Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9473 results about "High security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
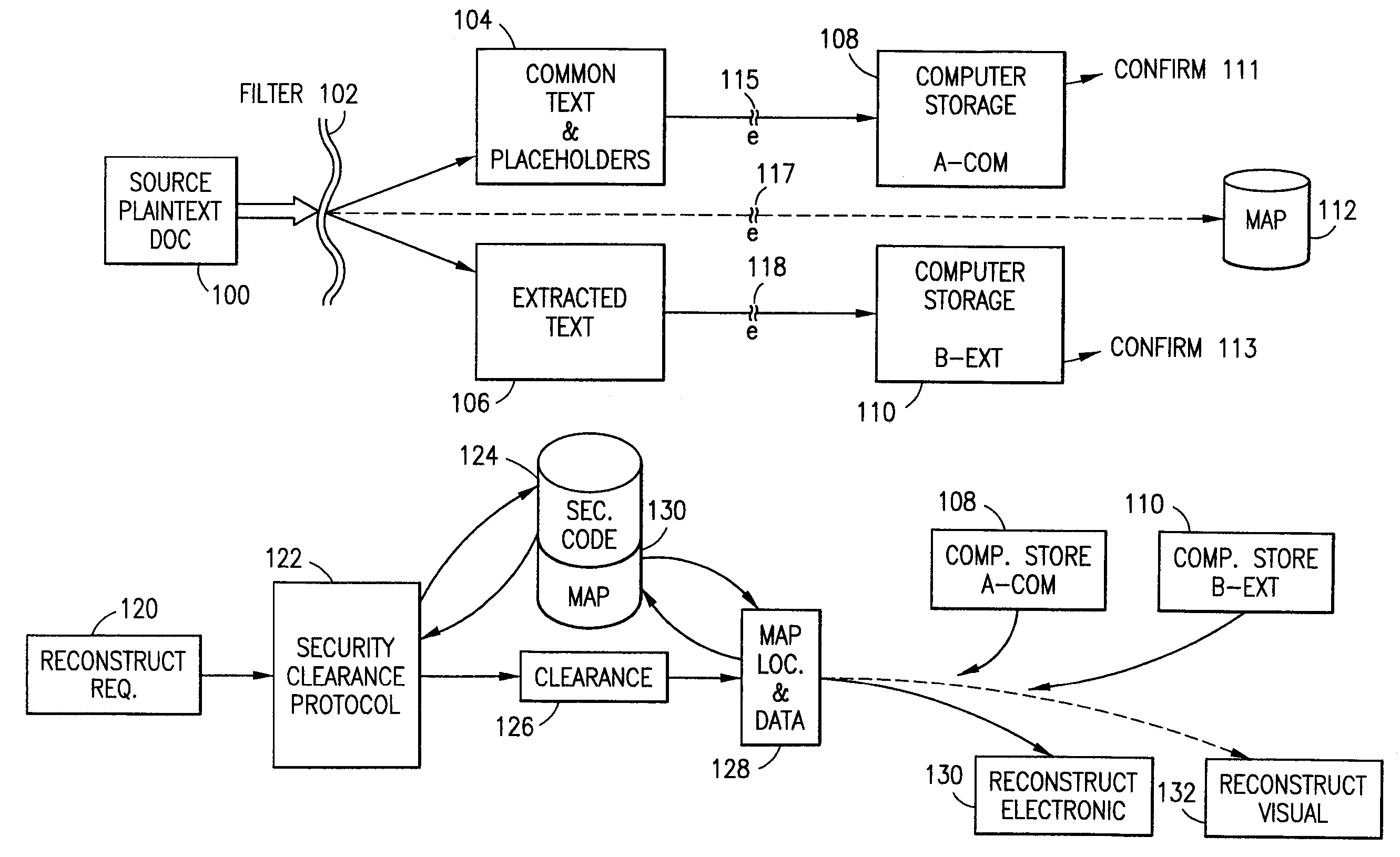
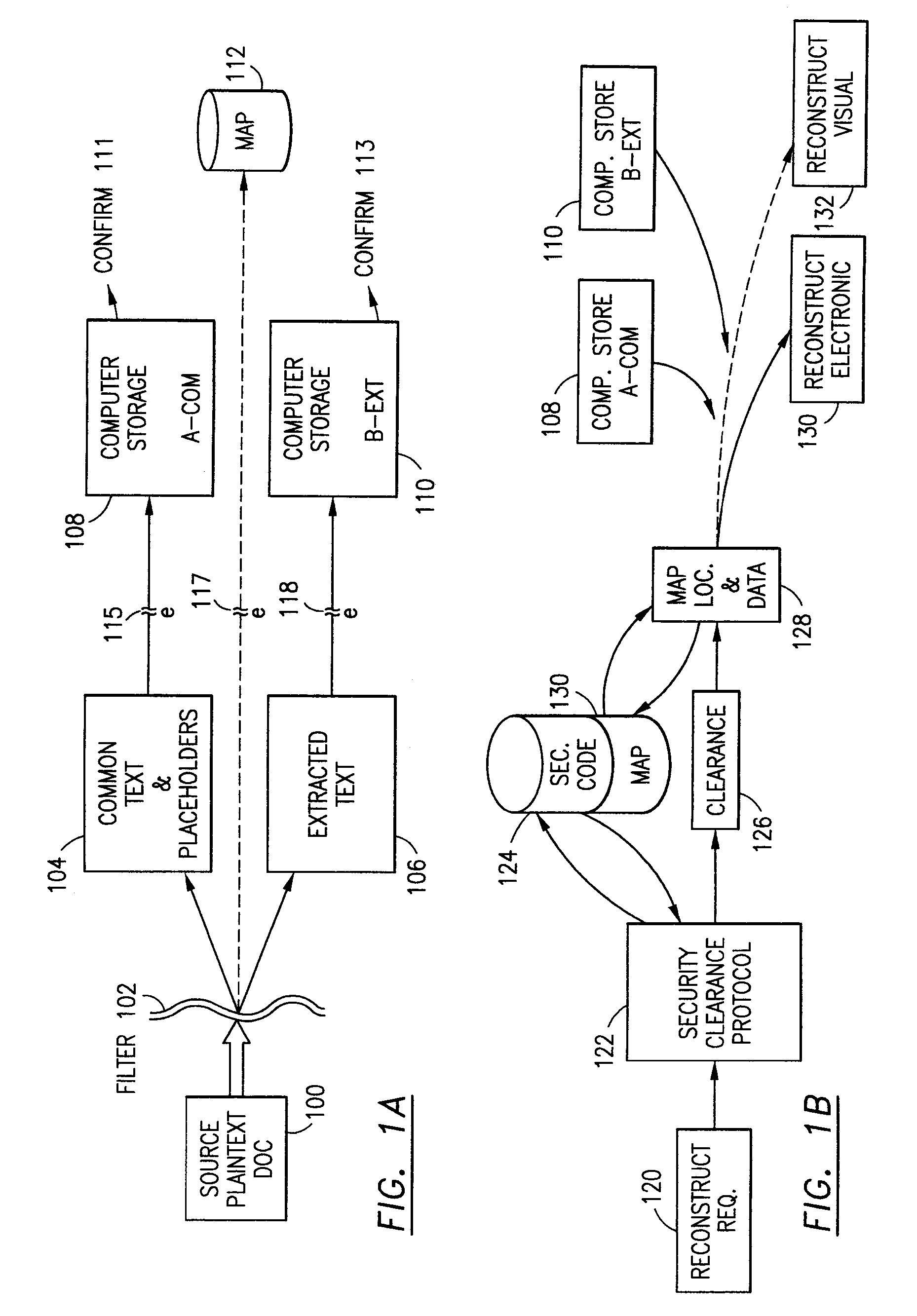
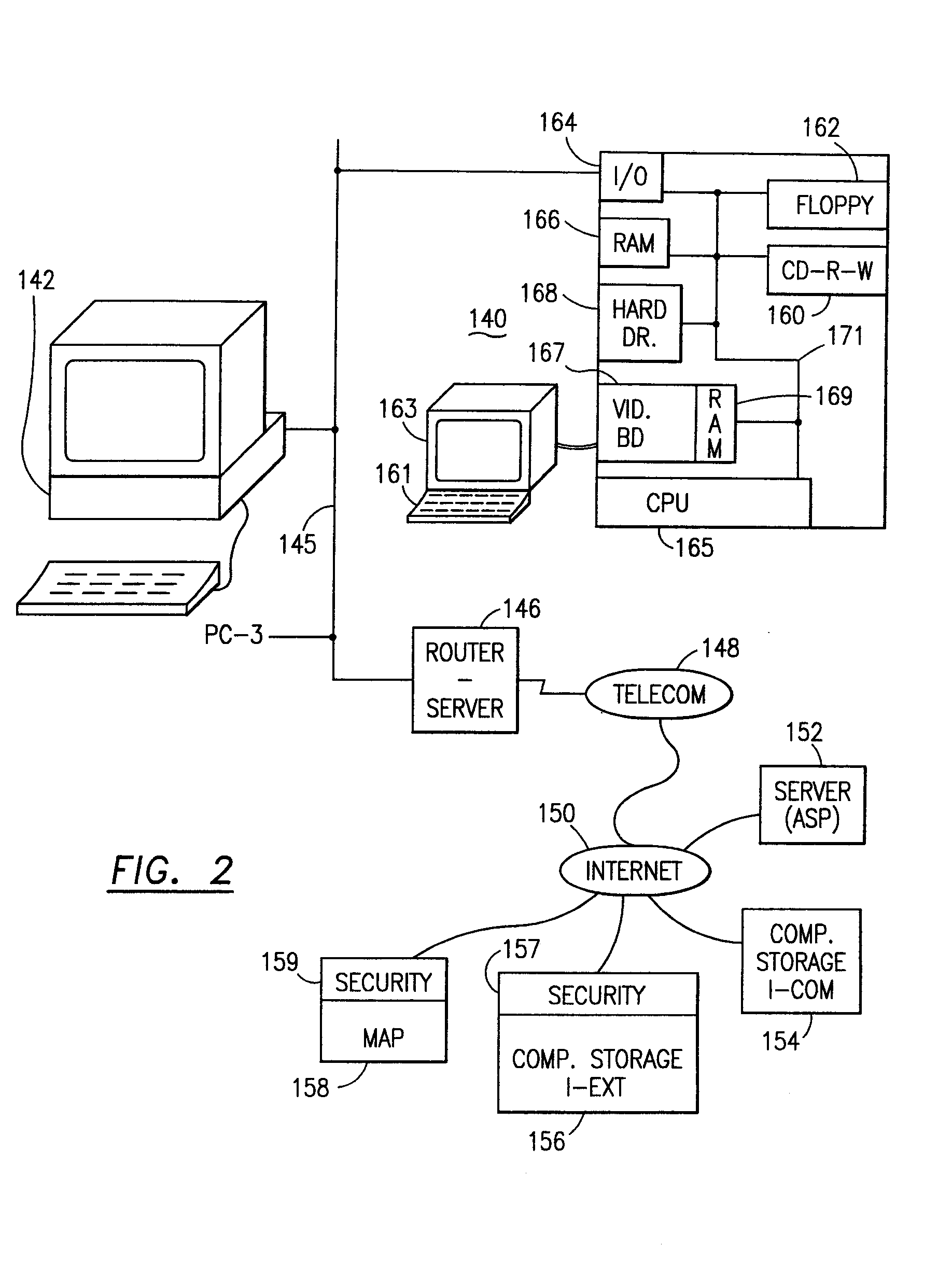
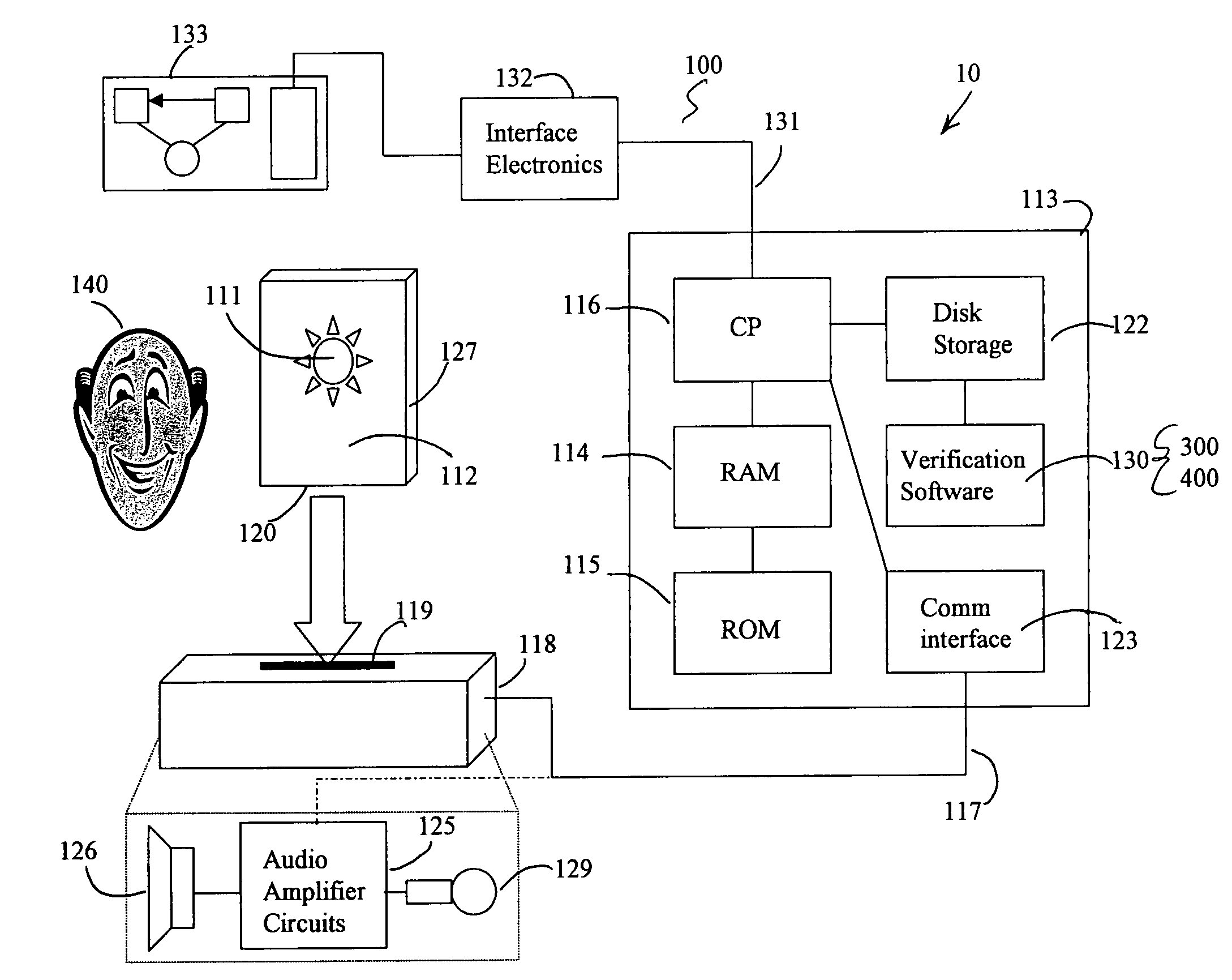
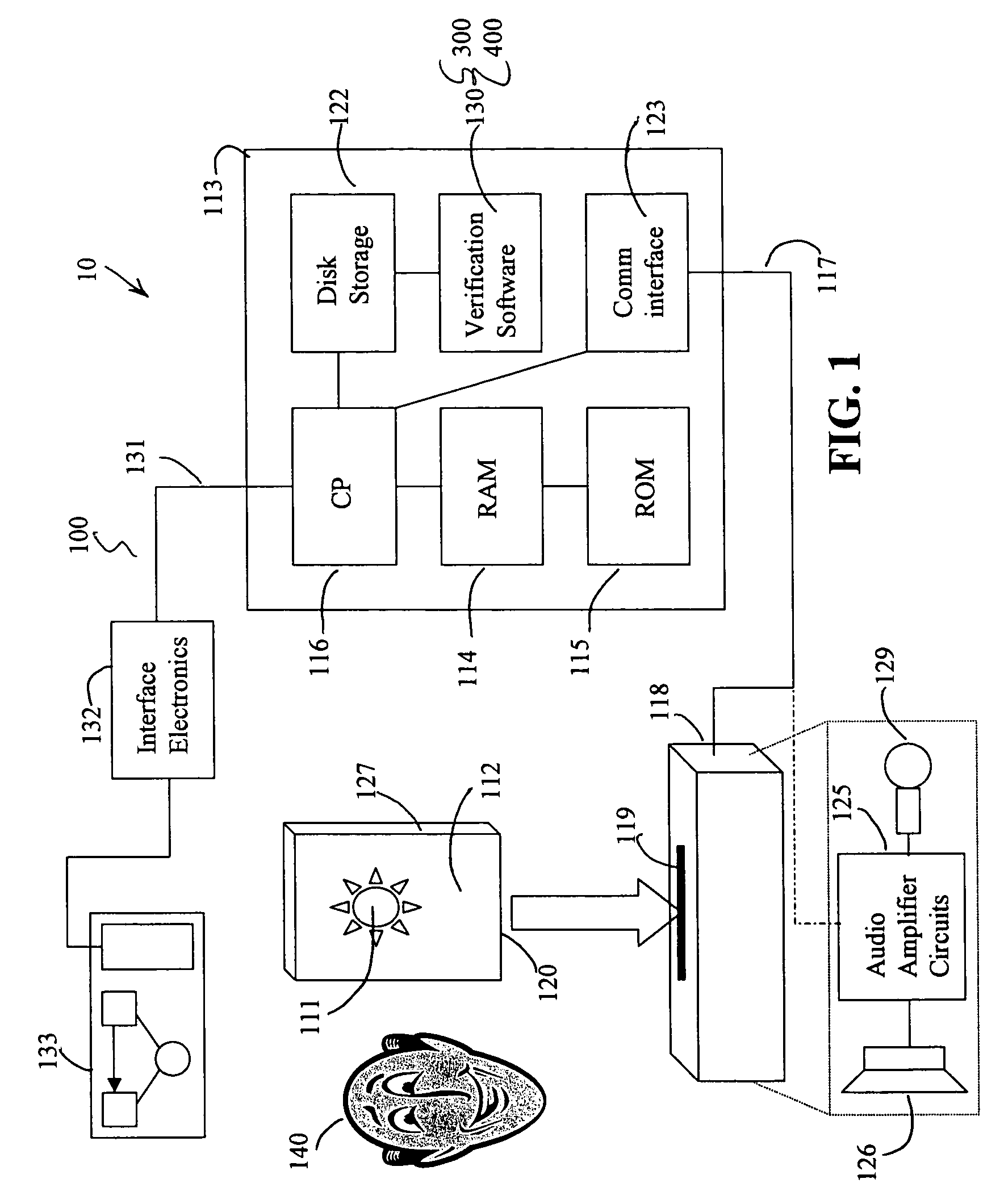
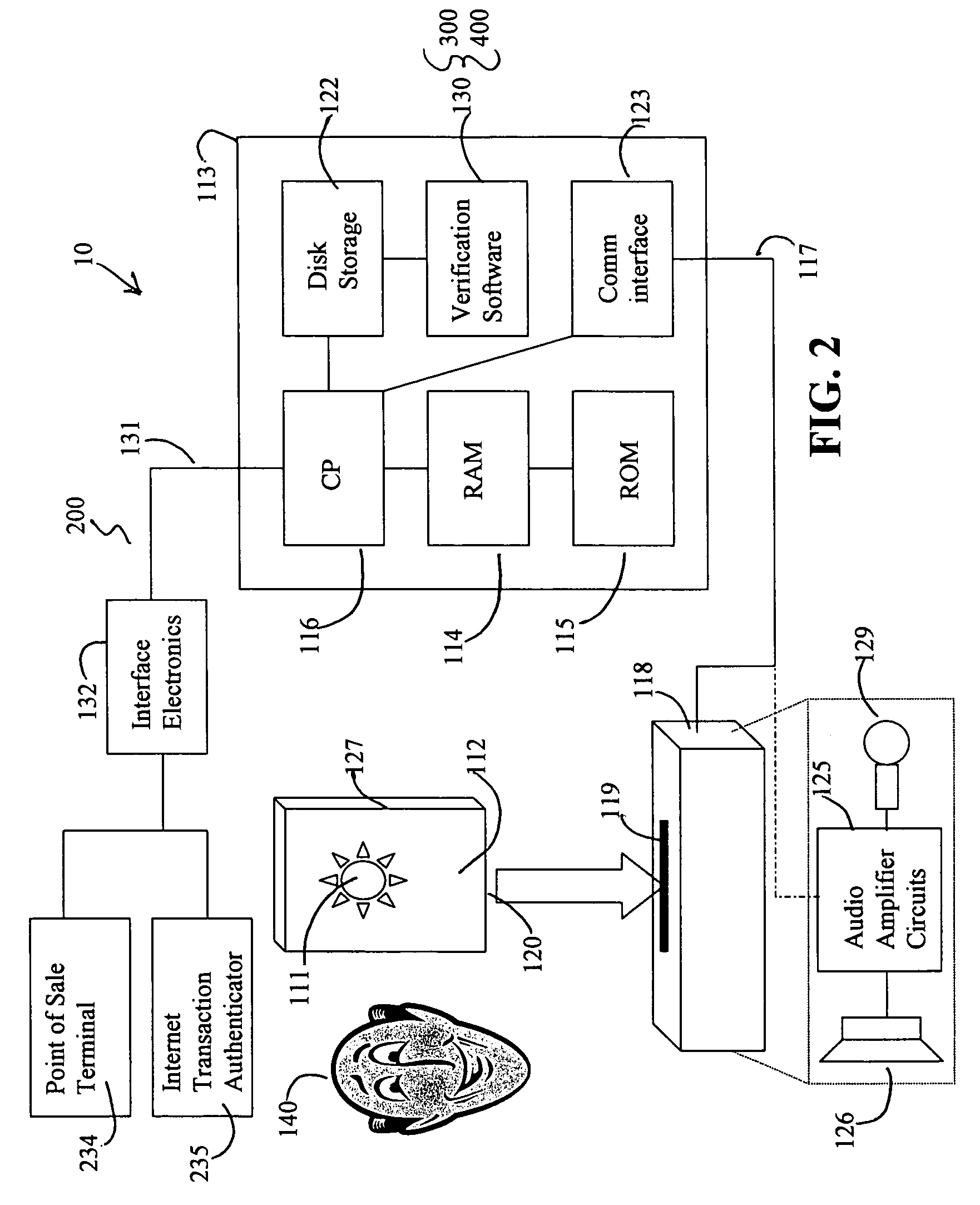
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
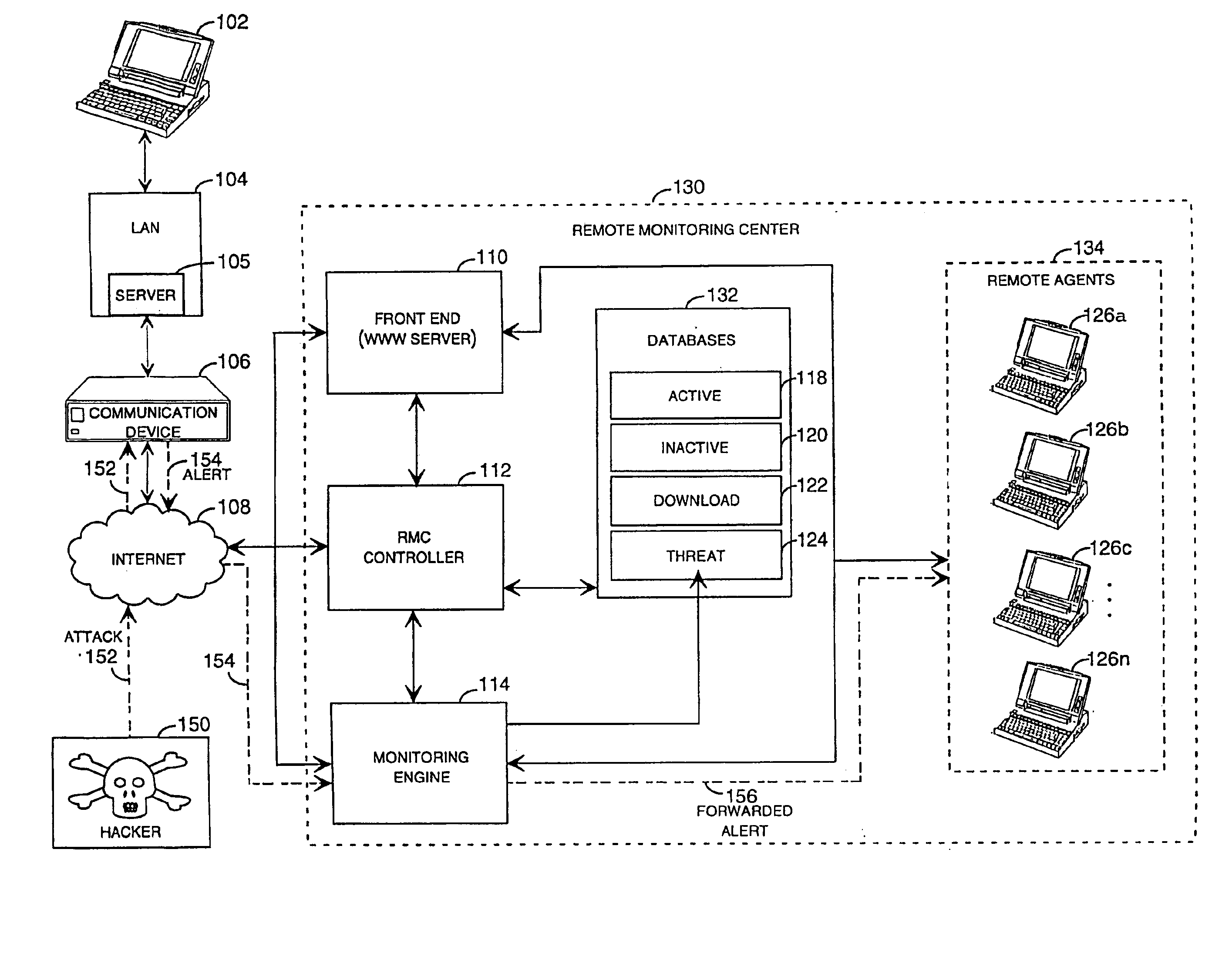
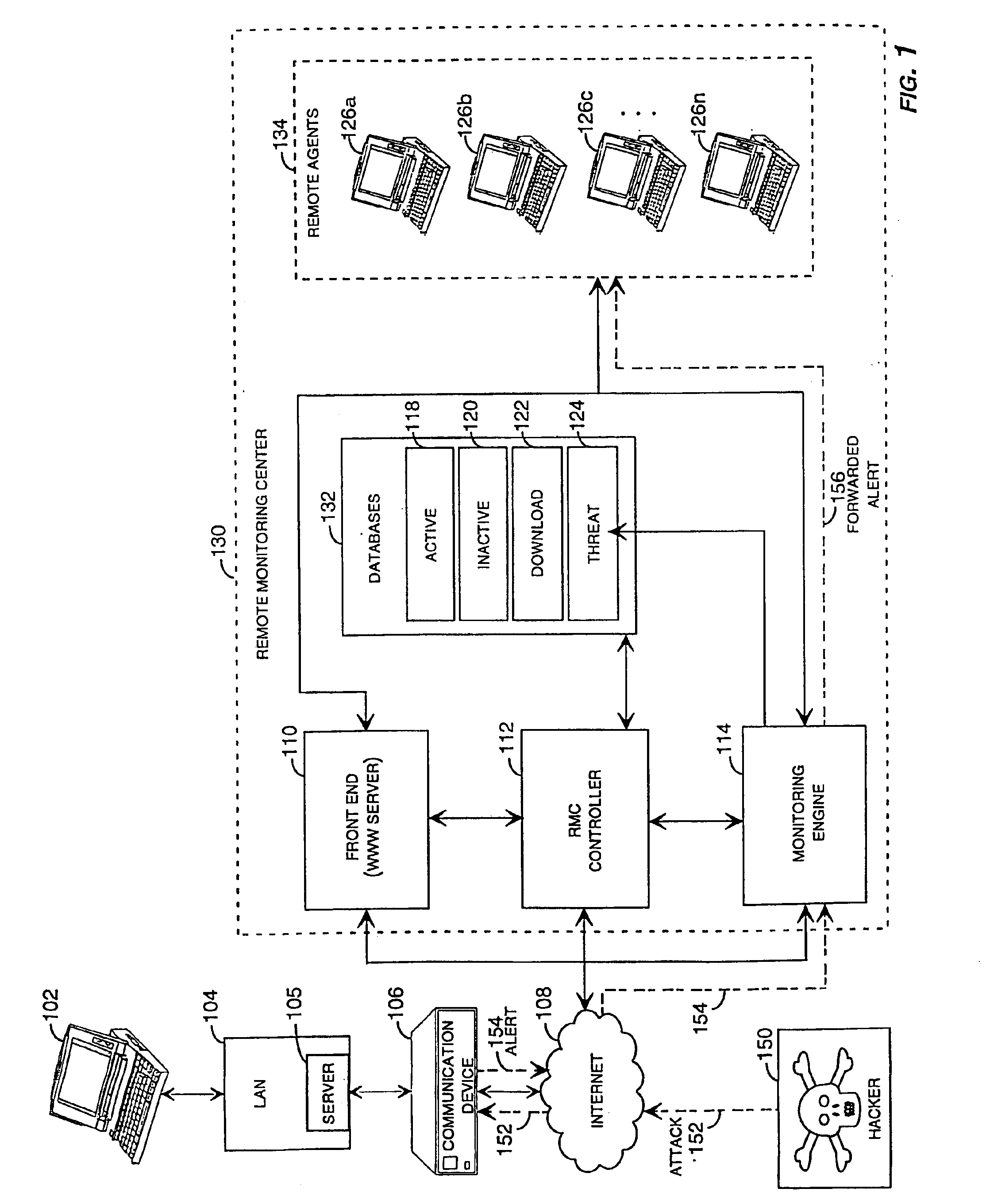
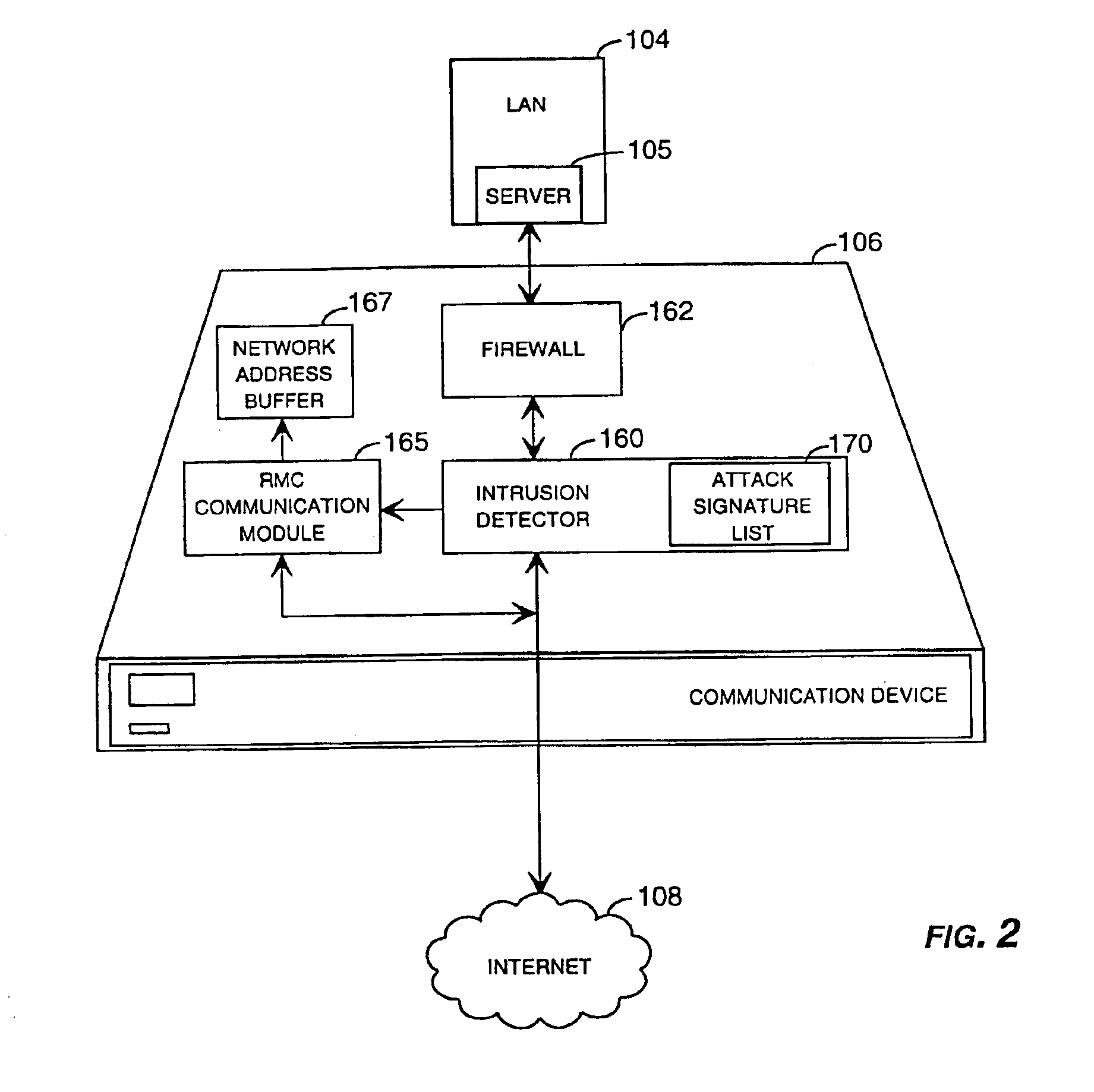
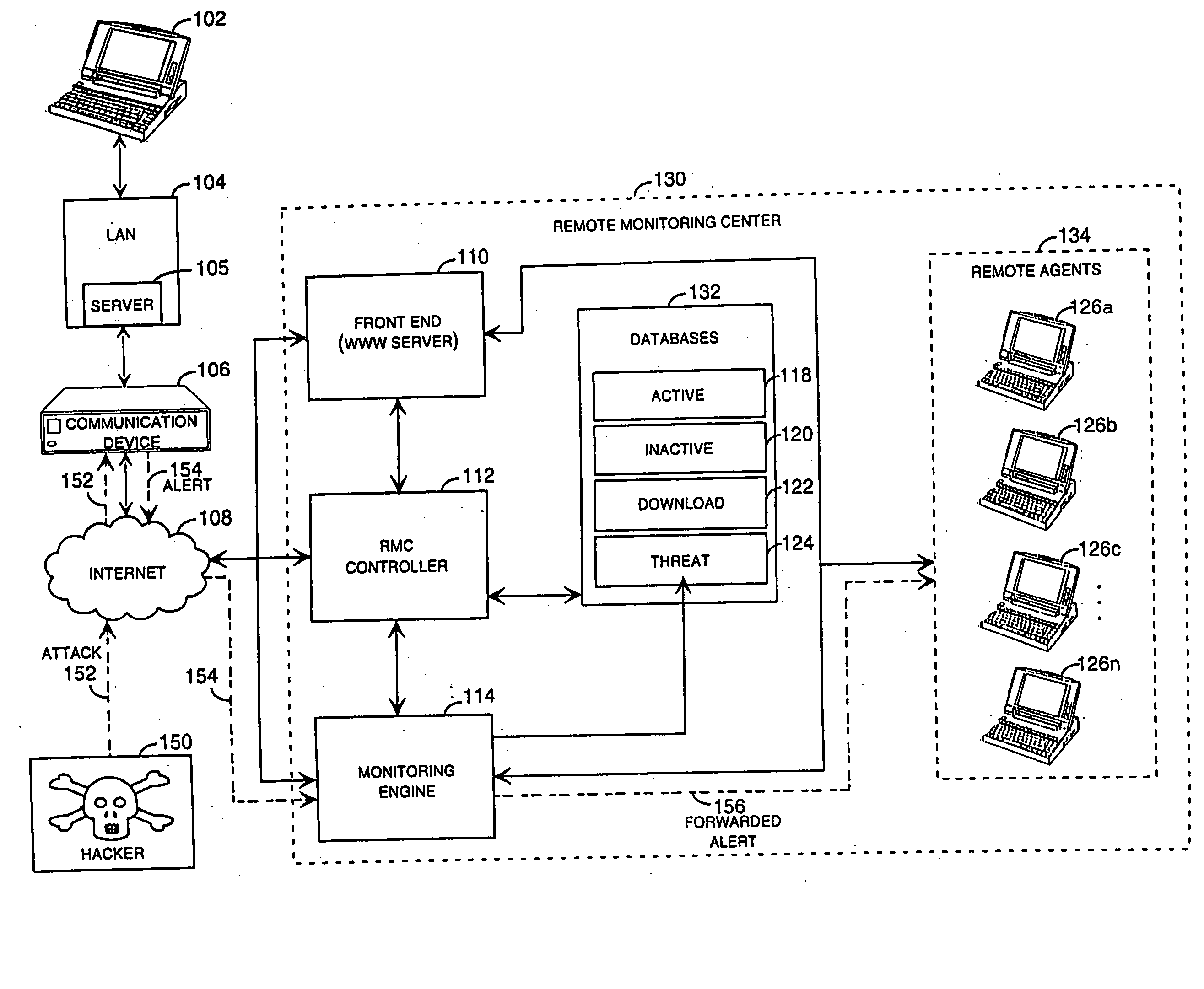
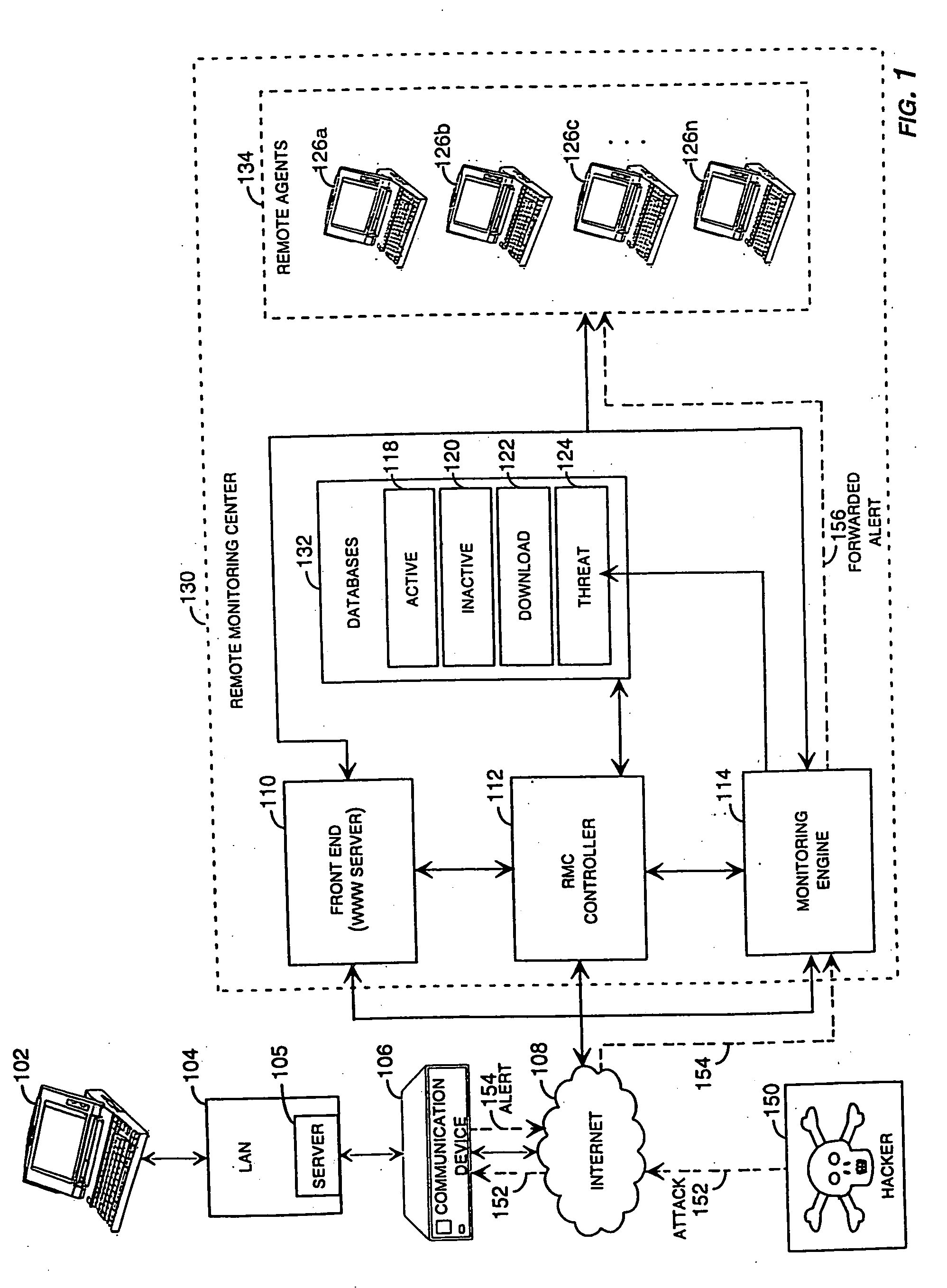
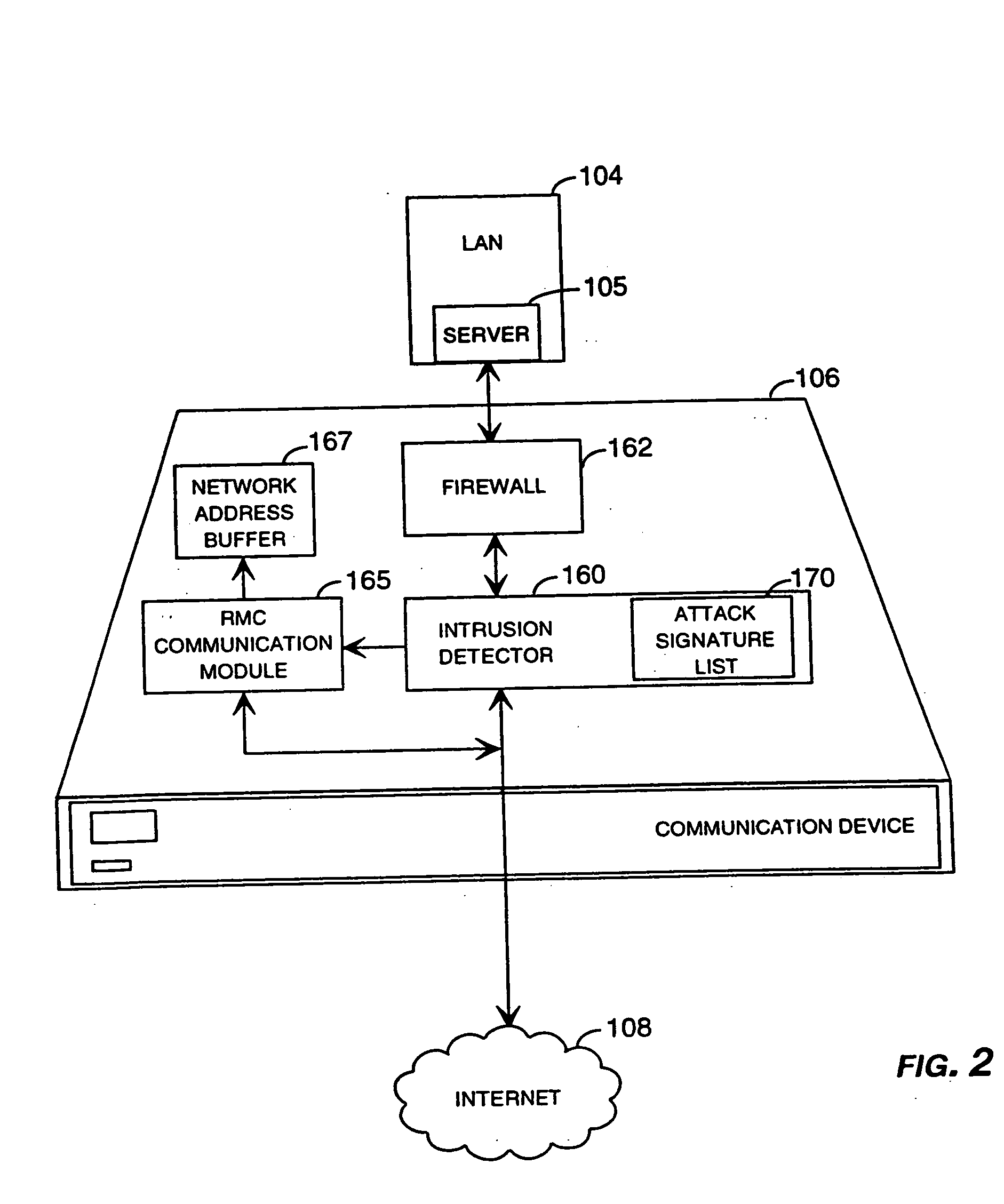
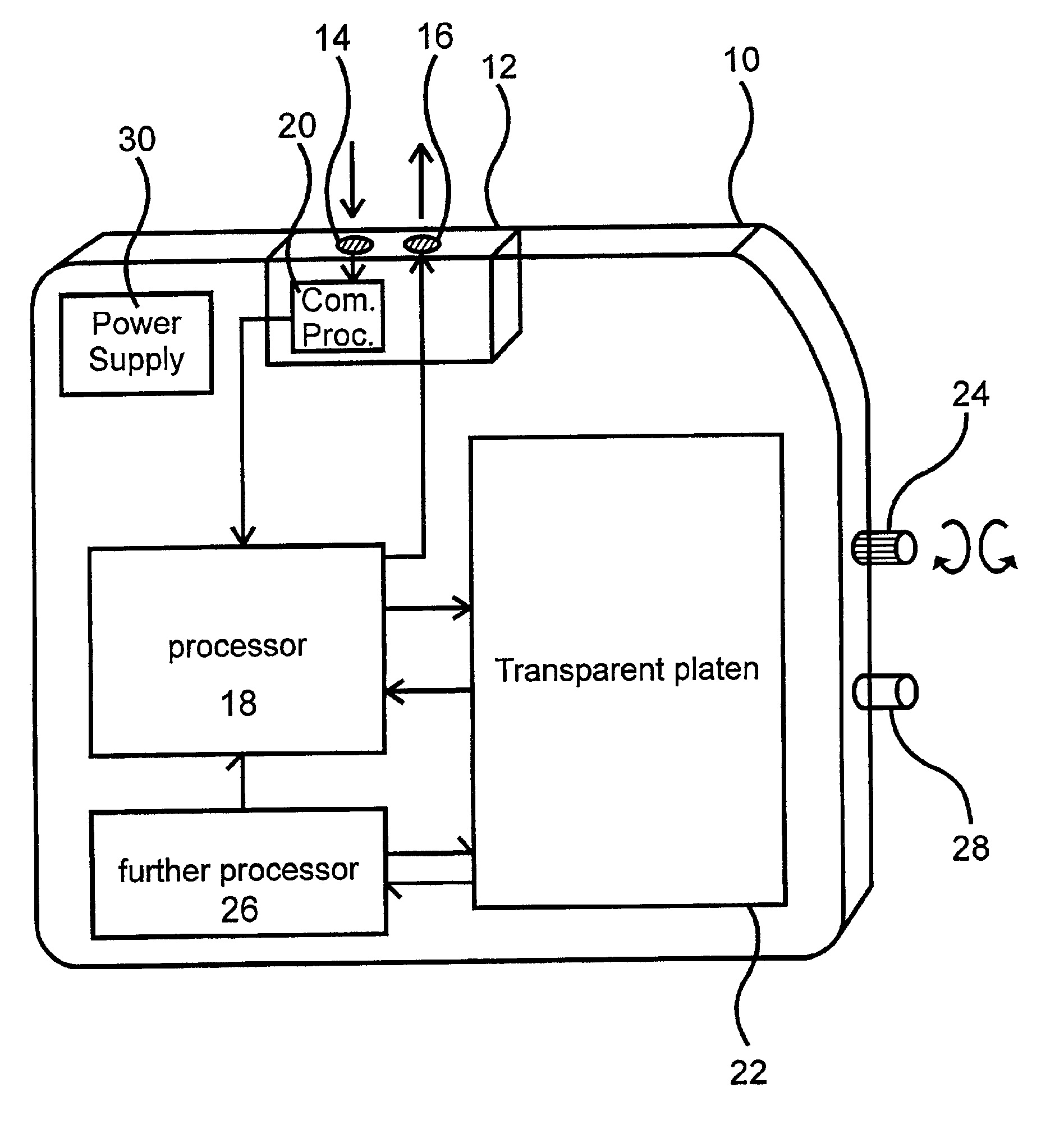
Method and system for remotely configuring and monitoring a communication device
InactiveUS6990591B1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Owner:SECUREWORKS
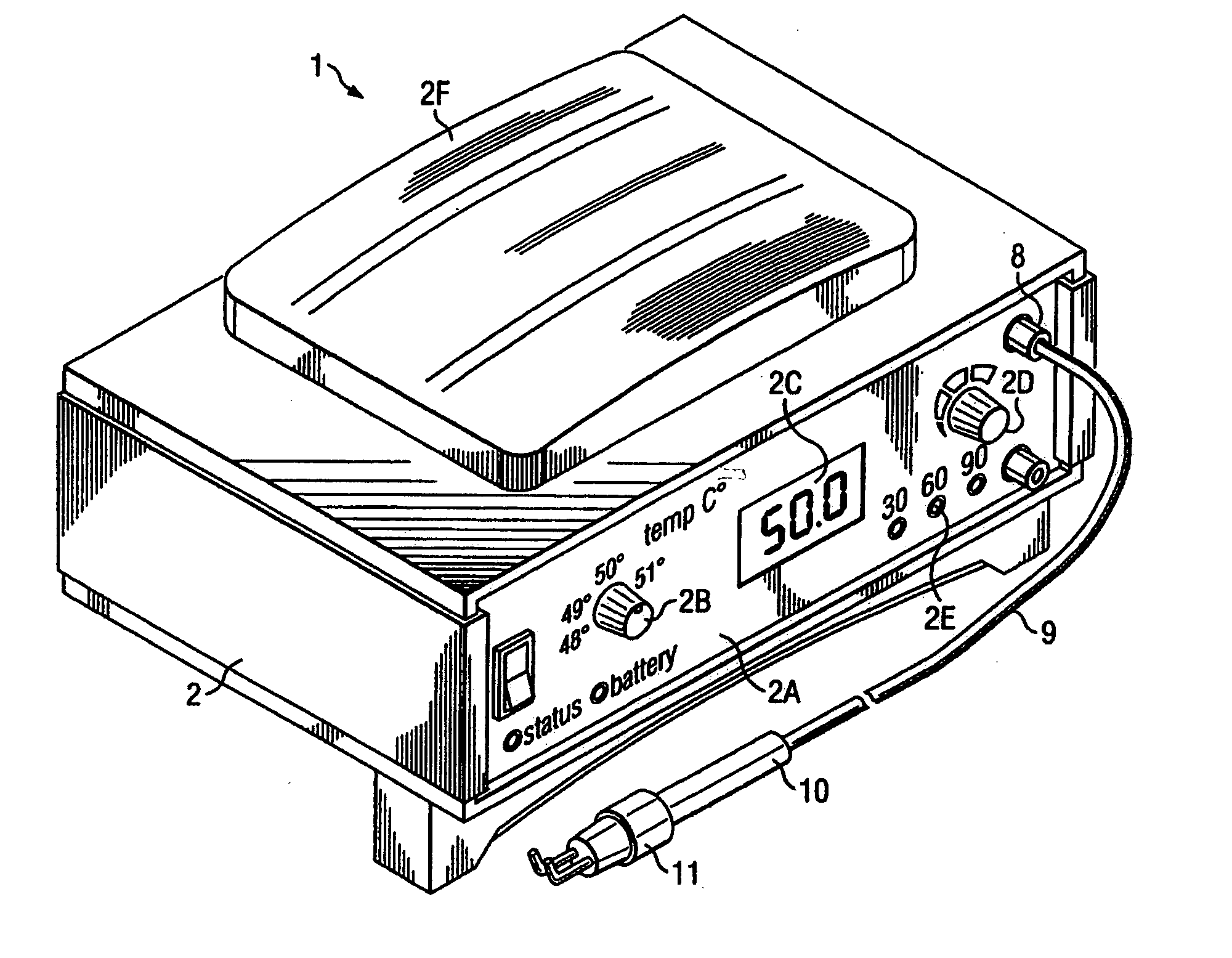
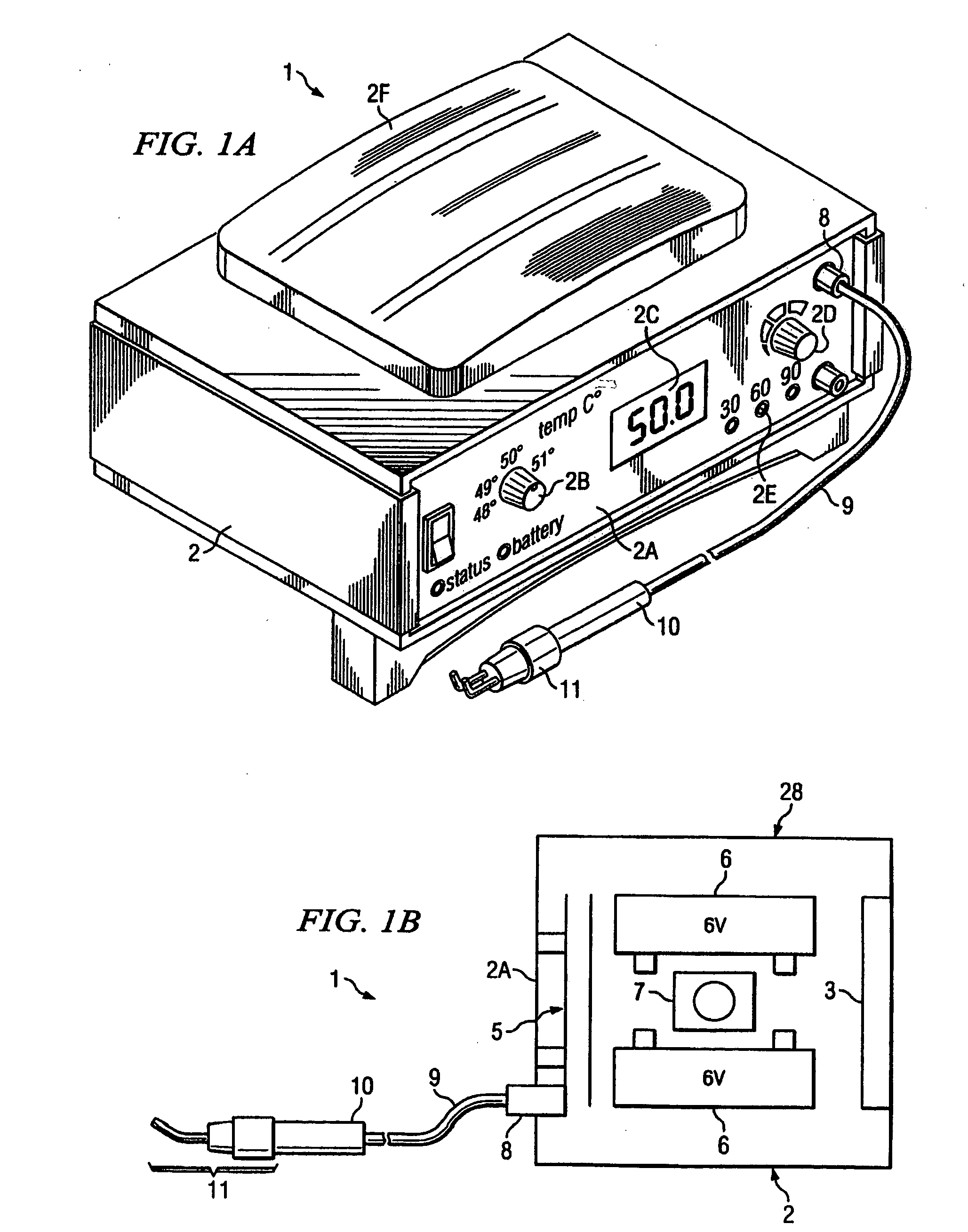
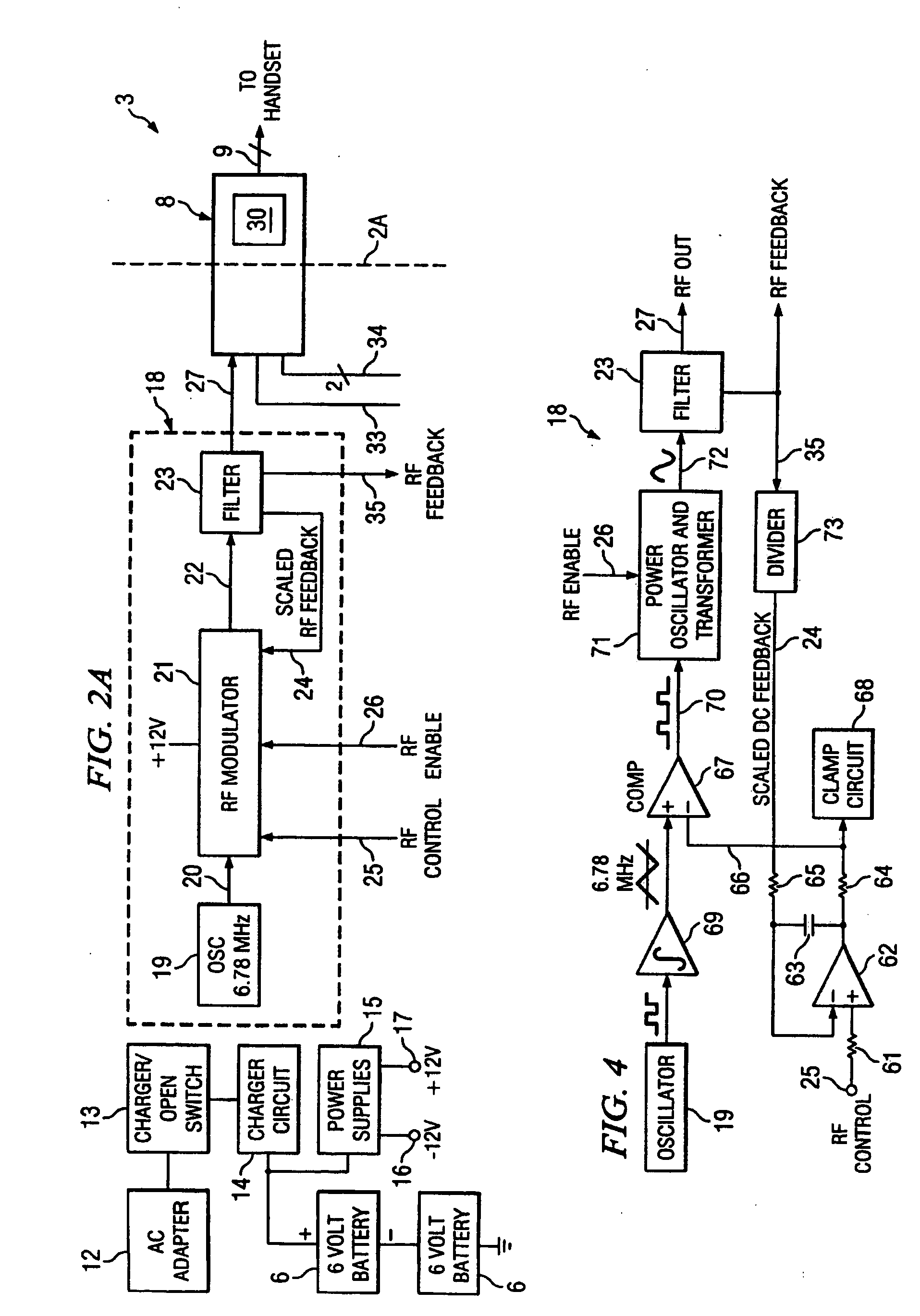
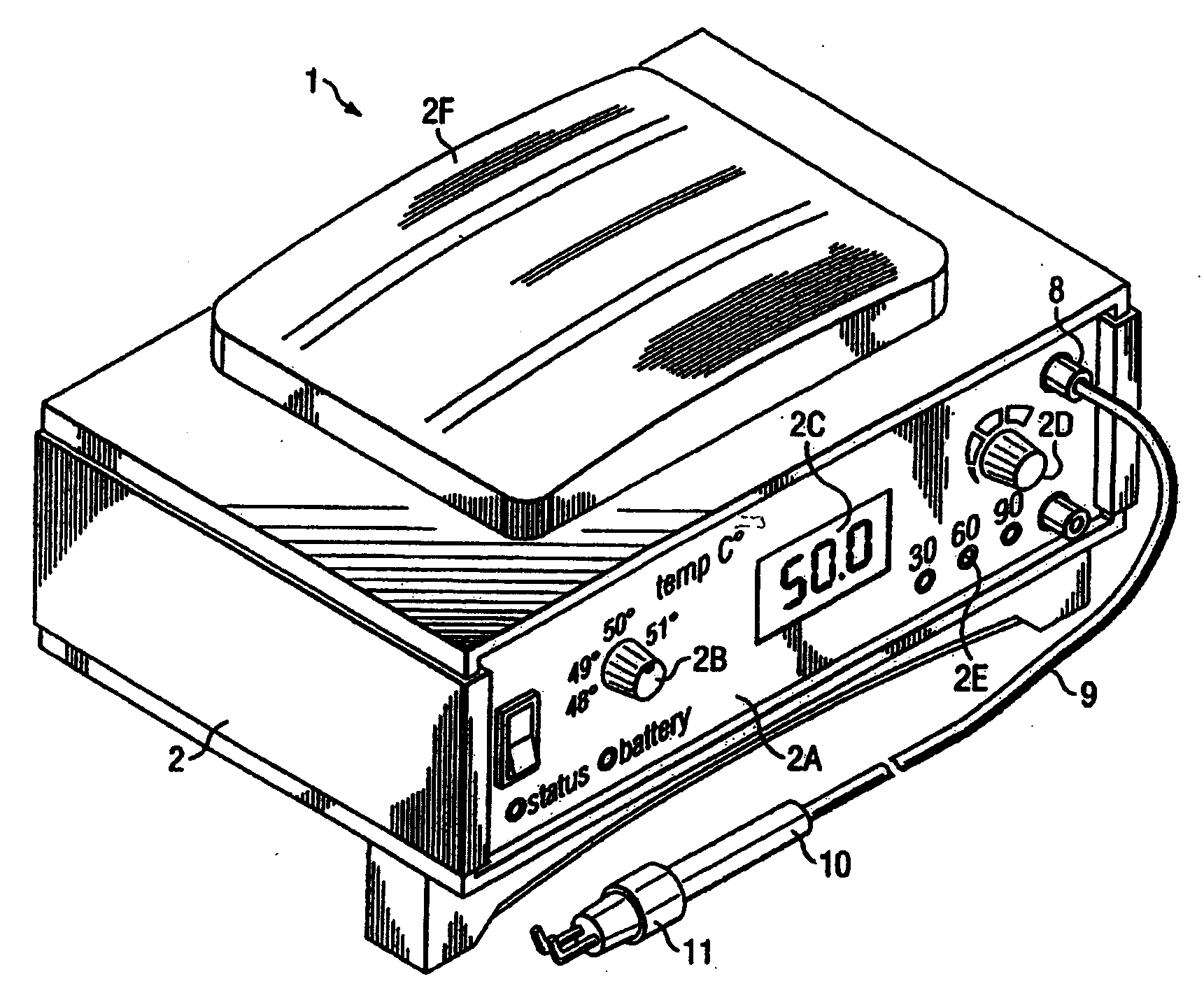
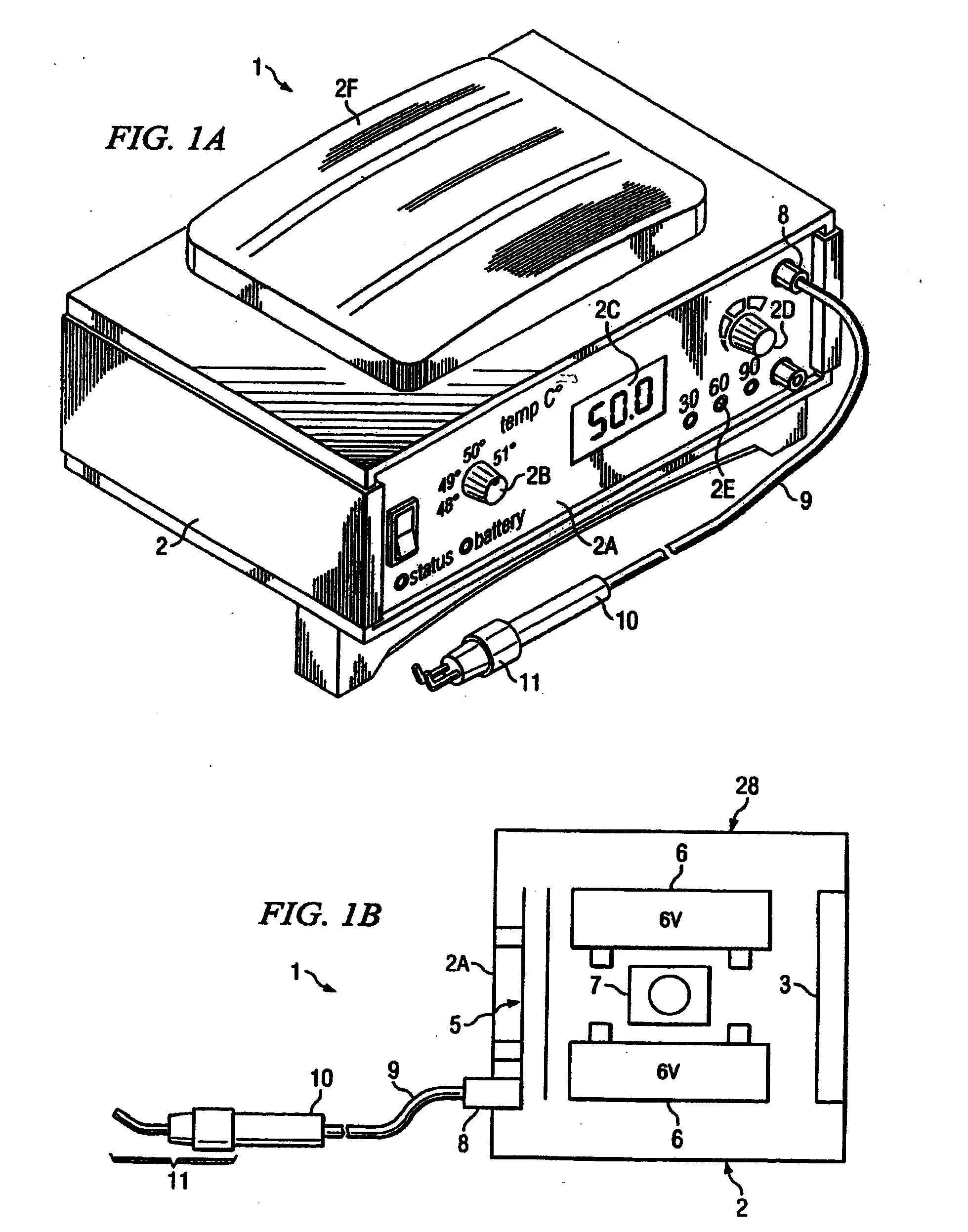
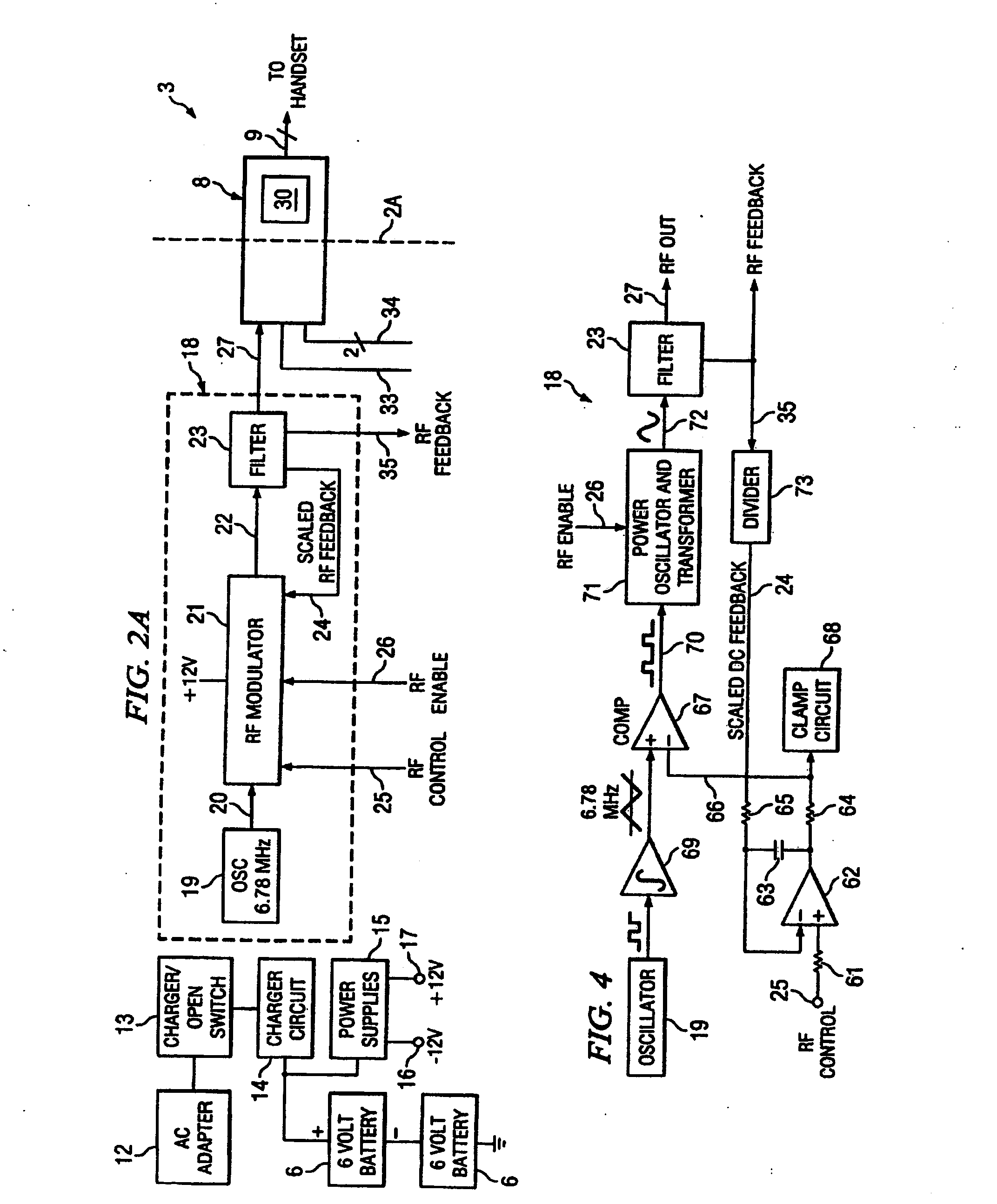
Hyperthermia treatment systems and methods
InactiveUS20050015125A1Reduce stepsSurgical instruments for heatingTherapeutic coolingTemperature differenceRadio frequency
Systems and methods are disclosed to control the temperature of an RF hyperthermia system with minimum overshoot and to improve safety by, among other things, detecting a defective temperature sensor. Temperature overshoot may be minimized by compensating for the short-term