Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6271 results about "Software system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A software system is a system of intercommunicating components based on software forming part of a computer system (a combination of hardware and software). It "consists of a number of separate programs, configuration files, which are used to set up these programs, system documentation, which describes the structure of the system, and user documentation, which explains how to use the system".
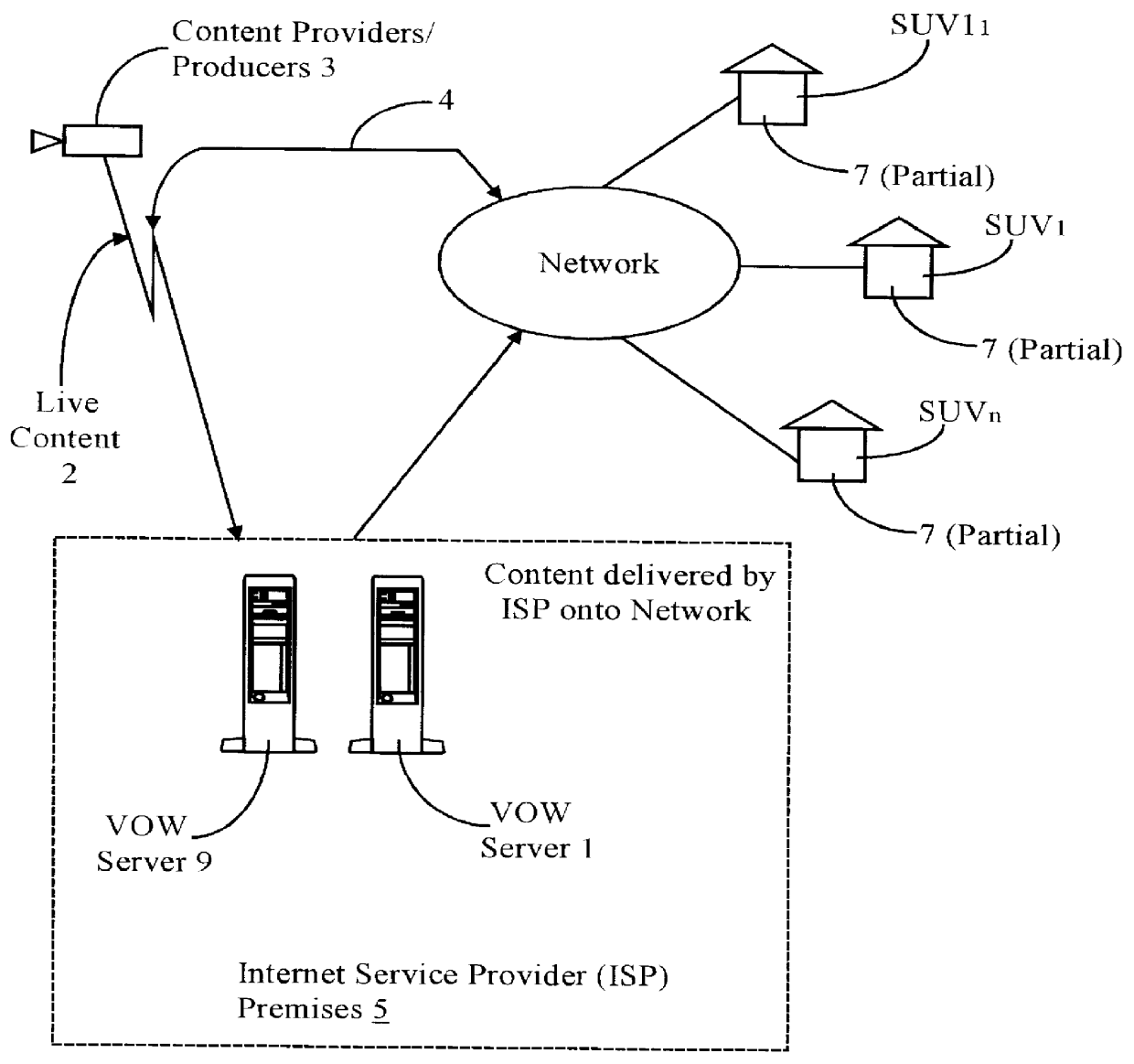
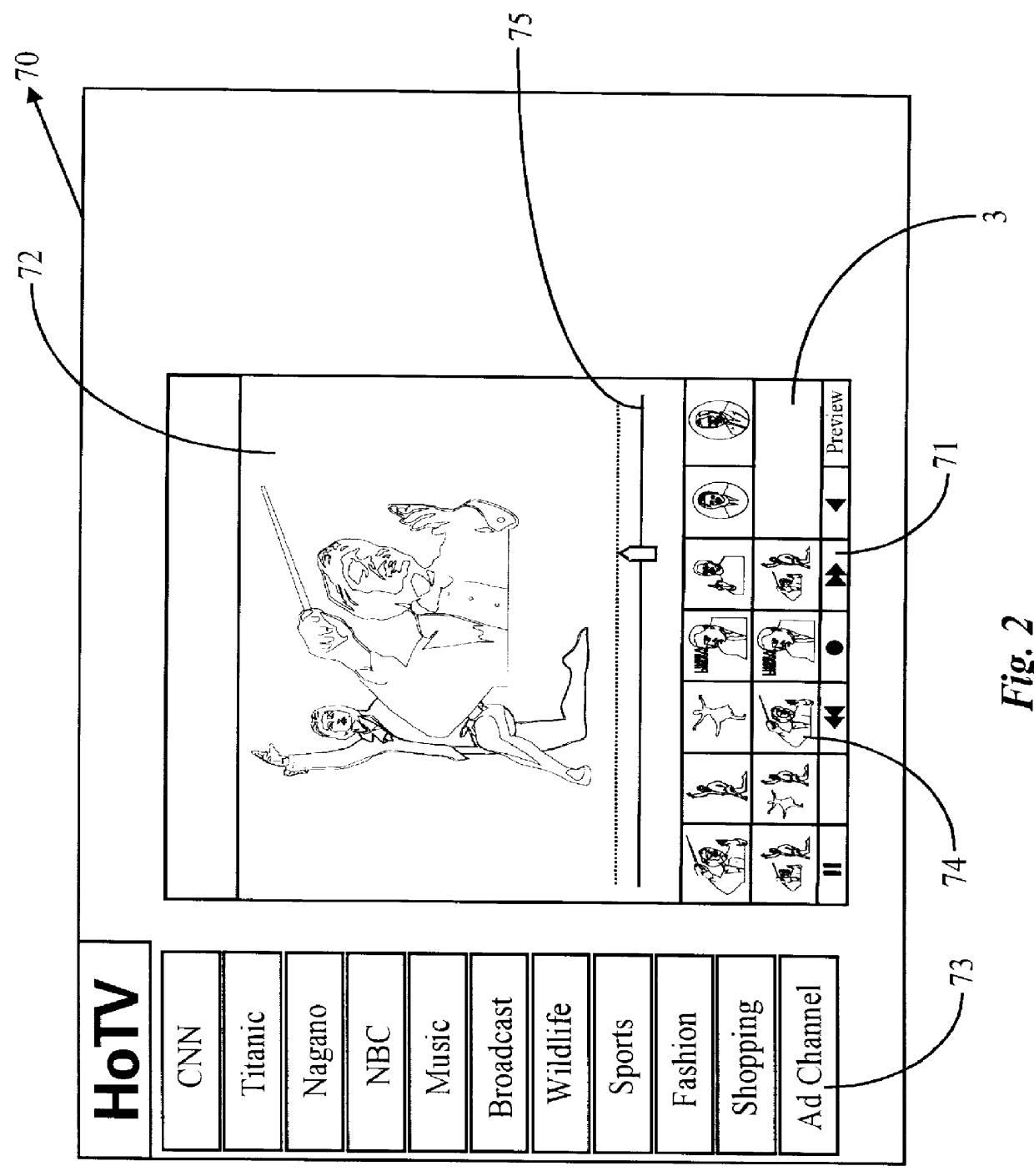
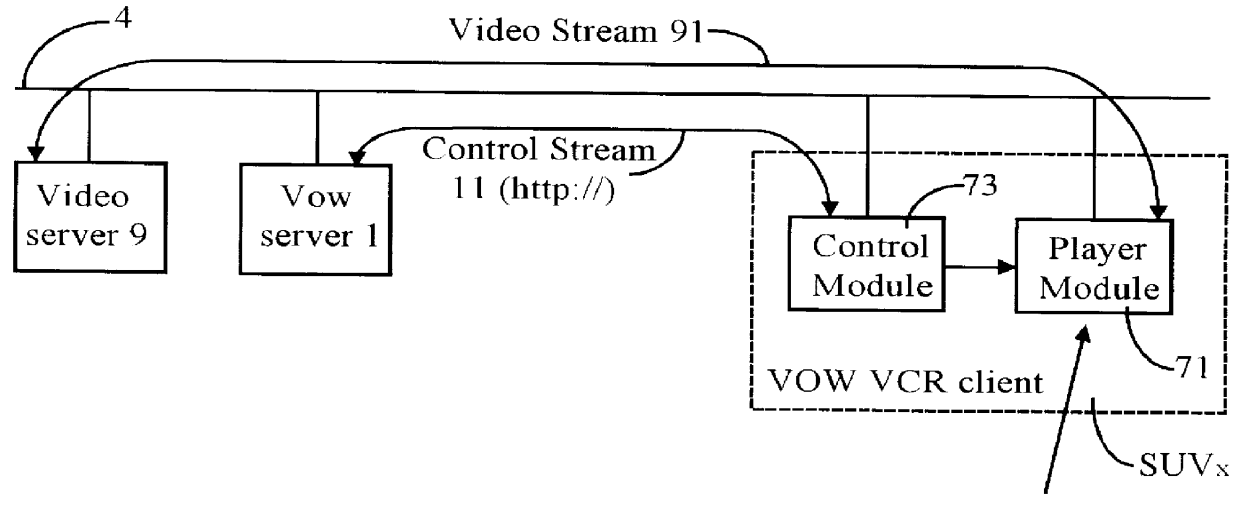
Real-time receipt, decompression and play of compressed streaming video/hypervideo; with thumbnail display of past scenes and with replay, hyperlinking and/or recording permissively intiated retrospectively
InactiveUS6154771AEfficient multicastingEasy to seeTelevision system detailsDigital data information retrievalFull customSoftware system
Streaming compressed digital hypervideo received upon a digital communications network is decoded (decompressed) and played in a client-computer-based "video on web VCR" software system. Scene changes, if not previously marked upstream, are automatically detected, and typically twenty-one past scenes are displayed as thumbnail images. Hyperlinks within the main video scene, and / or any thumbnail image, show as hotspots, with text annotations typically appearing upon a cursor "mouse over". All hyperlinks-as are provided and inserted by, inter alia, the upstream network service provider (the "ISP")-may be, and preferably are, full-custom dynamically-resolved to each subscriber / user / viewer ("SUV") upon volitional "click throughs" by the SUV, including retrospectively on past hypervideo scenes as appear within the thumbnail images. Hyperlinking permits (i) retrieving information and commercials, including streaming video / hypervideo, from any of local storage, a network (or Internet) service provider ("ISP"), a network content provider, and / or an advertiser network site, (ii) entering a contest of skill or a lottery of chance, (iii) gambling, (iv) buying (and less often, selling), (v) responding to a survey, and expressing an opinion, and / or (vi) sounding an alert.
Owner:TATA AMERICA INT
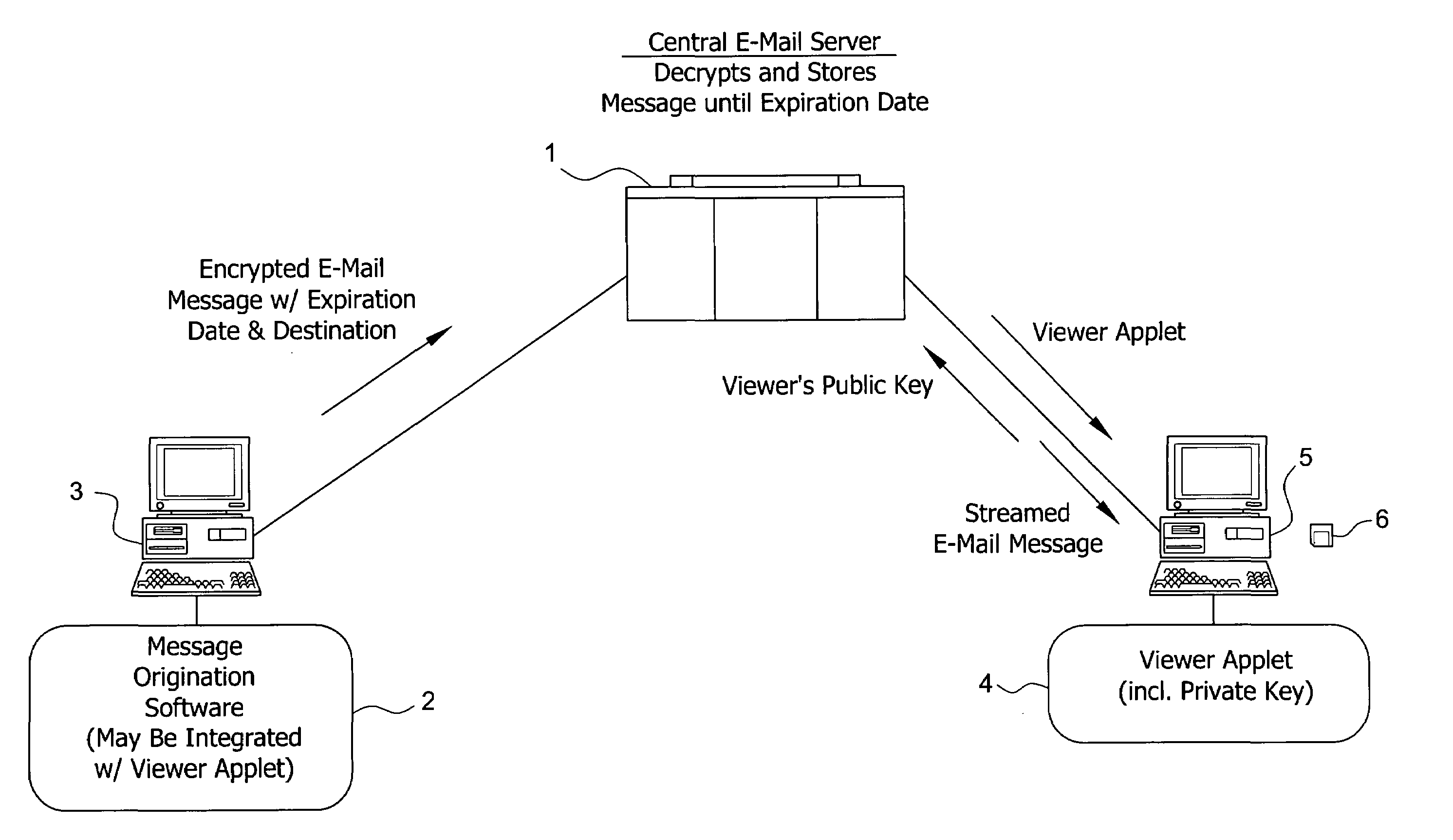
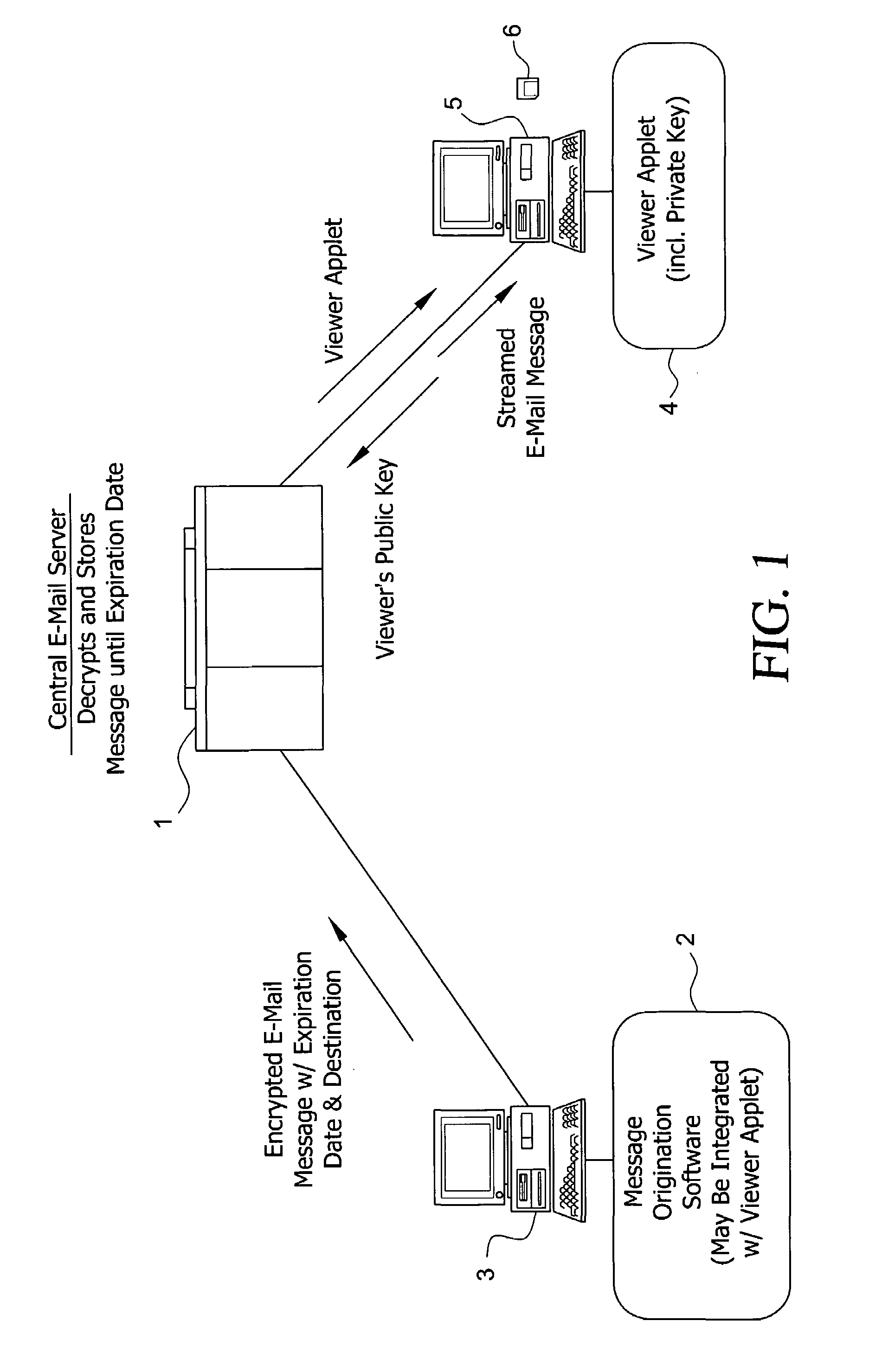
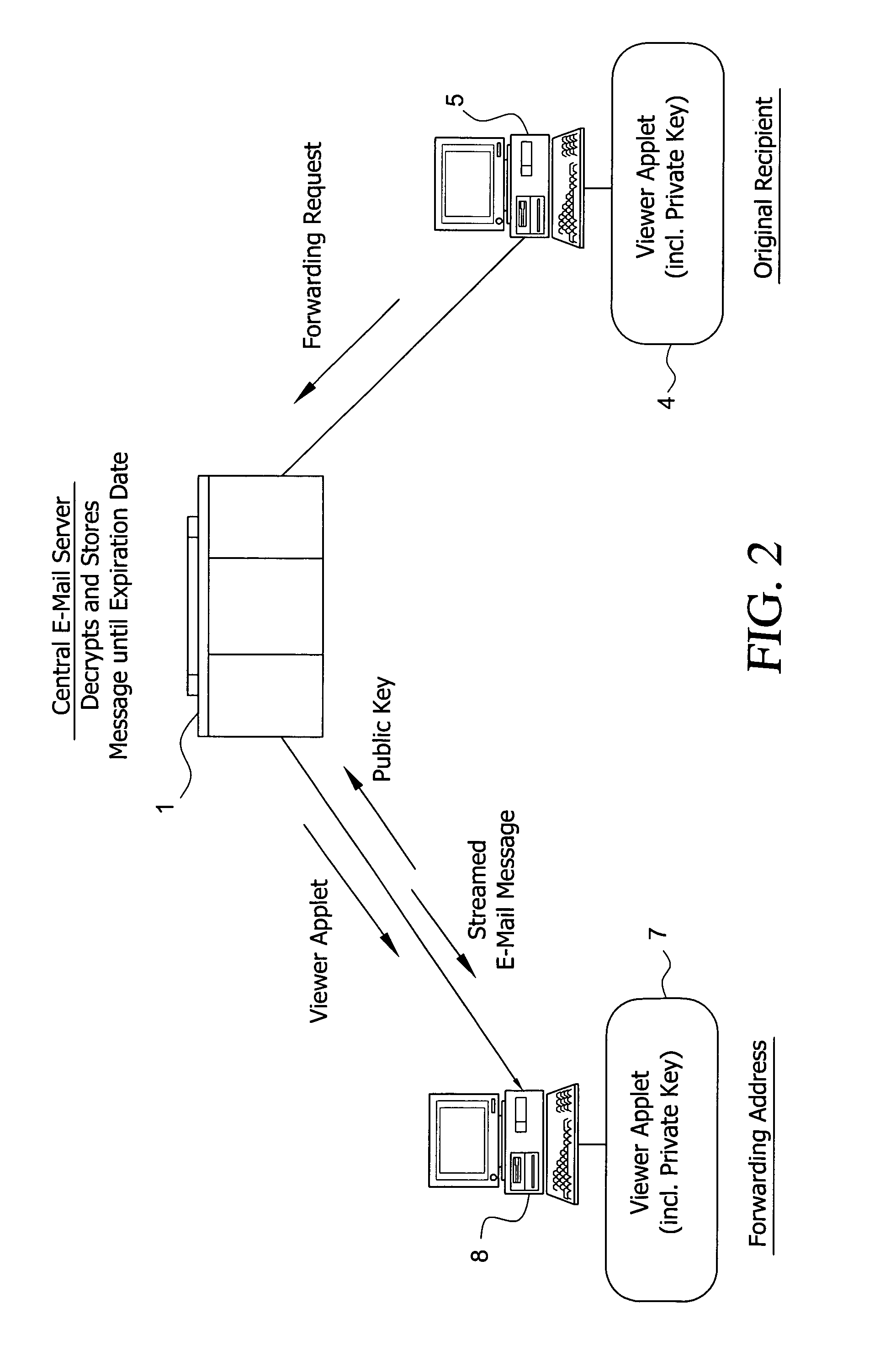
System and method for enabling the originator of an electronic mail message to preset an expiration time, date, and/or event, and to control processing or handling by a recipient
InactiveUS7149893B1Limited lifespanRapid and efficient mannerDigital data processing detailsAnalogue secracy/subscription systemsExpiration TimeComputer hardware
An electronic mail system and method enables the originator of a message sent by electronic mail to select a date, time, or event at which the message and all incarnations of the message to self-destruct, regardless of the number and types of computers or software systems that may have interacted with the message. The system and message also permits the originator to include processing and handling limitations. The necessary control over the message is achieved by encrypting the message and enabling viewing only through a viewer applet arranged to facilitate destruction of the message upon the occurrence of the selected expiration time, date, or event, and to implemented the handling and processing limitations. A central server can be used to exercise additional control over the message by serving as a proxy destination, and by streaming the encrypted message to the viewer applet. The viewer applet can be transmitted to new recipients with the message so that the system and method can direct mail to any electronic mail user.
Owner:RESOURCE CONSORTIUM LTD LLC
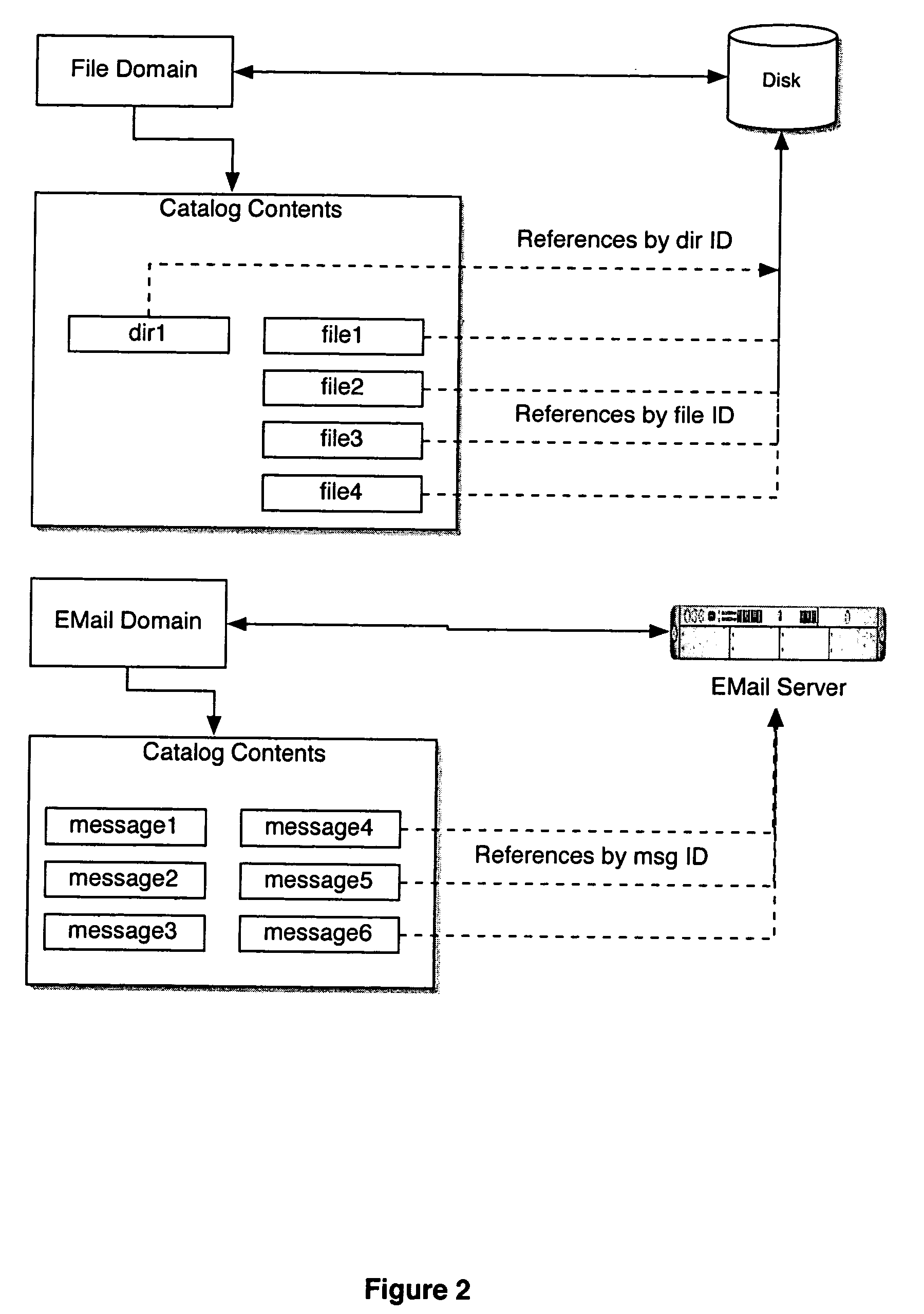
Computer system for automatic organization, indexing and viewing of information from multiple sources
ActiveUS7275063B2Facilitate communicationMultimedia data indexingFile access structuresPathPingSoftware system
Owner:EHIERARCHY LLC
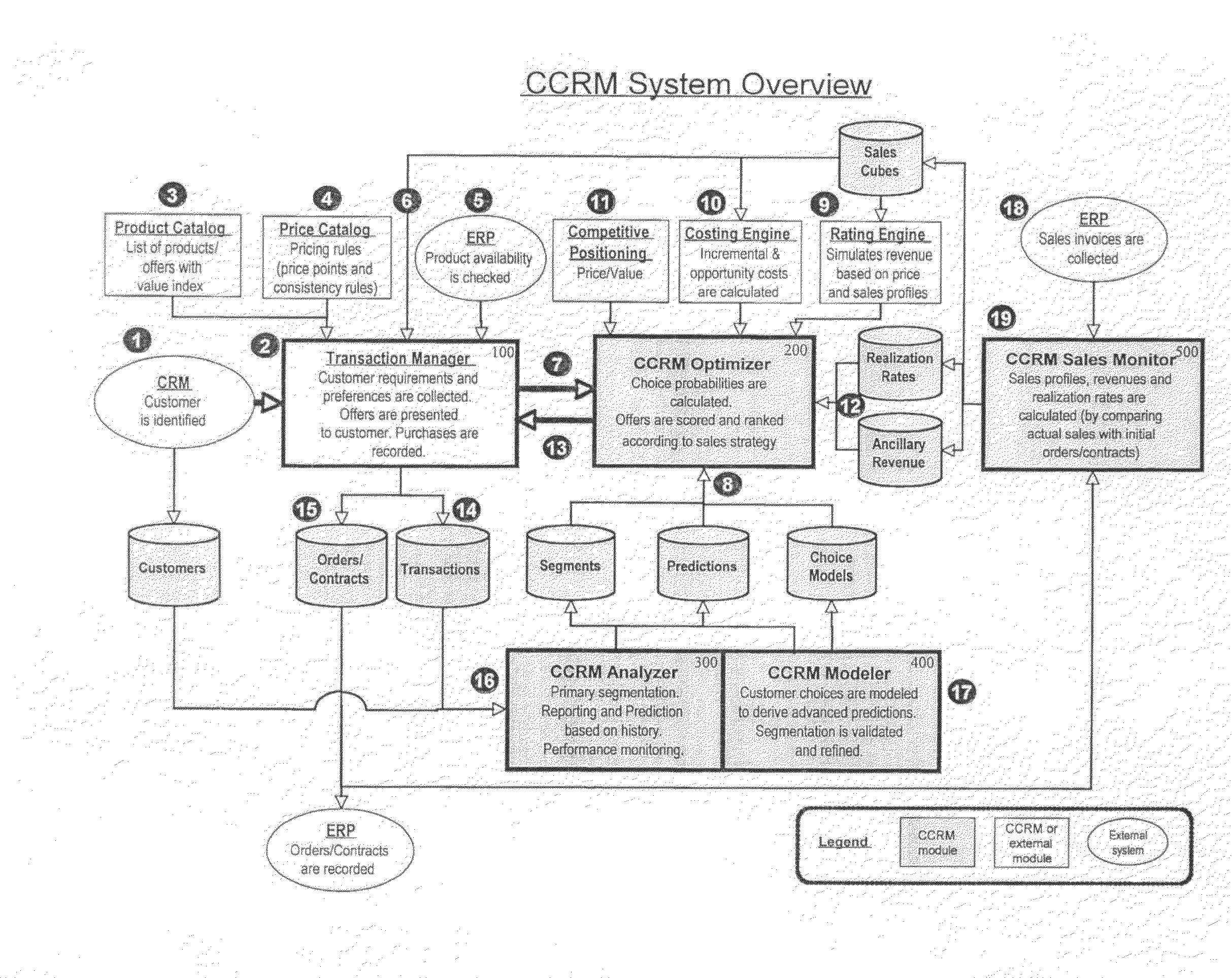
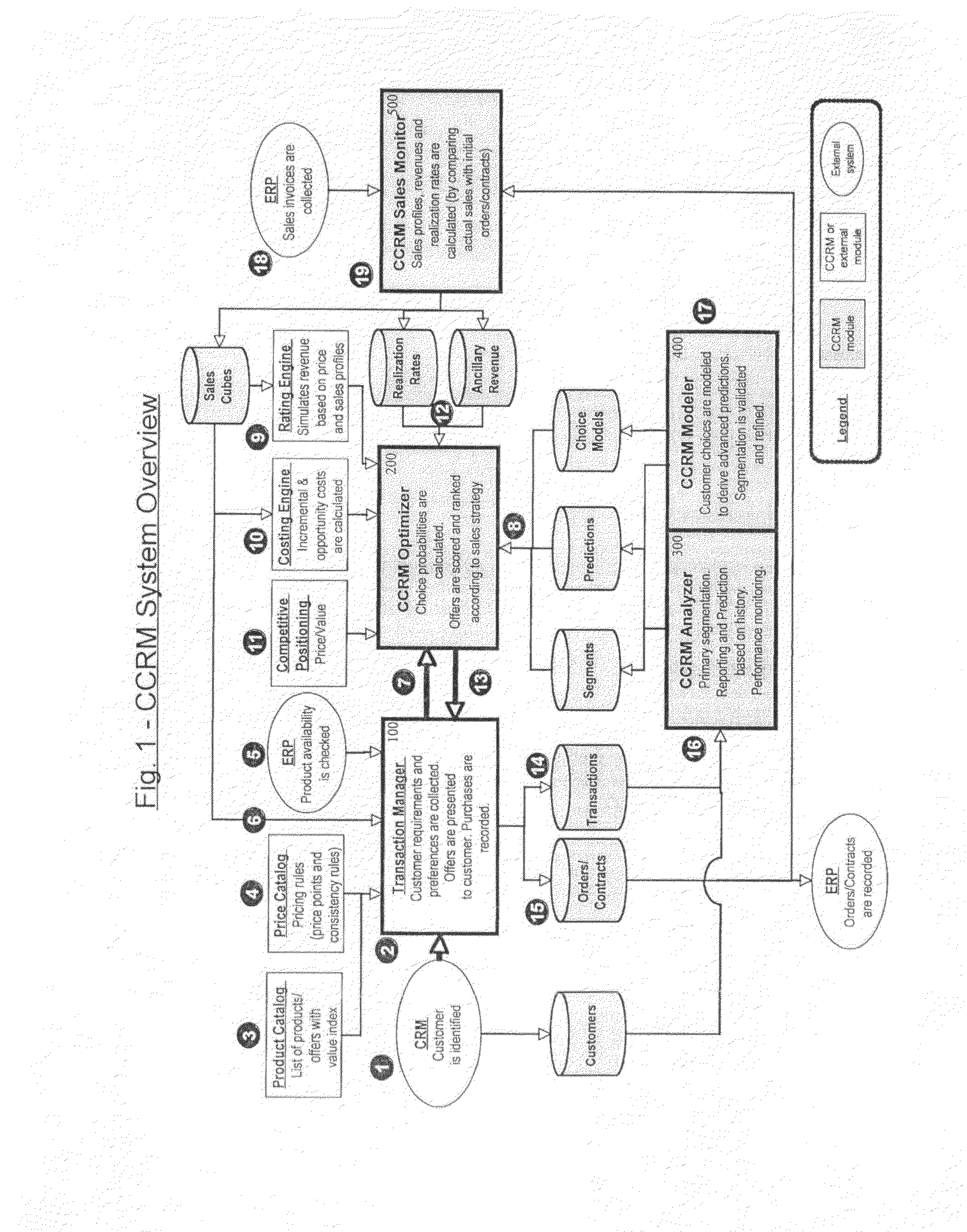
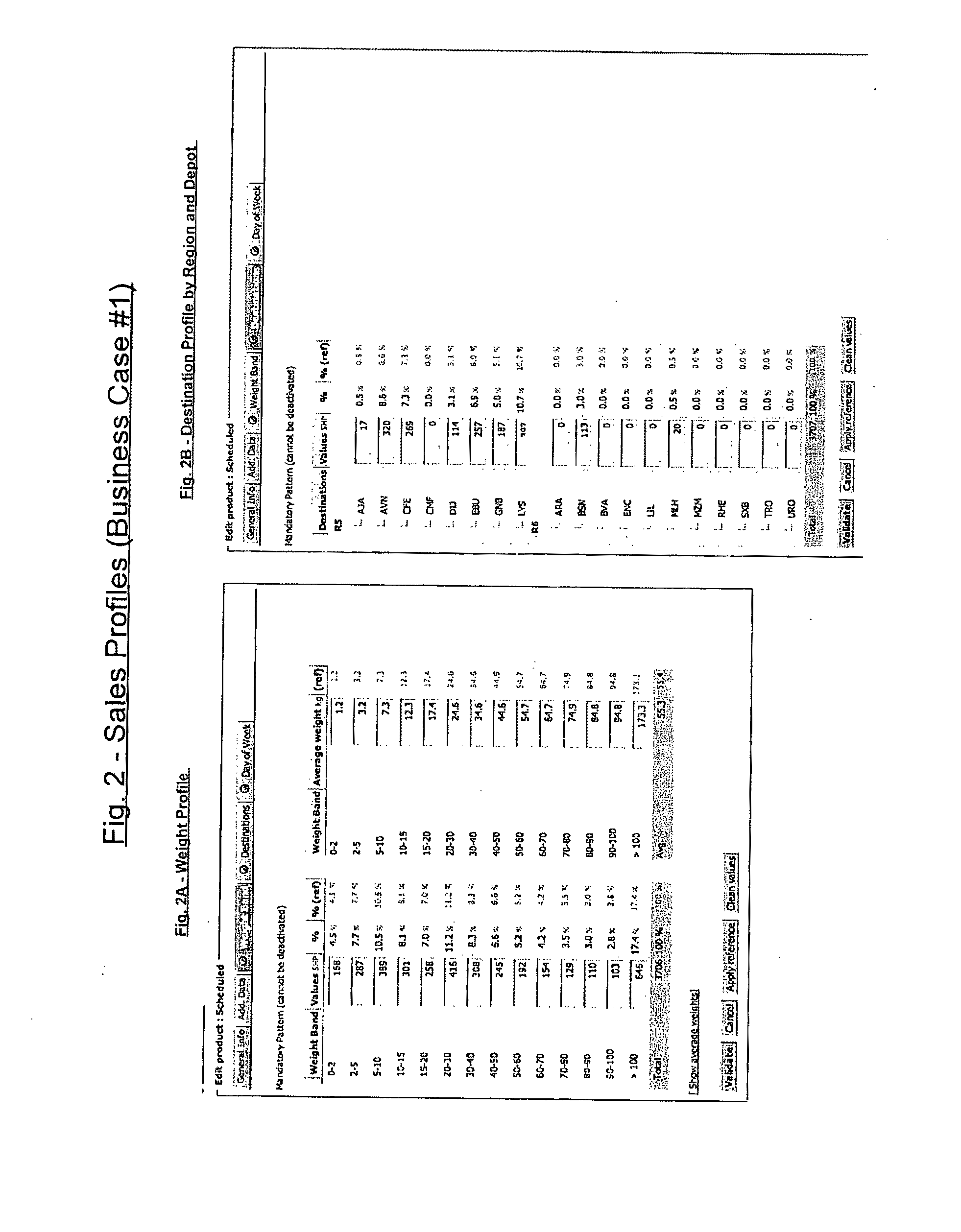
Customer centric revenue management
InactiveUS20090234710A1Improve recommendationsImprove definitionMarket predictionsSpecial data processing applicationsCustomer centricSoftware
CCRM is a business method and computer software system, to be used by Enterprises selling portfolios of products / services, aiming to optimize the expected value of transactions (or contracts) with consumers or business customers. At a transaction level, CCRM estimates the probability of choice of potential offers by the customer. These offers may be presented alone with possible variation of their attributes (such as price), or in combinations / sets, or in sequences. CCRM calculates the probability of consequent conversion and realization of the sale. Probabilities of choice and conversion are forecasted based on a disaggregated customer choice model, taking into account customer characteristics and stated preferences as well as product / service attributes such as price. Offers are then scored and ranked by expected value based on their revenue, cost and choice probability. Finally, CCRM recommends which offer(s) to present to the customer, at which price(s) and in which display / sequence order, to maximize a business objective function such as the expected value of the transaction / contract.
