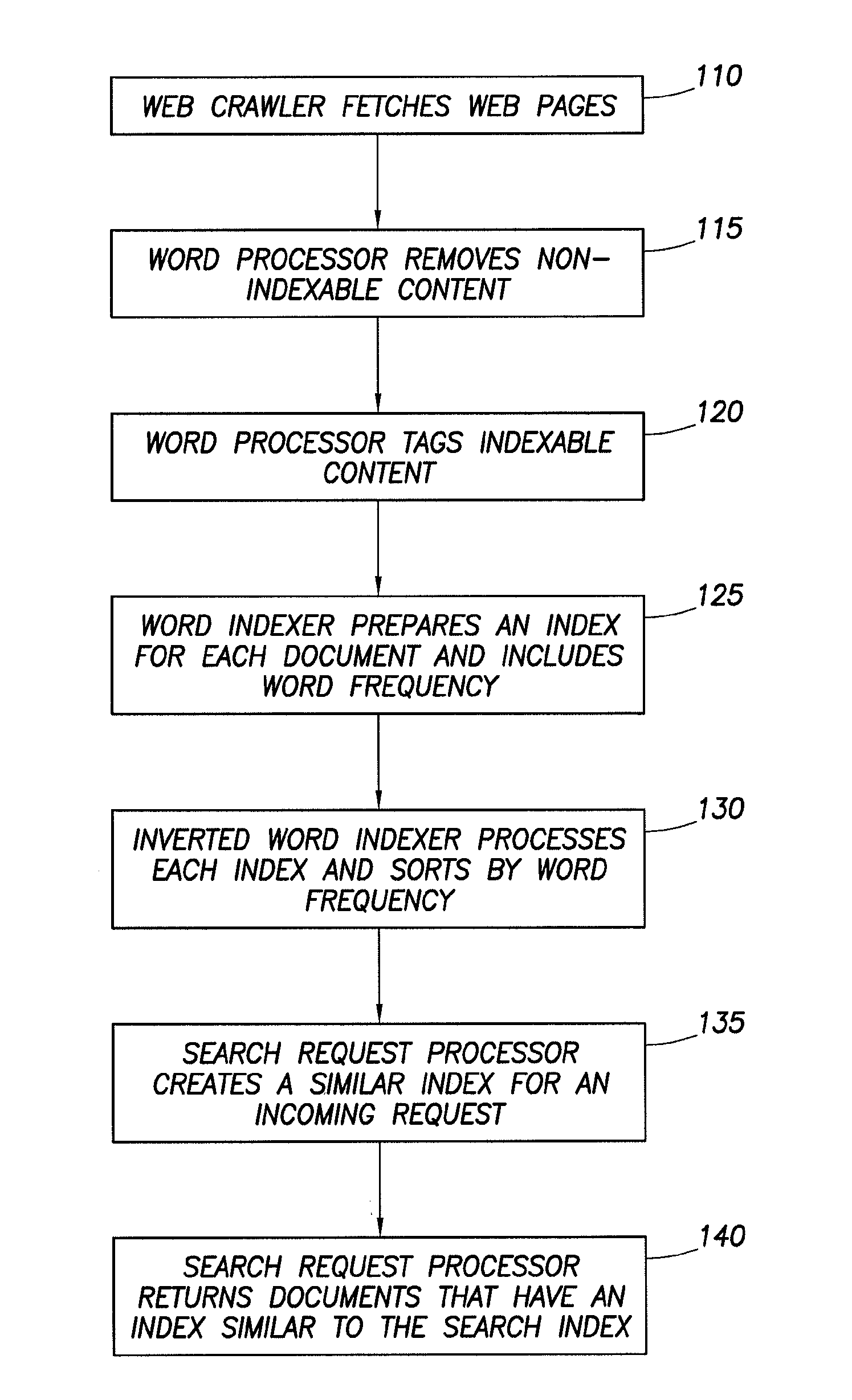
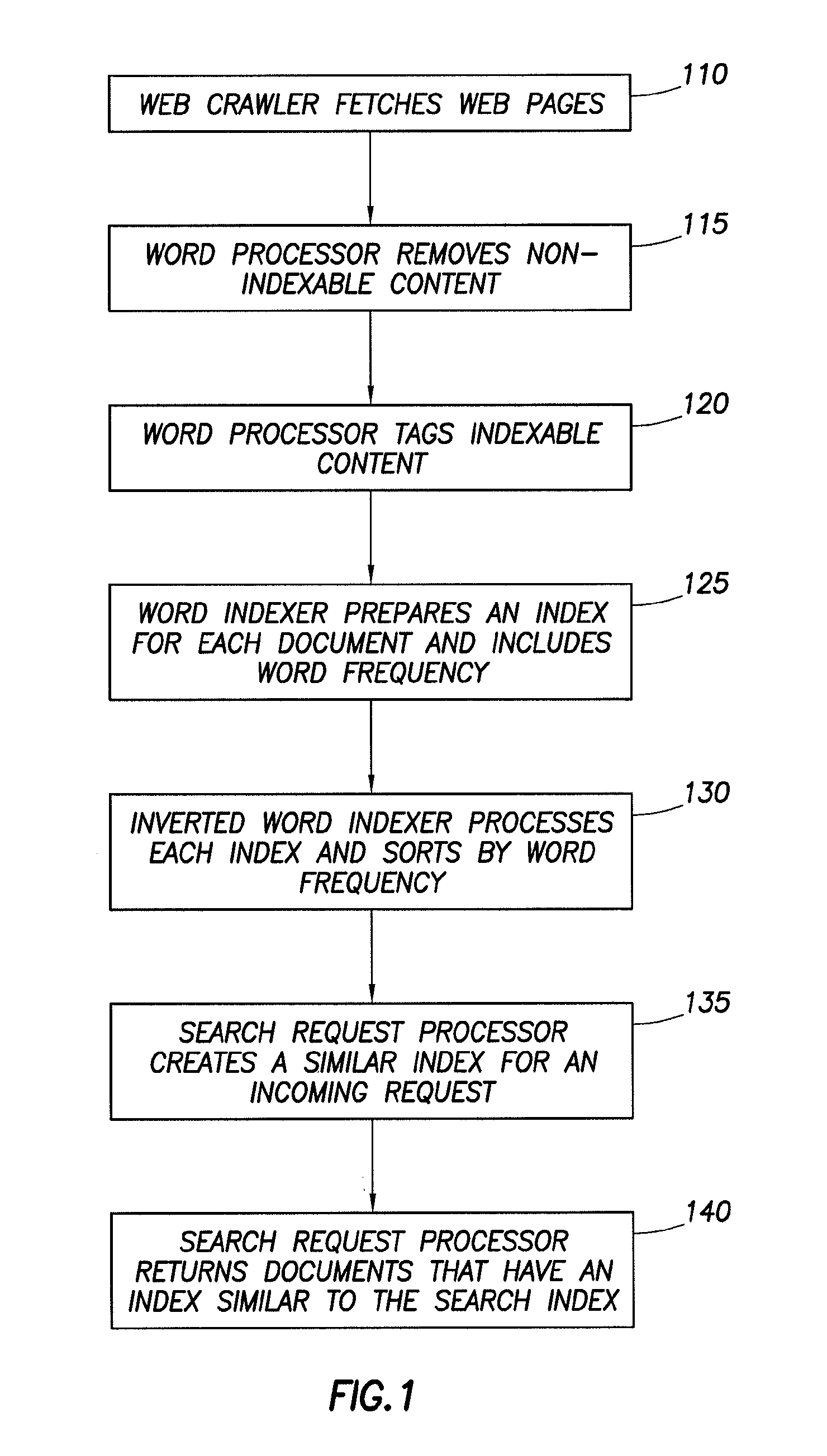
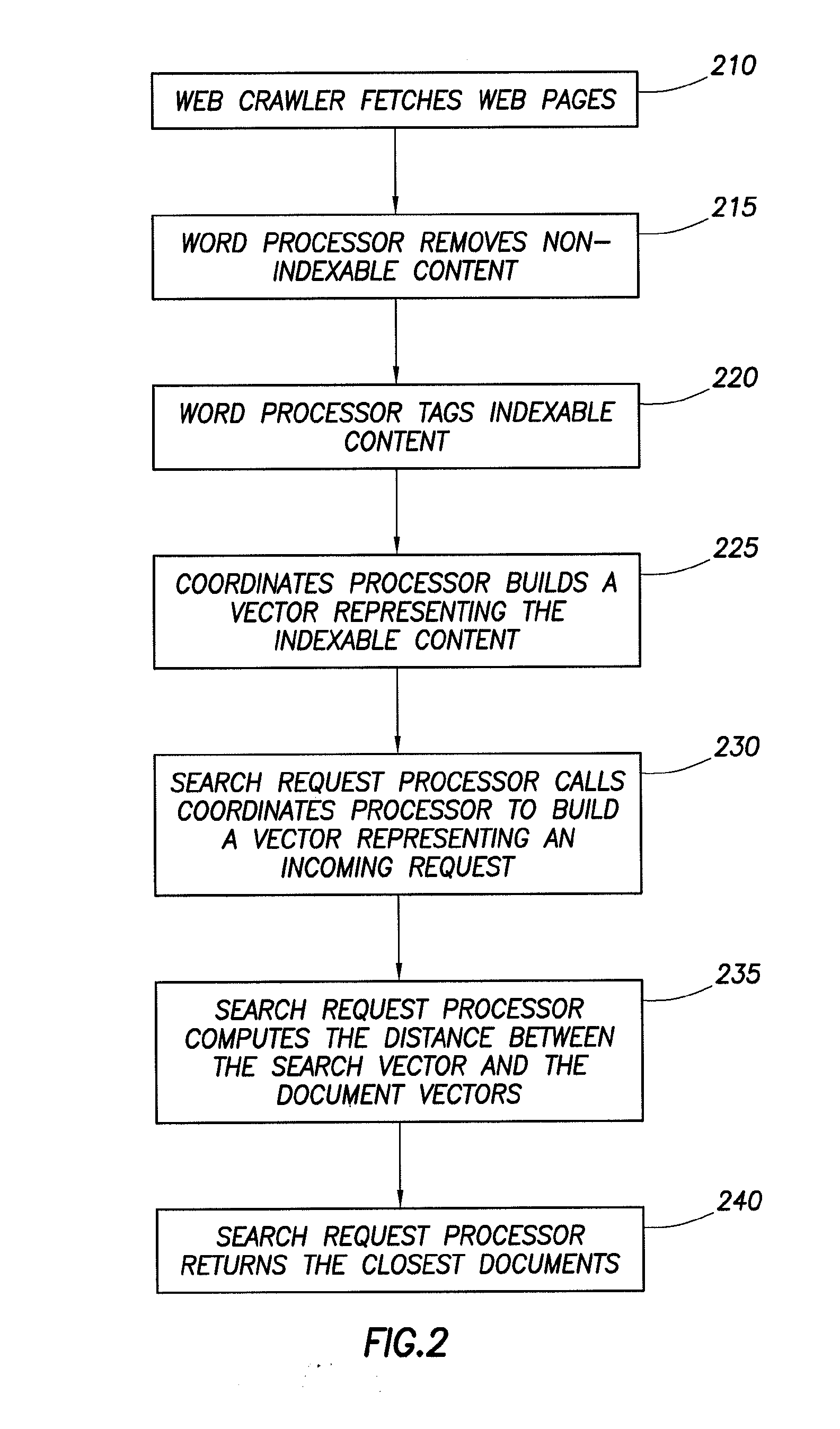
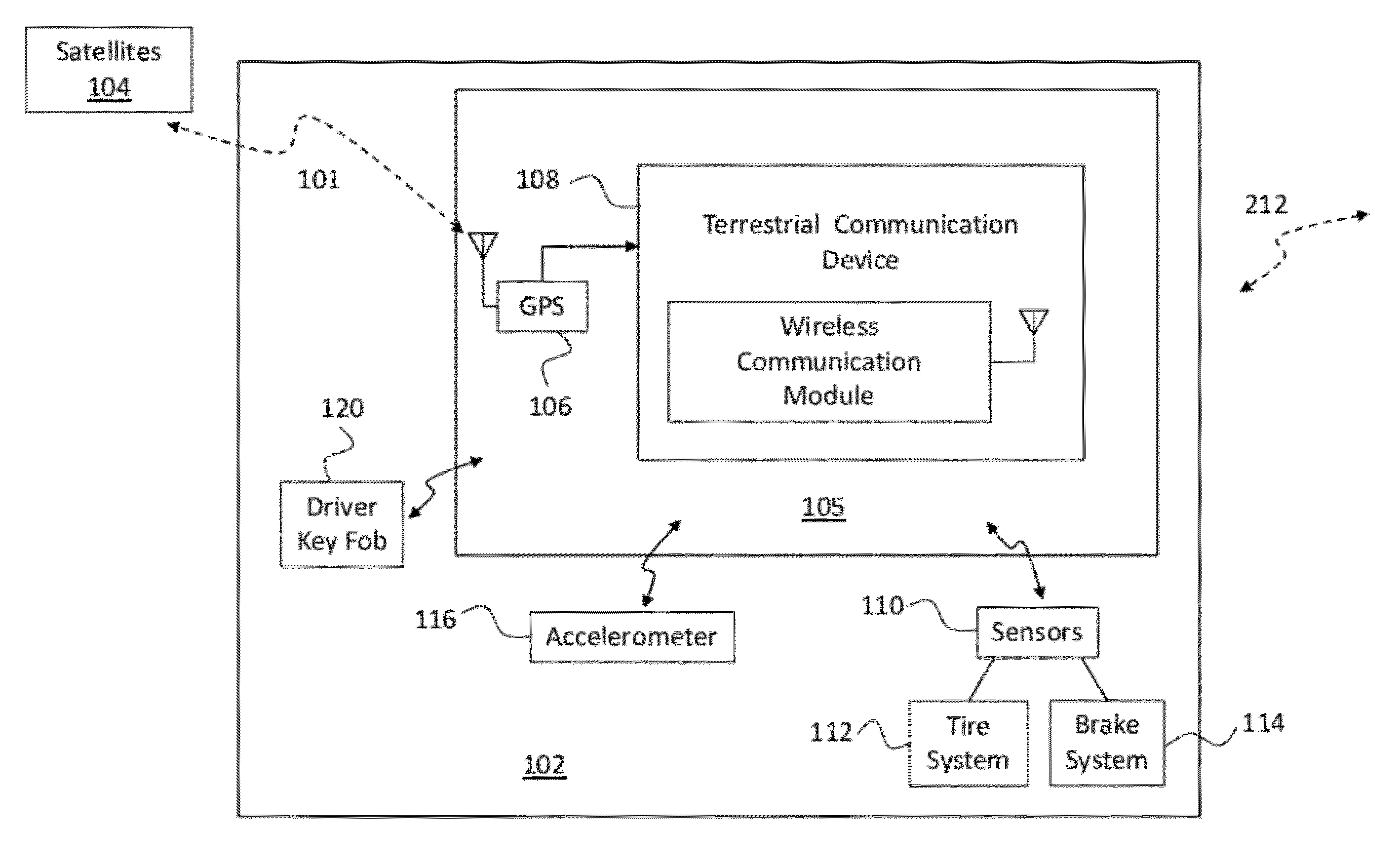
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10616 results about "Information handling system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
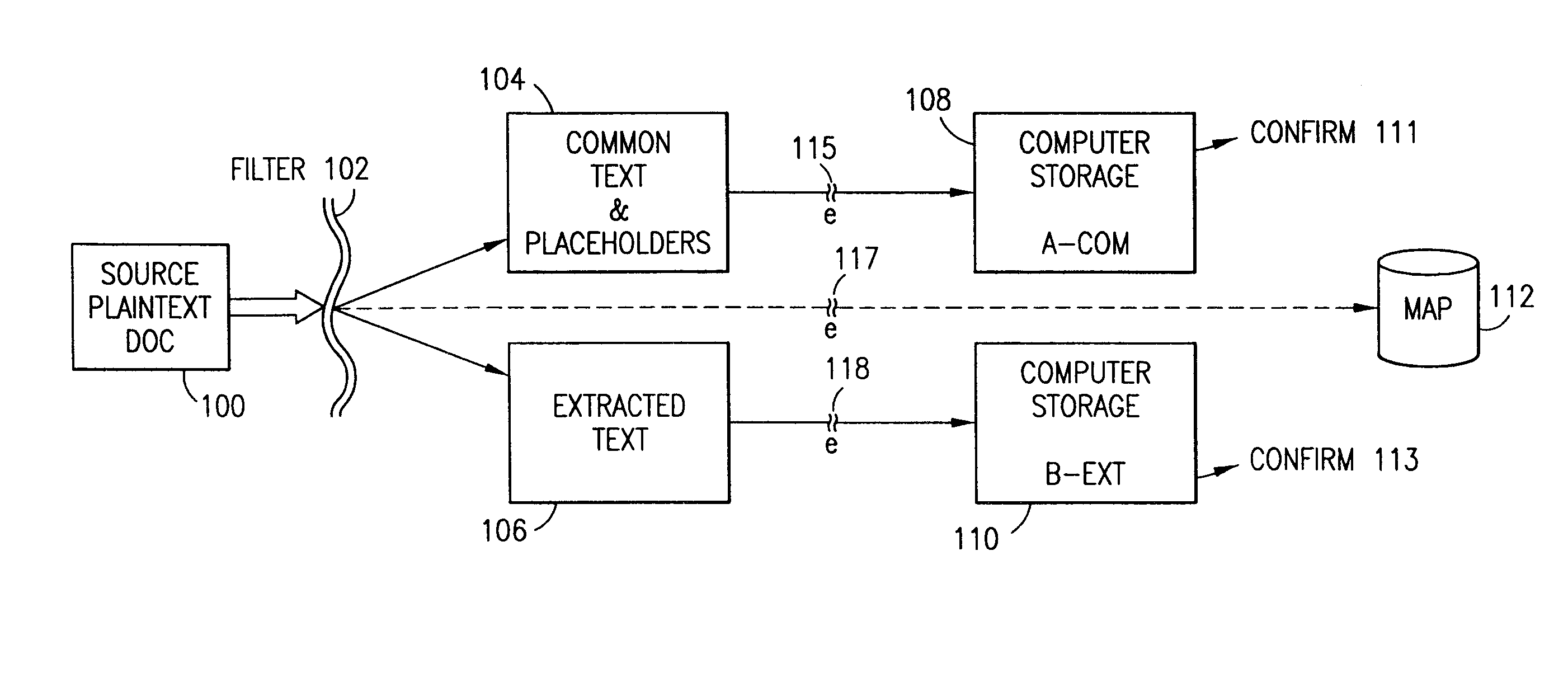
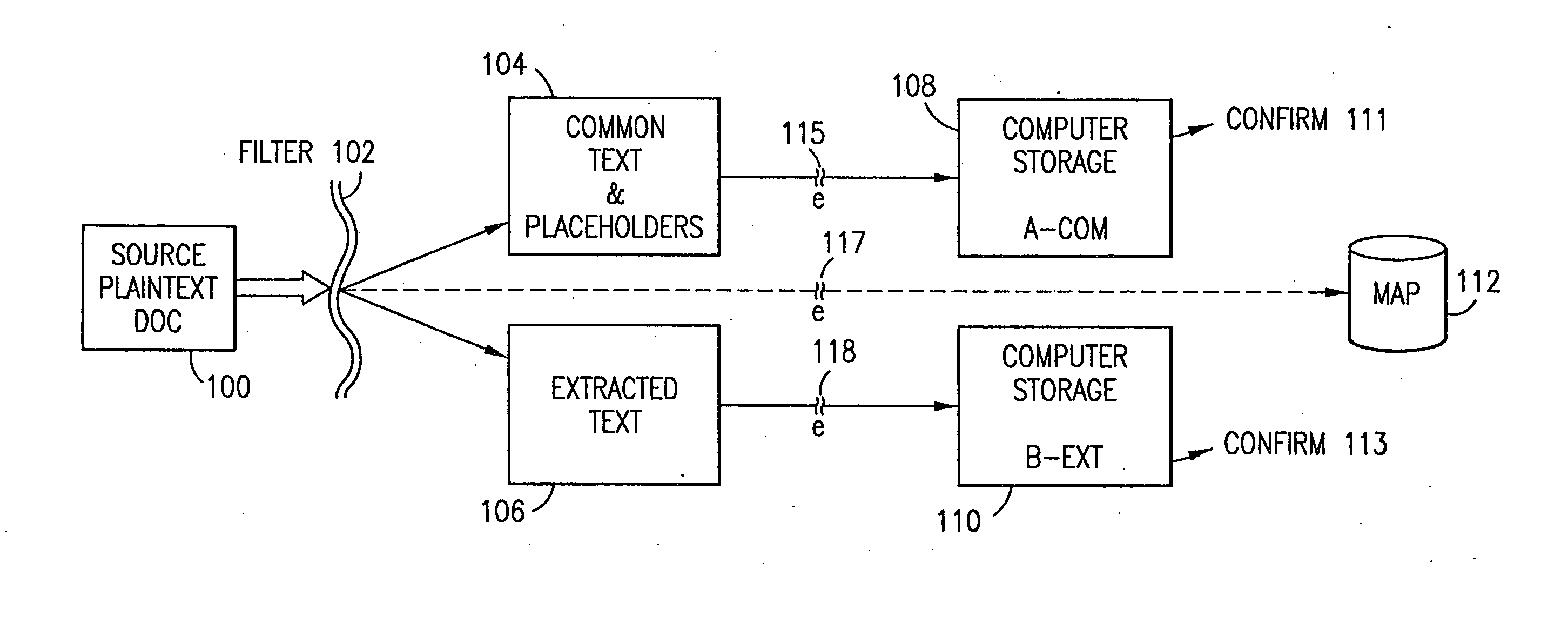
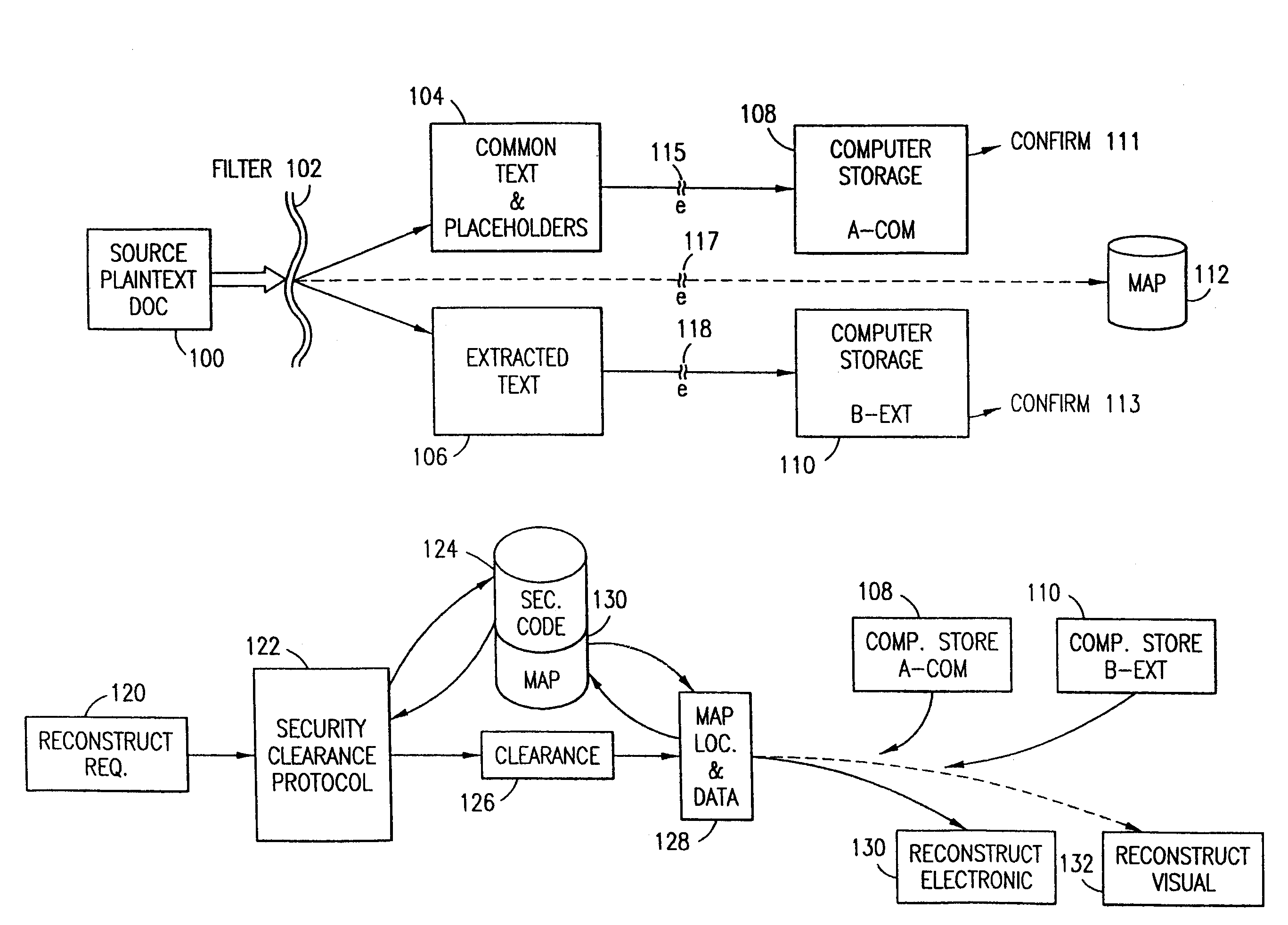
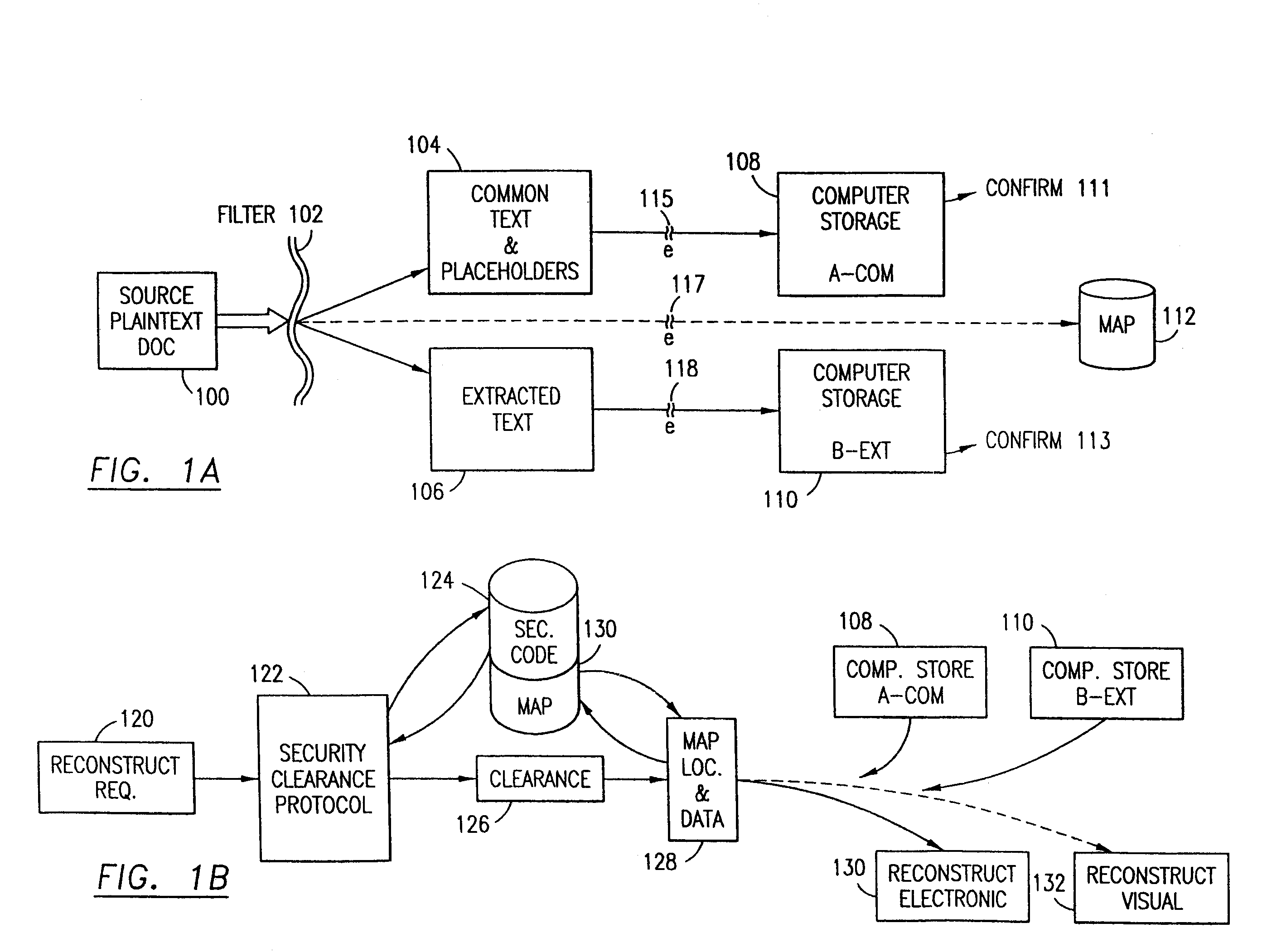
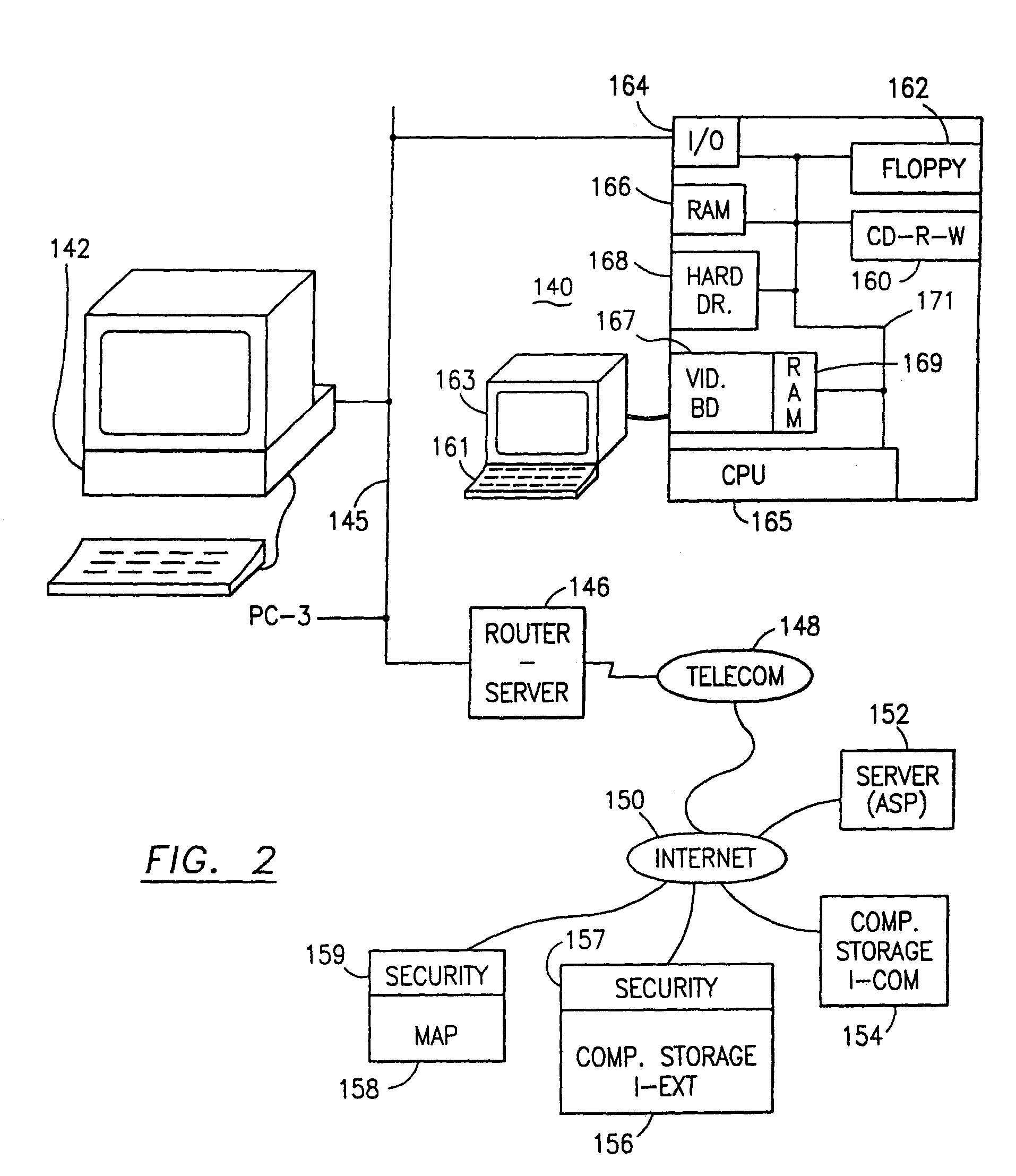
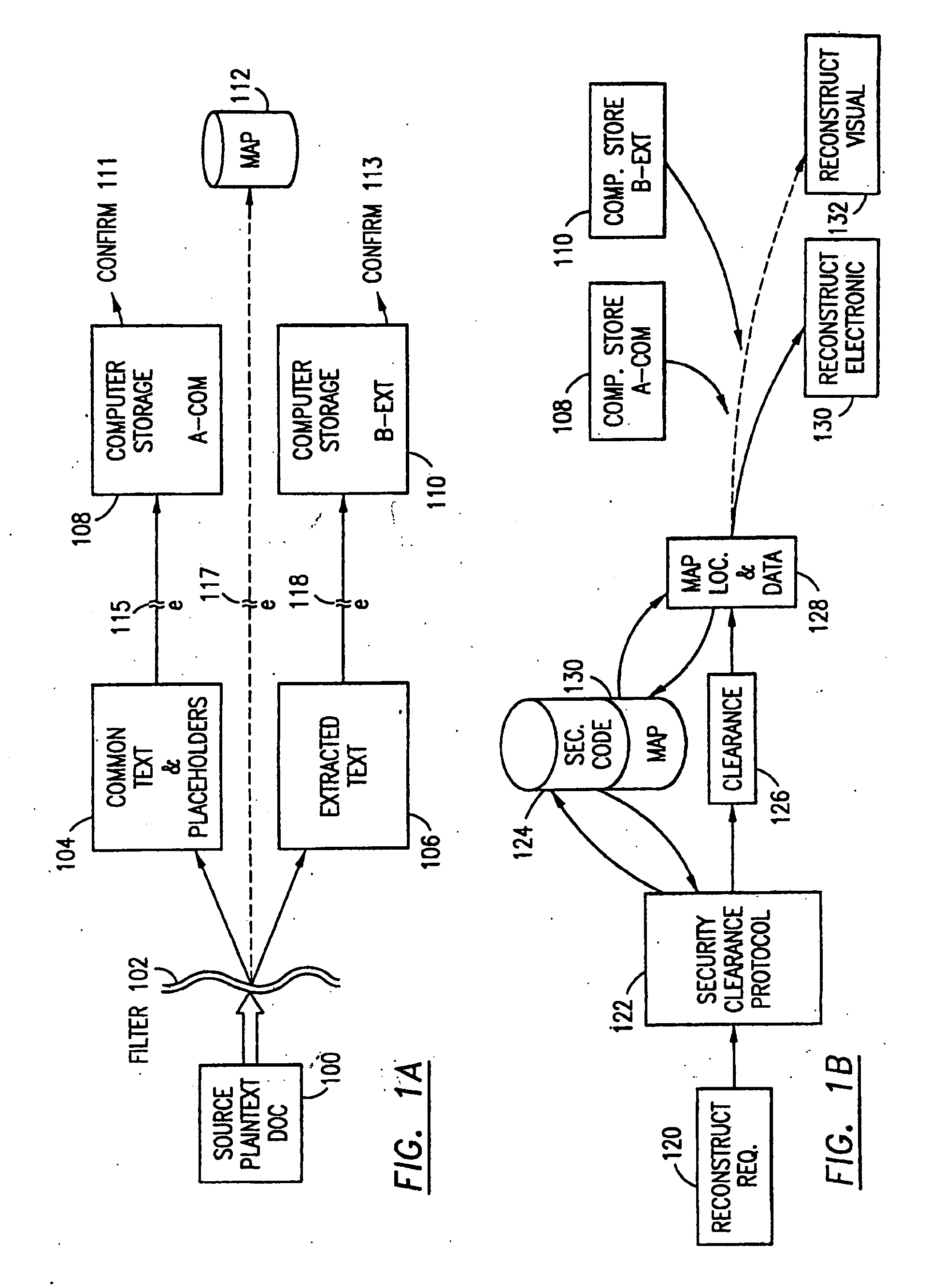
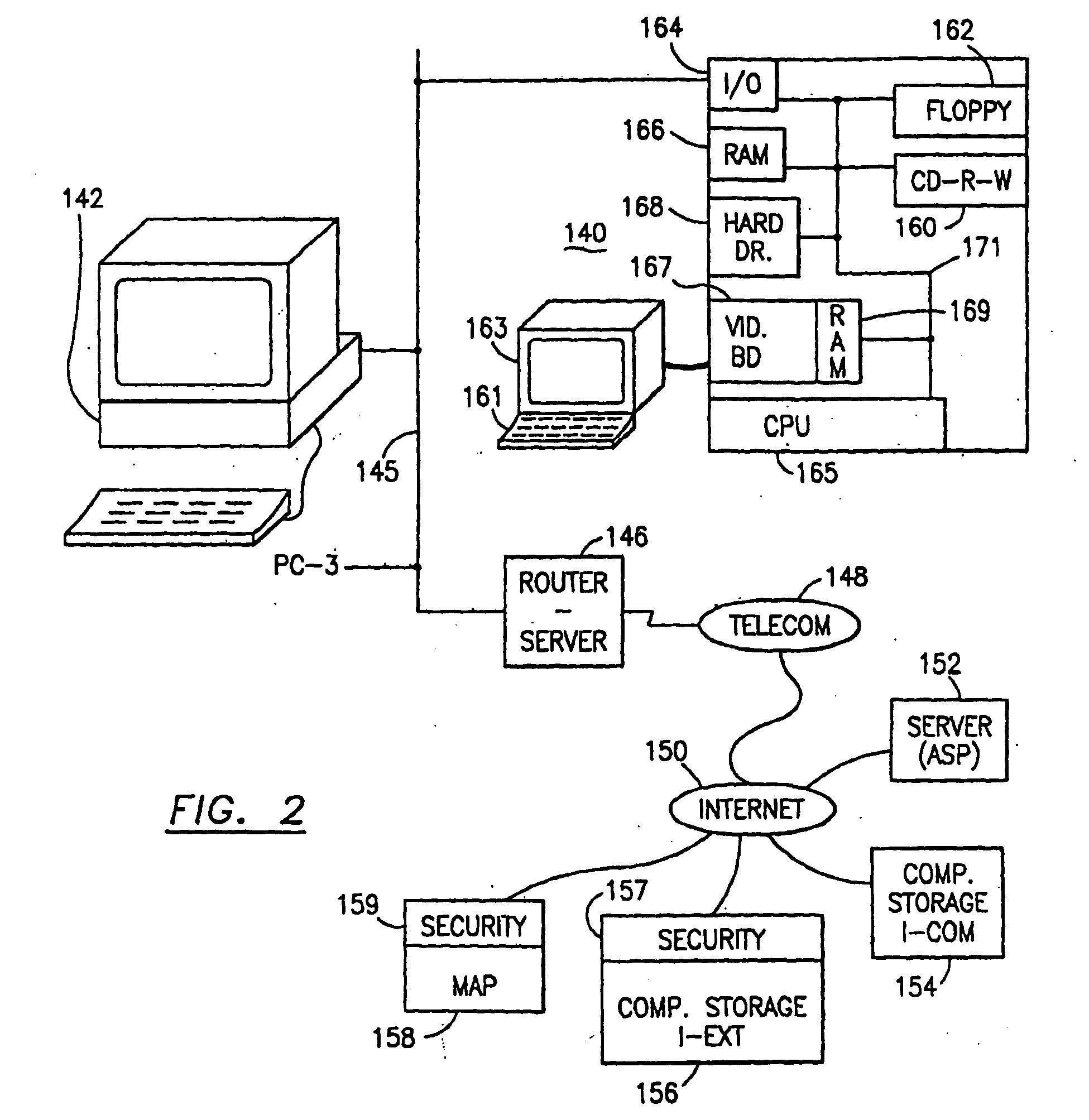
Data security system and method for separation of user communities
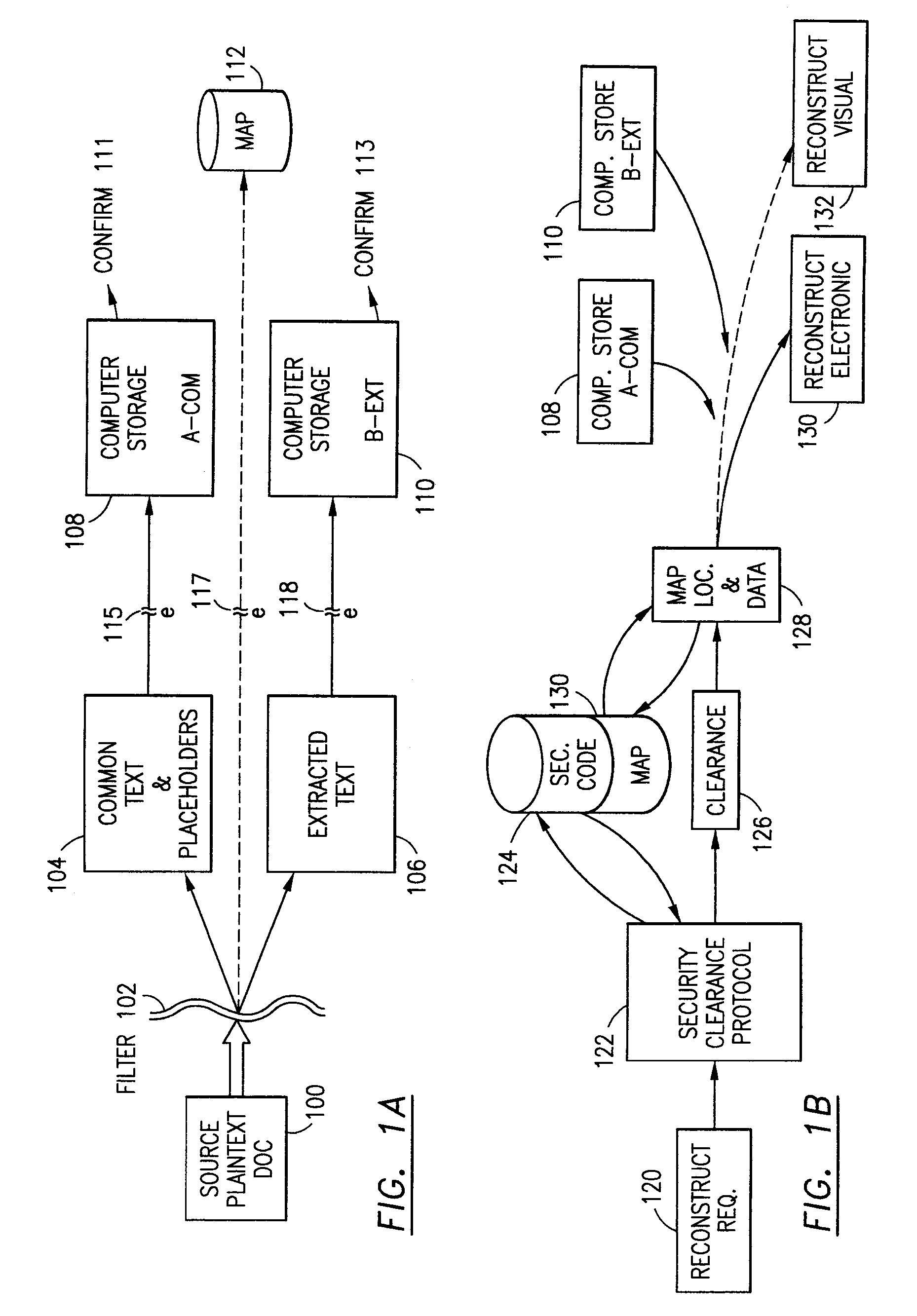
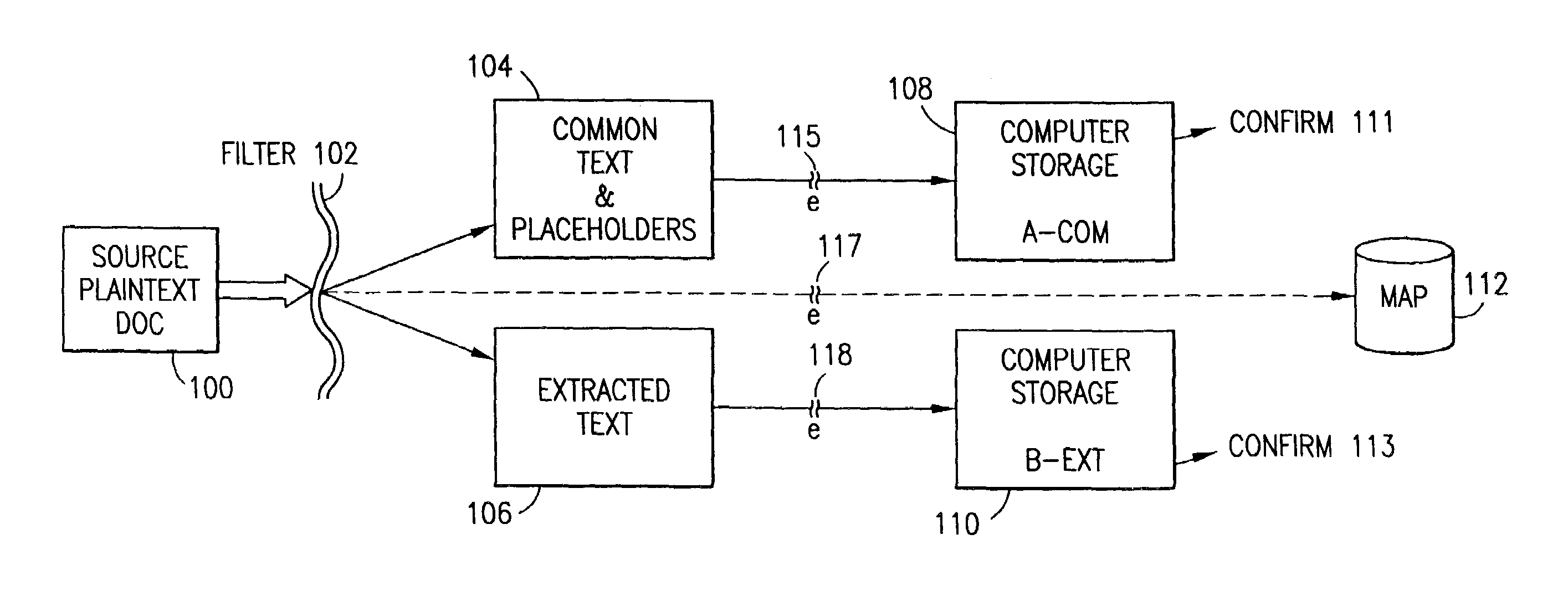
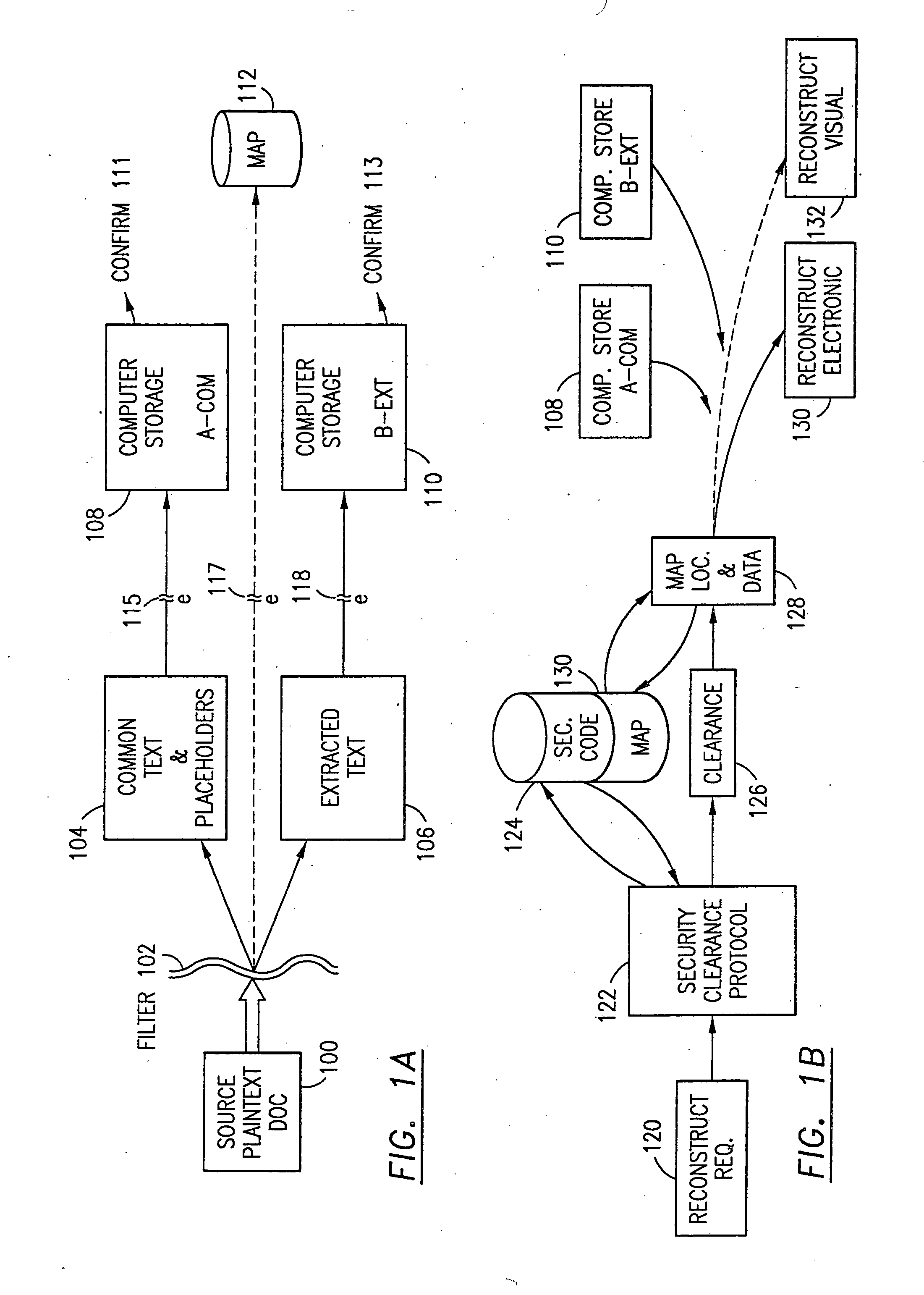
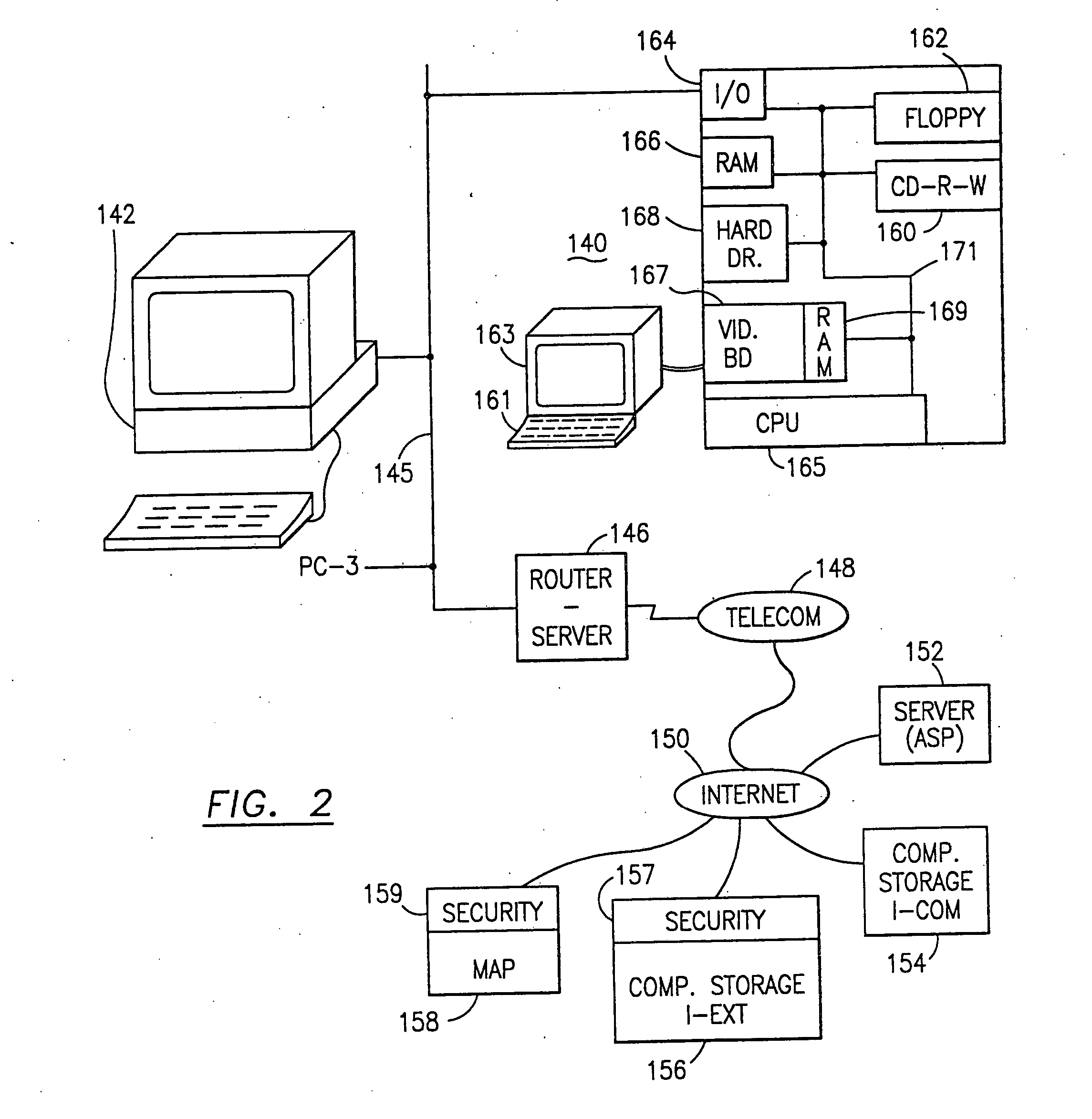
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
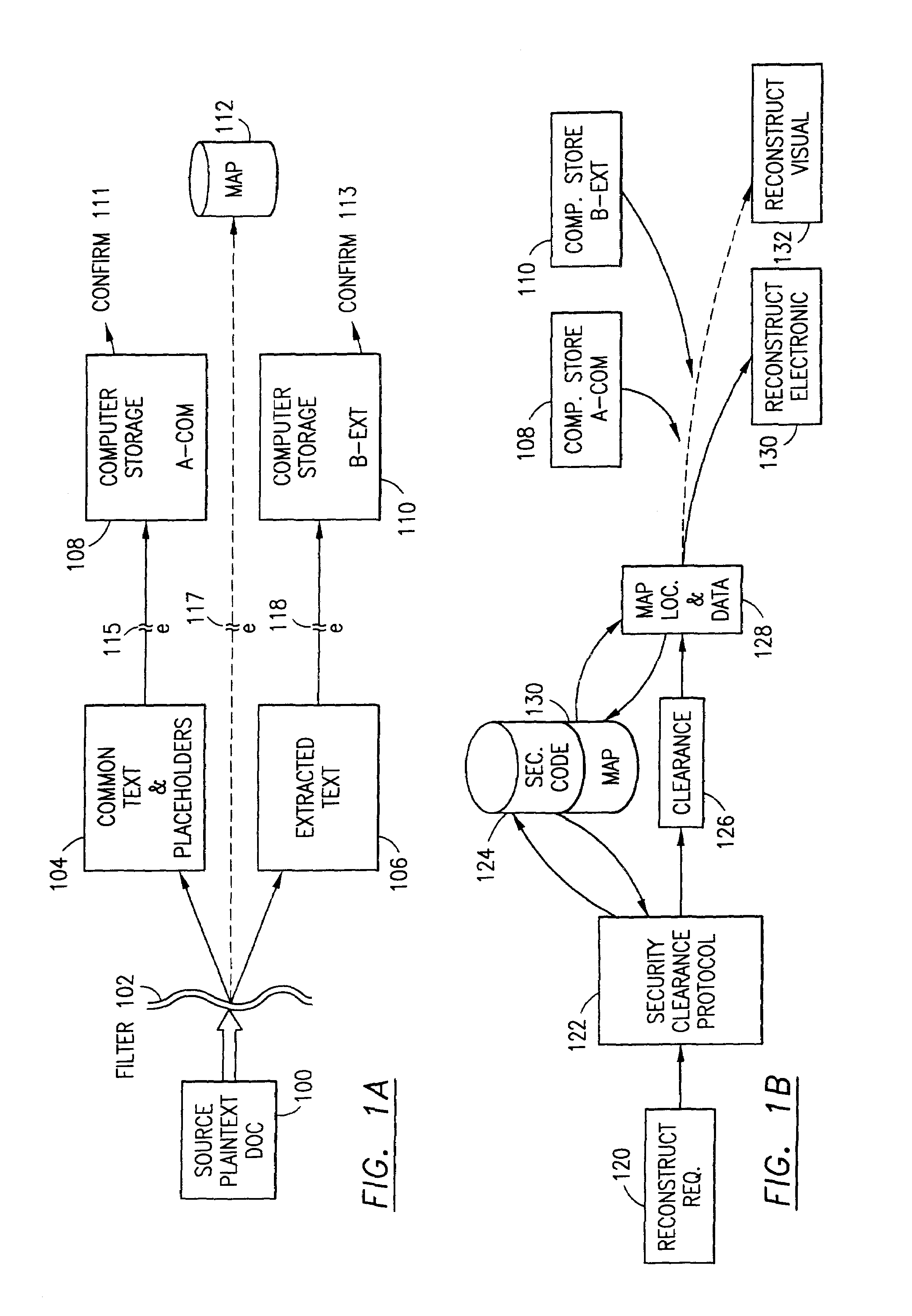
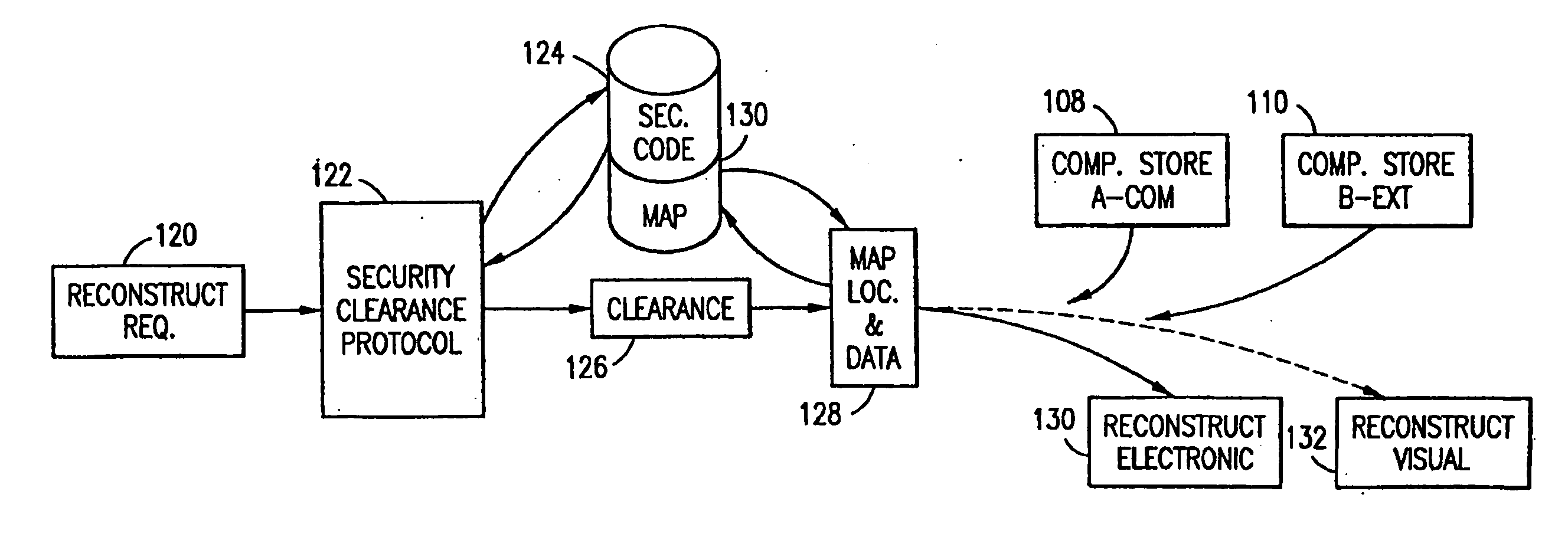
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
Data security system and method
