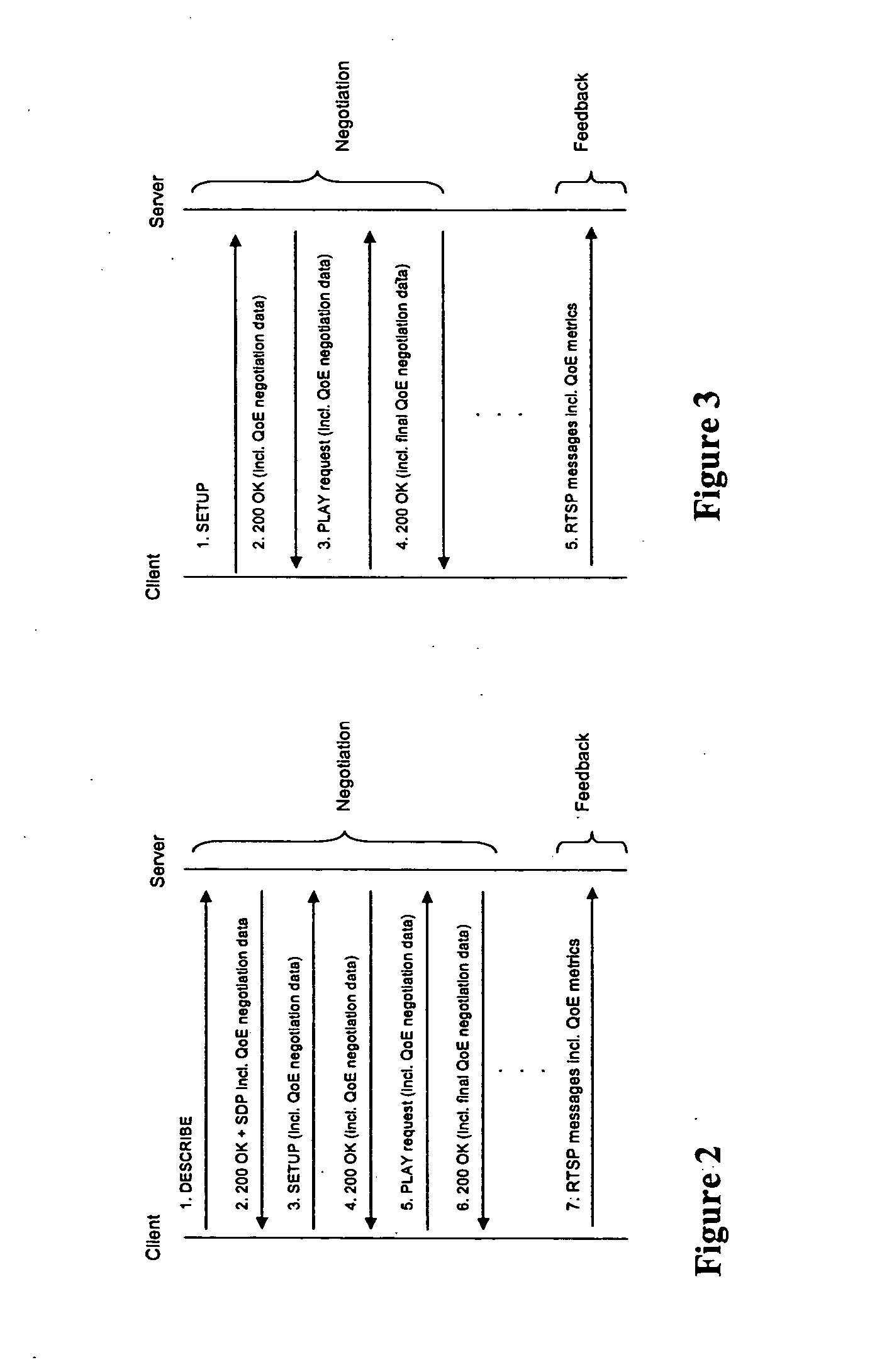
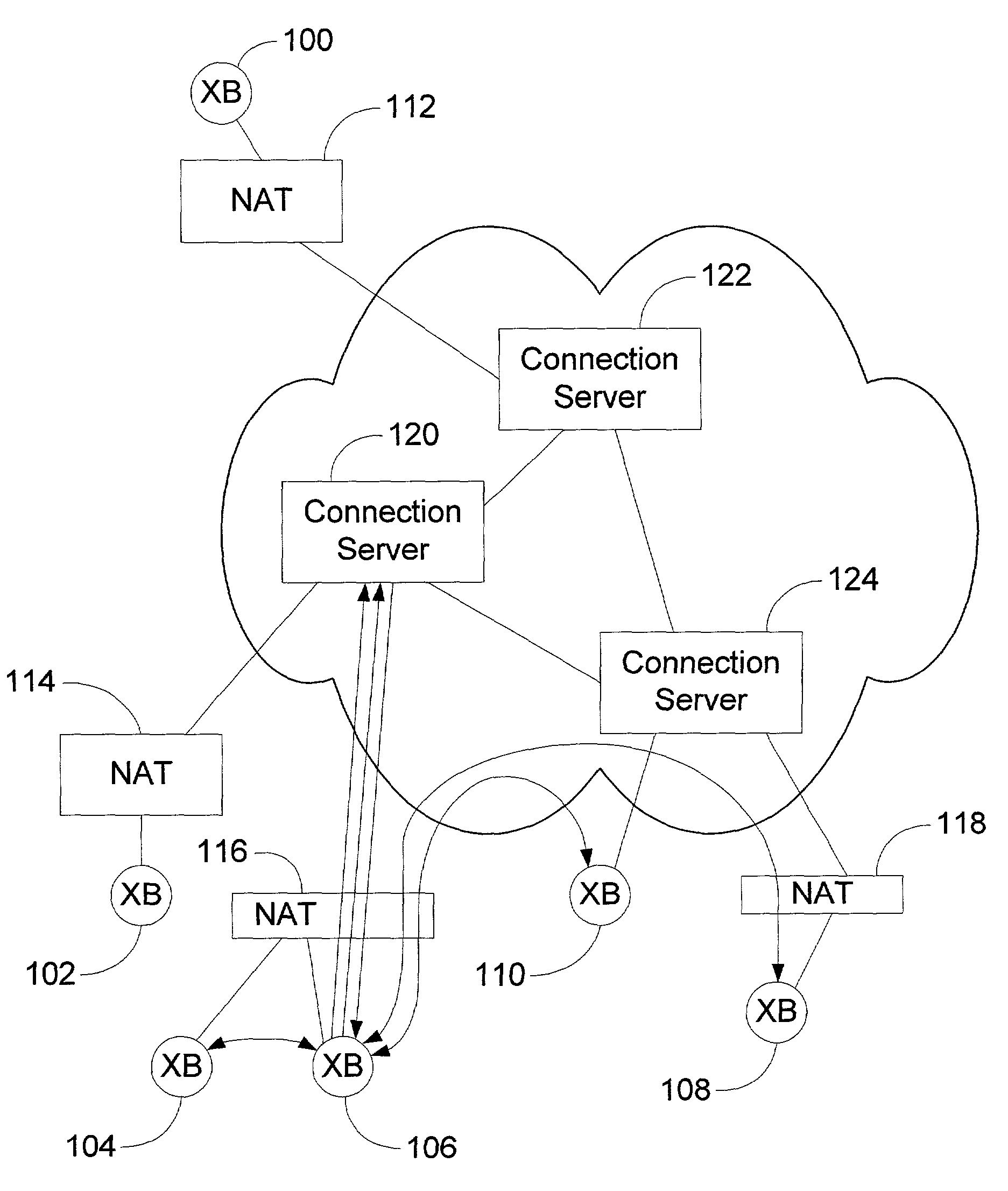
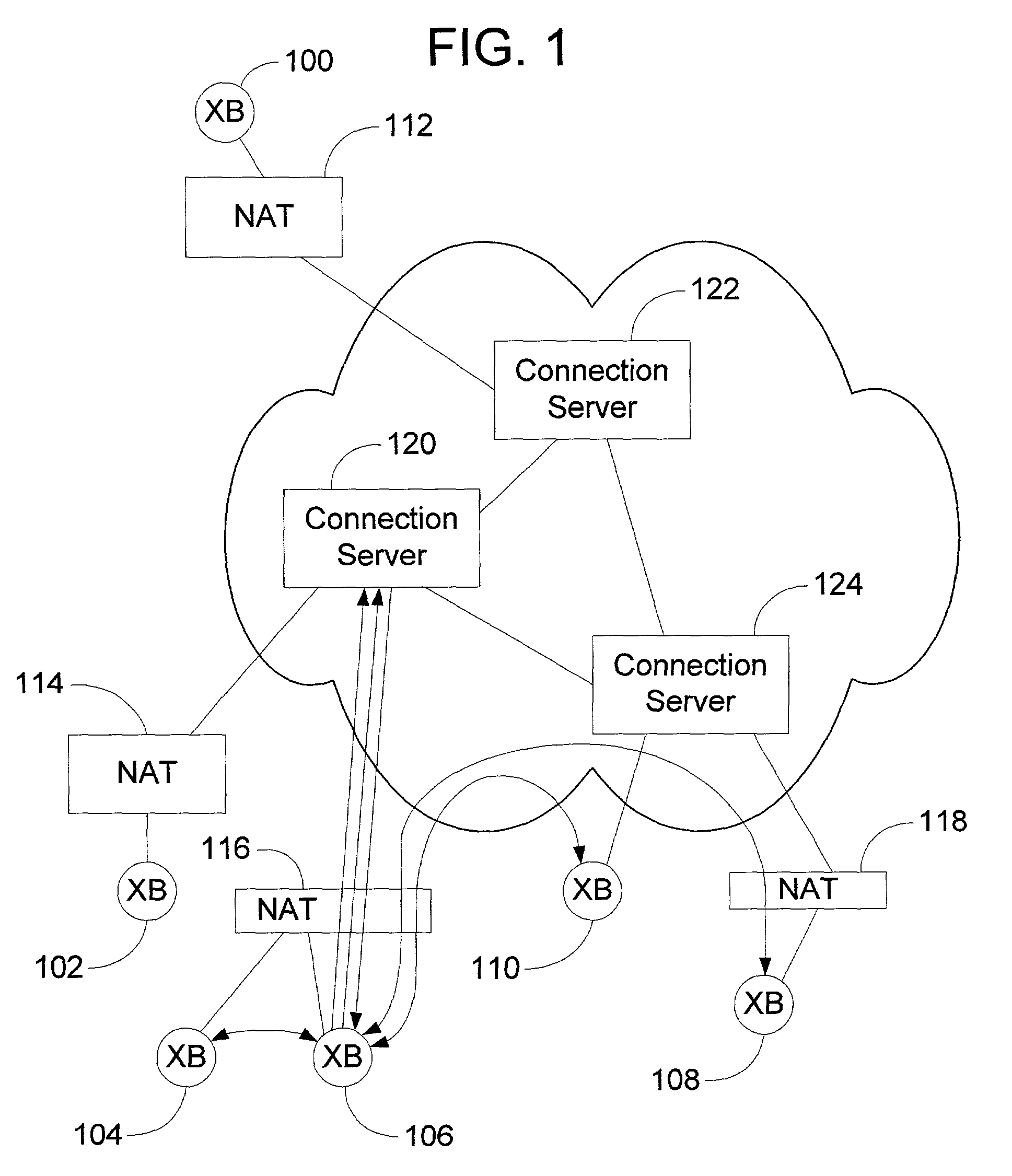
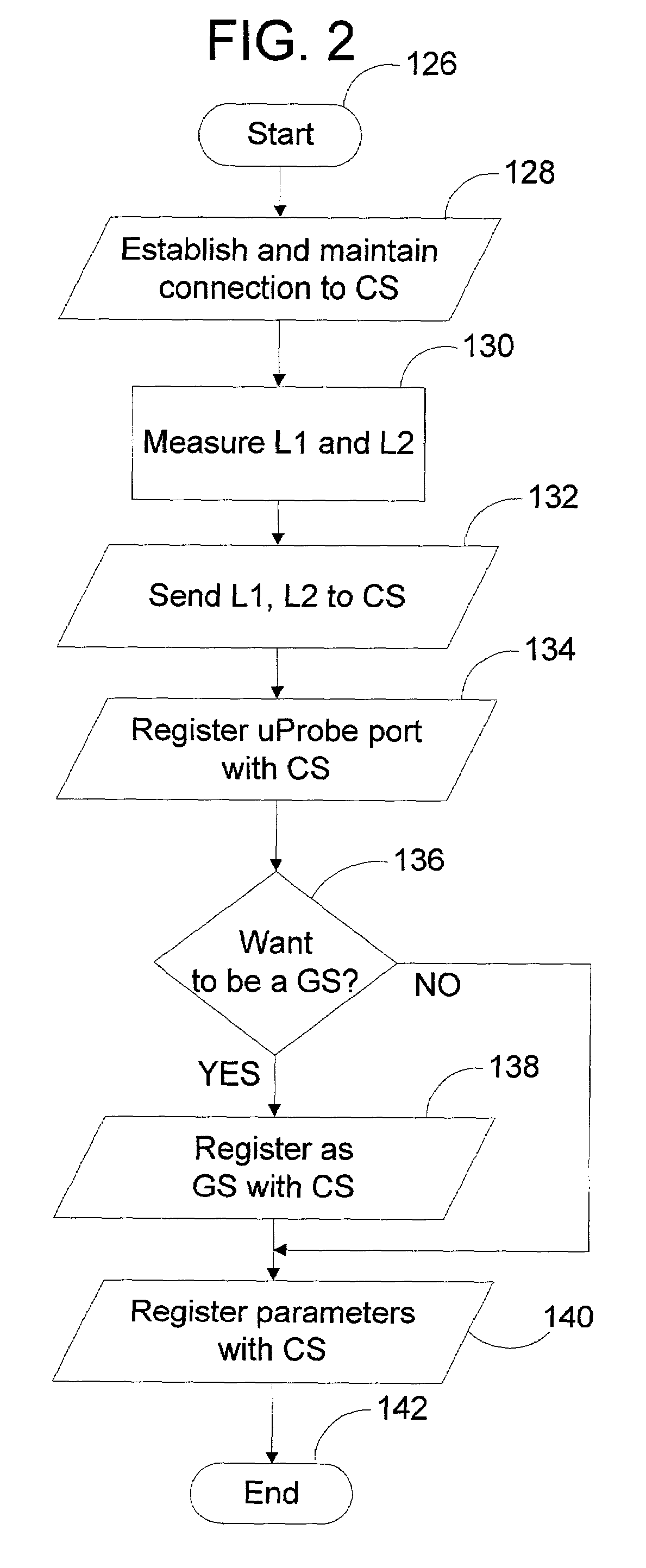
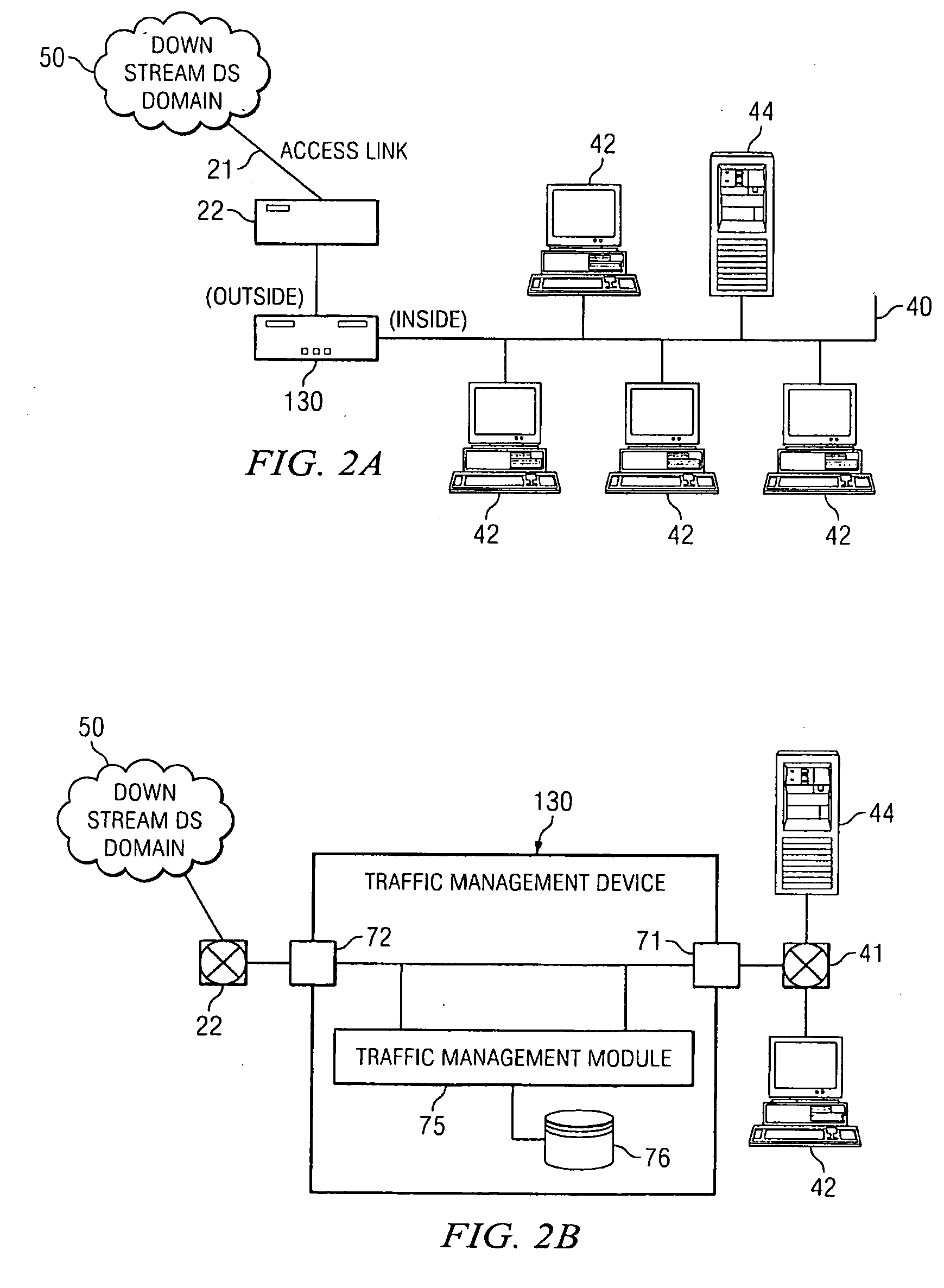
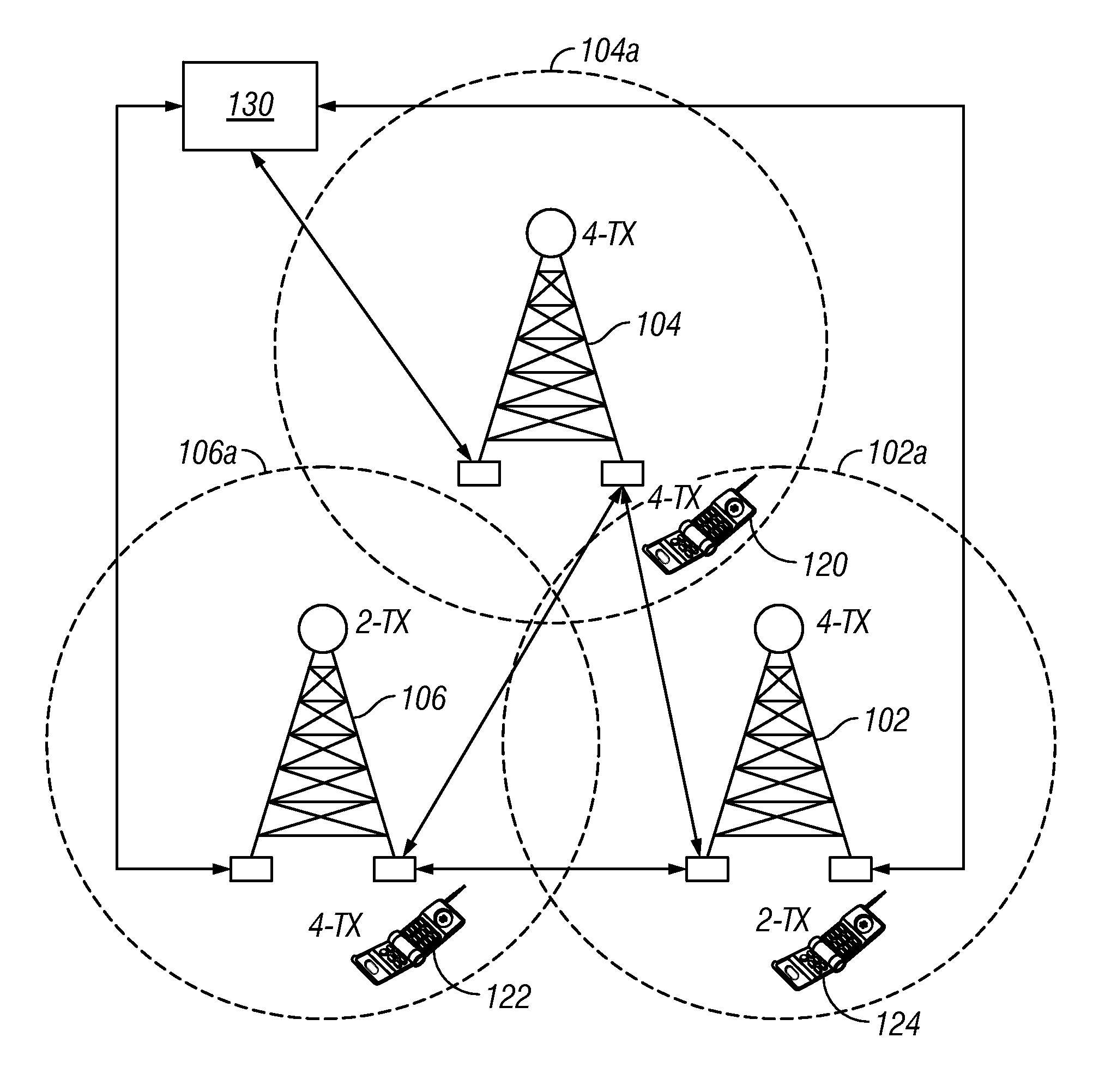
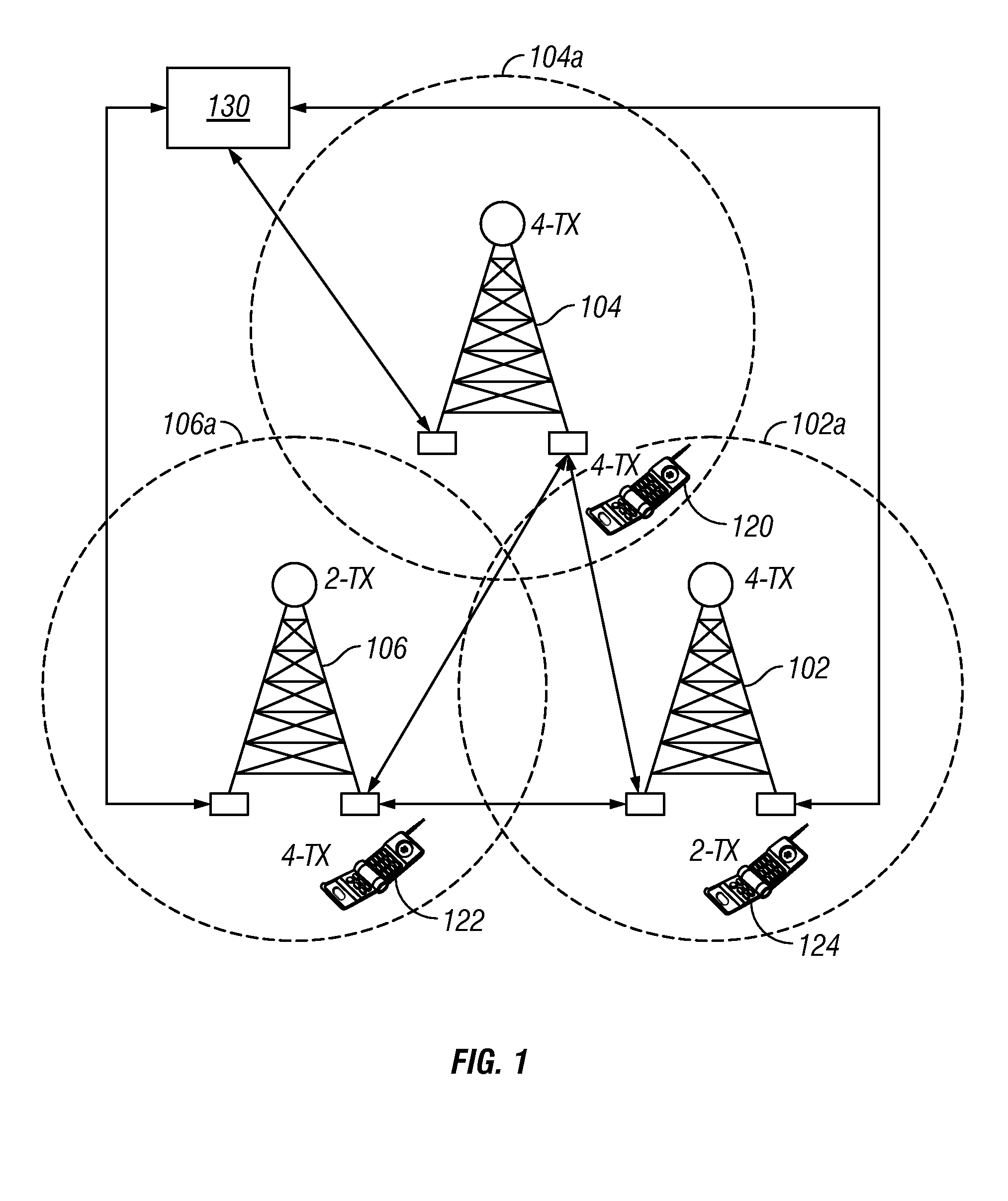
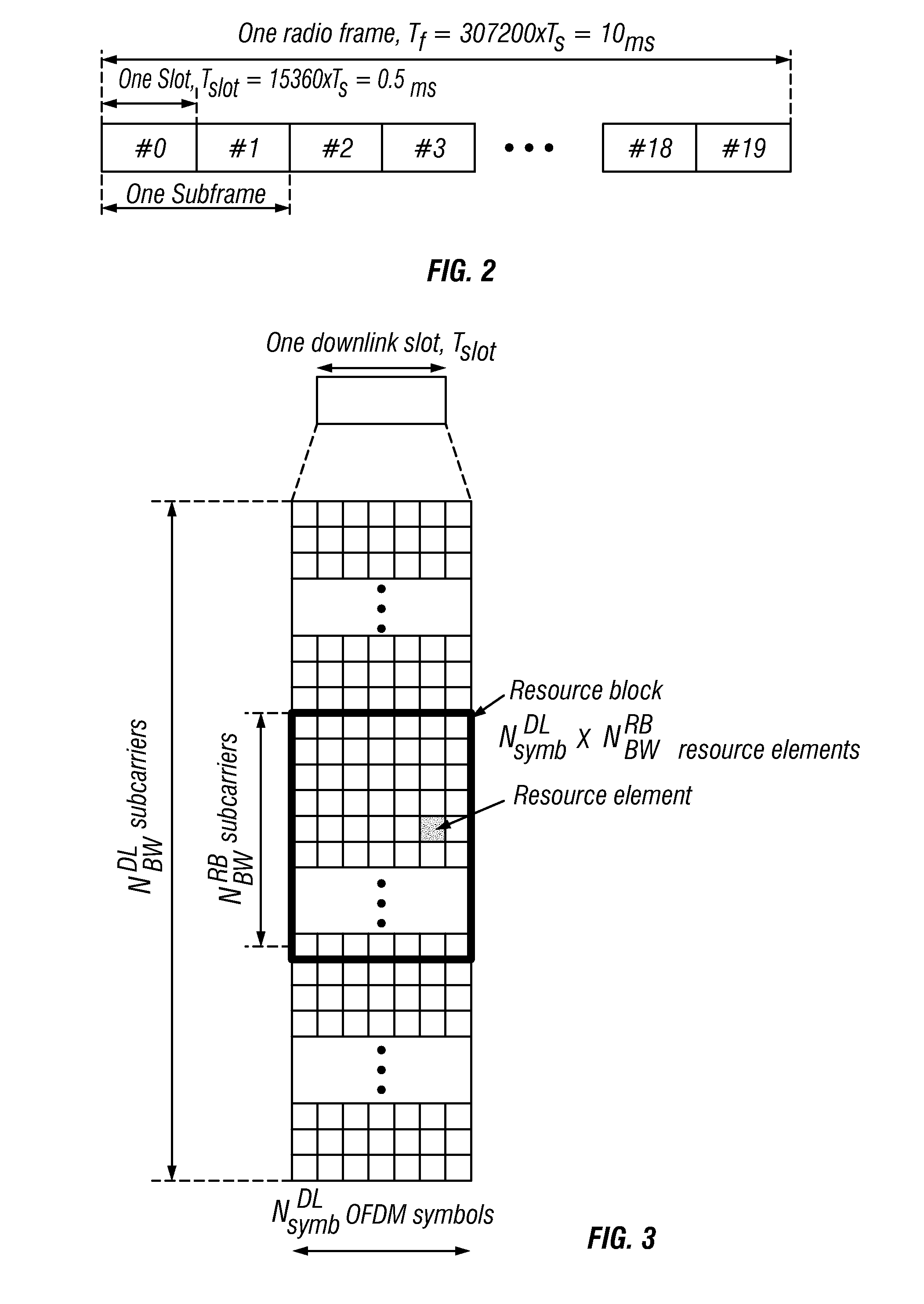
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2378 results about "Network conditions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
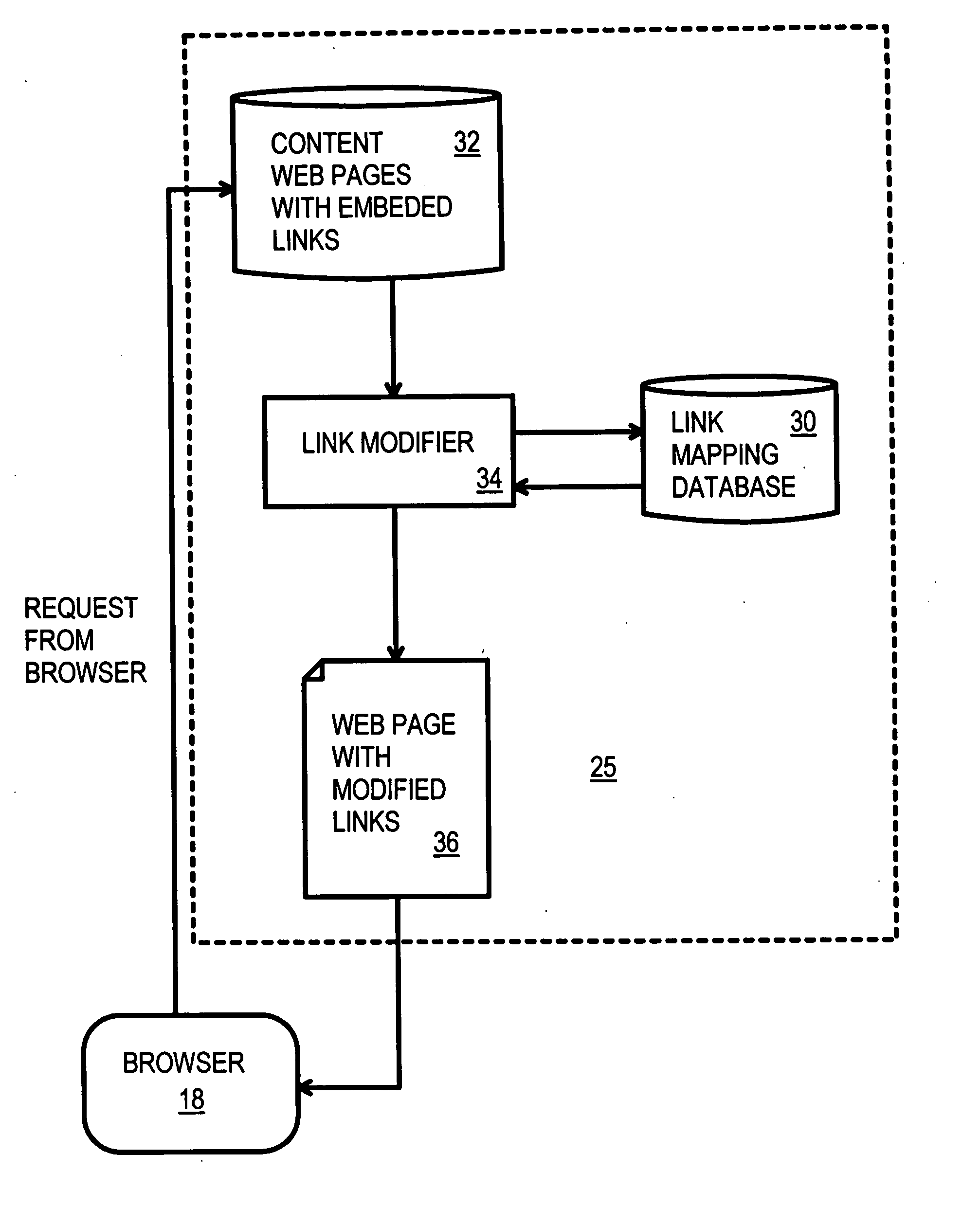
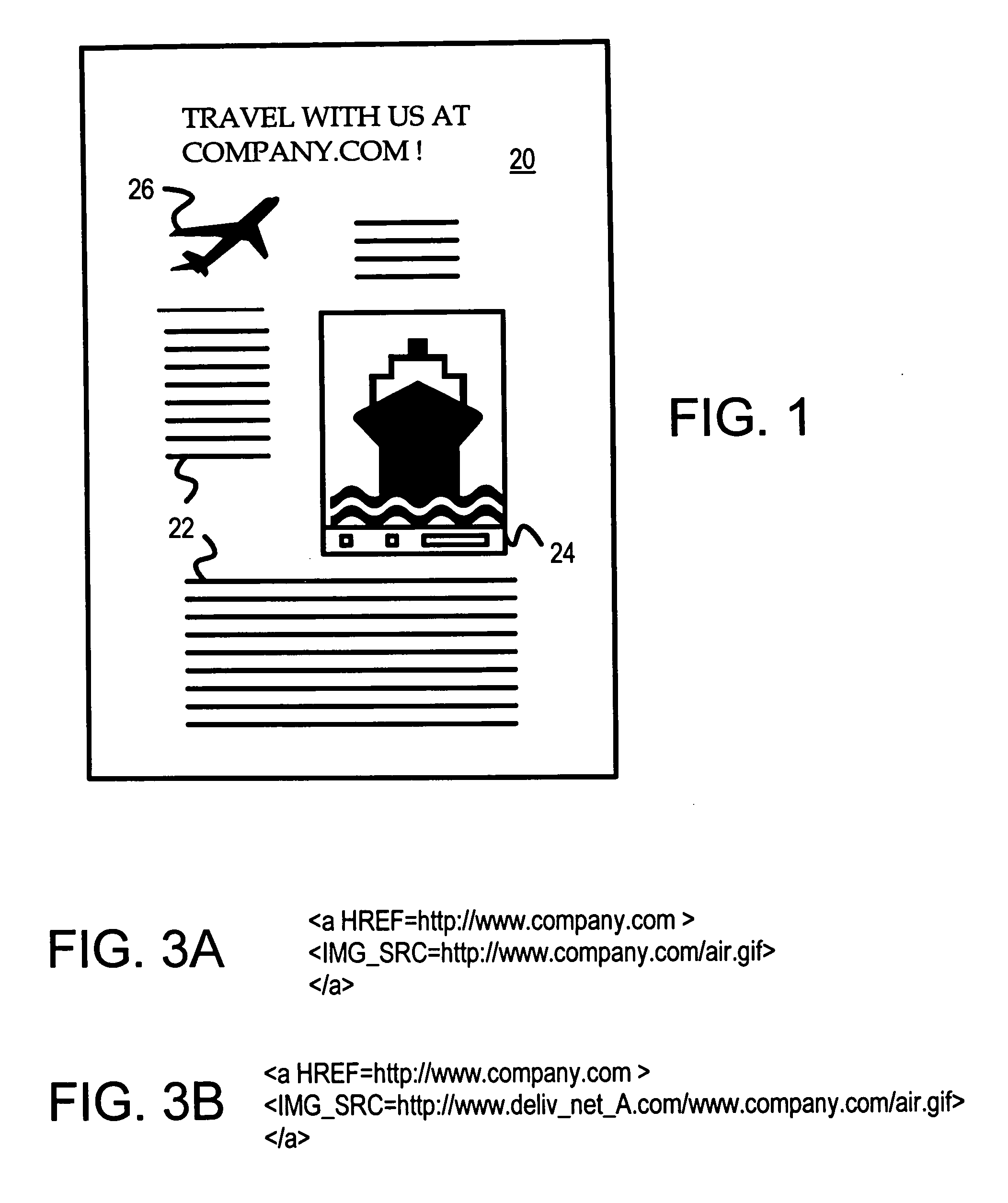
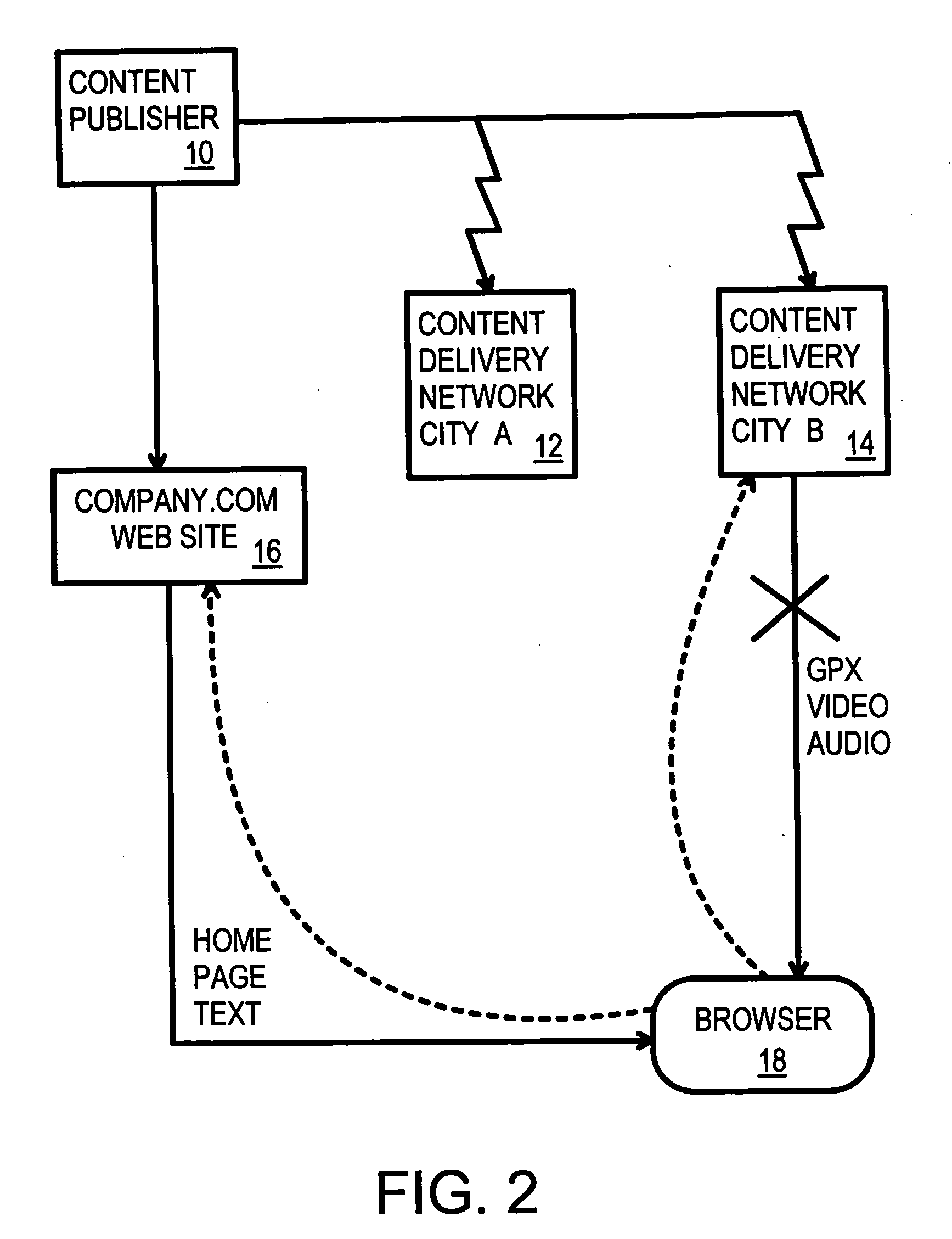
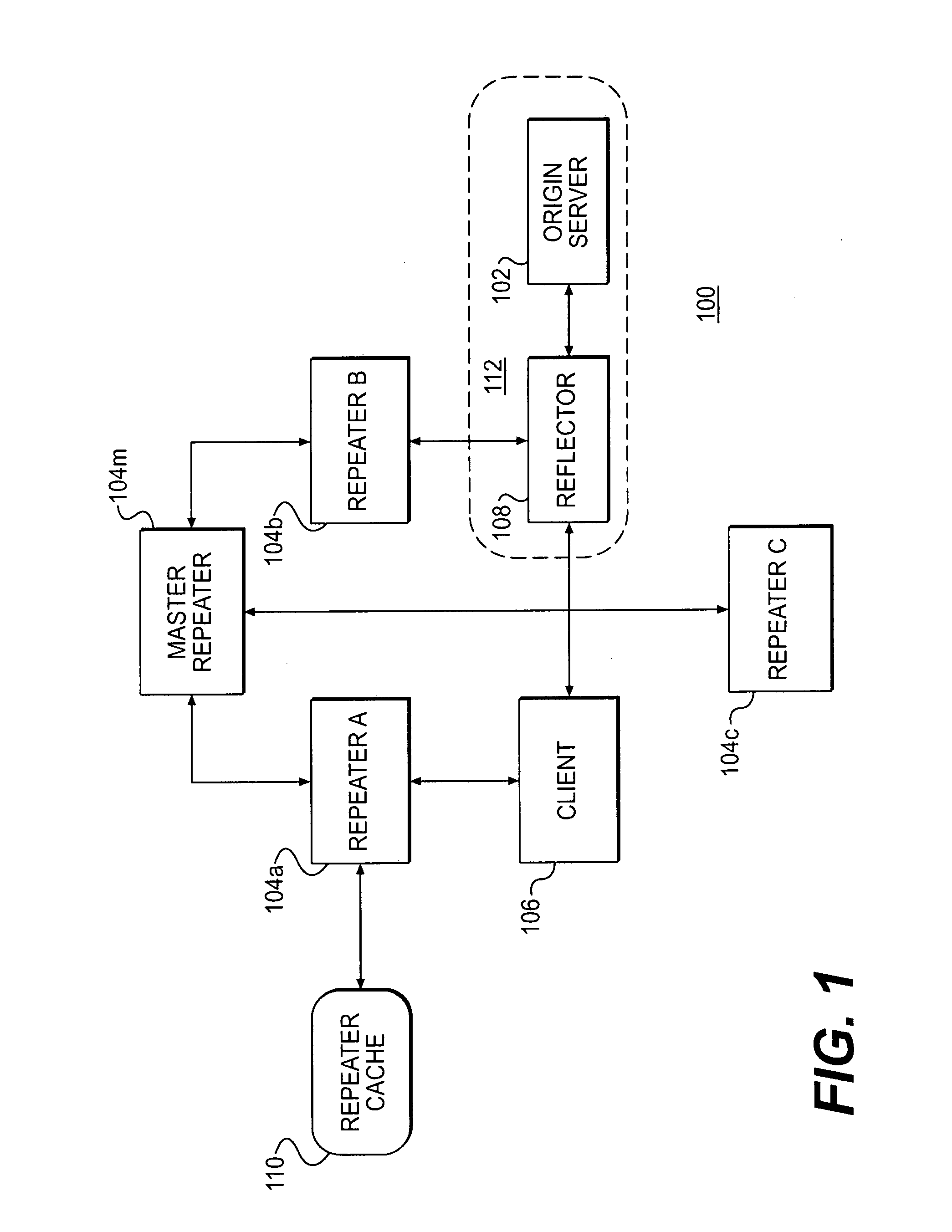
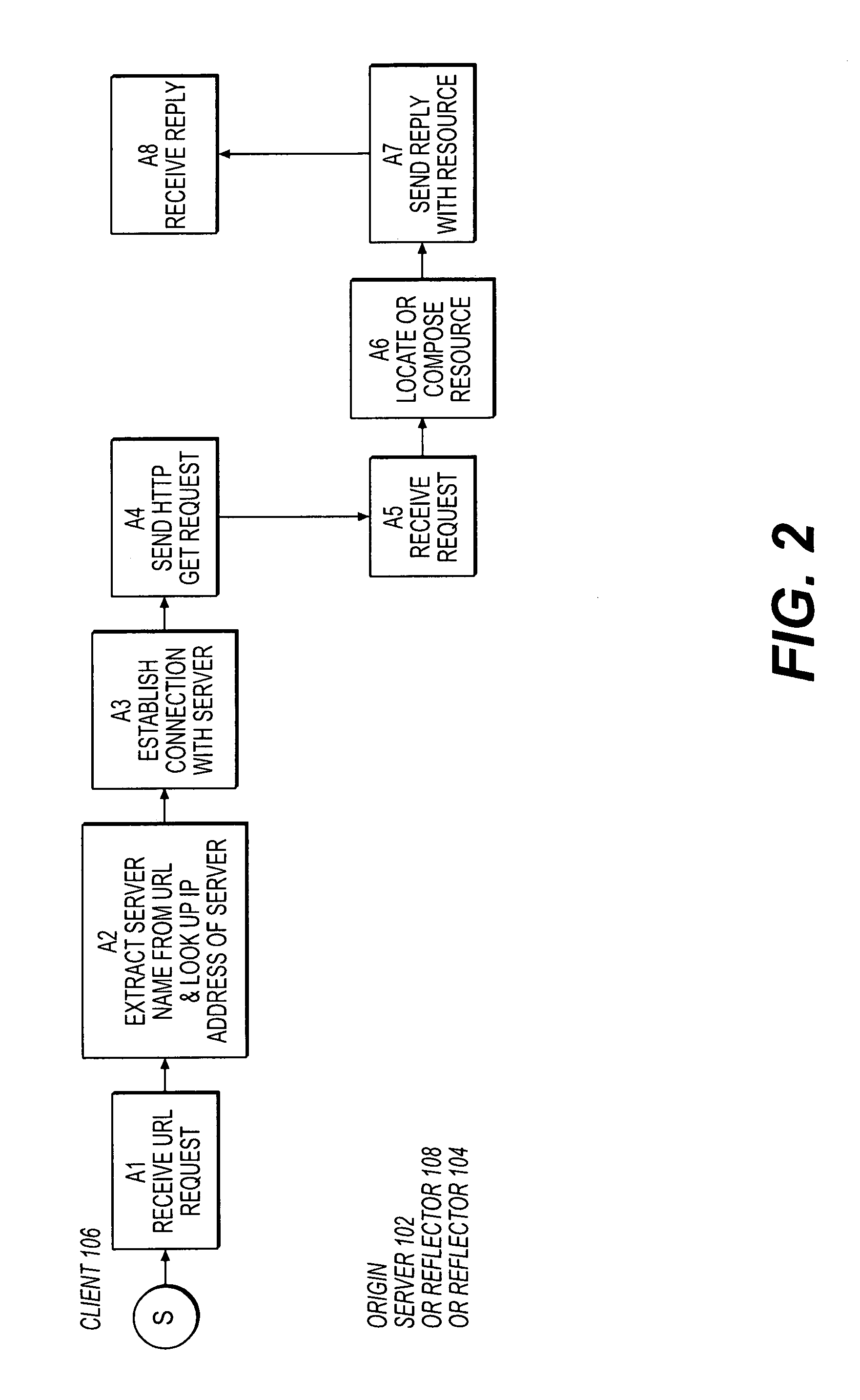
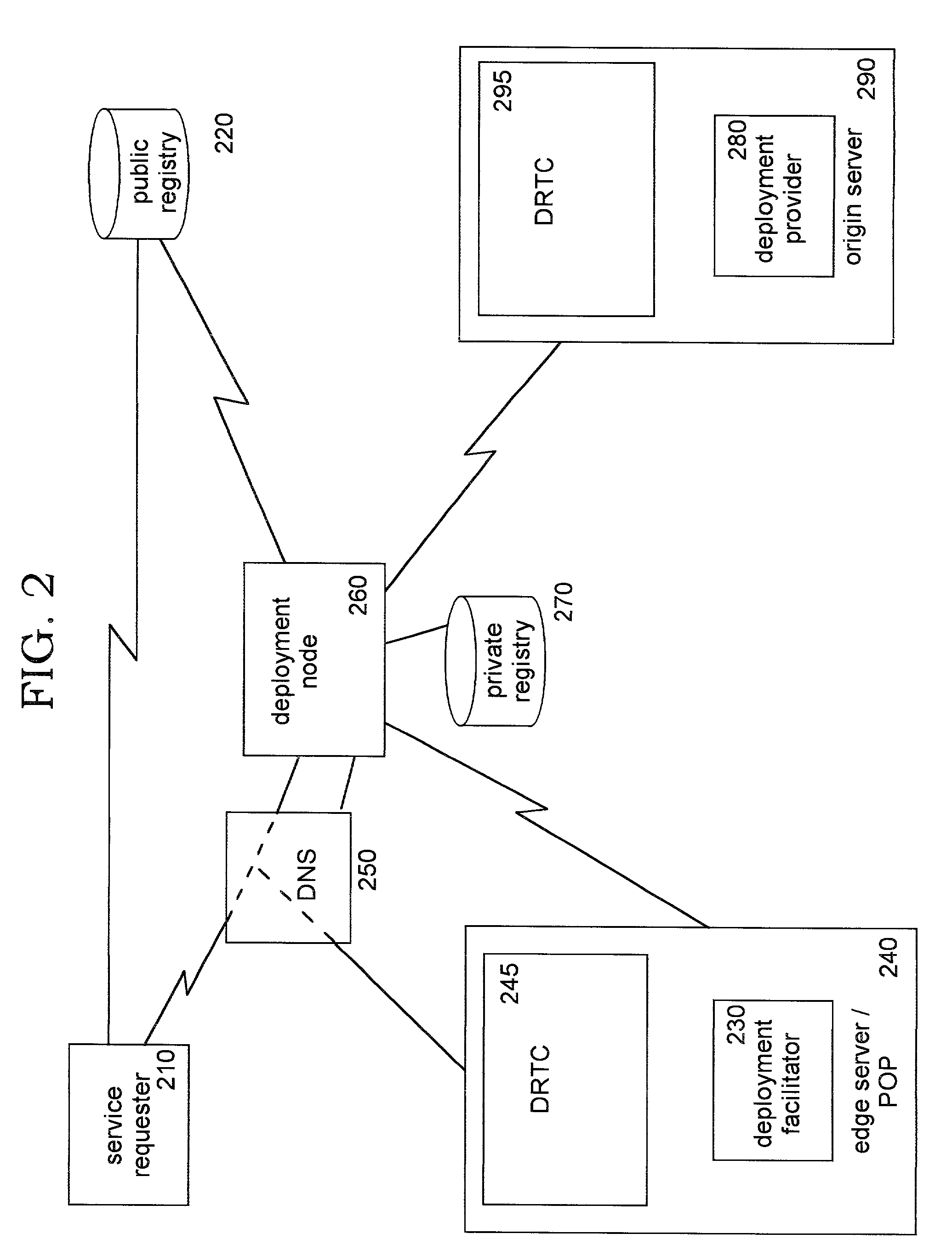
Automatic selection of content-delivery provider using link mapping database
InactiveUS20050021862A1Reduce the possibility of errorPossibility of errorMultiple digital computer combinationsSpecial data processing applicationsNetwork conditionsClient-side
A link-modifying web server automatically modifies links in each web page as it is served to a client browser. The web page is parsed for links, and the links are looked up in a link mapping database. A replacement field is read from the database. A link modifier alters the link using the replacement field to point to a different server at one of several content delivery providers. One of several replacement links can be selected from the link mapping database depending on network conditions and user account data. A replacement link to one content delivery provider can be chosen rather than another replacement link to a different content delivery provider when one provider's network is responding more quickly or has a lower cost. A provider monitor continuously checks provider performance at each of the content delivery providers. When one provider's network is slow or fails, the provider monitor instructs a delivery rule processor to choose link replacements at other content delivery providers. Thus the links in the web page served to the client are modified to point away from slow or failed providers.
Owner:DICKENS COAL
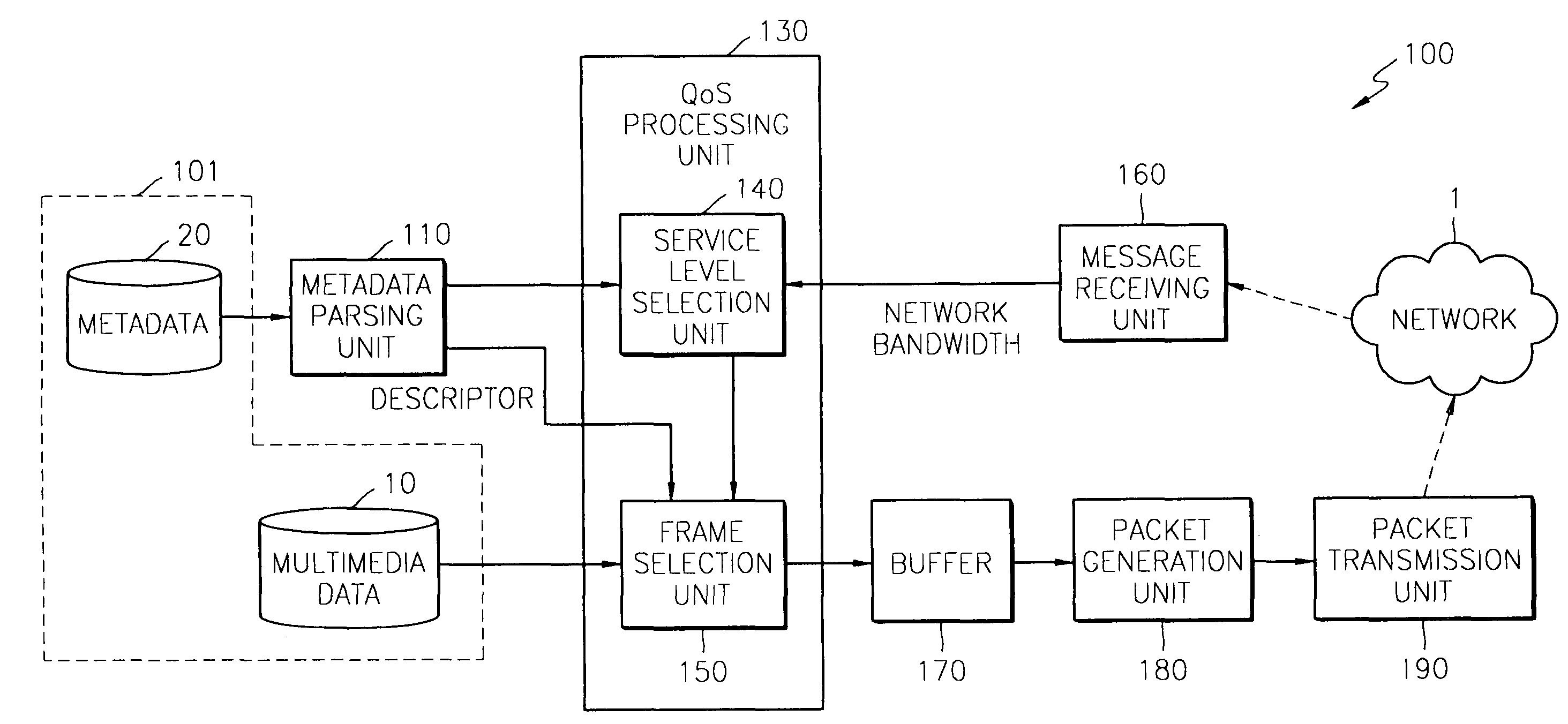
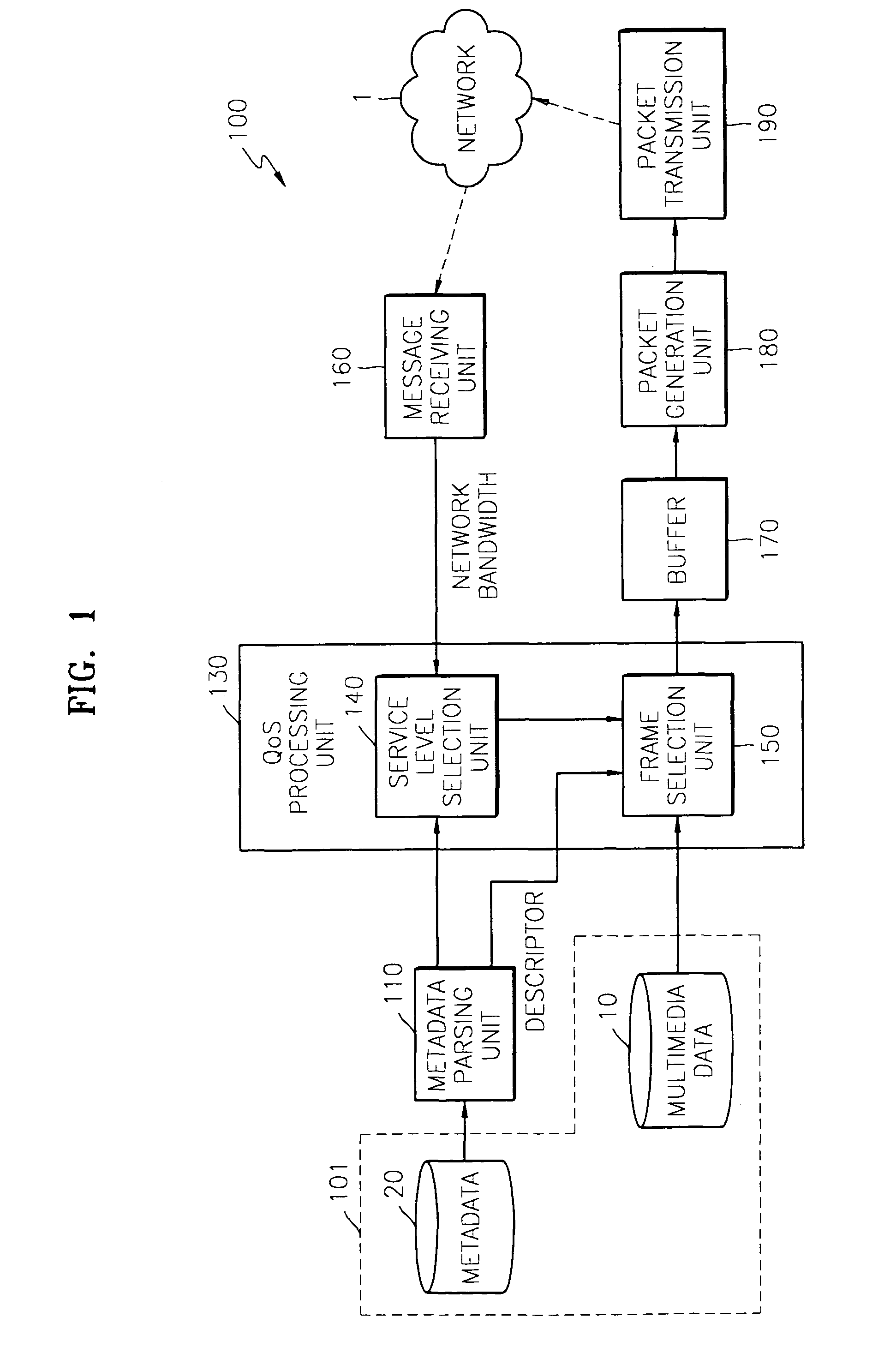