Owner:OPEN PRICER
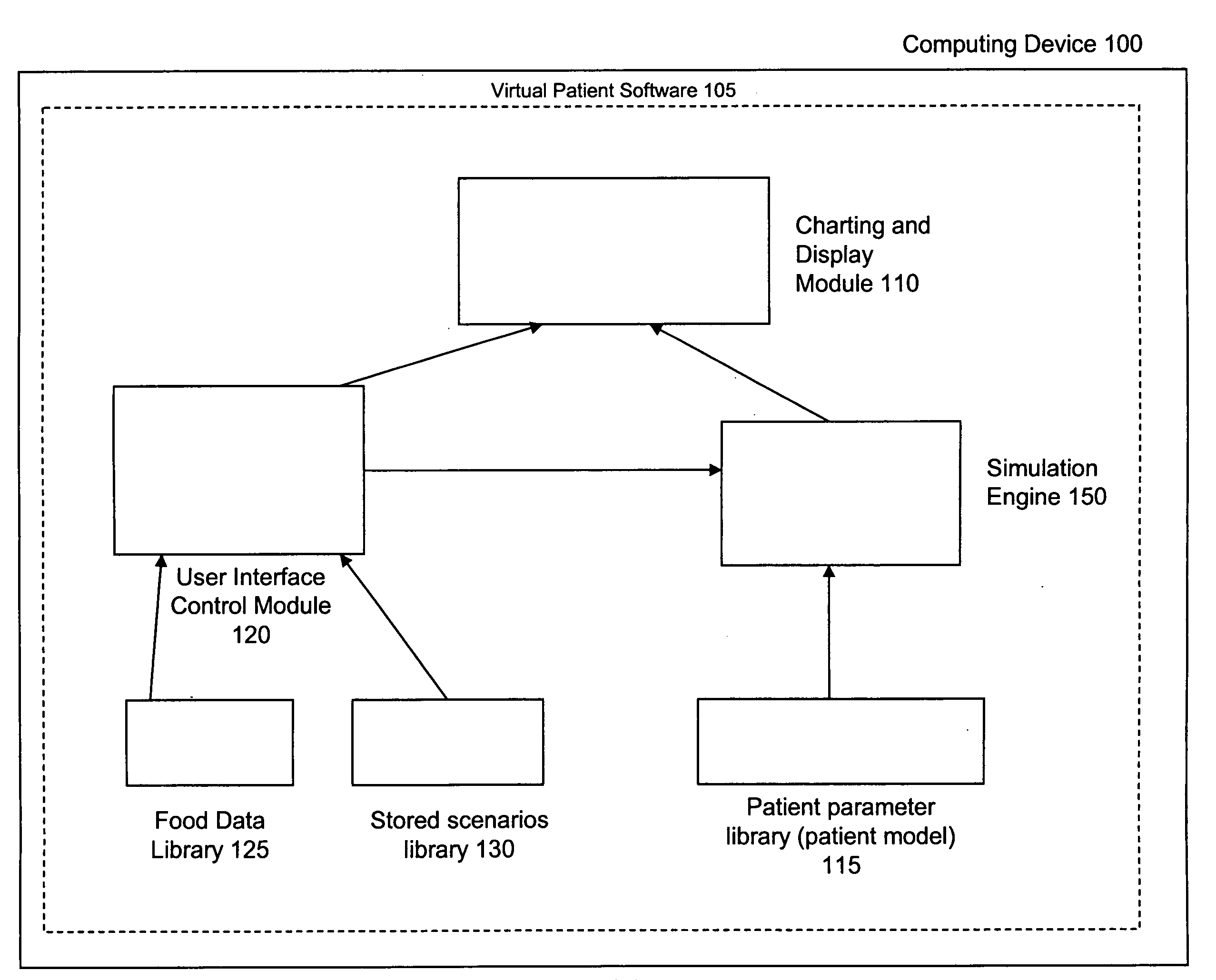
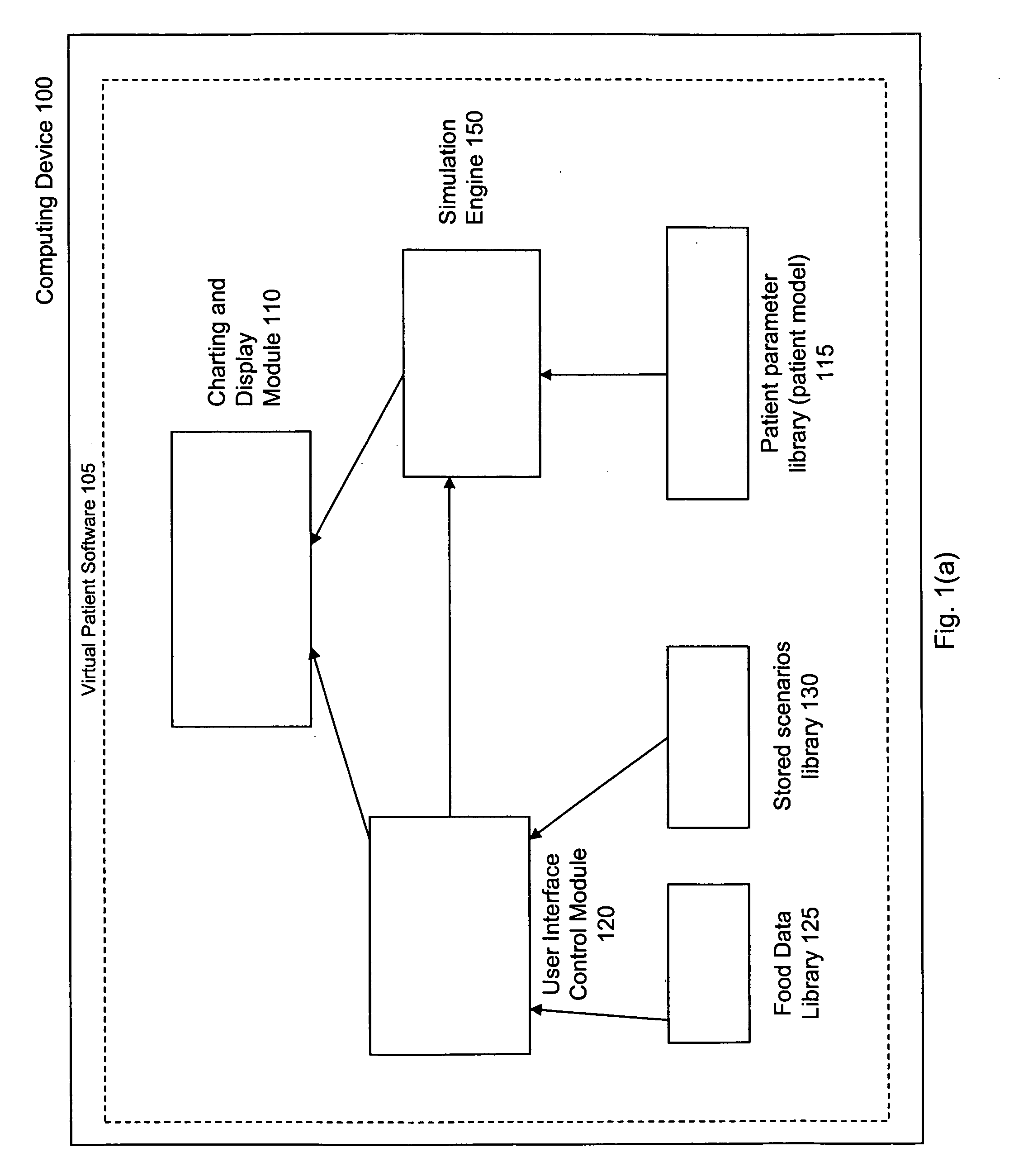
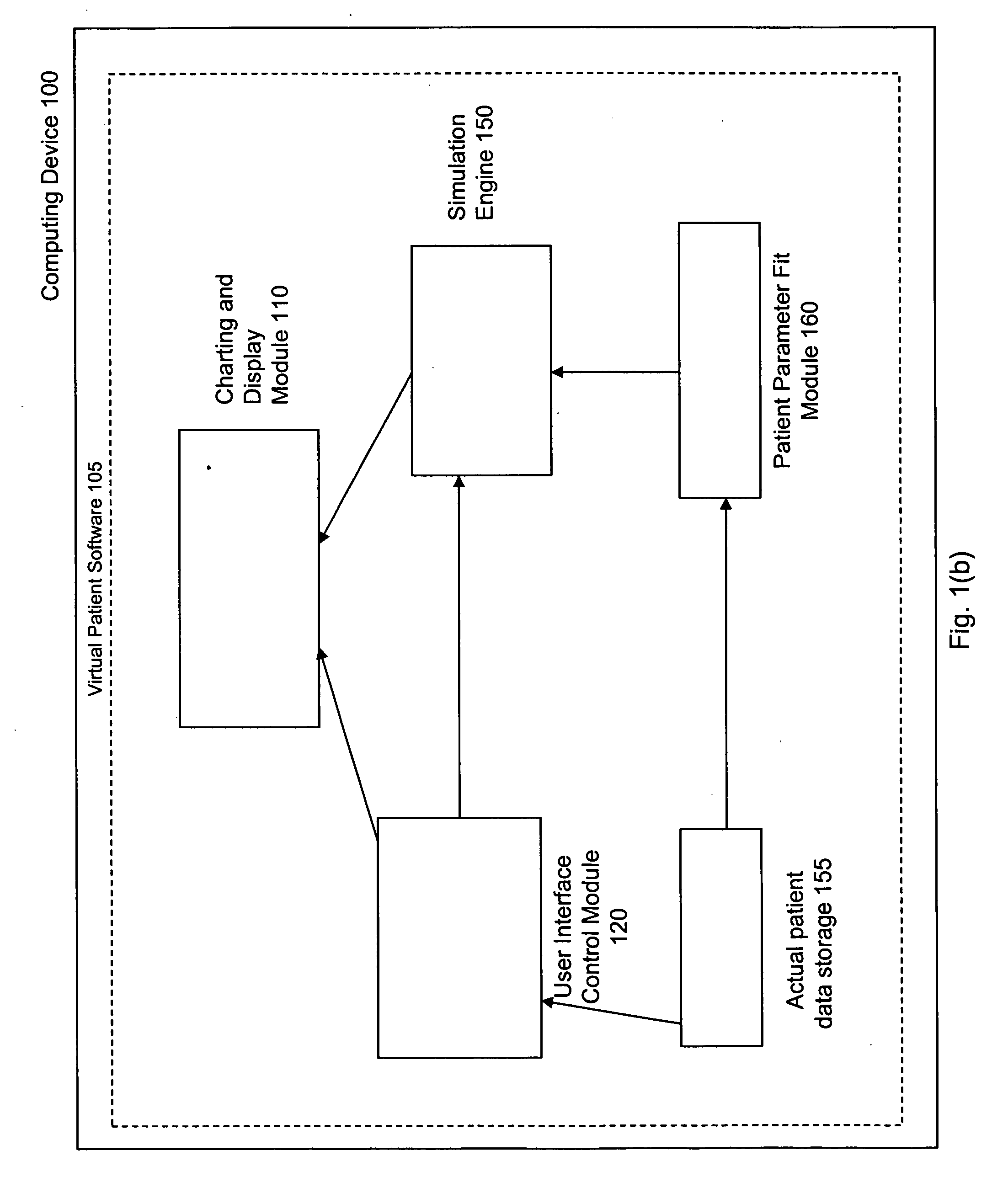
Virtual patient software system for educating and treating individuals with diabetes
A system to assist an individual in developing a therapy in diabetes treatment of a patient includes a user interface control module, a simulation engine, a charting and display module. The user interface control module receives an input related to the patient and captures a current time of the simulation. The simulation engine receives the input, generates a plurality of blood glucose readings for the patient up to the current time of the simulation based on the input, and to transfers the plurality of blood glucose readings. The charting and display module receives the plurality of blood glucose readings and display the plurality of blood glucose readings. The simulation engine receives patient parameters from a patient parameter library based on a selected patient model.
Owner:MEDTRONIC MIMIMED INC
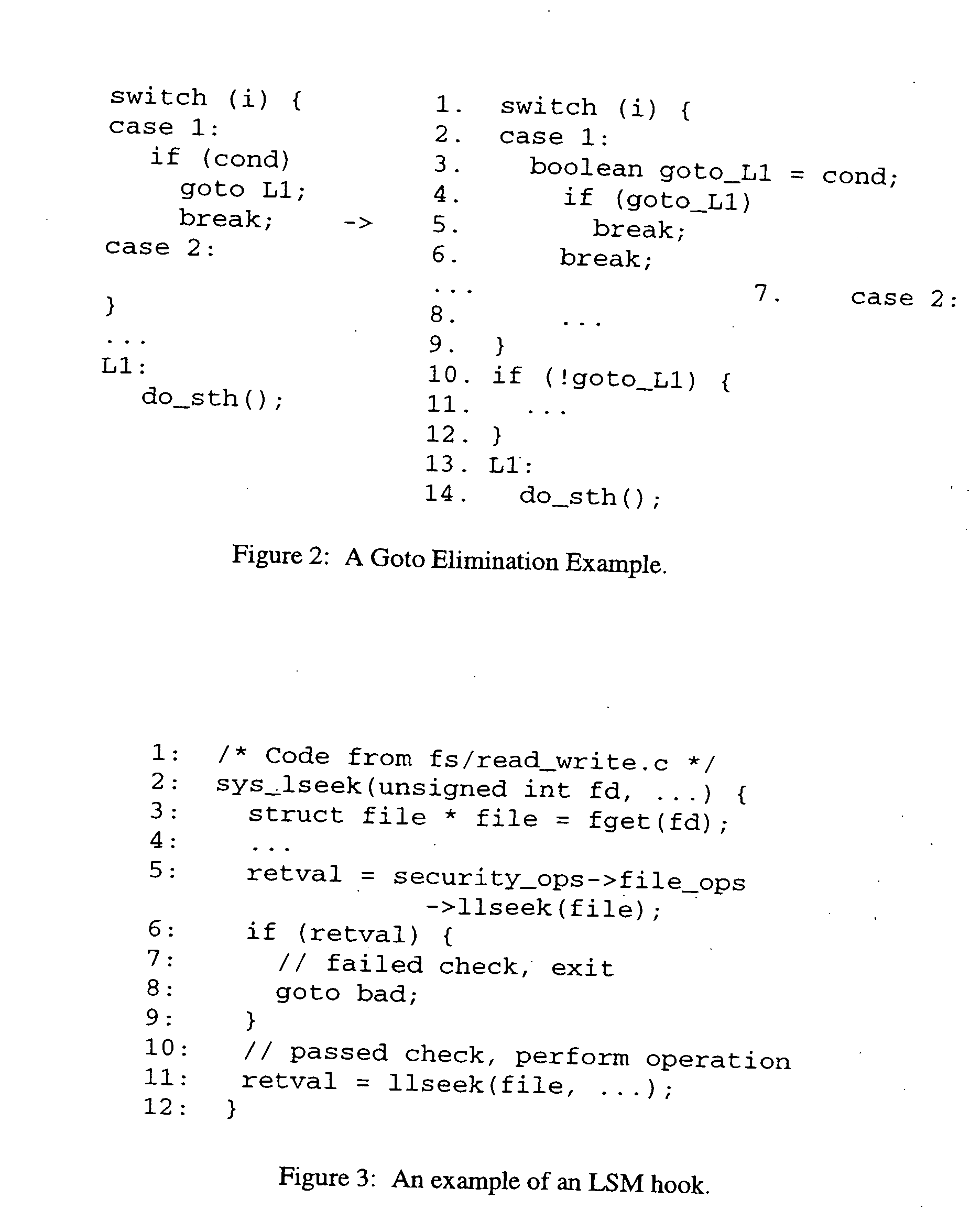
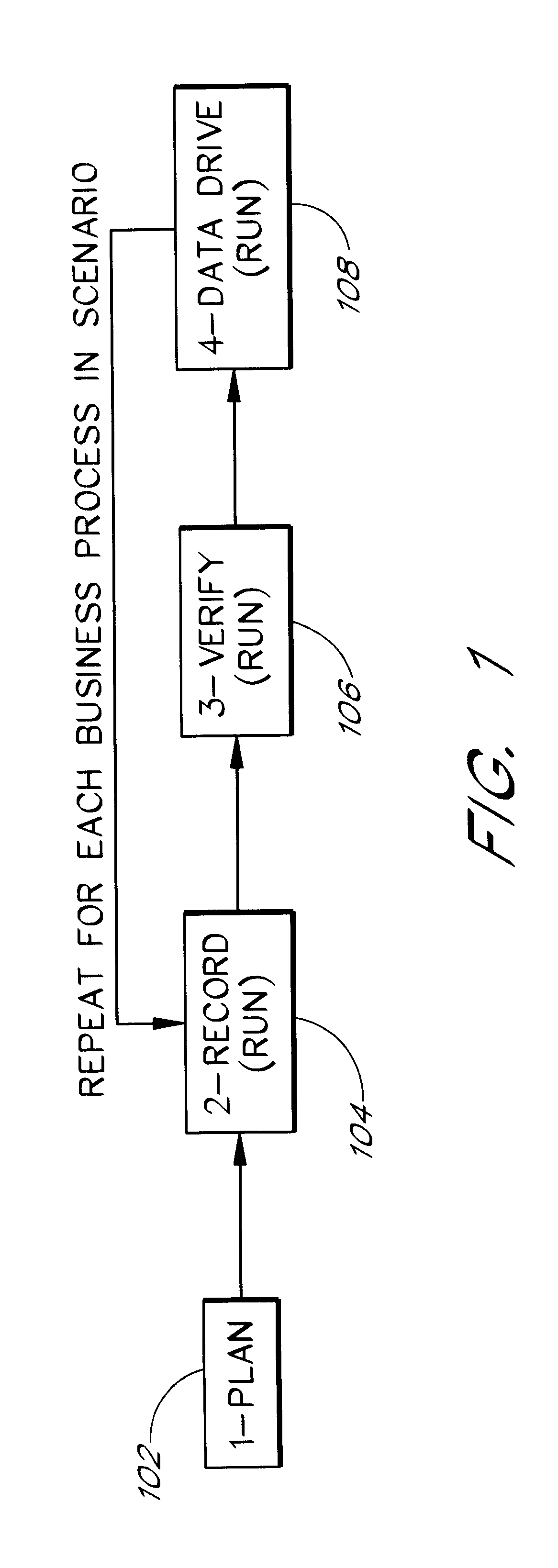
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS20050166094A1Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
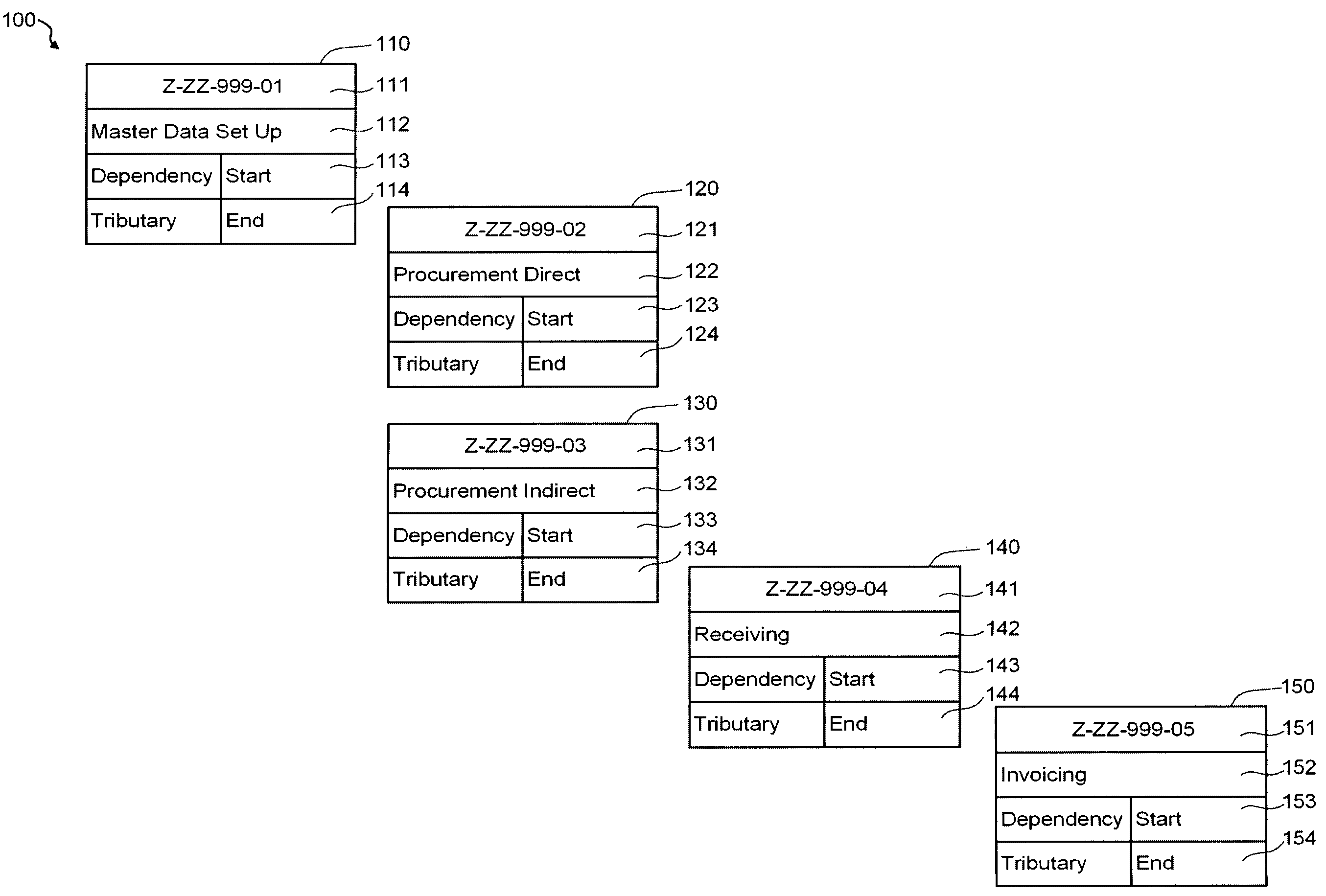
The present invention relates to a testing tool for testing of complex software systems having a plurality of interrelated system components and a suite of test scenarios for testing the performance of the plurality of interrelated system components. The testing tool includes an Automated Multidimensional Traceability Matrix system for determining linkages between interrelated system components, a means for identifying a change in one or more of the interrelated system components, a means for applying the Automated Multidimensional Traceability Matrix, a means for executing all of or a subset of the test scenarios associated with the interrelated system components that may be affected by the change and a means for evaluating the results of the executed test scenarios.
Owner:KIMBERLY-CLARK WORLDWIDE INC
Scalable system for monitoring network system and components and methodology therefore
InactiveUS20020078382A1Memory loss protectionDigital computer detailsScalable systemSecurity software
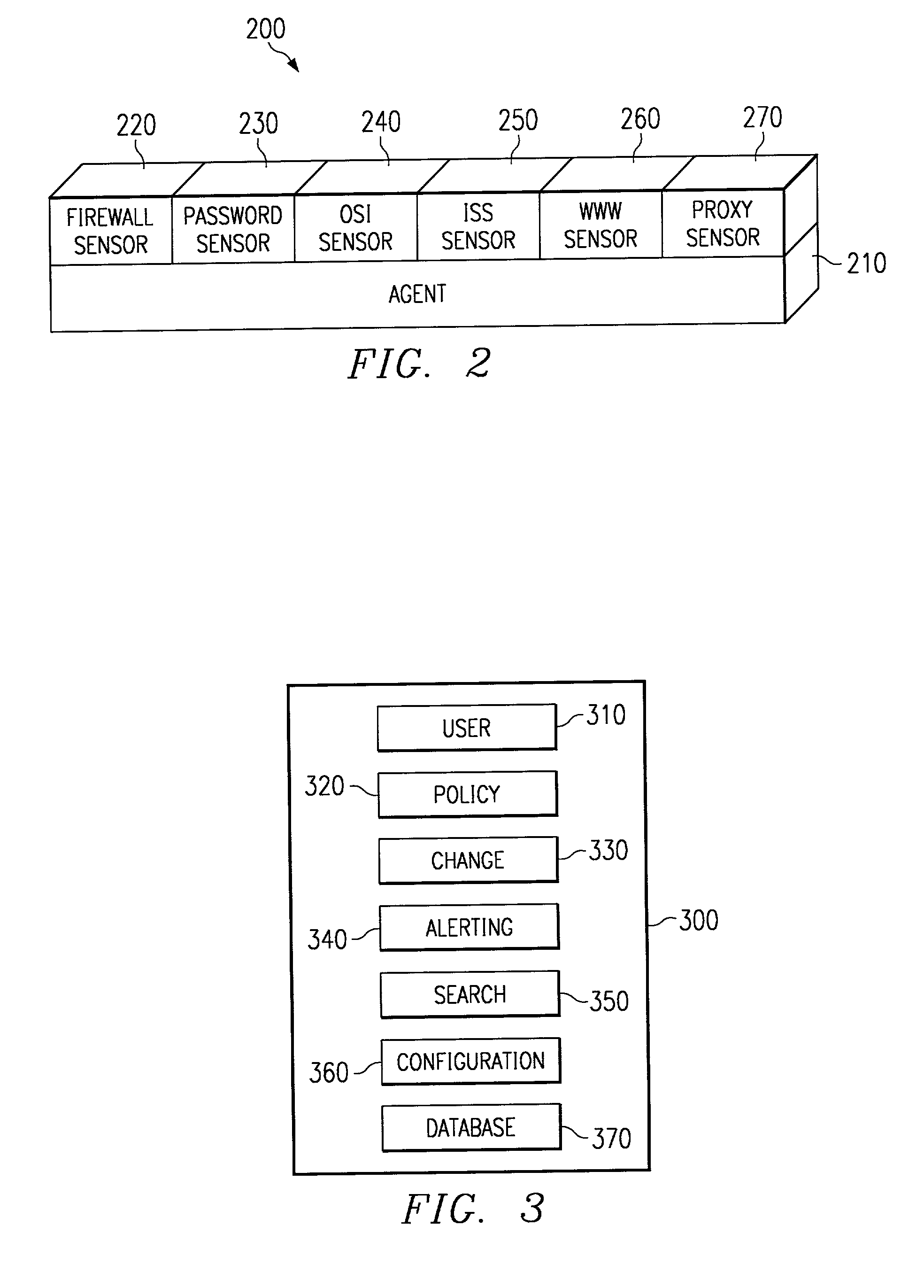
The present invention is a security software methodology and system that takes an internal approach to mitigating security risks from authorized and unauthorized users. The security software system uses the methodology of monitoring, in great detail, any configuration changes made to information systems within a network. These systems and applications include web servers, firewalls, proxy servers, log servers, intrusion detection software systems, routers and any other device or application which can be considered a part of the enterprise information system infrastructure.