ActiveUS7103915B2Memory loss protectionDigital data processing detailsPlaintextInformation processing
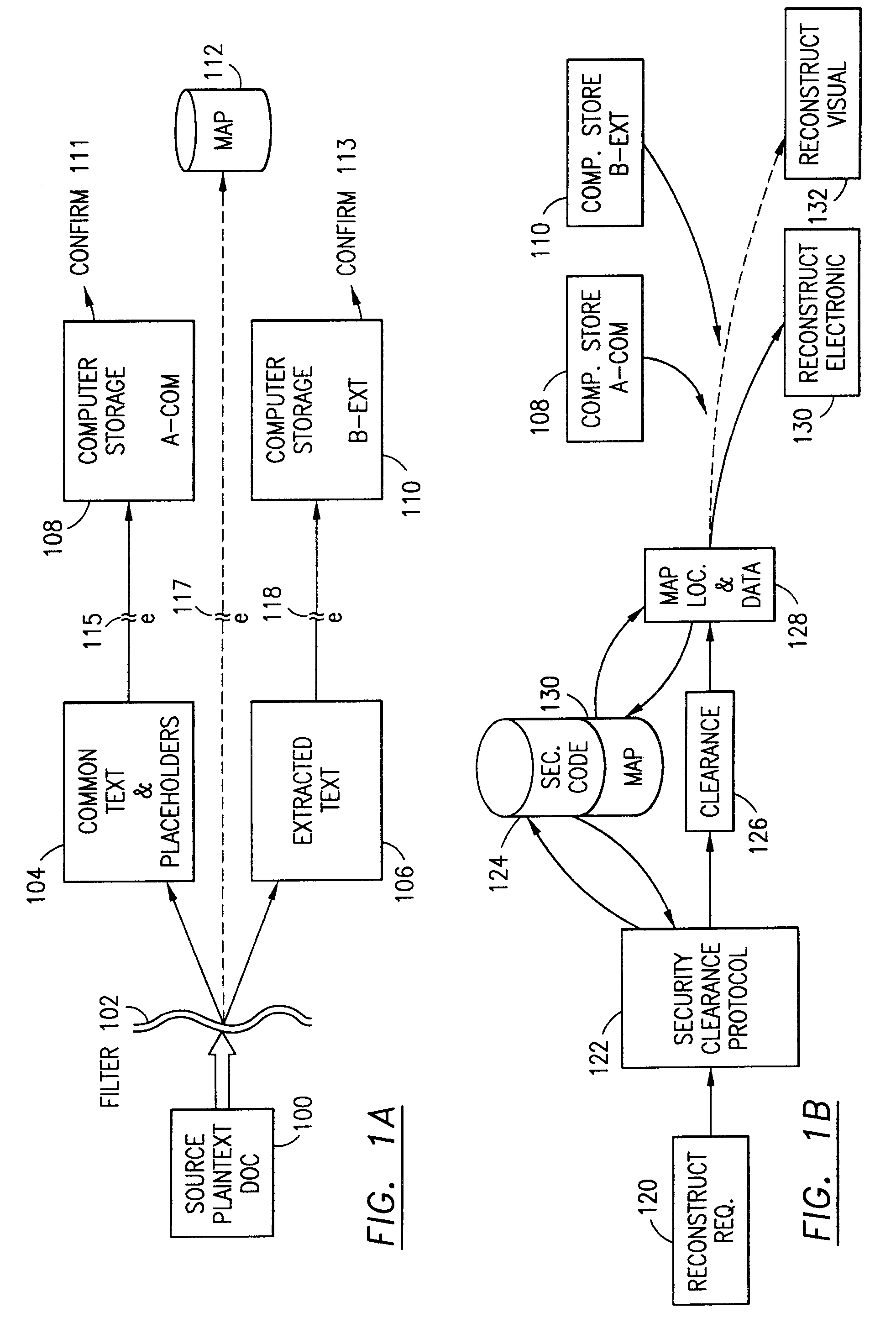
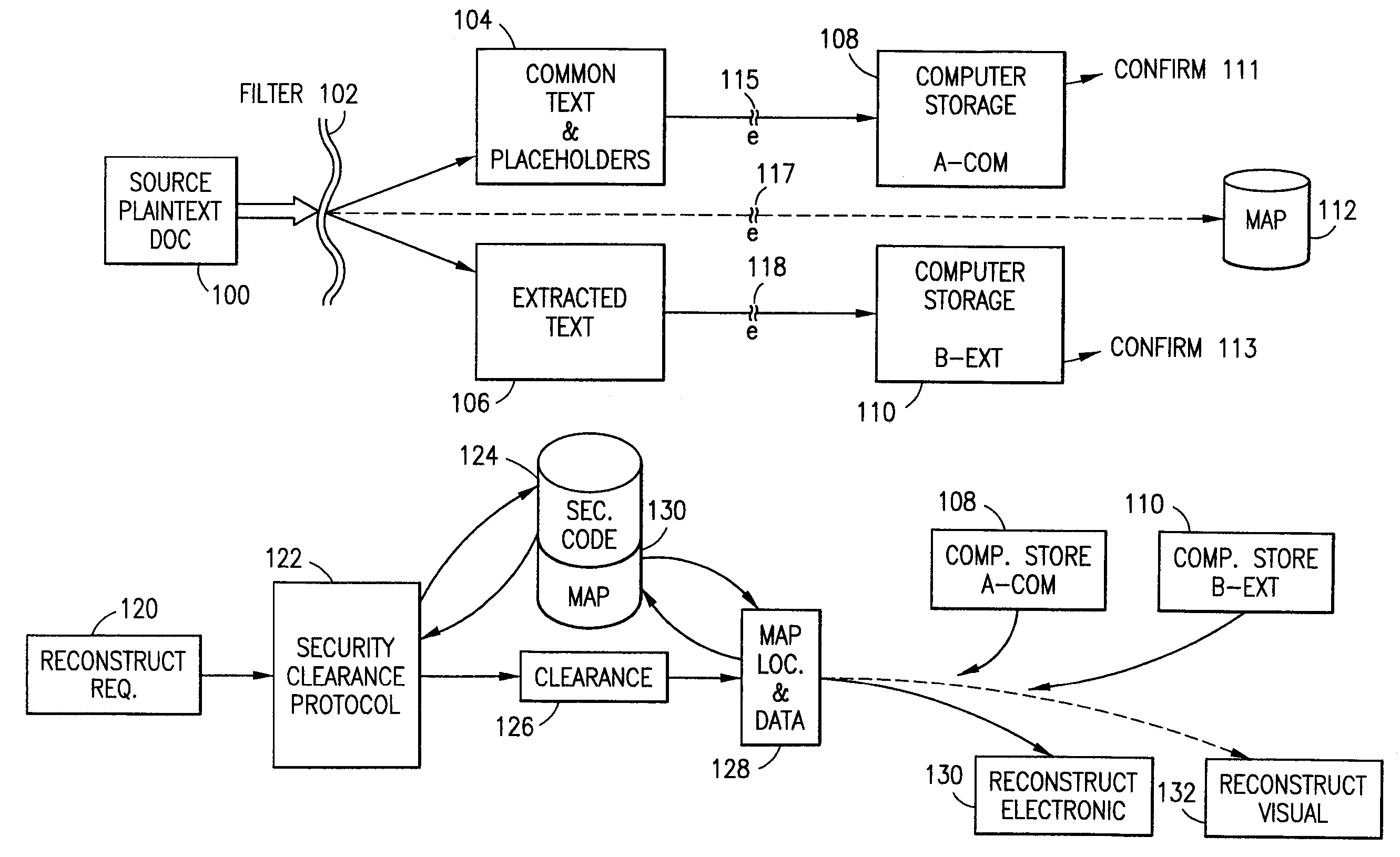
The method for securing data includes establishing a group of security sensitive items, filtering data and extracting and separating the security items from remainder data. The filtered data are separately stored (locally on a PC or on another computer in a LAN or WAN or on the Internet.) A map may be generated. The filter and / or map may be destroyed or stored. The data input, extracted data and remainder data may be deleted from the originating computer. Encryption may be utilized to enhance security (including transfers of data, filter and map). Reconstruction of the data is permitted only in the presence of a predetermined security clearance. A plurality of security clearances may be used to enable a corresponding plurality of partial, reconstructed views of the plaintext (omitting higher security words). A computer readable medium containing programming instructions and an information processing system is encompassed.
