Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4112 results about "User management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
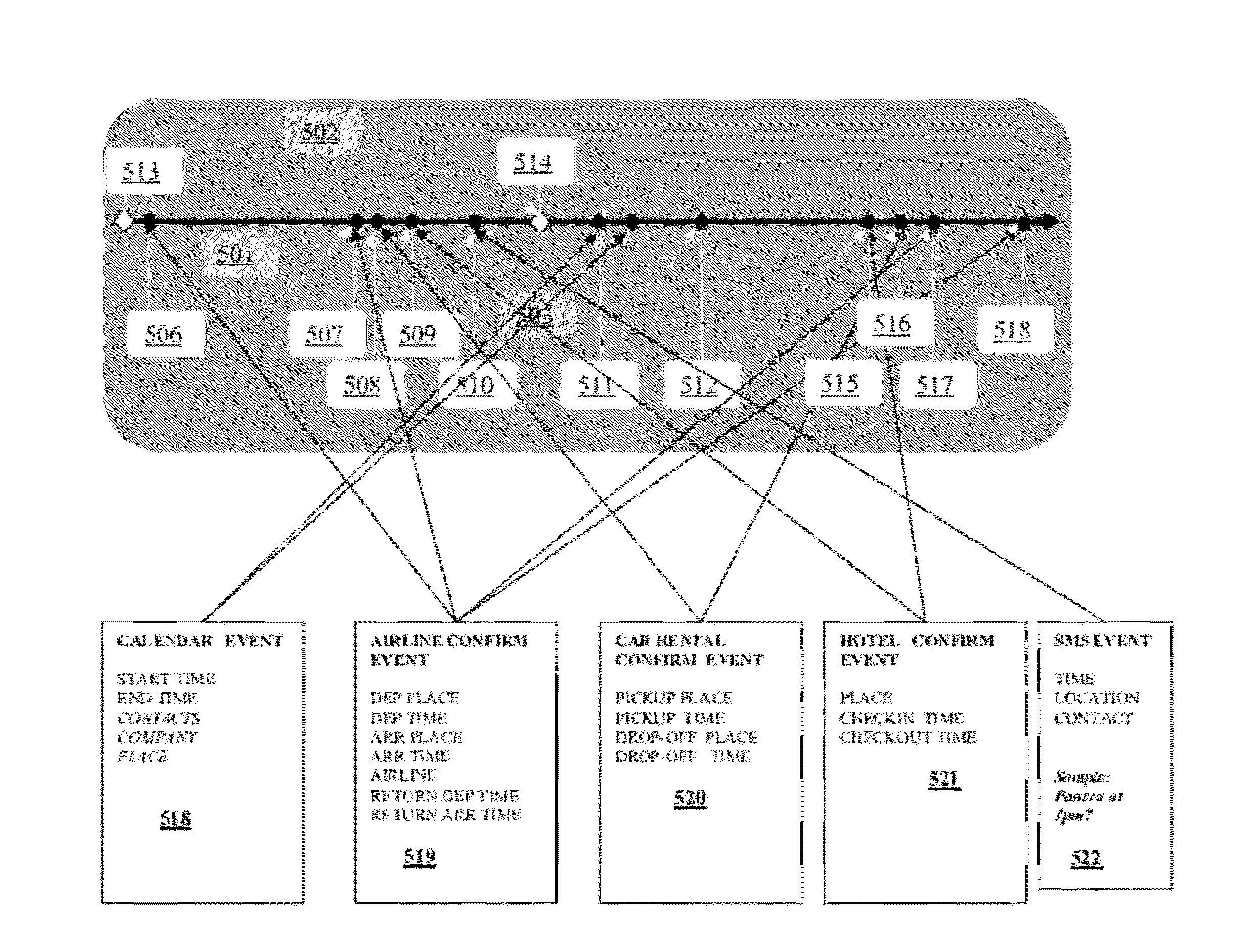
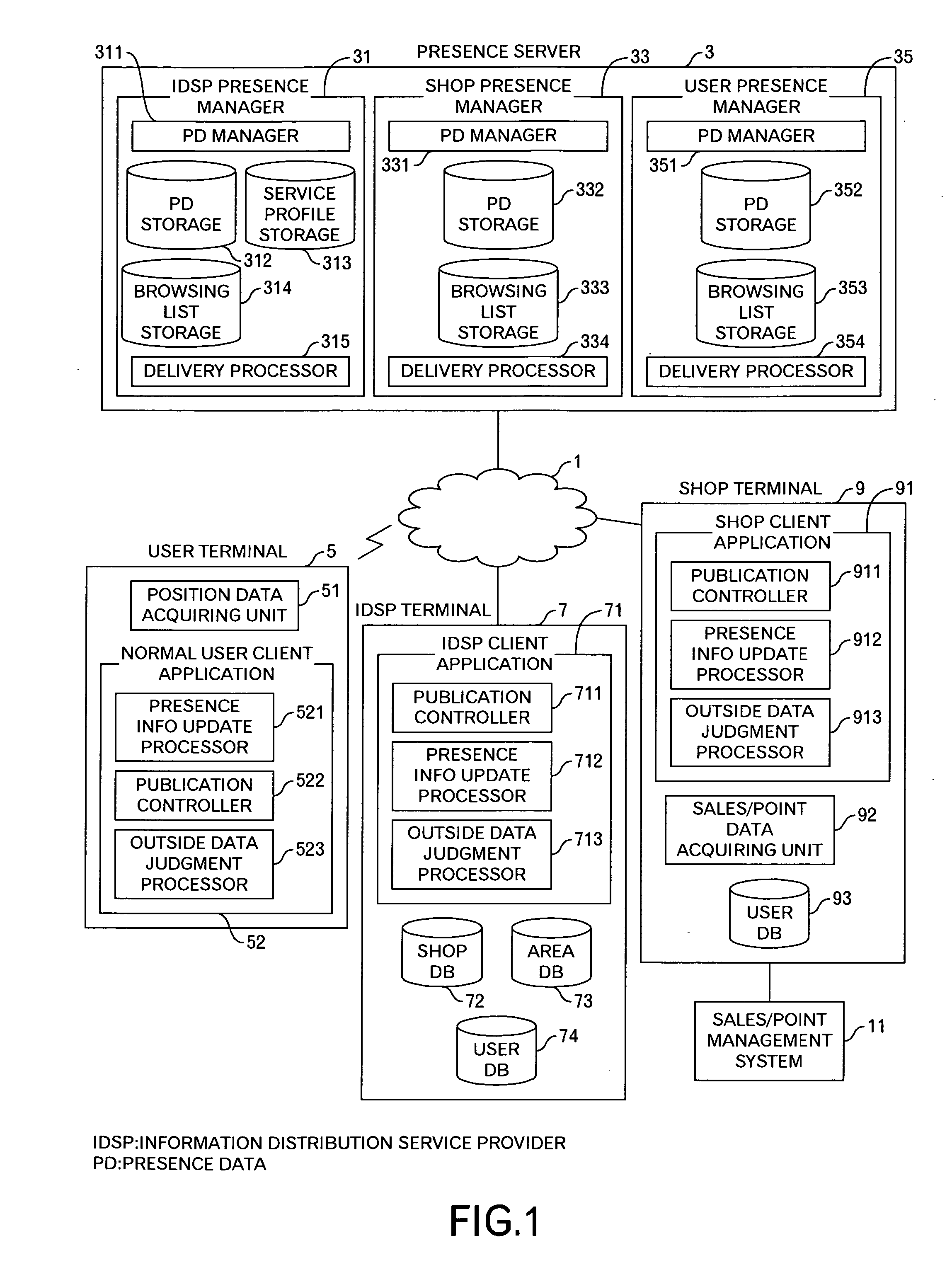
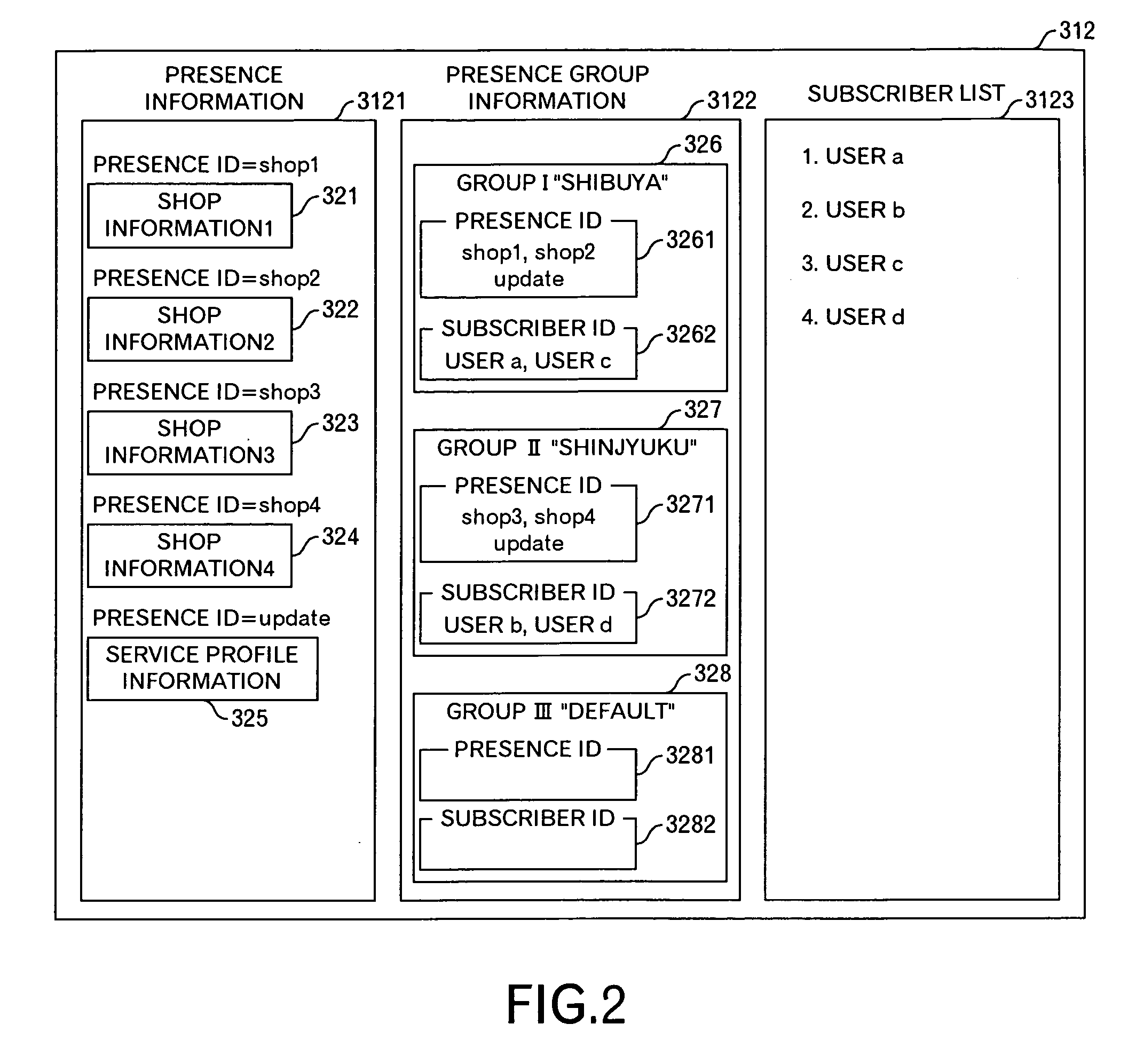
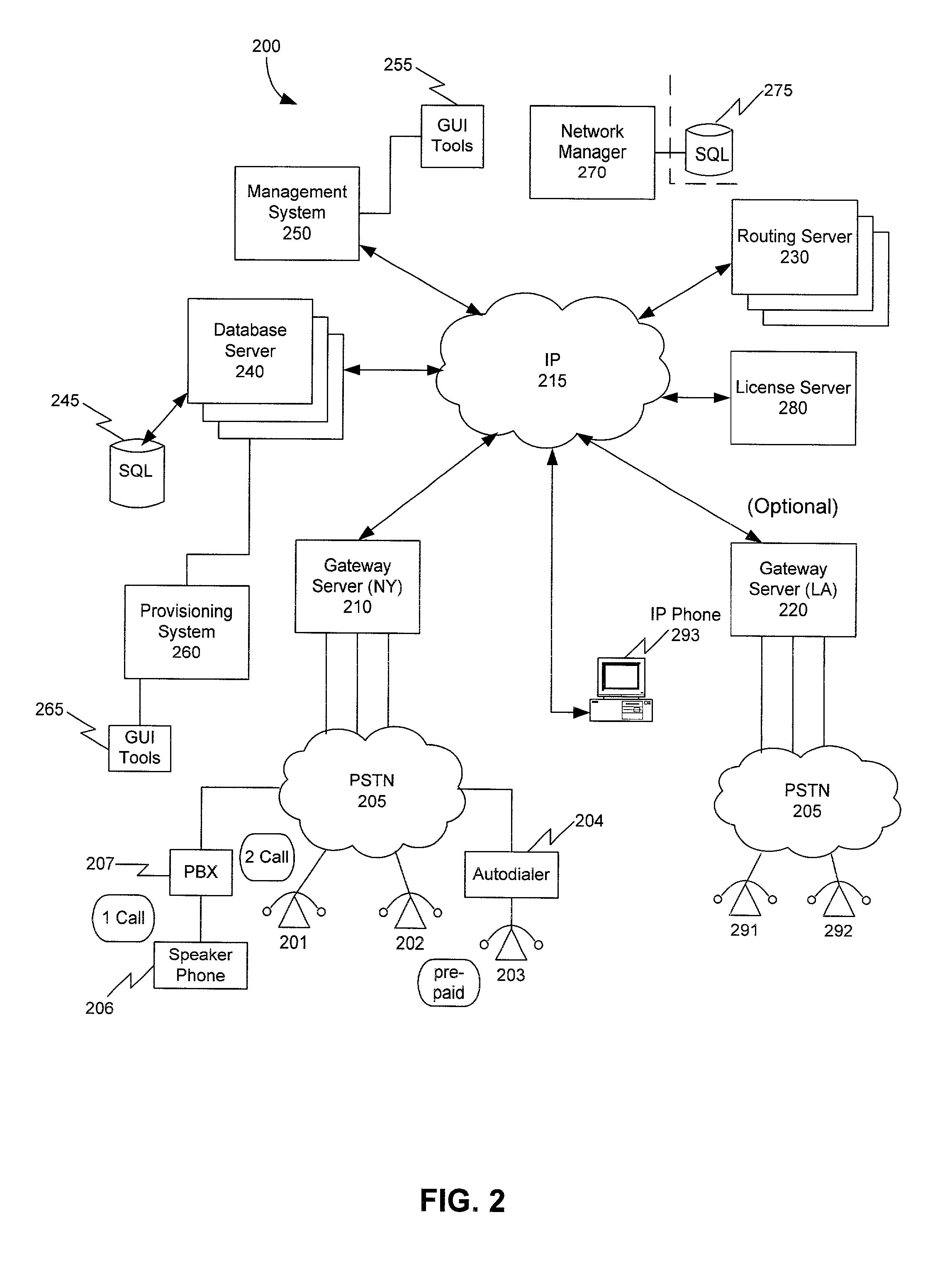
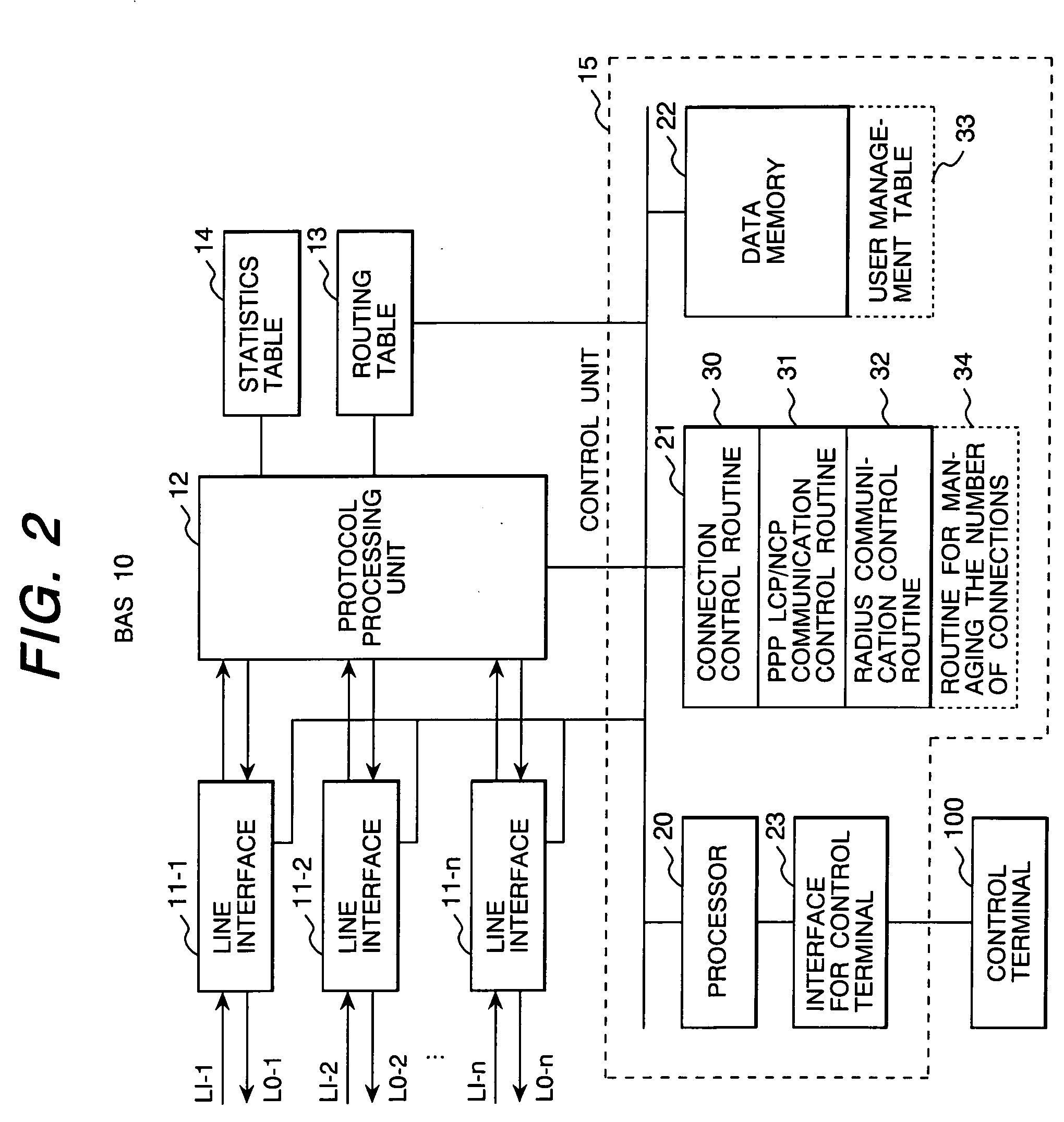
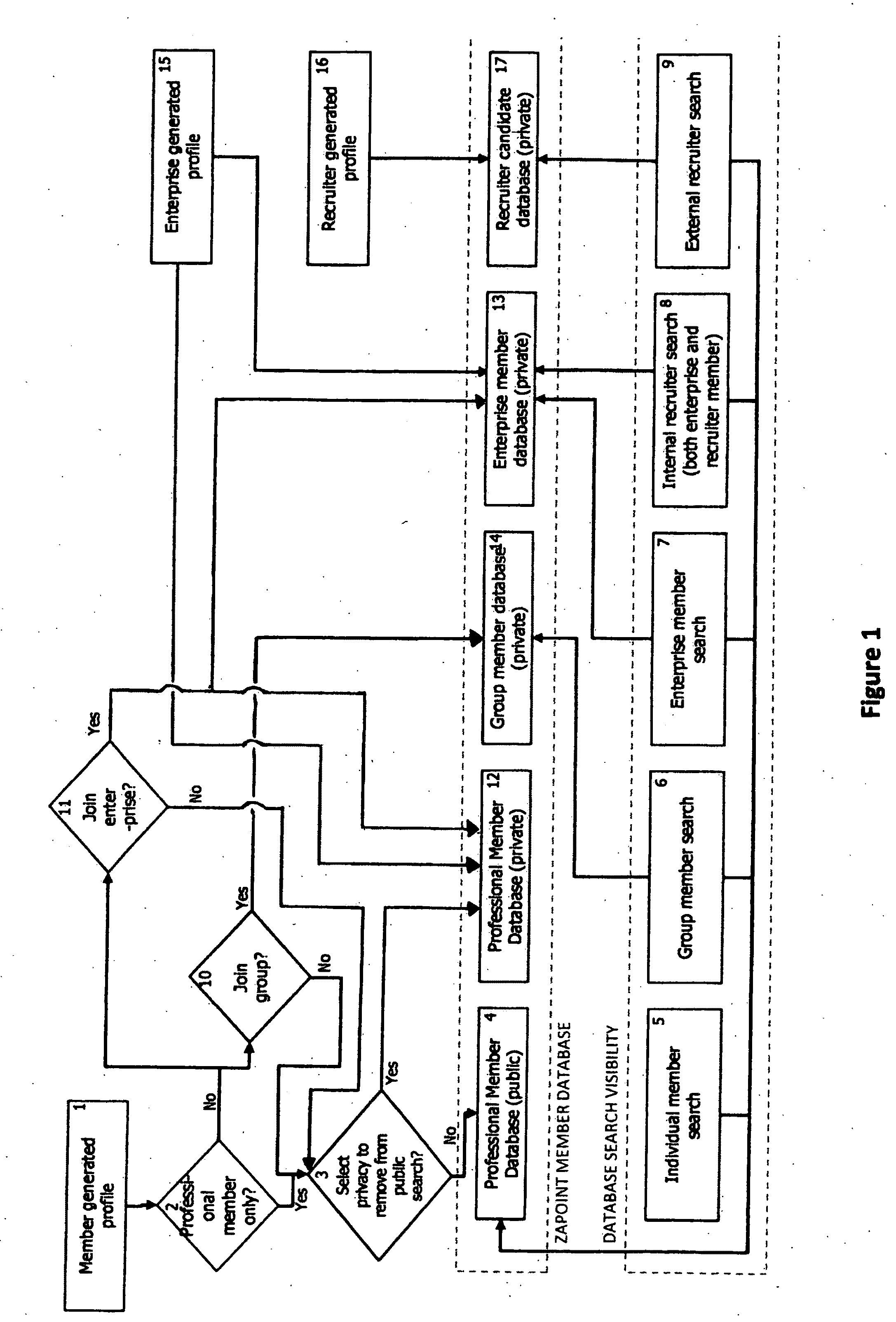
Presence information processing method and computer
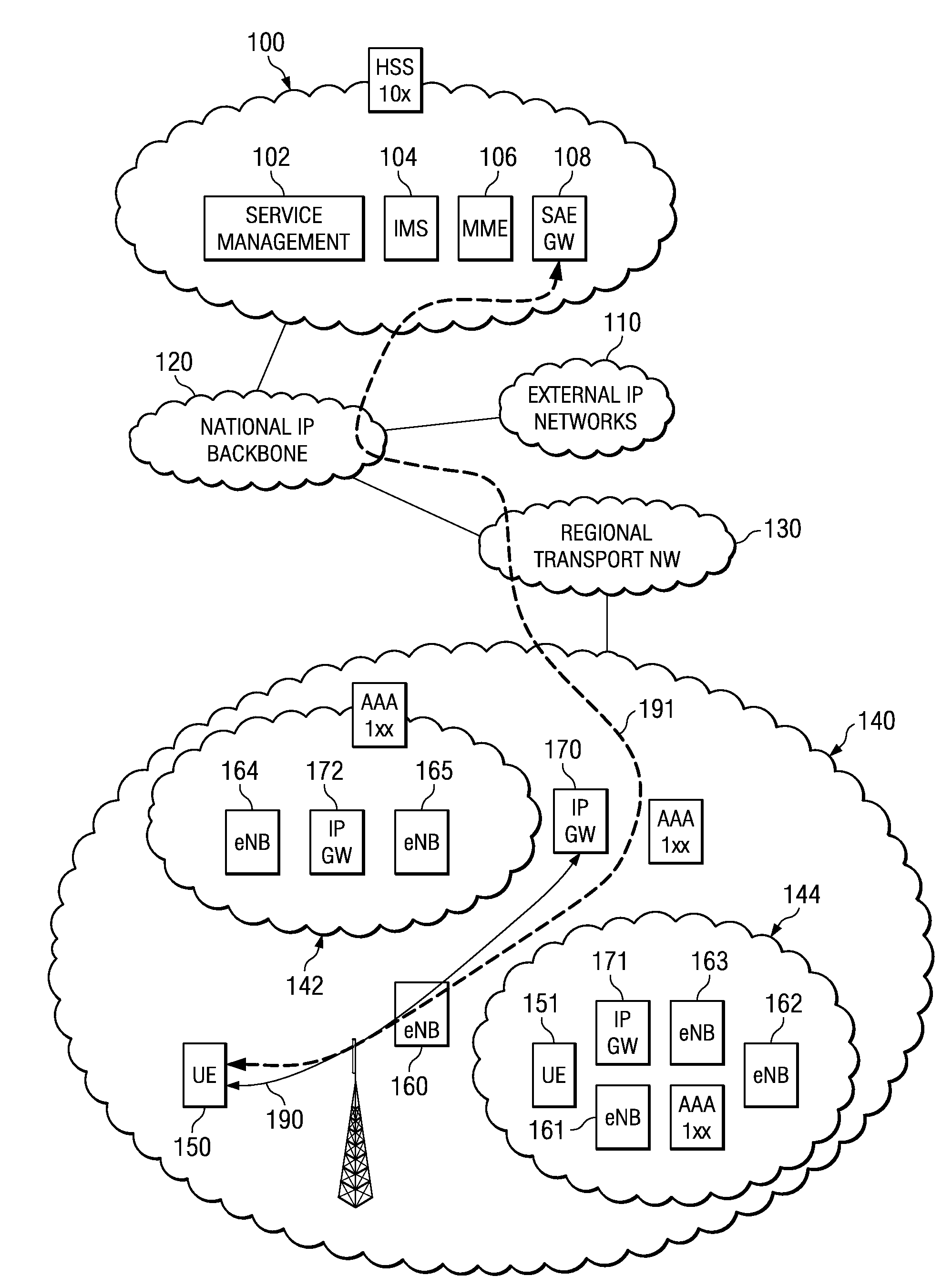
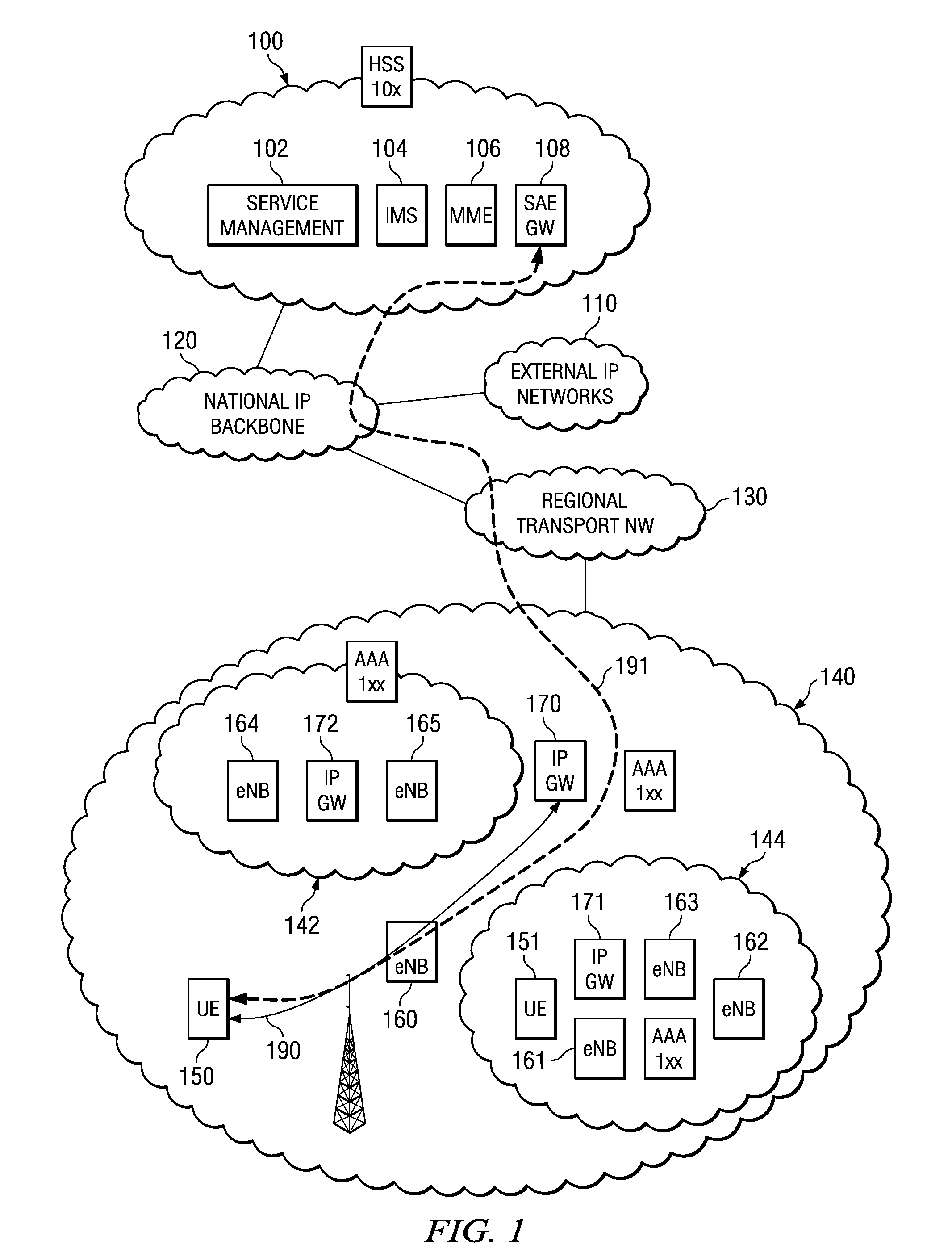
InactiveUS20060242239A1Easy delivery settingSpecial service provision for substationMultiple digital computer combinationsInformation processingUser management
The presence information delivery system according to this invention manages, for each user, data of one or plural presence group so as to associate one or plural presence information items for the presence information to be delivered with an ID or IDs of one or plural delivery destination user of the presence information relating to the presence information item. With this configuration, by generating a new presence group associating the presence information item with the delivery destination user, by registering the presence information item to another presence group, and by registering the delivery destination user into another presence group, the flexible information delivery is enabled according to characteristics or the like of the delivery destination user and presence information.