Owner:SECURITY & INTRUSION DETECTION RES LABS
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS7490319B2Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
Owner:KIMBERLY-CLARK WORLDWIDE INC
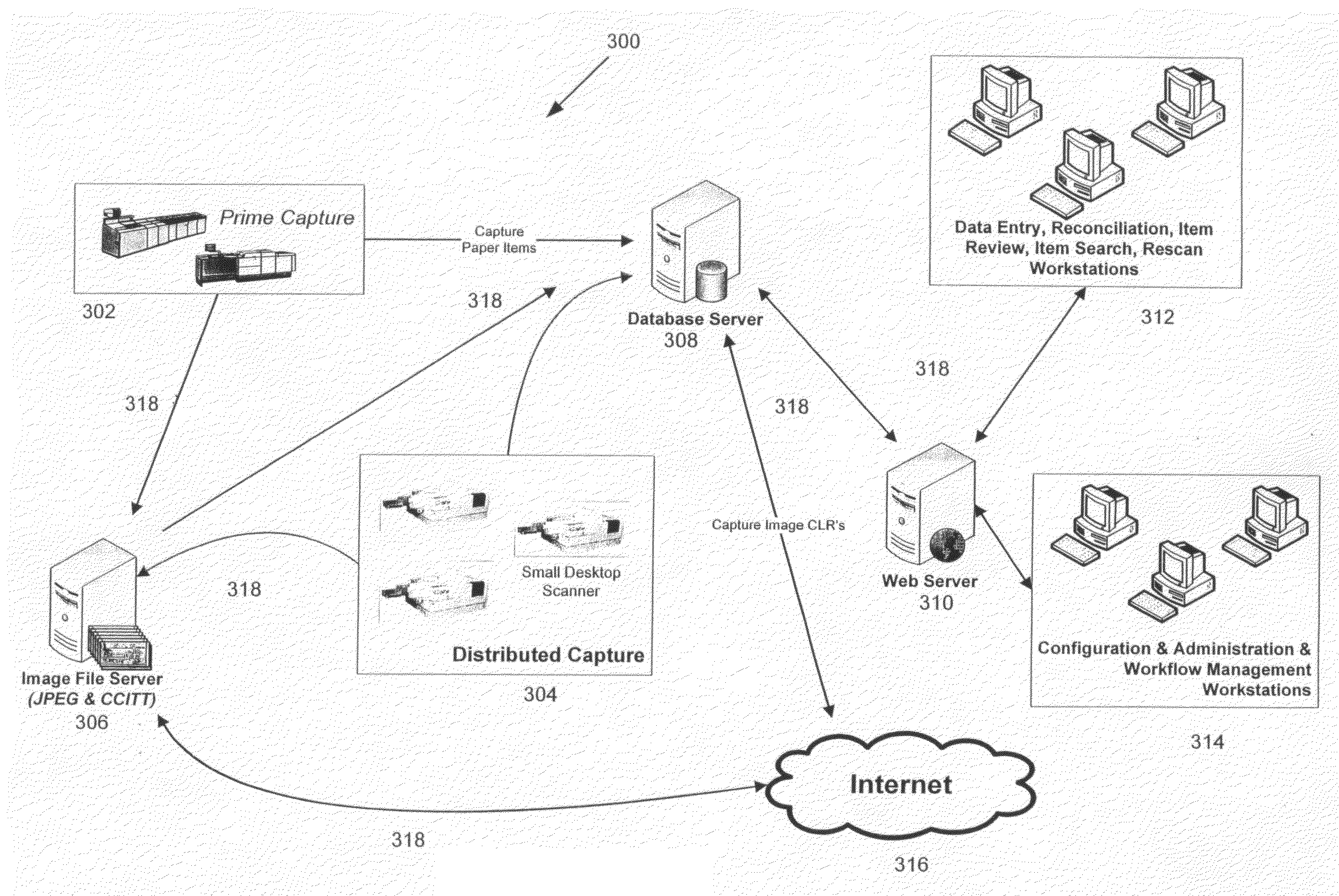
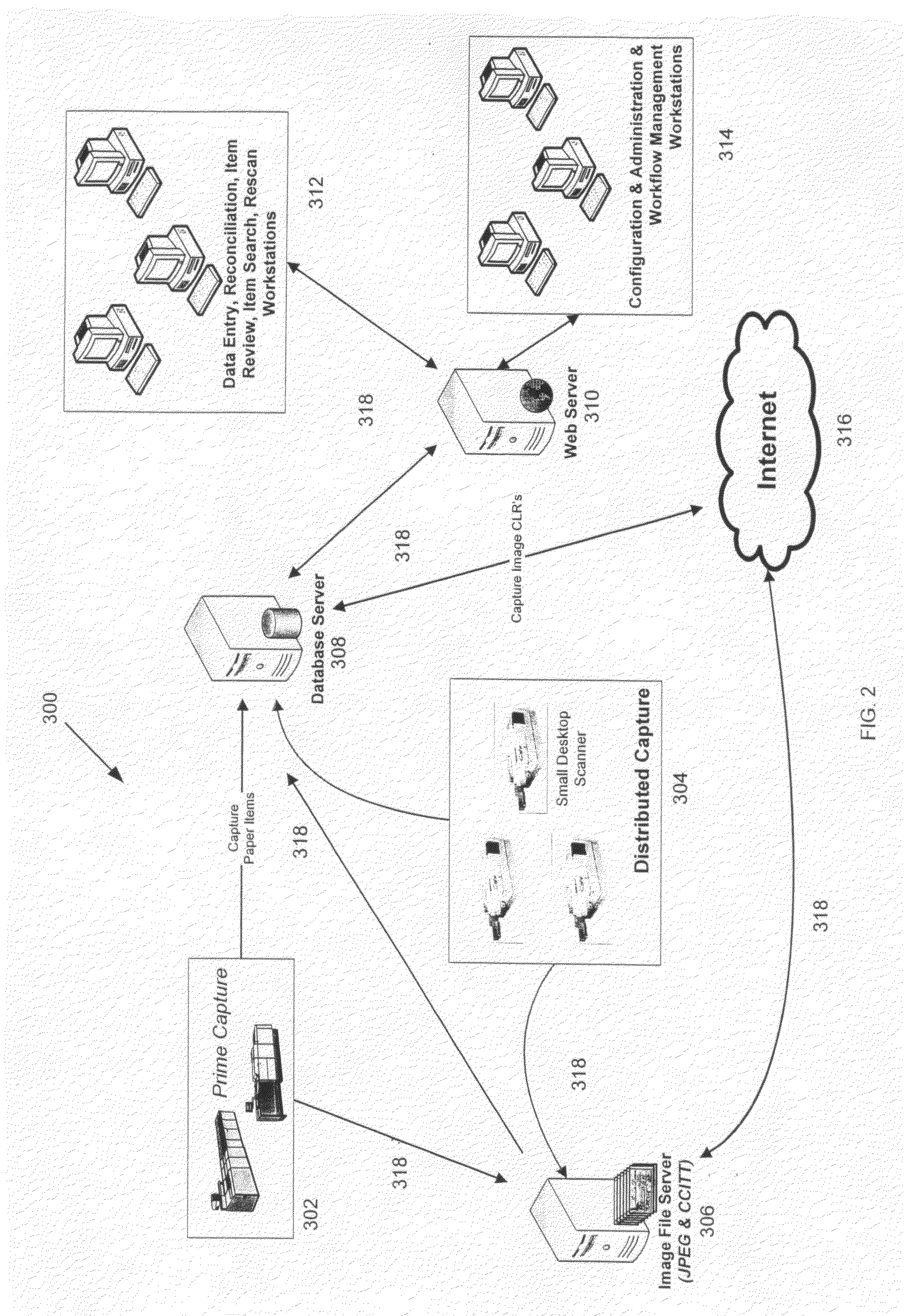
Check21 image based document and processing system
InactiveUS20070288382A1Easy to removeEasy to addFinanceCharacter and pattern recognitionSoftware systemModularity
A Check21 Act image based document and processing system, comprising a modular hardware and software image-based financial processing system with independent software modules supporting specific hardware and or processing applications; thereby, simplifying the process for the removal or addition of support for new computer platforms, components, features, peripherals, applications and / or interoperating with legacy hardware and software systems.
Owner:AVALON INT
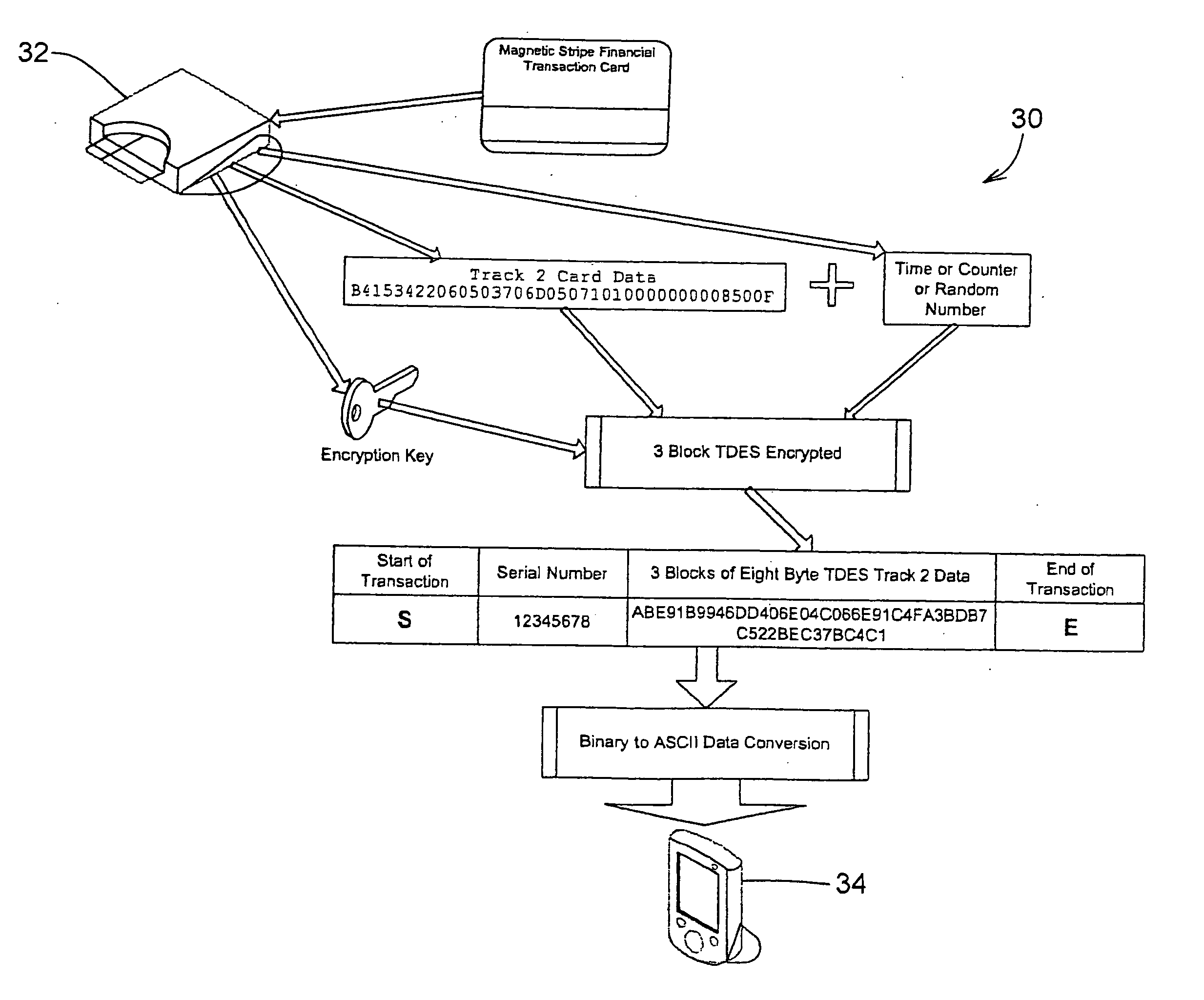
Transparently securing data for transmission on financial networks
ActiveUS20060049256A1Easy to operateIncrease powerAcutation objectsFinanceInformation processingSoftware system
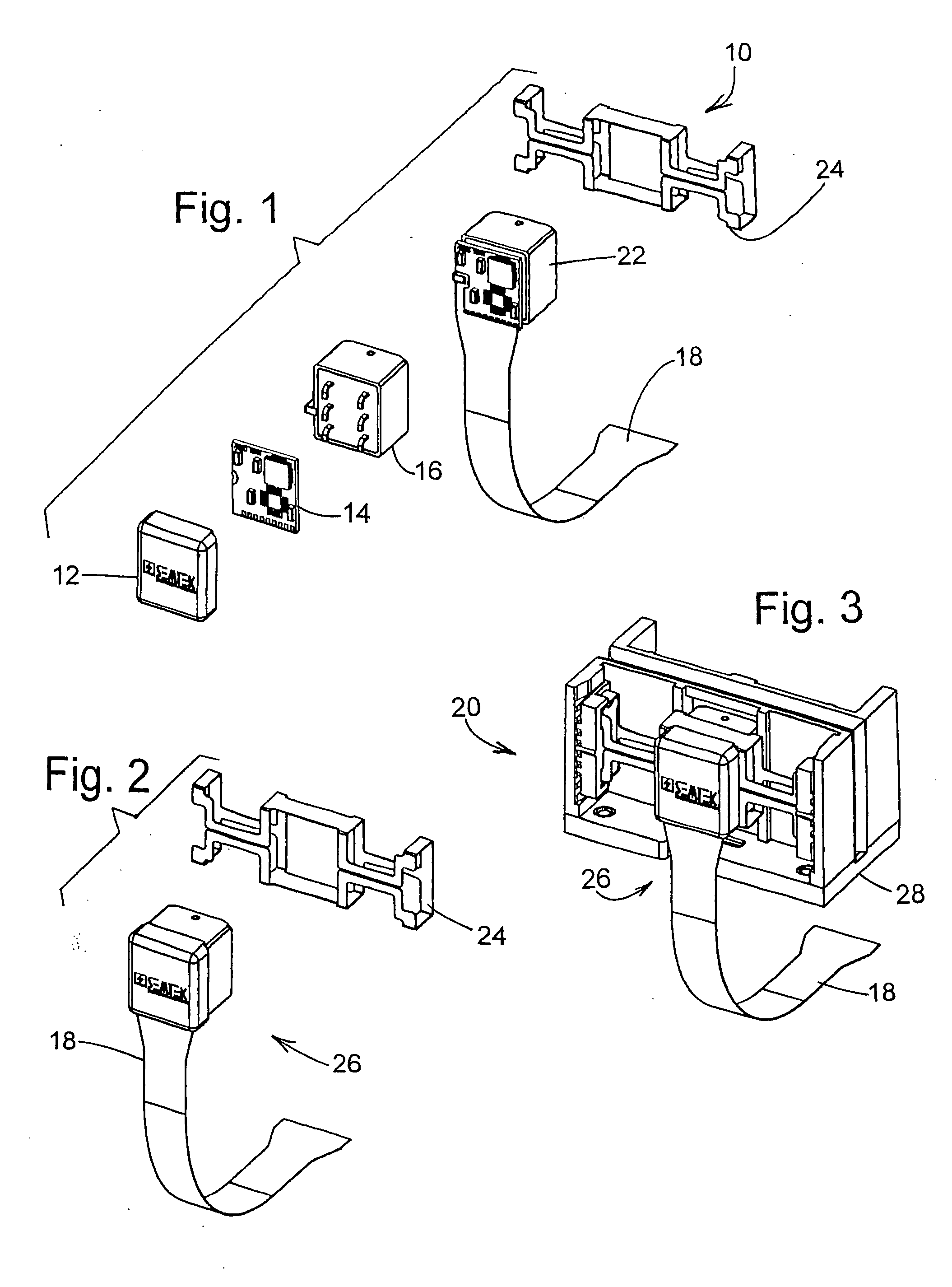
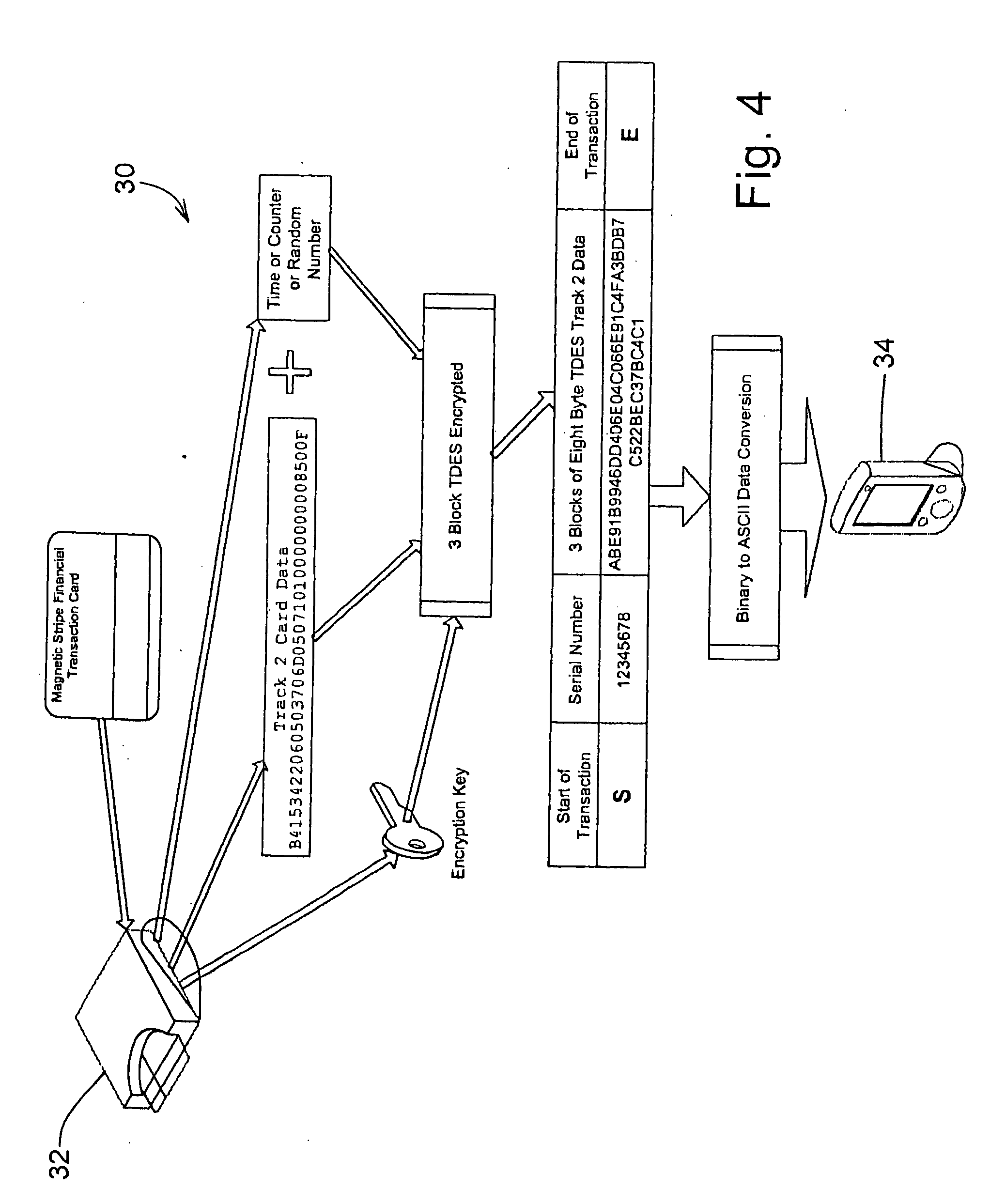
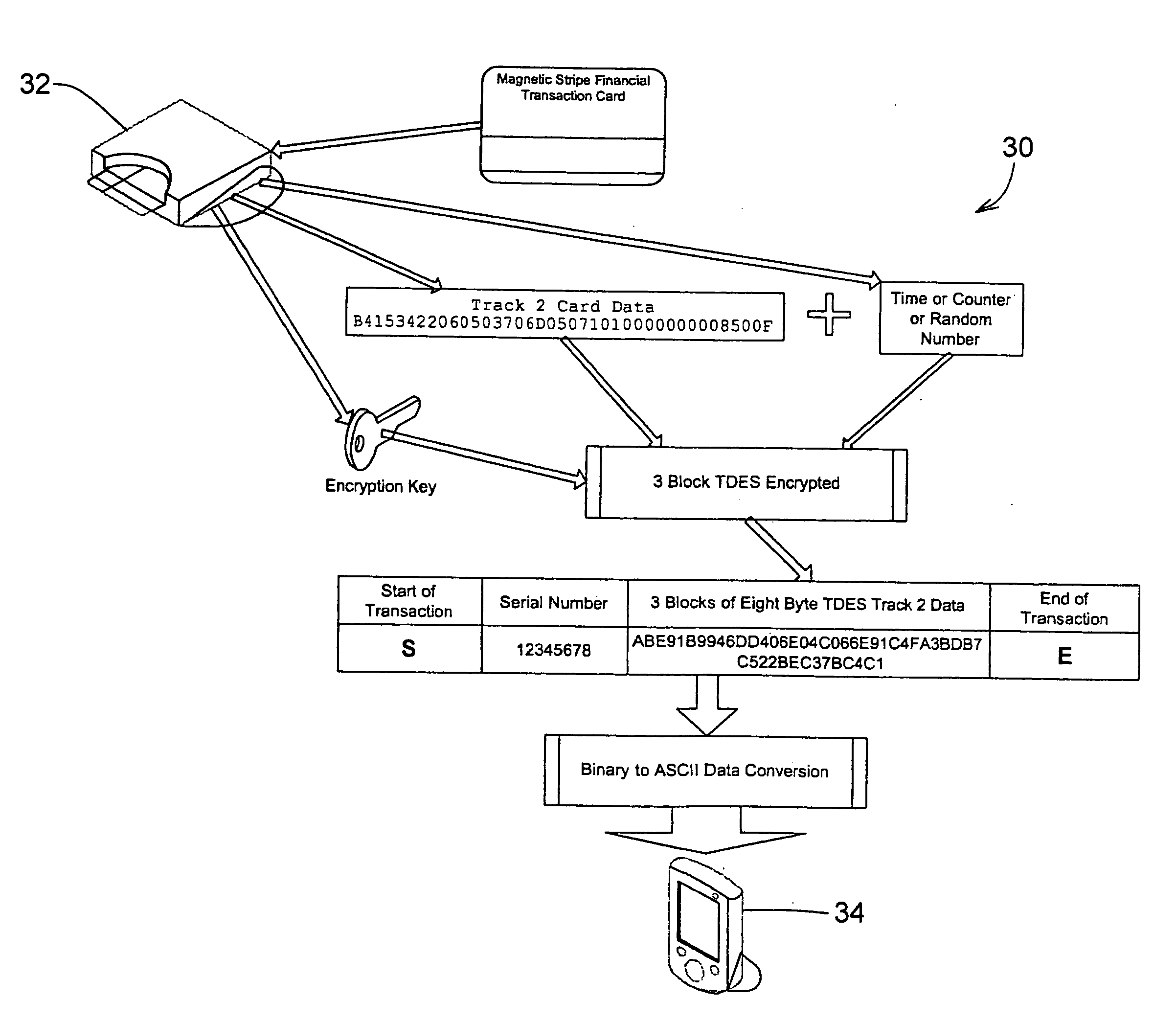
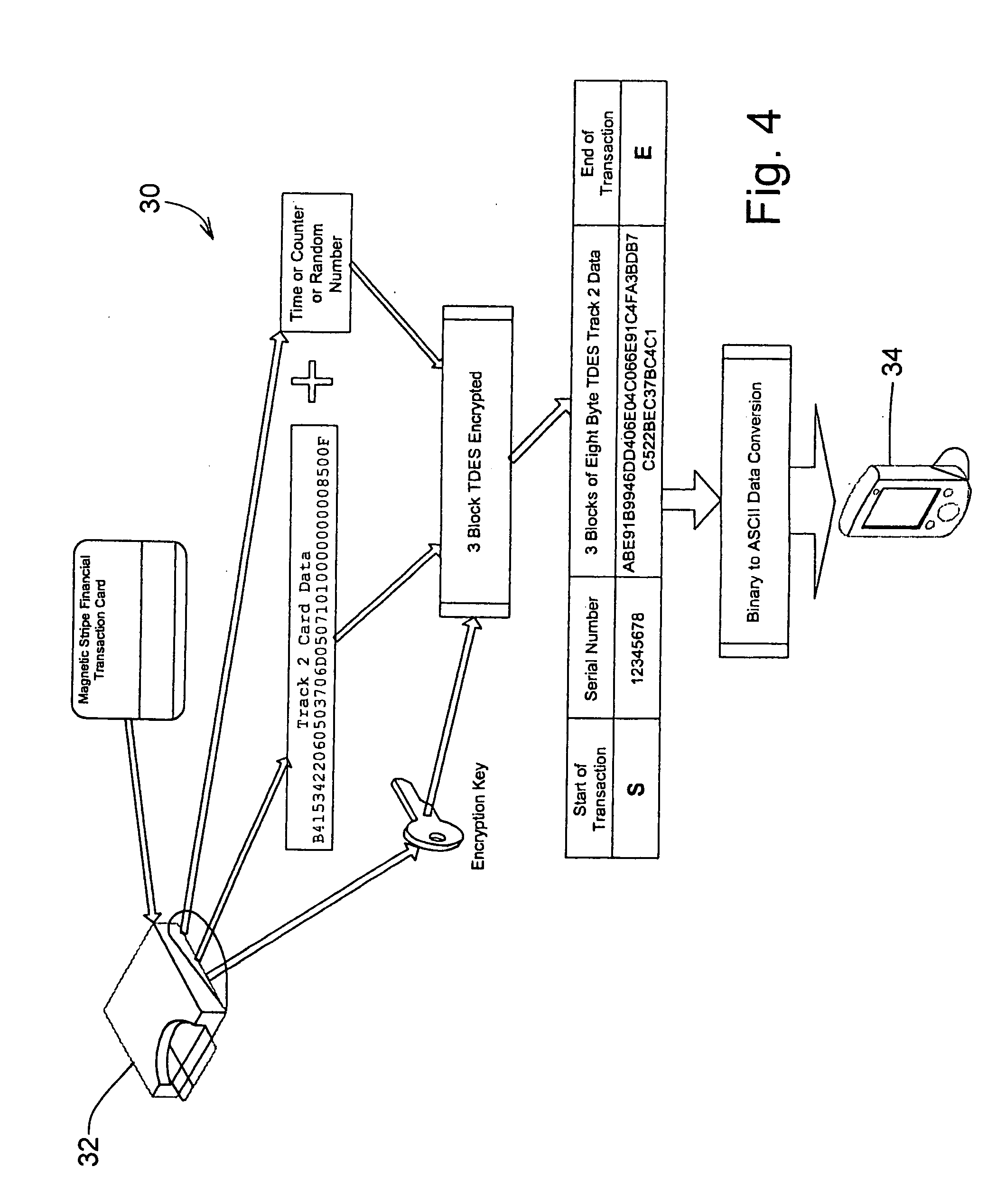
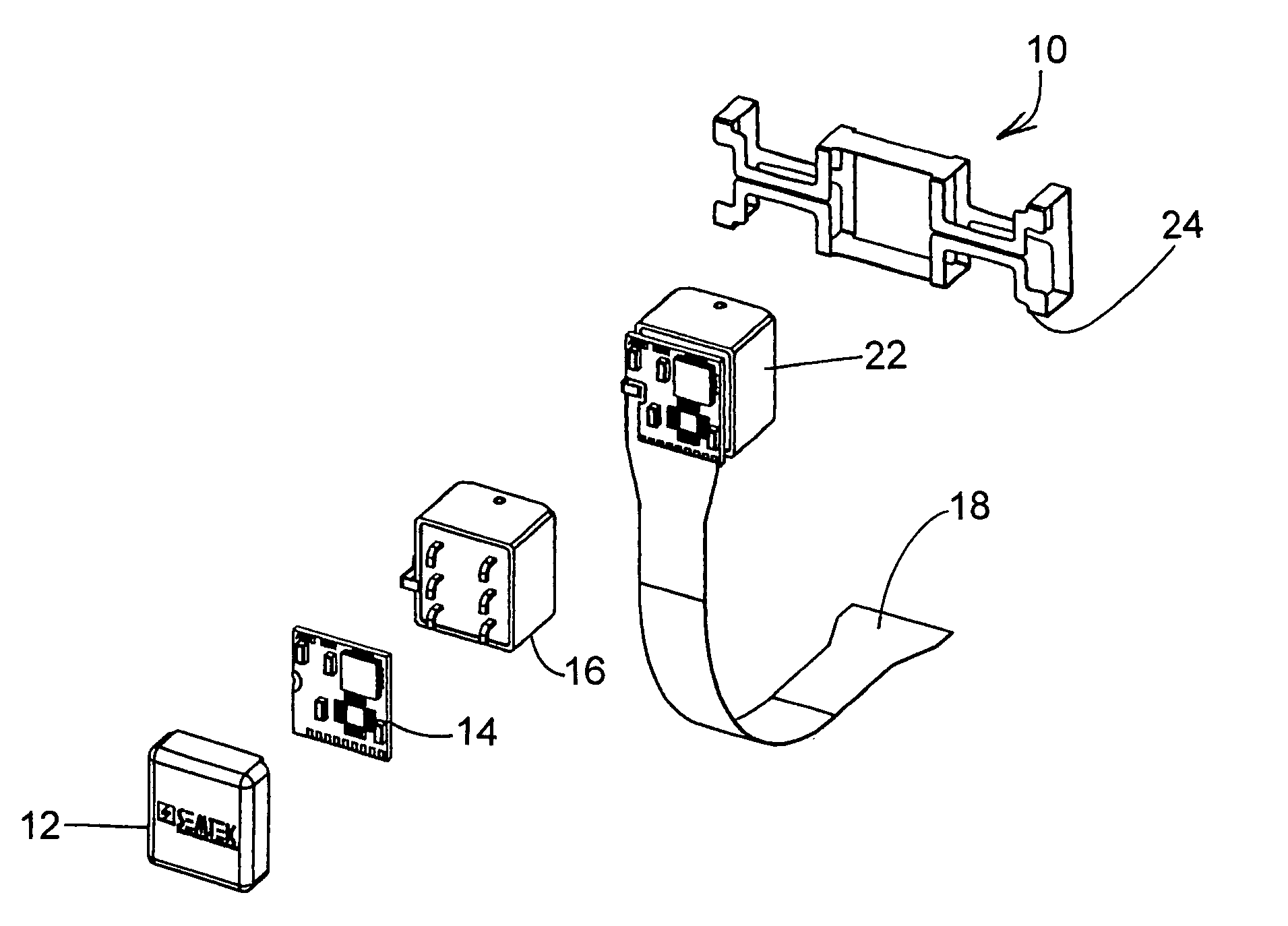
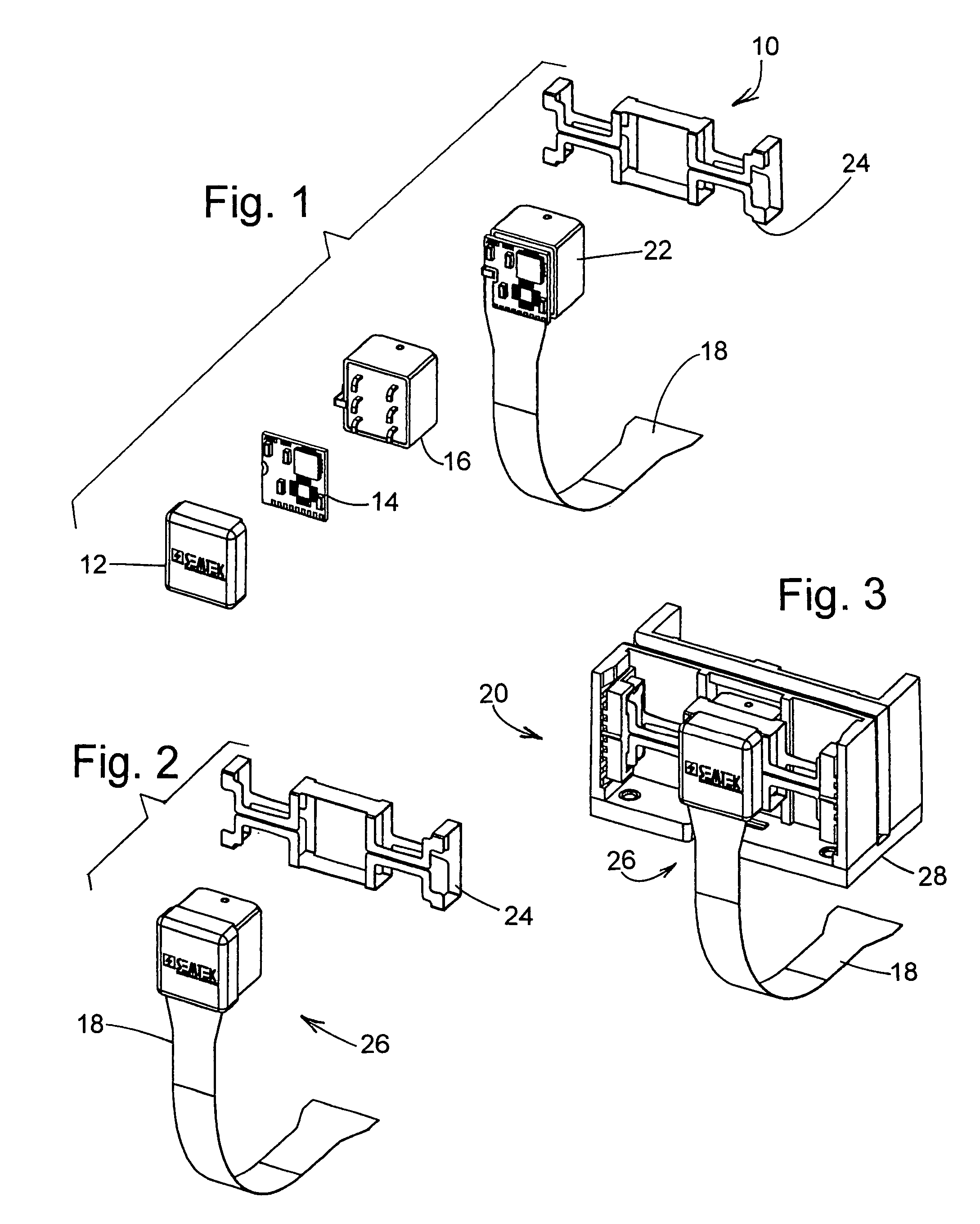
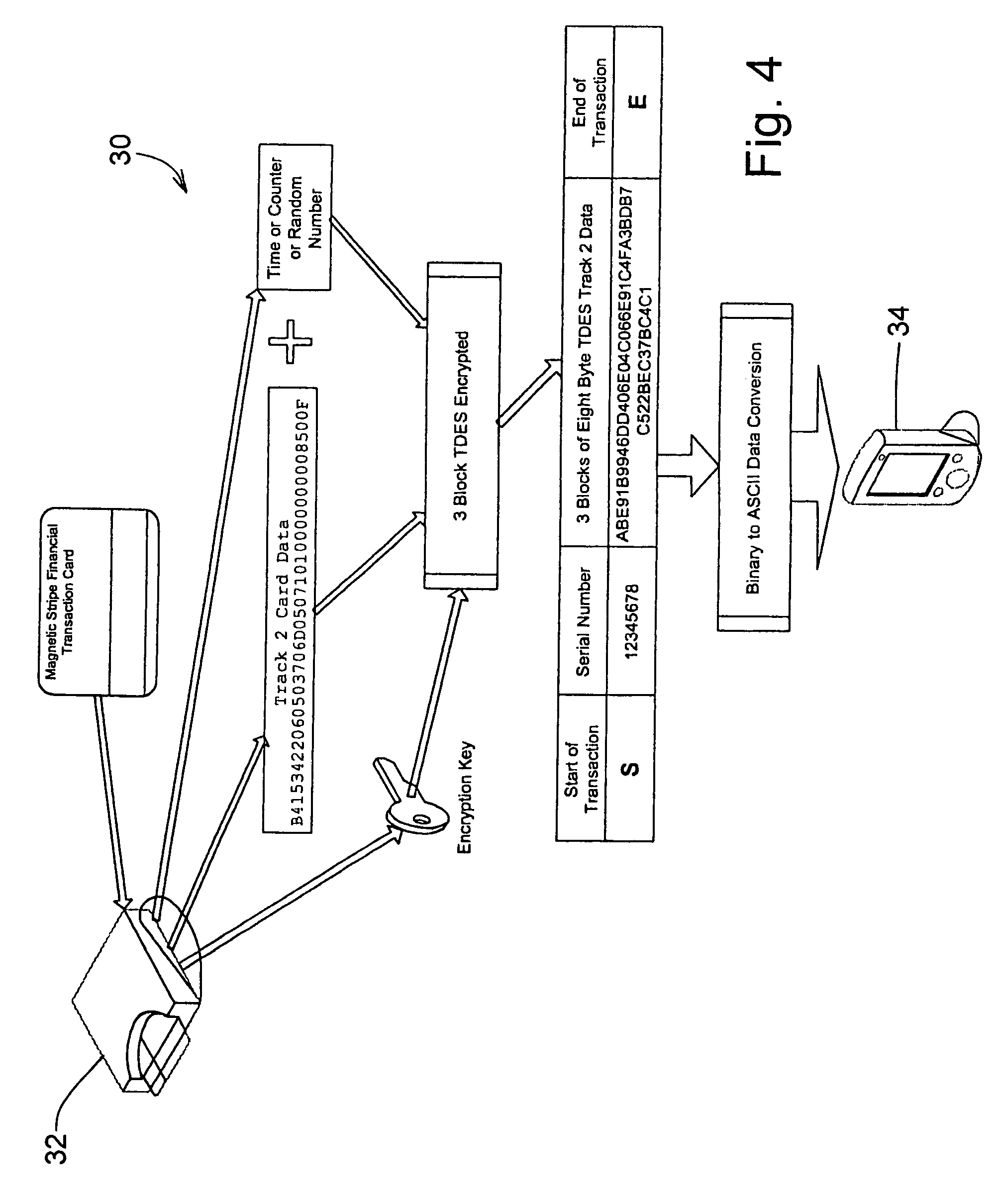
A secure magnetic stripe card stripe reader (MSR) module and software system capable of encrypting the magnetic stripe data to CPI, SDP and CISP standards for use in point of sale (POS) and other applications requiring data security using non secure networks and computing devices. Additionally, when incorporated within an attachment for conventional personal digital assistant (PDA) or cell phone or stationary terminal, provides encrypted data from the magnetic head assembly providing compliance with Federal Information Processing Standards Publication Series FIPS 140 covering security and tampering standards. Moreover, this module and software system includes the capability of providing secure POS transactions to legacy transaction processing systems and POS terminals transparently to the existing infrastructure. Furthermore, this module and software system includes the capability of transparently providing detection of fraudulently copied magnetic stripe cards.
