Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
604 results about "Program analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, program analysis is the process of automatically analyzing the behavior of computer programs regarding a property such as correctness, robustness, safety and liveness. Program analysis focuses on two major areas: program optimization and program correctness. The first focuses on improving the program’s performance while reducing the resource usage while the latter focuses on ensuring that the program does what it is supposed to do.
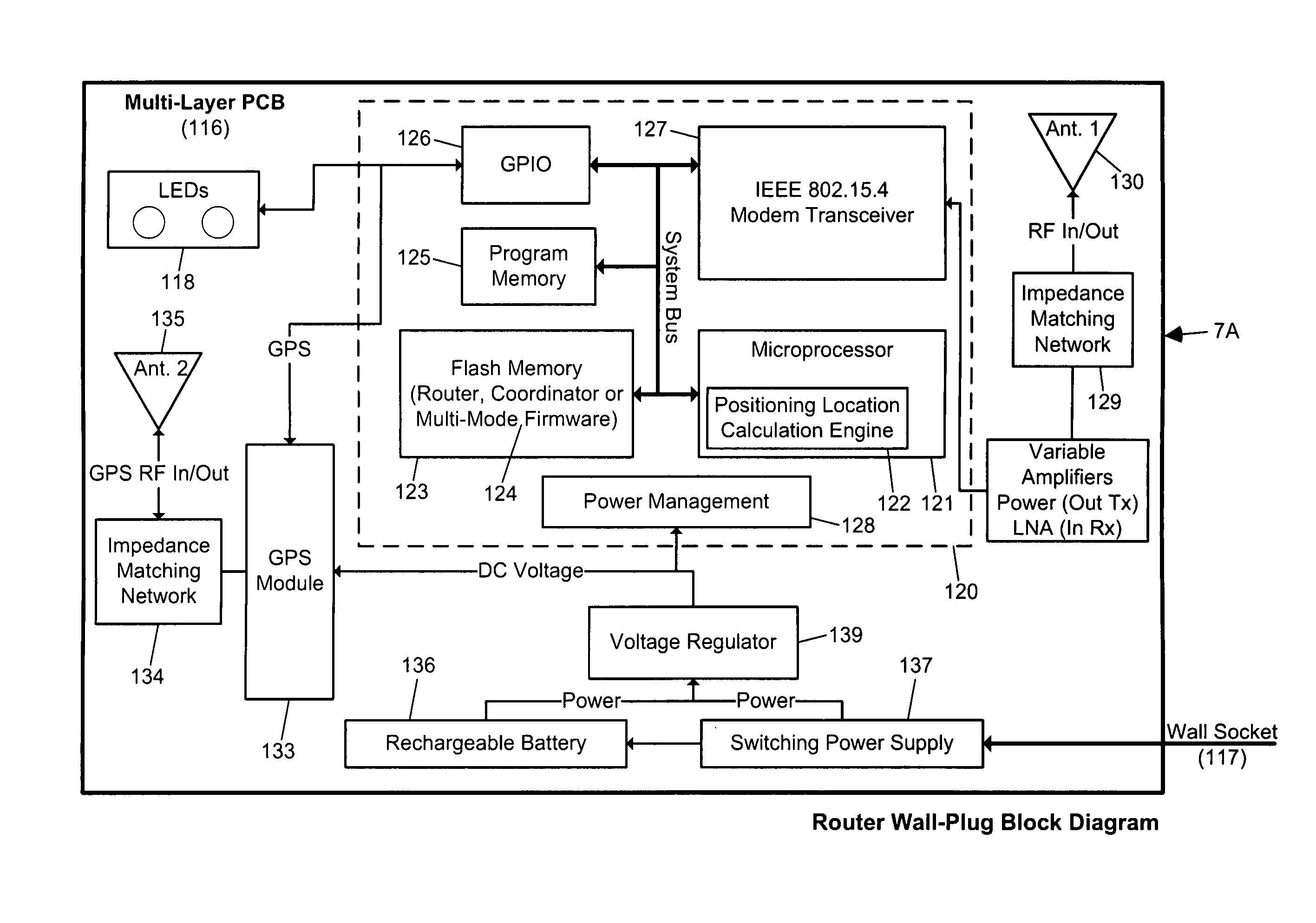
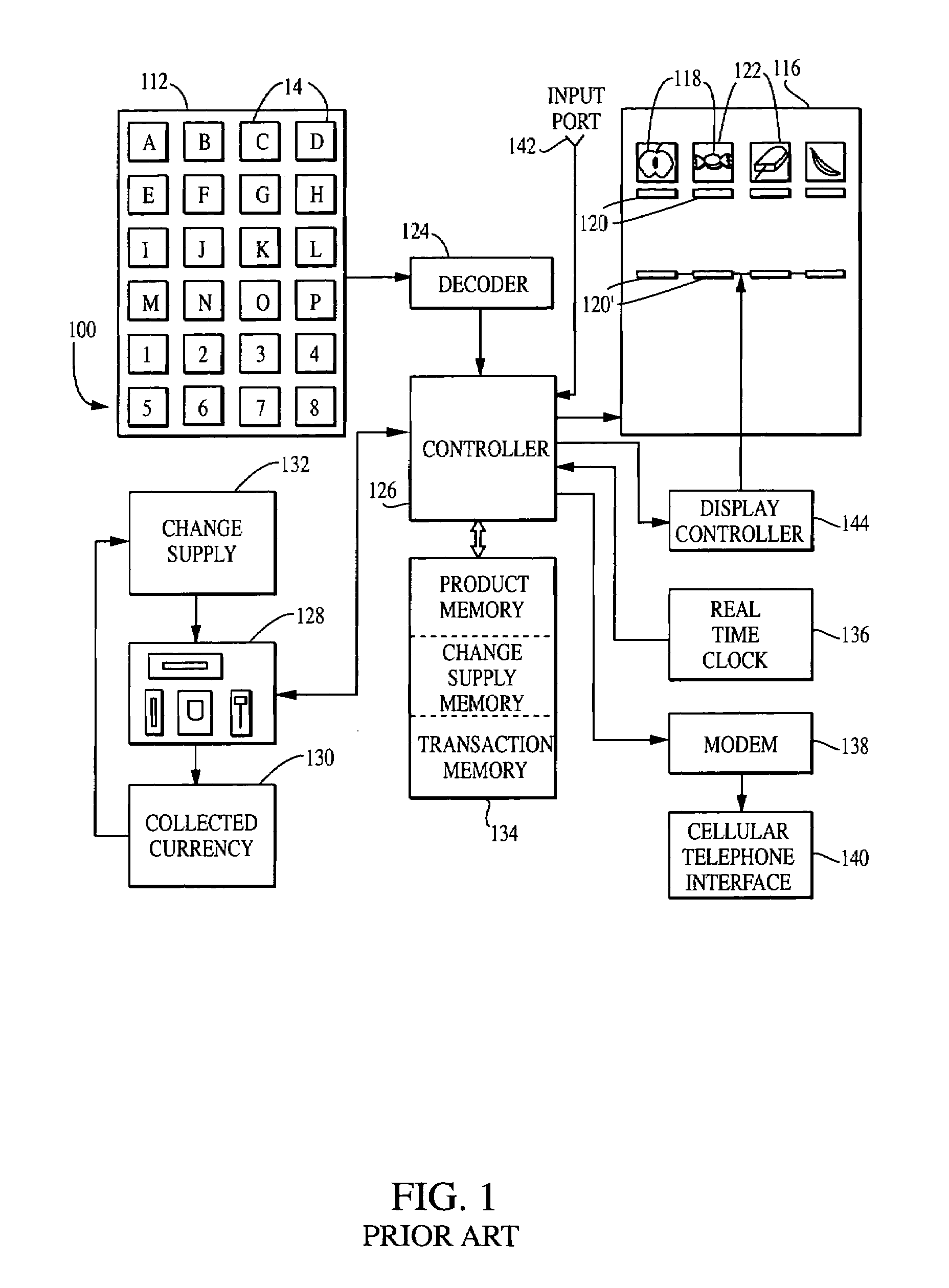
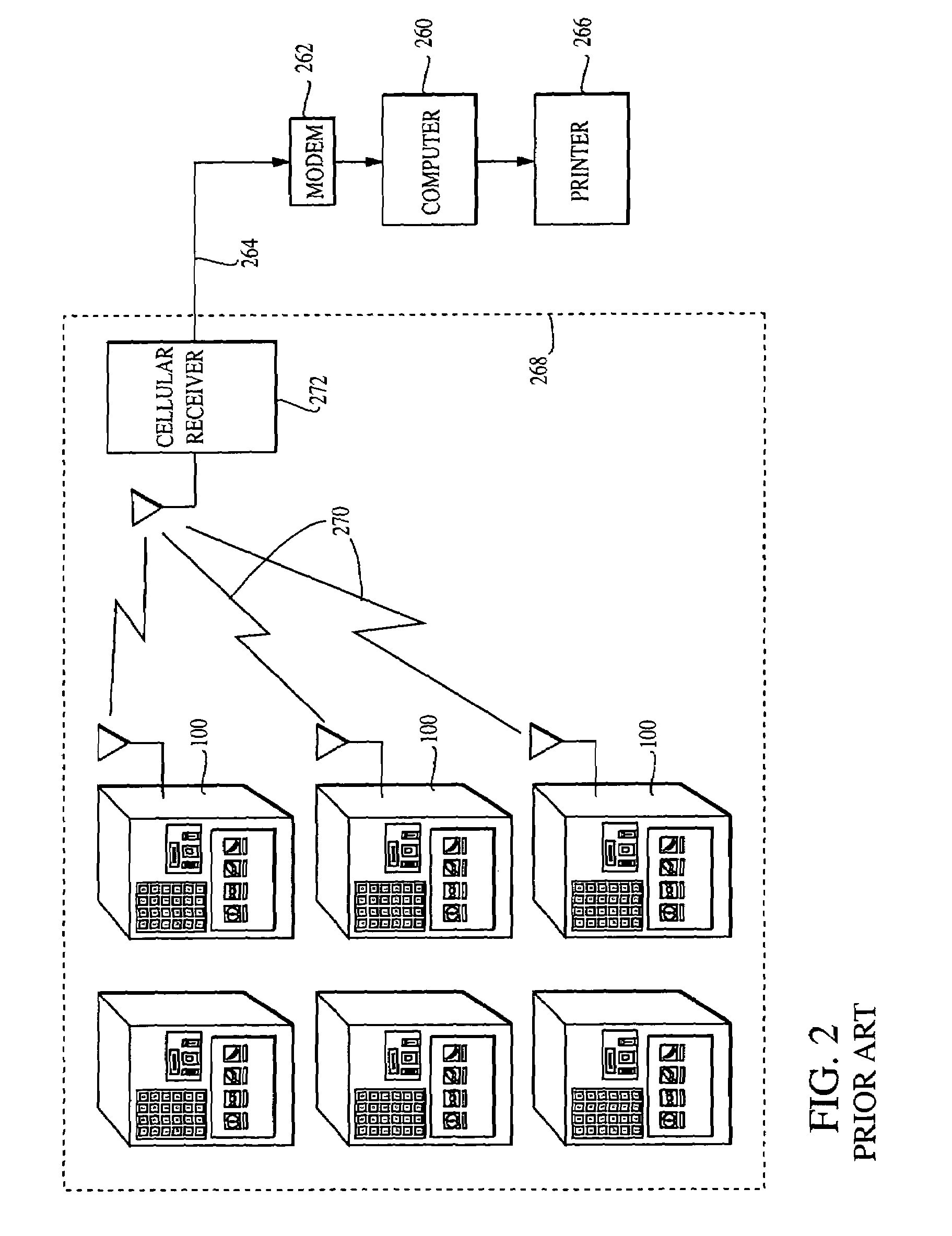
Edge-lit electronic-ink display device for use in indoor and outdoor environments
InactiveUS20100177076A1Easily identifiableCathode-ray tube indicatorsInput/output processes for data processingAmbient lightingControl signal
A wireless electronic-ink based display device for use in indoor and outdoor environments characterized by low and / or dynamic ambient lighting conditions. The wireless electronic-ink based display device has an ambient light level sensor for sensing ambient lighting conditions about the wireless electronic-ink based display device, and generating a drive control signal in response to sensed ambient lighting conditions. The wireless electronic-ink based display device also has an edge-lit LED-based illumination module, responsive to the drive control signal generated by the ambient light level sensor, for illuminating the display surface of its addressable electronic-ink display module during low-illumination ambient lighting conditions detected by the ambient light level sensor, under the control of a processor. In the illustrative embodiment, the processor runs a firmware routine which analyzes detected ambient light conditions made by the ambient light level sensor, and automatically generates the drive control signal provided to the edge-lit LED illumination module.
Owner:METROLOGIC INSTR
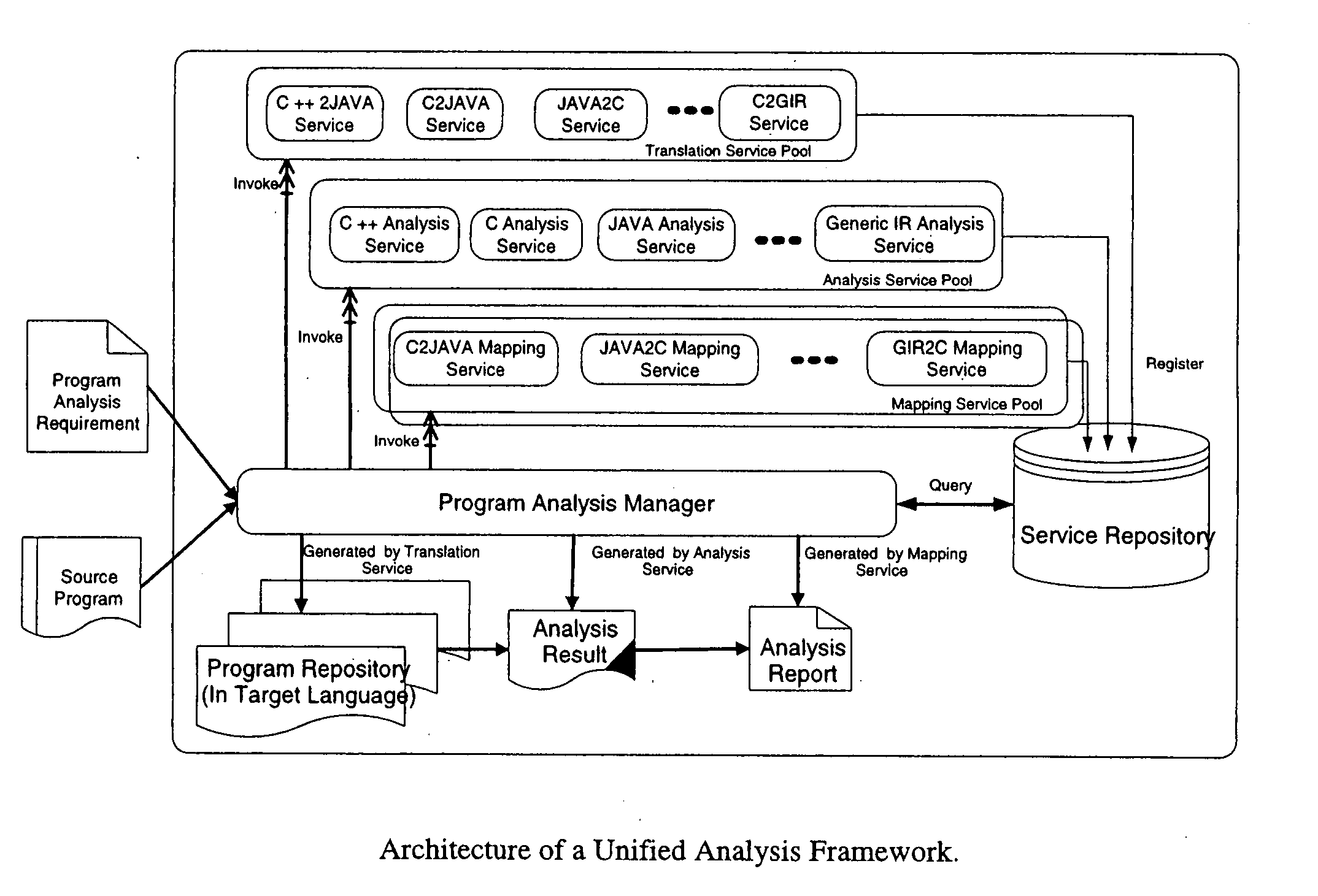
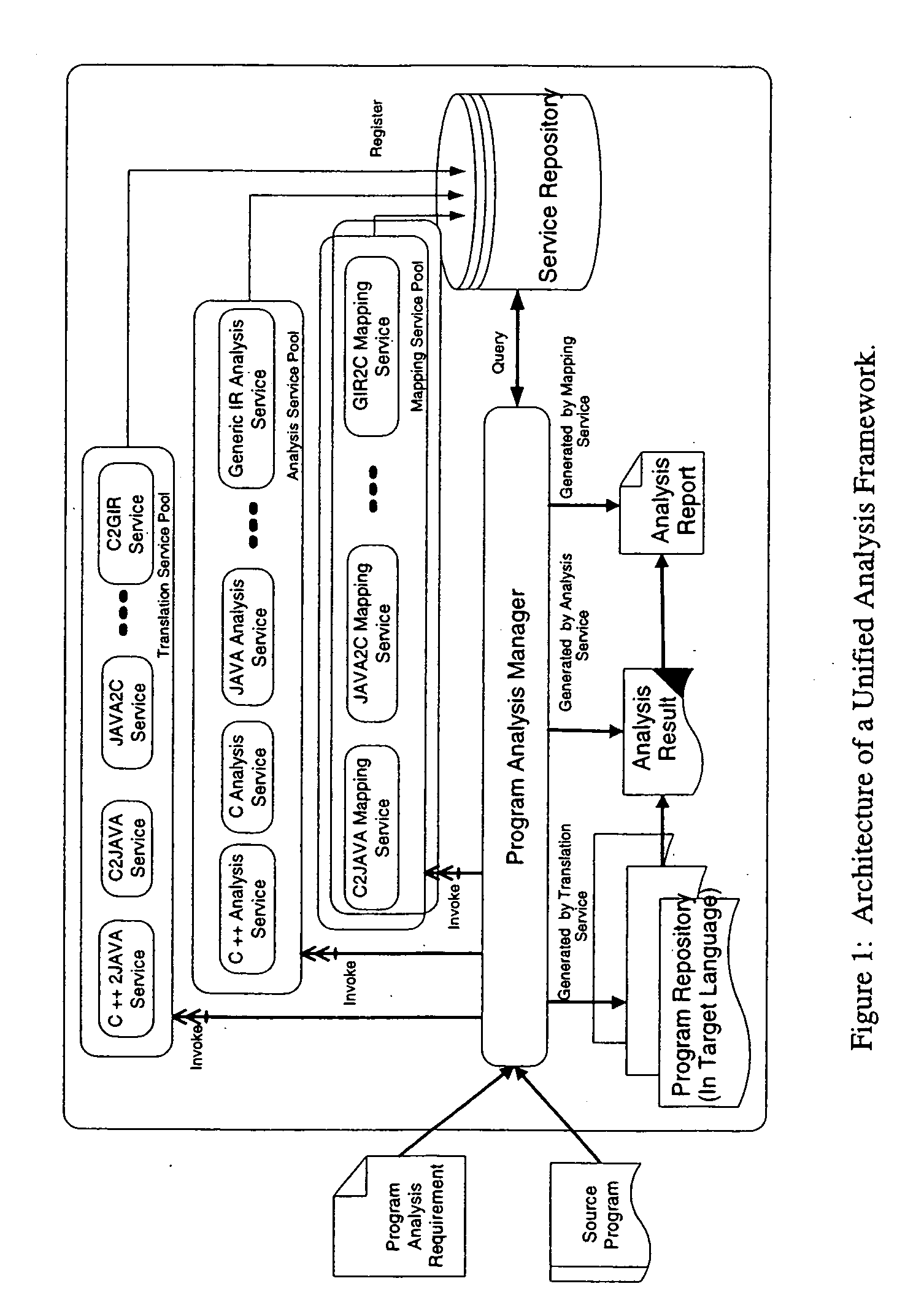
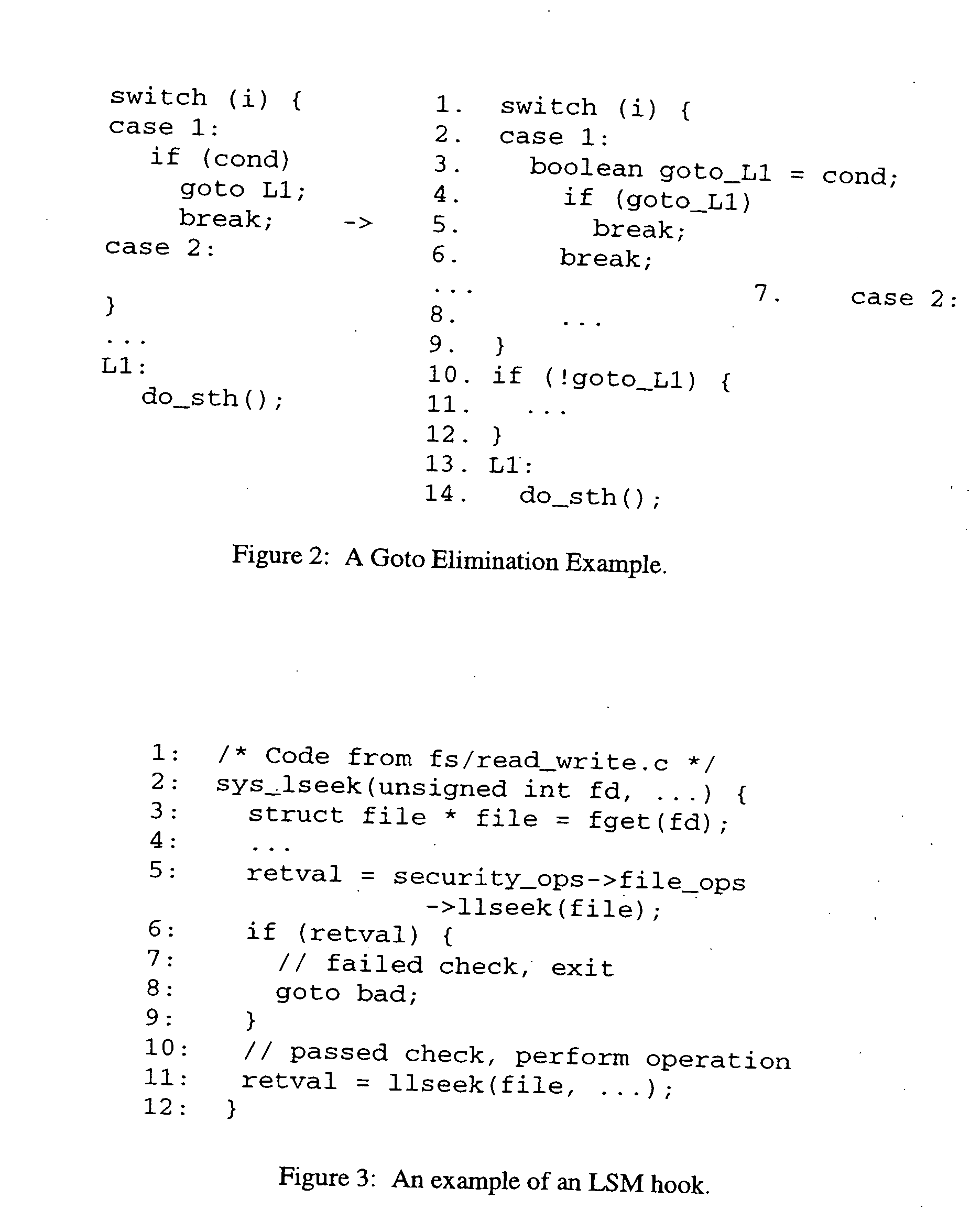
Methods and arrangements for unified program analysis
InactiveUS20060248519A1Low costMaximize returnError detection/correctionSpecific program execution arrangementsMulti languageSoftware system
A unified program analysis framework that facilitates the analysis of complex multi-language software systems, analysis reuse, and analysis comparison, by employing techniques such as program translation and automatic results mapping, is presented. The feasibility and effectiveness of such a framework are demonstrated using a sample application of the framework. The comparison yields new insights into the effectiveness of the techniques employed in both analysis tools. These encouraging results yield the observation that such a unified program analysis framework will prove to be valuable both as a testbed for examining different language analysis techniques, and as a unified toolset for broad program analysis.
