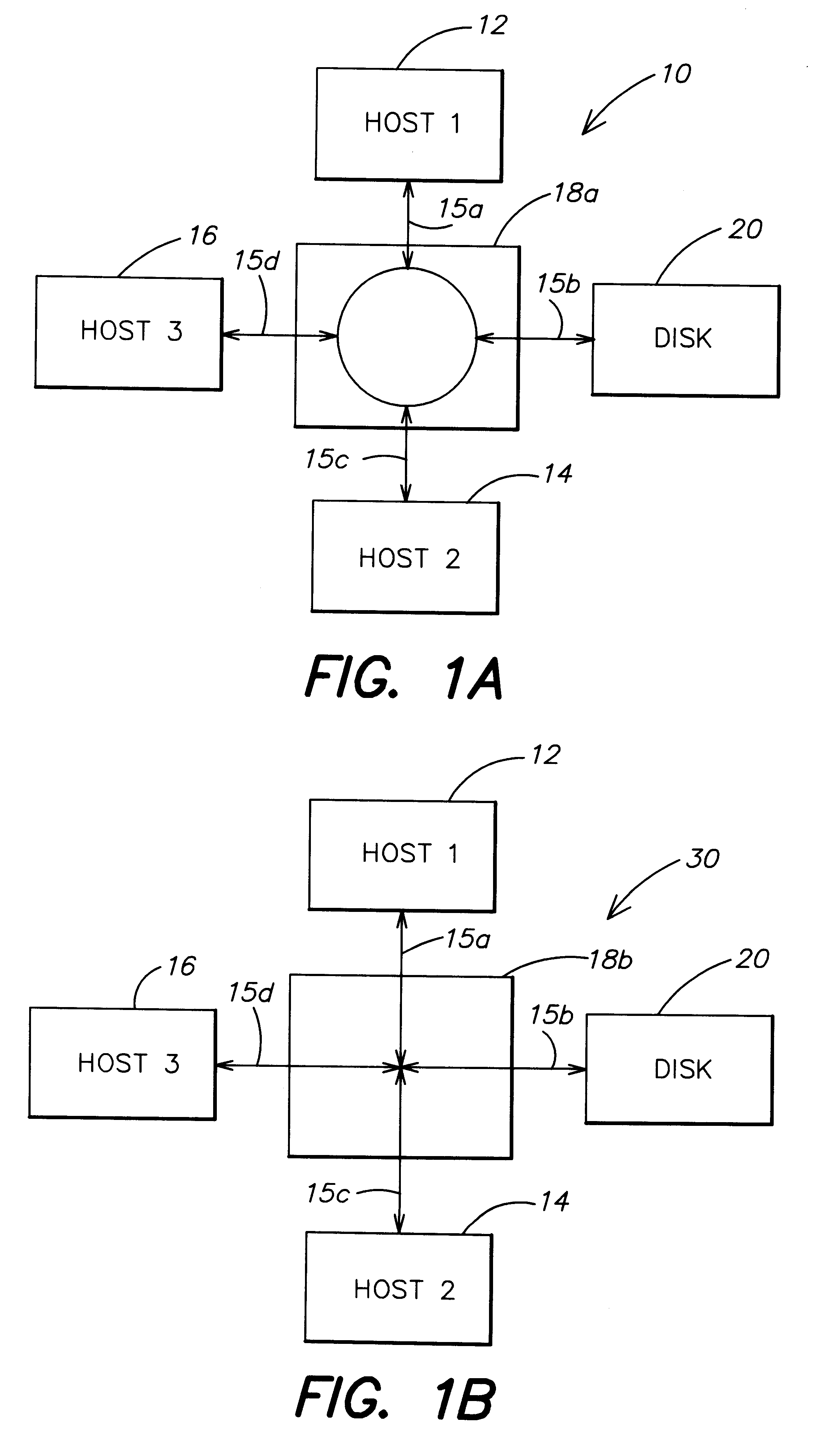
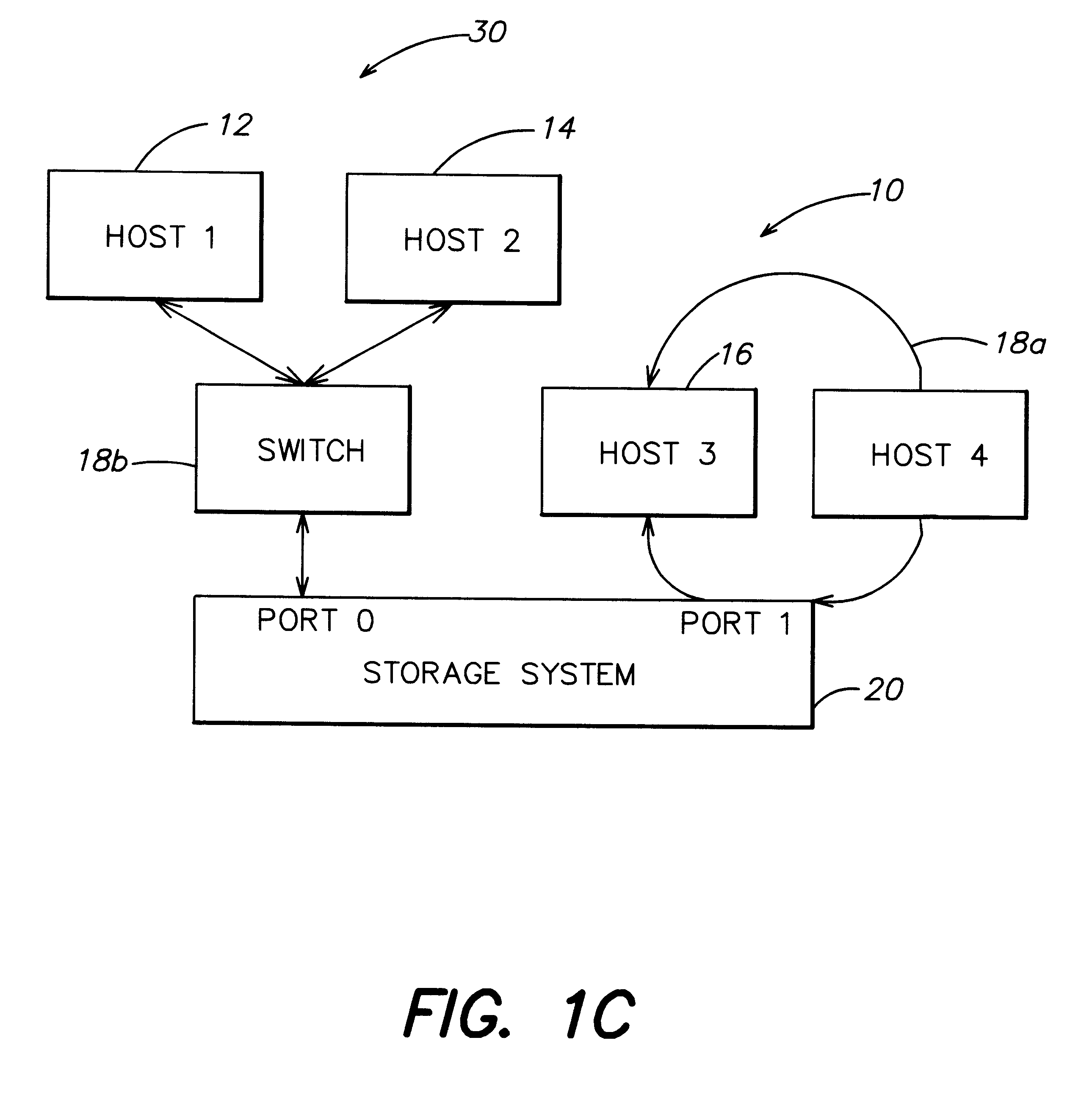
Method and apparatus for authenticating connections to a storage system coupled to a network
InactiveUS6263445B1Key distribution for secure communicationInput/output to record carriersData accessData management
A data management technique for managing accesses to data at a shared storage system includes a filter at the storage system. The filter is coupled to a configuration table, which identifies which of a number of coupled host processors have accesses to each of the resources at the device. During operation, requests received from the host devices are filtered by the filter, and only those requests to resources that the individual host devices have privilege to access are serviced. Advantageously, data security is further enhanced by authenticating each of the requests received by the storage system to verify that the host processor that is represented as forwarding the request is the indicated host processor. In addition, transfers of data between the storage system and the host processor may be validated to ensure that data was not corrupted during the data transfer.