temperature difference between the area being treated and the applicator delivering the RF energy. The RF energy may heat the tissue and then the tissue may transfer heat to the applicator sensor. The system may also adapt to various applicator sizes and shapes by modifying control loop coefficients based on initial probe response.
Owner:THERMOSURGERY TECH
Personal choice biometric signature
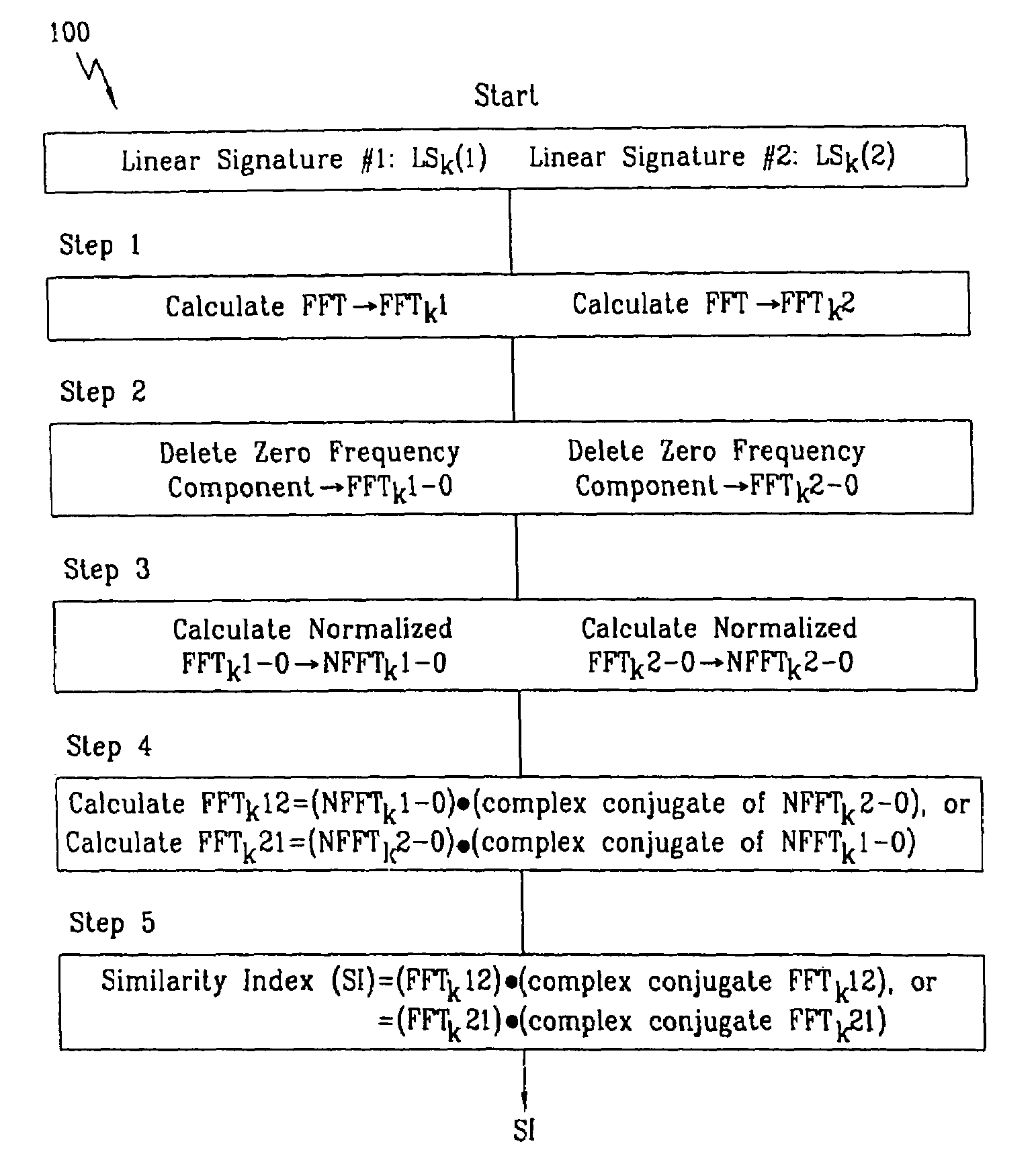
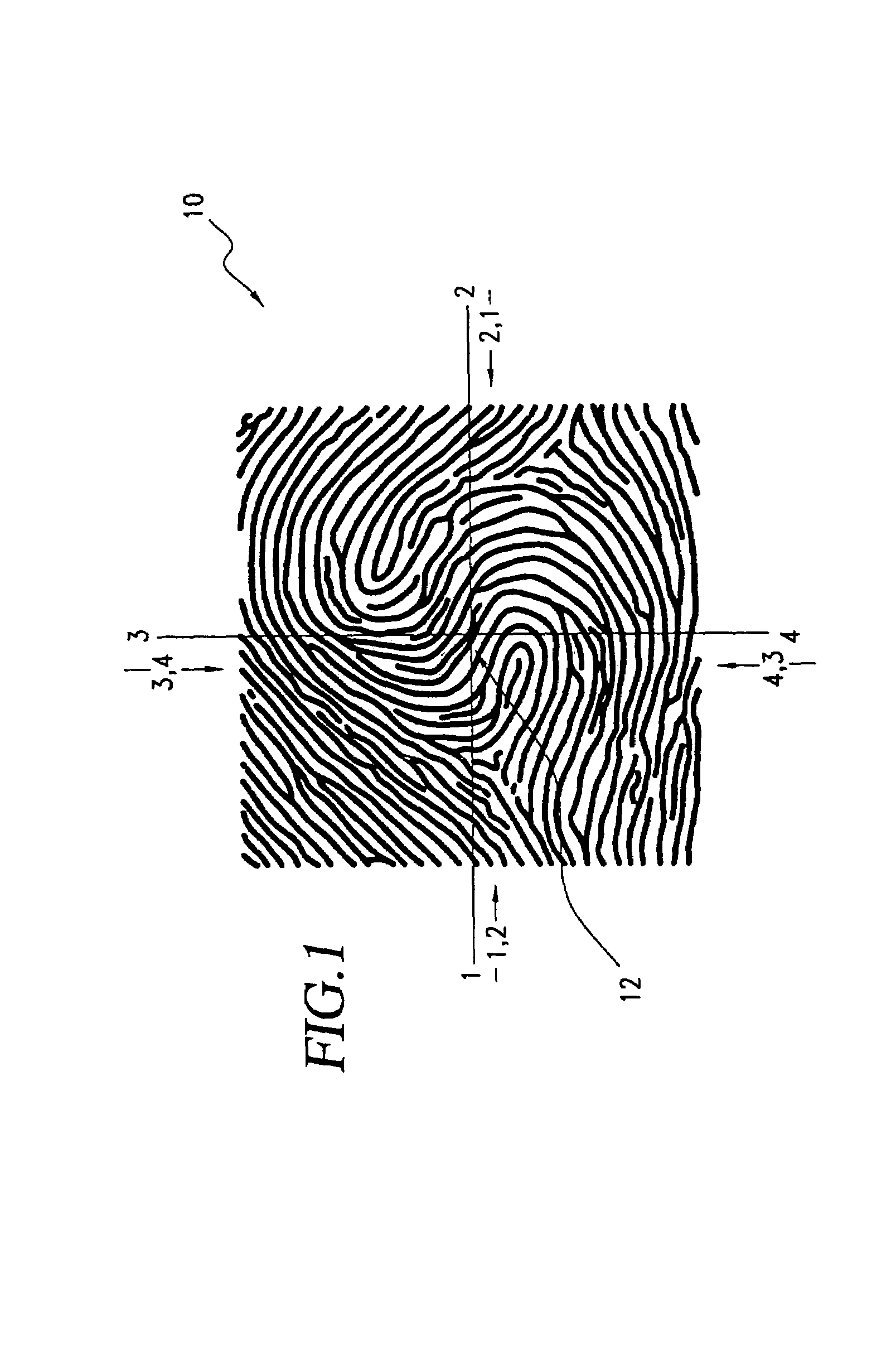
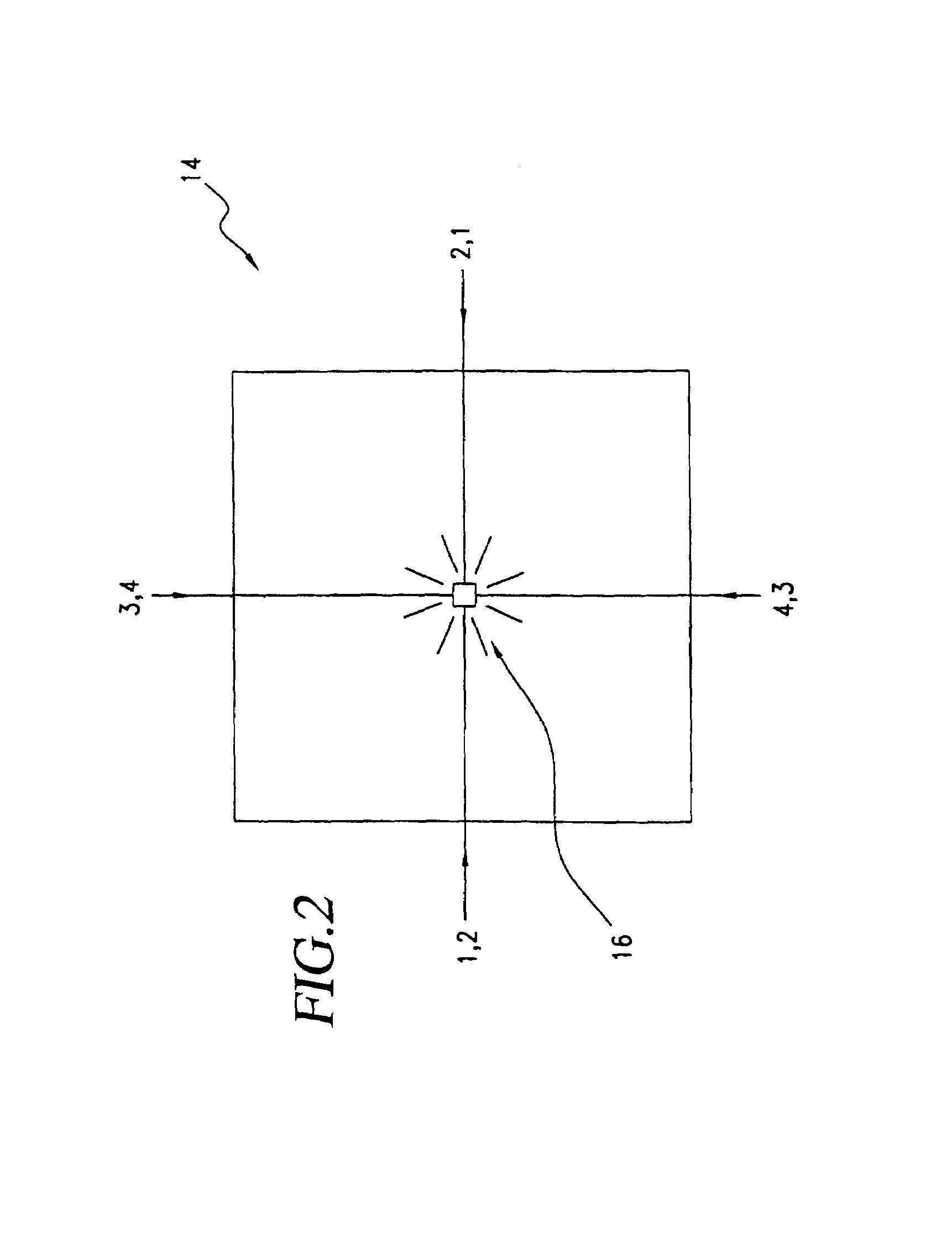
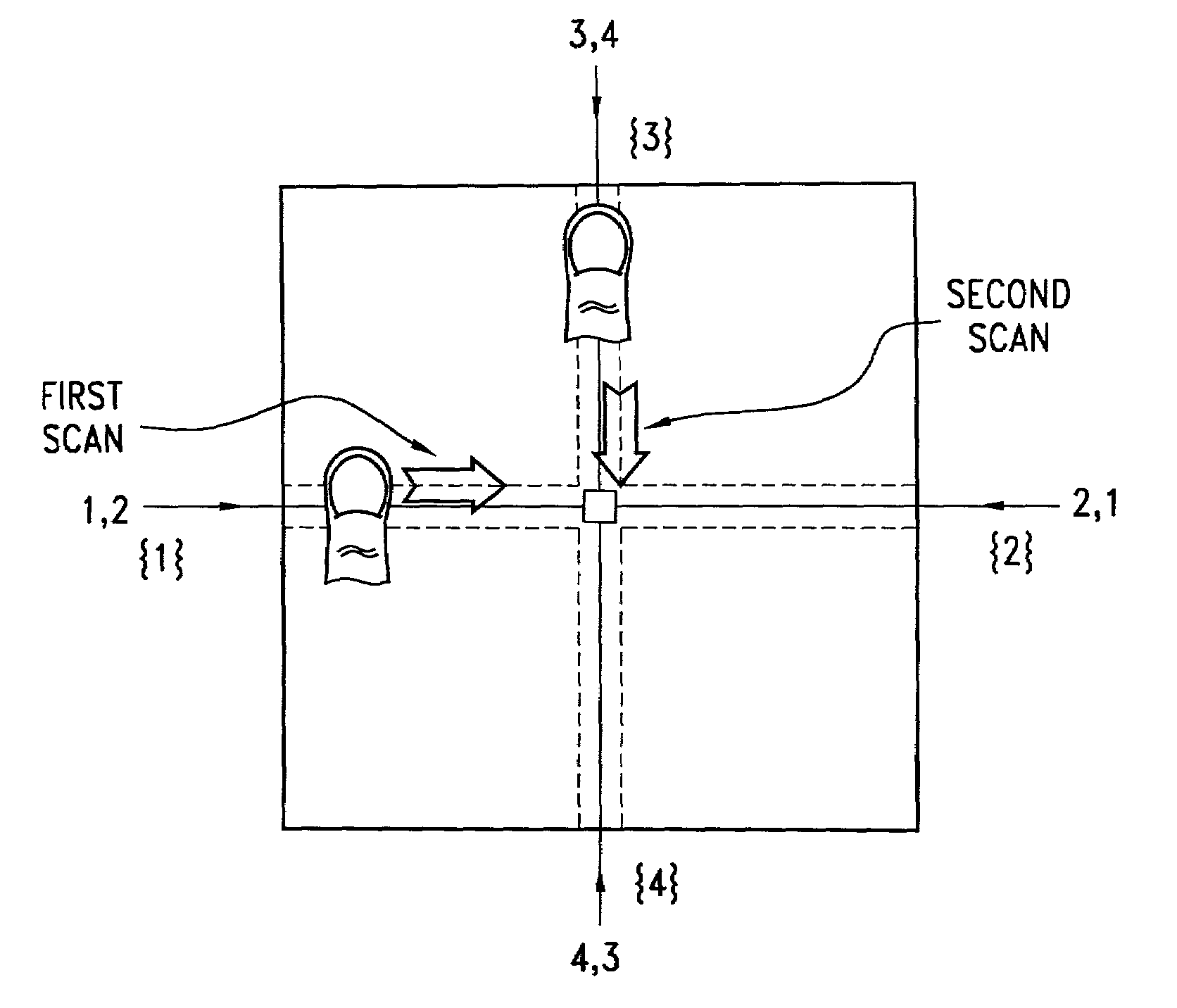
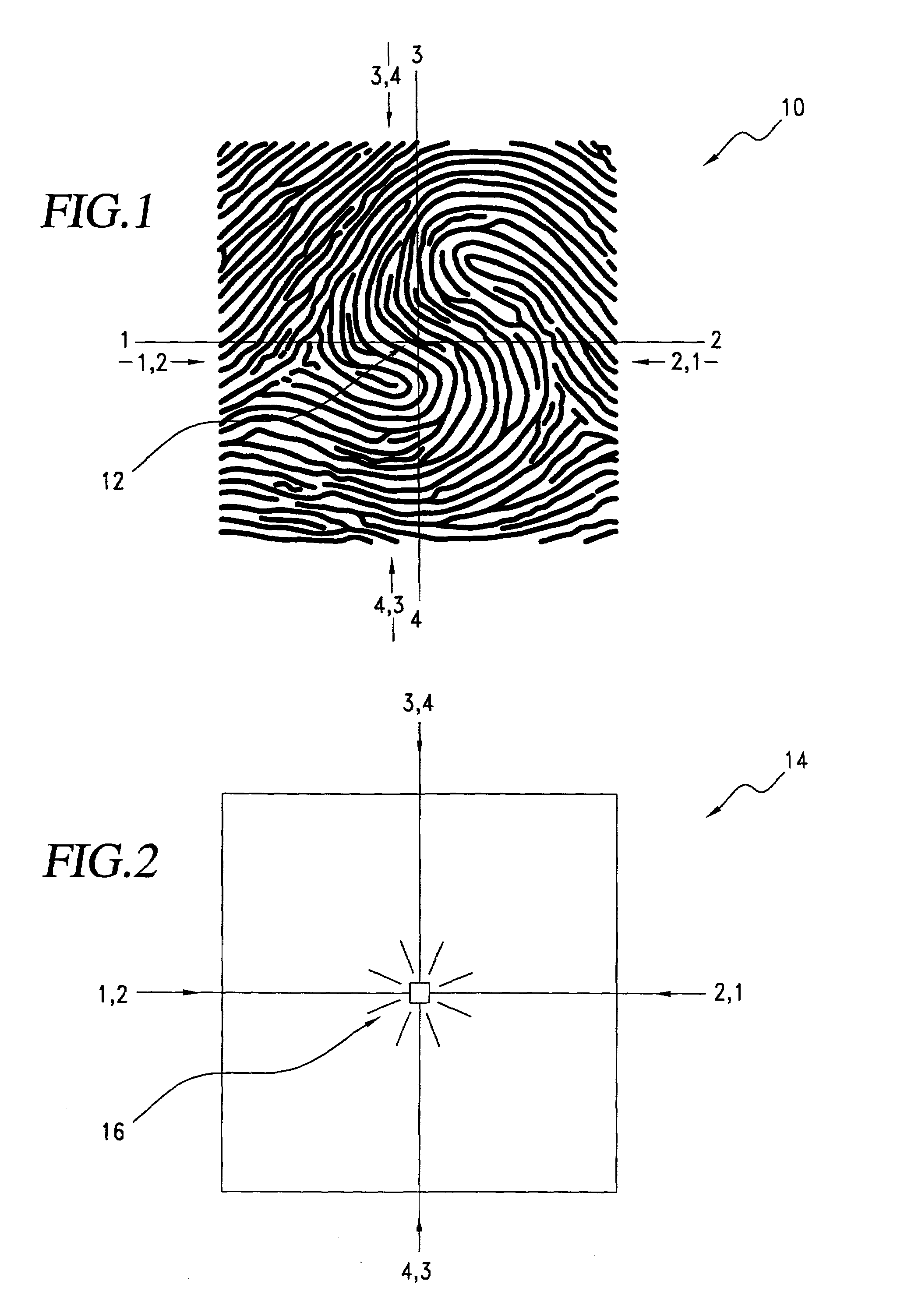
InactiveUS7013030B2Improved high security method and systemEasy to useElectric signal transmission systemsImage analysisCombined useLinearity
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains four (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, the same two candidate signatures in the chosen sequence are processed in a unique FFT / DFT process to produce a highly reliable Similarity Index to authenticate or verify the identity of individuals. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y +1
Personal choice biometric signature
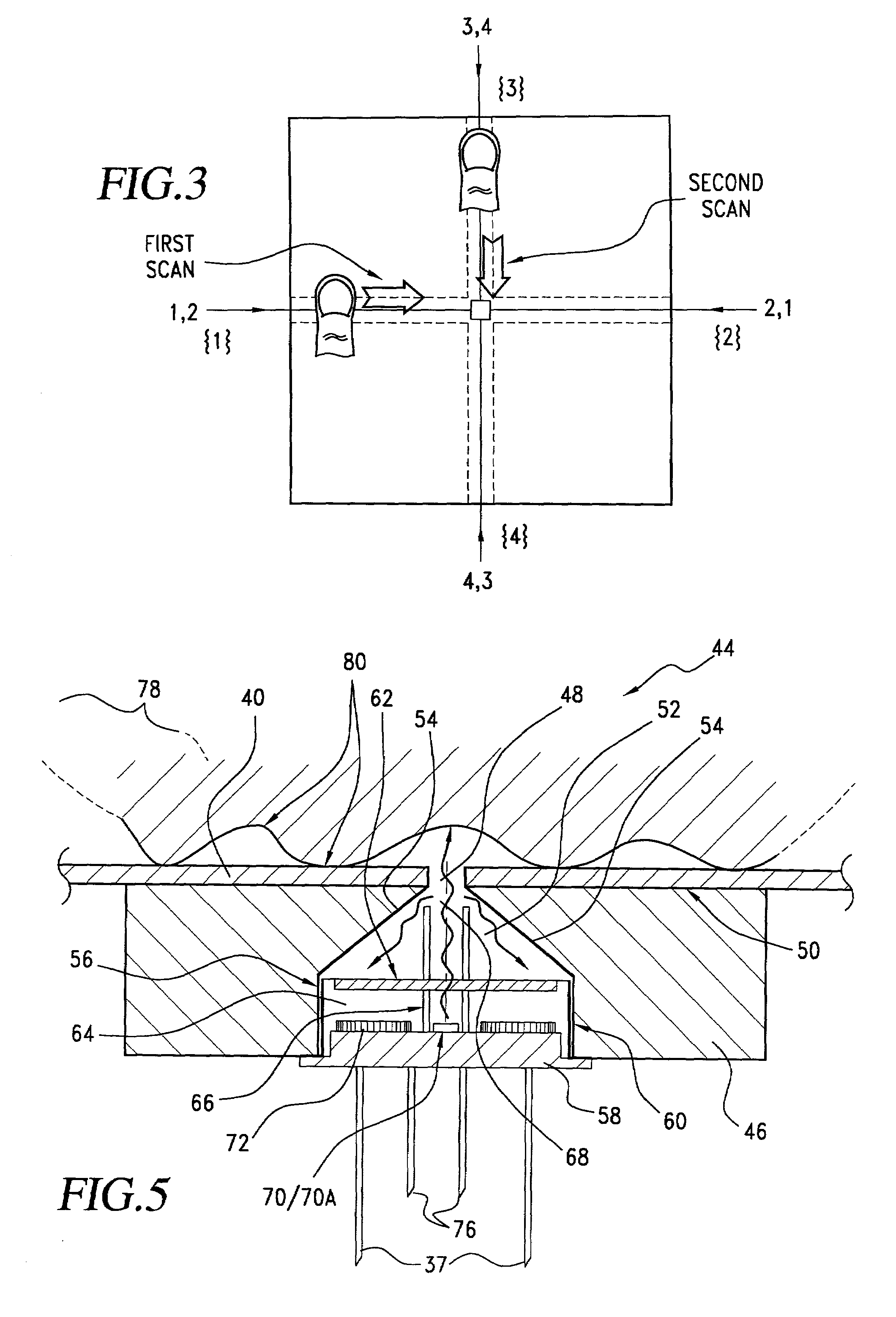
InactiveUS7035443B2Complicated processSpatial variation is minimizedElectric signal transmission systemsImage analysisPattern recognitionProximity sensor
A biometric method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. This approach is further enhanced by employing a frequency domain technique for calculating a Similarity Index of the partial fingerprint signatures. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains a reference set of linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. In an advanced embodiment, a pair of proximity sensors located along each of the linear tracks used for developing the linear partial signatures produce finger sensing signals which compensate for finger movement speeds and hence significantly improves the calculated Similarity Index values. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
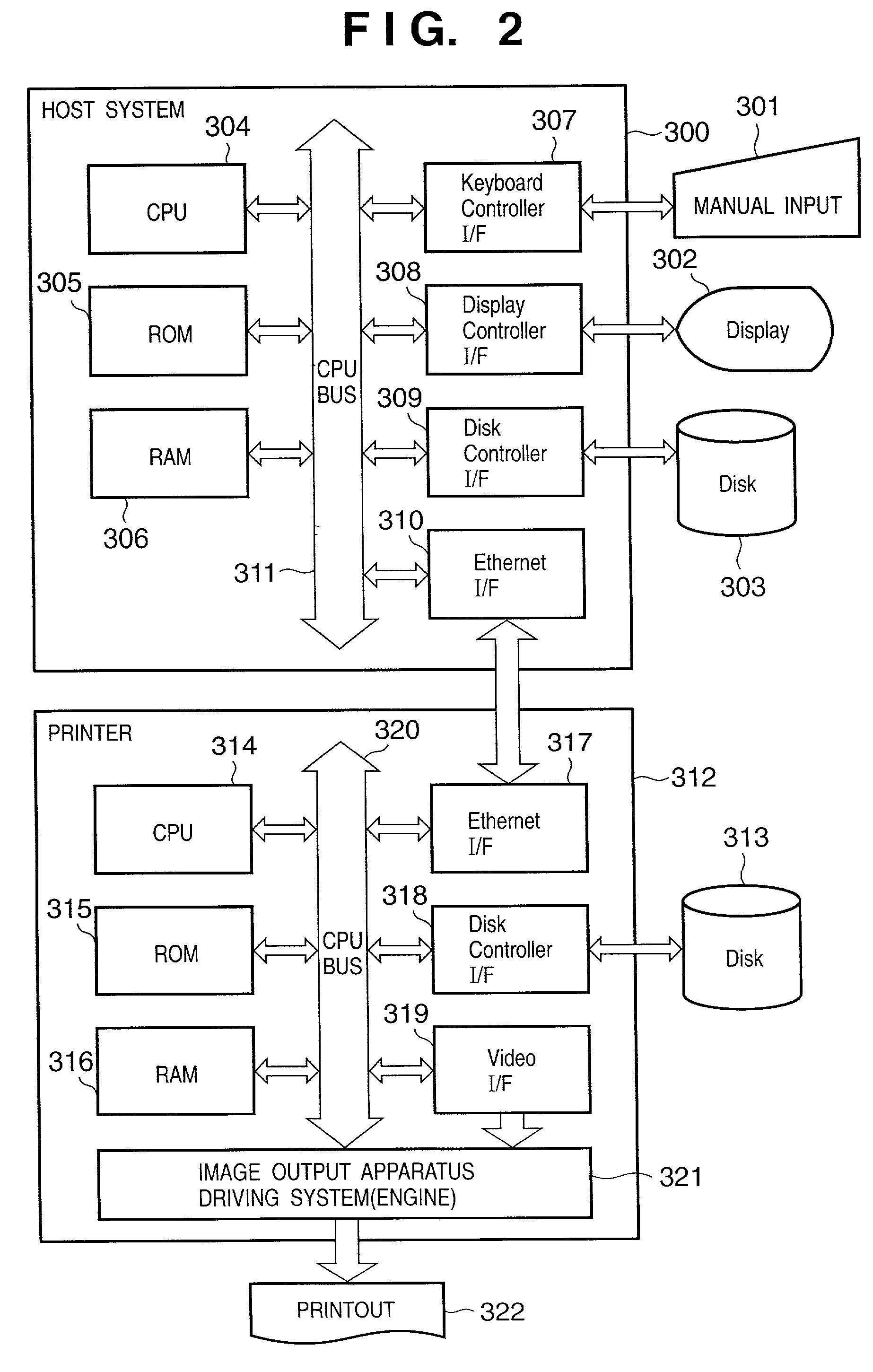
Automatic authentication method and system in print process
ActiveUS7313699B2Improve securityEliminate needDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
This invention provides an automatic authentication method and system in a print process, which can obviate the need for user's input operations of the user ID and password and can improve security since authentication is automatically done based on print information embedded in a file or information from an application program without any user's input.In a print process that requires user authentication, a printer driver extracts information related to an application and / or a document for the print process as attribute information, and user authentication is made by comparing the attribute information with information stored in a user registration information database of a server. If user authentication has succeeded, the printer driver controls a printer to print, and the server manages and stores accounting information and the like for respective departments in a department management information database.