Apparatus and method for streaming multimedia data
InactiveUS20050076136A1Imposing burdenMultiple digital computer combinationsTelevision signal transmission by single/parallel channelsNetwork conditionsClient-side
A multimedia streaming apparatus and method by which multimedia data is adaptively transmitted according to the conditions of a network are provided. The multimedia streaming apparatus streams multimedia data corresponding to a predetermined QoS level in response to a parsing result of metadata corresponding to multimedia data intended to be provided and information on a network bandwidth measured by a client which receives the multimedia data. Accordingly, adaptive multimedia streaming corresponding to the bandwidth change of the network can be performed without imposing an additional burden on a server.
Owner:SAMSUNG ELECTRONICS CO LTD
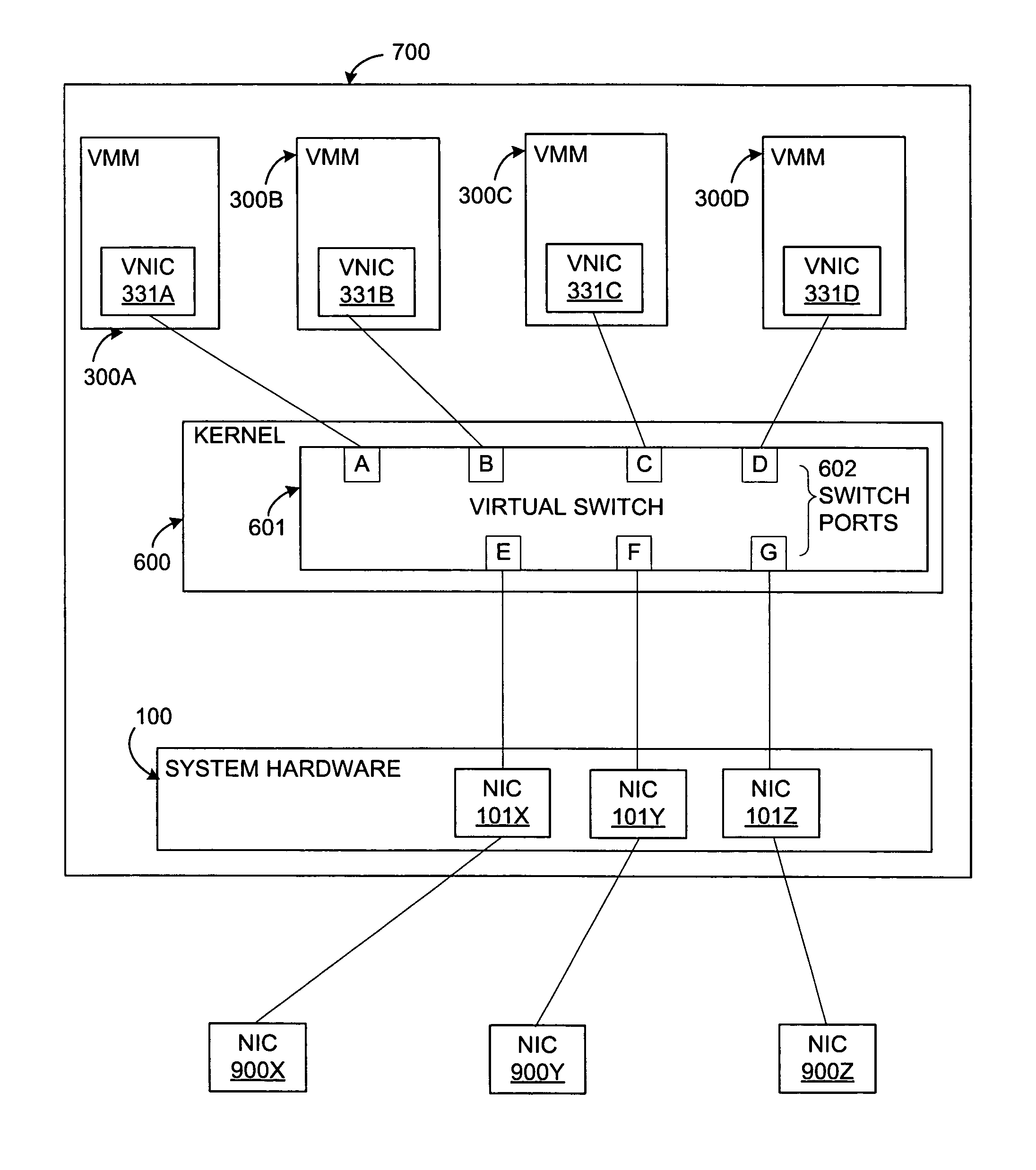
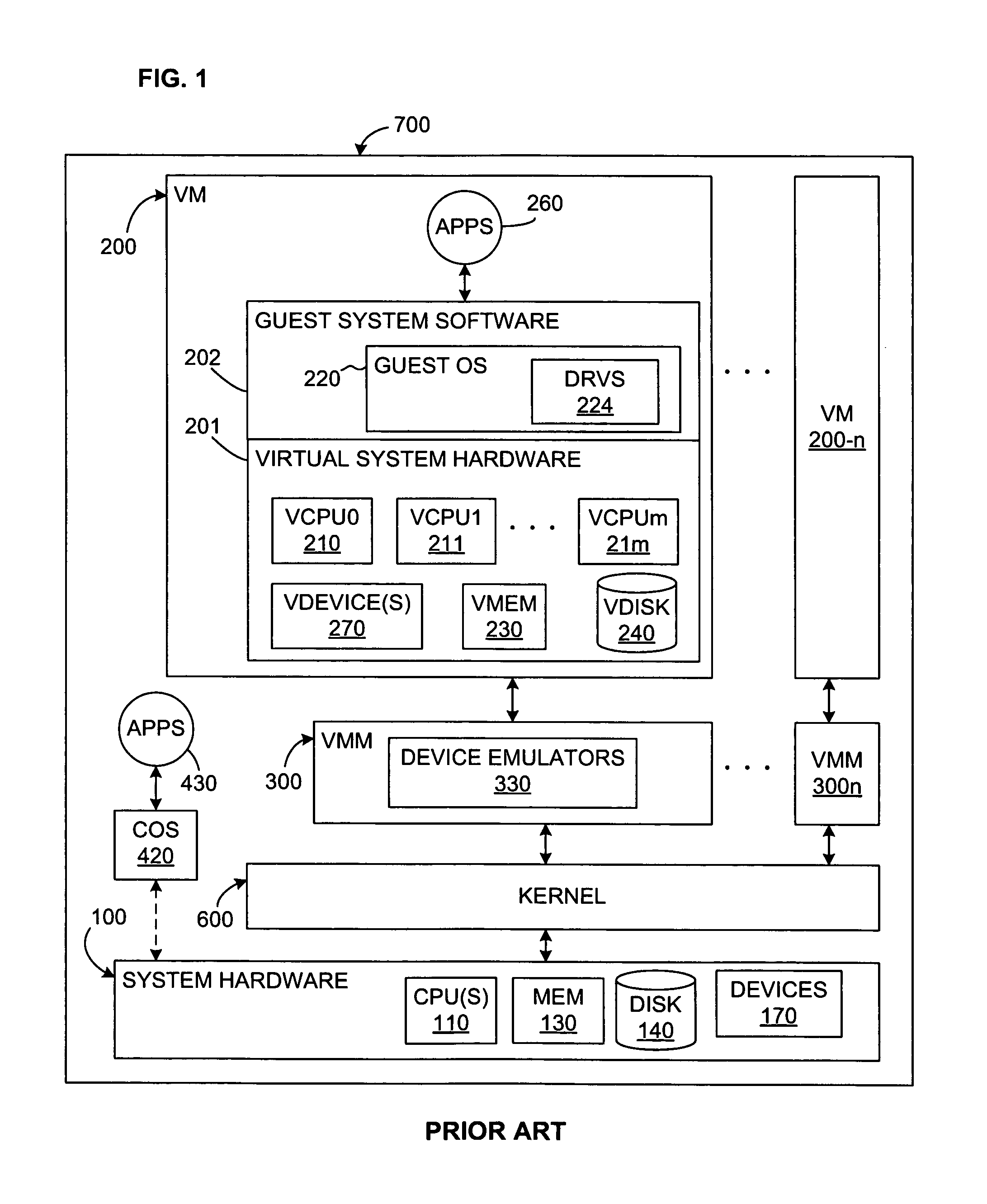
System and method for multiple virtual teams
ActiveUS8060875B1Flexible managementMultiprogramming arrangementsMultiple digital computer combinationsNetwork conditionsVirtual team
A system and method for assigning virtual machines to network interfaces. A first virtual machine is assigned to a network interface according to a first rule and a second virtual machine is assigned to a network interface according to a second rule. The assignment rules are dependent on network conditions as determined through at least one of the network interfaces. The first rule and the second rule may specify assignments differently, such that the same network conditions may result in different assignments for the first and second virtual machines.
Owner:VMWARE INC
Adaptive, application-aware selection of differntiated network services
ActiveUS7843843B1Sacrificing application performanceReduce bandwidth costsError preventionFrequency-division multiplex detailsNetwork conditionsNetwork service
Methods, apparatuses and systems that dynamically adjust the selection of differentiated network services for selected classes of traffic or network applications in response to changing network conditions or application performance levels.
