Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
615results about How to "Limit scope" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
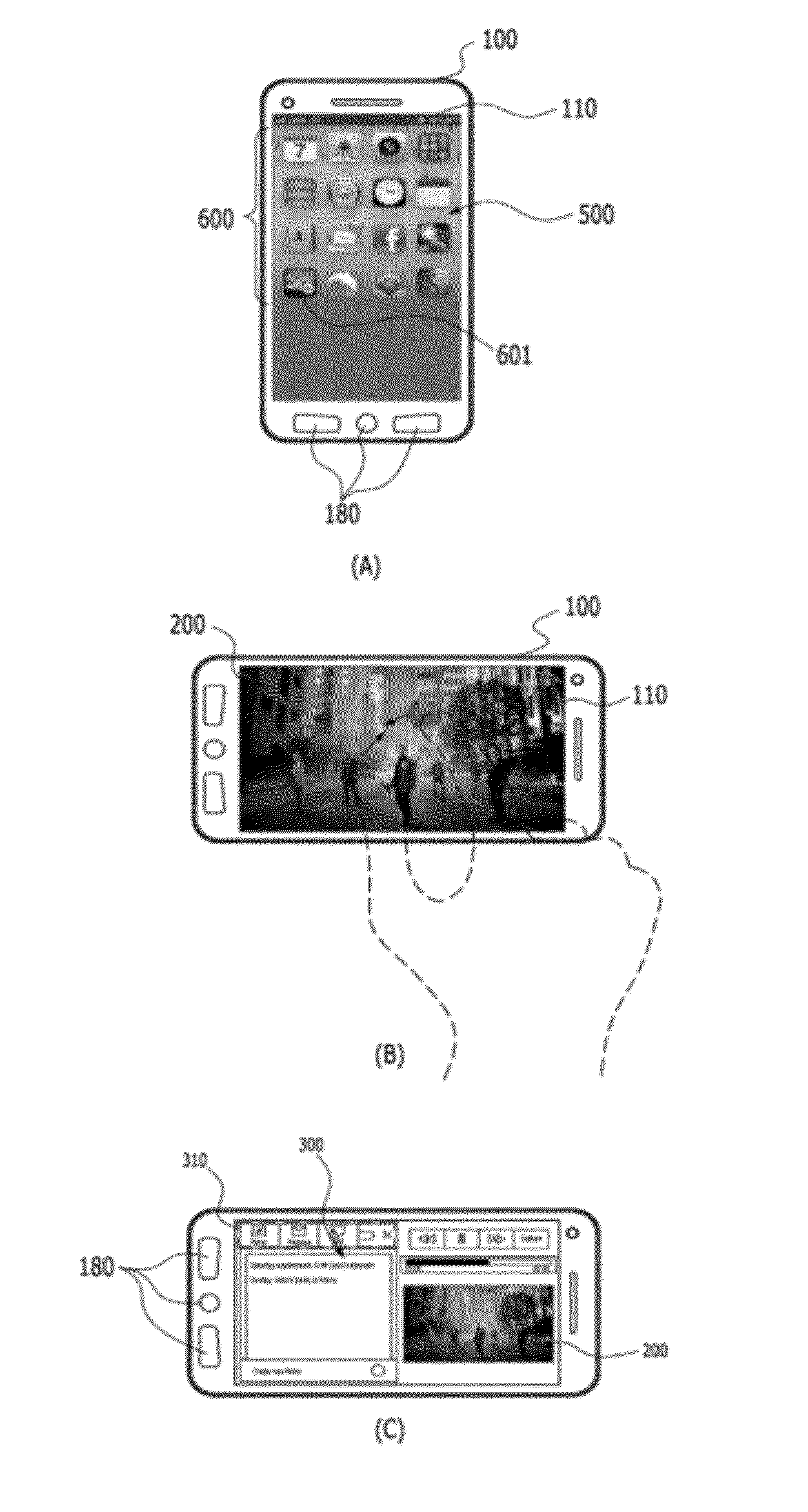
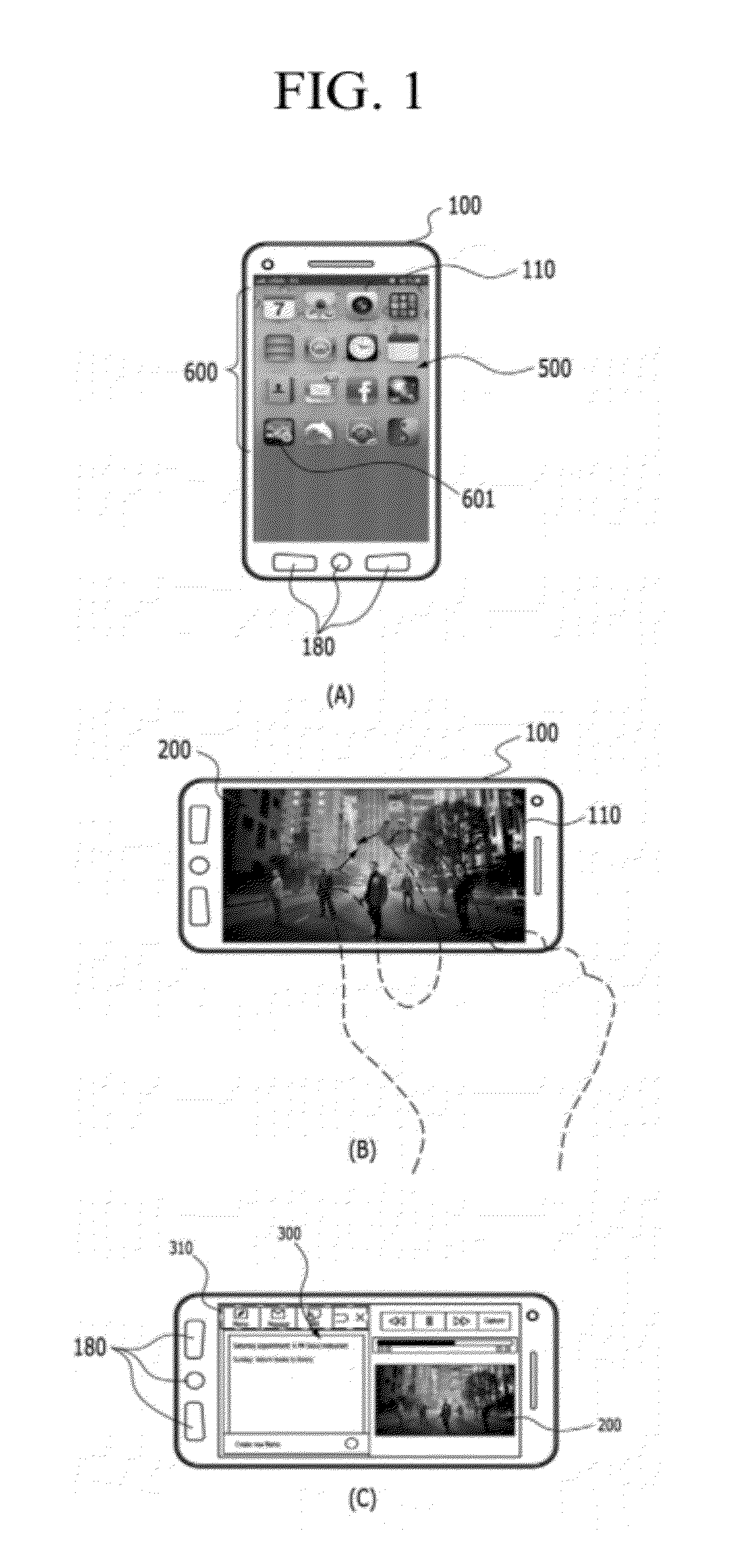
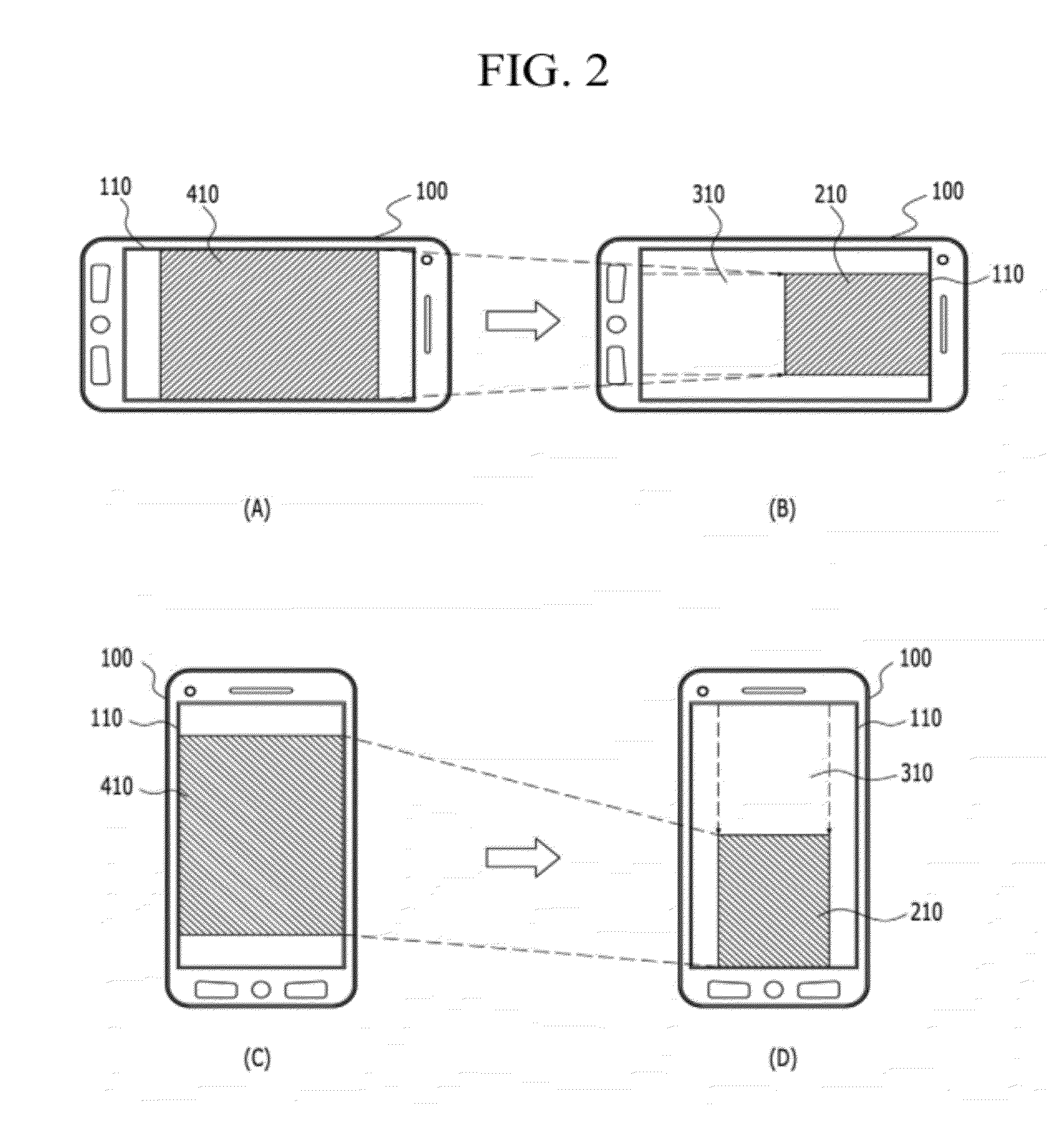
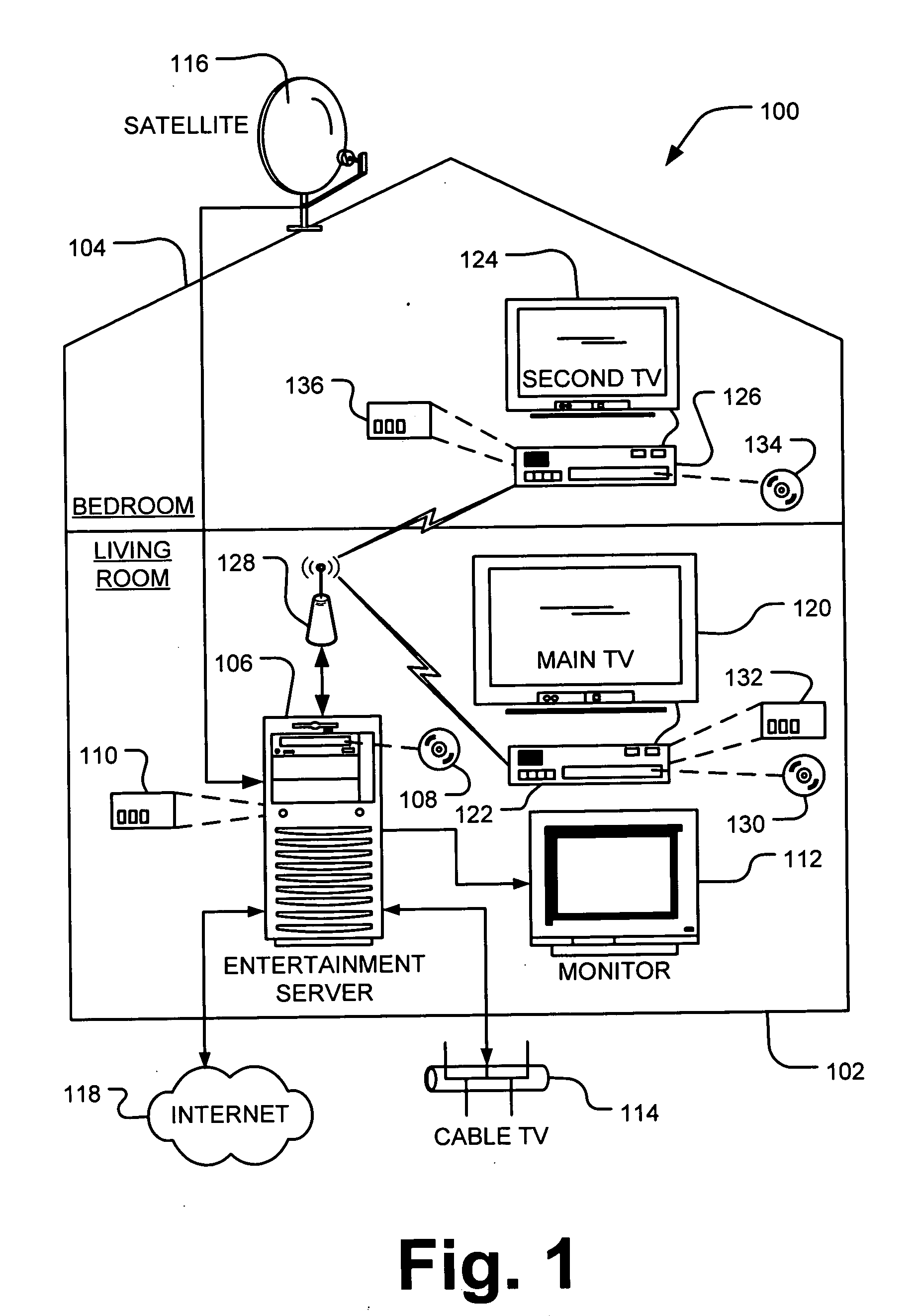
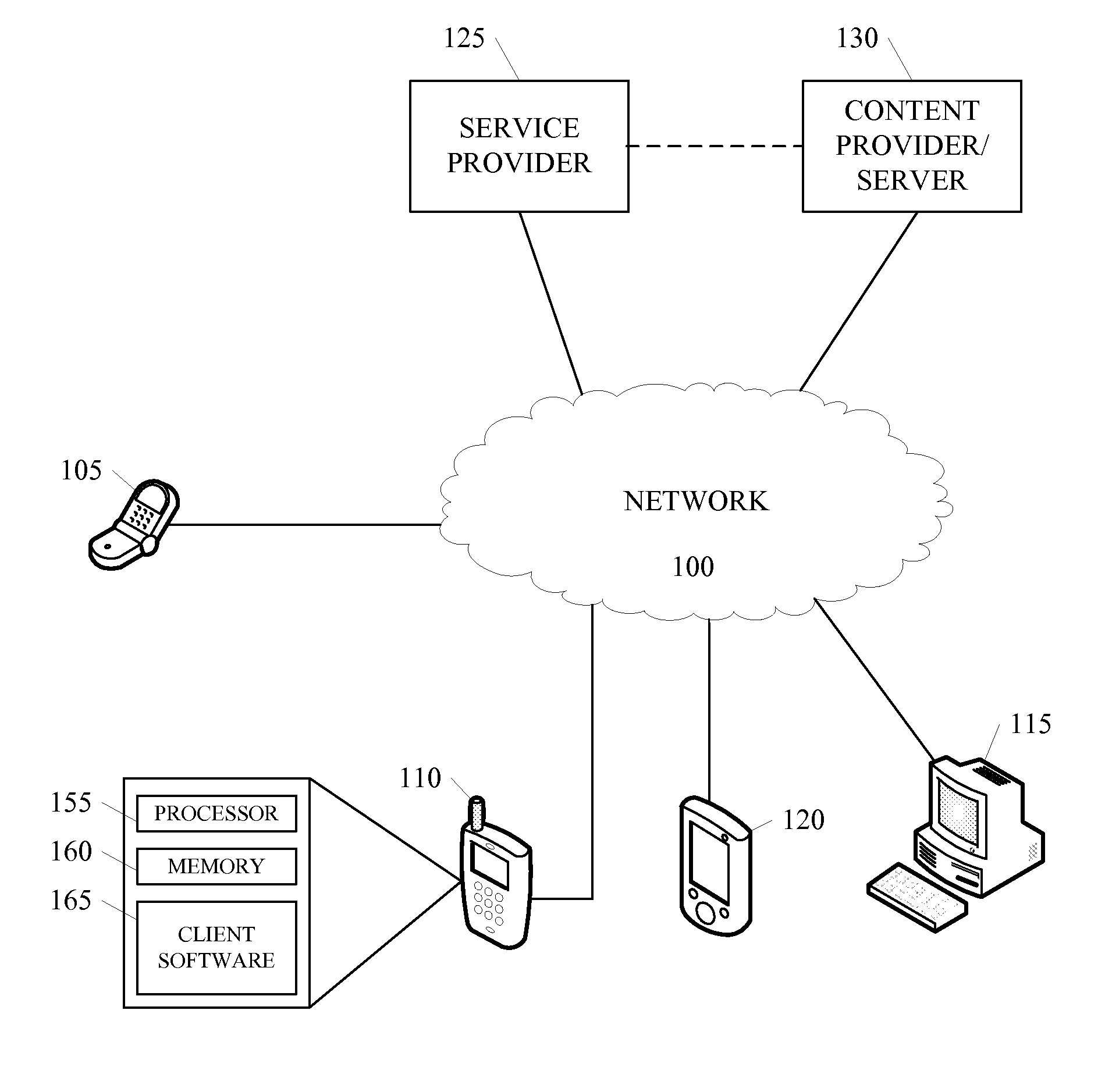
Transferring objects between application windows displayed on mobile terminal
InactiveUS20120289290A1Limit scopeInterprogram communicationCathode-ray tube indicatorsComputer hardwareTransfer mode
Provided are a mobile terminal and a method for transferring objects from a source application window to a destination application window, which are simultaneously displayed on a display unit of a mobile terminal. The method may include displaying the first application window and the second application window simultaneously on the display unit in response to a multi_screen mode initiation input, and transferring at least one of a portion of and an entire object in one of the first application window and the second application window to another application window in response to an object transferring mode initiation input.
Owner:KT CORP
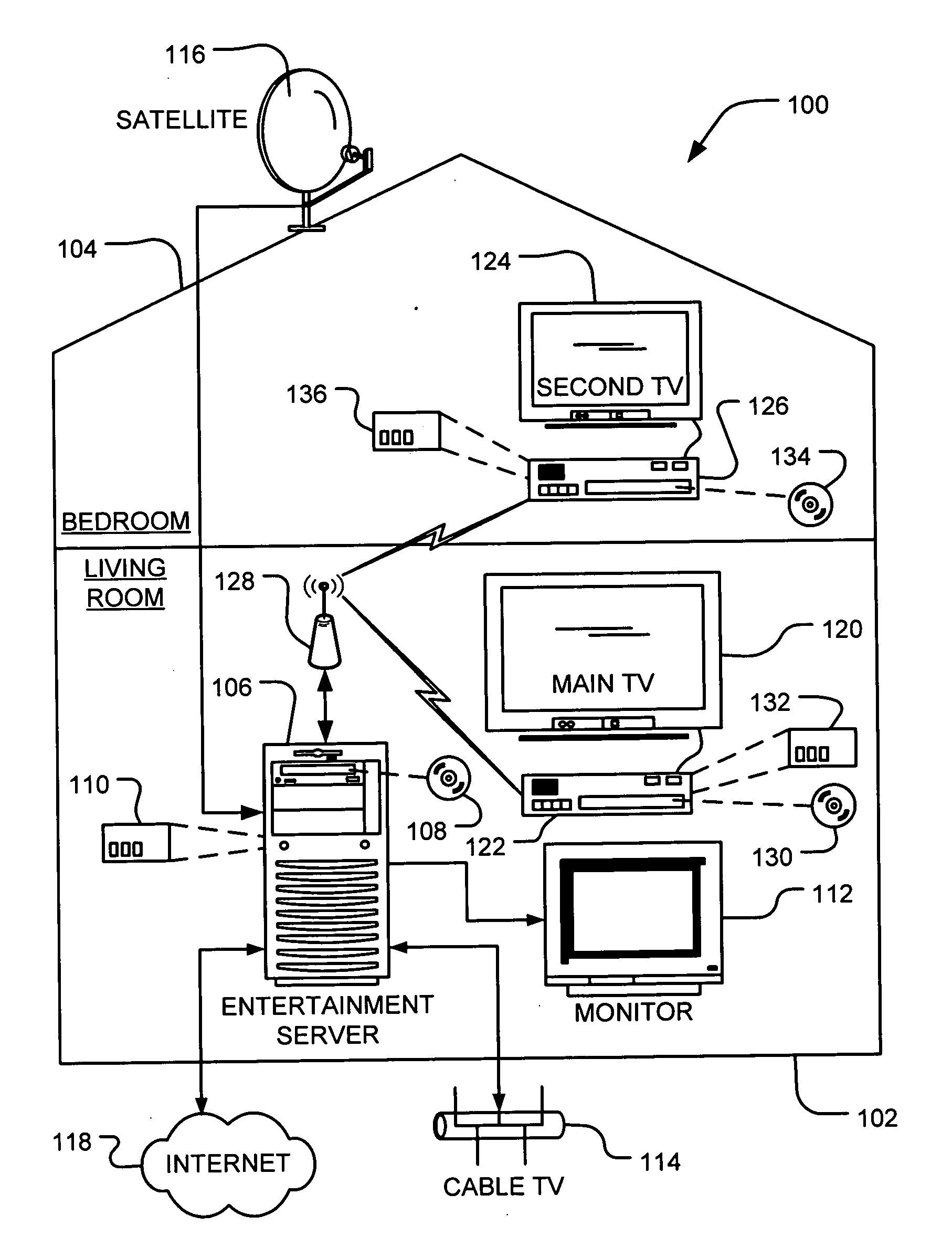
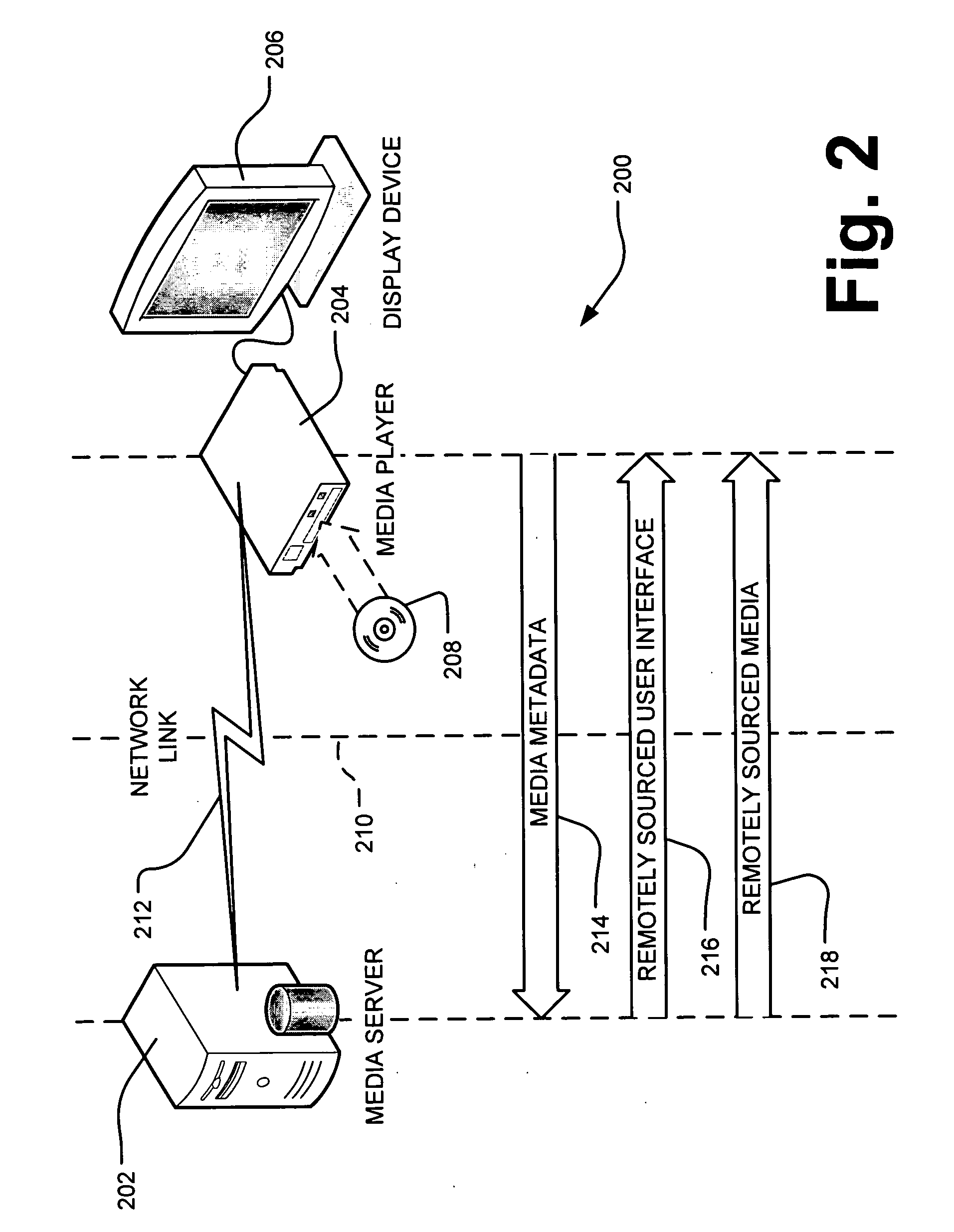
Composition of local media playback with remotely generated user interface
InactiveUS20080034029A1Limit scopeMultiple digital computer combinationsSelective content distributionNetwork mediaMetadata
A media server in a home entertainment network coordinates with a media player connected with the network to provide a media presentation with a combined user interface (UI) on an attached display device. Media content is sourced locally on a networked media player. The media player extracts metadata related to the media content and transmits the metadata to the media server. The media server creates the UI to include components related to the media content rendered by the media player. The media server then transmits the UI to the media player for combination with the rendered media content for a composite output to a presentation device. The media server may further develop and transmit compositing instructions and additional media content to the media player for inclusion in the composite output.
