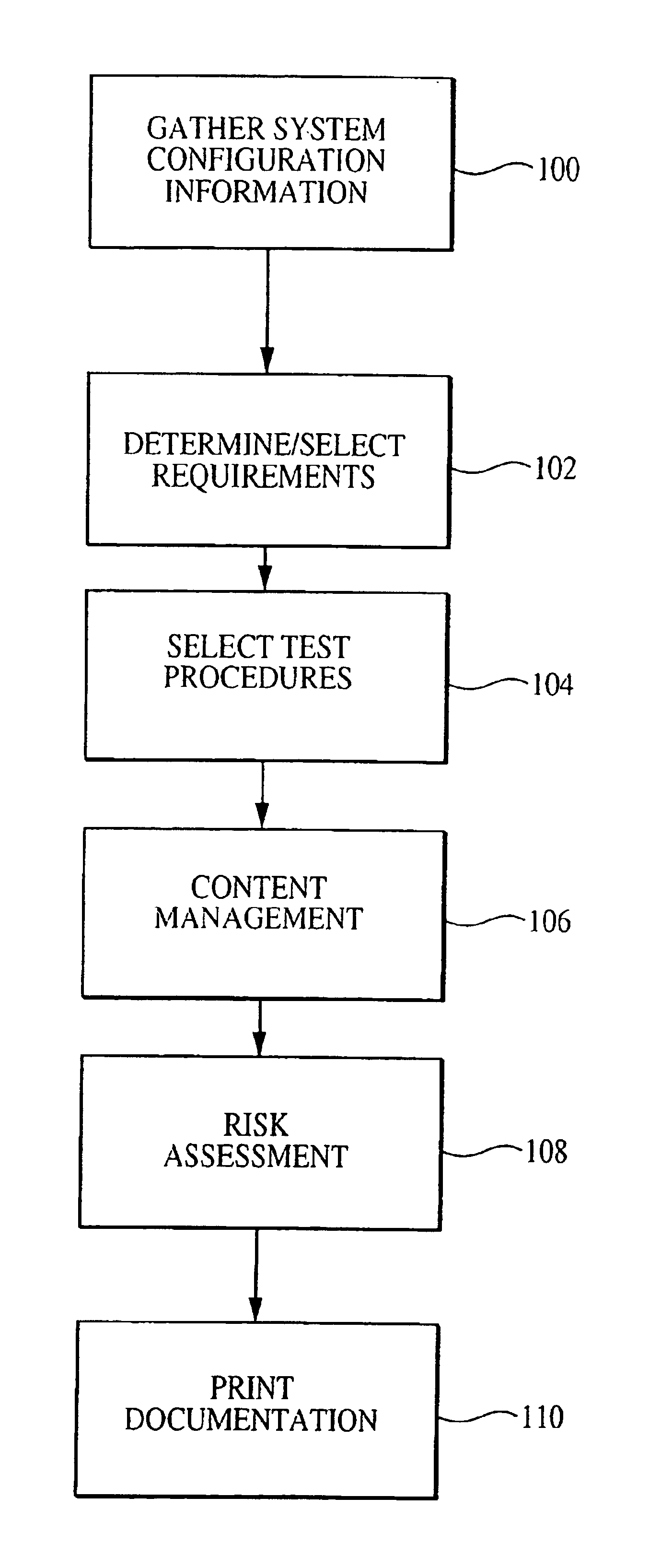
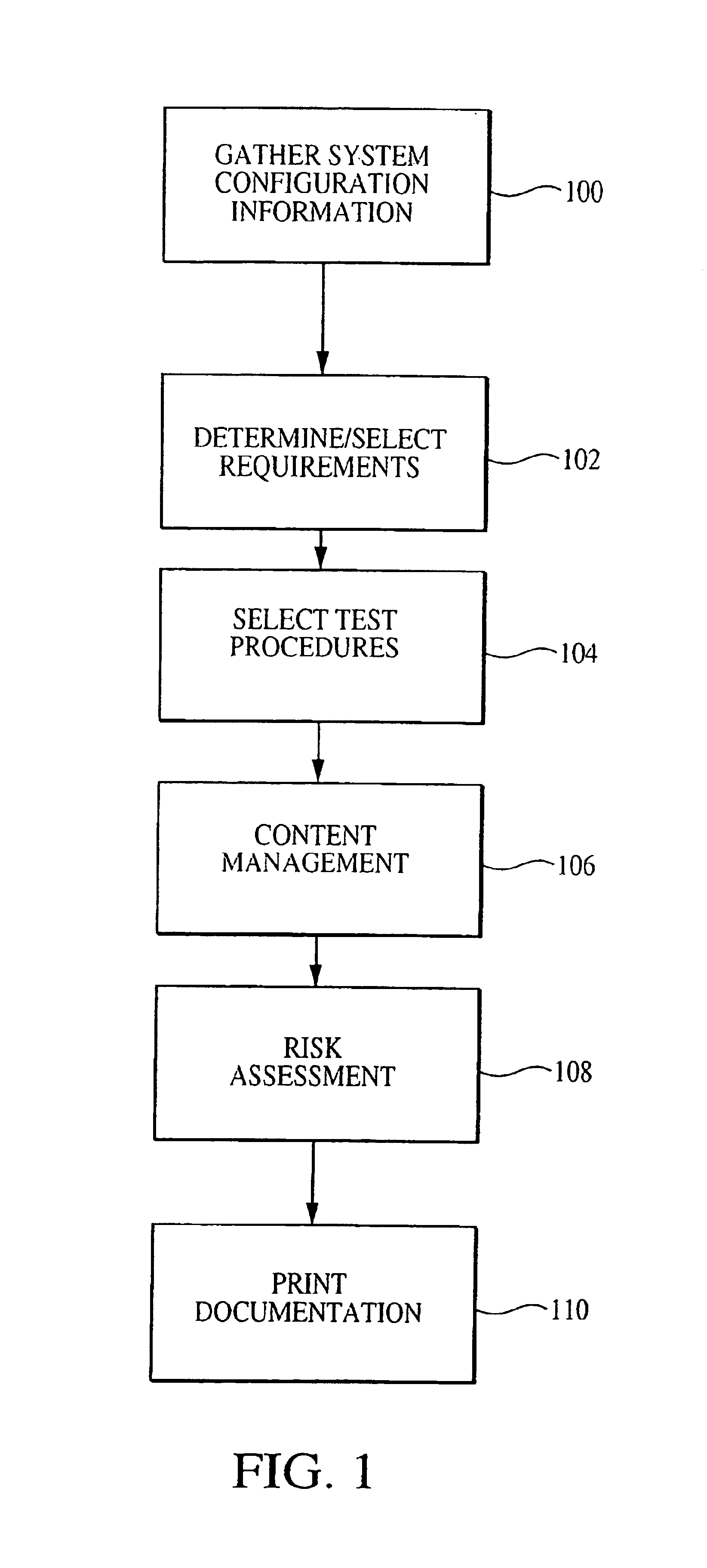
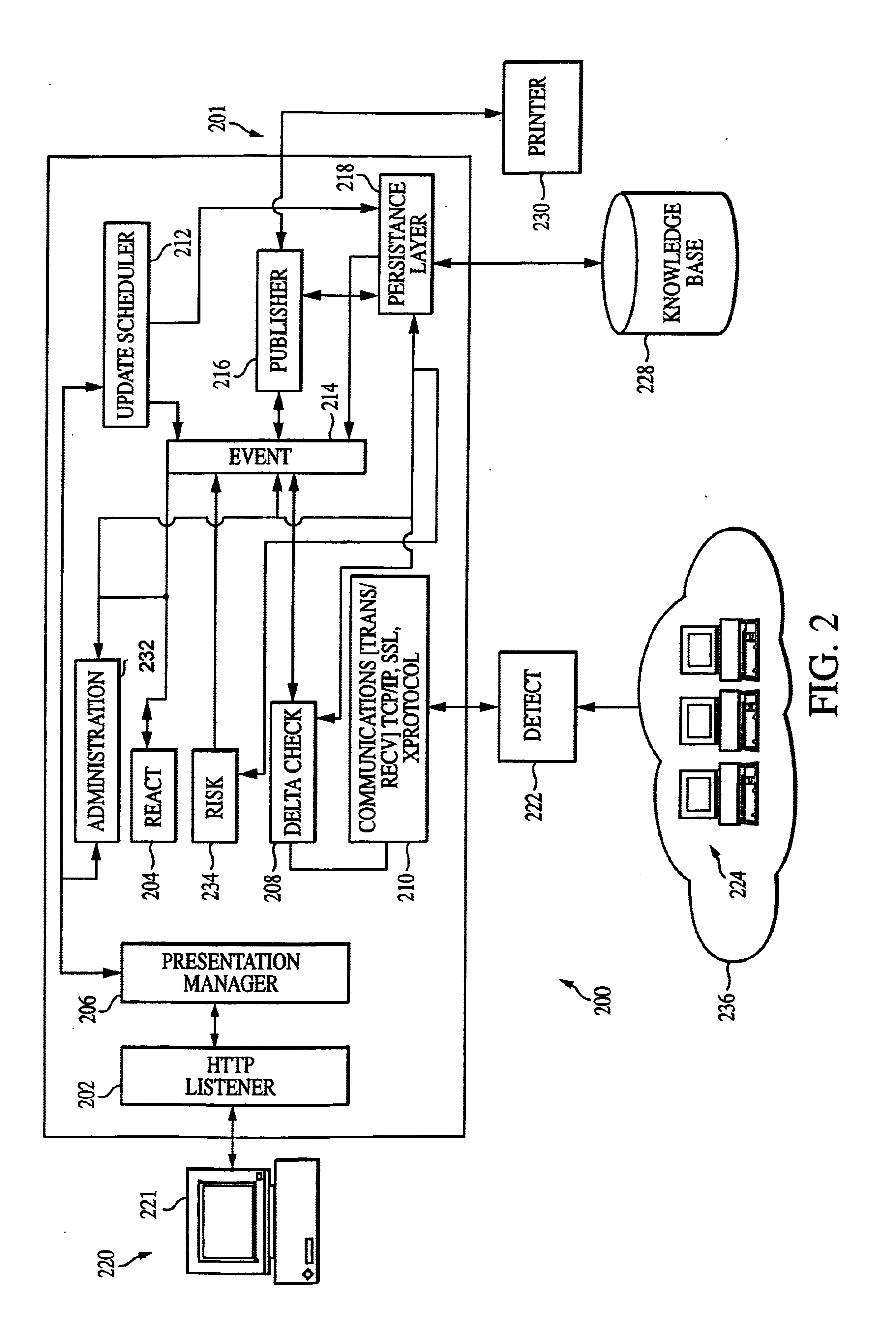
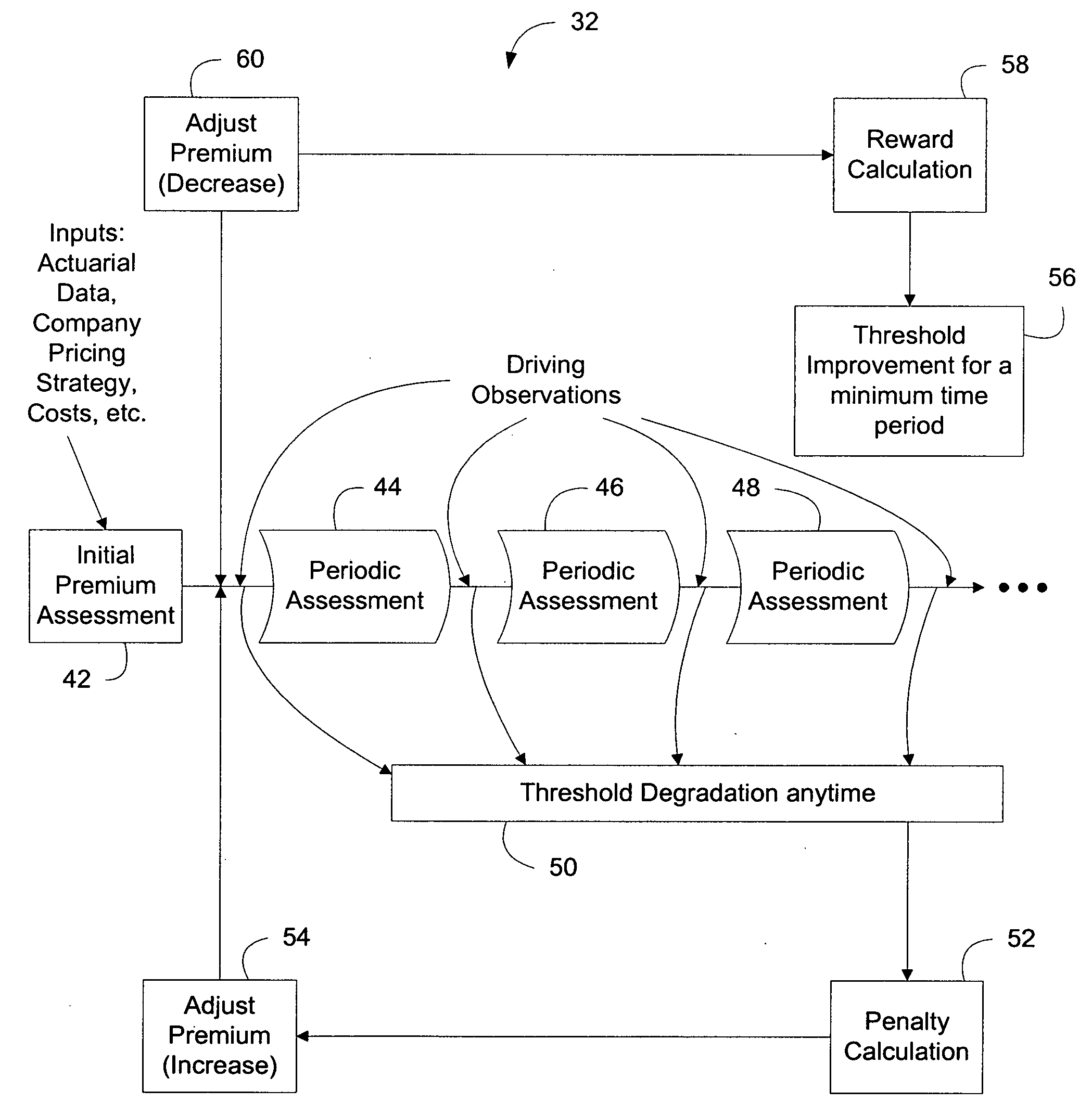
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4831 results about "Risk assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
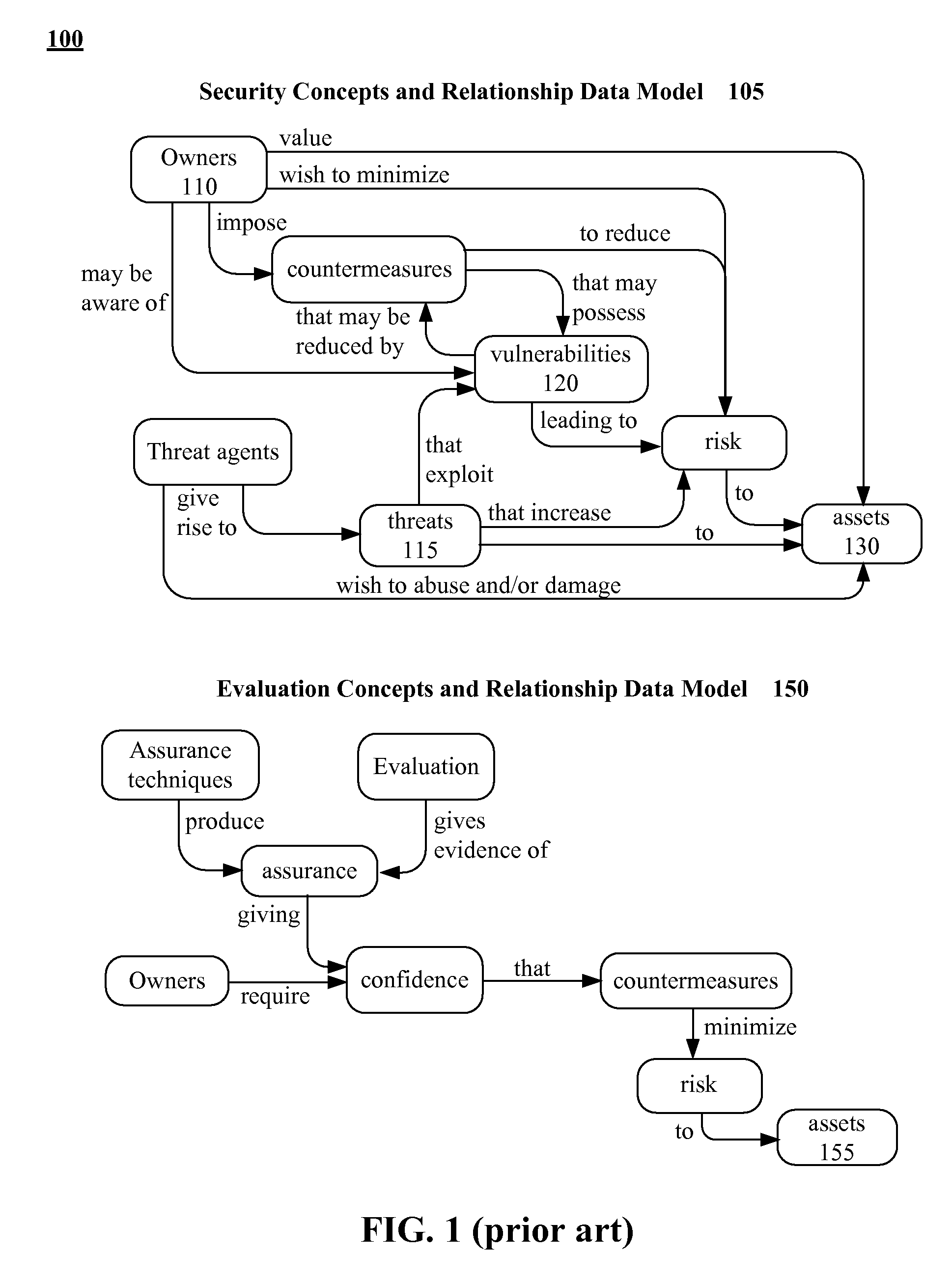
Broadly speaking, a risk assessment is the combined effort of...
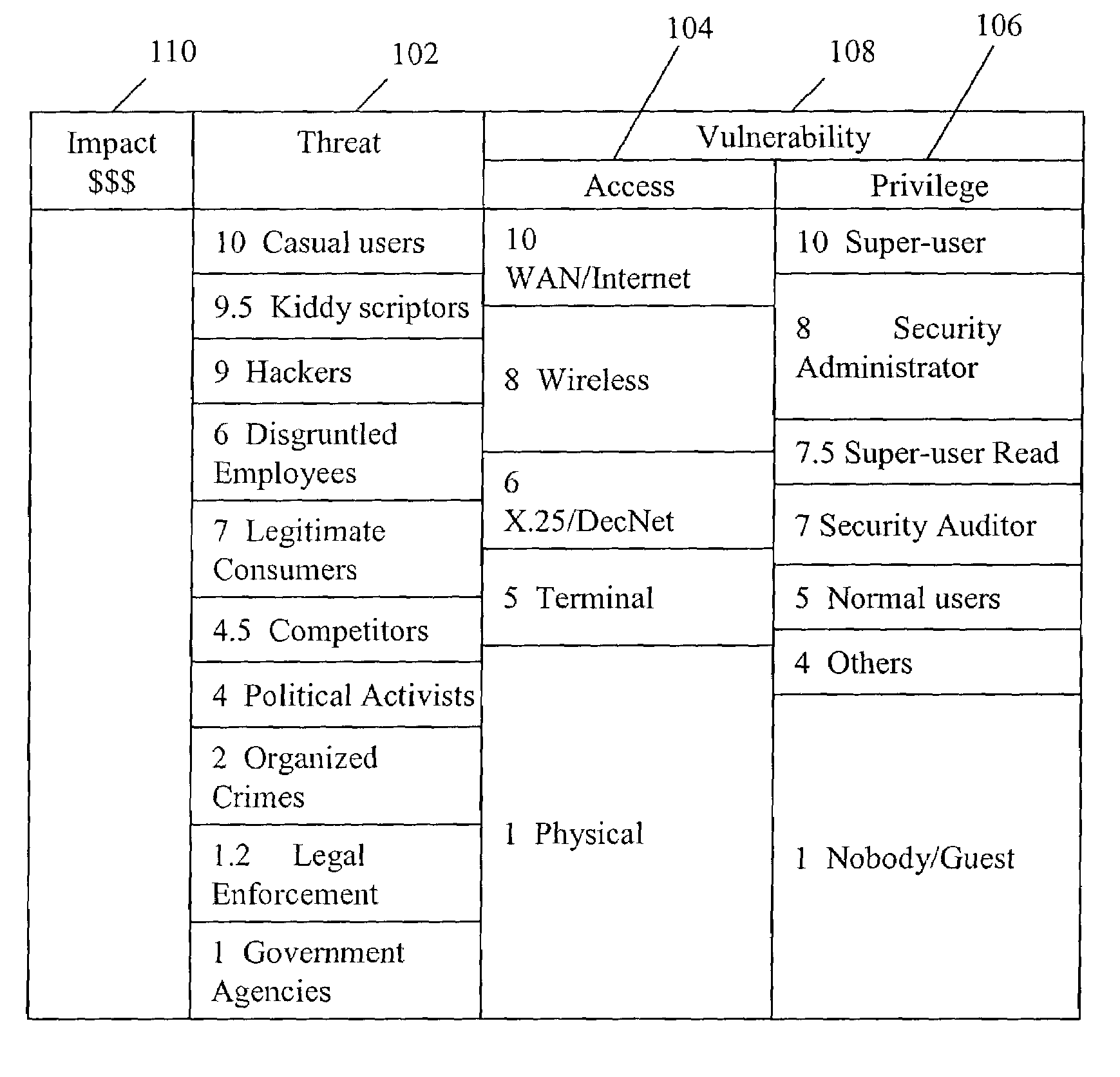
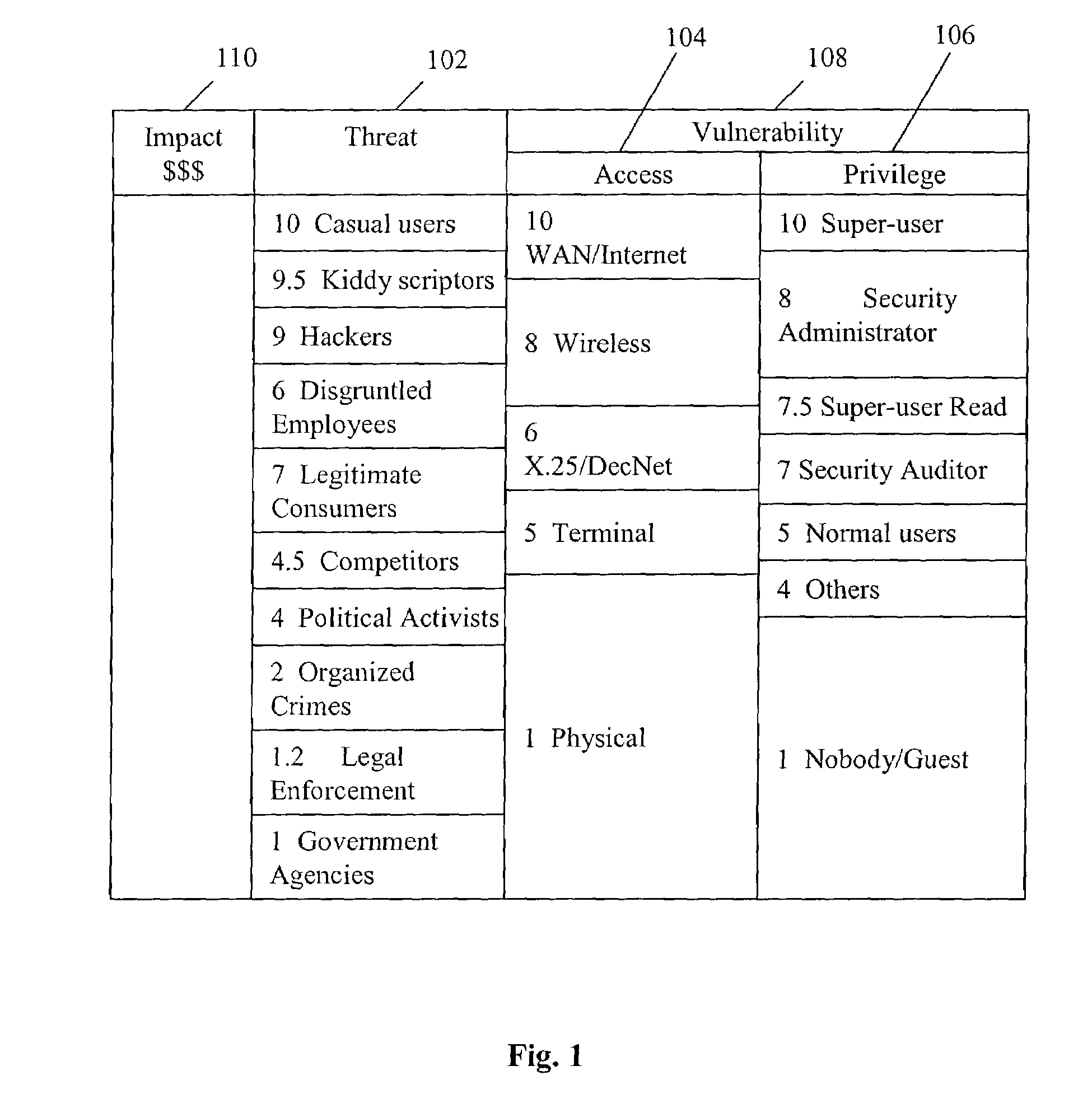
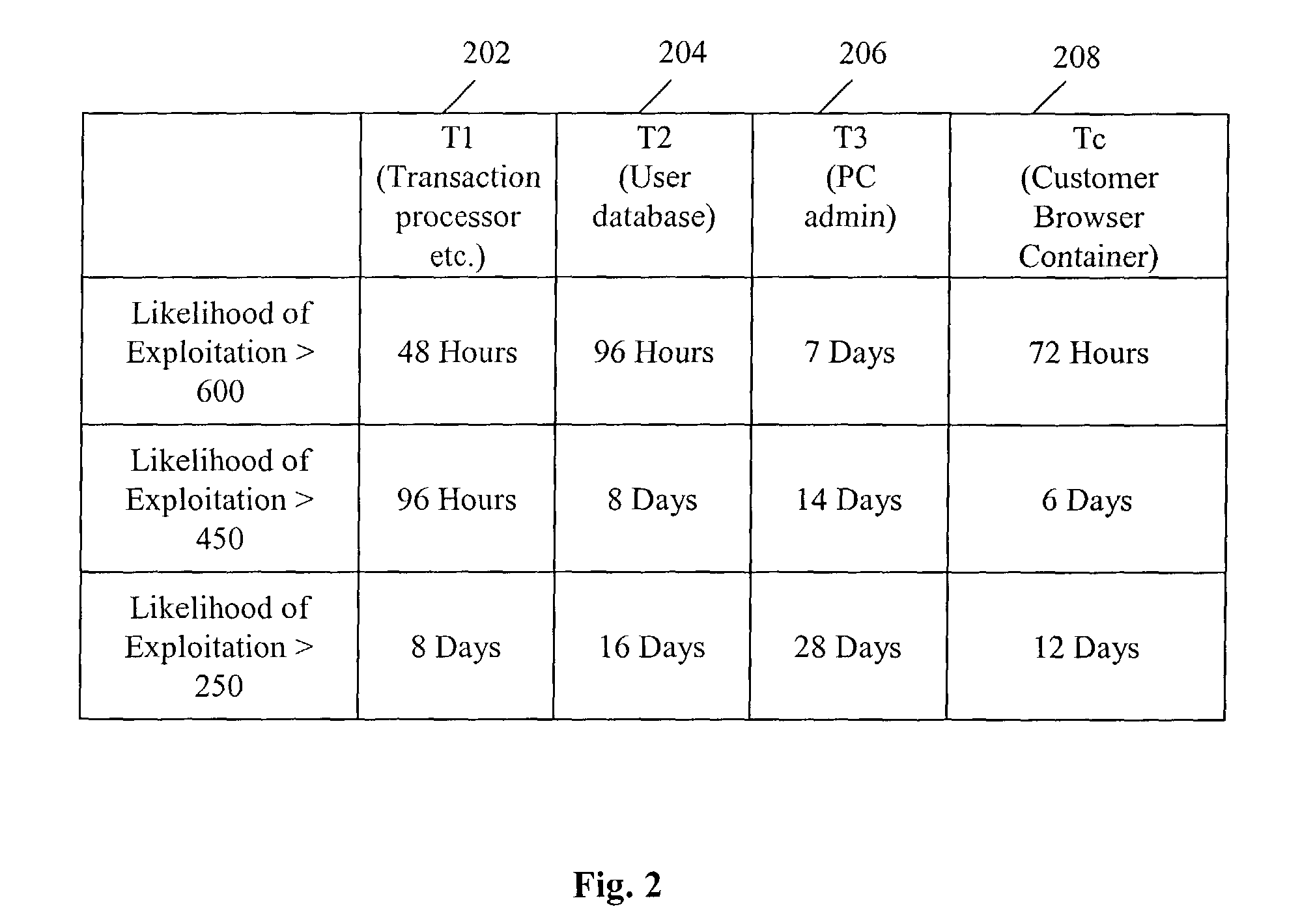
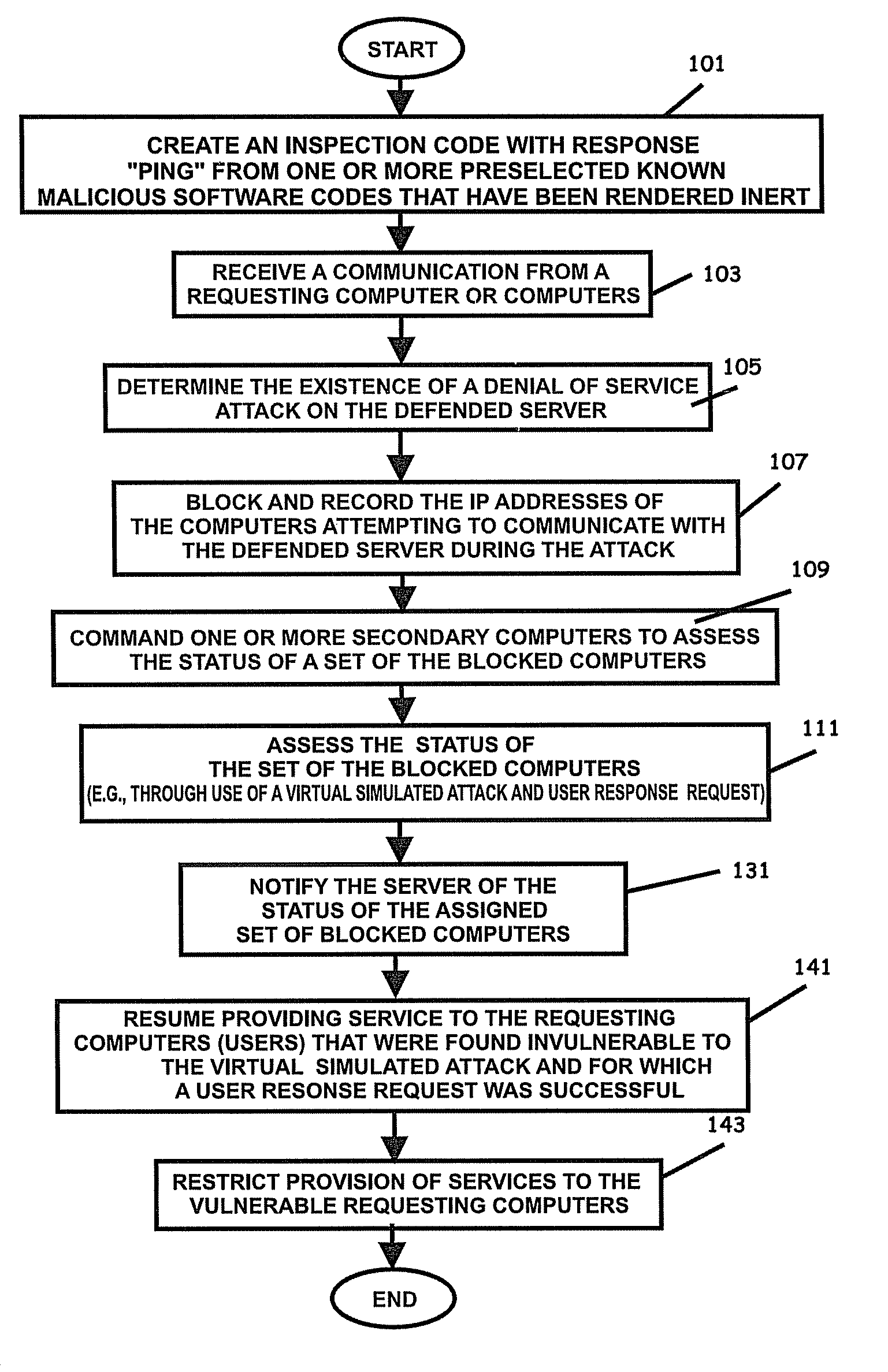
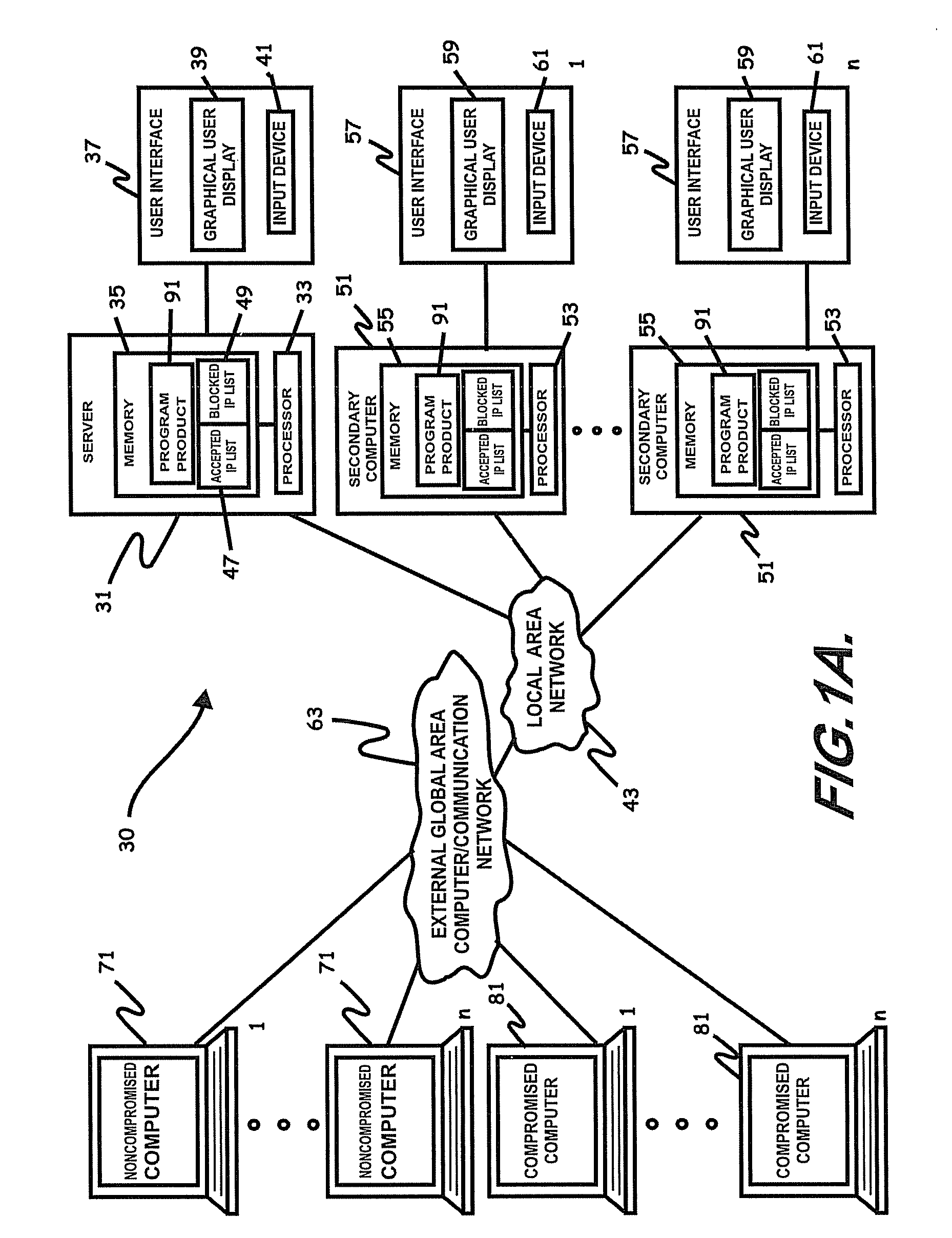
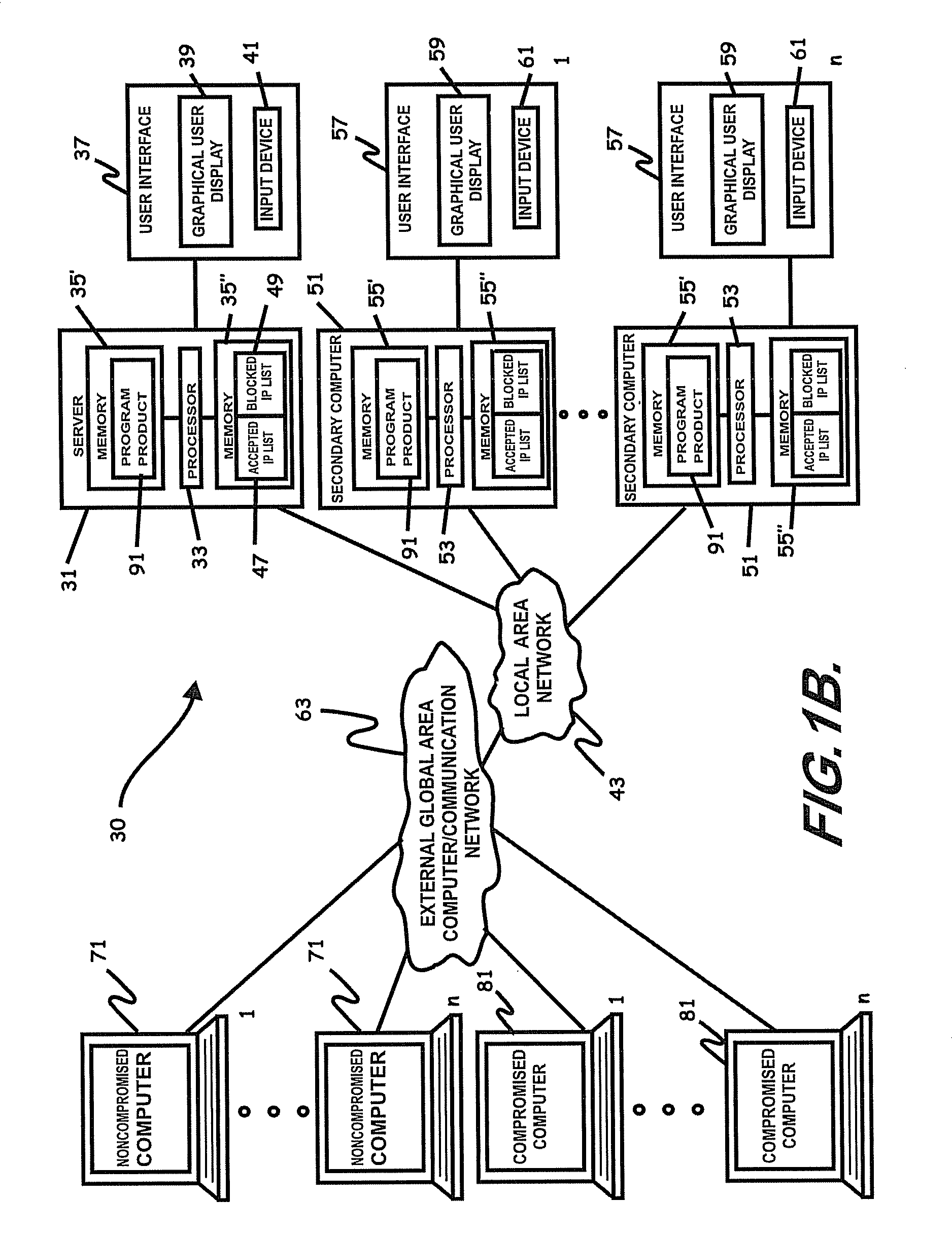
Method and system of assessing risk using a one-dimensional risk assessment model
A quantitative model combines a one-dimensional risk-assessment approach with expert knowledge to enable calculation of a probability or likelihood of exploitation of a threat to an information system asset without referring to actuarial information. A numerical value is established for one or more threats of attack on the information system asset based on expert knowledge without reference to actuarial data, and likewise, based on expert knowledge without reference to actuarial data, a numerical value is established for each of one or more access and privilege components of one or more vulnerabilities to attack on the information system asset. A security risk level for the information system asset is computed based upon the numerical values for threat and the access and privilege components for vulnerability so established.