Owner:CA TECH INC
Method and apparatus for providing end-to-end high quality services based on performance characterizations of network conditions
ActiveUS20060285489A1Improve service qualityError preventionFrequency-division multiplex detailsQuality of serviceNetwork conditions
A method and apparatus enforcing and improving end-to-end service quality, based on end-to-end service performance characterization of network conditions, for a convergence enabled end-user device during a user session for service.
Owner:ALCATEL LUCENT SAS
Delivering resources to clients in a distributed computing environment with rendezvous based on load balancing and network conditions
InactiveUS20080215755A1Low costResource allocationMultiple digital computer combinationsDistributed Computing EnvironmentNetwork conditions
A plurality of repeater servers form a shared content delivery network (CDN) to serve resources to clients on behalf of a plurality of content providers. First and second resources are associated with a first content provider, the first resource referencing the second resource. The second resource is associated with a domain of the shared CDN. Responsive to a request that causes the first resource to be served to a client from a server in a domain associated with the first content provider, a CDN server is identified in the domain associated with the shared CDN to serve the second resource to the client. The CDN server is selected based, at least in part, on load conditions on at least some of the CDN servers, and on the client's location. Responsive to the CDN server being requested to serve the second resource: if a copy of the second resource is available on the CDN server, the copy is served to the client from the CDN server; otherwise, the second resource is replicated on the CDN server and then served to the client from the CDN server.
Owner:MOUNT SHASTA ACQUISITION +1
Quality of experience (QOE) method and apparatus for wireless communication networks
A Quality of Experience (QoE) framework provides a technique to assess the end user experience in a mobile wireless communication environment, such as 2.5G or 3G networks, or in any other wireless or hardwired communication environment. The framework is usable in conjunction with media streaming applications and enables a combination of network layer, transport layer, codec layer, and application layer measurements in extracting results. The extracted results can be used to monitor and improve, if necessary, the end user experience over severely variable network conditions.
Owner:VIDIATOR ENTERPRISES INC
Peer-to-peer method of quality of service (QoS) probing and analysis and infrastructure employing same
InactiveUS7133368B2Improve gaming experienceImprove performanceError preventionTransmission systemsQuality of servicePacket loss
A peer-to-peer (P2P) probing / network quality of service (QoS) analysis system utilizes a UDP-based probing tool for determining latency, bandwidth, and packet loss ratio between peers in a network. The probing tool enables network QoS probing between peers that connect through a network address translator. The list of peers to probe is provided by a connection server based on prior probe results and an estimate of the network condition. The list includes those peers which are predicted to have the best QoS with the requesting peer. Once the list is obtained, the requesting peer probes the actual QoS to each peer on the list, and returns these results to the connection server. P2P probing in parallel using a modified packet-pair scheme is utilized. If anomalous results are obtained, a hop-by-hop probing scheme is utilized to determine the QoS of each link. In such a scheme, differential destination measurement is utilized.
Owner:MICROSOFT TECH LICENSING LLC
Adaptive prefetching for computer network and web browsing with a graphic user interface
InactiveUS6385641B1Multiple digital computer combinationsElectric digital data processingGraphicsGraphical user interface
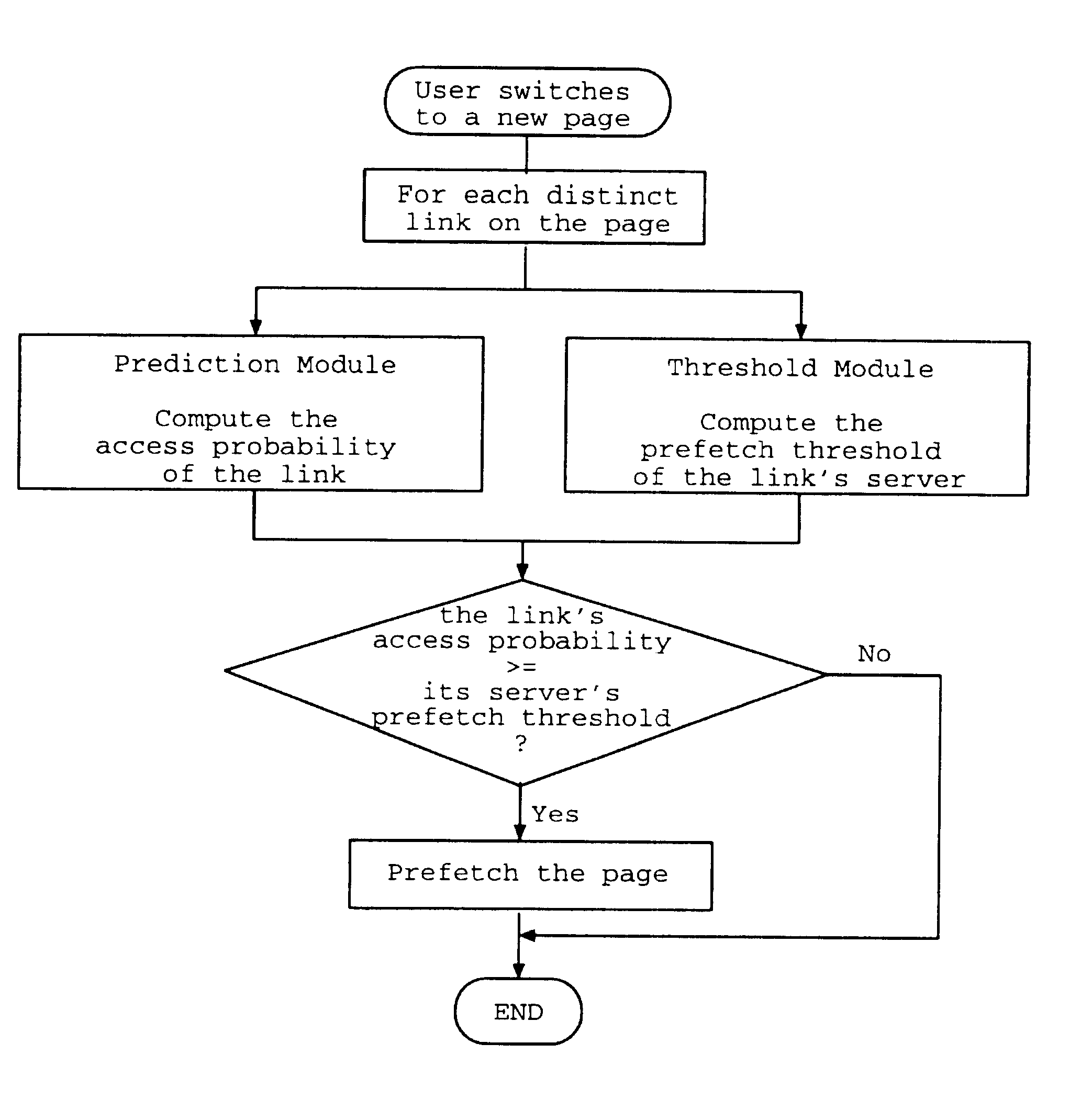
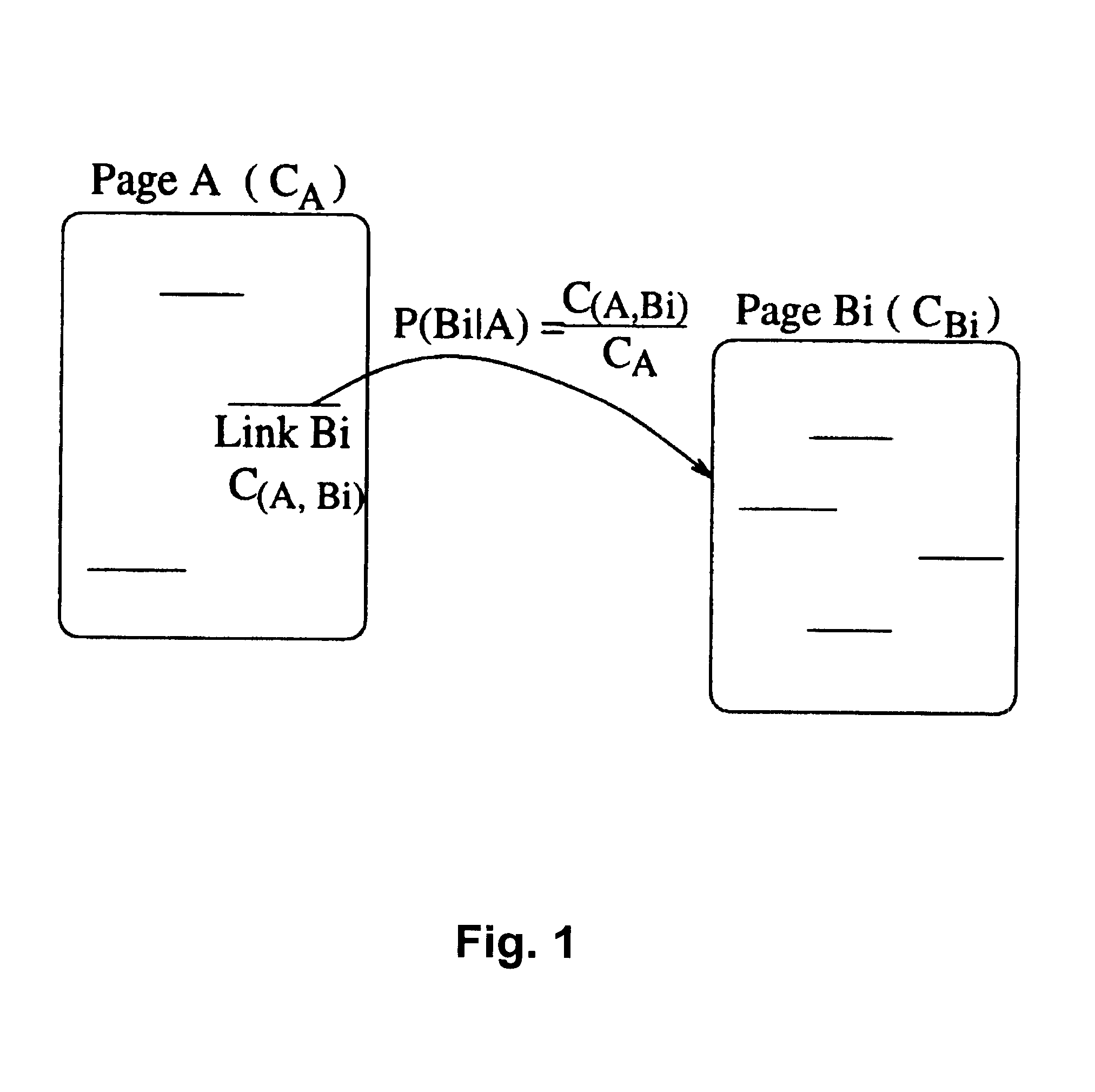
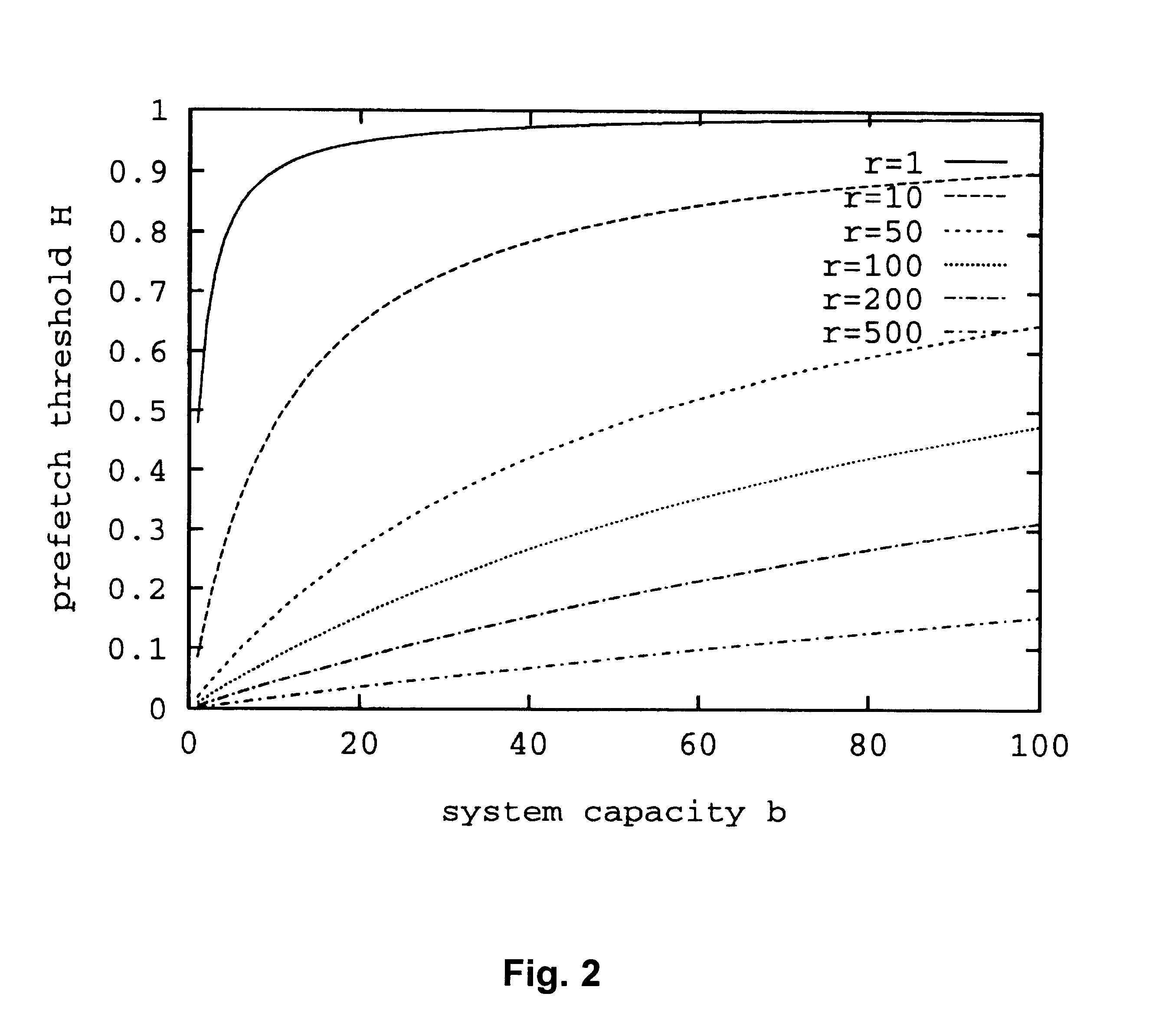
The present invention is based on a prefetching scheme consisting of two modules: a prediction module and a threshold module. After a use's request for a new file is satisfied, the prediction module immediately updates a database of history information if needed, and computes the access probability for each candidate file, where the access probability of a file is an estimate of the probability with which that file will be requested by the user in the near future. Next the threshold module determines the prefetch threshold for each related server, which contains at least one candidate file with nonzero access probability. The threshold is determined in real time based on then current network conditions. Finally, each file whose access probability exceeds or equals its server's prefetch threshold is prefetched. When prefetching a file, the file is actually downloaded if and only if no up-to-date version of the file is available on the local computer; otherwise no action is taken. Although web browsing is an important application for prefetching, the prefetch scheme of the present invention may be advantageously applied to any network application in which prefetching is possible.
Owner:RGT UNIV OF CALIFORNIA
Method and system of bandwidth management for streaming data
InactiveUS20050120128A1Bandwidth management/data qualityReadily apparentTelevision system detailsMachine supportsStreaming dataMass storage
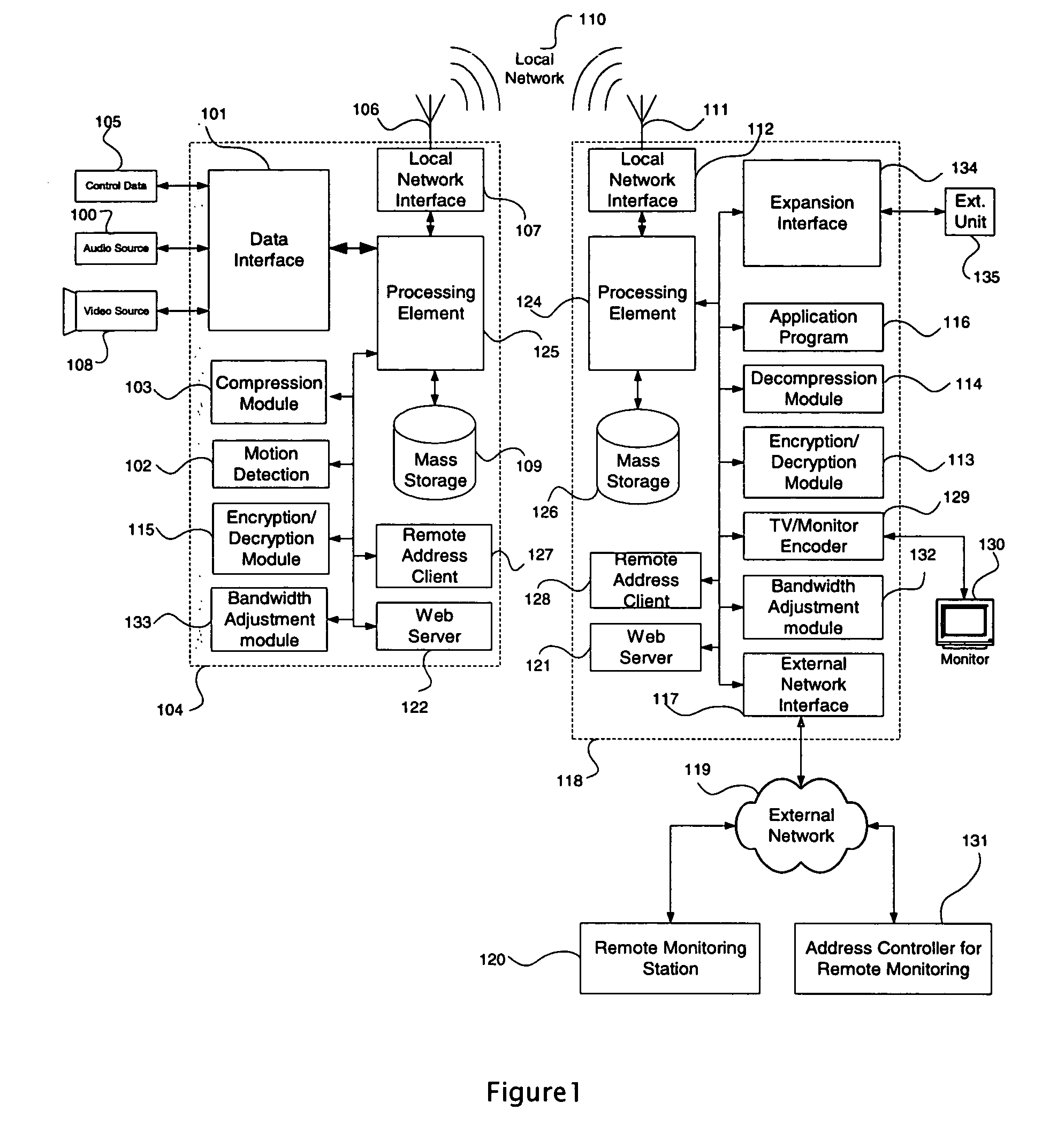
A data networking system and method which allows efficient use of bandwidth for data streams such as video and audio. This invention allows network nodes to dynamically identify changing network conditions which are typical on wireless and power line networks. The system and method dynamically adapt to the changes which affect network bandwidth by changing compression rates, compression types, audio / video quality, motion masks, throughput for specific connections, or mass storage of data streams until the network is capable of sending the data. The result is an improved system that requires little or no user intervention as network conditions change.
Owner:WILIFE
Cost-aware, bandwidth management systems adaptive to network conditions
ActiveUS8489720B1Improve load conditionsLow costMultiple digital computer combinationsData switching networksNetwork conditionsApplication software
Methods, apparatuses, and systems directed to cost-aware bandwidth management schemes that are adaptive to monitored network or application performance attributes. In one embodiment, the present invention supports bandwidth management systems that adapt to network conditions, while managing tradeoffs between bandwidth costs and application performance. One implementation of the present invention tracks bandwidth usage over an applicable billing period and applies a statistical model to allow for bursting to address increased network loading conditions that degrade network or application performance. One implementation allows for bursting at selected time periods based on computations minimizing cost relative to an applicable billing model. One implementation of the present invention is also application-aware, monitoring network application performance and increasing bandwidth allocations in response to degradations in the performance of selected applications.
Owner:CA TECH INC
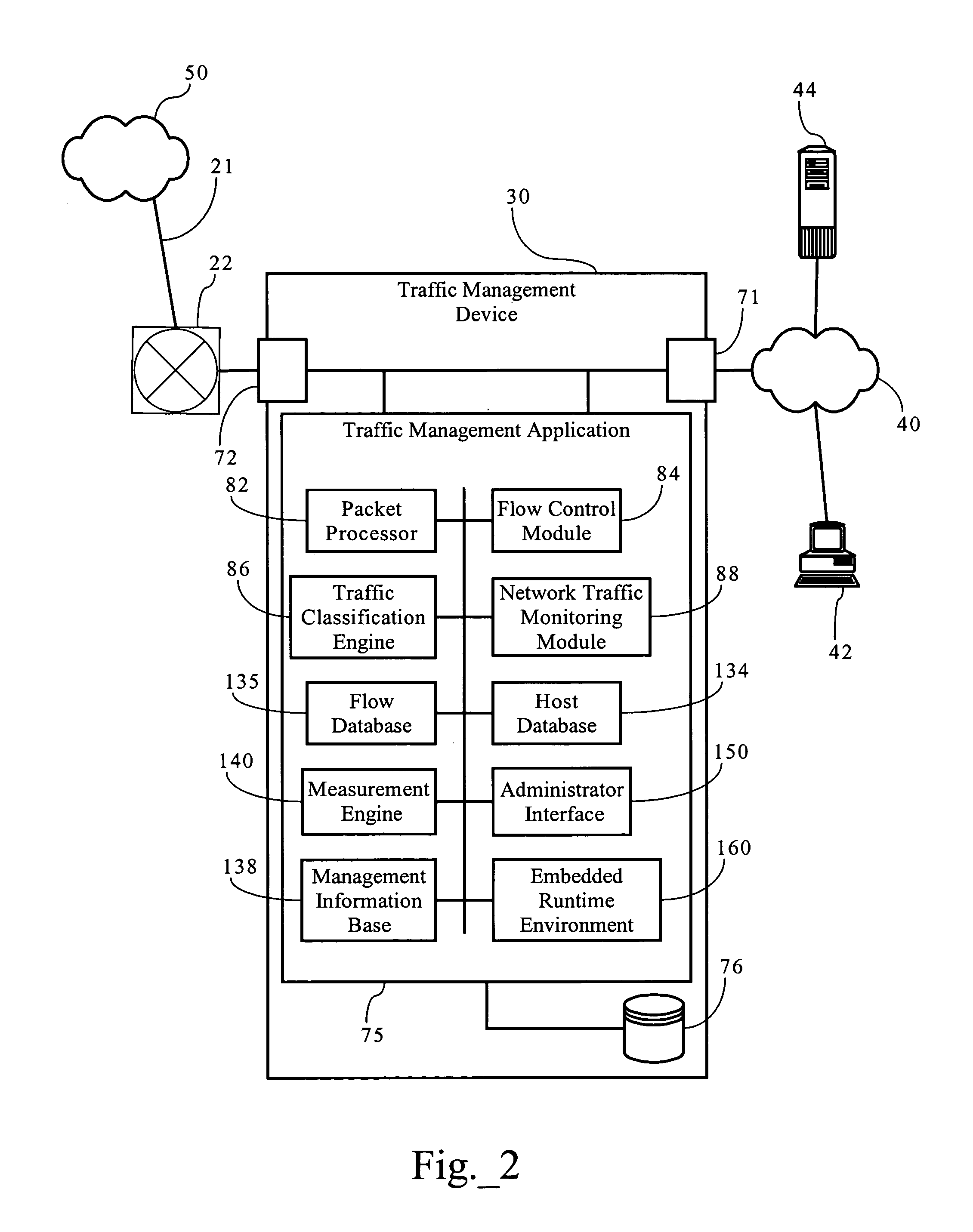
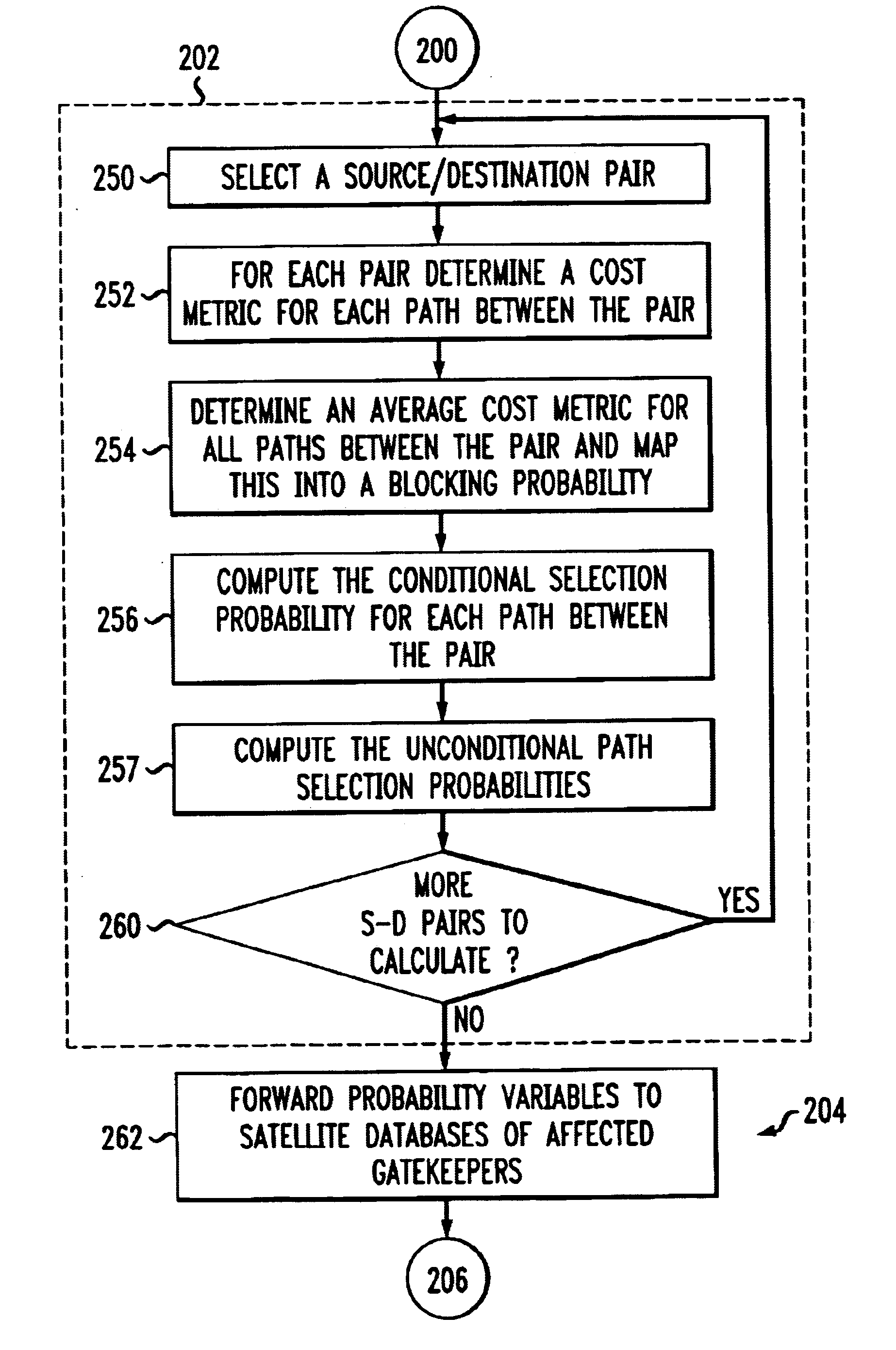
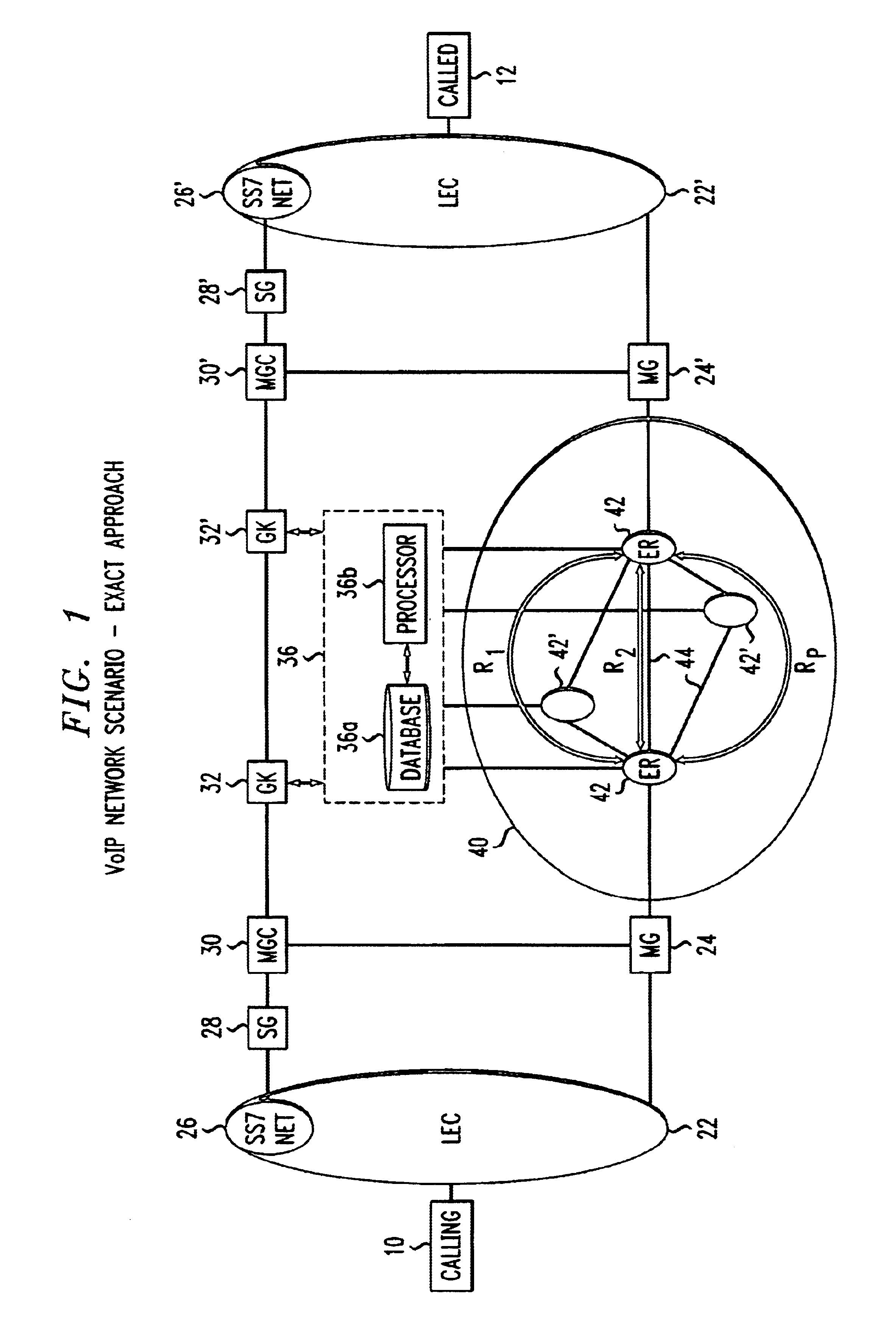
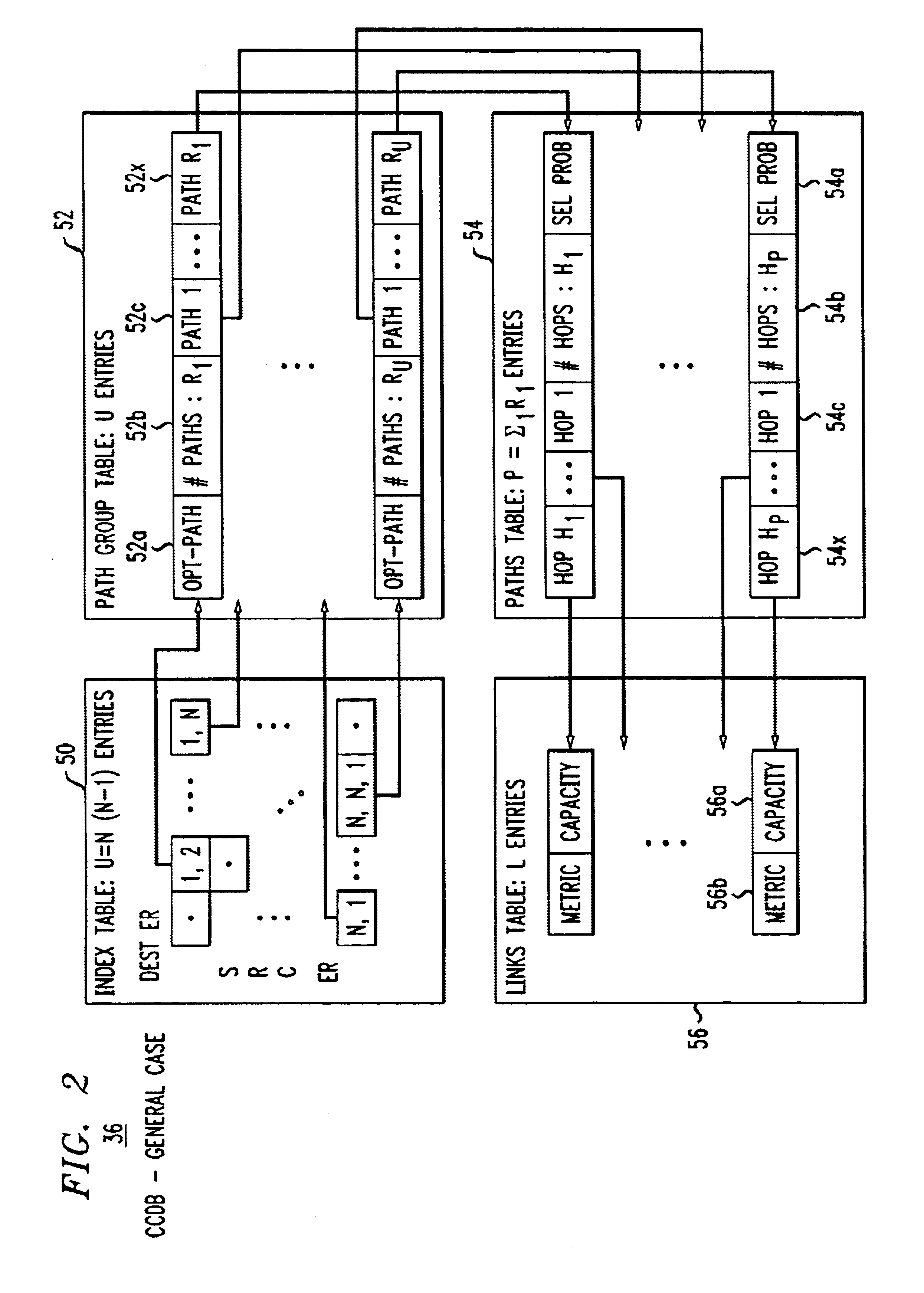
Method and apparatus to provide centralized call admission control and load balancing for a voice-over-IP network
InactiveUS6904017B1Improve service qualityBandwidth sharingInterconnection arrangementsError preventionExtensibilityBalancing network
An admission control and load balancing system controls admission of packet streams or calls to a network and balances the packet traffic across the network, improving quality of service. The system includes a central database which stores information including cost data associated with individual paths and links across the network. A processor, in communication with the database, coordinates the admission control and load balancing decisions, and updates of the database cost data to reflect the dynamic network conditions, based on input from appropriate data sources. In one embodiment, referred to as the exact algorithm, the database is consulted by the admission control points or gatekeepers prior to admitting each arriving packet stream, and the database contents are updated call-by-call to reflect the allocation of resources to each admitted stream. In another embodiment, referred to as the inexact algorithm, control decision as well as database updates occur on a periodic rather than on a call-by-call basis to promote better scalability. In this embodiment, the processor periodically calculates admission decisions based on cost data in the central database. These admission decisions are then periodically forwarded to a satellite database associated with each gatekeeper, for storage and use in admission decisions until the next update epoch.