Owner:IBM CORP
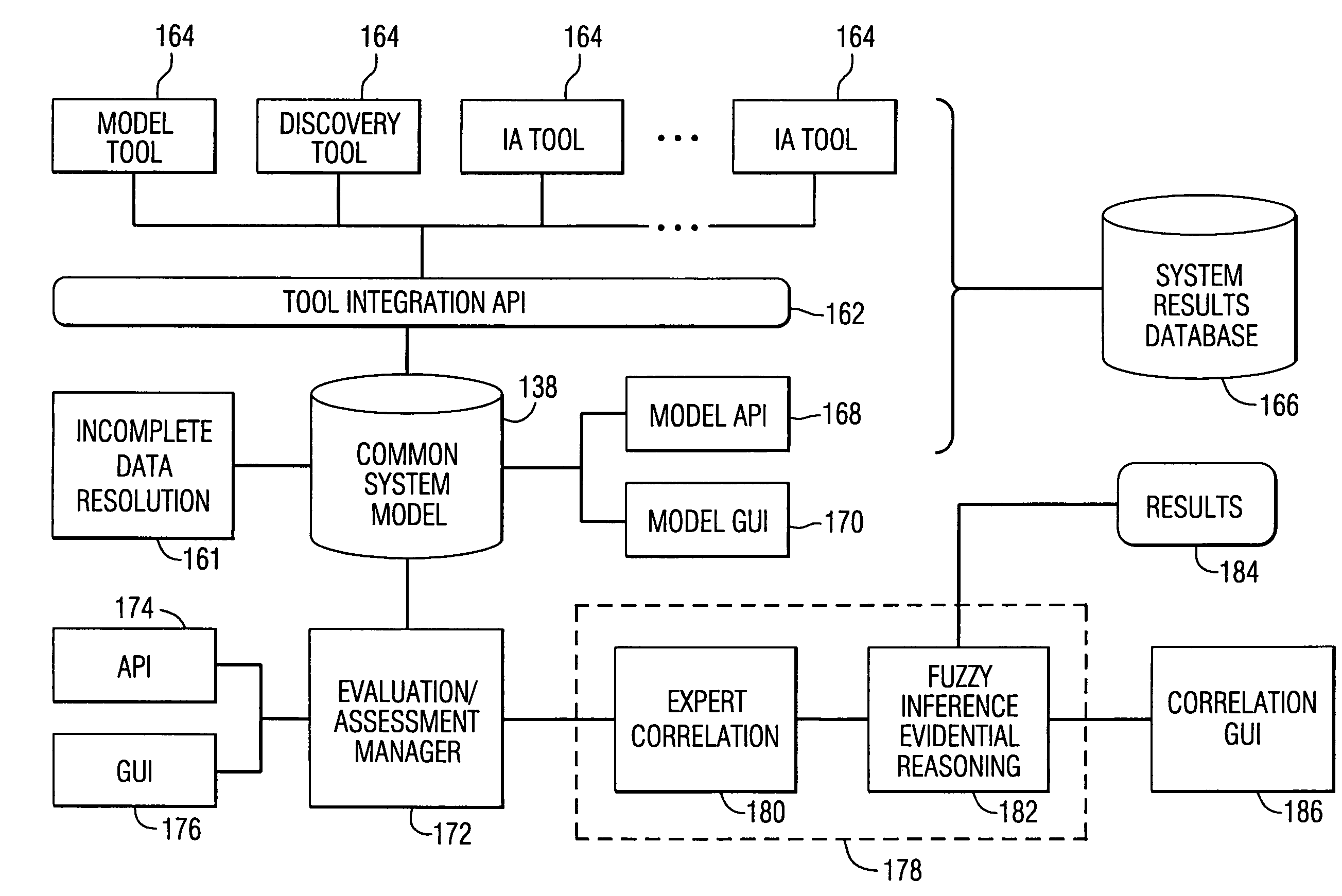
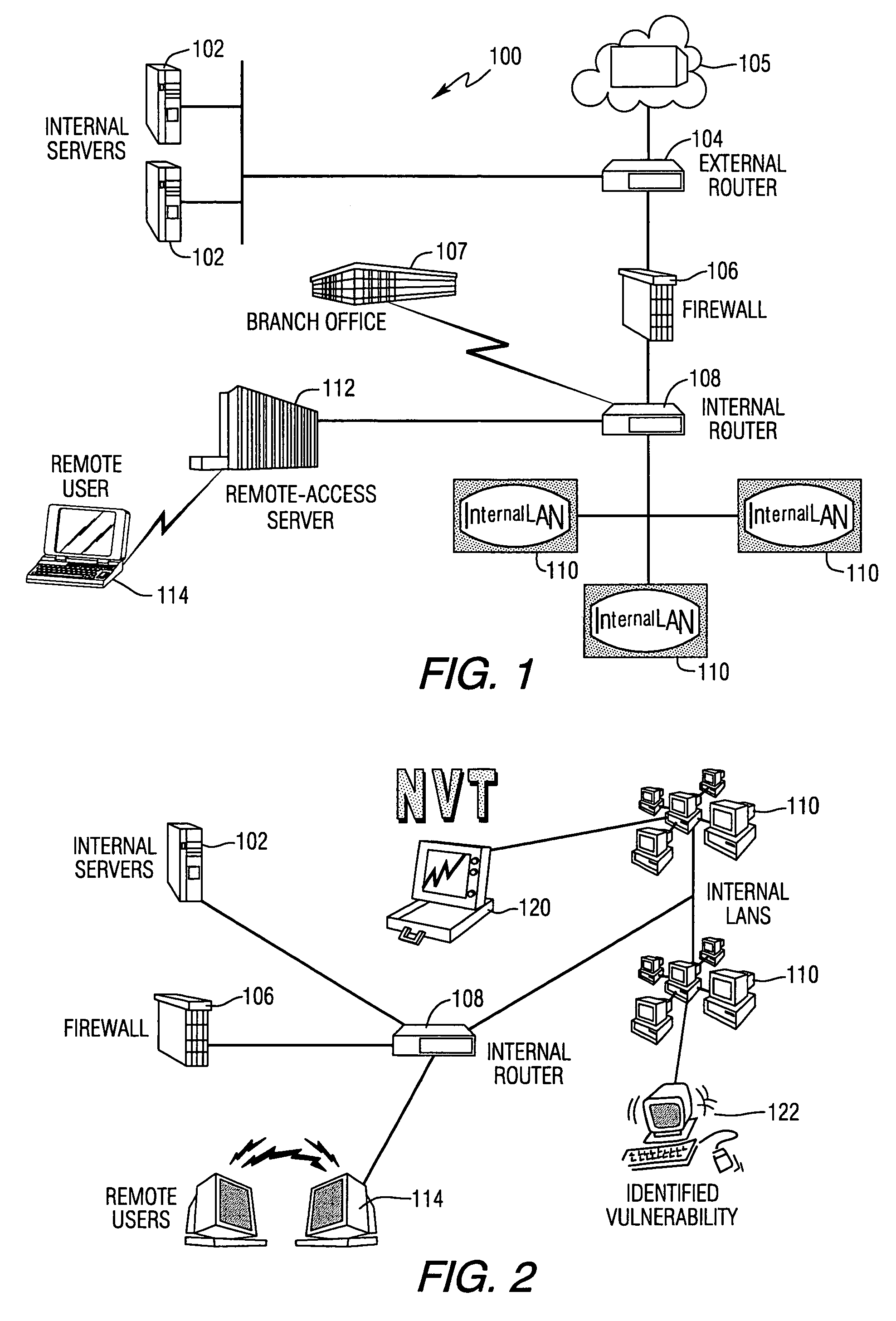
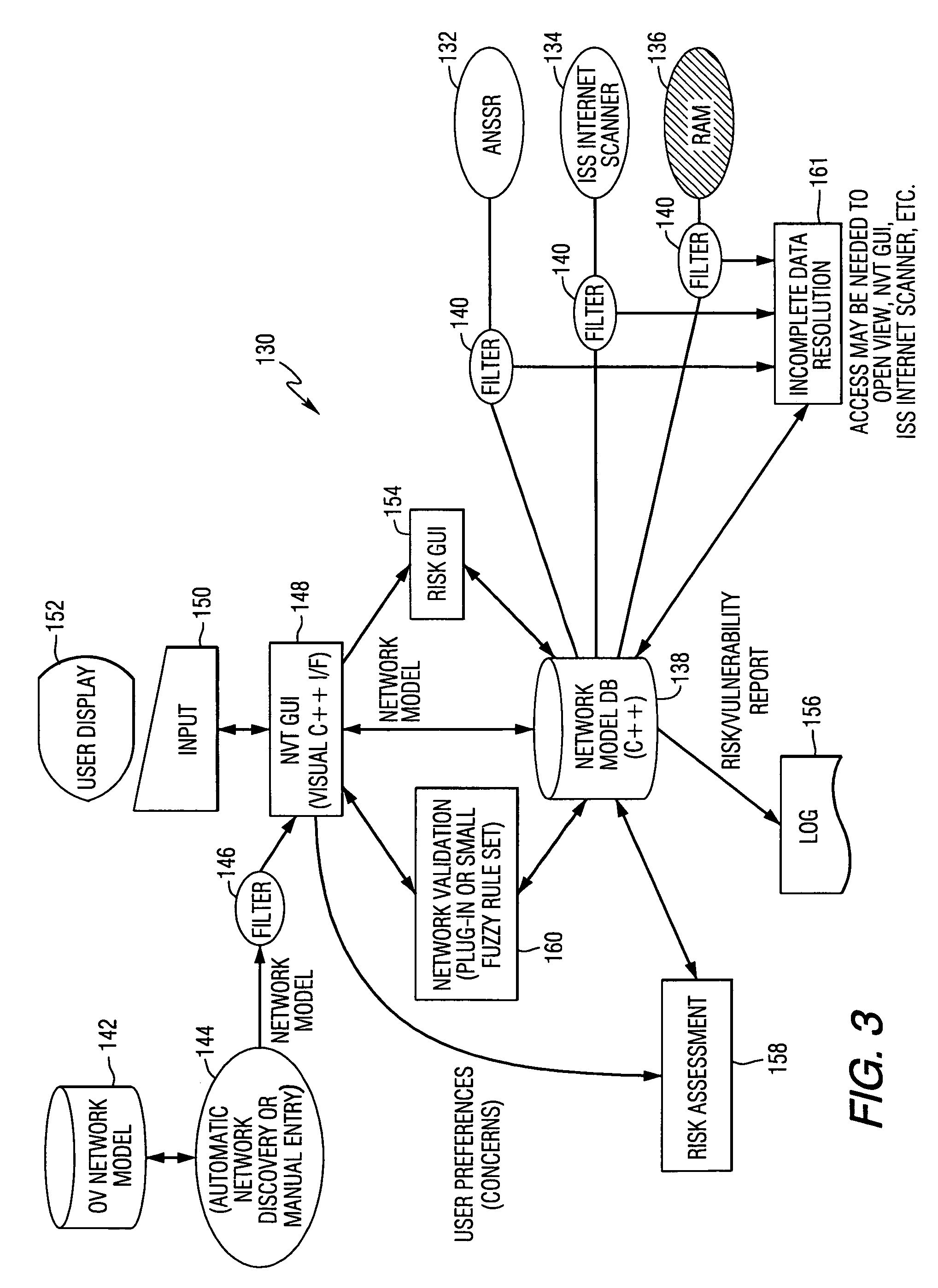
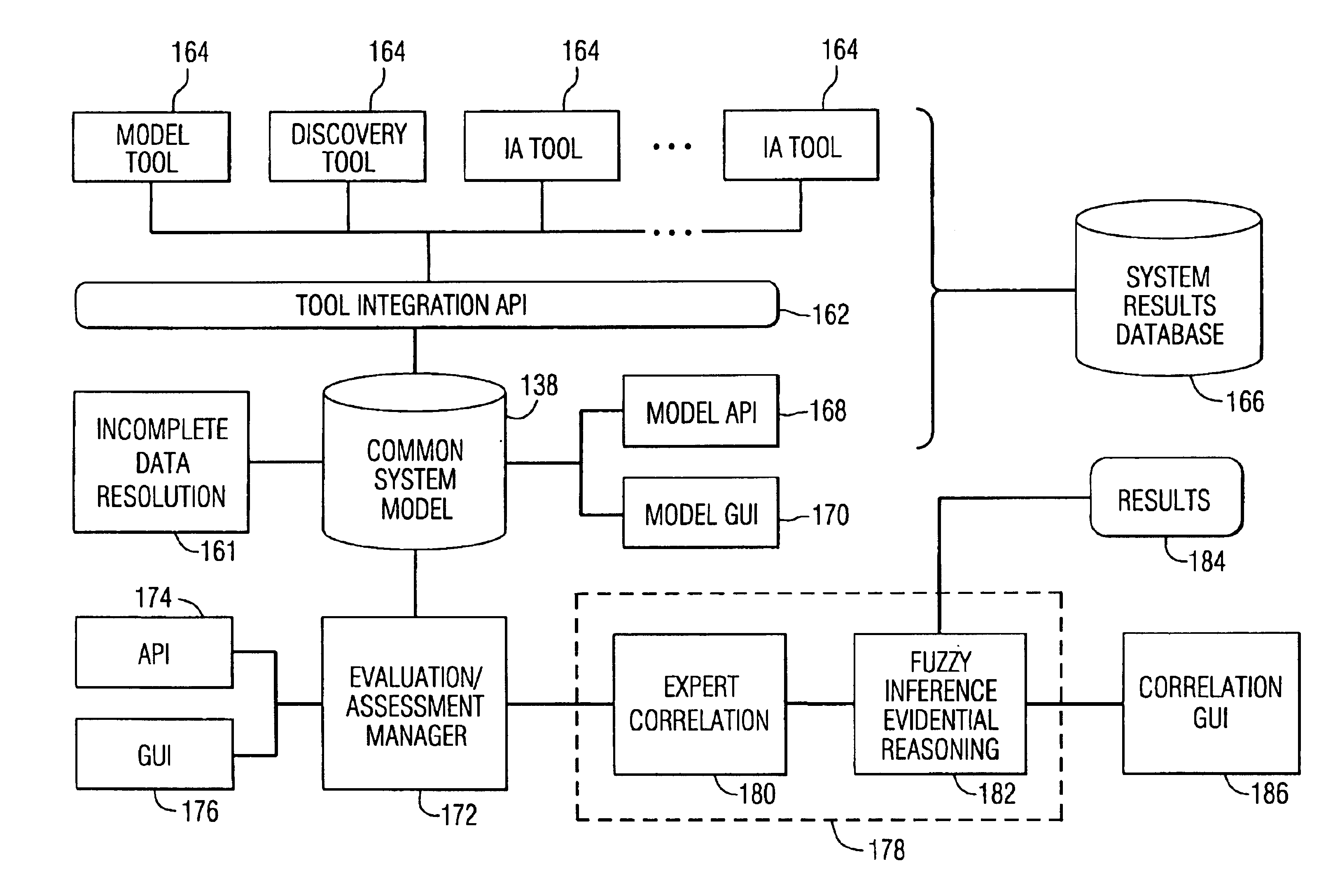
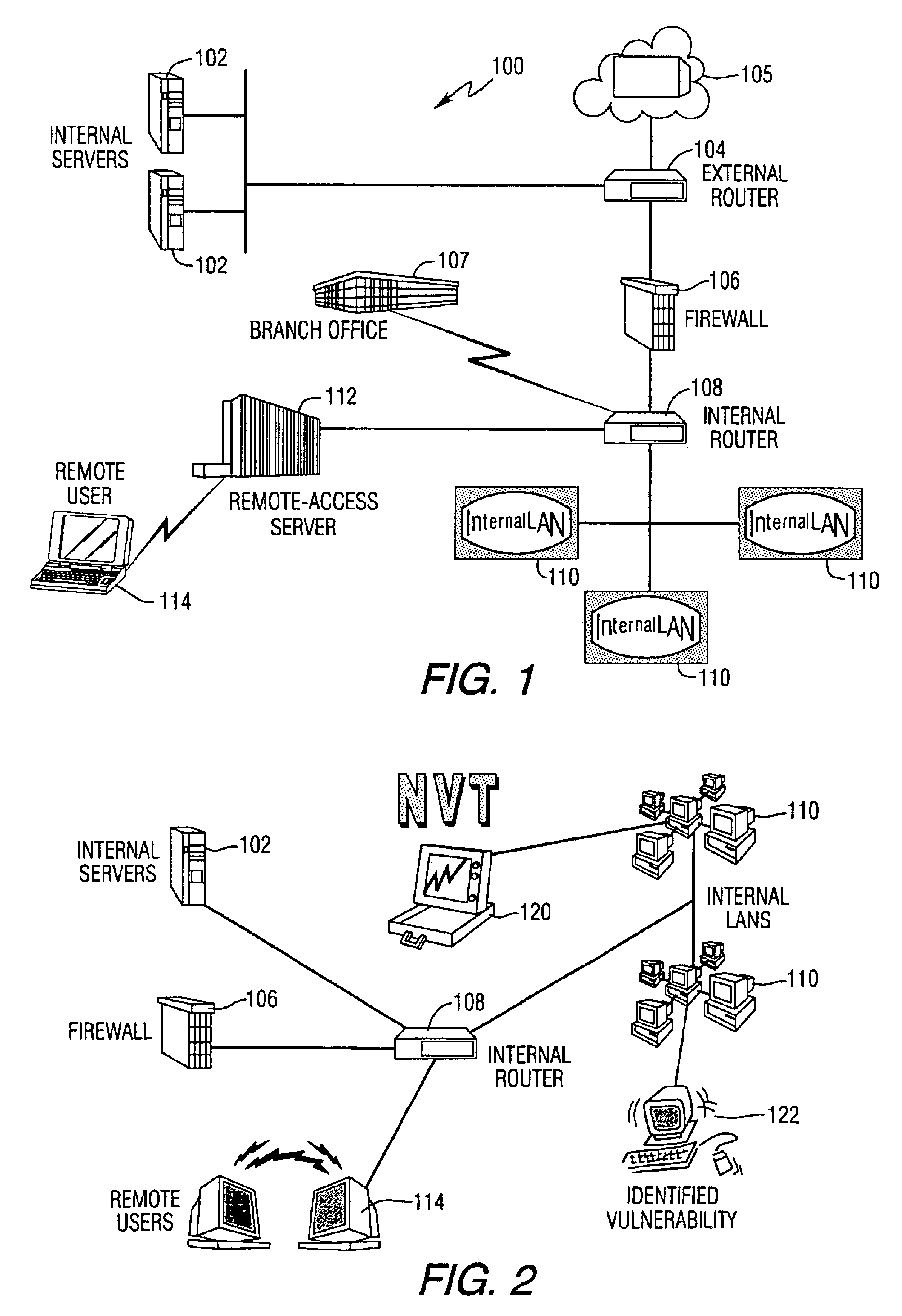
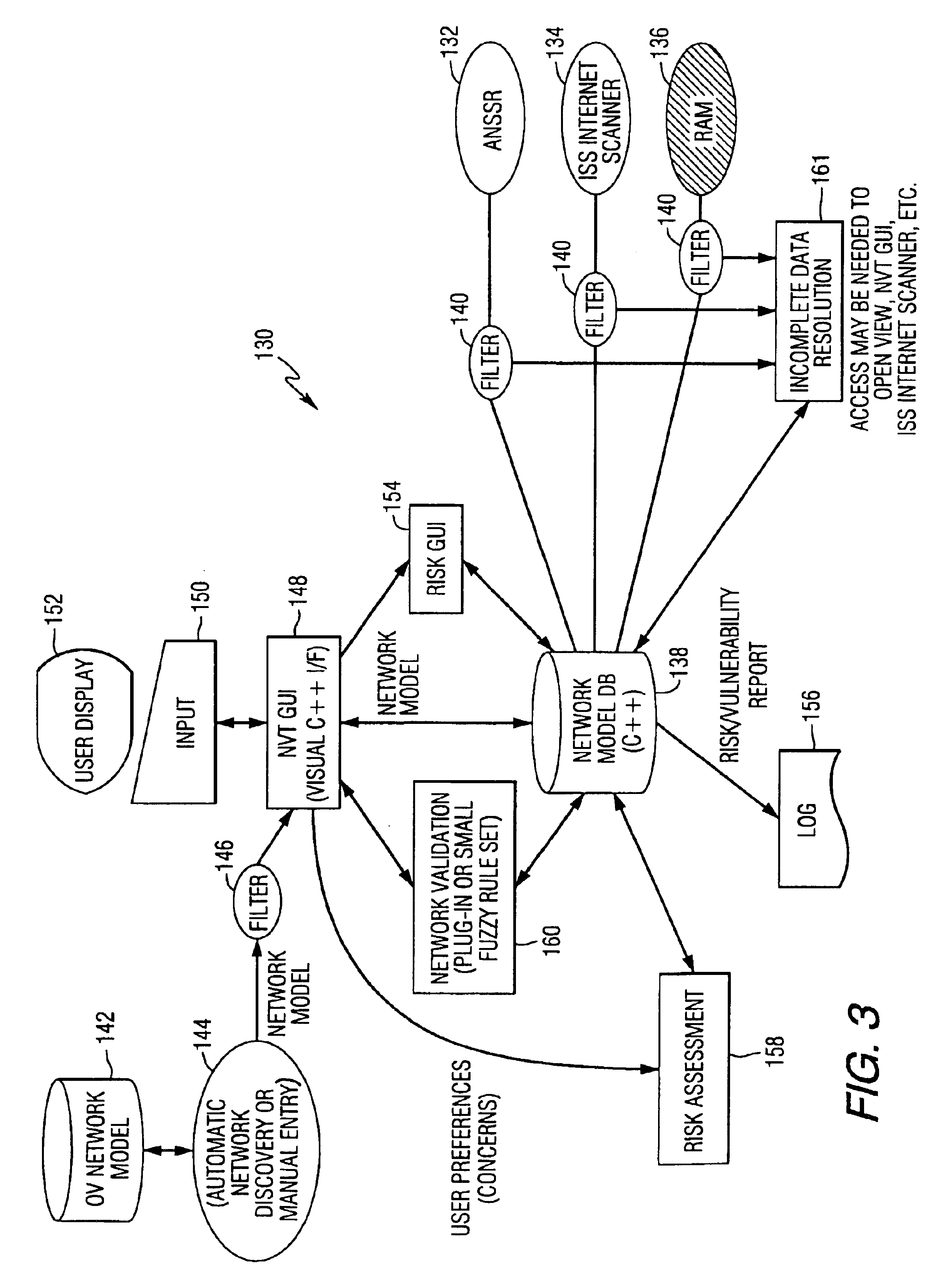
System and method for assessing the security posture of a network
InactiveUS7096502B1Data processing applicationsMemory loss protectionData processing systemSecure state
A method and data processing system assesses the security vulnerability of a network by creating a system object model database representing a network. The system object model database supports the information data requirements of disparate network vulnerability analysis programs. The system object model database is exported to the disparate network vulnerability analysis programs. The network is analyzed with each network vulnerability analysis program to produce data results from each program. Data results are correlated to determine the security posture of the network.
Owner:HARRIS CORP
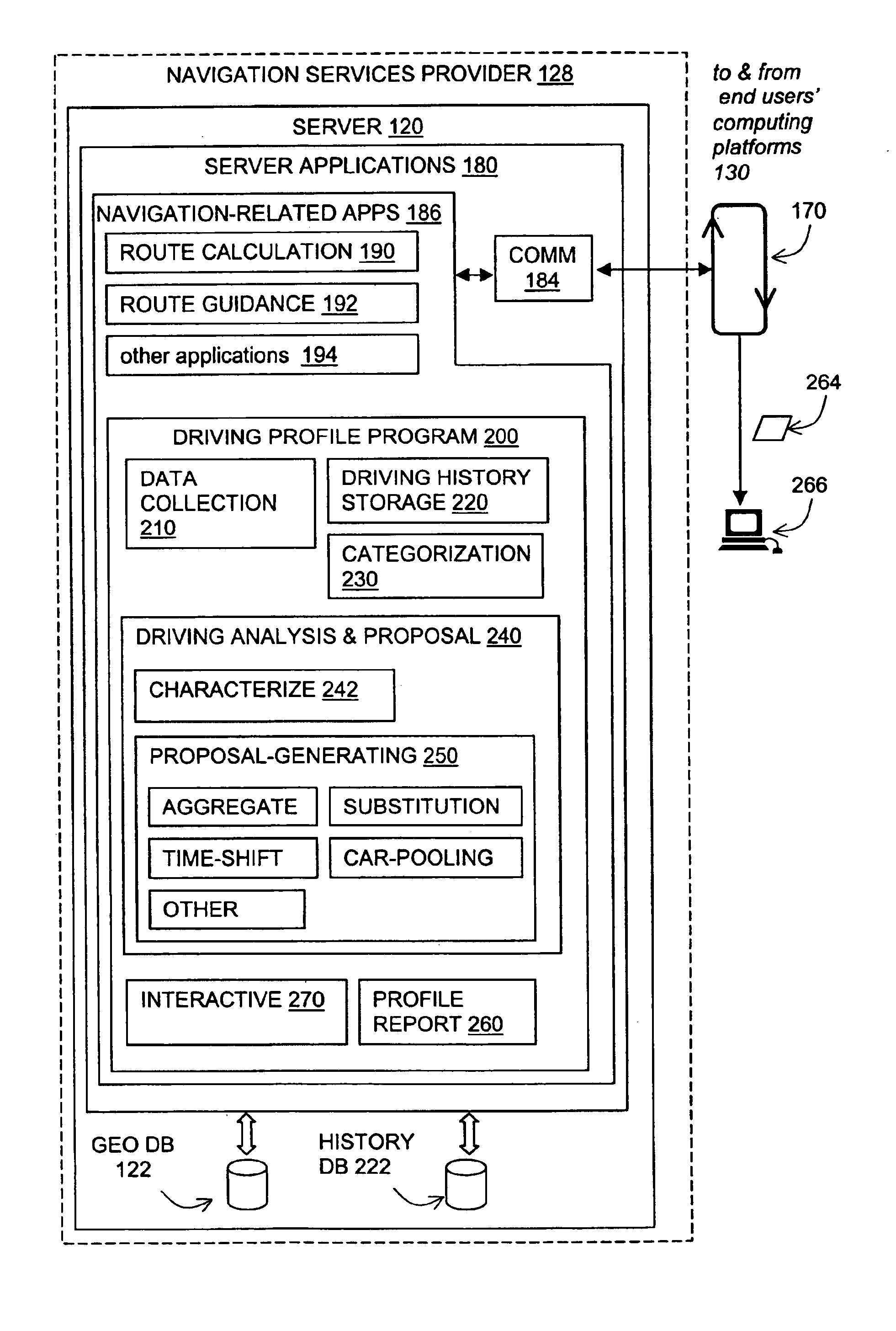
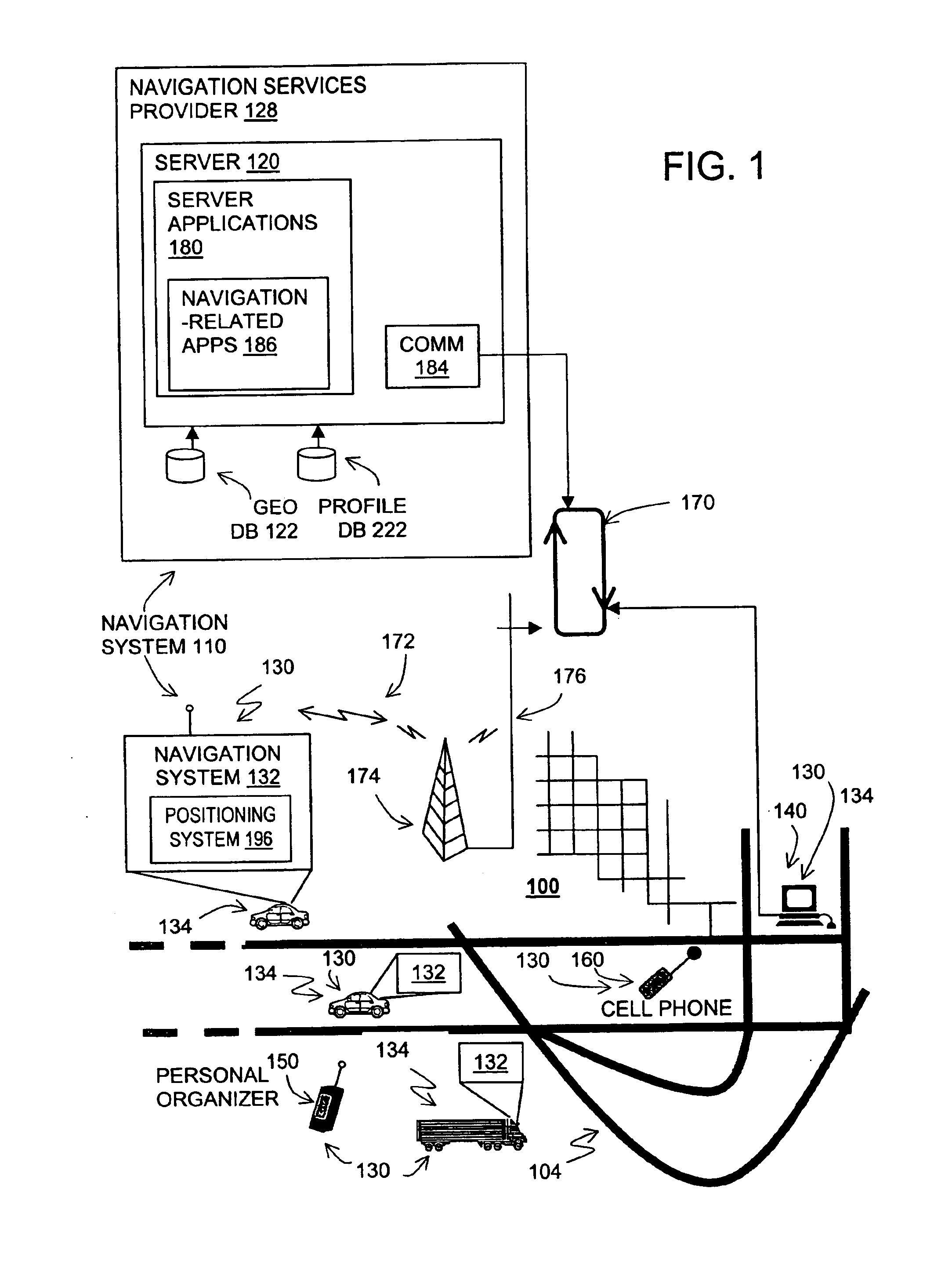
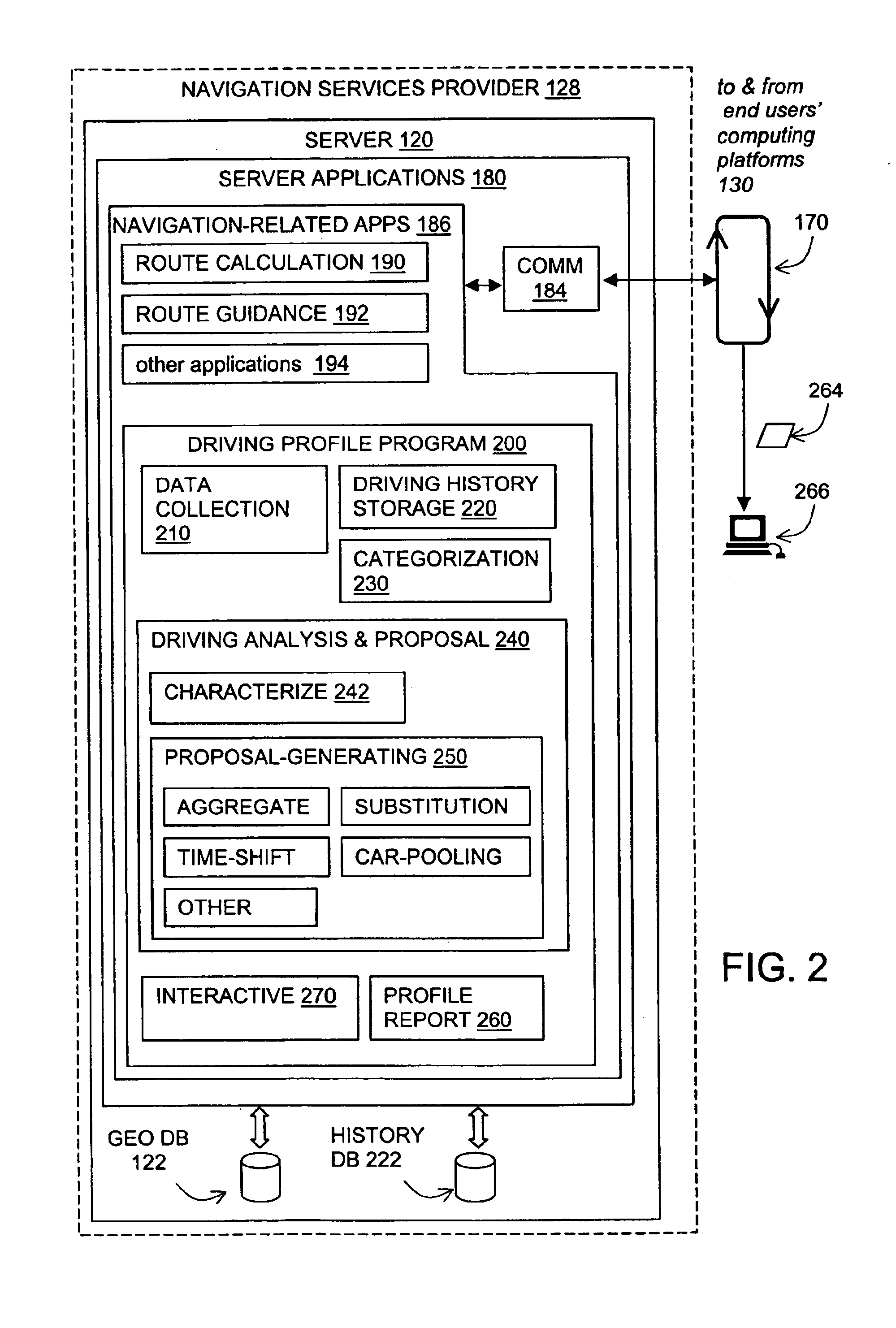
Method of operation of a navigation system to reduce expenses on future trips and to provide other functions
InactiveUS6944533B2Reduce the amount requiredReduce expensesInstruments for road network navigationRoad vehicles traffic controlArrival timeNavigation system
A navigation system includes a driving profile program. The driving profile program collects information about an end user's driving activity. The information relates to trips made by the end user. The information includes departure times, intermediate stops, arrival times, purposes of the trips, and so on. After collecting this information over a period of time, the driving profile program analyzes the end user's driving activity. The driving profile program provides the end user with a driving activity profile. In addition, the driving profile program determines ways to reduce the amount of time and / or expense that the end user spends traveling in his / her vehicle and suggests modifications to the end user's driving activity that would save the end user time or expense.