Owner:DIGITAL DOORS
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
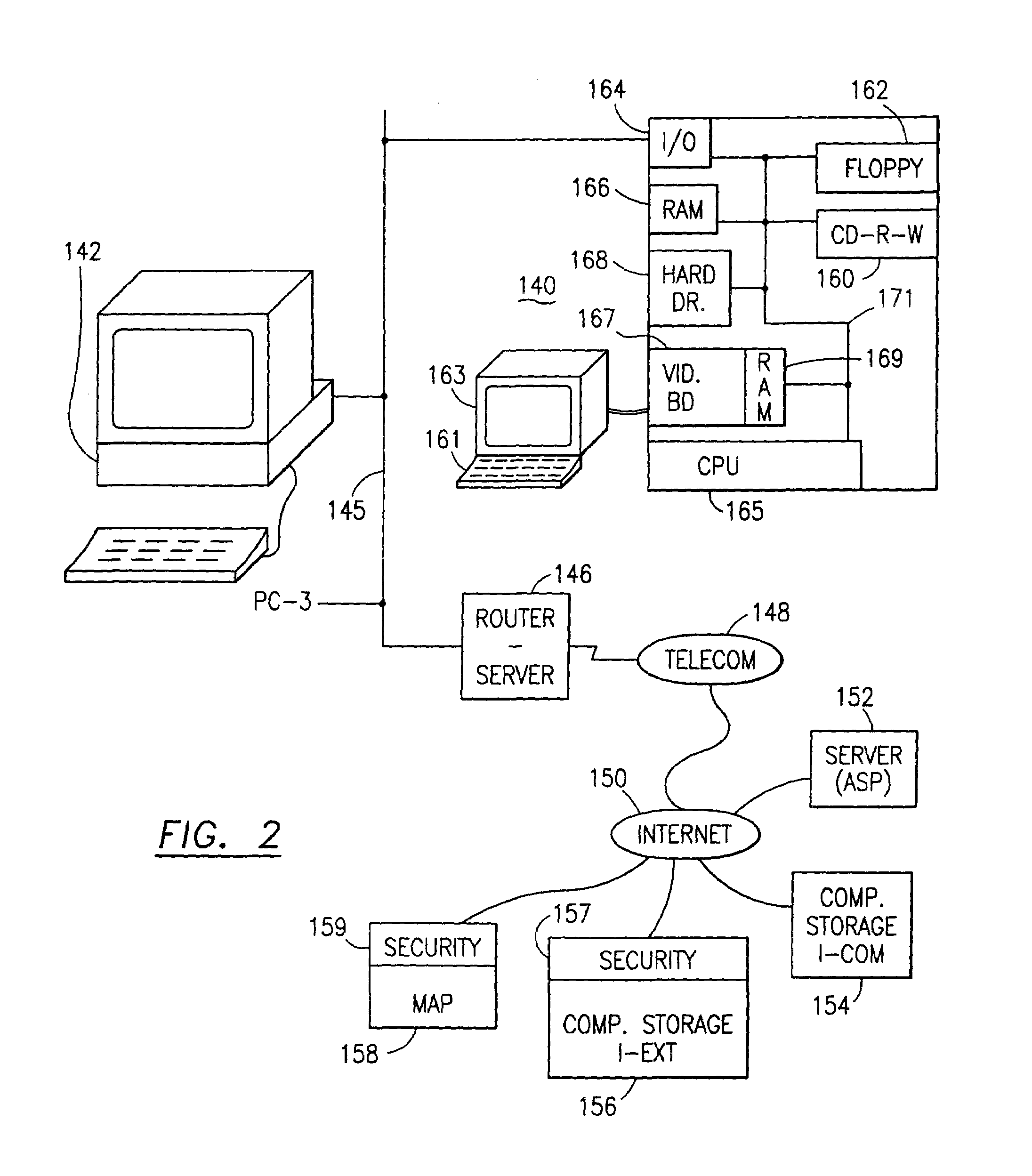
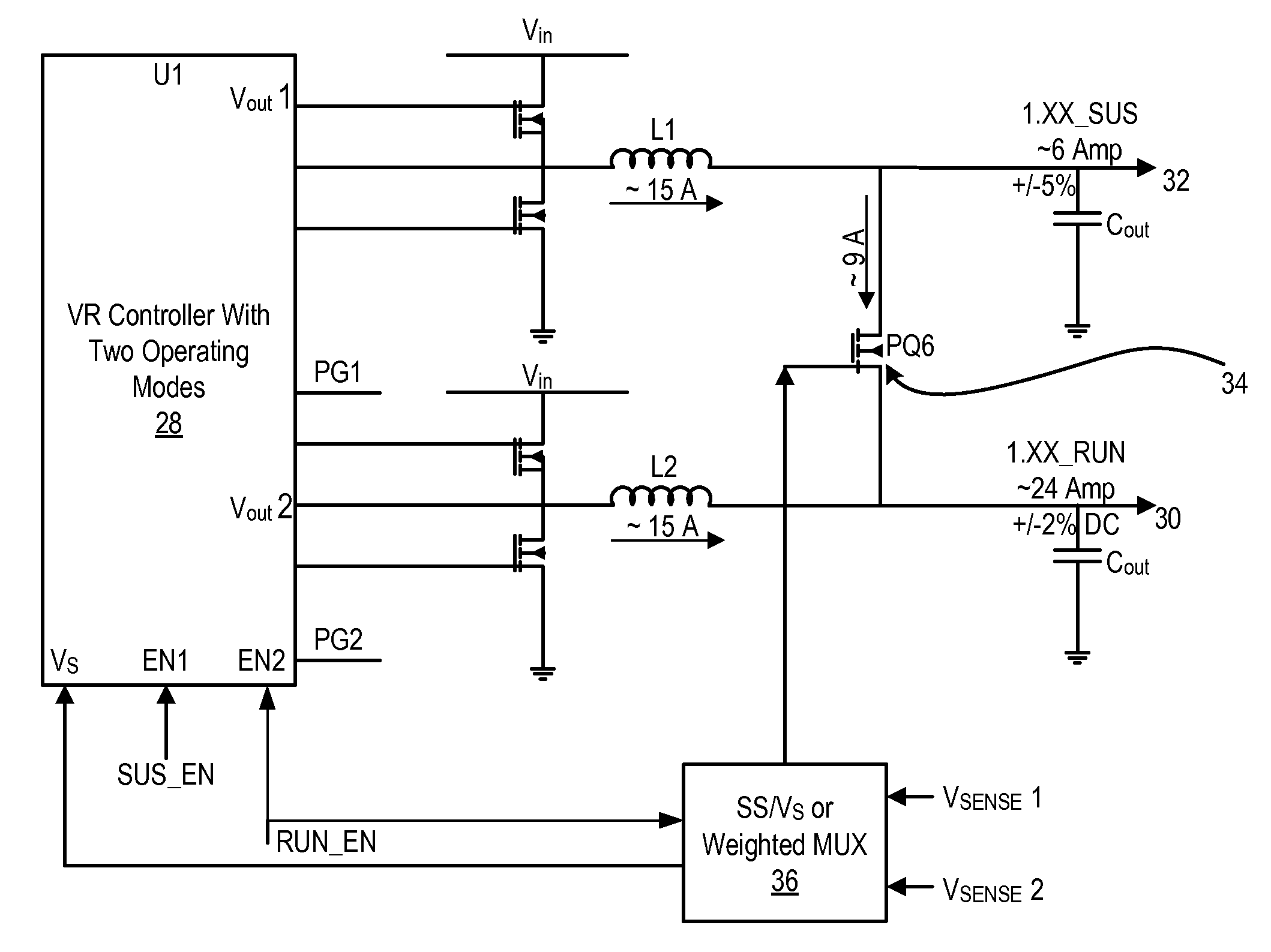
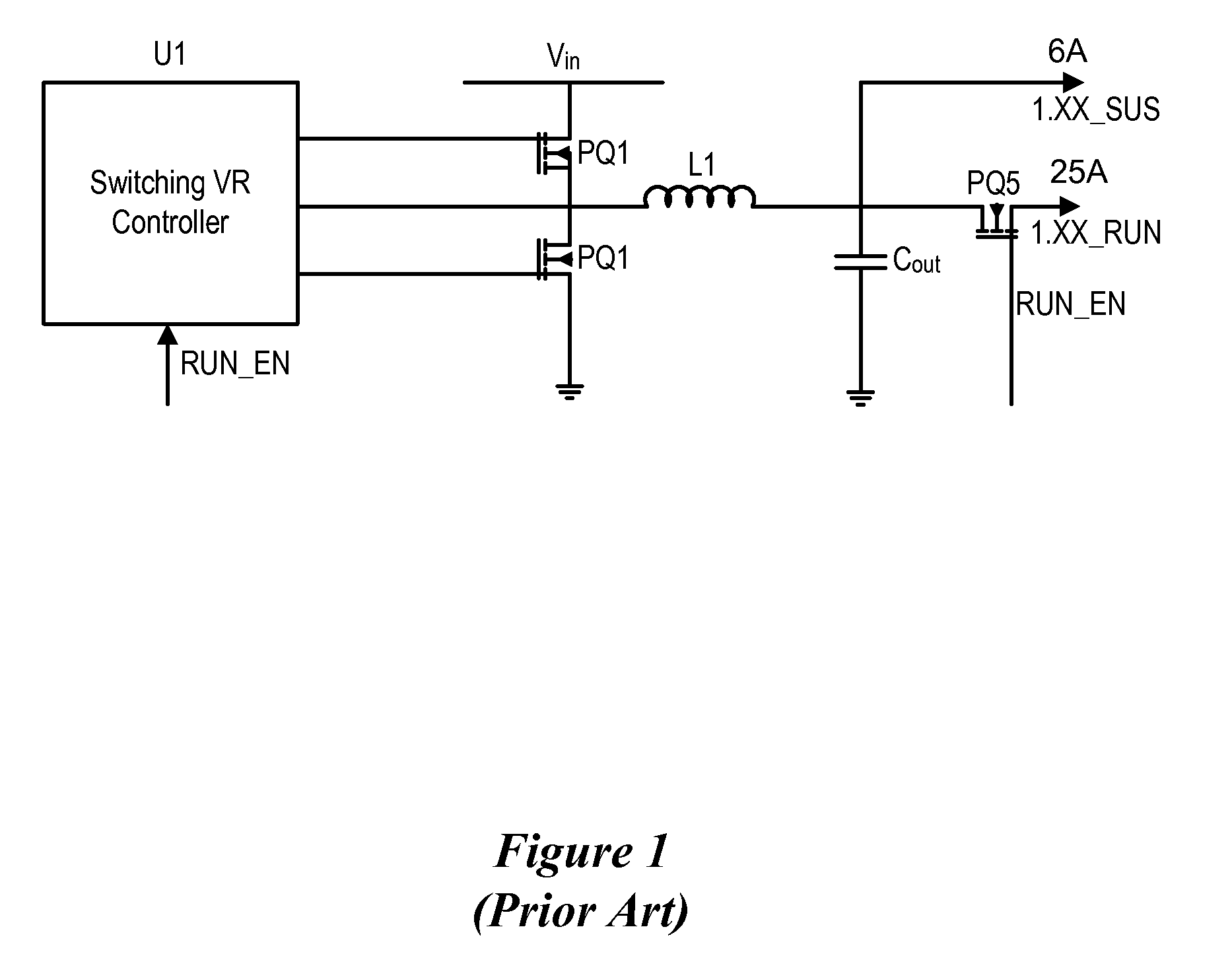
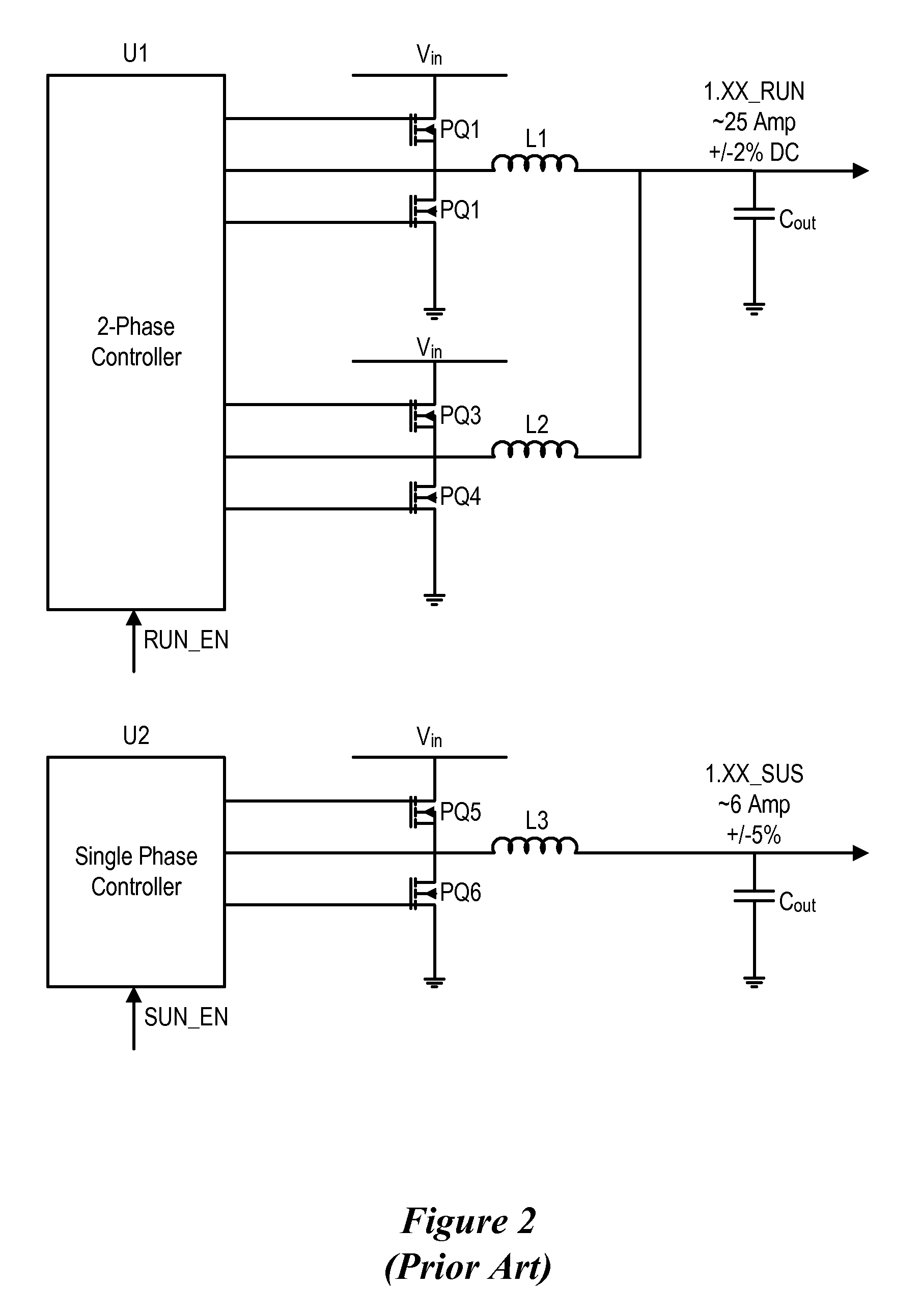
System and method for powering an information handling system in multiple power states
ActiveUS8063619B2Reduce disadvantagesReduce problemsElectric signal transmission systemsDc network circuit arrangementsMOSFETVoltage regulation
Power is supplied to an information handling system chipset with a single voltage regulator having dual phases. A first phase of the voltage regulator provides power to a low power state power rail in an independent mode to support a low power state, such as a suspend or hibernate state. A second phase of the voltage regulator provides power to a run power state power rail in combination with the first phase by activation of a switch, such as a MOSFET load switch, that connects the low power state power rail and the run power state power rail. Voltage sensed from both power rails is applied to control voltage output so that the run power state power rail is maintained within more precise constraints than the low power state power rail.
Owner:DELL PROD LP
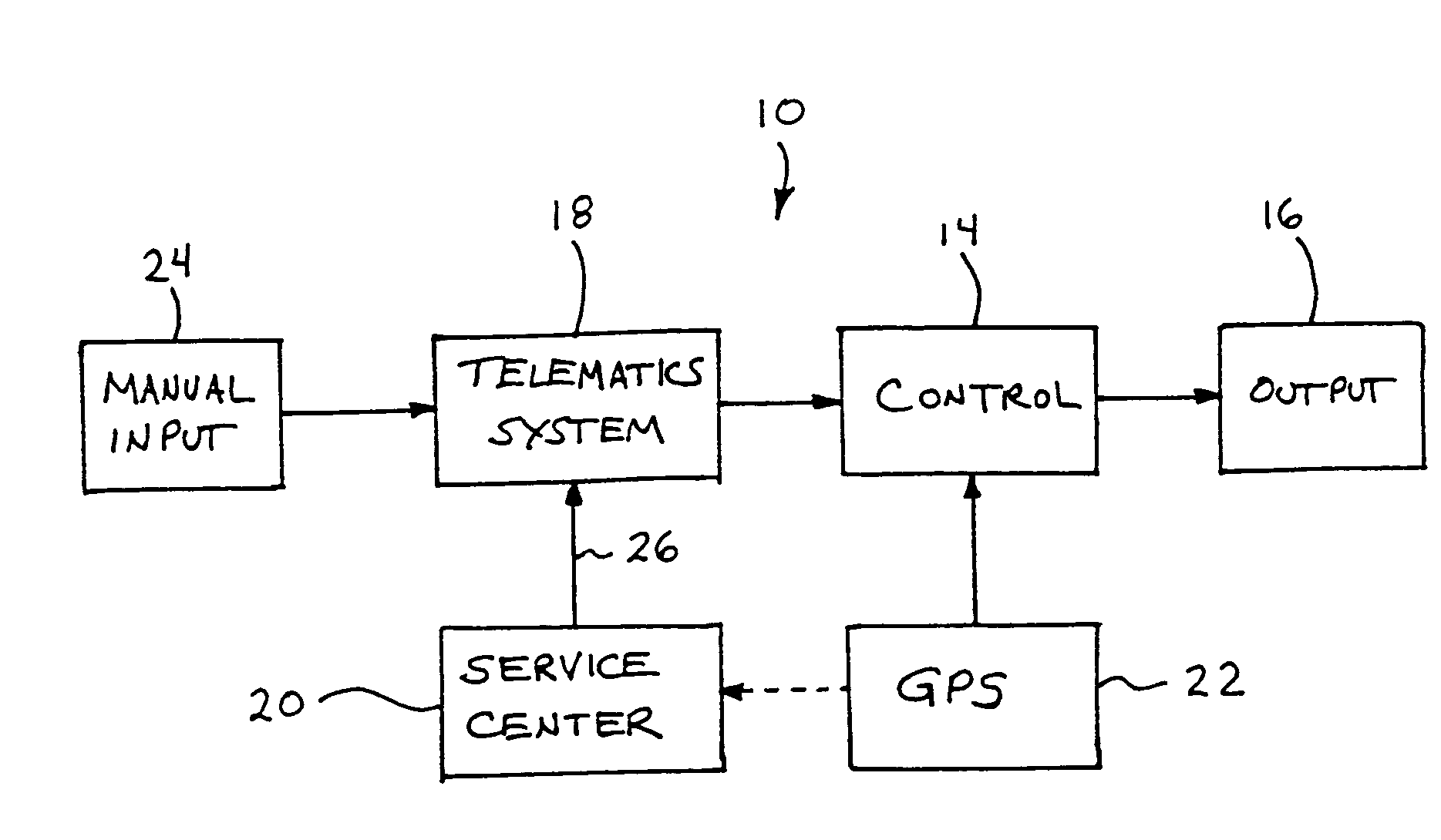
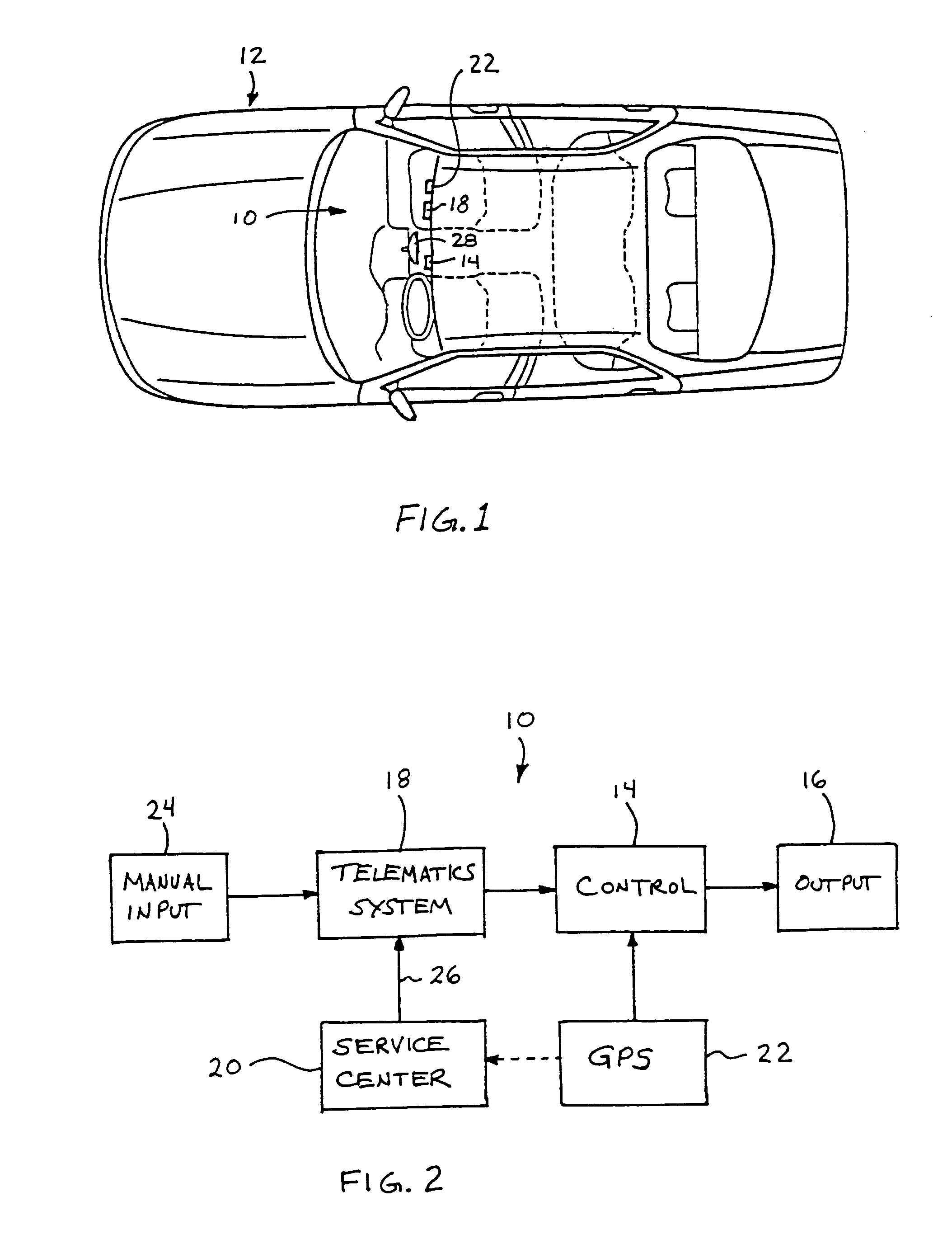
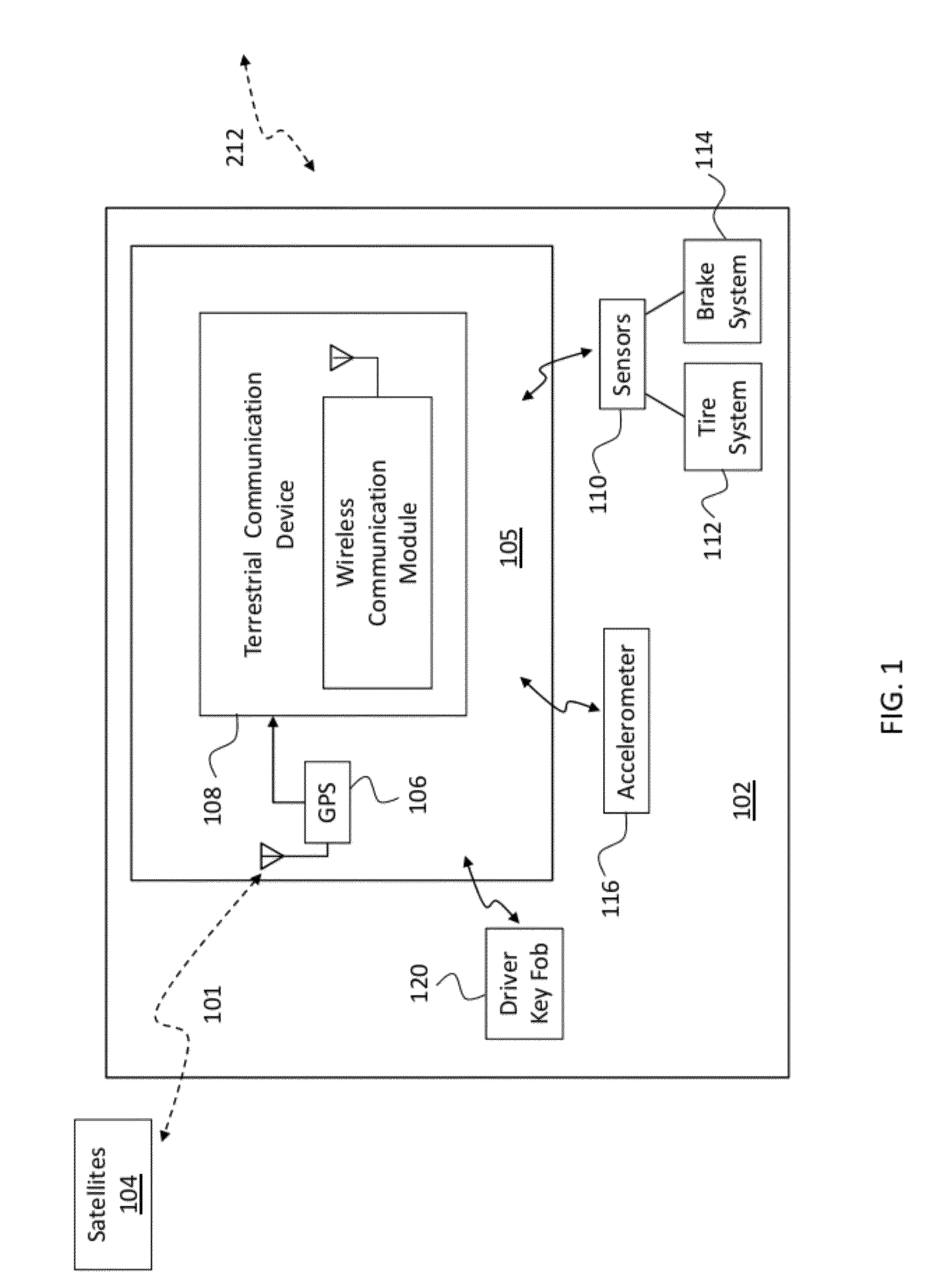
Vehicle navigation system for use with a telematics system
InactiveUS7167796B2Low costImage enhancementTelevision system detailsDriver/operatorService provision
A navigation system for a vehicle includes a vehicle-based telematics system, a vehicle-based global positioning system and a control. The telematics system is operable to receive a user input from a driver of the vehicle and to download directional information from an external service provider to the control in response to the user input and an initial geographic position of the vehicle. The directional information comprises at least two instructions with each of the instructions being coded or associated with or linked to a respective geographic location. The control is operable to provide an output corresponding to each of the instructions in response to a current actual geographic position of the vehicle. The control is operable to provide each instruction only when the then current actual geographic position of the vehicle at least generally corresponds to the particular geographic location associated with the instruction.
Owner:DONNELLY CORP
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
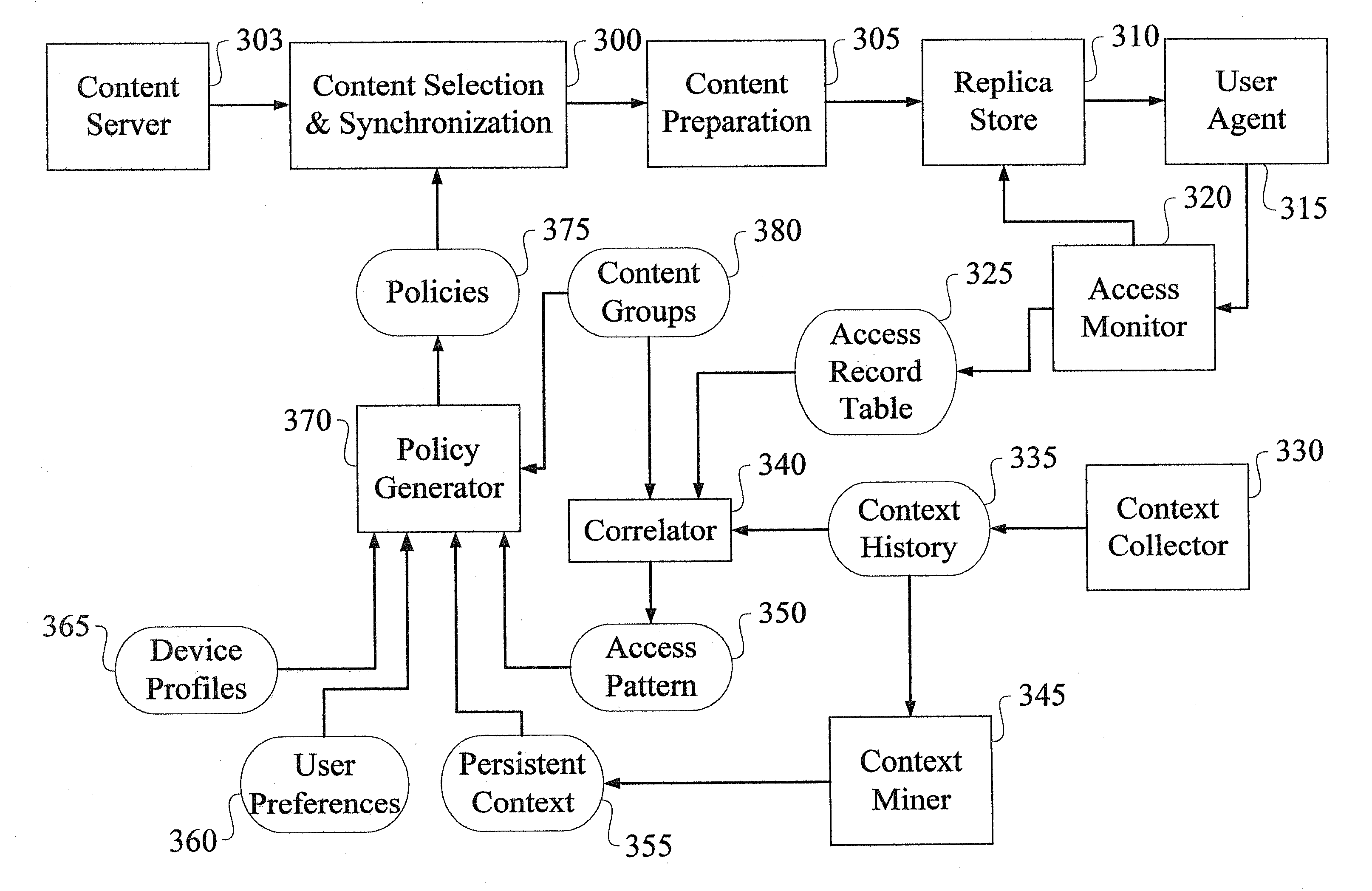
Method and Apparatus for Content Pre-Fetching and Preparation
InactiveUS20090287750A1Improve responsivenessMemory adressing/allocation/relocationInformation formatInformation processingProgram planning
A method of pre-fetching and preparing content in an information processing system is provided. The method includes the steps of generating at least one content pre-fetching policy and at least one content preparation policy, wherein each of the policies are at least in part a function of context information associated with a user. The content is pre-fetched based on information contained within the at least one content pre-fetching policy. Once the content has been pre-fetched, it is prepared based on information contained within the at least one content preparation policy. The context information associated with the user includes at least one of the user's usage patterns, current location, future plans and preferences.
