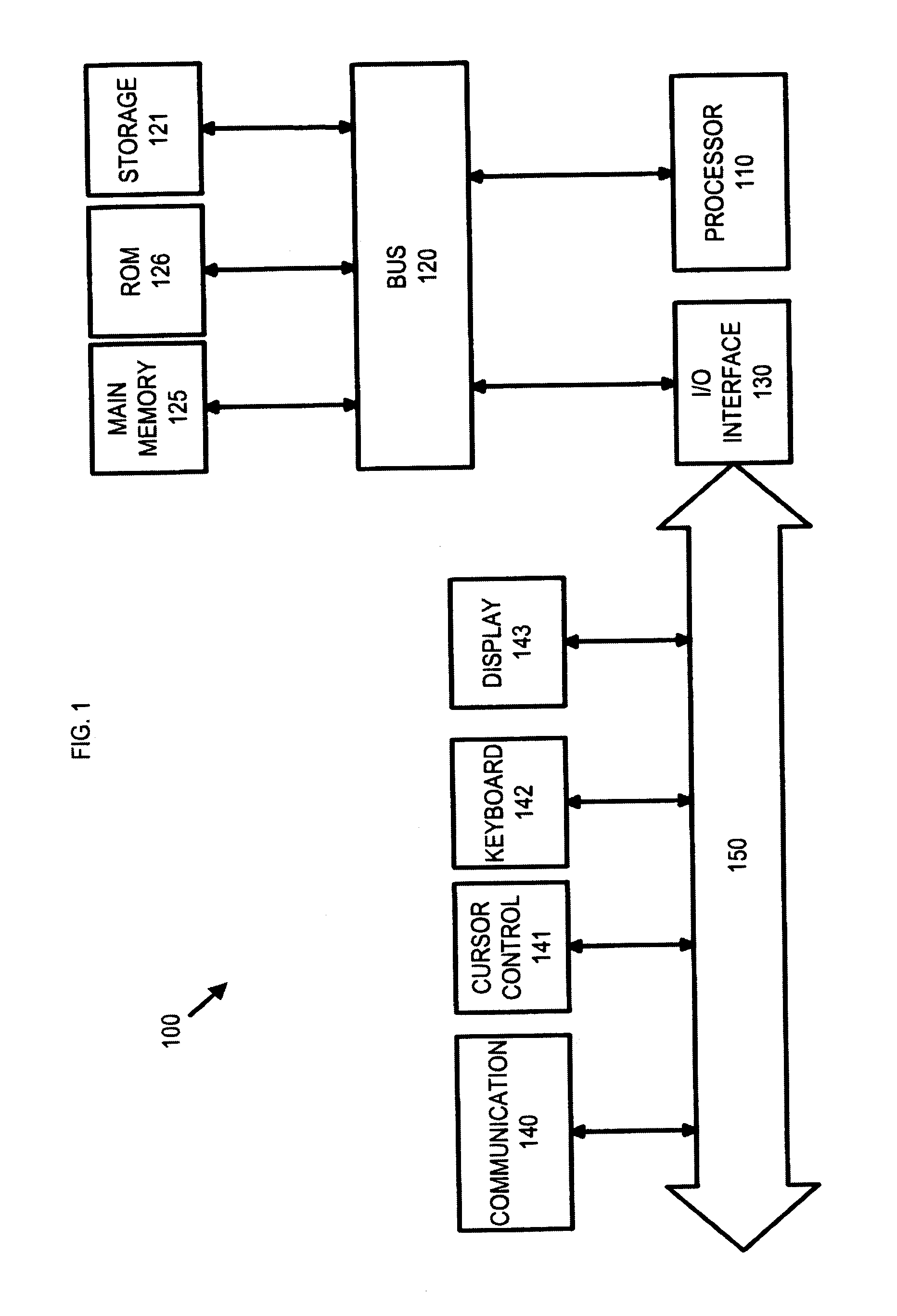
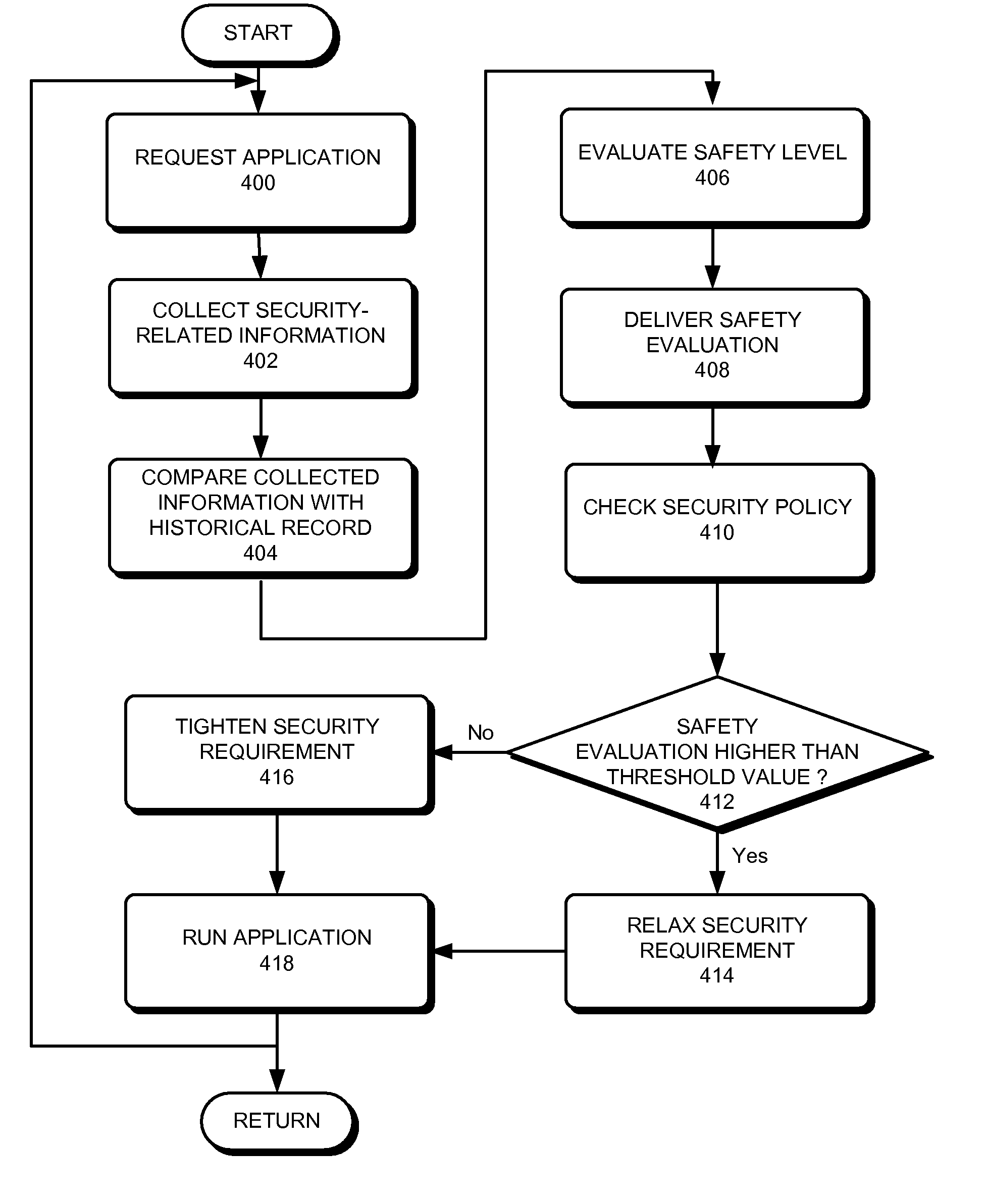
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1496 results about "Secure state" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
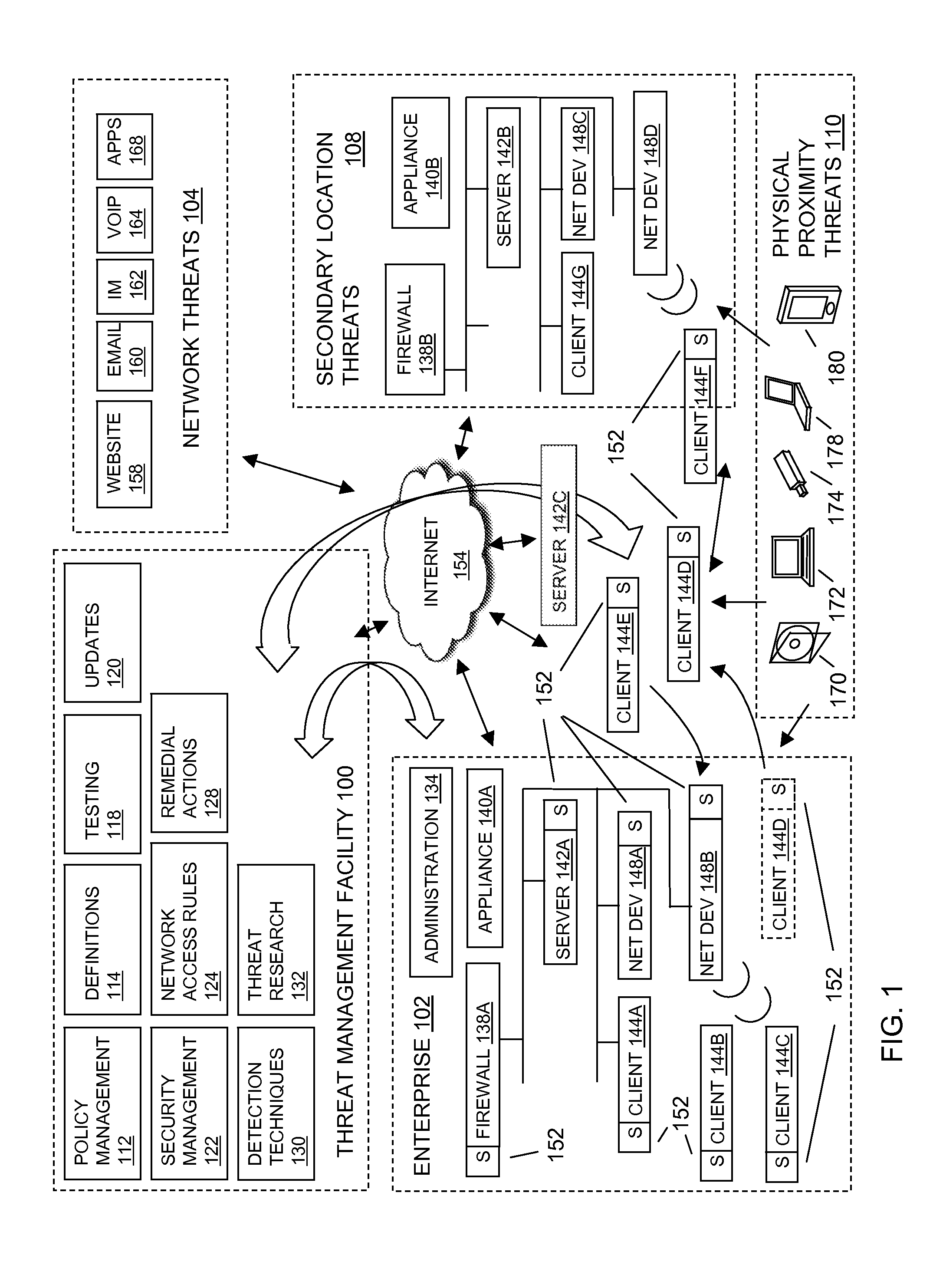
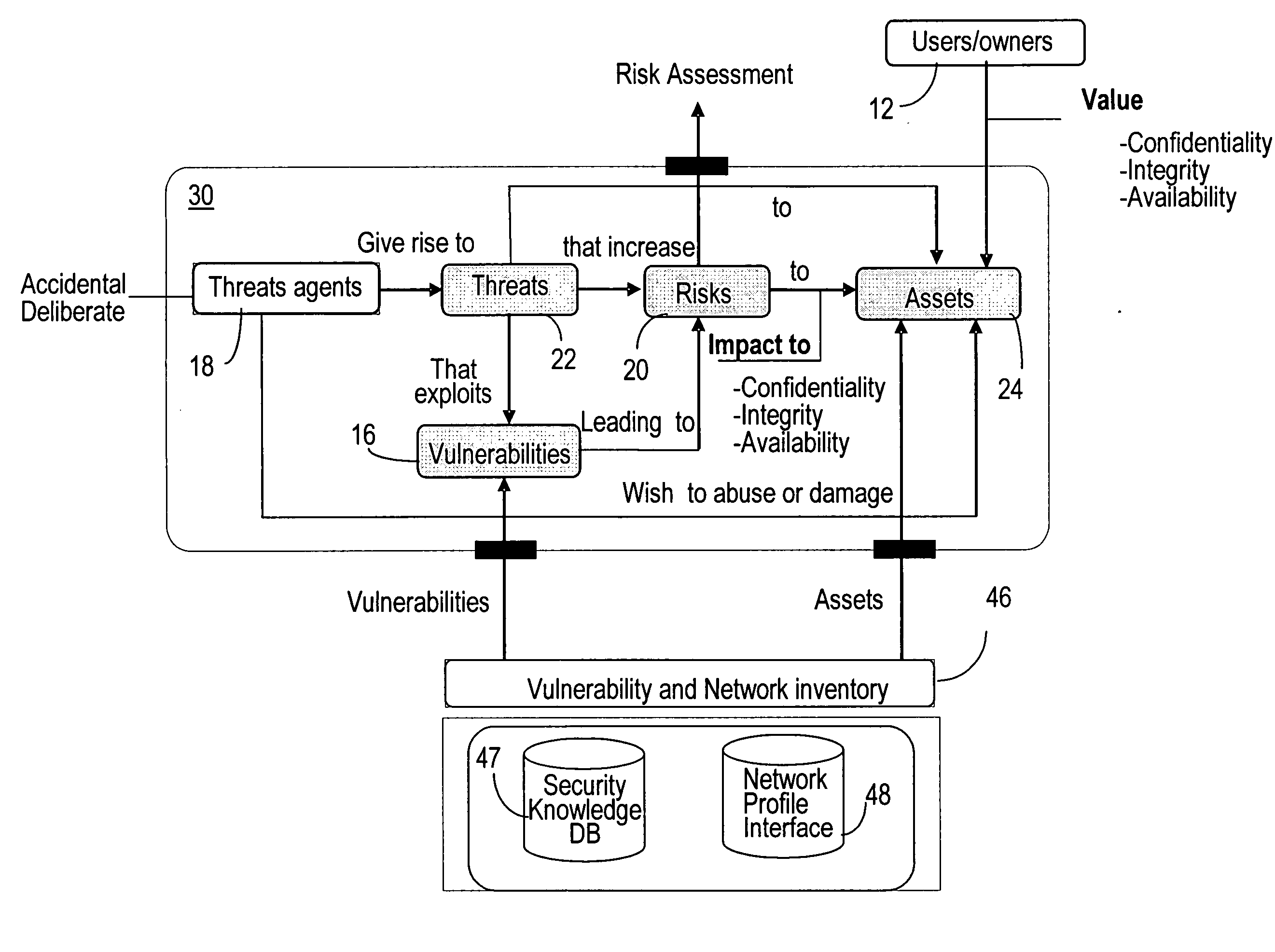
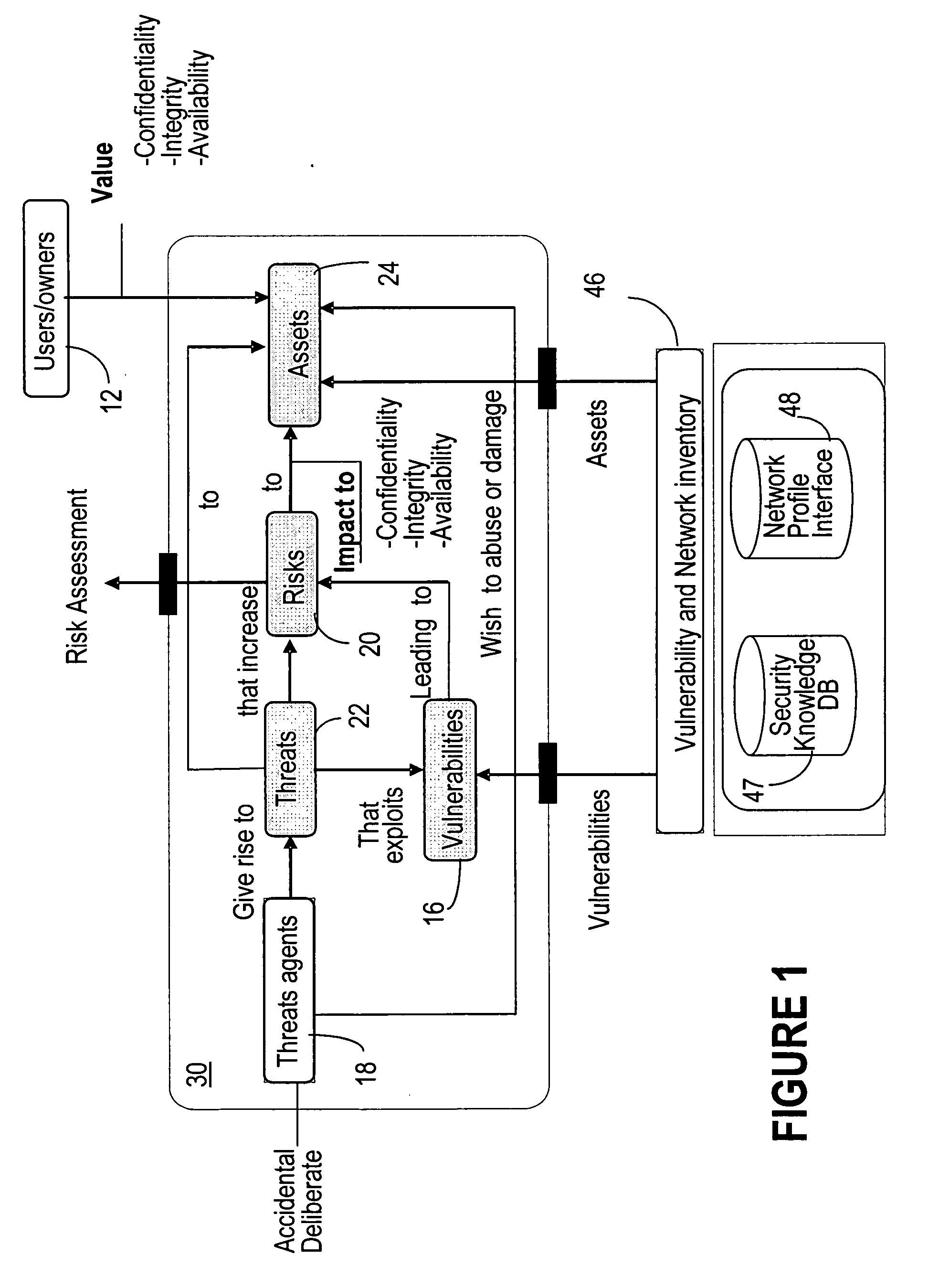
A secure state is an information systems security term to describe where entities in a computer system are divided into subjects and objects, and it can be formally proven that each state transition preserves security by moving from one secure state to another secure state. Thereby it can be inductively proven that the system is secure. As defined in the Bell–LaPadula model, the secure state is built on the concept of a state machine with a set of allowable states in a system. The transition from one state to another state is defined by transition functions.
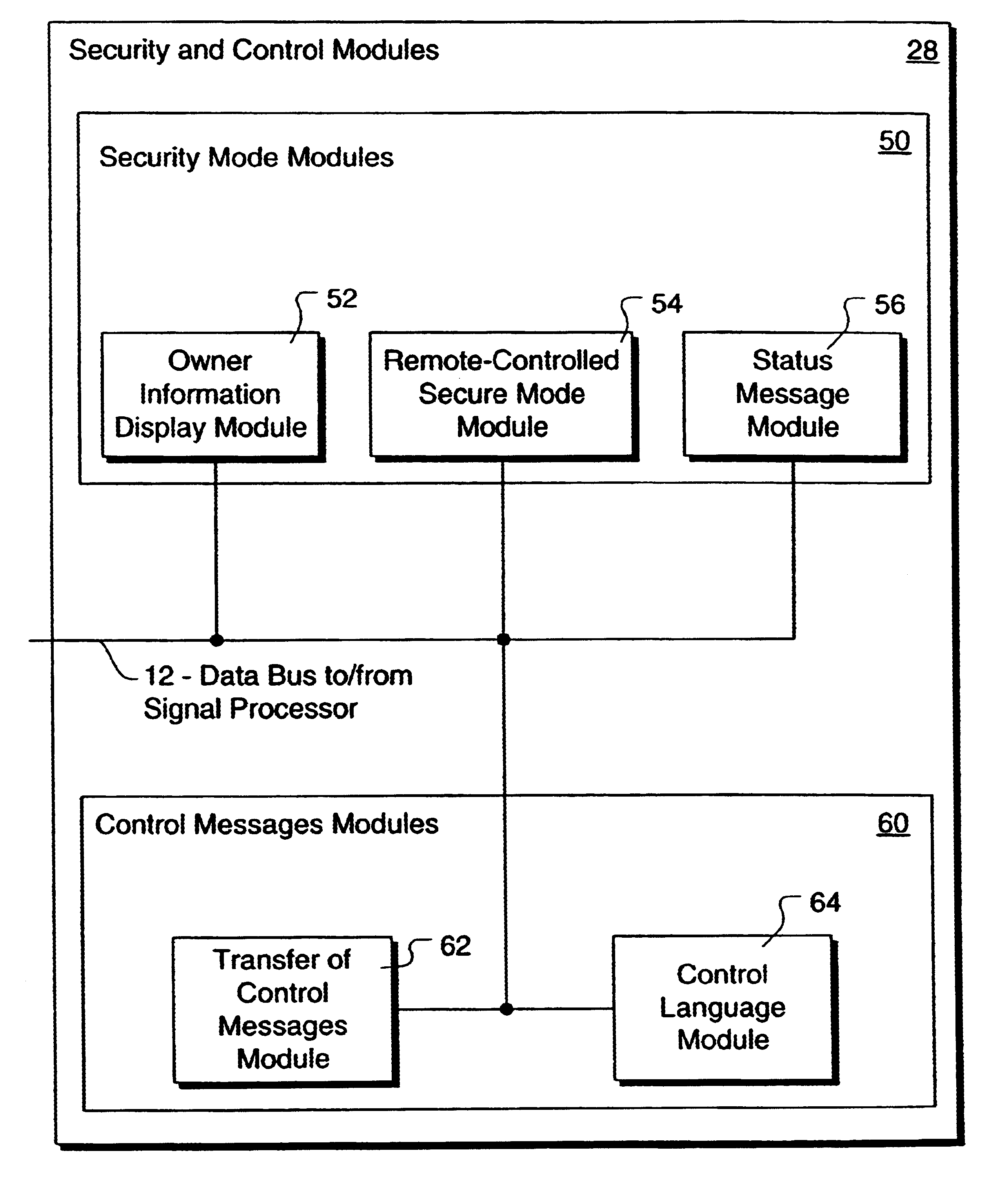
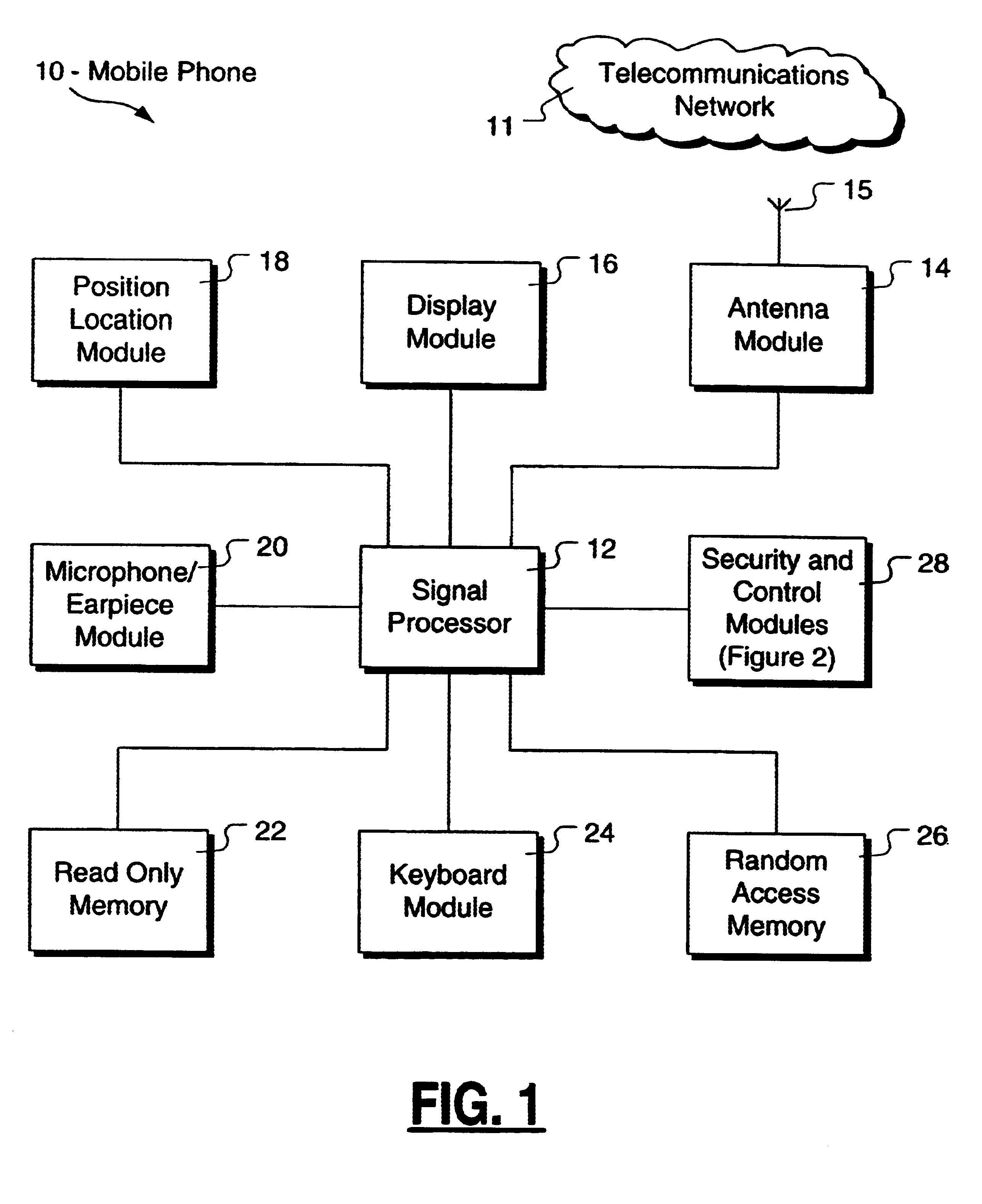
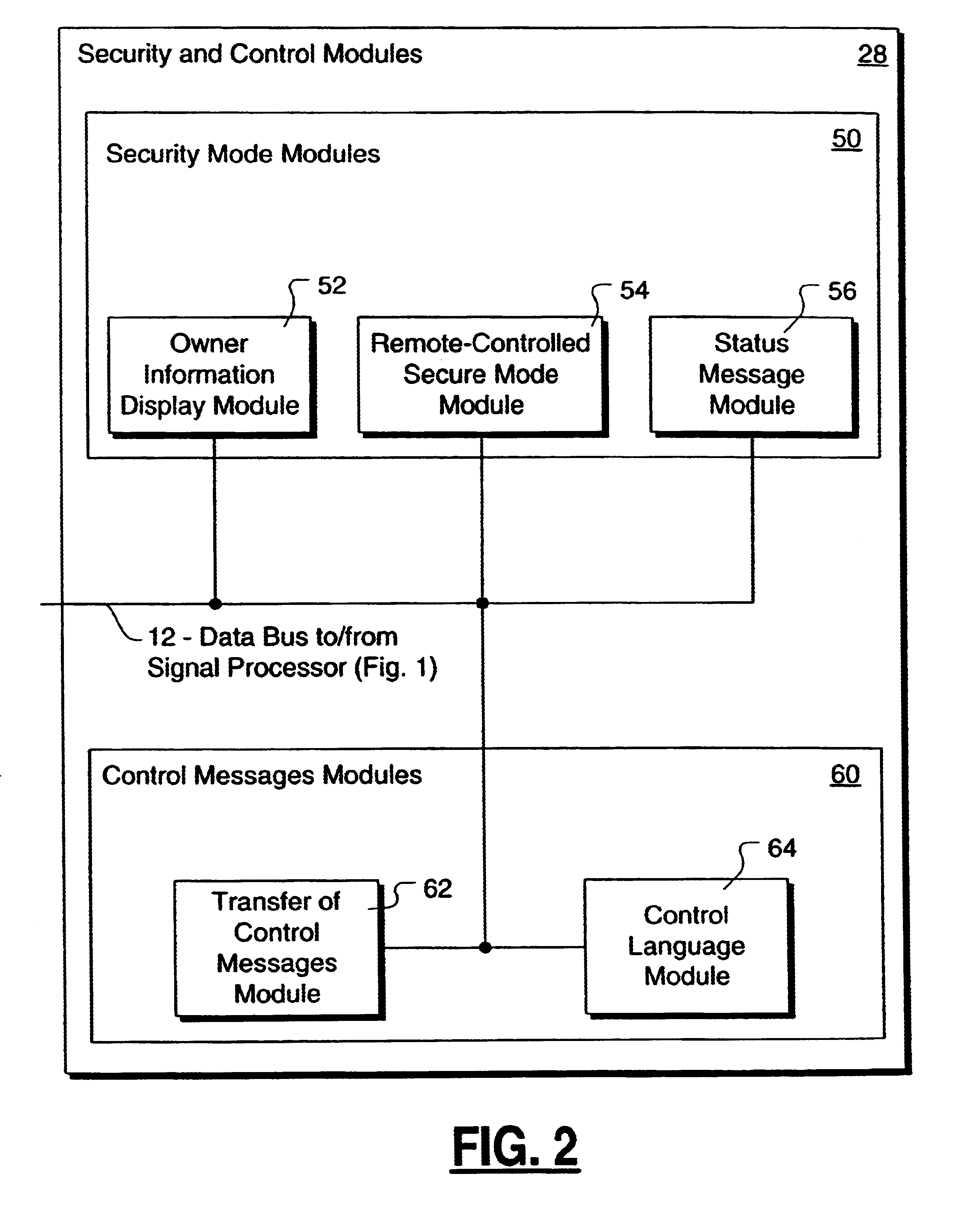
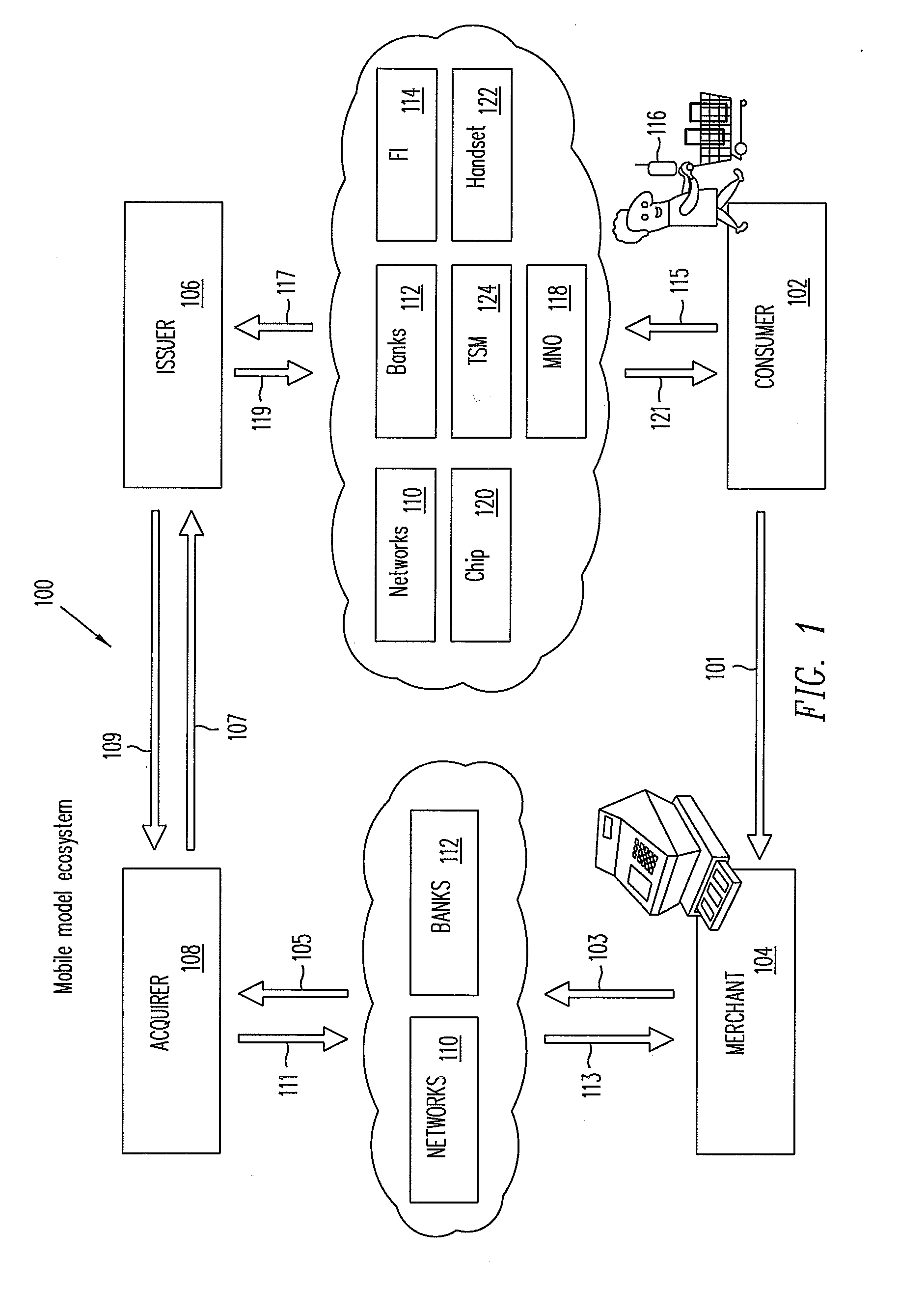
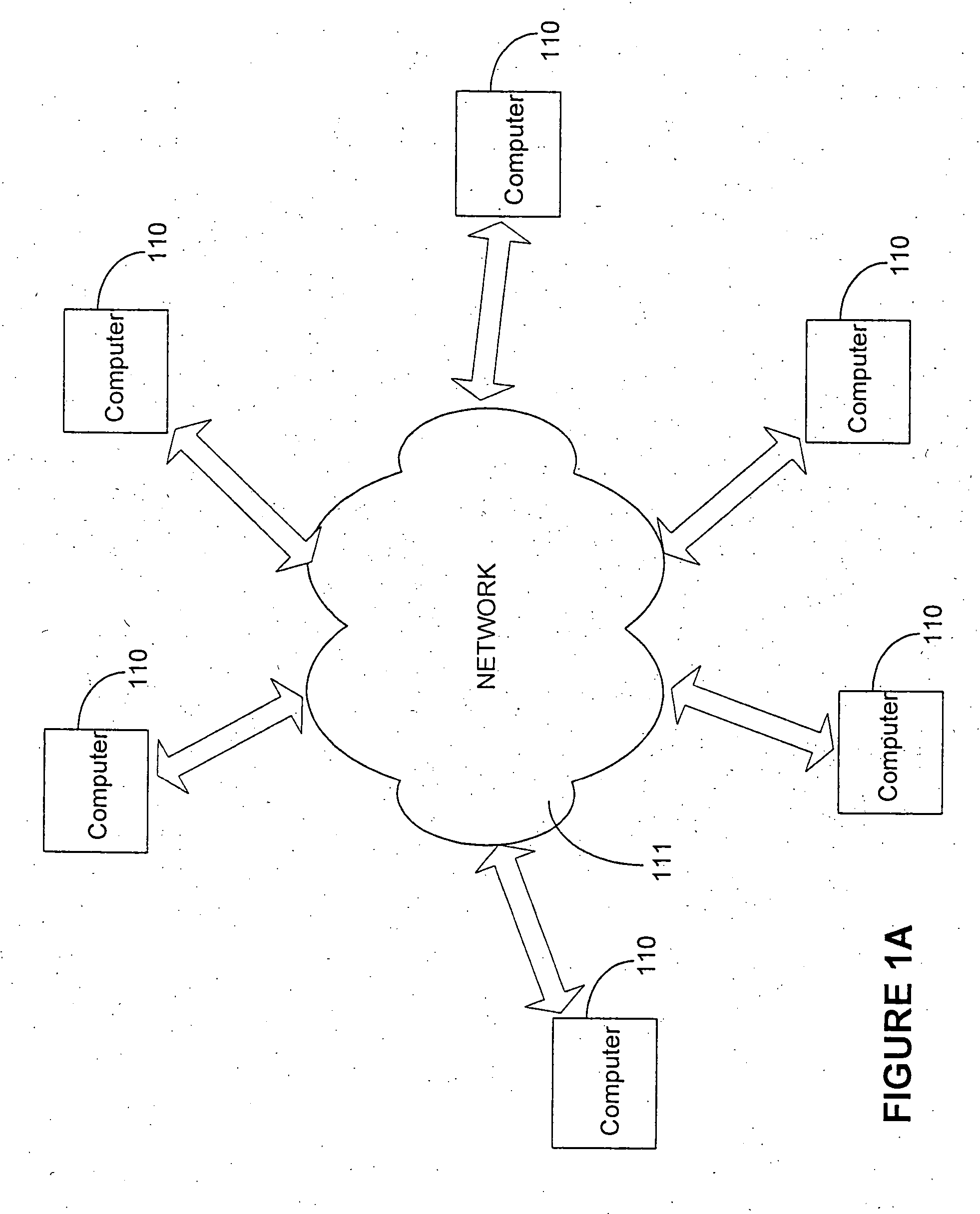
Method and apparatus for controlling and securing mobile phones that are lost, stolen or misused
InactiveUS6662023B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateStart up
A method and apparatus is provided for controlling a mobile phone when it has been lost or stolen in order to prevent its use except to help the owner find it. Controlling the phone remotely may be implemented via a known Short Messaging System, for example. The security features provided are as follows: (1) Displaying contact information (phone number) of the owner on screen when the mobile phone can not start up normally, for example, due to an incorrect security code entry; (2) Setting the mobile phone in a secure state where it can only be used to call one number (Emergency calls are of course always possible.); and (3) Commanding the mobile phone to send information about its location and usage via SMS to a given number.
