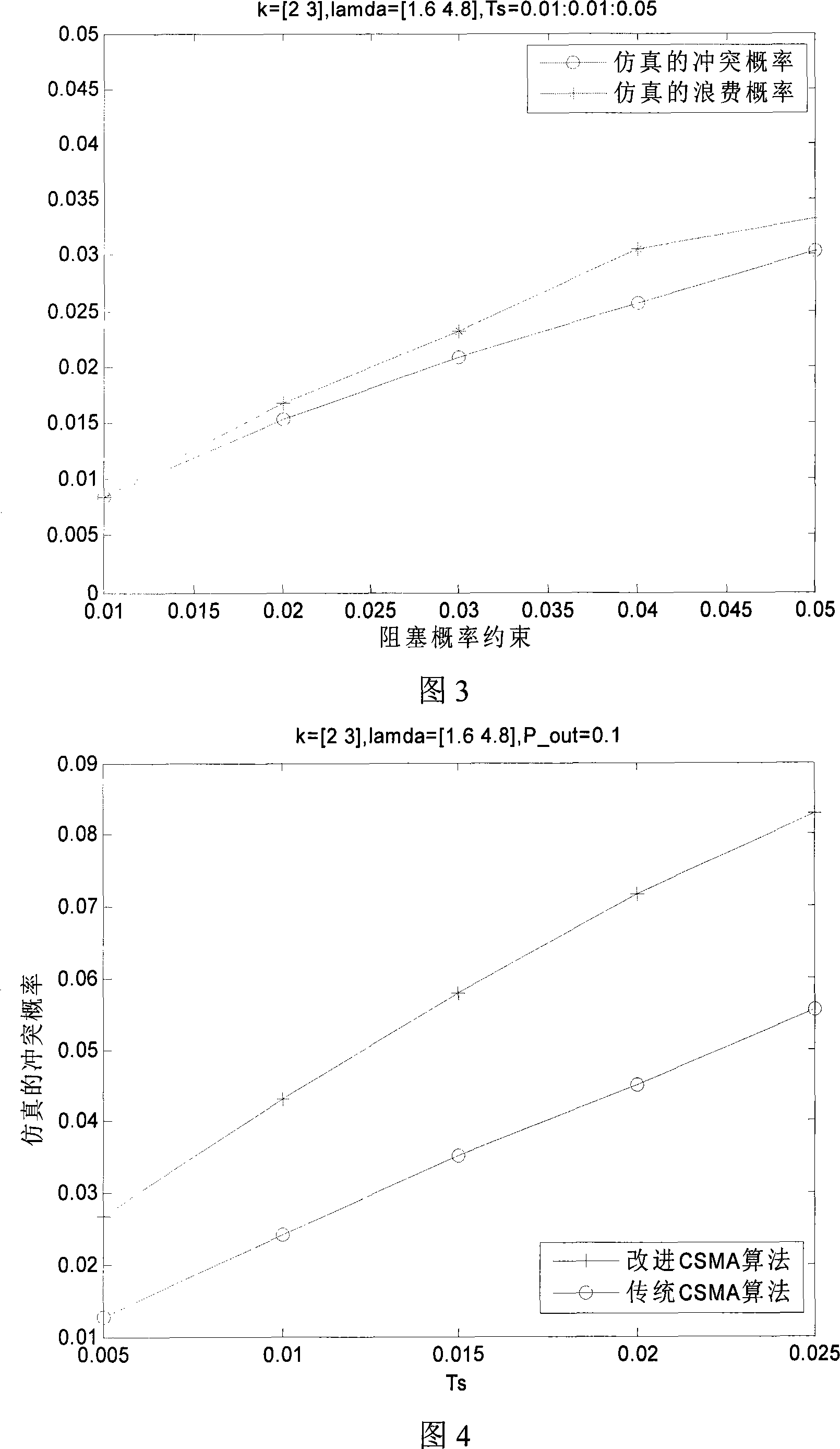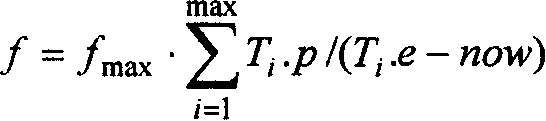Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
80 results about "Restrict" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the C programming language, as of the C99 standard, restrict is a keyword that can be used in pointer declarations. The restrict keyword is a declaration of intent given by the programmer to the compiler. It says that for the lifetime of the pointer, only the pointer itself or a value directly derived from it (such as pointer + 1) will be used to access the object to which it points. This limits the effects of pointer aliasing, aiding optimizations. If the declaration of intent is not followed and the object is accessed by an independent pointer, this will result in undefined behavior. The use of the restrict keyword in C, in principle, allows non-obtuse C to achieve the same performance as the same program written in Fortran.
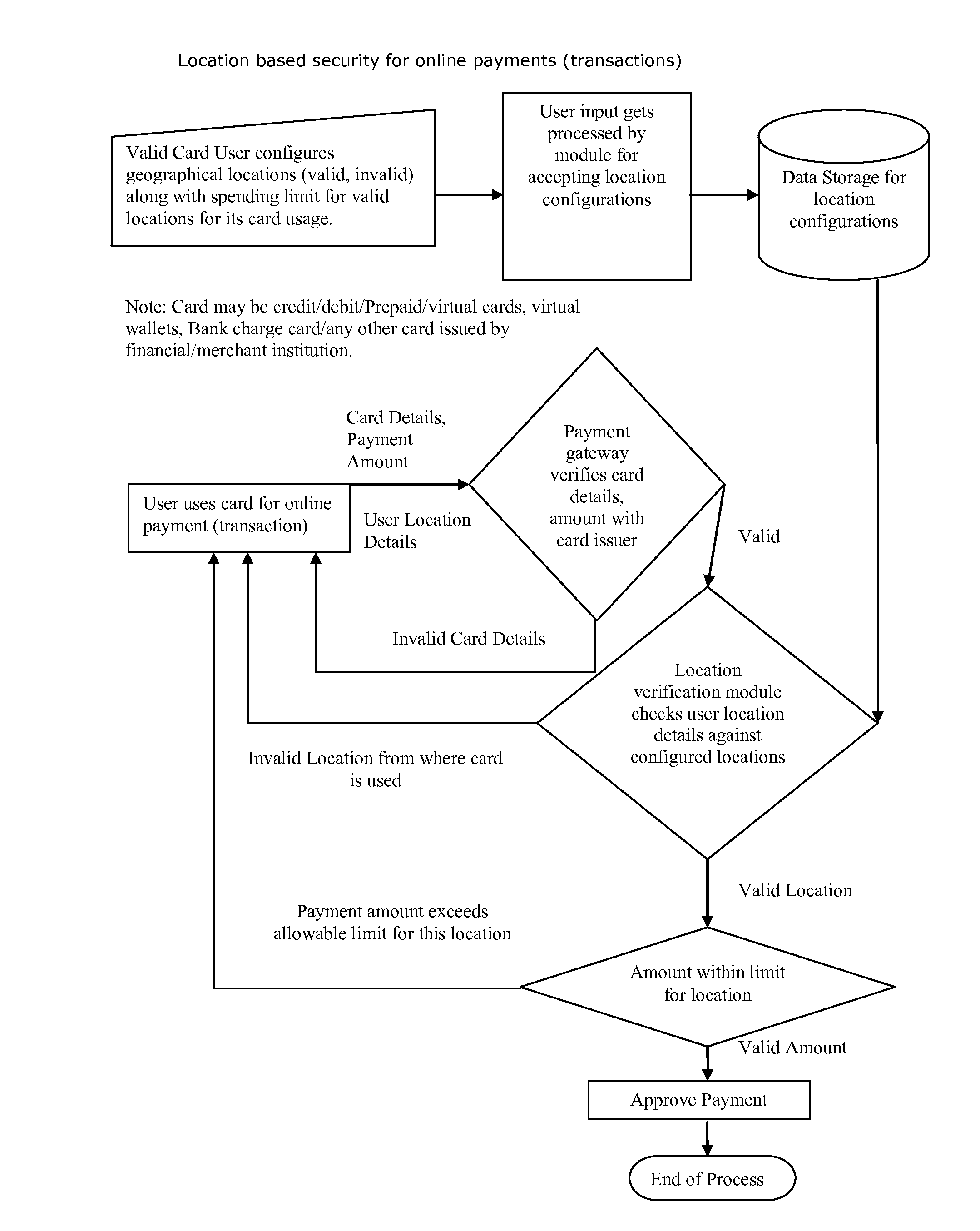
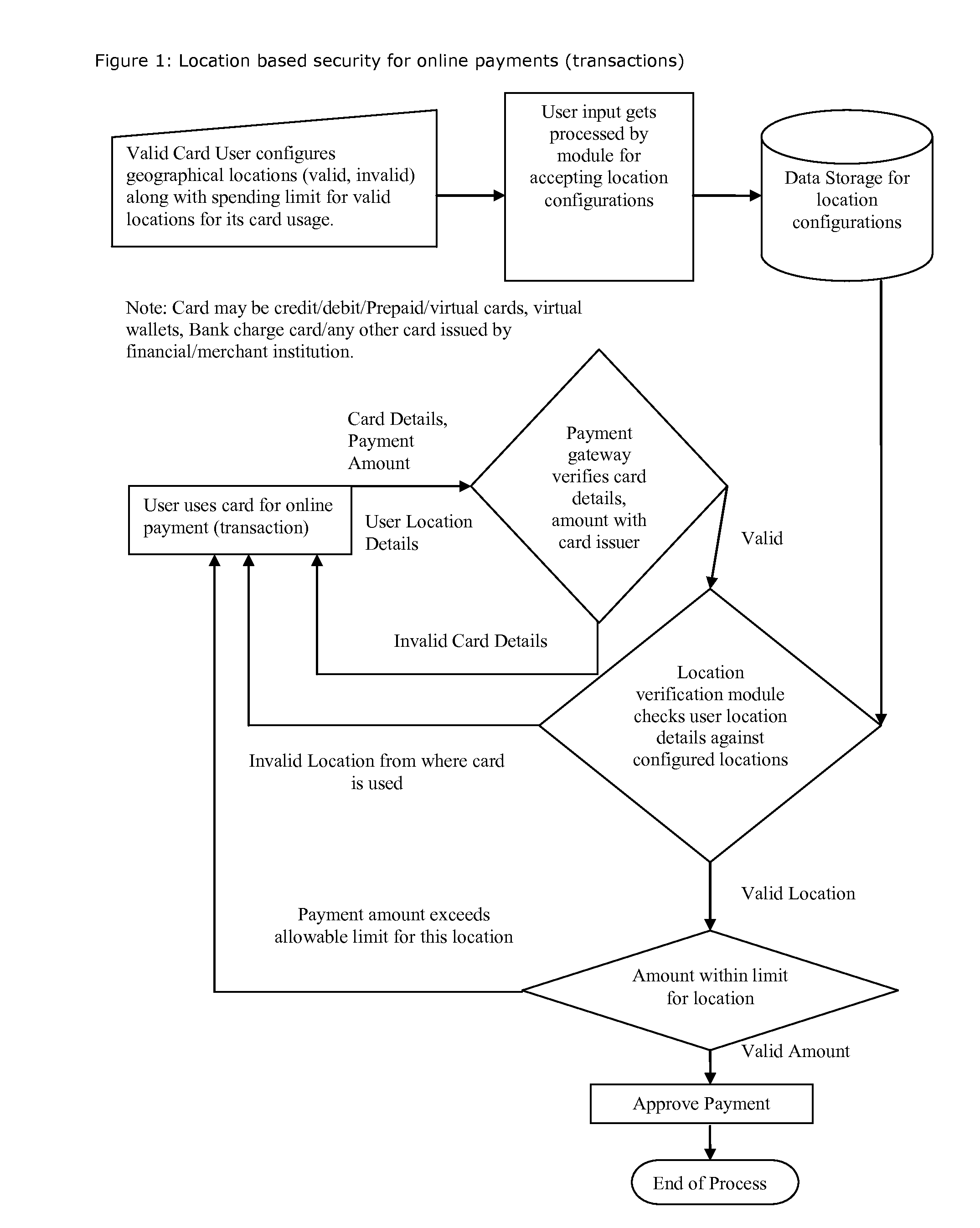
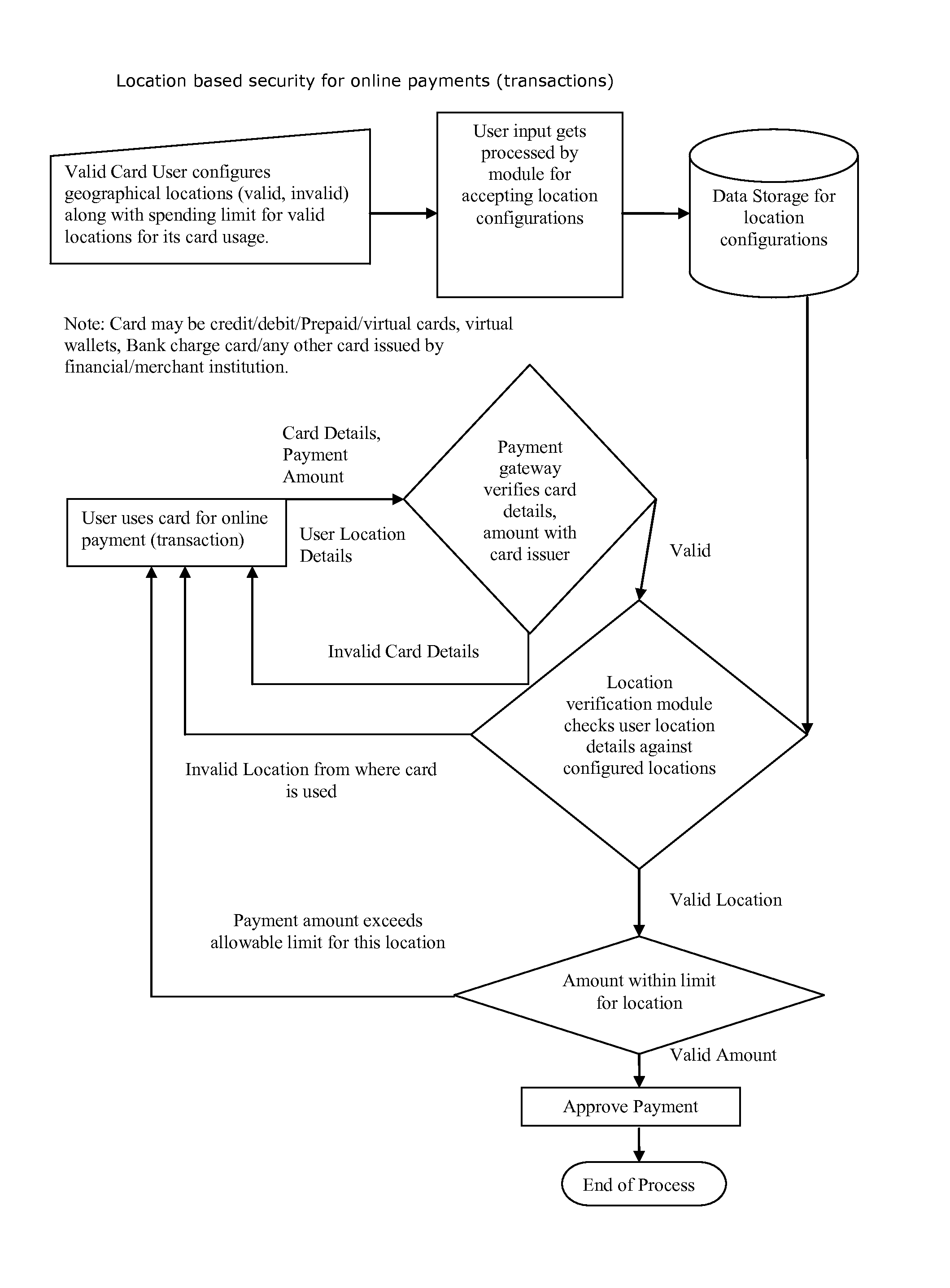
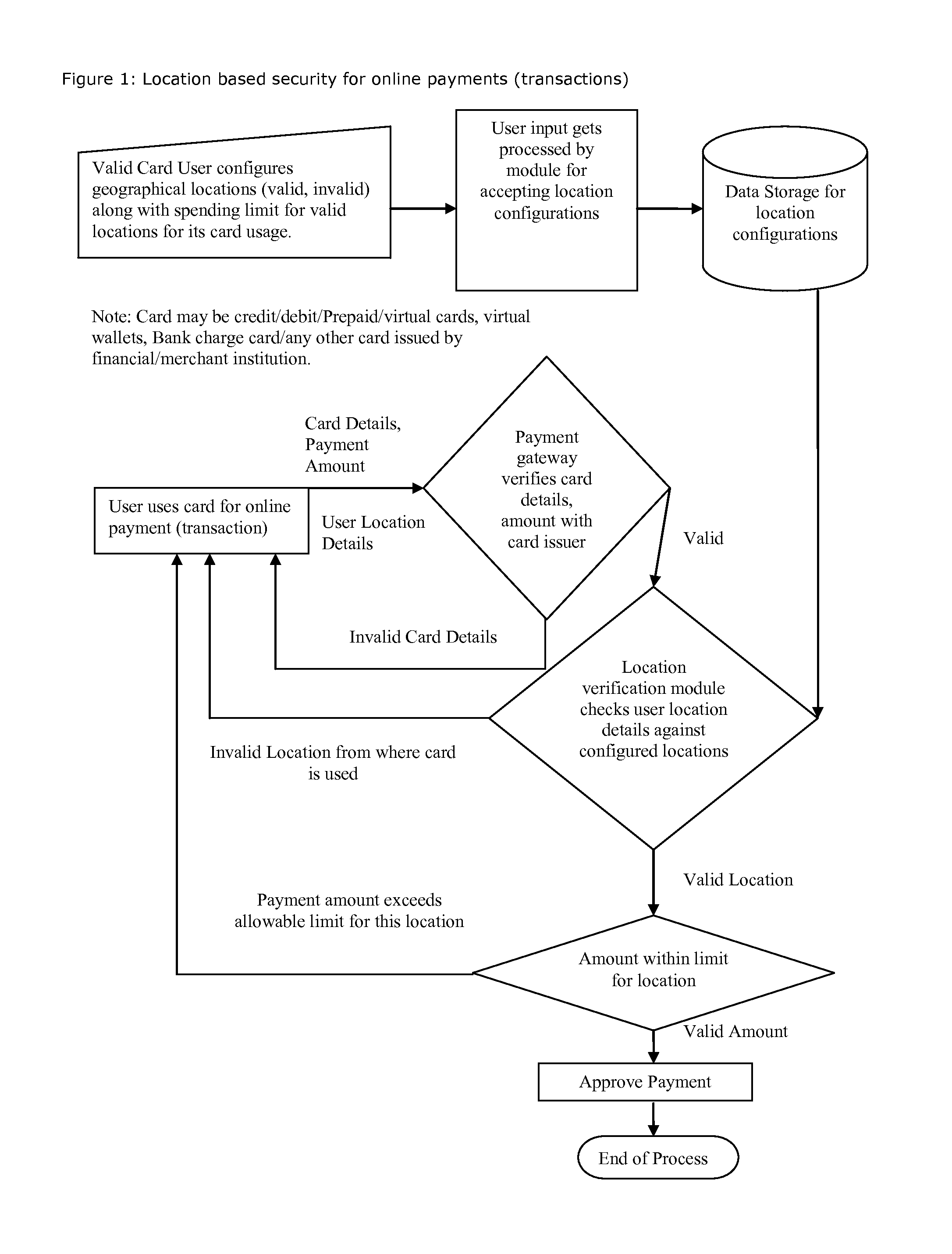
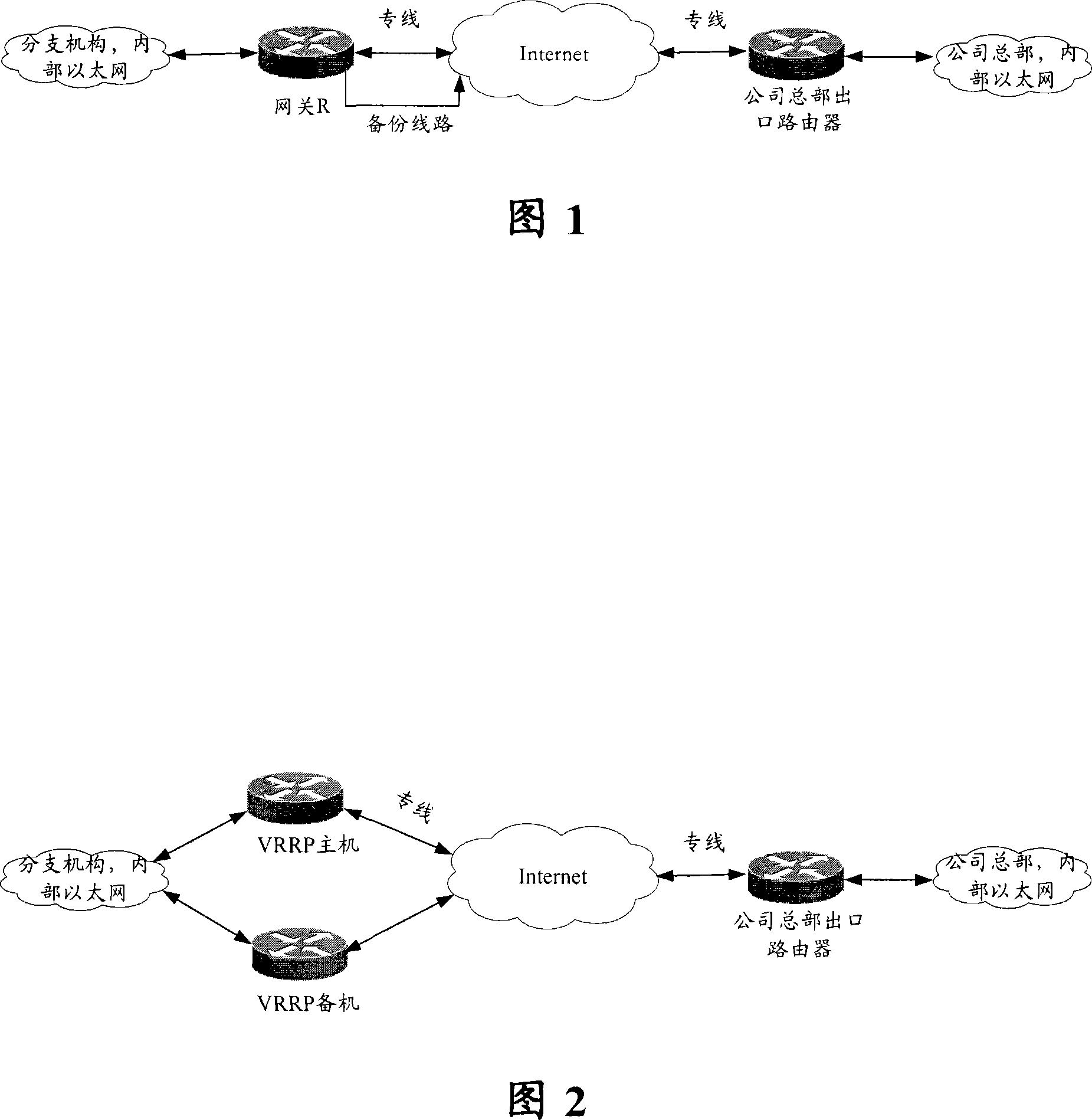
Method for providing geographical location-based security, restrict, permit access of varying level to individual's any kind of data, information, credit, finances, services obtained(online and or offline)
Proposed method and security system provide geographical location-based security with varying levels of access, allows users to select entities to protect, configure geographical locations, geographical boundaries as well as permissions, access level for given geographical locations, geographical boundaries and configure security alerts. It takes decision to grant, deny permission or provide coven access level based on user's current geographical location and user's own configuration for that geographical location or boundary and sends out security alerts.
Owner:SHAH DHAVALKUMAR M
Reverse identity profiling system with alert function
The present invention is a universal biometric monitoring system designed to locate and track terrorists, criminals, and missing or displaced persons. Via various checkpoints and a plurality of identity verification or observation ports, defining identity characteristics or biometric data is transmitted to a system that cumulatively creates a database and identity related profiles. The uses of the system are three-fold. Data is retrieved and examined in order to: Find, isolate, and restrict wanted individuals; Locate missing children; Bring order and identity resolution to groups of individuals, most specifically individuals displaced resultant to disaster situations. The system is capable of retrieving, capturing, transmitting, analyzing, and otherwise examining biometric data, cumulatively building identity profiles, and has the ability to search, match, find, trace and track identities through this system as well as set off a multiplicity of alert outputs and alarms.
Owner:OKUN SHERI LEE
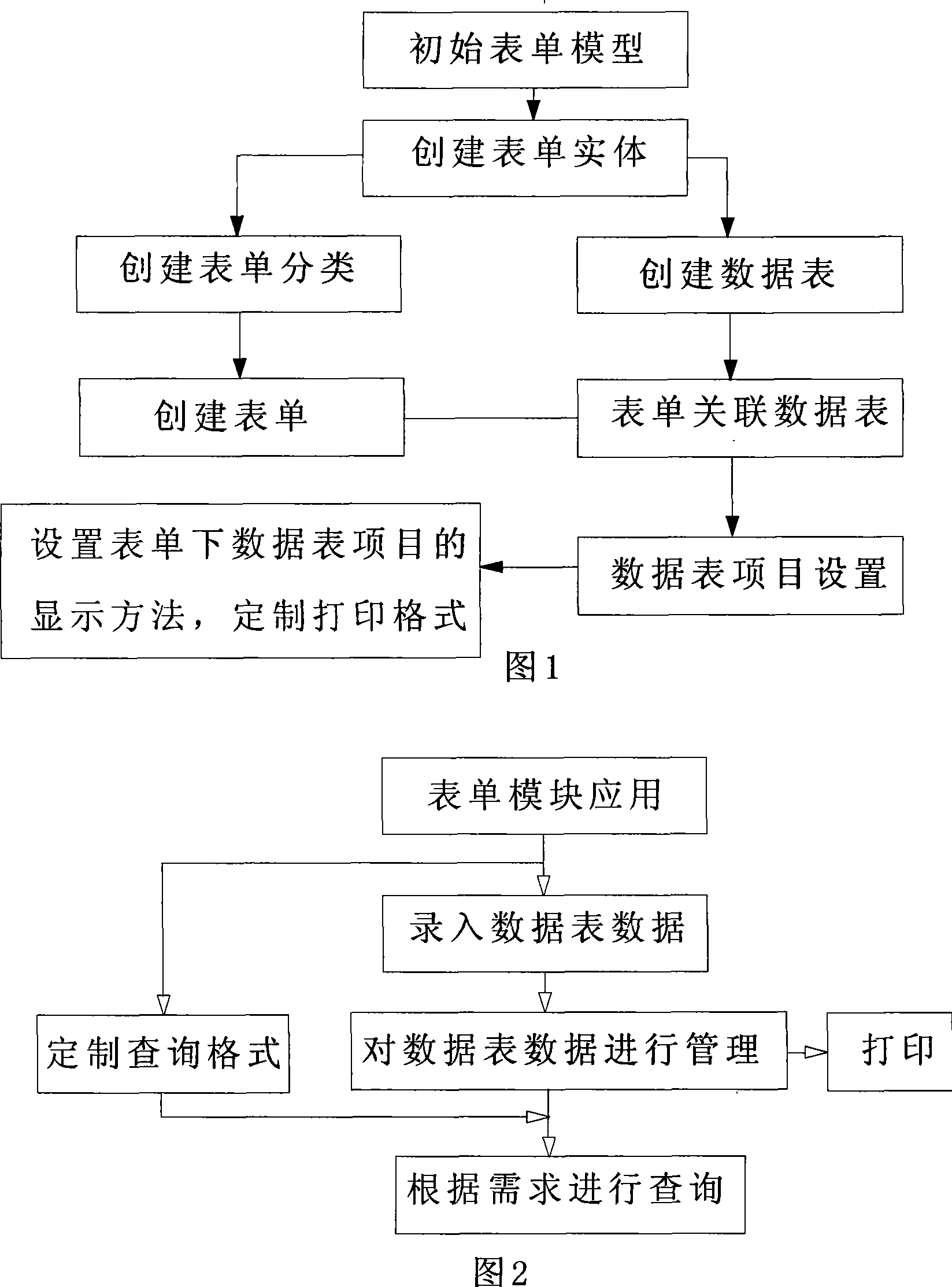
Form self-defining method
InactiveCN101241434AFlexible customization of printing formatsConvenient query functionSpecific program execution arrangementsSoftware developmentBusiness requirements
The present invention provides a flexible customizing method of all kinds of sheets aim to the sheets business requirement of different users. The method effectively resolves contradictions of continuous changes of sheets business requirement of different users and the passive maintaining adjustment of software development, at the same time provides integrated sheets set tool, report query output, print output. The component is based on multiple reusable controls, used for showing sheet module and providing inner and outer operating interfaces, the control is placed in the WinForm window, and complete coding control when developed. User more controls the sheet, setting more complex restrict, providing friendly navigation maintenance mode, expanding supporting function range, breaking seal performance of platform to achieve aim of directly felxible control final sheet.