Owner:VERIFONE INC
Methods and arrangements for unified program analysis
InactiveUS20060248519A1Low costMaximize returnError detection/correctionSpecific program execution arrangementsMulti languageSoftware system
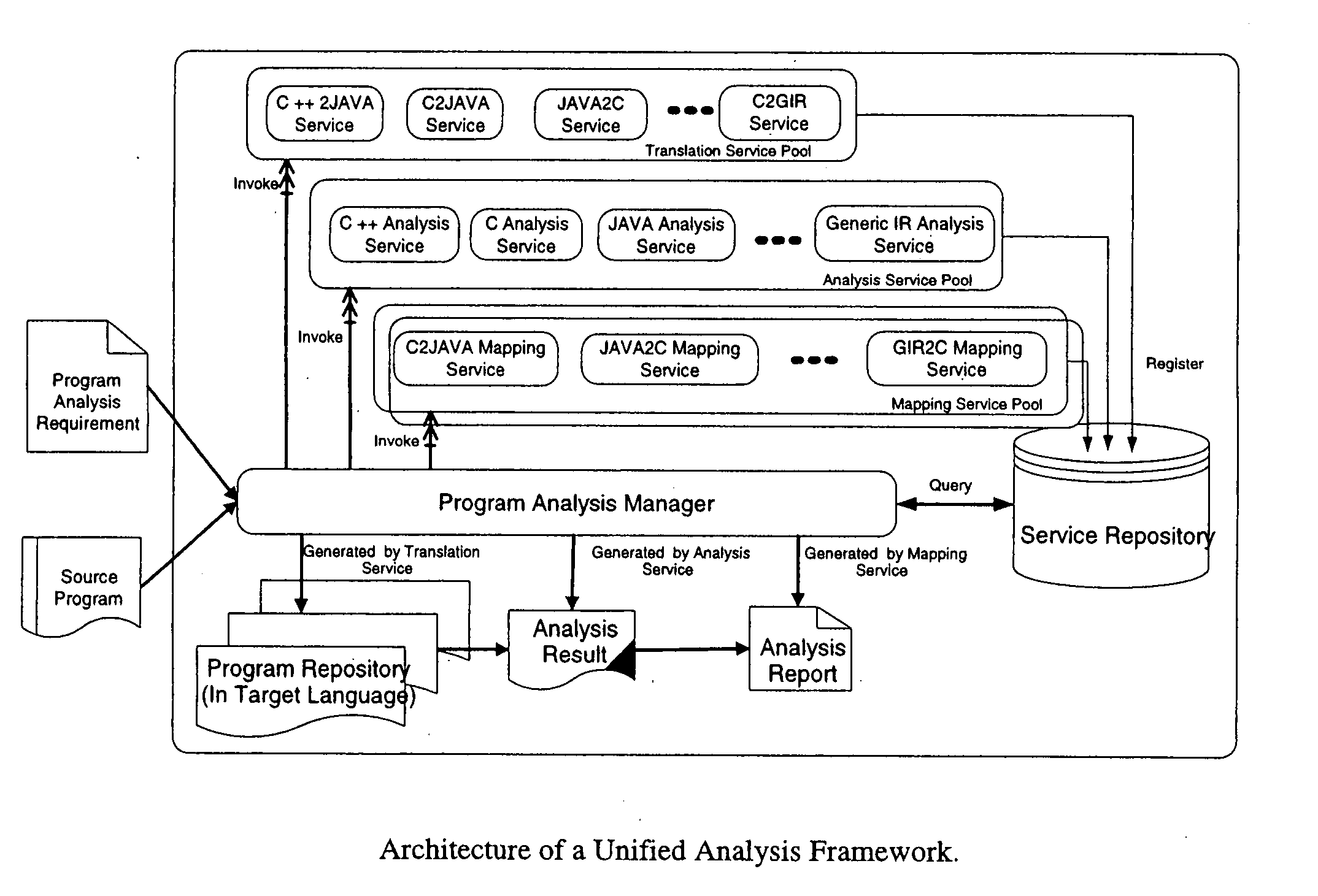
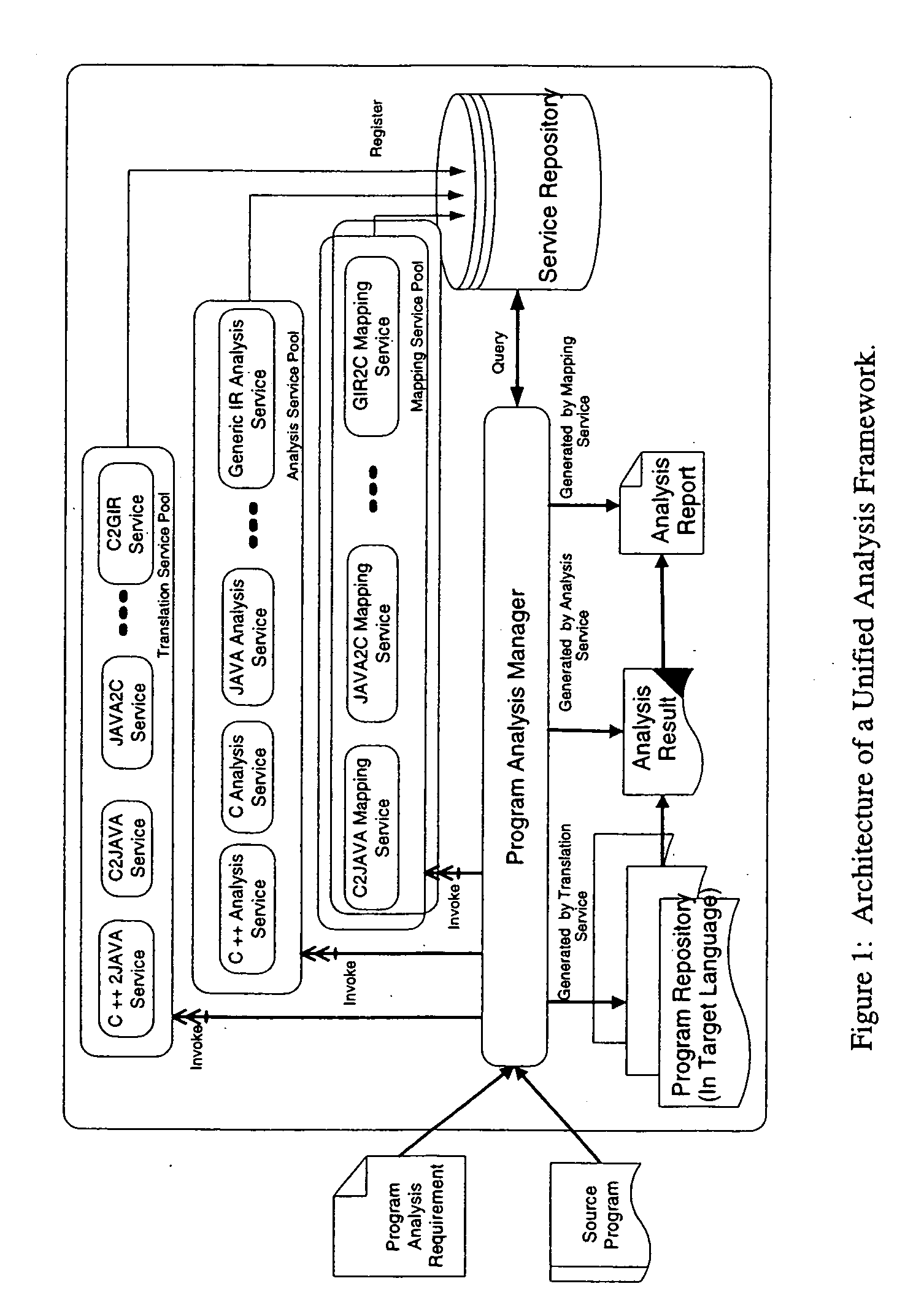
A unified program analysis framework that facilitates the analysis of complex multi-language software systems, analysis reuse, and analysis comparison, by employing techniques such as program translation and automatic results mapping, is presented. The feasibility and effectiveness of such a framework are demonstrated using a sample application of the framework. The comparison yields new insights into the effectiveness of the techniques employed in both analysis tools. These encouraging results yield the observation that such a unified program analysis framework will prove to be valuable both as a testbed for examining different language analysis techniques, and as a unified toolset for broad program analysis.
Owner:IBM CORP
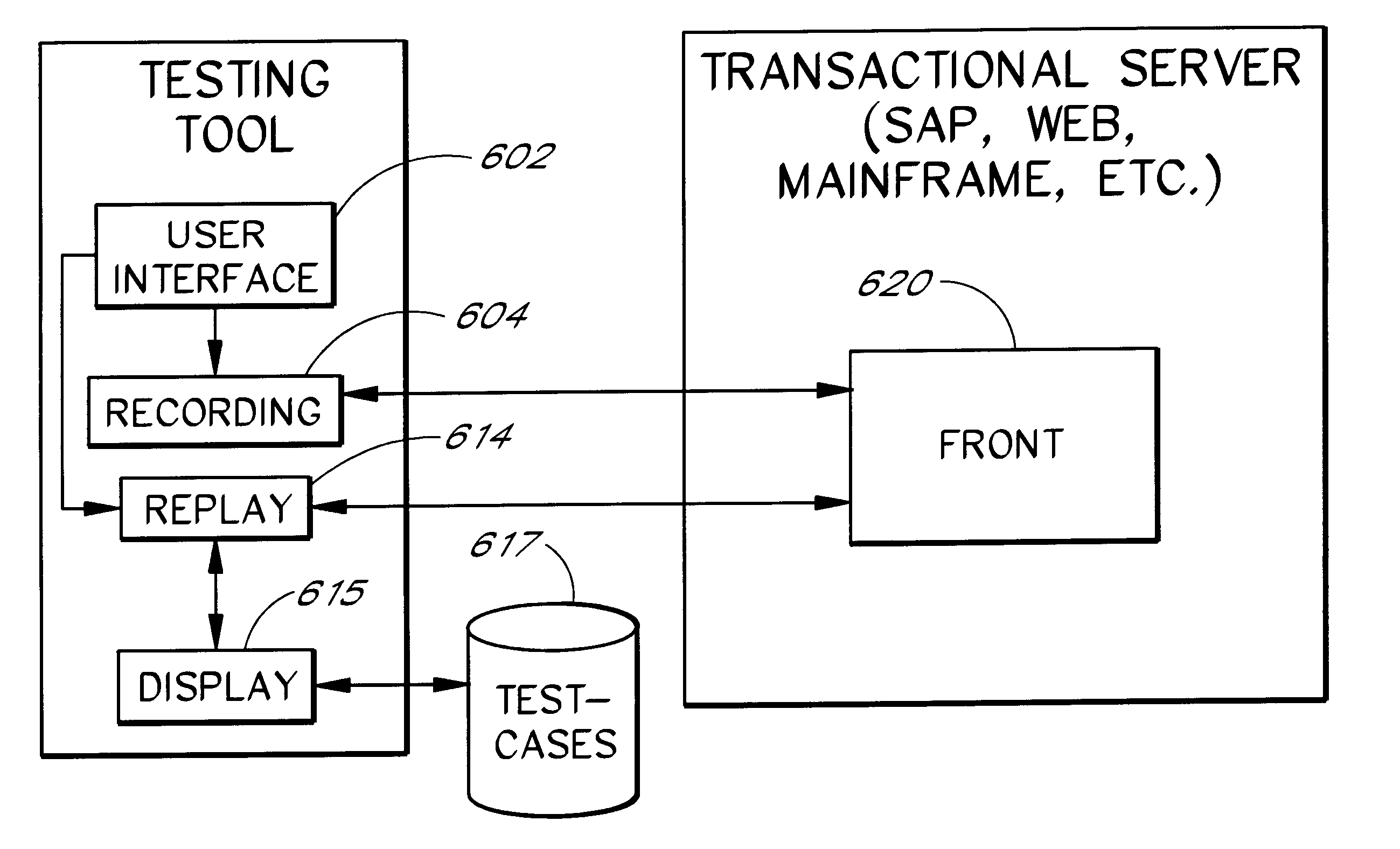
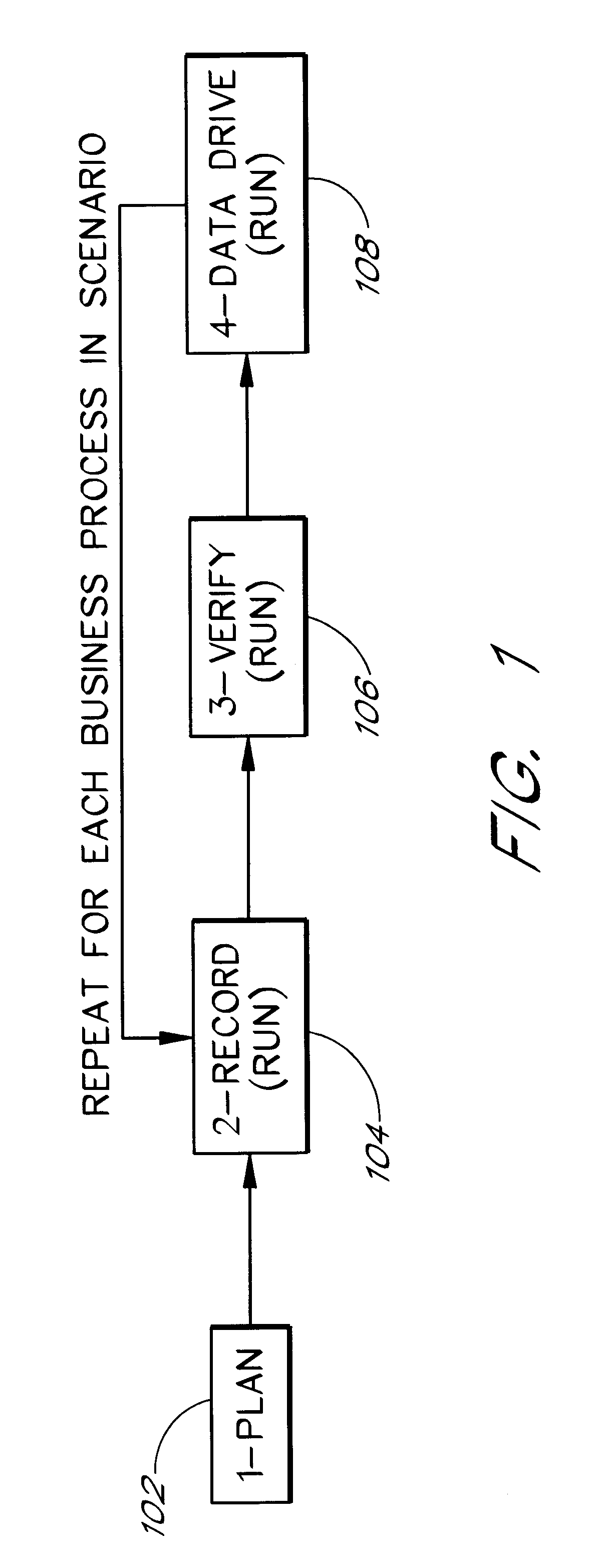
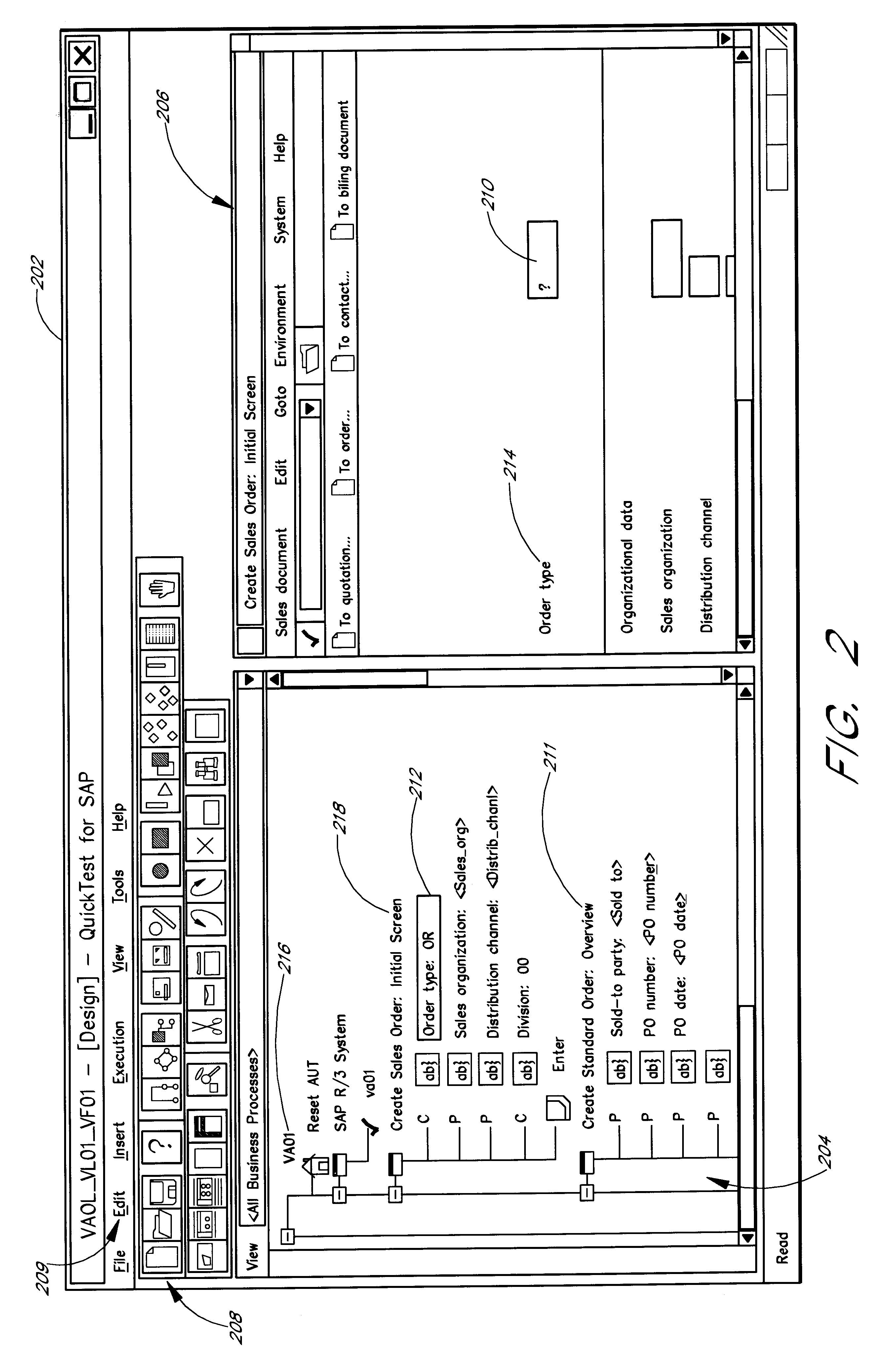
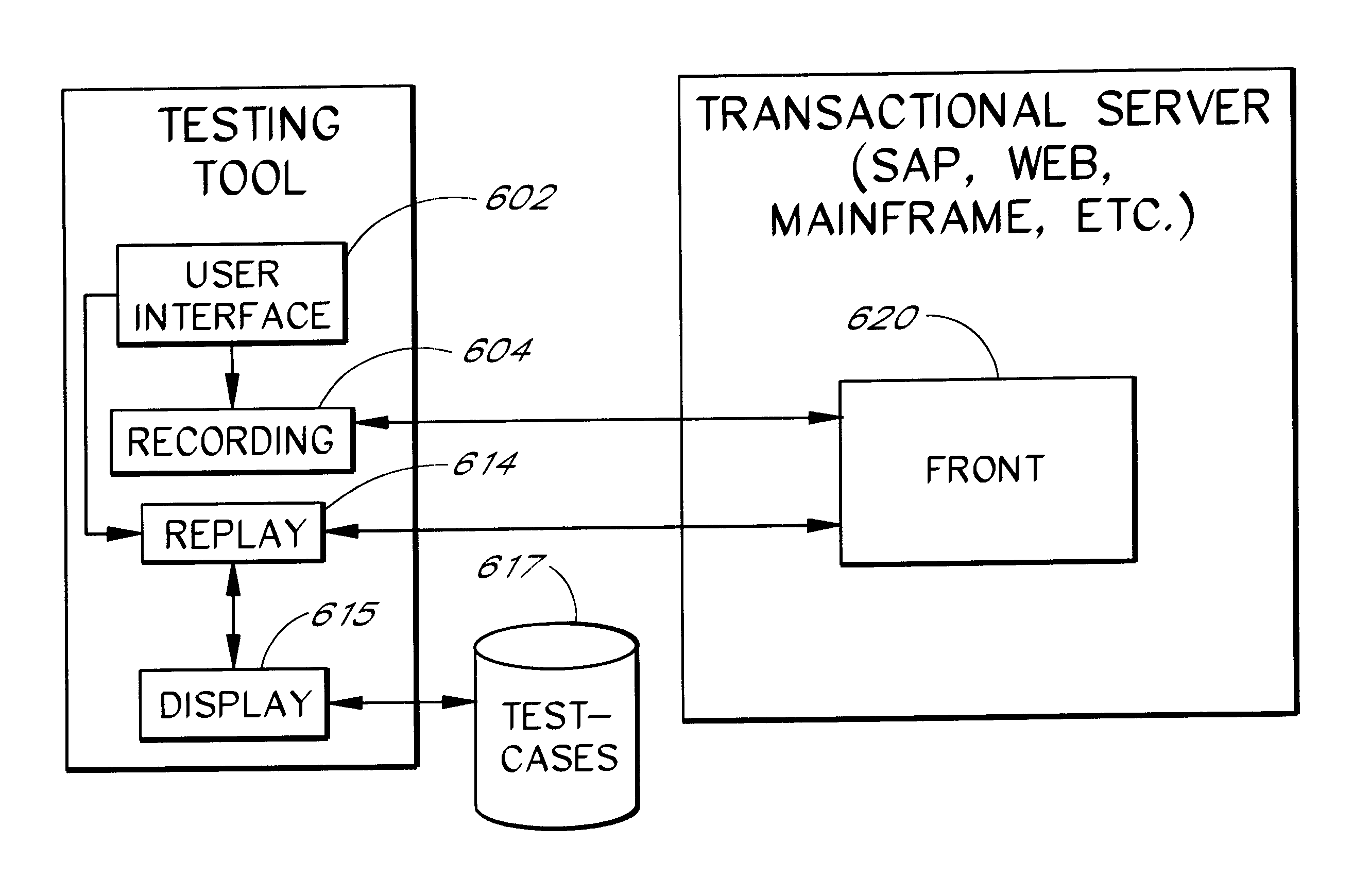
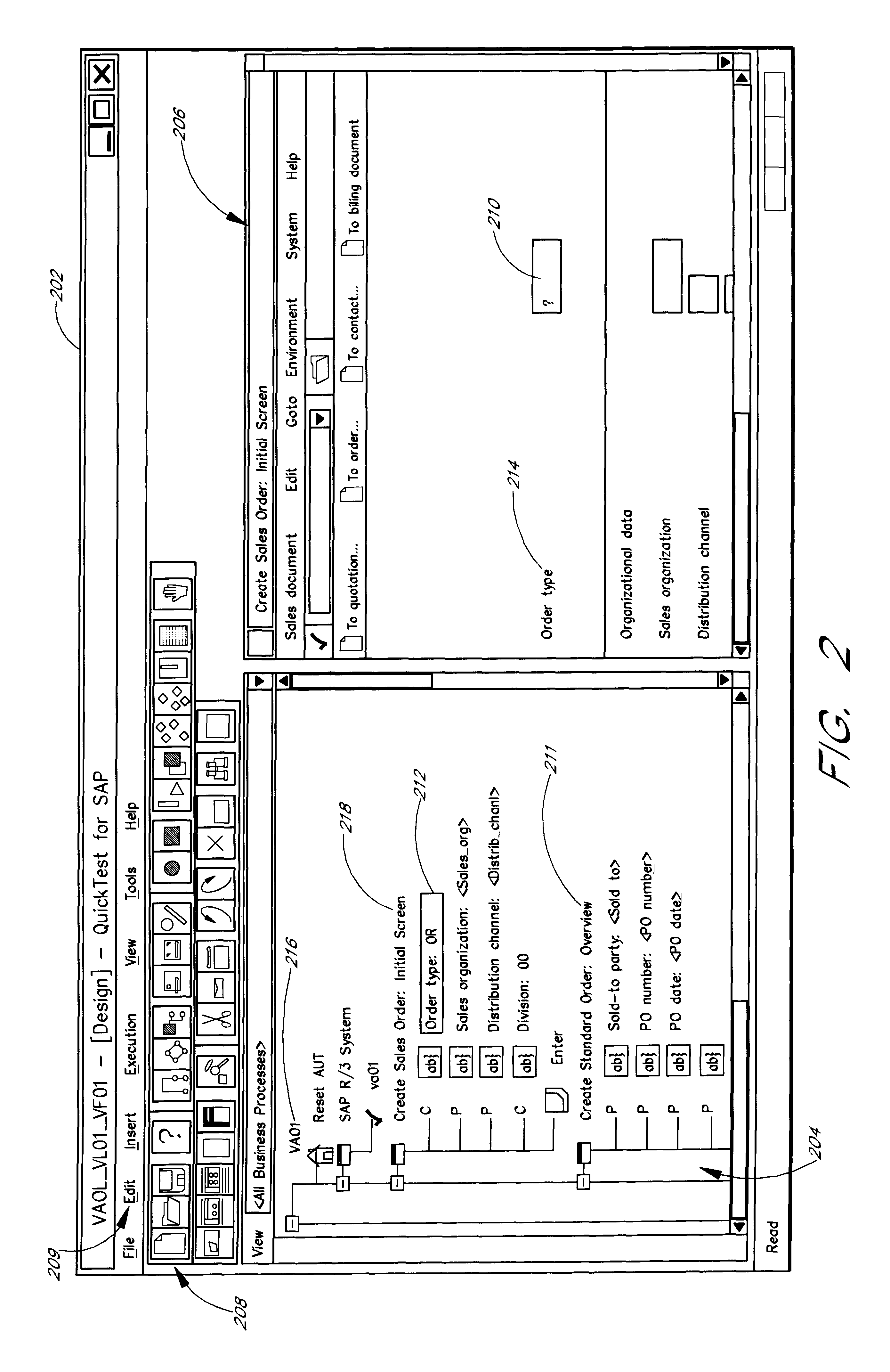
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:MICRO FOCUS LLC
Secure magnetic stripe reader for handheld computing and method of using same
ActiveUS20060049255A1Support easily and efficientlyFunction increaseAcutation objectsFinanceInformation processingSoftware system
A secure magnetic stripe card stripe reader (MSR) module and software system capable of encrypting the magnetic stripe data to CISP standards for use in point of sale (POS) and other applications requiring data security using non secure networks and computing devices. Additionally, when incorporated within an attachment for conventional personal digital assistant (PDA) or cell phone or stationary terminal, provides encrypted data from the magnetic head assembly providing compliance with Federal Information Processing Standards Publication Series FIPS 140 covering security and tampering standards. Moreover, this module and software system includes the capability of providing secure POS transactions to legacy transaction processing systems transparently to the existing infrastructure. Furthermore, this module and software system includes the capability of transparently providing detection of fraudulently copied magnetic stripe cards.
Owner:VERIFONE INC
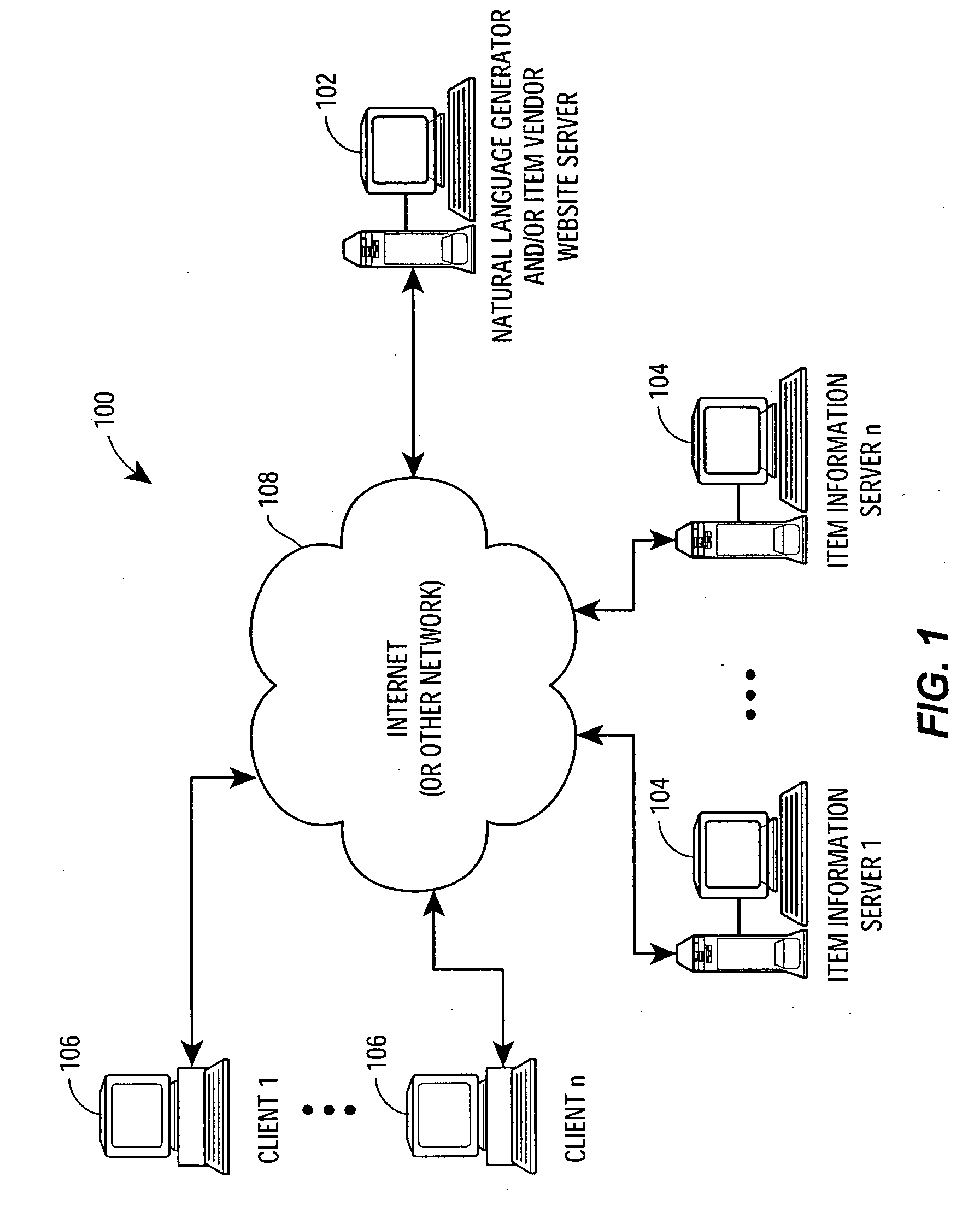
Methods and systems for generating natural language descriptions from data
ActiveUS20060178868A1Natural language translationSpecial data processing applicationsDocumentation generatorSoftware system
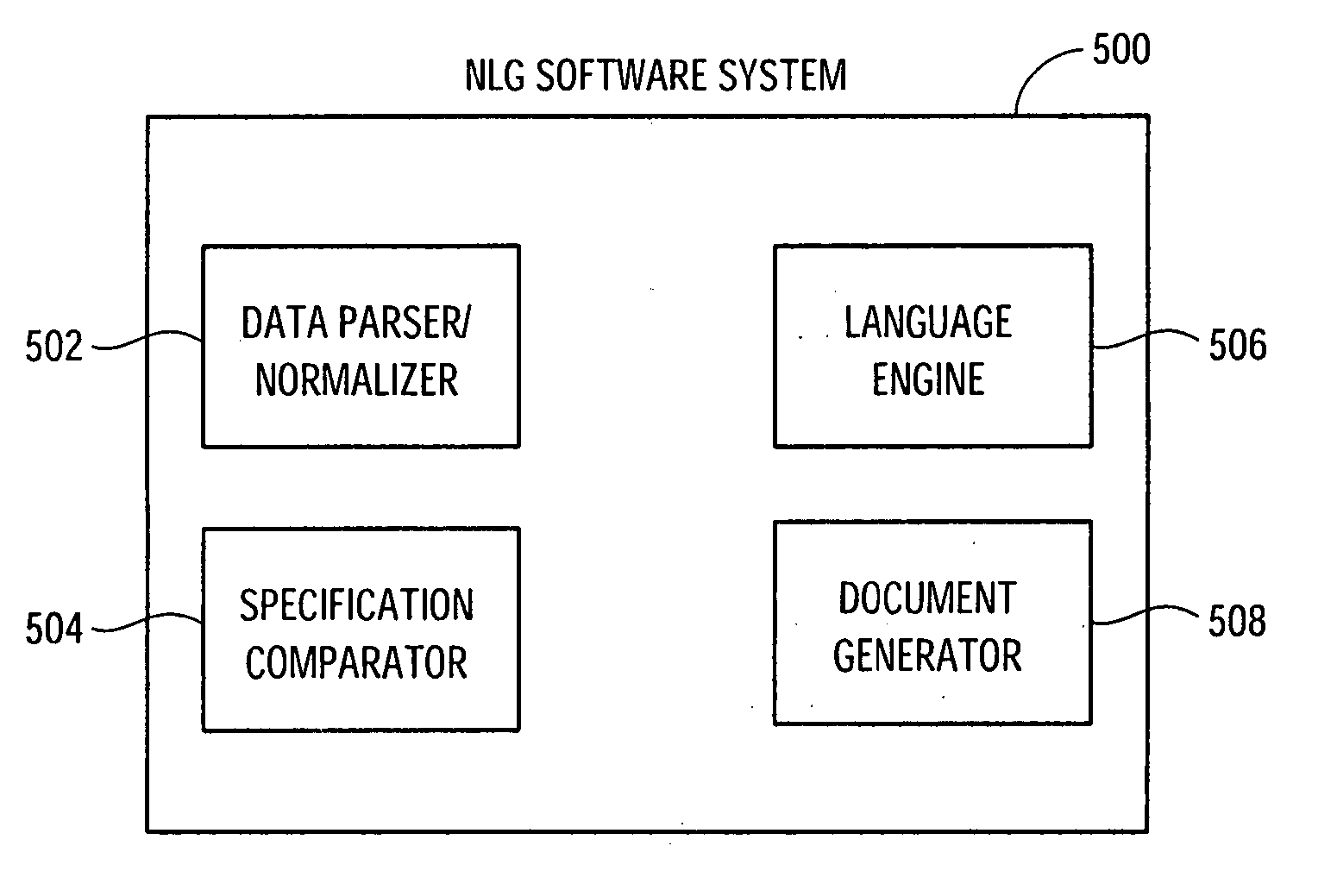
The invention is directed to a natural language generation (NLG) software system that generates rich, content-sensitive human language descriptions based on unparsed raw domain-specific data. In one embodiment, the NLG software system may include a data parser / normalizer, a comparator, a language engine, and a document generator. The data parser / normalizer may be configured to retrieve specification information for items to be described by the NLG software system, to extract pertinent information from the raw specification information, and to convert and normalize the extracted information so that the items may be compared specification by specification. The comparator may be configured to use the normalized data from the data parser / normalizer to compare the specifications of the items using comparison functions and interpretation rules to determine outcomes of the comparisons. The language engine may be configured to cycle through all or a subset of the normalized specification information, to retrieve all sentence templates associated with each of the item specifications, to call the comparator to compute or retrieve the results of the comparisons between the item specifications, and to recursively generate every possible syntactically legal sentence associated with the specifications based on the retrieved sentence templates. The document generator may be configured to select one or more discourse models having instructions regarding the selection, organization and modification of the generated sentences, and to apply the instructions of the discourse model to the generated sentences to generate a natural language description of the selected items.