Owner:HERE GLOBAL BV
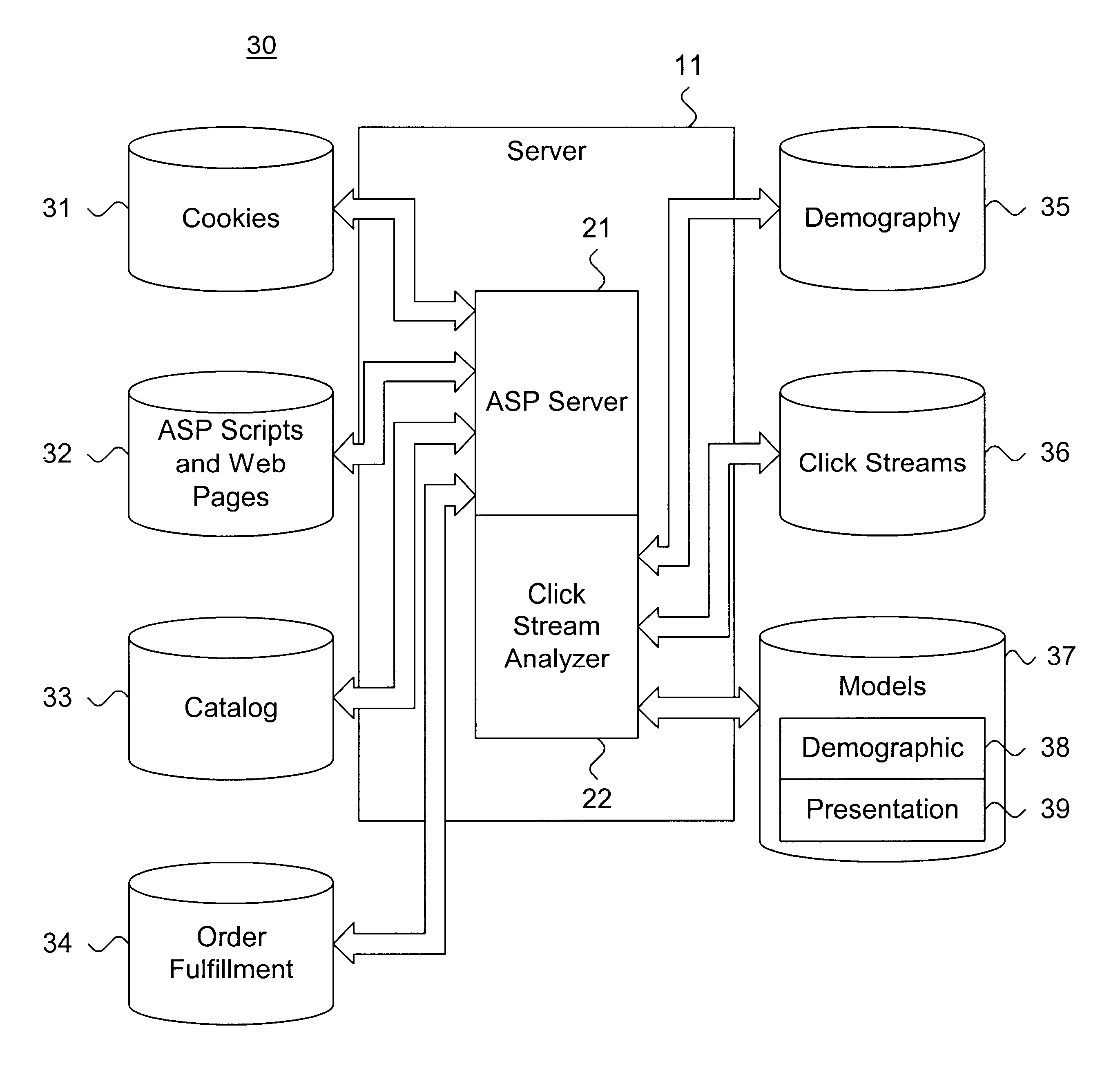
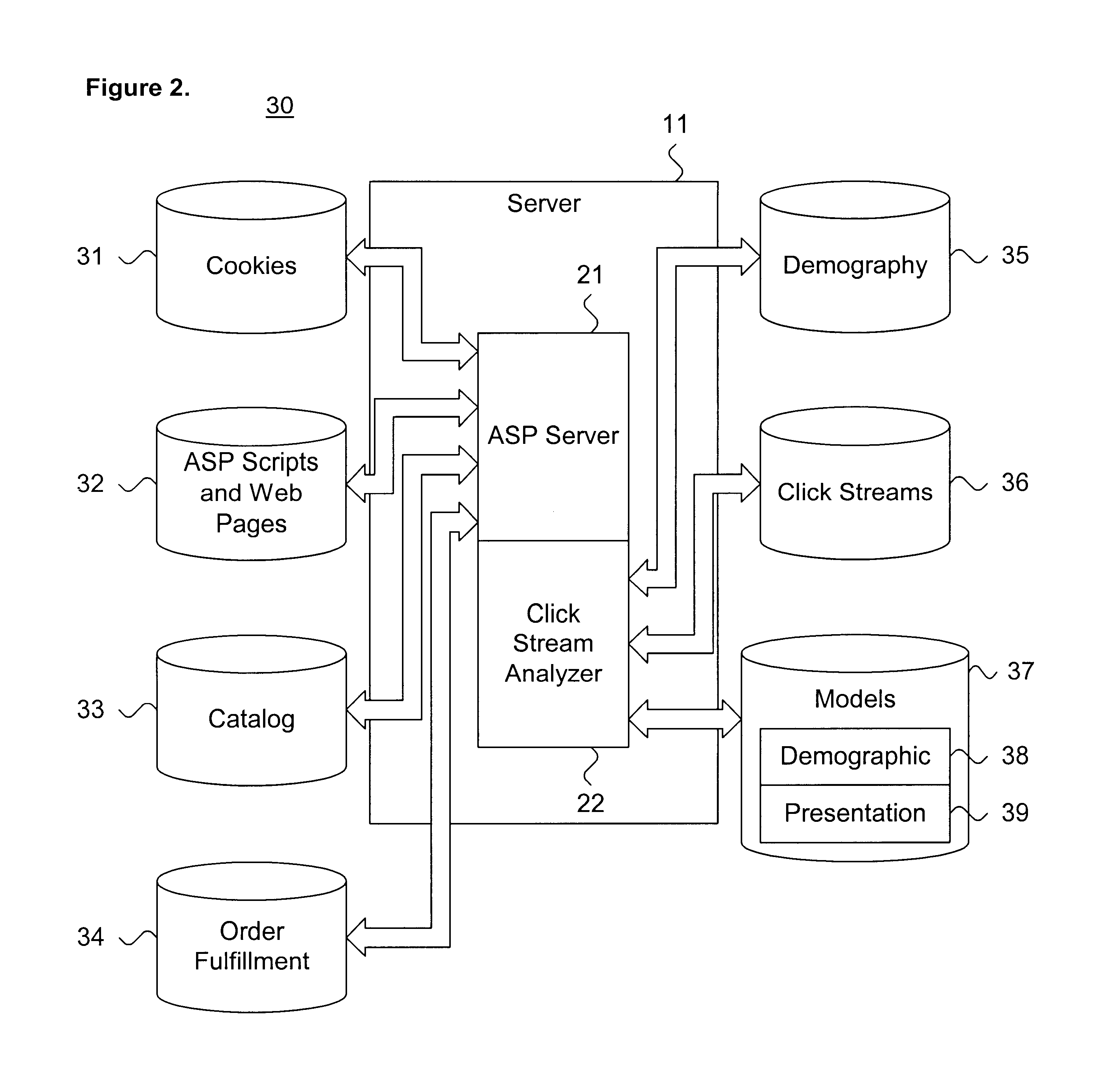
System and method for dynamically evaluating an electronic commerce business model through click stream analysis
A system and method for dynamically evaluating an electronic commerce business model through click stream analysis is disclosed. An electronic commerce business model is incorporated into a Web site. The Web site includes a plurality of related Web pages structured in a hierarchical manner. Each Web page includes one or more hyperlinks selectable by a user. A plurality of data vectors is stored. Each data vector represents a click stream path through the Web site. Each data vector includes a set of data entries that each corresponds to Web content selected via the hyperlinks in the related Web pages. Each click stream path is classified based on at least one such data entry in the data vector. The classified click stream path shares at least one common characteristic with one or more other click stream paths. The classified click stream paths are analyzed according to a pre-defined evaluation procedure directed at determining at least one of efficacy of presentation and shifts in demography. The electronic commerce business model is compared to the classified click stream paths analysis.
Owner:ORACLE INT CORP
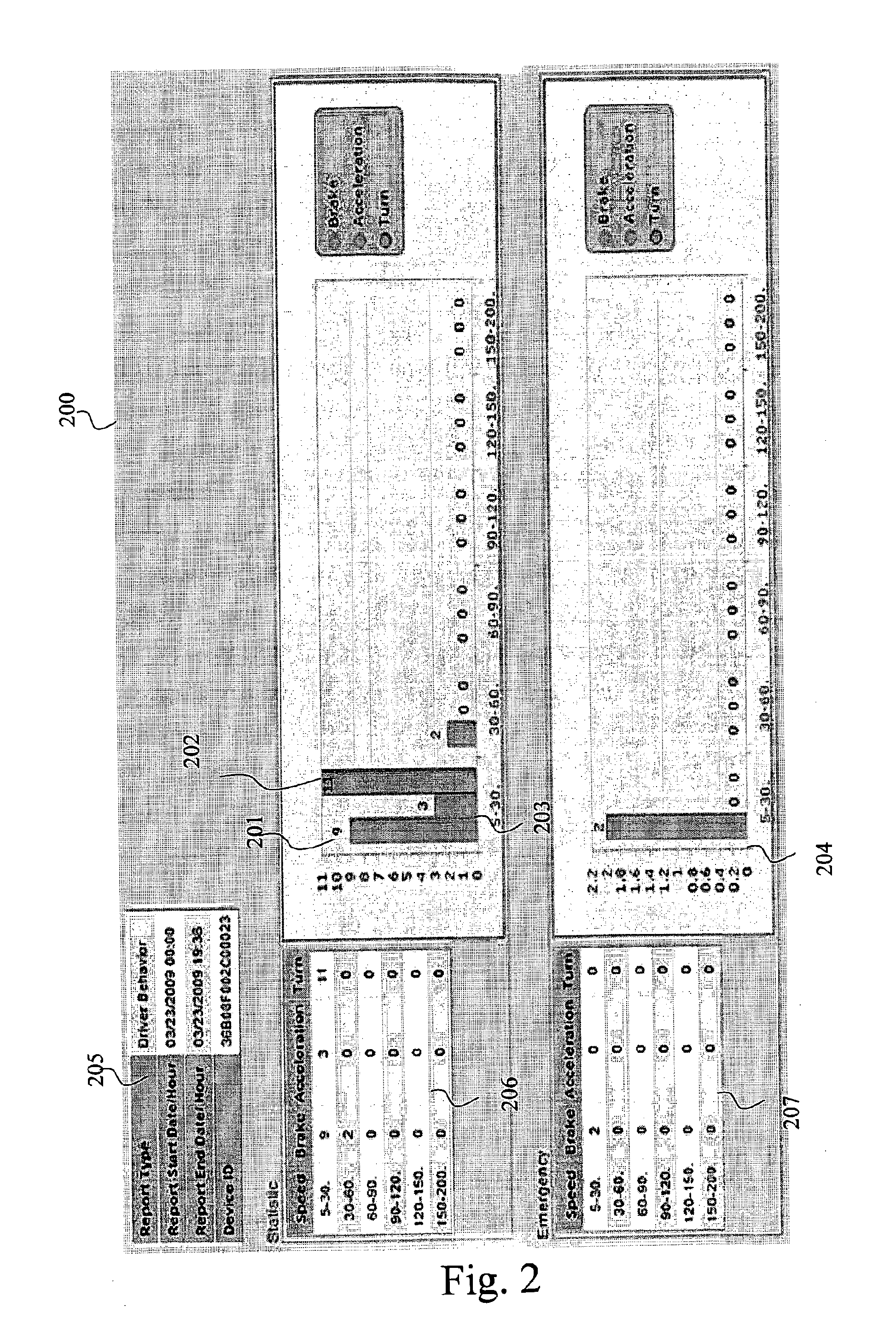
Driver profiling
InactiveUS20120109418A1FinanceRegistering/indicating working of vehiclesProgram analysisComputer science
The present invention discloses a driver profiling system comprising: at least one sensor adapted to measure vehicle parameters; computing means in communication with said sensors, provided with storage means adapted to store said vehicle parameters, and provided with means for issuing warnings based on said vehicle parameters; a remote server adapted to receive, store, analyze, and display said vehicle parameters; and, communication means adapted to transfer said vehicle parameters and associated data to said remote server; whereby historical vehicle parameter data may be analyzed to identify driver characteristics.
Owner:TRACKTEC
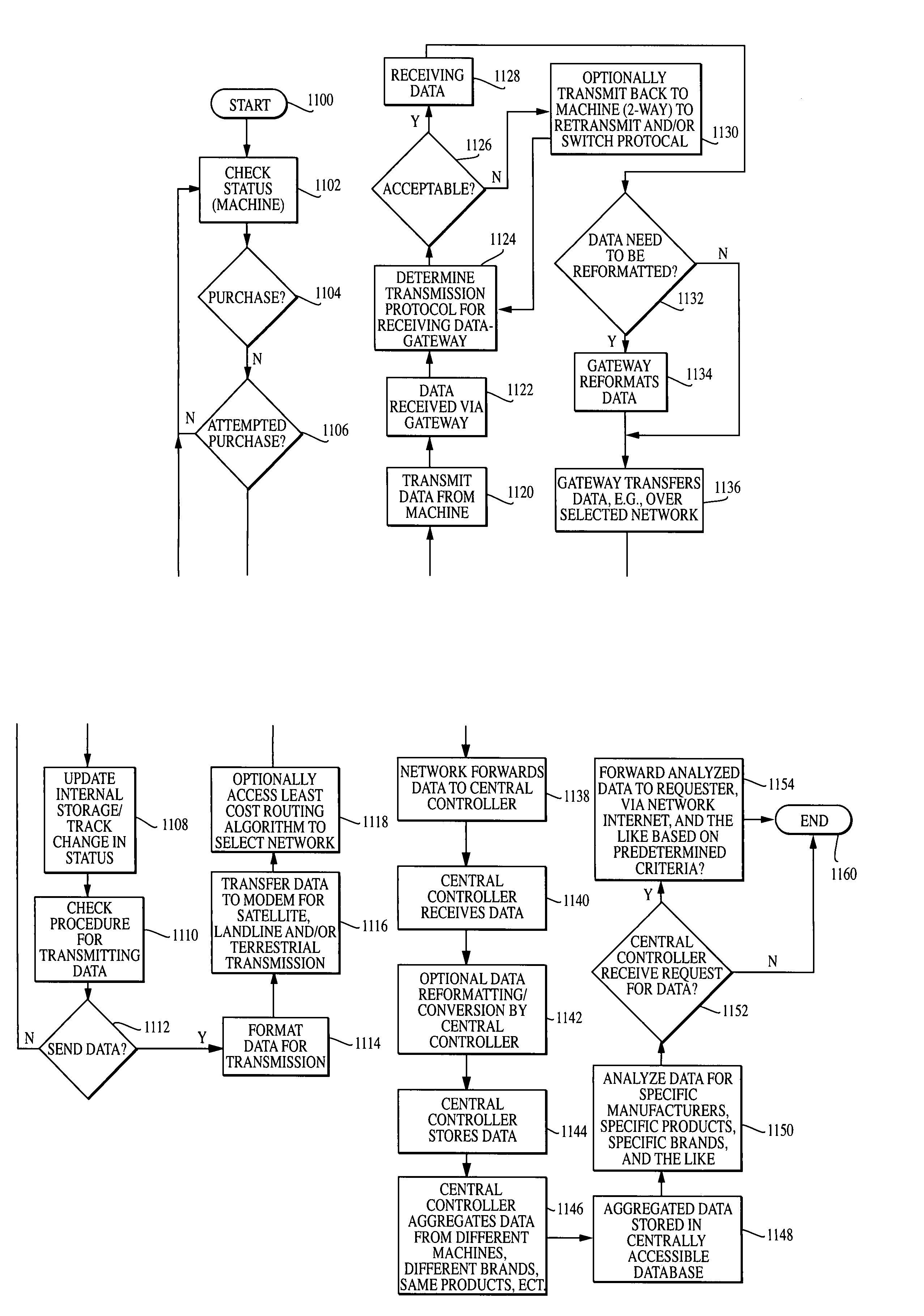
System and method of aggregating data from a plurality of data generating machines
InactiveUS7089322B1Easy to trackIncrease salesHand manipulated computer devicesDigital computer detailsTransceiverThe Internet
A system and method for collecting and aggregating data from a plurality of data generating machines. The system includes a plurality of data generating machines each having a transceiver for transmitting data pertaining to a monitored sales event of each of the plurality of data generating machines via at least one of a terrestrial, Internet, satellite, and landline network. At least one first computer receives and cumulatively stores the data transmitted by each of the plurality of data generating machines. At least one second computer is operatively communicable with the at least one first computer and runs at least one application software program that analyzes the data to determine consumer buying habits and / or preferences. Advertising data can be transmitted that provides message content at least partially determined by an analysis of the data.
Owner:XRS CORPORATION
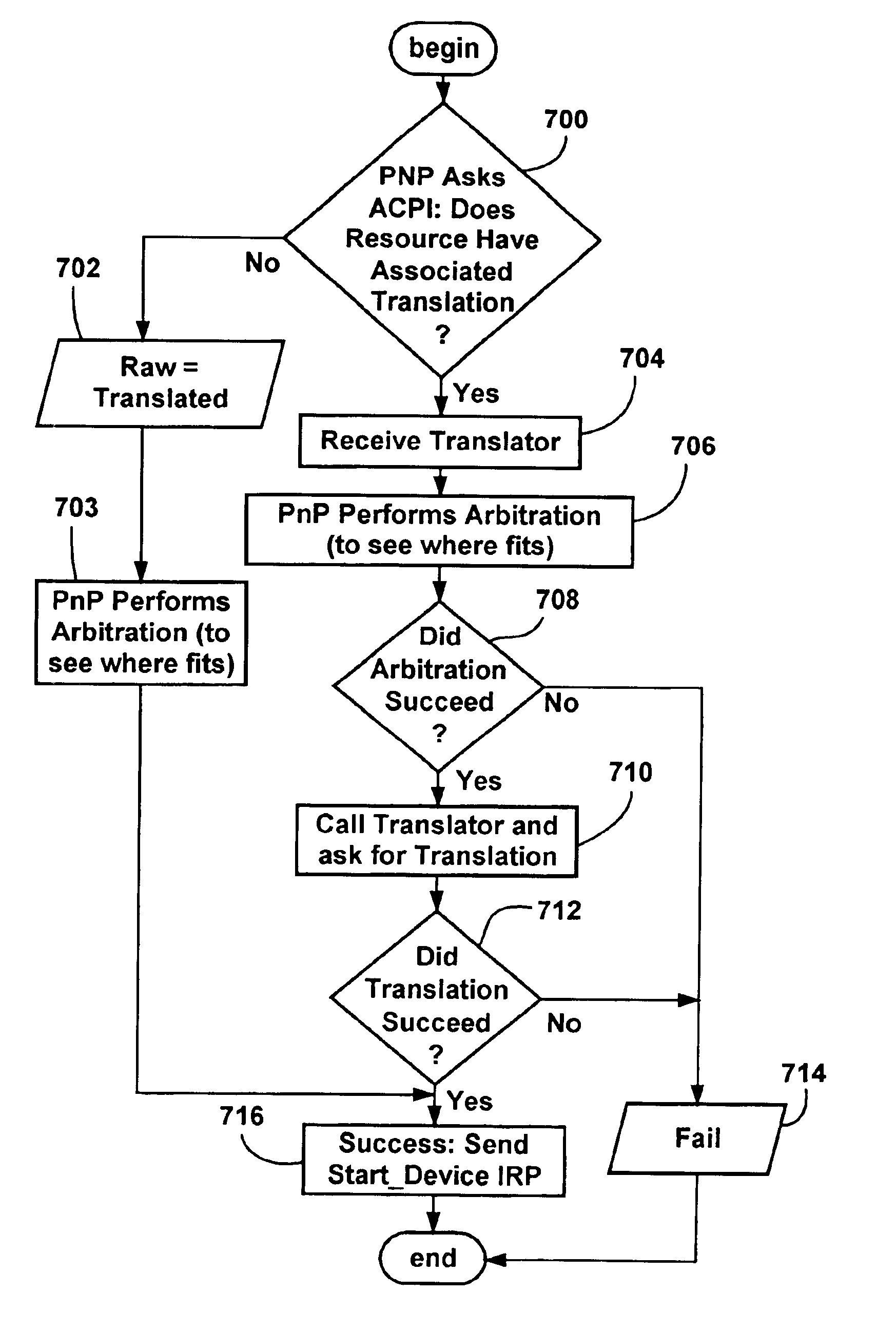
Dynamically configuring resources for cycle translation in a computer system
InactiveUS6970957B1Program controlGenerating/distributing signalsAdvanced Configuration and Power InterfaceOperational system
Owner:MICROSOFT TECH LICENSING LLC
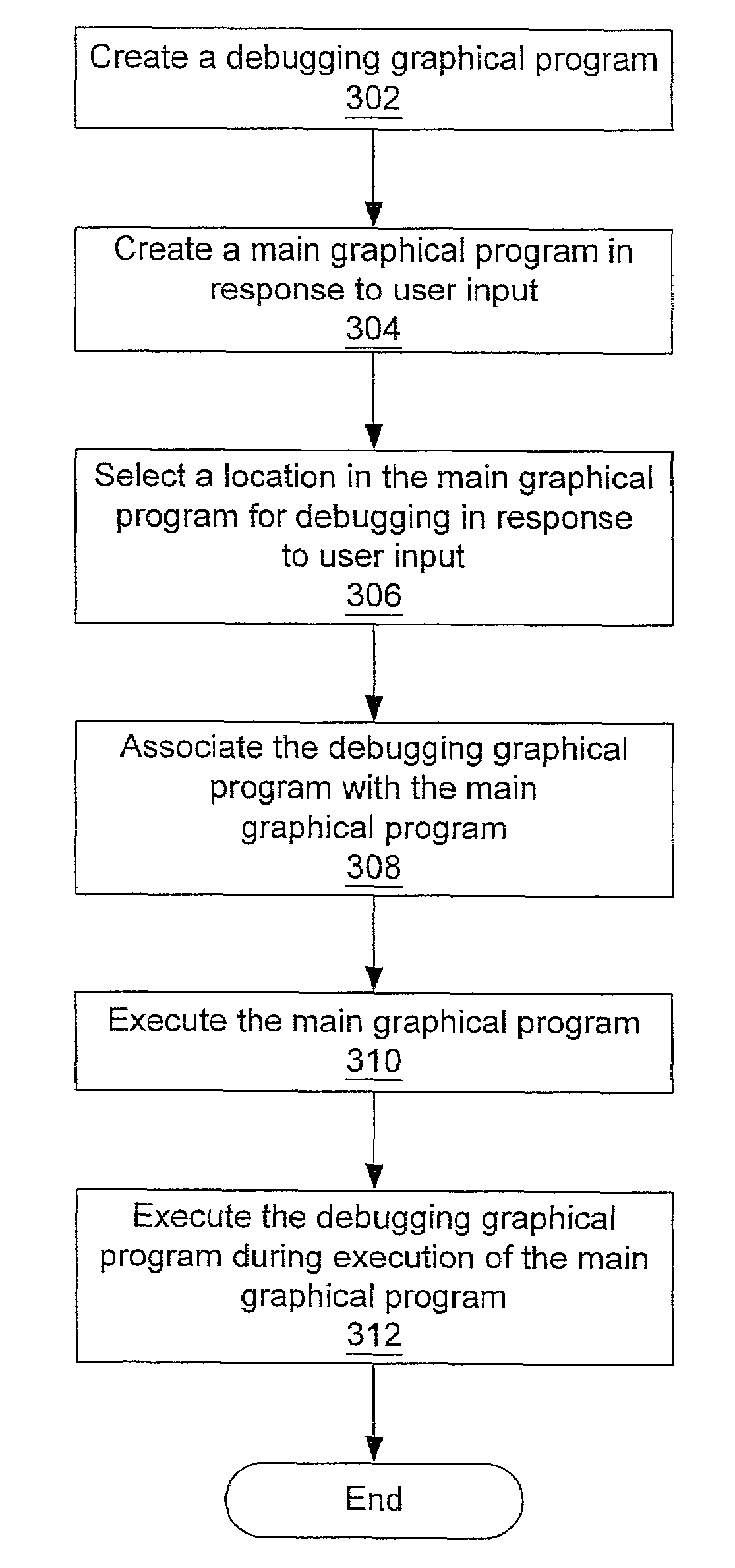
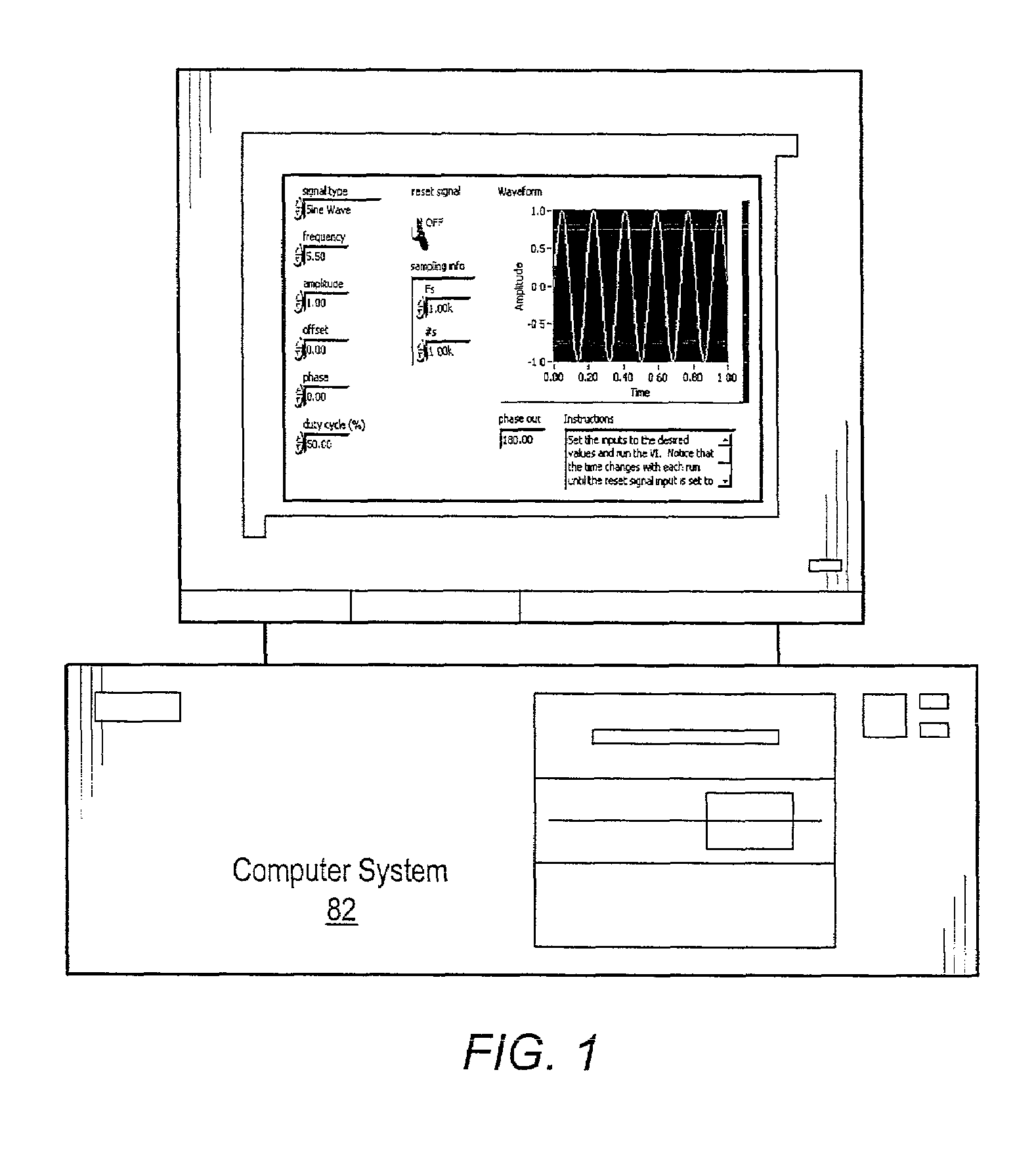
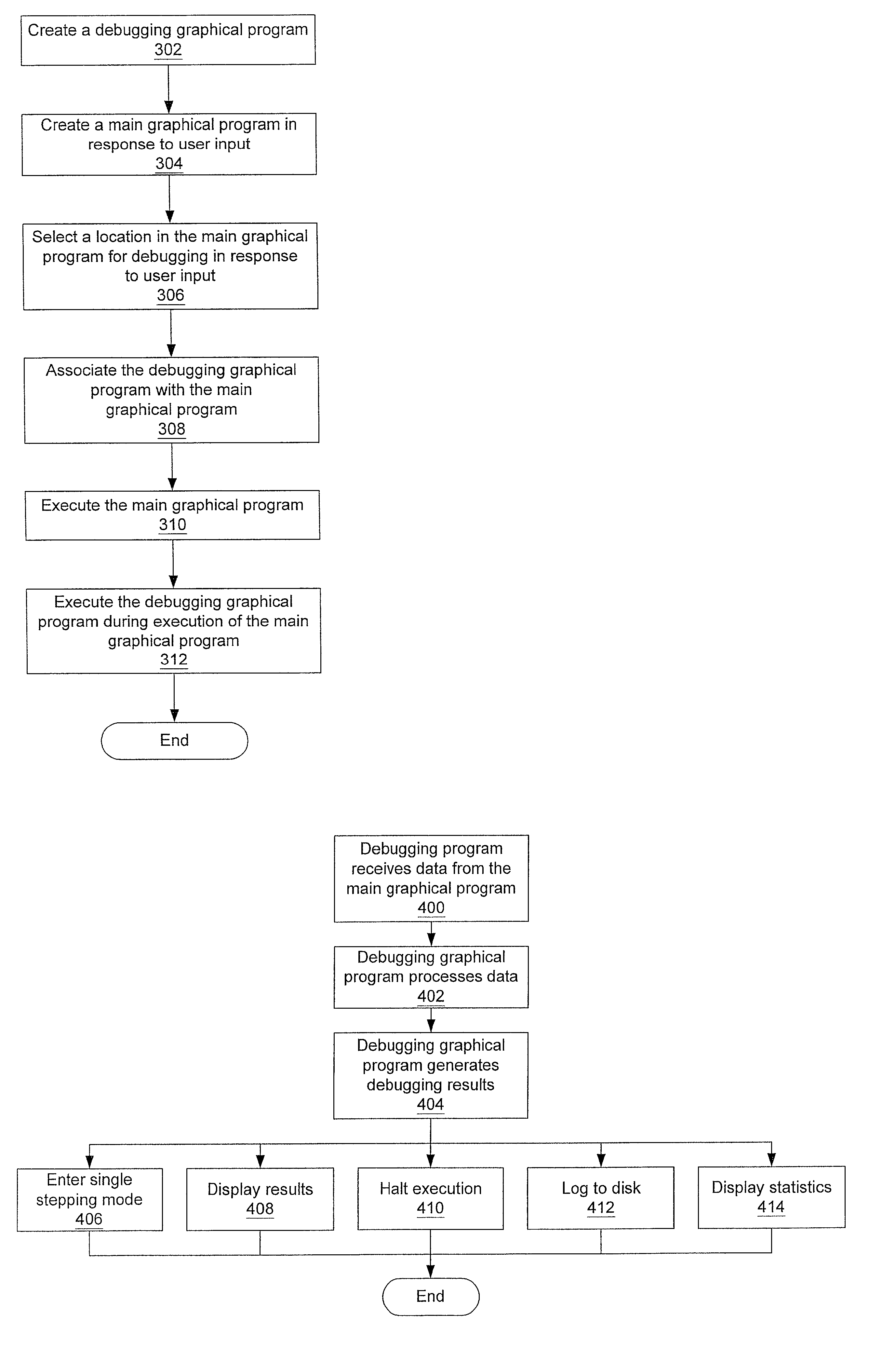
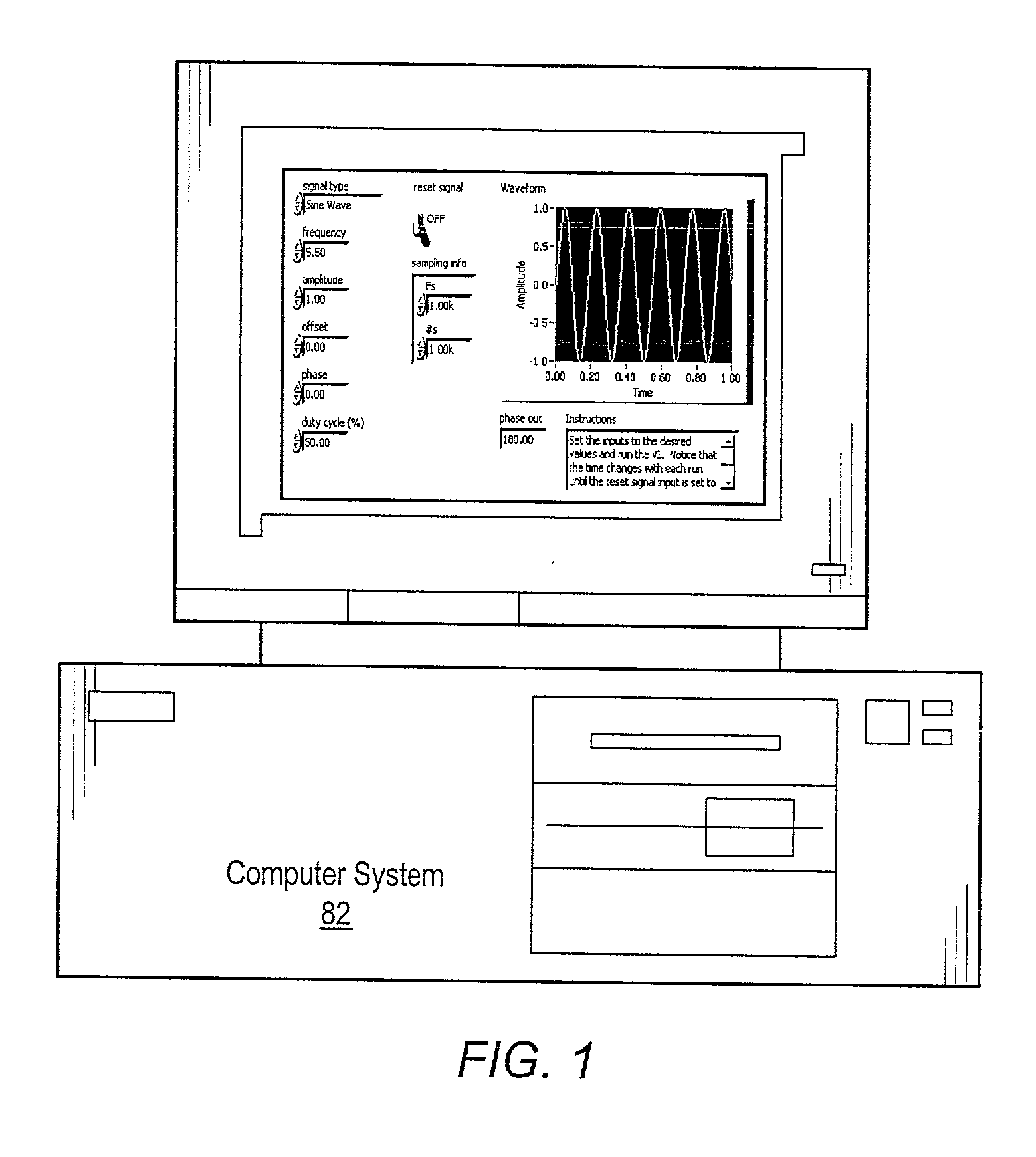
System and method for analyzing a graphical program using debugging graphical programs
InactiveUS7302675B2Easy to createSimplify the commissioning processSoftware testing/debuggingVisual/graphical programmingGraphicsData recording
Owner:NATIONAL INSTRUMENTS
System and method for analyzing a graphical program using debugging graphical programs
A system and method for implementing a debugging graphical program in a main graphical program. A user can associate a debugging graphical program with a wire in a data flow diagram in order to debug and / or analyze the main graphical program. This association does not change or require recompilation of the main graphical program. The debugging graphical program, or smart probe, receives the data from the main graphical program, analyzes this data, and can perform one of several actions. The debugging graphical program can display the data in the wire, generate statistics based on received data, log statistics or data to a file, or perform other analysis functions. The debugging graphical program can also cause the main graphical program into halting execution, entering single stepping mode, etc. The user may choose a debugging graphical program already present, or create one using graphical programming techniques.