Owner:CANON KK
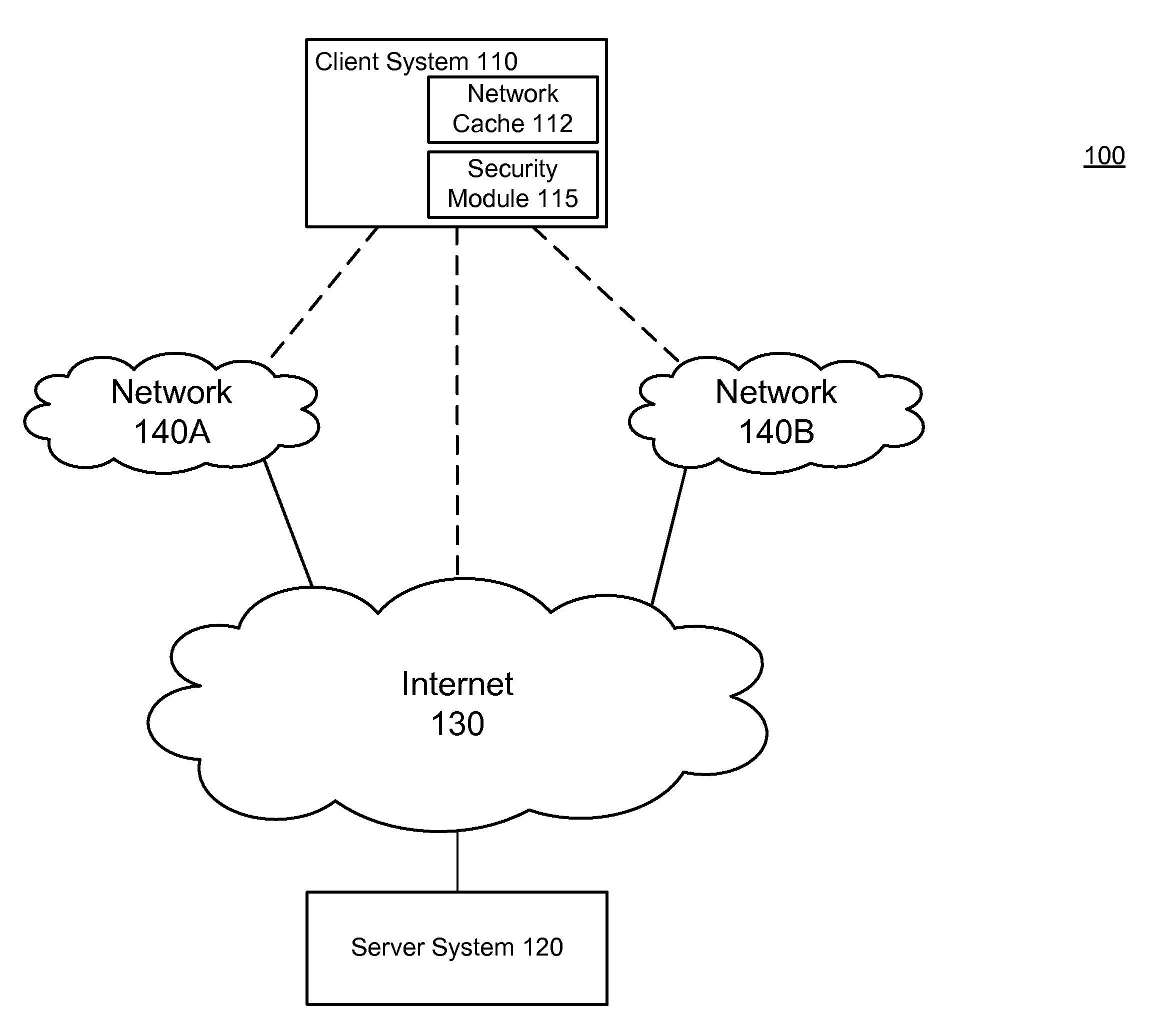
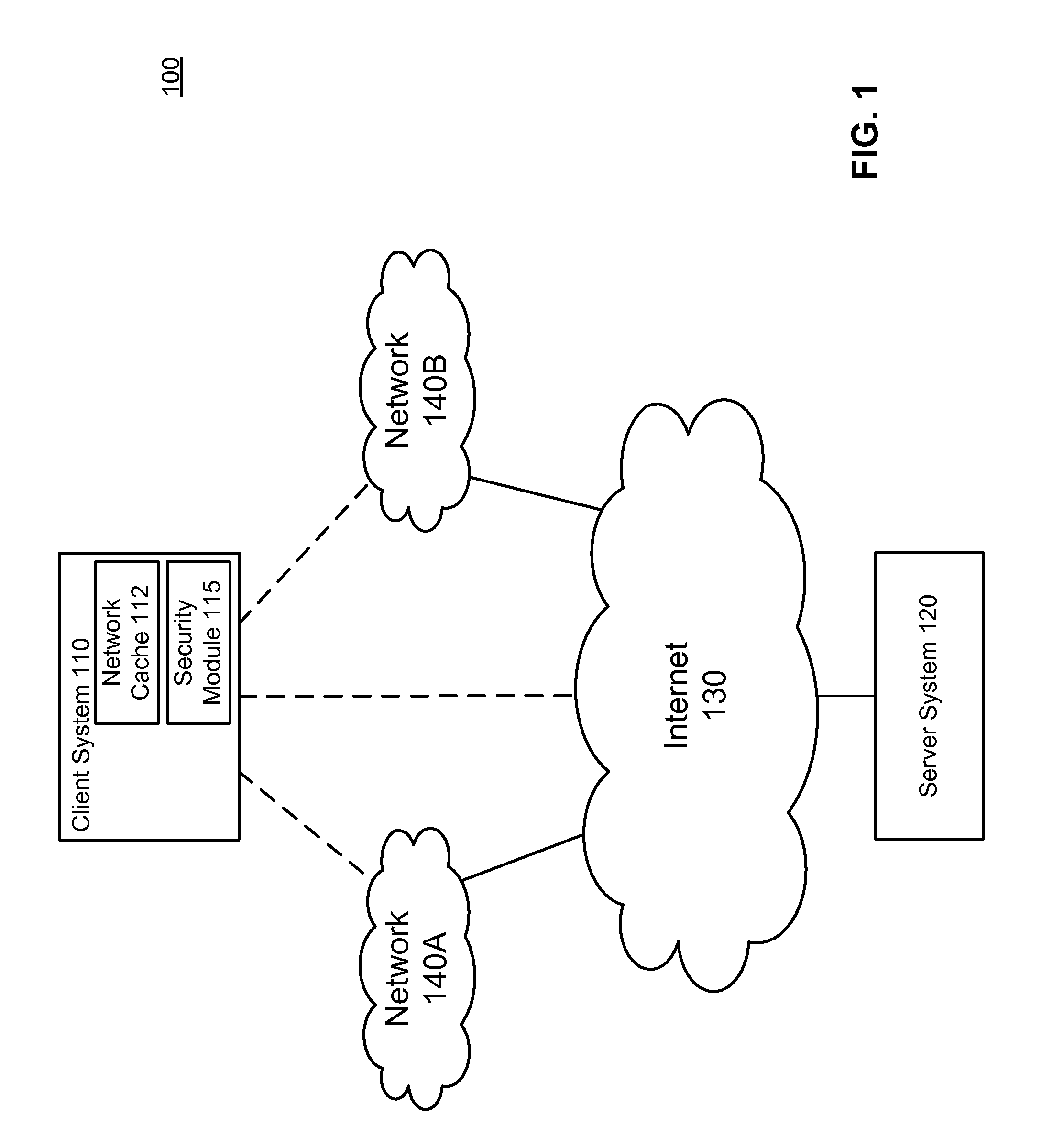
Secure network cache content
ActiveUS8584234B1Prevent malicious activityMemory loss protectionError detection/correctionAccess networkSecurity rule
A security module on a computing device applies security rules to examine content in a network cache and identify suspicious cache content. Cache content is identified as suspicious according to security rules, such as a rule determining whether the cache content is associated with modified-time set into the future, and a rule determining whether the cache content was created in a low-security environment. The security module may establish an out-of-band connection with the websites from which the cache content originated through a high security access network to receive responses from the websites, and use the responses to determine whether the cache content is suspicious cache content. Suspicious cache content is removed from the network cache to prevent the suspicious cache content from carrying out malicious activities.
Owner:CA TECH INC
Facial image verification utilizing smart-card with integrated video camera
InactiveUS7039221B1Prevent fraudProvide securityAcutation objectsCharacter and pattern recognitionDocking stationPrincipal component analysis
A biometric facial image verification system capable of recognizing human users which includes a smart-card having stored thereon encoded first human facial images, a video camera and video digitizer embedded within said smart-card for acquiring data representative of a second human facial image. A computer-based device with a docking station capable of receiving said smart-card and software resident within said computer-based device for facial recognition, which includes Principal Component Analysis, Neural Networks, or another equivalent algorithm for comparing said first human facial images with said second human facial image and producing an output signal therefrom for use in verifying the identity of said human users. The apparatus can further include software for fingerprint and speech recognition. In addition, said smart-card is capable of acquiring and storing information pertaining to each of said human users such as would be required for use in a high-security environment or preventing fraud in point of sale and Internet-based financial transactions.
Owner:DONALD R STARKWEATHER
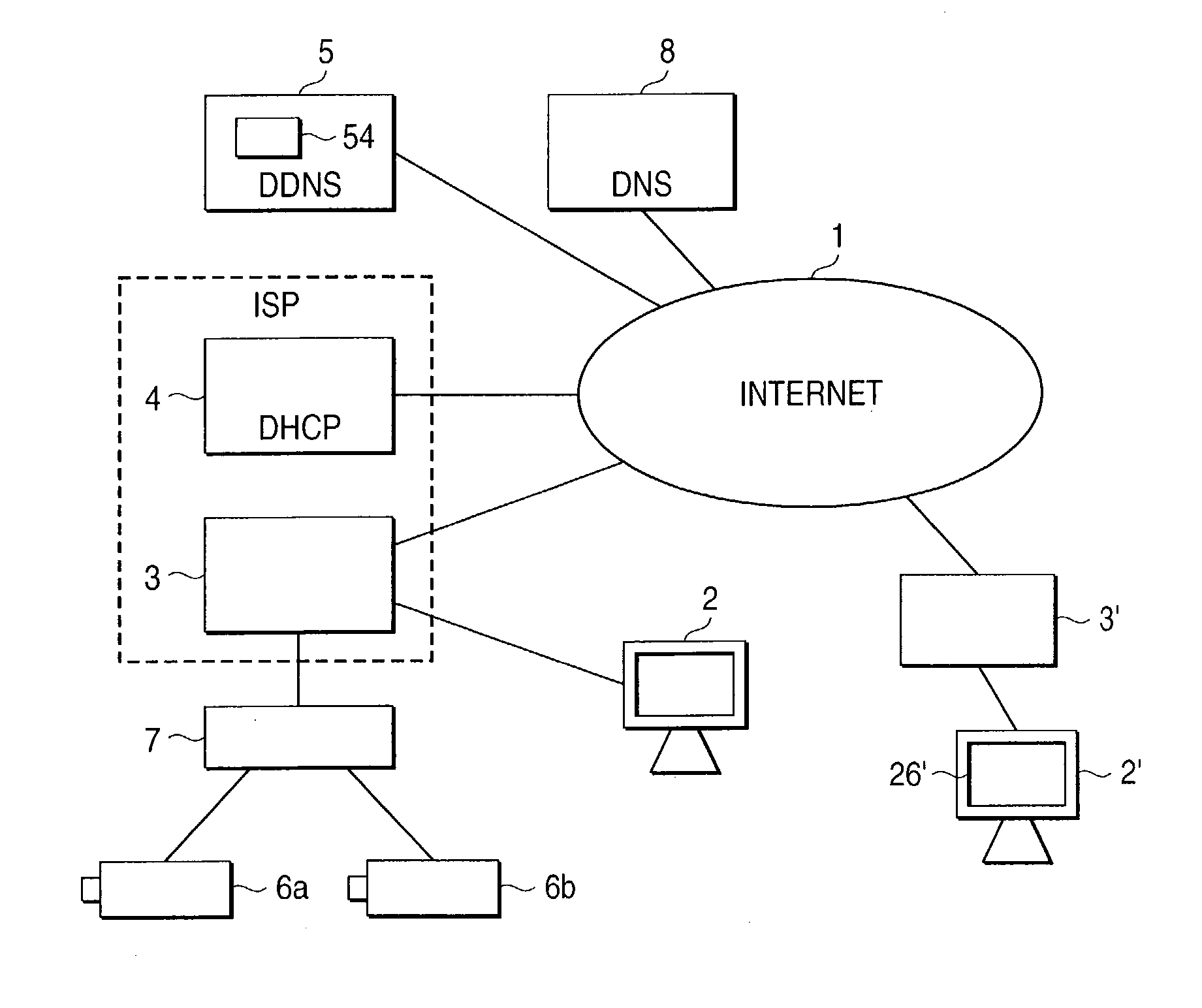
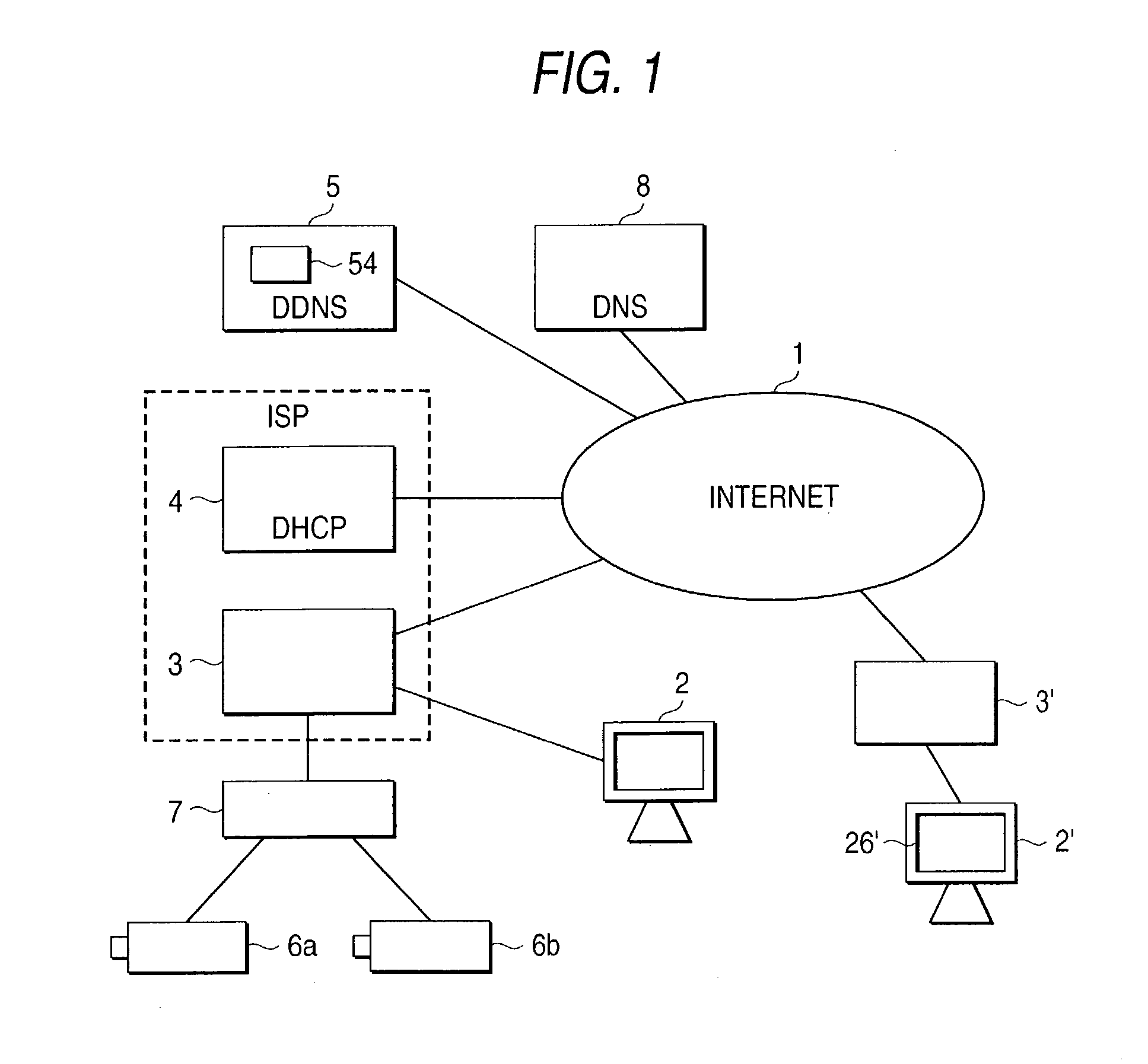
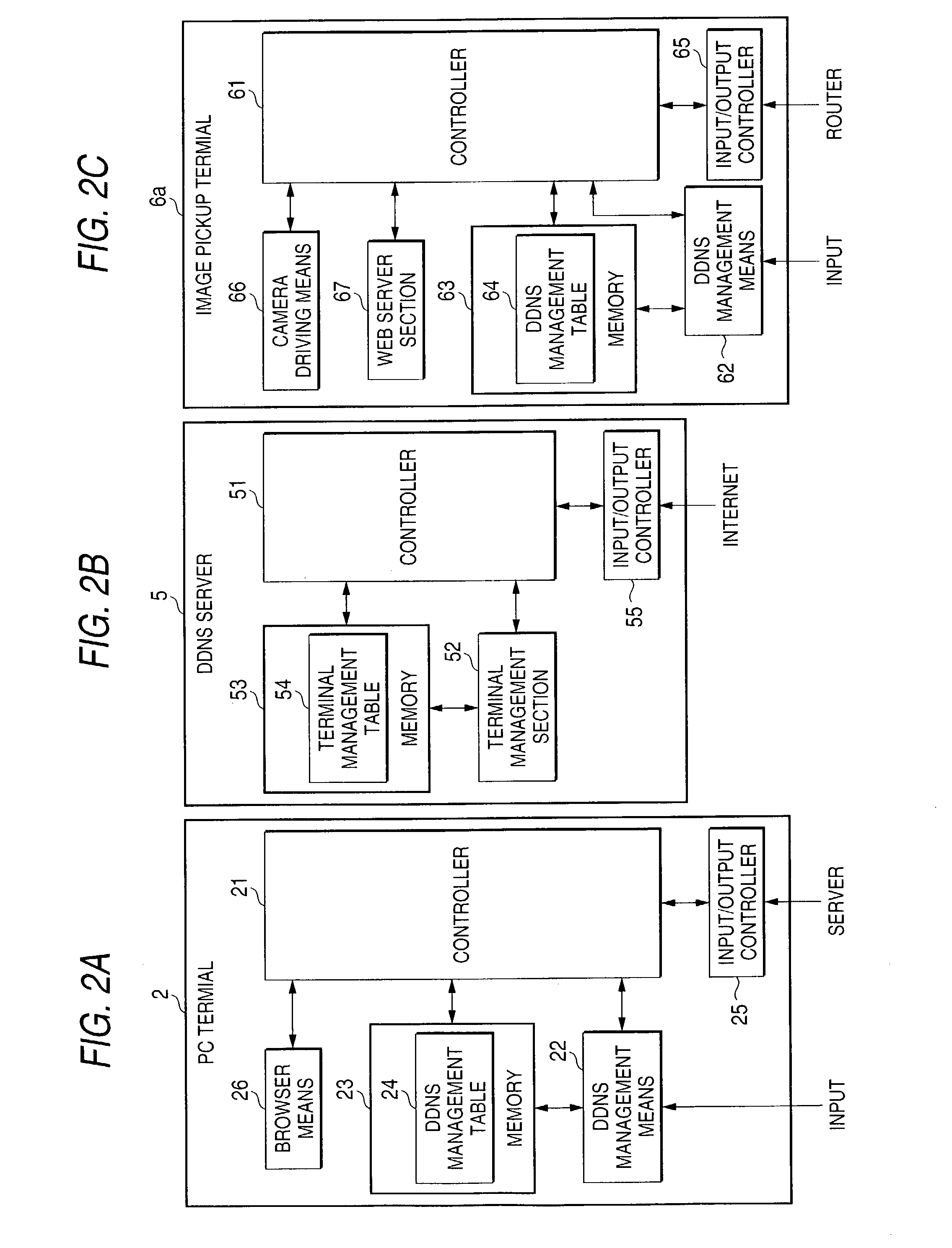
DDNS server, a DDNS client terminal and a DDNS system, and a web server terminal, its network system and an access control method
InactiveUS20030177236A1Readily and reliably prevent erroneous connectionImprove securityMultiple digital computer combinationsTransmissionDomain nameIp address
The present invention aims at providing a DDNS server, a DDNS client terminal and a DDNS system which maintains high security while using DHCP and allows an access to terminals having the same IP address as well as data updates. The DDNS server includes a terminal management table storing the domain name, global IP address and port number of a DDNS client terminal, characterized in that the terminal management section checks whether a same global IP address is present in the terminal management table when a request to overwrite a global IP address is made from a DDNS client terminal and, in case the same global IP address is absent, permits overwriting of the global IP address, and in case the same global IP address is present, checks the port number, and in case the same port number is detected, inhibits overwriting of the global IP address, and in case the port number is different, permits overwriting of the global IP address.
Owner:PANASONIC CORP
Authentication method utilizing a sequence of linear partial fingerprint signatures selected by a personal code
InactiveUS7039223B2Improved high security method and systemEasy to useProgramme controlElectric signal transmission systemsCombined usePersonal computer
A method and system for personal authentication using sequences of partial fingerprint signatures provides a high security capability to various processes requiring positive identification of individuals. In a baseline usage, the sequential partial fingerprint sequence techniques augments sentinel systems for gaining access to restricted areas, and when used in combination with financial cards, offer a unique and greatly simplified means for authenticating or identifying individuals. A highly automated technique initially obtains eight (illustratively) linear partial fingerprint signatures which serve as reference data against which later proffered candidate data in the form of at least two linear partial fingerprint signatures are compared for authentication. The particular two candidate signatures used and the sequence in which they are submitted are selected with the user's consent and serve as a PIN-like unique personal code. The use of only partial fingerprint data greatly allays the concerns of widespread fingerprint dissemination by many individuals.
Owner:WONG JACOB Y
Method and system for remotely configuring and monitoring a communication device
InactiveUS20050235360A1Rapid responseMemory loss protectionUnauthorized memory use protectionImage resolutionThe Internet
Methods and systems for remotely configuring and monitoring a communication device are provided, especially useful in a computer network environment such as the Internet. A communication device or network appliance compares communications entering the communication device to a list of communication types established as known security risks, for example hacker attacks, unauthorized attempted access to network resources, or similar network security threats. If the received communication corresponds to a known security risk, the communication is classified as either a high security risk or low security risk, and an alert signal is transmitted to a remote monitoring center. Upon receiving the alert signal, the remote monitoring center assigns a priority to the alert signal based upon the type of the communication that triggered the transmission of the alert signal. Based on the assigned priority, the prioritized alert signal is then forwarded to a remote monitoring agent for resolution. The remote monitoring agent may then analyze the communication, contact the end user of the communication device with an appropriate resolution, or take other appropriate action in response to the received communication. The communication device may also be remotely configured.
