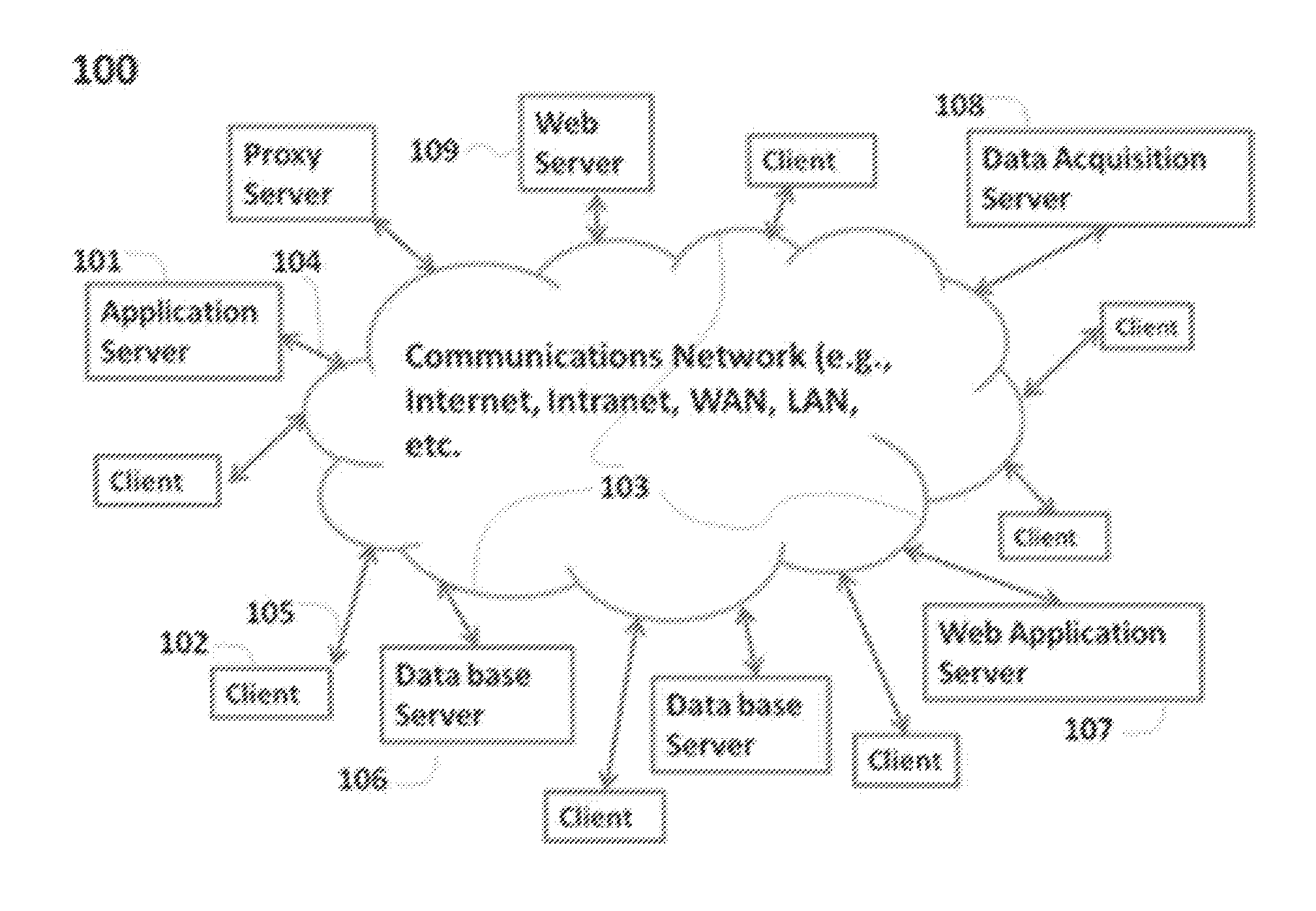
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
4853 results about "Safe system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
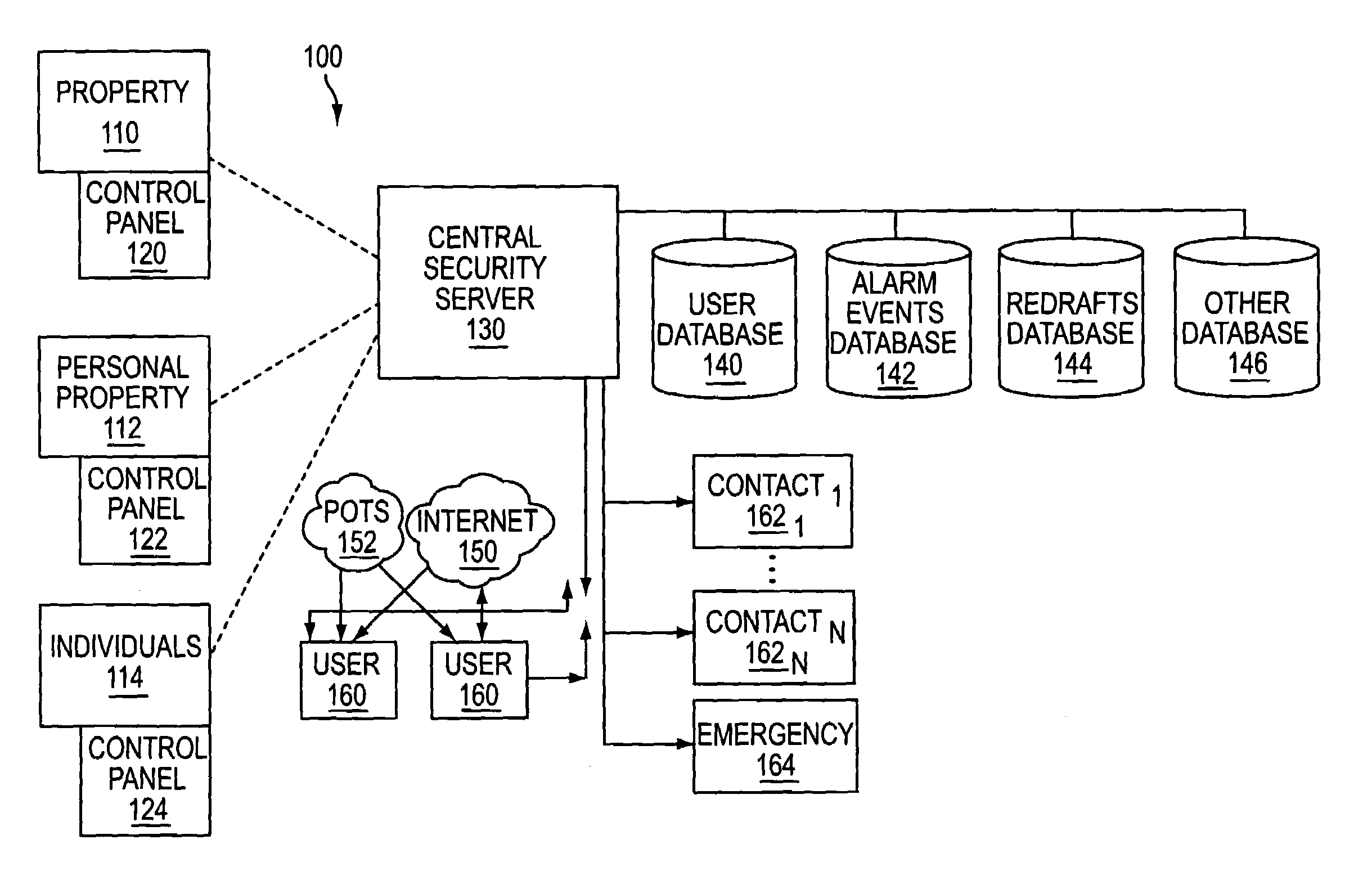
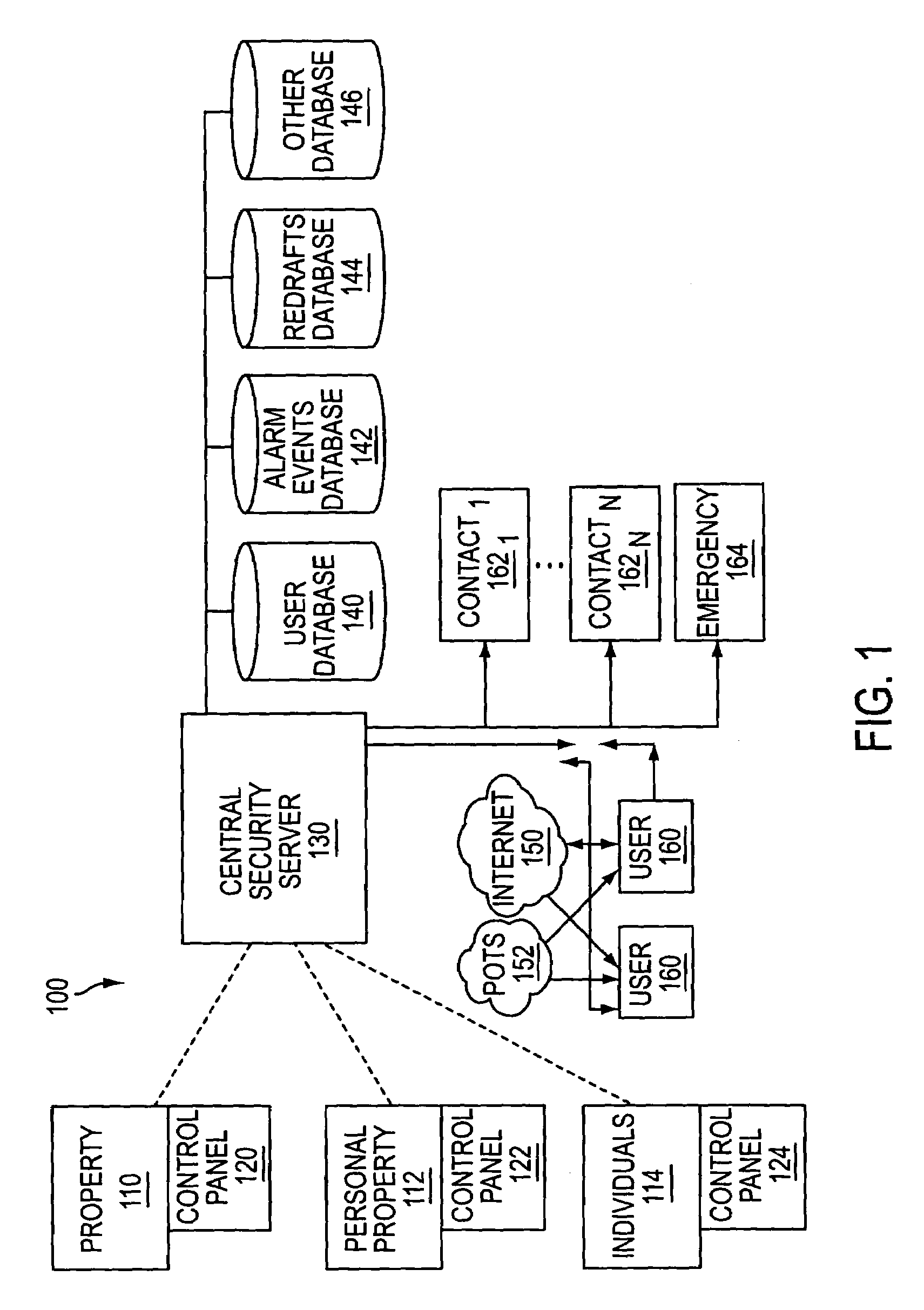
A safe system of work is a procedure to eliminate the risks that are involved in a specific operation. The 1st priority is to eliminate the risks. If that cannot be achieved, then priority falls to lowering the risks involved in the process to acceptable levels. A safe system of work is a part of risk assessment.
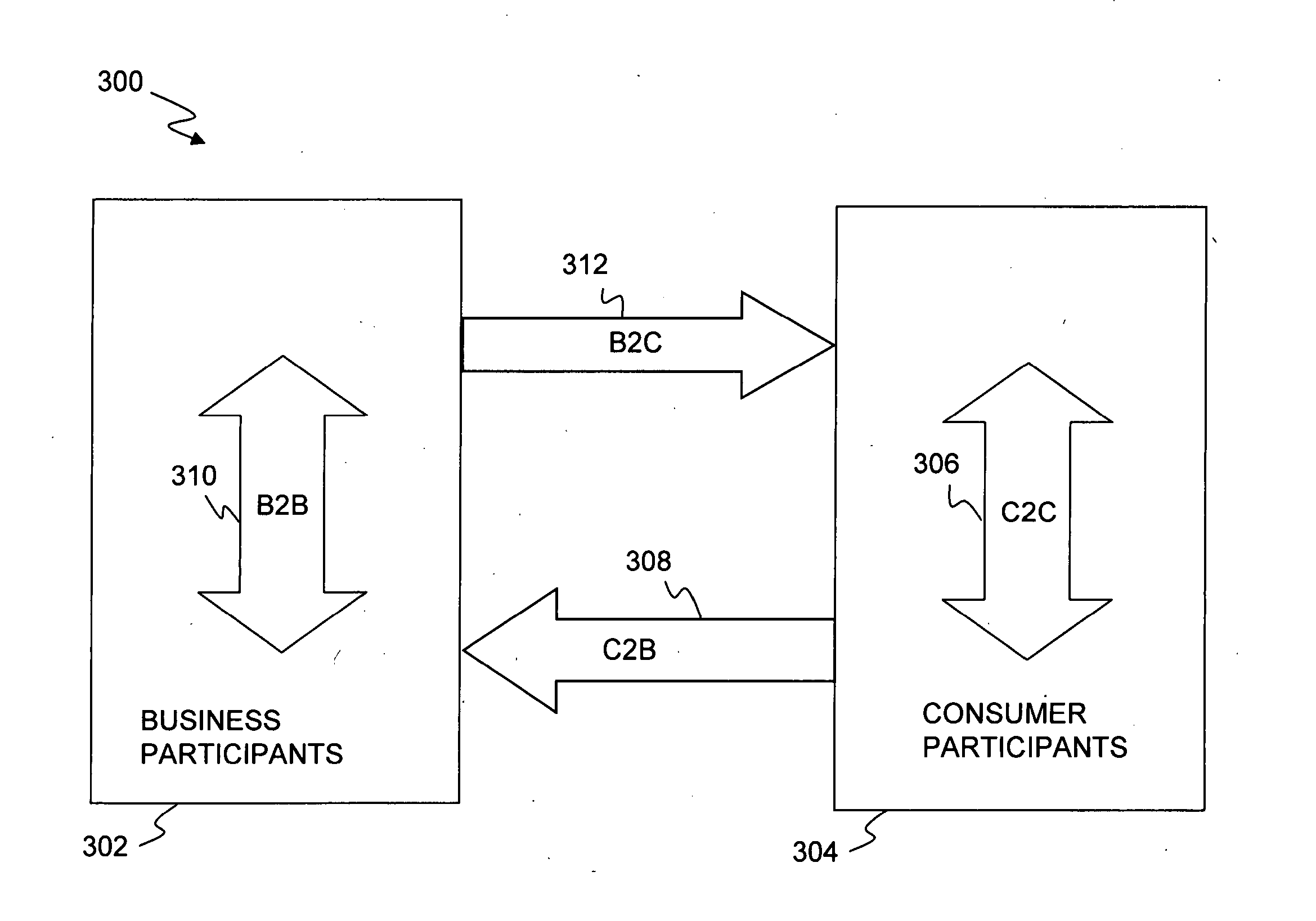
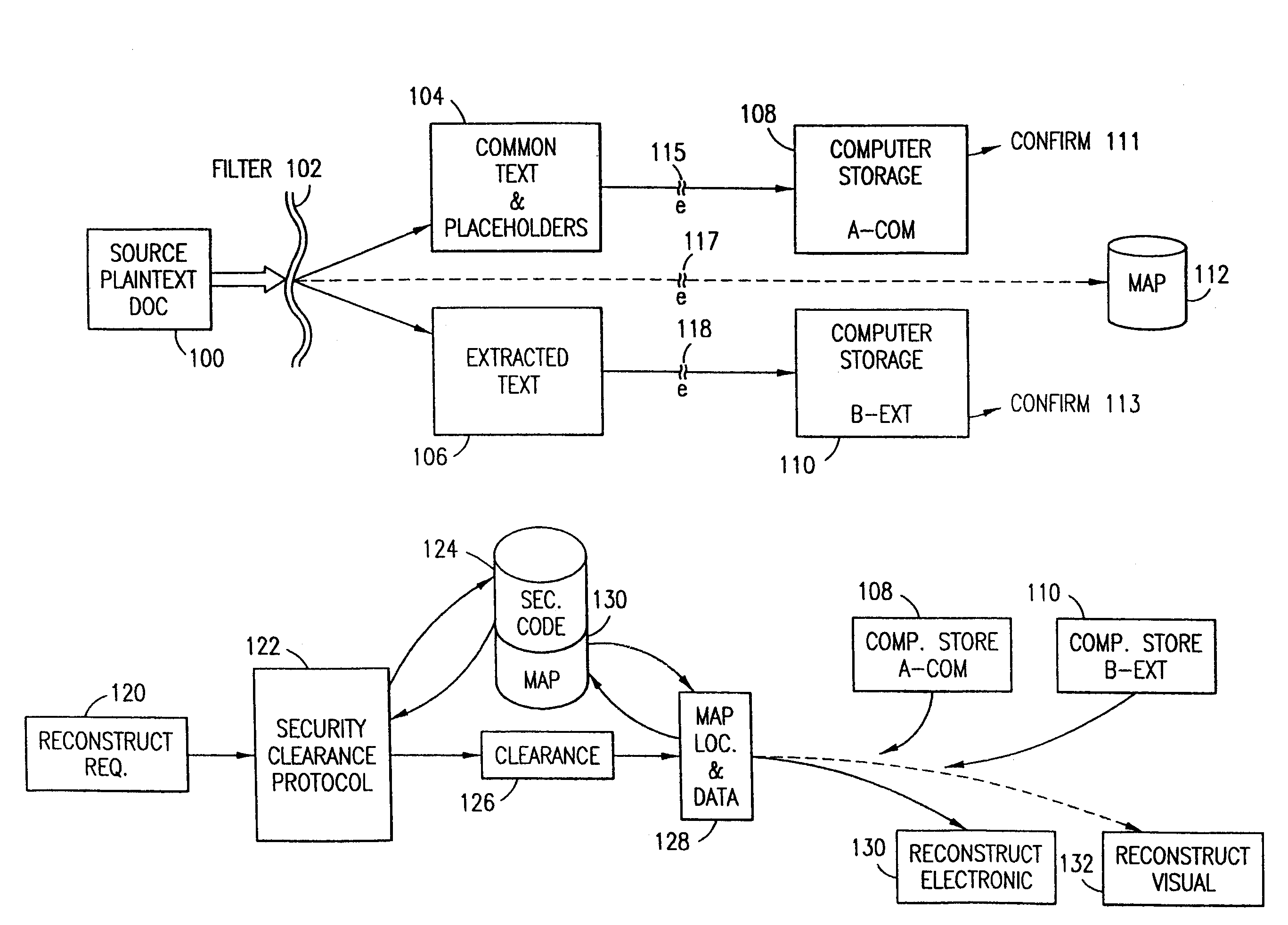
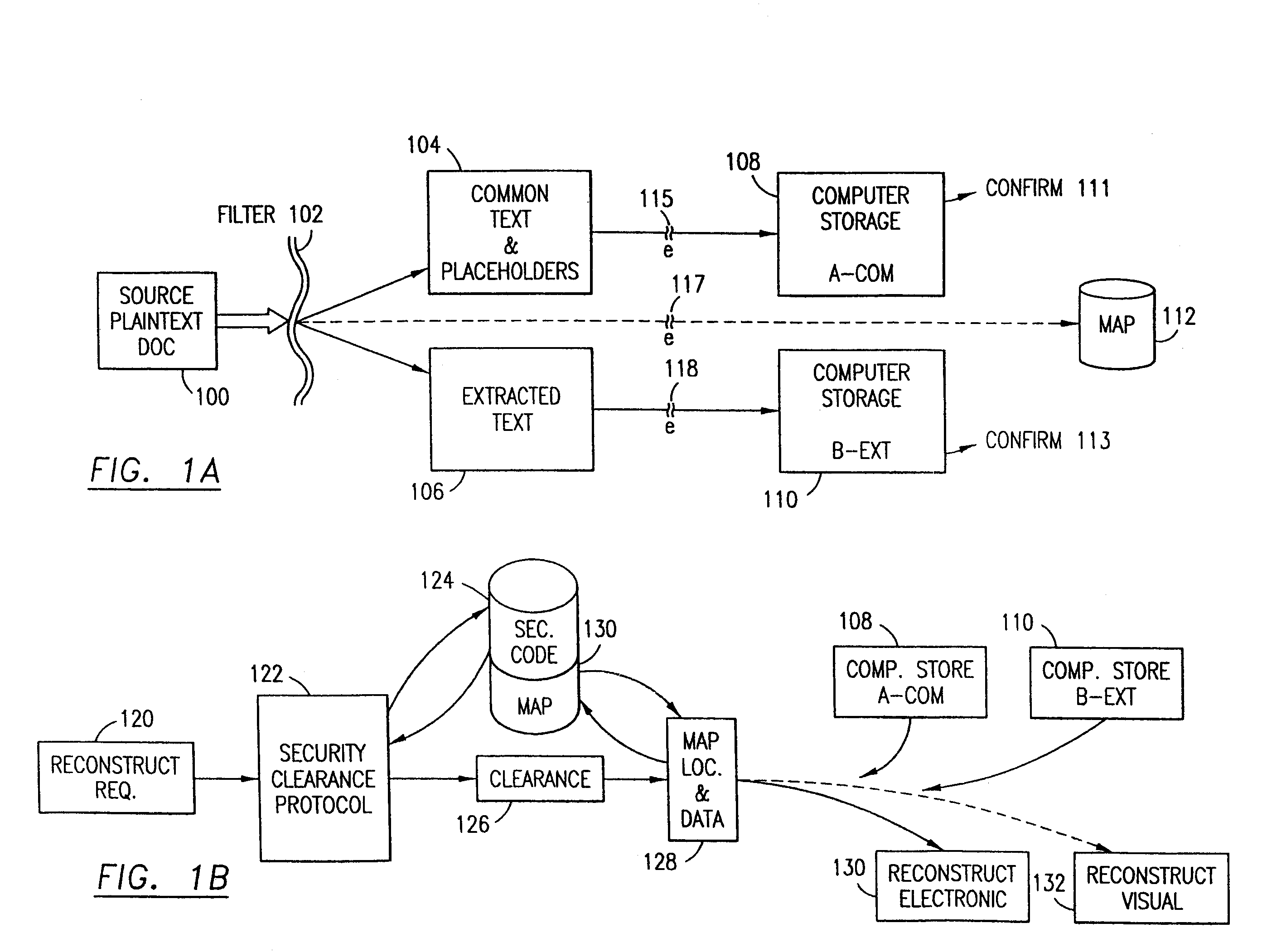
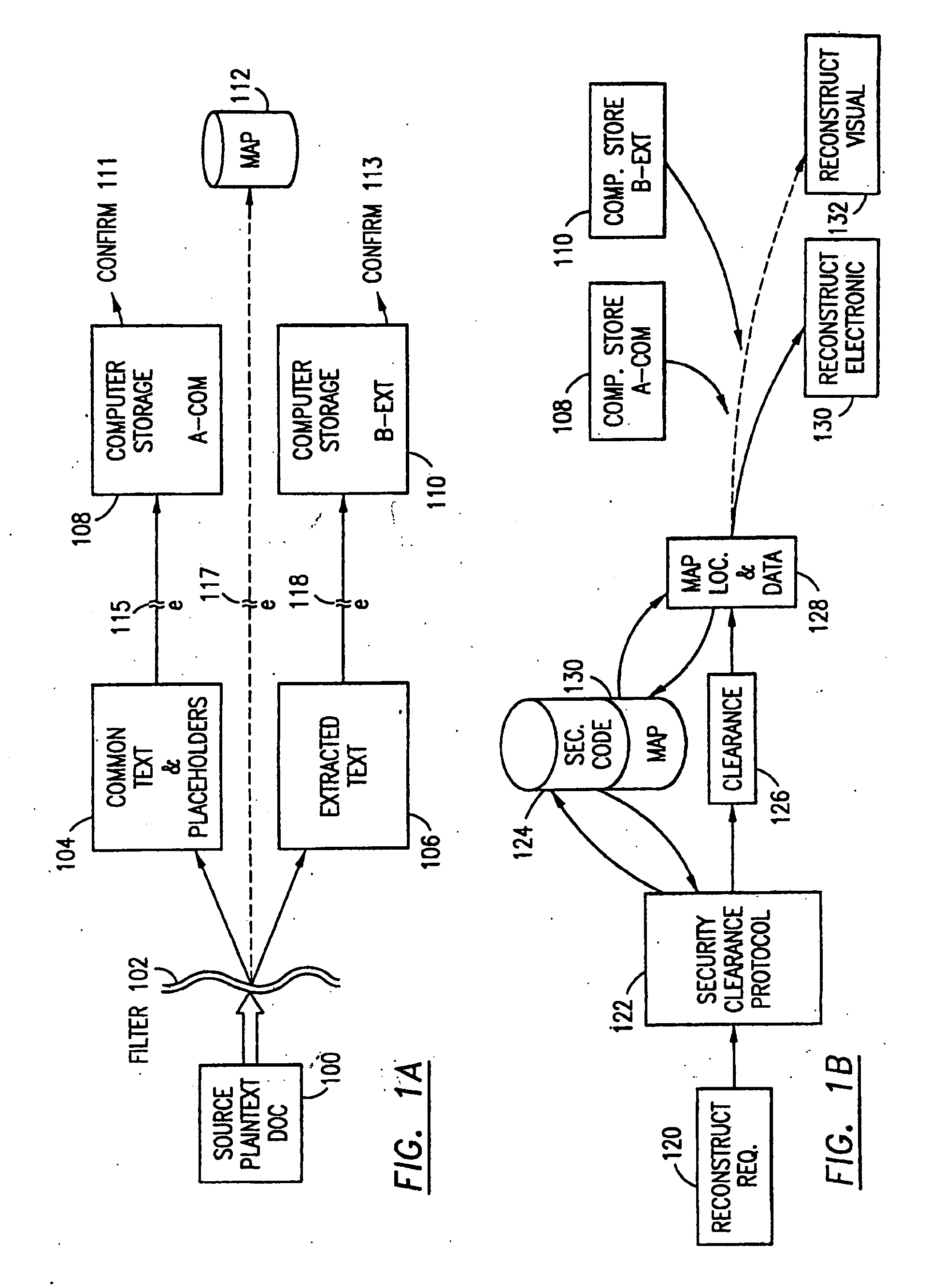
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
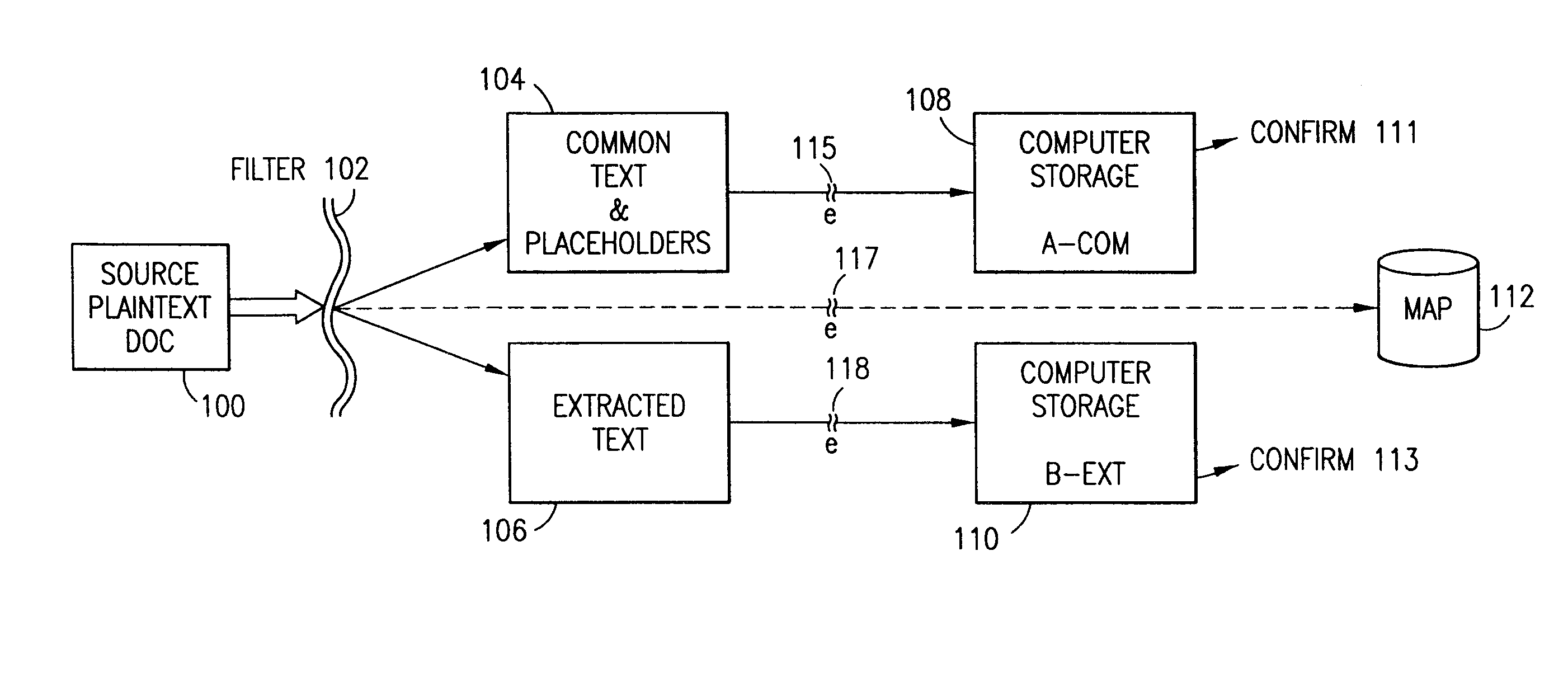
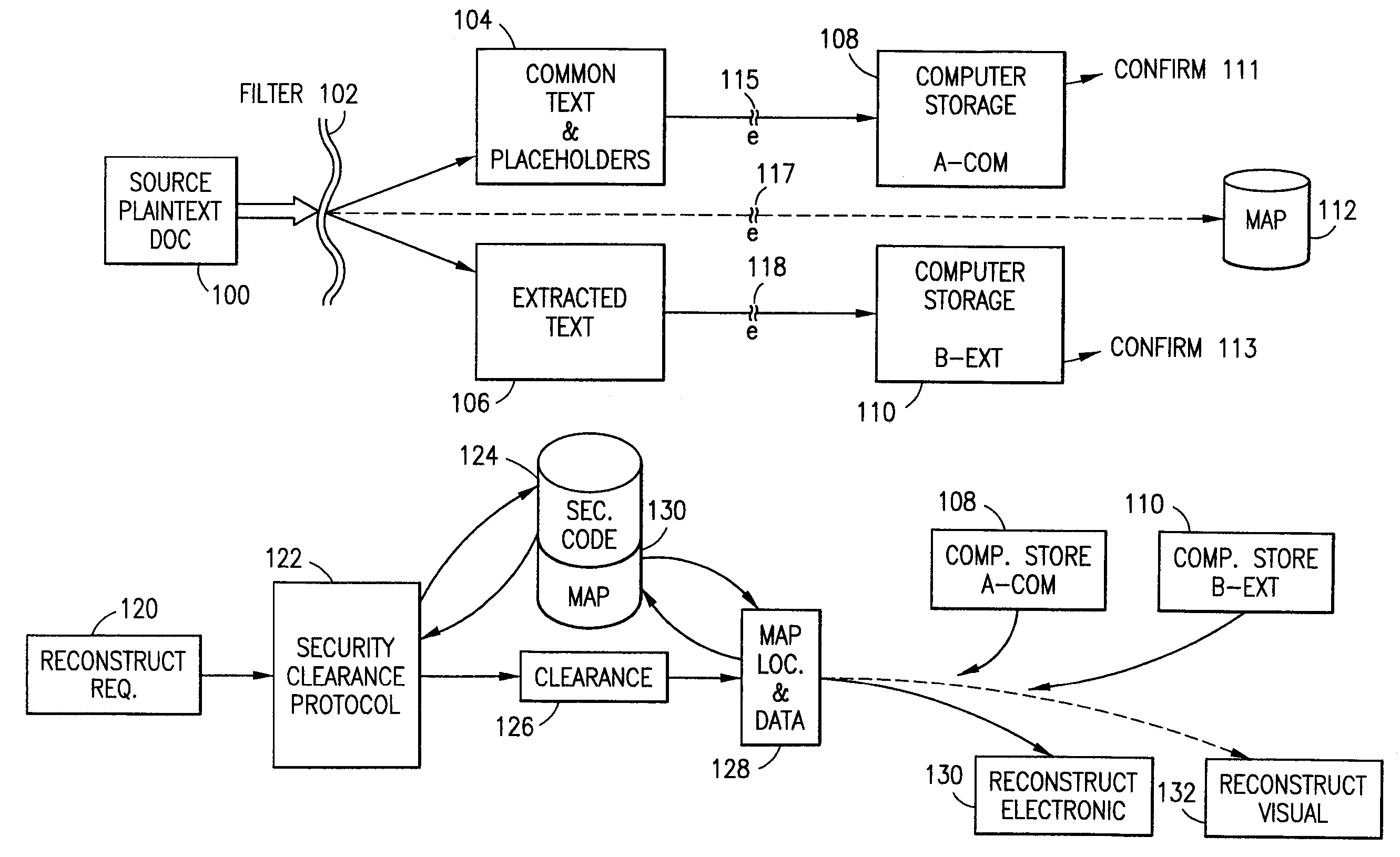
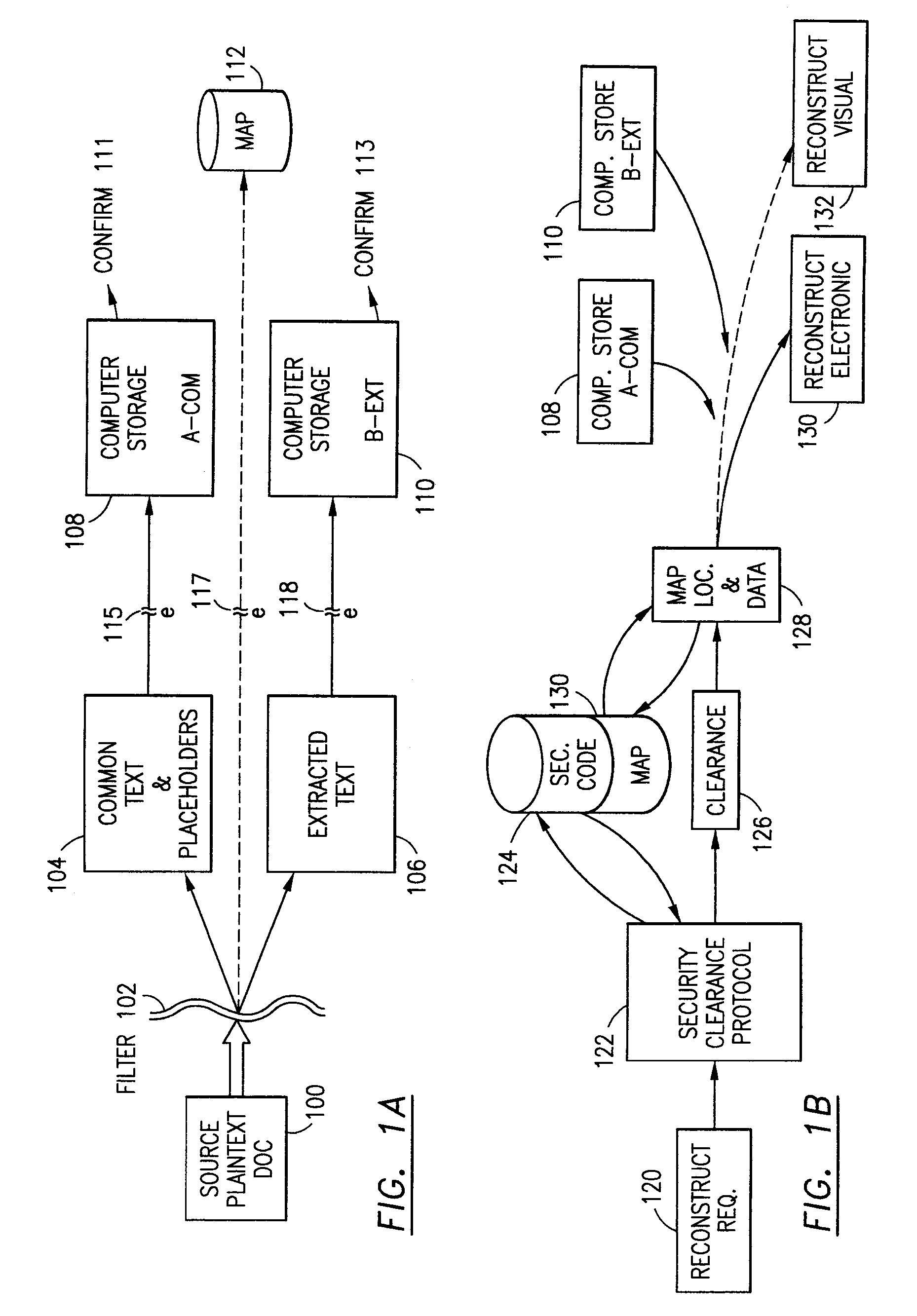
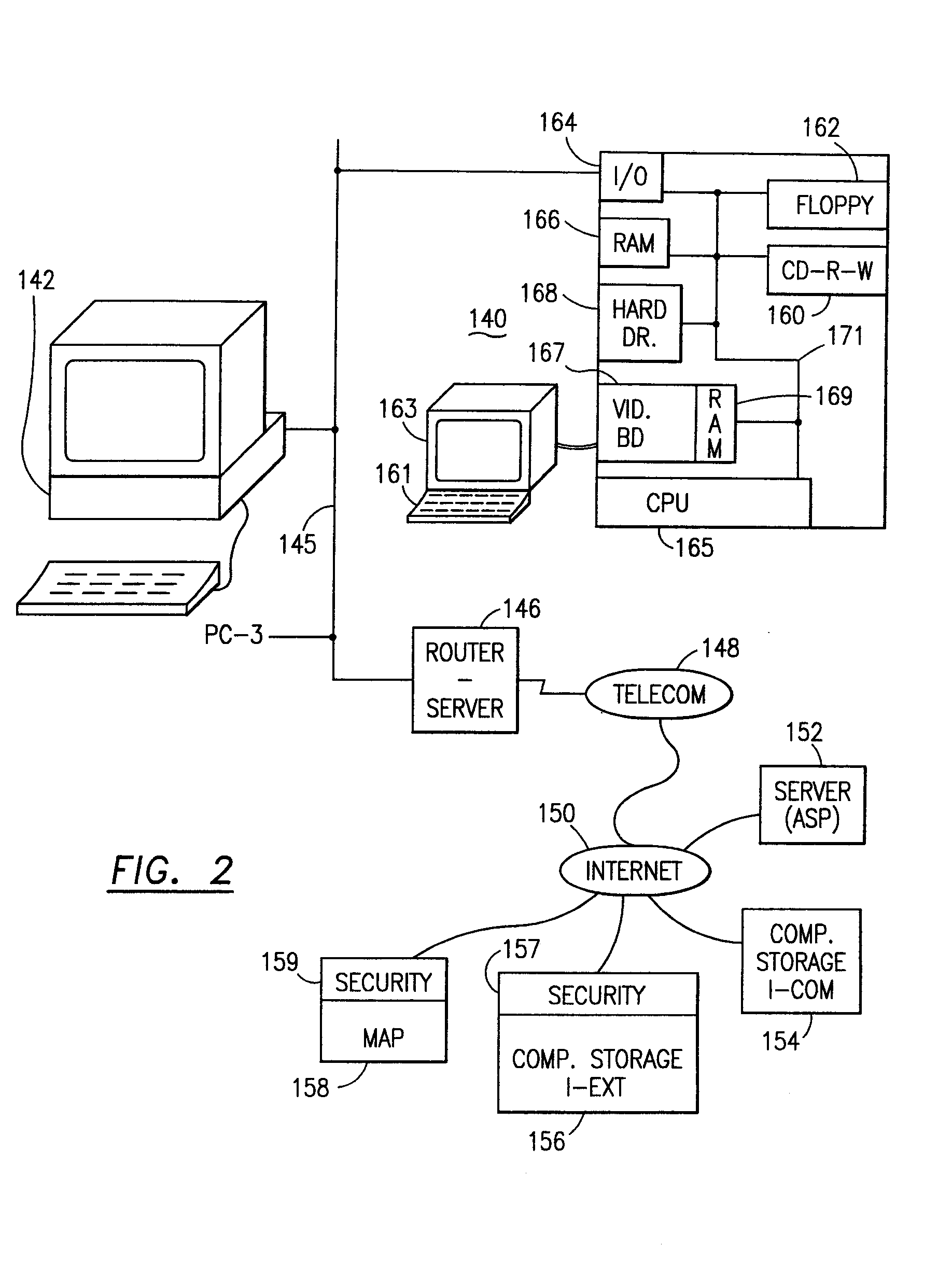
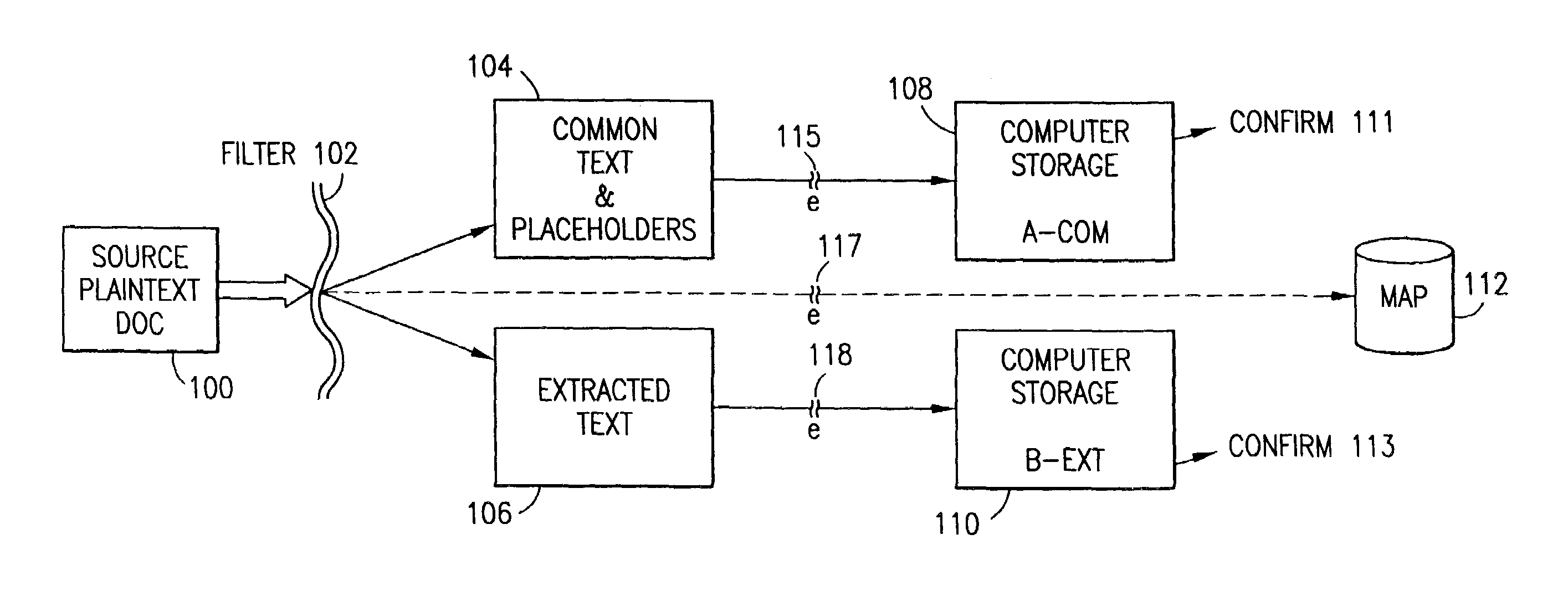
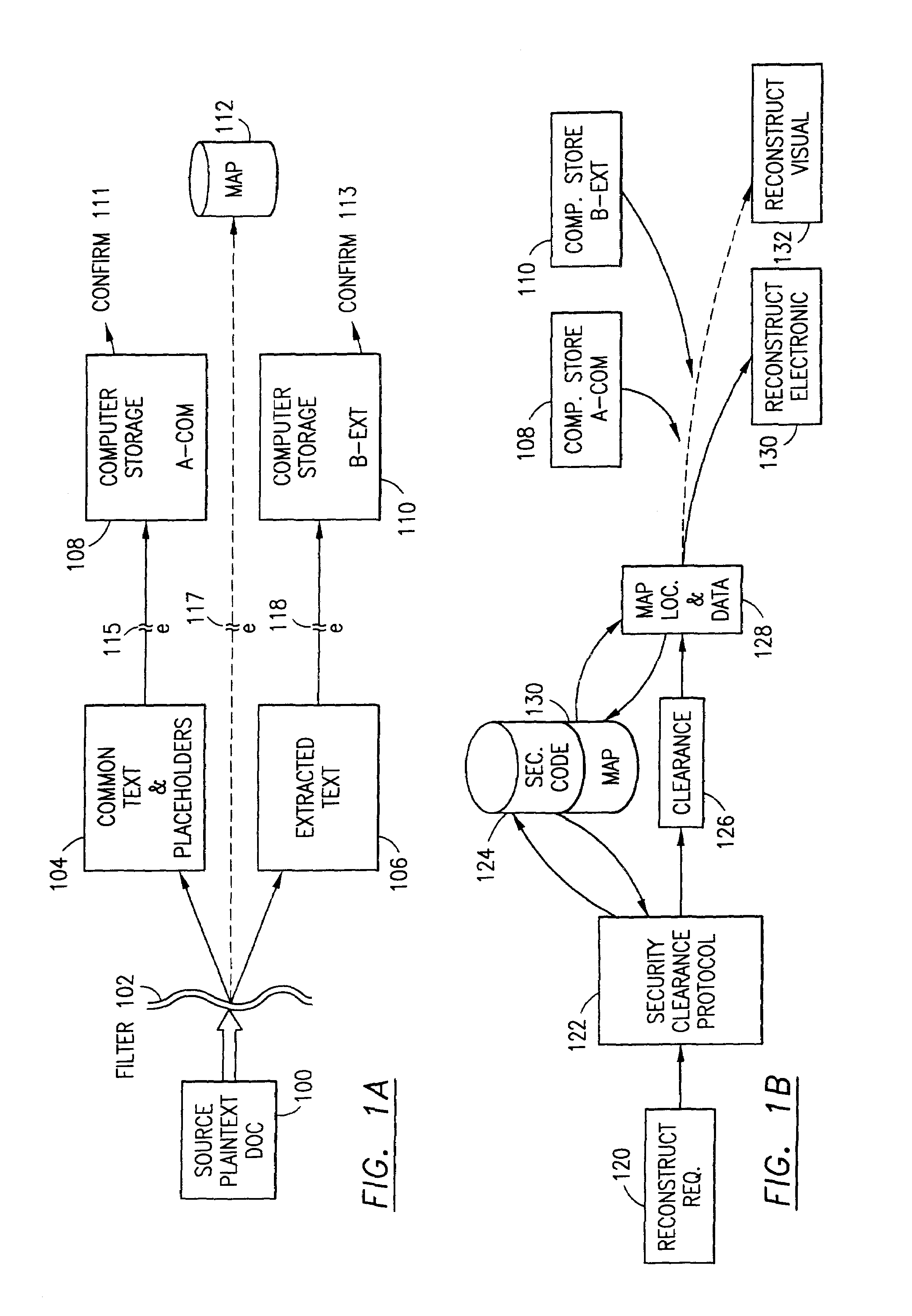
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
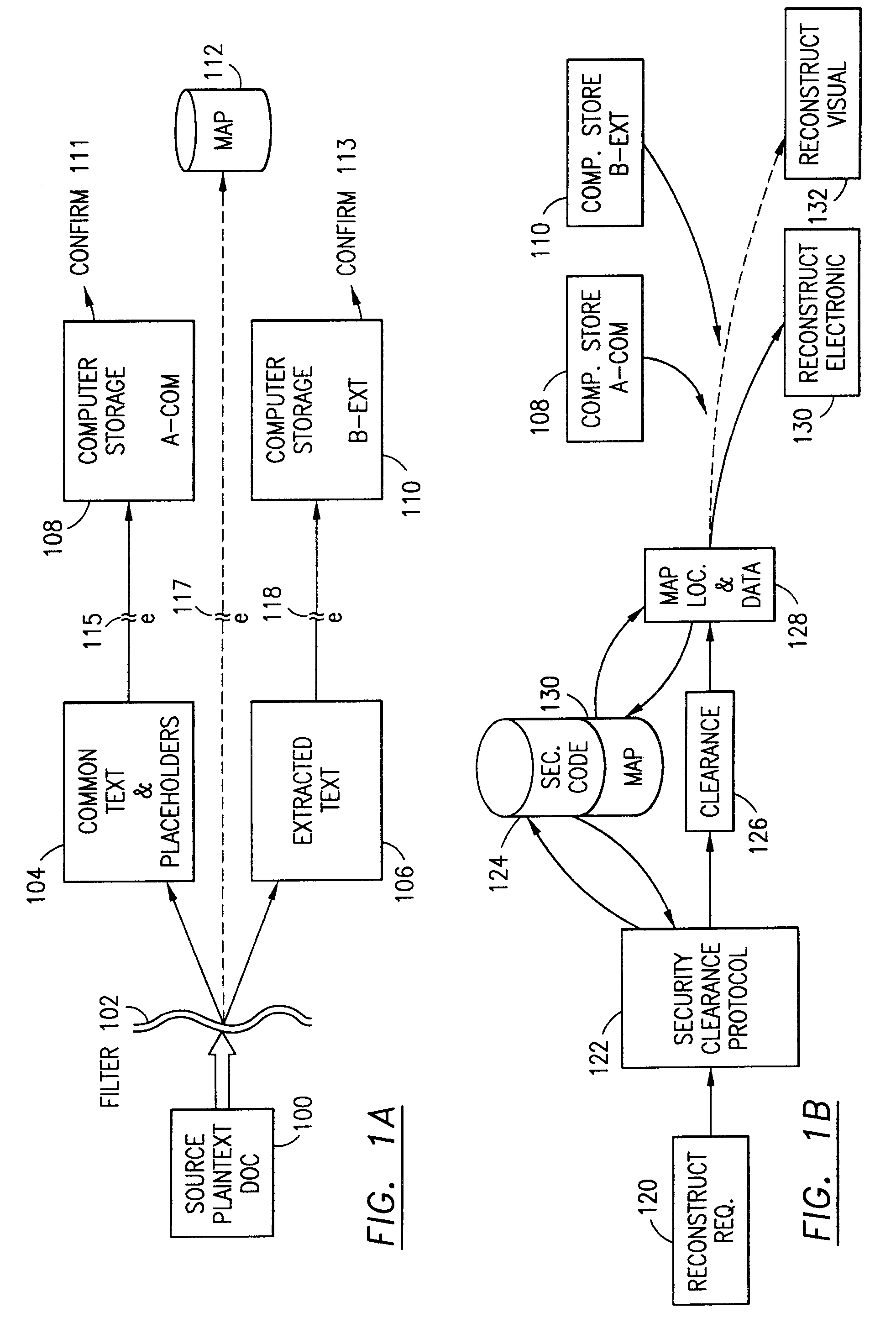
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
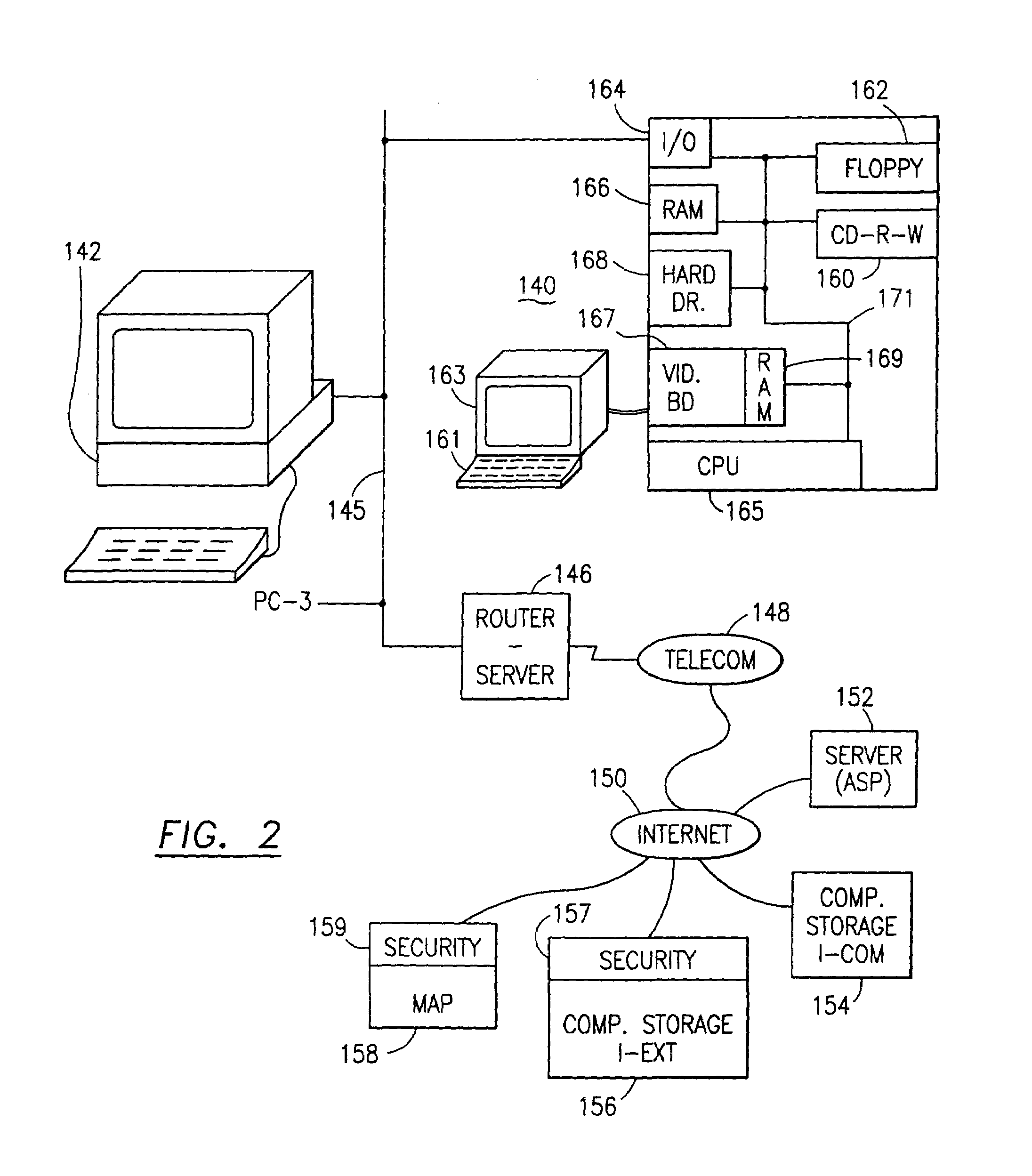
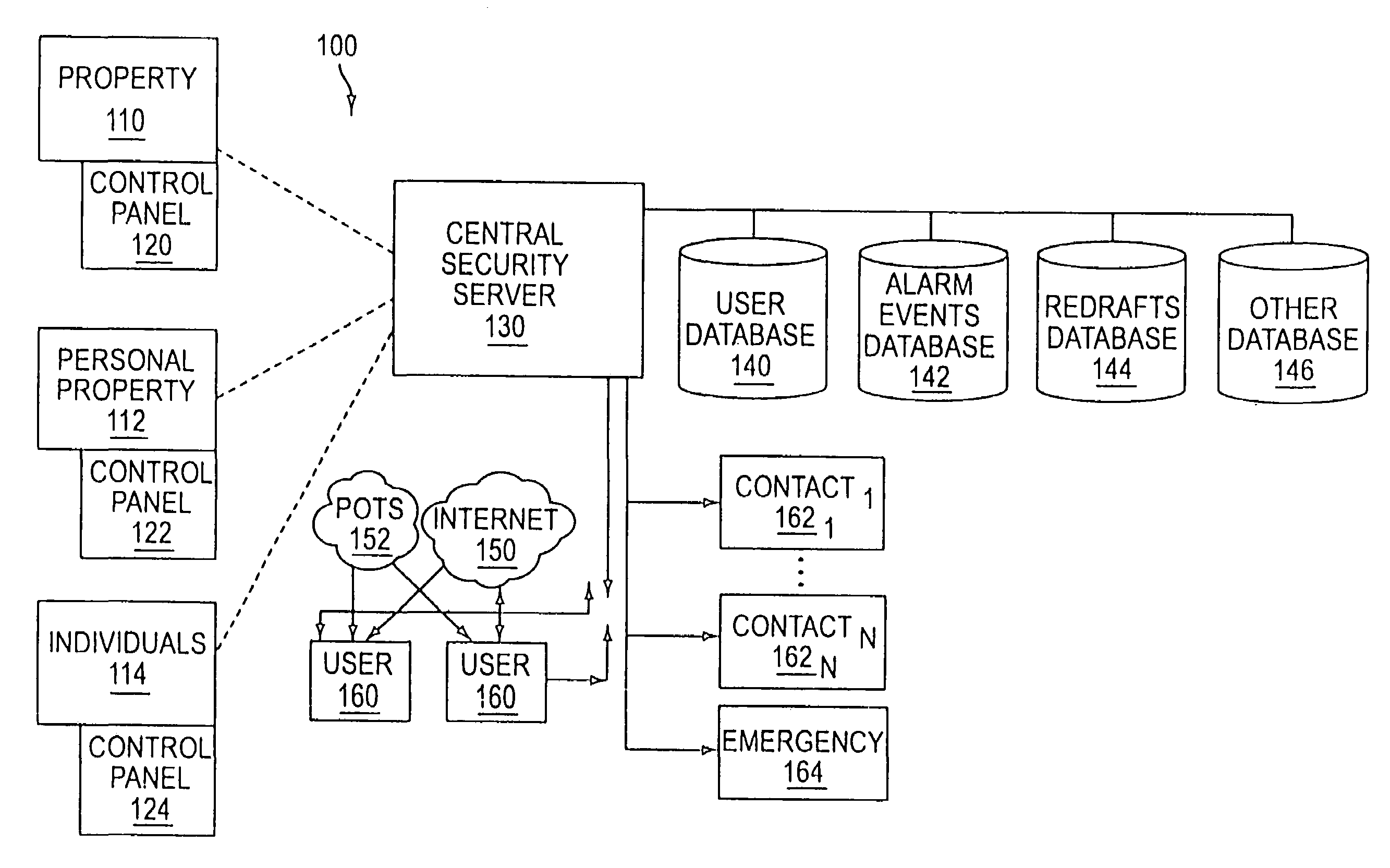
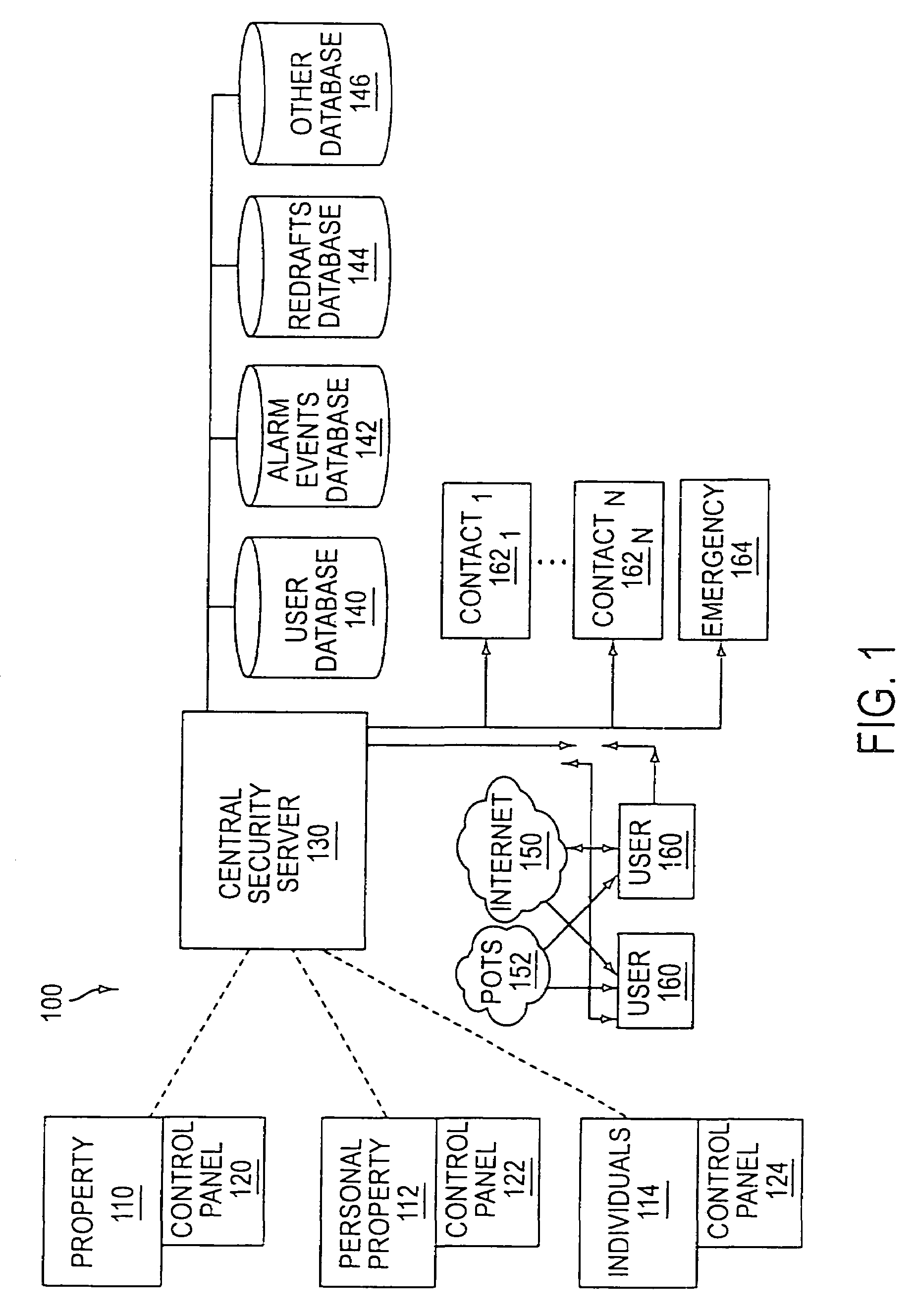
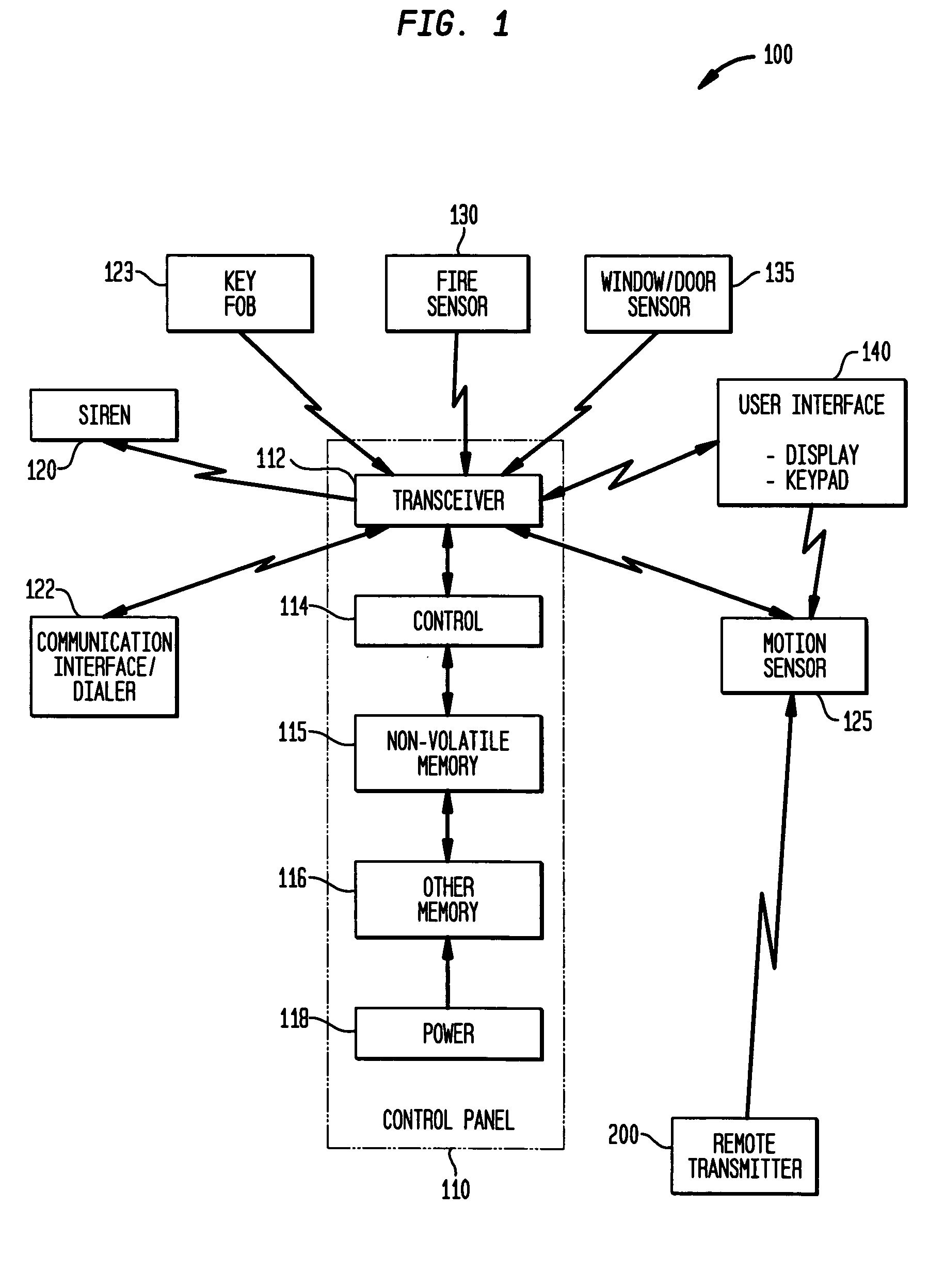
System and method for connecting security systems to a wireless device
InactiveUS7113090B1Electric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