Owner:INSPUR COMMON SOFTWARE
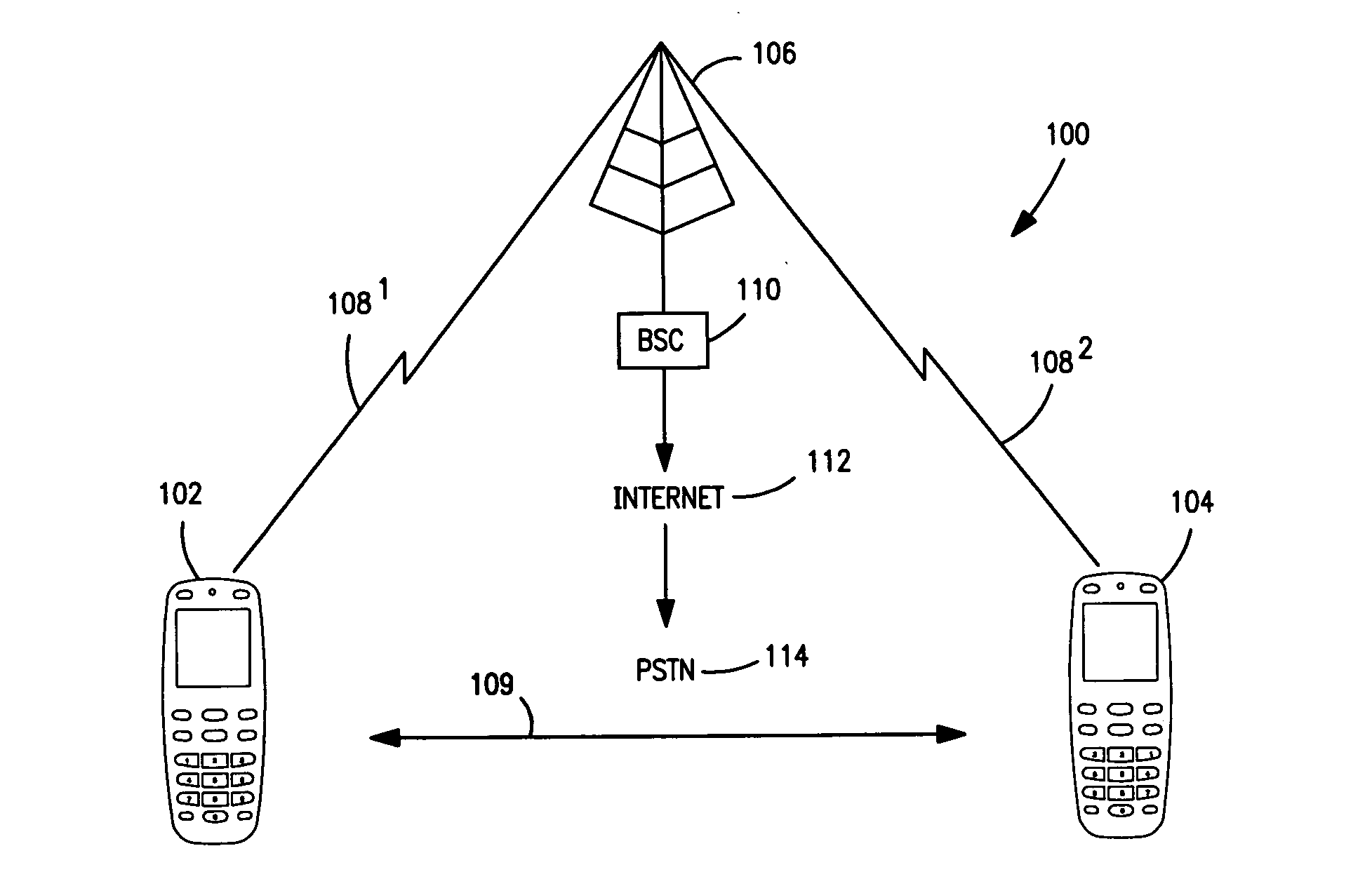
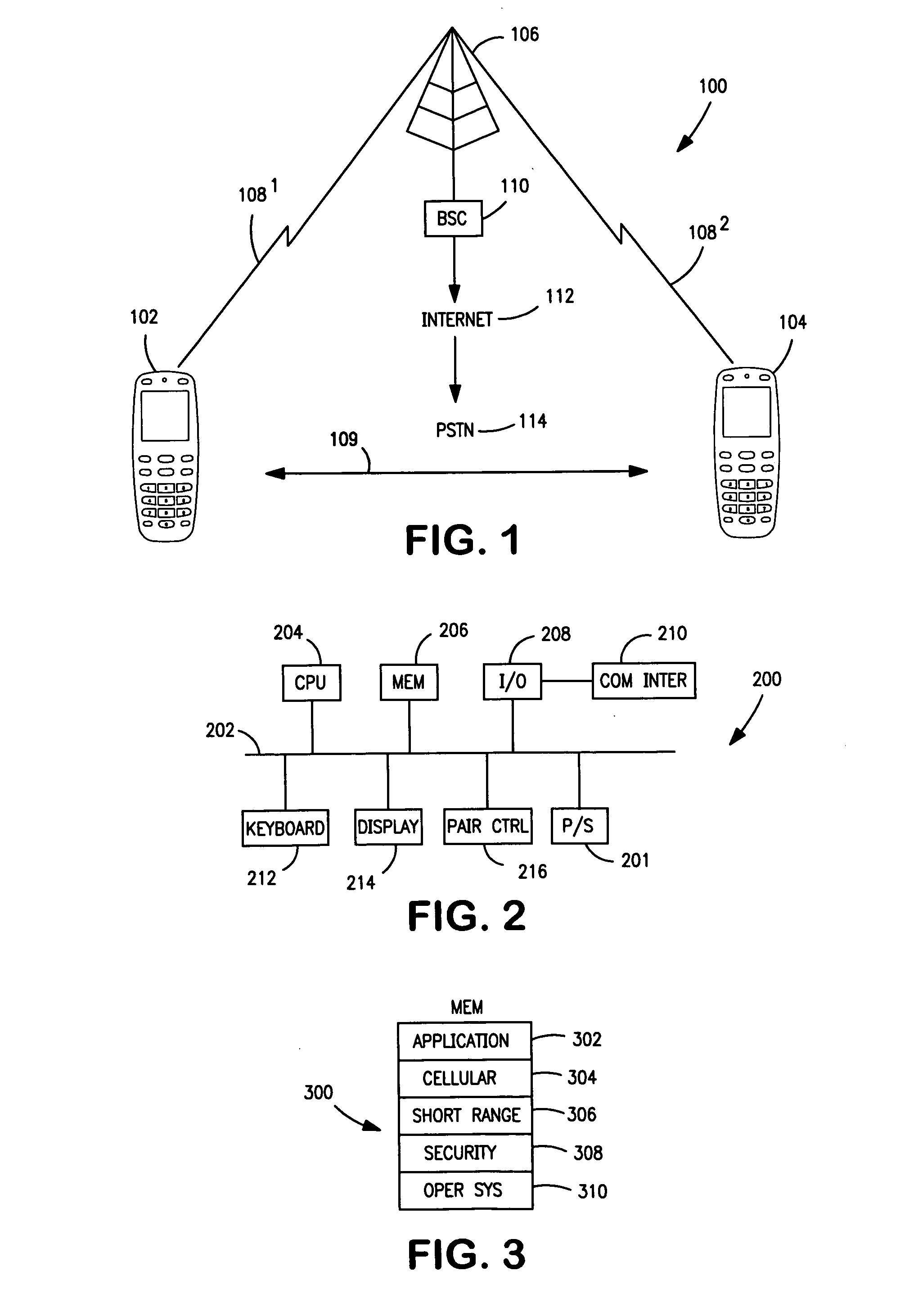
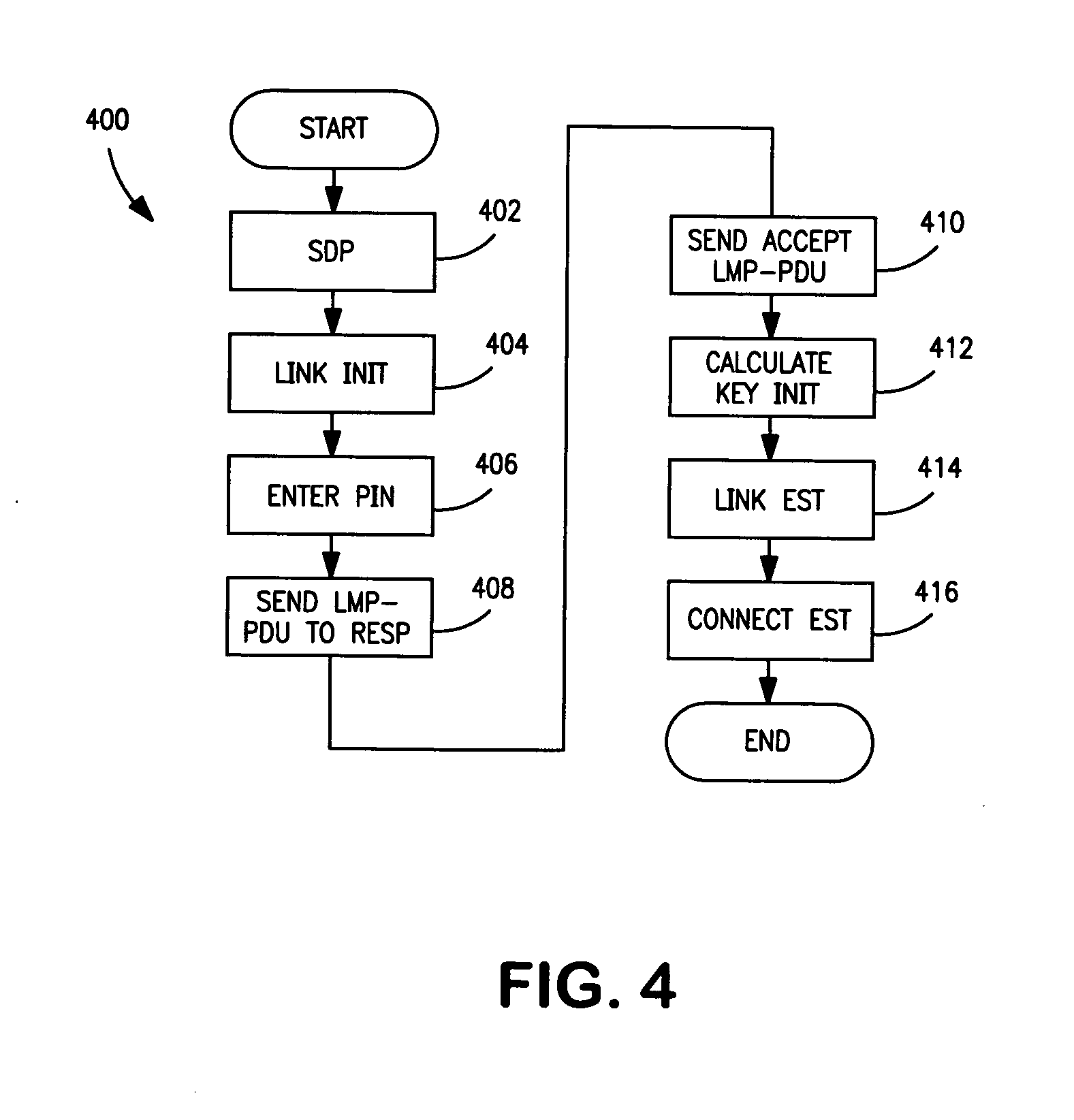
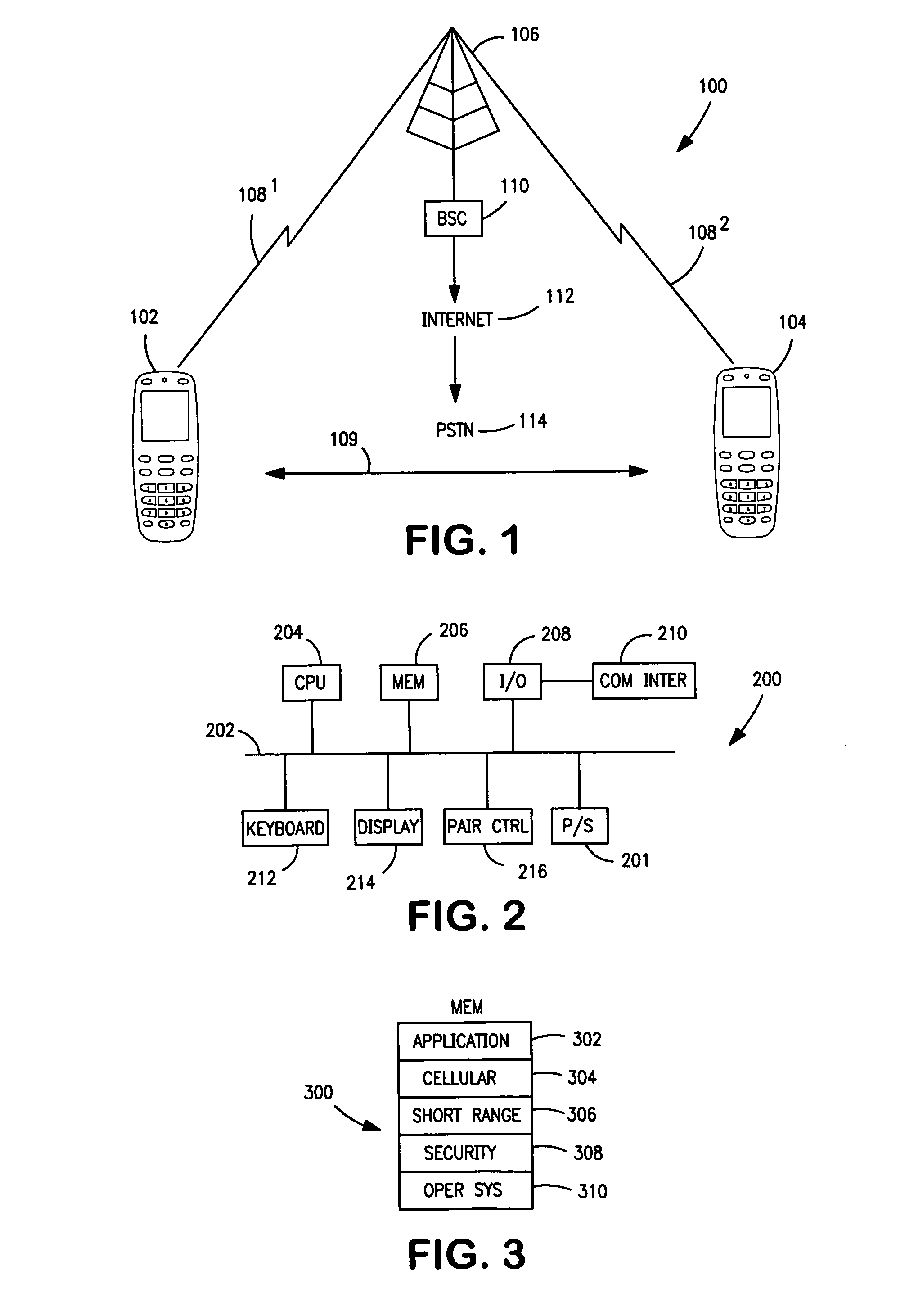
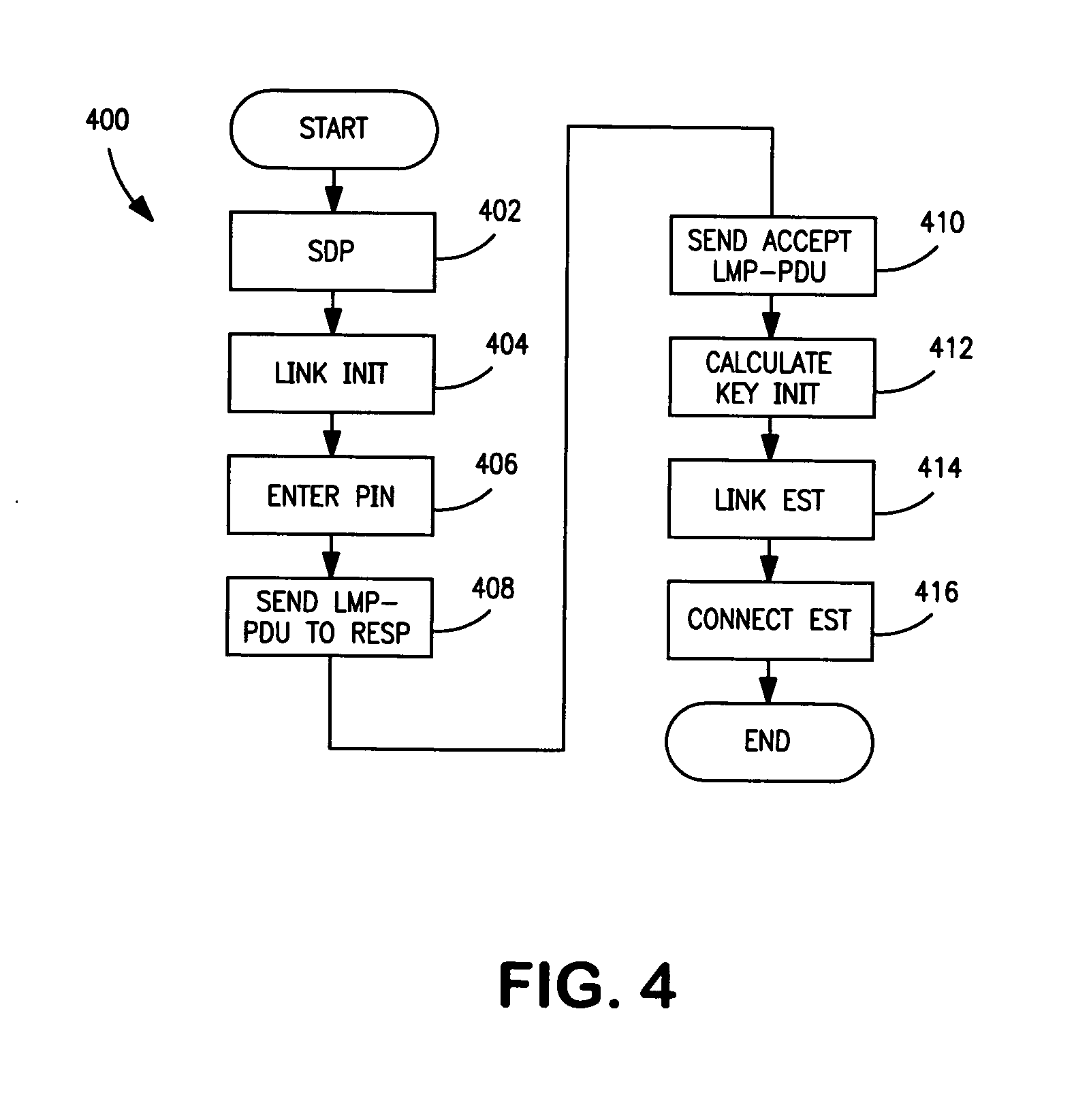
Restricting and preventing pairing attempts from virus attack and malicious software
A method, device and system restrict and prevent virus attack and malicious software to a wireless communication device from a pairing attempt by another wireless communications device. A switch is included in a transmission path coupling a first device to a second device, wherein the second device is attempting to pair with first wireless communications device. A detector coupled to the transmission path, detects an address of the second wireless communications device in a pairing communication protocol between the first and second devices. A counter coupled to the detector counts the pairing attempts of the second device. A compare circuit compares the pairing attempts to a selected number N. The compare circuit signals the switch to open when the number of attempts equals or exceeds the number N, breaking the connection, thereby preventing the first device from receiving virus attacks and malicious software.
Owner:NOKIA TECHNOLOGLES OY
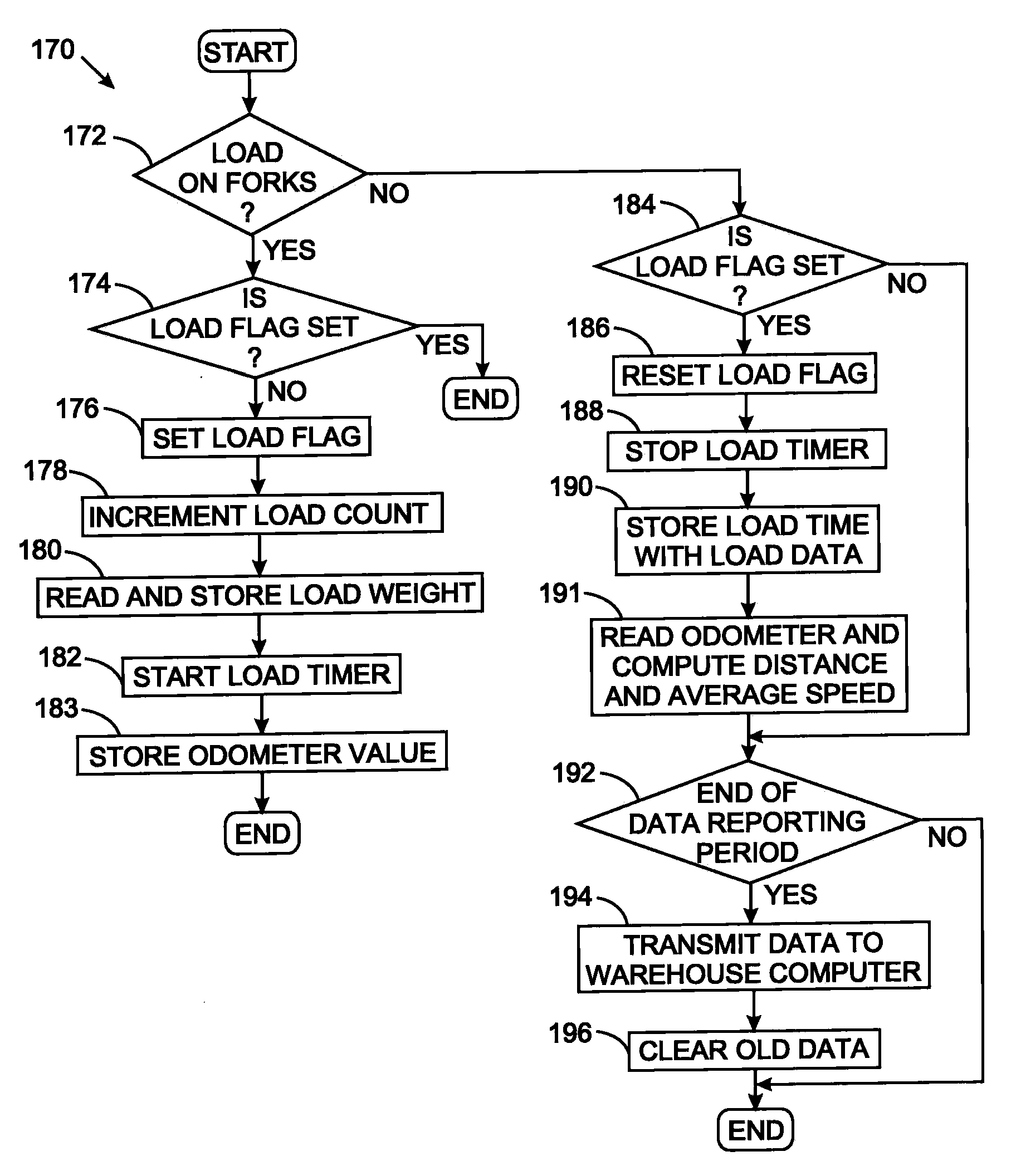
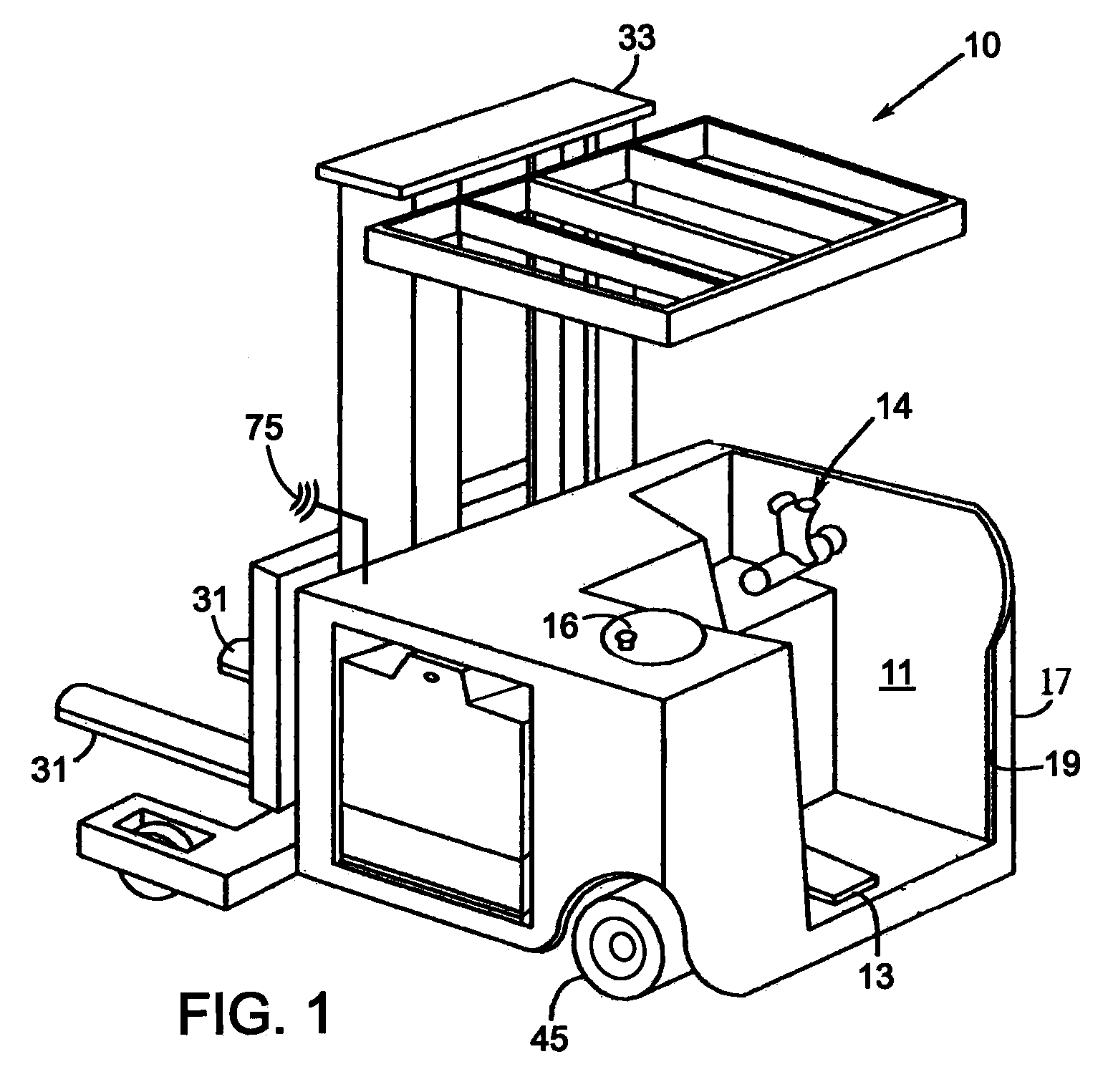
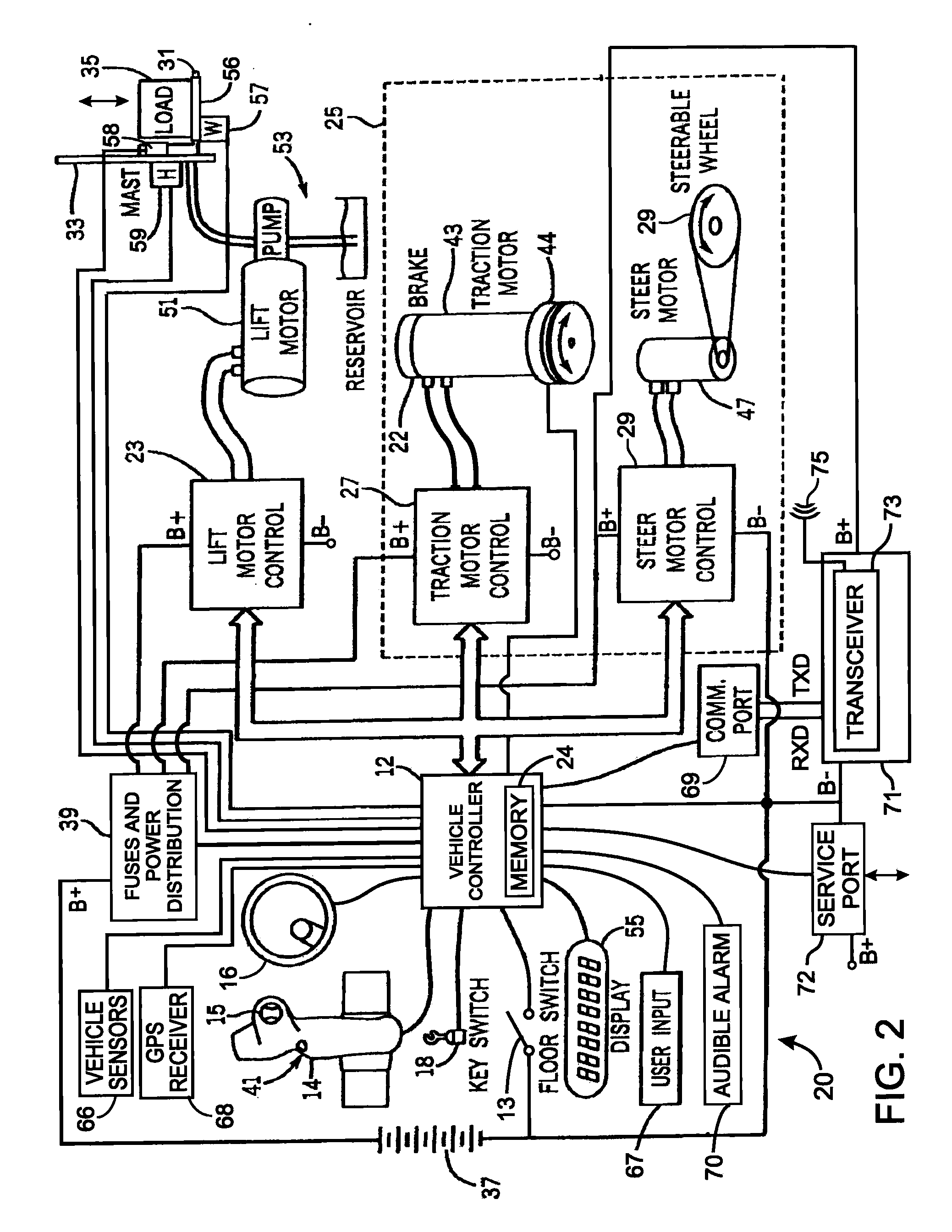
System for managing operation of industrial vehicles
ActiveUS20090265059A1Extend battery lifeUtilize battery powerVehicle testingAnalogue computers for trafficComputerized systemElectric power
An industrial vehicle has a controller connected to a plurality of sensors for accumulating information related to operation of the vehicle. The controller employs that information in governing further vehicle operation to reduce the likelihood of damage to the vehicle or a load being transported. The information also is analyzed to determine how efficiently the industrial vehicle and its operator are performing in relation to performance benchmarks for the vehicle and in comparison to other industrial vehicles. Performance of the industrial vehicle can be limited to conserve battery power and restrict recharging the battery to off-peak hours of an electrical utility. When the sensors detect a malfunction of the industrial vehicle, a fault code is produced. A service technician can use that fault code to automatically access service manuals stored in the computer system of the vehicle and obtain information for diagnosing and correcting the malfunction.