Owner:NOKIA TECHNOLOGLES OY
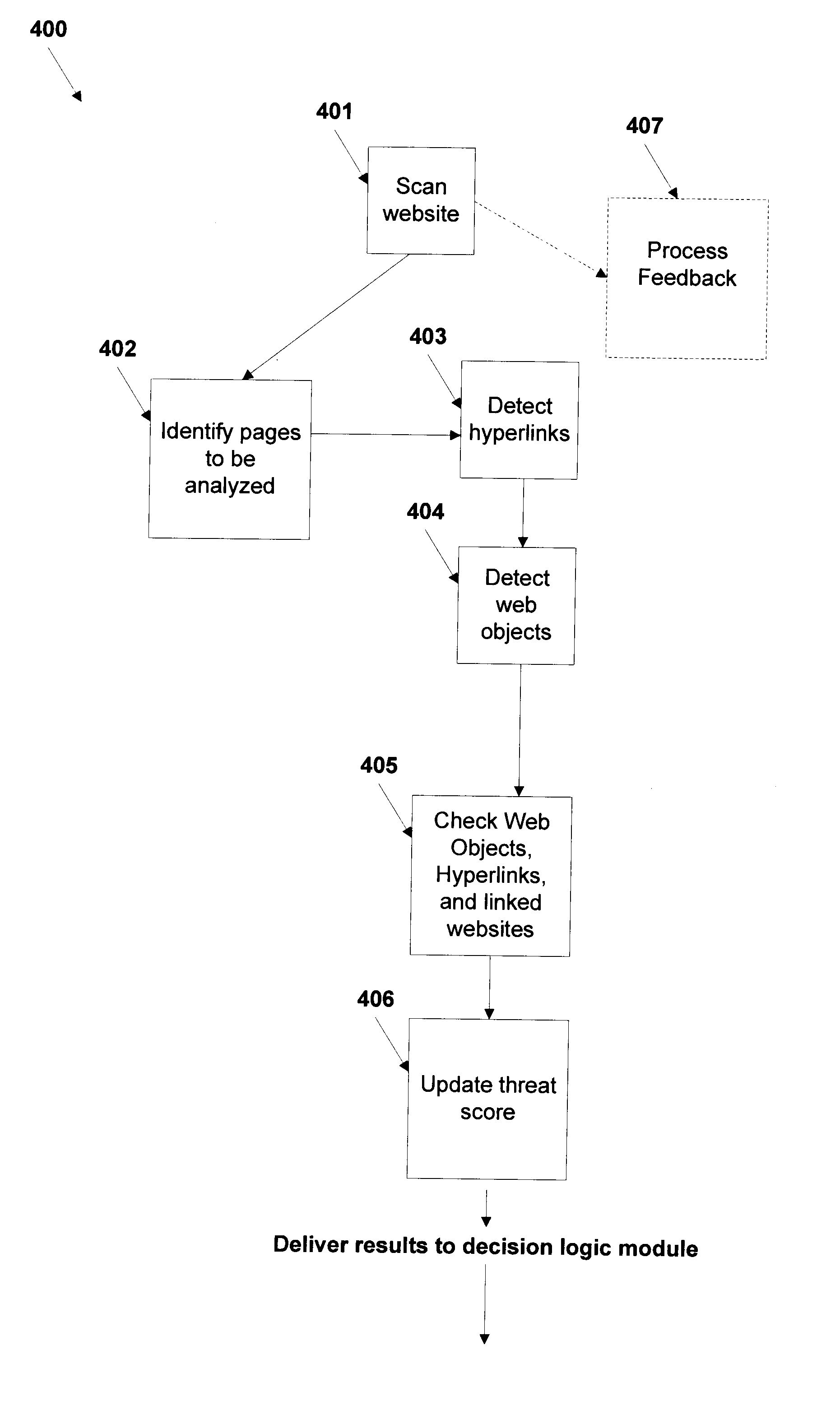
Automated identification of phishing, phony and malicious web sites
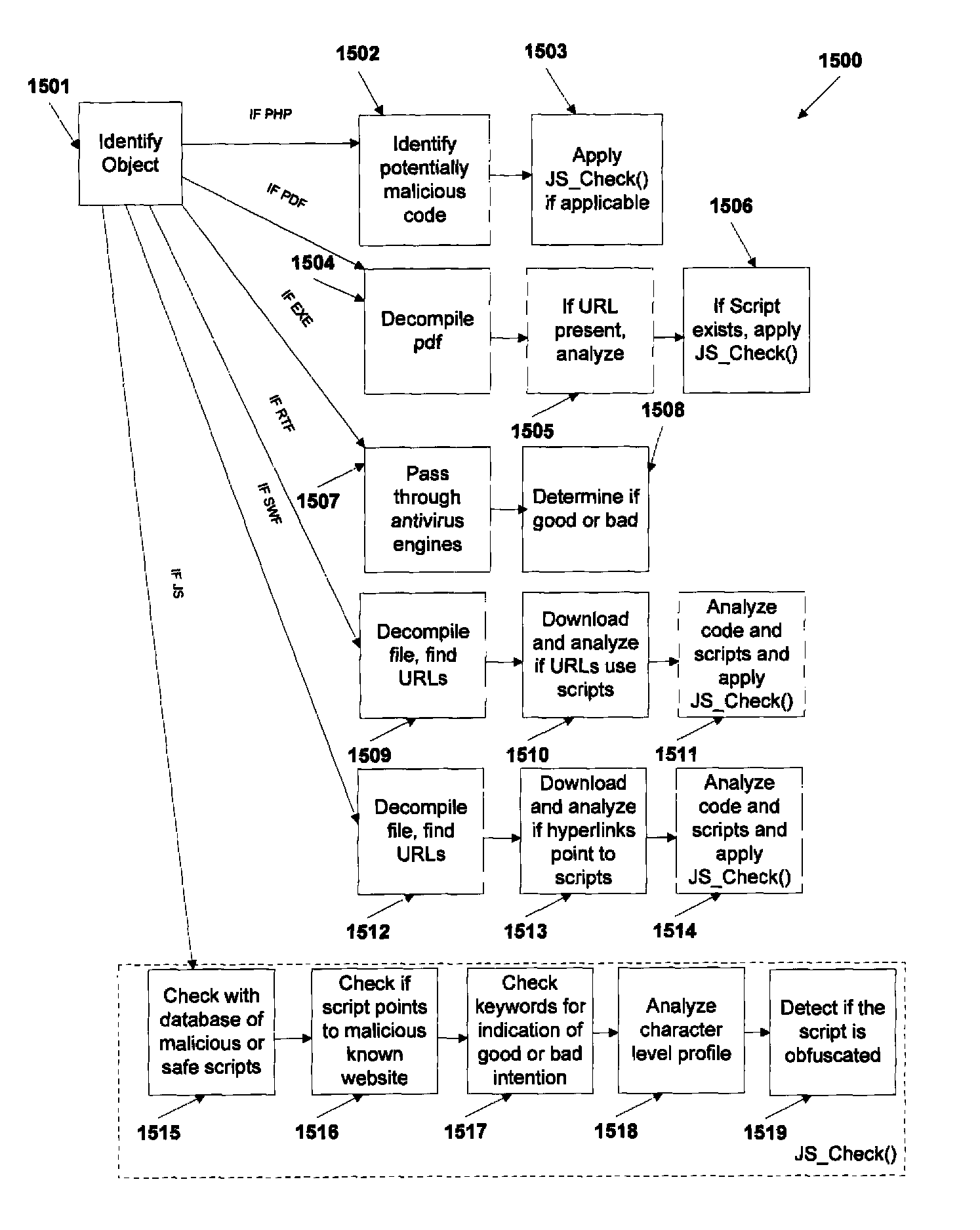
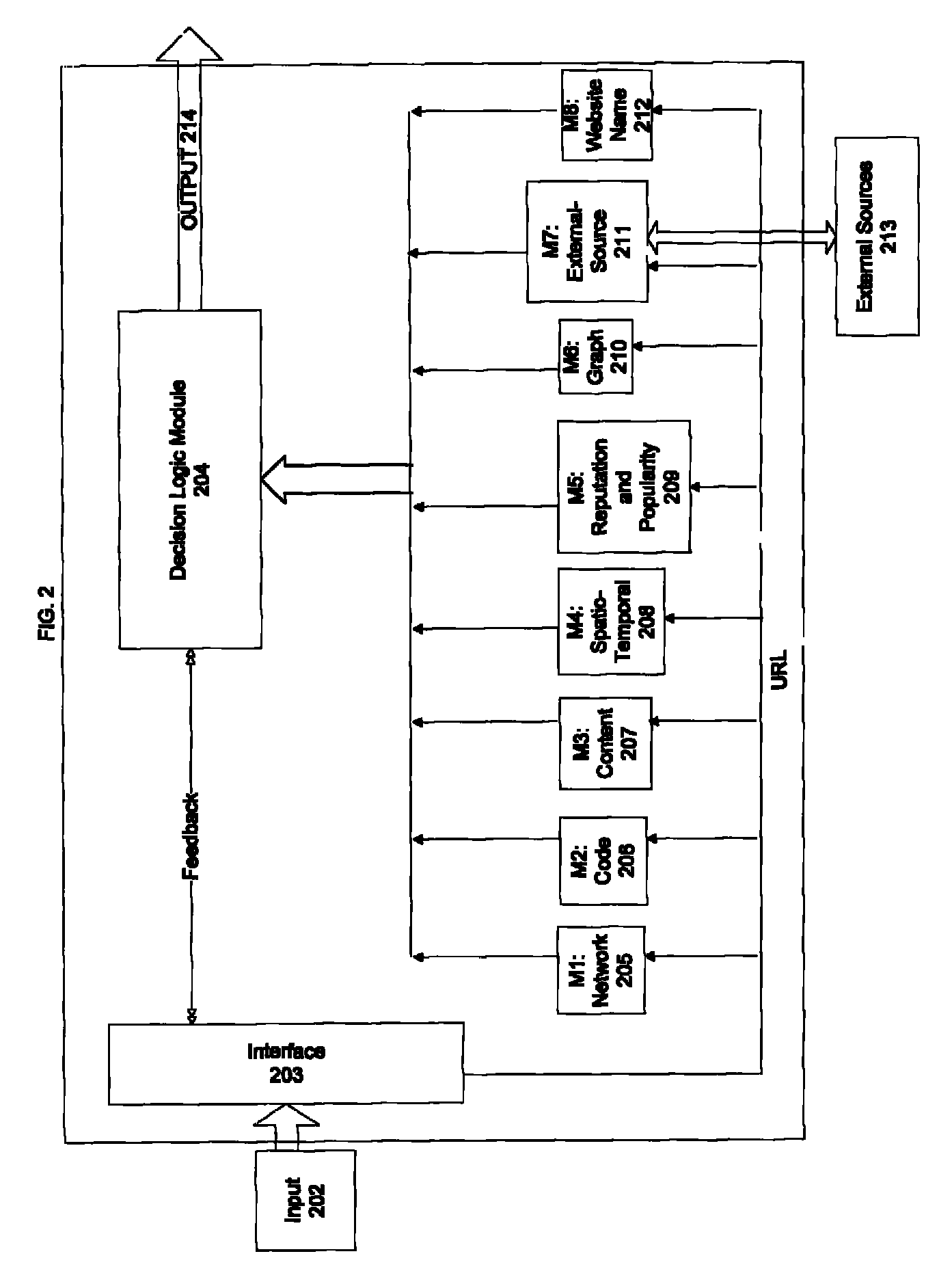
A method and system for automated identification of phishing, phony, and malicious web sites are disclosed. According to one embodiment, a computer implemented method, comprises receiving a first input, the first input including a universal resource locator (URL) for a webpage. A second input is received, the second input including feedback information related to the webpage, the feedback information including an indication designating the webpage as safe or unsafe. A third input is received from a database, the third input including reputation information related to the webpage. Data is extracted from the webpage. A safety status is determined for the webpage, including whether the webpage is hazardous by using a threat score for the webpage and the second input, wherein calculating the threat score includes analyzing the extracted data from the webpage. The safety status for the webpage is reported.
Owner:CLOUDFLARE
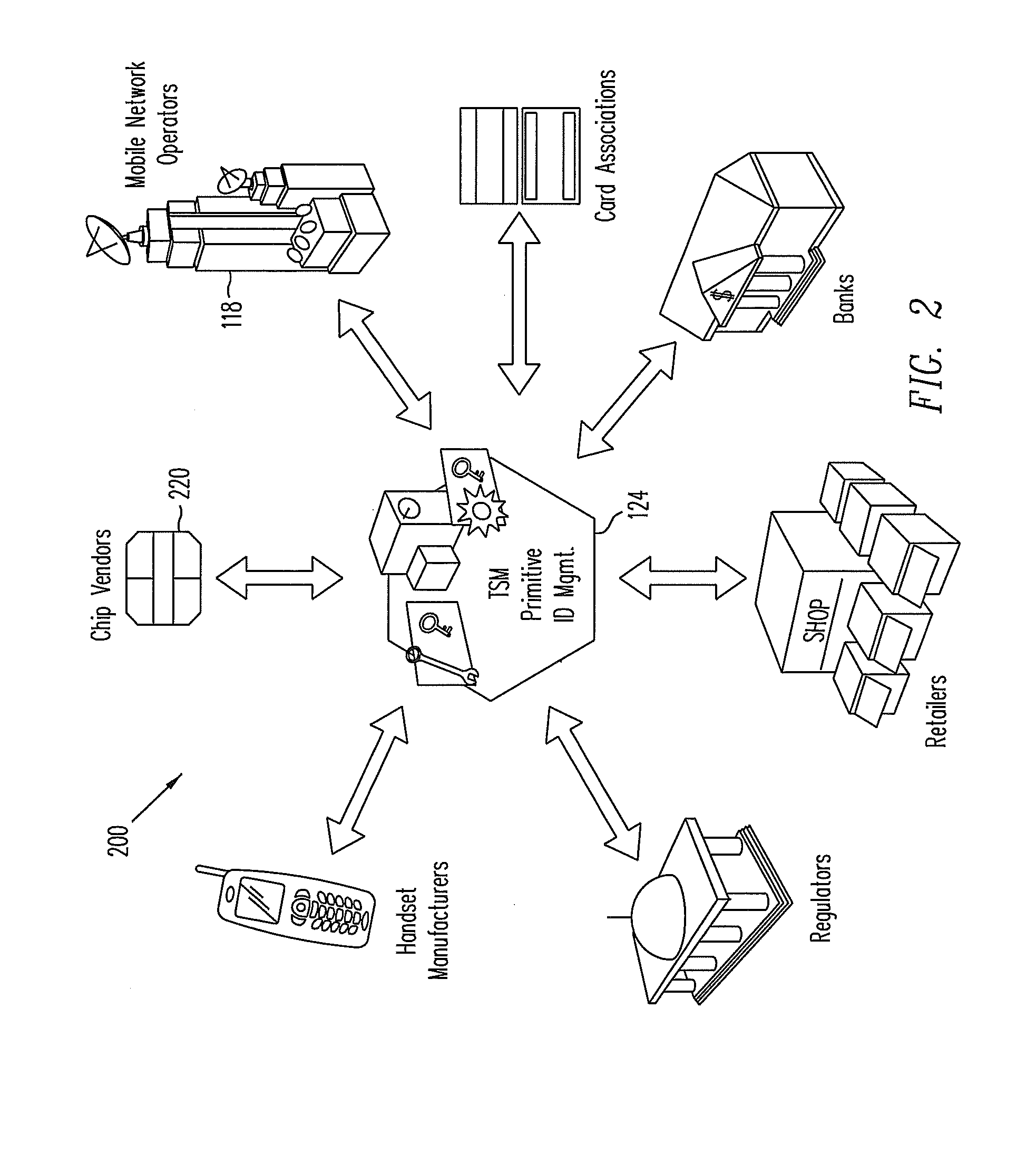
Adjusting security level of mobile device based on presence or absence of other mobile devices nearby
ActiveUS8095112B2Unauthorised/fraudulent call preventionDigital data processing detailsSecure stateGeolocation
One embodiment of the present invention provides a method for adjusting security status on a mobile device, the method comprising: collecting security-related contextual information which includes information of nearby mobile devices and / or the geographic location of the intelligent mobile device; evaluating a threat level based on the collected security-related contextual information; invoking a security policy; and adjusting the security status of the mobile device based on the threat level and the security policy.
Owner:XEROX CORP
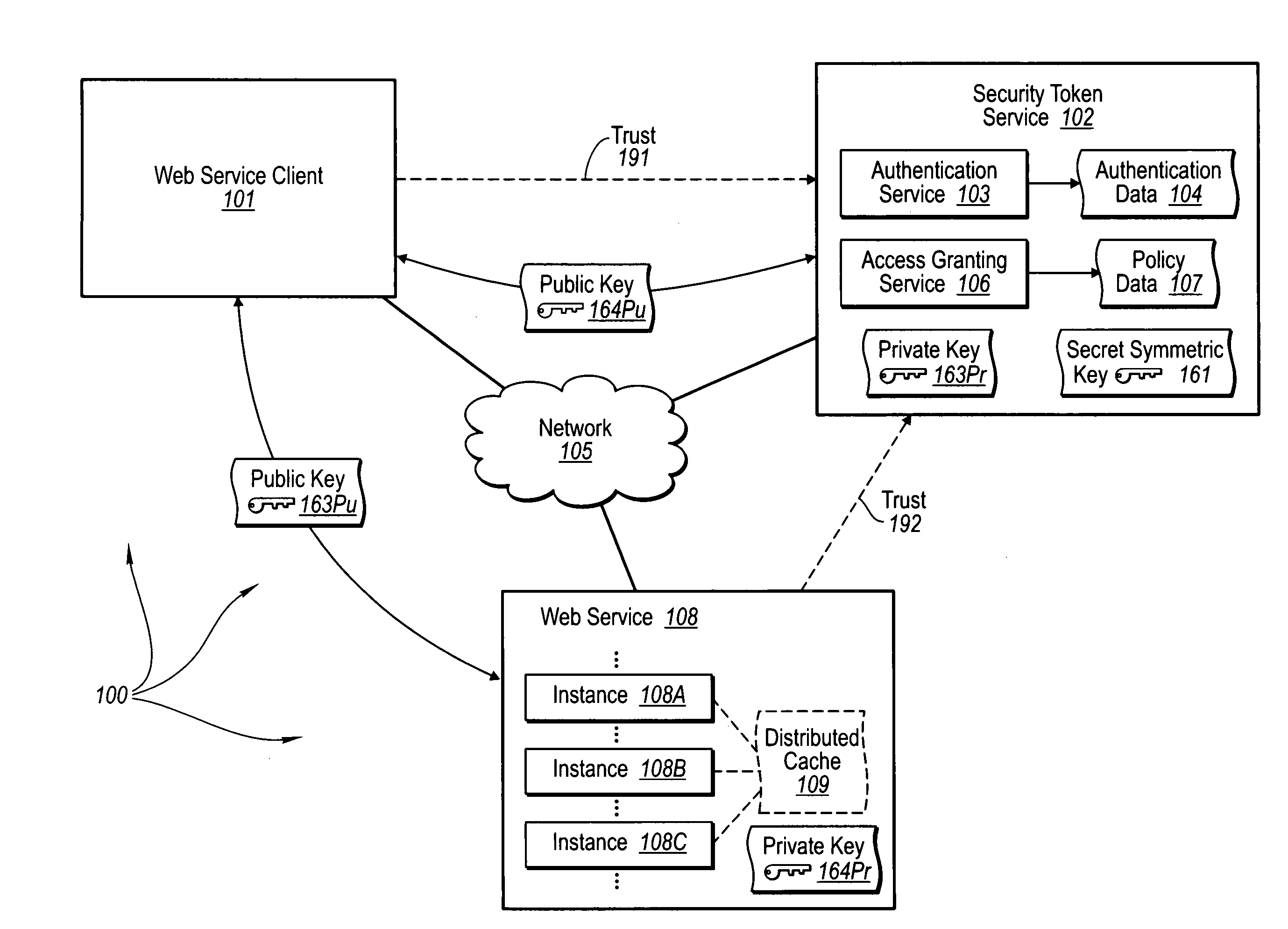
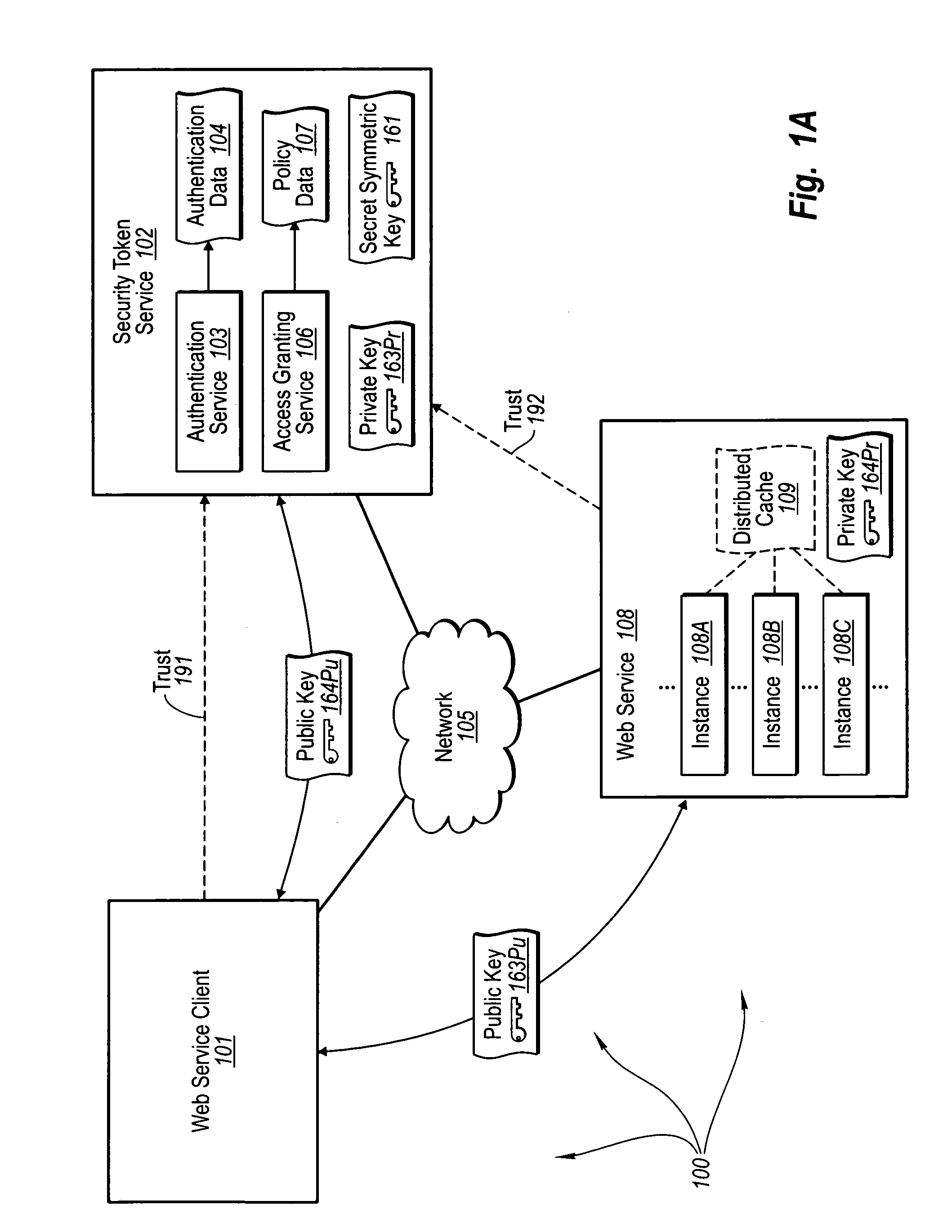
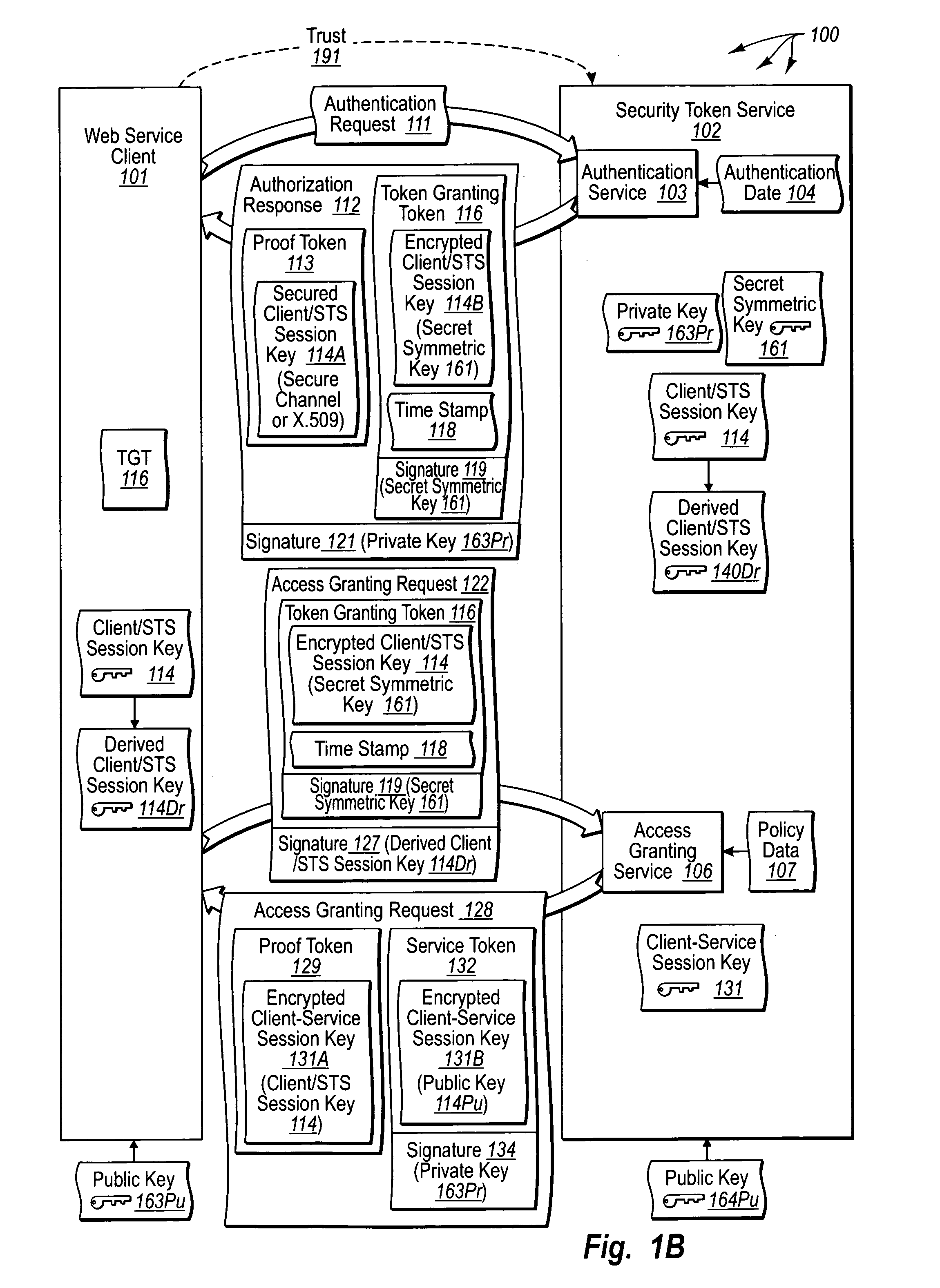
Trusted third party authentication for web services
InactiveUS20060206932A1Communication securityDigital data processing detailsUser identity/authority verificationWeb serviceInternet privacy
The present invention extends to trusted third party authentication for Web services. Web services trust and delegate user authentication responsibility to a trusted third party that acts as an identity provider for the trusting Web services. The trusted third party authenticates users through common authentication mechanisms, such as, for example, username / password and X.509 certificates and uses initial user authentication to bootstrap subsequent secure sessions with Web services. Web services construct user identity context using a service session token issued by the trusted third party and reconstruct security states without having to use a service-side distributed cache.