Owner:FUJITSU LTD
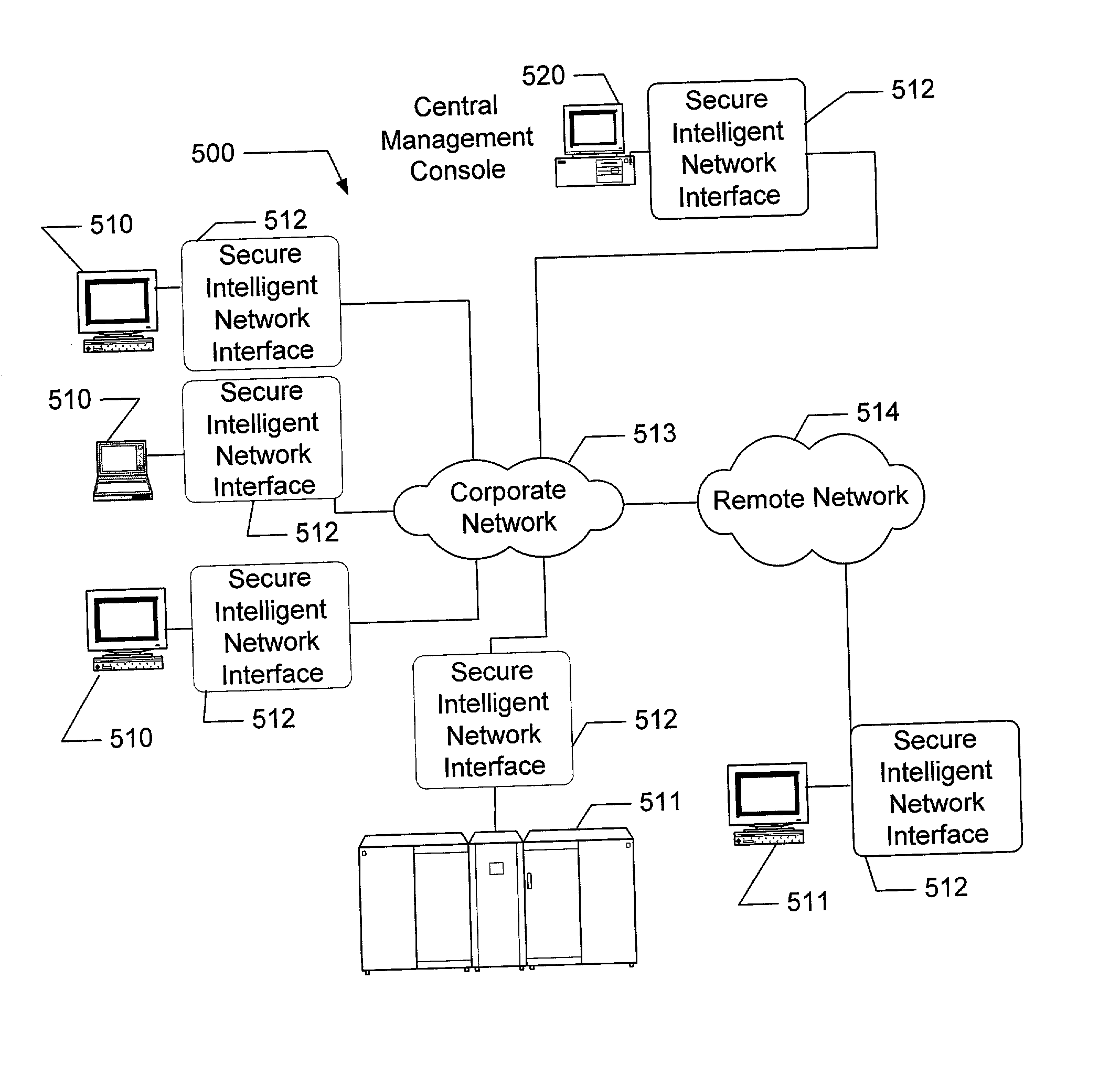
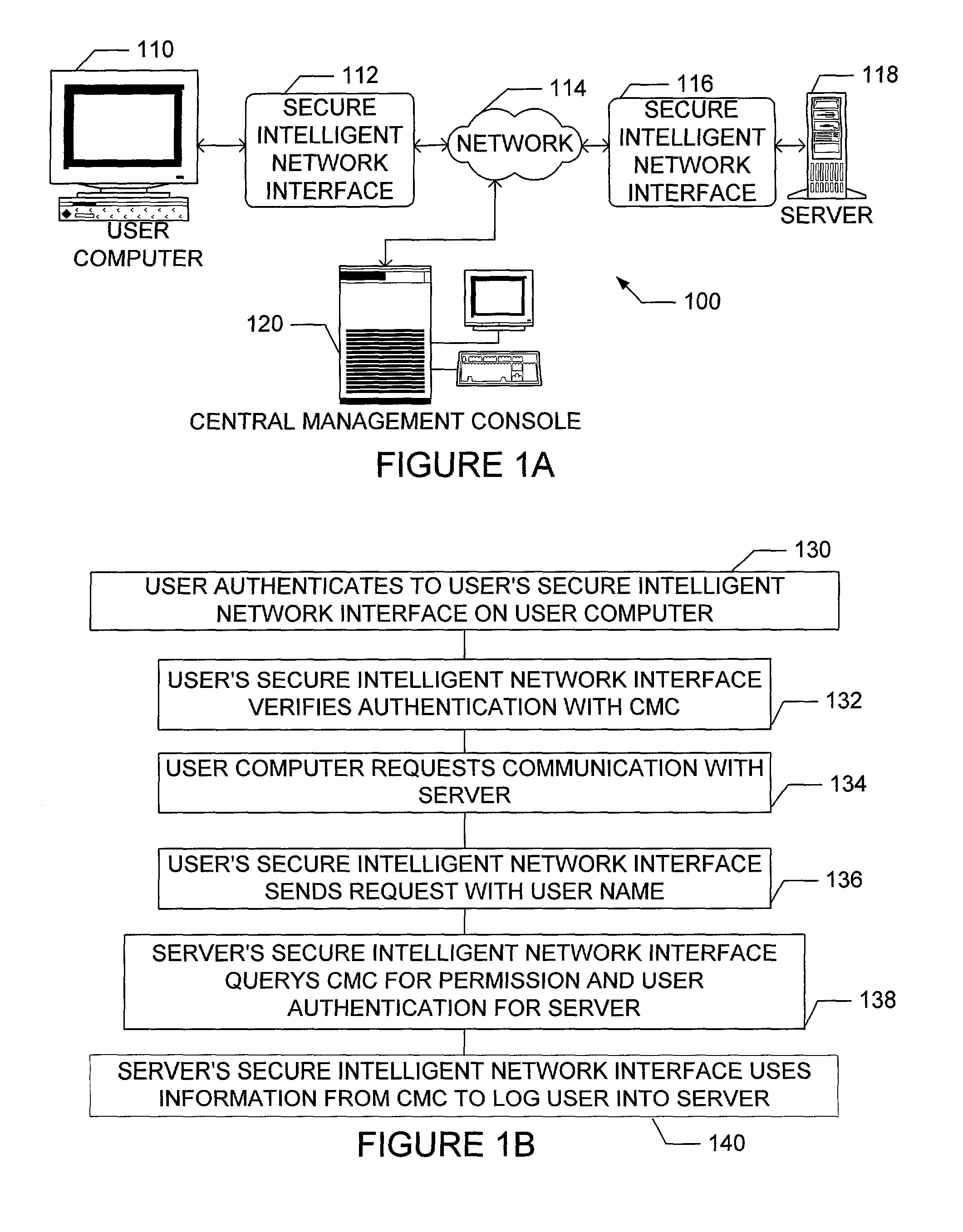
Apparatus and method for providing secure network communication
InactiveUS20020162026A1Eliminate attackEliminate needData taking preventionDigital data processing detailsFault toleranceIntelligent Network
The present invention is drawn to an apparatus and method for providing secure network communication. Each node or computer on the network has a secure, intelligent network interface with a coprocessor that handles all network communication. The intelligent network interface can be built into a network interface card (NIC) or be a separate box between each machine and the network. The intelligent network interface encrypts outgoing packets and decrypts incoming packets from the network based on a key and algorithm managed by a centralized management console (CMC) on the network. The intelligent network interface can also be configured by the CMC with dynamically distributed code to perform authentication functions, protocol translations, single sign-on functions, multi-level firewall functions, distinguished-name based firewall functions, centralized user management functions, machine diagnostics, proxy functions, fault tolerance functions, centralized patching functions, Web-filtering functions, virus-scanning functions, auditing functions, and gateway intrusion detection functions.
Owner:NEUMAN MICHAEL +1
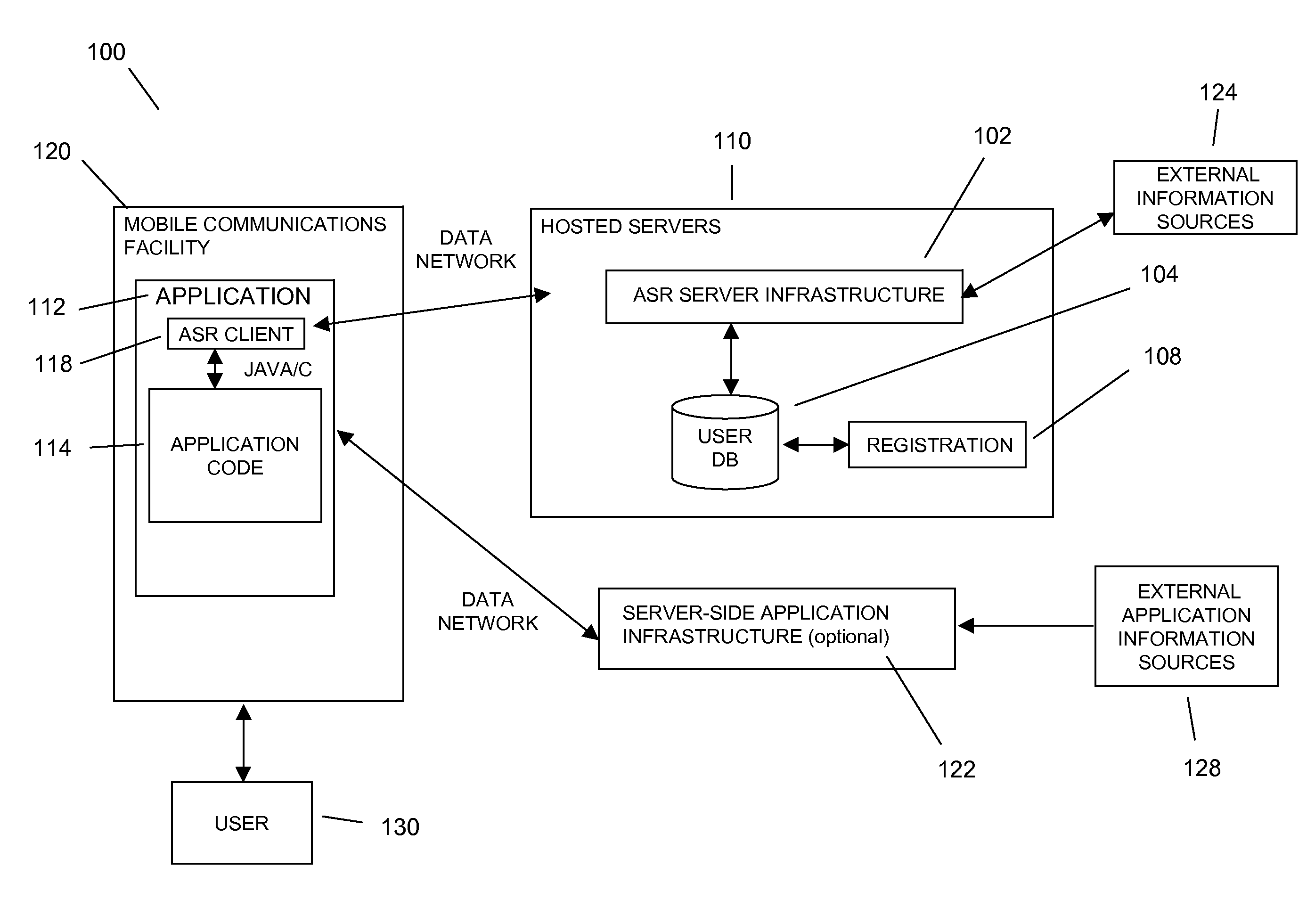
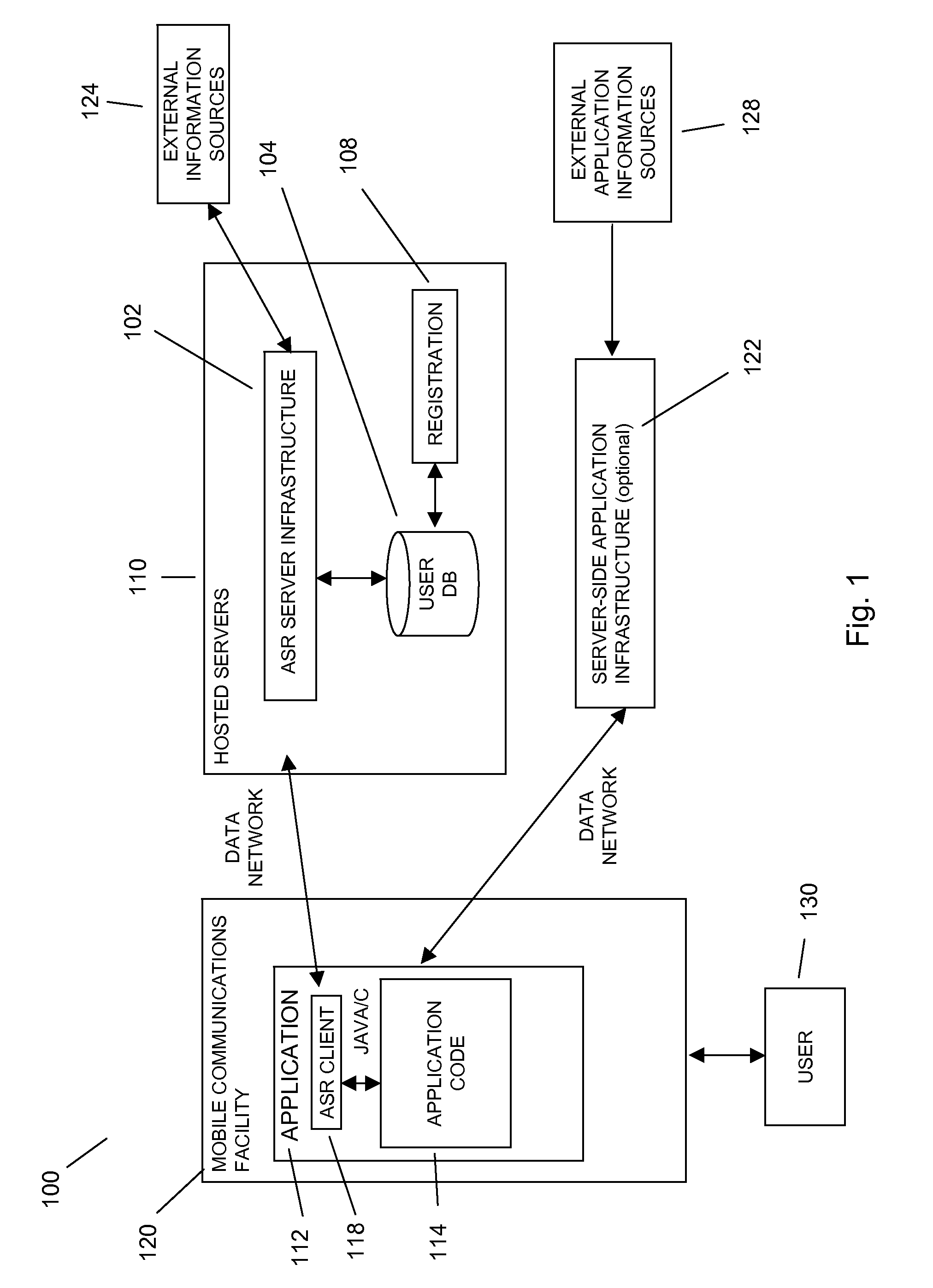
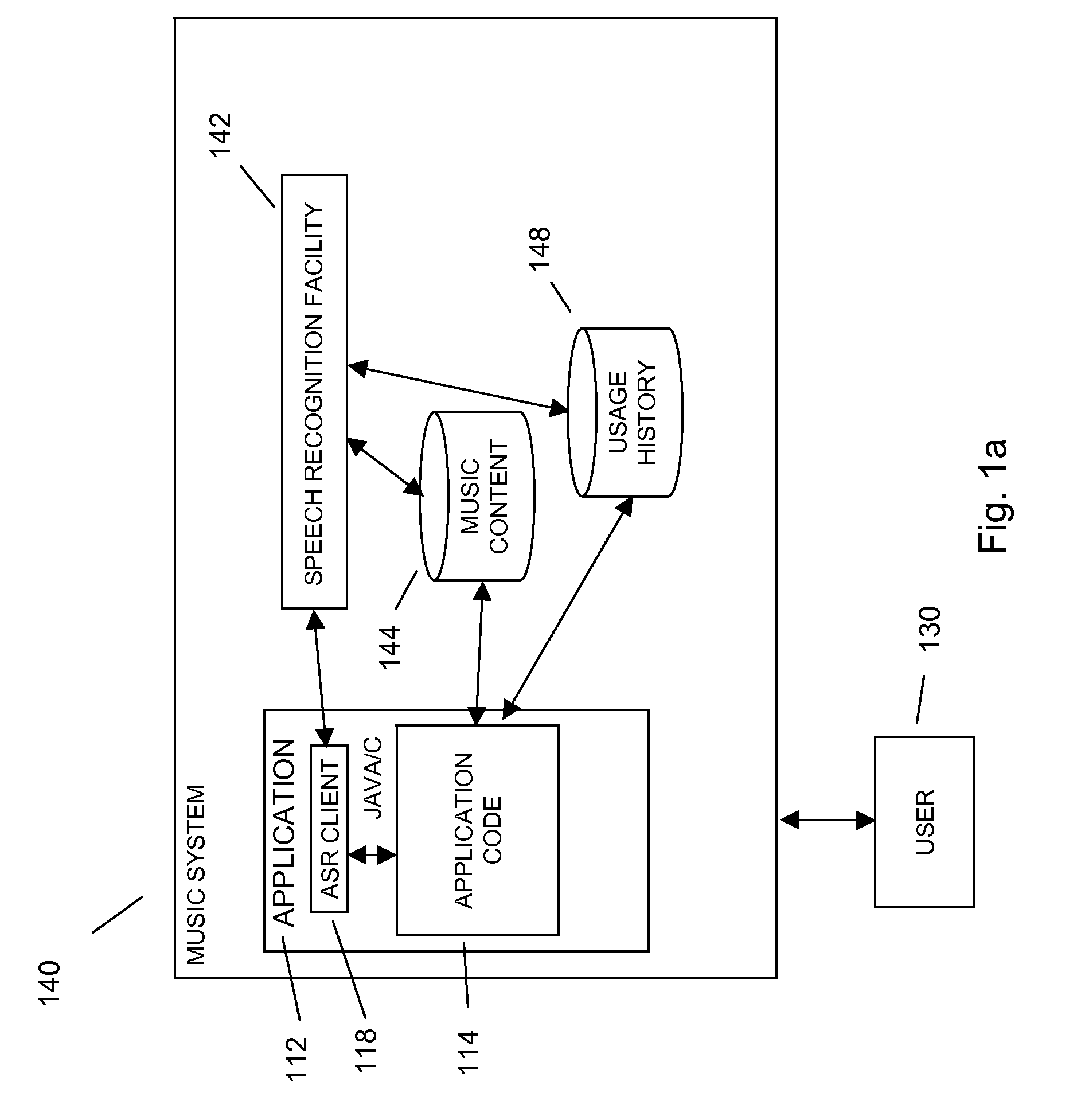
Speech recognition through the collection of contact information in mobile dictation application
In embodiments of the present invention improved capabilities are described for improving speech recognition through the collection of contact information on a mobile communication facility comprising capturing speech presented by a user using a resident capture facility on the mobile communication facility; transmitting at least a portion of the captured speech as data through a wireless communication facility to a speech recognition facility; prompting the user to manage contacts associated with usage of the mobile communication facility; transmitting contact names to the speech recognition facility, wherein the contact names are used by the speech recognition facility to at least one of tune, enhance, and improve the speech recognition of the speech recognition facility; generating speech-to-text results for the captured speech utilizing the speech recognition facility based at least in part on at least one of a contact name; transmitting the text results from the speech recognition facility to the mobile communications facility; and entering the text results into a text field on the mobile communications facility.
Owner:VLINGO CORP
System and Method for Providing Local IP Breakout Services Employing Access Point Names
A method, apparatus and system are provided for acquiring an access point name for an application employing a local Internet protocol breakout service. In one embodiment, the apparatus includes a user management subsystem (820) configured to initiate an Internet protocol application. The apparatus also includes a local breakout service monitoring subsystem (810) configured to monitor availability of a local Internet protocol local breakout service and to obtain an access point name from the local Internet protocol local breakout service when the local Internet protocol local breakout service is available. The apparatus also includes an access point name selection control subsystem (830) configured to bind the access point name to the Internet protocol application.
Owner:NOKIA TECHNOLOGLES OY
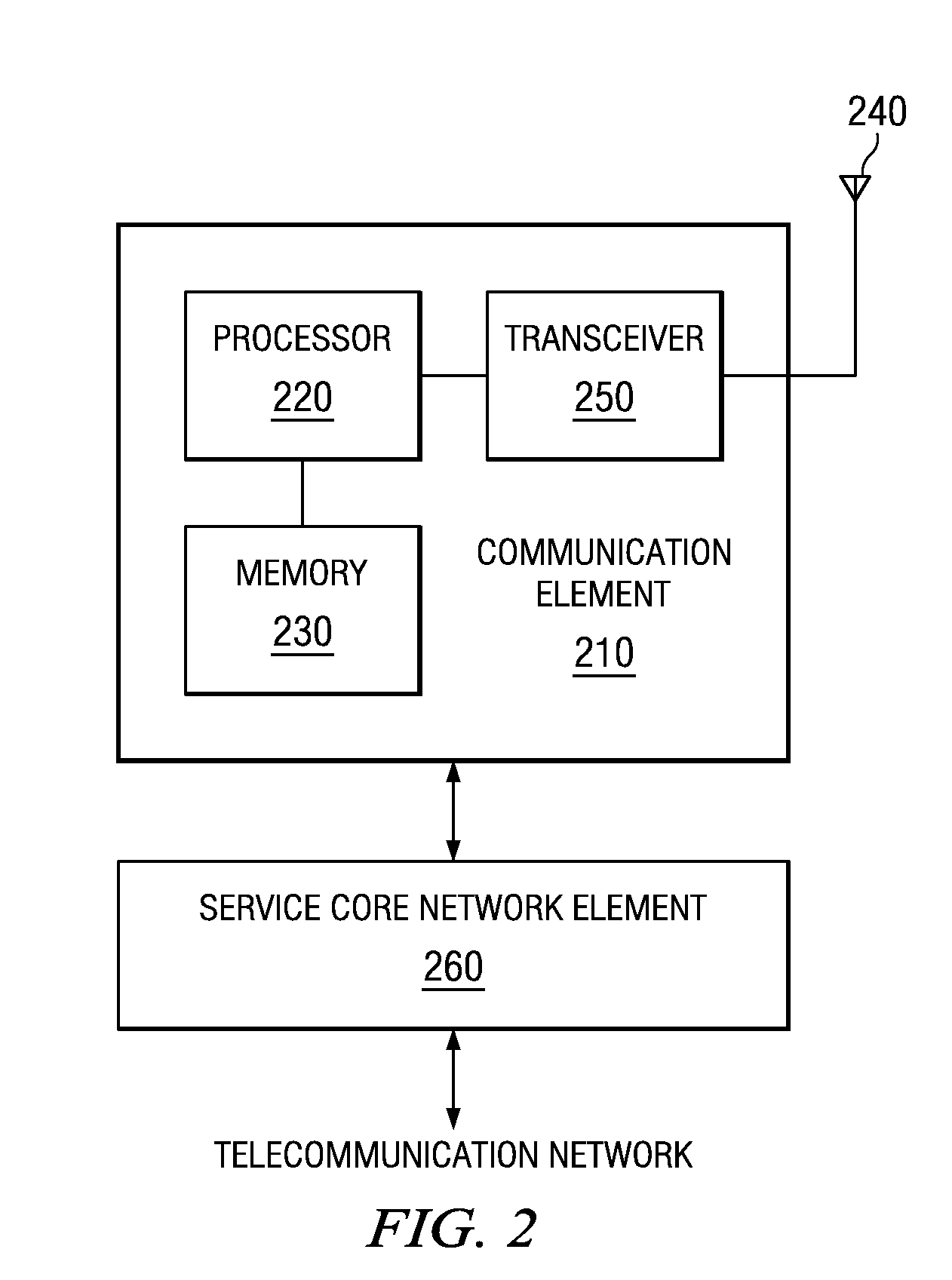
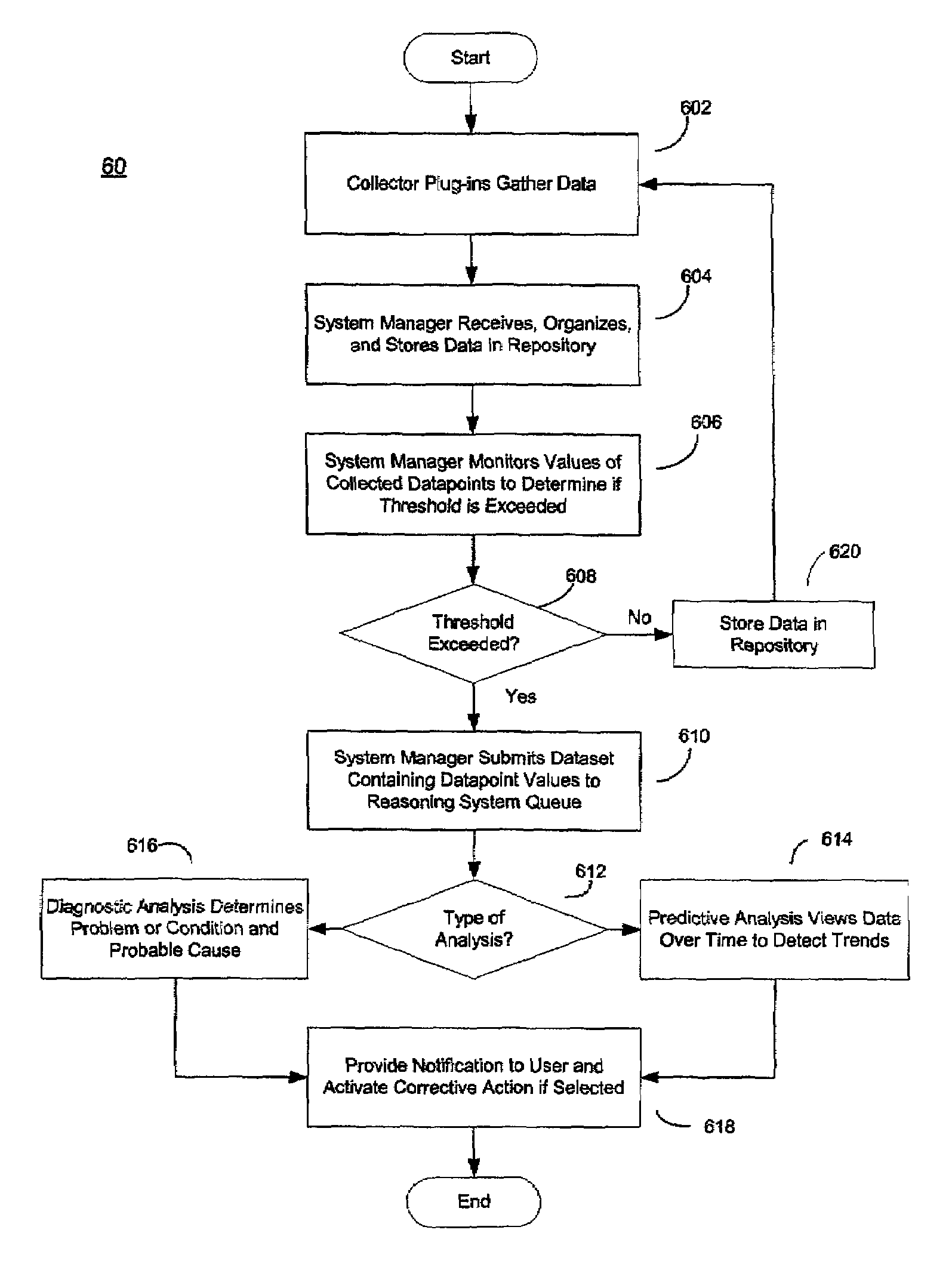
System and method for business systems transactions and infrastructure management
InactiveUS7065566B2Increase costImprove performanceDigital computer detailsBuying/selling/leasing transactionsSecure communicationCollection system
The system and method for business systems transactions and infrastructure management includes a client side collection system and a server side system having the capability to communicate with the other over a secure communication path. The collection system extracts transaction and infrastructure data from a business system and transmits the extracted data to the management server over a secure communication path. The management server receives the extracted data over the secure communication path, compares it to threshold analyzes the data that exceed threshold values, and notifies a user of the results of the analysis. The management server also has the capability to activate corrective scripts in the client business system and to reconfigure the client business system.