Owner:CLASSIFIED VENTURES
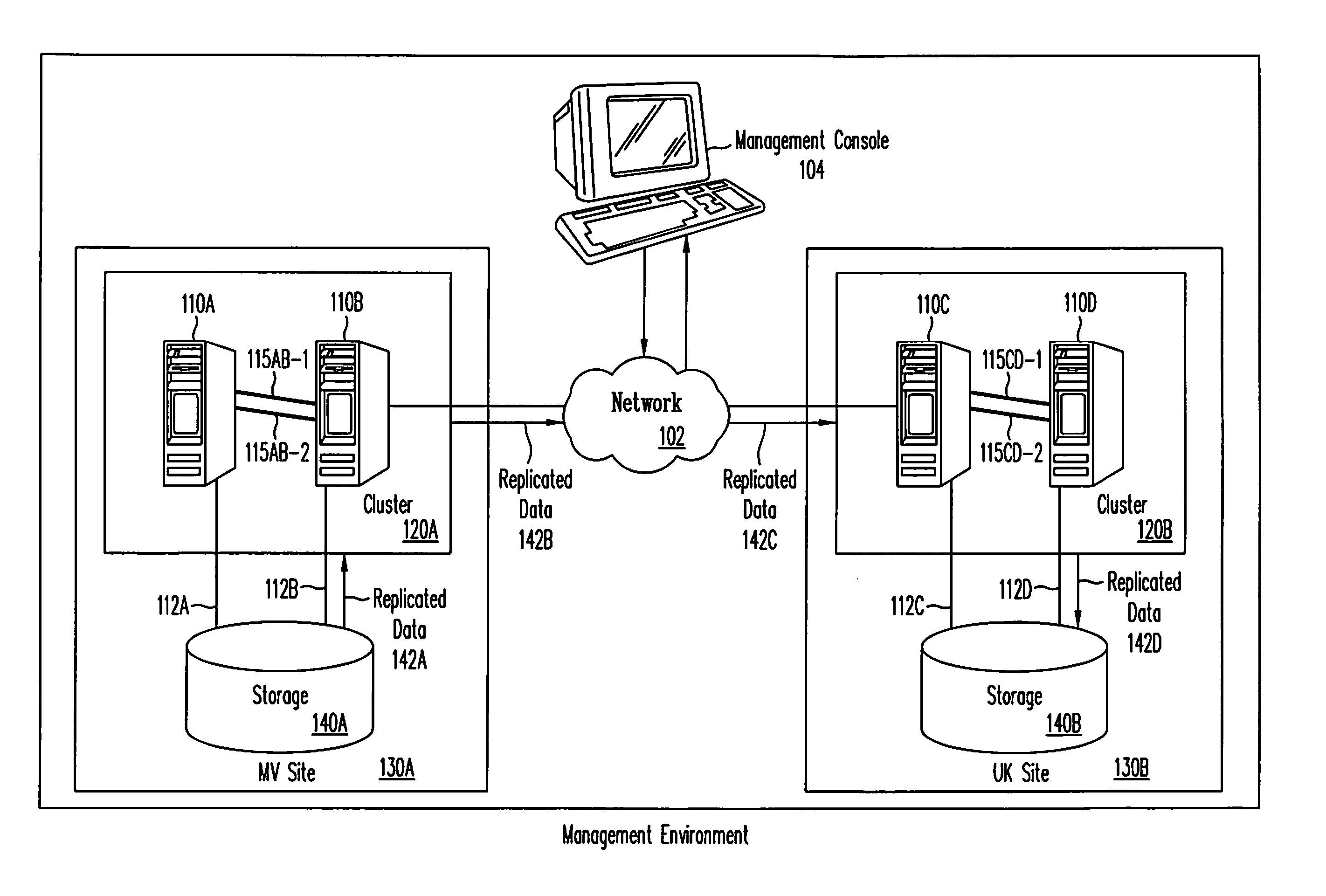
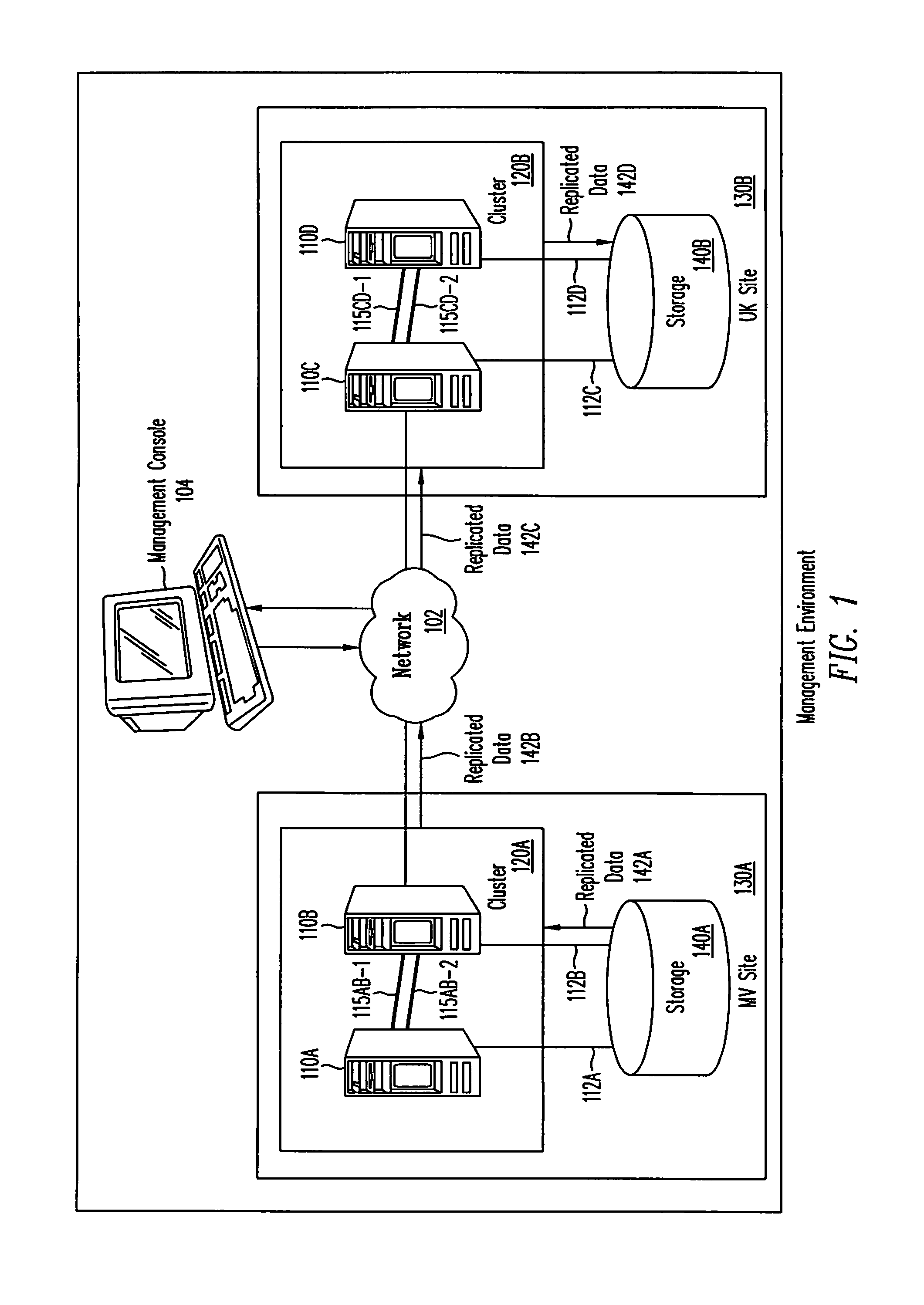
Framework for managing clustering and replication
The present invention provides a framework for managing both clustering and data replication in a software system distributed across multiple nodes. The framework includes at least one agent running at nodes comprising the distributed system. The framework also includes a master to coordinate clustering and replication operations. The framework further includes a library of software programs, called primitives, that are used by agents to communicate with the master. The agent(s) obtain cluster status information and replication status information, which are used by the master to manage clustering and replication operations. The framework is designed to work with existing cluster management applications and data replication facilities. The framework provides status information needed for coordinating clustering and replication operations to ensure that applications and data remain in a consistent state for disaster recovery purposes.
Owner:SYMANTEC OPERATING CORP
System and method for troubleshooting software configuration problems using application tracing
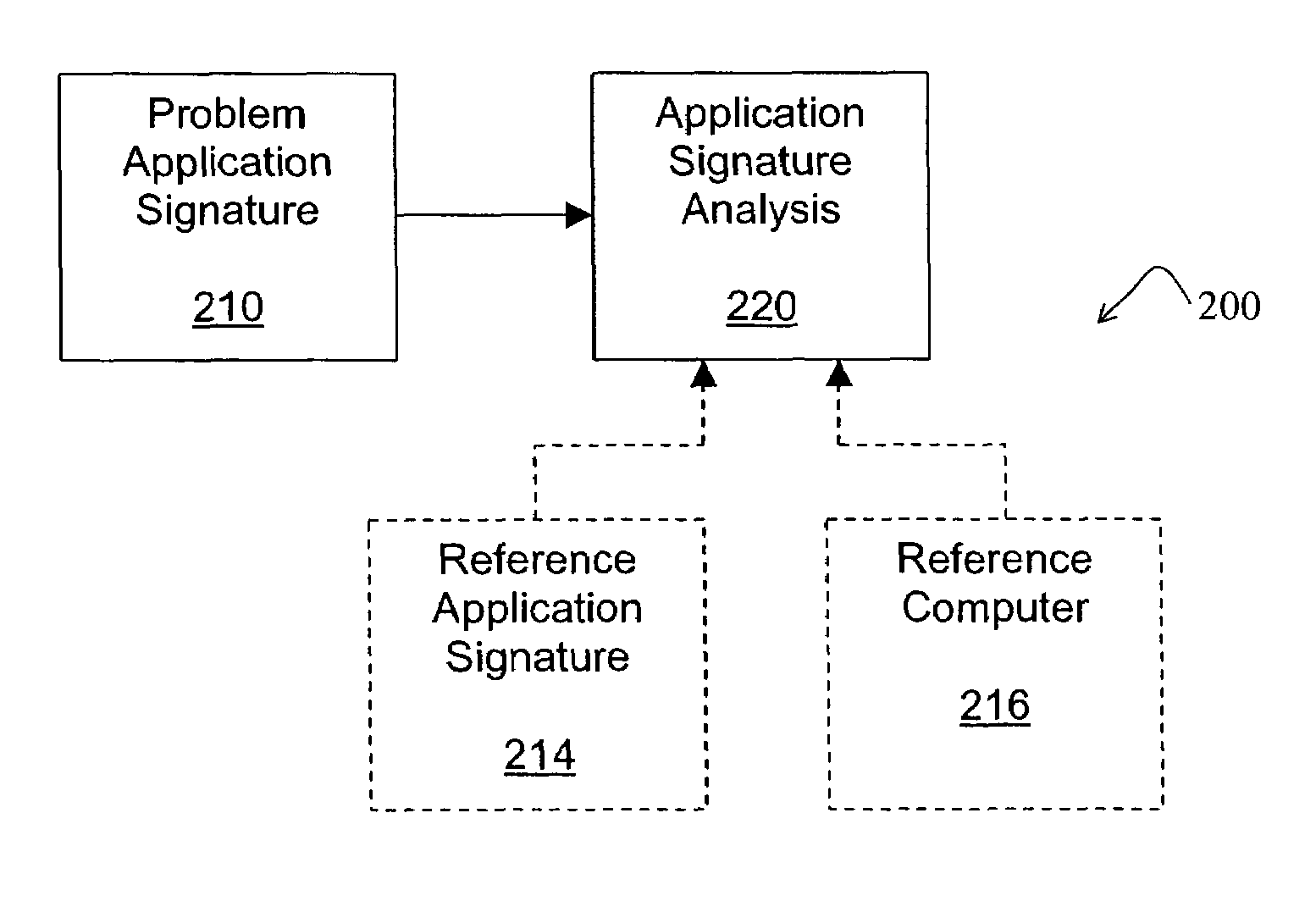
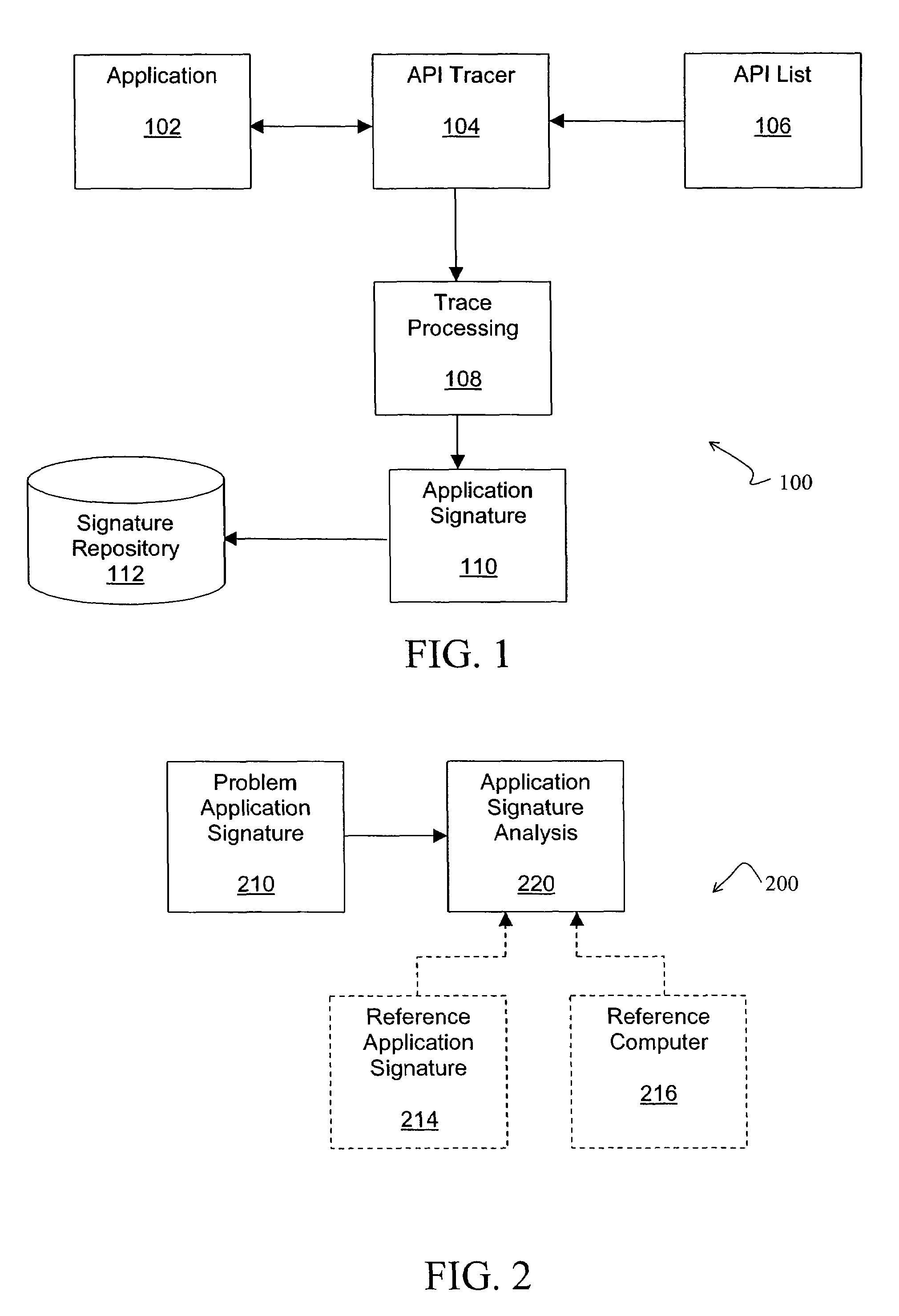
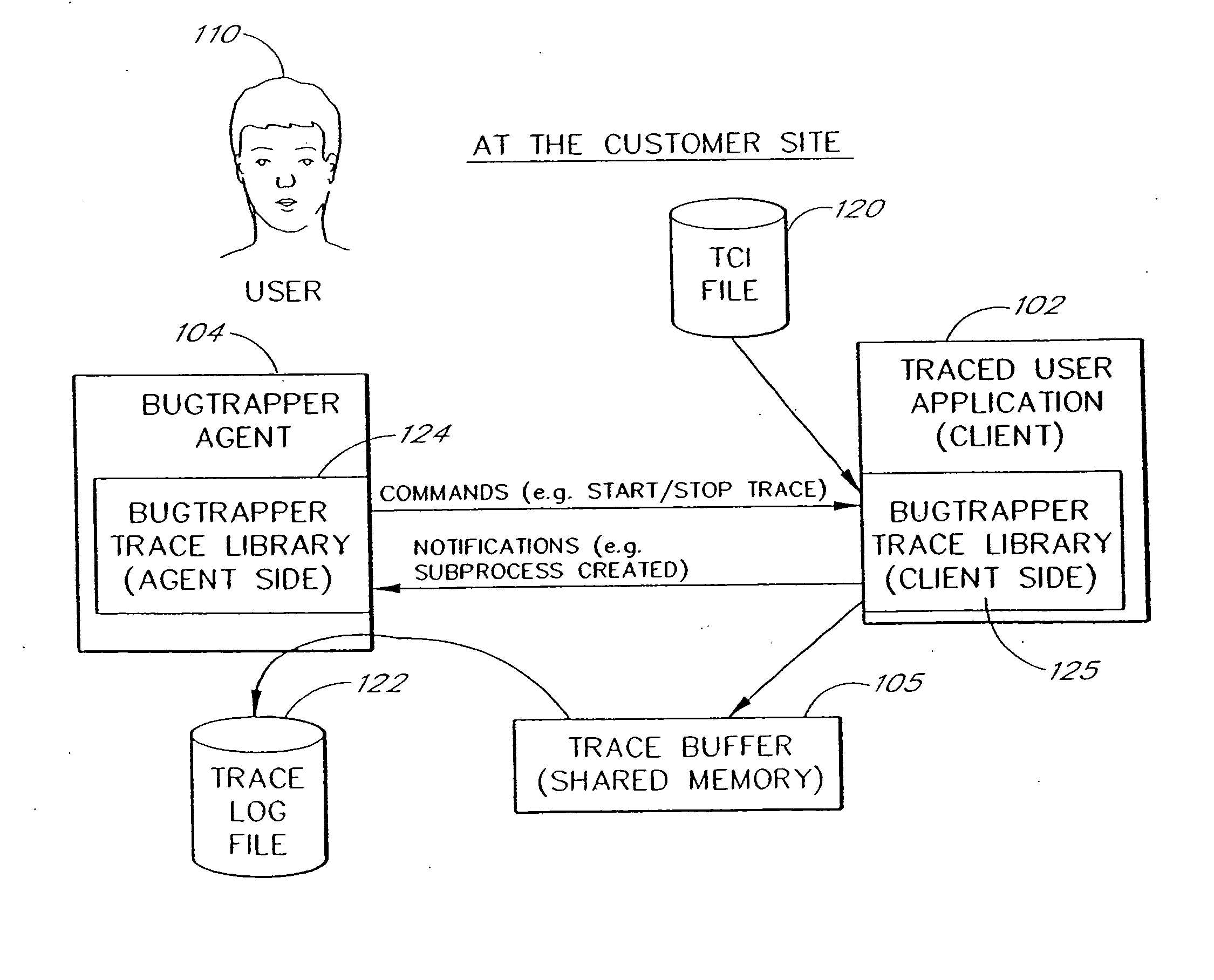
ActiveUS7386839B1Precise functionError detection/correctionSpecific program execution arrangementsSoftware systemComputerized system
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called a client or application. Trace data corresponding to selected system resources that interact with the execution of the application is collected during the tracing operation and stored in an application signature. A computer system user can generate trace options, trace the application, and compare the application signature to a known software configuration. The application signature is compared to a reference signature created by tracing the execution of the application on a system with the known software configuration. In another embodiment, the application signature is compared to a static configuration of a reference computer.
Owner:BMC SOFTWARE ISRAEL LTD
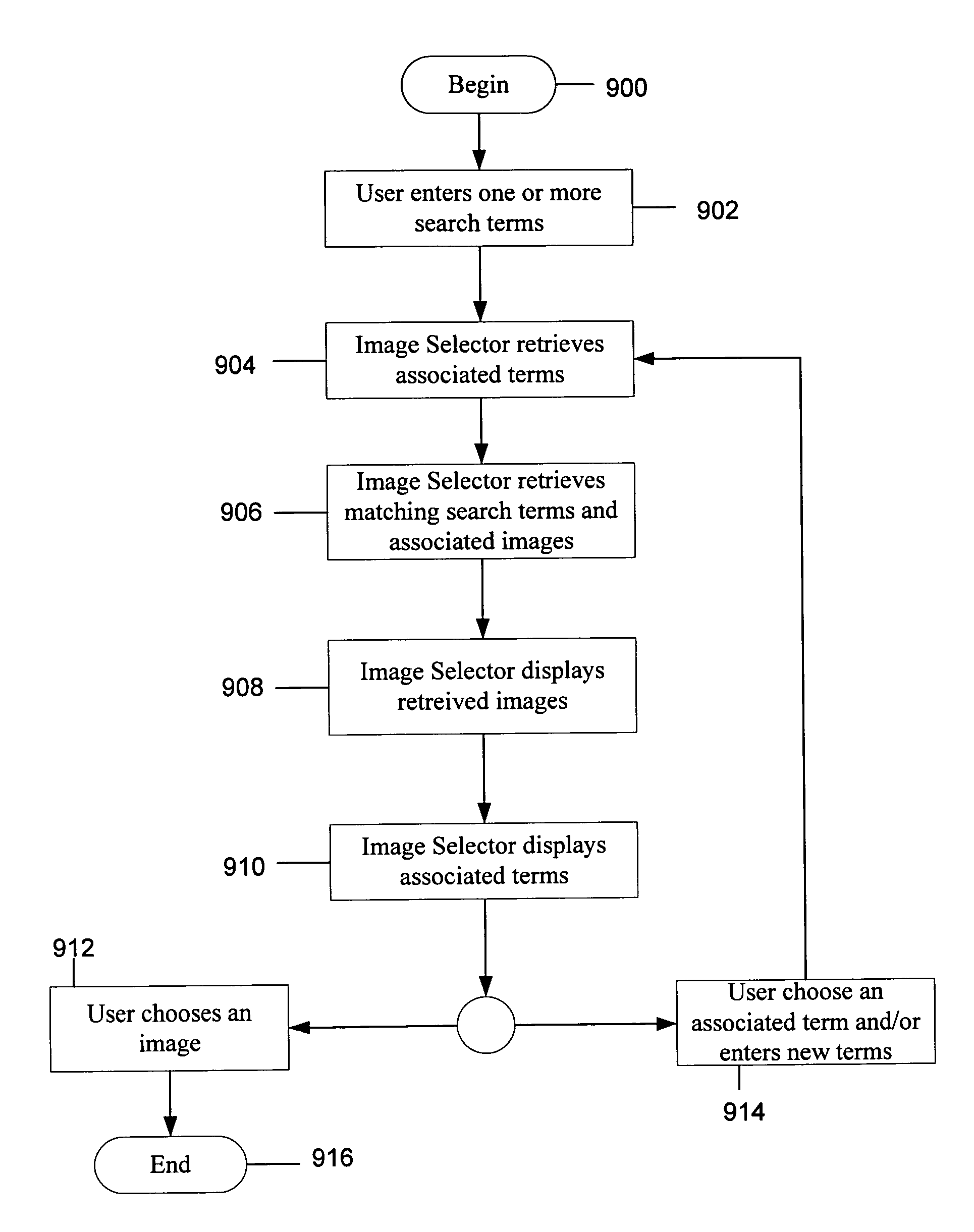
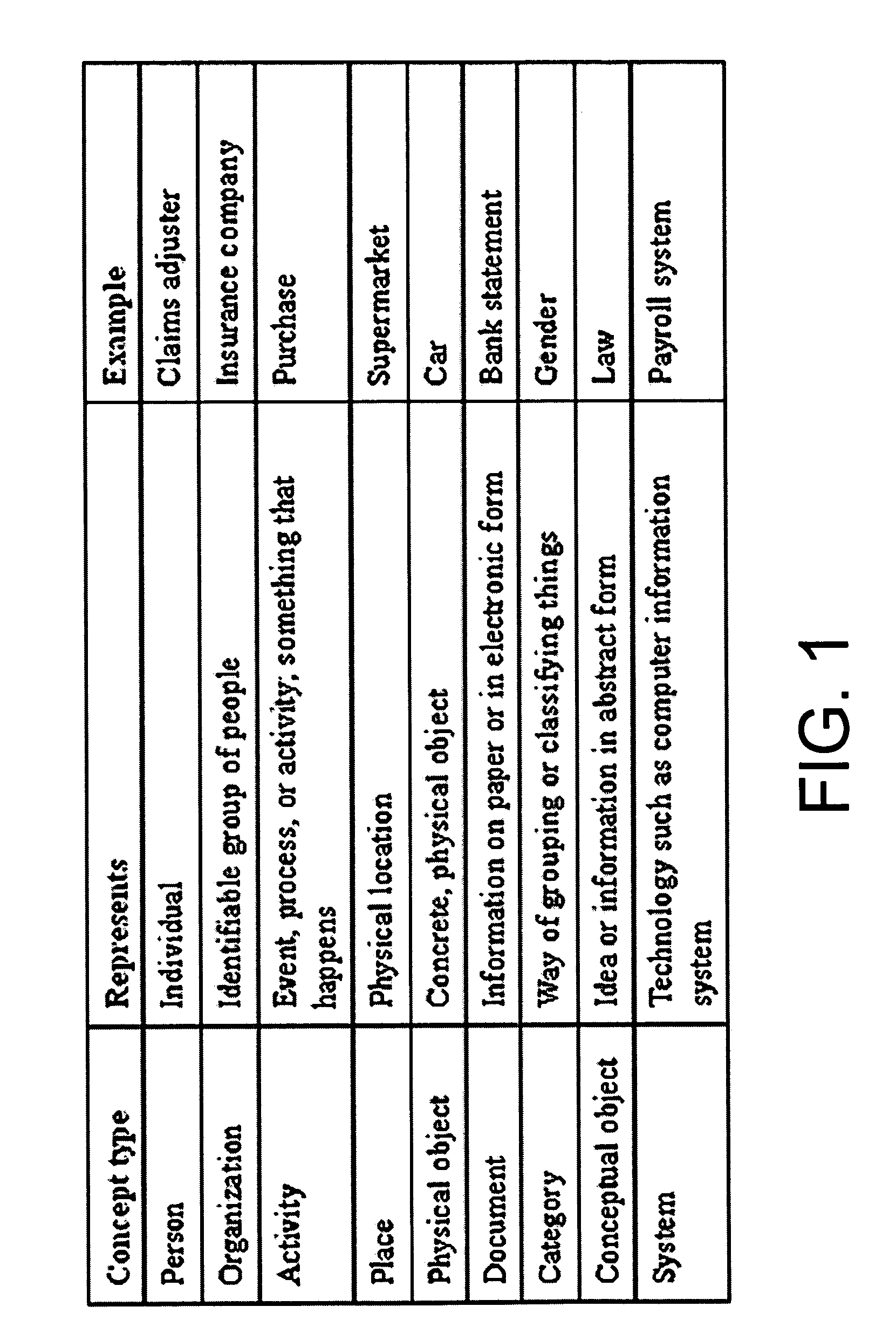
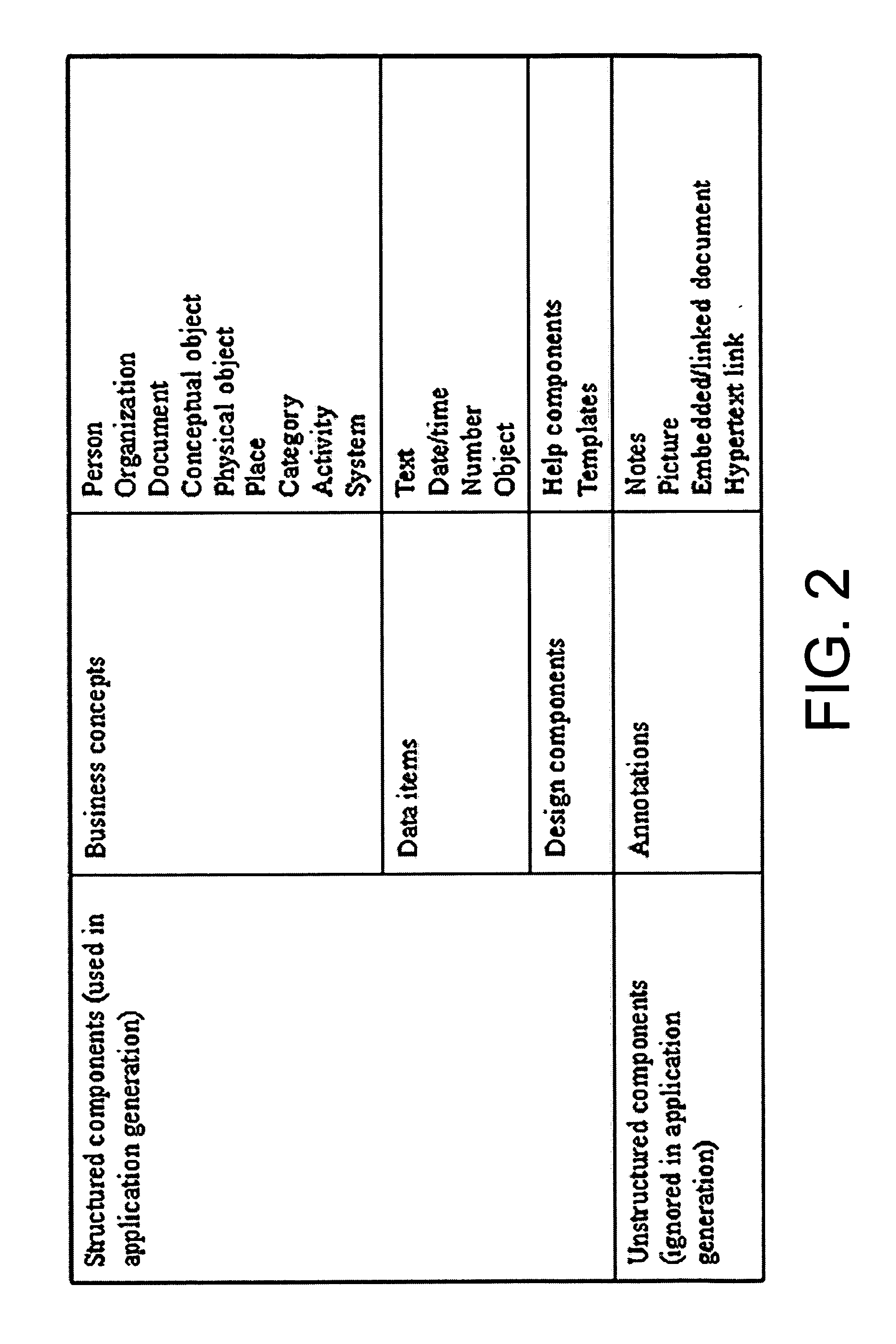
Systems and methods for software based on business concepts
InactiveUS20050289524A1Many taskEasy to understandSoftware designOffice automationSoftware systemPaper document
Business concept definitions may be utilized with software applications, components, tools, and system software. The business concepts definitions are each associated with archetypal definitions, which may also be known as innate concepts. These archetypal definitions may include a person, an organization, a system, a place, an activity, a document, a conceptual object, a physical object, and a category. The business concept definitions may also be represented by an image on a user interface, where the images may be selectable by a user. These business concept definitions may be manipulated and modified. Indeed, certain relationships may be denoted between business concept definitions through the positioning of the images on a user interface. Because these business concept definitions are associated with archetypal definitions, which may be intuitive for users, application definitions using these business concept definitions may be easily created by a user without programming skills.