Owner:EMC IP HLDG CO LLC
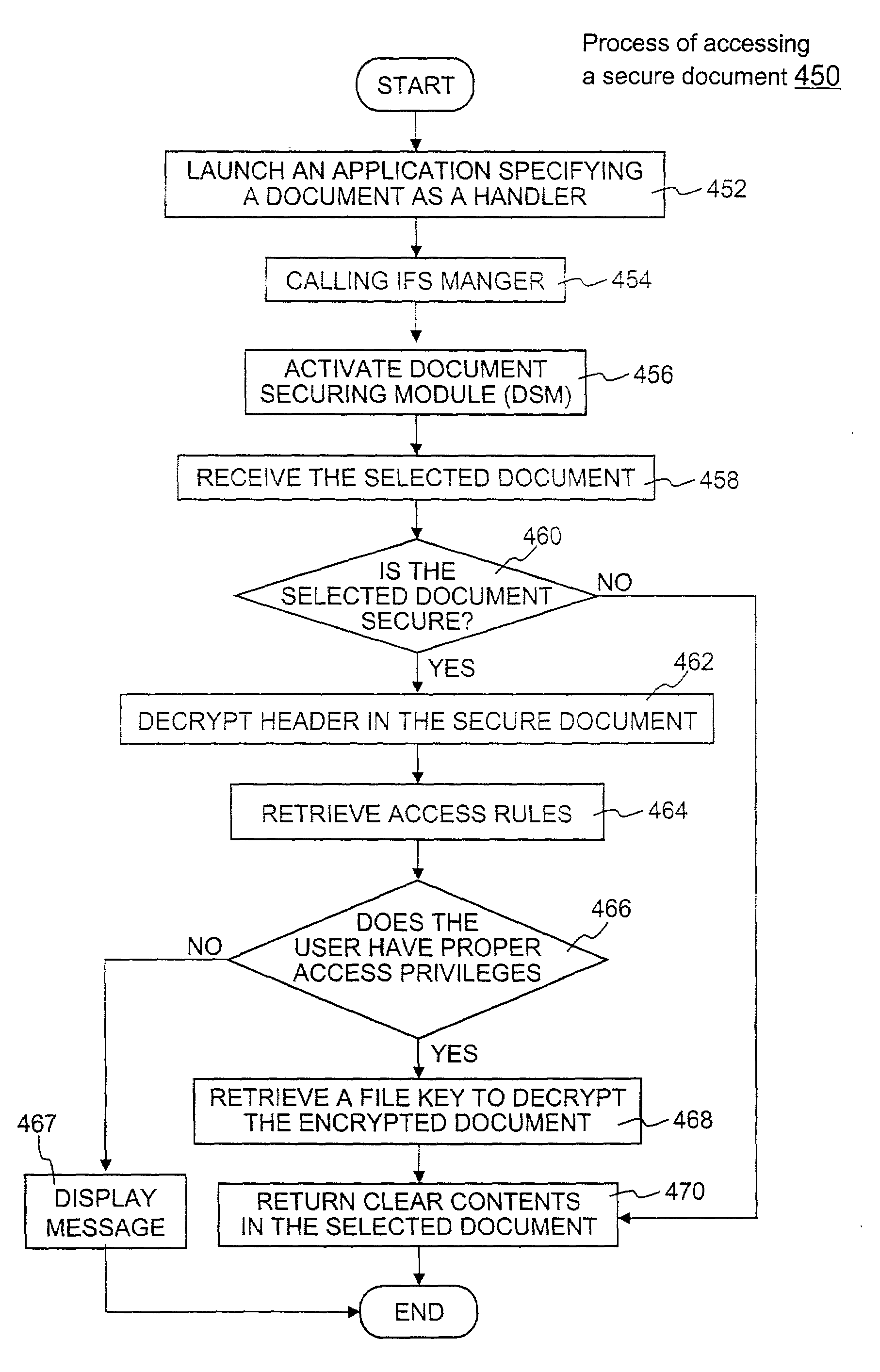
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
Secure magnetic stripe reader for handheld computing and method of using same
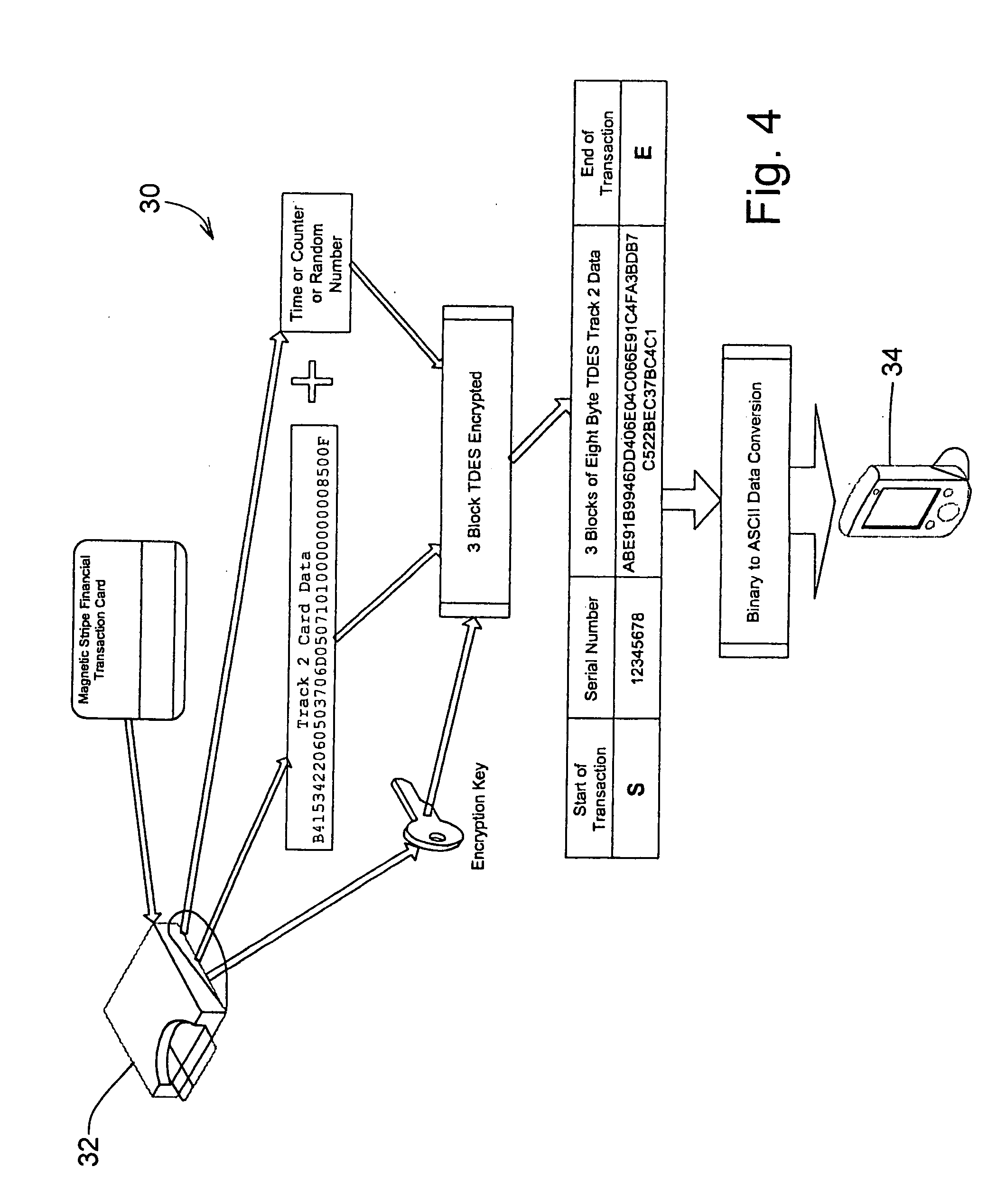
ActiveUS20060049255A1Support easily and efficientlyFunction increaseAcutation objectsFinanceInformation processingSoftware system
A secure magnetic stripe card stripe reader (MSR) module and software system capable of encrypting the magnetic stripe data to CISP standards for use in point of sale (POS) and other applications requiring data security using non secure networks and computing devices. Additionally, when incorporated within an attachment for conventional personal digital assistant (PDA) or cell phone or stationary terminal, provides encrypted data from the magnetic head assembly providing compliance with Federal Information Processing Standards Publication Series FIPS 140 covering security and tampering standards. Moreover, this module and software system includes the capability of providing secure POS transactions to legacy transaction processing systems transparently to the existing infrastructure. Furthermore, this module and software system includes the capability of transparently providing detection of fraudulently copied magnetic stripe cards.
Owner:VERIFONE INC
Data security system and method associated with data mining
ActiveUS7322047B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsMultiple keys/algorithms usagePlaintextInternet privacy
The data security method, system and associated data mining enables multiple users, each having a respective security clearance level to access security sensitive words, data objects, characters or icons. The method extracts security sensitive words, data objects, characters or icons from plaintext or other source documents to obtain (a) subsets of extracted data and (b) remainder data. The extracted data is, in one embodiment, stored in a multilevel security system (MLS) which separates extract data of different security levels with MLS guards. Some or all of the original data is reconstructed via one or more of the subsets of extracted data and remainder data only in the presence of a predetermined security level. In this manner, an inquiring party, with the proper security clearance, can data mine the data in the MLS secured storage.