Owner:MICROSOFT TECH LICENSING LLC
Trusted remote attestation agent (TRAA)
ActiveUS20100306107A1Reduce riskFinanceMultiple digital computer combinationsComputer hardwareRisk profiling
Systems and methods for use with a service provider and a consumer electronic device include a trusted remote attestation agent (TRAA) configured to perform a set of checking procedures or mechanisms to help ensure the security status of a consumer electronic device (e.g., a mobile terminal or phone) that holds financial instruments. The checking procedures may include: self-verifying integrity by the TRAA; checking for presence of a provisioning SIM card (one that was present when the financial instruments were enabled on the device); checking that a communication connection between the consumer electronic device and the service provider is available and active; and checking that communication connectivity to a home mobile network is available and active. The frequency of the checking mechanisms may be adjusted, for example, according to a risk-profile of a user associated with the device or the location (e.g., GPS location) of the device. The checks may be used, for example, to temporarily disable or limit the use of the financial instruments from the device.
Owner:PAYPAL INC
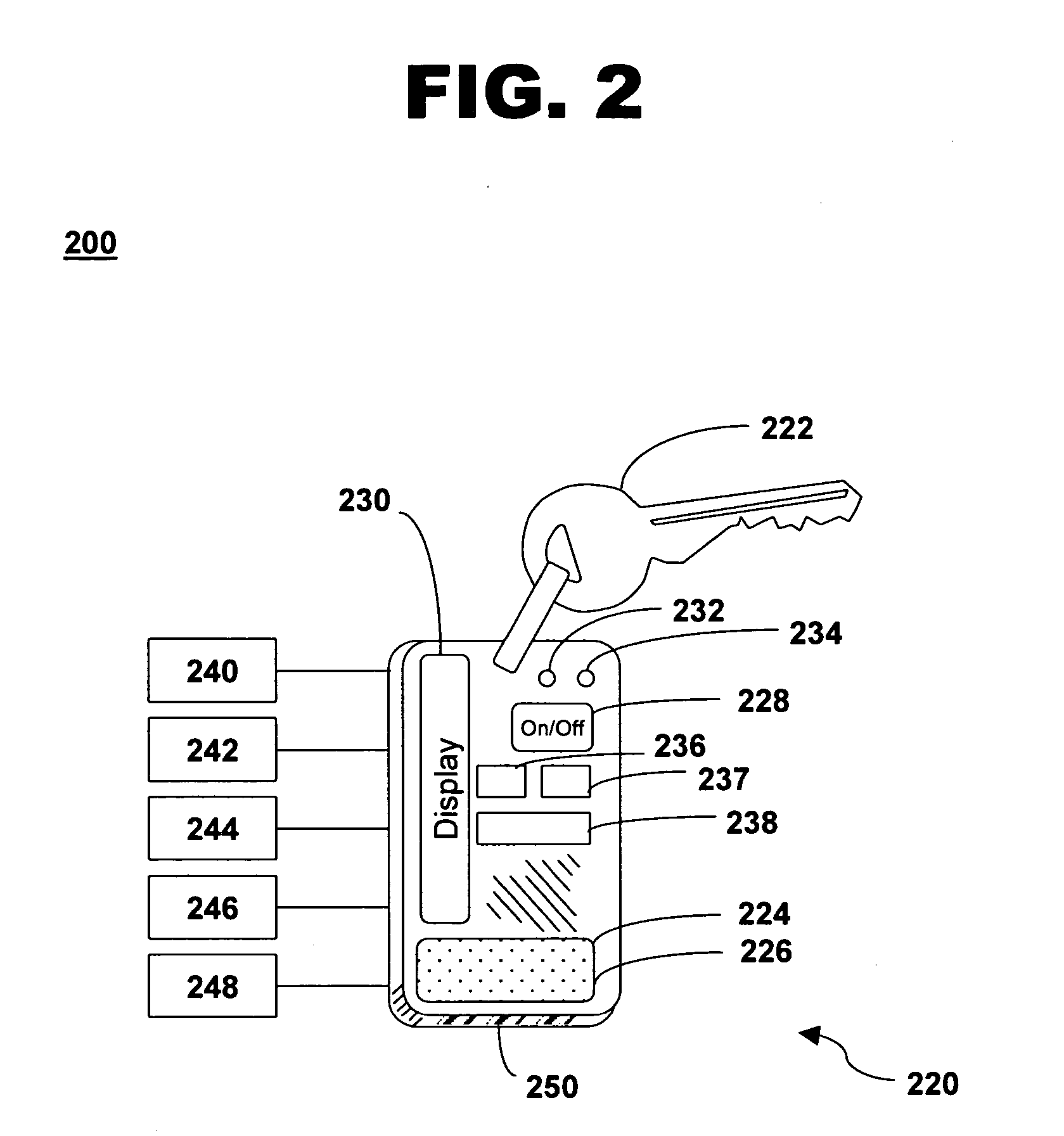
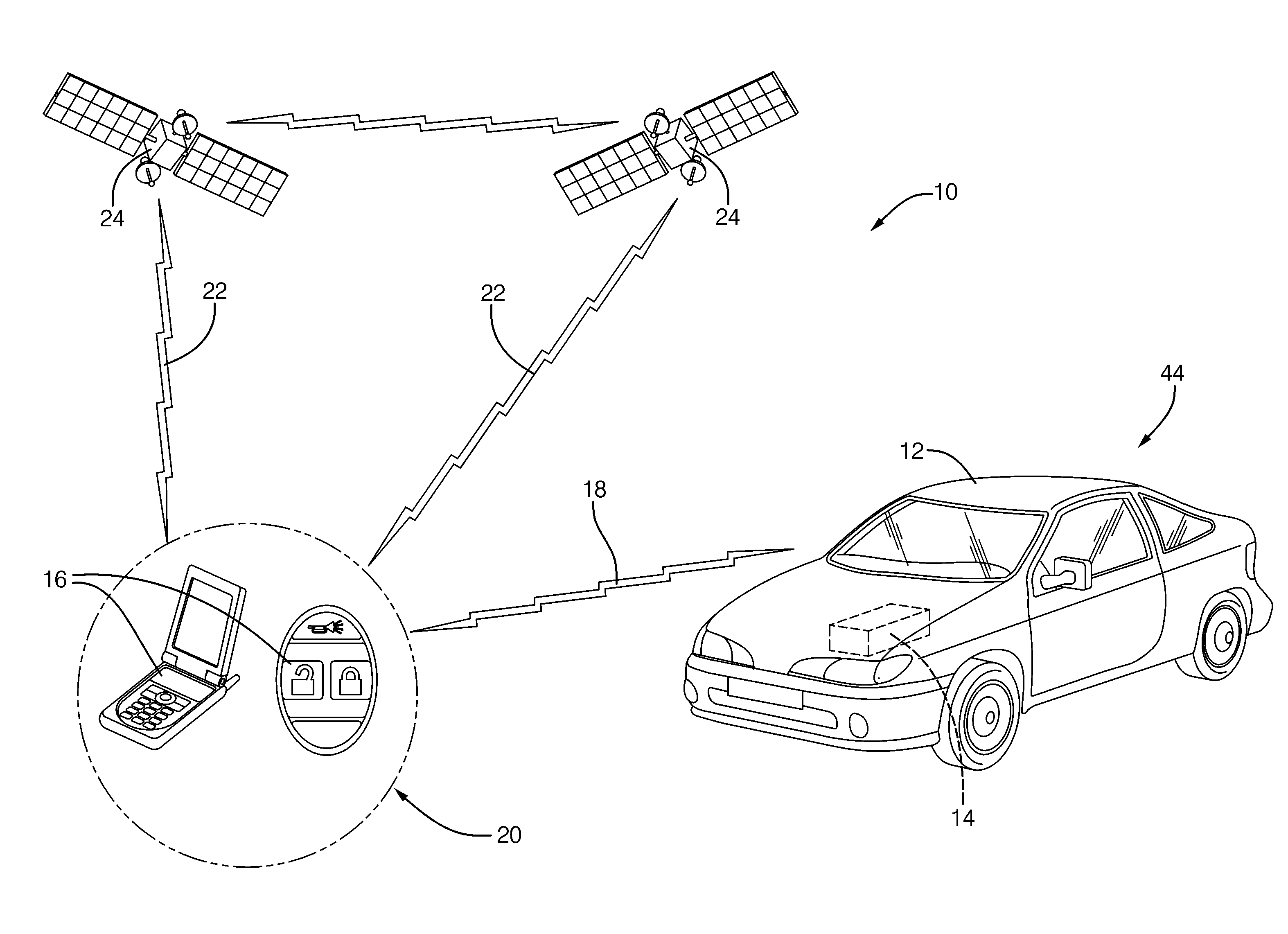
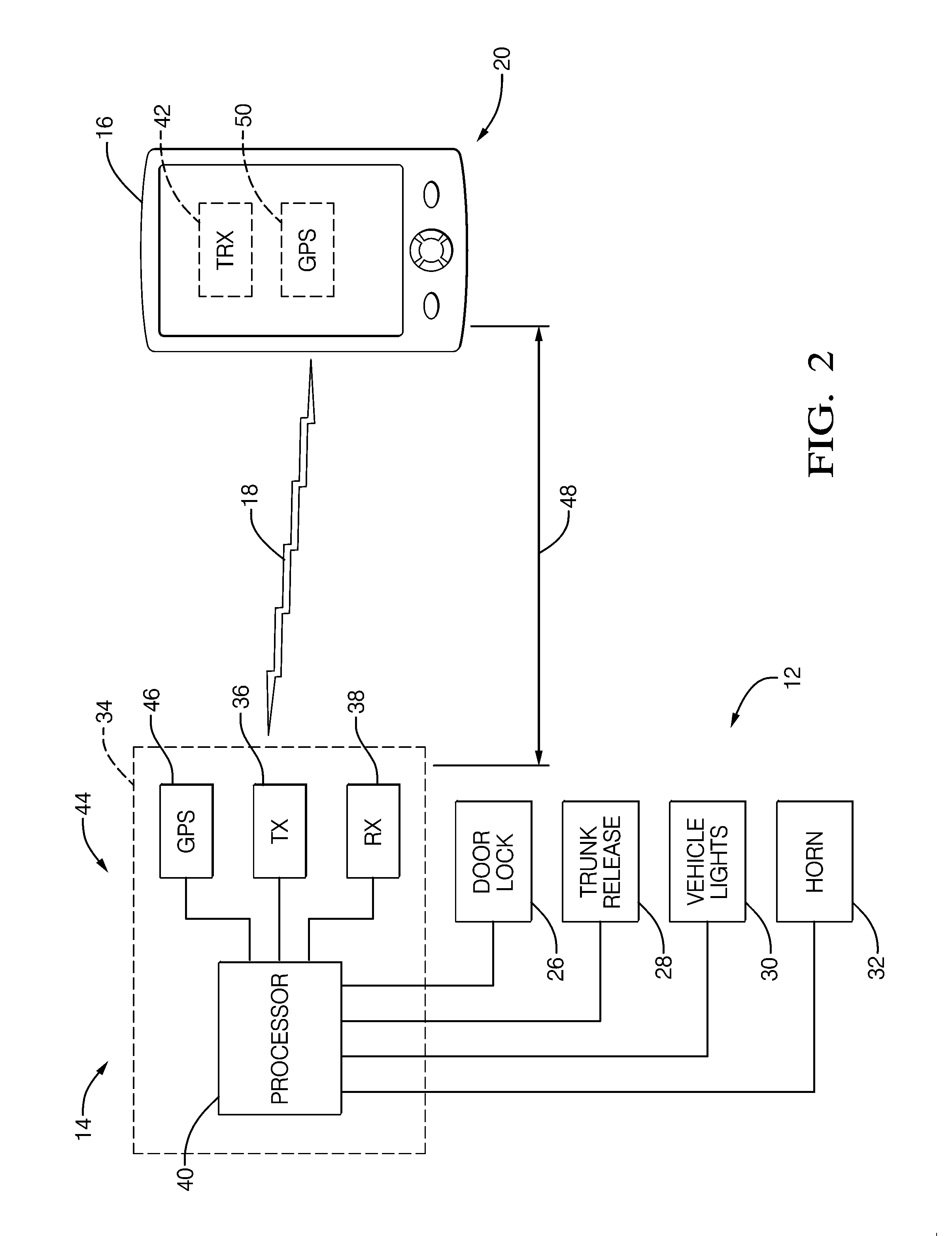
Method and system for status indication on a key fob
The invention provides a system for determining a vehicle security status and providing the status to the vehicle driver using a key fob wirelessly connected to a telematics unit located within the vehicle. A method for providing security status includes providing a key fob in wireless communication with a vehicle, the key fob including a status indicator, receiving sensor signals of vehicle components positions at the vehicle telematics unit determining whether the vehicle components positions are in an unsecured status position, sending a notification signal based on the determination from the vehicle telematics unit to the key fob and activating the status indicator of the key fob based on the notification.
Owner:GENERAL MOTORS COMPANY
Method for determining the security status of transmissions in a telecommunications network
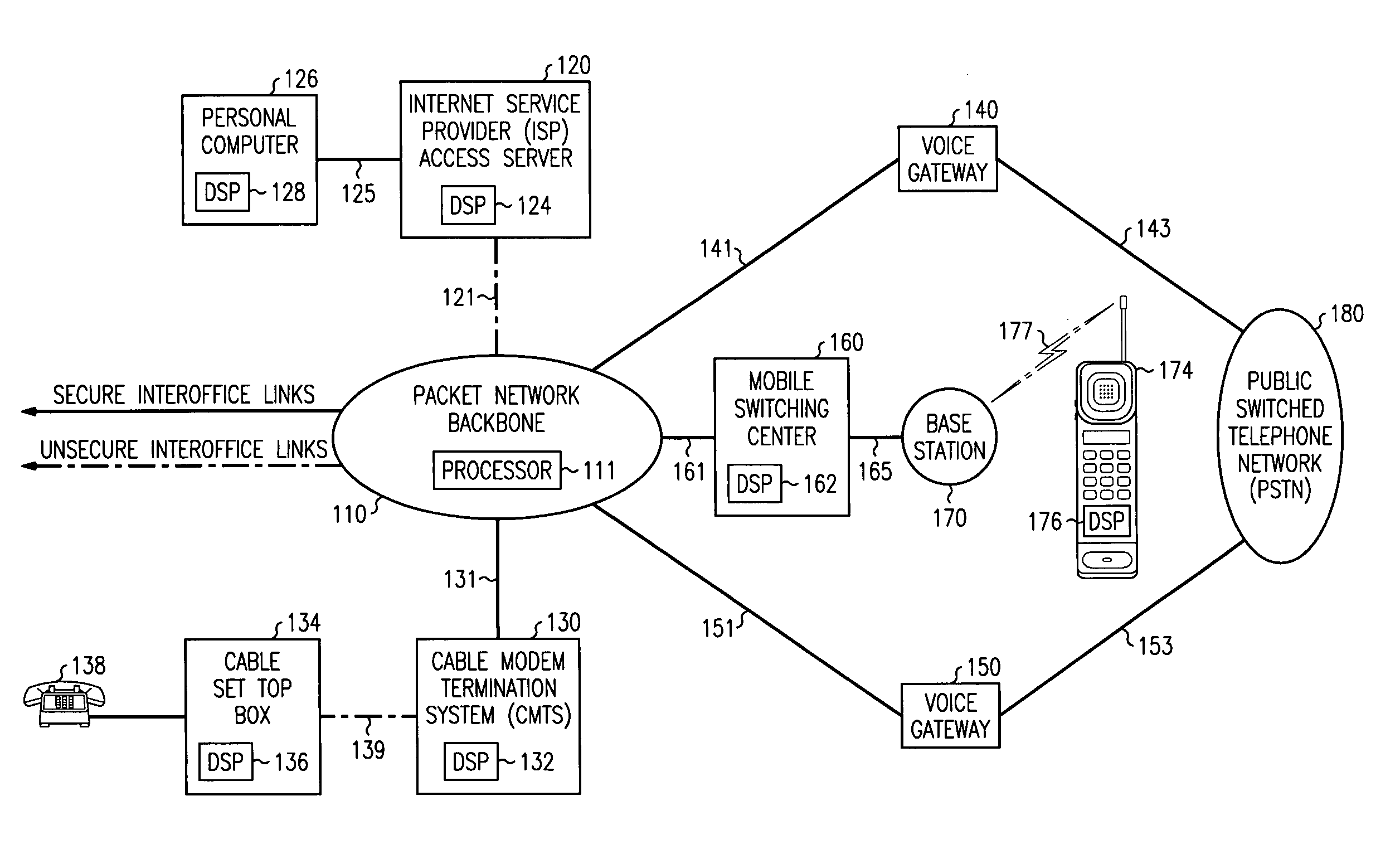
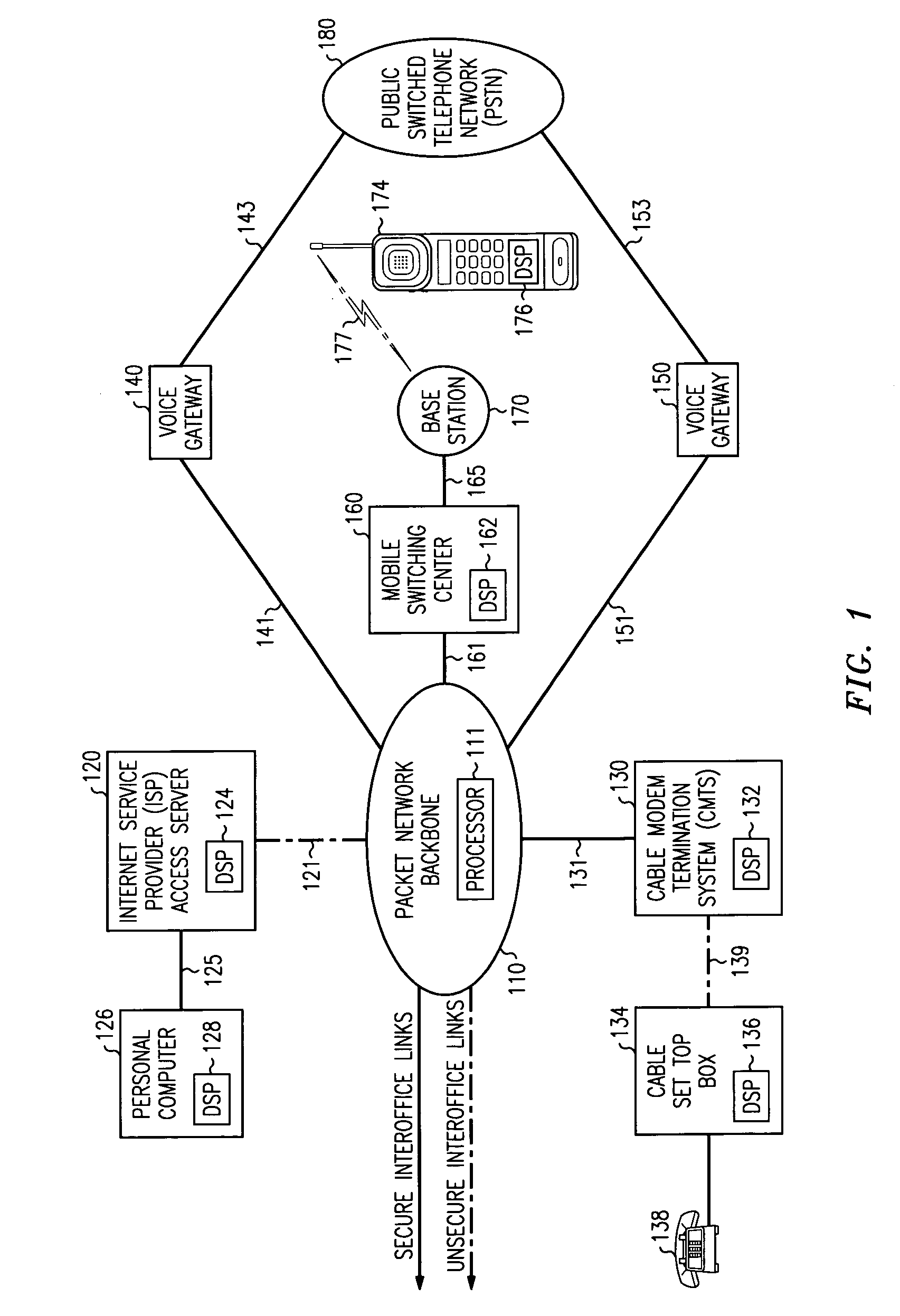
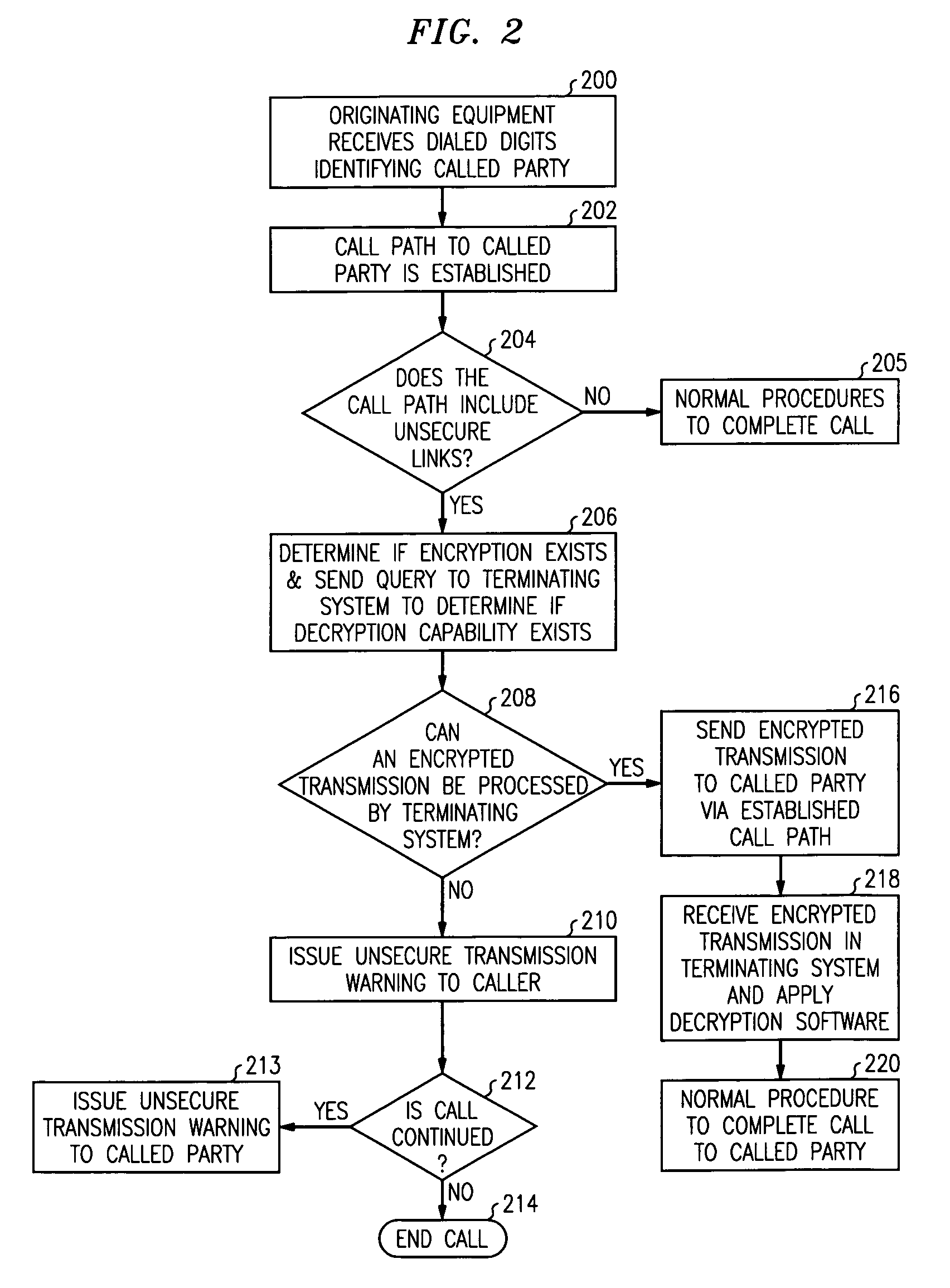
InactiveUS6959184B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications linkTelecommunications network
A method for determining the security level associated with transmissions in a telecommunications network includes means for alerting parties of the security status of the transmission. When a route interconnecting the parties includes an insecure link, an alert is provided so that the parties are aware of the insecure nature of the call before communications begin. Alternatively, the parties may elect to decline or alter content of the communications to preserve integrity.
Owner:LUCENT TECH INC
Adjusting security level of mobile device based on presence or absence of other mobile devices nearby
ActiveUS20100048167A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsSecure stateGeolocation
One embodiment of the present invention provides a method for adjusting security status on a mobile device, the method comprising: collecting security-related contextual information which includes information of nearby mobile devices and / or the geographic location of the intelligent mobile device; evaluating a threat level based on the collected security-related contextual information; invoking a security policy; and adjusting the security status of the mobile device based on the threat level and the security policy.