Owner:CITIBANK
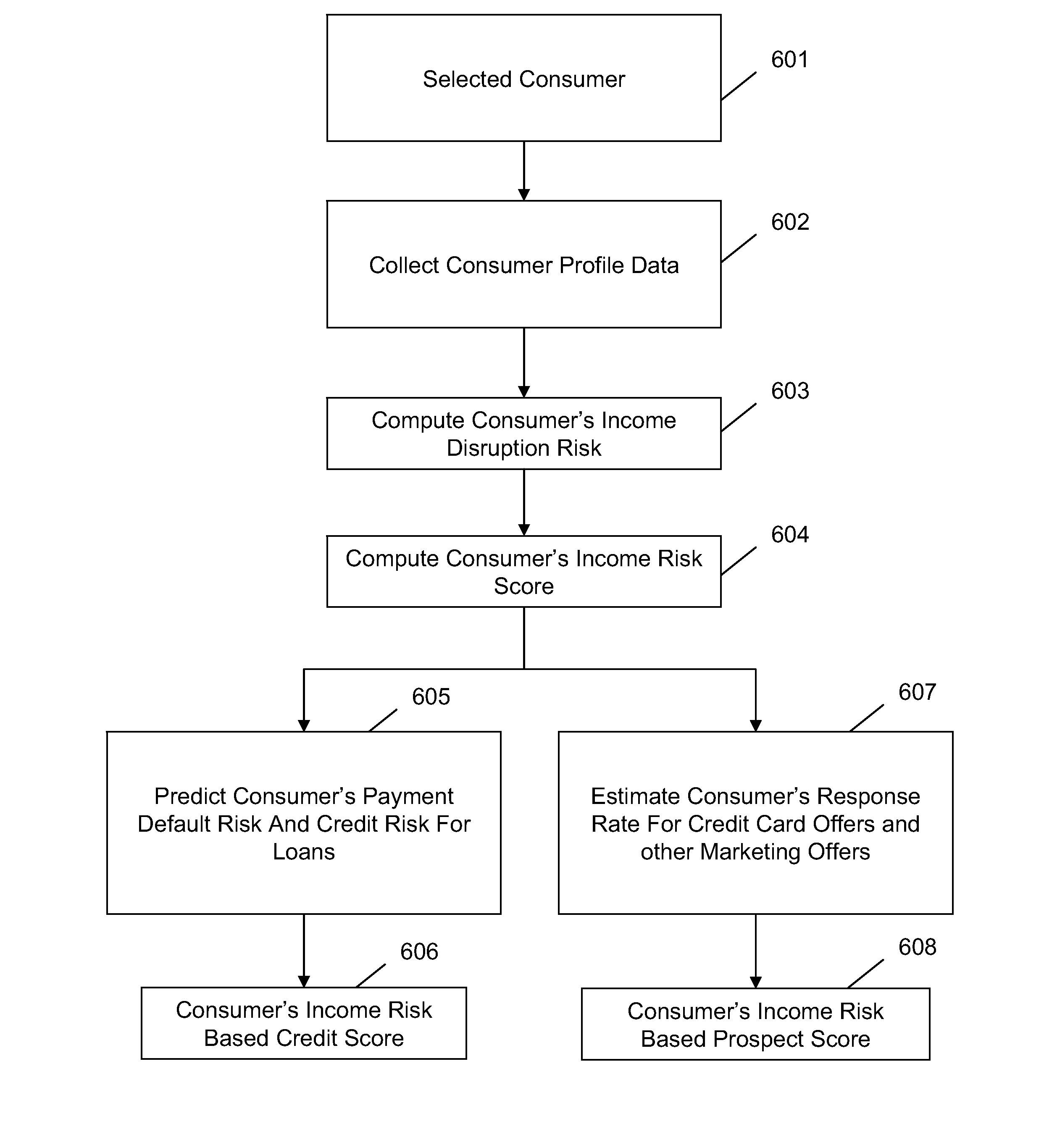
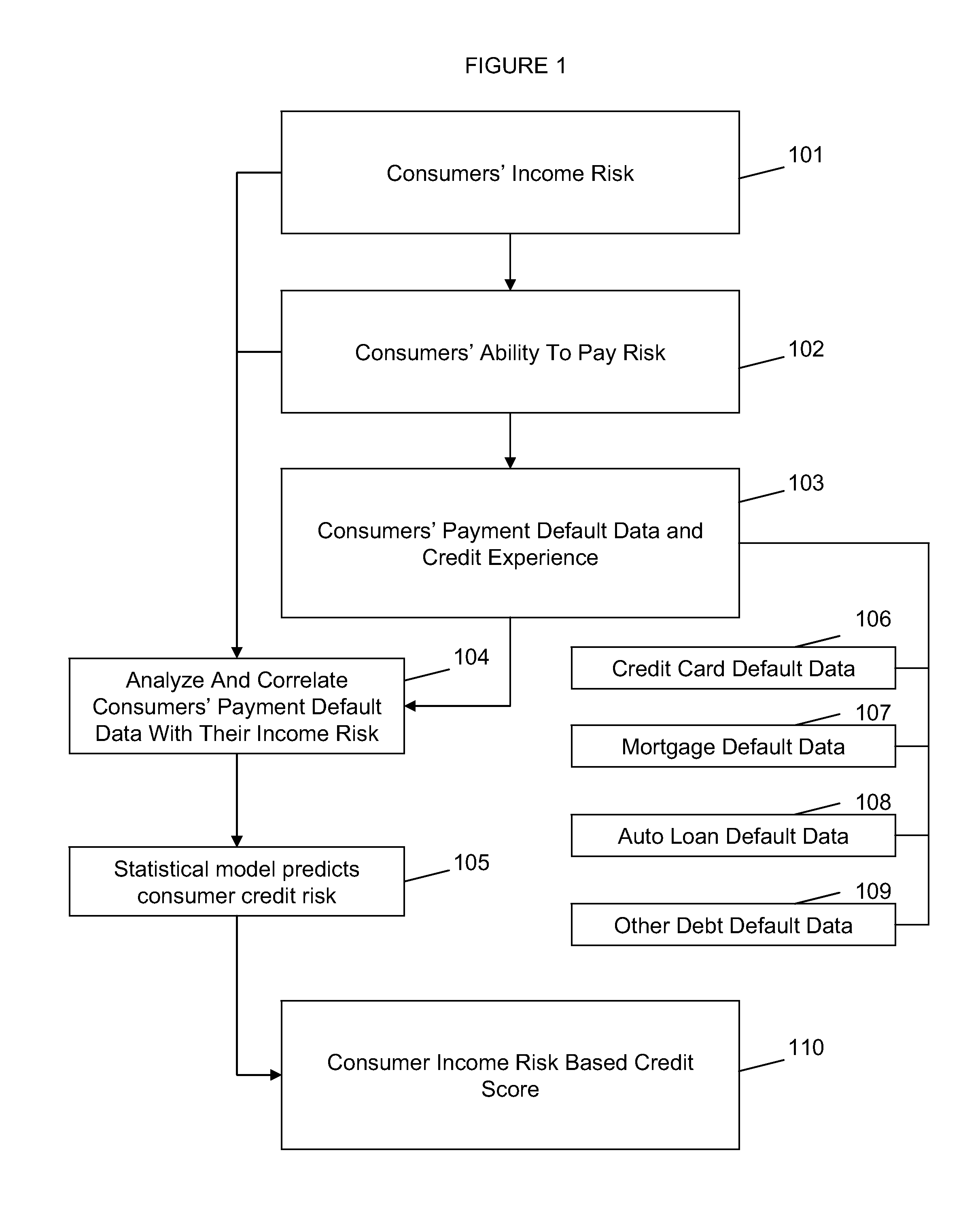
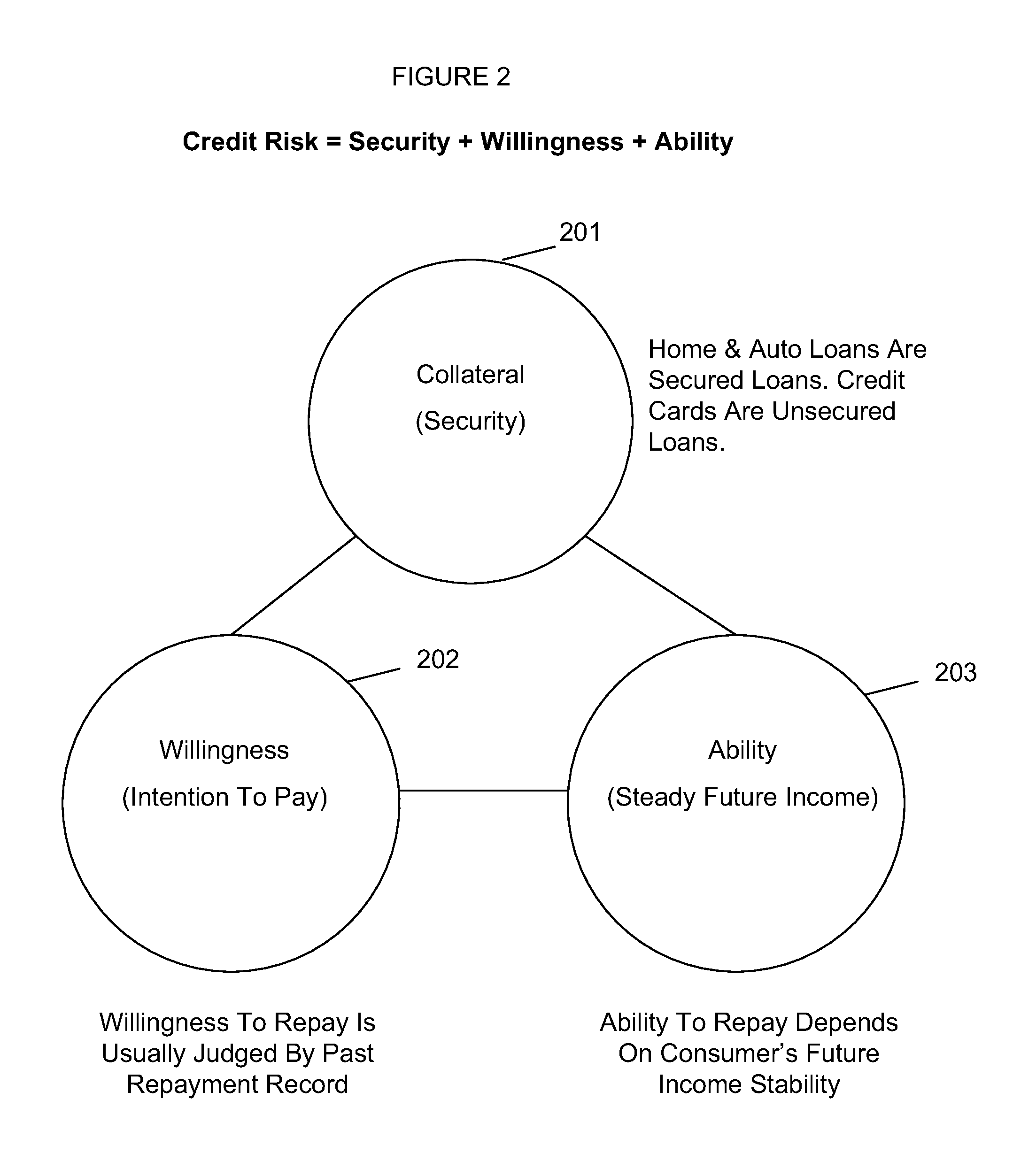
System and method for predicting consumer credit risk using income risk based credit score
InactiveUS20110078073A1Accurate assessmentImprove acquisitionFinanceIncome lossProspective evaluation
Systems and methods are described for scoring consumers' credit risk by determining consumers' income risk and future ability to pay. Methods are provided for measuring consumers' income risk by analyzing consumers' income loss risk, income reduction risk, probability of continuance of income, and economy's impact on consumers' income. In one embodiment, a method is provided to evaluate an individual's creditworthiness using income risk based credit score thereby providing creditors, lenders, marketers, and companies with deeper, new insights into consumer's credit risk and repayment potential. By predicting consumers' income risk and the associated creditworthiness the present invention increases the accuracy and reliability of consumers' credit risk assessments, results in more predictive and precise consumer credit scoring, and offers a new method of rendering a forward-looking appraisal of an individual's ability to repay a debt or the ability to pay for products and services.
Owner:SCORELOGIX
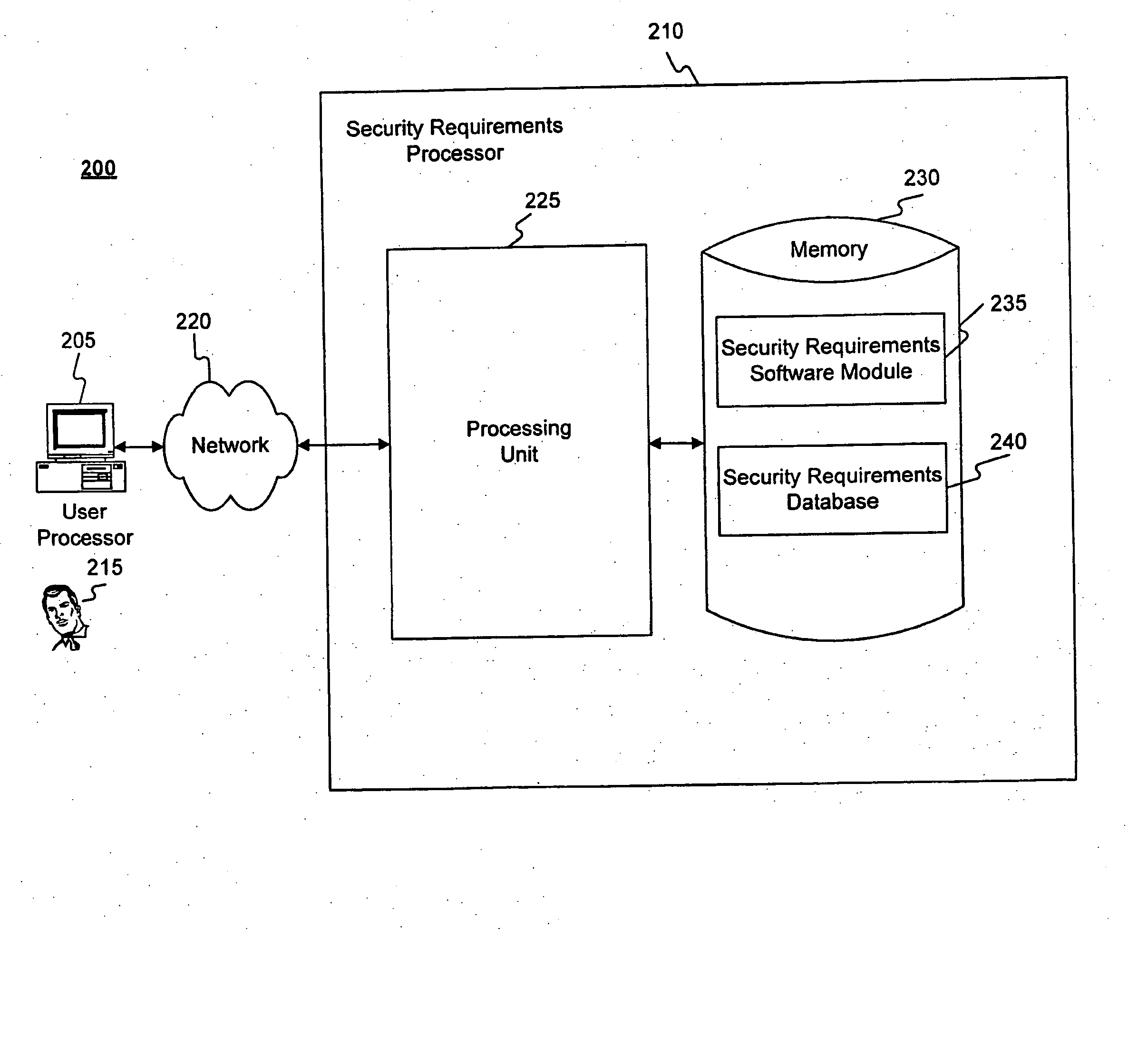
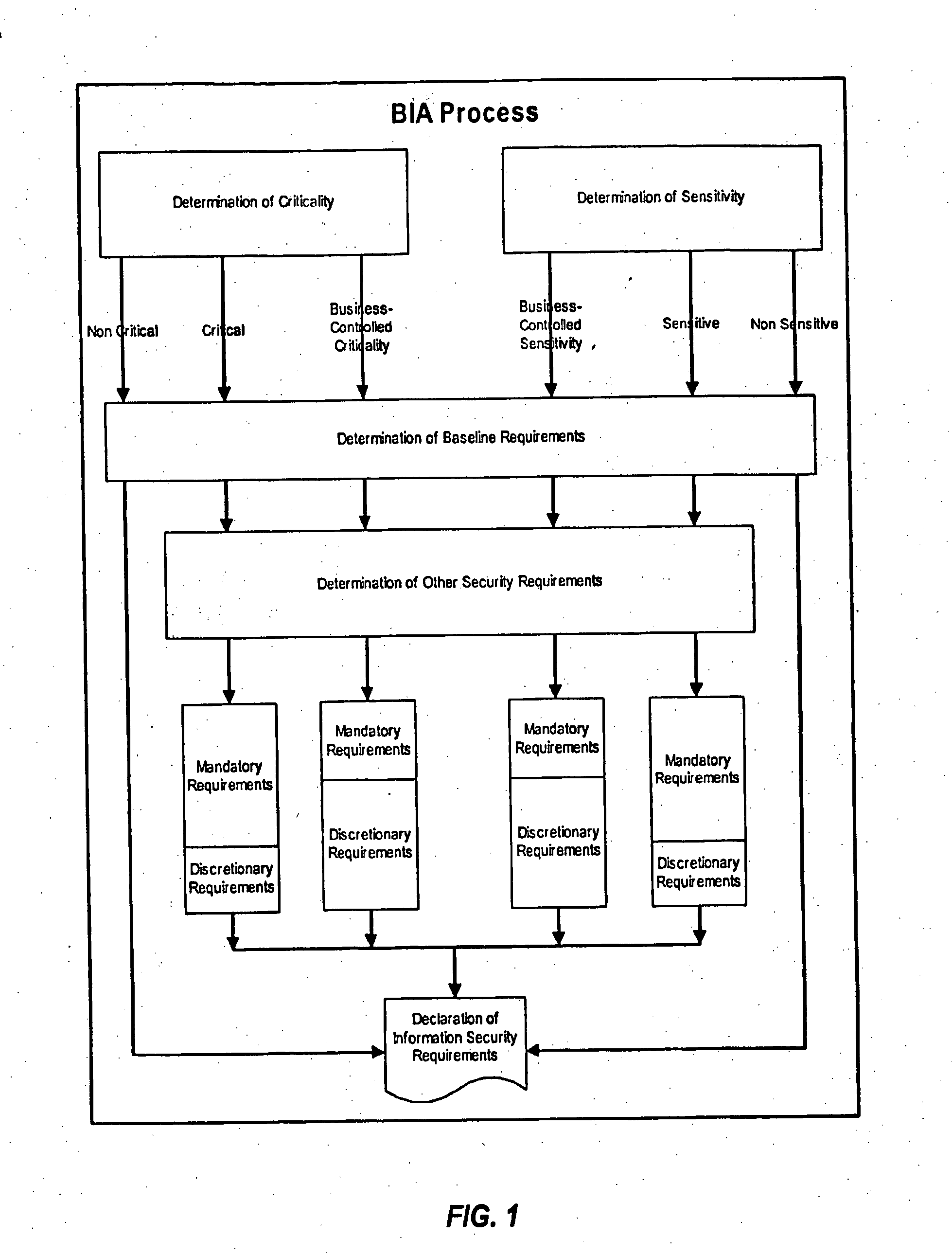
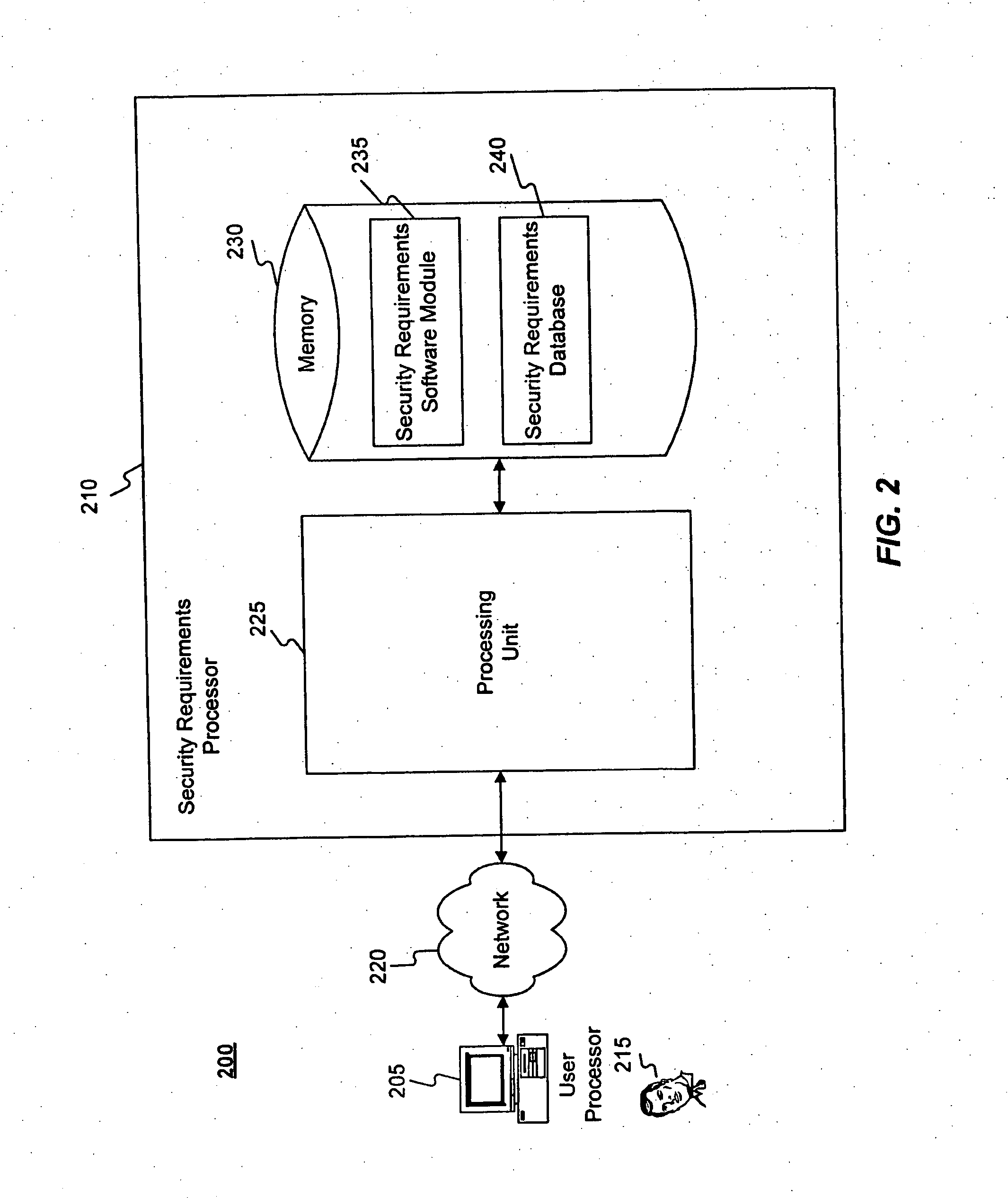
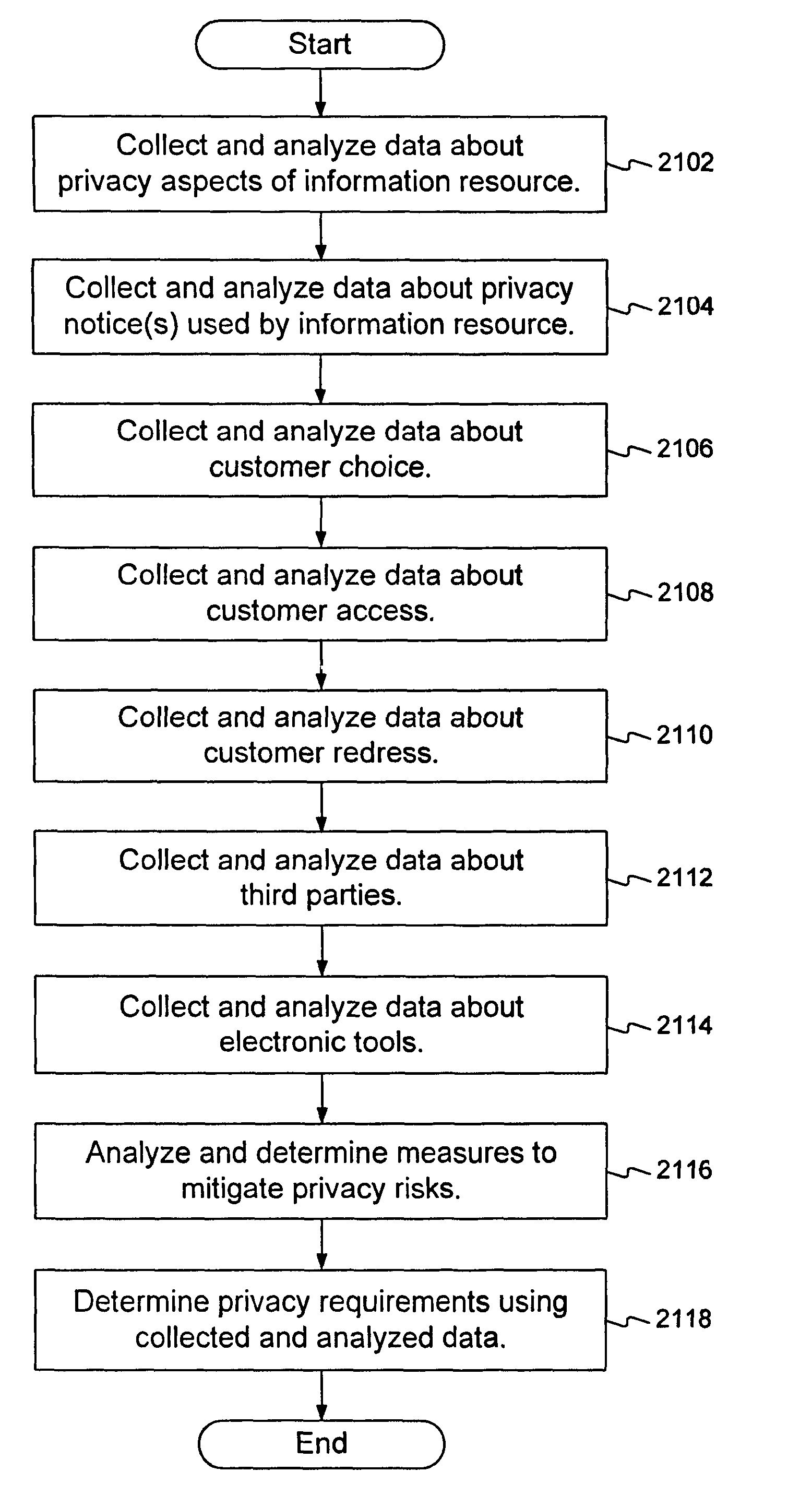
Methods and systems for determining privacy requirements for an informatin resource
InactiveUS20080028435A1Digital data processing detailsAnalogue secracy/subscription systemsRetention periodPrivacy Impact Assessment
A privacy impact assessment is performed to determine and implement privacy requirements for any information resource that uses personal information. Data may be collected and analyzed regarding the information resource and the personal information, and applicable laws, regulations, and policies may be considered to determine privacy requirements. Such requirements may include, for example, access controls, information retention periods, systems requirements, and risk assessments.
