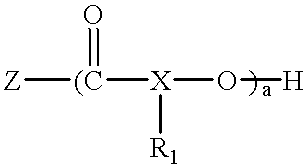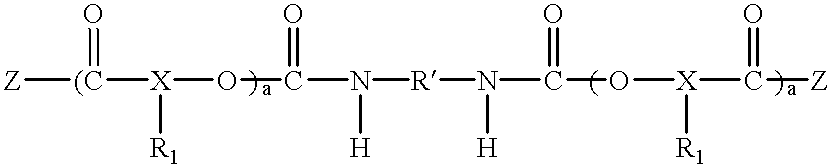Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35948results about How to "Easy to manage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
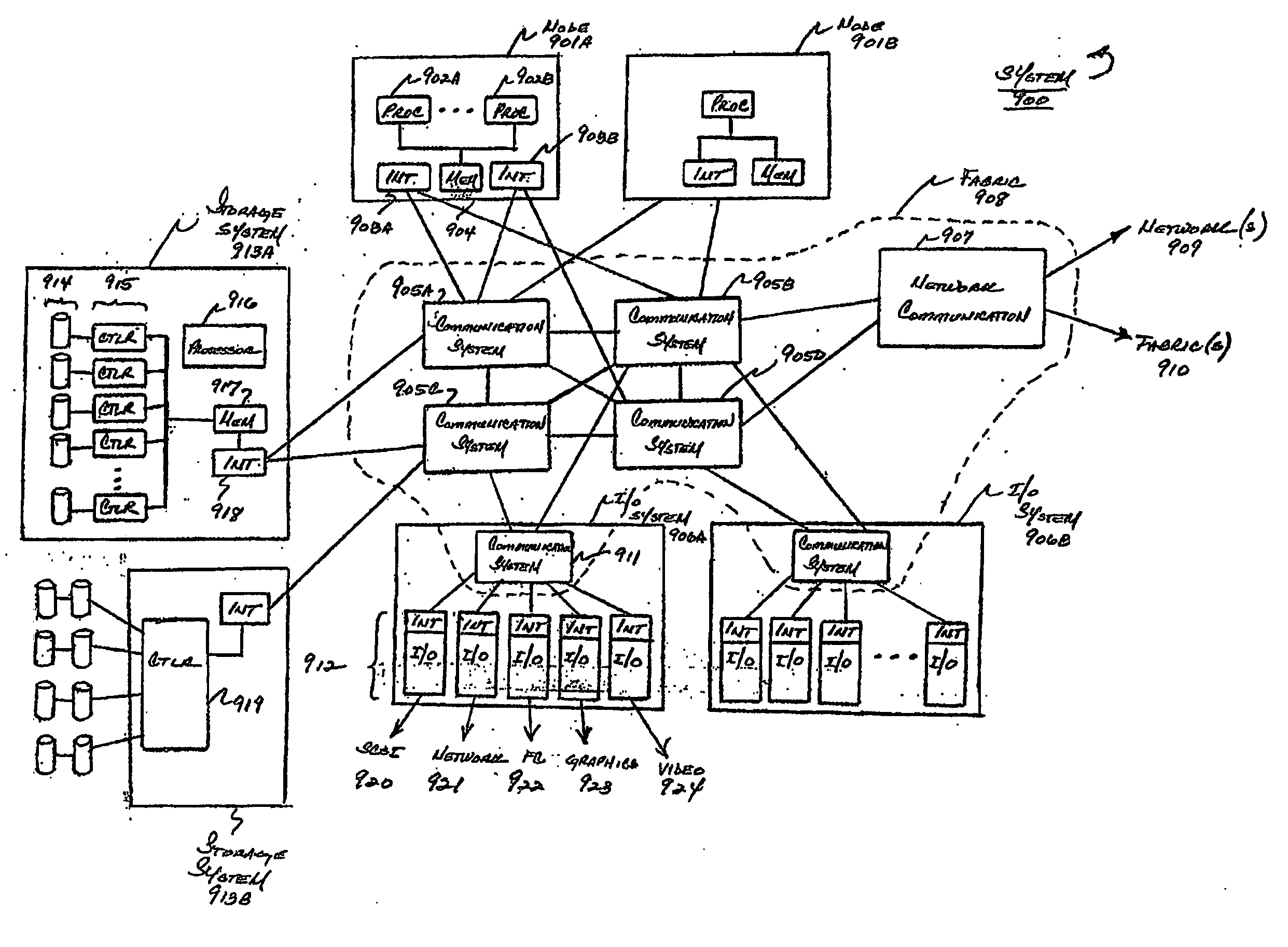
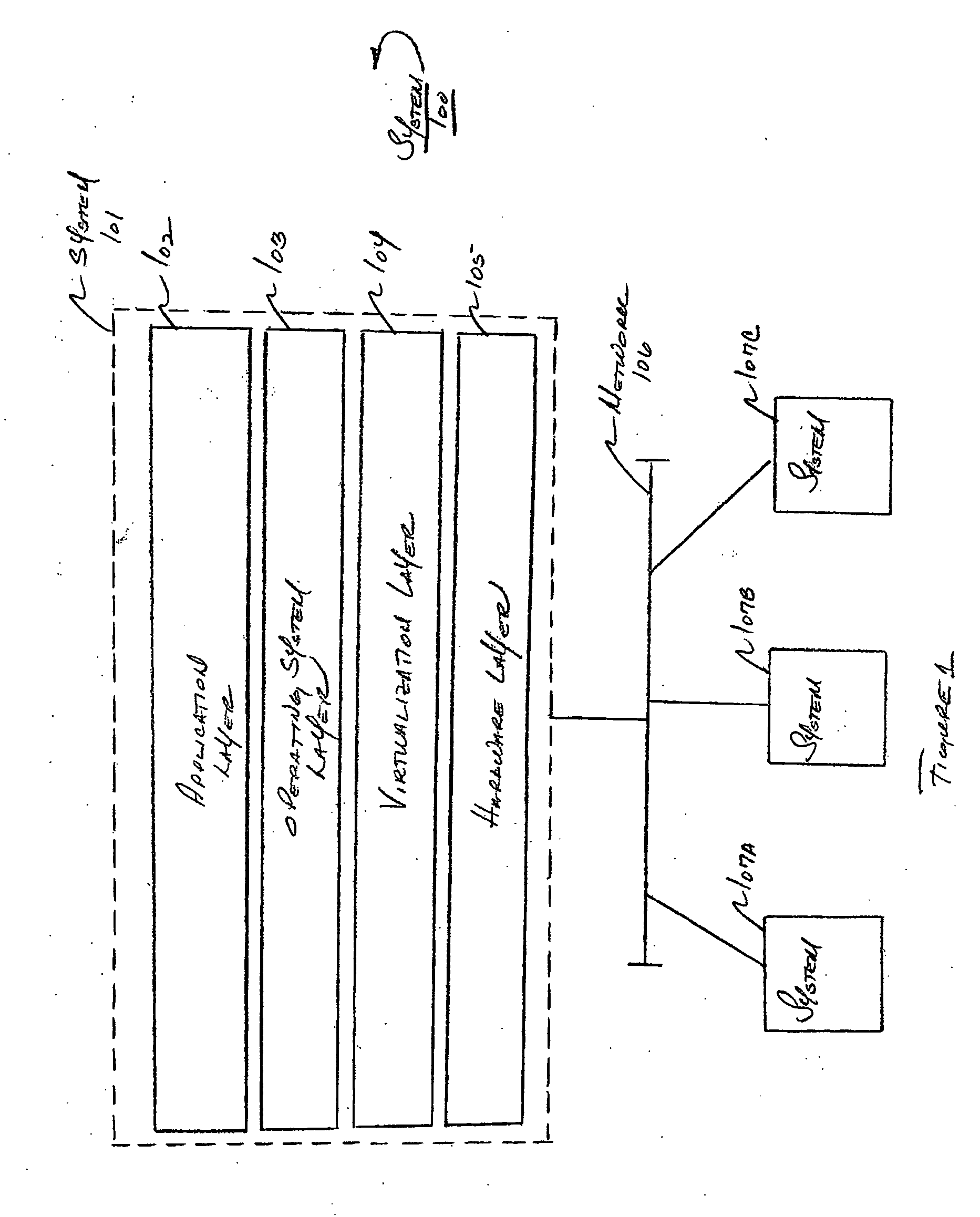
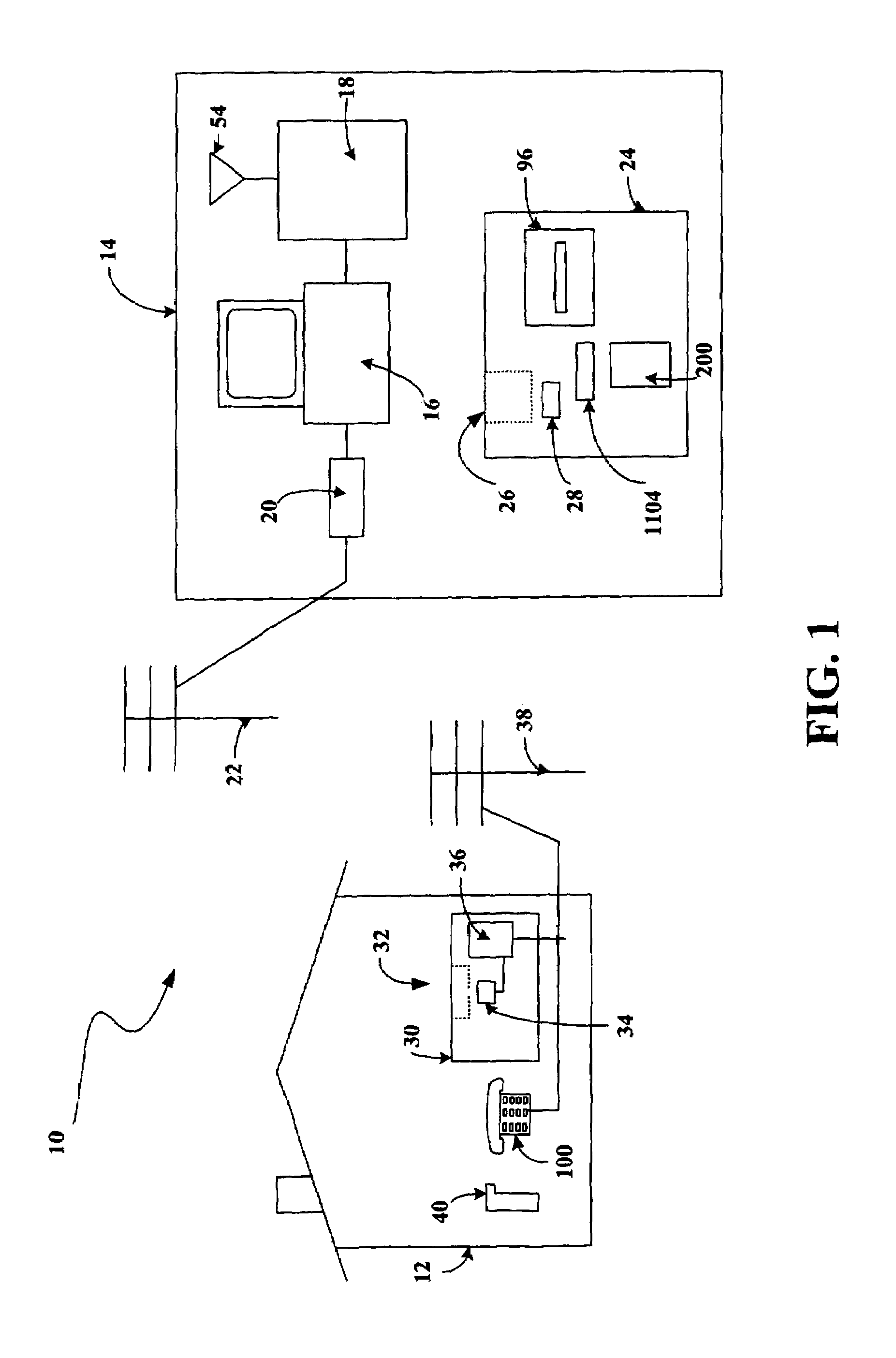
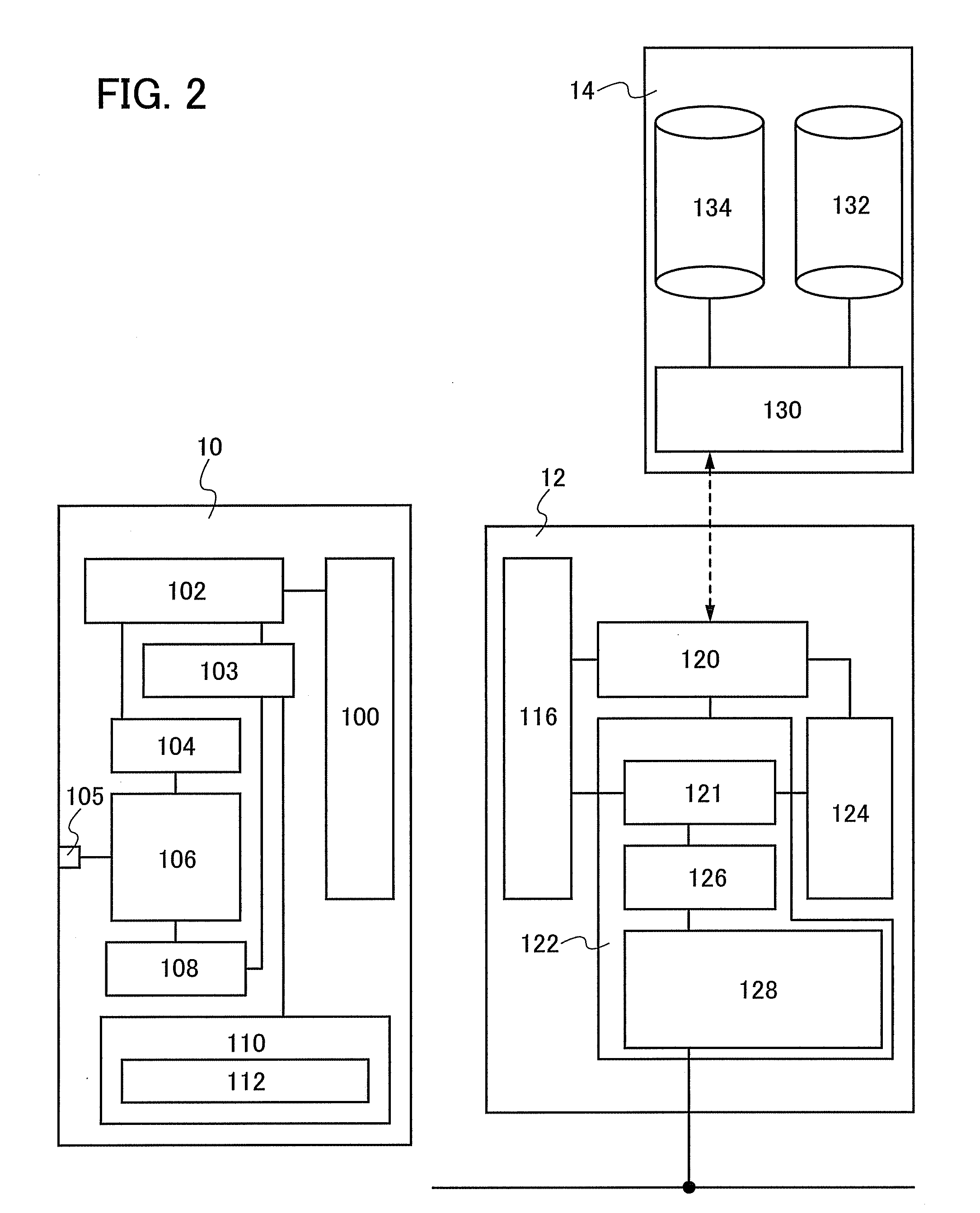
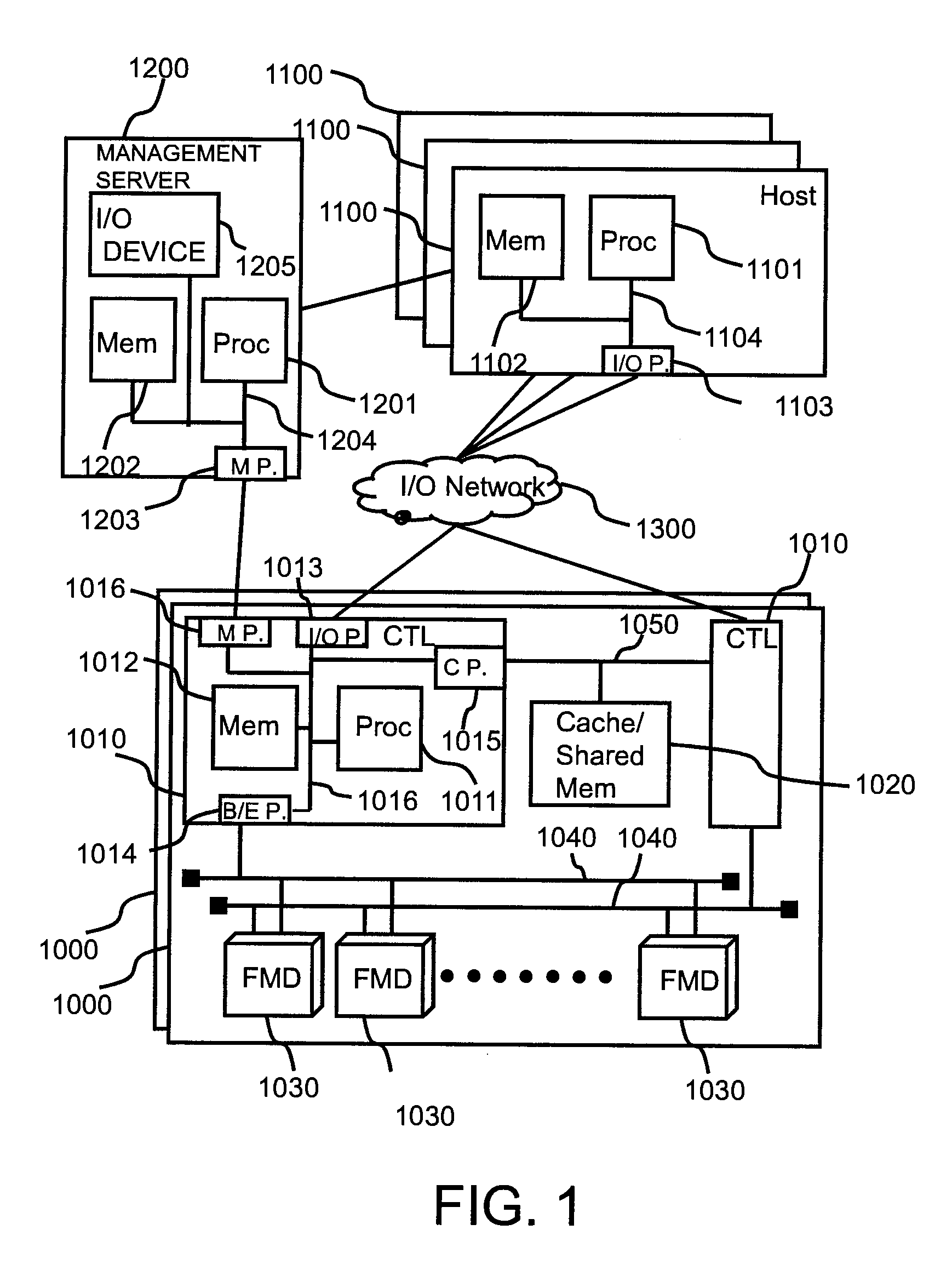
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
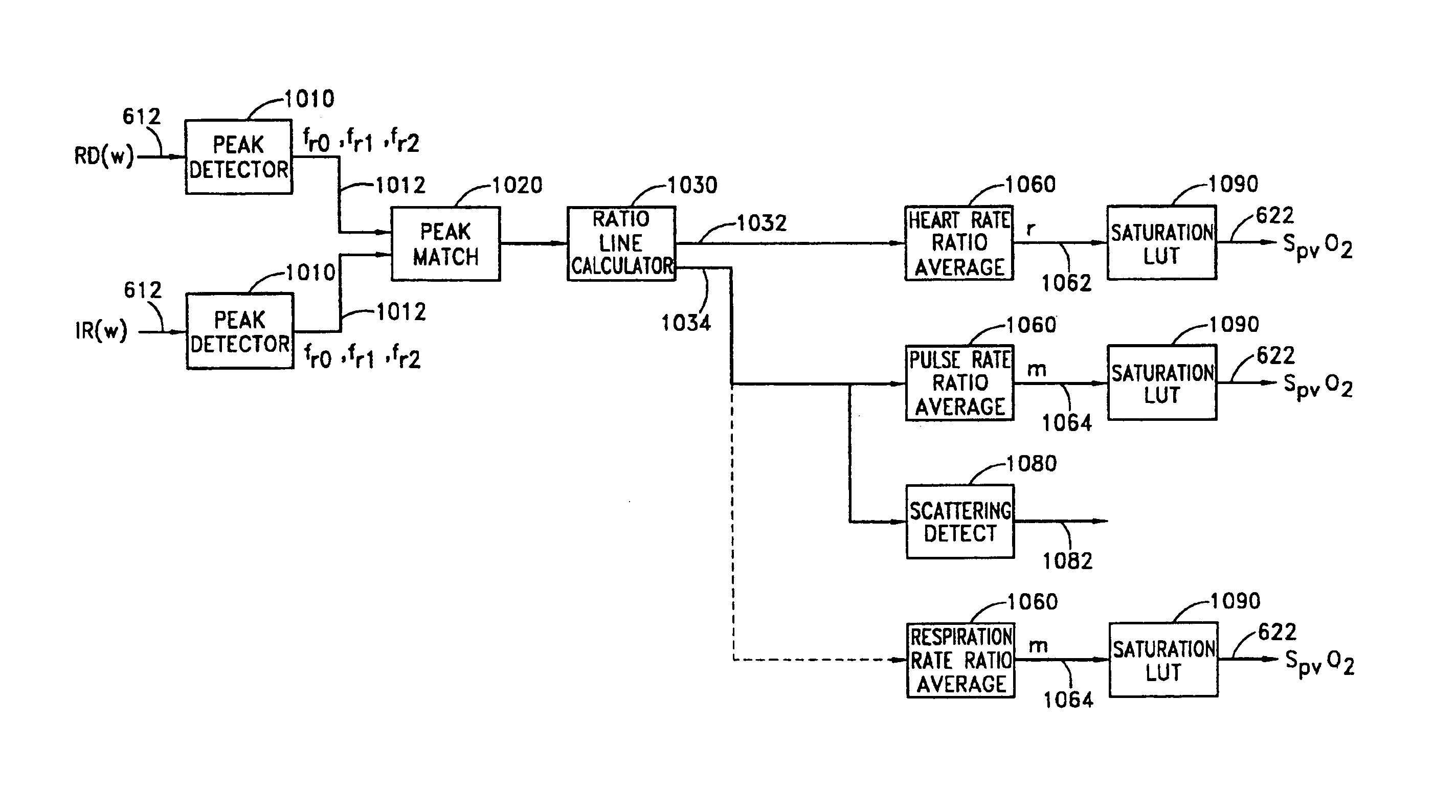
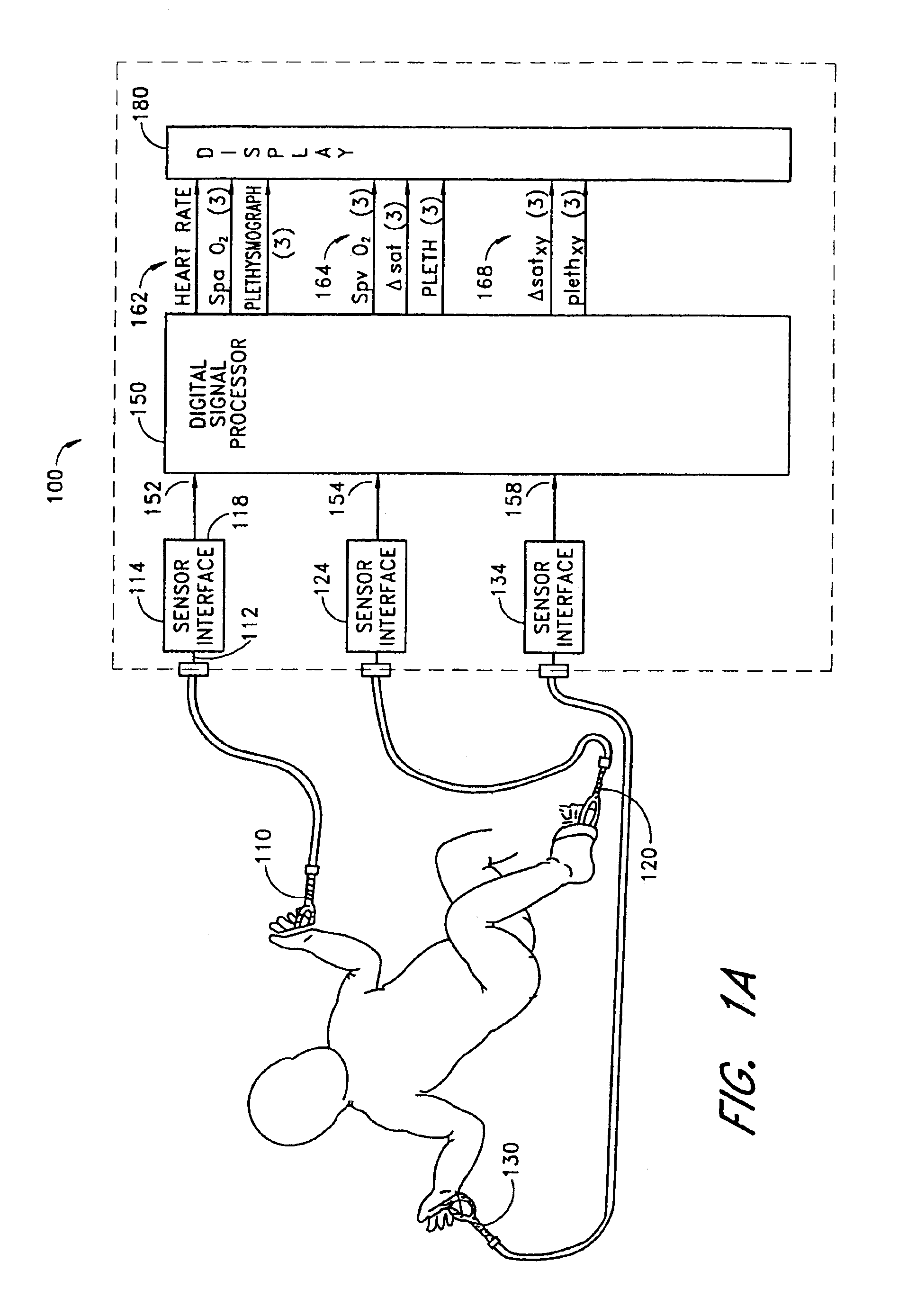
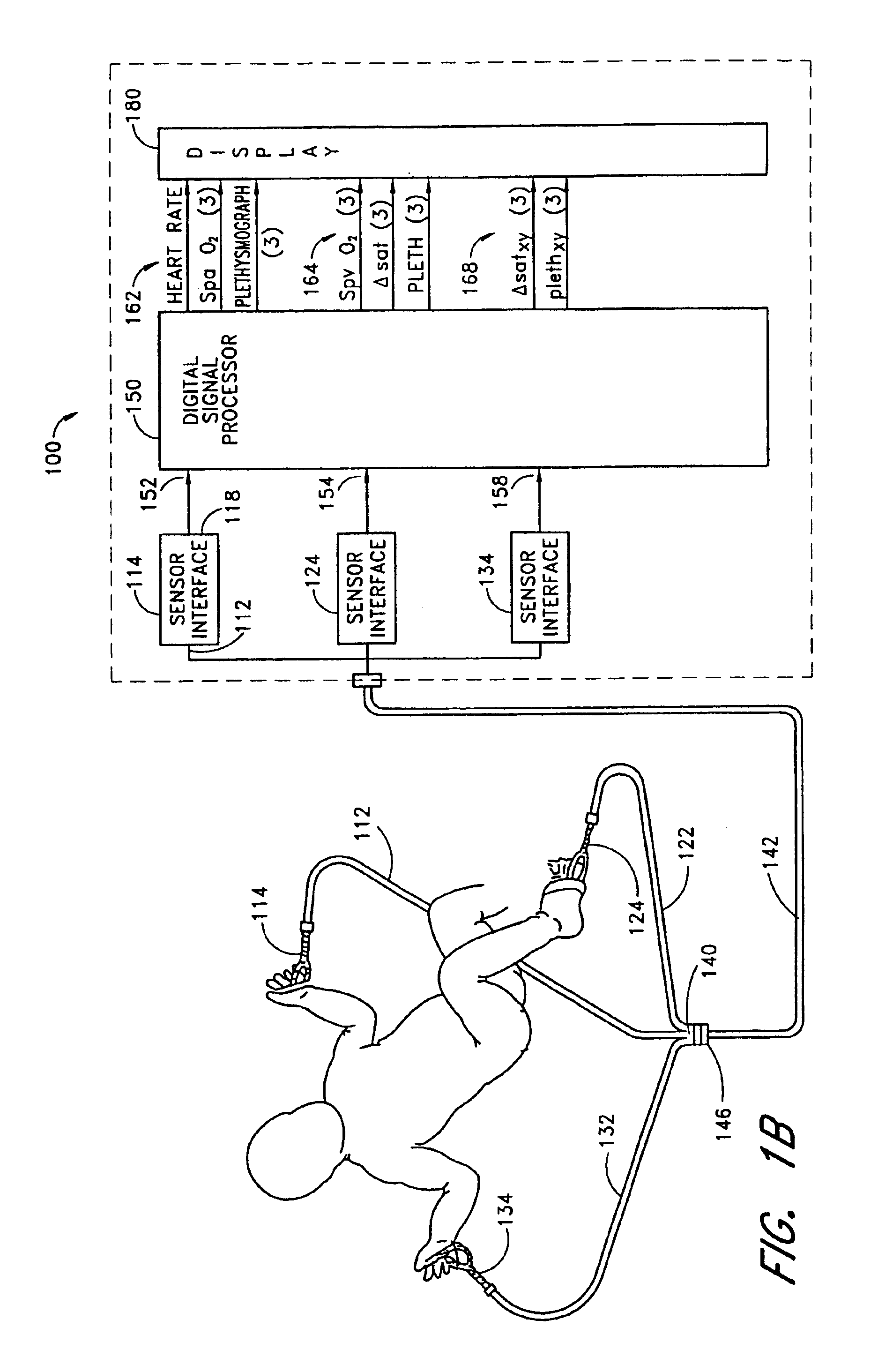
Stereo pulse oximeter
InactiveUS6898452B2Exact reproductionAccurate measurementRespiratorsMedical devicesVenous blood specimenVenous blood
An improved pulse oximeter provides for simultaneous, noninvasive oxygen status and photoplethysmograph measurements at both single and multiple sites. In particular, this multiple-site, multiple-parameter pulse oximeter, or “stereo pulse oximeter” simultaneously measures both arterial and venous oxygen saturation at any specific site and generates a corresponding plethysmograph waveform. A corresponding computation of arterial minus venous oxygen saturation is particularly advantageous for oxygen therapy management. An active pulse-inducing mechanism having a scattering-limited drive generates a consistent pulsatile venous signal utilized for the venous blood measurements. The stereo pulse oximeter also measures arterial oxygen saturation and plethysmograph shape parameters across multiple sites. A corresponding calculation of delta arterial saturation and comparison of plethysmograph shape parameters between multiple sites is particularly advantageous for the detection and management of persistent pulmonary hypertension in neonates (PPHN), a patent ductus arteriosis (PDA), and aortic coarctation.