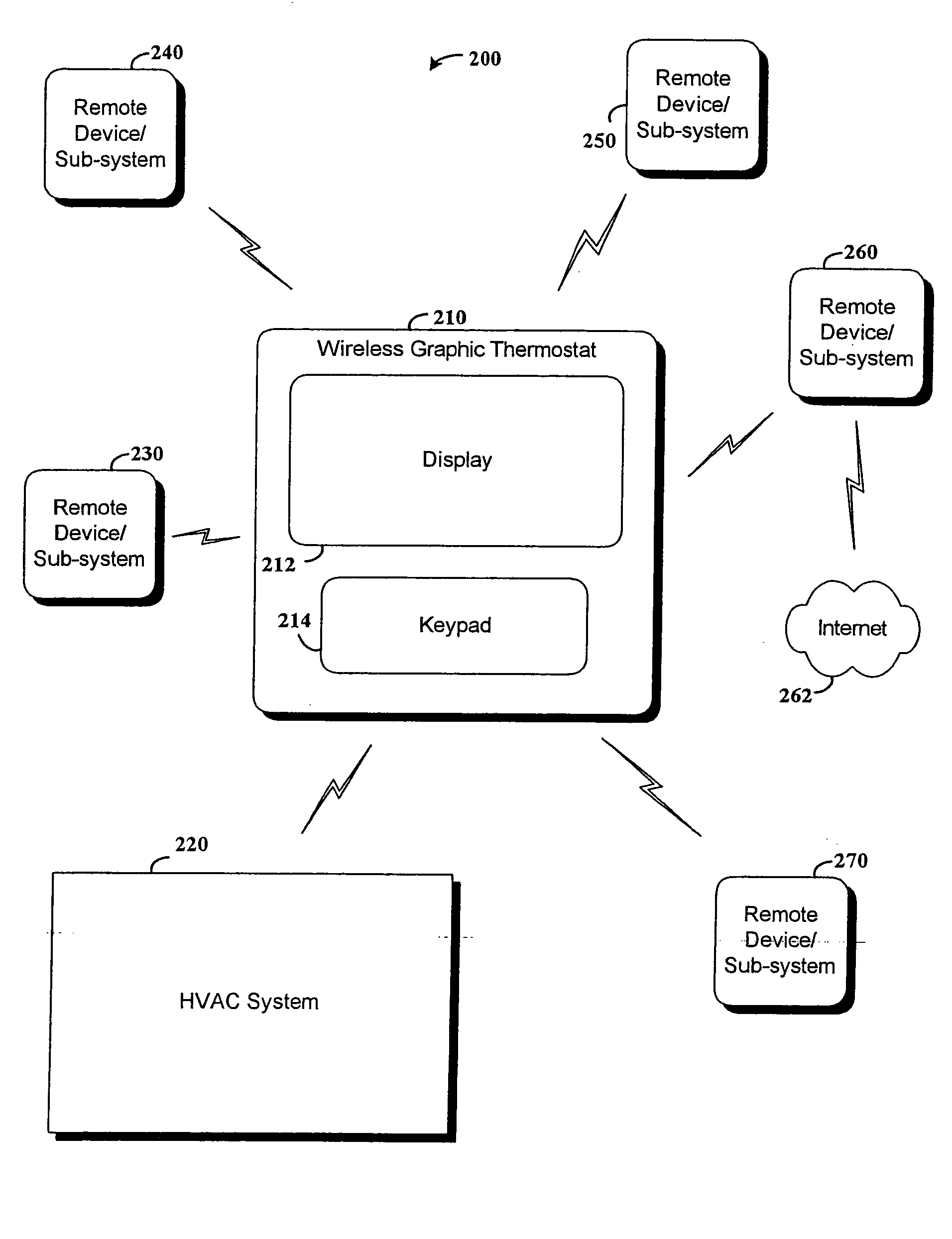
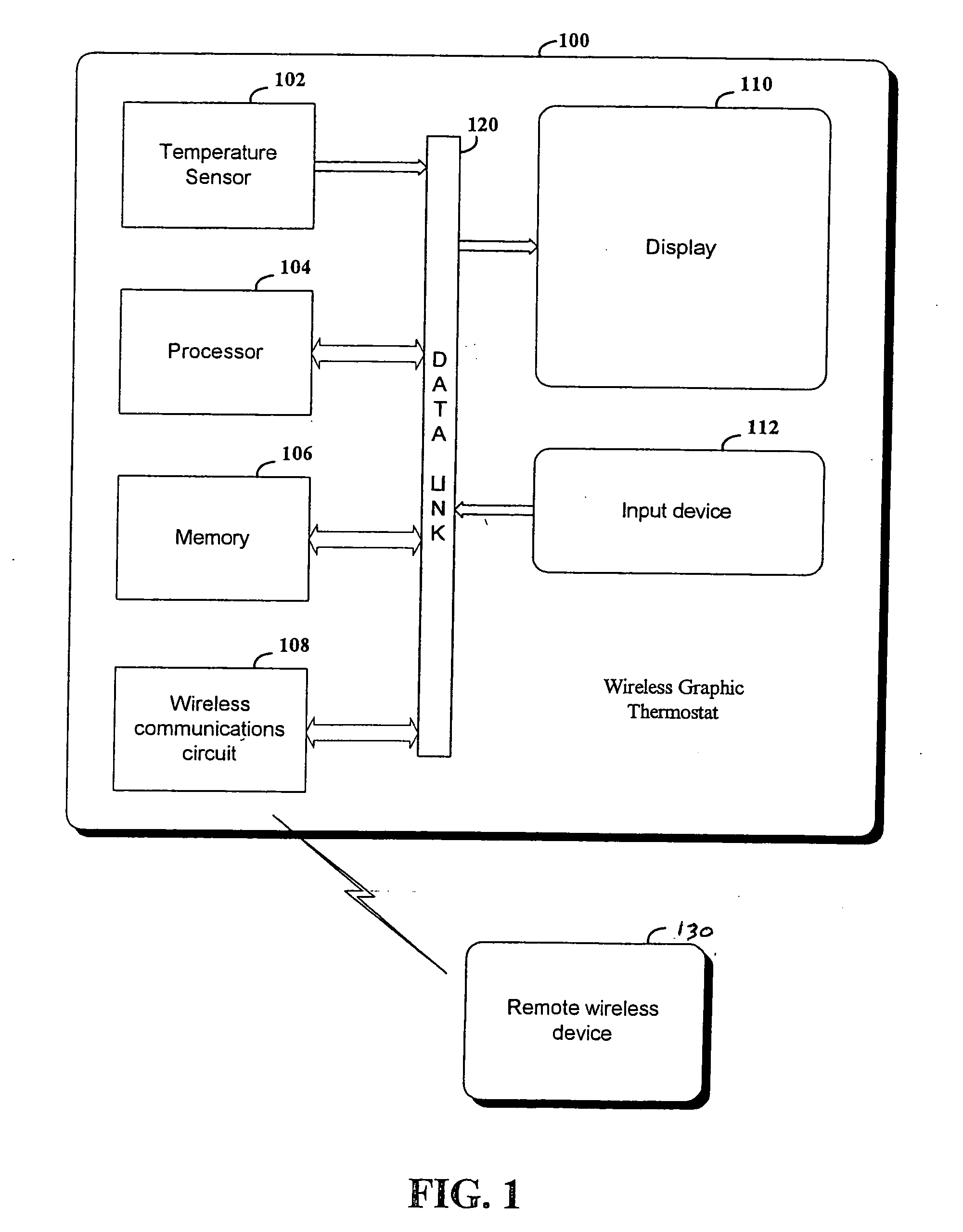
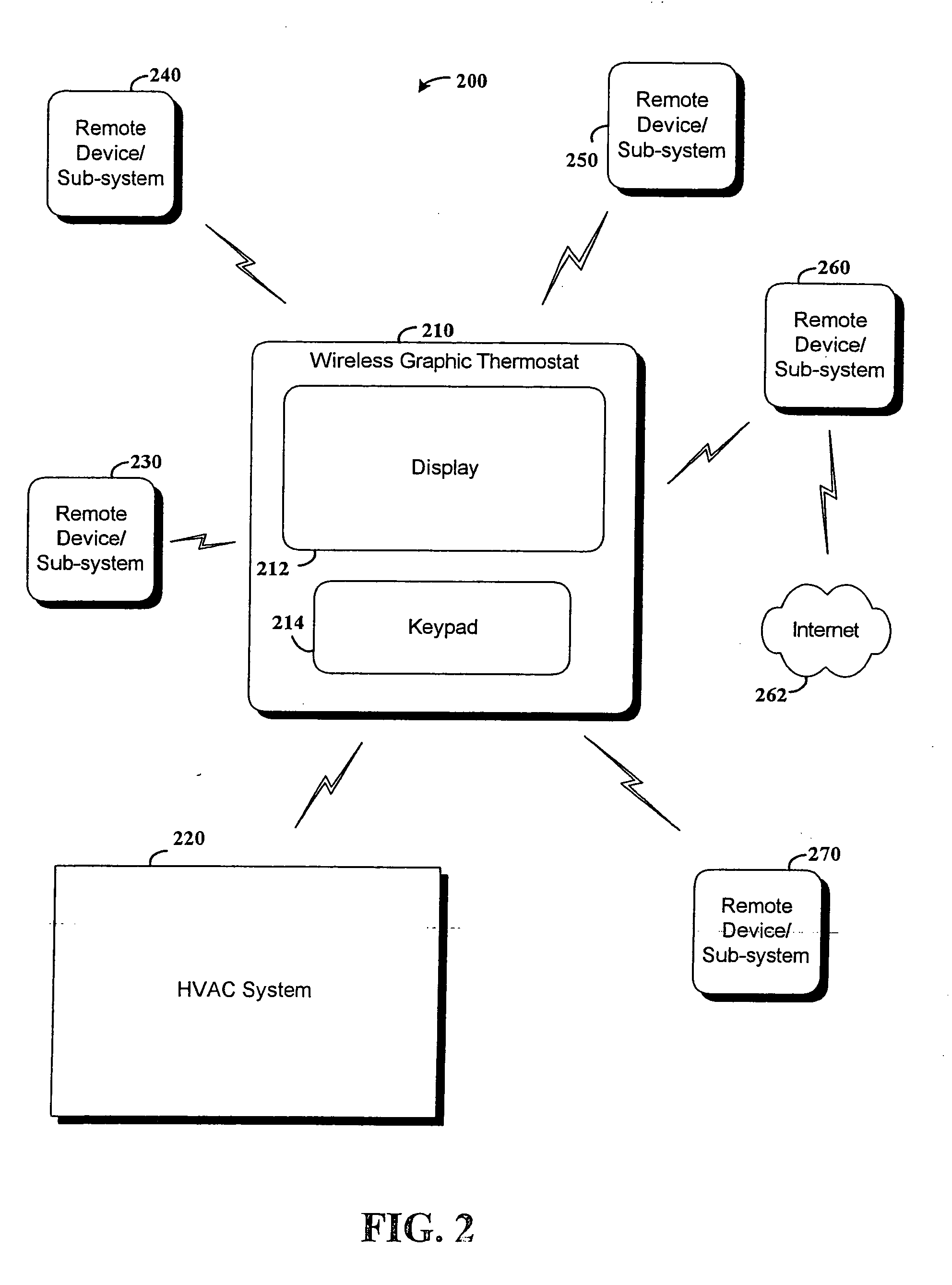
RF interconnected HVAC system and security system
InactiveUS20050270151A1Easy programmingMechanical apparatusSpace heating and ventilation safety systemsWireless controlThermostat
An interconnected wireless HVAC (heating, ventilation, air conditioning) system and wireless security system, which are interconnected and communicate with each other through the use of a common wireless technology, including the same selected frequency, modulation and a set of common protocols. The Wireless HVAC system includes wireless thermostats, which can communicate with and control both the HVAC system and the security system, and the wireless security system includes wireless controls or keypads, which can communicate with and control both the security system and the HVAC system. The universal wireless infrastructure can be expanded to provide communication or control of additional user or manufacturer installed wireless devices or systems through the universal wireless home infrastructure.
Owner:HONEYWELL INT INC
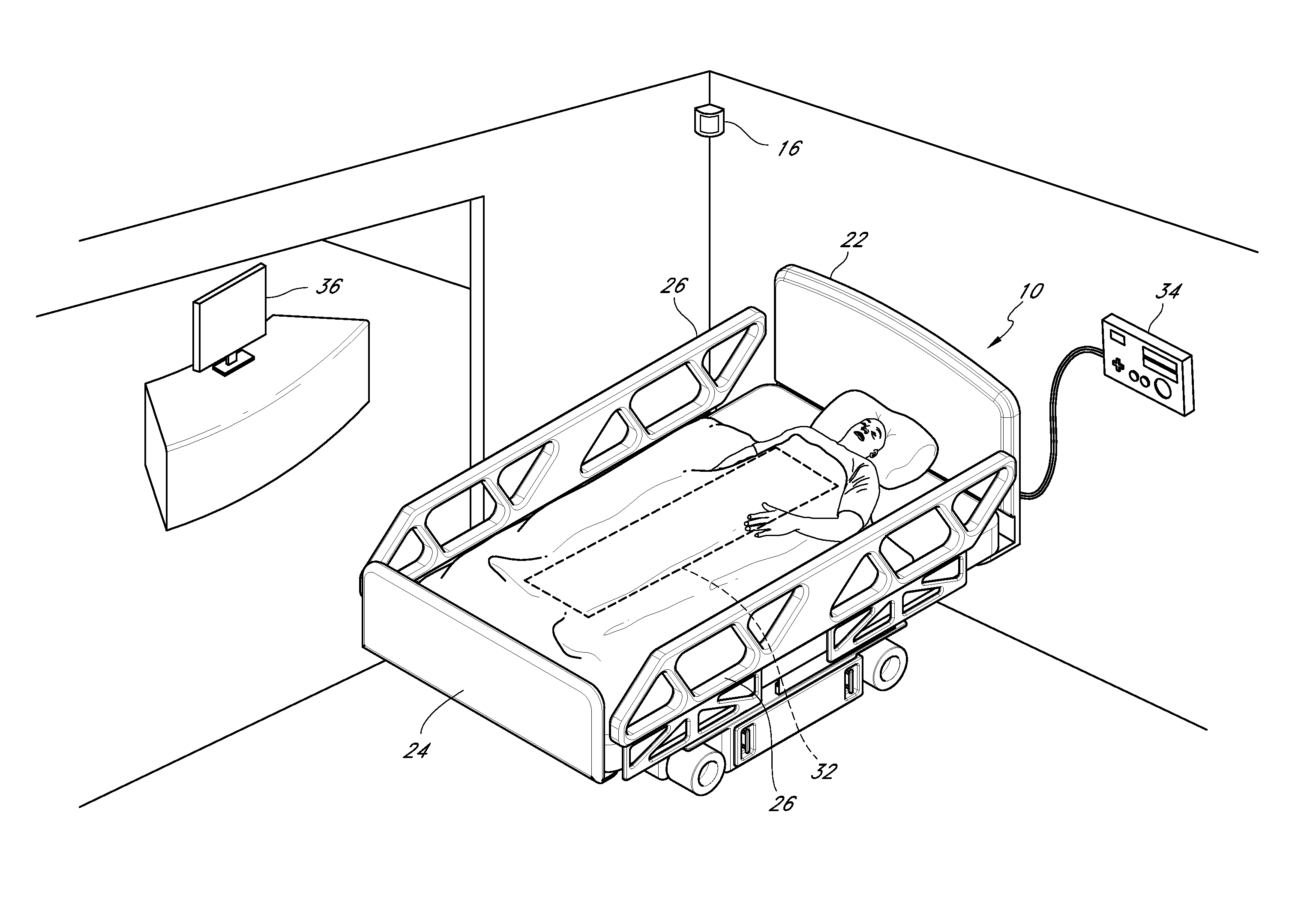
Patient safety system with automatically adjusting bed
A patient safety system including an adjustable bed and a patient monitoring system is disclosed herein. The adjustable bed can automatically adjust to a safe default configuration when the safety system detects that a care provider has