Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2466results about How to "Process safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
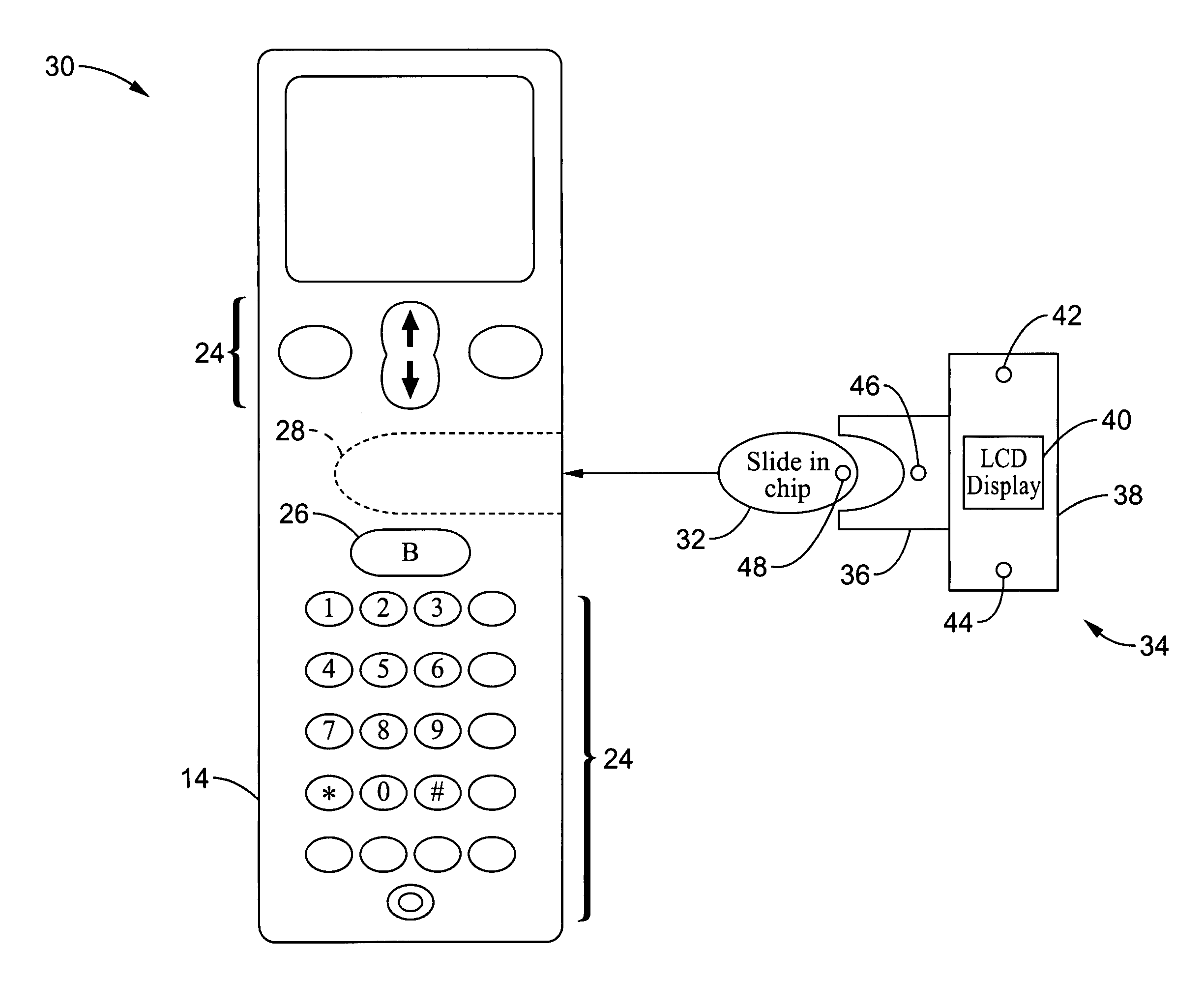
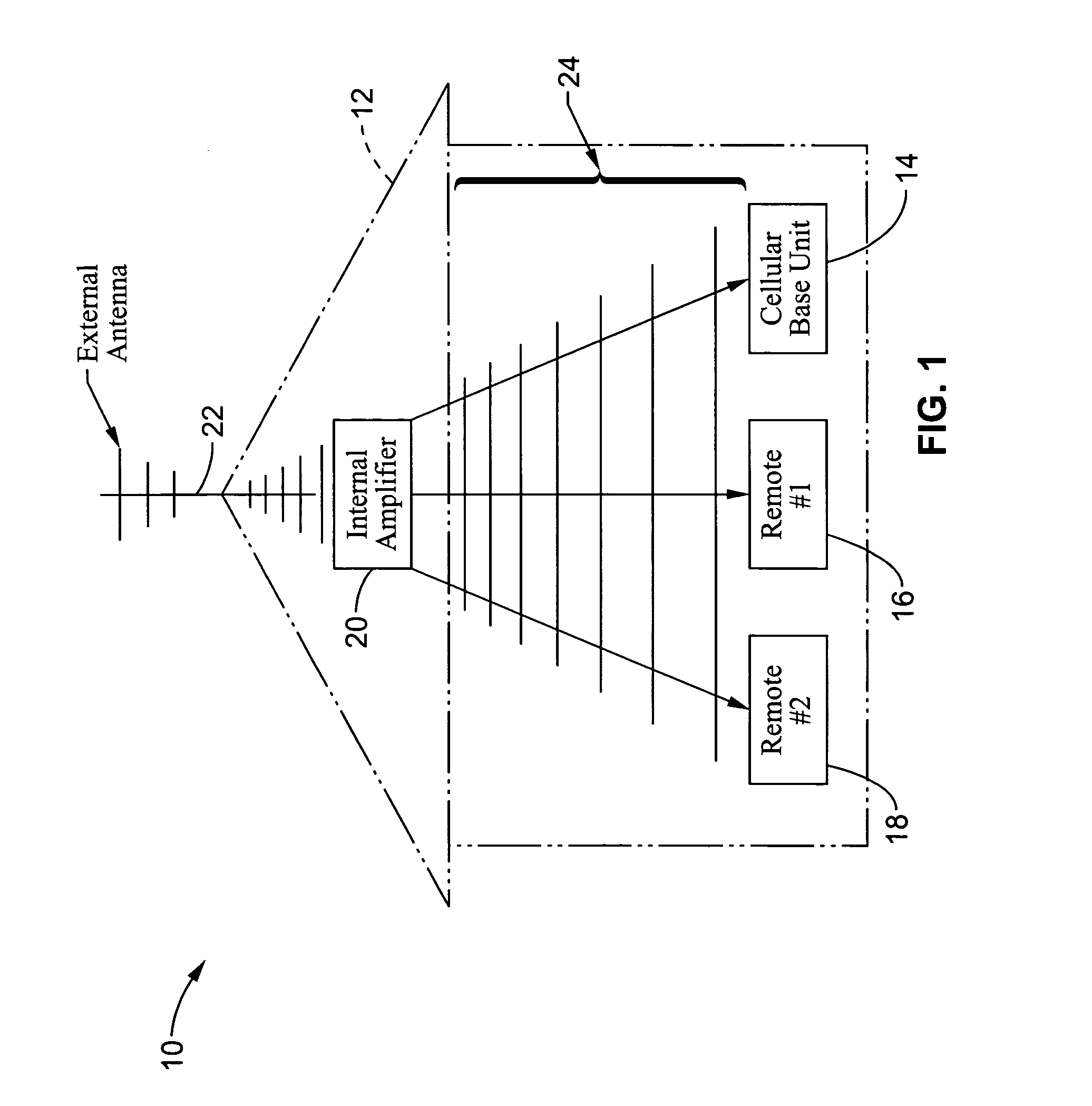
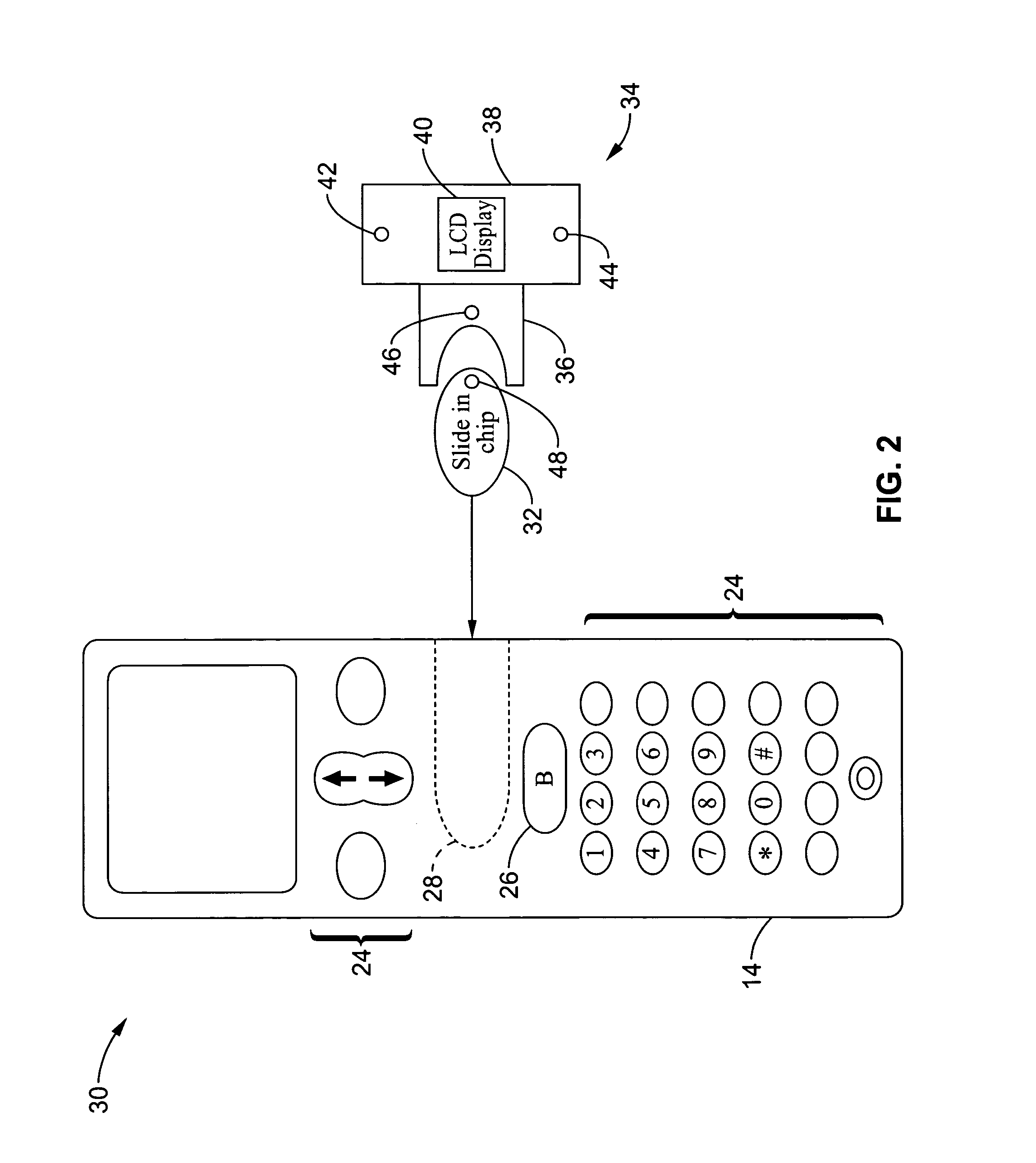
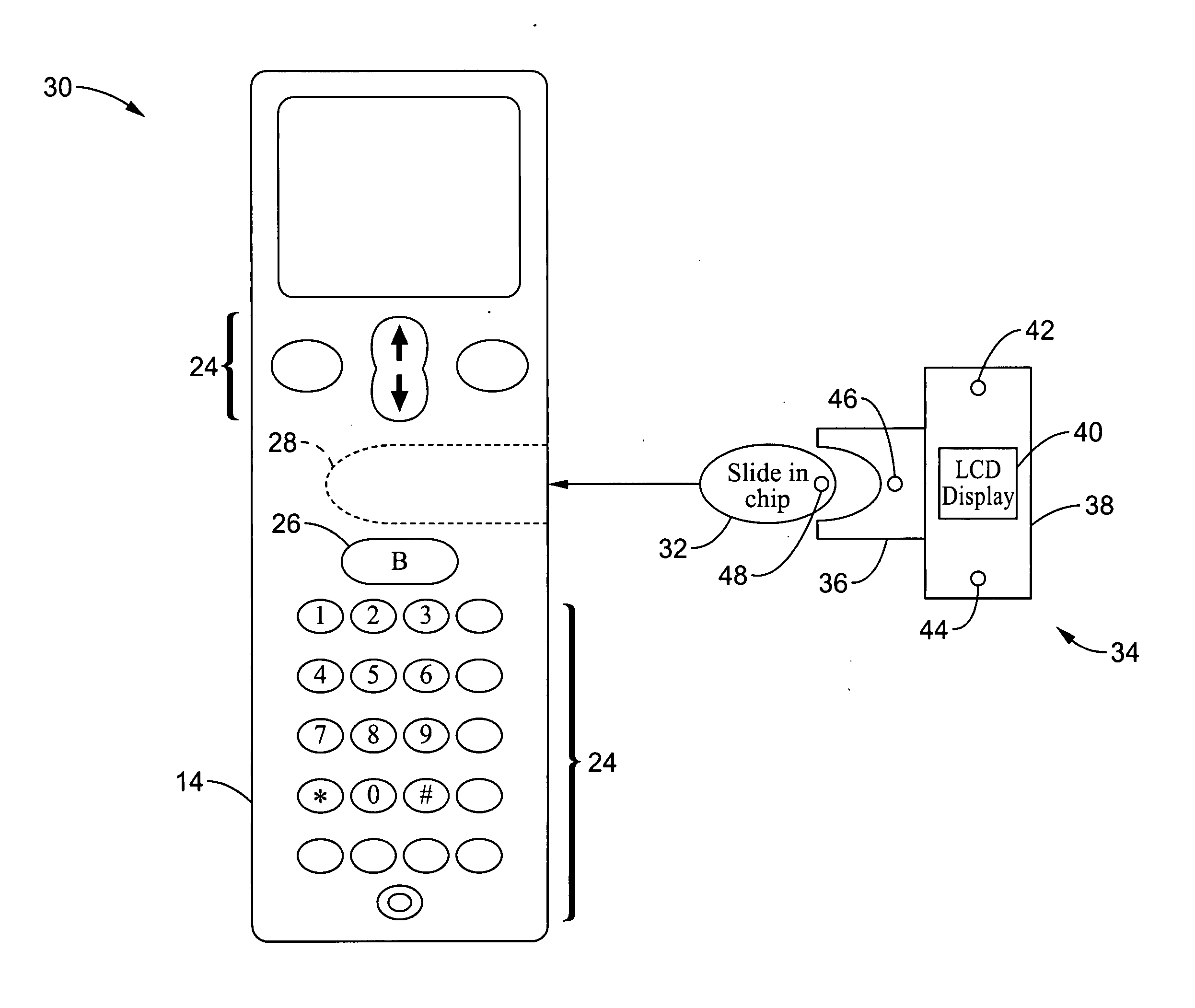
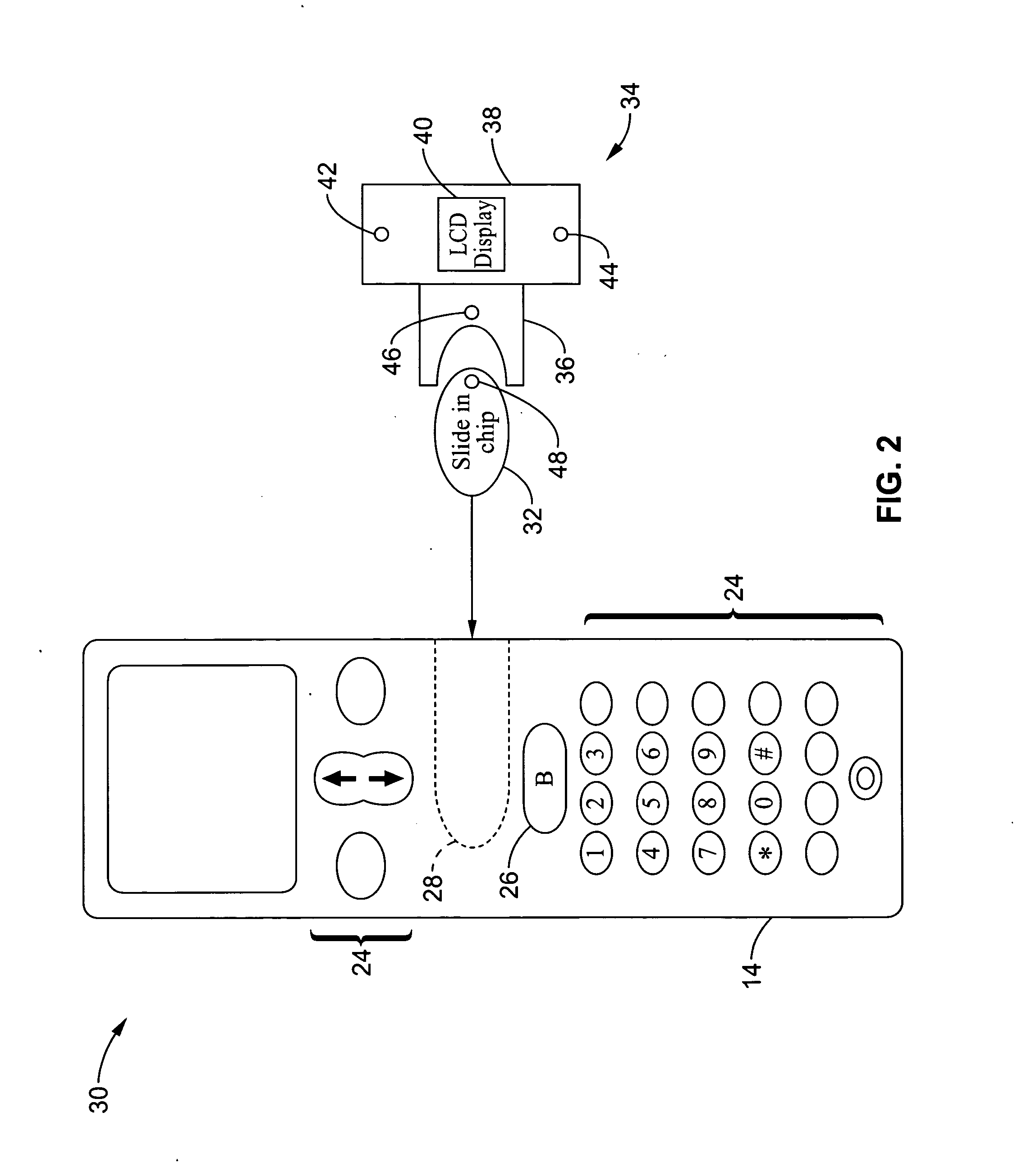
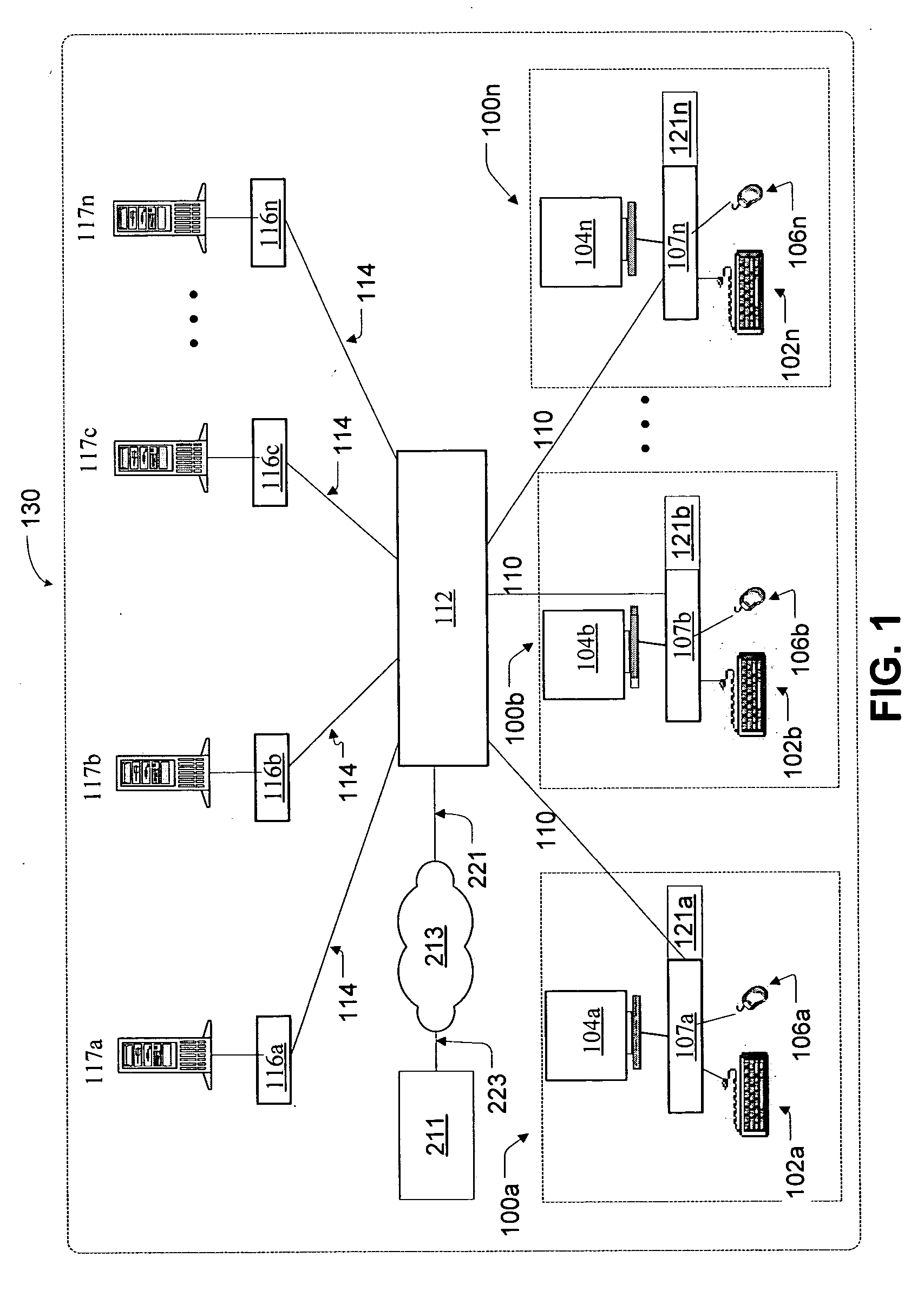
Wireless communications apparatus and method
InactiveUS7146191B2Easy to be stolenProcess safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInterconnectivityDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
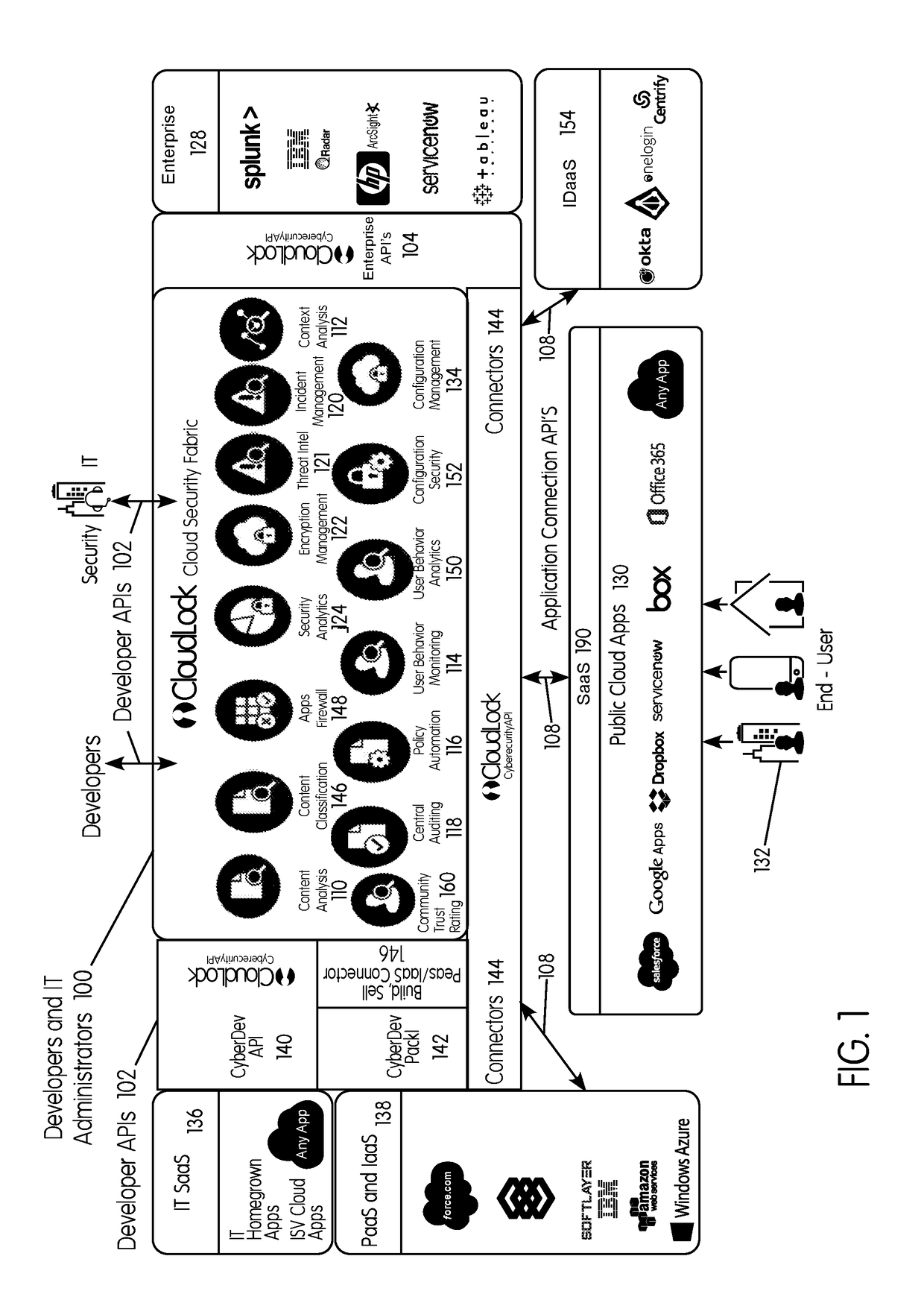
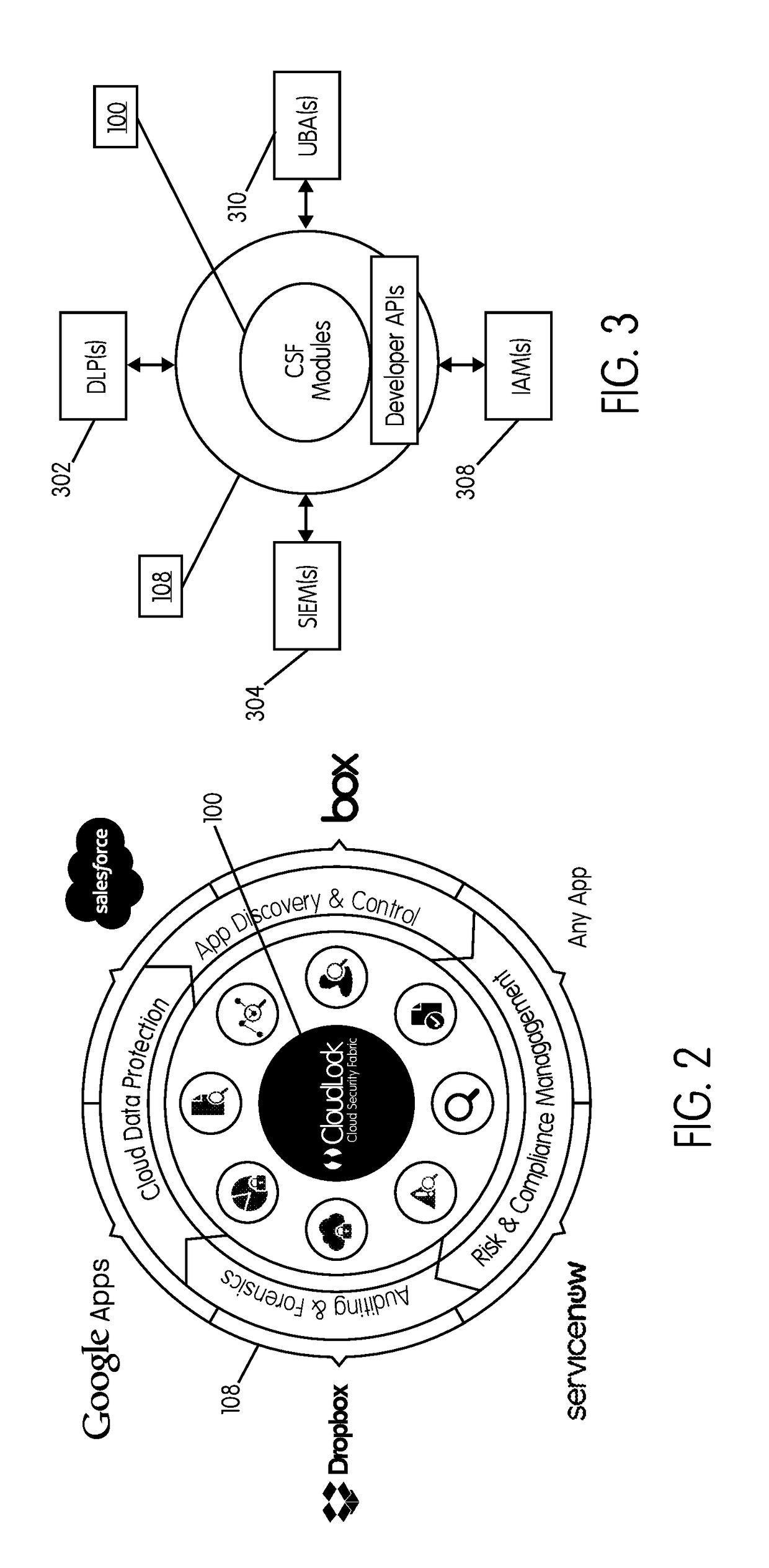
System and method for securing an enterprise computing environment
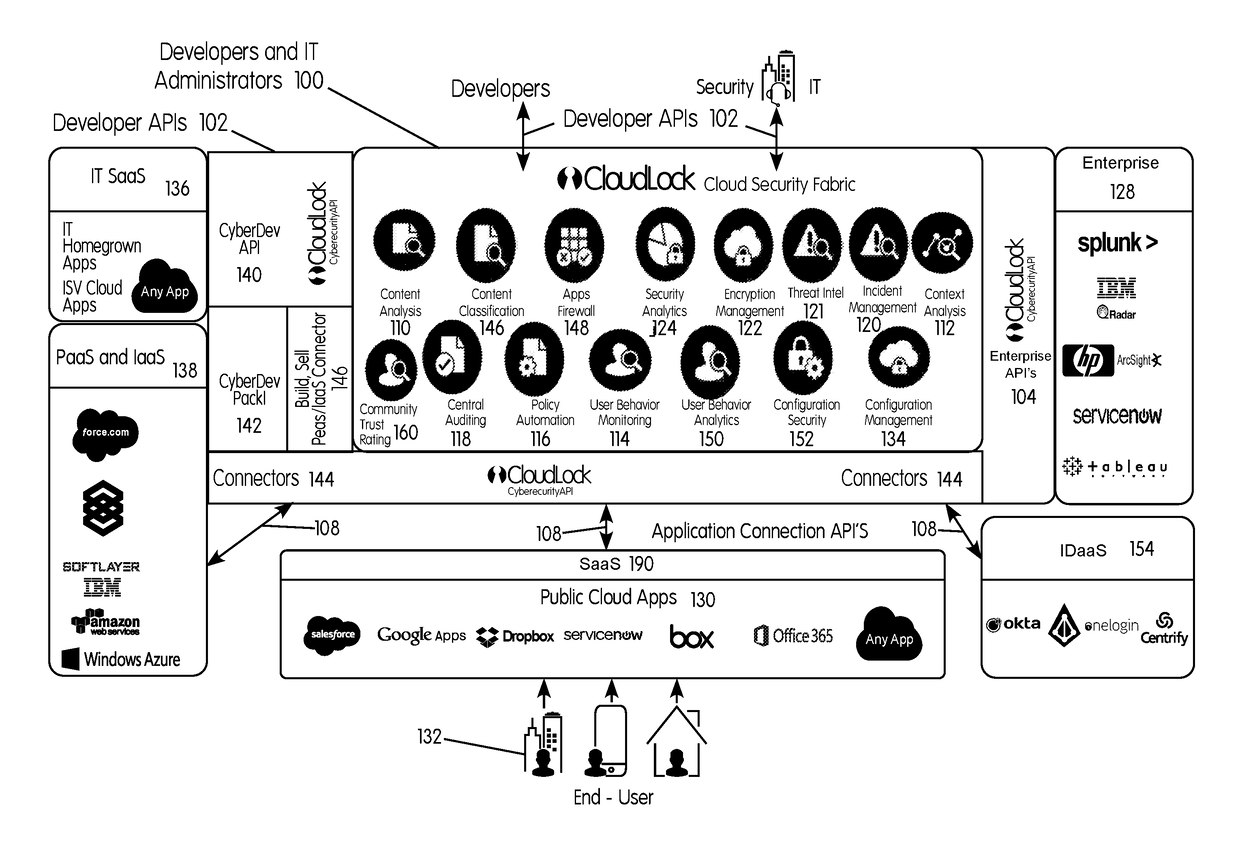
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
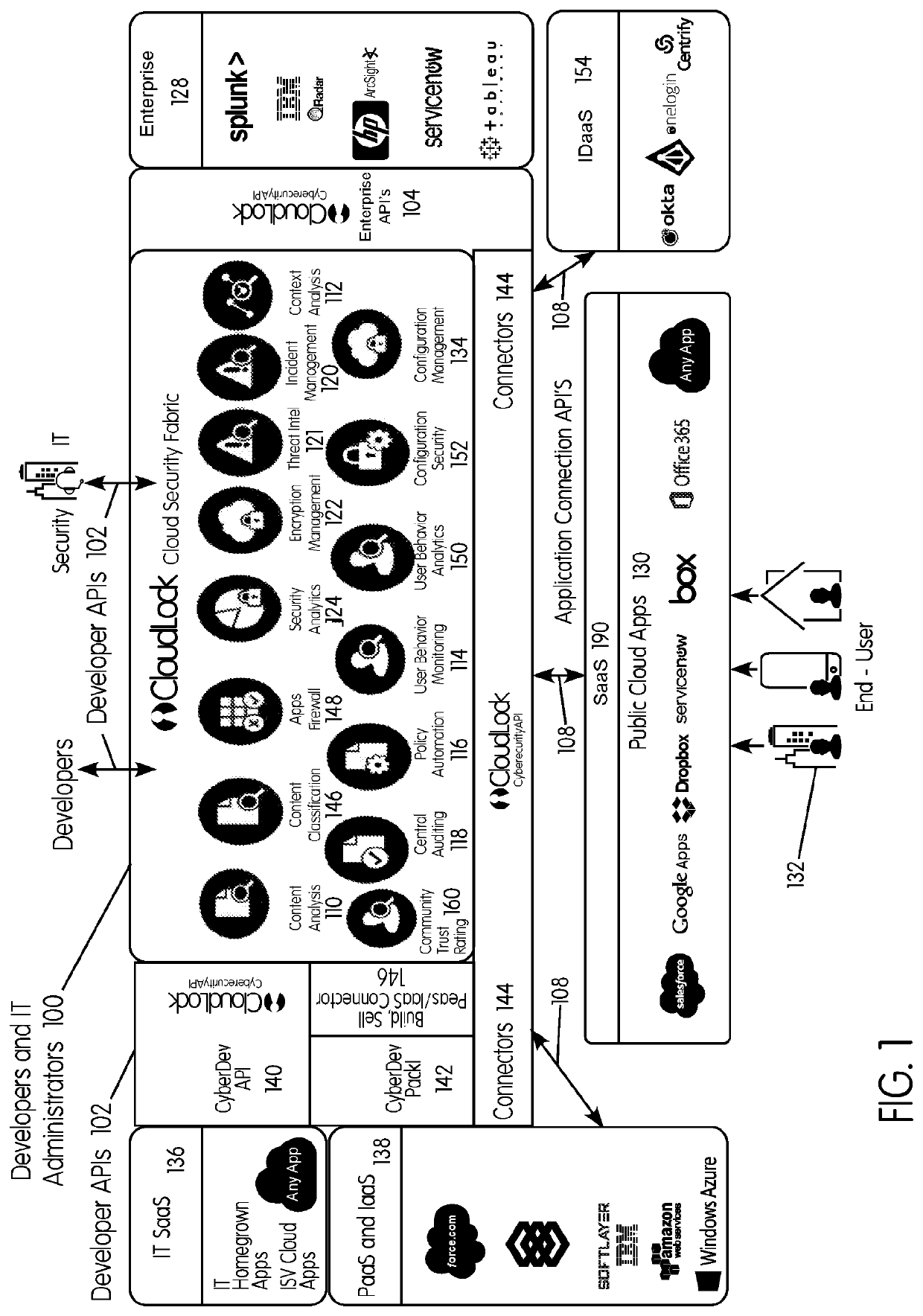
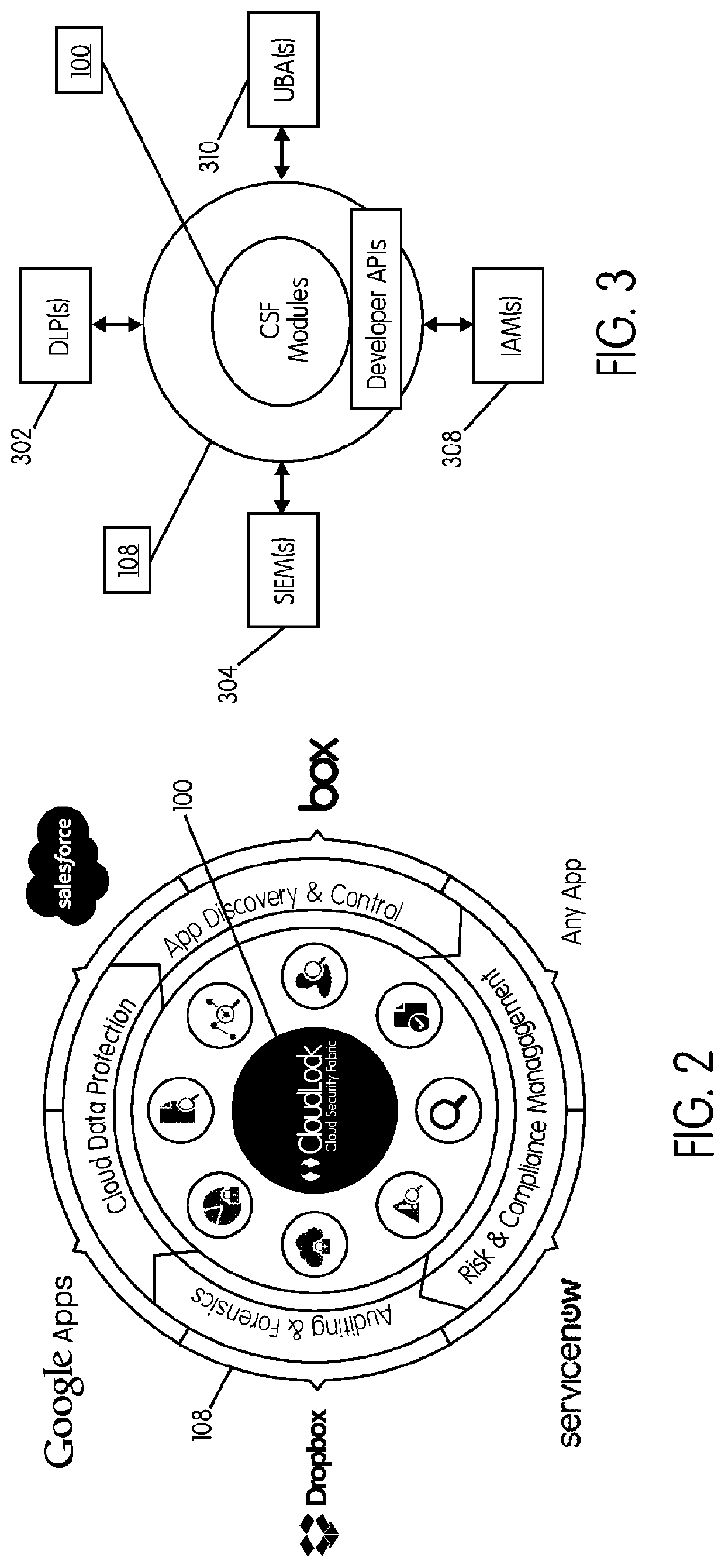
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
Wireless communications apparatus and method
InactiveUS20050159184A1Security and flexibility of systemEasy to be stolenUnauthorised/fraudulent call preventionEavesdropping prevention circuitsBase stationDisplay device
A wireless communication method and apparatus are described for increasing security for communication devices utilizing identification chips for accessing wireless networks and the associated billing for services. One aspect of the invention is an enhanced phone chip and a communications device adapted to engage the enhanced phone chip, which then cannot be installed or removed from the wireless communications device by unauthorized users. In one embodiment a security key mates to the identification