Owner:JPMORGAN CHASE BANK NA
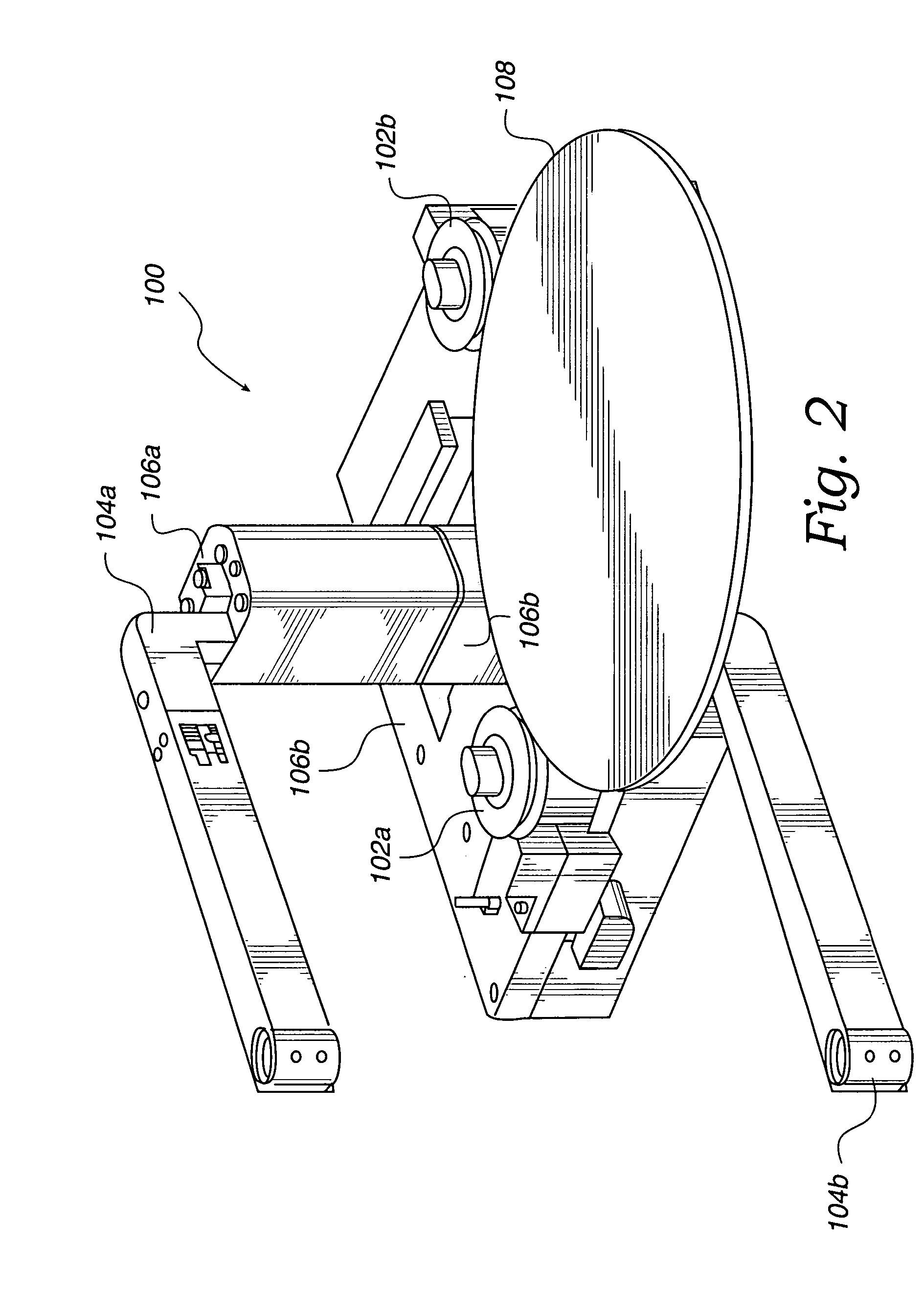
Concentric proximity processing head
InactiveUS20050217137A1Efficient processingImprove Wafer YieldDrying using combination processesDrying solid materials without heatEngineeringMeniscus
In one of the many embodiments, a method for processing a substrate is disclosed which includes generating a first fluid meniscus and a second fluid meniscus at least partially surrounding the first fluid meniscus wherein the first fluid meniscus and the second fluid meniscus are generated on a surface of the substrate.
Owner:LAM RES CORP
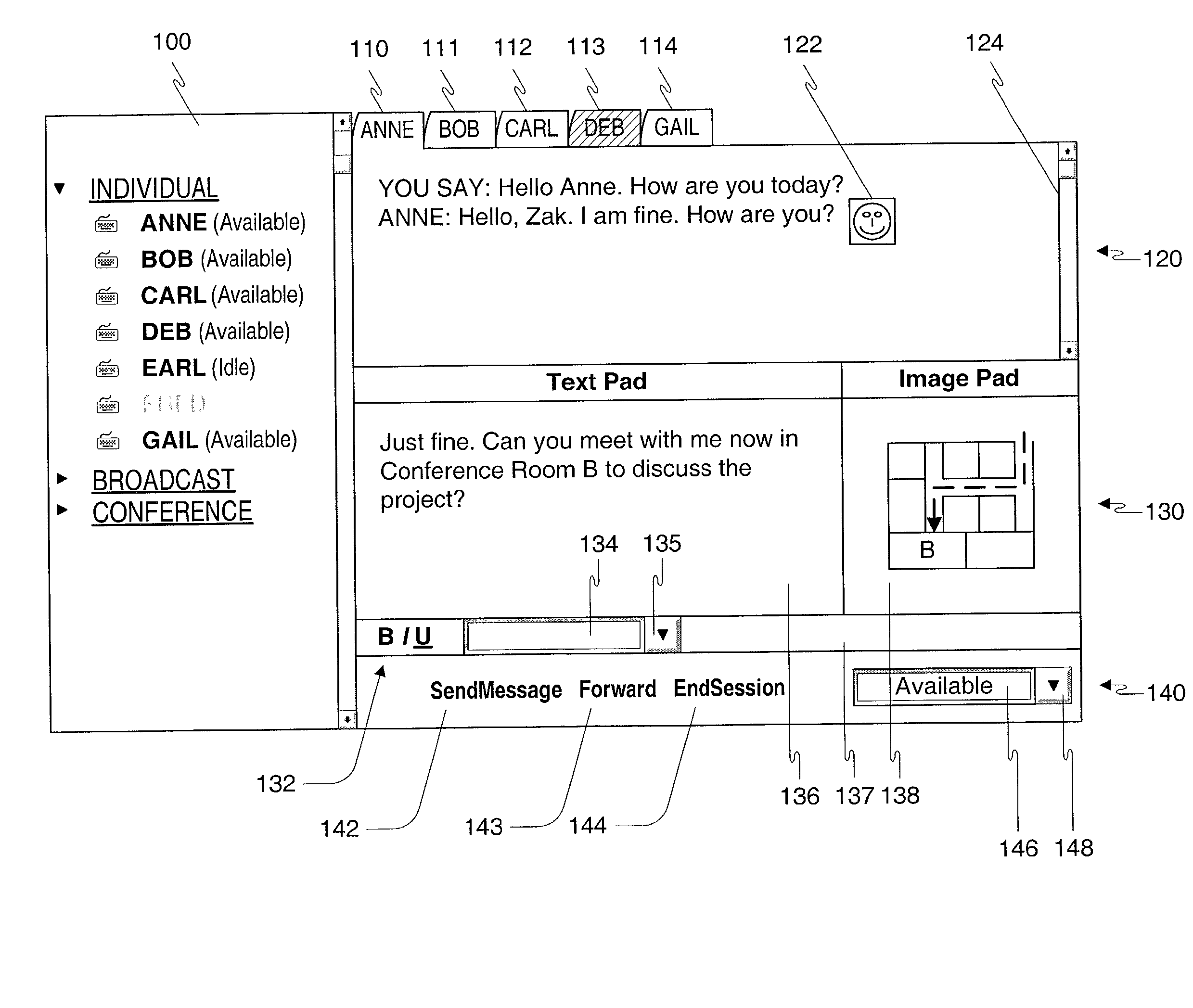
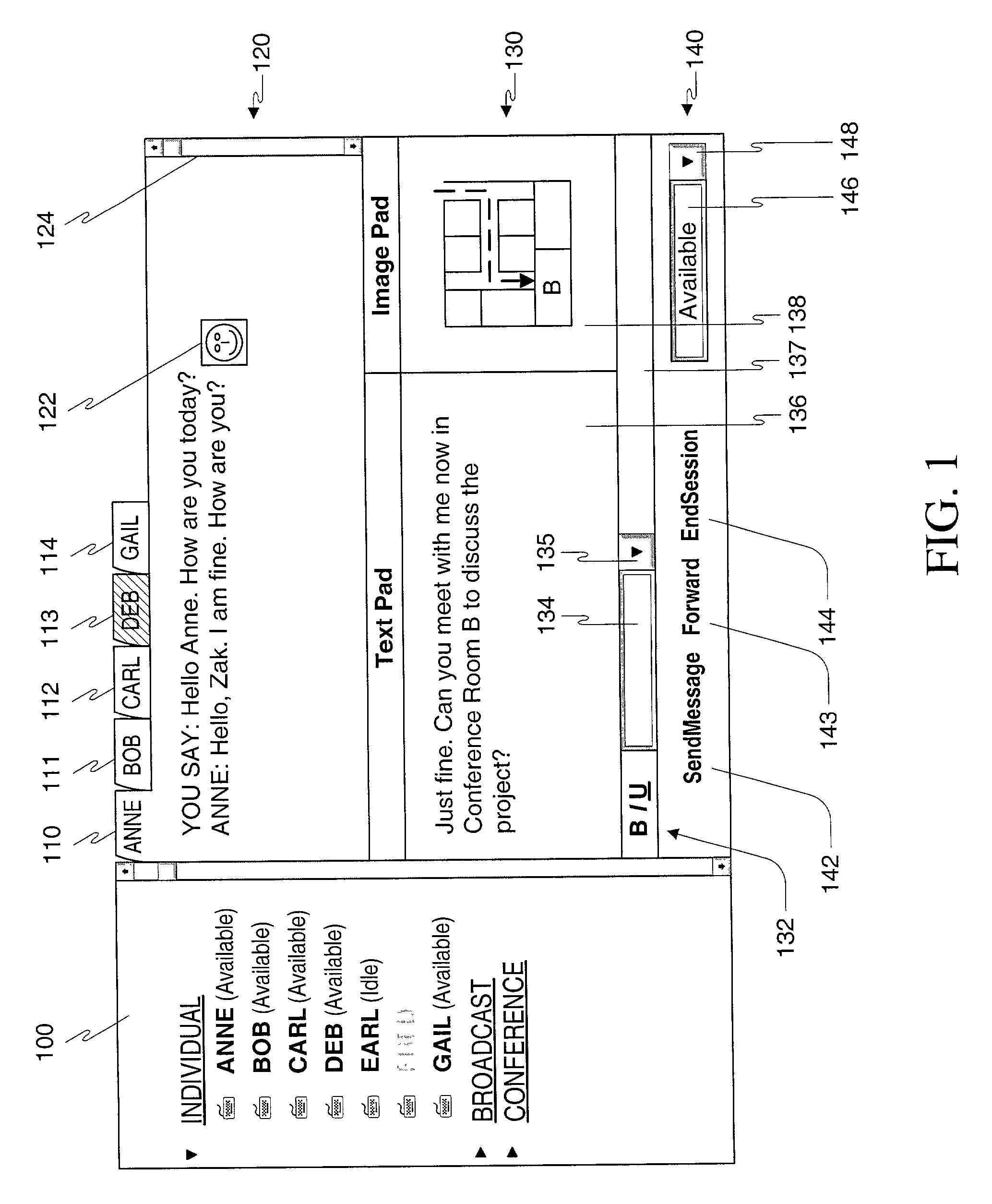
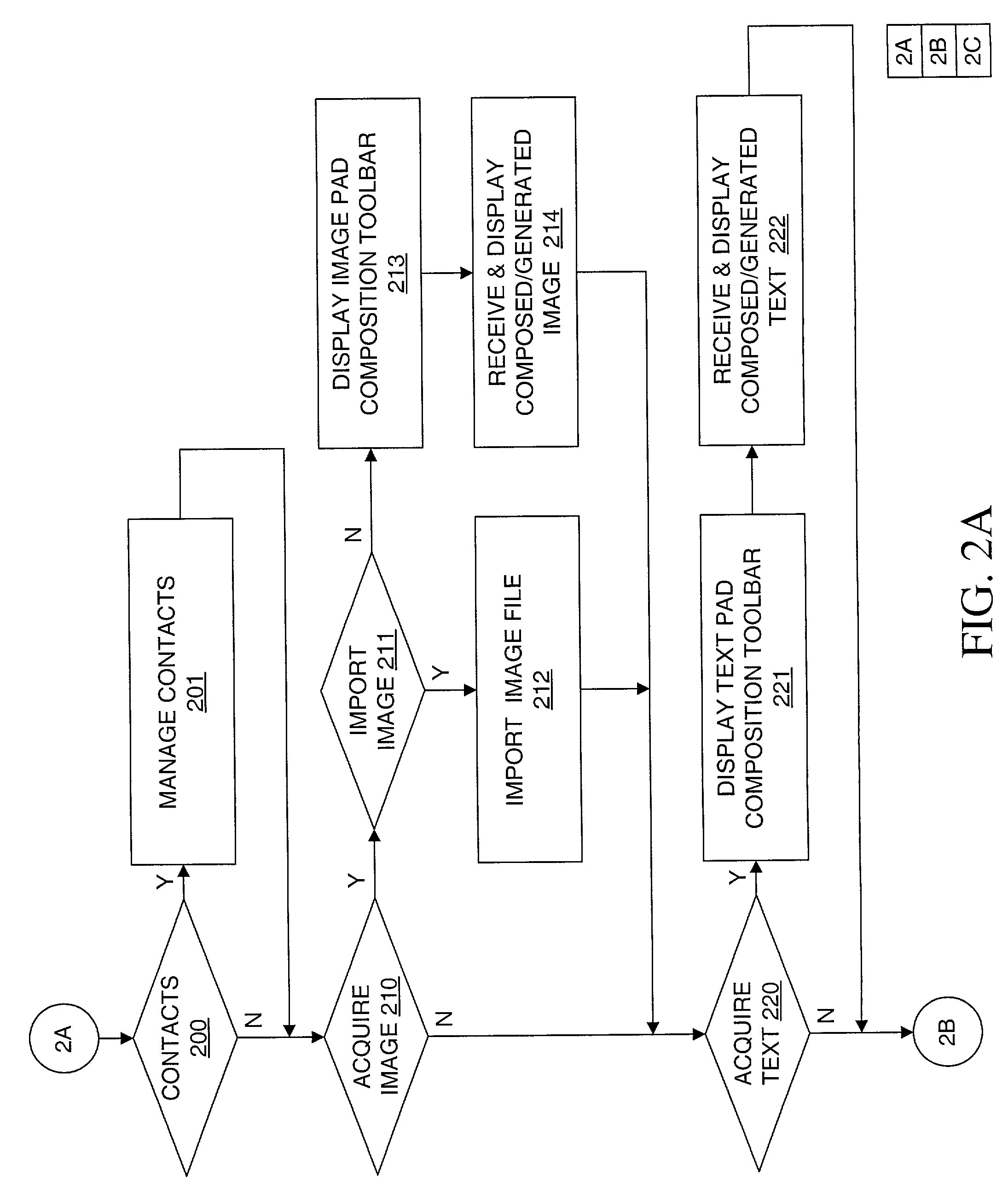
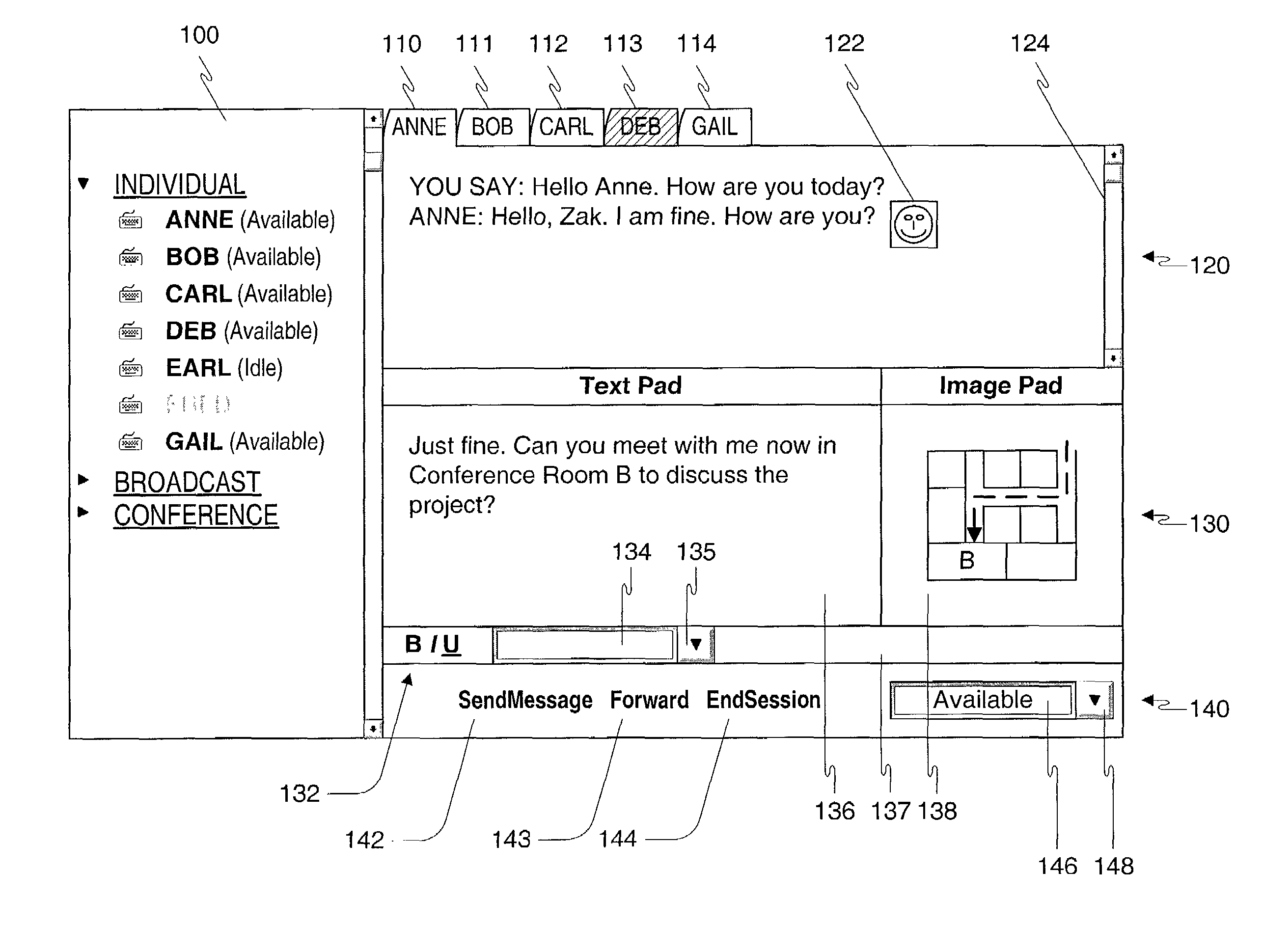
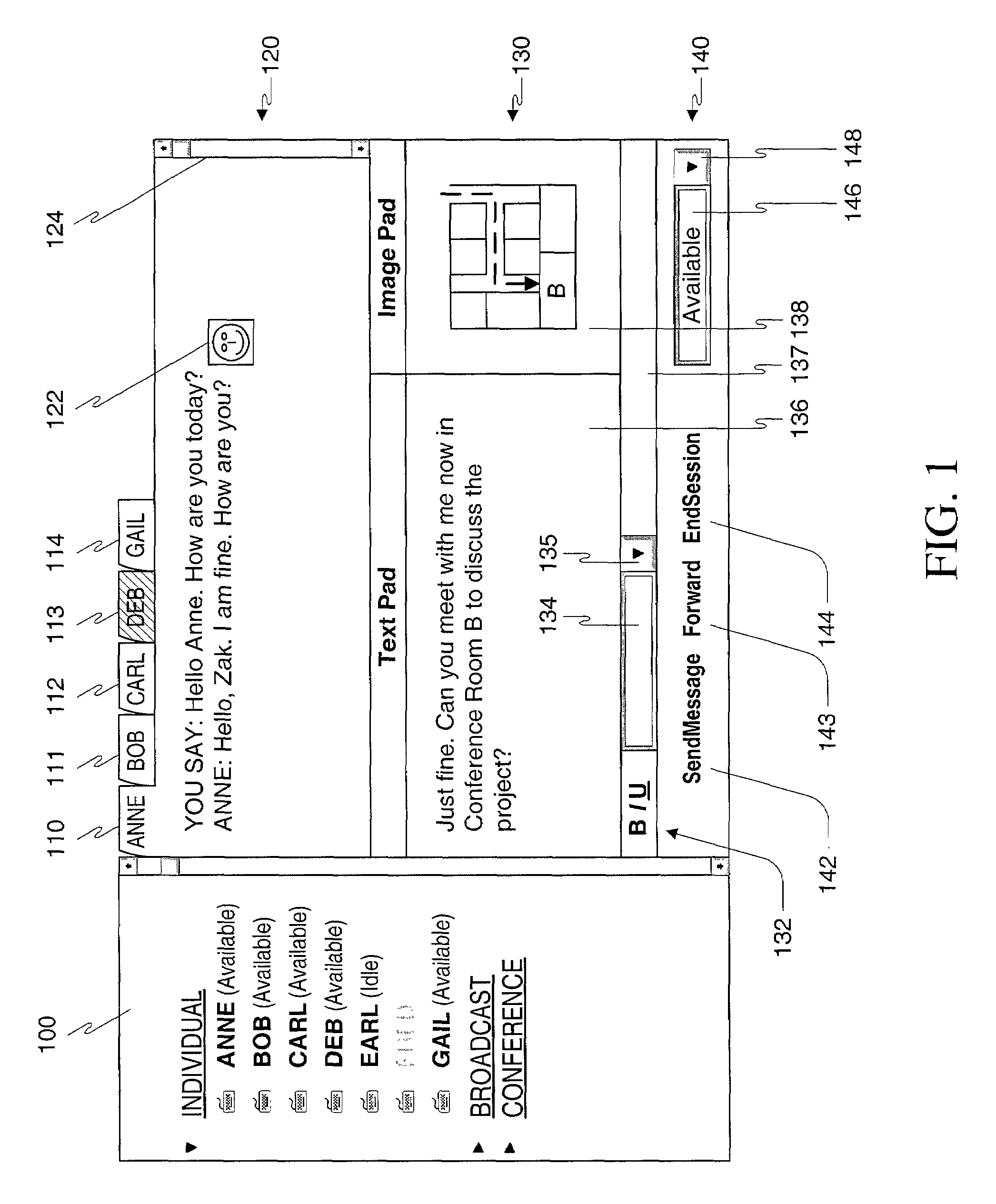
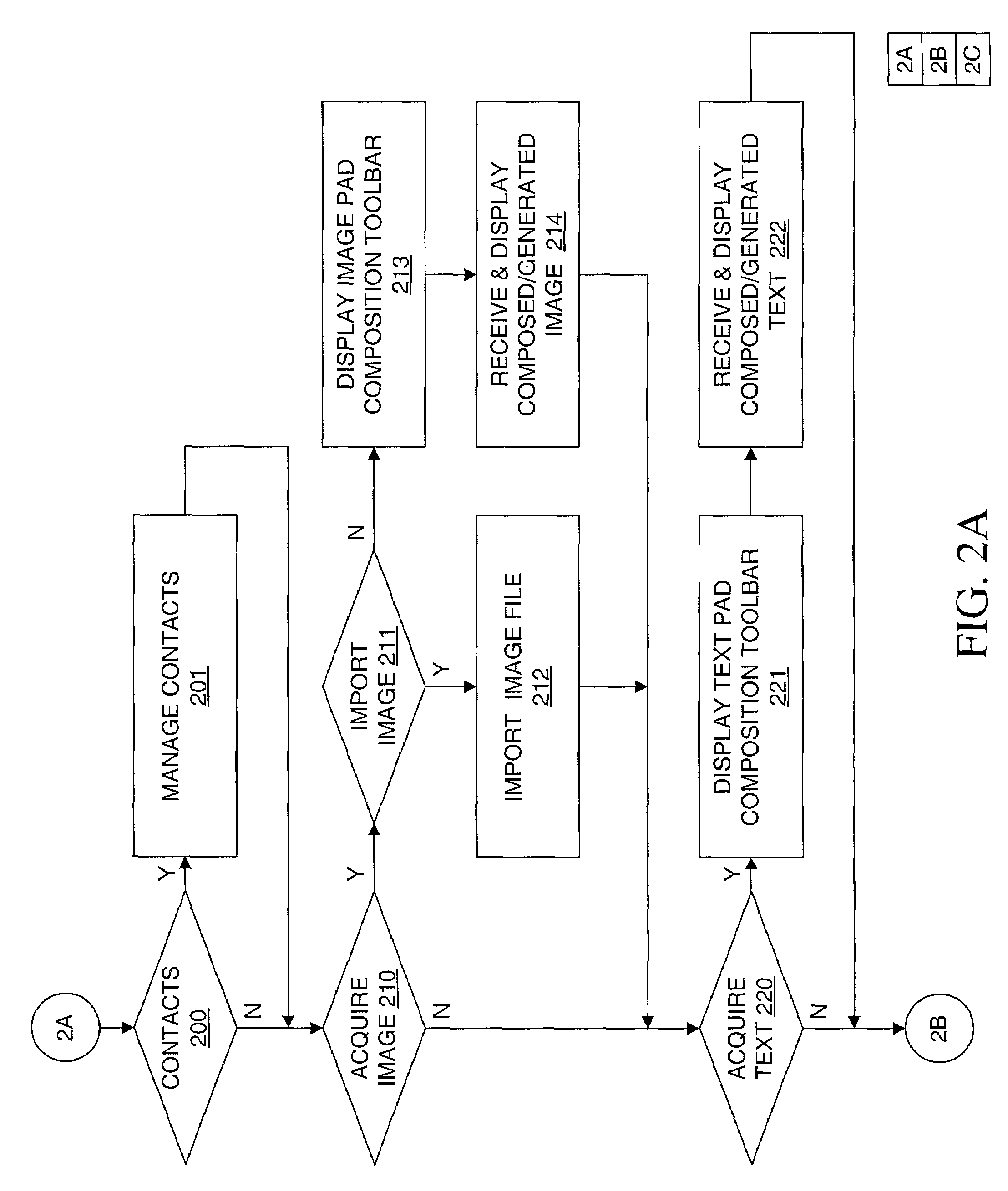
Method, apparatus and computer readable medium for multiple messaging session management with a graphical user interfacse
InactiveUS20020130904A1Easy to manageCathode-ray tube indicatorsTransmissionGraphicsSession management
A graphical user interface displays a unique graphical indexing element such as a tab for each engaged and non-engaged messaging session. The user chooses which messaging session to make engaged by selecting its graphical indexing element. The graphical indexing elements have various distinctive characteristics to indicate the status of their respective messaging sessions, such as engaged, non-engaged with no unread messages, or non-engaged with at least one unread message. The messaging sessions may all be docked, in which event the engaged messaging session is displayed in a window pane set and the other messaging sessions are not displayed, or may be selectively undocked, in which event the engaged messaging session and the undocked messaging sessions are displayed in respective window pane sets. The engaged window pane set supports the communication of original or predefined messages between the user's digital device and the pal's messaging-enabled digital device, regardless of capability.