Owner:RAYMOND LTD
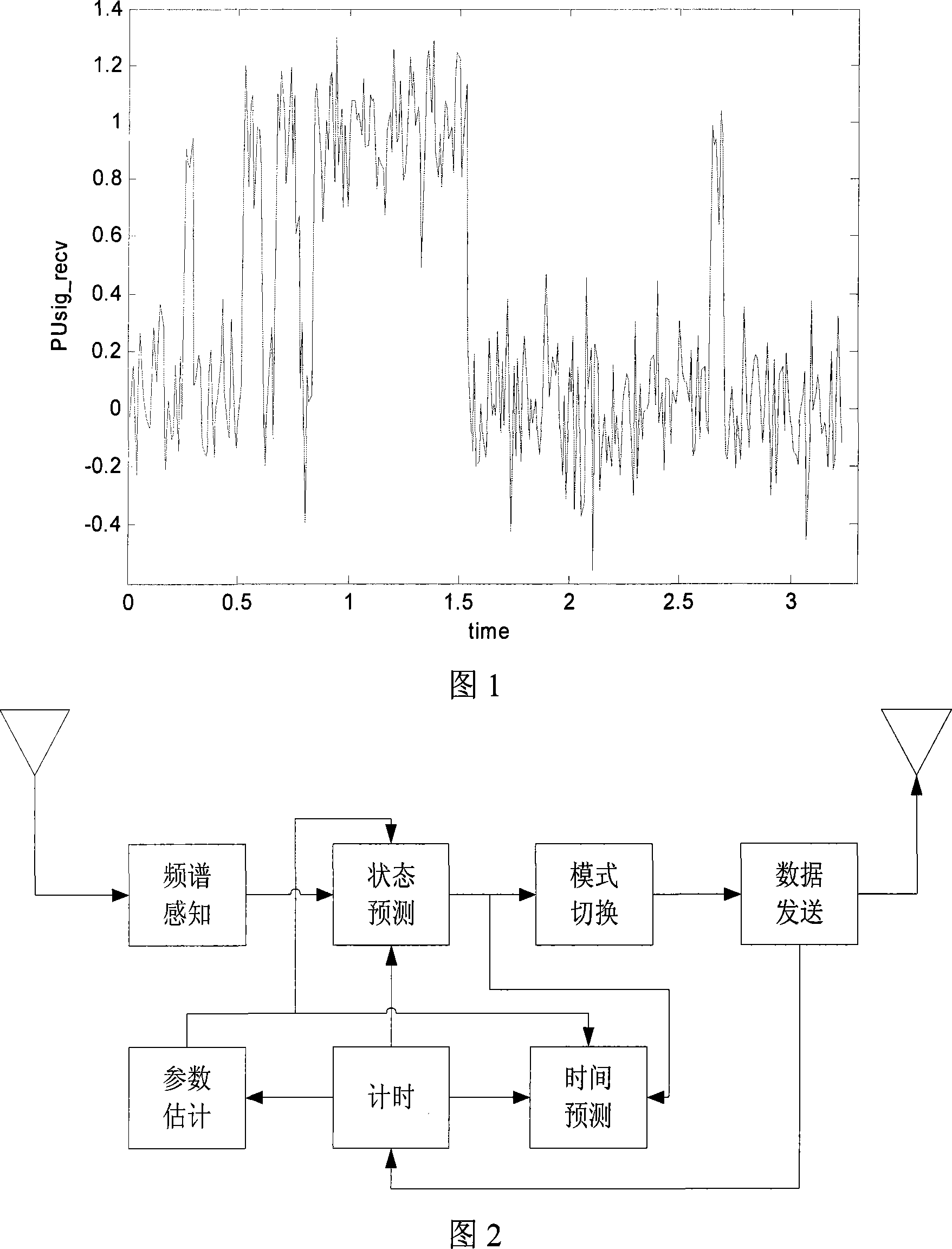
A multi-address access method based on channel sensing and prediction
InactiveCN101242333ATake advantage ofAvoid interferenceData switching networksFrequency spectrumAccess method
The invention discloses a multi access method based on channel sense and prediction. The method can self-adapting adjusts transmission time and backoff time of non-authorized user based on statistical law of authorized user busy channel. By using a modified carrier sense multi access arithmetic, the non-authorized user carries out a prediction on a frequency spectrum state and a state residual duration based on a present sensing time, a present time slot duration, the statistical law of authorized user busy channel and a blocking probability restrict of authorized user. Further, the invention provides a recursive parameter estimation method for avoiding a long-term observation to a non-authorized user required before frequency range is used. The method can increase a service efficiency of the channel under the premise of ensuring the blocking probability restrict of authorized user.
Owner:ZHEJIANG UNIV
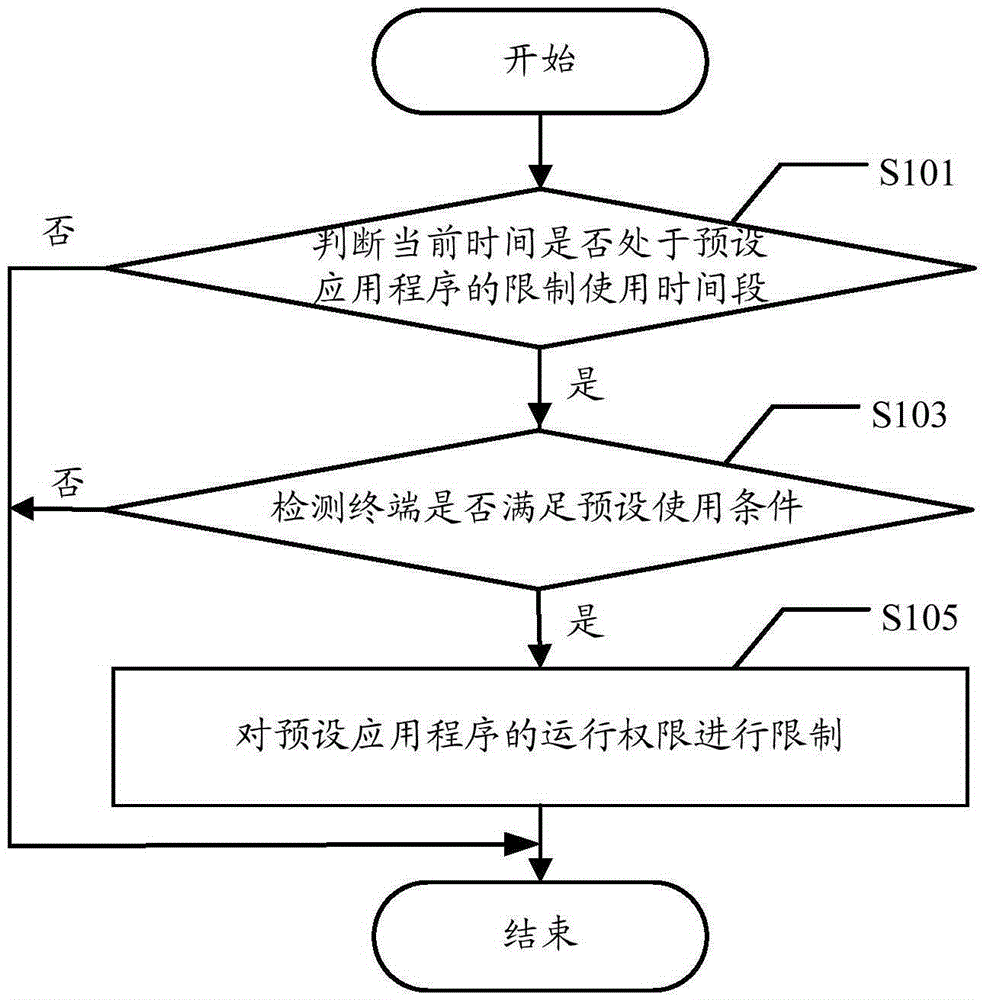
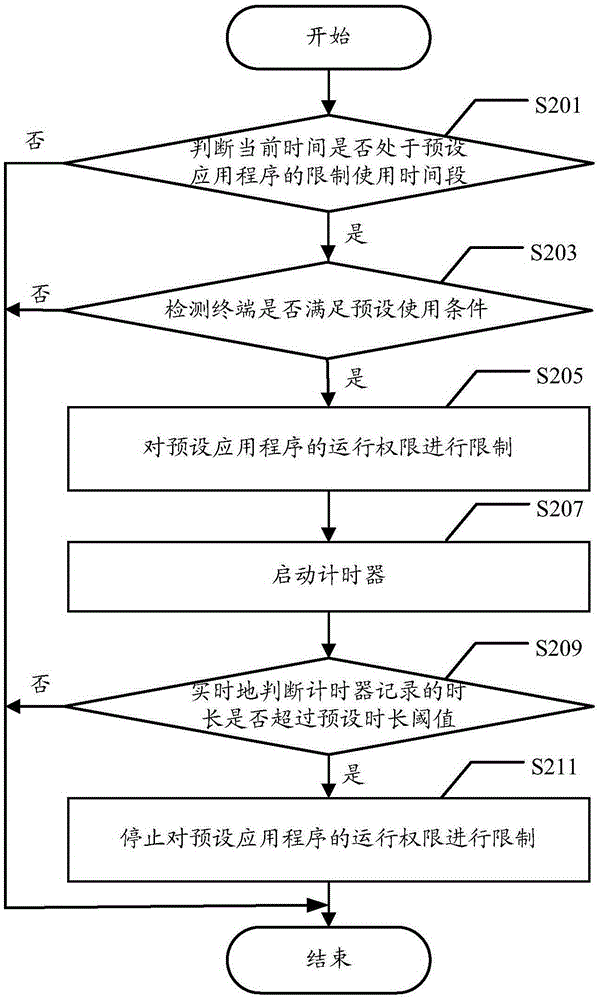
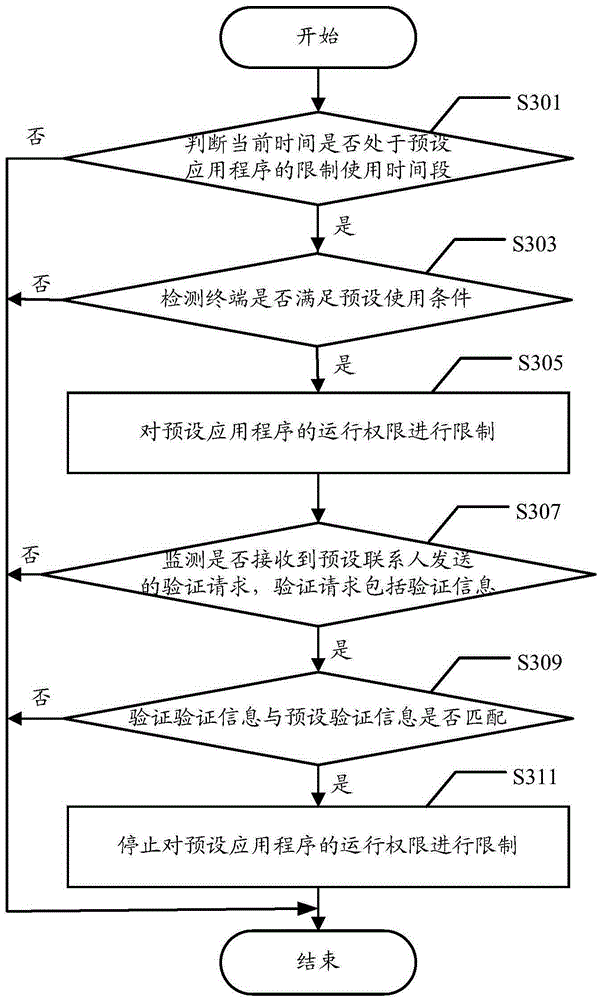
Application program control method and terminal
InactiveCN105243322AUse in moderationPrevent addictionDigital data authenticationSpecific timeReal-time computing
The embodiments of the present invention disclose an application program control method and a terminal. The method comprises: judging whether current time is in a restrict using time period of a preset application program; if judging that the current time is in the restrict using time period of the preset application program, detecting whether the terminal meets preset using conditions; and If yes, performing limiting on an operation permission of the preset application program. According to the embodiments of the present invention, the terminal can effectively limit the operation permission of the specific application program in a specific period of time so as to avoid the condition that users use the specific application program continuously in the specific period of time, thereby monitoring usage behaviors of the users and avoiding the condition that the users use the terminal immoderately.
Owner:SHENZHEN GIONEE COMM EQUIP
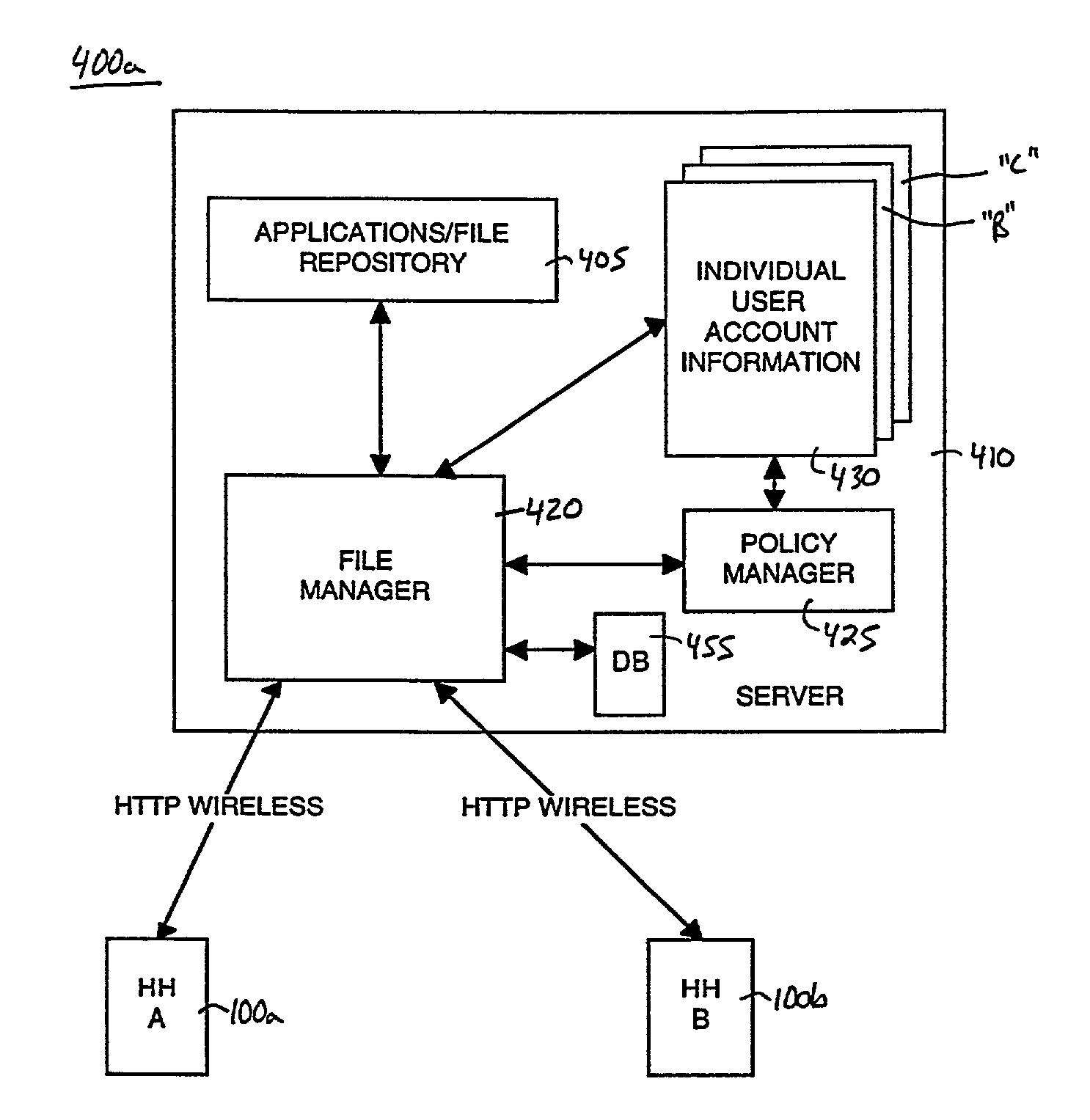
Method and system for using tokens to conduct file sharing transactions between handhelds and a web service
InactiveUS20090100149A1Reduces and eliminates impedimentEfficient transferMultiple digital computer combinationsElectric digital data processingWeb serviceComputerized system
A method and system supporting web file sharing transactions via a networked handheld computer system. In a system having a server that automatically detects when new versions of currently used applications are made available for a networked handheld computer system, a method is described for allowing one handheld computer system to facilitate the transfer of a file to another handheld computer system using the server. On the server, each registered handheld has account information indicating the applications (and versions) that it supports. As part of the file sharing transaction, using a token, a sending handheld computer system updates the account information of a receiving handheld to indicate that a download is required the next time the receiving handheld is networked with the server. A new file name may be recorded in the account information, or, a new version of an existing file name may be updated. The new information is then automatically downloaded to the receiving handheld during its next synchronization with the server. Security options on the receiver are available that restrict which handhelds have authority to send files to the receiving handheld. Synchronization can be performed with a host computer system, or directly between the server and the handhelds. The shared file may be any information, e.g., an application, data, images, electronic currency, etc.
Owner:QUALCOMM INC
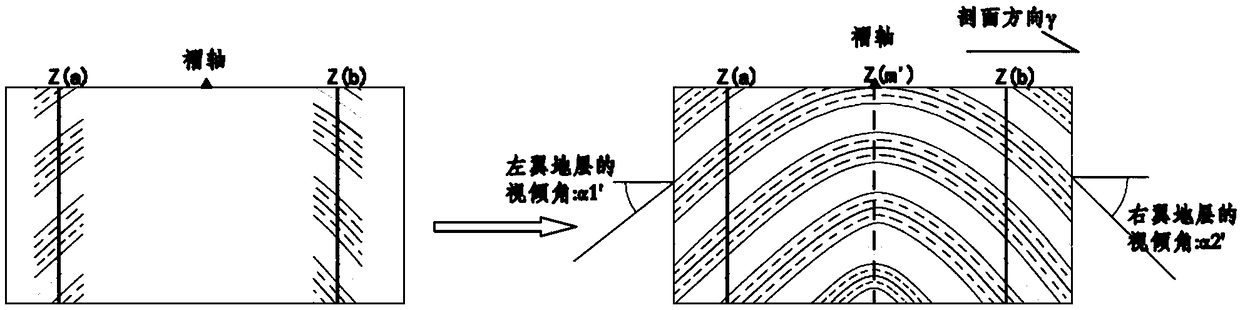
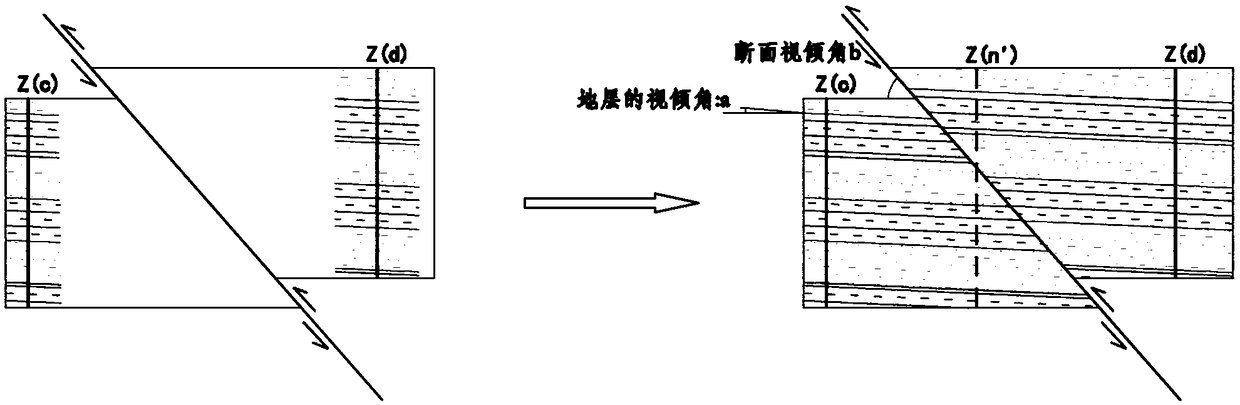
Method for measuring occurrence of non-contact structural surface
InactiveCN103697854AAchieving Occurrence MeasurementRealize multi-angle measurementAngle measurementRectangular coordinatesLight beam
The invention discloses a method for measuring the occurrence of a non-contact structural surface. The method comprises the following steps: establishing a descartes rectangular coordinate system of a right-hand space by taking a relocation site of a distance meter as an original point and a magnetic north direction as the positive direction of the x-axis by means of a space ranging function of a laser or infrared distance meter; rotating the distance meter to enable a measured light beam to be irradiated to three non-colinear points of a structural surface to be measured, and respectively recording the vertical rotation angle, horizontal rotation angle and measuring distance of each measured light beam; and quantitatively describing the inclination state of the structural surface to be measured by utilizing the relationship between a spatial vector and a geometric projection, and calculating the inclination angle, inclination and trend of the structural surface. By using the method, the application restrict for the contact measurement of the traditional geological compass is broken, the measurement for the occurrence of a long-distance or difficultly-contact structural surface is realized, and the measurement errors caused by the magnetism of minerals are effectively avoided.
