Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
14235 results about "Access network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
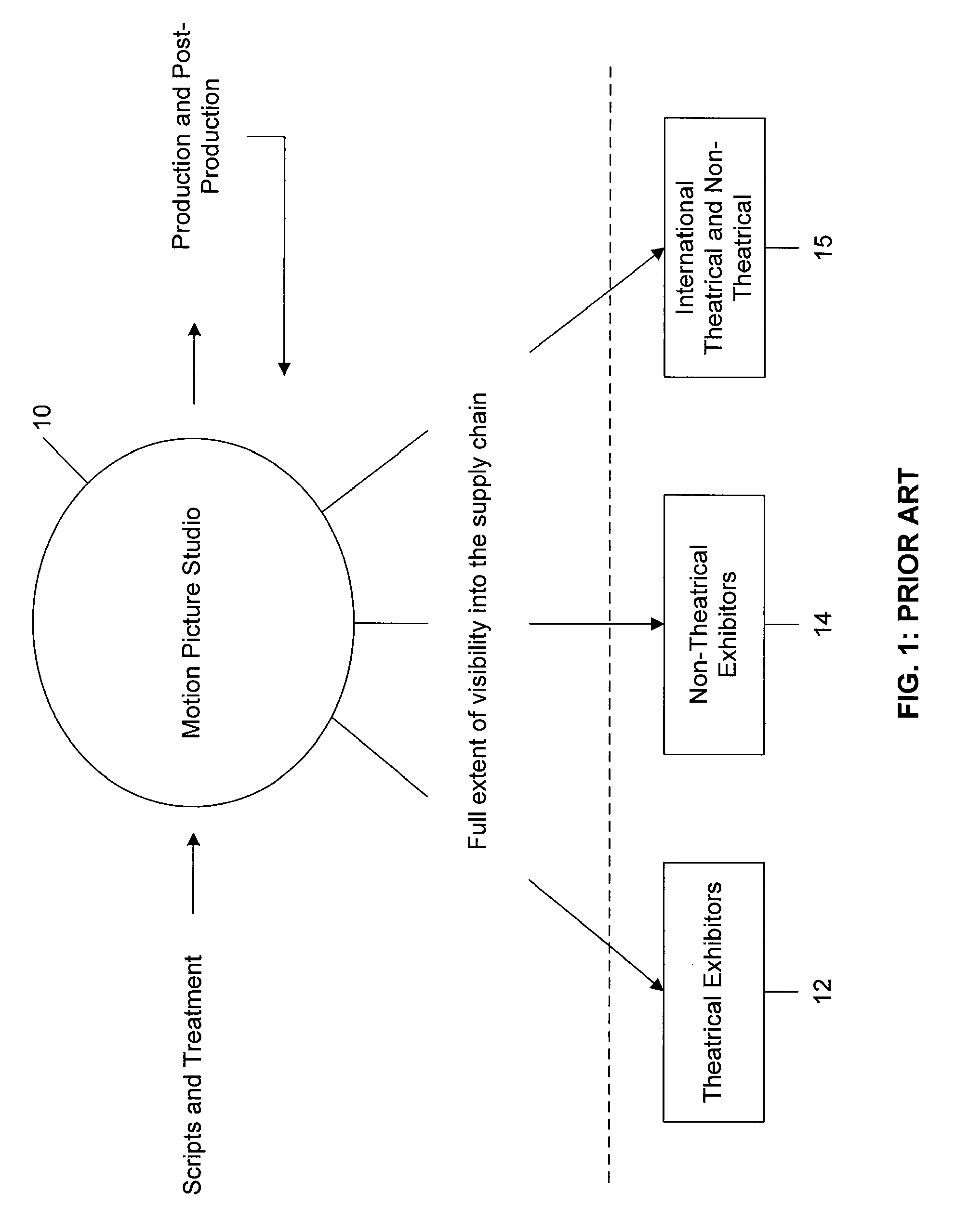
An access network is a type of telecommunications network which connects subscribers to their immediate service provider. It is contrasted with the core network, (for example the Network Switching Subsystem in GSM) which connects local providers to one another. The access network may be further divided between feeder plant or distribution network, and drop plant or edge network.
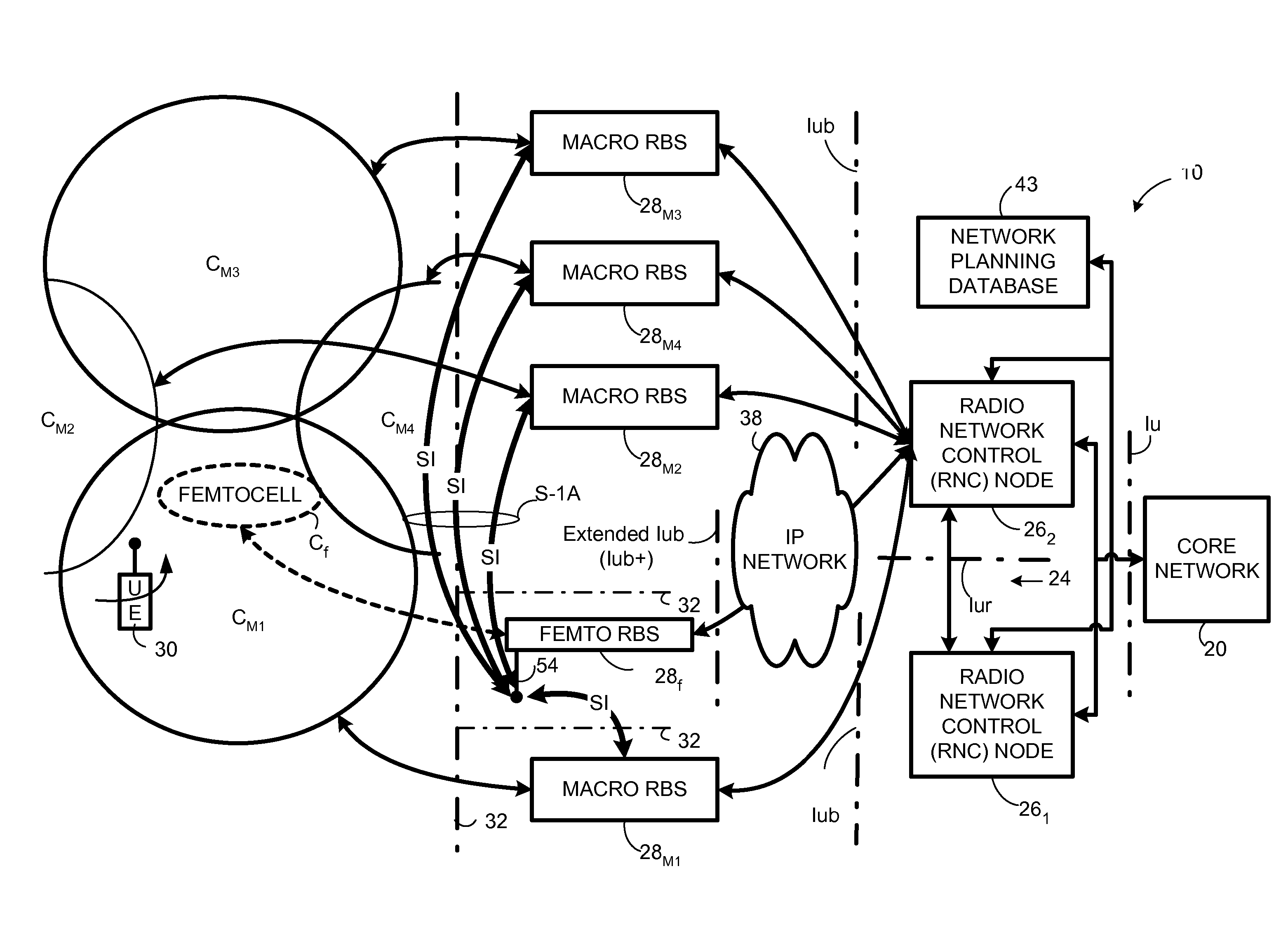
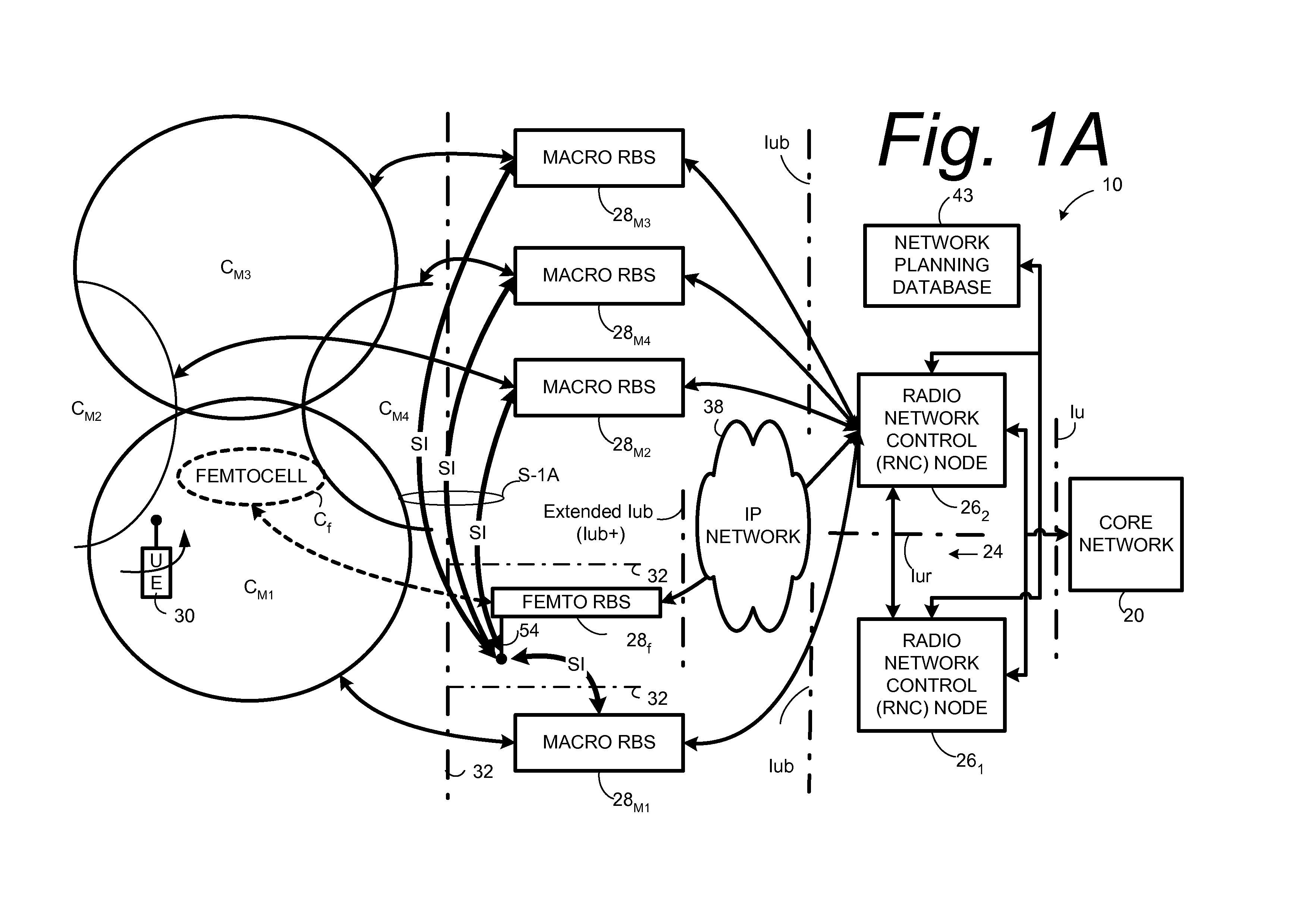
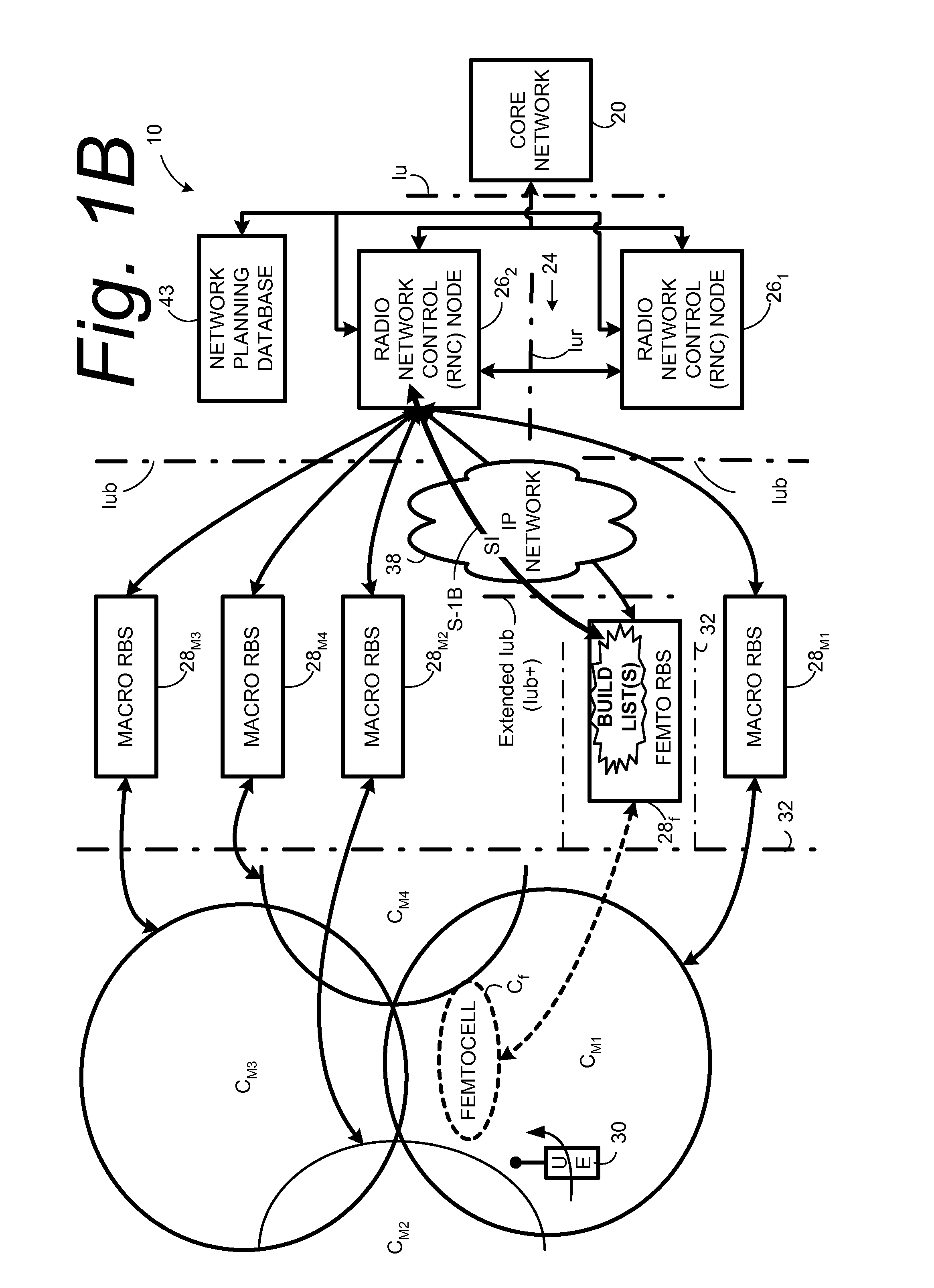
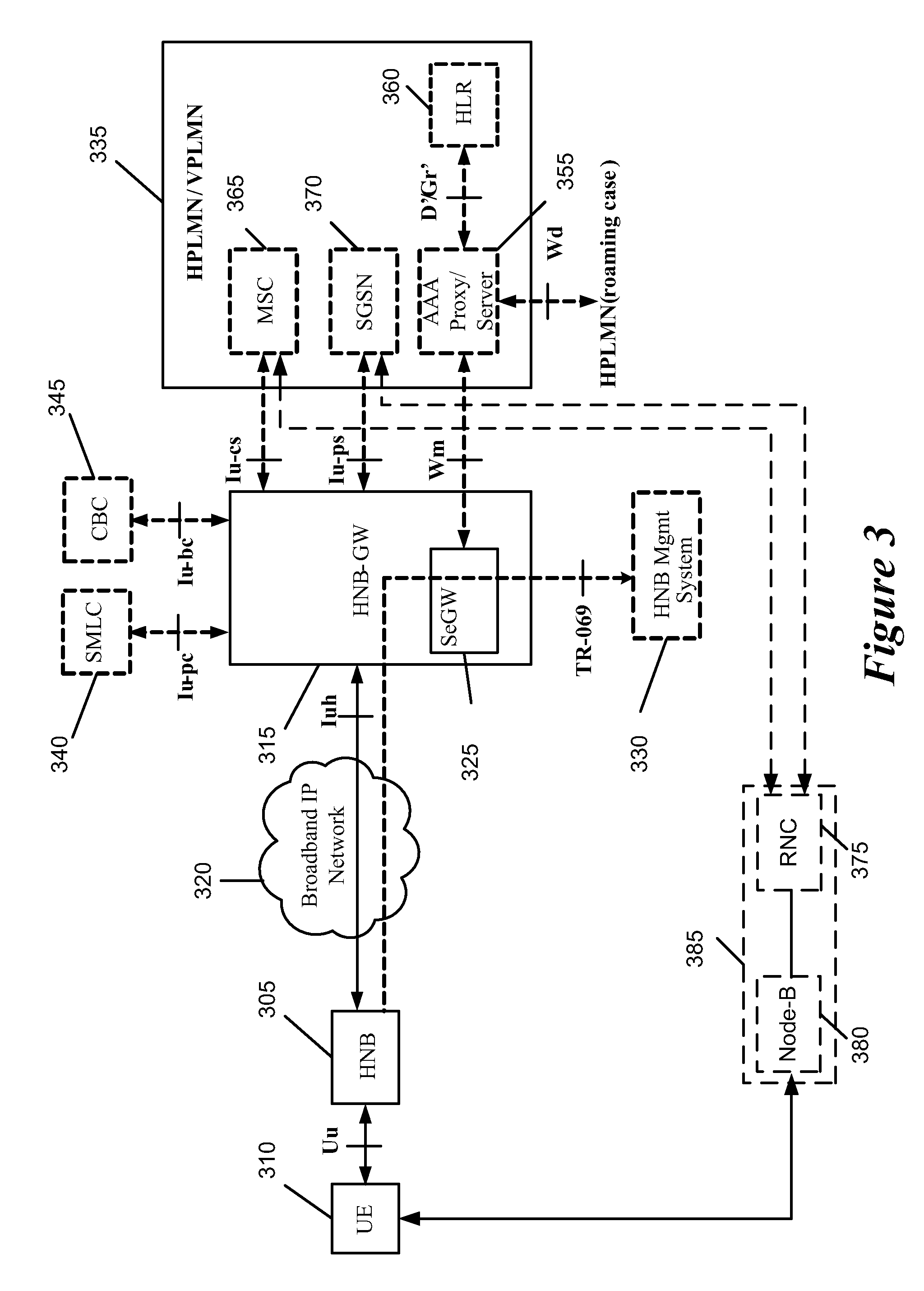
Automatic configuration of pico radio base station
Methods and apparatus configure a femto radio base station ( 28 f). A macro receiver of the femto radio base station ( 28 f) is used to acquire detected coverage information of a radio access network ( 24 ). The detected coverage information is used to determine an operation parameter for use by the macro transceiver ( 52 ) of the femto radio base station ( 28 f). In one embodiment, the detected coverage information is transmitted to a control node ( 26 ) of the radio access network. The control node ( 26 ) determines the operation parameter and communicates the operation parameter to the femto radio base station ( 28 f). The femto radio base station ( 28 f) is accordingly configured using the operation parameter for further operation towards UEs ( 30 ) accessing the femto radio base station ( 28 f).
Owner:TELEFON AB LM ERICSSON (PUBL)
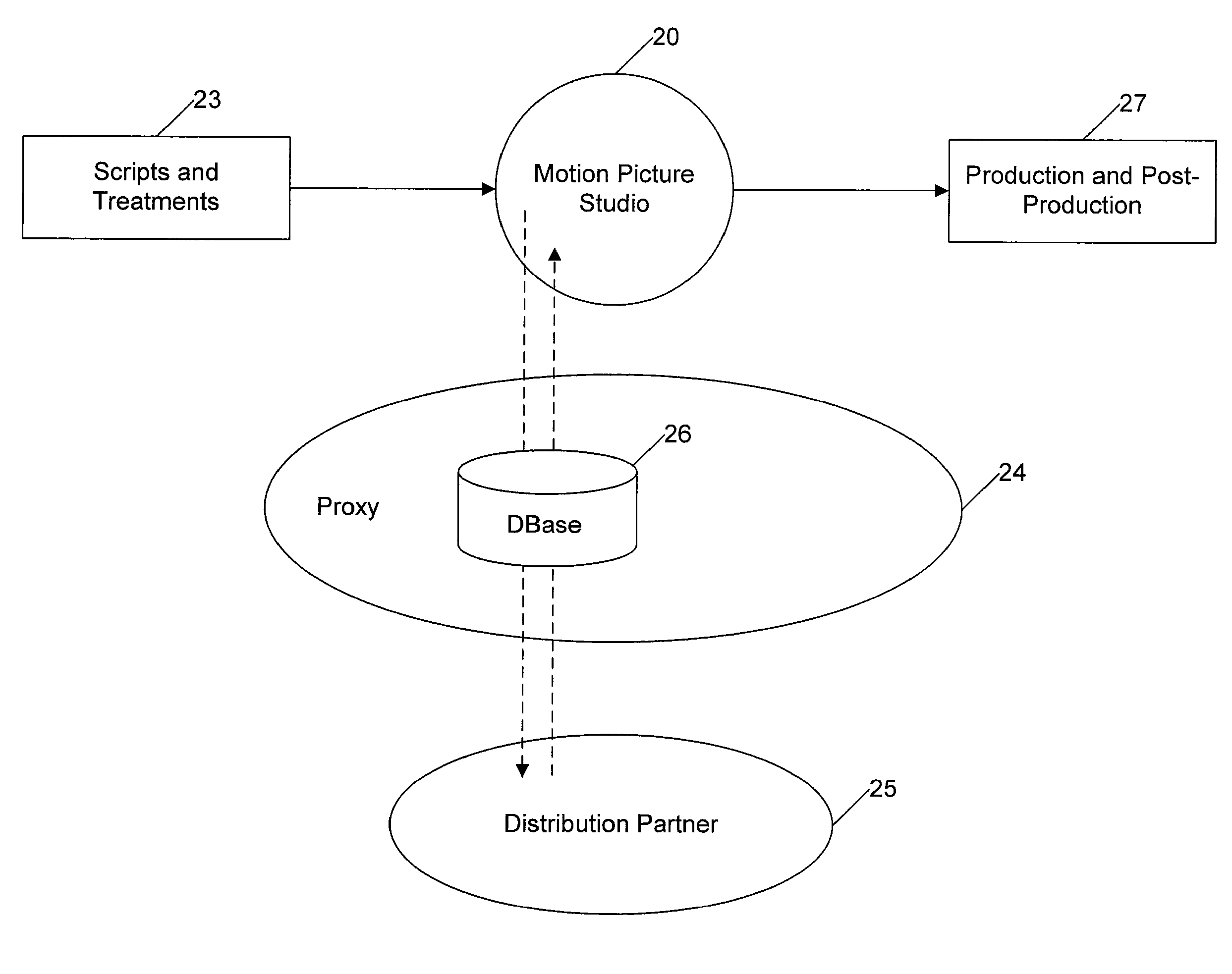
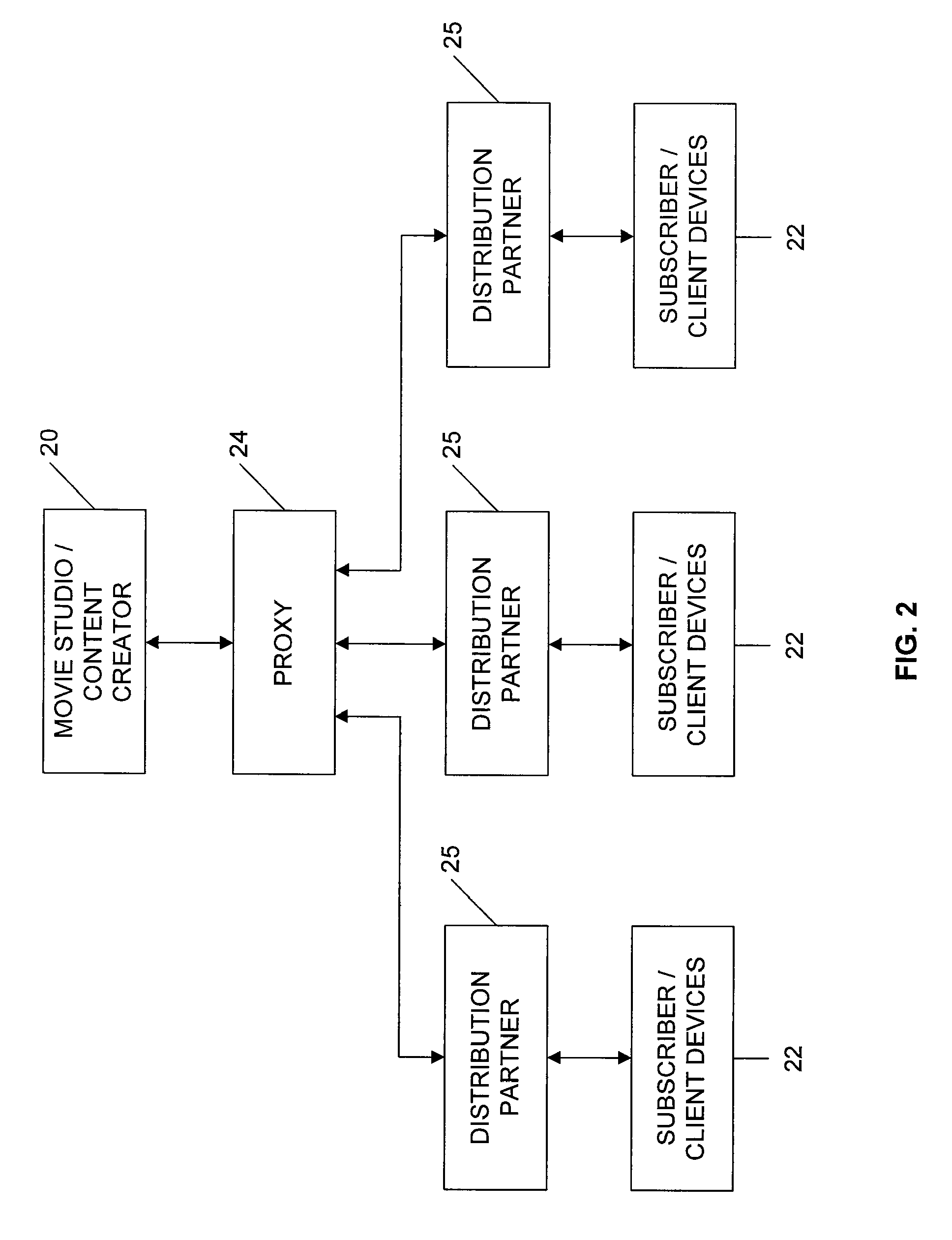
Movie studio-based network distribution system and method
ActiveUS20070220575A1Analogue secracy/subscription systemsTwo-way working systemsAccess networkDigital content
Digital content files containing entertainment media such as movies, TV shows, and the like are distributed from at least one content source primarily responsible for the original creation of the media to subscribers over a network system. The content source is connected over at least one content source network to a plurality of distribution partners, and each distribution partner is connected with a selected group of subscribers over an access network. A requested digital content file is distributed from the content source to a subscriber in a network distribution path comprising at least the content source network, the distribution partner associated with the subscriber, and the second network. A profile information package containing subscriber preferences is transmitted from the subscriber to the content source by way of a proxy over the network distribution path, and the profile information package is stored at the content source.
Owner:VERIMATRIX INC
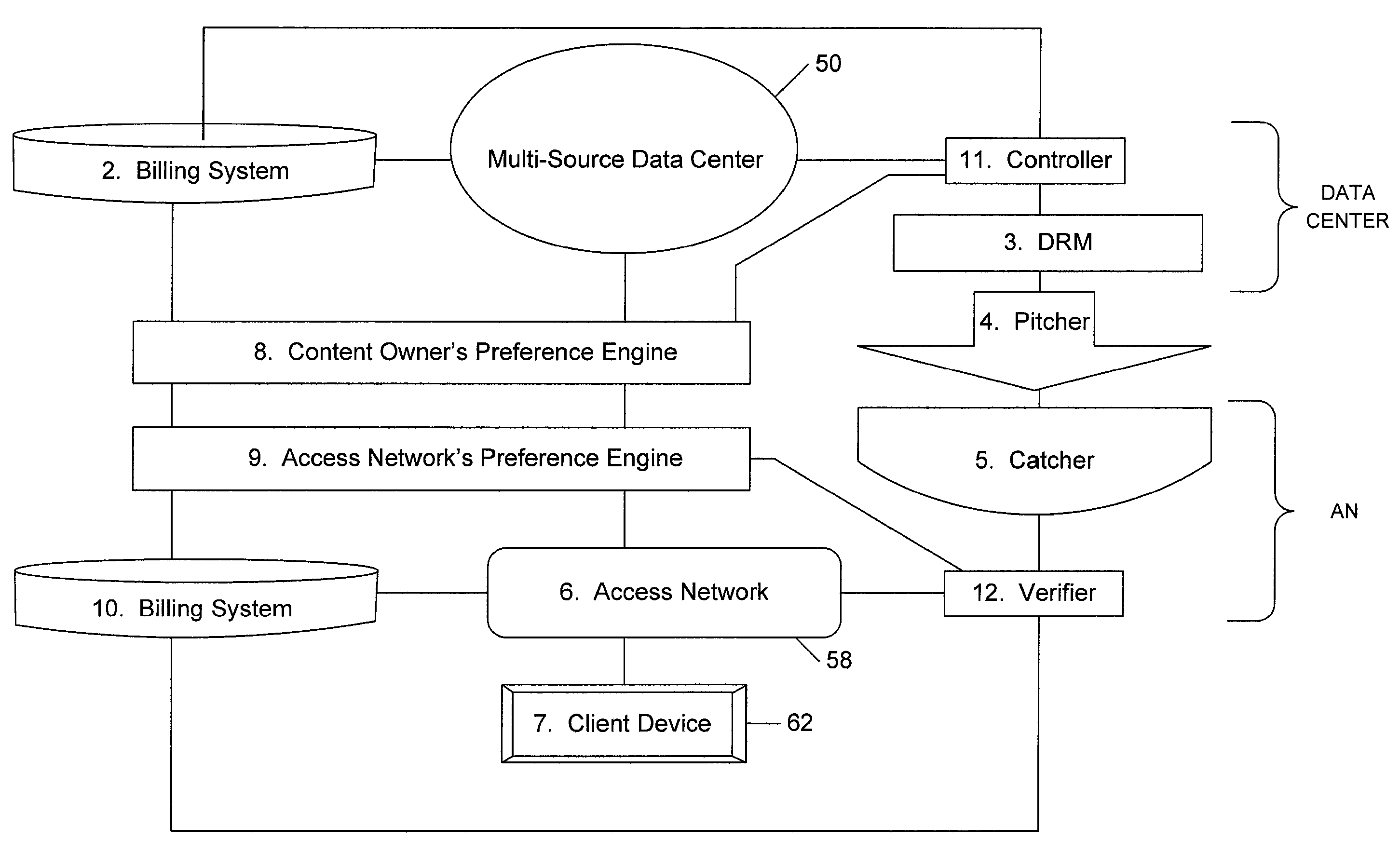
Multi-source bridge content distribution system and method
ActiveUS20080155614A1Appropriately sharedComplete banking machinesAdvertisementsContent distributionAccess network
A multi-source bridge content distribution system links multiple content owners with access network operators or content distribution providers leasing space on access networks so that multi-media content can be provided from multiple content owners to consumers through a multi-source bridge or data center. Content files and associated content owner preference settings are provided from a plurality of content sources or providers to the multi-source data center. Files stored at the data center or locally at an access network are provided to subscribers through the local access network Content files are provided if the content owner preference settings are a sufficient match with service provider access network preference settings set up by the service provider using the access network to provide content to subscribers.
Owner:VERIMATRIX INC
Mobile mesh Ad-Hoc networking
InactiveUS6879574B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsCyber operationsAccess network
An architectural solution in which standalone ad-hoc network cells are used as an extension of the backbone infrastructure in terms of network architecture or / and its service capabilities is provided. These Ad-Hoc networks will integrate to the Internet via cellular and other access networks. This integration brings new possibilities to network operators and ISP's. In its extended architecture, it is envisaged that the mobility issues are handled by utilizing the IP mobility capabilities, taking into account the mobile mesh Ad-Hoc specific requirements.