Owner:LUCENT TECH INC
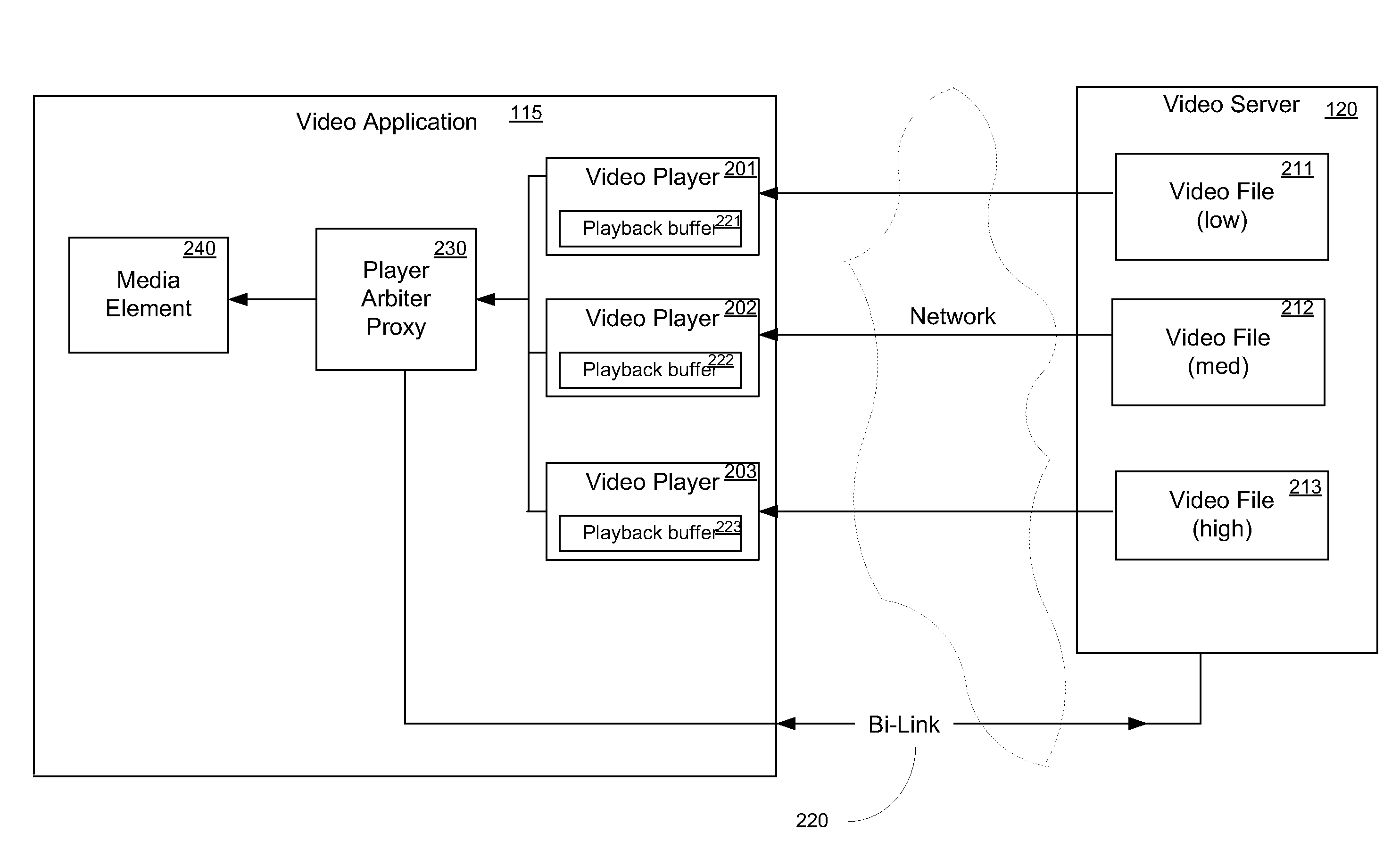
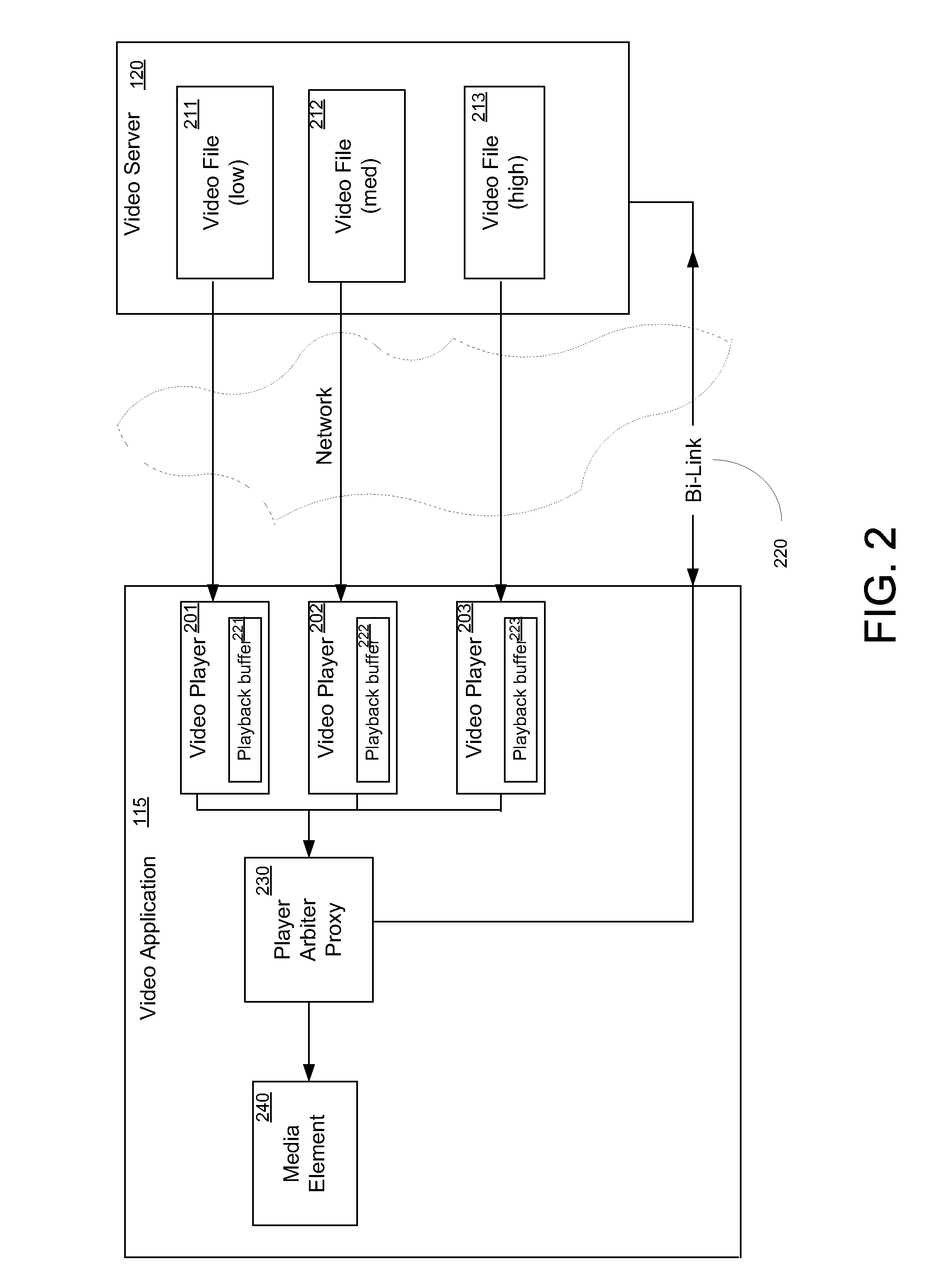
Adaptive video switching for variable network conditions
InactiveUS20090328124A1Color television with pulse code modulationColor television with bandwidth reductionComputer hardwareNetwork conditions
A method for video playback switching in response to changing network conditions. The method includes accessing a server to retrieve respective index files for a low bit rate version and a high bit rate version of the video file, and instantiating a low bit rate media player and a high bit rate media. Playback of the video file is begun by the high bit rate media player streaming the high bit rate version from the server. Upon an indication of impeded network conditions, a transition point is selected, wherein the transition point indicates where downloading of the high bit rate version stops and where downloading of the low bit rate version begins. The low bit rate media player is then positioned to begin playback at the transition point. Playback of the video file is then switched to the low bit rate player upon encountering the transition point.
Owner:MICROSOFT TECH LICENSING LLC
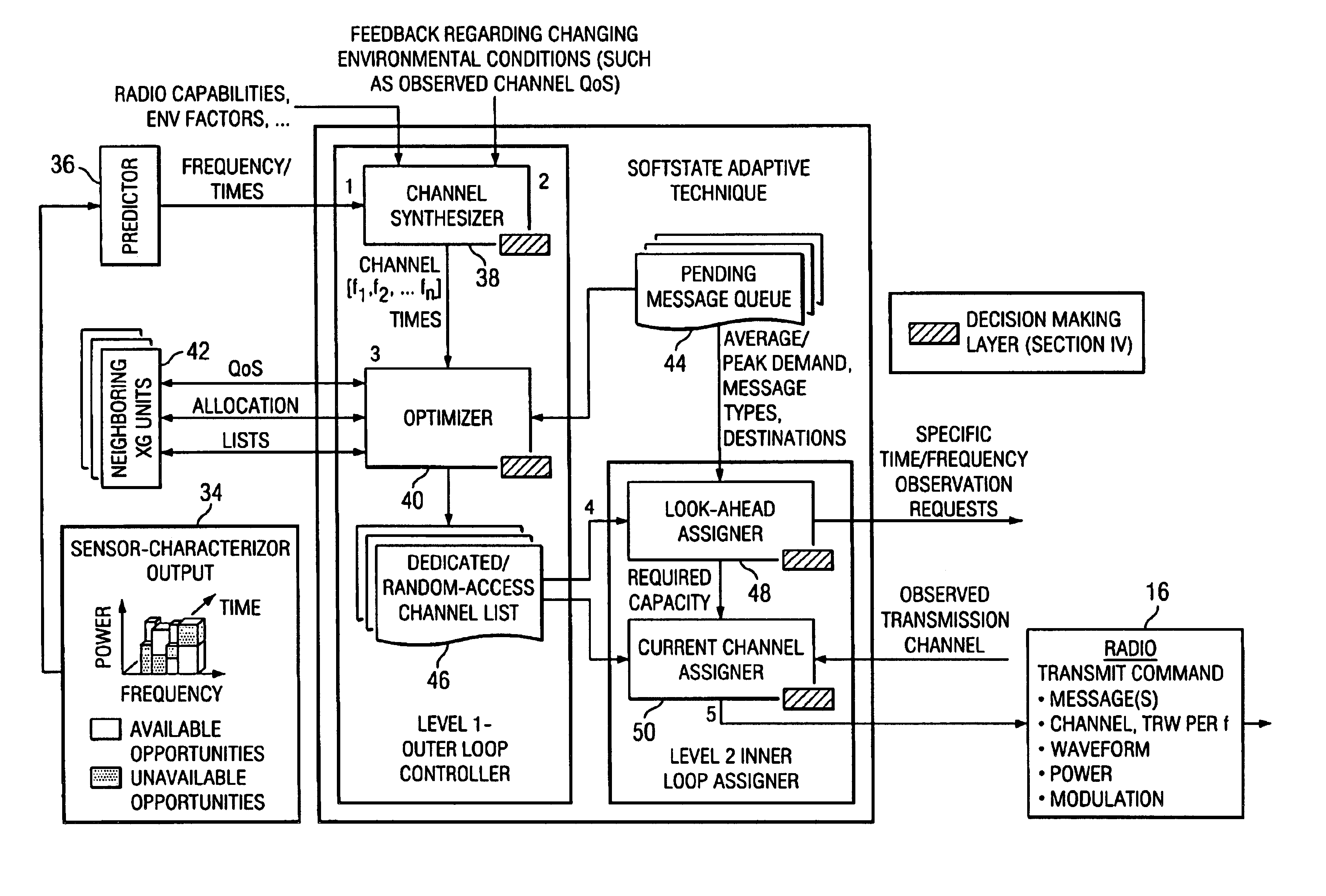
Dynamic wireless resource utilization
InactiveUS6990087B2Increase profitImprove efficiencyNetwork traffic/resource managementTime-division multiplexTelecommunicationsResource utilization
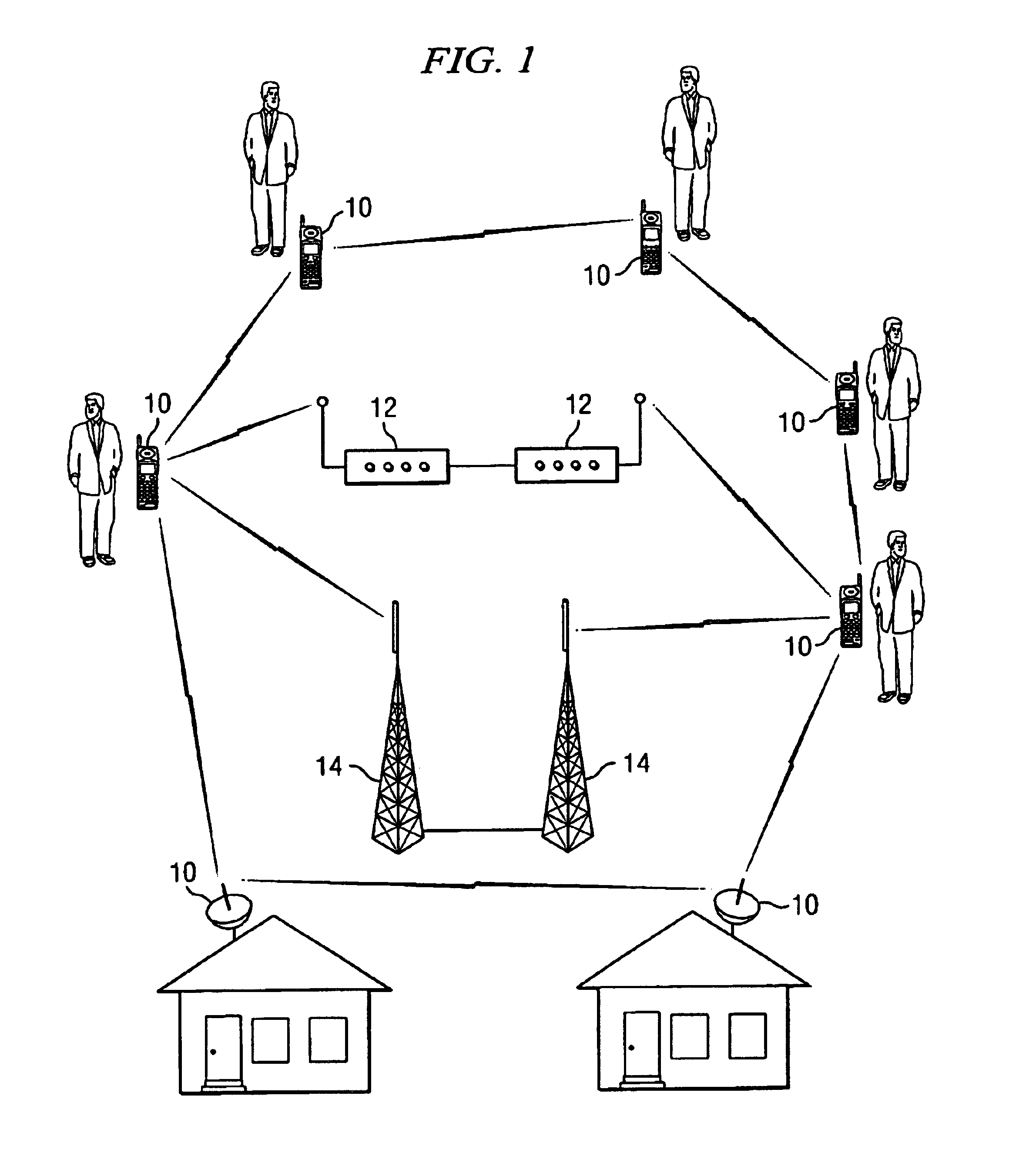
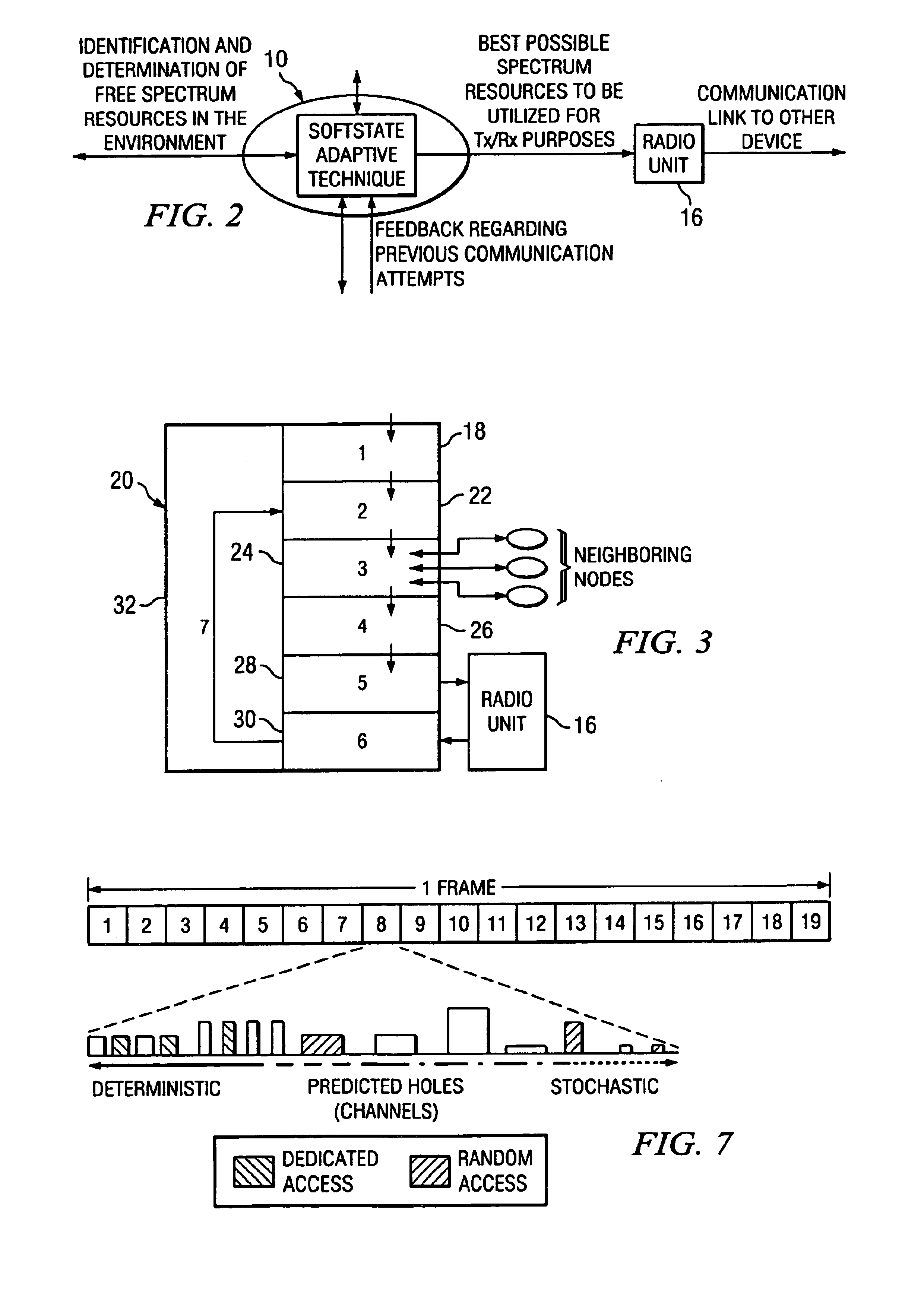
In one embodiment, a method for dynamic wireless resource utilization includes monitoring a wireless communication resource; generating wireless communication resource data; using the wireless communication resource data, predicting the occurrence of one or more holes in a future time period; generating hole prediction data; using the hole prediction data, synthesizing one or more wireless communication channels from the one or more predicted holes; generating channel synthesis data; receiving data reflecting feedback from a previous wireless communication attempt and data reflecting a network condition; according to the received data and the channel synthesis data, selecting a particular wireless communication channel from the one or more synthesized wireless communication channels; generating wireless communication channel selection data; using the wireless communication channel selection data, instructing a radio unit to communicate using the selected wireless communication channel; and instructing the radio unit to discontinue use of the selected wireless communication channel after the communication has been completed.
Owner:POWERWAVE COGNITION INC
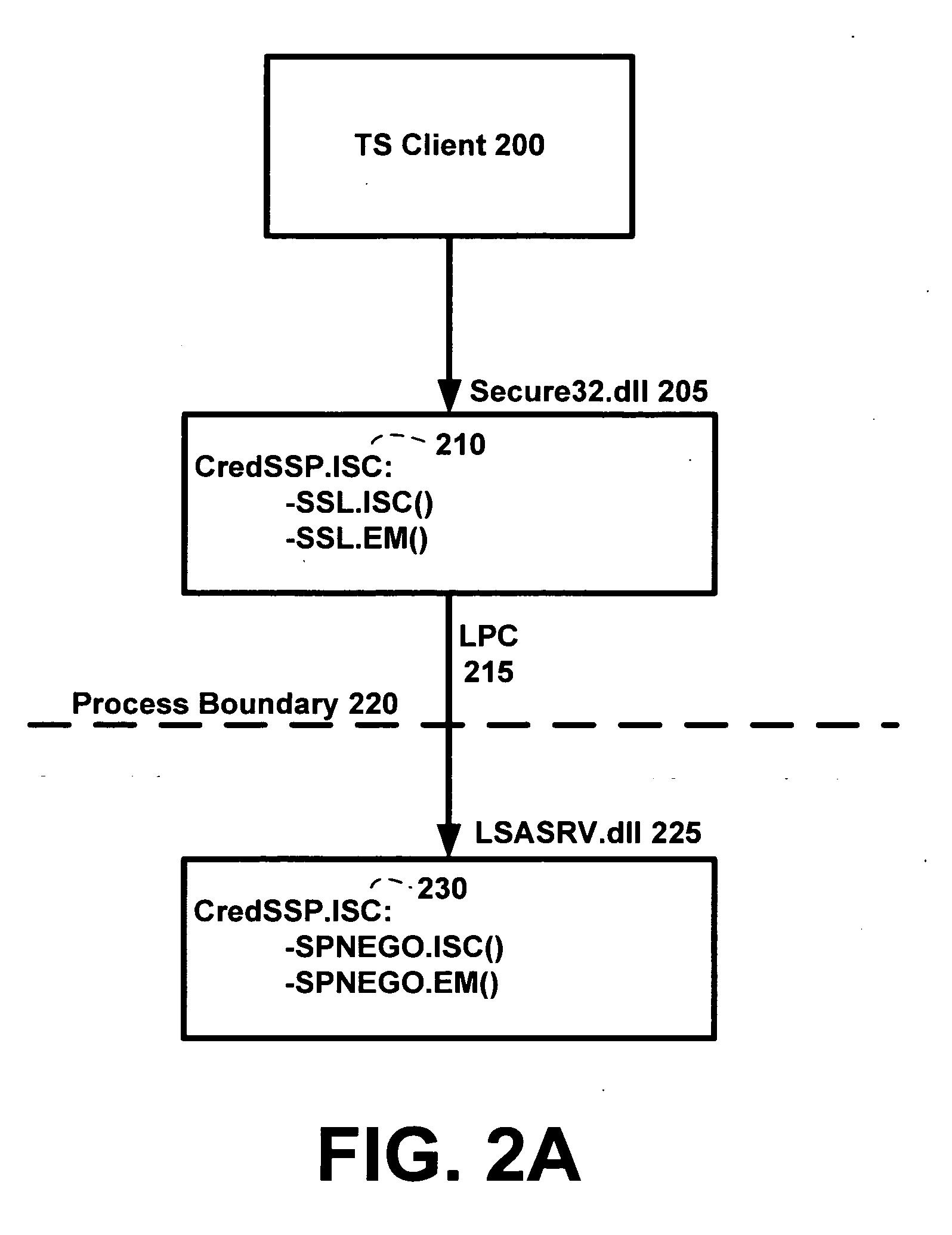
Policy driven, credential delegation for single sign on and secure access to network resources
ActiveUS20070277231A1Wide rangeMemory loss protectionError detection/correctionNetwork conditionsTrust level
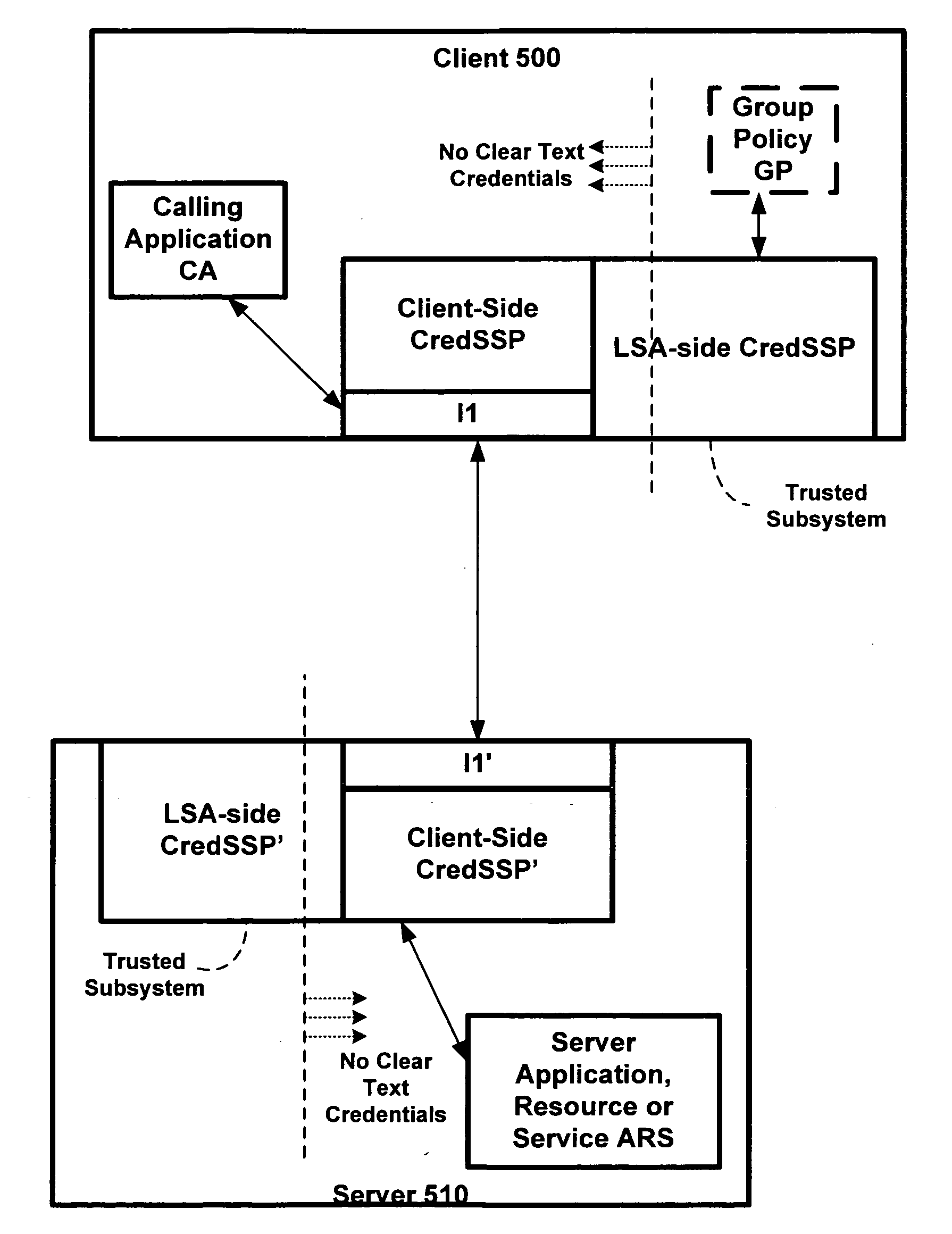
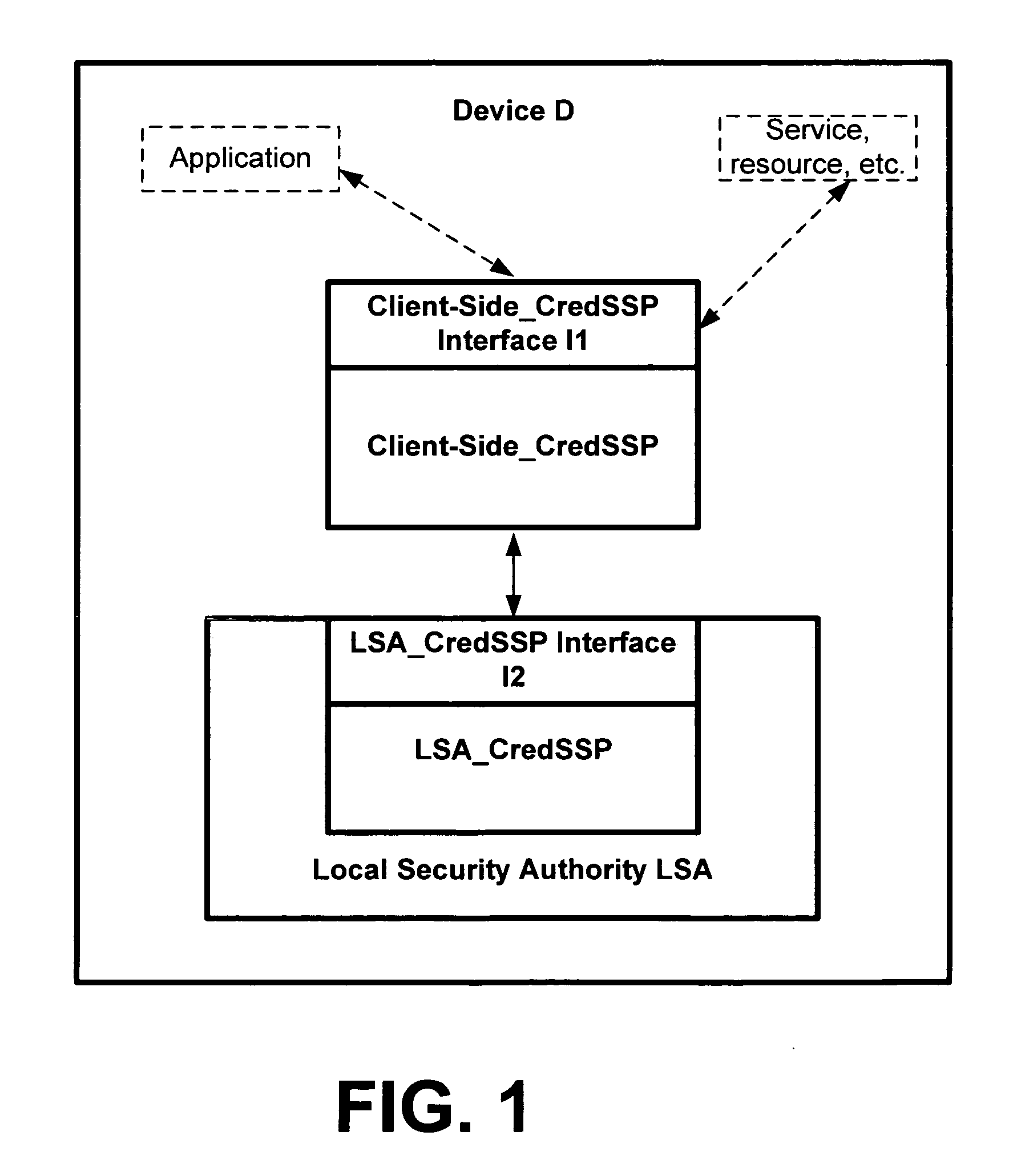
A credential security support provider (Cred SSP) is provided that enables any application to securely delegate a user's credentials from the client, via client side Security Support Provider (SSP) software, to a target server, via server side SSP software in a networked computing environment. The Cred SSP of the invention provides a secure solution that is based in part upon a set of policies, including a default policy that is secure against a broad range of attacks, which are used to control and restrict the delegation of user credentials from a client to a server. The policies can be for any type of user credentials and the different policies are designed to mitigate a broad range of attacks so that appropriate delegation can occur for given delegation circumstances, network conditions, trust levels, etc. Additionally, only a trusted subsystem, e.g., a trusted subsystem of the Local Security Authority (LSA), has access to the clear text credentials such that neither the calling application of the Cred SSP APIs on the server side nor the calling application of the Cred SSP APIs on the client side have access to clear text credentials.