left the patient's room or when the safety system detects that the patient is trying to leave the bed. The patient monitoring system can send an alert to the care provider and / or sound an alarm if the patient tries to leave the bed and a care provider is not present with the patient.
Owner:MASIMO CORP
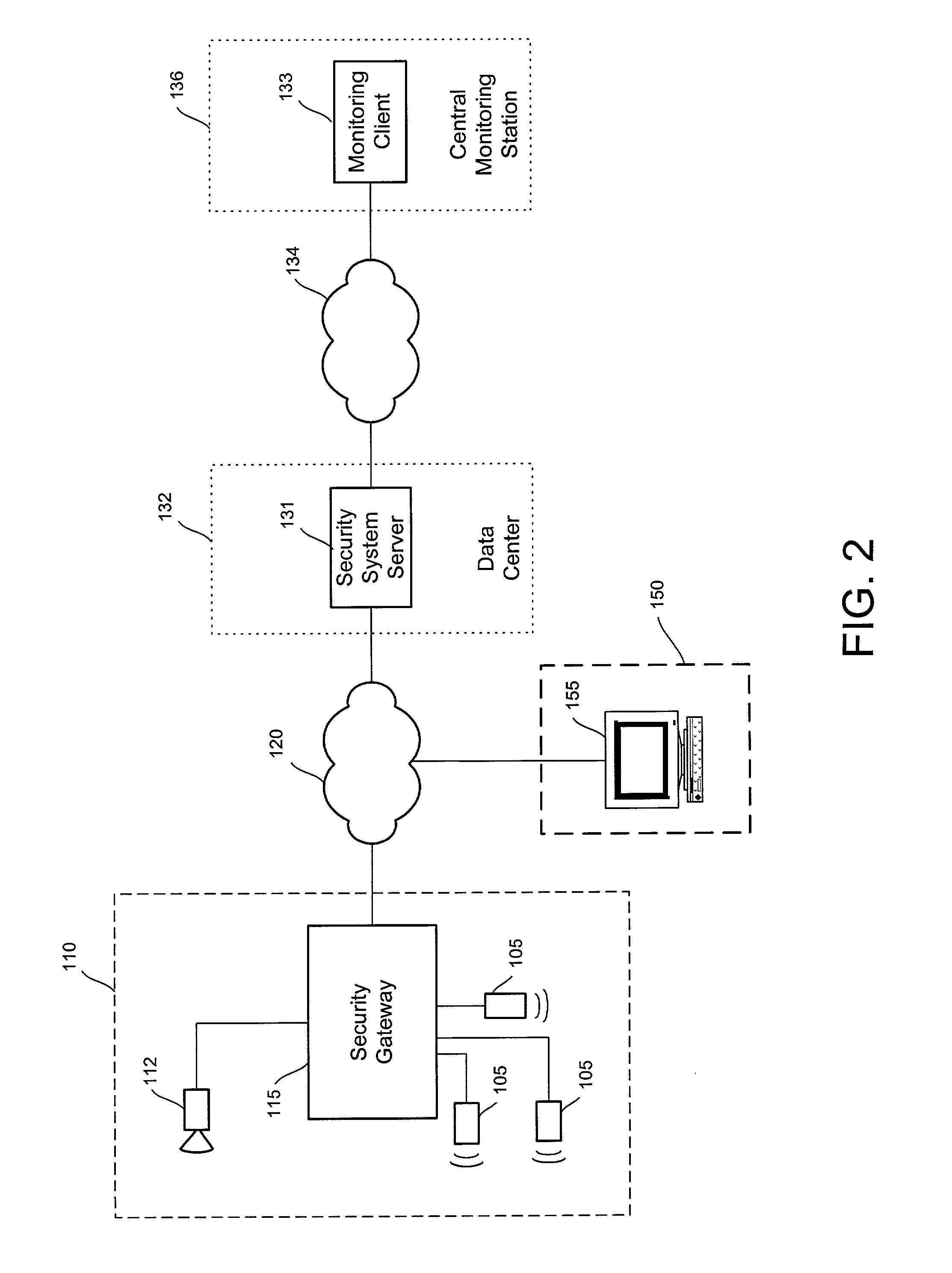
Video security system
InactiveUS20020147982A1Color television detailsClosed circuit television systemsSafe systemHybrid fibre-coaxial
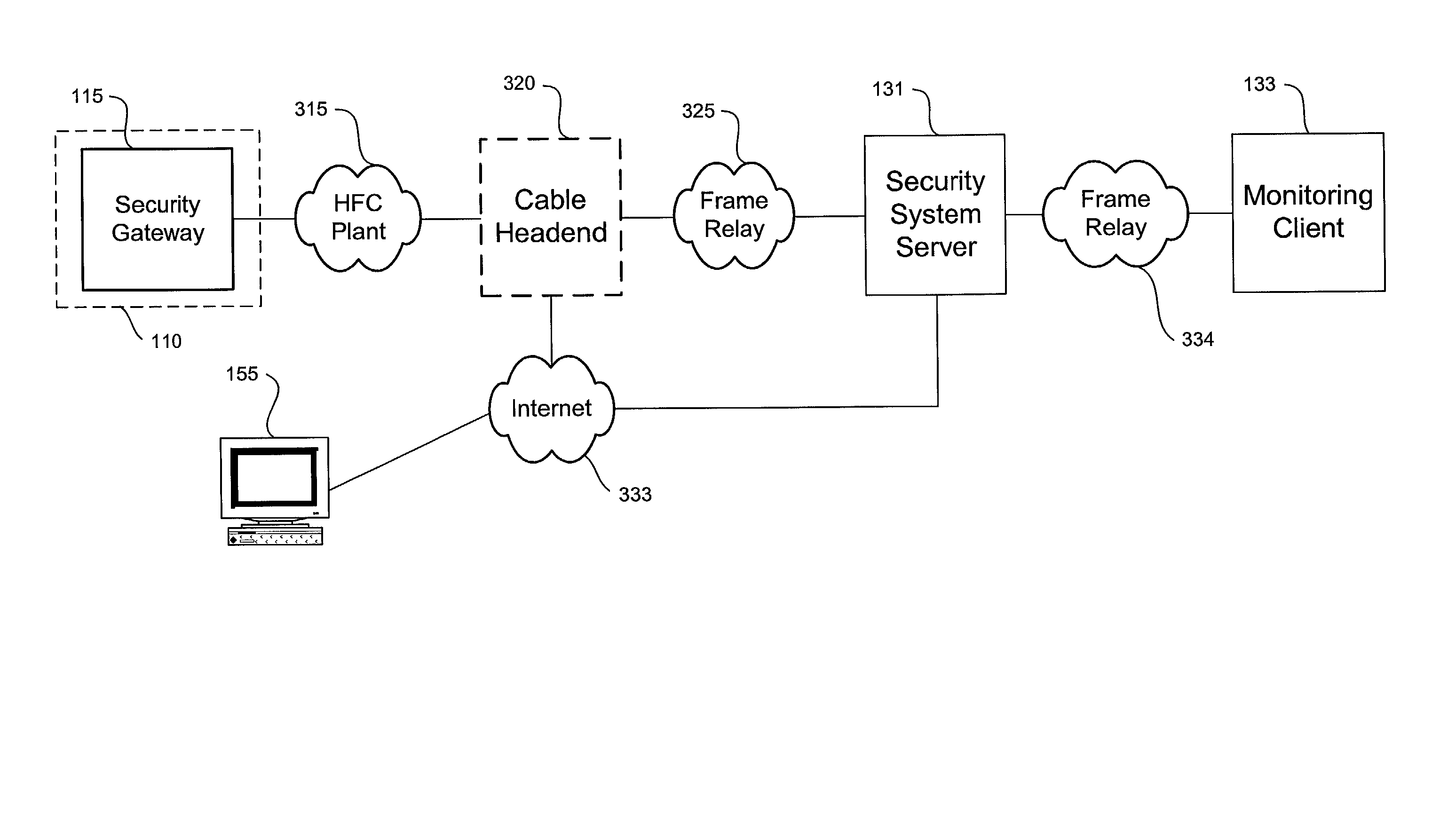
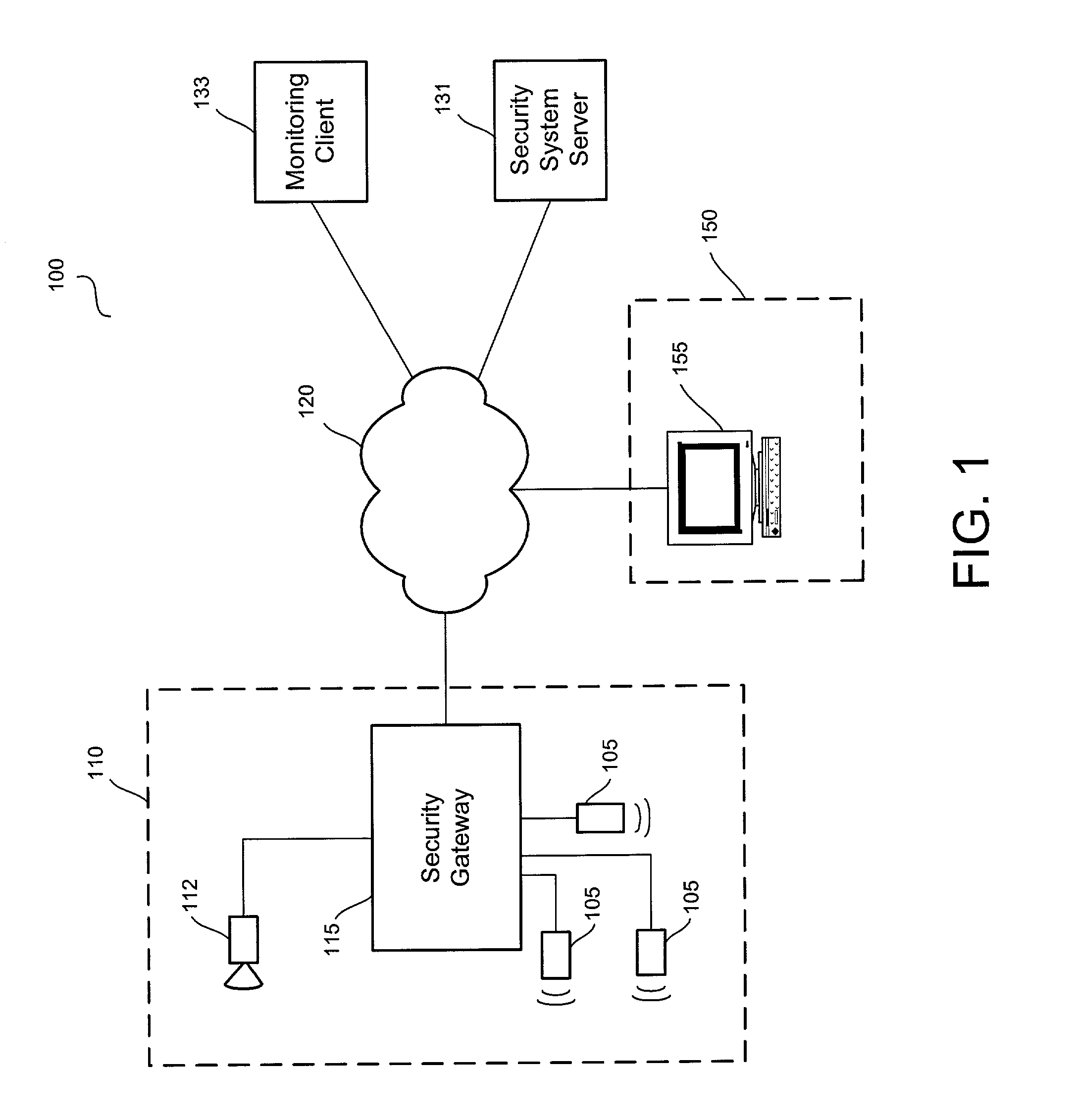
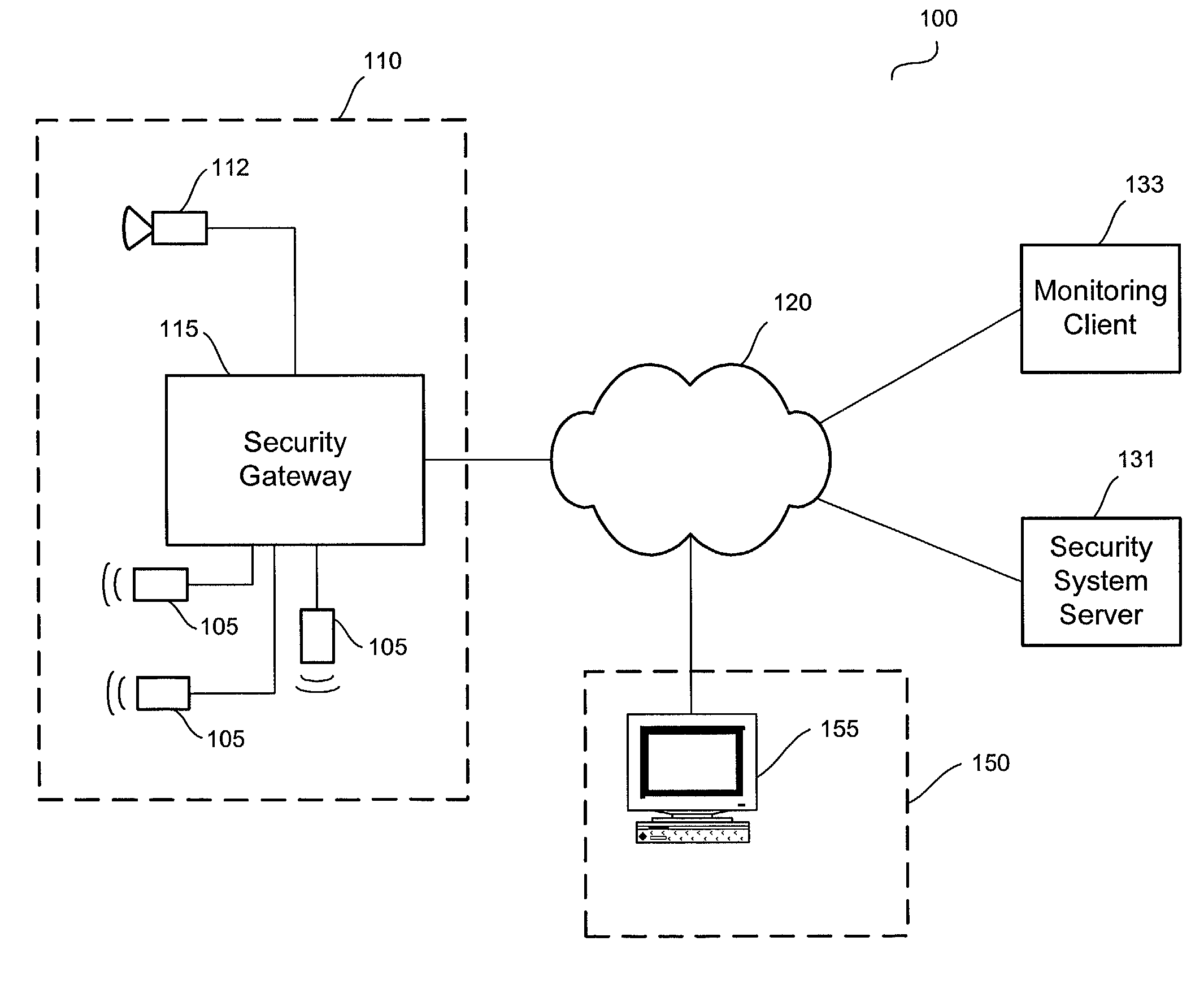
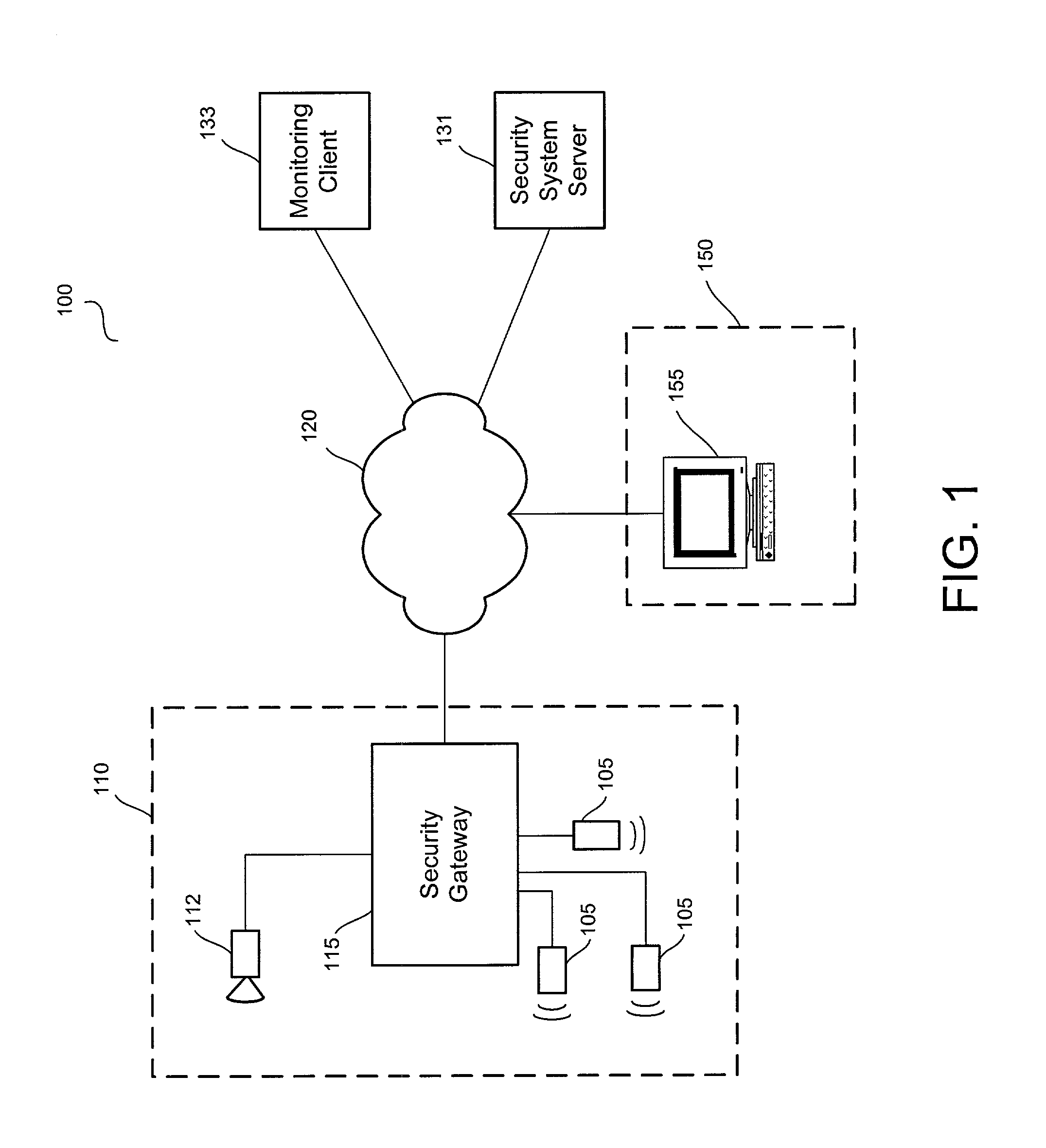
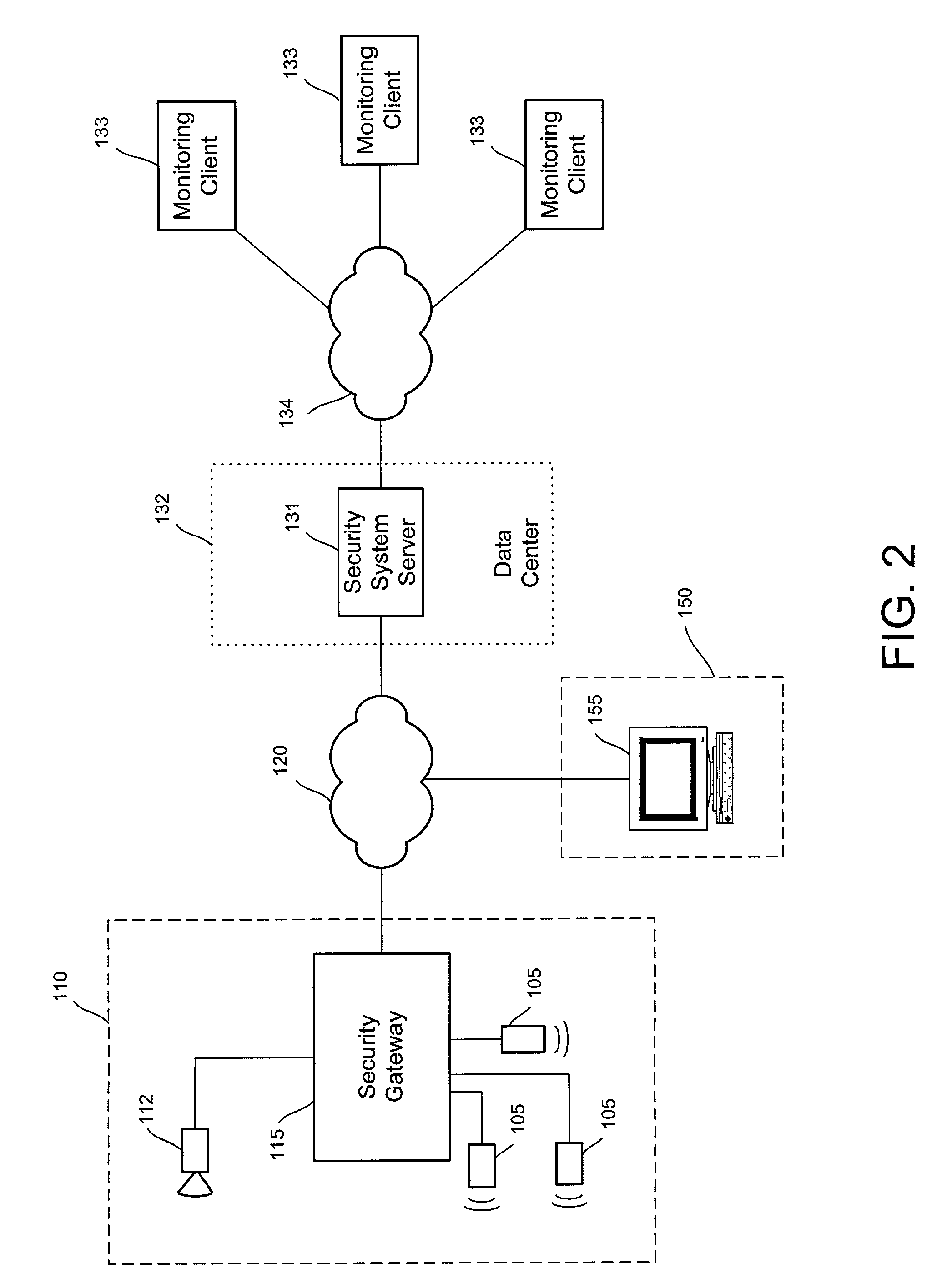
A video security system for the remote verification and monitoring of conditions surrounding an alarm signal. A security gateway at the monitored premises detects alarm conditions and transmits information and video relating to the alarm condition to personnel at a central monitoring station in substantially real time for verification. Various embodiments of the system transmit alarm information to the central monitoring station through hybrid-fiber coaxial, DSL, fiber-optic, high-speed fixed wireless and mobile communications networks. The security system may include secondary alarm notification from the security gateway to the central monitoring station via a second network, such as IP, Ethernet, Internet, frame relay, public switched telephone, wireless, and mobile communications networks.