Owner:US POSTAL SERVICE
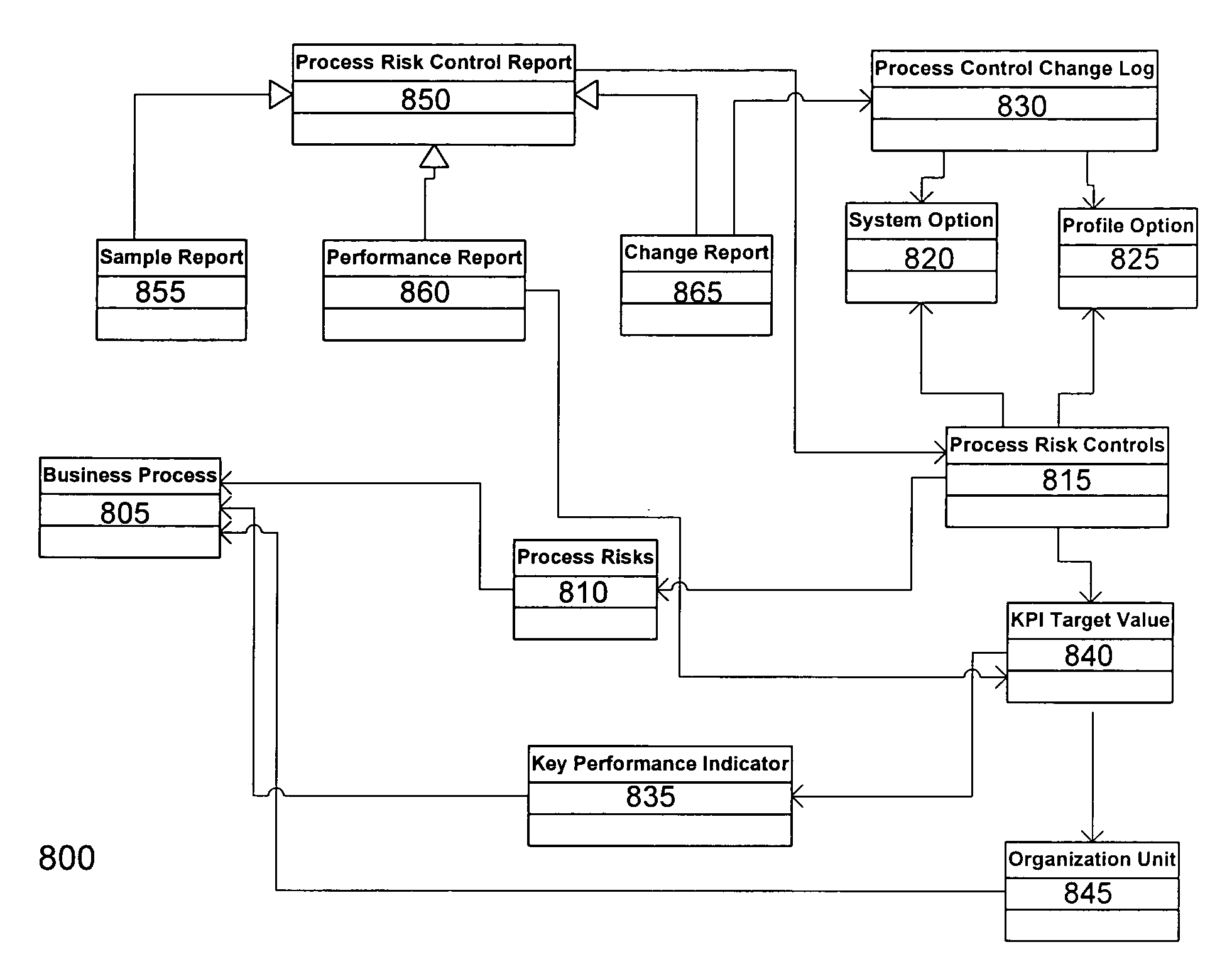
Internal audit operations for Sarbanes Oxley compliance
A system provides audit opinions on an enterprise's organizations, processes, risks, and risk controls. The system first evaluates the enterprise's set of risk controls. The audit opinions of the set of risk controls are used to evaluate the set of risks associated with the set of risk controls. The audit opinions of the set of risks and of the set of risk controls are in turn used to evaluate the set of processes associated with the set of risks. Finally, all of these audit opinions are used to evaluate the set of organizations associated with the set of processes. The system streamlines the evaluation of risk by determining suggested audit opinions. Suggested audit opinions for a given item can be determined from audit opinions previously determined and associated with the given item. Rules can be defined for a given item to specify how to determine the suggested audit result.
Owner:ORACLE INT CORP
Enhanced system, method and medium for certifying and accrediting requirements compliance utilizing robust risk assessment model
InactiveUS6983221B2Enhances and facilitates security risk assessmentsFinanceError detection/correctionComputer-aidedGoal system
Owner:TELOS CORP
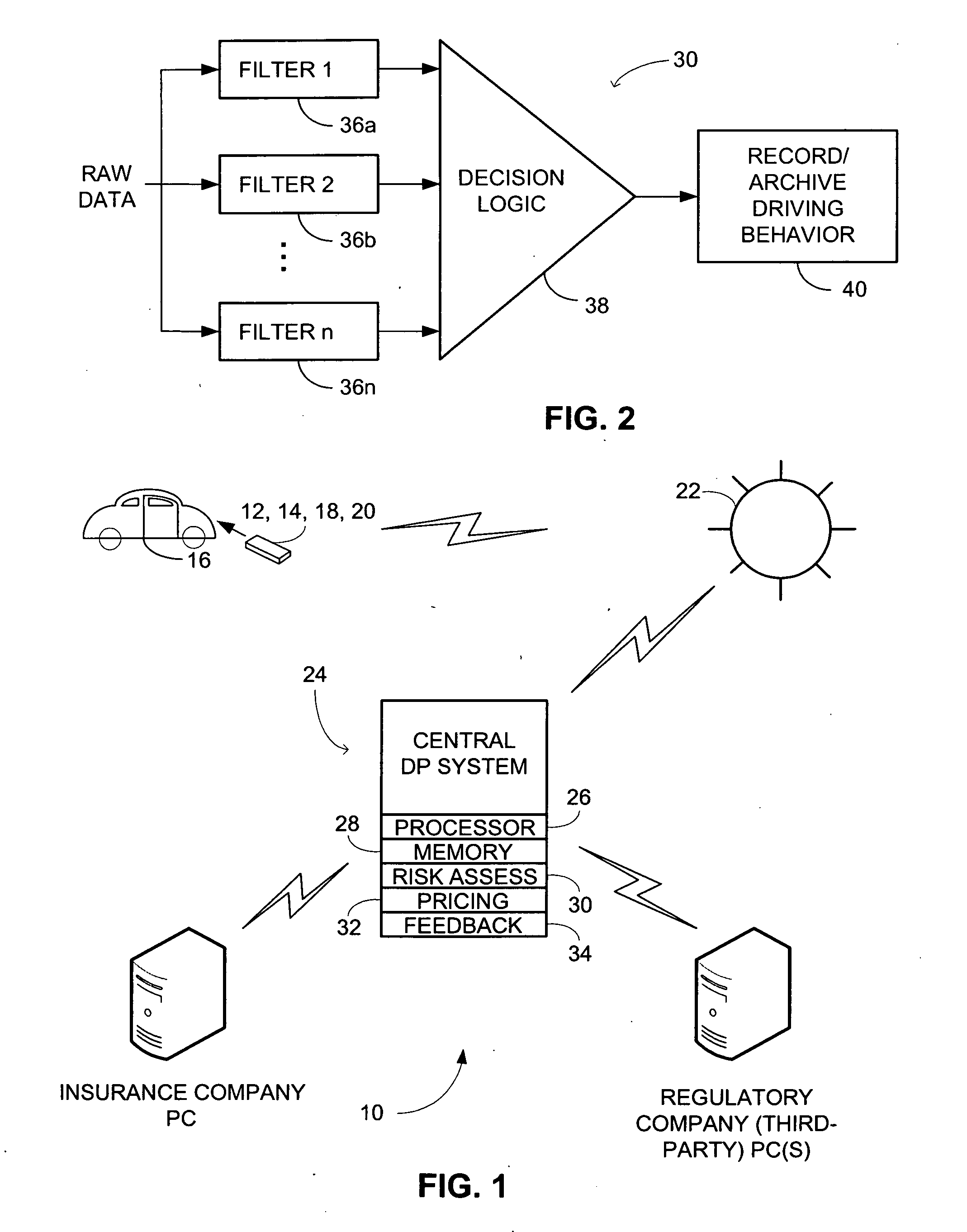
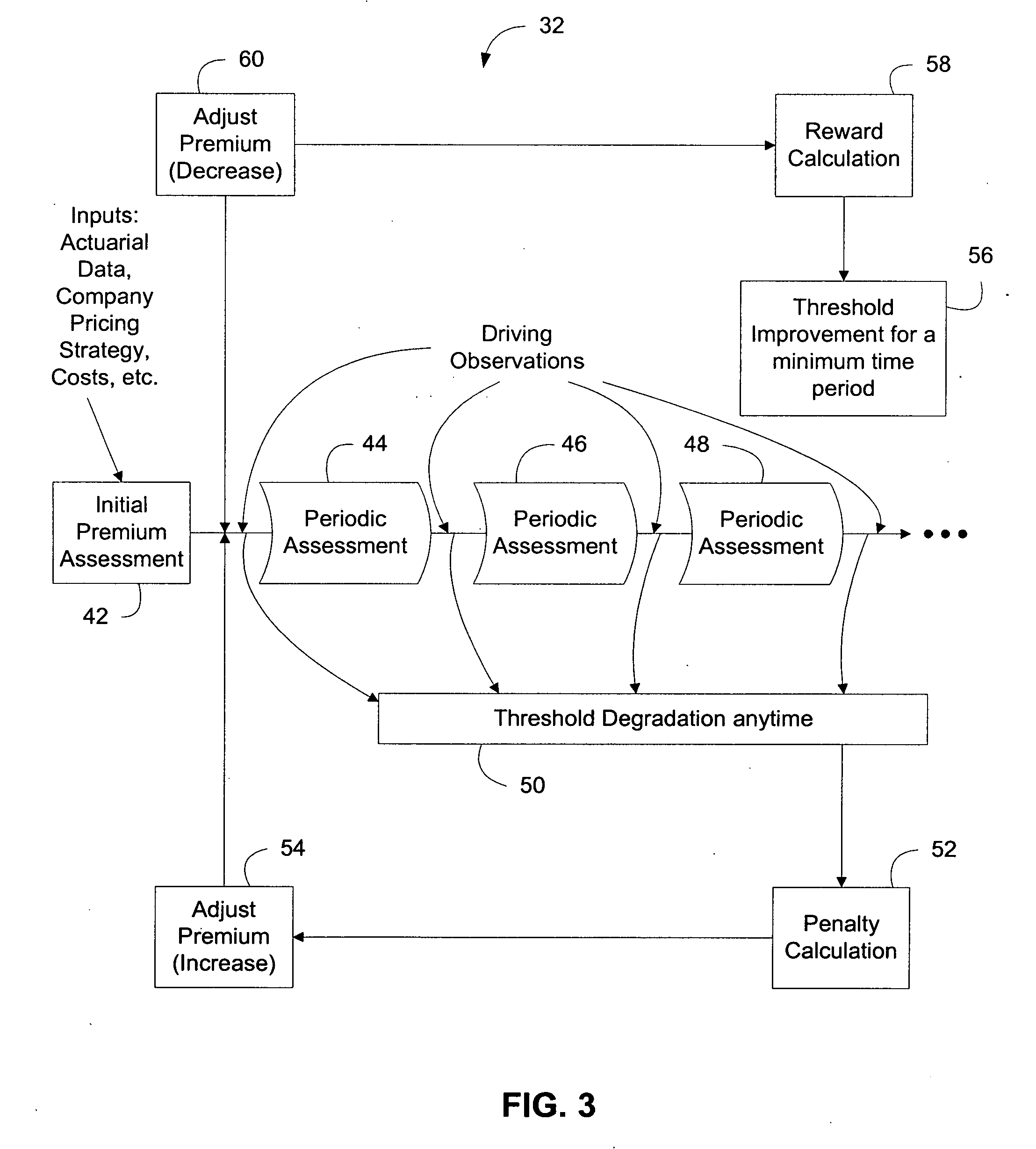
System and method for monitoring driving behavior with feedback
InactiveUS20080243558A1Accelerate emissionsReduce fossil fuel reservesFinanceRegistering/indicating working of vehiclesData processing systemAnalysis data
In accordance with an embodiment of the present invention, a network system for monitoring driving behavior comprises one or more vehicle-mountable motion sensing mechanisms that generate a plurality of data relevant to vehicle moving attitude. The data being indicative of manual or mental risks for a vehicle operator is wirelessly transmittable. The network system also comprises a central data processing system that collects the data transmitted from the motion sensing mechanisms. A risk assessment engine operatively coupled to the central data processing system analyzes the collected data to determine the manual or mental risks. The central data processing system further comprises a feedback engine operable to yield indicia based on the analyzed data that is reportable to the vehicle operator or an authorized data recipient. A reward engine operatively coupled to the feedback engine provides incentives to encourage good or improved driving behavior.
Owner:GUPTE ASH
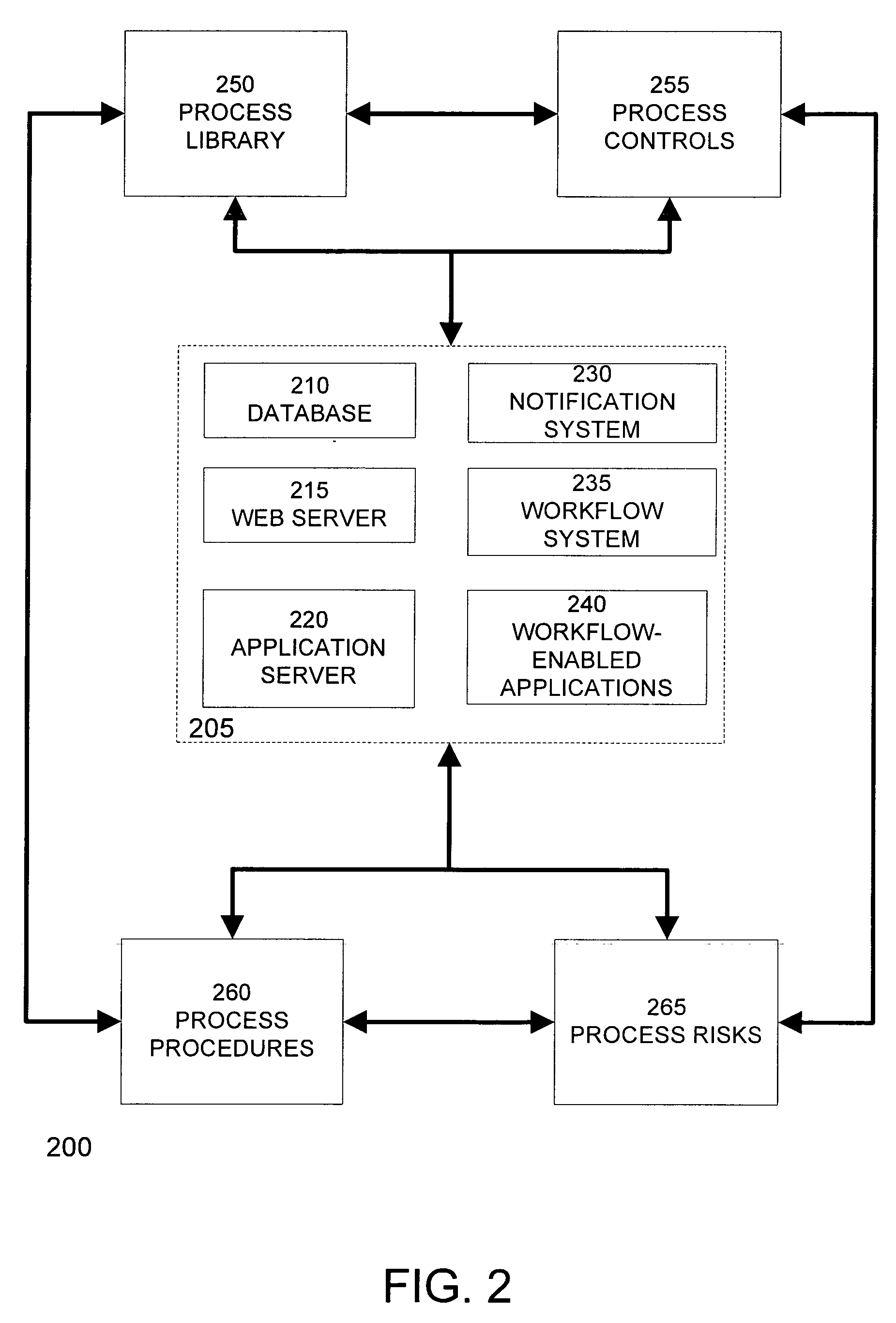
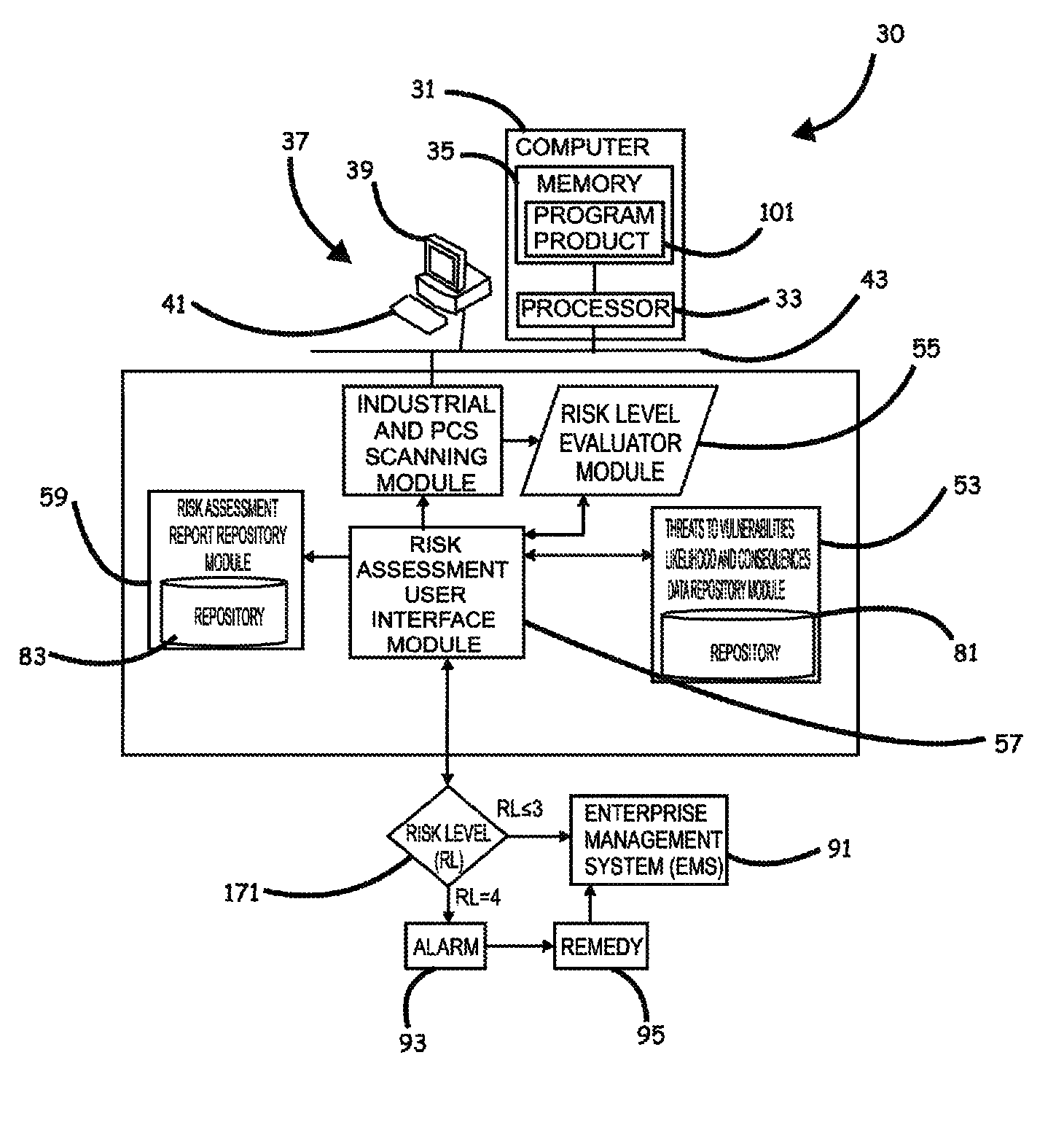
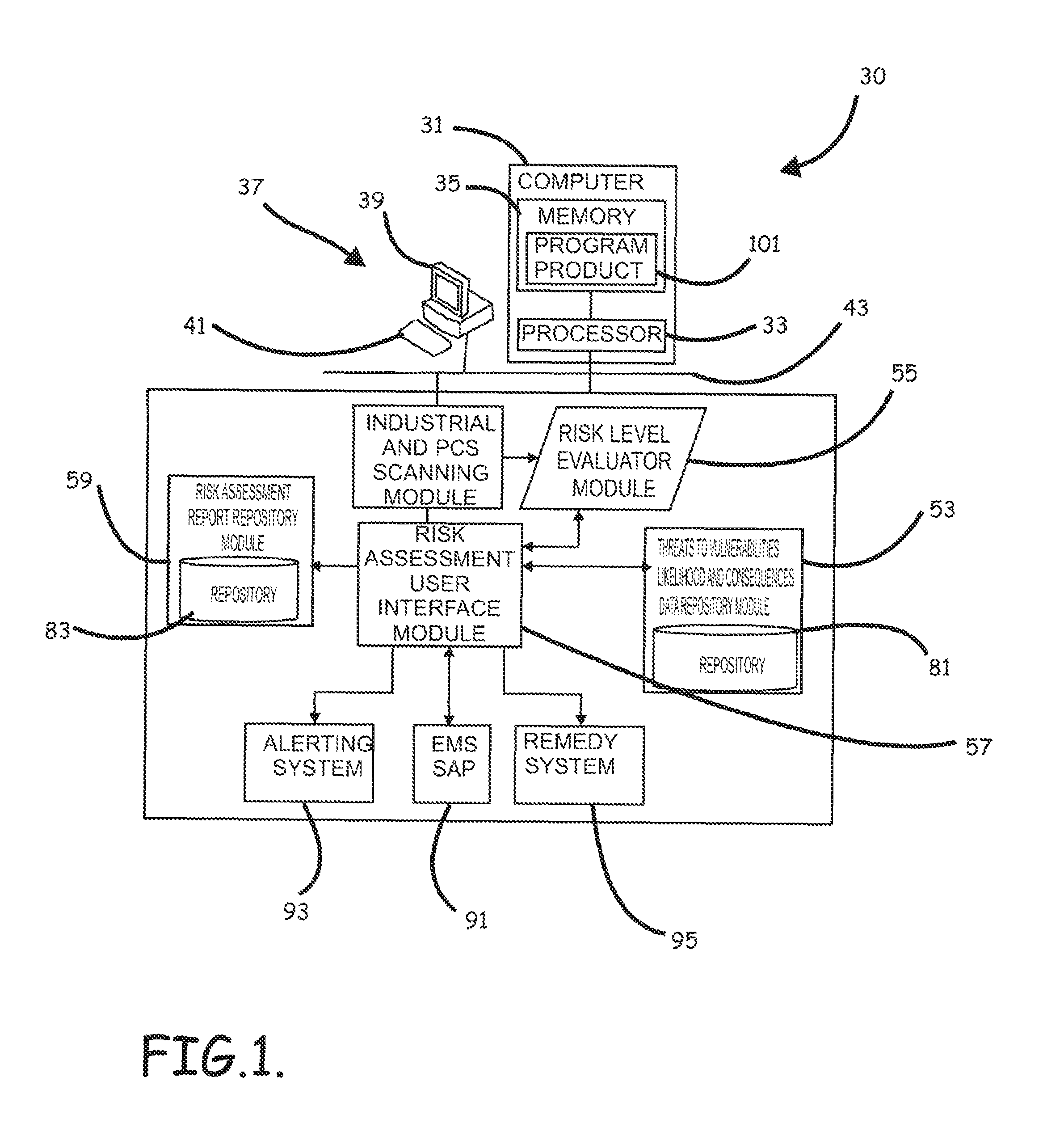
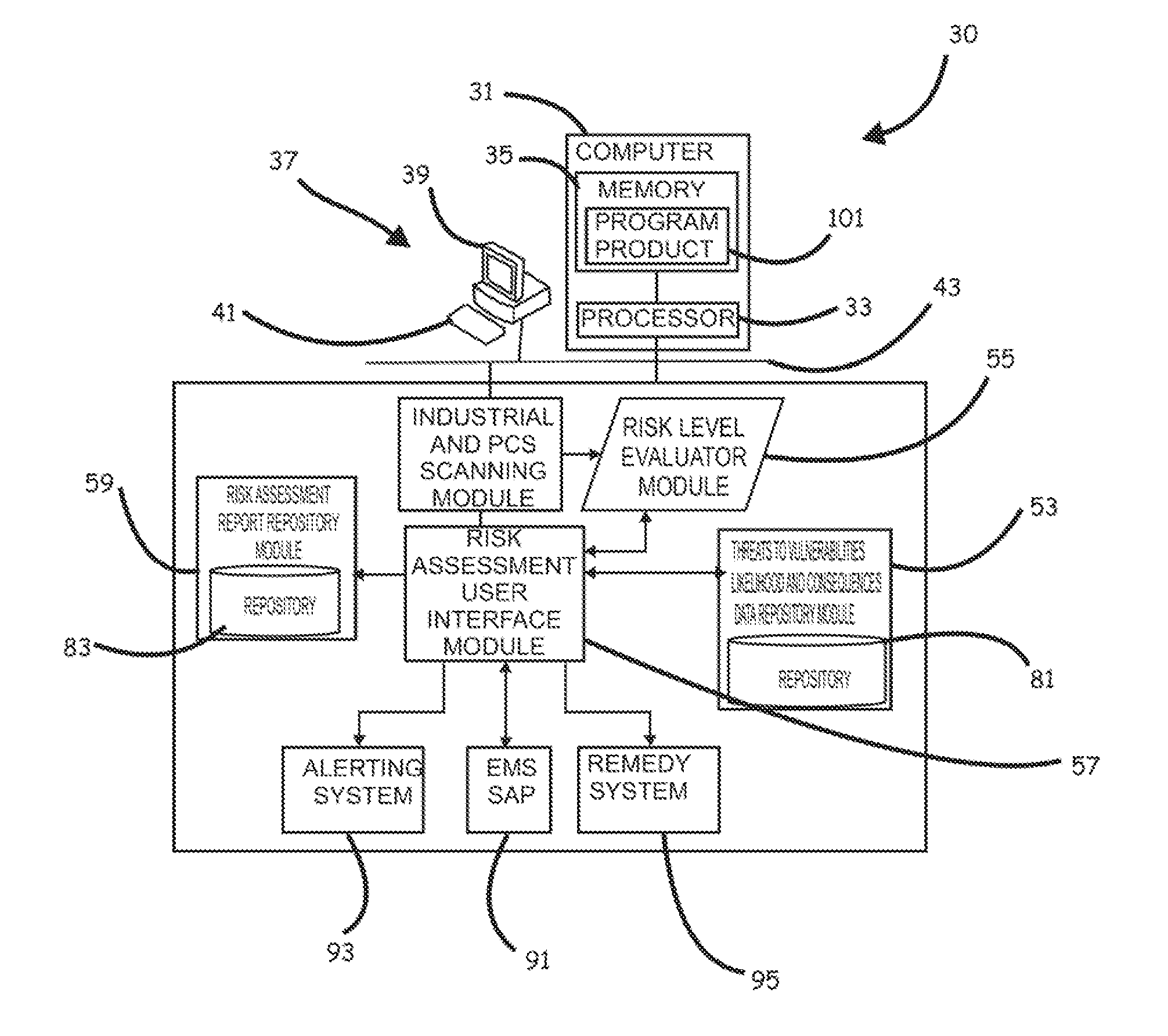
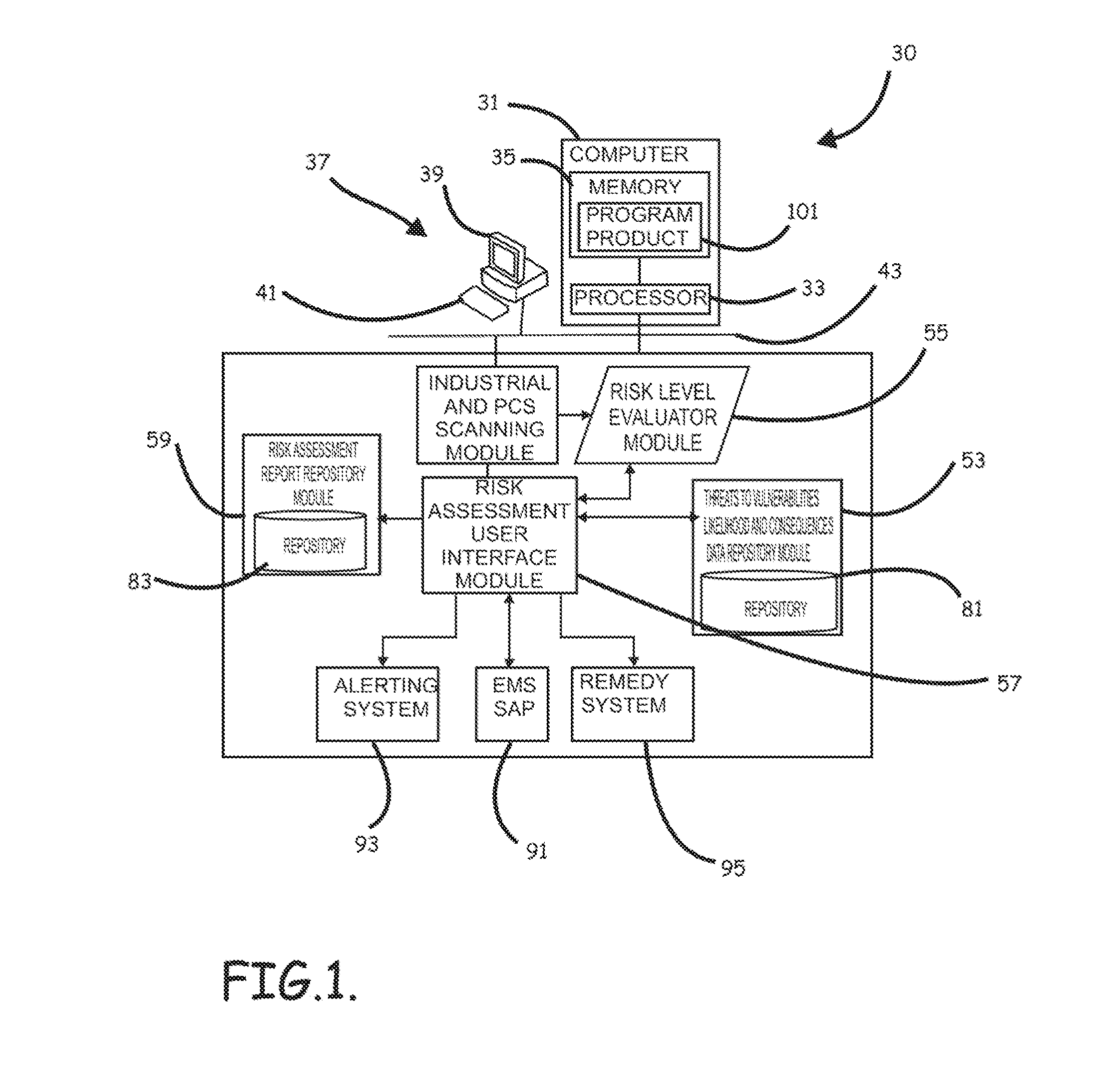
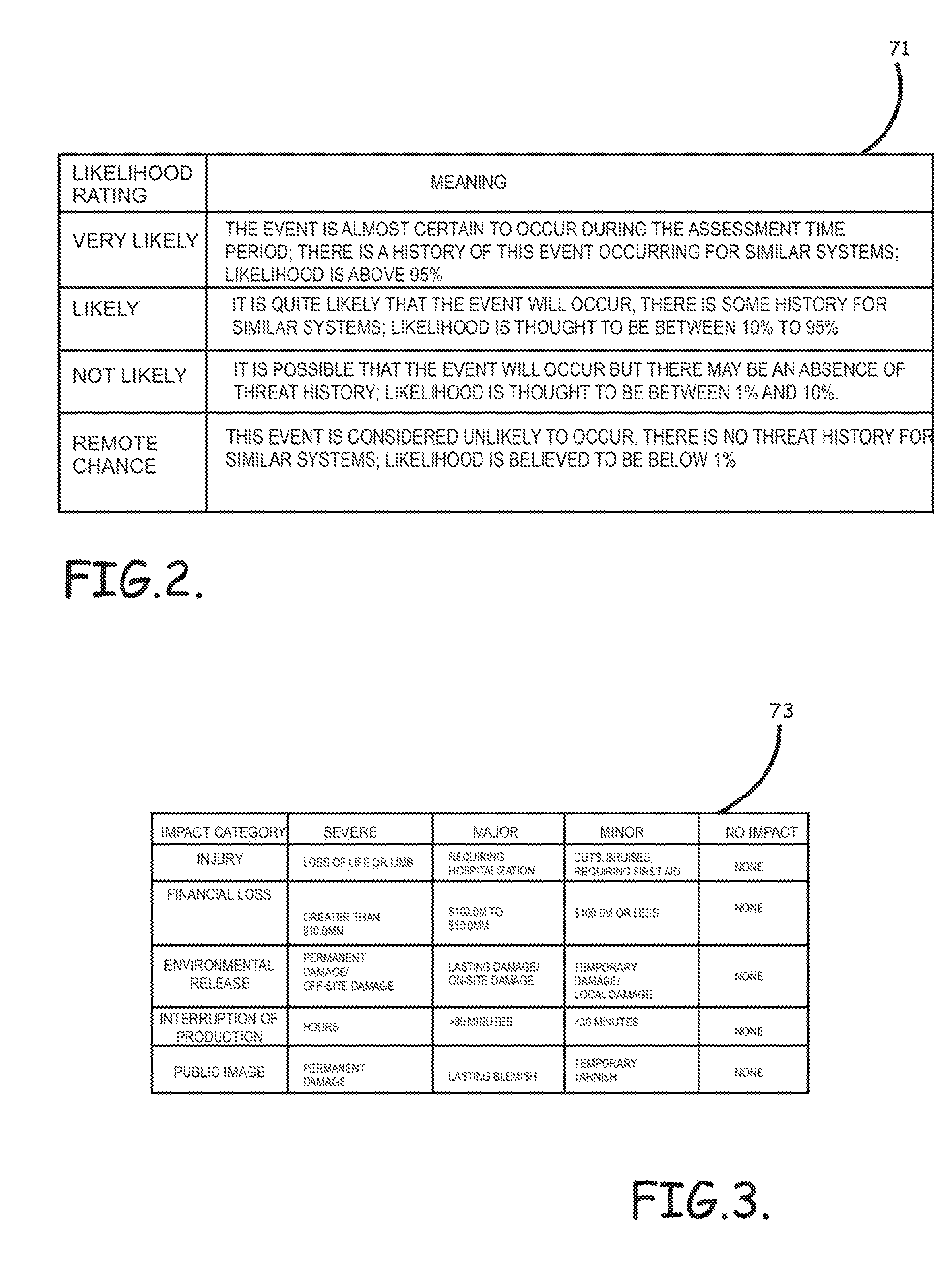
Systems, program product and methods for performing a risk assessment workflow process for plant networks and systems
ActiveUS8621637B2Minimizing human interactionEasy to implementProgramme controlMemory loss protectionRisk levelProcess control network
Systems, methods, and program product to perform a cyber security risk assessment on a plurality of process control networks and systems comprising a plurality of primary network assets at an industrial process facility, are provided. An example of a system and program product can include an industrial and process control systems scanning module configured to identify networks and systems topology and to execute system and network security, vulnerability, virus, link congestion, node congestion analysis to thereby detect susceptibility to know threats to define potential vulnerabilities; a threats to vulnerabilities likelihood and consequences data repository module configured to determine a likelihood of each of a plurality of known threats exploiting identified vulnerabilities and to identify consequences of the exploitation to individual impacted systems and to overall plant operation; and a risk level evaluator module configured to determine a risk level rating for any identified vulnerabilities and provide recommended corrective actions.