Owner:XEROX CORP
Method and system for evaluating network safety situation
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
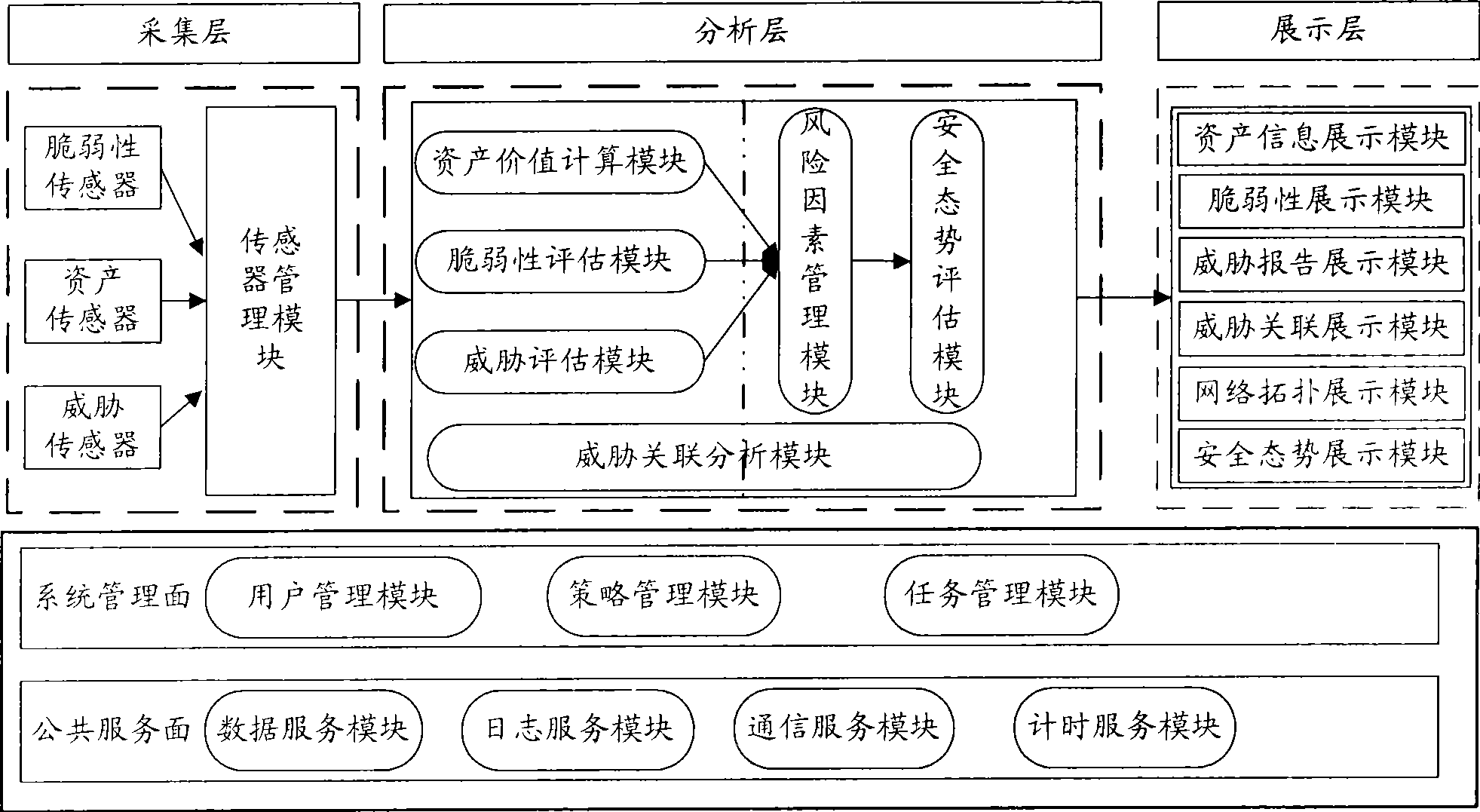
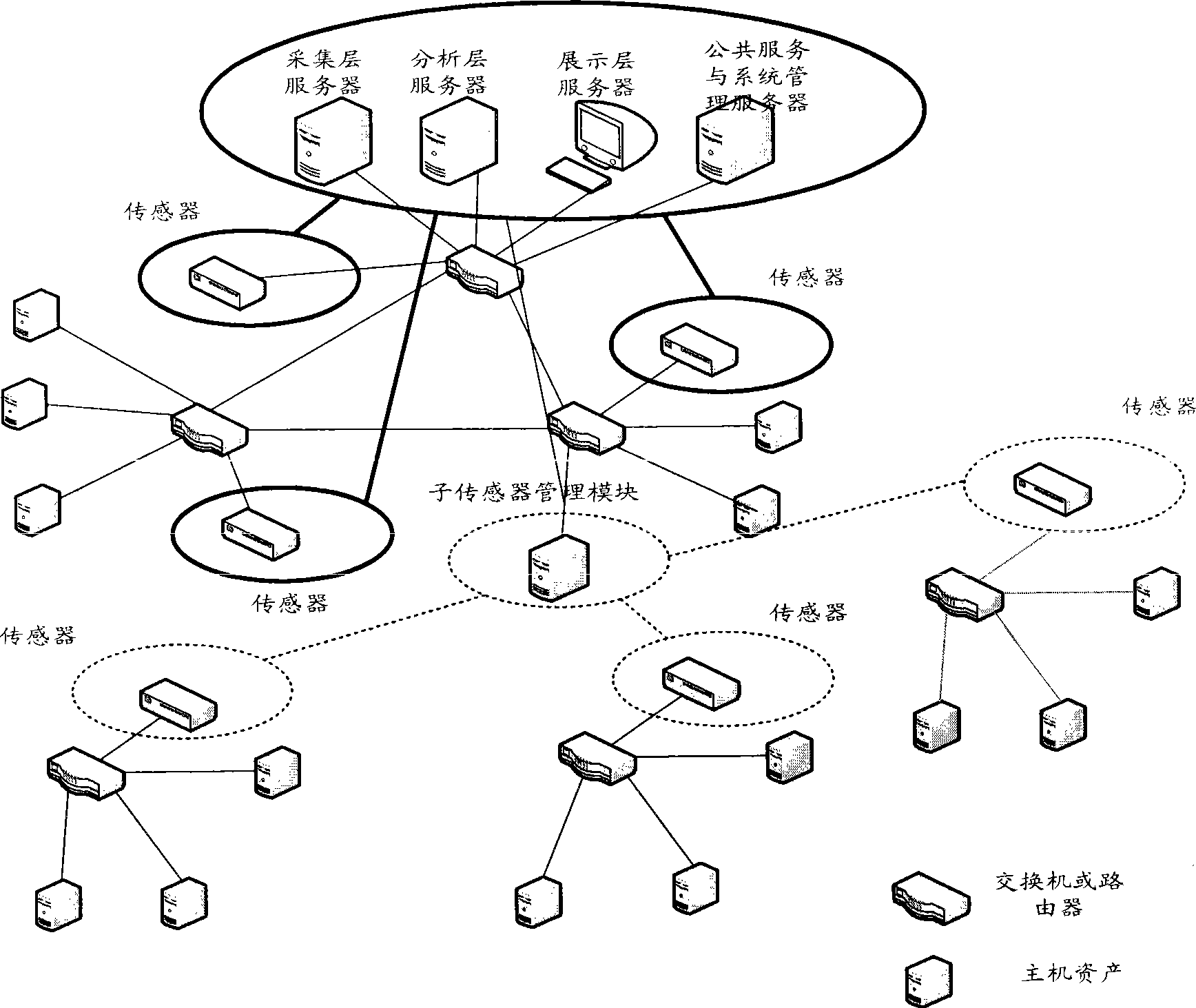
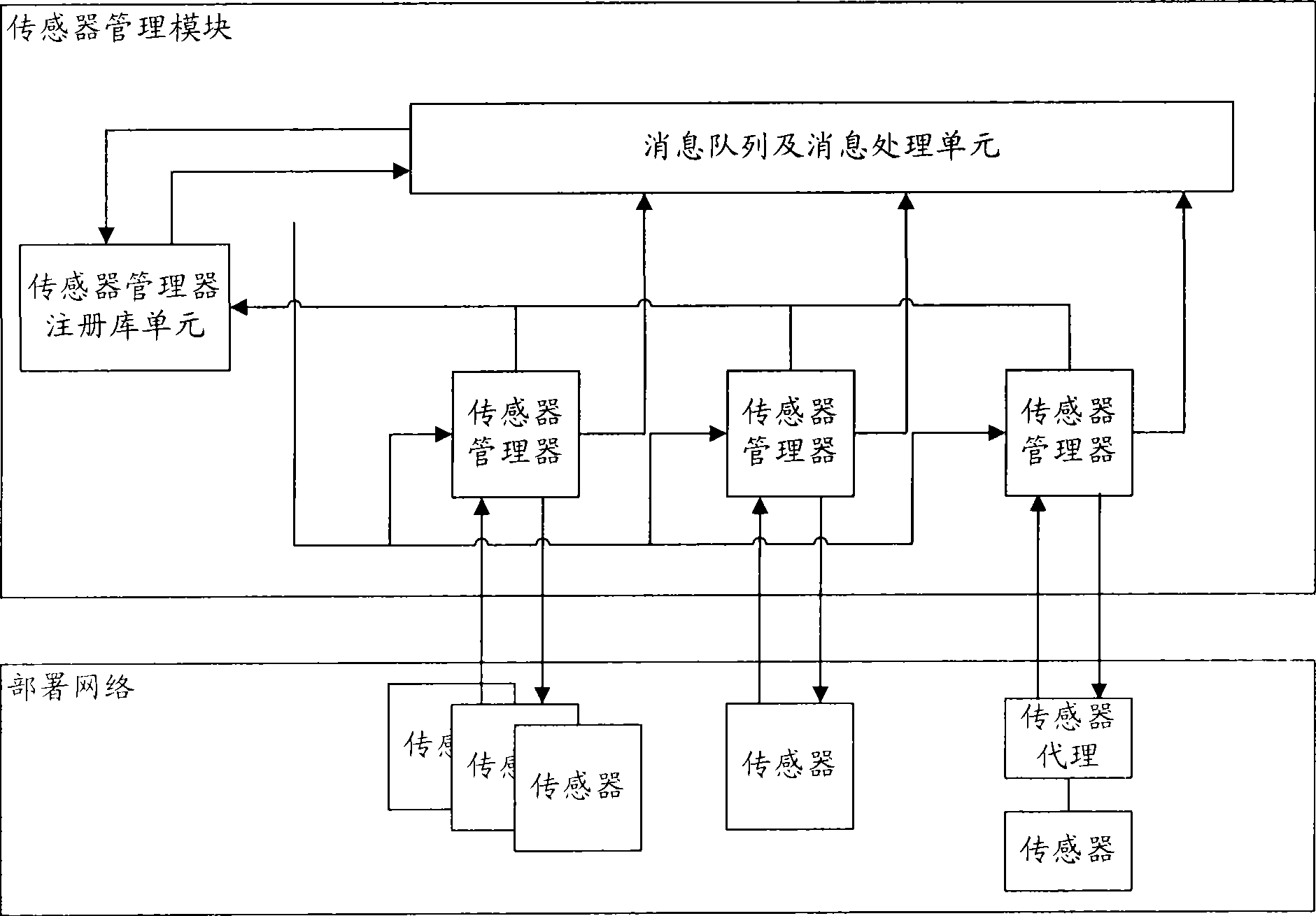
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
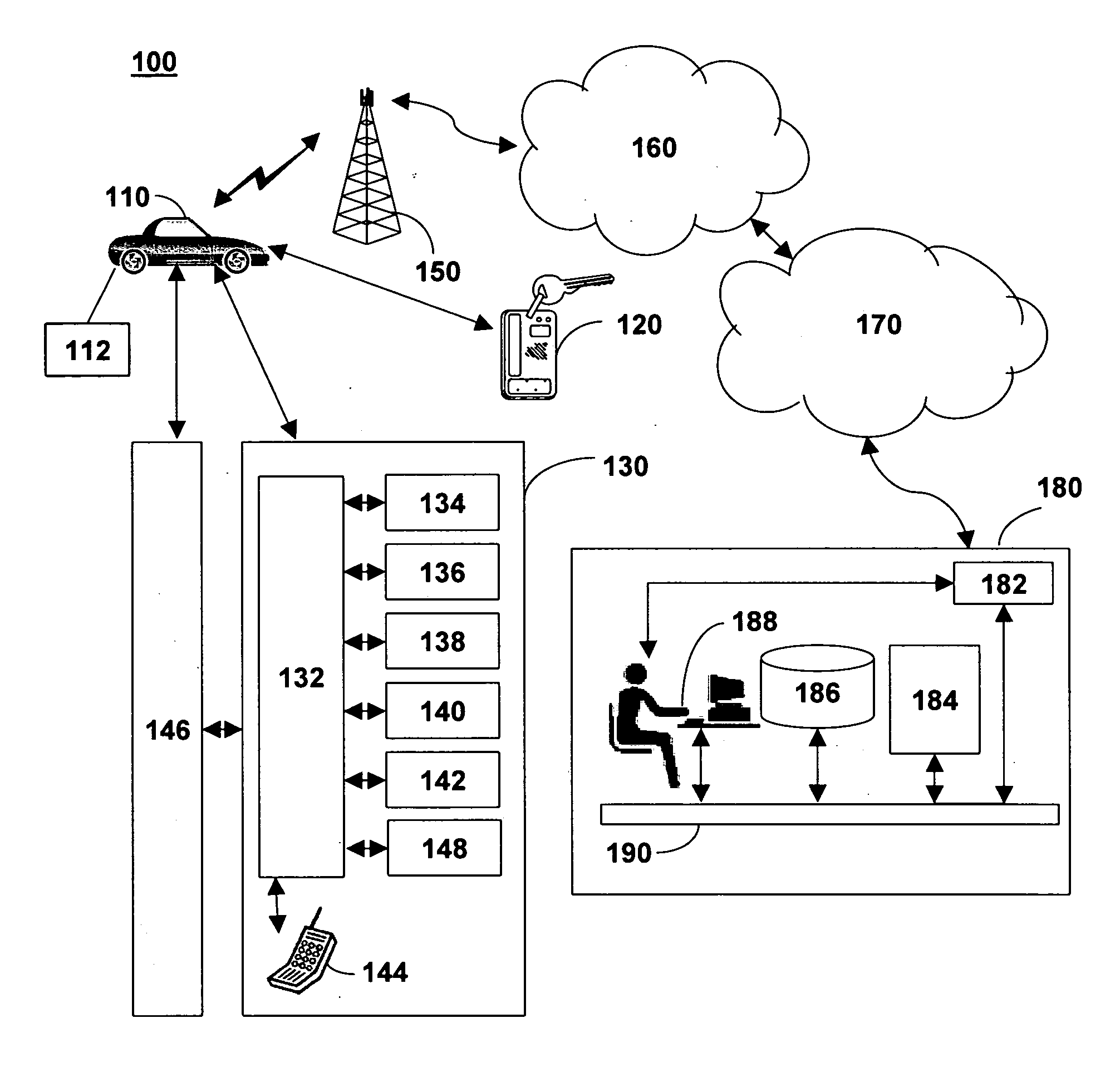
Vehicle security system and method of operation based on a nomadic device location
A vehicle security system for a vehicle equipped with a passive keyless entry / passive start (PEPS) security system including a nomadic device configured to determine a present location of the nomadic device (e.g. key fob, smart phone), and a controller configured to control a security-status based on the present location. The controller determines the security status based on the proximity of the nomadic device in order to thwart theft of the vehicle using a relay attack.
Owner:DELPHI TECH INC
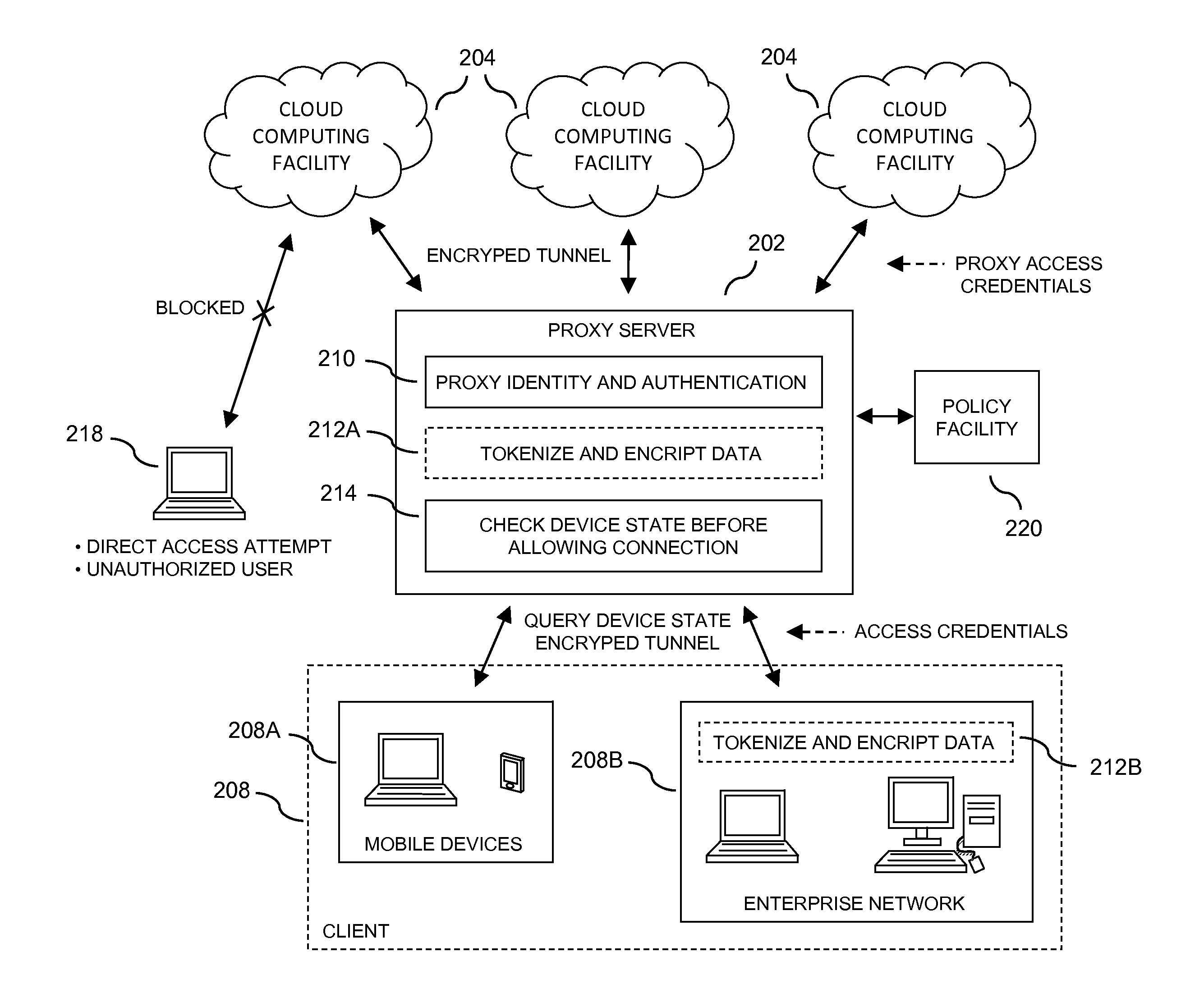
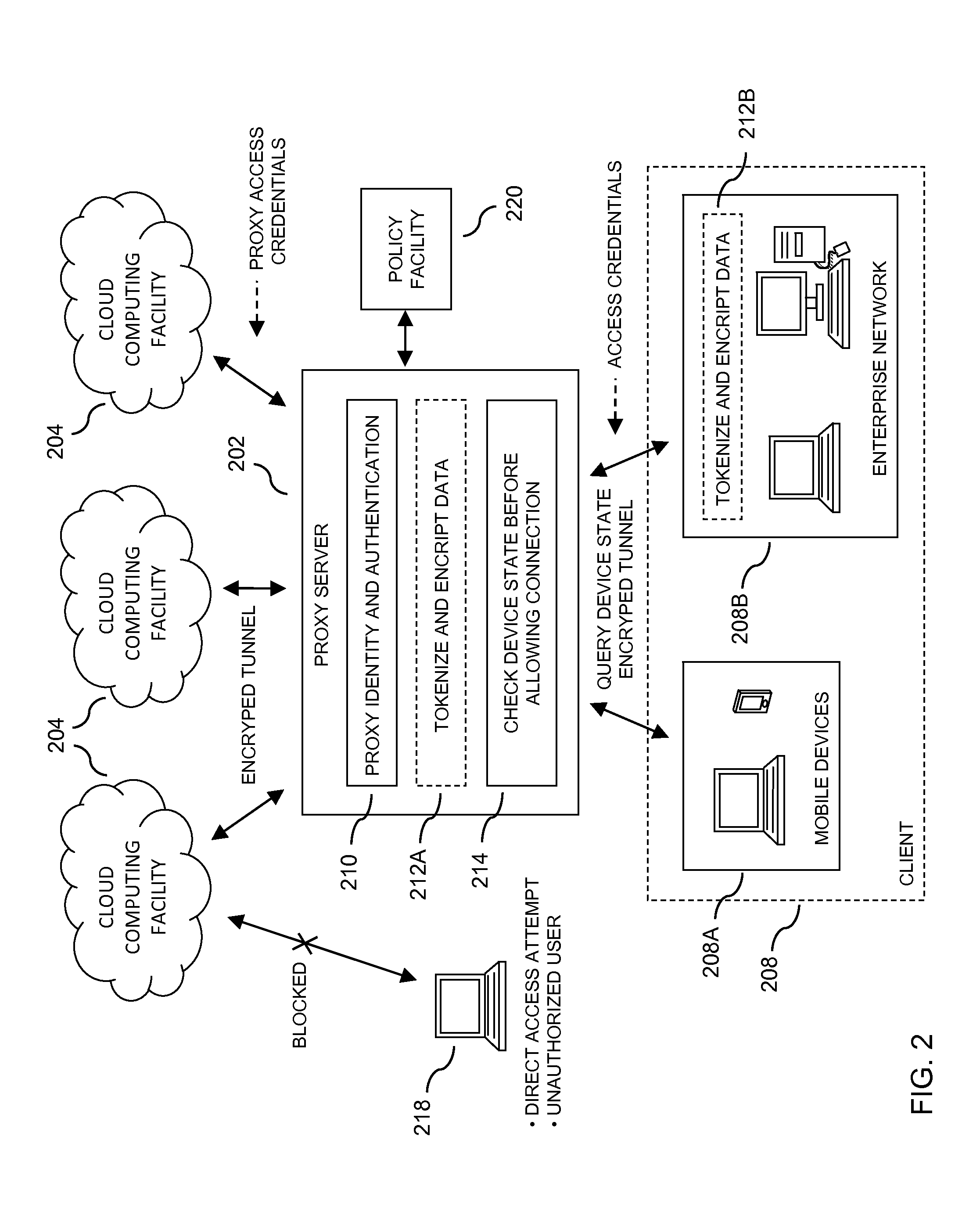
Security access protection for user data stored in a cloud computing facility
ActiveUS20140020072A1Digital data processing detailsUser identity/authority verificationTelecommunications linkSecure state
In embodiments of the present invention improved capabilities are described for a method and system including storing a plurality of proxy access credentials for a user to securely access each of a plurality of cloud computing facilities; receiving a request from a client device for access to one of the plurality of cloud computing facilities; securing a communication link to the client device, thereby providing a secure link; receiving access credentials from the user through the secure link; verifying an identity of the user with the access credentials; assessing a security state of the client device to determine if the client is in compliance with a security policy; and if the client is in compliance with the security policy, coupling the client to one of the plurality of cloud computing facilities through a second secure link using a corresponding one of the plurality of proxy access credentials for the user.
Owner:SOPHOS
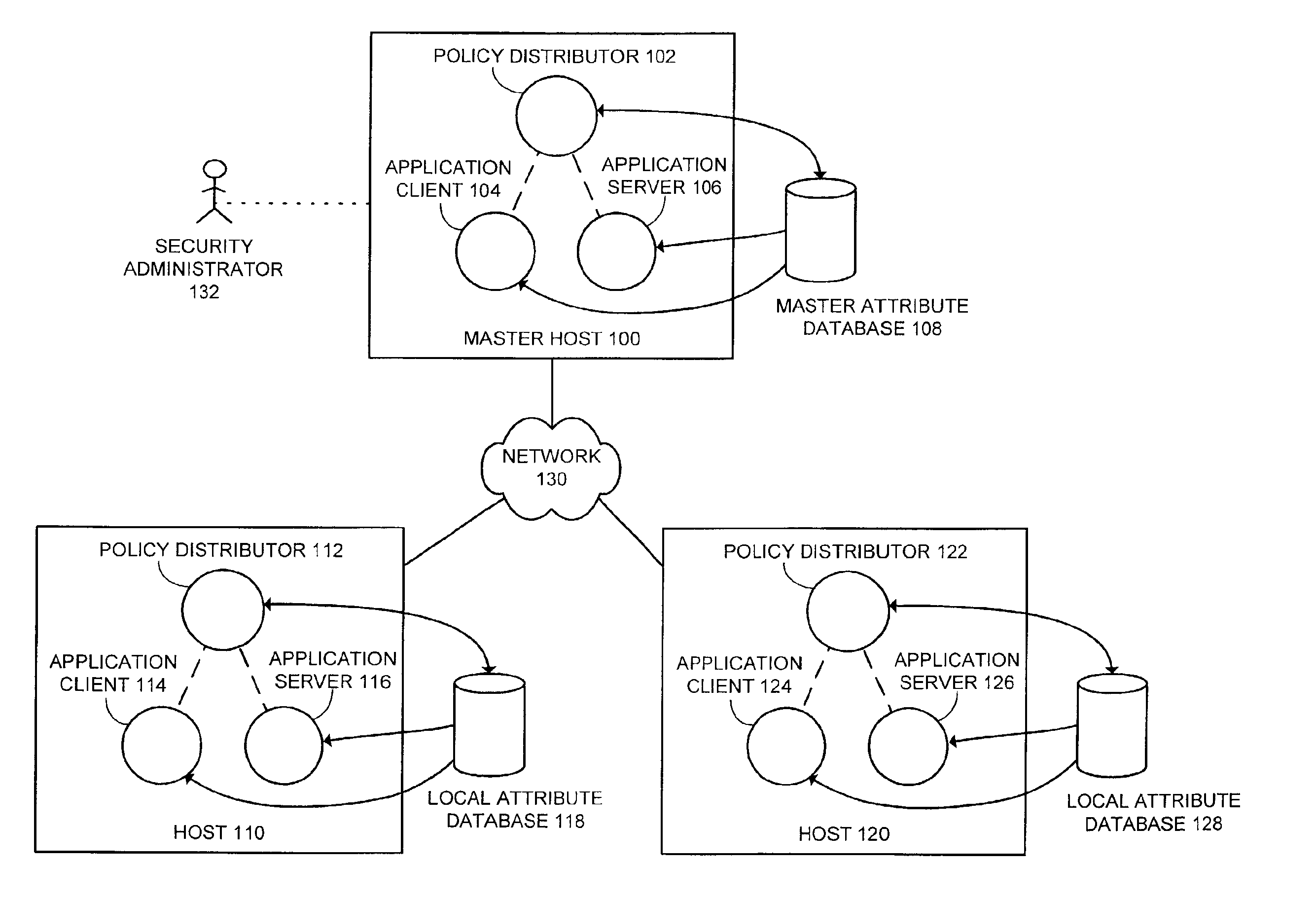
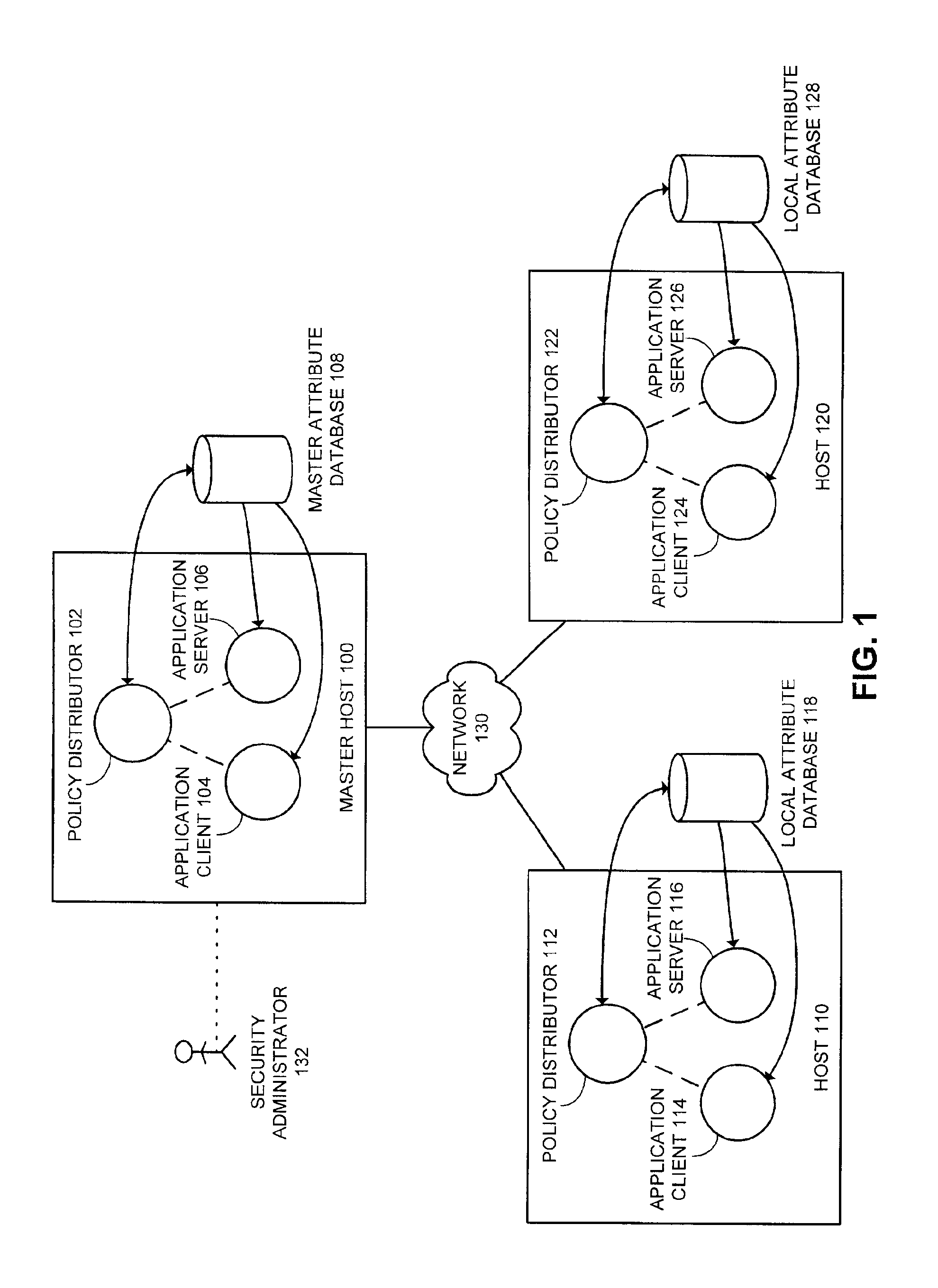
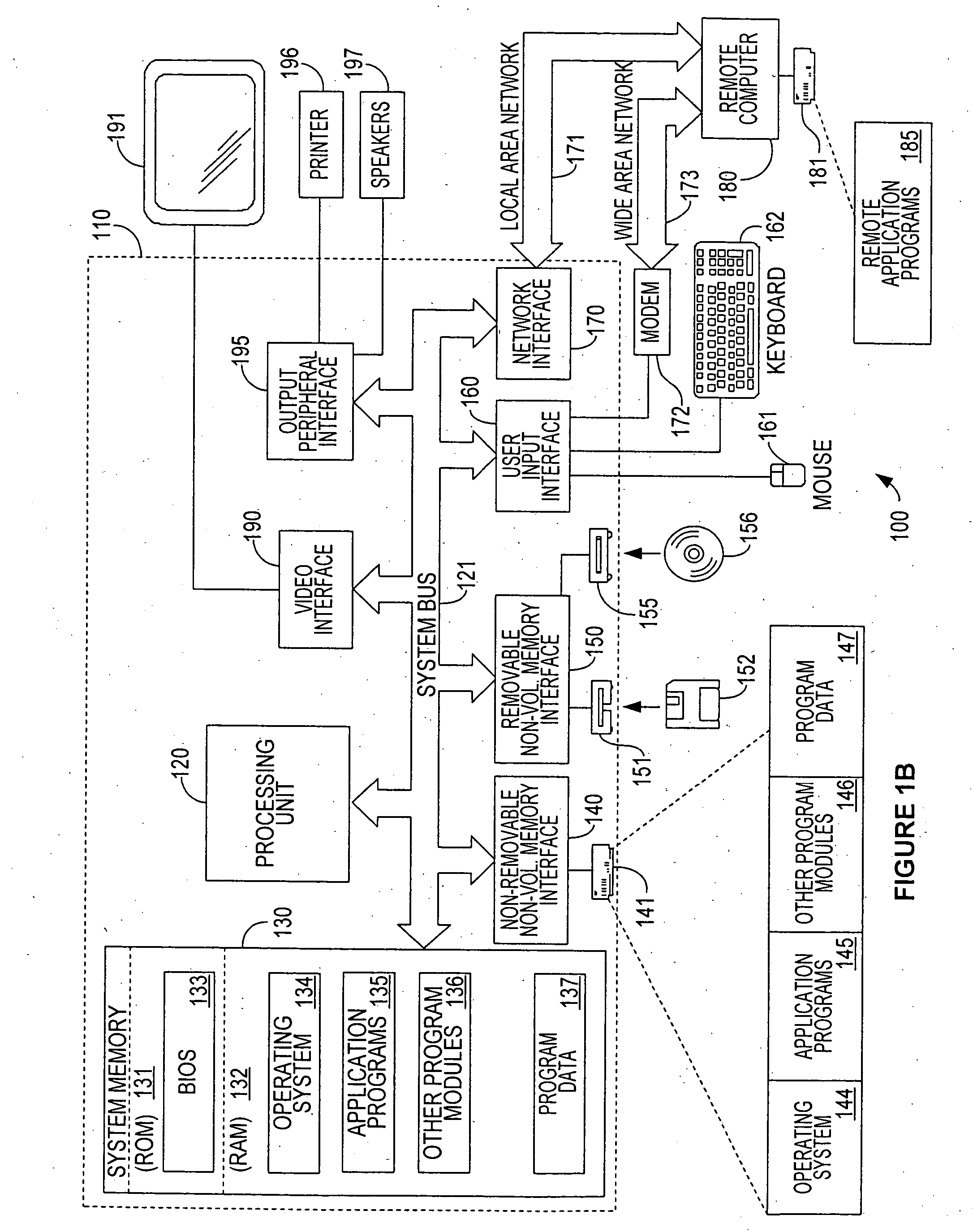
Method and apparatus for securely and dynamically modifying security policy configurations in a distributed system
InactiveUS6920558B2Computer security arrangementsSecret communicationSecure stateApplication software
One embodiment of the present invention provides a system for managing security policies in a distributed computing system. Security policies include, but are not limited to, a firewall policy, a policy for file access, a policy for application access, a policy for an encryption algorithm, a policy for audit trails, and a policy for activity logging. These security policies determine access rights to a computer application. The system operates by creating multiple security policies with individual security policies specifying a differing level of security for the distributed computing system. These security policies are then distributed to each computer in the distributed computing system. Next, a specific security policy is selected for use across the distributed computing system, and each computer in the distributed computing system is directed to use the specified security policy enforcing a selected security posture.