Owner:CA TECH INC
Method, system, and computer program product for managing database servers and service
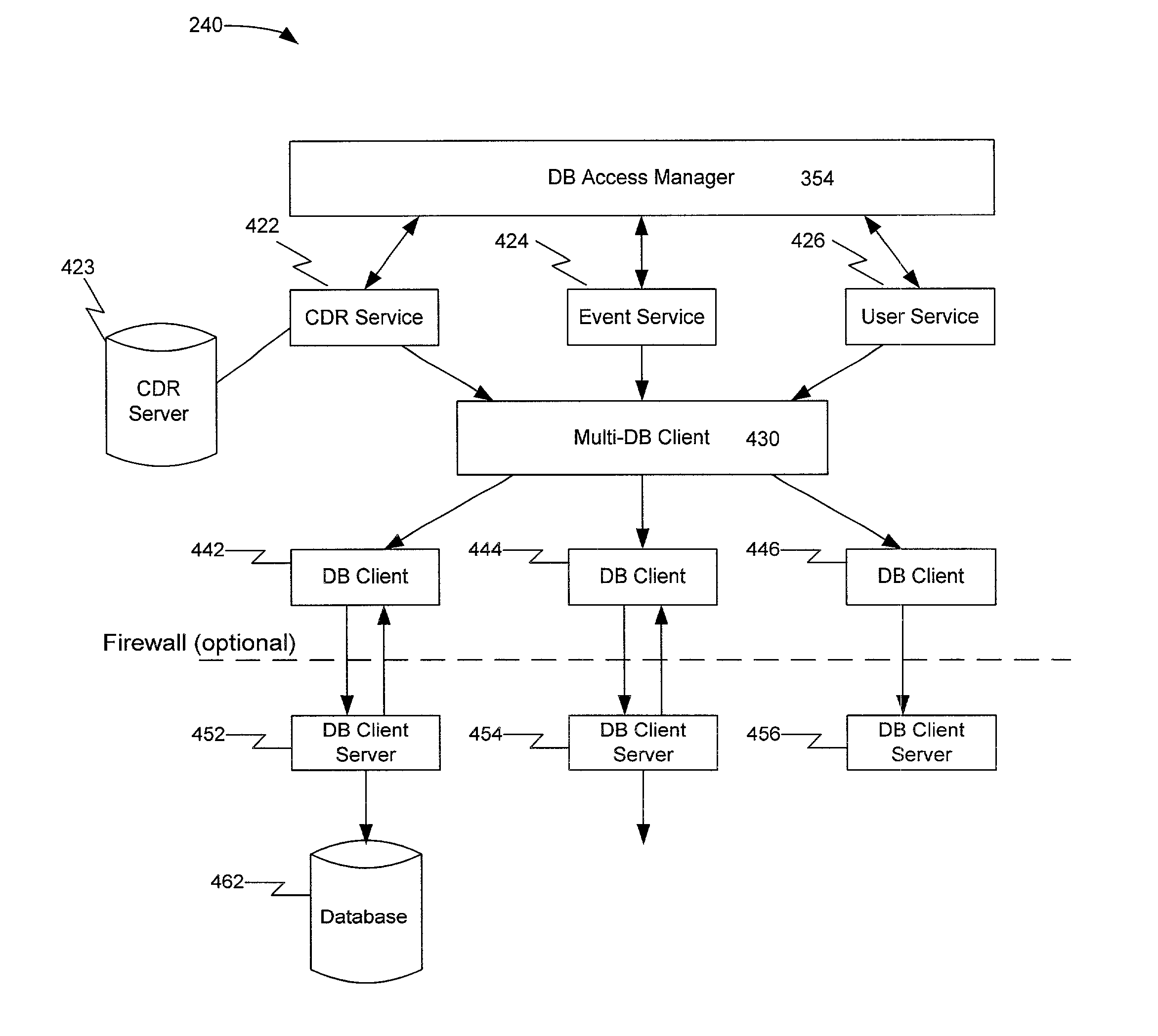
InactiveUS7123608B1Interconnection arrangementsDigital data processing detailsDatabase serverComputer module
A system, method, and computer program product for managing database servers and services is disclosed, which expands the capabilities of existing systems by providing better scalability and security. A database management system includes databases consisting of database clients and servers that handle the storing of information, a multi-database client that manages database servers, service modules which allow other systems to access the database servers, and a database access manager that manages requests from the service modules. A database access manager facilitates and coordinates interaction between the service modules and the multi-database client. Service modules provide interfaces from which other external or internal systems can access the managed databases. Requests can be sent between systems and the database access manager via the service modules. Two present and representative implementations of service modules are: user management and call detail record (CDR) collection. The user management service module allows systems to access user account information stored in the databases. The CDR collection service module inserts details for each call made on the network.
Owner:CHEMTRON RES
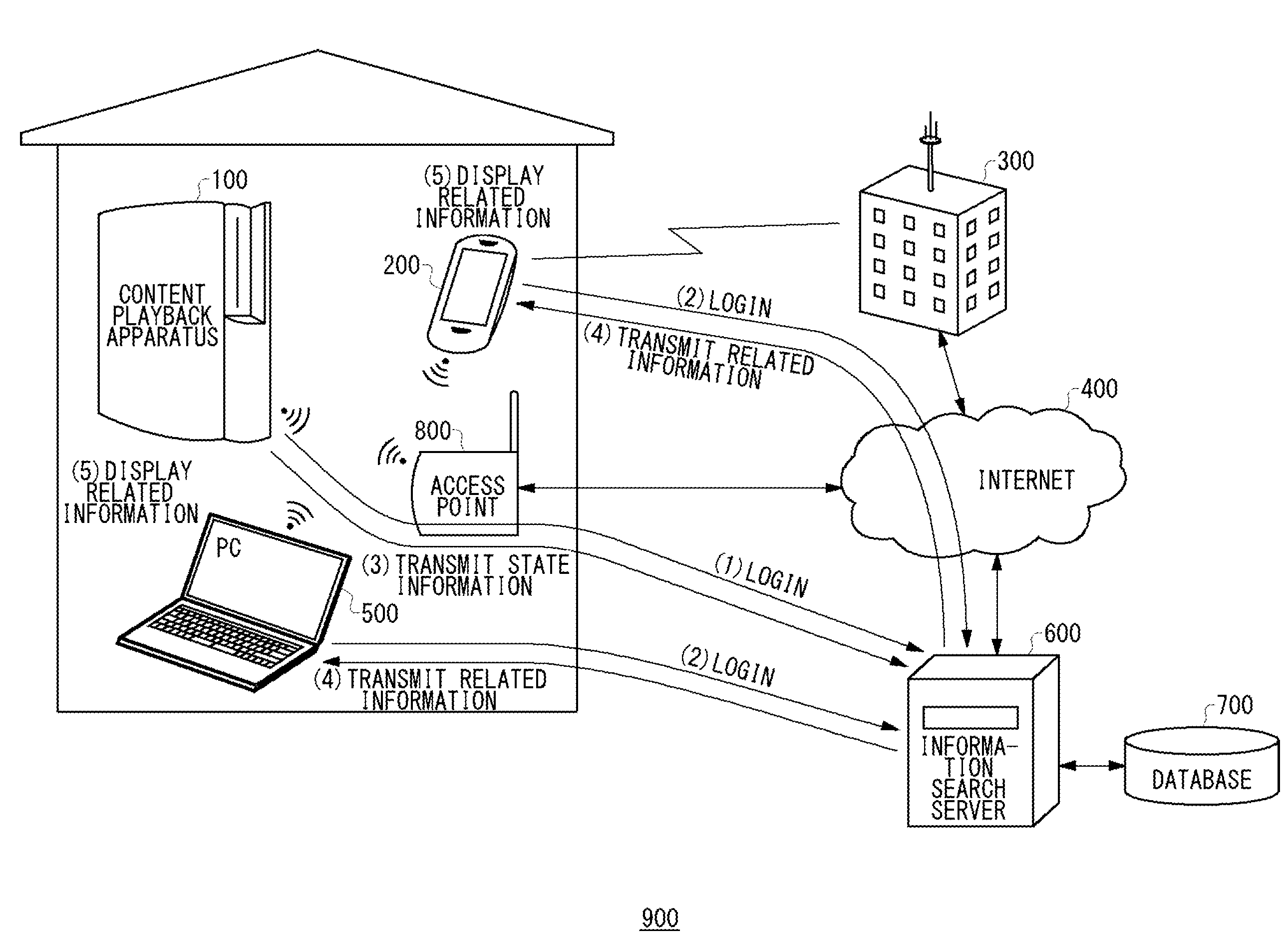
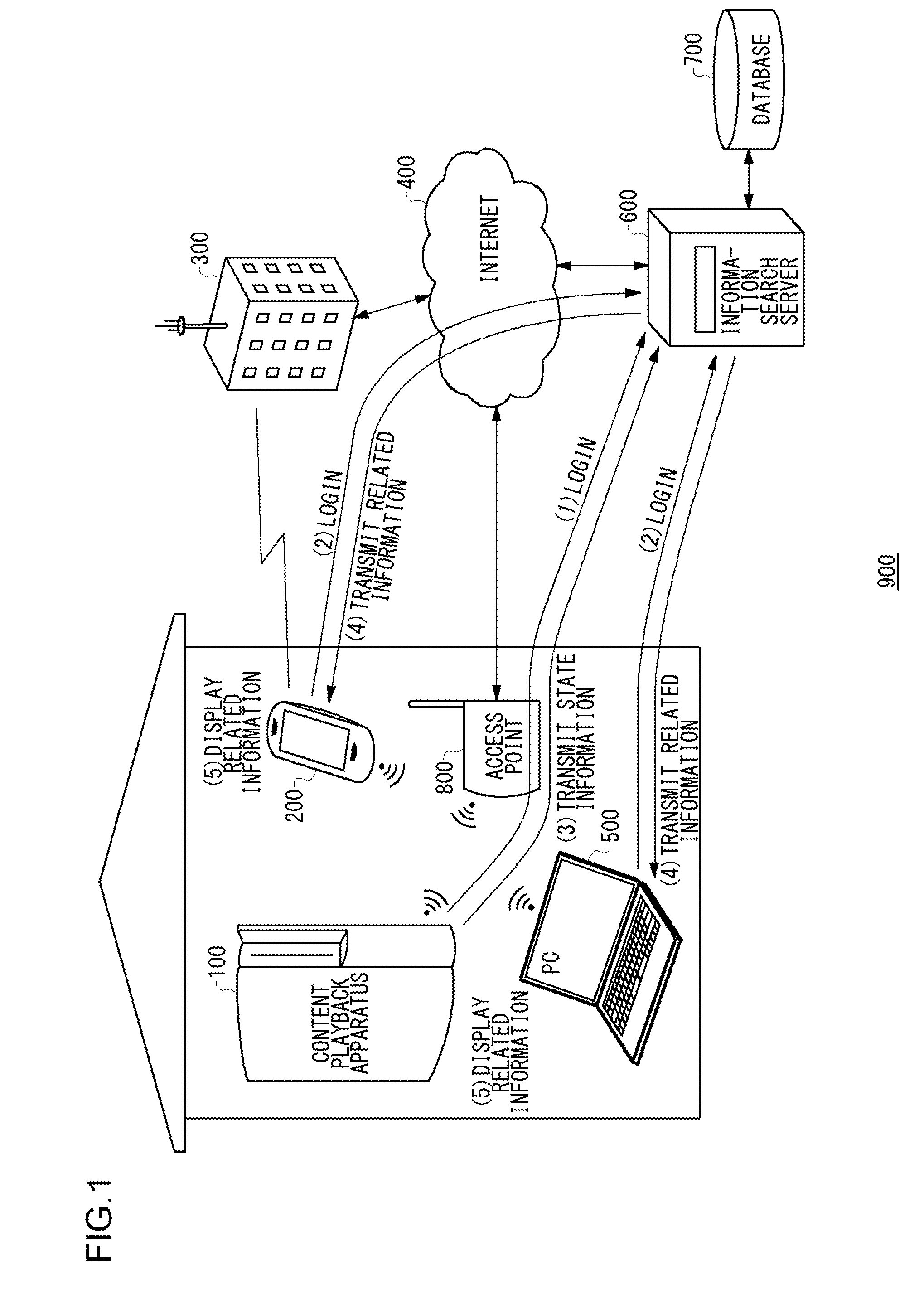
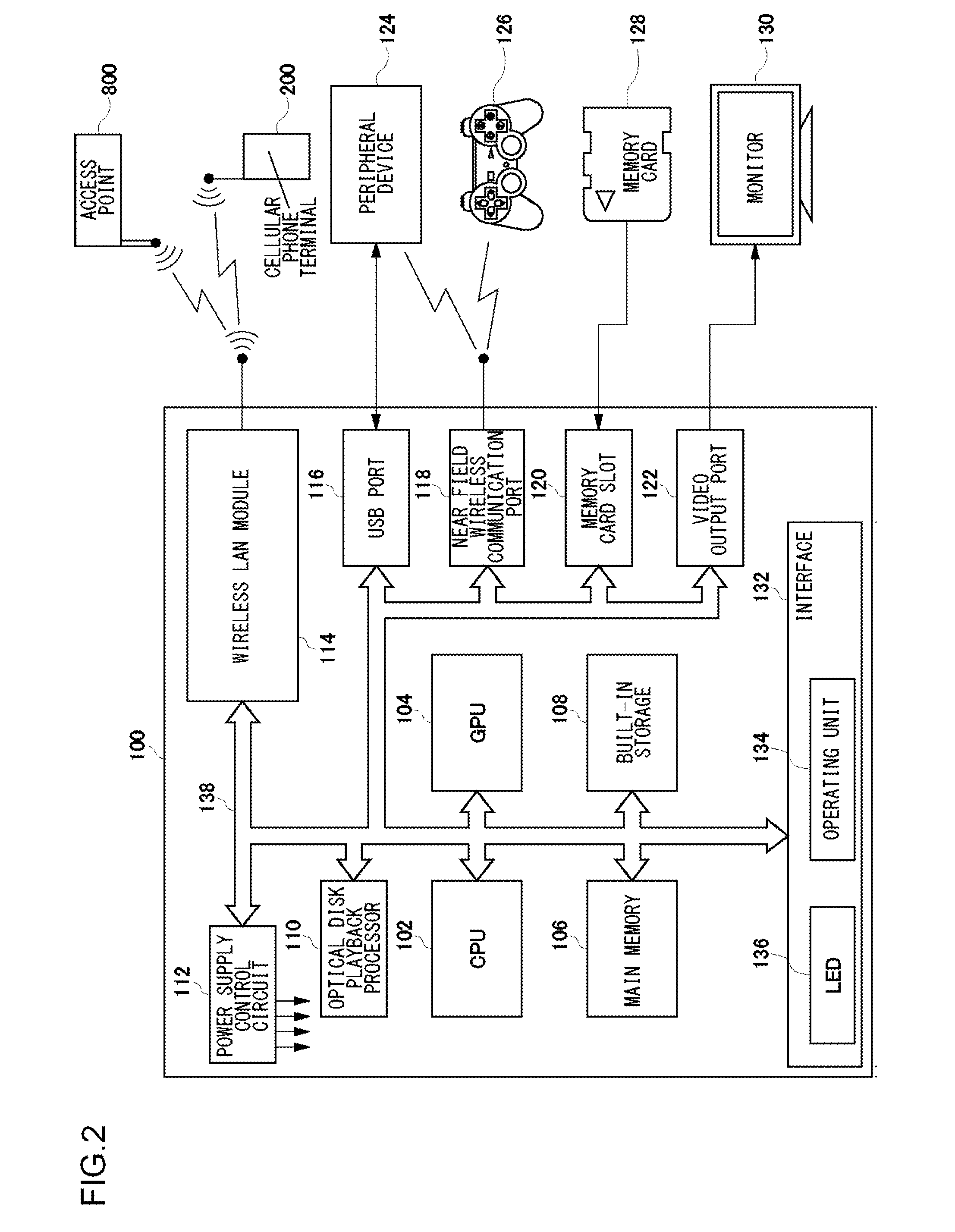
Information search method, information search server, and information search system
ActiveUS20120331112A1Digital data information retrievalMultiple digital computer combinationsRelevant informationManagement unit
In an information search server 600, a database includes a table storing a progress status of content, and information related to the content at the progress status, and a table storing user information with respect to a content playback apparatus, an identifier of the content playback apparatus, and an identifier of a terminal apparatus that differs from the content playback apparatus. A connecting user management unit manages user information with respect to the content playback apparatus connected to the information search server. A related information acquisition unit acquires a current progress status of content being played back on the content playback apparatus, and acquires information related to the content at the current progress status. A connecting user management unit identifies a terminal apparatus that differs from the content playback apparatus, and the related information acquisition unit transmits the related information to the terminal apparatus.
Owner:SONY COMPUTER ENTERTAINMENT INC
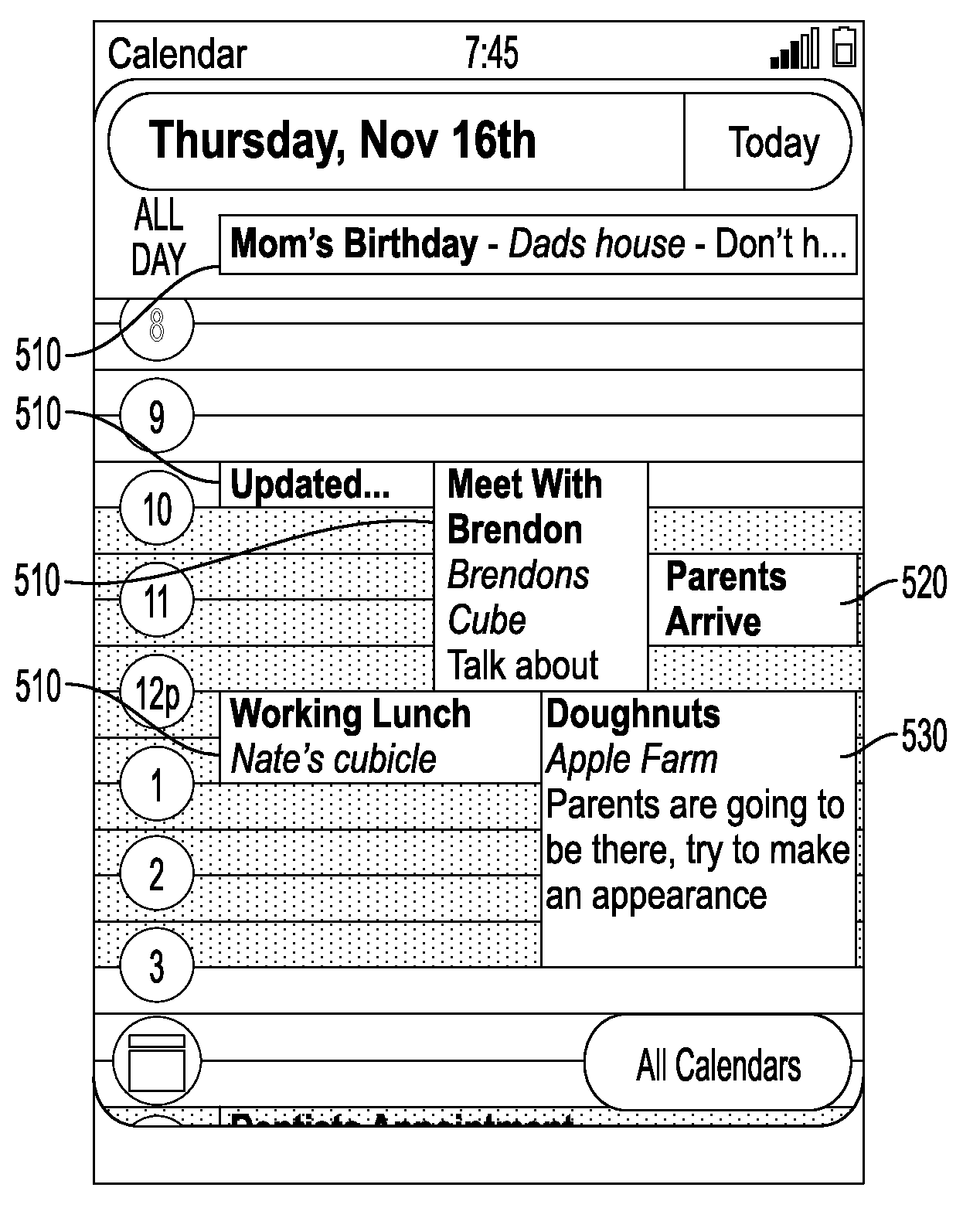
Access and management of cross-platform calendars
ActiveUS20100162105A1Data processing applicationsSpecial data processing applicationsTime scheduleScrolling
A system is disclosed for users to manage calendars in mobile computing devices. The system retrieves calendar entries from multiple calendars of distinct calendar platforms, extracts event information from the retrieved calendar entries, and aggregates extracted event information. The system can simultaneously display calendar entries extracted from multiple calendars of distinct platforms. The system provides various features for users to operate the calendars, such as (1) hiding calendar entries from some calendars and visually distinguishing the time scheduled for the hidden entries from free time; (2) compressing the display of extended free time periods; and enabling users to (3) navigate time as a scrolling list not subject to the limitations of arbitrary calendar units (e.g., month, week).
Owner:QUALCOMM INC
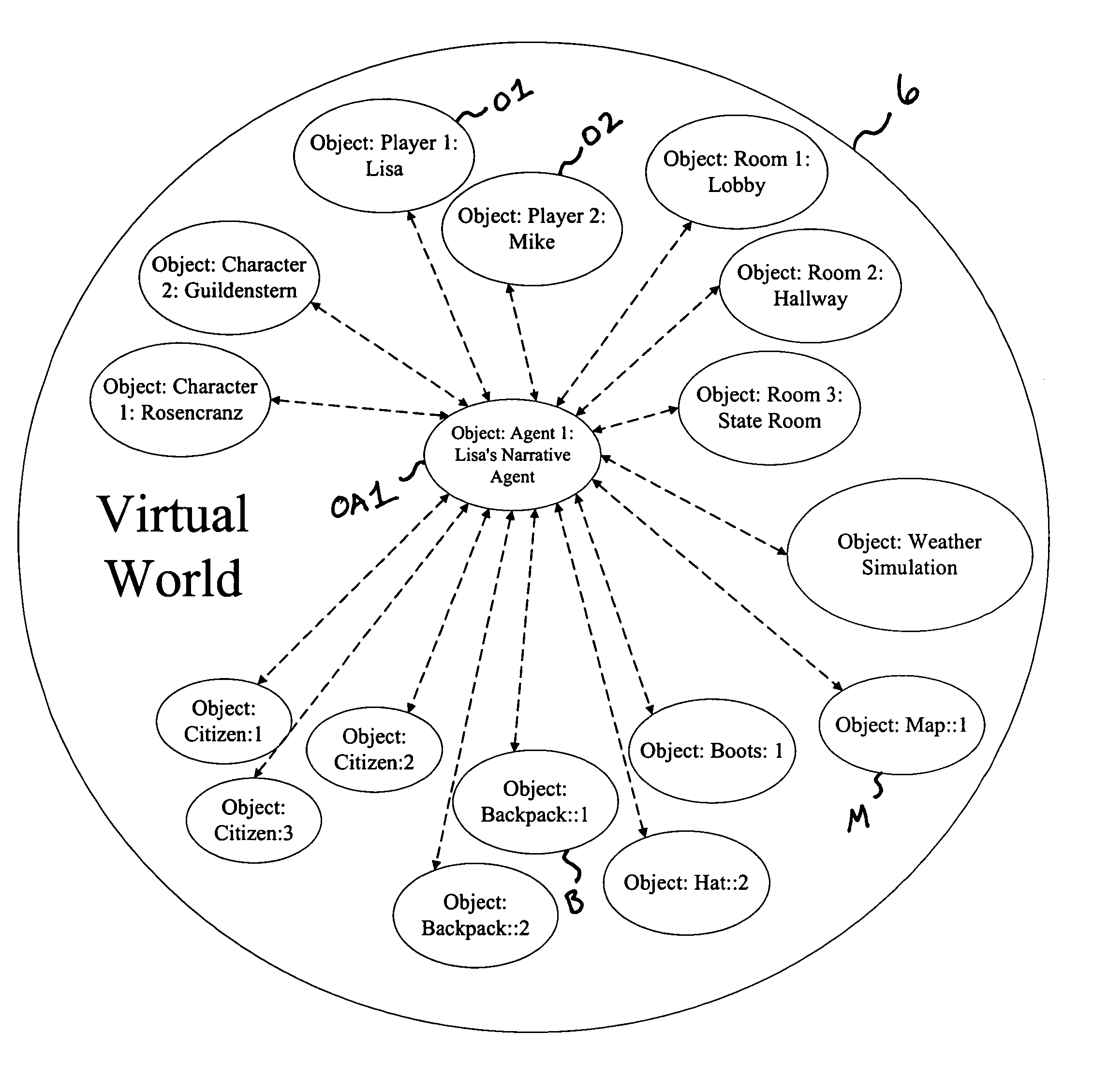
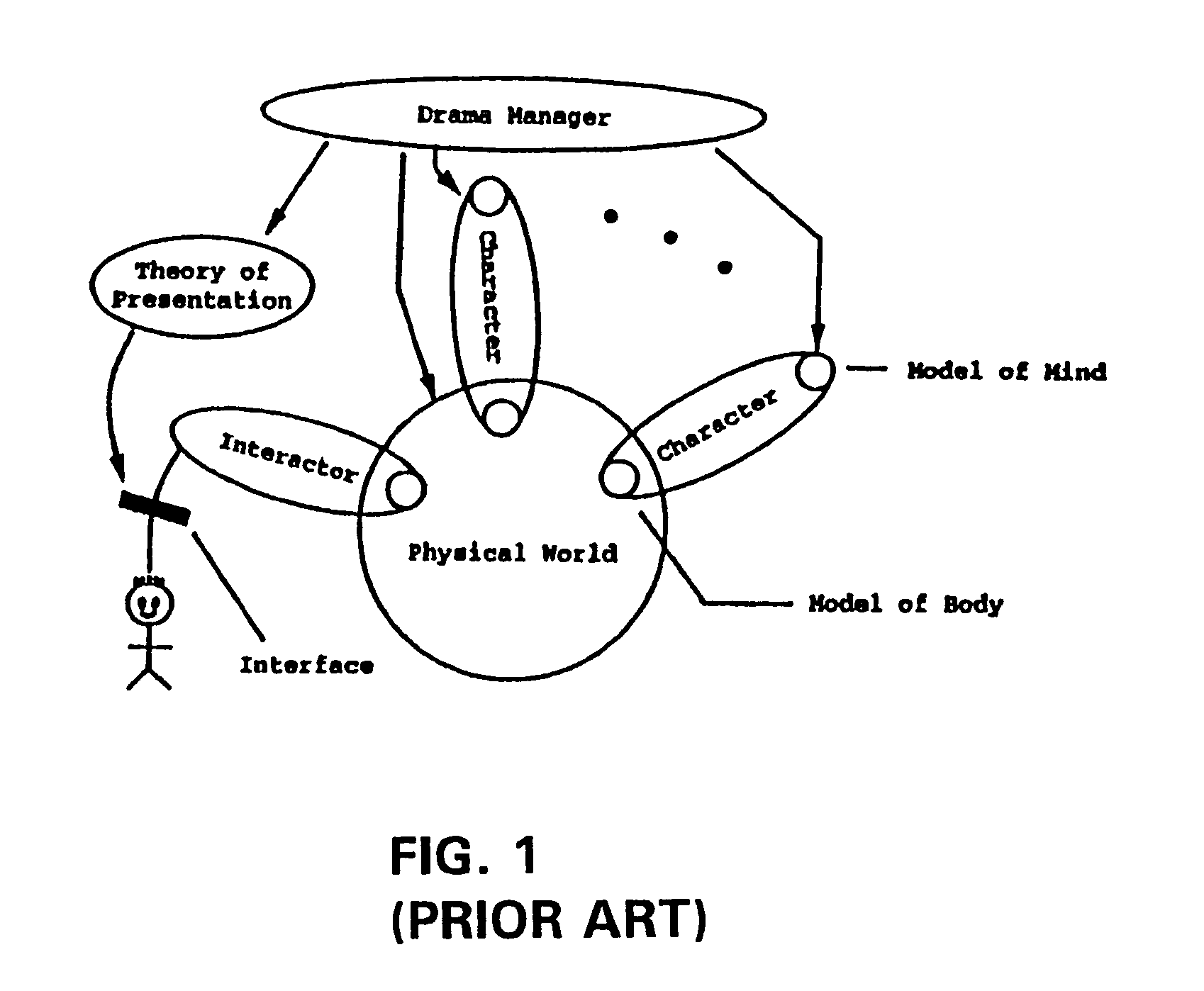
Interactive personal narrative agent system and method
InactiveUS7246315B1Data processing applicationsDigital computer detailsApplication softwareComputer science
A software application and method enables a personal narrative agent (PNA) to create and manage multiple dynamic customized story experiences for a subject user in a user-observable environment having one or more objects with which the subject user may interact. The PNA selectively interacts with one or more of those objects to manipulate the environment in furtherance of the story experiences. The PNA further maintains data relating to the subject user, the environment and the multiple story experiences of the subject user. The PNA also simultaneously manages each of the story experiences which each reach its own narrative conclusion consistent with input and characteristics of the subject user and any objects selected to influence the story experiences. A unique PNA may be assigned to each of multiple users which independently manage different story opportunities for their respective users, such as to enable each of the multiple users to pursue individual stories independent from the stories of the other user. A PNA of one user may interact with a PNA of another user to negotiate a story opportunity involving the second user for the first user, and vice-versa.