Owner:COMCAST CABLE COMM LLC
Vehicle charger safety system and method
InactiveUS20110074346A1Safety concern can be addressedFix security issuesMultiple-port networksBatteries circuit arrangementsForeign objectSystem identification
Wireless vehicle charger safety systems and methods use a detection subsystem, a notification subsystem and a management subsystem. The detection subsystem identifies a safety condition. The notification subsystem provides an indication of the safety condition. The management subsystem addresses the safety condition. In particular, undesirable thermal conditions caused by foreign objects between a source resonator and a vehicle resonator are addressed by sensing high temperatures, providing a warning and powering down a vehicle charger, as appropriate for the environment in which the charger is deployed.
Owner:WITRICITY CORP
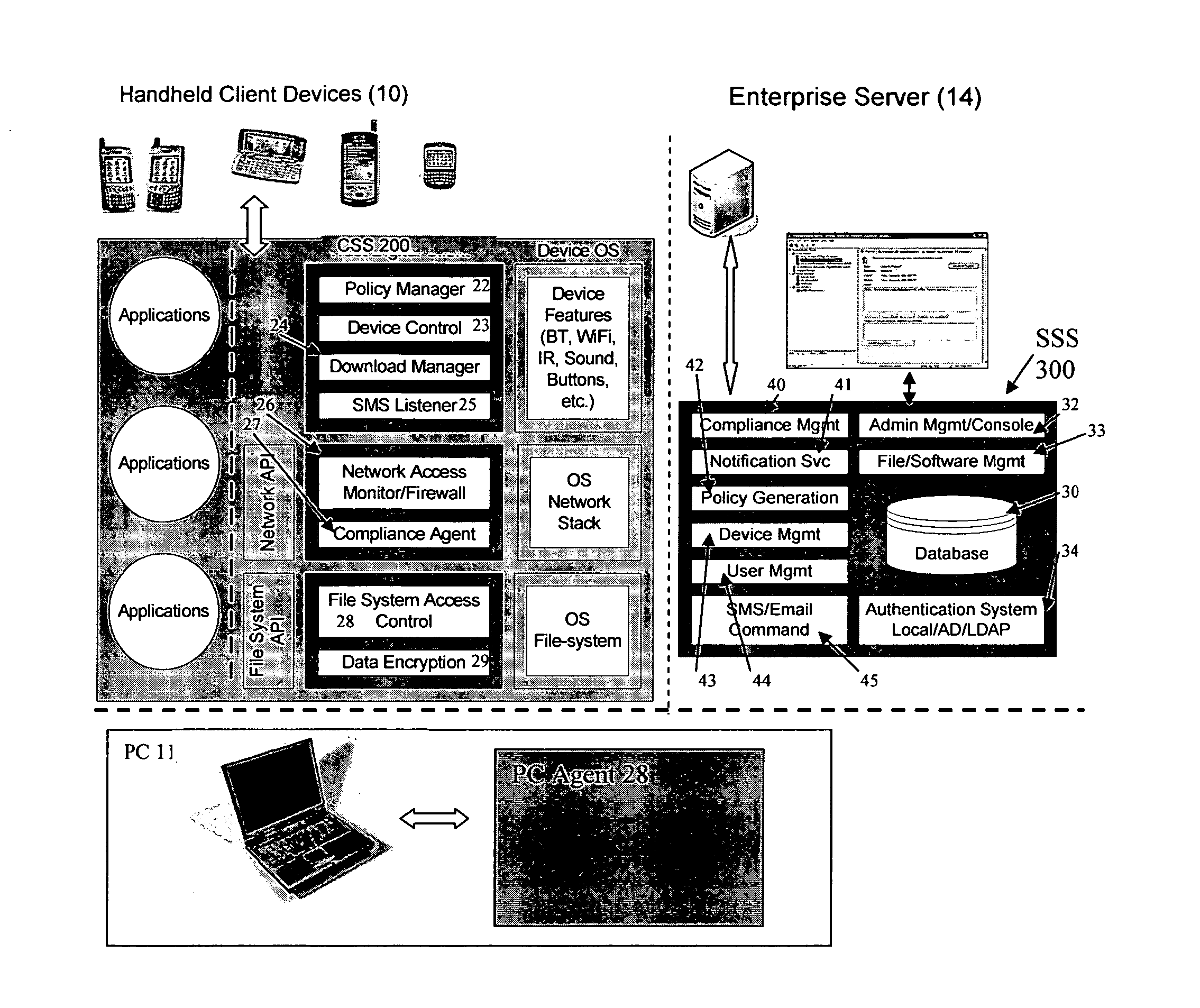
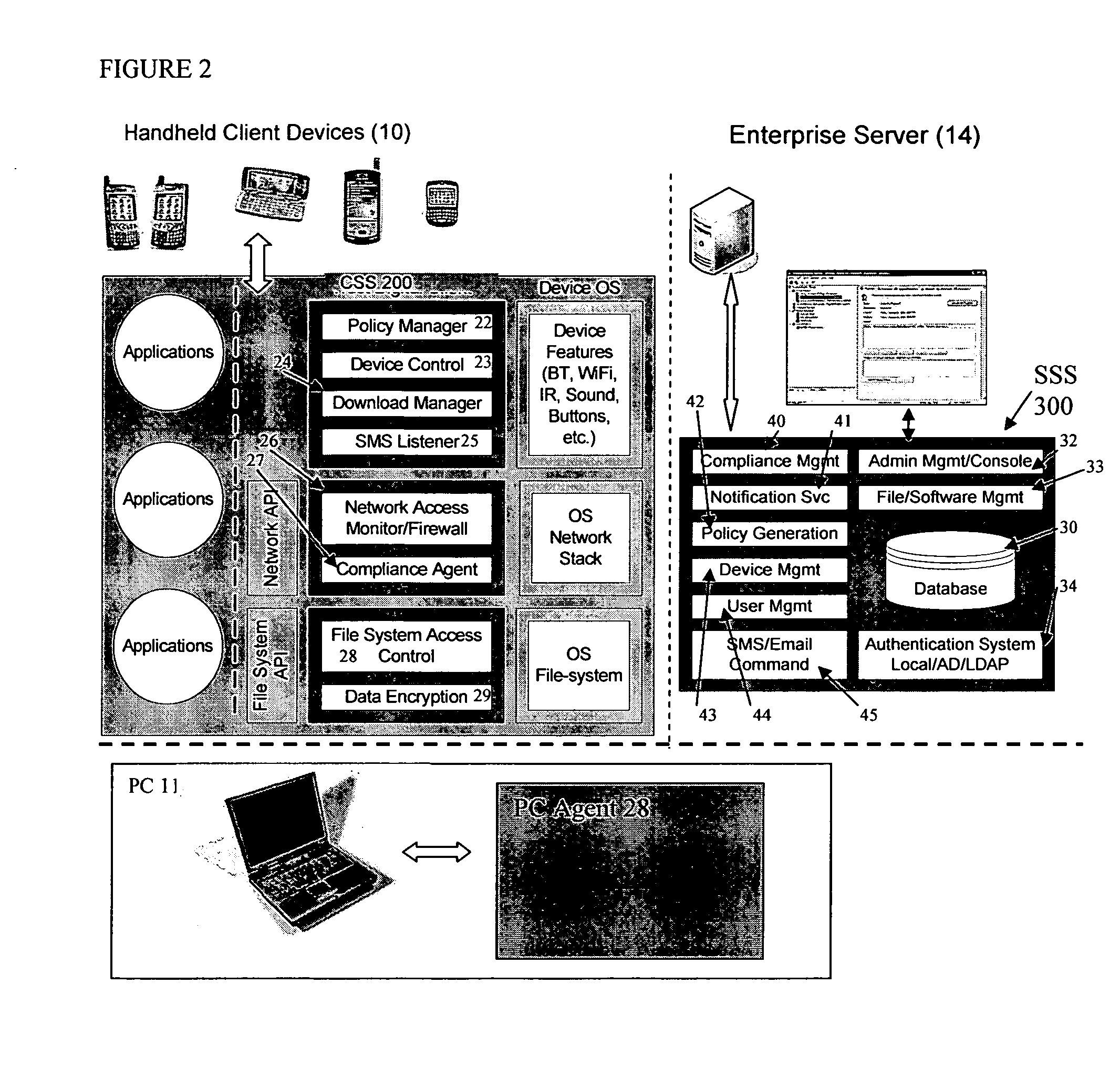
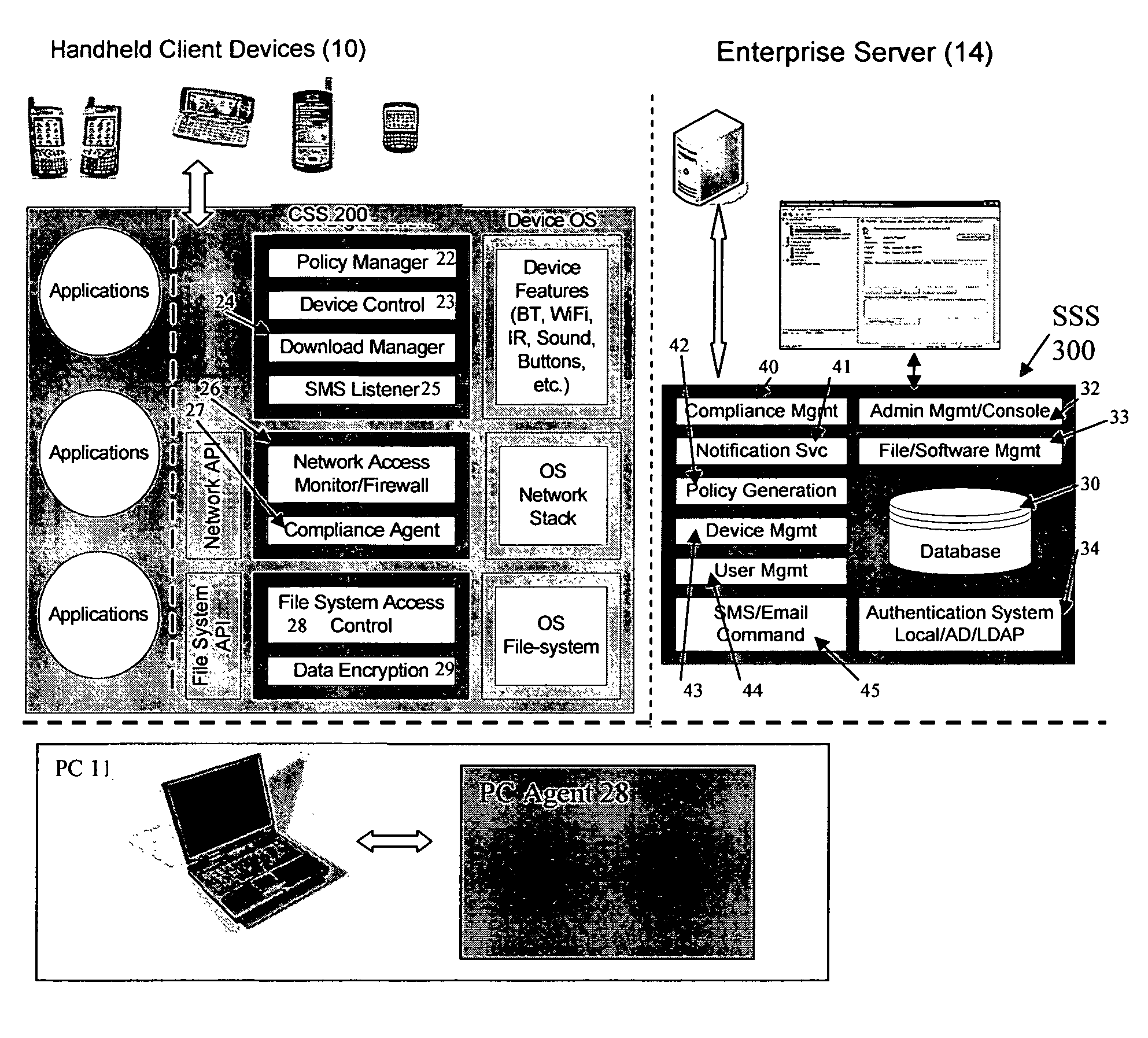
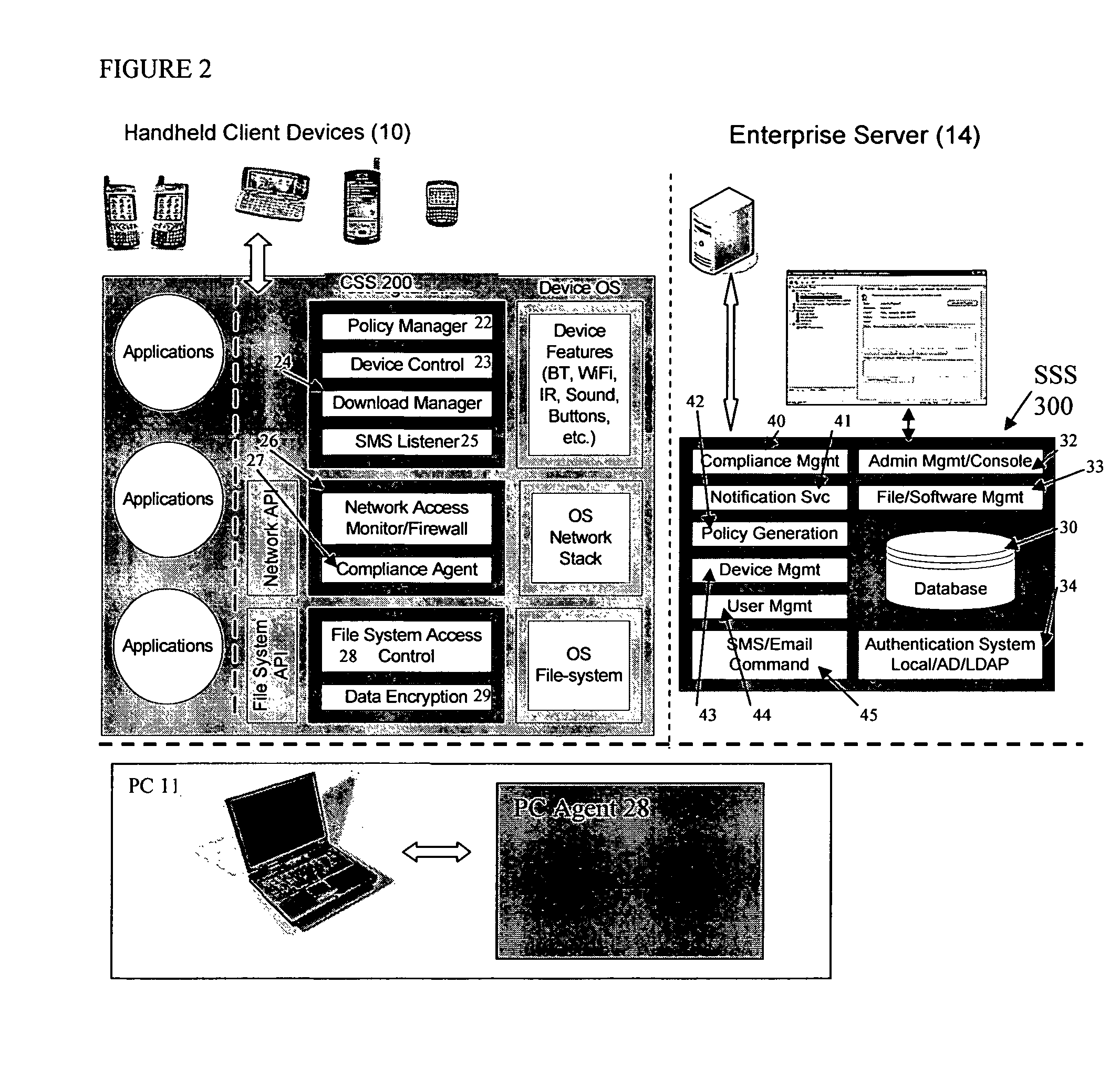
Mobile data security system and methods
ActiveUS20060224742A1Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securitySecurity system
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
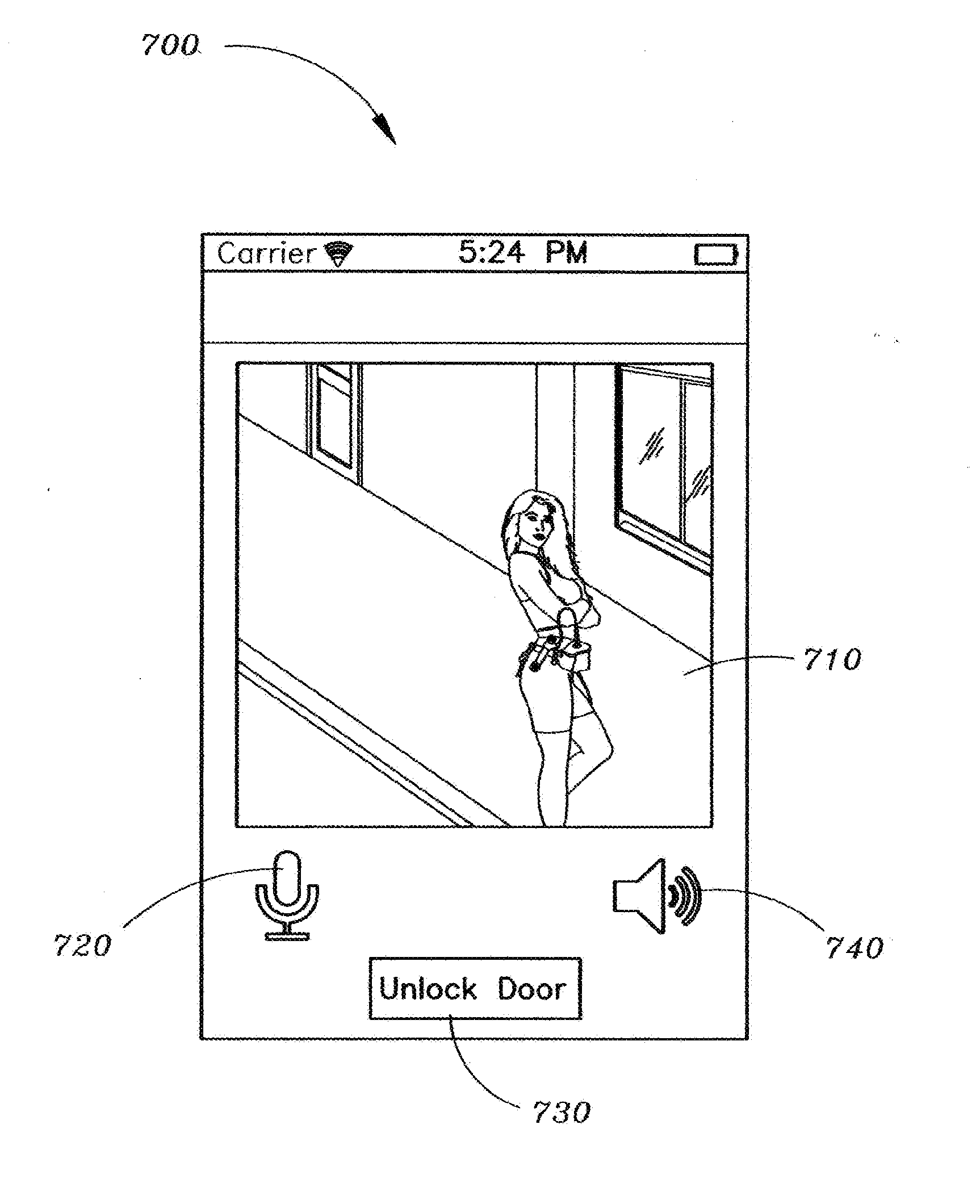
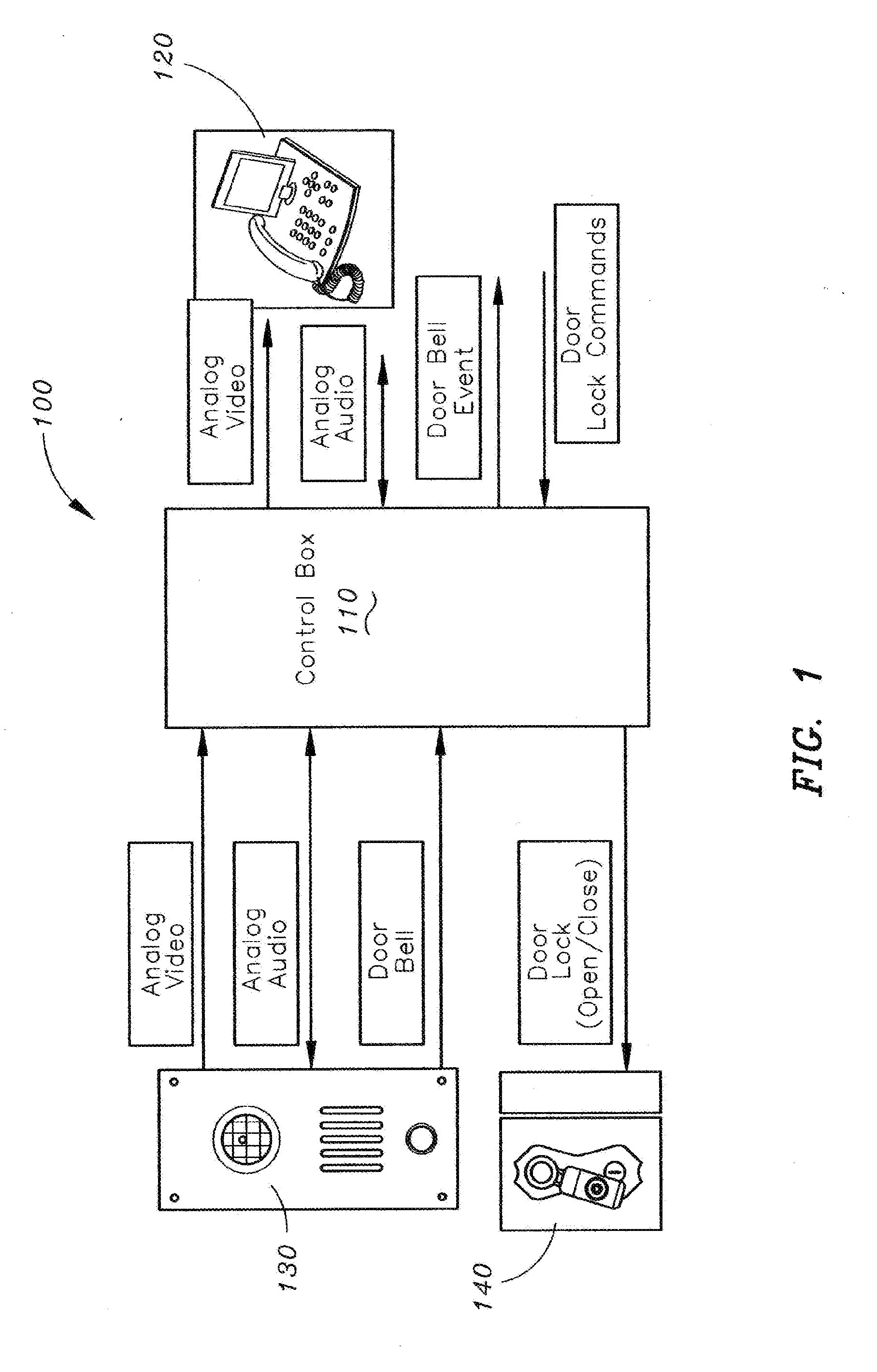
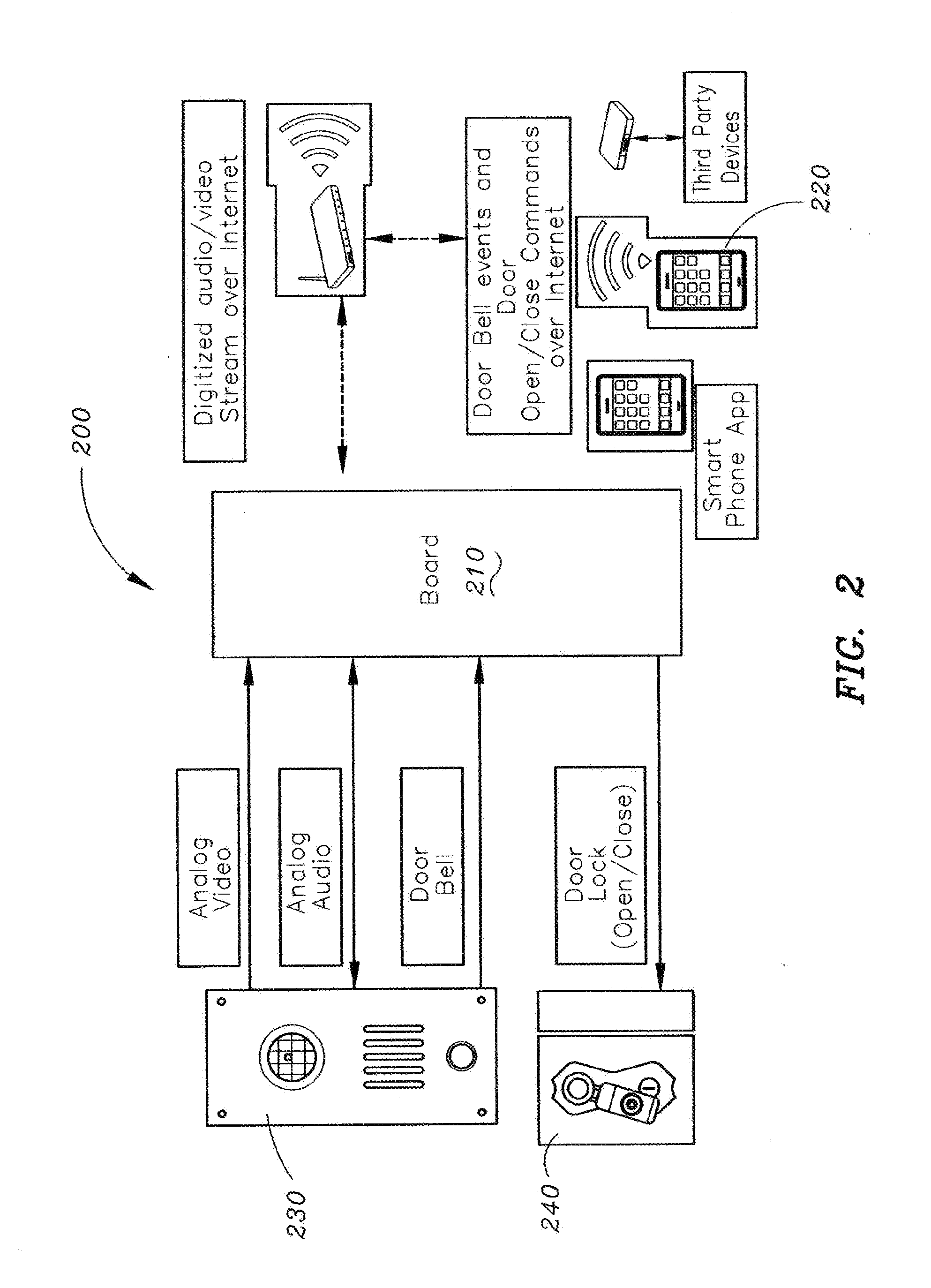
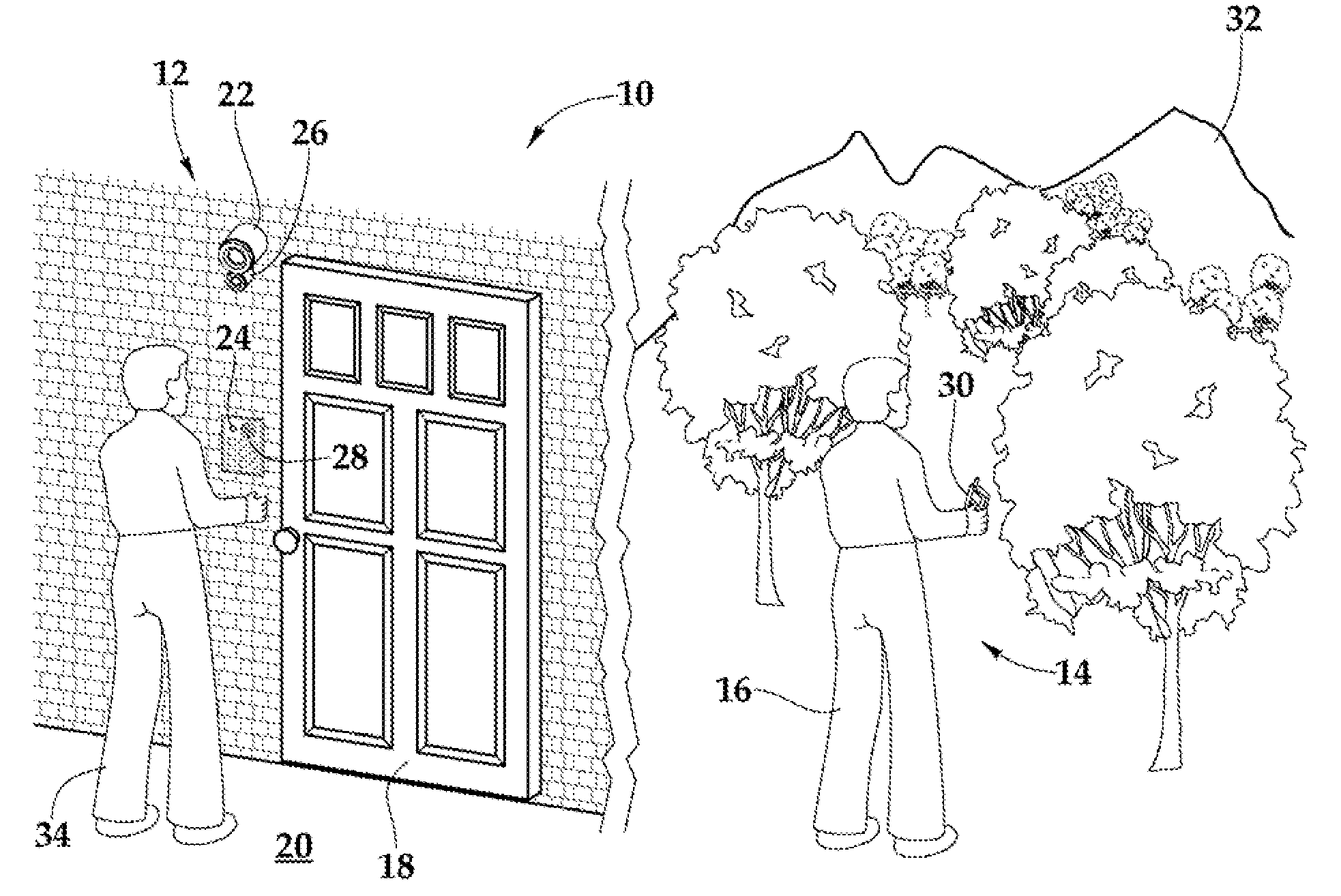
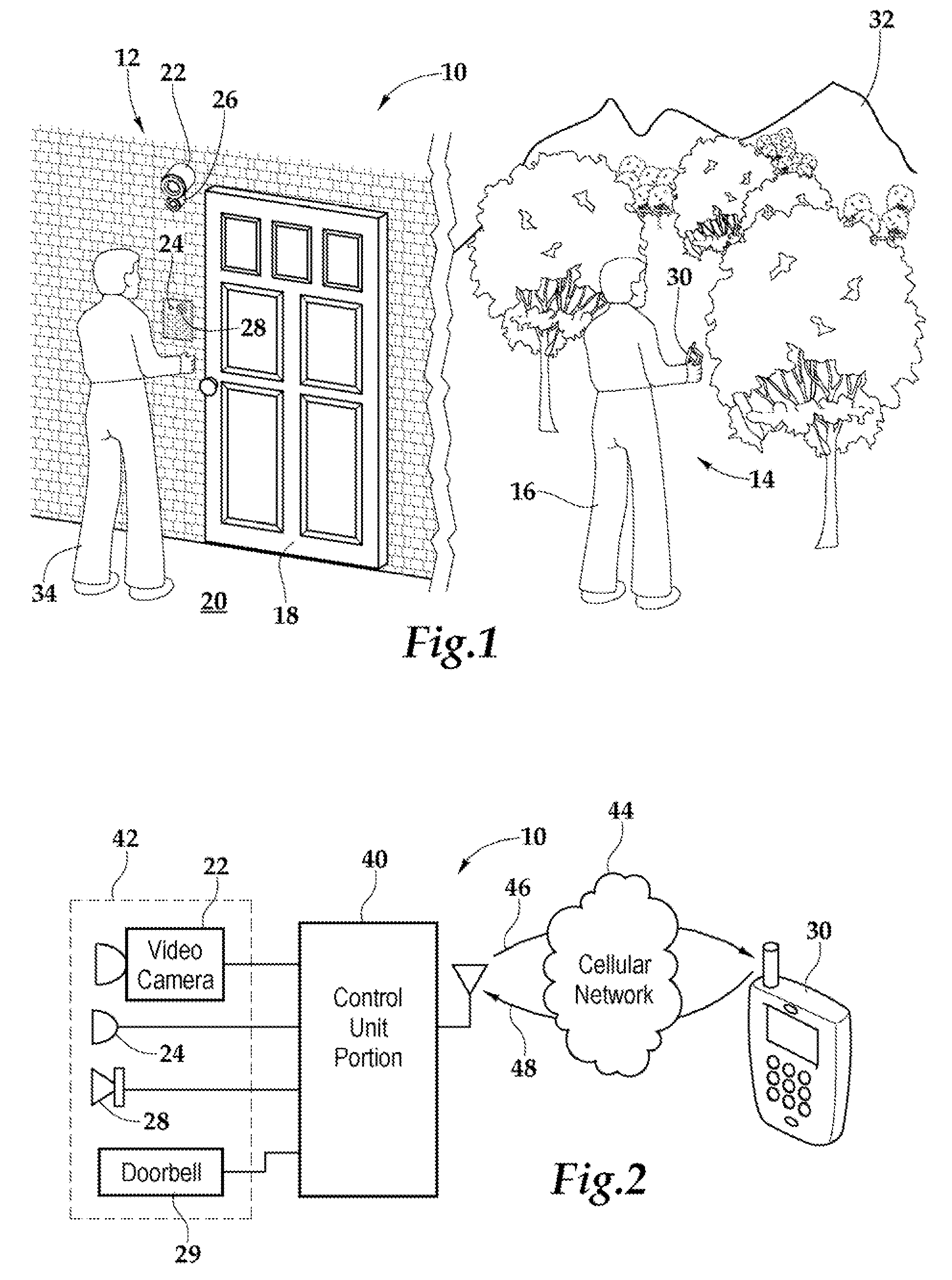
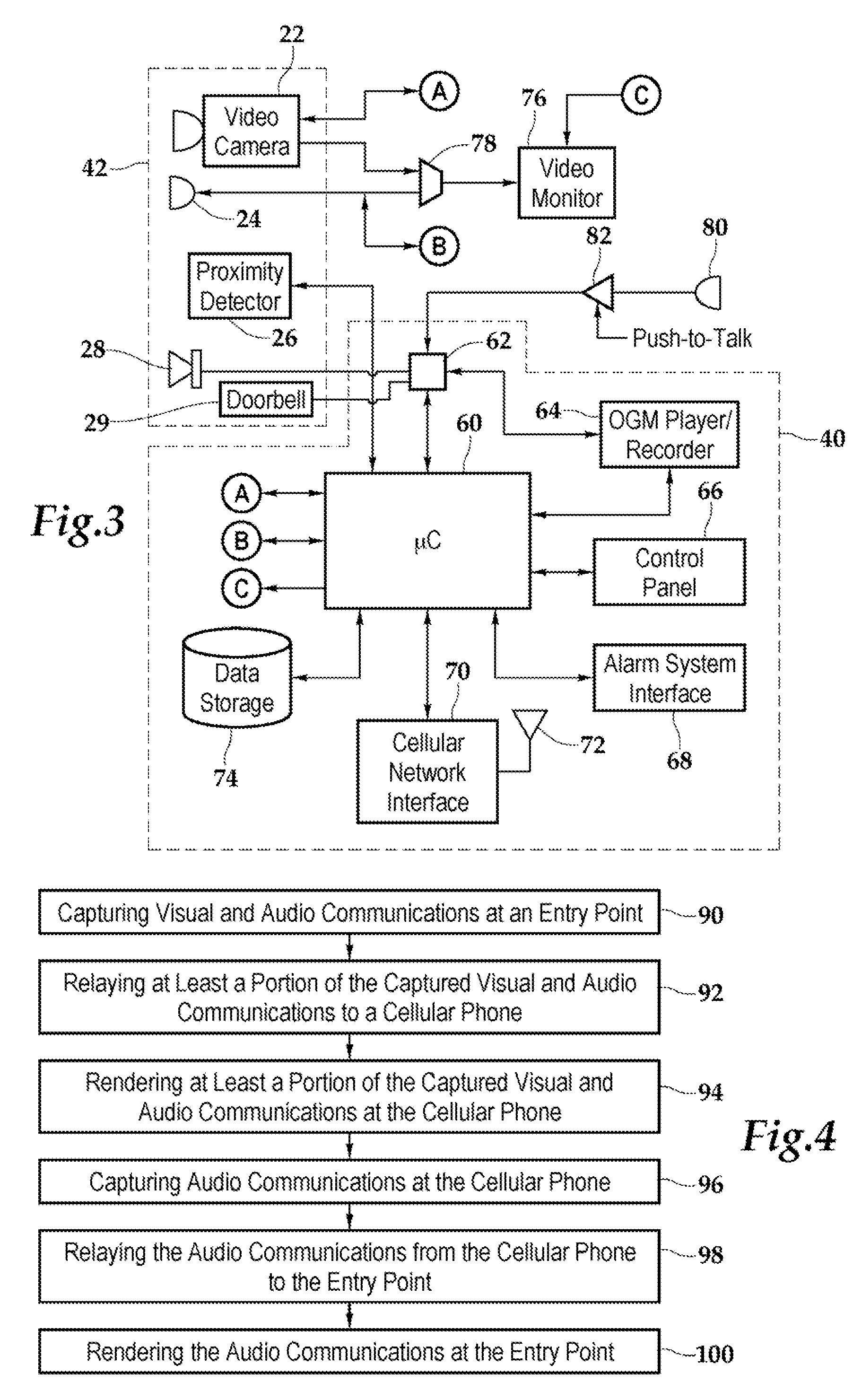
Method and apparatus for unlocking/locking a door and enabling two-way communications with a door security system via a smart phone
A method for operating a doorbell security system. The method may include receiving a doorbell press event signal and sending a doorbell press event notification to at least one mobile computing device. The method may further include receiving an acceptance response from a particular mobile computing device, wherein the acceptance response. The method may include receiving audio from a microphone and video from a camera located in proximity to a doorbell. The method may also include sending the audio from the microphone and the video from the camera to the particular mobile computing device. The method may additionally include receiving a command from the mobile computing device and unlocking, locking, opening, or closing a door.