Owner:ECRIO
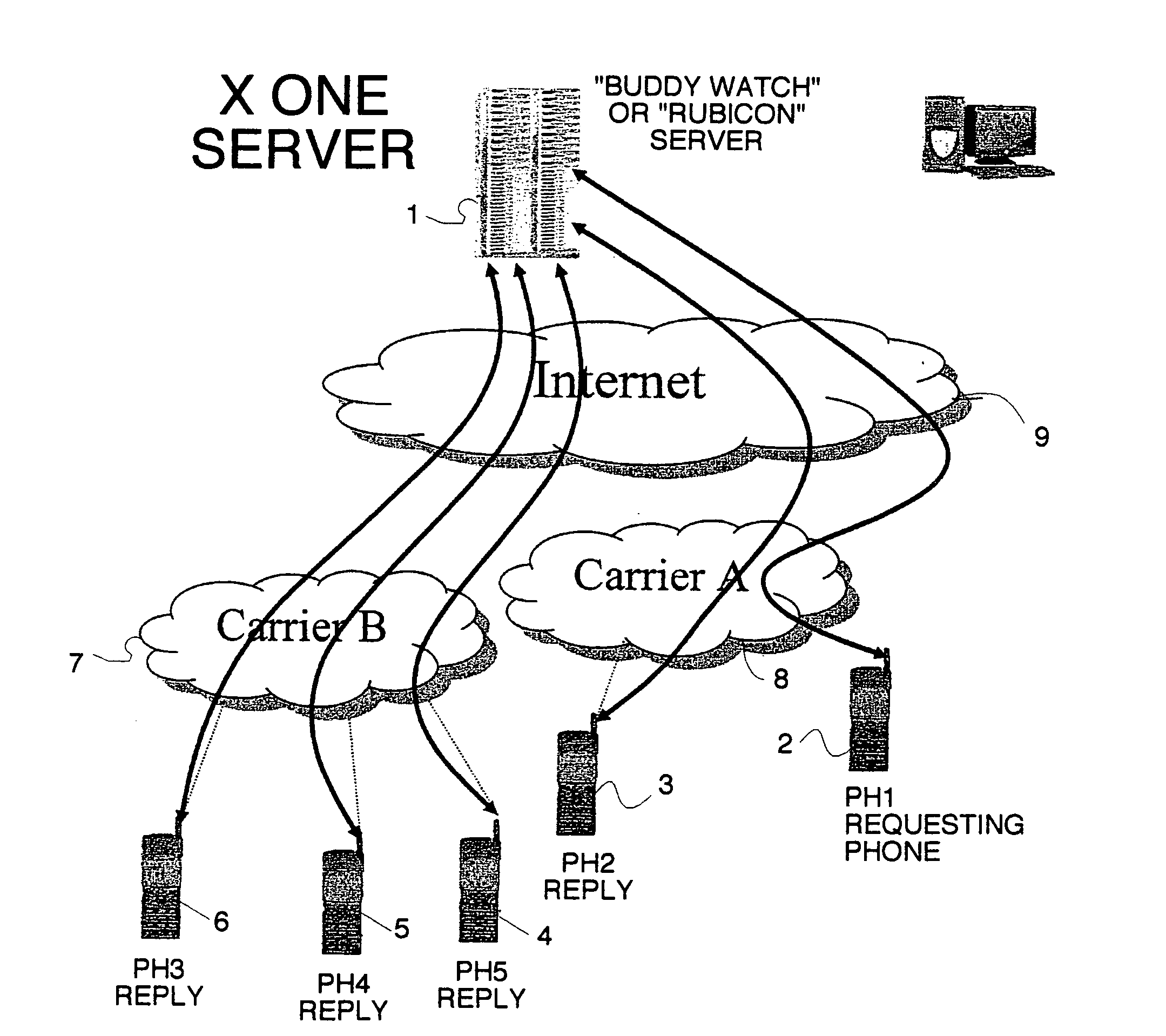
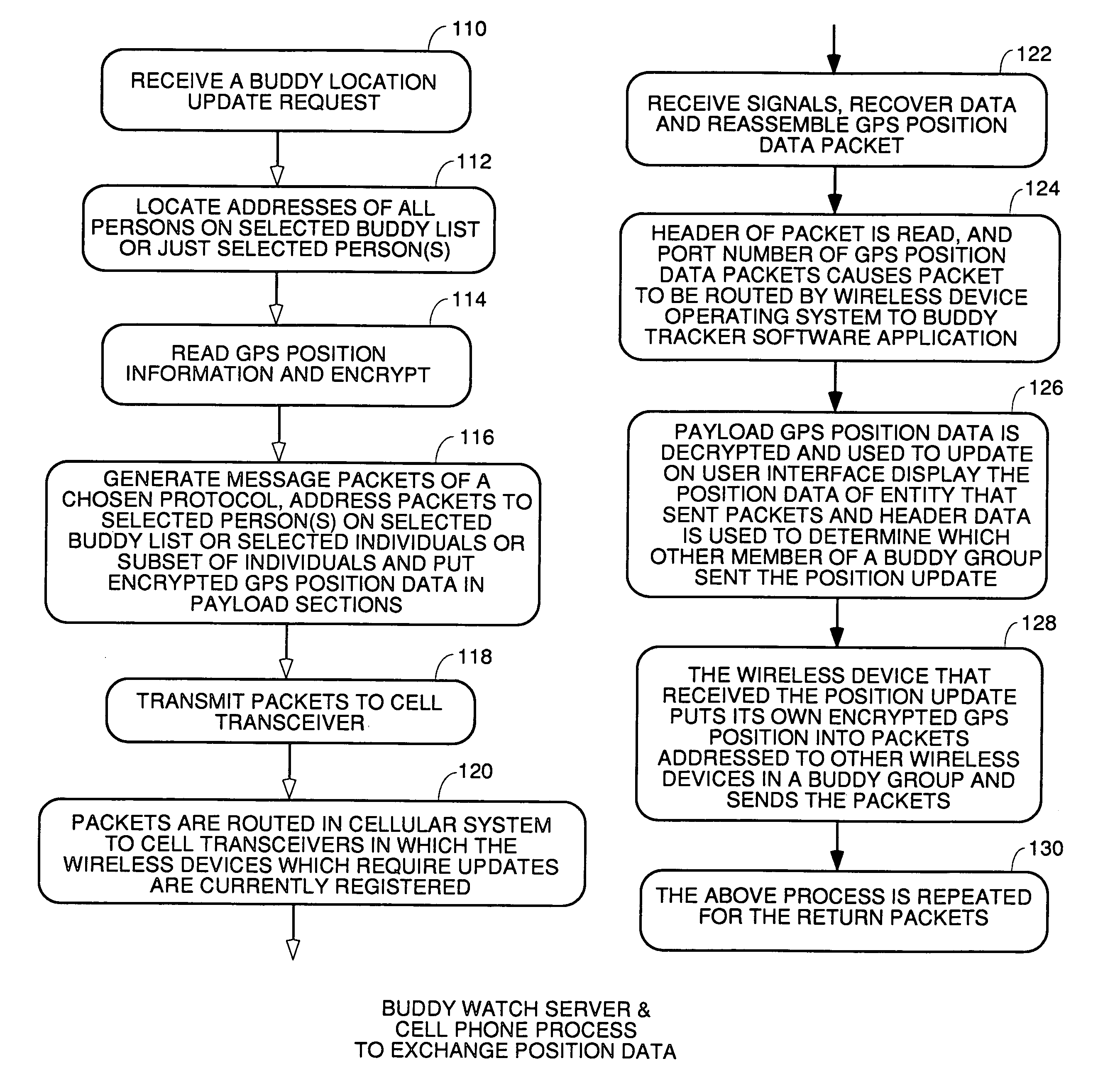
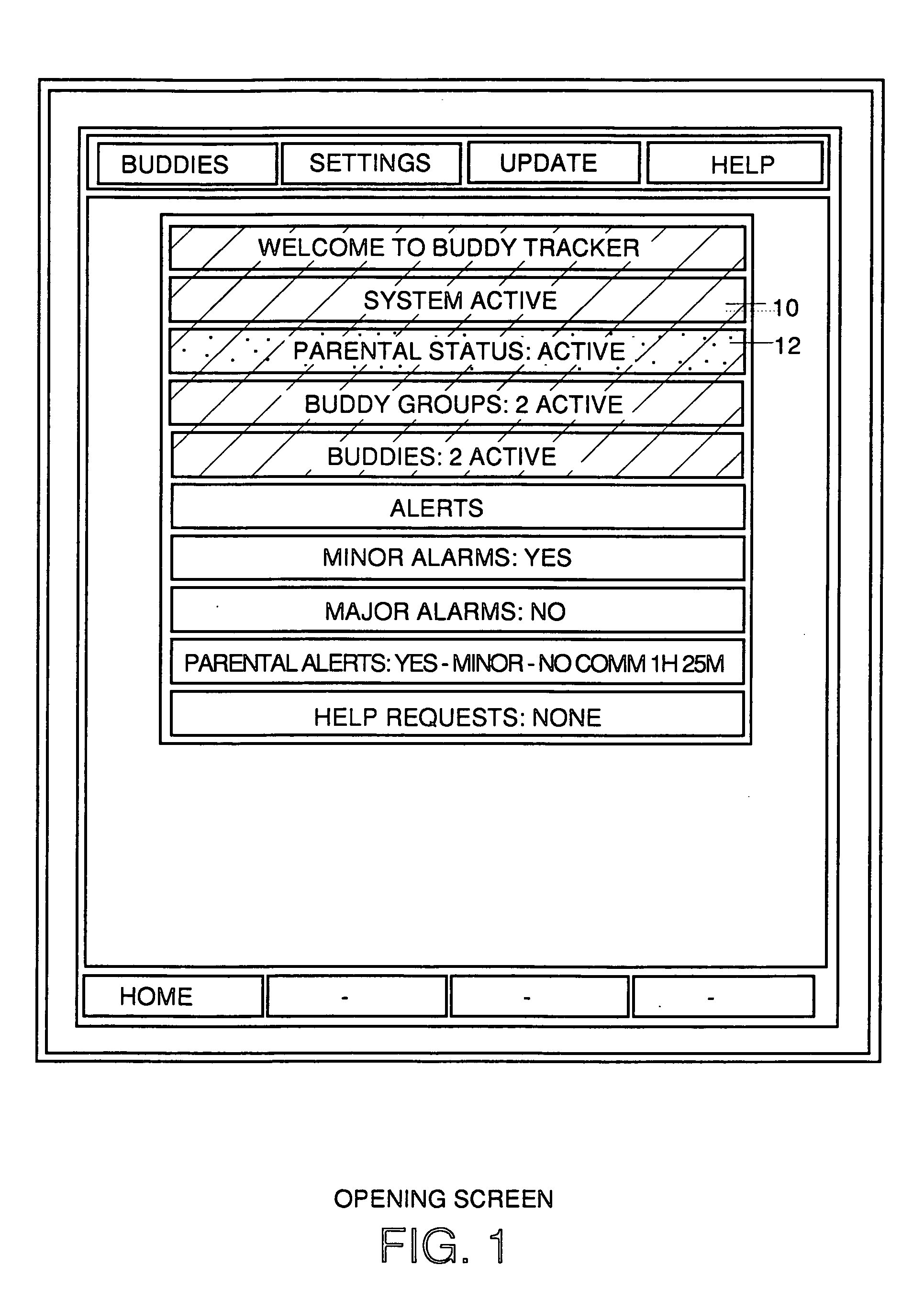
Location sharing and tracking using mobile phones or other wireless devices
ActiveUS20060223518A1Easy to identifyKeep trackNavigational calculation instrumentsDevices with GPS signal receiverLocation sharingGroup coordination
A system for exchanging GPS or other position data between wireless devices for purposes of group activities, child location monitoring, work group coordination, dispatching of employees etc. Cell phones and other wireless devices with GPS receivers have loaded therein a Buddy Watch application and a TalkControl application. The Buddy Watch application communicates with the GPS receiver and other wireless devices operated by buddies registered in the users phone as part of buddy groups or individually. GPS position data and historical GPS position data can be exchanged between cell phones of buddies and instant buddies such as tow truck drivers via a buddy watch server. Emergency monitoring services can be set up with notifications to programmable individuals in case an individual does not respond. Positions and tracks can be displayed. TalkControl simplifies and automates the process of joining talk groups for walkie talkie services such as that provided by Nextel.
Owner:X ONE
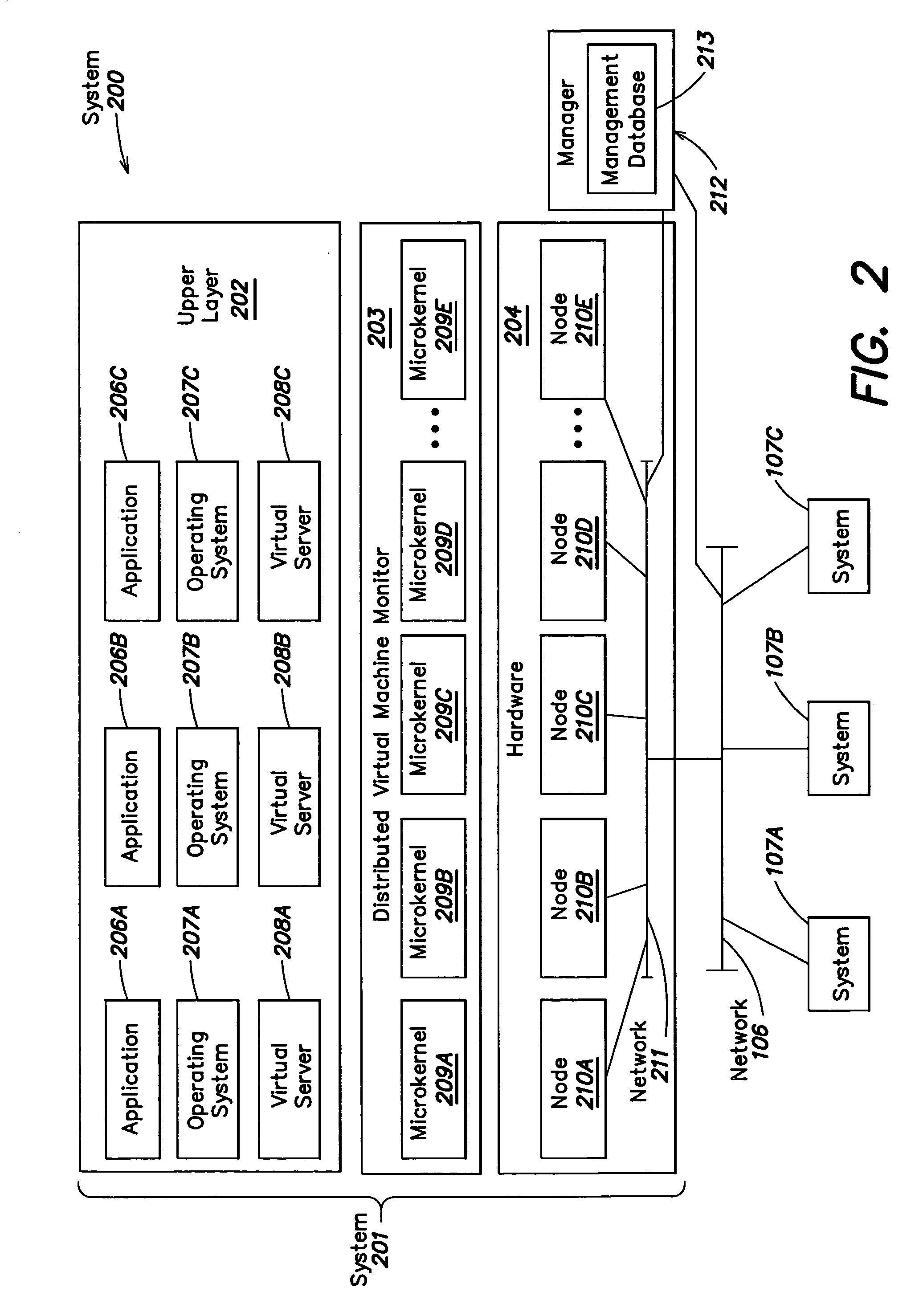
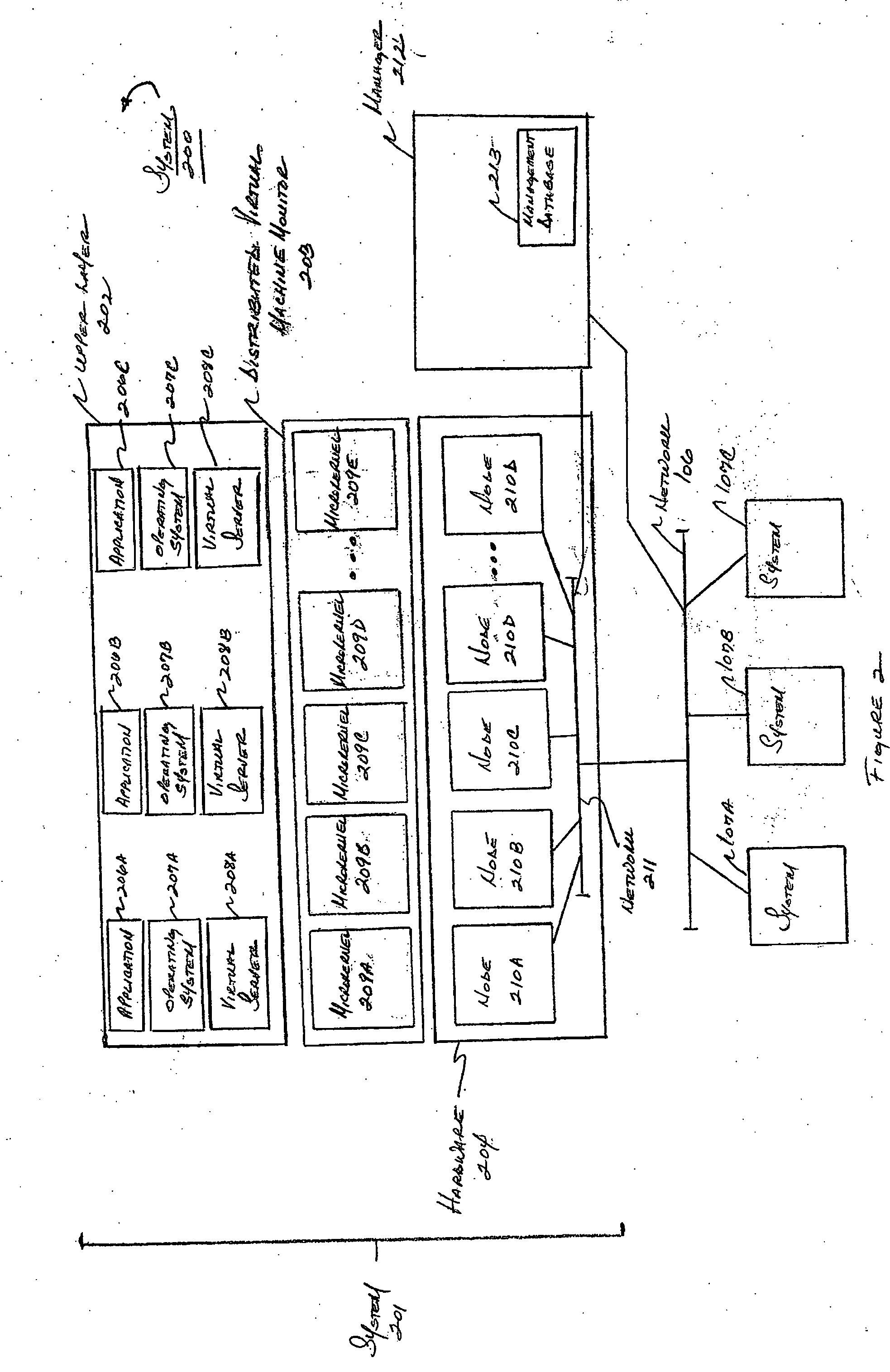
Method and apparatus for providing virtual computing services
InactiveUS20050044301A1Easy to manageLow costResource allocationMemory adressing/allocation/relocationVirtualizationOperational system
A level of abstraction is created between a set of physical processors and a set of virtual multiprocessors to form a virtualized data center. This virtualized data center comprises a set of virtual, isolated systems separated by a boundary referred as a partition. Each of these systems appears as a unique, independent virtual multiprocessor computer capable of running a traditional operating system and its applications. In one embodiment, the system implements this multi-layered abstraction via a group of microkernels, each of which communicates with one or more peer microkernel over a high-speed, low-latency interconnect and forms a distributed virtual machine monitor. Functionally, a virtual data center is provided, including the ability to take a collection of servers and execute a collection of business applications over a compute fabric comprising commodity processors coupled by an interconnect. Processor, memory and I / O are virtualized across this fabric, providing a single system, scalability and manageability. According to one embodiment, this virtualization is transparent to the application, and therefore, applications may be scaled to increasing resource demands without modifying the application.
Owner:ORACLE INT CORP
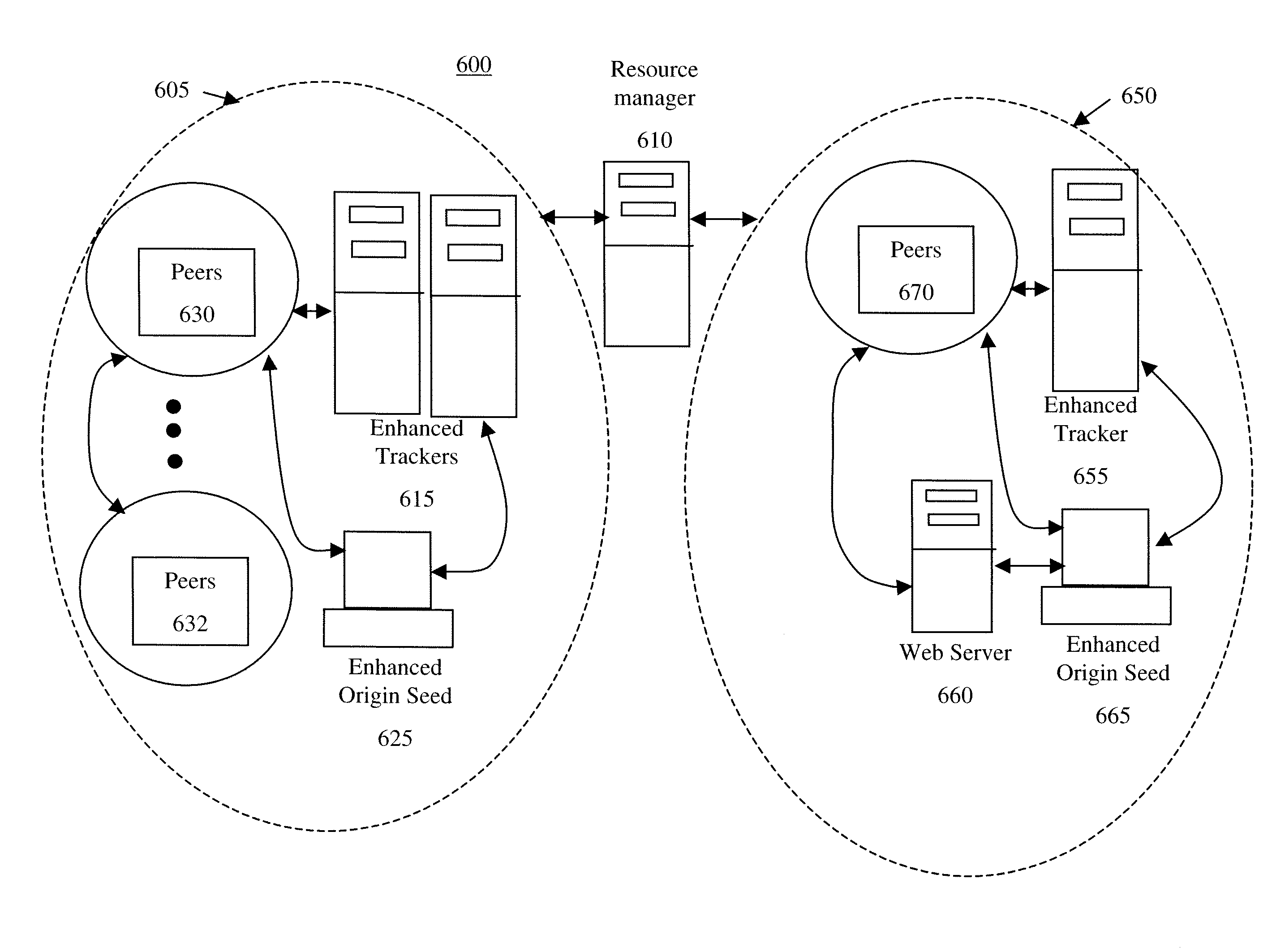
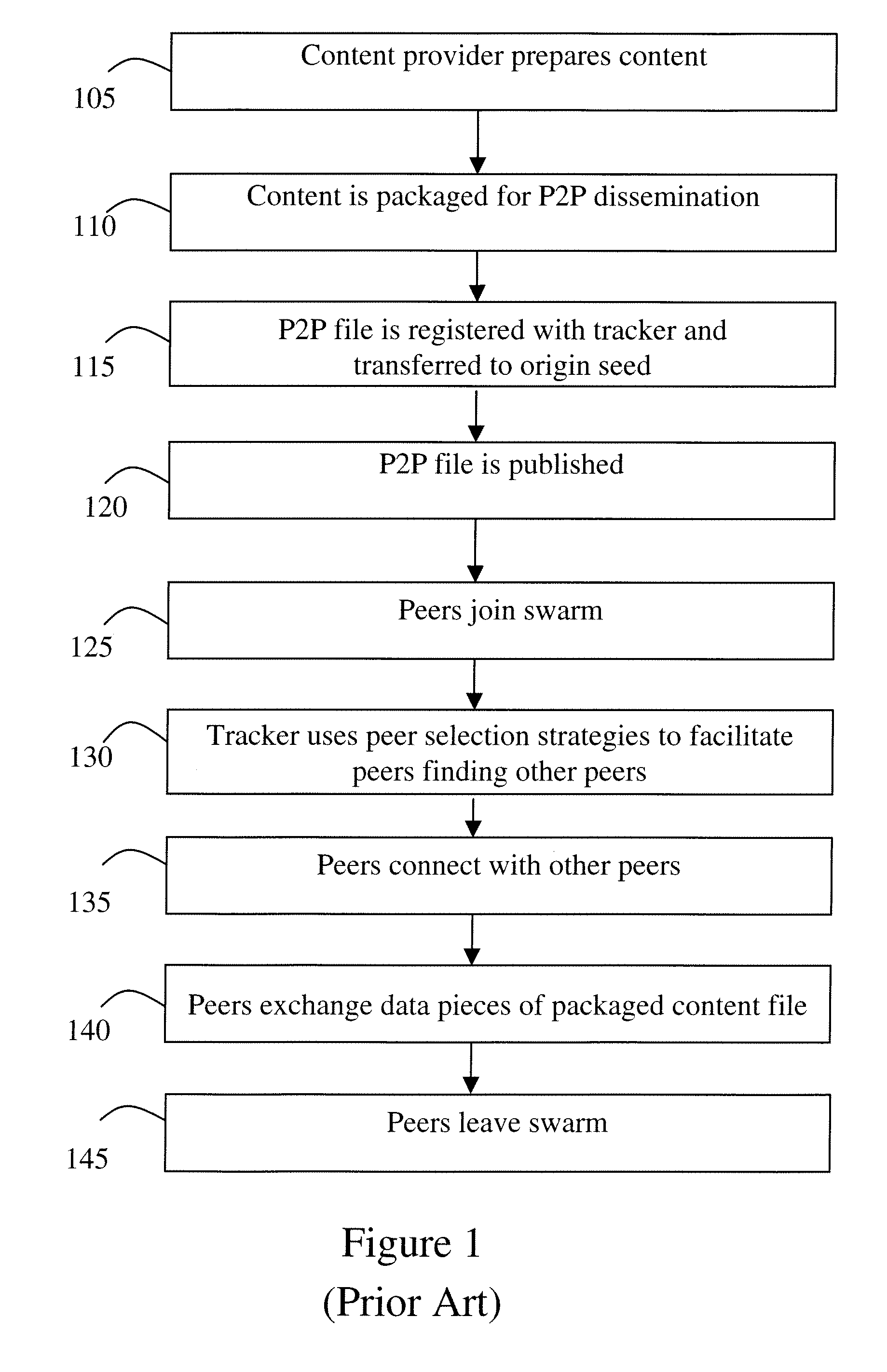
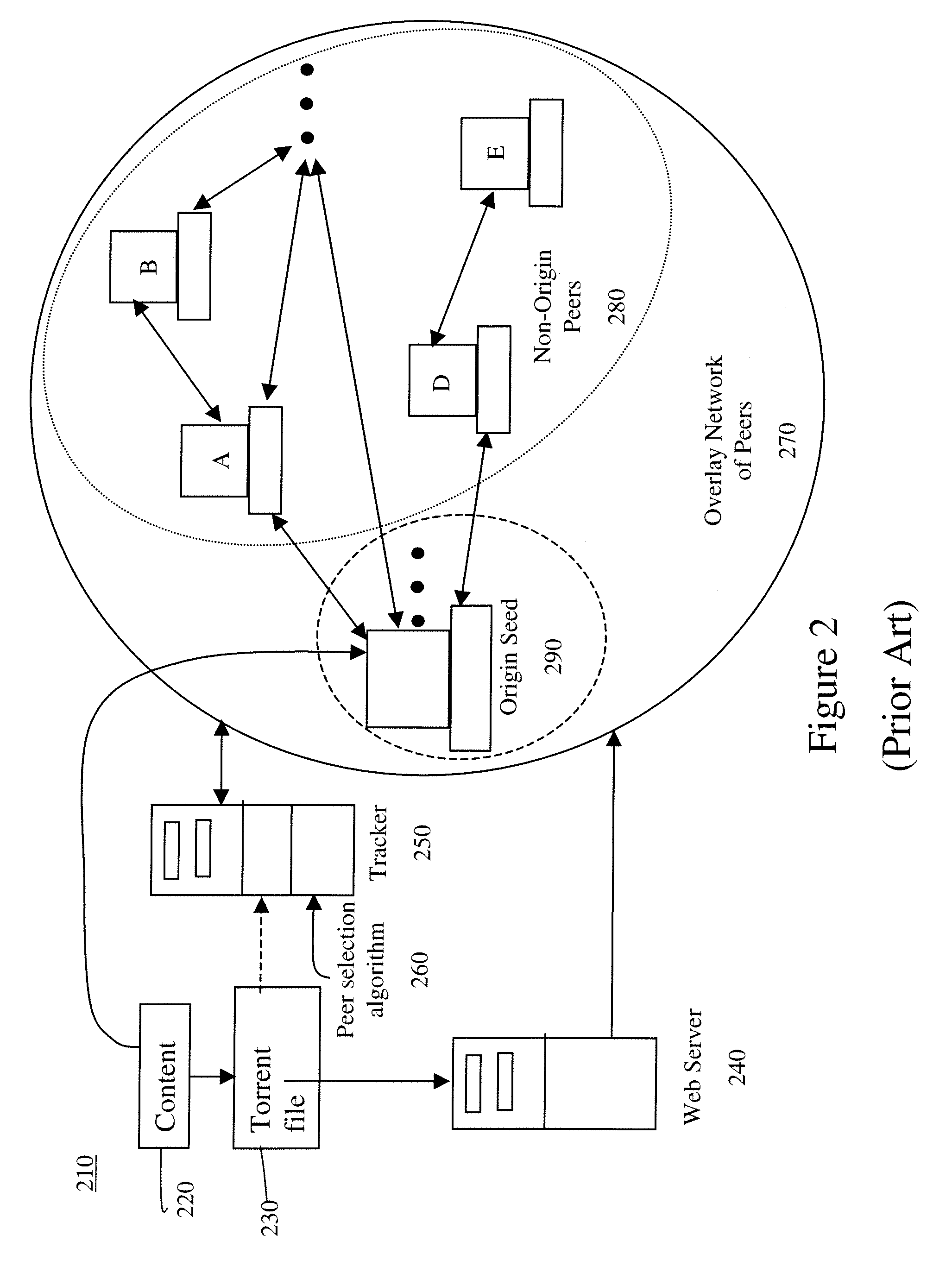
Accelerating peer-to-peer content distribution
ActiveUS20090182815A1Improving P2P performanceImprove service qualityMultiple digital computer combinationsElectric digital data processingContent distributionDistributed computing
The acceleration of peer-to-peer downloads of content files wherein a tracker performs a condition based peer selection that is dynamically adjustable. A further feature relates to the use of enhanced message scheme for communications. One embodiment is a system in a swarm having at least one origin seed capable of at least initially storing the content files with at least one tracker maintaining a list of peers wherein the tracker uses at least one dynamically adjusting peer selection algorithm to generate a condition based peer-list and provides the condition based peer-list to a requesting peer.