chip and is utilized for installing and removing the enhanced phone chip. The security key preferably has a display upon which information about the communication device is displayed prior to removing the security key after installing the enhanced phone chip. Other aspects of the invention include wireless base station communication devices which support wired (dedicated and non-dedicated), and more preferably wireless extensions, while providing sharing of wireless network resources and interconnectivity between base station and extensions.
Owner:US THERMOELECTRIC CONSORTIUM
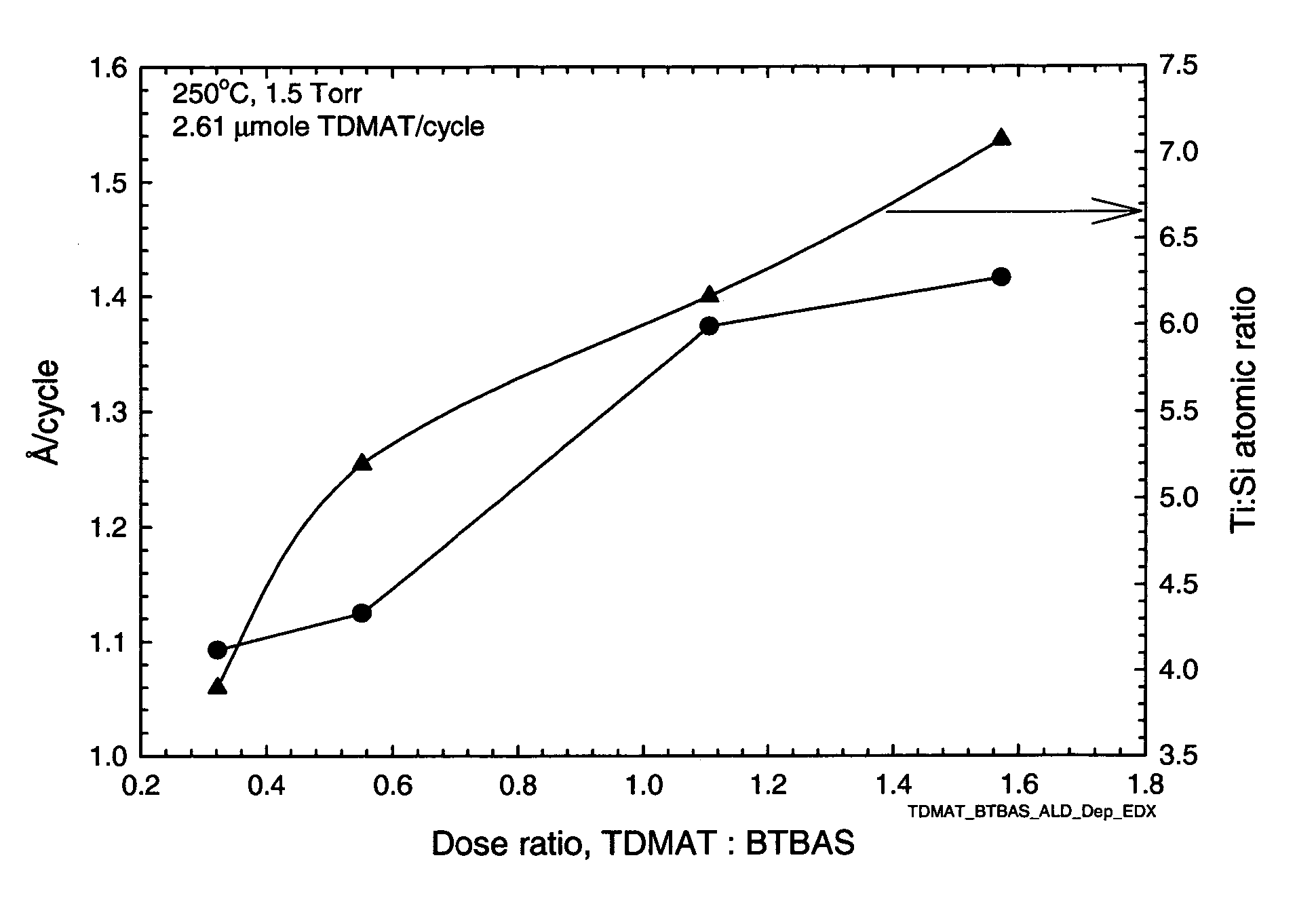
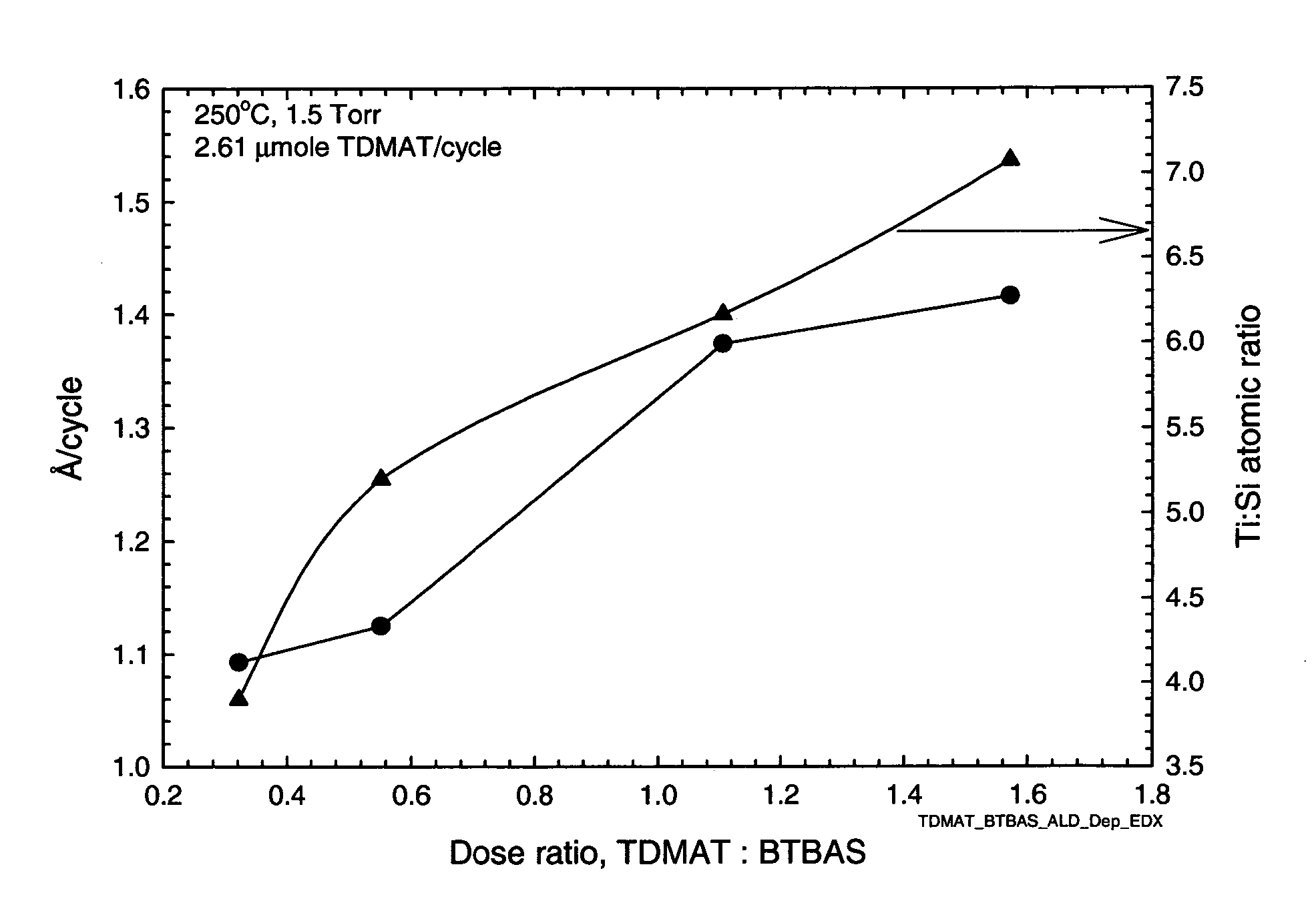
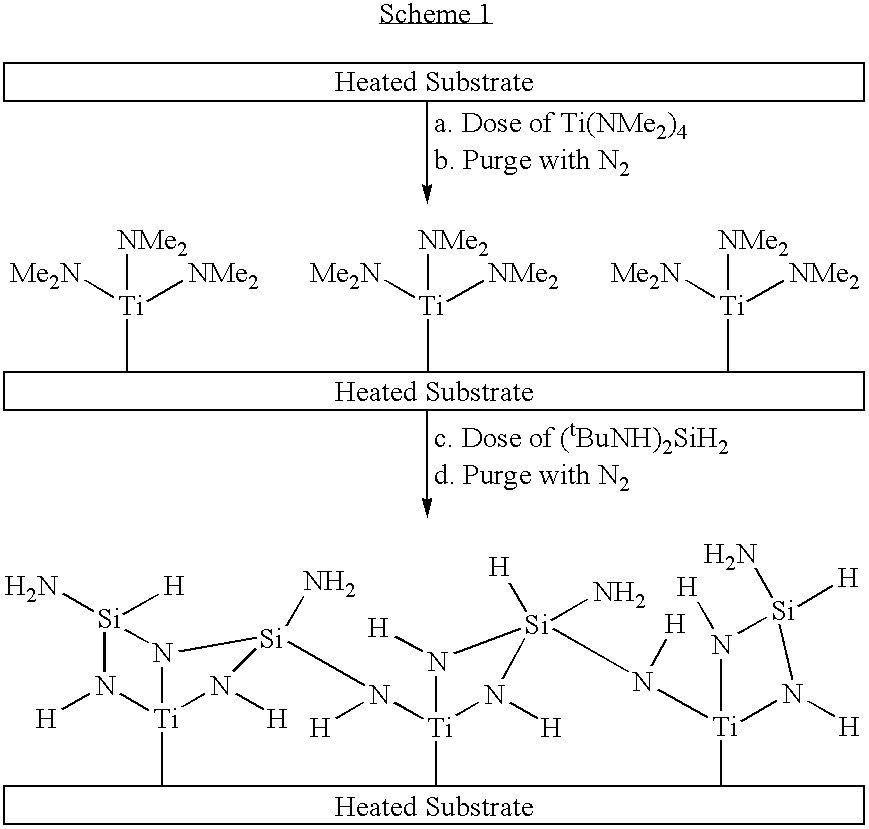
Preparation of metal silicon nitride films via cyclic deposition
InactiveUS20060182885A1Quality improvementProcess safetyLighting support devicesSemiconductor/solid-state device manufacturingSilyleneSilanes
This invention relates to an improved process for producing ternary metal silicon nitride films by the cyclic deposition of the precursors. The improvement resides in the use of a metal amide and a silicon source having both NH and SiH functionality as the precursors leading to the formation of such metal-SiN films. The precursors are applied sequentially via cyclic deposition onto the surface of a substrate. Exemplary silicon sources are monoalkylamino silanes and hydrazinosilanes represented by the formulas: (R1NH)nSiR2mH4-n-m (n=1,2; m=0,1,2; n+m=<3); and (R32N—NH)xSiR4yH4-x-y (x=1,2; y=0,1,2; x+y=<3) wherein in the above formula R1-4 are same or different and independently selected from the group consisting of alkyl, vinyl, allyl, phenyl, cyclic alkyl, fluoroalkyl, silylalkyls.