Owner:MICROSOFT TECH LICENSING LLC
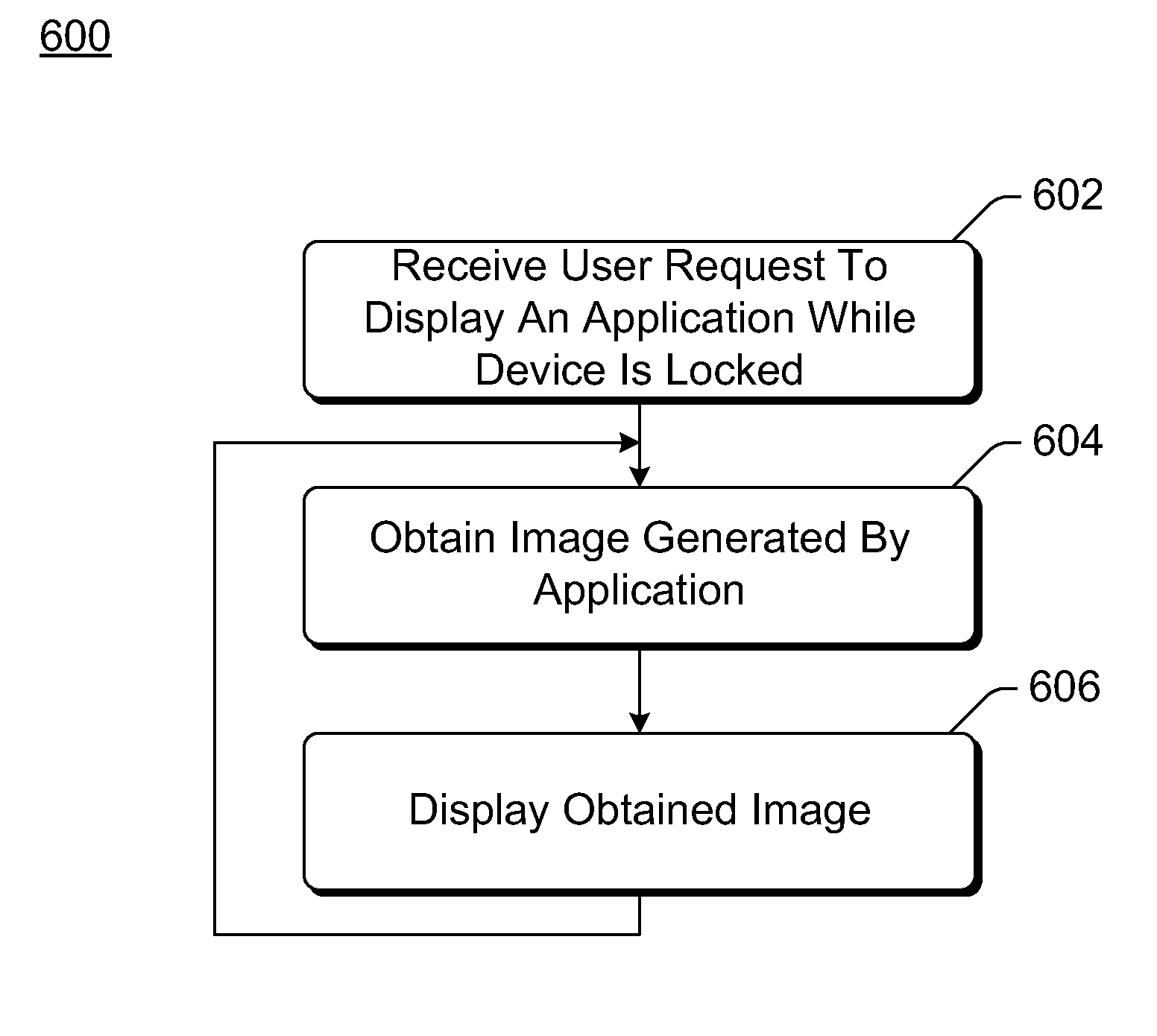
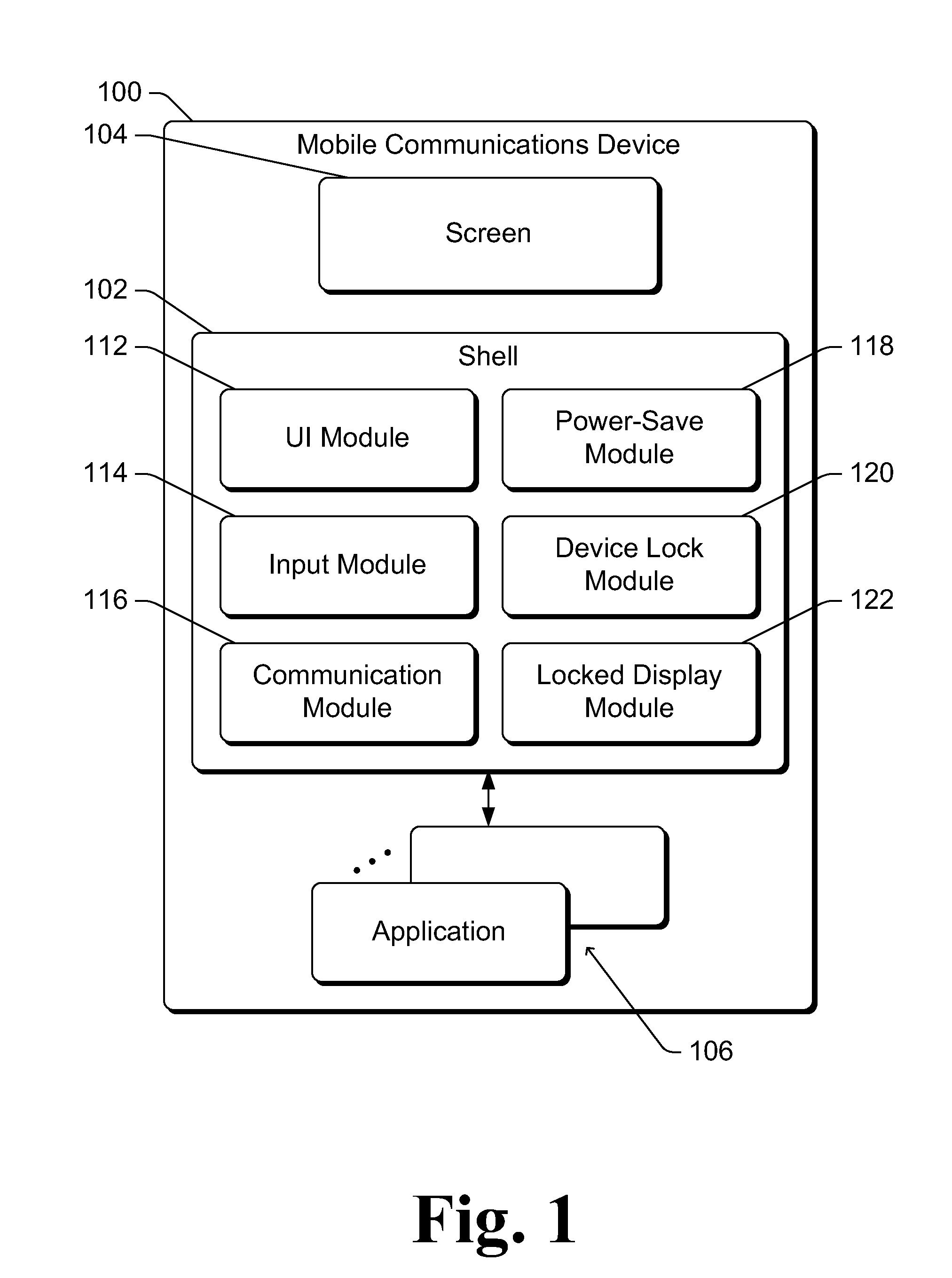
Application Display on a Locked Device
ActiveUS20110047368A1Limit scopePower managementUnauthorised/fraudulent call preventionPower savingApplication software
Owner:MICROSOFT TECH LICENSING LLC
System and method for in- and out-of-band multi-factor server-to-user authentication
ActiveUS20110197070A1More versatile security requirementPracticalDigital data processing detailsUser identity/authority verificationUser authenticationClient-side
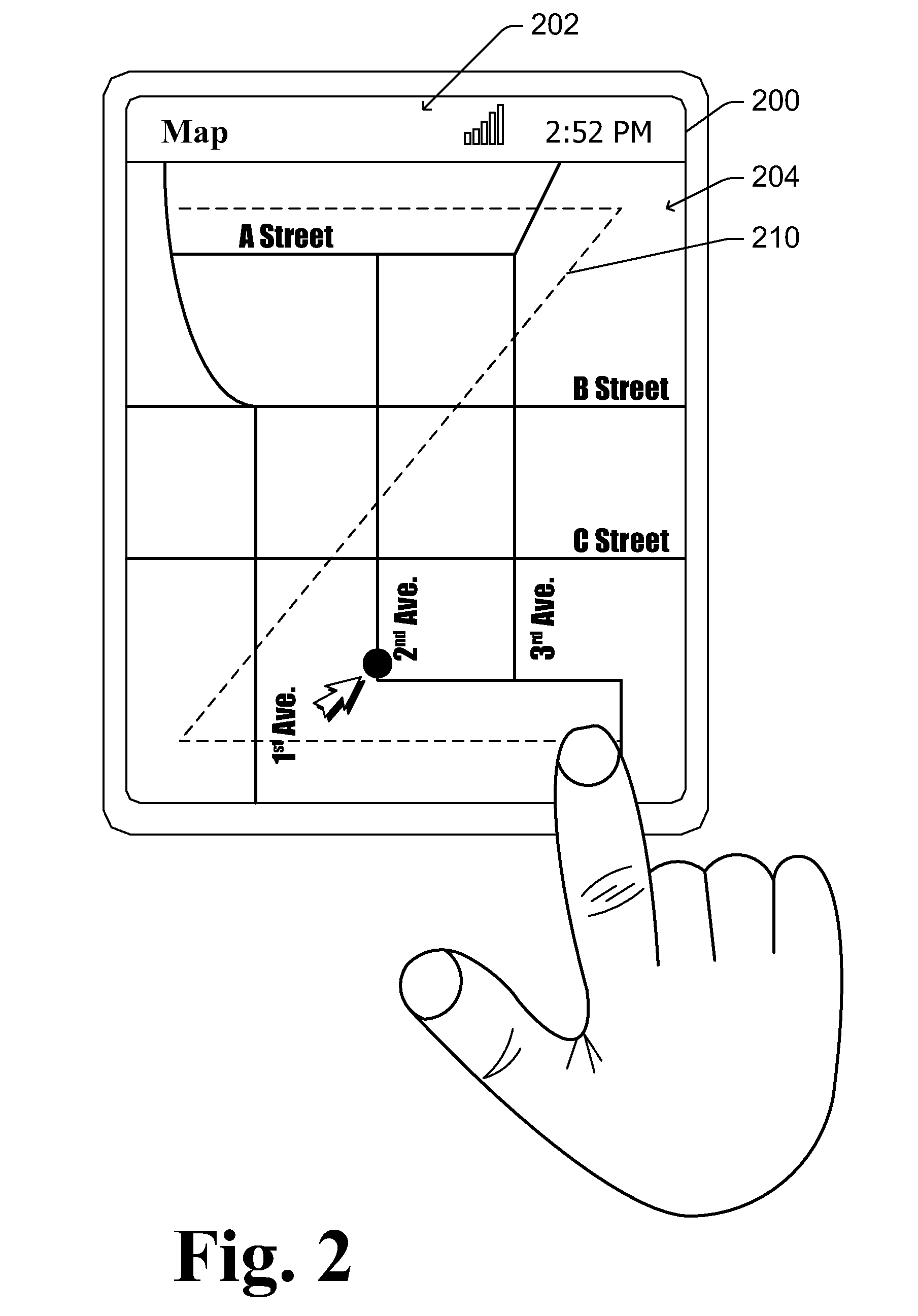
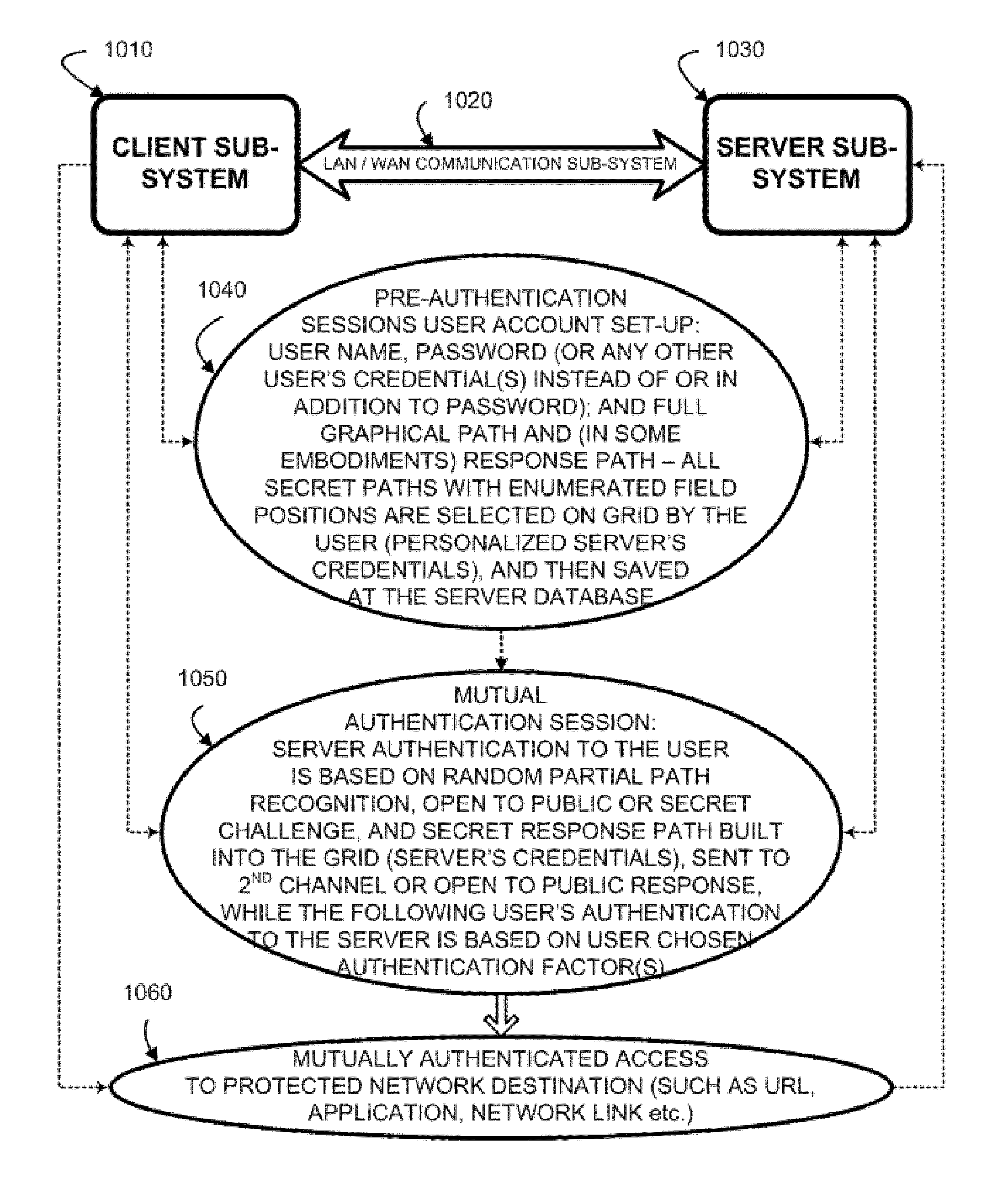
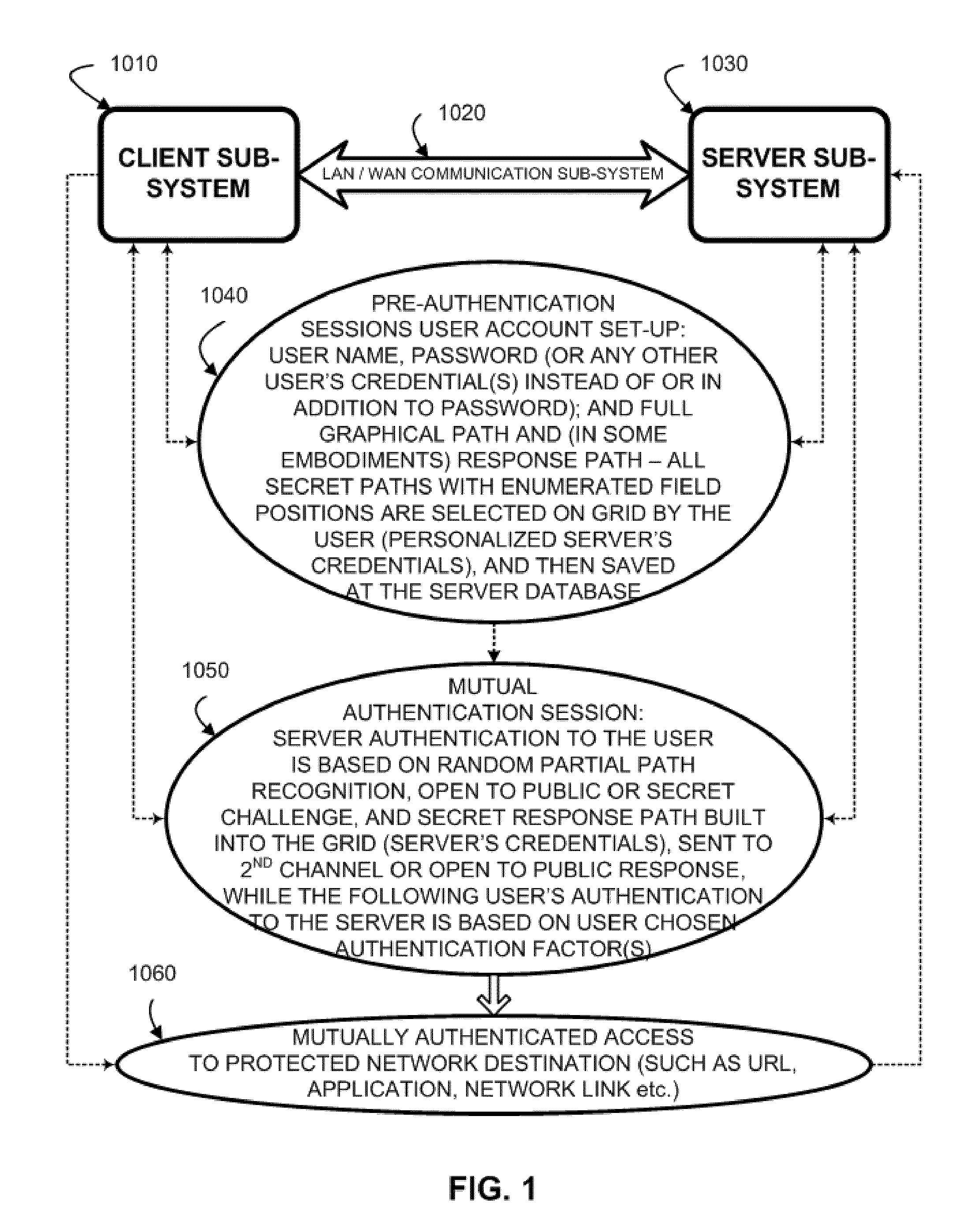
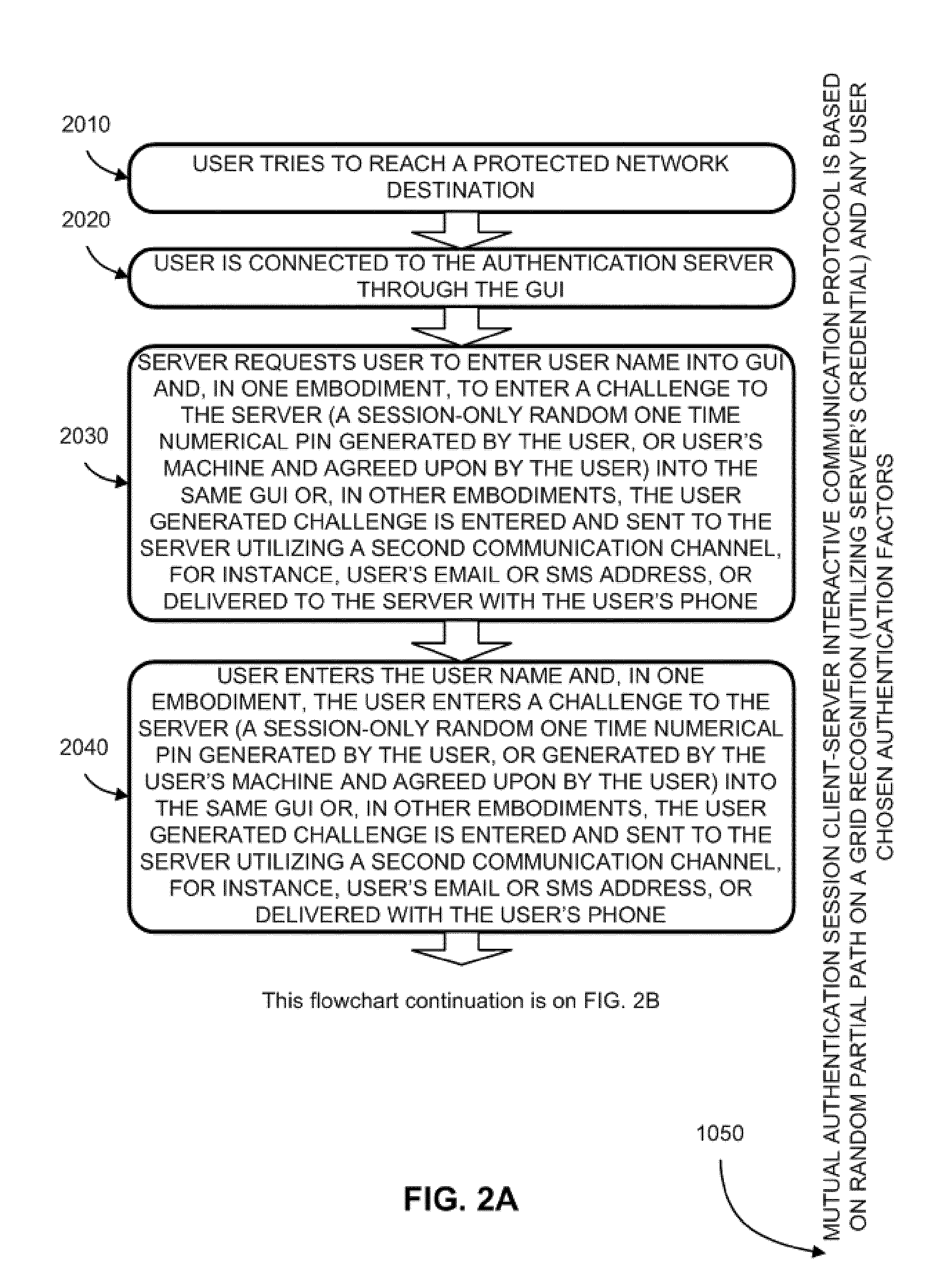
A method to authenticate a server to a client is provided, including in-band and out-of-band techniques. At least a first shared secret identifies a server path, including a plurality of pre-defined locations on a frame of reference (e.g. a grid). An authentication session is initiated upon receiving a client identifier at the server-side resources. A current session instance of the grid is presented to the client, populated with characters. The process includes sharing between the client and the server a challenge identifying a random subset of the plurality of predefined locations in the server path, and a response including characters that match the characters in the locations on the server path identified by the challenge. As a result, client is capable of verifying that the server has access to the first shared secret. Then a protocol is executed to authenticate the client to the server.
Owner:AUTHERNATIVE INC
Authentication methods for use in financial transactions and information banking
ActiveUS20090152343A1Limit scopeComplete banking machinesHand manipulated computer devicesBiometric dataFinancial transaction
A method for conducting a financial transaction can be used by a person using a mobile device to conduct the transaction. The mobile device receives information related to the person that can be used for authentication purposes, such as a PIN or biometric data. The mobile device then authenticates the person by verifying the information received. If the person is authenticated, the transaction is completed using the mobile device, and if the person is not authenticated, the transaction is prevented.
Owner:BANK OF AMERICA CORP
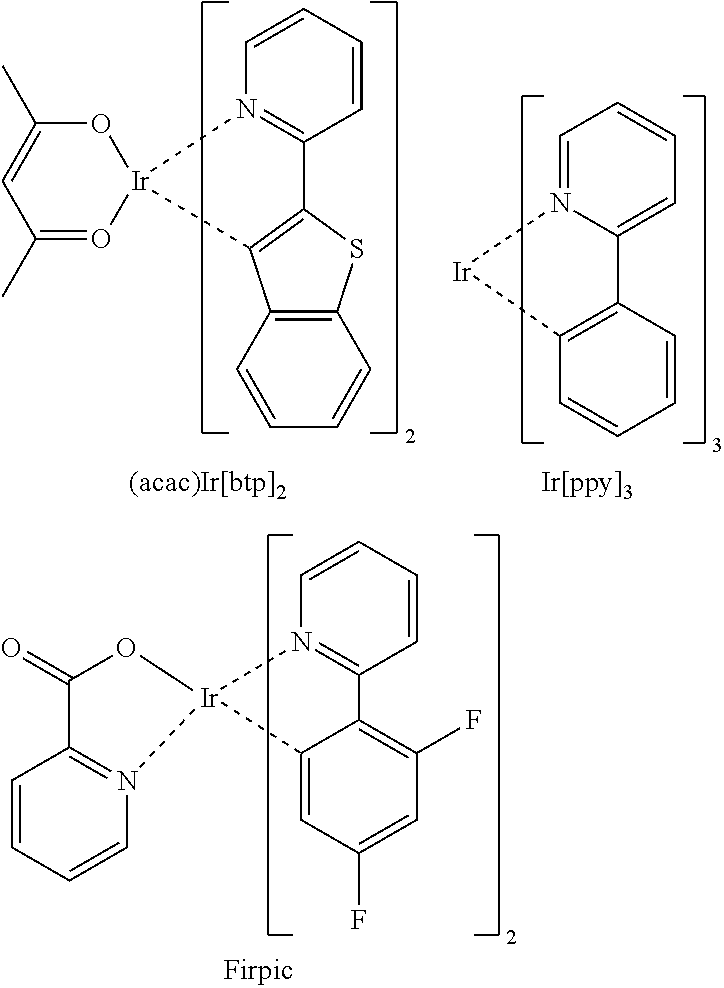
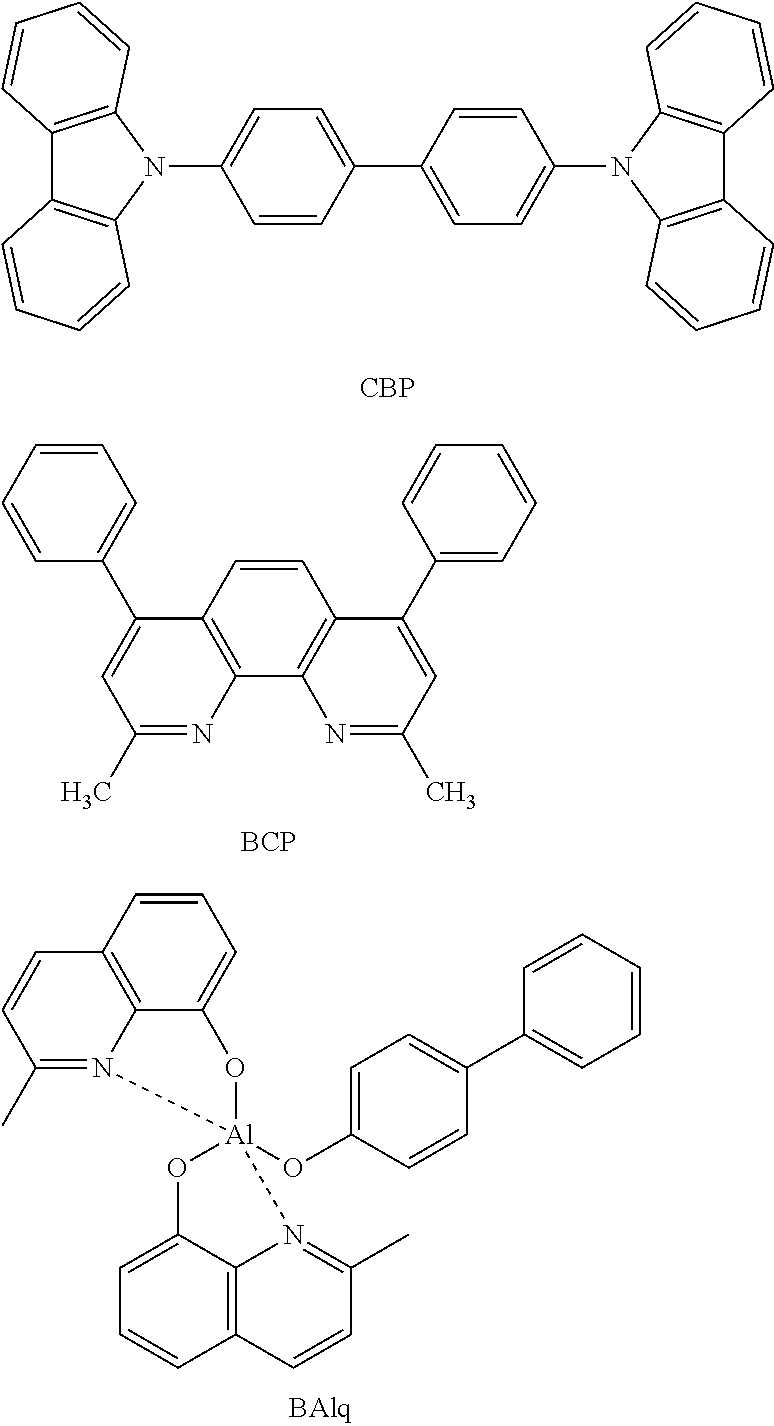
Electroluminescent device using electroluminescent compound as luminescent material
InactiveUS20140054564A1Improve luminous efficiencyIncreased operating lifeIndium organic compoundsElectroluminescent light sourcesEnergy transferOrganic electroluminescence
Provided is an organic electroluminescent device that exhibits an efficient host-dopant energy transfer mechanism, and thus, expresses a certain high-efficiency electroluminescent performance, based on improved electron density distribution. The organic electroluminescent device also overcomes low initial efficiency and short operation life property, and secures high-performance electroluminescent performance with high efficiency and long life property for each color.
Owner:ROHM & HAAS ELECTRONICS MATERIALS LLC
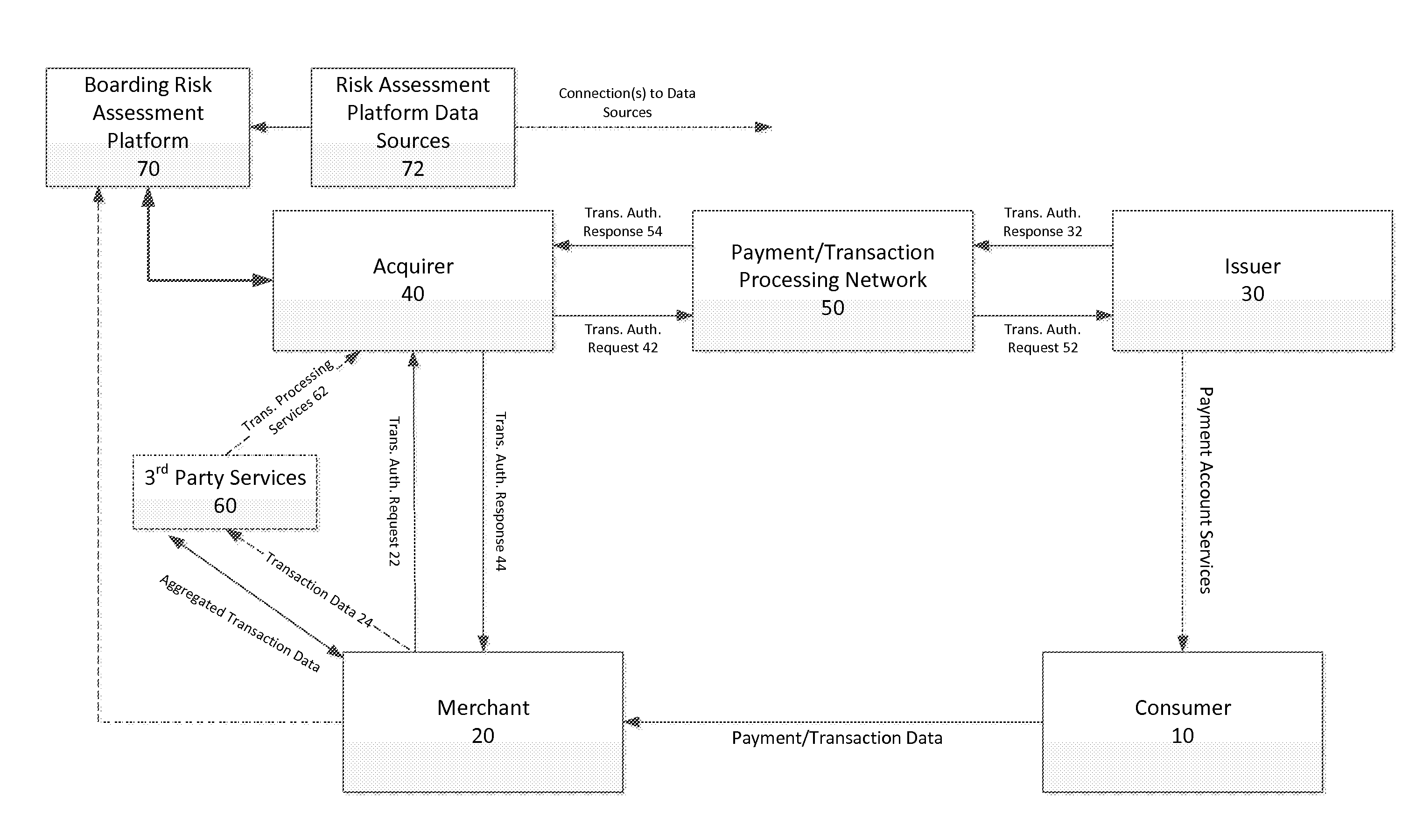
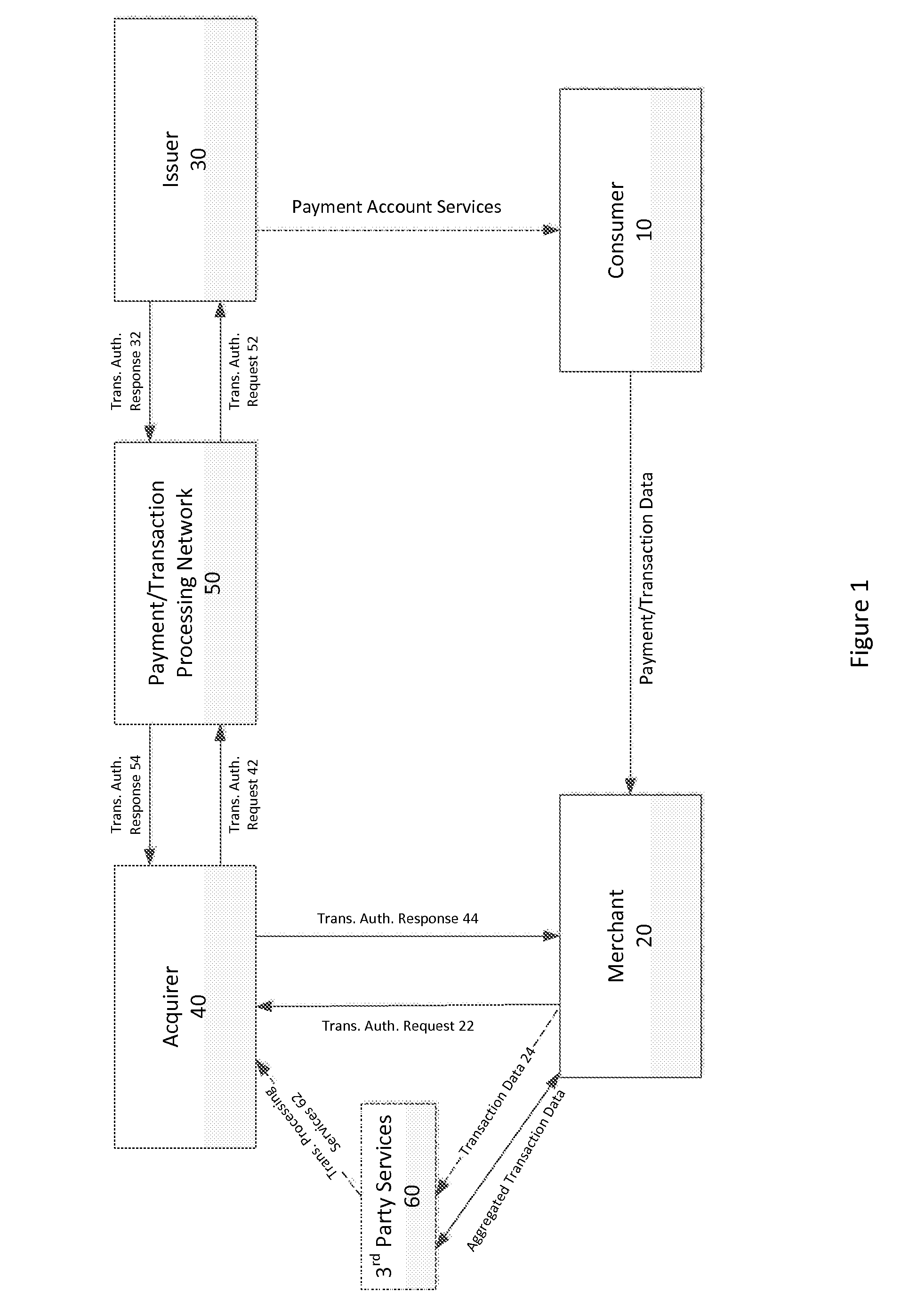
System and methods for global boarding of merchants
InactiveUS20150106260A1Limit scopeDetermination is accurate and reliableFinanceProtocol authorisationData sourceComputer science
Systems, apparatuses, and methods for determining if a Merchant should be provided transaction processing services by an Acquirer and / or continue to be provided such services by the Acquirer. In one embodiment, the inventive system and methods permit a more accurate and reliable determination of the risk to an Acquirer presented by a Merchant, based on a risk assessment engine and the described set of data sources.