Owner:MICROSOFT TECH LICENSING LLC
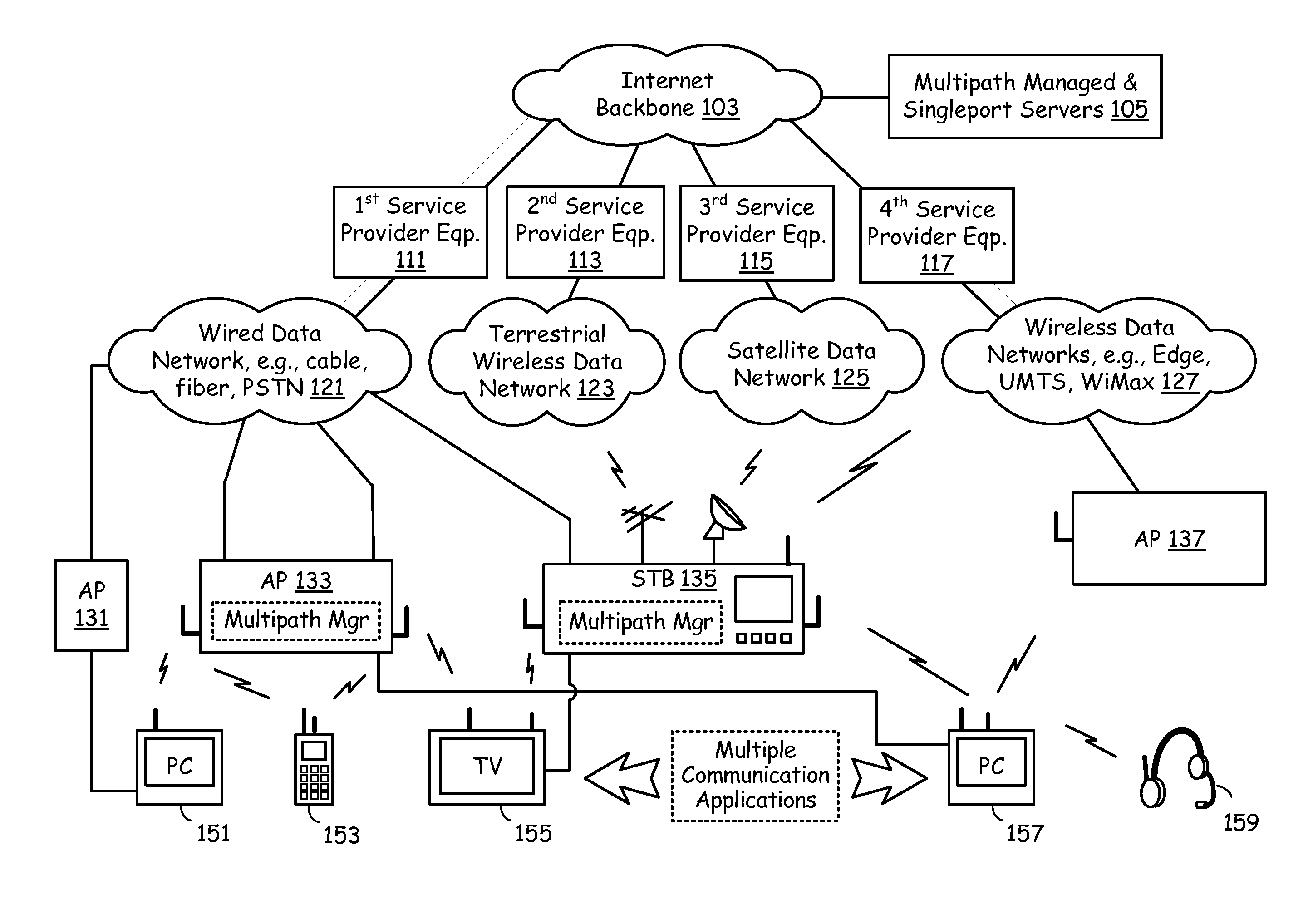
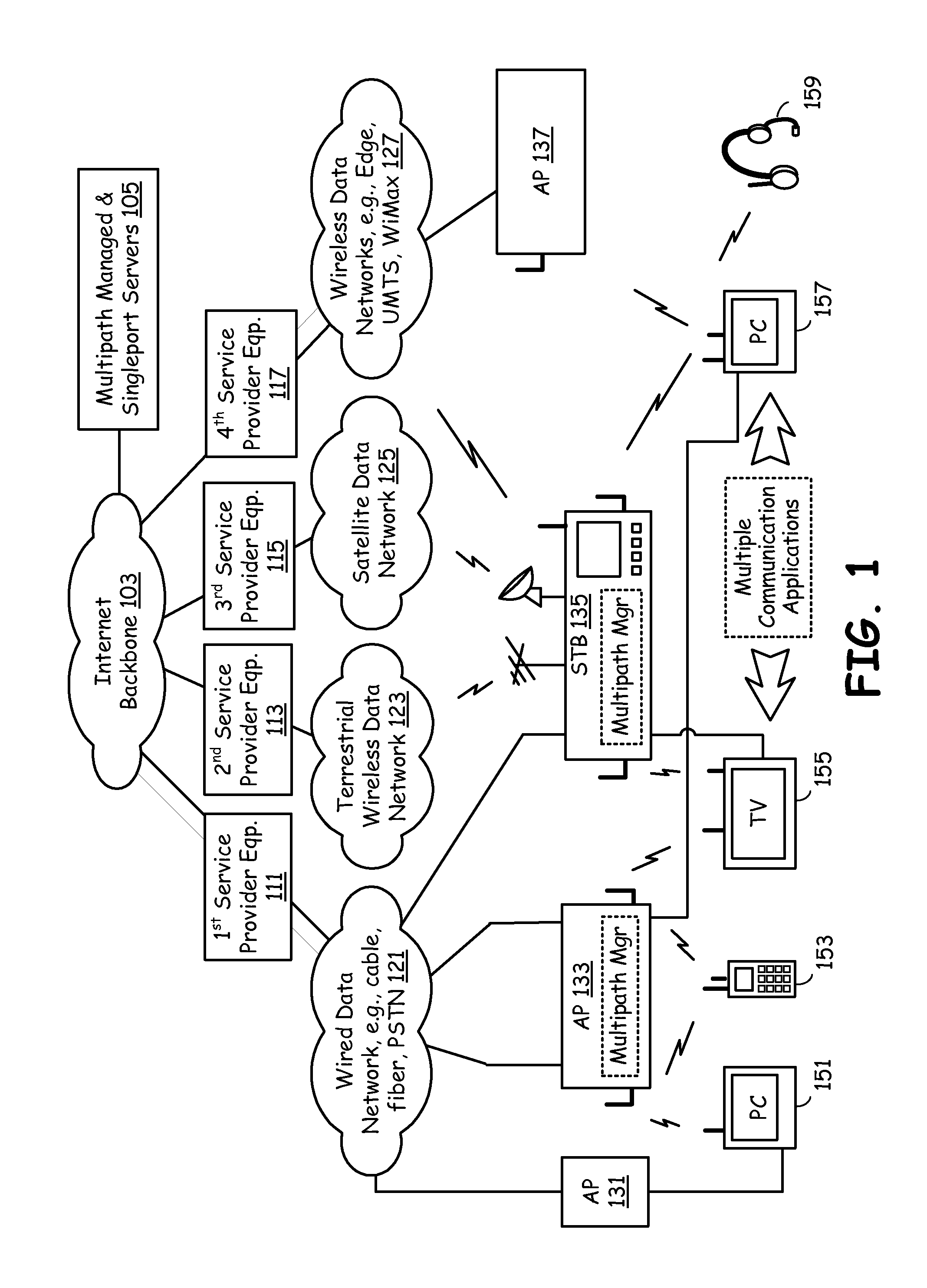
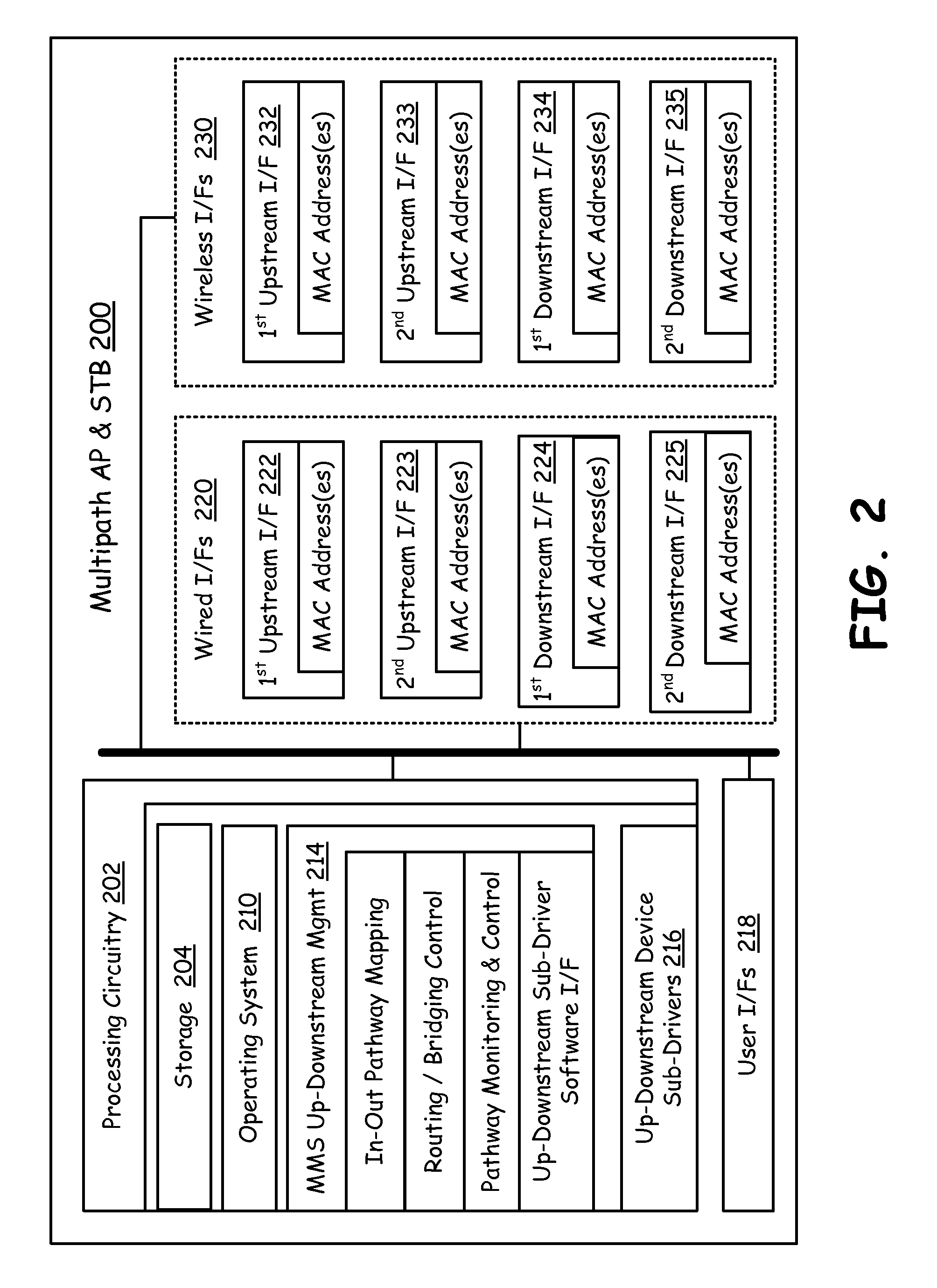
Network nodes cooperatively routing traffic flow amongst wired and wireless networks
InactiveUS20110110309A1Wireless commuication servicesData switching networksWireless mesh networkNetwork conditions
End-point devices, access points and other types of network nodes each employ multi-path management software to manage communication via multiple possible paths to the Internet backbone from communication applications that run on an end-point device. The multi-path management software on an end-point device may operate independently and / or cooperate with the local communication applications and the multi-path management software located on the access points or other network nodes to select one or more pathways for the local communication applications. The multi-path management software depending on data types and data requirements also supports selection and maintenance of two or more paths that simultaneously serve a single communication application. The multi-path management software of an end-point device may pass all or a portion of multi-path management responsibility to a local communication application and / or to multi-path management software of another network node. In addition to managing the selection of one or more pathways, the multi-path management software seamlessly switches pathways as may become necessary to meet changing network conditions or bandwidth demands.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Scalable Secure Wireless Interaction enabling Methods, System and Framework
InactiveUS20120084364A1Avoiding self-configuringConnection securityNetwork topologiesMultiple digital computer combinationsNetwork conditionsOperation mode
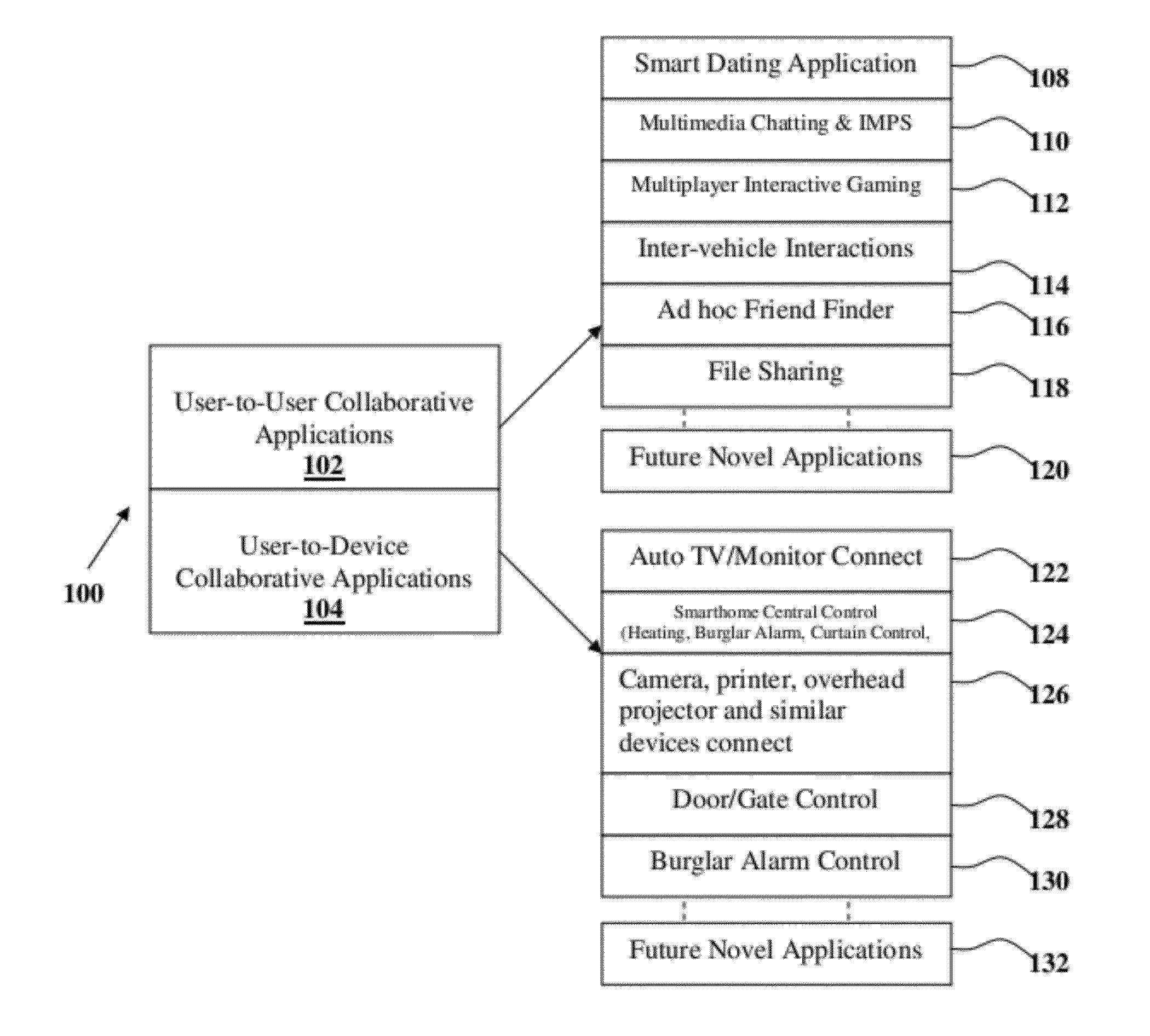
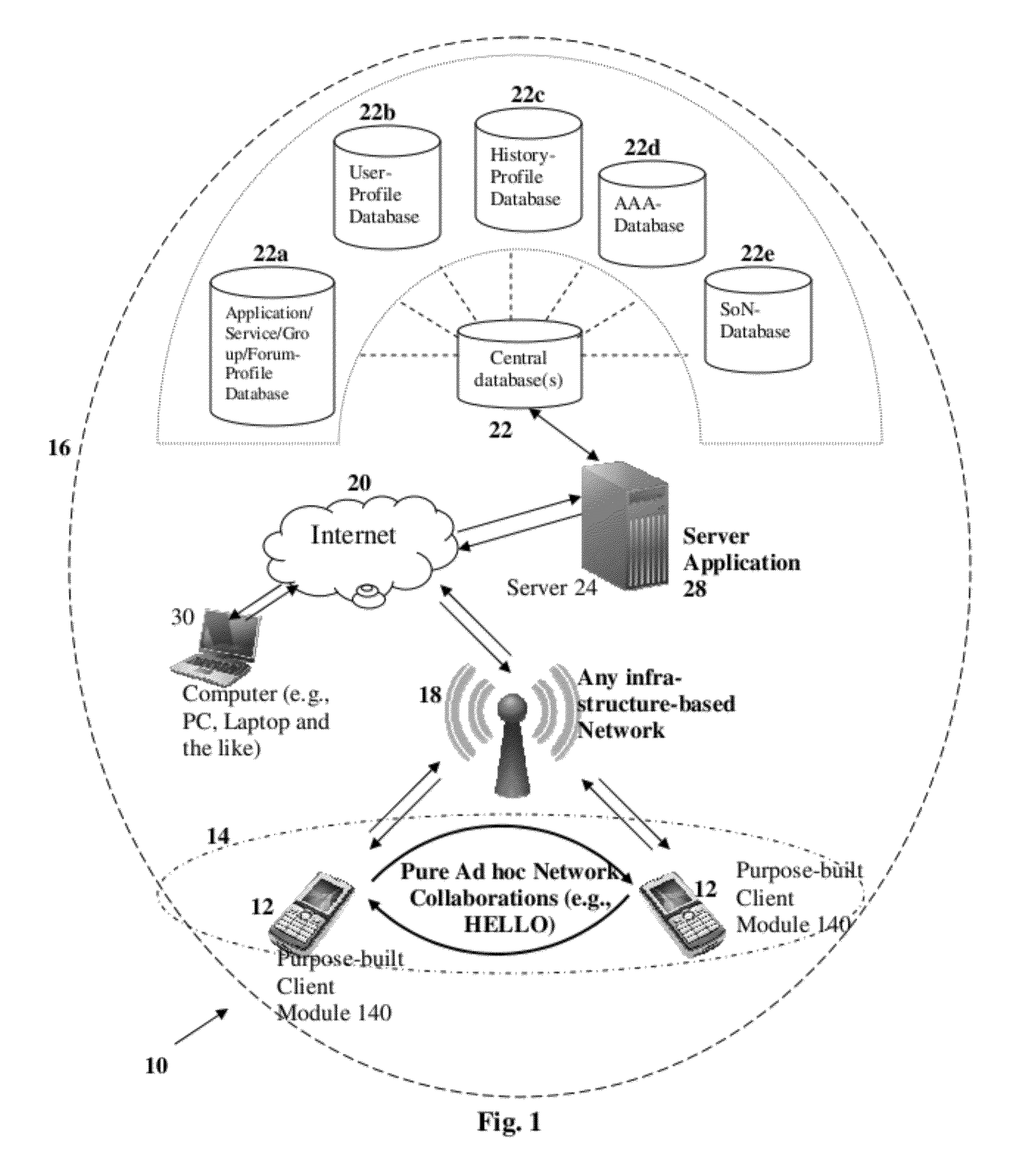
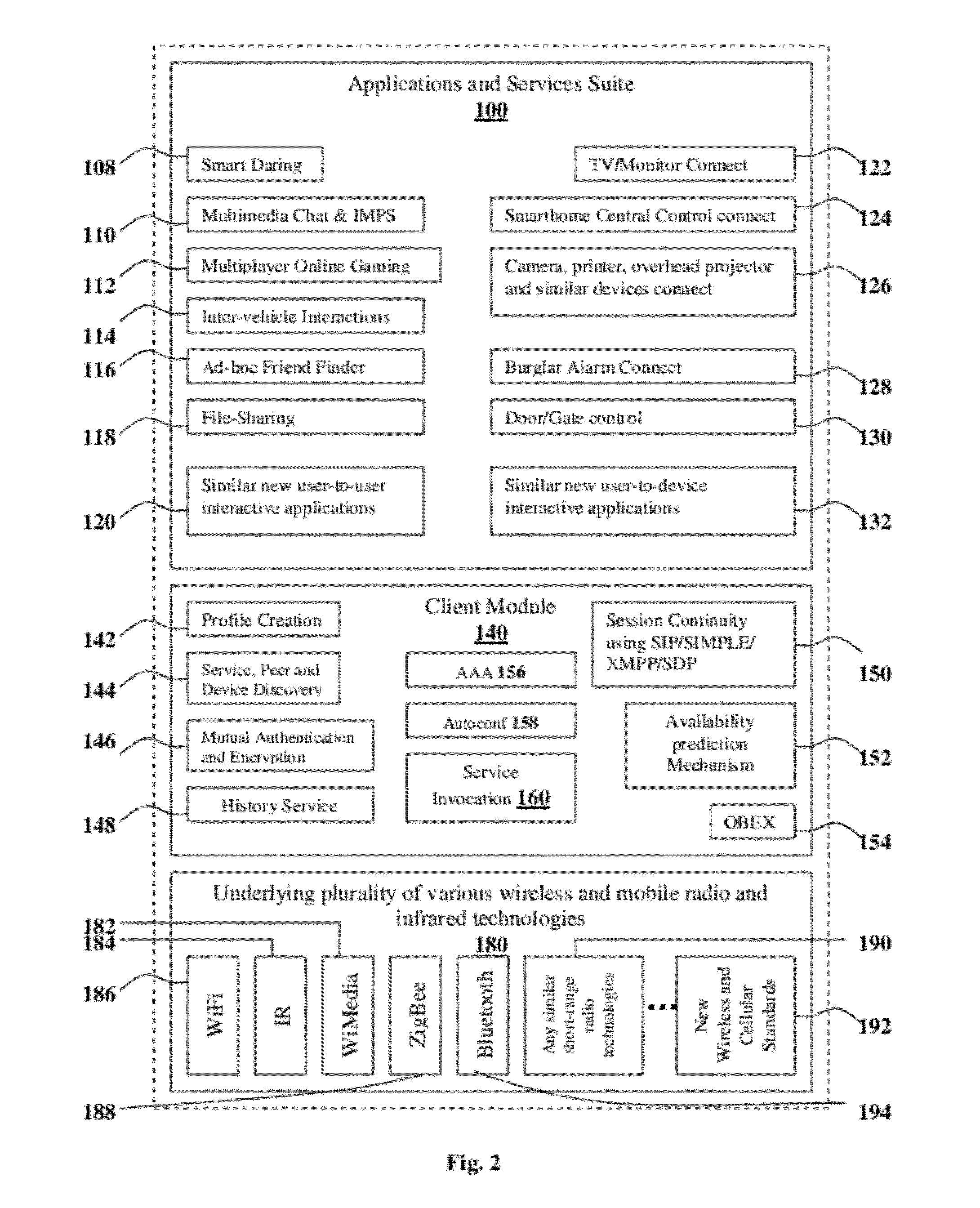
The present invention proposes methodologies, a system and a secure spontaneous collaboration framework along with a suitable application and services suite for enabling new paradigm of social networking among users of handheld devices by bridging gab between infra-structure-based networks and mobile ad hoc networks. While supporting three different operating modes for the spontaneous collaboration that suits the user preference and network conditions, the proposed solutions hide the complexity of finding the right peer / device for spontaneous collaboration, self-organising the network to be formed on-demand, mitigating the security threat, being aware of user mobility for service continuity across wide variety of networks. Binding a given user to user's handheld device and specifying the number of applications / services enabling spontaneous collaborations that a given user is interested in are possible through user-profile creations. By taking a holistic view, the proposed solutions enable very practical, scalable, secure and economical spontaneous collaborations.
Owner:SIVAVAKEESAR SIVAPATHALINGHAM
Telecommunication and multimedia management method and apparatus
InactiveUS8321581B2Telephonic communicationMultiple digital computer combinationsNetwork conditionsMediaFLO
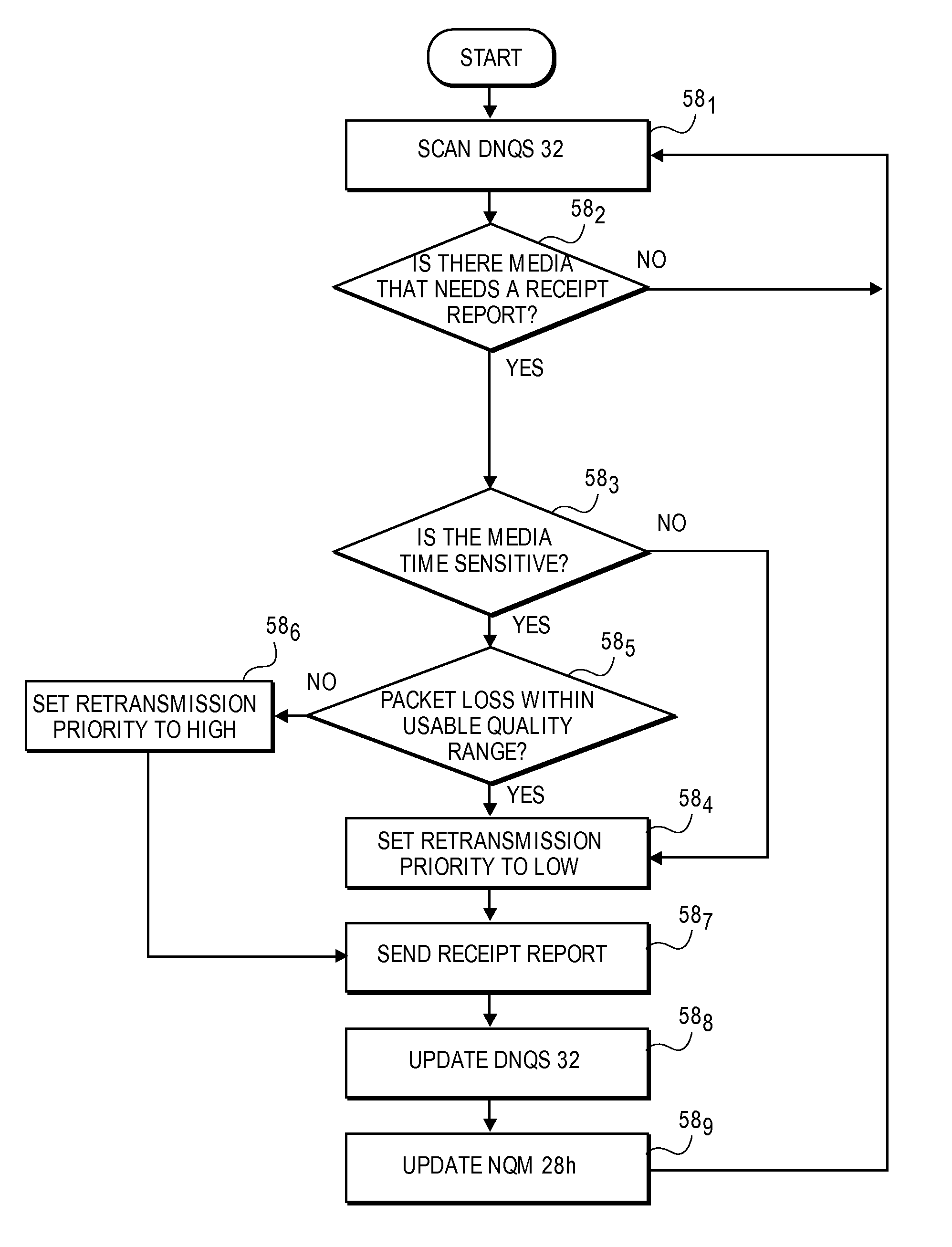
A method for reliably transferring media over a network from a sending node to a receiving node. The method includes ascertaining at the sending node if the media to be transmitted is either time-sensitive or not time-sensitive. For media ascertained as non time-sensitive, the media is transmitted by adjusting the rate of transmission at the sending node based on network conditions. As the non time-sensitive media is received, the receiving node generates one or more low priority requests for the retransmission of any missing non time-sensitive media lost during the transmission. The method also includes transmitting the time-sensitive media from the sending node to the receiving node. As the time-sensitive media is received, the receiving node ascertains if a predetermined acceptable network transmission loss level is met. If met, the receiving node generates one or more low priority requests for the retransmission of any missing time-sensitive media lost during transmission. The sending node retransmits the missing time-sensitive and non time-sensitive media in response to the low priority requests when bandwidth on the network becomes available in excess of what is needed for the transmission of time-sensitive media.
Owner:VOXER IP
Dynamic deployment of services in a computing network
InactiveUS20020178254A1Improve efficiencyMore efficient web hosting sitesResource allocationMultiple digital computer combinationsNetwork conditionsClient-side
Methods, systems, and computer program products for improving network operations by dynamically deploying services (such as web services or other network-accessible services) in a computing network. A process is defined whereby conditions such as usage metrics for incoming client requests (or other network conditions such as load balancing considerations) are monitored, and used to trigger dynamic deployment of web services to locations in the network in order to improve efficiency (e.g. by reducing response time to the client and / or reducing the burden on the back-end computing system resources). Service requests are dynamically routed to the destination where the service resides, in a manner which is transparent to the client. In an optional aspect, programmatic replication of system upgrades may be implemented by redeploying services using this same dynamic deployment approach, enabling the complexity of upgrading previously-deployed software to be reduced significantly. As another optional aspect, previously-deployed software may also be automatically and programmatically undeployed using disclosed techniques.
Owner:IBM CORP
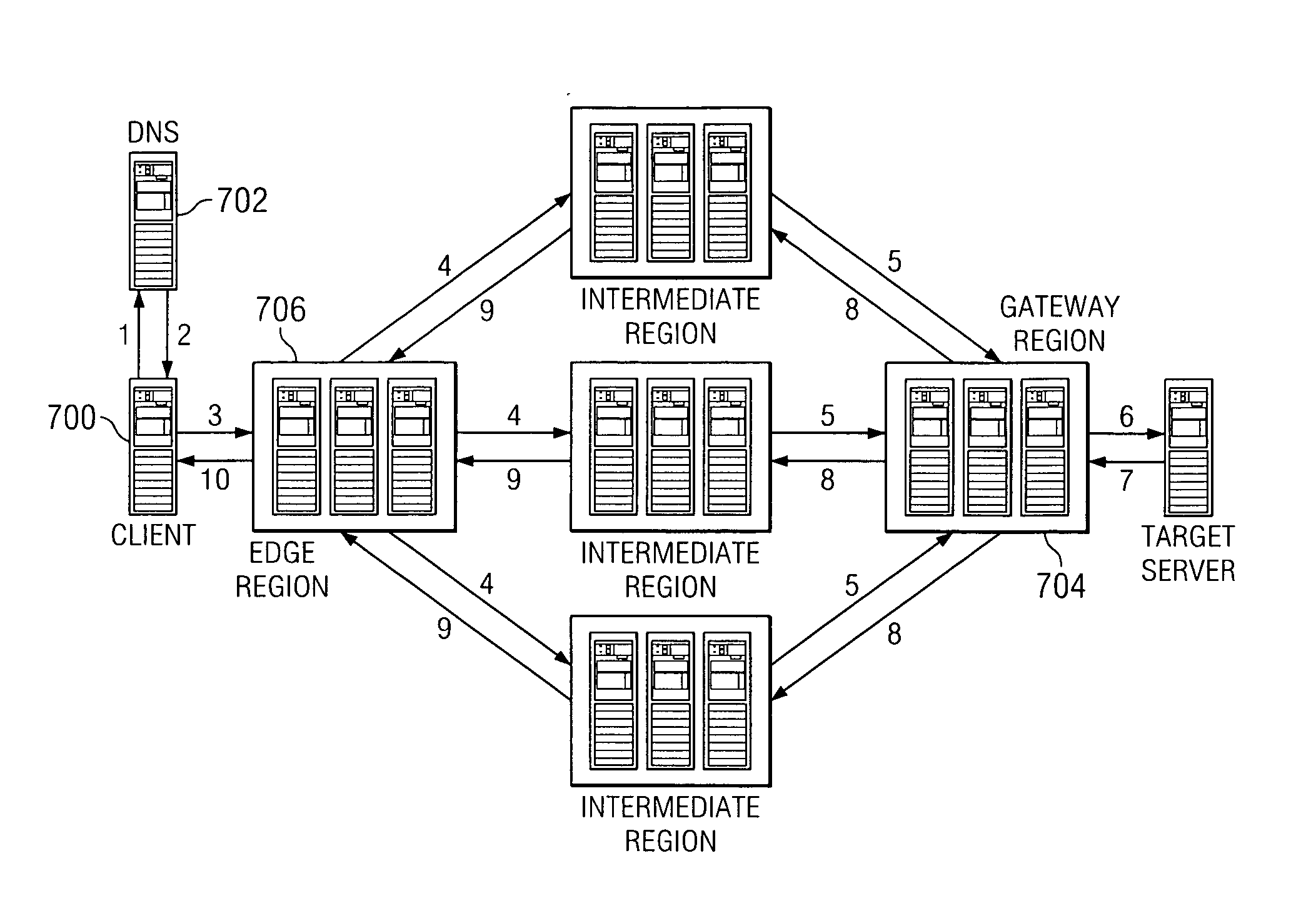
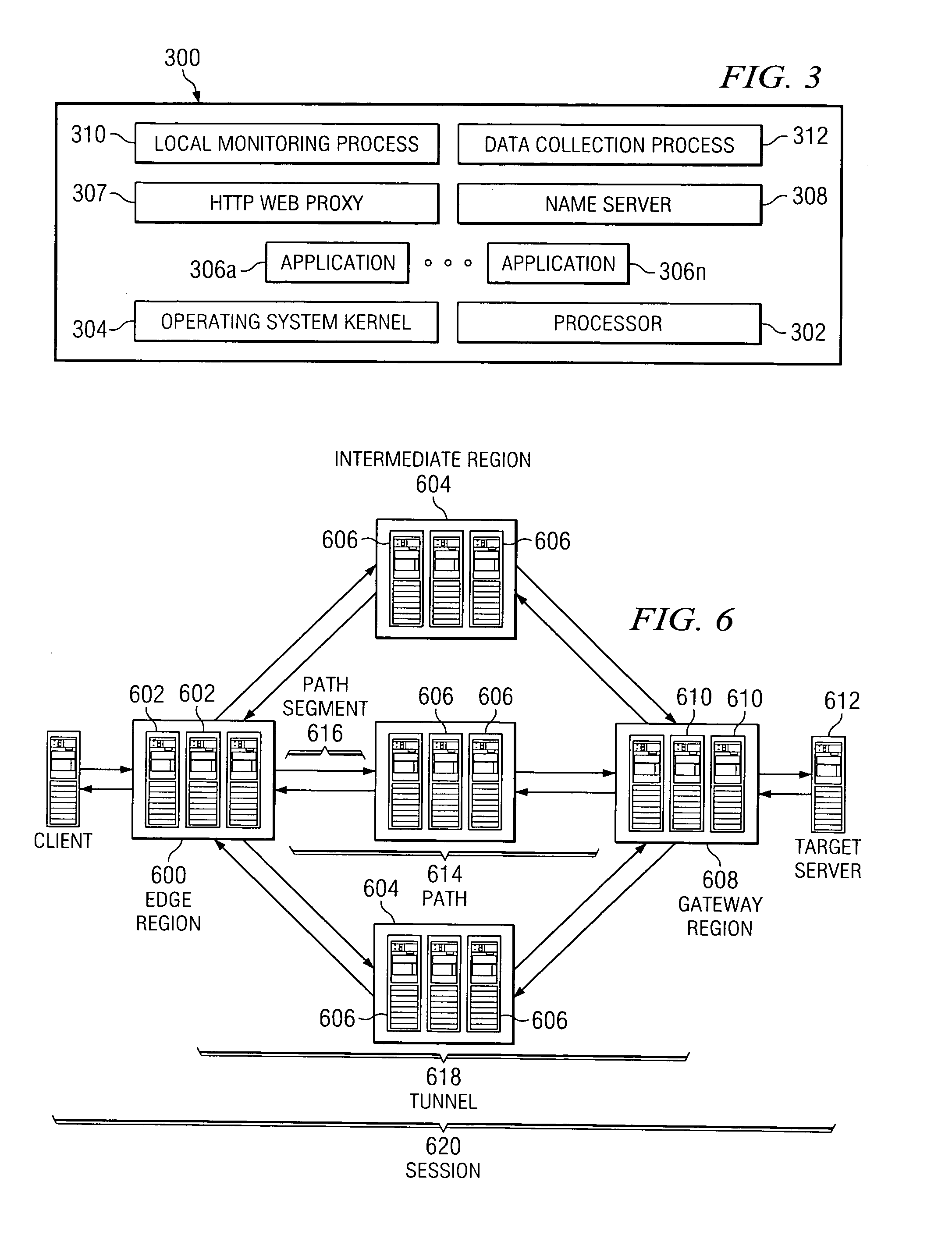
Reliable, high-throughput, high-performance transport and routing mechanism for arbitrary data flows
ActiveUS20070153782A1Minimum delayImprove performanceTime-division multiplexData switching by path configurationData streamEdge node
The present invention leverages an existing content delivery network infrastructure to provide a system that enhances performance for any application that uses the Internet Protocol (IP) as its underlying transport mechanism. An overlay network comprises a set of edge nodes, intermediate nodes, and gateway nodes. This network provides optimized routing of IP packets. Internet application users can use the overlay to obtain improved performance during normal network conditions, to obtain or maintain good performance where normal default BGP routing would otherwise force the user over congested or poorly performing paths, or to enable the user to maintain communications to a target server application even during network outages.