Owner:REALTIME DRAMA
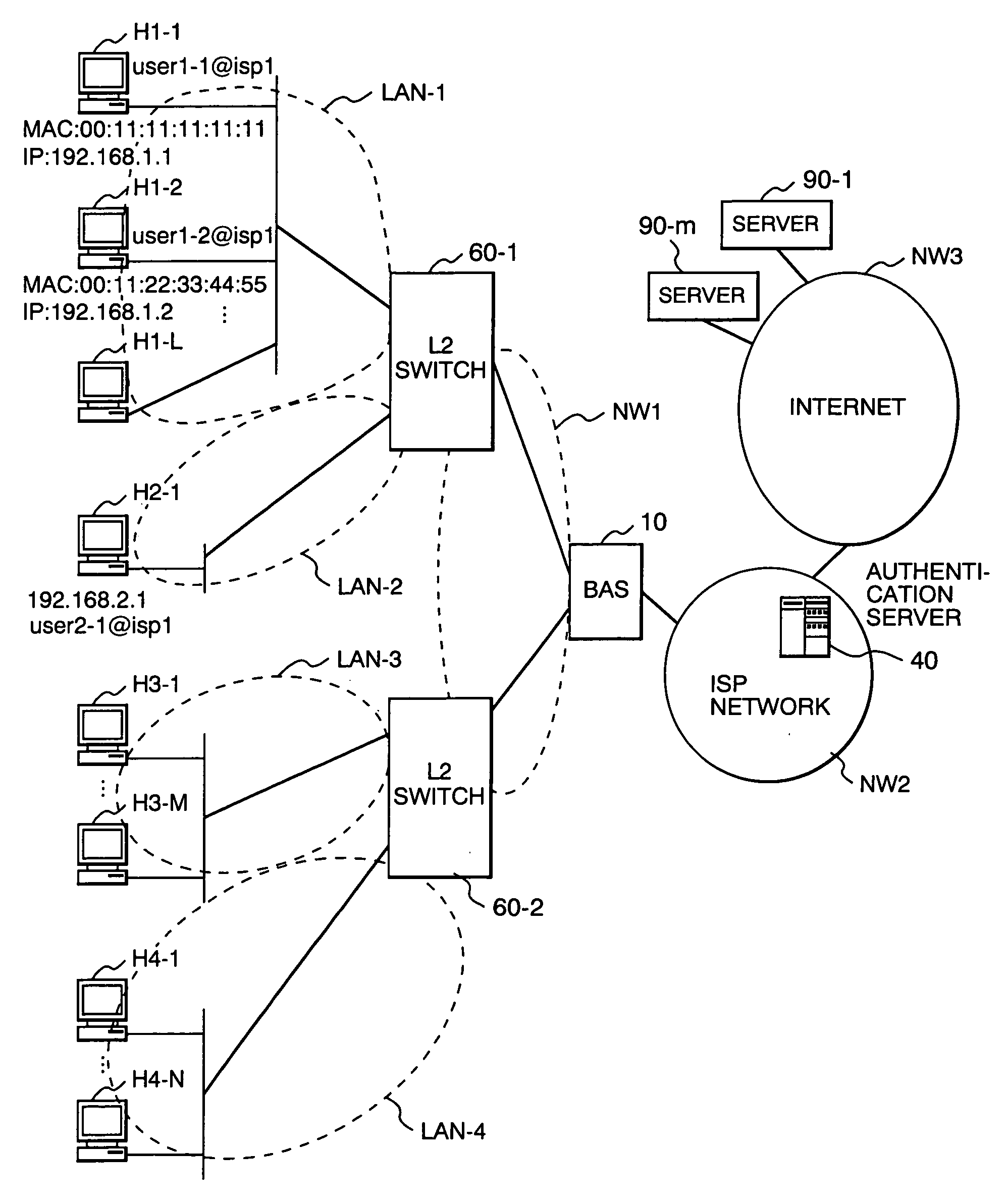
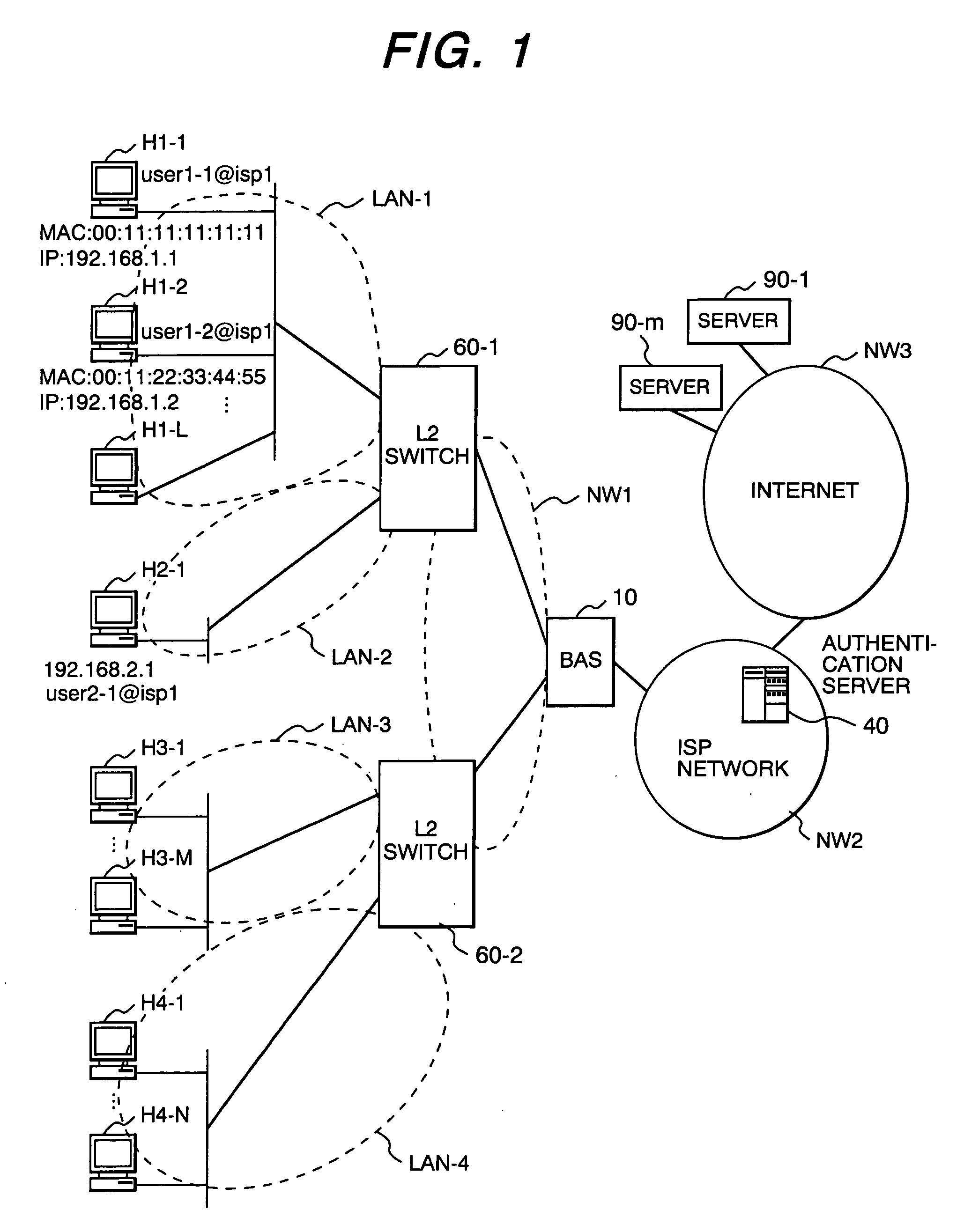
User terminal connection control method and apparatus
InactiveUS20060109839A1Reduce frequencyReduce in quantityError preventionTransmission systemsThe InternetAuthentication server
A user terminal connection control method to limit the number of sessions simultaneously connectable to the Internet, wherein an access server or authentication server has a user management table for specifying the maximum number of connections and a preferential terminal identifier indicating a user terminal to be preferentially connected to the Internet for each group comprising a plurality of user identifiers. The access server or authentication server determines, during a communication procedure for authenticating a user who requests to access to the Internet, whether the current number of connections for a group to which the user belongs has reached the maximum number of connections, and if so, determines whether to allow the user terminal to connect to the Internet depending on whether the user terminal identifier matches the preferential terminal identifier.
Owner:HITACHI LTD
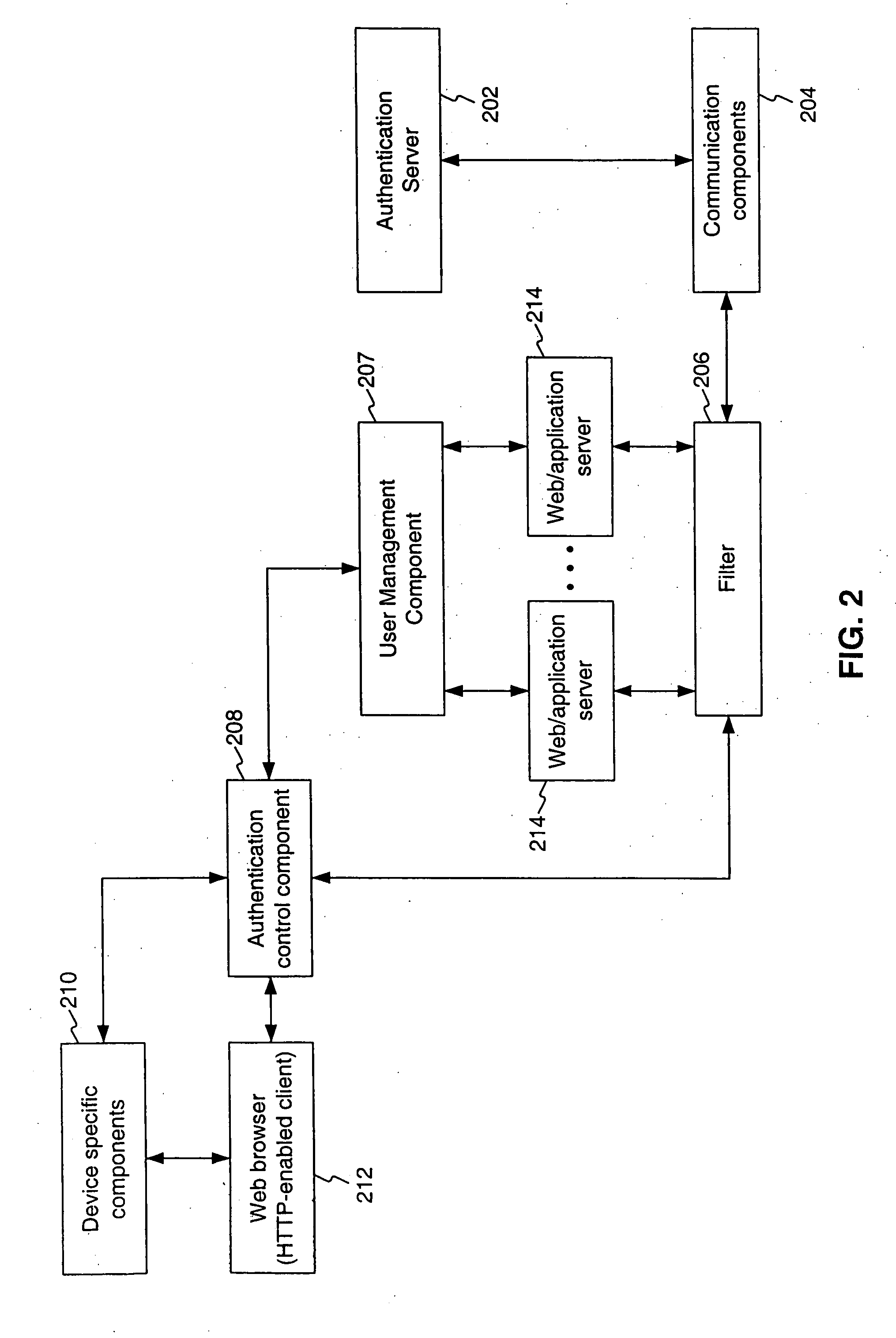
System, method and computer program product for providing unified authentication services for online applications
InactiveUS20090019534A1Digital data processing detailsUser identity/authority verificationInternet Authentication ServiceWeb application
A system and method remotely enrolls, authenticates and provides unified authentication services in an ASP setting to a user to access requested information via a communication medium. A filter is coupled to client side components via the communication medium and a user management component coupled to the client side components via the communication medium. The user management component allows end-users to register their credentials only once. In addition, the user management component allows end-users to define the level of protection of access to their web application accounts. This includes accounts that have been configured specifically for use with the present invention and particular user credentials and accounts that have been subsequently set up but configured to use the same user credentials. The present invention can then reuse those credentials to authenticate the user to one or more potentially unrelated web applications.
Owner:BIONETRIX SYST CORP
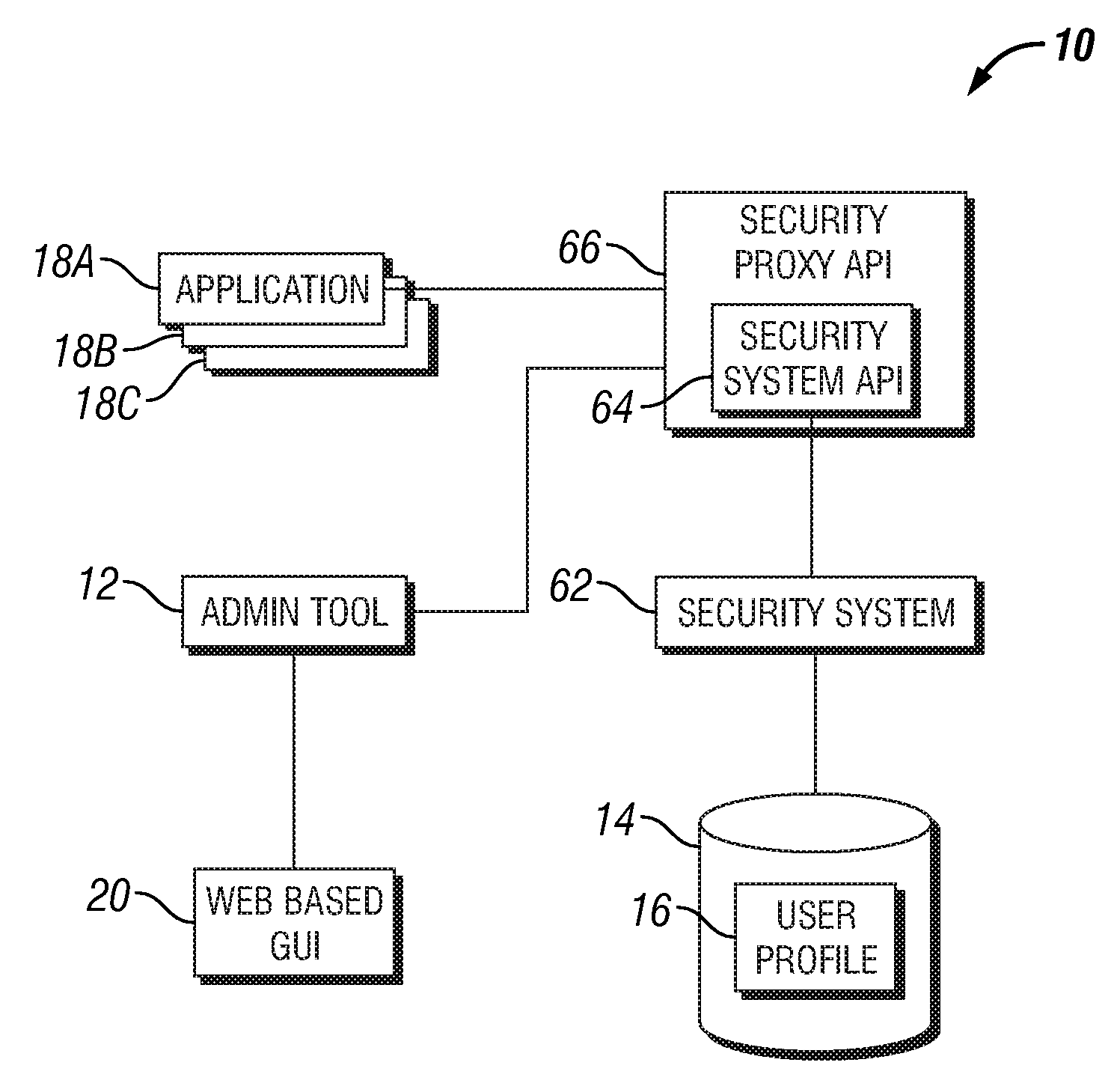
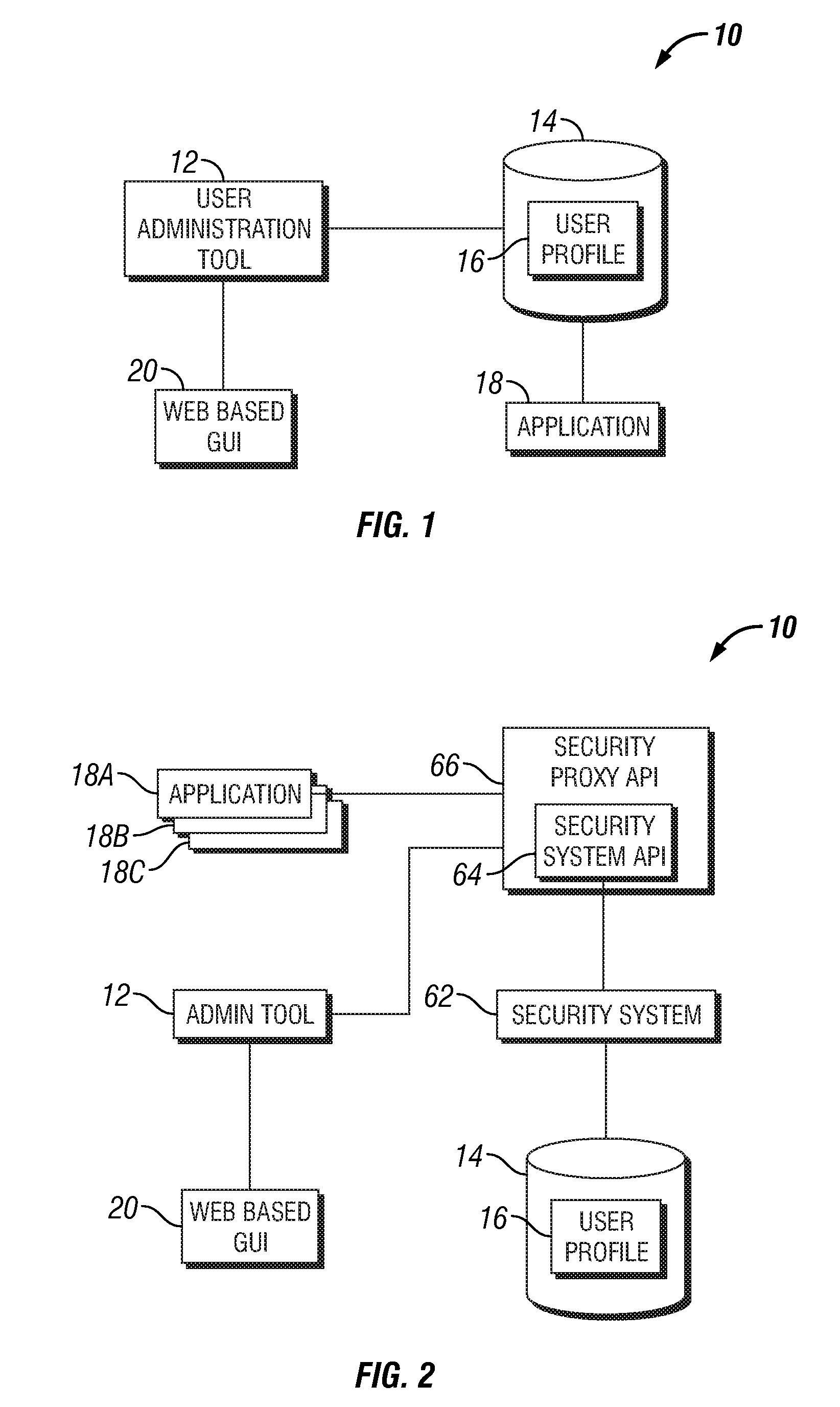
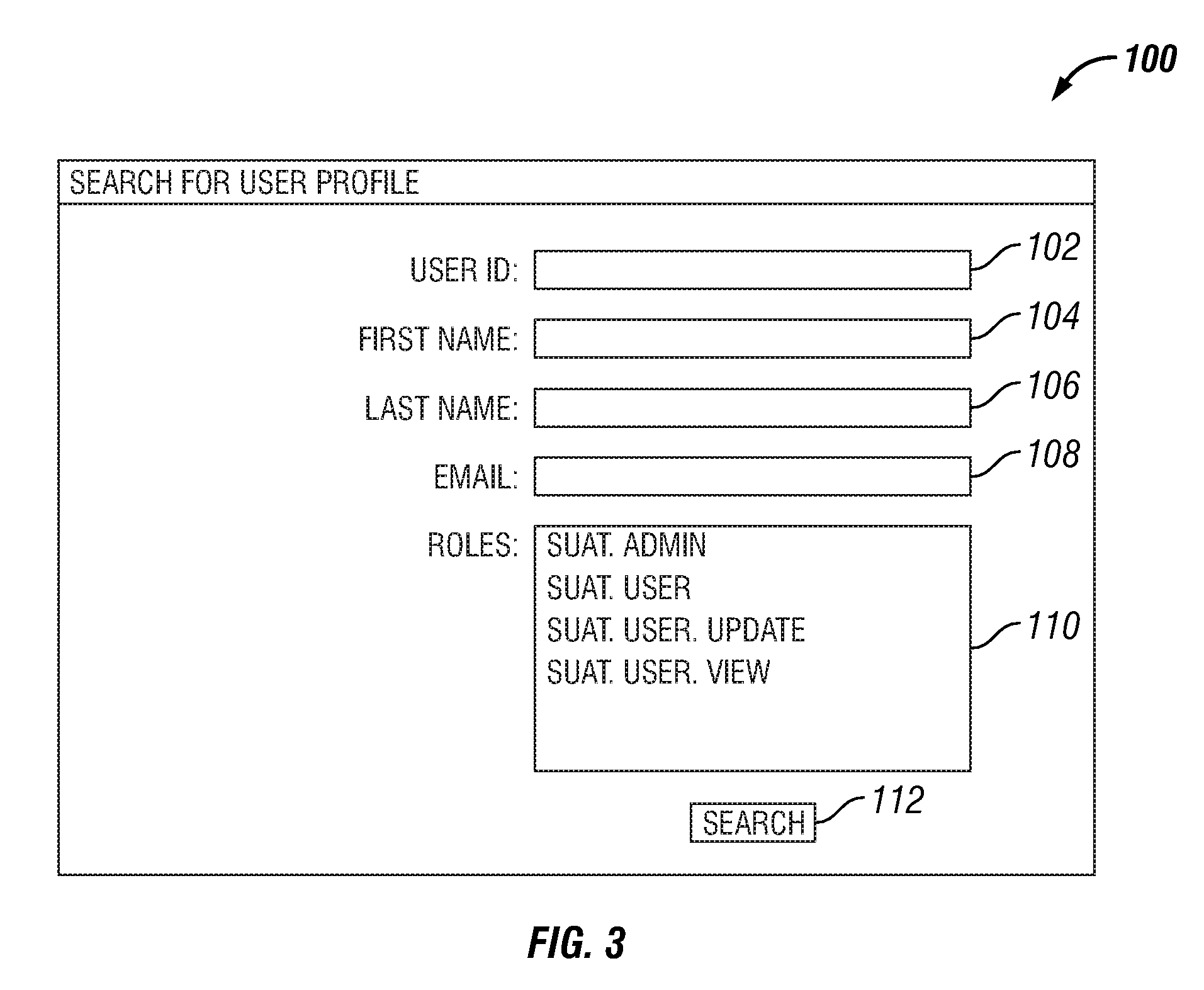
User administration tool
ActiveUS7523486B1Limited accessDigital data processing detailsUnauthorized memory use protectionThird partyGraphics
A tool for administering users of a security system is provided. The security system includes a storage component stored on a computer readable medium, a centrally located graphical user interface stored on a computer readable medium, and an engine stored on a computer readable medium. The storage component maintains roles data that includes an authorization component and an application component, wherein the application component includes at least one role defined by a third party application. The centrally located graphical user interface manages the application component and the authorization component. The engine communicates with the storage component via a security system application programming interface, uses the authorization component to determine whether to grant access to the third party application, and communicates the application component to the third party application which uses the application component to determine a level of access within the third party application.
Owner:T MOBILE INNOVATIONS LLC
Internet based achievement & skills management process & method
InactiveUS20100125475A1Easy to useUniversally functionalComplete banking machinesTelephonic communicationBase codeThird party
An Internet Based Achievement Management Process & Method of use thereof which generally comprises computer software, including internet web page based code, and methods of applications that allows a user to mange, track, and record events and or achievements which pertain to professional, educational, and or personal goals as well as the ability to measure or compare the events and or achievements against their peers by means of an impartial third party review and assessment process.
Owner:TWYMAN CHRISTOPHER
Systems and methods for providing and updating a unified client
InactiveUS20110126192A1Improved end user experienceImprove experienceProgram loading/initiatingMemory systemsClient-sideReceipt
The present invention is directed towards systems and methods for more efficiently managing installation of a plurality of application plug-ins for a client device. A client device executes, upon startup, a receiver application. The receiver application may manage installations of application plug-ins for a user of the client device. The receiver application may receive from an update server a delivery of application plug-ins to install on the client device. Upon receipt of the delivery, the receiver application may automatically install each of the application plug-ins on the client device transparently to the user of the client device. The receiver application may automatically start each of the application plug-ins.