Owner:NOKIA TECHNOLOGLES OY
Managing an access account using personal area networks and credentials on a mobile device
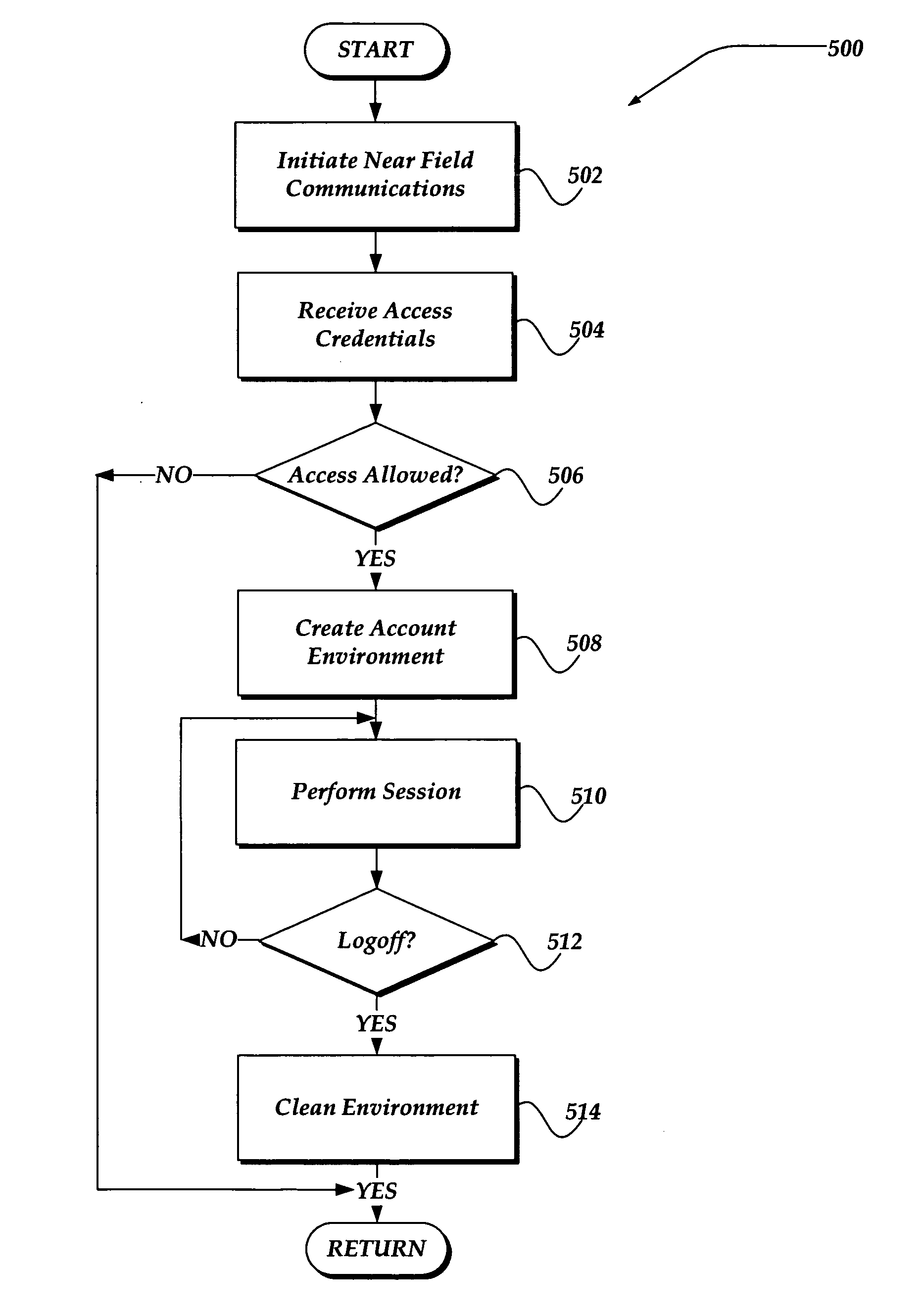
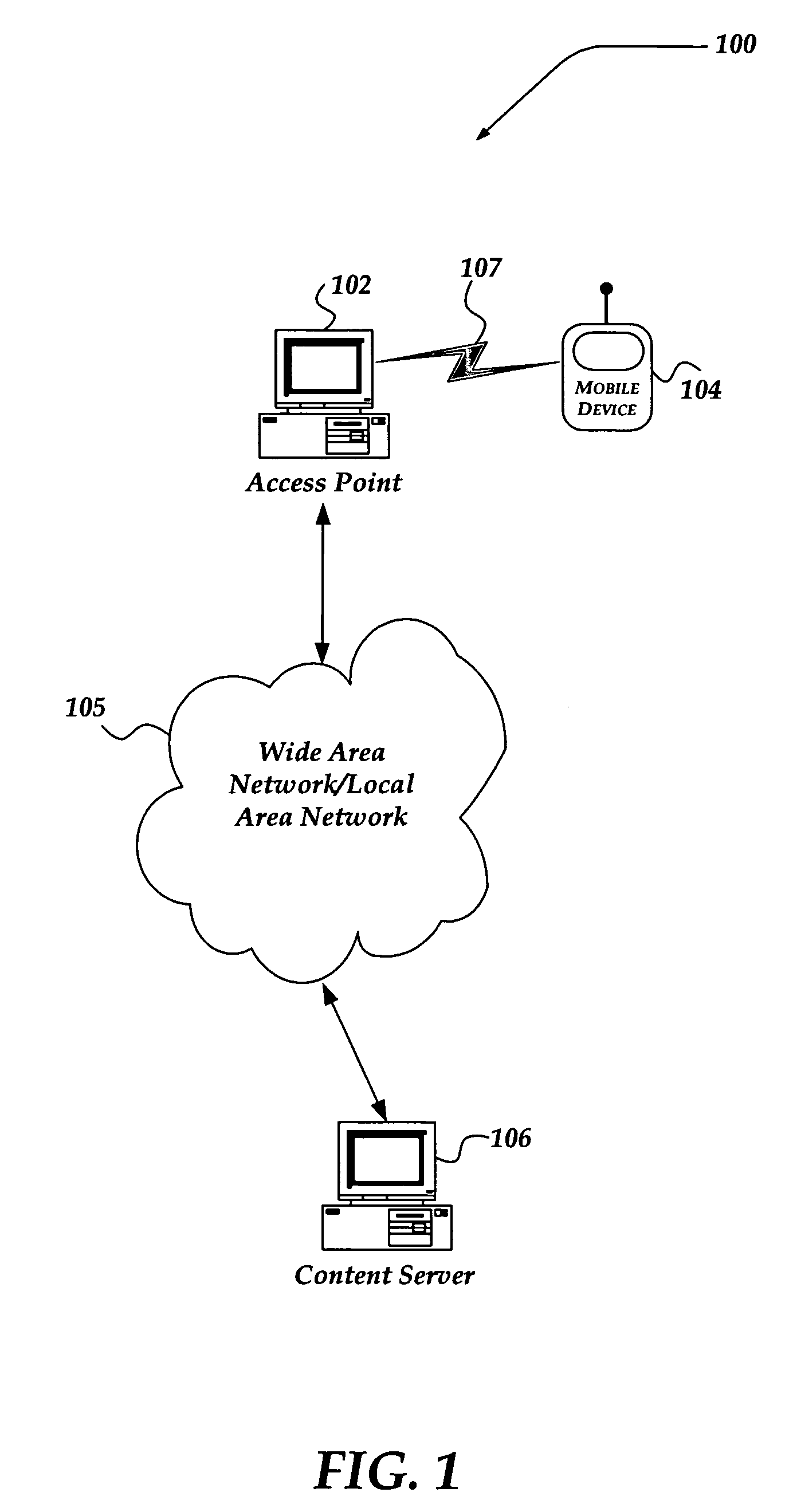
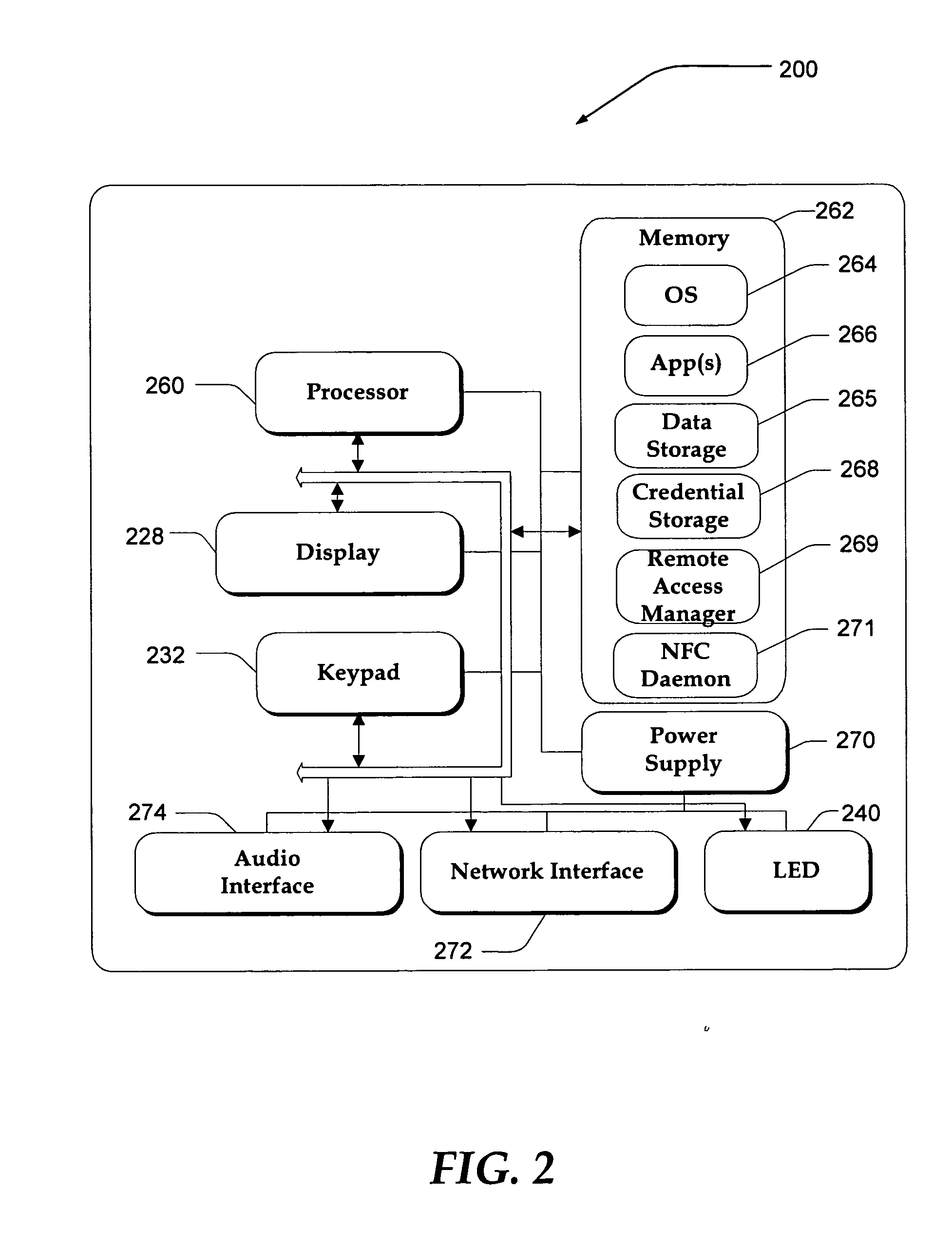
InactiveUS20060183462A1Near-field transmissionUnauthorised/fraudulent call preventionAccess networkRelevant information
A system, apparatus, and method are directed towards automatically managing an access account at an access point using near field communications and credentials stored on a mobile device. The mobile device receives, out-of-band, information for use in creating an account for accessing network resources from the access point. As the mobile device is brought into proximity with the access point, a wireless network connection is established using a near field communication (NFC) protocol. The information, which may include a user credential, account information, and so forth, is communicated to the access point. The access point employs the information to establish an account and create an environment from which access to the network resources may be obtained. Upon termination, the access point removes from itself any user specific data. The access point may provide also session related information useable in billing the user of the mobile device.
Owner:NOKIA CORP
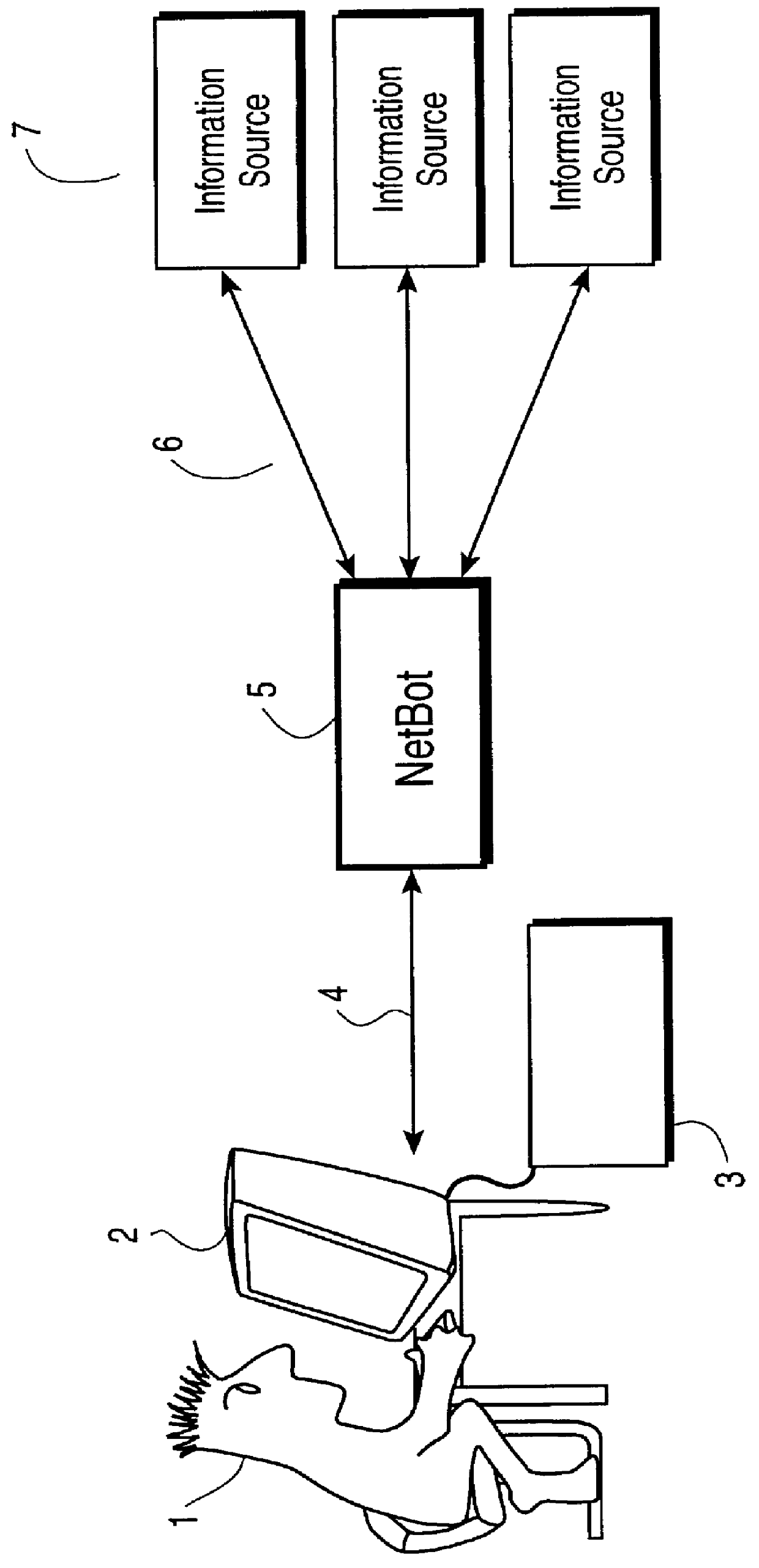
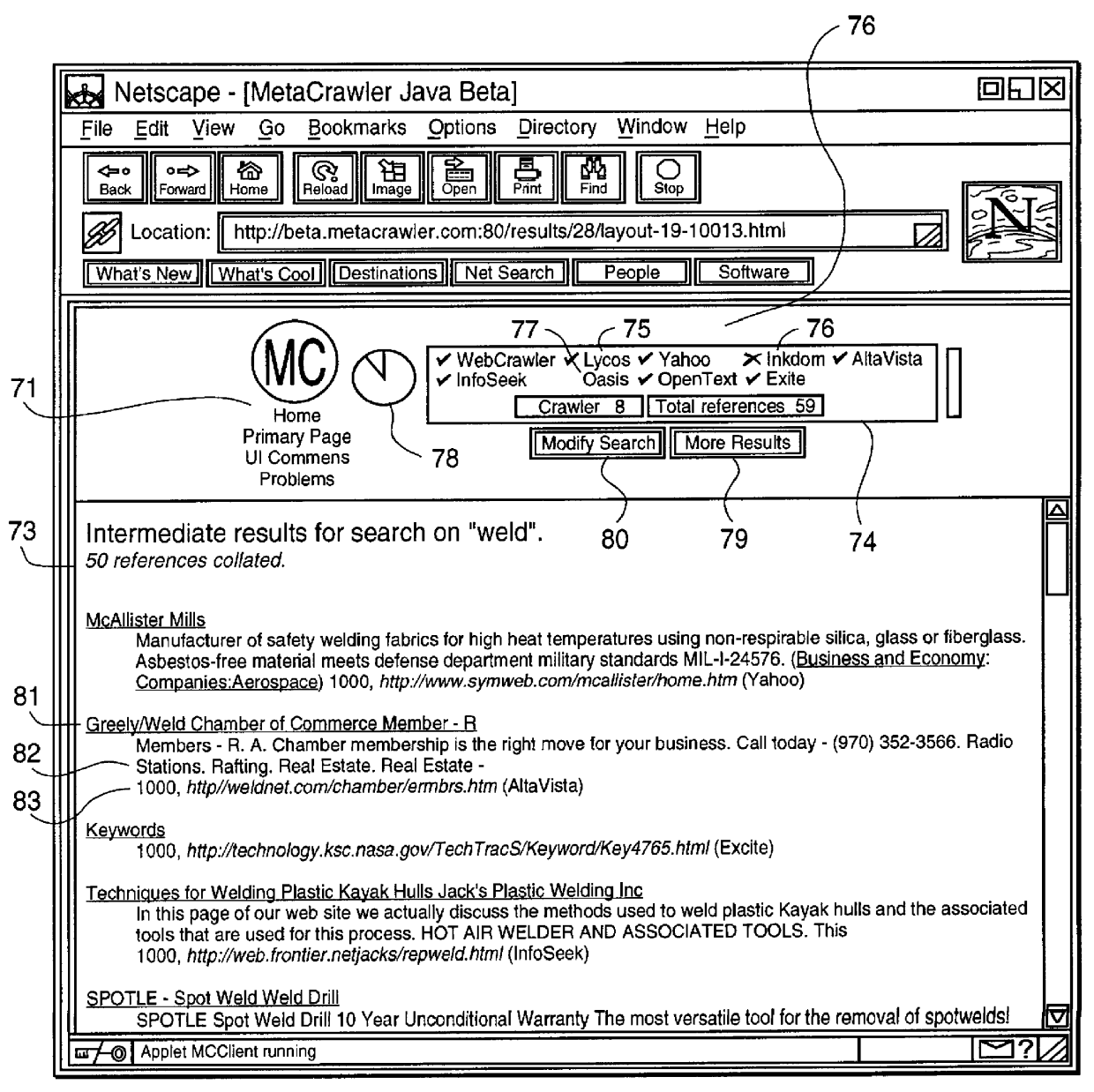
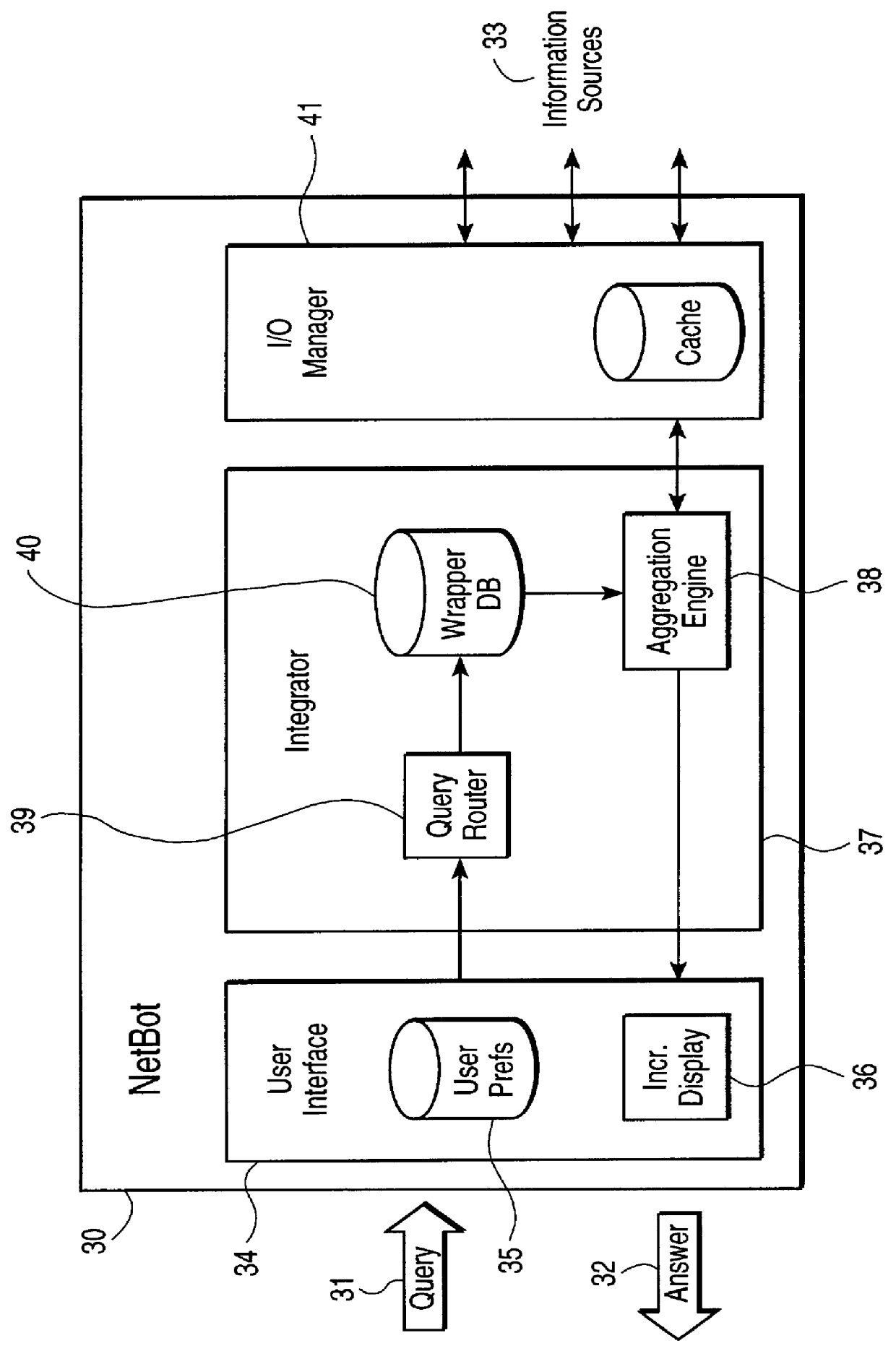
Method and system using information written in a wrapper description language to execute query on a network
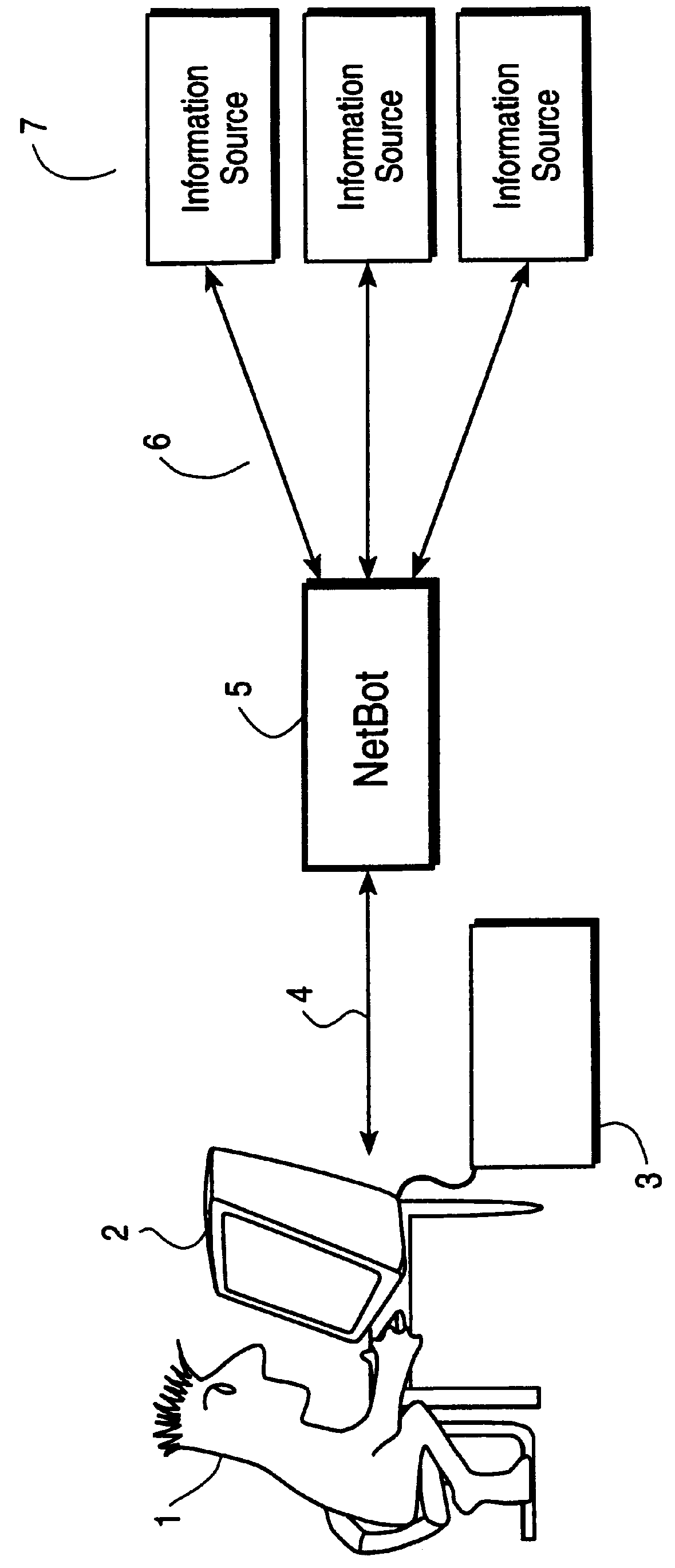
InactiveUS6085186AEasy to understandEasy maintenanceData processing applicationsWeb data indexingAccess networkNetwork connection
This invention provides assistance to a user in accessing network attached information sources. In one aspect, the invention is a method for intelligently routing a user query to information sources relevant to that query, extracting relevant data fields from received responses, and intelligently presenting the extracted data in order of estimated relevance. The system of this invention implements one or more steps of the method in a centralized or distributed manner on one or more network attached computers. Further, this invention provides a novel language and implementation that facilitates easily written and maintained descriptions of information source query and response formats.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST
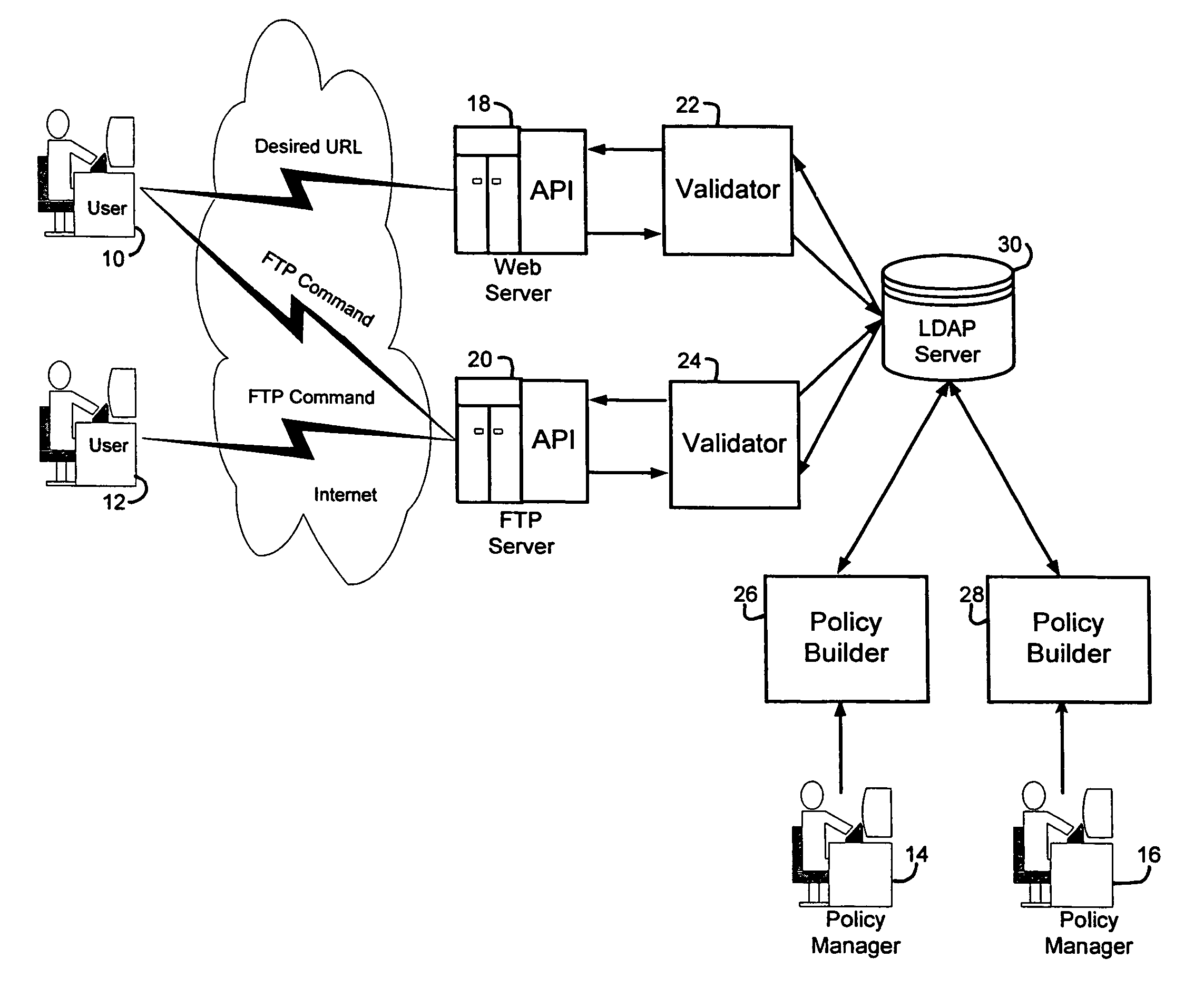
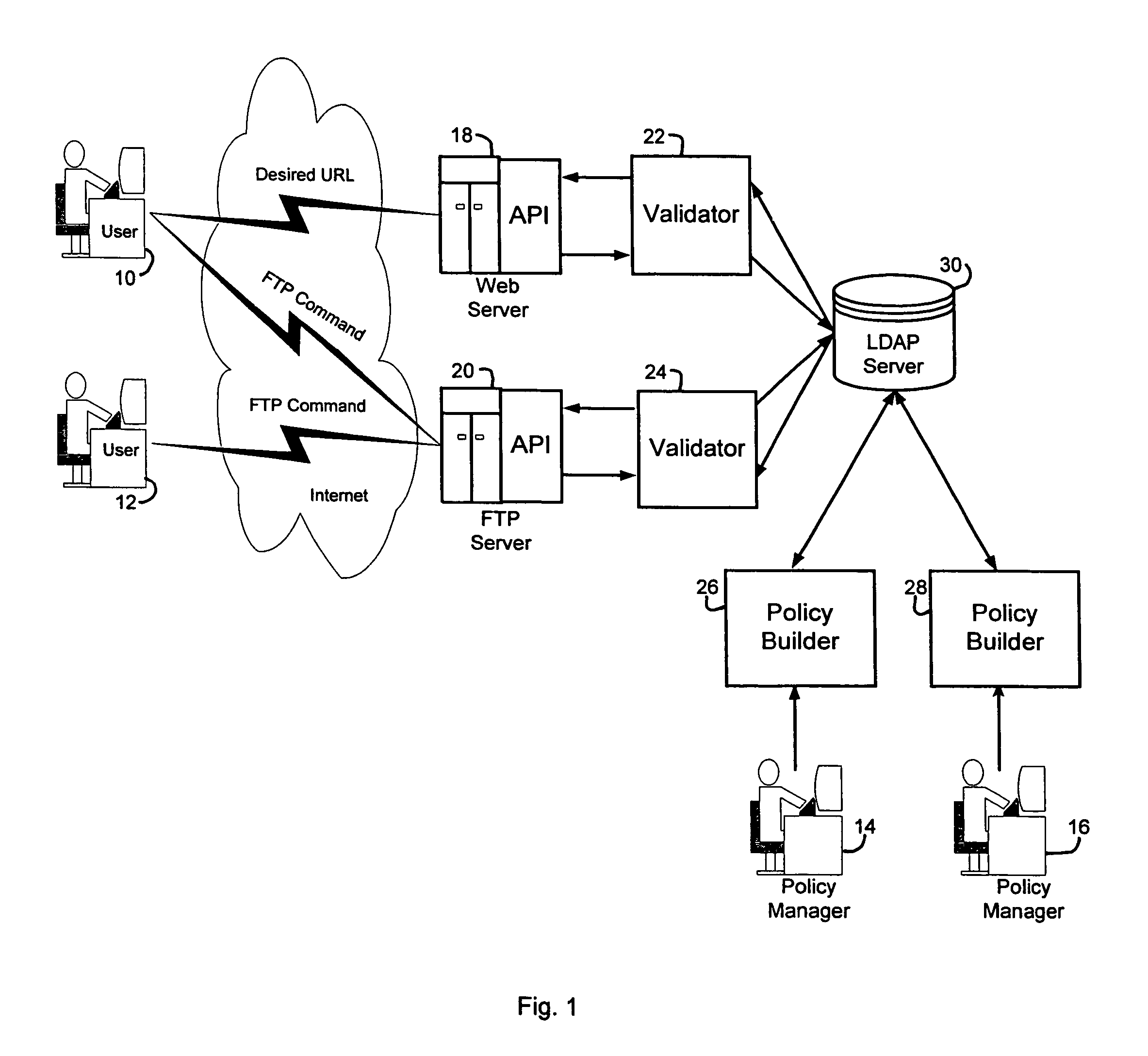
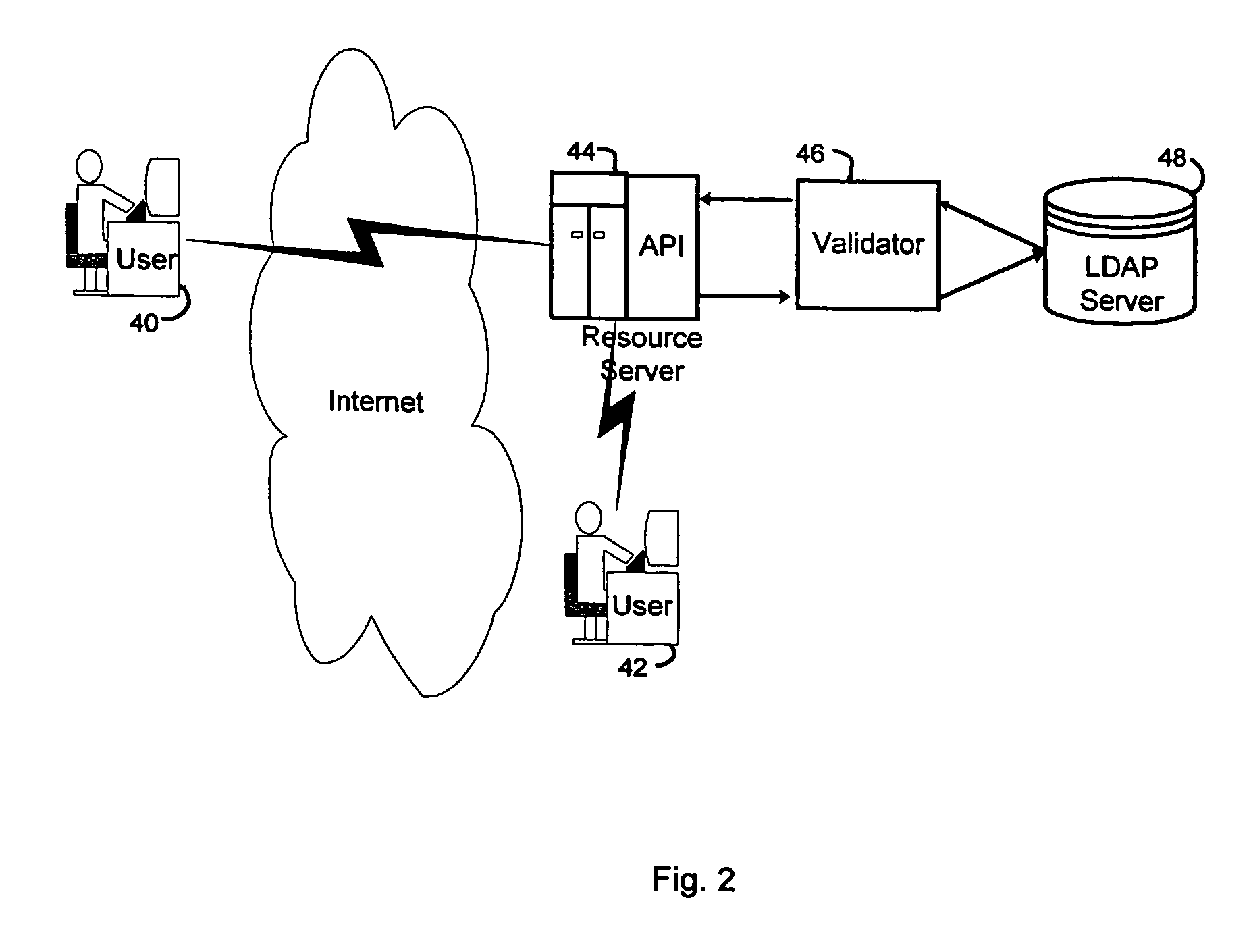
Computer system security service
A security service of computer networks having a policy builder, an LDAP-compliant database, a validator and an API. The policy builder component provides a graphical user interface to be used by a policy manager to define access policies for users seeking to access network services and resources. The graphical user interface has a grid of nodes representing access policies. The grid is arranged to correspond to a defined tree structure representing services and resources and a business relationship tree structure representing users. The graphical user interface permits the policy manager to define policy builder plug-ins for access policy customization. The LDAP-compliant database maintains the policy builder plug-ins. The validator component receives requests from users and queries the LDAP-compliant database to obtain relevant access policies as defined by the policy manager. The system provides for double inheritance of access policies such that where there is no express definition of an access policy for a node, the access policies are propagated according to the hierarchical structures of the data. The validator includes validator plug-ins for carrying out access policies corresponding to the access policies defined by policy builder plug-ins.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
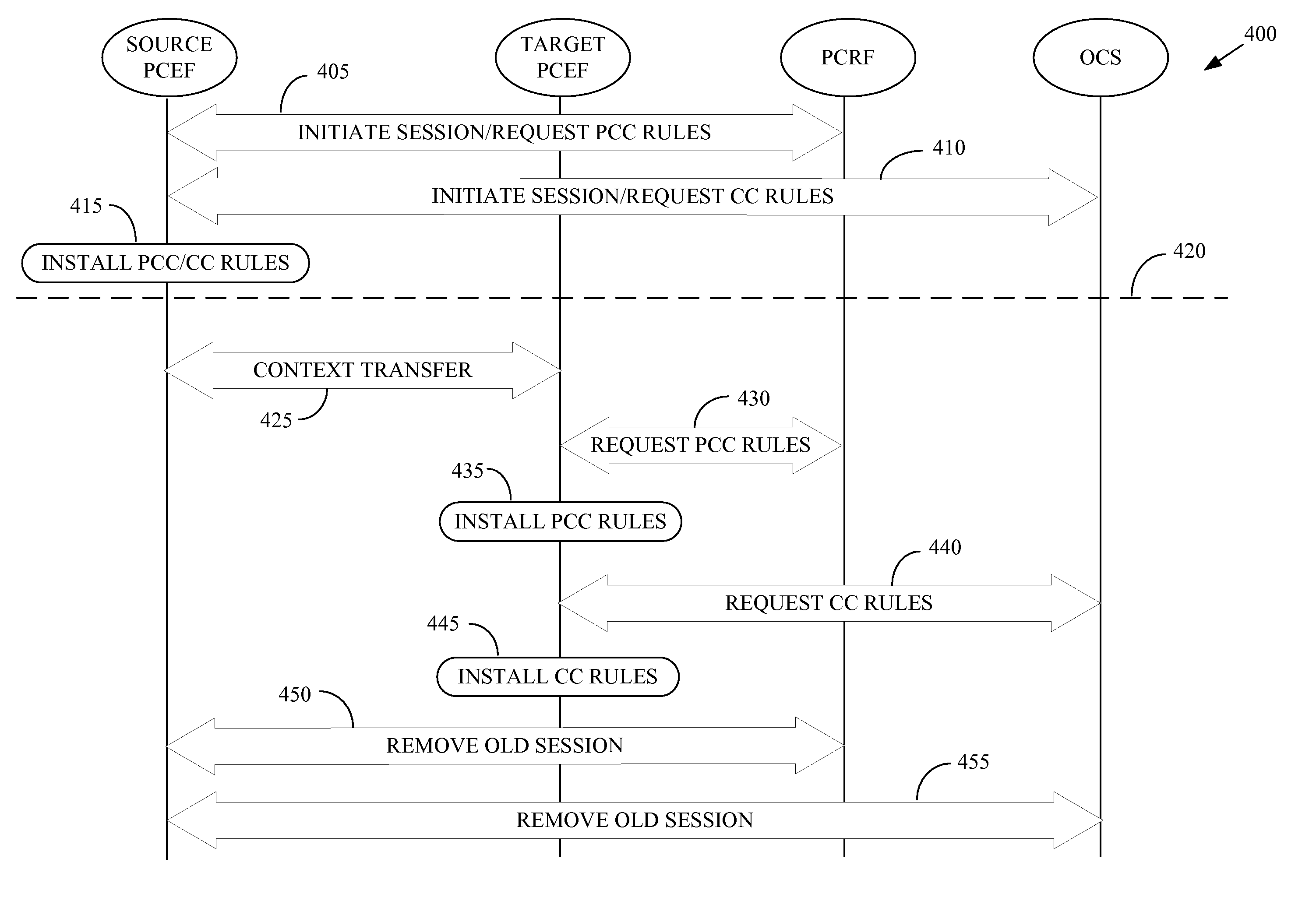
Mobility Aware Policy and Charging Control in a Wireless Communication Network
ActiveUS20080229385A1Metering/charging/biilling arrangementsTelephonic communicationAccess networkCommunications system
One embodiment of the present invention provides a method for implementation in a policy control and charging rules functional entity in a wireless communication system. The method includes receiving, from at least one of a source policy and charging enforcement function in a source access network or a target policy and charging enforcement function in a target access network, information indicative of a mobile unit that has handed off from the source access network to the target access network. The method also includes establishing a first session for communicating policy and charging rules associated with the mobile unit. The first session is concurrent with a second session for communicating policy and charging rules associated with the mobile unit. The second session was previously established with the source policy and charging enforcement function in the source access network. The method further includes transmitting at least one policy and charging rule to the target policy and charging enforcement function using the first session.