Owner:SAUDI ARABIAN OIL CO
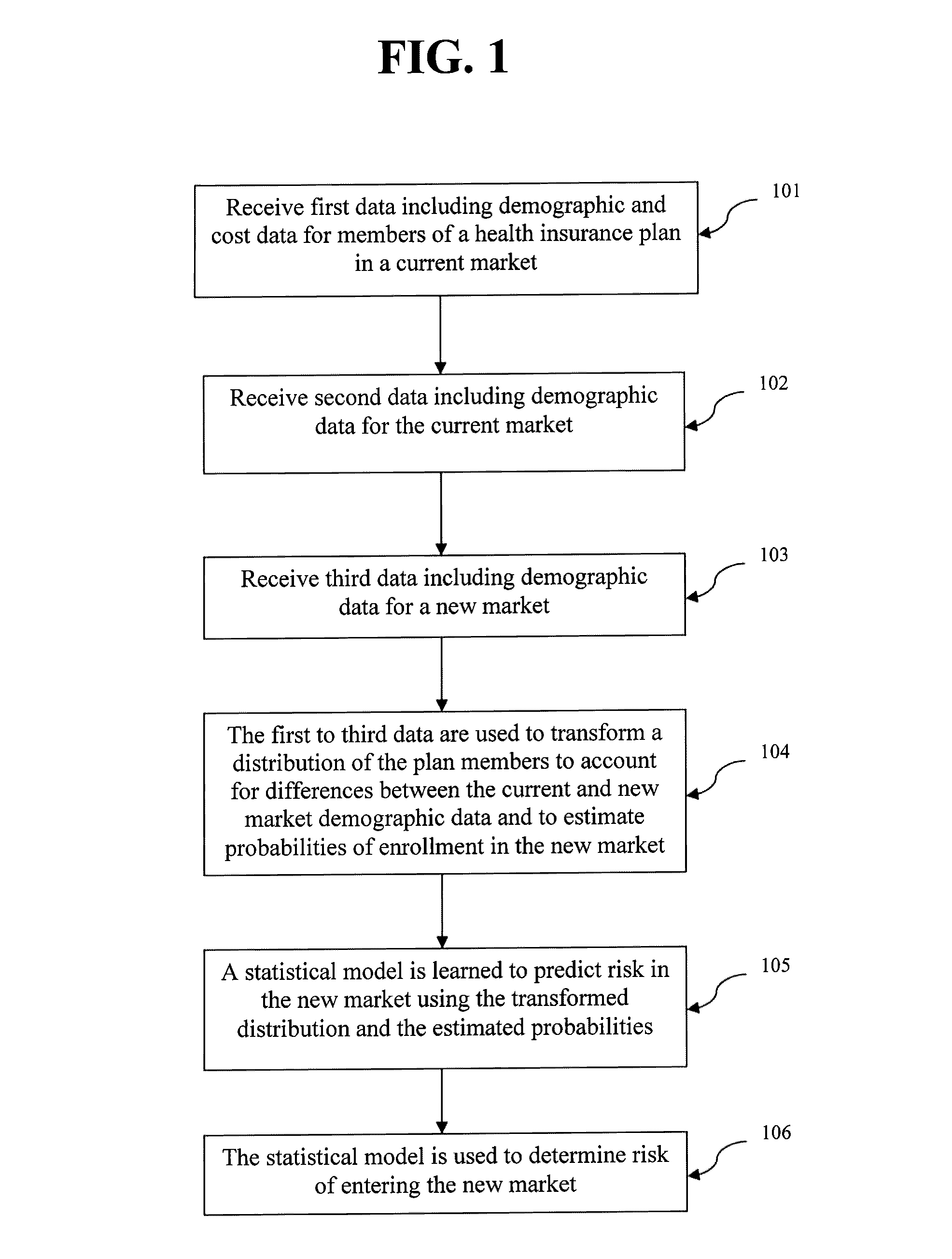
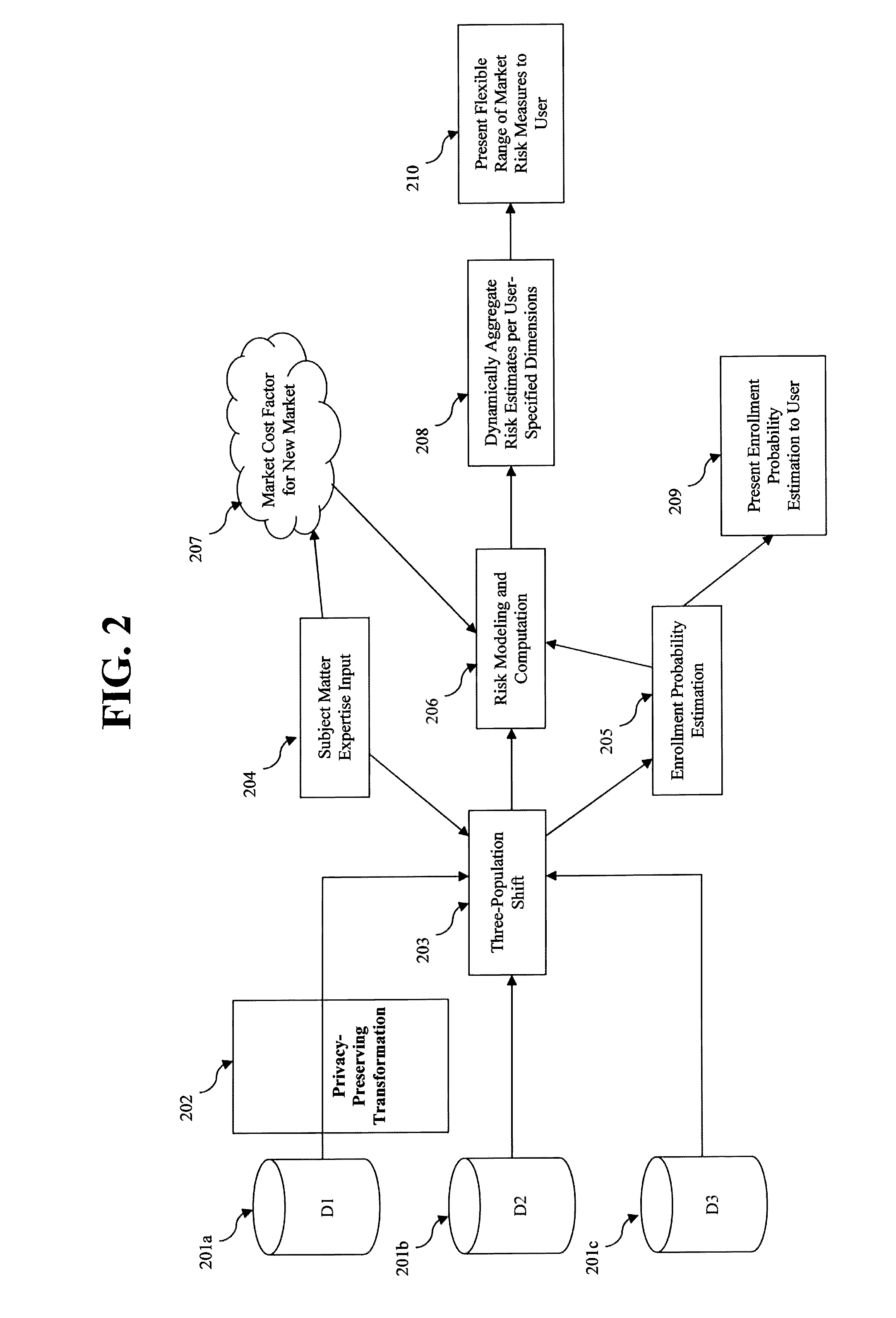
Method for market risk assessment for healthcare applications
Exemplary embodiments of the present invention provide a method of health insurance market risk assessment including receiving first data including demographic and cost data for members of a health insurance plan in a current market, receiving second data including demographic data for the current market, and receiving third data including demographic data for a new market. The first to third data are used to transform a distribution of the plan members to account for differences between the current and new market demographic data and to estimate probabilities of enrollment in the new market. A statistical model is learned to predict risk in the new market using the transformed distribution and the estimated probabilities. The statistical model is used to determine risk of entering the new market.
Owner:IBM CORP
Methods and systems for determining privacy requirements for an information resource
InactiveUS7966663B2Digital data processing detailsAnalogue secracy/subscription systemsRetention periodPrivacy Impact Assessment
A privacy impact assessment is performed to determine and implement privacy requirements for any information resource that uses personal information. Data may be collected and analyzed regarding the information resource and the personal information, and applicable laws, regulations, and policies may be considered to determine privacy requirements. Such requirements may include, for example, access controls, information retention periods, systems requirements, and risk assessments.
Owner:US POSTAL SERVICE
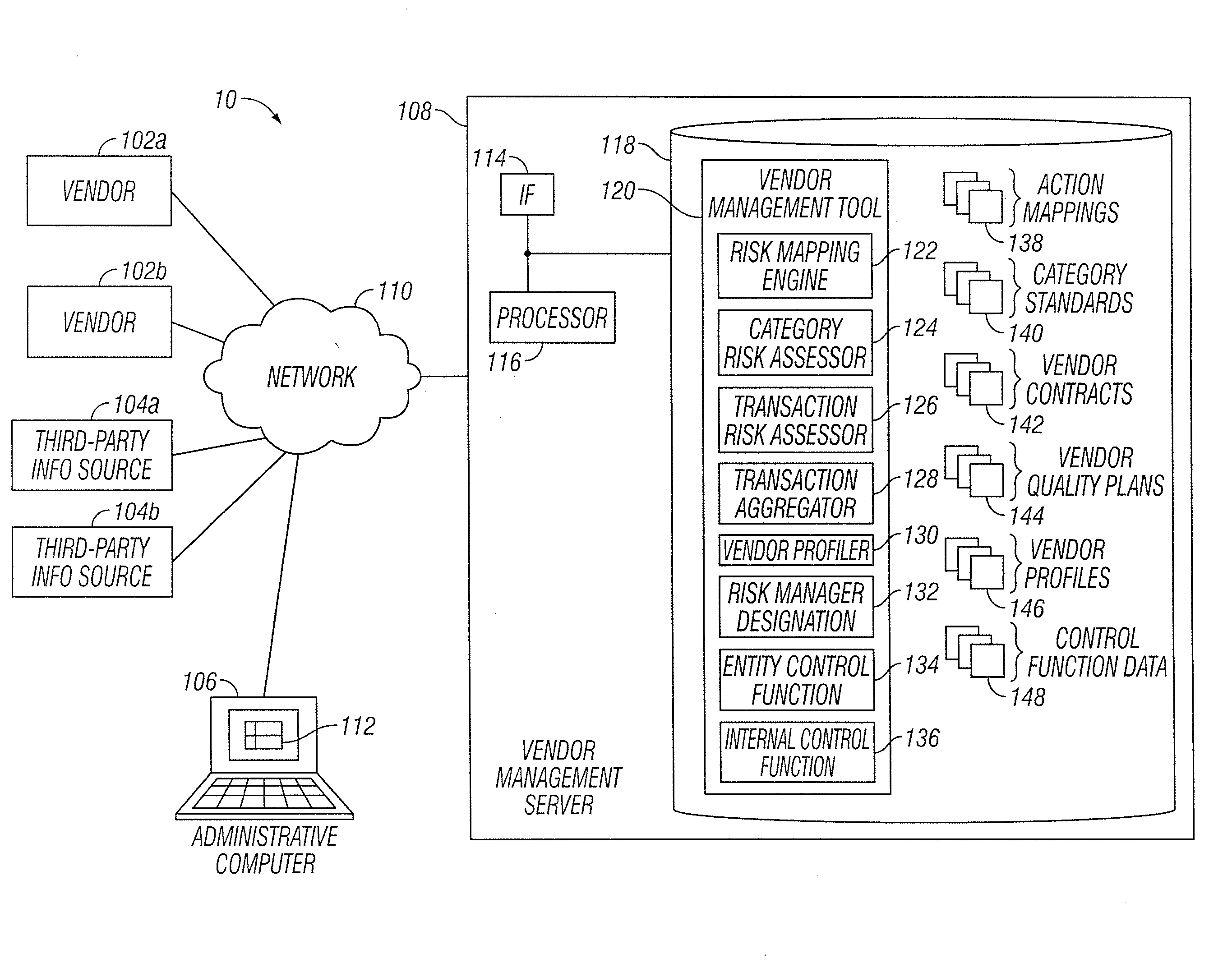
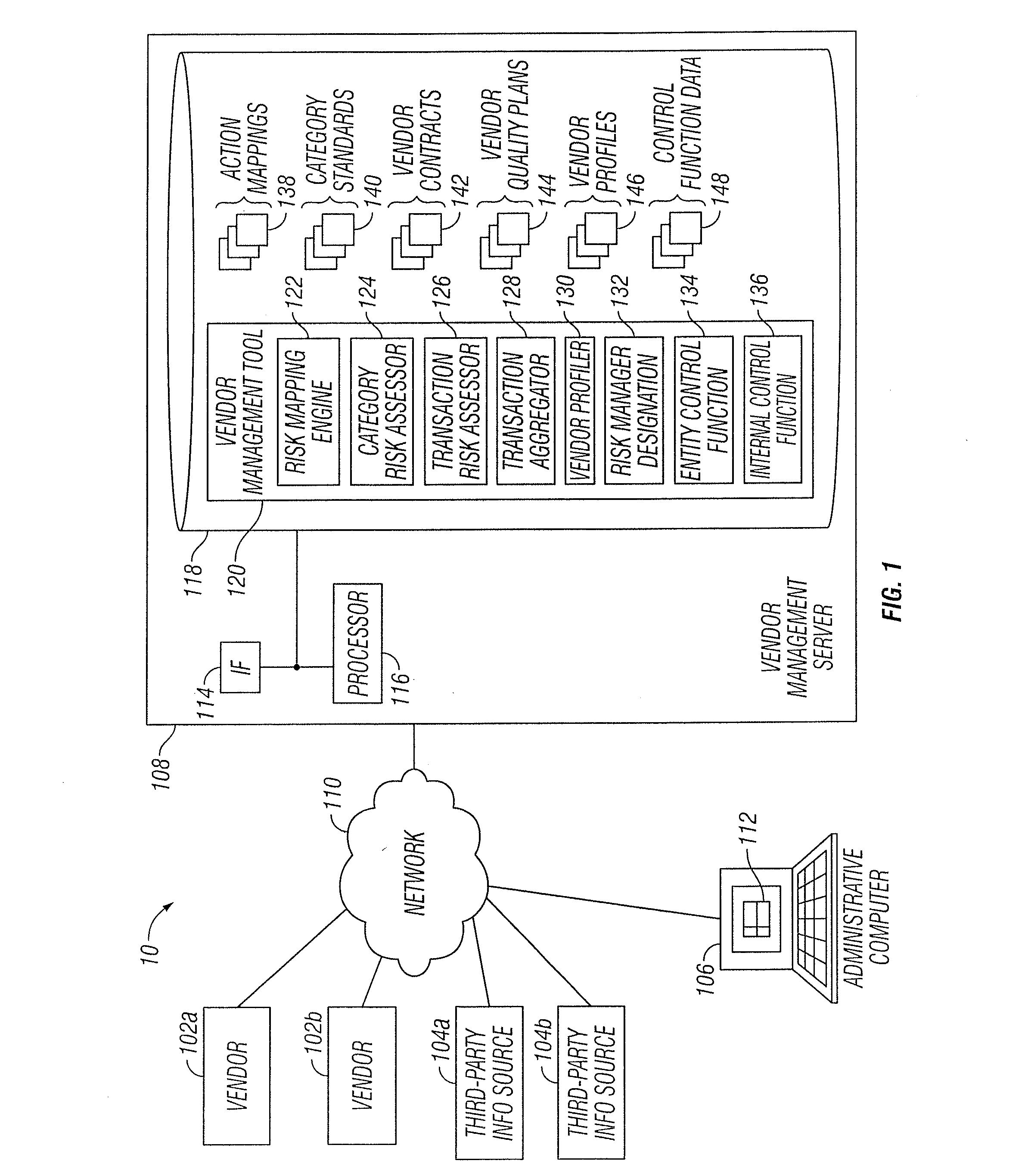
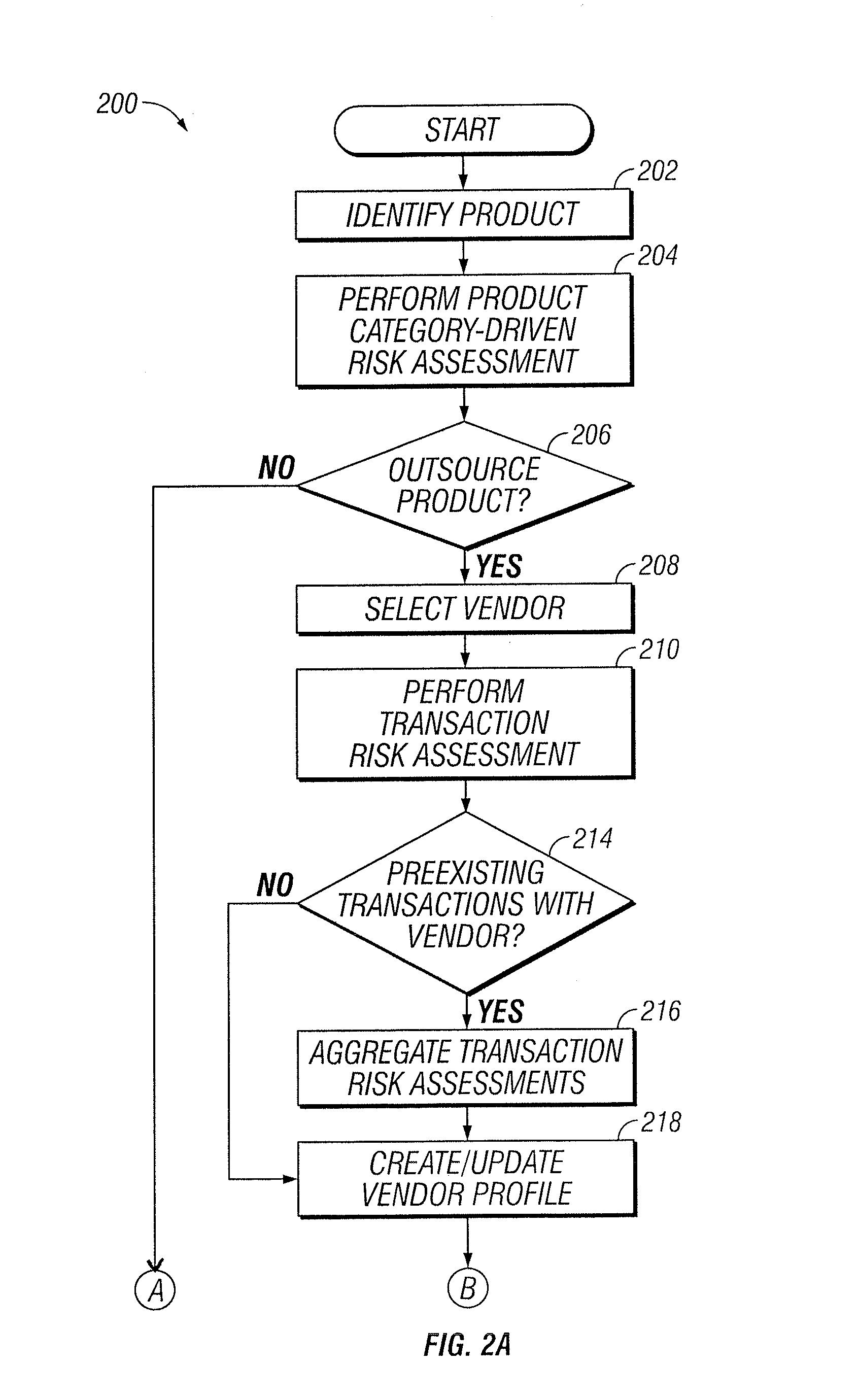
Vendor Management System
InactiveUS20150242778A1Disadvantages can be reduced eliminatedProblems be reduced eliminatedFinanceResourcesDriving riskEngineering
Managing a vendor may comprise identifying a product to be supplied to an entity. Risk elements associated with the product may be determined by performing a product category-driven risk assessment. A transaction level risk assessment is performed for one or more vendors proposed to supply the product to the entity. At least one management action is determined for reducing risk for a risk element of the plurality of risk elements associated with supplying the product to the entity by a selected vendor from a group comprising the one or more vendors proposed to the supply the product to the entity, wherein the at least one management action is determined according to results of the product category-driven risk assessment and the transaction level risk assessment for the selected entity. A vendor level quality plan for the selected vendor is created that comprises the at least one management action.
Owner:BANK OF AMERICA CORP
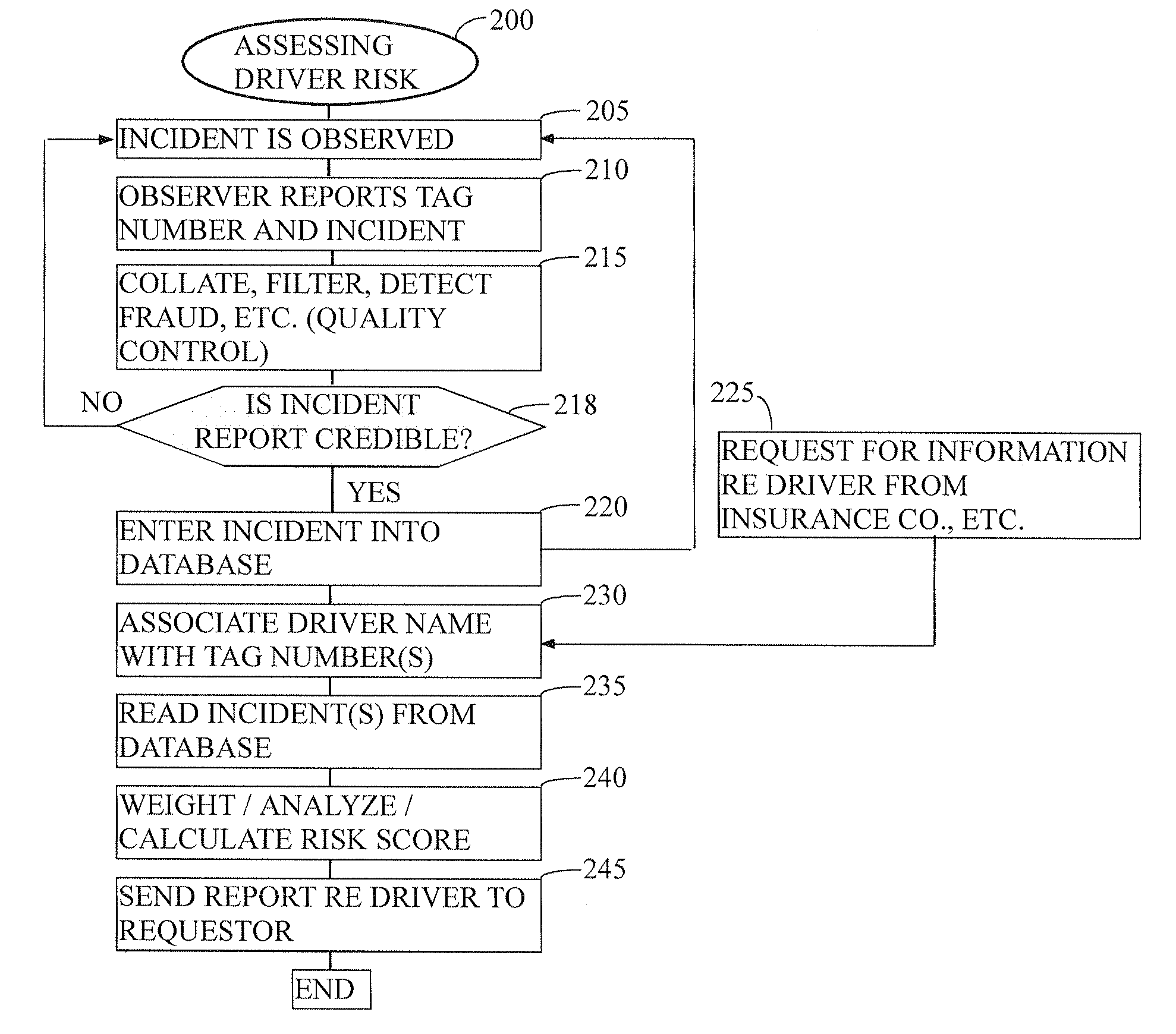
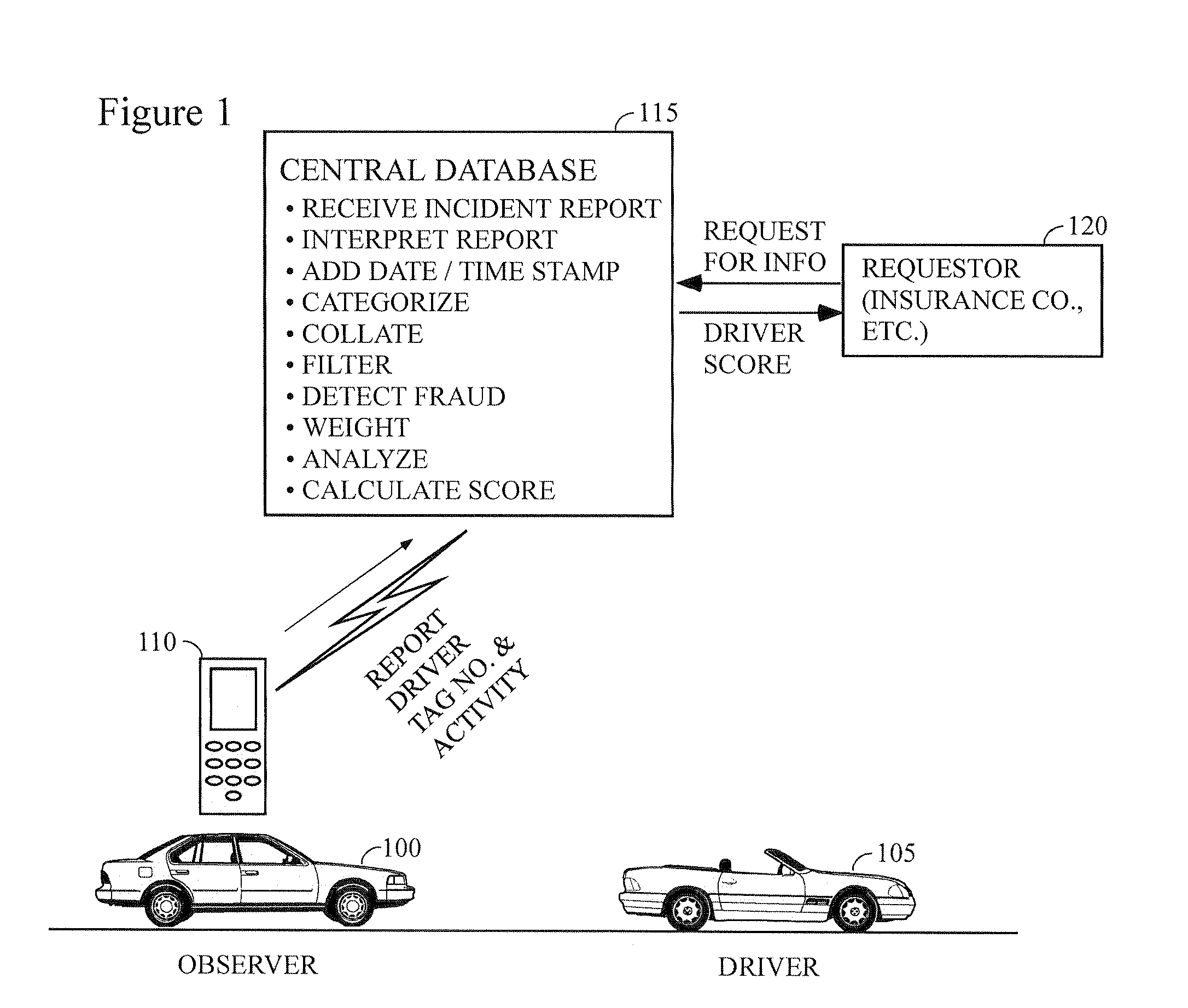
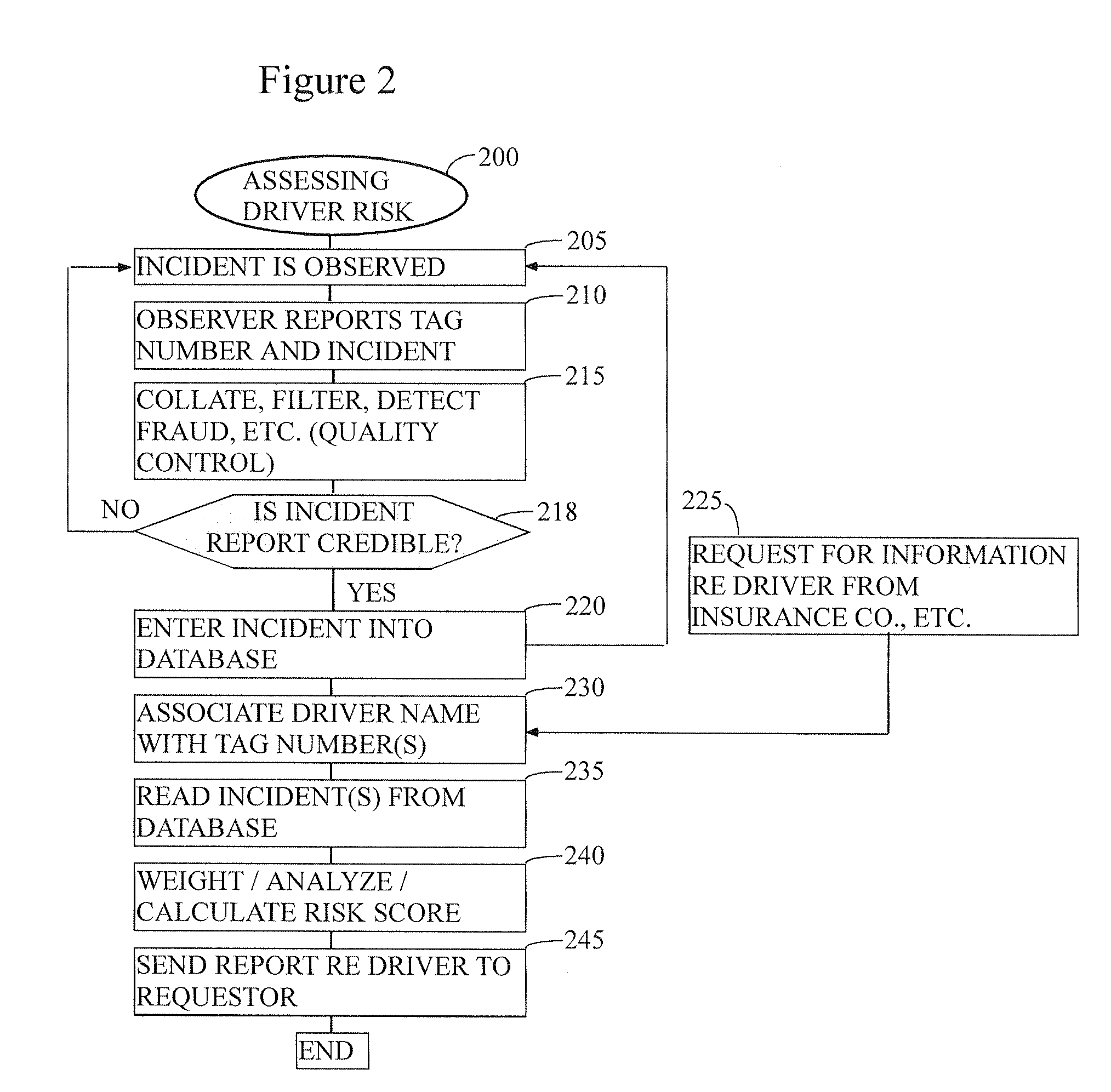
Method for ranking driver's relative risk based on reported driving incidents
InactiveUS20090132294A1Understand clearlyAnalogue computers for vehiclesFinanceDriver/operatorDriving risk
The present invention relates generally to the field of improvement in the driving risk assessment arts. More particularly, but not by way of limitation, the present invention generally relates to a method of rating the driving risks of individuals based on that driver's actual driving record as obtained from his or her fellow drivers.