Owner:VERSUM MATERIALS US LLC
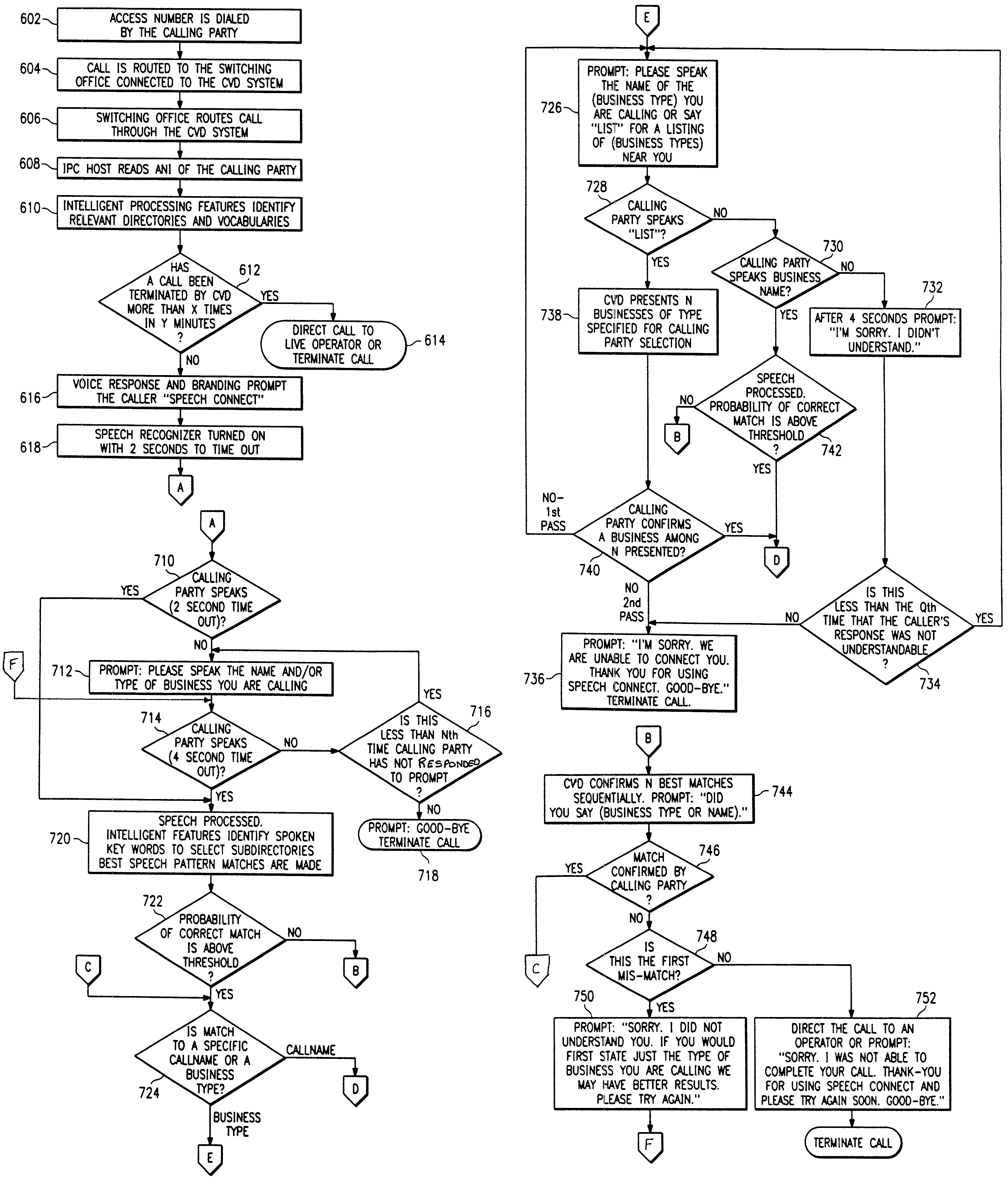
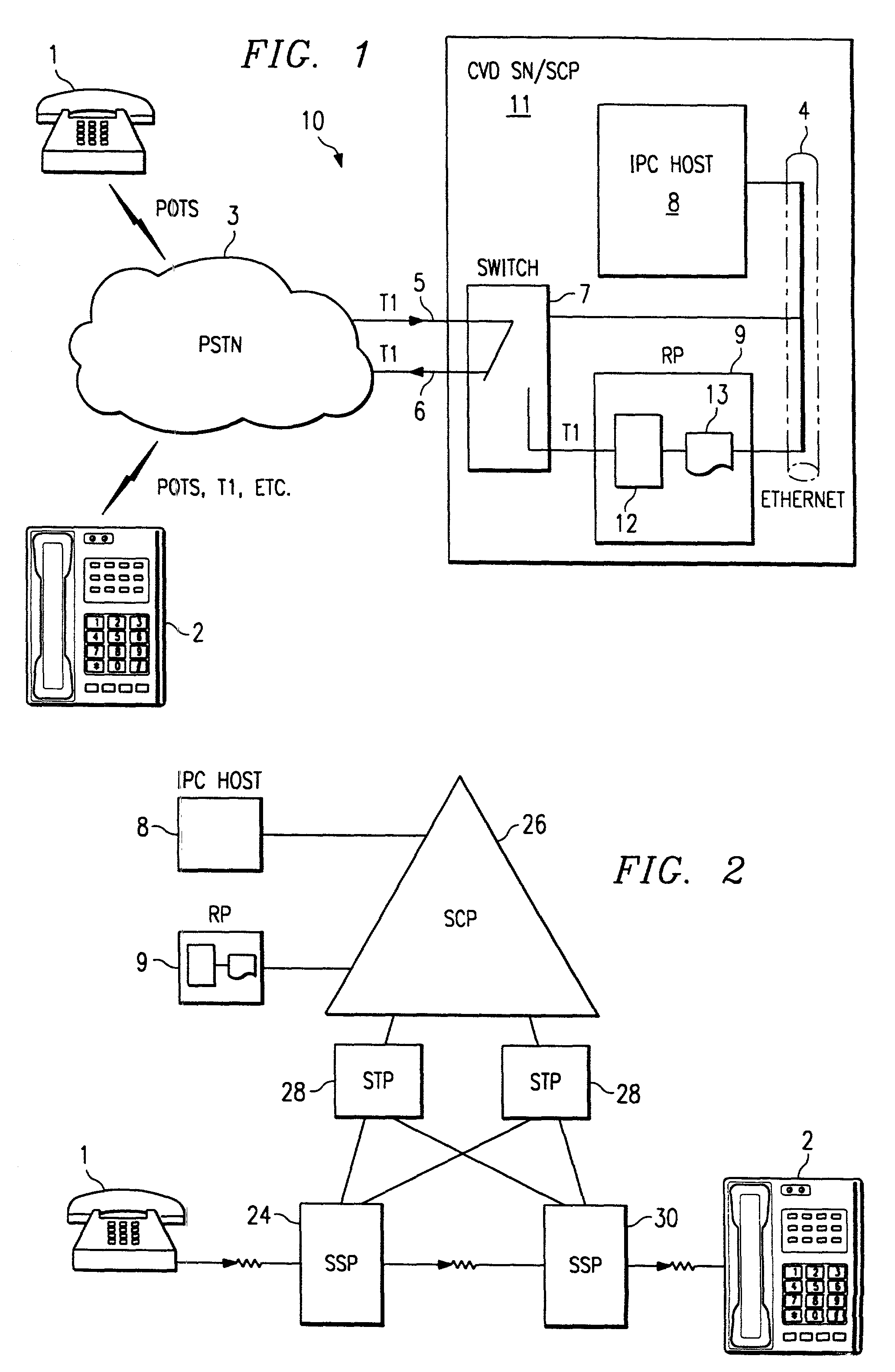
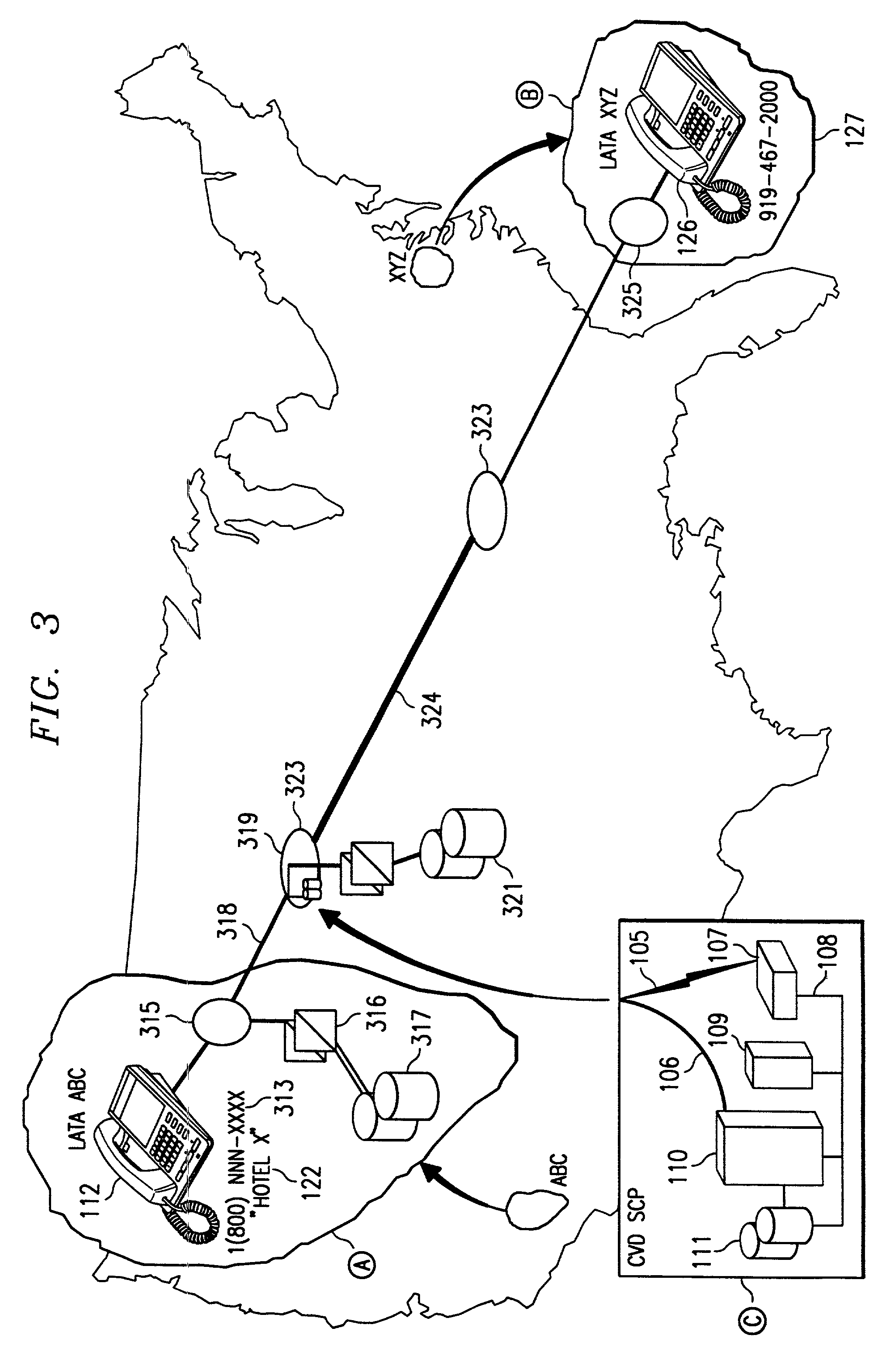
Voice-activated call placement systems and methods
InactiveUS7127046B1Easily reachableEasy to adaptIntelligent networksAutomatic call-answering/message-recording/conversation-recordingSpoken languageService control
System and method for deriving call routing information utilizing a network control data base system and voice recognition for matching spoken word sound patterns to routing numbers needed to set up calls. Public access is provided to a common database via a common access number or code. Terminating parties sponsor the call and originating parties need not be pre-subscribed to use the service. The common access number is used to initiate or trigger the service. The system advantageously operates under the direction of a service control point, which combines technologies for switching, interactive voice response, and voice recognition with the data base to automate the processes of assisting callers in making calls for which they do not know the phone number. Usage information is gathered on completed calls to each terminating party for billing. Three alternative deployments in the U.S. telephone network are described, and vary based on the location of the service control points or intelligent processors and the degree of intelligence within the network.
Owner:GOOGLE LLC
Methods and systems for assessing clinical outcomes
InactiveUS20090318775A1Increased futureImproved labelingBiostatisticsDiagnostic recording/measuringComputer terminalEnd user
Described herein are methods and systems useful for characterizing clinical outcomes of a subject. Provided herein includes computer-assessed methods, medical information systems, and computer-readable instructions that can aid an end-user in diagnosis, prognosis, and treatment of a clinical outcome.
Owner:THERANOS
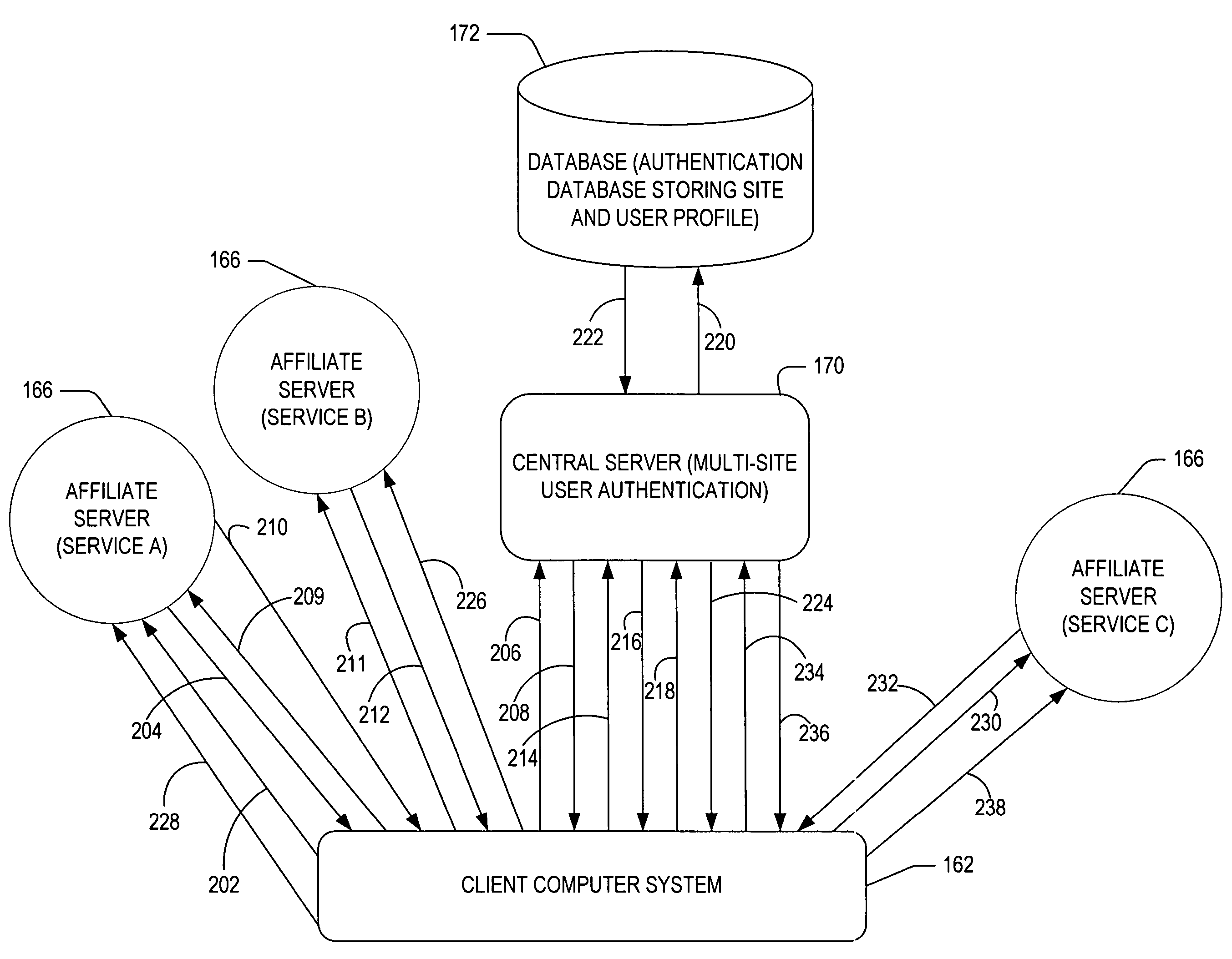
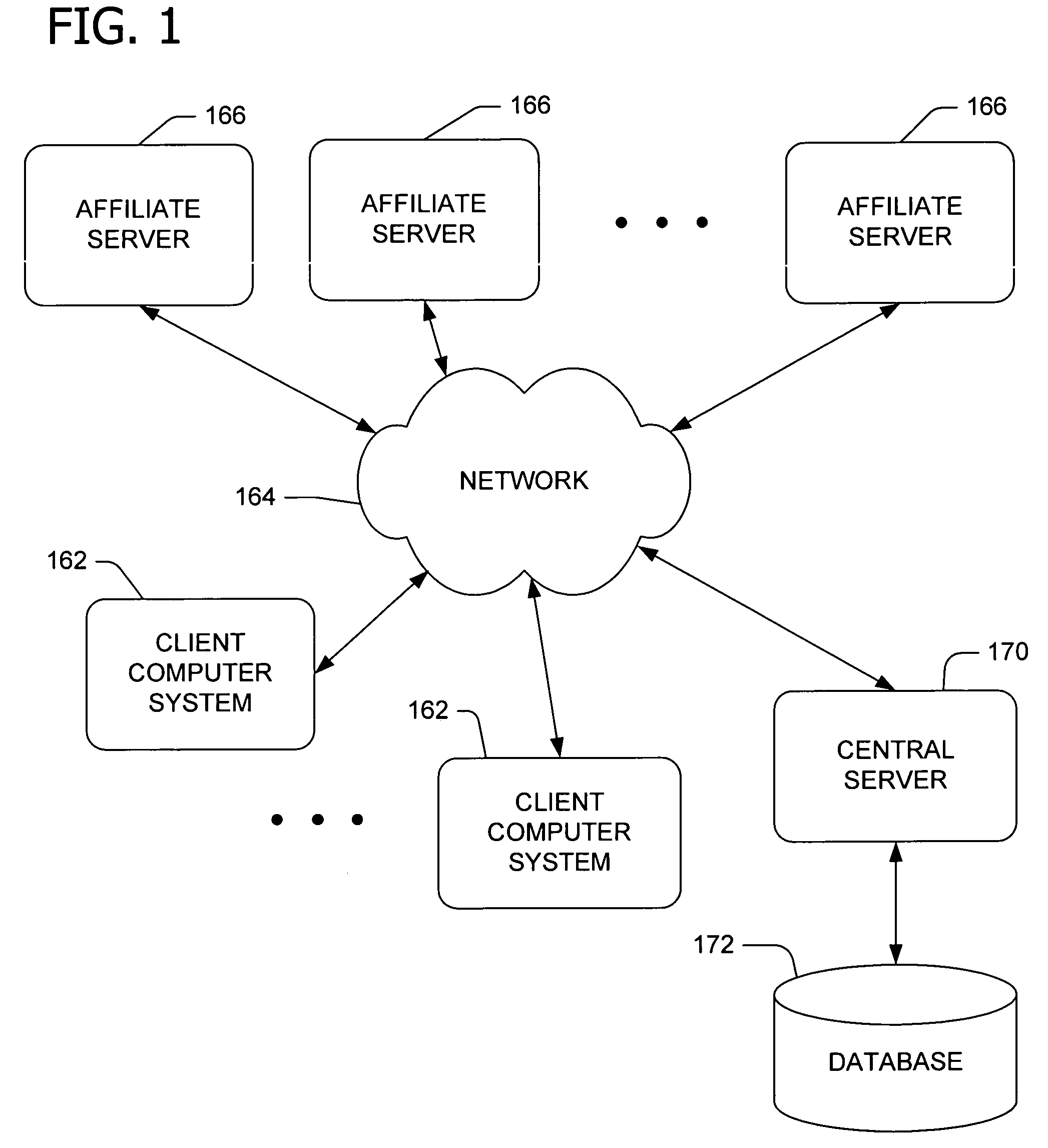
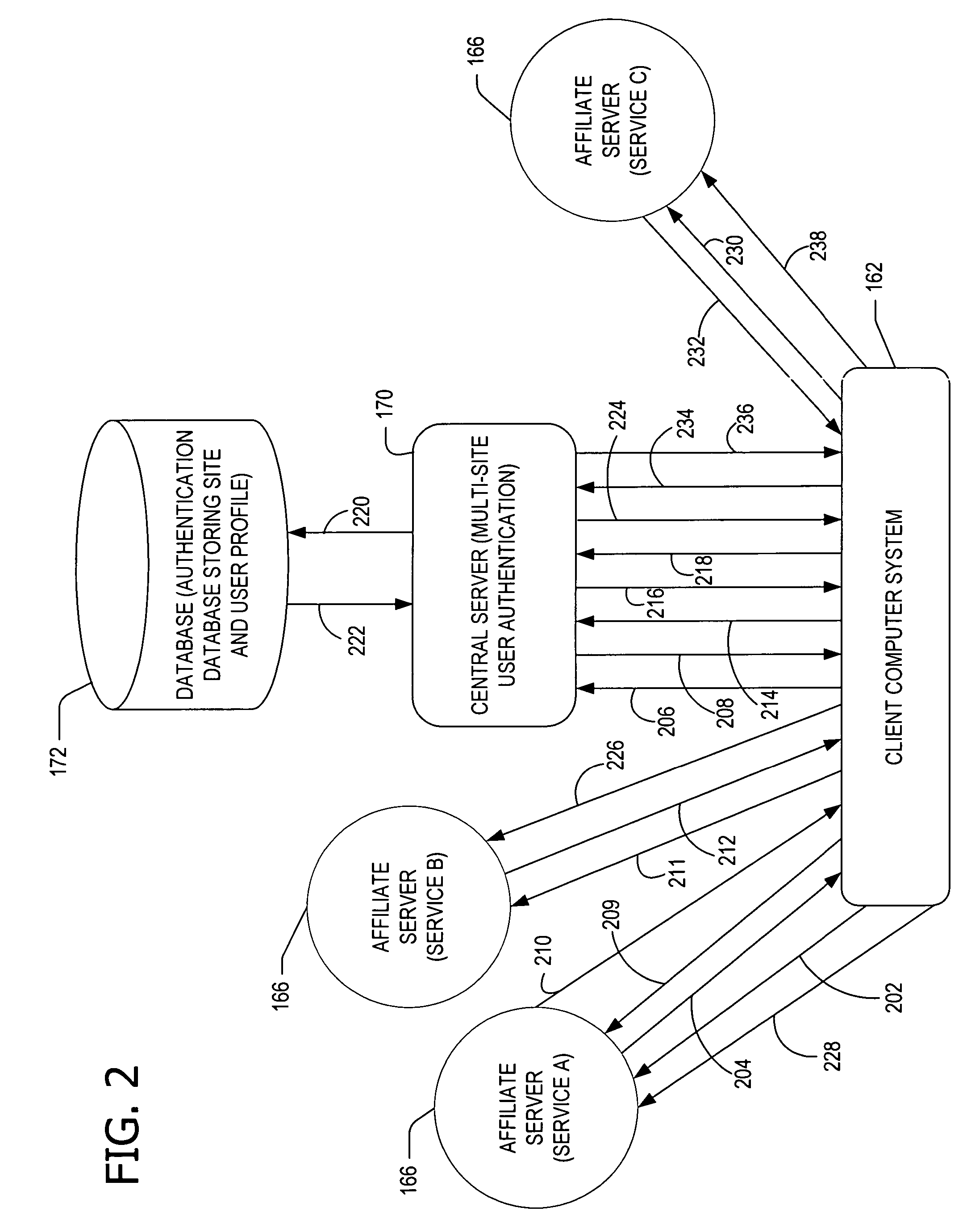
Cross-domain authentication
InactiveUS20050204041A1Overcome deficienciesAvoid the needDigital data processing detailsDigital computer detailsService provisionClient-side
Providing services within a network of service providers sharing an authentication service and a set of business rules. A central server receives a first request from a first server to provide a first service to a user via a client without forcing the user to present credentials. In response to the received first request, the central server stores data identifying the first service on the client. The central server further receives a second request from a second server to provide a second service to the user via the client after the user presents the credentials to the second service. After receiving the second request and the presented credentials, the central server allows the user access to the second service. In response to allowing the user access to the second service, the central server further allows the user access to the first service as a result of the stored data.