Owner:NOKIA TECHNOLOGLES OY
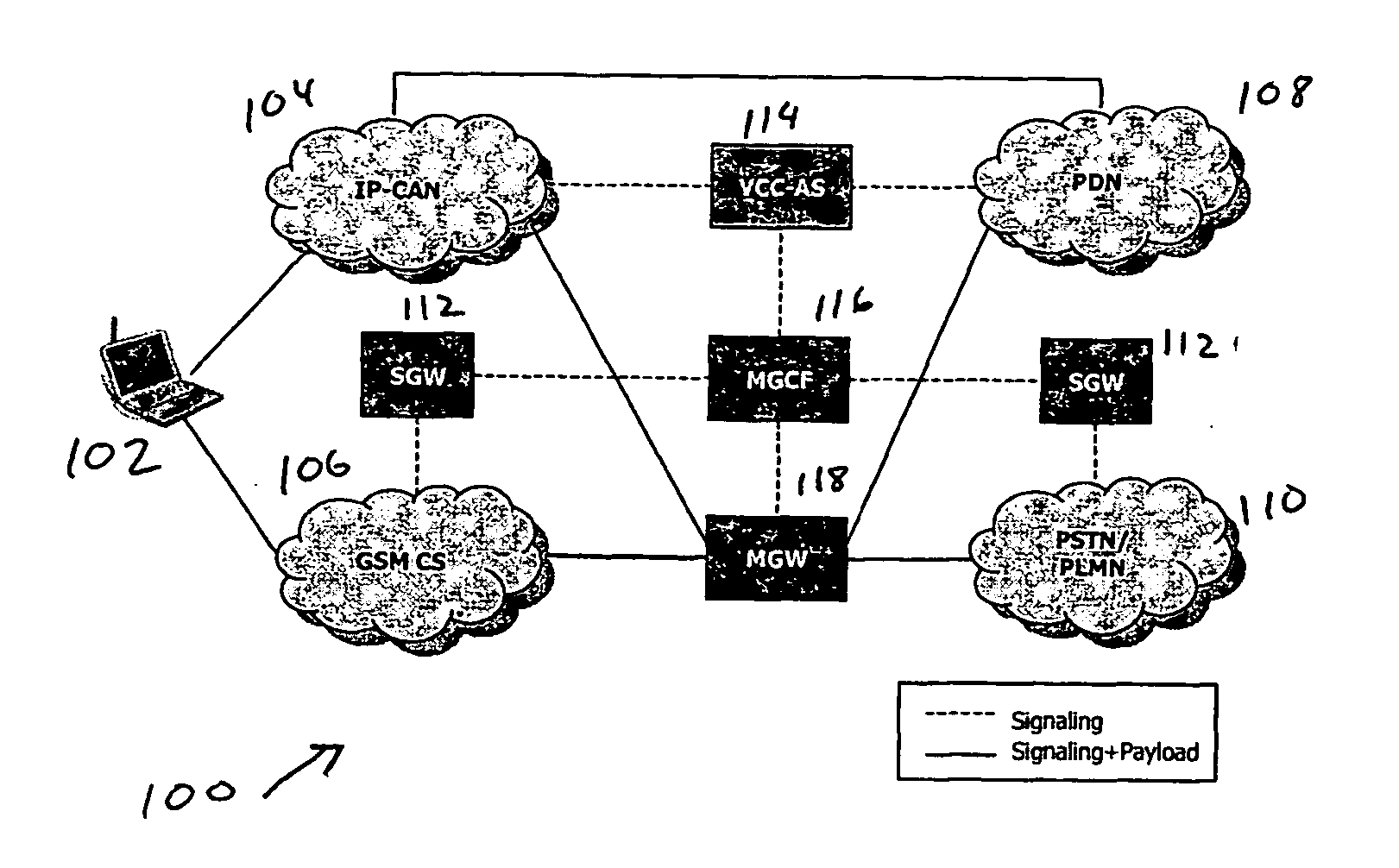
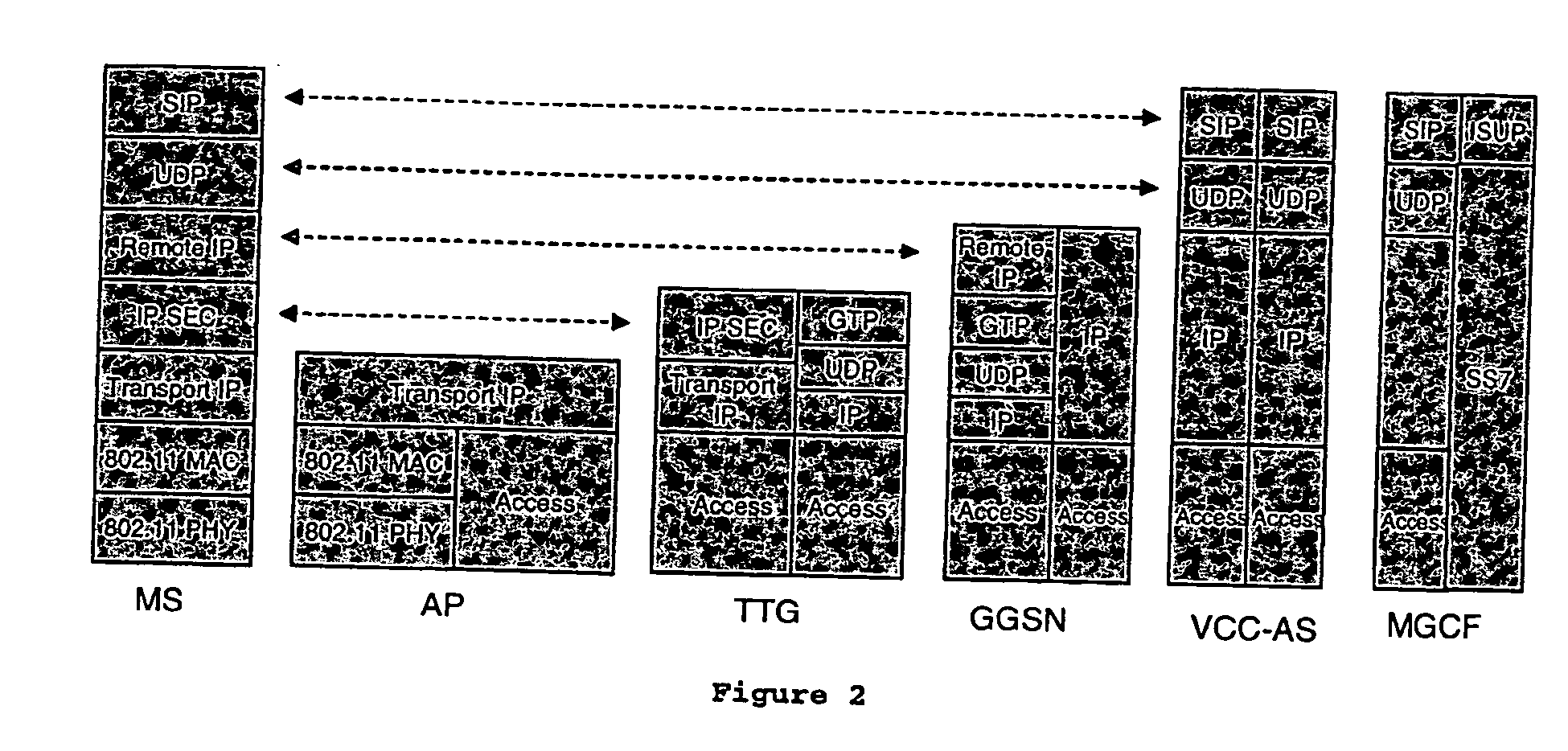
Voice call continuity application server between IP-CAN and CS networks
InactiveUS20070014281A1Accurate processingMultiplex system selection arrangementsConnection managementAccess networkApplication server
A system and method for continuous voice calls when a user switches between packet data and circuit switched access networks. In one example embodiment, the present innovations include an interworking system that supports voice call continuity for a user that moves between IP-CAN and CS networks (e.g., PSTN or GSM). In one example embodiment, the present innovations comprise a voice call continuity application server (VCC-AS) that serves as an anchor point for a voice call (i.e., it is the node from which a handover is initiated) and controls and handles voice calls to and from the user equipment (UE) regardless of the access network.
Owner:INTELLINET TECH
Application access control in a mobile environment
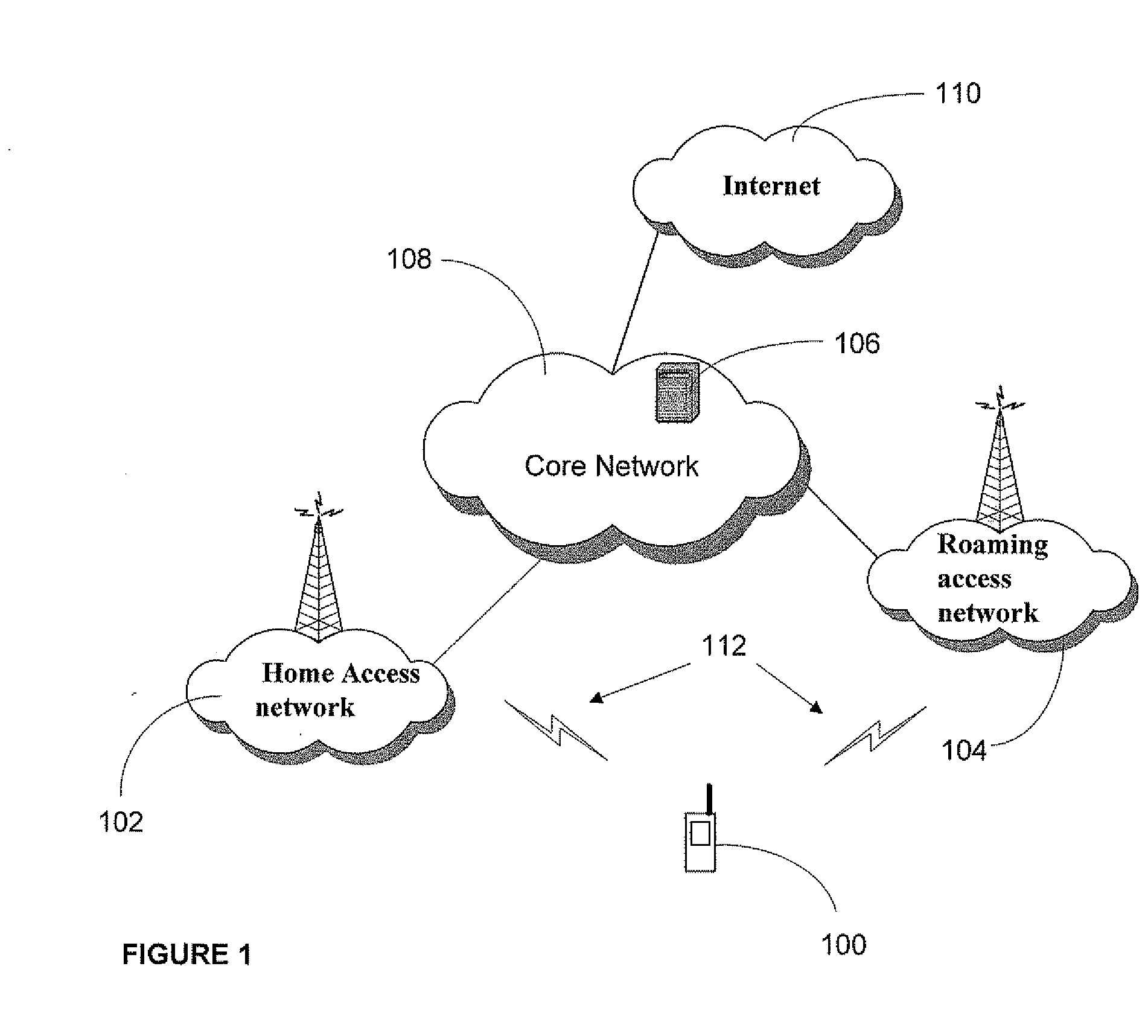
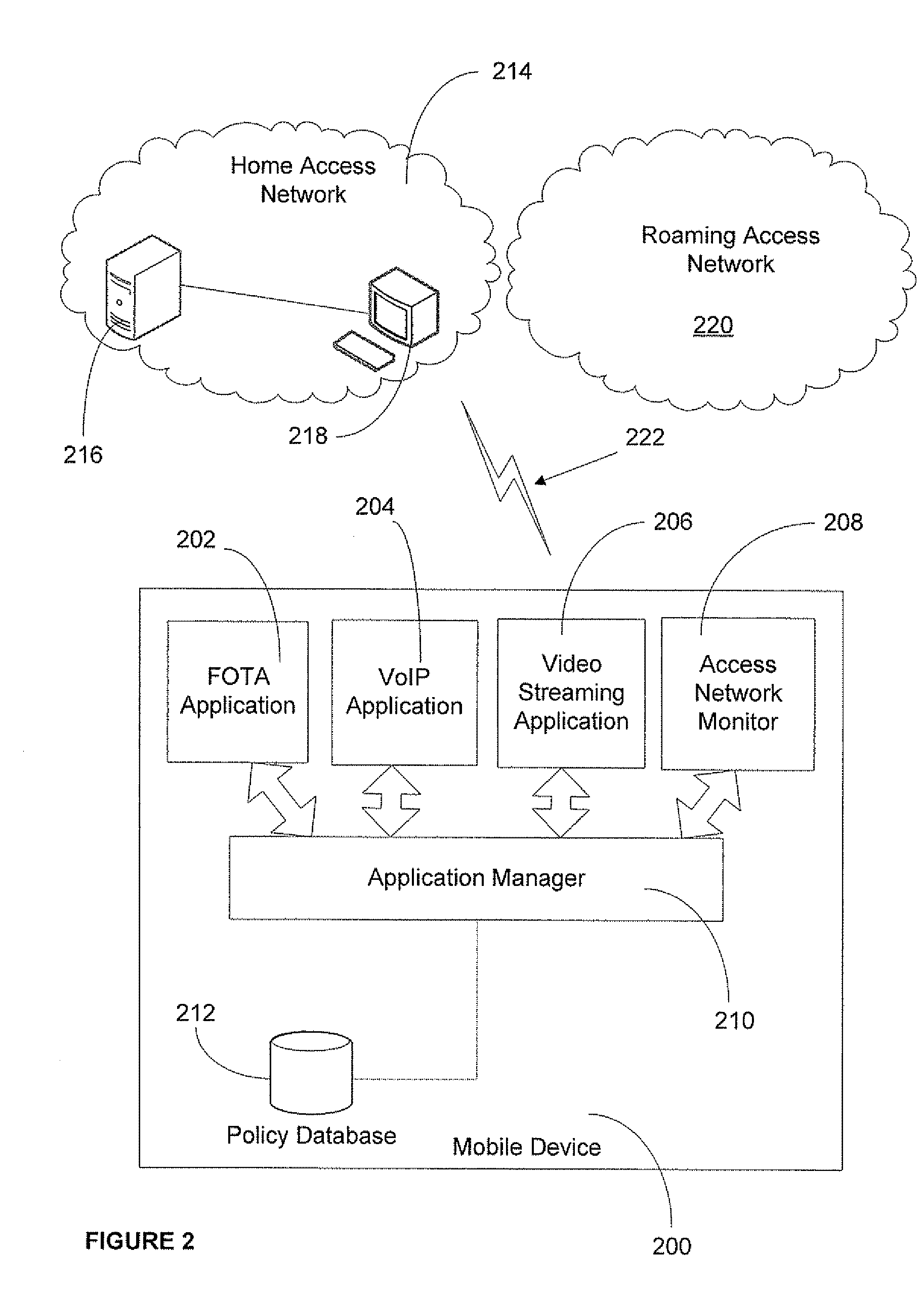
ActiveUS20080160958A1Avoid unwanted roaming chargeAvoid runningUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData connectionAccess network
A system and method are described whereby a mobile device controls access to mobile applications based on access conditions associated with a current access network. To prevent mobile applications from running when the access conditions are not suitable, the mobile device includes a policy database used to store a list of access conditions that are inappropriate for launching the installed applications. The access conditions are based on the type of the current access network used by the mobile device for launching or maintaining the requested application session. The access conditions indicate whether the mobile device is currently accessing its home network or roaming on another provider's network. Similarly, the access conditions indicate the type of network access interface used by the current network to provide the data connection necessary to run the requested application. The policy database correlates predetermined actions with the access conditions associated with a given application session.
Owner:U S CELLULAR
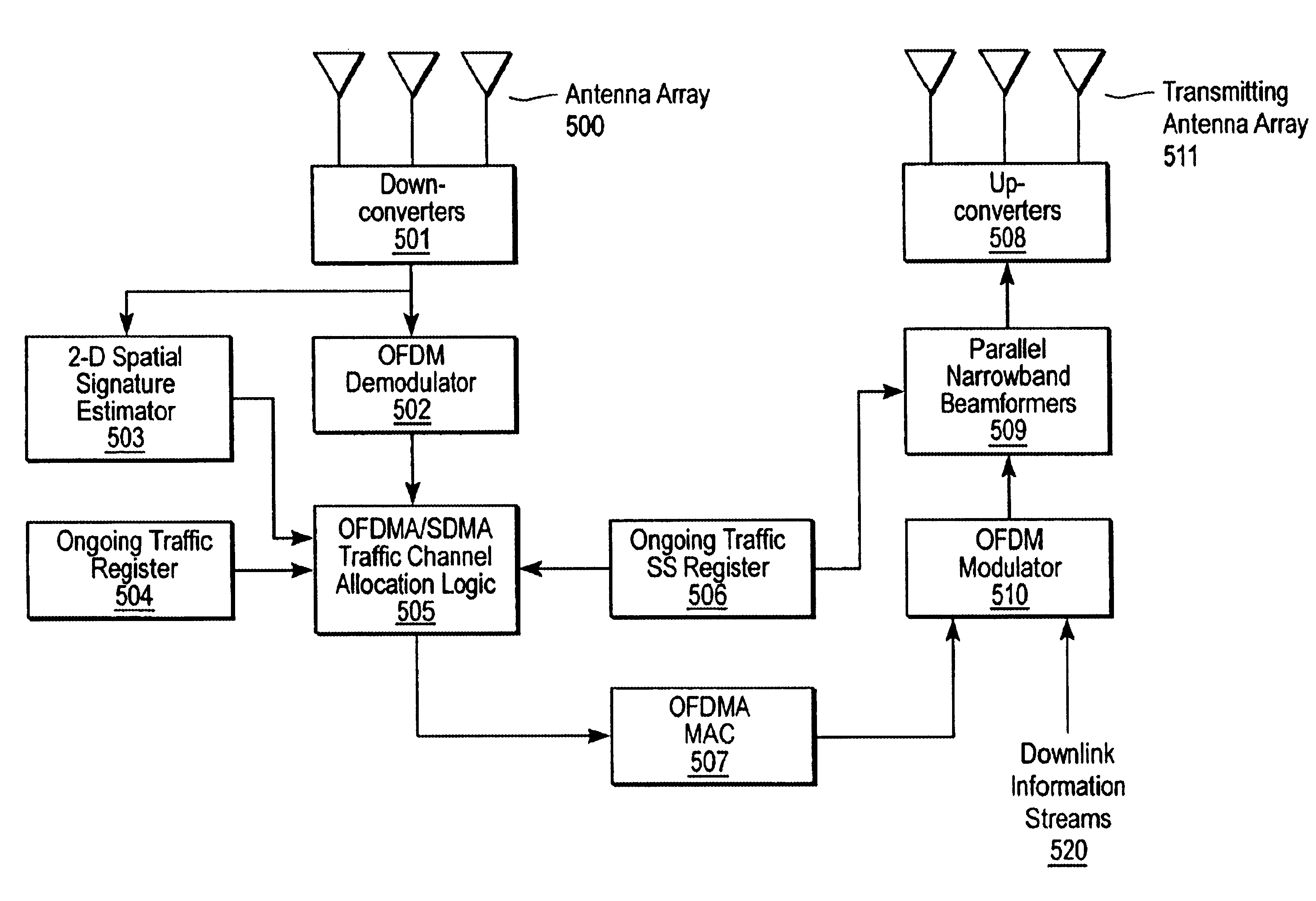
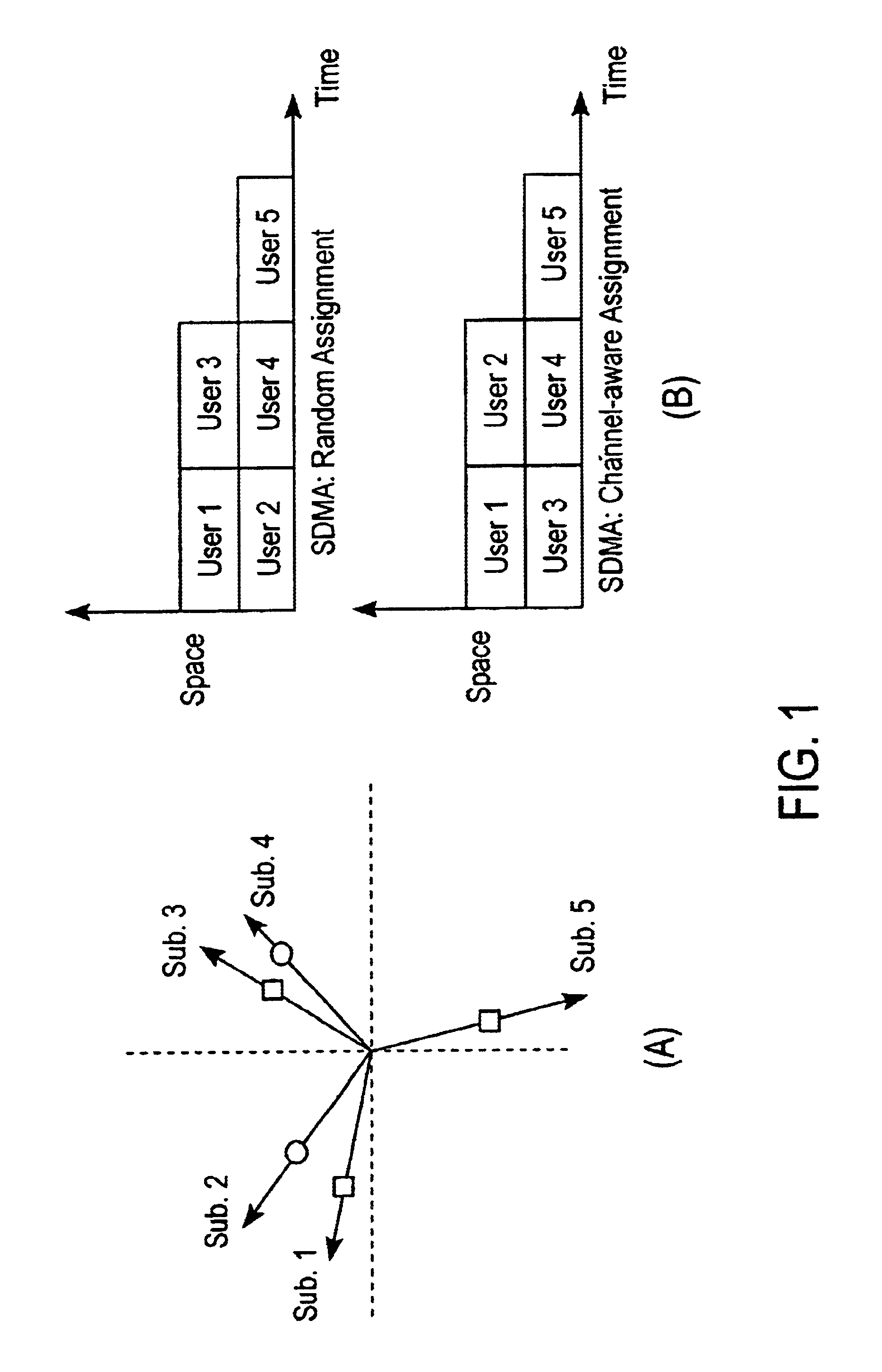
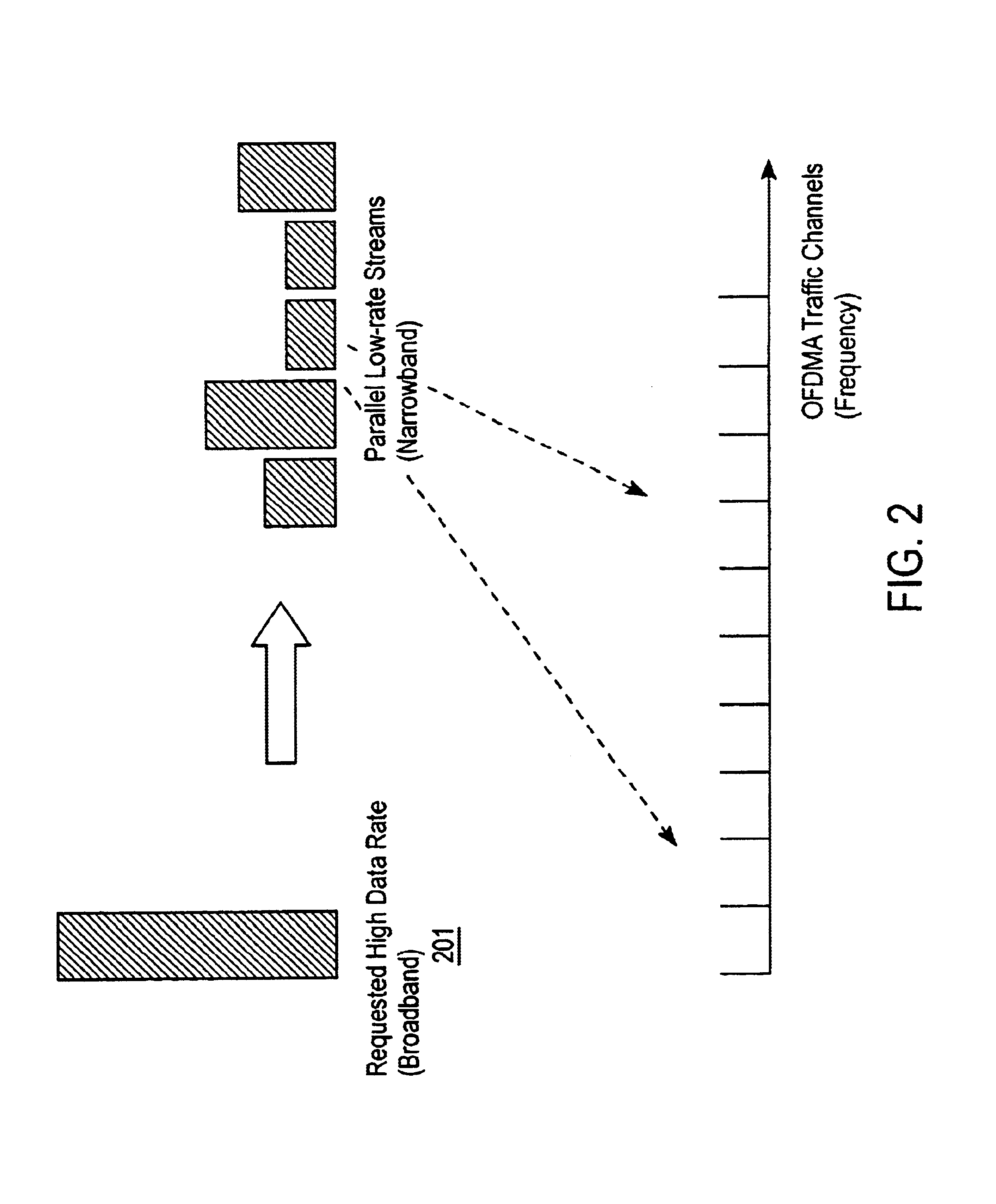
Channel allocation in broadband orthogonal frequency-division multiple-access/space-division multiple-access networks
A network is described. In one embodiment, the network comprises multiple subscriber units to communicate with the base station using an orthogonal frequency-division multiple-access (OFDMA) protocol, and a base station. The base-station includes a memory unit to store broadband spatial signature vectors associated with each subscriber and traffic channel allocation logic. The vectors are a function of frequency. The traffic channel allocation logic allocates OFDMA channels using the broadband spatial signature vectors of the subscribers.