Owner:MCAFEE LLC
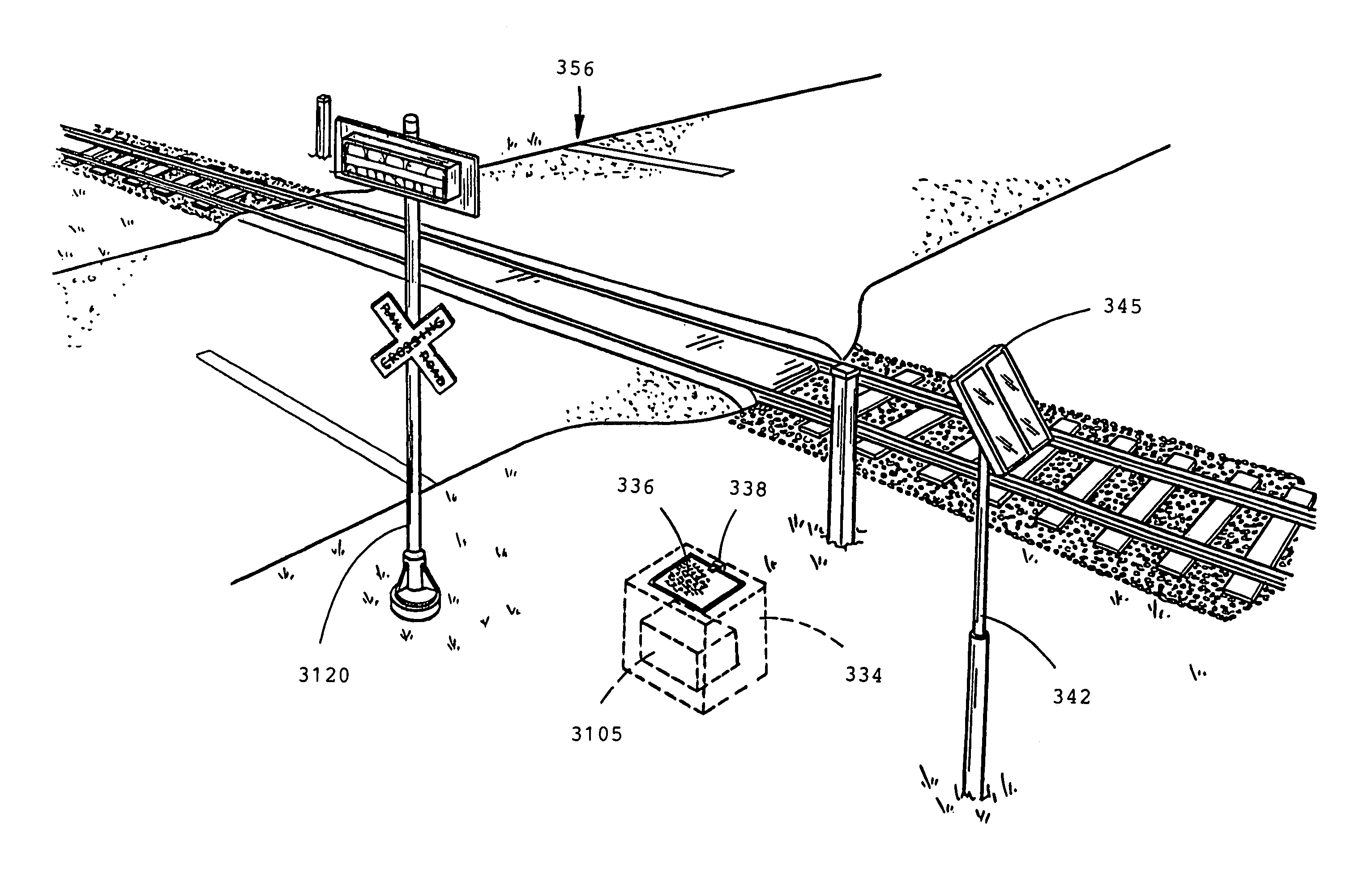
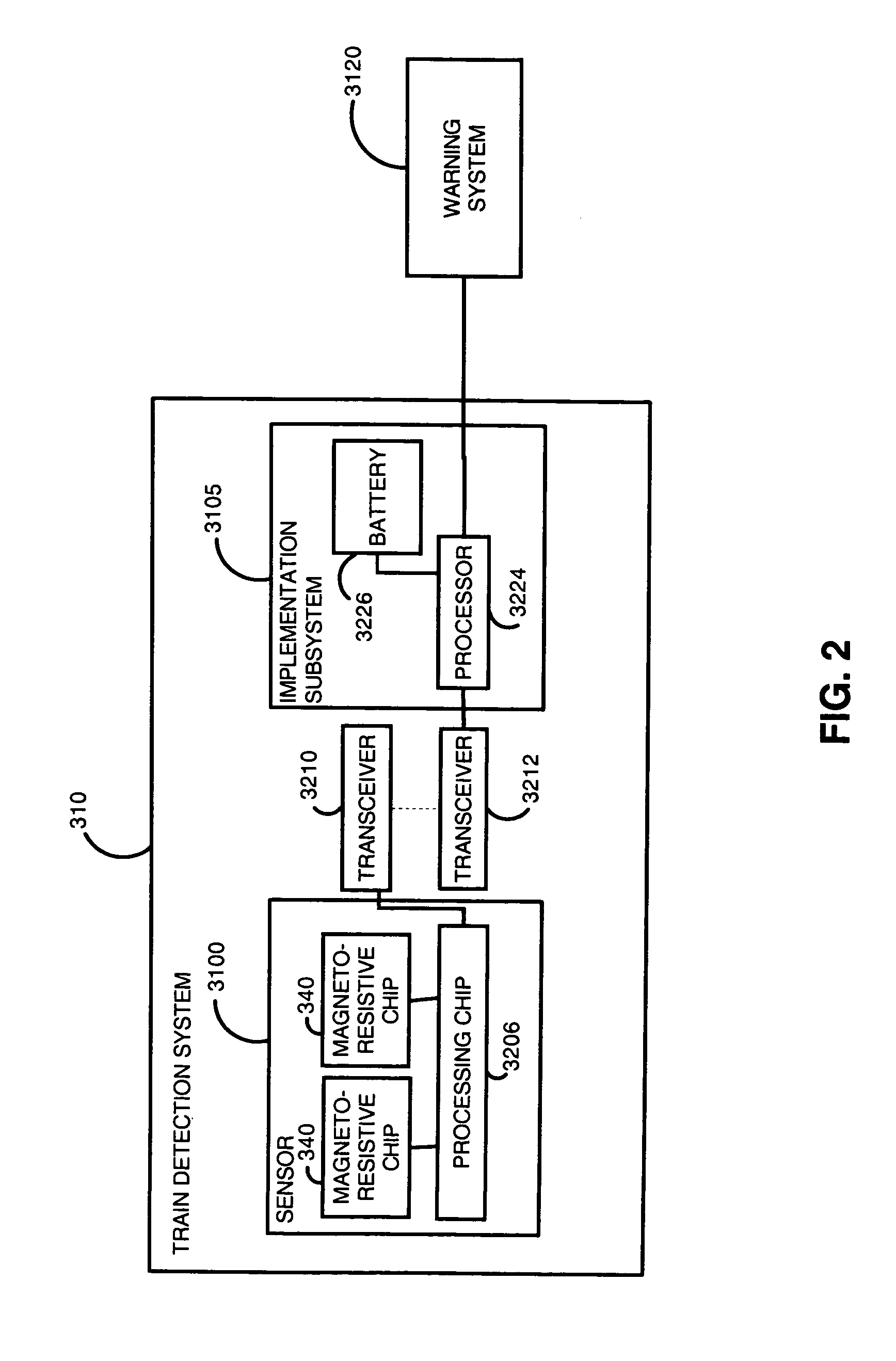
Traffic warning system
InactiveUS7075427B1Increase awarenessProvide informationDetection of traffic movementAnti-collision systemsSecure stateLevel crossing
The present invention is directed to a train detection system for detecting the velocity, presence, and direction of a railroad car which may be utilized in existing railroad crossing installations. The train detection system is suitable for self-testing of its components and if an anomaly has been detected, the train detection system is capable of placing the system in a fail-safe state. The train detection system of the present invention is also capable of constant communication between the sensor of said system and the implementing device of the train detection system via a wireless link.
Owner:EVA SIGNAL CORP
System and method for assessing the security posture of a network
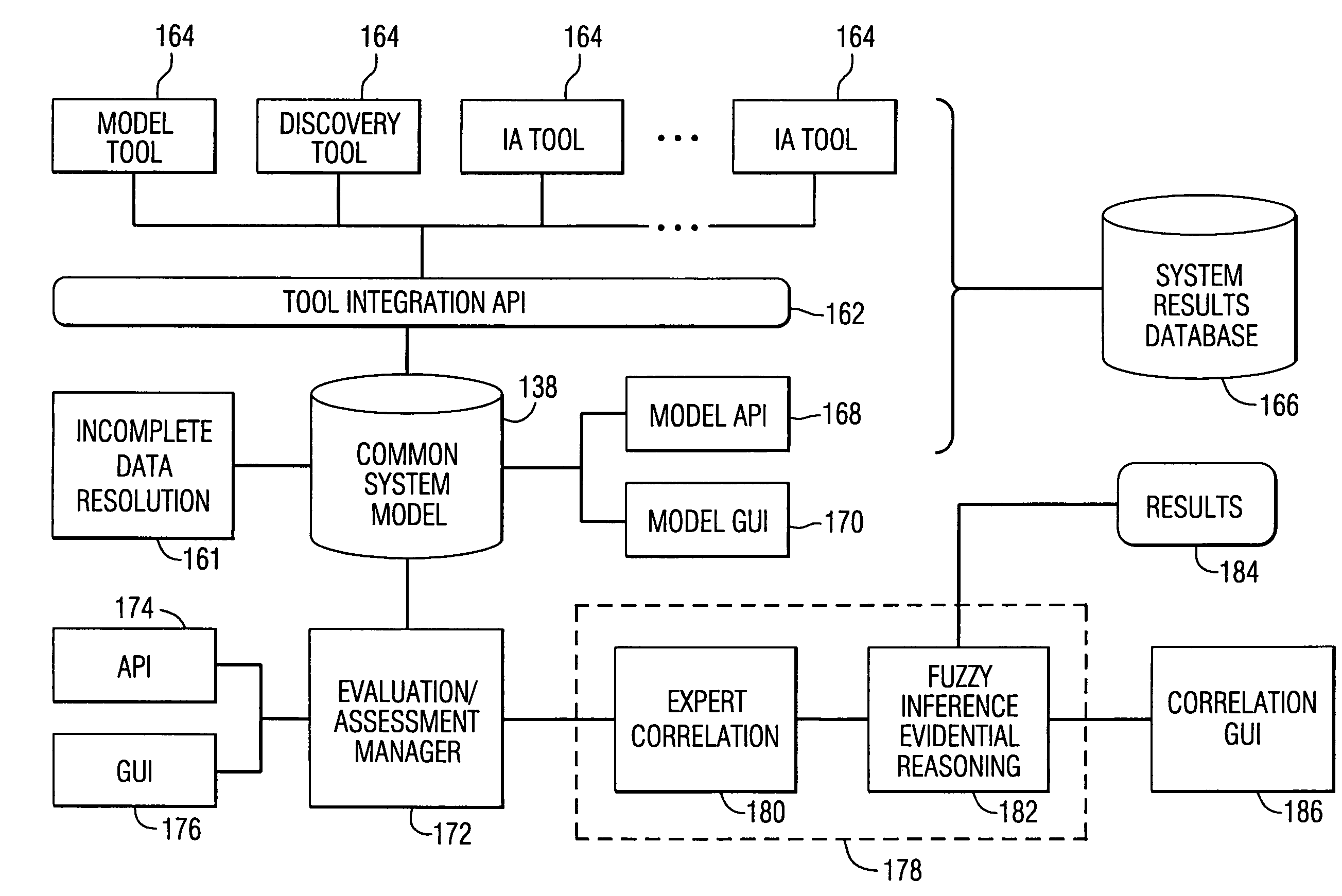
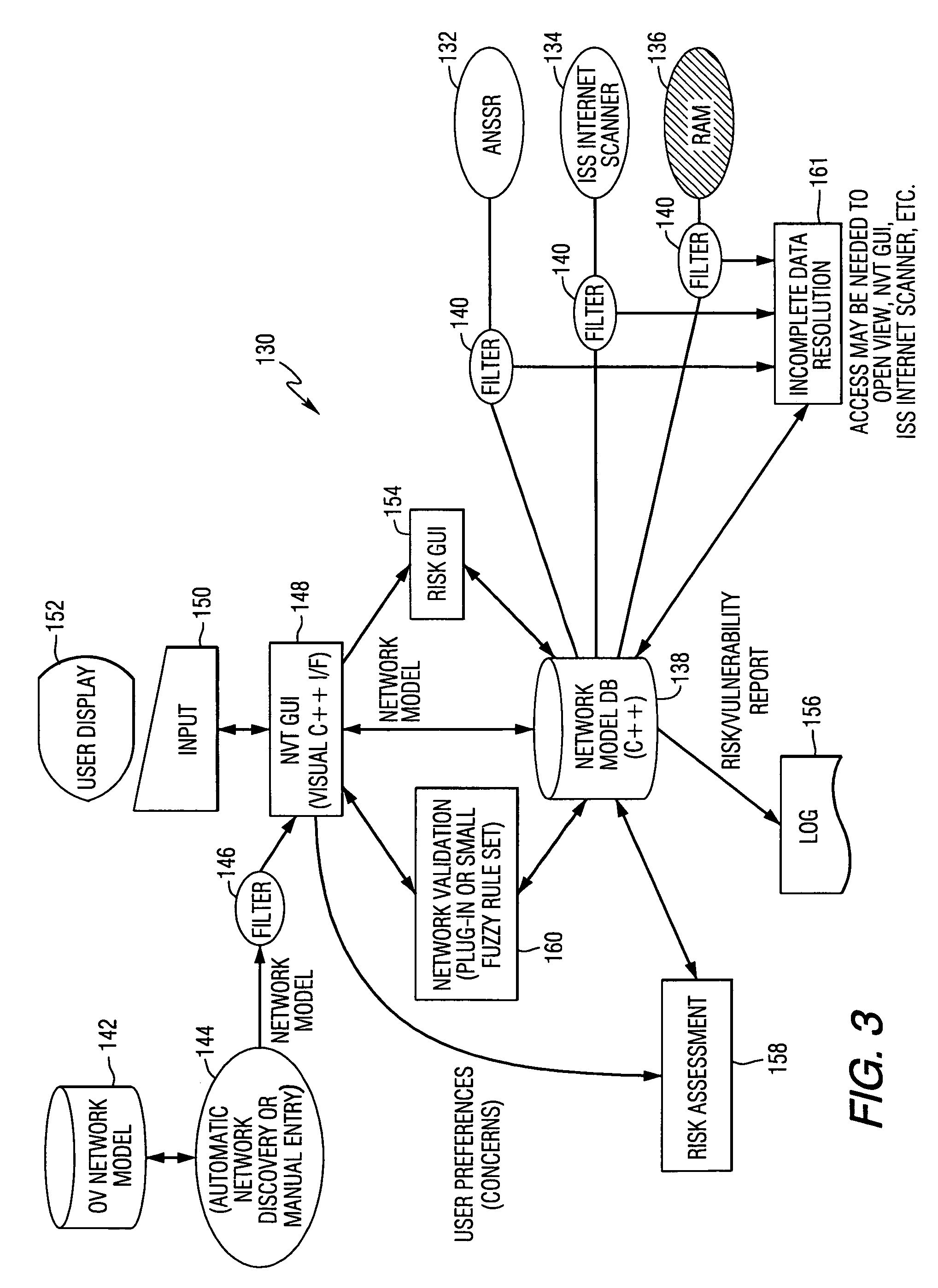
InactiveUS7096502B1Data processing applicationsMemory loss protectionData processing systemSecure state
A method and data processing system assesses the security vulnerability of a network by creating a system object model database representing a network. The system object model database supports the information data requirements of disparate network vulnerability analysis programs. The system object model database is exported to the disparate network vulnerability analysis programs. The network is analyzed with each network vulnerability analysis program to produce data results from each program. Data results are correlated to determine the security posture of the network.
Owner:HARRIS CORP
System and methods for providing network quarantine
InactiveUS20050131997A1Network resource is limitedMemory loss protectionDigital data processing detailsAccess networkSecure state
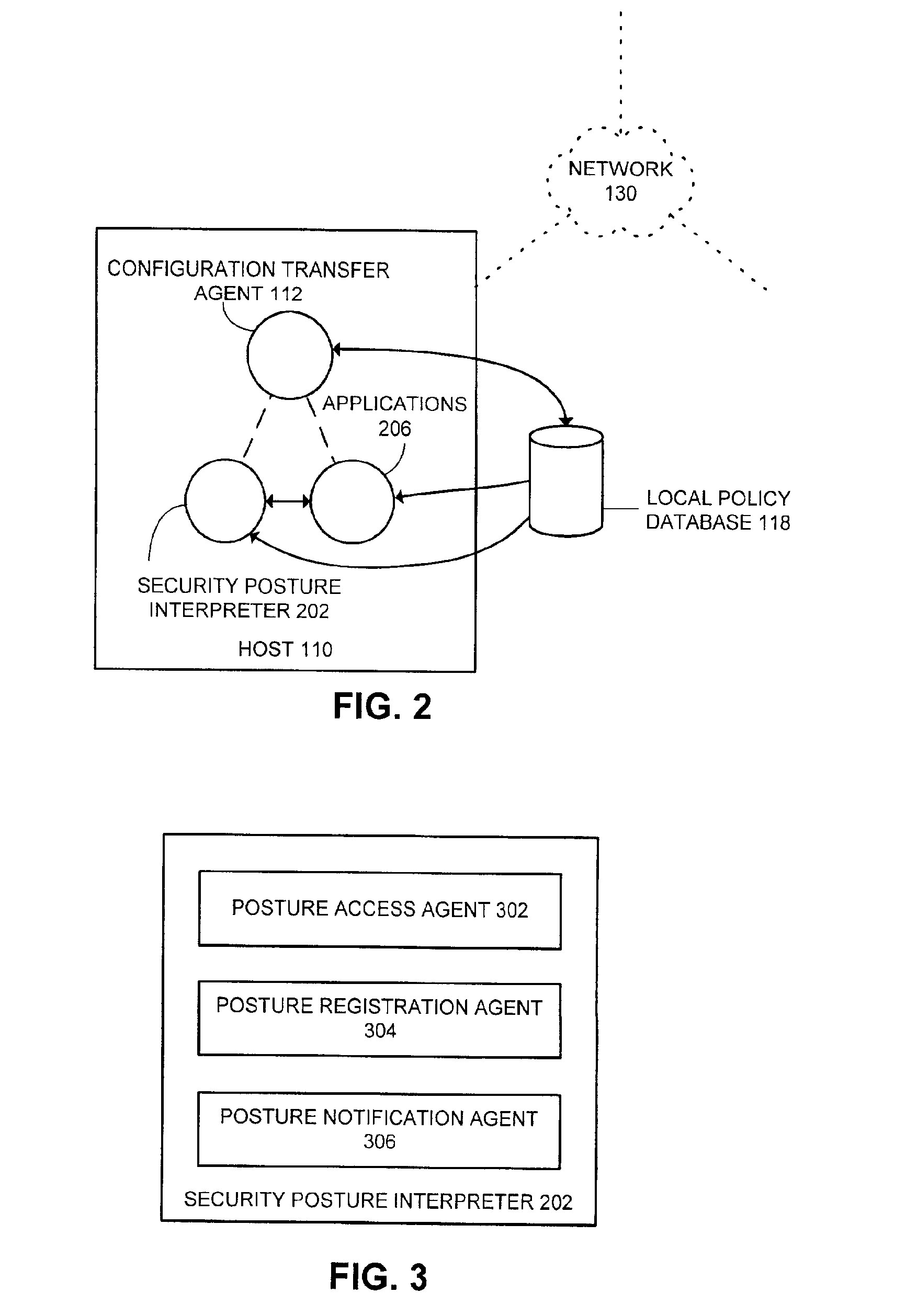
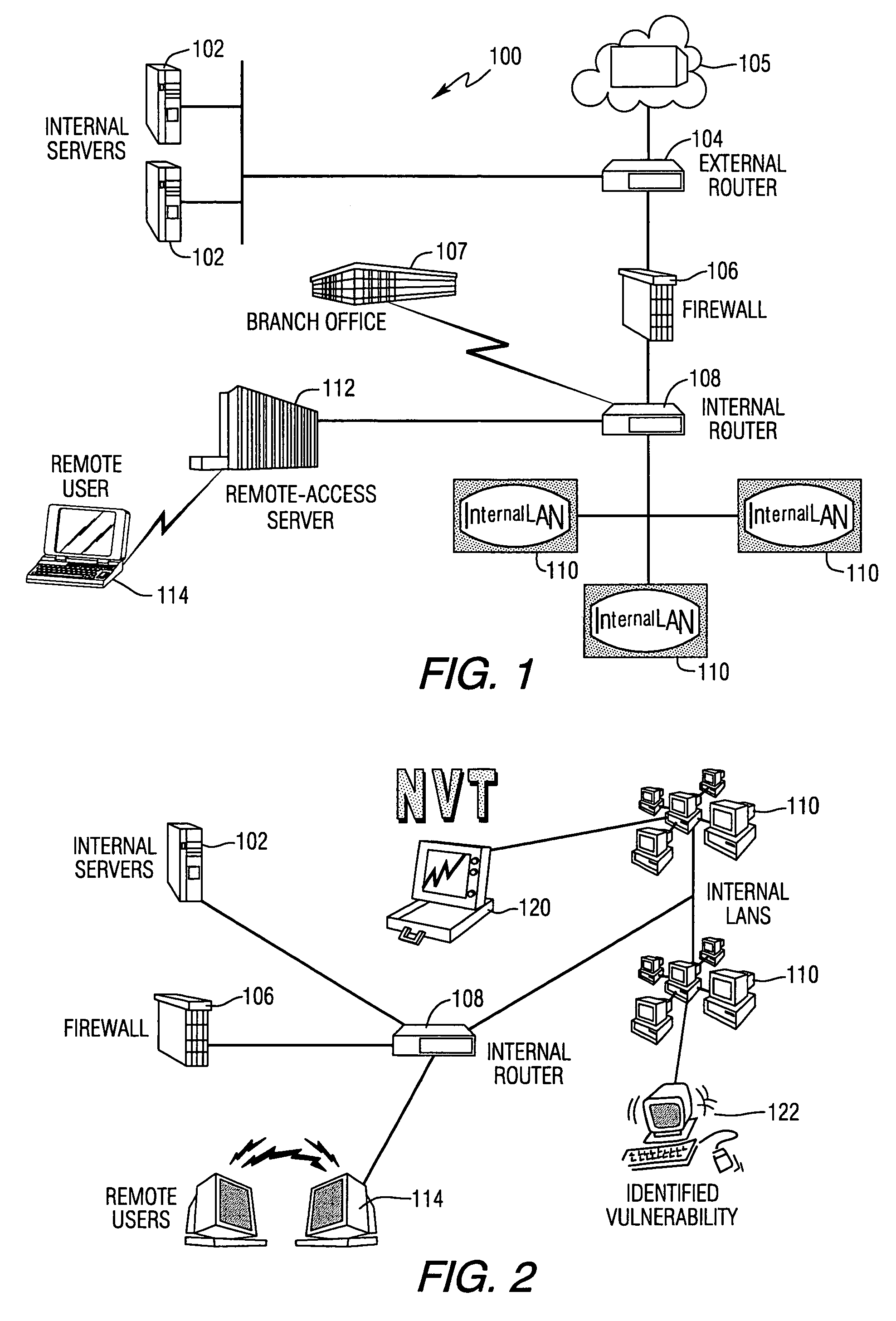
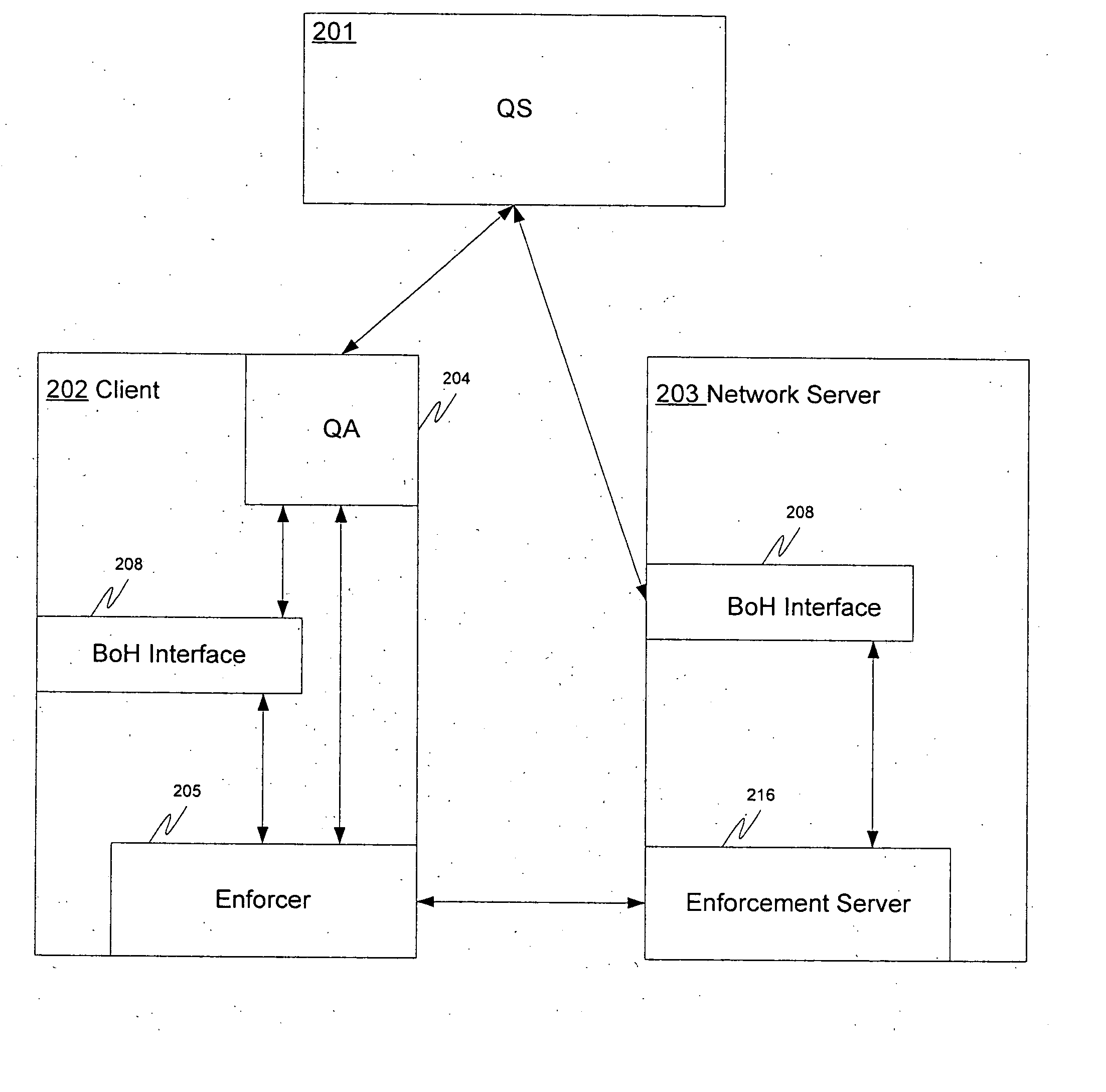
A system and method for ensuring that machines having invalid or corrupt states are restricted from accessing network resources are provided. A quarantine server located on a trusted machine in a network provides a bill of health to a quarantine agent located on a client computer that wishes to gain access to network resources administered by an organization. The quarantine agent requests bill of health from the quarantine server, and receives a manifest of checks that the client computer must perform. The quarantine agent then sends a status report on the checks back to the quarantine server. If the client computer is in a valid security state, the bill of health is issued to the client. If the client computer is in an invalid state, the client is directed to install the appropriate software / patches to achieve a valid state. When a client requests the use of network resources from a network administrator, the network administrator requests the client's bill of health. If the bill of health is valid, the client is admitted to the network. If the bill of health is invalid, or if the client does not have a quarantine agent, the client is placed in quarantine, in which the only network resources accessible to the client are those necessary to install the quarantine agent and requisite software / patches to achieve a valid state.
Owner:MICROSOFT TECH LICENSING LLC
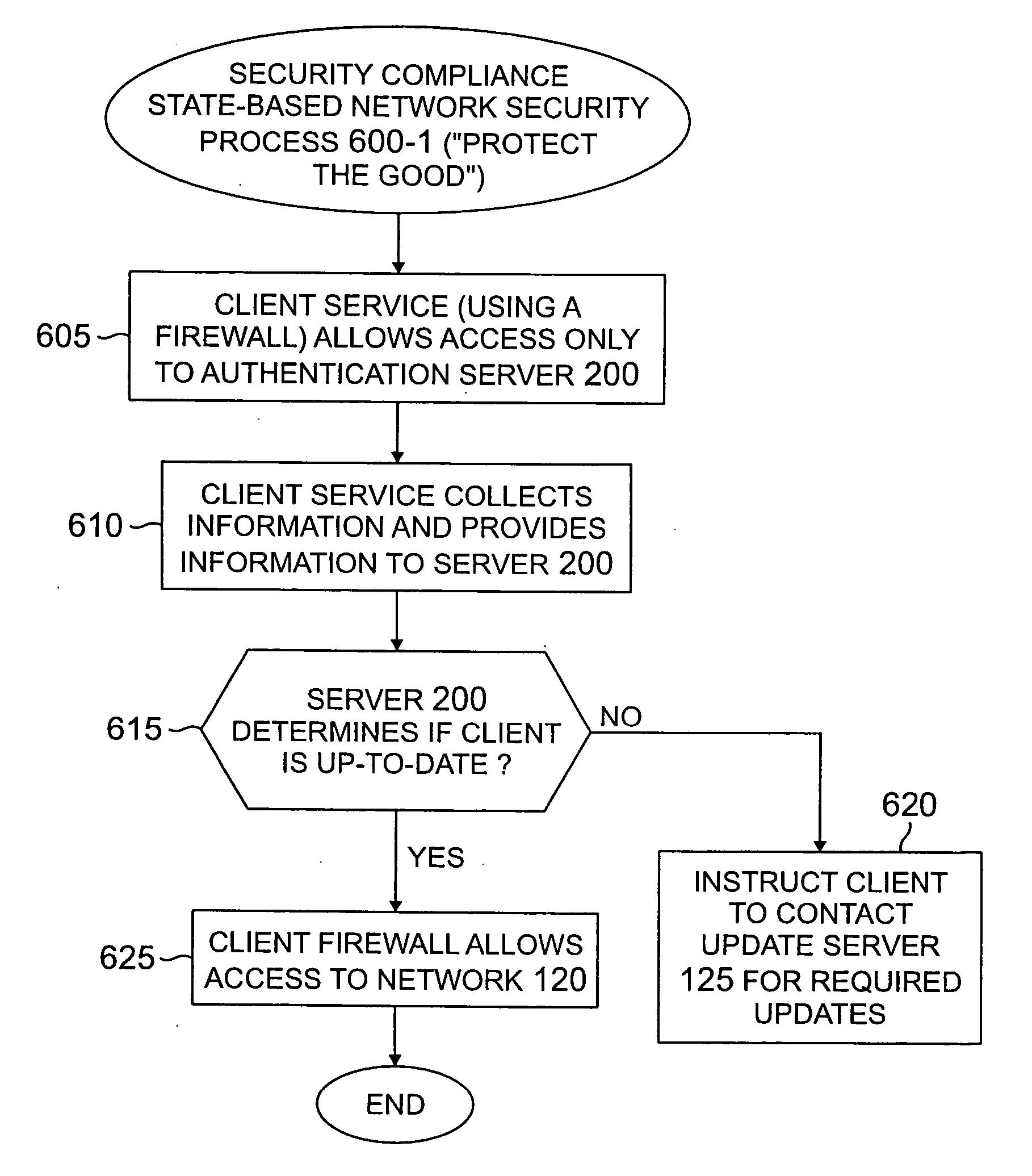
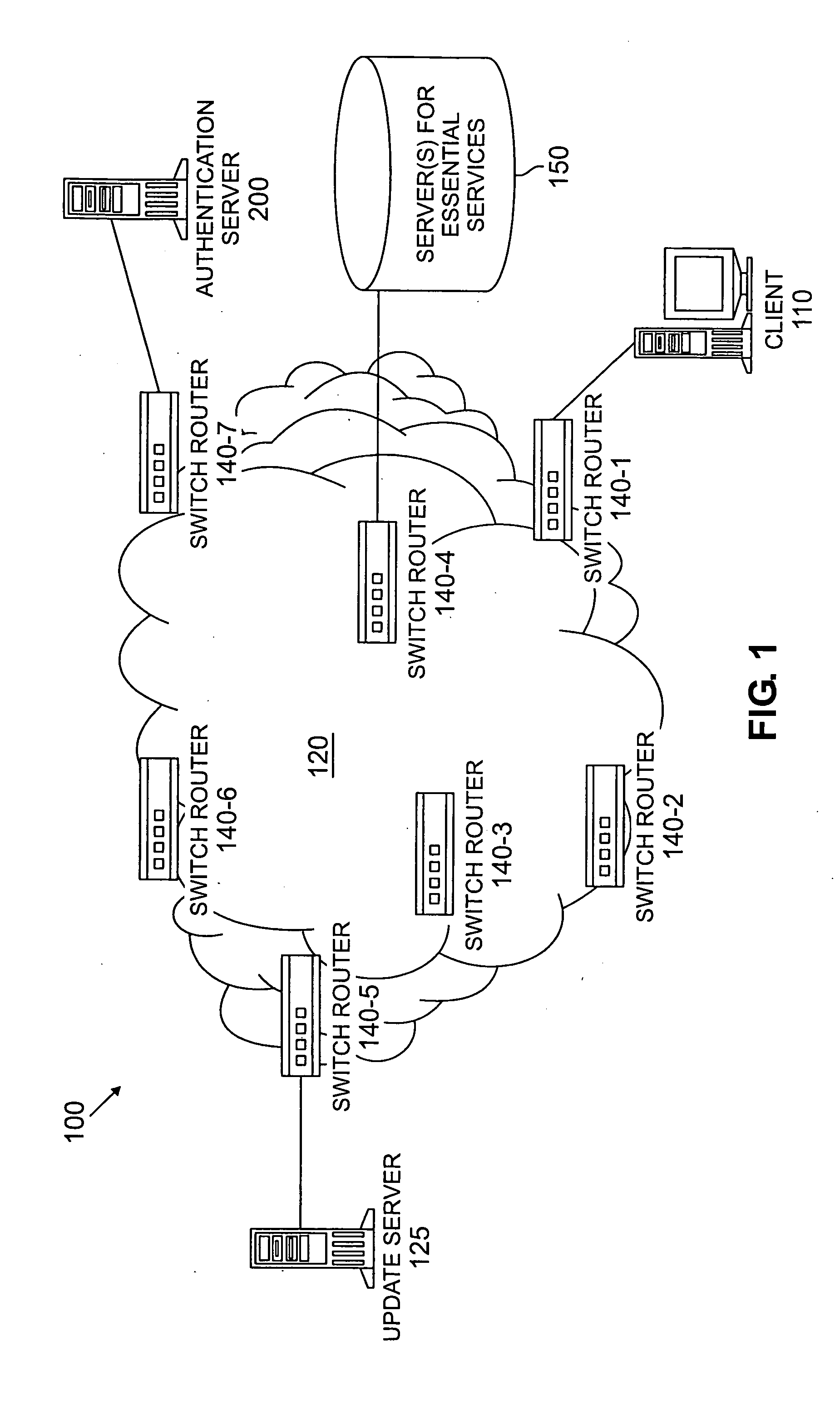
Method and apparatus for network security based on device security status
A method and apparatus are provided for network security based on a security status of a device. A security update status of a device is evaluated; and one or more of a plurality of security policies are selected to apply to the device based on the security update status. The available security philosophies may include, for example, a “protect the good” philosophy, an “encourage the busy” philosophy and a “shut off the non-compliant” philosophy. The security update status can evaluate, for example, a version level of one or more security features installed on the device or can be based on a flag indicating whether the device satisfies predefined criteria for maintaining one or more computer security protection features up-to-date.