Owner:HUISKING TIMOTHY J
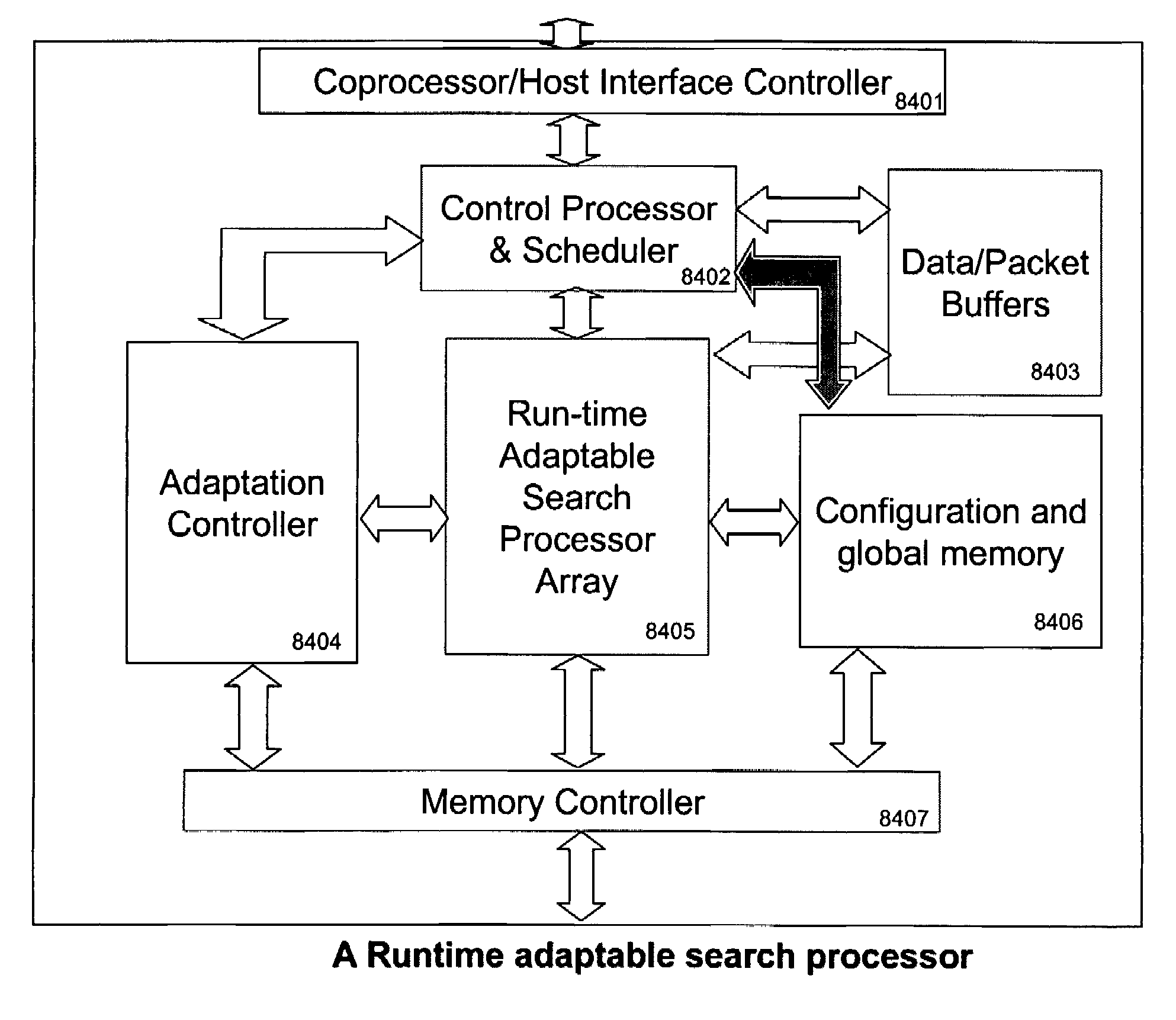
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Distributed monitoring for a video security system
A system and method for distributed monitoring and remote verification of conditions surrounding an alarm condition in a security system. A security gateway detects alarm conditions at a premises and records video relating to the alarm condition. The security gateway transmits an alarm notification and the video across a network to a security system server in substantially real time. The security system server relays information to one or more distributed monitoring clients using rules-based routines for verification of the alarm condition. An operator at a monitoring client determines whether the alarm condition represents an actual alarm event and activates an appropriate response.
Owner:COMCAST CABLE COMM LLC
Security systems and methods for use with structured and unstructured data
InactiveUS20130104251A1Increase flexibilityEasy accessDigital data processing detailsAnalogue secracy/subscription systemsUnstructured dataDistributed database
Disclosed herein are systems and methods including hardware, software and electronic service components and systems to provide large-scale, reliable, and secure foundations for distributed databases and content management systems combining unstructured and structured data, and allowing post-input reorganization to achieve a high degree of flexibility.
Owner:NEWSILIKE MEDIA GROUP
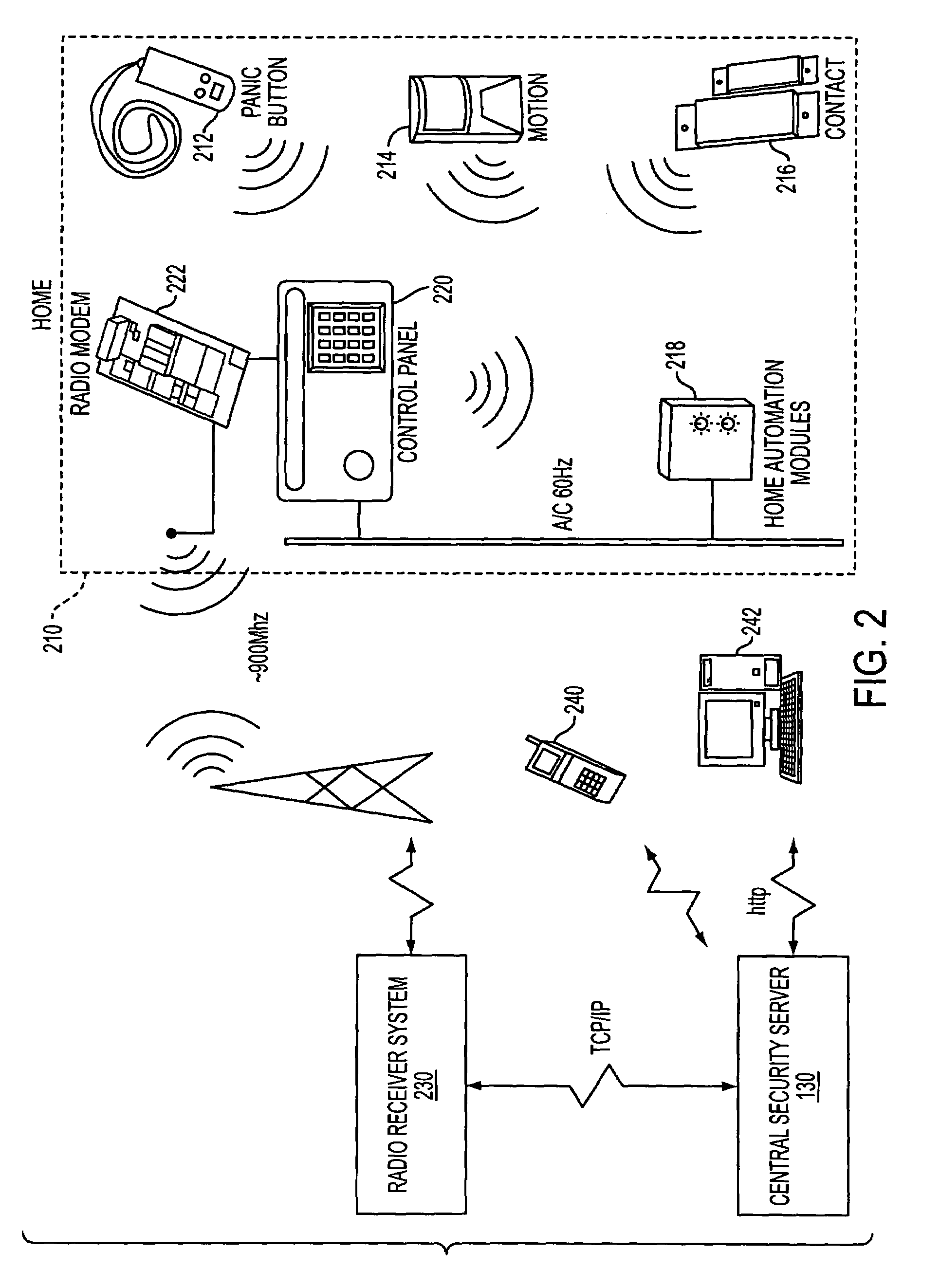
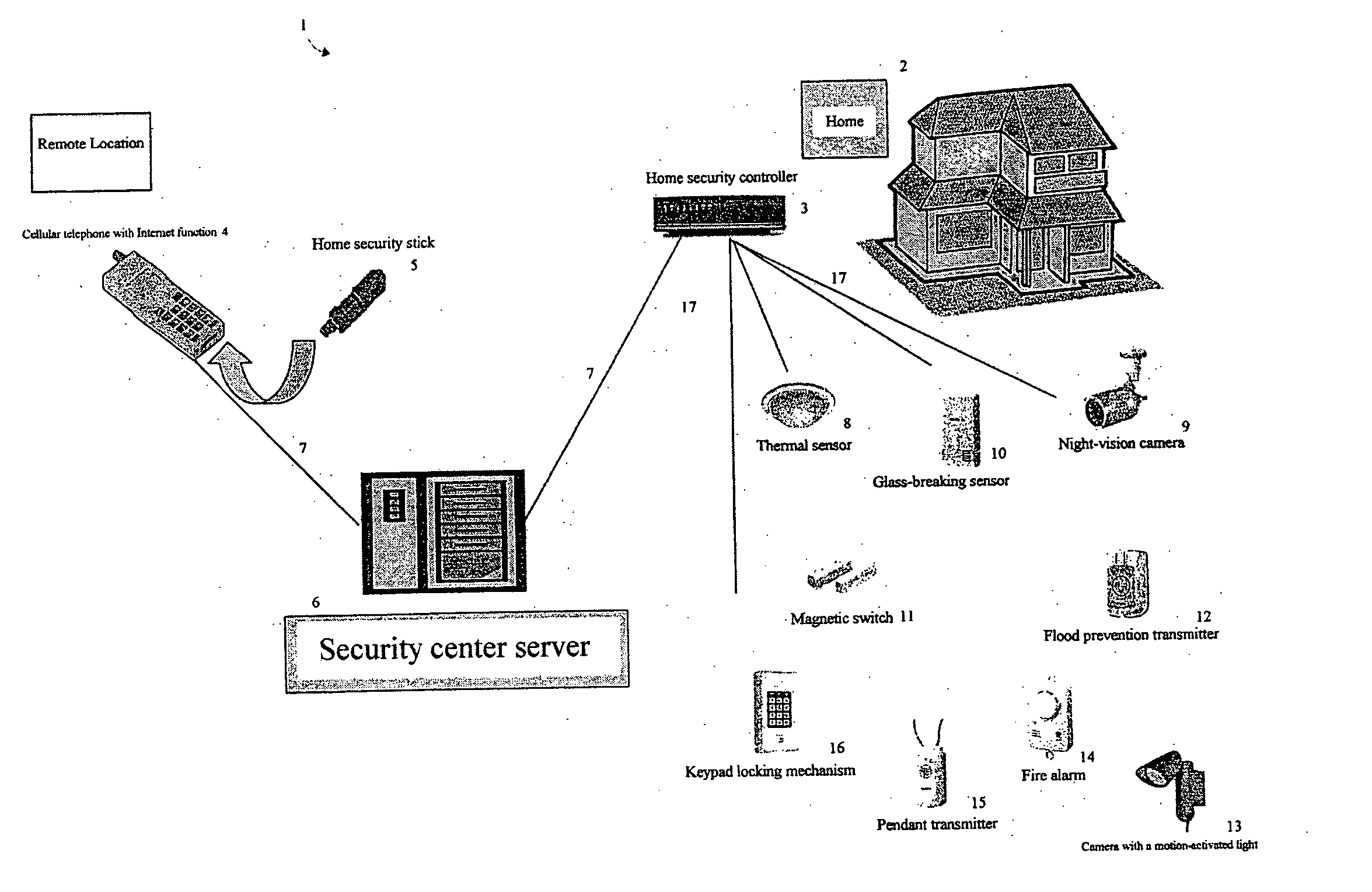
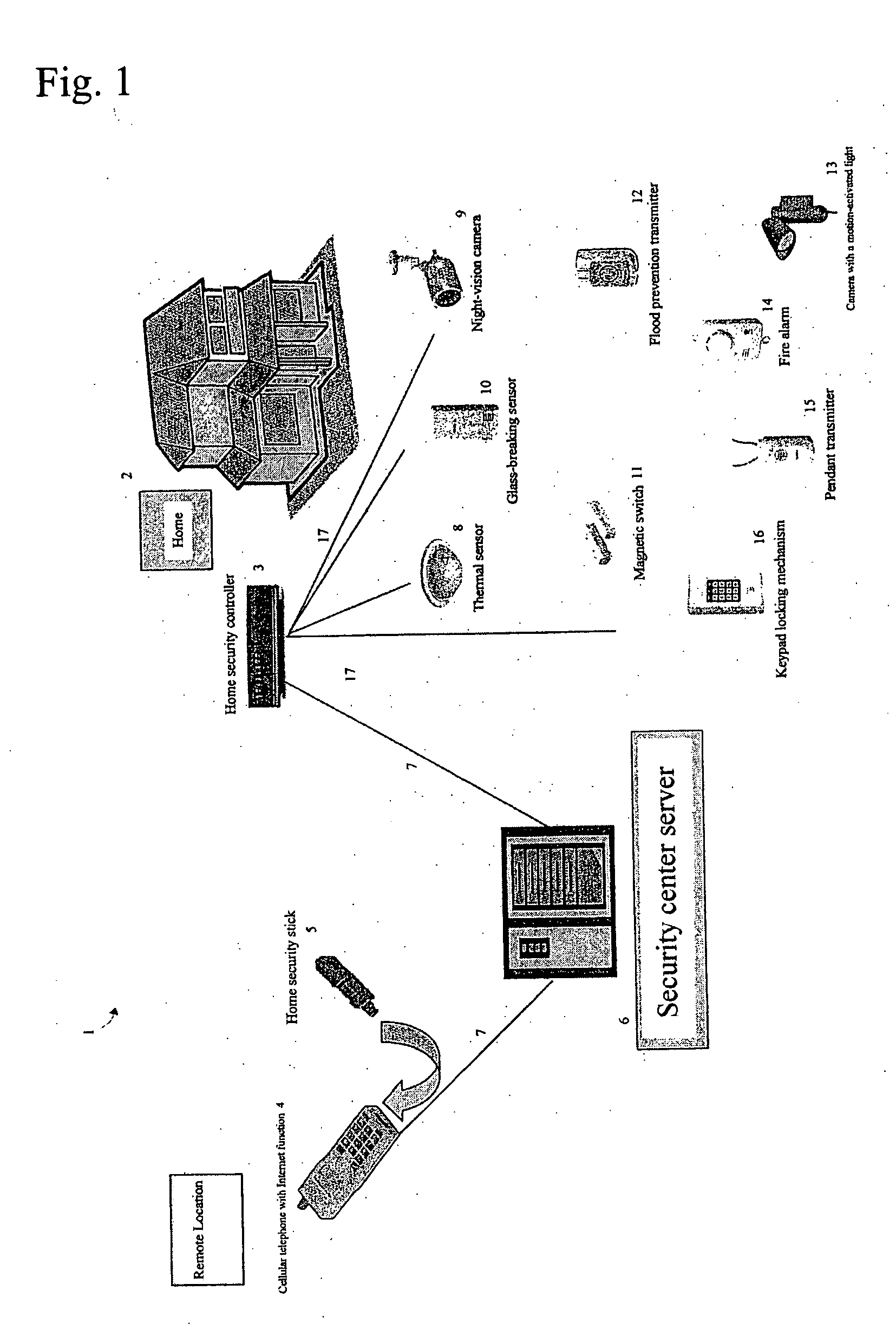
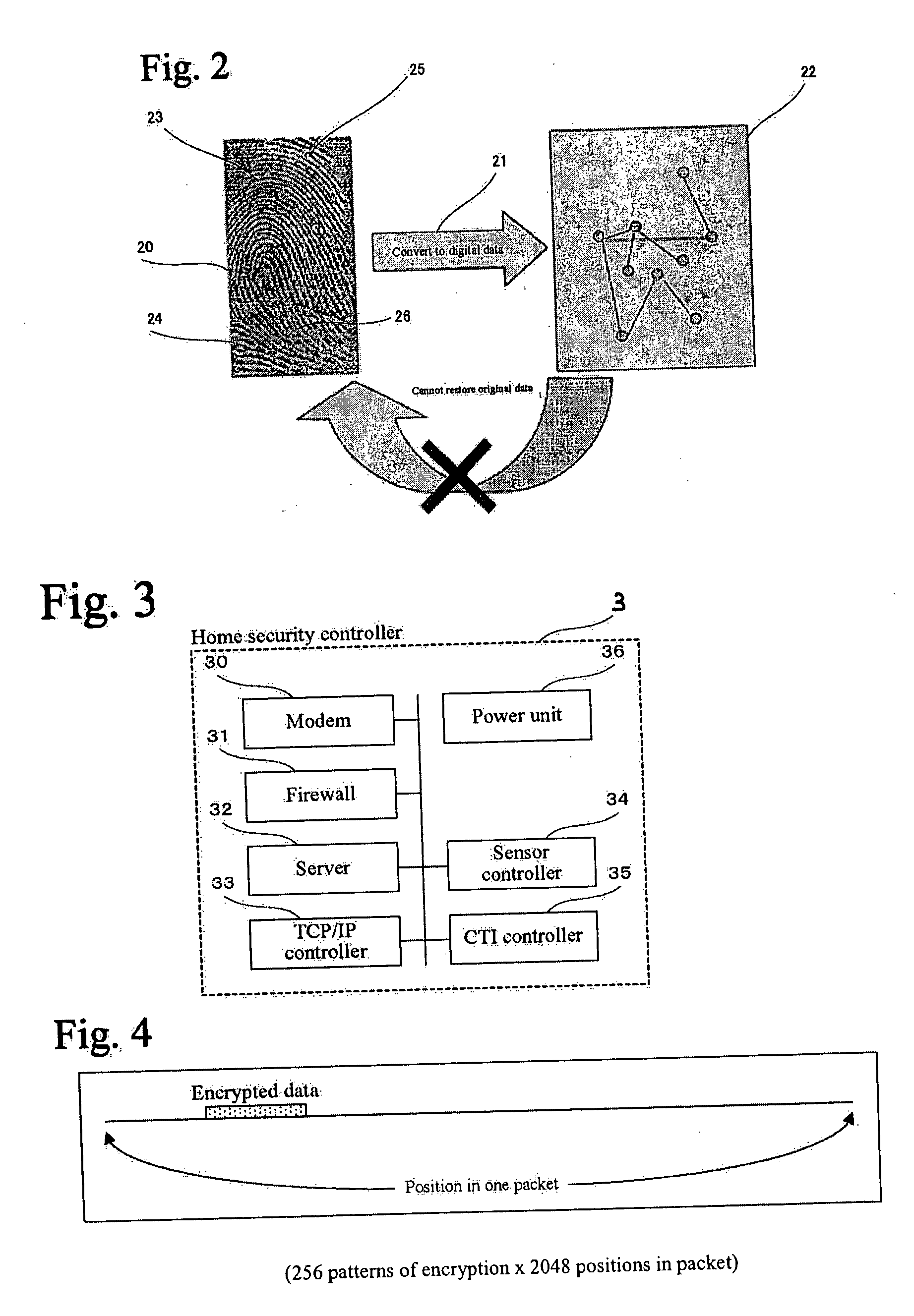
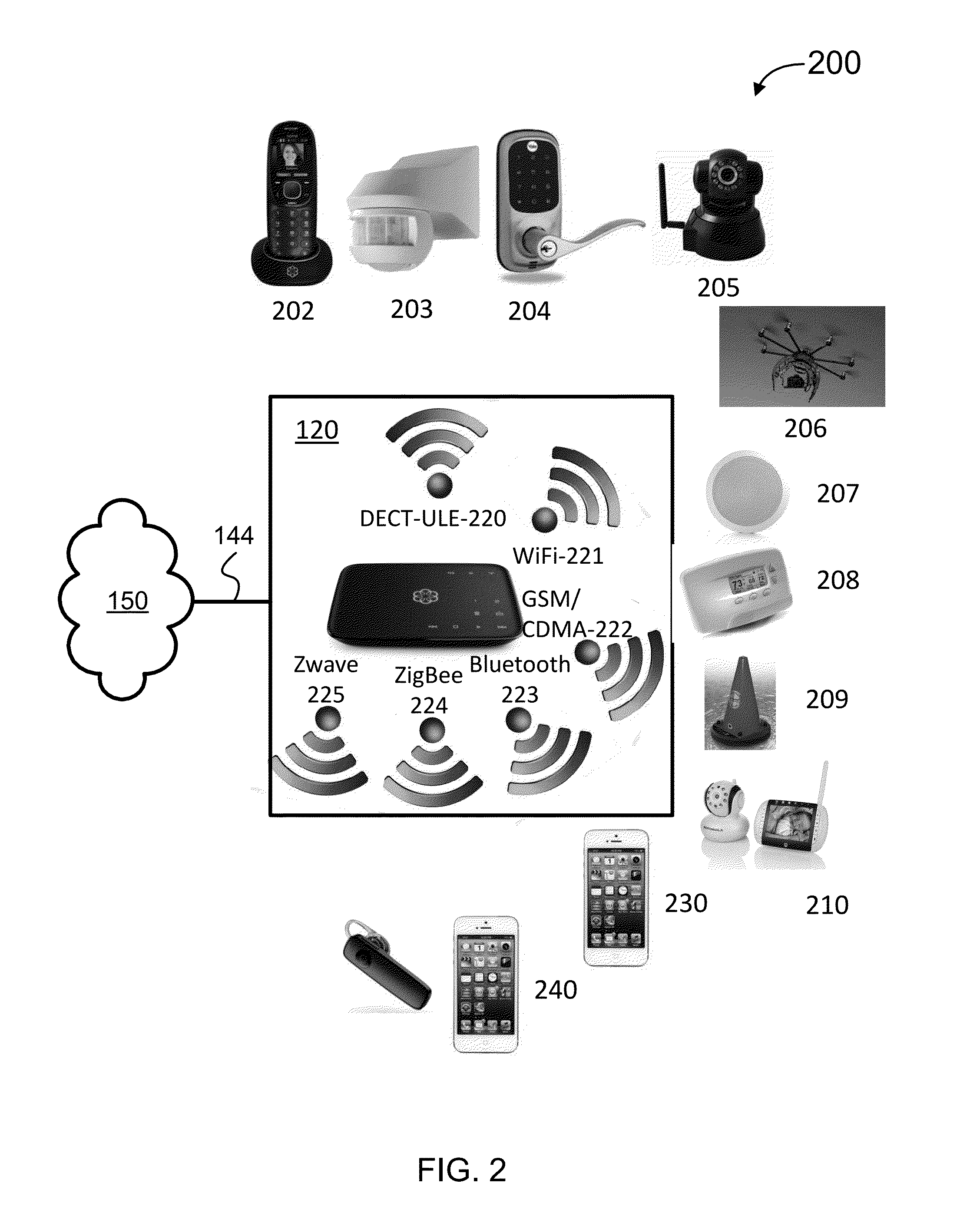
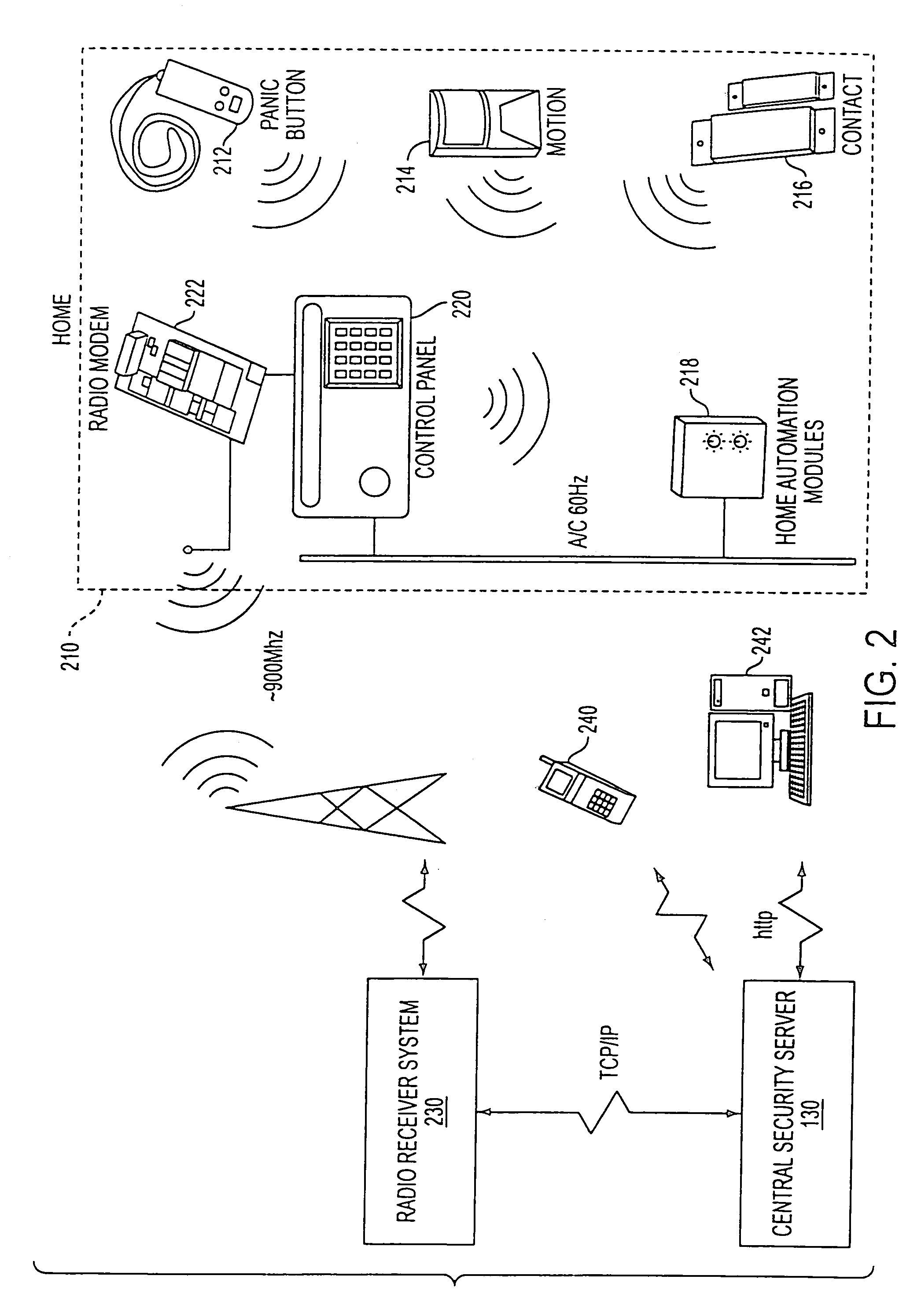
Home security system
InactiveUS20060022816A1Prevent intrusionEasy to operateElectric signal transmission systemsImage analysisRemote controlEngineering
The present invention provides a home security system that includes a home security controller for collecting monitor data from various crime prevention and disaster prevention sensors installed in a home via a home network and notifying the portable terminal when a state of emergency occurs. The home security controller also enables devices in the home to be operated through remote control signals via an external network. The home security system further includes a portable terminal capable of connecting to the external network and having fingerprint data inputting means mounted on the body of the portable terminal for inputting fingerprints used for authentication. The fingerprint data inputting means has an assigned ID number. The home security system further includes a security center server having fingerprint authenticating means for receiving fingerprint data from the portable terminal via the external network and authenticating the fingerprint data through comparisons with registered fingerprint data. The fingerprint authenticating means completes authentication by checking the assigned ID number of the fingerprint data inputting means and matching the received fingerprint data with fingerprint data registered in association with the ID number. The security center server allows a connection between the portable terminal and the home security controller and controls bi-directional communications between the two after the security center server has completed authentication, enabling the portable terminal to receive monitor data from and transmit remote control signals to the home security controller via the external network.