Owner:ADAPTIX +1
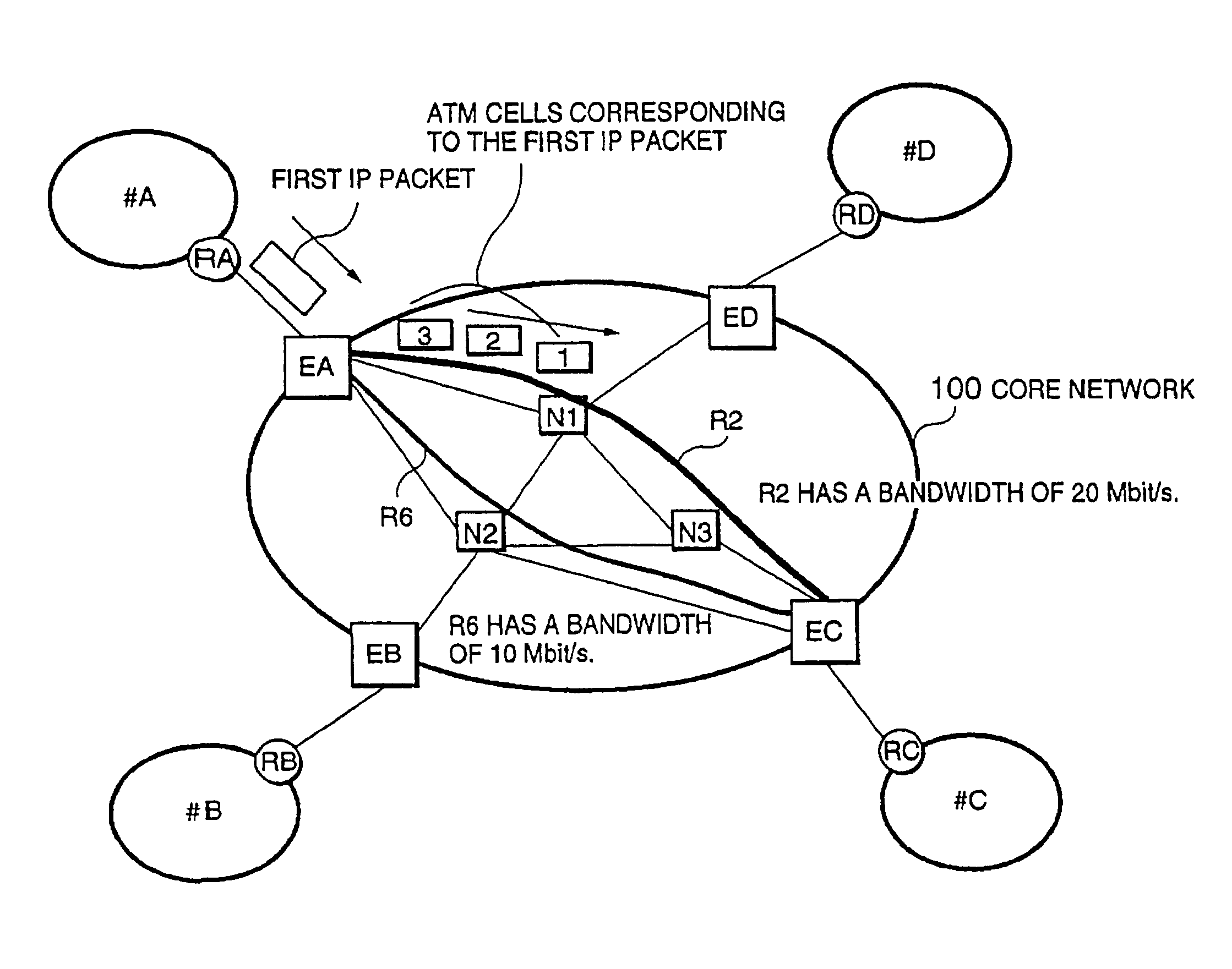
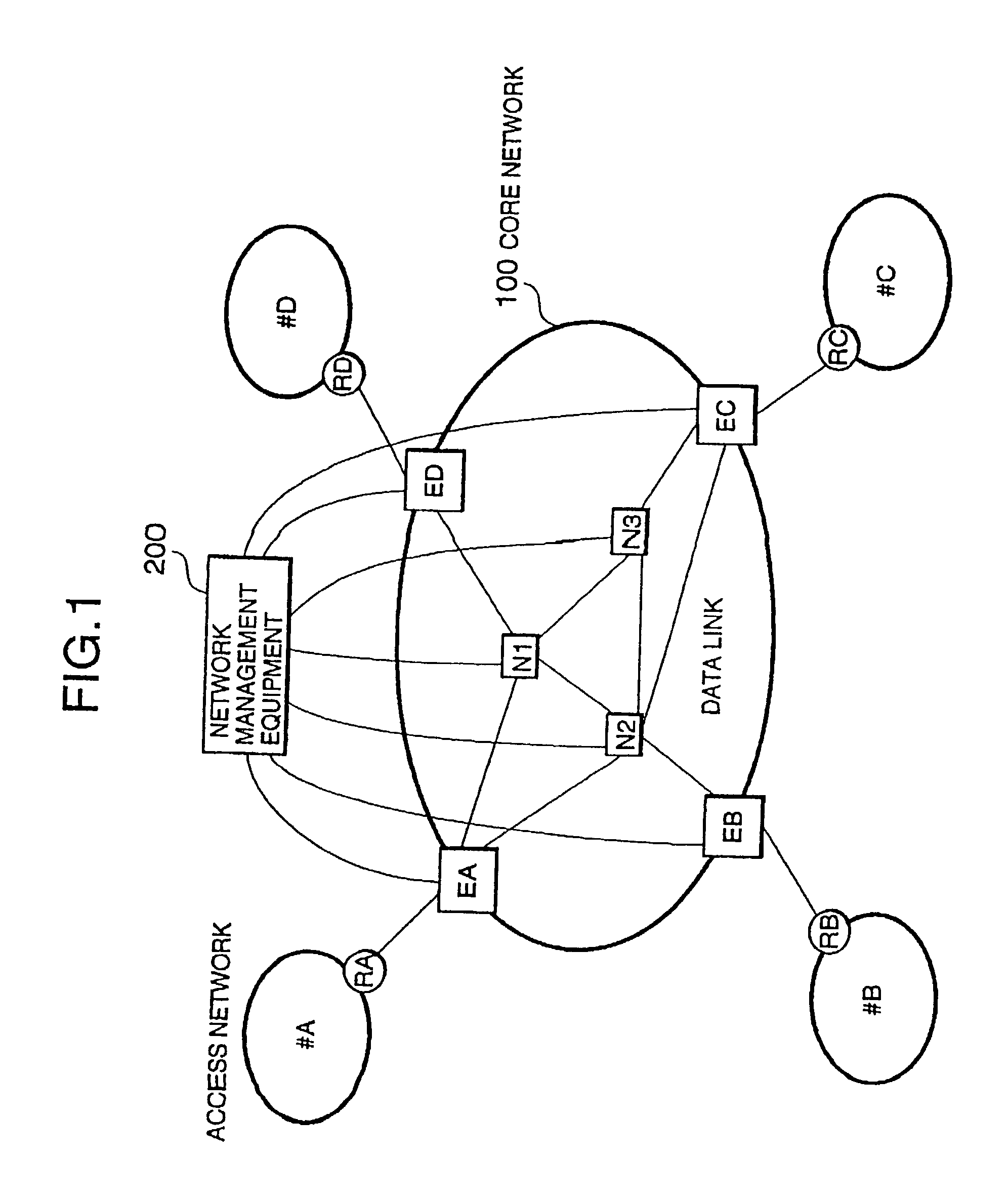
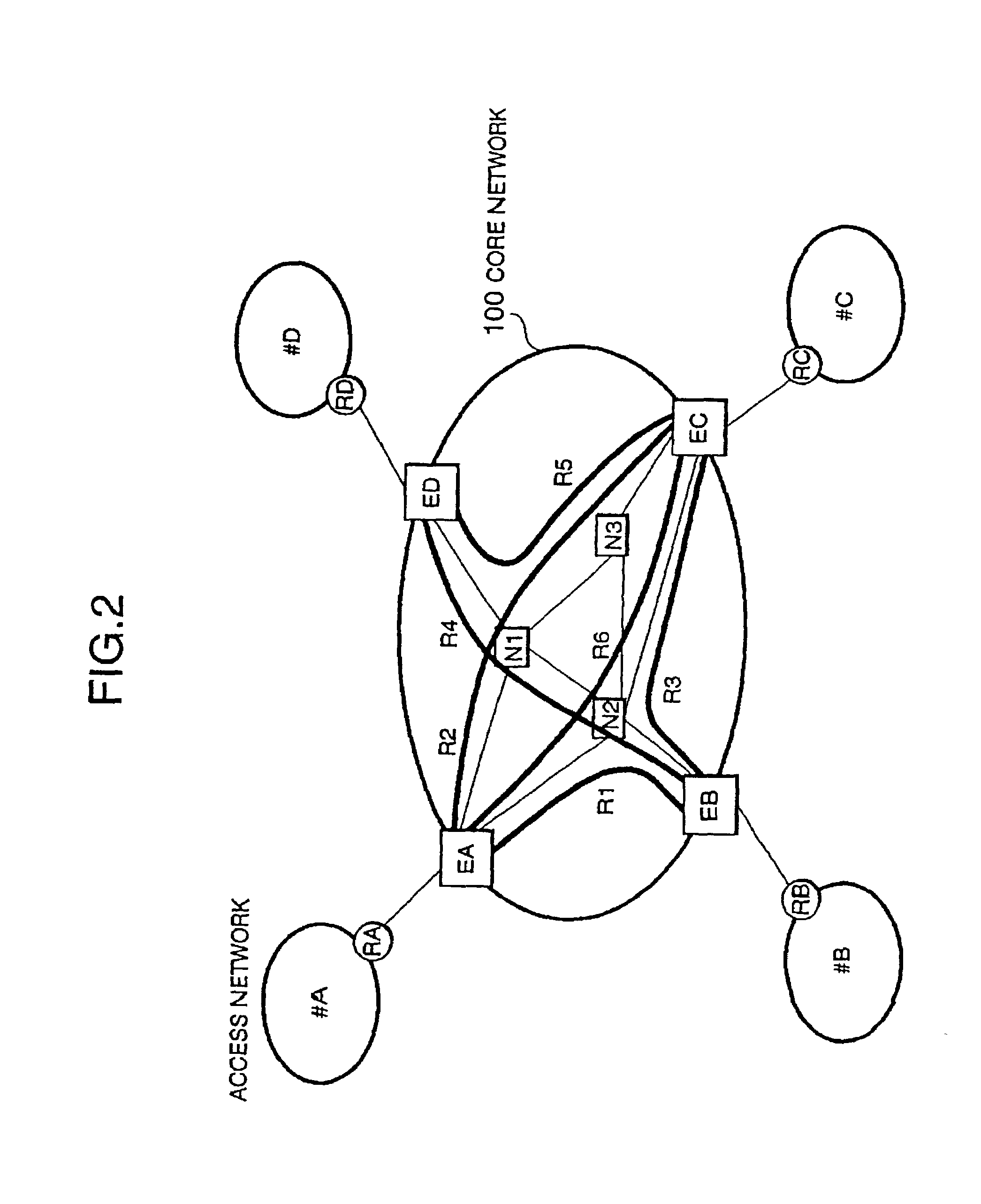
Packet switching network, packet switching equipment and network management equipment
InactiveUS7046630B2Reduces delay variationReduce in quantityError preventionTransmission systemsAccess networkDelayed time
This invention provides a network management equipment and a packet switching equipment which eliminate a connection setup delay time, reduce a delay and a delay variation involved in data transfer, and effectively perform connectionless data flow processing in a large data network. The network is divided into a connection-oriented core network and a plurality of connectionless access networks connected to the core network where a plurality of connections (called permanent virtual route (PVR)) are set up among a plurality of edge nodes. The network management equipment selects one route from a plurality of PVRs for connectionless data flow received from one of the access networks and transfers data along the PVR.
Owner:HITACHI LTD
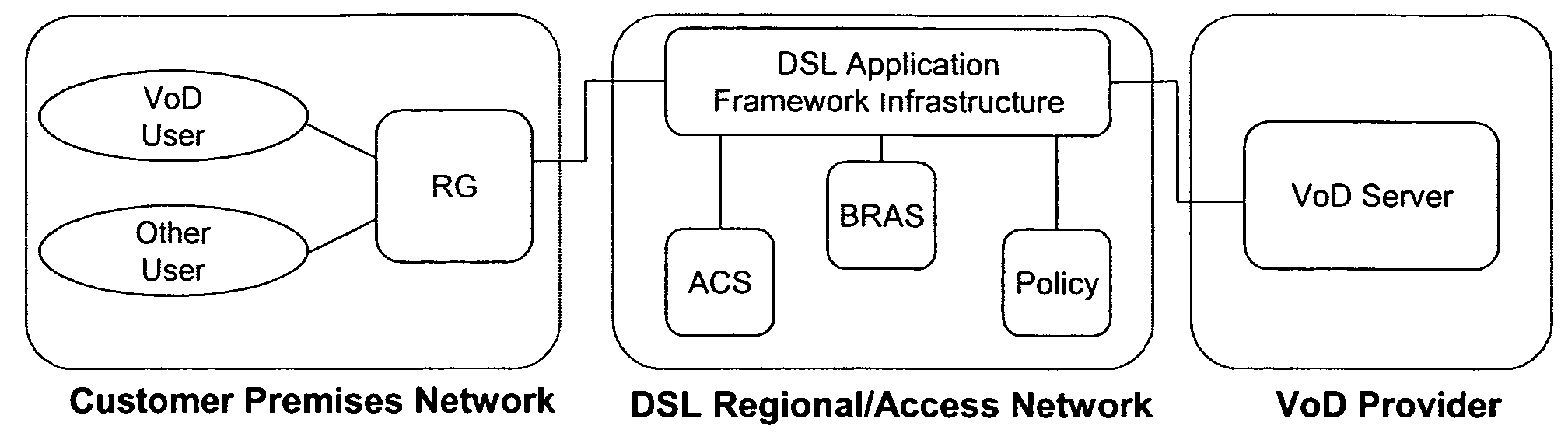
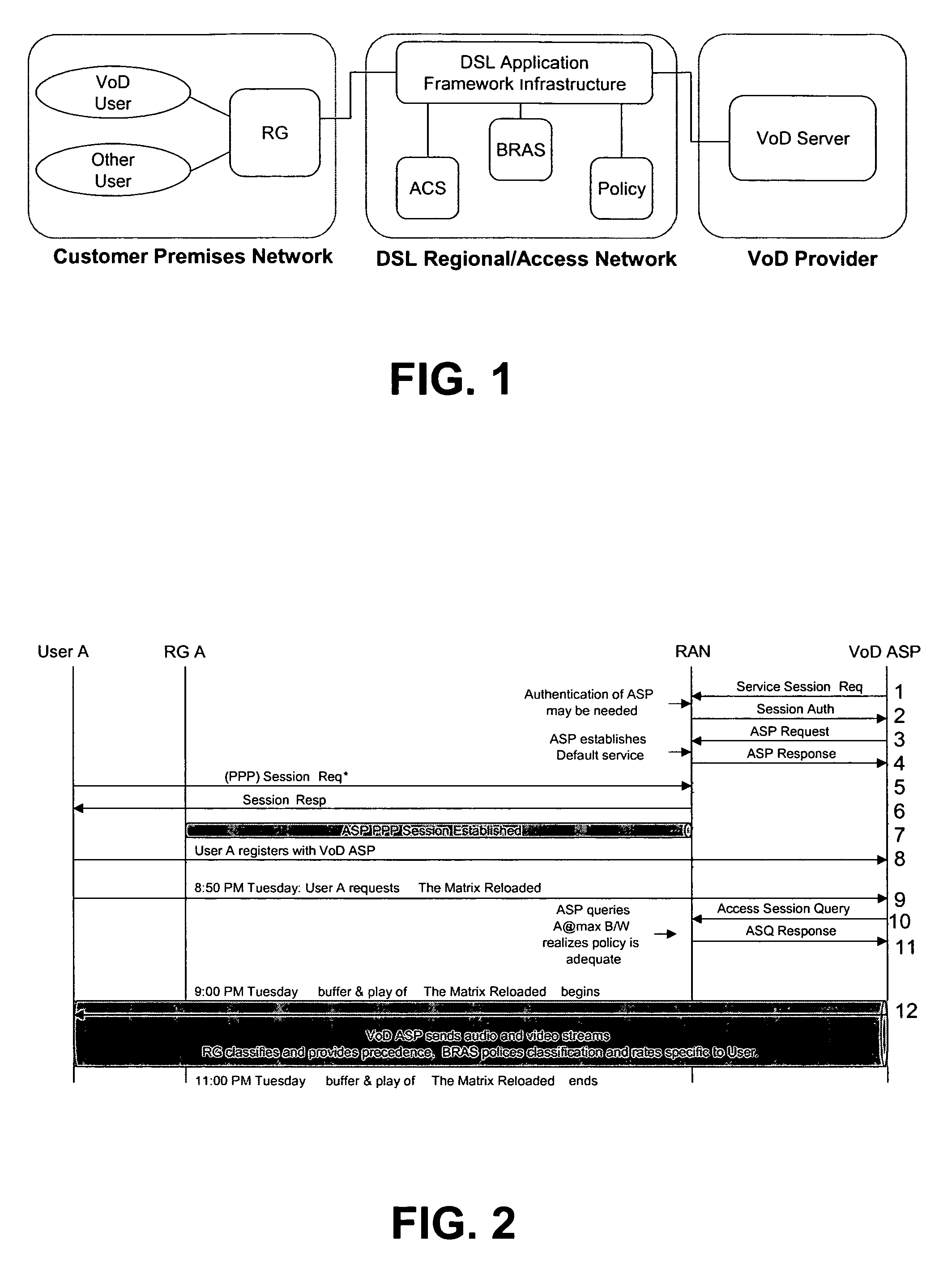
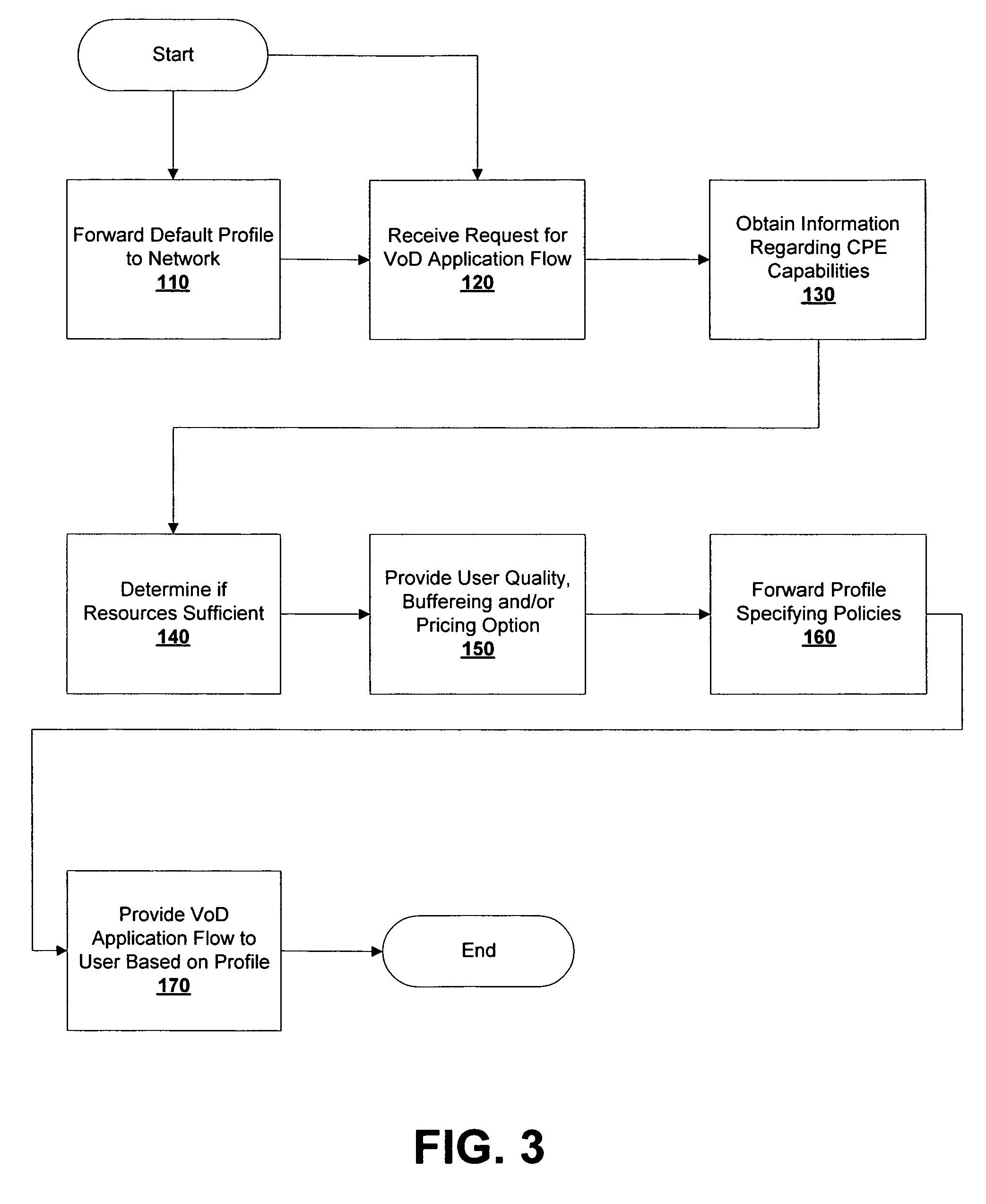
Methods and systems for providing video on demand over a communication network using managed quality of service, bandwidth allocation and/or user profiles
ActiveUS7617516B2Multiplex system selection arrangementsTelevision conference systemsAccess networkDynamic bandwidth allocation
Methods for providing video on demand service from an Application Service Provider (“ASP”) to a user over a Regional / Access Network (“RAN”) are provided. A request for a video on demand application flow may be received from the user. In response to the request, information may be obtained from the RAN regarding the capabilities of the user's Customer Premises Equipment (“CPE”). A profile may then be forwarded from the ASP to the RAN that specifies at least one policy regarding the transmission of data associated with the video on demand application flow across the RAN. The data associated with the video on demand application flow may then be forwarded across the RAN in accordance with the profile. The RAN may also be provided a default profile that specifies default policies that apply with respect to video on demand application flows that are transmitted across the RAN prior to obtaining information from the RAN regarding the capabilities of the CPE of any specific user. The user specific profiles may then be used to alter one or more policies specified in the default profile.
Owner:BELLSOUTH INTPROP COR
Method and system using information written in a wrapper description language to execute query on a network
InactiveUS6102969AEasy to understandEasy maintenanceData processing applicationsWeb data indexingAccess networkNetwork connection
This invention provides assistance to a user in accessing network attached information sources. In one aspect, the invention is a method for intelligently routing a user query to information sources relevant to that query, extracting relevant data fields from received responses, and intelligently presenting the extracted data in order of estimated relevance. The system of this invention implements one or more steps of the method in a centralized or distributed manner on one or more network attached computers. Further, this invention provides a novel language and implementation that facilitates easily written and maintained descriptions of information source query and response formats.
Owner:AT HOME BONDHOLDERS LIQUIDATING TRUST
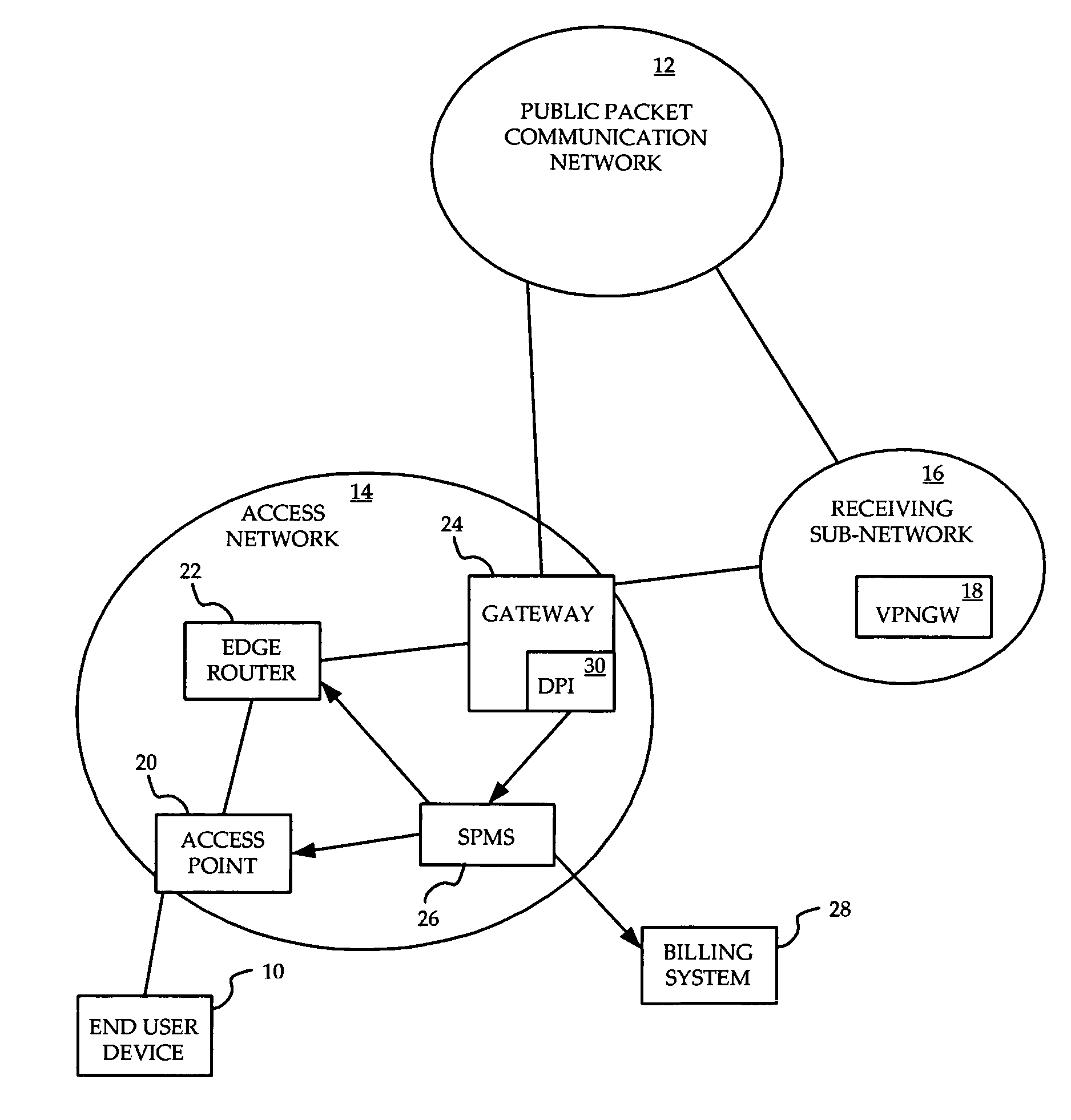
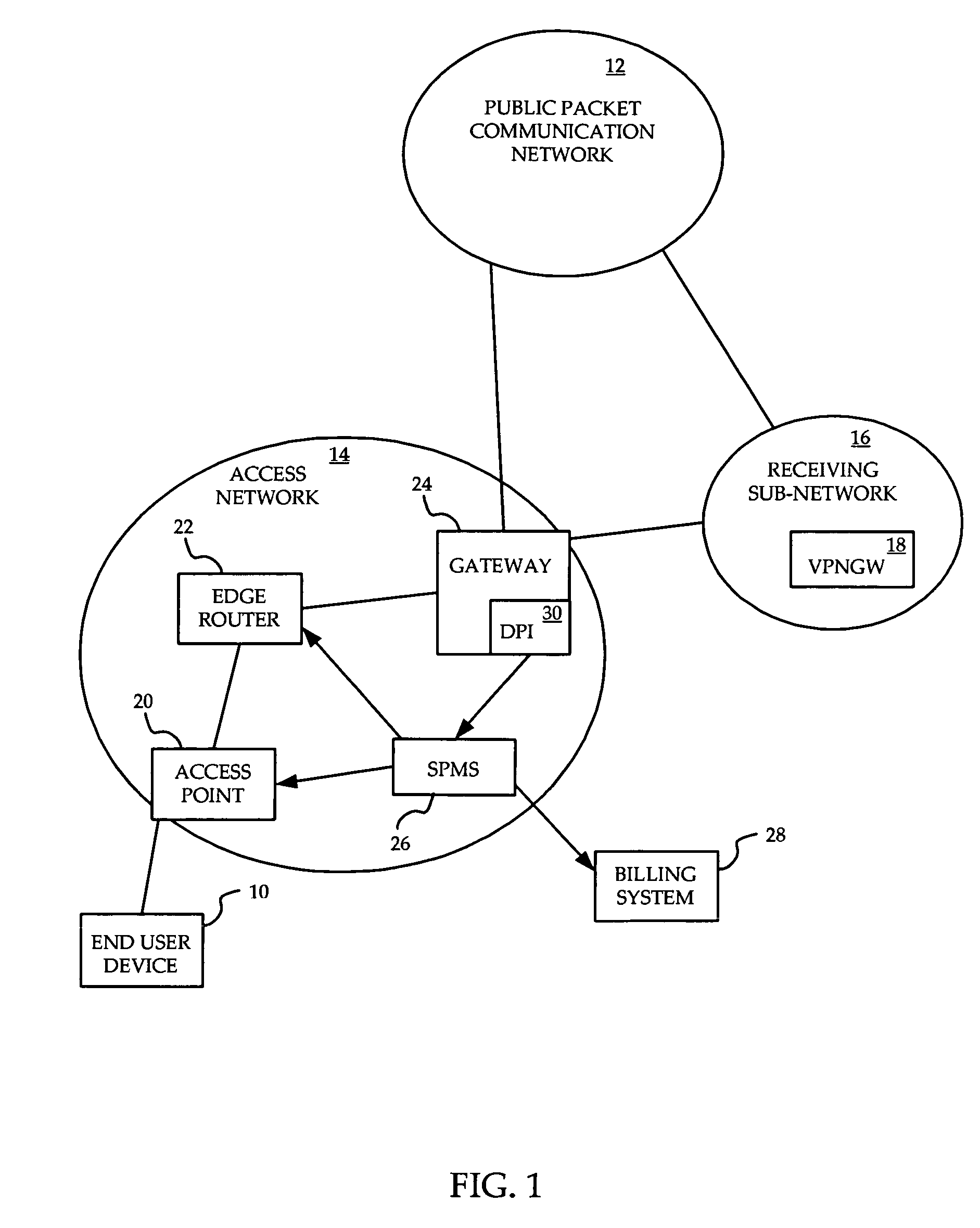
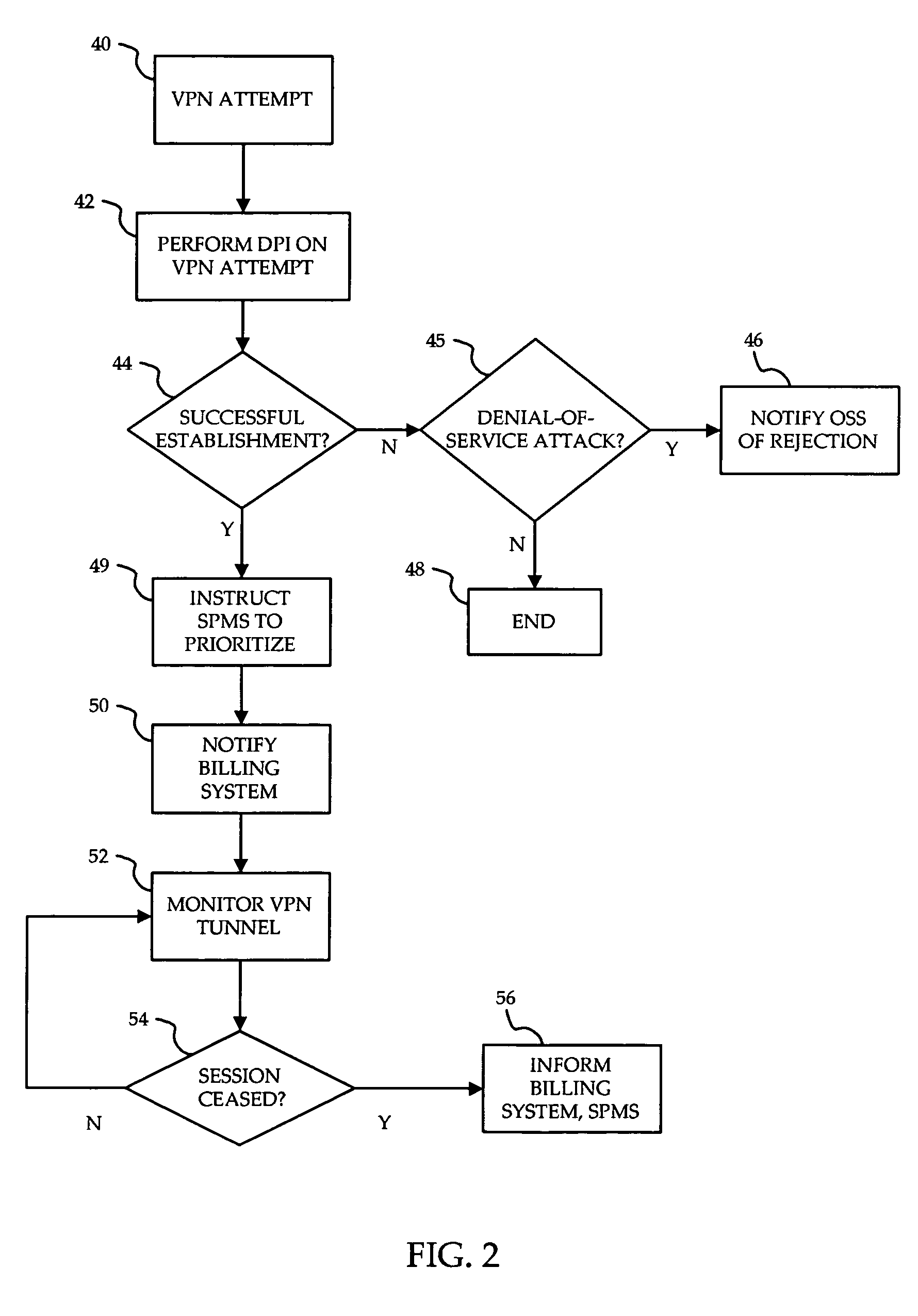
System and method for prioritization of traffic through internet access network
InactiveUS7881199B2Avoid allocation problemsRaise priorityError preventionTransmission systemsPacket communicationTraffic capacity
A method is provided for ensuring that specific traffic flows are adequately prioritized in a public packet communication network even when the network is heavily congested. Per-flow QoS capability is added to VPN tunnels. Connection requests are routed through a specific port in an access provider's network to designated VPN gateway. Deep packet inspection is performed on traffic through the port in an attempt to determine whether the connection request was accepted. If the connection request was accepted, the traffic flows associated with that session may be given a specific priority of QoS level when transiting a packet access network.