Owner:AKAMAI TECH INC
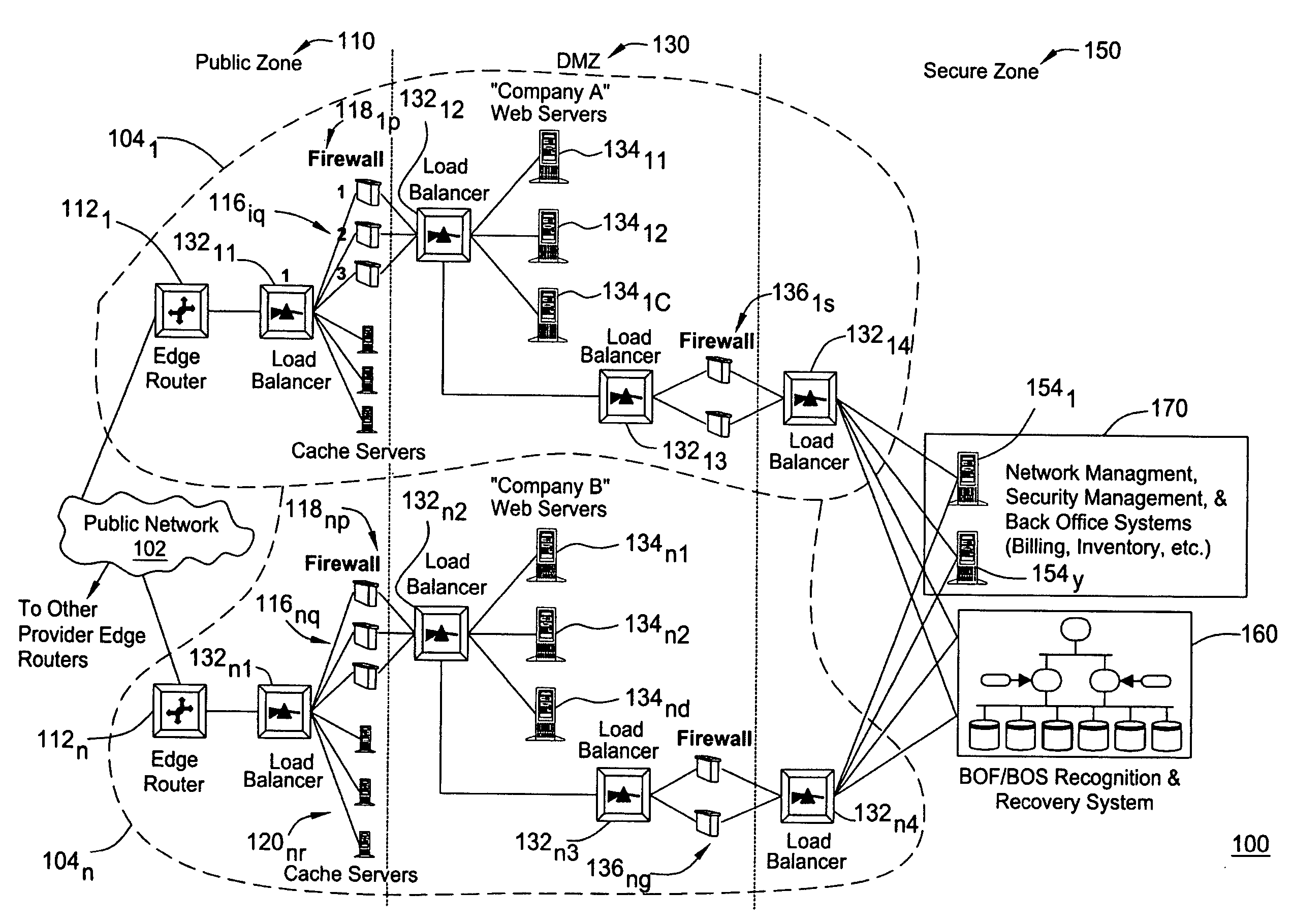
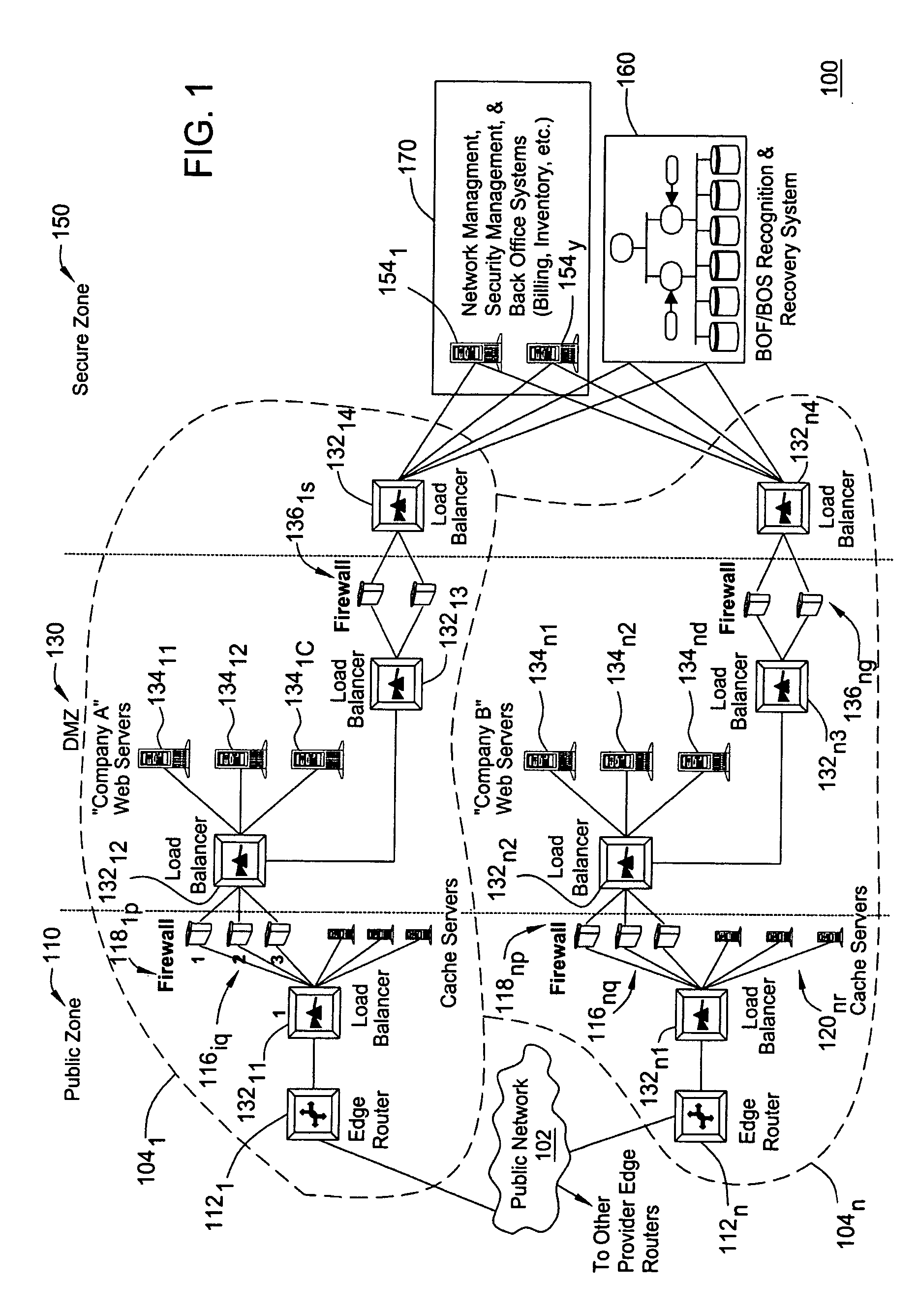
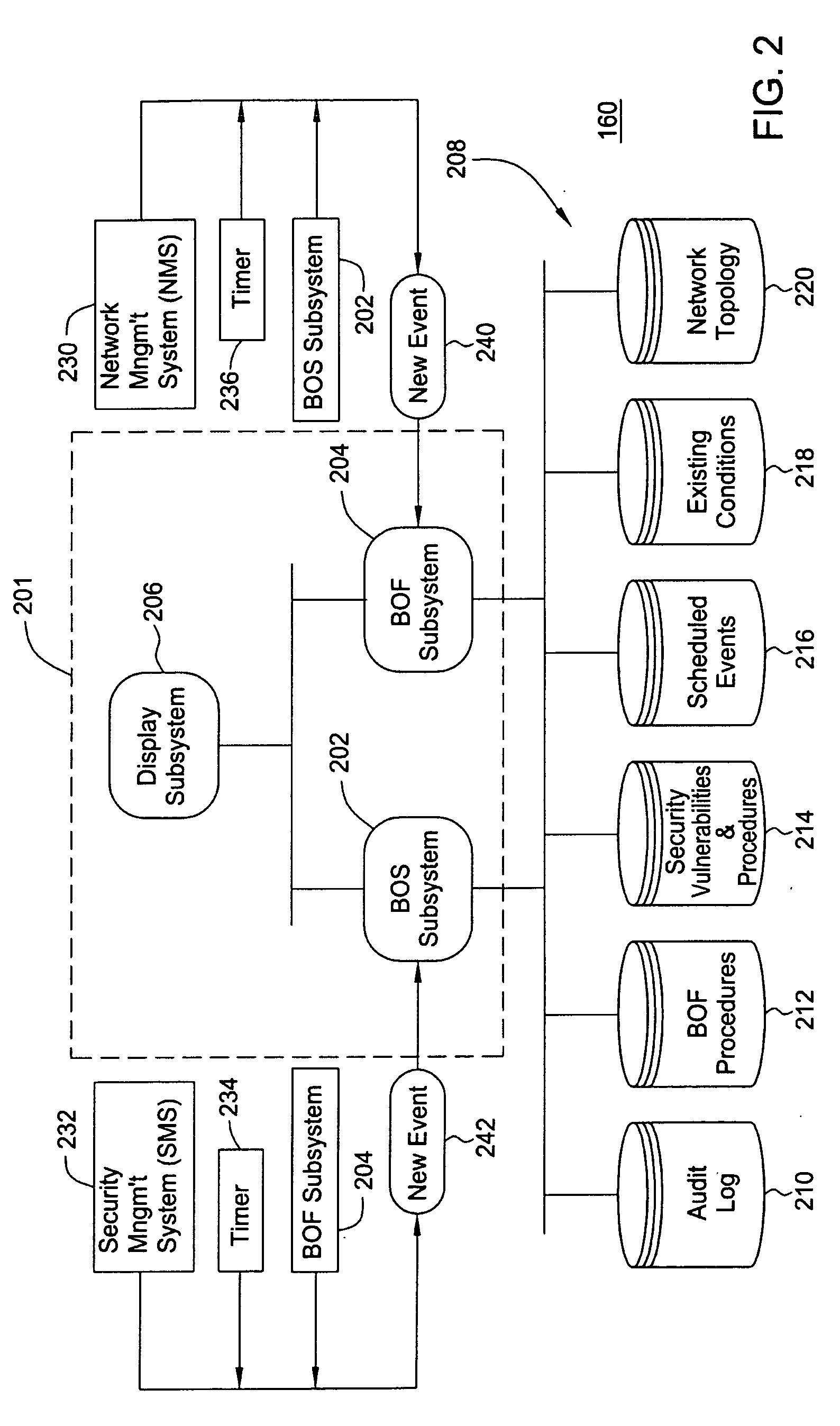
Brink of failure and breach of security detection and recovery system
ActiveUS20050050377A1Reduce the impactAvoid power outagesError detection/correctionTransmissionTelecommunications linkProgram planning
A method and apparatus for managing a network includes detecting occurrence of a network event associated with a new network condition including unplanned and planned macro-events associated with network elements and communication links of the network. The network event is classified as being associated with at least one of a network element failure, communications link failure, and a security breach. In response to the network event exceeding a network degradation threshold, the network event is identified as a network degradation event, and an alert is sent to a network administrator to normalize the network degradation event.
Owner:ALCATEL-LUCENT USA INC +1
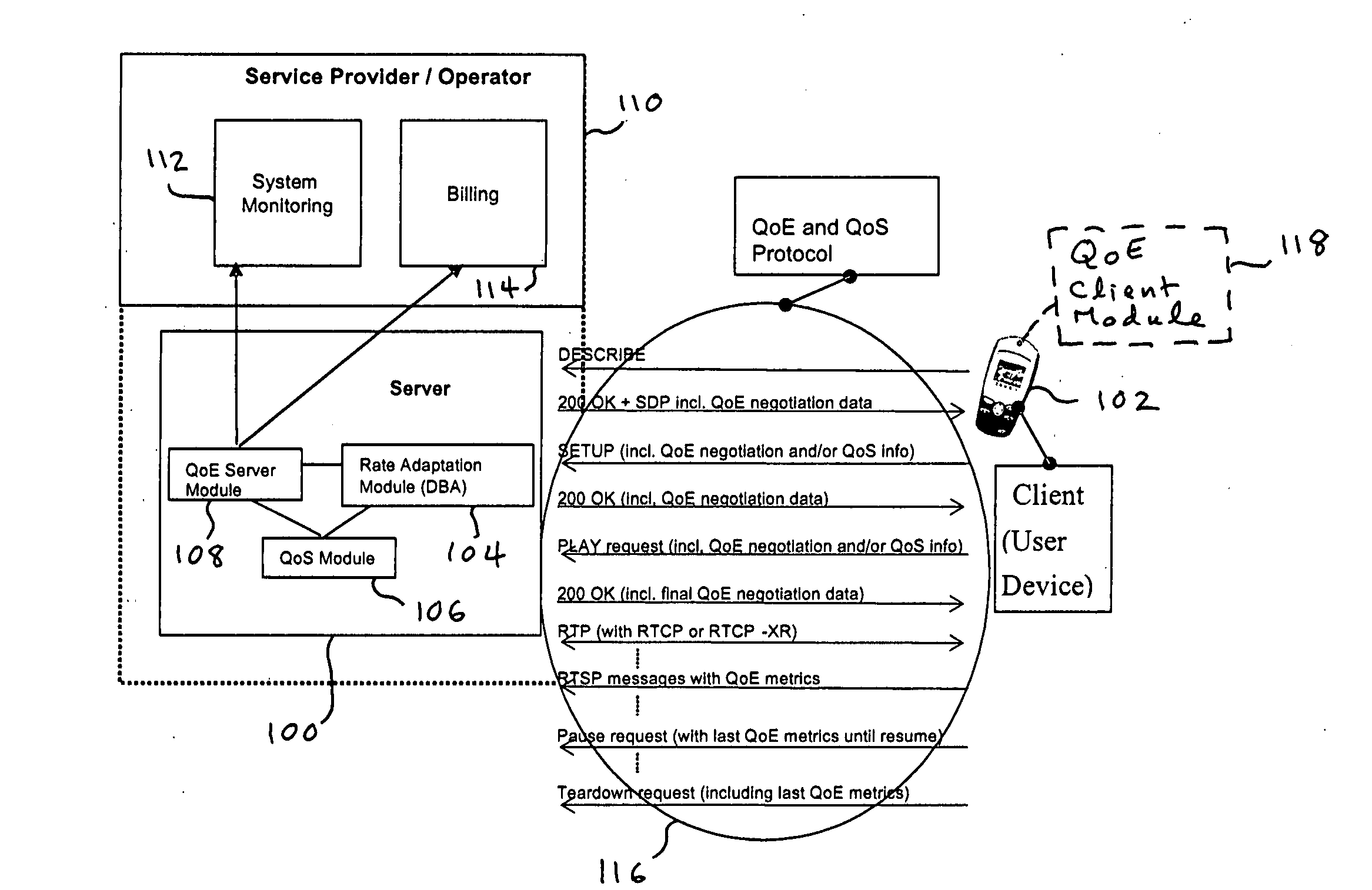
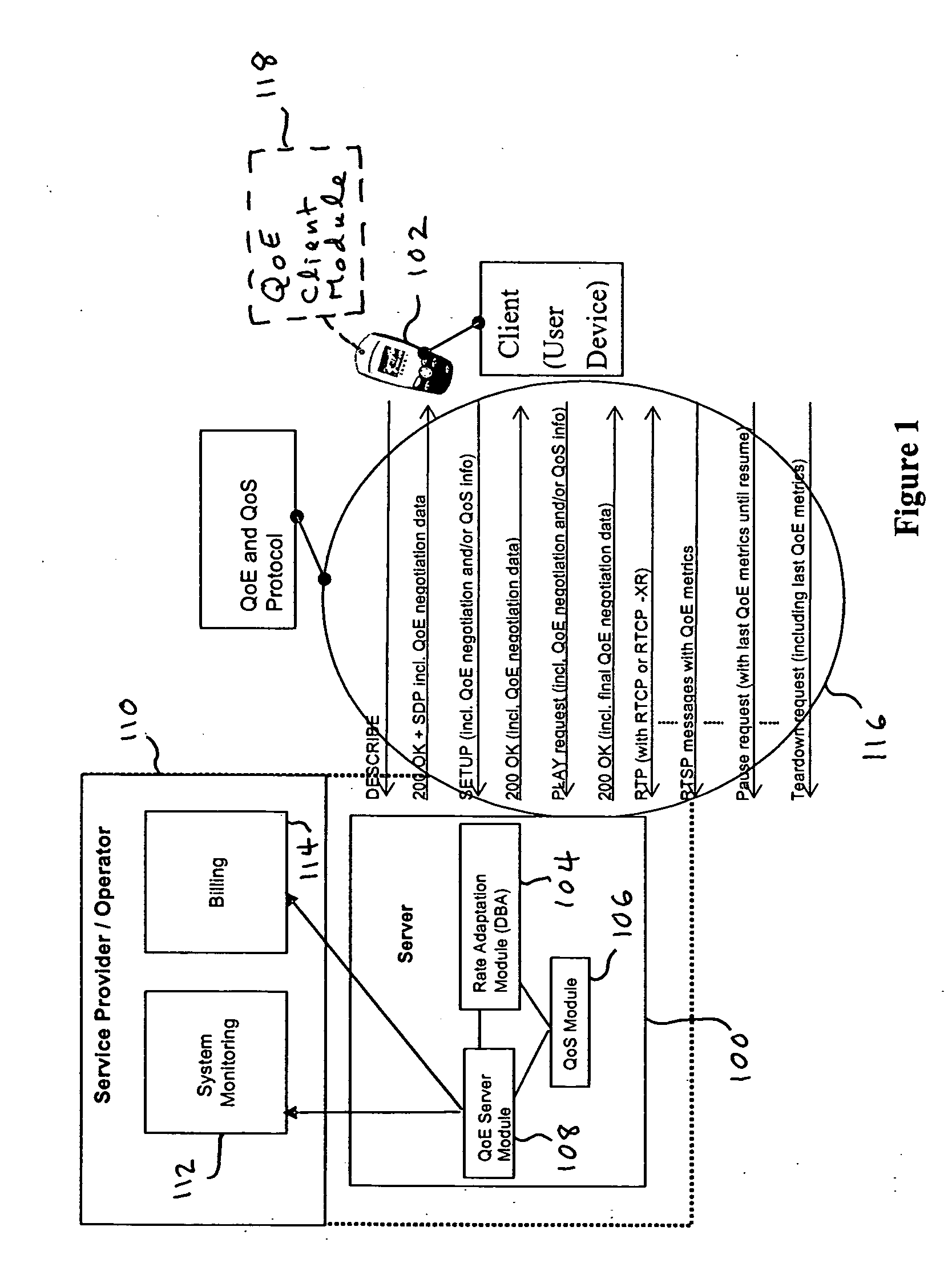
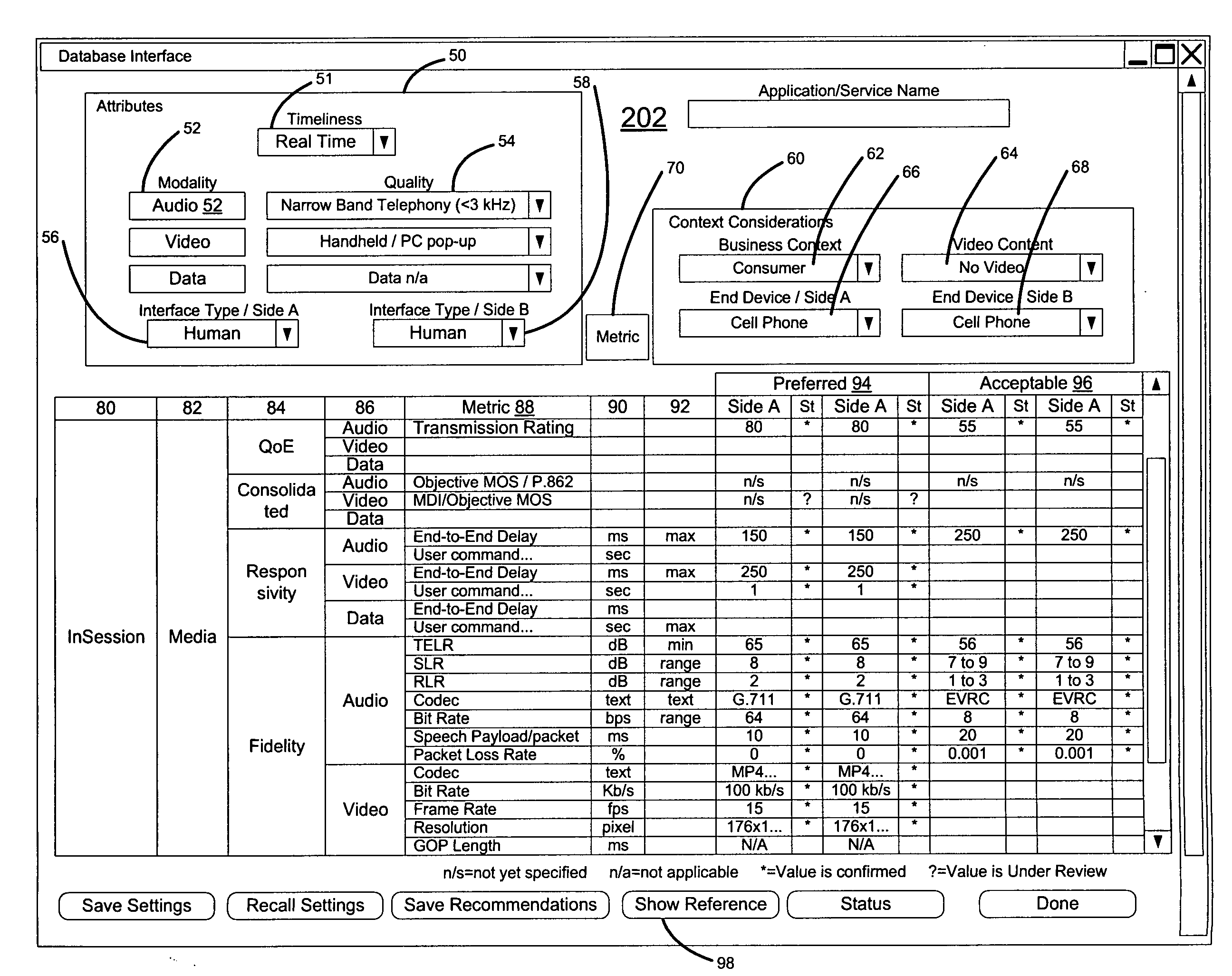
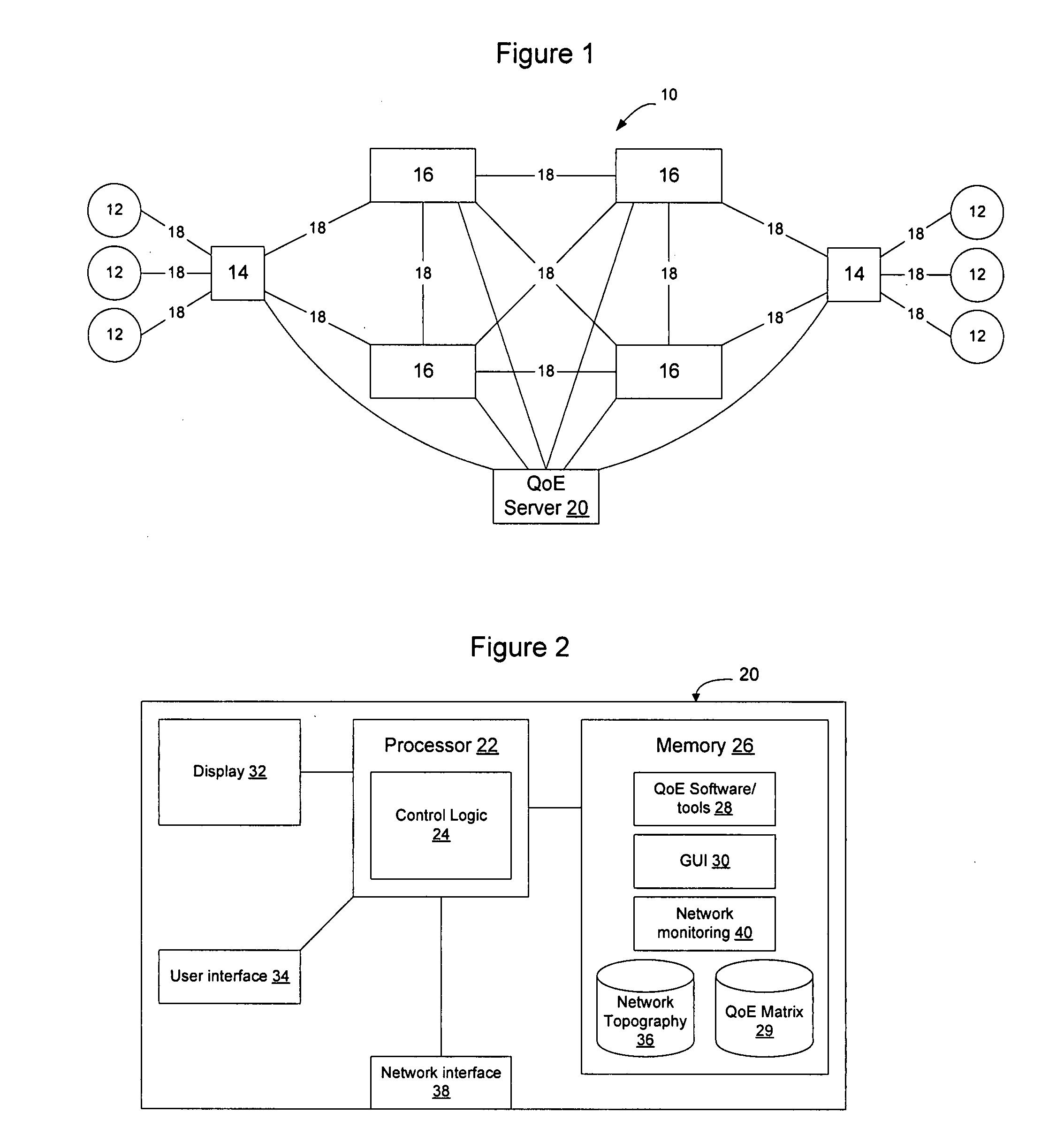
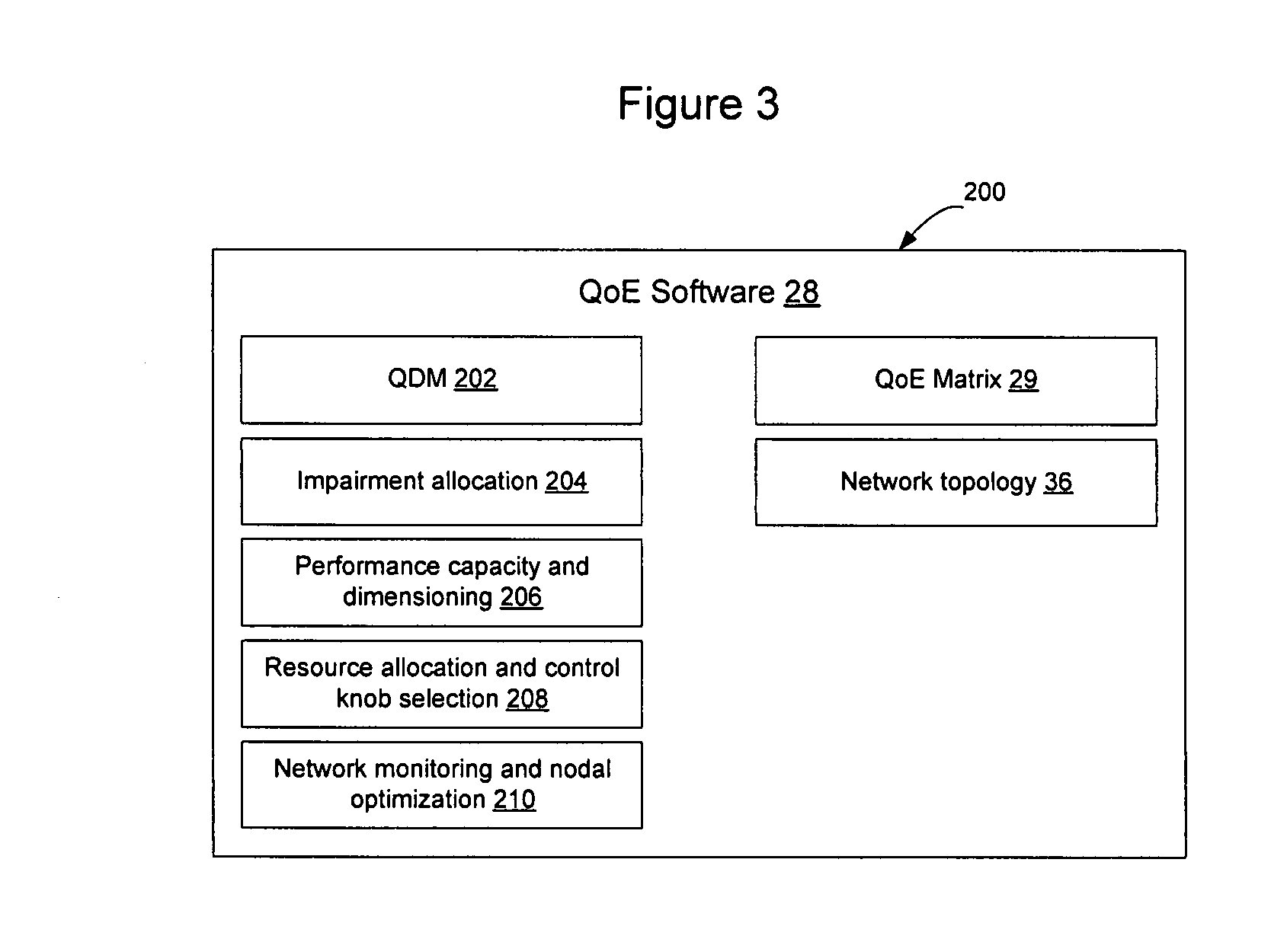
Method and apparatus for designing, updating and operating a network based on quality of experience
A software program or a set of software tools allows end user quality of experience to be quantified and translated into network conditions required to achieve that end user quality of experience. By focusing on the Quality of Experience (QoE) for the applications that will use the network rather than the traditional bottom up approach, and then looking to design the network based on those end user requirements, the network may be designed and / or operated to achieve a high quality of experience. The program and tools may be used at different phases of the networking cycle, including design, planning, deployment, and operational phases, to allow the QoE requirements to be obtained while optimizing network cost and utilization. A QoE server may be implemented off line and used for network design / planning, or may be included on the network to monitor the network and control operation of the network to achieve the intended QoE.