Owner:MICROSOFT TECH LICENSING LLC
Process for producing flexible optical waveguide
InactiveUS7120345B2Peeling can be safelyReduce adhesionCoupling light guidesOptical waveguide light guideFoaming agentWaveguide
Owner:NITTO DENKO CORP
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
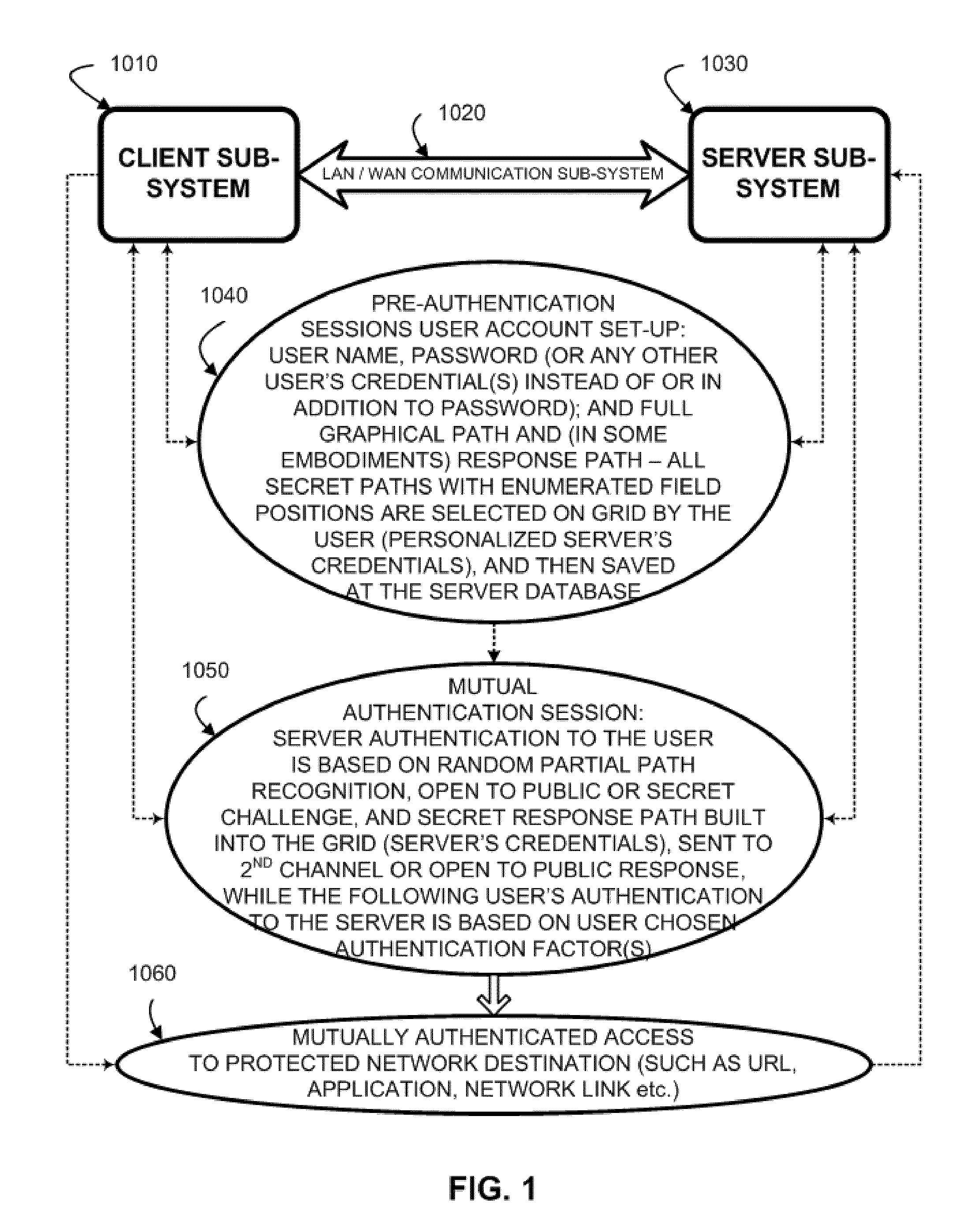
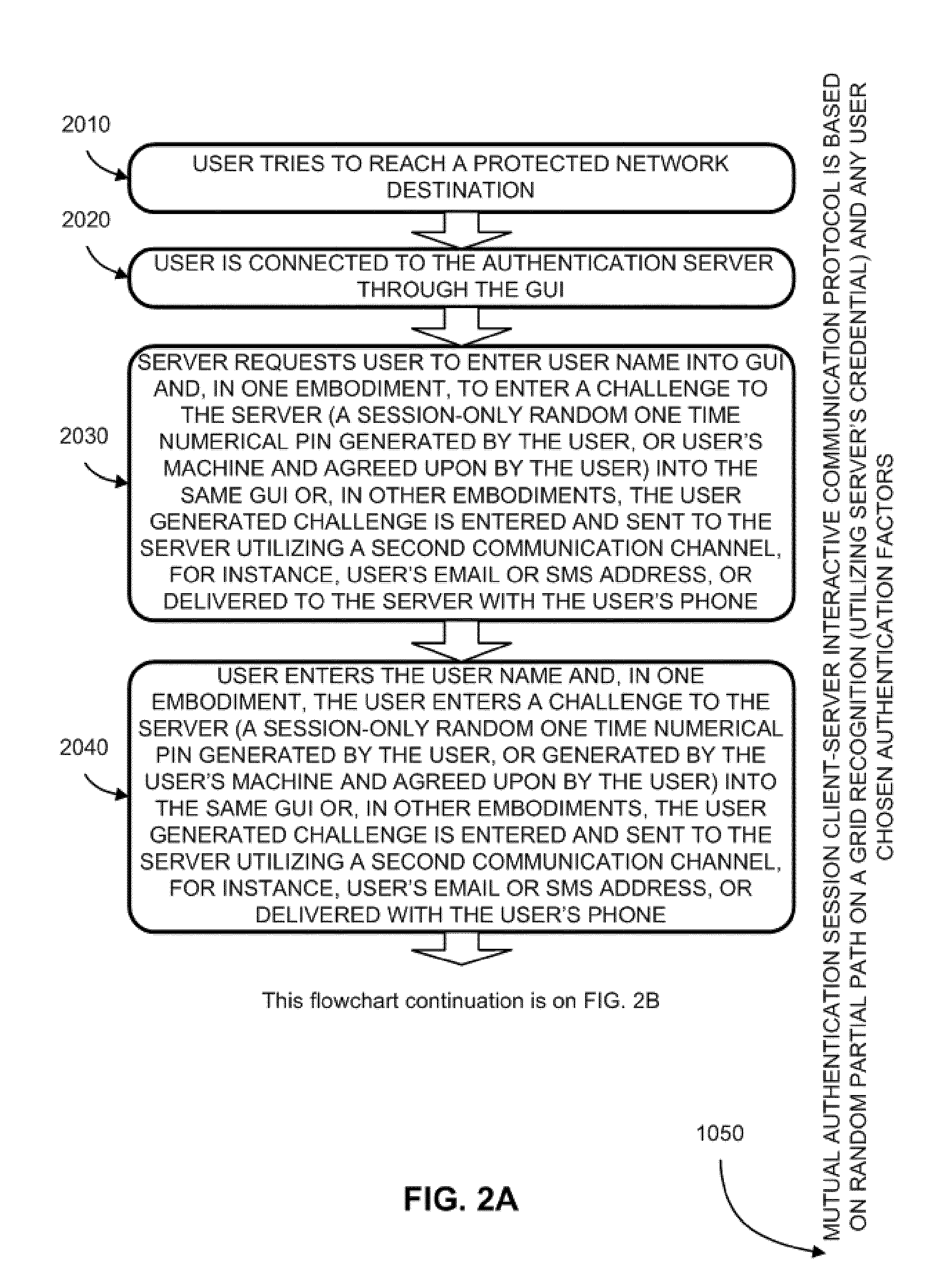
System and method for in- and out-of-band multi-factor server-to-user authentication
ActiveUS20110197070A1More versatile security requirementPracticalDigital data processing detailsUser identity/authority verificationUser authenticationClient-side
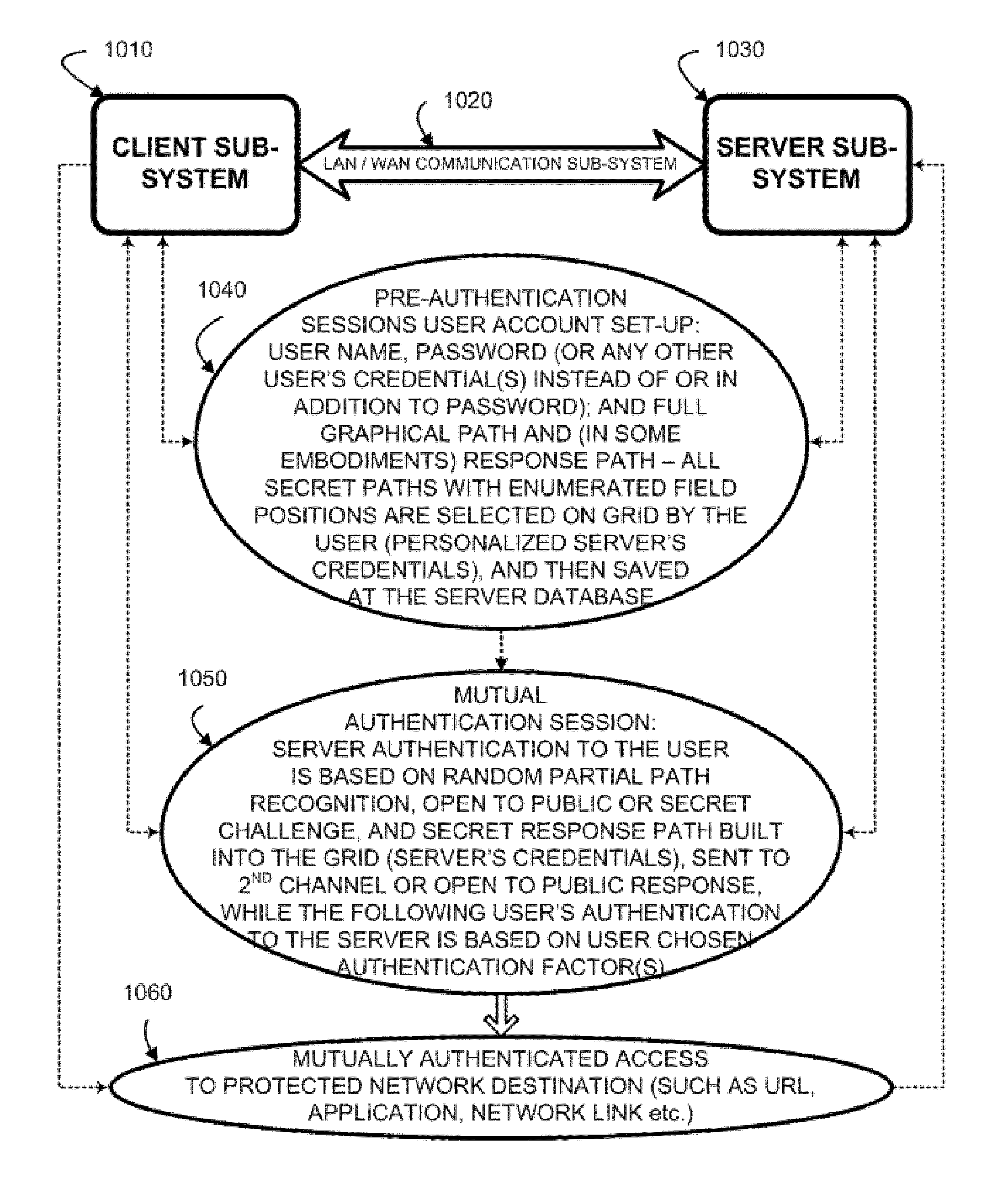
A method to authenticate a server to a client is provided, including in-band and out-of-band techniques. At least a first shared secret identifies a server path, including a plurality of pre-defined locations on a frame of reference (e.g. a grid). An authentication session is initiated upon receiving a client identifier at the server-side resources. A current session instance of the grid is presented to the client, populated with characters. The process includes sharing between the client and the server a challenge identifying a random subset of the plurality of predefined locations in the server path, and a response including characters that match the characters in the locations on the server path identified by the challenge. As a result, client is capable of verifying that the server has access to the first shared secret. Then a protocol is executed to authenticate the client to the server.
Owner:AUTHERNATIVE INC
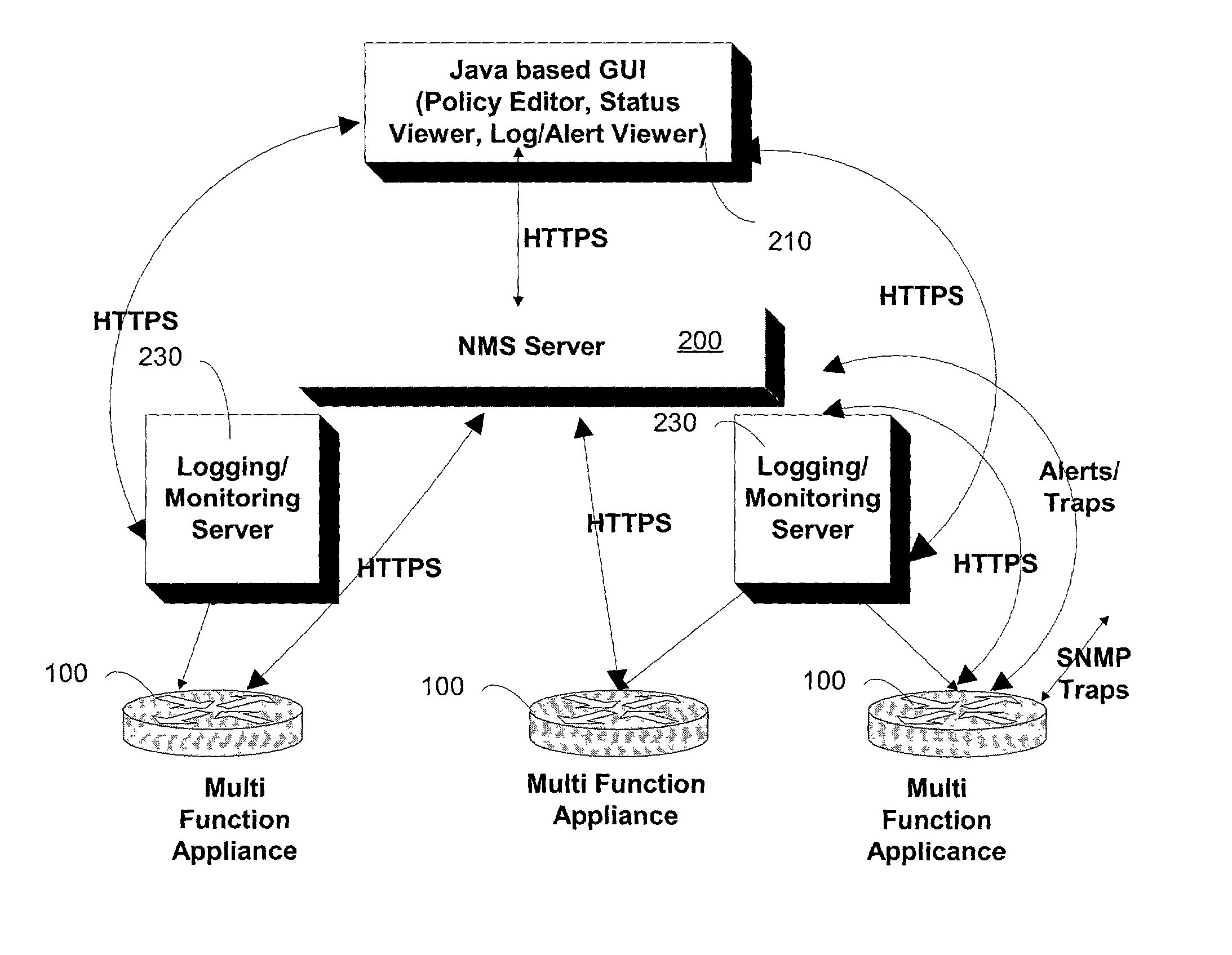
Network management system
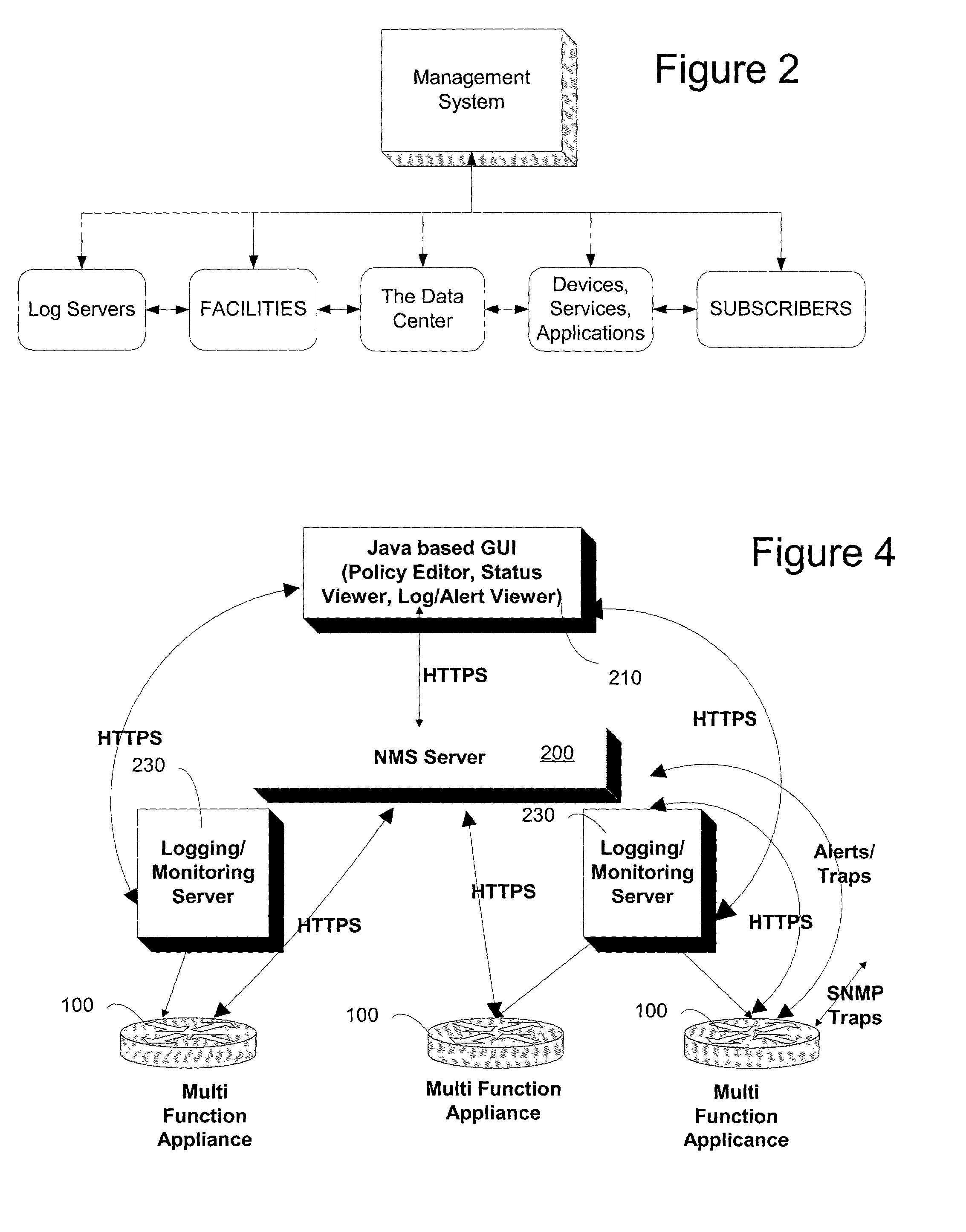
InactiveUS20030028624A1Low costMinimizing cross-configurationMultiple digital computer combinationsData switching networksData centerThe Internet
A virtual management system for a network facility, such as a data center, or any facility having a plurality of components which can be organized as objects for presentation in a virtualized environment, is disclosed. The system includes a management topology presenting devices, facilities, subscribers, log servers, and services as objects to an administrative interface; and a configuration manager implementing changes to objects in the topology responsive to configuration input from an administrator via the administrative interface. In an exemplary embodiment, the user interface is a graphical user interface designed to work in a platform independent environment. The system may include a management server coupled to the plurality of objects. In one aspect, the management server communicates with the devices, downloading configuration data to and uploading configuration data from, the devices. The management server and the interface may communicate via a LAN, WAN or the Internet.
Owner:NEXSI SYST
Process for production of steviosides from stevia rebaudiana bertoni
A process for the production of steviosides from Stevia rebaudiana Bertoni includes extraction of comminuted plant material by directly injecting steam into the extractor followed by filtration to get aqueous extract and alkali treatment to remove unwanted compounds in the form of precipitate. The treated aqueous extracted was filtered and the filtrate was first treated with gel or macroporous strong acid cation exchange resin and then with gel or macroporous weak base anion exchange resin. The aqueous eluant containing steviosides was concentrated to obtain purified steviosides.
Owner:COUNCIL OF SCI & IND RES
Mechanism for downloading software components from a remote source for use by a local software application
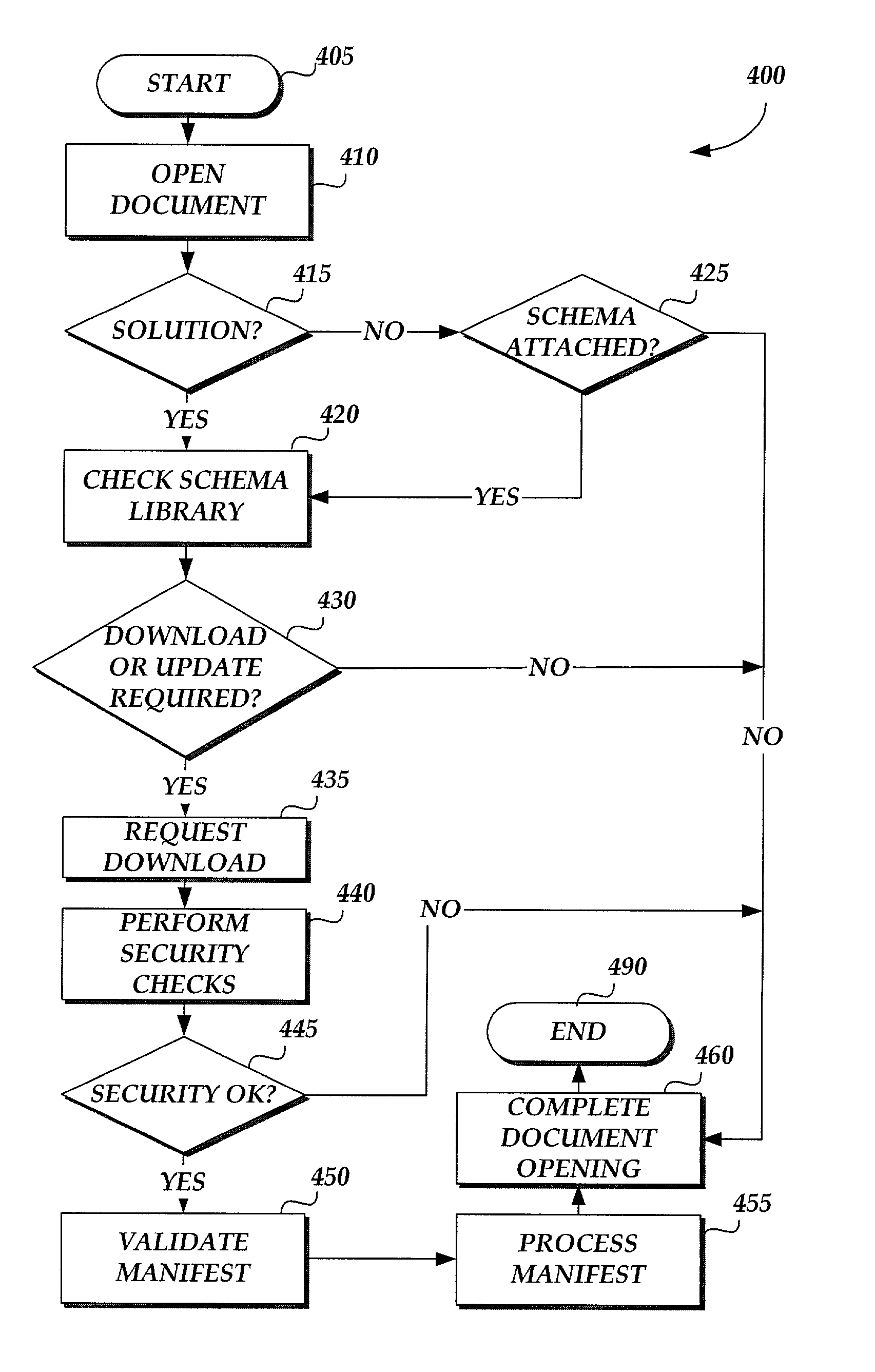
InactiveUS7281245B2Process safetyPlurality of obstructionProgram loading/initiatingSpecial data processing applicationsWeb serviceApplication software
A method and system are provided for downloading software components from a remote source to a software application for providing updates or additions to the application's functionality. All components and files that may be utilized to update or add to functionality available to the application are identified and are assembled on a manifest that may be located on a remote web server accessible by the application. If components of the application should be updated, or corrections or improvements to existing components are available, or new functionality is available that will transform the user's existing application and document into a “smart” application and “smart” document, the application may connect to the web server to download the required components.