Owner:广西华锡集团股份有限公司
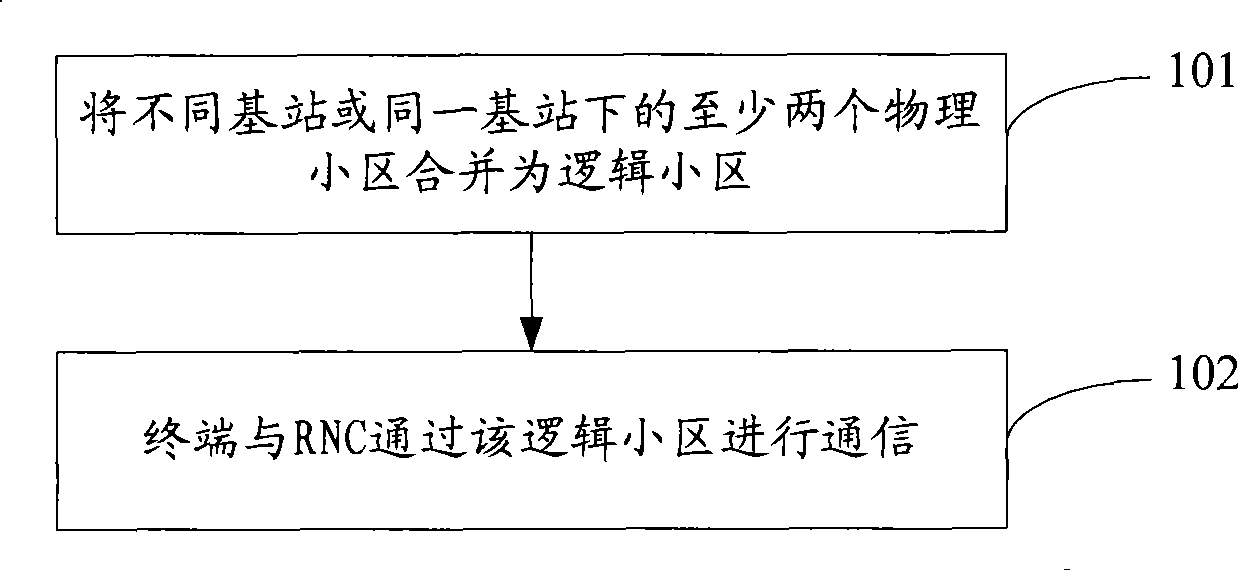
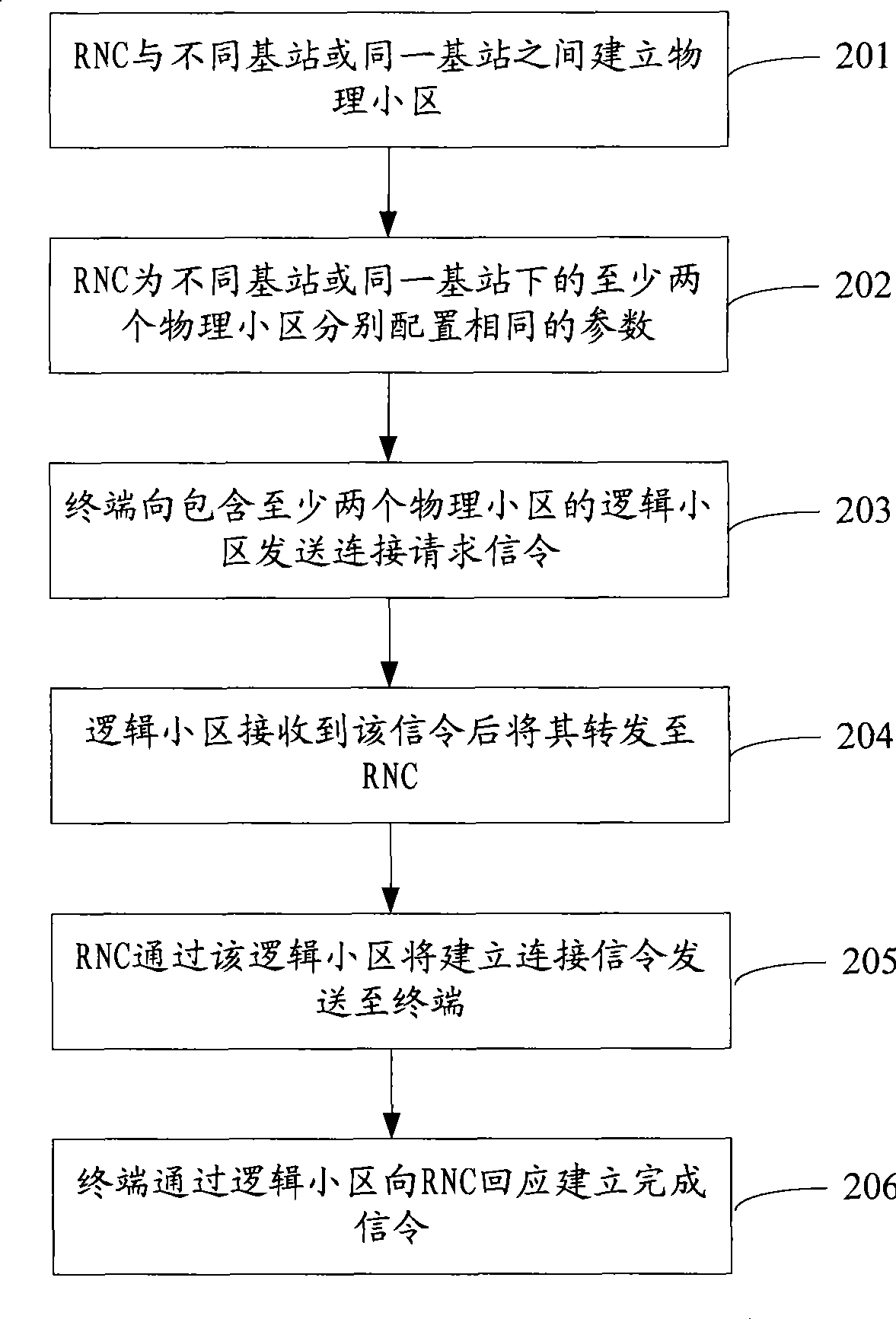
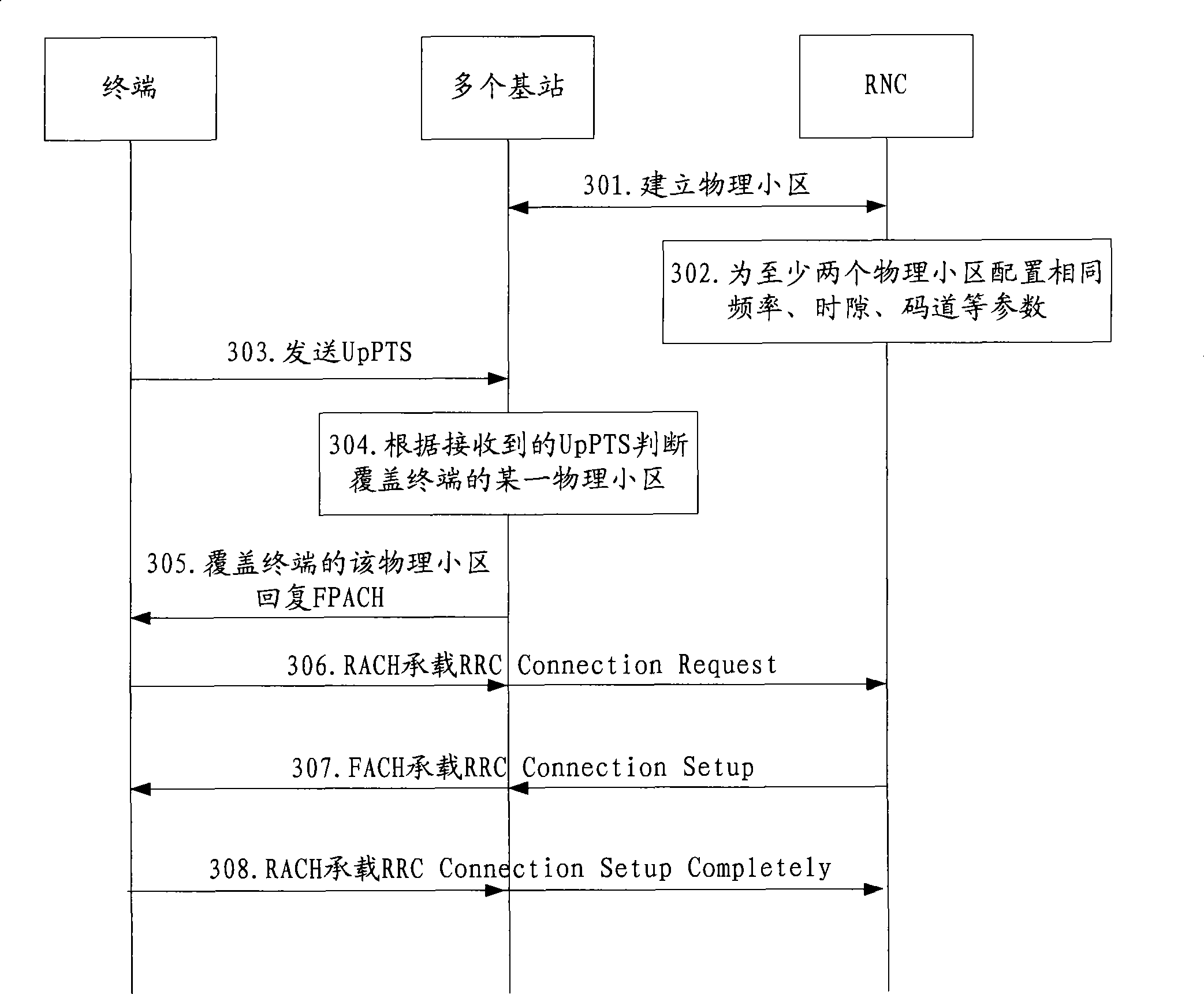
Cell communication method, system and radio network controller
InactiveCN101400111AImprove communication qualitySimple accessAssess restrictionNetwork planningCommunications systemRadio Network Controller
The invention discloses a method of district communication, comprising: combining at least two physical districts under different base stations or the same base station into a logic district; communicating through the logic district between terminals and a radio network controller RNC. The invention also discloses a district communication system and a radio network controller. According to the invention, district coverage range of the wireless communication system is added through the logic district constituting a plurality of physical districts, avoiding restrict of a transmitting device and special terminals to increasing transmitting power and receiving sensitivity, requirement of distributivity antennas or repeater stations on transmission bandwidth is adopted, wherein realization is convenient. Due to the increased coverage range of the district after combining the logic district, the terminal are easy to access into the district, increasing switching success ratio, avoiding drop call.
Owner:CHINA ACAD OF TELECOMM TECH
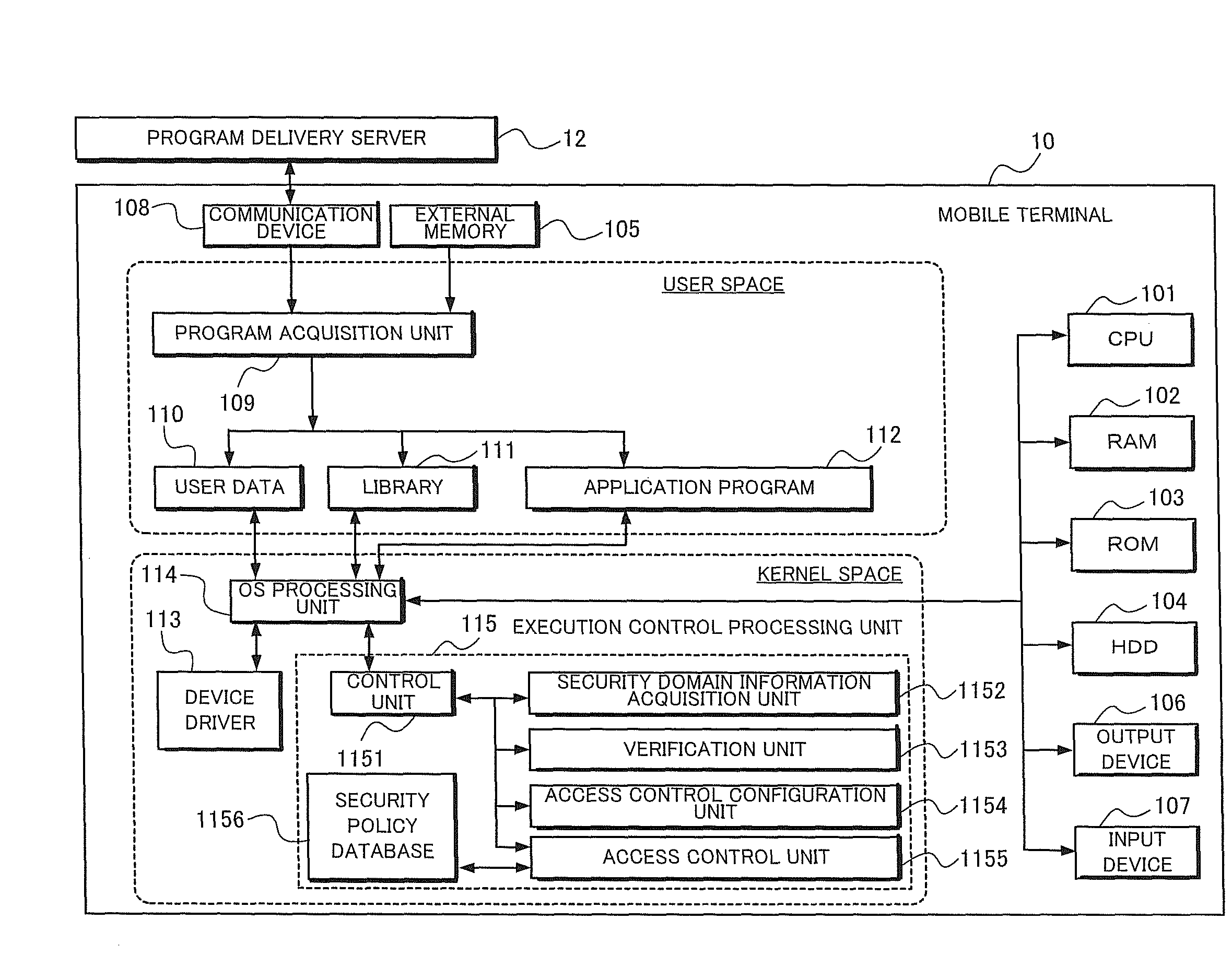
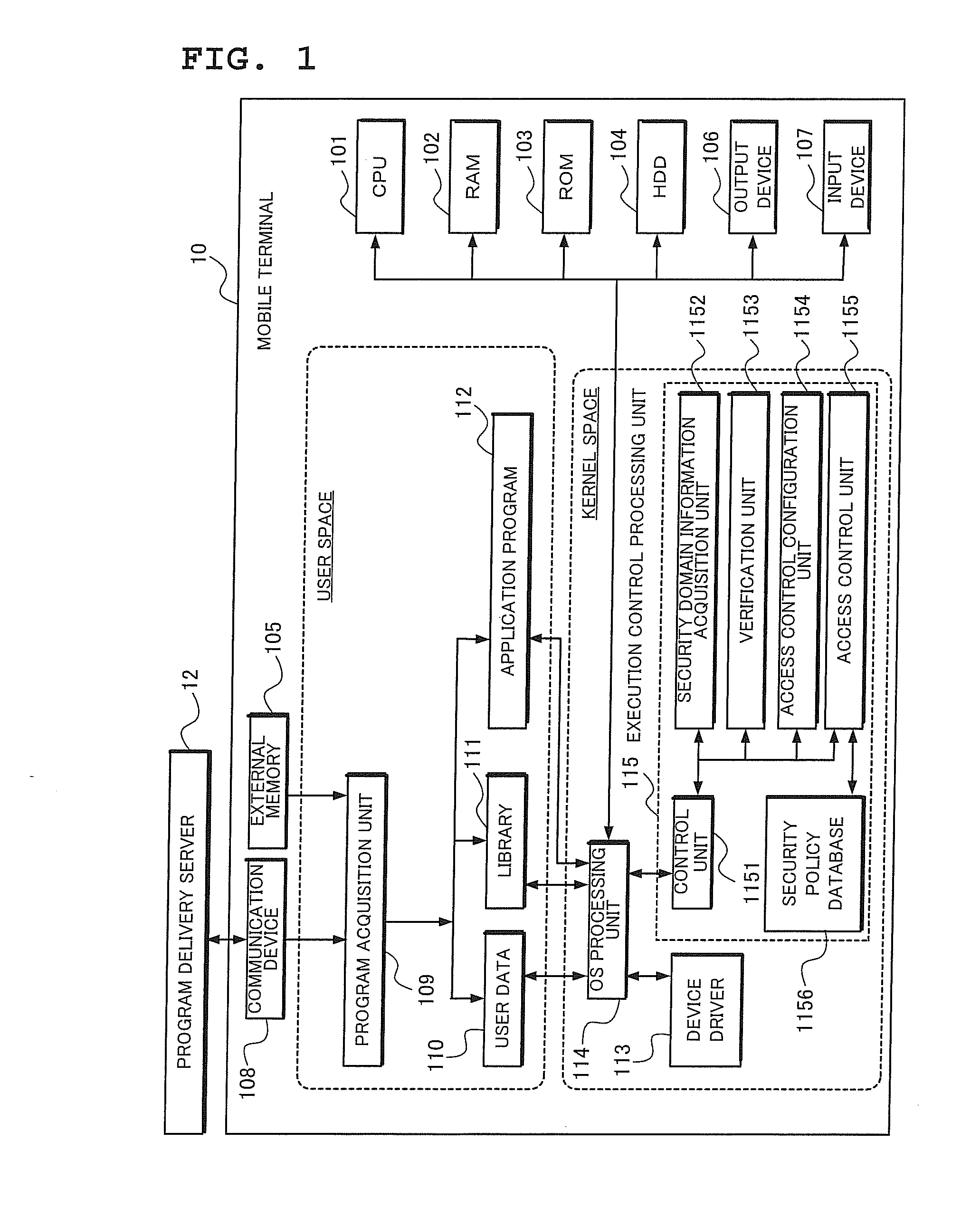
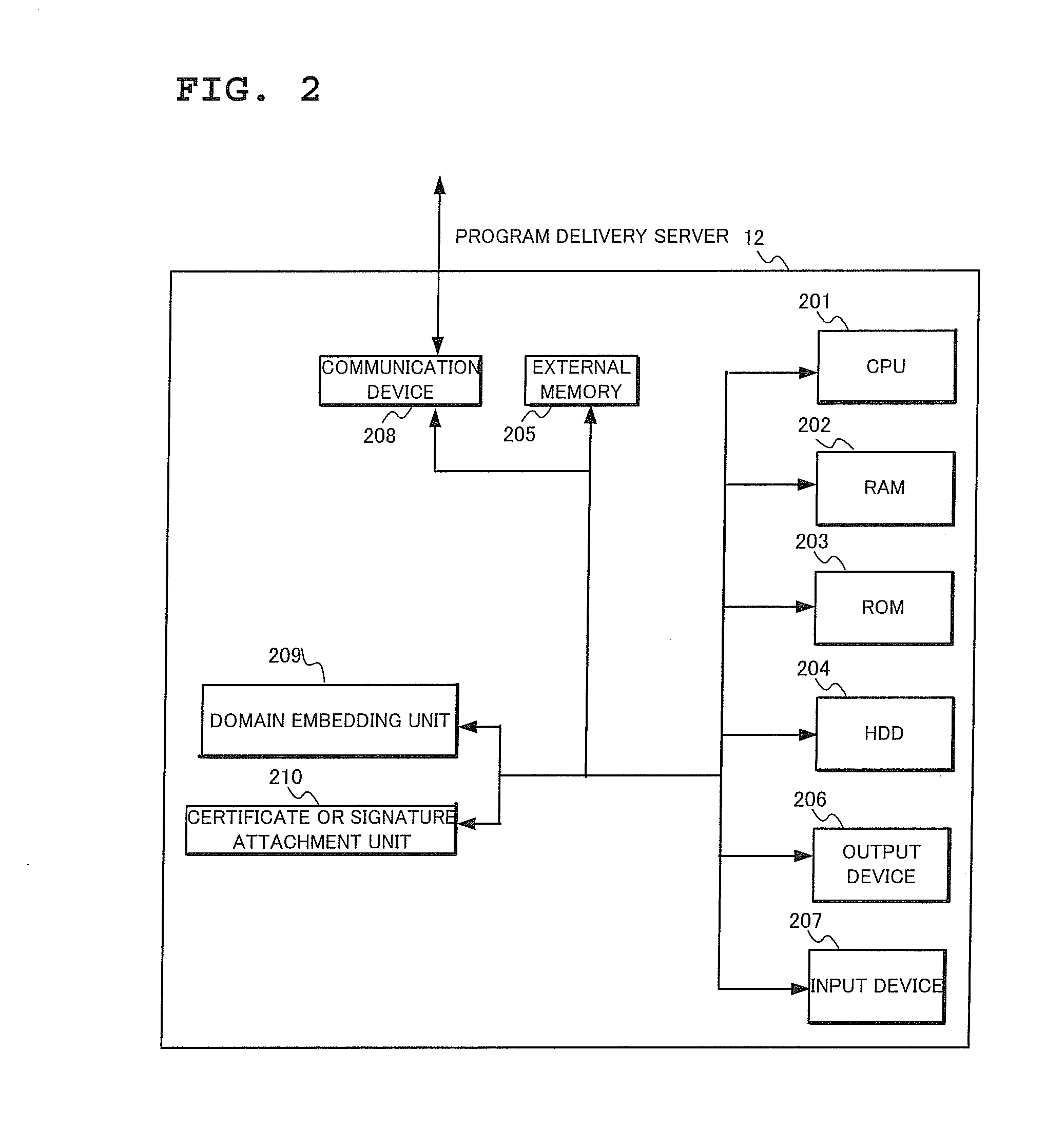
Program execution control system, program execution control method and computer program for program execution control
InactiveUS20100229242A1Ensuring Safe ExecutionDigital data processing detailsAnalogue secracy/subscription systemsControl systemSecurity domain
When a program is introduced into a computer terminal from an external source via a wired or wireless network or by using an external memory card, unauthorized access by the introduced program to various functions within the terminal is prevented by verifying the source from which the program was distributed and performing execution control appropriately according to the identity of the program. In order to reference the security policy data which specifies functions available to each program given from an external source and restrict functions used by the program, the information concerning the security domain or the certificate or signature attached to the program is extracted, and the extracted information is associated with one of a plurality of function access types held as security policy data.
Owner:NEC CORP
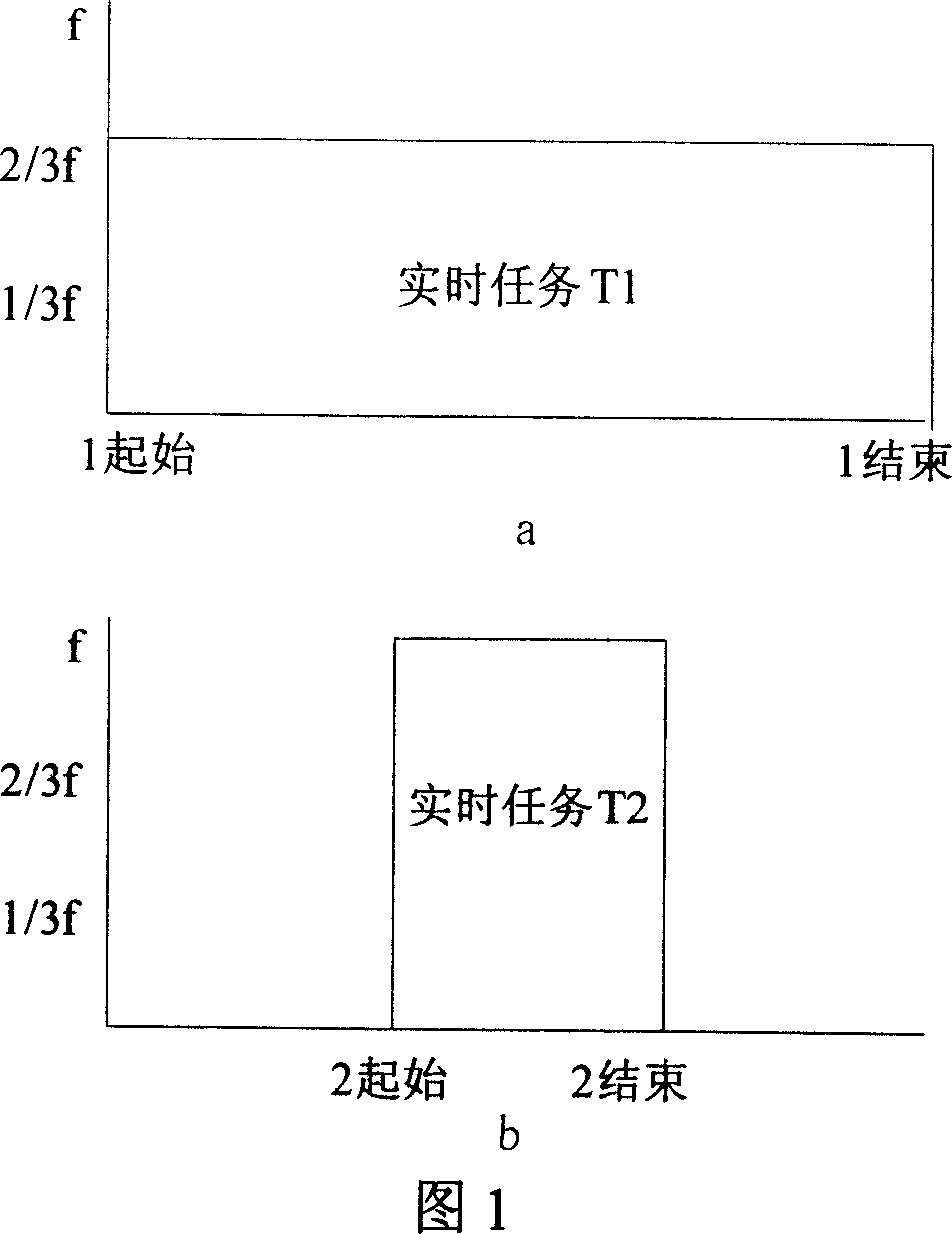
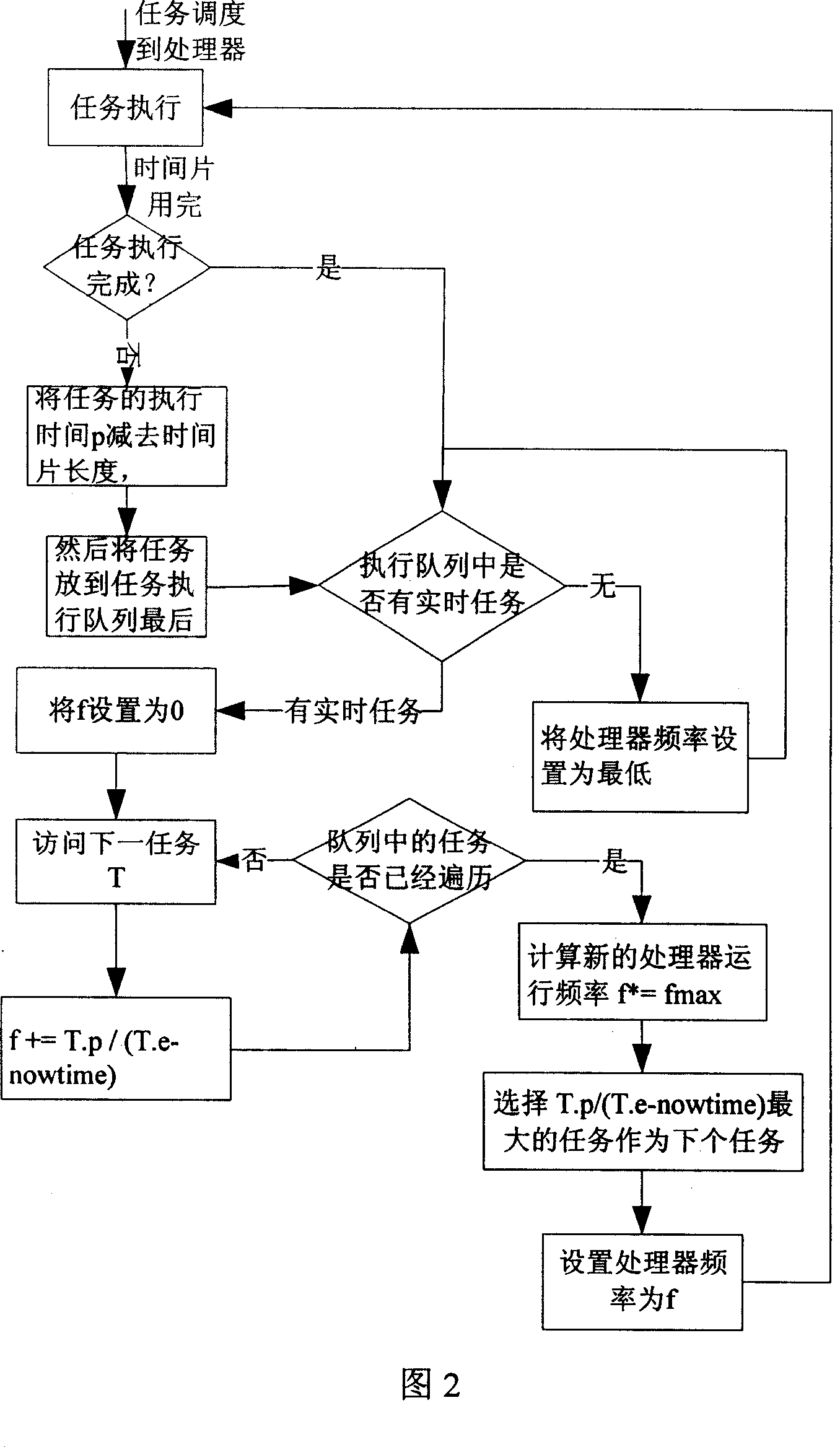
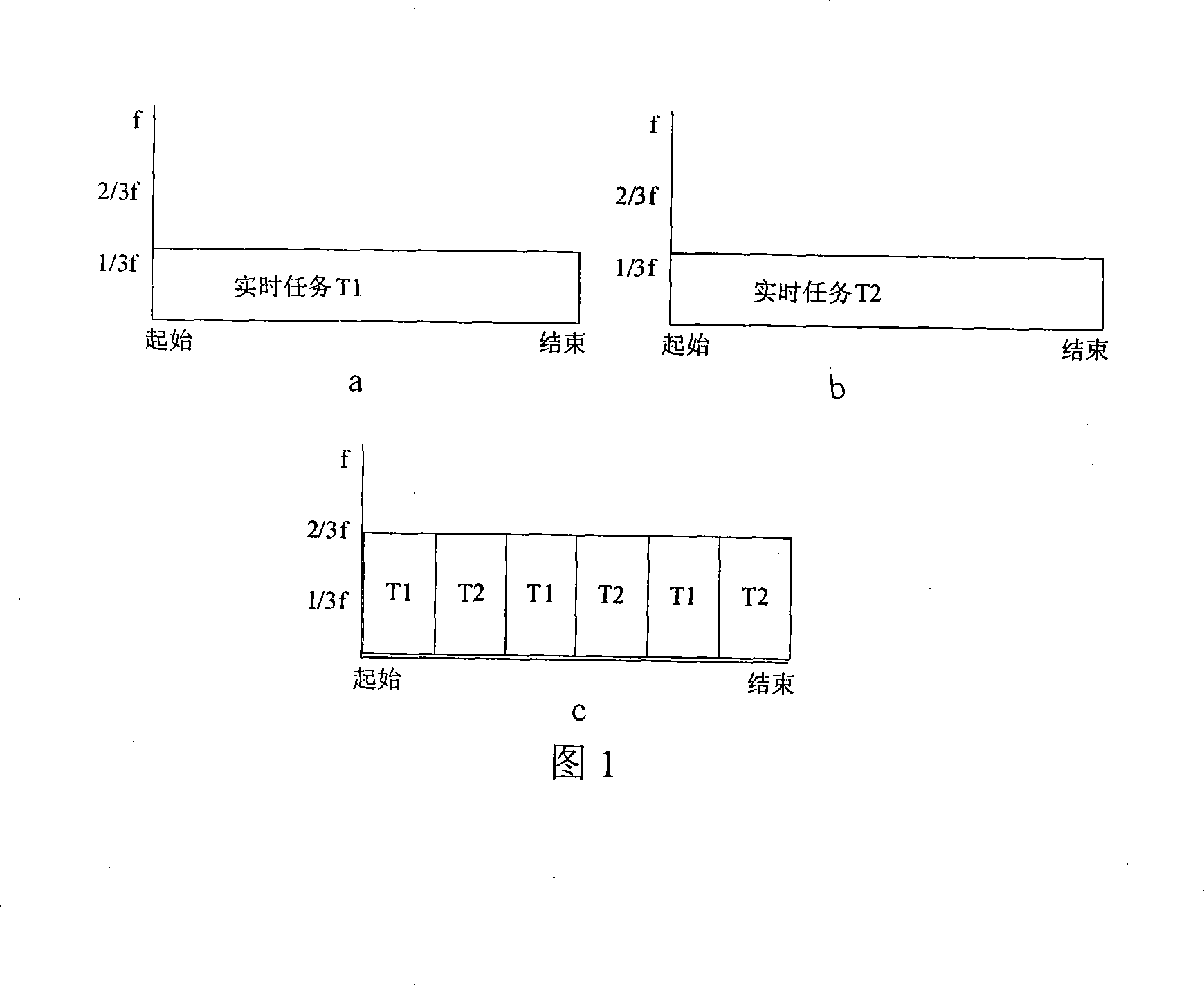
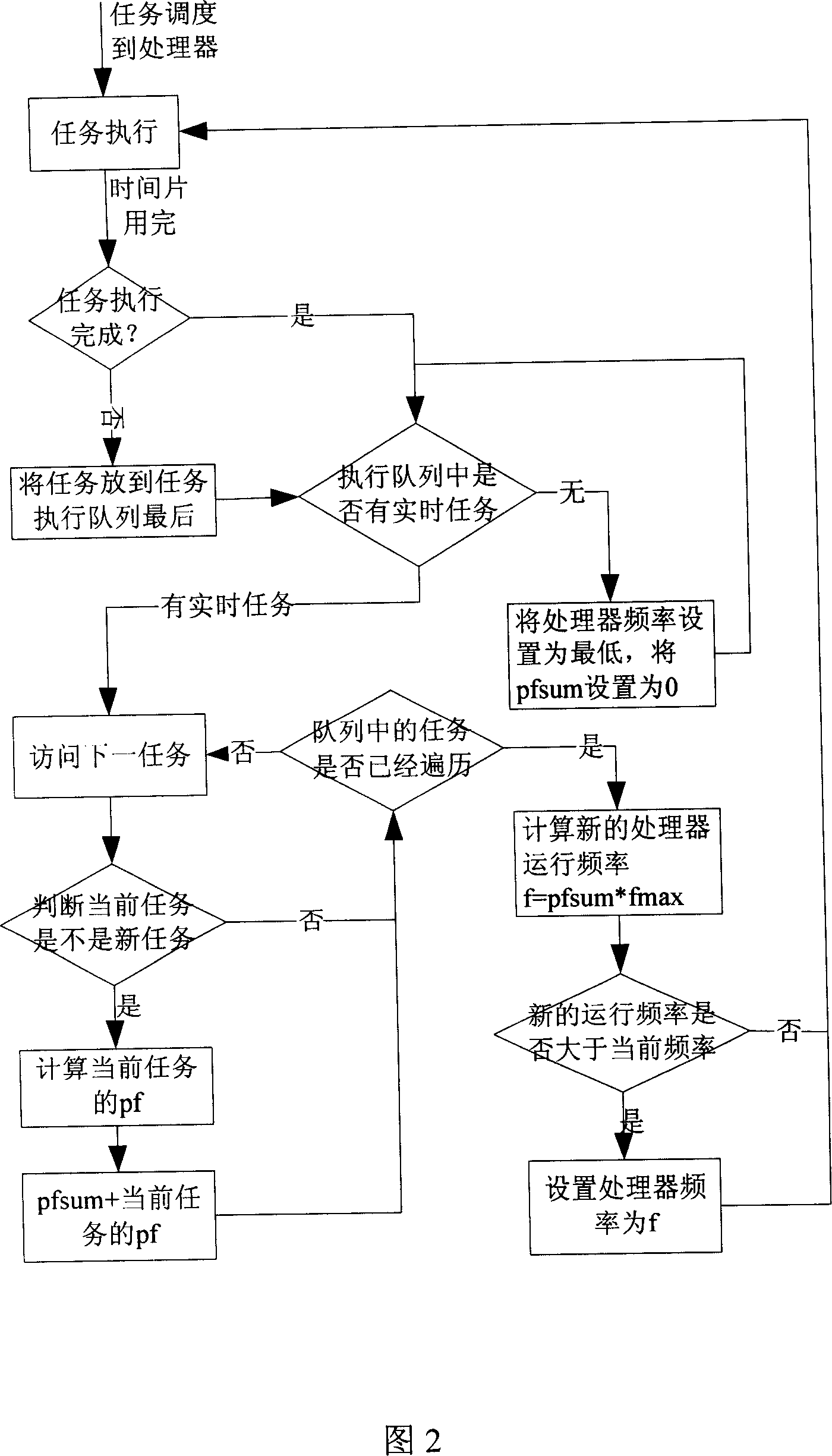
Low power consumption real time task parameter model dispatching method facing embedded system
InactiveCN1945498AEnsure real-time requirementsExtended use timeEnergy efficient ICTMultiprogramming arrangementsTime functionOperational system
This invention provides a low power real-time task scheduling method oriented embedded system for modeling, solution and optimization of real-time task scheduling for low power. It achieves low power consumption by using the technology and Real-time dynamic FM_PM Web tablet model, real-time scheduling. It ensures a real-time function based on the Real-time tasks in the model with a real-time restrict. Meanwhile, the program use of dynamic FM_PM operating systems, real-time processor to adjust to state Energy-saving way to achieve the objective during the process of implementing the mandate.