Owner:AVAYA INC
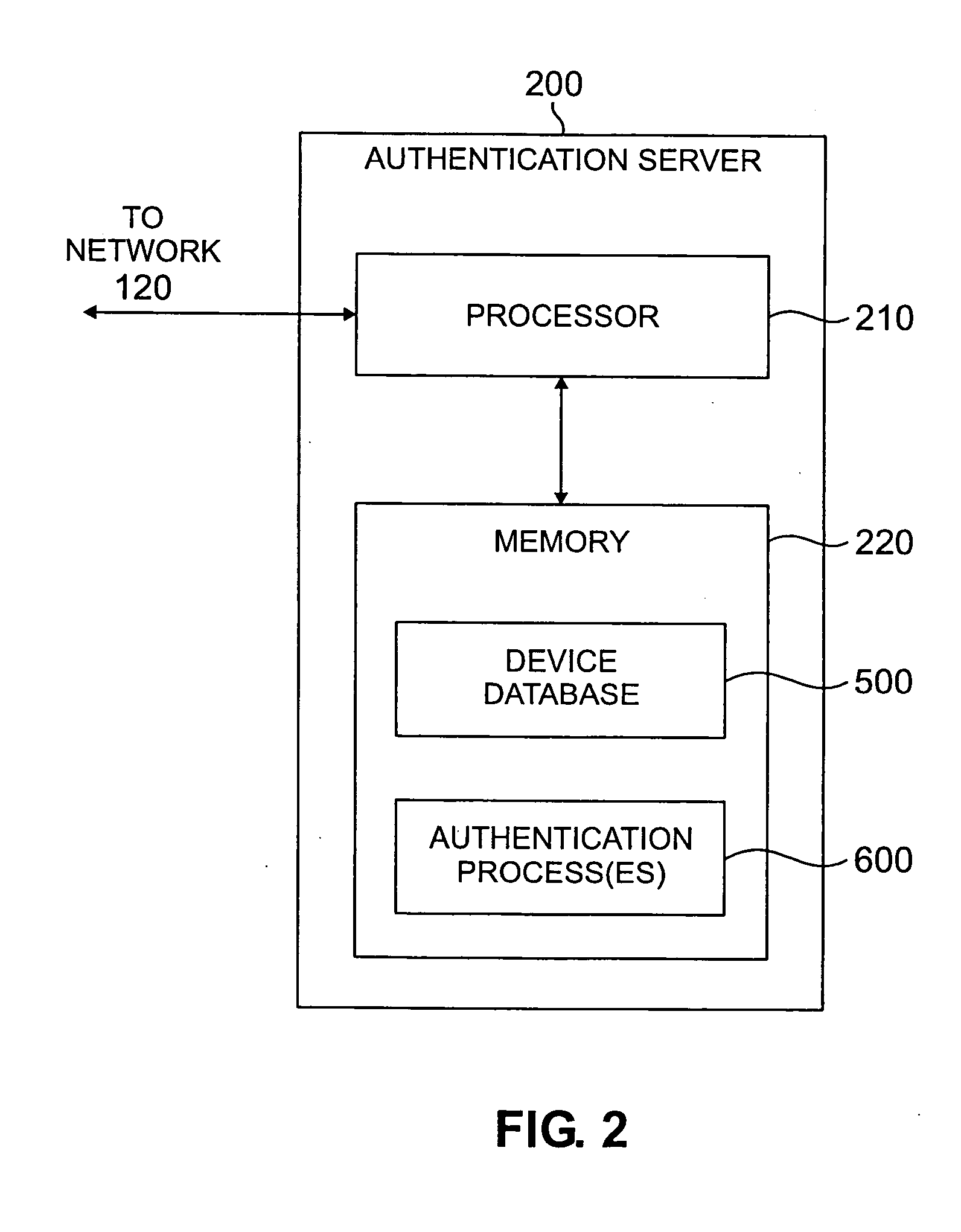
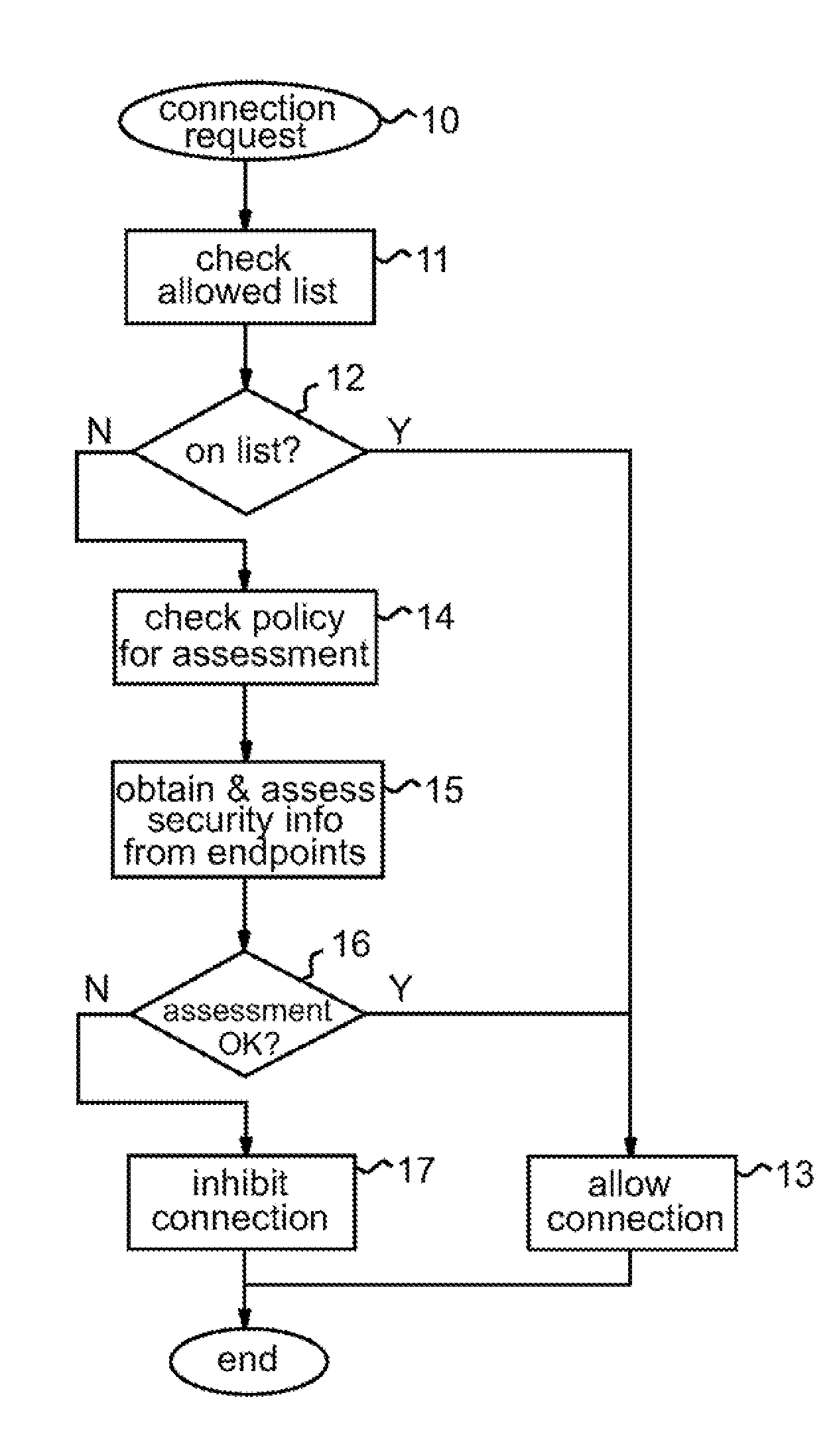
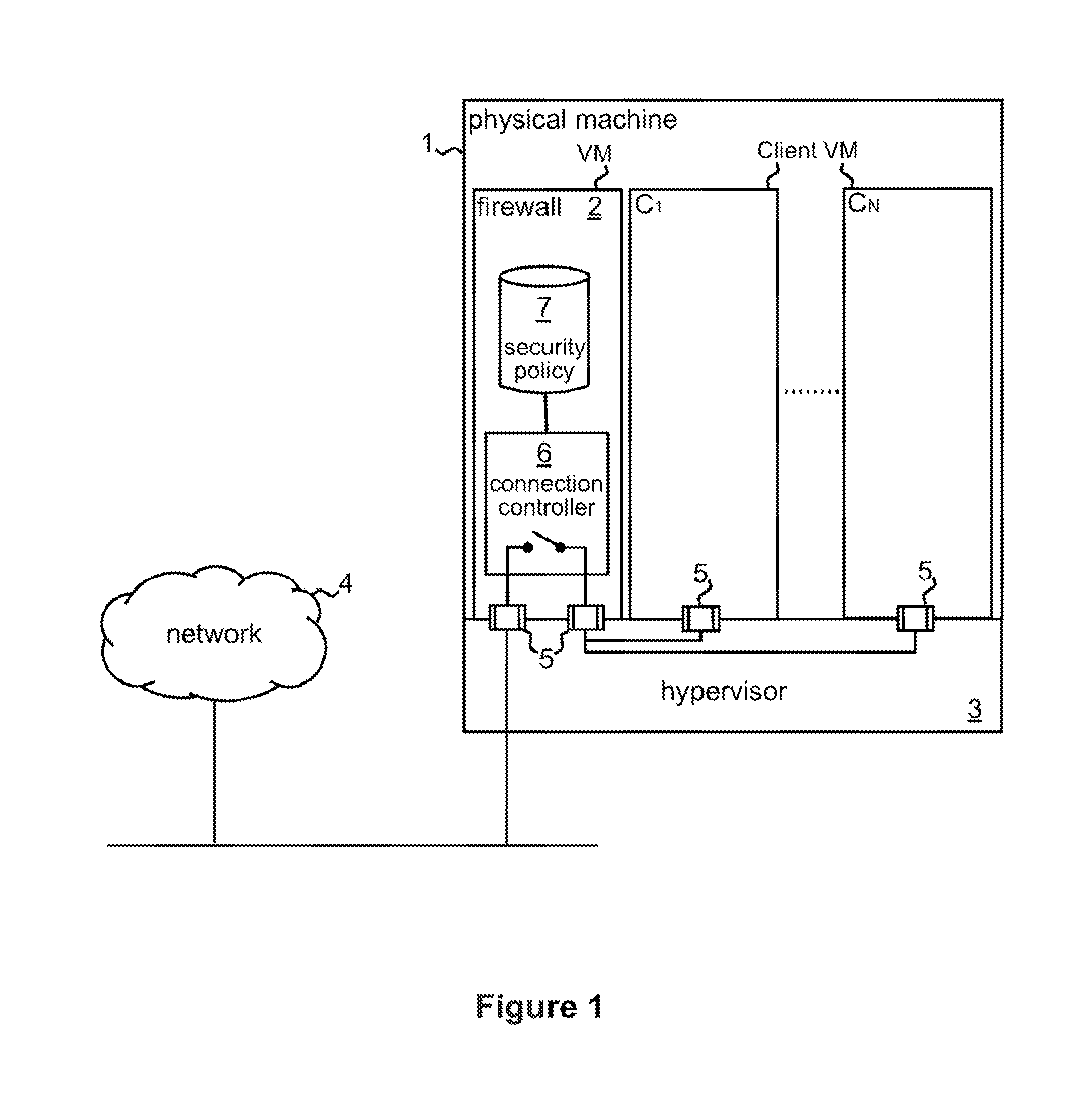
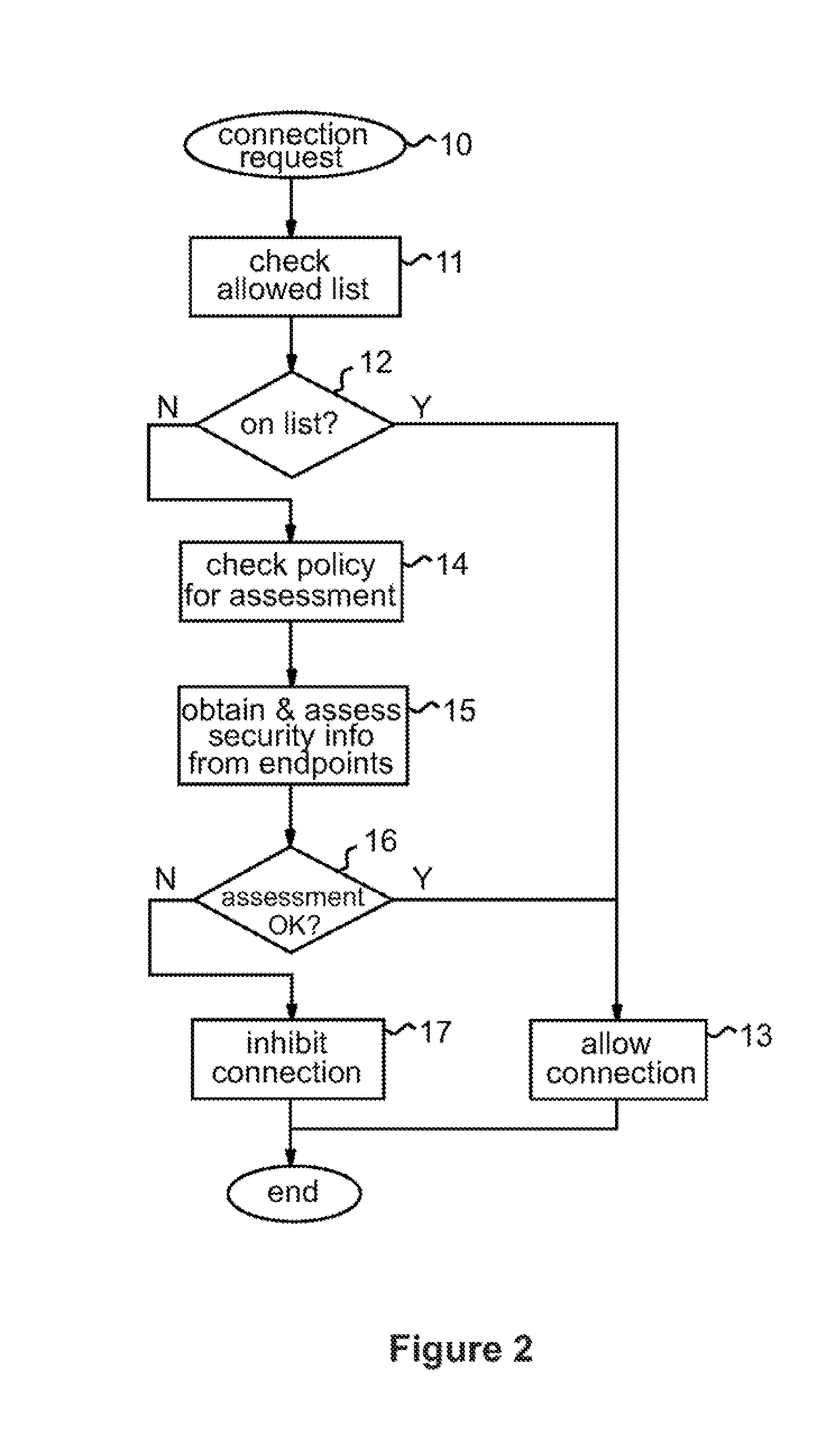
Firewall for controlling connections between a client machine and a network
ActiveUS20080289028A1Function increaseAvoid problemsComputer security arrangementsMultiple digital computer combinationsSecure stateClient-side
A firewall system adapted for location outside the client machine, preferably in the same data processing device as the client machine but outside a virtual machine containing the client machine. Control logic of the firewall system receives incoming and outgoing connections from the network and client machine respectively. In response to a connection request initiating a connection between respective endpoints in the network and client machine, the control logic performs a security assessment comprising obtaining from at least one of the network and client machine information indicative of the security state of the endpoint therein, and allows or inhibits the connection in dependence on the result of the security assessment. The security assessment may be performed in accordance with a security policy of the system, and different security assessments may be performed for different connection requests in accordance with the security policy.
Owner:GLOBALFOUNDRIES US INC
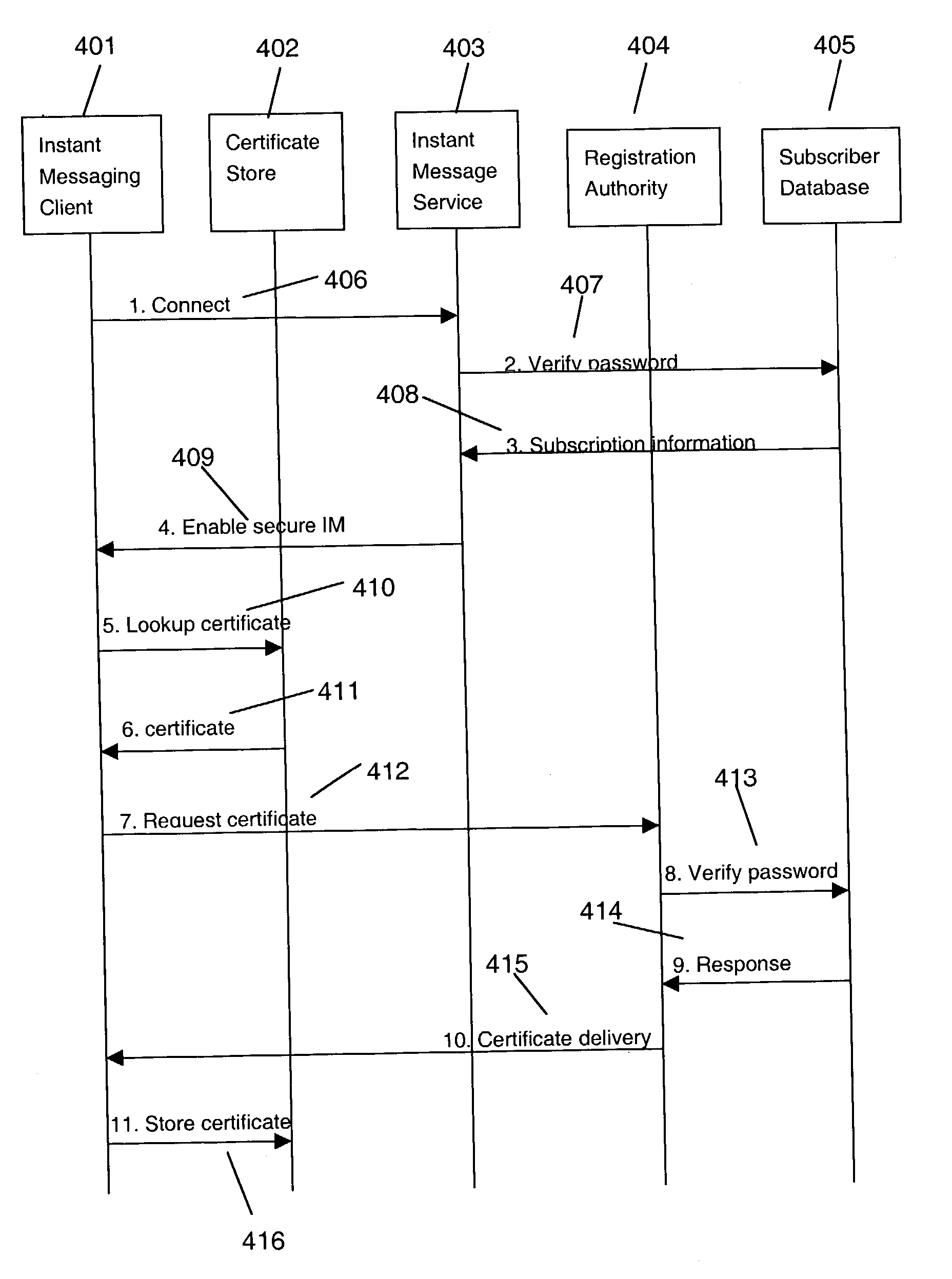
Secure instant messaging system
ActiveUS7131003B2Multiple keys/algorithms usagePublic key for secure communicationRelevant informationSecure state
A secure instant messaging system integrates secure text instant messaging and secure file transfers into existing instant messaging systems. At least one certificate authority (CA) is provided that issues a security certificate to a user that binds the user's instant messaging screen name to a public key which is used by other users to encrypt messages and files sent to the user and by the user to decrypt the received messages and files. A subscriber database is used by the CA to keep track of valid users and their associated information, such as: user screen names, user subscription expiration dates, and enrollment agent information. A user sends his certificate to the invention's instant messaging server which publishes the user's certificate to other users by creating a hash value of the user's certificate and sending it to the other users which allows the recipients to decide if they need to update their caches with a new copy of the user's certificate. Instant messages and files are encrypted by a sending user using an encryption algorithm and the recipient's certificate. The sending user can sign instant messages using his private signing key. The security status of each received instant message is displayed to the user.
Owner:GOOGLE LLC
Security system for power and display of consumer electronic devices
InactiveUS7327276B1Prevent rotationEliminate needBurglar alarm by hand-portable articles removalDisplay deviceSecure state
A security system for powering and displaying a handheld electronic device includes a stand assembly mounted to a support and a housing removably mounted on a top portion of the stand assembly. The handheld electronic device is secured to a top portion of the housing and a sensor is coupled to the handheld electronic device. The sensor has a secure and a non-secure state and produces a detectable signal in the non-secure state. An output voltage controller controls an output voltage to the handheld electronic device which can be set only when the sensor is in the non-secure state. The output voltage is set to zero if the sensor is not placed in the secure state within a predetermined time.
Owner:VANGUARD PRODS GROUP
Safe state recognition system for people on basis of machine vision
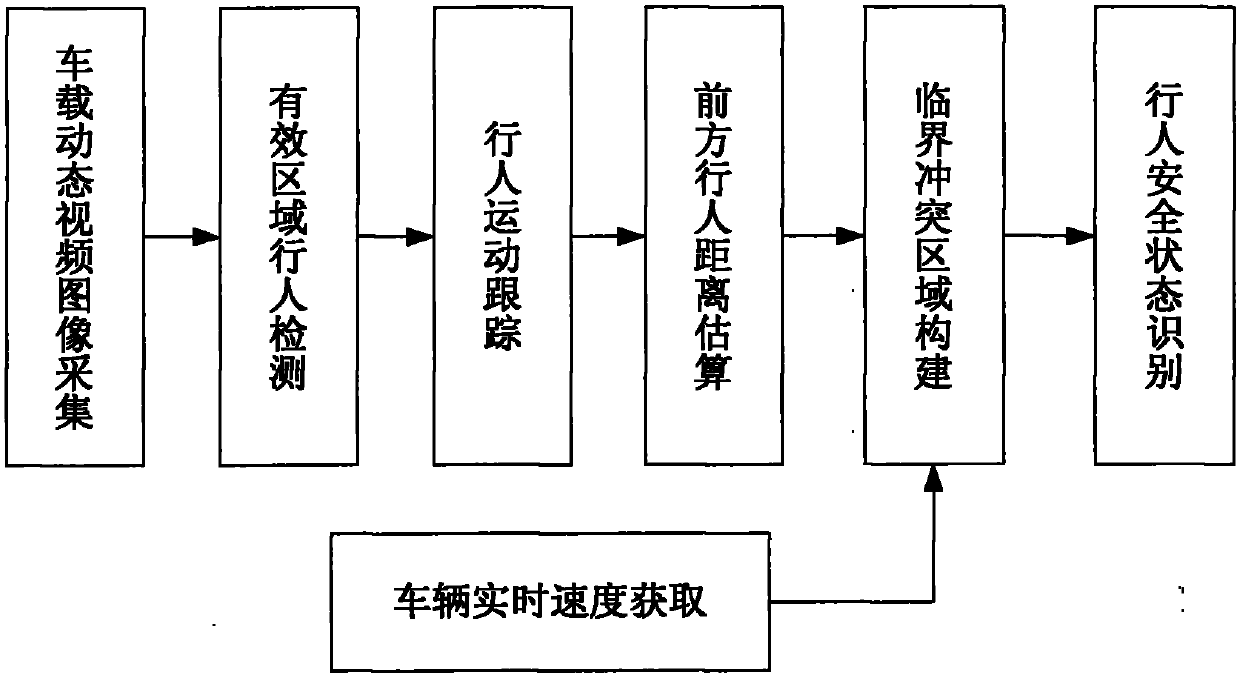
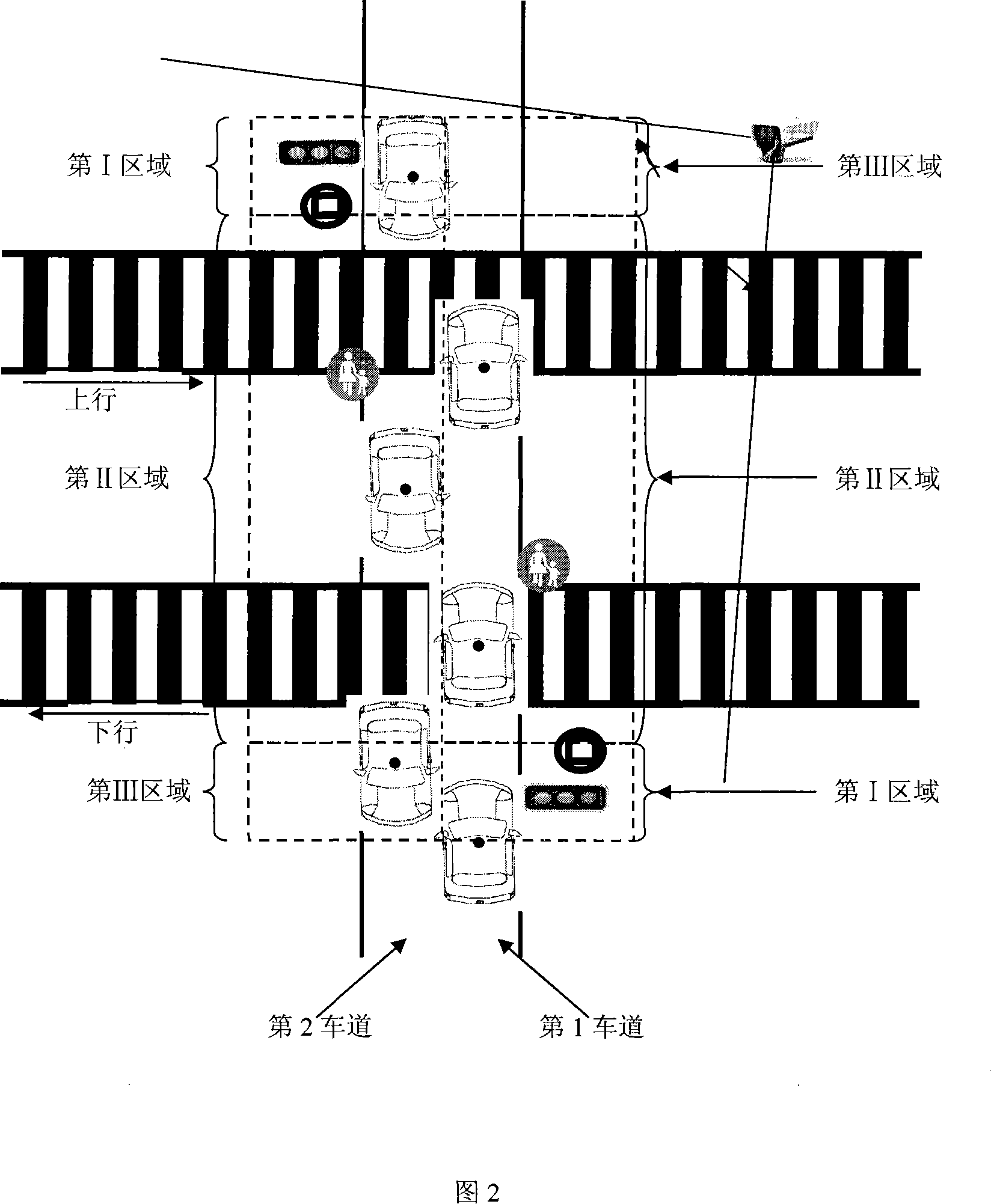
InactiveCN102096803AEnsure safetyHigh technology contentImage analysisAnti-collision systemsDriver/operatorSecure state
The invention discloses a safe state recognition system for people on the basis of machine vision, aiming to solve the problem that the corresponding intelligent control decision for the vehicle driving behaviour can not be formulated according to the safe state of the people in the prior art. The method comprises the following steps: collecting a vehicle-mounted dynamic video image; detecting and recognizing a pedestrian in an interested area in front of a vehicle; tracking a moving pedestrian; detecting and calculating the distance of pedestrian in front of the vehicle; and obtaining vehicle real-time speed; and recognizing the safe state of the pedestrian. The process of recognizing the safe state of the pedestrian comprises the following steps: building a critical conflict area; judging the safe state when the pedestrian is out of the conflict area in the relative moving process; and judging the safe state when the pedestrian is in the conflict area in the relative moving process. Whether the pedestrian enters a dangerous area can be predicted by the relative speed and the relative position of a motor vehicle and the pedestrian, which are obtained by a vision sensor in the above steps. The safe state recognition system can assist drivers in adopting measures to avoid colliding pedestrians.