Owner:G2 WEB SERVICES
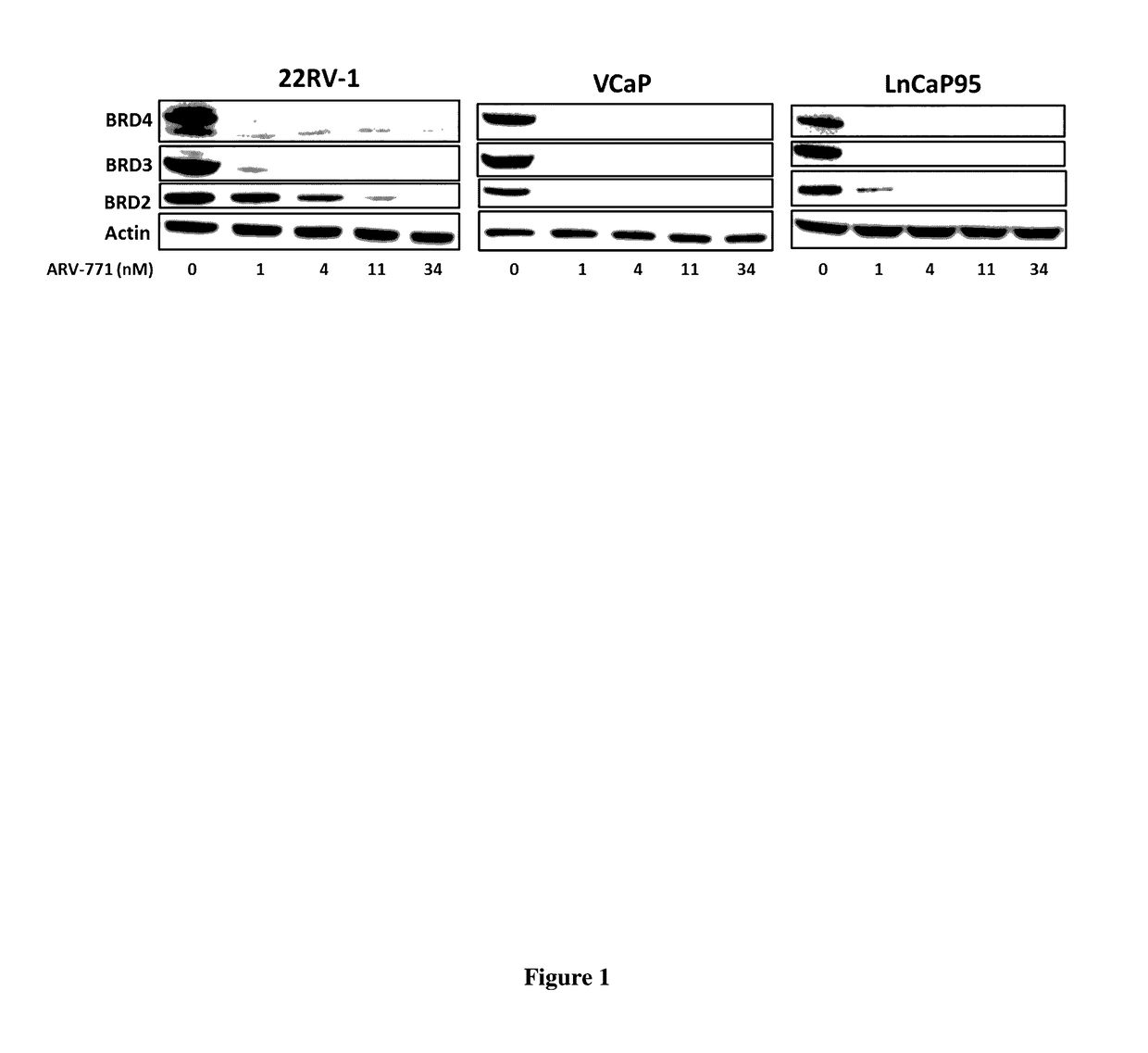
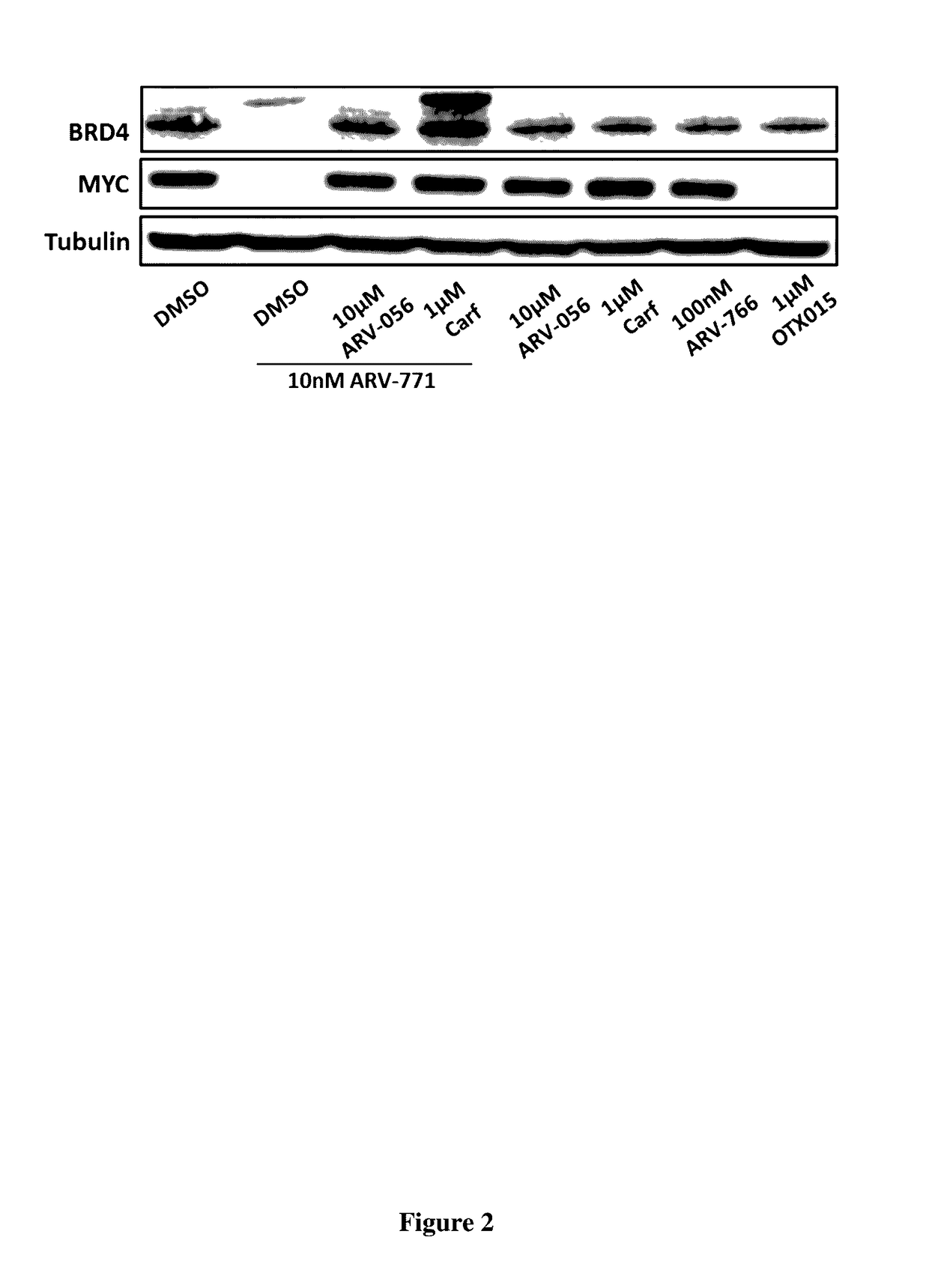
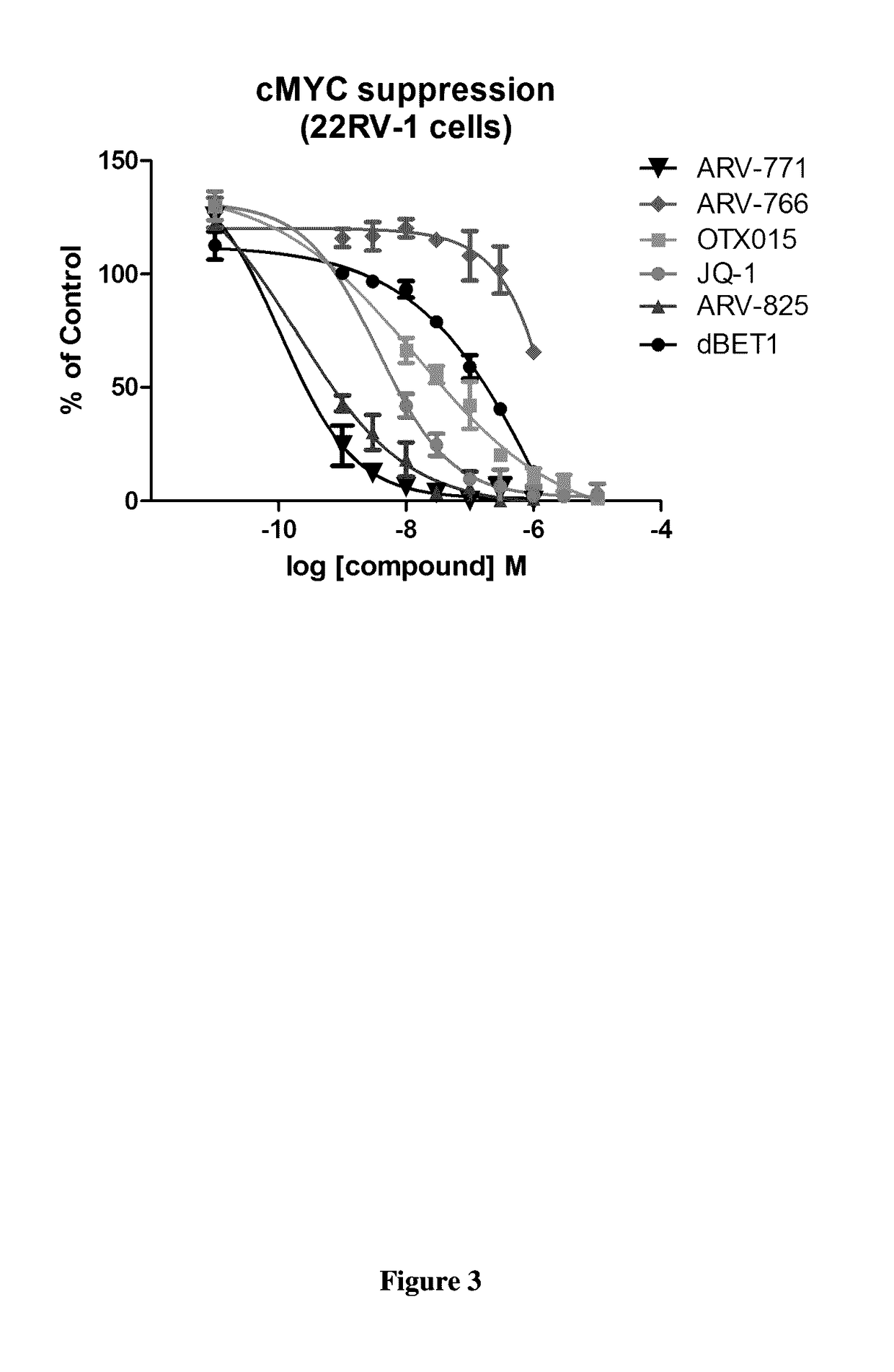
Compounds and methods for the targeted degradation of bromodomain-containing proteins
ActiveUS20170065719A1Symptoms improvedLimit scopeOrganic active ingredientsOrganic chemistryProteinUbiquitin ligase
The present invention relates to bifunctional compounds, which find utility as modulators of targeted ubiquitination, especially inhibitors of a variety of polypeptides and other proteins which are degraded and / or otherwise inhibited by bifunctional compounds according to the present invention. In particular, the present invention is directed to compounds, which contain on one end a VHL ligand which binds to the ubiquitin ligase and on the other end a moiety which binds a target protein such that the target protein is placed in proximity to the ubiquitin ligase to effect degradation (and inhibition) of that protein. The present invention exhibits a broad range of pharmacological activities associated with compounds according to the present invention, consistent with the degradation / inhibition of targeted polypeptides.
Owner:ARVINAS OPERATIONS INC +1
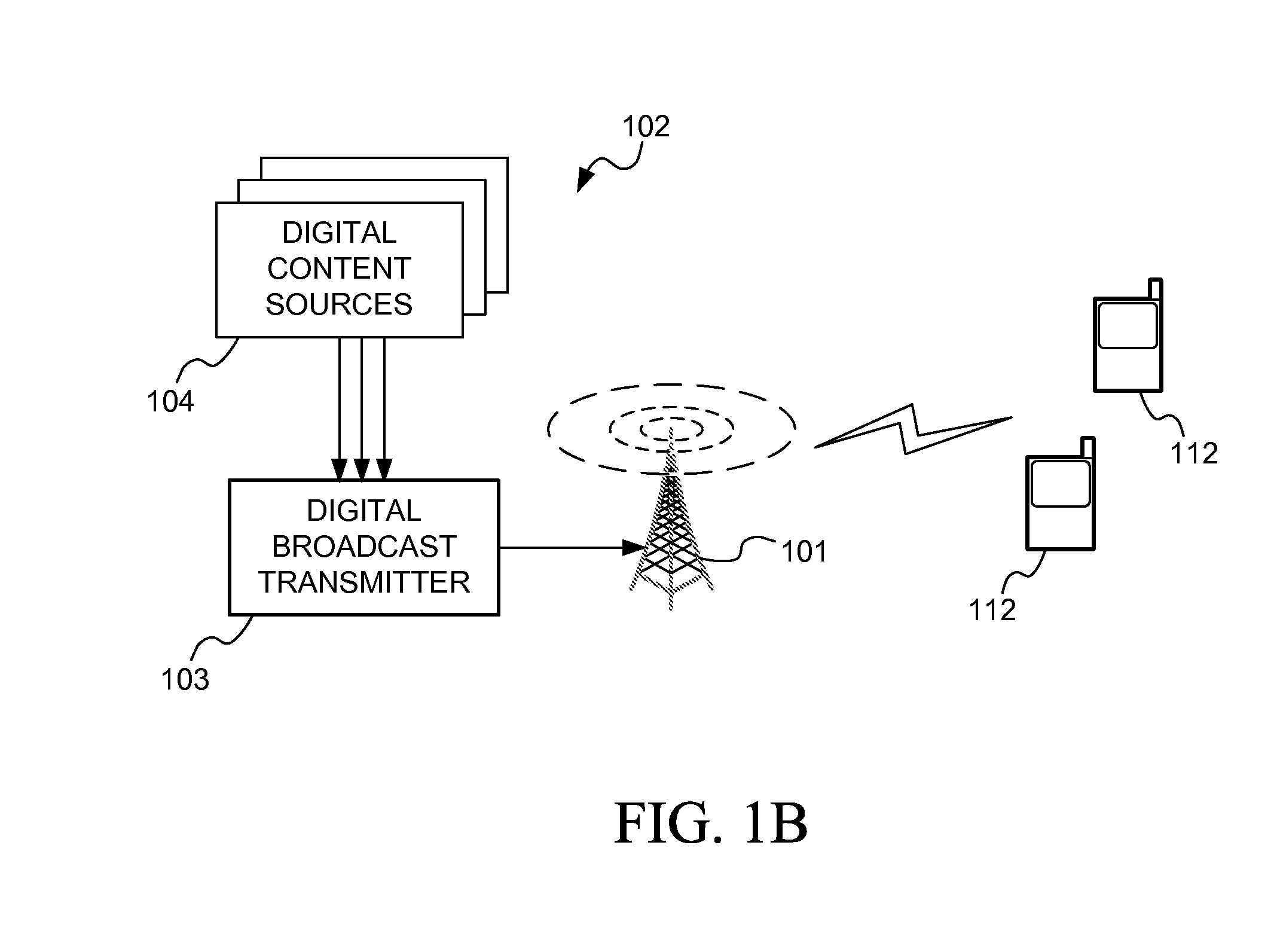
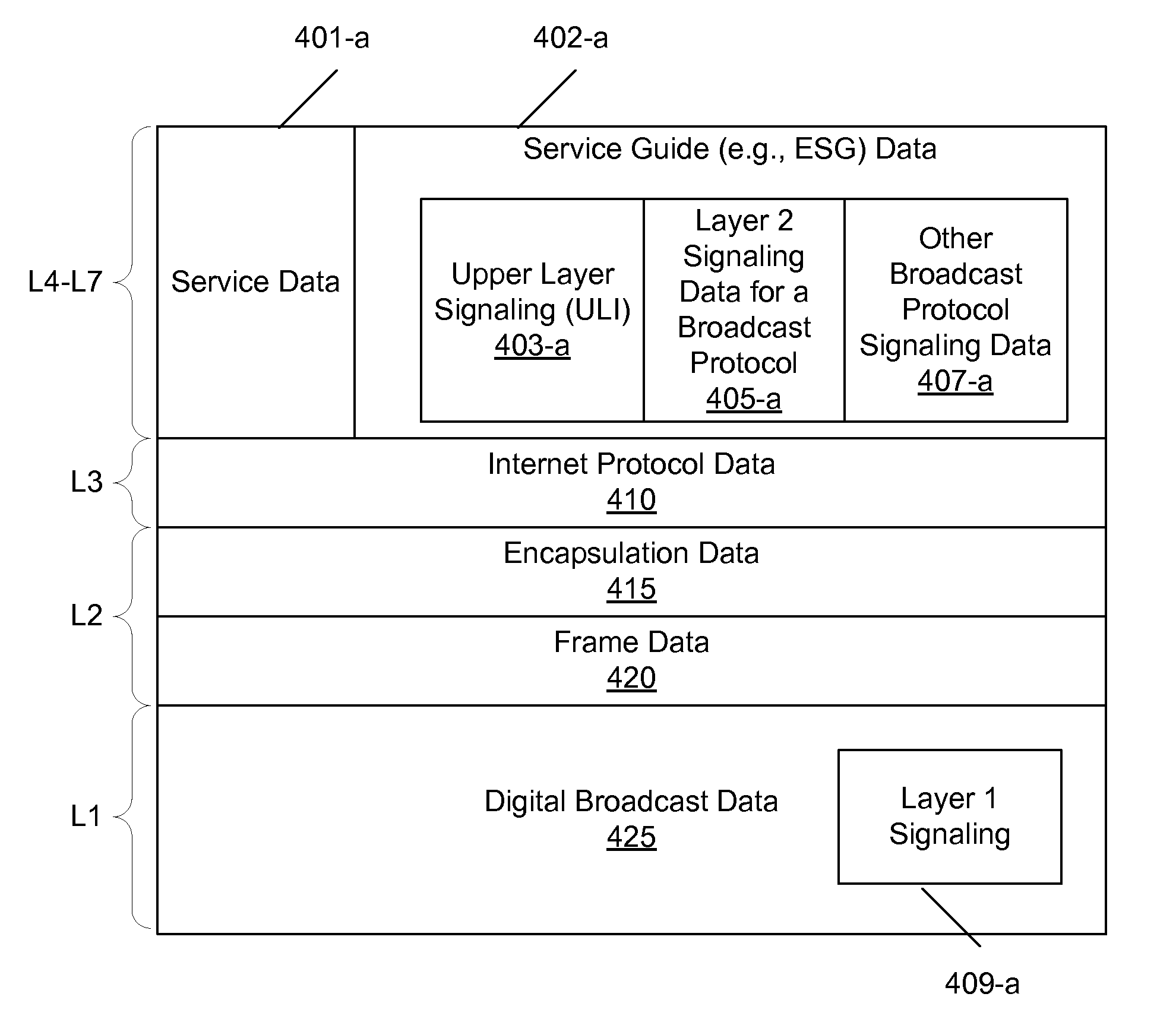
Accessing Service Guide Information in a Broadcast System
InactiveUS20130034032A1Limit scopeSimple formBroadcast service distributionRadio transmissionBroadcast systemOperating system
Apparatuses may perform and methods may include receiving a broadcast signal that includes a physical layer pipe identified by a predetermined identifier indicating that the physical layer pipe includes service guide bootstrap information. The bootstrap information may identify one or more service guides available for download. The physical layer pipe may include a header that includes version values that identify changes in signaling data and changes in the service guides. Based on receiving the header only, an apparatus may determine whether the signaling data and / or service guides previously stored in the apparatus need to be updated.
Owner:NOKIA CORP
Aqueous compositions comprising polymeric duller particle
ActiveUS7829626B2Limit scopeImprove consistencyLiquid surface applicatorsLayered productsSingle stageTert-butyl acrylate
The present invention provides aqueous matte coating compositions comprising a binder component B) and a polymeric duller component A) composed of particles of one or more multi-stage copolymer or single stage crosslinked (co)polymer, e.g. crosslinked t-butyl (meth)acrylate, the duller component particles A) having an average diameter of 1-20 μm. Components A) and B) are compatible. Preferably, the duller component A) is acrylic; more preferably, components A) and B) are acrylic. The aqueous compositions provide matte coatings having haptic or feel (soft touch) properties, film and appearance properties, including burnish resistance and low color loss.
Owner:ROHM & HAAS CO
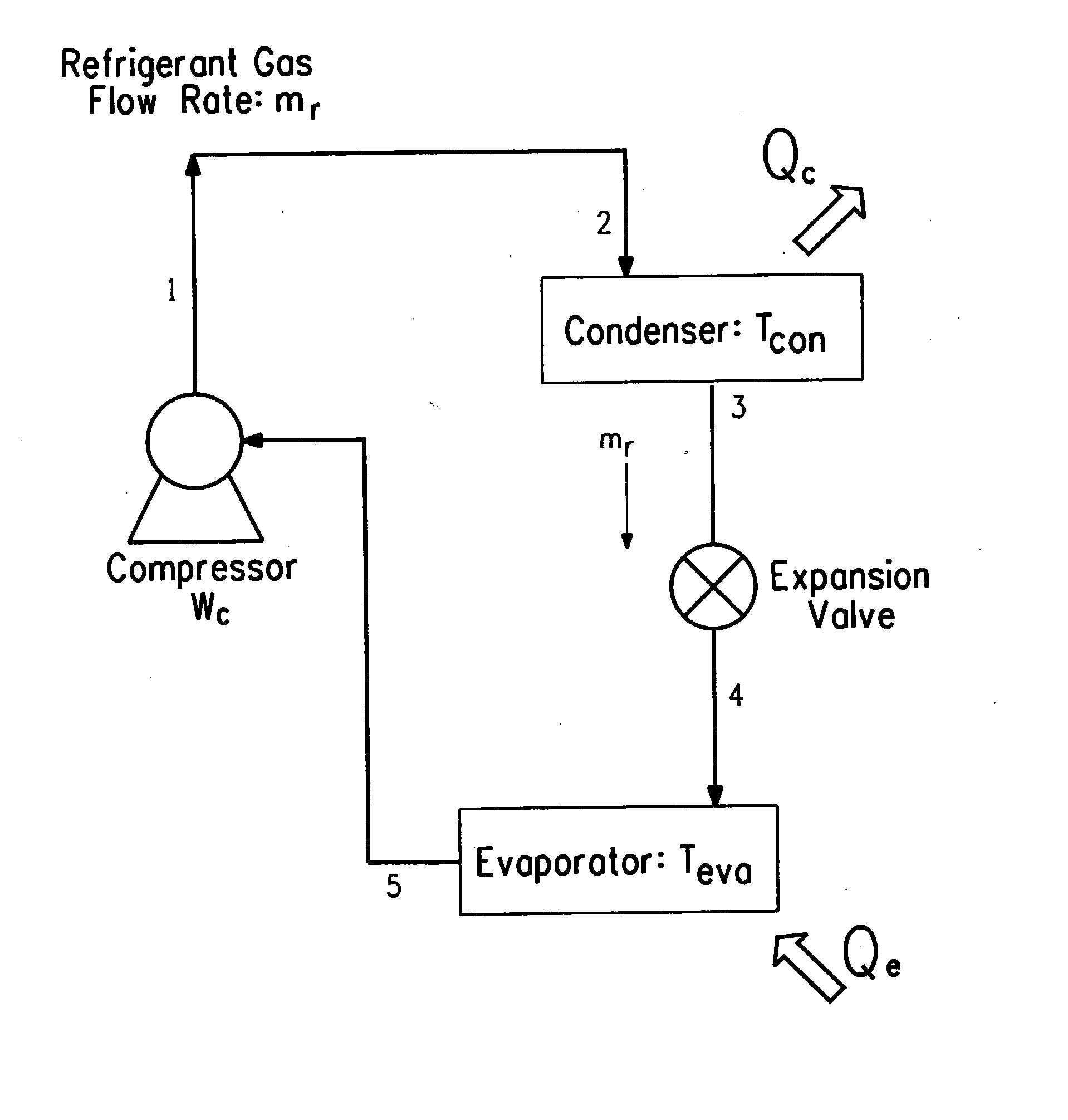
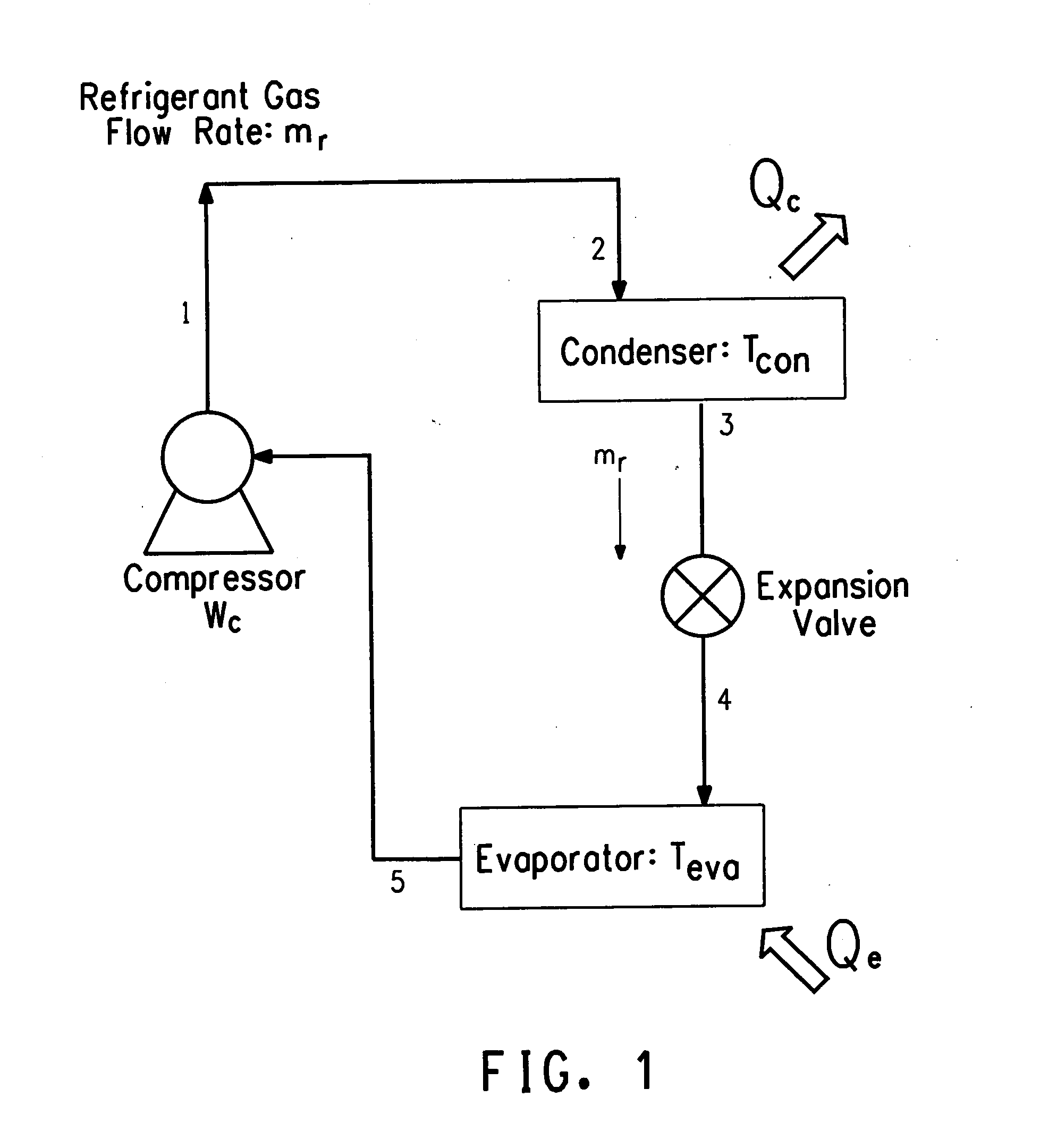
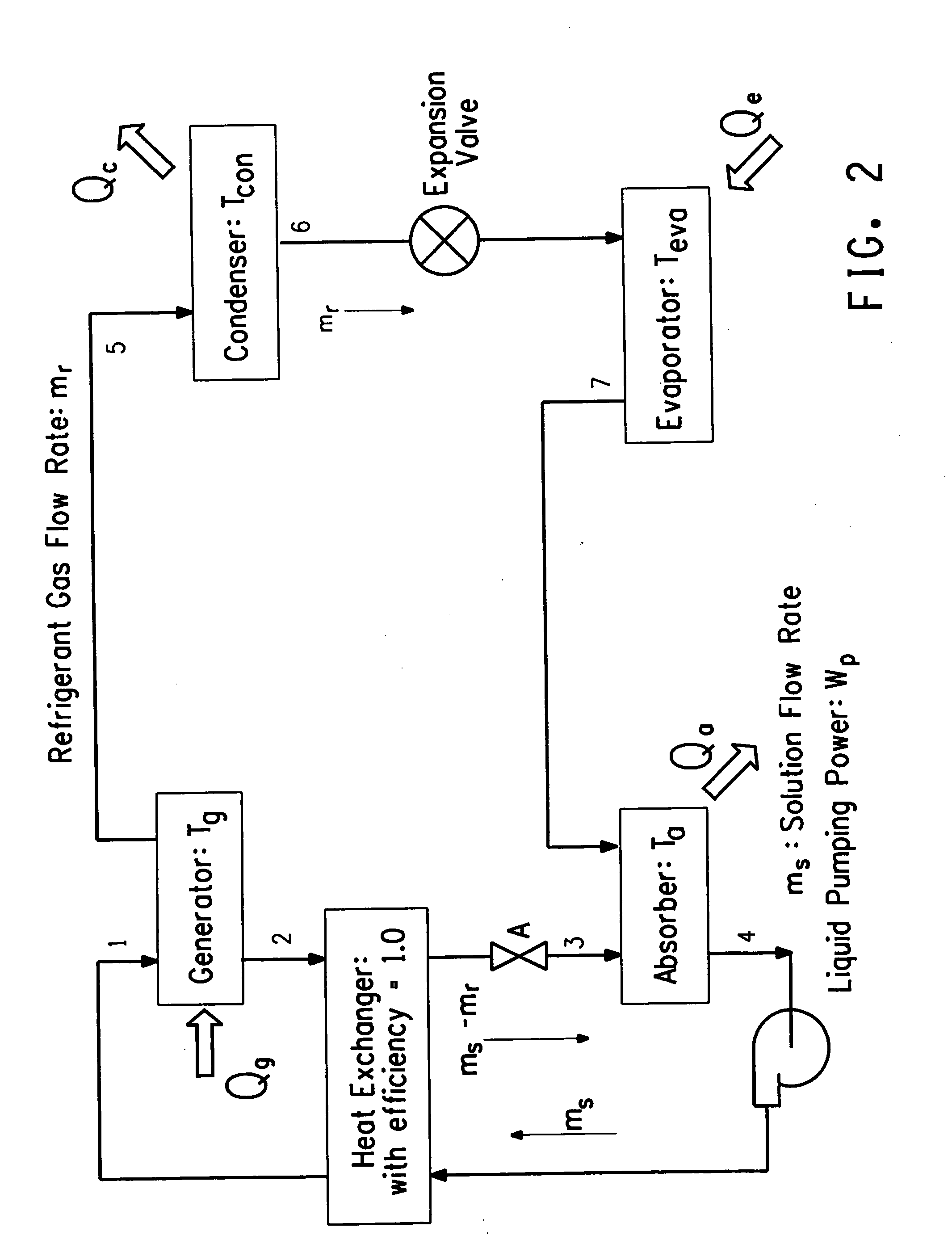
Hybrid vapor compression-absorption cycle
InactiveUS20070019708A1Limit scopeCompression machines with non-reversible cycleThermometers using electric/magnetic elementsFluorocarbonRefrigerant
The present invention relates to a hybrid vapor compression-absorption cooling or heating system and apparatus containing a refrigerant pair comprising at least one refrigerant and at least one ionic liquid. The present invention also provides for the performance of a hybrid vapor compression-absorption cycle that utilizes refrigerants and absorbents such as fluorocarbon gases in fluorinated ionic liquids. The present invention also provides a method of cooling by the execution of a hybrid vapor compression-absorption cycle using a refrigerant pair comprising at least one refrigerant and at least one ionic liquid. The present invention also provides a method of heating by the execution of a hybrid vapor compression-absorption cycle using a refrigerant pair comprising at least one refrigerant and at least one ionic liquid.