Owner:NATIONAL INSTRUMENTS
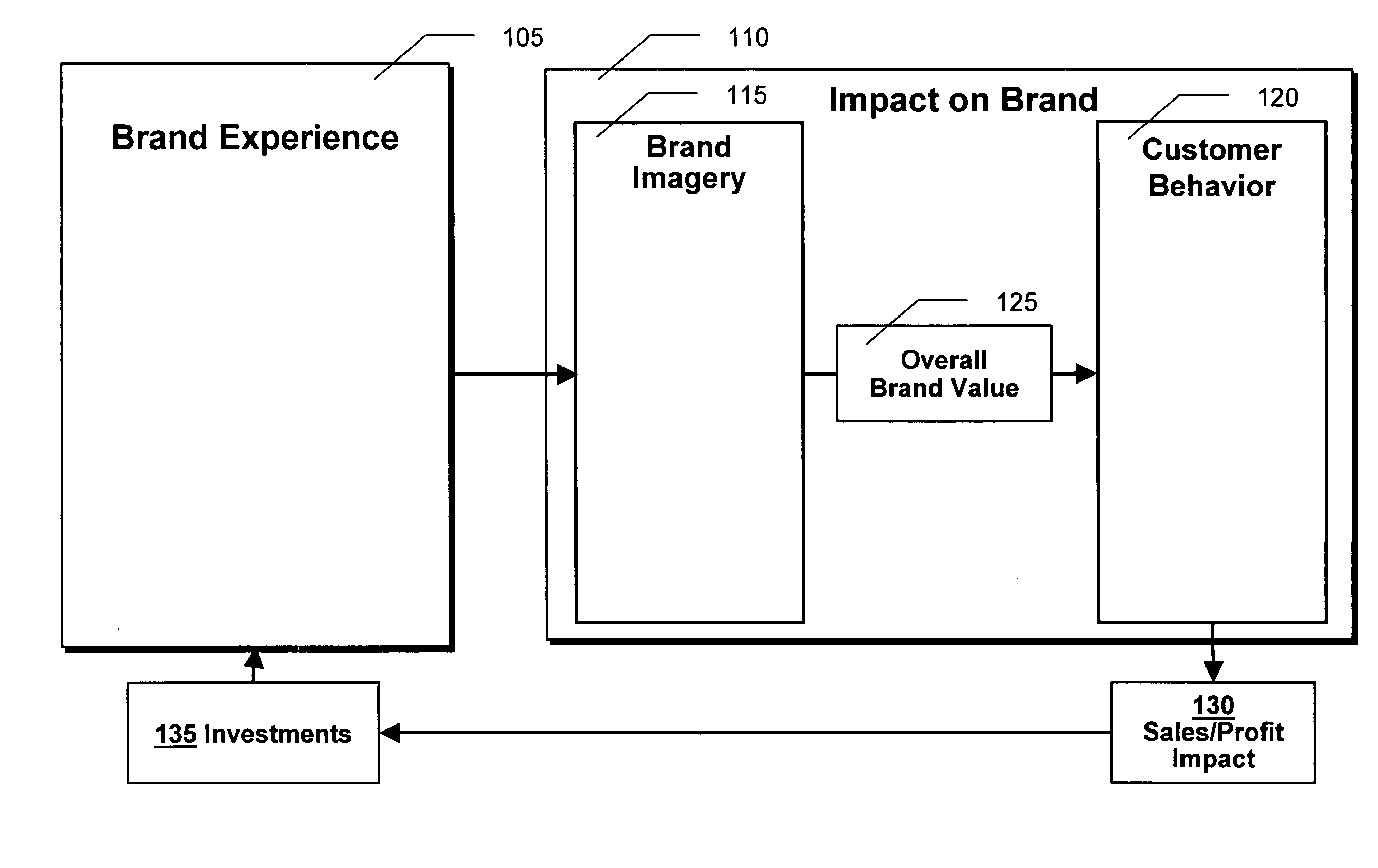
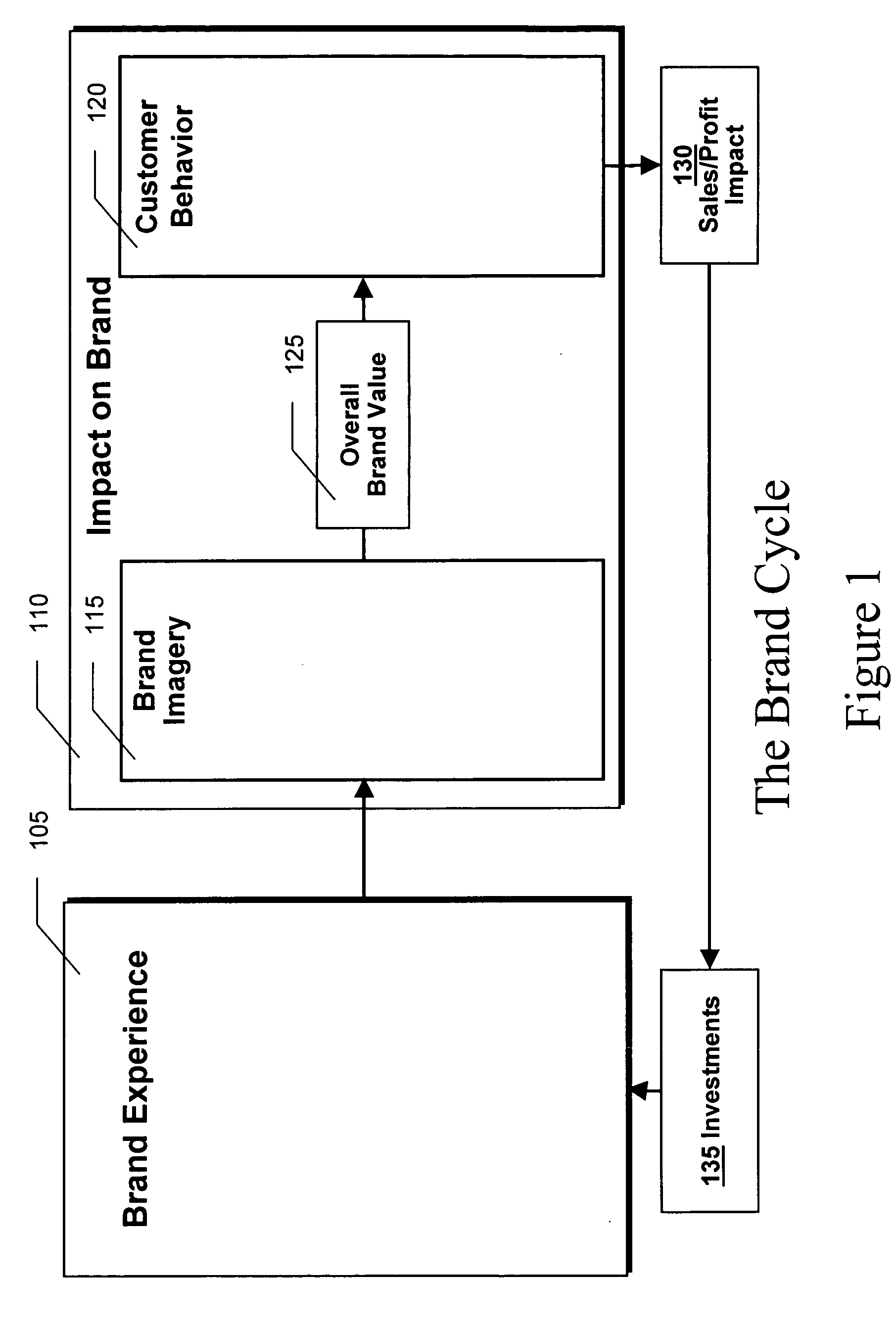
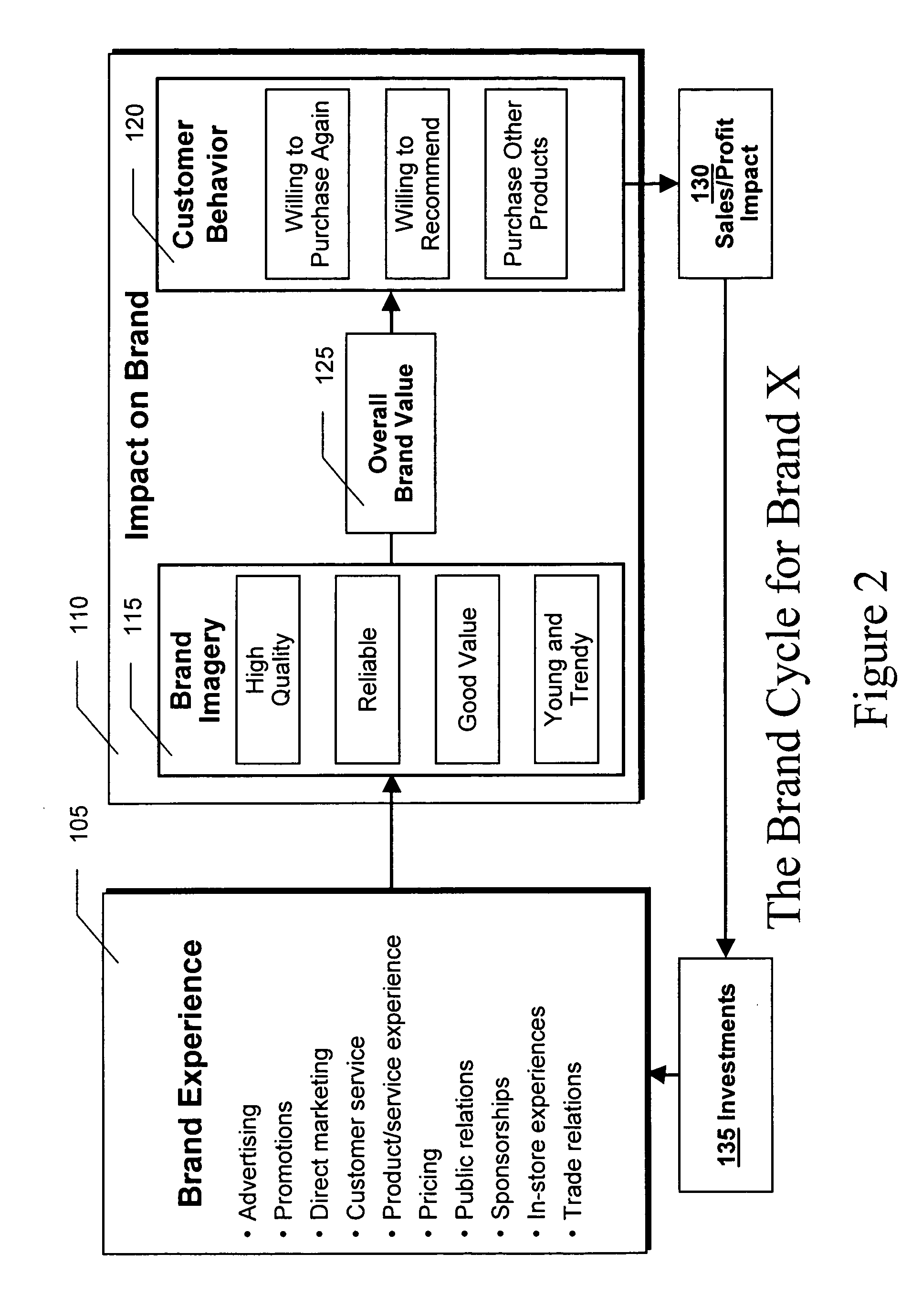
Brand value management
InactiveUS20050209909A1Enhance brand valueProfit maximizationMarket predictionsFinanceTrade offsProgram analysis
A combination of several analytical computer-assisted modeling techniques may be used to evaluate the value of a brand, the relative value of competitive brands and may identify the opportunities to increase brand value and the priority of those opportunities. Image / Attitudinal driver analysis, pyramid analysis, probability analysis, trade-off analysis, and other regression techniques may be used in novel combinations to quantify brand development, impacts and the overall estimate of brand value. For example: (1) image driver analysis may be applied to each level of a brand pyramid to understand how to most effectively move customers through to the next level in the pyramid; (2) probability analysis may be used to estimate the impact of each movement through the pyramid; and (3) tradeoff analysis may be used to improve the value customers perceive at any particular level of the pyramid.
Owner:ACCENTURE GLOBAL SERVICES LTD
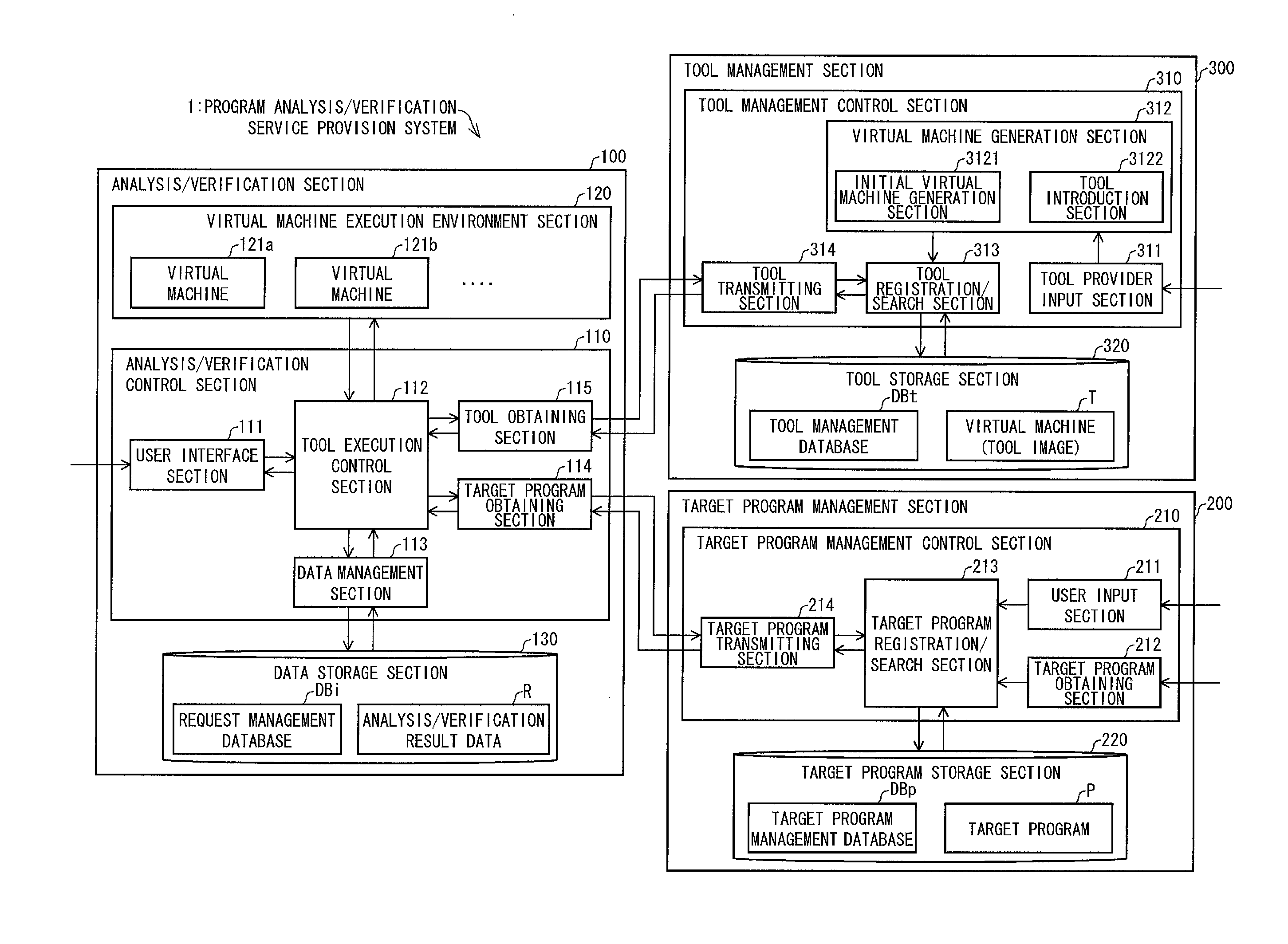
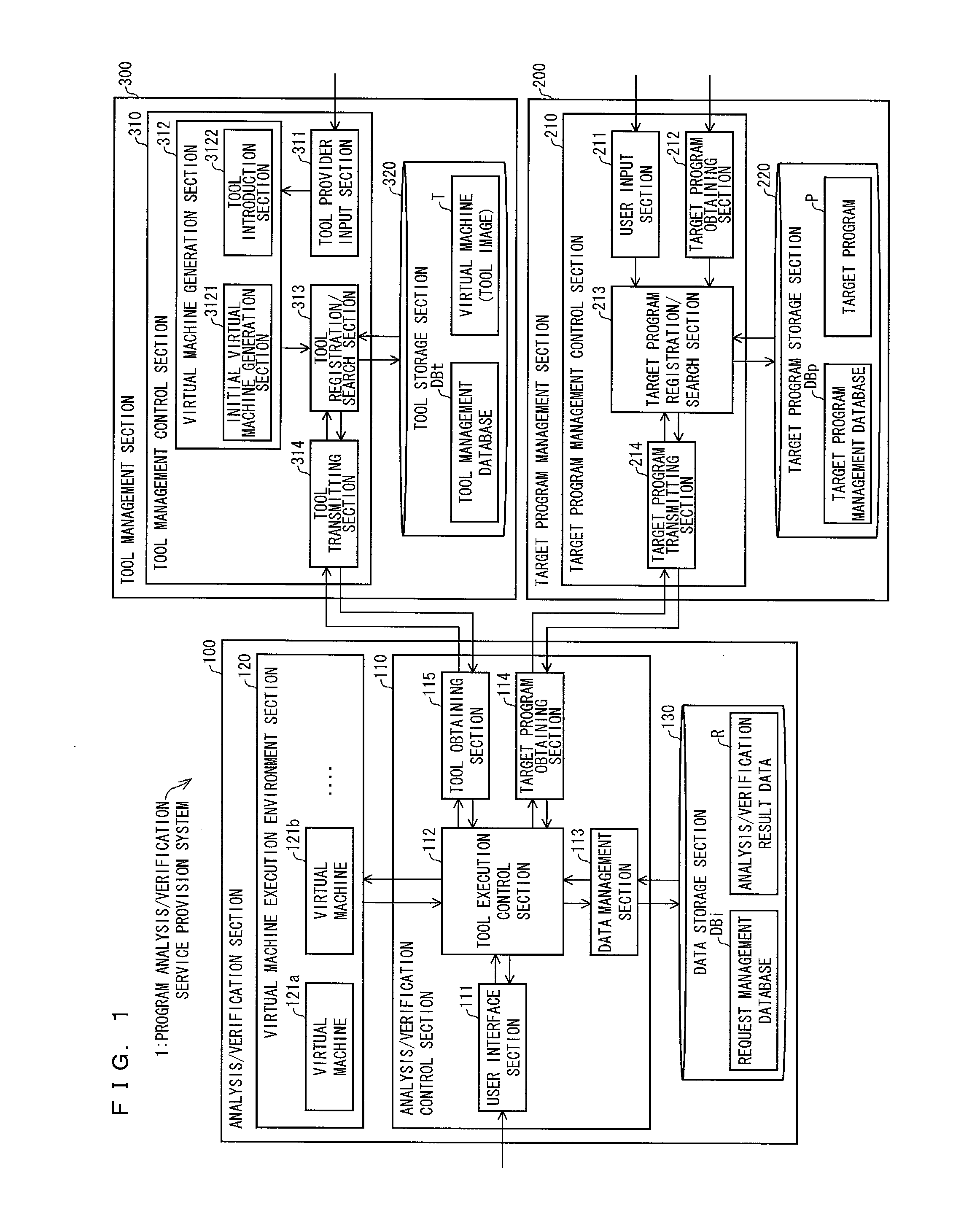
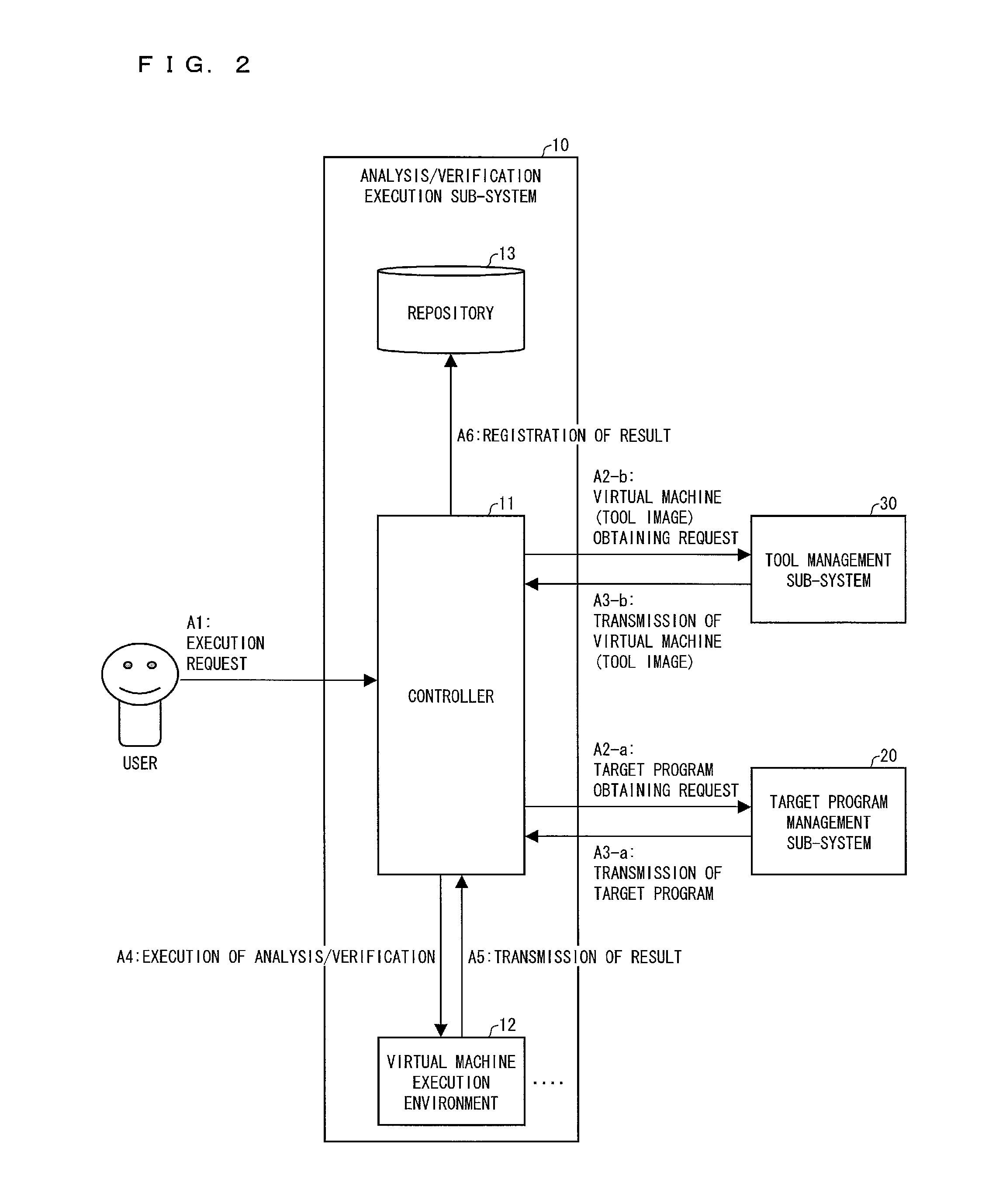
Program analysis/verification service provision system, control method for same, control program, control program for directing computer to function, program analysis/verification device, program analysis/verification tool management device
ActiveUS20140304815A1Easily analyze/verifyMemory loss protectionError detection/correctionService provisionProgram analysis
A program analysis / verification service provision system (1) includes: a tool registration / search section (313) for extracting, from a plurality of program analysis / verification tools (virtual machines) stored in a tool storage section (320), a virtual machine (T) in which a program analysis / verification tool for use in analysis / verification of a target program (P) has been installed and set; and a virtual machine execution environment section (120) for analyzing / verifying the target program (P) with use of the virtual machine (T) thus extracted.