Owner:IBM CORP
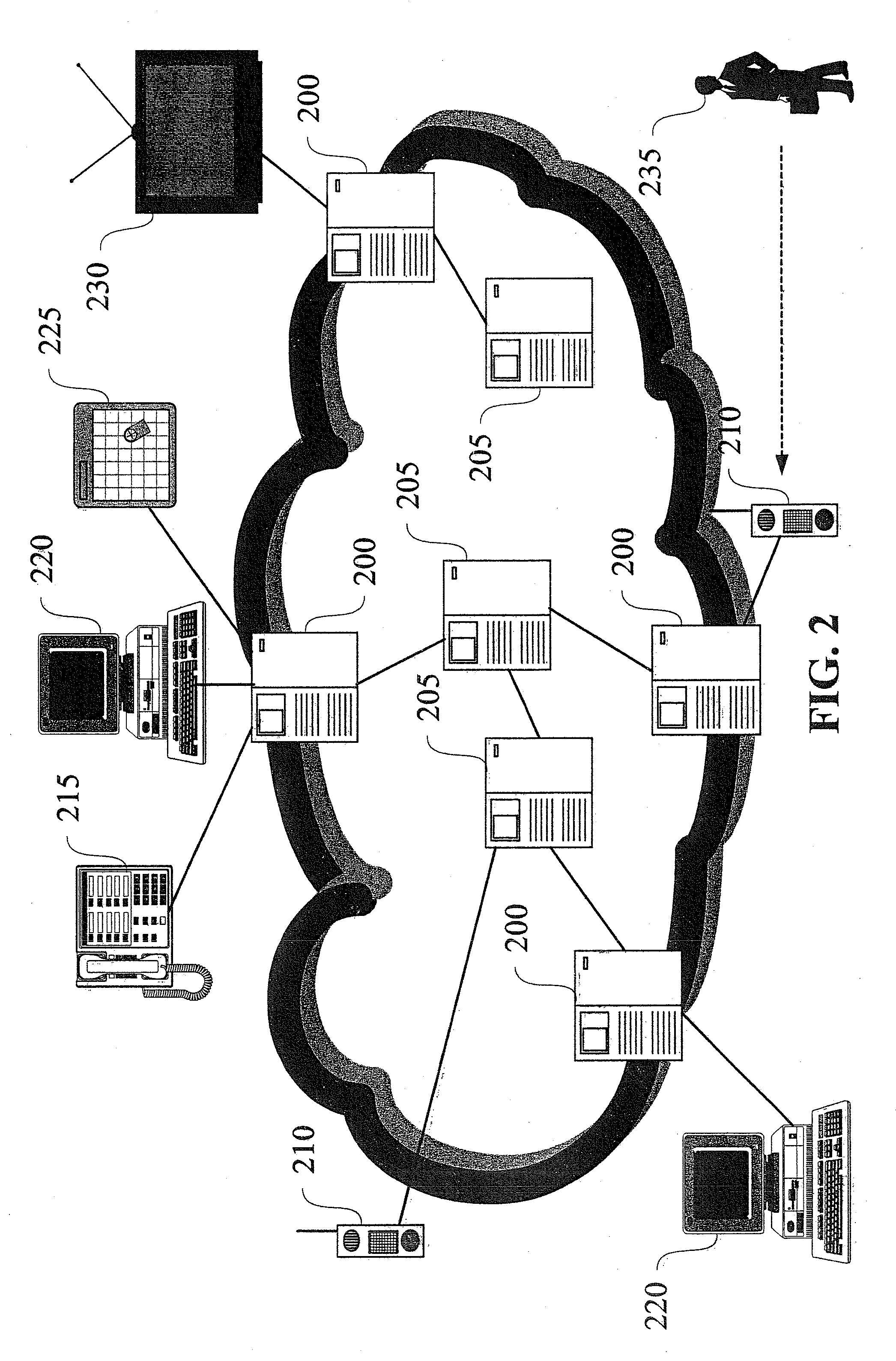
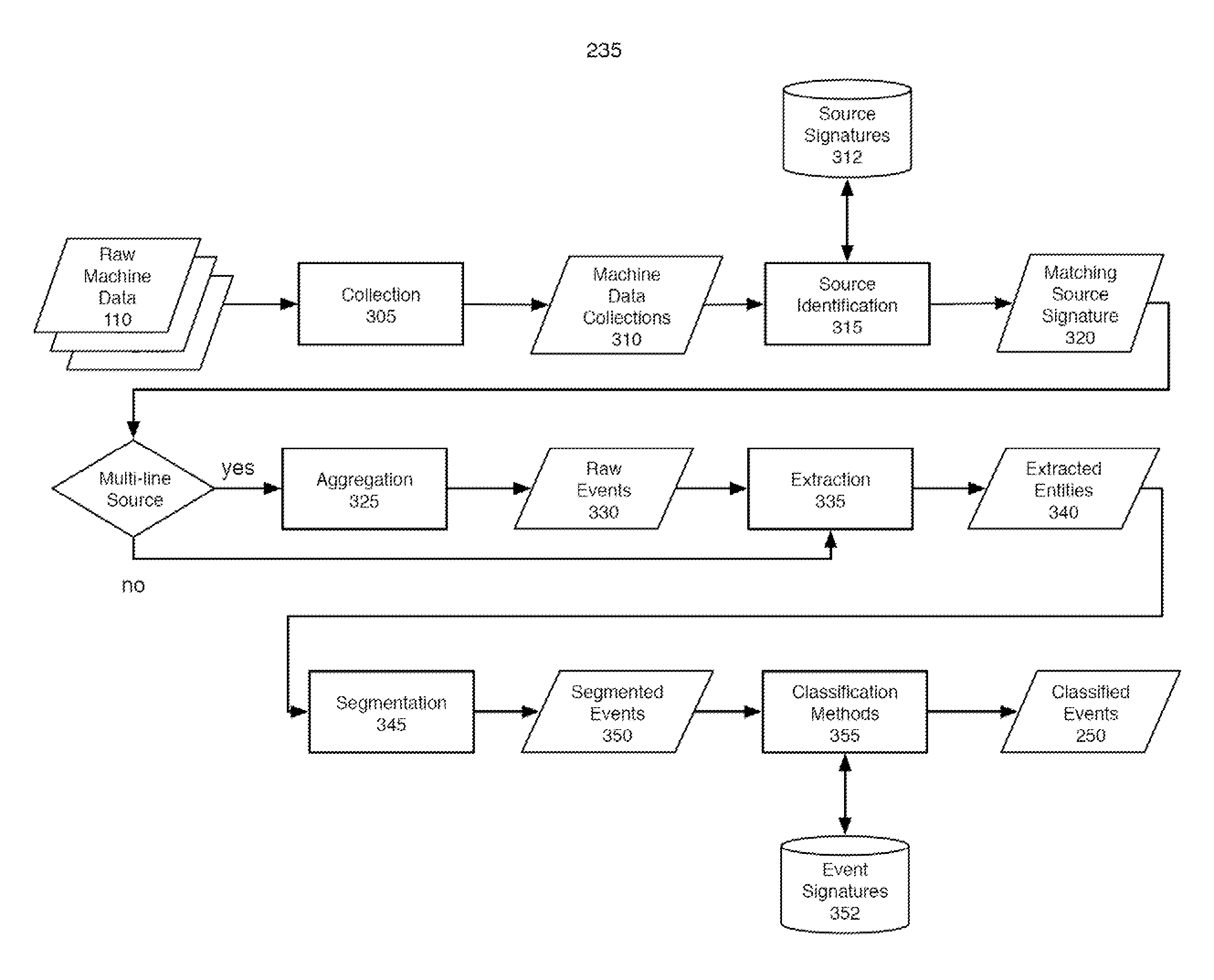
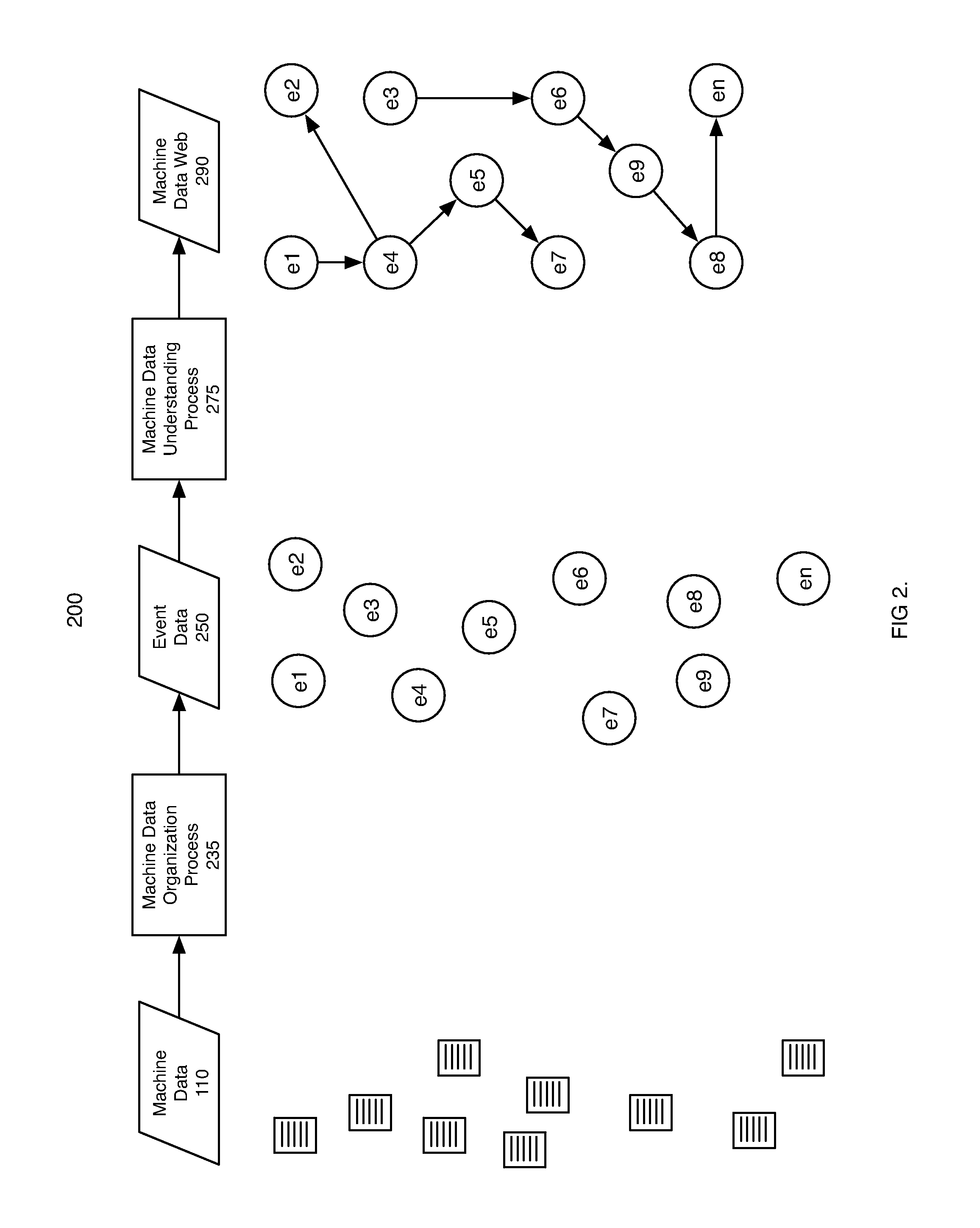
Machine data web
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
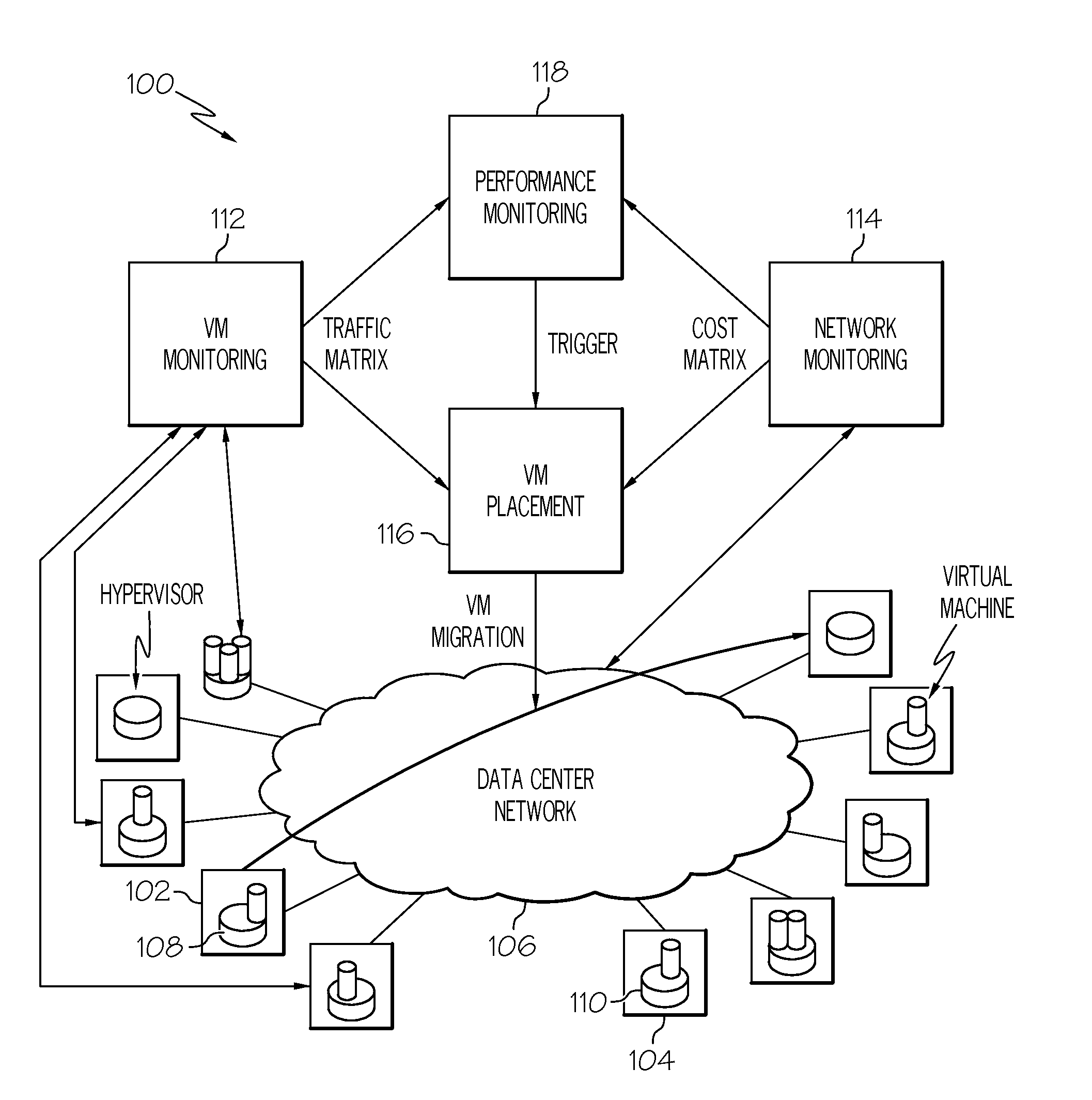
Placement of virtual machines based on server cost and network cost
InactiveUS20110225277A1Digital computer detailsMultiprogramming arrangementsInformation processingInformation handling system
A method, information processing system, and computer program product manage server placement of virtual machines in an operating environment. A mapping of each virtual machine in a plurality of virtual machines to at least one server in a set of servers is determined. The mapping substantially satisfies a set of primary constraints associated with the set of servers. A plurality of virtual machine clusters is created. Each virtual machine cluster includes a set of virtual machines from the plurality of virtual machines. A server placement of one virtual machine in a cluster is interchangeable with a server placement of another virtual machine in the same cluster while satisfying the set of primary constraints. A server placement of the set of virtual machines within each virtual machine on at least one mapped server is generated for each cluster. The server placement substantially satisfies a set of secondary constraints.
Owner:IBM CORP
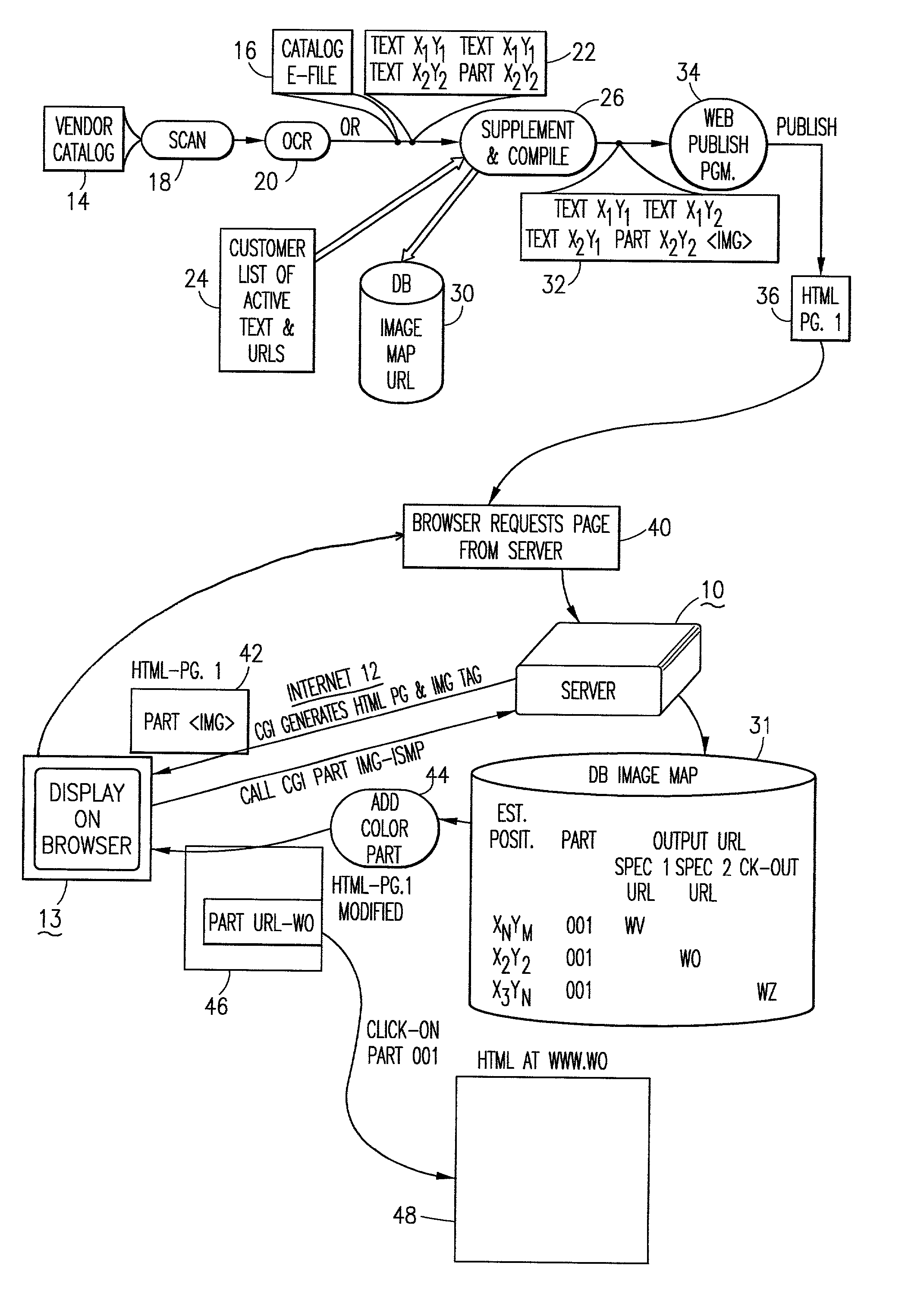
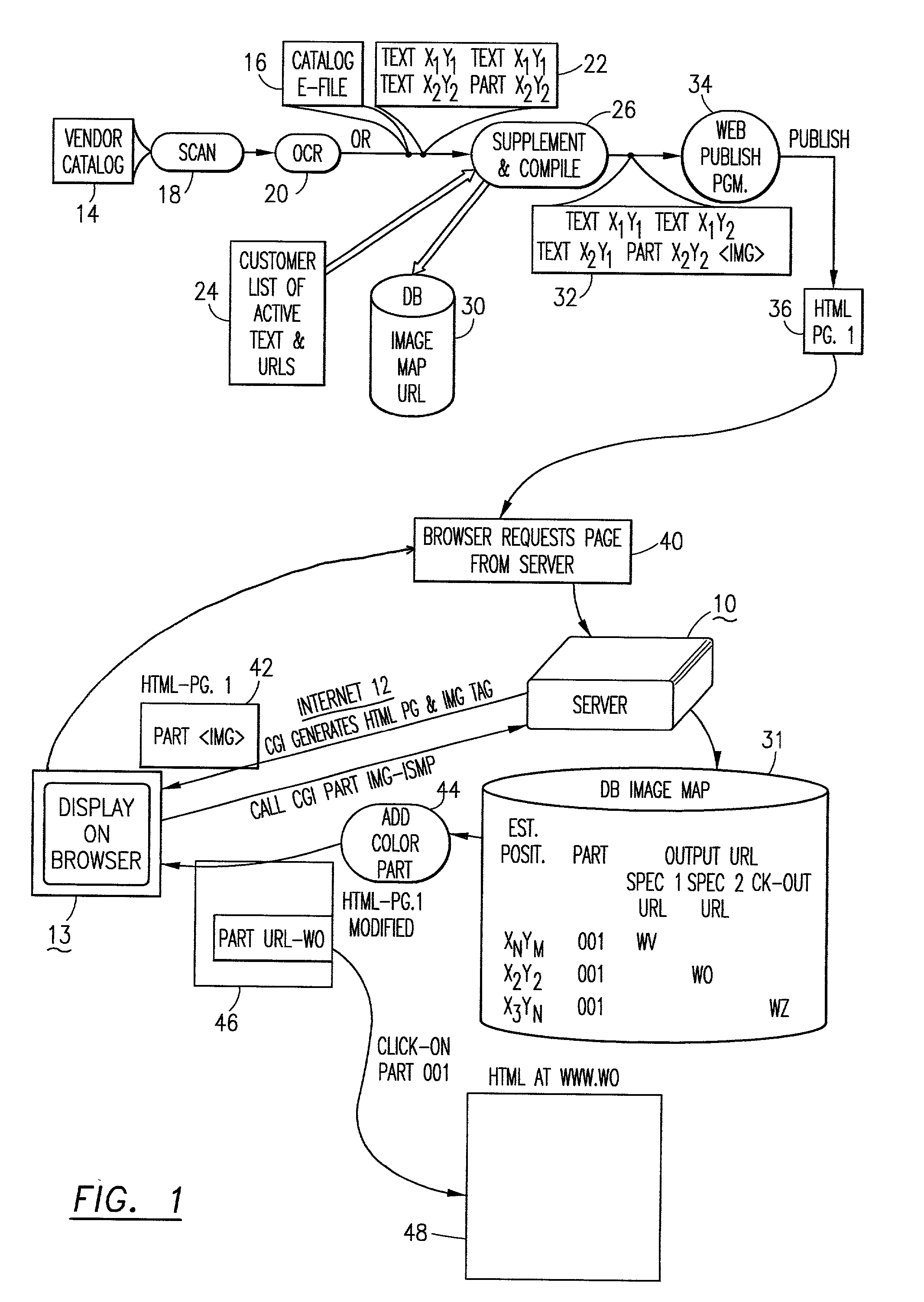
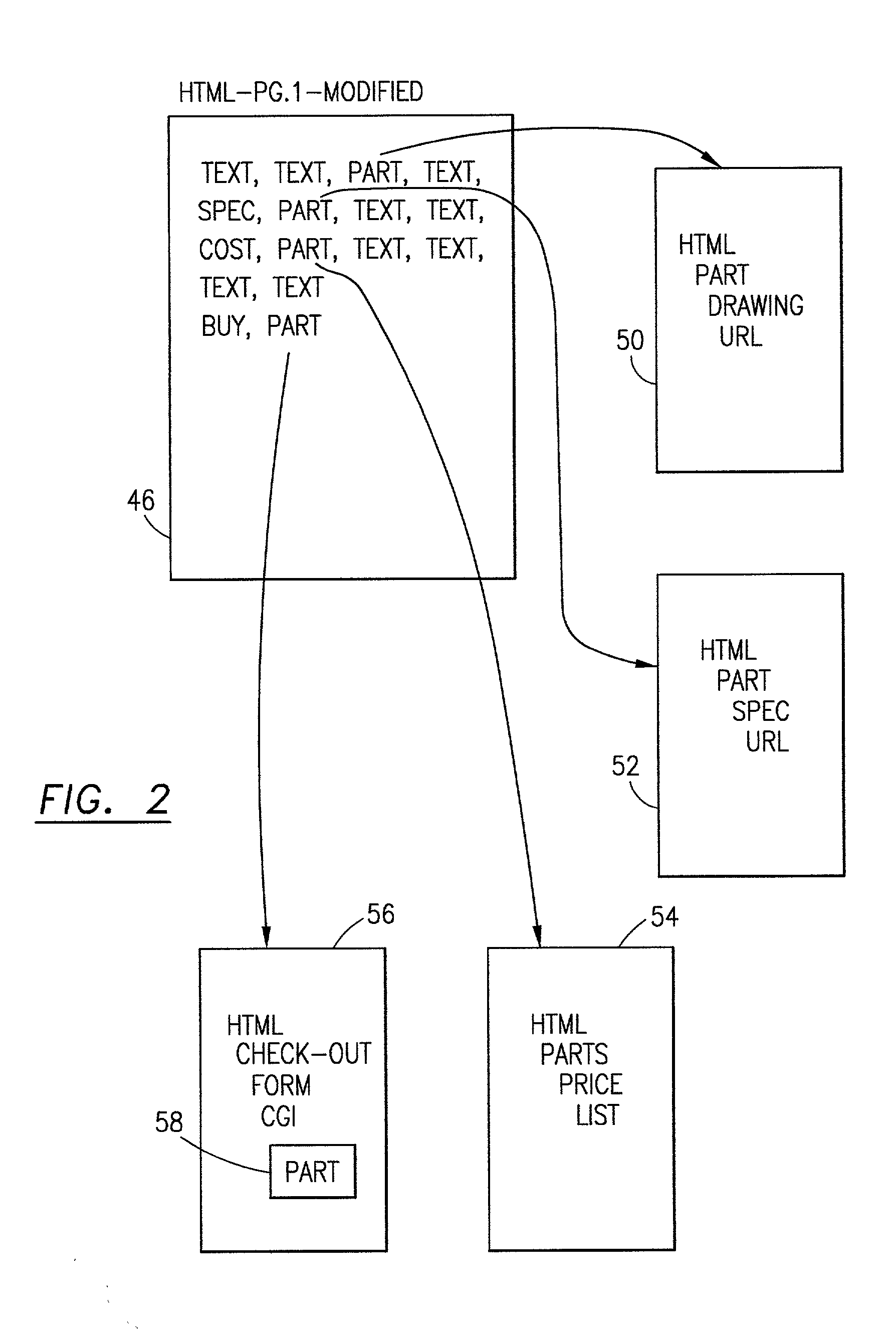
System and method for placing active tags in HTML document
InactiveUS20020069222A1Quick conversionNatural language data processingSpecial data processing applicationsInformation processingDocument preparation
The method and the information processing system dynamically creates an HTML document with at least one embedded hyperlink code therein. The HTML document is based upon a source document provided by a manufacturer or a supplier of services. Typically, the system and the method is operable in a client-server computer environment. A database is provided on the server computer system which database associates location data of a plurality of data strings in the source document with hyperlink addresses. The location data in the database maps at least one predetermined data string in the source document. An HTML document, based upon the source document, is published with an image tag on, in or near the predetermined data string. As an example, the string may be a "part number" or a string of words "SONY PLAYSTATION II.". The published HTML document has an image tag on, at or near the part number and a map attribute command which supplies or generates an HTML location data unique to the image tag location in the HTML document when the browser calls the server's common gateway interface (CGI). The image tag URL points to the database on the server. The server, via the database provides a corresponding hyperlink address, associated with the unique location data correlated to the HTML location data, to the browser on the client computer system. The method and the system then publishes and embeds in the original or initial HTML document at, on or near the predetermined data string or part number an active hyperlink tag (an embedded code) with the corresponding hyperlink address obtained from the database.