Owner:EI DU PONT DE NEMOURS & CO
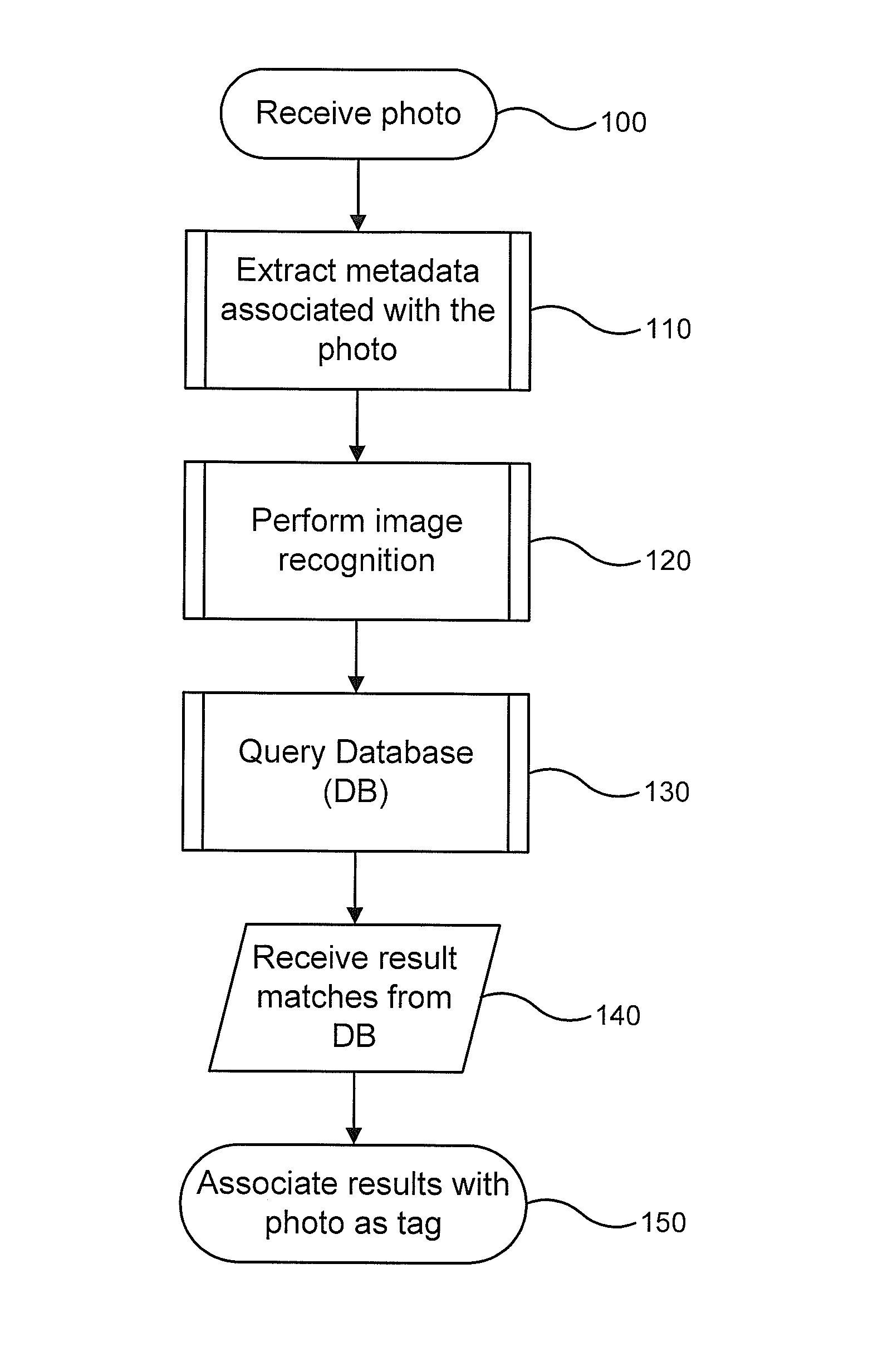
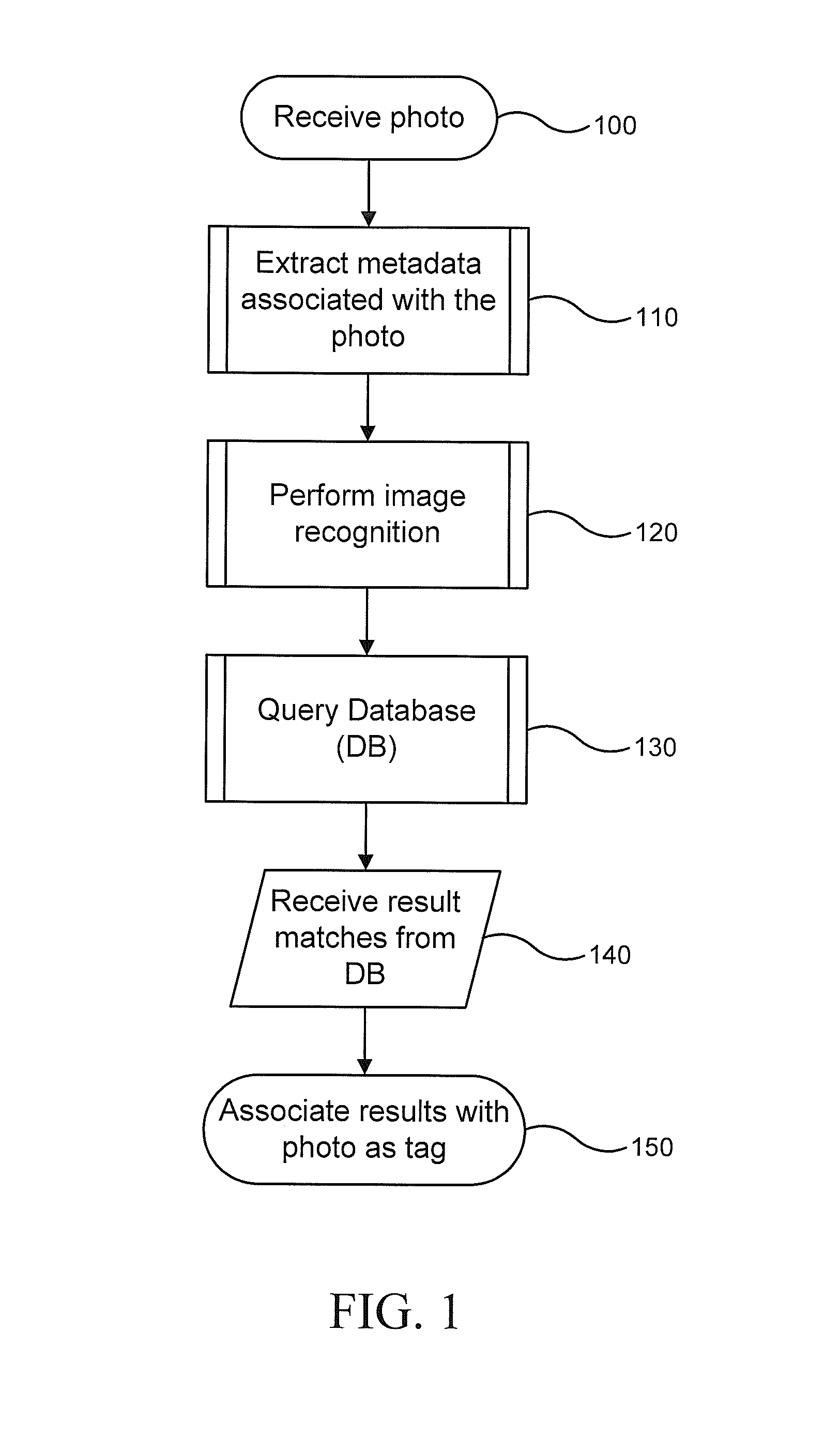
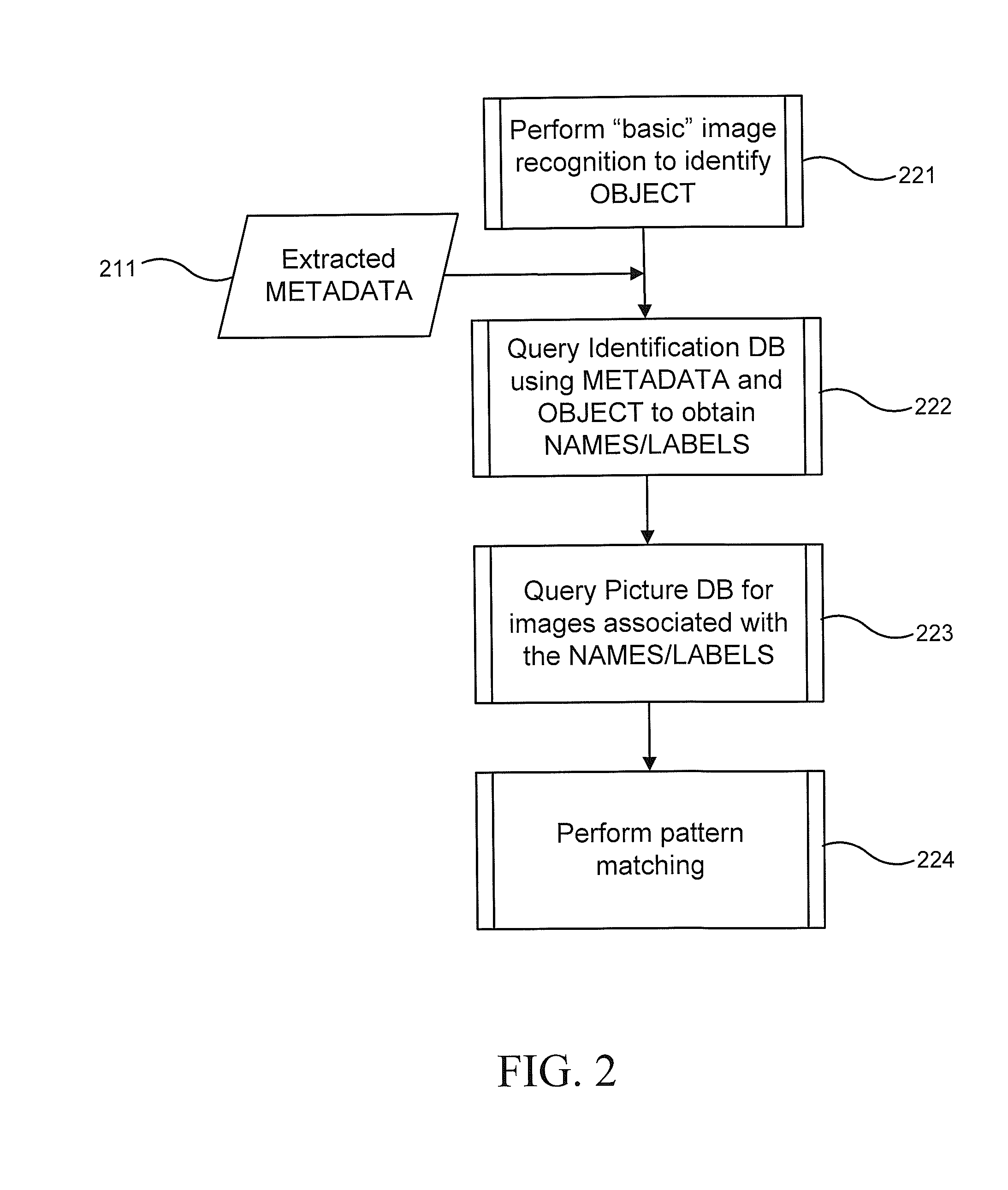
Automatic tag generation based on image content
InactiveUS20130129142A1Limit scopeMetadata video data retrievalCharacter and pattern recognitionMetadataImage based
Automatic extraction of data from and tagging of a photo (or video) having an image of identifiable objects is provided. A combination of image recognition and extracted metadata, including geographical and date / time information, is used to find and recognize objects in a photo or video. Upon finding a matching identifier for a recognized object, the photo or video is automatically tagged with one or more keywords associated with and corresponding to the recognized objects.
Owner:MICROSOFT TECH LICENSING LLC
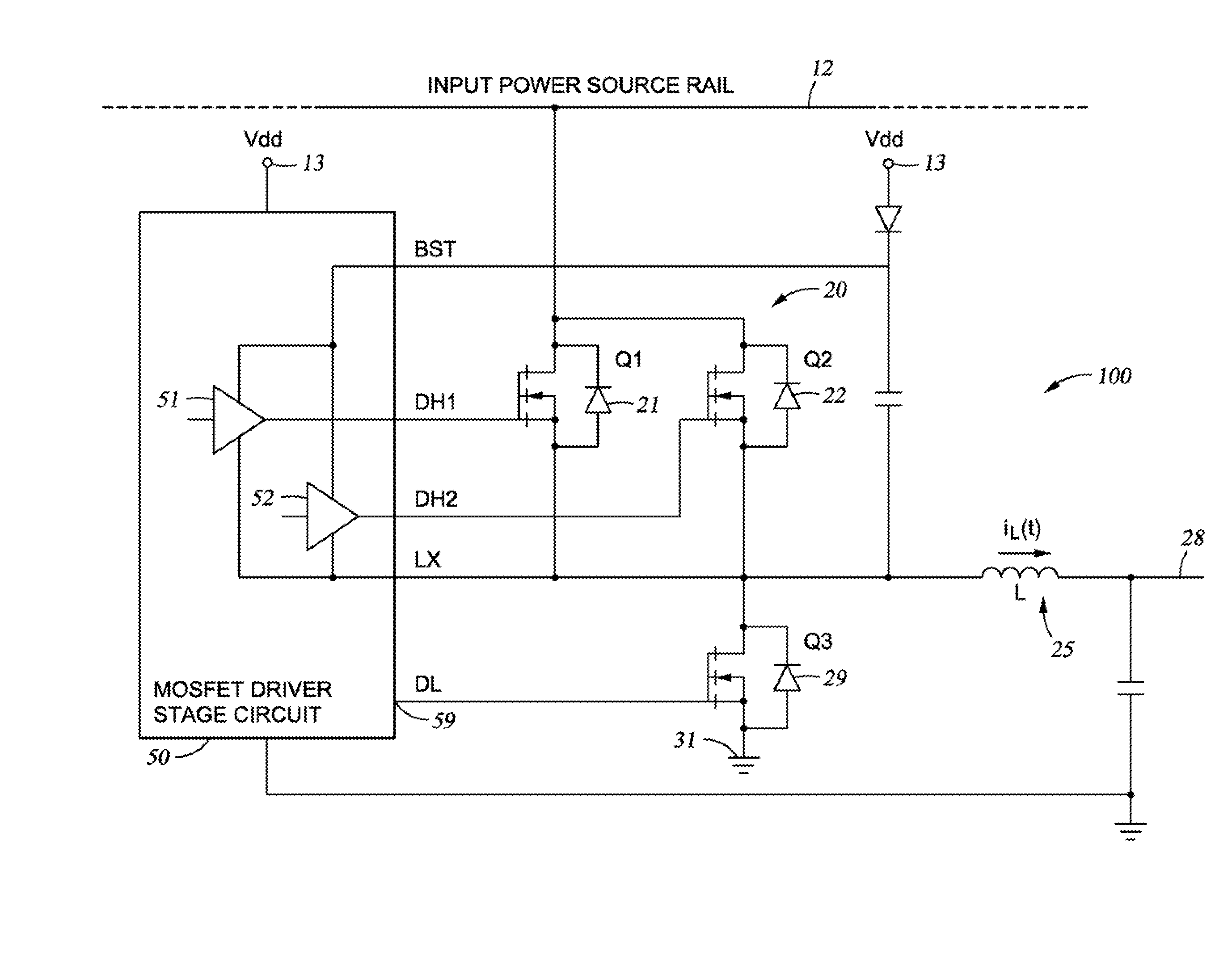
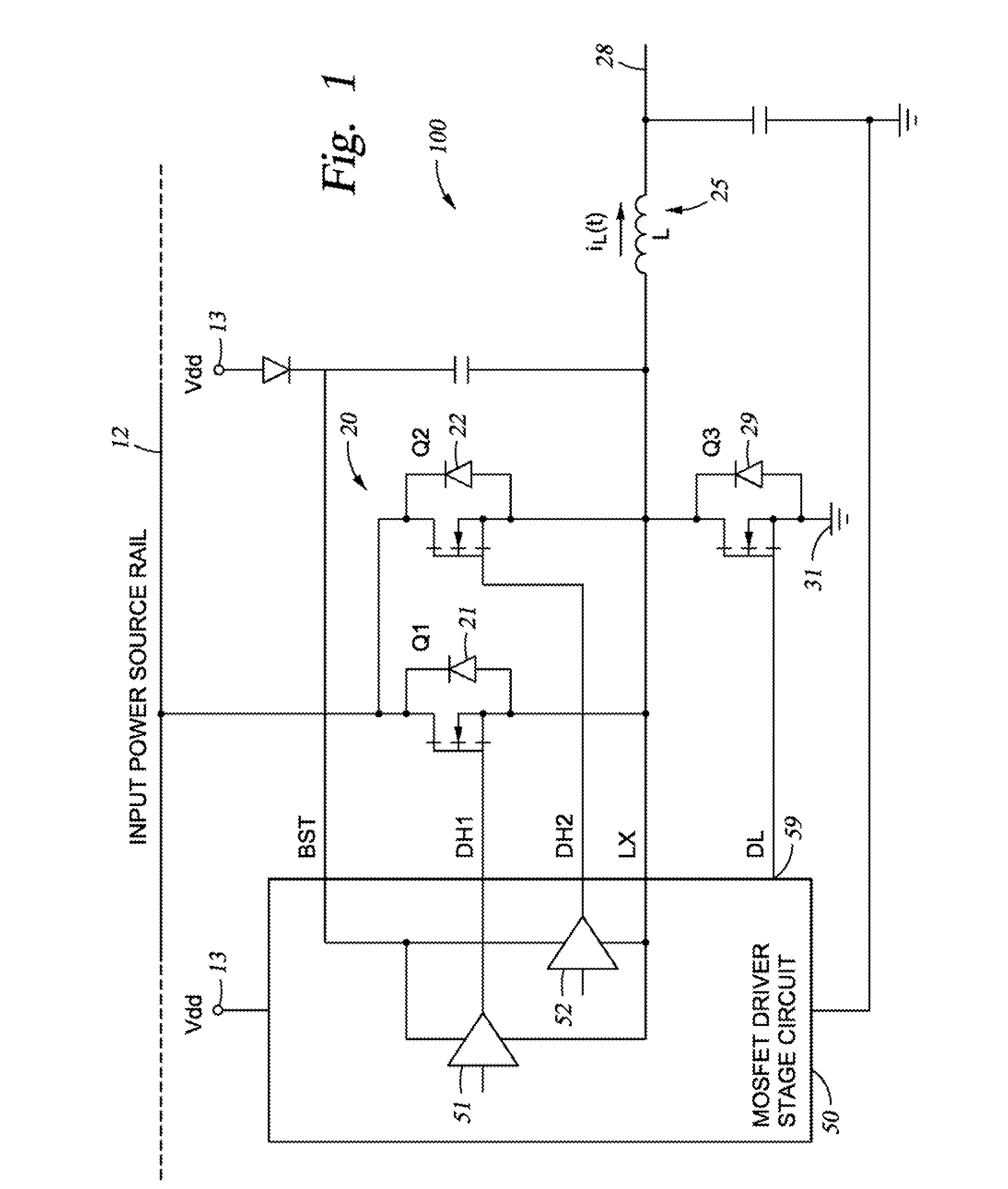
Methods, apparatus and media for control scheme for parallel high-side switching mosfets
InactiveUS20080111529A1Limit scopeEfficient power electronics conversionDc-dc conversionMOSFETInductor
The present disclosure relates to a power regulator including an inductor and a high-side switch comprising a first MOSFET and a second MOSFET in parallel. The regulator may also include an electrical pathway between the high-side switch and the inductor. A controller may also be communicatively coupled to the high-side switch. The controller may comprise logic to operate the high-side switch by simultaneously enabling the first MOSFET and disabling the second MOSFET.
Owner:DELL PROD LP
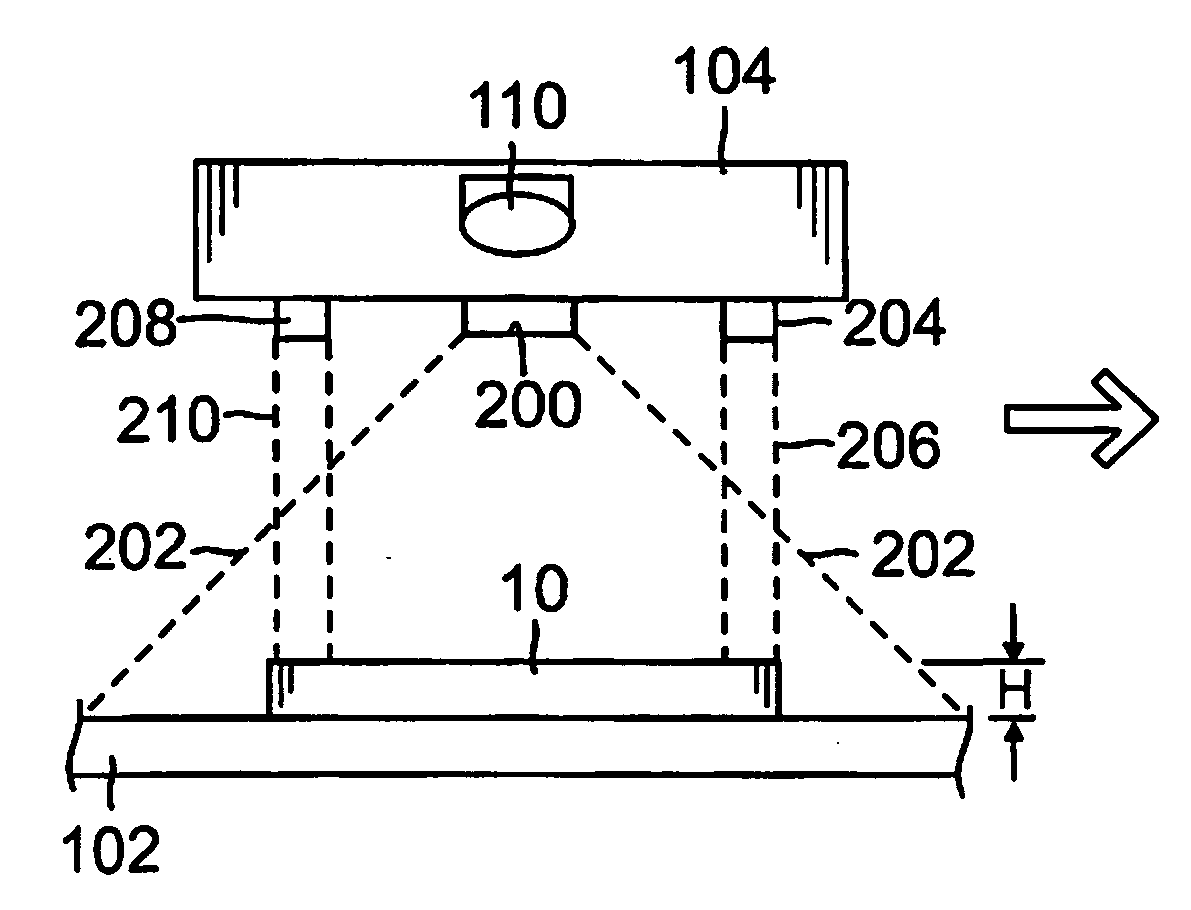
Package dimensioner and reader
InactiveUS20090323084A1Limit scopeDigital computer detailsMechanical clearance measurementsImage ViewCard reader
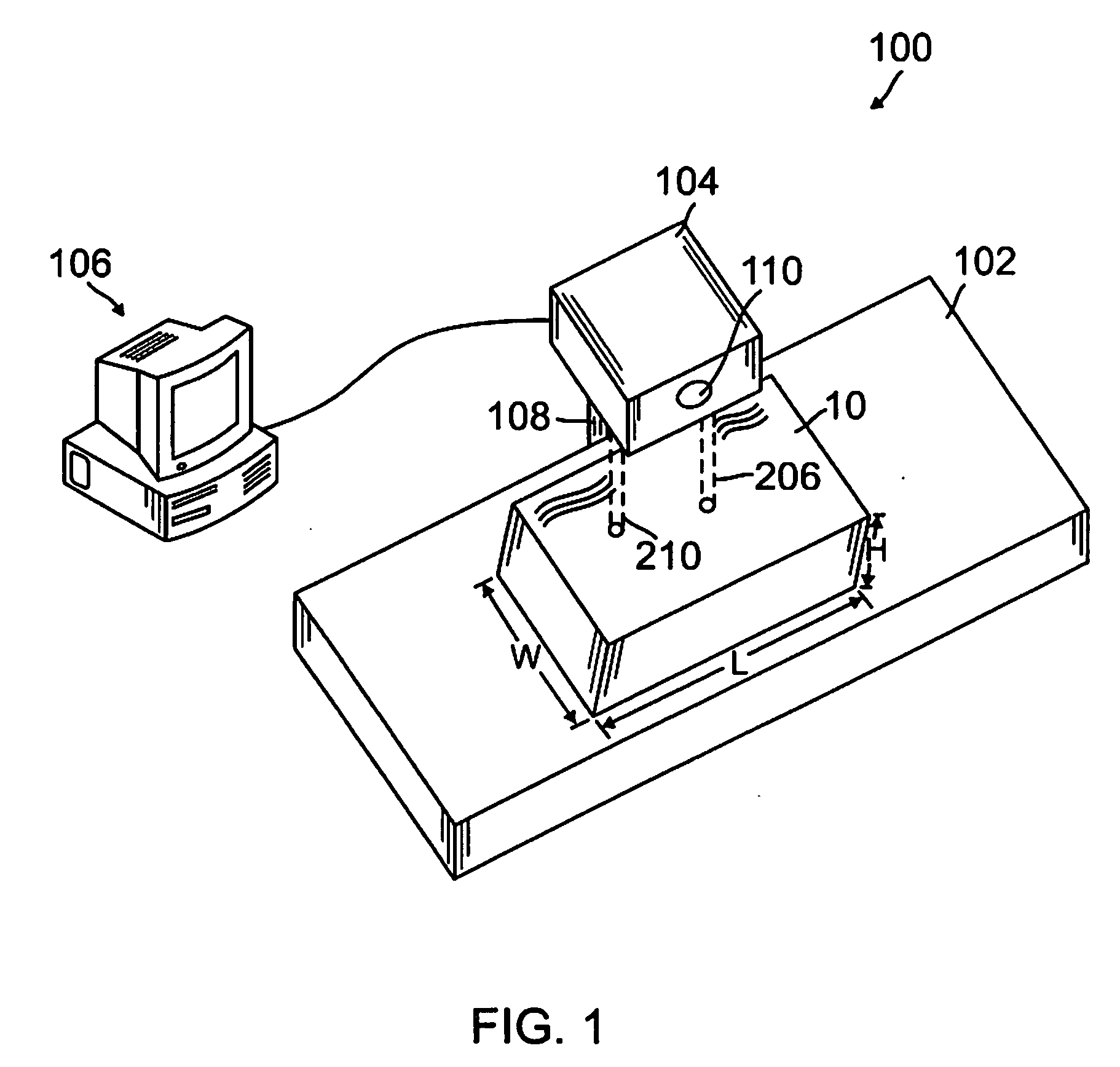
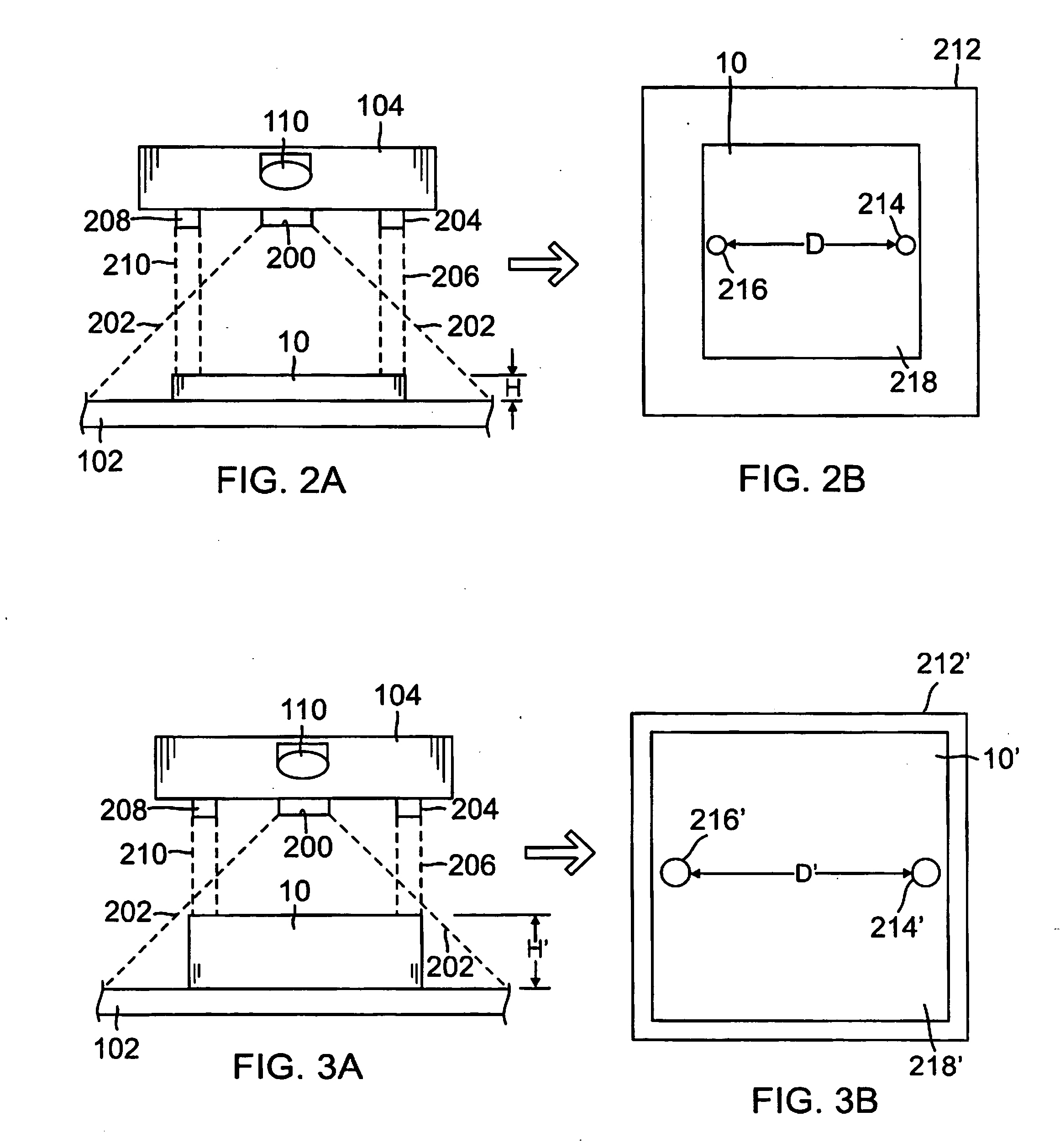
A package dimensioner and reader having a reference surface to support an object; a measurement system comprising at least one laser above the reference surface generating at least one laser beam directed towards the reference surface, and a first optical detection device above the reference surface and adjacent to the at least one laser; and a processor operatively connected to the measurement system to process an image view captured by the optical detection device. The image view comprises an object image and a laser beam image. Based on the image view the processor calculates characteristics of the box such as the height. Other characteristics of the object may be determined such a length, width, and weight, sender or receiver information, and other related information regarding the transit of the object. The package dimensioner and reader may further comprise a second optical detection device to capture other information regarding the object.