Owner:SECUREWORKS
Ultra-wide band wireless / power-line communication system for delivering audio/video content
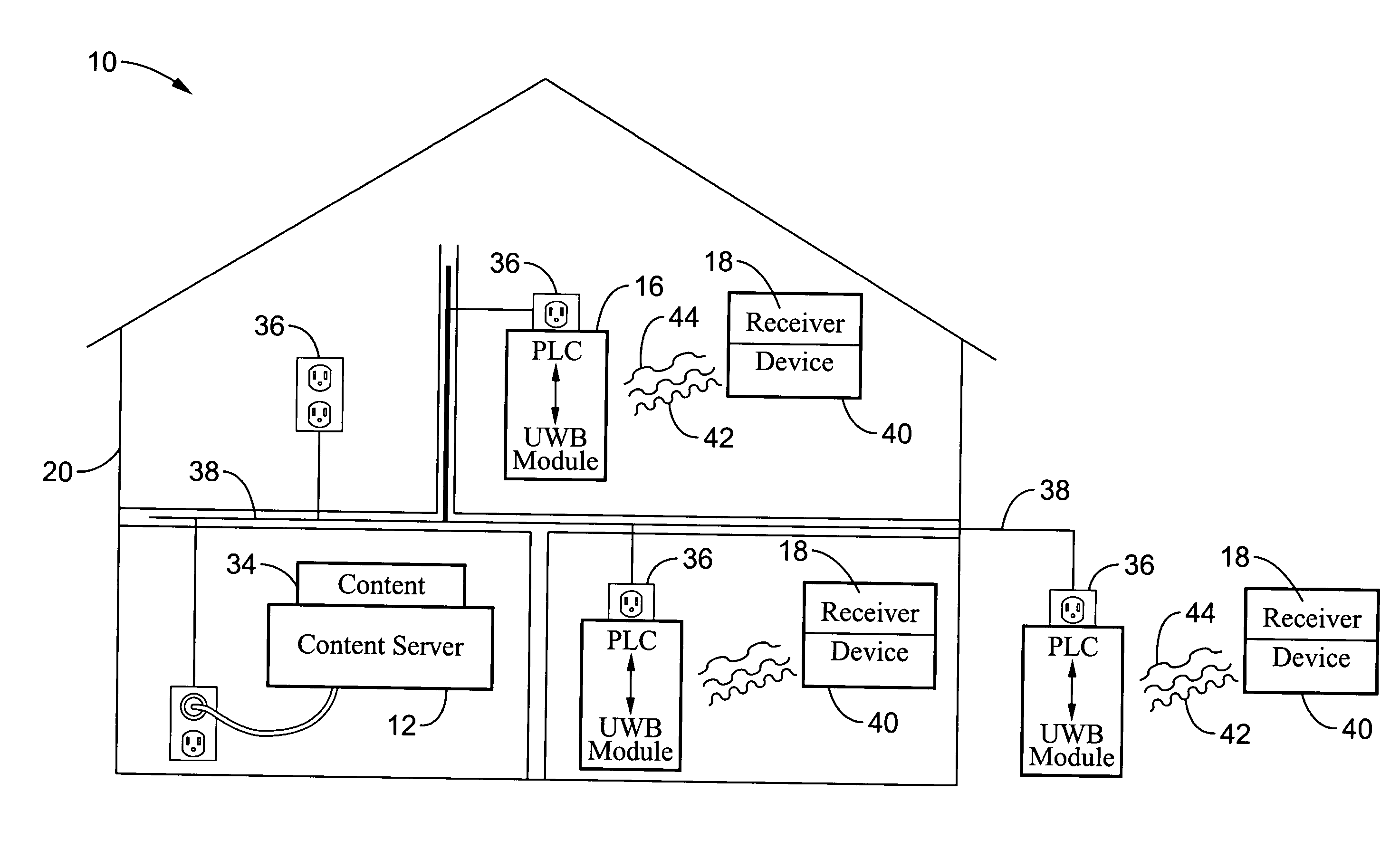
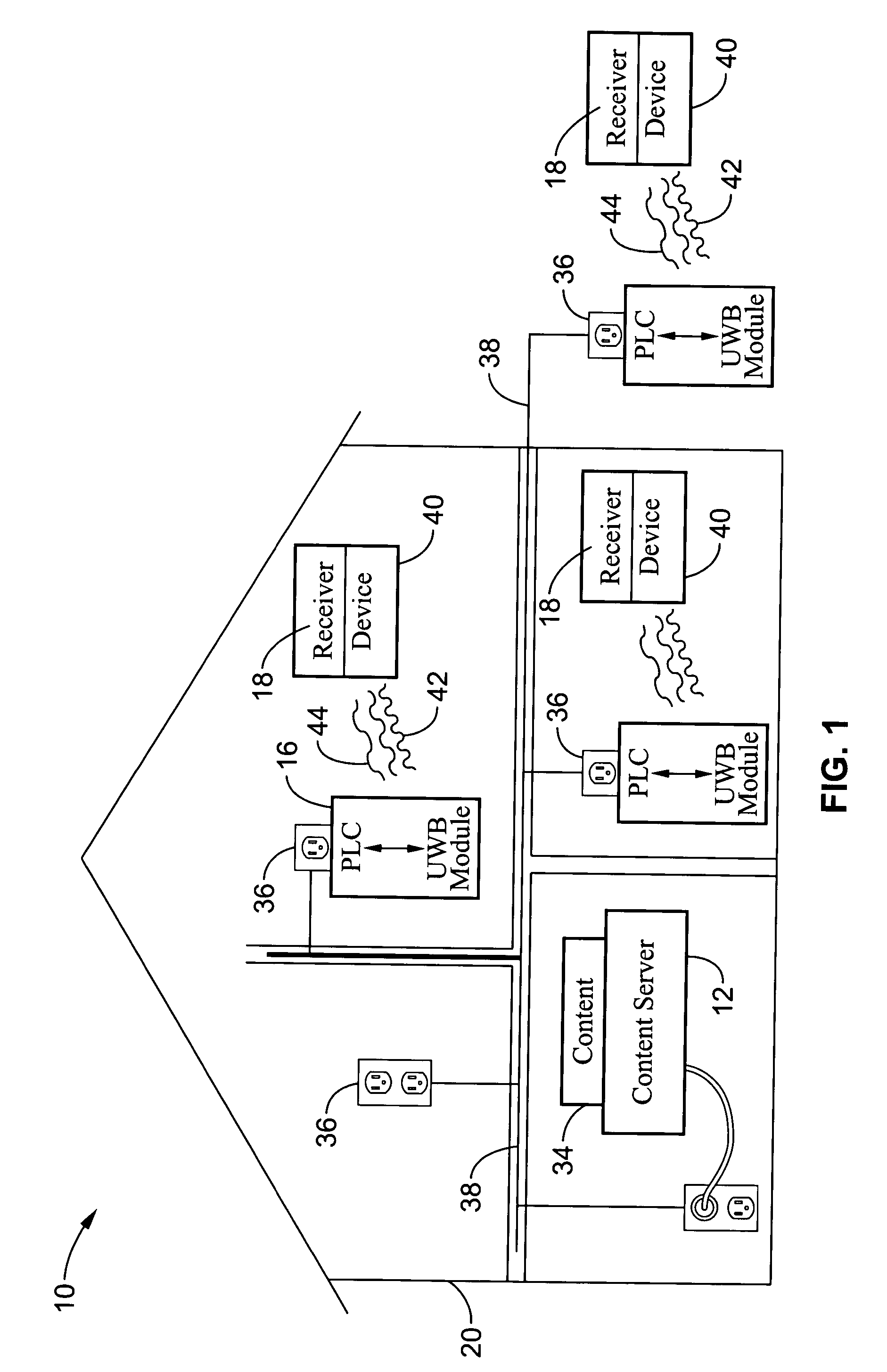
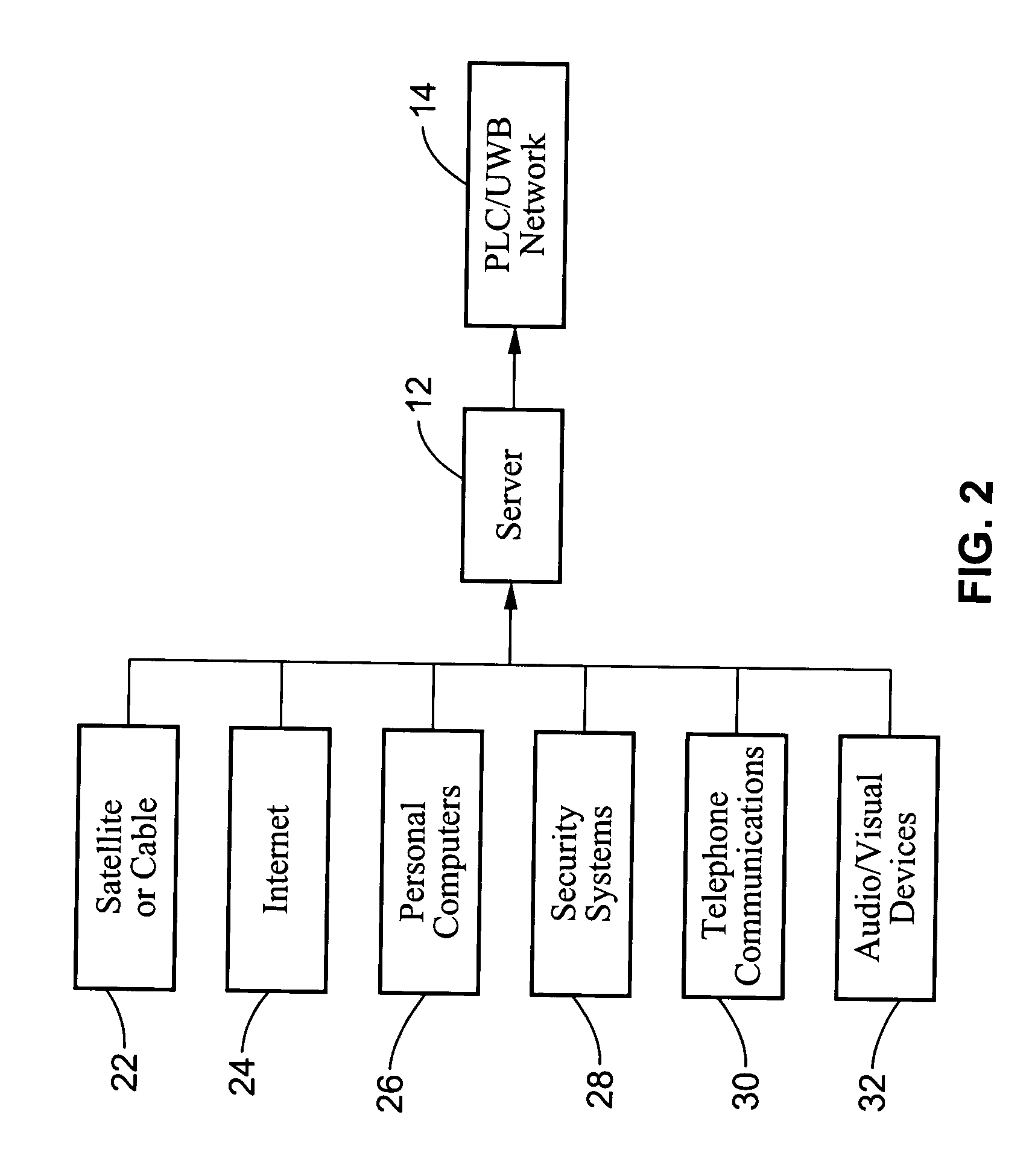
ActiveUS20050047379A1Need can be overcomeInterconnection arrangementsPower distribution line transmissionPower line networkBroadband
A system for communicating content streams (i.e. voice, video, data) between a content server connected to a power-line communications network and a remote electronic device having ultra-wide band connectivity with an interface module. The interface module is a power-line communication / ultra-wide band (PLC / UWB) module preferably connected to a conventional power outlet upon the power-line network. The interface module converts the power-line signals from the server to ultra-wide band signals which are broadcast for reception by the wireless electronic device. Return communications with the server from the wireless electronic device are also preferably supported. The power-line communication and / or ultra-wide band signal can also be encrypted for improved security. The content server and interface module are preferably configured to communicate content streams only within the portions of the bandwidth allocated by a bus master, which may comprise a content server with programming for controlling bandwidth use on the physical power-line communications network.
Owner:SONY CORP +1
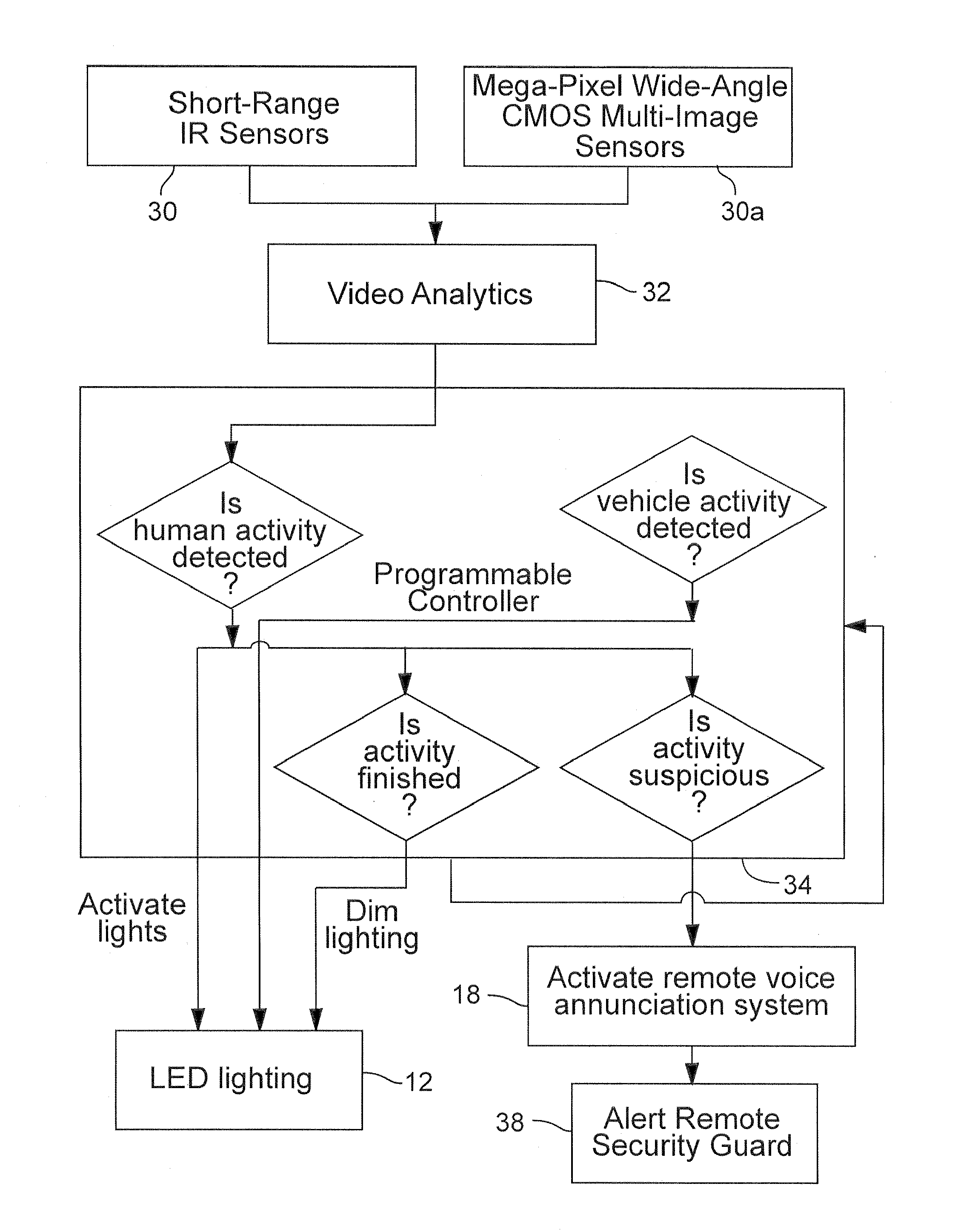
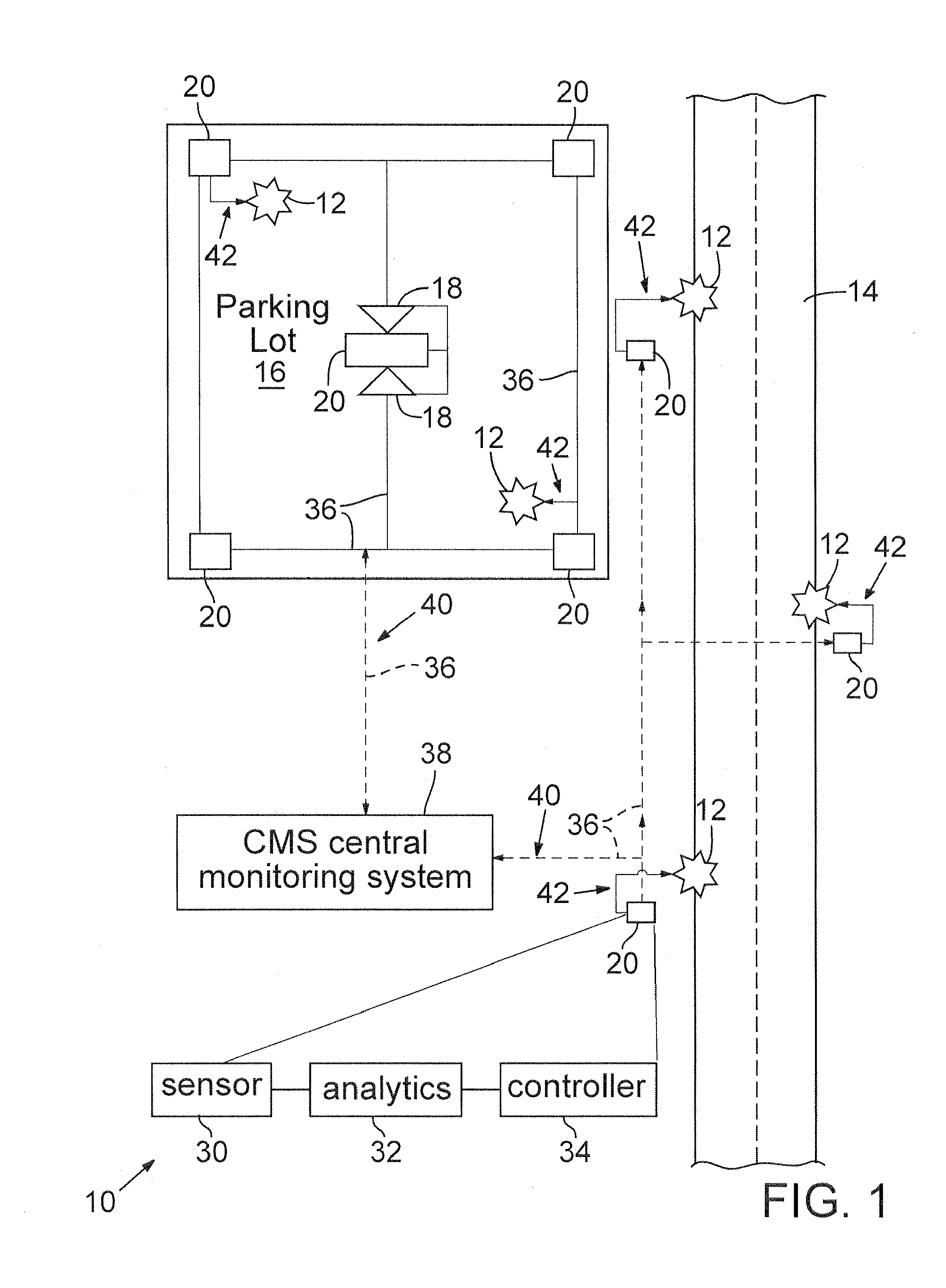
Energy savings and improved security through intelligent lighting systems
ActiveUS20090262189A1Facilitates proactiveFacilitates appropriate security responseImage analysisElectroluminescent light sourcesIntelligent lightingLight equipment
An intelligent lighting system employs energy efficient outdoor lighting and intelligent sensor technology in cooperation with video analytics processing. The lighting system selectively illuminates outdoor spaces and identifies and evaluates events in a scene monitored by a video camera, thereby to facilitate proactive and appropriate security responses to those events. Selective use of advanced lighting fixtures may significantly reduce costs of lighting areas that are monitored by security systems such as streets, public parks, and parking lots, while simultaneously improving security, safety, and traffic control. Energy savings alone, for a properly designed system, are estimated at 50%-90% of current usage. When combined with remote monitoring, such systems may prevent accidents and criminal activity.
Owner:MOTOROLA SOLUTIONS INC
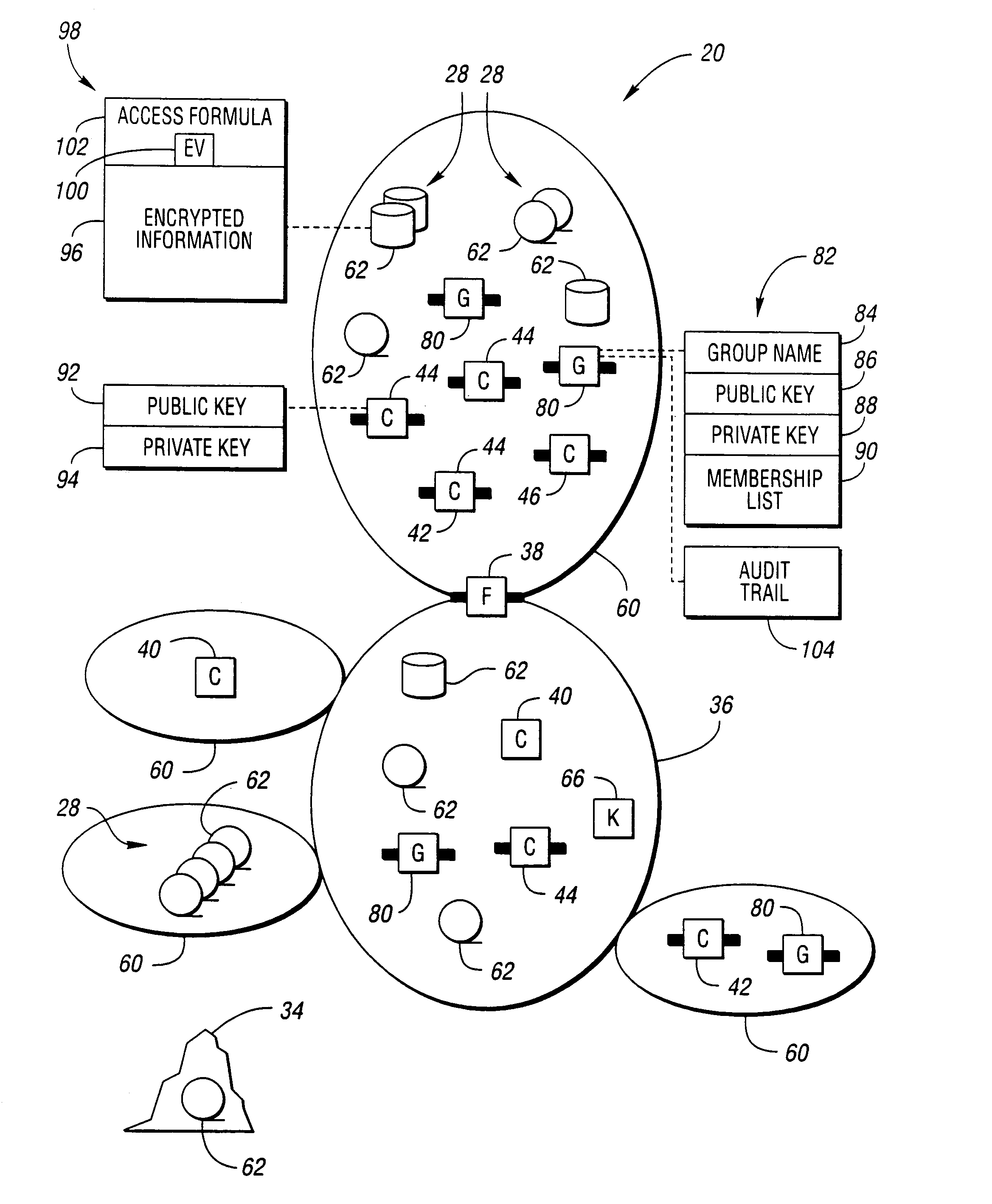
Method and system for secure information handling
InactiveUS6957330B1Safe handlingSafe storageKey distribution for secure communicationUser identity/authority verificationClient-sideSecurity information
Information that must remain secure is often stored on untrusted storage devices. To increase security, this information is encrypted by an encryption value prior to storing on the untrusted storage device. The encryption value itself is then encrypted. The encryption value is decrypted by correctly solving an access formula describing a function of groups. Each group includes a list of at least one consumer client. A requesting consumer client is granted access to the information if the requesting consumer client is a member of at least one group which correctly solves the access formula.
Owner:ORACLE INT CORP
Distortion resistant double-data correcting color transition barcode and method of generating and using same
InactiveUS6070805AEliminate useDigitally marking record carriersRecord carriers used with machinesError checkingLinear growth
A color barcode symbology is disclosed that can be accurately decoded despite severe distortions, misreads or altered symbols. This disclosed barcode is a color transition barcode having linear growth properties designed to resist the single or combined effects of: scaling distortions, perspective distortions, shear distortions, and wave distortions of both the uniform and non-uniform type distributed across the barcode's vertical or horizontal axis. This color barcode symbology is also resistant to missing symbols and altered symbols while offering, high security, error checking, and double error correcting capability.