Owner:HAINES SAMUEL H
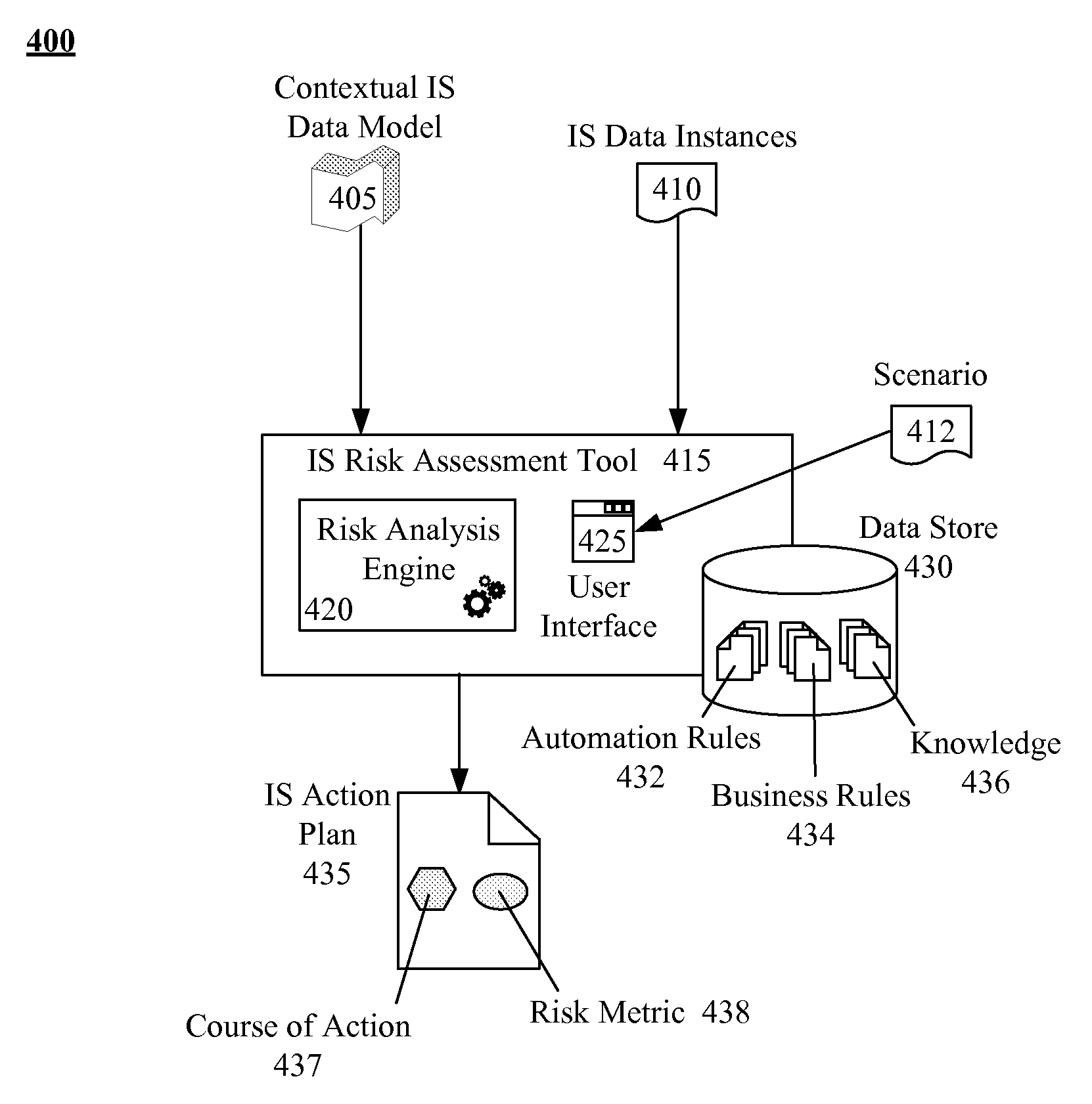
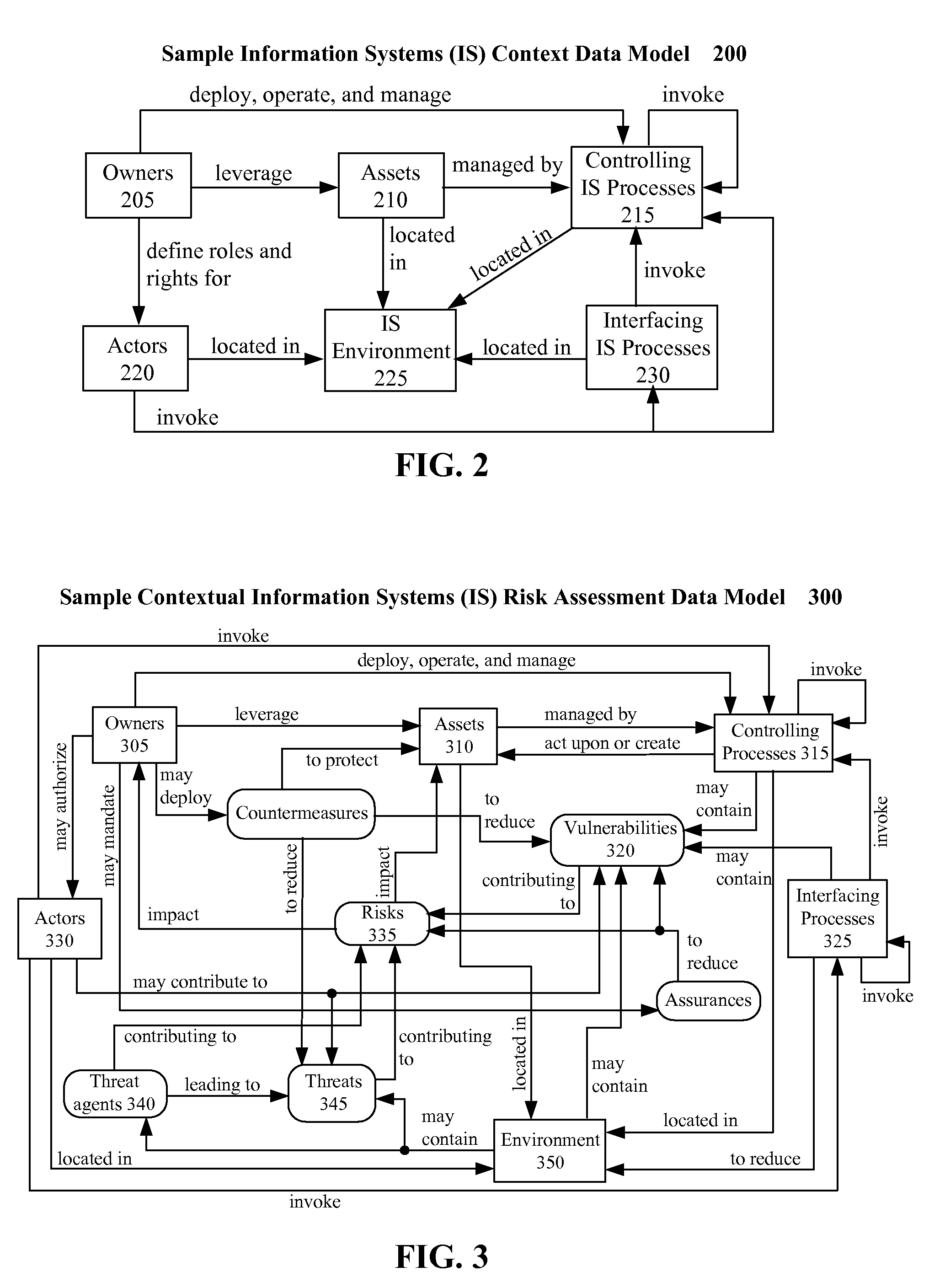
Automated risk assessments using a contextual data model that correlates physical and logical assets
An automated method, system, device, and / or computer program for performing risk assessment for an information system. A risk assessment tool can receive a scenario for which to perform a risk assessment. A contextual data model and a set of data instances for the information system can be accessed. The contextual data model can define relationships between physical and logical assets of the information system. The contextual data model and set of data instances can be analyzed in relation to the scenario. An action plan can be generated that addresses the scenario.
Owner:INT BUSINESS MASCH CORP
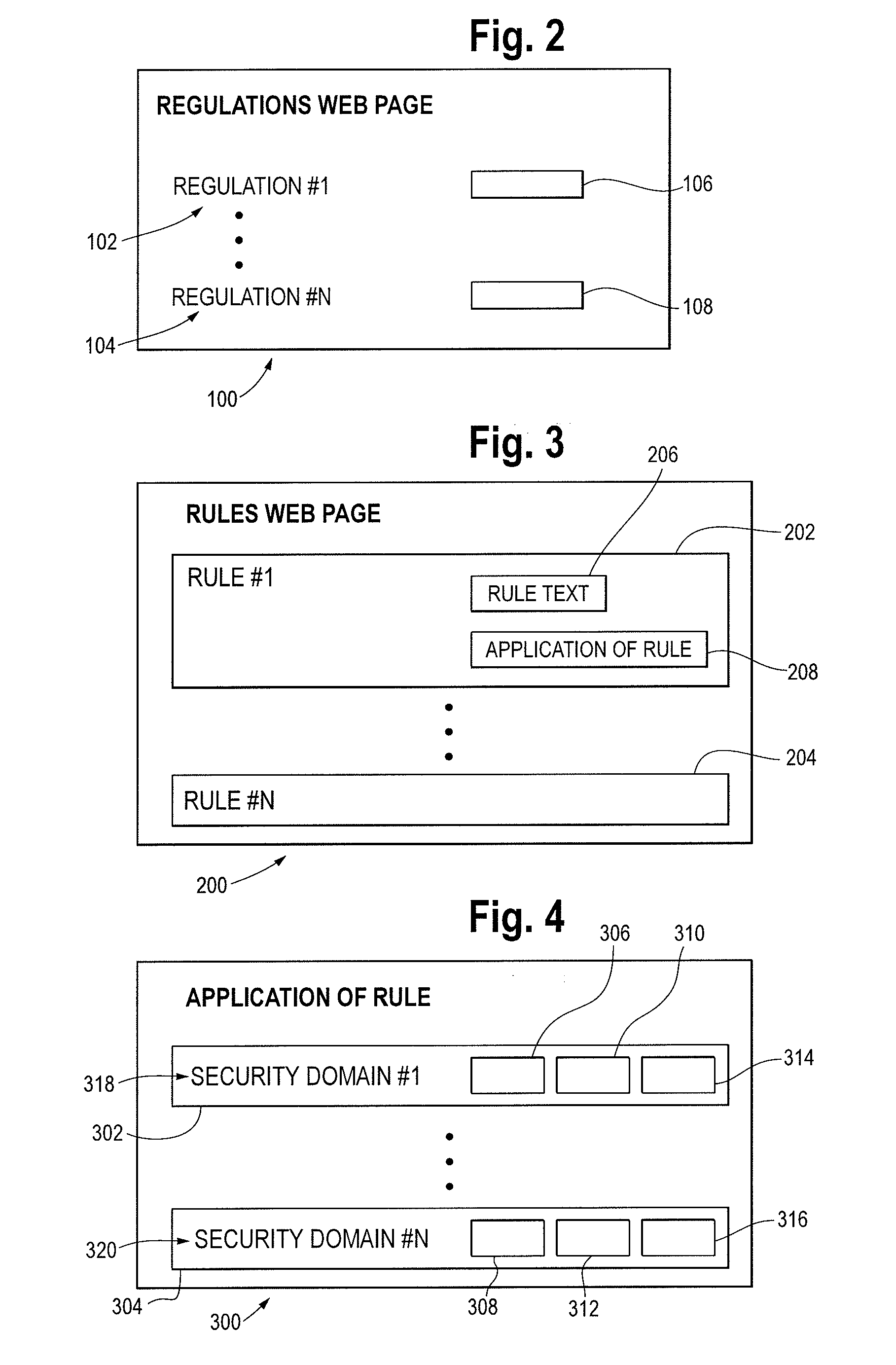
Security Compliance Methodology and Tool
An apparatus is provided for evaluating risk to an organization. The apparatus includes a plurality of governmental rules directed to protecting shareholders, a plurality of security domains of the organization wherein each security domain is associated with a different asset of the organization and a request for an information risk assessment within at least one of the plurality of security domains of the organization formed under the plurality of governmental rules from a set of initializing inputs. The apparatus further includes a information risk assessment plan formed from the request for the information risk assessment, a set of information assessment templates and test cases formed from the information risk assessment plan, a set of information risk assessment tests conducted on the IT system using the assessment templates and test cases, a set of test results generated by the risk assessment tests, one or more security control gaps identified by the assessment responses and one or more gap remediation plans formed from the identified security gaps.
Owner:DENOVO ANDREW +1
Point of care diagnostic systems
InactiveUS6867051B1Accurate concentrationAccurately presenceComputer-assisted medical data acquisitionMedical imagesPoint of careDiagnostic test
Systems and methods for medical diagnosis or risk assessment for a patient are provided. These systems and methods are designed to be employed at the point of care, such as in emergency rooms and operating rooms, or in any situation in which a rapid and accurate result is desired. The systems and methods process patient data, particularly data from point of care diagnostic tests or assays, including immunoassays, electrocardiograms, X-rays and other such tests, and provide an indication of a medical condition or risk or absence thereof. The systems include an instrument for reading or evaluating the test data and software for converting the data into diagnostic or risk assessment information.
Owner:CYTYC CORP
Internet security dynamics assessment system, program product, and related methods
ActiveUS8069471B2Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Owner:LOCKHEED MARTIN CORP
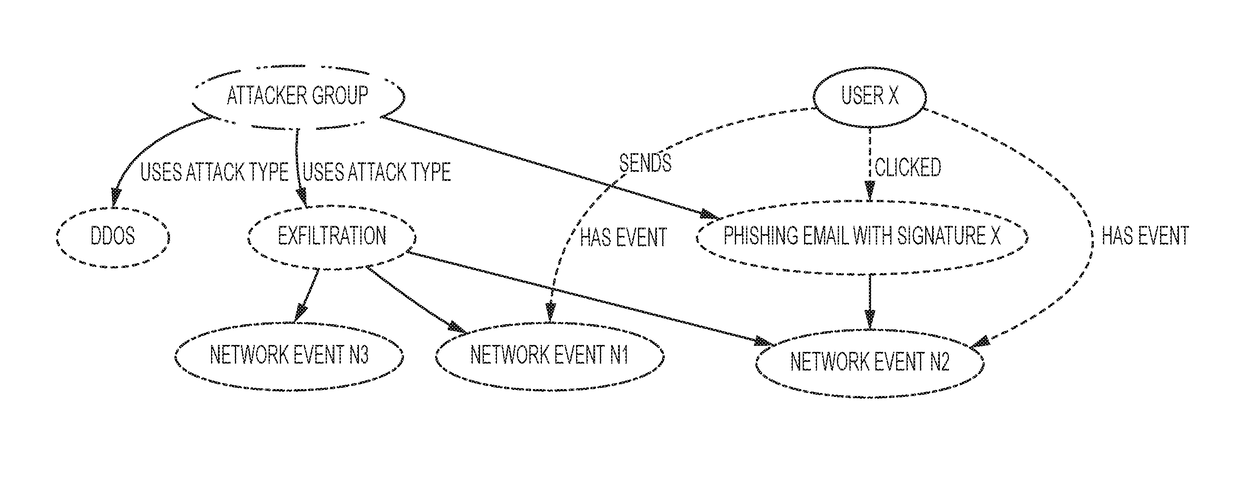
System and methods for automated detection, reasoning and recommendations for resilient cyber systems
ActiveUS20180103052A1Improve applicabilityLarge capacityDigital data information retrievalComputer security arrangementsElastic networkKnowledge extraction
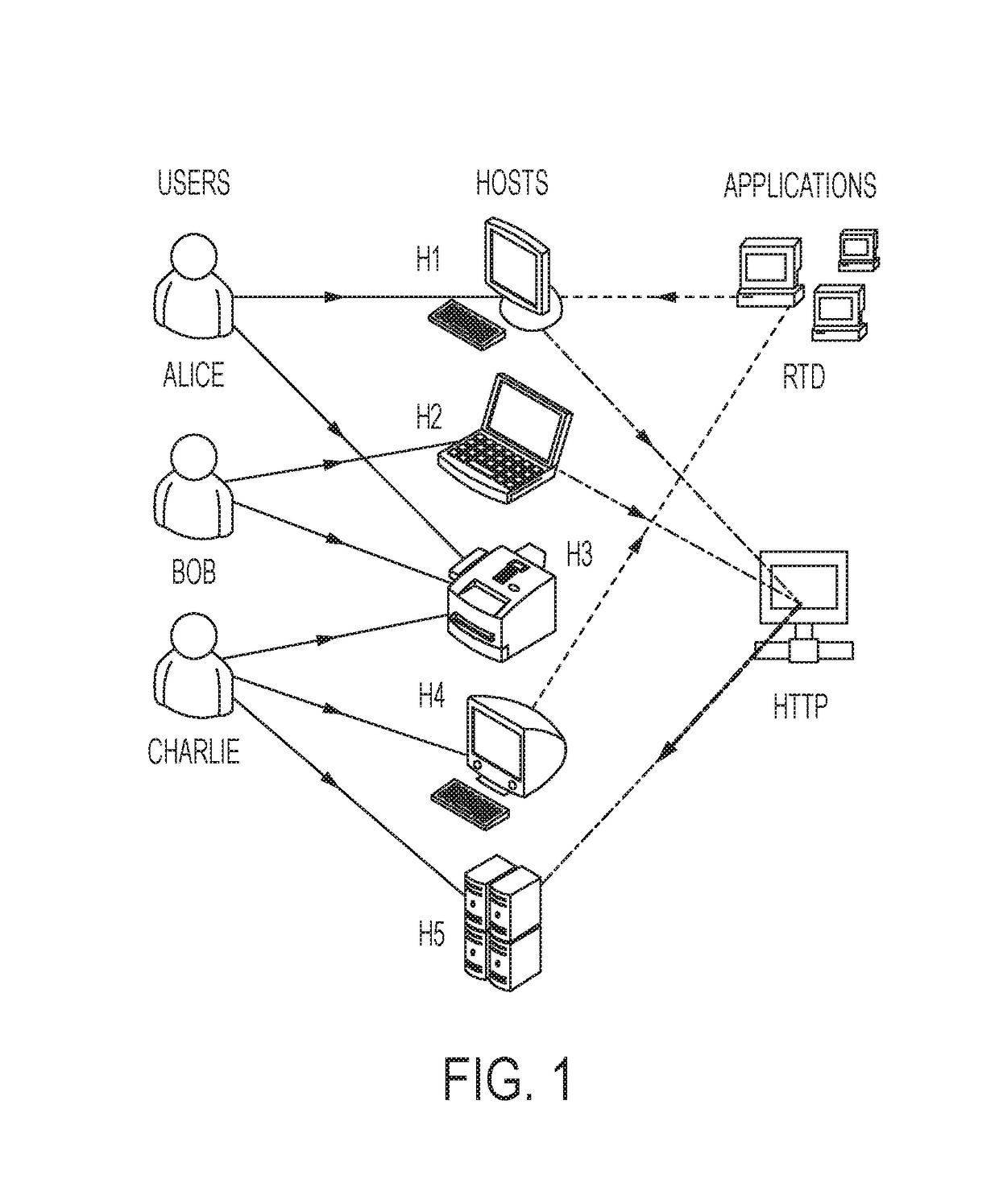
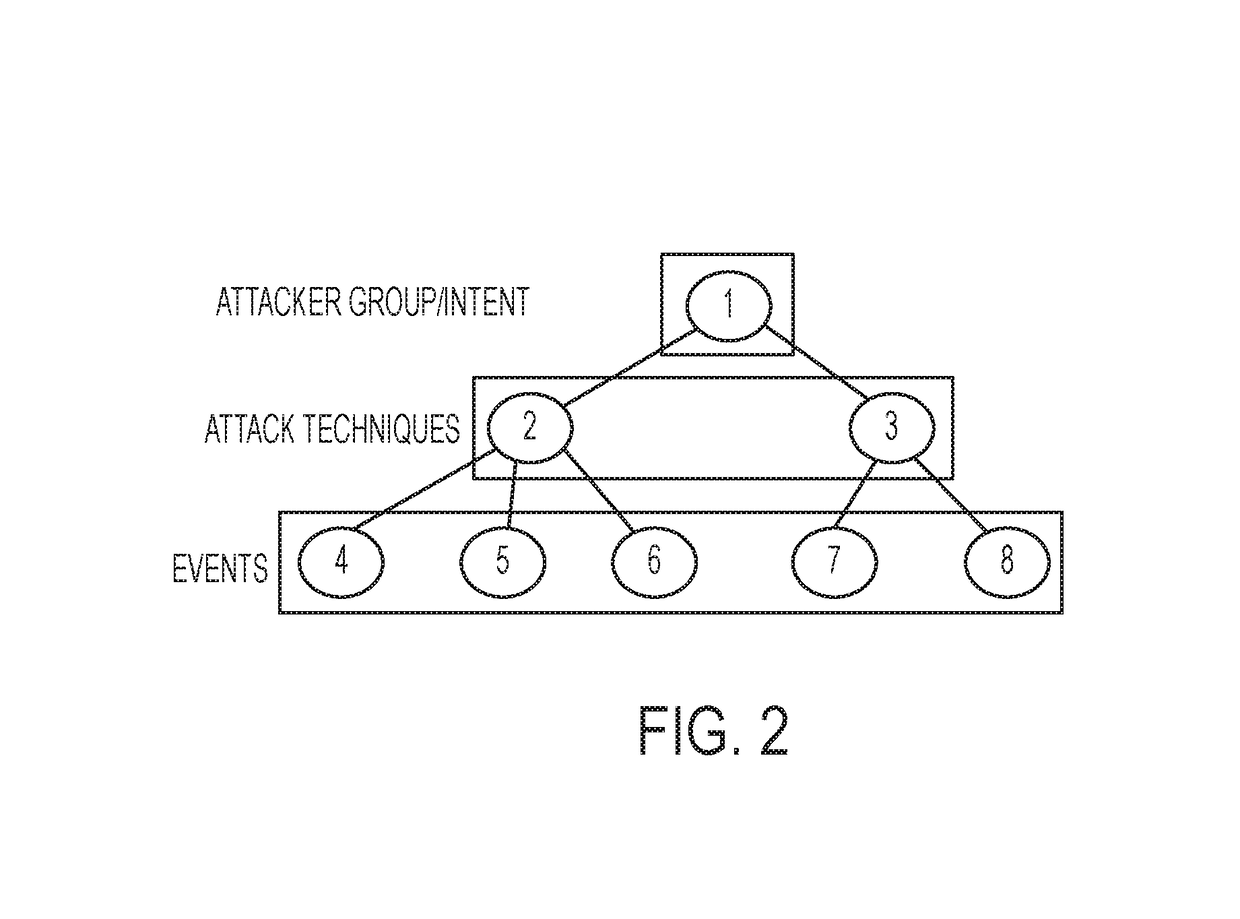
A method for securing an IT (information technology) system using a set of methods for knowledge extraction, event detection, risk estimation and explanation for ranking cyber-alerts which includes a method to explain the relationship (or an attack pathway) from an entity (user or host) and an event context to another entity (a high-value resource) and an event context (attack or service failure).