Owner:DIGITAL DOORS
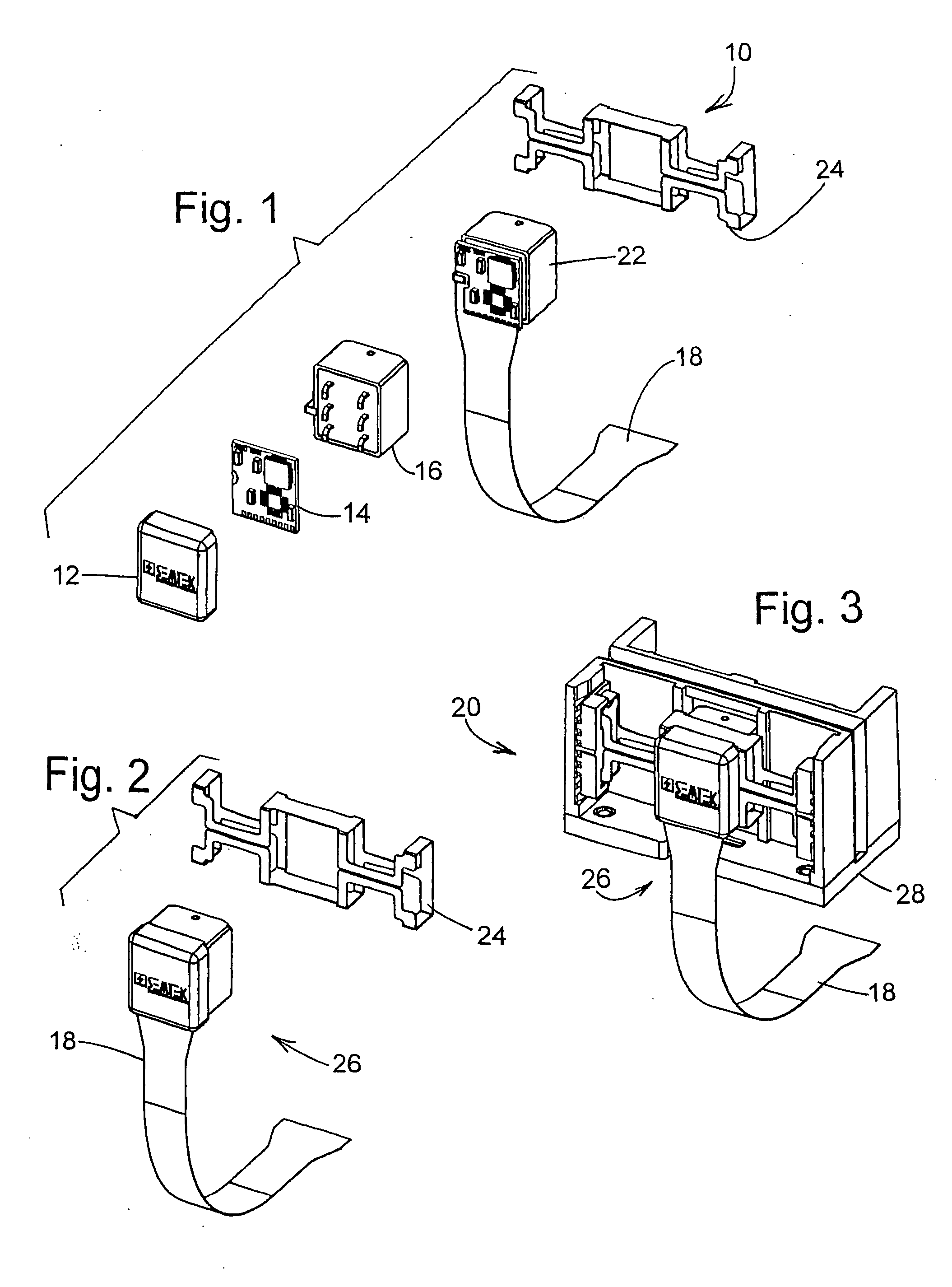
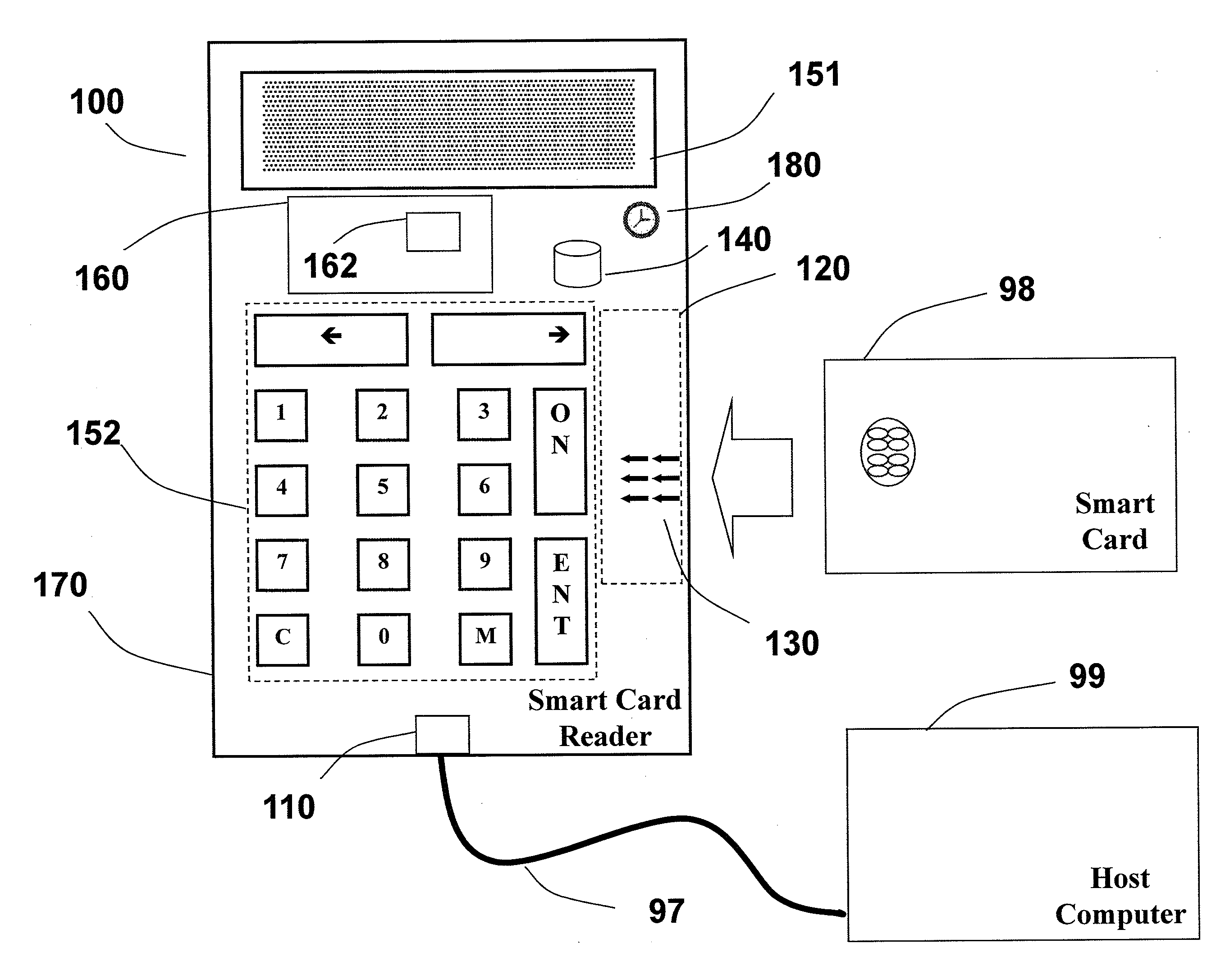
Smart card reader with a secure logging feature
A secure smart card reader is disclosed that is enabled to make reader signatures on data representative of events and actions which may be security related and which may include data representative of reader commands received from a host or remote application, smart card commands exchanged with an inserted smart card, data presented to a user for approval, and / or configuration parameters applied when dealing with any of the foregoing. The smart card reader may be adapted to maintain logs of events and actions which may include exchanging reader commands, exchanging smart card commands, and / or interactions with a user. The logs may include data representative of the reader commands received, the smart card commands exchanged, data presented to the user for approval, and / or configuration parameters applied when dealing with any of the foregoing. The secure smart card reader may be adapted to generate a reader signature over the logs.