Owner:DUNN JOSEPH CHRISTEN +2
Housing Case, Method for Manufacturing Housing Case, and Glass Insert Molding Die Used in Same
ActiveUS20100014232A1Limit scopeDigital data processing detailsCasings with display/control unitsEngineeringGlass sheet
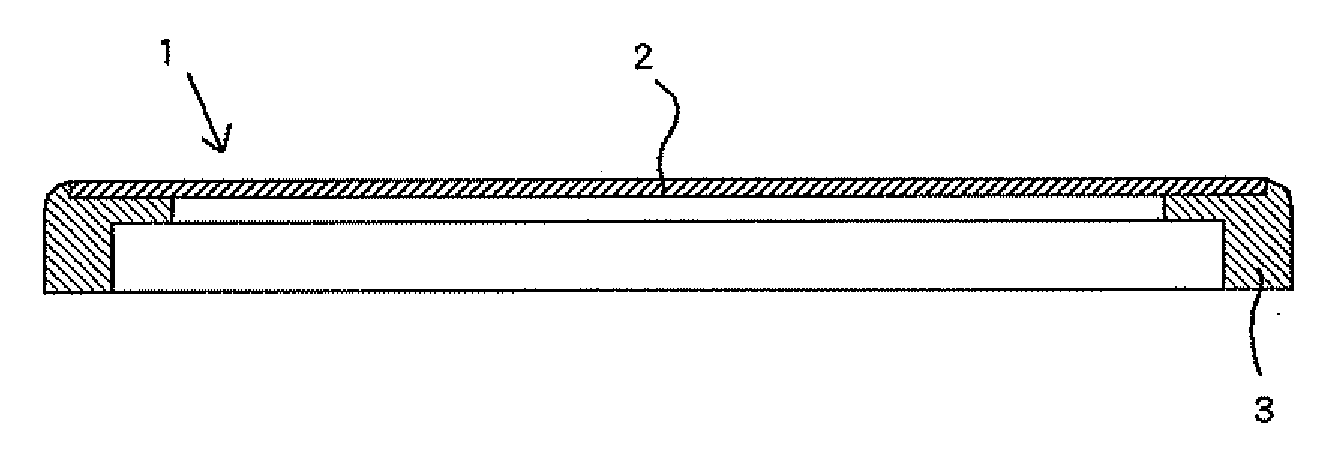
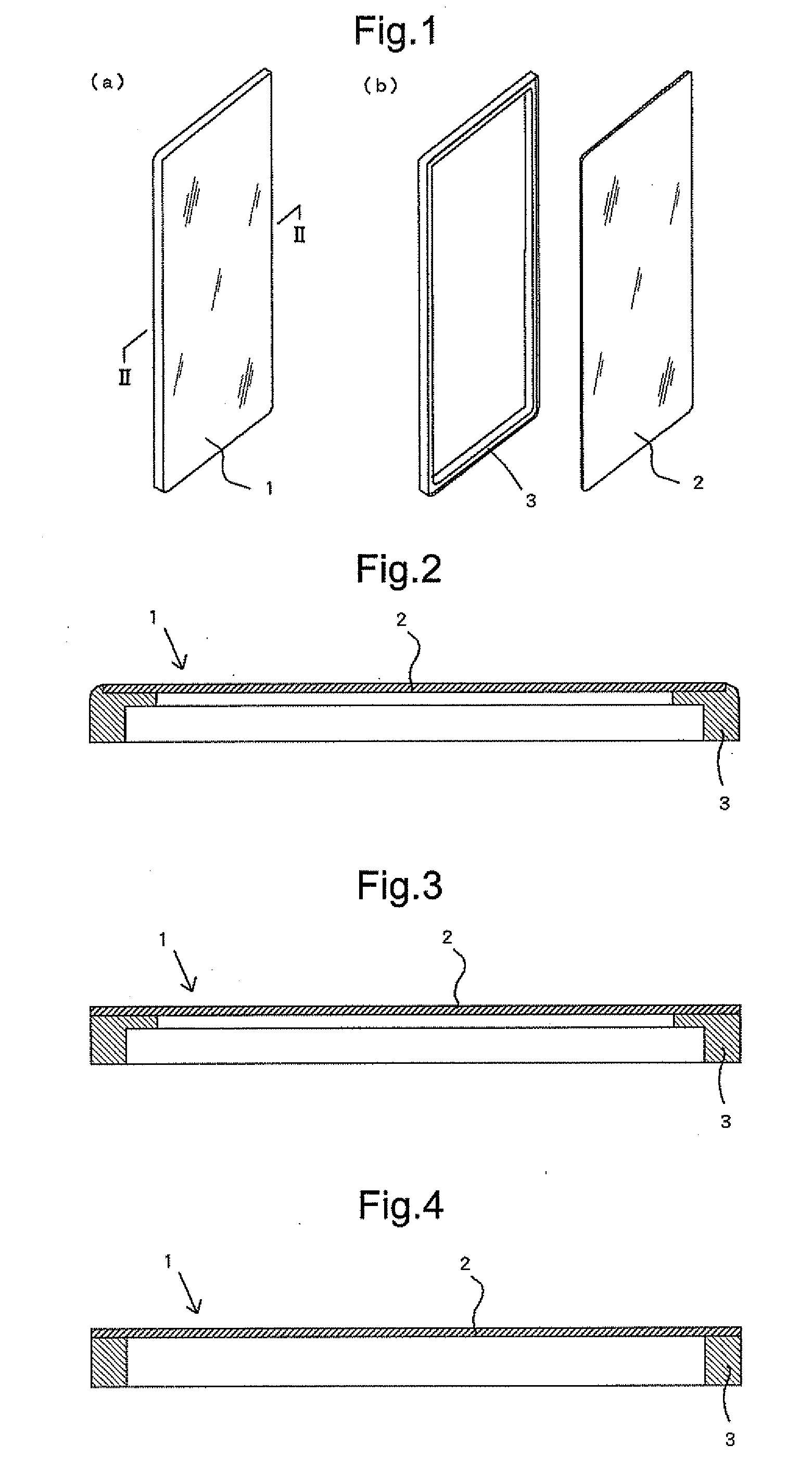
A housing case for a small electric device and communication device includes a flat plate having a dimension substantially the same as that of the front portion of the housing case and comprising at least a glass plate, and a resin frame integrated with the flat plate to support the backside periphery of the flat plate.
Owner:NISSHA PRINTING COMPANY
Communication device auto negotiate reconnect
ActiveUS20070274488A1Limit scopeSpecial service for subscribersConnection managementComputer hardwareSpeech sound
The embodiments contemplate a negotiation and reconnection method between two devices for use when an original call connection is dropped. In order to allow a reconnected call to be easily made without multiple calls from each user, a negotiation between the two devices is made during the original call, assigning reconnection authority to one of the devices. If the original call is inadvertently dropped, due to for example environmental conditions, the assigned device initiates reconnection by bypassing voicemail options that are typically encountered in a reconnection situation. The reconnection may be used when each of the two devices is attempting to reconnect. Alternatively, if the device that lost coverage is without coverage for an extended period of time, a message may be sent to the other device to inform the user of that device of the situation.
Owner:MICROSOFT TECH LICENSING LLC
Accessing Service Guide Information In A Digital Video Broadcast System
ActiveUS20120331508A1Limit scopeWell formedTelevision system detailsSpecific information broadcast systemsDigital videoTelecommunications
Apparatuses may perform and methods may include receiving a digital broadcast signal that includes a physical layer pipe identified by a predetermined identifier indicating that the physical layer pipe includes service guide bootstrap information. The bootstrap information may identify one or more service guides available for download. The physical layer pipe may include header information that identifies one or more other physical layer pipes containing portions of the service guides identified in the bootstrap information. Based on the bootstrap information and header information, a selected service guide is retrieved and presented to a user.
Owner:SAMSUNG ELECTRONICS CO LTD
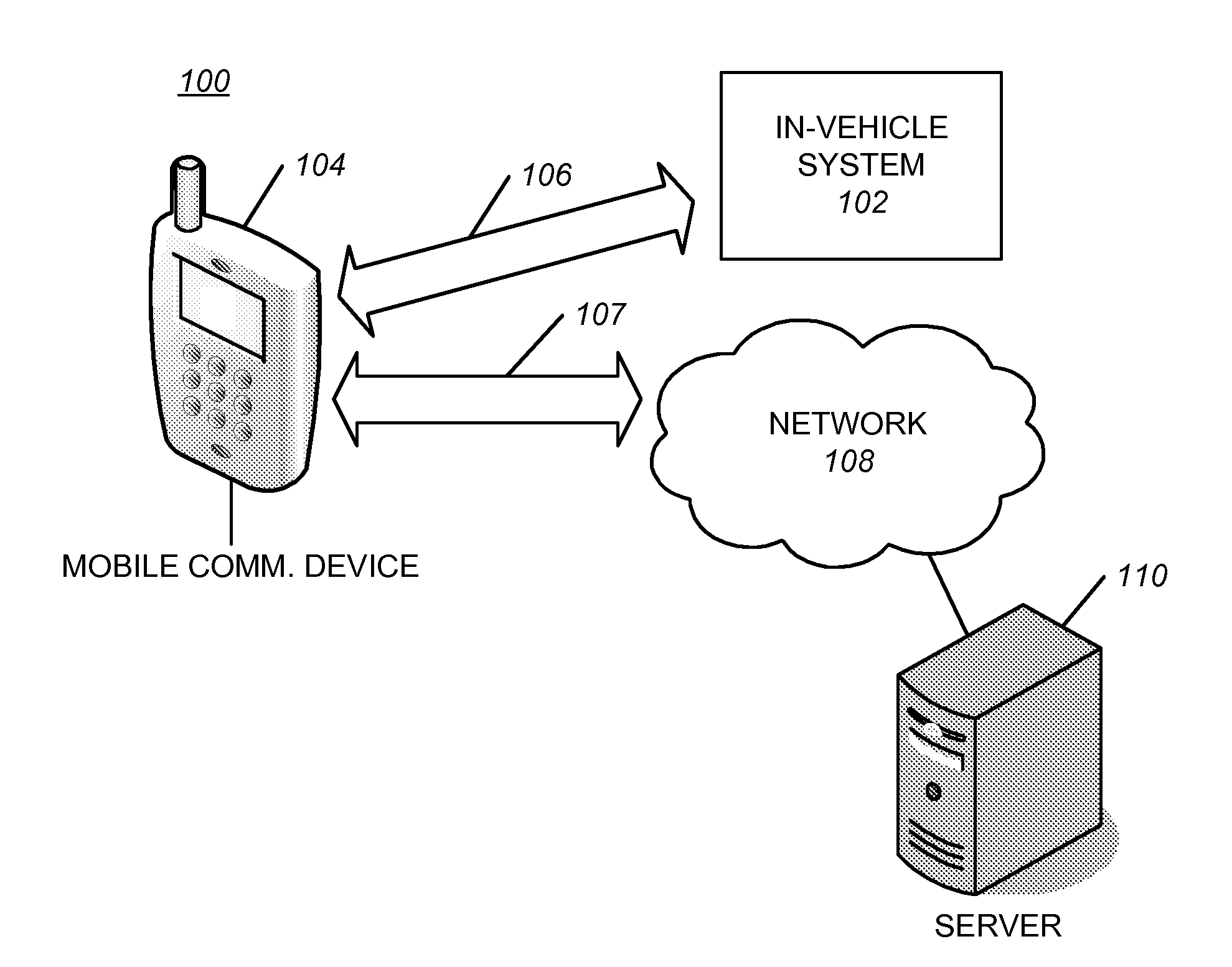
Destination information sharing for the automobile environment
ActiveUS20110184789A1Limit scopeInstruments for road network navigationDiscounts/incentivesIn vehicleReal-time computing
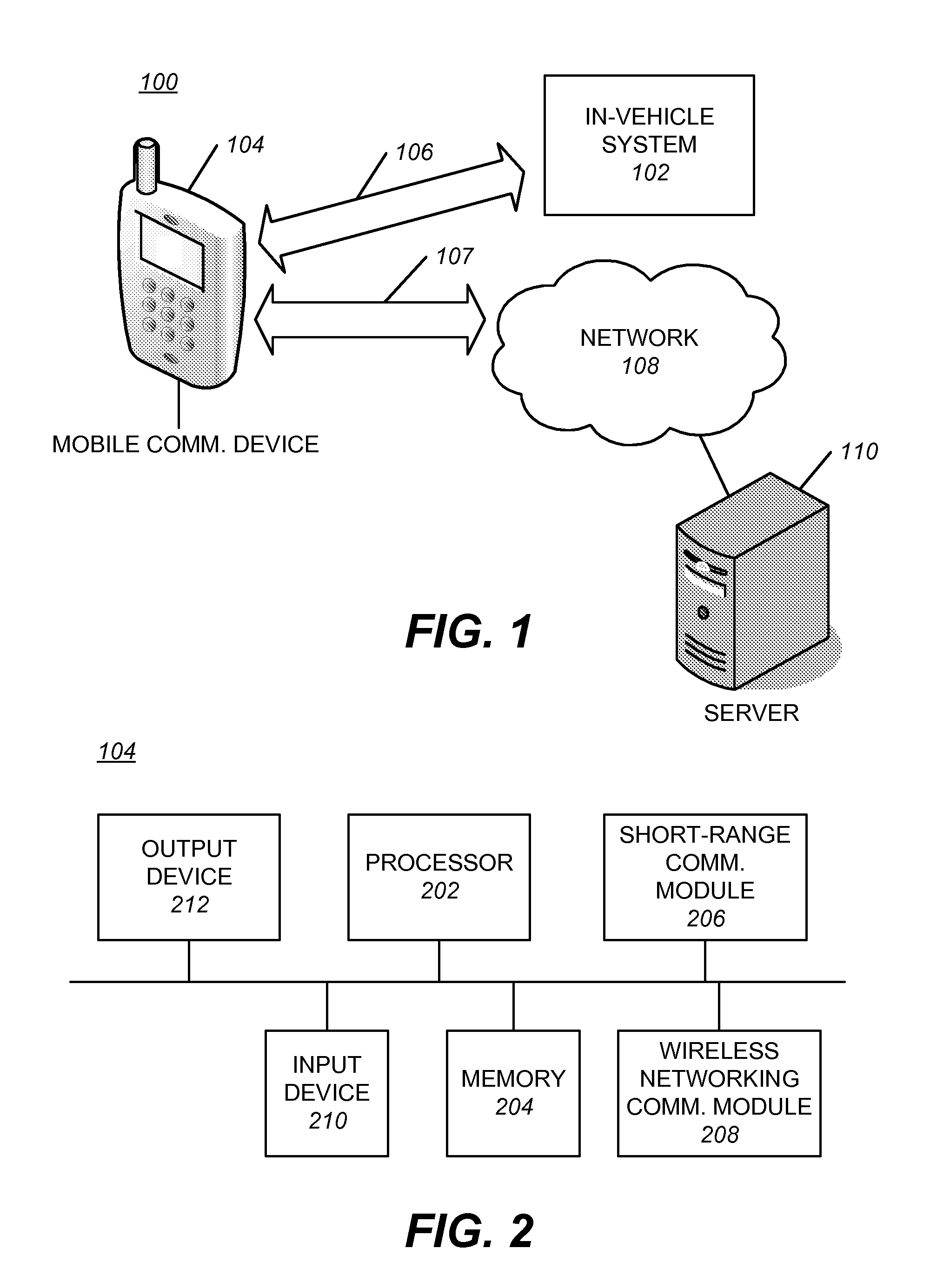
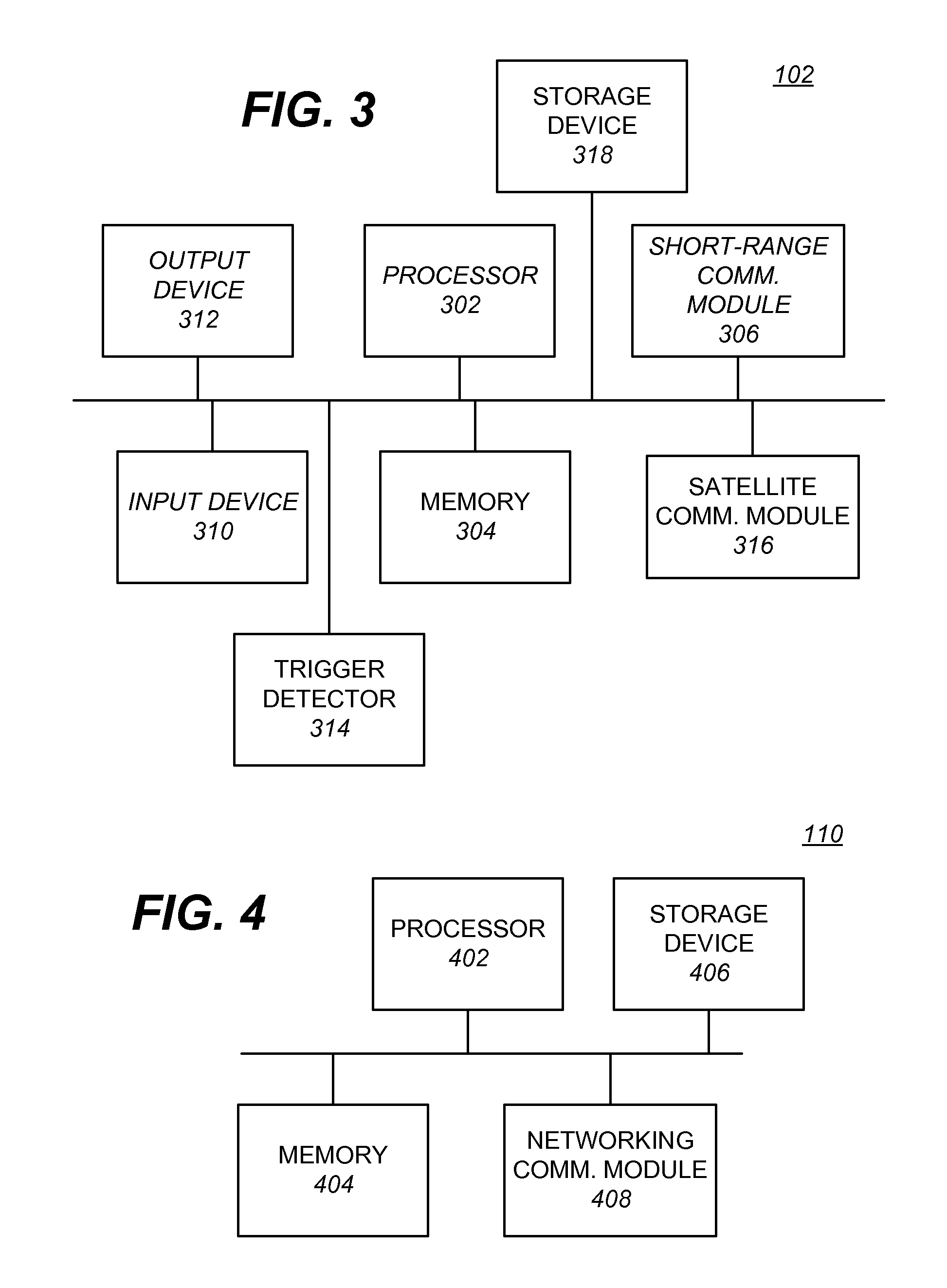
An in-vehicle system may detect an occurrence of a triggering event, detect a short-range communication connection between the in-vehicle system and a mobile communication device, send a prompt, including a request for information, to the mobile communication device, and receive a response, including the requested information, from the mobile communication device via the short-range communication module. In some embodiments, a business review, an advertisement, or a redeemable electronic coupon may be sent to the mobile communication device after the requested information is provided. Furthermore, destination information may be shared between the in-vehicle system and the mobile communication device in response to the triggering event.
Owner:HONDA MOTOR CO LTD
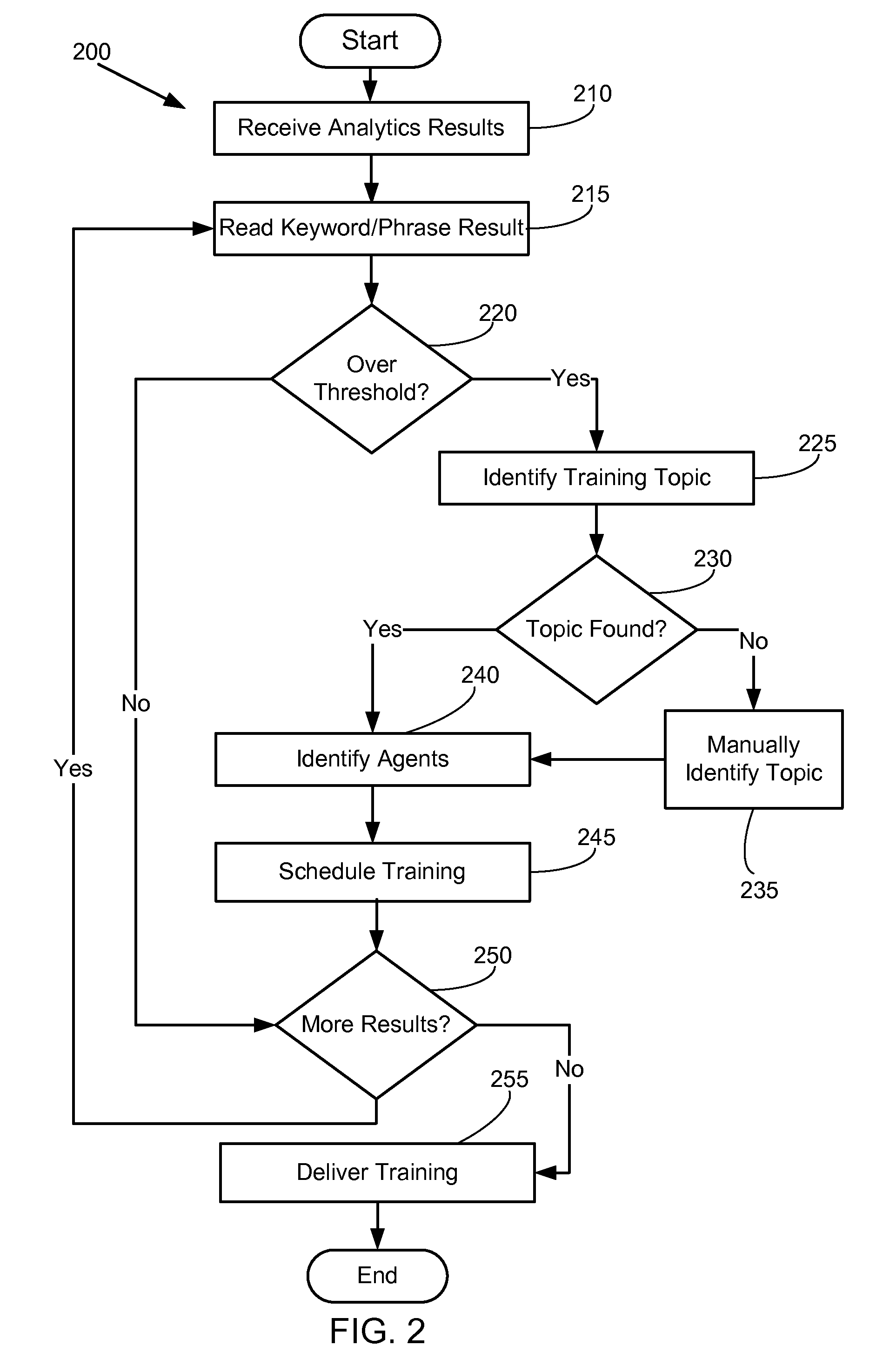
Communication analytics training management system for call center agents
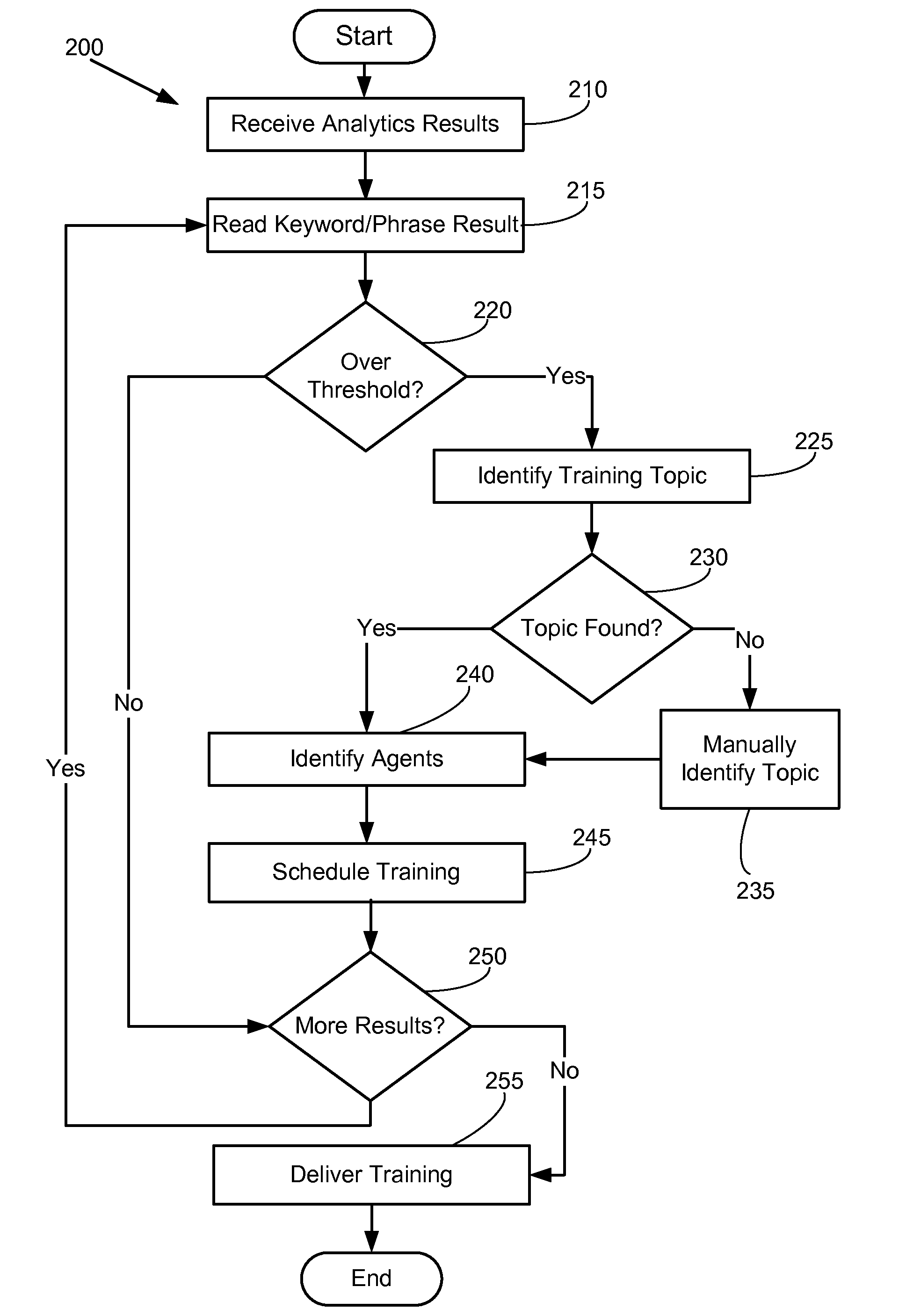
Technologies are generally presented herein pertaining to identifying a training topic for agents at a contact center. In various embodiments, these technologies comprise performing an analysis on communications conducted between agents at the contact center and contact parties over a time period. In particular embodiments, the analysis performed on the communications involves identifying a number of occurrences of a keyword or a keyphrase found in the communications between the agents and the contact parties. Further, in various embodiments, in response to the number of occurrences of the keyword or the keyphrase over the time period being more than a predetermined threshold, the technologies presented herein comprise automatically identifying a training topic associated with the keyword or the keyphrase, and then providing a training course to the agent.