Owner:BATTELLE MEMORIAL INST
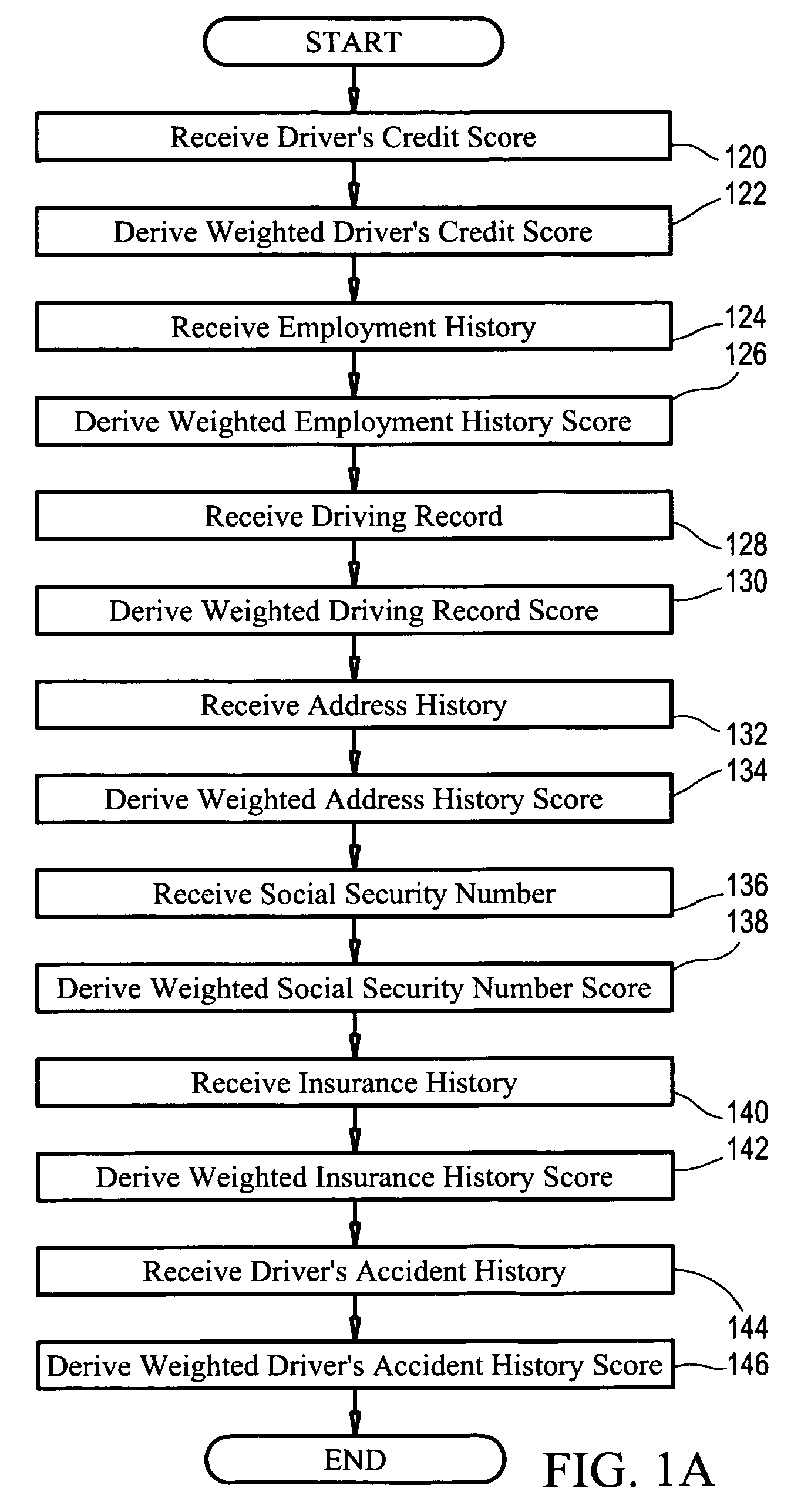
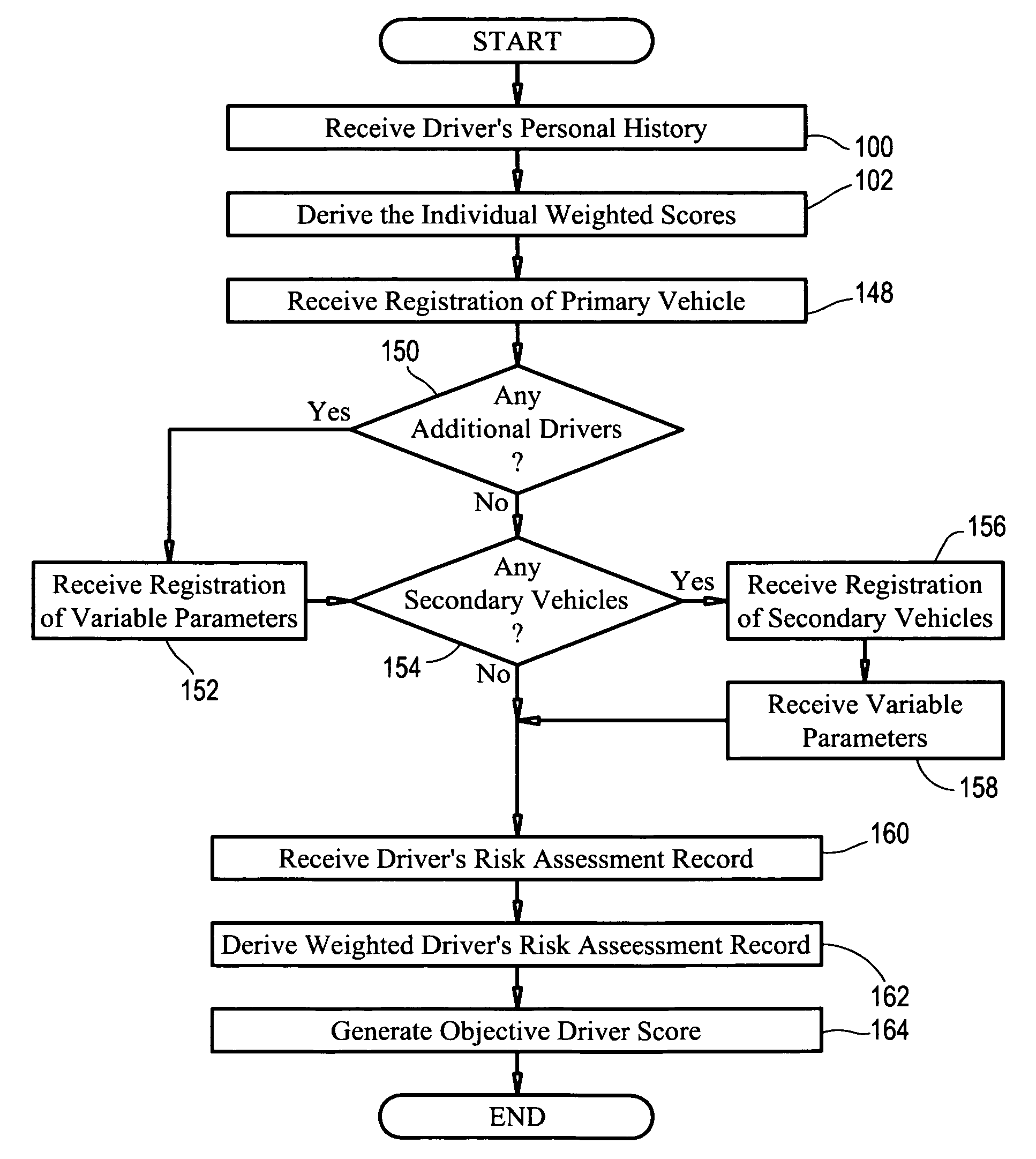
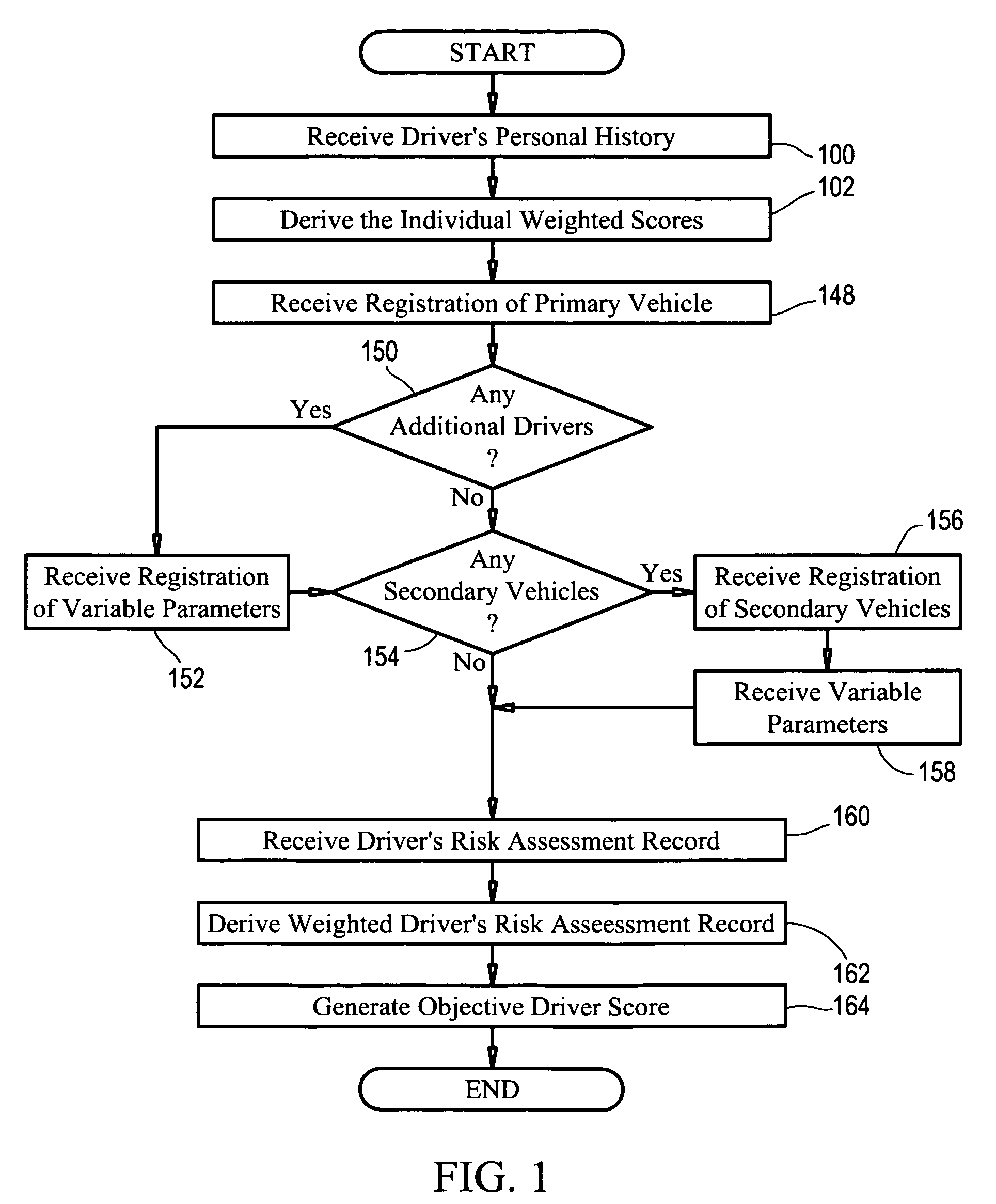
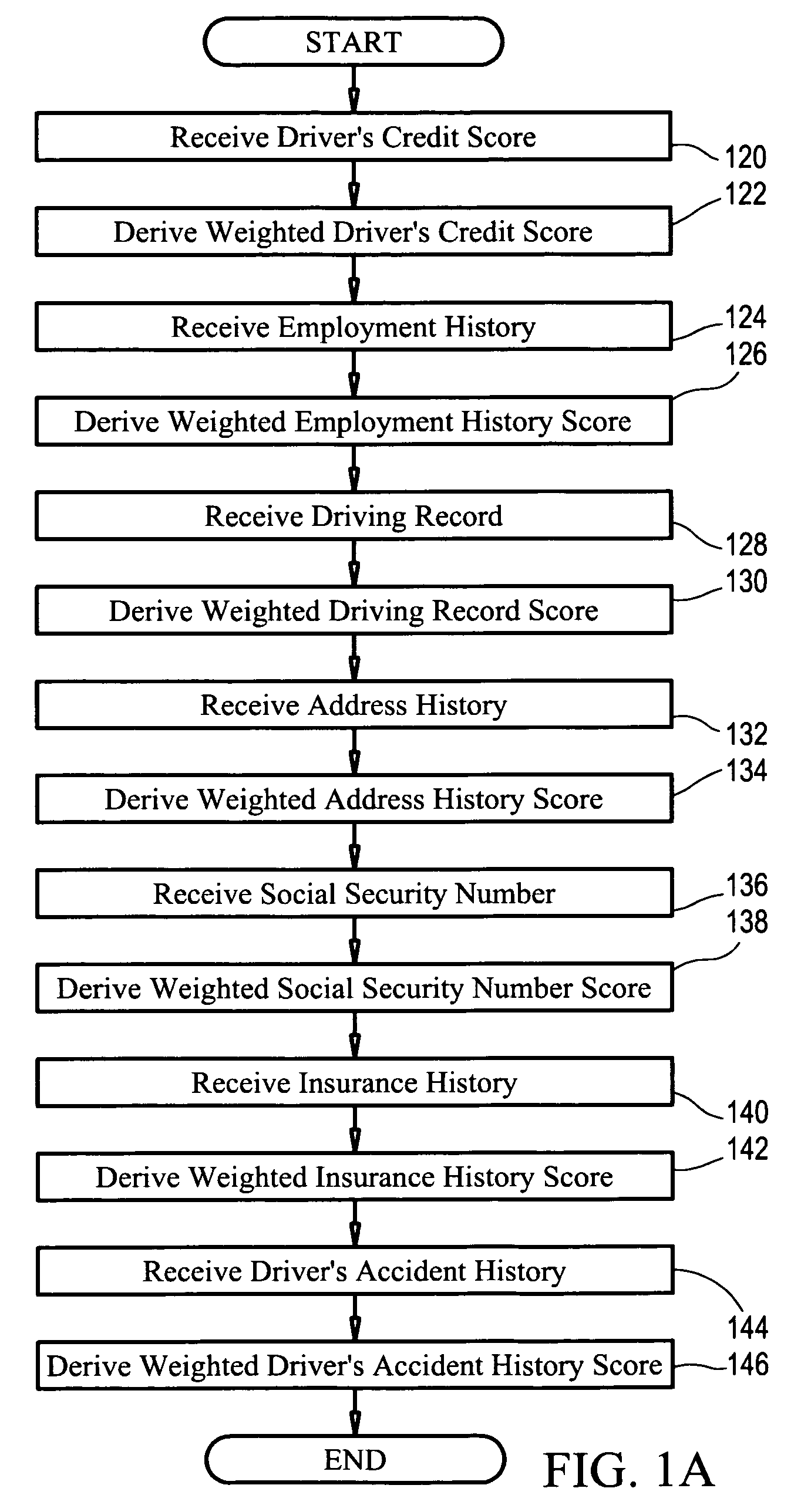
System and method for determining an objective driver score
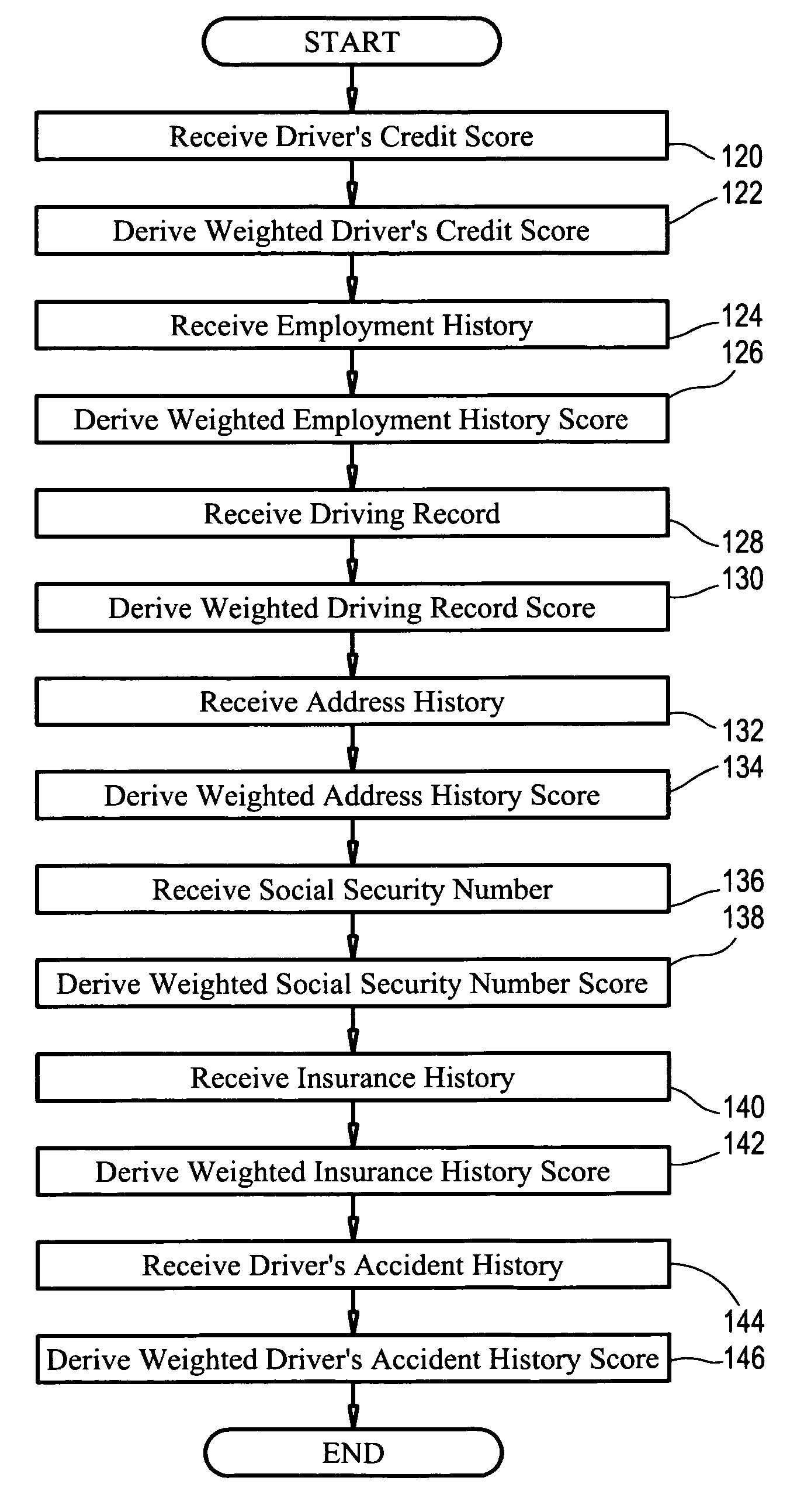
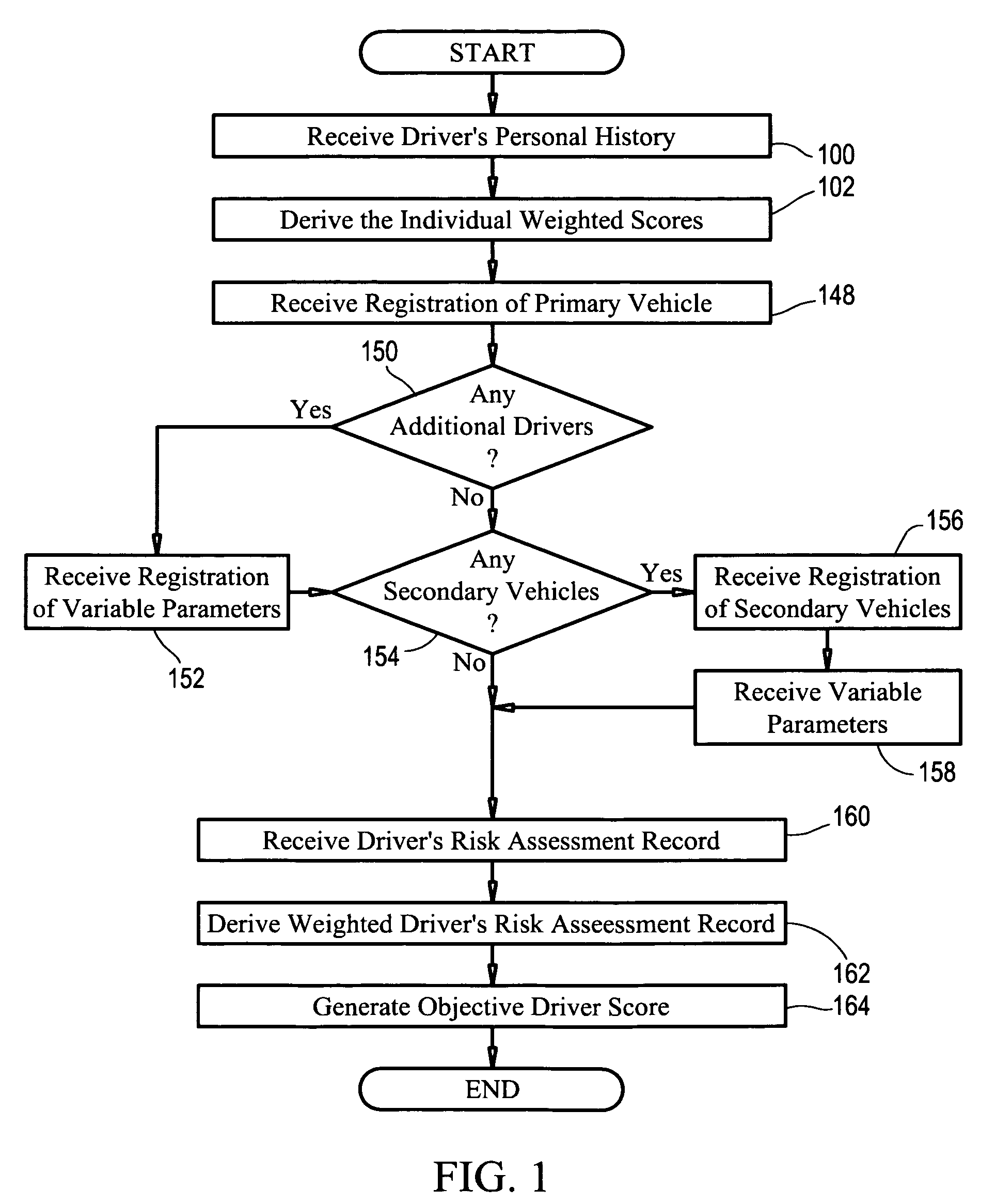
The present invention is directed to a business method in the field of automobile insurance, more specifically, a system and method of determining an objective driver score that may be used universally by independent insurers to evaluate the risk of insuring a driver by employing certain risk assessment factors concerning the driver's personal history which are each analyzed to derive weighted scores. Each driver is provided with a portable pin with an electronic key unique to the driver that is encoded for selective activation of a monitoring unit in a vehicle such that solely the activities of the driver being assessed is recorded and communicated to an evaluation center. Once activated, the monitoring unit records and generates the driver's risk assessment record based on the driver's operation of a vehicle equipped with the monitoring unit, as well as other variable parameters concerning operation of the vehicle. Said driver's risk assessment record is analyzed to derive a weighted driver risk assessment score that is aggregated with the individual weighted scores derived from the risk assessment factors to generate an objective driver score.
Owner:F3M3
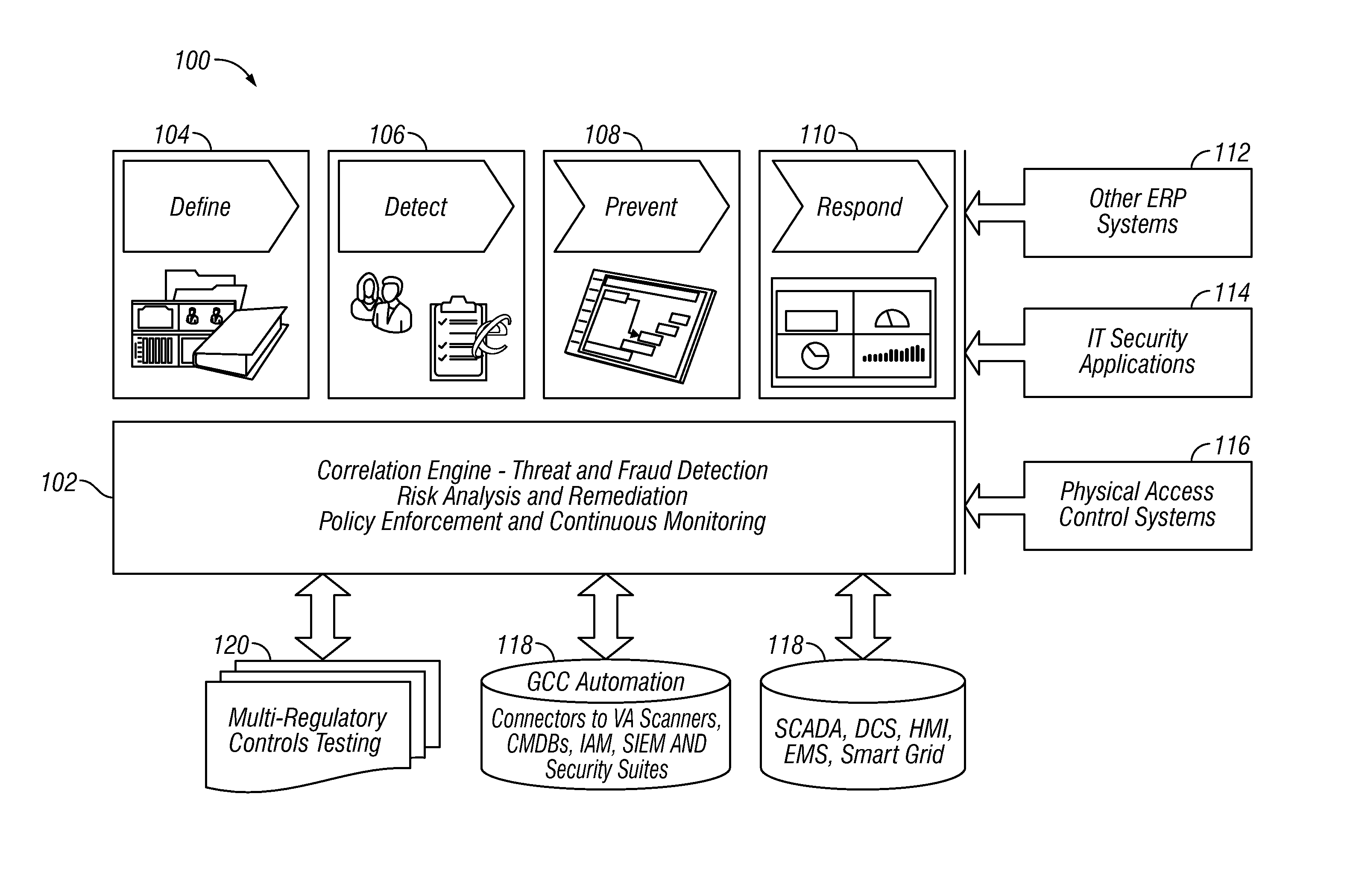
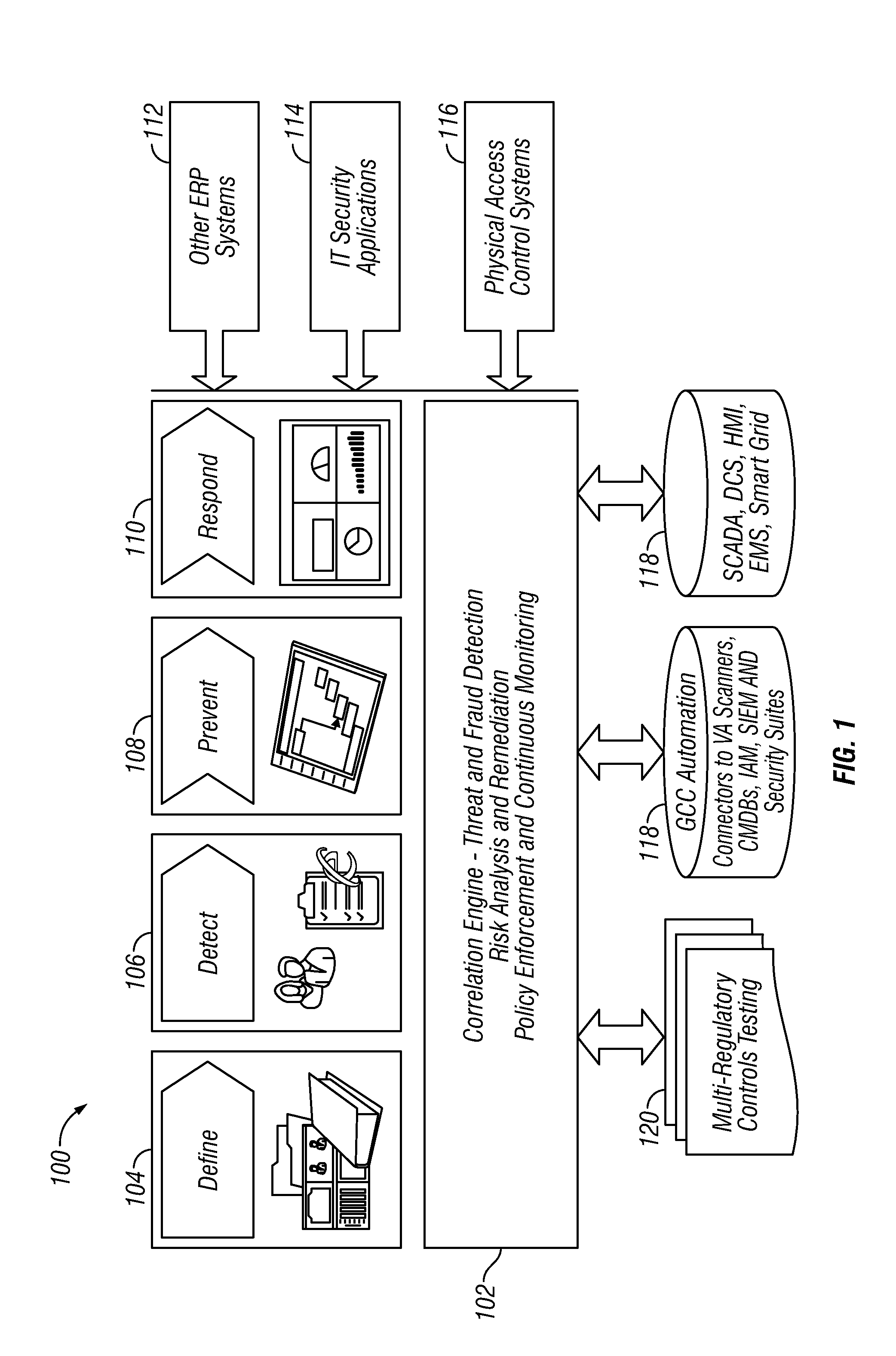
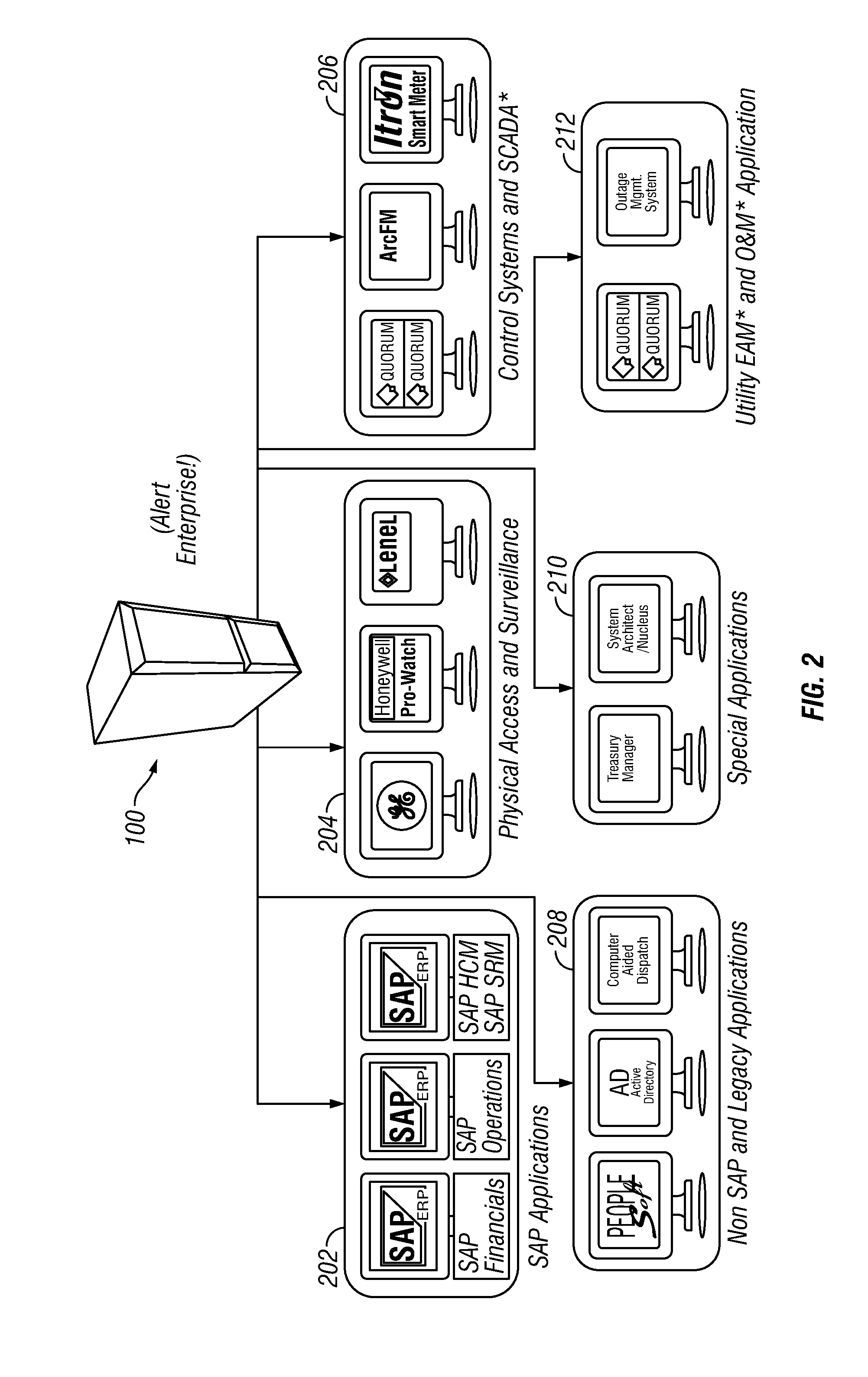
Situational intelligence
ActiveUS20120224057A1Color television detailsClosed circuit television systemsDashboardRemedial action
A method and apparatus is provided that includes techniques for providing complete solutions for role-based, rules-driven access enforcement, the techniques including situational awareness and video surveillance. An embodiment addresses blended risk assessment and security across logical systems, IT applications, databases, and physical systems from a single analytic dashboard, with auto-remediation capabilities. Further, an embodiment provides capability and functionality for co-relating seemingly innocent events and activities to detect real threats and risks, while providing powerful alerting and automated remedial action strategies for decisive action.
Owner:ALERT ENTERPRISE
Systems, Program Product and Methods For Performing a Risk Assessment Workflow Process For Plant Networks and Systems
ActiveUS20120180133A1Easy to editEasy to customizeProgramme controlMemory loss protectionProcess control networkRisk level
Systems, methods, and program product to perform a cyber security risk assessment on a plurality of process control networks and systems comprising a plurality of primary network assets at an industrial process facility, are provided. An example of a system and program product can include an industrial and process control systems scanning module configured to identify networks and systems topology and to execute system and network security, vulnerability, virus, link congestion, node congestion analysis to thereby detect susceptibility to know threats to define potential vulnerabilities; a threats to vulnerabilities likelihood and consequences data repository module configured to determine a likelihood of each of a plurality of known threats exploiting identified vulnerabilities and to identify consequences of the exploitation to individual impacted systems and to overall plant operation; and a risk level evaluator module configured to determine a risk level rating for any identified vulnerabilities and provide recommended corrective actions.
Owner:SAUDI ARABIAN OIL CO