Owner:ONESPAN NORTH AMERICA INC
Data privacy
ActiveUS8412837B1Public key for secure communicationComputer security arrangementsTokenization (data security)Coding decoding
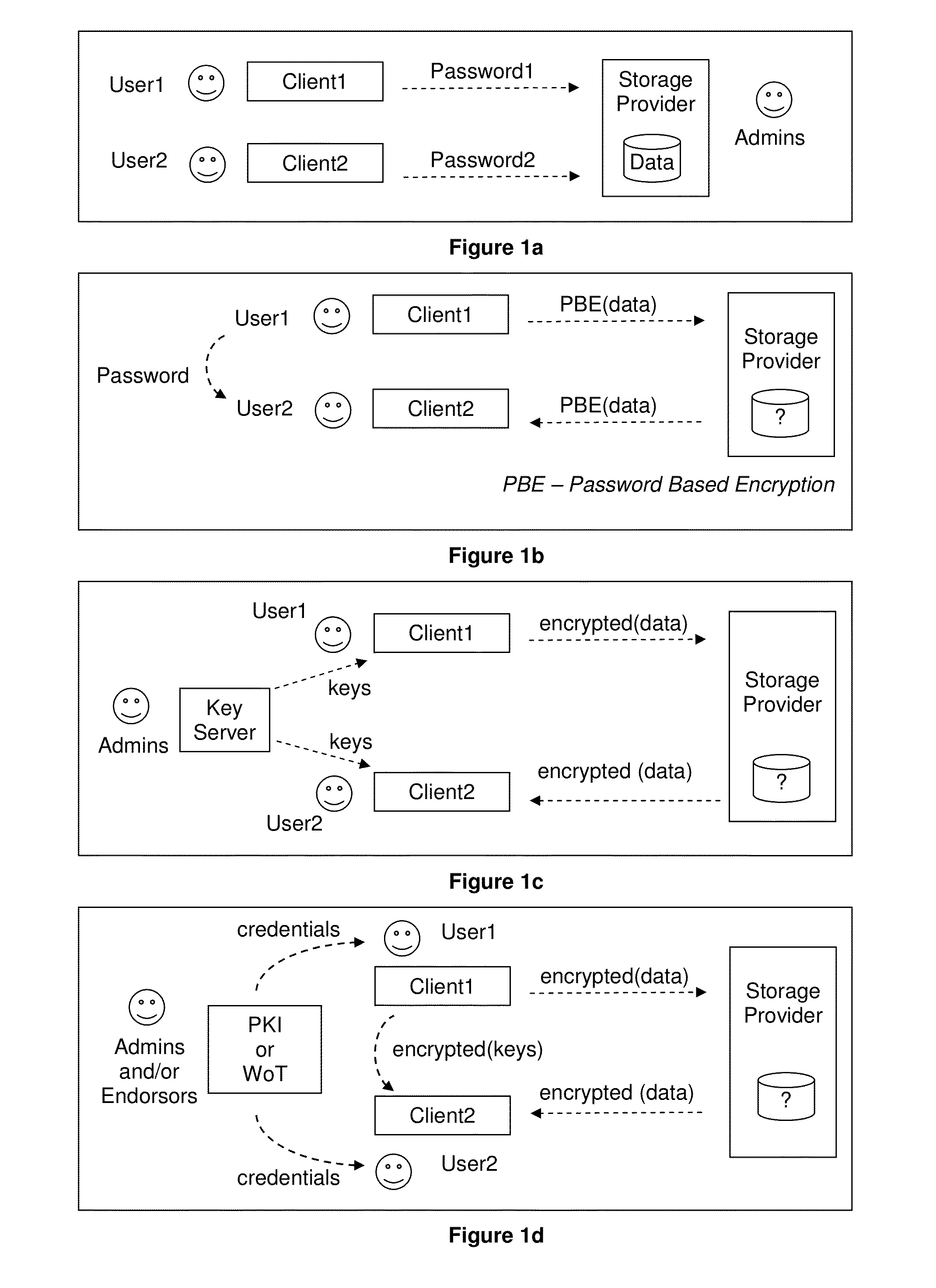
In some embodiments, techniques for data security may include encoding and decoding unreadably encoded data, such as data encrypted with a public key or tokenized. In some embodiments, techniques for data security may include distributing an encrypted private key. In some embodiments, unreadable data may be encrypted and / or decrypted using time-varying keys.In some embodiments, techniques for data security may include combining information and a policy, and encoding the combined information and policy, wherein encrypting the combined information and policy is performed using a public key, or via tokenization.In some embodiments, techniques for data security may include receiving data, wherein the data has been encoded, decoding the data, determining a first datum and a second datum, wherein the first datum and the second datum are associated with the decoded data, and determining a policy, wherein the policy is associated with the first datum.