Owner:CITRIX SYST INC
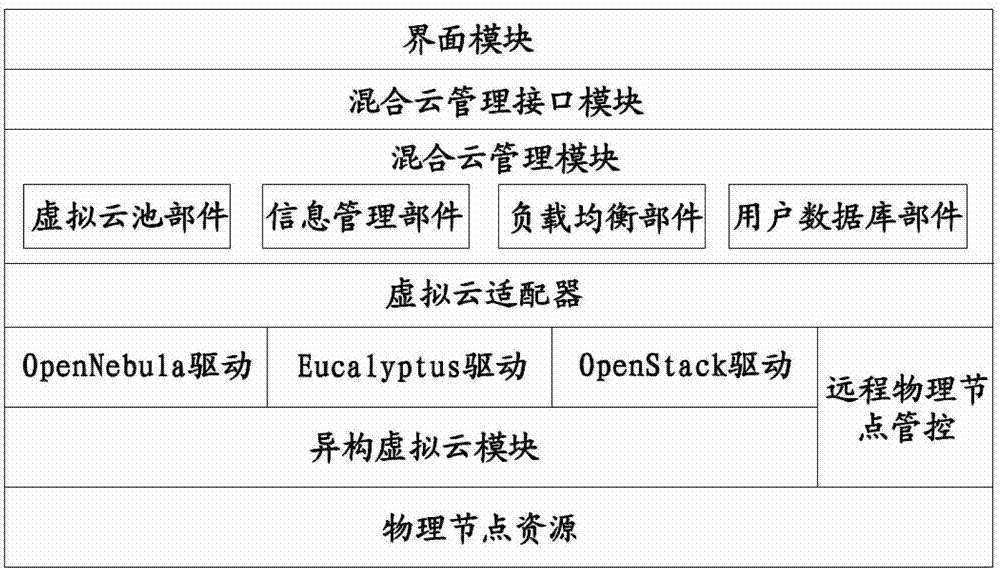
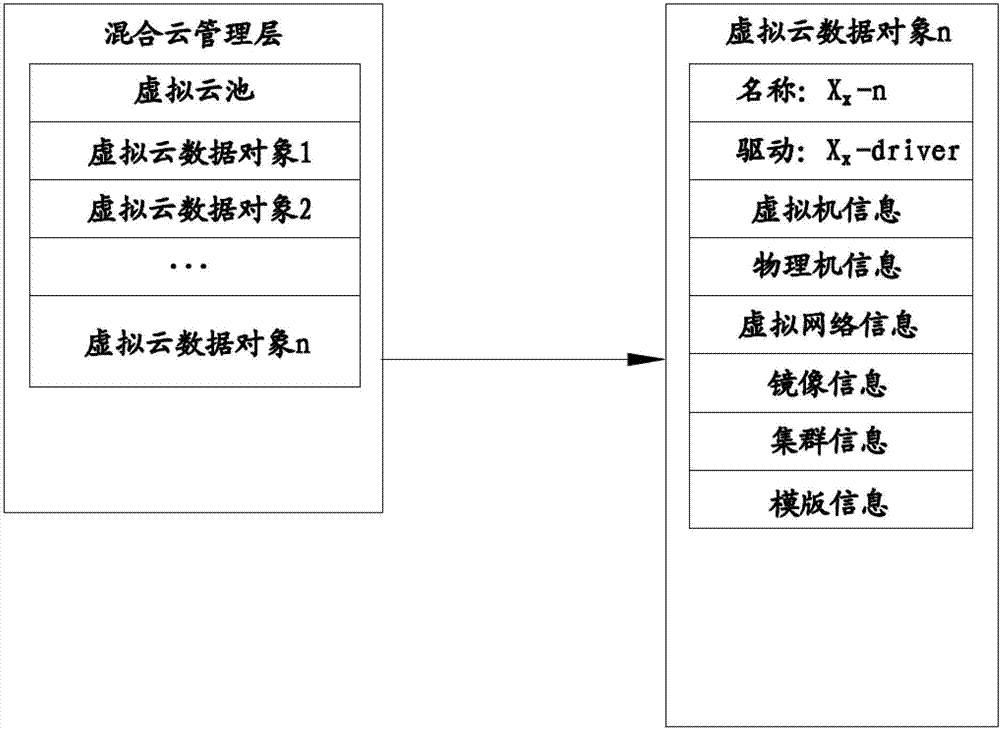
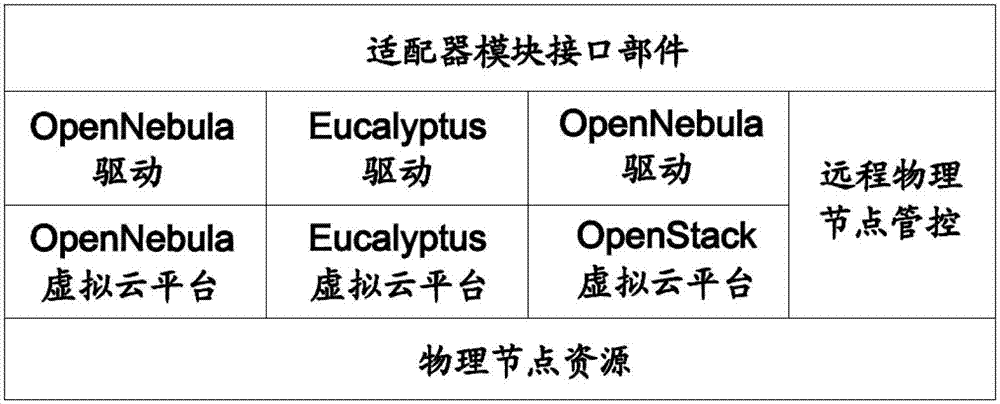
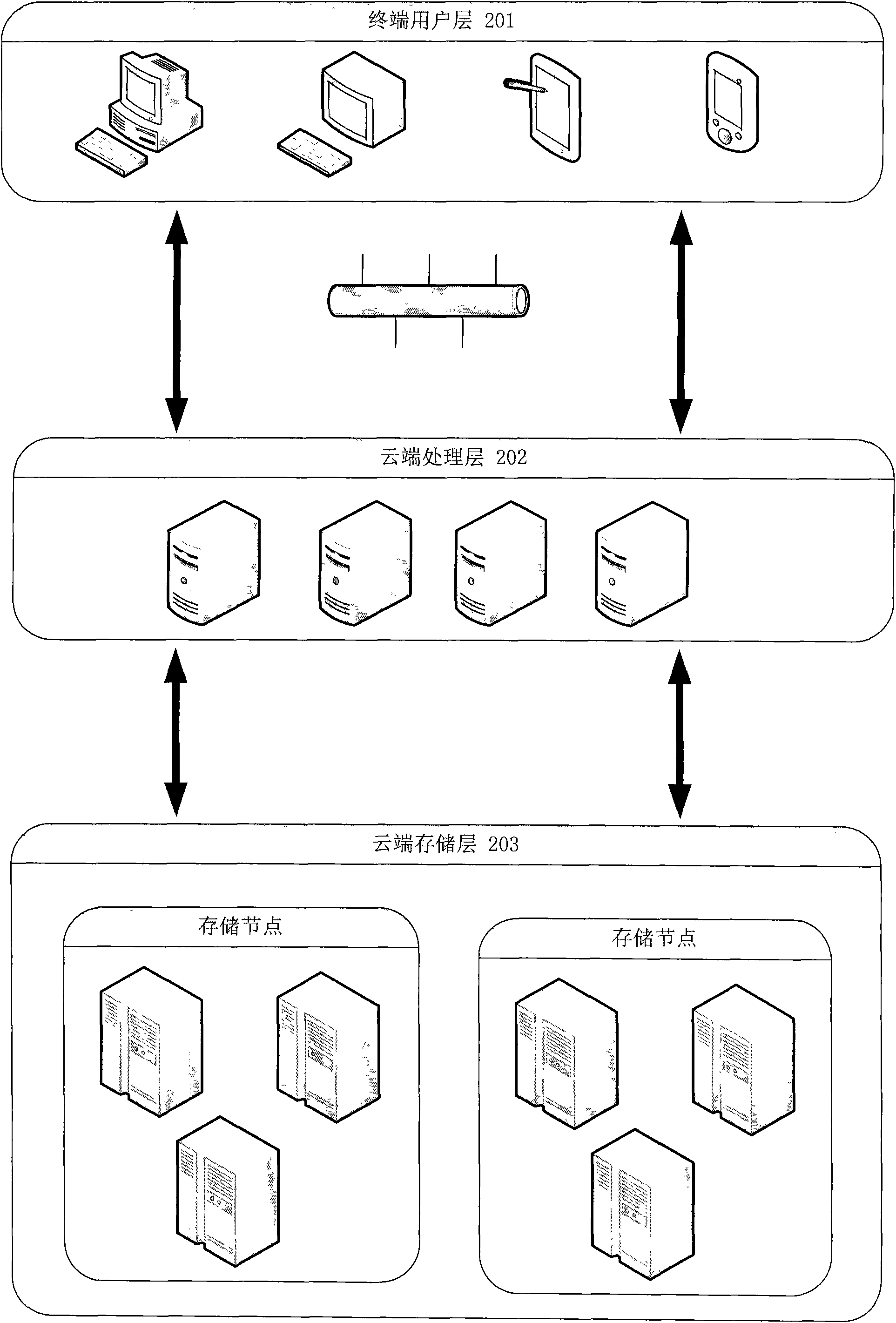
Virtual cloud platform management system and method
The invention belongs to the technical field of cloud computing, and particularly relates to a virtual cloud platform management system and a virtual cloud platform management method. The a virtual cloud platform management system comprises an interface module and an isomerous virtual cloud module, wherein the interface module is a window through which a user interacts with a virtual cloud platform; and the isomerous virtual cloud module comprises various virtual cloud platforms, a hybrid cloud management module for managing various virtual cloud platforms in the isomerous virtual cloud module, and a virtual cloud adapter for providing a uniform programmatic interface for managing and shielding the difference among a plurality of different virtual cloud platforms on a bottom layer for the hybrid cloud management module. According to the virtual cloud platform management system and the virtual cloud platform management method disclosed by the embodiment of the invention, a way for managing a plurality of isomerous virtual cloud modules in a single way is provided, so that the transparency of the management of isomerous platforms by different users is realized.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
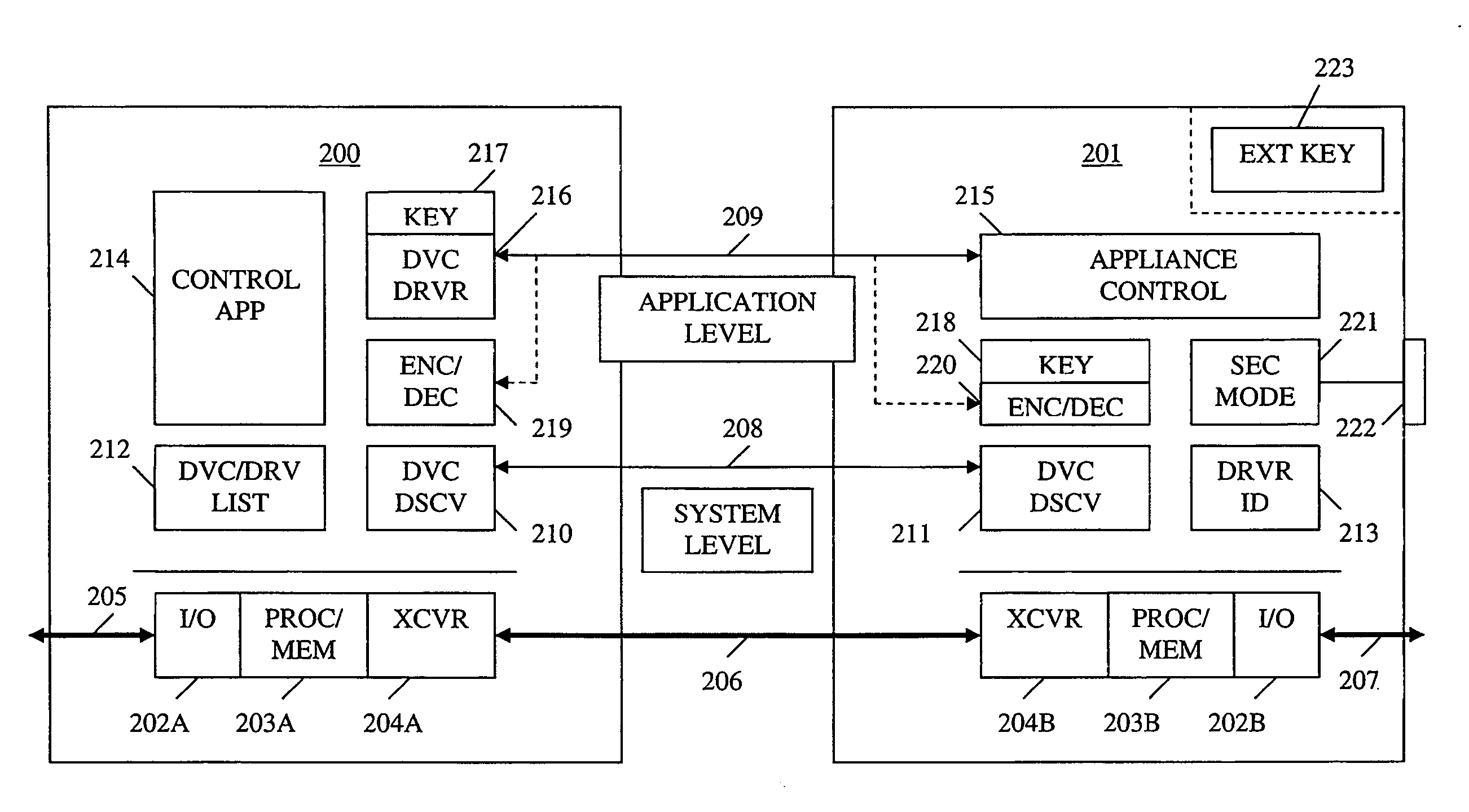
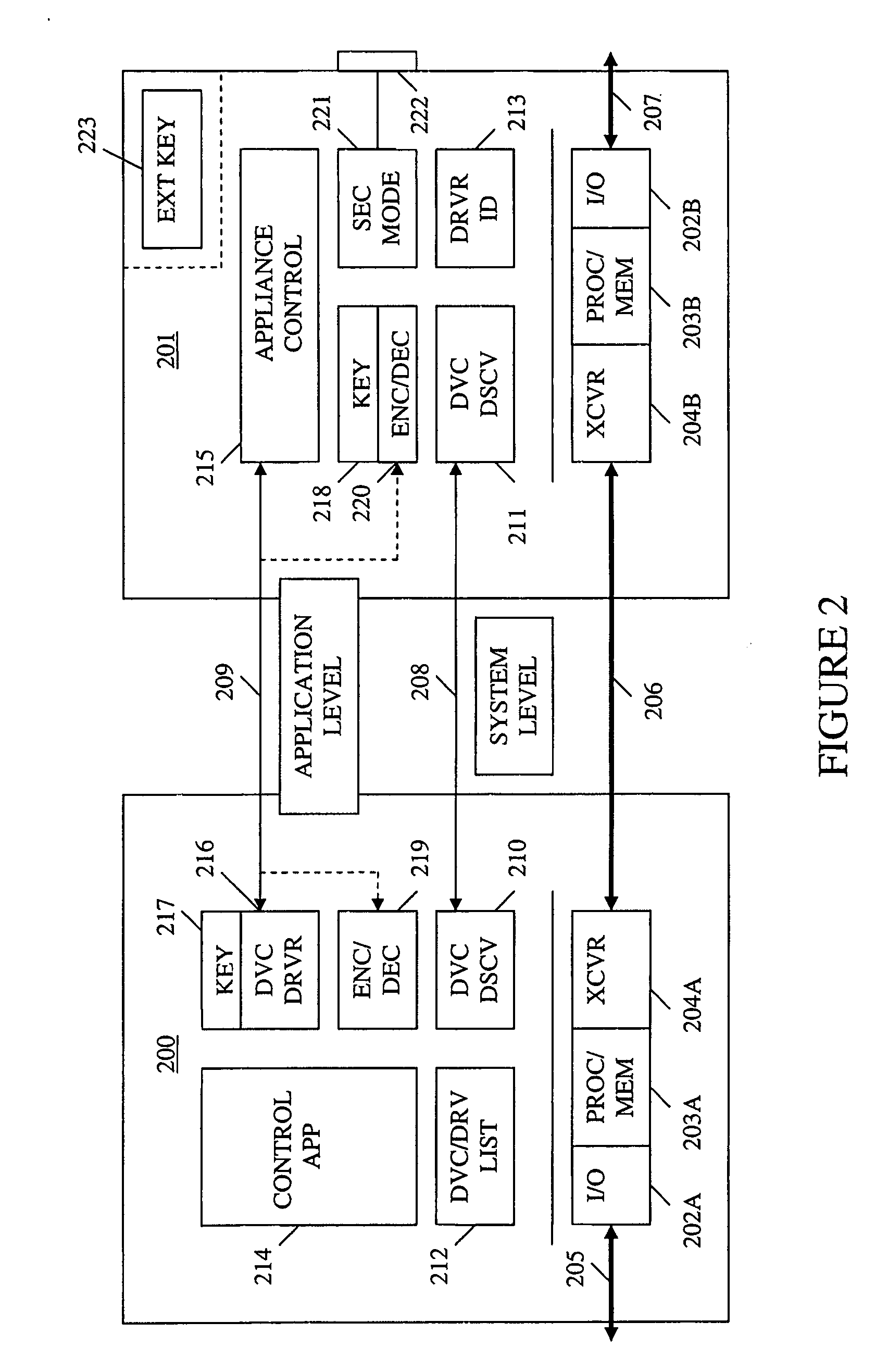
Method and apparatus for device detection and multi-mode security in a control network
ActiveUS20060174102A1Facilitate key exchangeAvoid reconfigurationSecurity arrangementSecuring communicationWireless controlUser management
A method and apparatus for device discovery and multi-mode security in a wired and / or wireless control network are described. A controlled device is configured with discovery-level instructions and application-level control instructions. The controlled device includes a user-configurable parameter for selecting between multiple security modes. In one or more security modes, the controlled device may ignore application-level messages until encrypted communications are established with a controller. In one mode, the encrypted communication is established with an encryption key exchange using a predetermined security key. In another mode, a specific key is manually entered into the controller by the user / administrator to facilitate the encryption key exchange. Additionally, for control applications where security is not important, an unencrypted security mode may be implemented. A driver ID provided by the controlled device facilitates loading of a preferred device driver by the controller.
Owner:SNAP ONE LLC
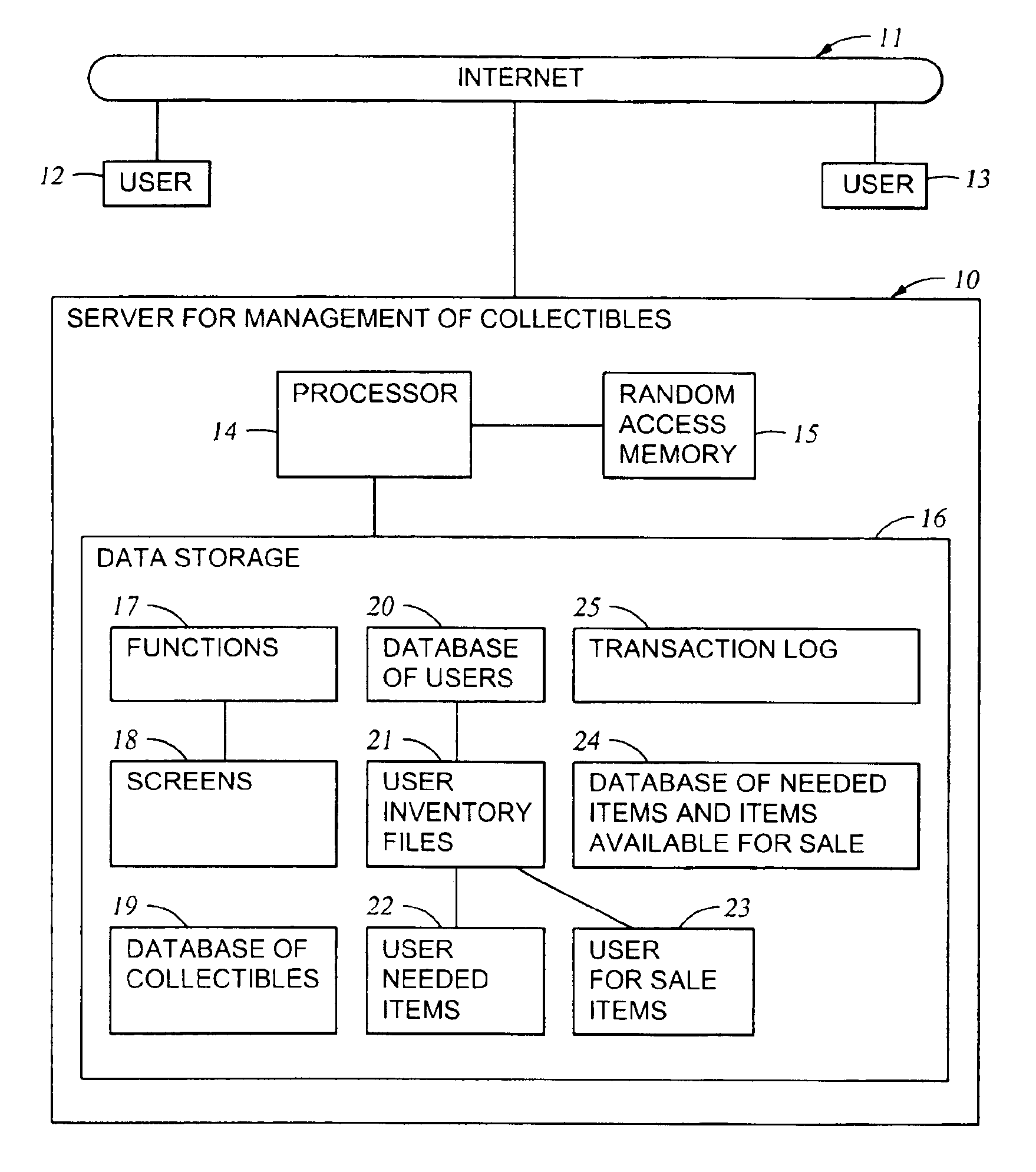
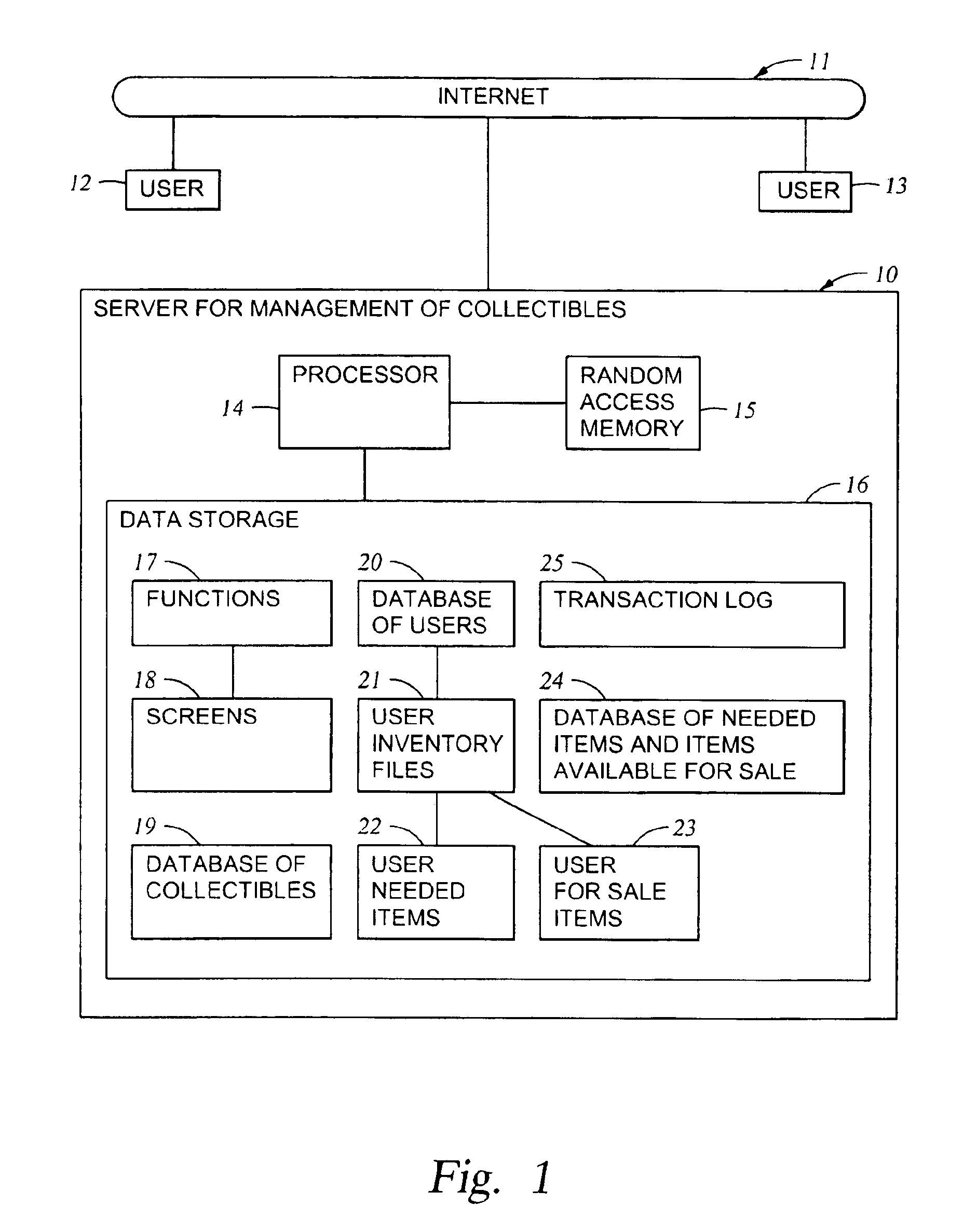
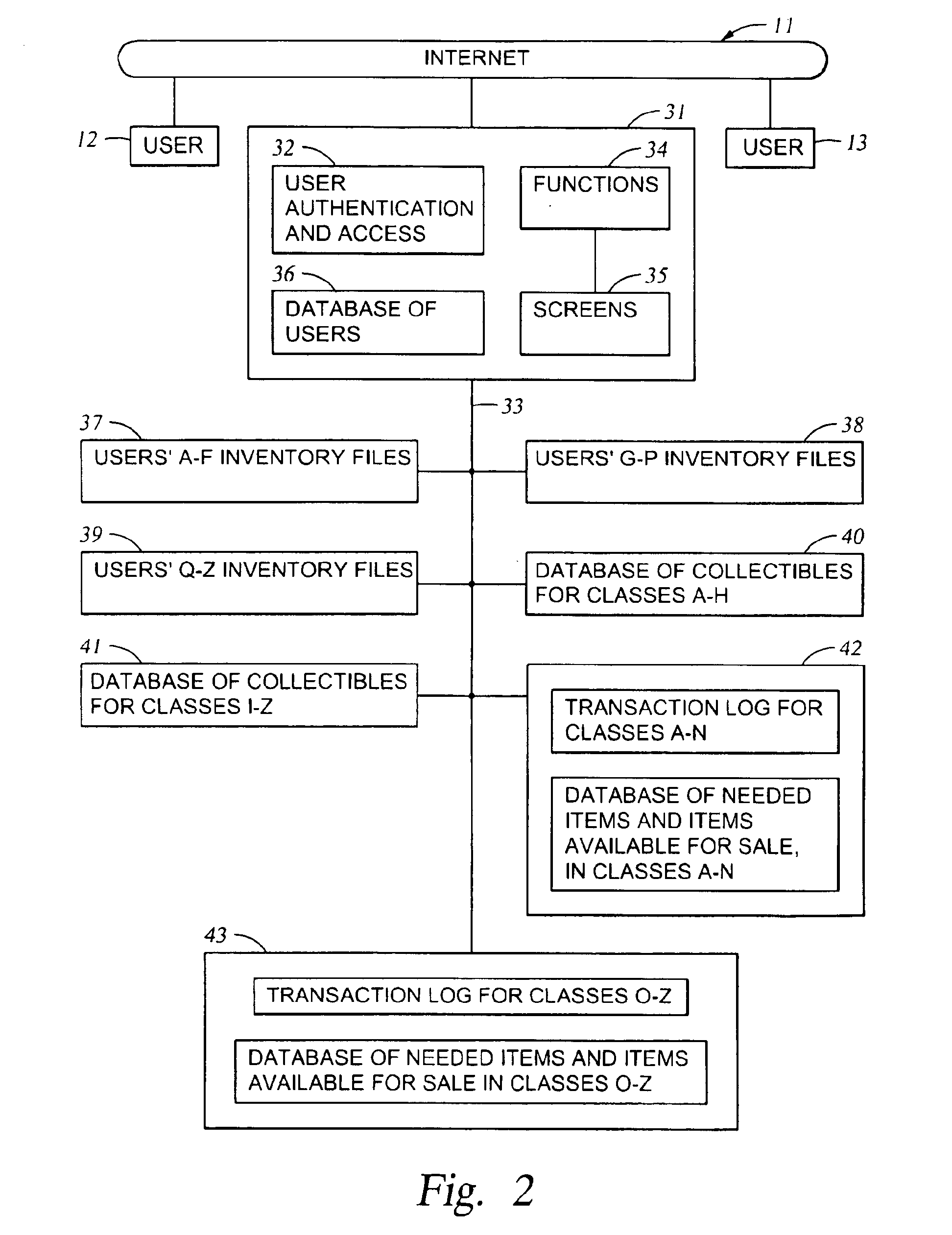
Online method and system for management of collectibles
An online system for permitting users in a data network to manage inventories of their collectibles (including antiques) includes a database of collectibles, user inventory files, user information files, a database of needed items and items available for sale, and a server-based task for managing and searching the database of needed items and items available for sale. The database of collectibles includes object classes indexed by primary classes and subclasses, and user inventory files storing inventories of instances of the object classes, including instances that each user has, instances that each user would like to sell, and instances that each user would like to buy. Users may access their respective inventories by inspecting, editing, and adding the instances to the user inventories; obtaining valuations of instances in their inventories; and insuring instances in their inventories. The server-based task finds buy-sell opportunities between the users when one user has an instance of at least one object class that said one user would like to buy and another user has an instance of said at least one object class that said another user would like to sell.