Owner:MICROSOFT TECH LICENSING LLC
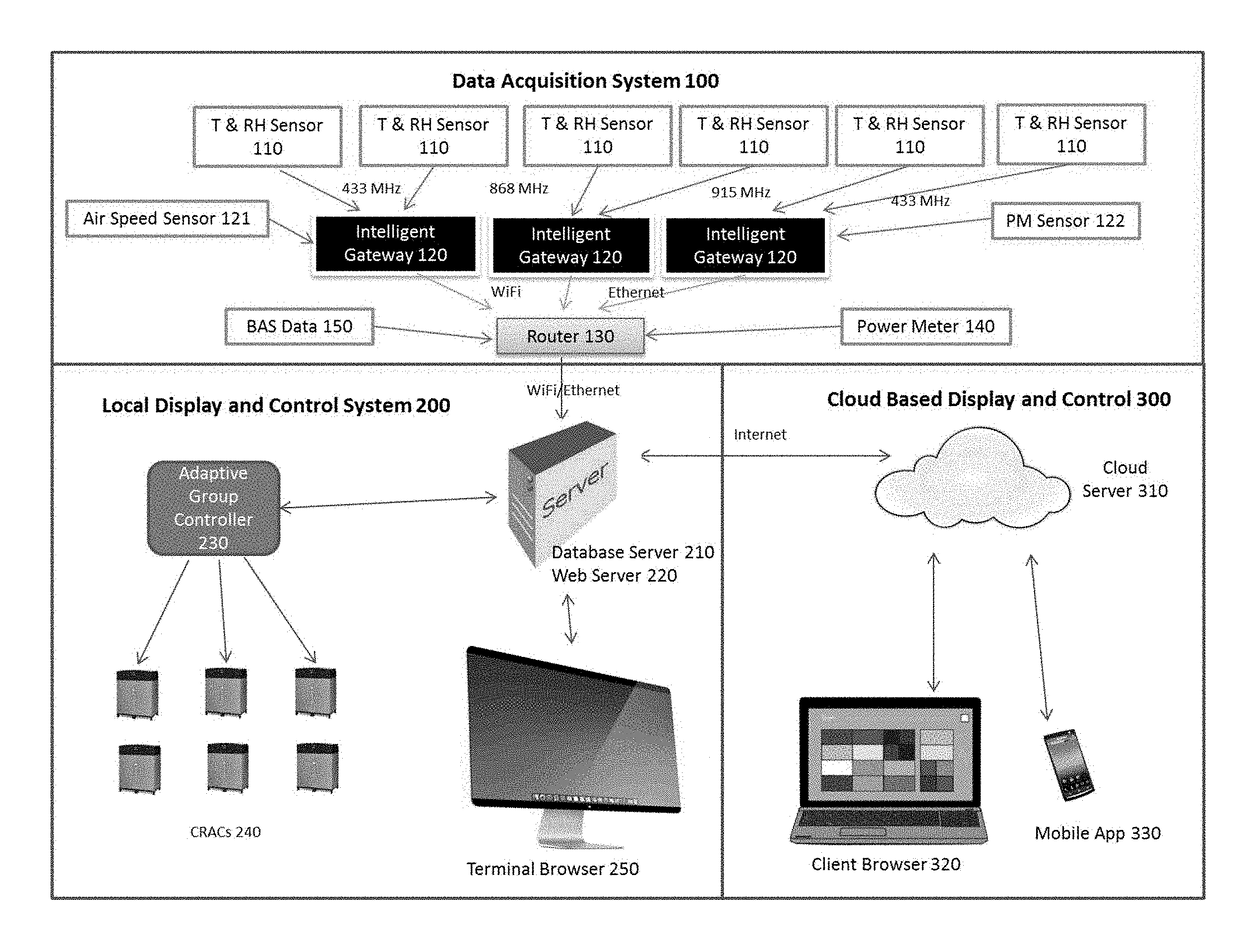
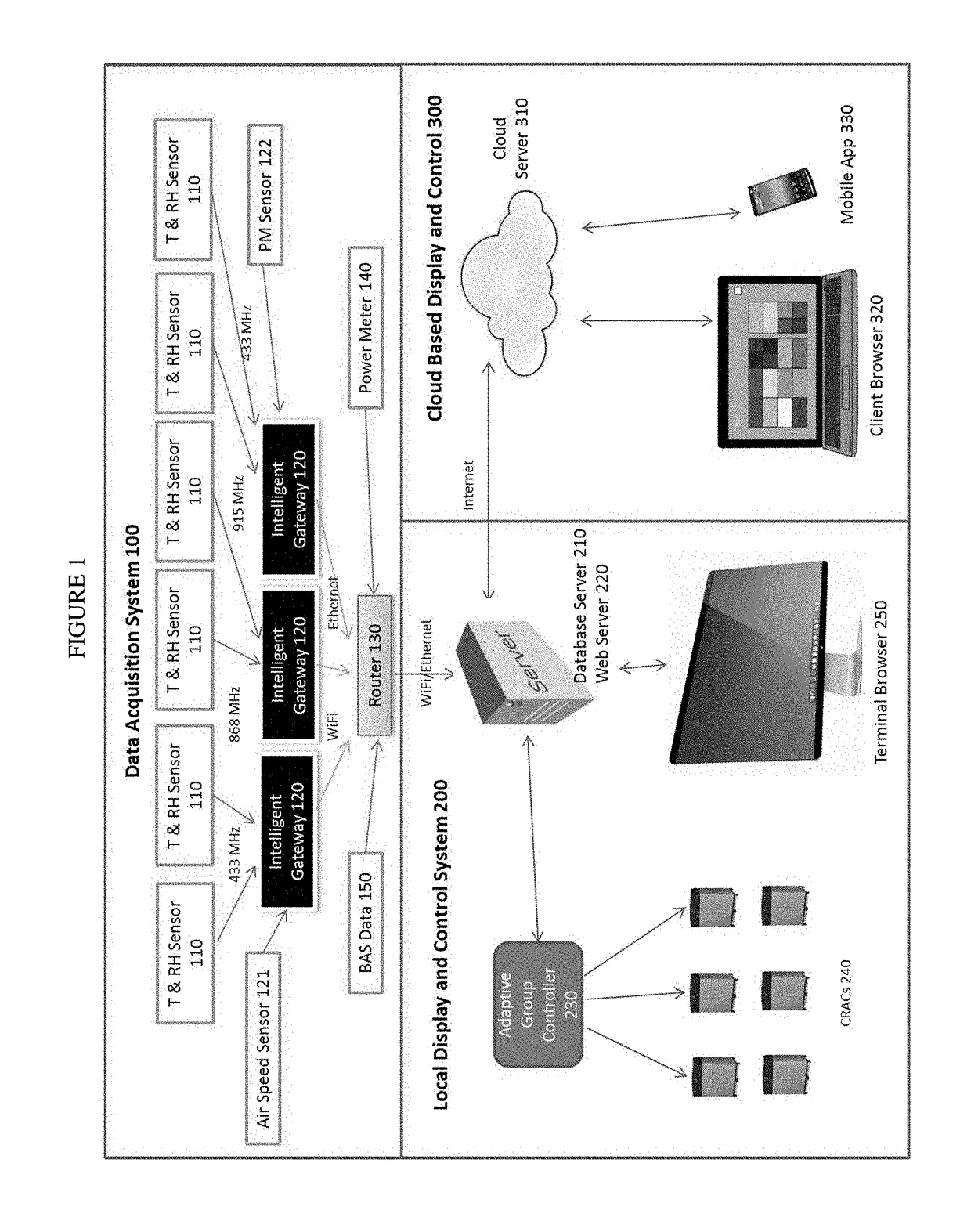
Intelligent mission critical environmental monitoring and energy management system
InactiveUS20170176033A1Process safetyEnergy efficiencyProgramme controlMechanical apparatusDashboardUser management
The present invention is a complete solution for mission critical facilities to create a safe environment and energy efficient CRAC system. The invented system collects mission critical facility volume environmental and energy data in real time, and uses big data analytics to provide adaptive group control to CRACs. The data is visualized in 2D and 3D graphs, dashboard, history curves and reports locally and through the cloud. The present invention also provides user management to allow authorized users to view and control the racks / servers owned or rented by these users. The present invention is comprised of four companion patents: 1) A Battery-powered Wireless Long Life Temperature and Humidity Sensor Module, 2) An Intelligent Multi-channel Wireless Data Acquisition Gateway, 3) Mission critical facility Three Dimension Temperature Contour Generator, and 4) An Adaptive Automatic CRAC Master Control Method.
Owner:ARCHIMEDES CONTROLS CORP
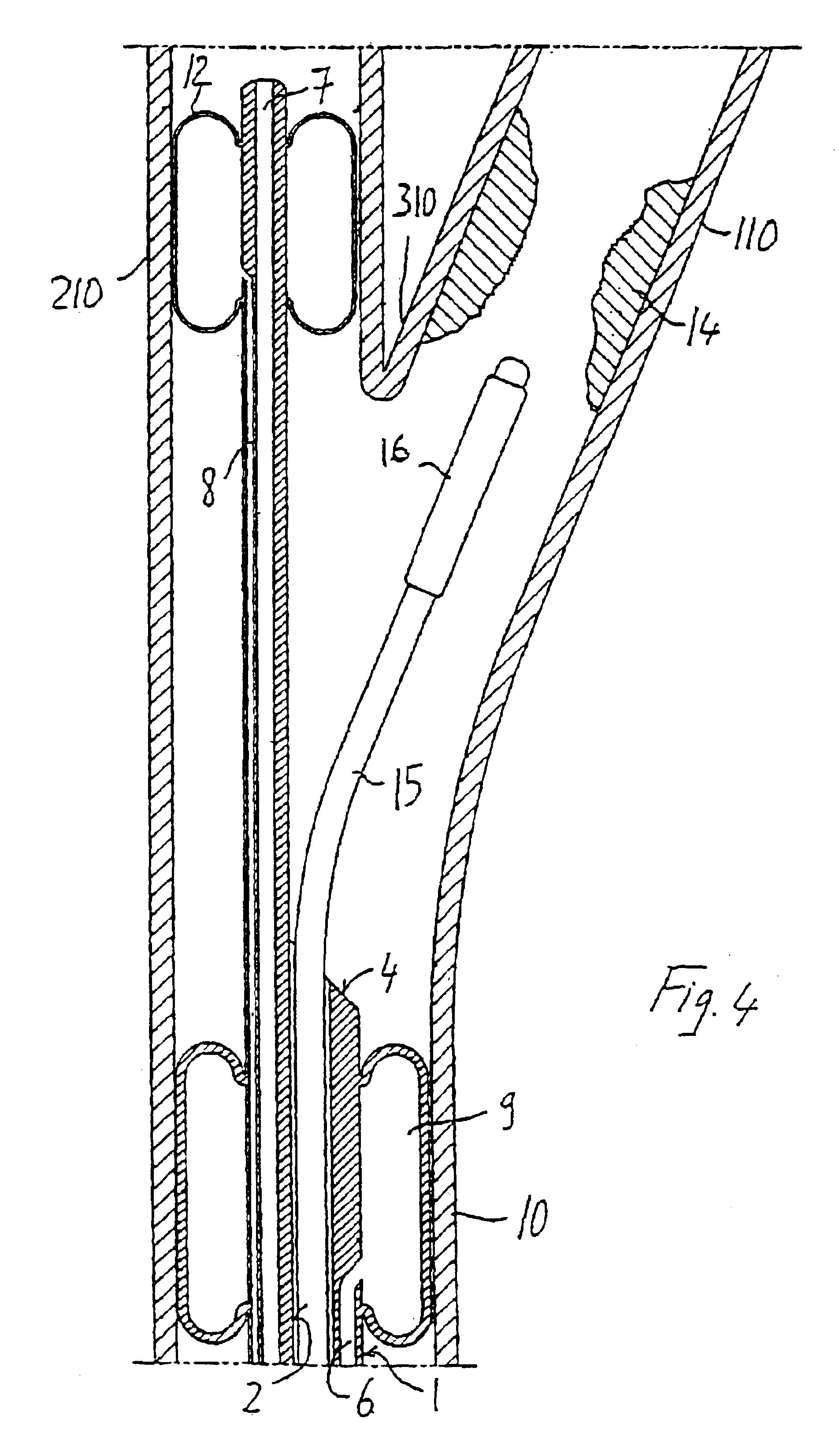
Endovascular system for the treatment of stenoses of the carotid and catheter for this system
A catheter, in particular for endovascular applications, including a long and flexible, hollow, tubular body having an insertion end and a connection end intended to remain outside the body. The catheter includes in the insertion end at least two elements which are expandable / contractible by means of external operations. Those elements are located at a distance from each other, one upstream and the other downstream of a given section of a vessel. With the catheter it is possible to operate in the section between the two expandable elements and, if necessary, in the intermediate arterial branch which, on account of the two elements upstream and downstream, will have a zero flow.
Owner:INVATEC +3
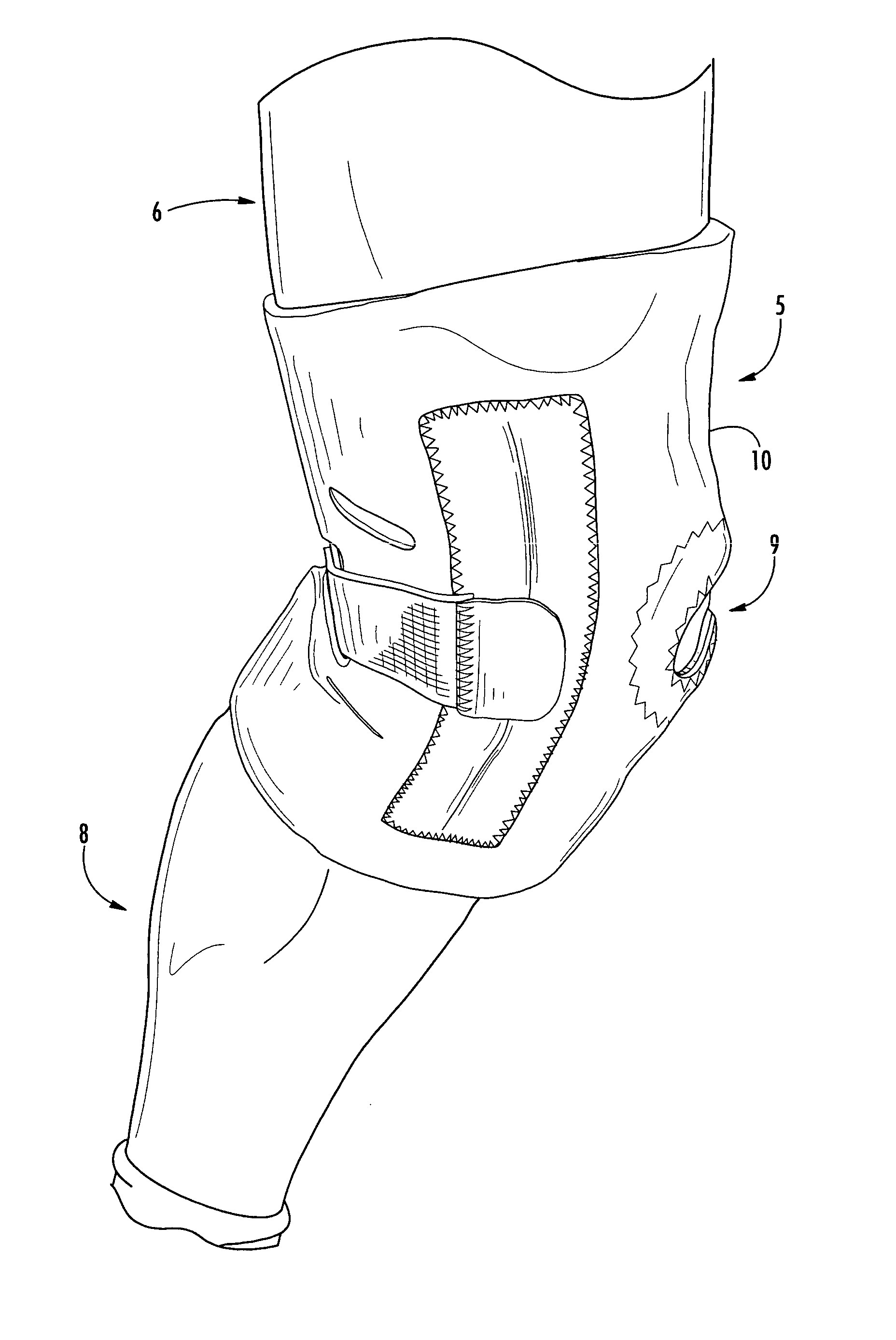
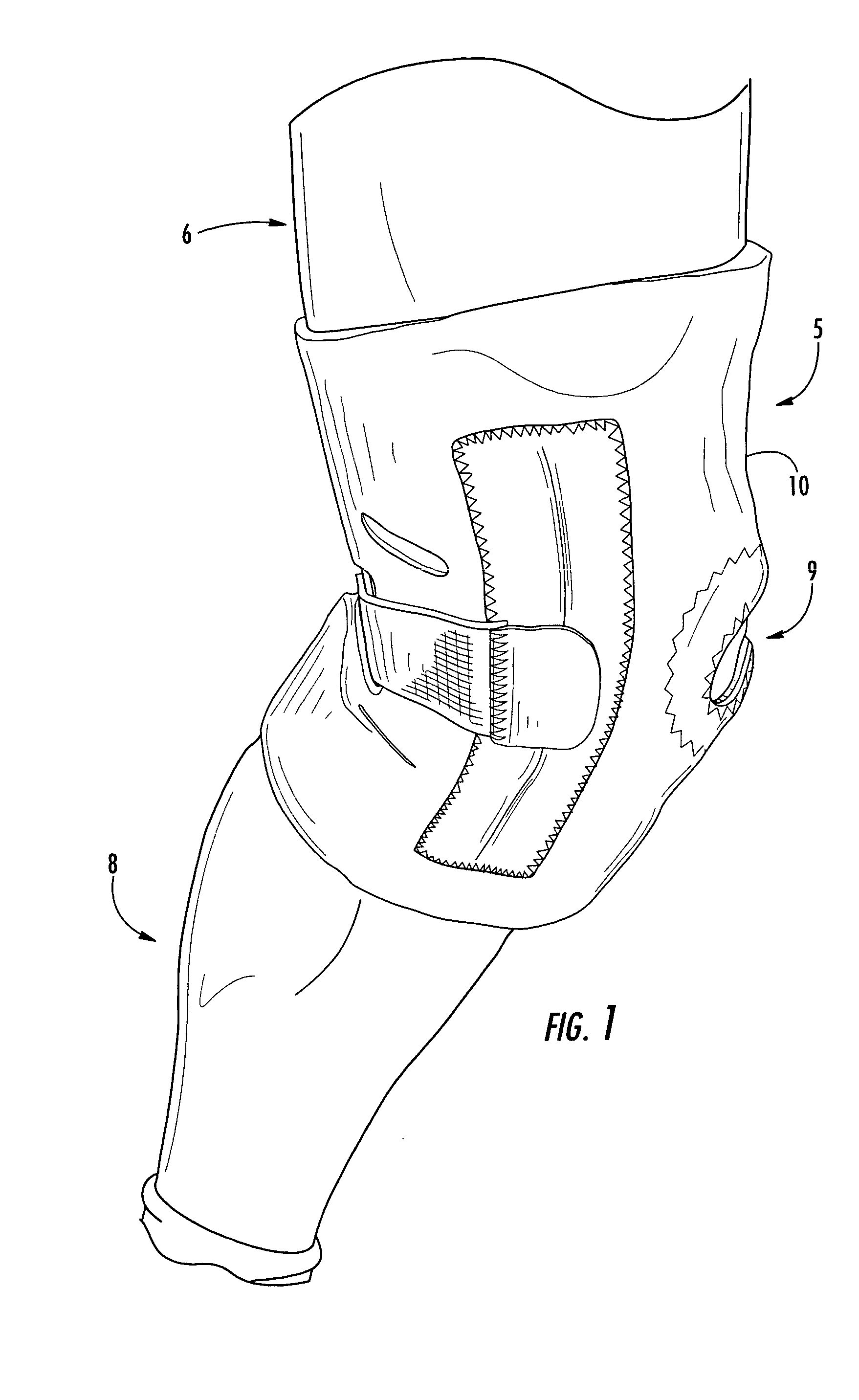
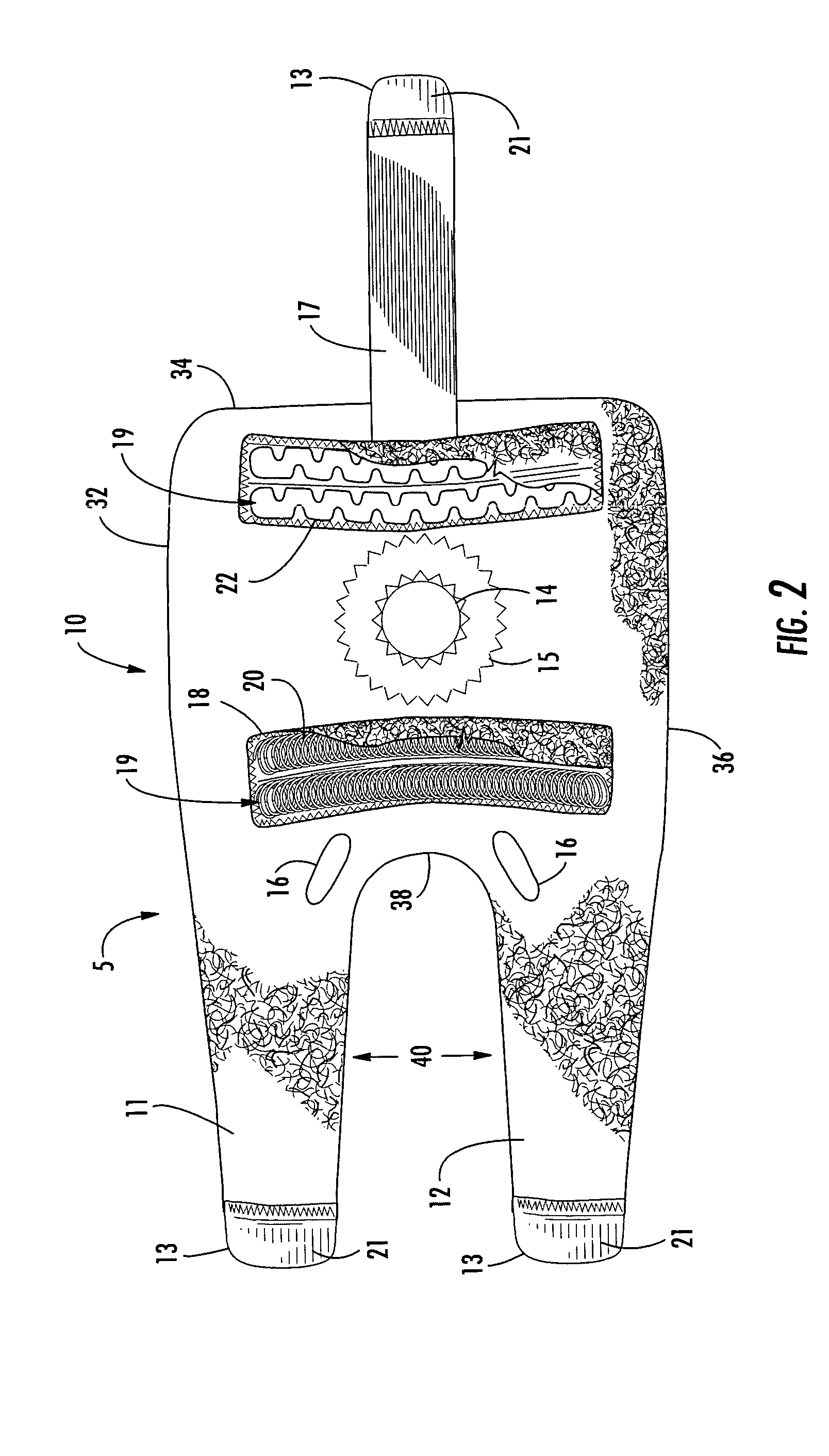
Adjustable knee stabilizer
InactiveUS20050038367A1Efficient use ofImprove material efficiencyNon-surgical orthopedic devicesEngineeringNormal flexion
Owner:BEIERSDORF INC
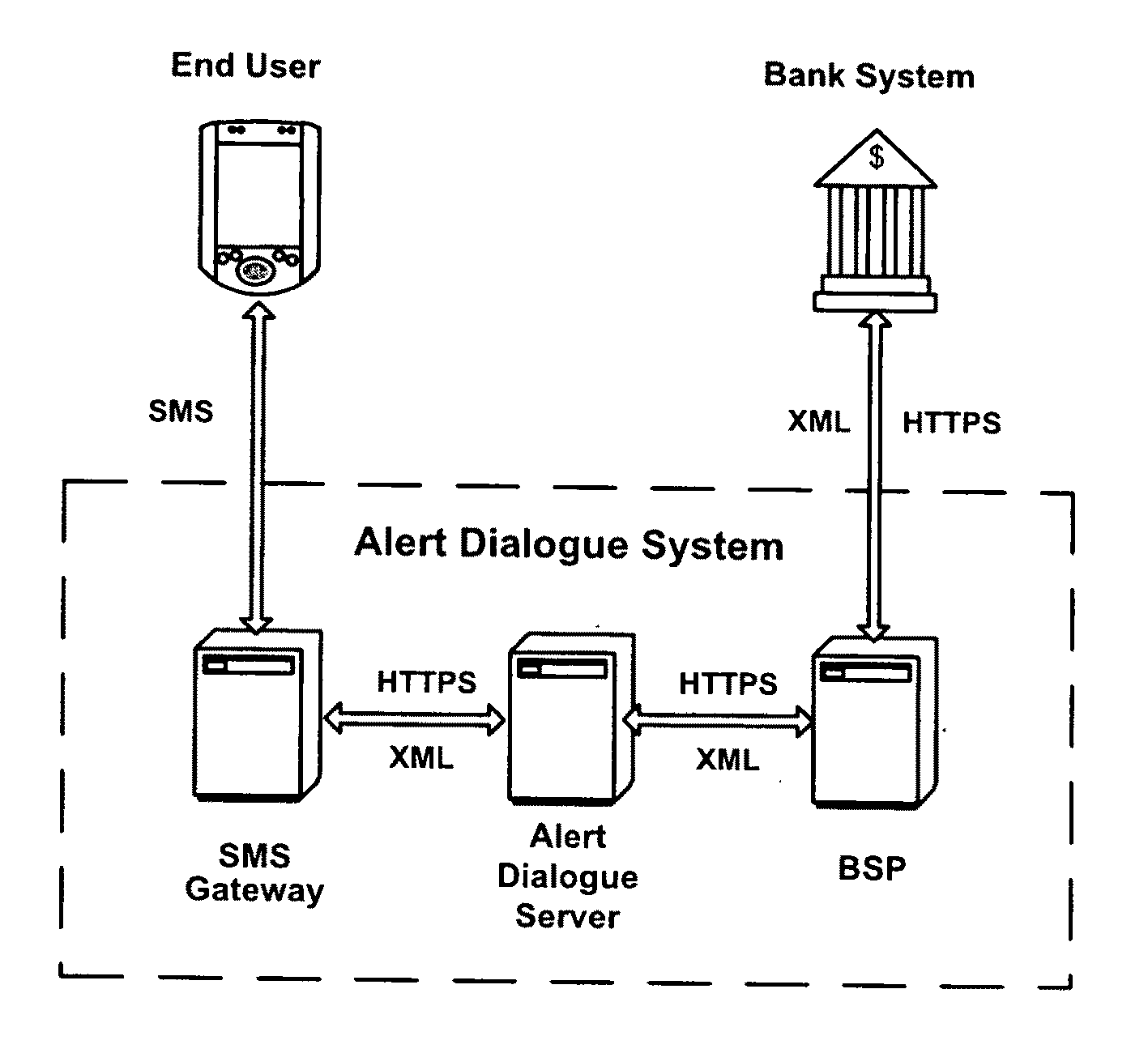
Mobile banking and payment platform
InactiveUS20100191602A1Fast transferProcess safetyFinanceUser identity/authority verificationPaymentComputer network
To eliminate, or at least substantially eliminate, the security concerns of conventional Internet-enabled mobile banking operations, and mobile banking operations in general, the present invention provides perhaps the most secure mobile banking and payment or product / service purchase method extent which avoids security problems of the Internet and provides a rapid transfer of transactional information and other information as desired, inclusive of revenue generating advertisements with the architecture and techniques of the present inventive Internet data protocol (DTP).