Owner:ZEBRA TECH CORP
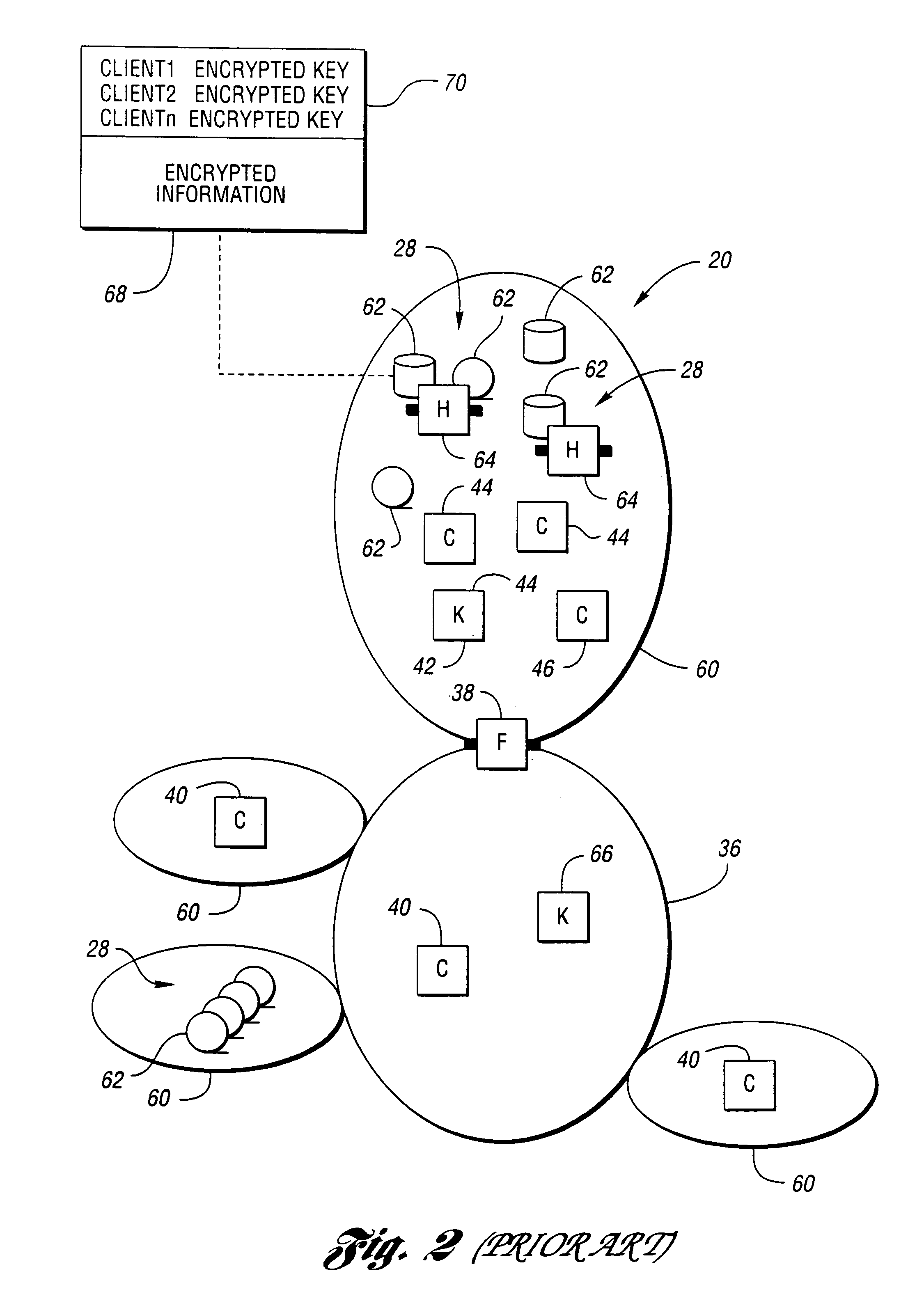
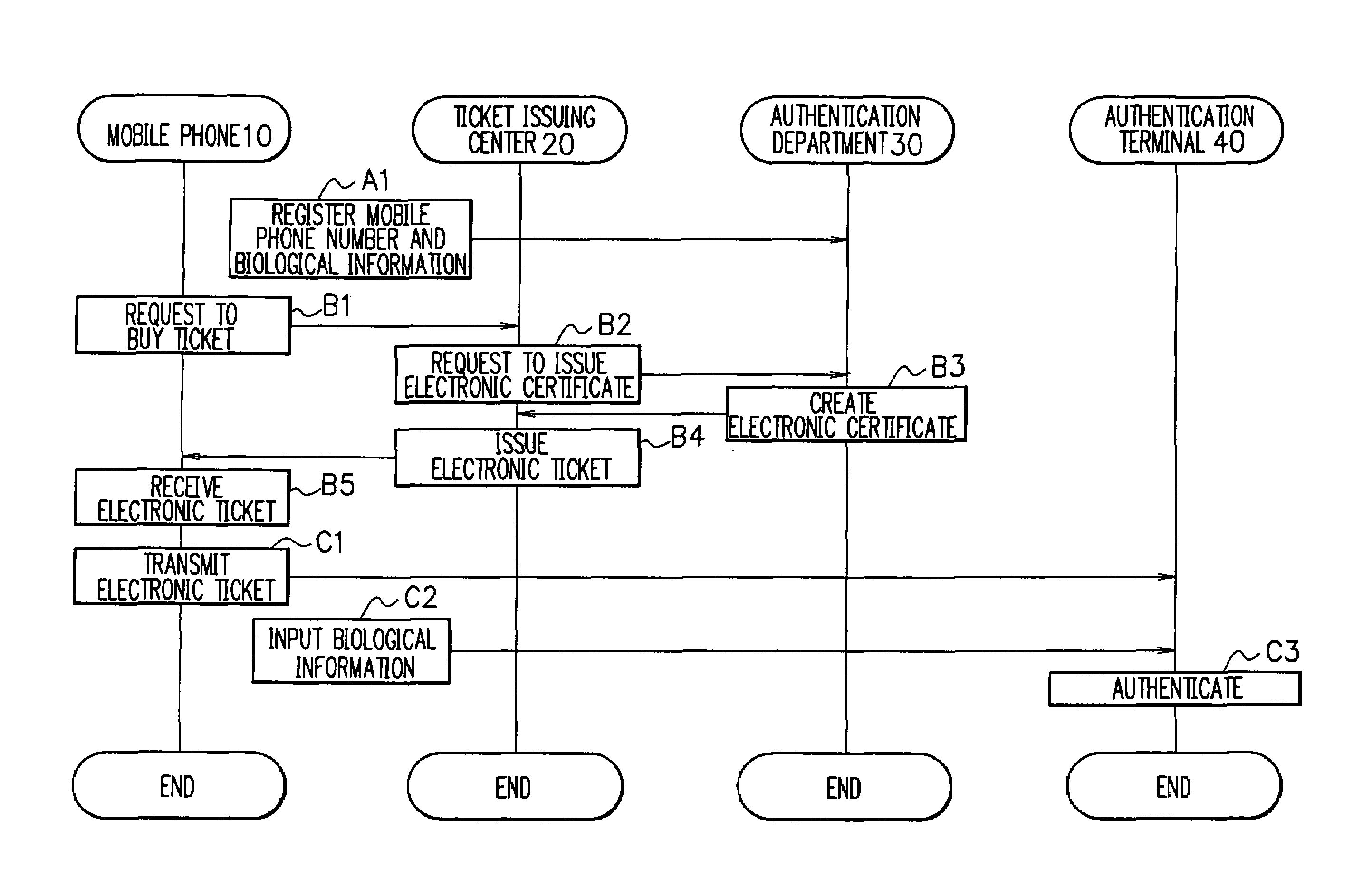
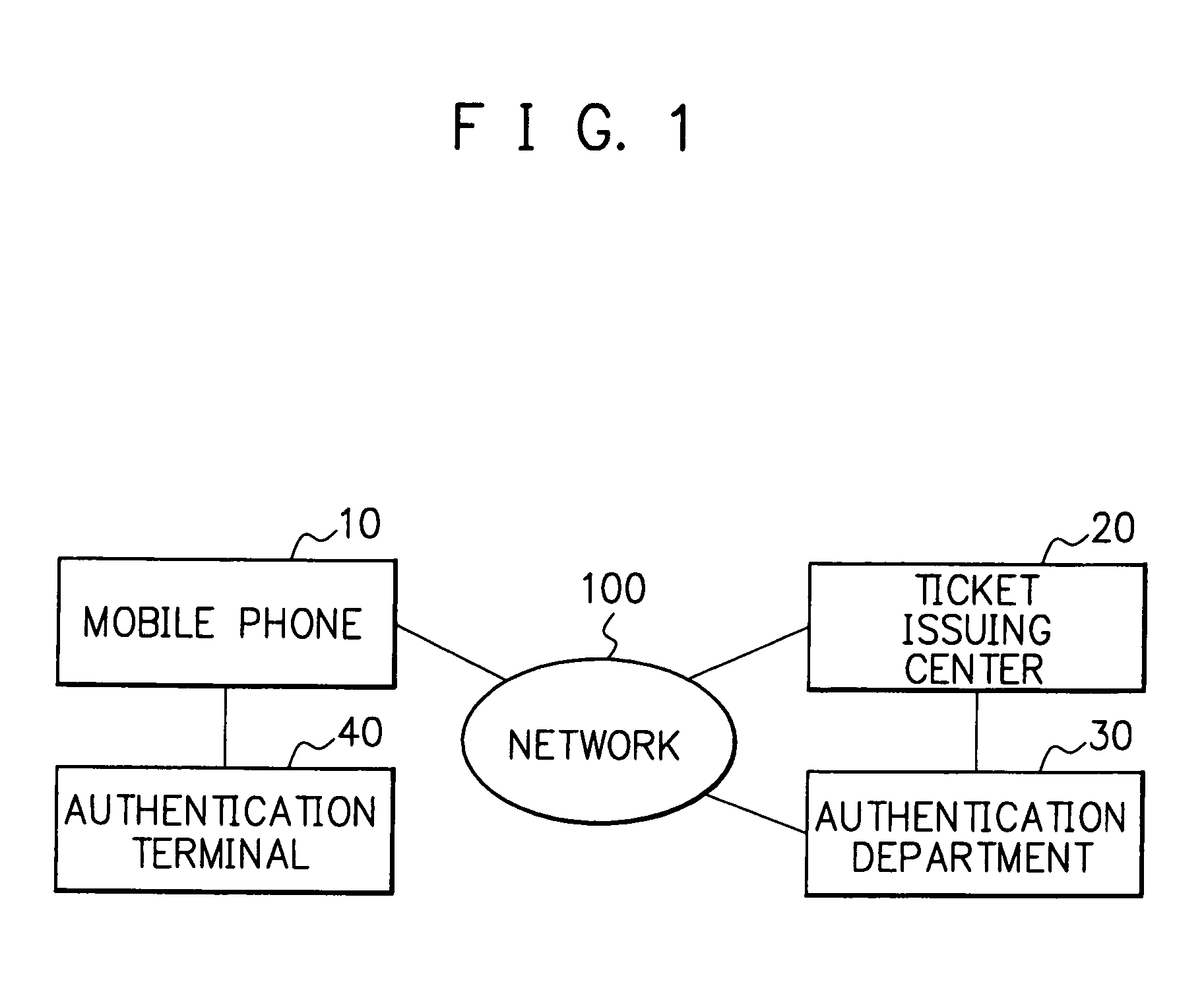
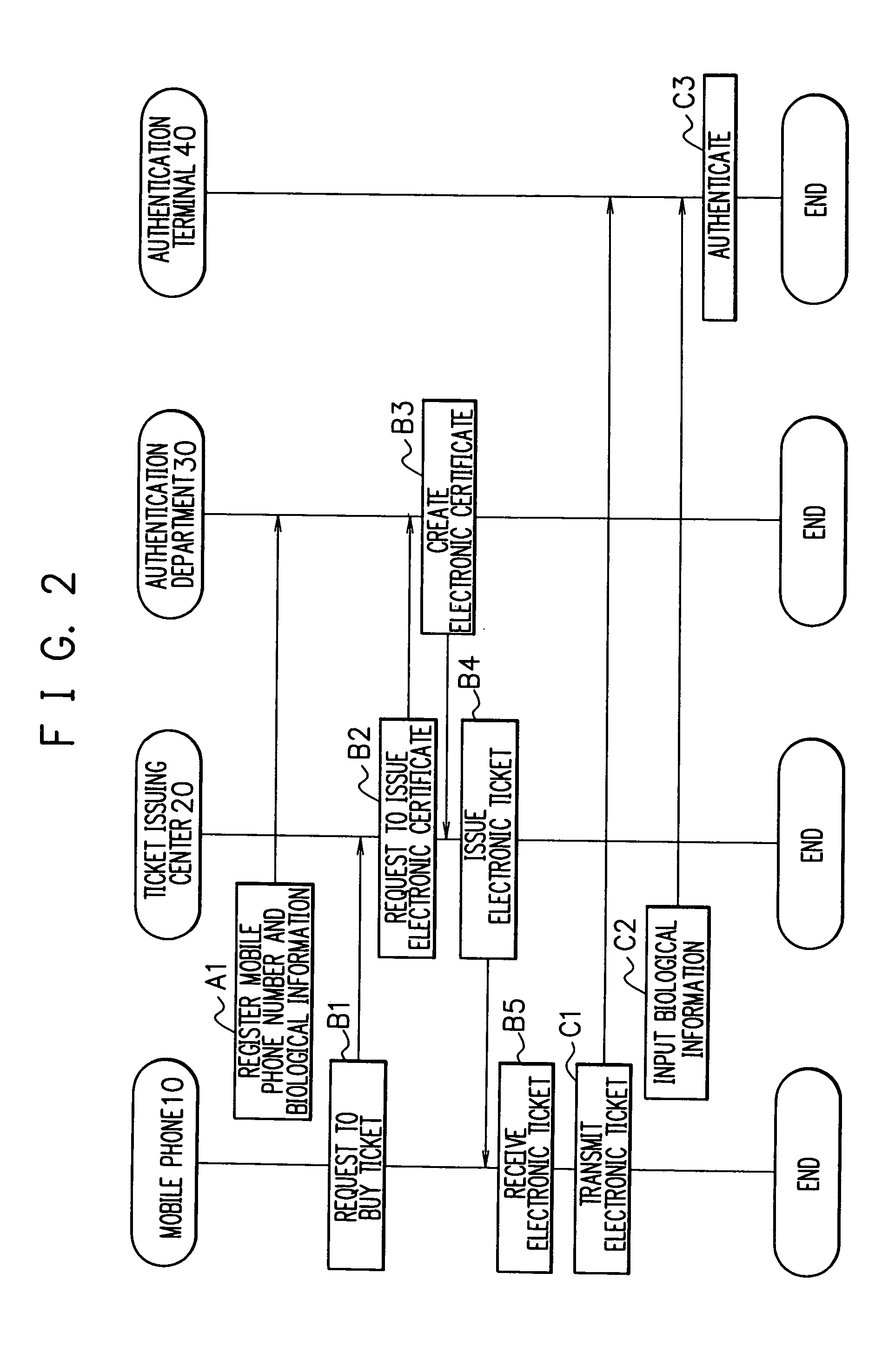
Electronic ticket issuing system and electronic ticket issuing method
InactiveUS7004388B2Simplifying purchase procedure and procedureSimple procedureCredit registering devices actuationTicket-issuing apparatusMobile phoneFingerprint
An electronic ticket issuing system and an electronic ticket issuing method for simplifying authentication procedures by the use of biological information such as a fingerprint and voiceprint. First, a ticket buyer sends a request for ticket purchase to a ticket issuing center using his / her mobile terminal. The ticket issuing center transmits a request for issue of an electronic certificate to request an authentication department to issue an electronic certificate. The authentication department creates an electronic certificate to which the biological information about the ticket buyer is added. The ticket issuing center transmits an electronic ticket including the electronic certificate to the mobile phone. When the ticket buyer participates in an event with the electronic ticket, the ticket buyer transmits the electronic ticket with the biological information to an authentication terminal. In addition, the ticket buyer inputs his / her biological information at the moment into the authentication terminal. Subsequently, the authentication terminal compares the two pieces of biological information for authentication. Since the electronic ticket includes the biological information, the authentication terminal can perform high-security authentication without exchanging the biological information with the authentication department via a network.
Owner:NEC CORP
Hyperthermia Treatment Systems and Methods
InactiveUS20090118802A1Surgical instruments for heatingTherapeutic coolingTemperature differenceHyperthermia Treatment
Owner:THERMOSURGERY TECH
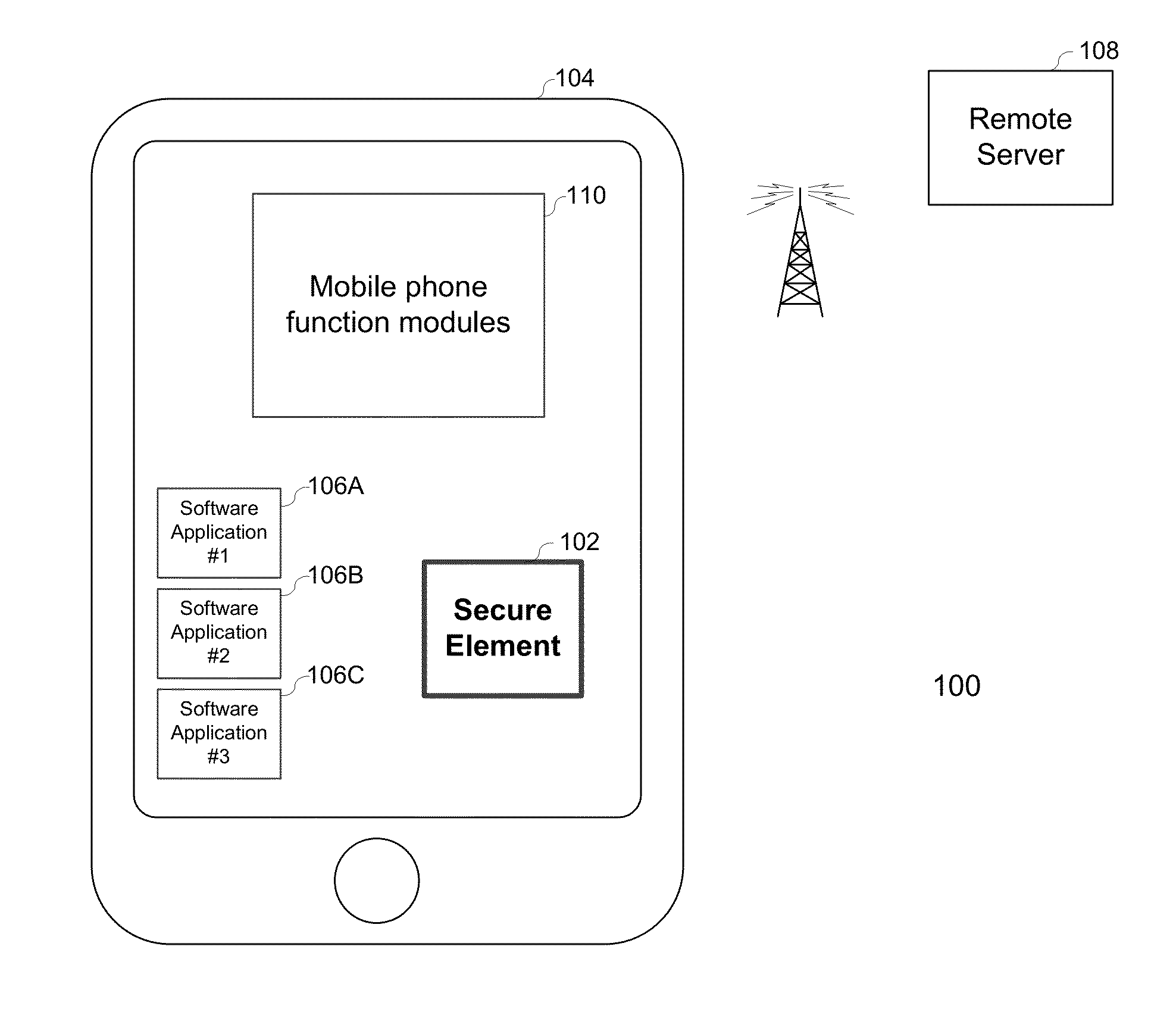
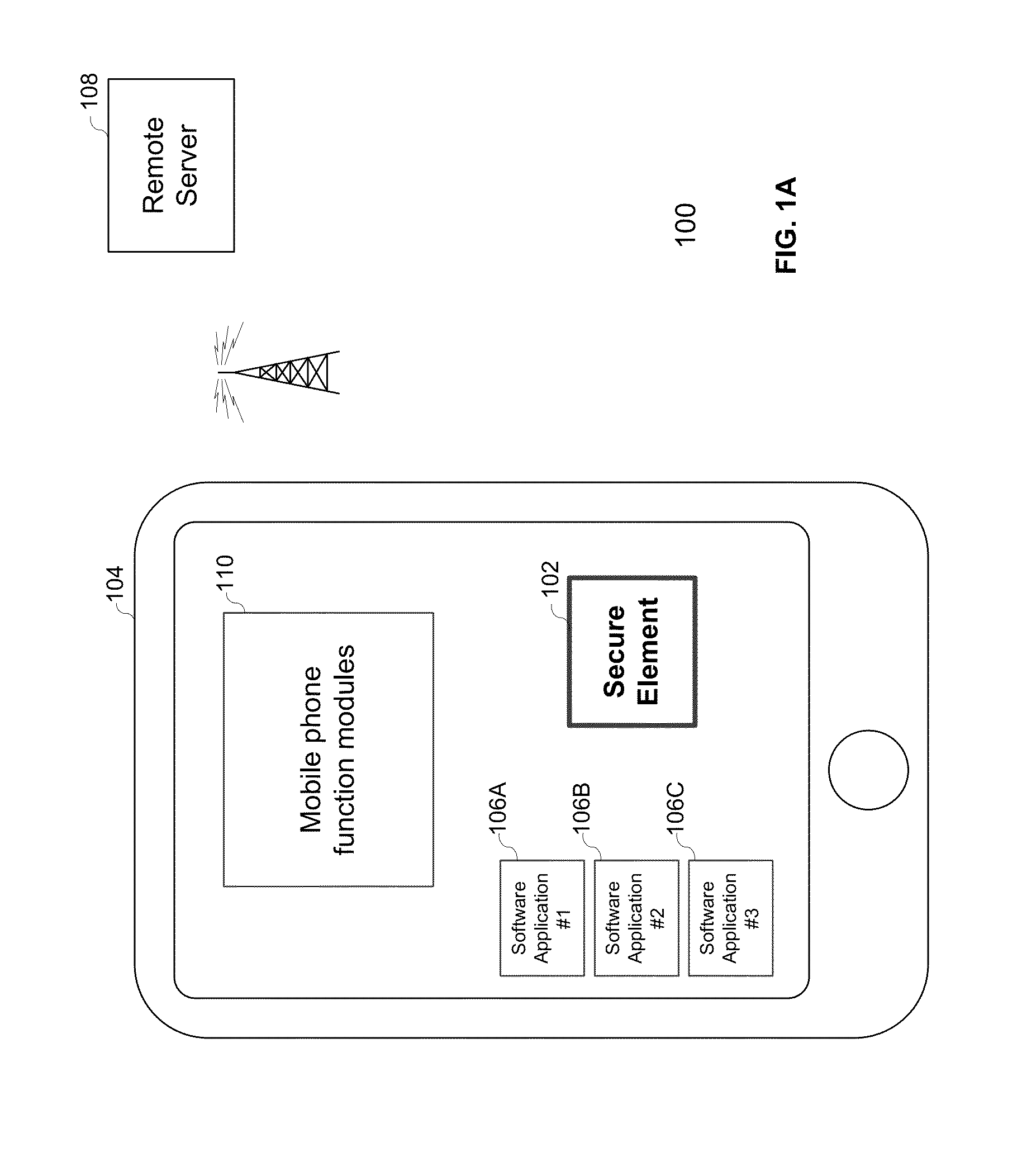
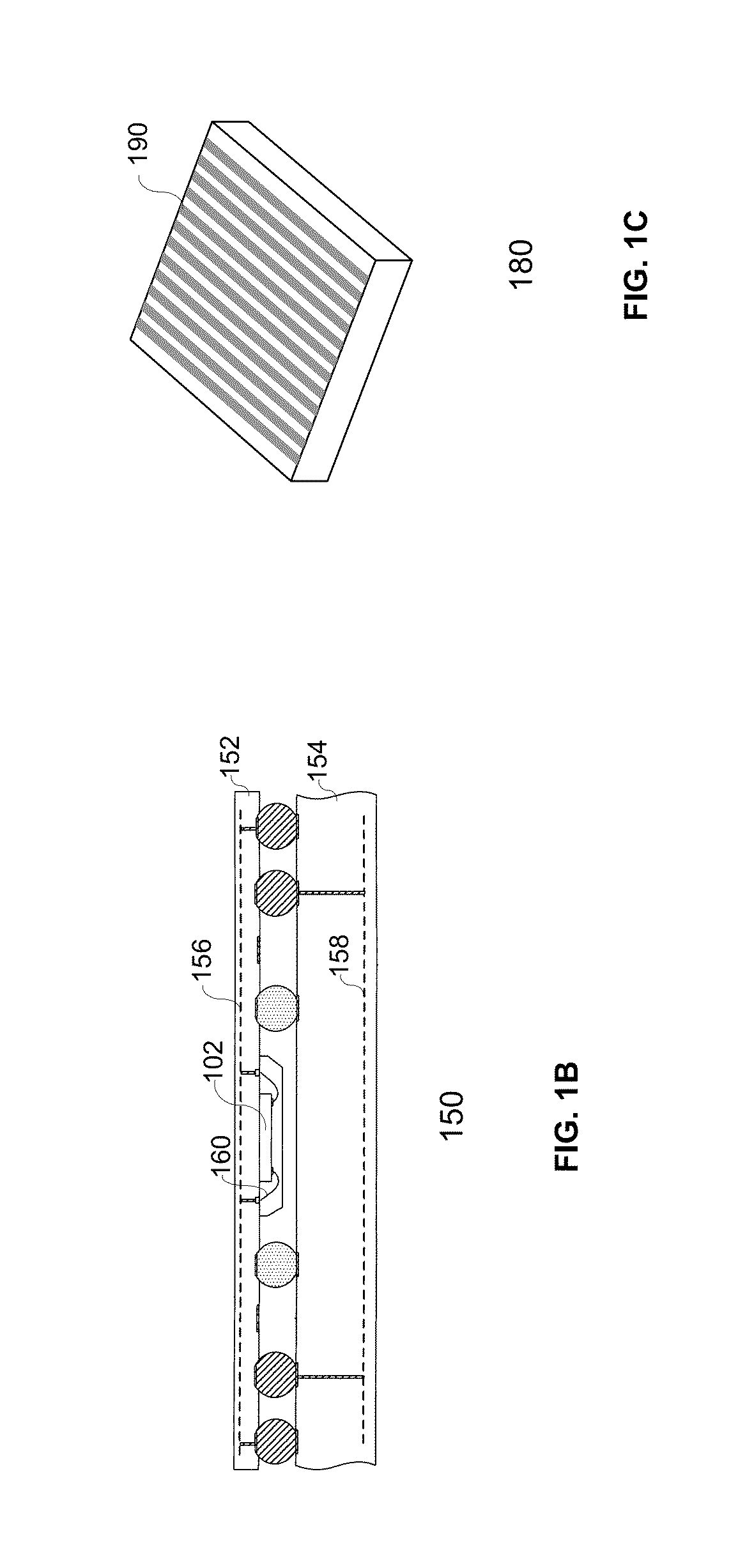
Embedded secure element for authentication, storage and transaction within a mobile terminal
ActiveUS20140013406A1Improve security levelImprove securityNear-field transmissionDigital data processing detailsEmbedded securityApplication software
Various embodiments of the present invention relate to incorporating an embedded secure element into a mobile device, and more particularly, to systems, devices and methods of incorporating the embedded secure element into a mobile device for identity authentication, data storage and processing in trusted transactions. These trusted transactions require a high security level to protect sensitive data or programs in bank account management, purchasing orders, contactless payment, passport verification, and many other high-security applications. The secure element will provide a root of trust such that that applications running on the mobile device are executed in a controlled and trusted environment. In addition to conventional password or encryption protection, alternative security features are introduced from both software and hardware levels based on the embedded secure element. Therefore, the security level of the mobile device is not only enhanced, but also may potentially exceed that of the conventional POS terminals.
Owner:MAXIM INTEGRATED PROD INC
High security personalized wireless portable biometric device
The present application discloses a wireless hand held portable security device in the form of a wireless hand held portable biometric device in communication with a plurality of ubiquitous items for receiving information from, and sending information to the plurality of ubiquitous items, comprising a processor for selecting at least one item of the plurality of ubiquitous items and for sending information to the selected item in order to activate or deactivate or send a programming to the selected item. The level of security and the personalization is achieved by using a fingerprint or a combination of fingerprints for accessing communication with a selected item.
Owner:ACTIVCARD IRELAND
Secure Biometric Verification of Identity
InactiveUS20080019578A1Reduce computational complexityReduce probabilityImage analysisCharacter and pattern recognitionComputer hardwareData matching
A high security identification card includes an on-board memory for stored biometric data and an on-board sensor for capturing live biometric data. An on-board processor on the card performs a matching operation to verify that the captured biometric data matches the locally stored biometric data. Only if there is a positive match is any data transmitted from the card for additional verification and / or further processing. Preferably, the card is ISO SmartCard compatible. In one embodiment, the ISO SmartCard functions as a firewall for protecting the security processor used for storing and processing the protected biometric data from malicious external attack via the ISO SmartCard interface. In another embodiment, the security processor is inserted between the ISO SmartCard Interface and an unmodified ISO SmartCard processor and blocks any external communications until the user's fingerprint has been matched with a previously registered fingerprint. Real-time feedback is provided while the user is manipulating his finger over the fingerprint sensor, thereby facilitating an optimal placement of the finger over the sensor. The card may be used to enable communication with a transactional network or to obtain physical access into a secure area.
Owner:IVI HLDG
Fetal oximetry system and sensor
InactiveUS20050283059A1Improve accuracyUsable signal timeSensorsBlood characterising devicesFetal monitoringLength wave
Owner:RIC INVESTMENTS LLC
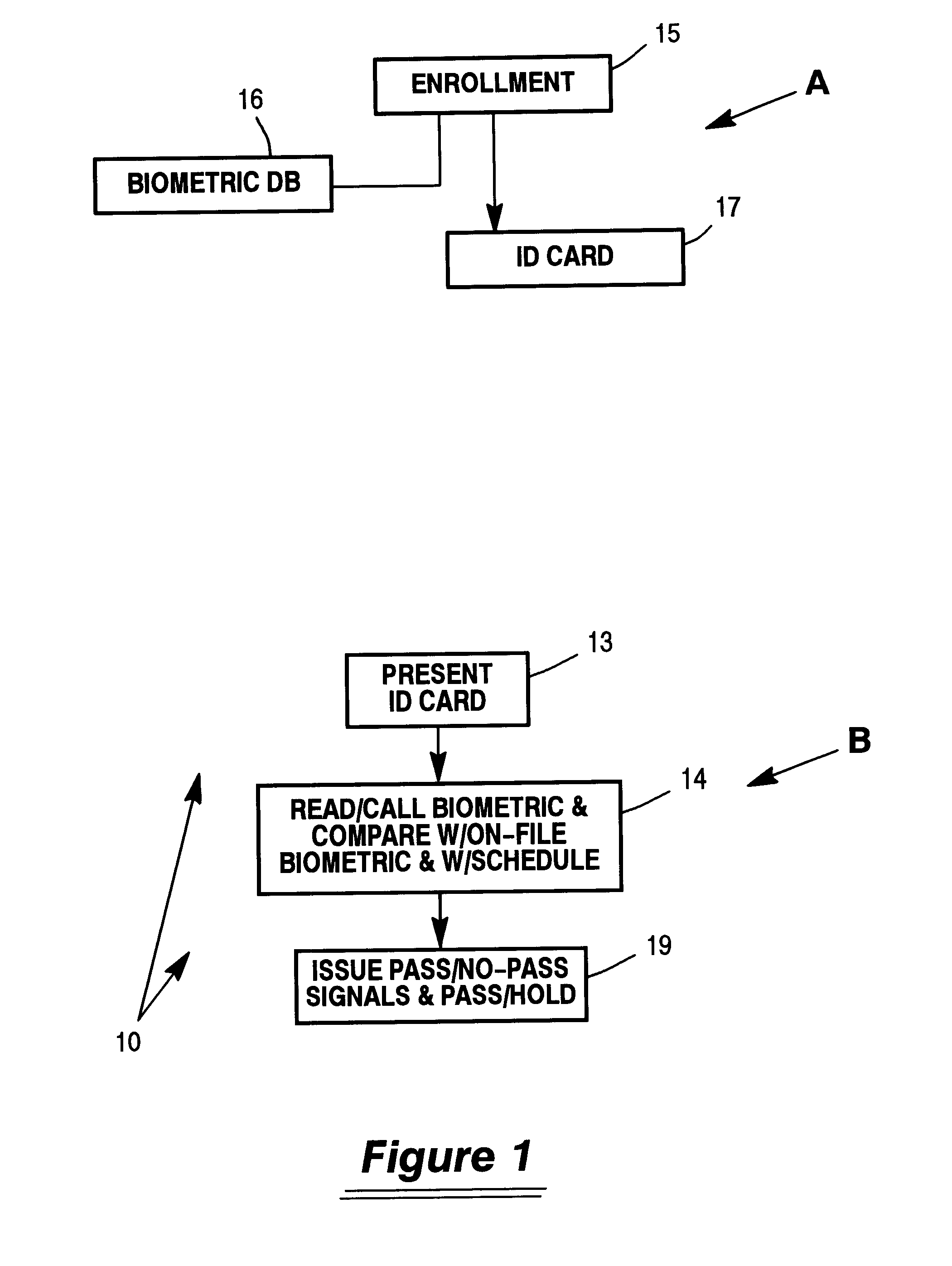
High security identification system for entry to multiple zones
InactiveUS6867683B2Less-expensive and flexibleReduce usageProgramme controlElectric signal transmission systemsData fileBiometrics
Control over access by individuals to a group of high security facilities and zones within such facilities is accomplished with use of biometric readers at each access door as well as a quick ID reading device that is not required to contain biometric information. Enrollment at a secure facility where biometrics are maintained for each individual establishes a multipart data file for each individual, each part of which may be accessed by different actors in the system. The individuals allowed security to various facilities can only be in a single facility at a given time and also control their own schedule.