Owner:ALCATEL LUCENT SAS
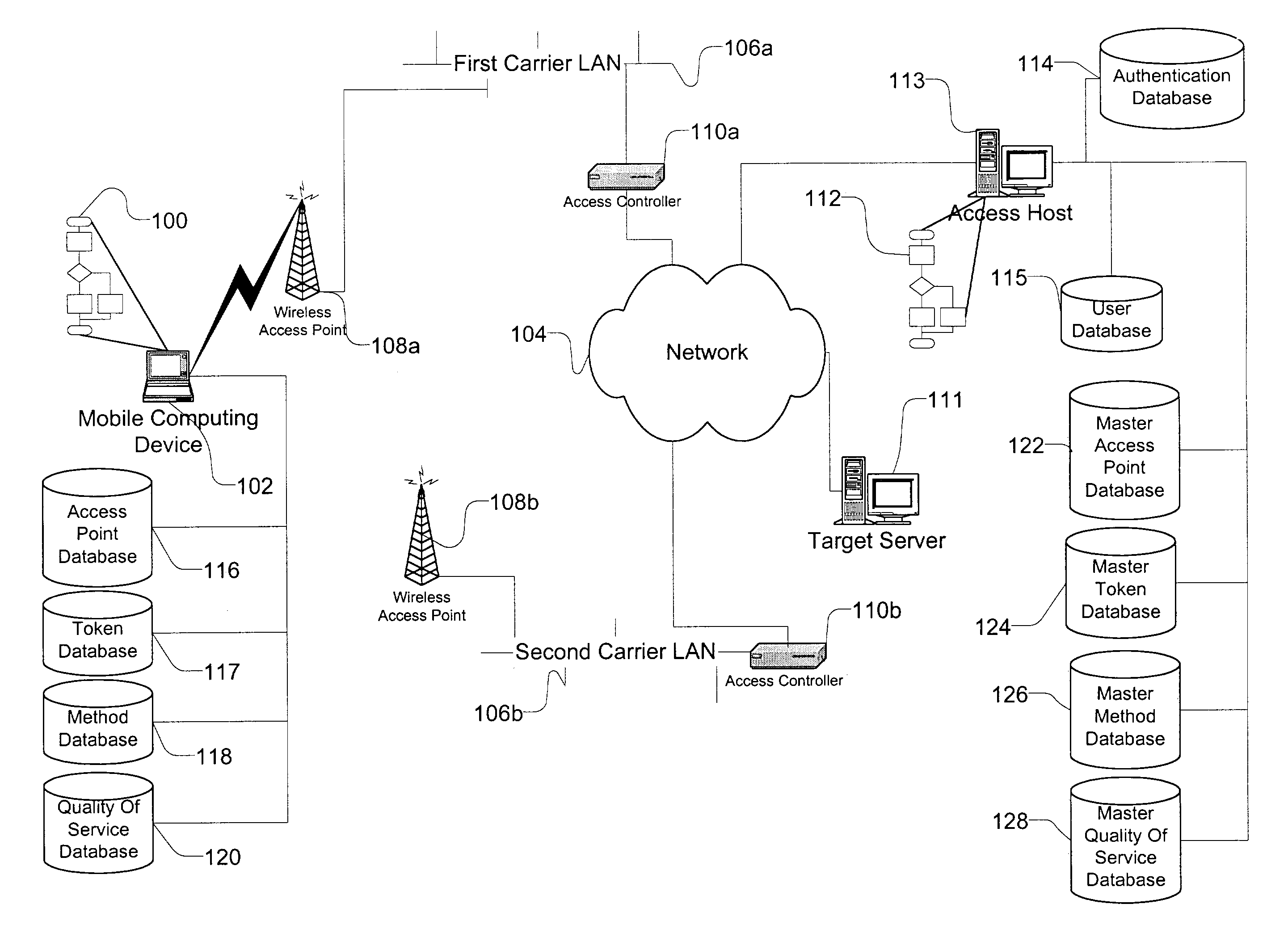
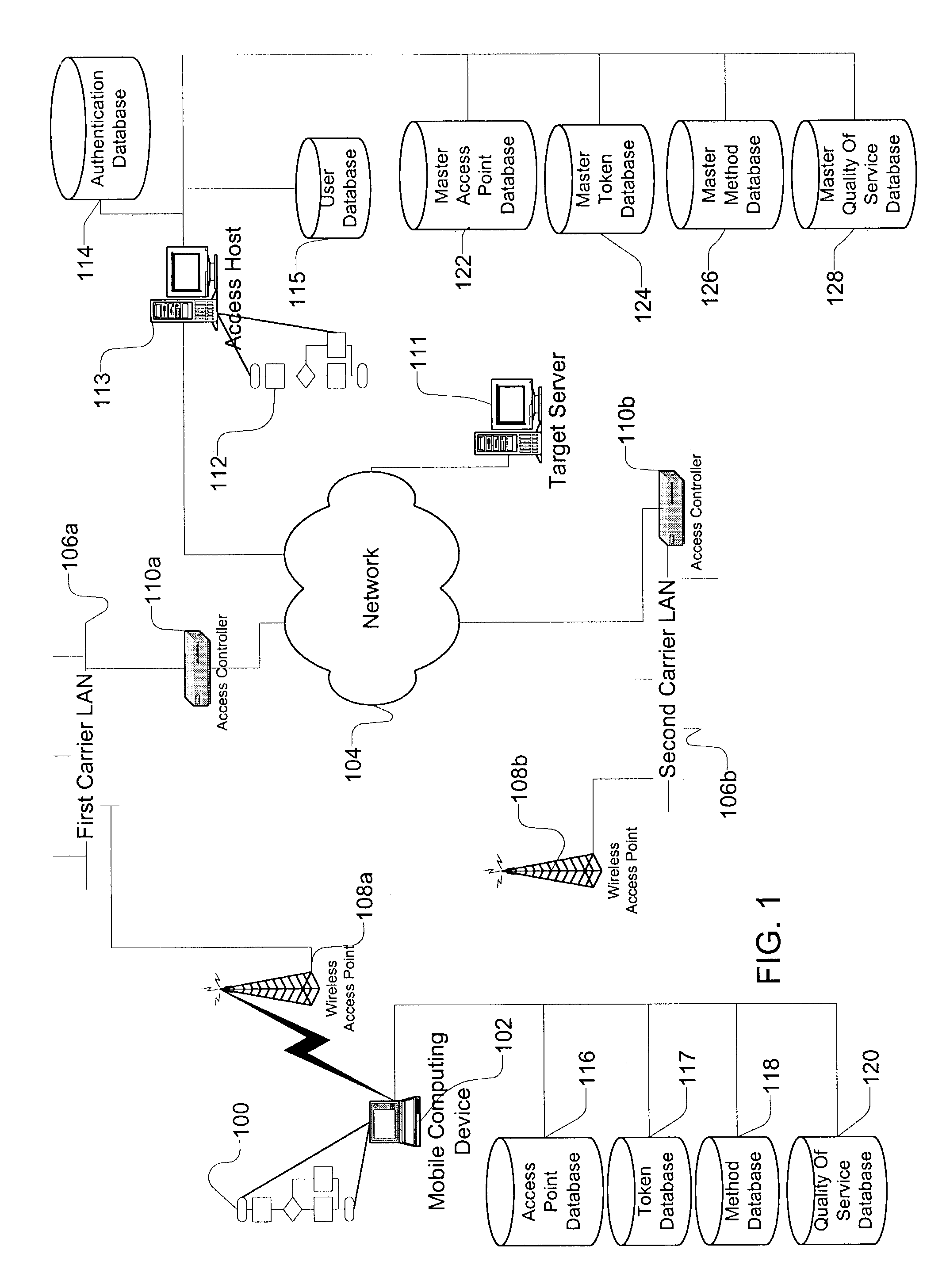
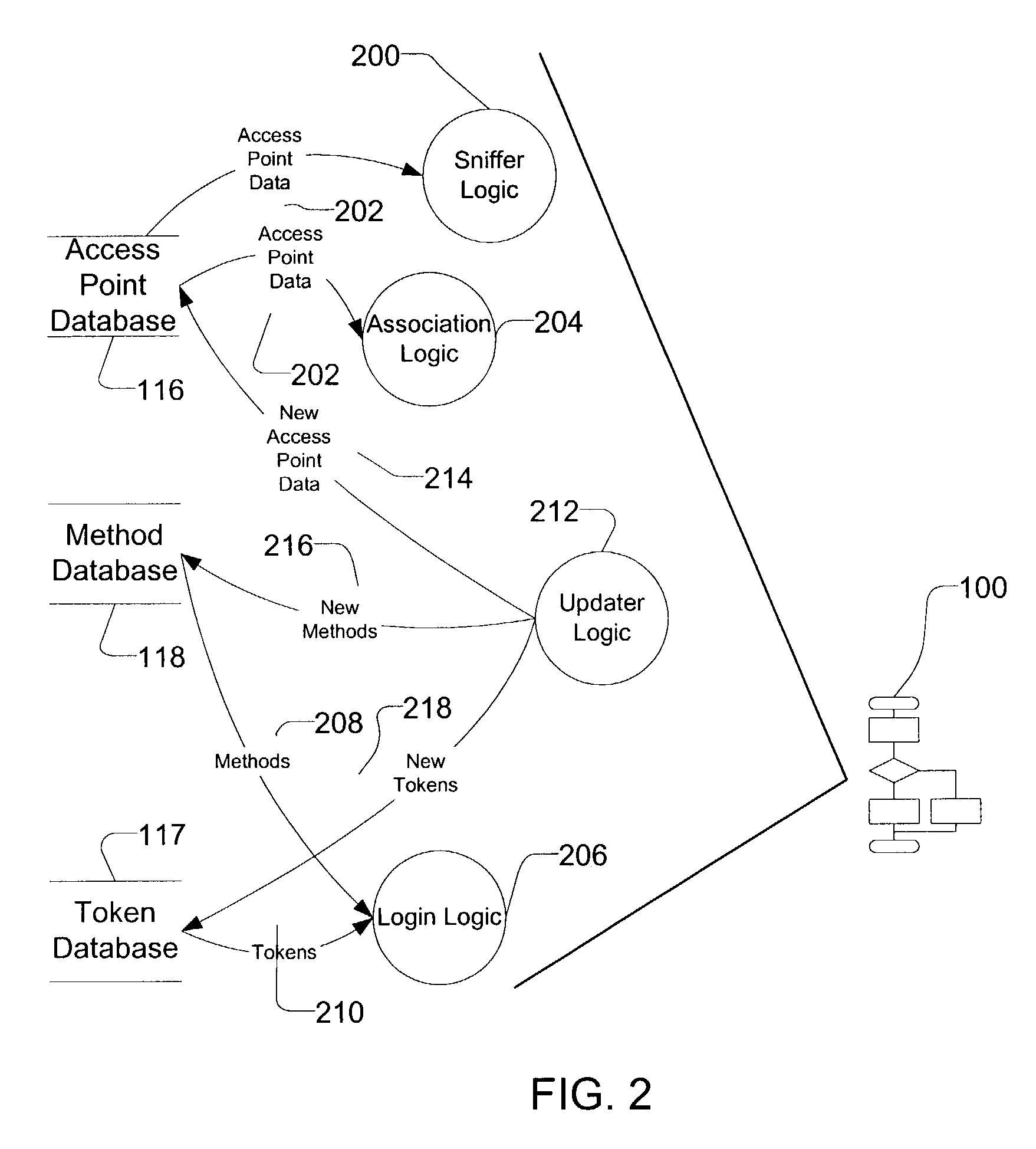
Method and apparatus for accessing networks by a mobile device
InactiveUS7483984B1Assess restrictionMultiple digital computer combinationsAccess networkNetwork generation
A method and apparatus for accessing wireless carrier networks by mobile computing devices. An access client hosted by a mobile computing device accesses carrier networks using wireless access points. The access client uses an access point database to identify access points and carrier networks. The access client uses a methods database and a tokens database to access the carrier networks. The access client updates the access point database, the methods database, and the token database using an access server when the access client is operably coupled to a carrier network. The access client transmits user information to the carrier network. The carrier network uses the user information to authenticate the user and to generate session data while the user is accessing the carrier network. The carrier network transmits the session data to the access server. The access server uses the session data to generate billing information for the user. The access client also collects network performance data for individual access points and carrier networks. The access client transmits the network performance data to the access server. The access server aggregates network performance data from a plurality of access clients to generate quality of server reports for both individual access points and carrier networks. The access client further includes access point detection and evaluation features for use by a user in selecting access points available at a single location.
Owner:BOINGO WIRELESS
Secure network cache content
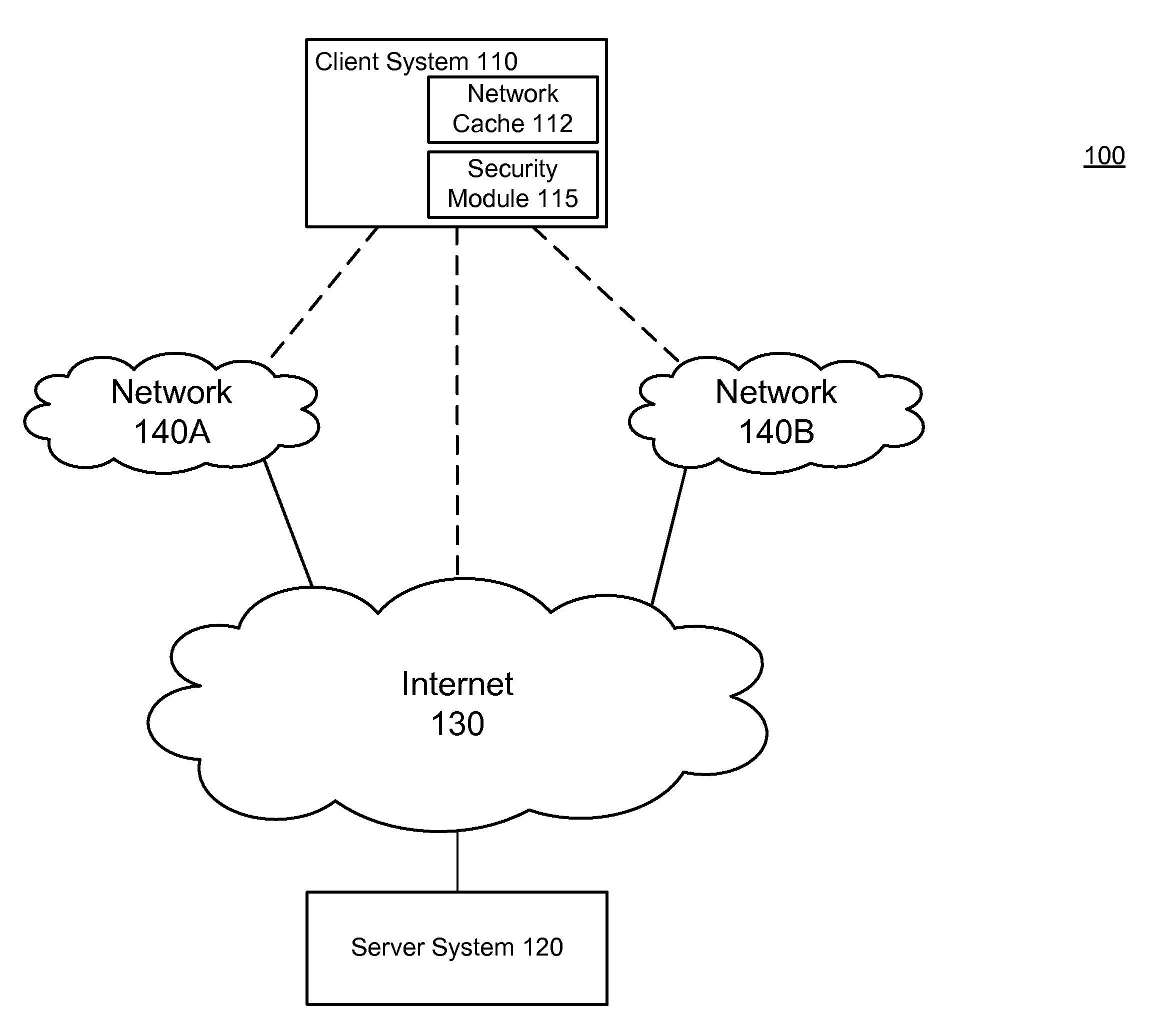
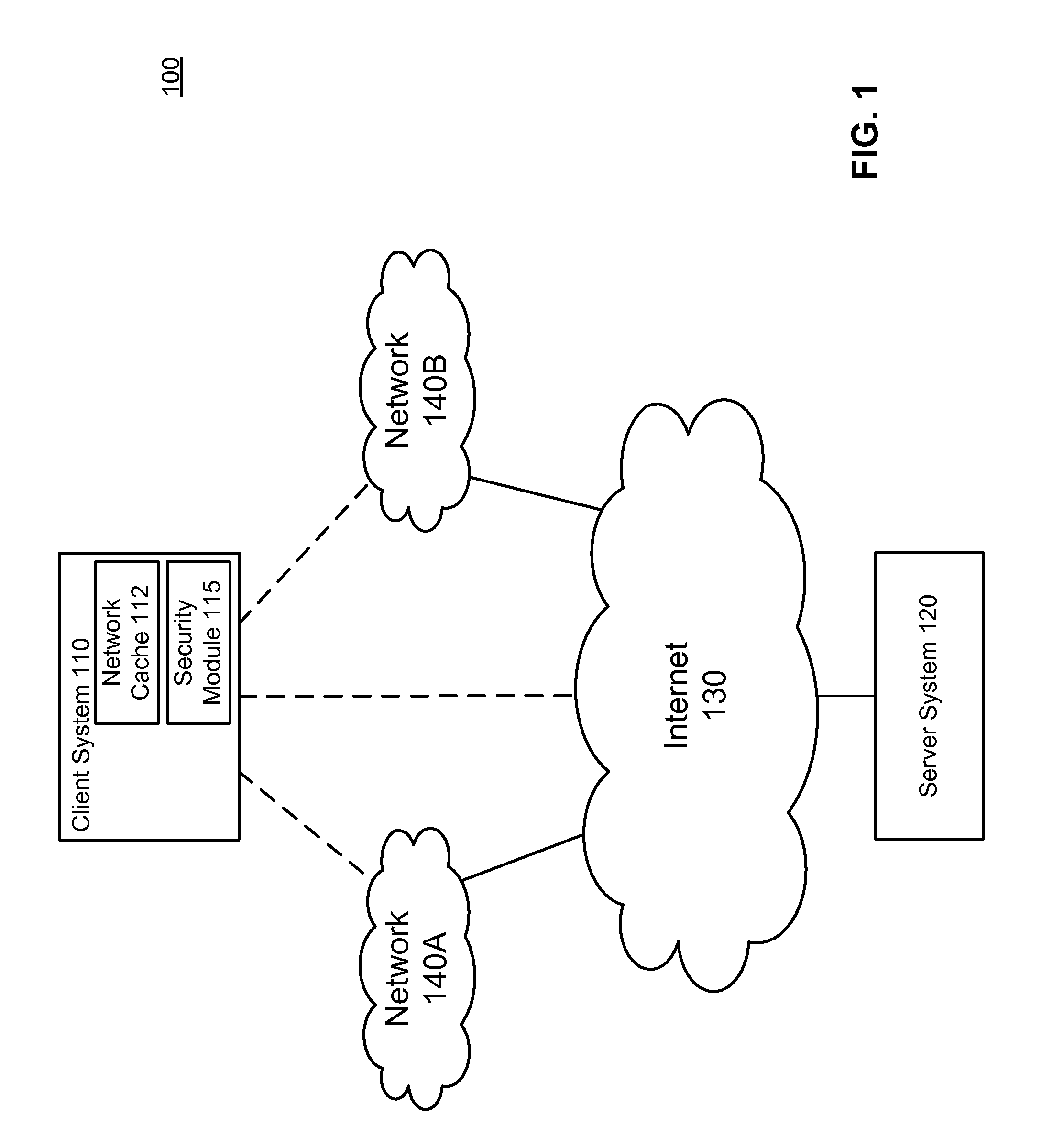
ActiveUS8584234B1Prevent malicious activityMemory loss protectionError detection/correctionAccess networkSecurity rule
A security module on a computing device applies security rules to examine content in a network cache and identify suspicious cache content. Cache content is identified as suspicious according to security rules, such as a rule determining whether the cache content is associated with modified-time set into the future, and a rule determining whether the cache content was created in a low-security environment. The security module may establish an out-of-band connection with the websites from which the cache content originated through a high security access network to receive responses from the websites, and use the responses to determine whether the cache content is suspicious cache content. Suspicious cache content is removed from the network cache to prevent the suspicious cache content from carrying out malicious activities.
Owner:CA TECH INC
Network discovery mechanisms
InactiveUS20060187858A1Reduce degradationReduce transient data lossAssess restrictionData switching by path configurationAccess networkMobile device
In some of the preferred embodiments, a method for network discovery of a mobile device to use at least one of a plurality of access networks within an IP network includes: obtaining specified network information in the vicinity of a given location based on a set of criteria when a mobile is connected to the IP network from any location.
Owner:FOUR BATONS WIRELESS LLC +2
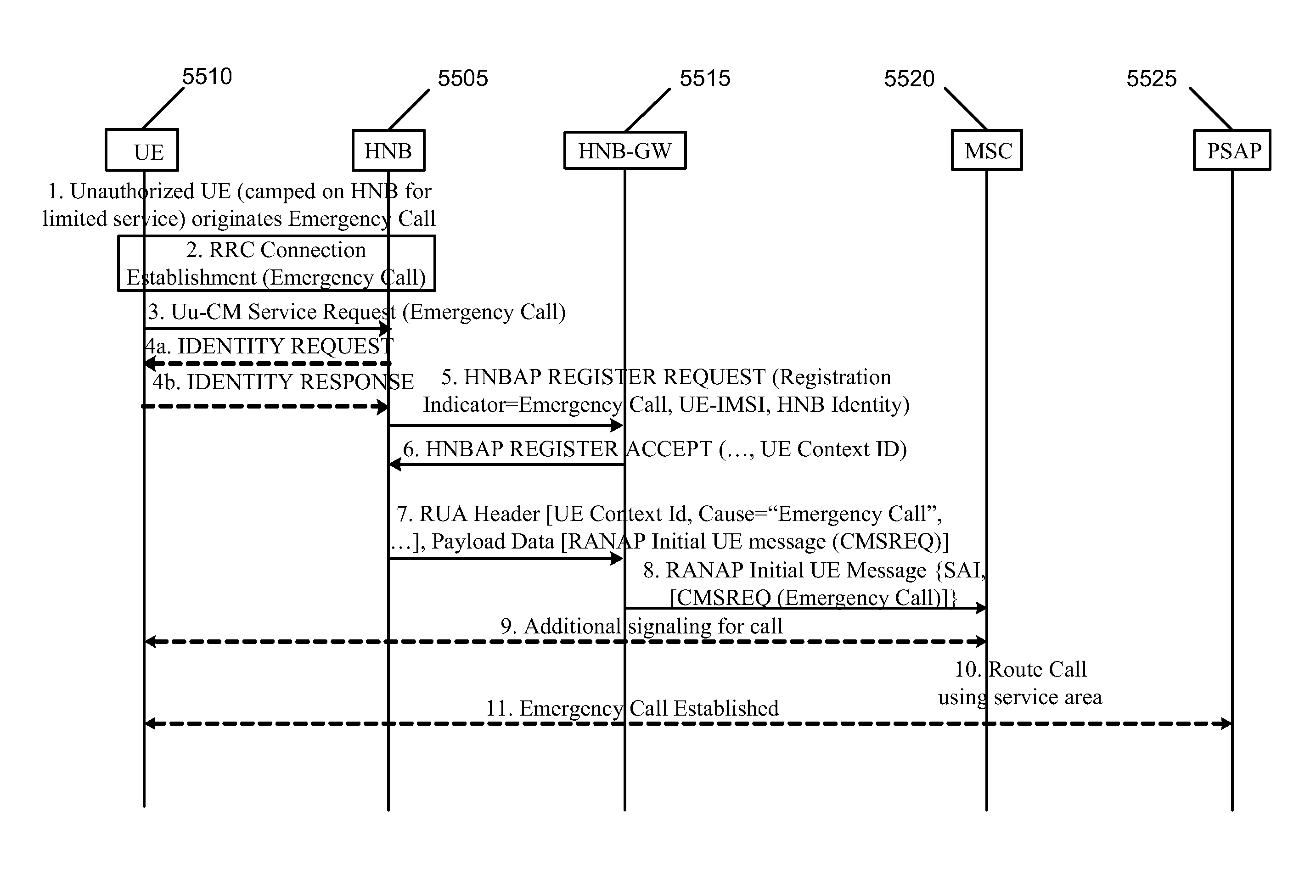
Method and apparatus for routing of emergency services for unauthorized user equipment in a home Node B system
ActiveUS8041335B2Lower deployment costsQuality andAssess restrictionNetwork topologiesAccess networkHome Node B
Some embodiments are implemented in a communication system that includes a first communication system comprised of a licensed wireless radio access network and a core network, and a second communication system comprising a plurality of user hosted access points and a network controller. In some embodiments, each access point operates using short range licensed wireless frequencies to establish a service region. In some embodiments, the network controller communicatively couples the core network to the plurality of access points. The method enables an unauthorized user equipment to call from an access point it is not allowed to use for emergency purposes. The method receives at an access point a service request from an unauthorized user equipment with an establishment cause of emergency call. The method sends a registration request to the network controller. The method sends a message to the core network indicating the location of the user equipment.
Owner:RIBBON COMM OPERATING CO INC
Transceiver for fixed wireless access network applications
InactiveUS20020128009A1Low costConveniently mountedRadio/inductive link selection arrangementsWireless commuication servicesTransceiverWireless transceiver
A combined wireless transceiver and signal conversion unit comprises a radio receiver for receiving a wireless radio signal, and a converter for converting the signal into a form having a communications protocol supported by a communications port of a user digital device. An output device is provided for transmitting the converted signal to a user digital device via a wireline or other suitable medium for carrying the converted signal. The unit includes an input device for receiving a communications signal from the communication port of a user digital device via a wireline or other suitable signal transmission medium, and a transmitter for converting the received signal to a form for wireless transmission.