Owner:NBCUNIVERSAL
Potentiation of immune responses with liposomal adjuvants
InactiveUS6090406AGood water solubilityPractical and convenientBacterial antigen ingredientsViral antigen ingredientsLipid formationOrganic acid
A high integrity liposome comprising at least one stabile lipid and at least one peptide-like therapeutic agent associated with said liposome, adapted for parenteral administration to an animal, including a human, and method according to manufacture and use. Immunizing dosage forms comprising a liposome and an immunogen, wherein said liposome and immunogen are present in an immunization dose. Additionally, a dosage form, including such form particularly adapted to producing an immune response, comprising a salt according to an organic acid derivative of a sterol and an immunogen wherein said organic acid derivative of a sterol and immunogen are present in an immunization dose, and method according to use is disclosed. Further, a dosage form, including such form particularly adapted to producing an immune response, comprising dimyristoylphosphatidylcholine (DMPC) / cholesterol liposomes, optionally in an aluminum hydroxide gel, and an immunogen wherein said DMPC / cholesterol and immunogen are present in an immunization dose, and method according to use.
Owner:TRANSAVE
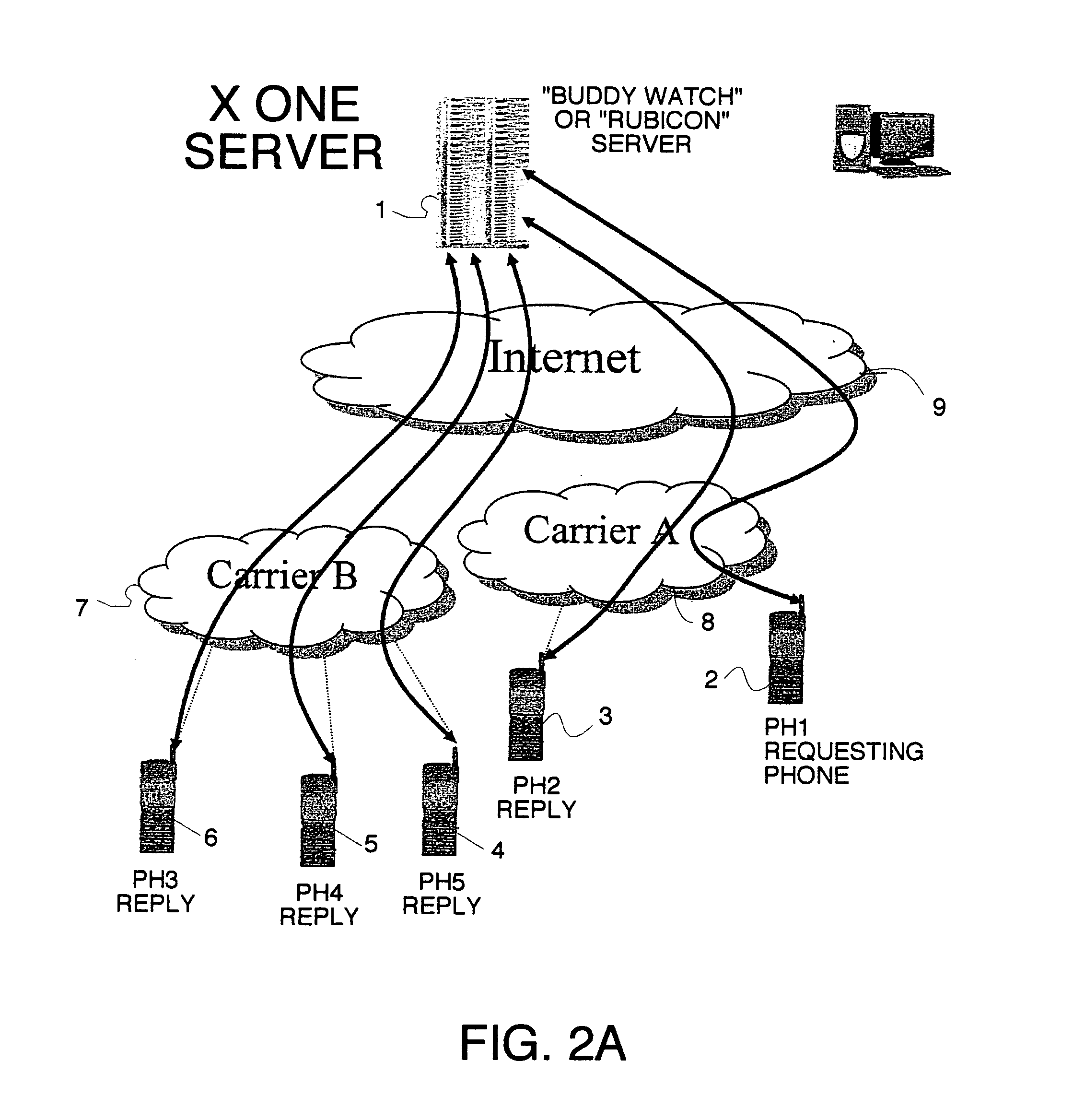
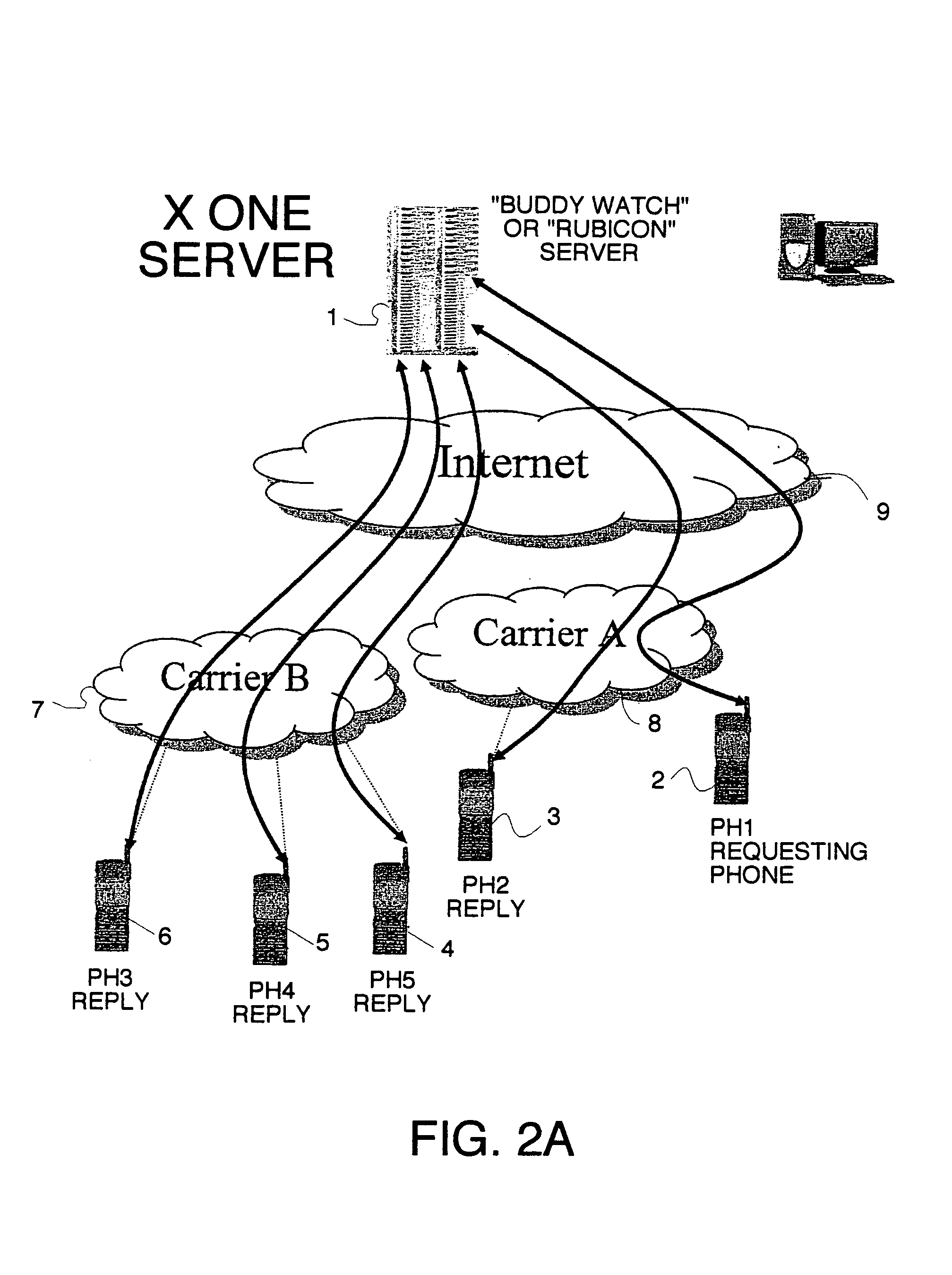
Location sharing and tracking using mobile phones or other wireless devices
ActiveUS7353034B2Easy to manageEasy SetupNavigational calculation instrumentsUnauthorised/fraudulent call preventionLocation sharingGroup coordination
A system for exchanging GPS or other position data between wireless devices for purposes of group activities, child location monitoring, work group coordination, dispatching of employees etc. Cell phones and other wireless devices with GPS receivers have loaded therein a Buddy Watch application and a TalkControl application. The Buddy Watch application communicates with the GPS receiver and other wireless devices operated by buddies registered in the users phone as part of buddy groups or individually. GPS position data and historical GPS position data can be exchanged between cell phones of buddies and instant buddies such as tow truck drivers via a buddy watch server. Emergency monitoring services can be set up with notifications to programmable individuals in case an individual does not respond. Positions and tracks can be displayed. TalkControl simplifies and automates the process of joining talk groups for walkie talkie services such as that provided by Nextel.
Owner:X ONE
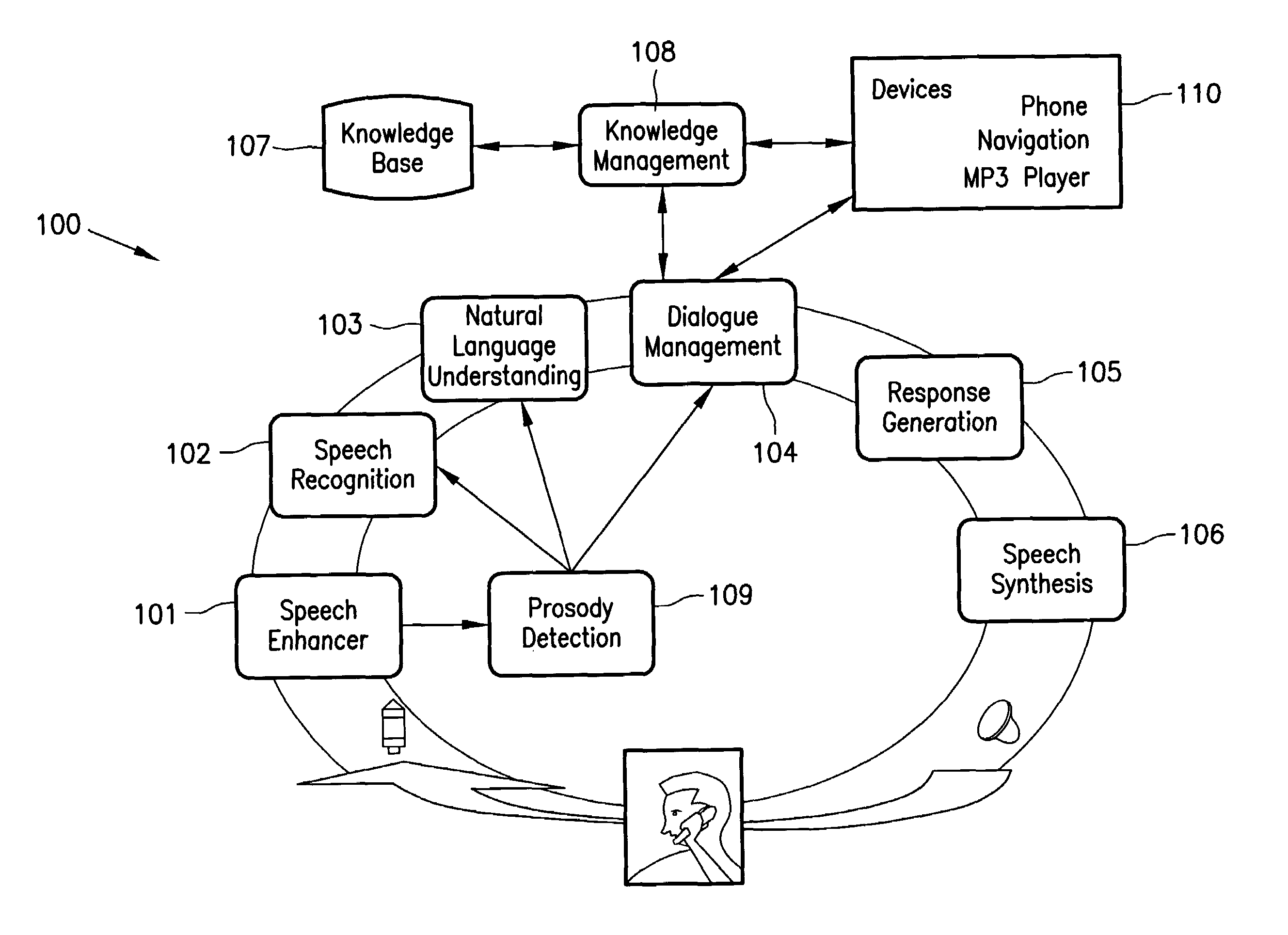
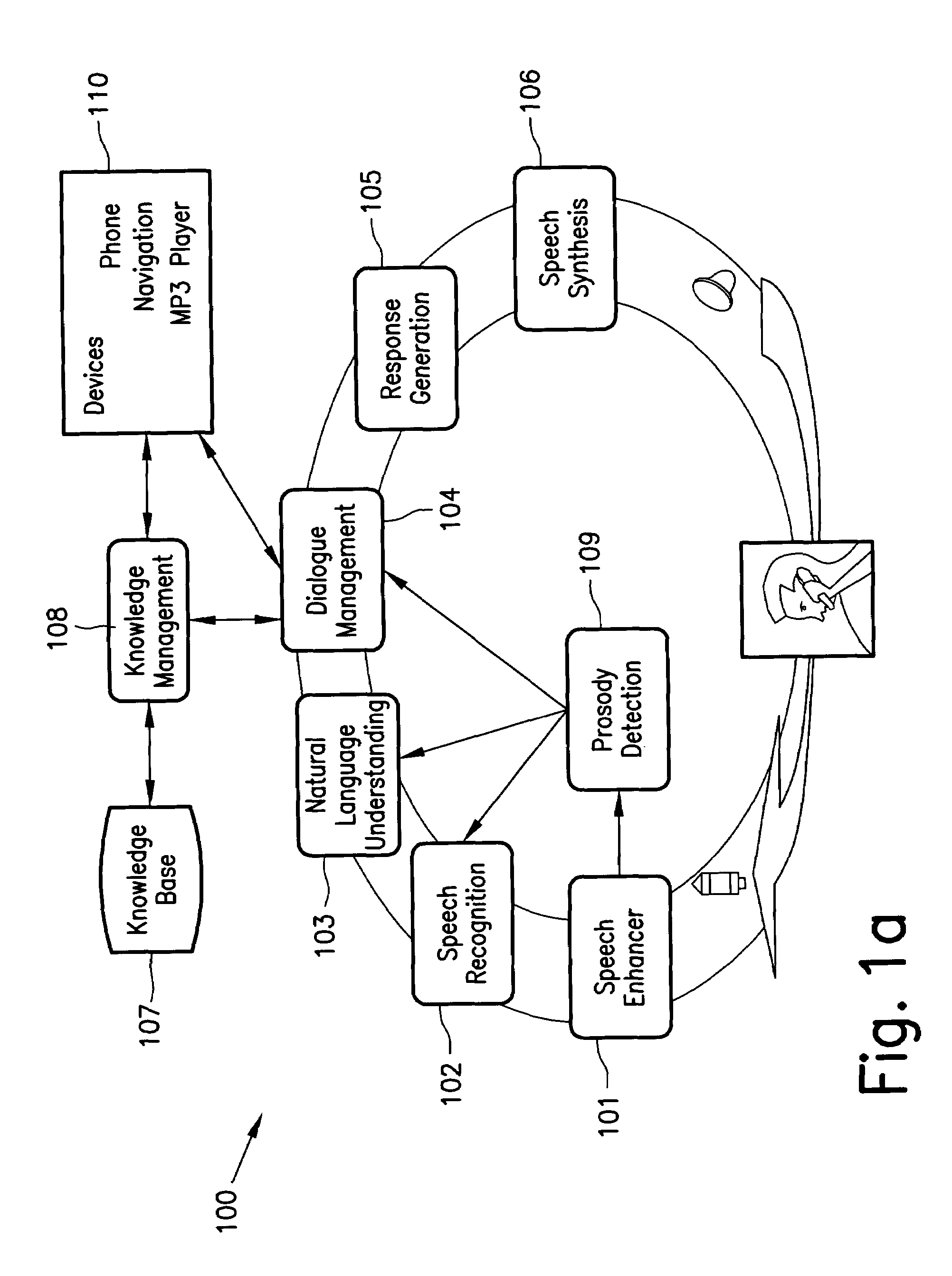
Method and system for interactive conversational dialogue for cognitively overloaded device users
ActiveUS7716056B2Easy and efficientAdapt quicklyNatural language data processingSpeech recognitionNatural language processingWave form
A system and method to interactively converse with a cognitively overloaded user of a device, includes maintaining a knowledge base of information regarding the device and a domain, organizing the information in at least one of a relational manner and an ontological manner, receiving speech from the user, converting the speech into a word sequence, recognizing a partial proper name in the word sequence, identifying meaning structures from the word sequence using a model of the domain information, adjusting a boundary of the partial proper names to enhance an accuracy of the meaning structures, interpreting the meaning structures in a context of the conversation with the cognitively overloaded user using the knowledge base, selecting a content for a response to the cognitively overloaded user, generating the response based on the selected content, the context of the conversation, and grammatical rules, and synthesizing speech wave forms for the response.
Owner:ROBERT BOSCH CORP +1
Personal shopping system
The present invention relates to a personal shopping system for combined use in both the home of a user and a shopping establishment. The system includes a host computer which is coupled to a host modem and, optionally, to at least one wireless multi-access point. The portable terminal can be used in both the shopping establishment and the home of the user. It is configured to read bar codes associated with items related to shopping, and includes a memory, a bar code reader, a wireless transceiver, and a data interface. The data interface of the terminal communicates with a data interface of the shopping establishment kiosk cradle or directly with the shopping establishment's communications network.
Owner:SYMBOL TECH LLC
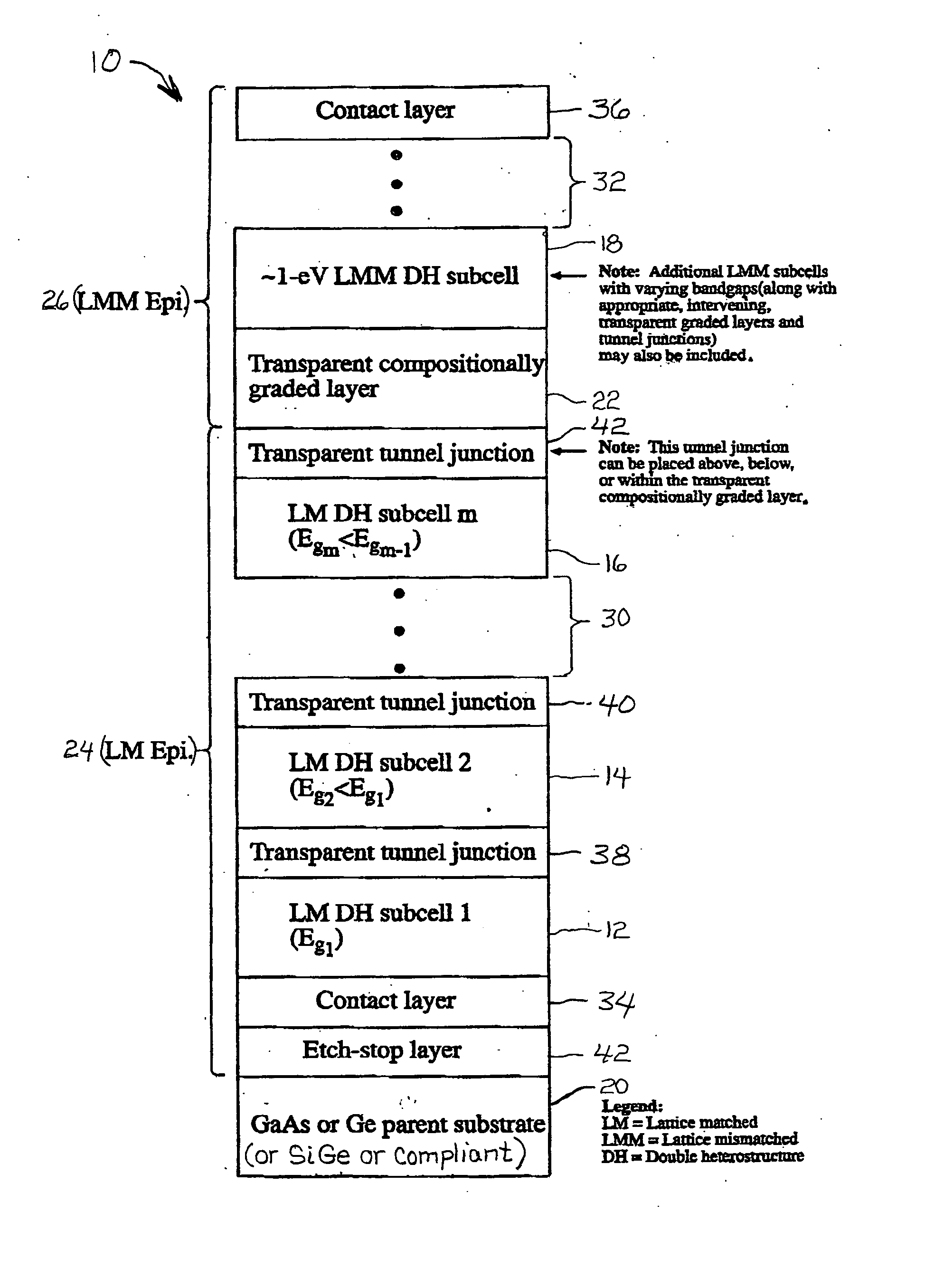
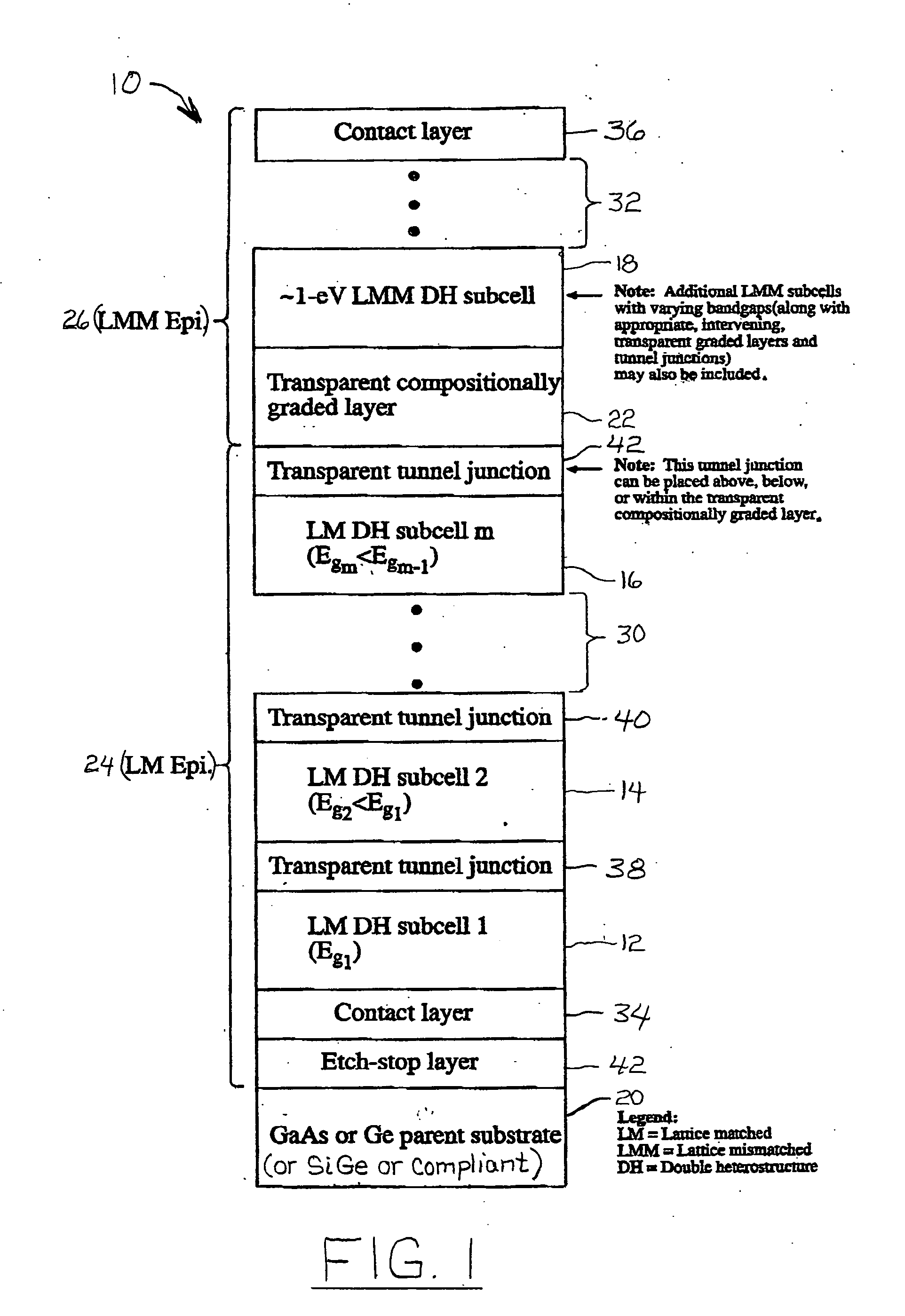
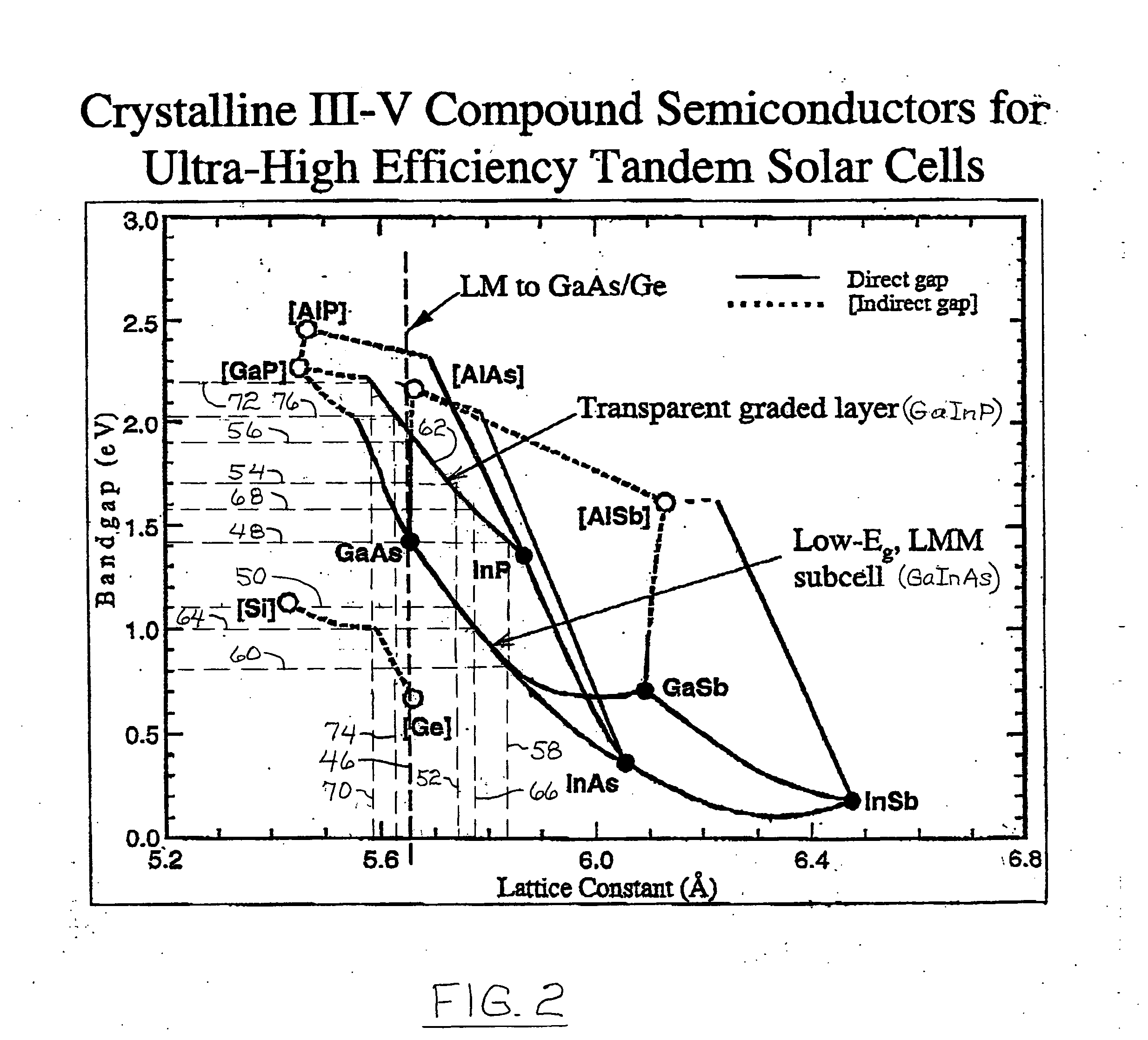
High-efficiency, monolithic, multi-bandgap, tandem photovoltaic energy converters
ActiveUS20060144435A1Improved thermal managementIncrease flexibilityPV power plantsSemiconductor/solid-state device manufacturingHigh energyLattice mismatch
A monolithic, multi-bandgap, tandem solar photovoltaic converter has at least one, and preferably at least two, subcells grown lattice-matched on a substrate with a bandgap in medium to high energy portions of the solar spectrum and at least one subcell grown lattice-mismatched to the substrate with a bandgap in the low energy portion of the solar spectrum, for example, about 1 eV.