Owner:ZHEJIANG UNIV
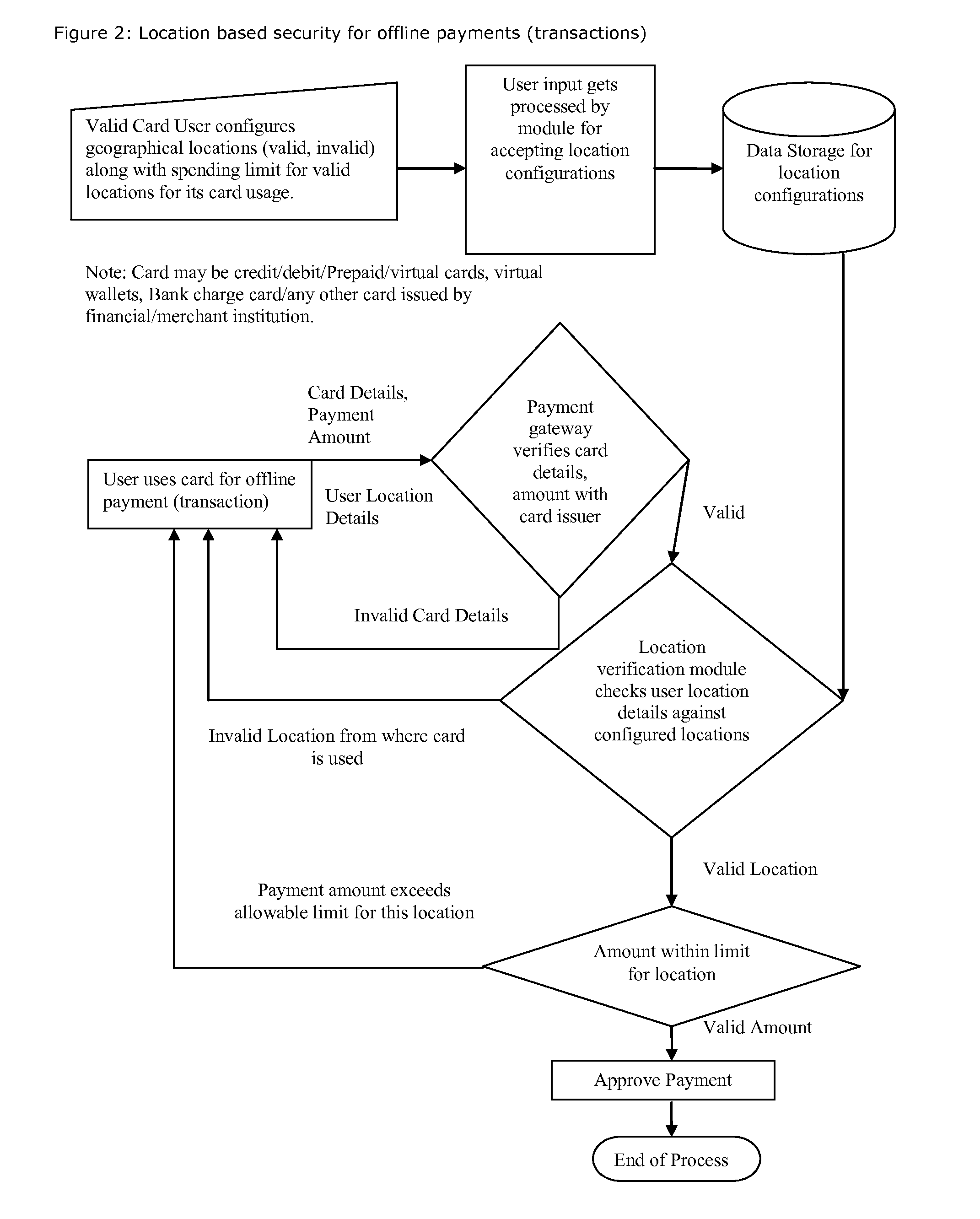
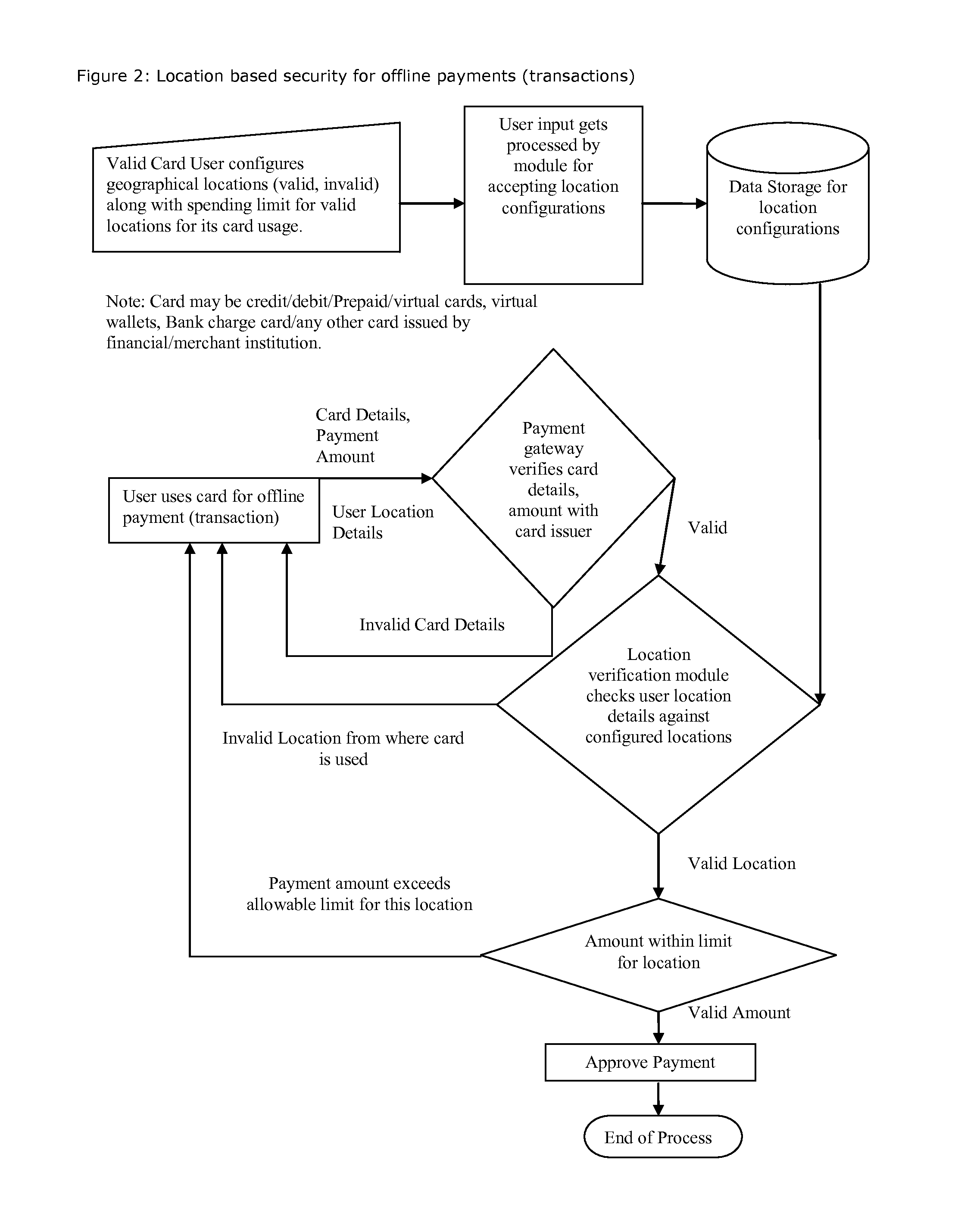
Method for providing geographical location-based security, restrict, permit access of varying level to individual's any kind of data, information, credit, finances, services obtained(online and or offline)
Proposed method and security system provide geographical location-based security with varying levels of access. It allows users to select entities to protect, configure geographical locations, geographical boundaries as well as permissions, access level for given geographical locations, geographical boundaries and configure security alerts. It takes decision to grant, deny permission or provide given access level based on user's current geographical location and user's own configuration for that geographical location or boundary and sends out security alerts.
Owner:SHAH DHAVALKUMAR M
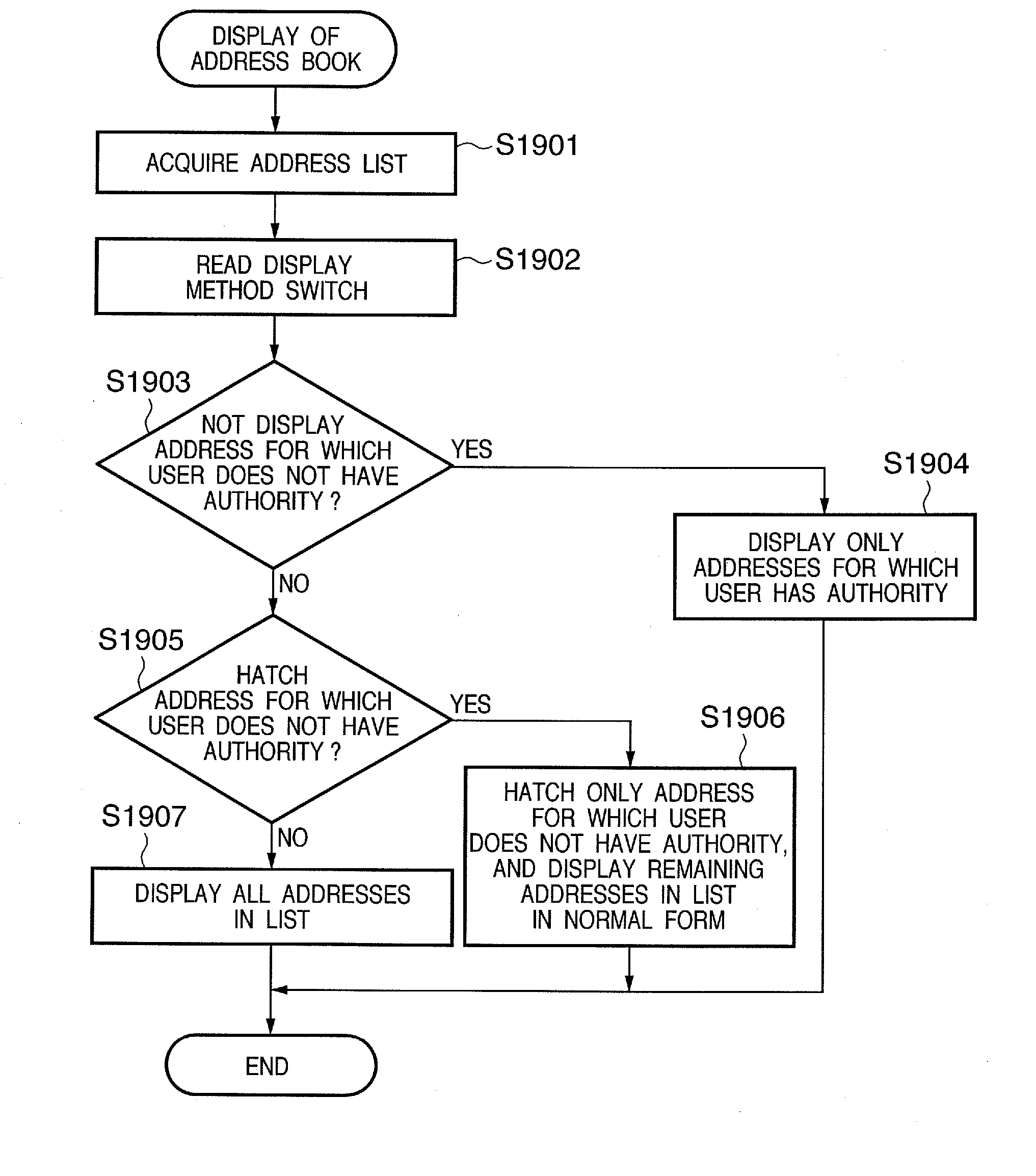
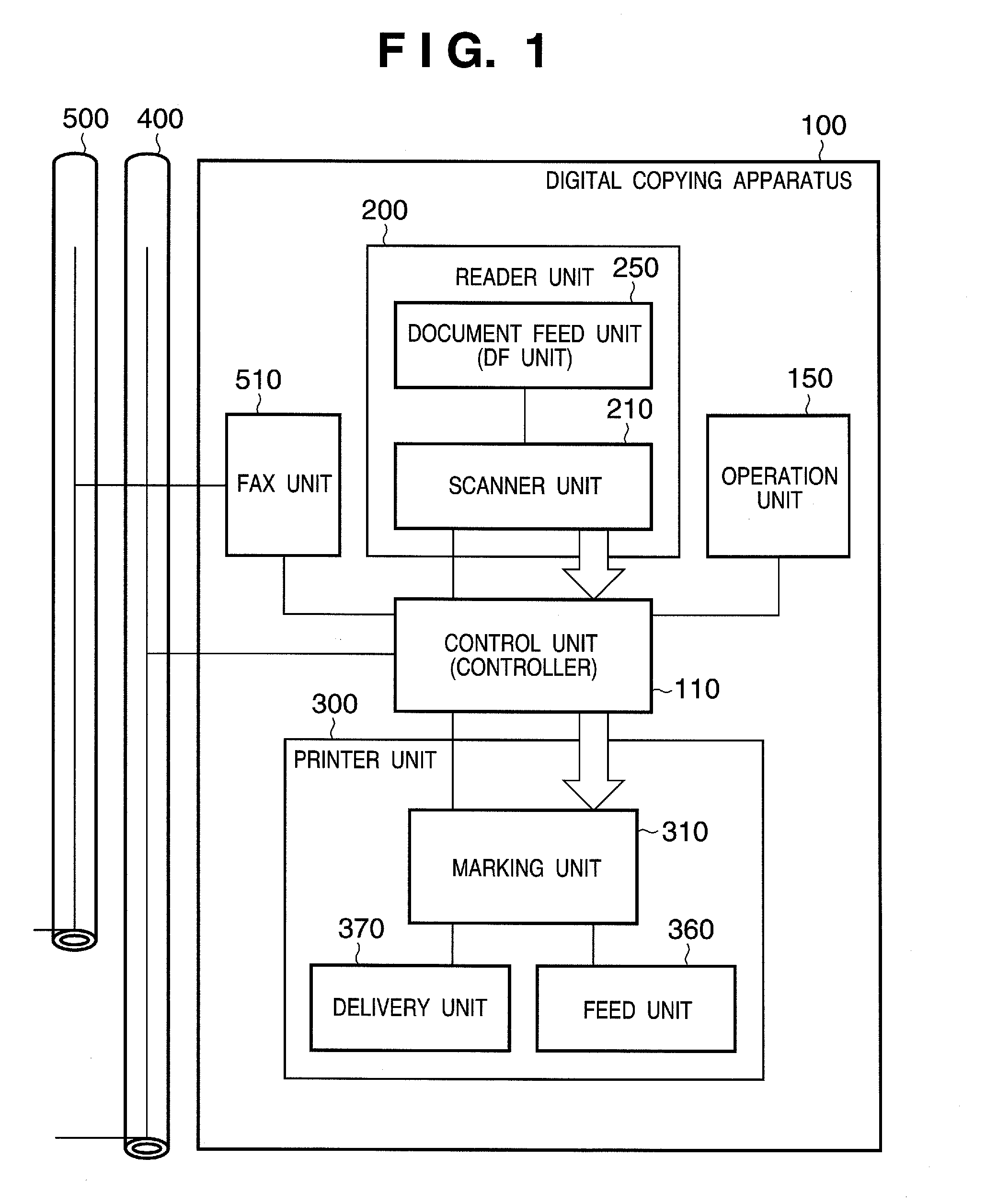
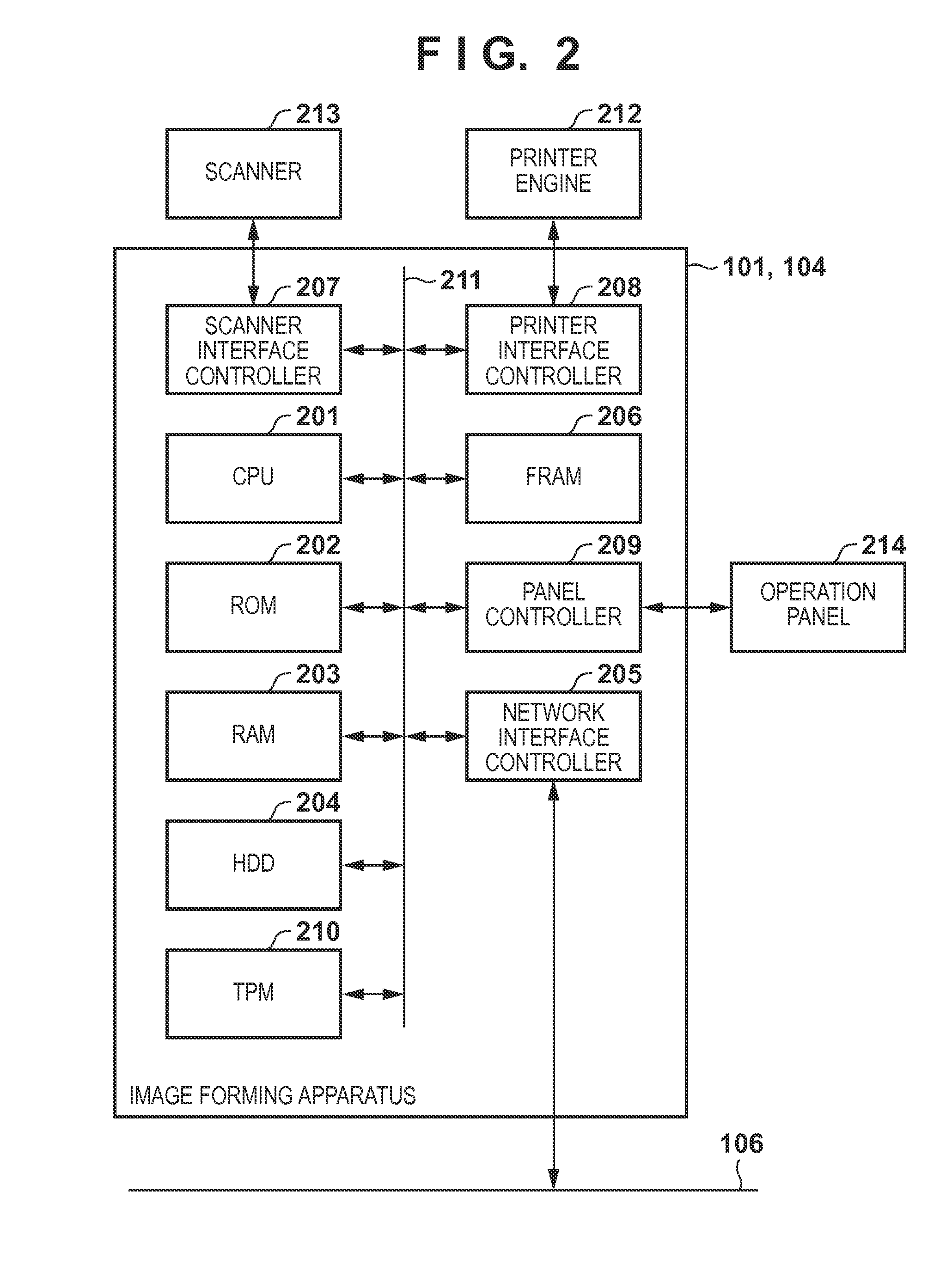
Data transmission apparatus, control method therefor, and image input/output apparatus
ActiveUS20070089173A1Digital data processing detailsDigital computer detailsComputer hardwareData transmission
According to the present invention, a data transmission apparatus capable of transmitting data by using a plurality of transmission media, comprises an authority storage unit, adapted to store authority information representing use authority to use each transmission medium by each user; and a transmission control unit, adapted to, in transmitting data, restrict data transmission to a destination corresponding to a transmission medium for which a current user does not have the use authority.