Owner:WIZNET
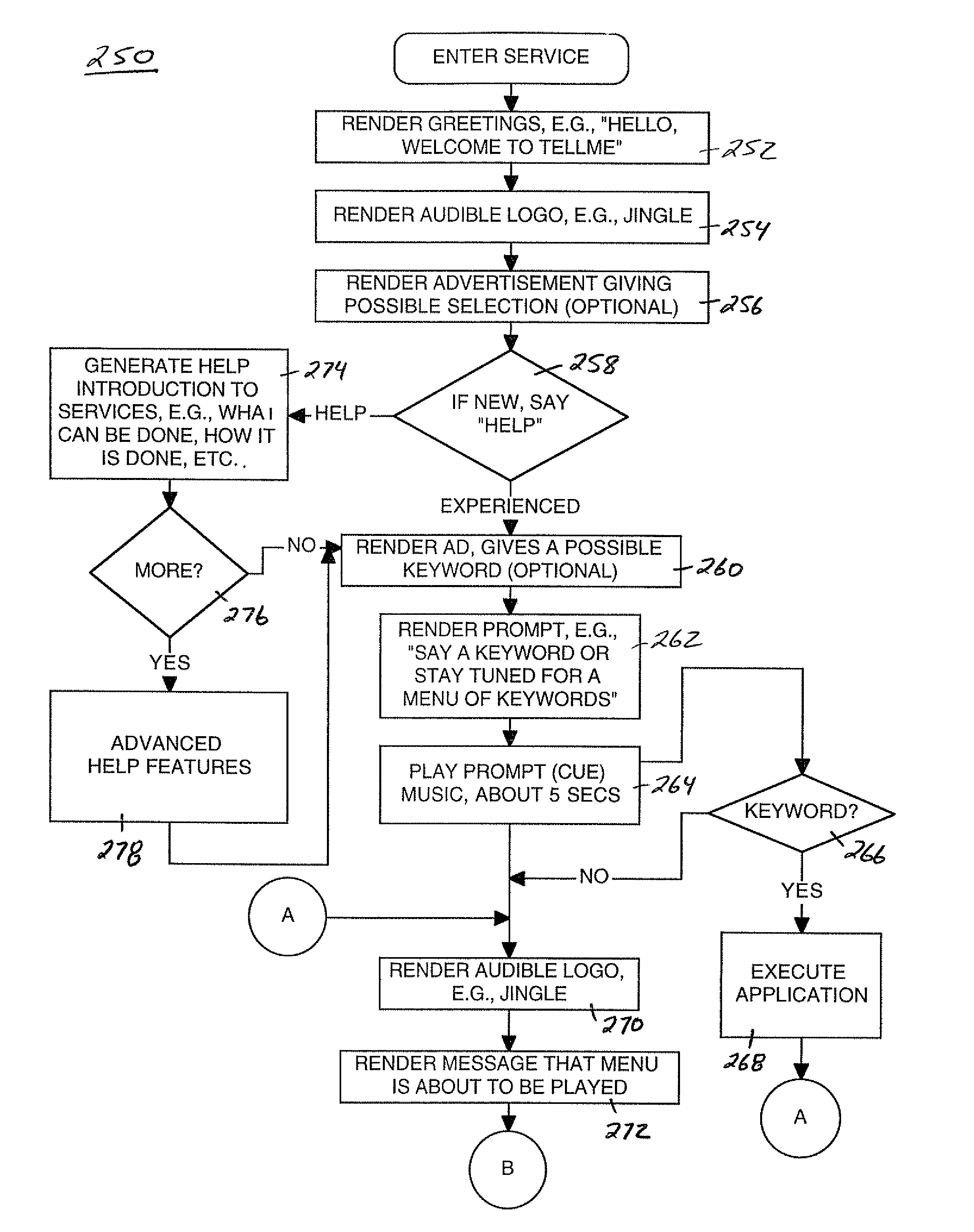
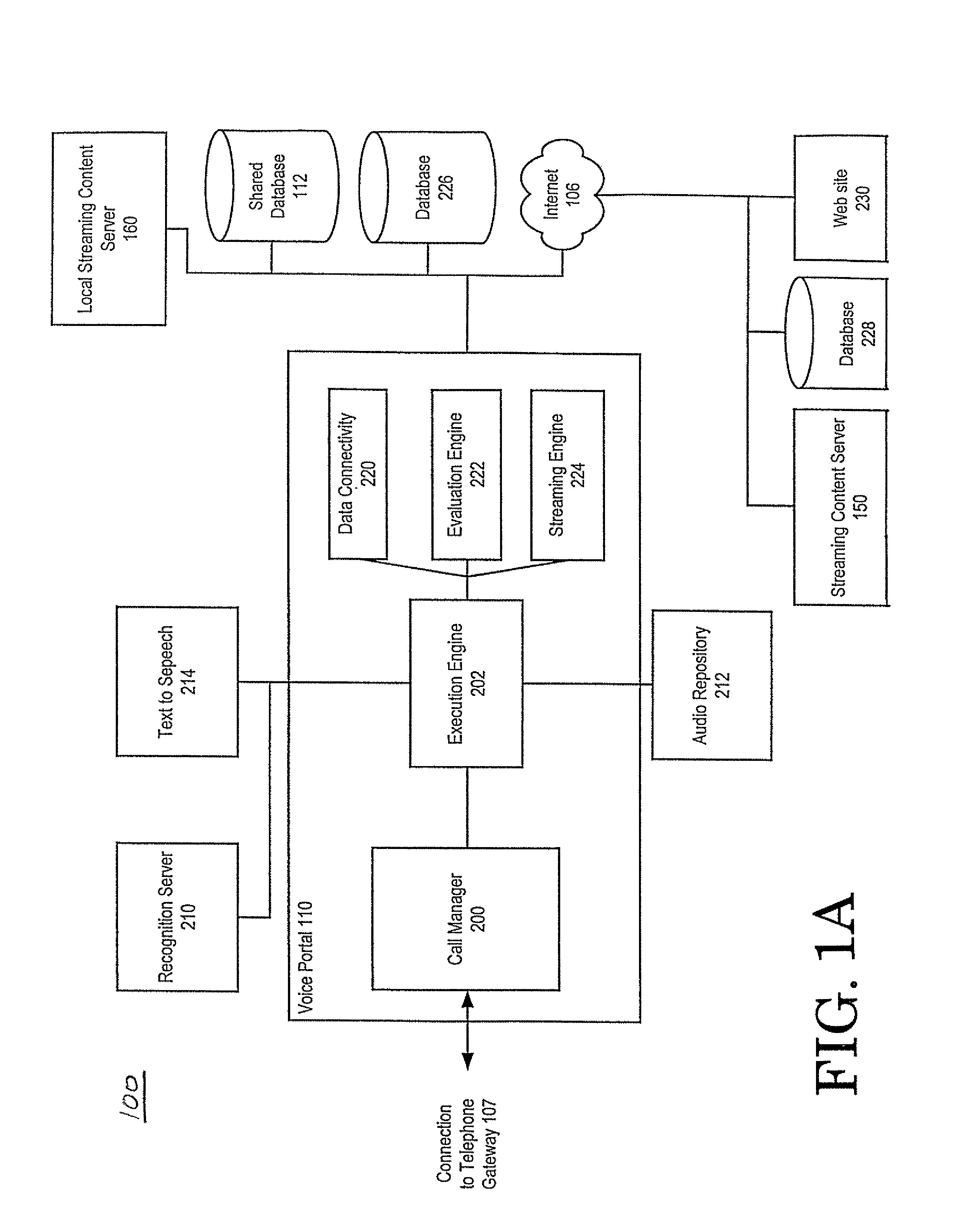
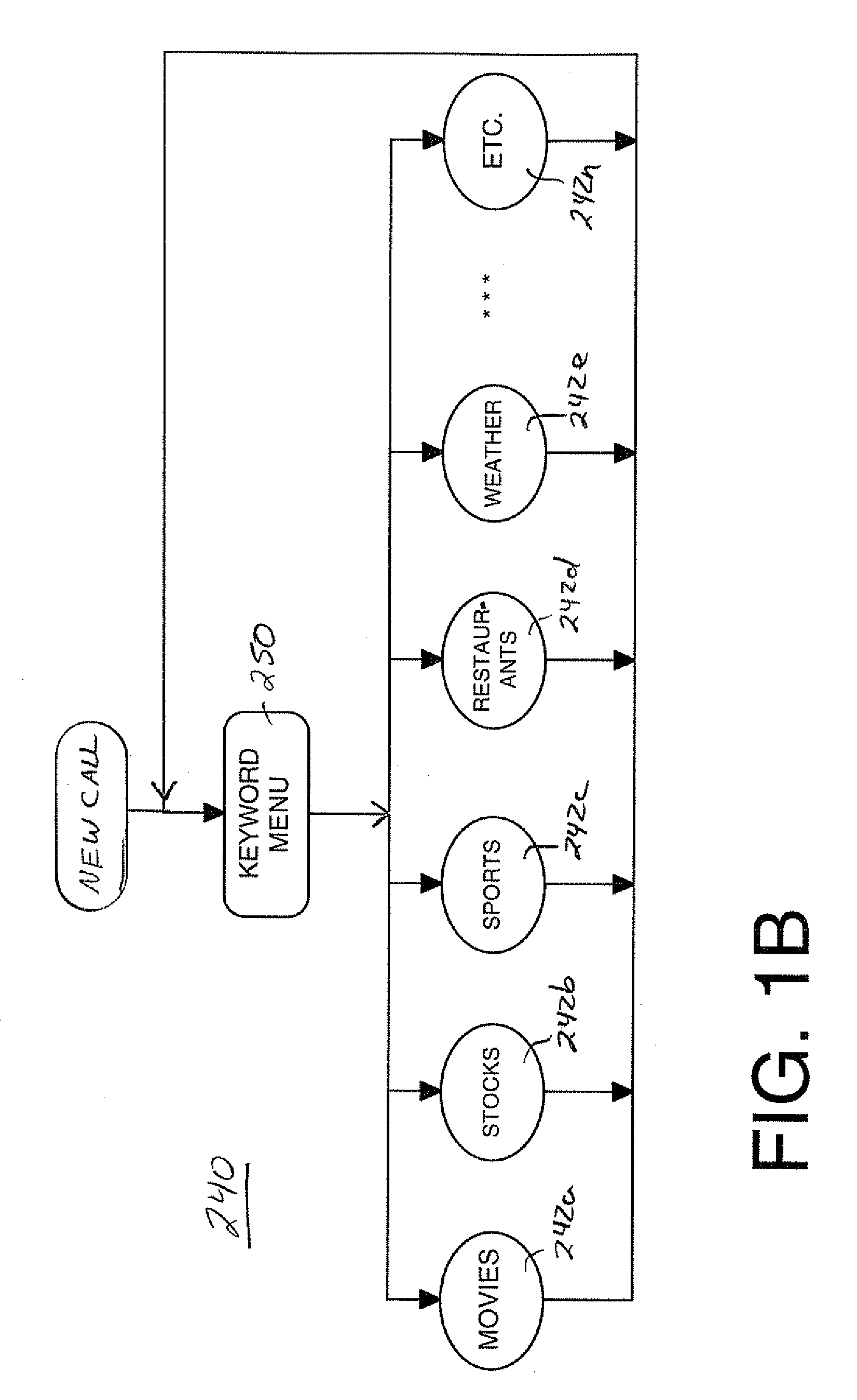
Providing services for an information processing system using an audio interface
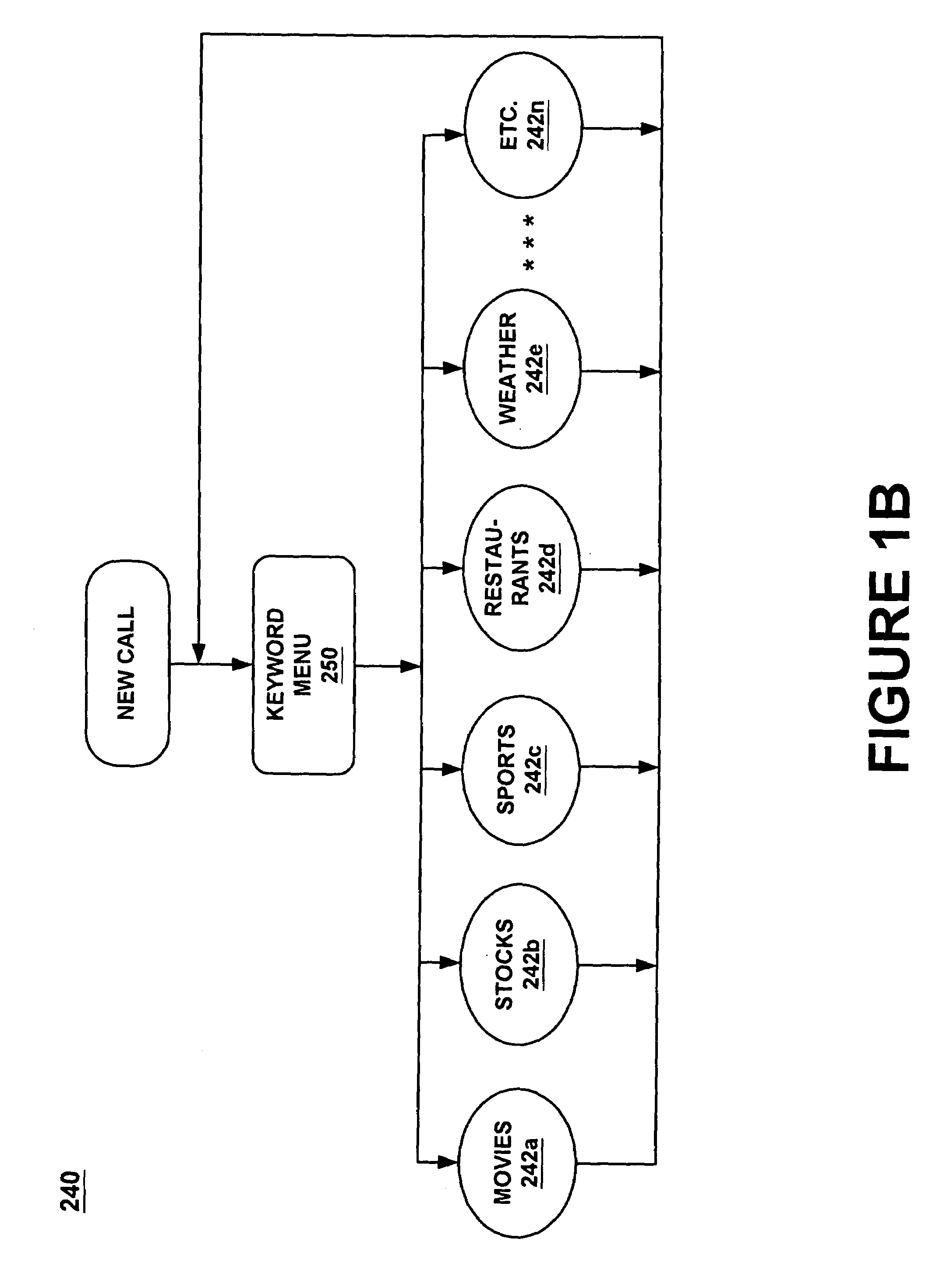
InactiveUS7308408B1Structured and efficient and effectiveEffectivelyAutomatic exchangesSpeech recognitionInformation processingSpeech identification
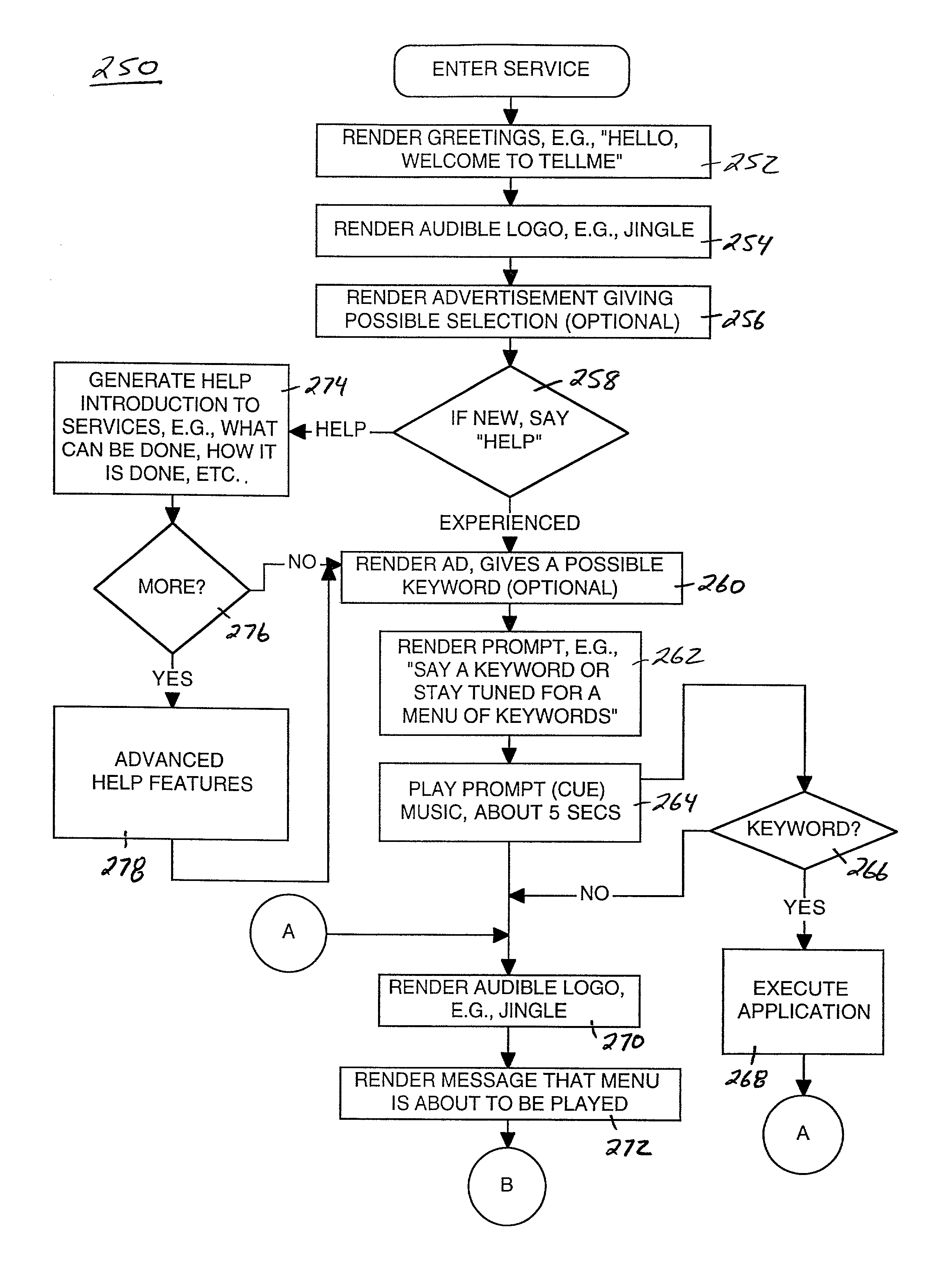
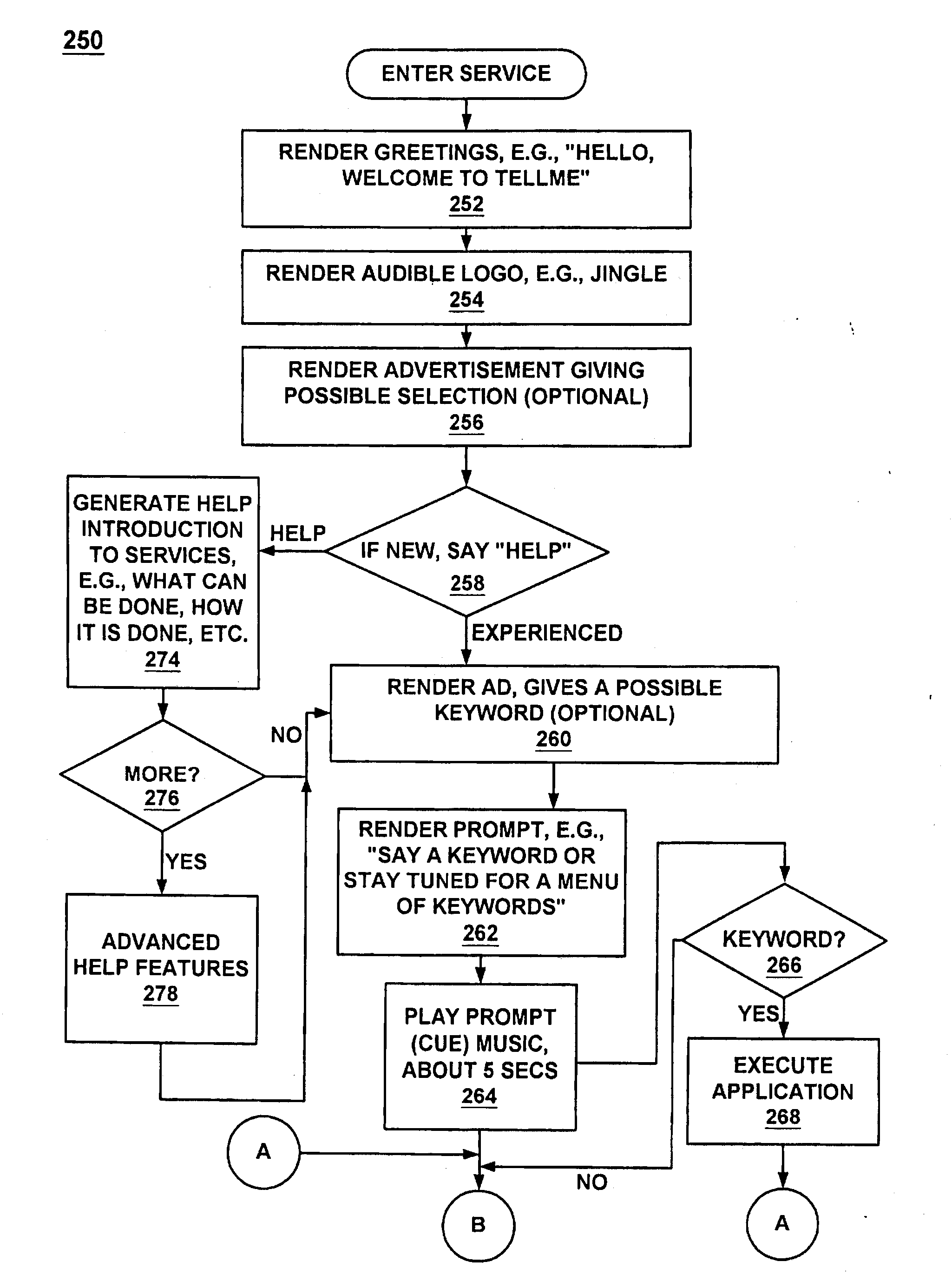
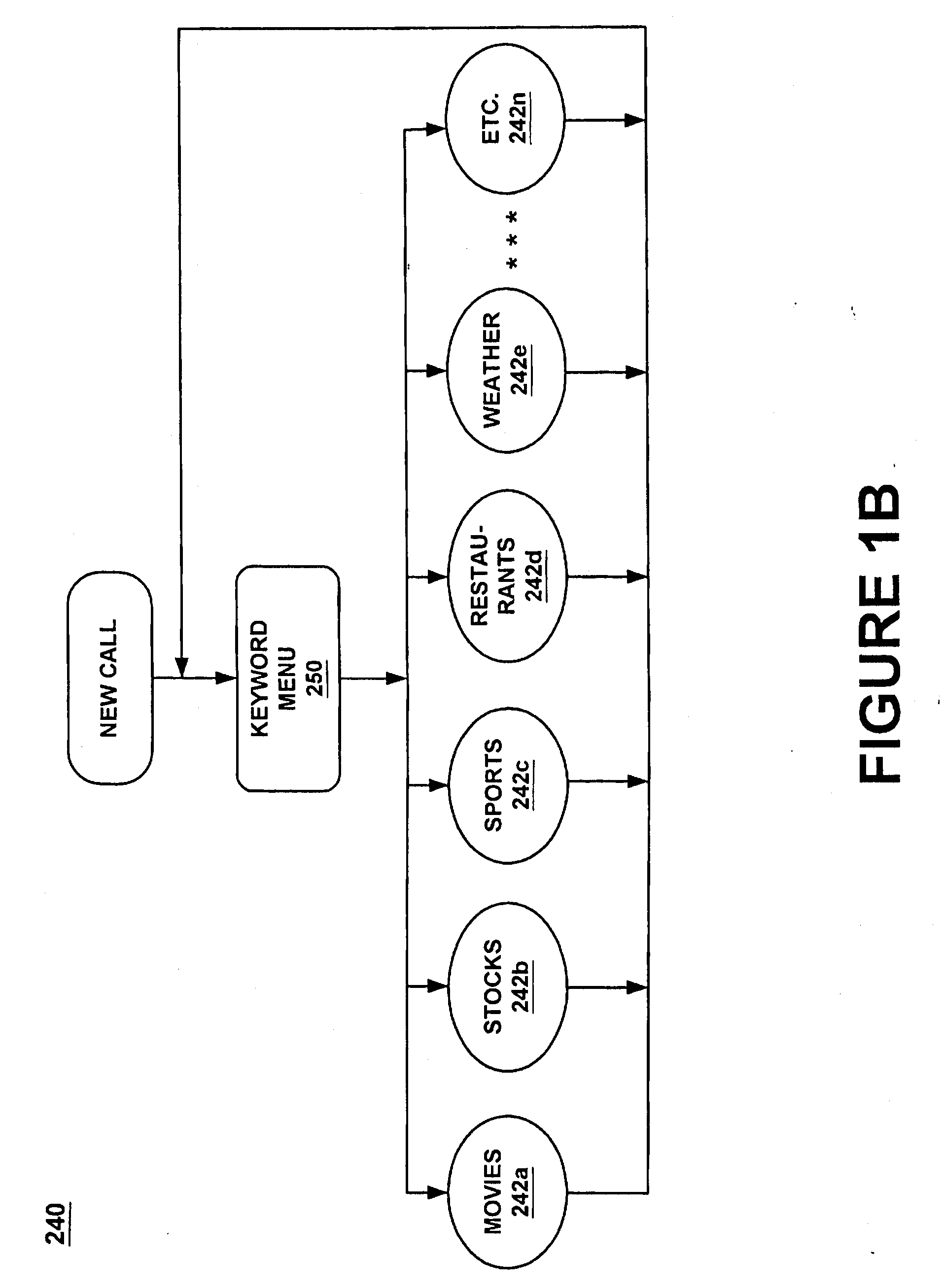
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
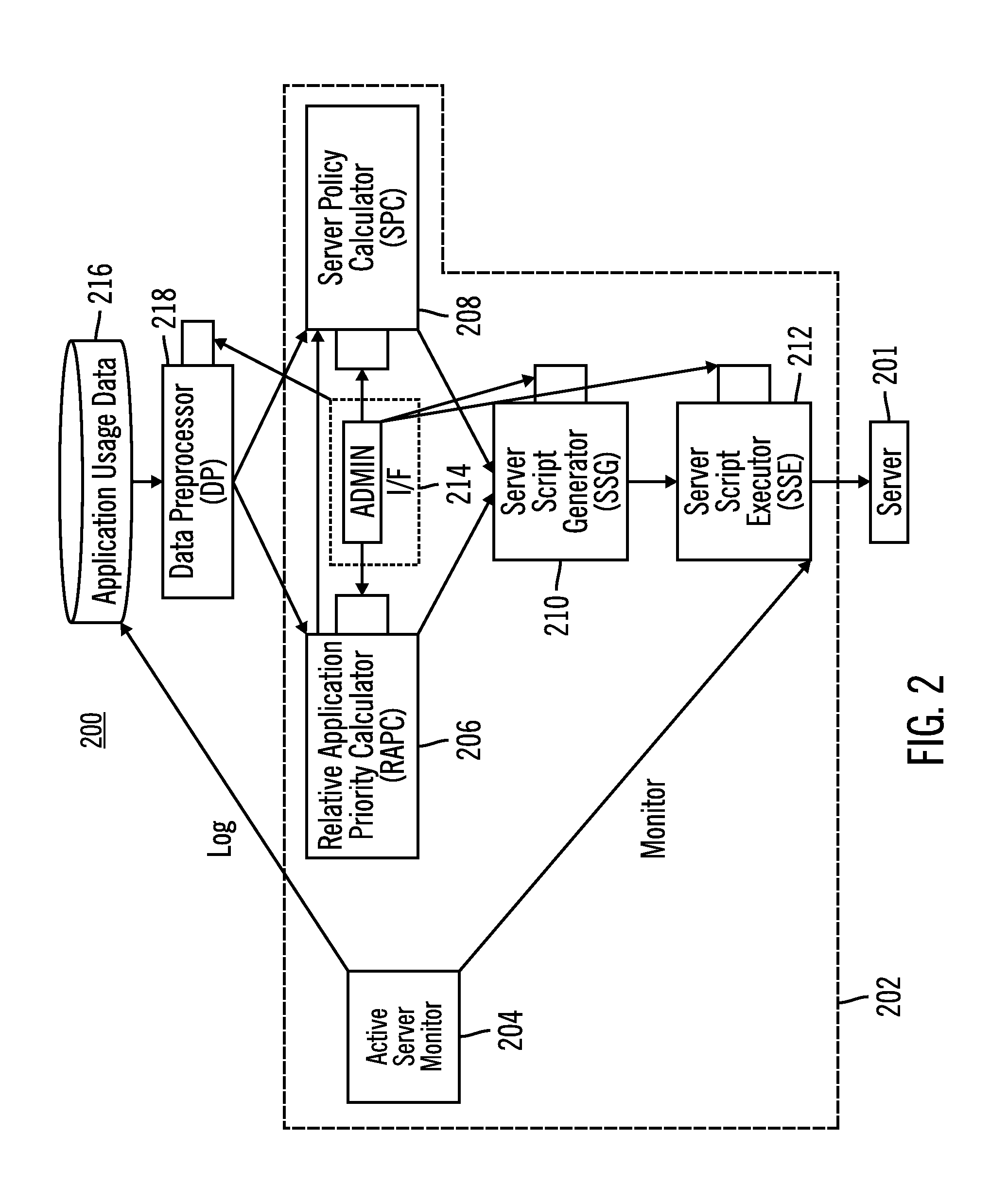
SAN Performance Analysis Tool
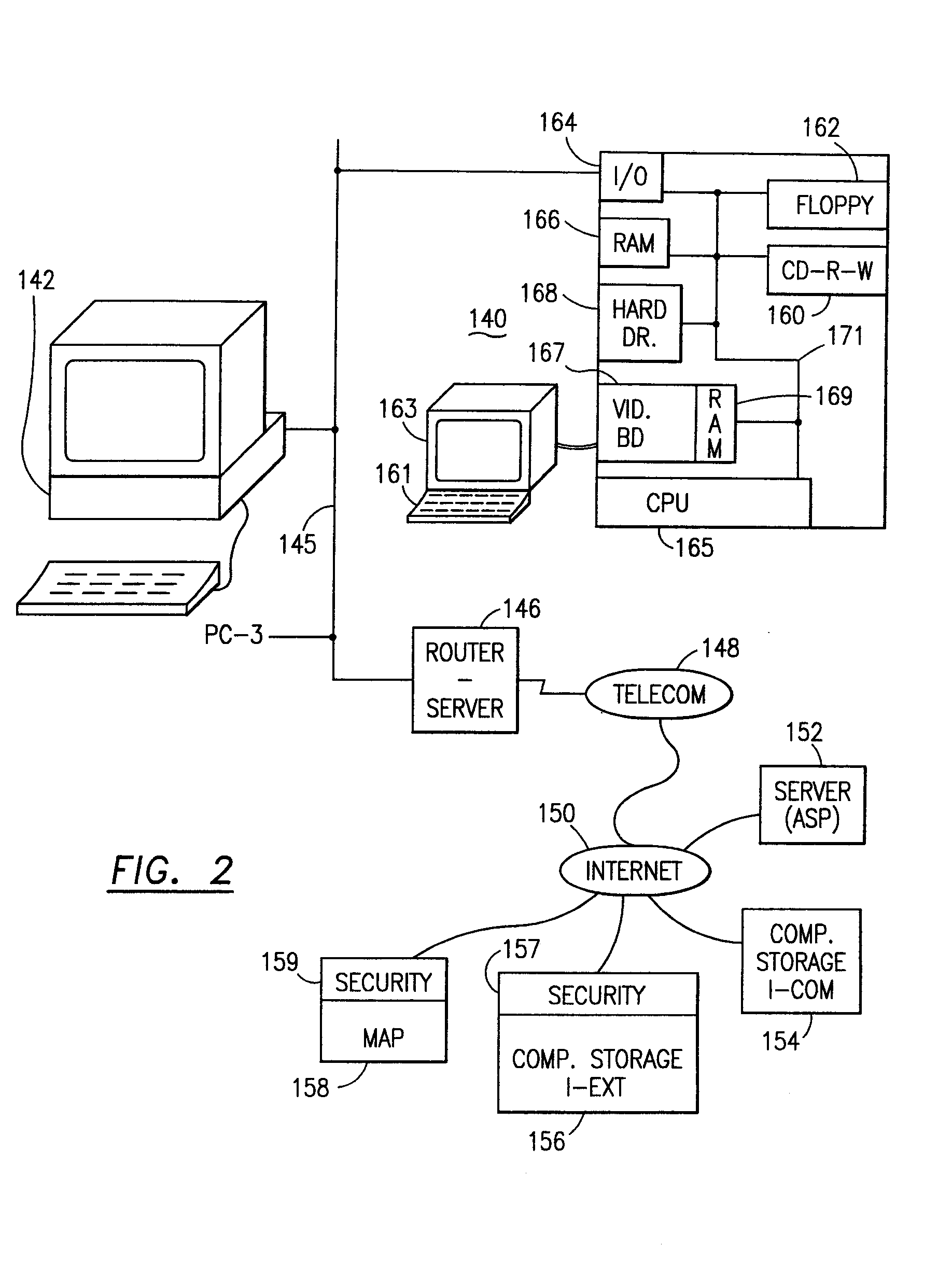
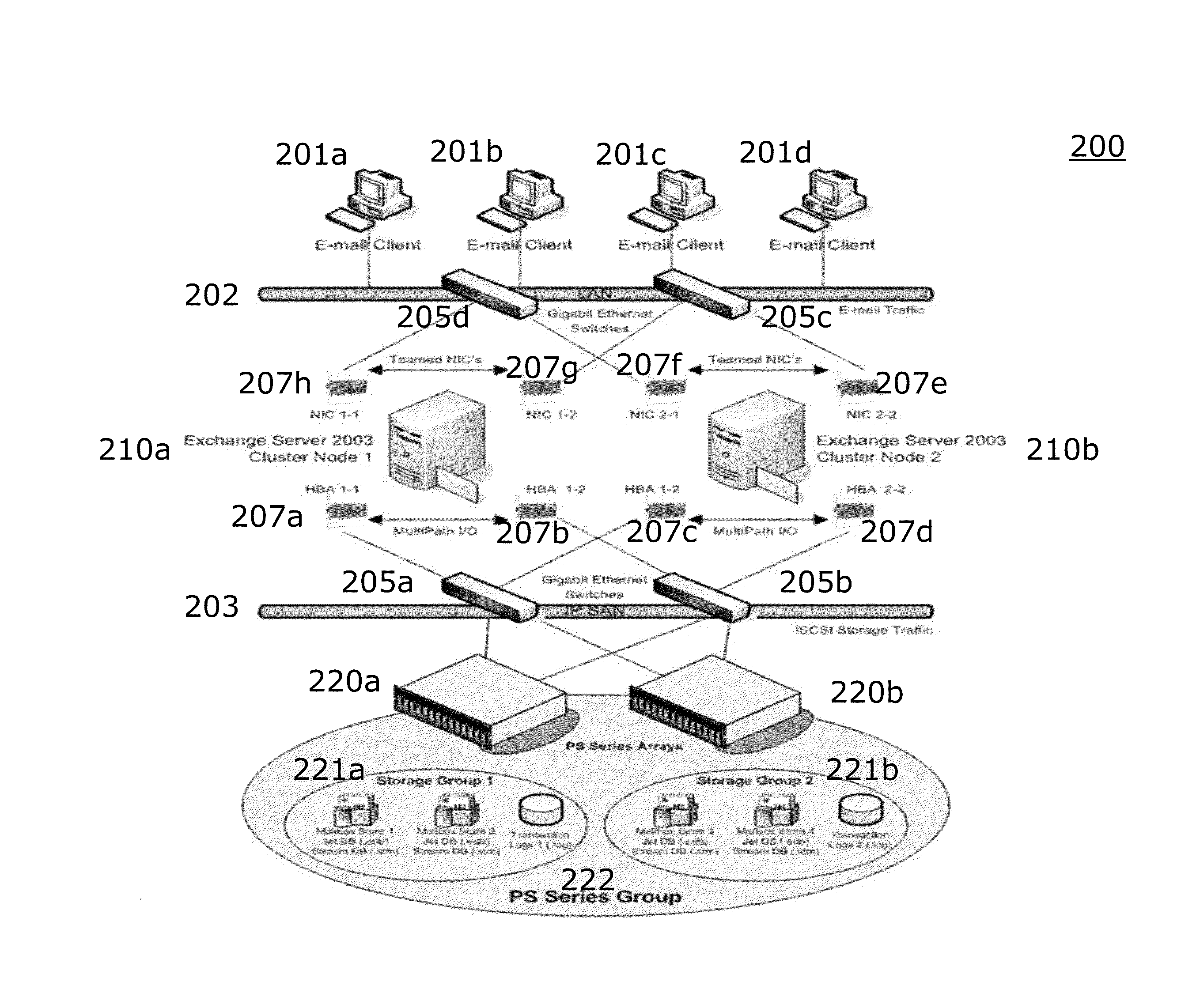
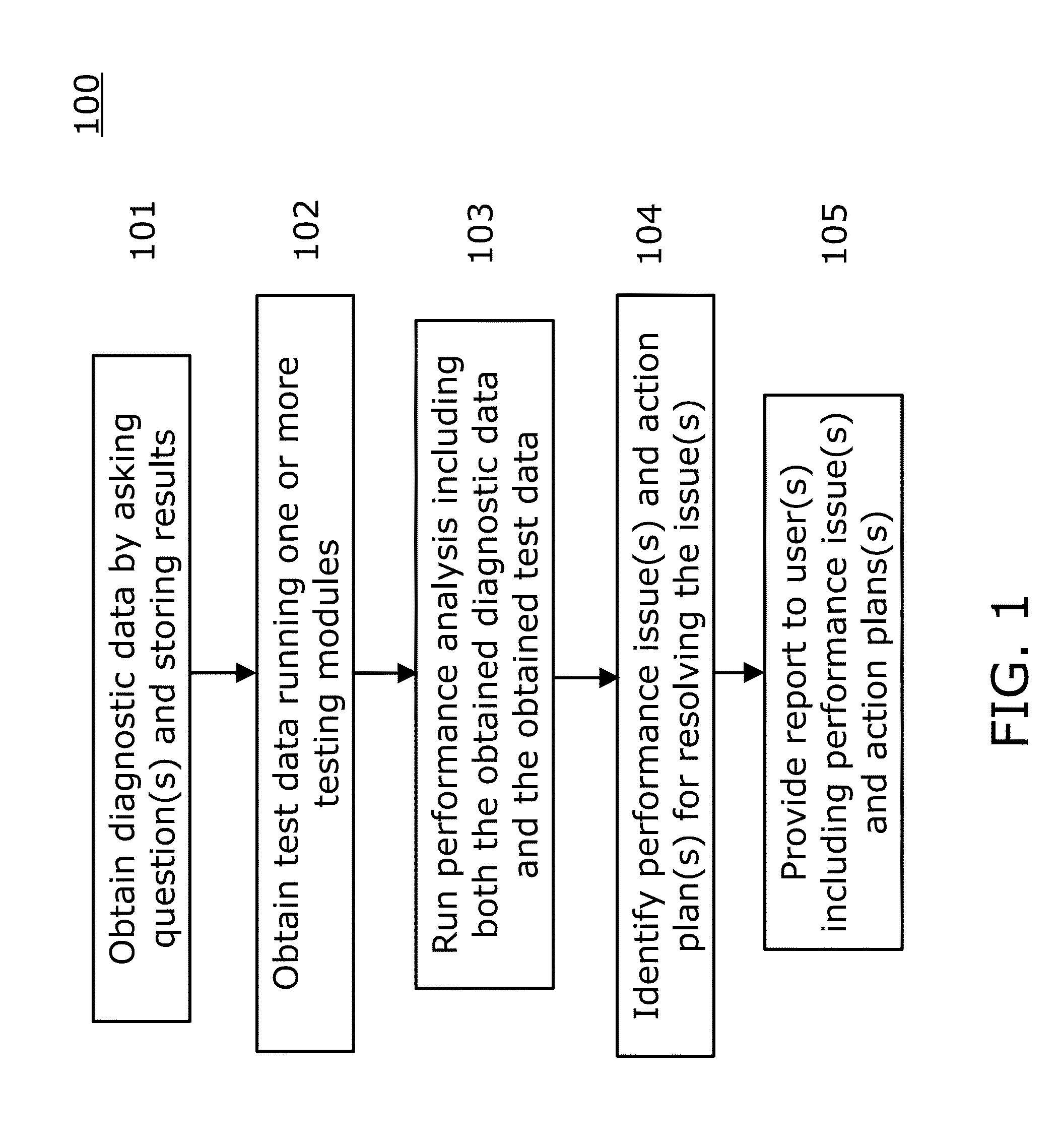
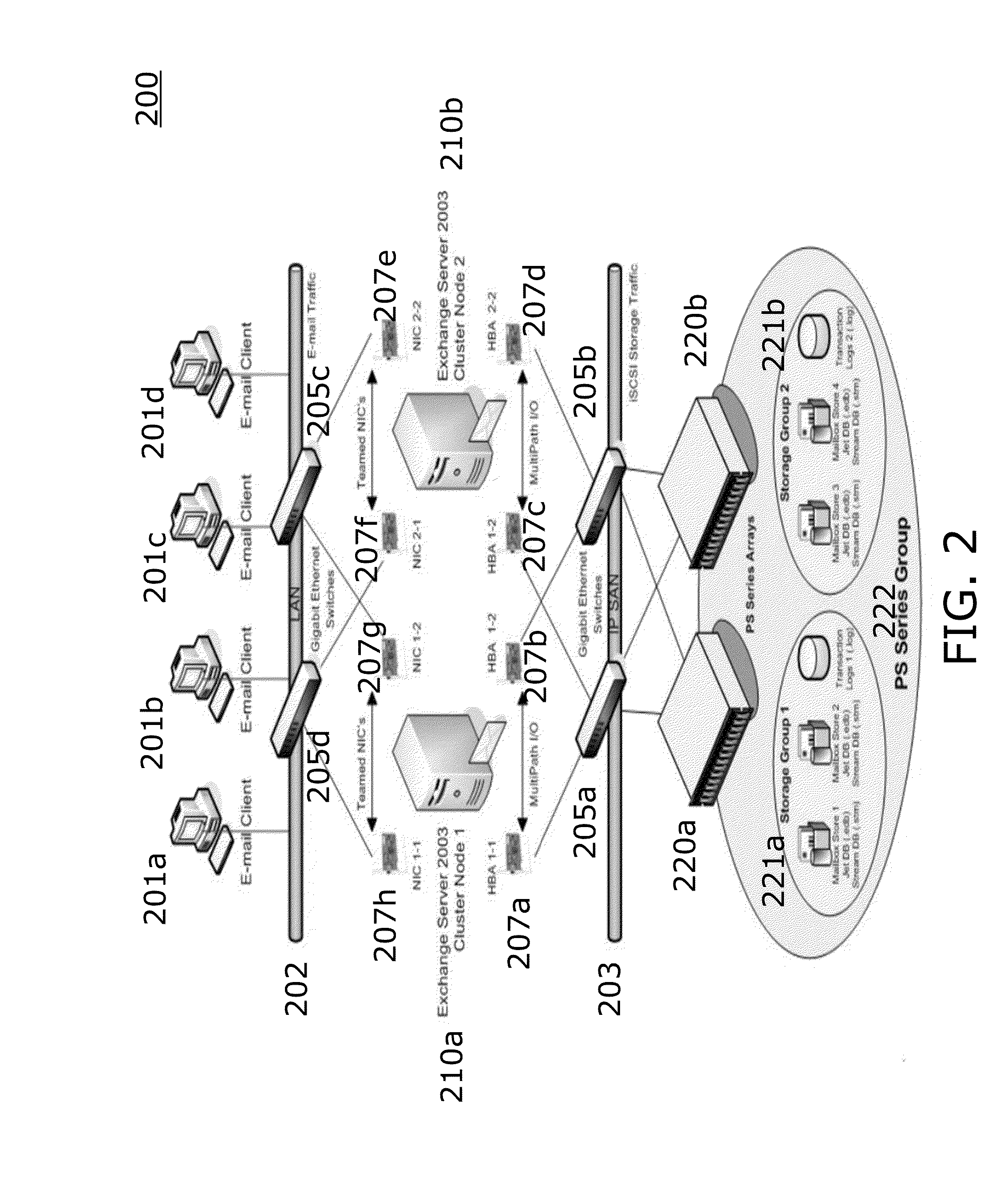
The present invention is directed to a method and information handling system (IHS) for improving system performance in a storage area network. An embodiment of the present invention begins by obtaining diagnostic data for the storage area network by asking a user one or more questions and storing results to the one or more questions. Next, test data is obtained by running one or more testing modules on at least one component of the storage area network. A performance analysis of the storage area network is executed, including the obtained diagnostic data and the obtained test data. Then, one or more performance issues and one or more action plans for resolution are identified based upon the analysis. Finally, a report to one or more users is provided including the one or more identified performance issues and the one or more action plans.