Owner:ALLIANCE FOR SUSTAINABLE ENERGY
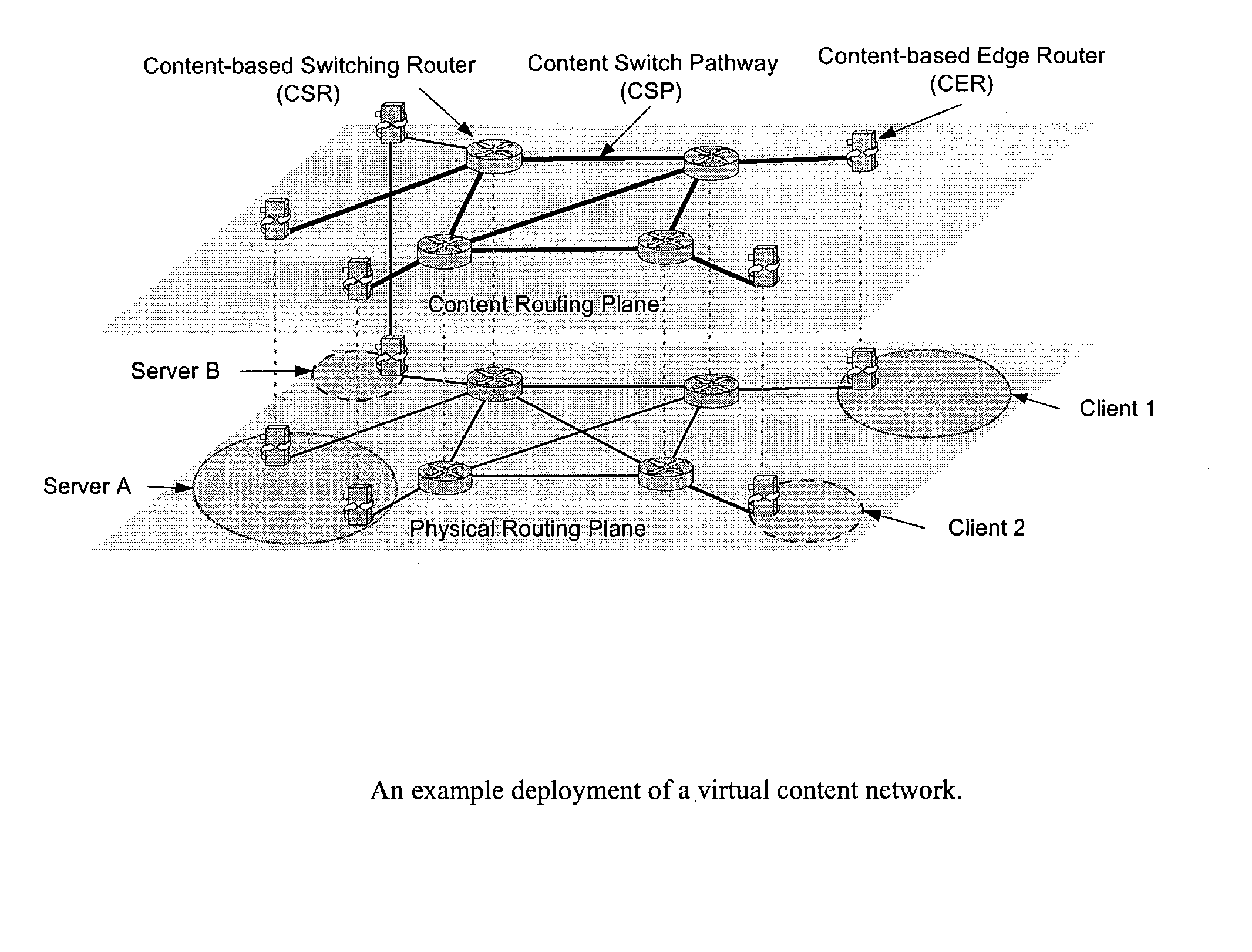
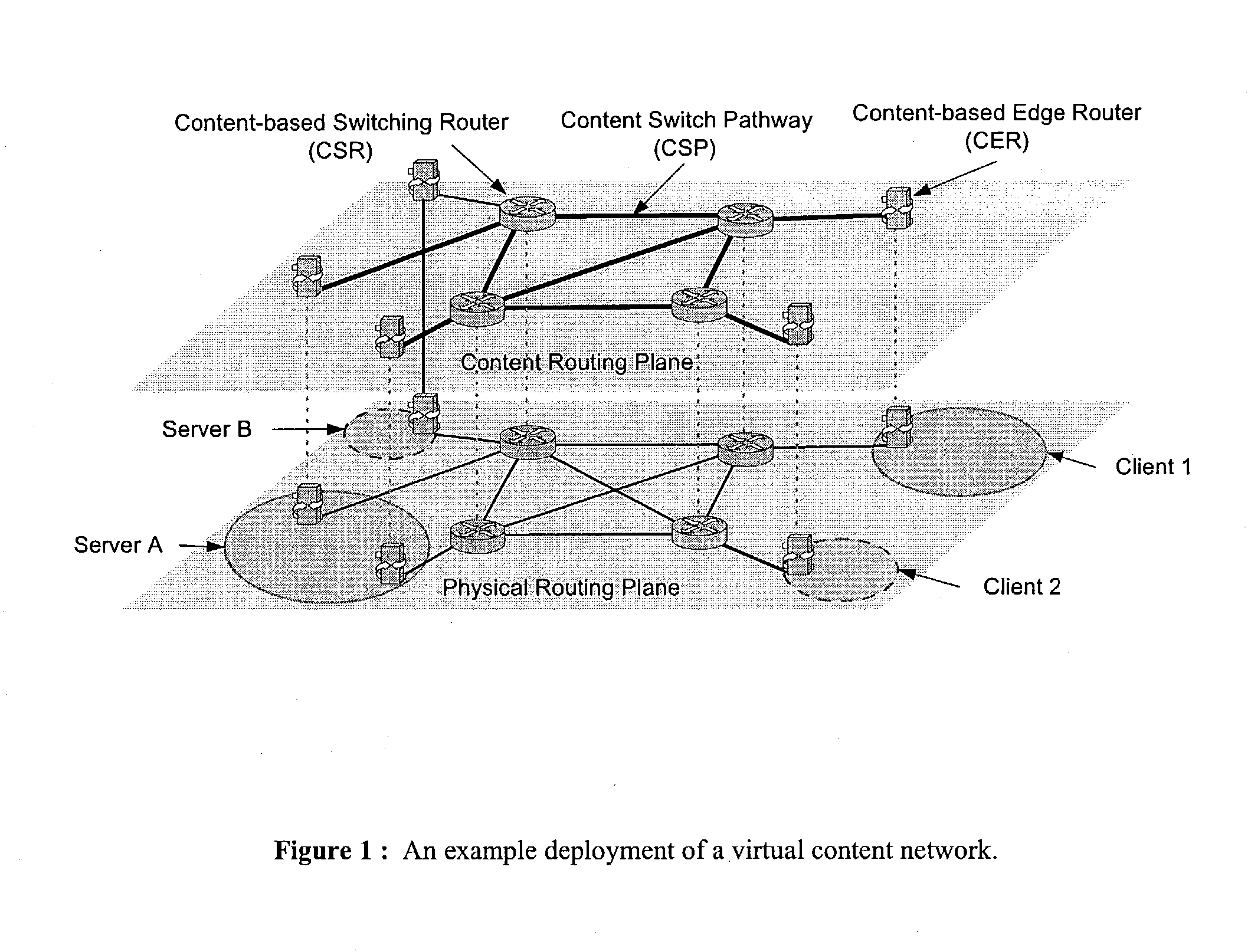
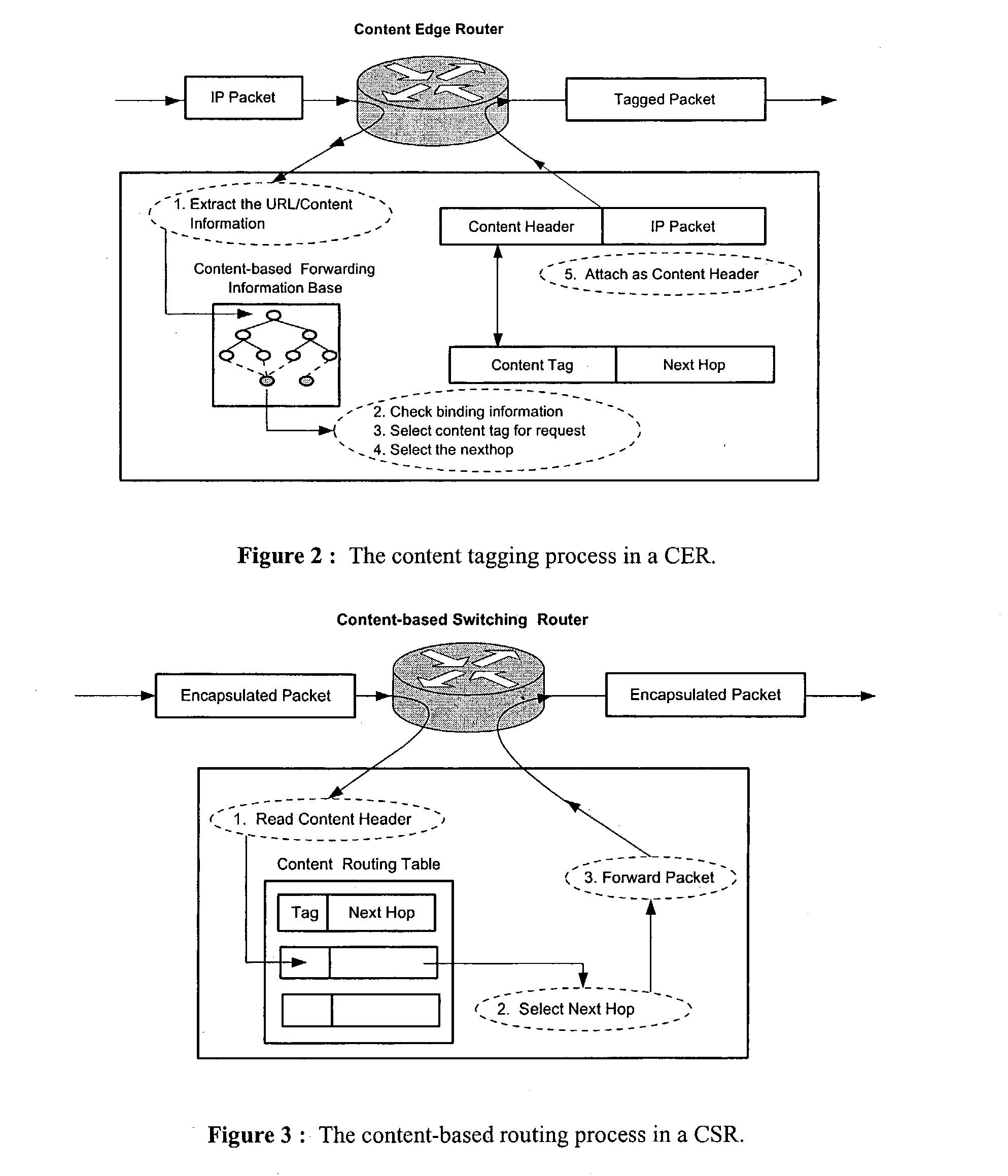
Wide-area content-based routing architecture
InactiveUS20030099237A1Easy to manageMaximum connectivityData switching by path configurationWide areaVirtualization
Content networking is an emerging technology, where the requests for content accesses are steered by "content routers" that examine not only the destinations but also content descriptors such as URLs and cookies. In the current deployments of content networking, "content routing" is mostly confined to selecting the most appropriate back-end server in virtualized web server clusters. This invention presents a novel content-based routing architecture that is suitable for global content networking. In this content-based routing architecture, a virtual overlay network called the "virtual content network" is superimposed over the physical network. The content network contains content routers as the nodes and "pathways" as links. The content-based routers at the edge of the content network may be either a gateway to the client domain or a gateway to the server domain whereas the interior ones correspond to the content switches dedicated for steering content requests and replies. The pathways are virtual paths along the physical network that connect the corresponding content routers. The invention is based on tagging content requests at the ingress points. The tags are designed to incorporate several different attributes of the content in the routing process. The path chosen for routing the request is the optimal path and is chosen from multiple paths leading to the replicas of the content.
Owner:TELECOMM RES LAB
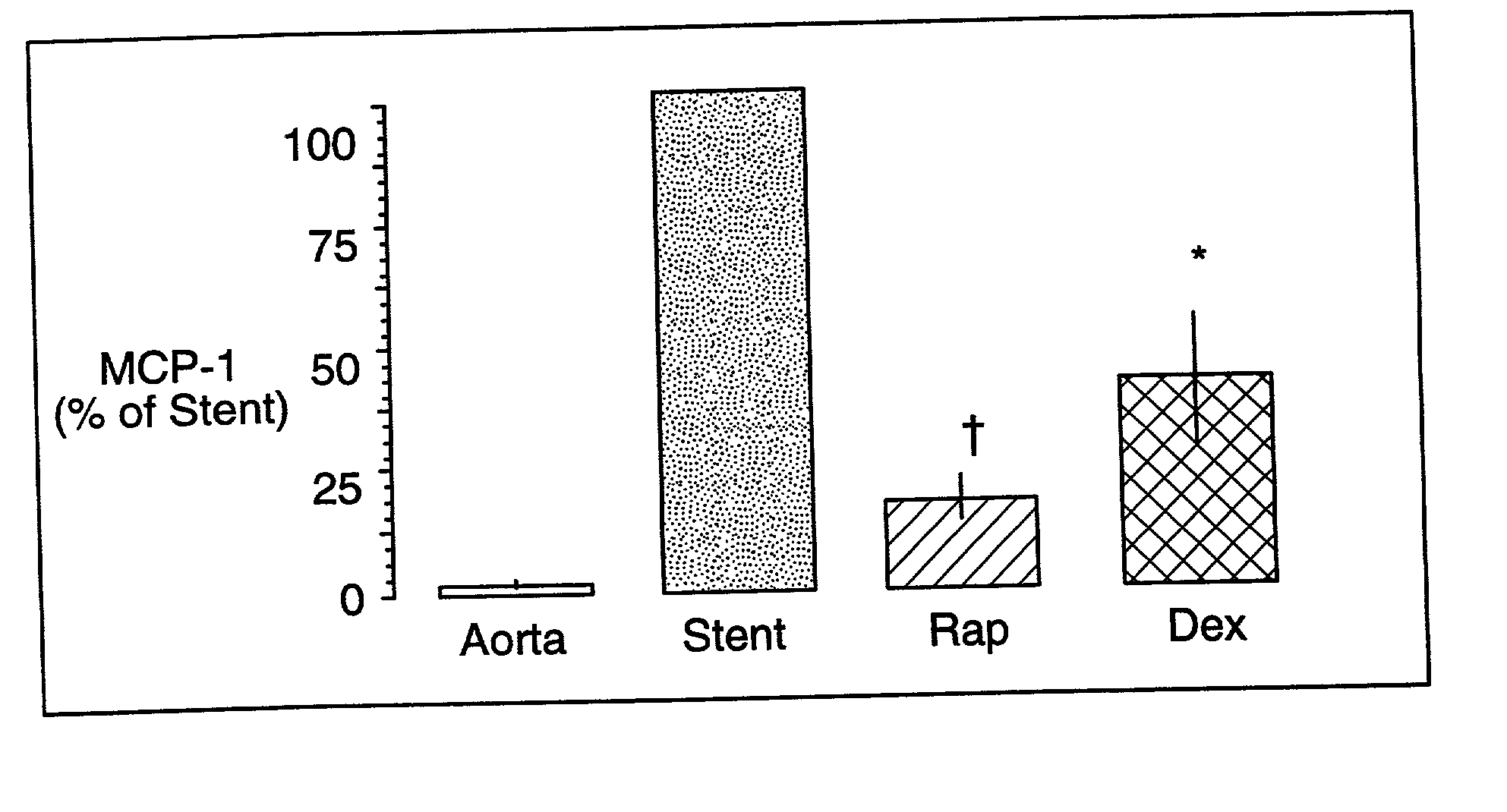
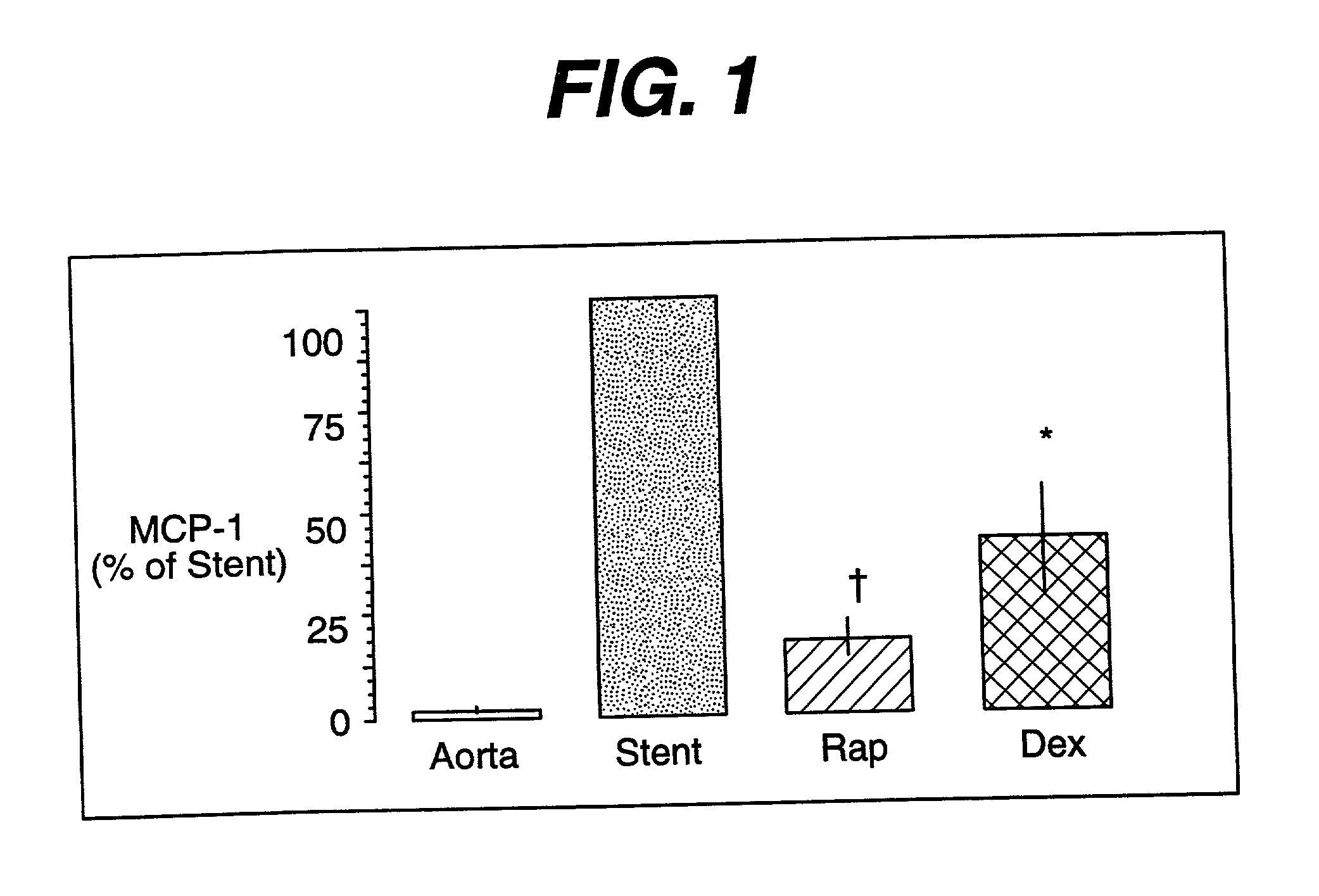
Drug/drug delivery systems for the prevention and treatment of vascular disease
InactiveUS20020007215A1Prevent proliferationGood effectOrganic active ingredientsStentsVascular diseaseWhole body
A drug and drug delivery system may be utilized in the treatment of vascular disease. A local delivery system is coated with rapamycin or other suitable drug, agent or compound and delivered intraluminally for the treatment and prevention of neointimal hyperplasia following percutaneous transluminal coronary angiography. The local delivery of the drugs or agents provides for increased effectiveness and lower systemic toxicity.
Owner:WYETH LLC
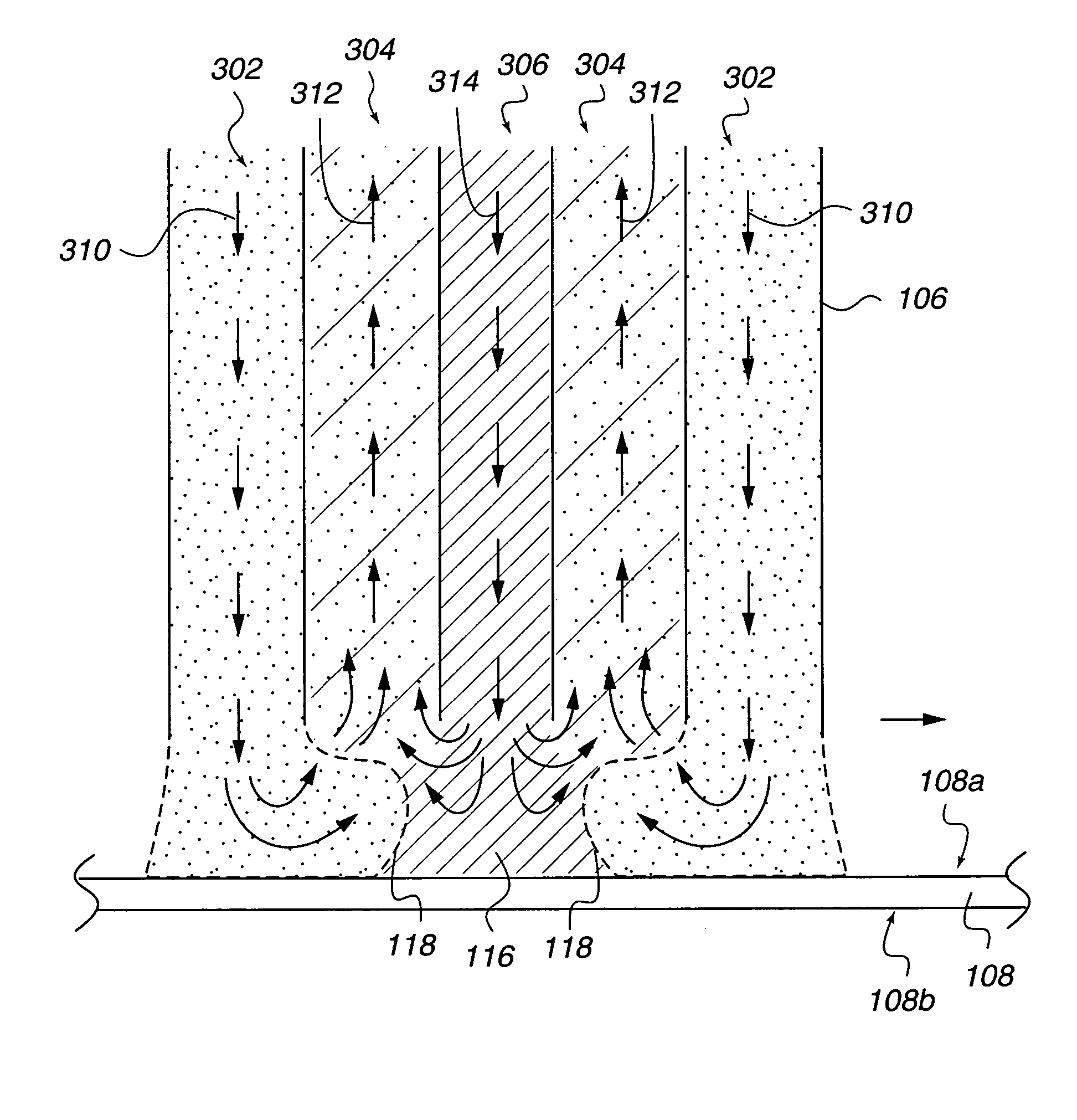
Method and apparatus for processing wafer surfaces using thin, high velocity fluid layer
InactiveUS20050145265A1Efficient processingReducing unwanted fluidElectrolysis componentsDrying solid materials without heatHigh velocityBiomedical engineering
Among the many embodiment, in one embodiment, a method for processing a substrate is disclosed which includes generating a fluid layer on a surface of the substrate, the fluid layer defining a fluid meniscus. The generating includes moving a head in proximity to the surface, applying a fluid from the head to the surface while the head is in proximity to the surface of the substrate to define the fluid layer, and removing the fluid from the surface through the proximity head by a vacuum. The fluid travels along the fluid layer between the head and the substrate at a velocity that increases as the head is in closer proximity to the surface.
Owner:LAM RES CORP
Wireless Power Supply System and Wireless Power Supply Method
ActiveUS20080122297A1Improve convenienceMeet needsElectrical testingLoop antennasElectric power systemComputer terminal
An object is to provide a system for improving convenience for users, by which a portable electronic device or the like can be charged even in a place where utility power is not available. Another object is to provide a system which allows a service provider to easily perform customer management. A wireless power supply system includes a power storage device having a power storage portion, a terminal charging device for wirelessly supplying electric power to the power storage device, and a management server having user information. Electric power can be supplied to specified users by intercommunication of user information between the power storage device and the terminal charging device and between the terminal charging device and the management server.
Owner:SEMICON ENERGY LAB CO LTD
Method, apparatus and computer readable medium for multiple messaging session management with a graphical user interface
A graphical user interface displays a unique graphical indexing element such as a tab for each engaged and non-engaged messaging session. The user chooses which messaging session to make engaged by selecting its graphical indexing element. The graphical indexing elements have various distinctive characteristics to indicate the status of their respective messaging sessions, such as engaged, non-engaged with no unread messages, or non-engaged with at least one unread message. The messaging sessions may all be docked, in which event the engaged messaging session is displayed in a window pane set and the other messaging sessions are not displayed, or may be selectively undocked, in which event the engaged messaging session and the undocked messaging sessions are displayed in respective window pane sets. The engaged window pane set supports the communication of original or predefined messages between the user's digital device and the pal's messaging-enabled digital device, regardless of capability.