Owner:JAPAN SCI & TECH CORP
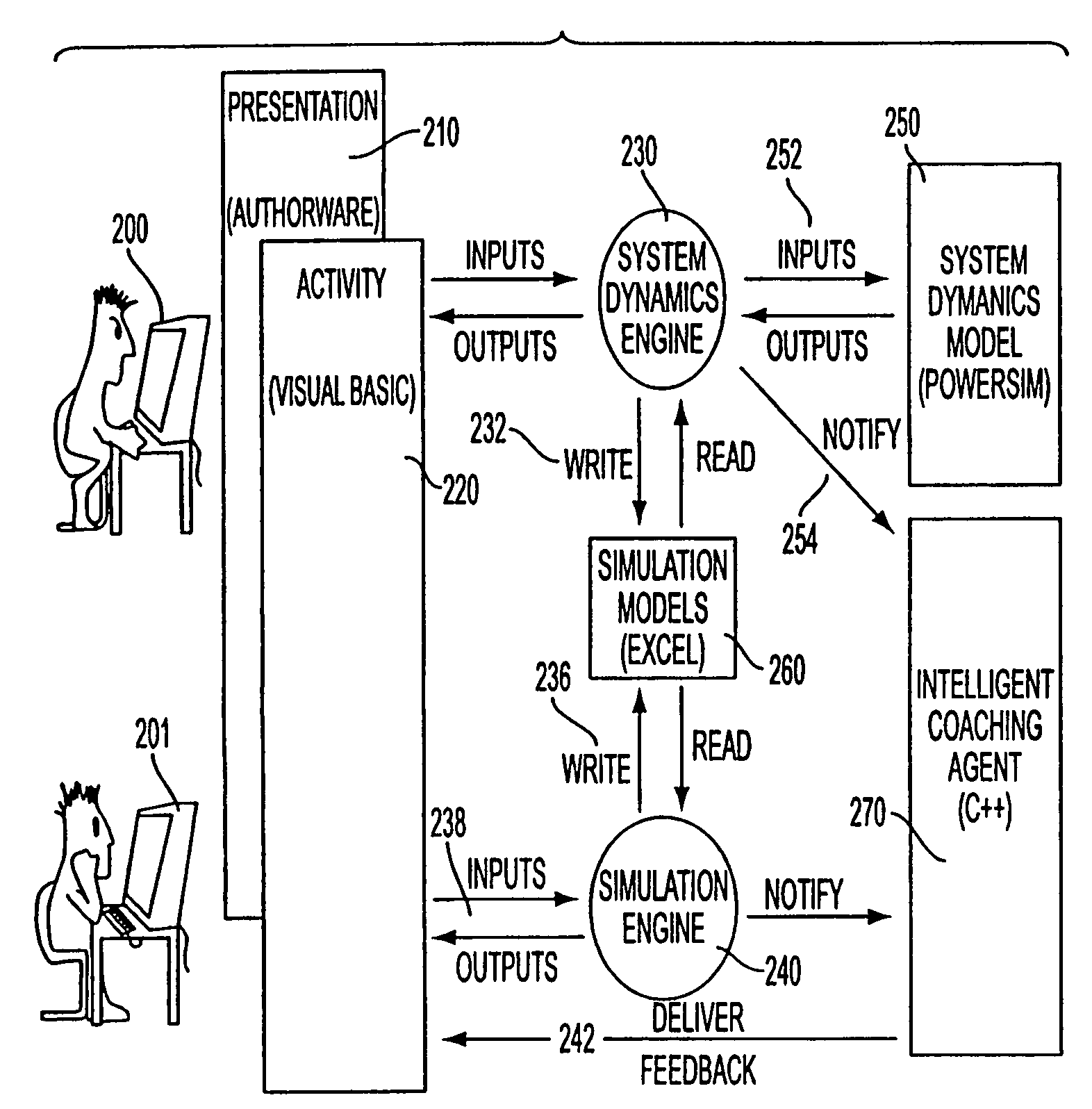
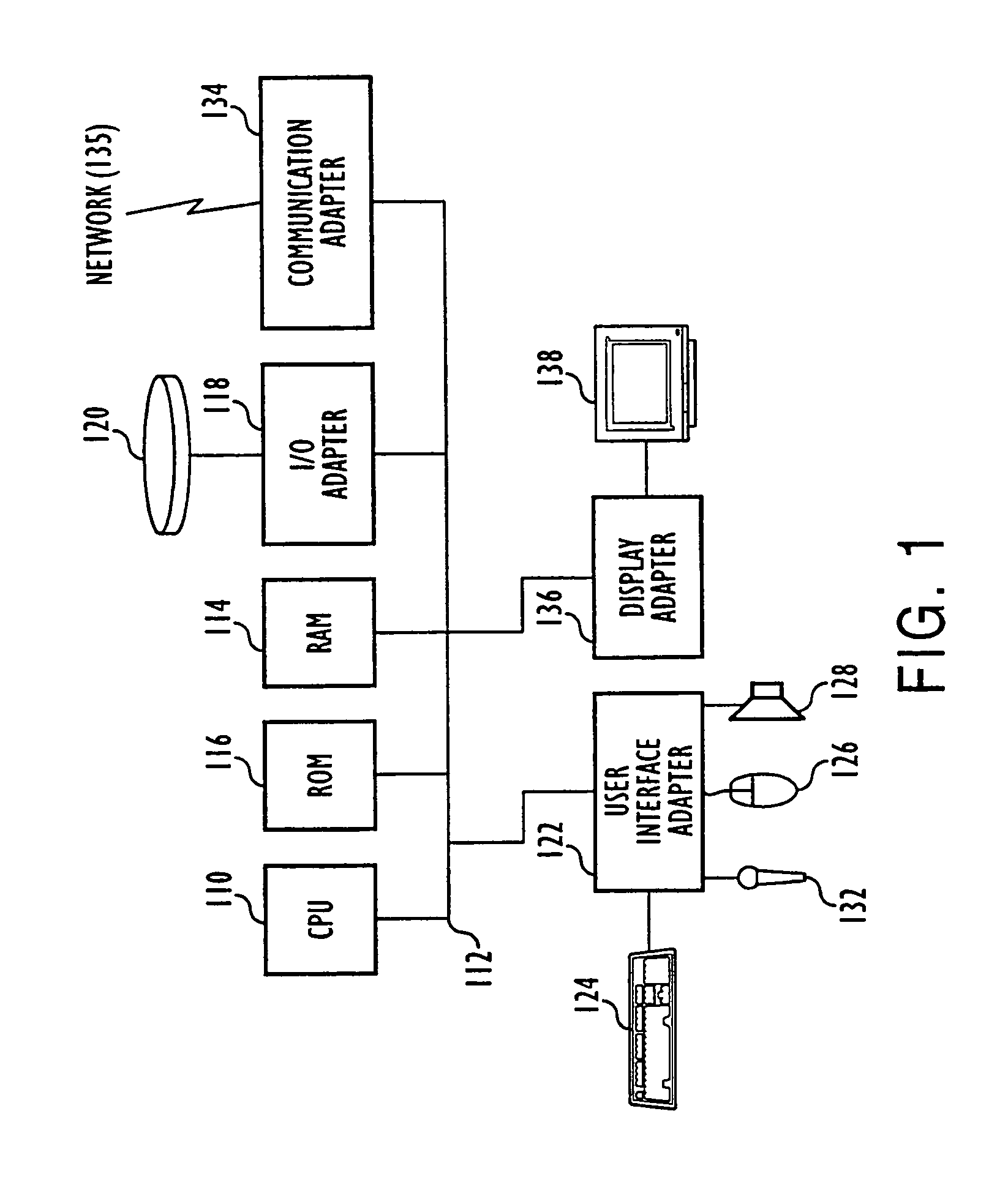
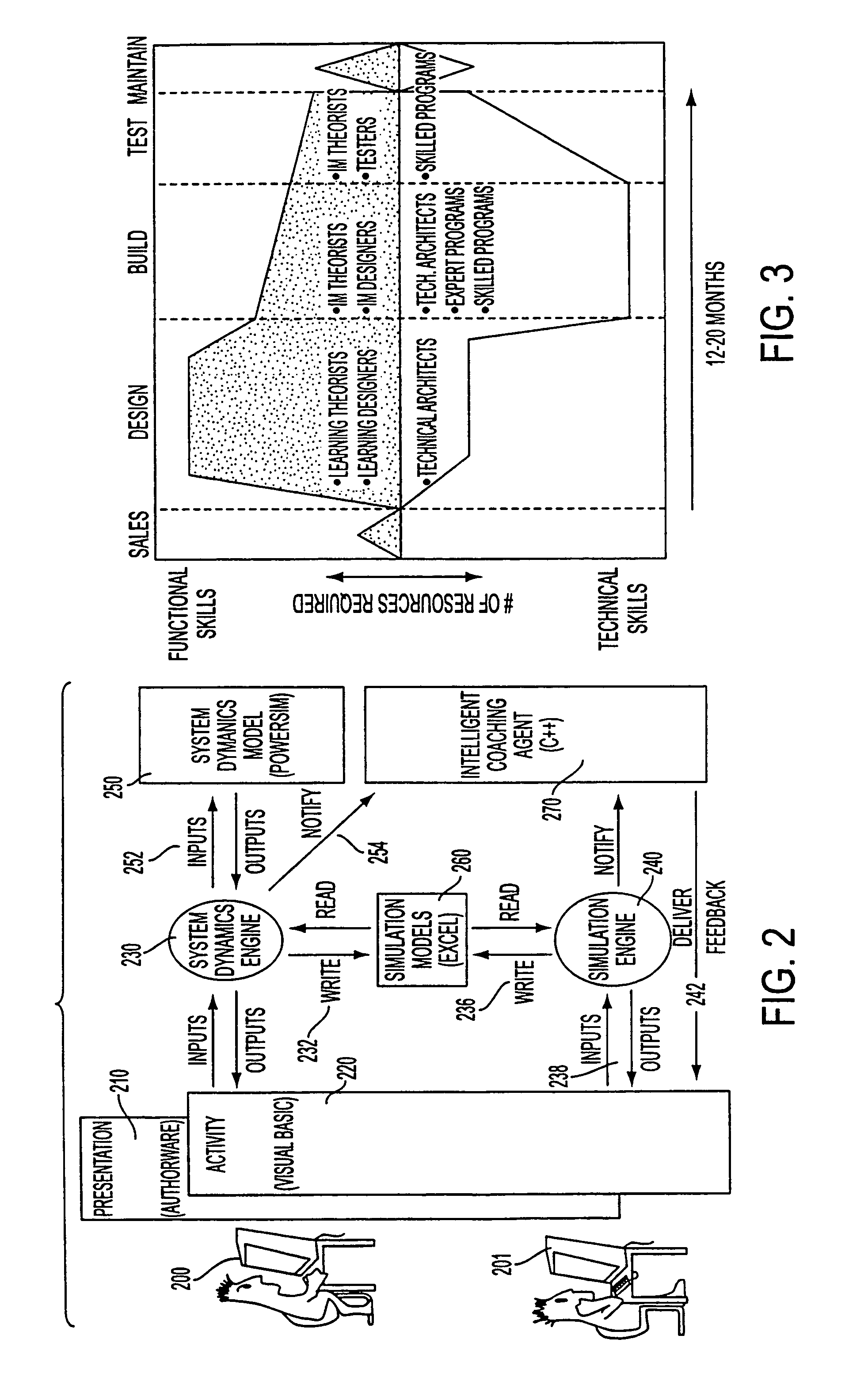
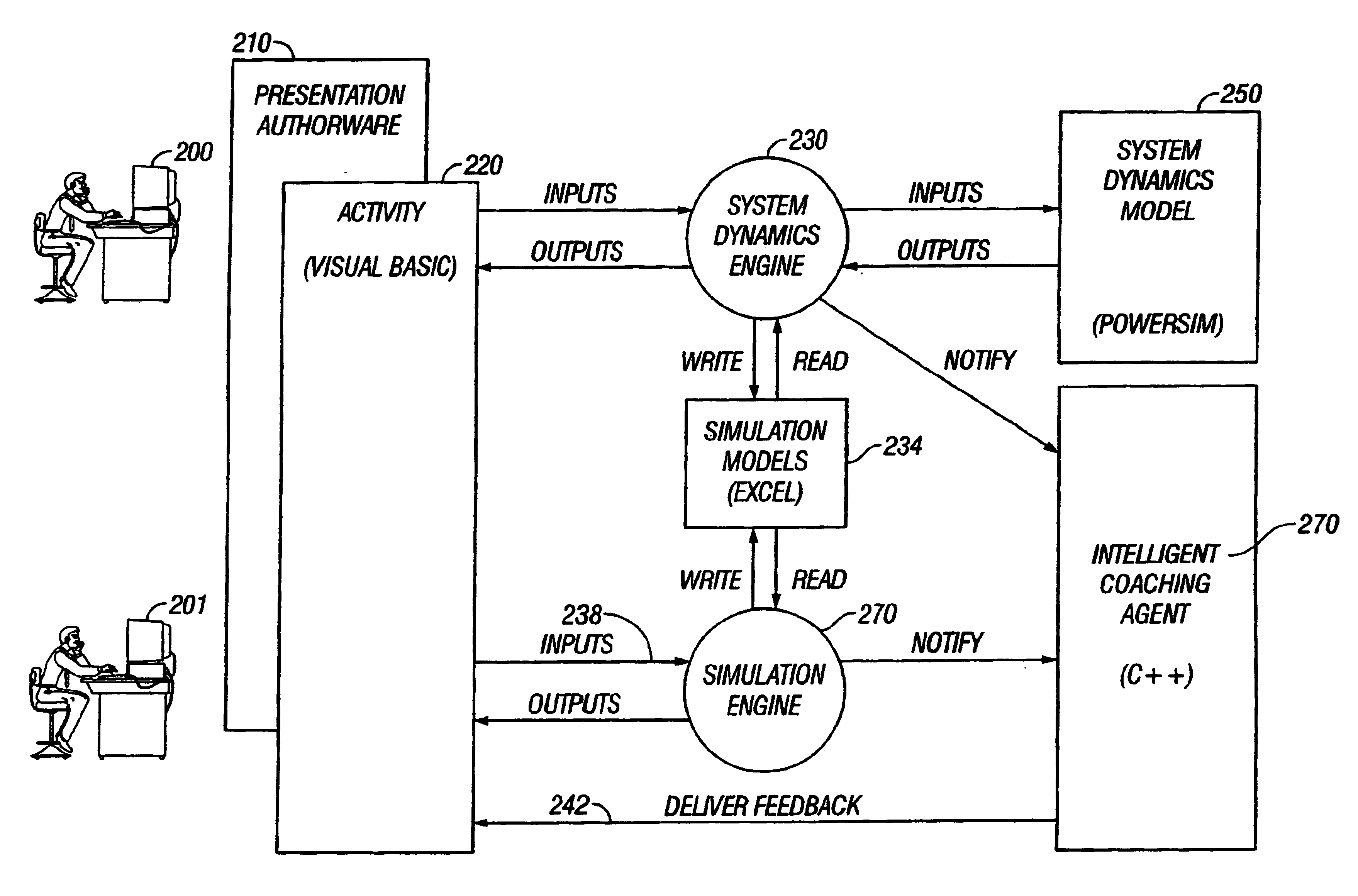
Runtime program analysis tool for a simulation engine
A system is disclosed that provides a goal based learning system utilizing a rule based expert training system to provide a cognitive educational experience. The system provides the user with a simulated environment that presents a business opportunity to understand and solve optimally. Mistakes are noted and remedial educational material presented dynamically to build the necessary skills that a user requires for success in the business endeavor. The system utilizes an artificial intelligence engine driving individualized and dynamic feedback with synchronized video and graphics used to simulate real-world environment and interactions. Multiple “correct” answers are integrated into the learning system to allow individualized learning experiences in which navigation through the system is at a pace controlled by the learner. A robust business model provides support for realistic activities and allows a user to experience real world consequences for their actions and decisions and entails realtime decision-making and synthesis of the educational material. The system includes tools for analysis and display of a presentation as it is presented.
Owner:ACCENTURE GLOBAL SERVICES LTD
System and method for assessing the security posture of a network using goal oriented fuzzy logic decision rules
A method and data processing system assesses the security vulnerability of a network. A system object model database is created and supports the information data requirements of disparate network vulnerability analysis programs. Only the required data from the system object model database representing the network is imported to the programs, which then analyze the network to produce data results from each program. These data results are stored in a common system model database and within the data fact base. Goal oriented fuzzy logic decision rules are applied to determine the vulnerability posture of the network.
Owner:HARRIS CORP
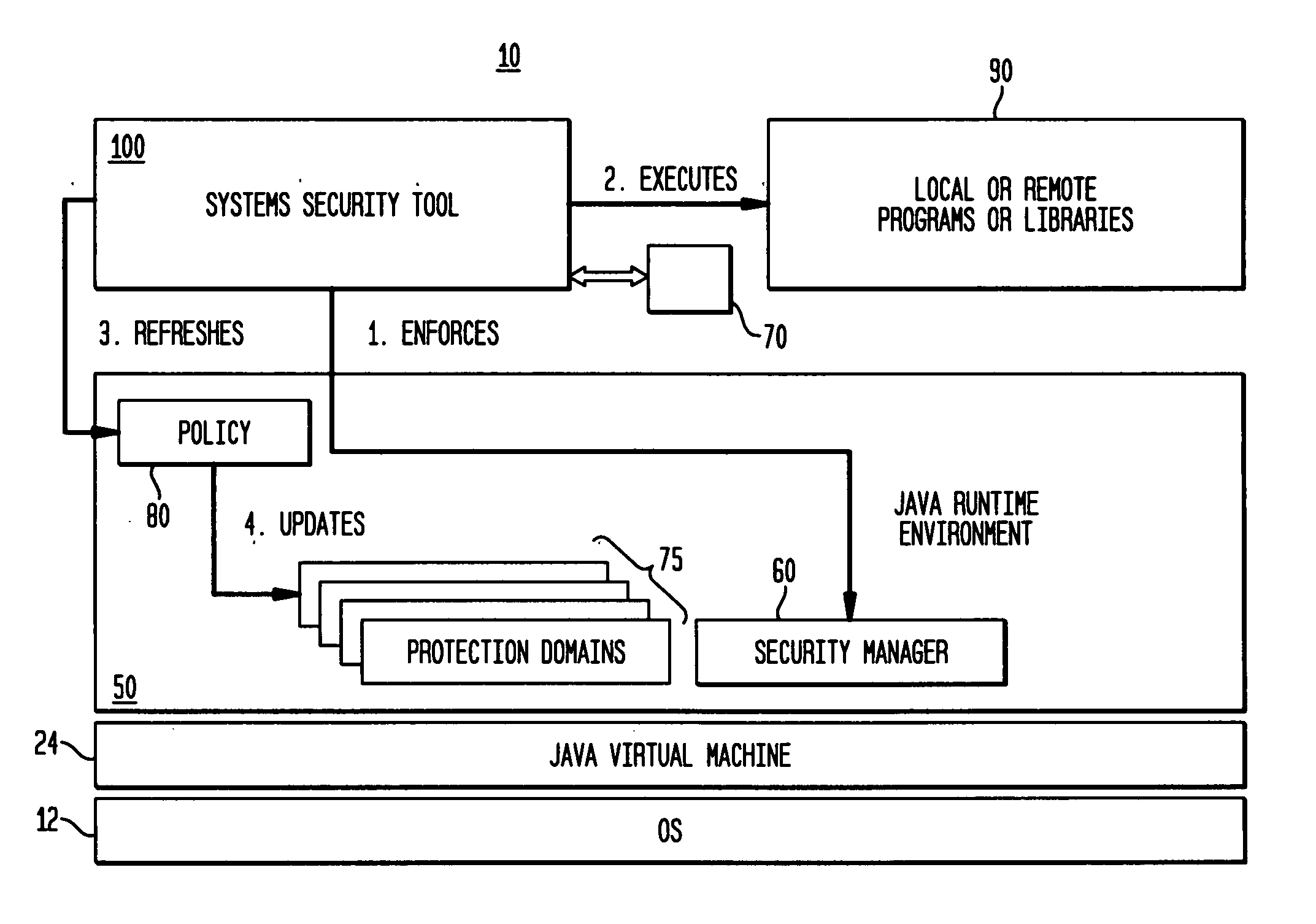
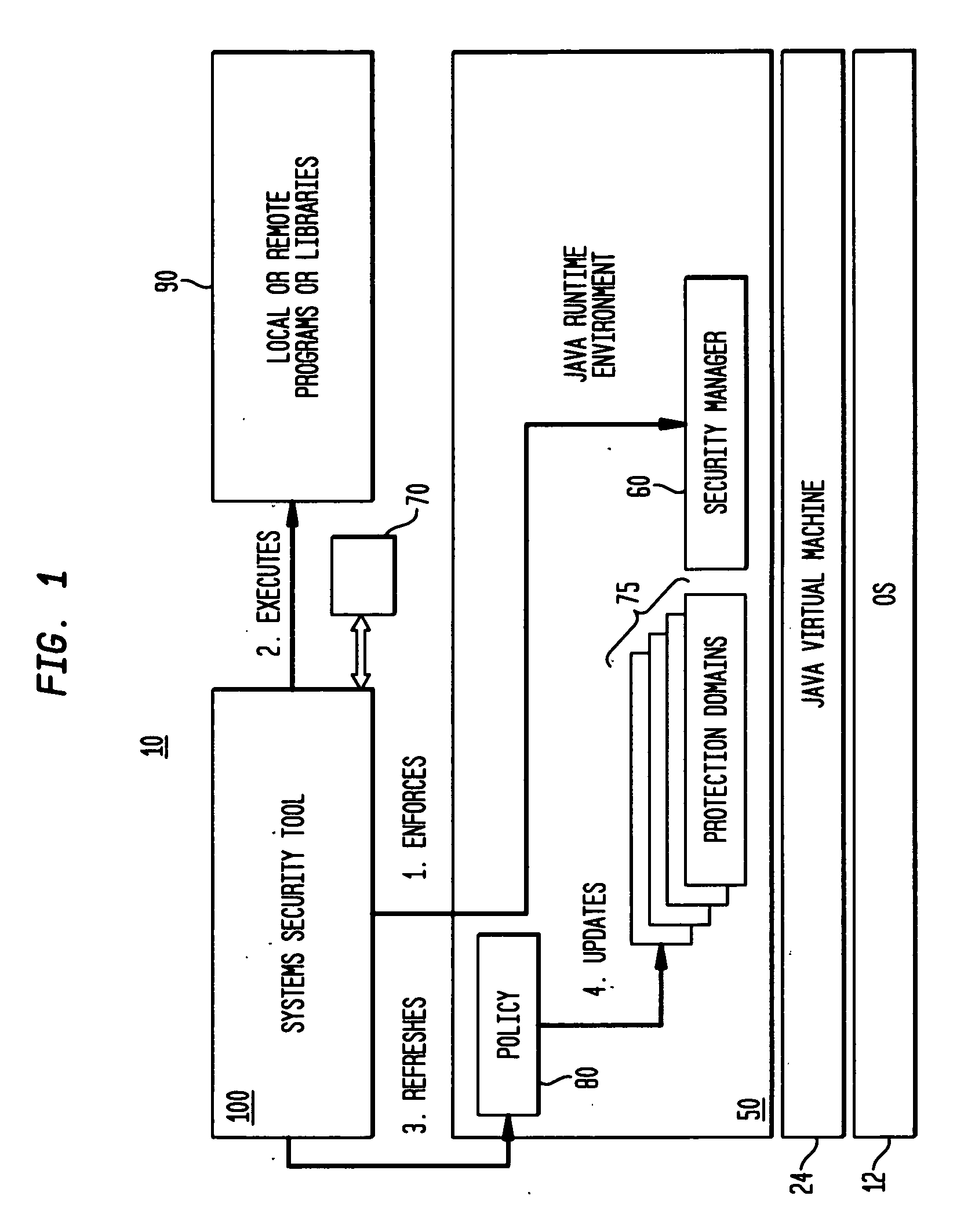
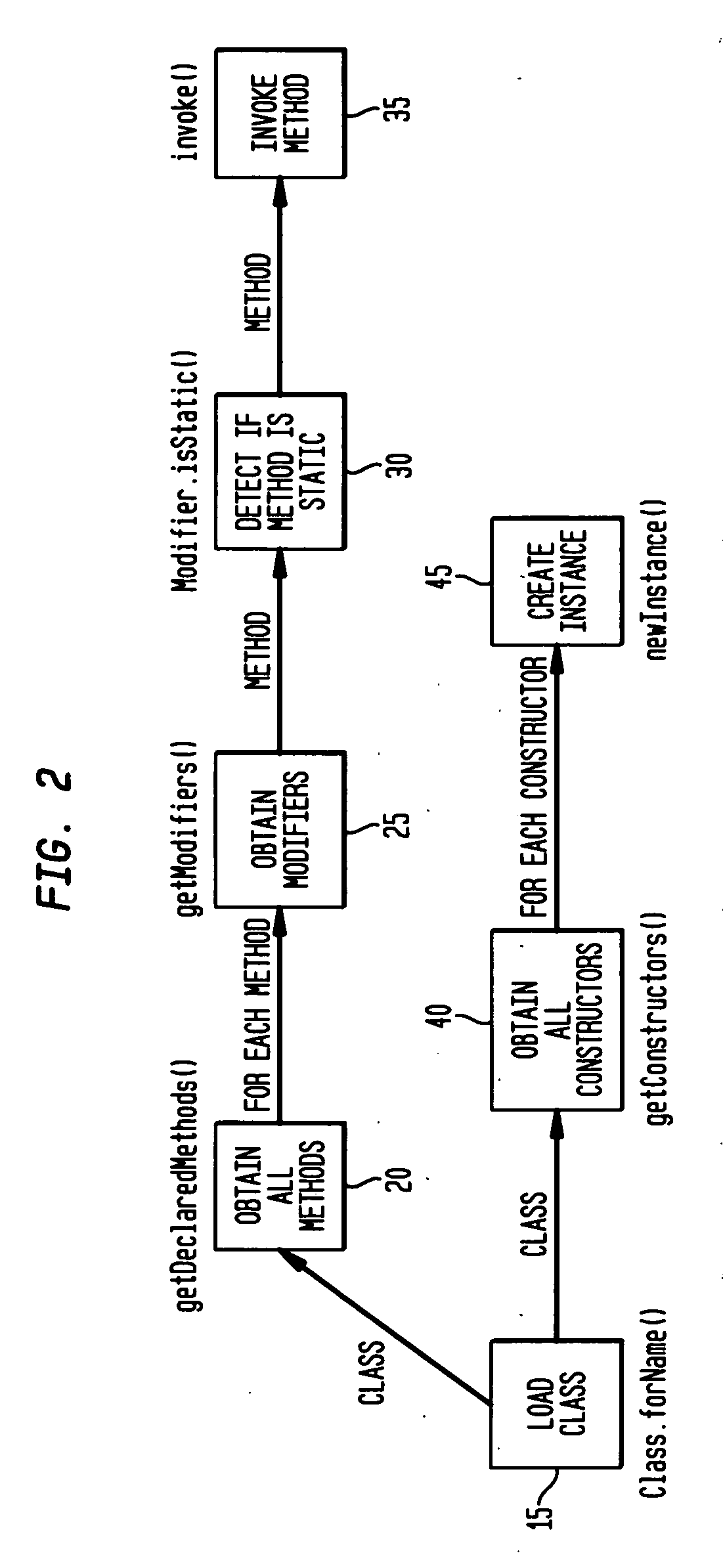
Method and system for run-time dynamic and interactive identification of software authorization requirements and privileged code locations, and for validation of other software program analysis results
InactiveUS20070261124A1Digital data processing detailsUser identity/authority verificationProgram analysisSecurity policy
A system, method and computer program product for identifying security authorizations and privileged-code requirements; for validating analyses performed using static analyses; for automatically evaluating existing security policies; for detecting problems in code; in a run-time execution environment in which a software program is executing. The method comprises: implementing reflection objects for identifying program points in the executing program where authorization failures have occurred in response to the program's attempted access of resources requiring authorization; displaying instances of identified program points via a user interface, the identified instances being user selectable; for a selected program point, determining authorization and privileged-code requirements for the access restricted resources in real-time; and, enabling a user to select, via the user interface, whether a required authorization should be granted, wherein local system, fine-grained access of resources requiring authorizations is provided.