Owner:UNISYS CORP
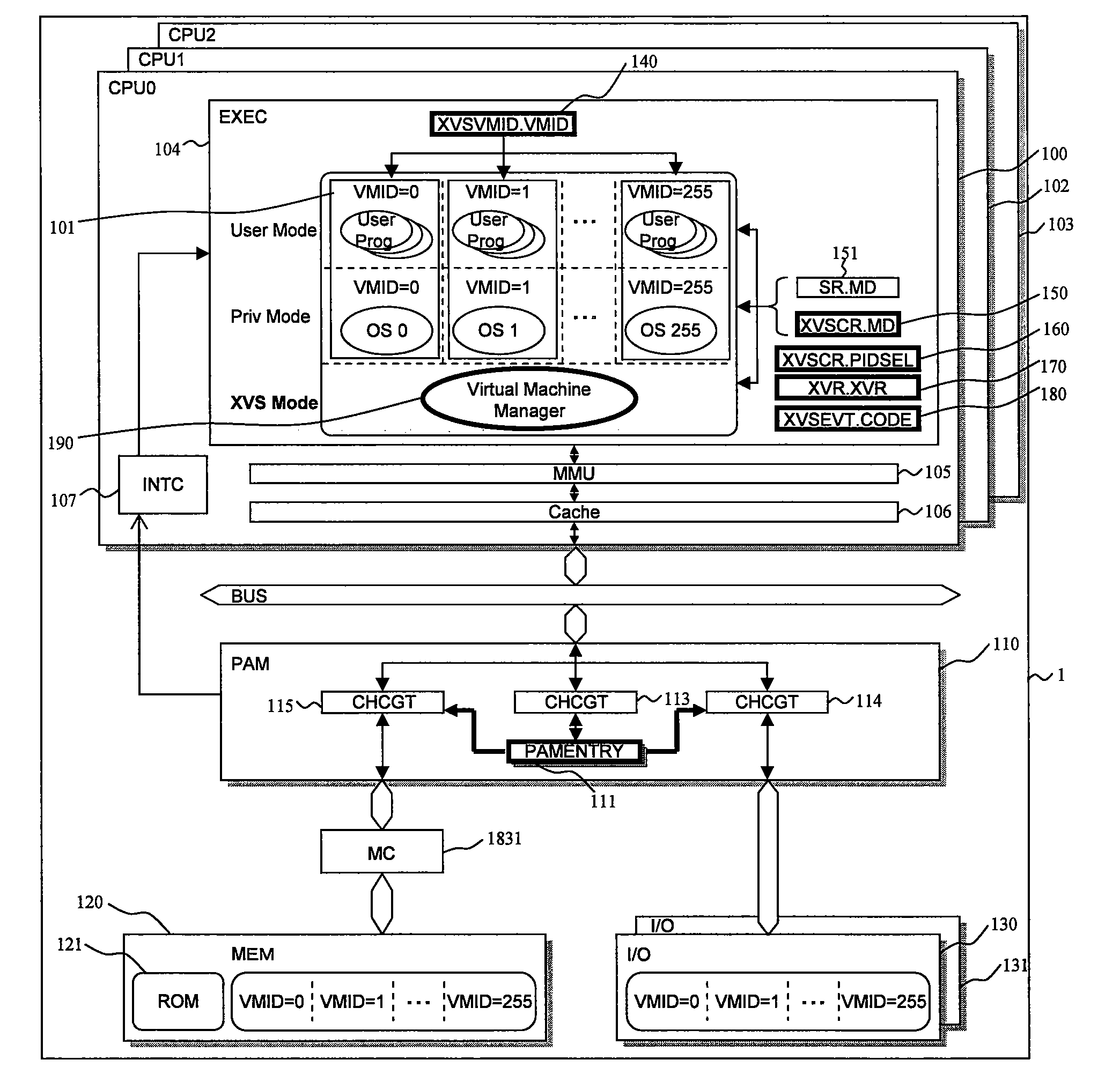
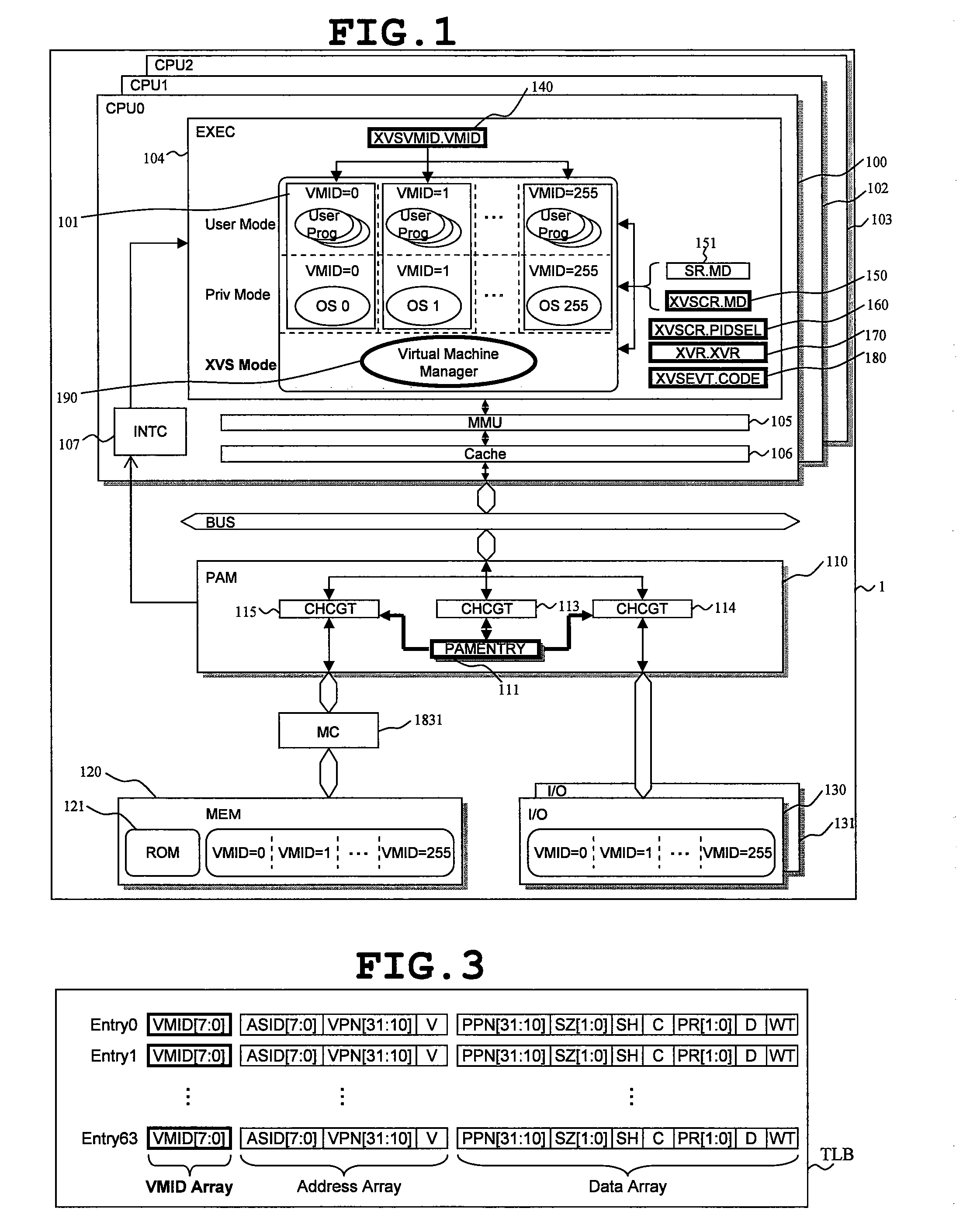
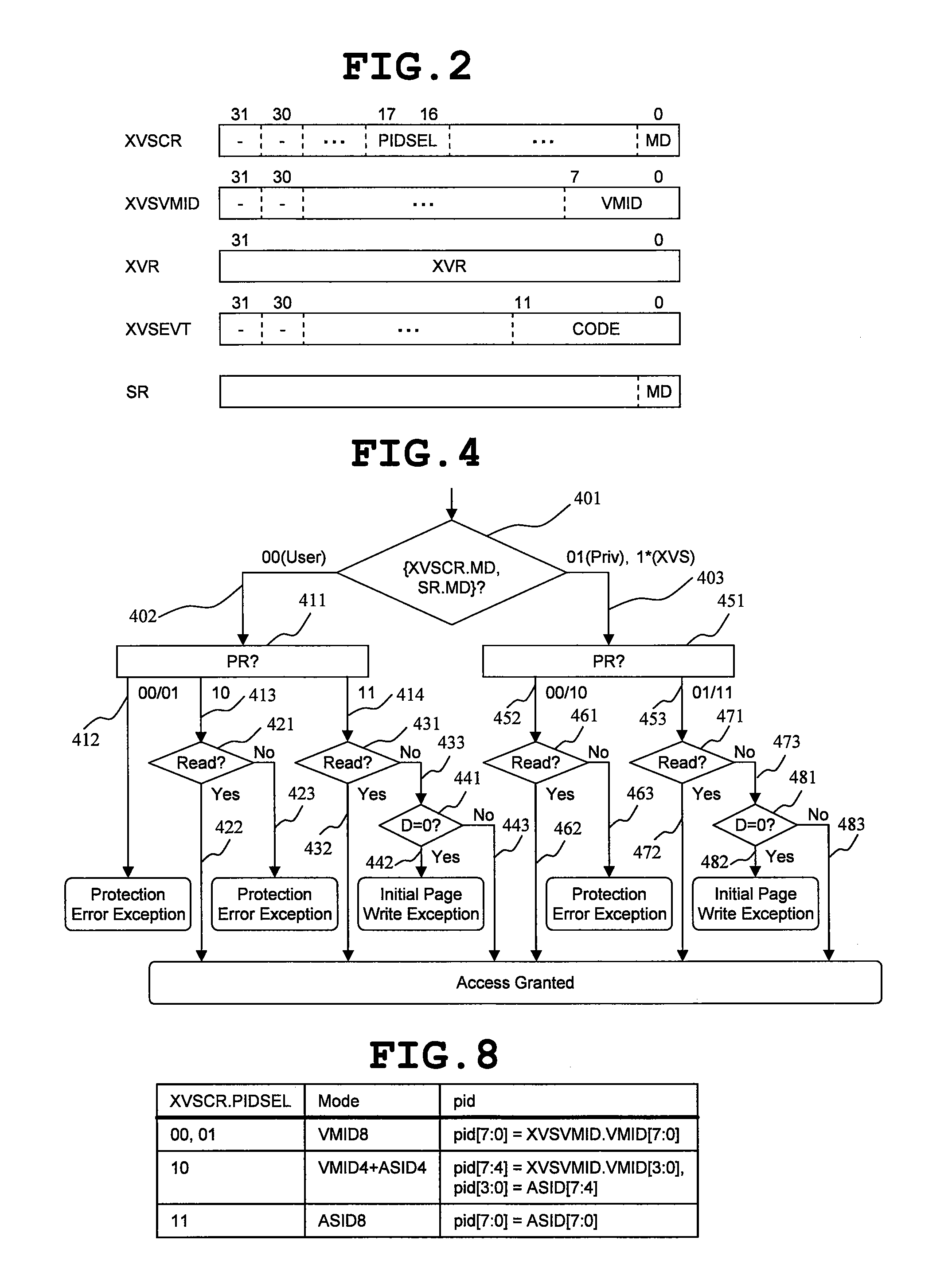
Data processor
ActiveUS20080086729A1Reduce needImprove system reliabilityResource allocationSoftware simulation/interpretation/emulationOperational systemControl register
A data processor includes: a central processing unit (CPU), in which a plurality of virtual machines (101), each running an application program under controls of different operating systems, and a virtual machine manager (190) for controlling the plurality of virtual machines are selectively arranged according to information set in mode registers (140, 150, 151); and a resource access management module (110) for managing access to hardware resource available for the plurality of virtual machines. The resource access management module accepts, as inputs, the information set in the mode registers and access control information of the central processing unit to the hardware resource, compares the information thus input with information set in a control register, and controls whether or not to permit access to the hardware resource in response to the access control information. As a result, redesign involved in changes in system specifications can be reduced, and a malfunction owing to resource contention can be prevented. The invention contributes to increase of security.
Owner:RENESAS ELECTRONICS CORP
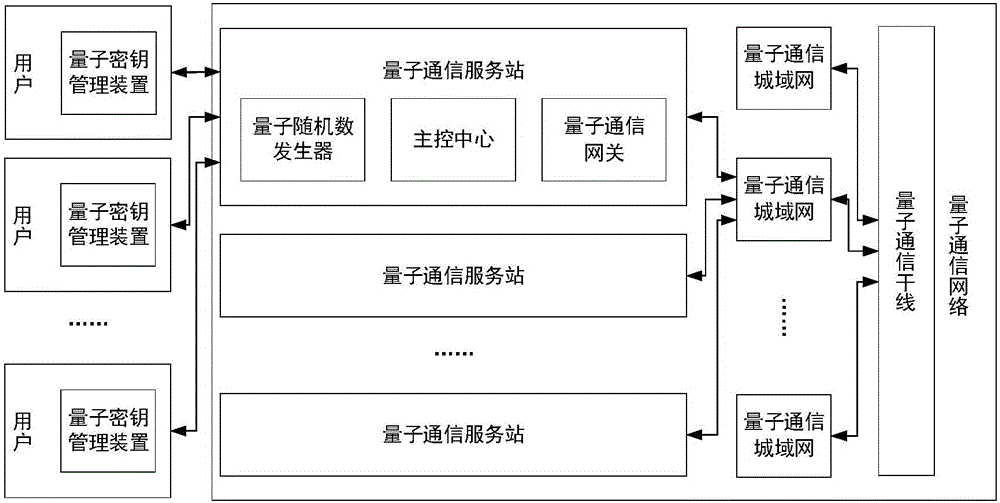
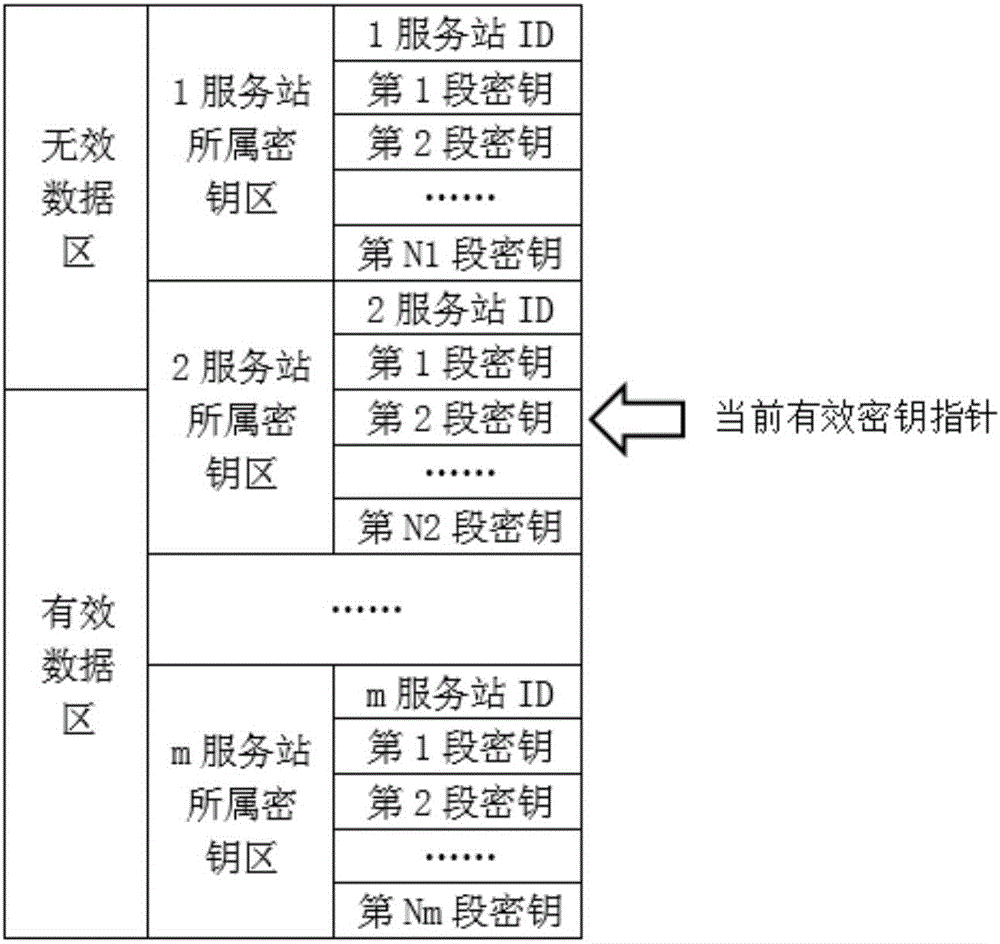
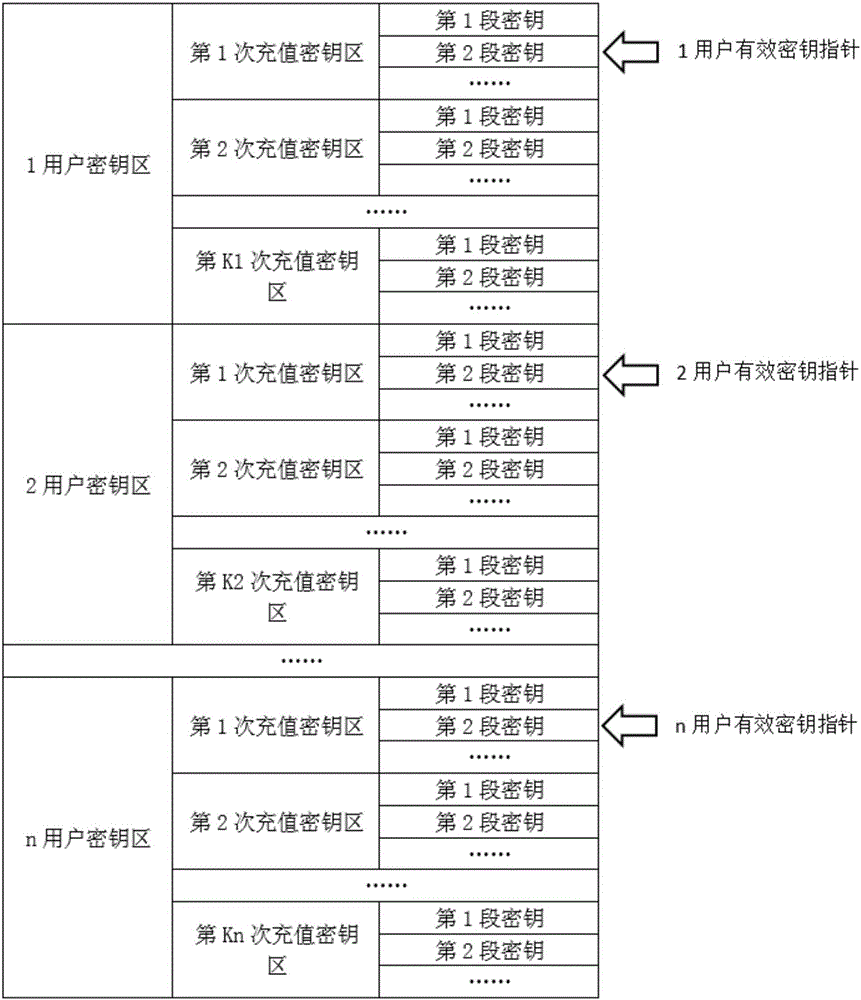
Quantum communication service station, quantum key management device, key configuration network, and key configuration method
ActiveCN106452740AAddress access security issuesAchieve coverageKey distribution for secure communicationSecurity questionKey distribution
The invention discloses a quantum communication service station, a quantum key management device, a key configuration network, and a key configuration method. The key configuration method comprises the following steps: responding to a key distribution request; authenticating a user of the key distribution request; writing a key generated with a true random number into a quantum key management device of the authenticated user. The key configuration method is different from the existing quantum key distribution QKD method in that key distribution of ultra high security is realized by pairing quantum key management devices and service stations at the end of a quantum communication network, the problem about access security at the end of a quantum communication network is solved, and terminal access is not a weak link of a quantum communication scheme. The quantum communication network can completely cover and replace the classic communication network in service.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
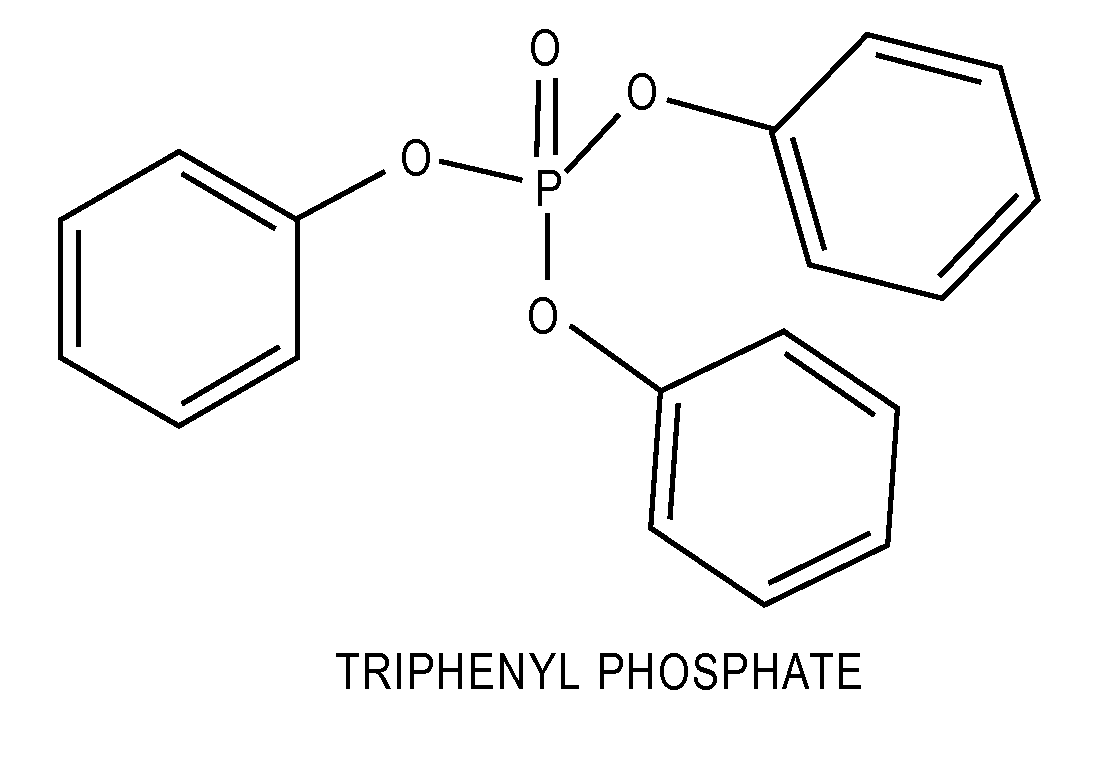
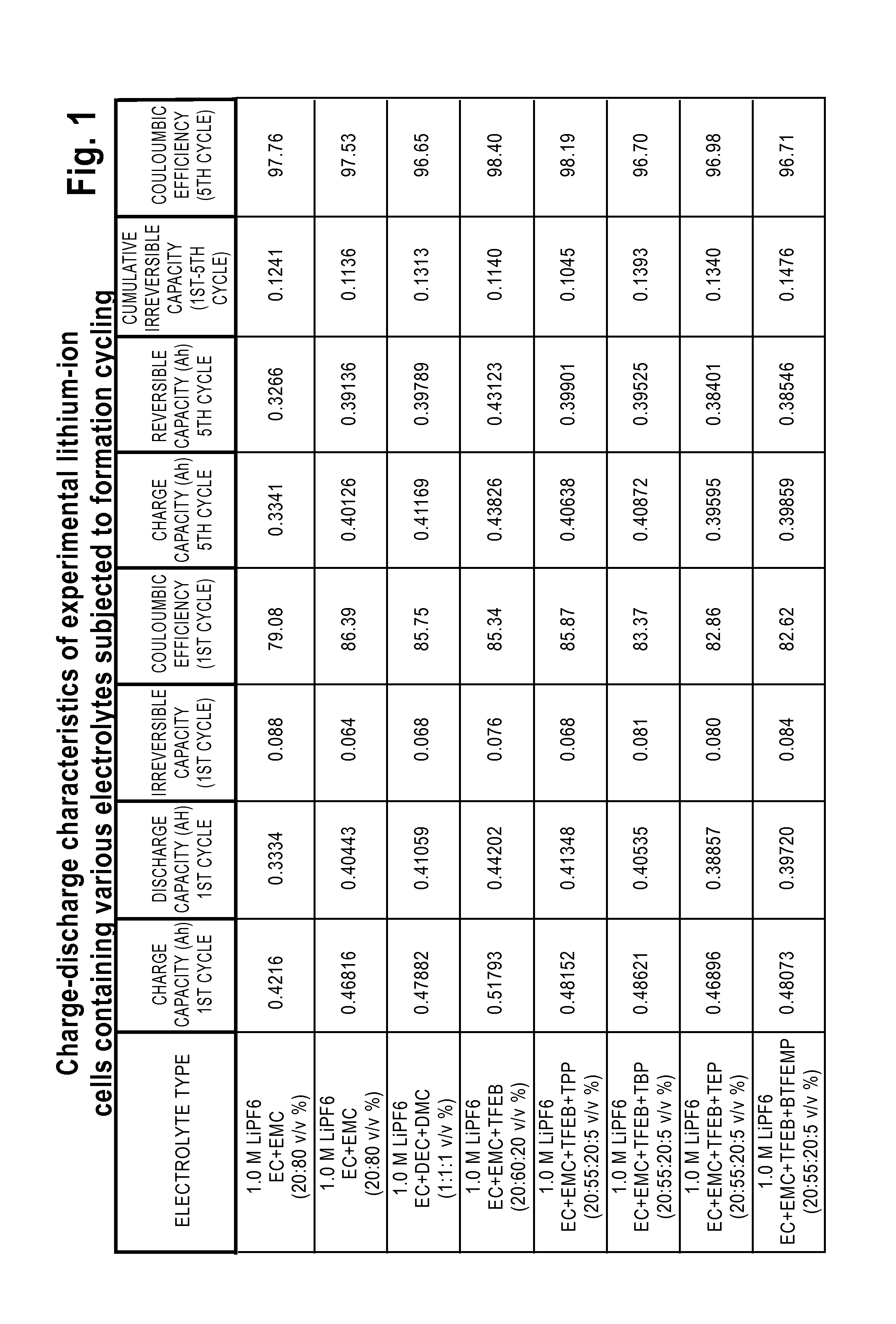
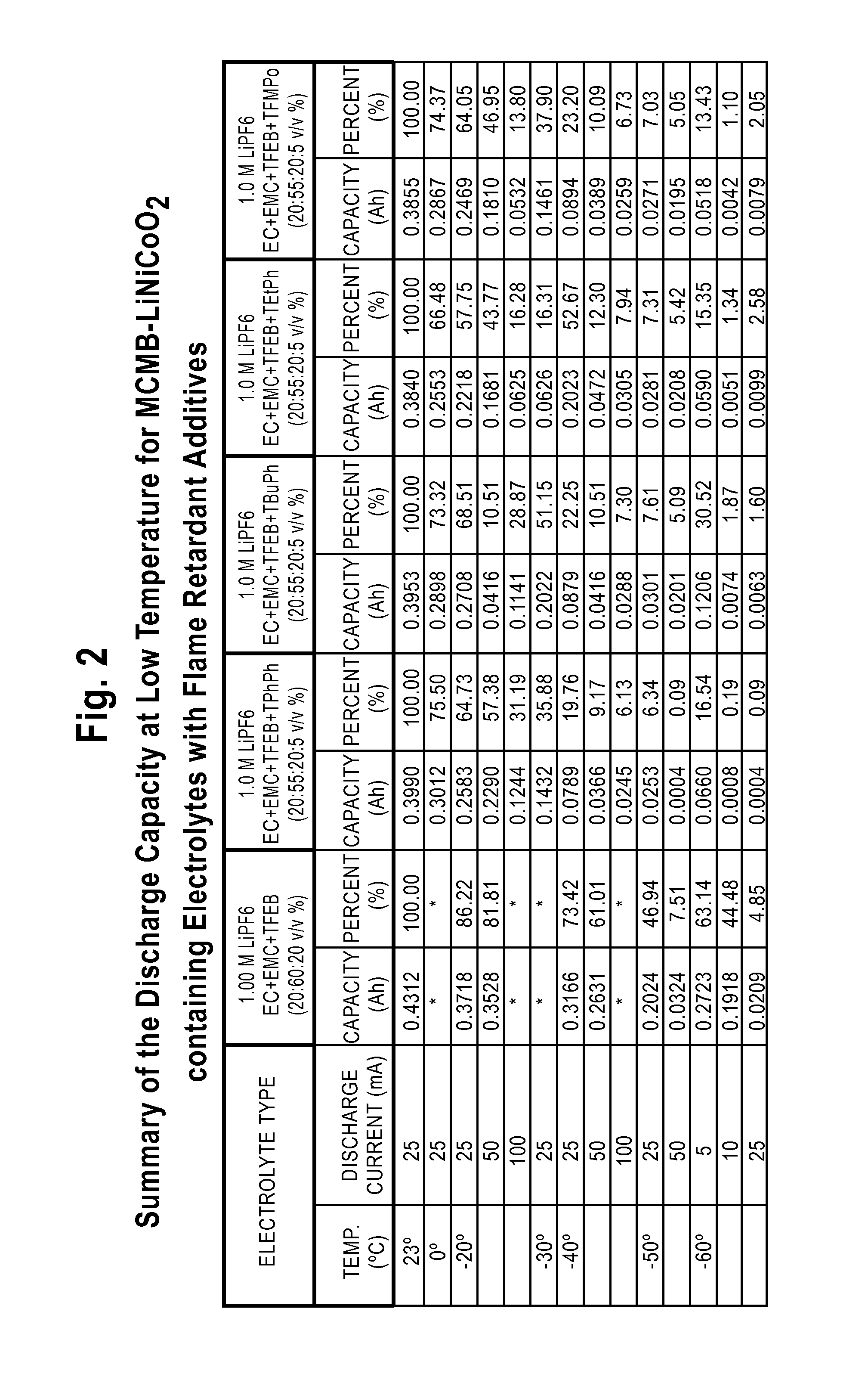
Lithium-Ion Electrolytes Containing Flame Retardant Additives for Increased Safety Characteristics
InactiveUS20100047695A1Improve performanceImprove security featuresOrganic electrolyte cellsSecondary cellsMethyl carbonatePhysical chemistry
The invention discloses various embodiments of Li-ion electrolytes containing flame retardant additives that have delivered good performance over a wide temperature range, good cycle life characteristics, and improved safety characteristics, namely, reduced flammability. In one embodiment of the invention there is provided an electrolyte for use in a lithium-ion electrochemical cell, the electrolyte comprising a mixture of an ethylene carbonate (EC), an ethyl methyl carbonate (EMC), a fluorinated co-solvent, a flame retardant additive, and a lithium salt. In another embodiment of the invention there is provided an electrolyte for use in a lithium-ion electrochemical cell, the electrolyte comprising a mixture of an ethylene carbonate (EC), an ethyl methyl carbonate (EMC), a flame retardant additive, a solid electrolyte interface (SEI) film forming agent, and a lithium salt.