Owner:HAVENEED COM
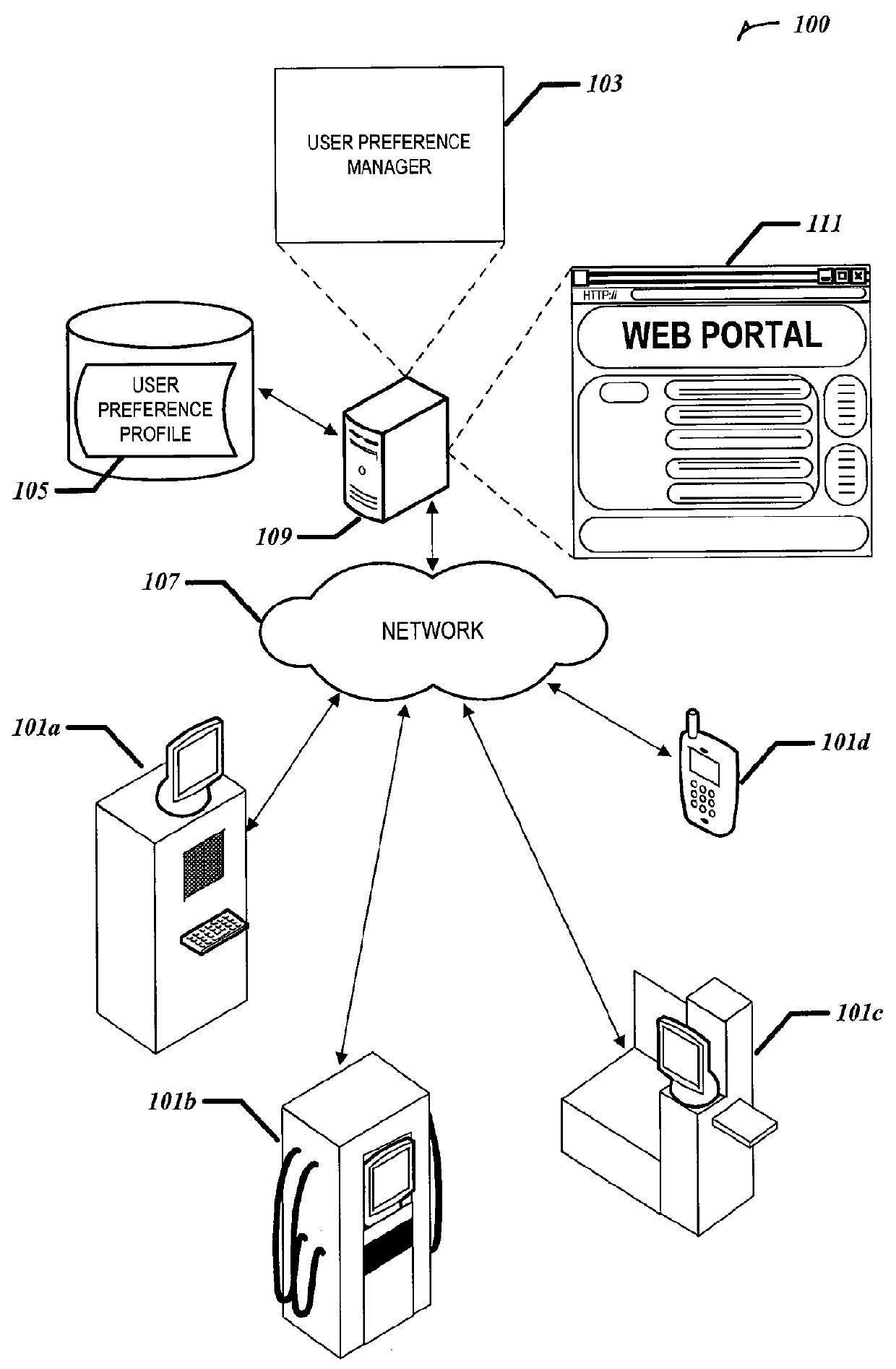
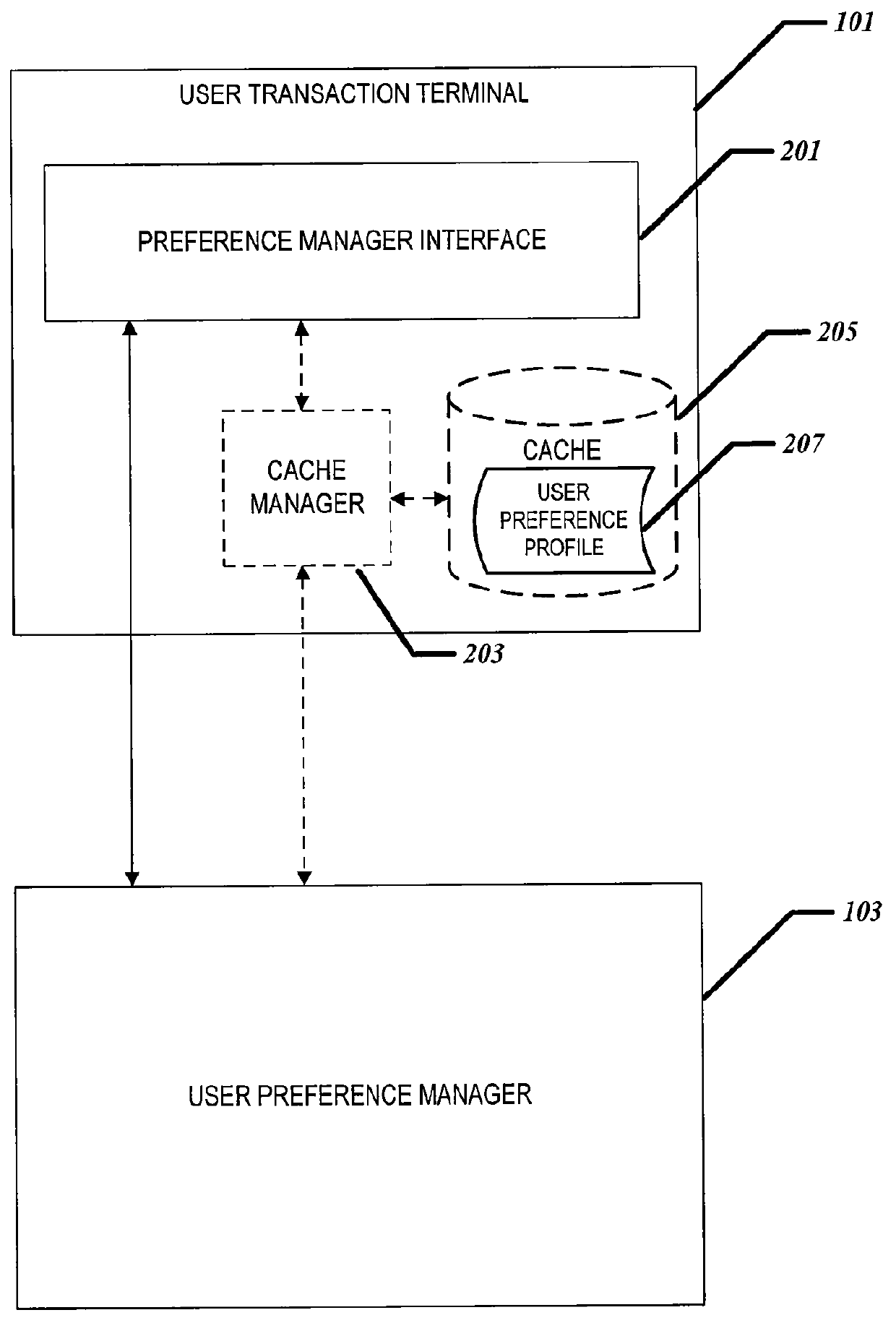
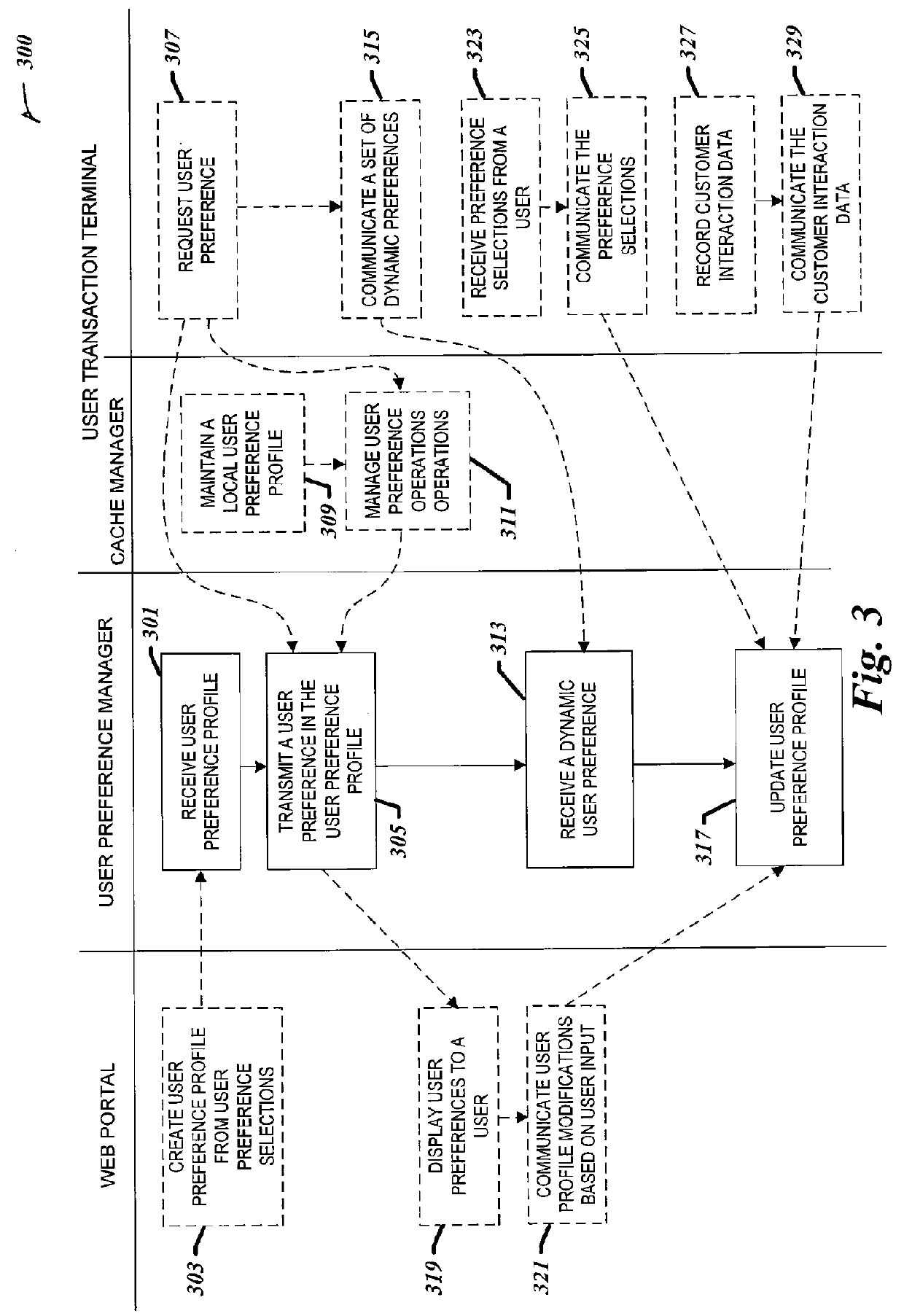
Centralized user preference management for electronic decision making devices
ActiveUS20120110467A1Multiple digital computer combinationsExecution for user interfacesComputer scienceUser management
Systems and techniques for centralized user preference management for electronic decision making devices are provided. A user preference profile is received. A user preference profile manager may transmit a user preference from the user preference profile to a requesting user transaction terminal. the user preference manager may also receive a dynamic user preference from a user preference profile and extend the user preference profile with the dynamic user preference, where the dynamic user preference includes a preference definition and the preference definition includes read and write access controls for the dynamic user preference. Then the user manager may update the user preference profile based on data received from the user transaction terminal.
Owner:NCR CORP
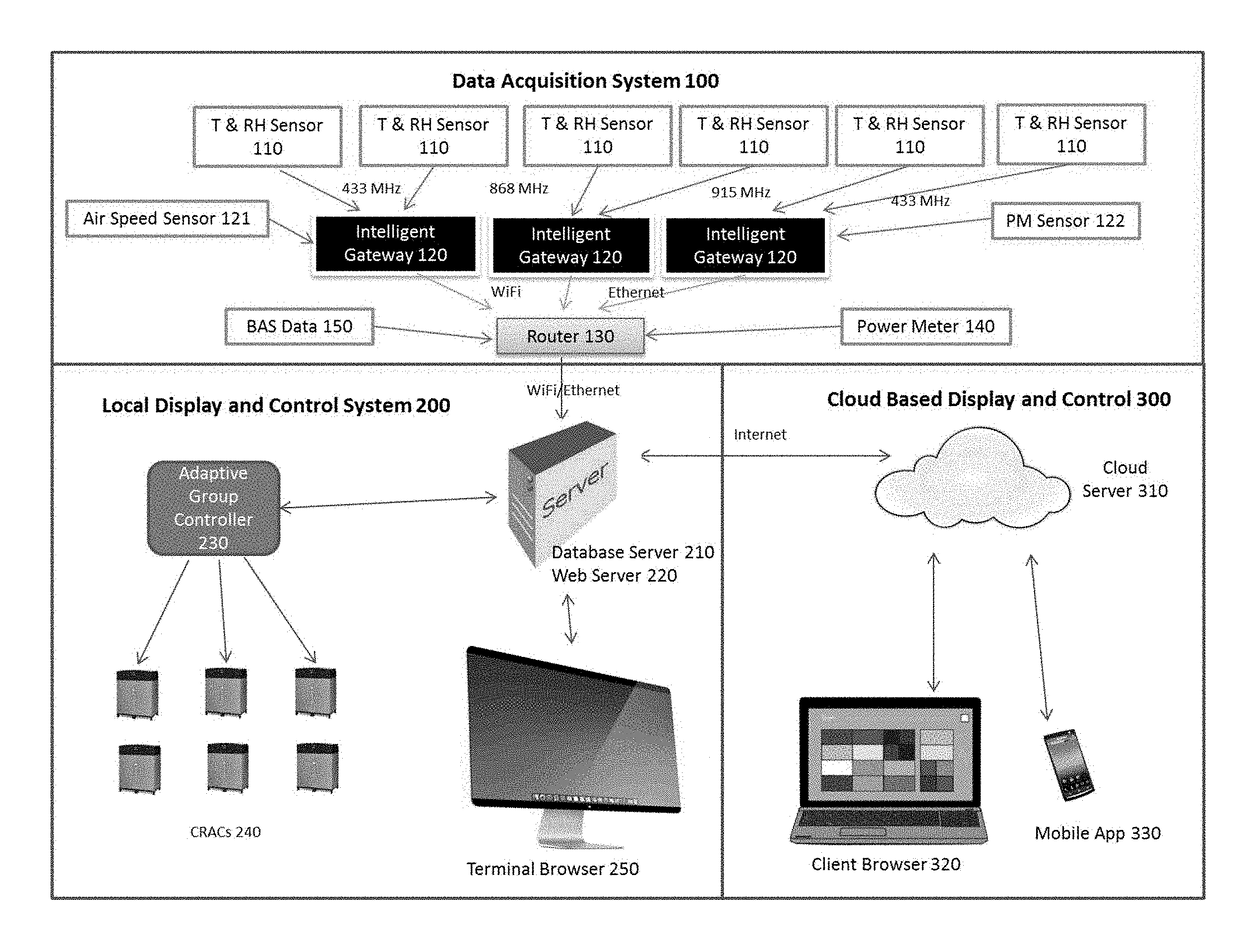
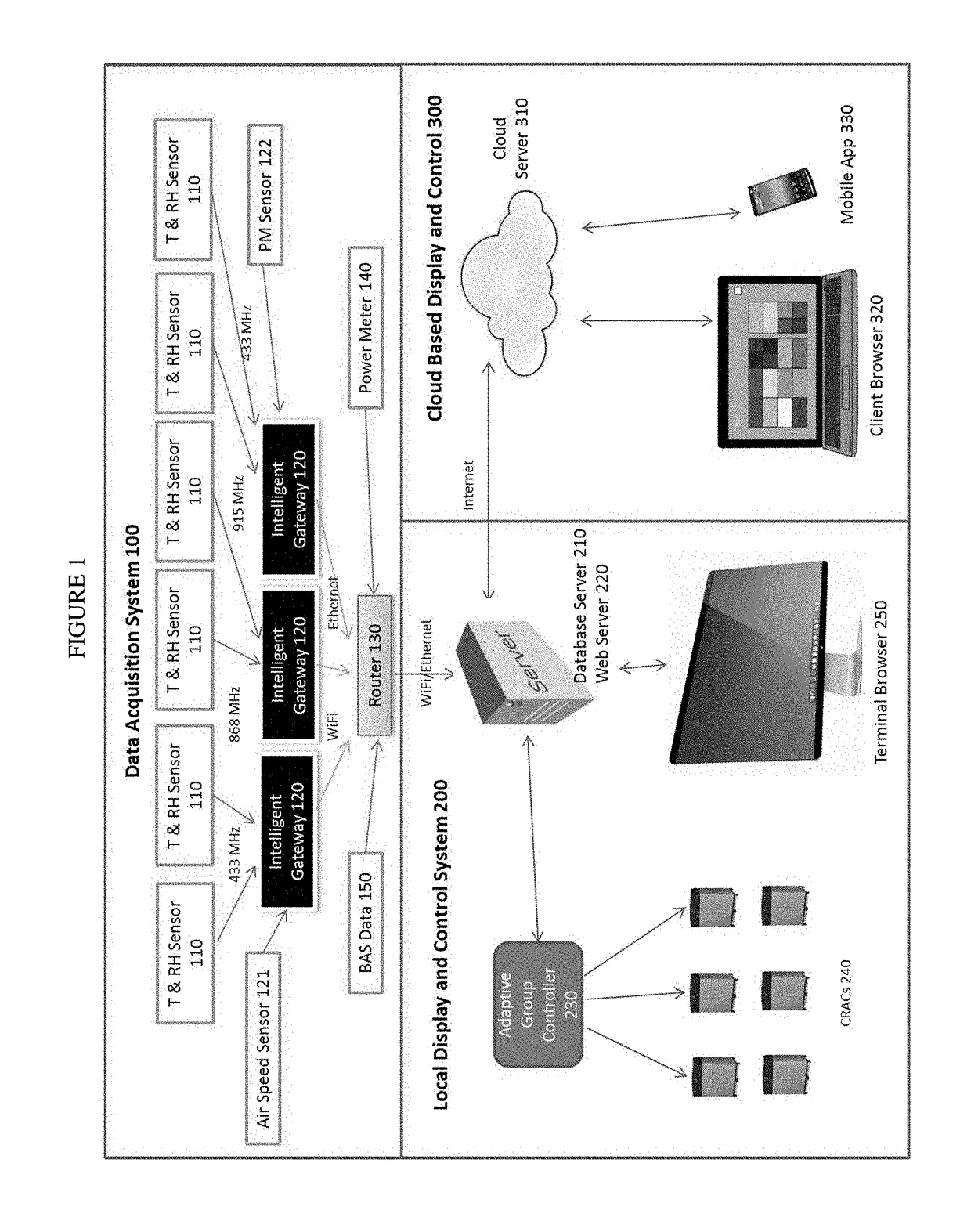
Intelligent mission critical environmental monitoring and energy management system
InactiveUS20170176033A1Process safetyEnergy efficiencyProgramme controlMechanical apparatusDashboardUser management
The present invention is a complete solution for mission critical facilities to create a safe environment and energy efficient CRAC system. The invented system collects mission critical facility volume environmental and energy data in real time, and uses big data analytics to provide adaptive group control to CRACs. The data is visualized in 2D and 3D graphs, dashboard, history curves and reports locally and through the cloud. The present invention also provides user management to allow authorized users to view and control the racks / servers owned or rented by these users. The present invention is comprised of four companion patents: 1) A Battery-powered Wireless Long Life Temperature and Humidity Sensor Module, 2) An Intelligent Multi-channel Wireless Data Acquisition Gateway, 3) Mission critical facility Three Dimension Temperature Contour Generator, and 4) An Adaptive Automatic CRAC Master Control Method.
Owner:ARCHIMEDES CONTROLS CORP
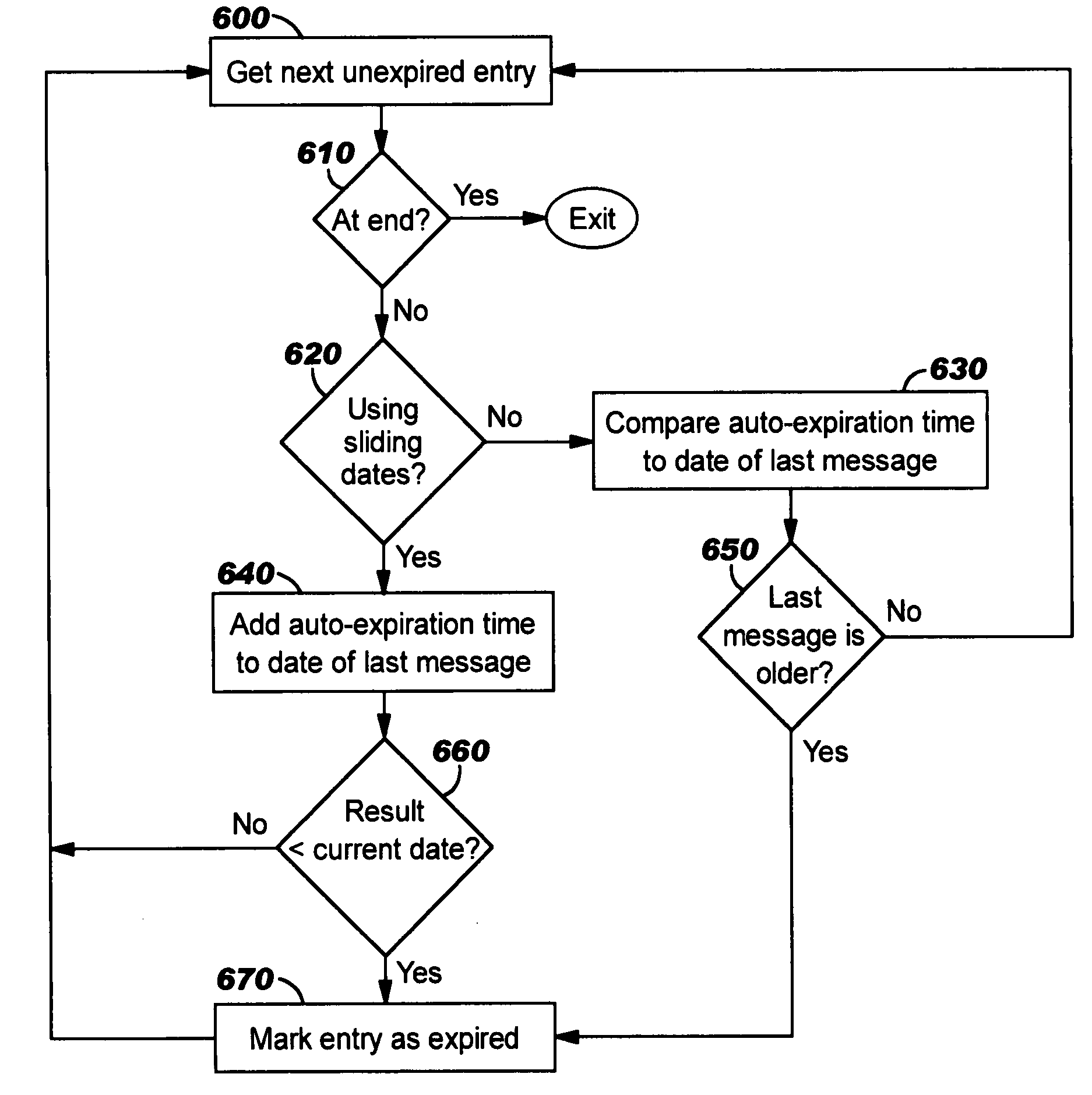
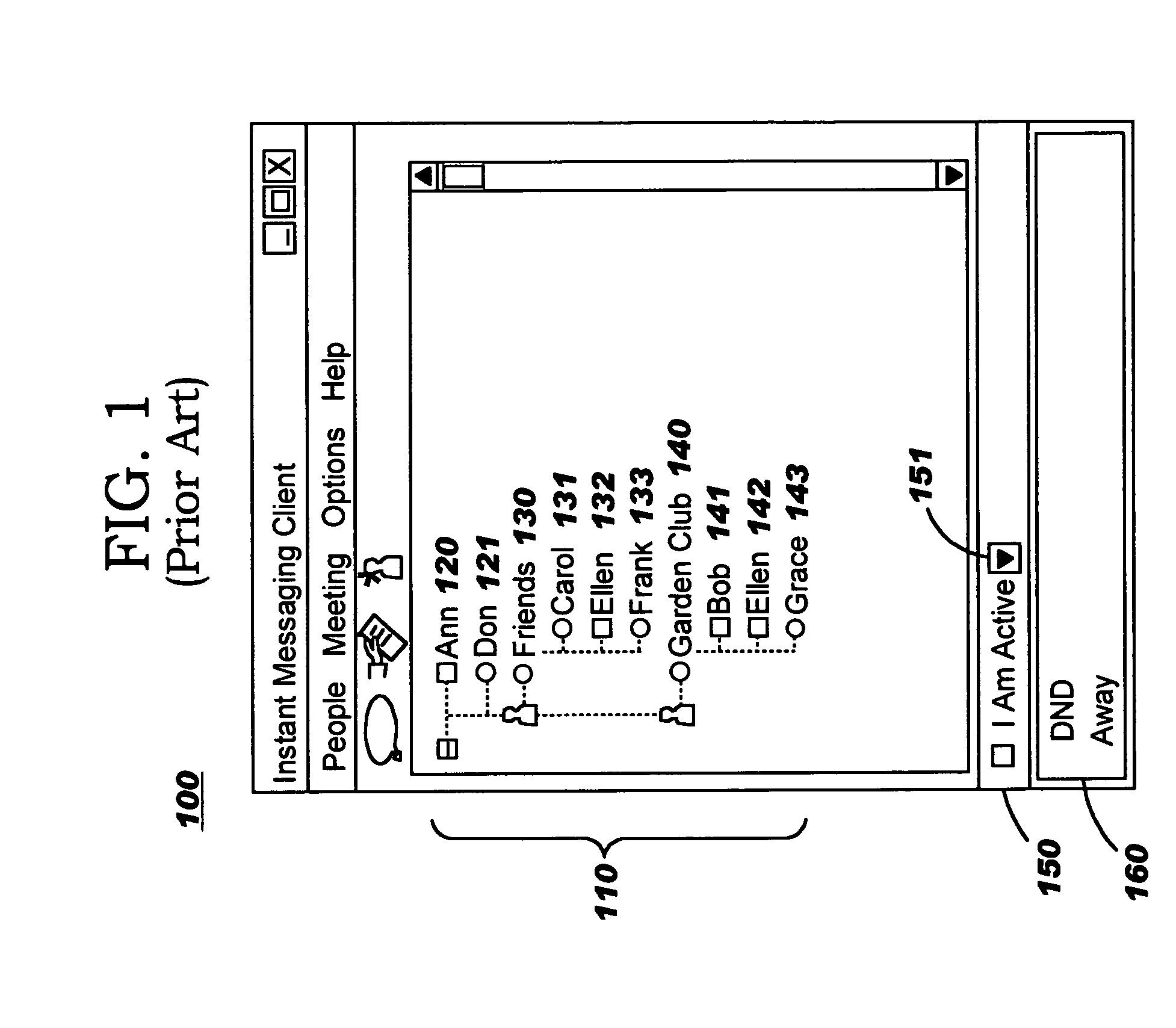
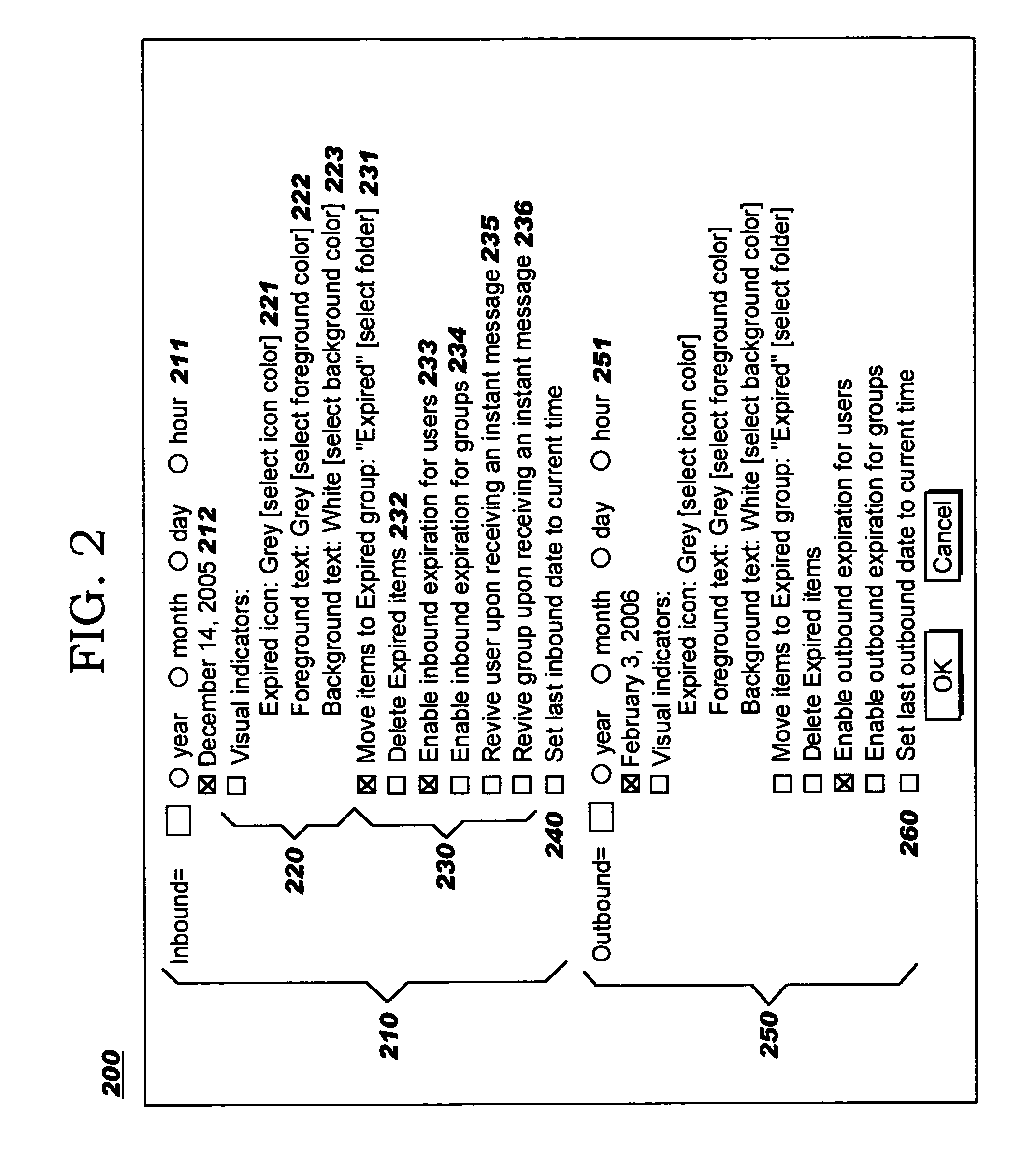
Instant message user management
InactiveUS20050071435A1Easy to manageImprove efficiencyMultiple digital computer combinationsData switching networksMessage passingUser management
Techniques are disclosed for improving management of user information in instant messaging systems. Expiration criteria are defined, whereby one or more users or user groups may be considered as having “expired” from consideration by instant messaging functions such as presence determination. In particular, instant messaging activity is preferably used as an expiration criterion. Absence of inbound or outbound messages for a specified amount of time (or since a particular date / time) can therefore be used as a trigger for treating a user or group of users as expired. As a result, efficiency of an instant messaging system is improved by omitting the expired users and groups from subsequent management operations. Optionally, an expired user or group may be revived upon occurrence of certain events (such as a newly-arriving instant message from, or a change in presence status of, the user or group). “On-demand” expiration and revival are preferably provided as well.