Owner:ECRIO
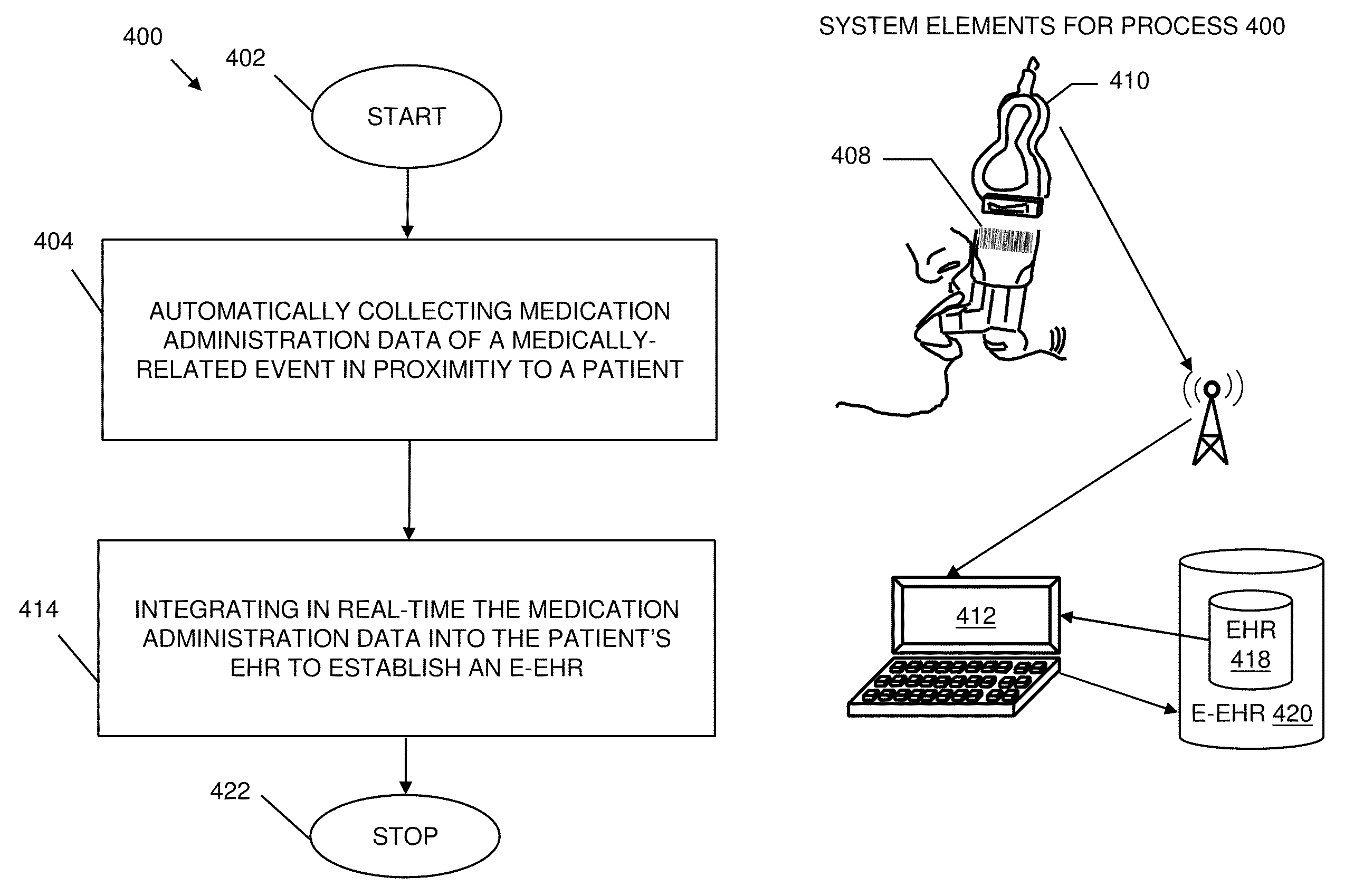
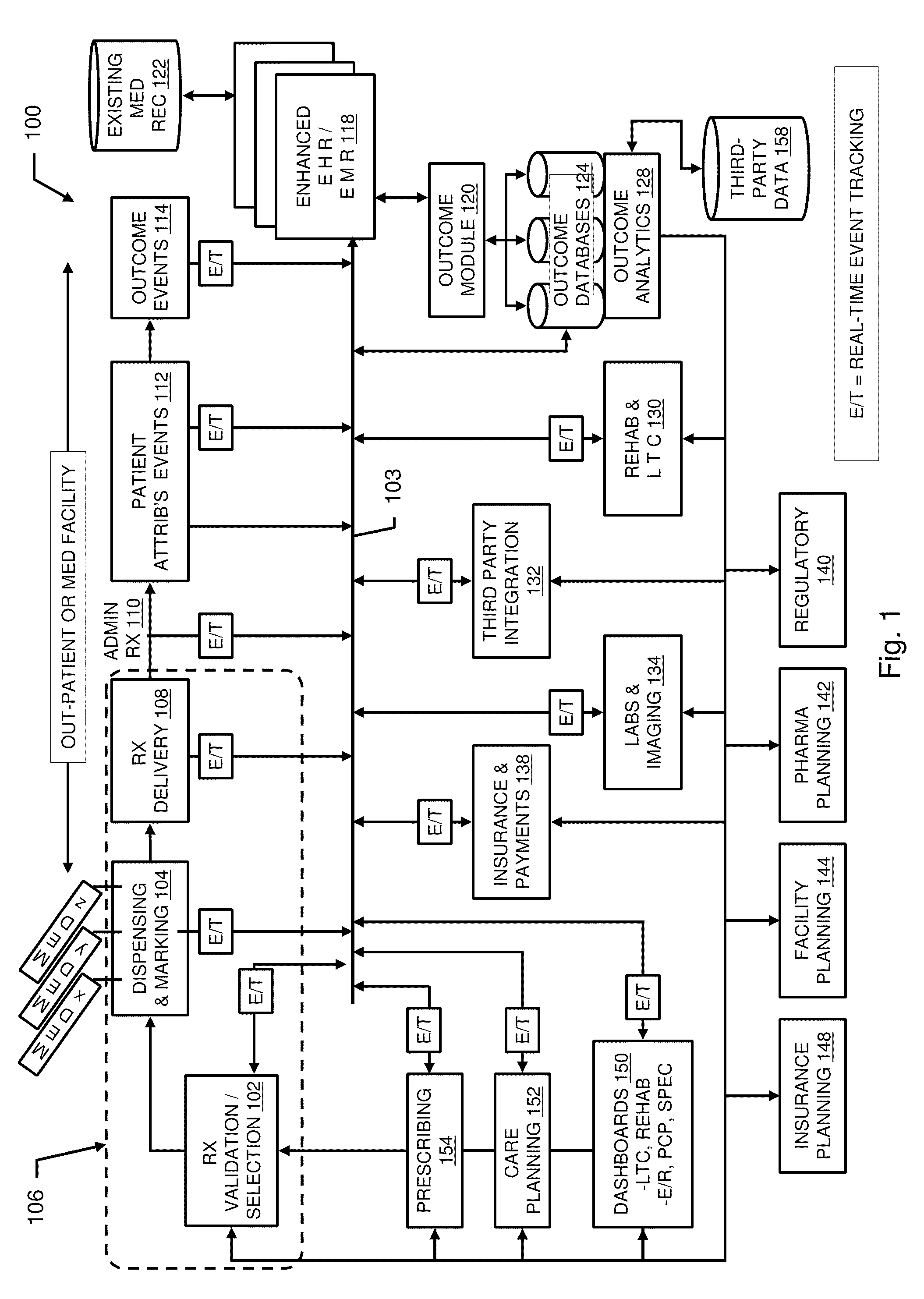
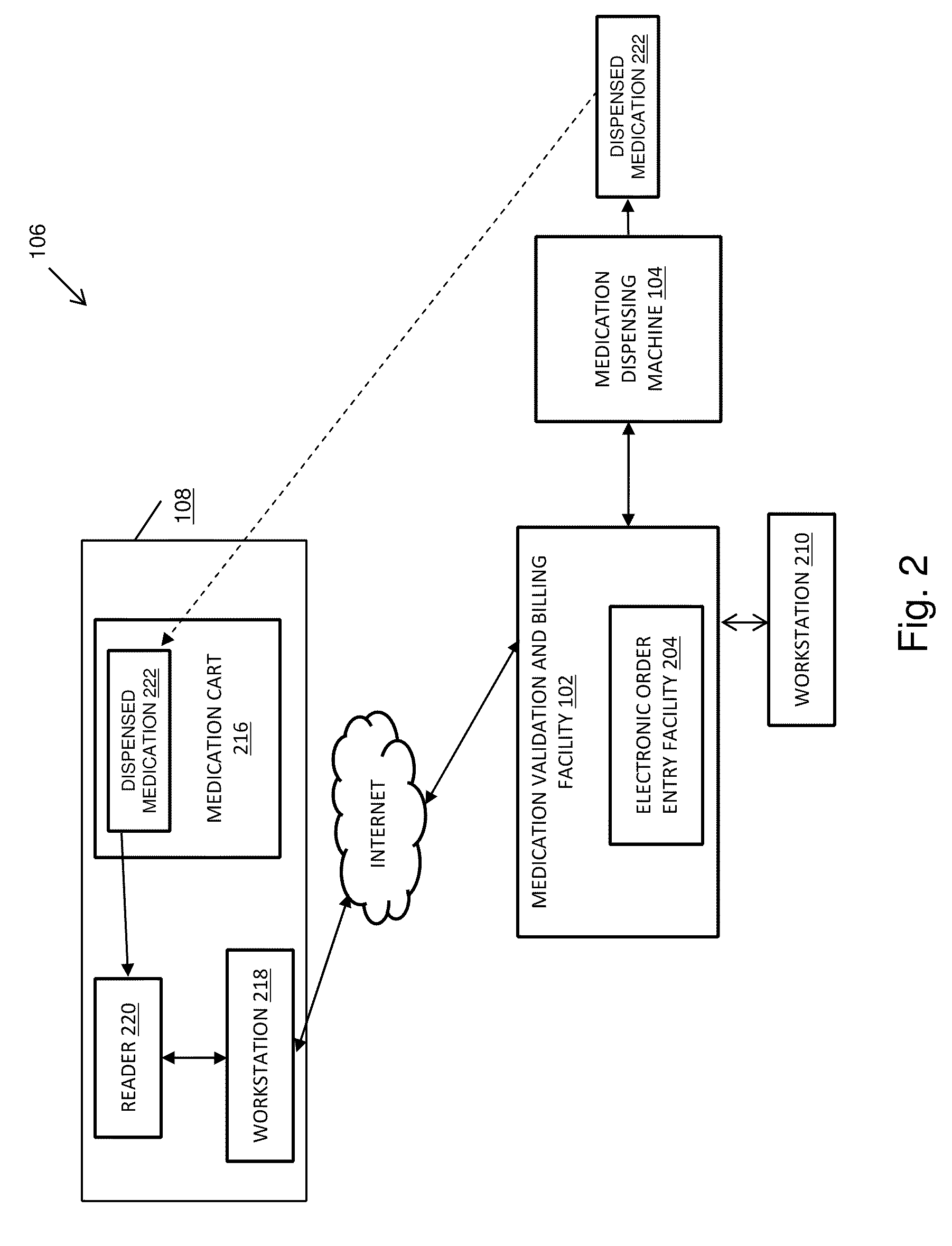
Pharmacy management and administration with bedside real-time medical event data collection
Methods and systems for automatically establishing an enhanced electronic health record (EHR) for a patient include an automatic data collection facility that collects data of a medically related event in proximity to a patient upon occurrence of the event. The collected data may include medication administration data such as medication, time of administration, administration of a dosage of medication, reaction data, and the like. The collected data is communicated to a real-time data integration facility that automatically integrates the data with a patient's electronic health record to establish an enhanced electronic health record.
Owner:MILLENNIUM PHARMACY SYST LLC
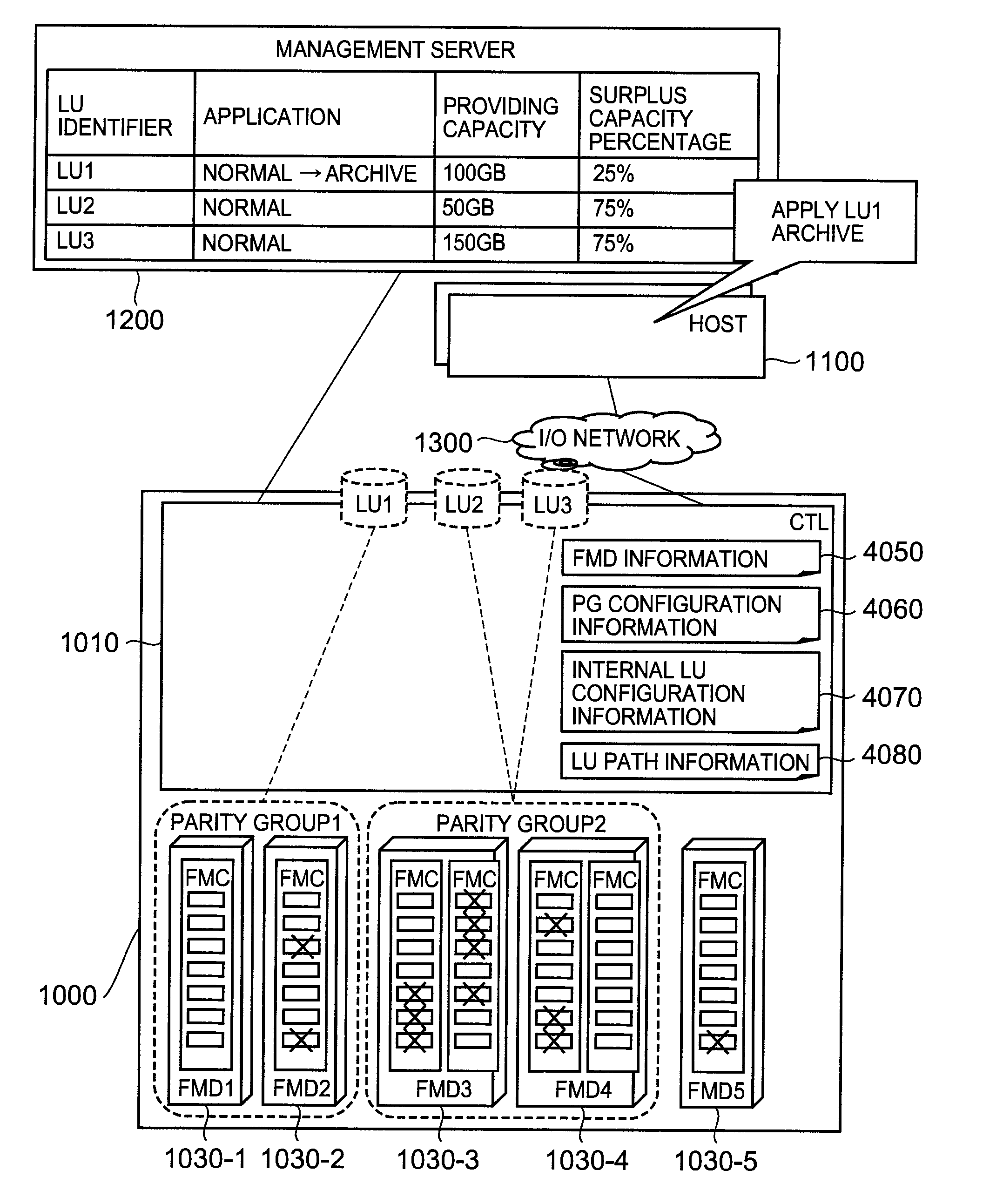
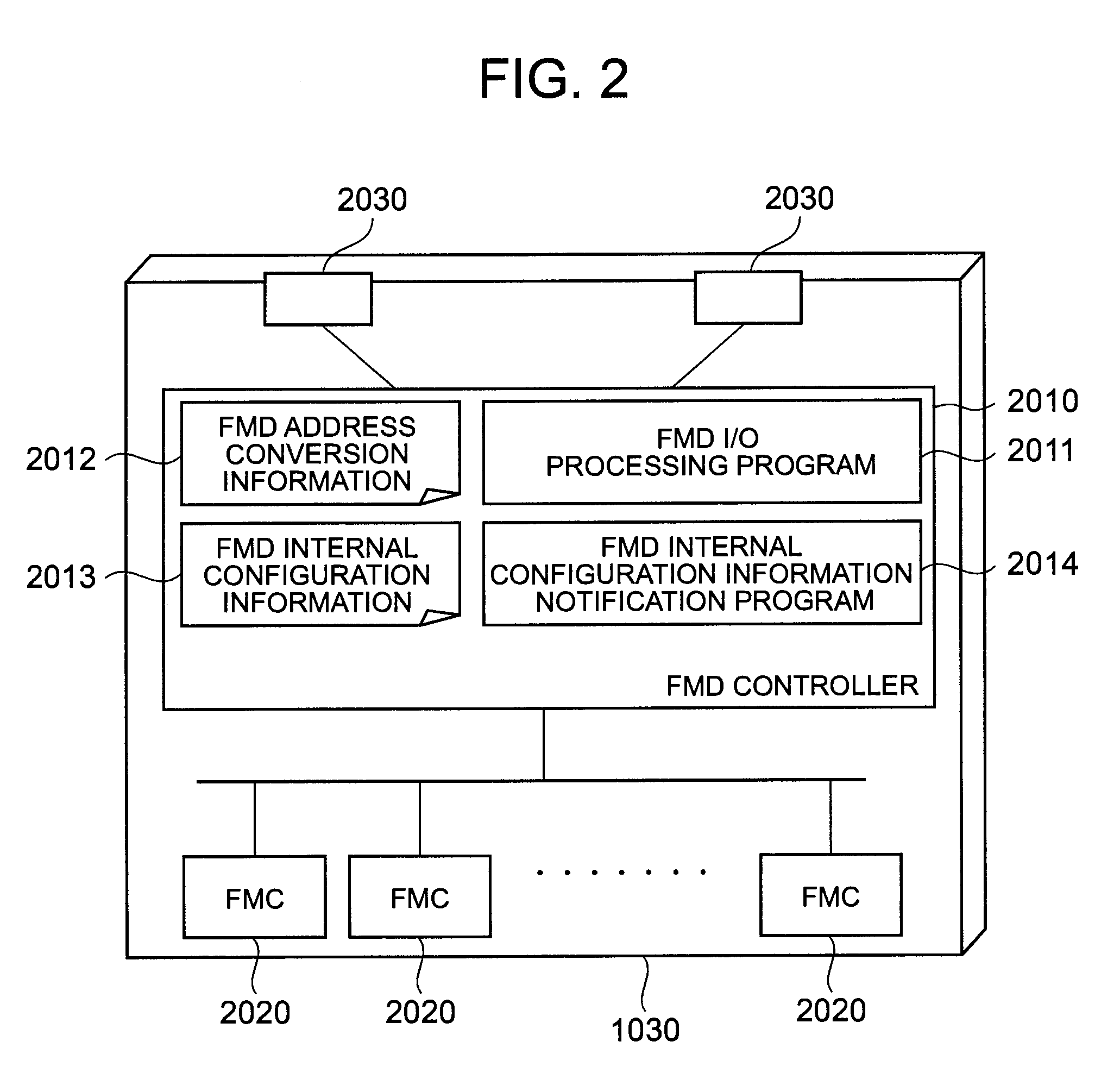
Method for managing storage system using flash memory, and computer
ActiveUS20100325345A1Easy to manageError detection/correctionMemory adressing/allocation/relocationAnd logic unitFlash memory
To facilitate the management of a storage system that uses a flash memory as a storage area. A controller of the storage system provided with a flash memory chip manages a surplus capacity value of the flash memory chip, and transmits a value based on the surplus capacity value to a management server, on the basis of at least one of a definition of a parity group, a definition of an internal LU, and a definition of a logical unit. The management server displays a state of the storage system by using the received value based on the surplus capacity value.
Owner:HITACHI LTD
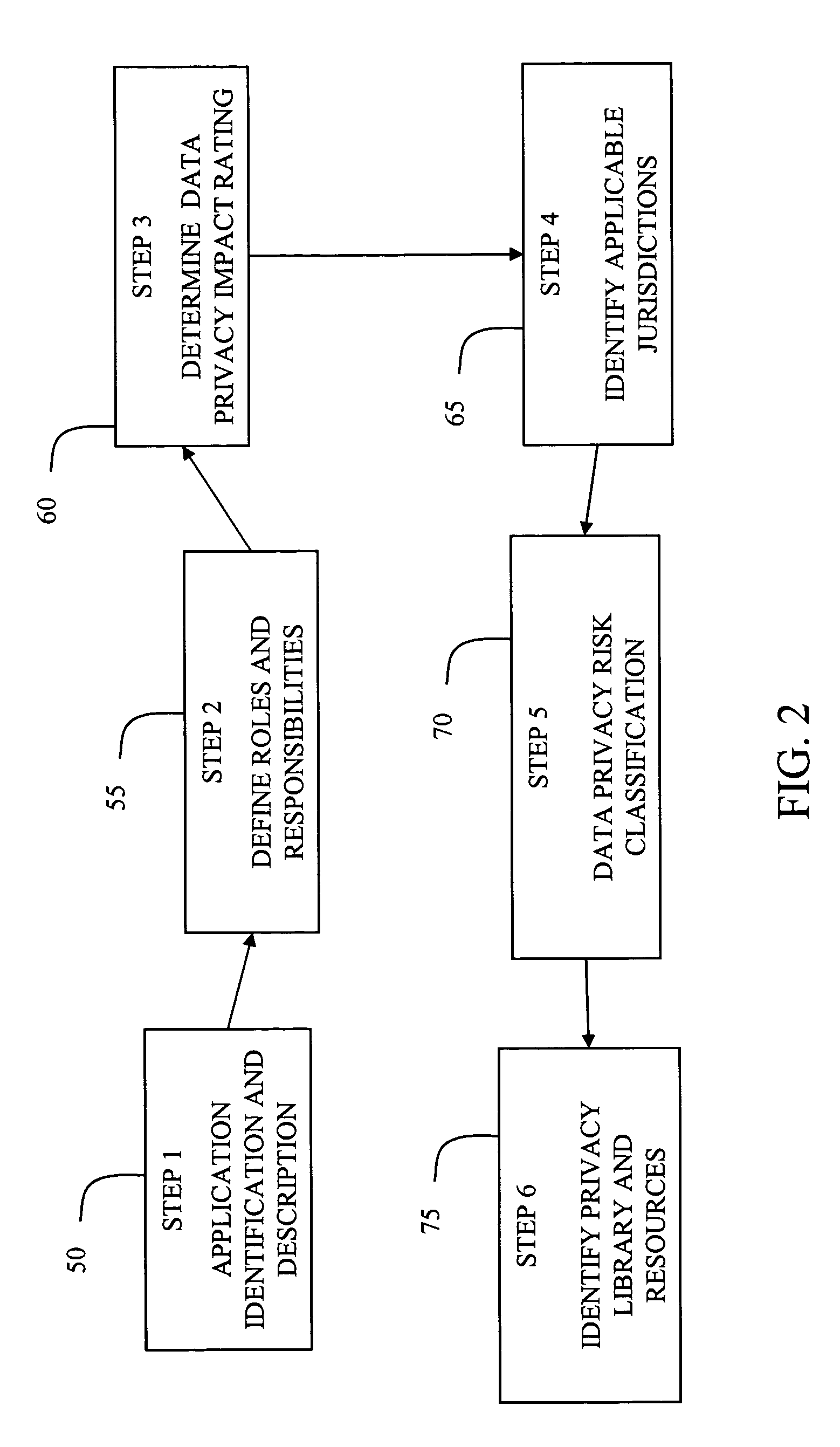
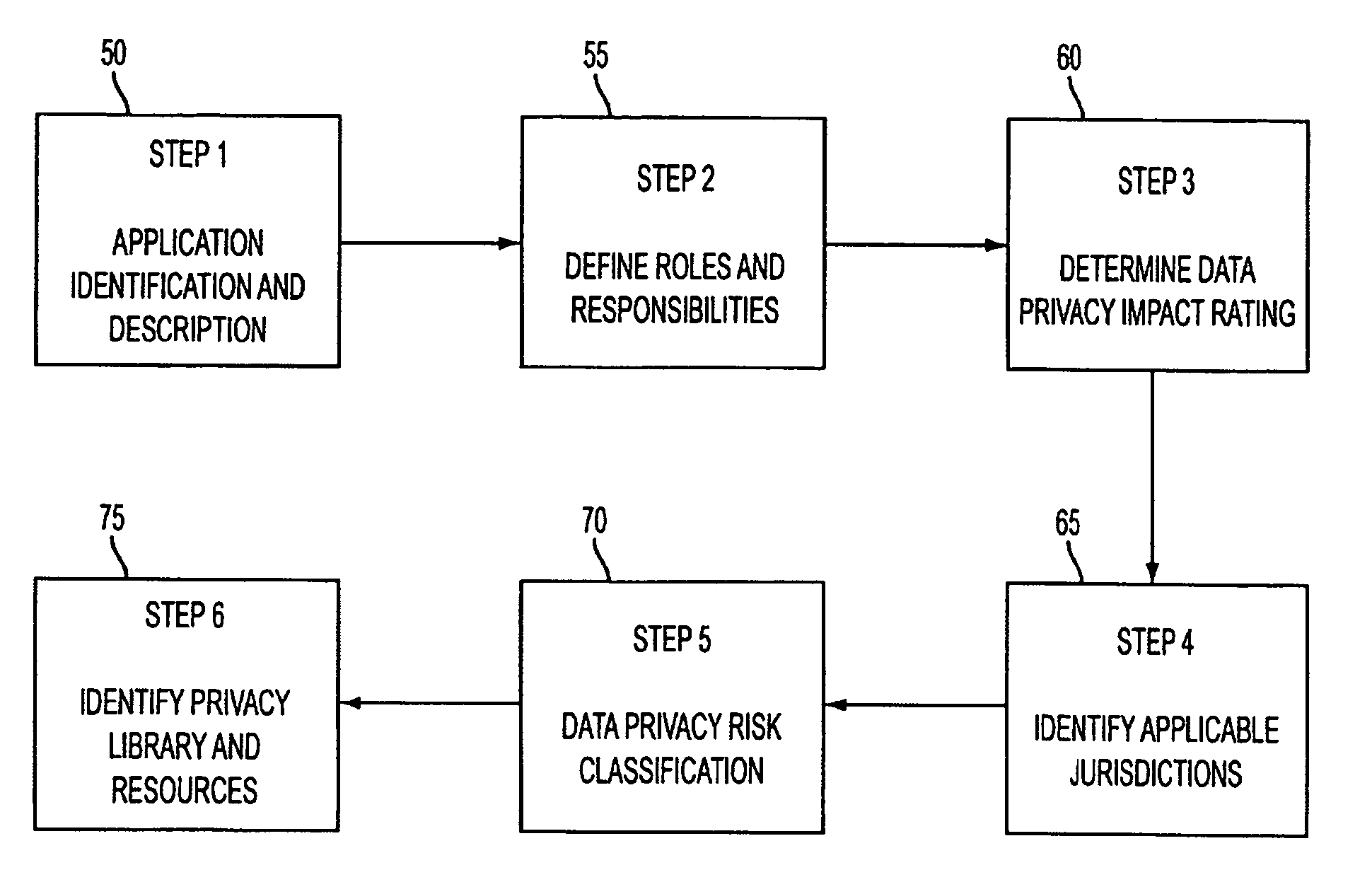
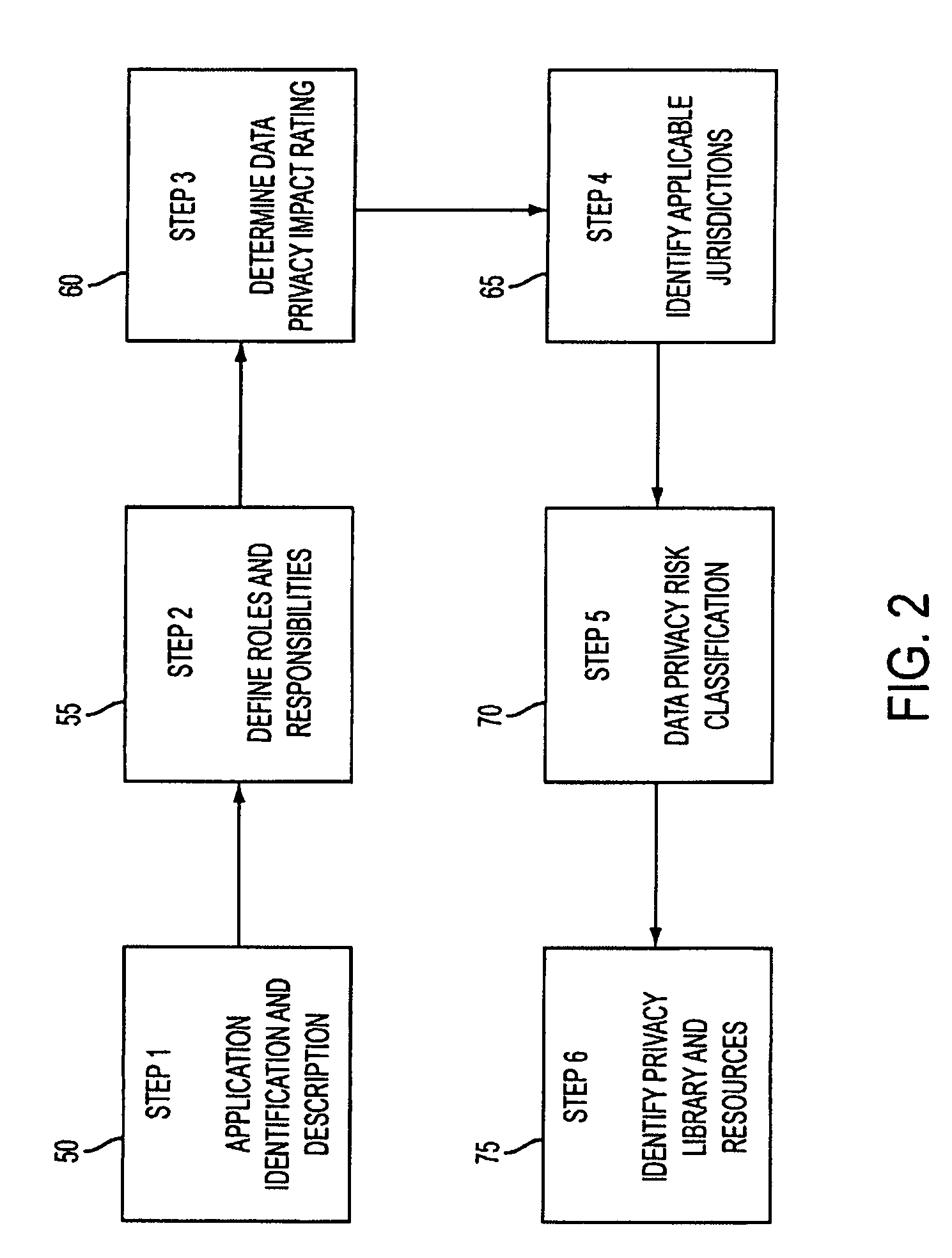
System and method for managing data privacy
ActiveUS7234065B2Easy to manageSpeed up the processUser identity/authority verificationUnauthorized memory use protectionInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
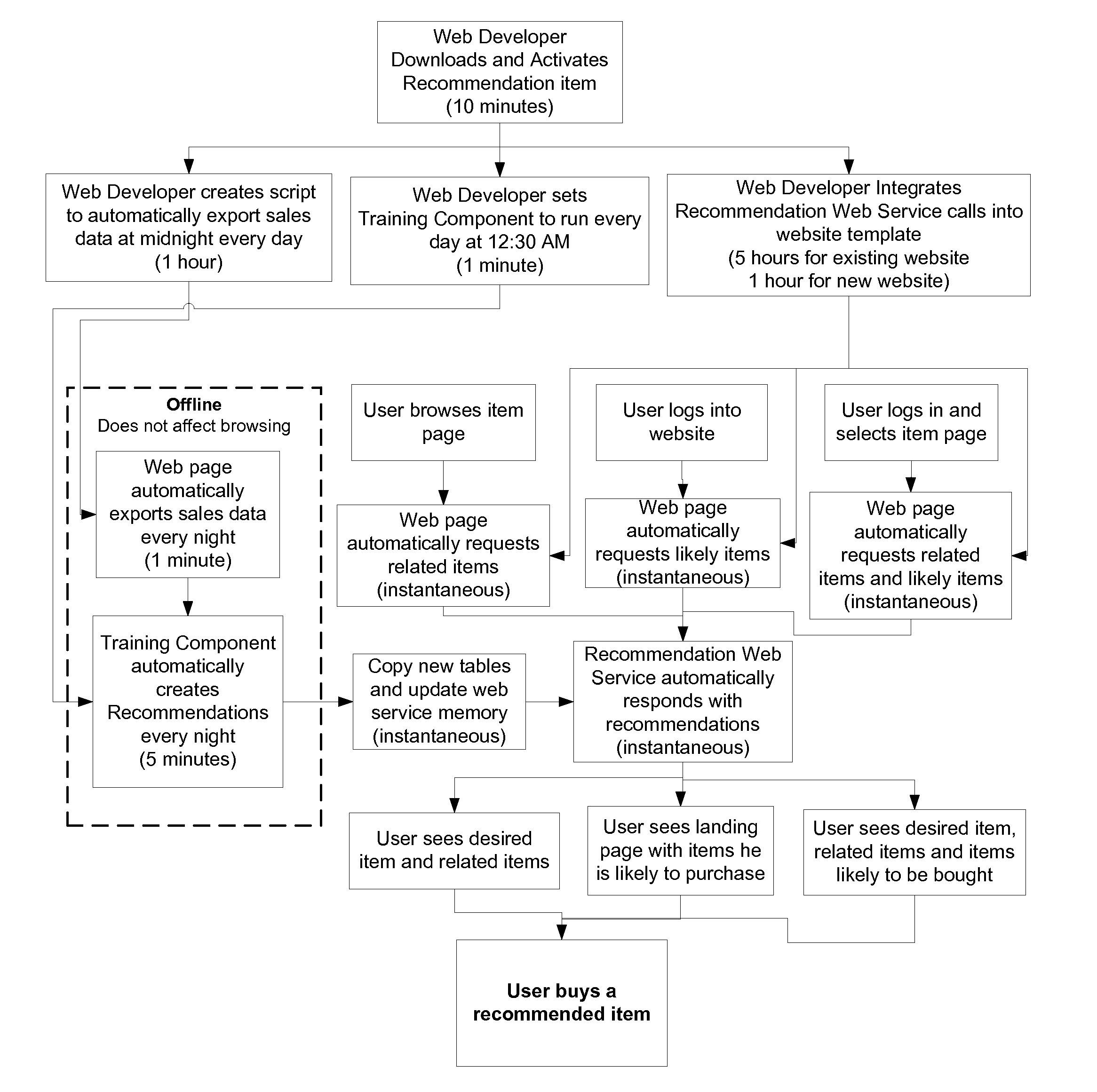
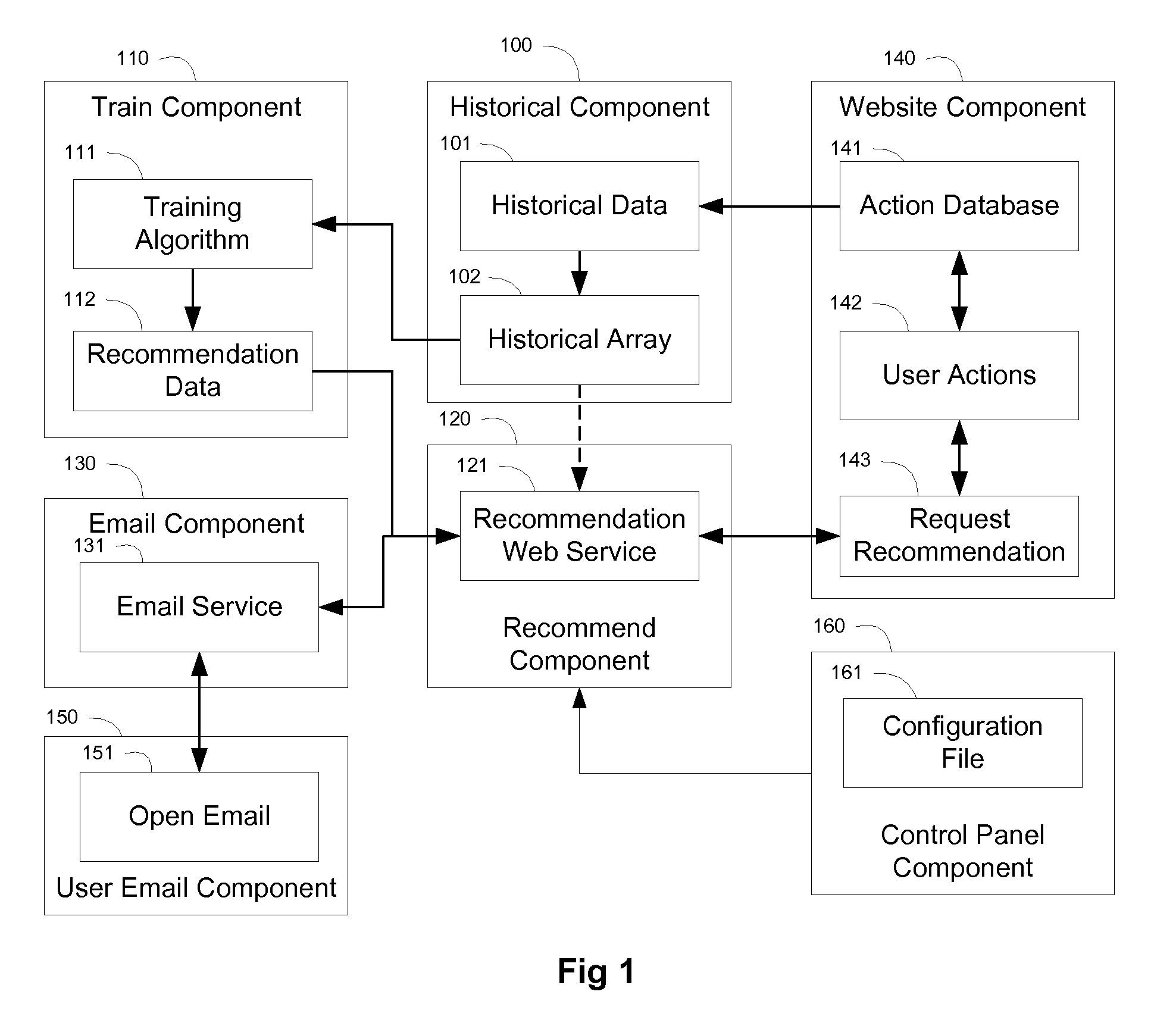
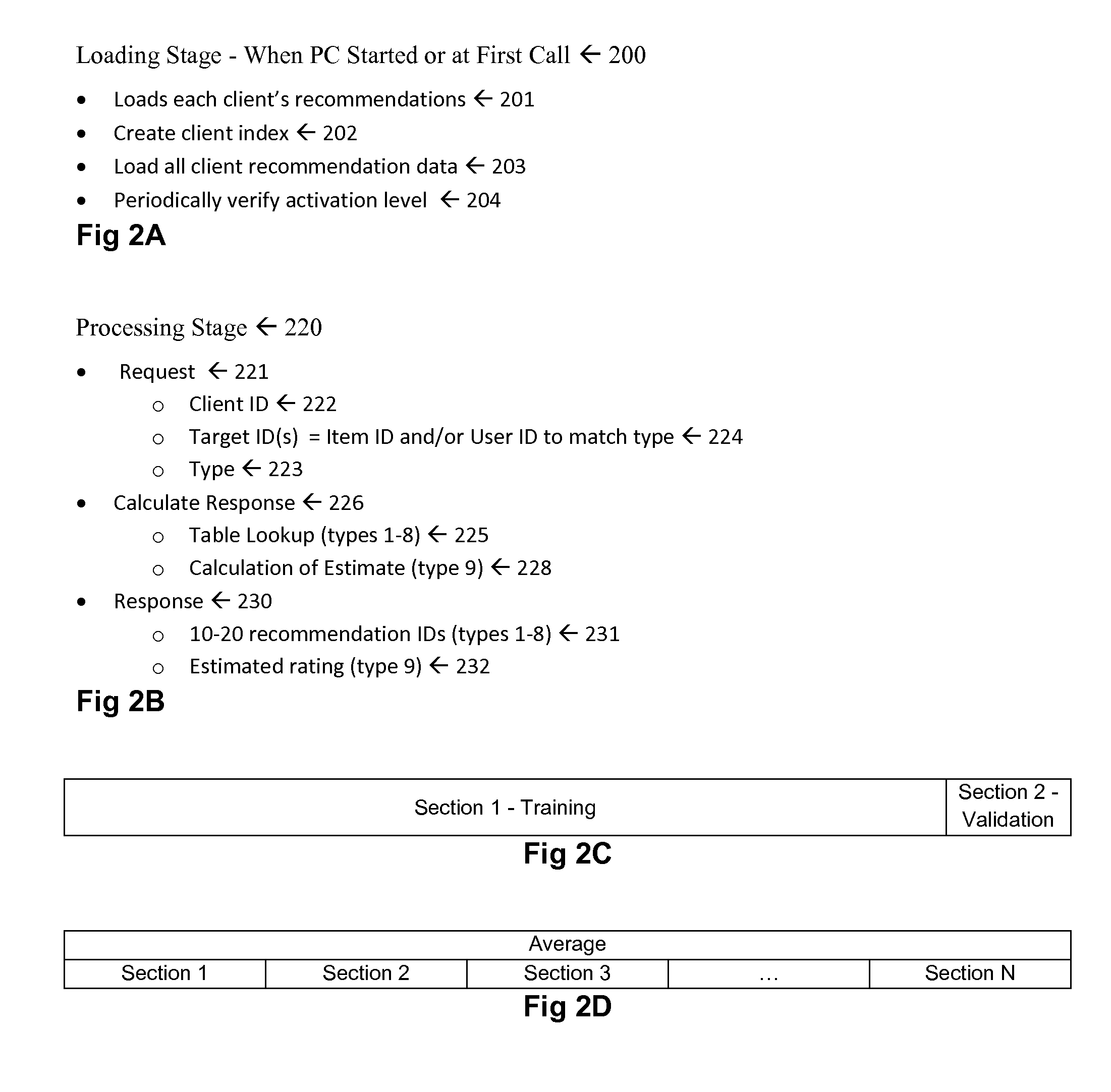
Recommendation Systems
InactiveUS20100268661A1Increase diversityFirmly connectedDigital data processing detailsSpecial data processing applicationsClient-sideOff the shelf
This invention deals with recommendation systems. The first embodiment is an off-the-shelf recommendation system is described, where it is easy to integrate with the website database and uses a web service for recommendations, as well as easy to integrate with email. The system receives client ID, item ID and user ID, and returns recommended item IDs. The recommendations include similar items, related items, related users, items likely to be acted upon by a given user (labeled likely items), and users likely to act upon an item (labeled likely users). The recommendations include categorical training, where recommended items are based upon similar categories, where the category types include as product type and brand. The recommendations include similar-to-related training, where similar items are used to find related items. These two intelligent methods work for items with no, few or numerous actions.