Owner:DELL PROD LP
Providing menu and other services for an information processing system using a telephone or other audio interface
InactiveUS7143039B1Reduce generationStructured and efficient and effectiveAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesInformation processingWord selection
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
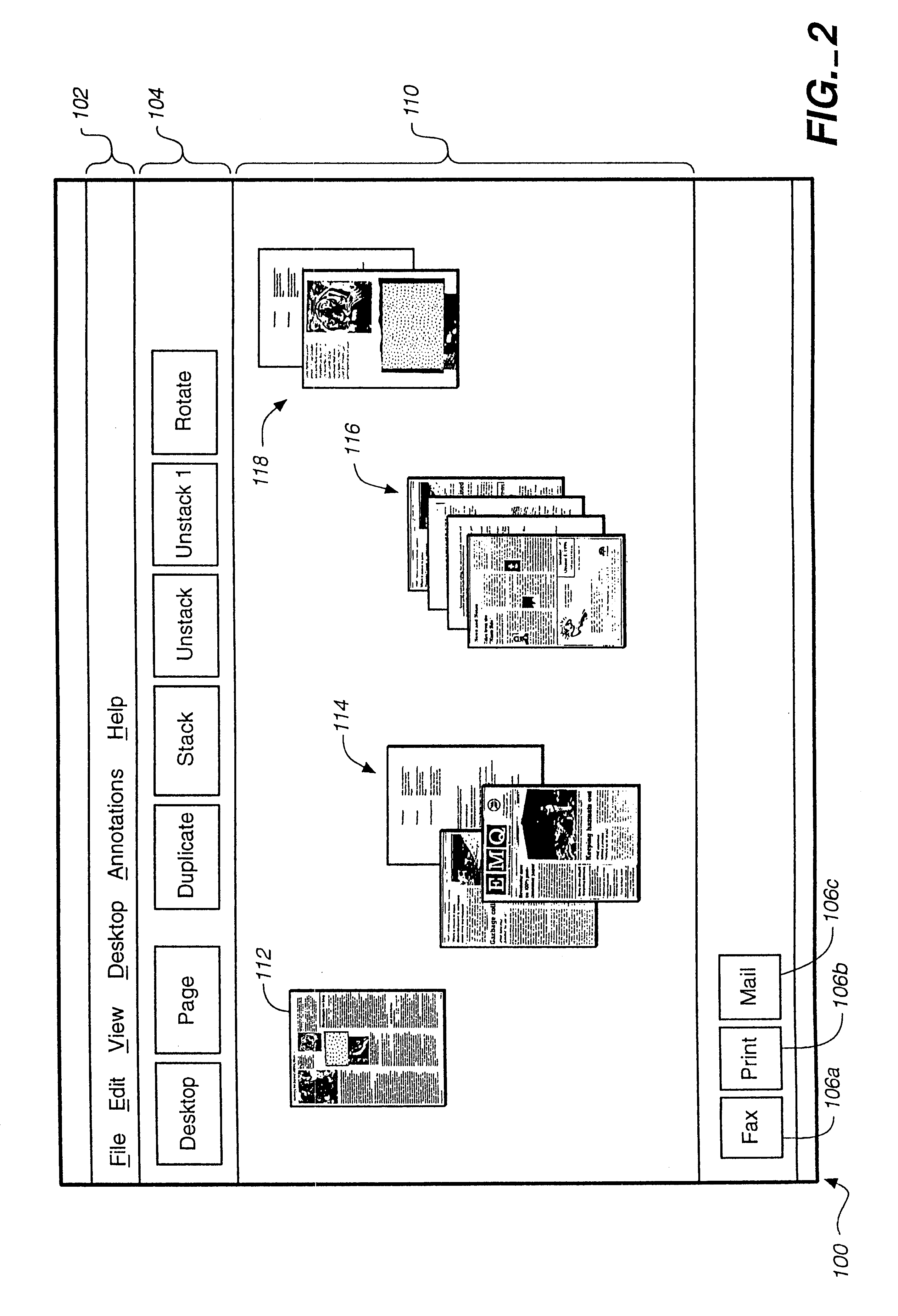
Method and apparatus for managing and navigating within stacks of document pages
InactiveUS6262732B1Easy to operateSimplifies movingDigital data information retrievalDigital computer detailsInformation processingDocumentation procedure
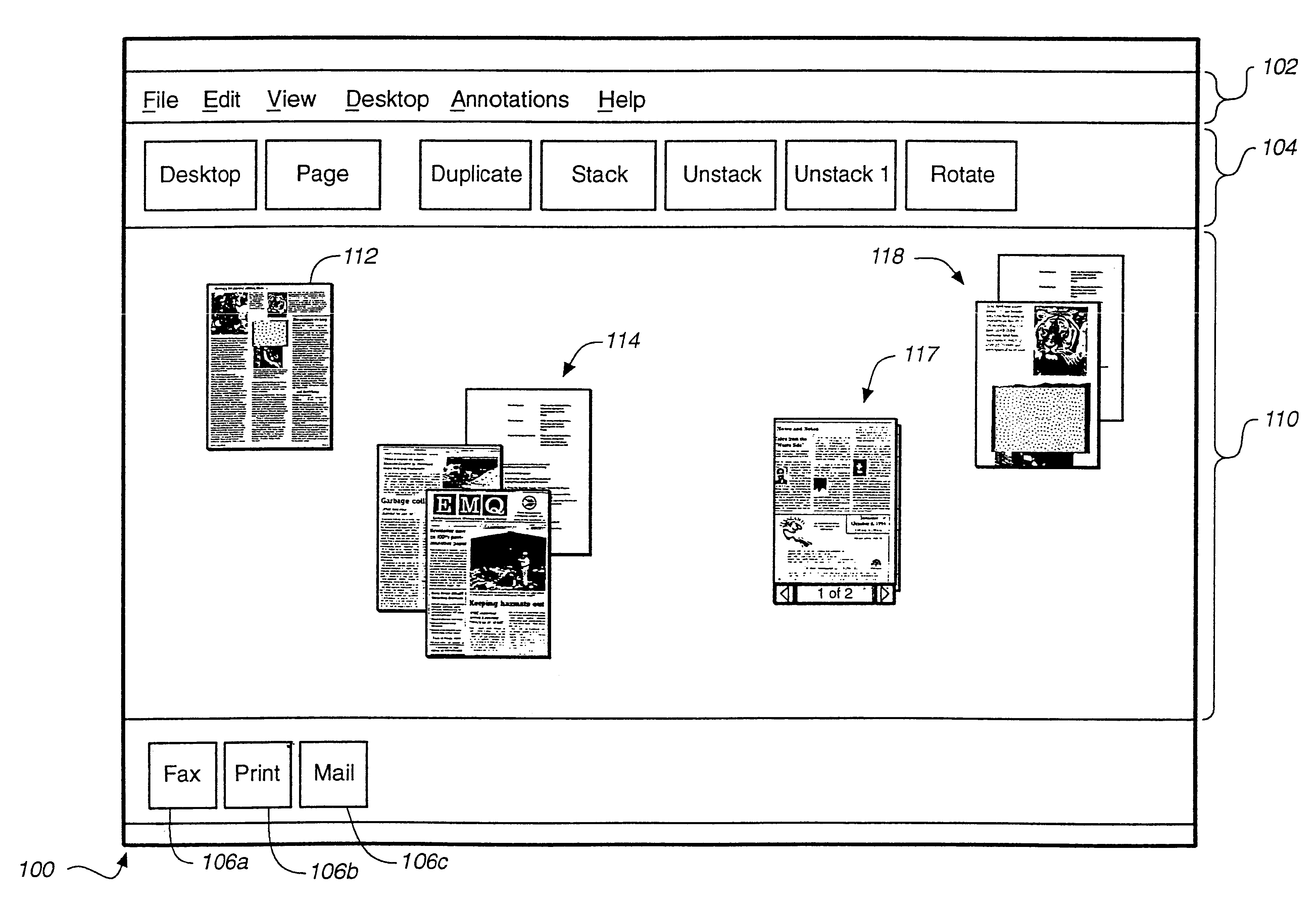
An apparatus and method for an information processing system are disclosed for improved manipulation of documents consisting of multiple pages. In one embodiment, a multi-page document is depicted by a representation of a stack of pages and a request area through which an operator may navigate within the stack. In another embodiment, a multi-page document is depicted by static icon representing the stack and a dynamic miniature replica of a current page within the stack. Additional functions are disclosed such as adding one or more pages to a document, removing a page from a stack, rotating a page within a stack, and adding annotations to a page.
Owner:CANON KK
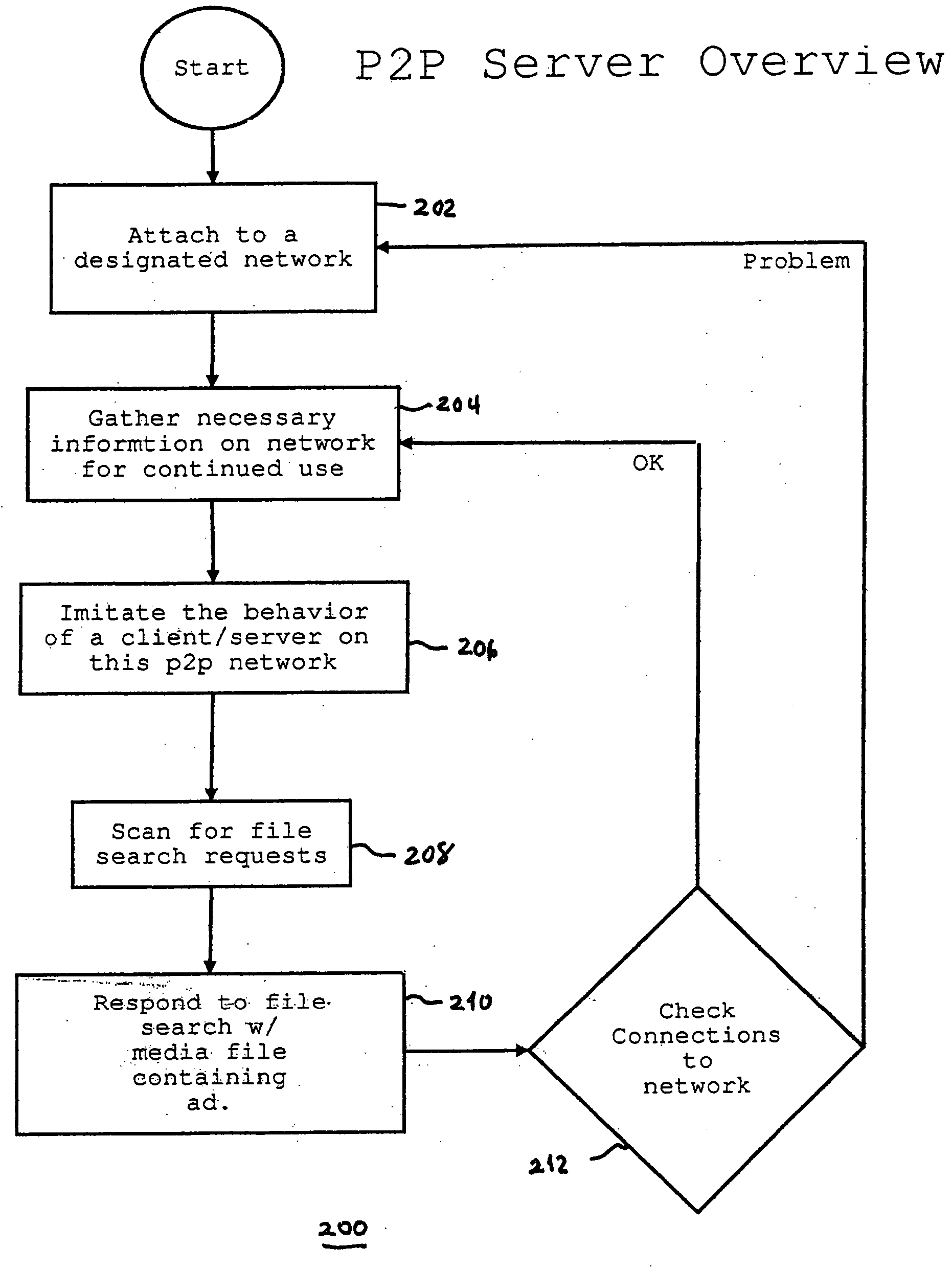
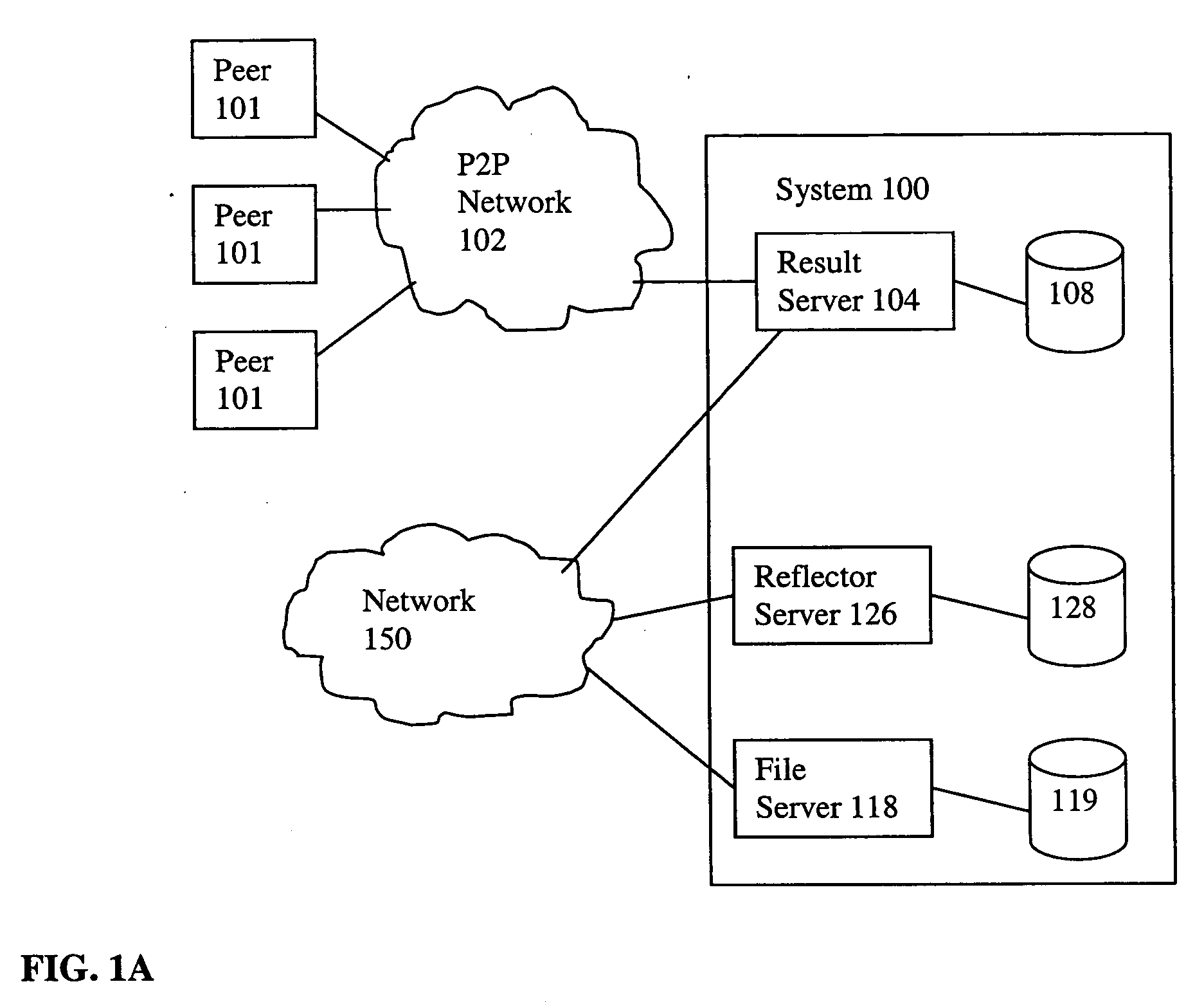
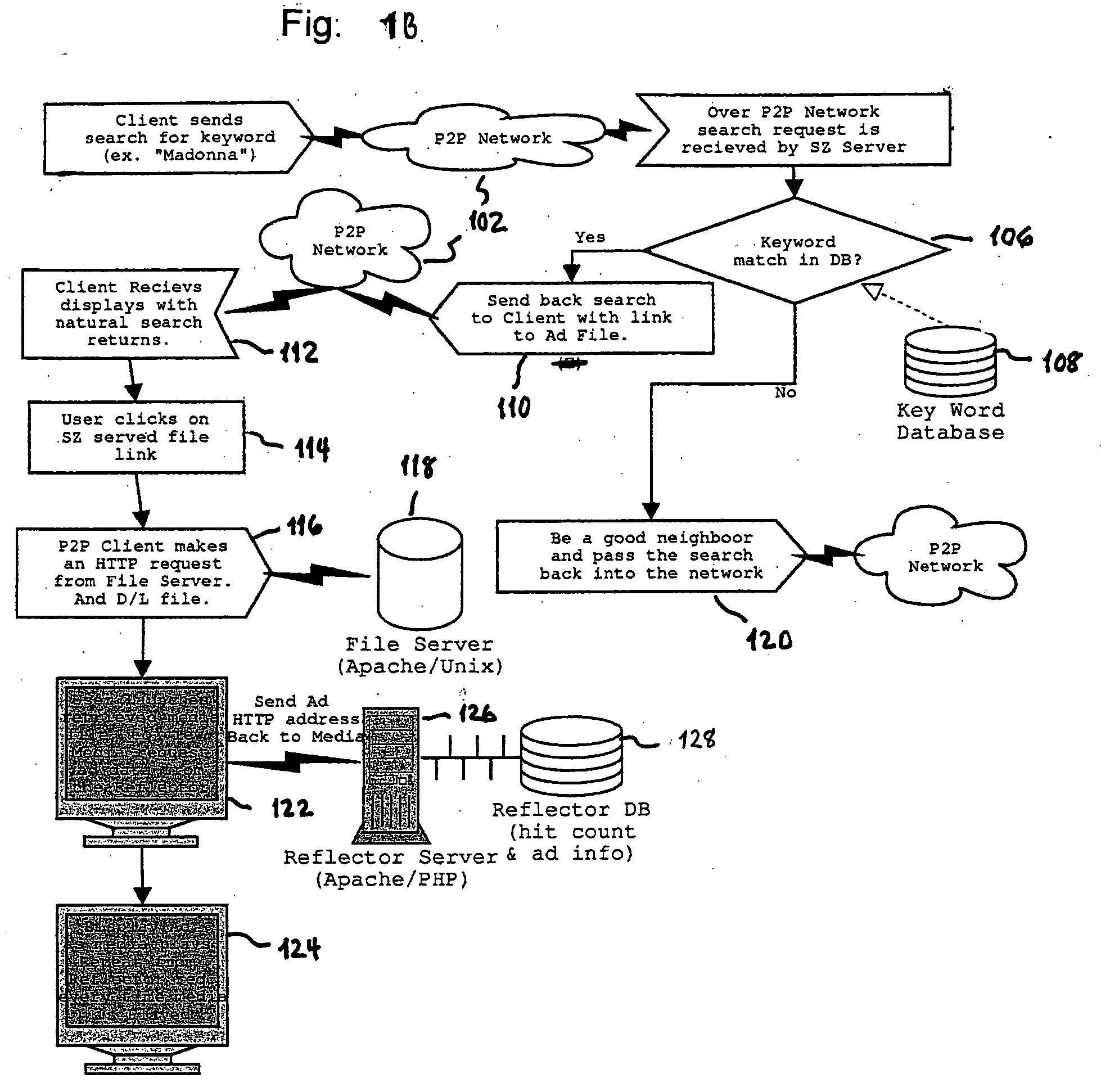
System and methods for direct targeted media advertising over peer-to-peer networks
An information handling system according to the invention comprises an input for receiving search requests seeking one or more specified files; a search engine for searching a database for names of files satisfying a received search request; and server logic for serving a results page comprising the names of files satisfying a received search request and a hyperlink associated with each file name. Each hyperlink in the results, when activated causes transmission of a request for the selected file that is associated with the link. The request for the selected file is directed to a file server controlling a database of files including the selected file. The file server responds to the request by serving a content (or media) file comprising a copy of the selected file with an embedded request for information for presentation to the person from whom the search request was received. When the user runs the downloaded content file the content file sends a request for service to a site (e.g., a reflector server) that responds by serving information such as advertising to the requester.
Owner:MOGANSTEIN DAVID MR
Data security system and method for portable device
ActiveUS7313825B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsDigital data processing detailsInformation processingEvent trigger
The method, used with a portable computing device, secures security sensitive words, icons, etc. by determining device location within or without a predetermined region and then extracting the security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only in the presence of a predetermined security clearance and within certain geographic territories. A computer readable medium containing programming instructions carrying out the methodology for securing data is also described herein. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
System and Method for a Vector-Space Search Engine
InactiveUS20110179002A1Reduce delaysImprove usabilityWeb data indexingDigital data processing detailsGraphicsGeneral purpose graphical processing unit
A system and method for a search engine is disclosed. A method for operating a search engine may include calculating a plurality of document vectors, receiving a search request, calculating a search request vector, calculating a distance between the search request vector and the plurality of document vectors, and returning a list of documents that are within a predetermined distance of the search request vector. An information handling system for a search engine may include a central processing unit that is coupled to a general purpose graphical processing unit. The central processing unit is able to calculate a plurality of document vectors, receive a search request, calculate a search vector, and return a list of documents that are within a predetermined distance of the search request vector. The general purpose graphical processing unit is able to calculate a distance between the search request vector and the plurality of document vectors.
Owner:DELL PROD LP
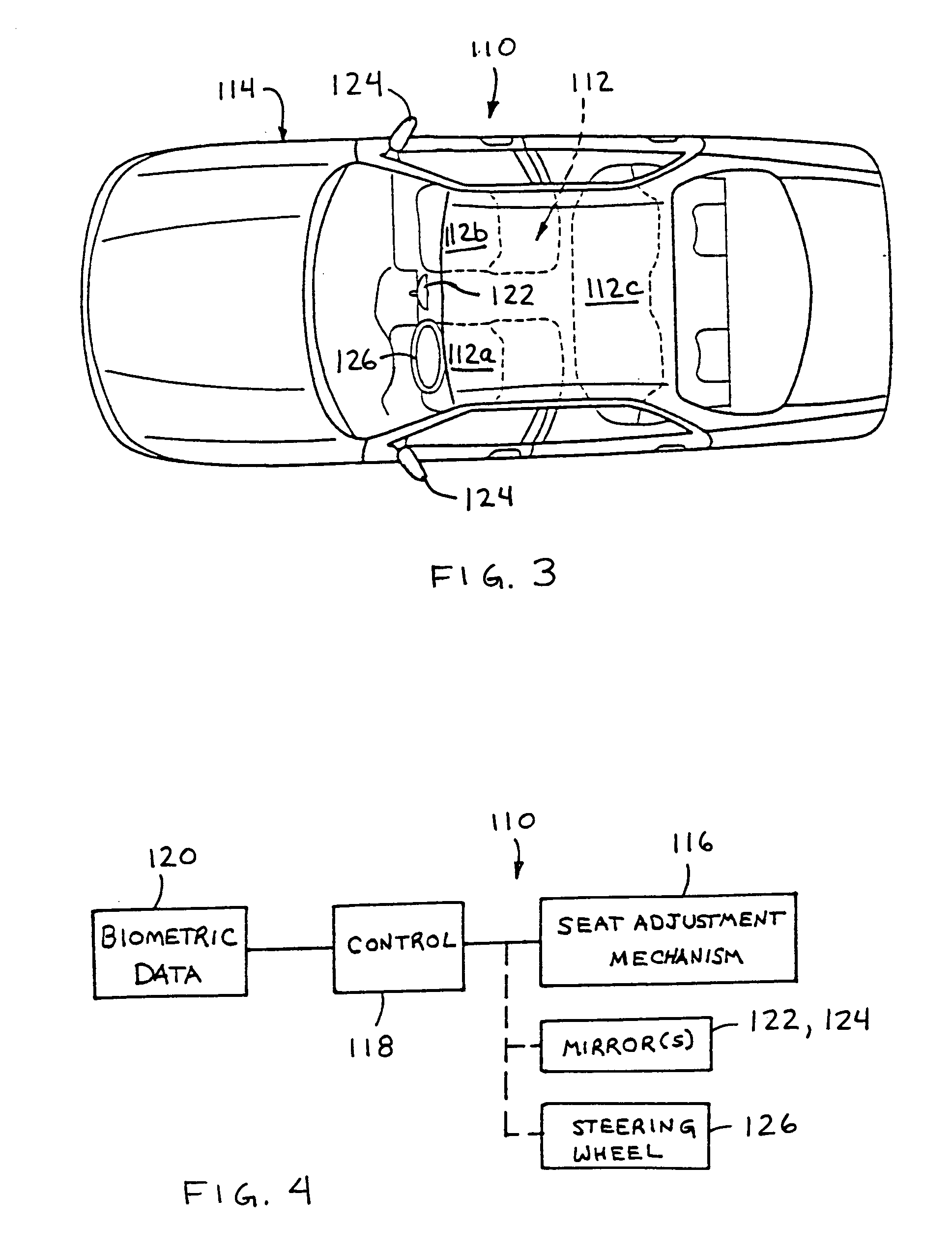
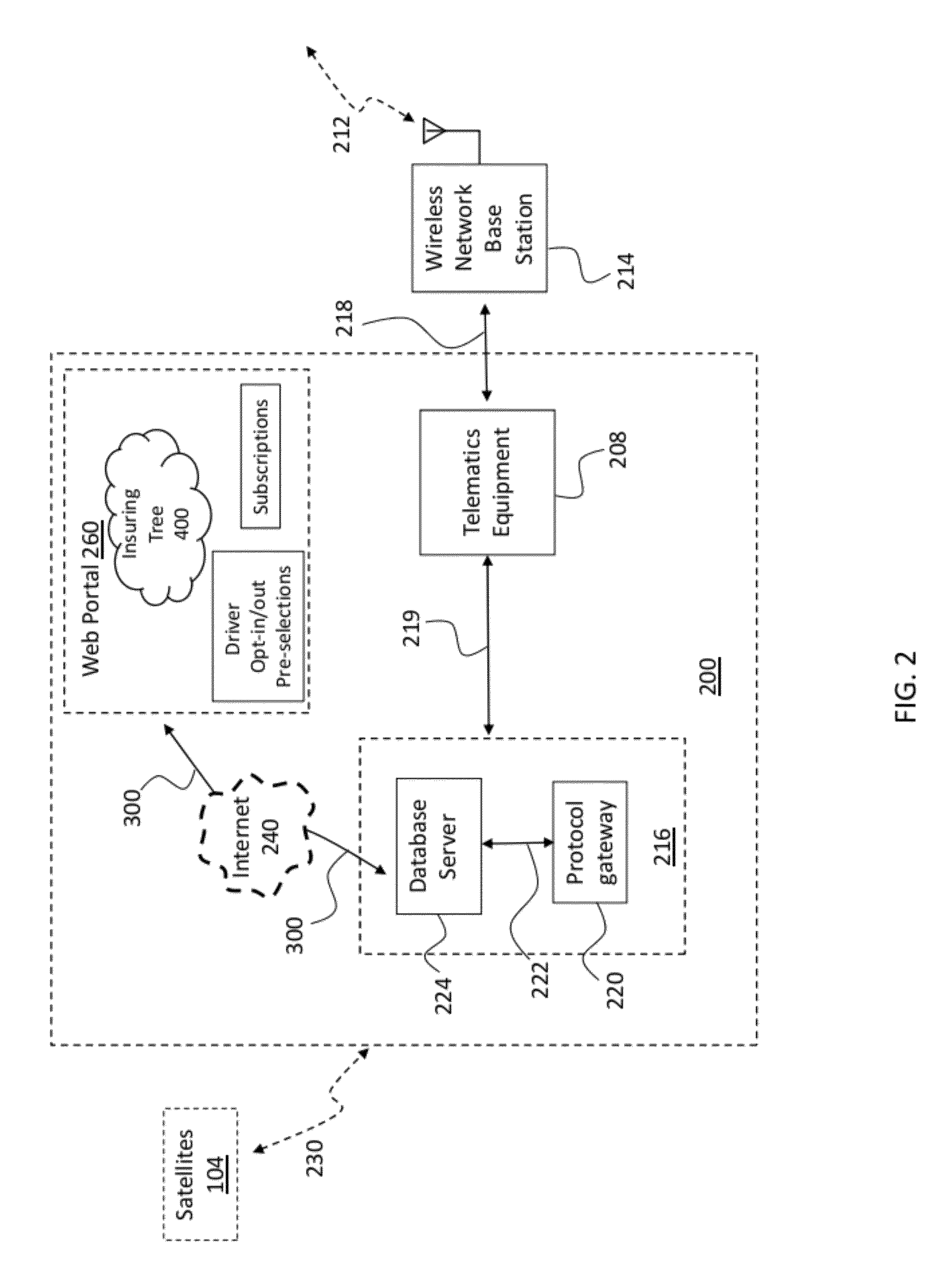
System and Method for Tracking and Sharing Driving Metrics with a Plurality of Insurance Carriers
InactiveUS20120066007A1Overcome disadvantagesIncrease chanceFinanceCommerceDriver/operatorTelecommunications link
A method for determining an insurance premium cost to insure a vehicle. A wireless communication link exists between a vehicle telematics system of the vehicle and a control center remote from the vehicle. The control center has a data center including a database server and a protocol gateway exchanging data with the server, and a web portal connected to the data center. Driver metrics data associated with the vehicle and / or the driver are communicated by a vehicle telematics system to the data center and are analyzed to create a driver profile. The driver profile is shared with at least one insurance carrier who can assign a rating to the profile and, thereby, determines an insurance premium cost to insure the vehicle, which is sent to an owner or a driver of the vehicle.