Owner:UNIV OF SOUTHERN CALIFORNIA +1
System and Method for Video Distribution Management with Mobile Services
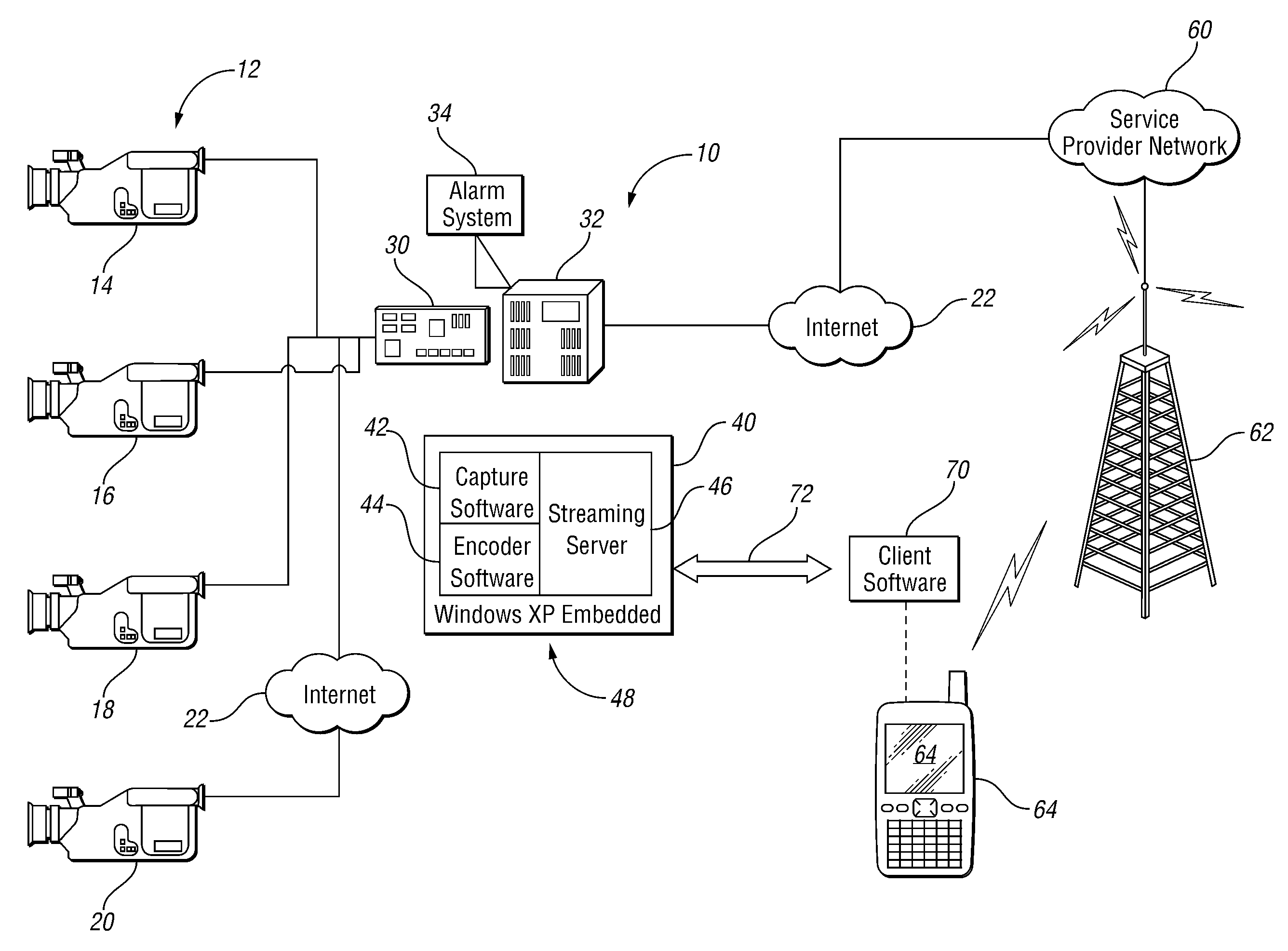
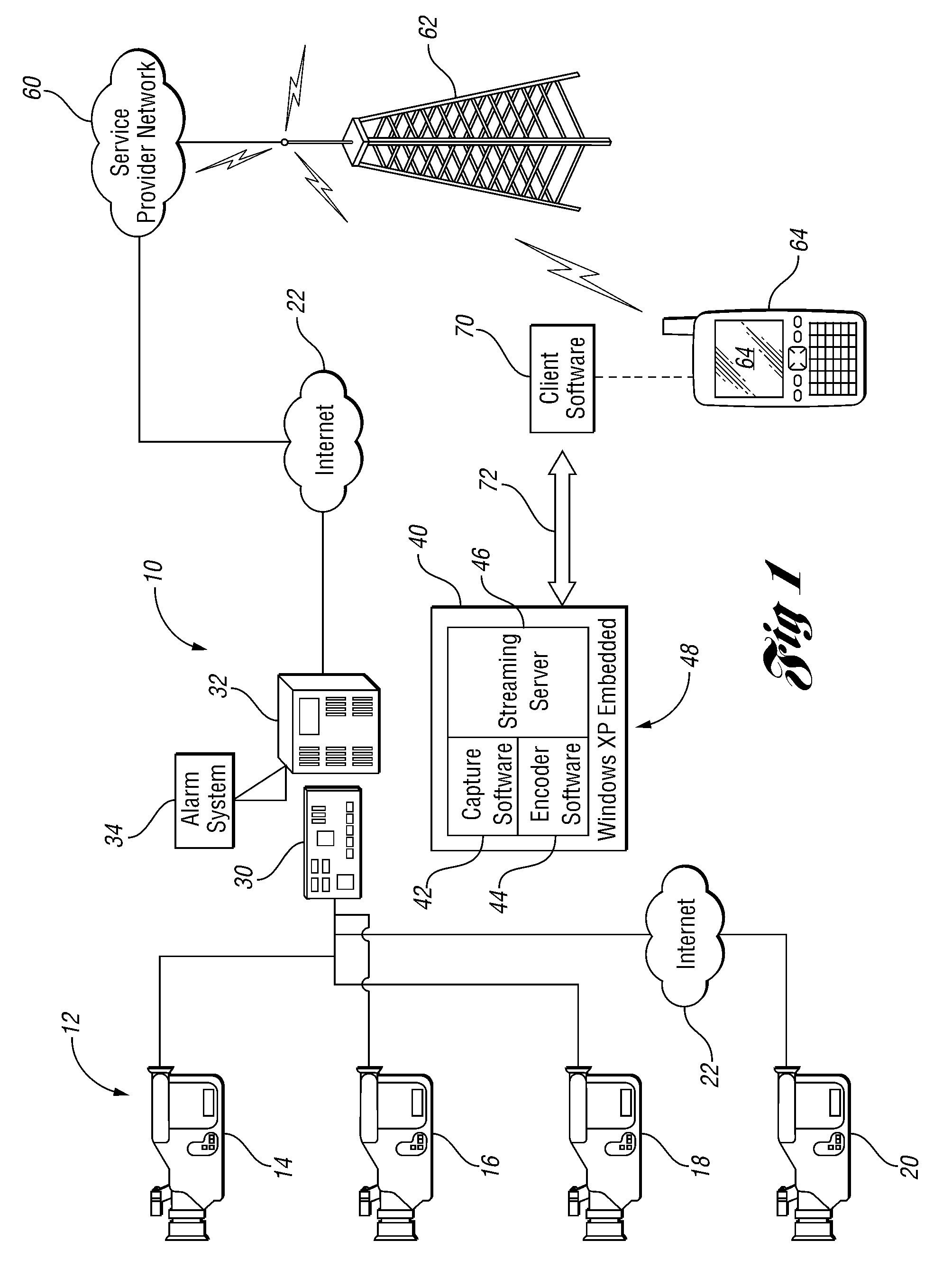
InactiveUS20110119716A1Convenient registrationEasy to downloadAnalogue secracy/subscription systemsSelective content distributionDisplay deviceHand held
Systems and methods for managing video distribution to display devices including mobile devices capture video from one or more cameras and apply a selected compression strategy suitable to broadcast video over a computer network and cellular network to at least one mobile device only when requested by a user to improve security and reduce required bandwidth and usage. The system and method may include controlling broadcast bandwidth by dynamically changing the selected compression strategy or algorithm to facilitate management of the video stream and adapt to changing network conditions. In one embodiment, the system and method include dynamically modifying video image properties of captured video frames to generate video data packets of a size suitable for transmission over a low bit-rate channel to a hand-held device for viewing.
Owner:MIST TECH HLDG
Print apparatus, print system, print method, job processing method, storage medium, and program
InactiveUS20050100378A1Maintain securityImprove securityDigital data processing detailsUser identity/authority verificationComputer scienceAuthentication
In order to maintain high security of a job that requires a high security level even after a print interrupt factor has been removed, and to achieve both the effect of maintaining high security of a job that requires a high security level even after the print process is interrupted, and the effect of improving the productivity of jobs other than a job of this type, when a print apparatus which can process a plurality of print jobs including a print job of a first type and that of a second type restarts a print operation of a print job, which is interrupted in the print apparatus, and when the print job is a print of the first type, the print apparatus is controlled to execute an authentication process, and then allowed to restart the print operation of the print job. When the print apparatus restarts a print operation of a print job, which is interrupted in the print apparatus, and when the print job is a print of the second type, the print apparatus is allowed to restart the print operation of the print job without executing the authentication process.
Owner:CANON KK
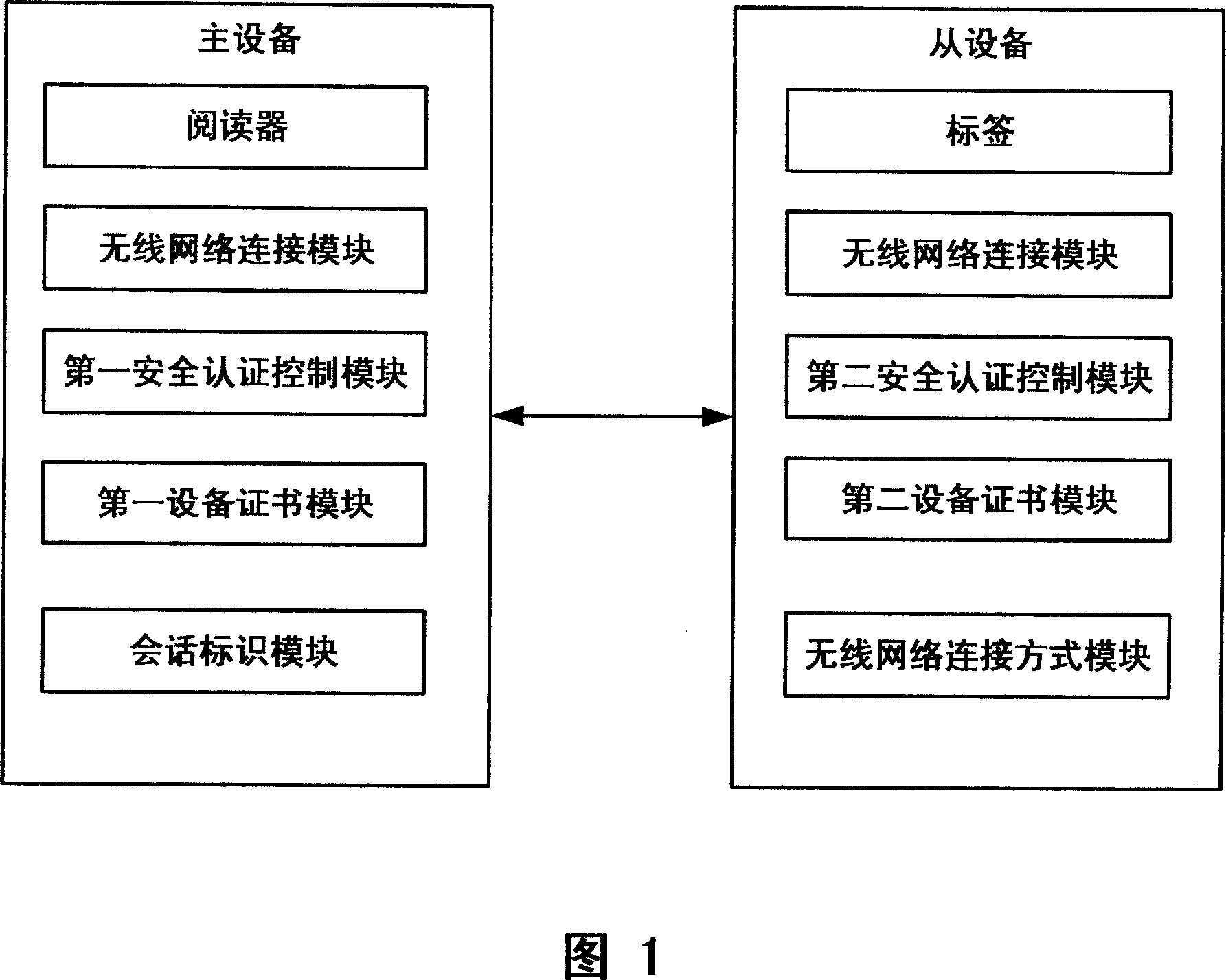
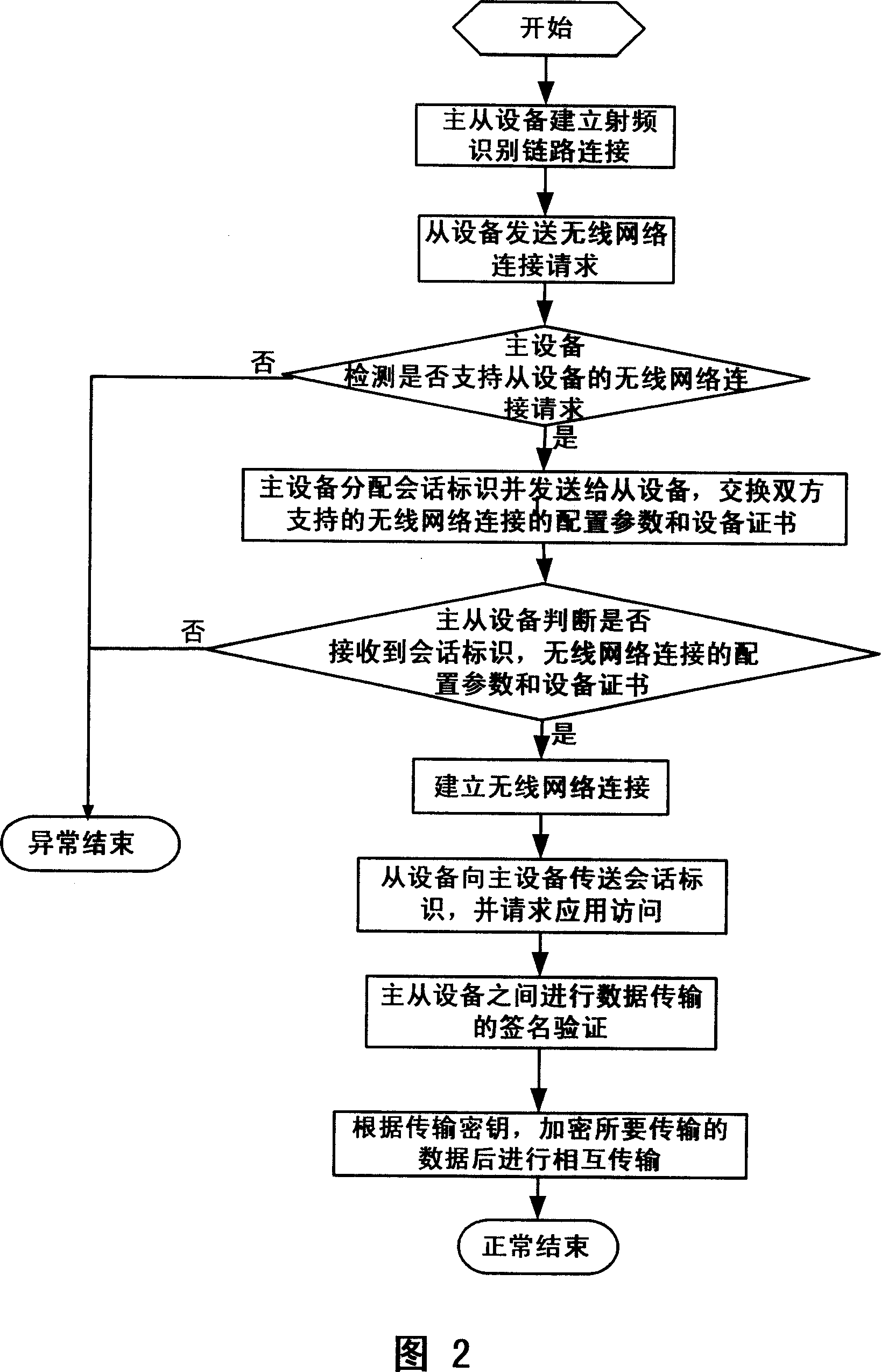
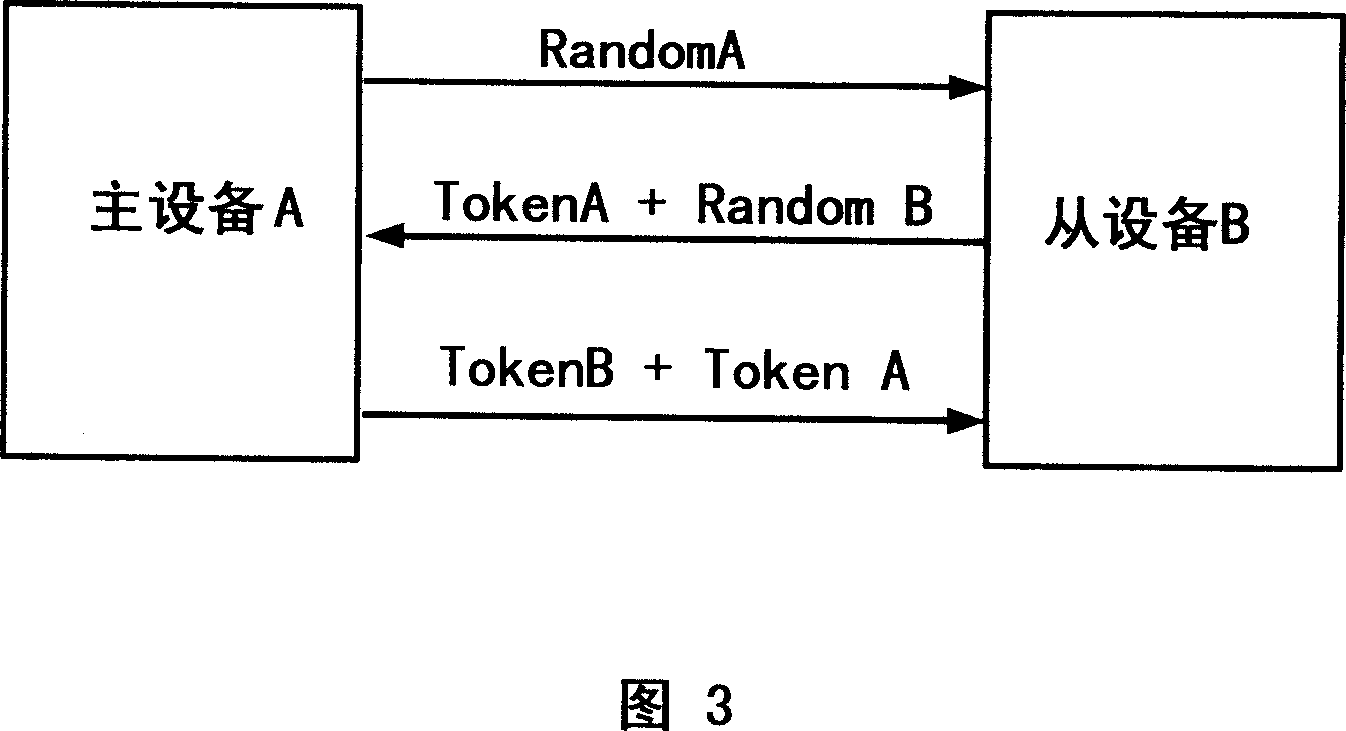
Safety authentication system, apparatus and method for non-contact type wireless data transmission
ActiveCN101114901AReduced usabilityImprove securityNear-field transmissionPublic key for secure communicationContact typeUsability
The invention discloses a system, a device and a method of a non-contact wireless data transmission safety certification. The method comprises the following steps that: when the examination of a main equipment enters a short-range RF-induced (radio frequency) area from the equipment, a radio frequency identification link connection is built between the main equipment and a slave equipment; then the safety certification parameter of the wireless network connection supported by both the main and the slave equipments is exchanged; then the main and the slave equipments judges whether the safety certification parameter is successfully received or not; if so, the wireless network connection is built; if not, users are prompted to restart or end the radio frequency identification communication connection; finally a signature verification of the non-contact equipment wireless data transmission is carried out on the wireless network link connection between the main and the slave equipments. Under the premise of convenience of users, the higher security is ensured.
Owner:LENOVO (BEIJING) CO LTD
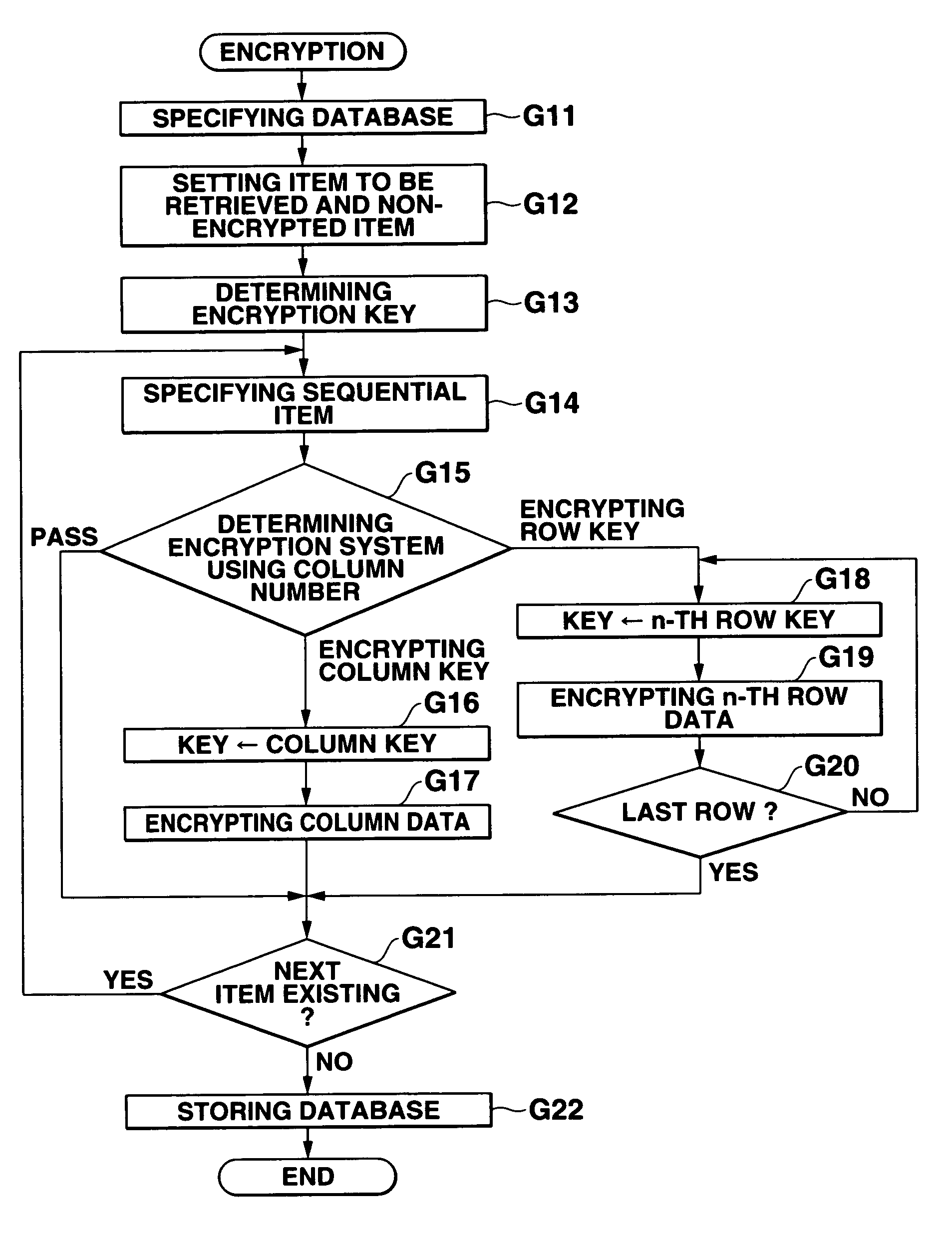
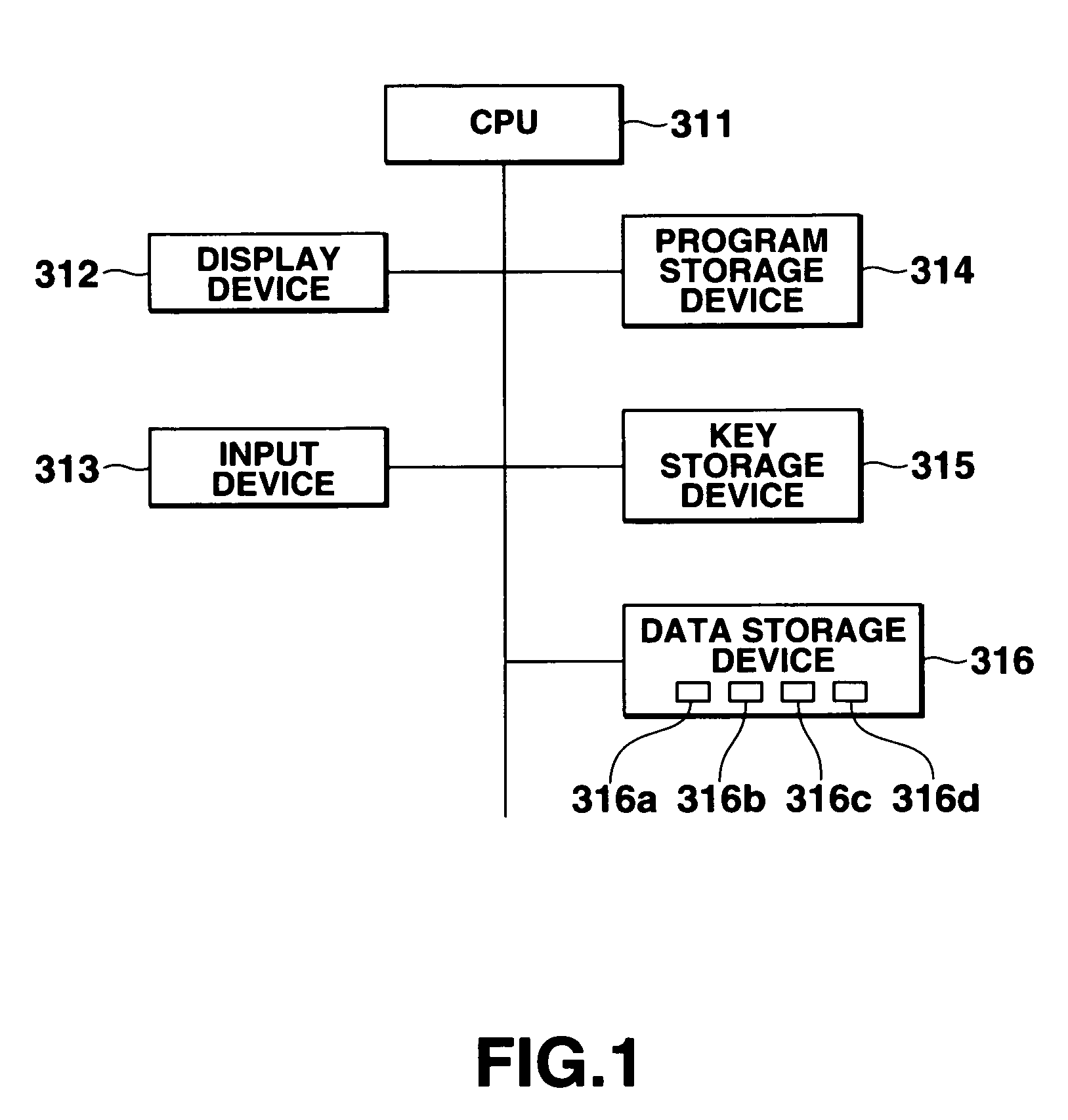
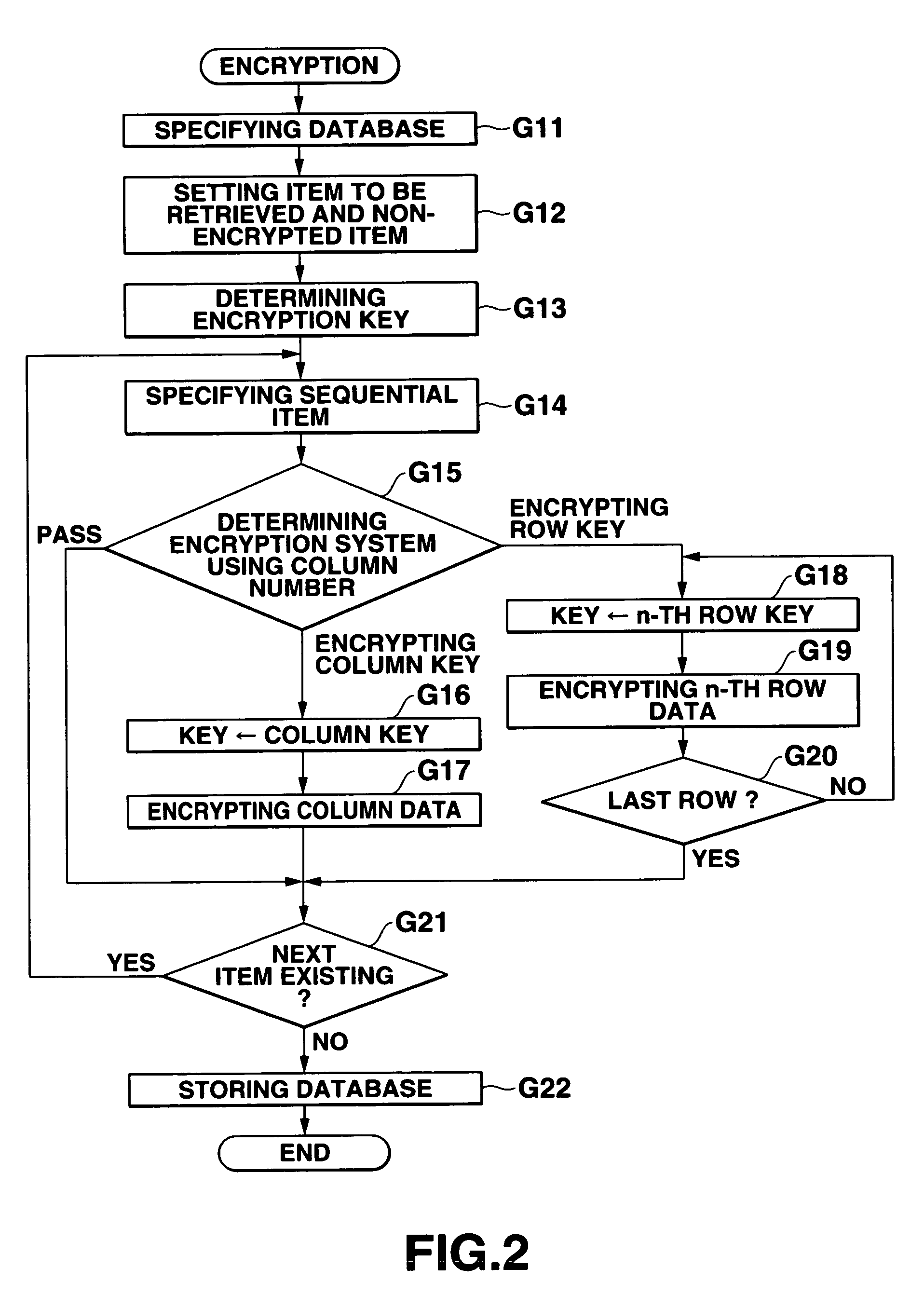
Database management apparatus and encrypting/decrypting system
InactiveUS7093137B1Easy to addEasy to changeData processing applicationsUnauthorized memory use protectionPlaintextTheoretical computer science
In a database, a frequently retrieved column is encrypted using a common key, and other columns are encrypted using a specific row key. Thus, a retrieving process can be performed at a high speed, and the security can be improved. Then, the row and column of the database are encrypted by assuming the plaintext to be encrypted as a bit string, and performing a binary operation with a random bit string. A random bit string is obtained by sequentially generating multidimensional vectors using a nonlinear function by defining a predetermined bit length as 1 word and a plurality of words as components of the multidimensional vector.
Owner:CASIO COMPUTER CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com