Owner:DRAGONWAVE
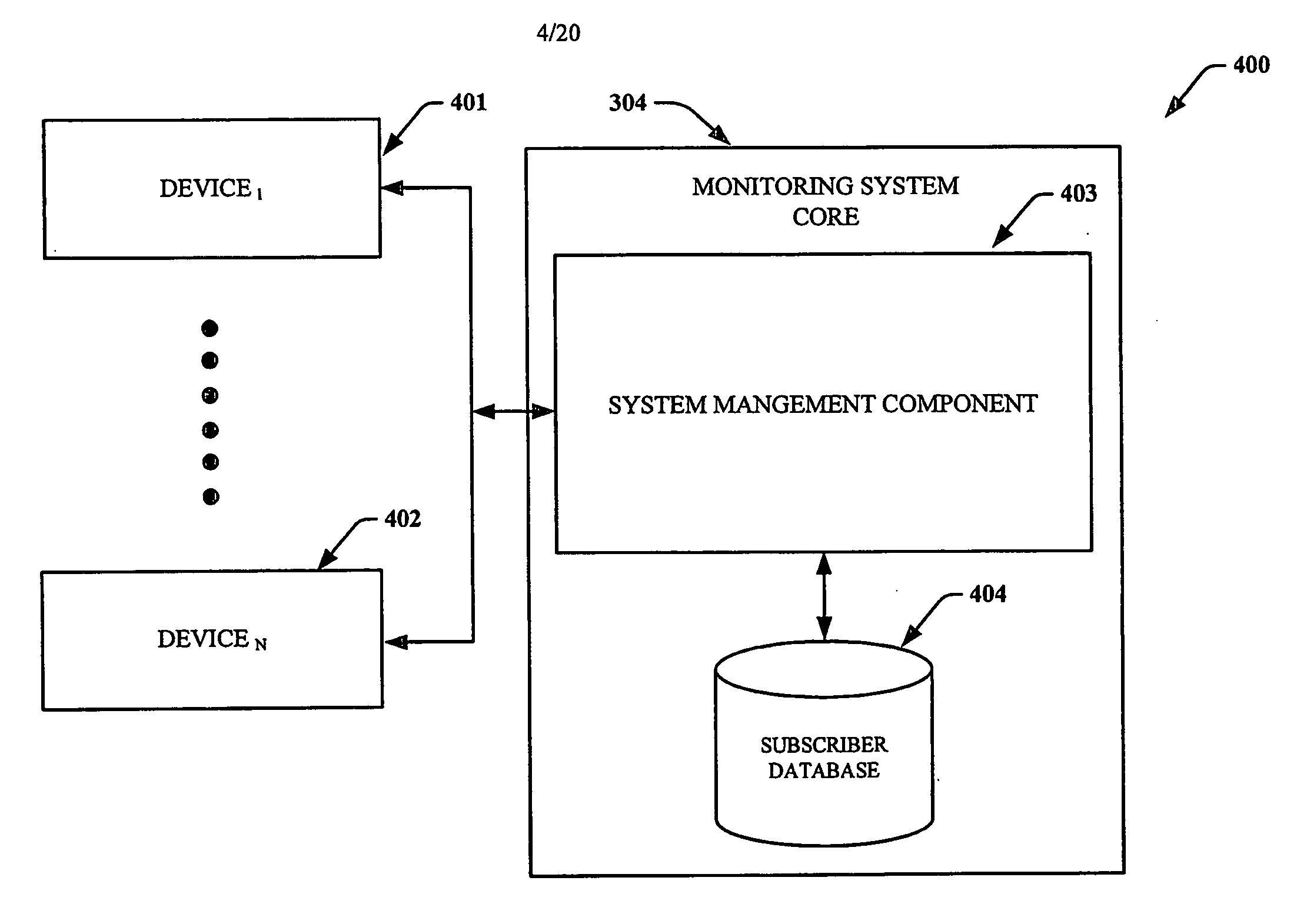
Usage data monitoring and communication between multiple devices
A system and method for by which real-time monitoring and communication of usage data is conducted between a set of N numbered of devices where N is and integer. According to an embodiment, a communication network provides a common core architecture in which the devices connected to the system are converged regardless of their access network requirements or functional capacity. The system has the capacity to monitor and analyze all the usage information of each device connected to the system in regards to content, identity, type, quality, quantity, time, status, activity level, and metadata associated with the functions and applications utilized on a device. The analysis is further based on information governing a subscriber's devices, preferences, and features held in a subscriber database integrated within the system. The analyzed usage data is further processed through a variety of applications in order to generate a response, such as; a report, an alarm, or tailored options for interacting with the generating device which is deliverable in any format within the capacity of the receiving device including all multimedia aspects and non-multimedia aspects. The system further communicates the response in real-time to any device within the set as designated by the subscriber. In another aspect of the invention, the analyzed usage data can be stored for on demand requests of a communication response from past analysis.
Owner:CINGULAR WIRELESS II LLC
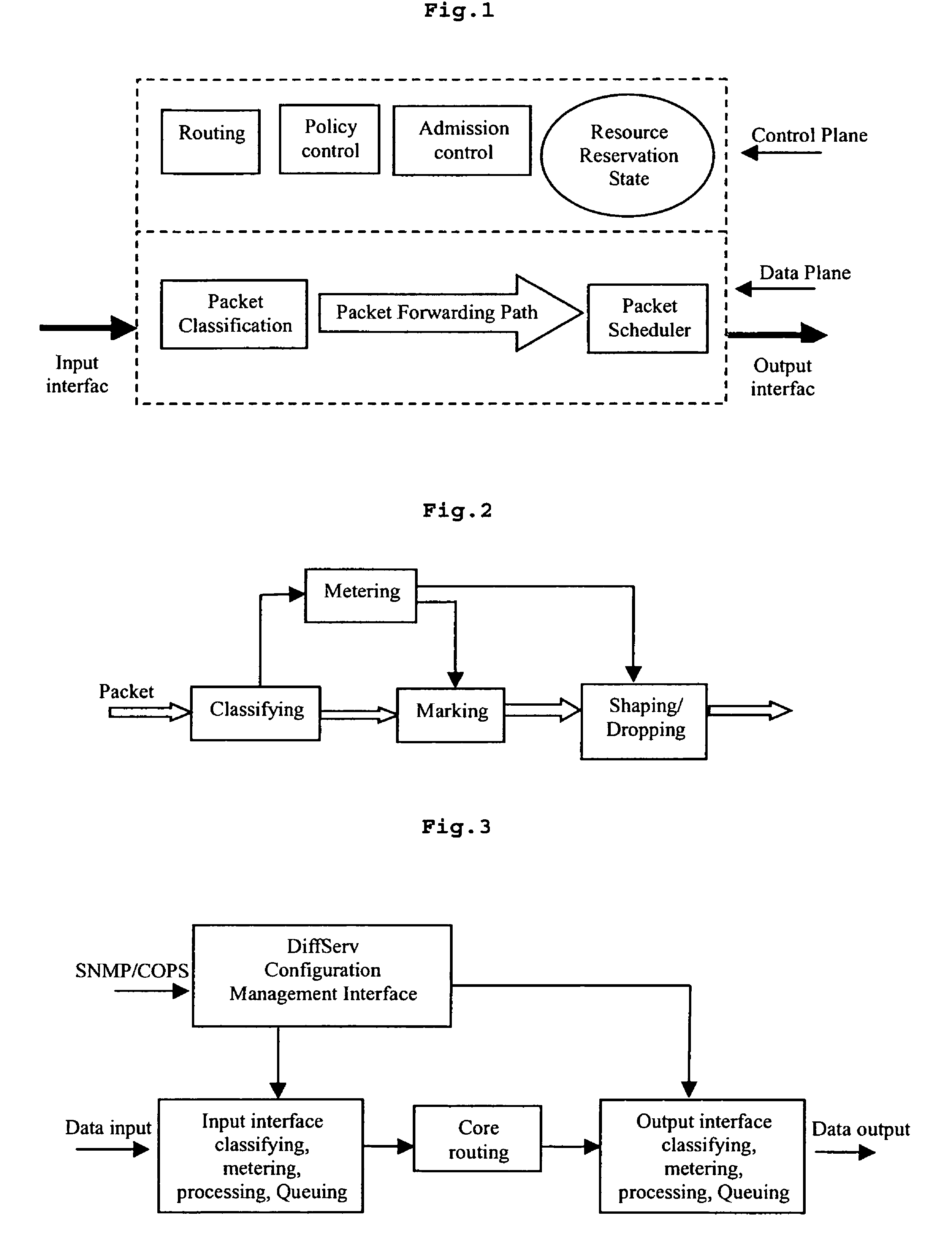
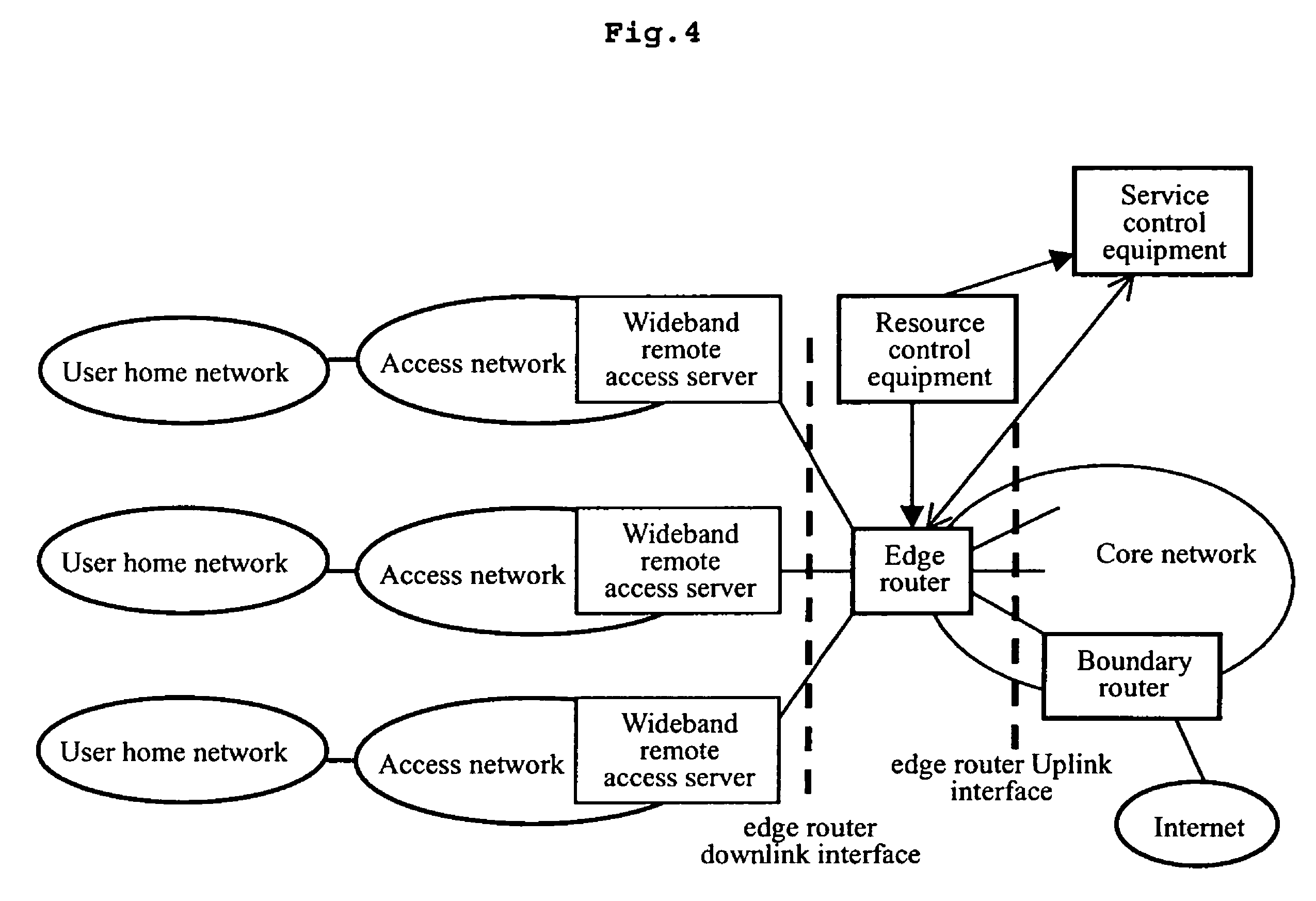
Method, apparatus, edge router and system for providing QoS guarantee
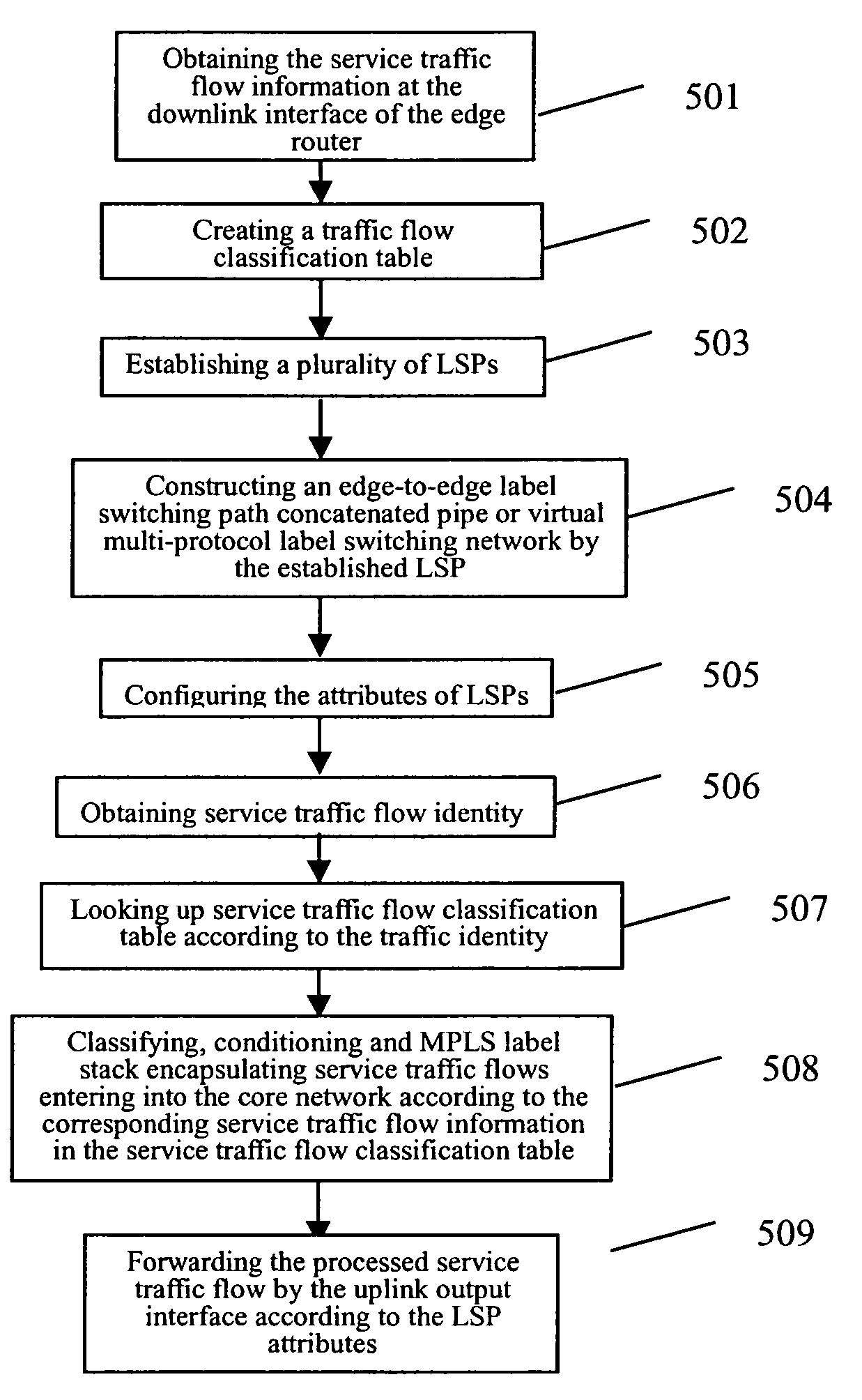
ActiveUS7903553B2High-speed capabilityHigh-speed simplicityError preventionFrequency-division multiplex detailsTraffic capacityAccess network
The present invention discloses a method for providing QoS guarantee by an edge router, the edge router transporting user traffic between the access network and core network, the method comprising: creating a service traffic flow classification table; establishing a plurality of label switching paths; configuring the attributes of the label switching paths; classifying and conditioning the service traffic flows entering into the core network at a downlink interface of an edge router according to the service traffic flow classification table; forwarding the processed traffic by an uplink interface of the edge router according to the attributes of the label switching paths. The present invention also discloses an apparatus for providing QoS guarantee by an edge router. Using the present invention, an edge router can provide exact QoS guarantee and QoS routing control for the application flows.
Owner:HUAWEI TECH CO LTD
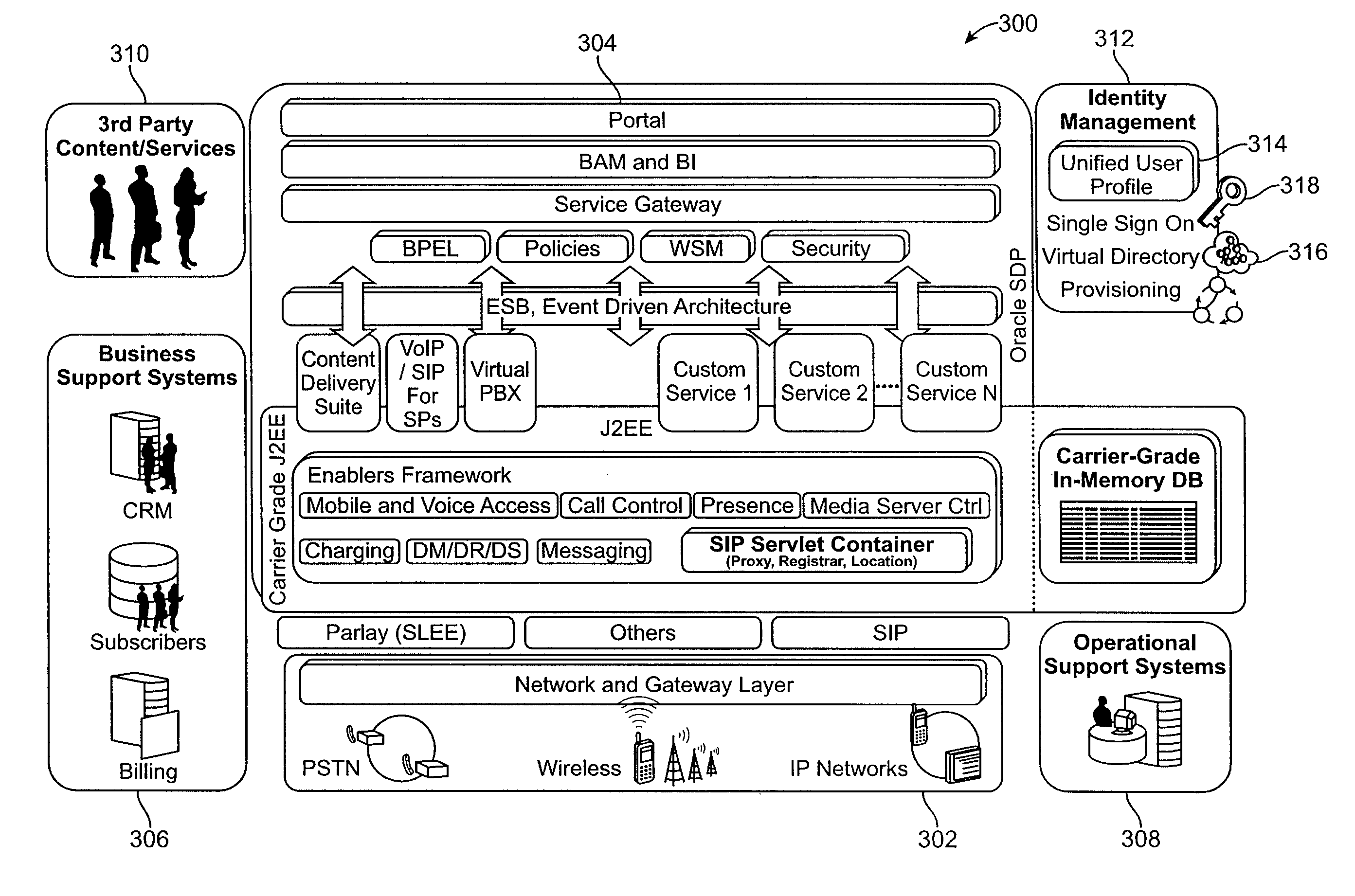
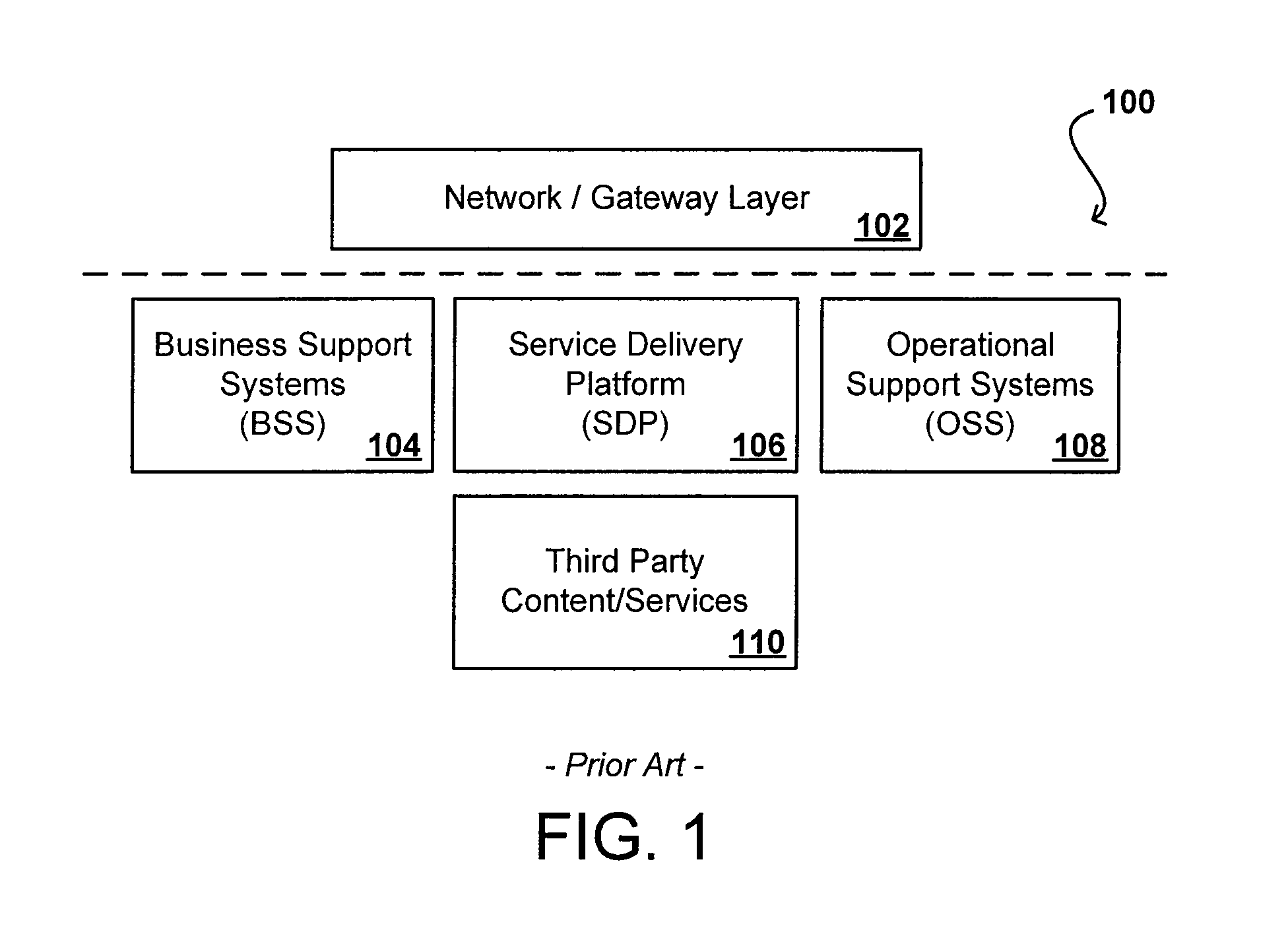
Shared view of customers across business support systems (BSS) and a service delivery platform (SDP)
ActiveUS8073810B2Overcome deficienciesDigital data processing detailsDatabase distribution/replicationData aggregatorCustomer information
Owner:ORACLE INT CORP
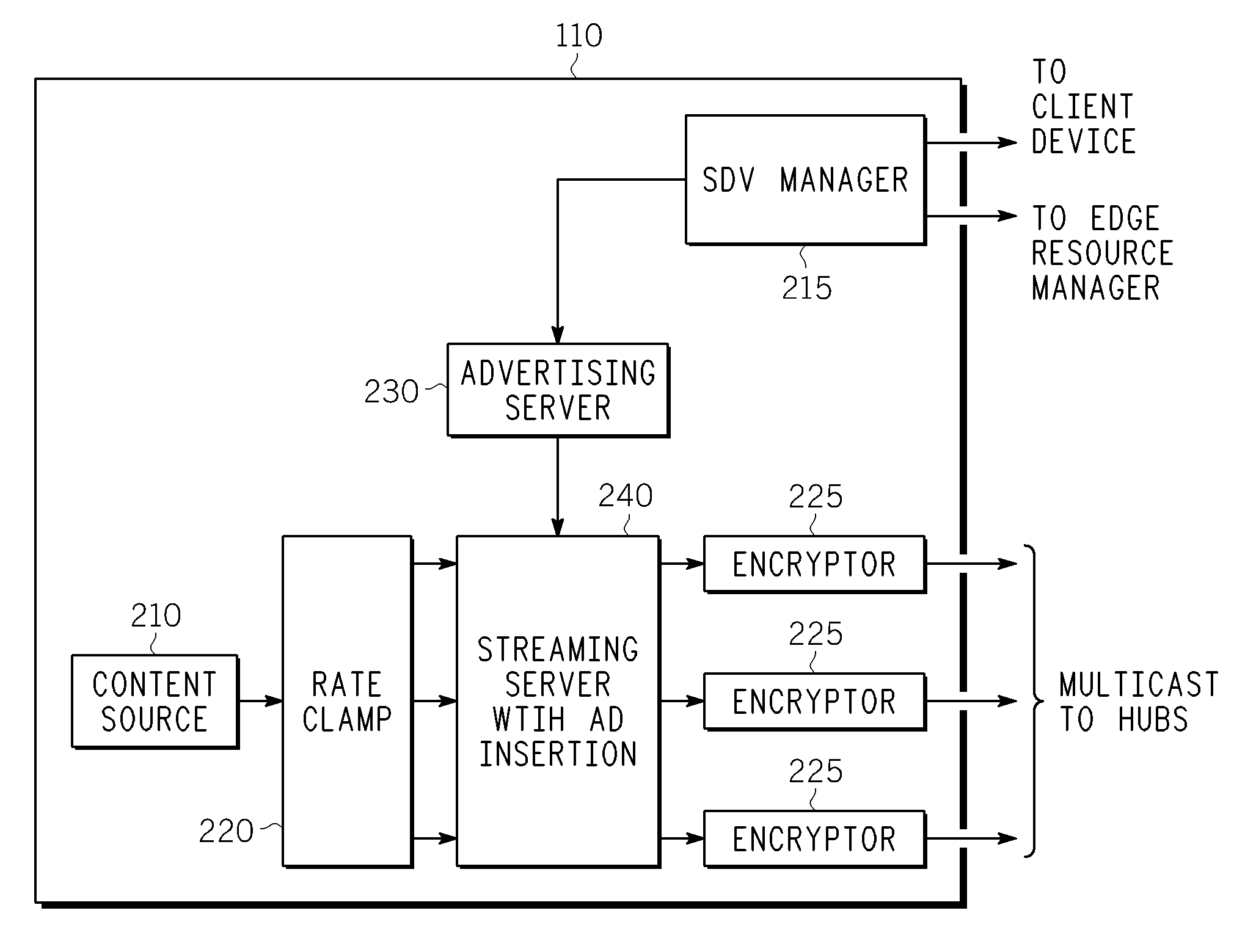
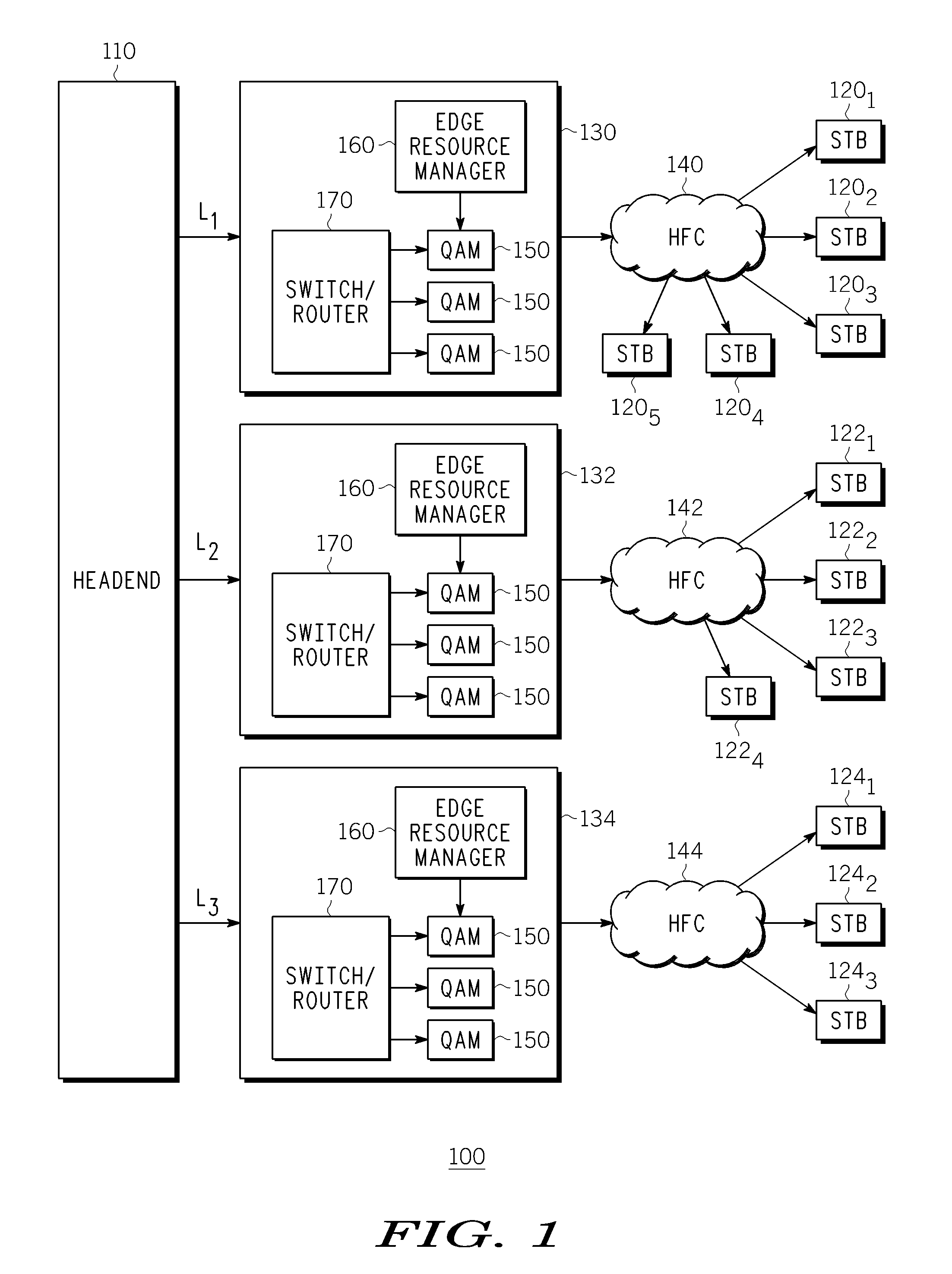
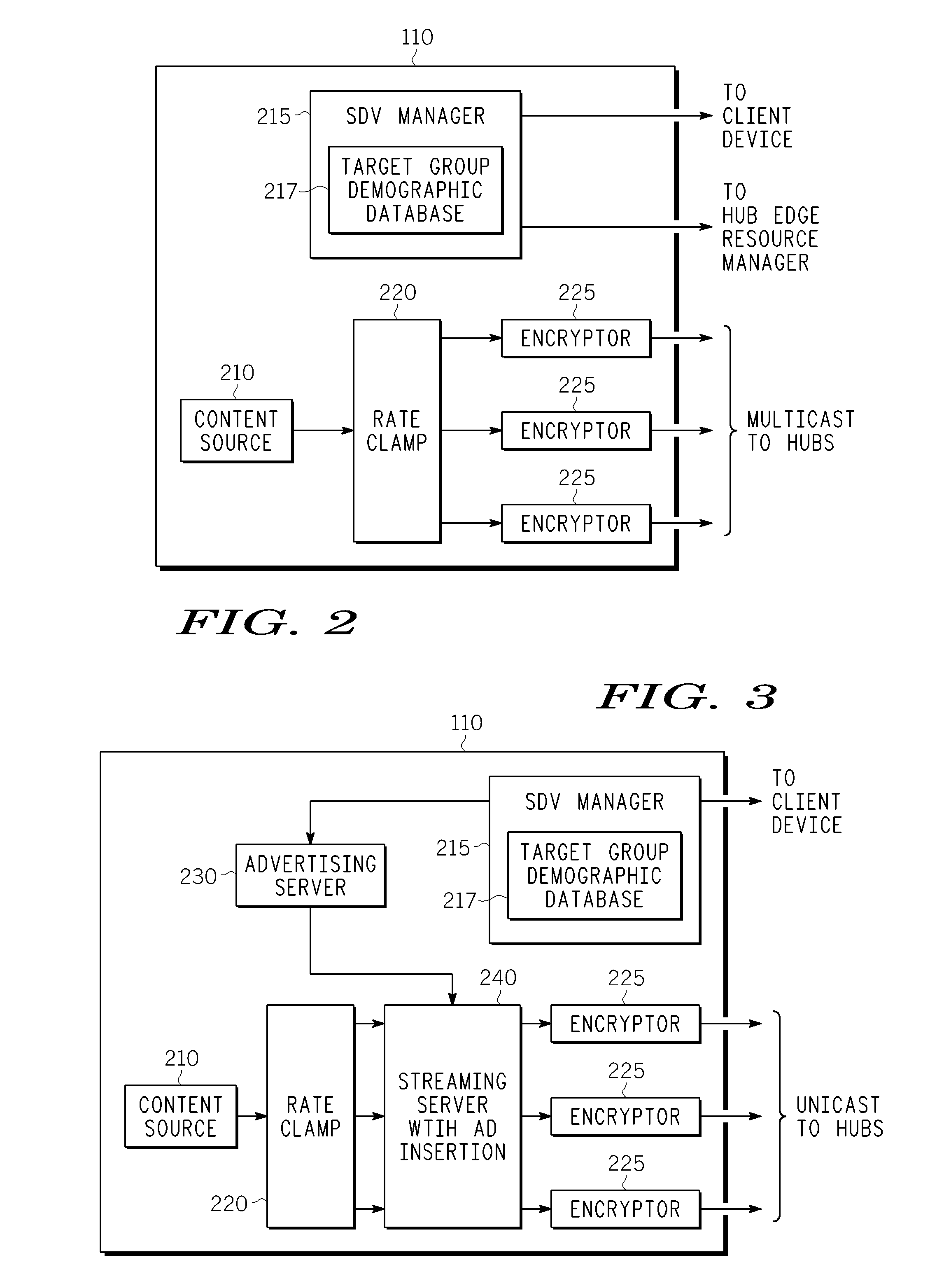
Method And Apparatus For Delivering SDV Programming With Targeted Advertising To Selected Groups Of Subscribers
InactiveUS20090150926A1Broadband local area networksTwo-way working systemsAccess networkDigital video
A switched digital video (SDV) system includes an SDV manager for coordinating a SDV session requested by a subscriber terminal and a storage medium on which resides content to be transmitted during the SDV session. The system also includes a plurality of edge devices for receiving a transport stream that includes content provided by the storage medium and transmitting the transport stream over an access network to the subscriber terminal on one of a plurality of SDV channels. The SDV manager is configured to cause different renditions of an SDV program to be provided by the edge devices to subscriber terminals associated with different target groups. The target groups each include a plurality of subscriber terminals that is less than a number of subscriber terminals serviced by a distinct edge device or devices.