Owner:JILIN UNIV
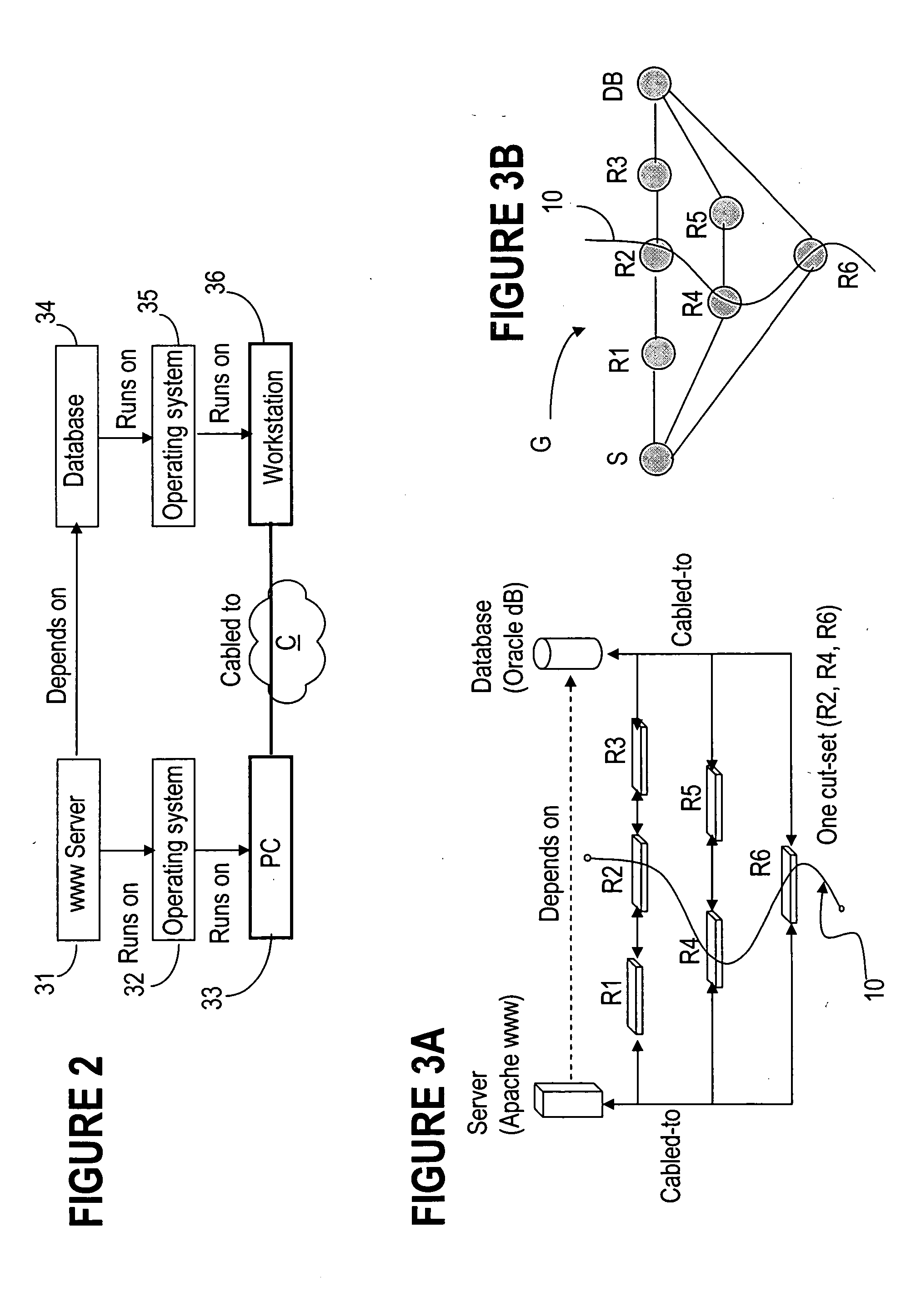
Application of cut-sets to network interdependency security risk assessment
InactiveUS20070067845A1Memory loss protectionError detection/correctionTraffic capacityRisk profiling
The invention is directed to providing threat and risk analysis for a network that has a high degree of inter-relationships and interdependencies among the assets comprising it, using a “cut set” enumeration method. The identified cut sets are used as the basis to the threat and risk analysis, since each cut set may affect the traffic between two dependent assets in the network, and thereby affect the security state of the dependent assets themselves. The affected security state may be confidentiality, integrity, availability, or other network or security relevant parameter.
Owner:ALCATEL LUCENT SAS
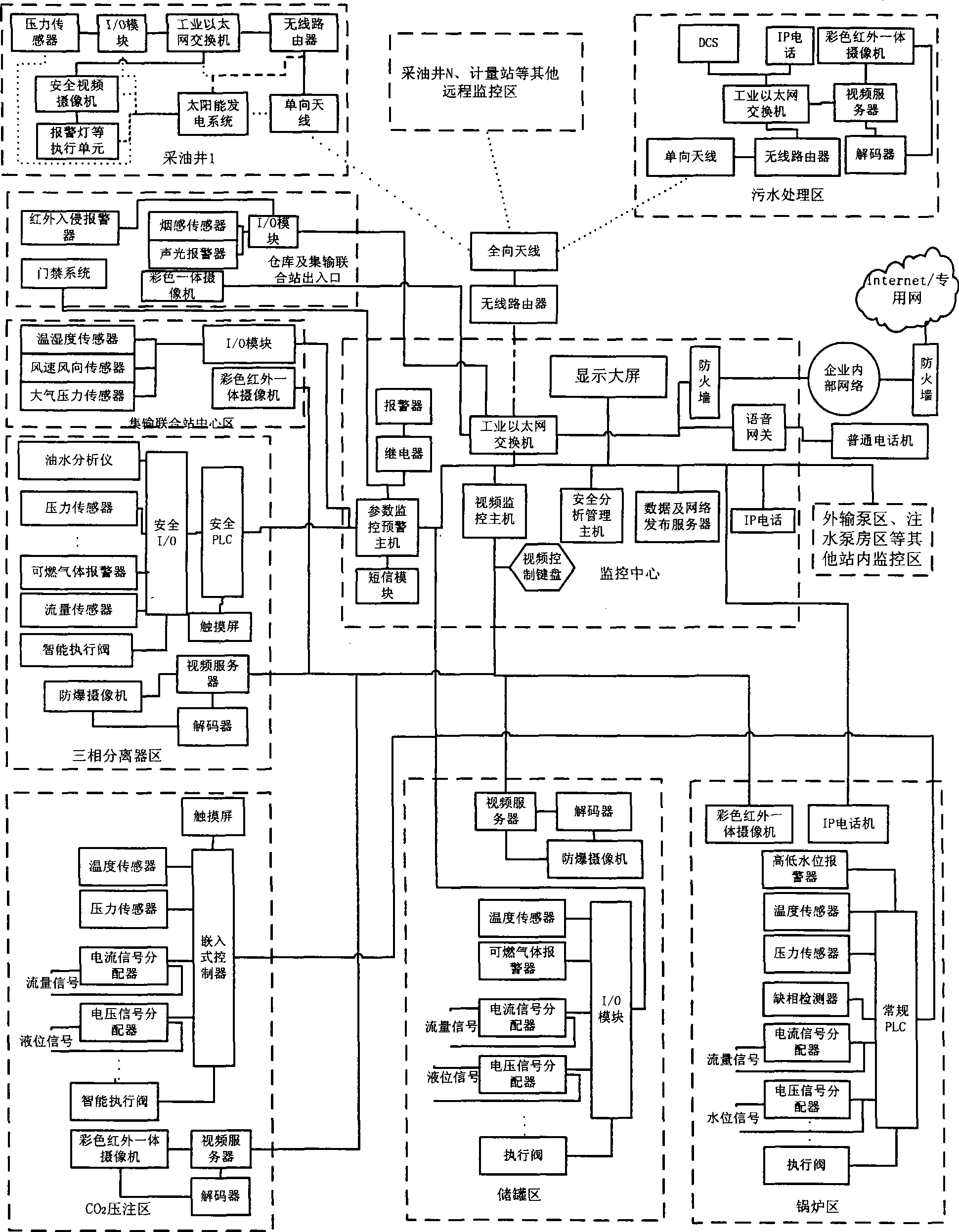
Safety monitoring early warning and safety management system and method for oil gas extracting, gathering and transporting operation
InactiveCN101369152AManagement is easy to strengthenEasy to manageFluid removalProgramme total factory controlVideo monitoringSafety management systems
The invention relates to a safety monitoring early warning and safety management system of oil and gas extraction and gathering operations as well as a method thereof, belonging to the technique field of safety production monitoring and supervision, and the system is composed of a monitoring center arranged at an oil and gas extraction safety monitoring and management department and a plurality of on-site monitoring terminals disposed at all oil and gas extraction operation areas. The method comprises: collecting and transmitting safety-related parameter signals, video signals and audio signals in real time; implementing the analog-digital conversion or signal conversion and compression coding to the signals; then transmitting the signals to all hosts of the monitoring center; processing and analyzing the received three types of signal information by all the hosts and then carrying out the parameter monitoring, video monitoring and audio communication respectively; and outputting the processed three types of information to the spot for being controlled correspondingly. The invention can realize the risk assessment, dynamic intelligent monitoring, safety state analysis, accident early warning and alarming, safety guarantee control and safety management of the whole process of operations ranging from oil and gas extraction, heating, separation processing, storage to transportation for oil and gas production enterprises.
Owner:CHINA ACAD OF SAFETY SCI & TECH
Automated identification of phishing, phony and malicious web sites
A method and system for automated identification of phishing, phony, and malicious web sites are disclosed. According to one embodiment, a computer implemented method, comprises receiving a first input, the first input including a universal resource locator (URL) for a webpage. A second input is received, the second input including feedback information related to the webpage, the feedback information including an indication designating the webpage as safe or unsafe. A third input is received from a database, the third input including reputation information related to the webpage. Data is extracted from the webpage. A safety status is determined for the webpage, including whether the webpage is hazardous by using a threat score for the webpage and the second input, wherein calculating the threat score includes analyzing the extracted data from the webpage. The safety status for the webpage is reported.
Owner:CLOUDFLARE
Security state vector for mobile network platform
ActiveUS20050254654A1Minimal amountMemory loss protectionError detection/correctionRolloverCyber operations
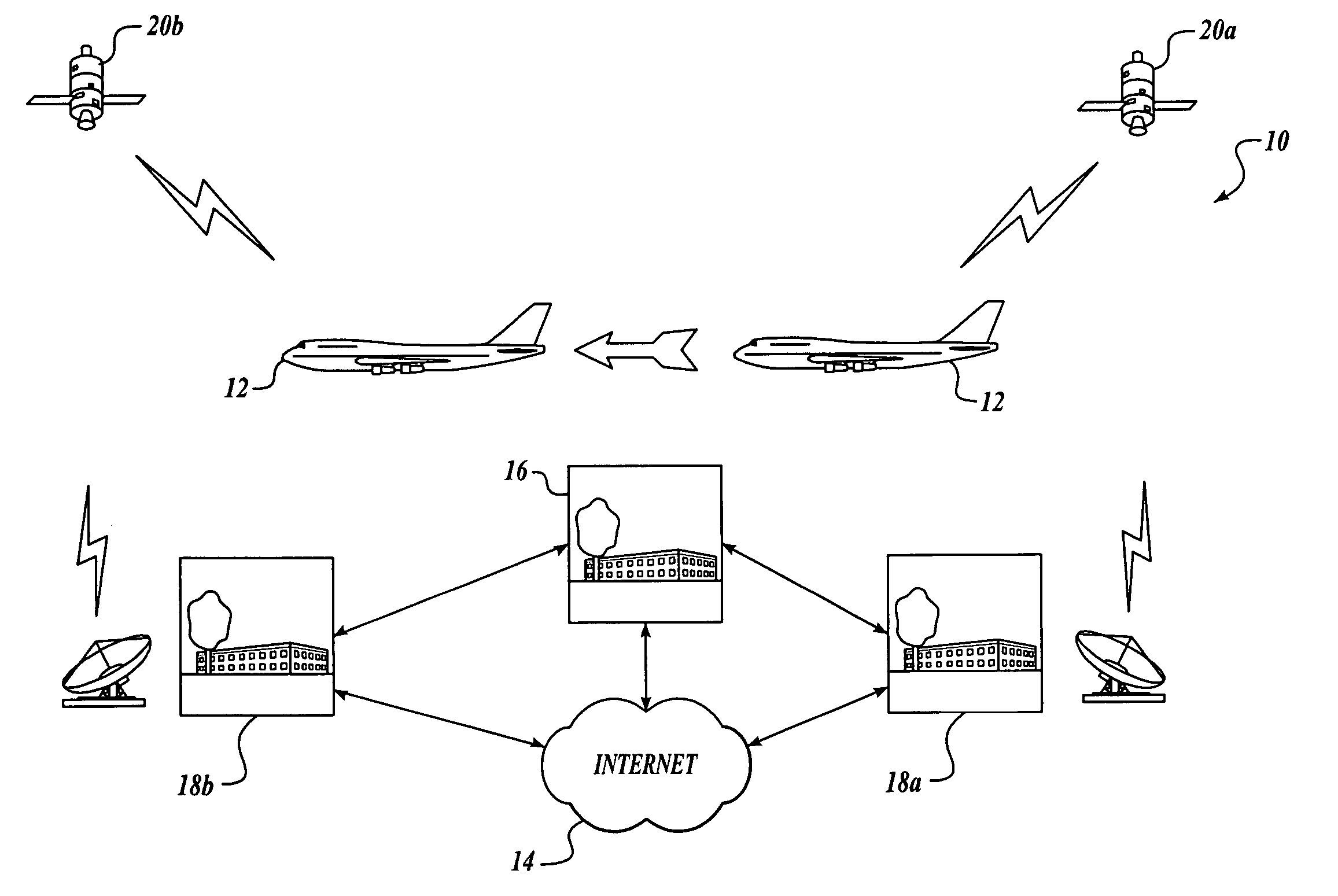
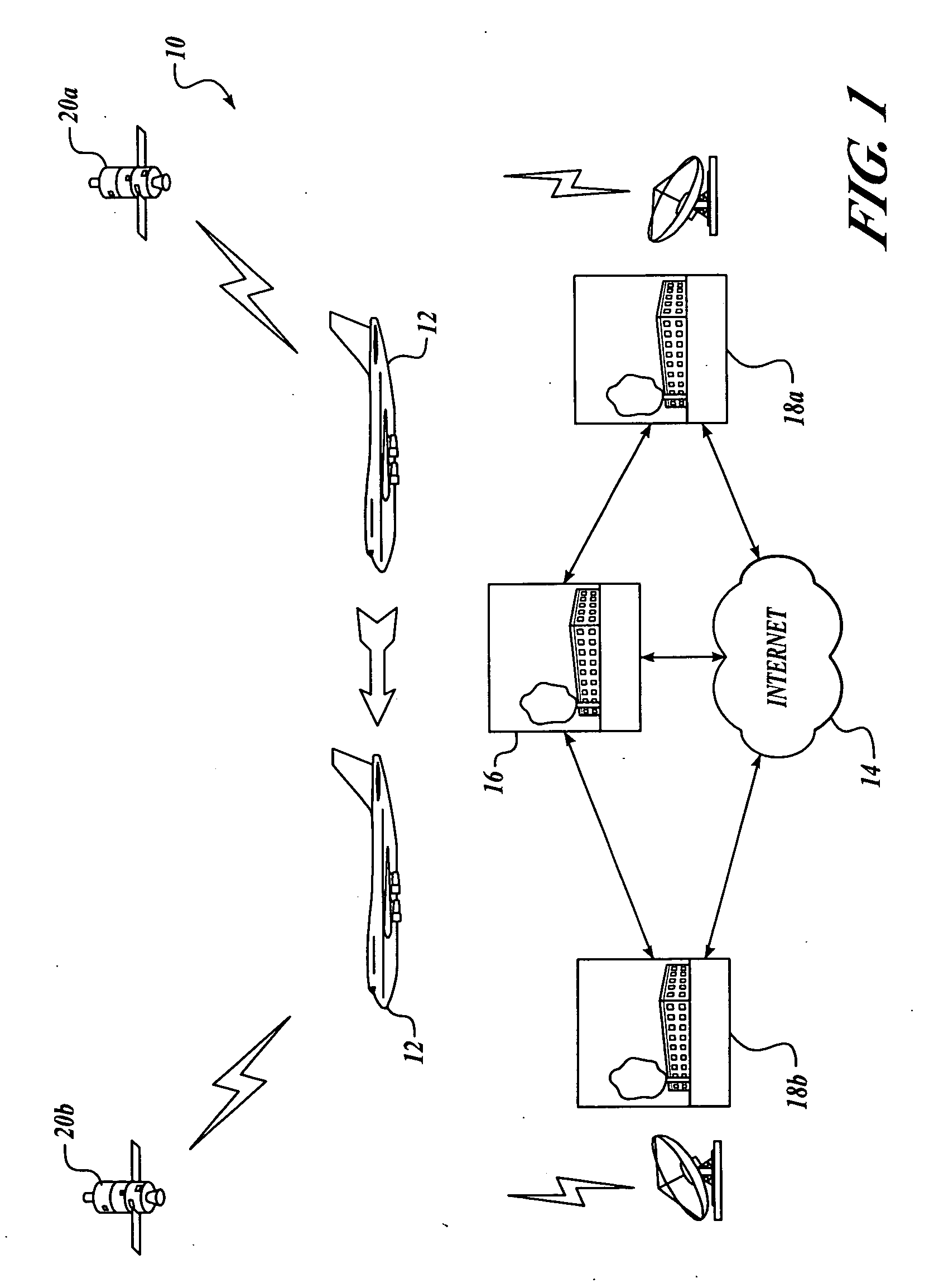
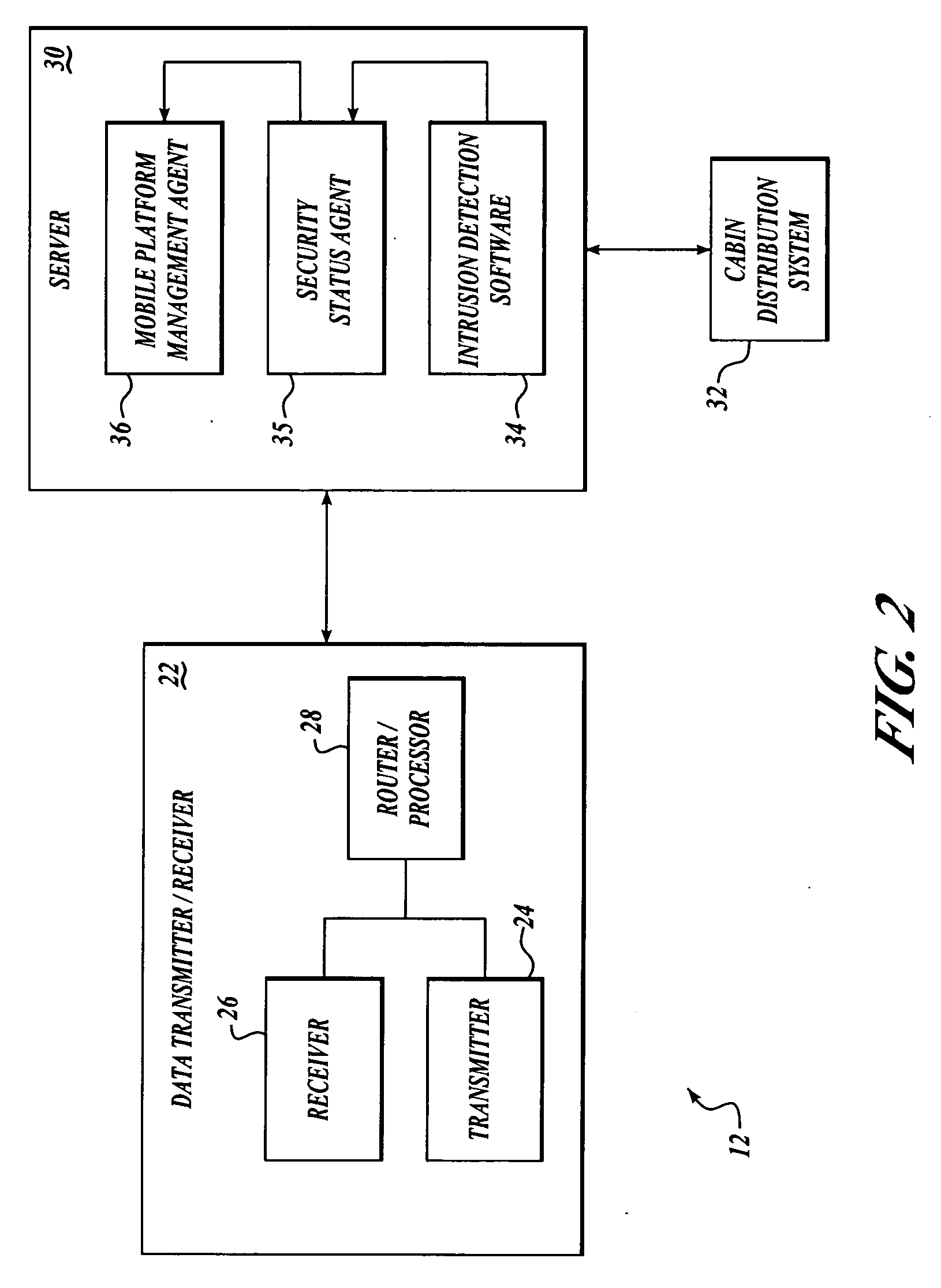
State of security in a mobile communications network is communicated. Data regarding nature and severity of security events onboard at least one mobile platform is generated and processed. A message that includes the processed data is generated and transmitted periodically. The processed data makes up a security state vector that includes the number of security events detected since power-up of the mobile platform node, sum of highest severity security events since power-up or counter rollover, sum of the second highest severity security events detected since power-up or counter rollover, sum of the third highest severity security events detected since power-up or counter rollover, highest security event classification, second-highest security event classification, and third-highest security event classification. The processed data may be used in a network operations center to prioritize mobile platforms from which logged data should be retrieved for further investigation and monitoring.
Owner:THE BOEING CO
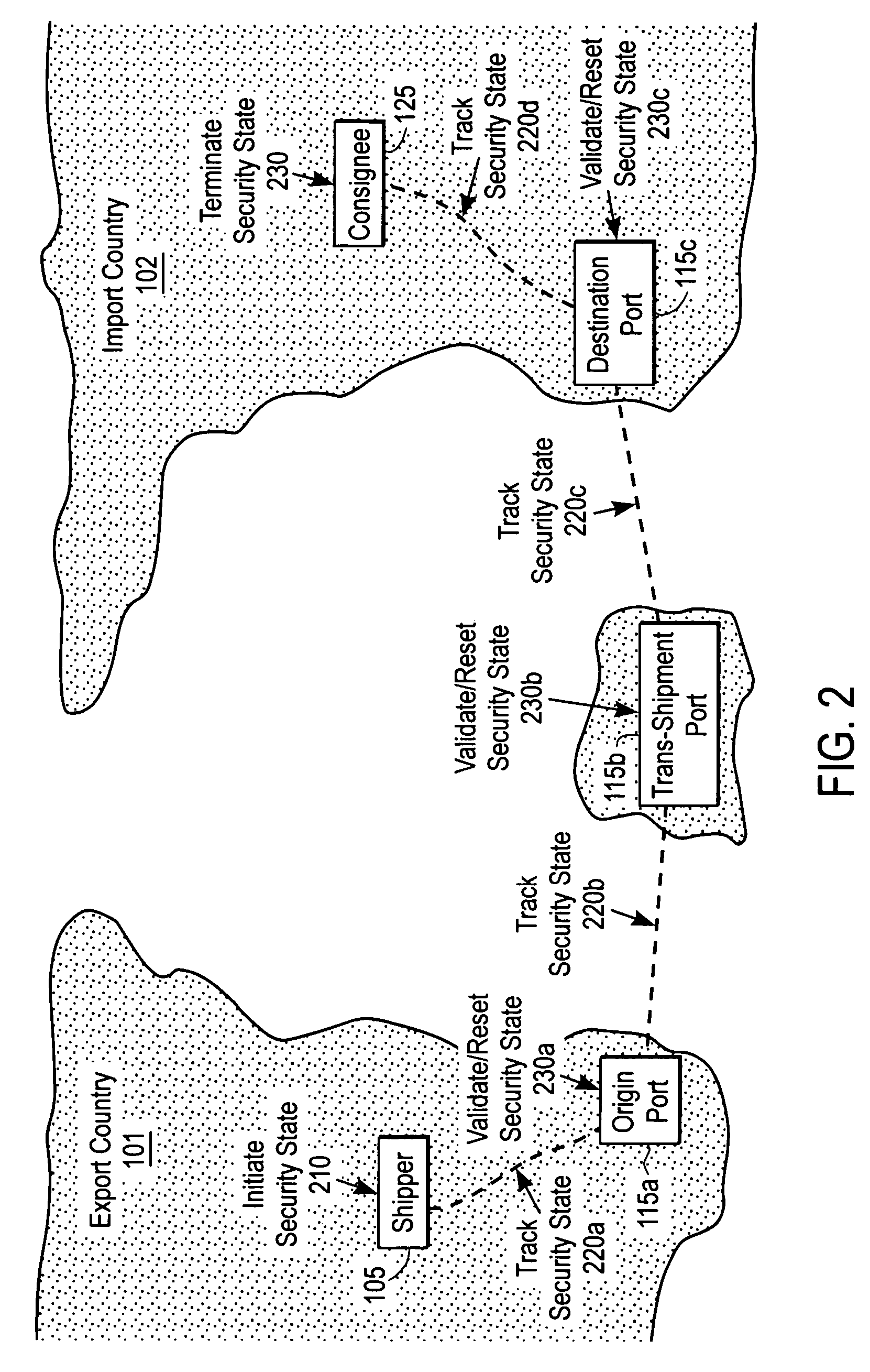
Continuous security state tracking for intermodal containers transported through a global supply chain
ActiveUS7129837B2Inhibitory activityReduce theftTicket-issuing apparatusCommerceSite managerData center
Owner:SAVI TECH INC
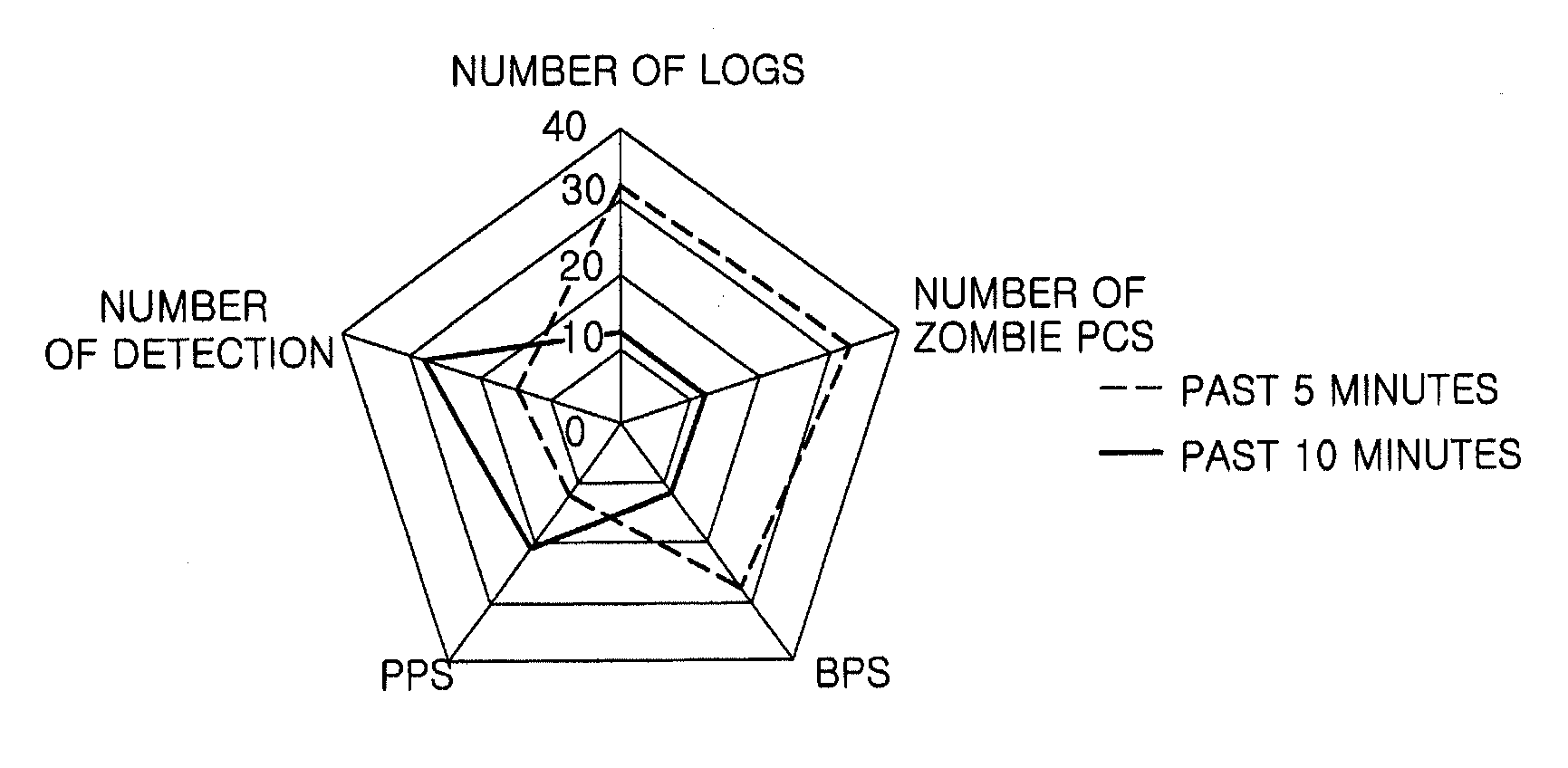
Network security control system and method, and security event processing apparatus and visualization processing apparatus for network security control
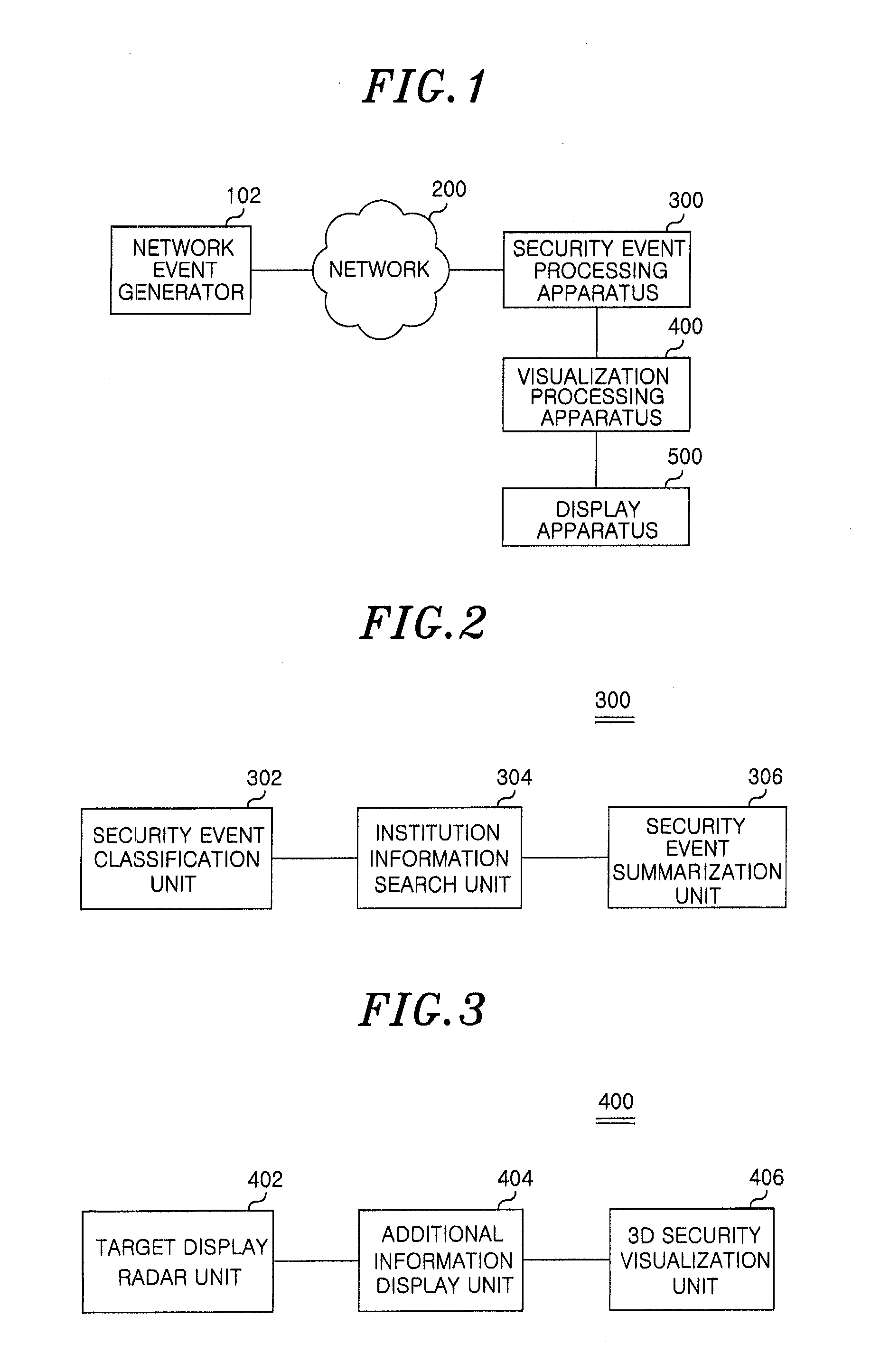
InactiveUS20120137361A1Memory loss protectionError detection/correctionControl systemEvent generator
A network security control system includes: a network event generator for generating network events; a security event processing apparatus for collecting the network events from the network event generator via a network and processing the collected network events as a target data for visualization; and a visualization processing apparatus for visualizing the target data to display a security status as a third-dimensional (3D) visualization information on an organization basis.