Owner:RPX CLEARINGHOUSE
Adaptive, Application-Aware Selection of Differentiated Network Services
InactiveUS20090182874A1Sacrificing application performanceReduce bandwidth costsDigital computer detailsTransmissionData streamNetwork conditions
Methods, apparatuses and systems that dynamically adjust the selection of differentiated network services for selected classes of traffic in response to changing network conditions or application performance levels. In one implementation, the present invention allows for a differentiated network services scheme that adapts to existing network conditions and, in one implementation, selects higher, generally more expensive classes of differentiated network service for certain data flows when the performance of selected applications degrades below a threshold level. The present invention, in one implementation, allows for bandwidth cost savings without sacrificing application performance.
Owner:CA TECH INC
Method and system for optimized reference signal downlink transmission in a wireless communication system
ActiveUS20080260062A1Reduce MAISignal allocationFrequency-division multiplexCommunications systemNetwork conditions
A method and system optimizes the transmission of a downlink reference signal (DLRS) in a wireless communication system that uses orthogonal division multiple access (OFDMA) for the downlink. Each Node-B (base station) is capable of transmitting the DLRS reference symbols in different subframes of the OFDM radio frame and changing both the number and location of the subframes in response to changing network conditions. The network conditions include the number of terminals being served by the Node-B and multiple access interference (MAI) from adjacent Node-Bs.
Owner:SNAPTRACK
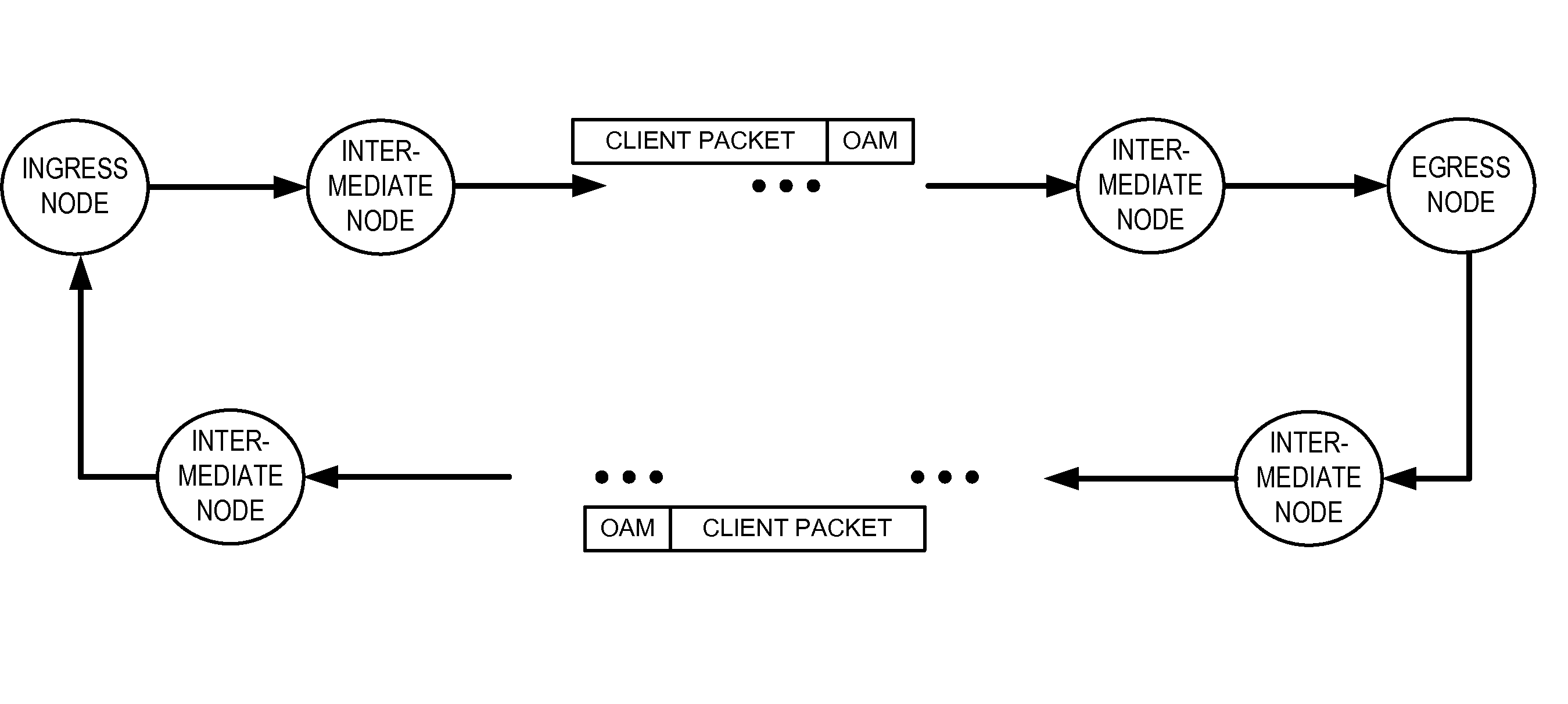
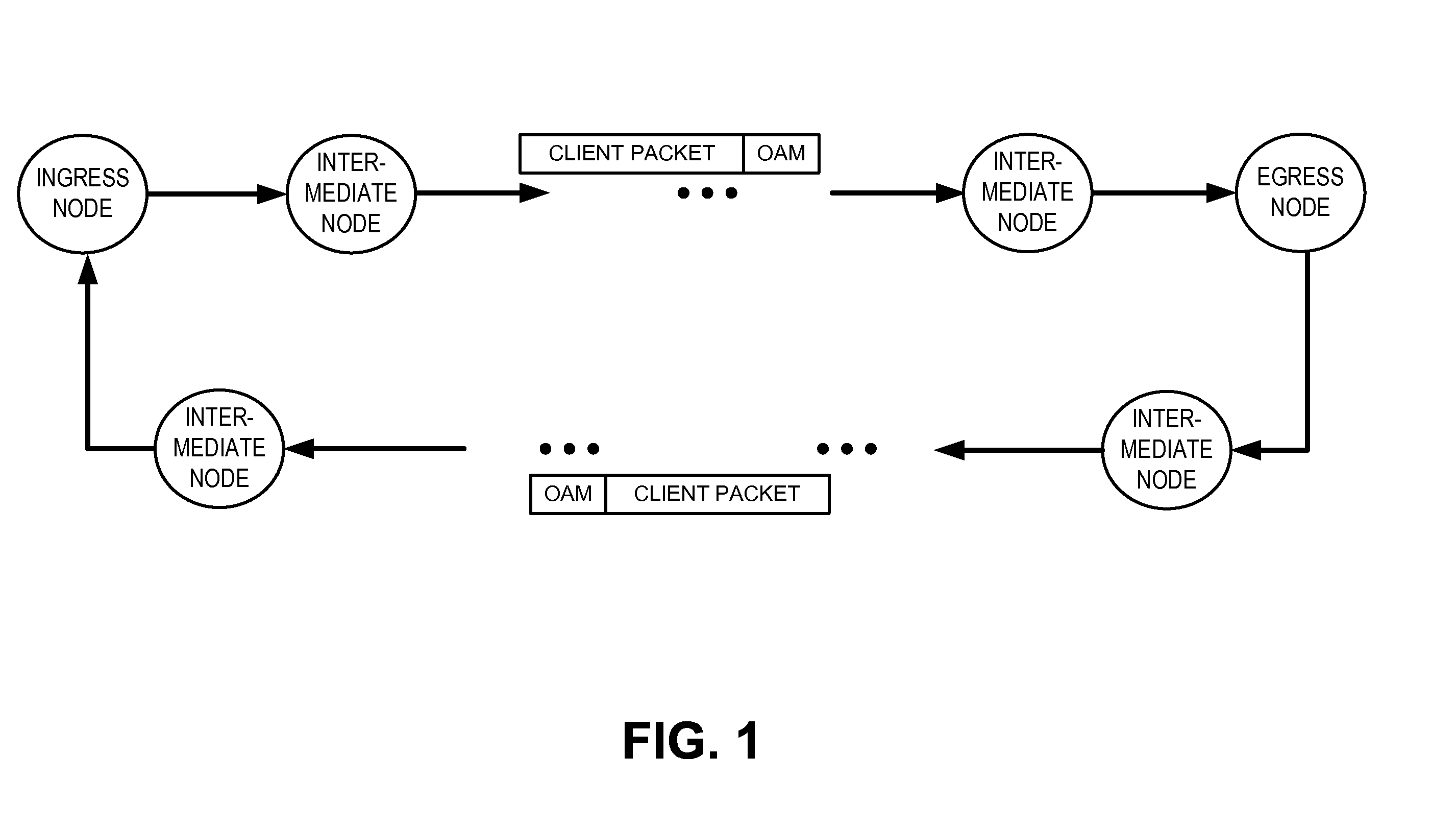
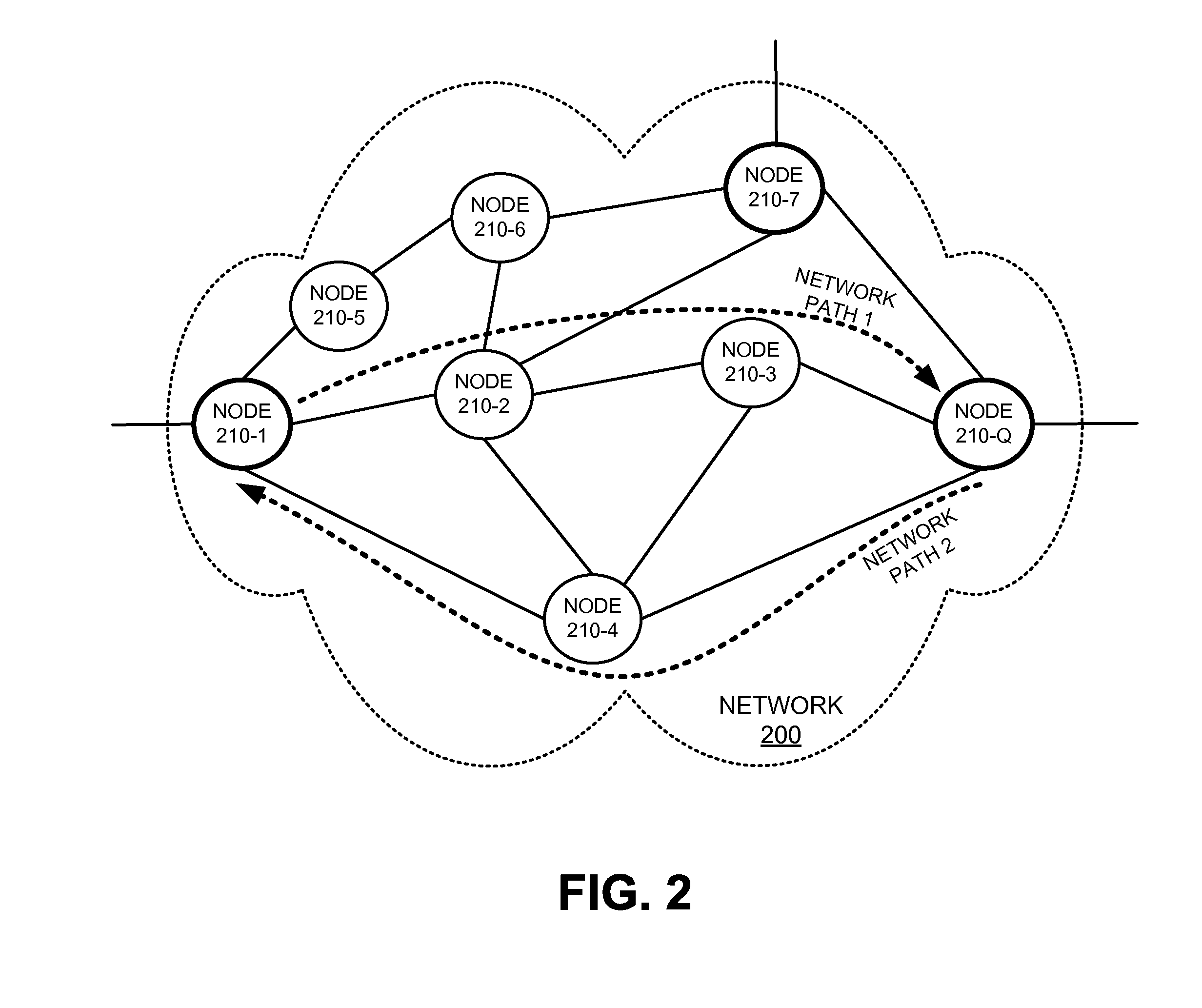
Operations, administration, and management fields for packet transport
Owner:JUMIPER NETWORKS INC
Method and system for monitoring a wireless communications network
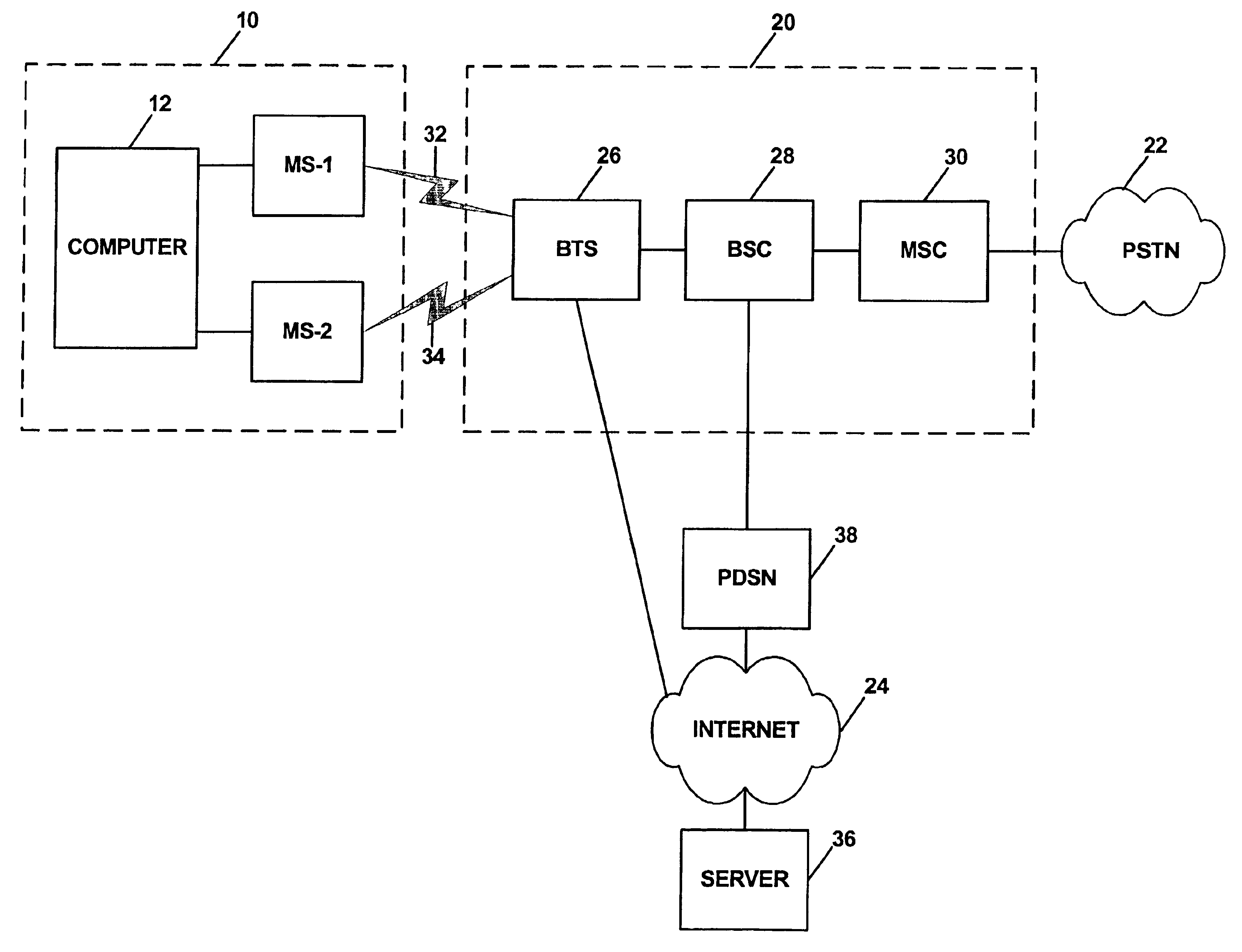
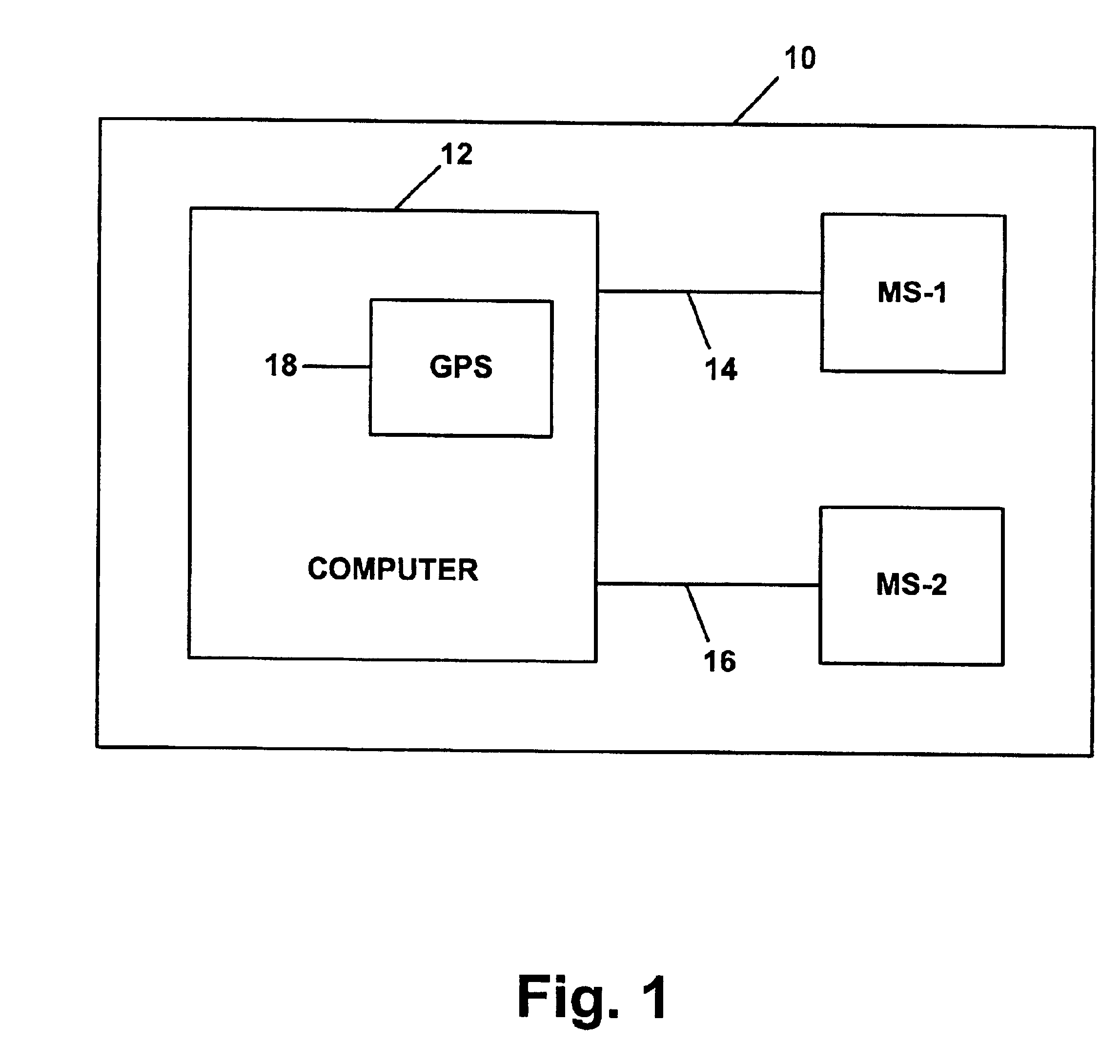
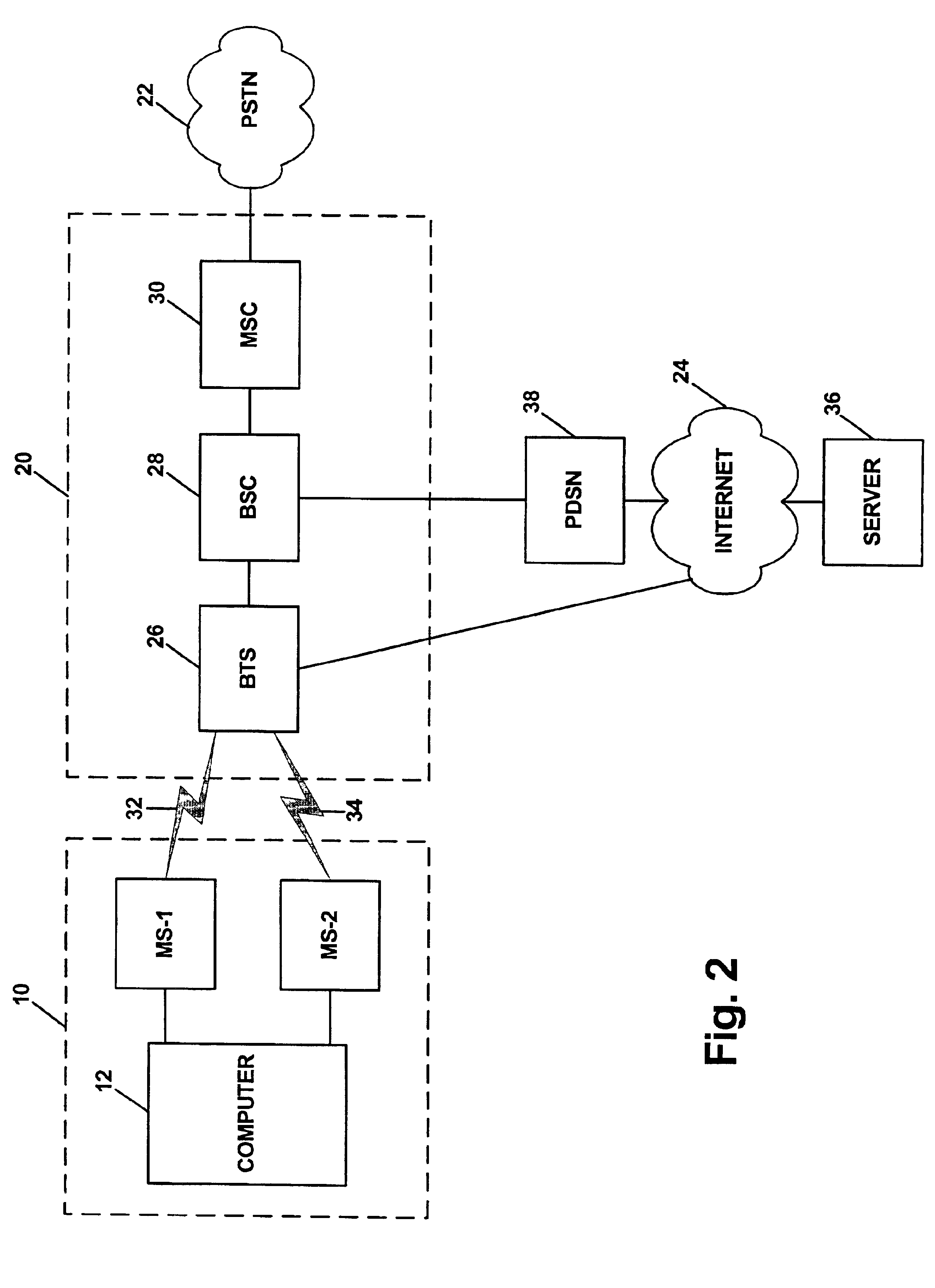
InactiveUS6915128B1Easy to manageImproved MDM arrangementRadio/inductive link selection arrangementsTransmission monitoringDiagnostic dataNetwork conditions
A method and system for monitoring wireless network conditions. Two mobile stations are coupled with a computer. The first mobile station interacts with the network and thereby establishes diagnostic data concerning network conditions. The first mobile station then reports that diagnostic data to the computer. As the computer receives the diagnostic data from the first mobile station, the computer obtains location data indicative of the current location of the first mobile station. The computer then provides the diagnostic data and corresponding location data to the second mobile station, which in turn transmits the data to a remote entity via the wireless communications network. As the remote entity receives the data, the remote entity may generate output reports and alerts as desired. Conveniently, the combination of the mobile stations and computer may be mounted in a vehicle and carried around a geographic area, so as to automatically report diagnostic data to the remote entity from a variety of locations.
Owner:SPRING SPECTRUM LP
Enhanced cross-network handoff for mobile IP service mobility
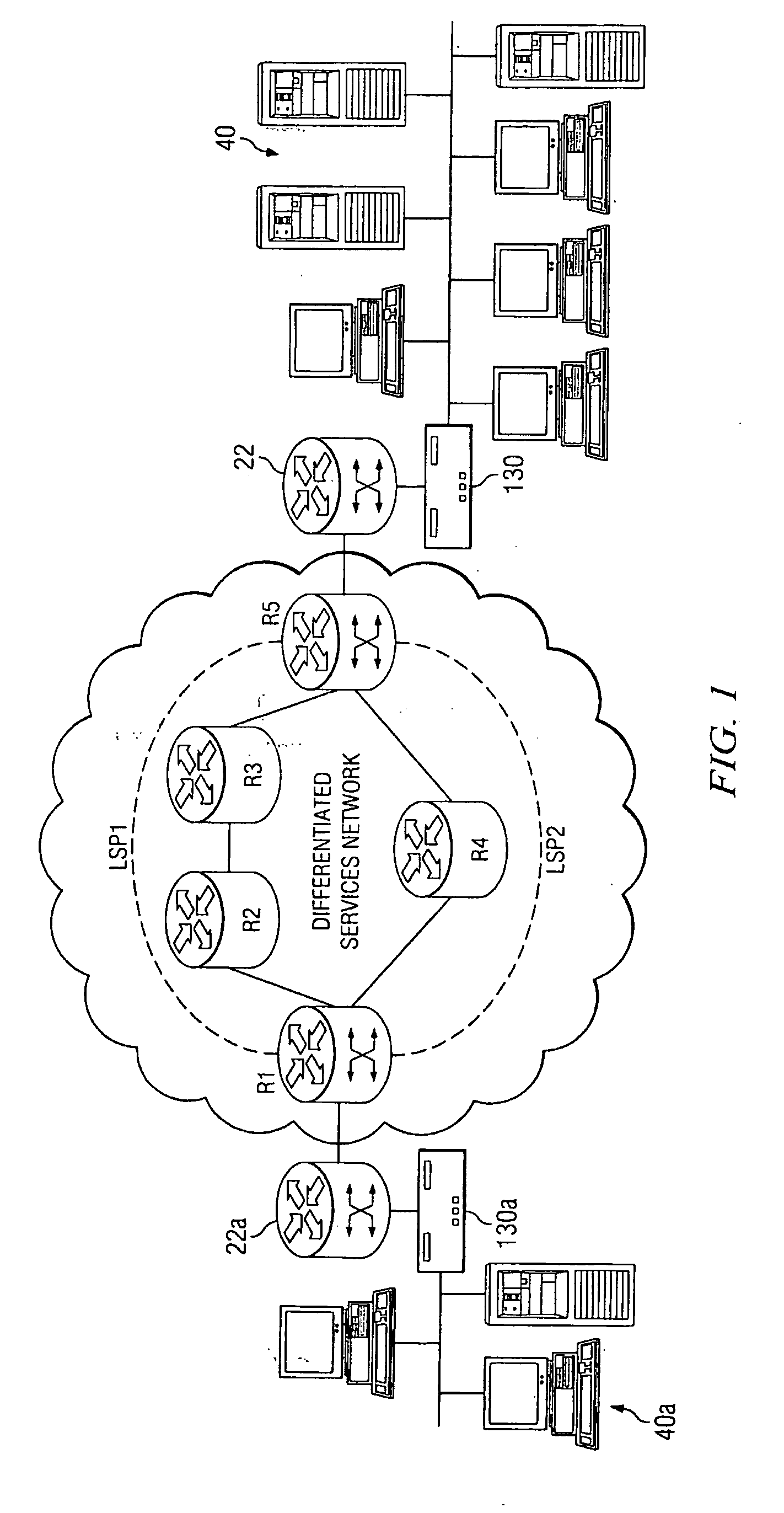
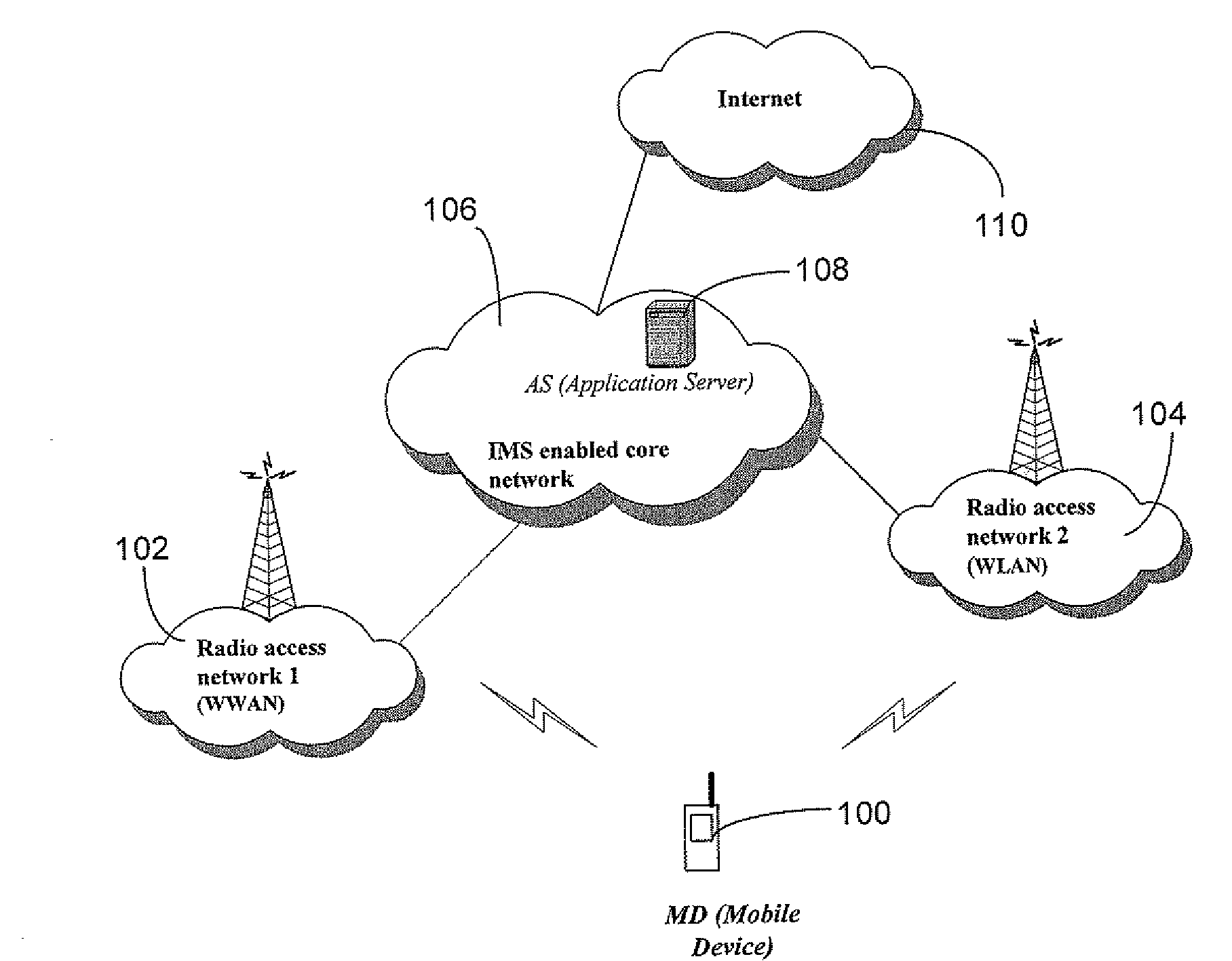
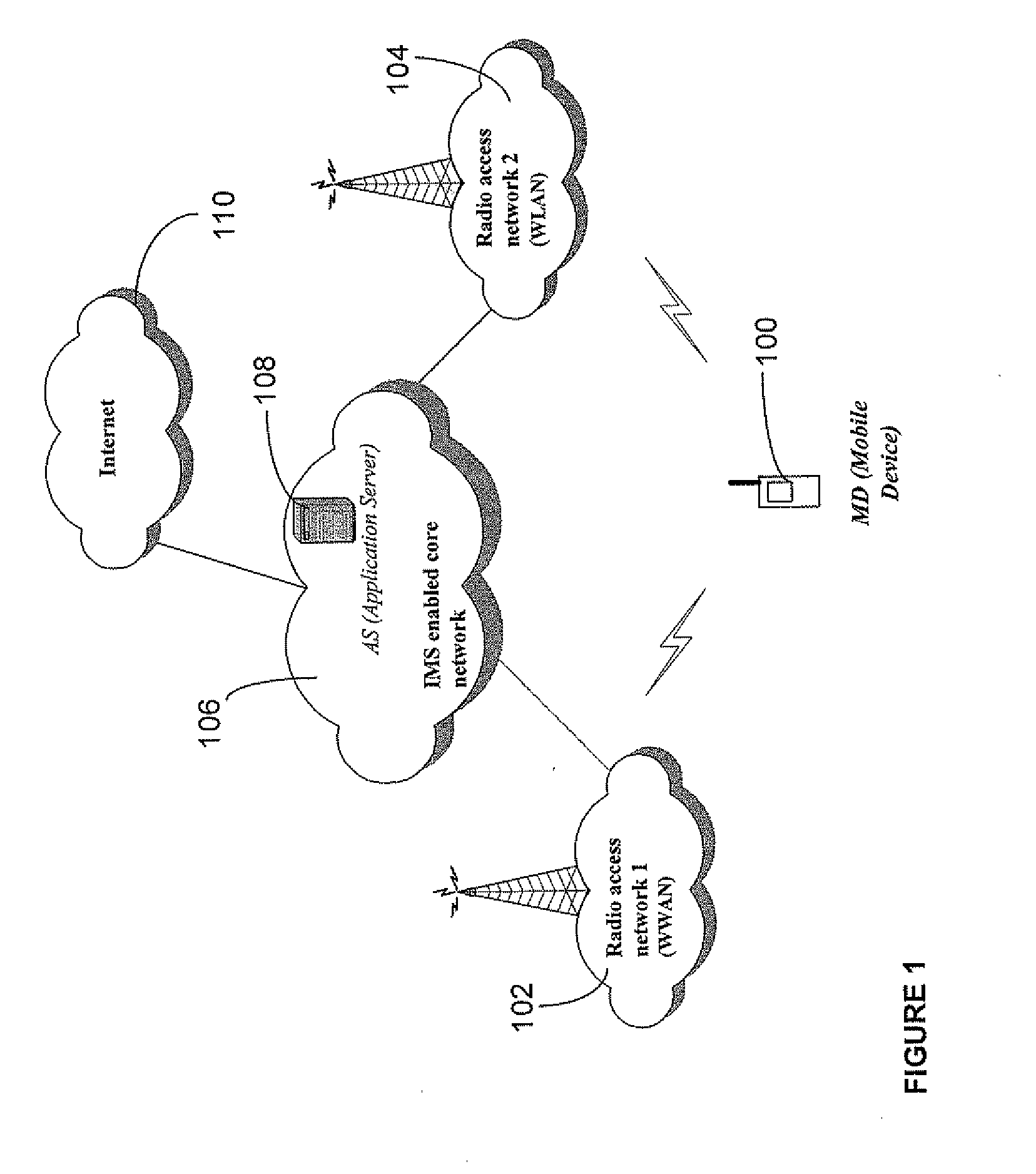
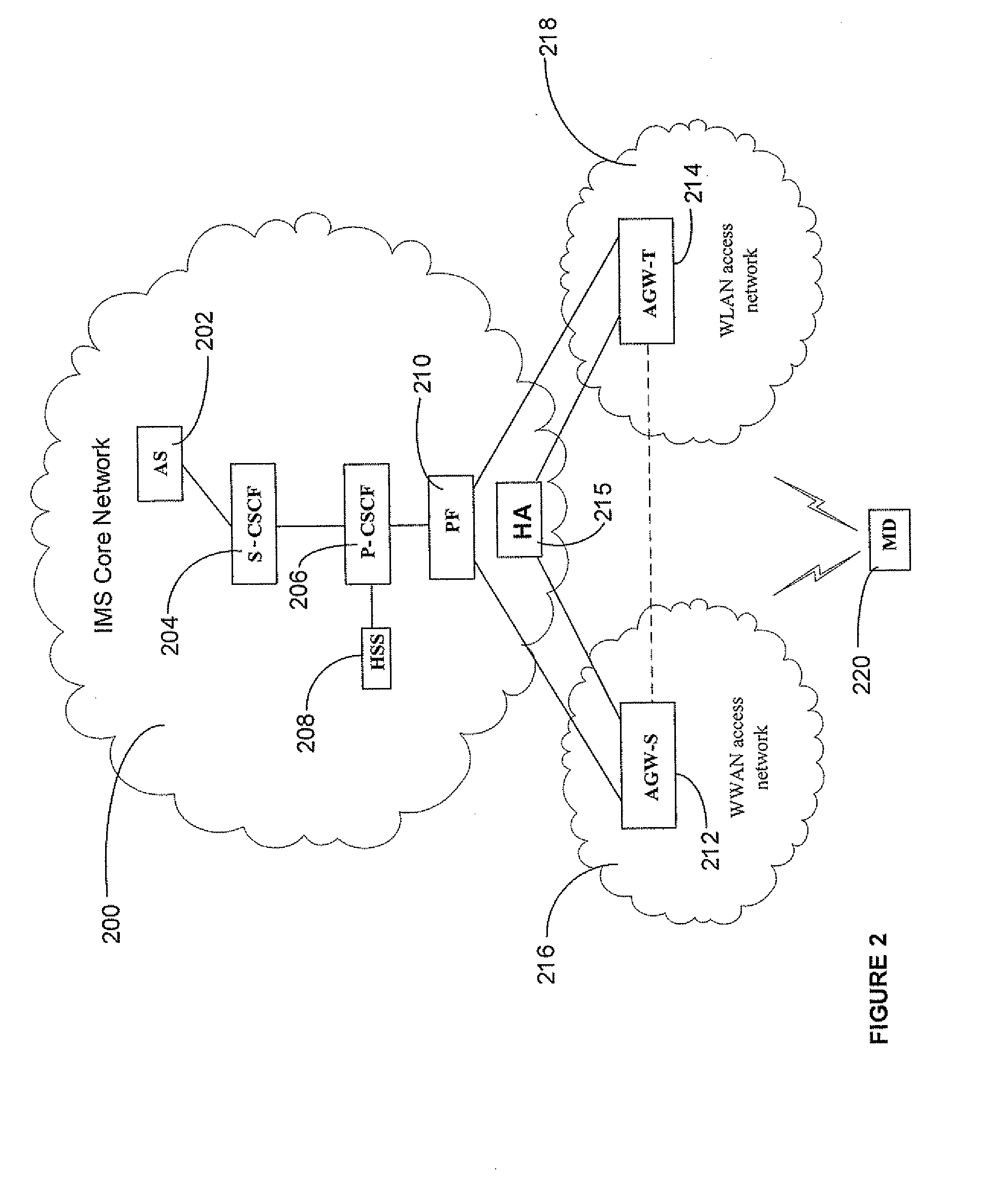
ActiveUS20080159232A1Assess restrictionData switching by path configurationAccess networkQuality of service
A system and method are described whereby an enhanced handoff scheme provides for monitoring of mobile device conditions and network conditions associated with a current access network attachment, as well as with a plurality of access networks on a preferred access network list, to proactively initiate a handoff operation, thereby preserving the QoS constraints necessary for seamless delivery of IP multimedia services. In an embodiment, each of the plurality of access networks is connected to an IMS core network, whereby a policy function receives quality of service constraints associated with the launched application from the mobile device and orders a list of preferred access networks accordingly. Preferably, the policy function selects an appropriate access gateway associated with a target access network based at least in part on the mobile device conditions reported by the mobile device and the access network conditions monitored by the policy function.