Owner:GOOGLE TECH HLDG LLC
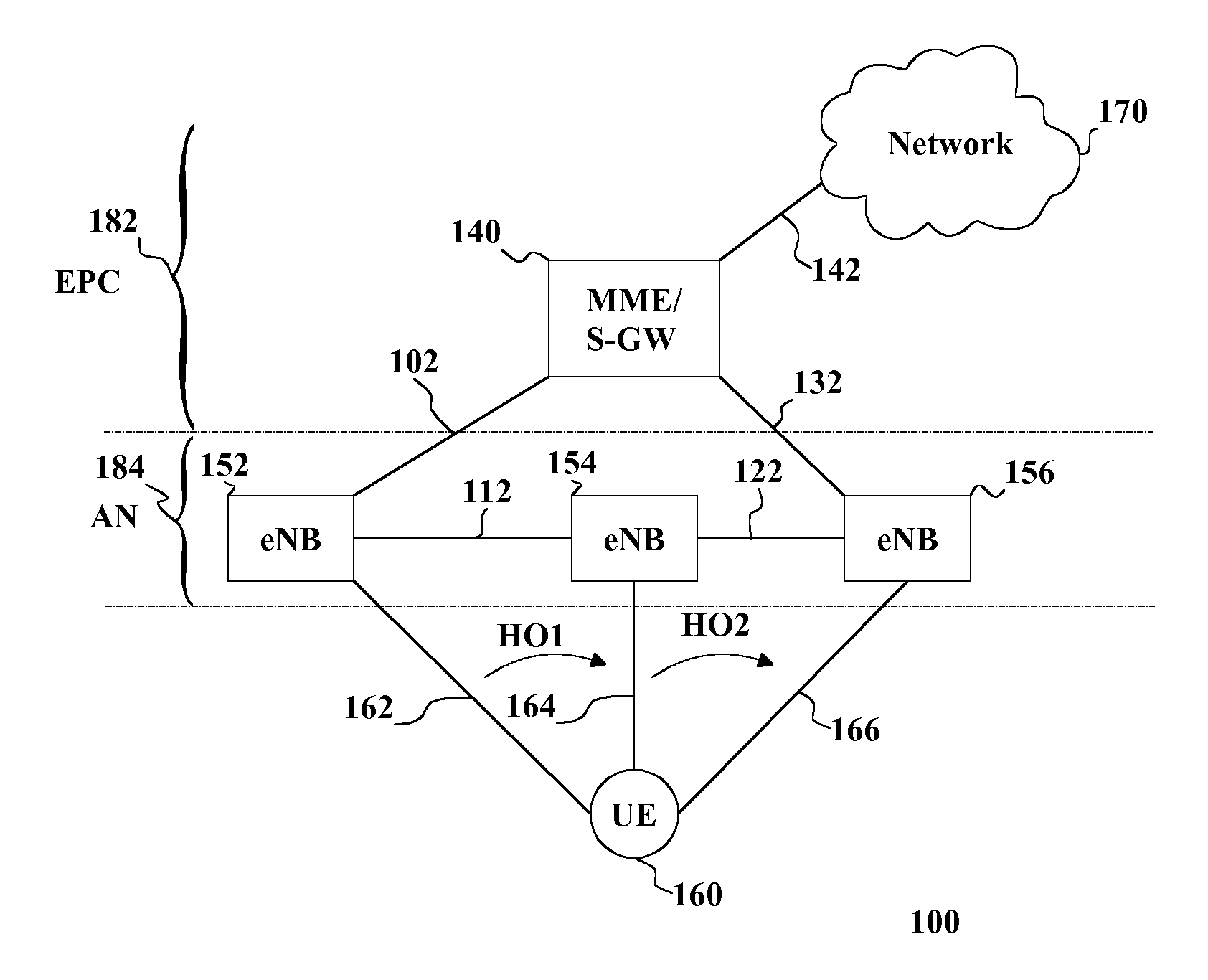
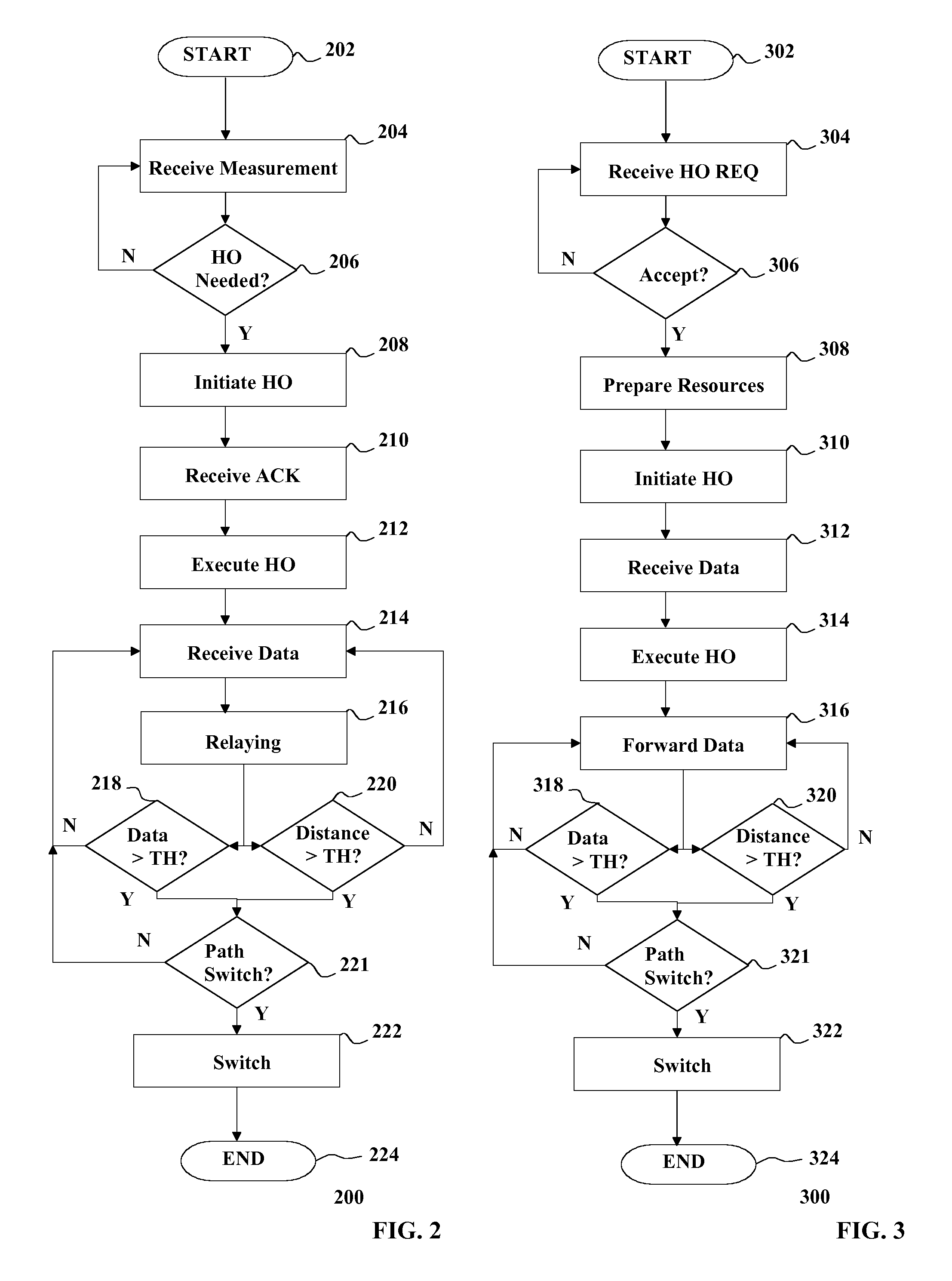
Handover of Connection of User Equipment
InactiveUS20130201904A1Increase profitLess capacityFrequency-division multiplex detailsTime-division multiplexAccess networkHandover
There is provided initiating a handover of a connection of user equipment, the connection including a path from an access network to a core network and switching the path to the core network on the basis of data received on the connection exceeding a threshold.
Owner:NOKIA SOLUTIONS & NETWORKS OY
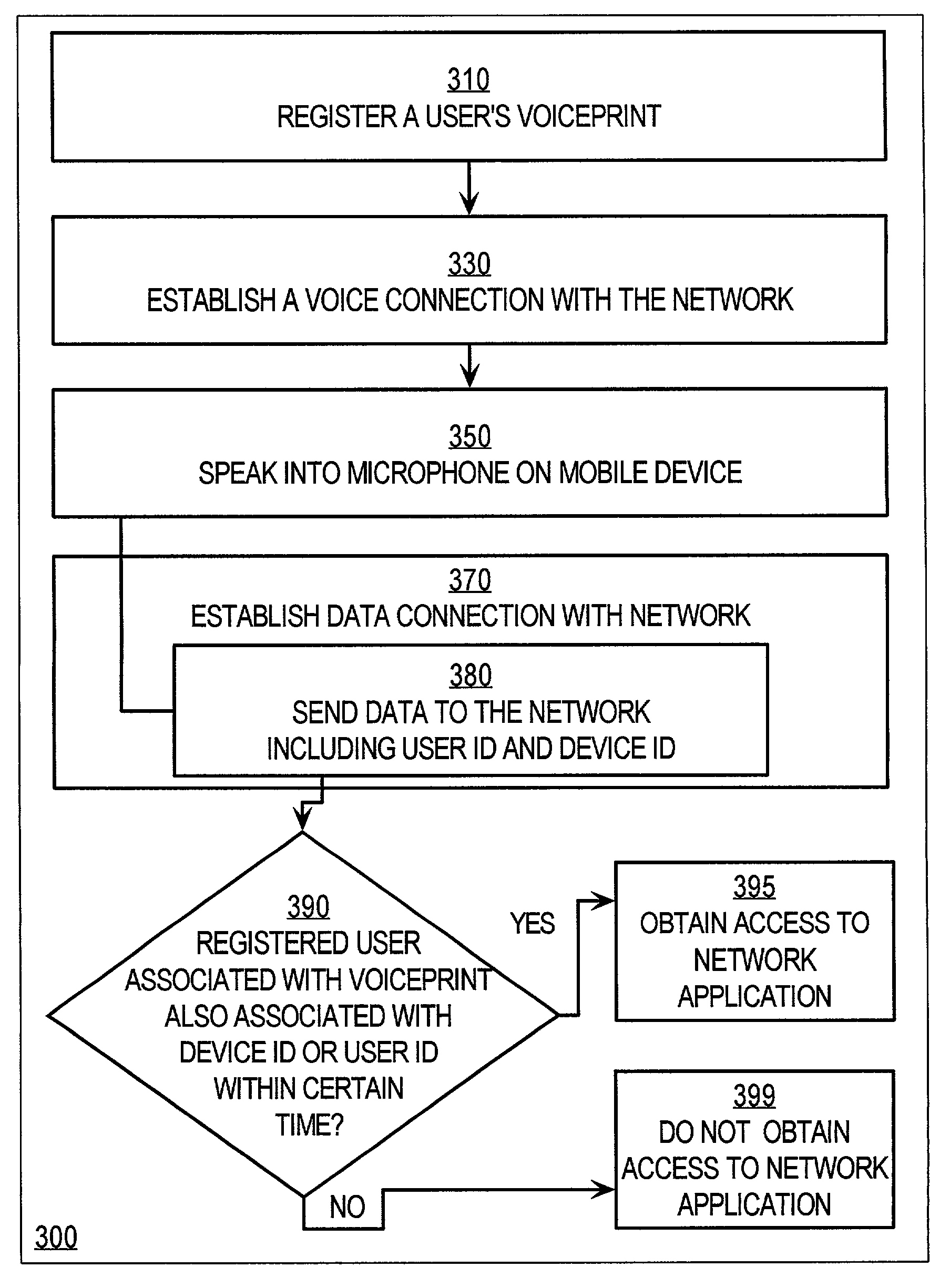
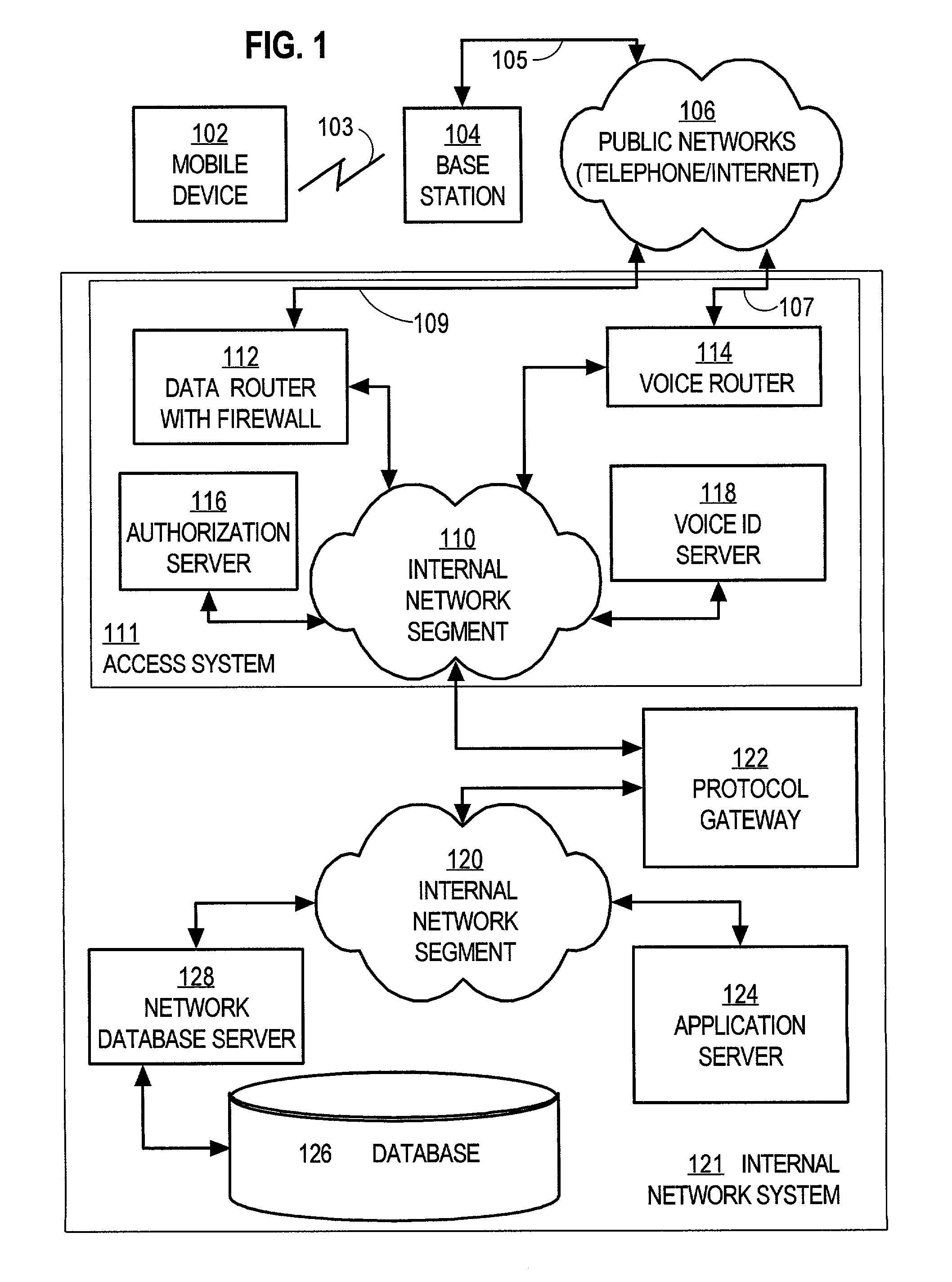
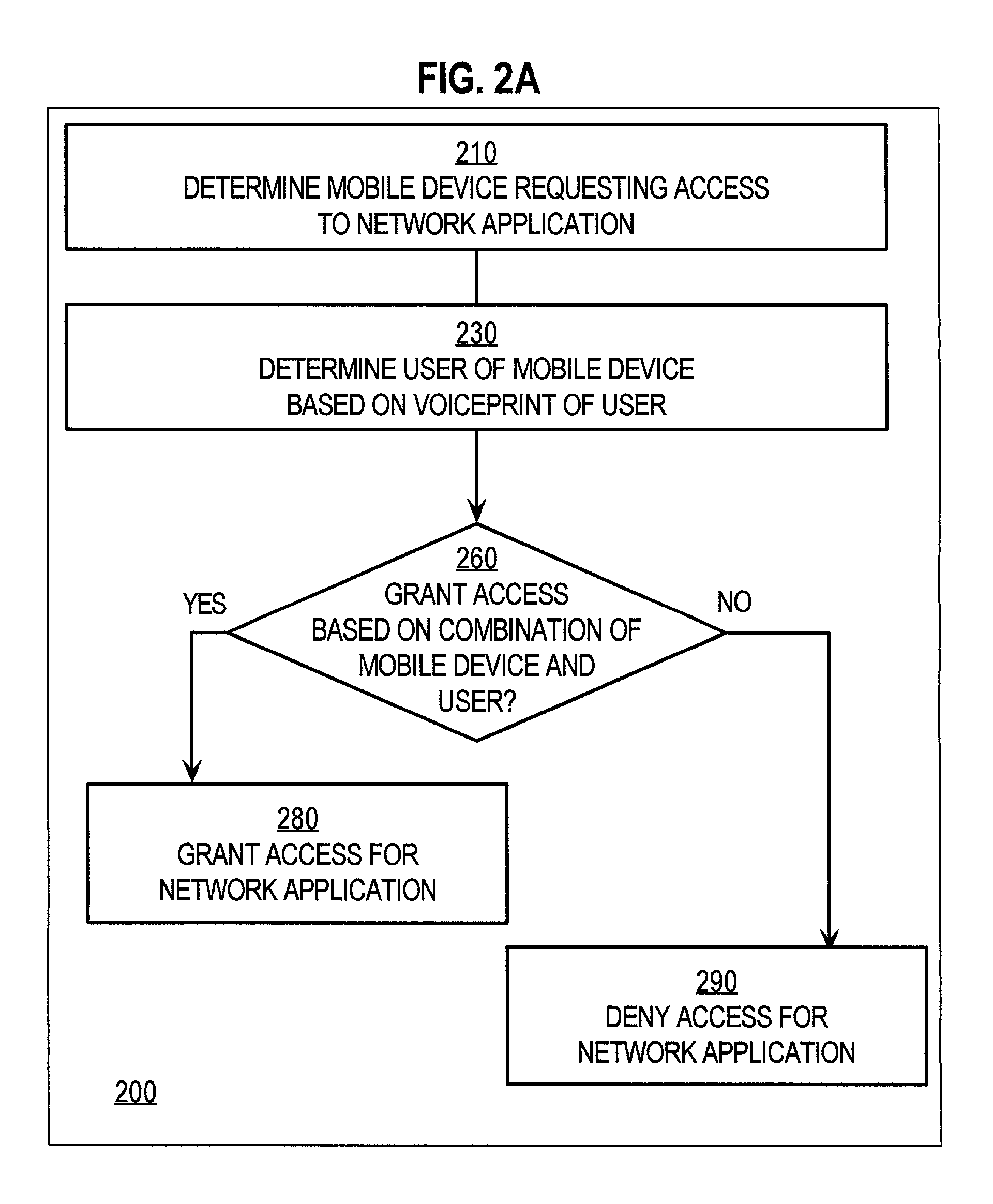
Techniques for voice-based user authentication for mobile access to network services
InactiveUS7158776B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsUser authenticationNetwork service
Techniques for granting access on a network having a network service to a user of a mobile device having a microphone includes determining a first identification uniquely associated with a registered user having a registered voiceprint that matches a voiceprint of the user of the mobile device. A second identification uniquely associated with the mobile device is also determined. It is then determined whether to grant access based on the first identification and the second identification. If it is determined to grant access, access is granted on the network to the user. Various aspects of the invention allow a user to be authenticated separately of the mobile device by the voice of the user, and granted access to a network service based on both the user's identity and the identity of the mobile device. Both the user's voice and the device identity are provided using the current capabilities of wireless telephones. Obtaining the first identification and second identification within a specified time interval makes confidently practical the technique of verifying that a certain user controls a certain mobile device, and then allowing access by that device to protected services.
Owner:CISCO TECH INC
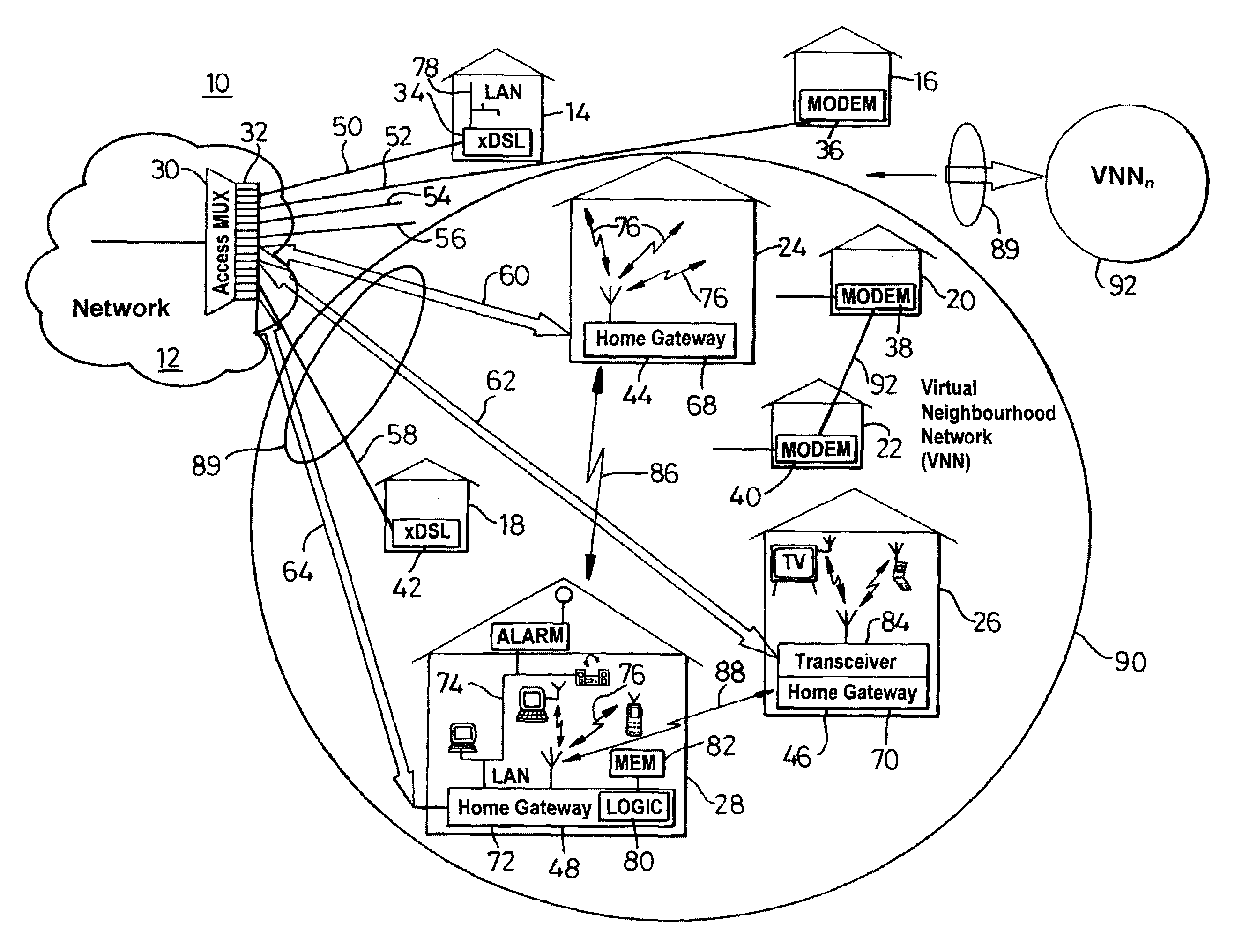
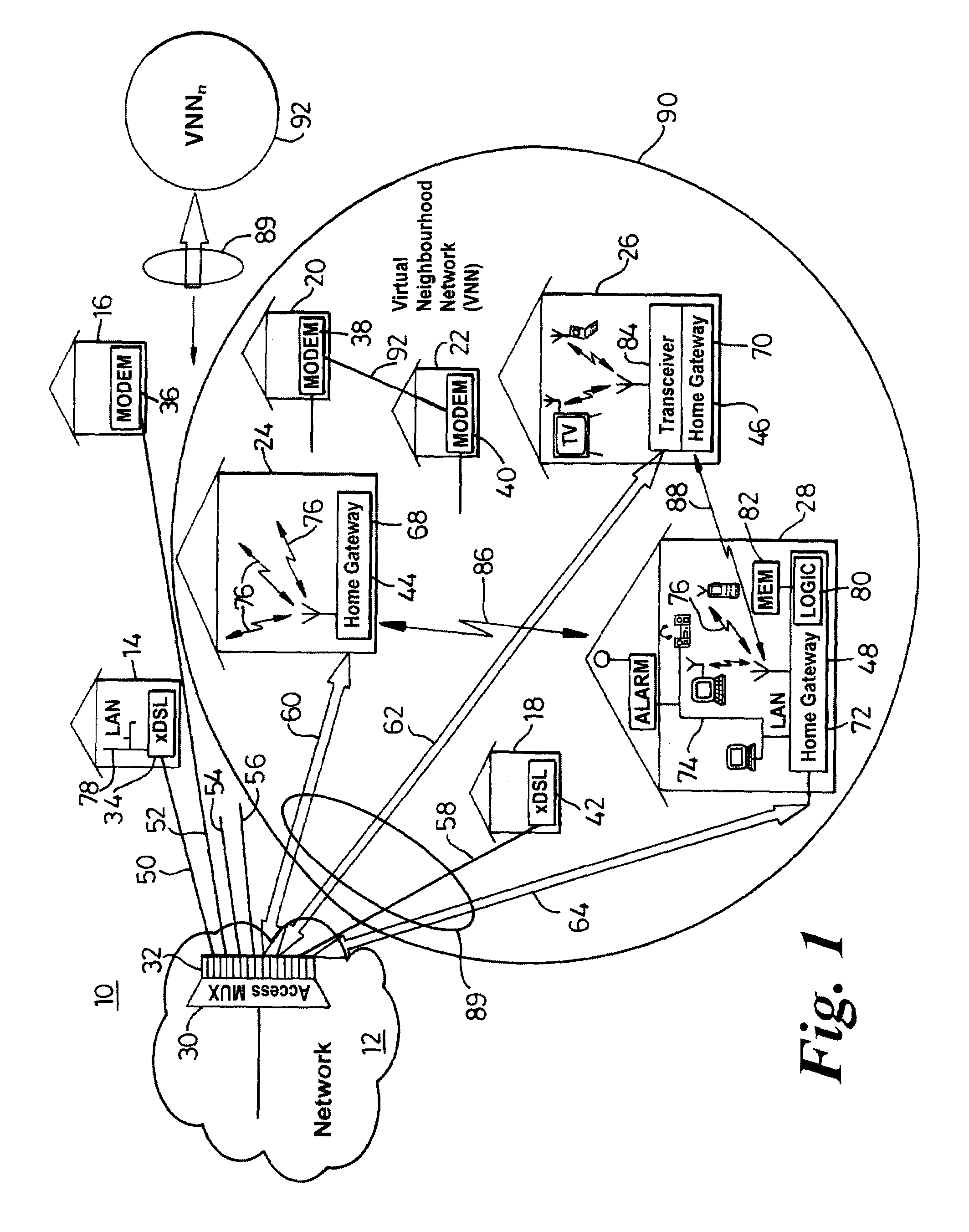
Communication system architecture and operating methodology providing a virtual neighborhood network
InactiveUS7142503B1Overcome bandwidth limitationIncreased peak bandwidth capacityError preventionFrequency-division multiplex detailsEnd-to-end encryptionTransceiver
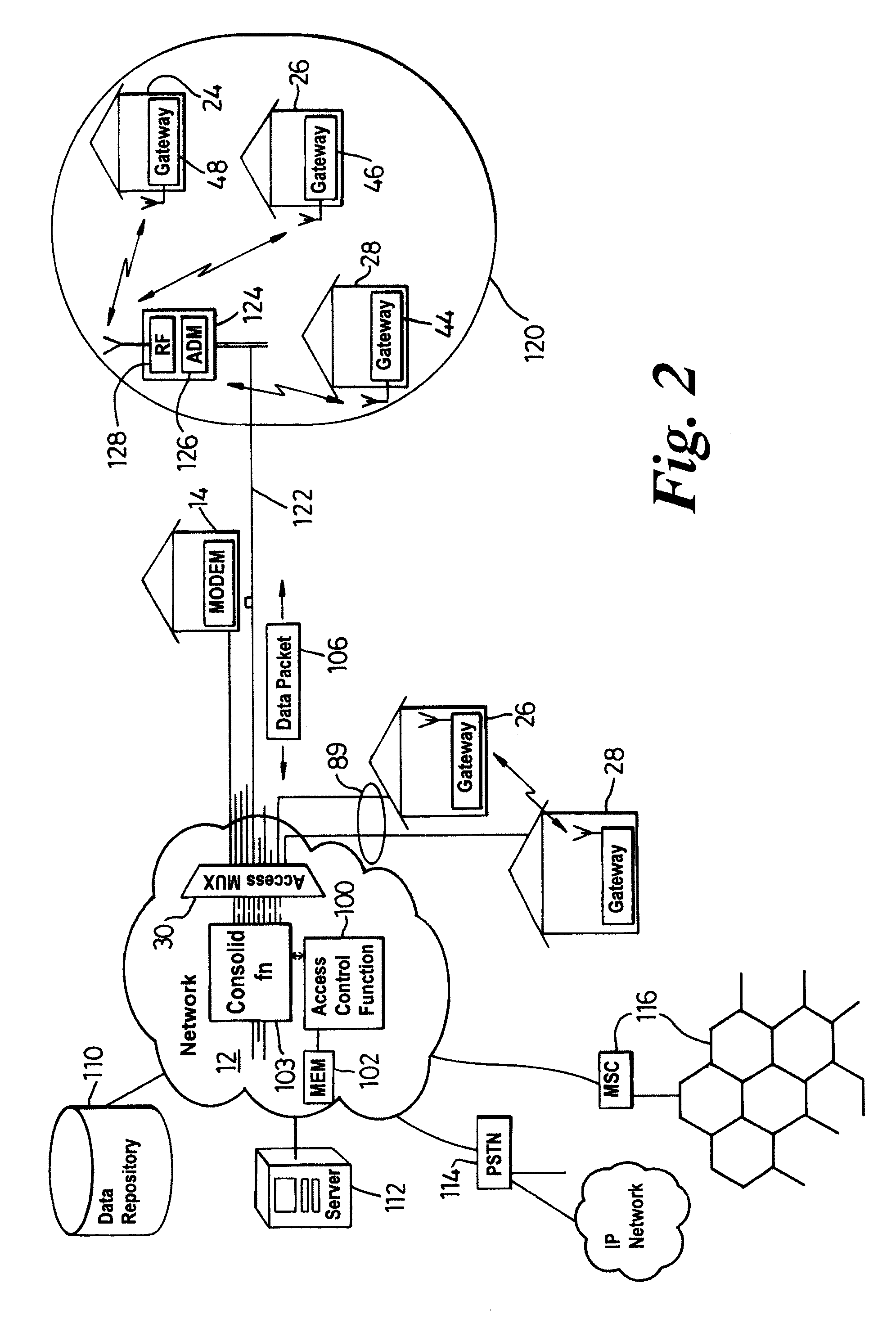
A communication system (10) supports the provision of a plurality of dedicated communication resources (50–64), such as copper drops, RF links and optical fibers, to dedicated home-gateway devices (44–48) or distribution points (124). The communication resources (50–64) support broadband interconnection (104) between the dedicated home-gateway devices (44–48) or distribution points (124) and an access multiplexor (30) in a network (12). Each gateway device (44–48) or distribution point (124) generally includes a local RF transceiver (84) and associated control logic (80–82) that allows local communication (86) between gateway devices (44–48) and hence statistically multiplexed access (60–64, 89) to multiple communication resources, thereby providing increased bandwidth in uplink and / or downlink directions. With the control logic (80) operable to provide a routing and prioritisation / arbitration function, each gateway (44–48) is able to selectively engage use of supplemental, non-reserved communication resources usually associated with a dedicated ono-to-one connection between the access network (12) and at least one secondary gateway. Physical layer access to information routed via a secondary gateway within a virtual neighborhood network (90–92) comprising several gateways is restricted through an end-to-end encryption algorithm between an originating gateway and, at least, the access multilpexor (30).