Owner:MCGINNES SIMON
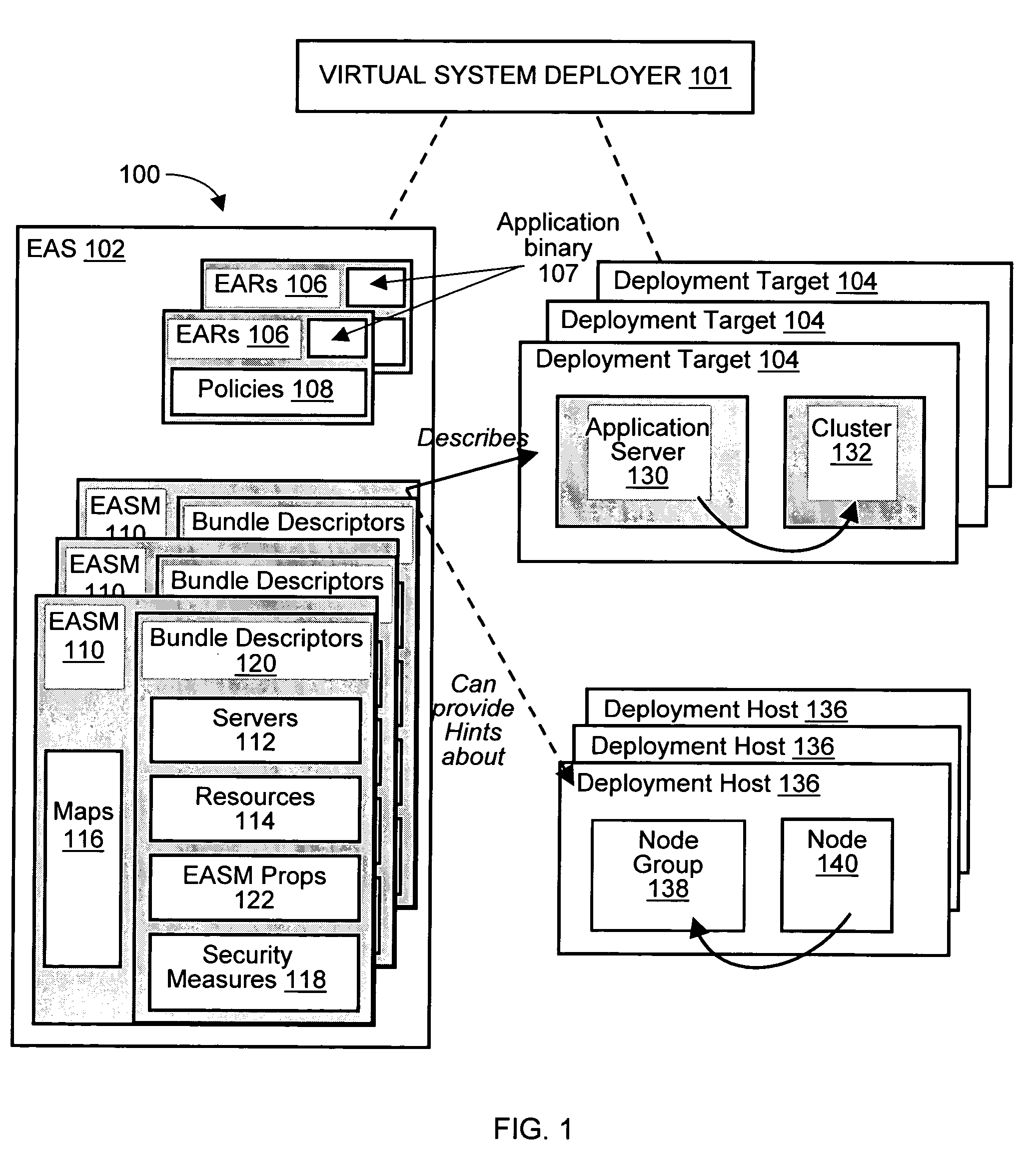
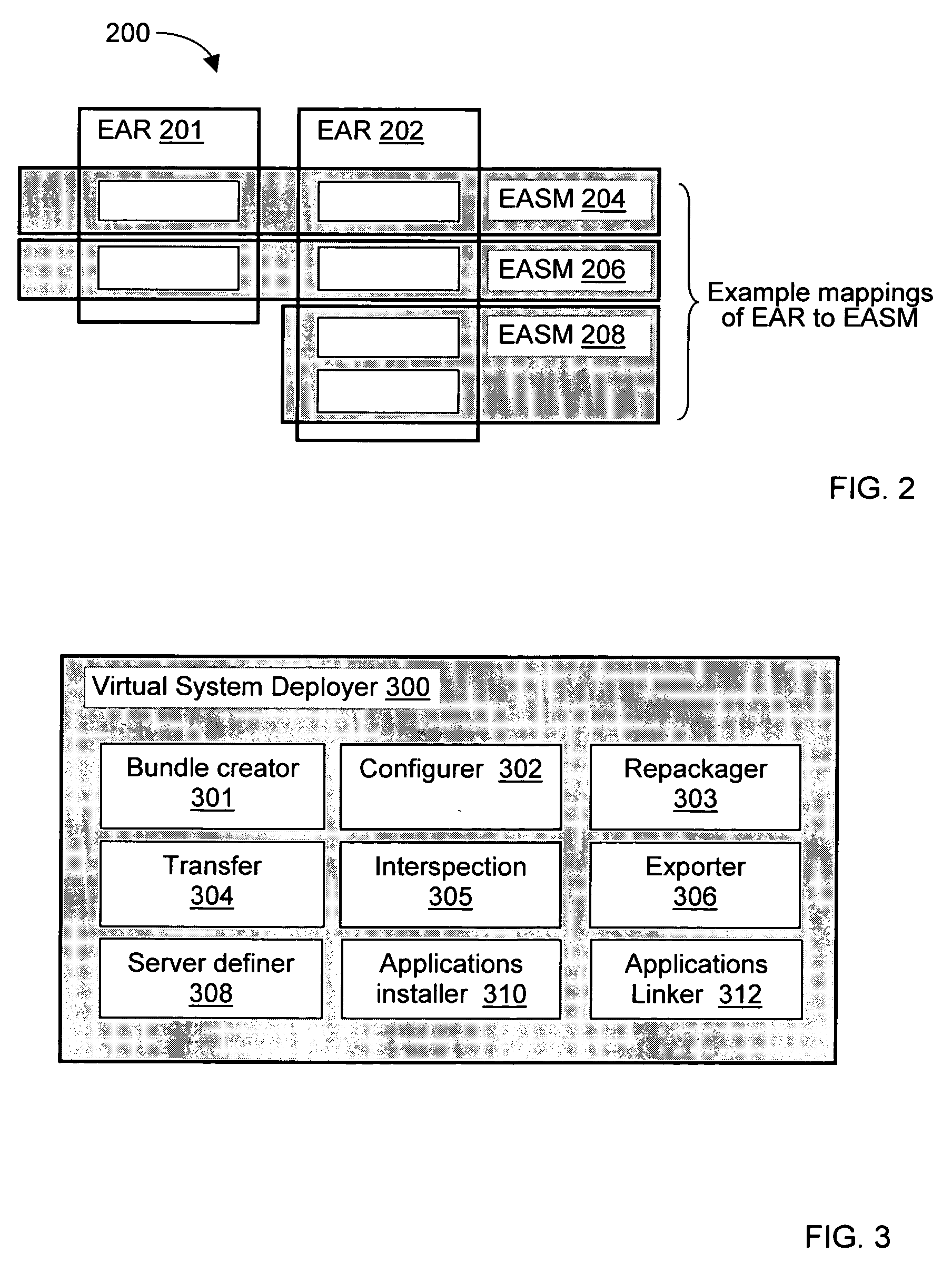
Deploying an application software on a virtual deployment target
InactiveUS20050289538A1Program loading/initiatingMemory systemsApplication program softwareRelevant information
Methods and arrangements to propagate application software to a virtual deployment target are contemplated. More specifically, a user may create multiple virtual deployment targets in a software system such as WebSphere™ and deploy applications to multiple the virtual deployment targets without having to manually fit policy-driven applications into each virtual deployment target. Embodiments are particularly advantageous when the application software is a business solution that needs to be deployed multiple times such as during the development and testing of the business solution. For example, application software of a business solution typically includes a group of applications designed to cooperatively function as a single entity. An application bundle such as an Enterprise Application Solution (EAS) file describes the application software and includes pertinent information about the application software, application configuration data, and runtime configuration data to implement the business solution. Then, the application bundle can be deployed automatically or substantially automatically.
Owner:IBM CORP
Integrated medical software system with clinical decision support
InactiveUS20110301982A1Readily apparentMedical data miningMedical automated diagnosisSoftware systemClinical decision support system
An integrated medical software system with embedded transcription functionality is disclosed. The system comprises a clinical module for capturing clinical data for a patient in a first electronic document and a communication component that communicates the clinical data to a rule-based clinical decision support (CDS) system and receives at least one of an alert, warning, reminder, and recommendation back from the CDS system based on the clinical data. The CDS system is configured to compare the clinical data against a knowledge base to identify the at least one of an alert, warning, reminder, and recommendation; the clinical data is serialized into a standardized database language and placed into a first electronic clinical document defined by a clinical document exchange standard before being communicated to the CDS system; and the at least one of an alert, warning, reminder, and recommendation is provided in a second electronic clinical document defined by the clinical document exchange standard when received back from the CDS system.
Owner:GREENWAY MEDICAL TECH
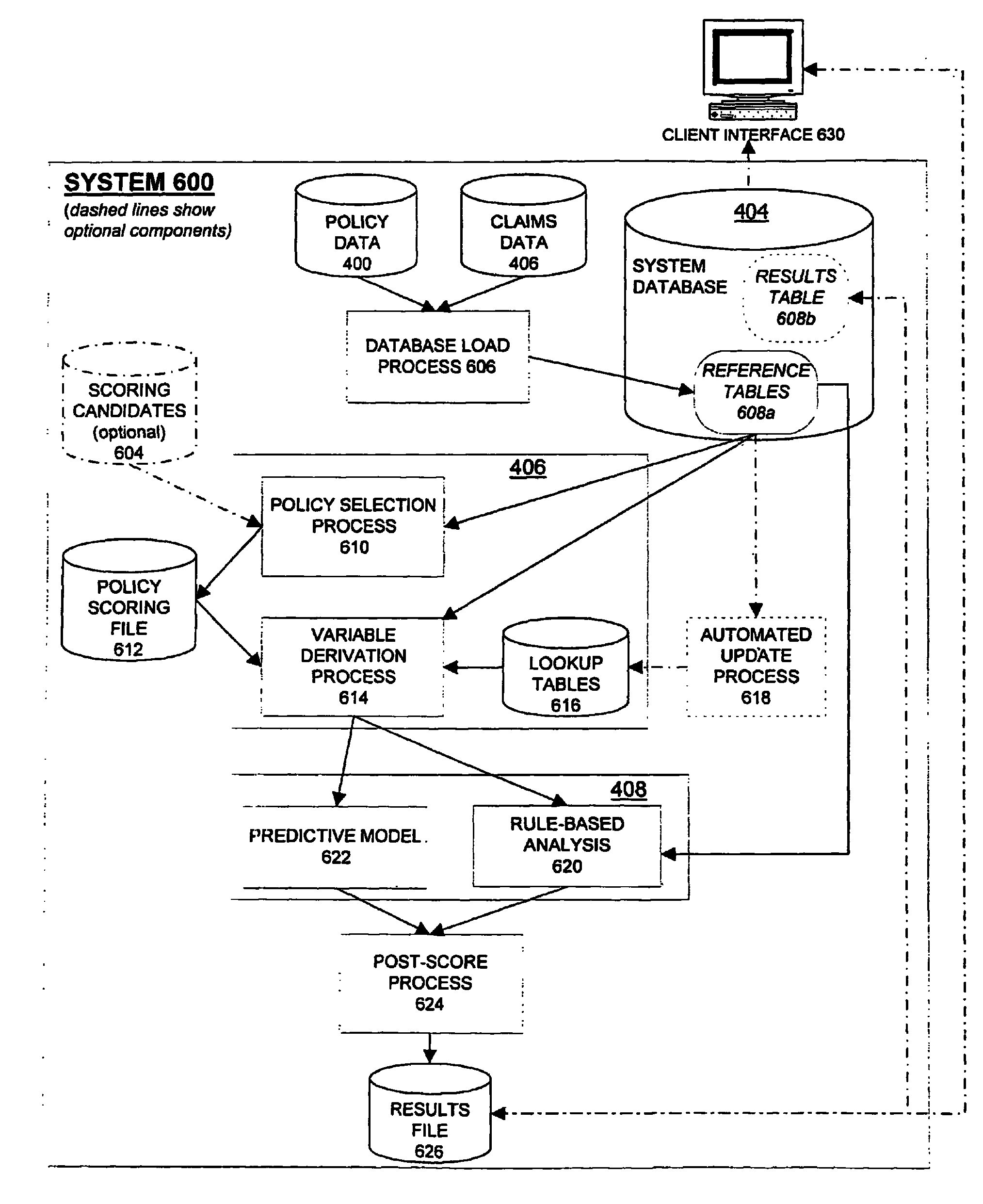
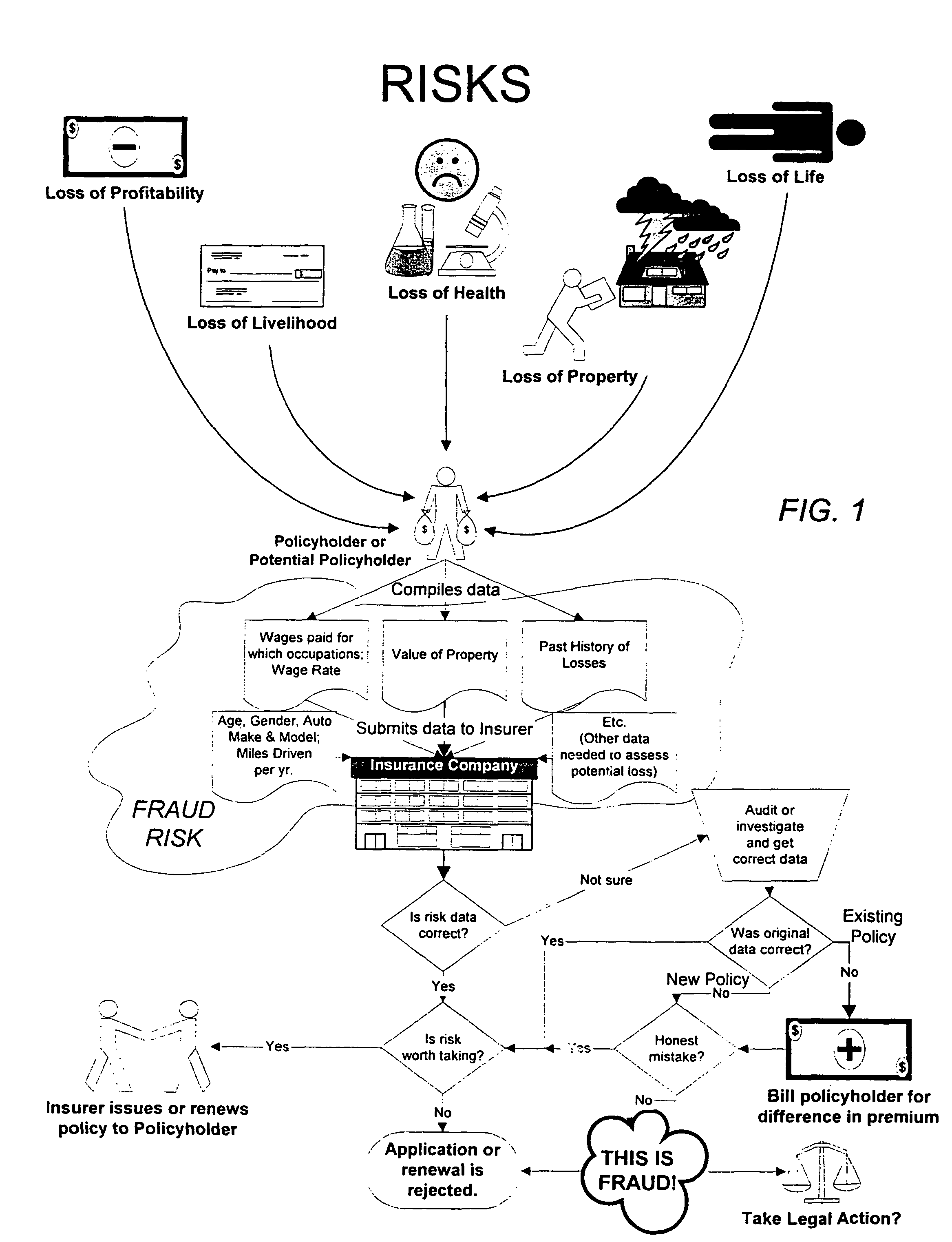
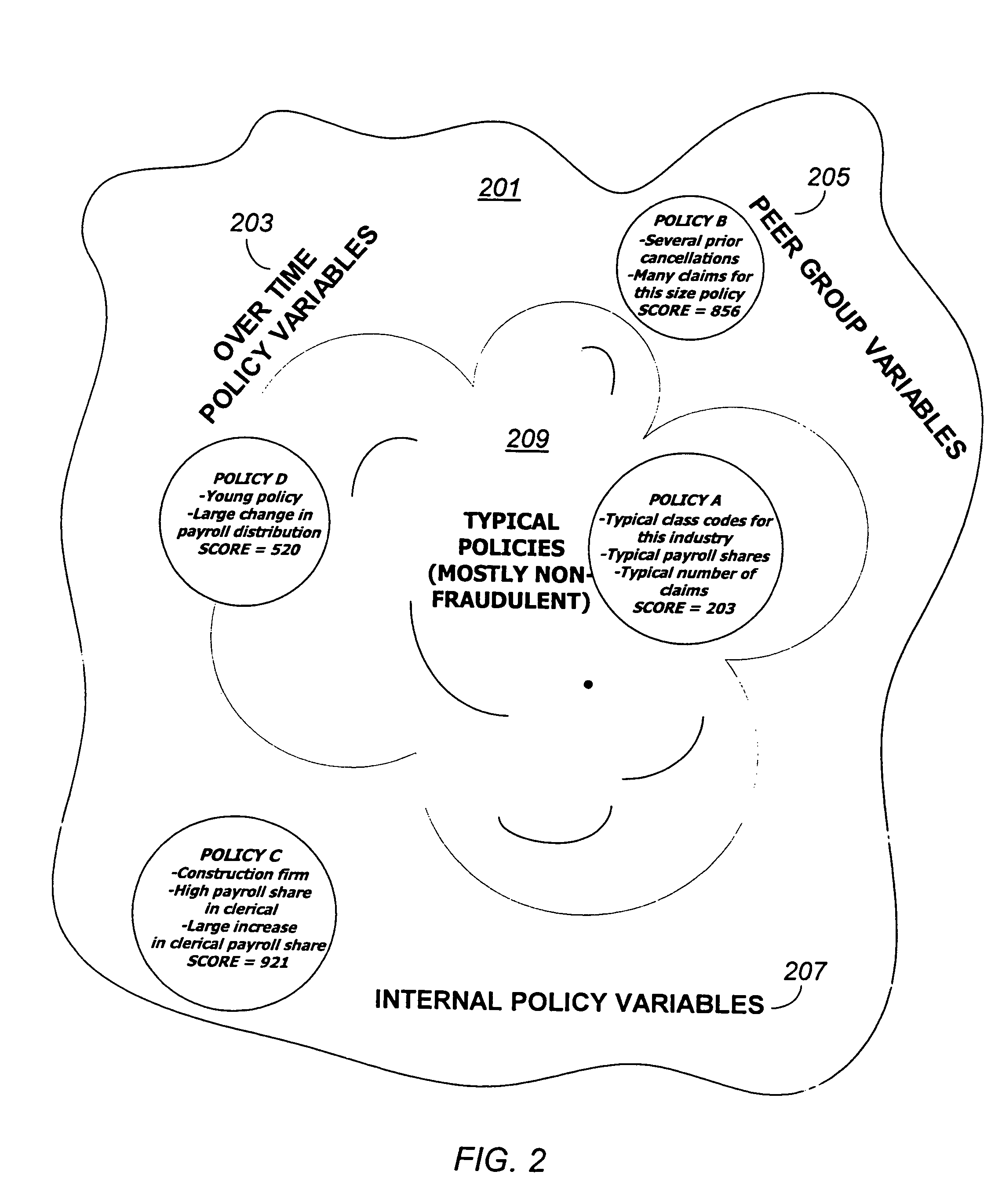
Detection of insurance premium fraud or abuse using a predictive software system
InactiveUS7813944B1Level of complexityIncrease ratingsFinanceOffice automationRelevant informationSoftware system
Detection of insurance premium fraud is provided by a predictive model, which uses derived variables to assess the likelihood of fraud for each policy. The predictive model produces a score, which is a measure of the likelihood of premium fraud or abuse. The predictive model is included in a system that accepts policies to be considered for scoring, selects which policies are appropriate for scoring, stores data about the policies in a database, uses the data to derive variables for the model, and processes and outputs the model scores and related information. A rule-based analysis, which detects specific inconsistencies in the data that are indicative of premium fraud, may also be part of the system. The model scores and red-flag indicators from the rule-based analysis may be further processed to provide customized output for users.
Owner:FAIR ISAAC & CO INC
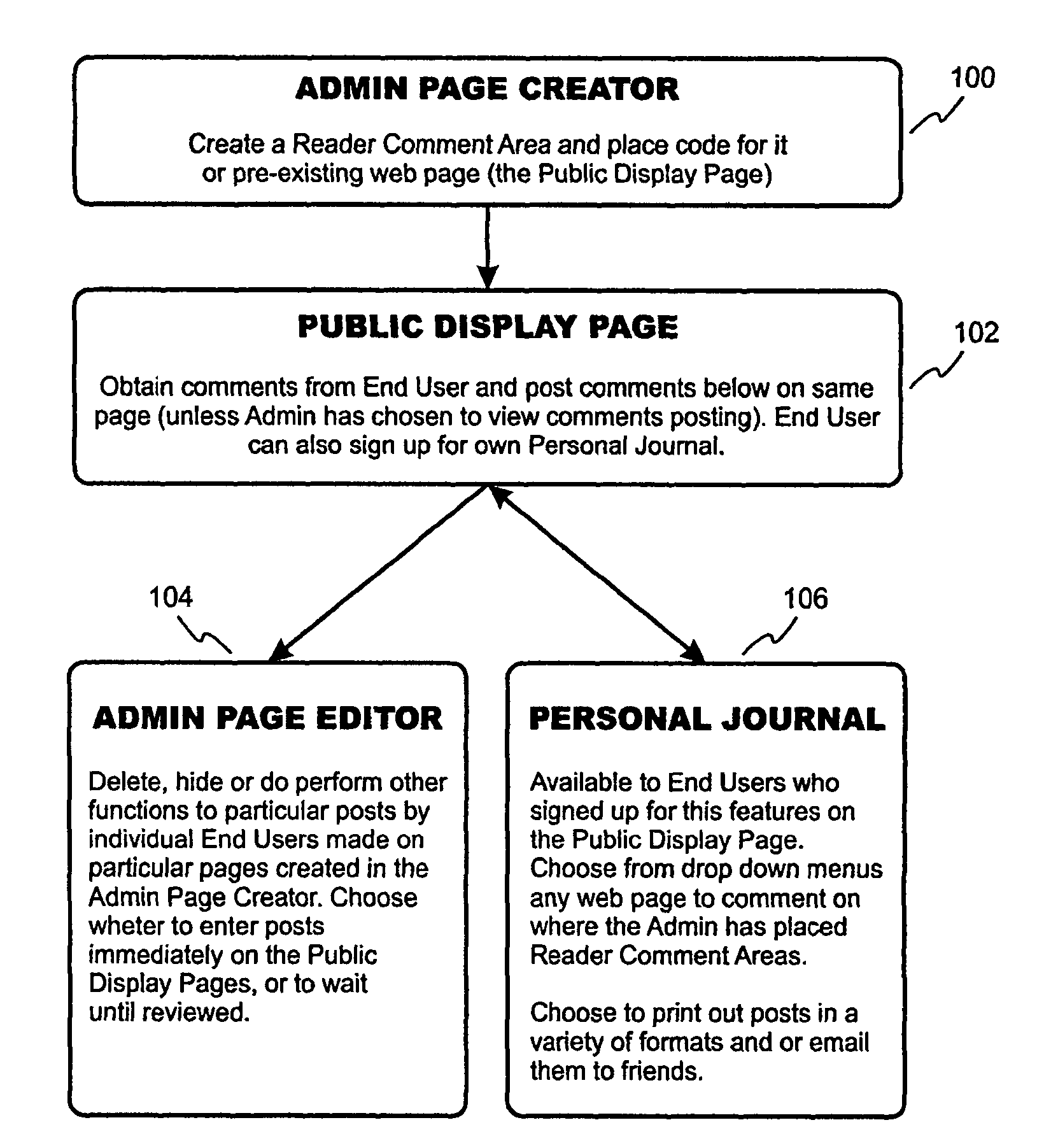
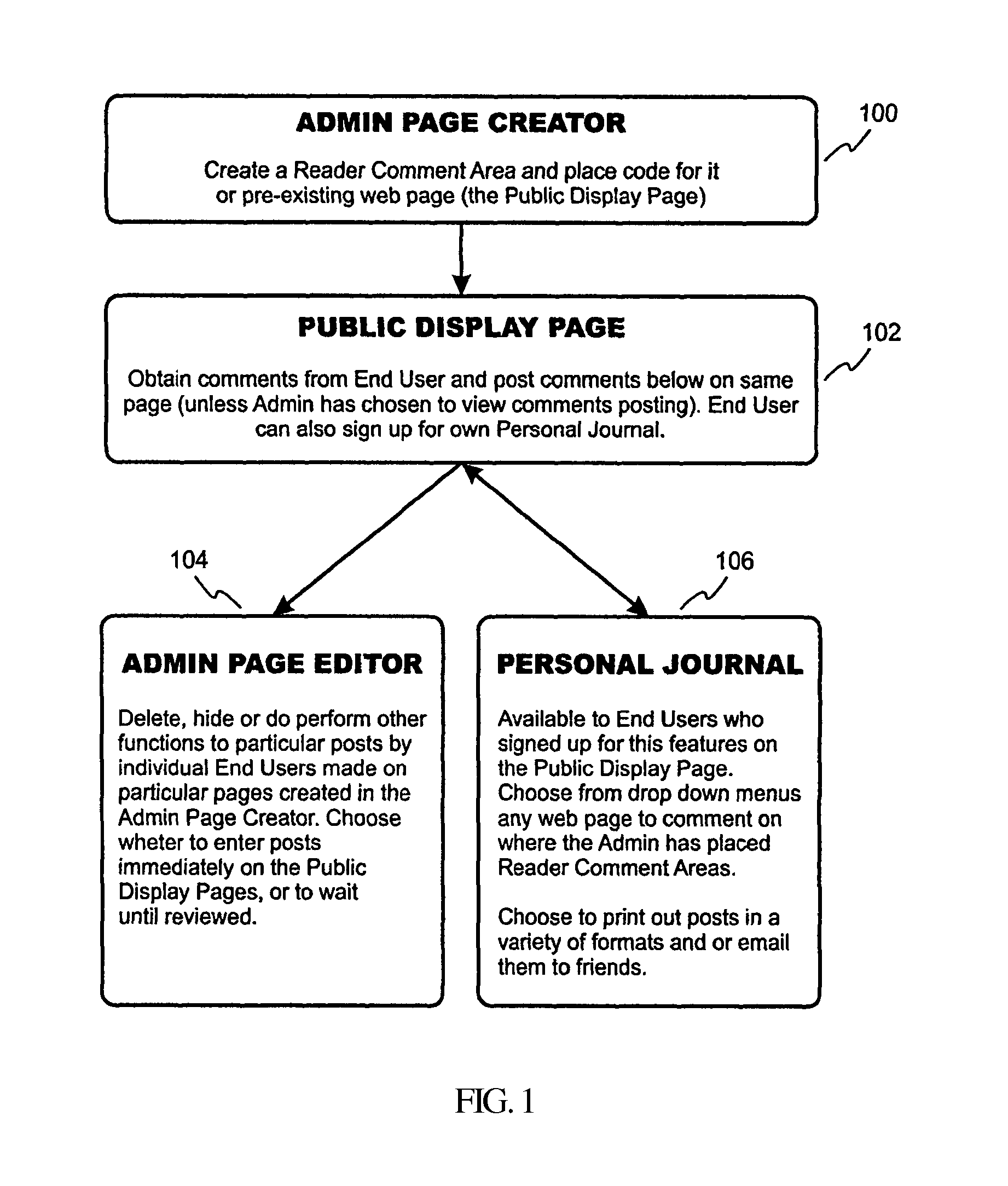
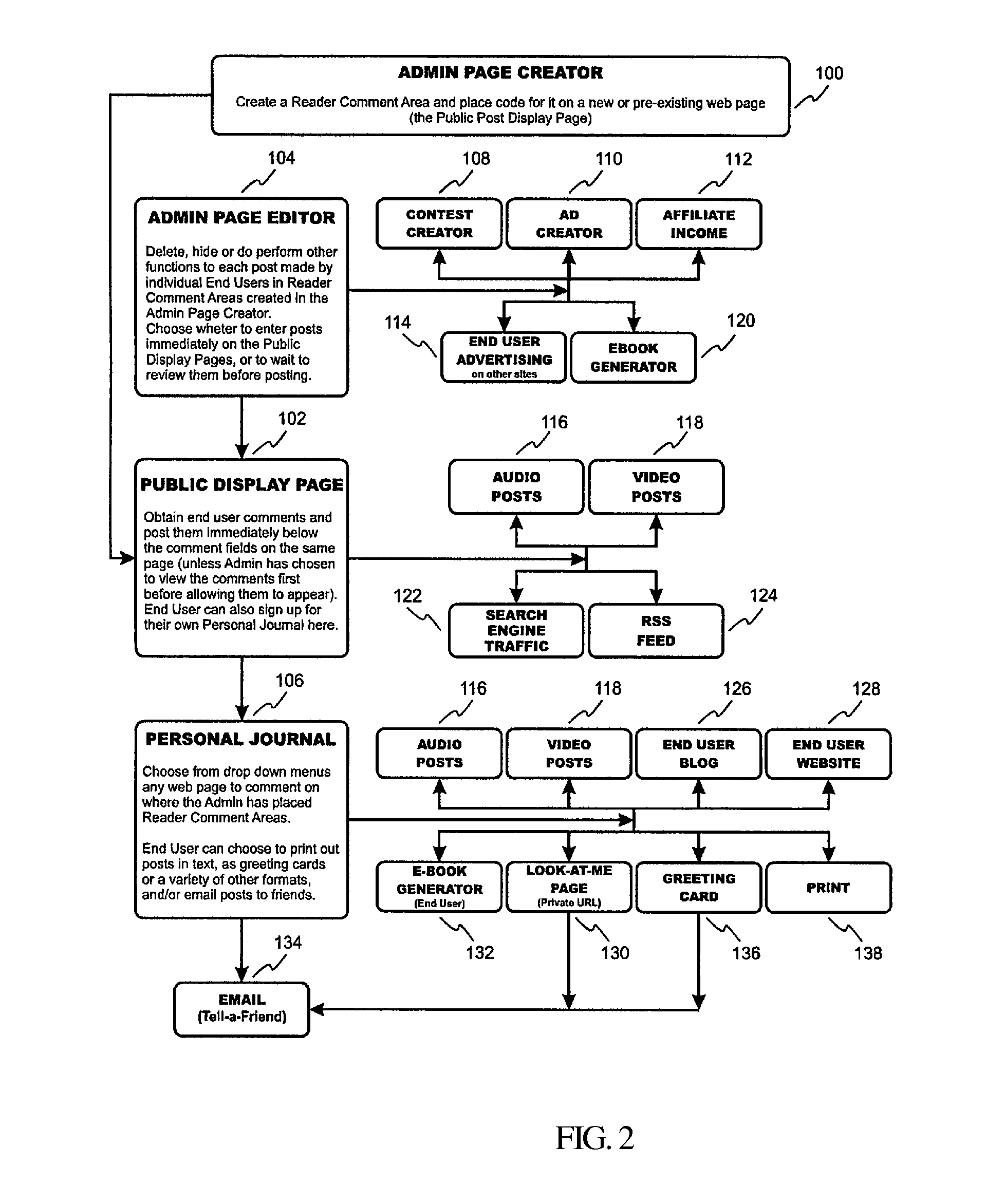
System and method for tagging content in a digital media display
InactiveUS20150033112A1Easy to adaptImprove rankingWeb data indexingNatural language data processingSoftware systemDisplay device
A software system and method that allows website readers to create and store comments pertaining to website content, with tags identifying the comment, so that the comments may be easily retrieved at a later time. An administrator accesses a website to enter data (e.g. HTML code) for creating reader comment and tag. When the webpage containing the code is posted to a website, the code results in a reader comment and tag display page where website visitors can comment on the content of the website, and create one or more tags that identify their comment. Comments and tags are then saved at a local or remote website database accessible to the reader. A reader can find their comments that they posted on various websites stored within their database record by searching the database for comments with a particular tag. They can also assign new tags to their stored comments.