Owner:CANON KK
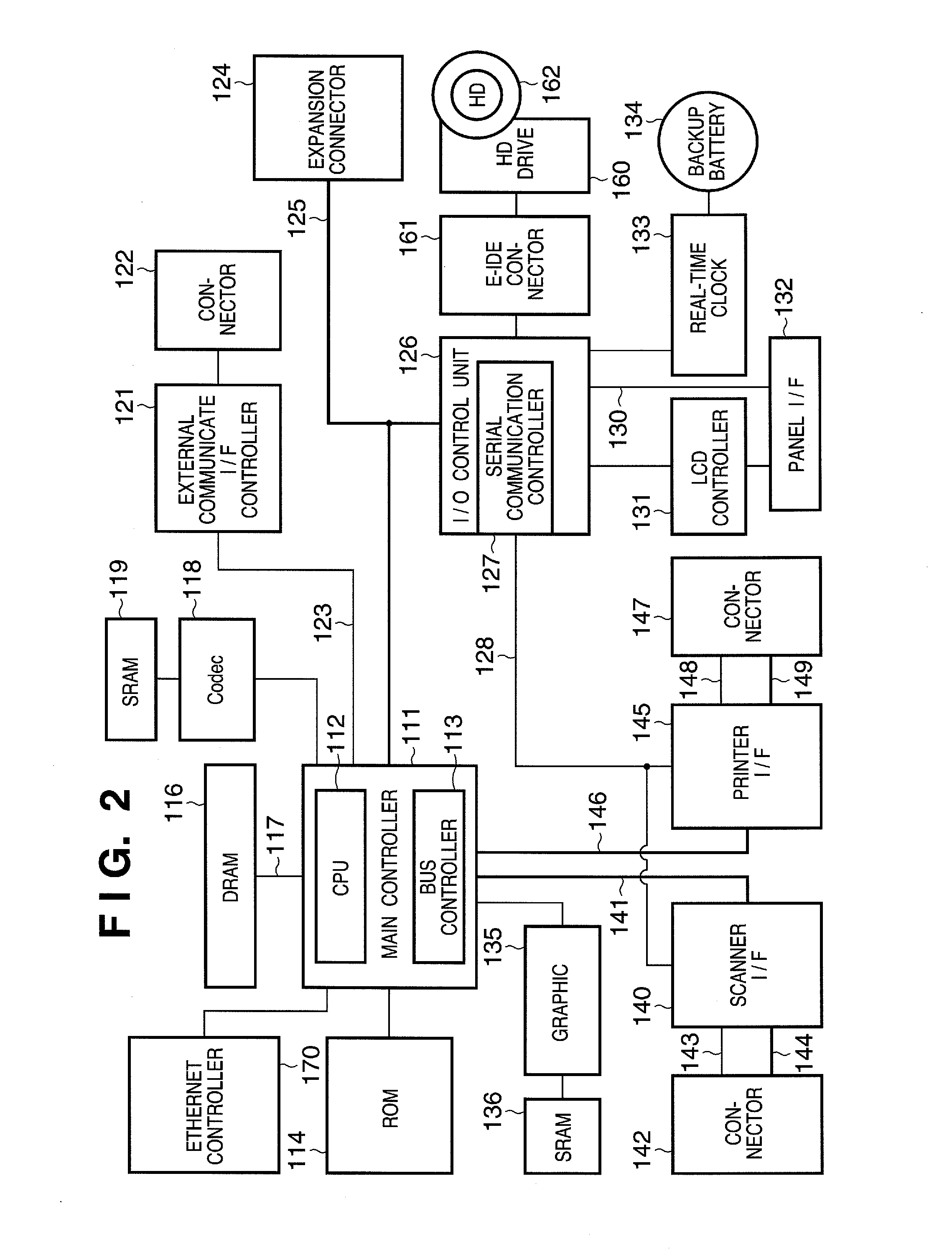
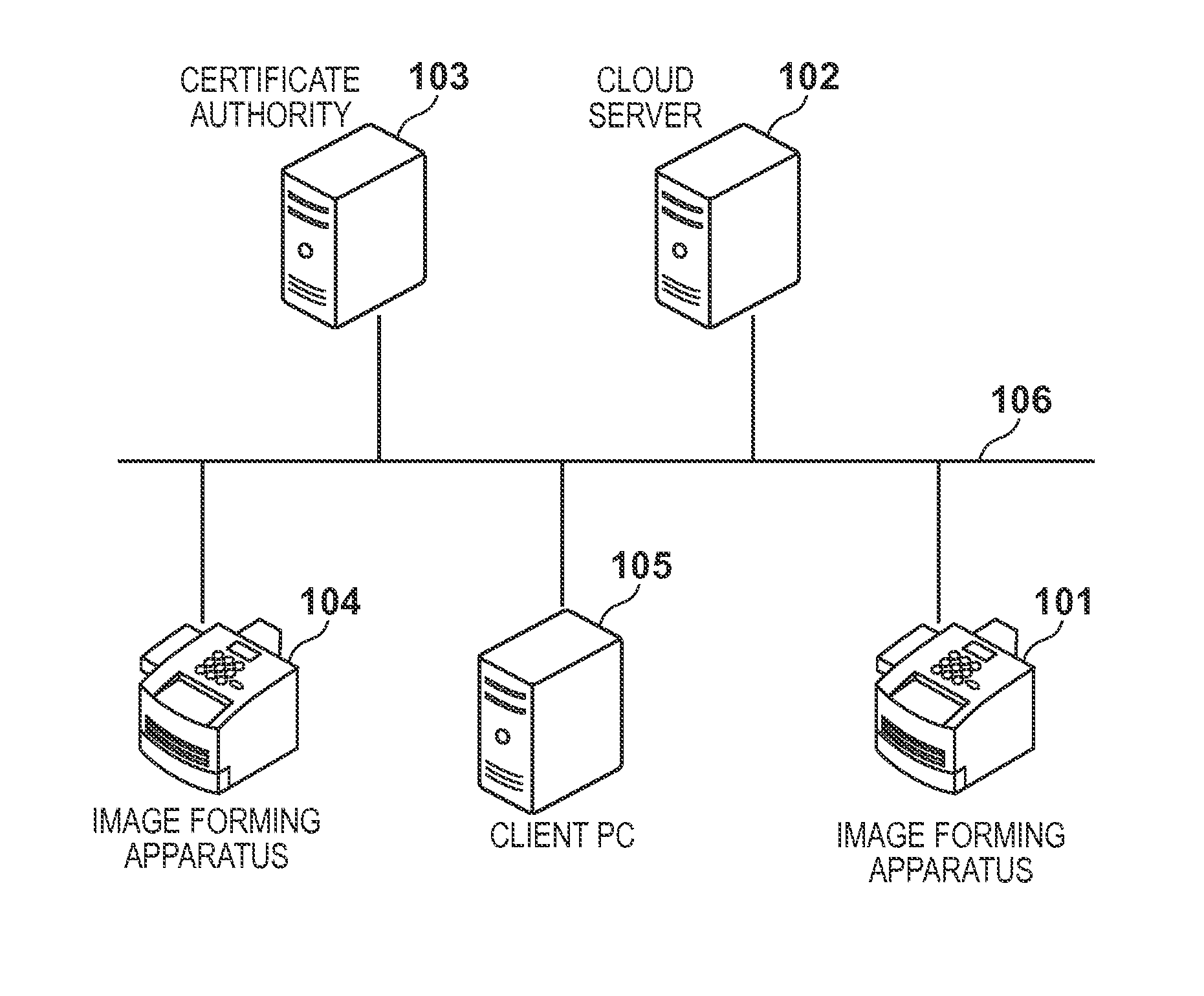
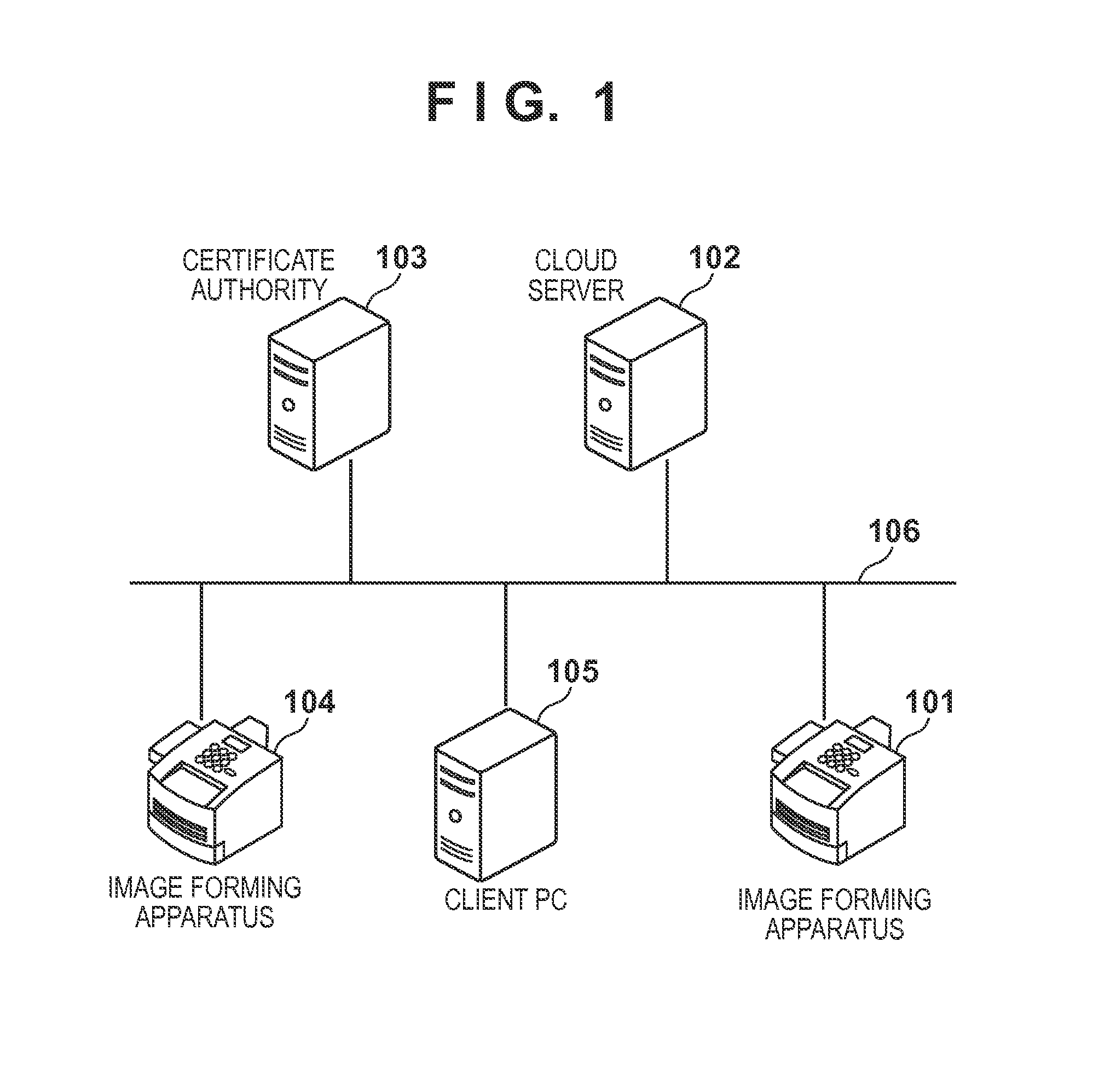
Information processing apparatus, server, method for controlling the same and storage medium
An information processing apparatus for accessing a server via a network transmits an issuance request of a certificate including information unique to the information processing apparatus to a certificate authority, and receives the certificate transmitted by the certificate authority in response to the issuance request. The apparatus determines whether or not it is possible to access the server by comparing information unique to the information processing apparatus with the unique information included in the received certificate, and restricts, if it is determined that it is not possible to access the server, issuance of a connection request to the server.
Owner:CANON KK
Method and device for implementing radio frequency link transmit-receive sharing by switch array in TDD mode
InactiveCN101321012AReduce usageIncrease profitRadio transmission for post communicationMultiplexingRadio frequency
The invention relates to a method for realizing the radio frequency link receiving share through a switch array in the TDD mode and the device. According to the invention, the functions of the uplink receiving share and the downlink receiving share or the partial branch receiving share are realized through adopting the switch array in the uplink and the downlink, the multiplexing restrict with the directivity radio frequency device is overcome, the utilance of the device in the receiving link is advanced, the complexity of the link is reduced and the cost and the volume of the device are reduced.
Owner:BEIJING XINWEI TELECOM TECH
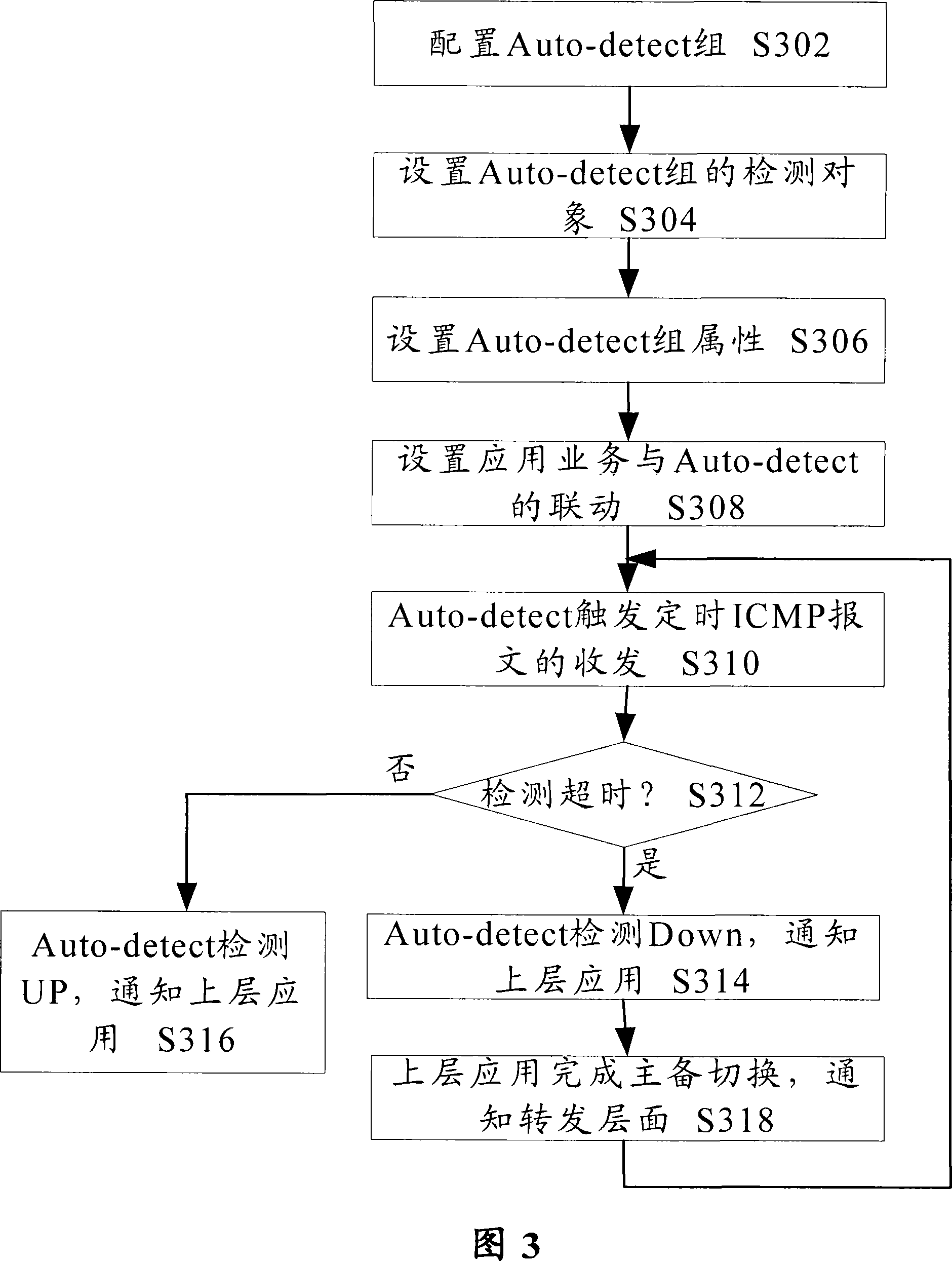
Automatic detection method and device for network connectivity
InactiveCN101197733ACheck interoperabilityImprove interoperabilityError preventionData switching networksThe InternetDistributed computing
The invention discloses a method for automatically detecting network connectivity and a device thereof, wherein the method includes the following procedures: (1) an automatic detection group is constructed, the automatic detection group is provided with one or more than one detecting object and detecting strategy; (2) an internet control information protocol request message is sent to one or more than one detecting object, whether the message reaches one or more than one detecting object is judged based on the detecting strategy; and(3) one or more than one application service is reported the detection result by sending the detection result message to the application service related to one or more than one automatic detection group. The invention can realize the detection of the network connectivity without restrict requirements on both detection sides, thereby effectively meeting needs of various application services.
Owner:ZTE CORP
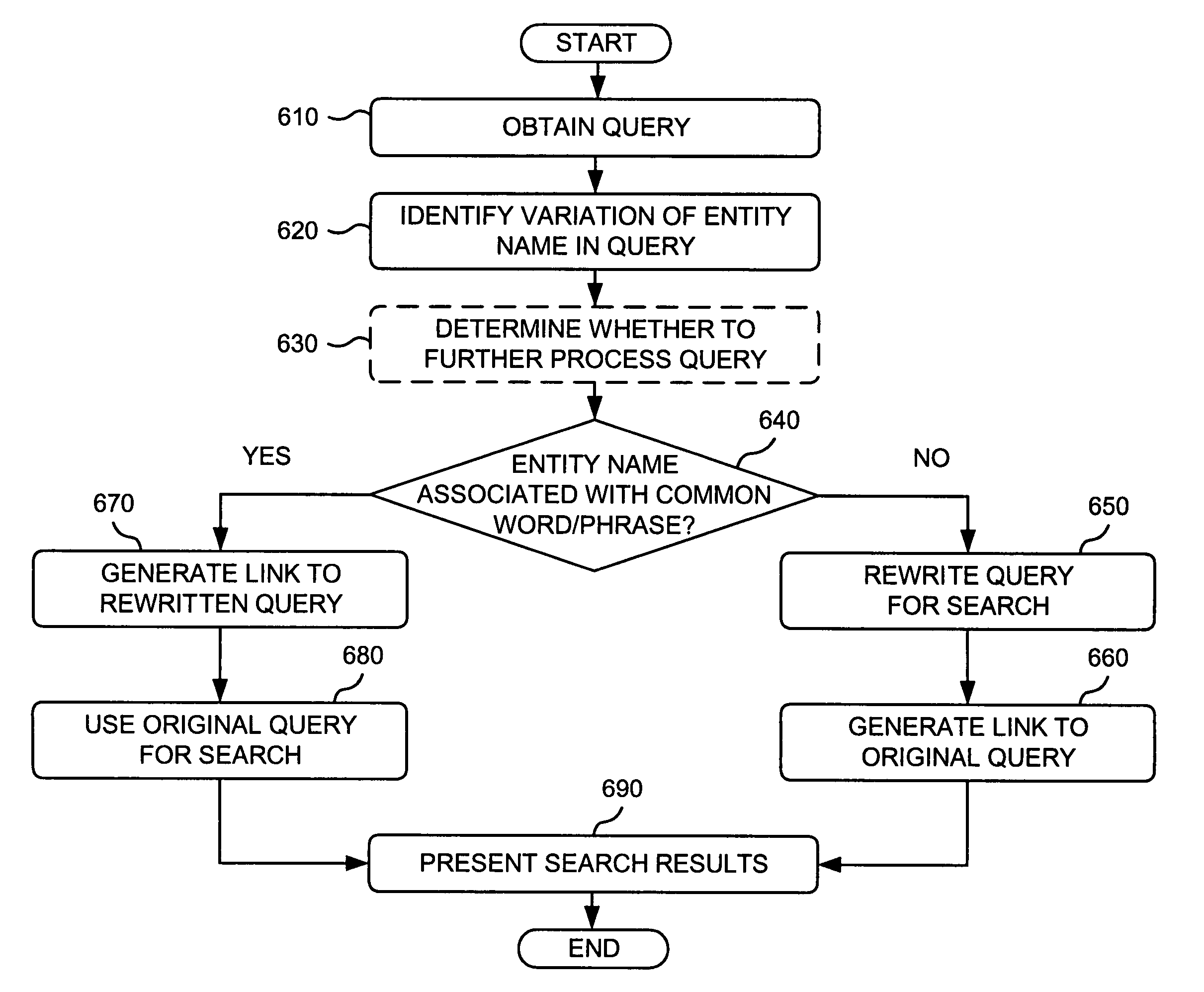
Query rewriting with entity detection
A system receives a search query, determines whether the received search query includes an entity name, and determines whether the entity name is associated with a common word or phrase. When the entity name is associated with a common word or phrase, the system generates a link to a rewritten query, performs a search based on the received search query to obtain first search results, and provides the first search results and the link to the rewritten query. When the entity name is not associated with a common word or phrase, the system rewrites the received search query to include a restrict identifier associated with the entity name, generates a link to the received search query, performs a search based on the rewritten search query to obtain second search results, and provides the second search results and the link to the received search query.
Owner:GOOGLE LLC
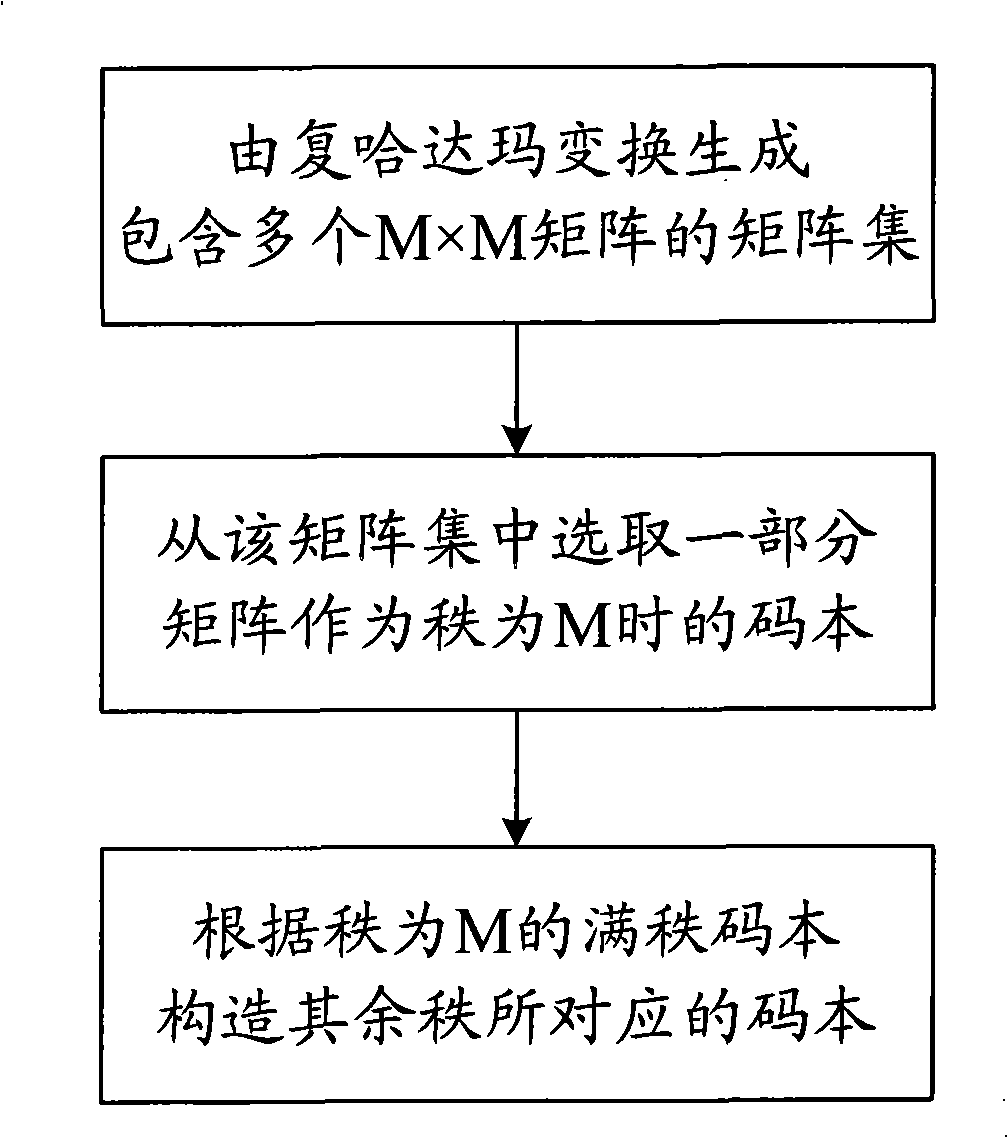
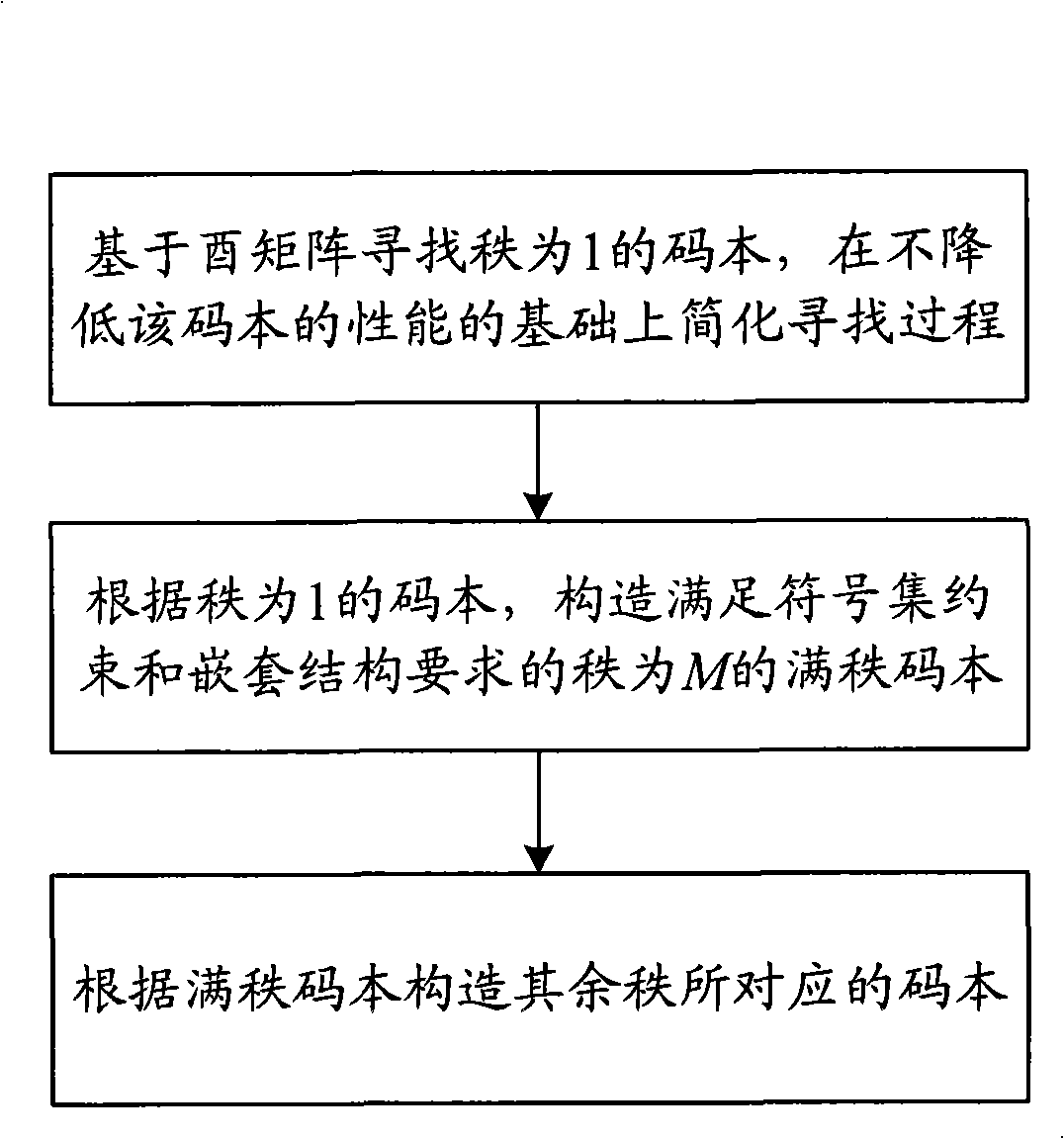
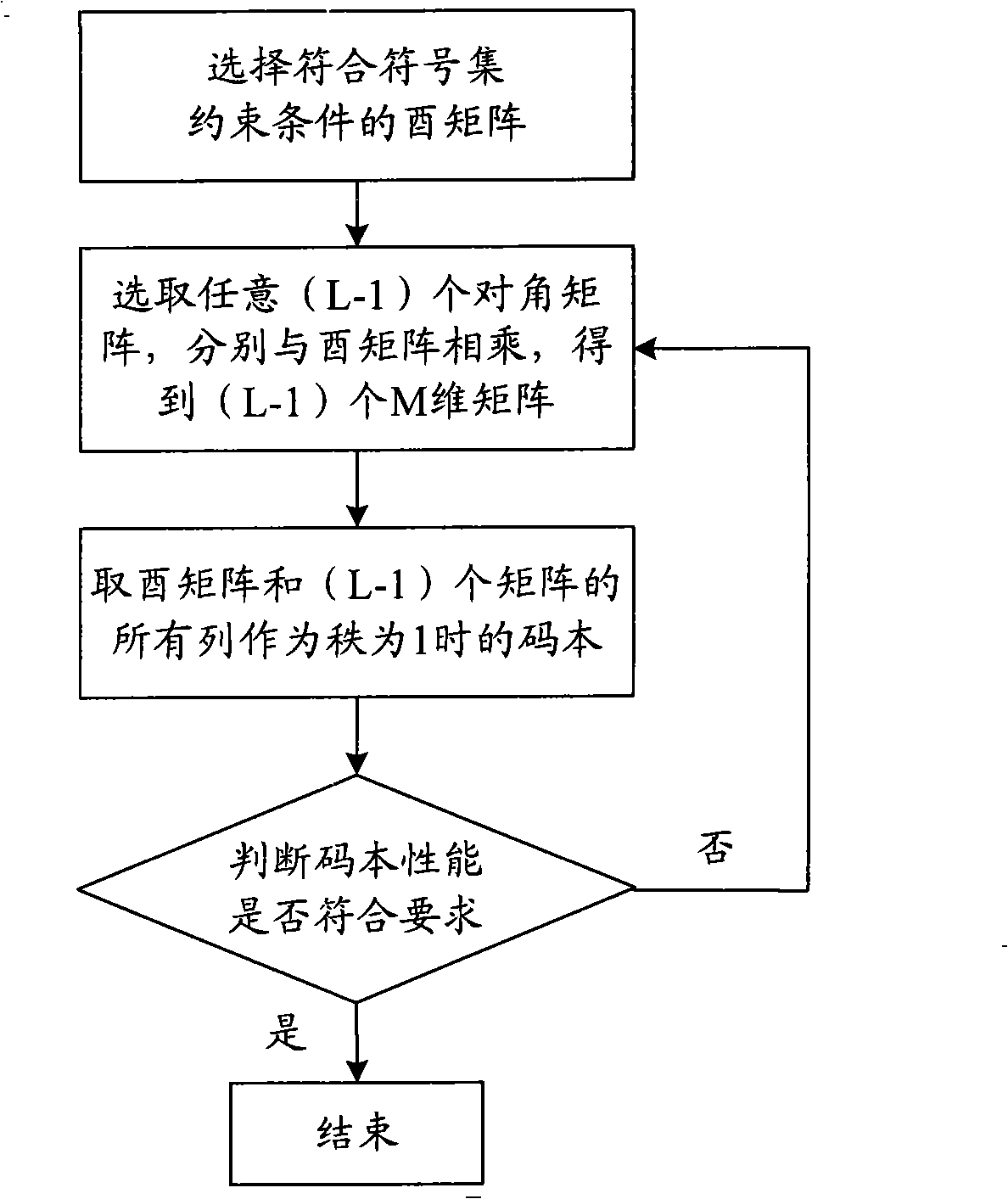
Constructing method of precoding codebook for high level MIMO system
InactiveCN101540663ALow efficiencyPurposefulSpatial transmit diversityTransmitter/receiver shaping networksUnitary matrixThroughput
The invention provides a constructing method of precoding codebook for high level MIMO system, comprising the steps as follows: (1) searching the codebook with the rank being 1 based on unitary matrix; (2) according to the codebook with the rank being 1, constructing full rank codebook with the rank being M satisfying symbol set restrict and nested structure requirements; (3) constructing the codebooks corresponding to other ranks according to the full rank codebook. The method of the invention can commendably solve the problems that the operation process of searching the codebook in the prior art has complicated calculation and low efficiency, so the method in the invention can fast and efficiently search the codebook; and the constructed codebook has simple structure and is easy to be realized and can achieve excellent performance under various scenes, and improves the throughput and spectrum utilization of the high level MIMO system. Furthermore, the invention can facilitating the possibility of searching the codebook in better performance by changing the construction mode of the codebook, and can improve the whole performance of the construction codebook.