Owner:AMERICAN TECH GRP JAPAN
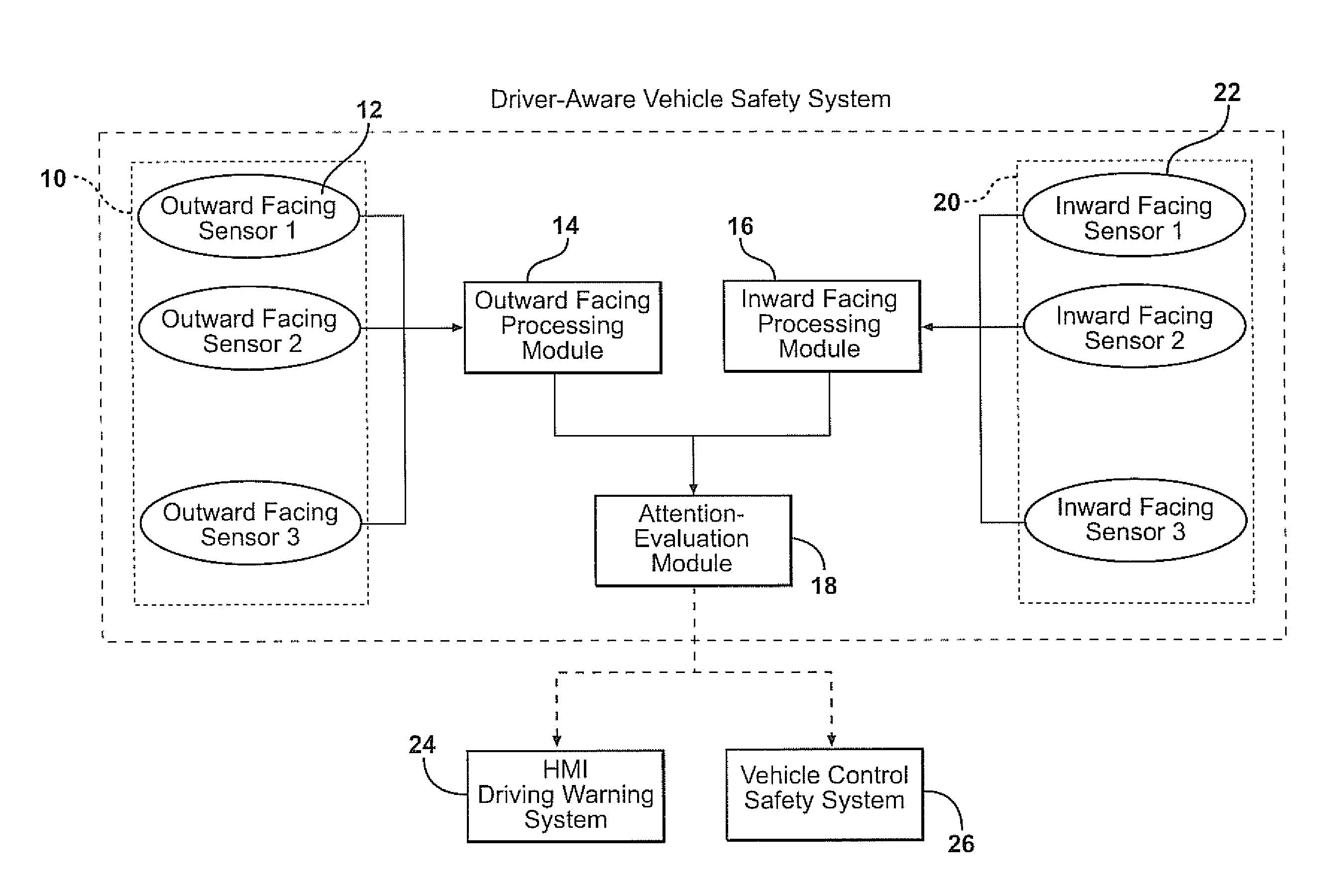
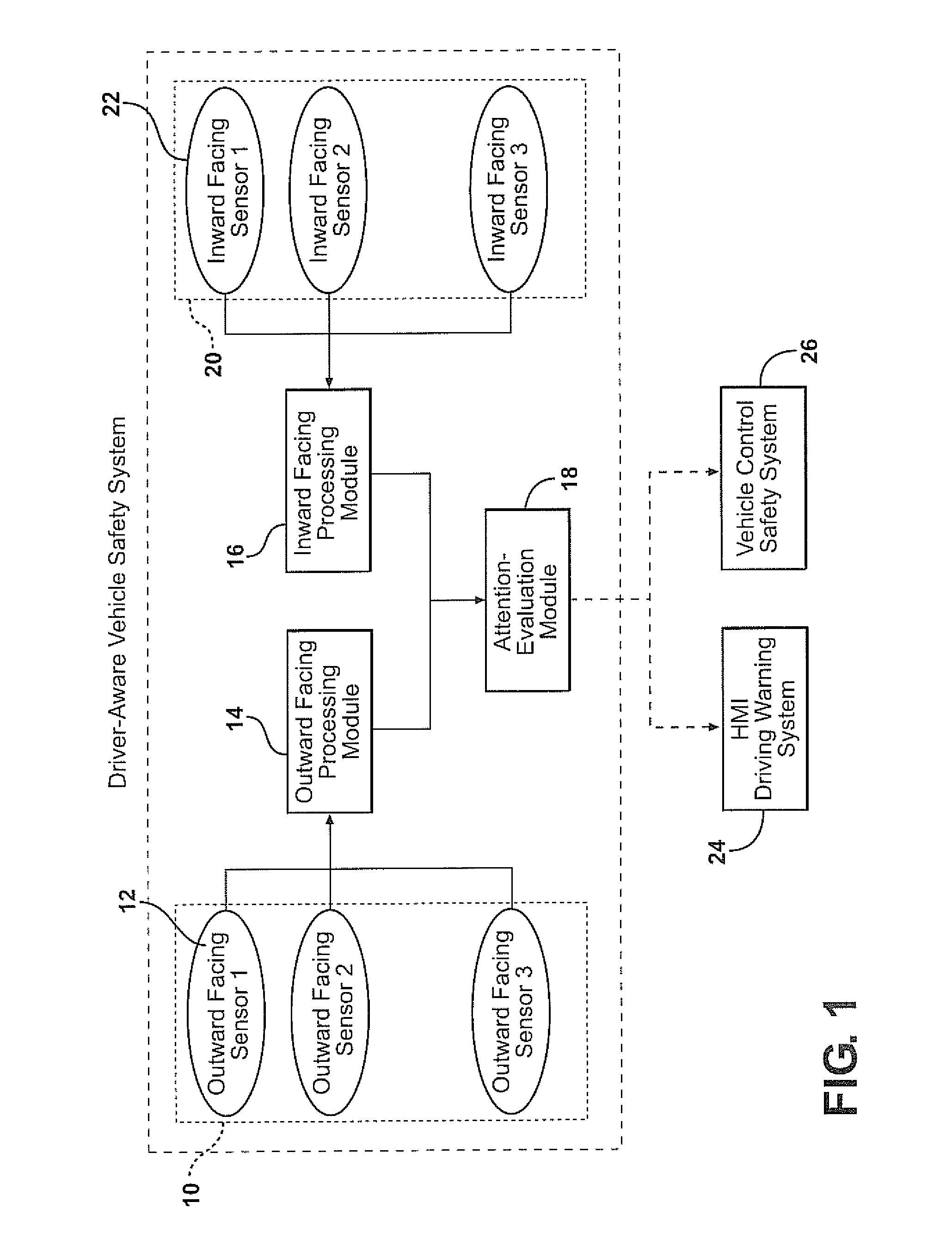
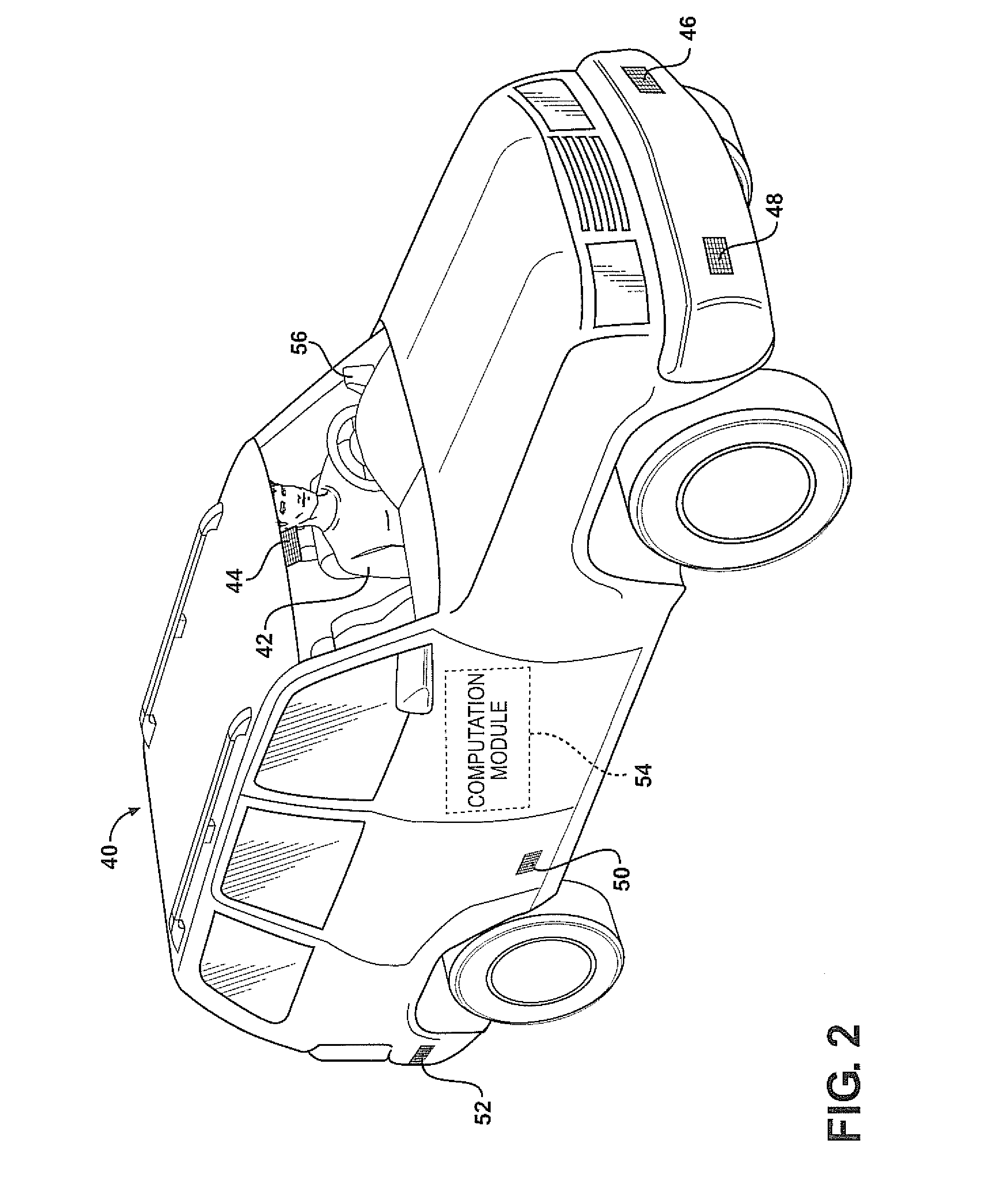
Combining driver and environment sensing for vehicular safety systems
ActiveUS20110169625A1Improve securityIncrease awarenessAnti-collision systemsCharacter and pattern recognitionDriver/operatorEngineering
An apparatus for assisting safe operation of a vehicle includes an environment sensor system detecting hazards within the vehicle environment, a driver monitor providing driver awareness data (such as a gaze track), and an attention-evaluation module identifying hazards as sufficiently or insufficiently sensed by the driver by comparing the hazard data and the gaze track. An alert signal relating to the unperceived hazards can be provided.
Owner:TOYOTA MOTOR CO LTD
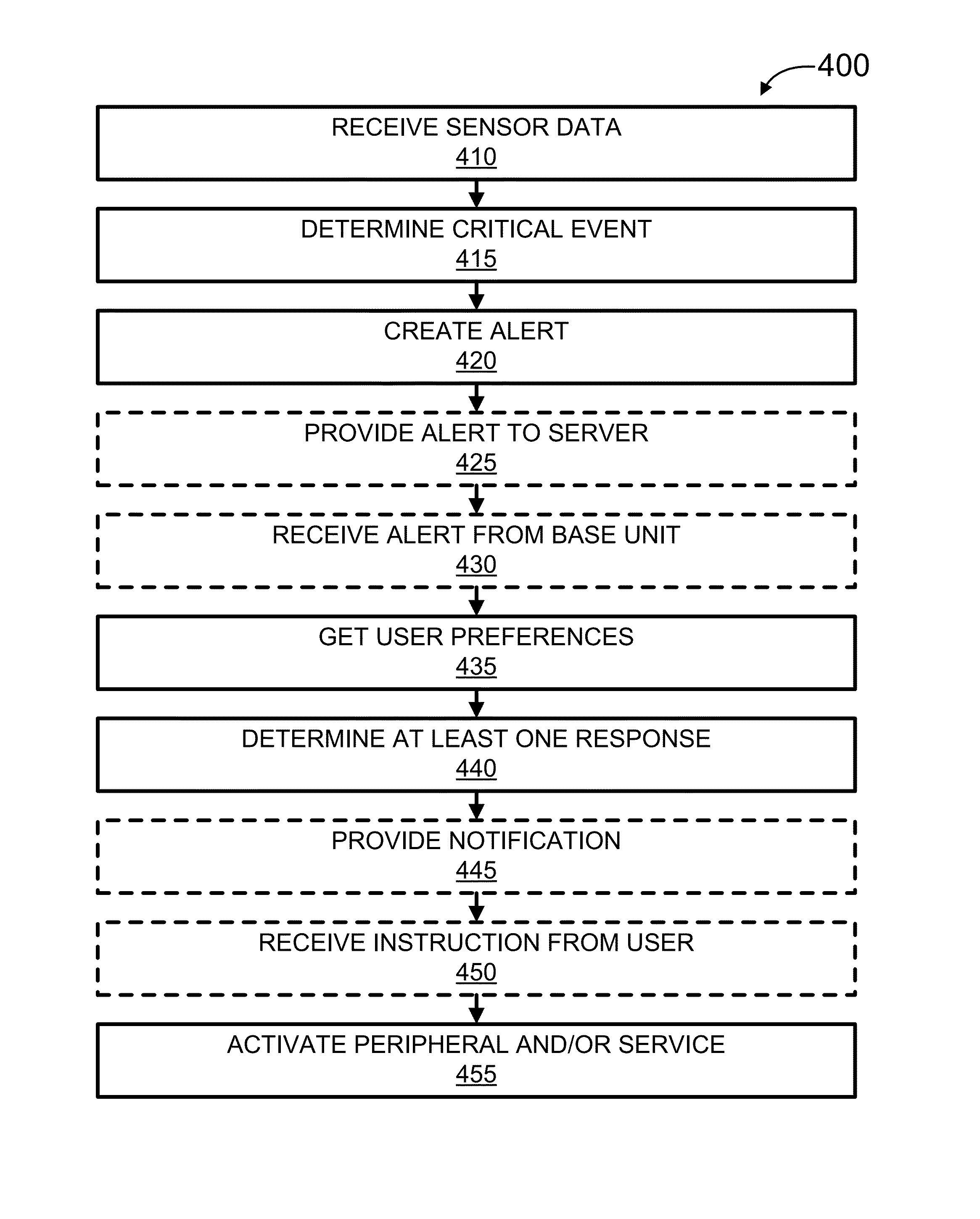
Security Monitoring and Control
ActiveUS20150339912A1Burglar alarm mechanical actuationControl systemStructure of Management Information
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
System and method for connecting security systems to a wireless device
InactiveUS6965313B1Not be preventElectric signal transmission systemsMultiple keys/algorithms usagePersonalizationMonitoring system
The present invention provides a personal security network where an individual's system or systems of security devices may be connected to a central security network. The central security network of the present invention may monitor a system's status and alert the individual when an alert situation occurs. The present invention provides a security network where a user may set up personalized alarms and alert services; identify various methods of contact; order at which to be contacted; individuals and entities to be contacted; type of situations to be alerted of and other relevant security and other information. The present invention may further provide a personalized web interface where authorized individuals may view current and historical security device status. A user may generate personalized reports based on aggregated historical data based on various user-defined factors. The reports may be displayed to the user in various formats, such as maps, graphs, statistics, and others.
Owner:ALARM COM INC
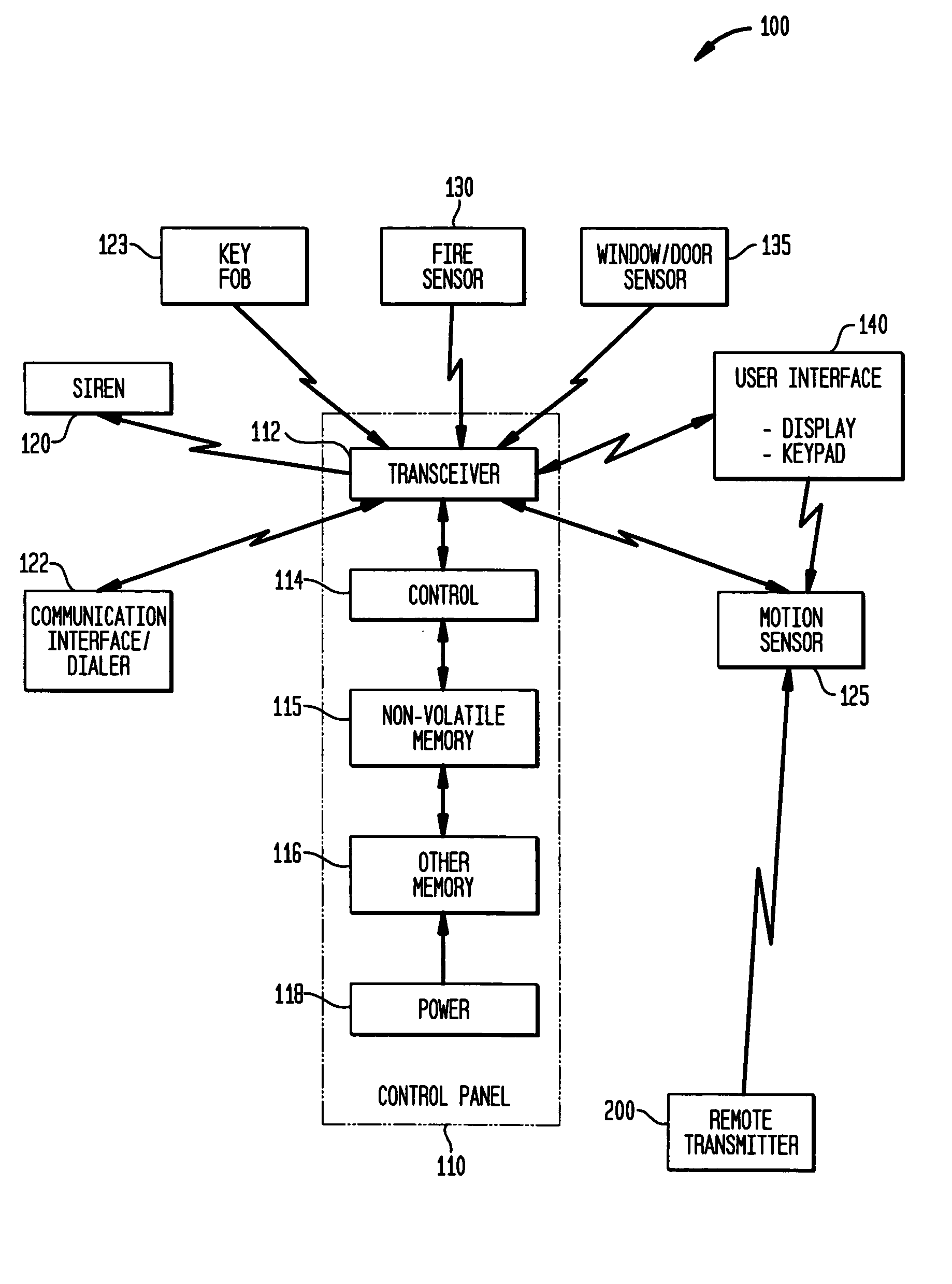
Automatic sensitivity adjustment on motion detectors in security system
InactiveUS20050128067A1Sensitivity adjustableSignalling system detailsAlarmsMotion detectorEngineering
The sensitivity of a motion sensor or detector in a security system is adjusted by a remotely-transmitted signal, such as from a user interface device in the security system. In another approach, a pet wears a transmitter on its collar that transmits a wireless signal to command the motion sensor to adjust its sensitivity, e.g., by entering a pet immune mode, when the pet is in the room that is protected by the motion sensor. In another approach, a remote monitoring site sends instructions to the motion sensor via a communication interface. The sensitivity can be adjusted by adjusting a pulse count, optical gain, or electrical or optical sensitivity of the motion sensor.
Owner:HONEYWELL INT INC
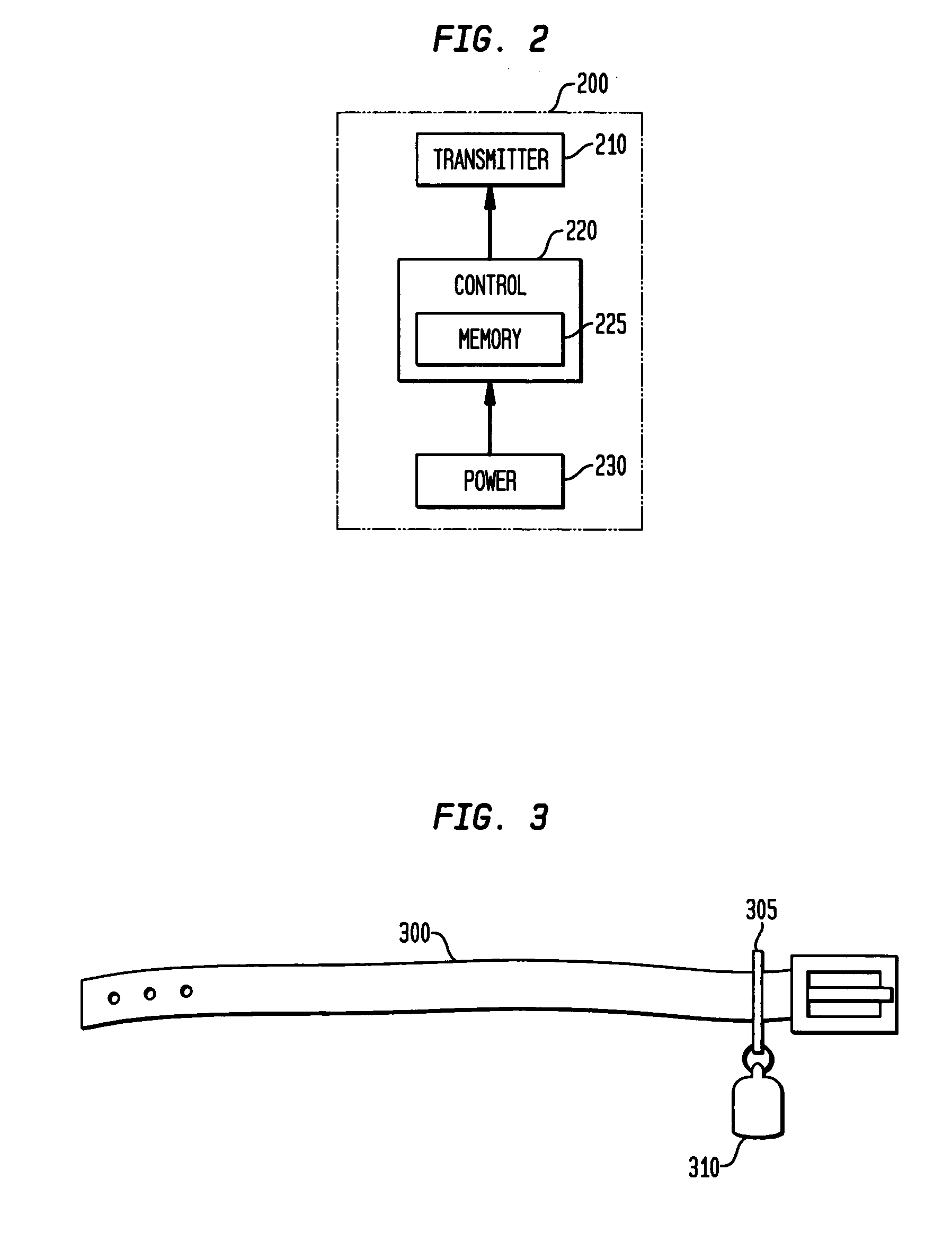
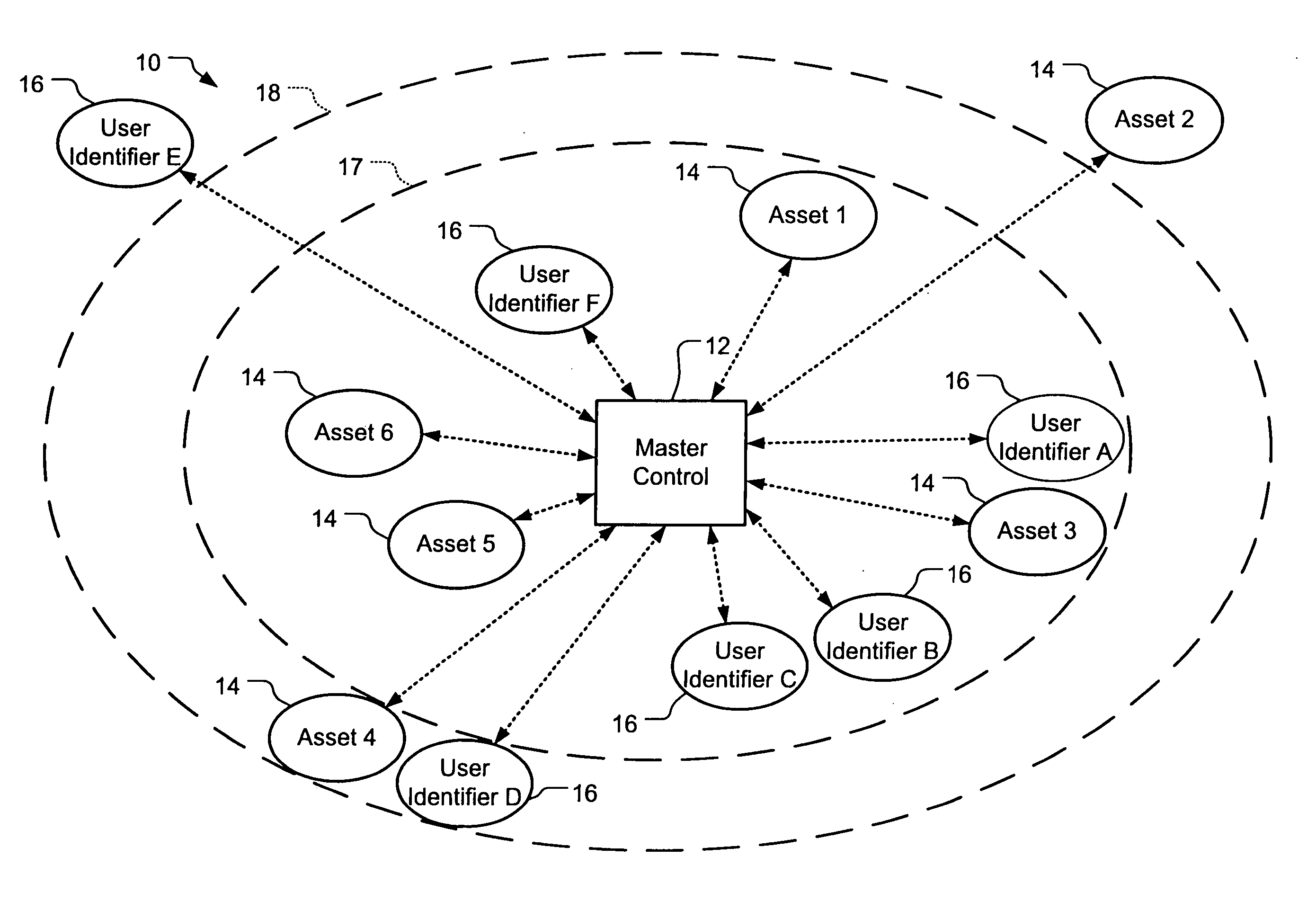
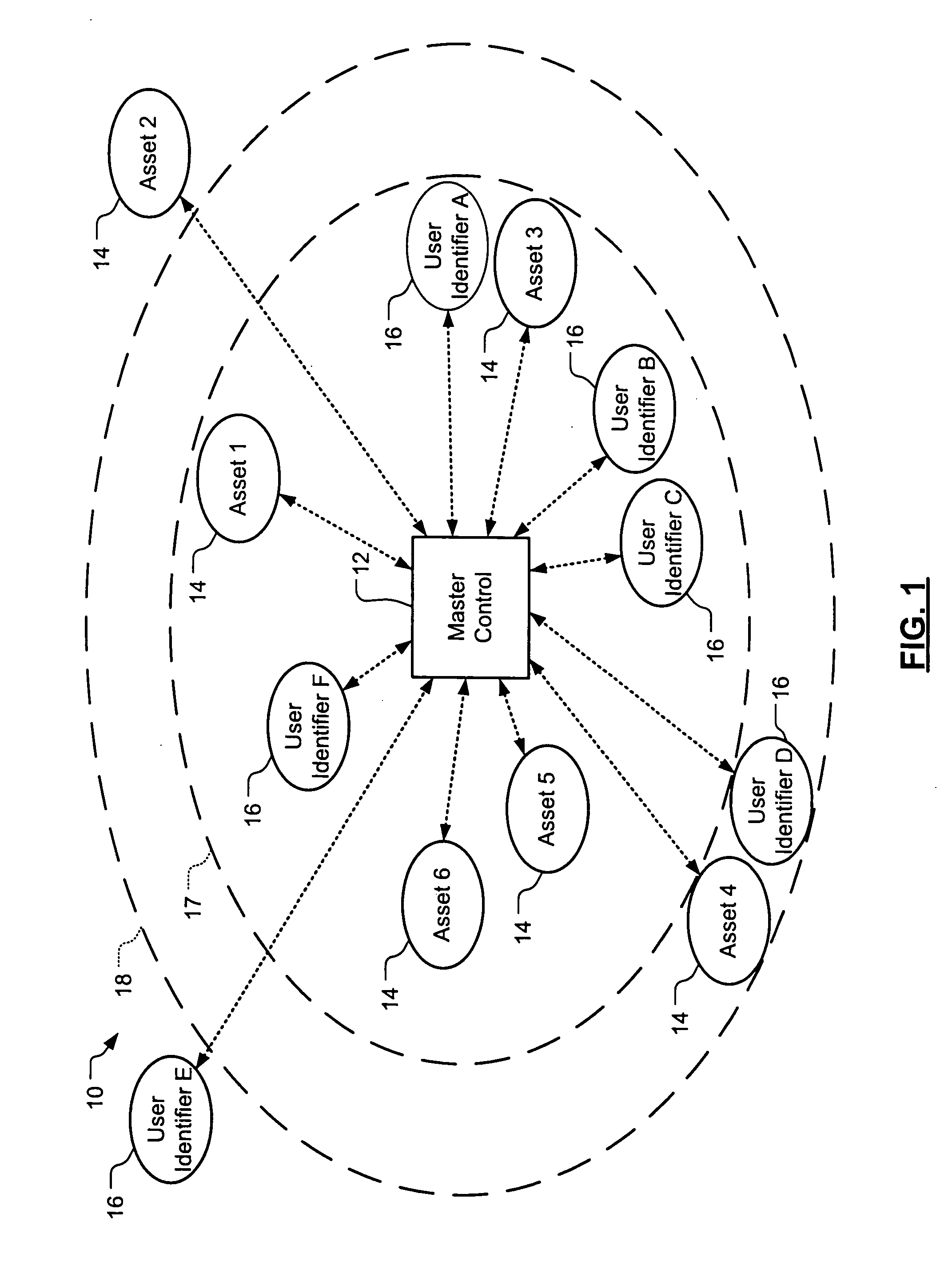
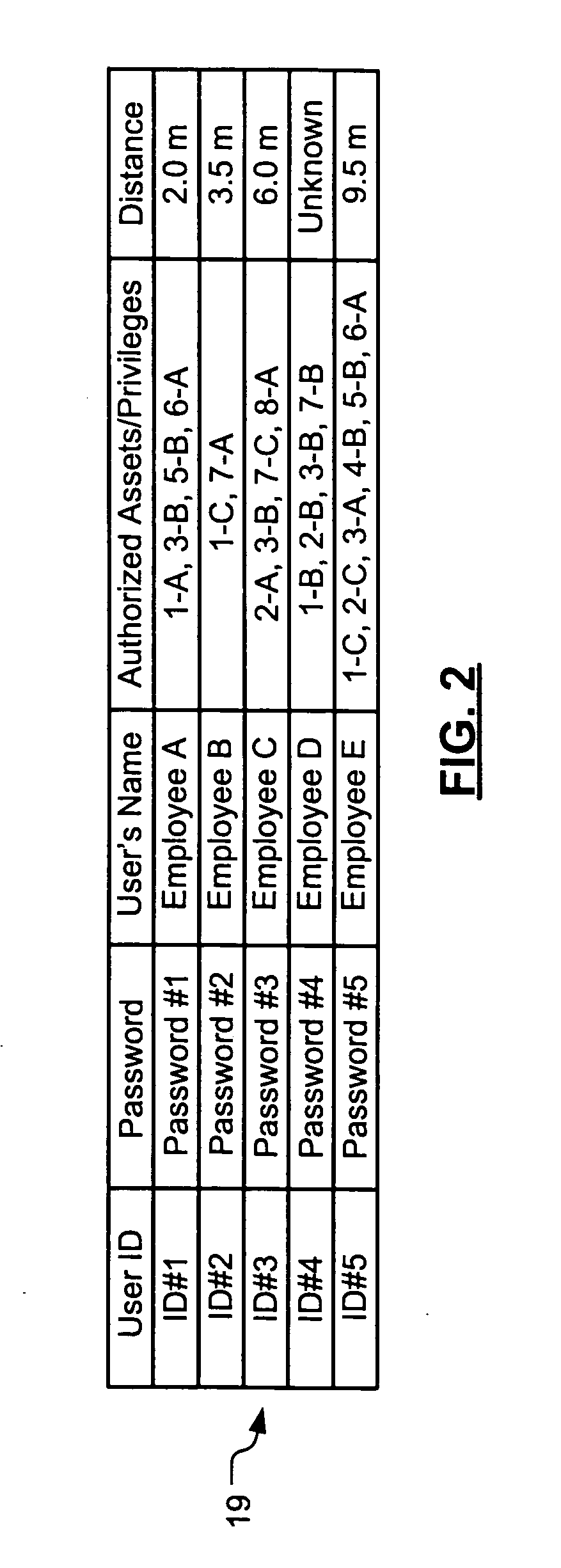
Wireless asset monitoring and security system
InactiveUS20050128083A1Electric signal transmission systemsMultiple keys/algorithms usageLocking mechanismUnique identifier
An asset monitoring and security system includes at least one asset assigned a unique identifier and operable wirelessly transmit an identification signal embodying the identifier. A data store maintains a list of the assets and privileges associated with the assets for authorized users of the assets. A control unit is adapted to receive identification signals from the assets and monitor positions of the assets within a defined area. The control unit communicates with the data store and is further operable to initiate an alarm event when privileges associated with a given asset for authorized users of the asset are exceeded. Each of the assets includes a lock-out mechanism that impedes use of the asset when the lock-out mechanism is activated. The control unit activates the lock-out mechanism of a given asset when the privileges associated with the asset for authorized users of the asset are exceeded.