Owner:ELECTRONICS & TELECOMM RES INST
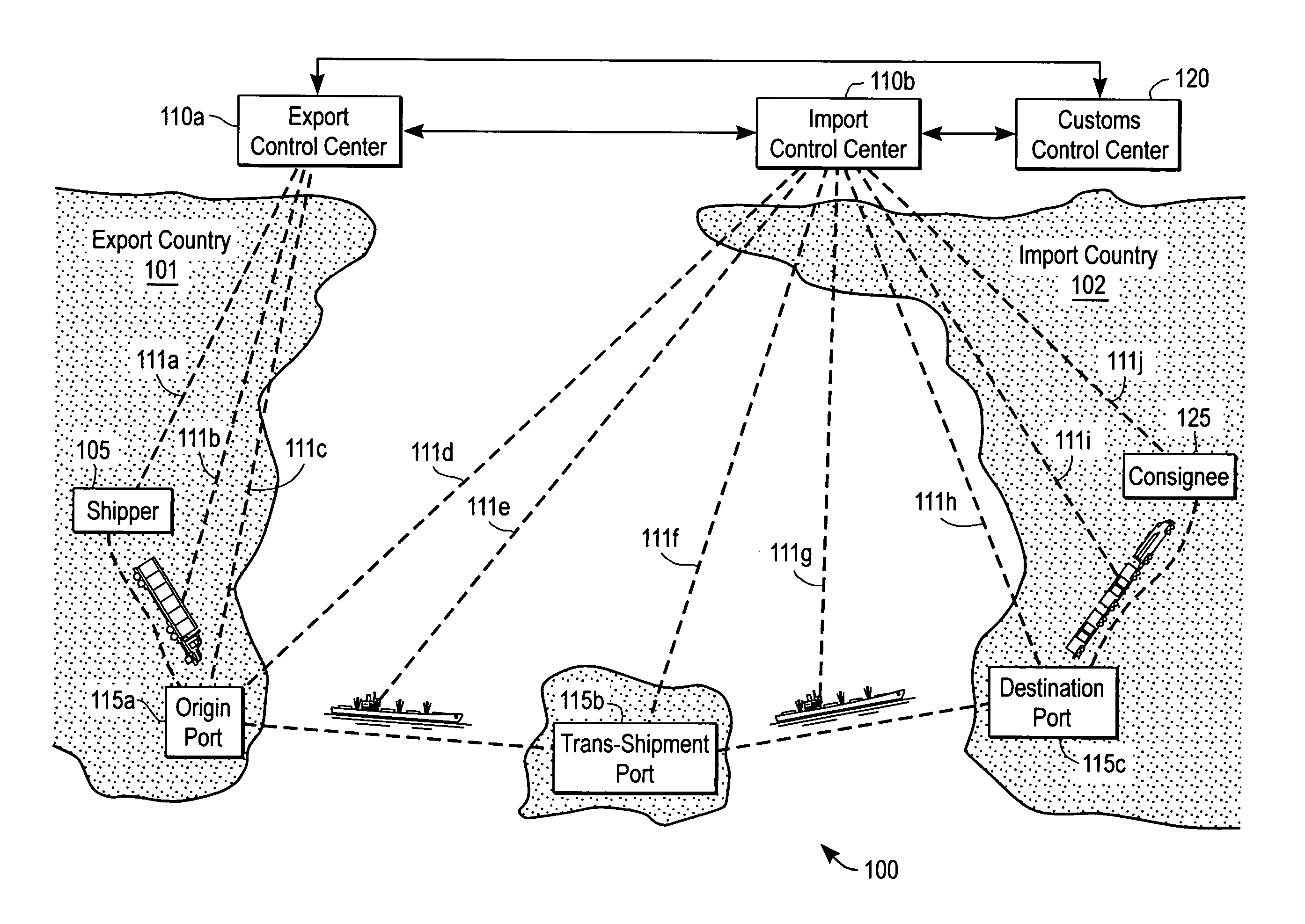
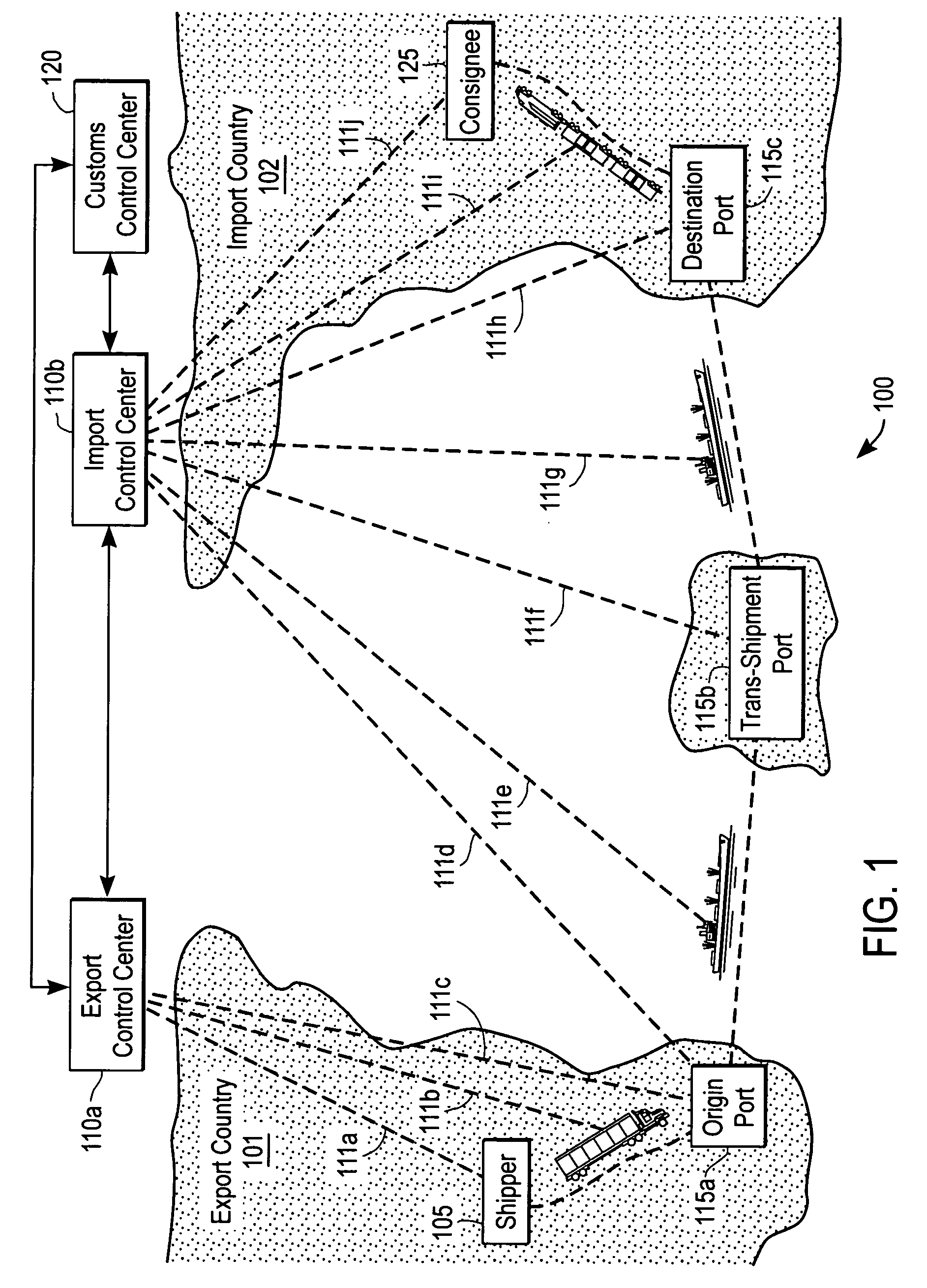
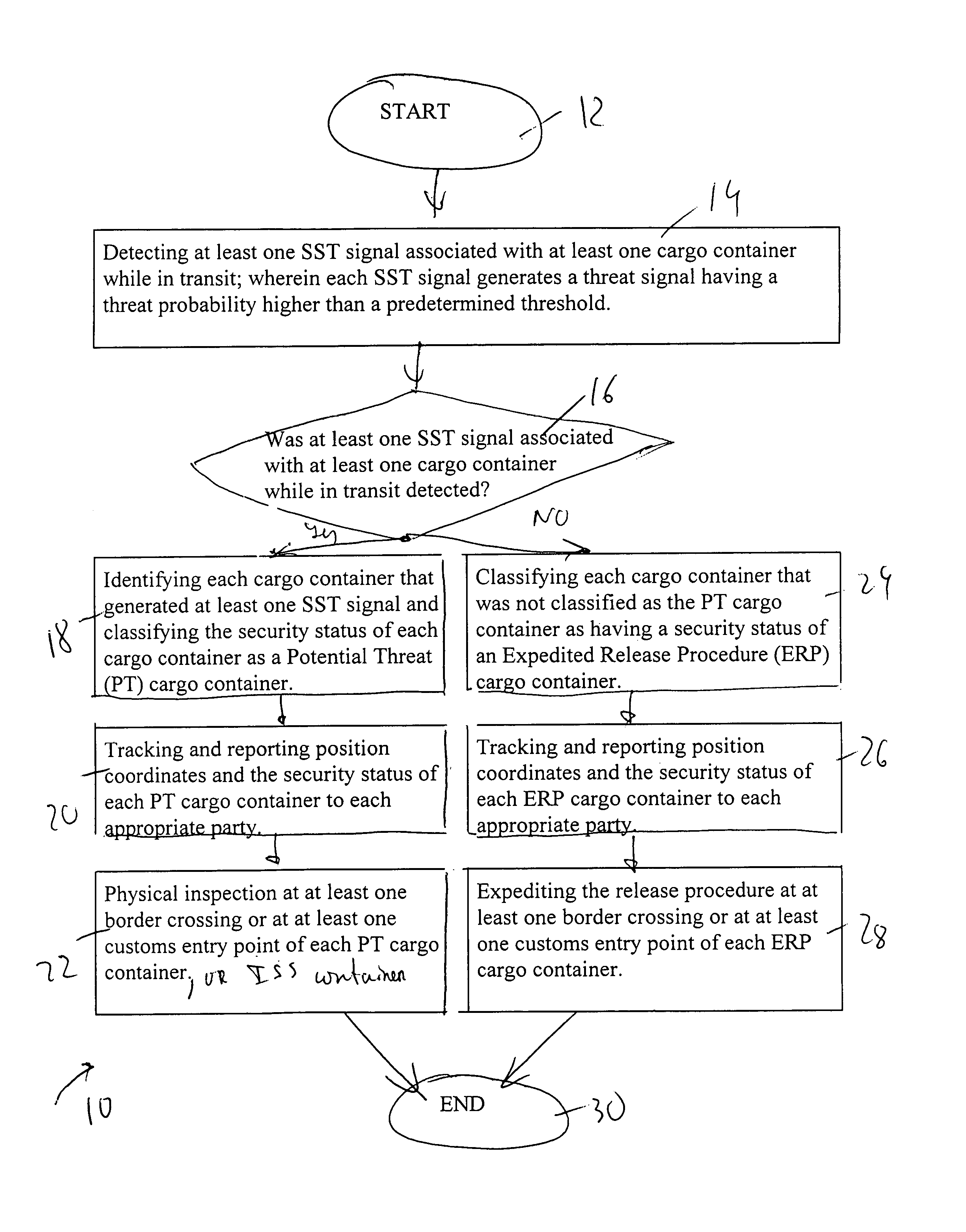
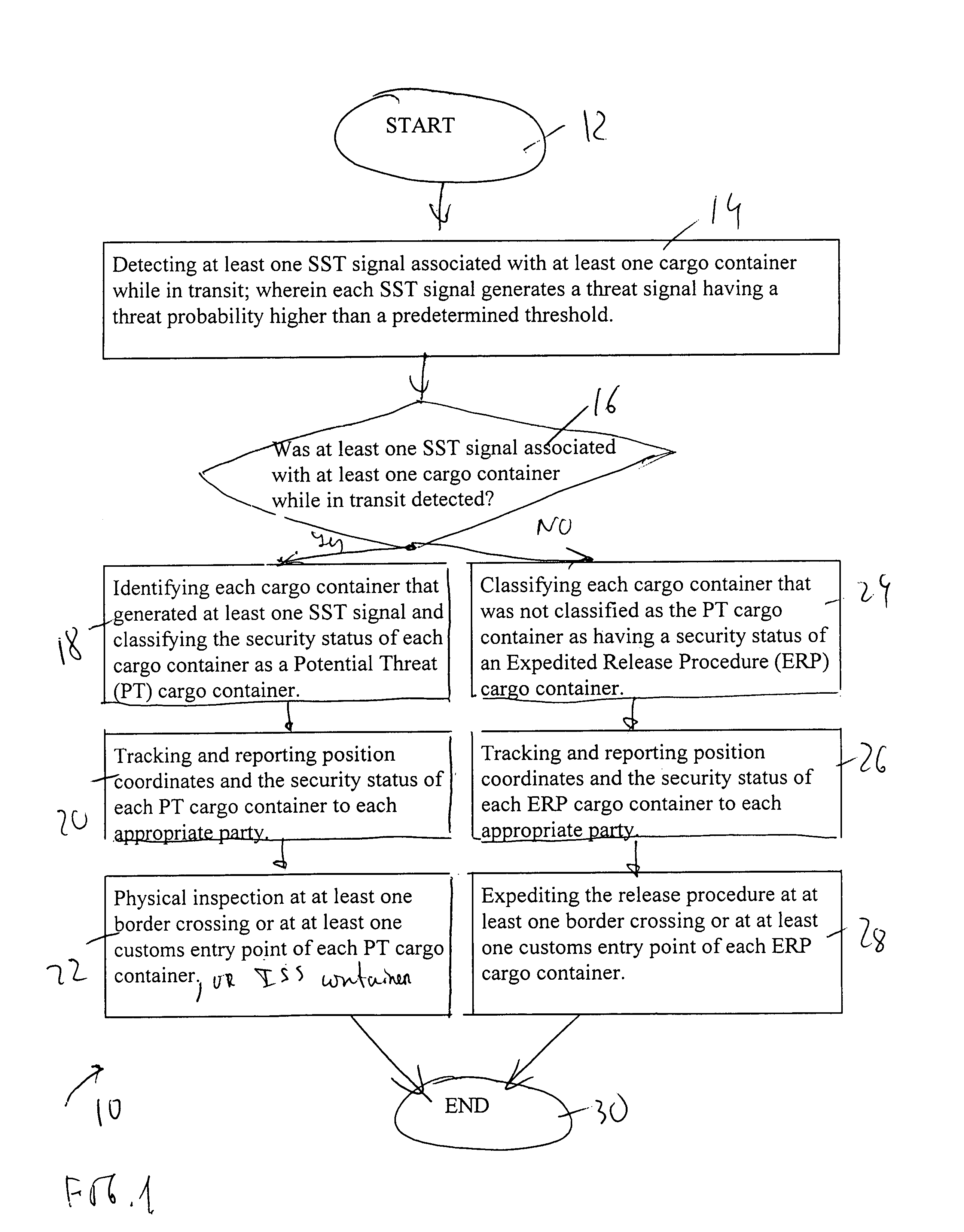
Expediting release procedure of cargo container at border crossing or at customs entry point by tracking and reporting threats while cargo container is in transit
A method of expediting a release procedure of at least one cargo container at least one border crossing or at least one customs entry point by detecting each statistically significant threat (SST) signal associated with at least one said cargo container while in transit, and by tracking and reporting to an appropriate party the position coordinates and a security status of each cargo container that generated at least one said SST signal. The appropriate party is selected from the group consisting of: {Homeland Security agency; and a cargo security agency}. The cargo security agency is further selected from the group consisting of: {a consignee; a steamship line; a customs broker; a freight forwarder; and a terminal operator}.
Owner:ERUDITE
Electronic lock box with multiple modes and security states
InactiveUS20050206499A1Avoid damageProlong lifeElectric signal transmission systemsMultiple keys/algorithms usageSecure stateMultiple modes
An electronic lock box contains a secure compartment for storing keys to a structure. A linear actuator moves in one direction opening the door to the secure compartment, and moves in the opposite direction releasing a shackle that holds the lock box to the structure. A lock box system uses an encryption algorithm to diversify user PIN data at a central computer, and stores that diversified information on a memory card for later use when the user attempts to access a lock box. The central computer and electronic lock box both keep track of system “epoch time,” and the memory card must be presented to the electronic lock box within a correct epoch time window for the diversified PIN data to be successfully decrypted and compared to the user's PIN data that is entered on a keypad of the electronic lock box.
Owner:SENTRILOCK
Intelligent video monitoring apparatus of railway crossing
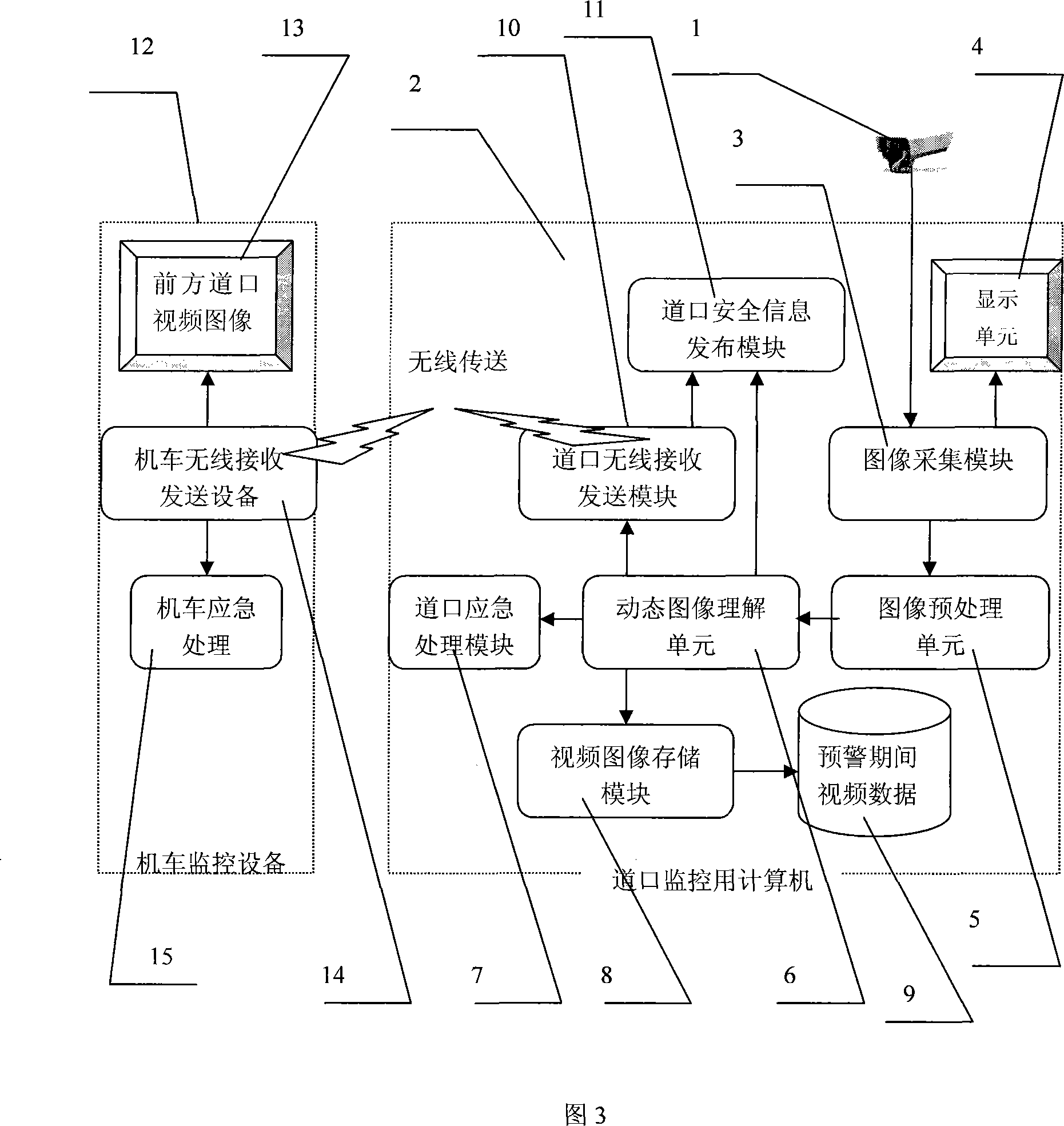
InactiveCN101179710ANormative behaviorFacilitate law enforcementPicture signal generatorsClosed circuit television systemsVideo monitoringVideo sensors
The invention discloses an intelligent video monitor of railway crossing, which includes a video sensor that is arranged on the railway crossing and is capable of covering the traffic condition of the entire crossing as well as a monitoring computer that is used for monitoring the condition of the entire crossing and is capable of dynamic image understanding; wherein, the monitoring computer includes a video image collecting module, a displaying unit, an image pretreatment module, a railway crossing customizing module, a dynamic image understanding module used for analyzing the safety condition of the crossing, a video information saving module, a crossing wireless receiving and transmitting module and an issuing module of crossing safety information; wherein, the issuing module of crossing safety information is connected with a crossing displaying unit and an alarming sound playing unit; and the monitoring computer is connected with the wireless receiving and transmitting device. The invention has a high intelligence level and is capable of automatically judging various dangerous conditions or failures of the crossing through the image understanding technique and is also capable of mutual communication between the train driver and safety condition of the crossing as well as between the passengers and vehicles passing through the crossing and the train running condition through the wireless communication technique.
Owner:ZHEJIANG UNIV OF TECH
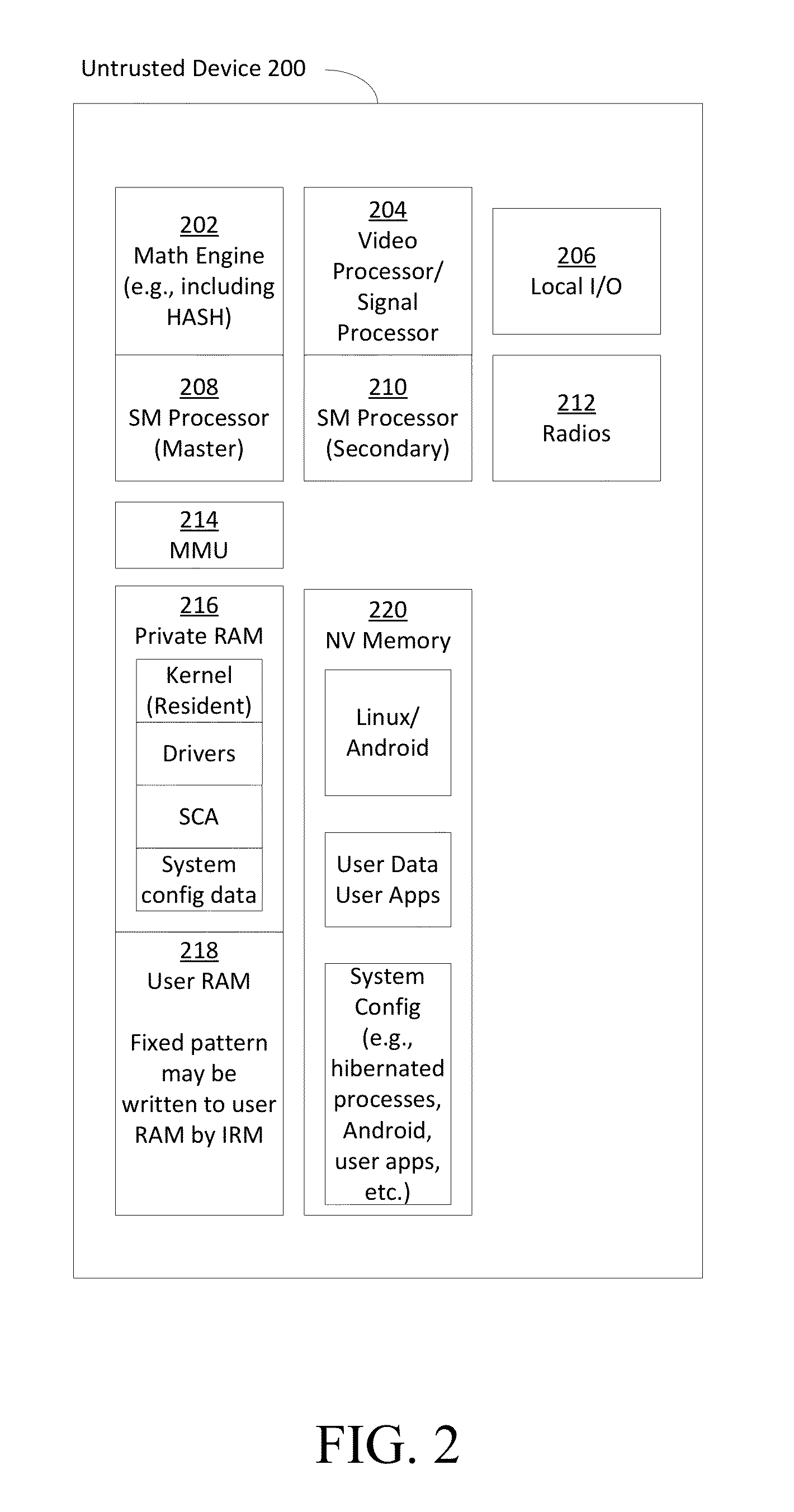
External Reference Monitor
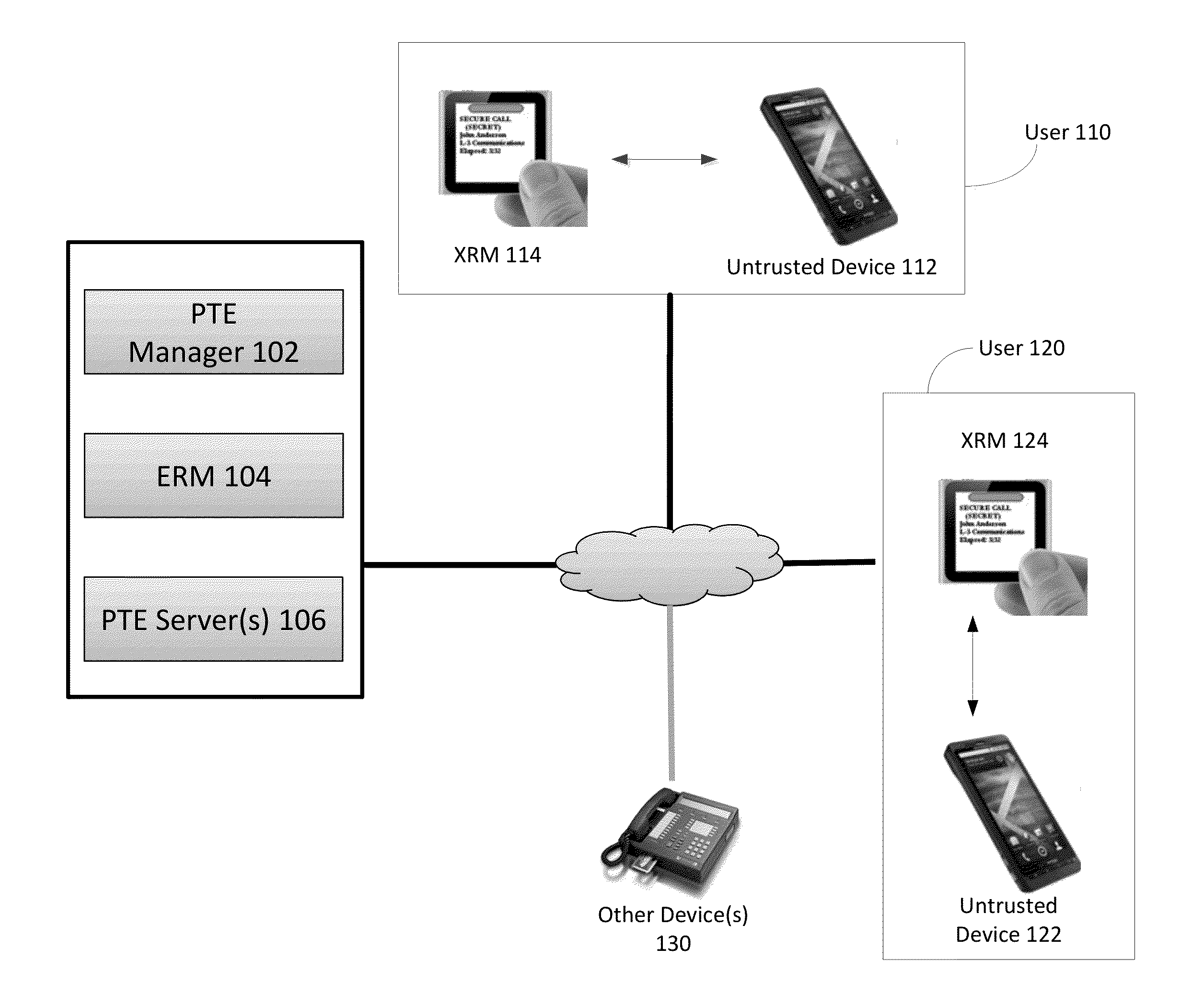
ActiveUS20130111211A1Improve trustPrevent cheatingDigital data processing detailsUser identity/authority verificationComputer hardwareTrusted hardware
Methods and systems for increasing the security or trust associated with an untrusted device are provided. For example, a trusted hardware component may send a request to the untrusted device. The request may indicate one or more challenges to be performed by a secure application executing on the untrusted device. The trusted hardware component may determine an expected response to the one or more challenges. The expected response may be determined at the secure hardware component based on an expected configuration of the untrusted device. The trusted hardware component may receive a response to the request from the untrusted device. The trusted hardware component may determine a security status of the untrusted device based on the expected response and the received response
Owner:LIONRA TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com