Owner:BEIJING UNIV OF POSTS & TELECOMM
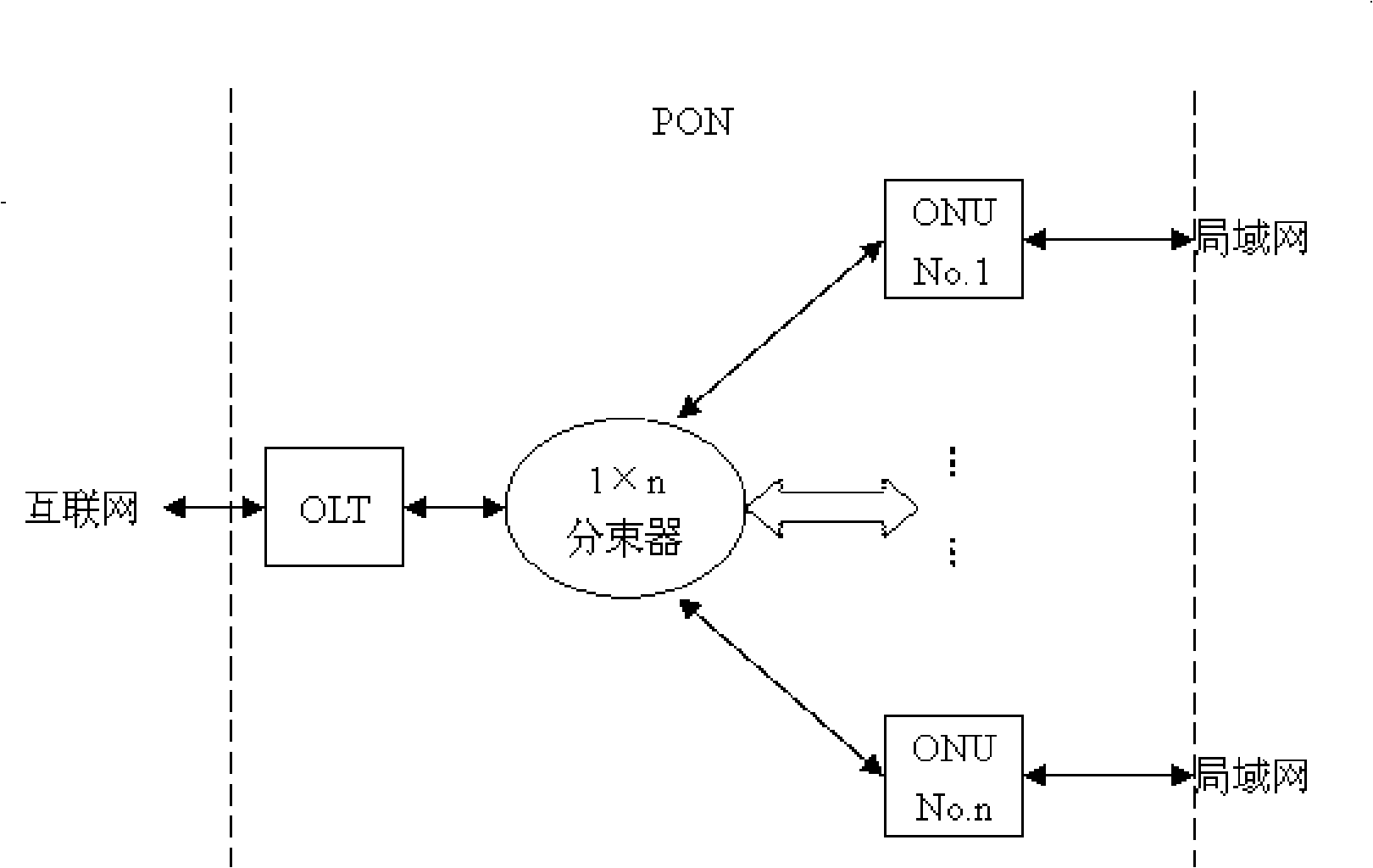
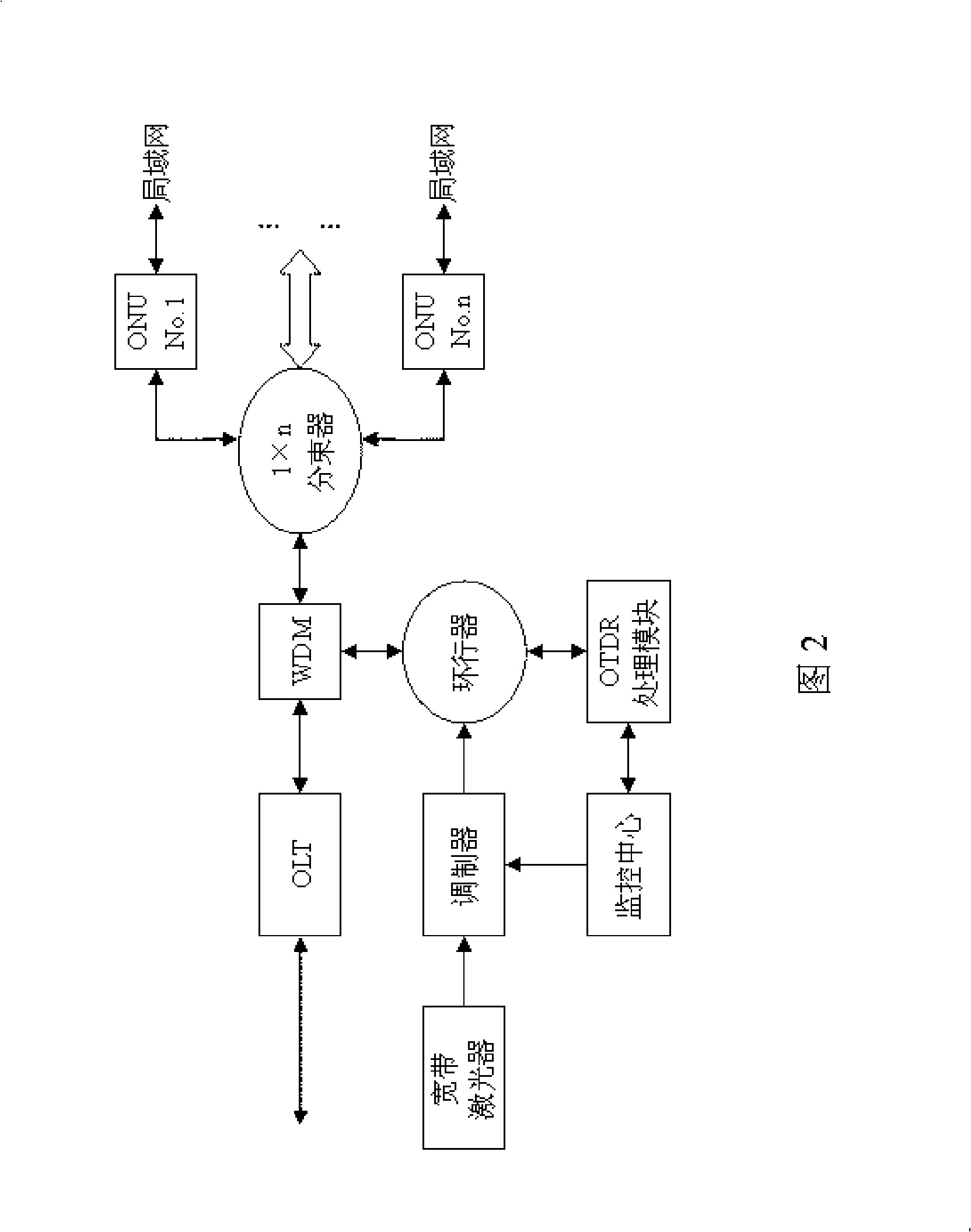
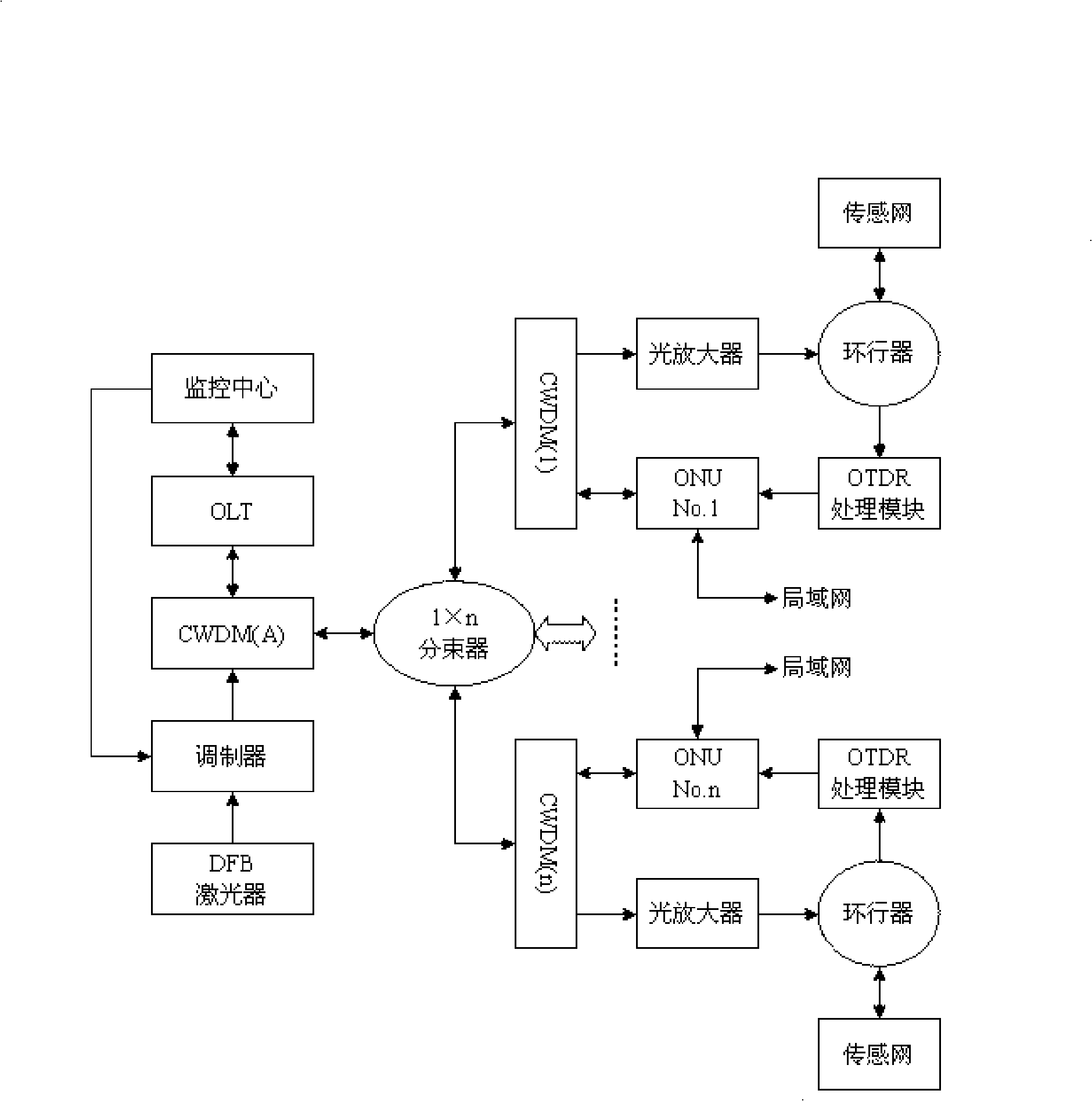
Optical fiber network sensing system
InactiveCN101321022AFacilitate customized servicesReduce the burden onData switching by path configurationFibre transmissionMultiplexerLength wave
The invention relates to a distributed fiber-optic sensor distributed fiber sensor, particularly to a sensing system based on a passive optical network (PON). The invention discloses a fiber optic network sensing system based on the wavelength division multiplexer and the distributed processing technique to overcome the deficiency aiming at the drawback which the sensing system can not recognize and detect each OUN branch optical path. The technical scheme is that, a sensing network is arranged in the prior PON system through using the ONU branch, to perform the distributed sensing laser receiving and processing, which reduces the request of the complexity and the real-time, applied in each PON structure at present free of the restrict of the PON standard restrain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Simplifying method facing to embedded system low-power consumption real time task scheduling
InactiveCN101135927AExtended use timeReduce power consumptionEnergy efficient ICTProgram initiation/switchingOperational systemProcessor frequency
The invention is used for optimizing the real-time task scheduling performance of the embedded system when it is running at low power consumption condition. It uses a real-time dynamical voltage-regulating and frequency-regulating technology and a real-time time flake cycle model to reach the real-time scheduling at low power consumption. Based on a time flake cycle task model, the invention adds a task real-time restrict to ensure the real-time capability of the task. Based on an original scheduling method, the invention adds a processor frequency controlling parameter to make the system get the lowest running frequency according to the real-time requirement of computing task.
Owner:ZHEJIANG UNIV
Preparation method of antibacterial finishing agent for textile apply
InactiveCN106436320AAchieve securityAchieve efficiencyBiochemical fibre treatmentLight touchWeakness
The invention relates to preparation method of antibacterial finishing agent of textile apply, belonging to textile assisting agent field. The antibacterial finishing agent for textile apply is prepared from zircoaluminate coupling agent, nanometer titanium dioxide, quaternary ammonium monomer, deionized water, and polymerization initiator synthetically react prepared; by mass, 7-11 parts of zircoaluminate coupling agent, 13-18 parts of nanometer titanium dioxide, 27-39 parts of quaternary ammonium monomer, 117-153 parts of deionized water, 0.8-1.3 parts of polymerization initiator. The method adopts the step of quaternary ammonium monomer after modification nanometer titanium dioxide ion surface grafting, restrict controls quaternary ammonium in basal body, compounds inorganic and organic antibacterial agent, overcomes the weaknesses that nanometer titanium dioxide light touch media loses antibacterial property at dim light and quaternary ammonium safety property appears poor and creates micro organism agent resistance, the finishing agent chemical stability stays poor, tolerates heat poor and more related weaknesses, helps achieves antibacterial agent safety, persistence, and efficiency property.
Owner:秦瑶
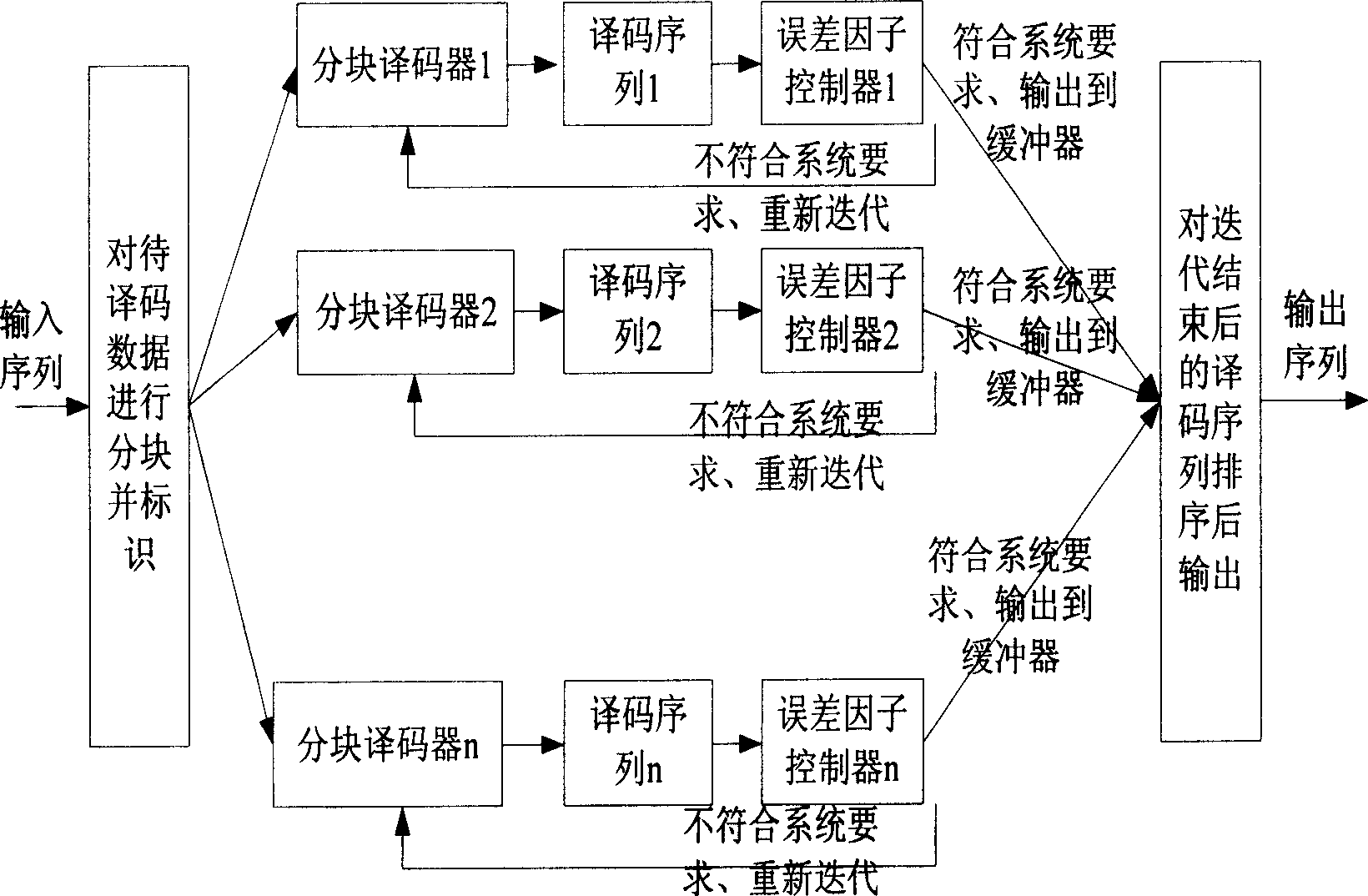
Method of adaptive turbo decode
InactiveCN1913368AReduce the number of iterationsReduce latencyCode conversionError correction/detection by combining multiple code structuresError factorSystem requirements
This invention relates to an adaptive turbo decoding method including the following steps: dividing received data into multiple blocks according to a code restrict length and the actual length of input data, identifying each divided sequence so as to merge and output in terms of the original sequence of the data to be input into multiple parallel decode processors to be decoded simultaneously then to be sent to the corresponding error factor controller after one time of coding to compute their error factors, continuing the iteration till the performance of which can meet the needs of the system or reach the top limit of the largest designed iteration times, outputting the sequence after decoding same to that before decoding in blocks, which reduces iteration times of part data blocks and system time delay.
Owner:ZTE CORP
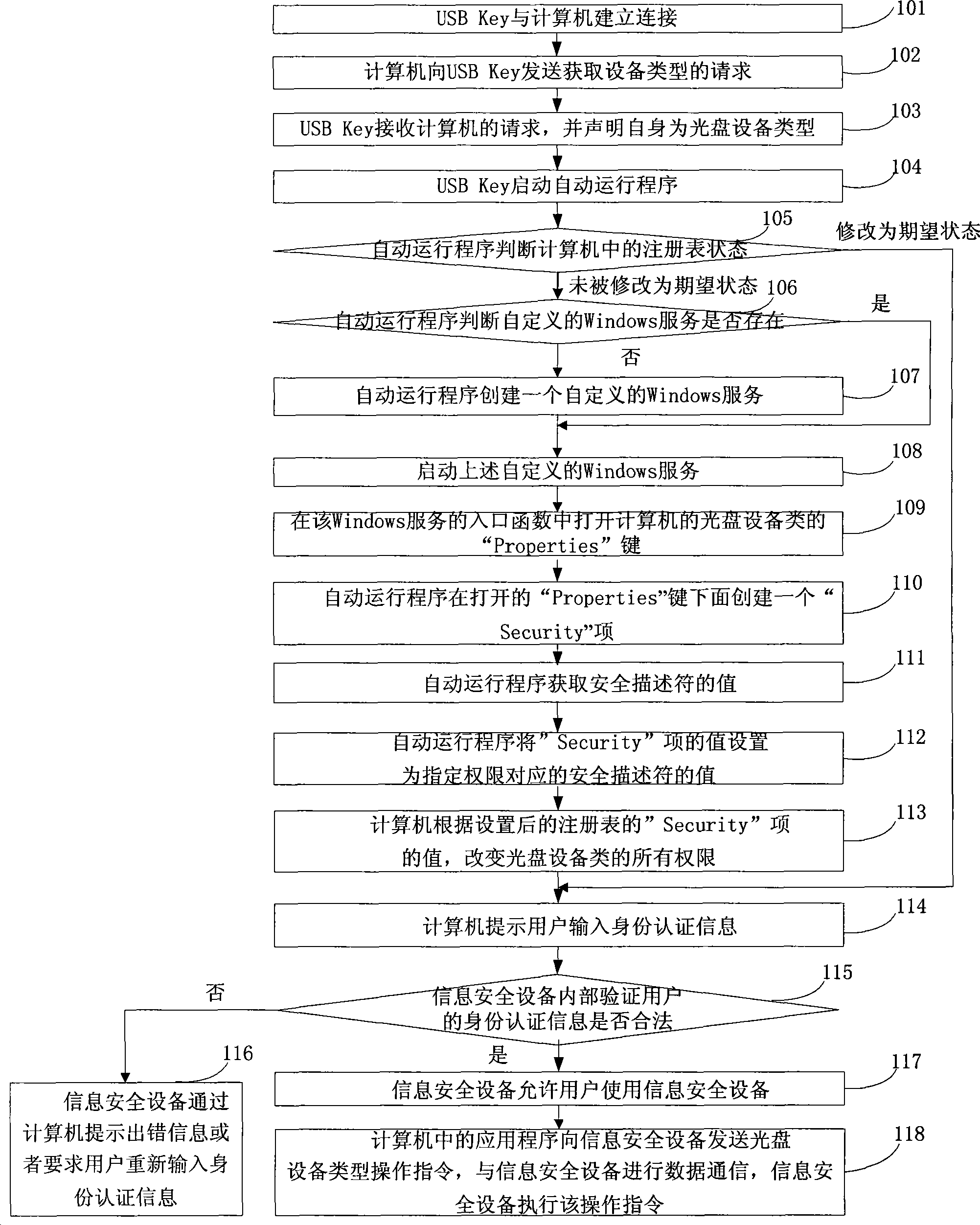
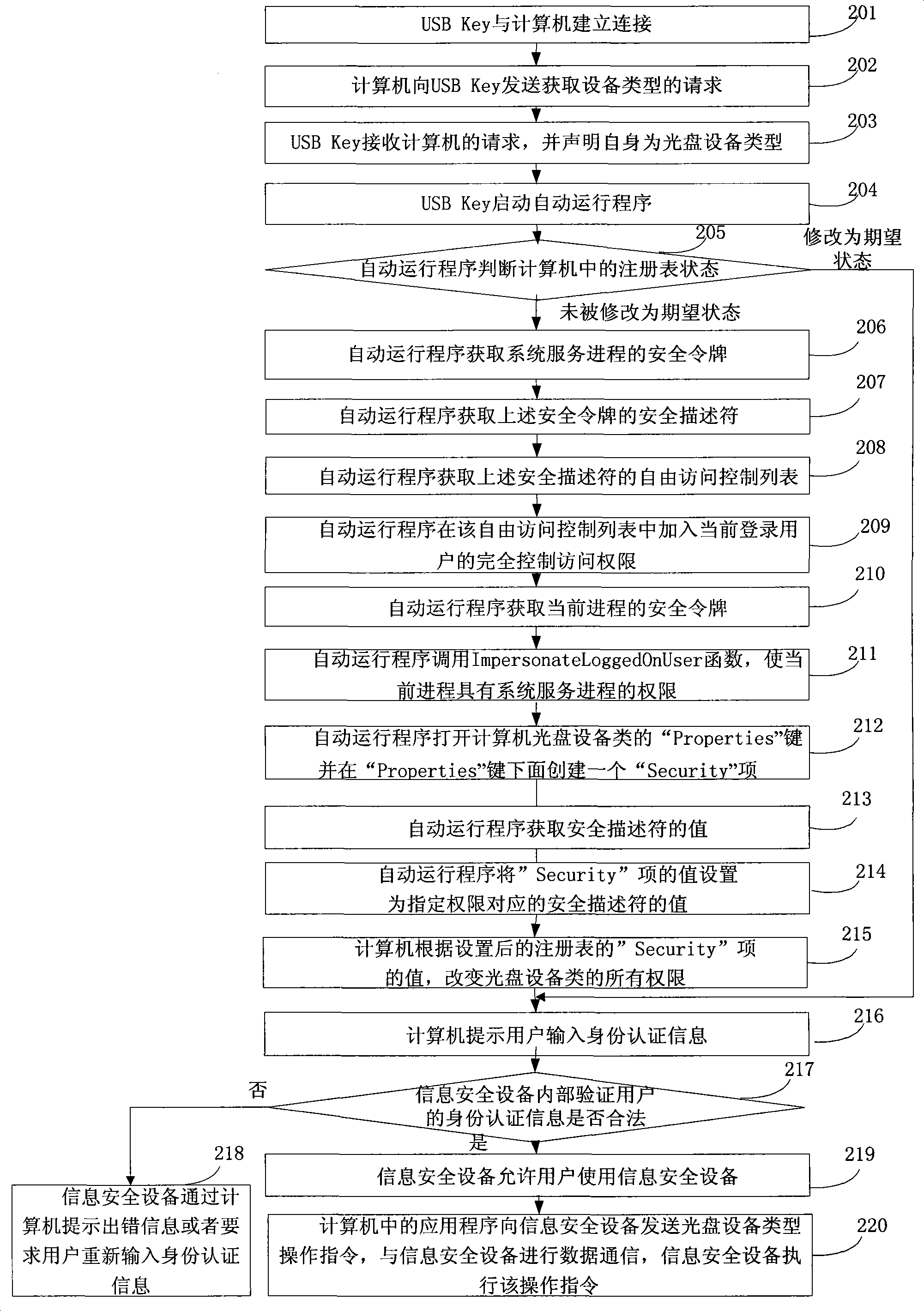
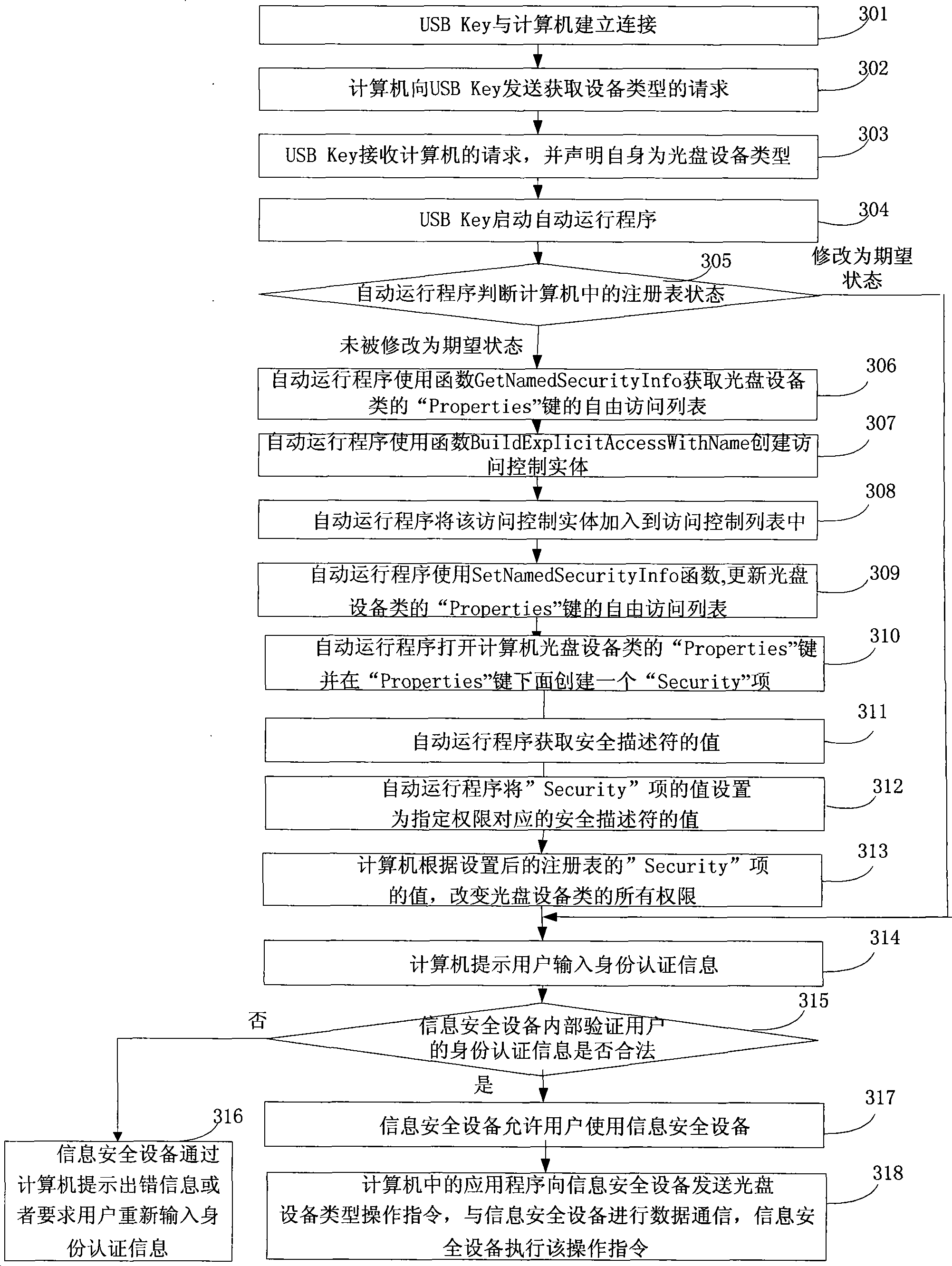
Method and system for controlling access authority of information safety equipment
ActiveCN101369302ASolve the problem that it cannot be used under ordinary usersDigital data authenticationComplete dataOperational system
The invention discloses a method of controlling access right of an information security device and a system, belonging to the field of controlling the access right of the device. The method comprises: starting an automatic operation program by an information security device; advancing the right of the automatic operation program, building Security items under Properties keys of CD devices in a register table of the computer; obtaining values of safe descriptors; setting values of the safe descriptors as values of Security items; modifying the access right of the CD devices in the computer according to the values of the Security items; transmitting operation instructions to the information security device by application programs in the computer, completing data communication of the computer and the information security device. The system comprises an information security device and a computer. According to the invention, the information security device is free of restrict of the user right in Windows operating system, and problems how the right of the information security device is modified are solved.