Owner:BLACK & DECKER INC
Mobile data security system and methods
ActiveUS8495700B2Transparent applicationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile Web
The present invention is directed to security systems and methods for mobile network-based data environments. The present invention provides an integration of security, mobile computing, wireless and IT infrastructure management technology, to create a new level of automation and enforcement to enable the transparent application of mobile security across an enterprise, while embracing end user “transparency” and “ease of use” and empowering IT administration.
Owner:TRUST DIGITAL
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
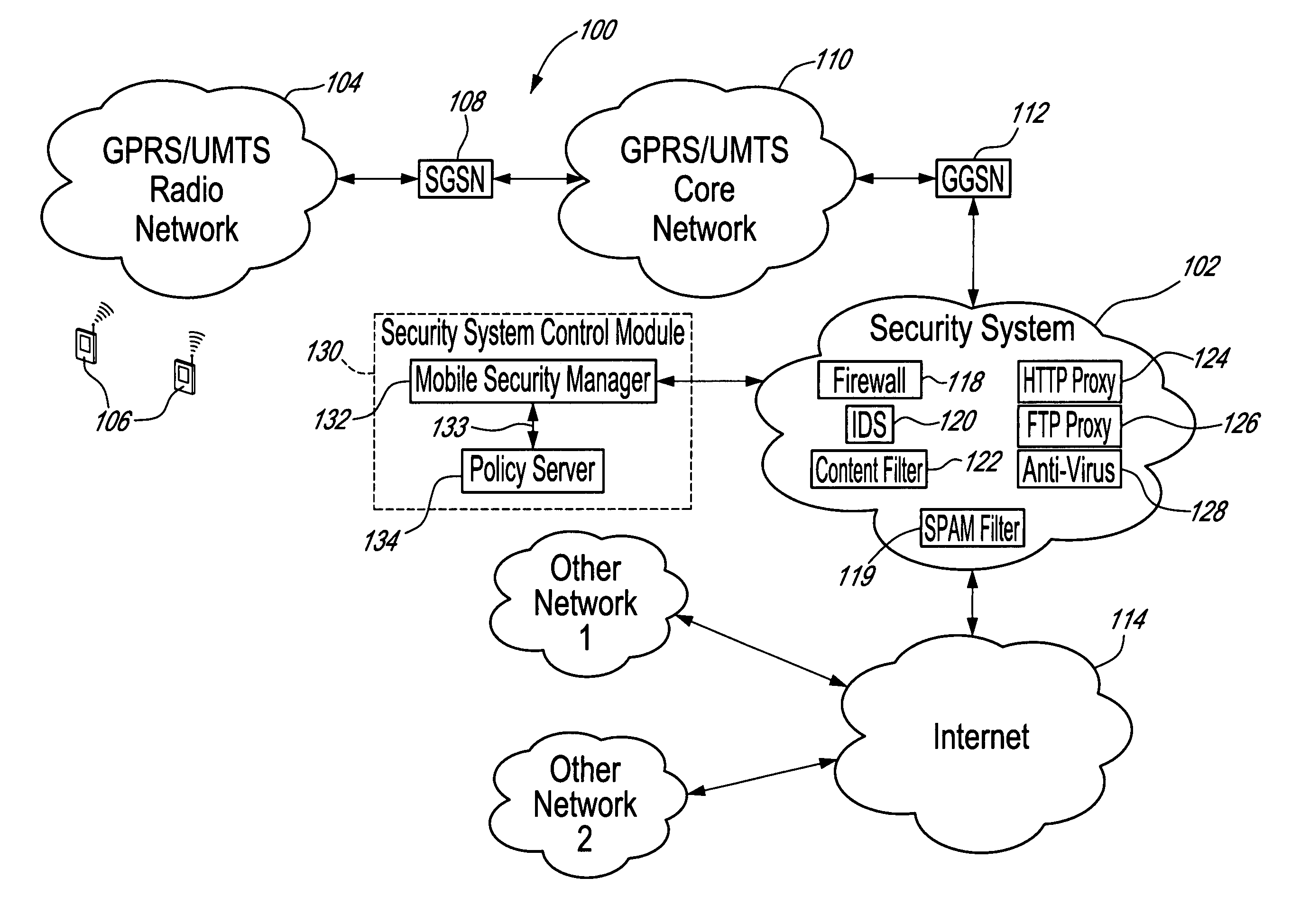
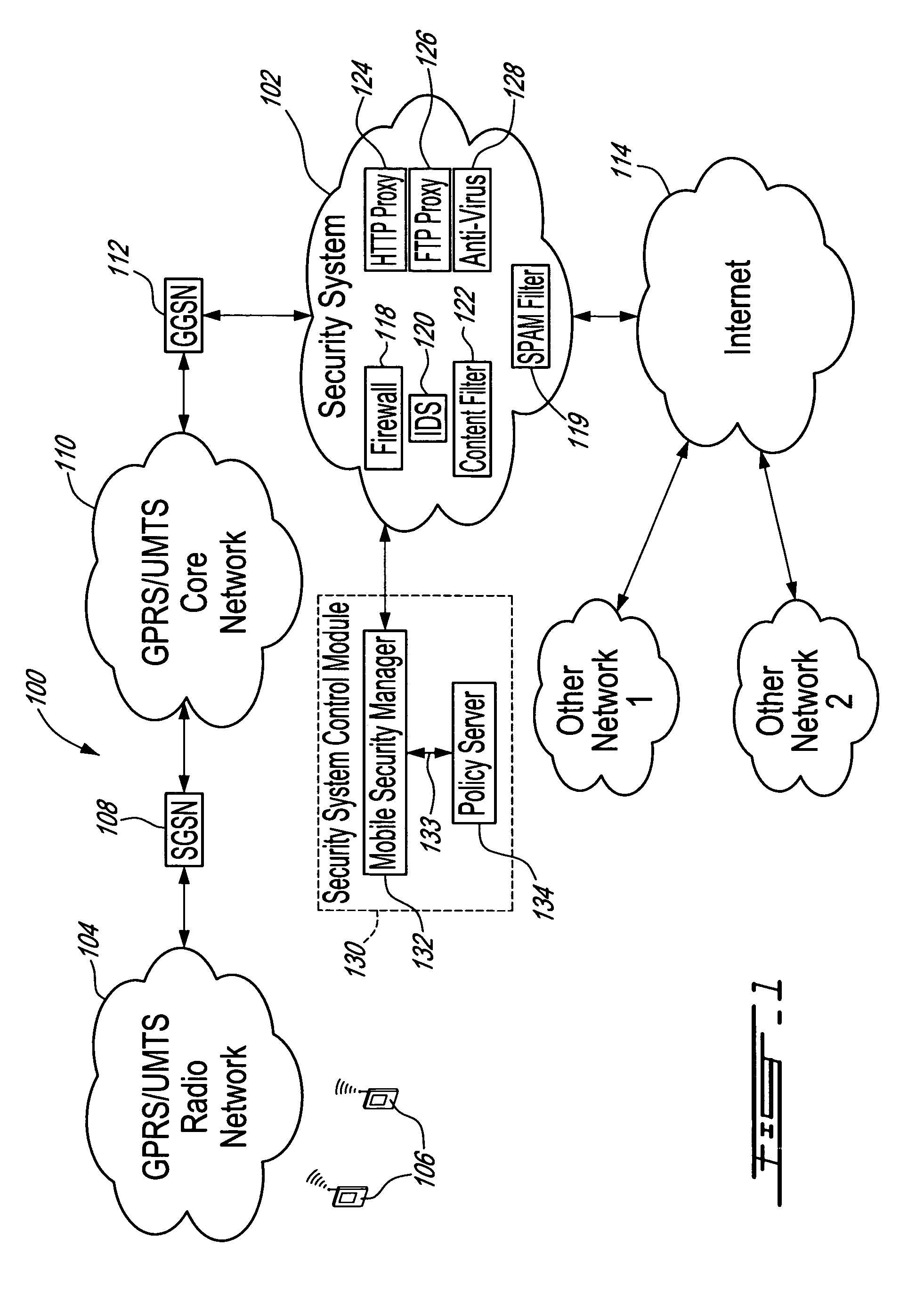
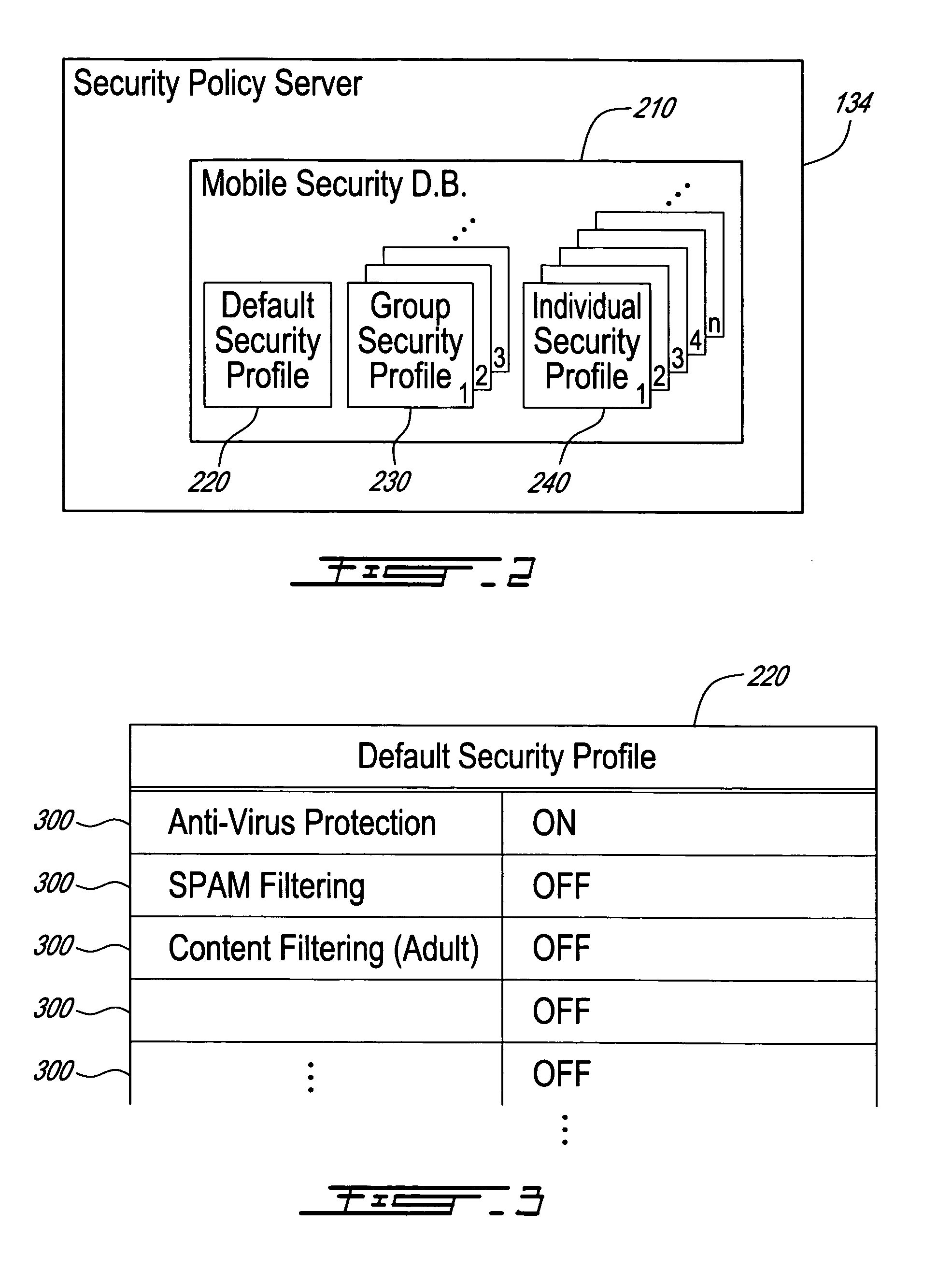
Method, security system control module and policy server for providing security in a packet-switched telecommunications system
ActiveUS7418253B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsMobile securityMobile station
A method, security system control module and policy server for providing security for Mobile Stations (MSs) in a Packet-Switched Telecommunications System. When an MS accesses the system, its identity is sent to a security system control module that retrieves a security profile associated with the MS. A policy server of the security system control module stores individual security profiles, default security profiles and group security profiles for registered subscribers. Security settings associated with the MS security profile are returned from the policy server to a mobile security manager of the control module, which then determines if they should be propagated in the system. When no previous network access was made in a given time period by an MS having similar security settings, i.e. belongs to the same group security profile, the settings are propagated in the system in order to be enforced, for providing security protection for the MS.
Owner:TELEFON AB LM ERICSSON (PUBL)
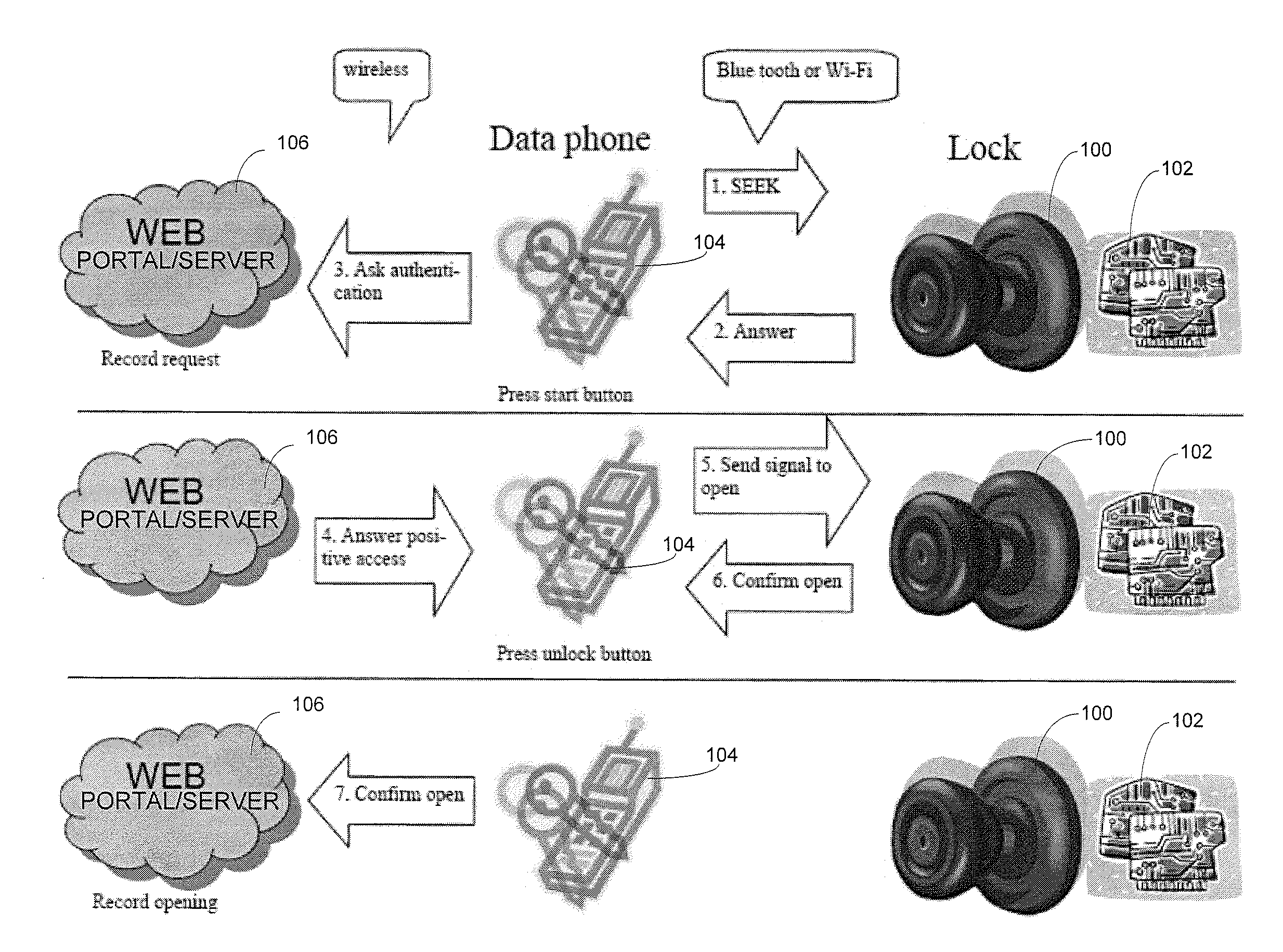
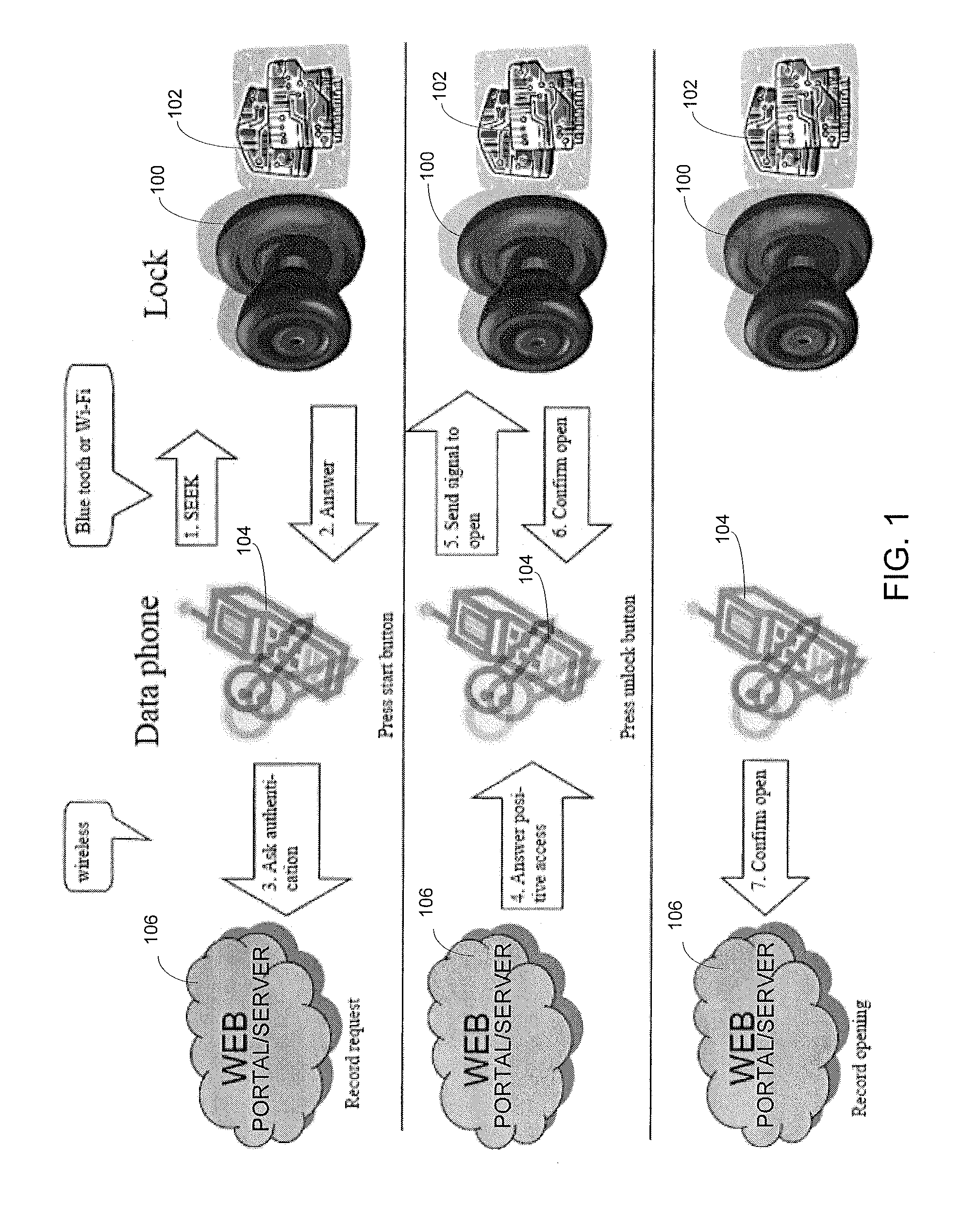
Wireless Device Enabled Locking System
ActiveUS20110311052A1Provide securityDigital data authenticationSecret communicationUnique identifierMobile device
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
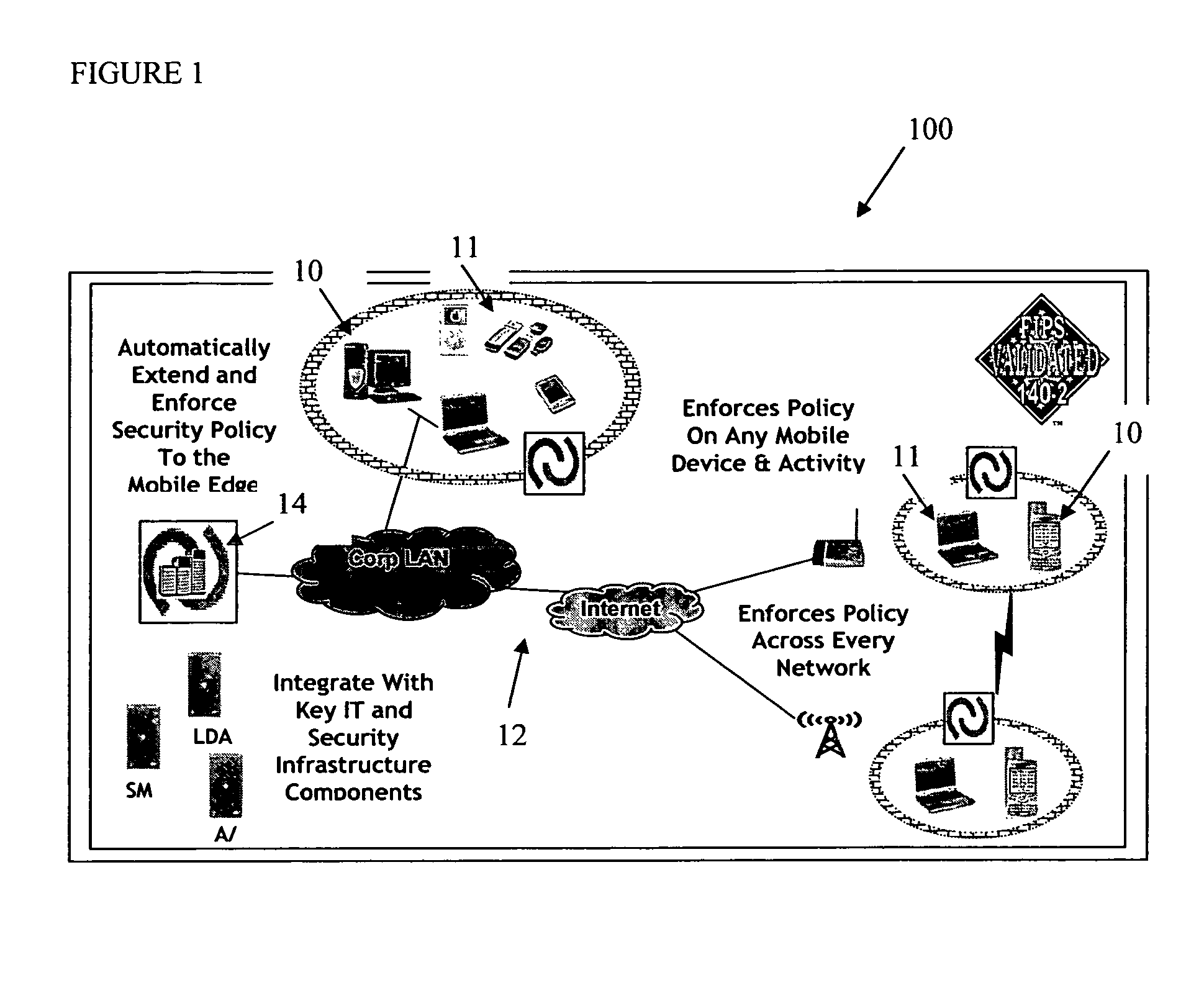
Centralized Dynamic Security Control for a Mobile Device Network
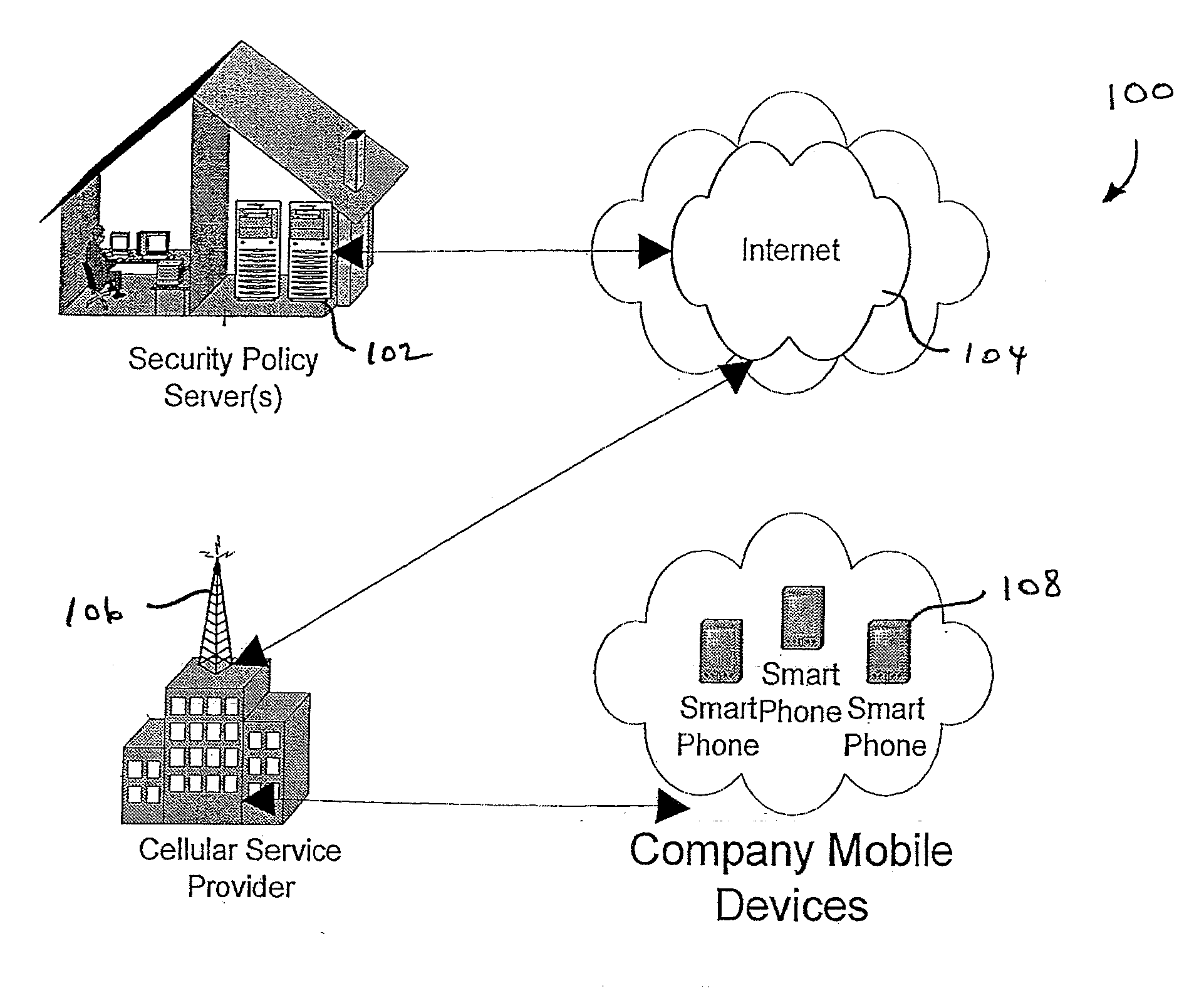
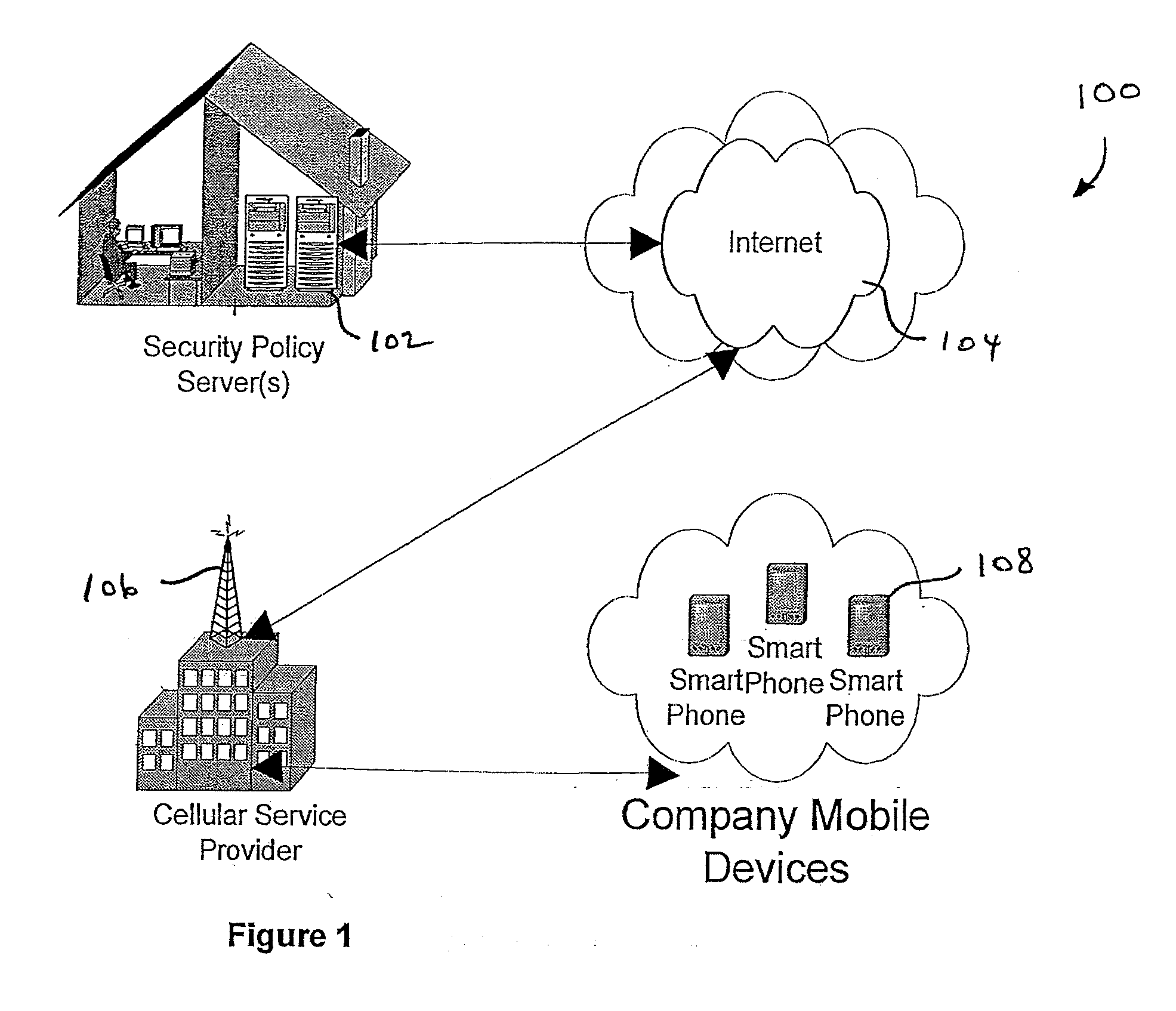
InactiveUS20070266422A1Well formedSecurity arrangementSpecial data processing applicationsTimerSecurity system
An security system for an enterprise network and data automates the revision, deployment, enforcement, auditing and control of security policies on mobile devices connected to said enterprise network, through automated communication between a security policy server and the mobile device. Control of the security system is centralized through administrative control of security policies stored on the security policy server. Automation of deployment of security policies to mobile devices occurs through transparent background communication and transfer of updated policies either triggered by a change in a security policy within the central repository of security policies or upon the expiration of a certain time period during which no policies were downloaded to the mobile device. When the mobile device is not in compliance with a security policy, a software security agent operating thereon limits access to said enterprise network and enterprise data. To aid in preventing the overwhelming of the enterprise network and the security policy server as a result of to many synchronization communications coming from too many mobile devices, a randomized timer is set by the software security agent upon receipt by the mobile device of a synchronization command from the security policy server.