Owner:IBM CORP
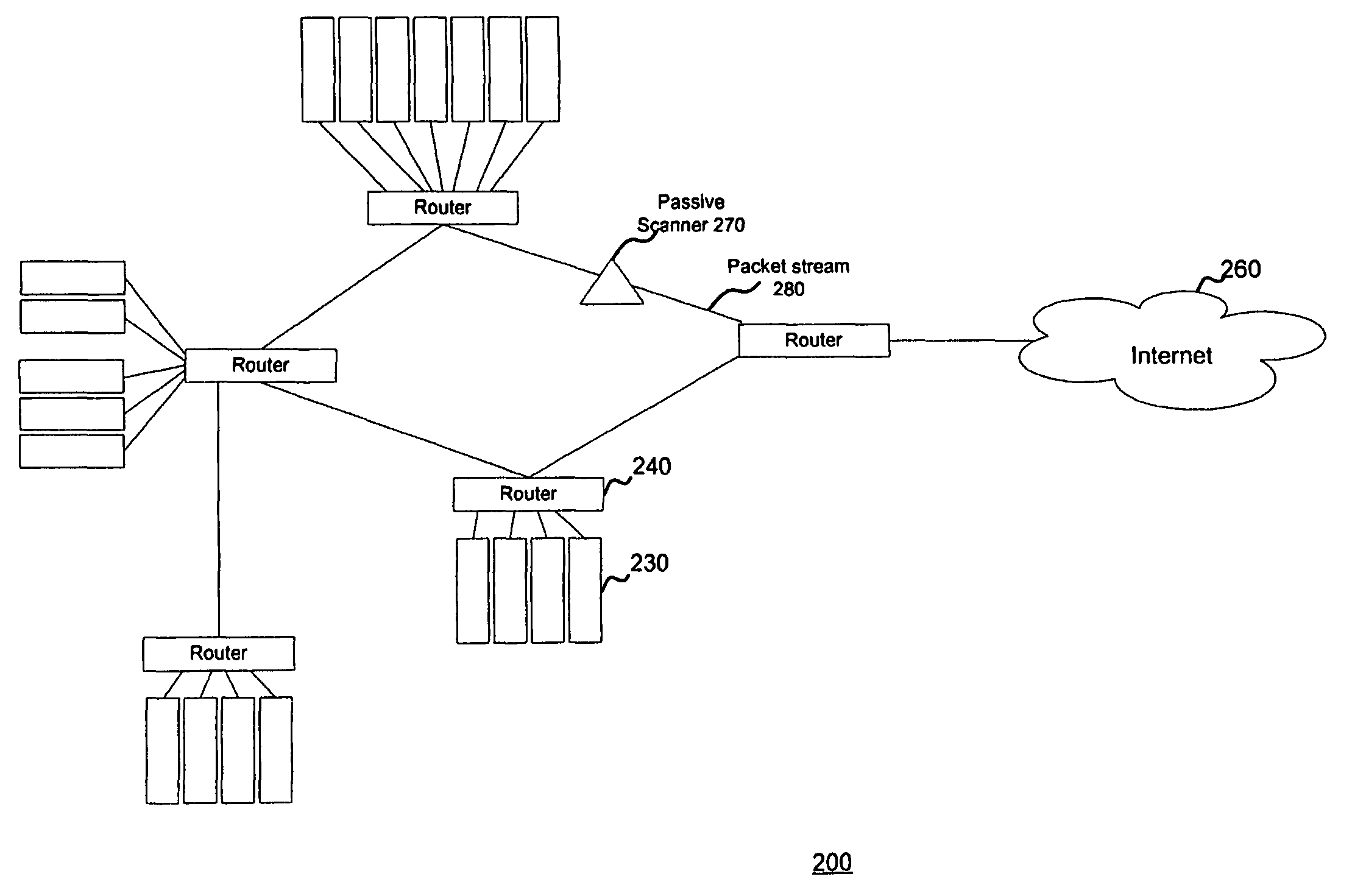
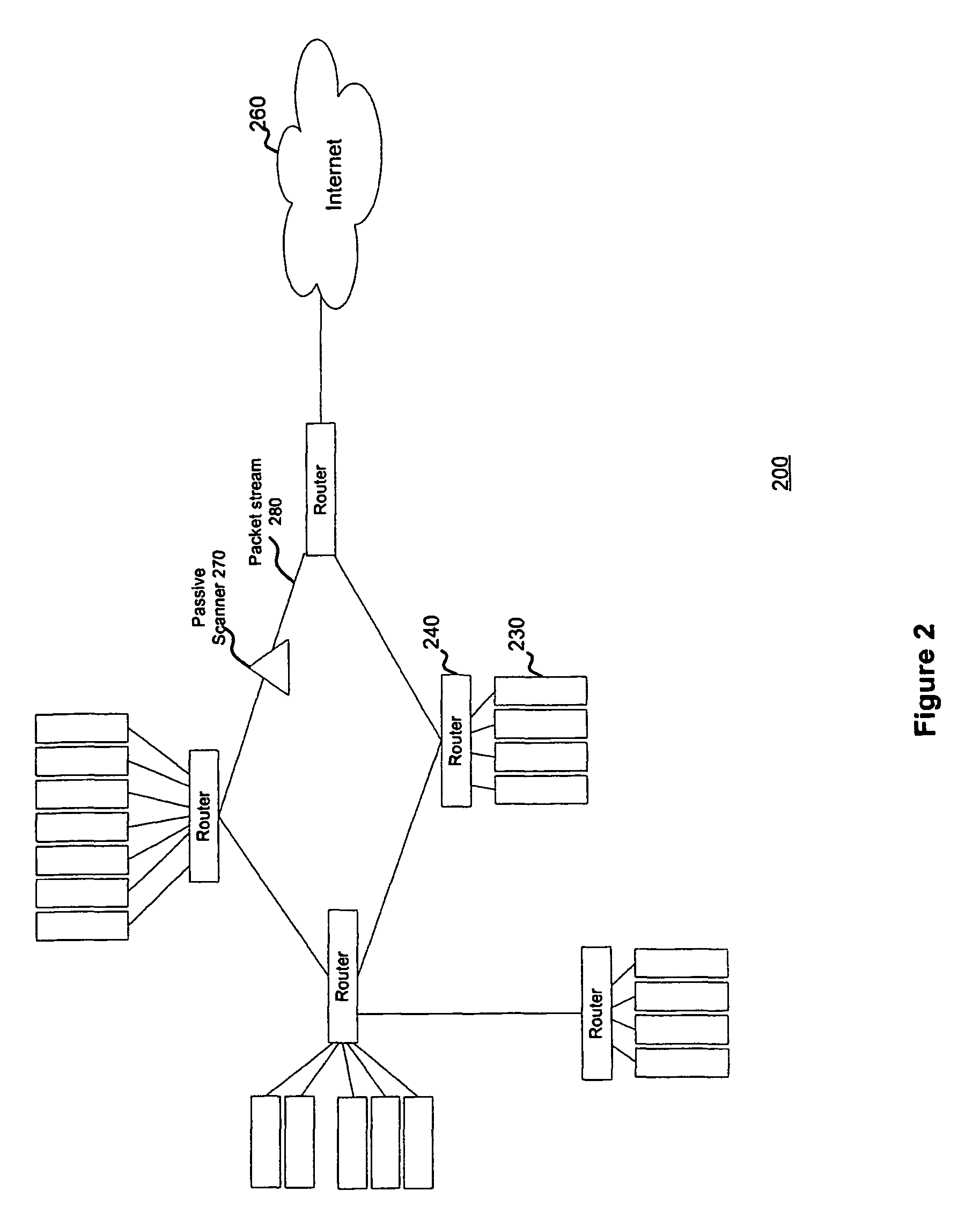
System and method for scanning a network
Systems and methods to passively scan a network are disclosed herein. The passive scanner sniffs a plurality of packets traveling across the network. The passive scanner analyzes information from the sniffed packets to build a topology of network devices and services that are active on the network. In addition, the passive scanner analyzes the information to detect vulnerabilities in network devices and services. Finally, the passive scanner prepares a report containing the detected vulnerabilities and the topology when it observes a minimum number of sessions. Because the passive scanner operates passively, it may operate continuously without burdening the network. Similarly, it also may obtain information regarding client-side and server side vulnerabilities.
Owner:TENABLE INC
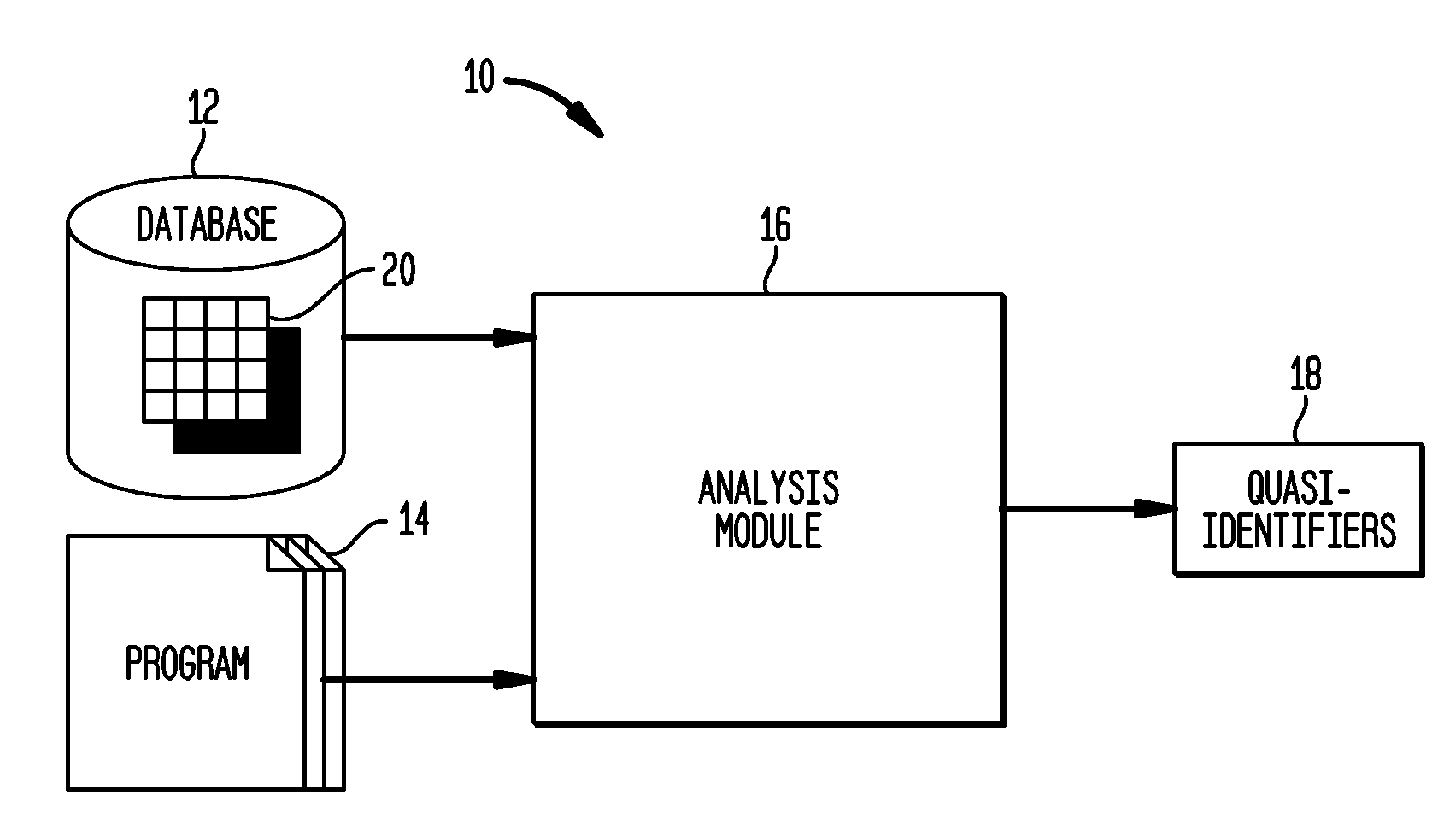
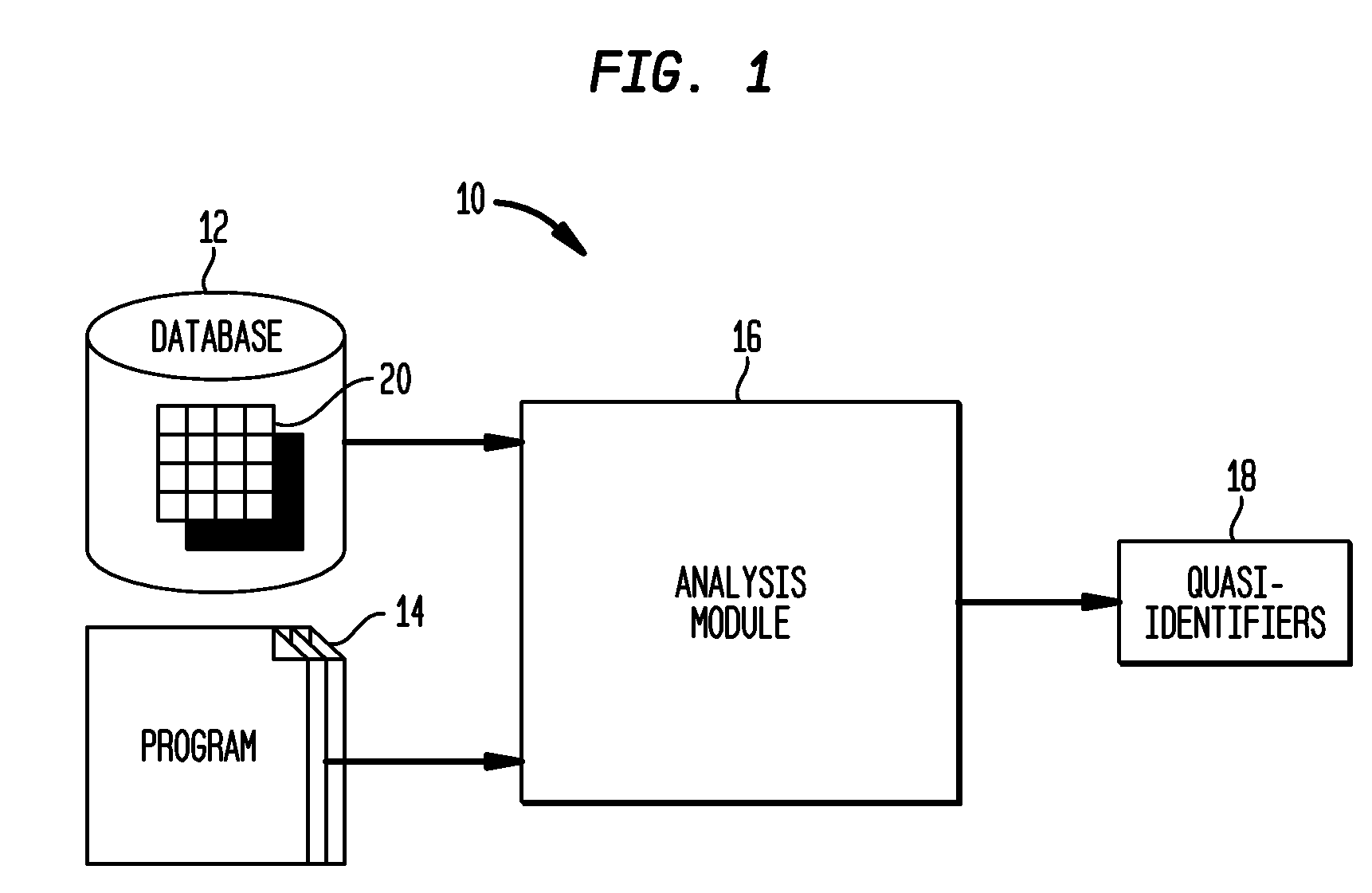
Automated Determination of Quasi-Identifiers Using Program Analysis
A system and method for automated determination of quasi-identifiers for sensitive data fields in a dataset are provided. In one aspect, the system and method identifies quasi-identifier fields in the dataset based upon a static analysis of program statements in a computer program having access to—sensitive data fields in the dataset. In another aspect, the system and method identifies quasi-identifier fields based upon a dynamic analysis of program statements in a computer program having access to—sensitive data fields in the dataset. Once such quasi-identifiers have been identified, the data stored in such fields may be anonymized using techniques such as k-anonymity. As a result, the data in the anonymized quasi-identifiers fields cannot be used to infer a value stored in a sensitive data field in the dataset.
Owner:TELCORDIA TECHNOLOGIES INC
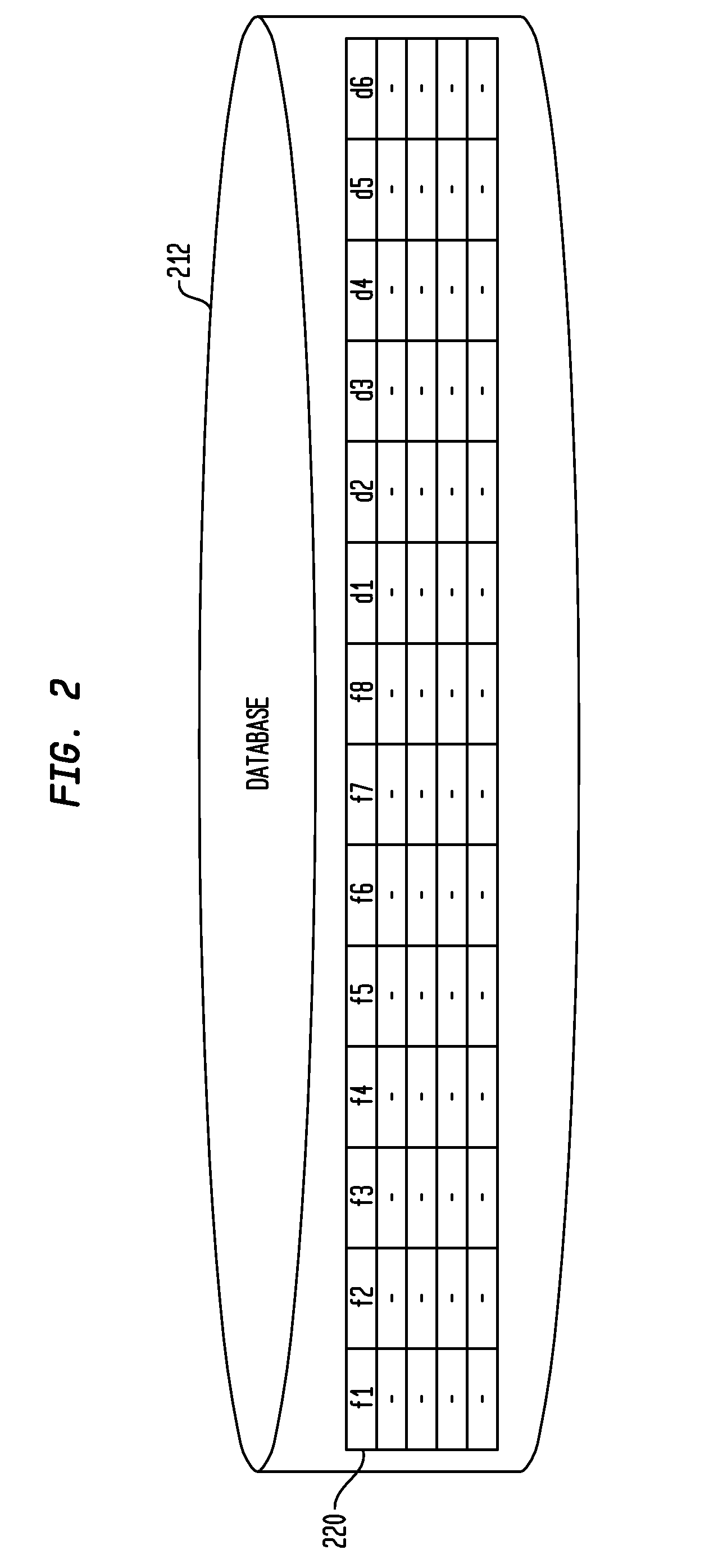
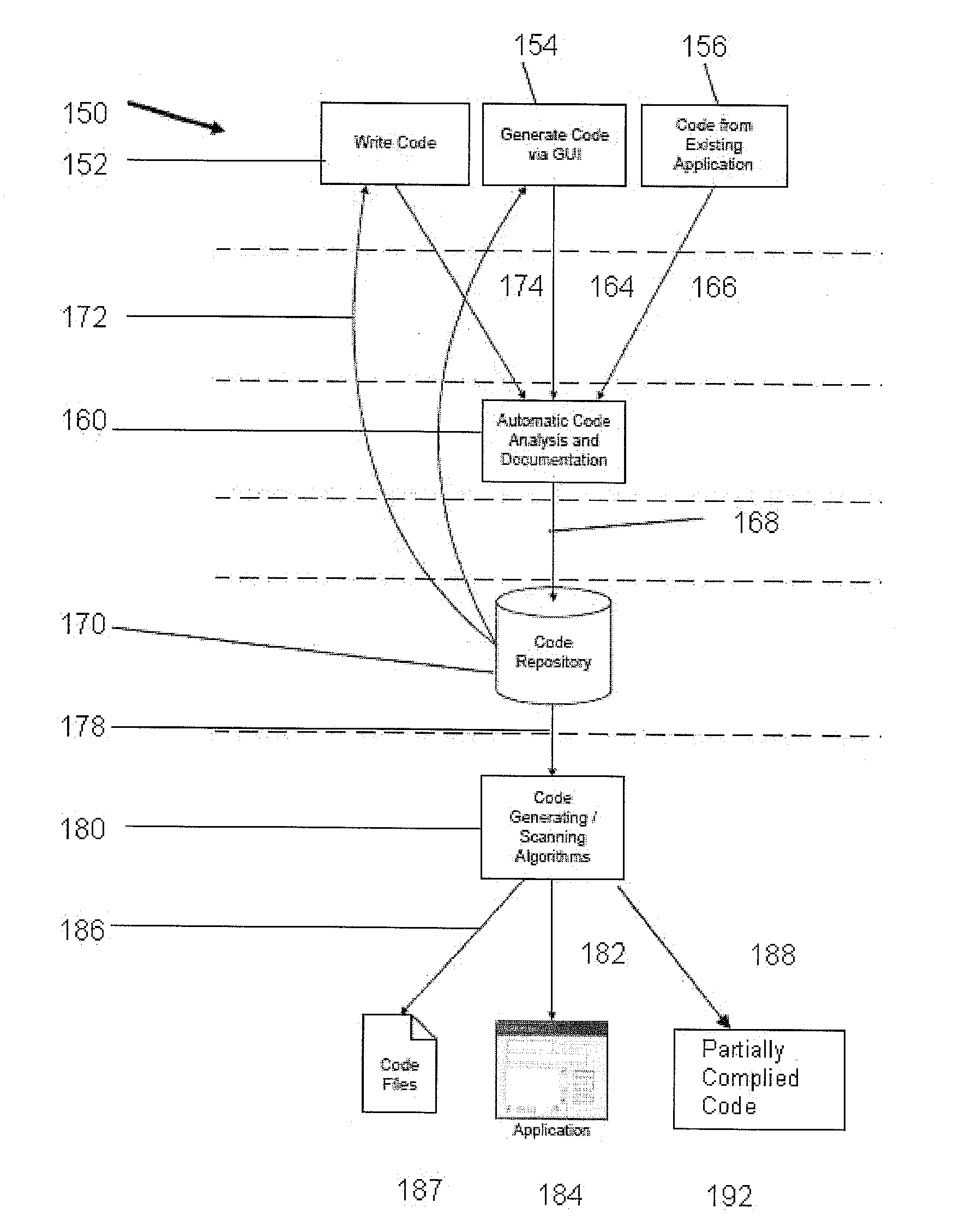
Software database system and process of building and operating the same
InactiveUS20120110030A1Digital data processing detailsCode refactoringDocumentation procedureProgram analysis
A software database system is provided that includes an automatic code analysis and self-documentation program. This program operating on a computer analyzes and fragments input code into constituent code segments and self-documents those segments. A code repository stores the code segments. A code-generating algorithm operating on a microprocessor extracts the code segments from the repository to generate a standard code page that is deployable on a server.
Owner:POMPONIO MARK
Method and system for run-time dynamic and interactive identification of software authorization requirements and privileged code locations, and for validation of other software program analysis results
ActiveUS20090007223A1Service is blockedOptimizationComputer security arrangementsTransmissionSystems approachesSecurity policy
Owner:INT BUSINESS MASCH CORP
Program analysis device, analysis method and program of same
InactiveUS20050204344A1Easy to trackImprove efficiencySoftware engineeringSpecific program execution arrangementsProgram analysisAnalysis method
A method for analyzing an original program to check an affected part by weaving an aspect and presenting the analysis result. An analysis device has an analysis processing portion for inputting a program based on aspect oriented programming, and acquiring data dependence information and control dependence information in the input program. A influence tracking portion tracks the data dependence and the control dependence acquired by the analysis processing portion starting from a position of weaving an aspect in the program, and searching a propagation path of the influence due the aspect weaving. A display control detects and displays a part undergoing the aspect weaving influence, based on the result of parsing by the analysis processing portion and information about the propagating path obtained by the influence tracking portion.
Owner:IBM CORP
Method for detecting code similarity based on semantic analysis of program source code
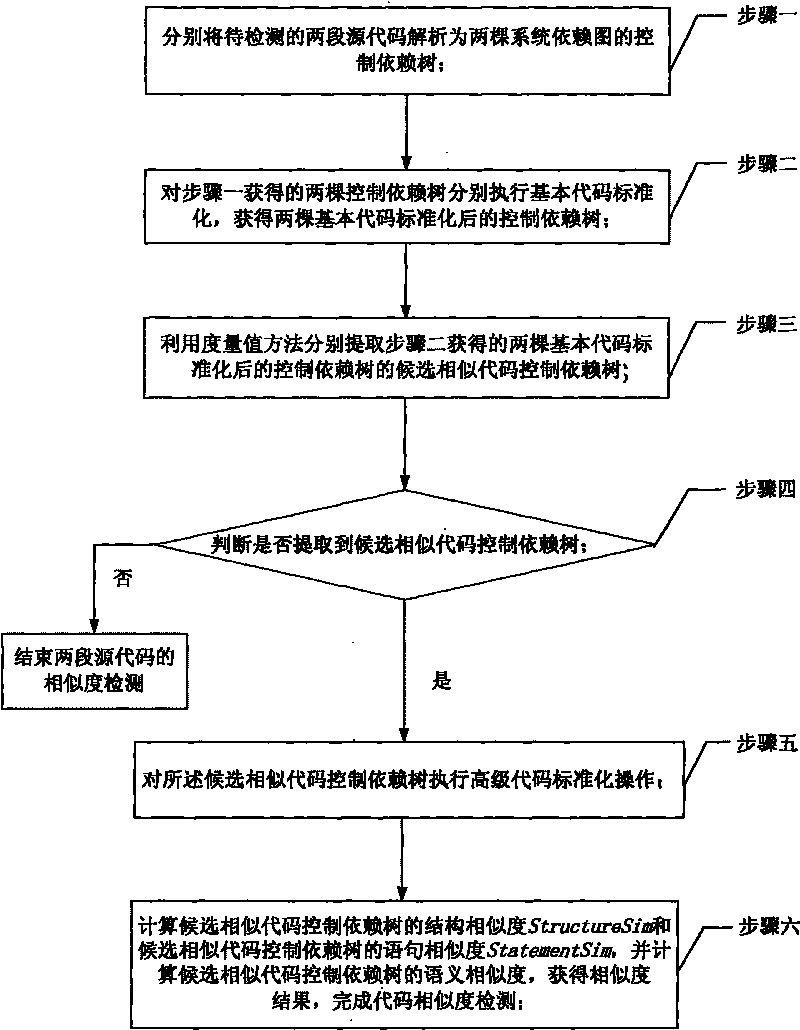
InactiveCN101697121AEliminate diversificationImprove accuracySpecial data processing applicationsSpecific program execution arrangementsComputation complexityProgram code
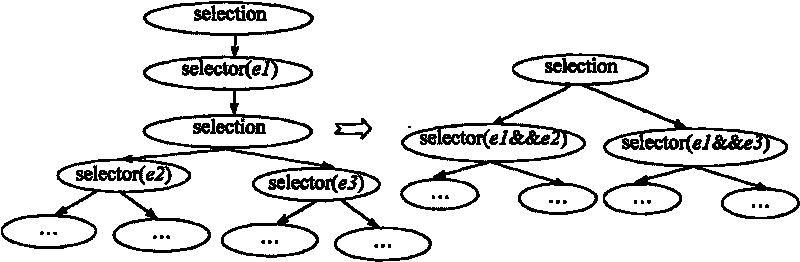
The invention discloses a method for detecting code similarity based on semantic analysis of a program source code, which relates to computer program analyzing technology and a method for detecting complex codes of computer software. The method solves the prior problems of low similarity detection accuracy and high computing complexity on the codes of different syntactic representations and similar semantemes, and also solves the problem of incapability of realizing large-scale program code similarity detection. The method comprises the following steps: resolving two segments of source codes to be detected into two control dependence trees of a system dependence graph respectively and executing basic code standardization respectively; utilizing a measure method to extract candidate similar code control dependence trees of the control dependence trees which are subjected to the basic code standardization; executing an advanced code standardization operation on extracted candidate similar codes; and computing semantic similarity to obtain a similarity result so as to finish the code similarity detection. The method is applied to source code piracy detection, software component library query, software defect detection, program comprehension and the like.