Owner:IBM CORP
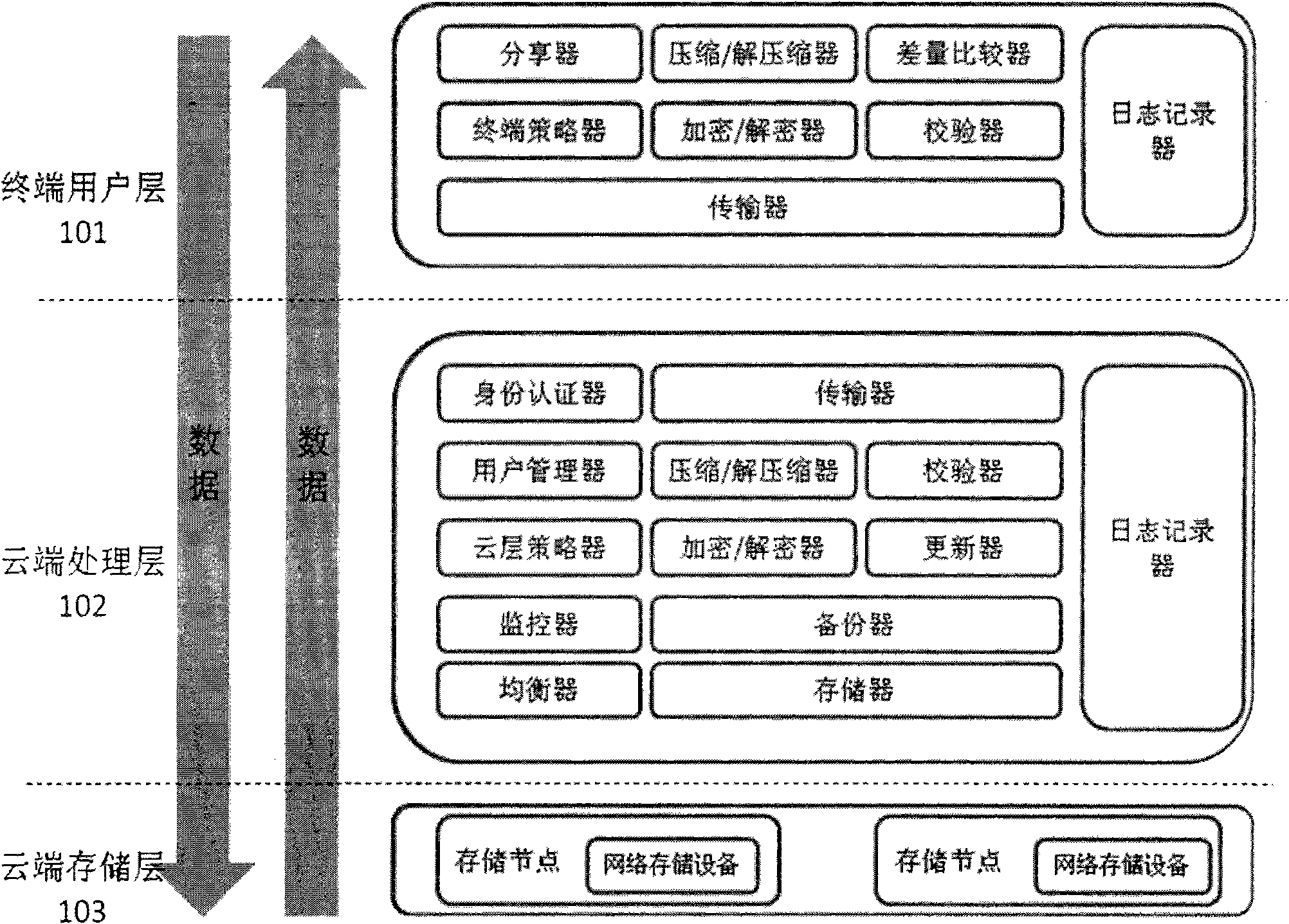
Efficient and safe data cloud storage system implementation method and device
The invention, which relates to the cloud storage field, provides a data cloud storage system that is composed of a plurality of servers and a plurality of data storage equipment. The method is characterized in that: an identity authentication mechanism and flexible operation authority setting are employed in cloud storage; each verification is carried out on data after each network transmission of the data; the network transmission is carried out after data compression; data in cloud are stored after encryption; backup is carried out on the data in cloud storage; the data that have been uploaded to the cloud storage can be updated only by uploading difference information; automatic load balancing is carried out to better utilize an idle processor and a network memory in cloud; both a user and an administrator can customize a strategy conveniently; and an administrator can monitor a serving state of the cloud storage. A cloud storage system that utilizes the technical scheme of the method enables security, integrity, availability of data storage and adaptive capability of the system to be improved; meanwhile, an operational efficiency and controllability of the system are also enhanced.
Owner:程旭
Managing objects and sharing information among communities
InactiveUS20050022132A1Much good performanceShorten the timeDigital computer detailsUnstructured textual data retrievalCommunity settingEngineering
A method for managing objects for users including providing a set of attributes and a set of containers each having attributes from the set. The method further provides a user interface for dynamically assigning attributes to the objects. The method further provides for selectively displaying, through a user interface, containers and objects in the containers. An object is displayed in a container if a condition is met. The condition is applied to the attributes of the container and the attributes of the object.
Owner:QUADRANT EPP +1
PDA workspace interface using application icons for downloading remote user file
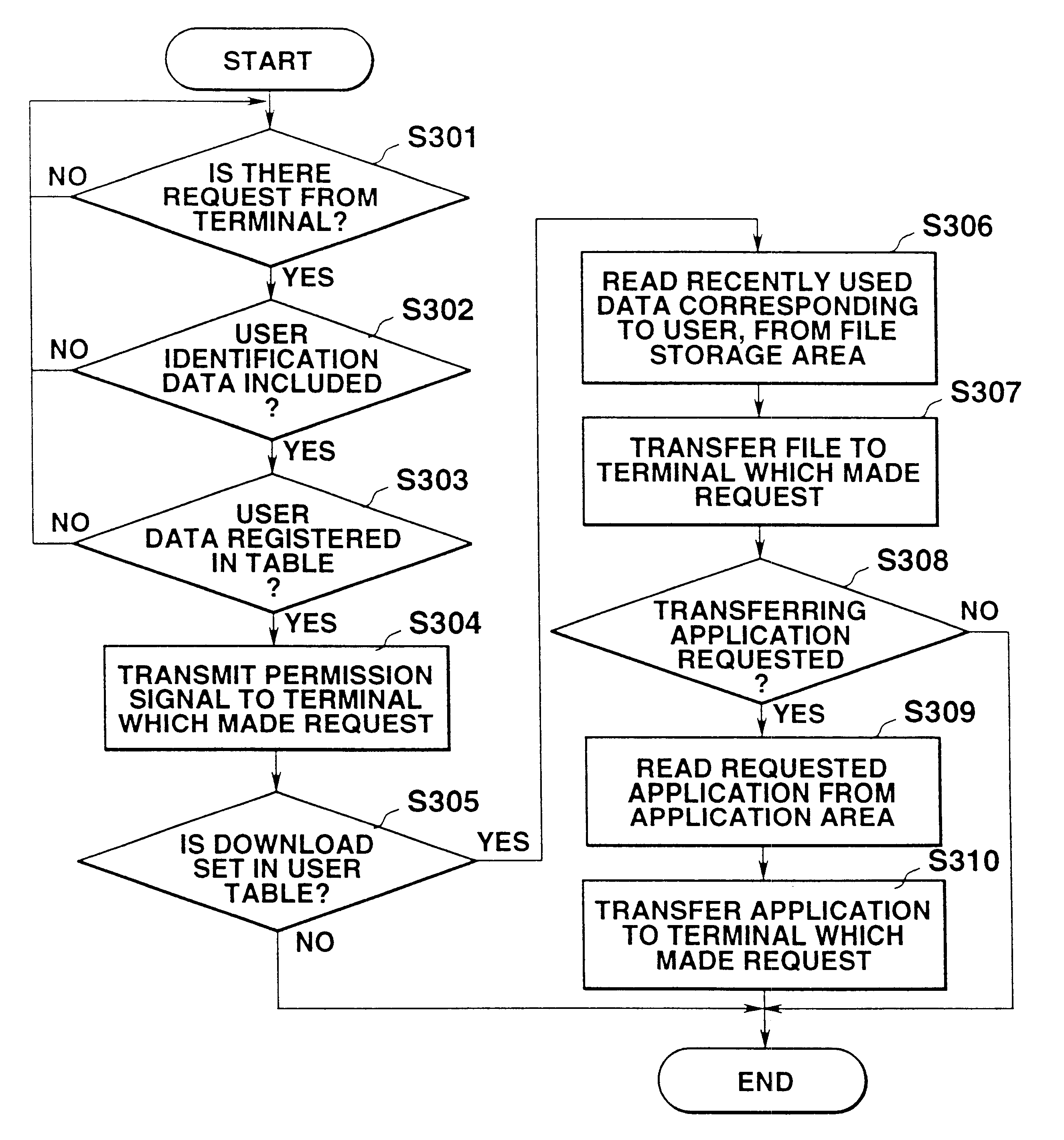
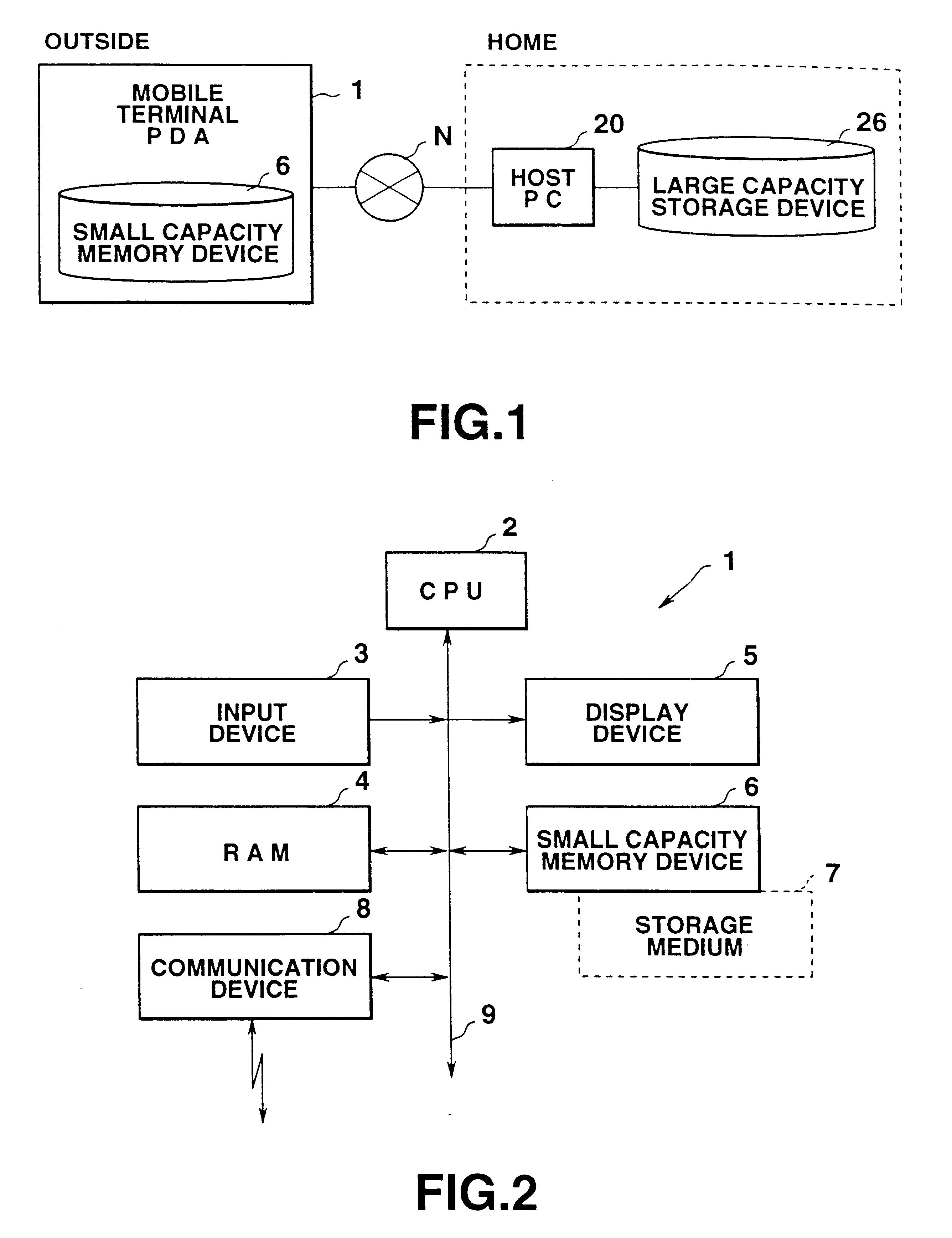
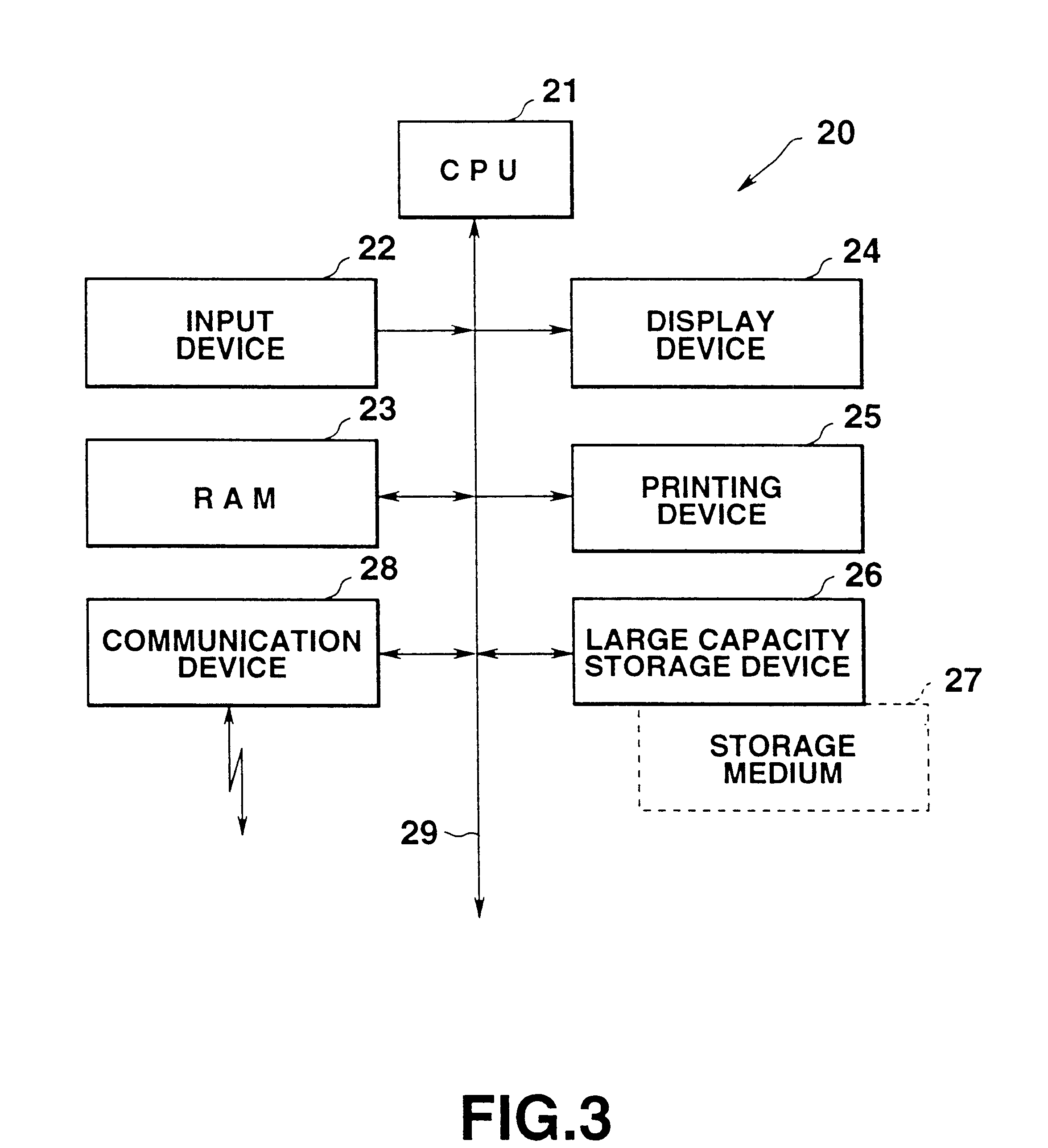
InactiveUS6493743B2Digital data information retrievalMultiple digital computer combinationsNetwork terminationComputer hardware
In the network terminal device (200), the computer main body (202) transmits a download request containing user identification data to the host device (300) via a network (100) at the time of starting the terminal device (200). In the host device (300), of various types of files corresponding to the user identification data, a designated file which is set by the user table in advance, is selected from the user management file which stores various types of files corresponding to each and individual user, in reply to the download request, and the designated file is transferred to the network terminal device (200) which made the request. The designated file is a recently used data file.
Owner:HANGER SOLUTIONS LLC
Security cloud storage system based on increment synchronization
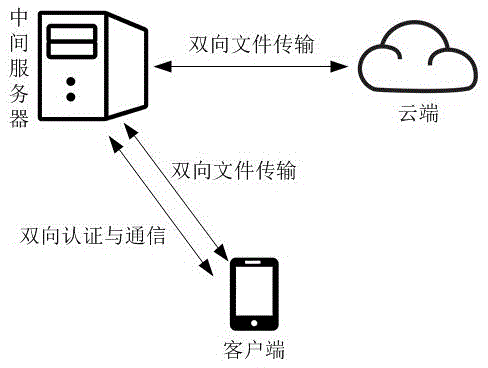
InactiveCN104023085AImprove user experiencePrevent leakageTransmissionTransmission protocolFile synchronization
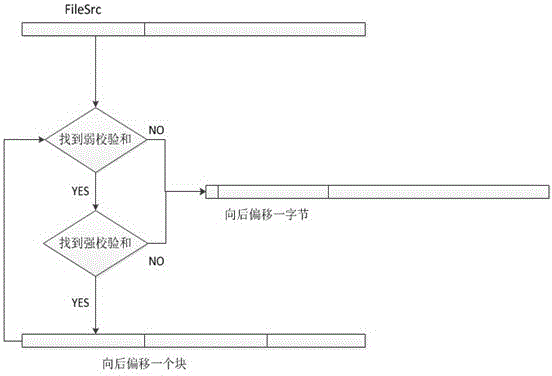
The invention discloses a security cloud storage system based on increment synchronization. A three-tier architecture of client-intermediate server-private cloud terminal is adopted, and data security is guaranteed by multiple security protection technology. After being blocked and encrypted, a user file is transmitted to a cloud terminal through an SSL (security socket layer) security transmission protocol; after finishing the work of user management and key management, the intermediate server terminal adopts a mutual authentication mechanism and an access control mechanism to realize the safe data share so as to completely prevent original data from leaking from the server terminal; the binding of the file and a mobile device is realized at a client, the specific file can be only opened on a specific device, and even though the file is leaked by an insider, a leaking device can be traced; moreover, the unique increment synchronization technology is realized, and the file can be synchronized by only synchronizing modified file blocks, so that the flow consumption in the file transmission process is reduced, the transmission efficiency is improved, the system usability is enhanced, and user experience is promoted.
Owner:WUHAN UNIV
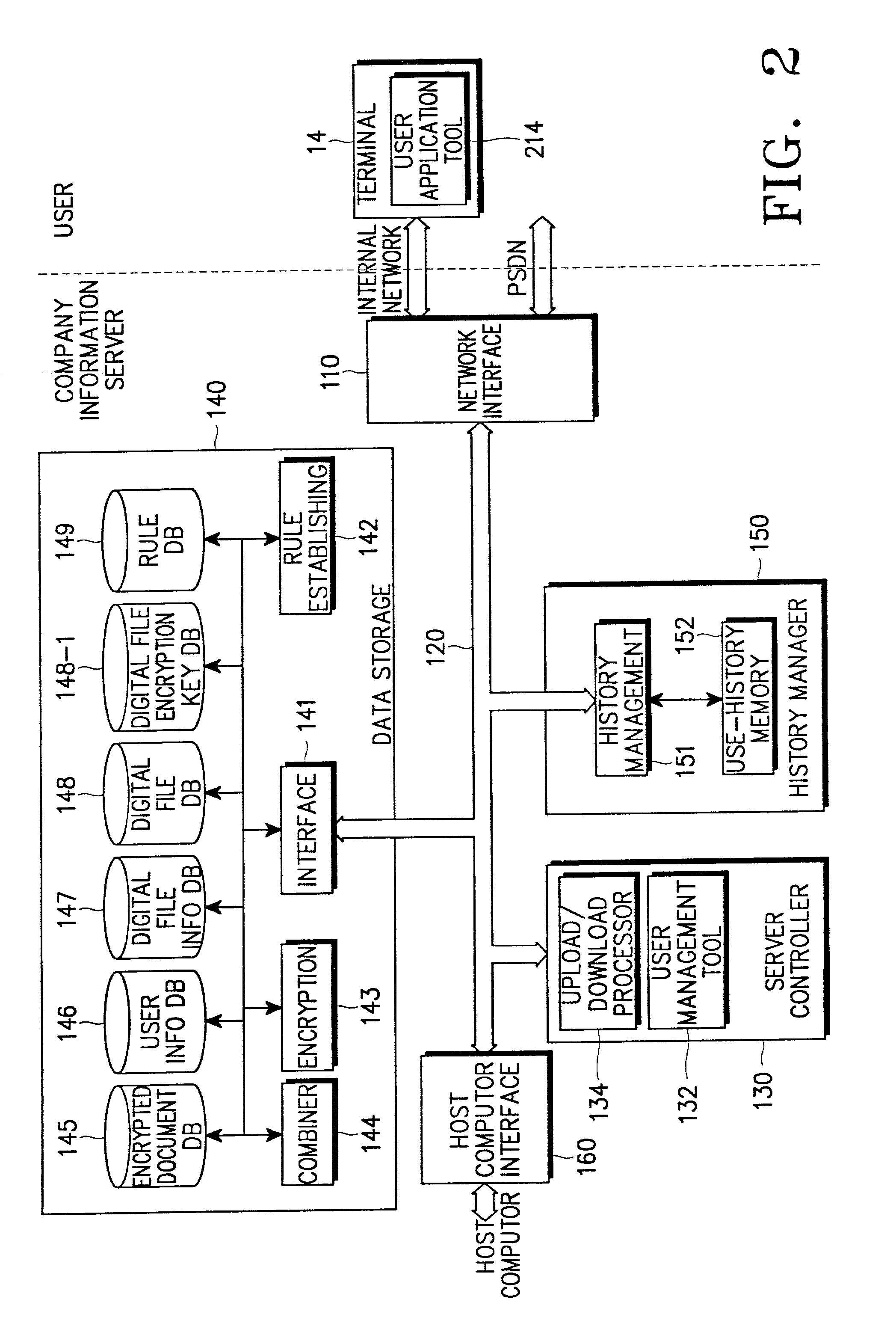
Method for securing digital information and system therefor
InactiveUS20030023559A1Key distribution for secure communicationData taking preventionUser authenticationInformation security
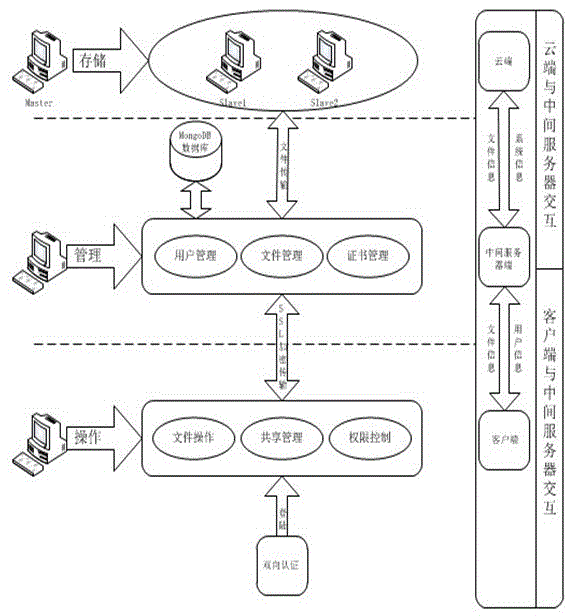
A digital information security system is disclosed. A user application tool installed in a user terminal, creates a unique user key using unique system information of the user terminal. A data storage unit stores user information and digital information. A user management tool installed in a server, receives the unique user key created by the user application tool, stores the received unique user key in the data storage unit as part of the user information, and compares, during user authentication, the stored unique user key with a unique user key provided from the user application tool of a user currently being subjected to authentication.
Owner:MARKANY
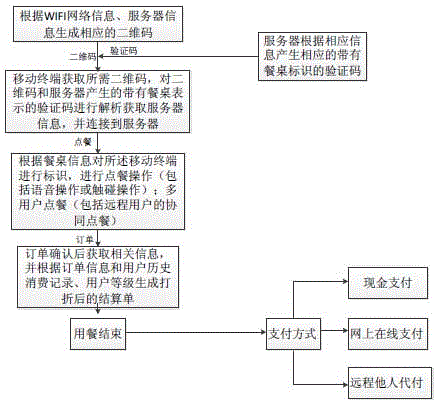
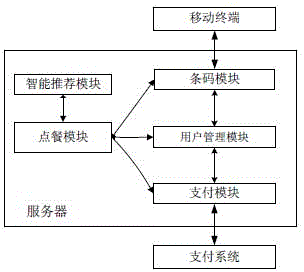
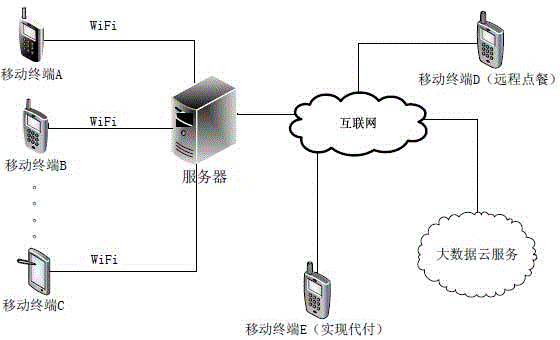
Two-dimensional code-based cooperative intelligent ordering method and system
InactiveCN104978697AOptimize dish informationAvoid the situation of "one dish is fried many times"Data processing applicationsTablet computerPayment
The invention discloses a two-dimensional code-based cooperative intelligent ordering method and system. The system comprises a mobile terminal with a two-dimensional code scanning function and a server supporting ordering and payment functions. The mobile terminal can be an intelligent mobile phone and a tablet computer. The server is used for processing ordering information, and mainly comprises a barcode module, an ordering module, a user management module, an intelligent recommendation module and a payment module; the barcode module mainly comprises two-dimensional code and verification code generation and verification functions; the ordering module is used for supporting ordering (including remote ordering) of multiple persons and voice ordering; the user management module is mainly used for automatically identifying user identities and storing user consumption information; the intelligent recommendation module is mainly used for providing big data cloud services for merchants, digging user consumption habits, tastes and the like according to user consumption records and providing personalized dish and service recommendations for users; and the payment module is mainly used for supporting transaction of cash, electronic payment (including remote payment for another) and the like.