Owner:AGERO
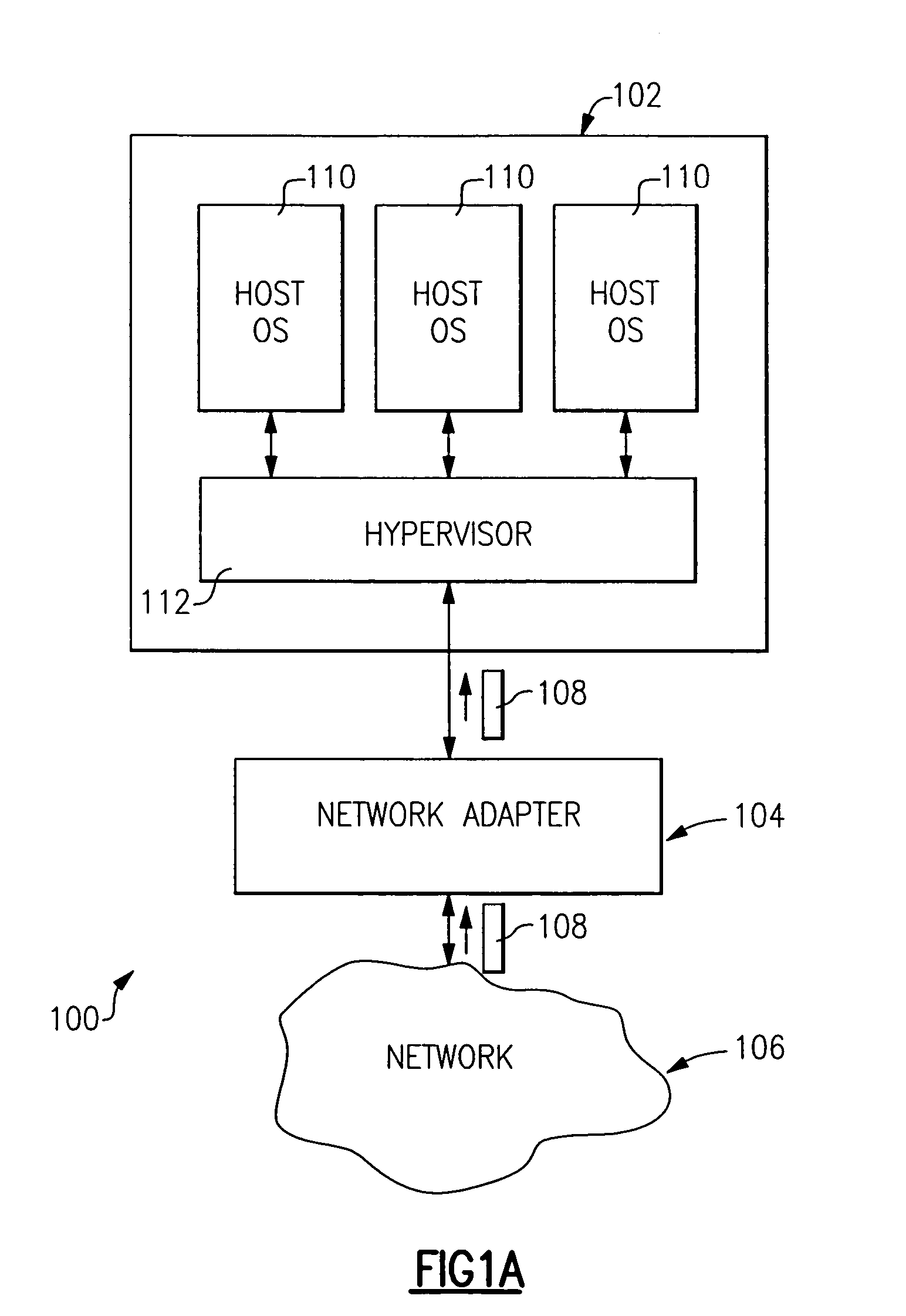
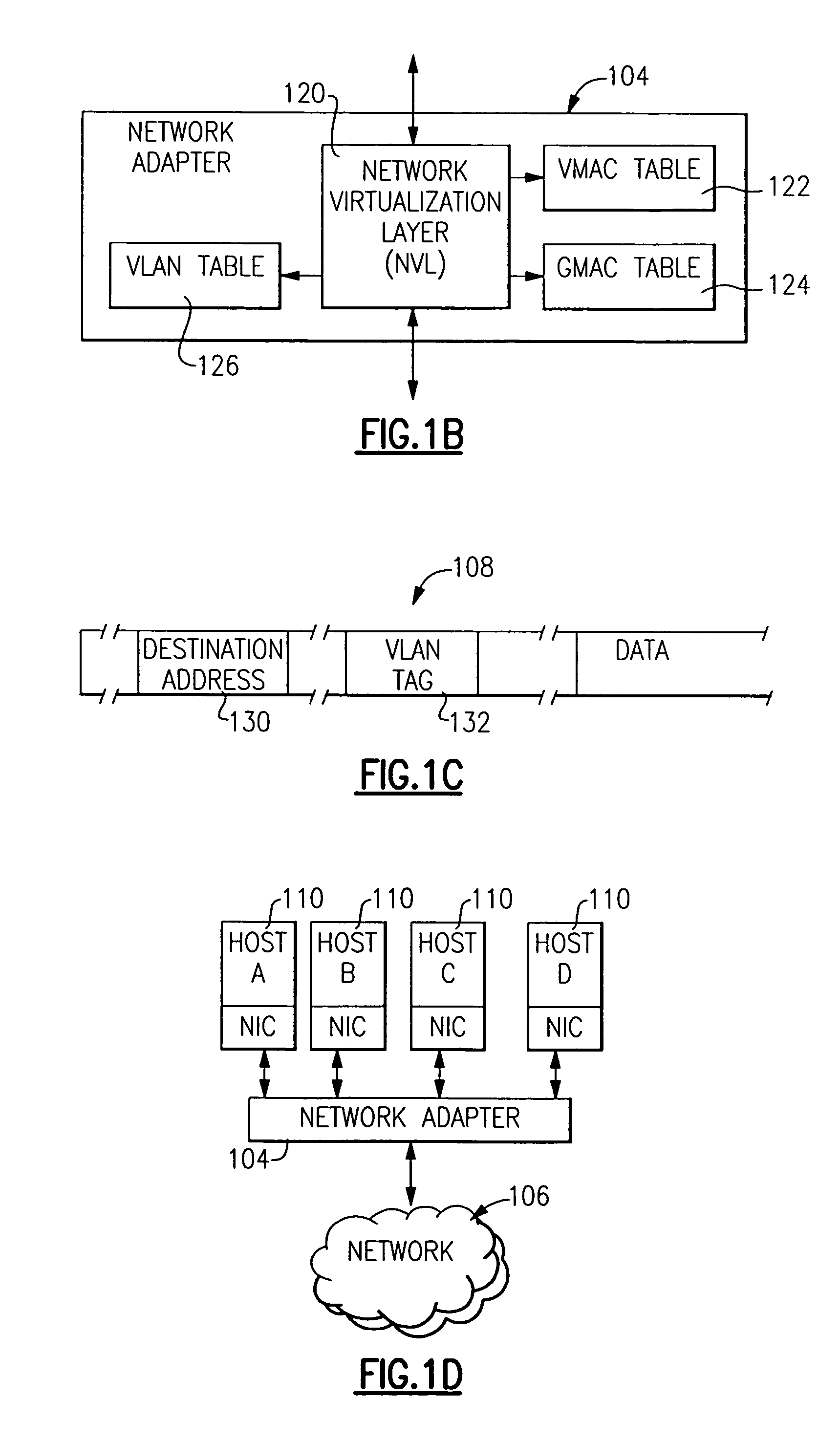
Method and apparatus for providing network virtualization
A network virtualization layer for an information handling system in which a physical machine coupled to a network is divided into a plurality of logical partitions, each of which has a host system residing thereon. In response to receiving a set command from one of the host systems specifying a data link layer (layer 2) address, the virtualization layer associates the data link layer address with the host system and forwards to the host system data packets specifying the data link layer address as a destination address. Unicast packets are forwarded to the single host system specifying the destination address as an individual MAC address, while multicast packets are forwarded to each host system specifying the destination address as a group MAC address. A host system may also specify a virtual LAN (VLAN) ID, which is used to scope the forwarding of packets to host systems sharing that VLAN ID.
Owner:IBM CORP
Interactive process for recognition and evaluation of a partial search query and display of interactive results
InactiveUS6862713B1Data processing applicationsDigital data information retrievalInformation processingGraphics
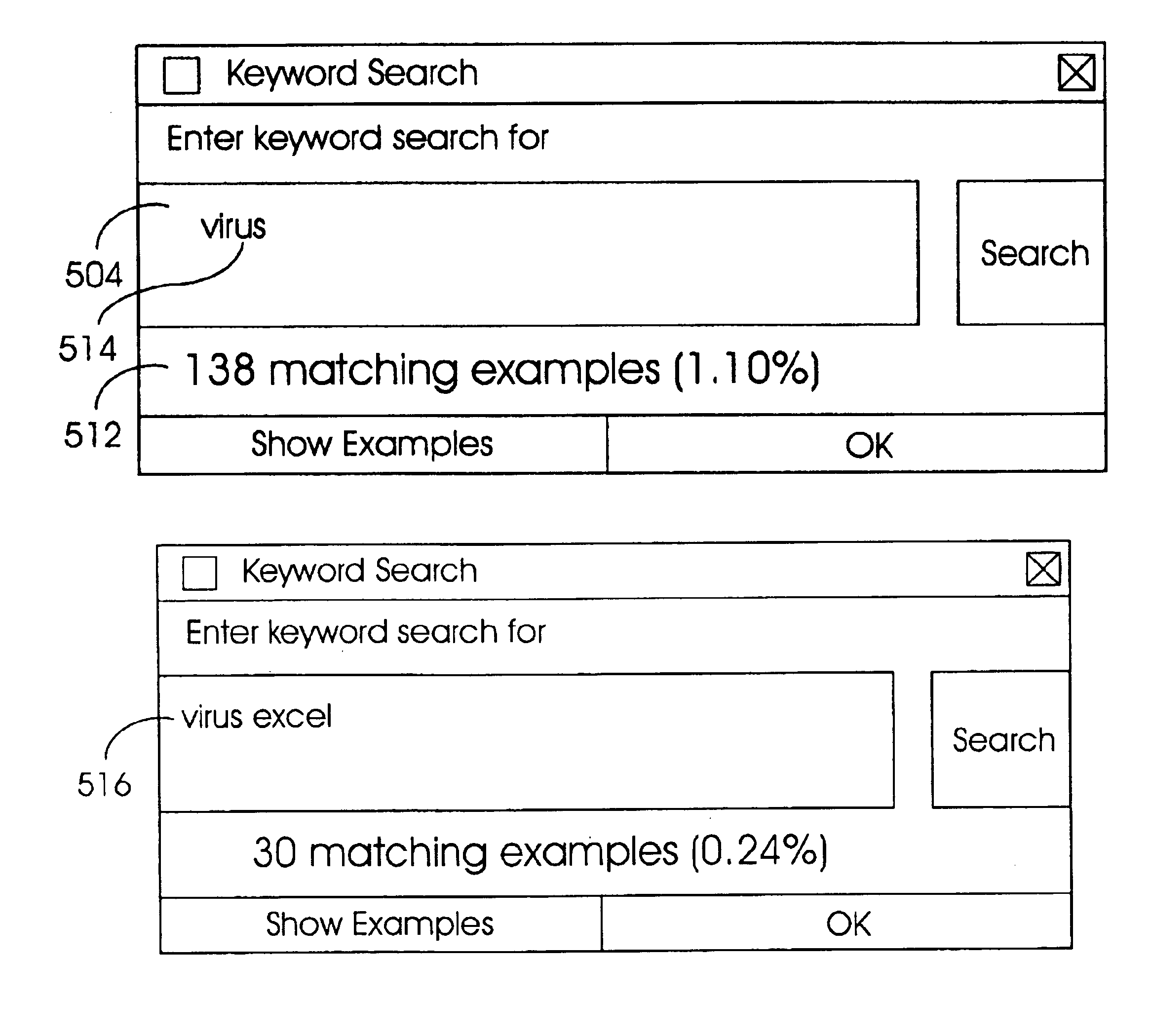
A method for presenting to an end-user the intermediate matching search results of a keyword search in an index list of information. The method comprising the steps of: coupling to a search engine a graphical user interface for accepting keyword search terms for searching the indexed list of information with the search engine; receiving one or more keyword search terms with one or more separation characters separating there between; performing a keyword search with the one or more keyword search terms received when a separation character is received; and presenting the number of documents matching the keyword search terms to the end-user, and presenting a graphical menu item on a display. In accordance with another embodiment of the present invention, an information processing system and computer readable storage medium carries out the above method.
Owner:IBM CORP
Data Security System and with territorial, geographic and triggering event protocol
ActiveUS20090178144A1Ease overhead performanceHigh overhead performanceDigital data processing detailsAnalogue secracy/subscription systemsInformation processingEvent trigger
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with territorial, geographic and triggering event protocols. The method and system determines device location within or without a predetermined region and then extracts security data from the file, text, data object or whatever. The extracted data is separated from the remainder data and stored either on media in a local drive or remotely, typically via wireless network, to a remote store. Encryption is used to further enhance security levels. Extraction may be automatic, when the portable device is beyond a predetermined territory, or triggered by an event, such a “save document” or a time-out routine. Reconstruction of the data is permitted only with security clearance and within certain geographic territories. An information processing system for securing data is also described.
Owner:DIGITAL DOORS
Providing menu and other services for an information processing system using a telephone or other audio interface
InactiveUS7552054B1Structured and efficient and effectiveEffectivelyMultiple digital computer combinationsAutomatic exchangesInformation processingApplication software
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
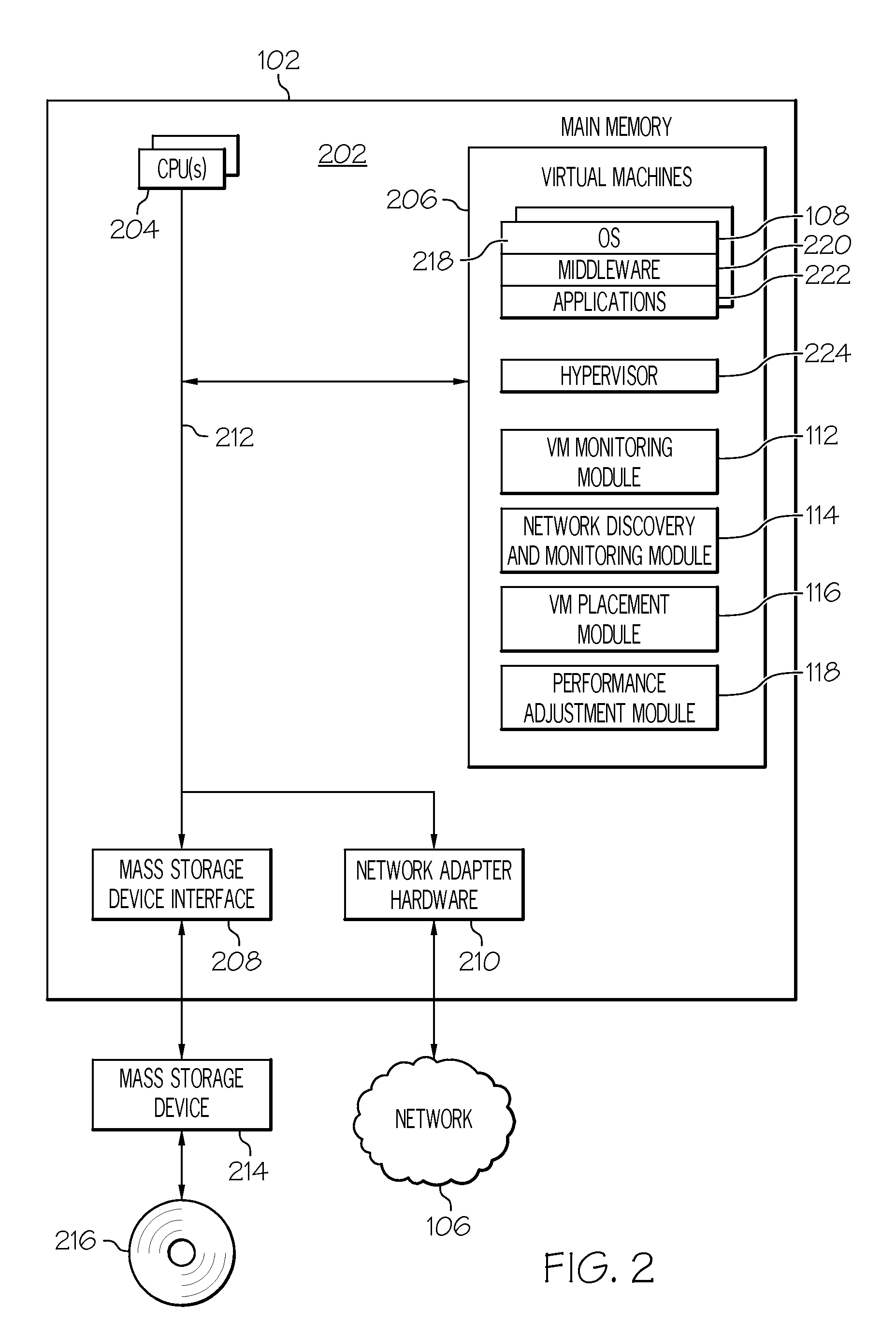
Autonomic definition and management of distributed appication information
ActiveUS20090125619A1Facilitates adoptionDigital computer detailsMultiprogramming arrangementsInformation processingInformation handling system
A method, information processing system, and computer program storage product for associating jobs with resource subsets in a job scheduler. At least one job class that defines characteristics associated with a type of job is received. A list of resource identifiers for a set of resources associated with the job class is received. A set of resources available on at least one information processing system is received. The resource identifiers are compared with each resource in the set of resources available on the information processing system. A job associated with the job class with is scheduled with a set of resources determined to be usable by the job based on the comparing.
Owner:DAEDALUS BLUE LLC
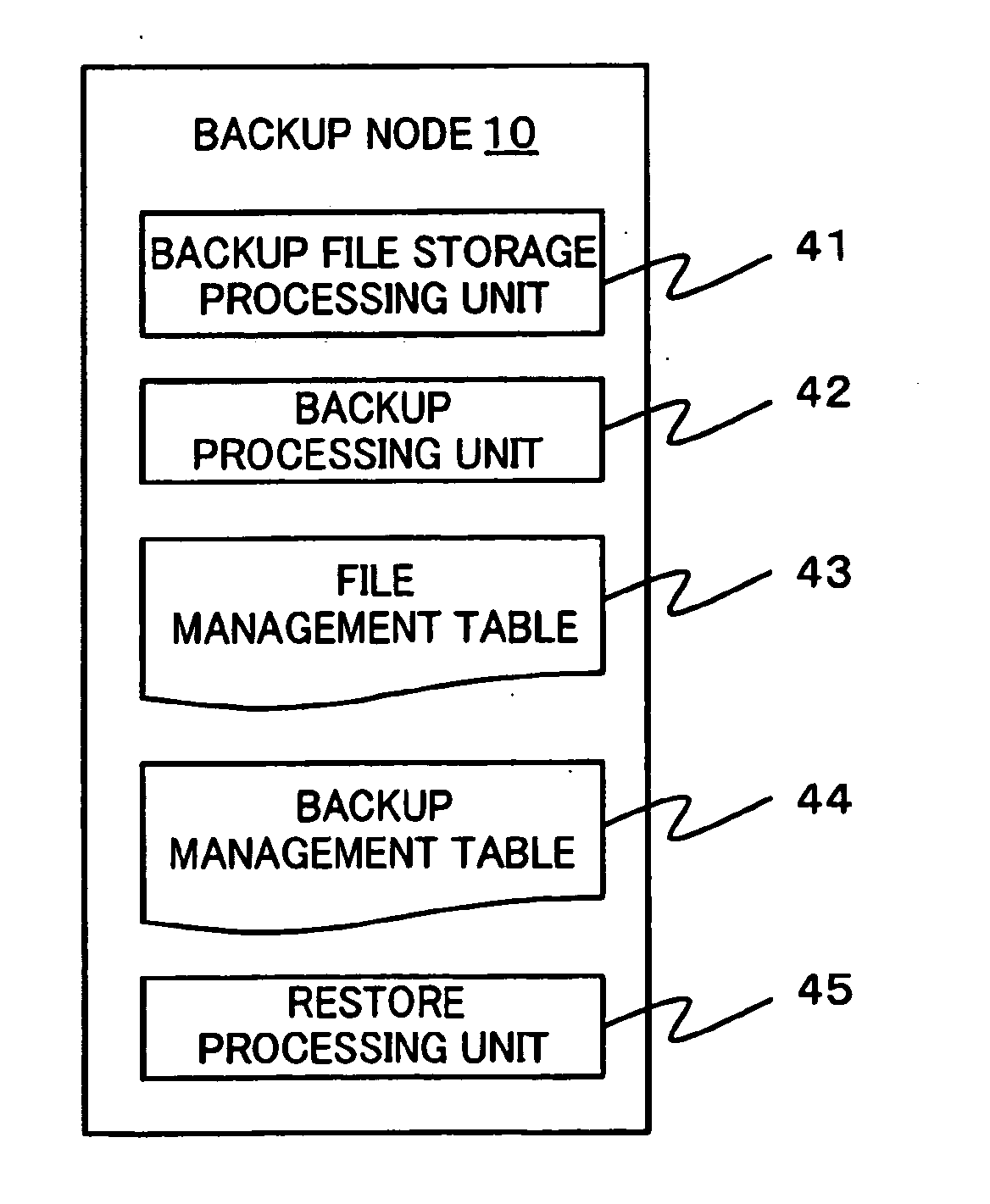
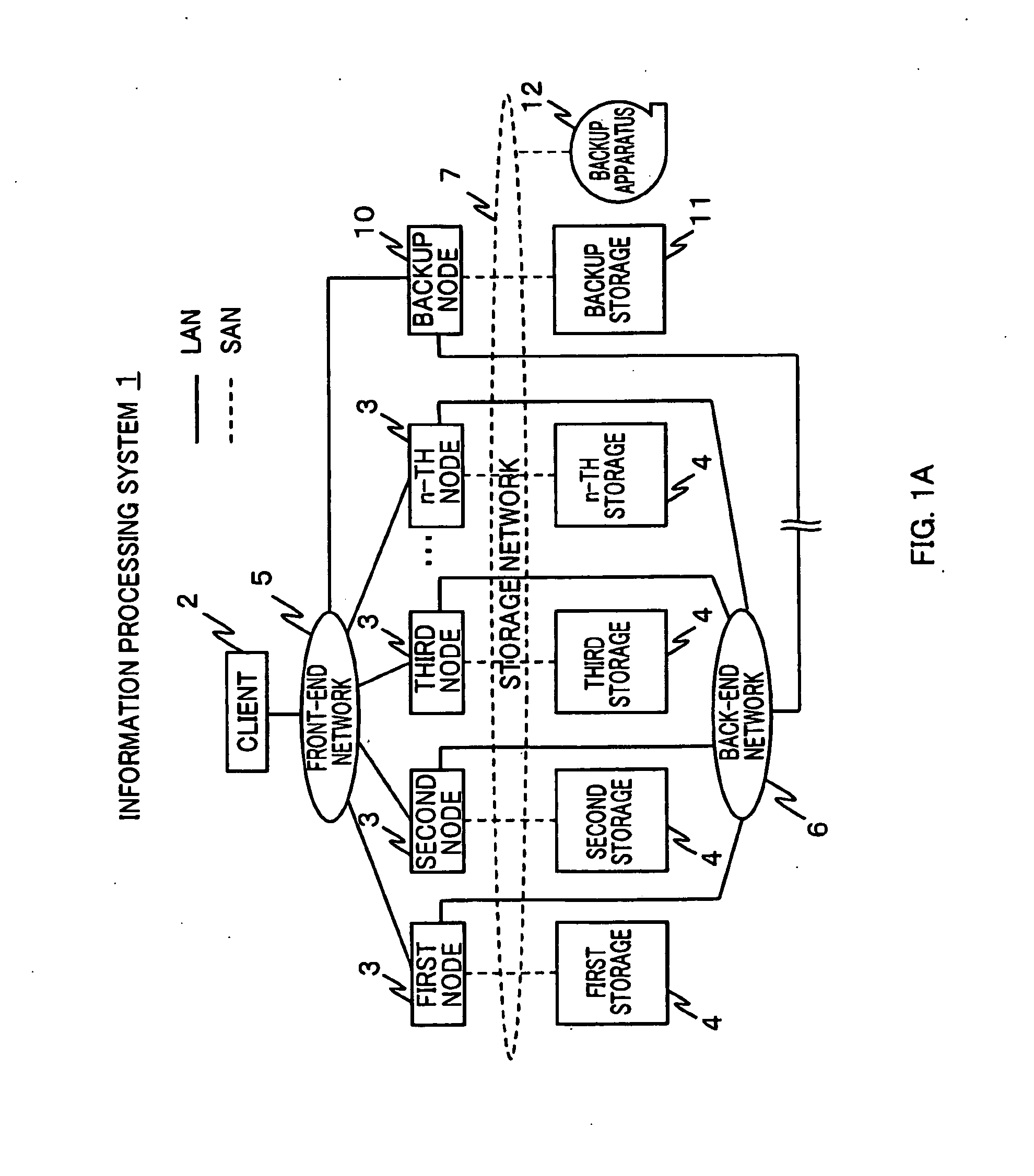
Information processing system and method of acquiring backup in an information processing system
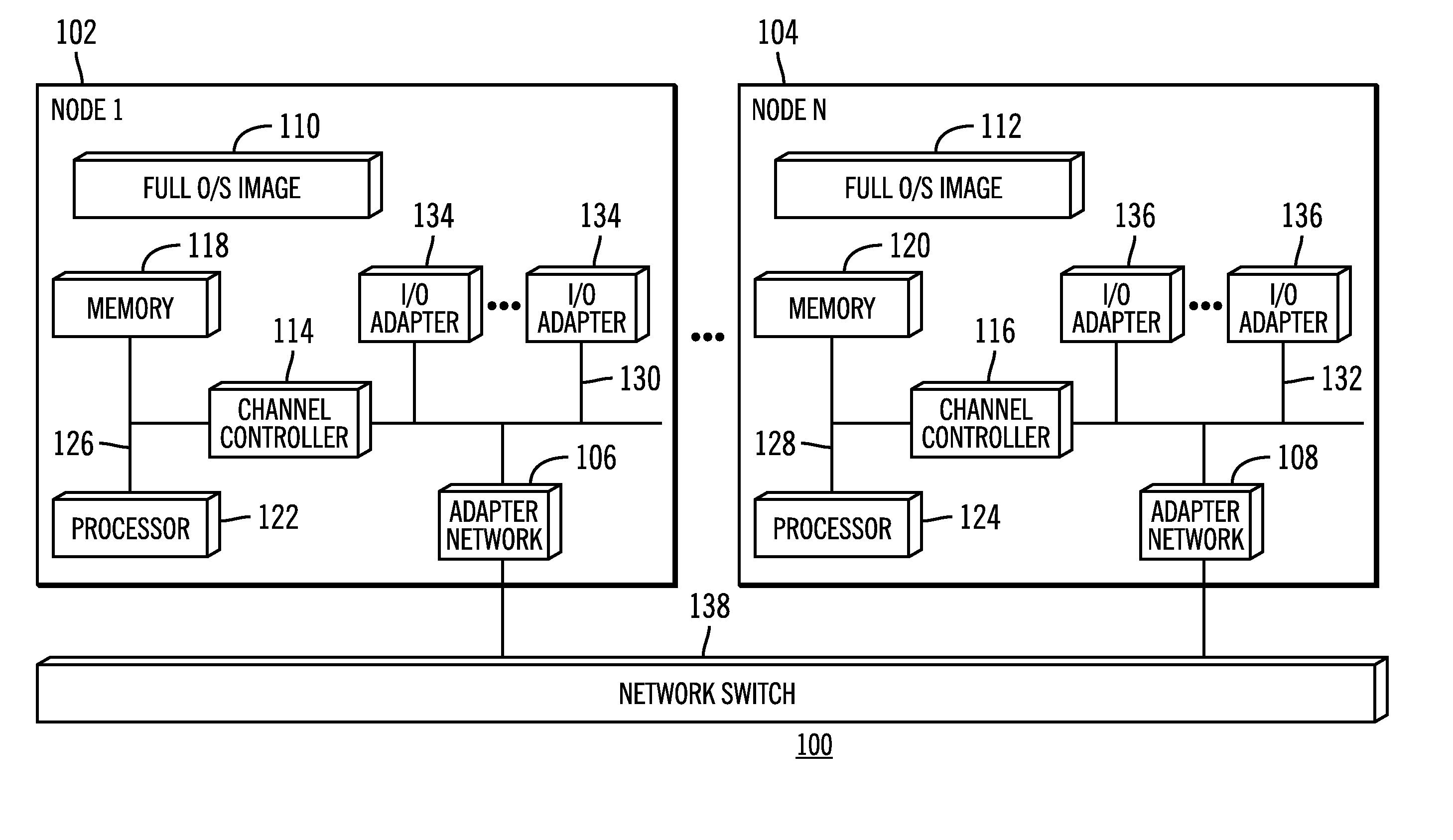
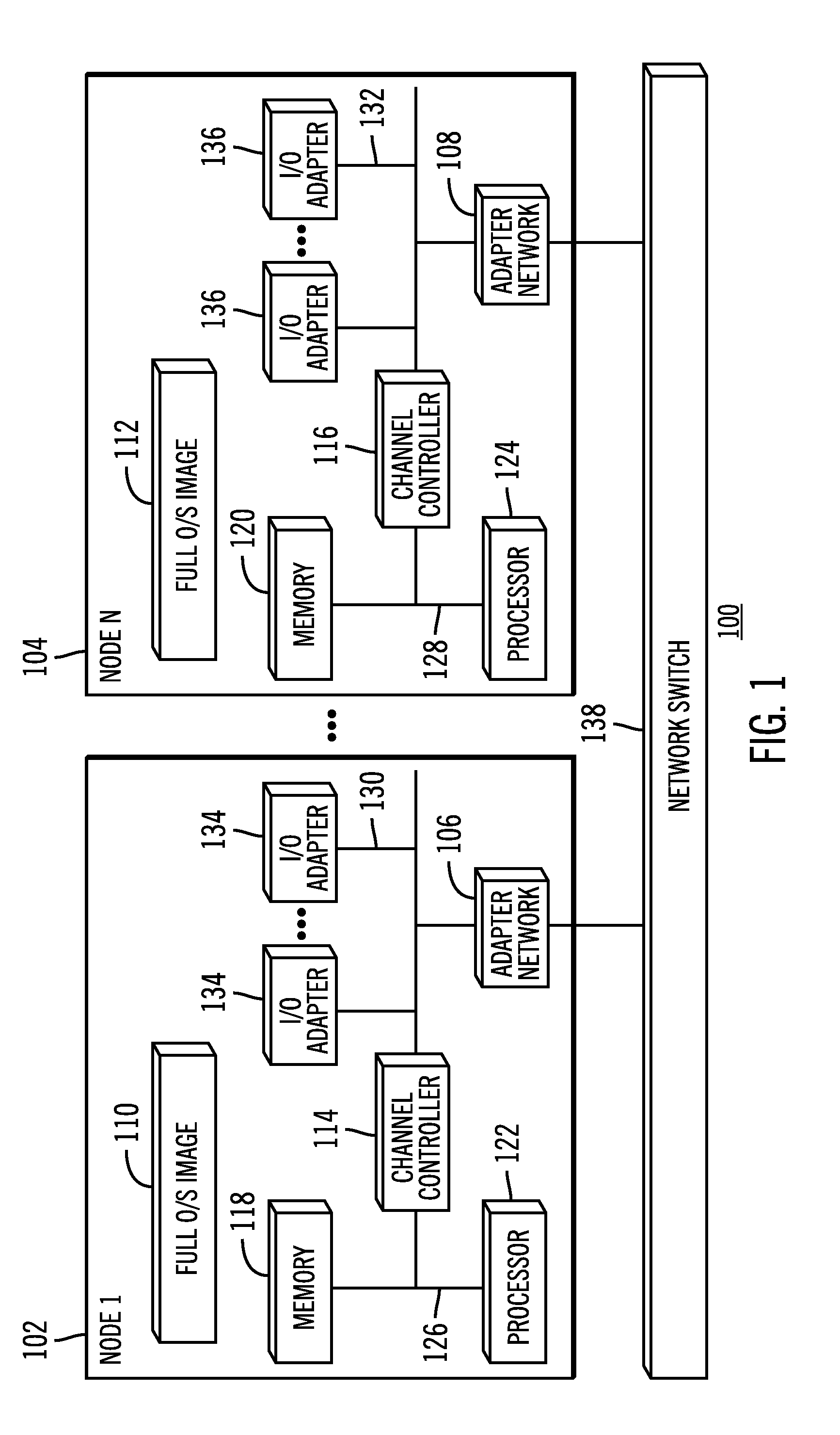
InactiveUS20110238625A1Backup fileCreate efficientlyError detection/correctionDigital data processing detailsInformation processingVirtual file system
Provided is an information processing system including a plurality of nodes 3 and a plurality of storages 4 coupled subordinately to each of the nodes 3, each of the nodes 3 functioning as a virtual file system that provides a client 2 with storage regions of each of the storages 4 as a single namespace. This information processing system is further provided with a backup node 10 and a backup storage 11 coupled subordinately to the backup node 10. The backup node 10 synchronizes and holds location information (file management table 33) held by each of the nodes 3. Then, the backup node 10 creates a backup file, and stores the backup file in the backup storage 11 by accessing a location identified by the location information (file management table 43) synchronized and held by the backup node 10 itself to acquire a file.