Owner:B7 INTERACTIVE LLC
Methods and devices for managing gaming networks
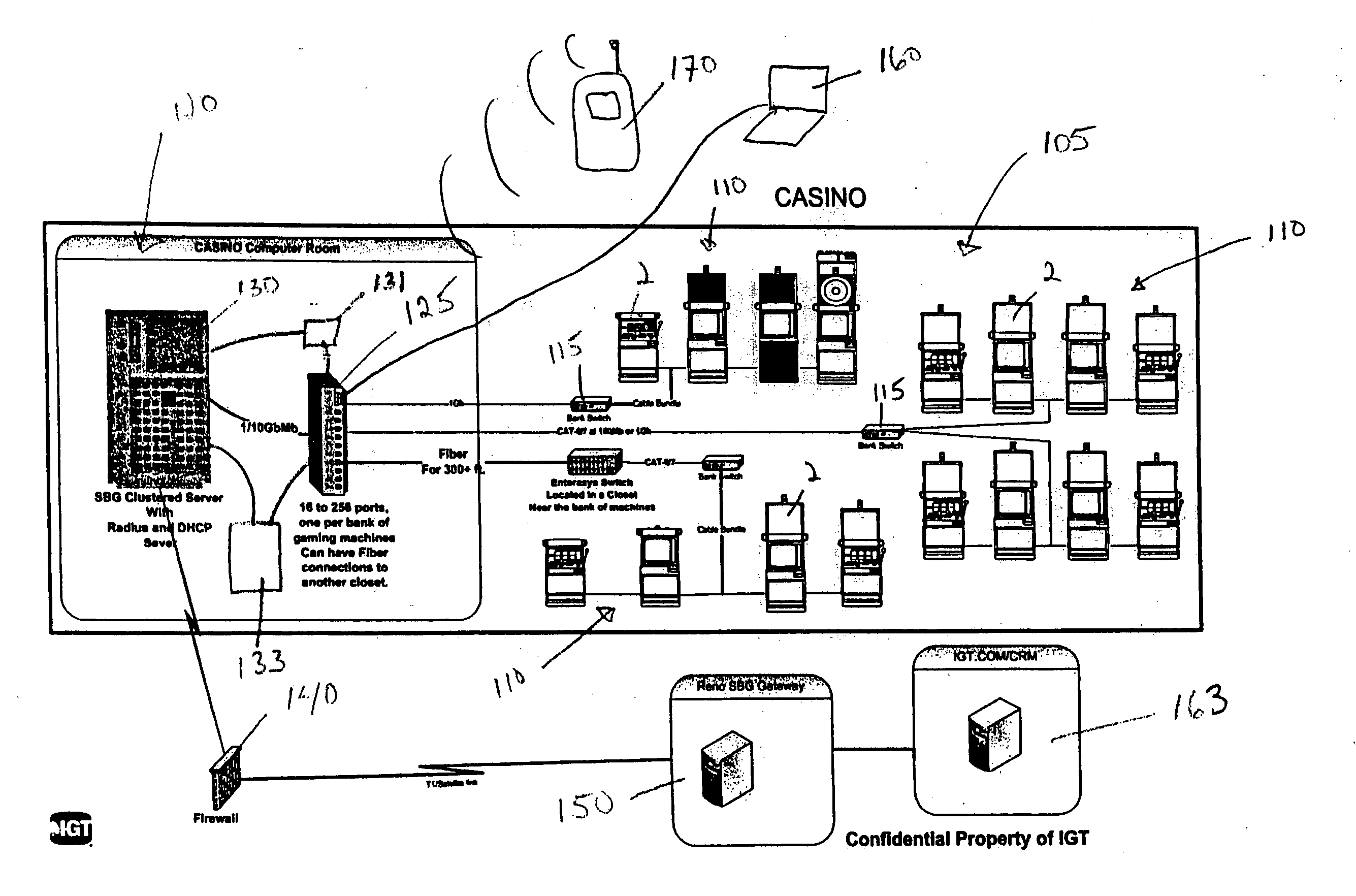
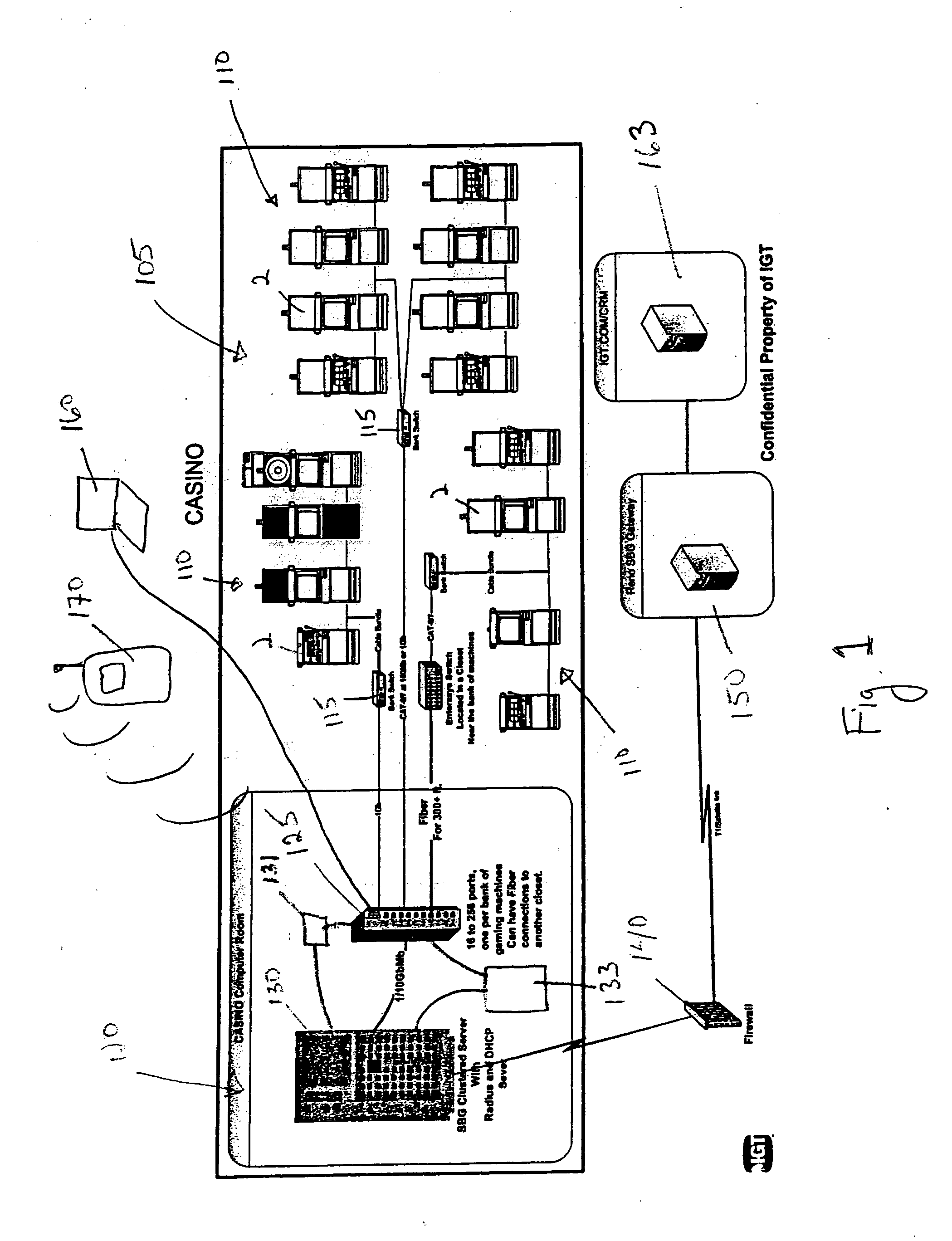
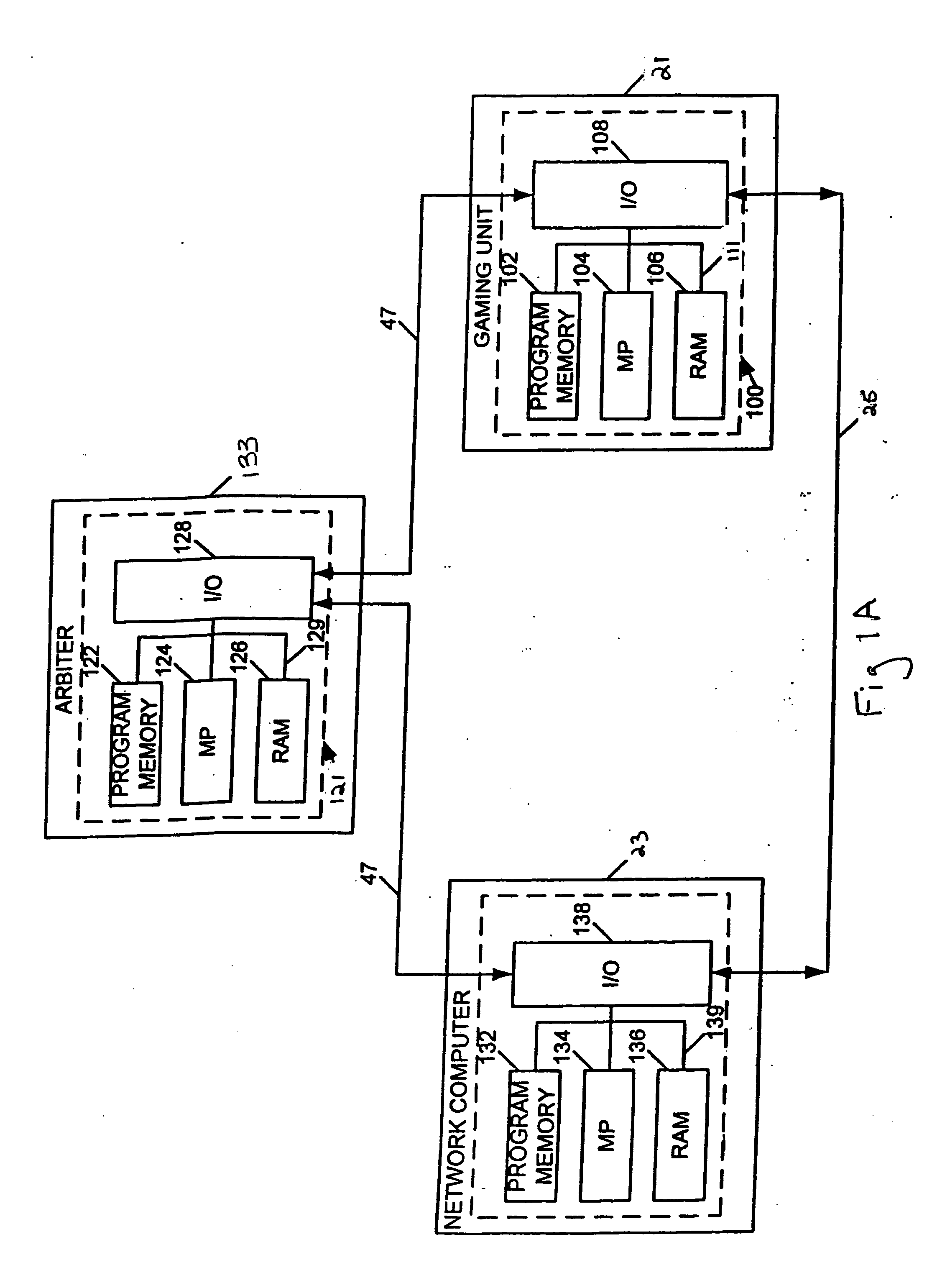
InactiveUS20070026935A1Easy to manageApparatus for meter-controlled dispensingVideo gamesHuman–computer interactionAuthentication
Some implementations of the invention provide methods and devices for managing gaming establishments and for provisioning and configuring gaming machines. Some such implementations allow a user to configure one or more gaming machines via an easy-to-use GUI displayed on a wired or a wireless device, such as a laptop, a PDA, a work station or other host device. Gaming machine parameters that can be changed according to some implementations of the invention include game denominations, games to enable or disable, game payback percentage, deal speed, volume level and enabling or disabling a tournament. Some preferred implementations of the invention provide an event scheduler that allows a user either to cause events to occur immediately or schedule certain events to occur at a future time. Some implementations of the invention allow a user to generate activity reports highlighting configuration changes, user logins, game set additions, and / or game downloading. Novel methods and devices for authentication are also provided herein. Some implementations of the invention allow a user to manage easily game downloads to a local server and / or to each gaming machine.
Owner:IGT
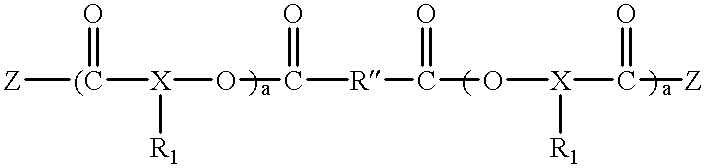
Polyester polyether block copolymers
The present invention relates to novel bioabsorbable polymeric compositions based upon AB polyester polyether or related diblocks and triblocks. Compositions according to the present invention may be used in medical applications, for example, for reducing or preventing adhesion formation subsequent to medical procedures such as surgery, for producing surgical articles including stents and grafts, as coatings, sealants, lubricants, as transient barriers in the body, for materials which control the release of bioactive agents in the body, for wound and bum dressings and producing biodegradable articles, among numerous others.
Owner:YISSUM RES DEV CO OF THE HEBREWUNIVERSITY OF JERUSALEM LTD
System and method for managing data privacy
InactiveUS20070283171A1Easy to manageSpeed up the processUnauthorized memory use protectionHardware monitoringInternet privacyKey issues
A system and method for assessing the risk associated with the protection of data privacy by software application. A decision engine is provided to assess monitor and manage key issues around the risk management of data privacy. The system creates a core repository that manages, monitors and measures the data privacy assessments of applications across an institution (e.g., a corporation). The system and method employs automated questionnaires that require responses from the user (preferably the manager responsible for the application). The responses are tracked in order to evaluate the progress of the assessment and the status of the applications with respect to compliance with the enterprise's data privacy policies and procedures as well as the regulations and laws of the jurisdictions in which the application is operated. Once a questionnaire has been completed, the application is given ratings both with respect to the data privacy impact of the application and the application's compliance with the data privacy requirements. If a risk exists, a plan for reducing the risk or bringing the application into compliance can be formulated, and progress towards compliance can be tracked. Alternatively, an identified exposure to risk can be acknowledged through the system, which requires sign off by various higher level managers and administrators.
Owner:JPMORGAN CHASE BANK NA
Content delivery network system and method for building the same
InactiveUS20020116481A1Optimize networkSolve the real problemData switching by path configurationMultiple digital computer combinationsClient-sideContent delivery network
A content delivery network system is disclosed. The system comprises a communication network, a first network node for providing services for clients to access network, a second network node for managing hosts for network content providers and a third network node, wherein said third network node sets a default route and a VPN tunnel between the first and second network nodes, and provides a cache server at the bandwidth outlet of the first network node, said cache server stores a information content which has been requested and transmitted. When the client request an information content, the third network node searches the cache server. If the information content is found, the cache server provides said information content to the client directly. If the information content is not found, the cache server sends a request for catching the information content to the second network via the VPN tunnel, and transmits the information content to the client via the default route. The cache server records the data of the transmitted information content. The recorded data is provided to the second network node, so that the second network node can bill the network content provider accordingly.
Owner:LEE KIM MAN
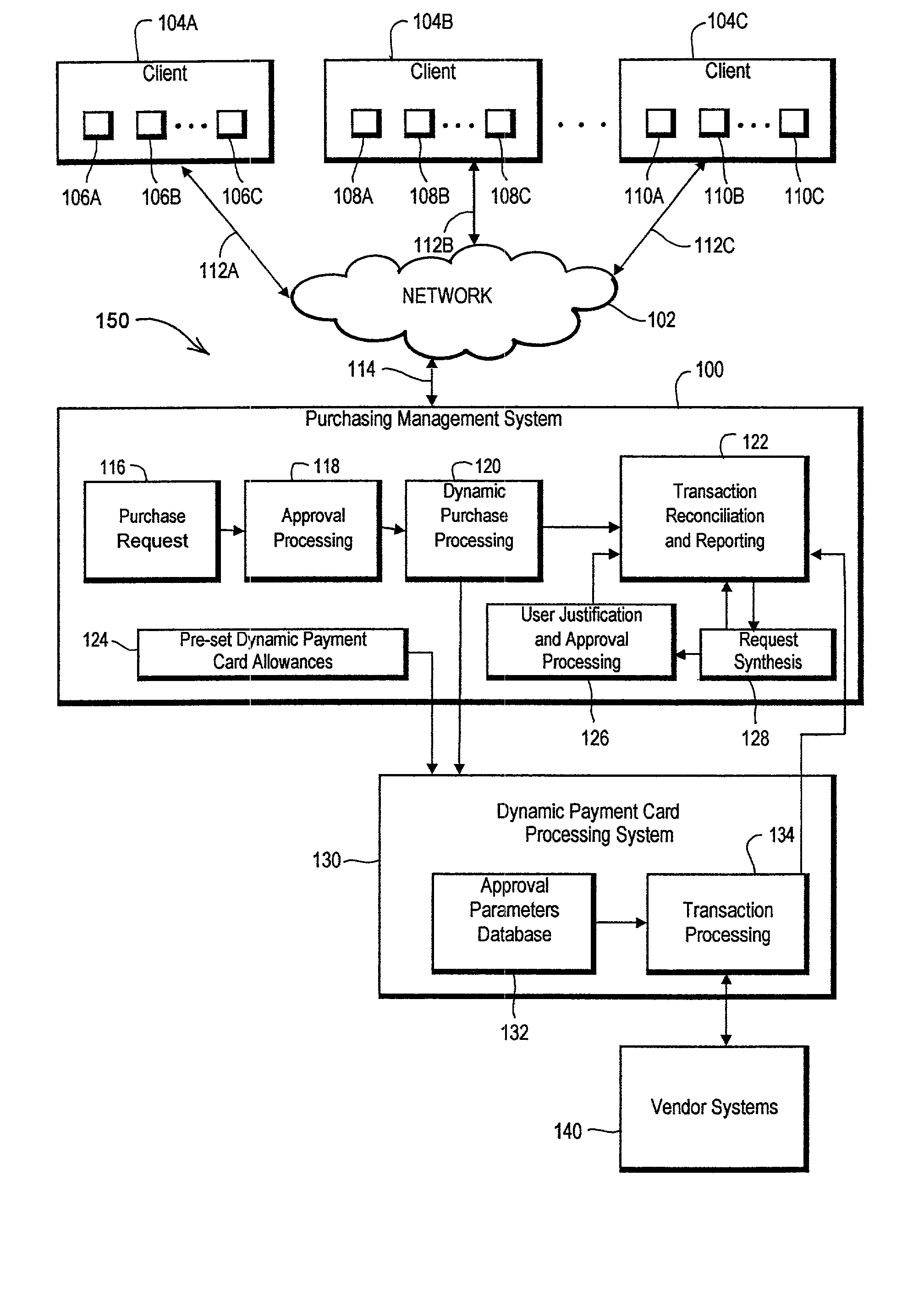
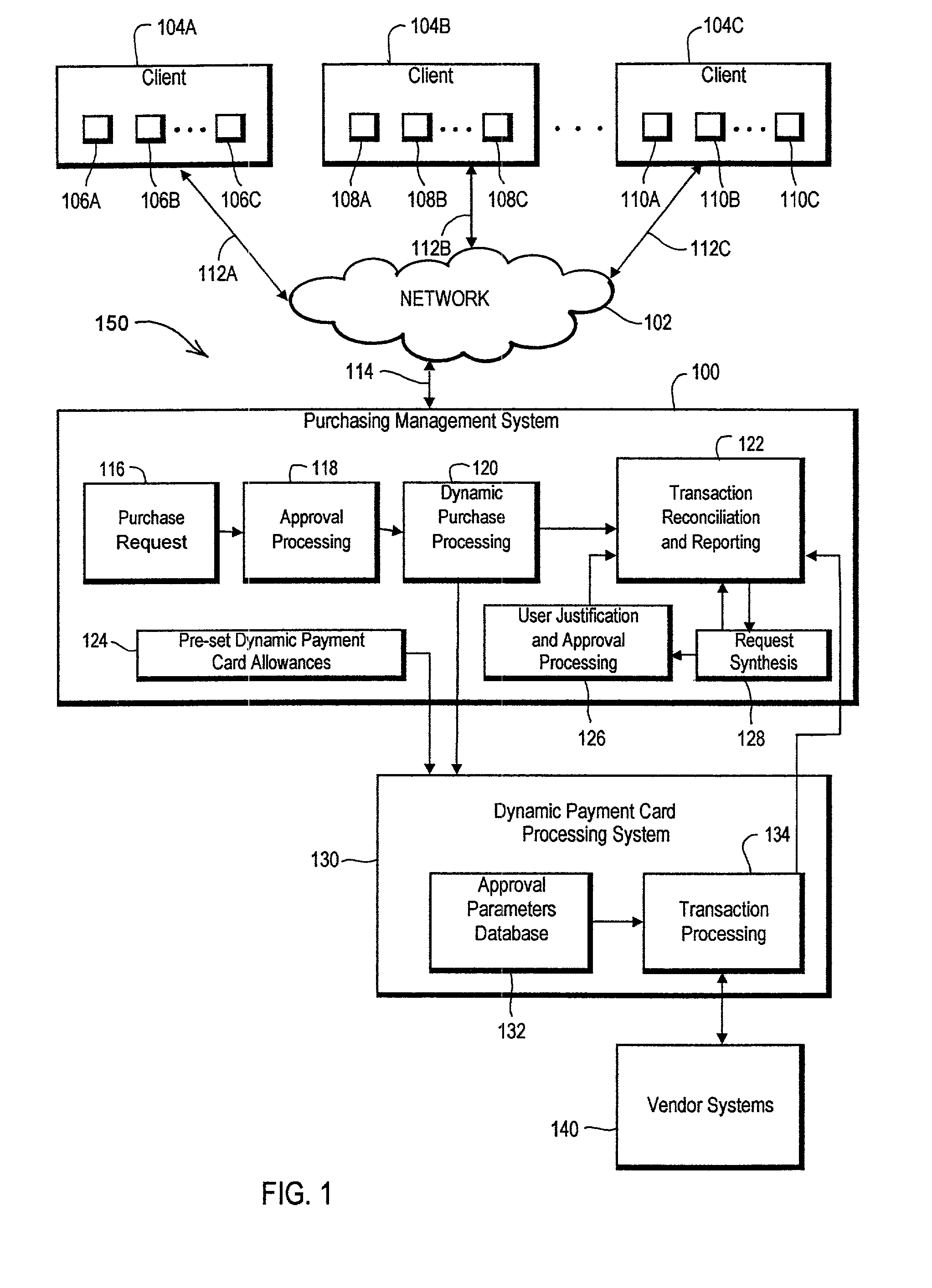
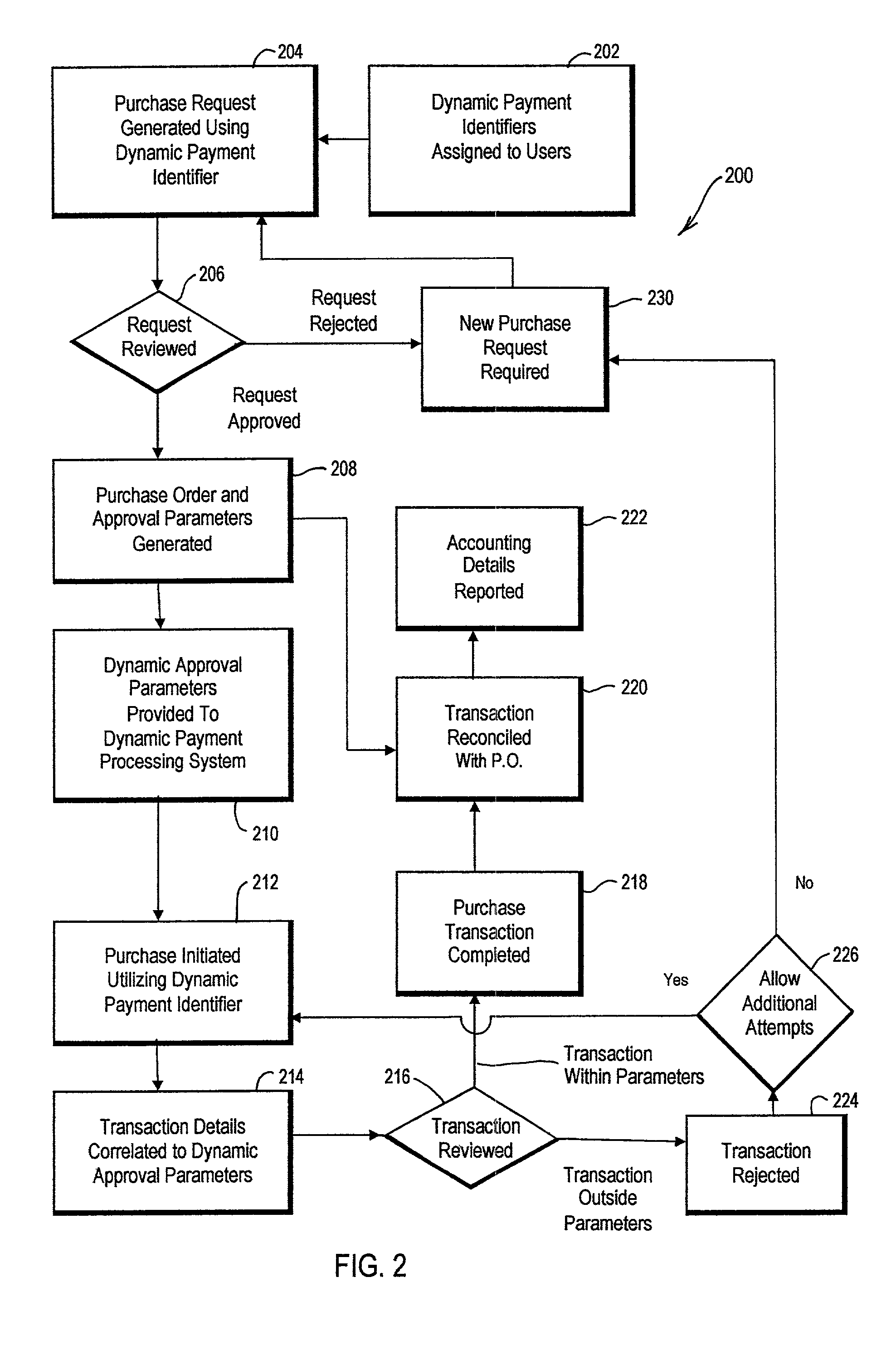
Dynamic payment cards and related management systems and associated methods
InactiveUS7319986B2Efficient managementEasy to manageFinanceCoded identity card or credit card actuationPaymentDynamic management
Dynamic payment cards and related dynamic payment card management systems and associated methods are disclosed that allow for the efficient management of corporate purchasing needs. The dynamic payment cards can be traditional payment cards with card control settings that are dynamically managed. In addition, a dynamic card management system can automatically interface with card processor systems to dynamically modify these card control settings, and a purchasing management system or other request and approval workflow engine can provide an interface between a company and the dynamic card management system. More generally, an advantageous solution for purchasing management is disclosed that utilizes dynamically or actively managed approval parameters to help control transaction authorization determinations associated with purchasing mechanisms. These dynamic approval parameters can be generated and / or managed through the application of configurable company purchasing policies and rules, and these dynamic approval parameters can be stored, for example, by a processing system that makes authorization determinations when transactions are initiated using the purchasing mechanisms.