Owner:U S CELLULAR
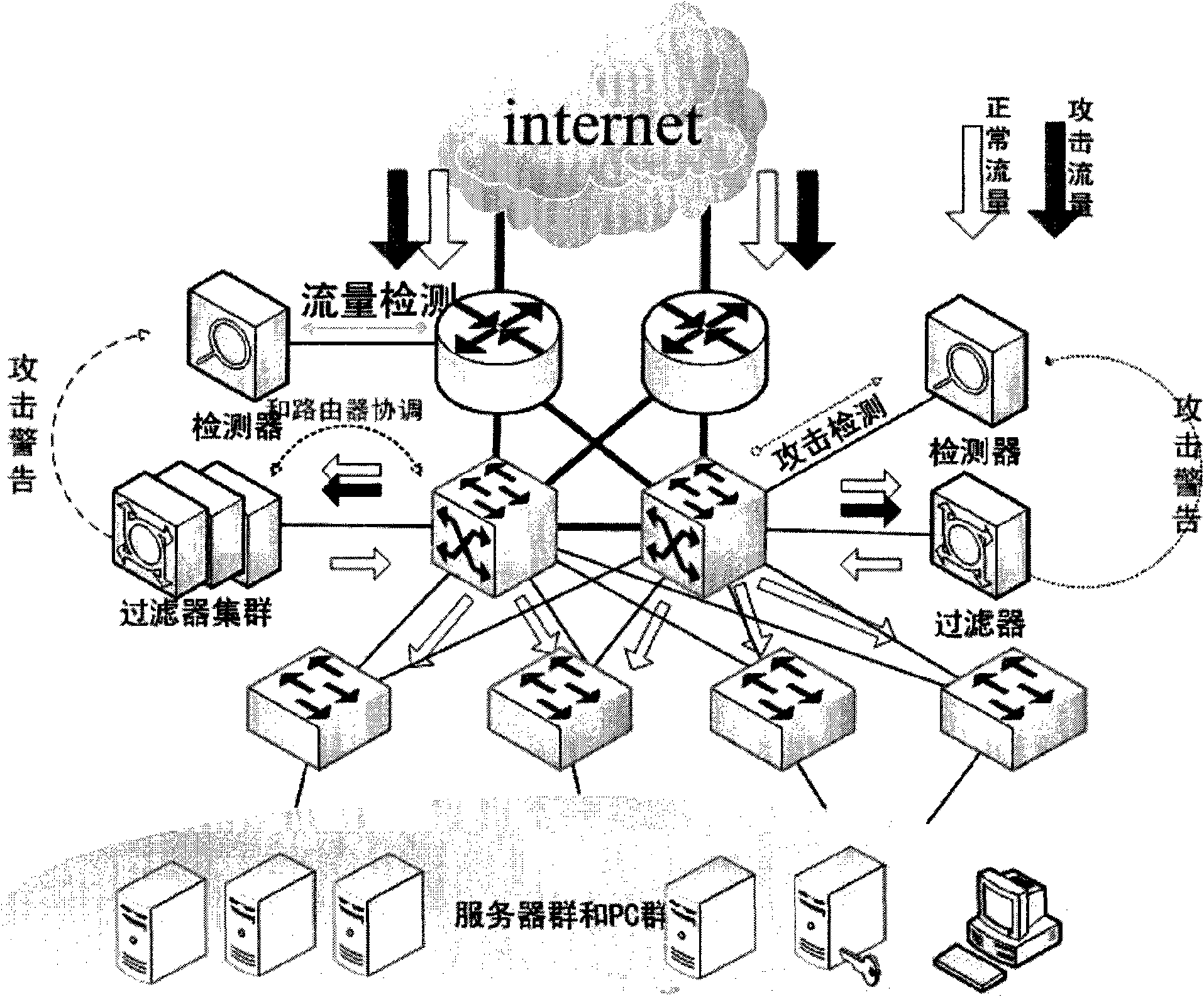
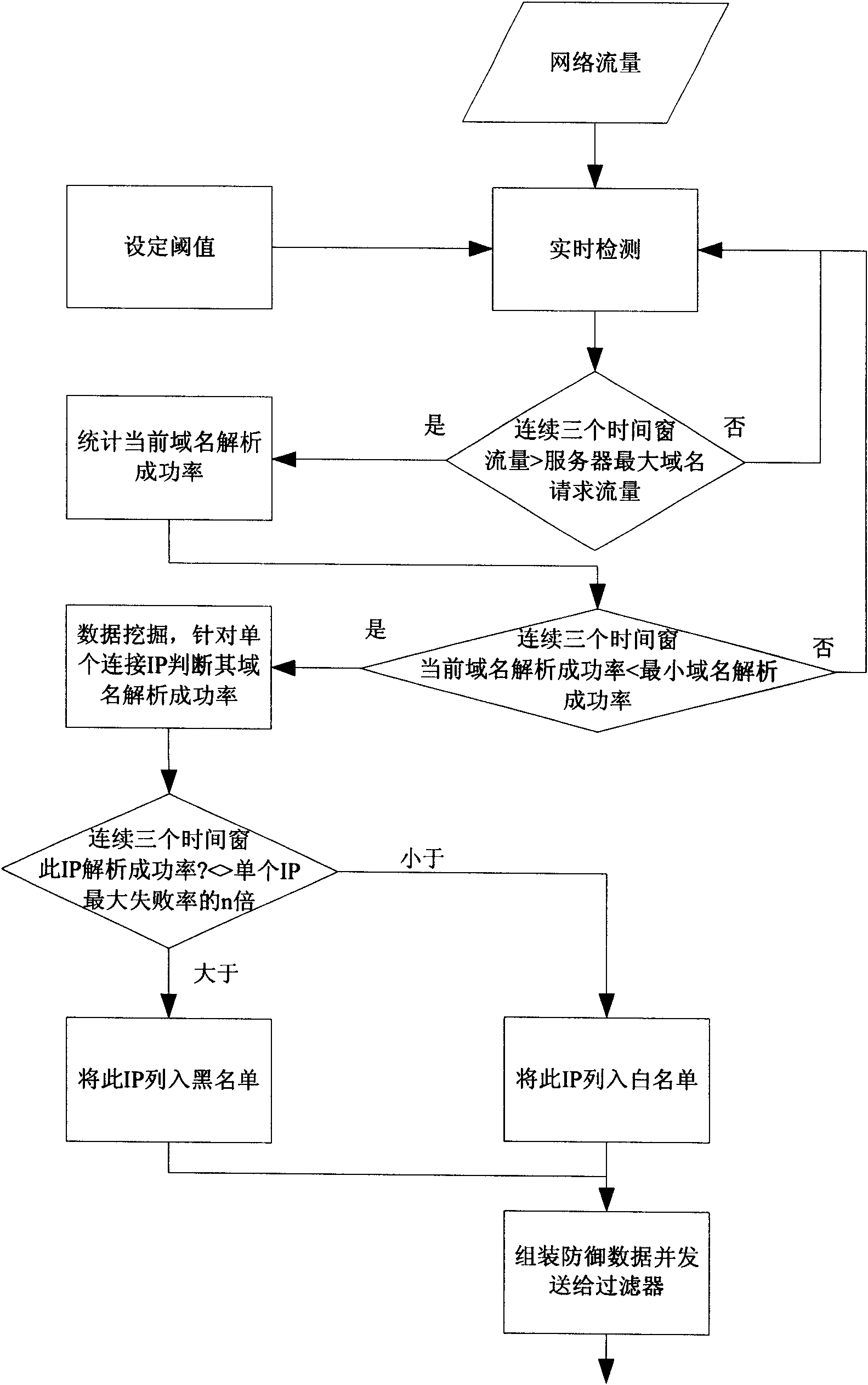
Security gateway system for resisting DDoS attack for DNS service
The invention discloses a high-efficiency anti-DDoS security gateway system, which can effectively detect and defend a DNS denial-of-service attack. The system comprises two core components, namely a detector and a filter. The system supports two deploying ways, namely serial connection and bypass. A detecting method is based on the self-learning network flow state statistic and characteristic disinterment, achieves the detection and positioning of the network abnormal flow by setting network performance parameter thresholds, and can effectively identify the suspected attack flow. A defending method carries out a thought of deep defense, and the system is deployed with two defense steps of attack characteristic defense and baseline defense so as to ensure the attack defending effect of thesystem under normal network condition and the basic defense capacity of the system in the individual and severe attack environment. The methods can effectively improve the security and attack resista nce of a DNS server and can ensure the normal operation of the DNS service.
Owner:ZHONGKE INFORMATION SECURITY COMMON TECH NAT ENG RES CENT CO LTD
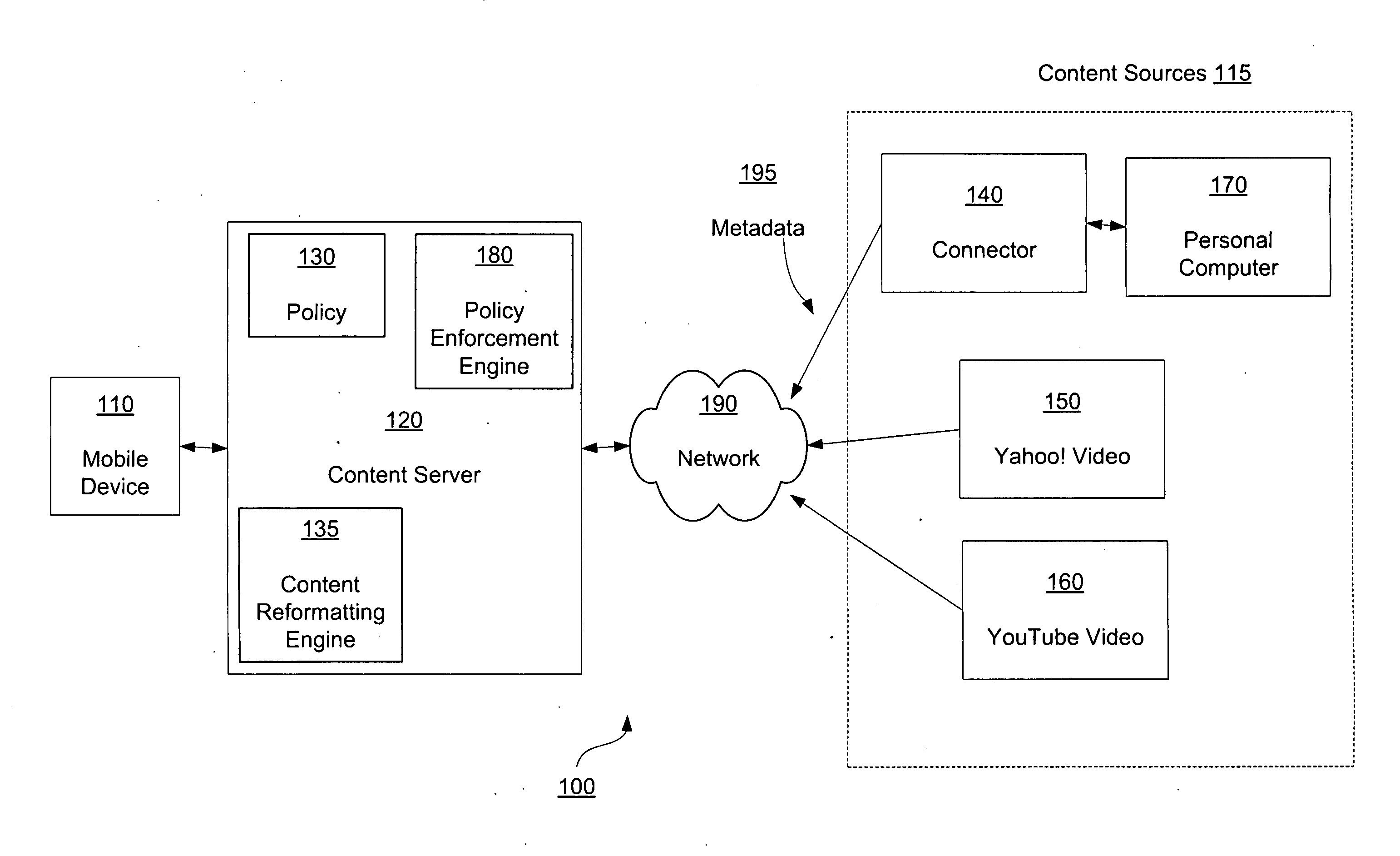
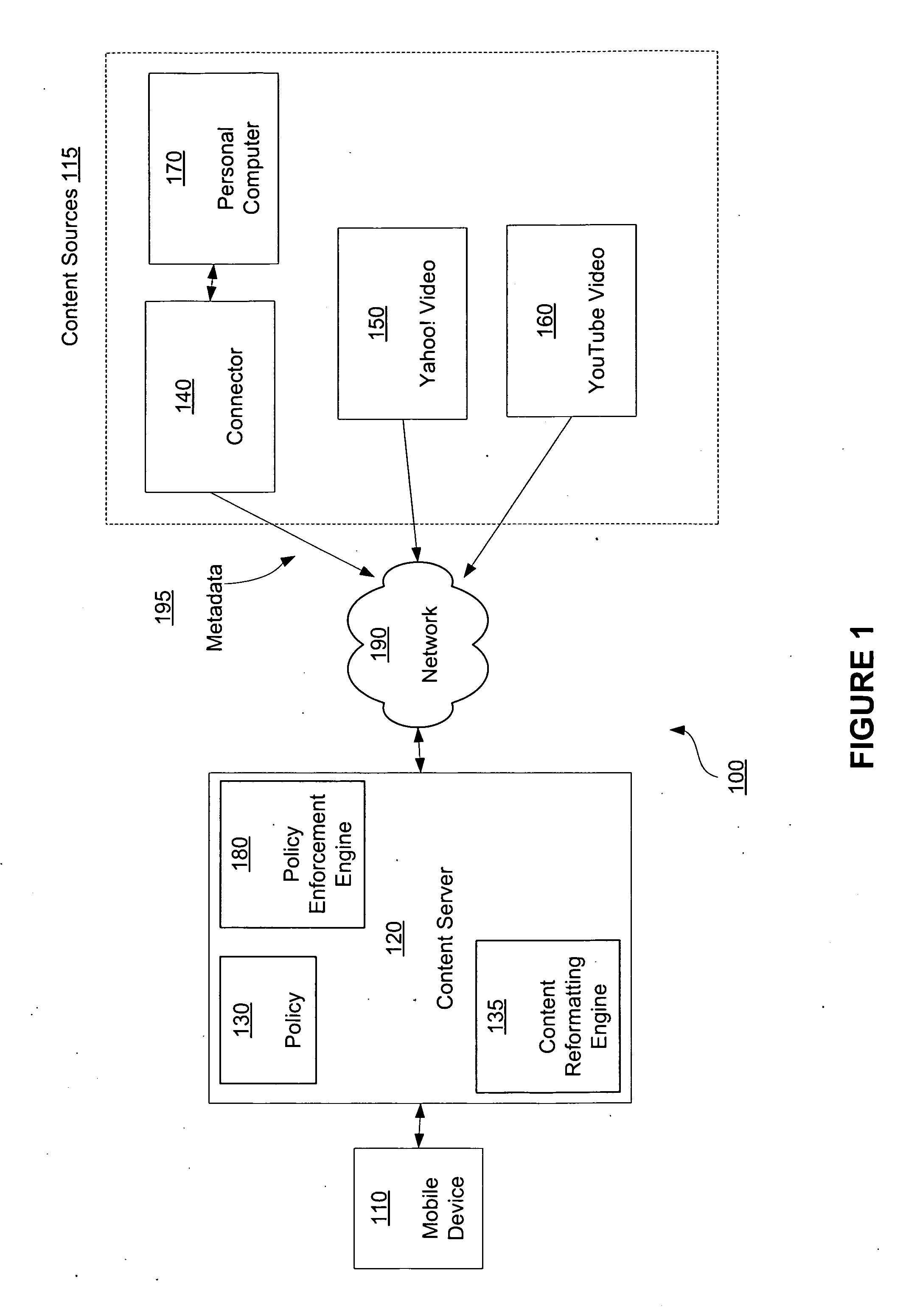
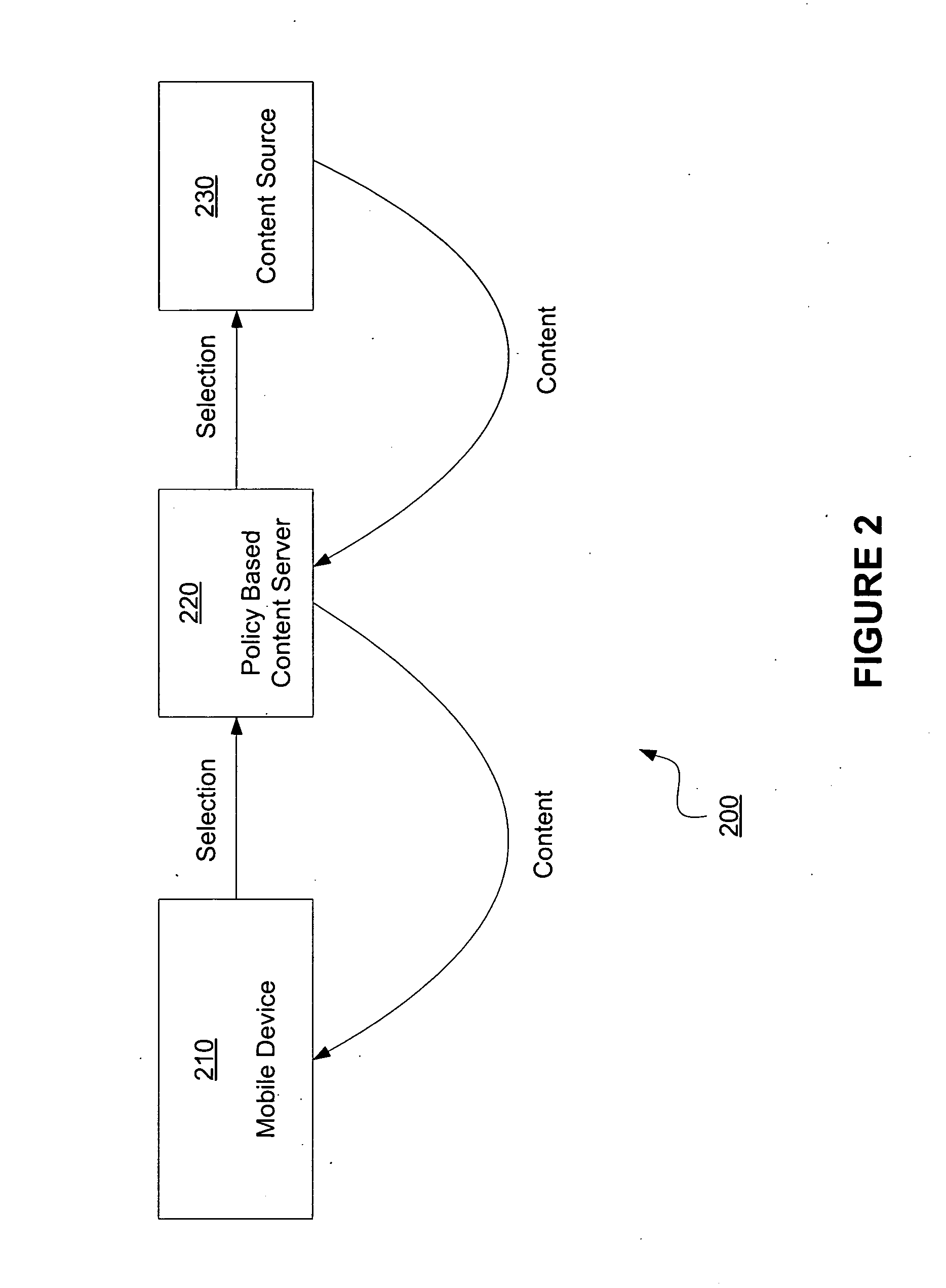
Policy based content service
InactiveUS20090164560A1Digital data information retrievalMultiple digital computer combinationsNetwork conditionsMobile device
Serving user selected content in accordance with a service policy is disclosed. The user may select content from a content source to be accessed at a mobile device. The desired content is modified as necessary such that transmission of the content complies with a policy. Alternatively, only content that complies with the policy may be made available for selection. The manner in which a policy is defined and the content provided may be determined by various factors including mobile device capabilities, user preferences, and network conditions.
Owner:SEVEN NETWORKS INC
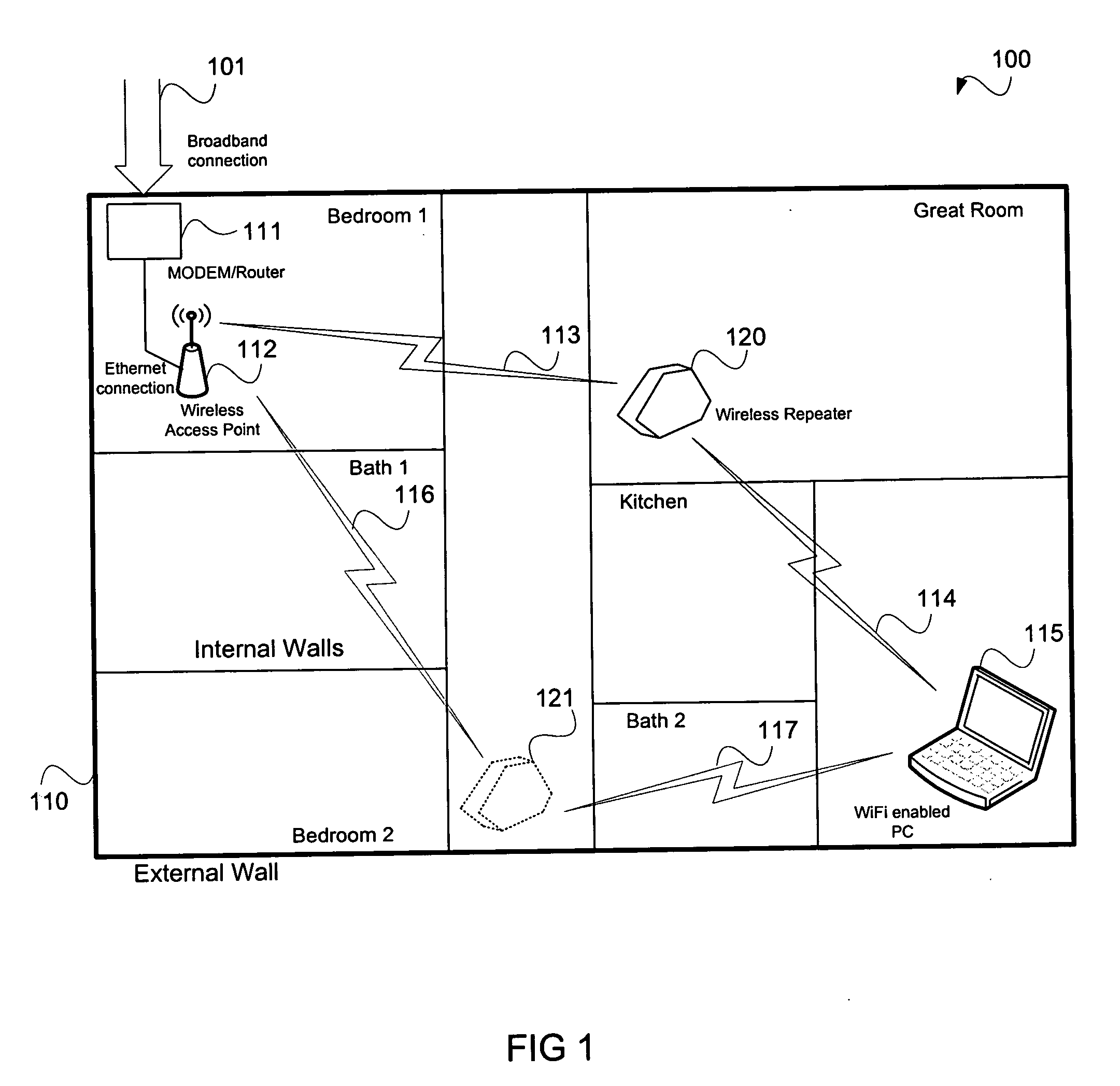
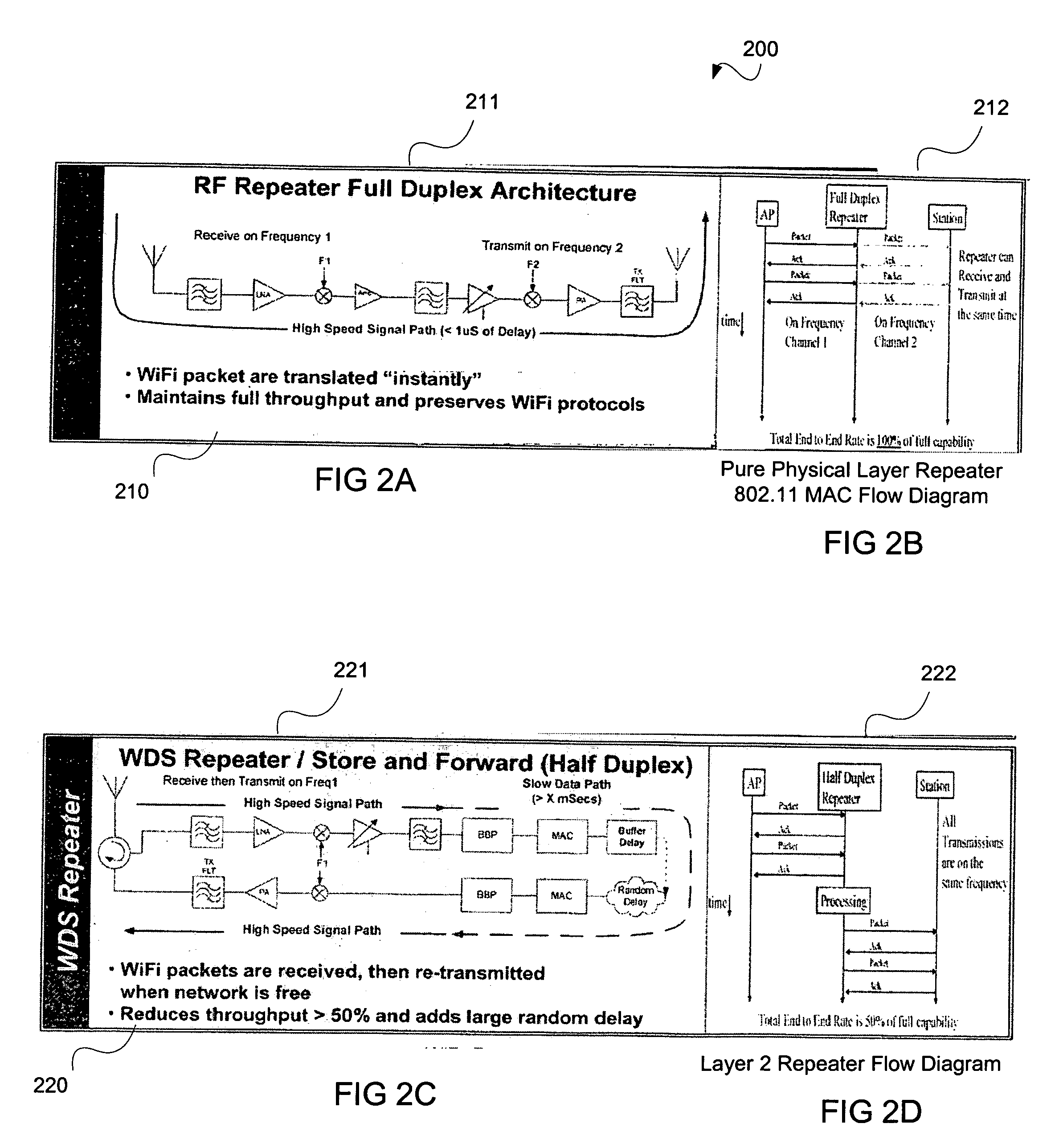
Physical layer repeater with selective use of higher layer functions based on network operating conditions
InactiveUS20060183421A1Increase capacitySolve the real problemFrequency-division multiplex detailsNetwork topologiesComputer hardwarePhysical layer
A physical layer frequency translating repeater (600, 700) for use in a wireless network includes signal processor (710-714) coupled with a signal processing bus (711), a processor (627) and a memory (650). The physical layer repeater conducts physical layer repeating and selectively conducts layer 2 and possibly layer 3 functions depending on network conditions and other factors. A demodulator (623) can extract address information such as media access control (MAC) addressing to enable packets to be redirected, terminated, stored and forwarded, if necessary, based on network conditions.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com