Owner:NOBLE SYSTEMS CORPORATION
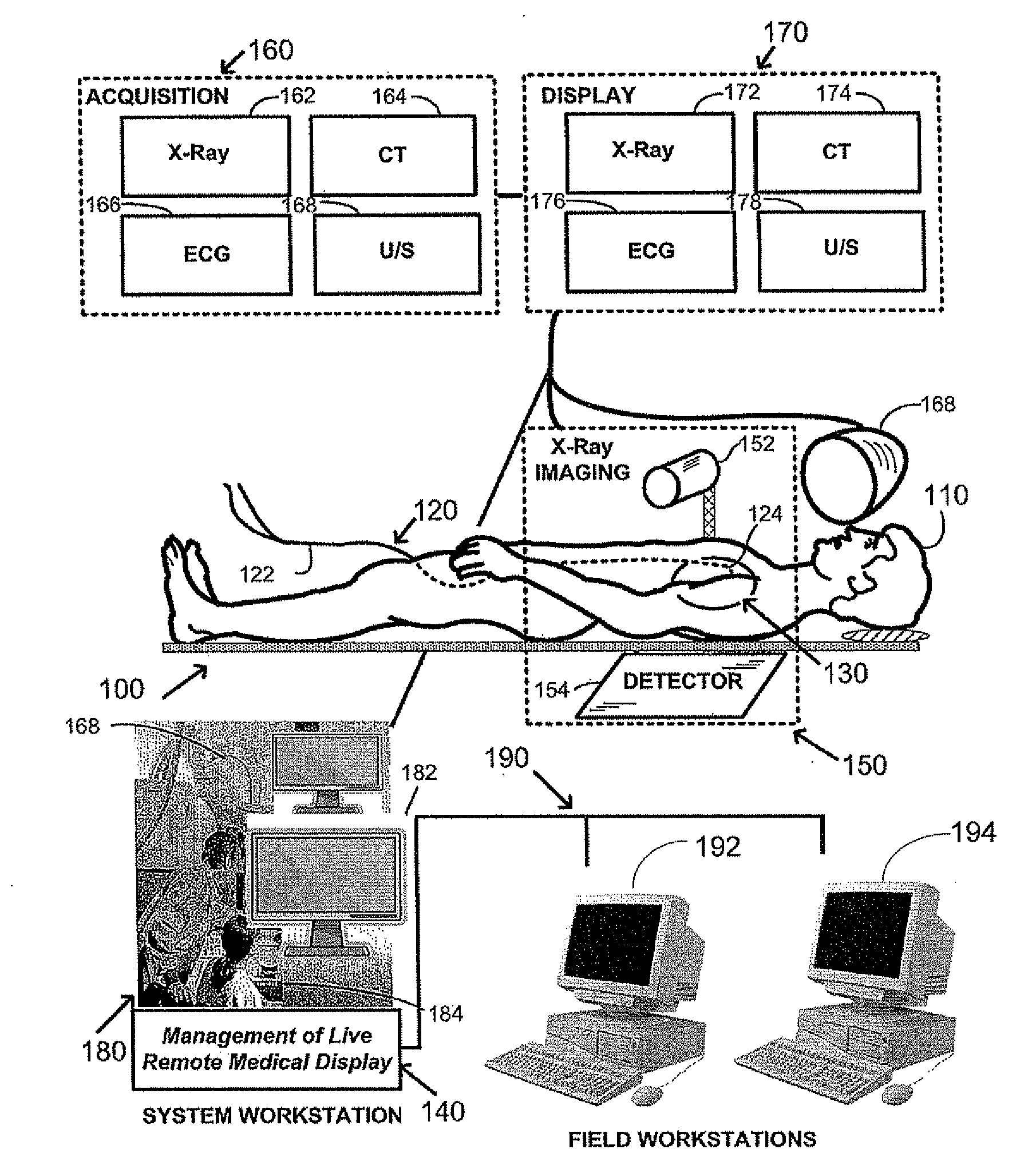
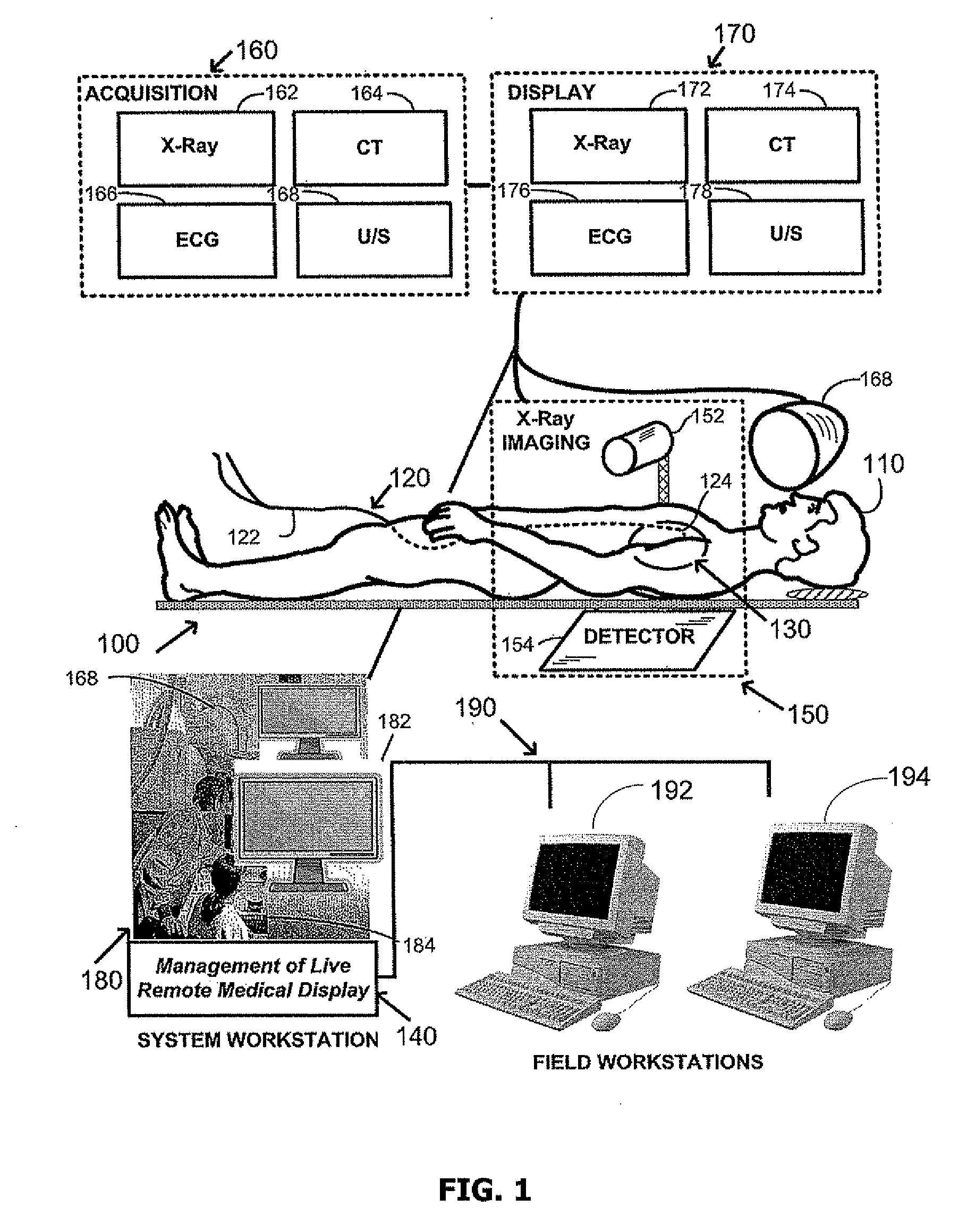
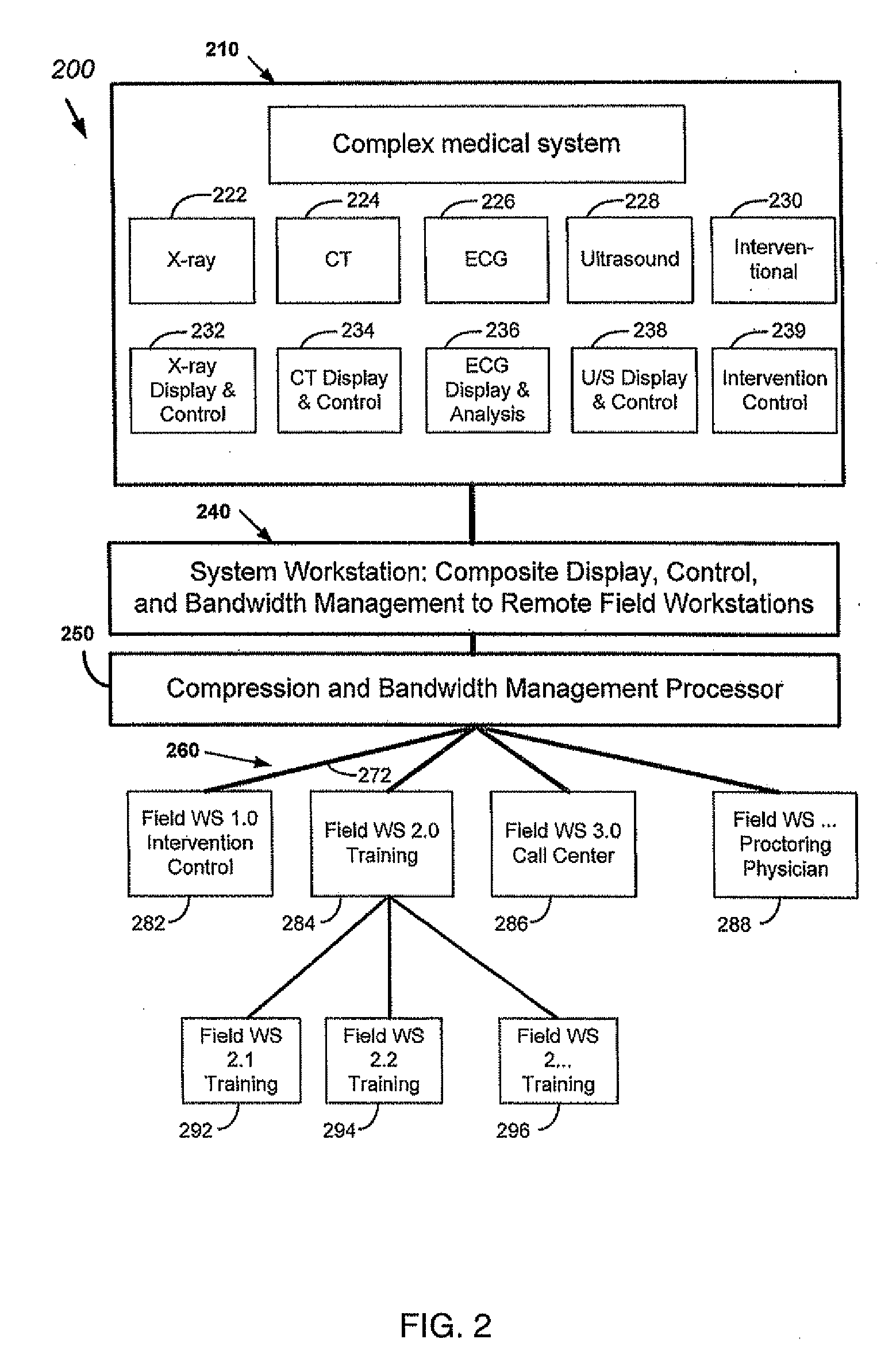
Management of live remote medical display
ActiveUS20090012821A1Less bandwidthLimit scopeMedical imagesSelective content distributionMedical systemsDisplay device
Owner:STEREOTAXIS
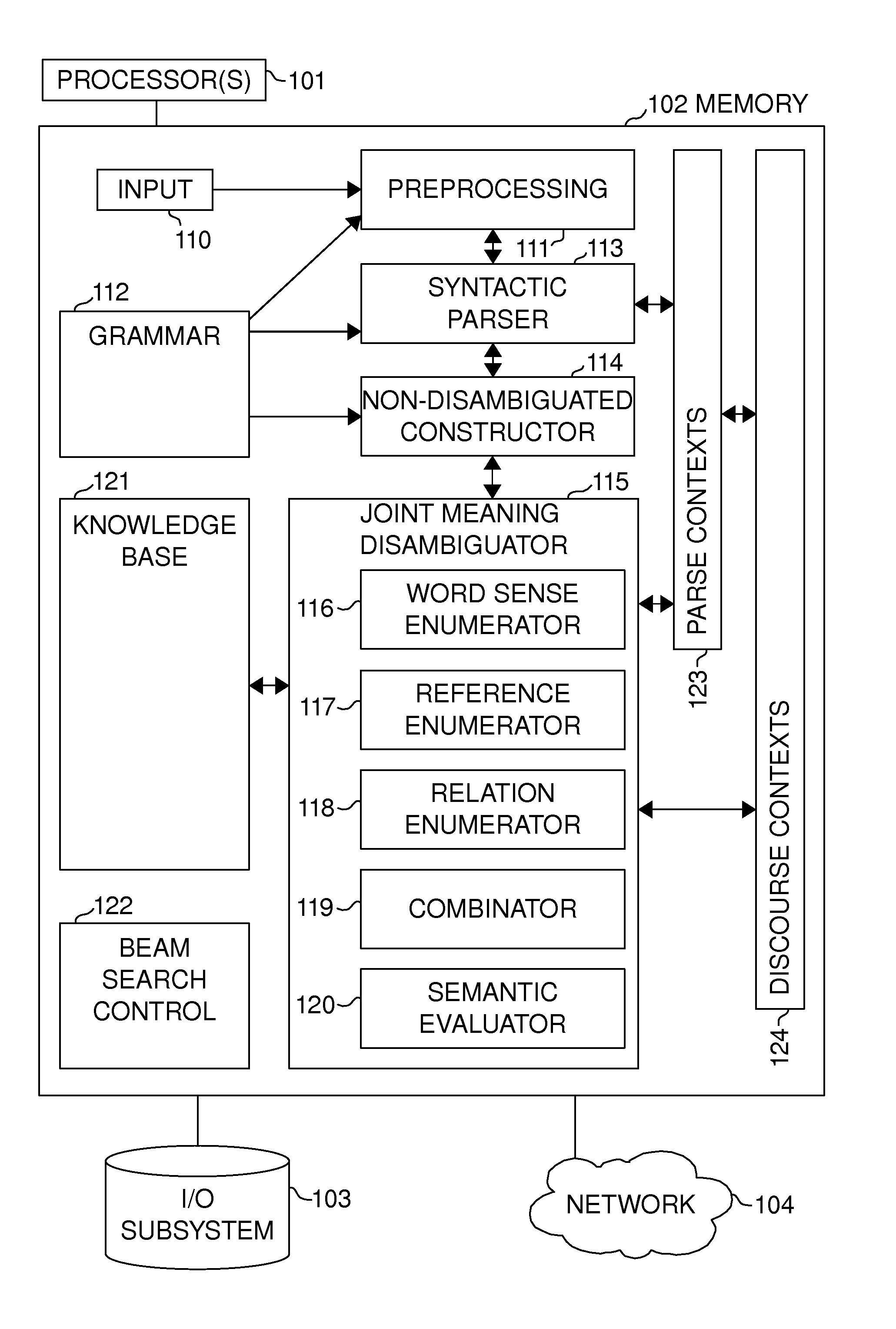
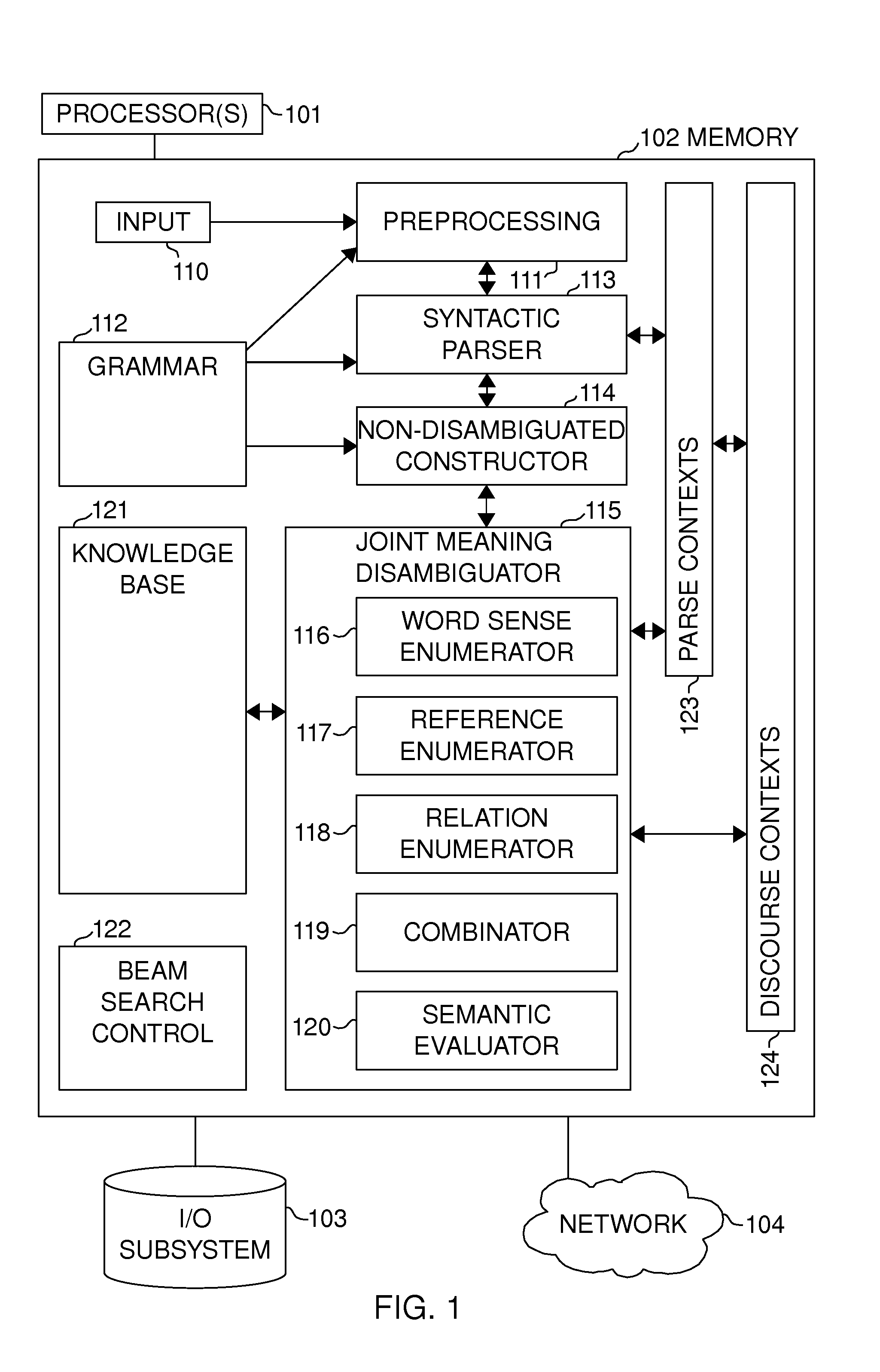
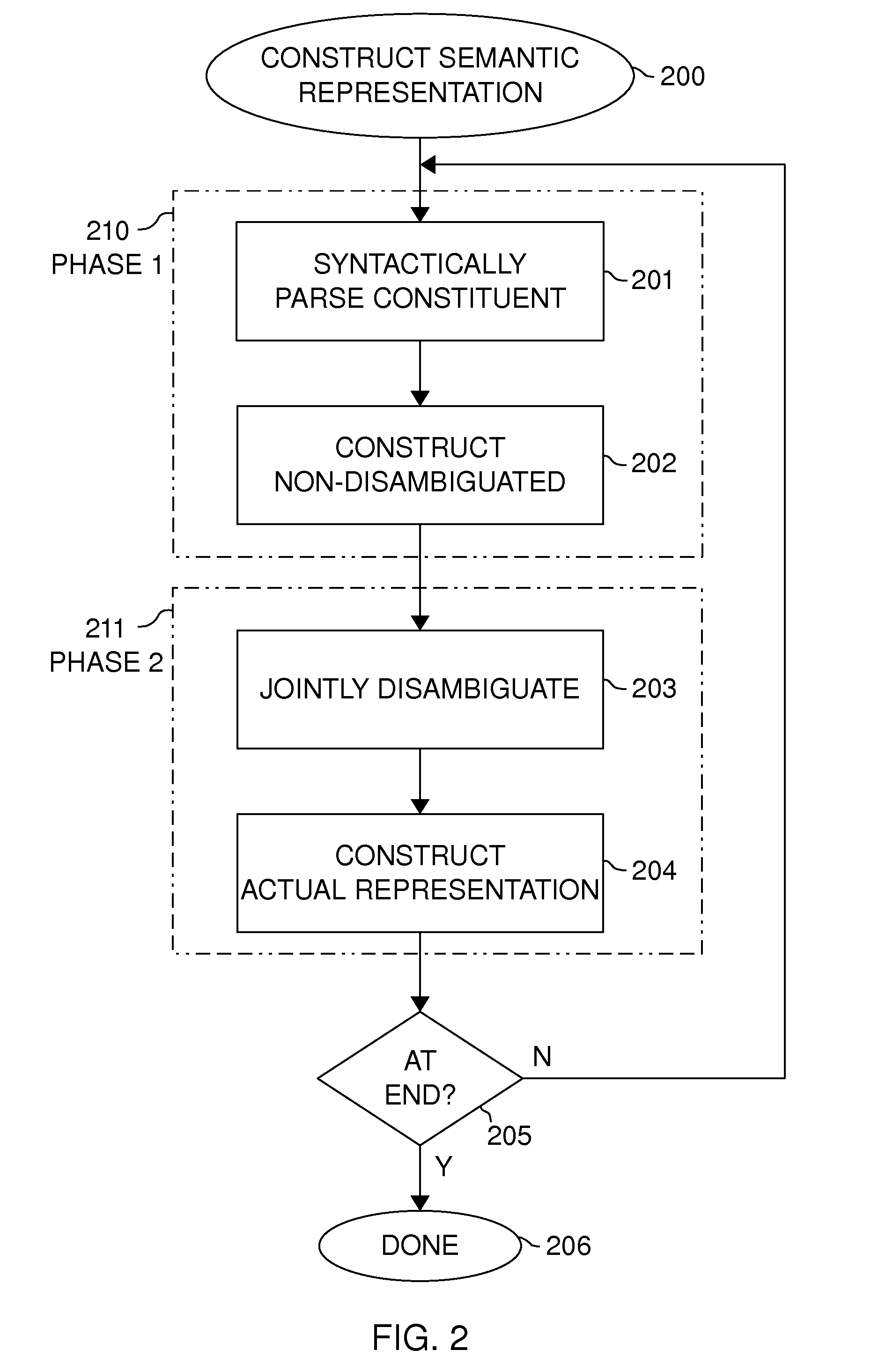
Joint disambiguation of the meaning of a natural language expression
InactiveUS20110119047A1Limit scopeSemantic analysisSpecial data processing applicationsNatural language generationAmbiguity
At least two ambiguous aspects of the meaning of a natural language expression are disambiguated jointly. In the preferred embodiment, word sense ambiguity, reference ambiguity, and relation ambiguity are resolved simultaneously, finding the disambiguation result(s) that simultaneously optimize the weight of the solution, taking into account semantic information, constraints, and common sense knowledge. Choices are enumerated for each constituent being disambiguated, combinations of choices are constructed and evaluated according to semantic information on which meanings are sensible, and the choices with the best weights are selected, with the enumeration pruned aggressively to reduce computational cost.
Owner:CLAUSAL COMPUTING
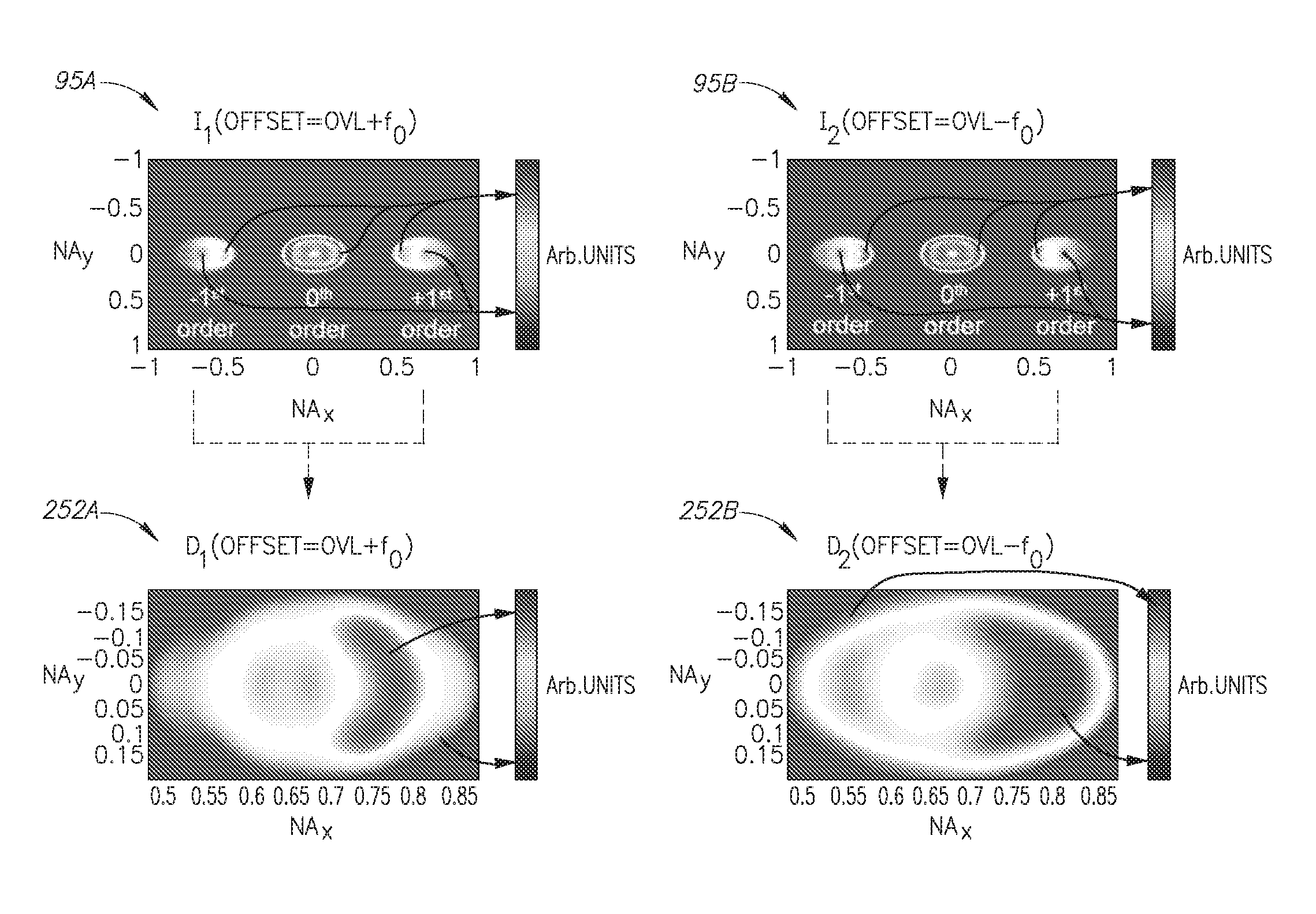
Methods of analyzing and utilizing landscapes to reduce or eliminate inaccuracy in overlay optical metrology
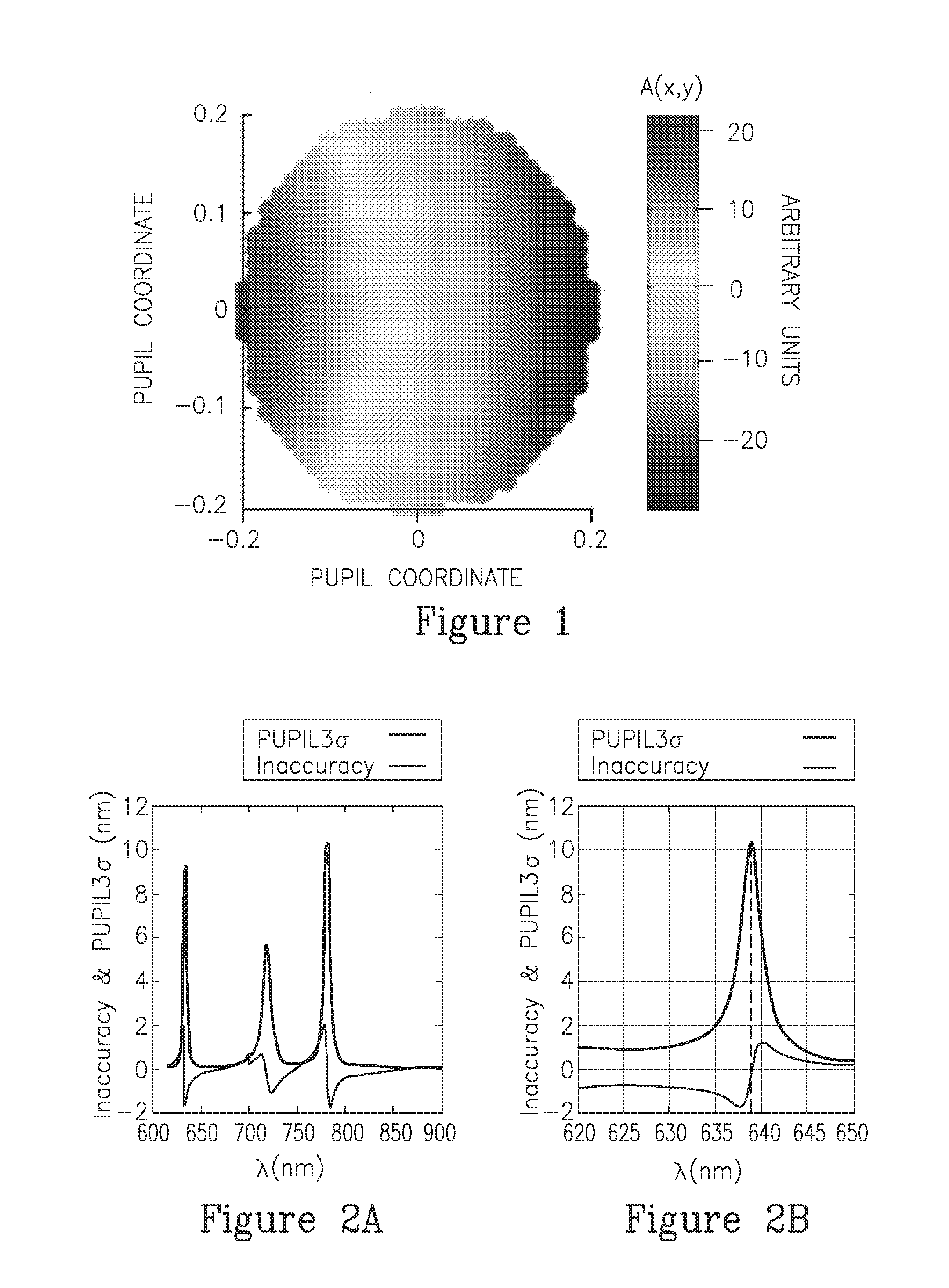
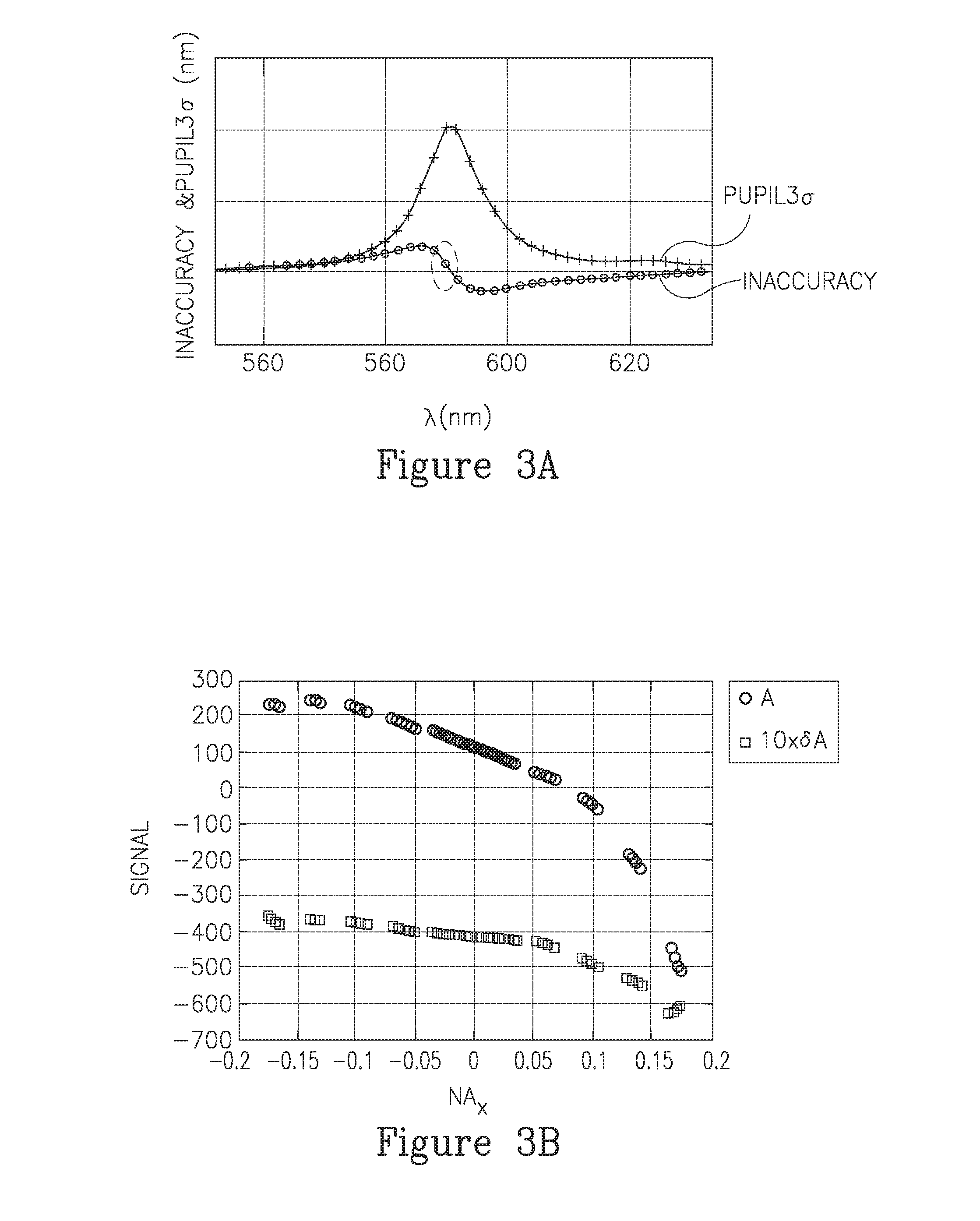
ActiveUS20160313658A1Limit scopeSemiconductor/solid-state device testing/measurementPhotomechanical apparatusOptical metrologyMeasurement precision
Methods are provided for deriving a partially continuous dependency of metrology metric(s) on recipe parameter(s), analyzing the derived dependency, determining a metrology recipe according to the analysis, and conducting metrology measurement(s) according to the determined recipe. The dependency may be analyzed in form of a landscape such as a sensitivity landscape in which regions of low sensitivity and / or points or contours of low or zero inaccuracy are detected, analytically, numerically or experimentally, and used to configure parameters of measurement, hardware and targets to achieve high measurement accuracy. Process variation is analyzed in terms of its effects on the sensitivity landscape, and these effects are used to characterize the process variation further, to optimize the measurements and make the metrology both more robust to inaccuracy sources and more flexible with respect to different targets on the wafer and available measurement conditions.