Owner:SKKY
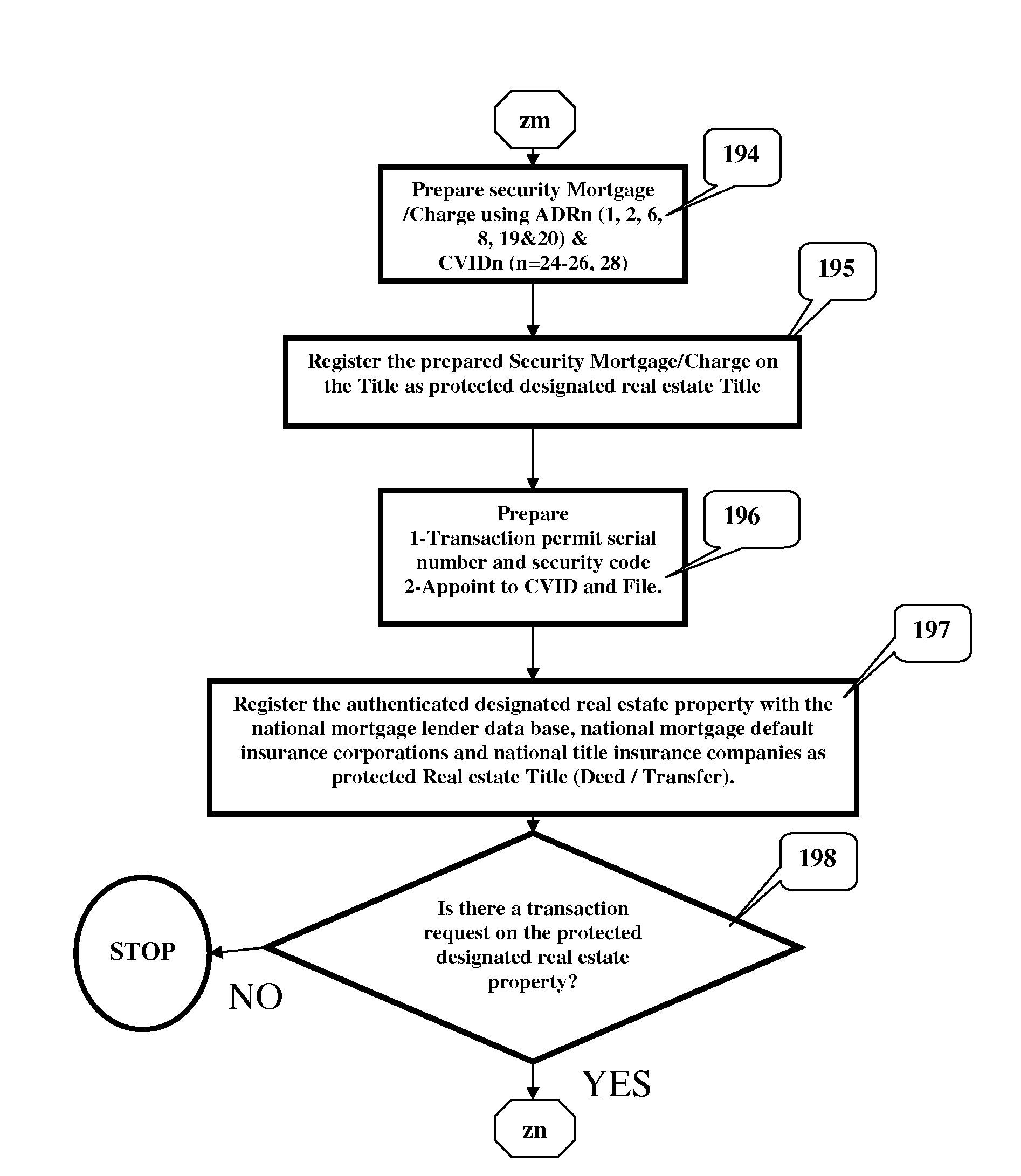
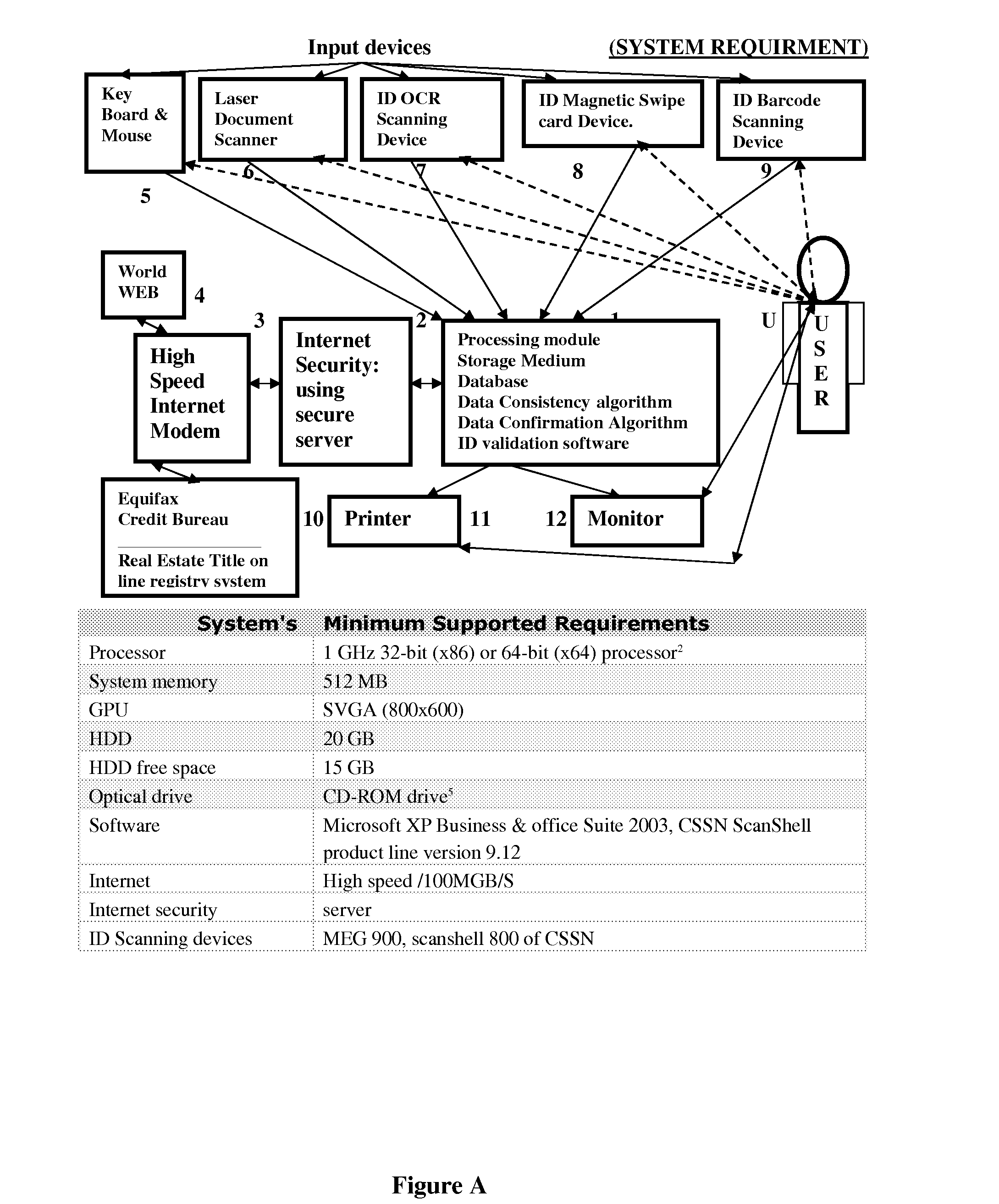
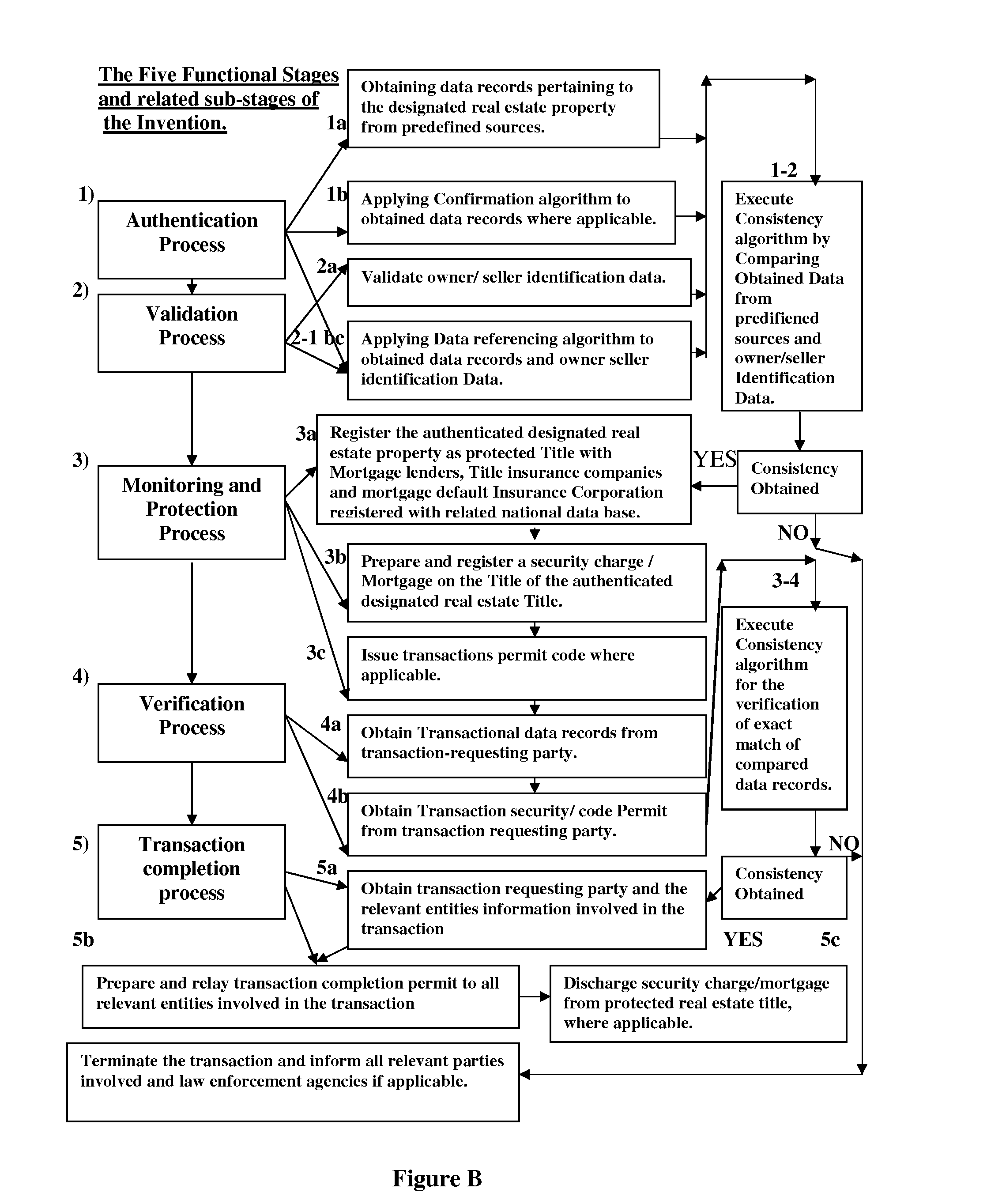
Method and System for Monitoring and Protecting Real Estate Title (Ownership) Against Fraudulent Transaction (Title Theft) and Mortgage Fraud
InactiveUS20080167883A1Prevented substantial financial losesRule out the possibilityCommerceData differencingTransaction data
A method for monitoring and protecting a designated real estate Title (Deed / Transfer) against title theft, fraudulent transaction, mortgage fraud includes process and steps of compiling selected data records associated with a designated real estate Title from plurality of predefined sources and storing the compiled data into an associated file within a computer database, number referencing stored selected data to further facilitate confirmation and authentication of the data records, execute monitoring process for an authenticated Title by preparing and registering security Charge / Mortgage on the Title, Issue transaction permit code, registering with local and national lender data base, Mortgage default insurers and Title insurance companies as protected Title, protect an authenticated Title from fraudulent transaction, mortgage fraud and illegal activity by further verifying transactional data of the requesting party with the stored authenticated data, stop transaction on detection of data discrepancies, issue transaction completion permit and discharge registered security charge by obtaining consistency in obtained data records. A system comprising of confirmation, authentication and verification algorithm and ID validation hardware components. The system further includes a computer database for storing data records, computer software to validate ID cards, reference number data records, execute confirmation, authentication and verification algorithm and issue transaction completion permit / Termination warning and security charge / discharge documents.
Owner:THAVILDAR KHAZANEH RAMIN
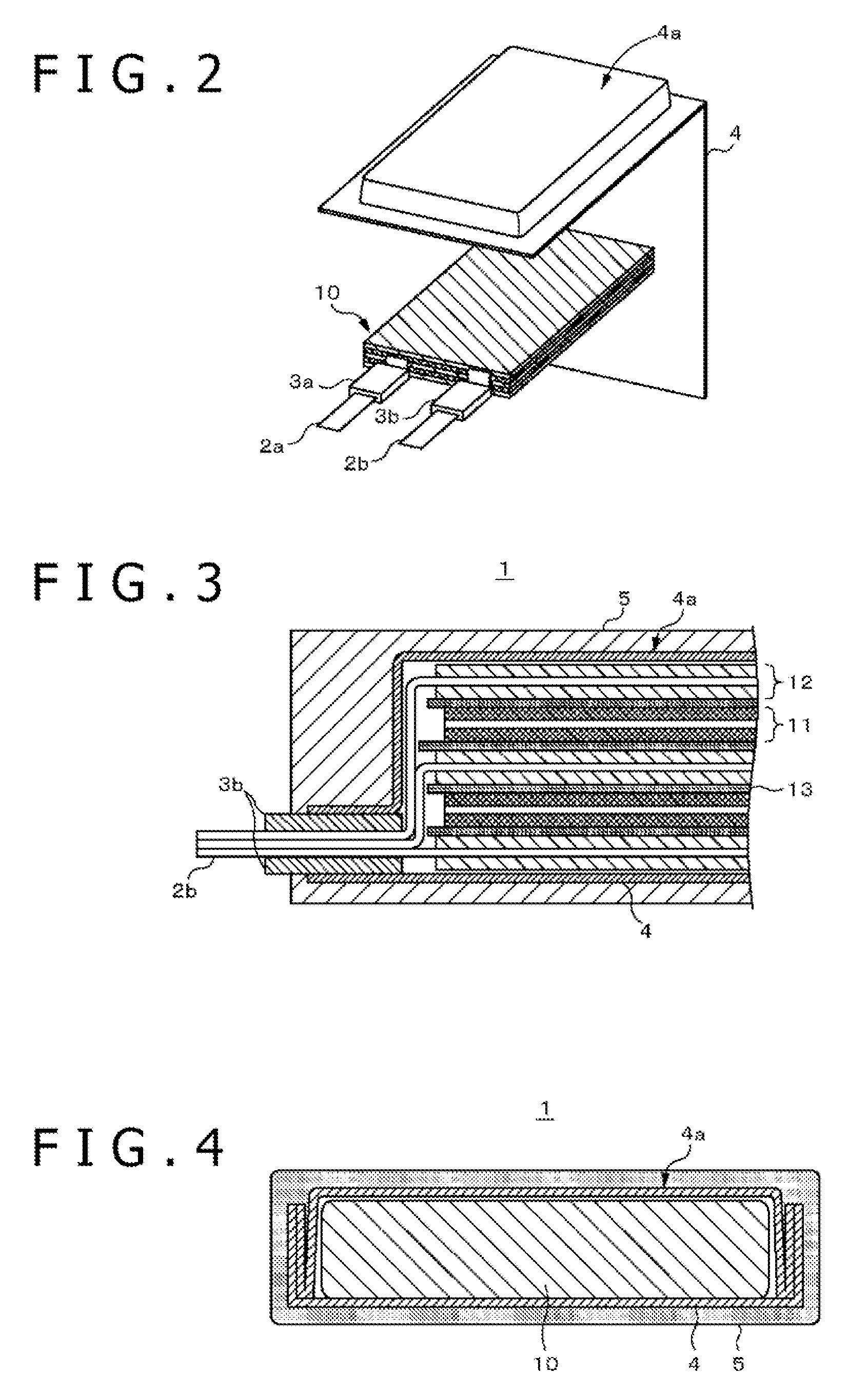
Non-aqueous electrolyte battery and method for producing the same
ActiveUS20090186270A1Improving battery strengthHigh strengthFinal product manufacturePrimary cellsEngineeringNon aqueous electrolytes
A non-aqueous electrolyte battery includes a battery element, a film-form casing member, and a resin protective layer. The battery element includes a positive electrode, a negative electrode, and a separator disposed between the positive electrode and the negative electrode. The film-form casing member contains the battery element and an electrolyte in an enclosed space thereof. The resin protective layer is formed along the surface of the film-form casing member and has a substantially uniform thickness.
Owner:MURATA MFG CO LTD
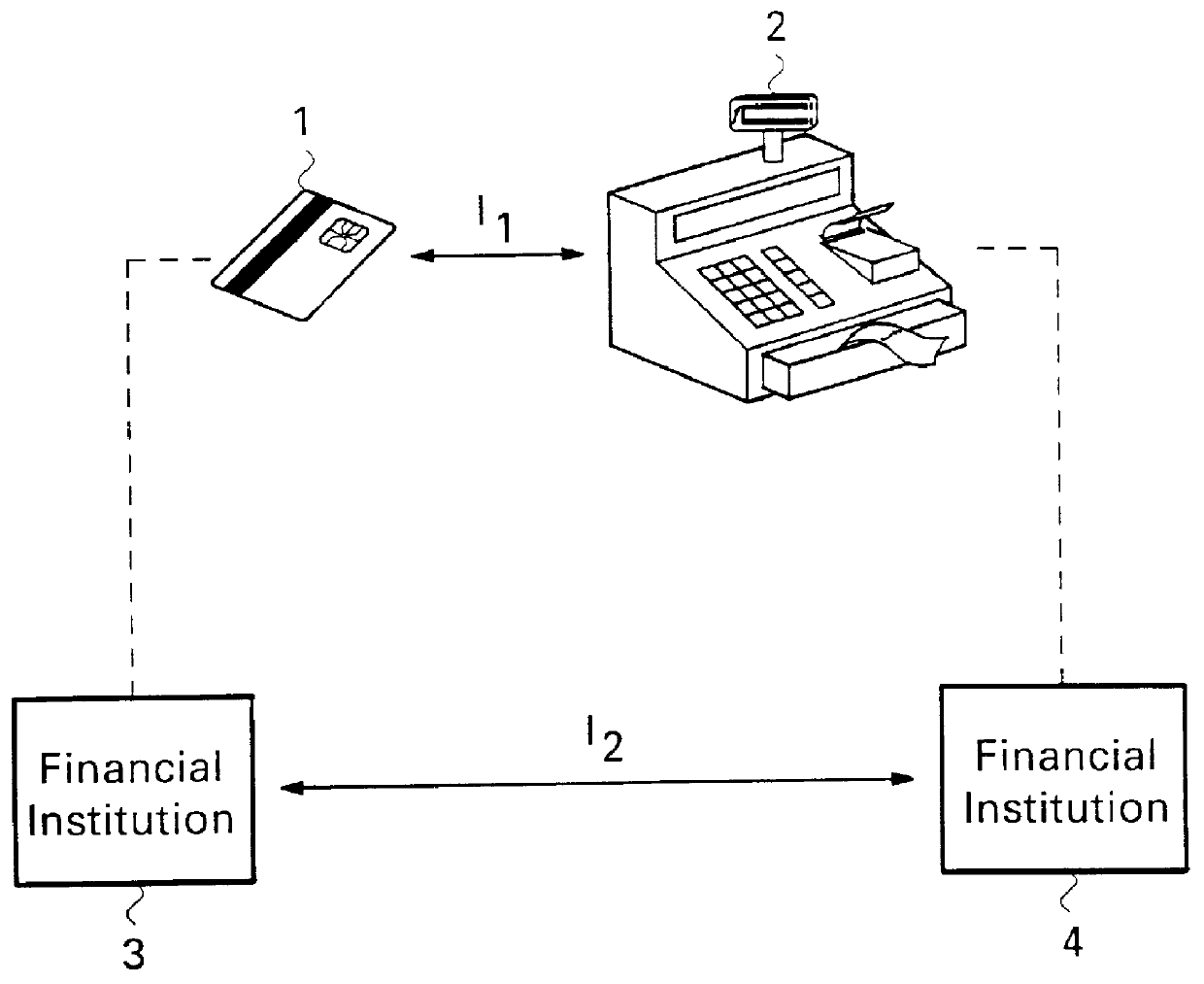
Electronic payment method and system having several calculation units and electronic payment devices
A payment system for use with electronic payment devices. Electronic payment cards (e.g. "Smart Cards"), may be used with one or more payment stations (e.g. electronic cash registers). The payment stations are designed for receiving, during a payment transaction, a monetary value by crediting, in the payment station, a first value, and debiting, in the payment means, a second value corresponding to the first value. The first and second values may be expressed in different calculation units, such as currencies of different countries. The system furthermore offers a payment device for application in such a system, and a method for effecting a payment transaction with an electronic payment means.