Owner:ROSKIND JAMES A DR
Processing, storing, and delivering digital content
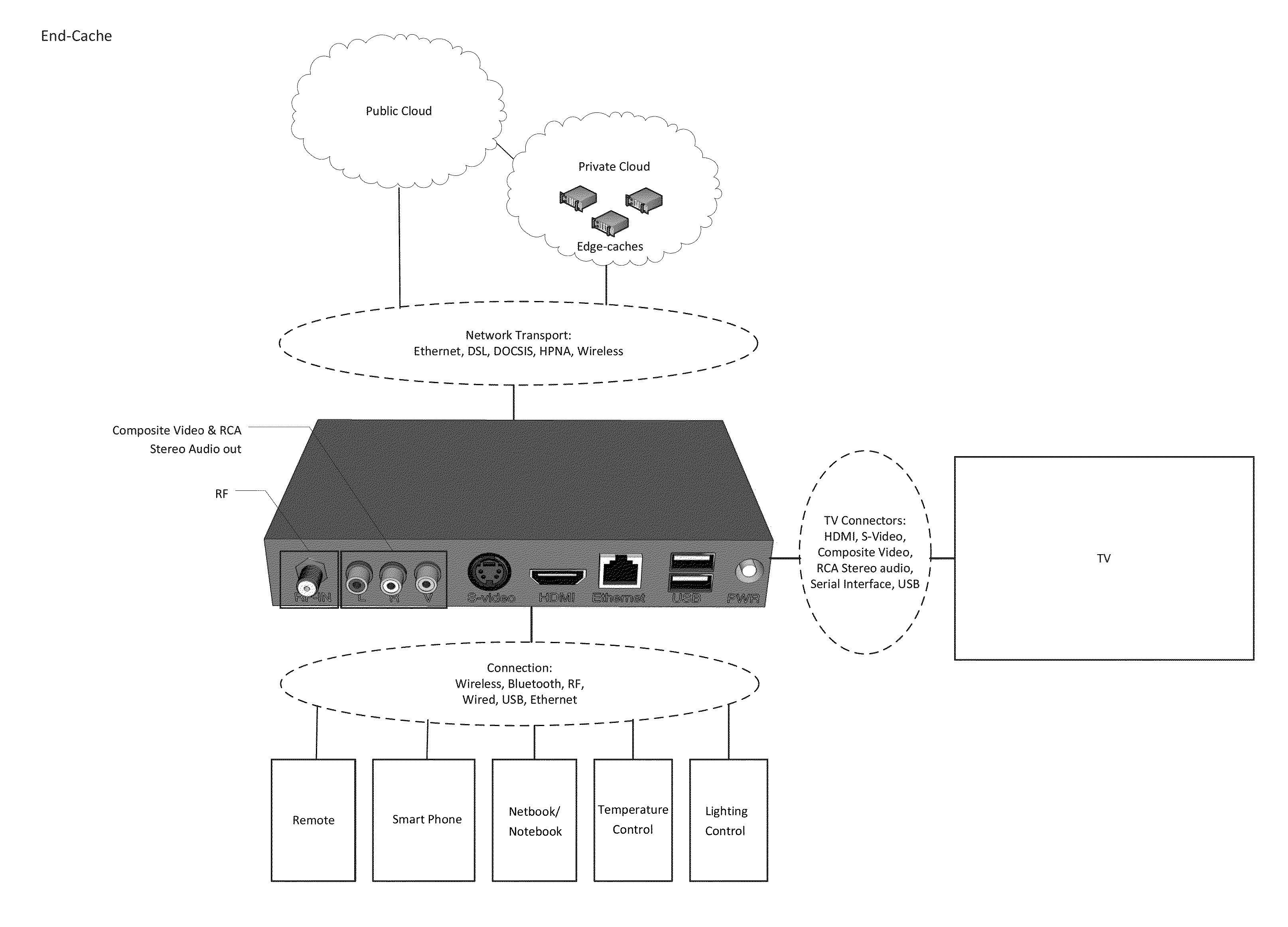
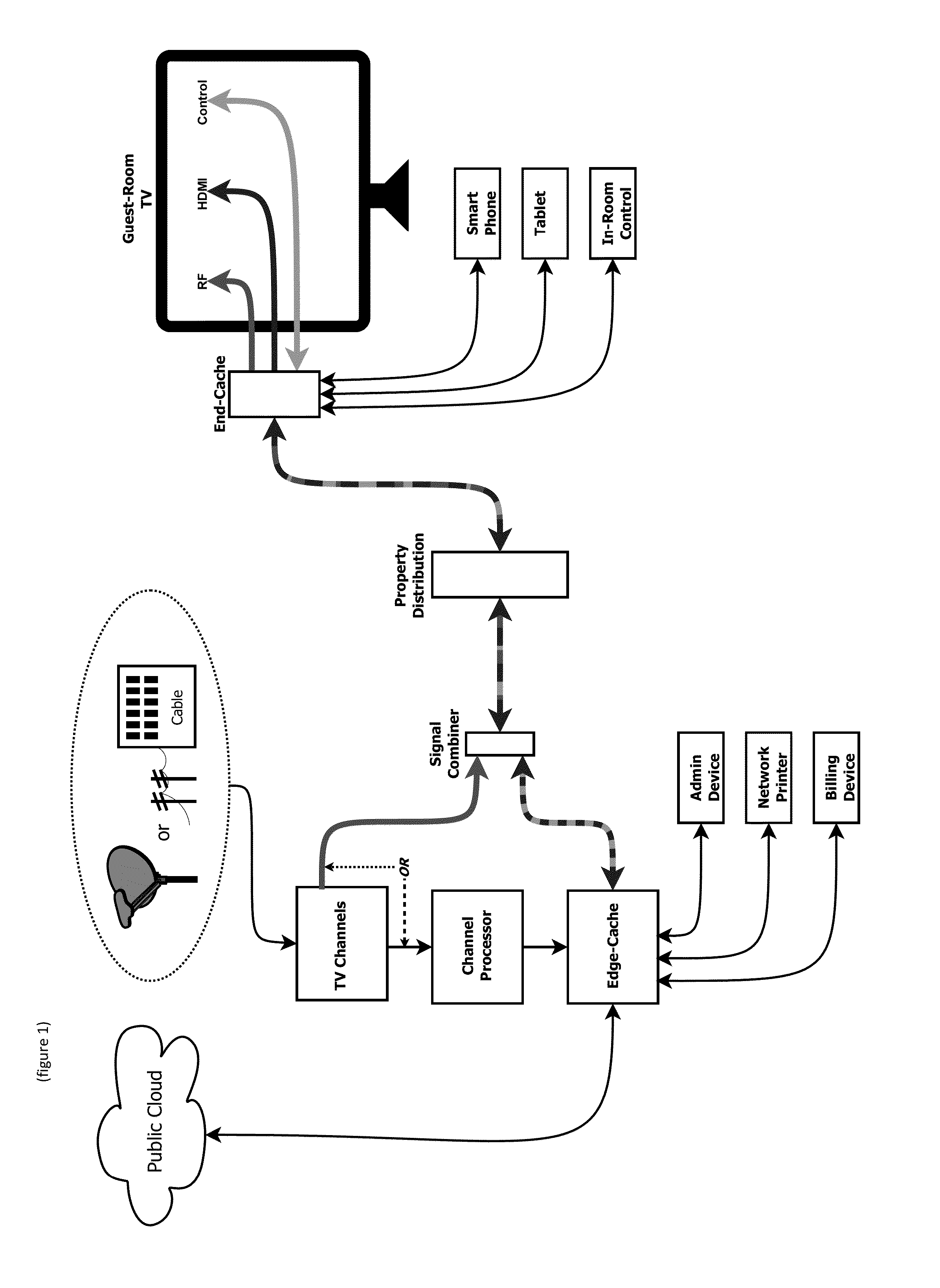
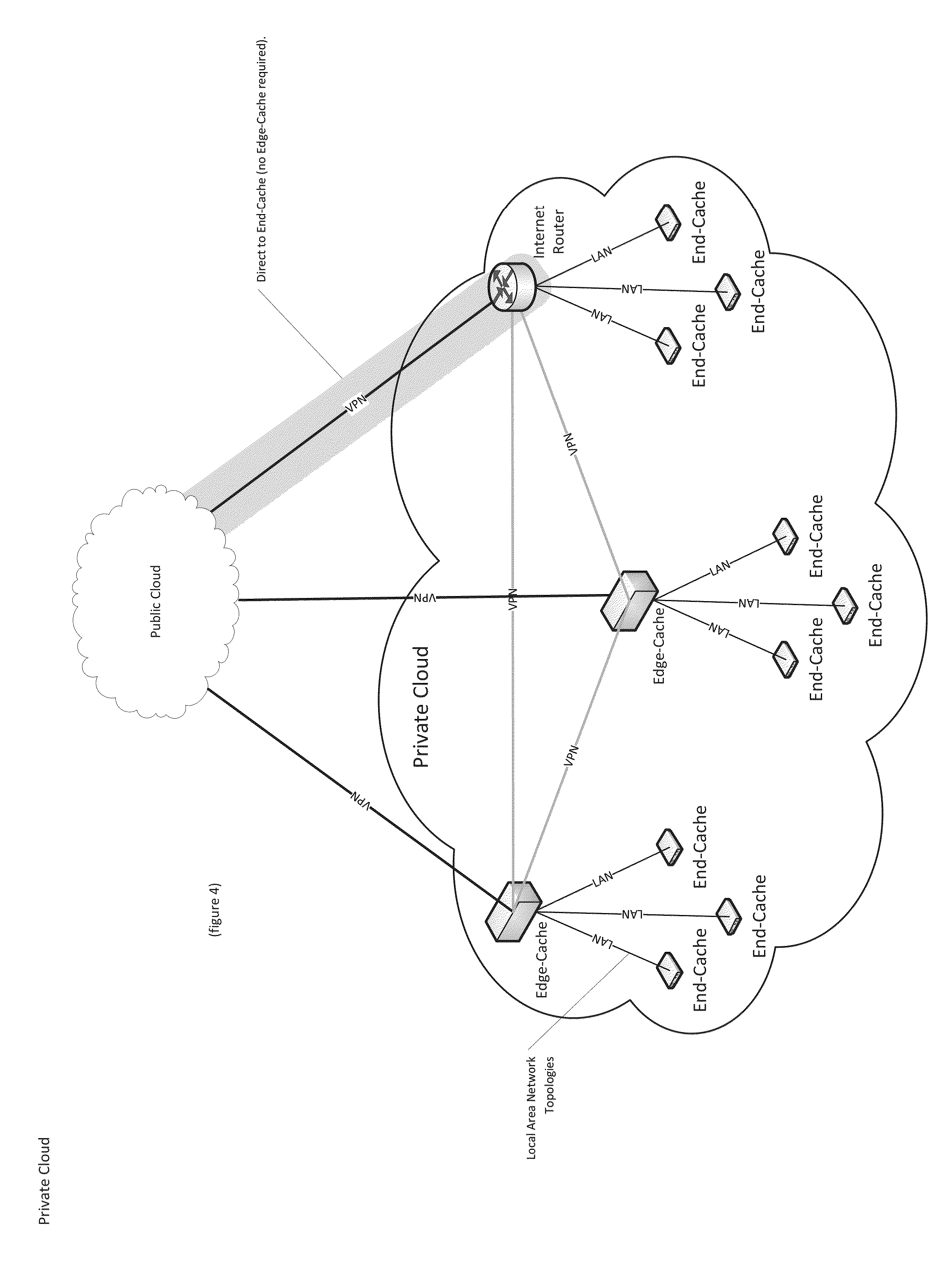
Implementations of the present invention include a Public Cloud, one or more End-Caches and optionally one or more Edge-Caches in computerized architecture that provides digital content, such as entertainment services and / or informational content, to a guest display (e.g., End-Cache connected to in-room TV, End-Cache connected to personal portable device) or control of one or more devices (e.g., in-room TV and / or in-room control). Implementations of the present invention also include a Content Distribution Architecture that uses the public Internet to securely transmit digital content and data to all desired locations (e.g., End-Caches). Implementations of the present invention further include a