Owner:SOCIAL COMMENTING
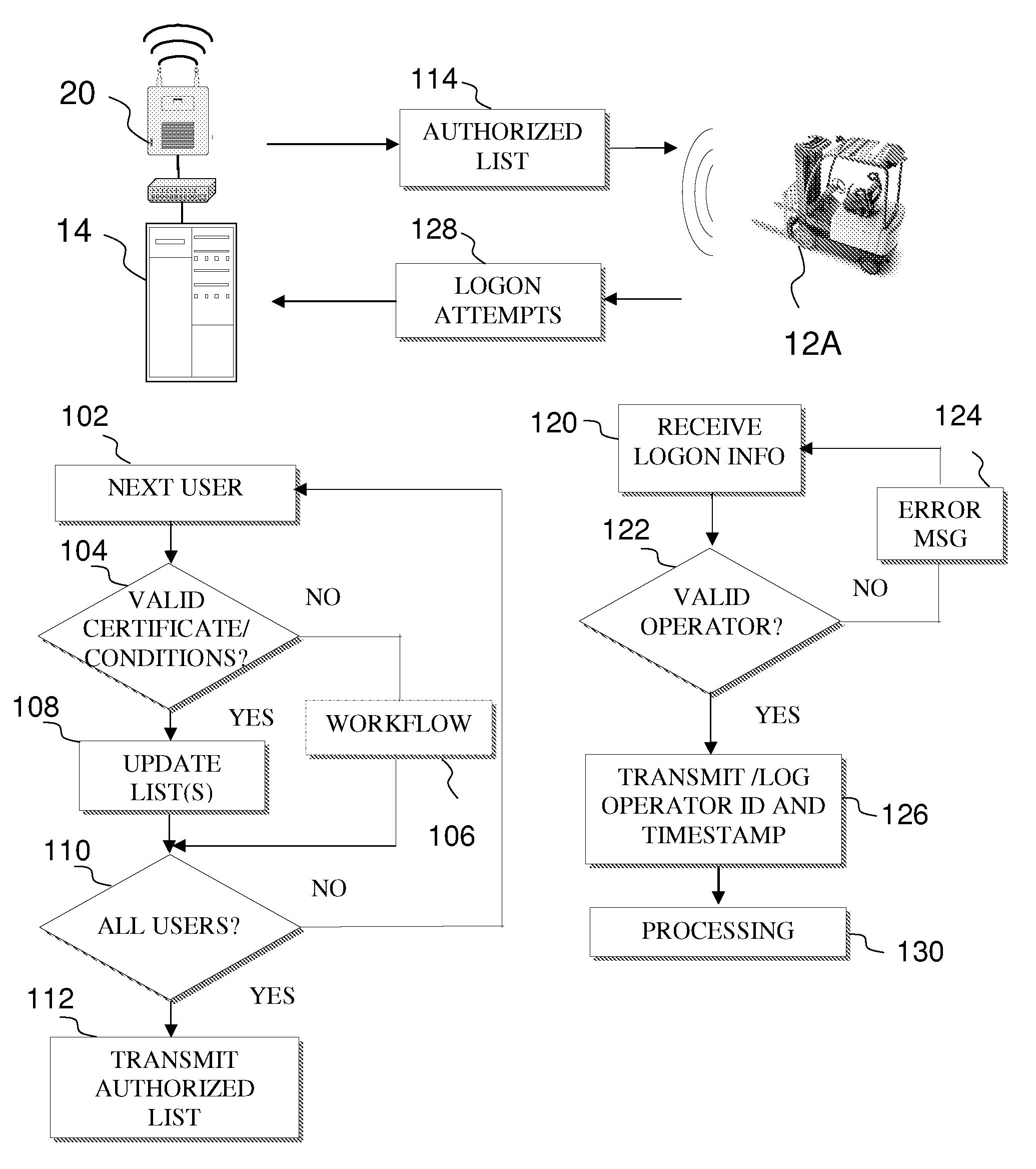
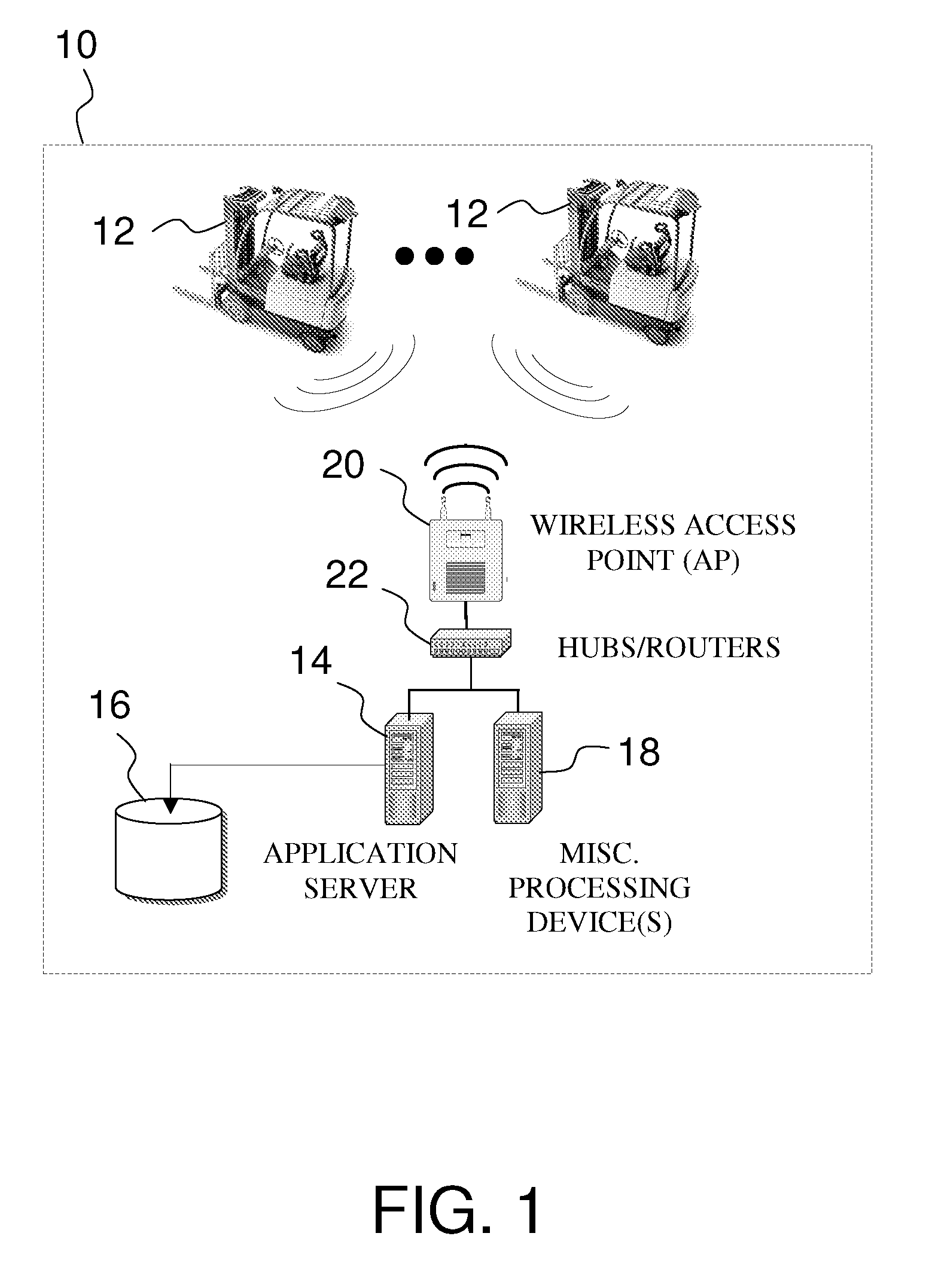
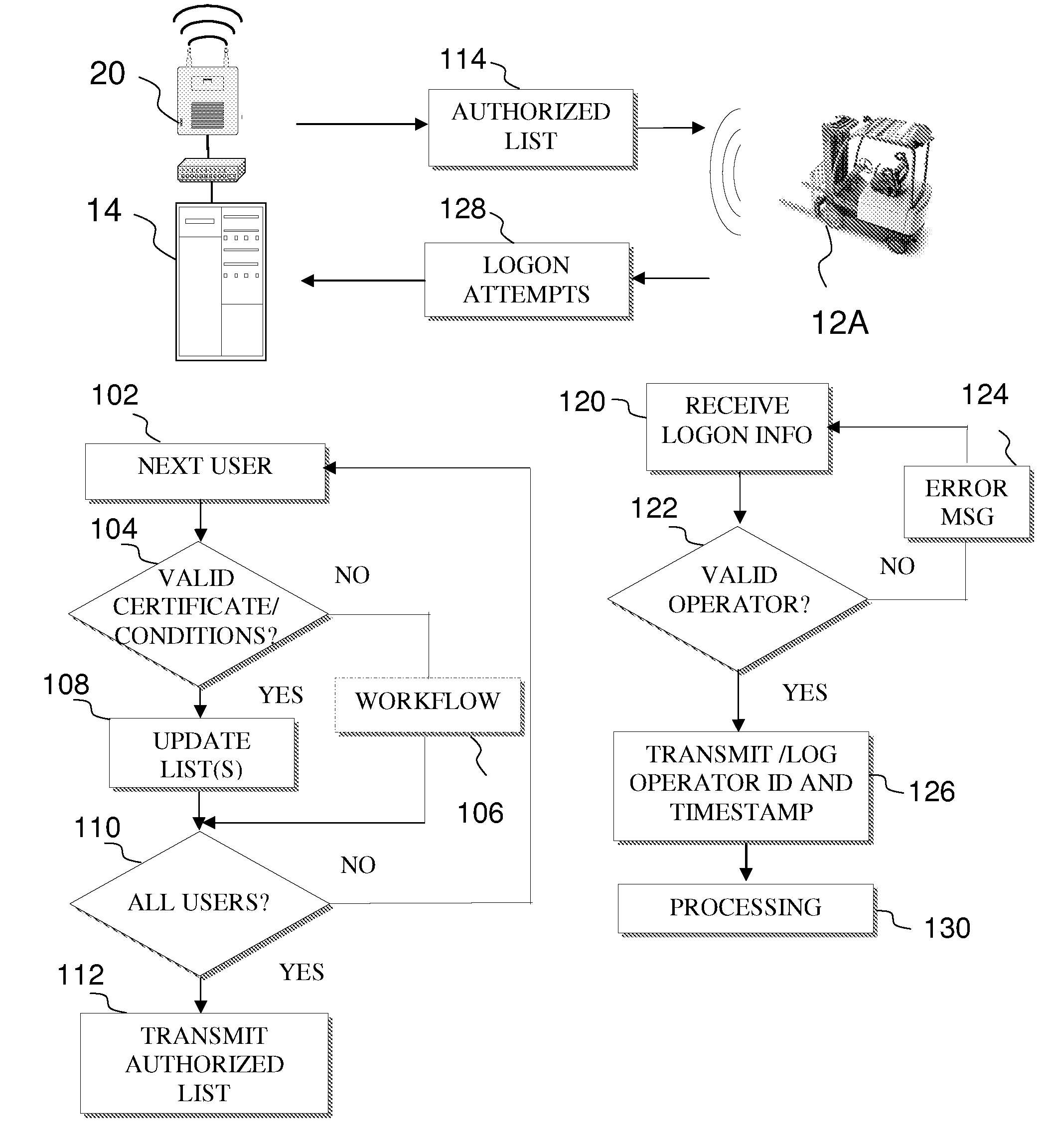
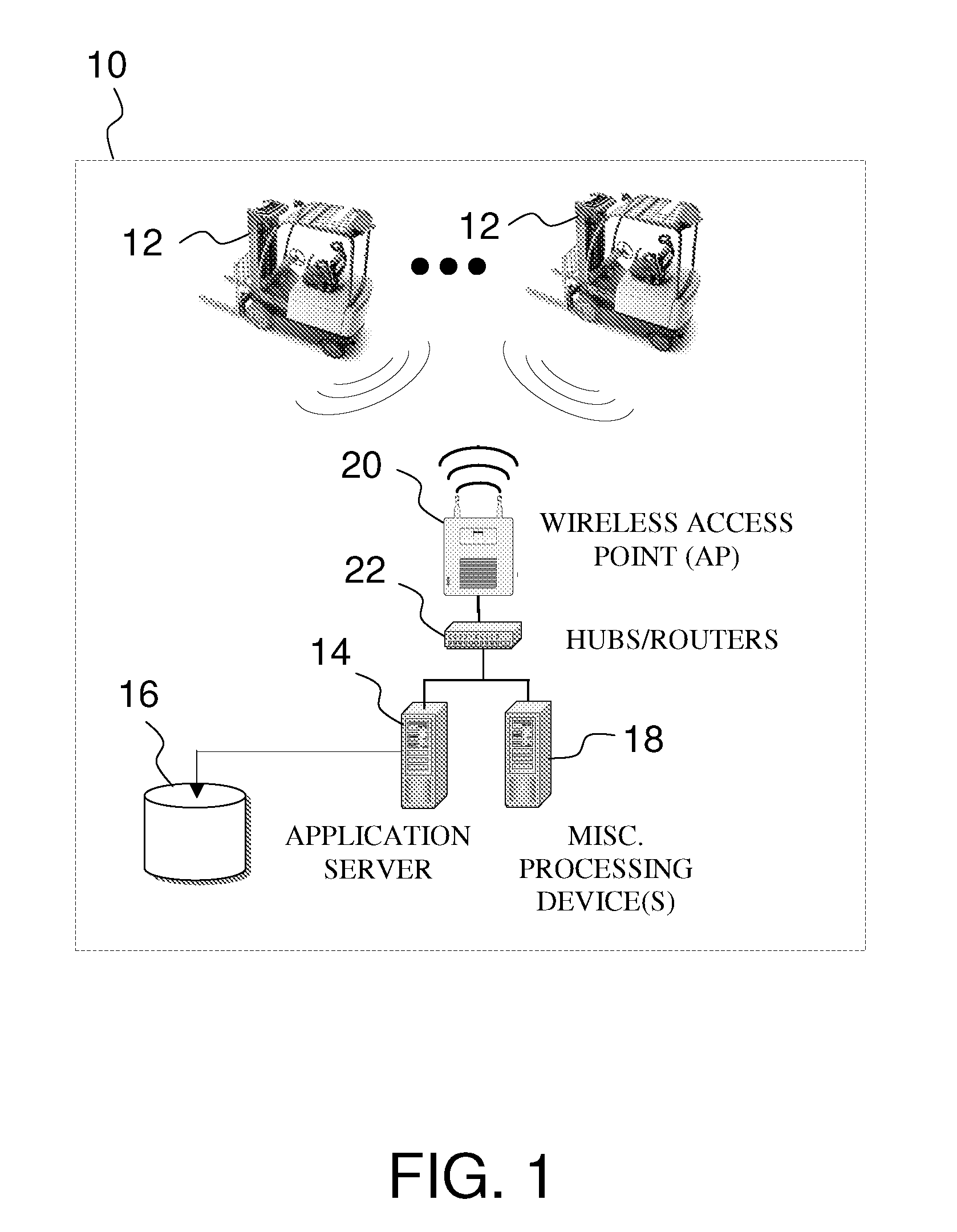
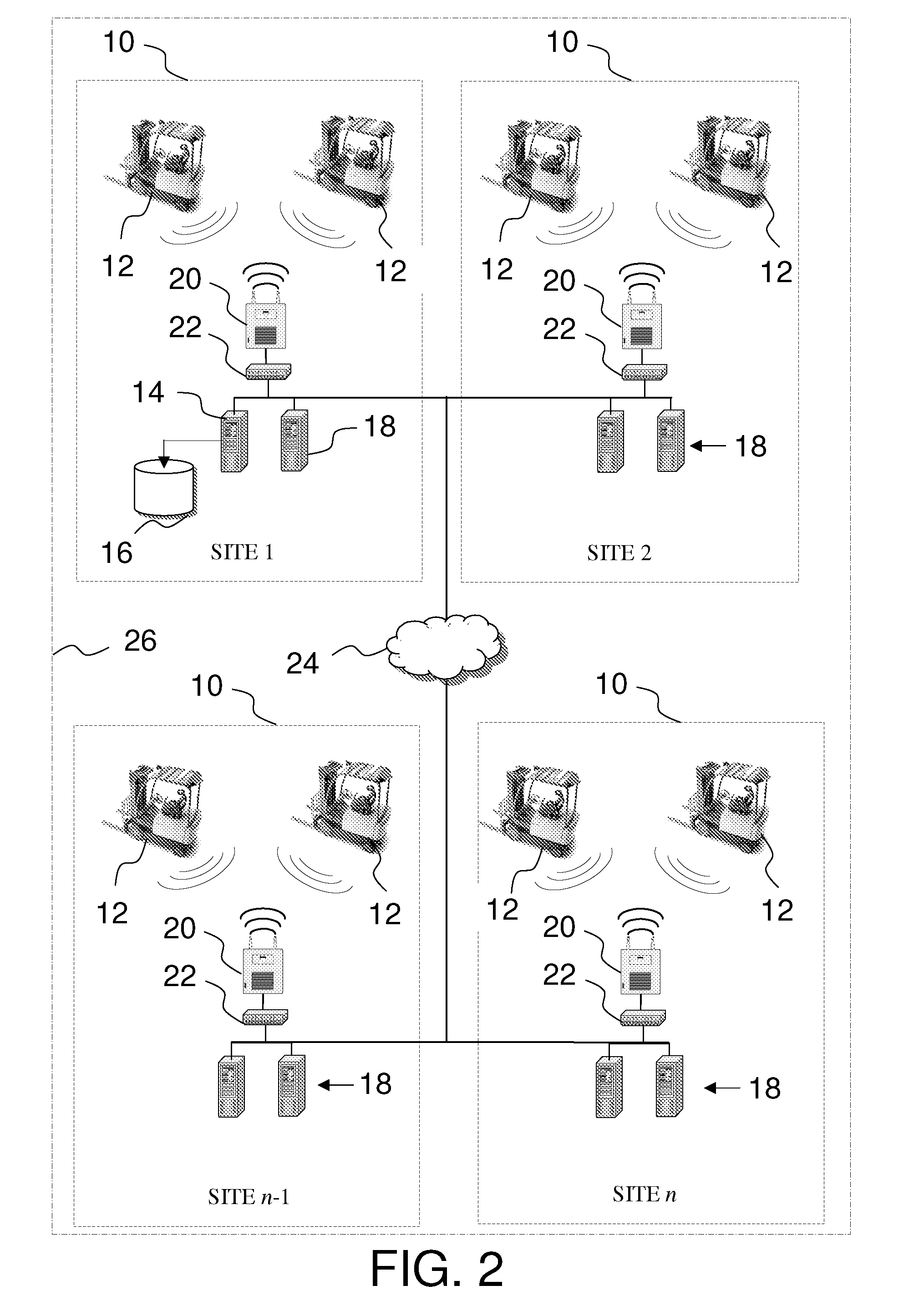
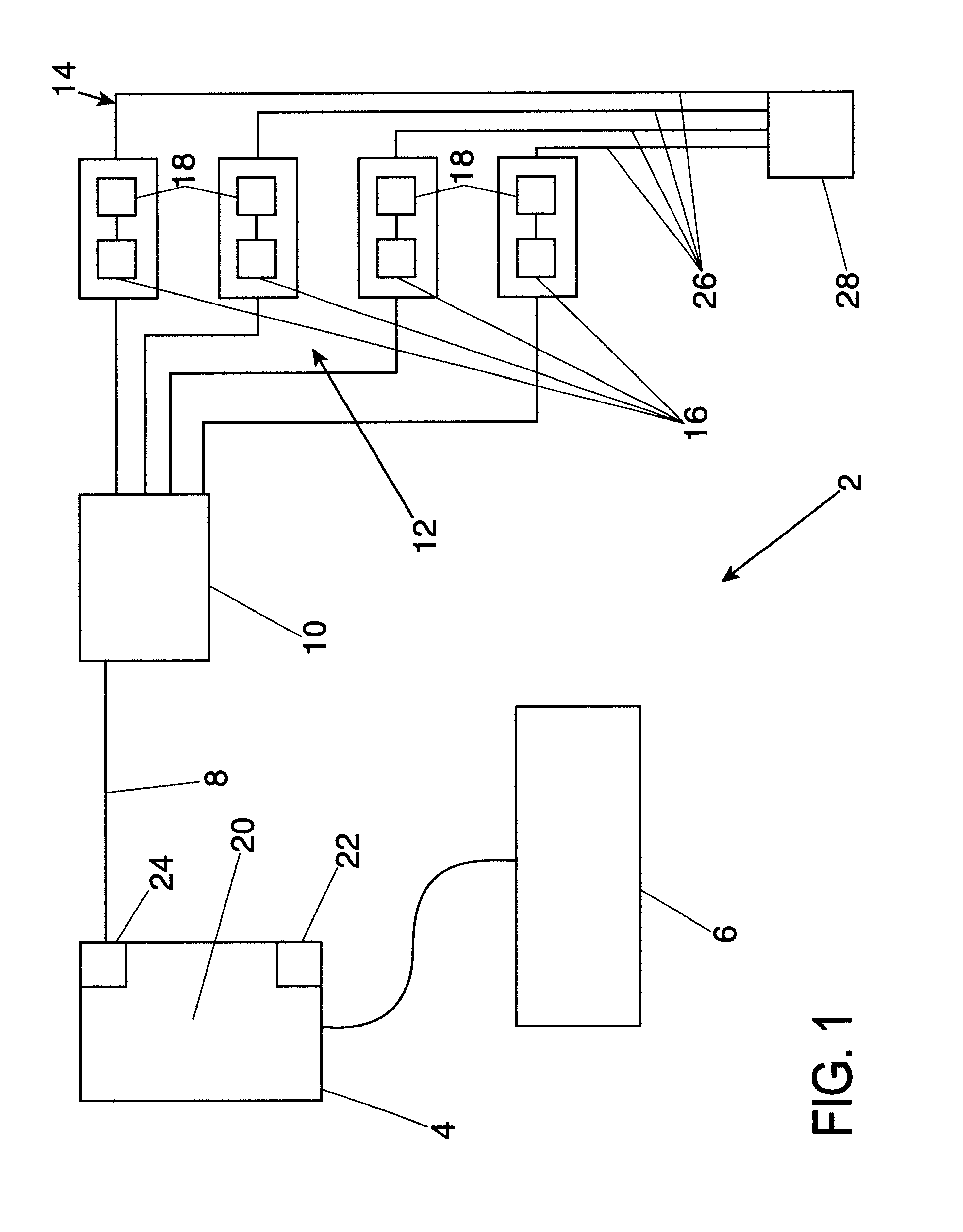
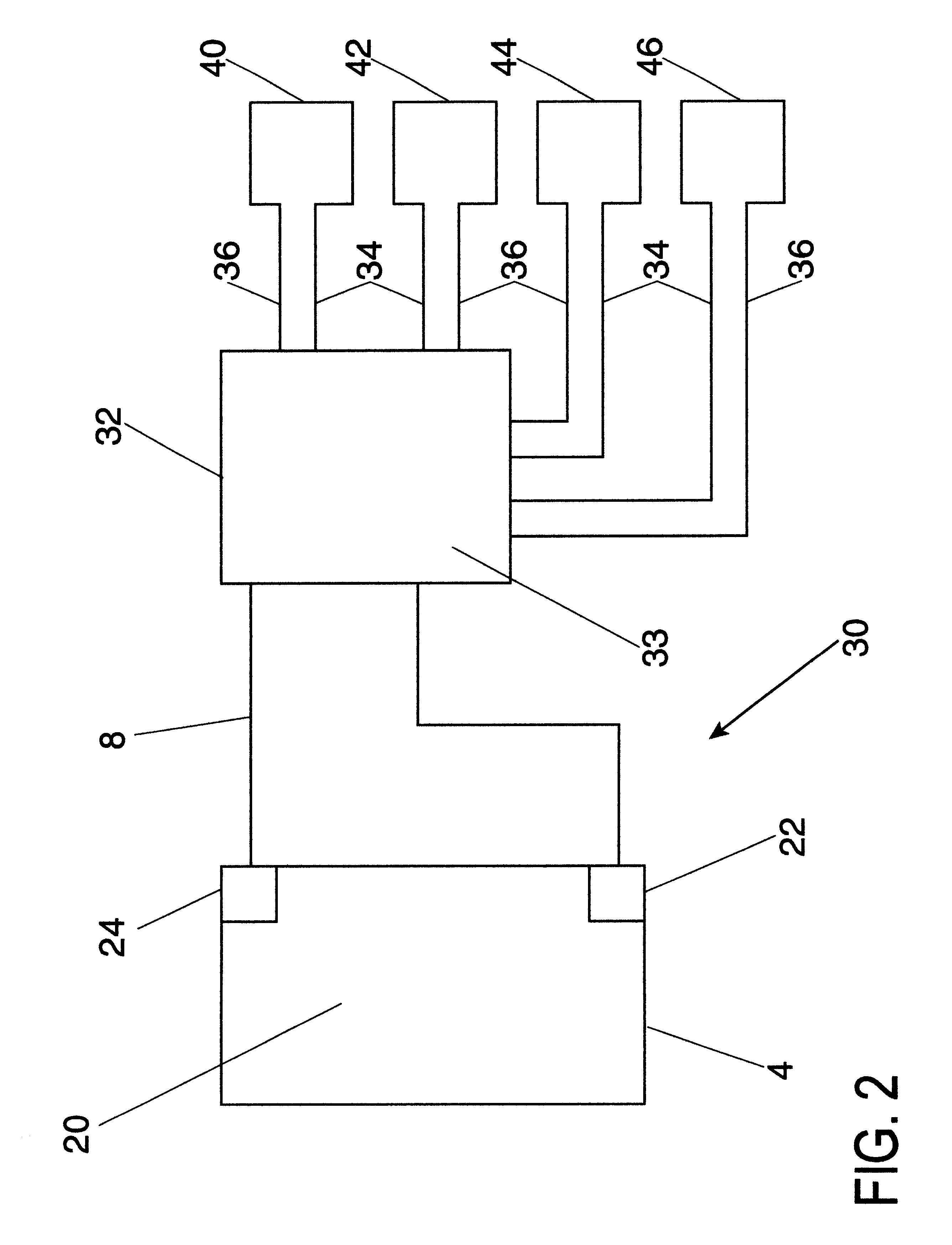
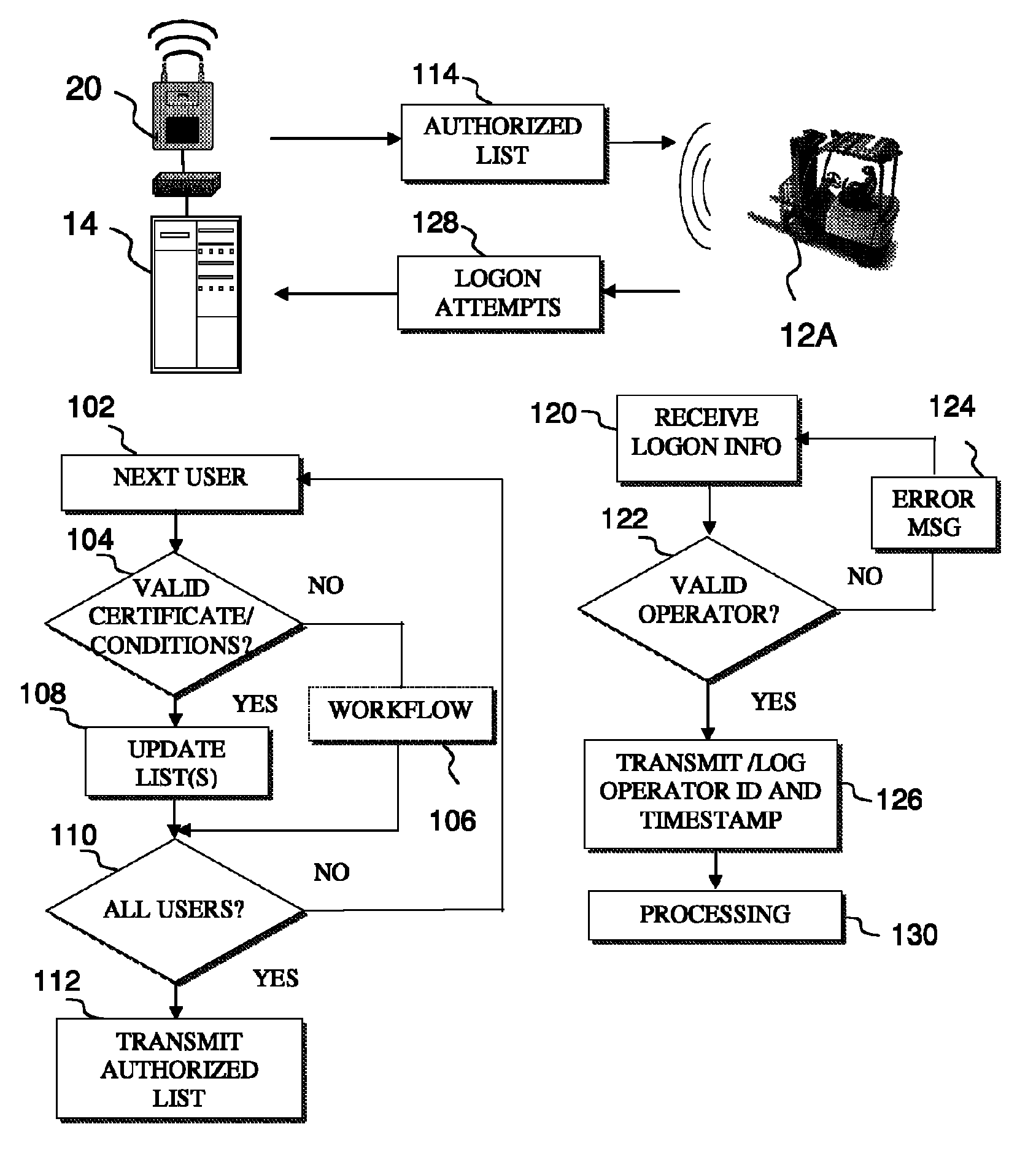
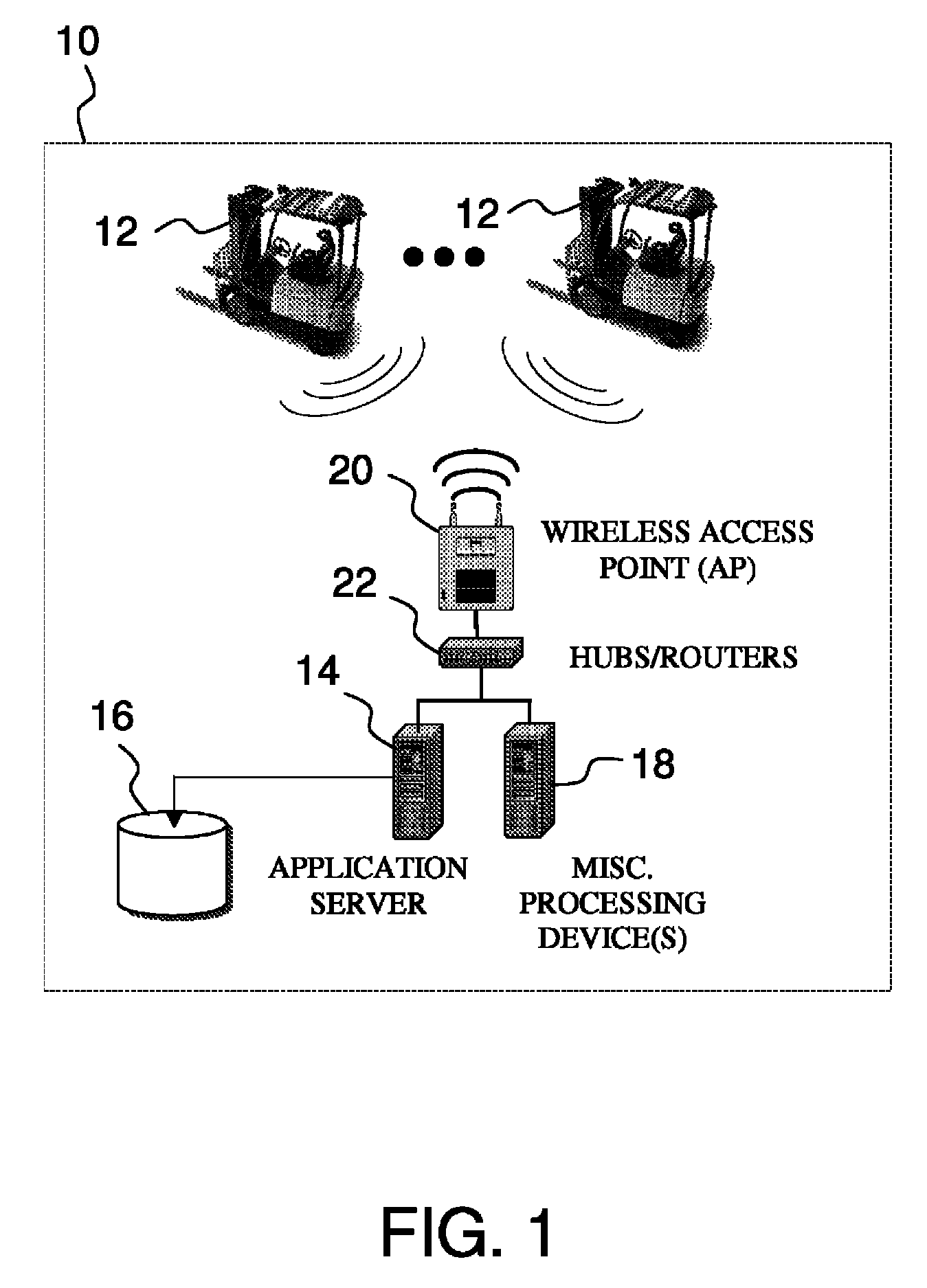
Fleet management system
ActiveUS20080154712A1Ticket-issuing apparatusRegistering/indicating working of vehiclesFleet managementSoftware system
Systems of hardware and software are provided for enabling mobile assets to communicate across a wireless network environment. Systems, computer-implemented methods and computer program products are also provided for leveraging wireless communication and / or processing capabilities of mobile assets against a robust software solution to implement enterprise wide asset management functions, to integrate mobile asset data into existing enterprise workflows and / or to enable trusted third party integration into the enterprise for enhanced asset and / or workflow management.