Owner:FEITIAN TECHNOLOGIES
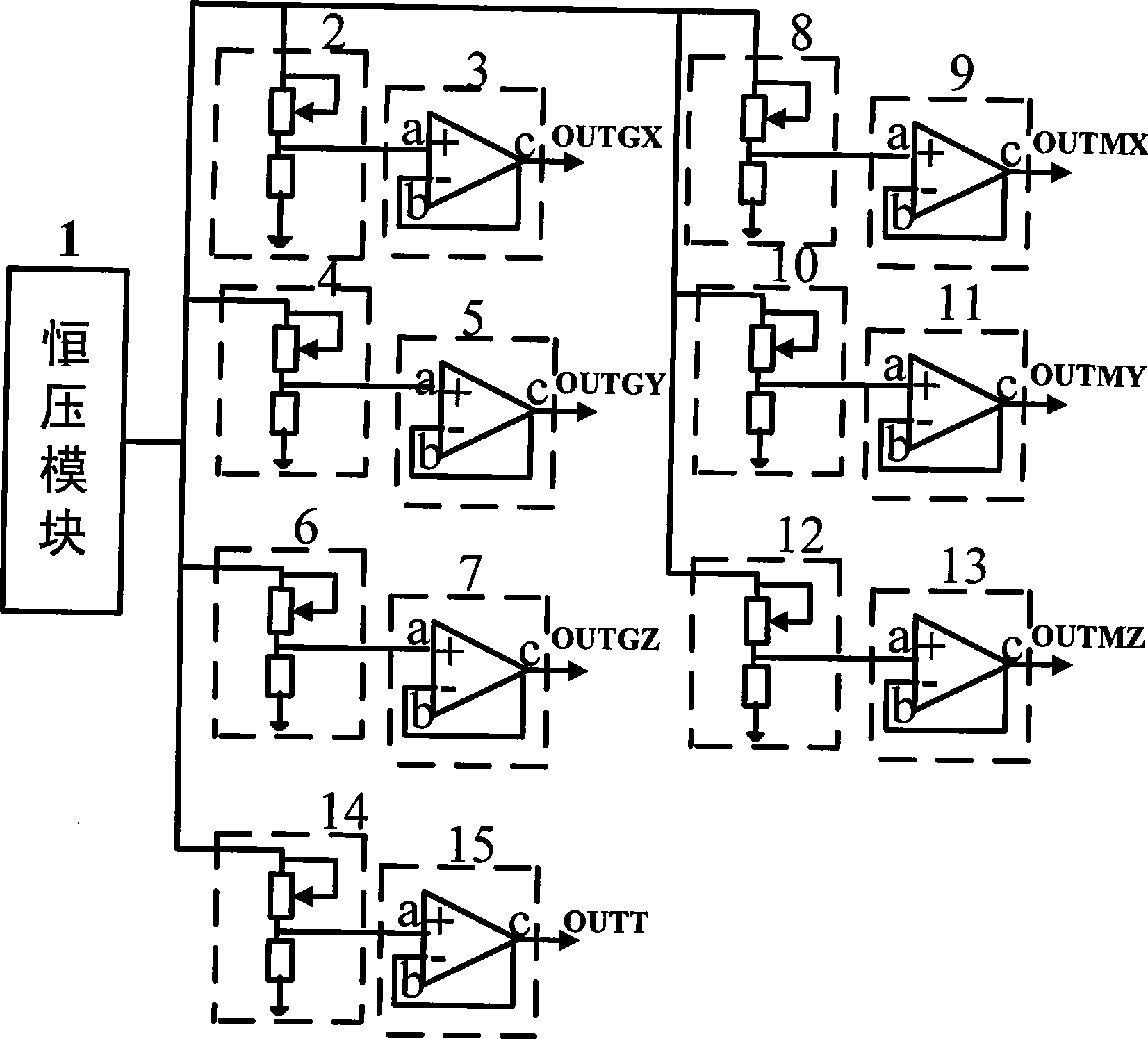
Measurement while drilling exploring tube sensor signal simulator
InactiveCN101469610AThe output signal is stableHigh precisionSurveyTest efficiencySignal conditioning circuits
The present invention discloses a exploring tube sensor signal simulator in petroleum well drilling MWD system, which includes a constant voltage module and seven channel identical structure circuit, which are used to simulate seven channel signal of the sensor as OUTGX, OUTGY, OUTGZ, OUTMX, OUTMY, OUTMZ, OUTT, and each channel analog signals circuit includes a signal conditioning circuit and a follower. The present invention is provided with advantages like output signal of the sensor signal simulator stable, accuracy high, no restrict to external conditions like parameter correction, environment and calibration frame when testing the exploring tube circuit, can measure exploring tube circuit conveniently, accurately and fully, and enhance exploring tube circuit test efficiency.
Owner:SHENGLI PETROLEUM ADMINISTRATION BUREAU DRILLING TECH ACAD SINOPEC
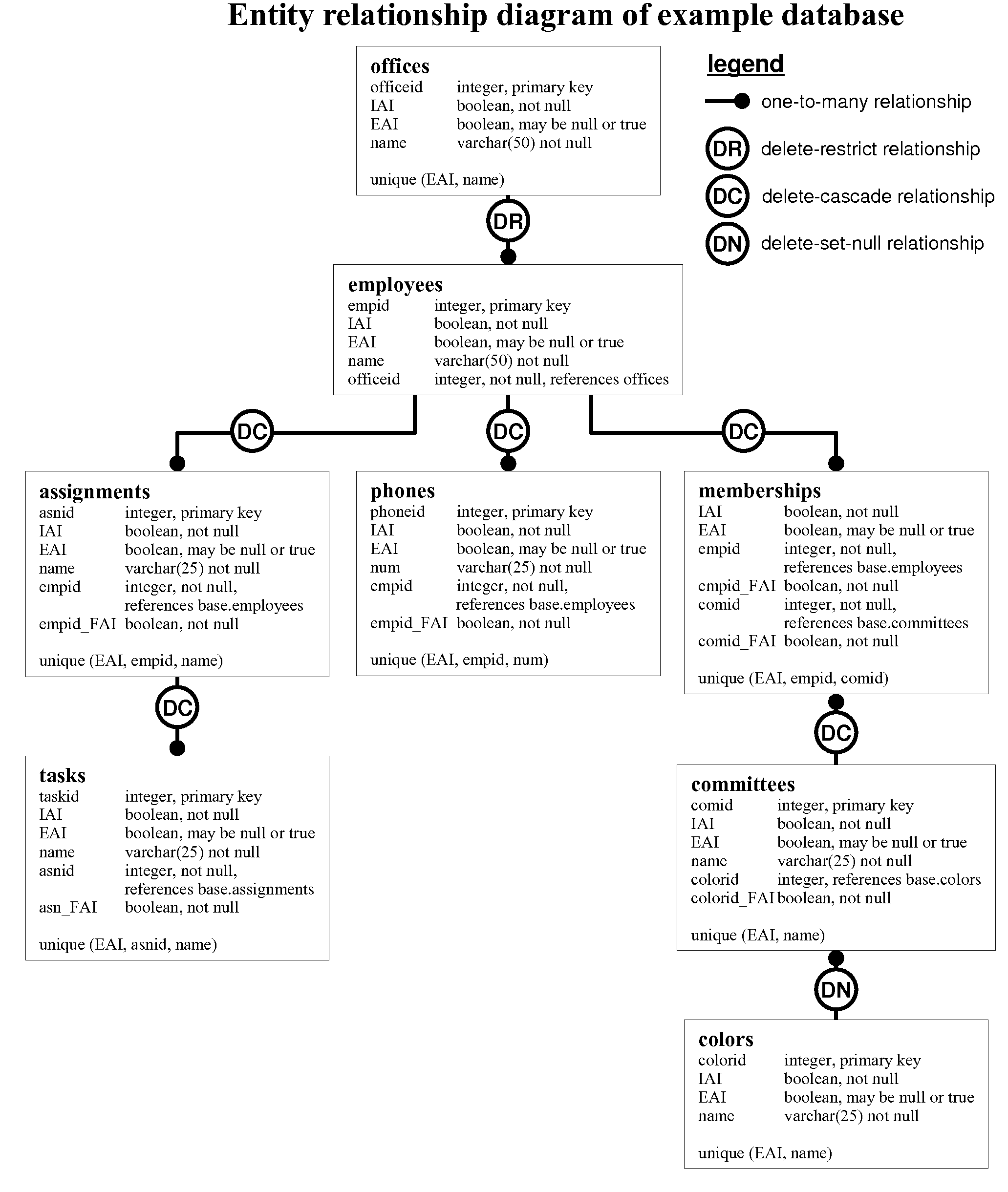
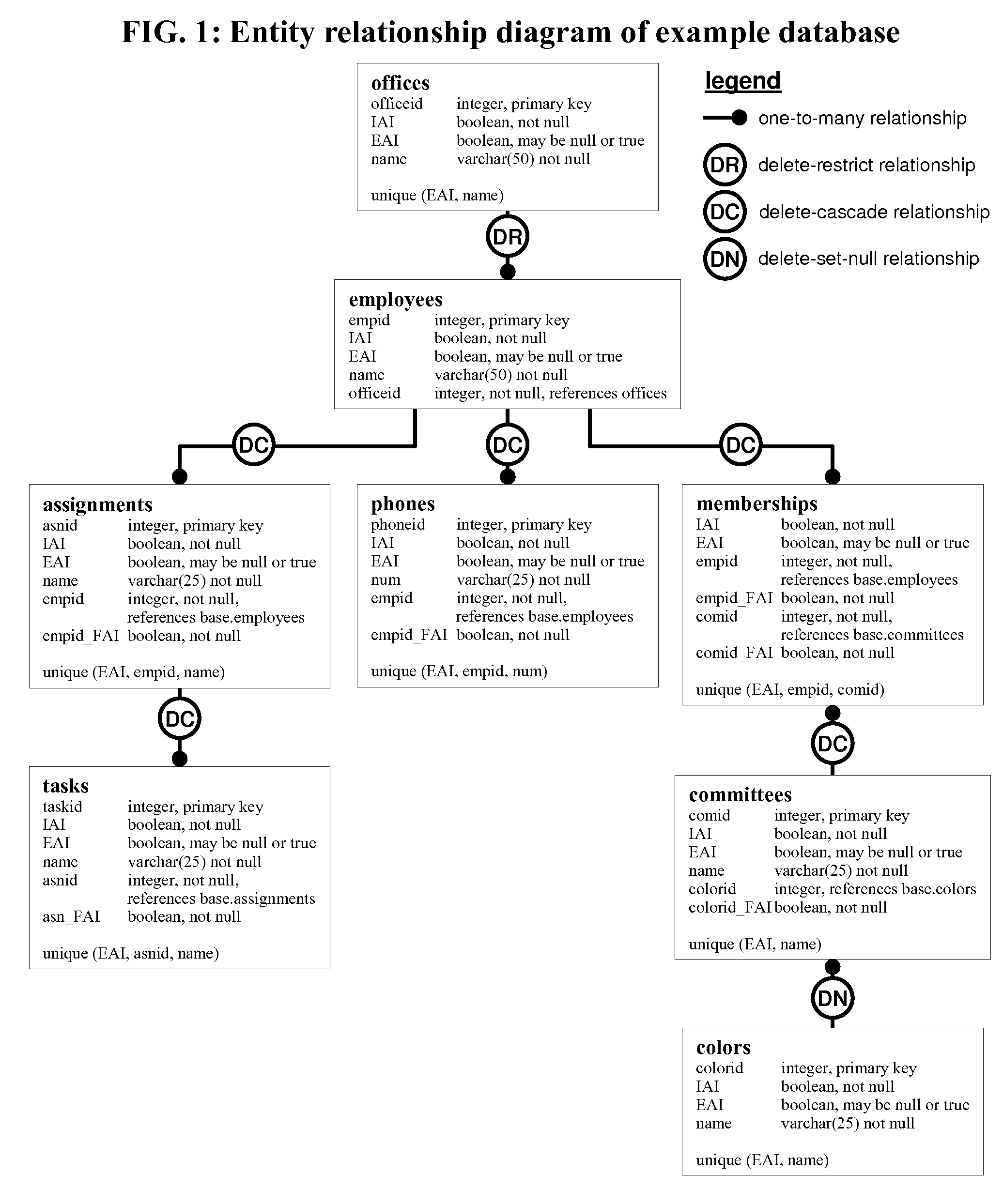
Method and system for the logical deletion of relational database records
InactiveUS20090300069A1Digital data information retrievalSpecial data processing applicationsForeign keyRelational database design
A method and system for relational database design that allows records to be flagged as deleted but still retained in the database. Deleted records are not included in table viewing or editing activities. Reversing a deletion flag undeletes the record. Records that reference deleted records in delete-cascade relationships are flagged as deleted. Such dependent records are undeleted if the independent records are undeleted, unless the dependent records were independently flagged as deleted. If an active record is dependent on a record in a delete restrict relationship then the independent record cannot be deleted. If a foreign key references a deleted record in a delete-set-null or delete-set-default relationship then the field evaluates to null or the default value, but if the independent record is undeleted then the field returns to referencing the independent record. Unique indexes are enforced without regard to deleted records.
Owner:OSULLIVAN MICHAEL PATRICK
Motion image code controlling method and code device
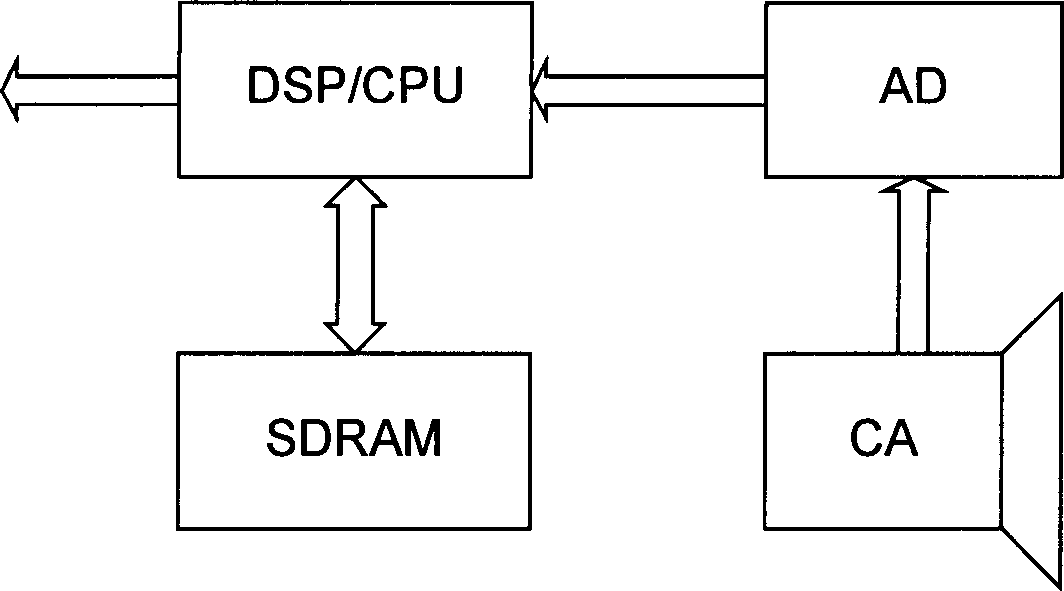
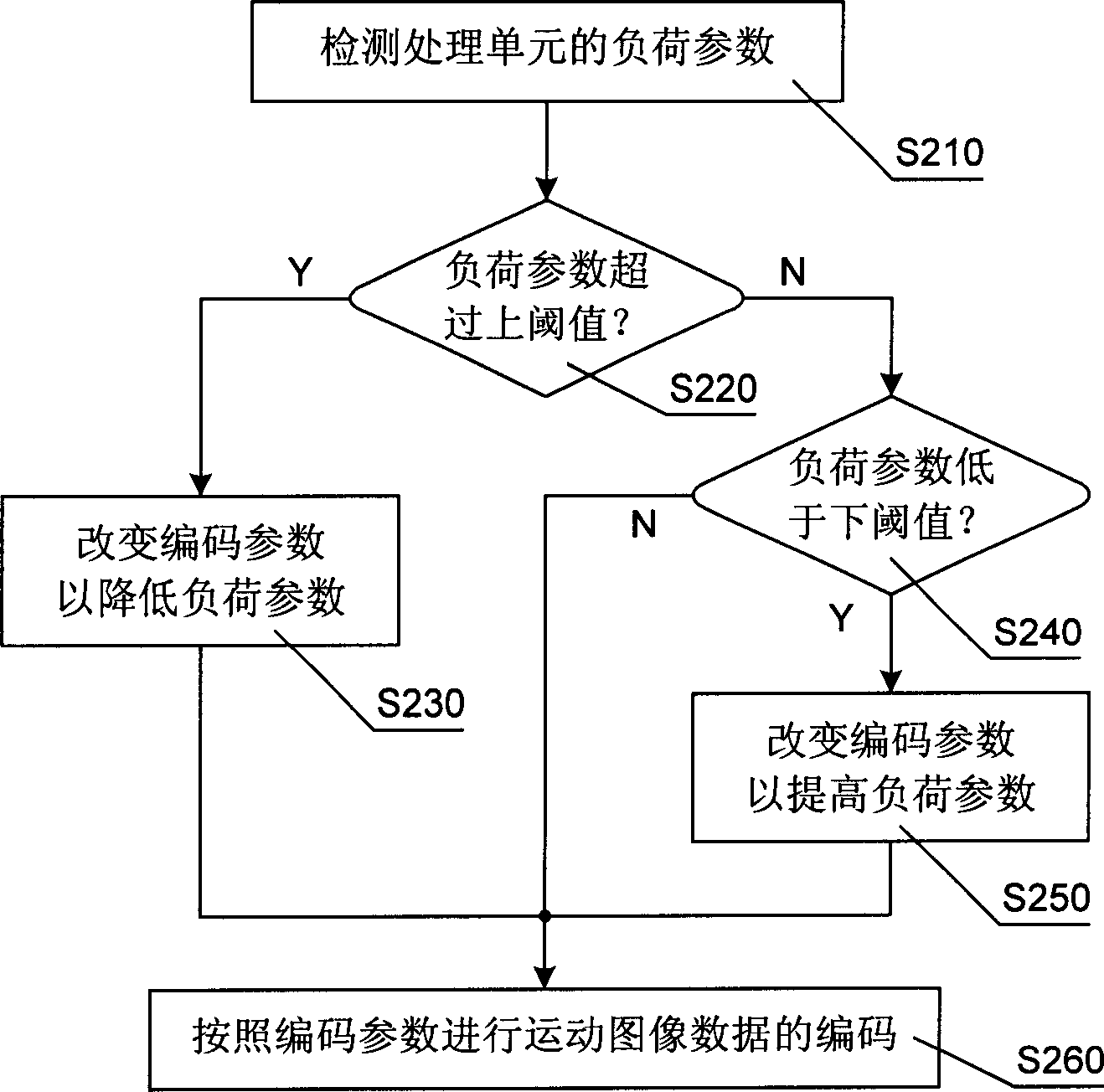
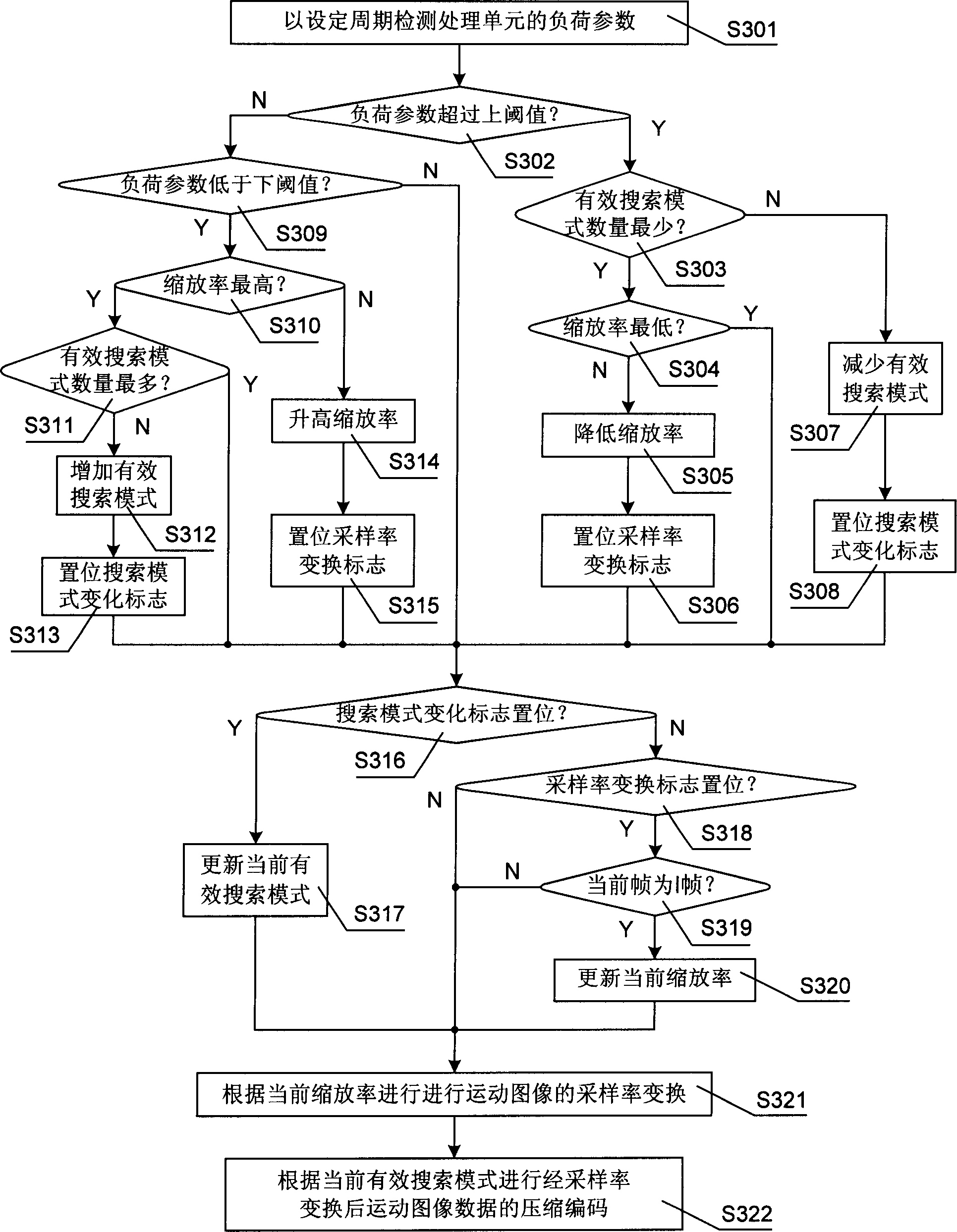
ActiveCN1801936AReal-timeQuality assuranceTelevision system scanning detailsModulated-carrier systemsTime informationImaging quality
Present invention discloses a method for movement image encoding control. It contains changing encoding parameter for adjusting said loading parameter as processing unit loading parameter exceeding restrict value. Present invention also discloses a movement image encoding image encoding device. Present invention can self adaptation regulate encoding algorithm according to video scene real-time information volume and processing unit practical processing ability, effectively utilizing processing unit calculating ability to ensure image quality.
Owner:XINHUASAN INFORMATION TECH CO LTD
Restricting and preventing pairing attempts from virus attack and malicious software
InactiveUS8787899B2Multiplex system selection arrangementsUnauthorised/fraudulent call preventionTelecommunicationsMalware
A method, device and system restrict and prevent virus attack and malicious software to a wireless communication device from a pairing attempt by another wireless communications device. A switch is included in a transmission path coupling a first device to a second device, wherein the second device is attempting to pair with first wireless communications device. A detector coupled to the transmission path, detects an address of the second wireless communications device in a pairing communication protocol between the first and second devices. A counter coupled to the detector counts the pairing attempts of the second device. A compare circuit compares the pairing attempts to a selected number N. The compare circuit signals the switch to open when the number of attempts equals or exceeds the number N, breaking the connection, thereby preventing the first device from receiving virus attacks and malicious software.
Owner:NOKIA TECHNOLOGLES OY
A modeling method of large geological building information model
The invention discloses a modeling method of a large geological building information model, which comprises the following steps: 1. Acquiring onsite scene data of a work area through tilt photographyand three-dimensional laser scanning technology, and constructing a three-dimensional scene model of the surface of the work area and a data set of point clouds; 2, extract DEM data and obtaining an optimal DEM model by fitting a curved surface; 3, primary drill restrict; 4, secondary terrain constraint; 5, plane geological constraint of the third time; 6, constrain that law of four geological evolution; 7, combine that surface three-dimensional real scene model and the underground three-dimensional geological body model and integrally displaying them to obtain a large geological build information model. The method of the invention is advanced, which combines the underground three-dimensional geological body and the three-dimensional real scene model of the ground surface for display, andhas the advantages of visualization, synergy, operability and the like. The method is Widely used, can effectively improve the management level.
Owner:SICHUAN INST OF GEOLOGICAL ENG INVESTIGATION
Circuit device of injection mold with single-side inlet and outlet cooling water
The invention discloses a circuit device of an injection mold with single-side inlet and outlet cooling water, which comprises a water-stop plate (1), a water faucet (2), a support plate (3), a plug (4), a water inlet channel (6), a folded-back channel (61), a water outlet channel (7), and a water-turning cooling hole (8). The present invention adopts such a technical scheme of cooling water circuit that the water-turning cooling hole consisting of several straight blind holes is arranged in the mold, an isolating device consisting of the water-stop plate, the water faucet and the support plate partitions the water-turning cooling hole into a water turning chamber and a water returning chamber from top to bottom; the water inlet channel and the water outlet channel provided with the straight holes are respectively communicated with the water turning chamber and the water returning chamber and then respectively connected with them by the folded-back channel of the straight hole, and the inlet and the outlet are arranged on the same outer side of the mold. By using the water faucet for partitioning the water inlet and the water outlet channels and the processing convenience of straight hole, the injection mold has inlet and outlet water on the single side, the purposes of simplifying structure, reducing processing cost, no restrict and improving cooling effect are achieved.
Owner:宁海县第一注塑模具有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com