Owner:HARBIN INST OF TECH
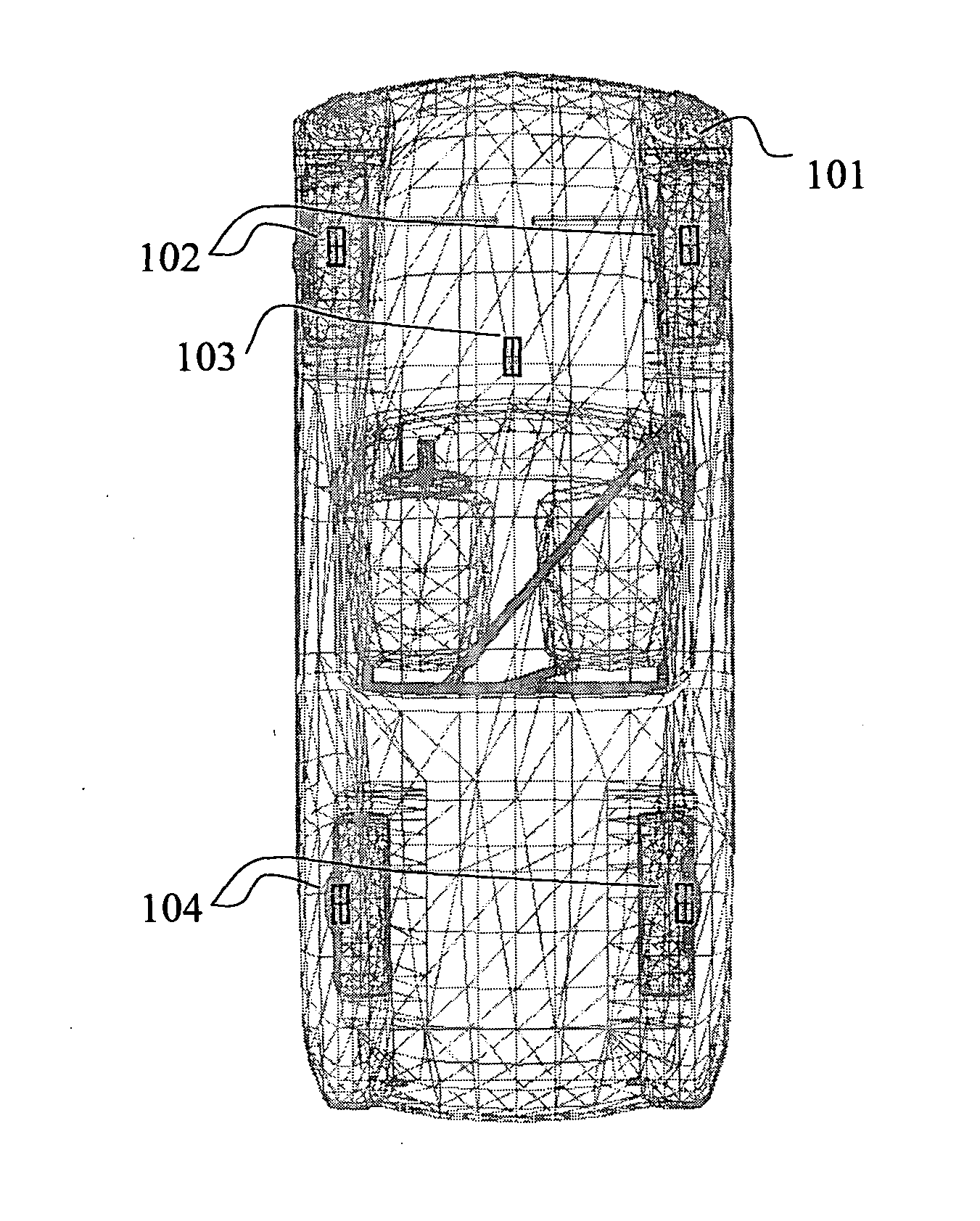
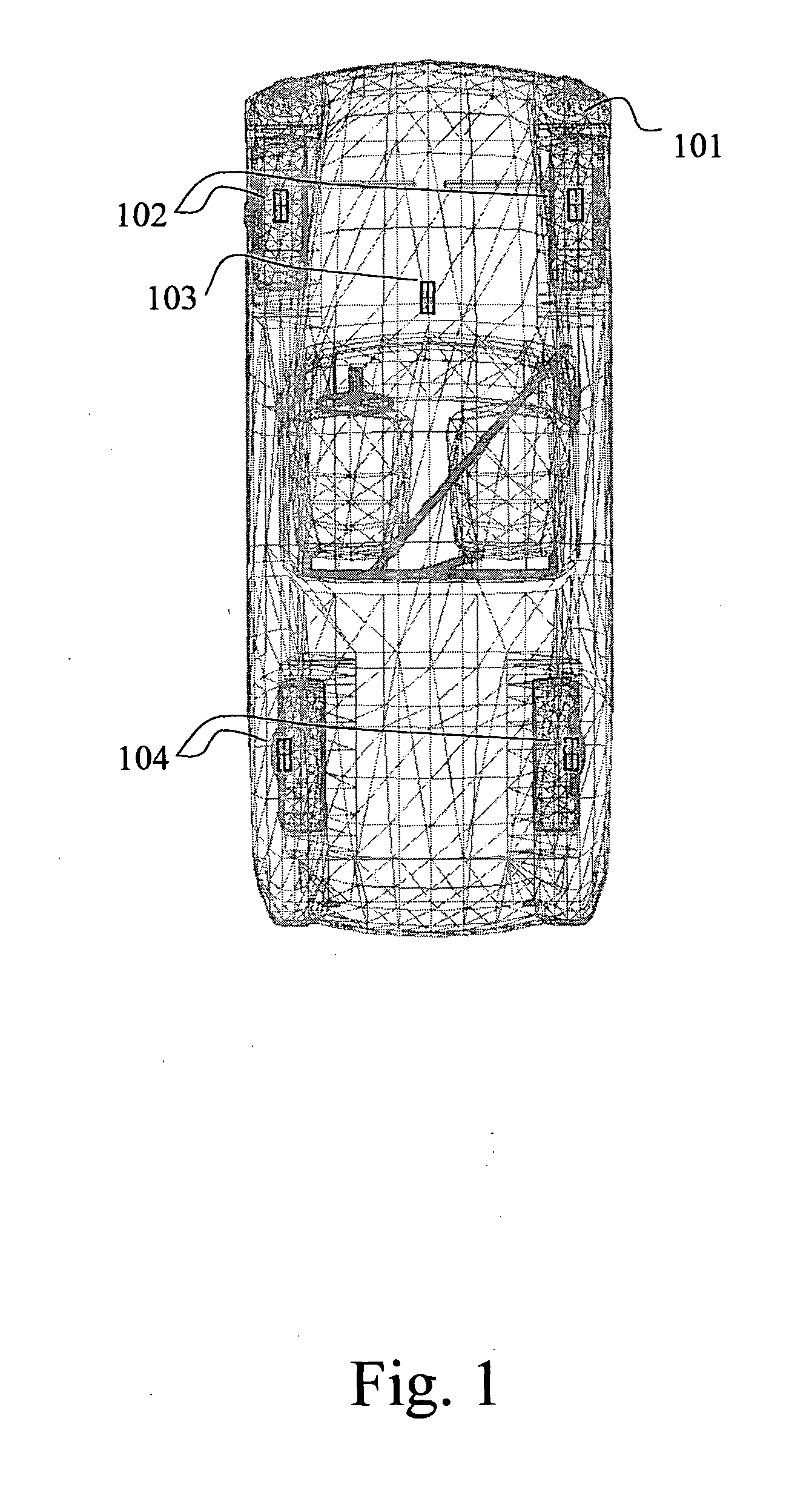
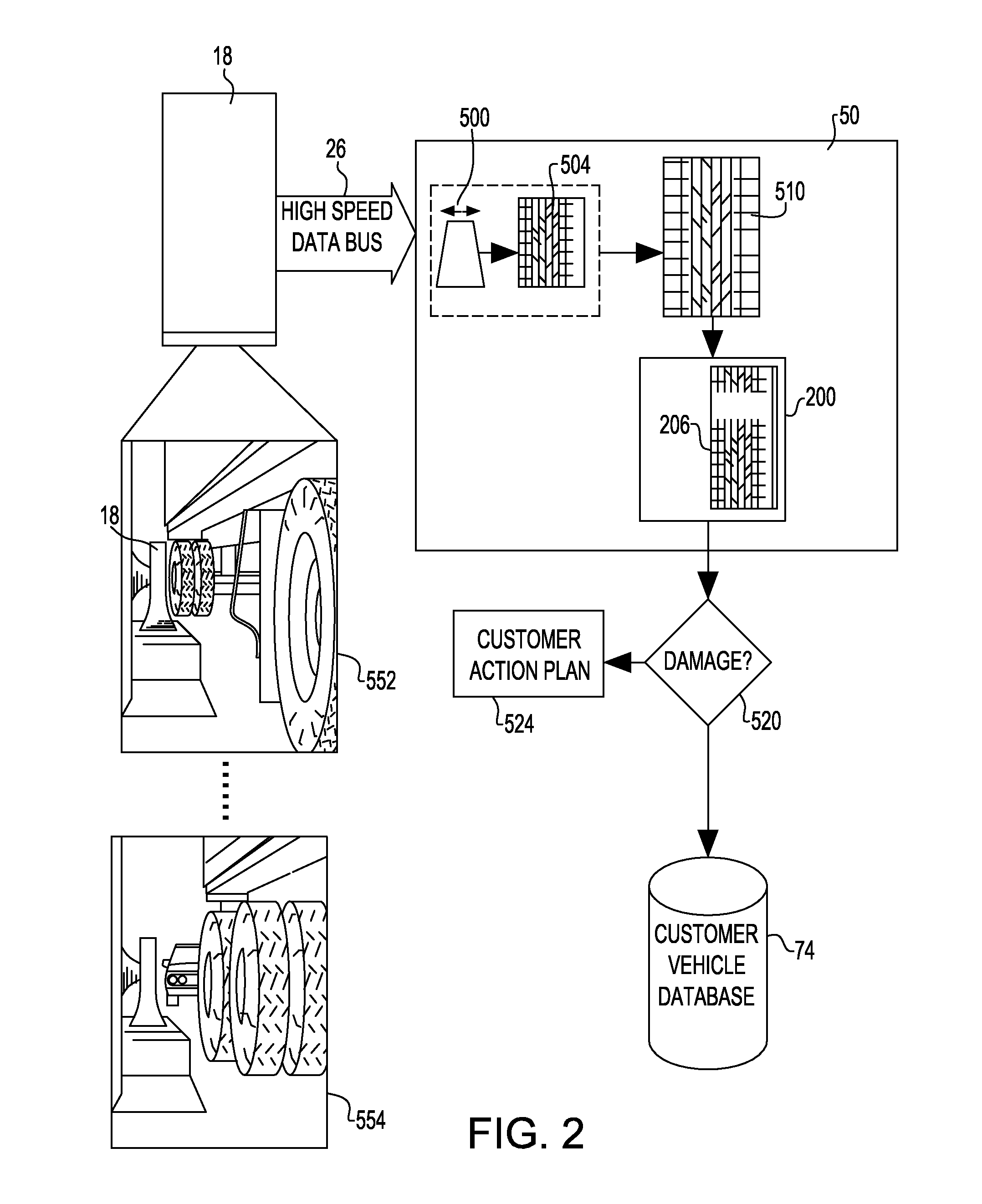
Computer vision aided automated tire inspection system for in-motion inspection of vehicle tires
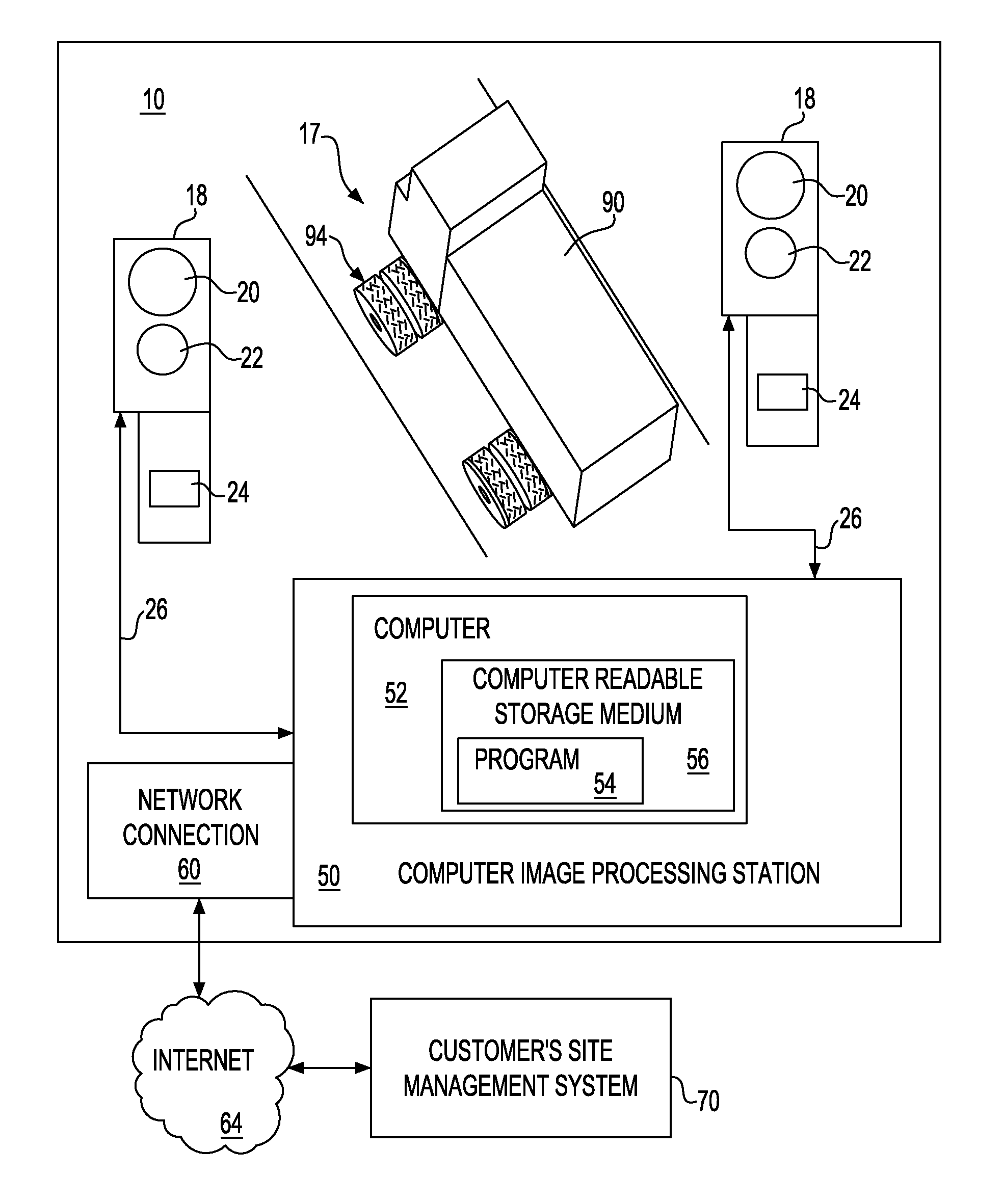
A system and method related thereto, for automatically inspecting at least one tire of a moving vehicle. The system includes an image acquisition device including at least one camera. The camera acquires multiple real-time images of at least one tire of a moving vehicle. As the tire of the vehicle enters a field of view of the camera, the camera component is configured to photograph and transmit the multiple photographs of the at least one tire. A light source illuminates the at least one tire of the vehicle in the field of view of the camera, and the light application may be synchronous with the imaging performed by the camera. A computer image processing component receives the multiple images transmitted from the camera and analyzes the multiple images using a detection program. The computer imaging processing component analyzing the photographs and provides an inspection analysis of each at least one tire.
Owner:NASCENT TECH
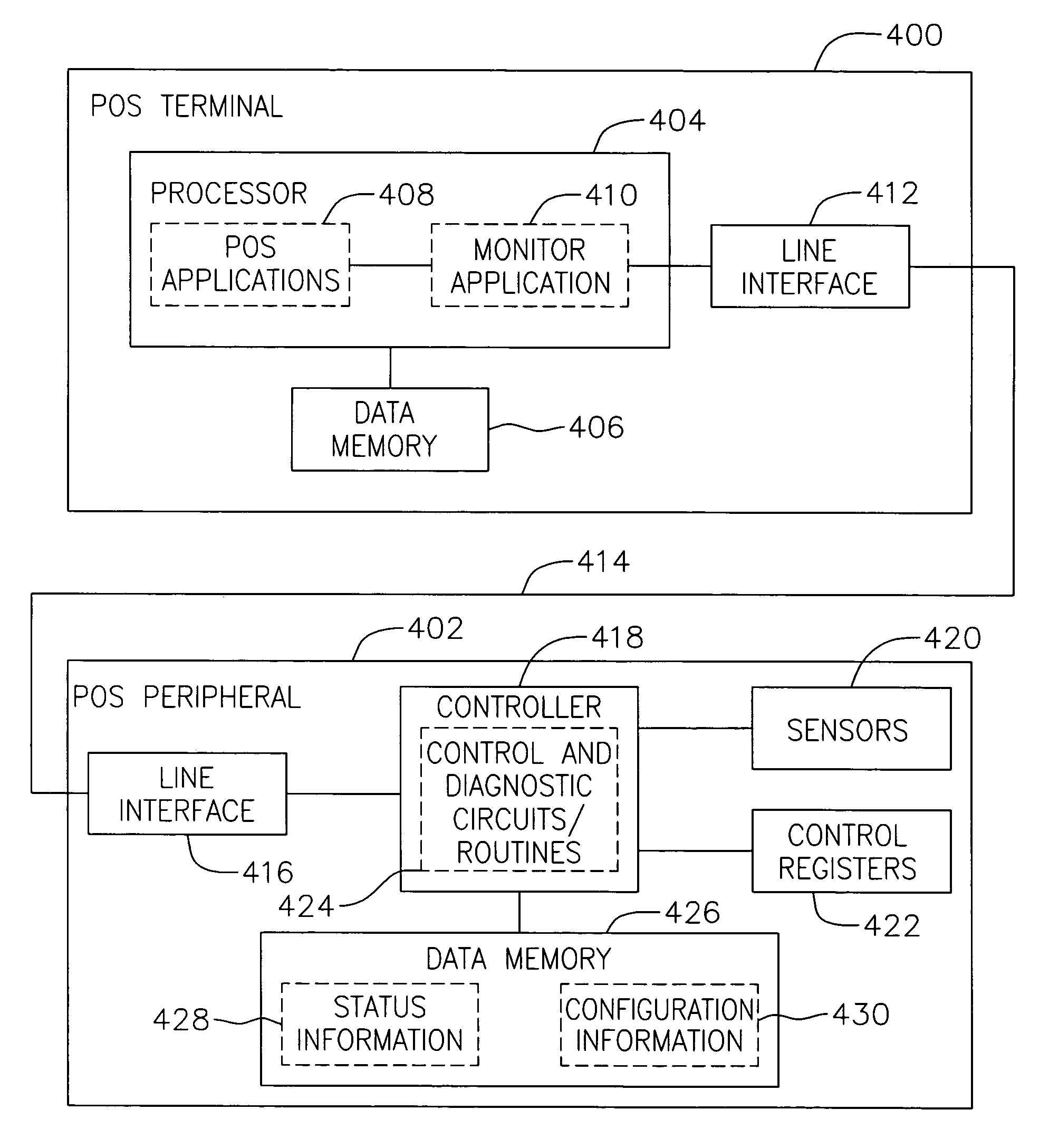
System and method for monitoring and diagnosis of point of sale devices having intelligent hardware
ActiveUS7232063B2Effective trackingDigital data processing detailsCash registersDevice MonitorDiagnostic information
A point-of-sale (“POS”) system includes POS devices and associated monitoring and diagnostic applications. POS peripherals in a POS device include data memory for storing device configuration and status information. A diagnostic application installed in the POS device monitors and diagnoses the POS device. The diagnostic application monitors the interactions between hardware in the POS device and applications that interface with the hardware. The diagnostic applications analyze these interactions, the configuration and status information and any logs it creates to provide diagnostic information. The POS device also includes several interfaces to access the diagnostic application.
Owner:FUJITSU FRONTECH NORTH AMERICA
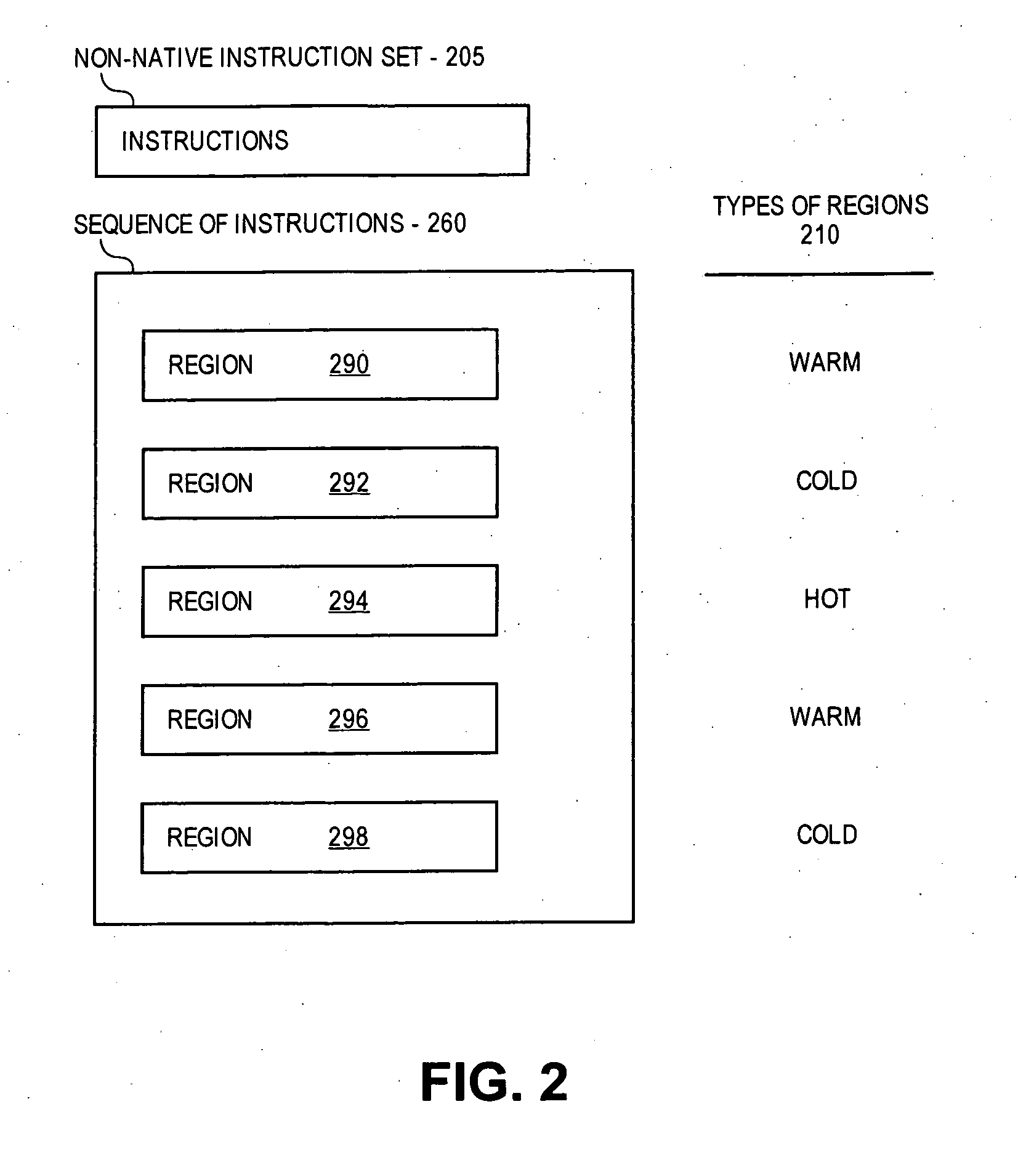
Compressing "warm" code in a dynamic binary translation environment
Selected regions of native instructions translated in a DBT environment from non-native instructions are compressed based on the independent compression of different fields of selected instructions using compression tables to reduce a length of selected fields. The regions of compressed instructions are stored and de-compressed into the native instructions during subsequent execution using de-compression tables. Specifically, for native instructions of a selected region, selected types of opcodes and / or operands may be compressed independently. The types may be selected by profiling the opcodes using benchmark programs and creating an opcode conversion table prior to compression, and scanning of the operands and creating an operand conversion table during compression of the opcodes.
Owner:INTEL CORP
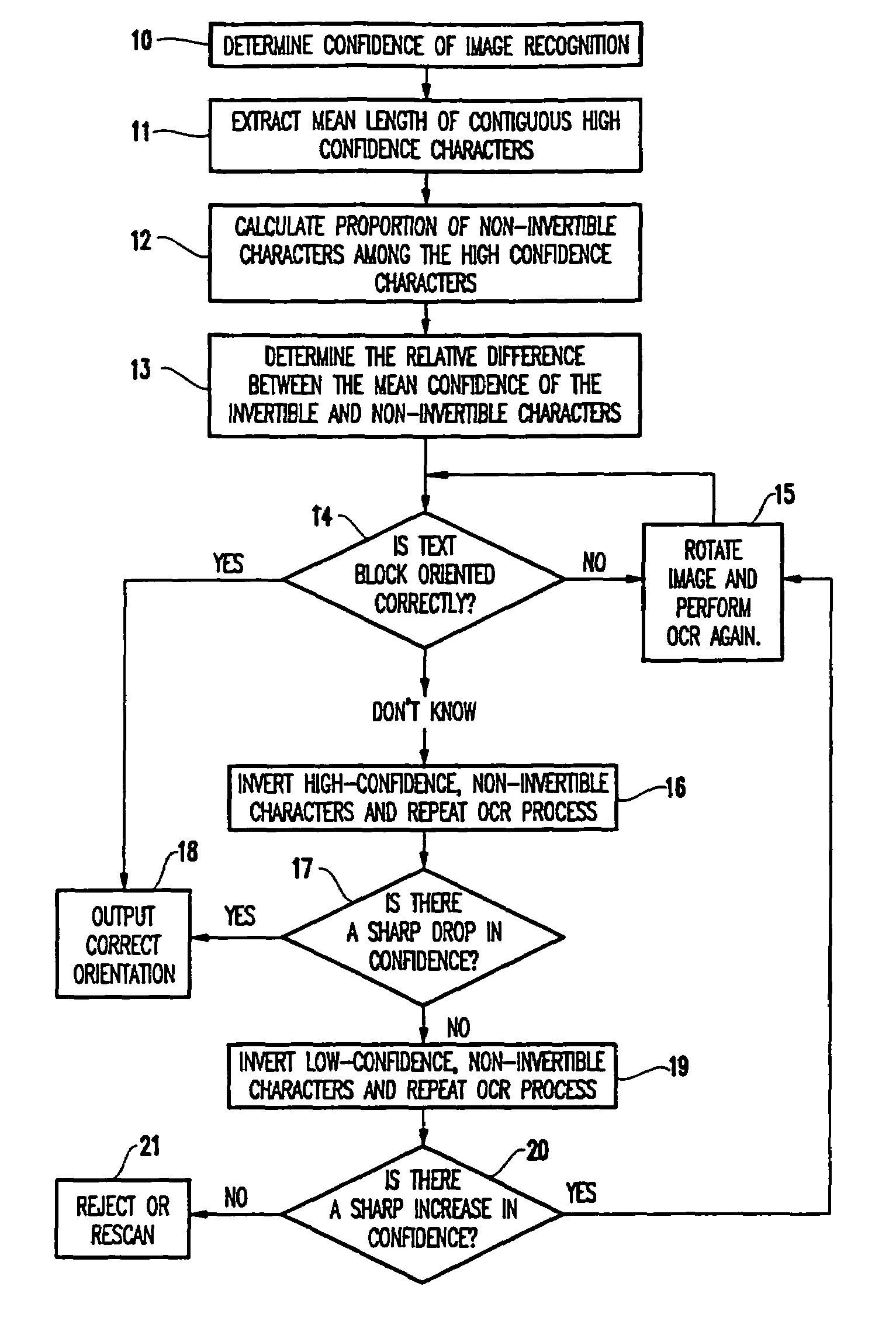
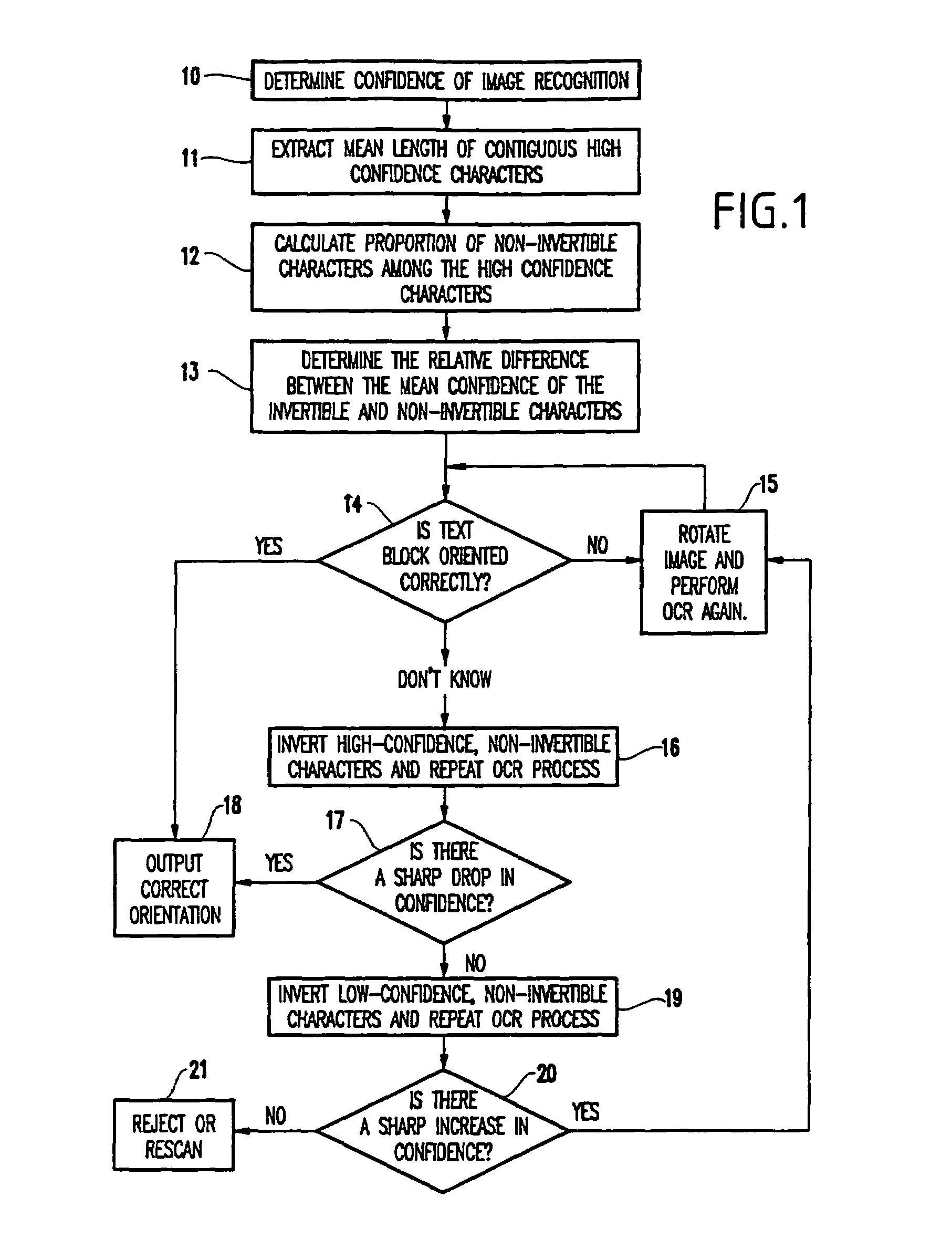
Automatic method of detection of incorrectly oriented text blocks using results from character recognition
InactiveUS6993205B1ConfidenceDecrease in confidenceCharacter recognitionProgram analysisConfidence measures
The invention determines the correct orientation of text blocks being processed with an optical character recognition computer program. The method determines a recognition confidence of characters in a text block being analyzed by the optical character recognition computer program and evaluates an orientation of the text block based on the recognition confidence.