Owner:KONINK KPN NV
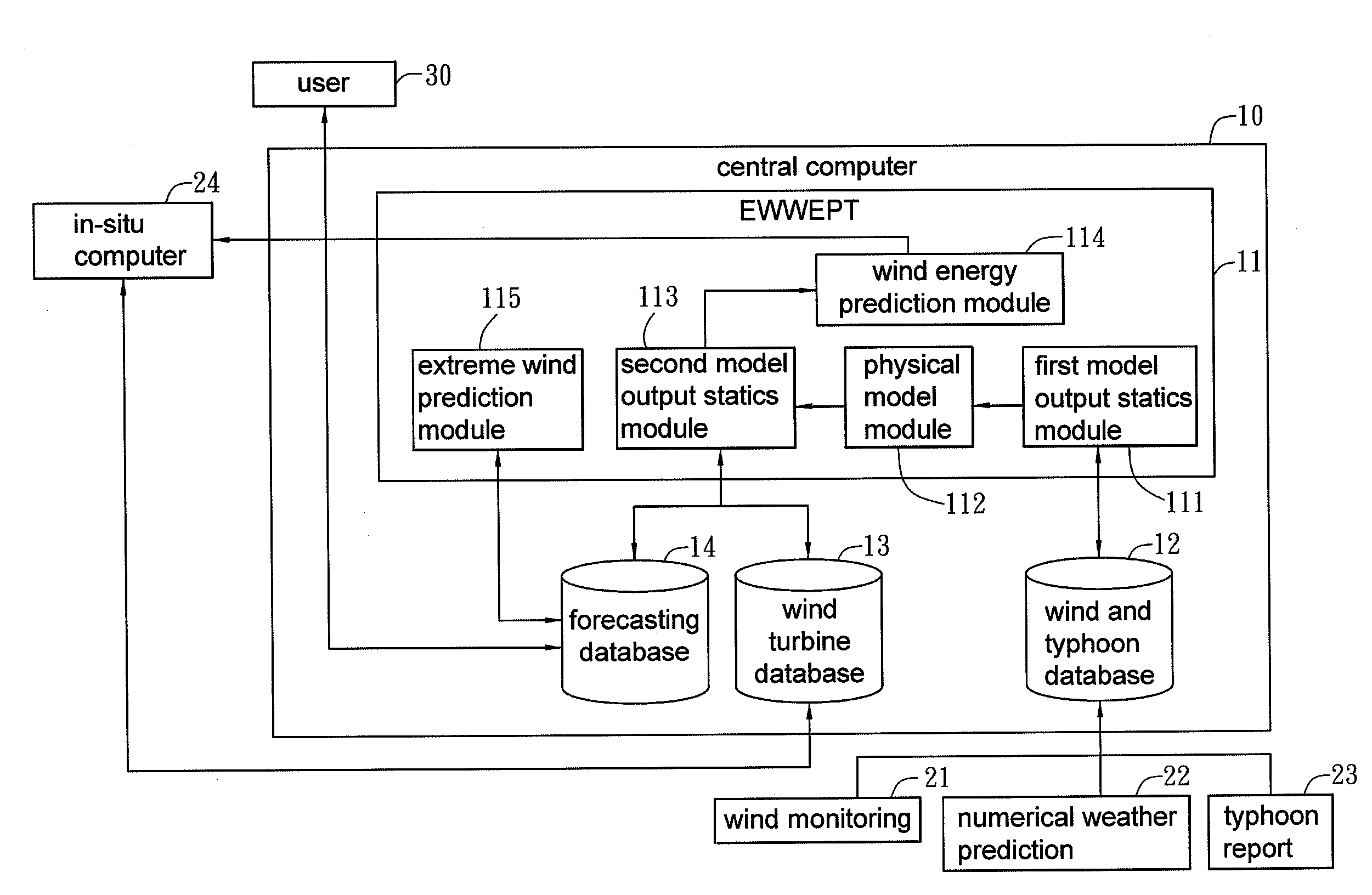
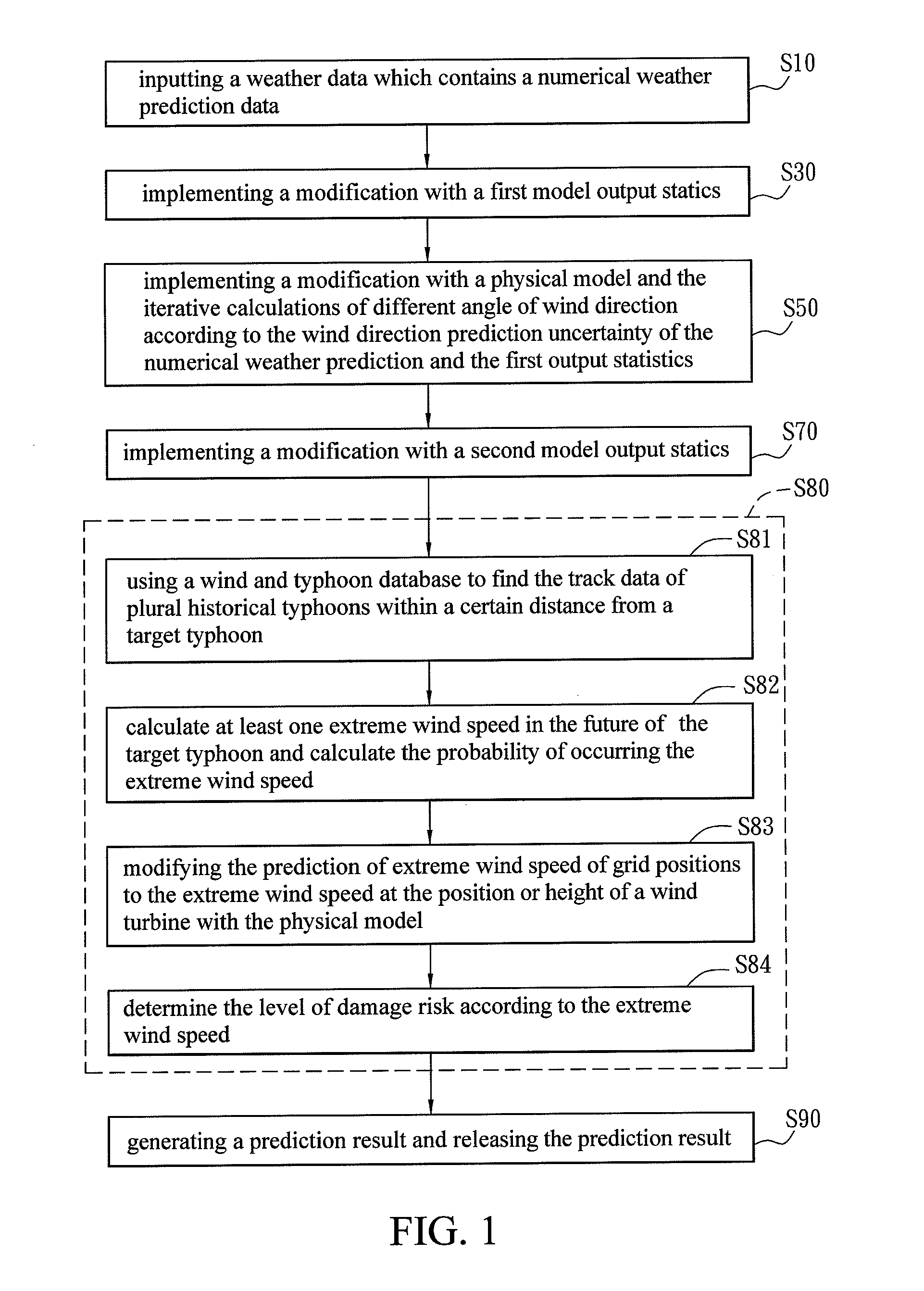
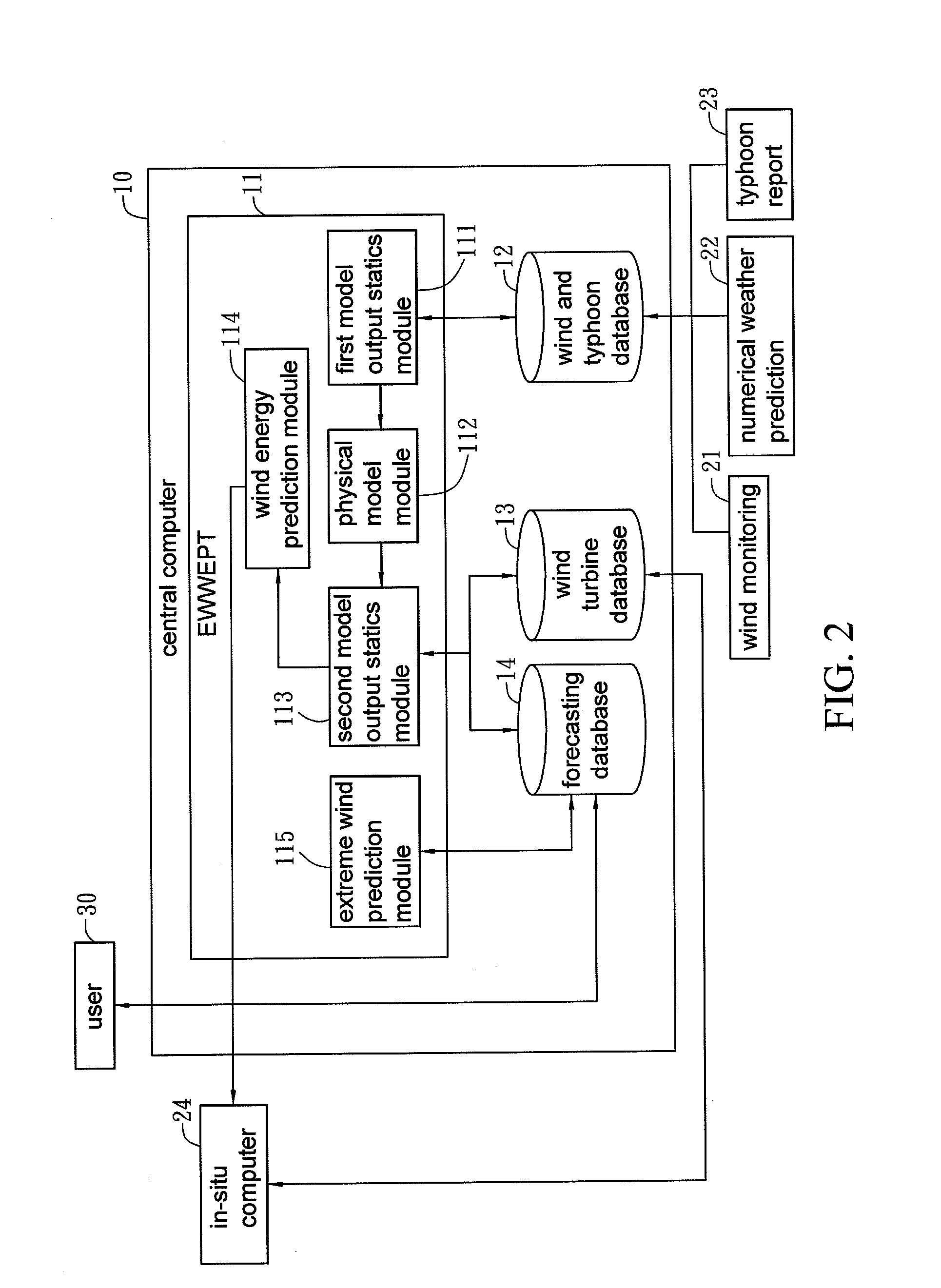
Wind energy forecasting method with extreme wind speed prediction function
InactiveUS20120046917A1Improve efficiencyProcess safetyWeather condition predictionEngine fuctionsNumerical weather predictionPhysical model
A wind energy forecasting method with extreme wind speed prediction function cooperated with a central computer, comprising the steps of: inputting a weather data which contains a numerical weather prediction data; implementing a modification with a first model output statistics; implementing a modification with a physical model in accordance with the output of the first model output statistics that can iteratively calculate the results by varying the angles of wind direction; implementing a modification with a second model output statistics; and implementing a prediction of extreme wind speed caused by typhoon, which comprises the following sub-steps of: using a wind and typhoon database to find track data of plural historical typhoons within a certain distance from a target typhoon; using an extreme wind and wind energy prediction tool to calculate at least one extreme wind speed in the future of the target typhoon and calculate the probability of occurring the extreme wind speed; and modifying the extreme wind speed with the physical model to the extreme wind speed at the position or height of a wind turbine.
Owner:INST NUCLEAR ENERGY RES ROCAEC
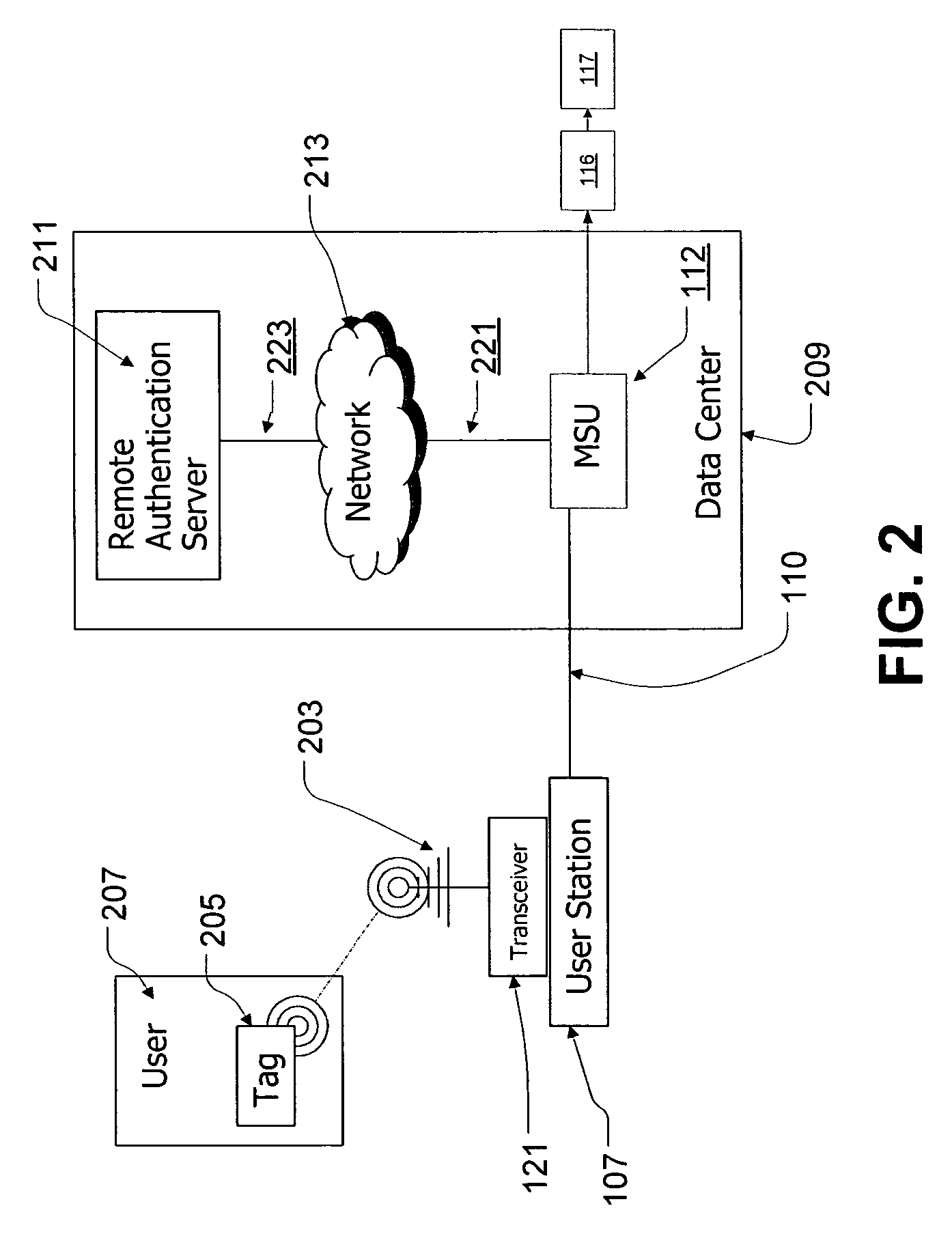
Means and method for providing secure access to KVM switch and other server management systems
ActiveUS20060107061A1Management moreSpace minimizationDigital data processing detailsUnauthorized memory use protectionTransceiverManagement system
Disclosed is a secure switching system that utilizes radio frequency identification (RFID) technology to allow only authorized users to access a remote management or keyboard, video, mouse (KVM) switching system. The system includes a plurality of user workstations that allow a user to select, monitor, and operate remote devices using a local keyboard, video monitor, and cursor control device. Coupled to or integrated with the system is an RFID transceiver that detects the presence of RFID tags that are within range of communications. A user workstation is only operable if the RFID transceiver detects a valid RFID tag.
Owner:RIIP
Cross-domain authentication
InactiveUS7636941B2Overcome deficienciesAvoid the needDigital data processing detailsDigital computer detailsService provisionClient-side
Providing services within a network of service providers sharing an authentication service and a set of business rules. A central server receives a first request from a first server to provide a first service to a user via a client without forcing the user to present credentials. In response to the received first request, the central server stores data identifying the first service on the client. The central server further receives a second request from a second server to provide a second service to the user via the client after the user presents the credentials to the second service. After receiving the second request and the presented credentials, the central server allows the user access to the second service. In response to allowing the user access to the second service, the central server further allows the user access to the first service as a result of the stored data.
Owner:MICROSOFT TECH LICENSING LLC
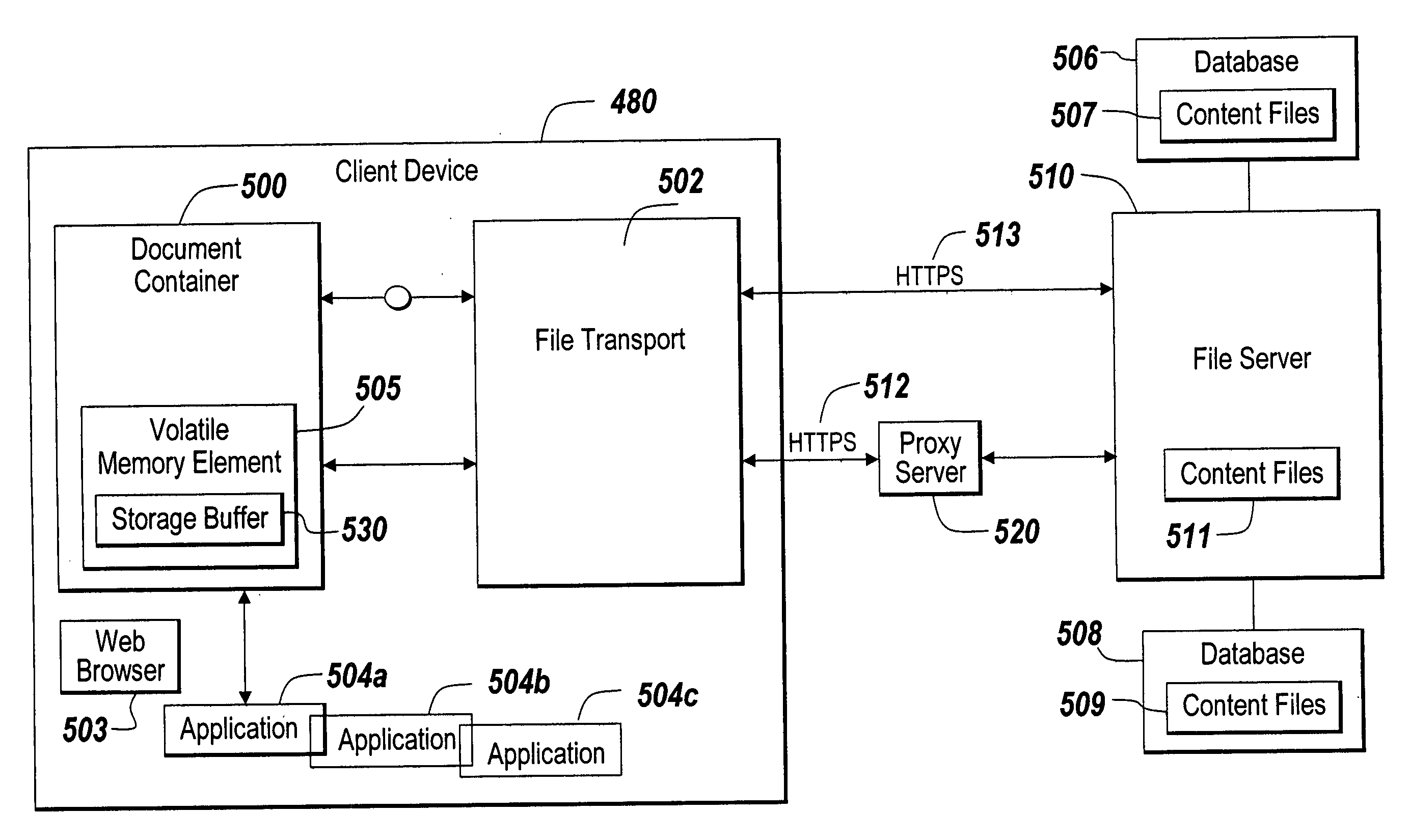
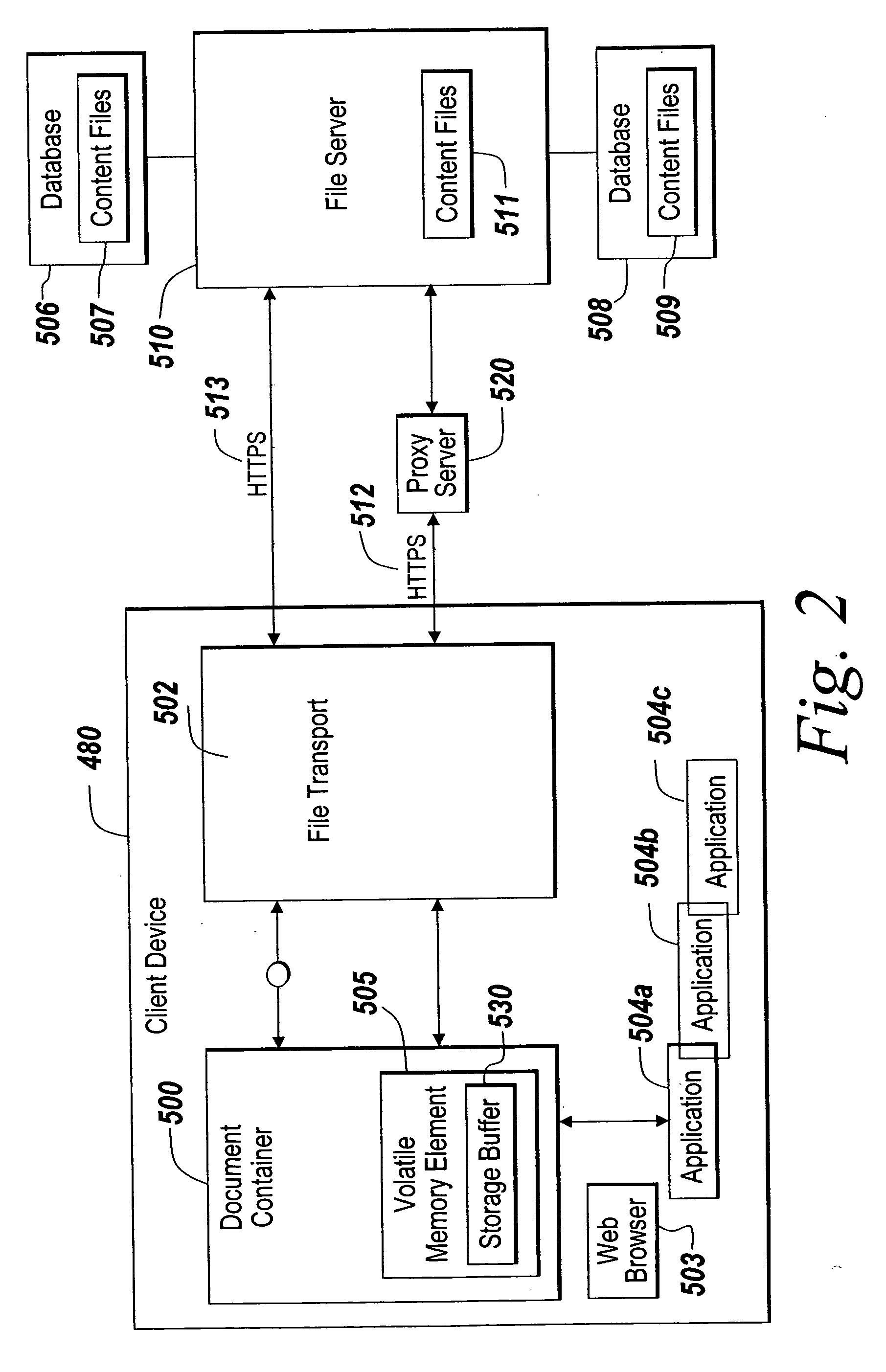
Methods and apparatus for secure online access on a client device
ActiveUS20060047956A1Prevent unwanted disclosure of confidential informationManipulation is limitedComputer security arrangementsSpecial data processing applicationsPaper documentDocument preparation
A method of securely accessing at a client device content from a server without using the non-volatile memory of the client device is disclosed. The bypassing of non-volatile memory lessens the security risk of unauthorized viewing of the server originated content. An transport mechanism is initiated on a client device and creates a document container. Downloaded documents from a server are mapped into the document container and saved within the document container in volatile memory. Substitute menus are generated within the container to replace application menus. User documents are saved directly to the originating server via the substitute menus. The downloaded copies in volatile memory automatically delete when the document container is destroyed thereby reducing security concerns of unauthorized viewing of the content at the client device.