Owner:CROWN EQUIP CORP
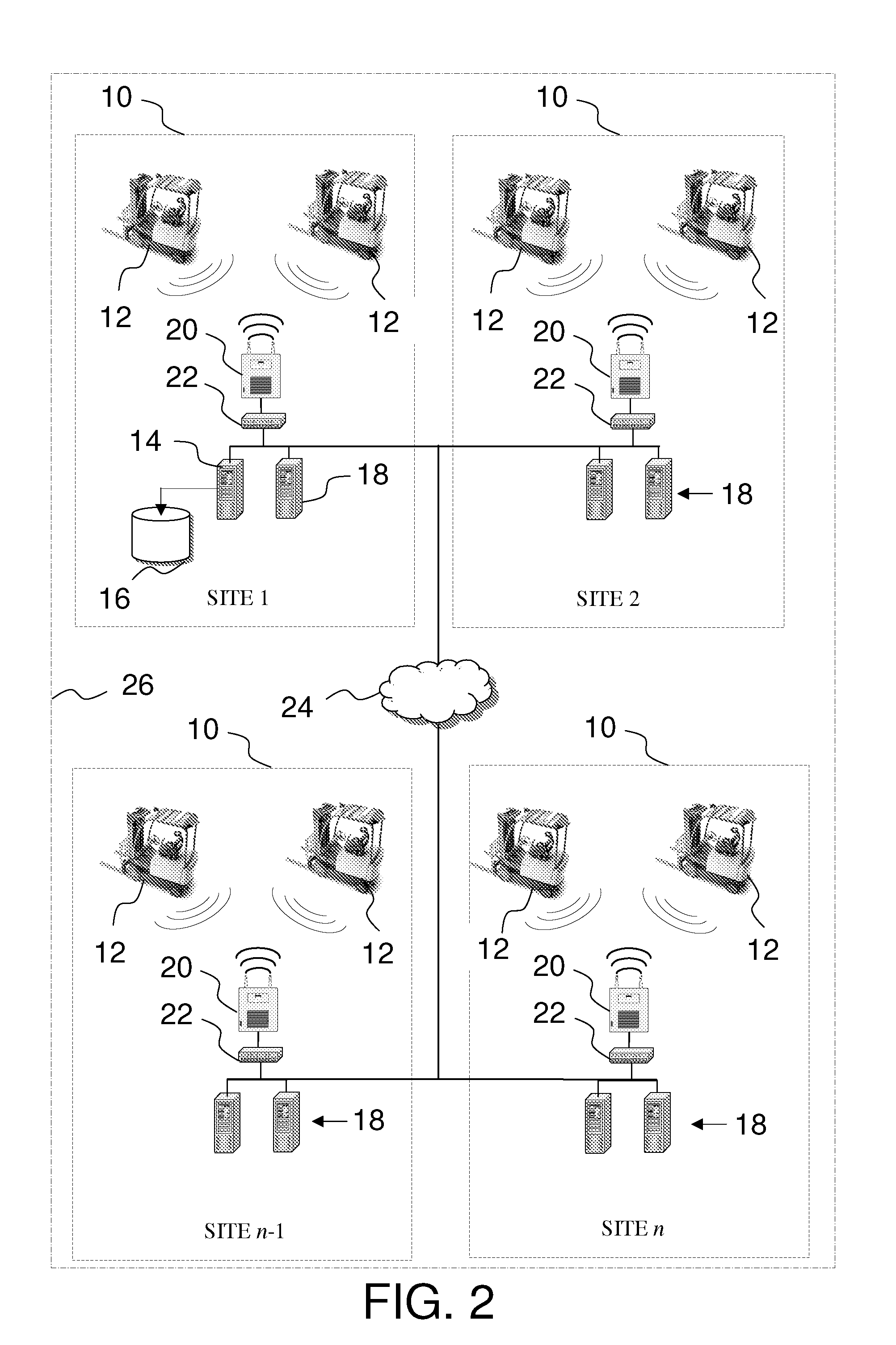
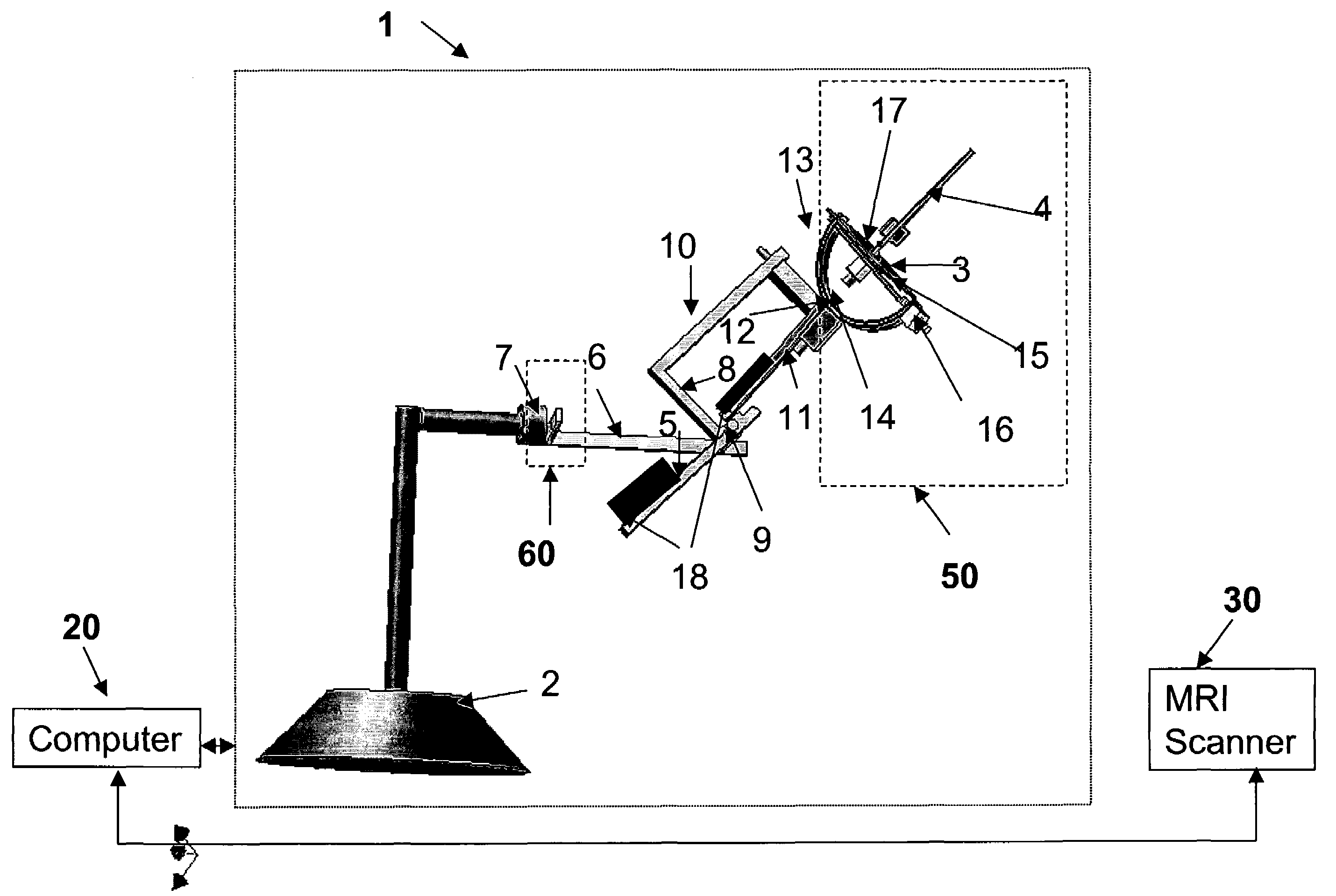
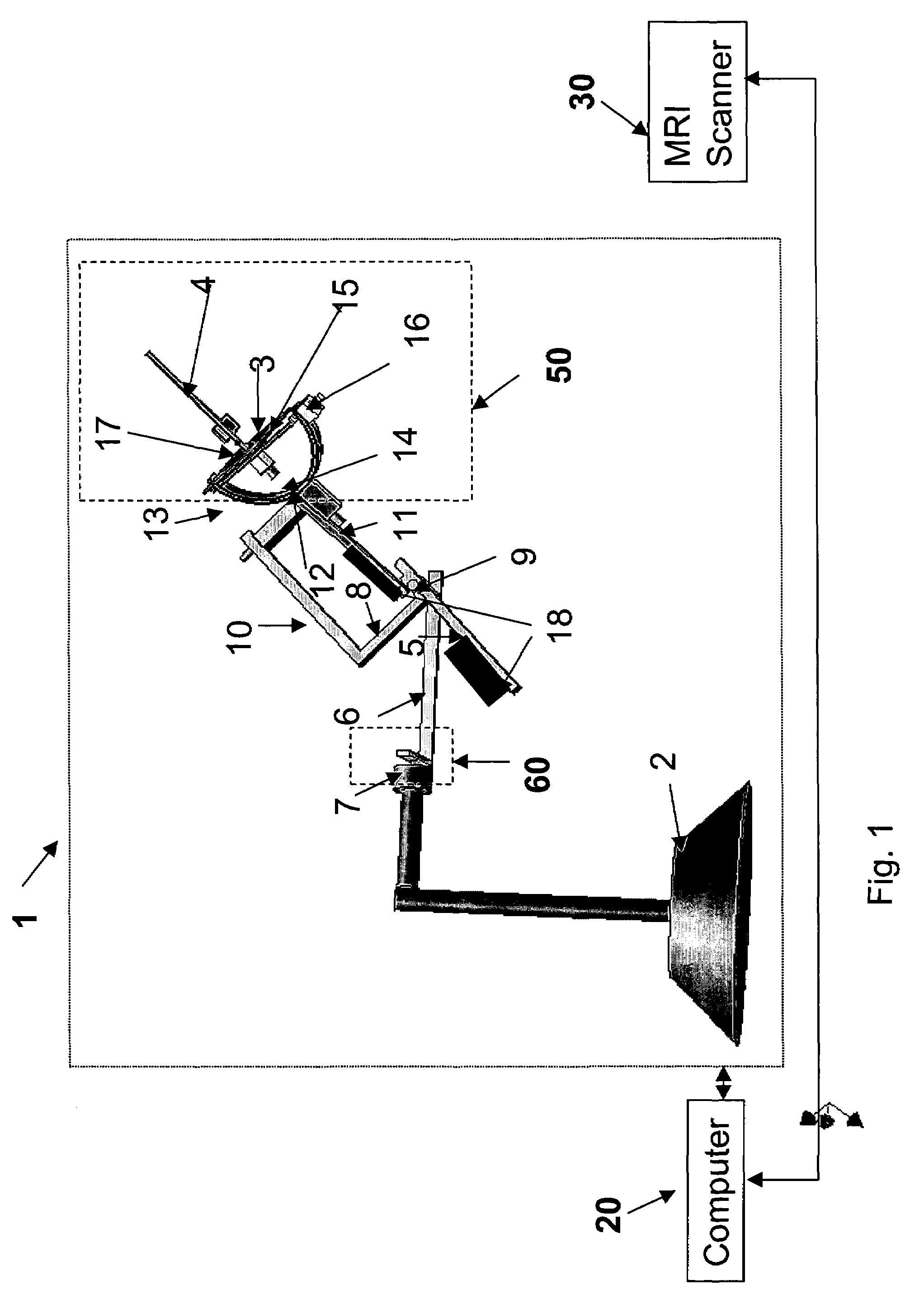
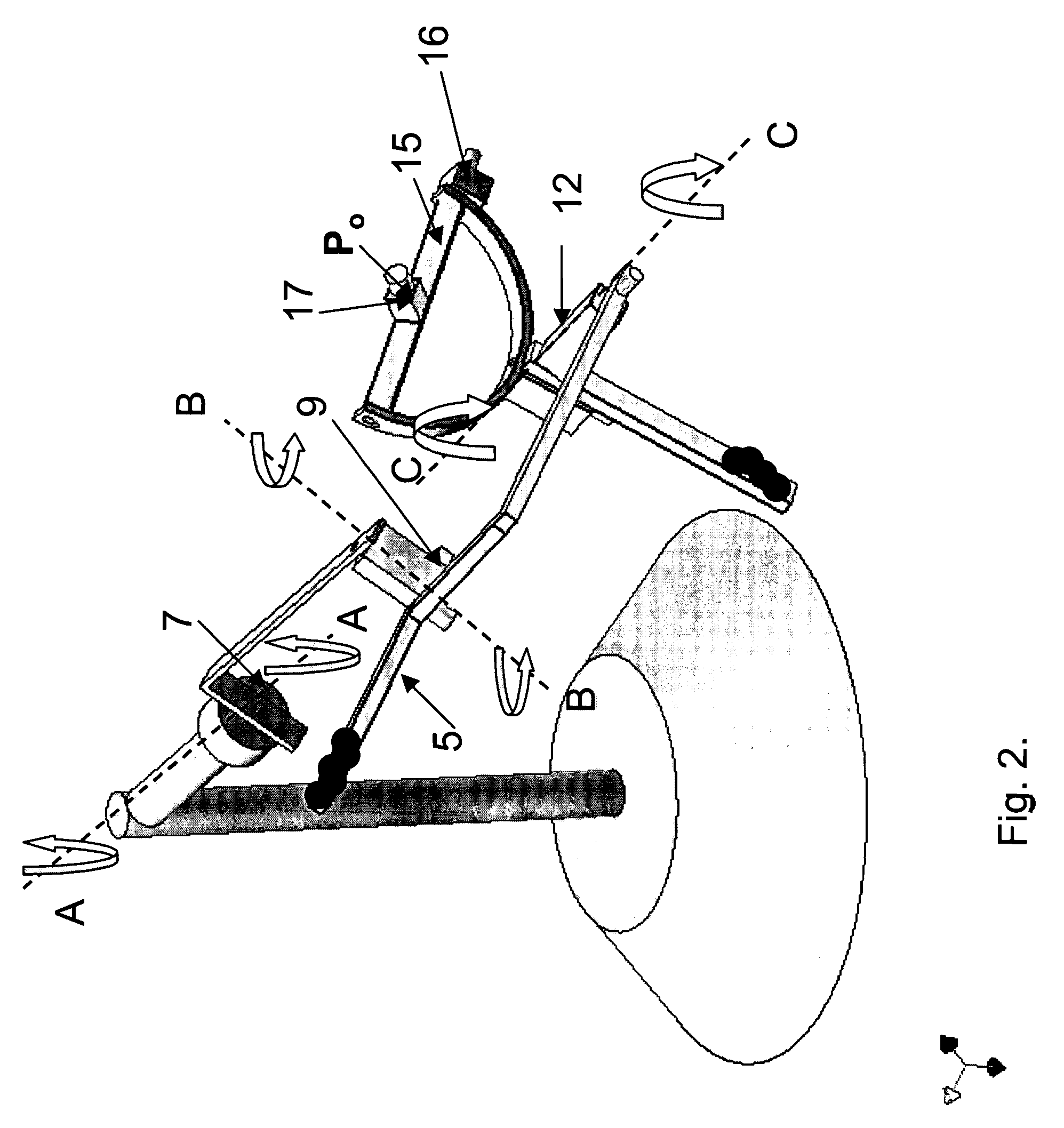
Device and process for manipulating real and virtual objects in three-dimensional space
InactiveUS7466303B2Rapid localizationAccurate detectionManual control with multiple controlled membersSurgeryRest positionThree-dimensional space
Owner:SUNNYBROOK HEALTH SCI CENT
Fleet management system
ActiveUS20080154691A1Registering/indicating working of vehiclesElectric testing/monitoringFleet managementSoftware system
Systems of hardware and software are provided for enabling mobile assets to communicate across a wireless network environment. Systems, computer-implemented methods and computer program products are also provided for leveraging wireless communication and / or processing capabilities of mobile assets against a robust software solution to implement enterprise wide asset management functions, to integrate mobile asset data into existing enterprise workflows and / or to enable trusted third party integration into the enterprise for enhanced asset and / or workflow management.
Owner:CROWN EQUIP CORP
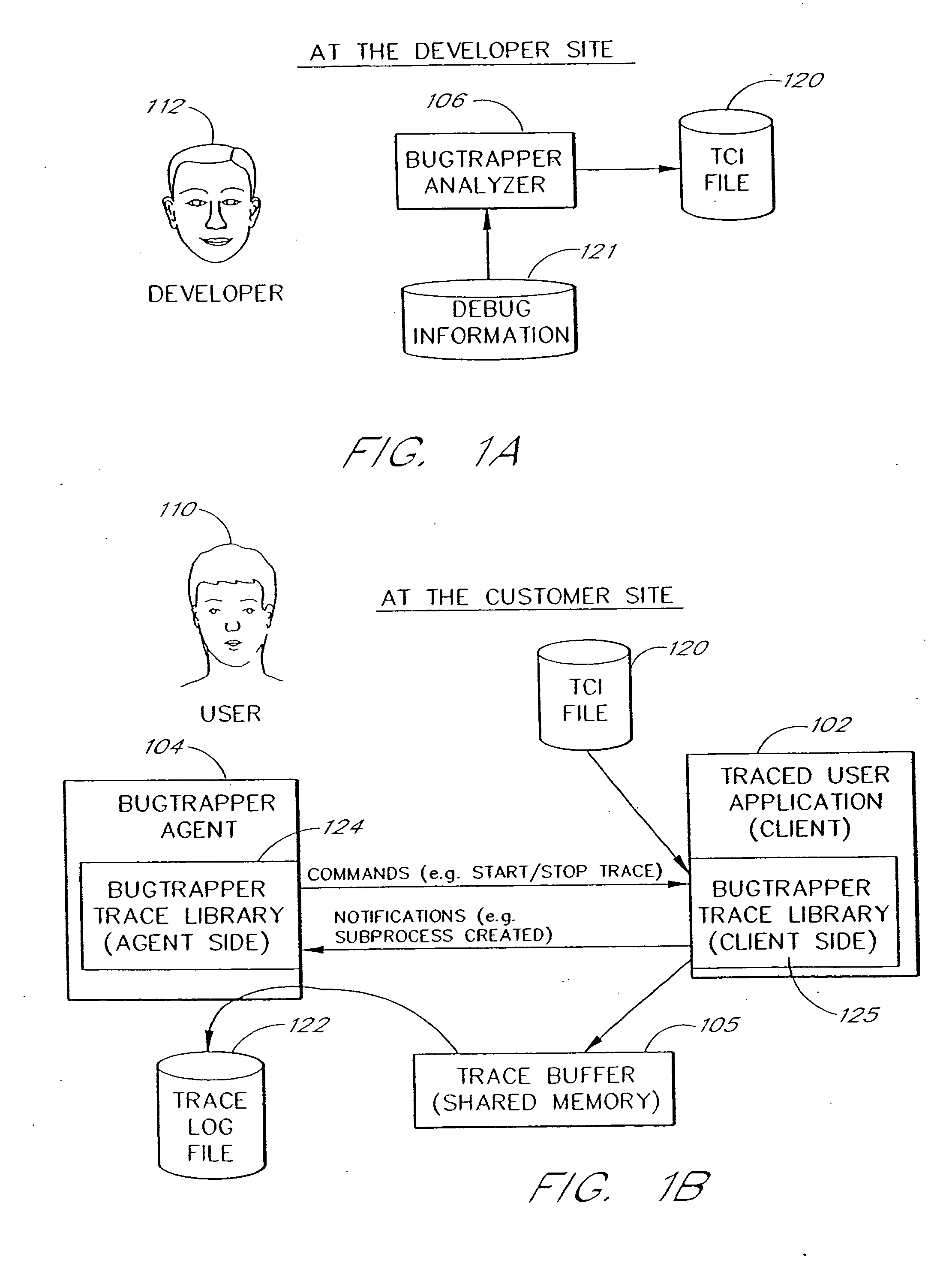
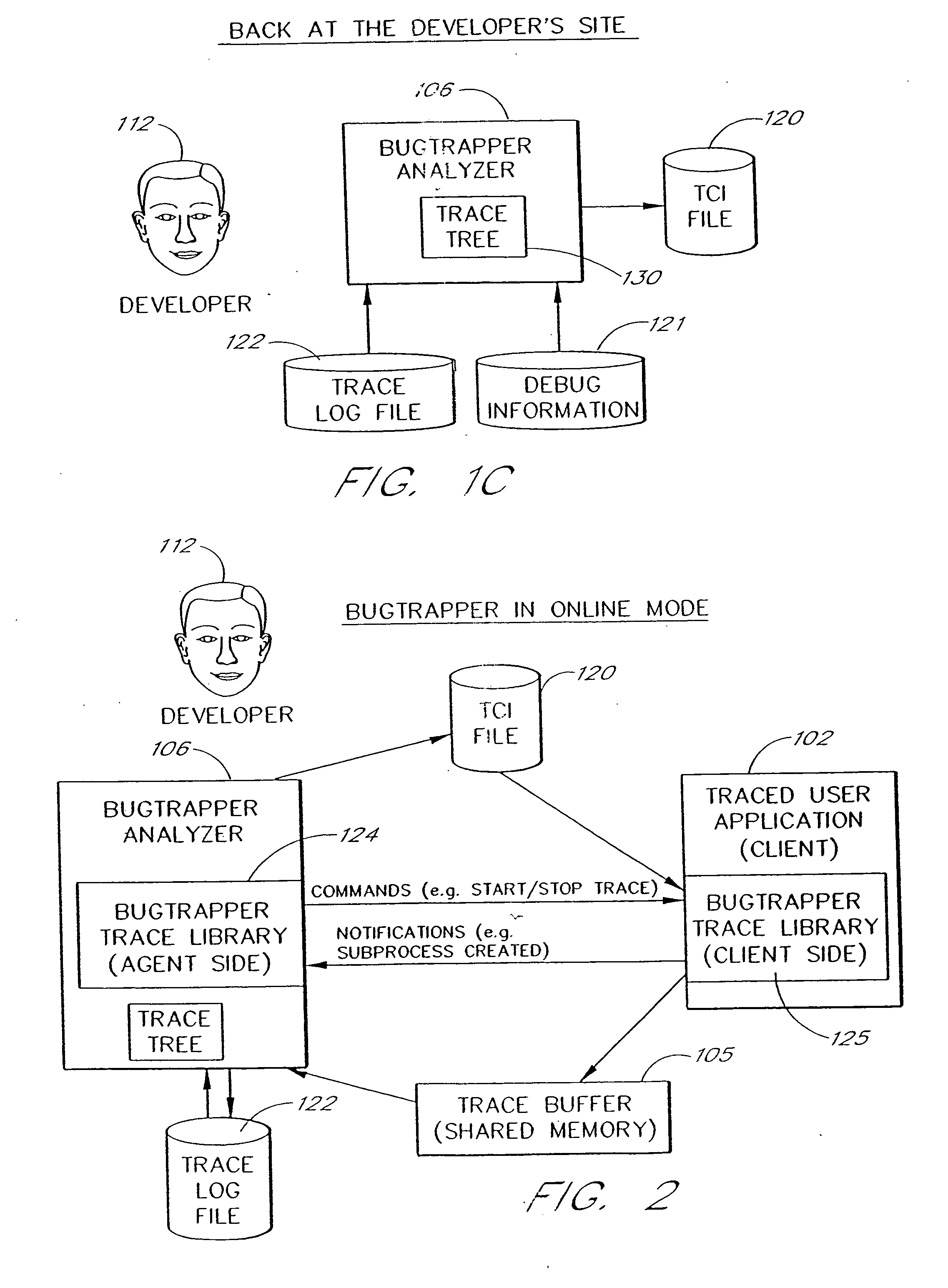
System and method for conditional tracing of computer programs
ActiveUS20060242627A1Small sizeRaise the possibilityError detection/correctionSpecific program execution arrangementsSource code fileTrace file
A software system is disclosed which facilitates the process of tracing the execution paths of a program, called the client. The tracing is performed without requiring modifications to the executable or source code files of the client. Trace data collected during the tracing operation is collected according to instructions in a trace options file. At run time, the tracing library attaches to the memory image of the client. The tracing library is configured to monitor execution of the client and to collect trace data, based on selections in the trace options file. Conditional tracing, through the use of triggers and actions taken in response to the triggers, allows the developer to control the tracing operation. The triggers can be conditional triggers in which the corresponding action is taken only if a conditional expression is satisfied. The system can trace multiple threads and multiple processes. The tracing system provides a remote mode and an online mode. In remote mode, the developer sends the trace control information (which can include triggers and corresponding actions) to a remote user site together with a small executable image called the agent that enables a remote customer, to generate a trace file that represents execution of the client application at the remote site. In online mode, the developer can generate trace options (including triggers and corresponding actions), run and trace the client, and display the trace results in near real-time on the display screen during execution of the client program.
Owner:BMC SOFTWARE ISRAEL LTD
Software system and methods for testing the functionality of a transactional server
A testing tool automatically records a series of user steps taken during a user session with a transactional server and generates a test for testing the functionality of server. Through a user interface of the testing tool, the user can define verification steps to automatically test for expected server responses during test execution. The testing tool displays the test to the user as a tree having nodes (displayed as icons) which represent steps of the test. Via the user interface, the user can modify node properties and perform other types of tree edit operations to edit the test, without the need to know a scripting or other programming language. When the user selects a node that corresponds to a particular field or other object of the server screen, the testing tool automatically displays the screen with the object highlighted. The testing tool also allows the test author to use a spreadsheet to conveniently specify data sets for running multiple iterations of a test; thus, the user can record a single transaction and then automatically test the transaction with other data sets.
Owner:AMAZON COM +1
Secure magnetic stripe reader for handheld computing and method of using same
ActiveUS7309012B2Limited useful battery lifeLow costAcutation objectsFinanceInformation processingSoftware system
A secure magnetic stripe card stripe reader (MSR) module and software system capable of encrypting the magnetic stripe data to CISP standards for use in point of sale (POS) and other applications requiring data security using non secure networks and computing devices. Additionally, when incorporated within an attachment for conventional personal digital assistant (PDA) or cell phone or stationary terminal, provides encrypted data from the magnetic head assembly providing compliance with Federal Information Processing Standards Publication Series FIPS 140 covering security and tampering standards. Moreover, this module and software system includes the capability of providing secure POS transactions to legacy transaction processing systems transparently to the existing infrastructure. Furthermore, this module and software system includes the capability of transparently providing detection of fraudulently copied magnetic stripe cards.
Owner:VERIFONE INC
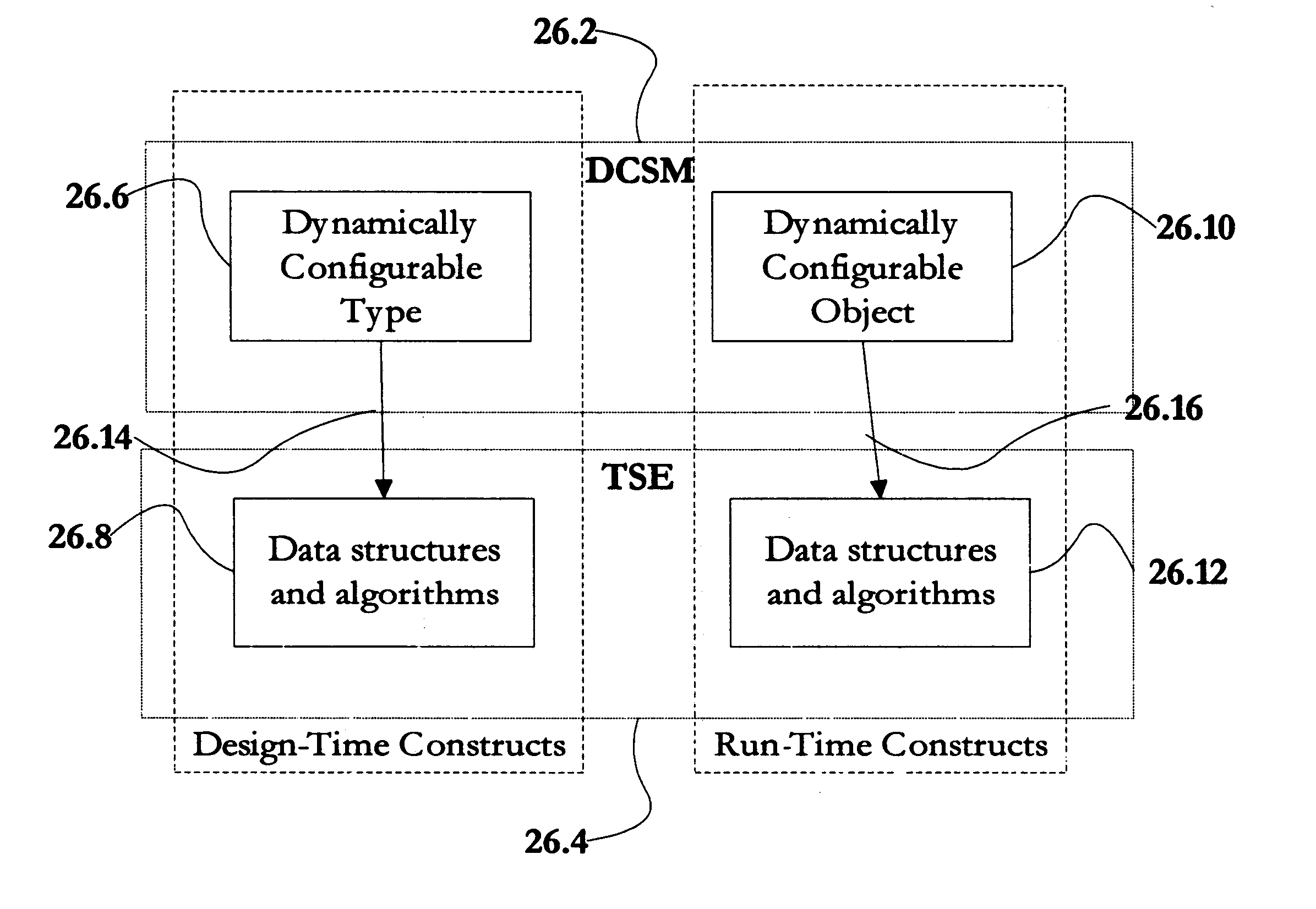
Method and apparatus for the development of dynamically configurable software systems
InactiveUS6269473B1Dynamic configurabilityImprove abilitiesData processing applicationsSoftware designSoftware systemSemantics
A software modeling environment is presented that supports the development and execution of software that can be dynamically configured. This is achieved by introducing a design-time object modeling construct called a dynamically configurable type (DCT) that supports the subdivision of an object into a plurality of subsets of semantics and allows dynamic merging of these semantic subsets together in different combinations in order to allow the resultant object to exhibit different semantics over time to serve different purposes. Specific process modeling constructs are included which take advantage of this semantic merging capability. Also included are other supporting design-time and run-time constructs and services. One embodiment of the present invention allows this software modeling environment to be integrated into a standard software development environment, enhancing the modeling capabilities already present.
Owner:EVOLVE SOFTWARE
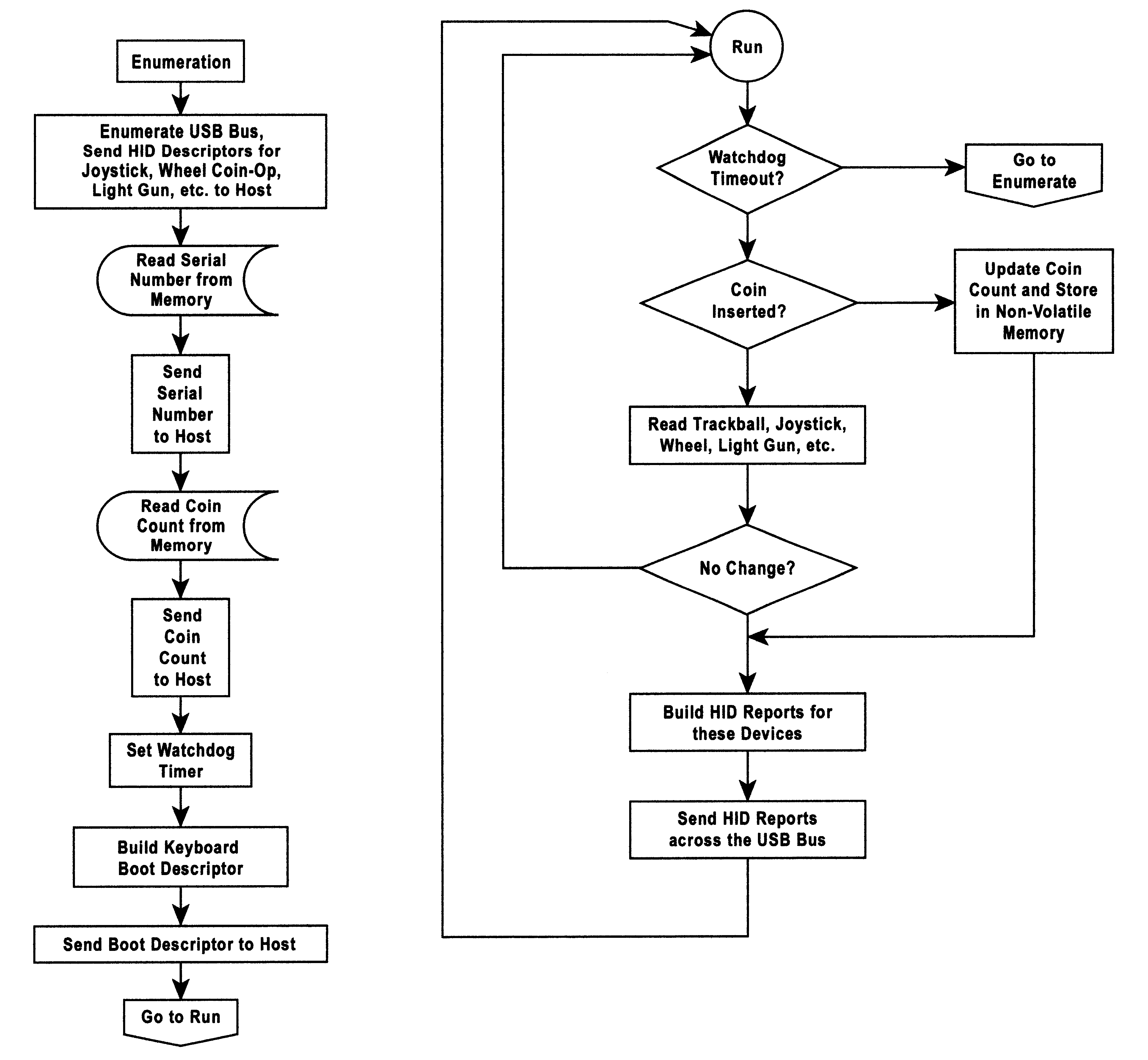
Method and apparatus for interfacing multiple peripheral devices to a host computer
InactiveUS6263392B1Discourage and prevent useUnauthorized useProgram loading/initiatingVideo gamesCredit cardJoystick
A method and an apparatus to interface multiple peripheral devices to a host computer is provided. An interface control module located in a multi-user computer game arcade system interfaces a host computer via a Universal Serial Bus (USB) to one or more joysticks, steering wheels, trackballs, coin op / bill counters, credit card readers and / or optical guns. A set of connectors allows the game builder or player to interface a variety of input peripherals to the interface control module. The interface control module recognizes the HID type of the input peripheral by the type of the selected connector, and then provides HD reports that describe each input device to the HID compliant software system of the host computer. The interface control module may support 127 HID peripherals. A watchdog function of the interface control module detects host computer malfunctions and crashes, and boots the host computer while retaining coin credit input data received proximate to and during the malfunction and recovery.
Owner:ACTIVISION PUBLISHING
Fleet management system
ActiveUS8060400B2Ticket-issuing apparatusRegistering/indicating working of vehiclesFleet managementSoftware system
Owner:CROWN EQUIP CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com