Owner:TWITTER INC
System, method and article of manufacturing for a runtime program analysis tool for a simulation engine
A system is disclosed that provides a goal based learning system utilizing a rule based expert training system to provide a cognitive educational experience. The system provides the user with a simulated environment that presents a business opportunity to understand and solve optimally. Mistakes are noted and remedial educational material presented dynamically to build the necessary skills that a user requires for success in the business endeavor. The system utilizes an artificial intelligence engine driving individualized and dynamic feedback with synchronized video and graphics used to simulate real-world environment and interactions. Multiple "correct" answers are integrated into the learning system to allow individualized learning experiences in which navigation through the system is at a pace controlled by the learner. A robust business model provides support for realistic activities and allows a user to experience real world consequences for their actions and decisions and entails realtime decision-making and synthesis of the educational material. The system includes tools for analysis and display of a presentation as it is presented.
Owner:ACCENTURE GLOBAL SERVICES LTD
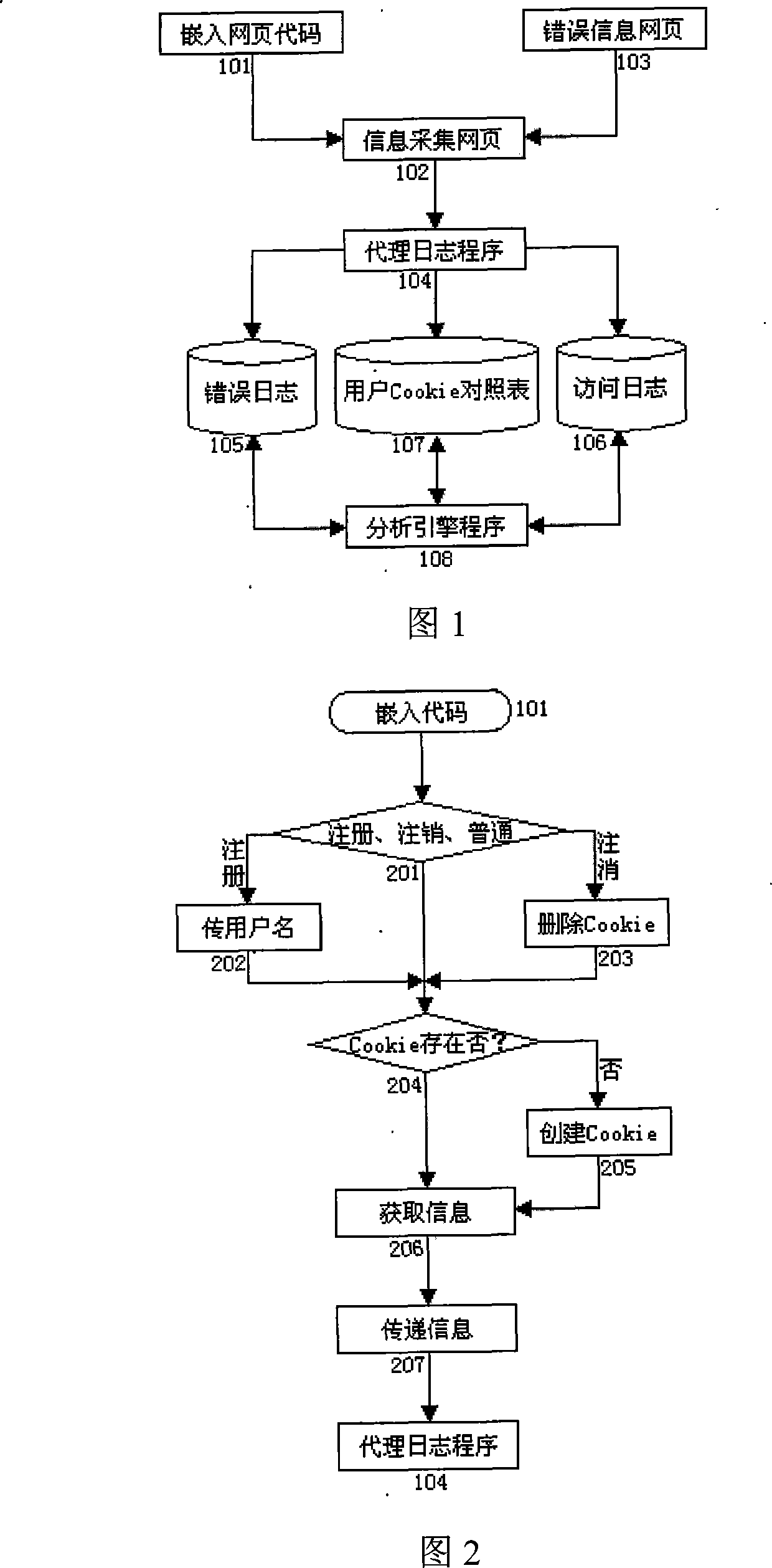
Website access analysis system and method based on built-in code proxy log
InactiveCN101242307AReflect real-timeAvoid statistical errorsData switching networksSpecial data processing applicationsWeb pageData mining
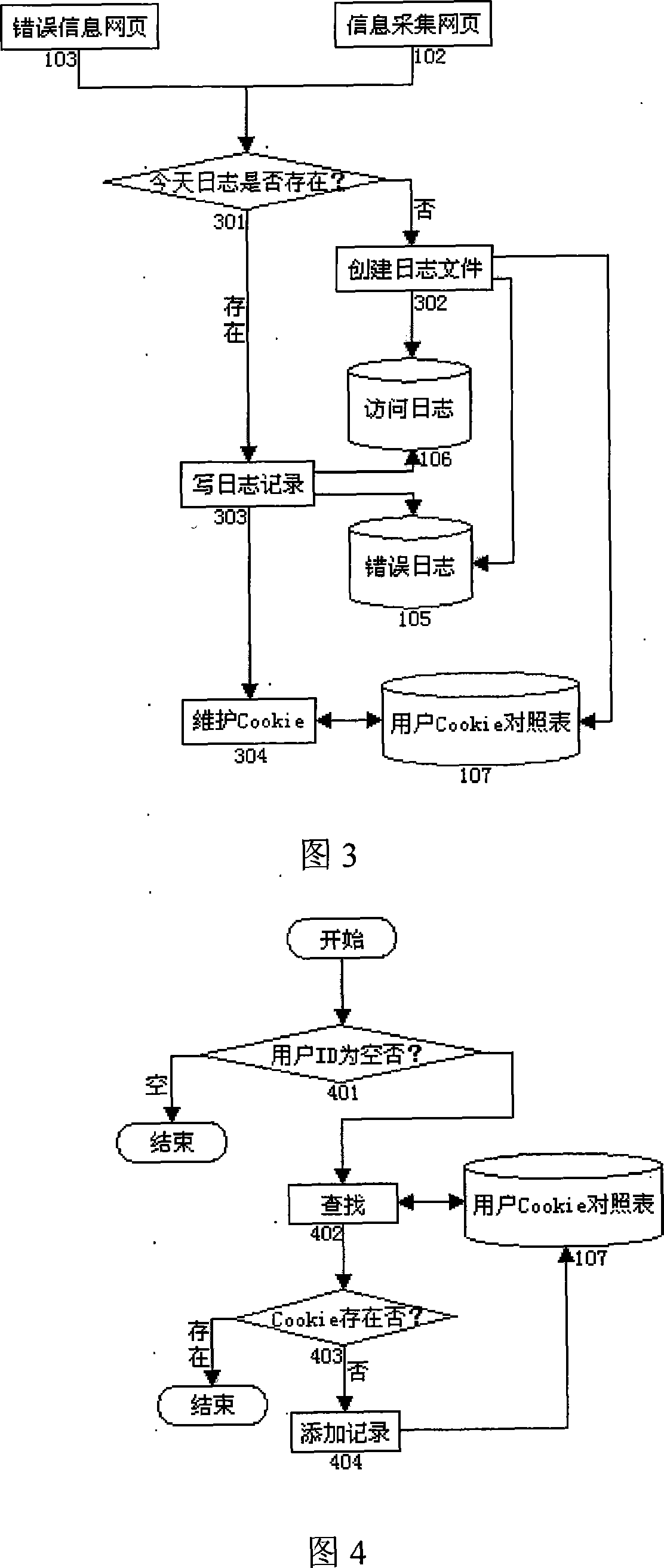
A system and a method for actualizing website access analysis by an agent log of embedded code relates to a website analysis system and a method, wherein the system comprises 'webpage-embedded code', 'information acquiring webpage', 'agent log server', 'agent log program', 'error information webpage', ' analysis engine server', and 'analysis engine program'; the webpage-embedded code and the error information webpage link invoke the information acquiring webpage, the information acquiring webpage invokes agent log program, and the agent log program records an access information to generate an access log, an error log and a cookie check list, and the analysis engine program analyzes the file generated by the agent log program. The invention combines two access analysis modes of 'embedded code' and 'log analysis', which satisfies require for rapid and real-time statistics, and uses log to record information to make a deep access analysis and data excavation convenient. The invention simplifies the complexity of the website access analysis system, and provides a better frame design solving scheme for the design of large-sized website access analysis system.
Owner:刘峰 +1
Method and apparatus for verifying data local to a single thread
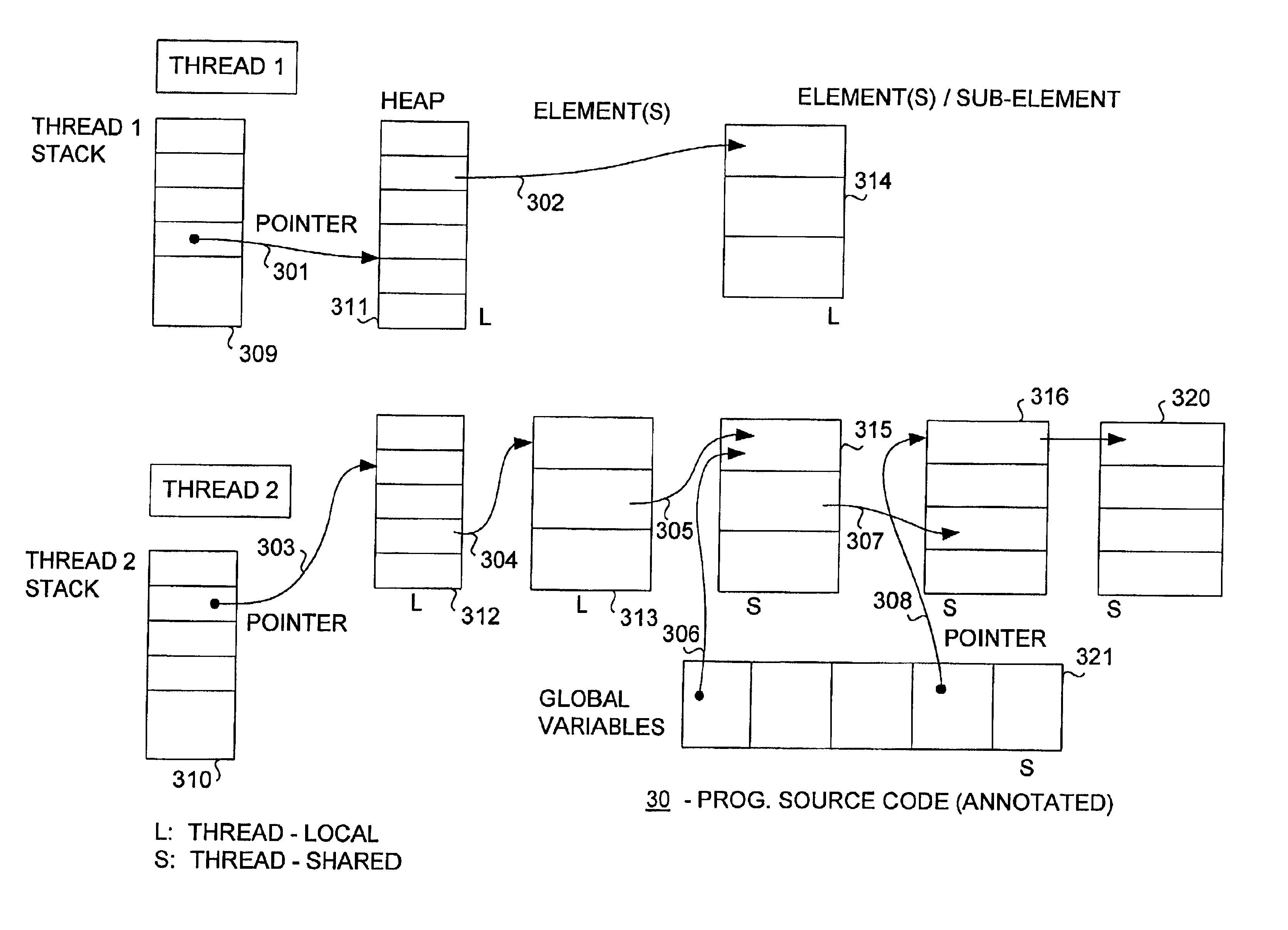
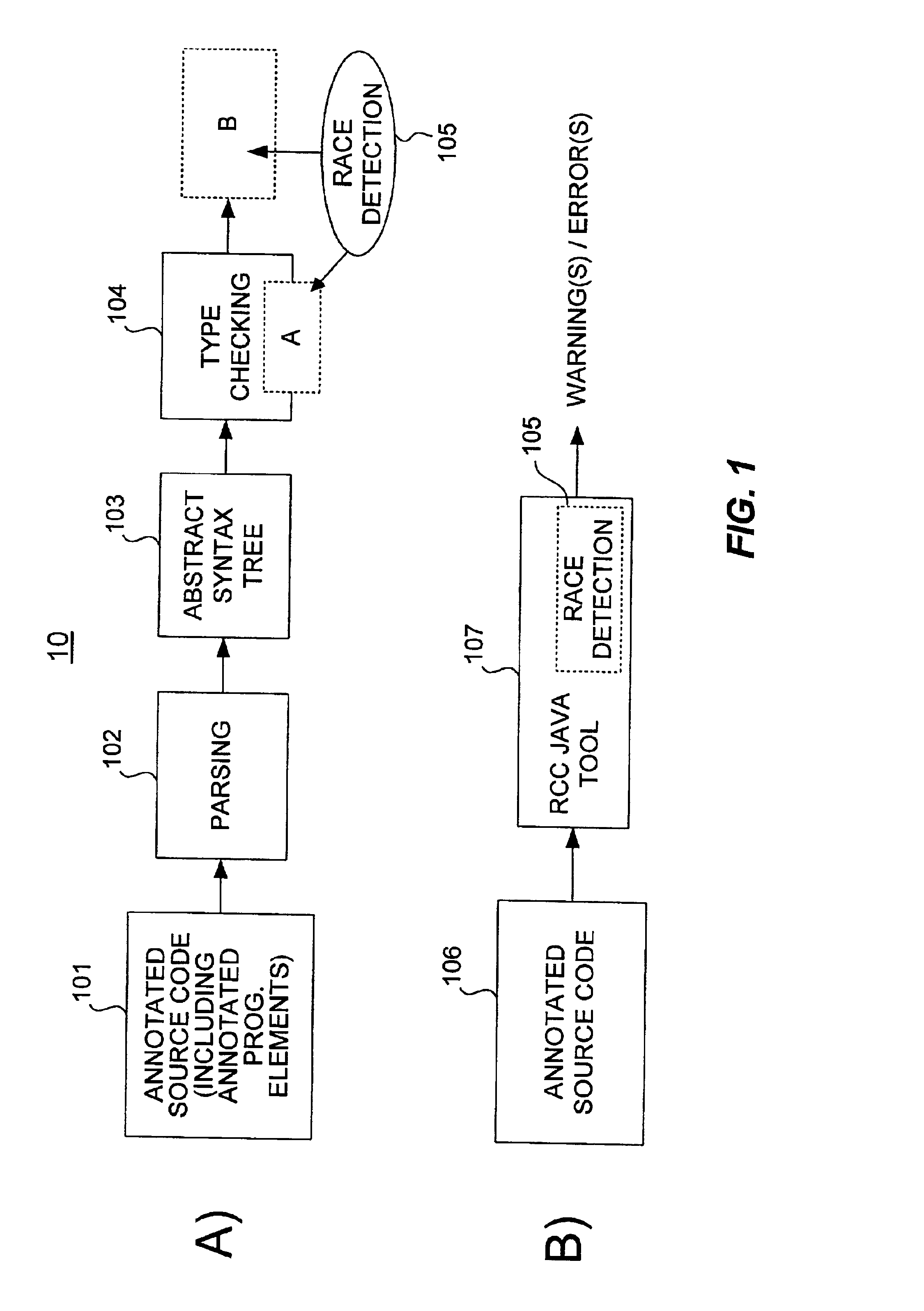
InactiveUS6817009B2Ensuring validityAccurate checkError detection/correctionSoftware engineeringProgram analysisSource code
Concurrent program analysis is fashioned for detecting potential race conditions such as data races in computer programs. One feature of this analysis is verifying annotations of addressable resources in a program. Annotations are verified by checking if thread-local resources are indeed thread-local, and that thread-shared data spaces are not in fact thread-local. Another feature is detecting potential race conditions, such as data races, in the computer program. The computer program can spawn a plurality of threads that are capable of being executed concurrently. The source code of the computer program being analyzed includes an element annotated as either thread-local or thread-shared. The validity of the thread-local annotation is verified if the element is annotated in the computer program as thread-local, wherein an invalid thread-local annotation may cause a race condition.
Owner:VALTRUS INNOVATIONS LTD +1
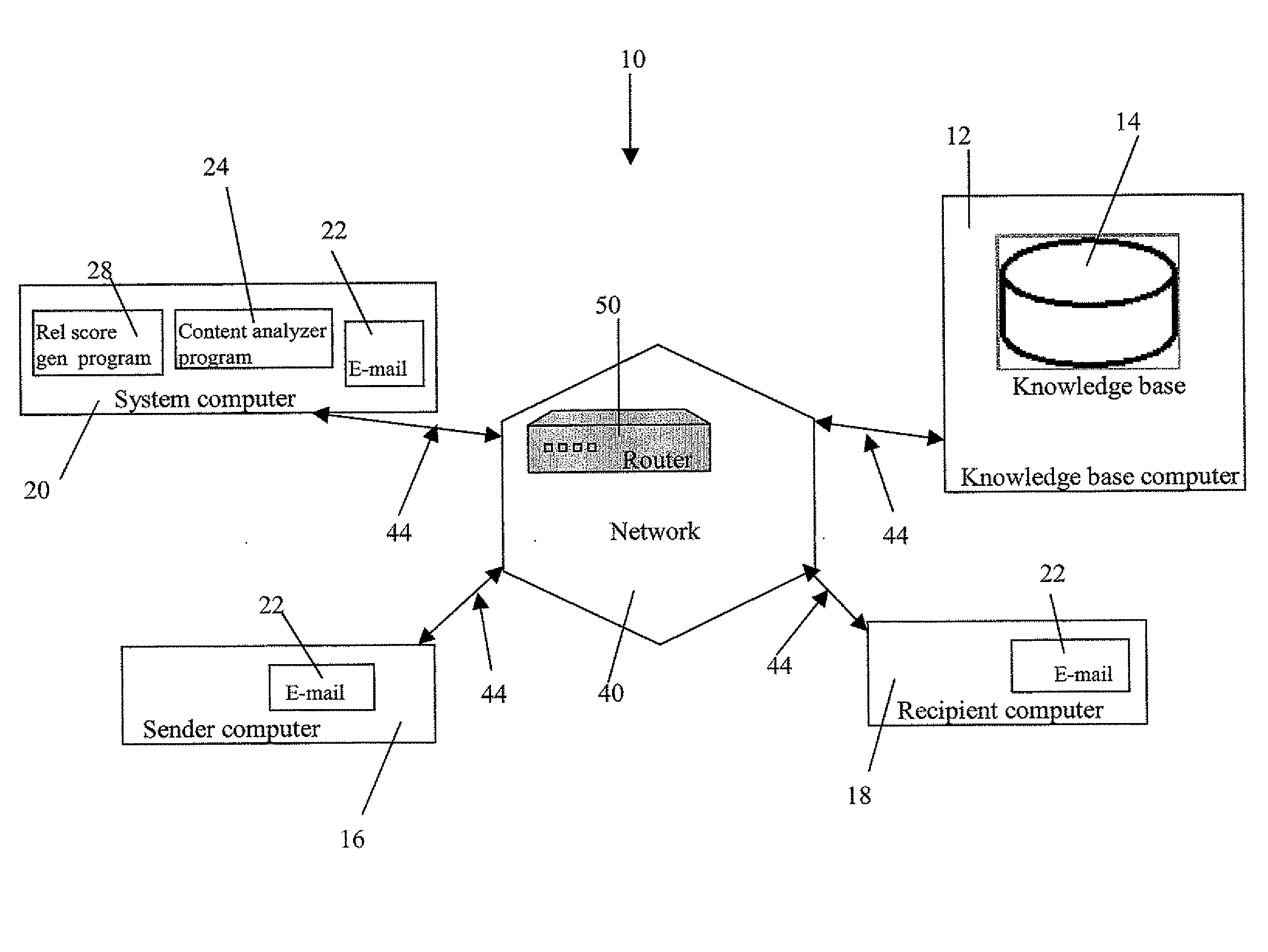
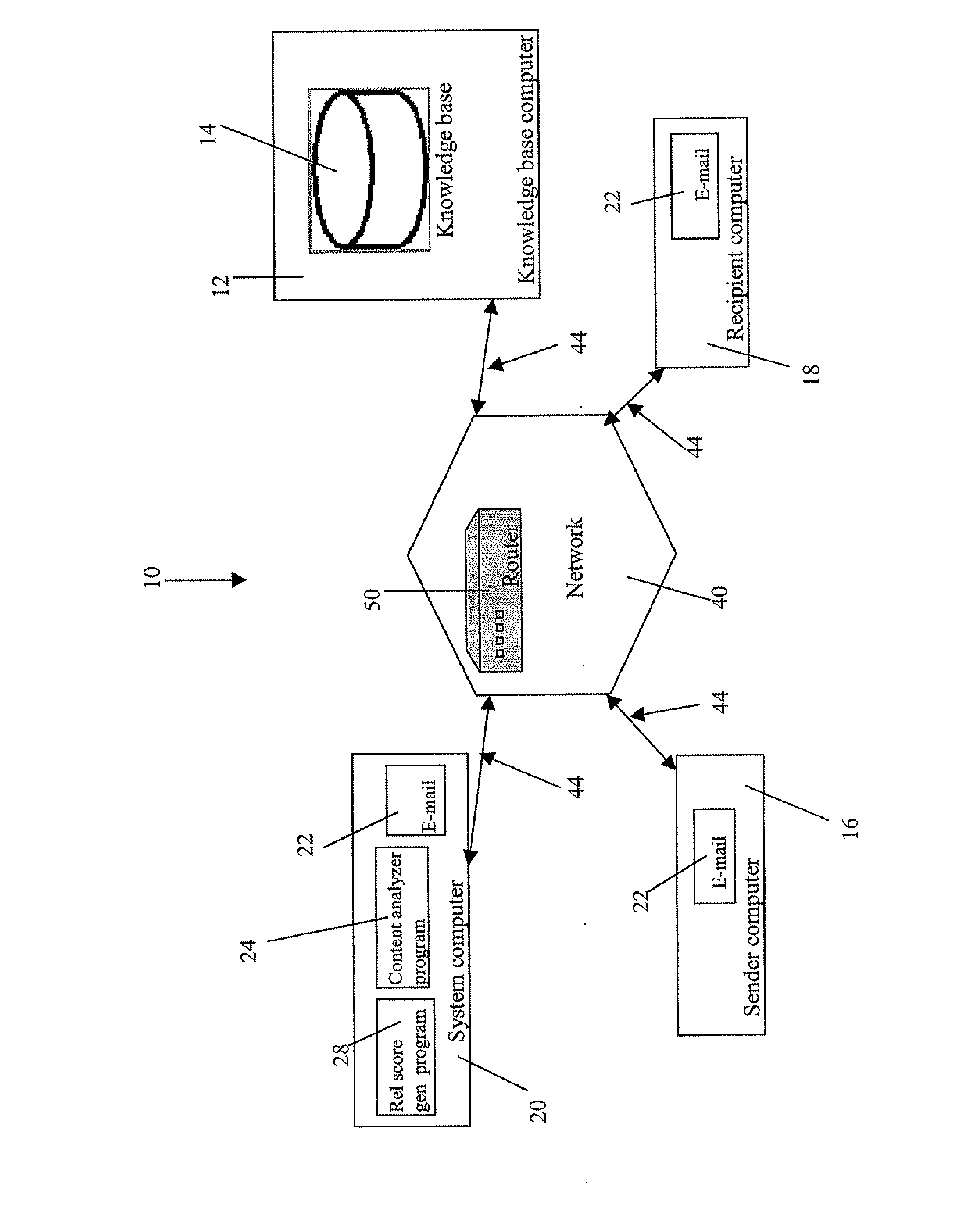
Content based routing of misaddressed e-mail
An e-mail routing system includes an e-mail program on a plurality of computers using a network for an e-mail system to minimize receipt of misaddressed e-mails. A knowledge base or database contains reference data associated with each of the recipient e-mail addresses in the e-mail system. A content analyzer program analyzes e-mail content data. A relevancy score generator program generates a relevancy score for each e-mail recipient. The relevancy score is derived from associating the reference data corresponding to each possible recipient e-mail addresses with the e-mail data. A specified minimal relevancy score is selected and low relevancy score recipient e-mails are associated by the content analyzer program with a plurality of possible recipient e-mail addresses having high relevancy scores. The relevancy score generator program selects at least one recipient from the possible recipient e-mail addresses and initiates sending the selected recipient the corresponding e-mail(s) using the e-mail program.
Owner:IBM CORP
Determination of regions of an analytical image that are subject to vital movement
ActiveUS20100125195A1Easy to detectEasy to identifyUltrasound therapyImage enhancementRadiologyProgram analysis
The present invention relates to a determination method for making it possible to determine the position of a body part subject to vital movement that is to be irradiated, by means of determining a region of an analytical image,wherein the region represents a body part subject to vital movement, in particular a tumor in an anatomical body, and performs a change in position from one analytical image to the next that reflects the vital movement, wherein the body parts subject to vital movement are parts of the body that are to be irradiated or are not to be irradiated and that move as a result of vital functions such as respiration and / or heartbeat even when the anatomical body is otherwise kept deliberately at rest,advance analytical image data, which includes the description of an advance analytical image having an advance region in which a first body part subject to vital movement is represented, is provided,procedure analytical image data that includes the description of a procedure analytical image of the body structure is provided,on the basis of the advance analytical image data and the procedure analytical image data, a procedure region, which corresponds to the advance region and occupies a procedure position in the procedure analytical image, is determined in the procedure analytical image,wherein a) determination of the procedure position of the procedure region is based on movement data that includes information on the vital movements of the body parts that are caused by the vital functions, and / or b) determination of the position of a second body part subject to vital movement is based on the determined procedure position and information on the relative position between the first and the second body part subject to vital movement.
Owner:BRAINLAB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com