Owner:RPX CLEARINGHOUSE
Mobile communication network system and method for composing network component configurations
ActiveUS20170070892A1Configuring networkAssess restrictionNetwork topologiesAccess networkNetworked system
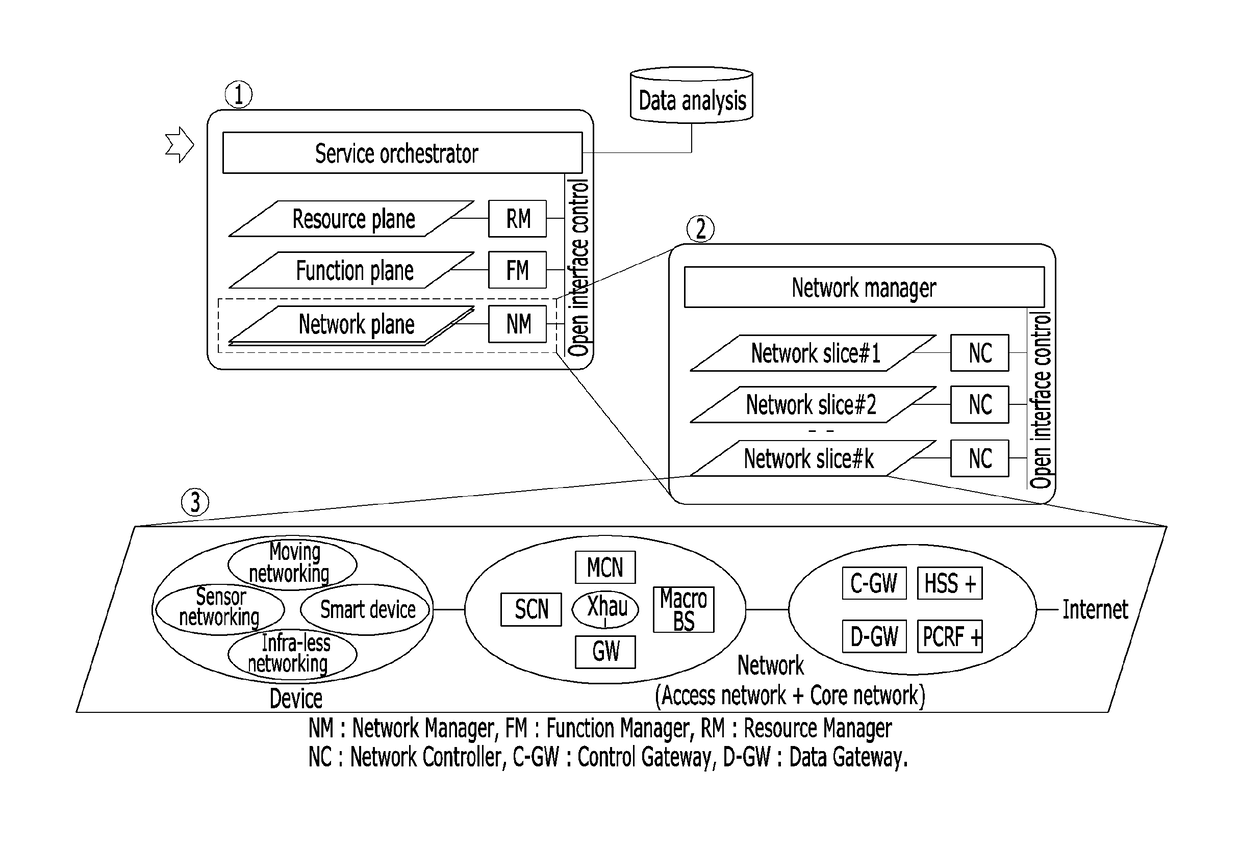
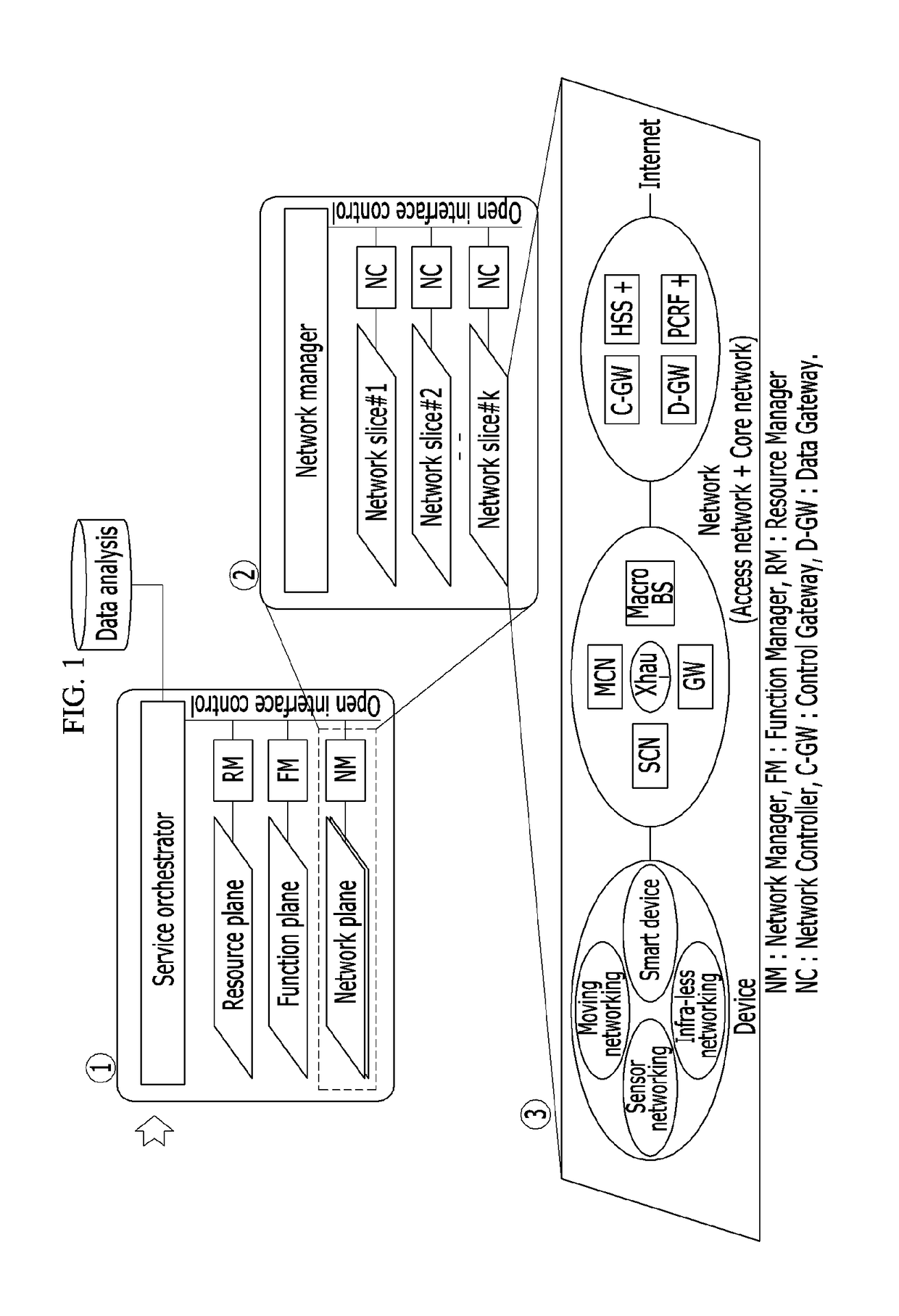
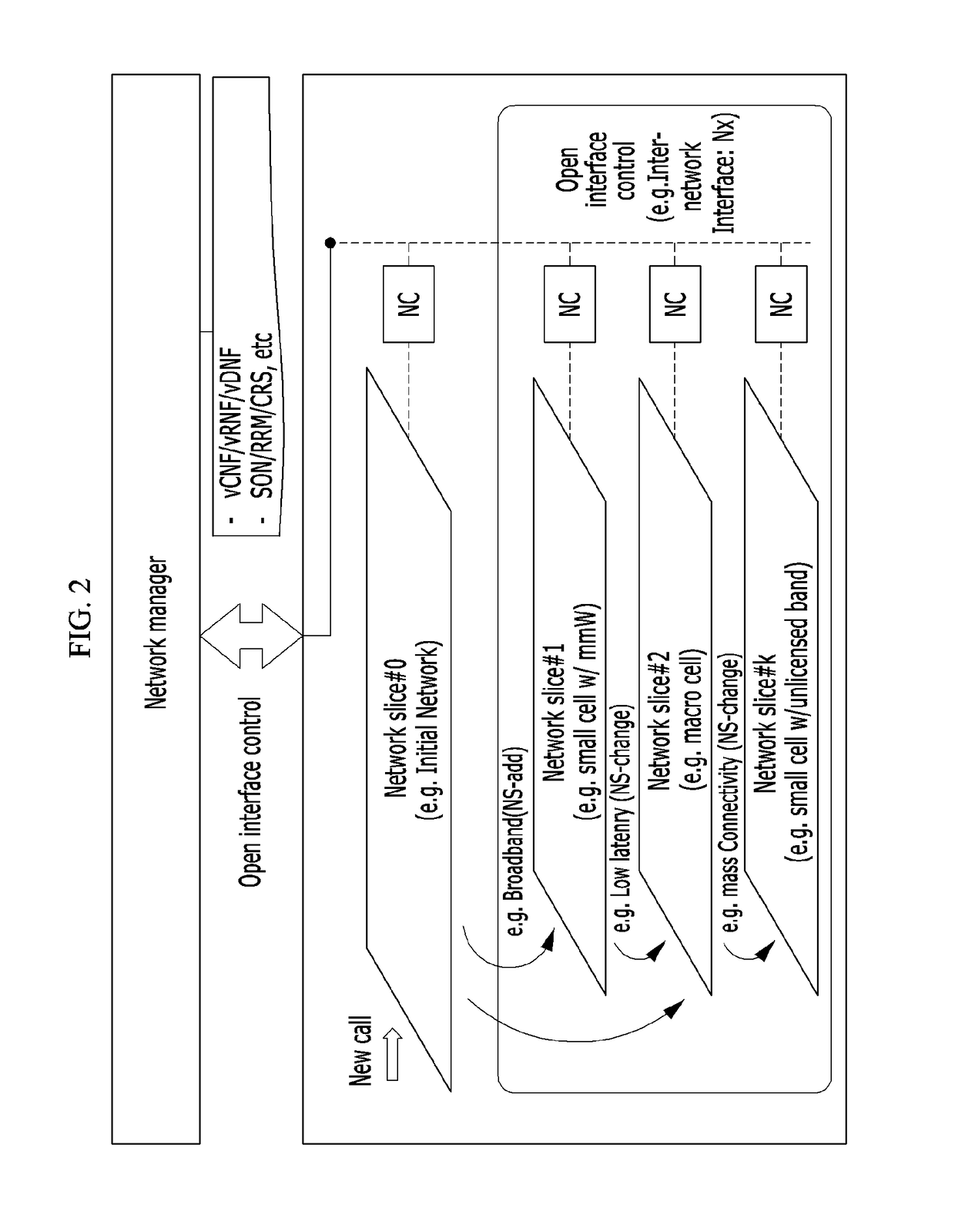
Disclosed is a mobile communication network system and a network configuring method. The communication network system includes: a common control access network; at least one access network slice added according to a service type requested by a device; a common control core network; and at least one core network slice added according to a service type requested by the device. The access network slice and the core network slice are determined by the service type requested by the device.
Owner:ELECTRONICS & TELECOMM RES INST
Video policy server
InactiveUS20050188415A1Analogue secracy/subscription systemsTwo-way working systemsAccess networkSession management
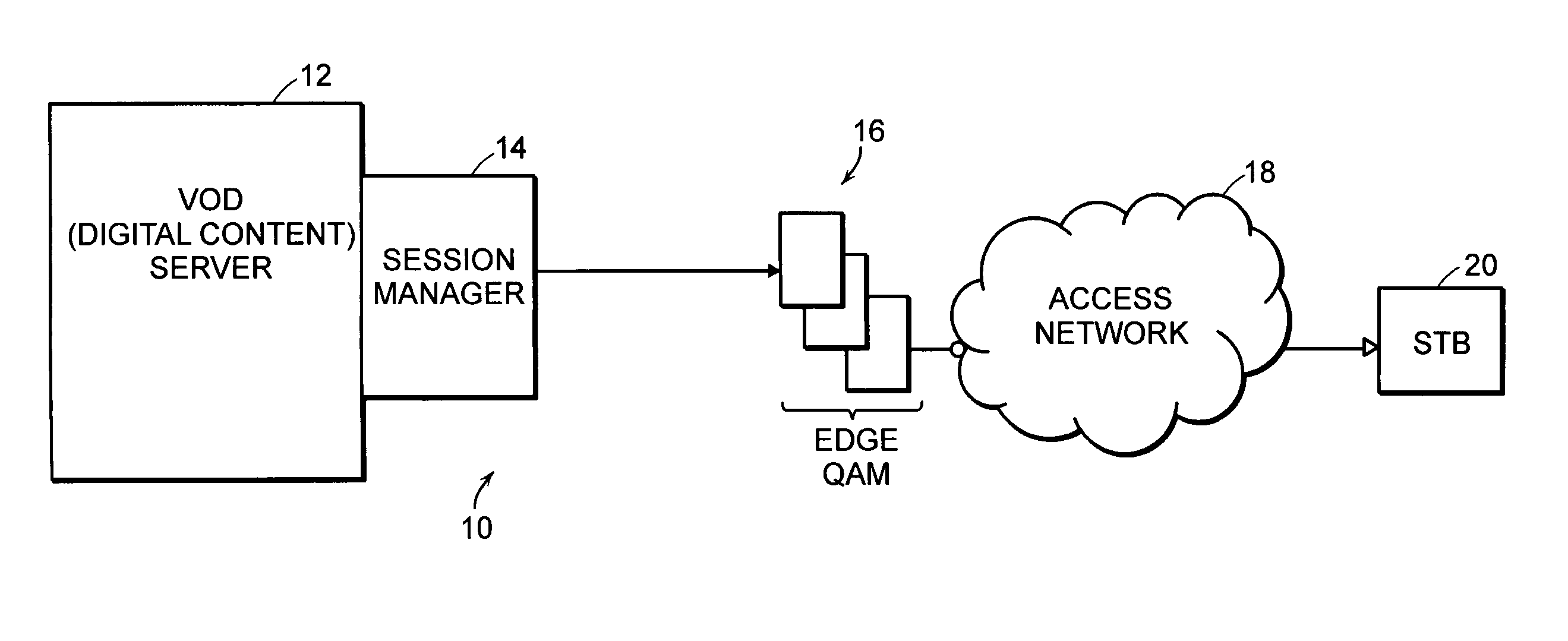
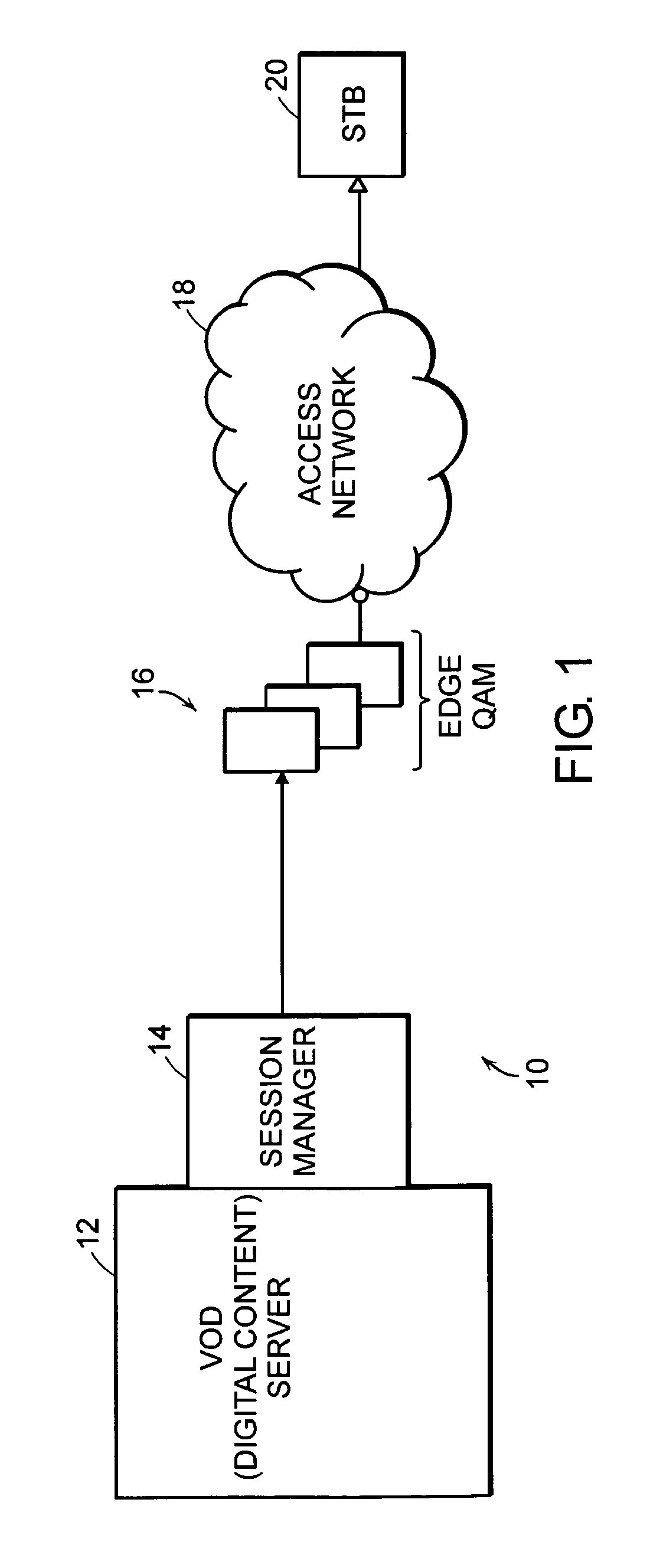
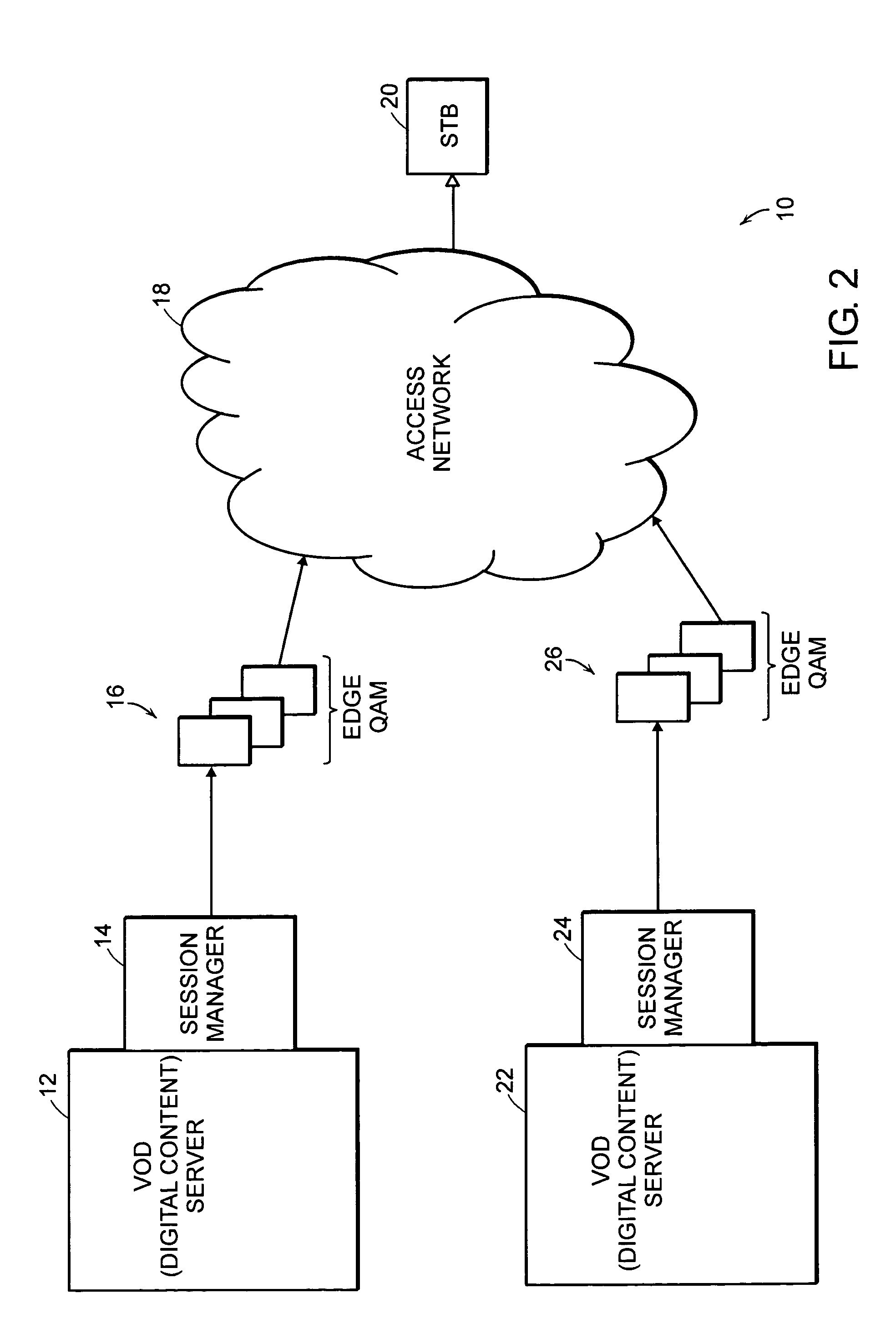
A system for distributing digital content includes two or more digital content sources. Each source has a separate session manager that is distinct from other session managers associated with other digital content sources. The system further includes at least one set of network resources that receive digital content from the two or more digital content sources, modulate the digital content onto a carrier signal suitable for transmission over an access network, and transmit the carrier signal over the access network. The system also includes a receiving device for terminating the carrier signal. The receiving device generates a digital content stream corresponding to the digital content from the two or more digital content sources. The system further includes a policy server for allocating bandwidth of the network resources to the digital content sources, and for monitoring a utilization state of the network resources.
Owner:CAMIANT INC
Methods and arrangement in a communication system
InactiveUS6333919B2Minimization requirementsMultiplex system selection arrangementsSpecial service provision for substationAccess networkCommunications system
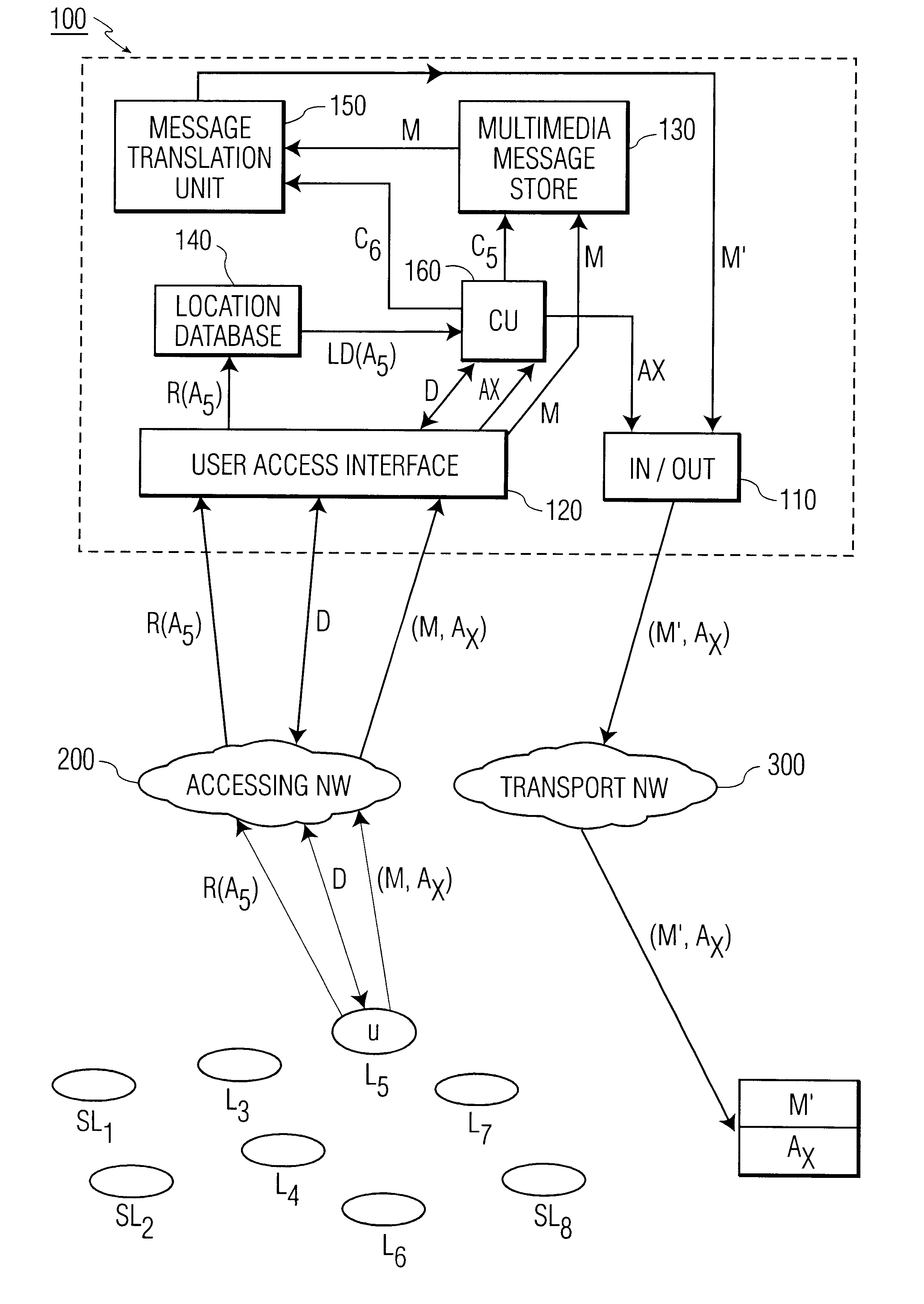
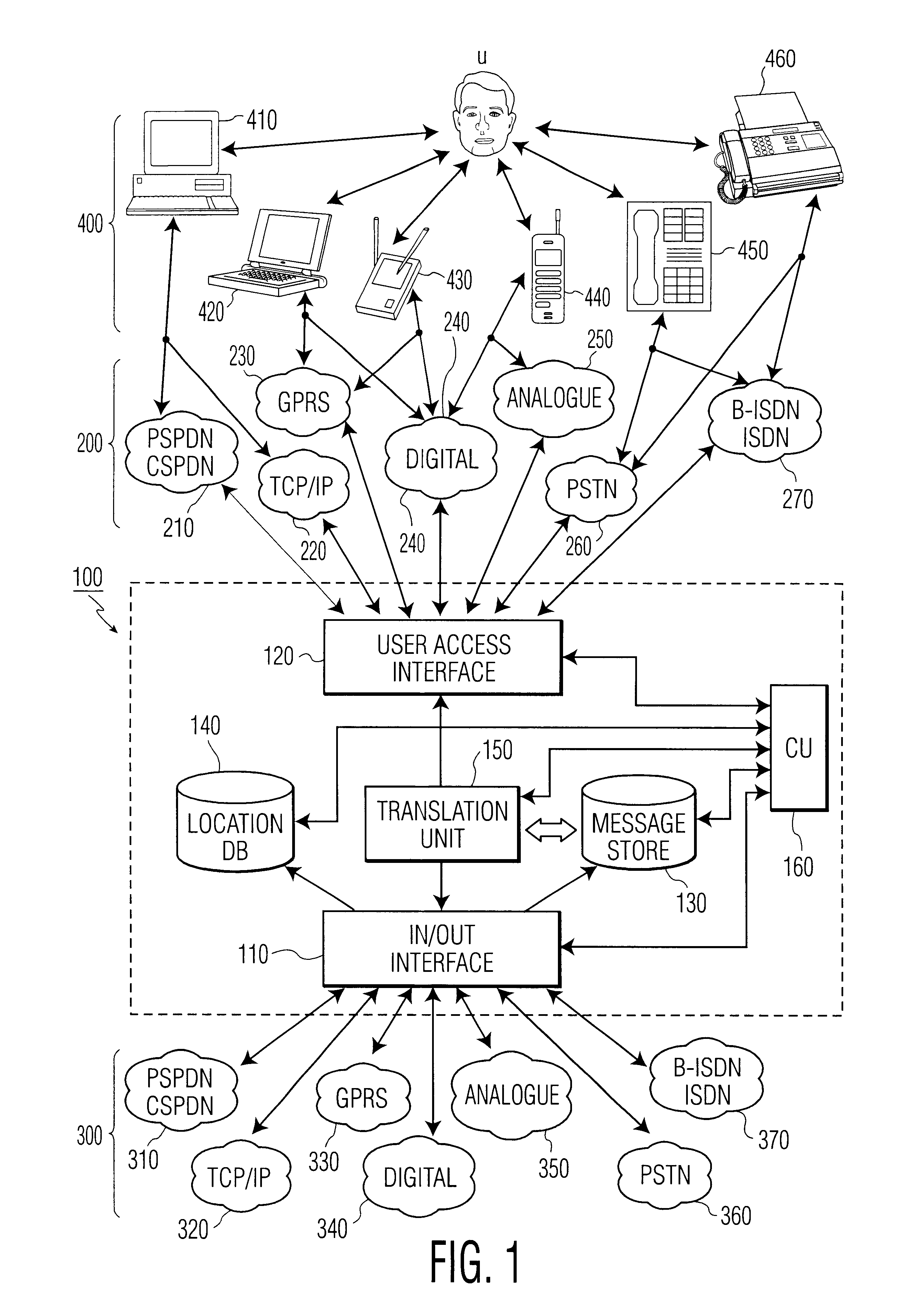
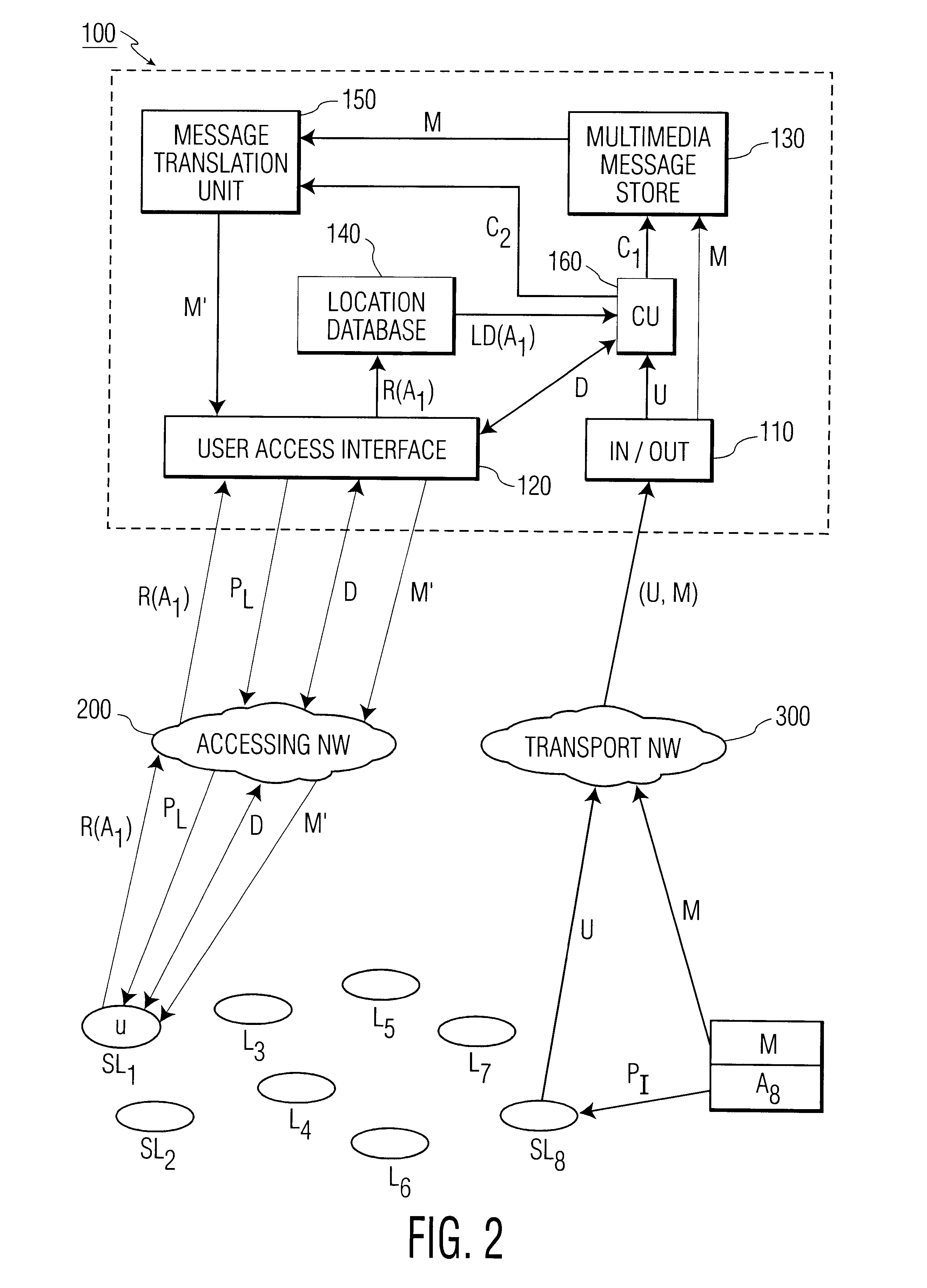
The present invention relates to methods and an arrangement for receiving, storing, and originating multimedia messages. An incoming message is transmitted to an in / out interface via a transport network. The message is stored in a message store, translated in a translation unit into a format adapted to the presentation capabilities of receiver's current terminal and delivered to the receiver over a user access interface and an access network with guidance from a location database. Earlier received messages, which are kept in the message store, can be accessed and edited via any standardized access network using media translation in the translation unit. A multimedia message is originated by a user in the system via any access network and the user access interface. The message is then stored in the message store, translated in the translation unit, and delivered to the destination through the in / out interface and an appropriate transport network.
Owner:IDTP HLDG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com