Owner:SQUARE 1 BANK
Security system and method for use of same
A security system and method for use of the same are disclosed that provide for remote surveillance. In one embodiment, a property's entry point such as a doorway is equipped with a video camera, an external microphone, and an external speaker. An individual, such as an owner of the property, is away from the property and equipped with a cellular telephone. When a person arrives at the entry point, a control unit relays audio and visual data captured by the video camera and the external microphone to the individual's cellular telephone. Similarly, the control unit relays audio data from the owner to the person at the entry point.
Owner:ZINSER DUKE W
Data security system and method for portable device
ActiveUS7313825B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsDigital data processing detailsInformation processingEvent trigger
The method, used with a portable computing device, secures security sensitive words, icons, etc. by determining device location within or without a predetermined region and then extracting the security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only in the presence of a predetermined security clearance and within certain geographic territories. A computer readable medium containing programming instructions carrying out the methodology for securing data is also described herein. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
Security System with Methodology for Defending Against Security Breaches of Peripheral Devices
ActiveUS20050138433A1Digital data processing detailsAnalogue secracy/subscription systemsAuthorizationSecurity system
A security system with methodology for defending against security breaches of peripheral devices is described. In one embodiment, for example, a method is described for protecting a computer from security breaches involving devices that may be attached to the computer, the method comprises steps of: when a device is first attached to the computer, specifying authorization information indicating that the device is allowed to communicate with the computer; detecting detachment of the device from the computer; updating the authorization information to indicate that the device is no longer authorized to communicate with the computer; and upon reattachment of the device, blocking communication with the device while the device remains unauthorized, thereby preventing a security breach involving the device.
Owner:CHECK POINT SOFTWARE TECH INC
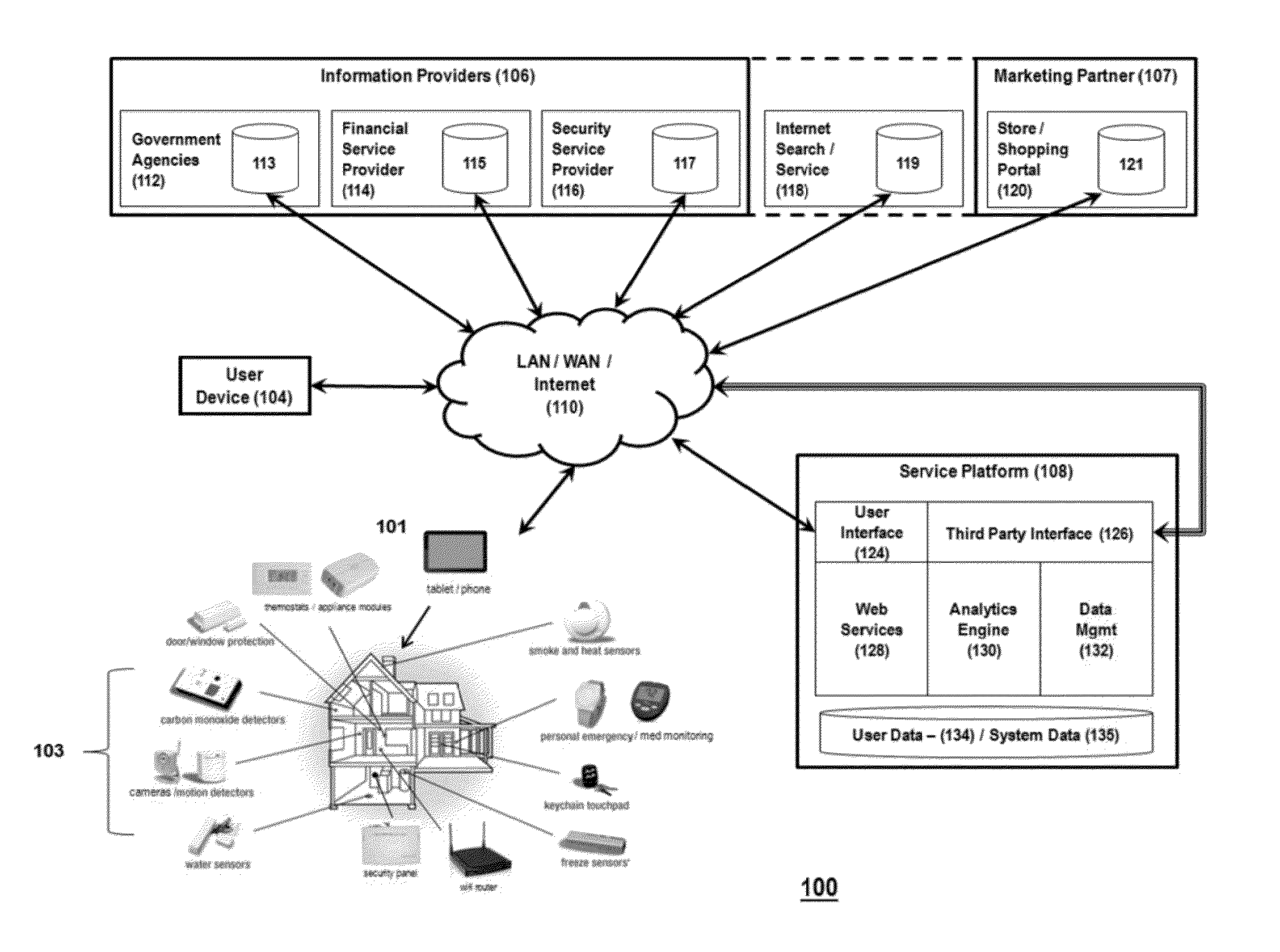
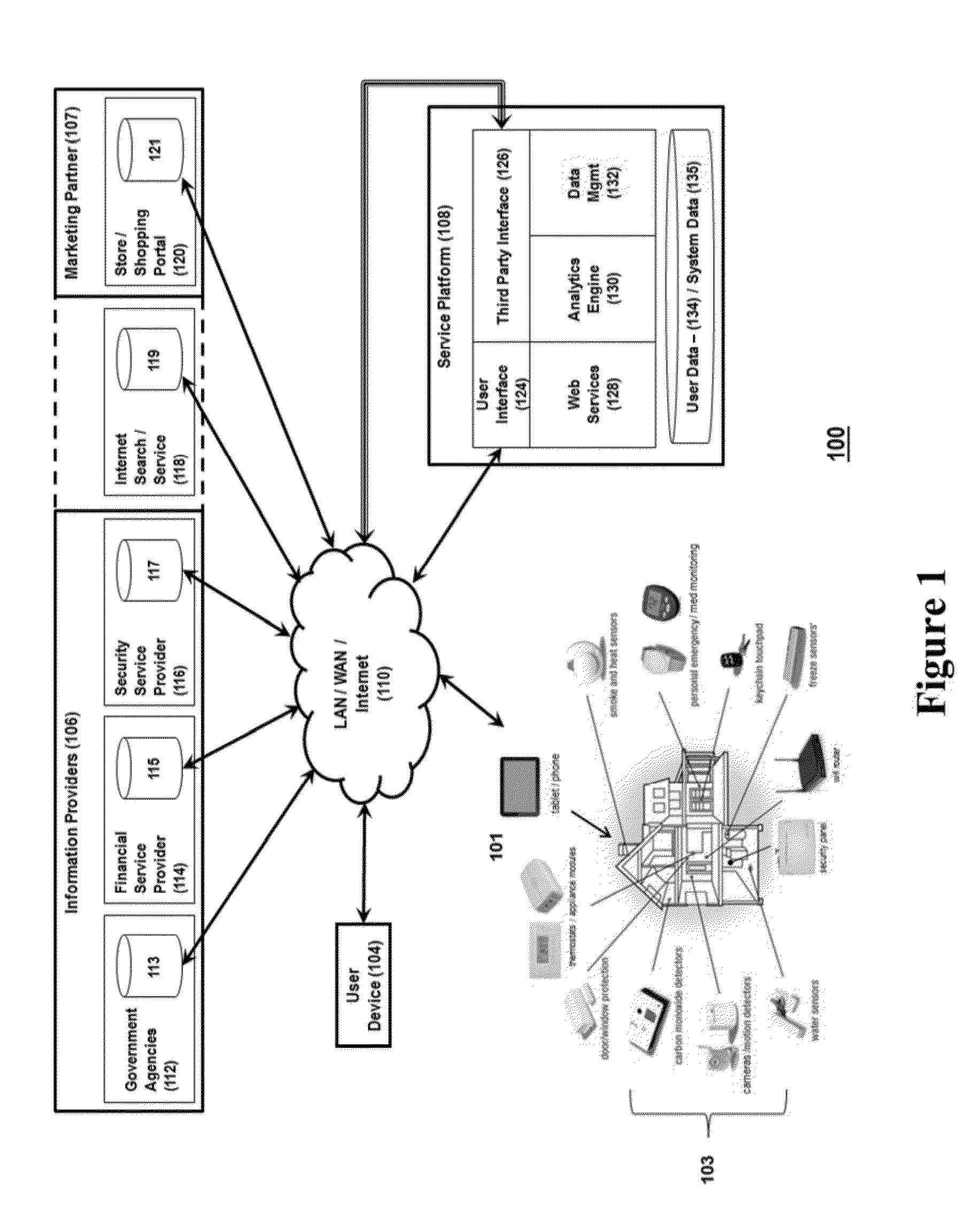
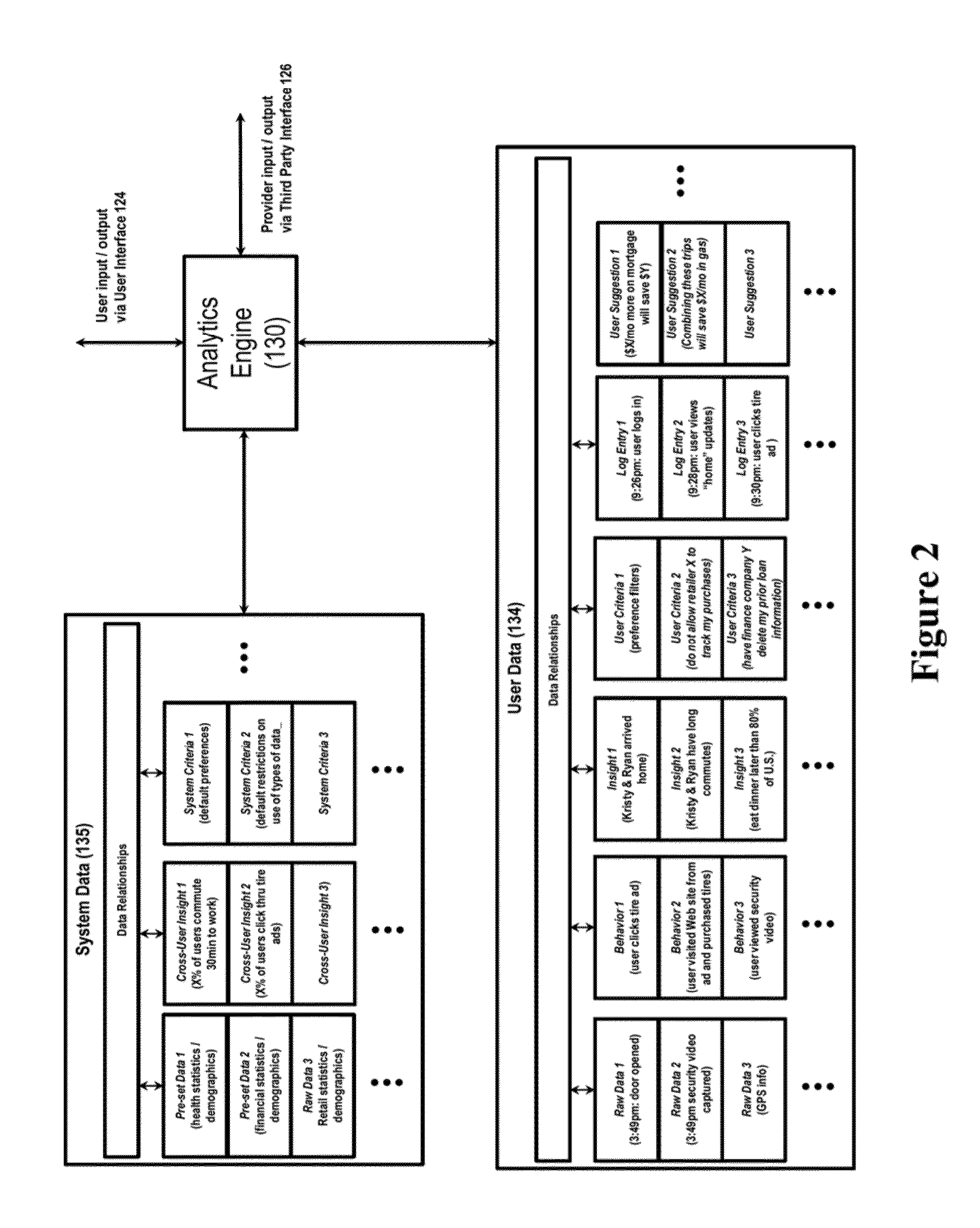
System for controlling use of personal data
InactiveUS20140244399A1Digital data processing detailsAnalogue secracy/subscription systemsInternet privacyPersonal details
The invention relates to a system configured to enable a user to track how his or her personal data is being used, and to control its collection, storage, and / or use, and delete certain personal data across information providers. A user may establish criteria regarding such collection, use, and storage of personal data generated by a security system device, capture the personal data at a control gateway before it is provided to an information provider; and applying the criteria to the personal data. The invention also relates to a system to present additional information to the user that is relevant to both the user and at least one marketing partner (such as targeted advertising); and to provide data to enable at least one marketing partner to provide value (a “reward”) to the user in exchange for the user allowing an information provider to collect and use personal data of the user.
Owner:ADT US HLDG INC
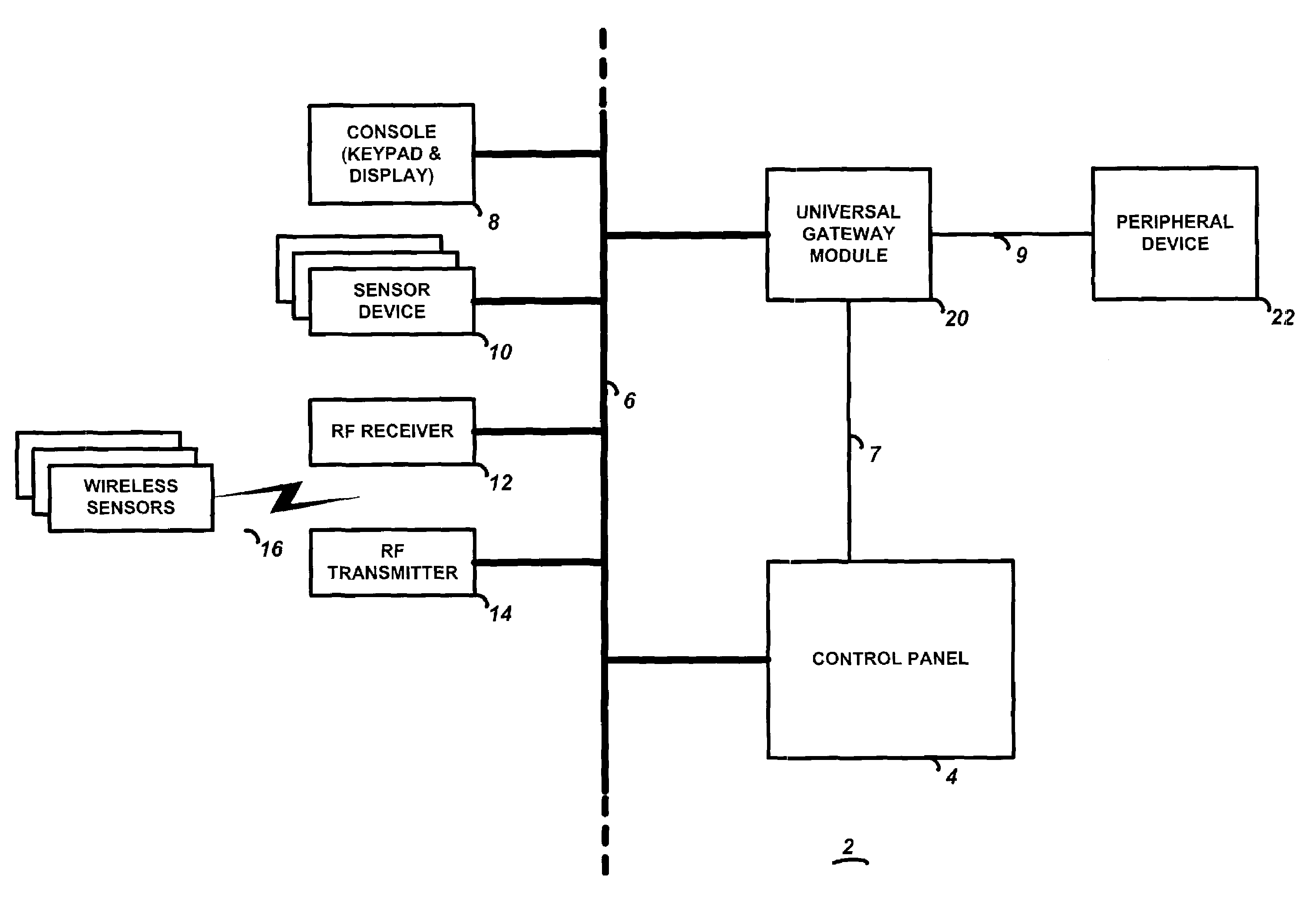
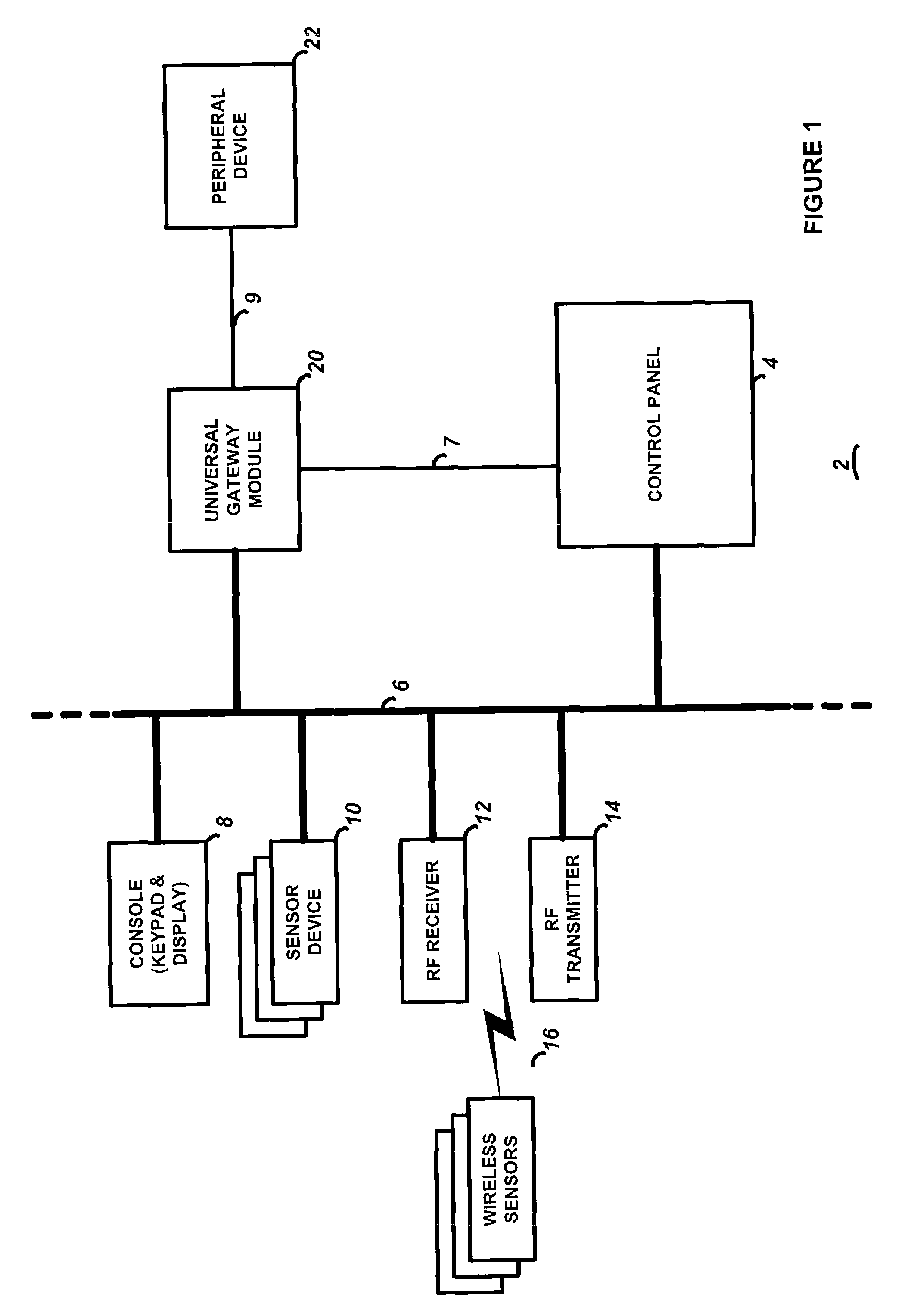
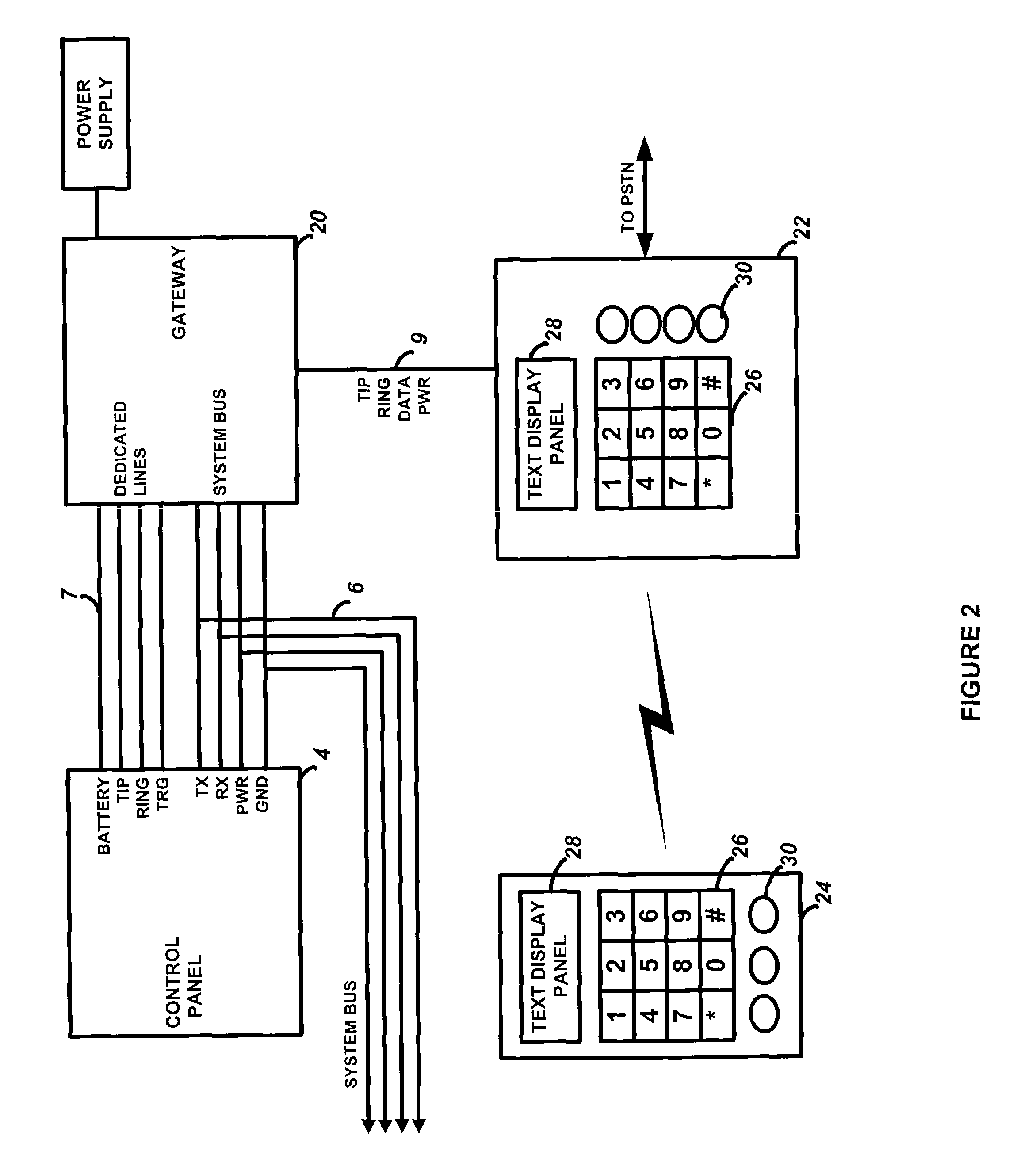
Universal gateway module for interfacing a security system control to external peripheral devices
InactiveUS7030752B2Simpler and more standardized communication channelEasily interfaceFrequency-division multiplex detailsTelephonic communicationComputer moduleSecurity system
A gateway module including a security system interface for interfacing with a security system control panel via a security system bus, a peripheral device interface for interfacing with a peripheral device, and processing circuitry for controlling operation. The processing circuitry transceives security system data to and from the security system interface, wherein the security system data is configured in a security system protocol suitable for communication with a security system control panel, and transceives peripheral device data to and from the peripheral device interface, wherein the peripheral device data is configured in a peripheral device protocol suitable for communication with a peripheral device. The processing circuitry is also adapted to translate security system data to peripheral device data, and also translate peripheral device data to security system data.
Owner:HONEYWELL INT INC
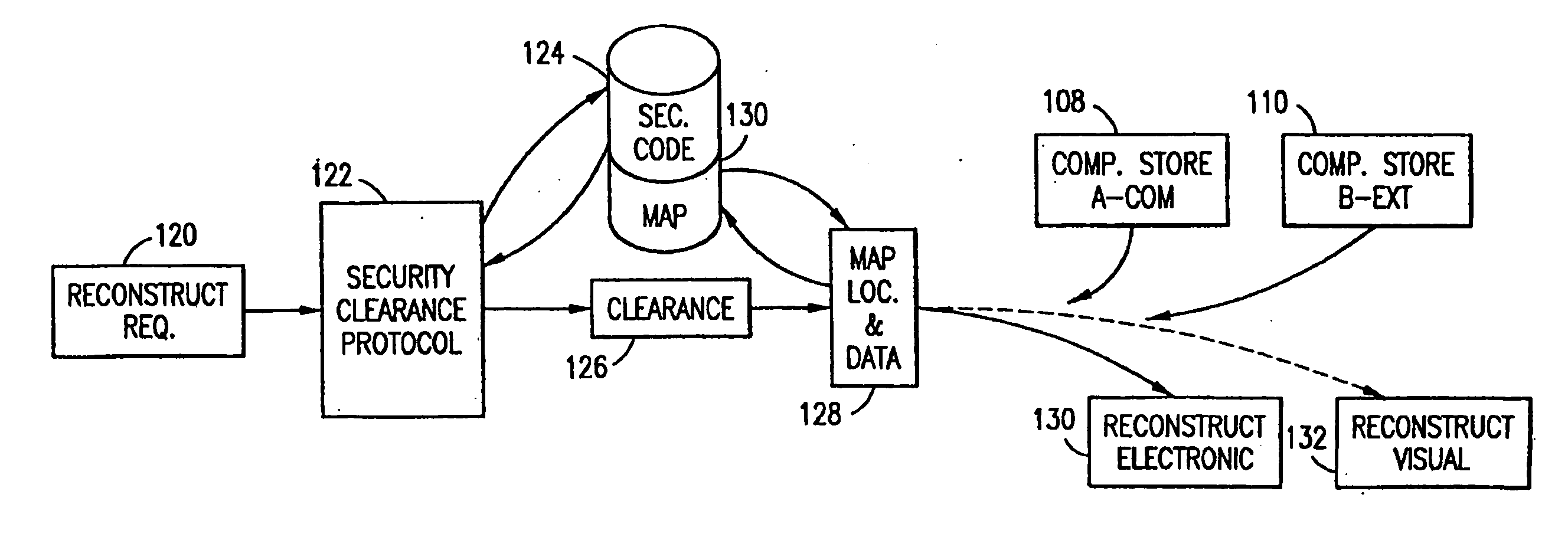
Data Security System and with territorial, geographic and triggering event protocol
ActiveUS20090178144A1Ease overhead performanceHigh overhead performanceDigital data processing detailsAnalogue secracy/subscription systemsInformation processingEvent trigger
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with territorial, geographic and triggering event protocols. The method and system determines device location within or without a predetermined region and then extracts security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only with security clearance and within certain geographic territories. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com