Channel Processor that takes one of more video signal(s) and prepares them for redistribution to an end user. Implementations of the present invention leverage existing wiring at the property (whether coax, Ethernet, home-run, or loop-thru) to transport content / data to / from End-Caches.
Owner:INNFLICKS MEDIA GRP
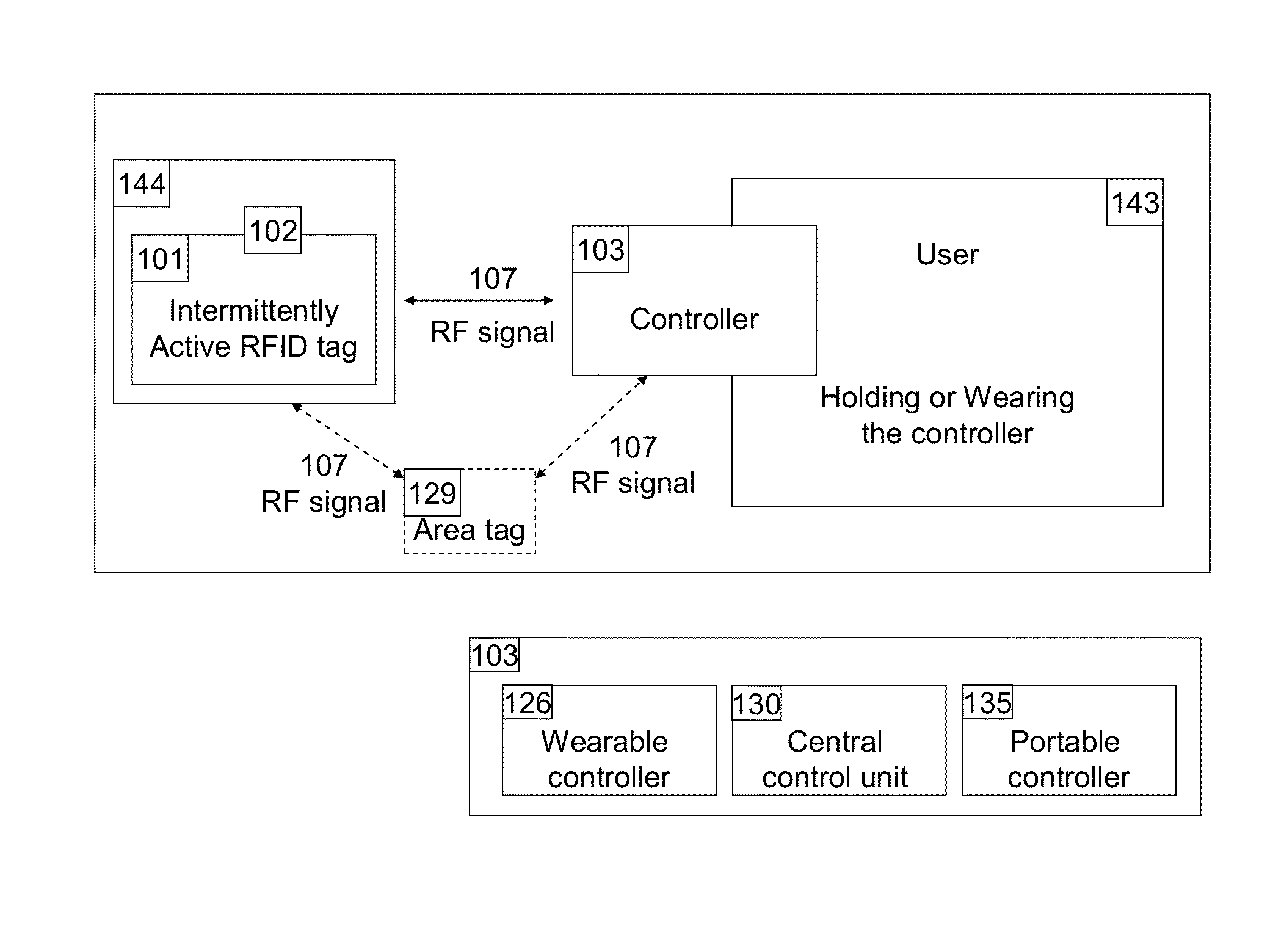
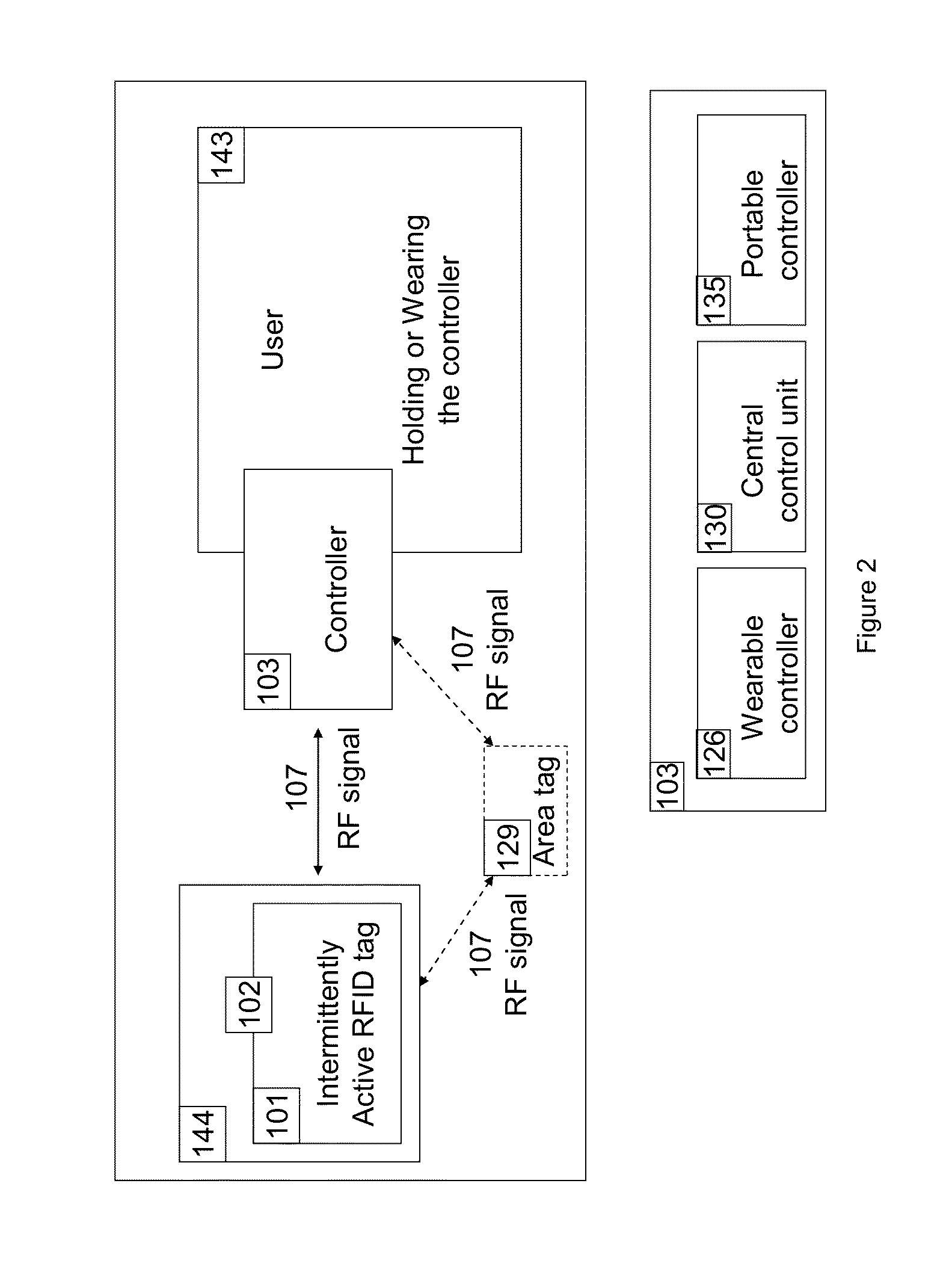
Apparatus and method for locating, tracking, controlling and recognizing tagged objects using active RFID technology
InactiveUS20140240088A1Avoid disturbanceEasy to changeProgramme controlElectric signal transmission systemsThe InternetUSB
A real-time automated data security system protects both data and devices from loss, theft, and unauthorized access or activity. A miniature active RFID circuit is embodied in tags, area tags, controllers, USB sticks and a universal interface software for computers (i.e., Java), smart phones, and gateway boxes written to interface with the system. These devices are customizable and can link in arrays to cover large areas, use sensors, and scale up in module configurations to meet any need. The system is independent of electricity, GPS, satellites, the Internet, other software, and IT personnel. Its novel software, inside the tags, area tags and controllers is inaccessible and cannot be copied. Wireless transmissions are encrypted to military grade levels and packets are never repeated, making it unhackable, even by brute force attack. A unique battery-conserving protocol ensures good range and long battery life. The system has the ability to ignore copied packages or relaying by attackers, and to prevent of unauthorized access to USB sticks by proximity checks to the active RFID circuit.
Owner:ROBINETTE JAMIE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com