Owner:SOUTHWEST PETROLEUM UNIV
System and method for managing electronic data transfer applications
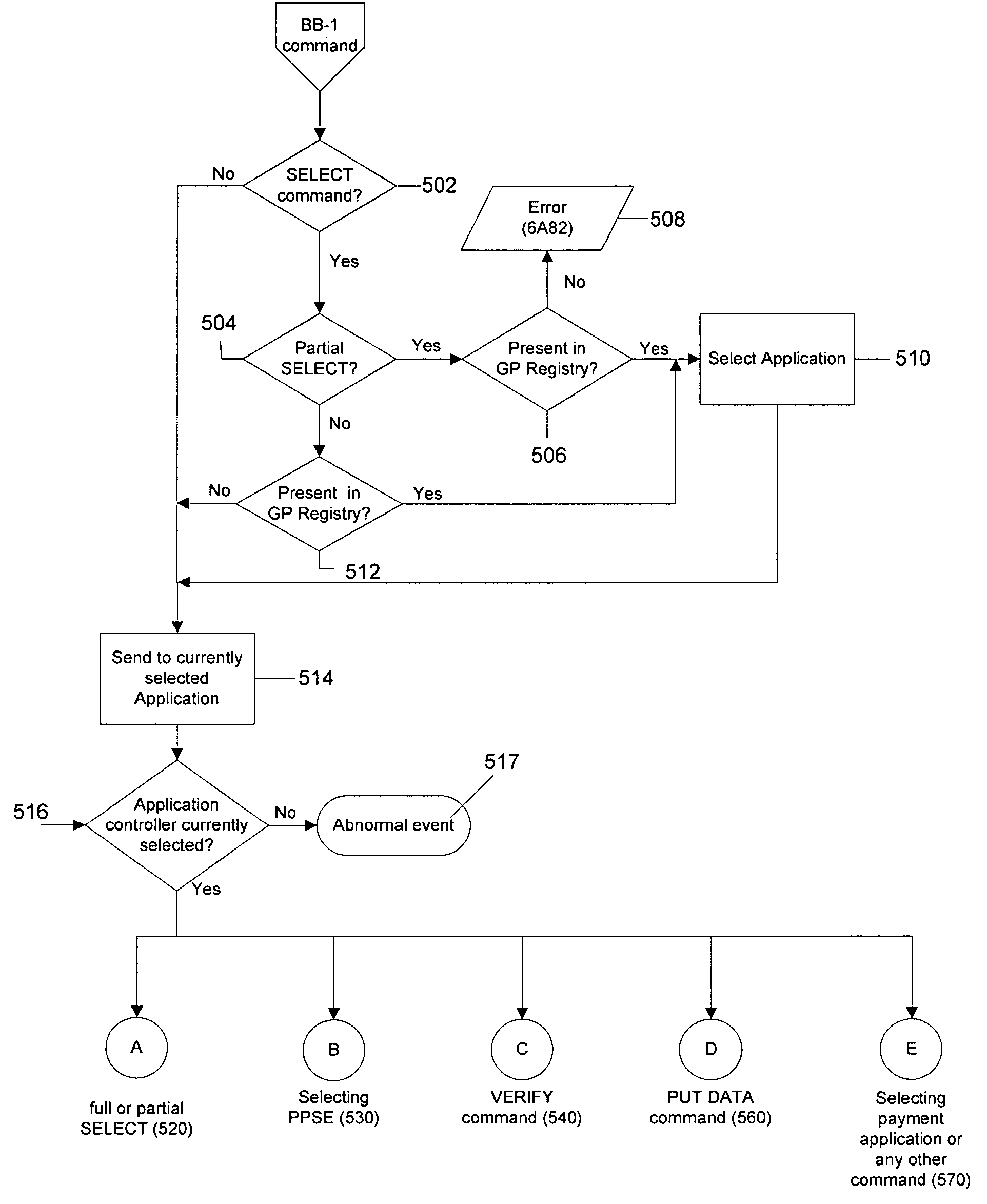
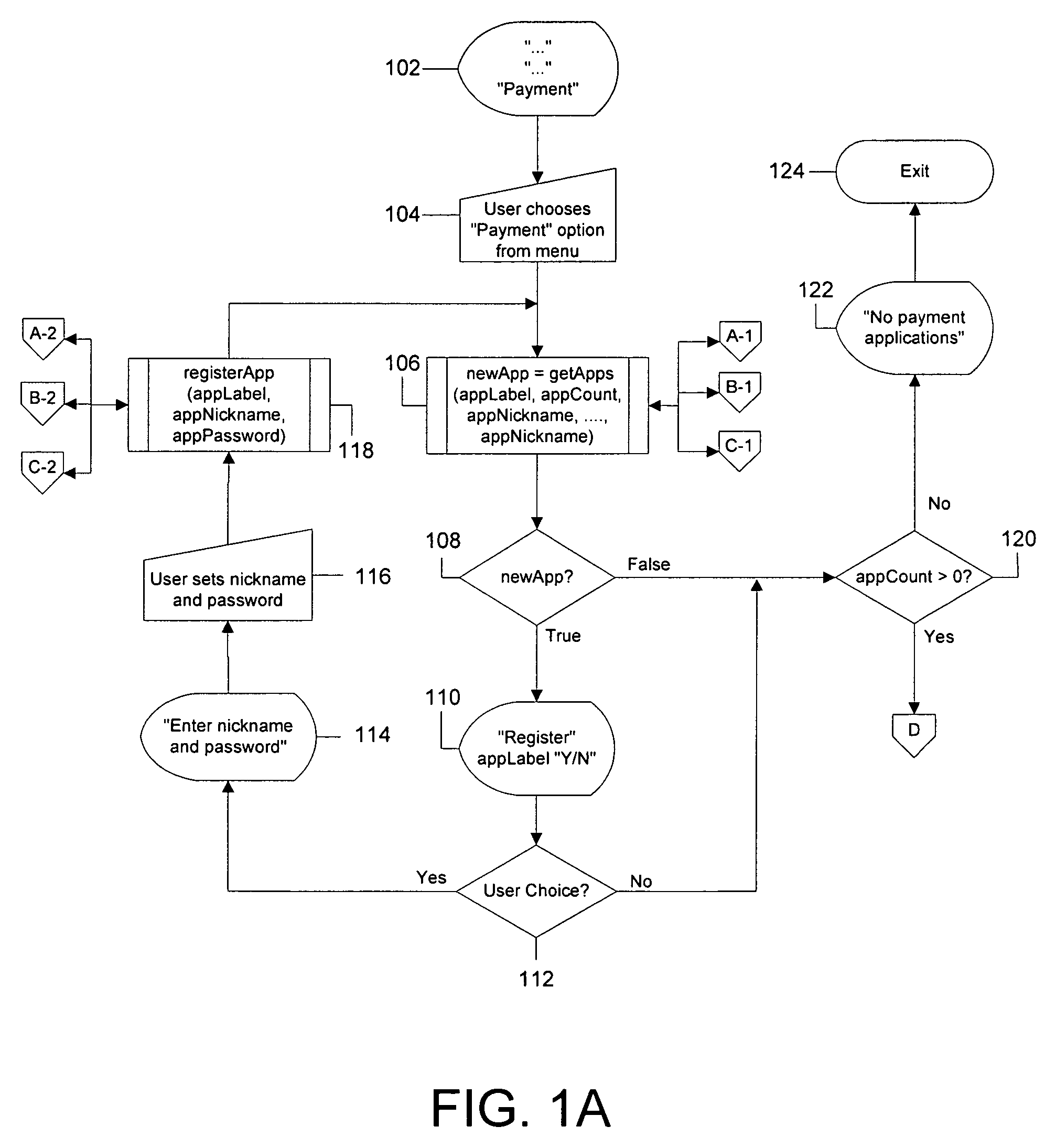
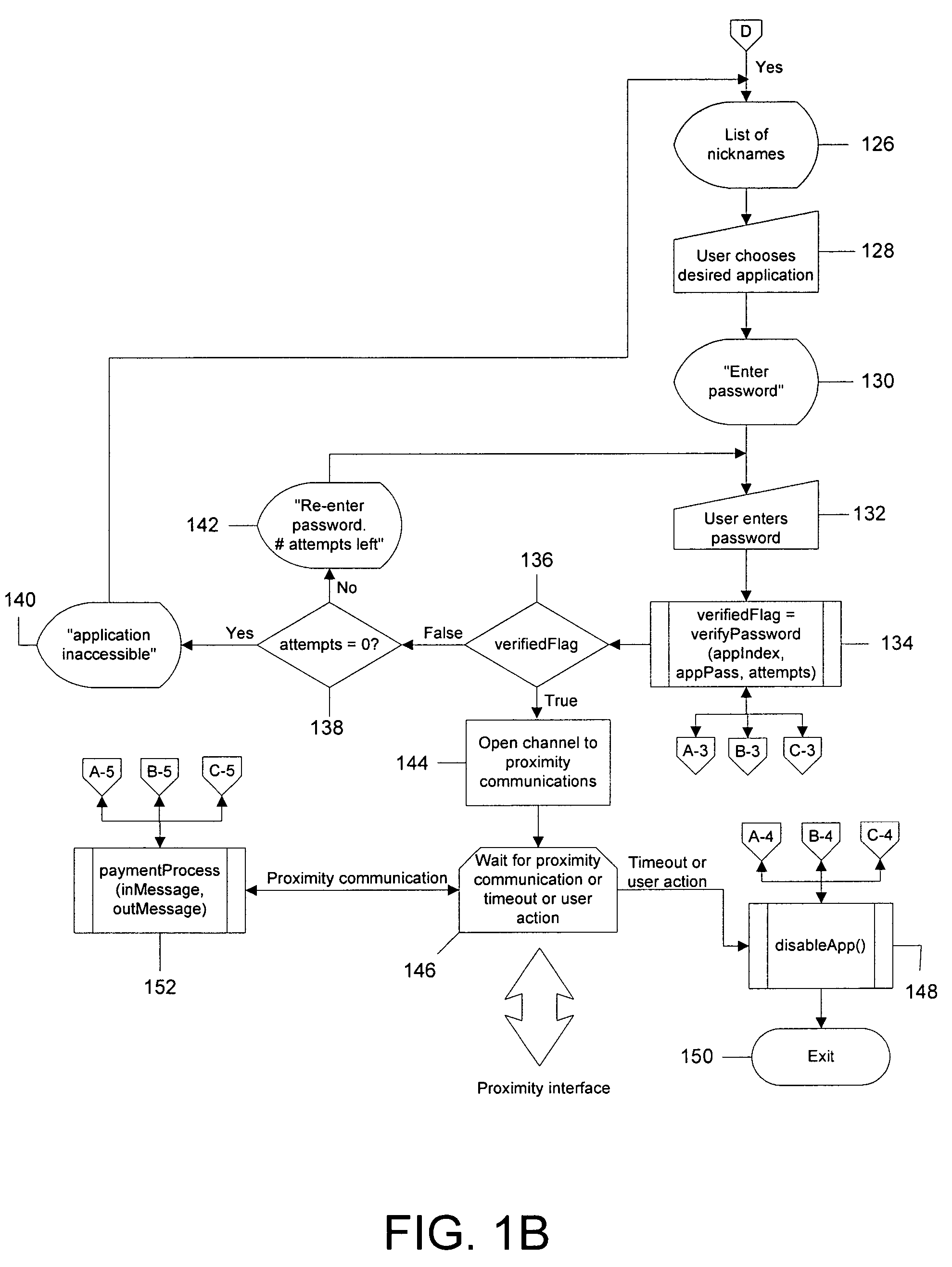
A system and method for managing one or more applications deployed on a mobile electronic device, such as a cellular phone, are disclosed. The system and method enable the user of a mobile electronic device to select one of a plurality of applications deployed on the mobile electronic device for use in a transaction and to authenticate himself or herself prior to initiating the transaction. The transaction may occur via a wireless interface and / or a contact-based interface. In addition, the system and method allow the user to manage applications deployed on a mobile electronic device, including adding new applications, designating nicknames for the applications and setting security codes for each application.
Owner:VISA INT SERVICE ASSOC
Transformer station three-dimensional real scene simulation system and implementation method
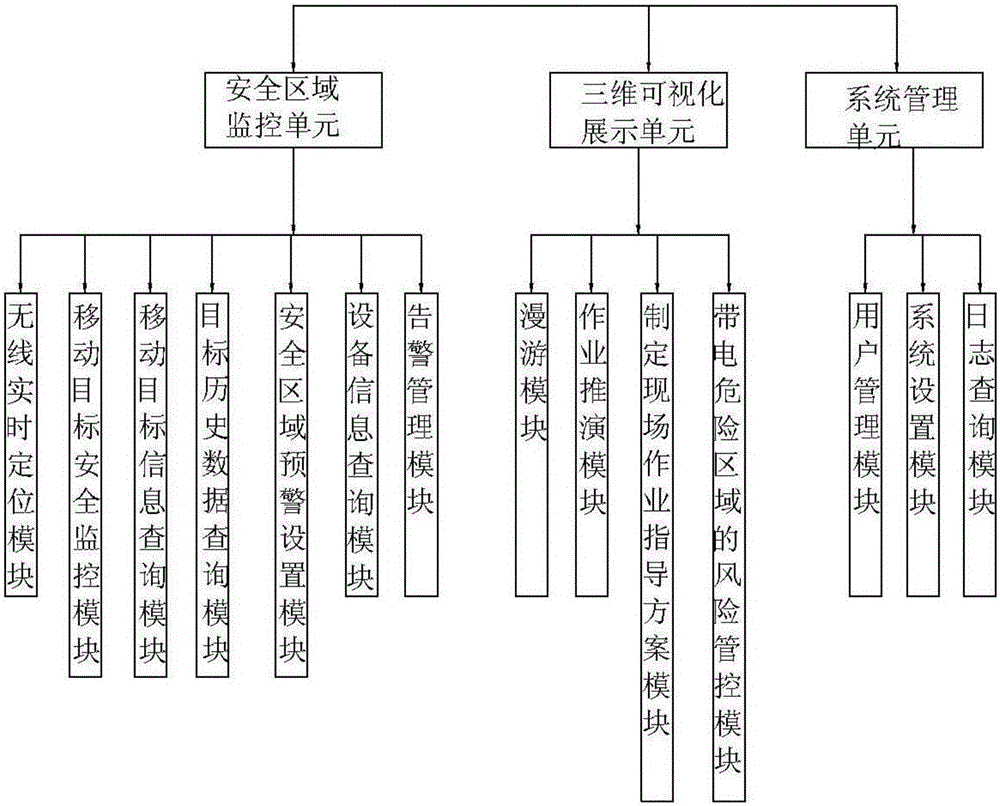
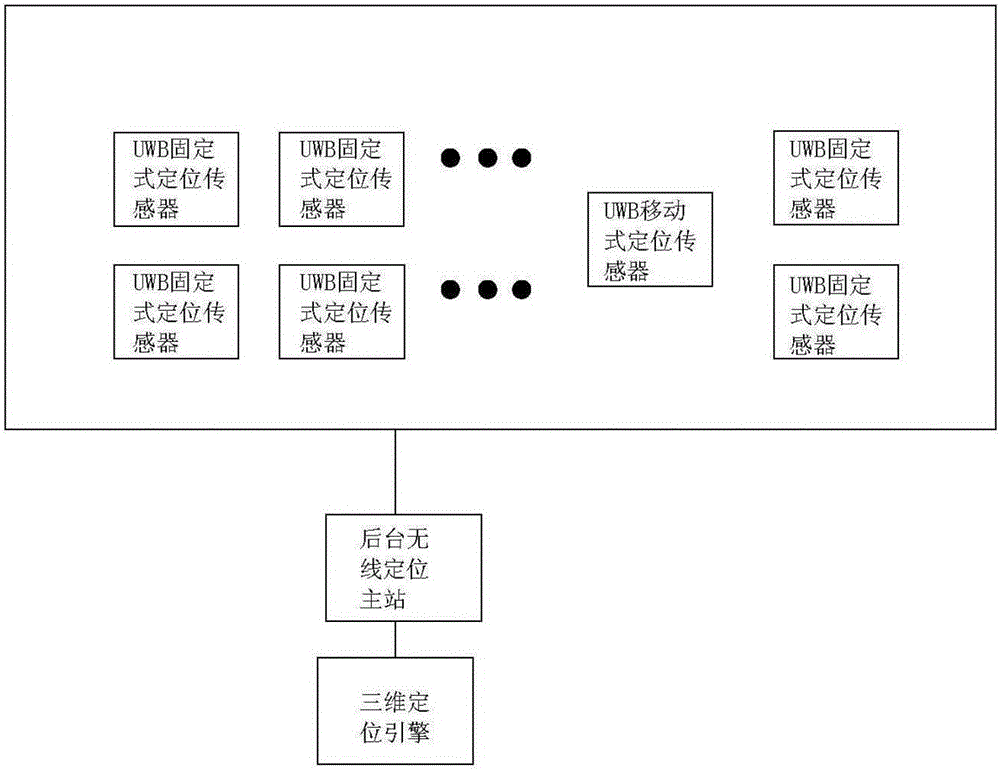
ActiveCN105956232ARealize 3D dynamic displayAvoid missingData processing applicationsDesign optimisation/simulationSystems managementTransformer
The invention relates to a transformer station three-dimensional real scene simulation system and an implementation method. The system comprises a safety region monitoring unit, a three-dimensional visualization display unit, and a system management unit. The safety region monitoring unit comprises a wireless real-time positioning module using a UWB positioning technology, a moving target security monitoring module, a moving target information query module, a target historical data query module, a safety region early warning setting module, an equipment information query module, and an alarm management module. The three-dimensional visualization display unit comprises a roaming module, an operation deduction module, a field operation instruction scheme making module, and a risk management and control module of an electrified dangerous region. The system management unit comprises a user management module, a system setting module, and a log query module. The system realizes functions of daily inspection and maintenance visual management of a transformer station, operating personnel daily inspection and maintenance process real-time tracking and monitoring, security alert alarm and intelligent recording management.
Owner:WUHAN NARI LIABILITY OF STATE GRID ELECTRIC POWER RES INST +1
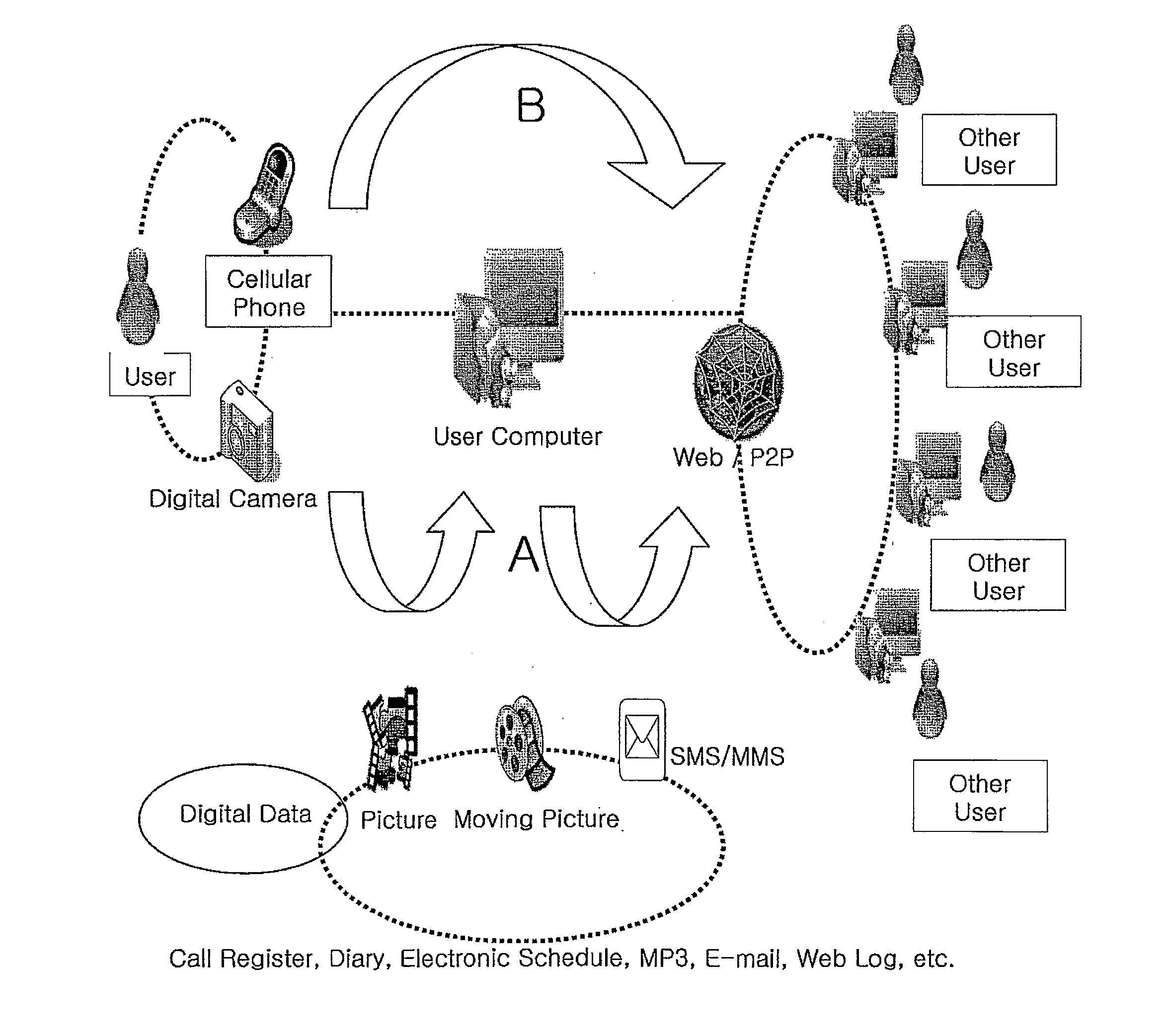
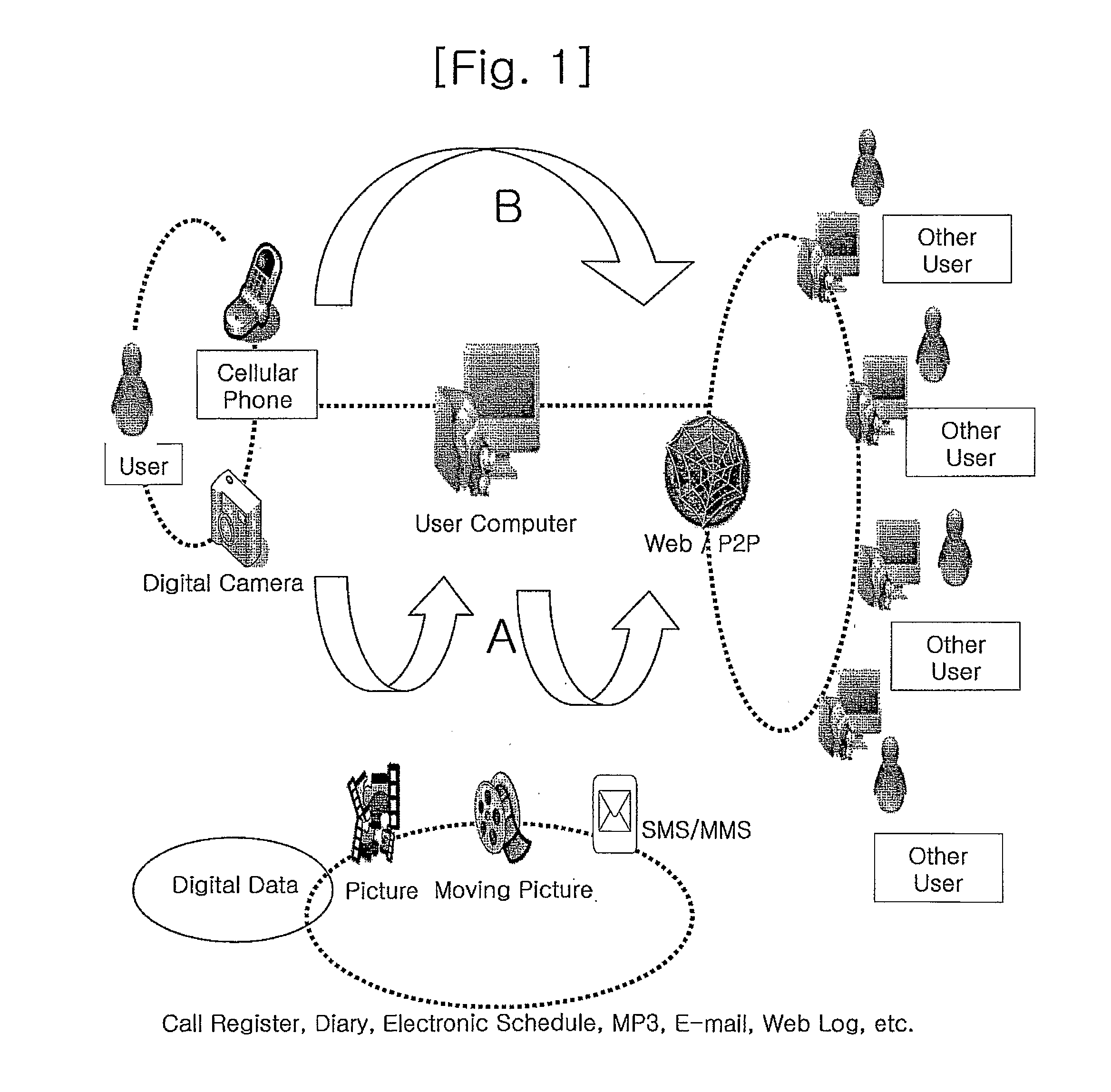
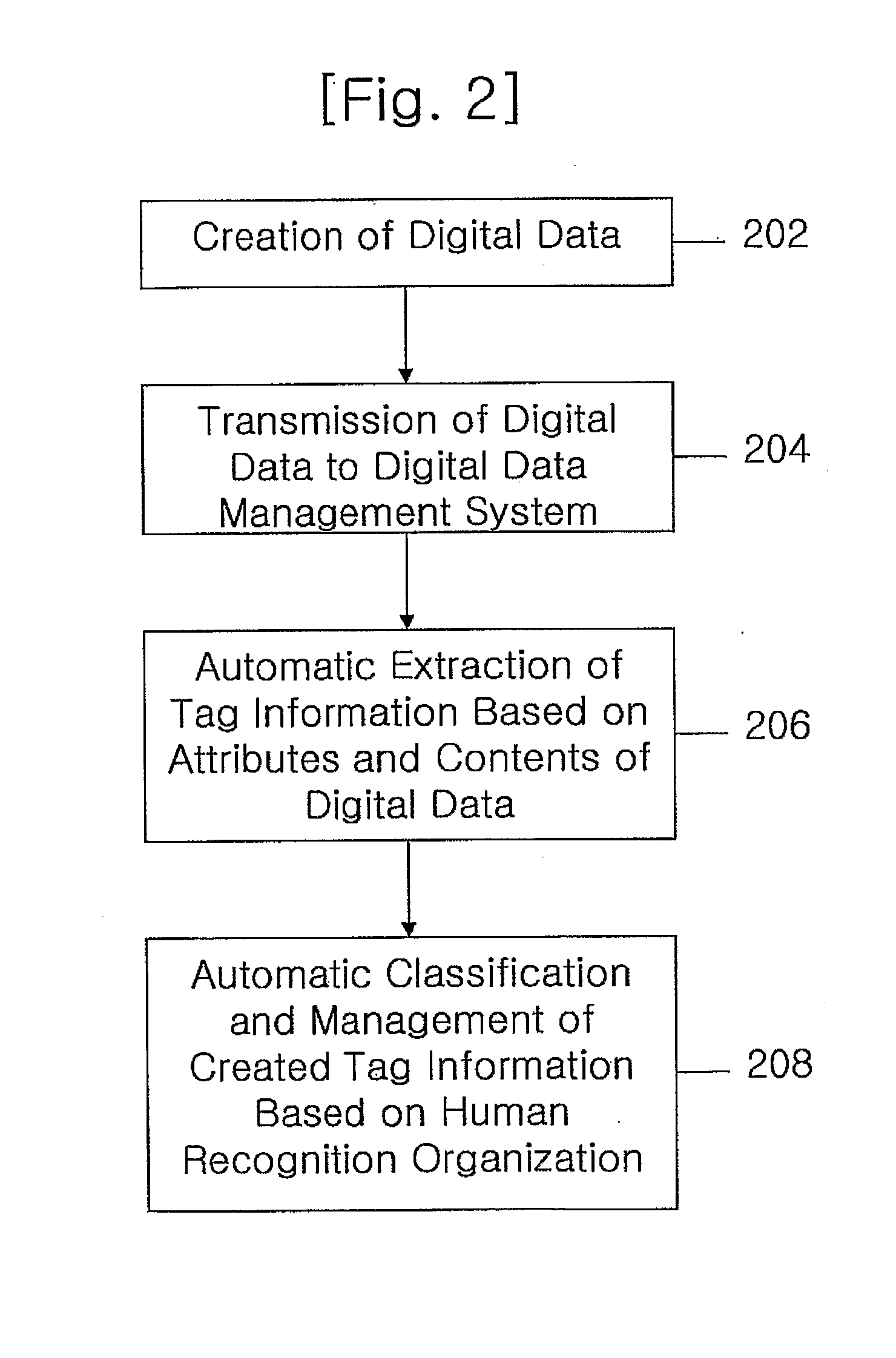
Method and System for Tagging Digital Data
InactiveUS20100232656A1Easy to shareEfficiently provideEqualizing valvesCharacter and pattern recognitionDigital dataTransceiver
A method for attaching a tag to digital data provided from a digital device in a digital data management system includes the steps of: attaching the tag to the digital data automatically according to attributes and contents of the digital data. Moreover, a system for managing digital data produced in a digital device includes: a transceiver for transmitting and receiving the digital data; a database for storing and managing the digital data; and a database engine including a processing unit for automatically extracting a tag from the digital data and then assigning the tag to the digital data. By using the method and the system, a user manages the digital data and shares them with other users. The notable effect is that it provides various tag information in a useful form to the users.
Owner:INTEL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com