Method and system for evaluating network safety situation
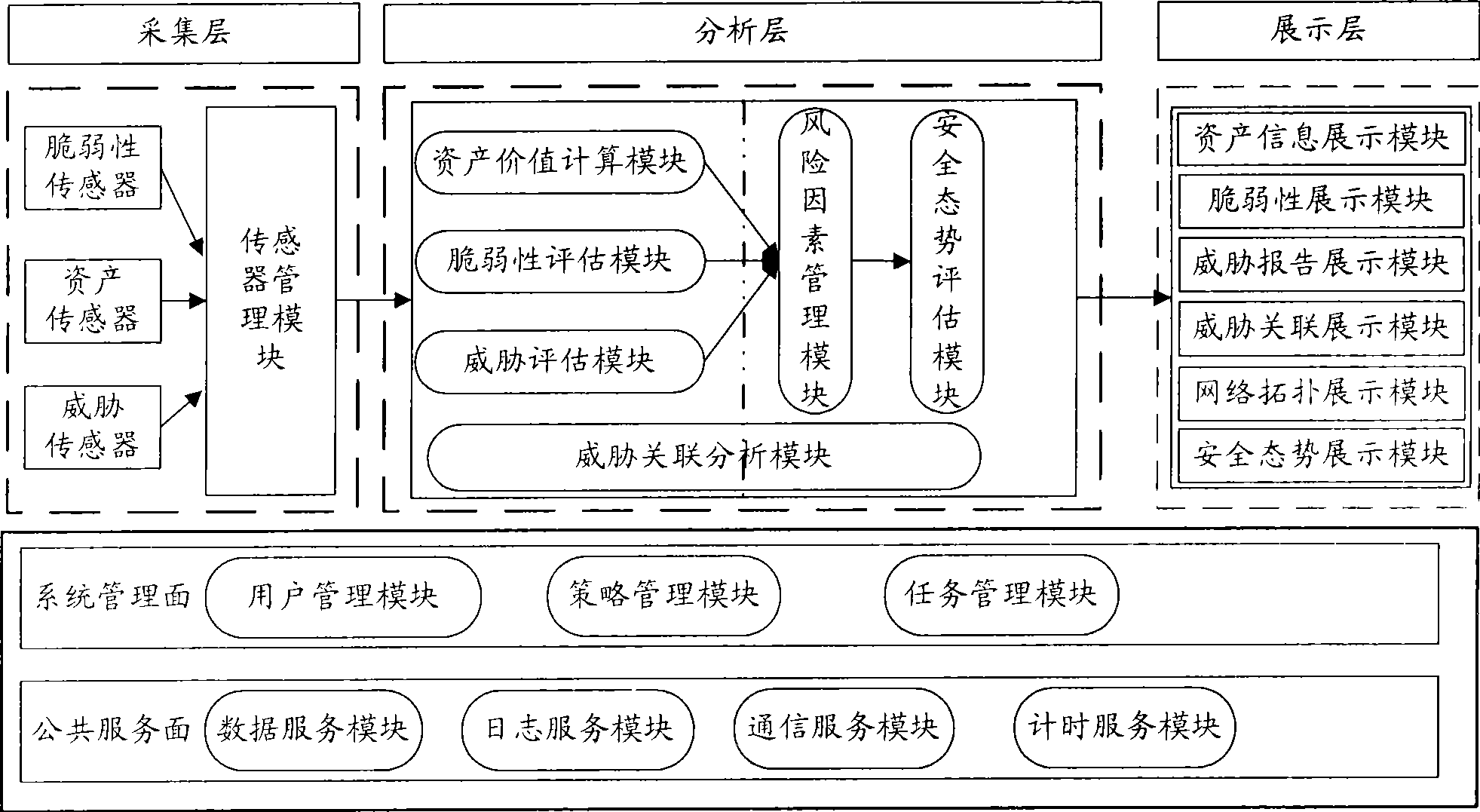
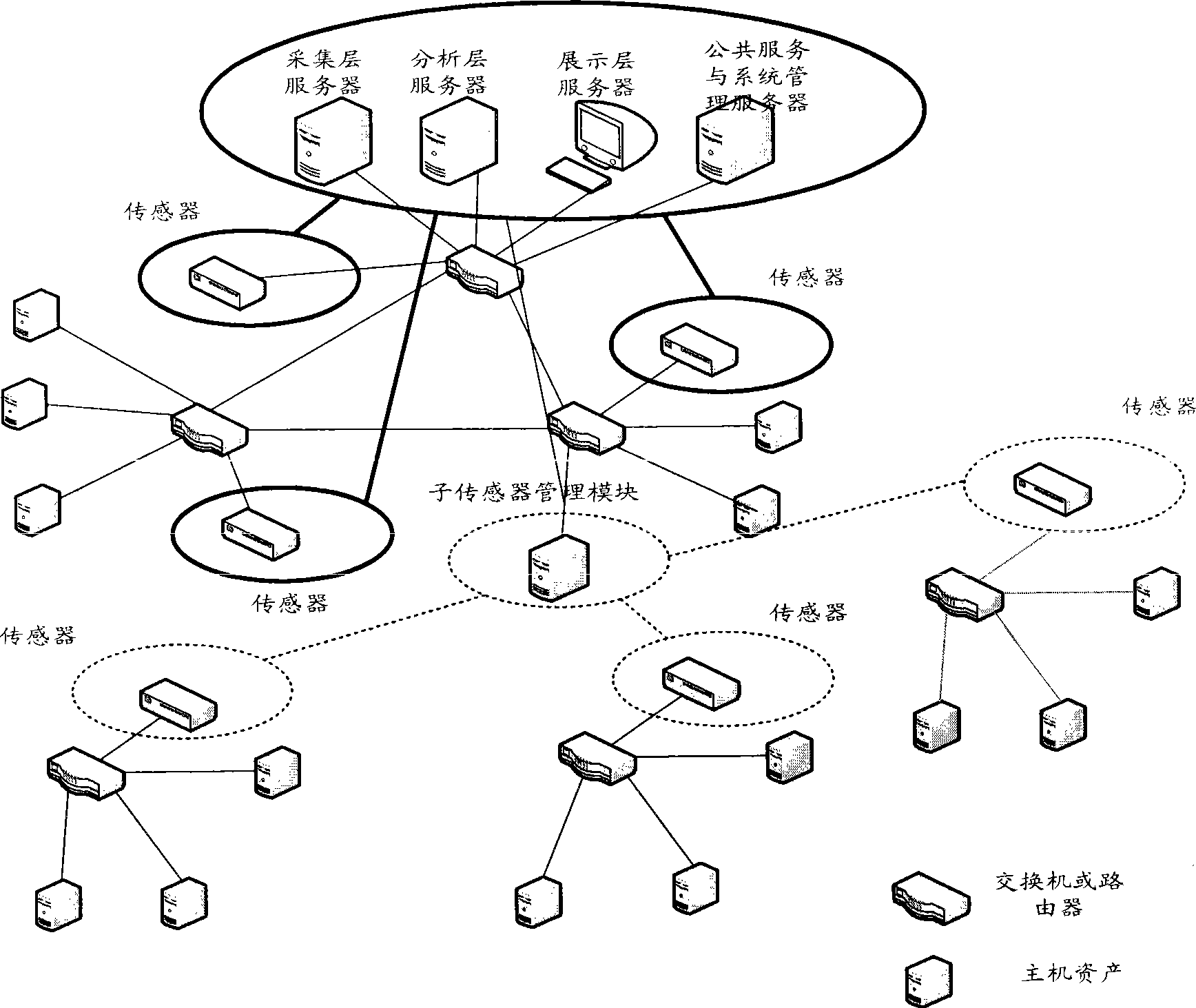
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
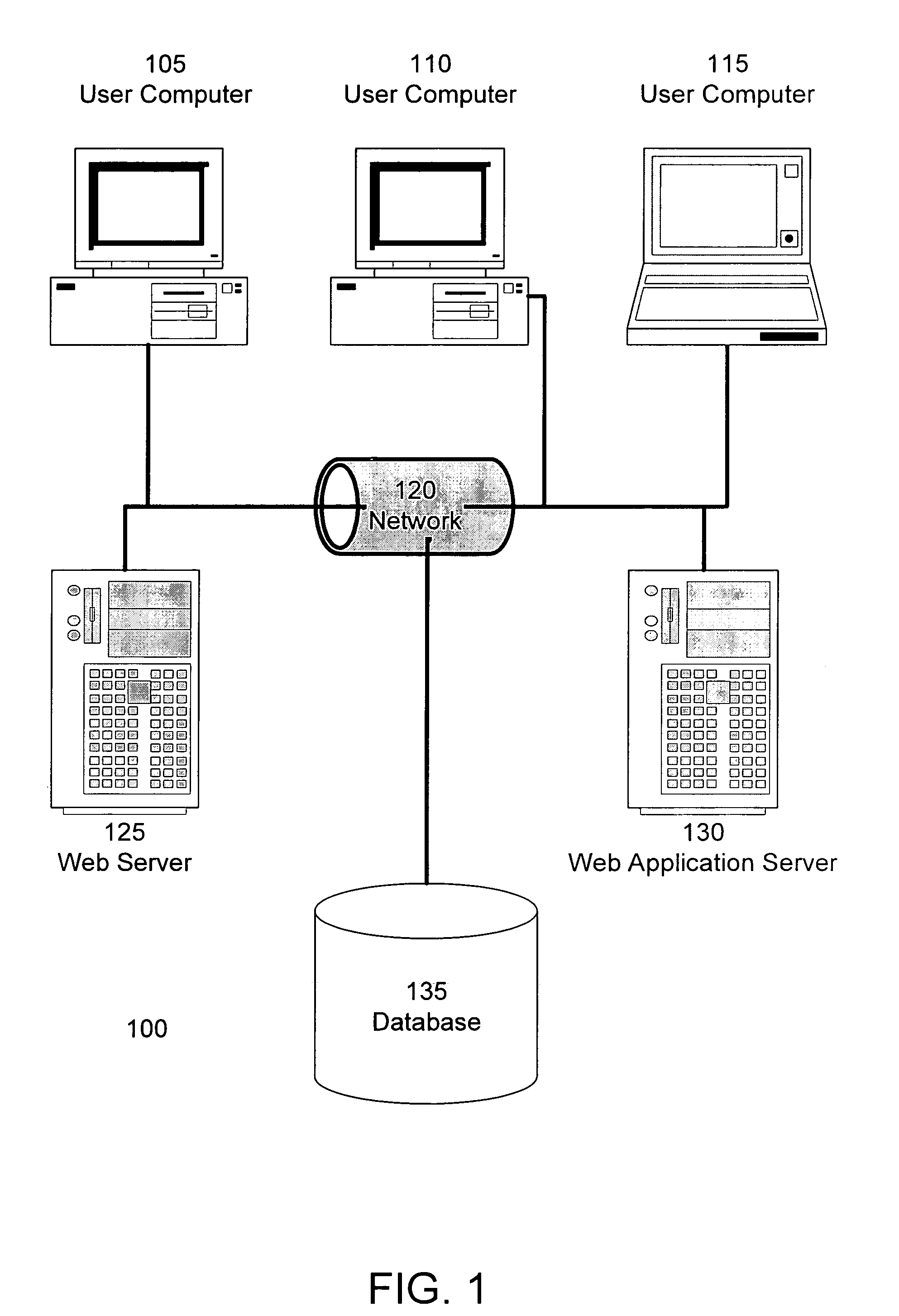
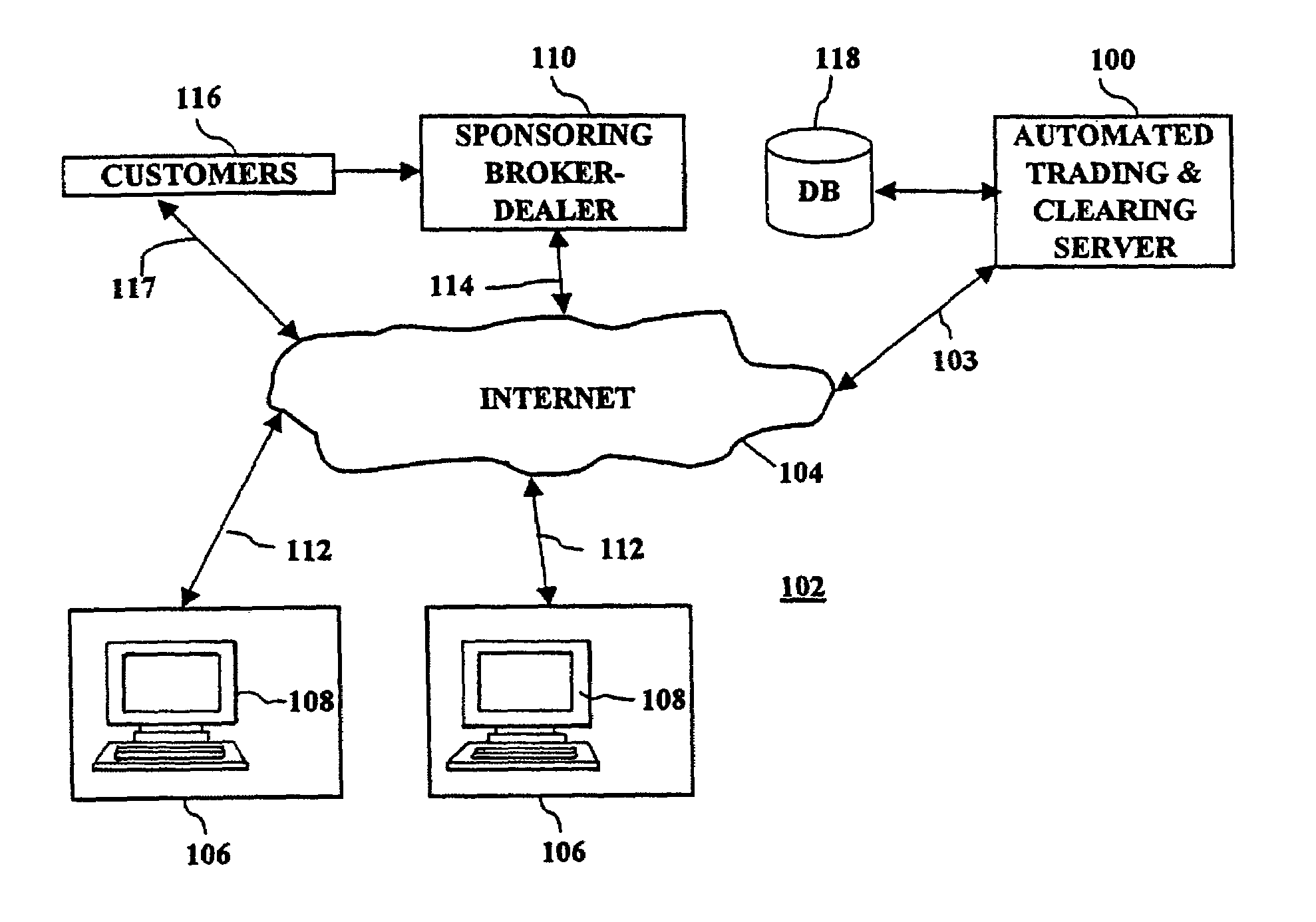
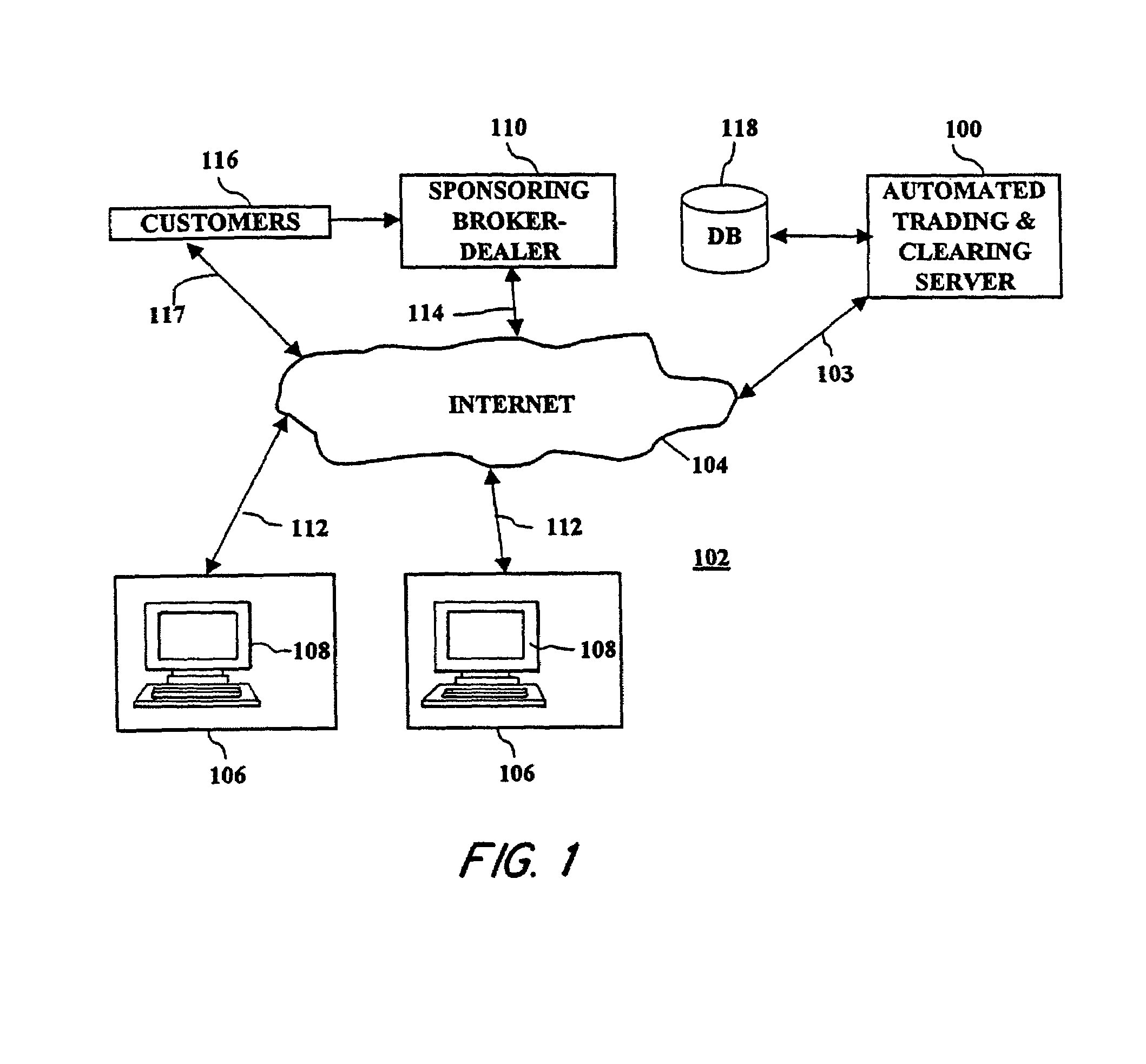
Network-based trading system and method
InactiveUS7165045B1Easy to implementLow costFinanceSpecial data processing applicationsCost effectivenessElectronic form
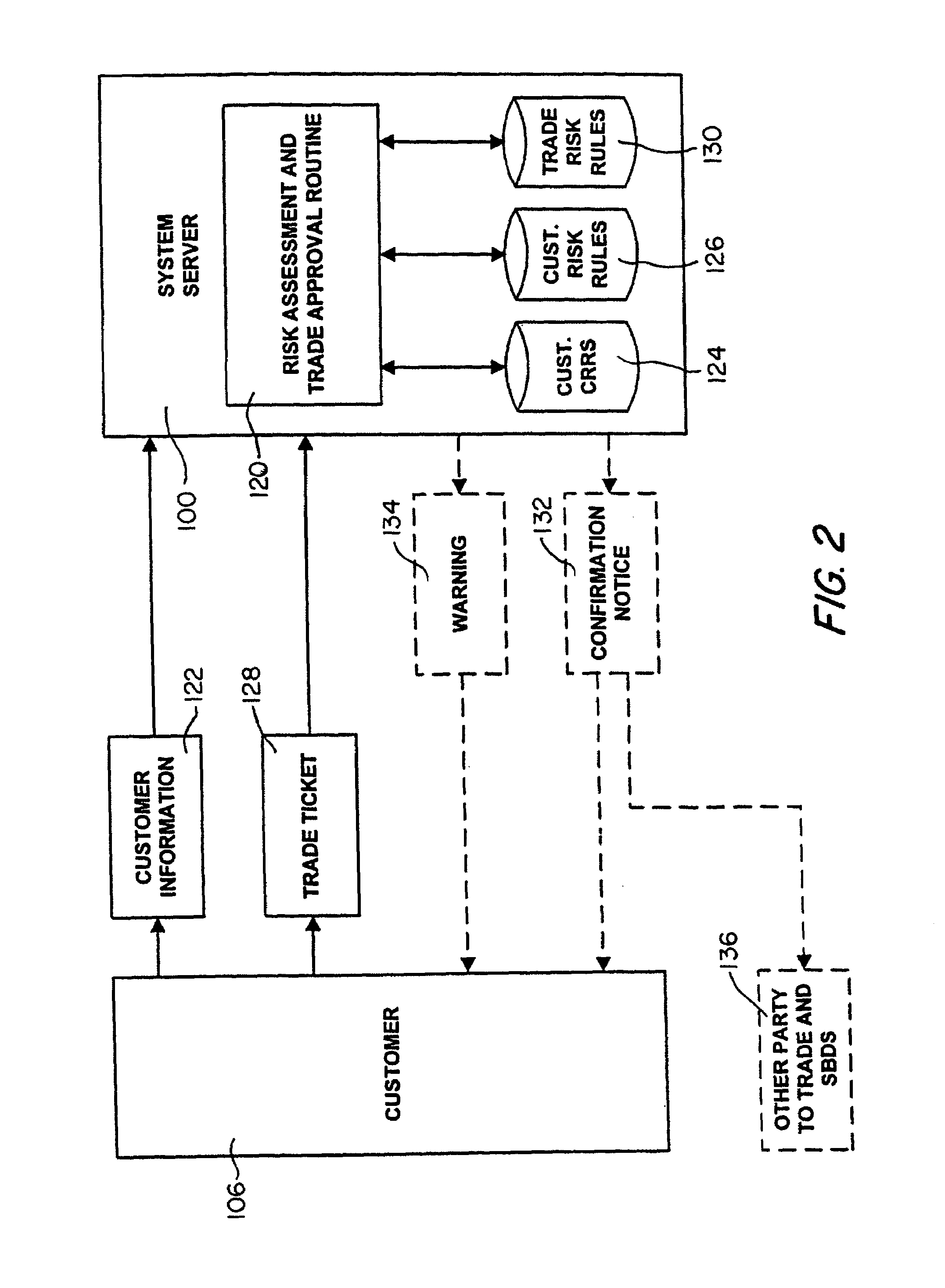
A network based trading system and method are provided which combine economies-of-scale enjoyed by institutional investors and mutual funds with direct ownership of securities to permit individual investors to participate in the bond market in a cost effective manner. Through team investing, institutional economies-of-scale are created for individuals by allowing groupings of individuals to buy and sell bonds as a “team,” thereby executing one cost-efficient trade in the institutional market rather than many smaller trades in the inefficient retail market. Also, through customer-to-customer (C2C) trading, customers are allowed to negotiate a trade directly with one another as an alternative to selling in the inter-dealer market. The system and method also incorporate an automatic risk assessment and trade approval routine for evaluating a proposed trade of a financial instrument which was received from a customer in an electronic form.
Owner:KIOBA PROCESSING LLC
Systems and methods for managing multi-region data incidents
ActiveUS10445508B2Digital data protectionPlatform integrity maintainanceInternet privacyPrivacy rule
Systems and methods for managing a multi-region data incident are provided herein. Example methods include receiving, via a risk assessment server, in response to an occurrence of the data incident, data incident data that including information corresponding to the data incident, wherein the data incident has a plurality of facets with each facet having any of unique and overlapping set of privacy data and media type and associated risk factors requiring facet specific incident risk assessment, automatically generating, via the risk assessment server, a risk assessment and decision-support guidance whether the facet is reportable, from a comparison of the facet to privacy rules, the privacy rules define requirements associated with data incident notification obligations, and providing, via the risk assessment server, the risk assessment to a display device that selectively couples with the risk assessment server.
Owner:RADAR LLC
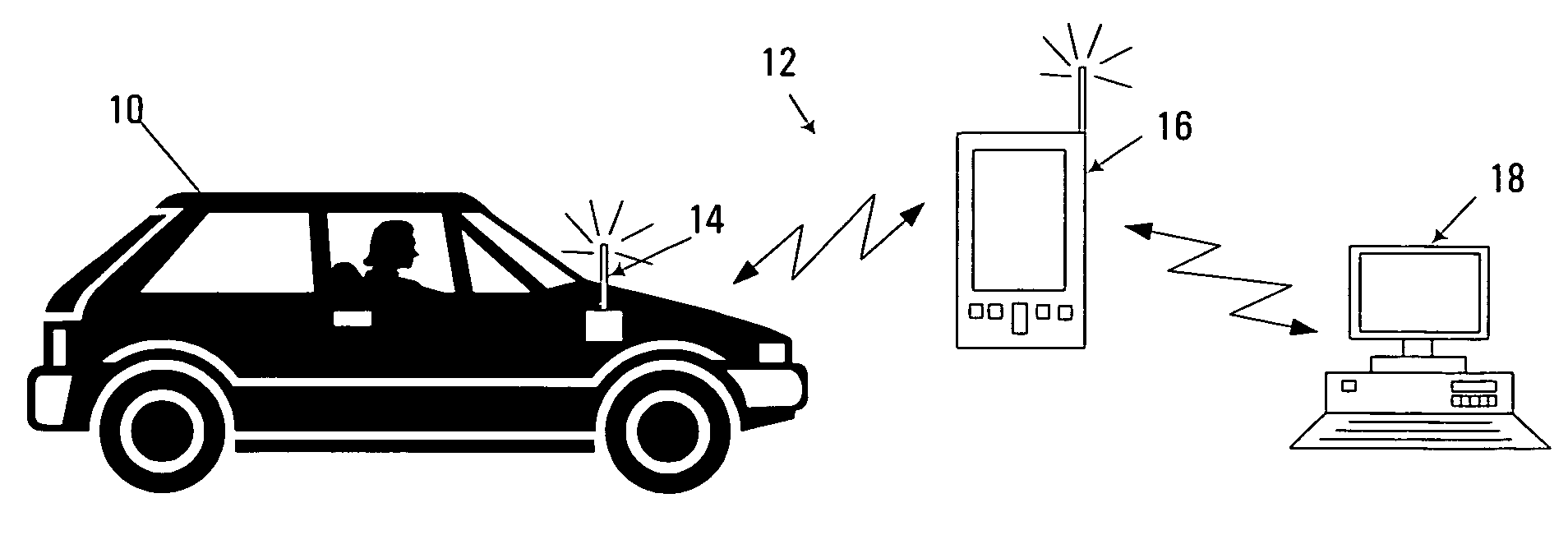
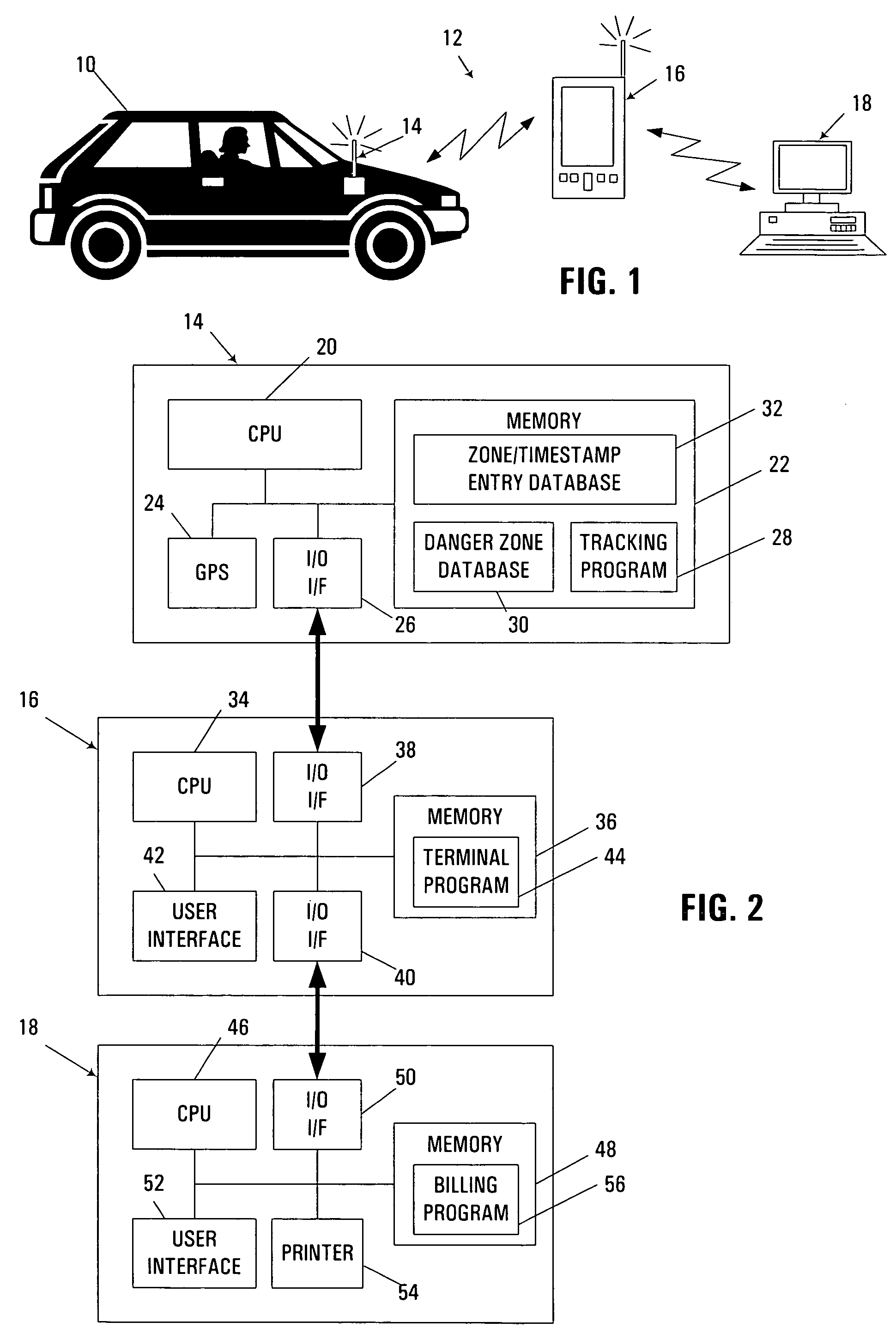
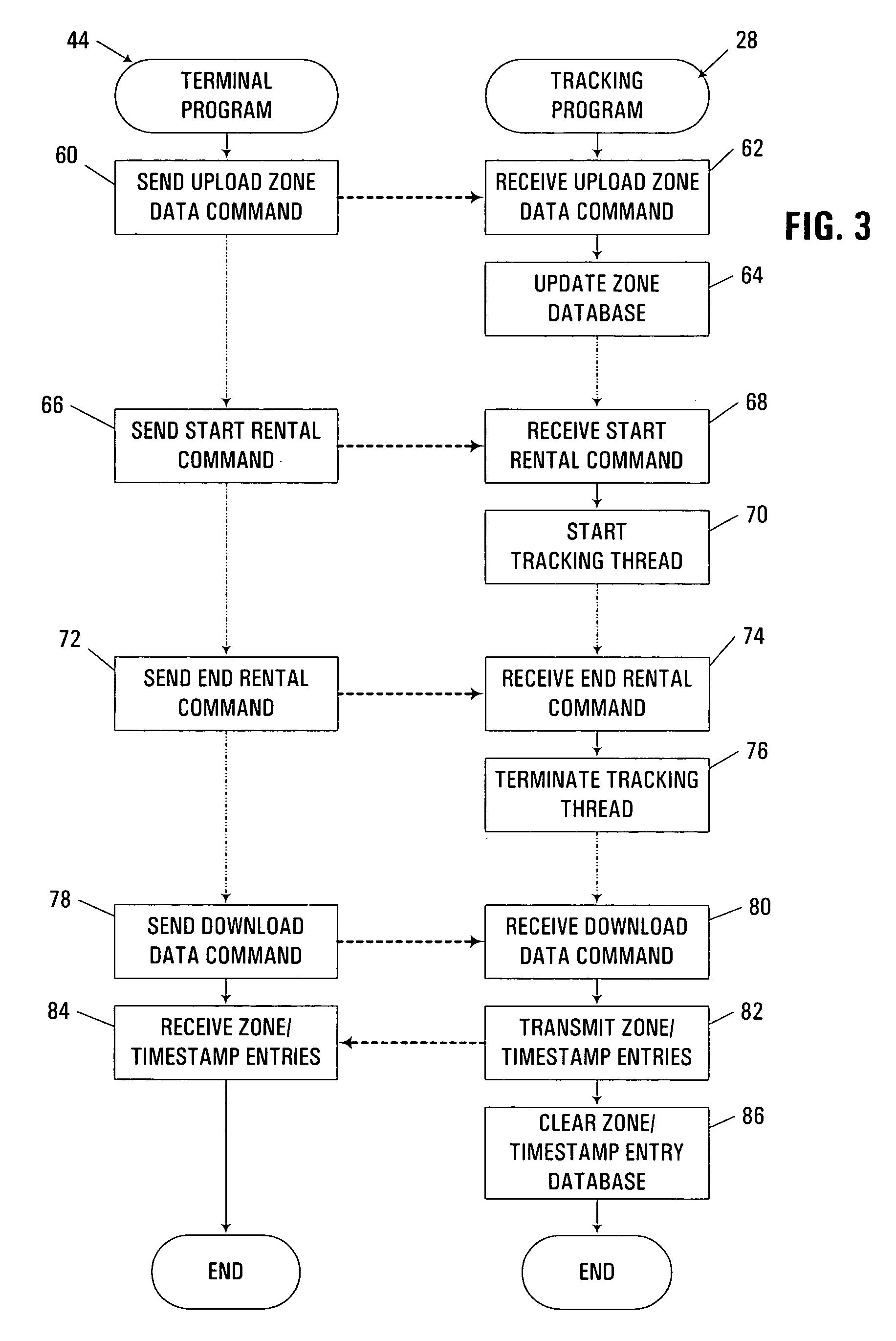
Location-based vehicle risk assessment system
Owner:GOOGLE LLC
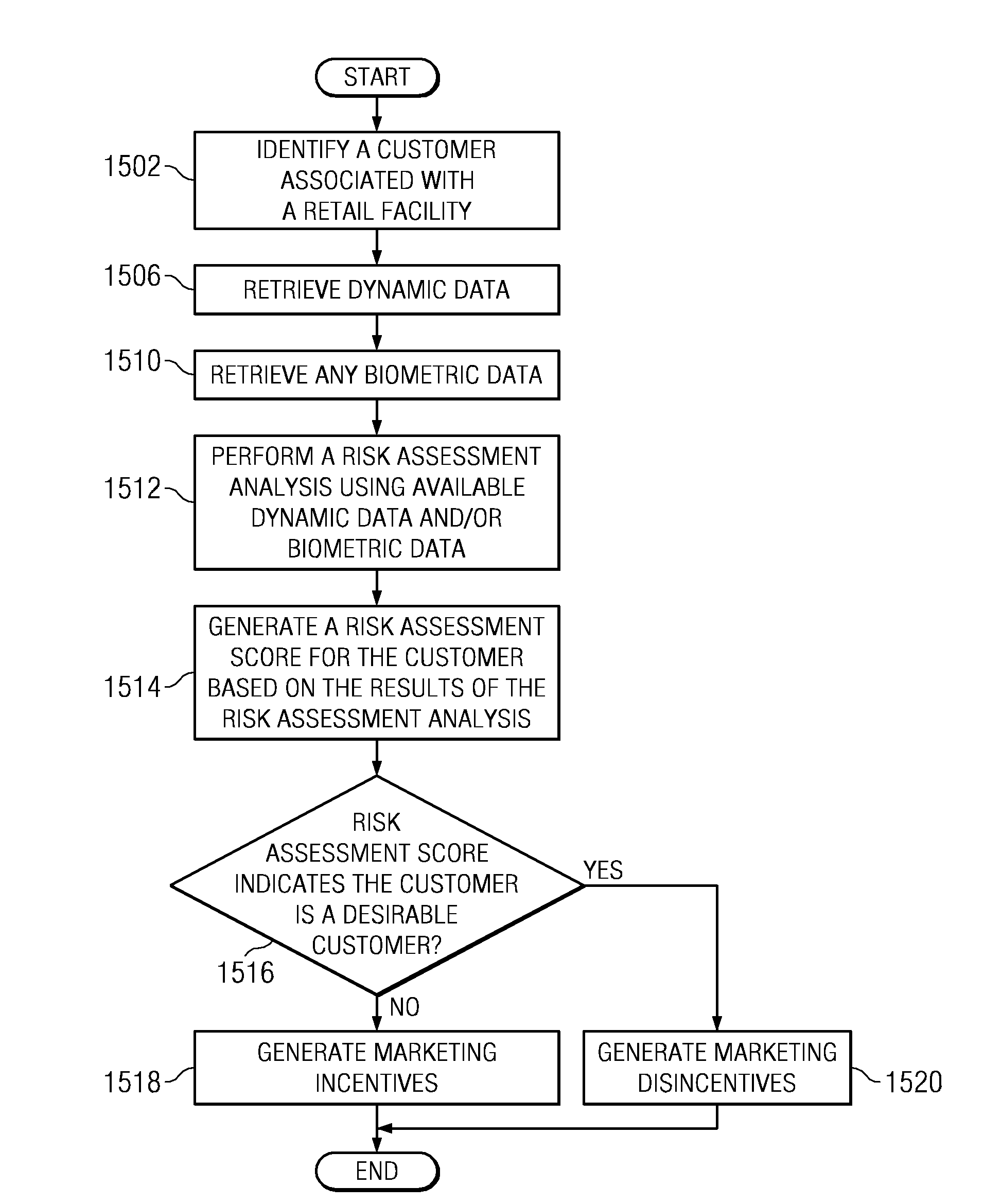
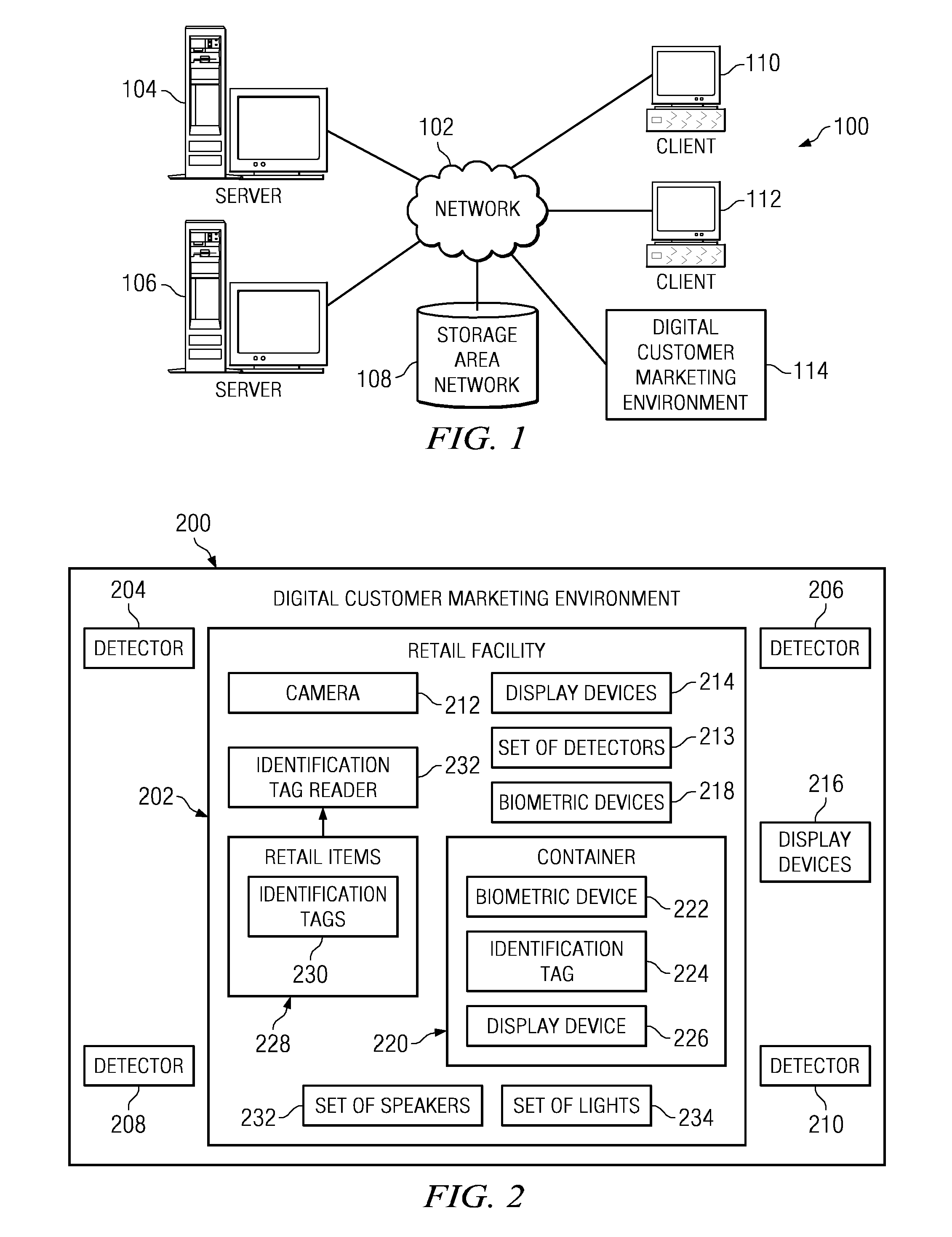
Method and apparatus for presenting disincentive marketing content to a customer based on a customer risk assessment
InactiveUS20080249869A1Discounts/incentivesSpecial data processing applicationsLibrary scienceRisk assessment
A computer implemented method, apparatus, and computer usable program product for managing a level of marketing disincentives directed towards a customer using a risk assessment score. In one embodiment, a risk assessment score for a customer associated with a retail facility is retrieved. The risk assessment score is analyzed to determine whether the customer is a desirable customer or an undesirable customer. In response to the risk assessment score indicating that the customer is an undesirable customer, aggressive marketing disincentives targeted to the undesirable customer are generated. If the risk assessment score indicates the customer is a desirable customer, marketing incentives targeted to the desirable customer are generated.