Owner:CITRIX SYST INC
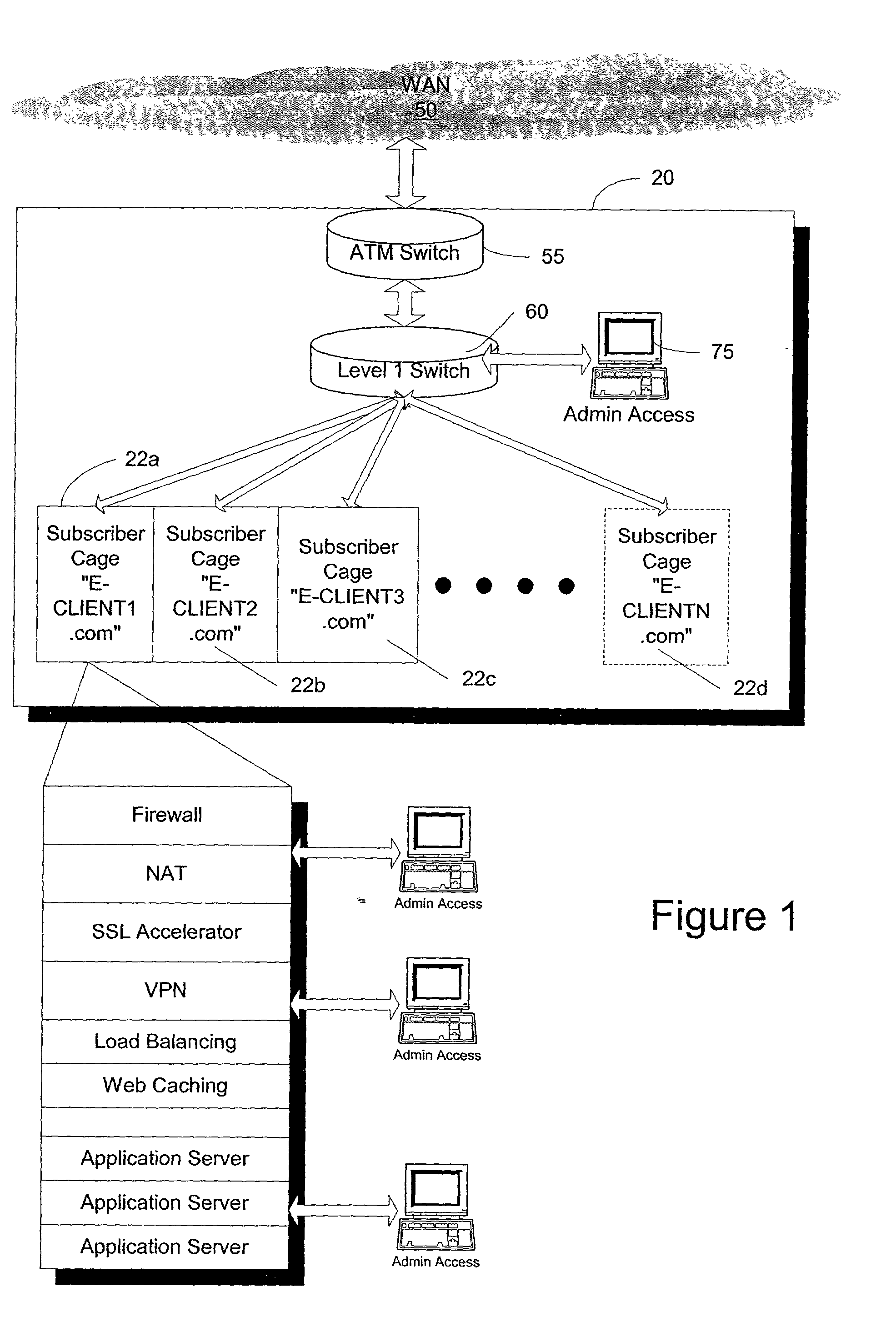
Distributed processing systems
InactiveUS20040128262A1Easy accessReduce decreaseFinanceElectric/magnetic computingData processing systemData set
A system for selecting one of a plurality of distributed processing entities that each are arranged to process a data set of user-specified criteria to determine a multi-parameter assessment of that data set is described. The system comprises: receiving means arranged to receive the data set via the Internet from an intermediary acting on behalf of the user; an estimation engine for executing a plurality of estimation algorithms, each algorithm being provided by one of the plurality of processing entities and being arranged to generate an approximation of the corresponding multi-parameter assessment by consideration of a processing-entity selected subset of the data set of user-specified criteria; and a selecting module for selecting of one of the processing entities, the selecting means being arranged to consider the generated approximations and select the processing entity whose approximation maximises one or more performance criteria for the intermediary.
Owner:BEST QUOTE DIRECT
Satellite downlink via patterns of uncollimated light
InactiveUS7925167B1Eliminate security concernsEliminating regulatory issueBroadcast transmission systemsSatellite communication transmissionLow earth orbitGround station
A satellite or spacecraft in low Earth orbit, when in eclipse and not illuminated by sunlight, represents a low-bandwidth datastream through modulation of a source of uncollimated light, such as a set of light emitting diodes. Transmission modes include generating patterns in the color, intensity or polarization of a light source, or precise timing control of a strobe signal. A ground station tracks the satellite in a telescope, stewing the telescope to follow the satellite as it moves across the sky, recording light generated by the satellite with a light sensor such as a video camera. The datastream is regenerated through analysis of recorded video. Satellite downlink is initiated by detection of eclipse, by command via radio uplink, or in response to a periodic automatic timer. In an alternative embodiment, the satellite represents the datastream through modulation of its effective albedo or reflective flux during periods of solar illumination.
Owner:KOZUBAL MAREK J +1
System and method for reducing effect of magnetic fields on a magnetic transducer
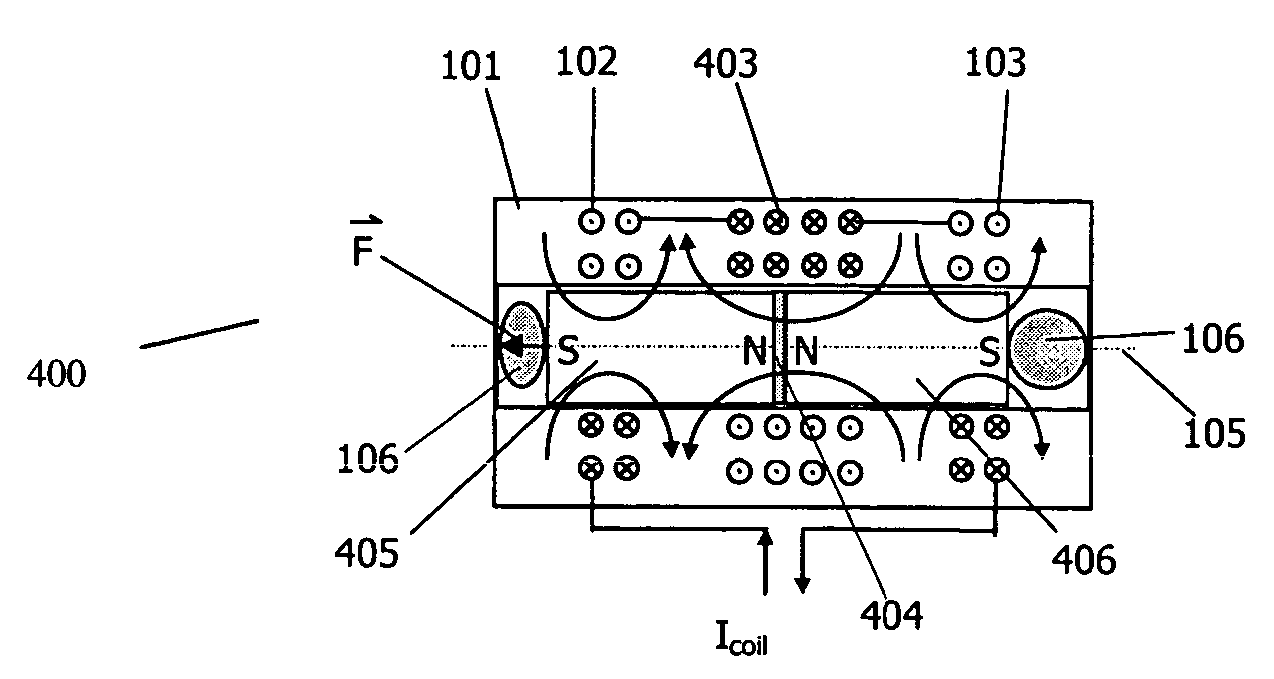
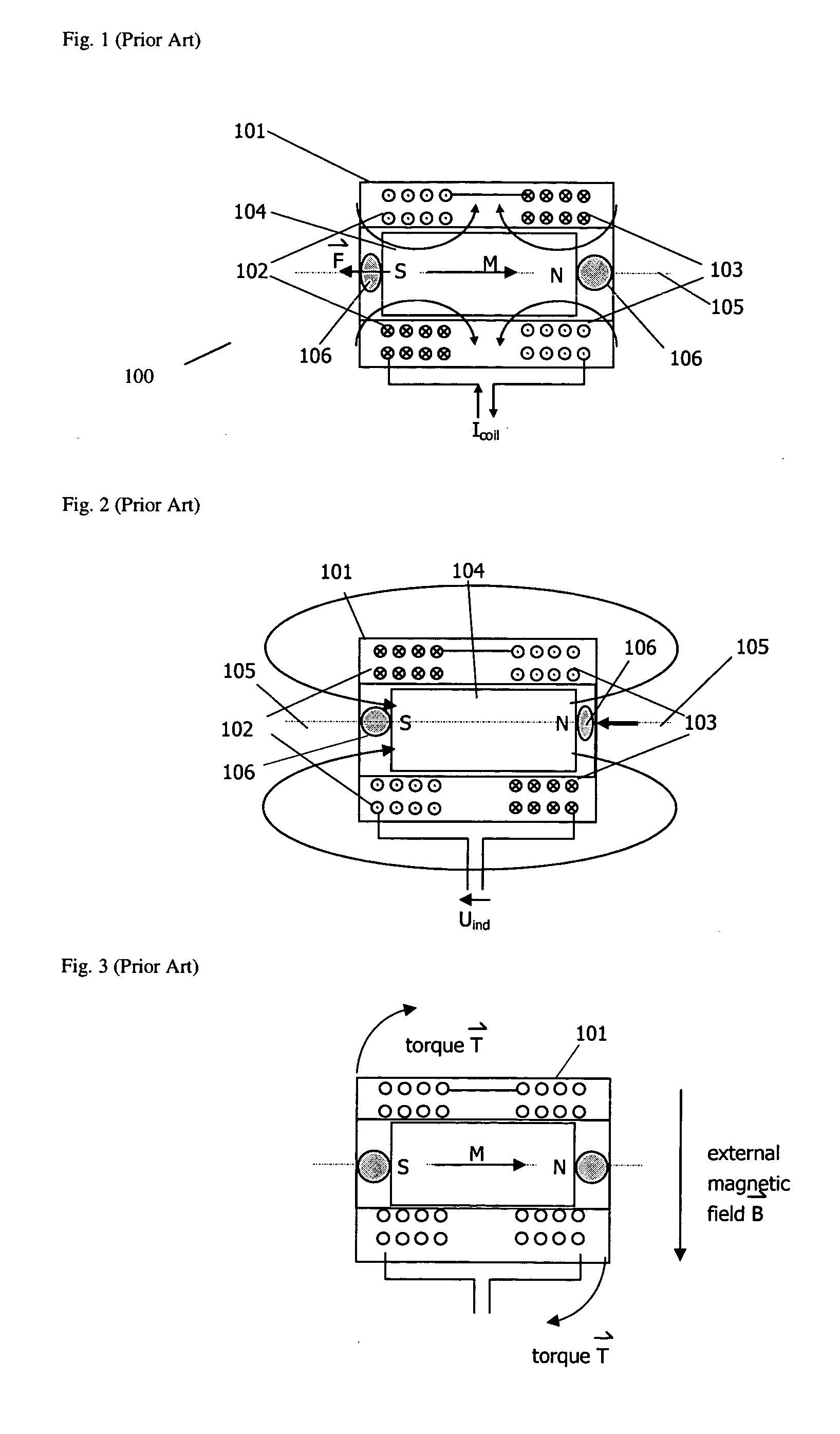
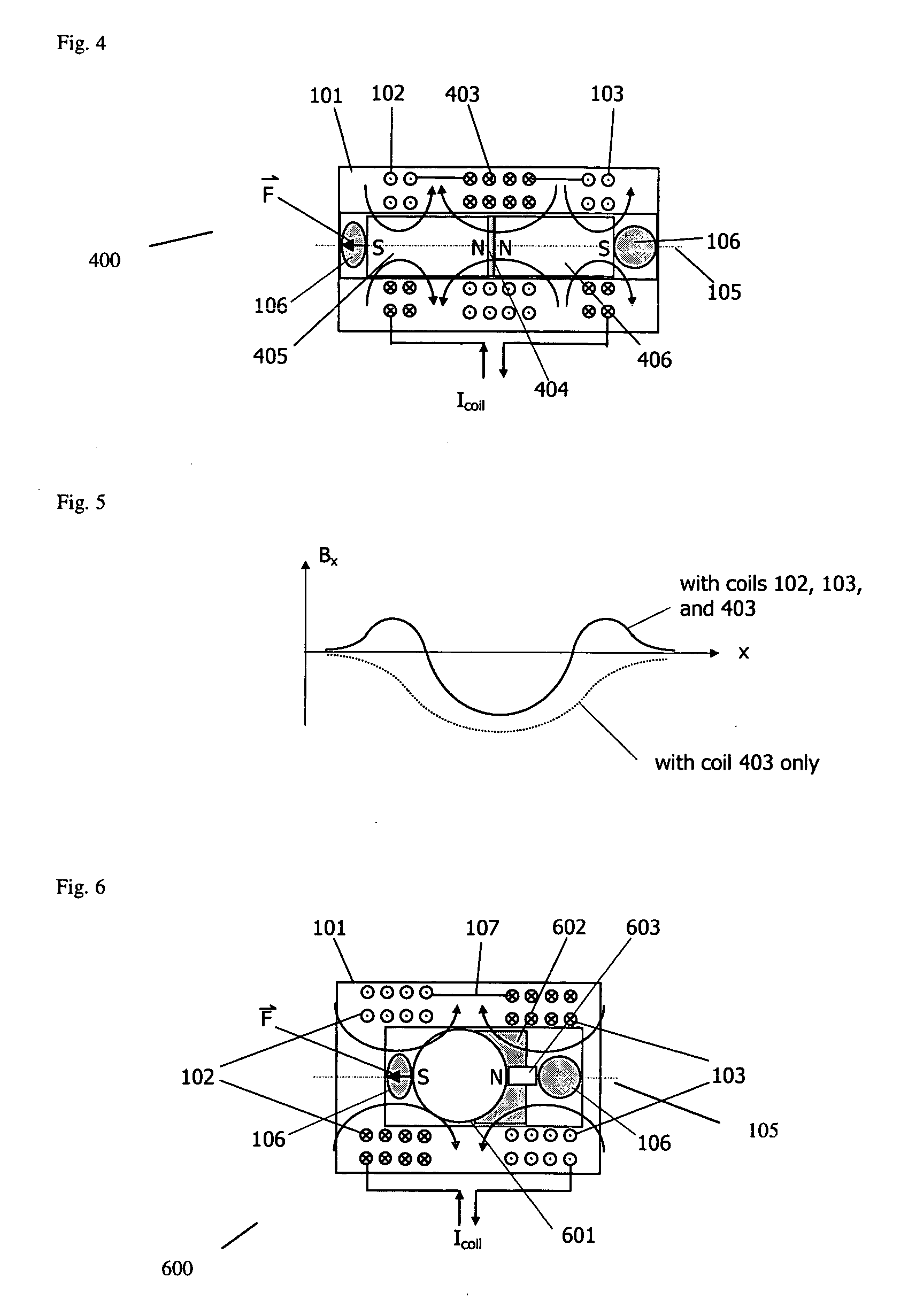
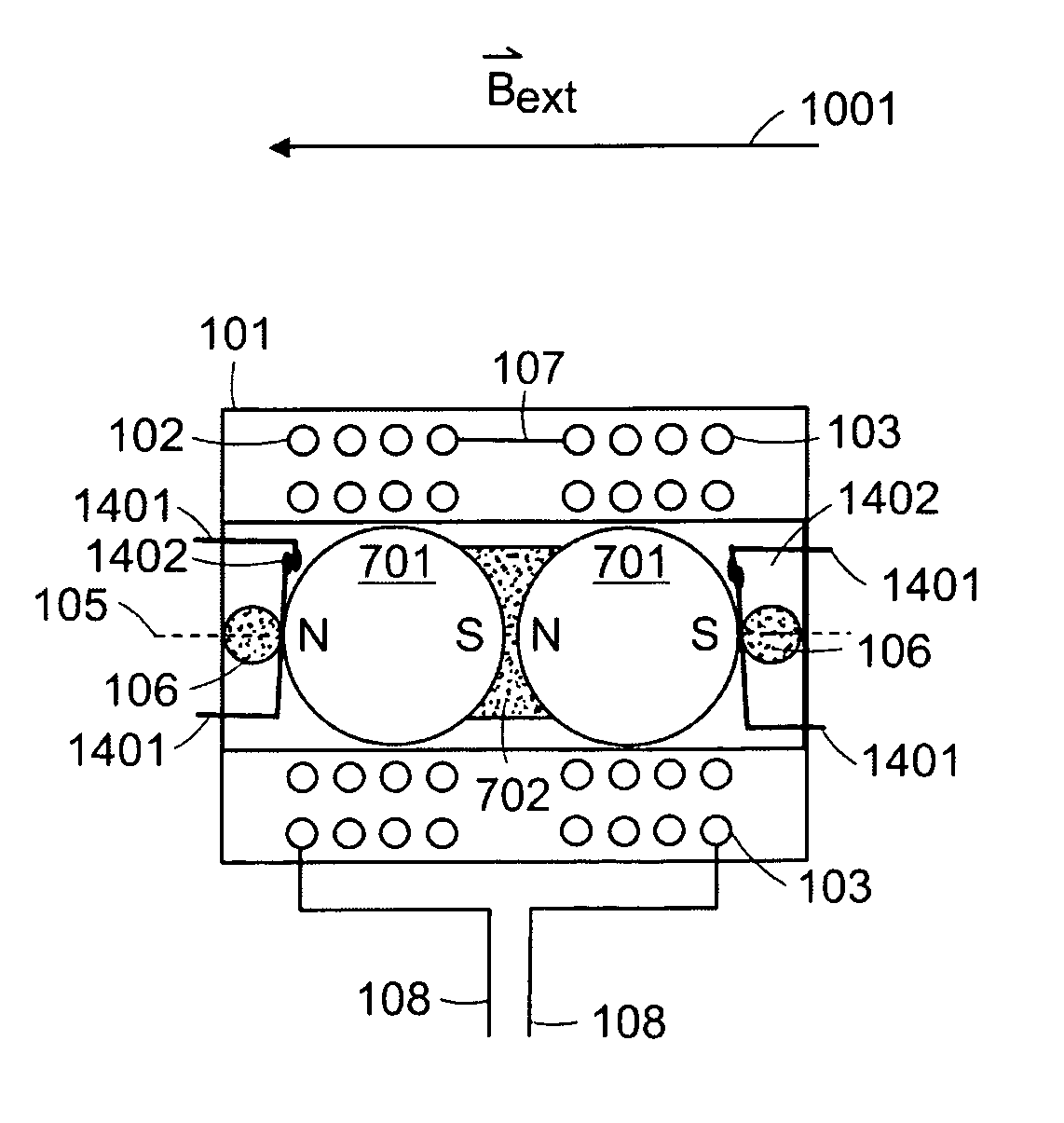
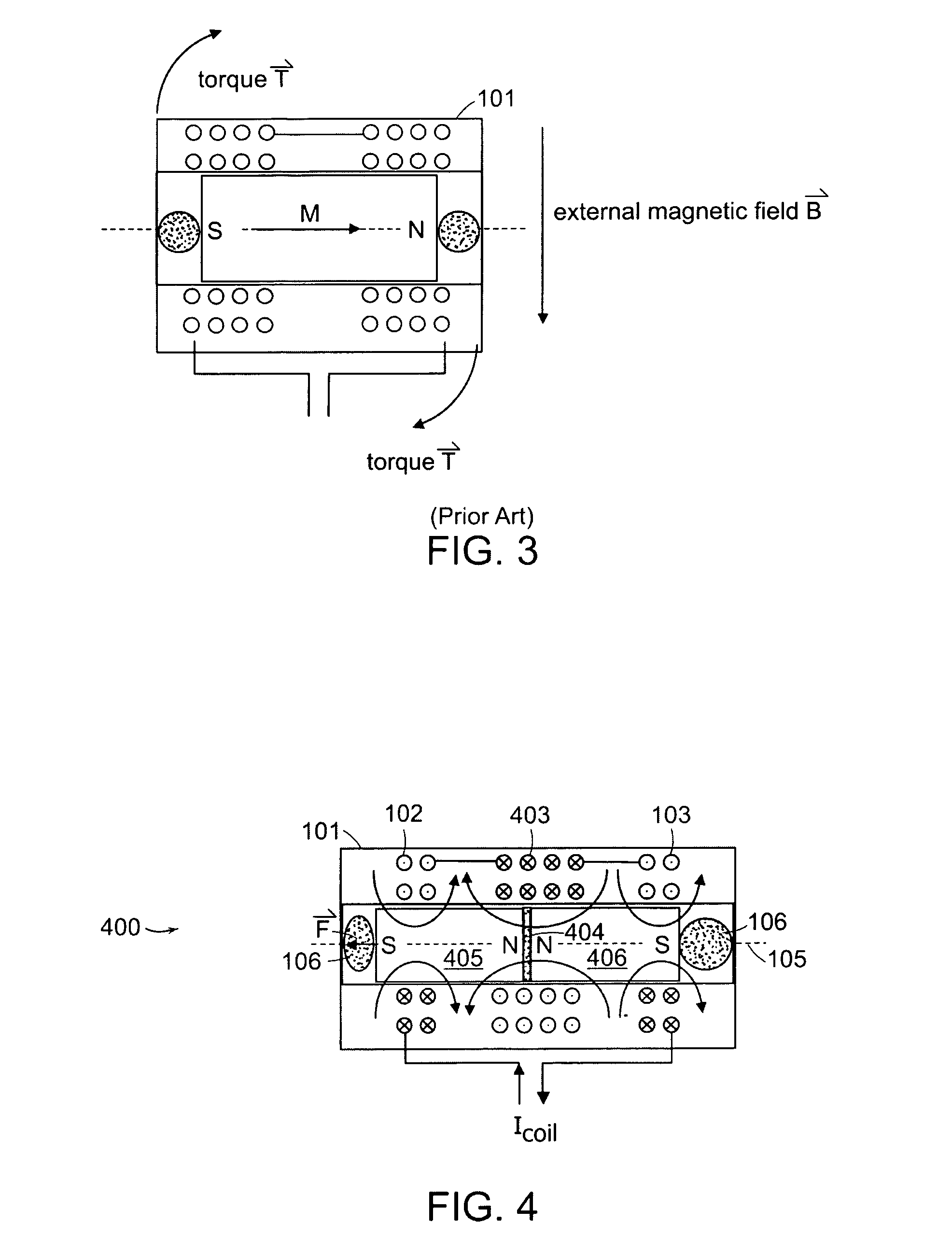
ActiveUS20050001703A1Low frictionReduce frictionVibration measurement in solidsMagnetic movement switchesMagnetMagnetic transducers
An electromagnetic driver transducer free of torque in the presence of an external magnetic field, of any direction and orientation (such as in a Magnetic Resonance Imaging environment). The transducer includes a housing. At least one coil is associated with the housing. A plurality of magnets within the housing are aligned along an axis in an anti-parallel orientation. The magnets are free to move along an axis, wherein vibration of the magnets causes vibration of the housing. The transducer may be, for example, fixed to an ossicle.
Owner:MED EL ELEKTROMEDIZINISCHE GERAETE GMBH
System and method for reducing effect of magnetic fields on a magnetic transducer
InactiveUS7190247B2Process safetyVibration measurement in solidsMagnetic movement switchesMagnetic transducersElectromagnetic drive
An electromagnetic driver transducer free of torque in the presence of an external magnetic field, of any direction and orientation (such as in a Magnetic Resonance Imaging environment). The transducer includes a housing. At least one coil is associated with the housing. A plurality of magnets within the housing are aligned along an axis in an anti-parallel orientation. The magnets are free to move along an axis, wherein vibration of the magnets causes vibration of the housing. The transducer may be, for example, fixed to an ossicle.
Owner:MED EL ELEKTROMEDIZINISCHE GERAETE GMBH
Nutritional supplement for caffeine-containing beverages
InactiveUS20060134300A1Increase alertnessSafe and yet high level of arousalCoffeeNutrition supplementationEnvironmental health
Owner:NEWMAN ARNOLD L
Single Use Centrifuge
InactiveUS20110319248A1Process safetyLow costBiological substance pretreatmentsRotary centrifugesBiotechnologyEngineering
The present invention relates to a device that incorporates a single use centrifuge that is sterilized prior to use in the pharmaceutical, biopharmaceutical, biotechnology or related industries and is used for the removal of solids and / or other undesirable materials from one or more fluids and is connected to a bioreactor, fermentor, container or process by way of single use tubing, connectors and / or various fluid flow components.
Owner:STARBARD NATHAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com