Owner:KLA TENCOR TECH CORP
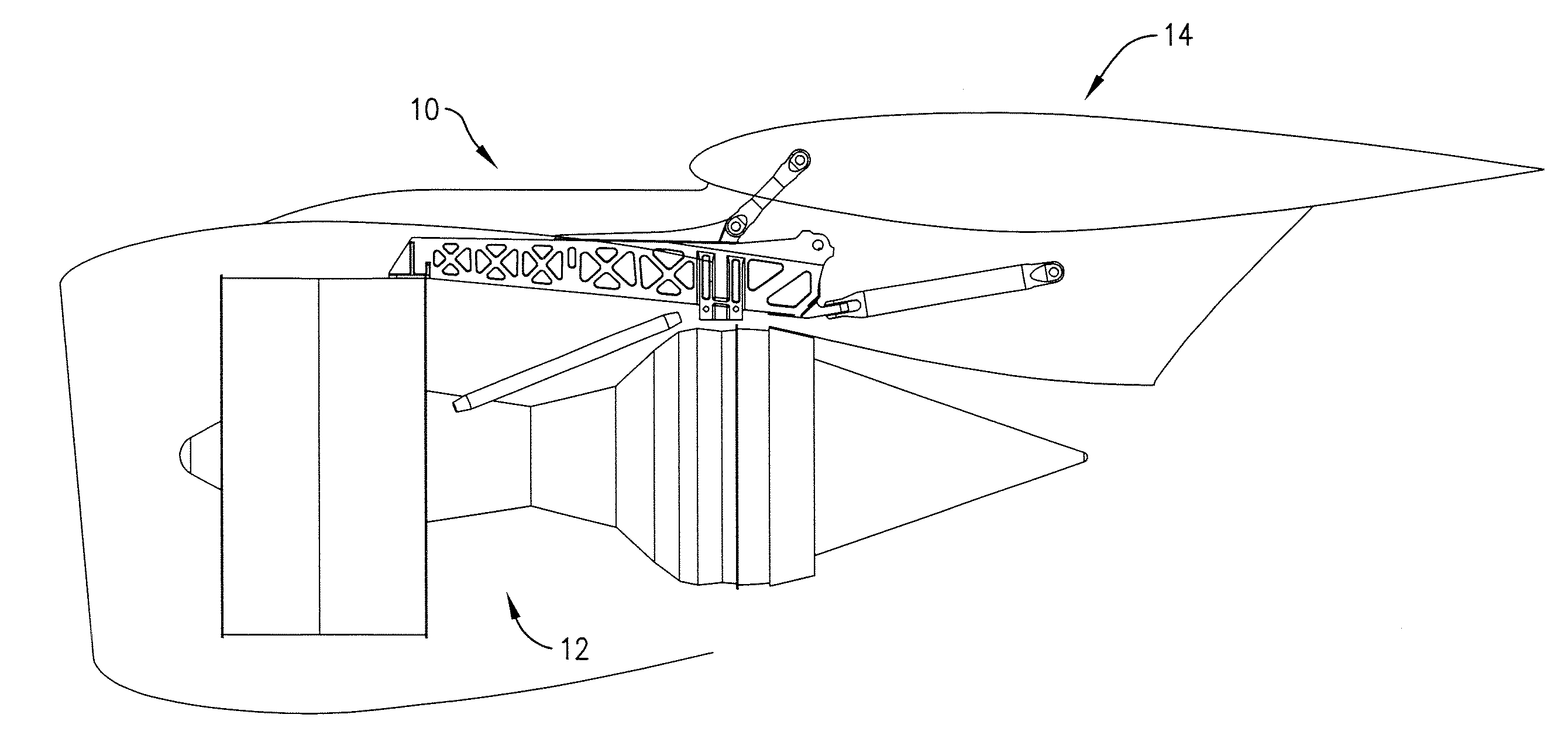
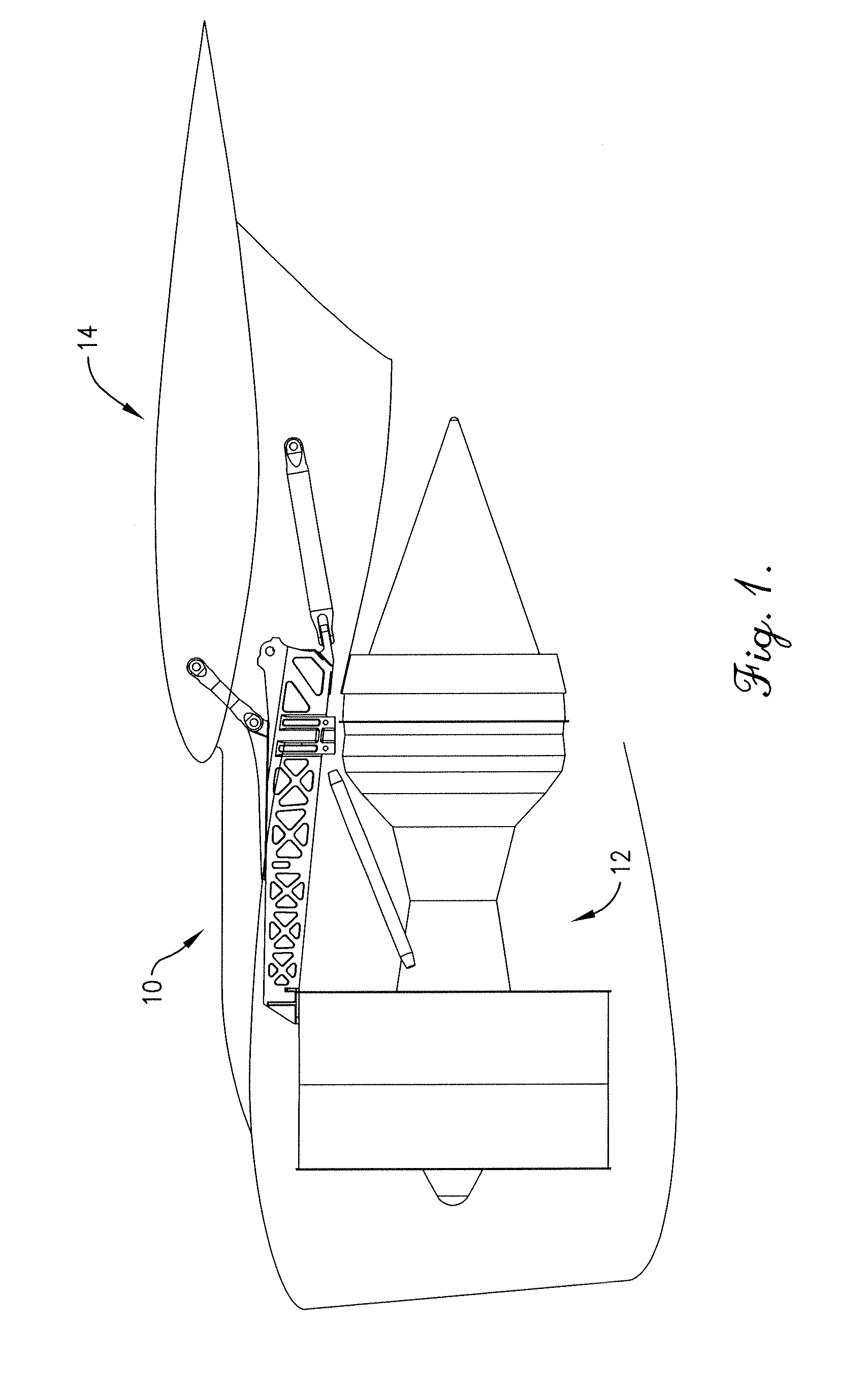
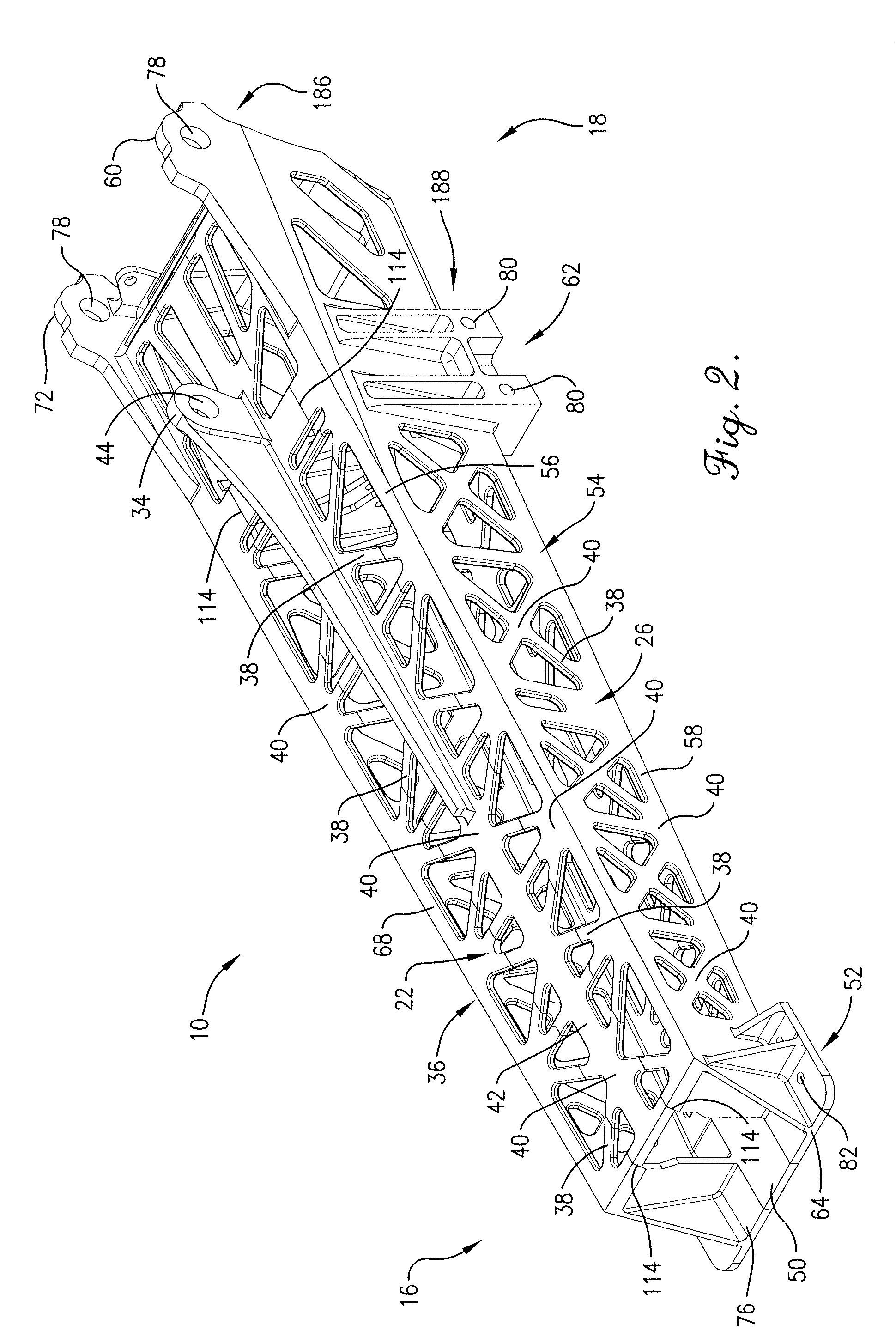
Truss-shaped engine pylon and method of making same
ActiveUS20110121132A1Limit scopeBuilding roofsMetal-working apparatusEngineeringStructural engineering
Owner:SPIRIT AEROSYSTEMS
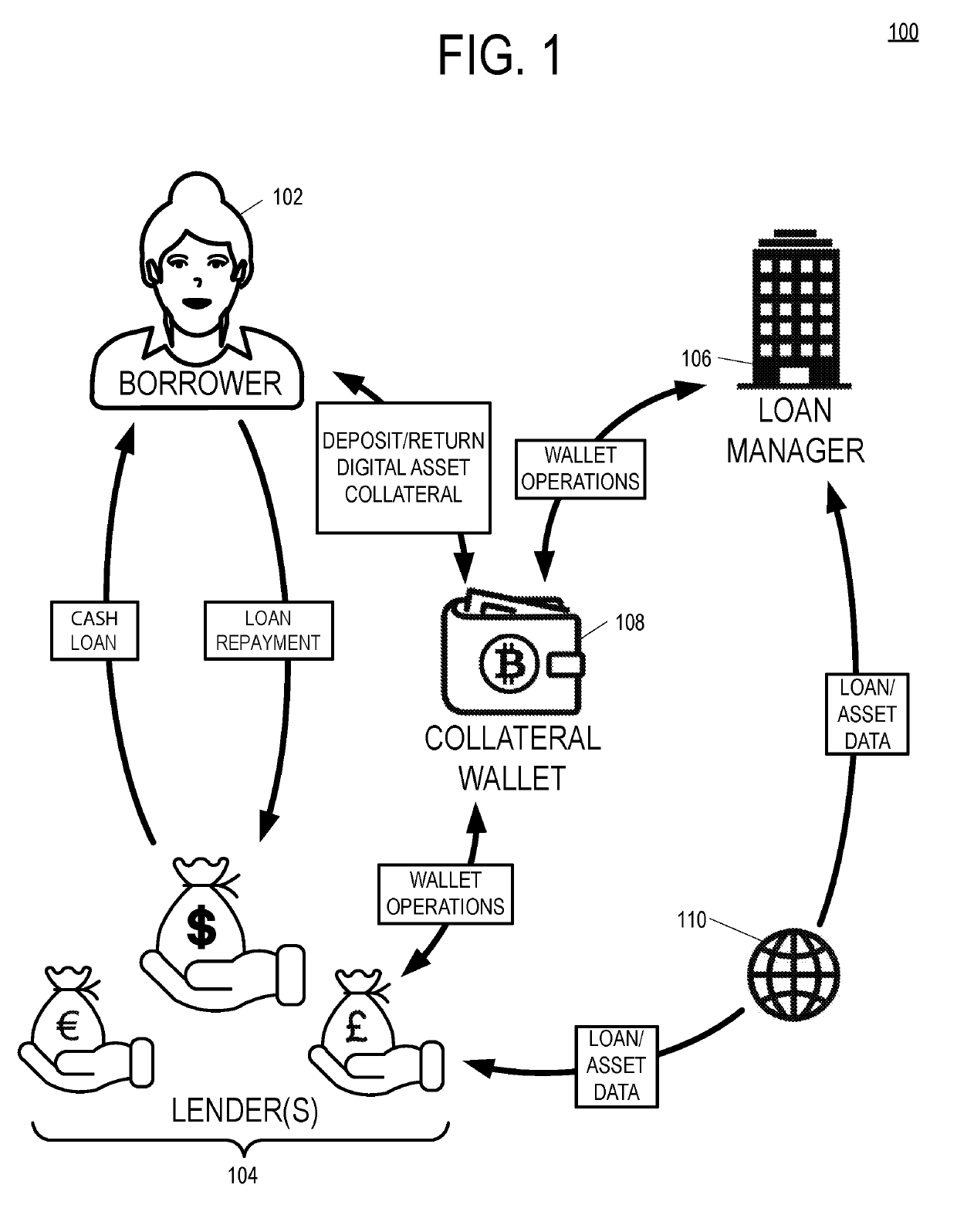
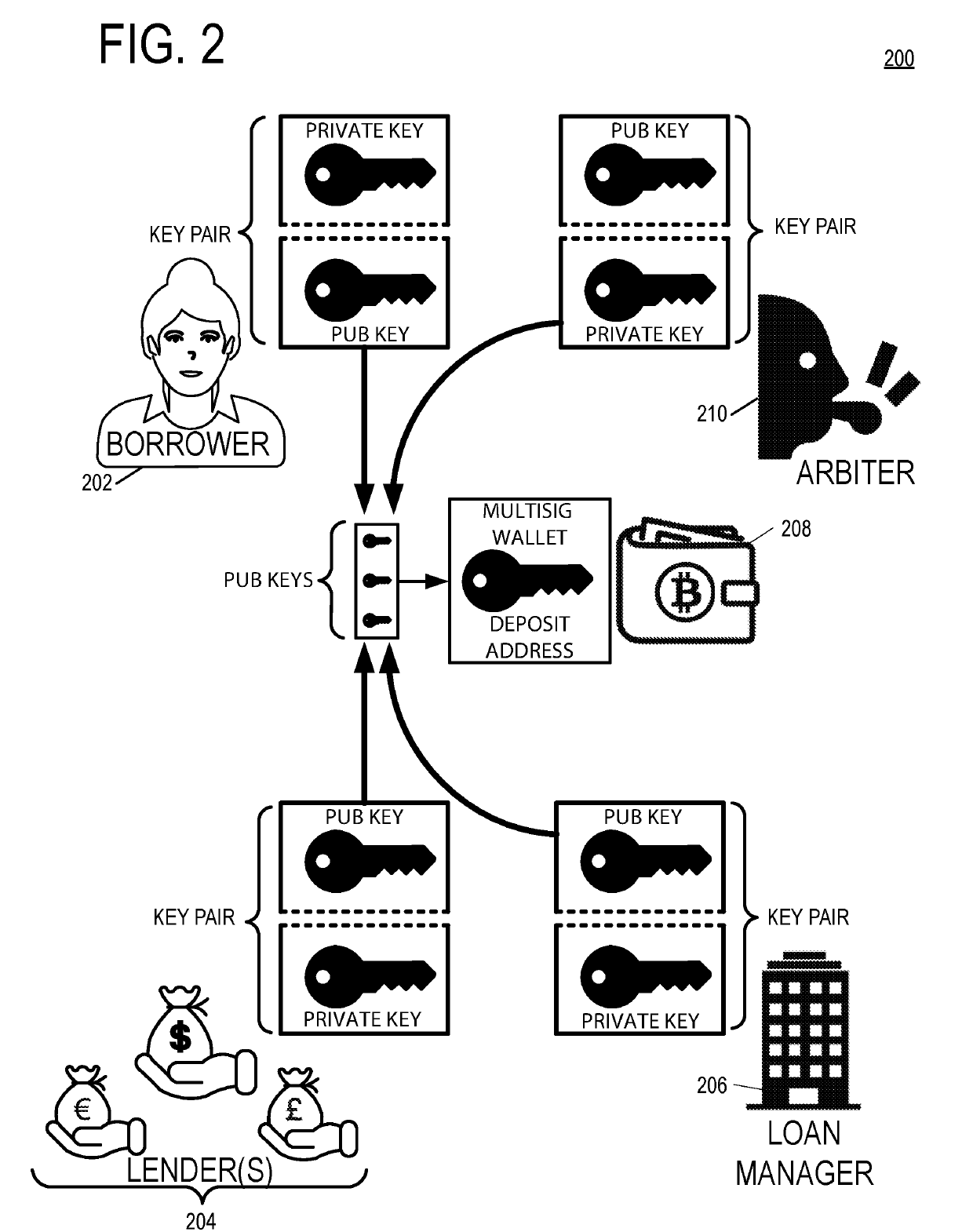
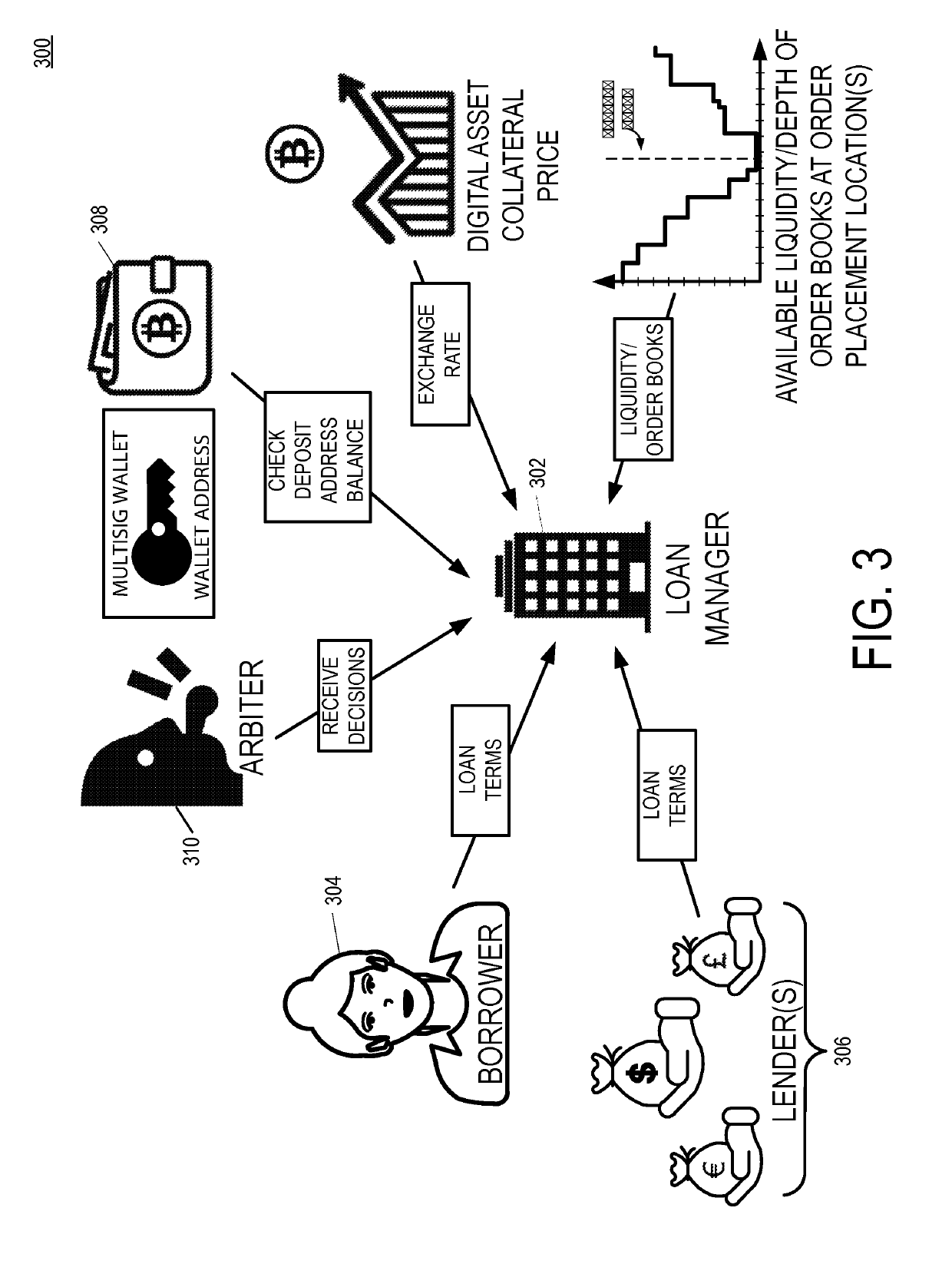
Incrementally Perfected Digital Asset Collateral Wallet
A multisig digital asset wallet stores collateral for a loan between a borrower and a lender. The borrower and lender agree to loan terms including collateralization requirements. Over the course of the loan repayment period, a Loan-to-Value (LTV) ratio between the digital asset collateral and the loan principal balance will change due to fluctuations in the market exchange value of the digital asset and a declining loan principal balance due to regular loan repayments by the borrower. If the LTV exceeds the collateral requirements by an overage amount, then the borrower may sign a transaction and request signatures from other participants to withdraw funds from the multisig collateral wallet. If the LTV fails to satisfy the collateral requirements, participants may spend funds from the multisig collateral wallet to improve the LTV, catch up after a missed payment by the borrower, or pay down the loan principal.
Owner:SALT BLOCKCHAIN INC
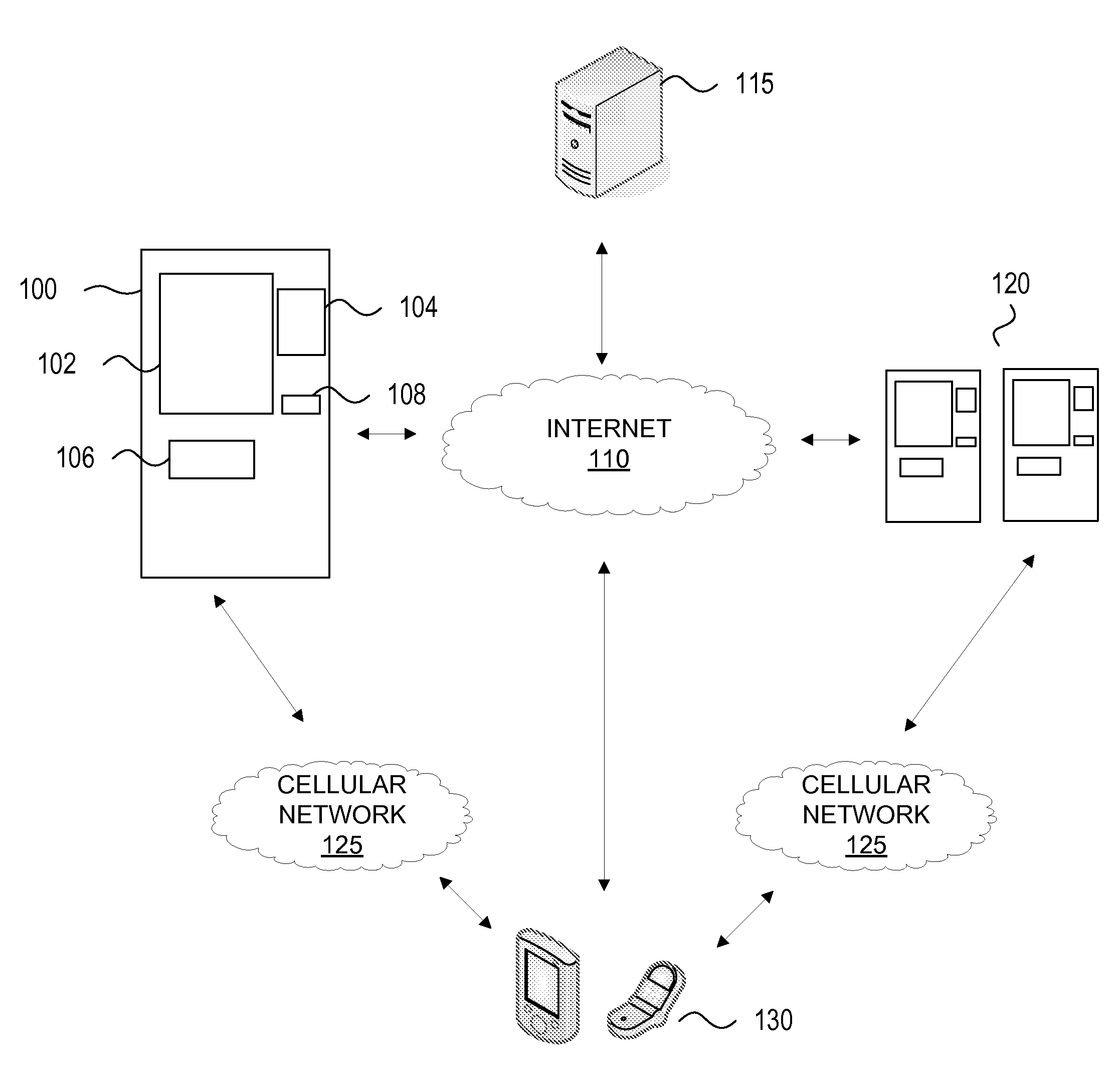
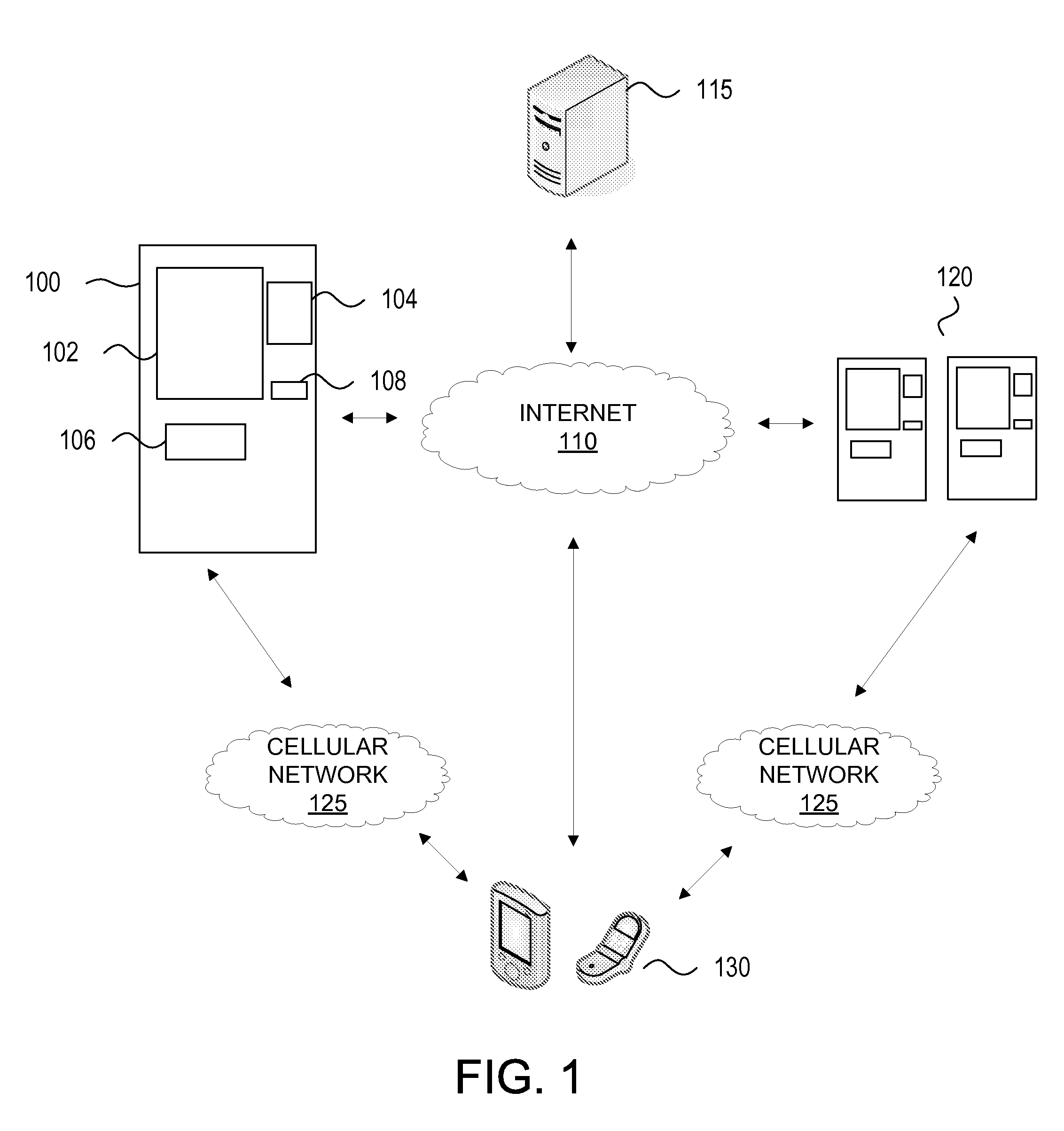
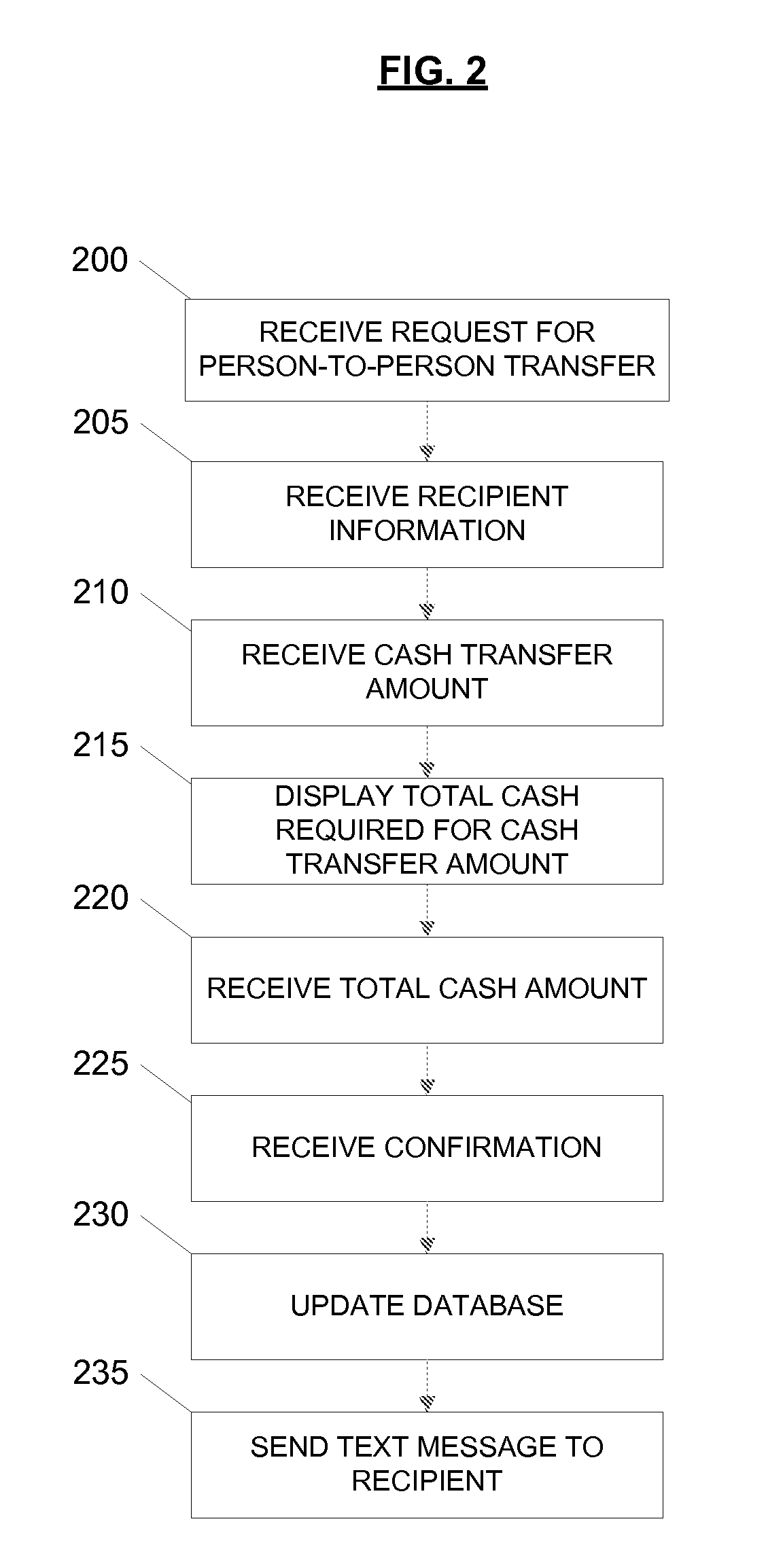
Person-to-Person Funds Transfer
ActiveUS20100174646A1Limit scopeWell formedFinanceProtocol authorisationInternet privacyTransfer system
Systems and methods are illustrated for performing a person-to-person funds transfer. A person-to-person funds transfer process may be divided into a funds transfer initiation process to receive the funds to be transferred and recipient information from a sender and a funds retrieval process to provide the funds to a recipient. The funds transfer initiation process may include a customizable authentication step that provides the sender an opportunity to determine the level of authentication. The funds transfer retrieval process may include determining whether the recipient is authenticated based on the authentication level chosen by the sender.