Owner:TERRACE LICENSING LLC
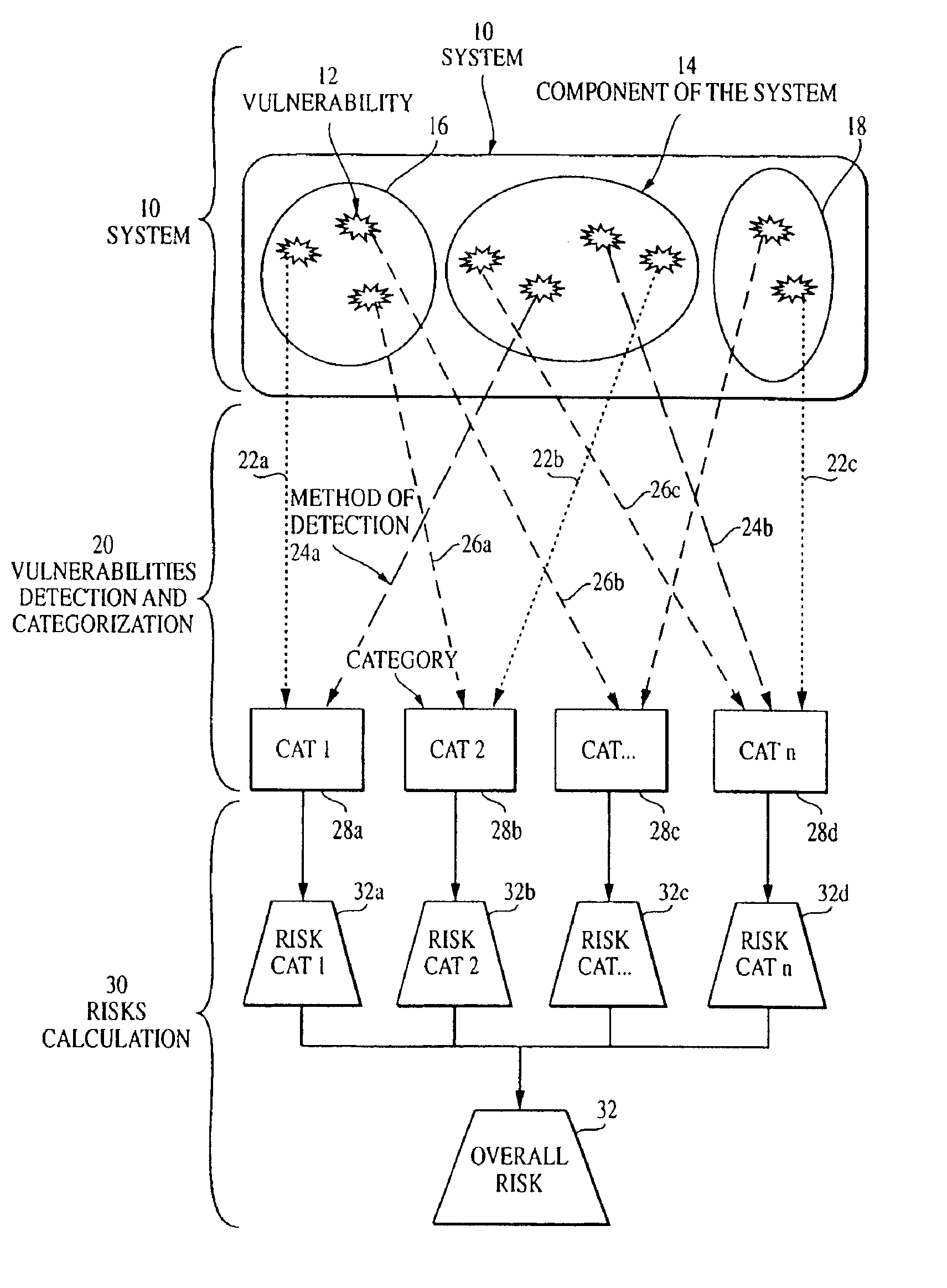
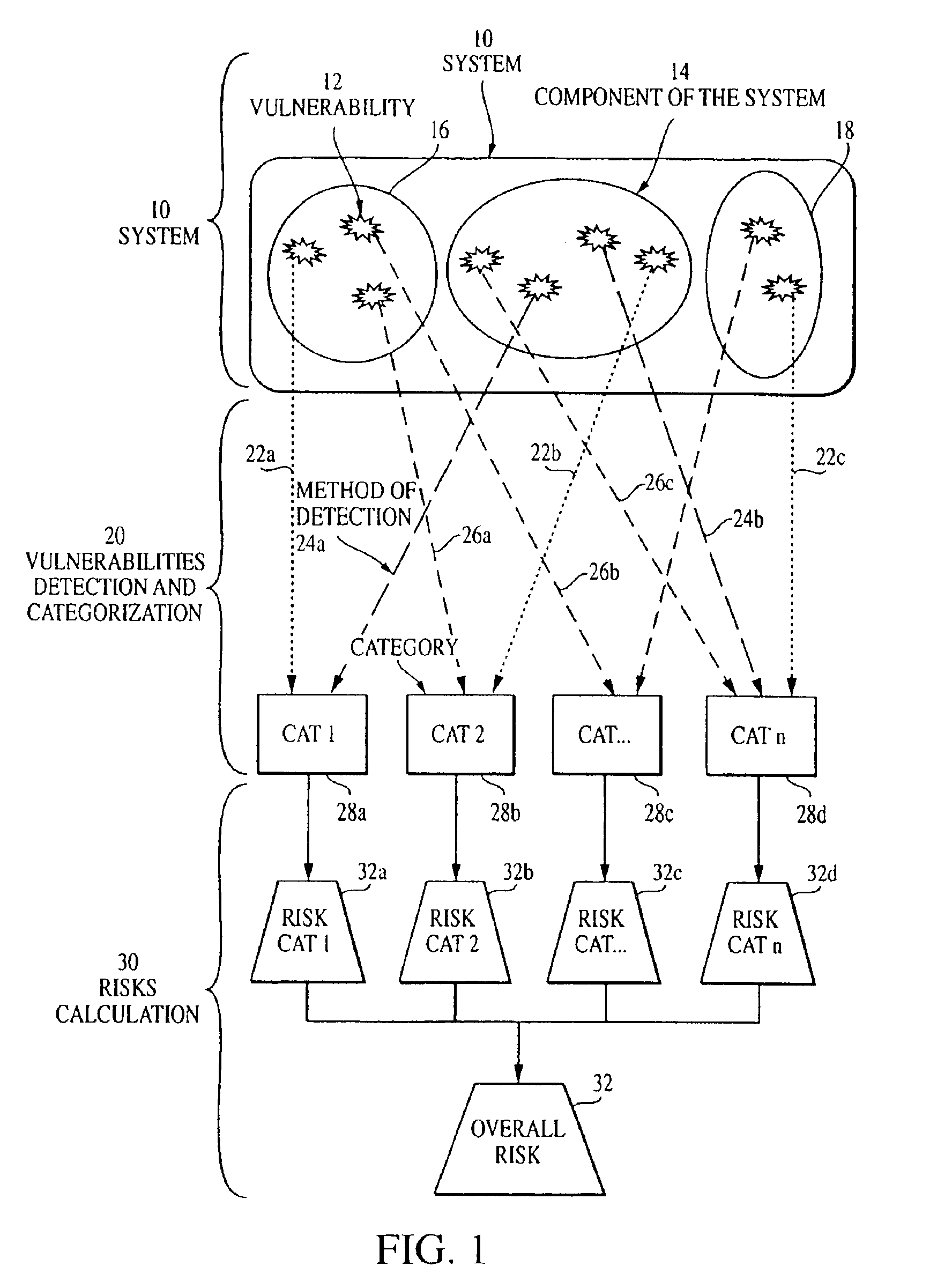
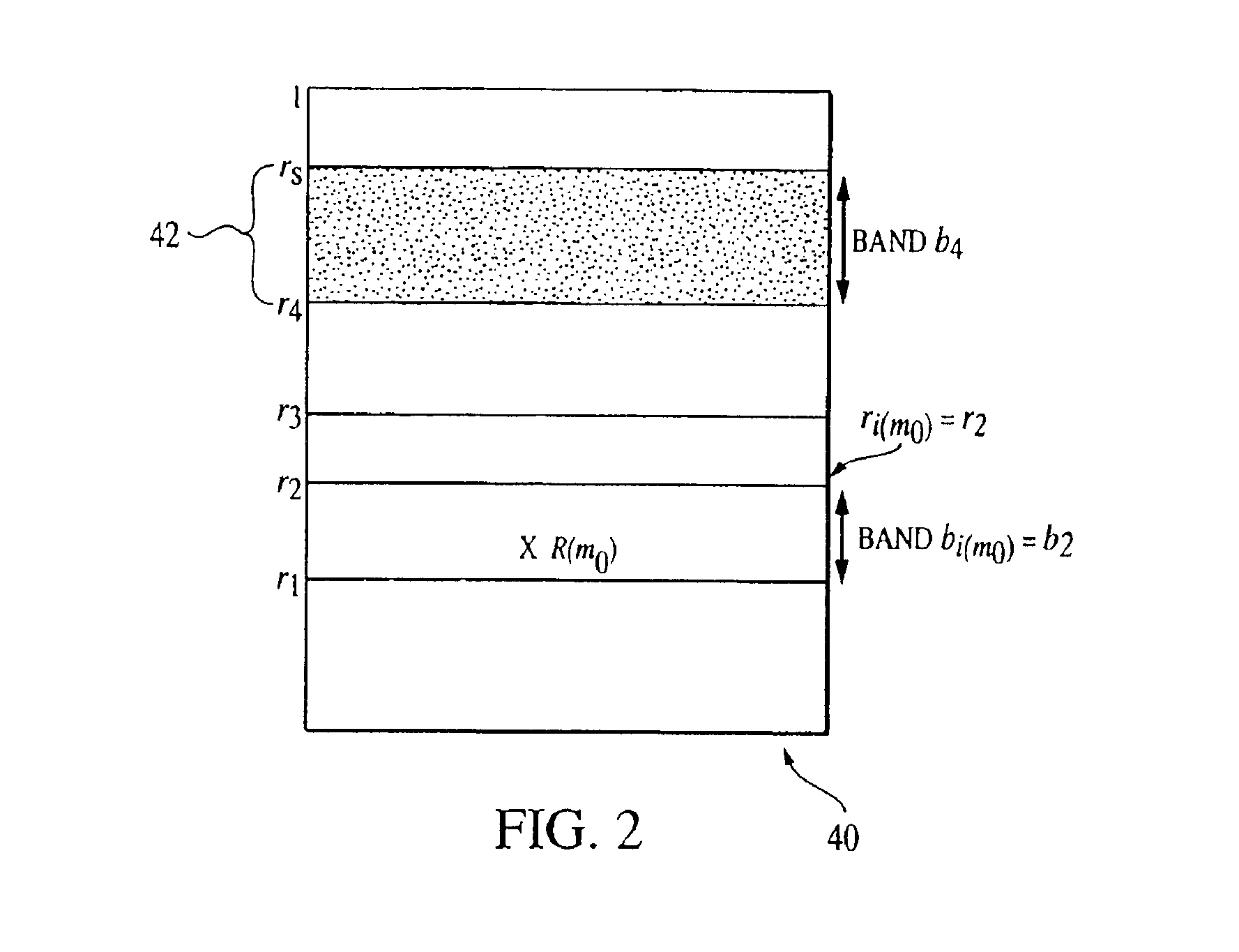
Overall risk in a system
A computer-implemented method and system for assessing the overall risk in at least part of an information technology system includes inputting into a risk assessment database a plurality of identified risks in a system; associating the risks to at least one severity band in a risk echelon; assigning a value to each risk; multiplying each risk value by a coefficient factor; and summing the factored risk values to determine the overall risk. The method preferably includes modifying the security implementation of the information technology system and determining the modified overall risk. The system preferably includes an automated vulnerability detection scanner to gather risk information, which is stored on a database and used in calculating the overall risk.
Owner:ACCENTURE GLOBAL SERVICES LTD
Driver risk assessment system and method having calibrating automatic event scoring
ActiveUS8508353B2Stable and reliableOptimizing data transmission bandwidthFinanceRegistering/indicating working of vehiclesEngineeringDependability
A Driver Risk Assessment System and Method Having Calibrating Automatic Event Scoring is disclosed. The system and method provide robust and reliable event scoring and reporting, while also optimizing data transmission bandwidth. The system includes onboard vehicular driving event detectors that record data related to detected driving events and selectively store or transfer data related to said detected driving events. If elected, the onboard vehicular system will score a detected driving event, compare the local score to historical values previously stored within the onboard system, and upload selective data or data types to a remote server or user if the system concludes that a serious driving event has occurred. Importantly, the onboard event scoring system, if enabled, will continuously evolve and improve in its reliability by being periodically re-calibrated with the ongoing reliability results of manual human review of automated predictive event reports. The system may further respond to independent user requests by transferring select data to said user at a variety of locations and formats.
Owner:DRIVECAM
System and method for determining an objective driver score
The present invention is directed to a business method in the field of automobile insurance, more specifically, a system and method of determining an objective driver score that may be used universally by independent insurers to evaluate the risk of insuring a driver by employing certain risk assessment factors concerning the driver's personal history which are each analyzed to derive weighted scores. Each driver is provided with a portable pin with an electronic key unique to the driver that is encoded for selective activation of a monitoring unit in a vehicle such that solely the activities of the driver being assessed is recorded and communicated to an evaluation center. Once activated, the monitoring unit records and generates the driver's risk assessment record based on the driver's operation of a vehicle equipped with the monitoring unit, as well as other variable parameters concerning operation of the vehicle. Said driver's risk assessment record is analyzed to derive a weighted driver risk assessment score that is aggregated with the individual weighted scores derived from the risk assessment factors to generate an objective driver score.
Owner:F3M3
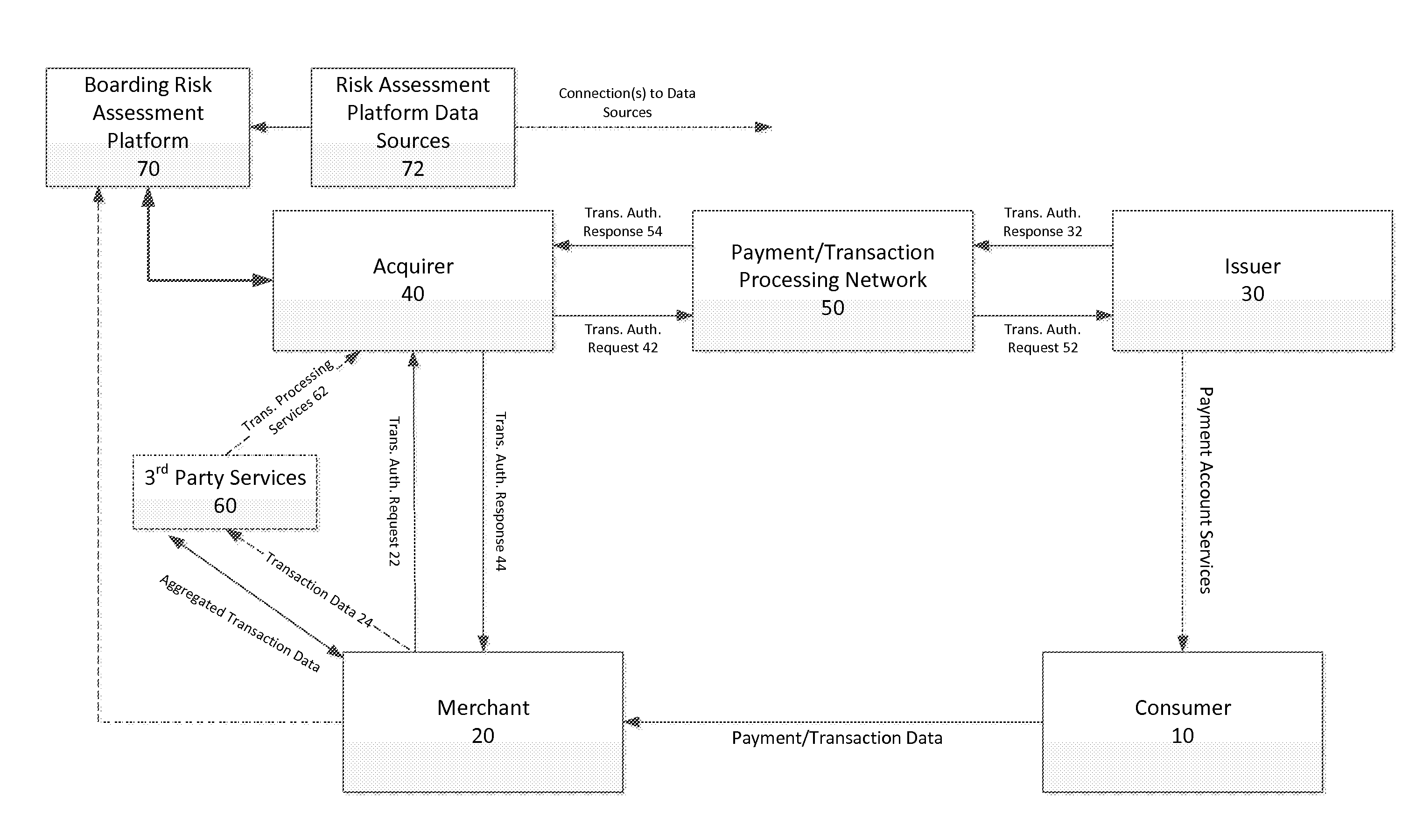
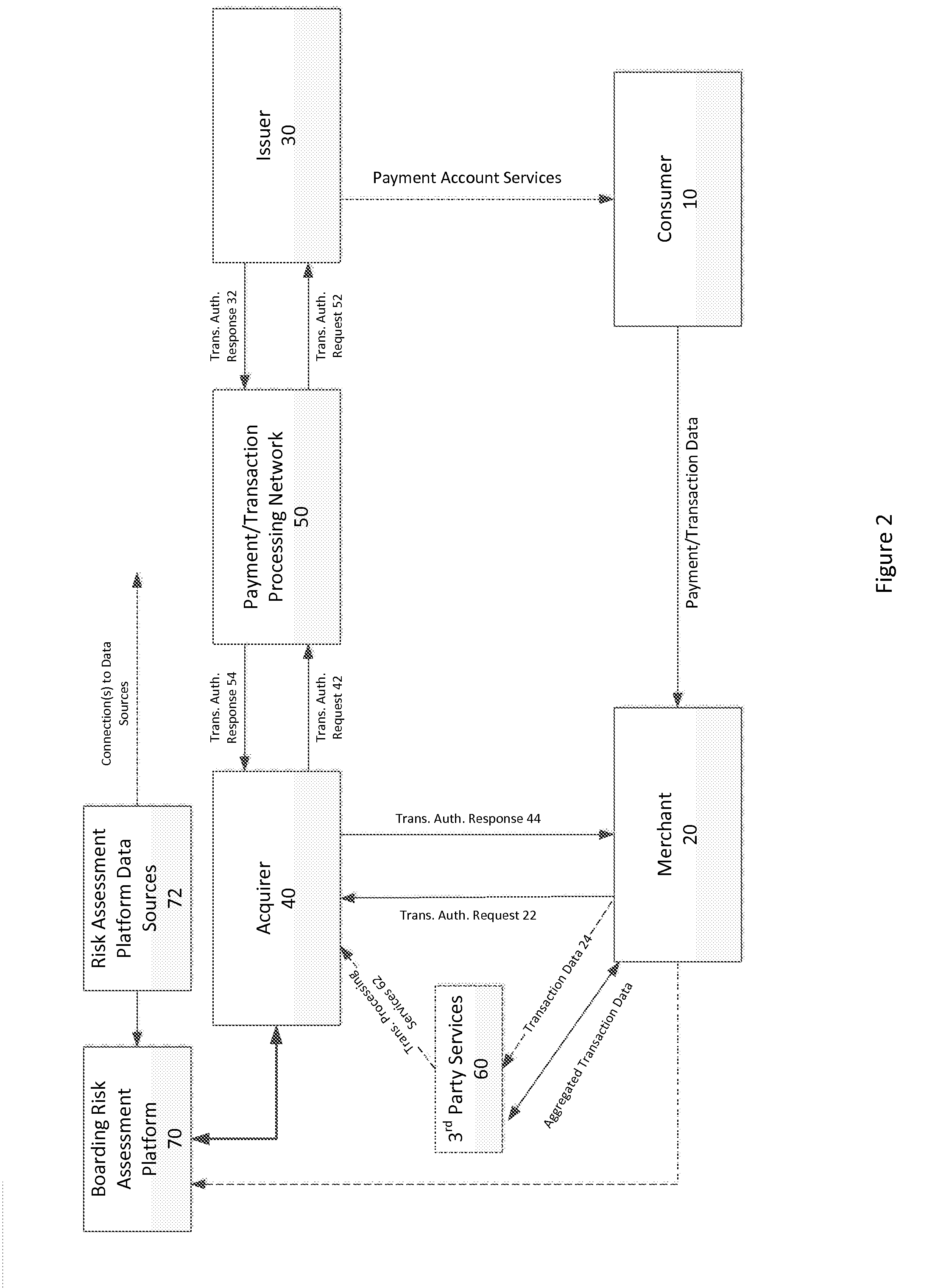
System and methods for global boarding of merchants
InactiveUS20150106260A1Limit scopeDetermination is accurate and reliableFinanceProtocol authorisationData sourceComputer science
Systems, apparatuses, and methods for determining if a Merchant should be provided transaction processing services by an Acquirer and / or continue to be provided such services by the Acquirer. In one embodiment, the inventive system and methods permit a more accurate and reliable determination of the risk to an Acquirer presented by a Merchant, based on a risk assessment engine and the described set of data sources.
Owner:G2 WEB SERVICES
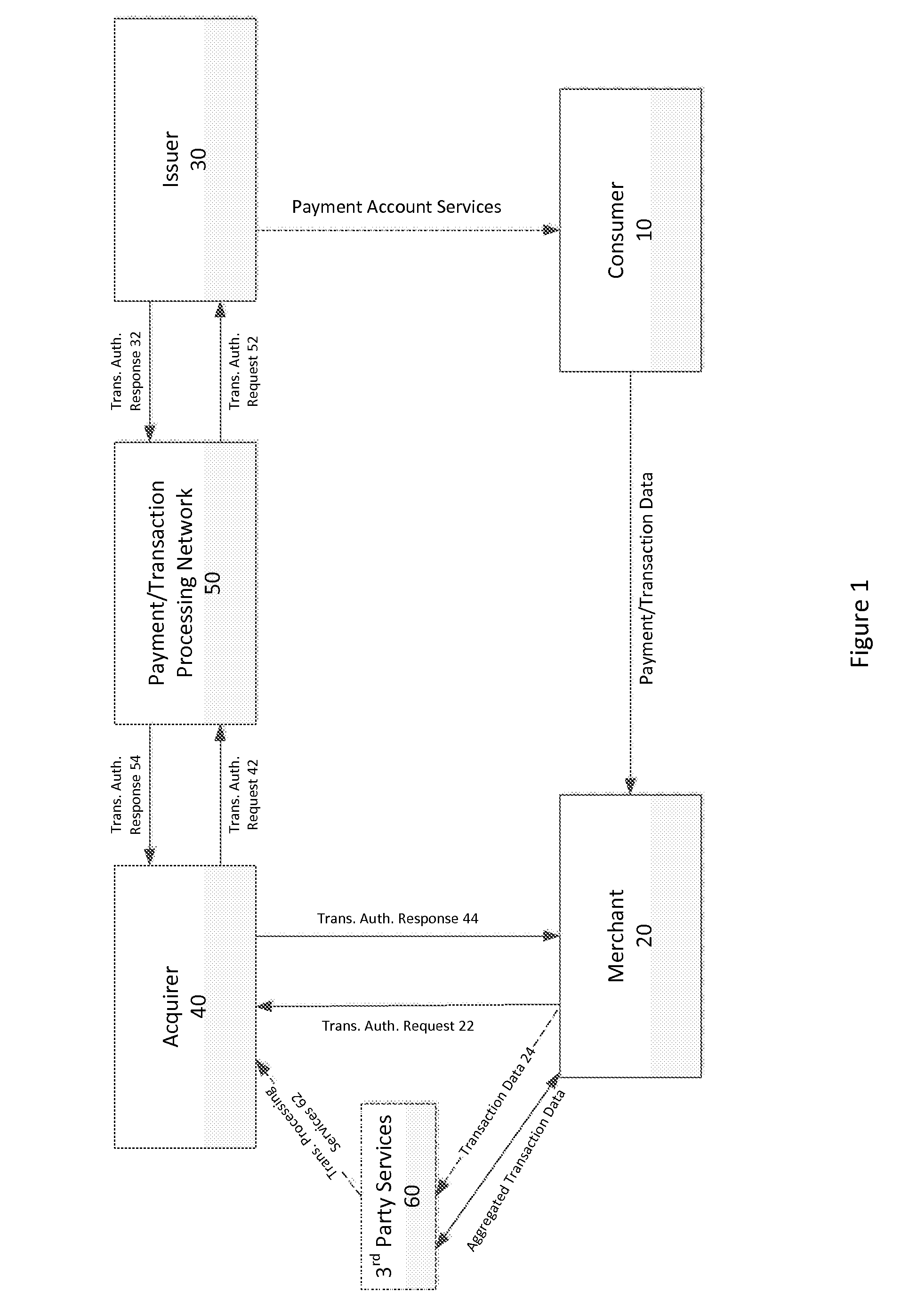
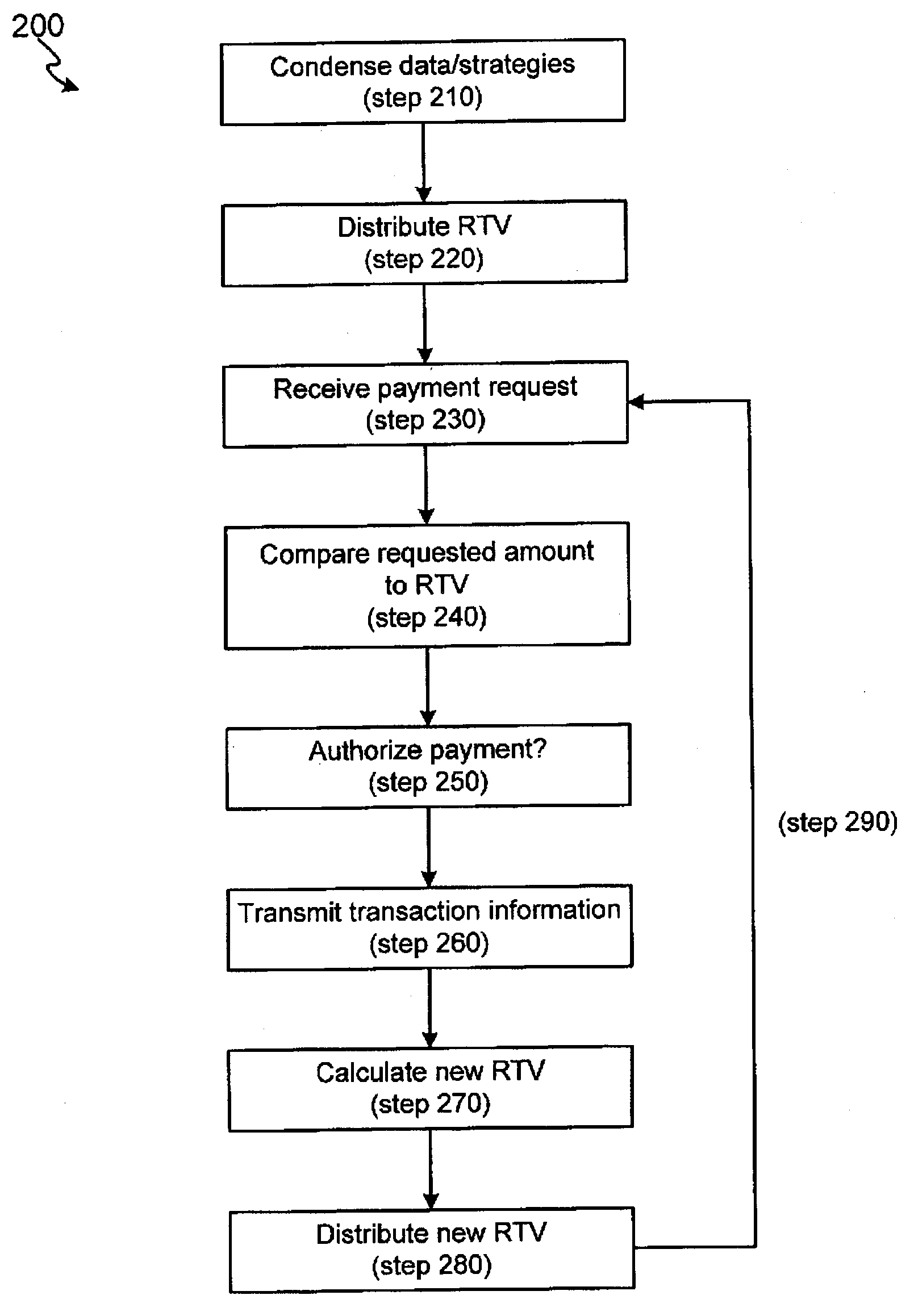
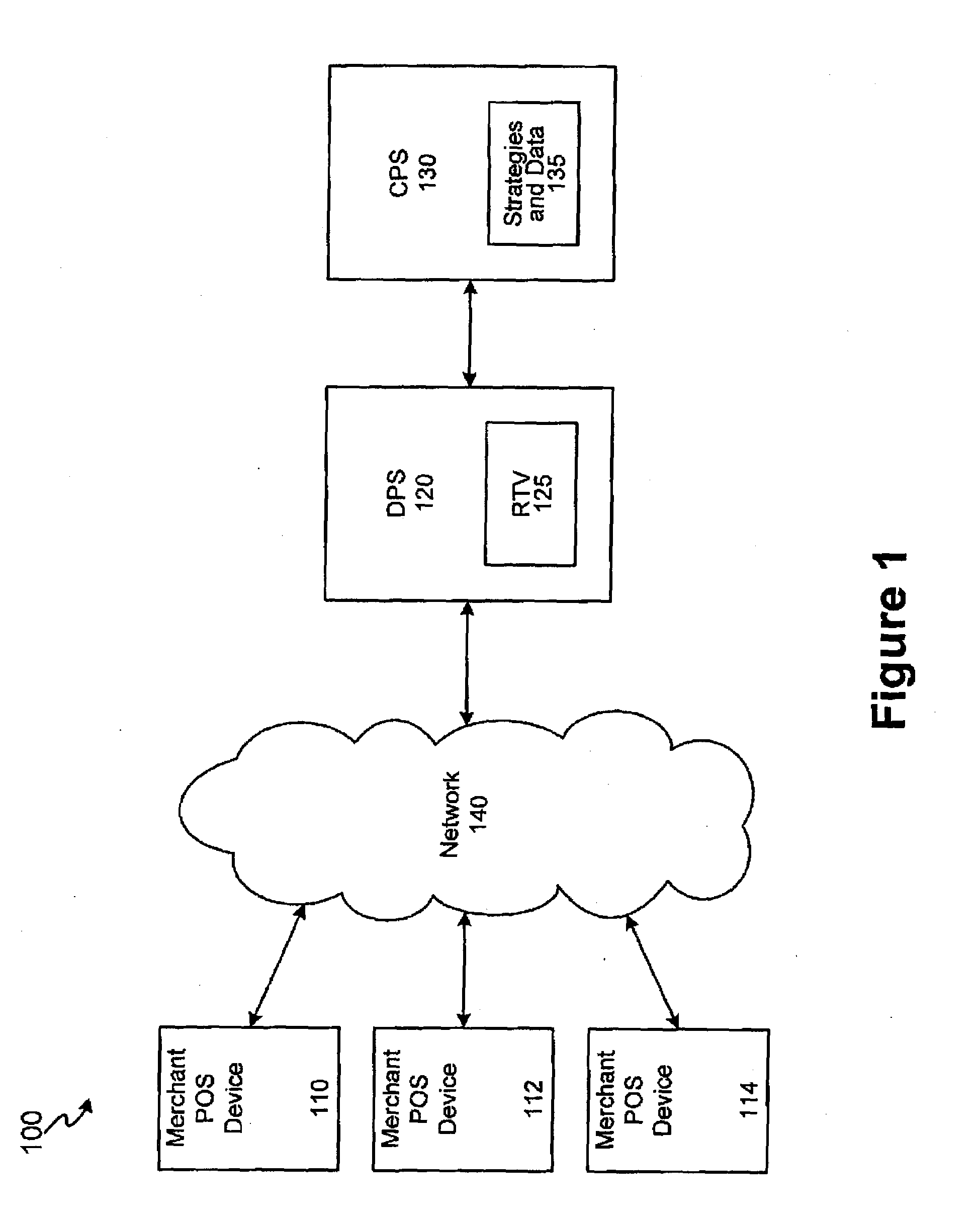
Systems and methods for risk triggering values
InactiveUS20080275821A1Facilitate authorizationComplete banking machinesFinancePaymentComputer science
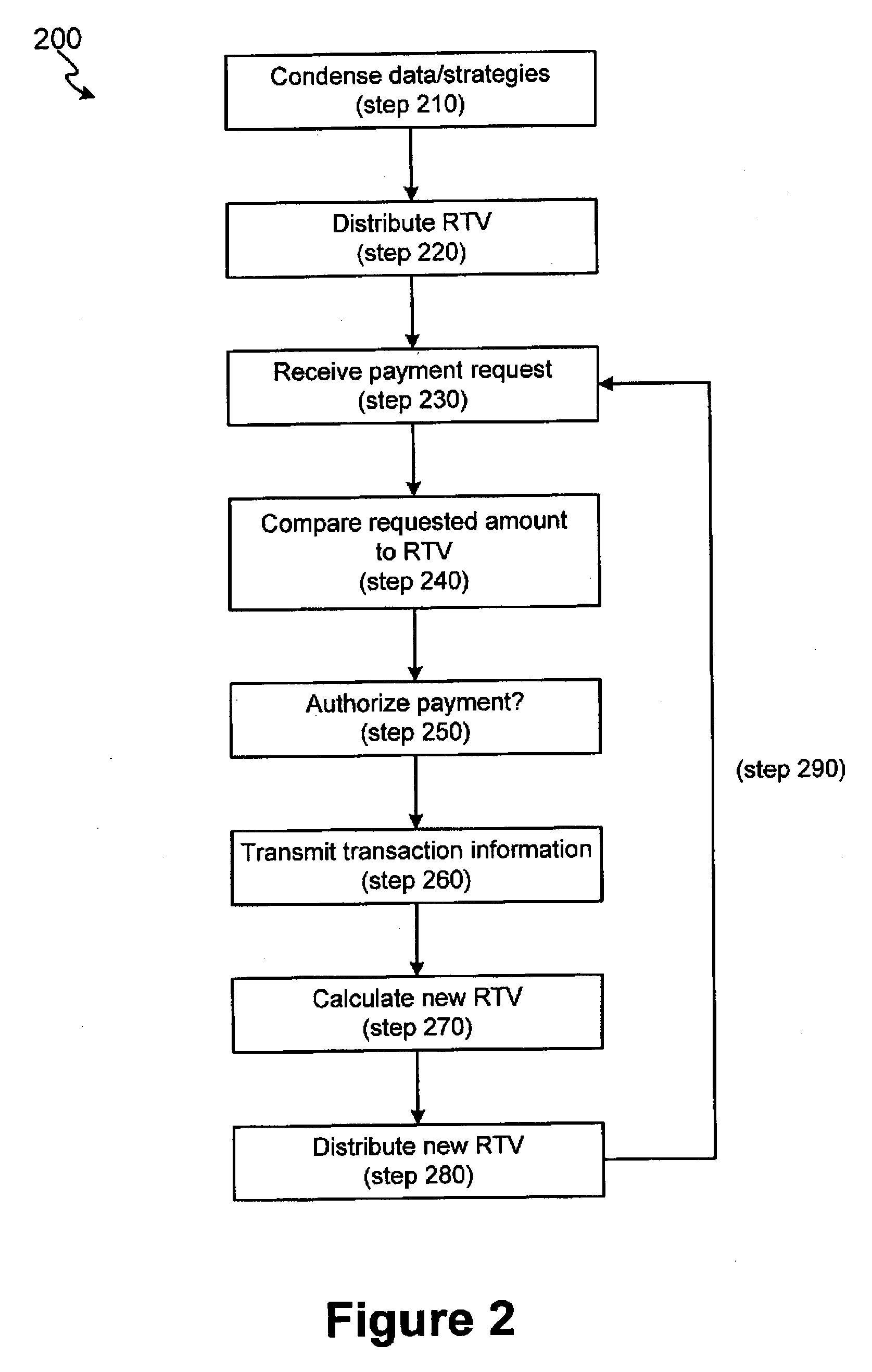
The invention includes systems and methods for facilitating risk assessment for point of sale transactions utilizing at least one risk triggering value (RTV) stored within a distributed (e.g., local and / or regional) processing site. An RTV is a condensed version of a set of complex risk data and strategies usually found in central processing sites. The distributed site, after receiving a request for payment authorization, a risk value is calculated for the request. The distributed processing site compares the risk value to the RTV to determine whether to authorize payment. If the risk value is less than or equal to the RTV, the payment is authorized while a risk value greater than the RTV will not be authorized. After one or more authorizations, the distributed processing site forwards the information from the transaction(s) to the central site, wherein the central site calculates a new RTV for the account and distributes the new RTV to the distributed processing site.
Owner:LIBERTY PEAK VENTURES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com