Owner:BANK OF AMERICA CORP
Delivering targeted advertising to mobile devices
InactiveUS20060190331A1Simple methodEasy to manageDigital data information retrievalAdvertisementsTargeted advertisingClient-side
A method of delivering advertising items to a client at a portable device is provided. A client ID is sent to a host server. A downloaded advertising item is produced relative to a product or service from the host server. The downloaded advertising item is parsed and stored. In response to the parsing and storing, displaying the advertising item is displayed to the client at the mobile device.
Owner:CELLFIRE
Fat analysis for optimized sequential cluster management
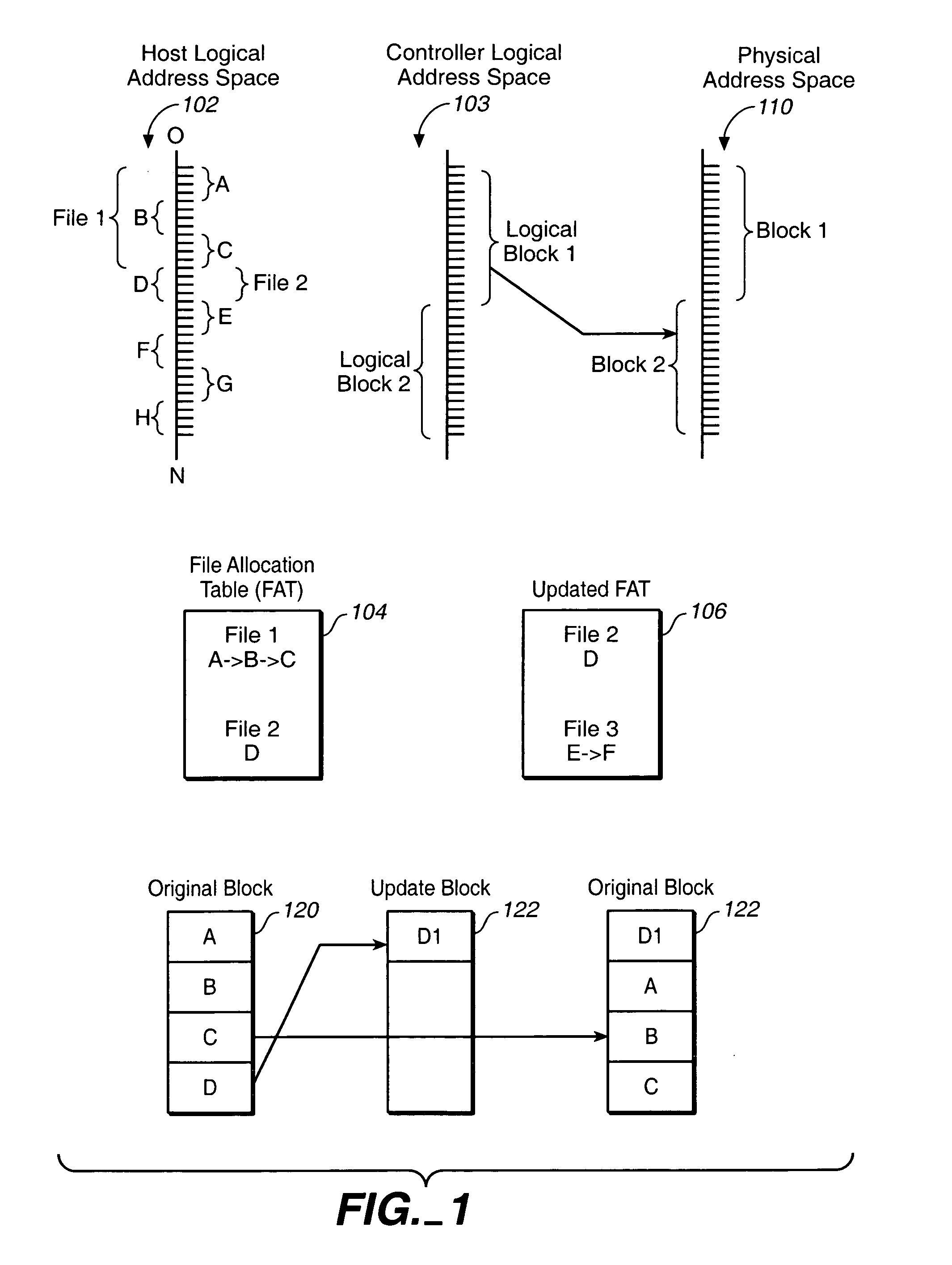
ActiveUS20060020745A1Free spaceEfficient in operationMemory adressing/allocation/relocationSpecial data processing applicationsFile systemVolatile memory
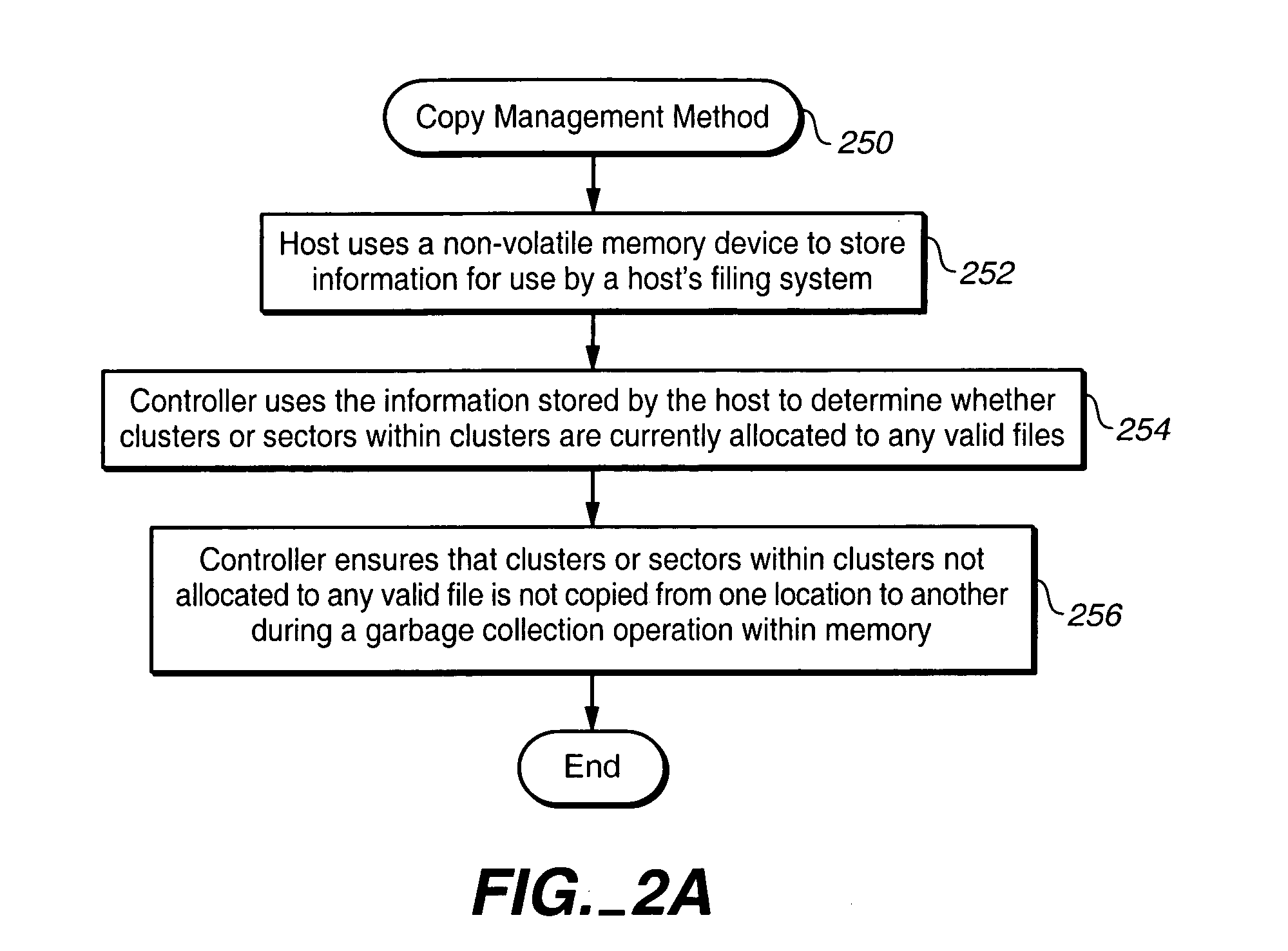
Techniques for managing data in a non-volatile memory system (e.g., Flash Memory) are disclosed. A controller can use information relating to a host's file system, which is stored by the host on non-volatile memory, to determine if one or more clusters (or sectors with clusters) are currently allocated. The controller can use the information relating to the host's file system to identify when the host is sending data to the next free cluster and to store such data in a sequential format by copying data from other locations in the non-volatile memory.
Owner:SANDISK TECH LLC
Social Help Network
InactiveUS20110238763A1Error minimizationFirmly connectedMultiple digital computer combinationsOffice automationGeographic siteGeolocation
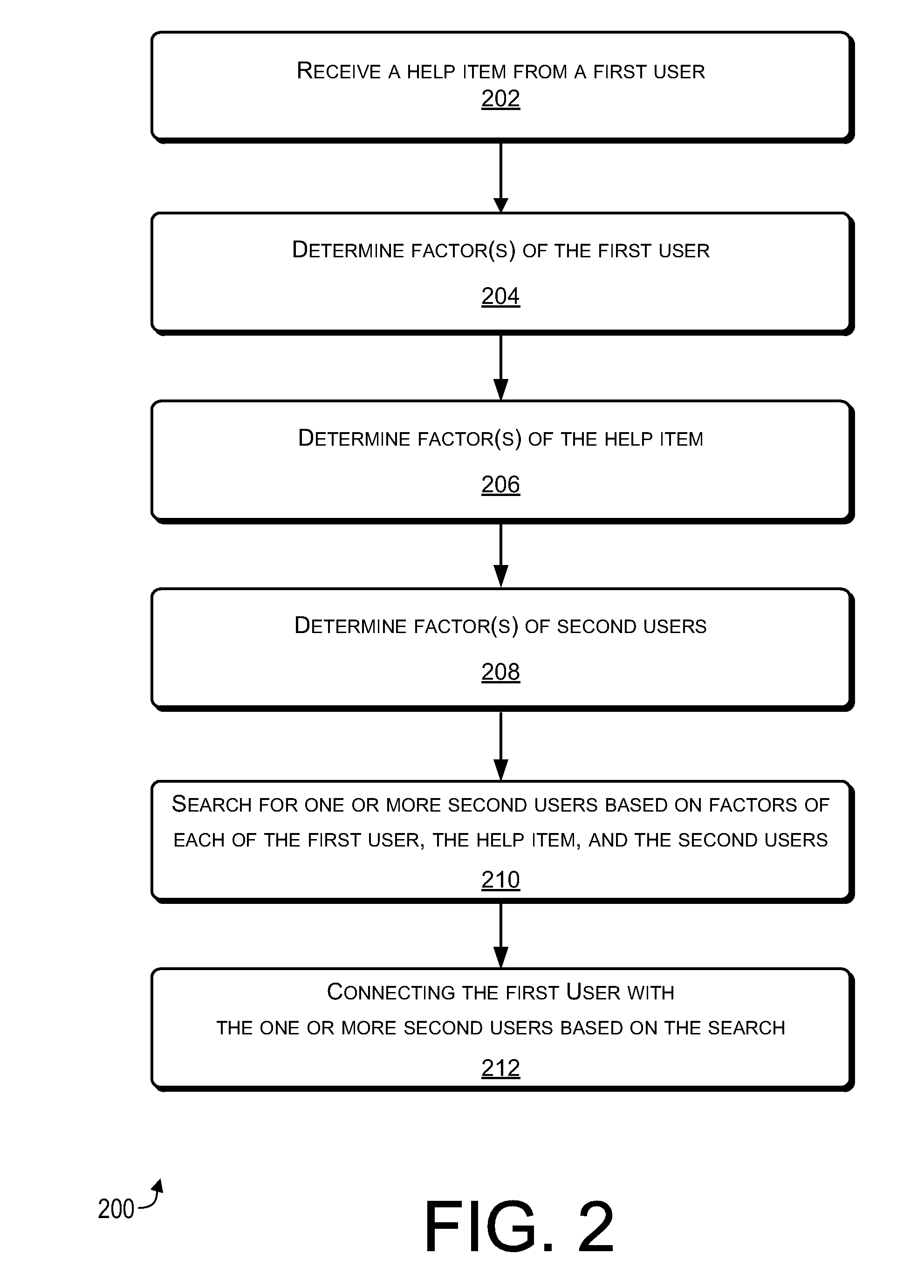
A help item is received from a first user by using a social help network. The help item indicates a help service to be performed for the first user by a second user of the social help network, or by the first user for the second user. Factor(s) of the first user and other users of the social network are determined, such as a geographical location of each user. Factor(s) of the help item are determined, such as a geographical location where the help service is to be performed. Based on the factor(s) of each of the first user, the help item, and the other users, a search for potential second users is performed. Each potential second user can perform the help service for the first user, or each potential second user can have the help service performed by the first user.
Owner:MOMO NETWORKS
Broadband power combining device using antipodal finline structure
ActiveUS7215220B1Easy to manageThermal resistance minimizationWaveguidesCoupling devicesWedge angleHermetic seal
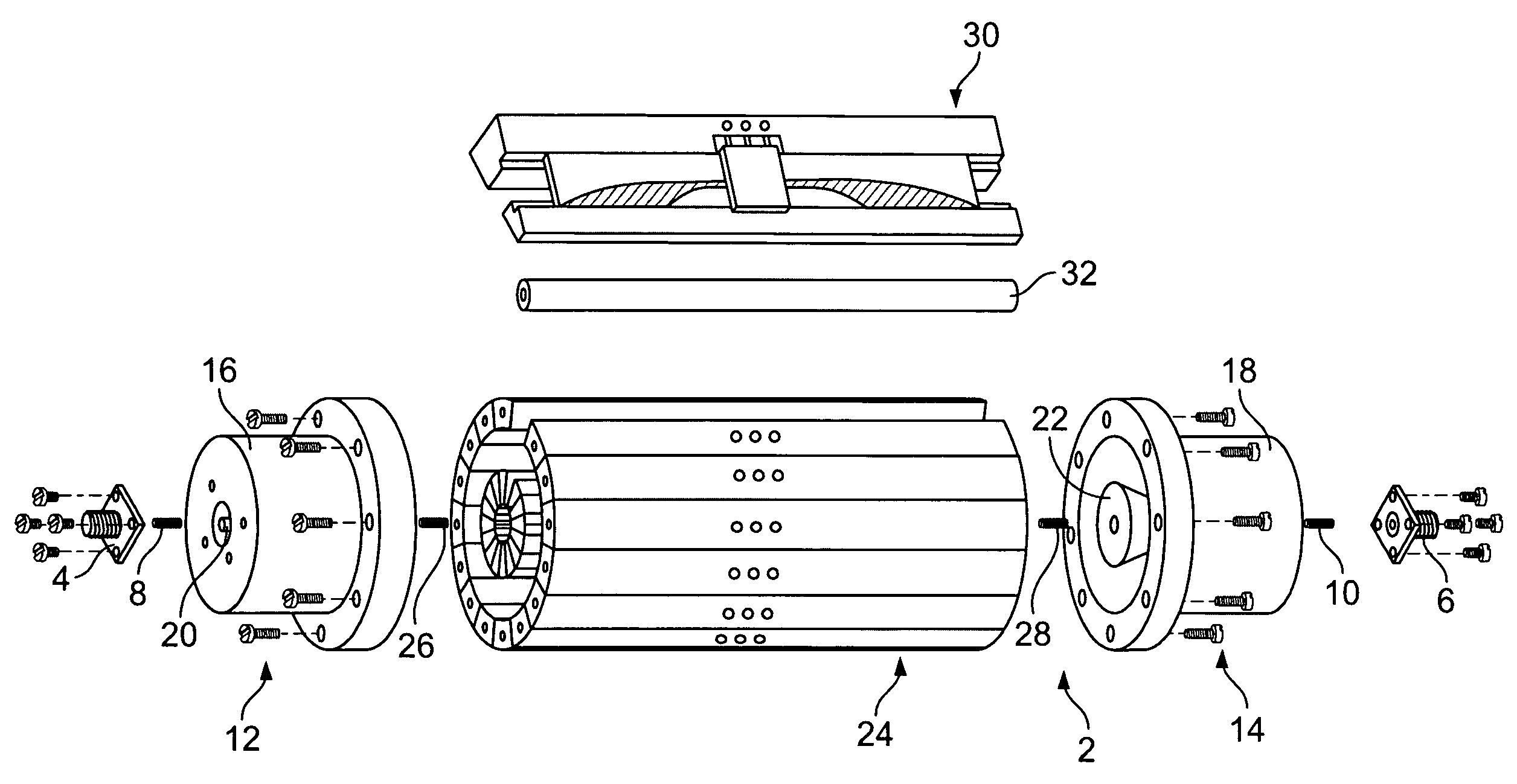
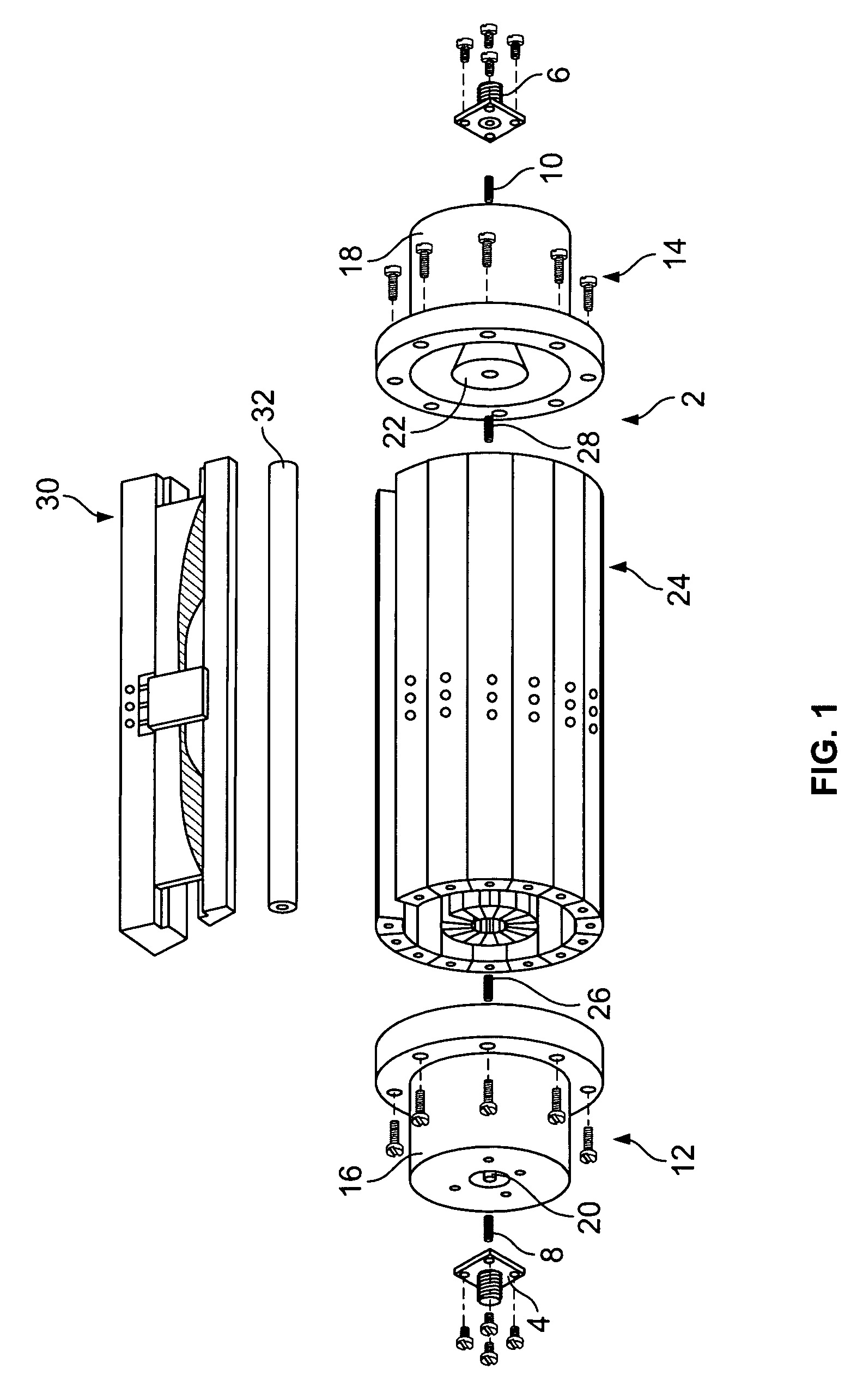
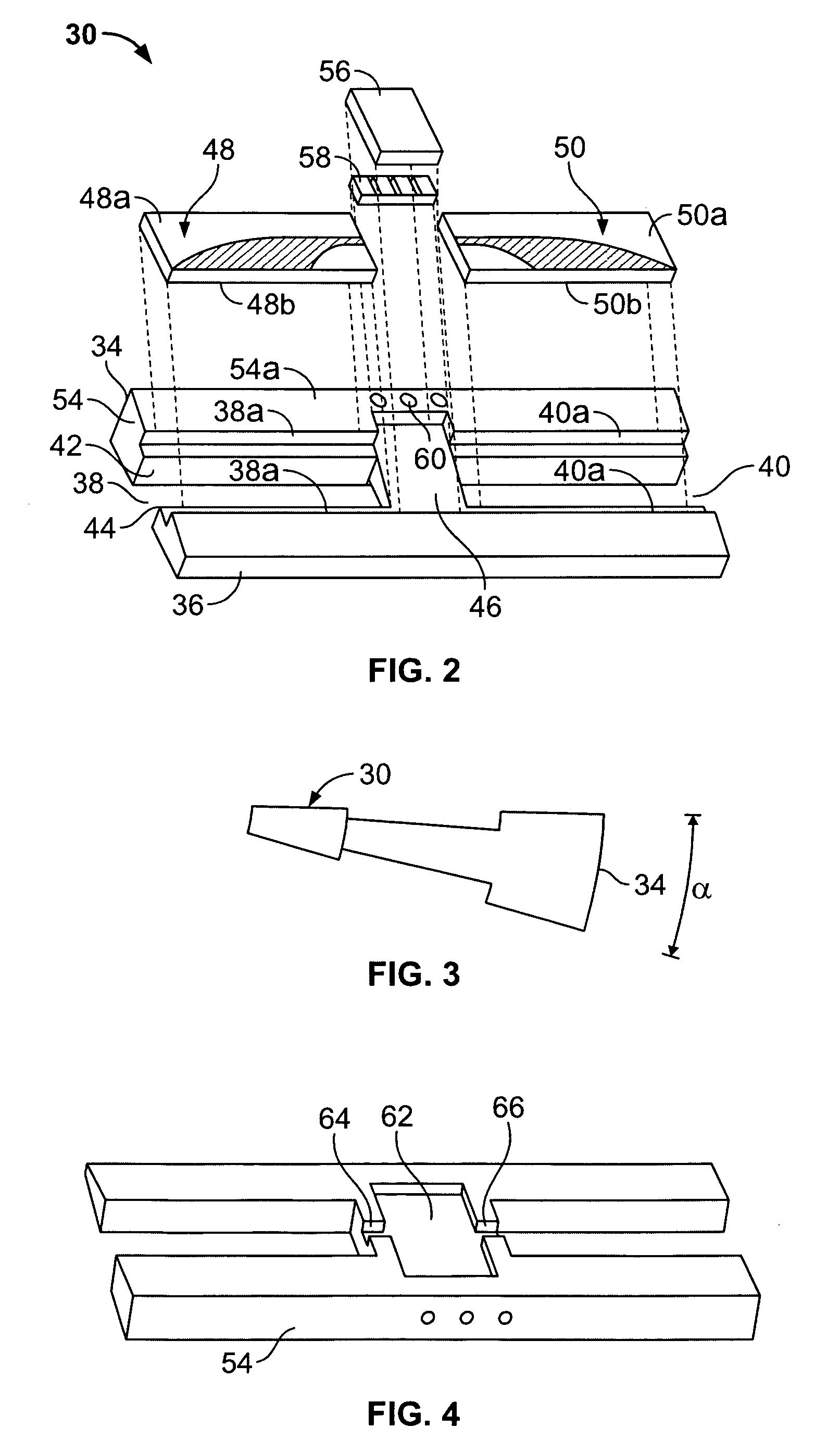
A broadband power combining device includes an input port, an input waveguide section, a center waveguide section formed by stacked wedge-shaped trays, an output waveguide section, and an output port. Each tray is formed of a wedge-shaped metal carrier, an input antipodal finline structure, one or more active elements, an output antipodal finline structure, and attendant biasing circuitry. The wedge-shaped metal carriers have a predetermined wedge angle and predetermined cavities. The inside and outside surfaces of the metal carriers and surfaces of the cavity all have cylindrical curvatures. When the trays are assembled together, a cylinder is formed defining a coaxial waveguide opening inside. The antipodal finline structures form input and output arrays. An incident EM wave is passed through the input port and the input waveguide section, distributed by the input antipodal finline array to the active elements, combined again by the output antipodal finlines array, then passed to the output waveguide section and output port. A hermetic sealing scheme, a scheme for improving the power combining efficiency and thermal management scheme are also disclosed. The broadband power combining device operates with multi-octave bandwidth and is easy to manufacture, well-managed thermally, and highly efficient in power combining.
Owner:CW ACQUISITION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com