Owner:BANK OF AMERICA CORP
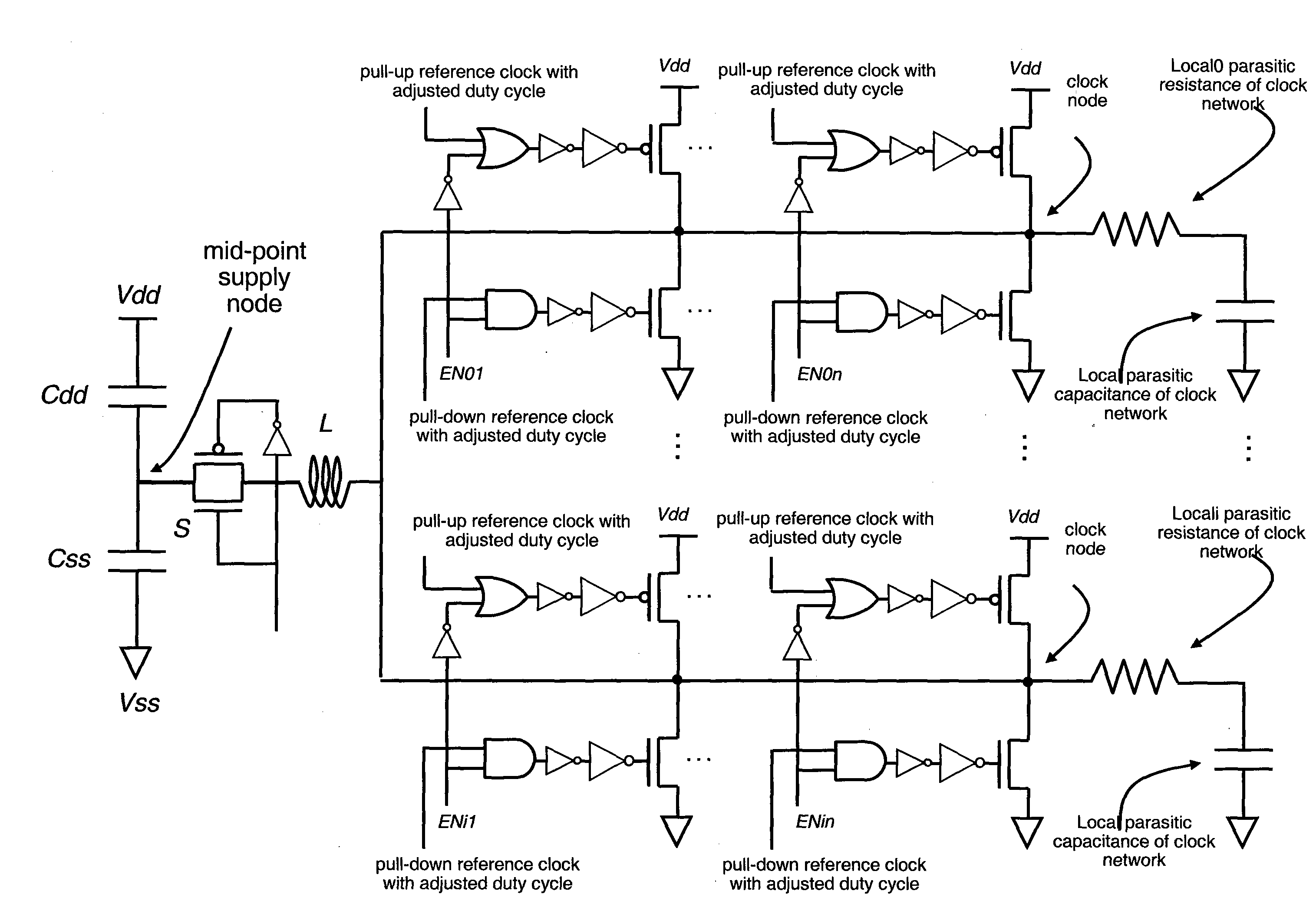
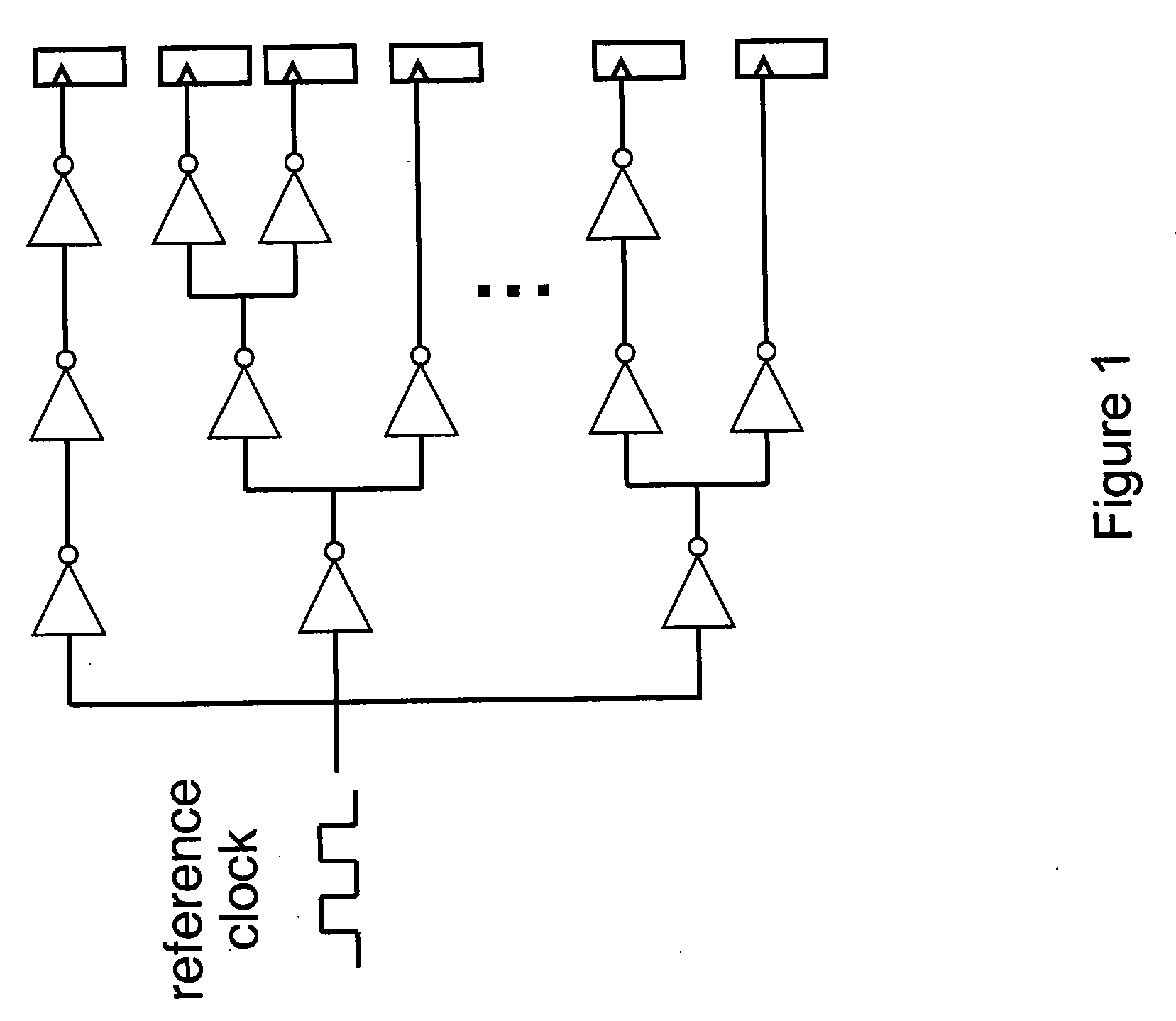
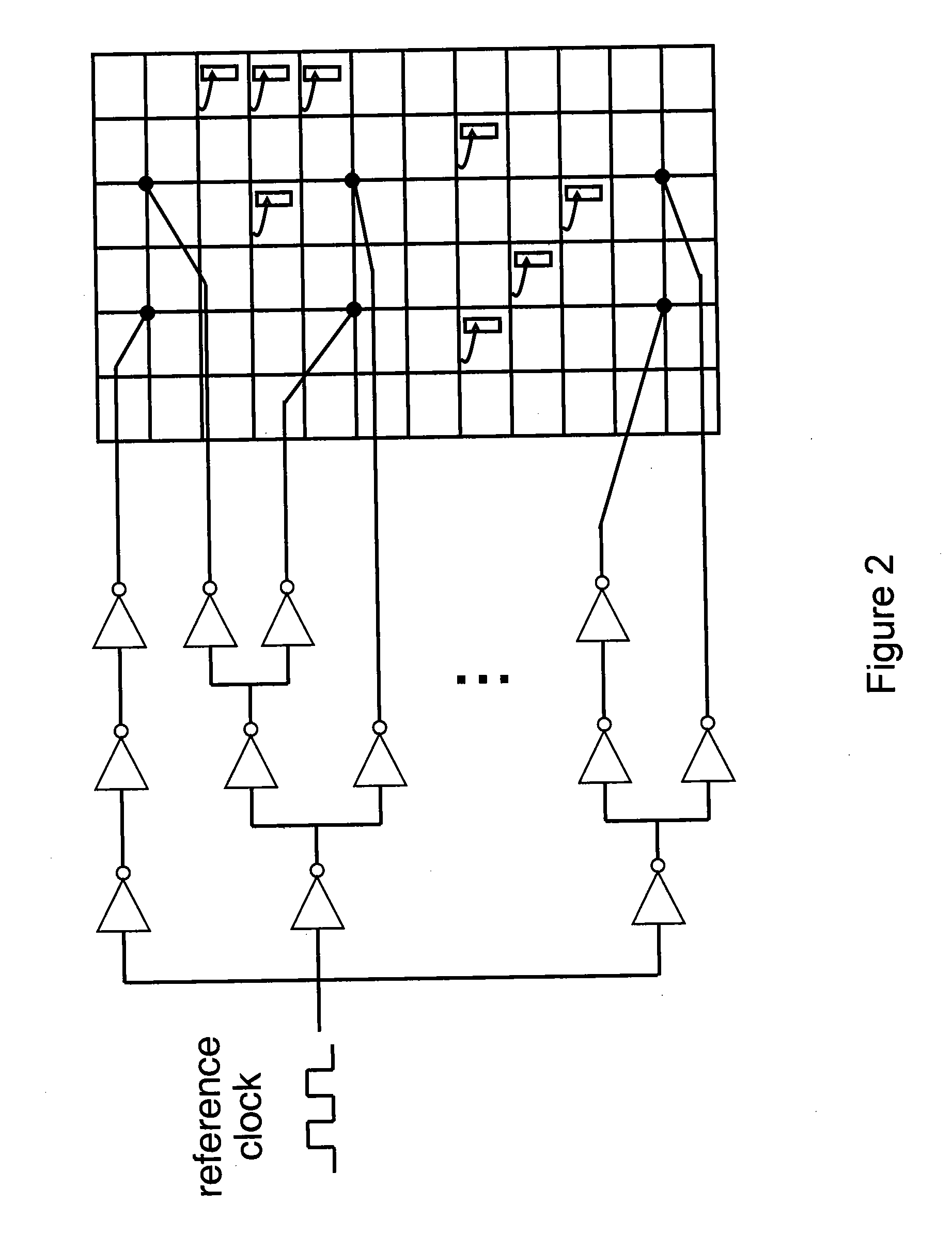
Architecture for controlling clock characteristics
An architecture for controlling the clock waveform characteristics, including but not limited to the clock amplitude and clock rise and / or fall times, of resonant clock distribution networks is proposed. This architecture relies on controlling the size of clock drivers and the duty cycles of reference clocks. It is targeted at resonant clock distribution networks and allows for the adjustment of resonant clock waveform characteristics with no need to route an additional power grid. Such an architecture is generally applicable to semiconductor devices with multiple clock frequencies, and high-performance and low-power clocking requirements such as microprocessors, ASICs, and SOCs.
Owner:CYCLOS SEMICON
Reactor System and Process for the Manufacture of Ethylene Oxide
A reactor system for the epoxidation of ethylene, which reactor system comprises an elongated tube having an internal tube diameter of more than 40 mm, wherein contained is a catalyst bed of catalyst particles comprising silver and a promoter component deposited on a carrier, which promoter component comprises an element selected from rhenium, tungsten, molybdenum and chromium; a process for the epoxidation of ethylene comprising reacting ethylene with oxygen in the presence of the catalyst bed contained in the reactor system; and a method of preparing ethylene glycol, an ethylene glycol ether or an ethanol amine comprising obtaining ethylene oxide by the process for the epoxidation of ethylene, and converting the ethylene oxide into ethylene glycol, the ethylene glycol ether, or the ethanol amine. Preferably, the internal tube diameter is at least 45 mm.
Owner:SHELL OIL CO
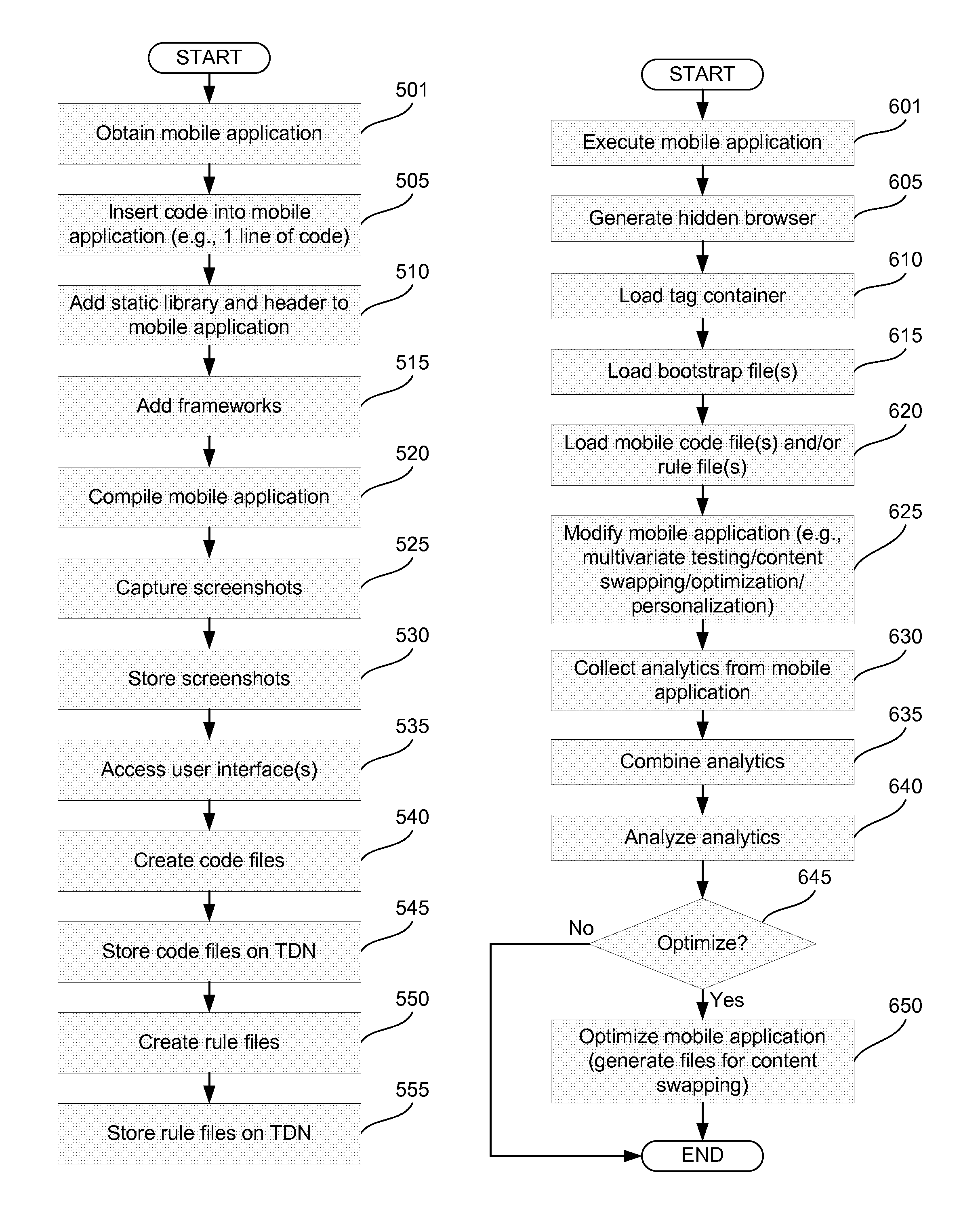
Analytics for mobile applications
A tag delivery network is disclosed for delivering tags to collect analytics related to use of mobile applications. The tag delivery network may include multiple servers for communicating with mobile devices executing mobile applications. The mobile applications may be any mobile application that has been recompiled with, for example, a particular line of code and a static library. A recompiled mobile application may initiate a browser when executed by a mobile device. The tag delivery network may deliver a tag container to the browser. The tag container may load a bootstrap file which in turn may load one or more rule files and code files. These files may cause the mobile device to modify an appearance of the mobile application. The modification may be performed to carry out multivariate testing (e.g., A / B testing), content swapping, optimization of the mobile application, or personalization of the mobile application.
Owner:ENSIGHTEN
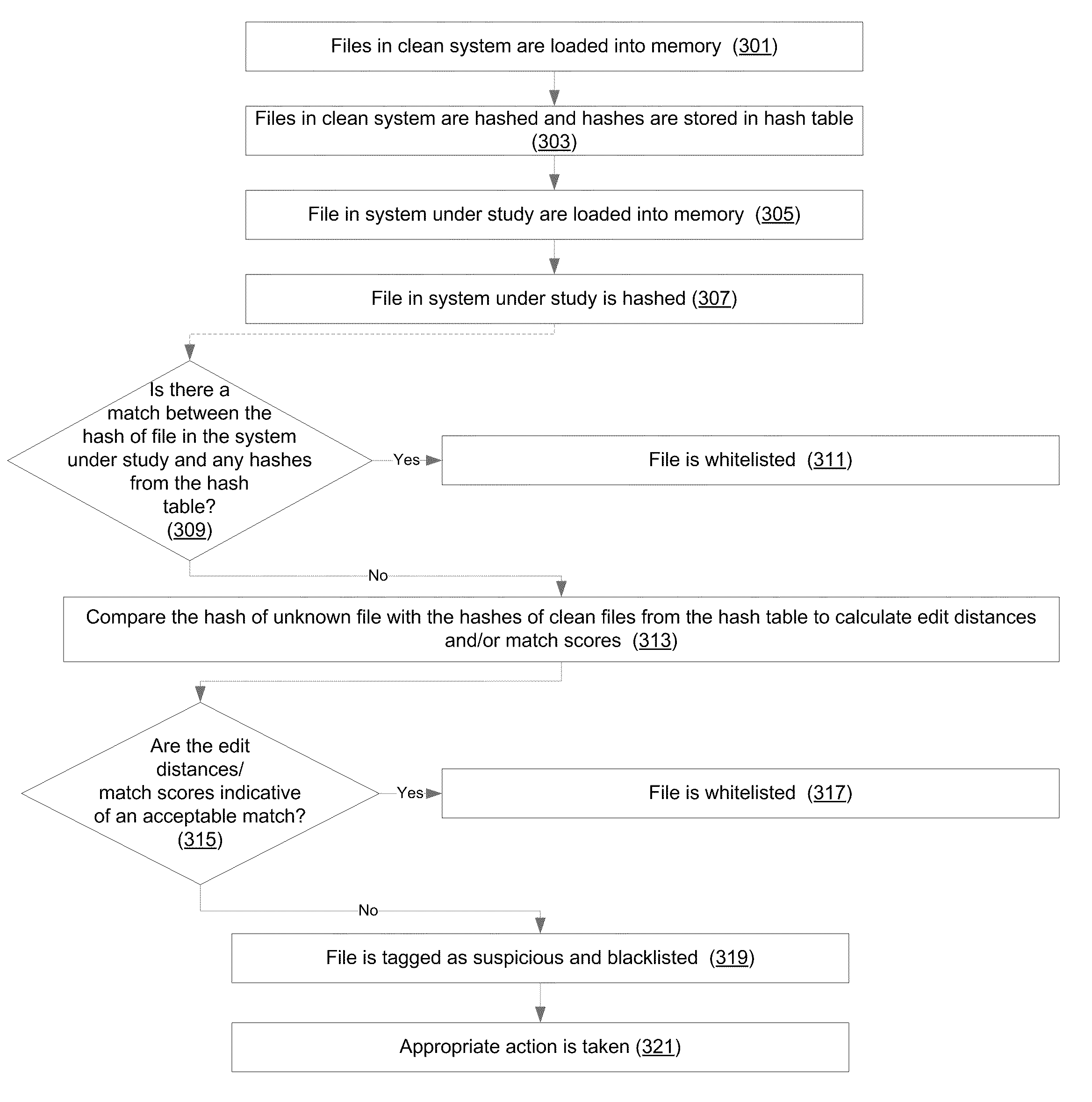
Memory Whitelisting
ActiveUS20110185417A1Limit scopeMemory loss protectionError detection/correctionRolling hashHash table
An enhanced whitelisting module associated within a system whitelists unknown files for execution on the system. The whitelisting module may oversee the computation of a hash of a file loaded into the memory and comparison of the hash to hashes within a hash table generated from clean files located on a clean system. The whitelisting module may communicate to a device internal and / or external to the system to retrieve the hash table of clean files. In certain embodiments, a rolling hash (or other piecewise hash) may be used to determine the location and / or extent of the differences between a modified file and a clean file.
Owner:BANK OF AMERICA CORP
Tactile overlay for virtual keyboard
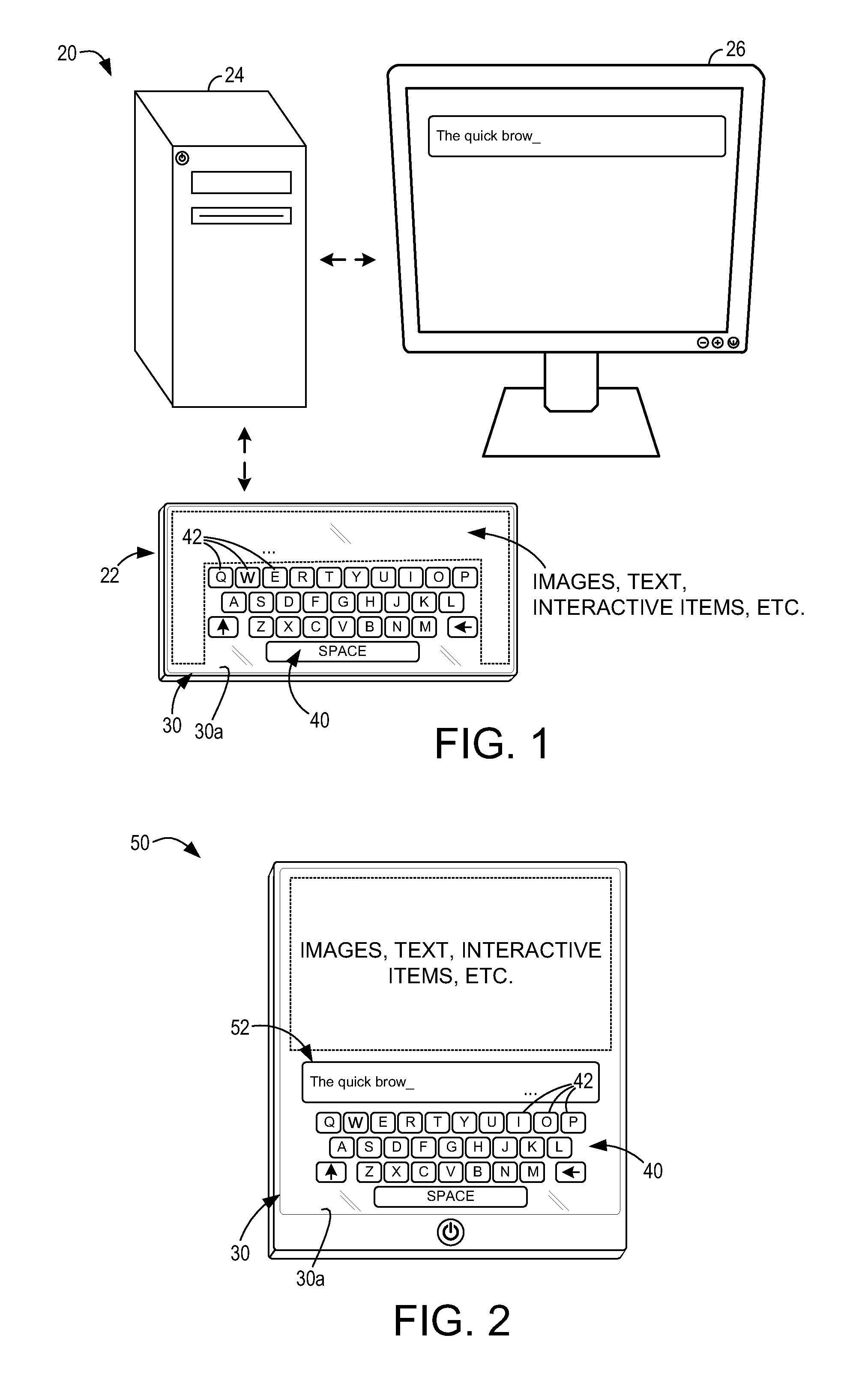
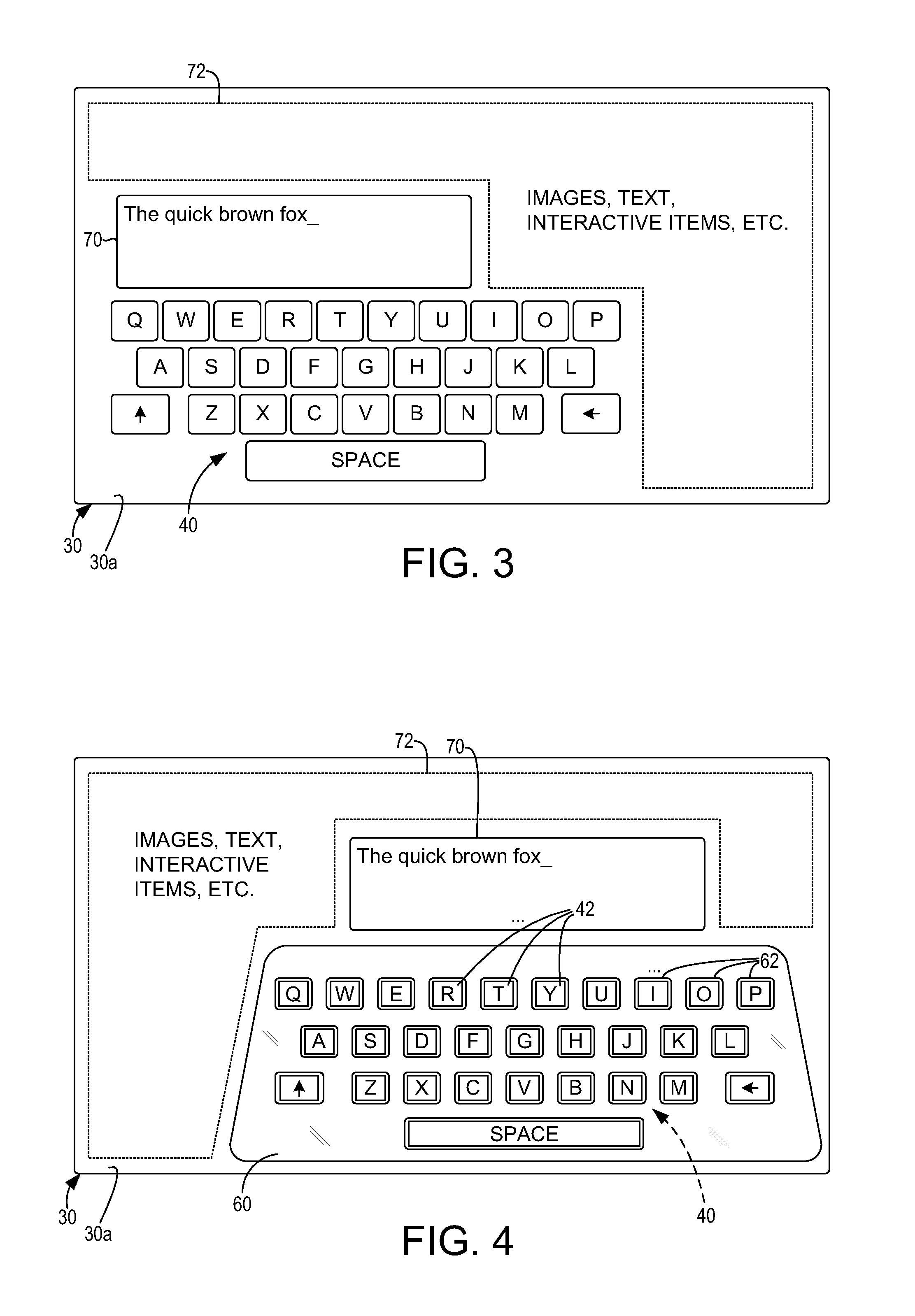
InactiveUS20110260976A1Enhance functionalityLimit scopeInput/output for user-computer interactionCathode-ray tube indicatorsVirtual keyboardDisplay device
The present disclosure provides for a computing system having virtual keyboard functionality that can be selectively enhanced through use of a tactile keyboard overlay. The tactile keyboard overlay includes a plurality of depressible key portions, and is placed onto an operative surface of a touch interactive display. The computing system configures the virtual keyboard functionality, so that each of the depressible key portions is operable to produce a touch input on the touch interactive display that causes performance of a corresponding input operation. The virtual keyboard functionality is dynamically and automatically located on the touch interactive display based on user placement of the tactile keyboard overlay.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com