Owner:HITACHI LTD
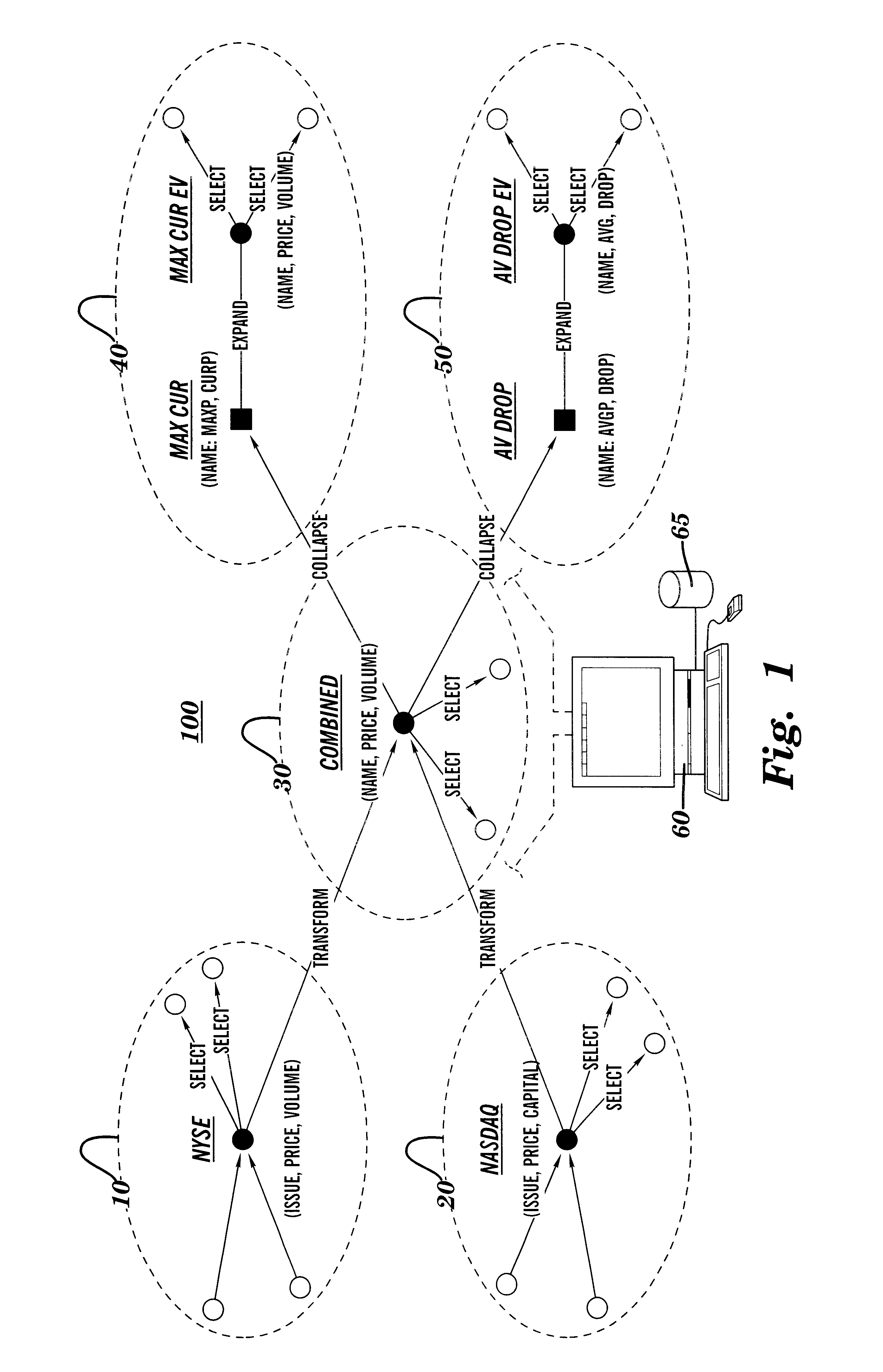
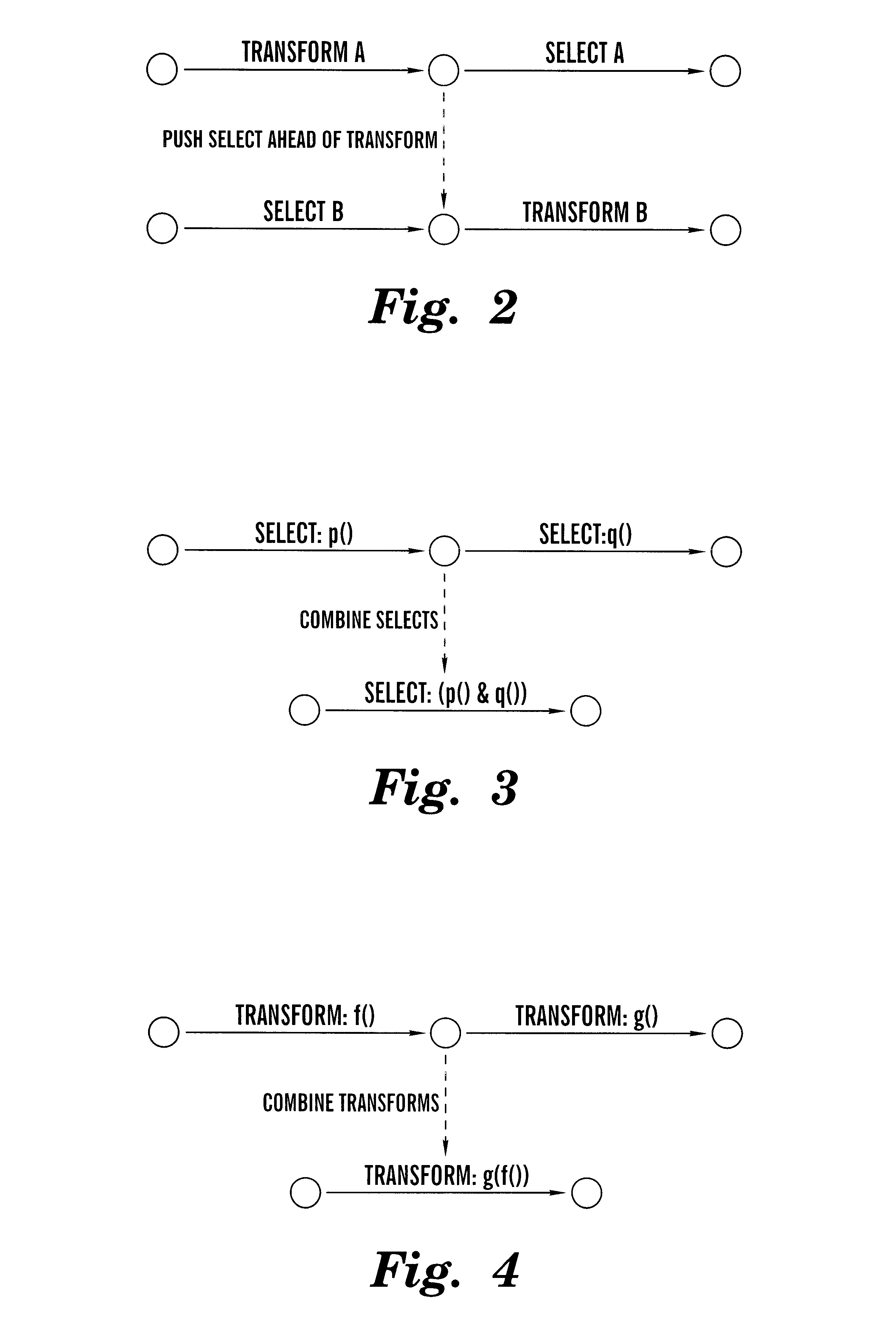
Reduction and optimization of operational expressions applied to information spaces between nodes in a publish/subscribe system
InactiveUS6681220B1Advanced technologyEfficient implementationData processing applicationsDigital data processing detailsInformation processingInformation space
Techniques for arranging operations performable on information in an information processing system are provided. In a system having a plurality of information producers and a plurality of information subscribers, paths are identified over which information traverses, and within which the information is subject to select and / or transform operations. The present invention optimizes the system by reorganizing the sequence of select and transform operations so that transforms follow select operations; and by combining multiple select and transform operations into single select and transform operations, respectively. Using these optimizations, the processing resources of the system can be reorganized, and / or information flow graphs describing the system can be designed, so that the select operations are "pushed" toward the producers, and transform operations are "pushed" toward the subscribers. Efficient content-based routing systems can then be used to implement the select operations.
Owner:IBM CORP
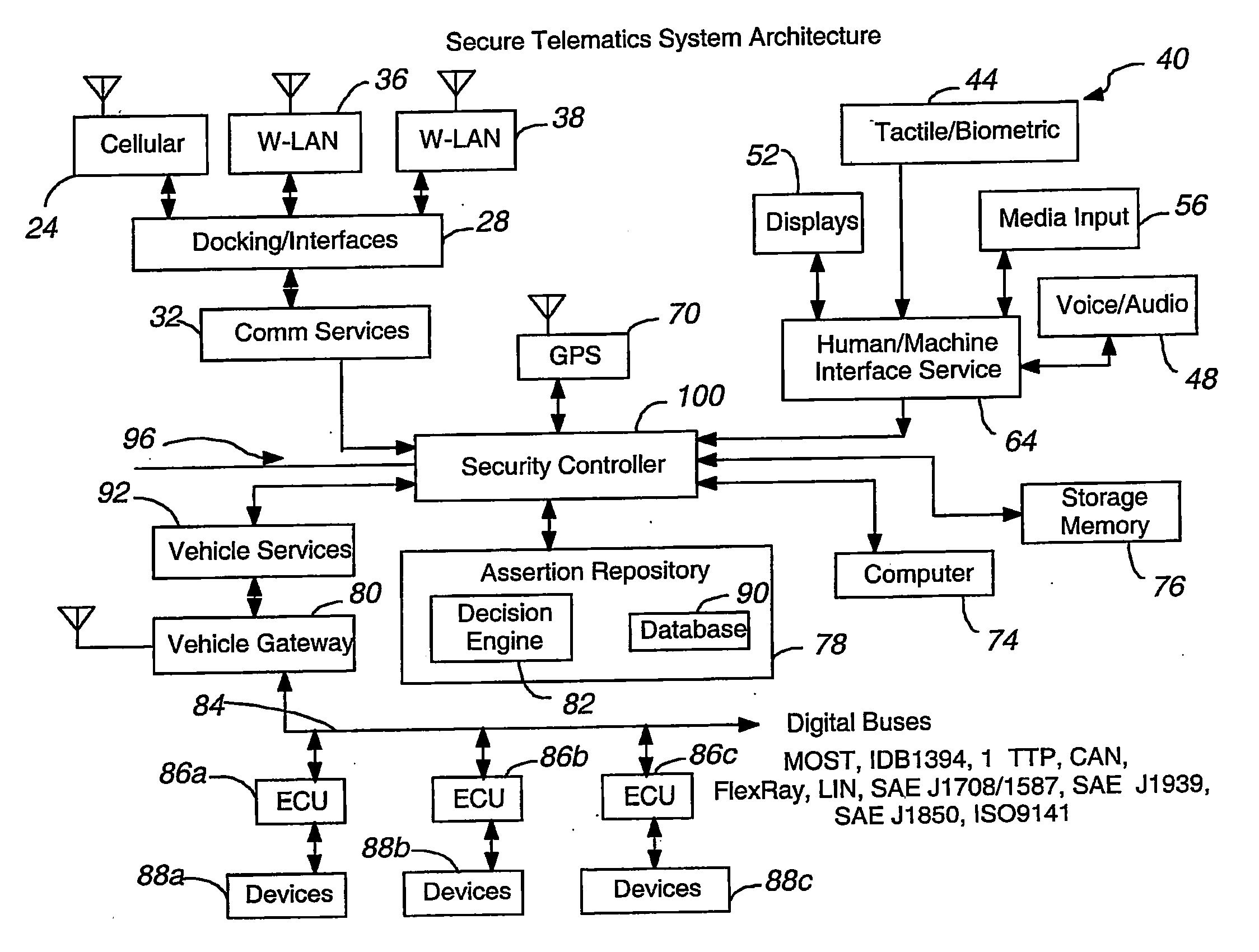
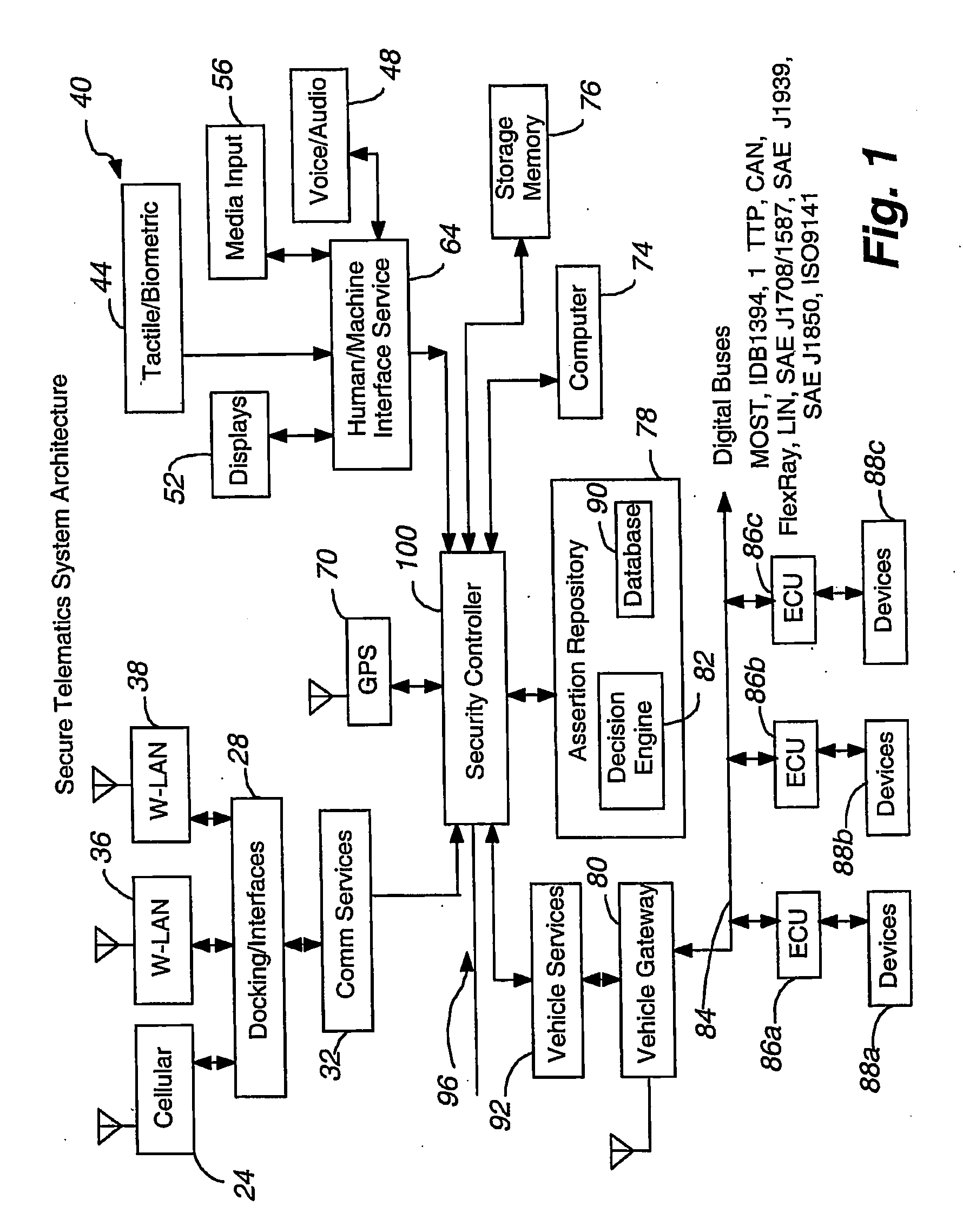
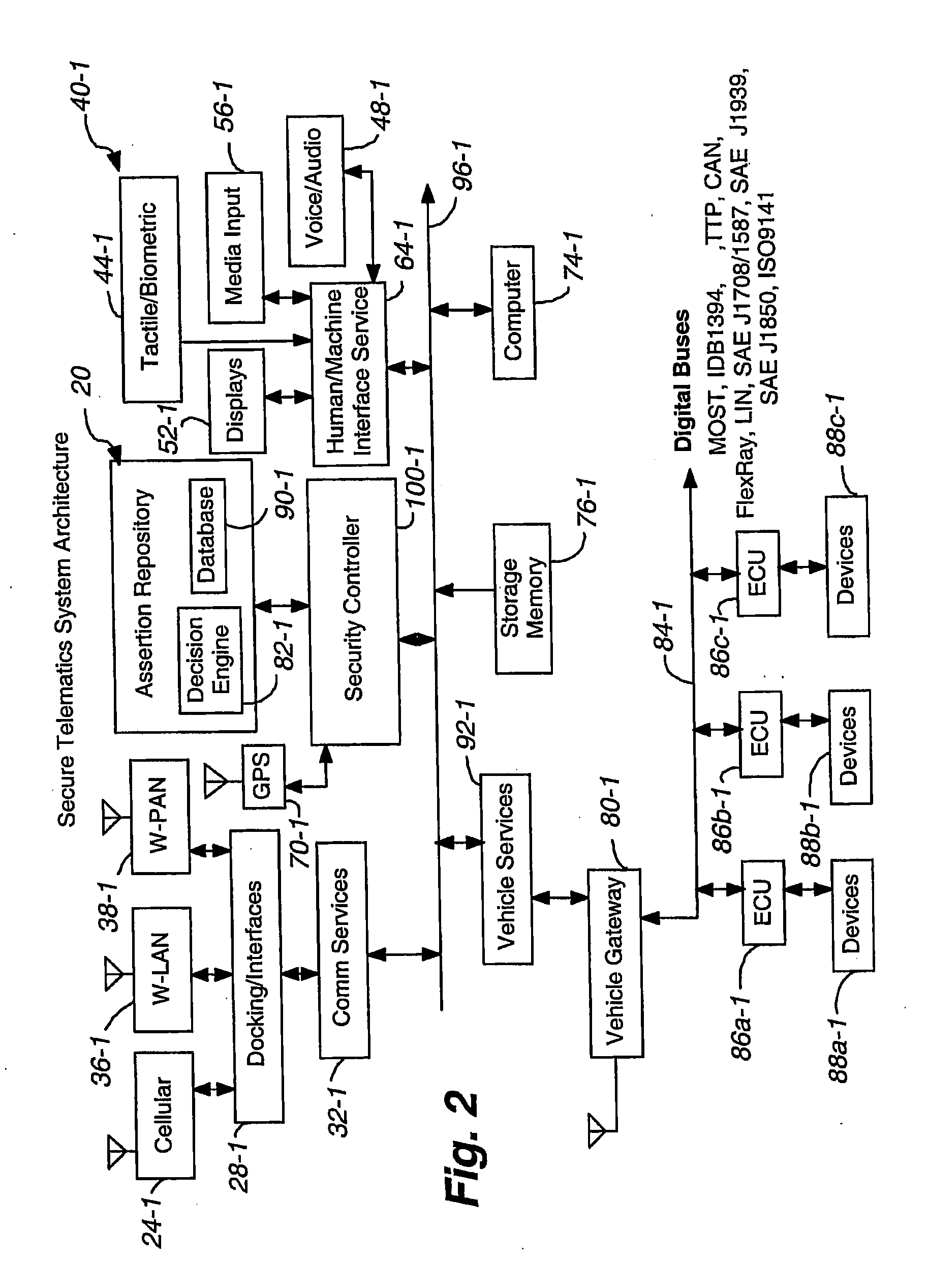
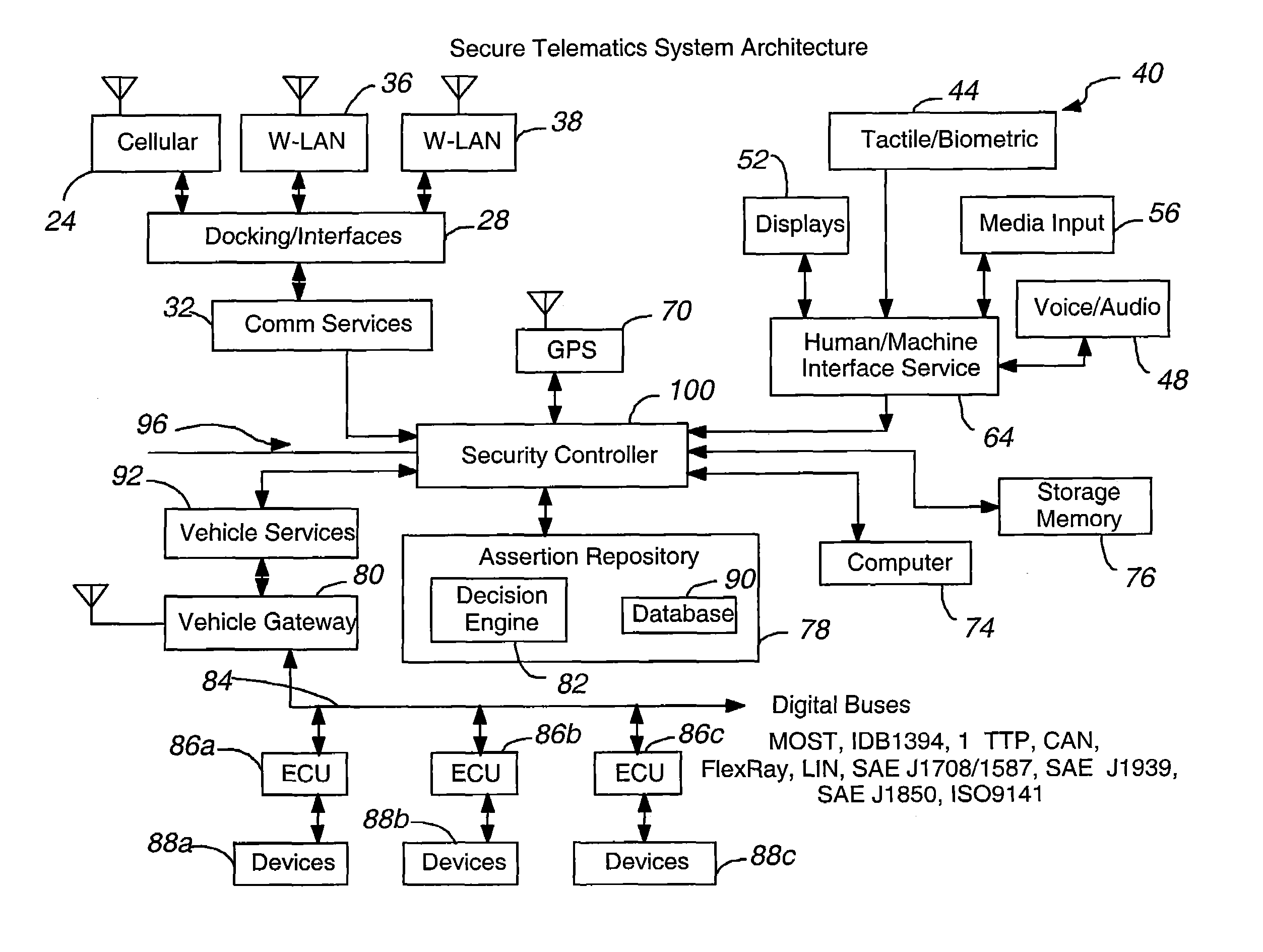
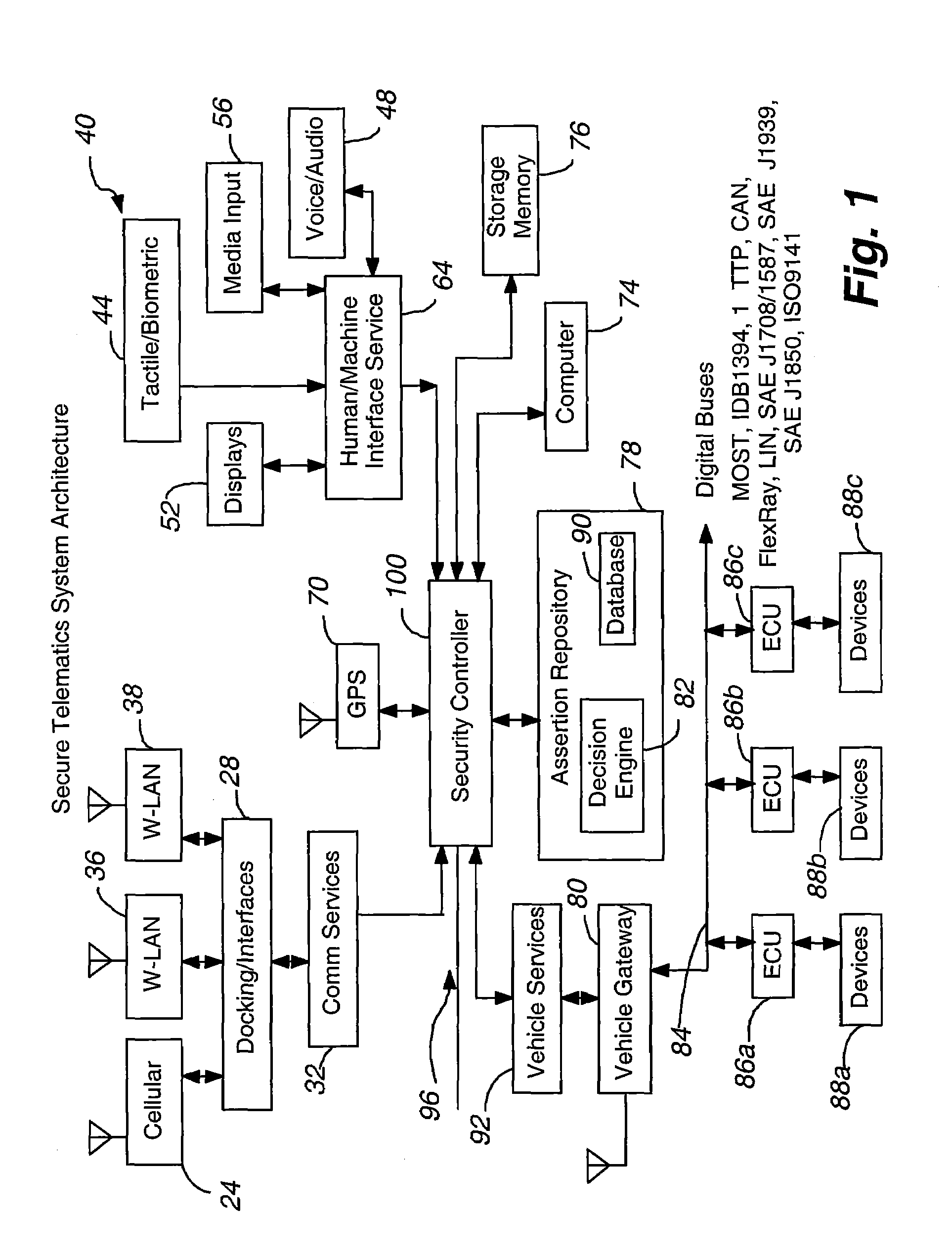
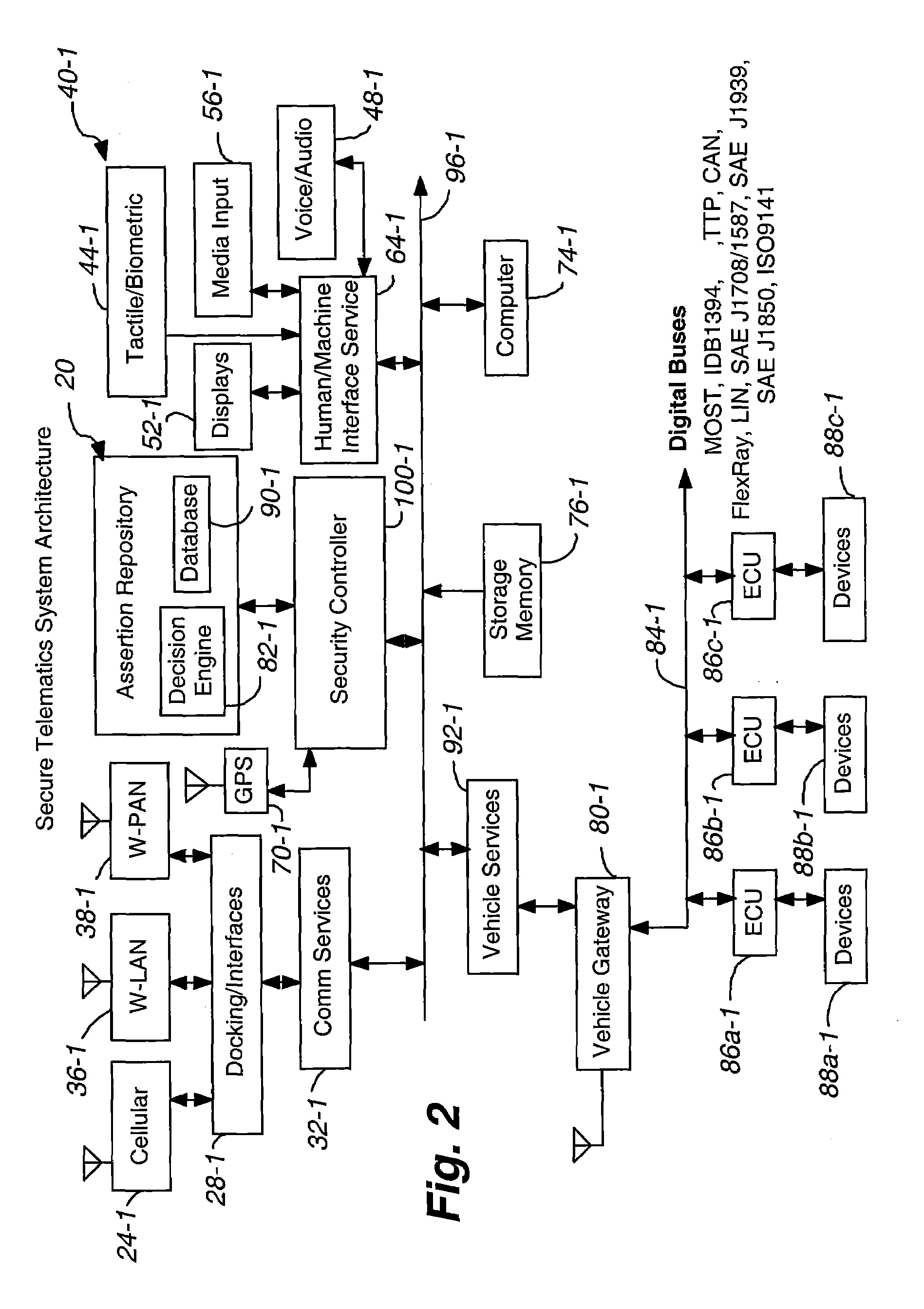
Secure telematics
InactiveUS20080148374A1Expands telematics usageImprove integrityVehicle testingRegistering/indicating working of vehiclesComputer networkService provision
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resources' security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Secure telematics
ActiveUS7366892B2Expands telematics usageLow costUnauthorised/fraudulent call preventionRegistering/indicating working of vehiclesService provisionSecurity Measure
A telematics system that includes a security controller is provided. The security controller is responsible for ensuring secure access to and controlled use of resources in the vehicle. The security measures relied on by the security controller can be based on digital certificates that grant rights to certificate holders, e.g., application developers. In the case in which applications are to be used with vehicle resources, procedures are implemented to make sure that certified applications do not jeopardize vehicle resource'0 security and vehicle users' safety. Relationships among interested entities are established to promote and support secure vehicle resource access and usage. The entities can include vehicle makers, communication service providers, communication apparatus vendors, vehicle subsystem suppliers, application developers, as well as vehicle owners / users. At least some of the entities can be members of a federation established to enhance and facilitate secure access and usage of vehicle resources.
Owner:CYBERCAR INC
Method and system for providing menu and other services for an information processing system using a telephone or other audio interface
InactiveUS20080154601A1Reduce generationStructured and efficient and effectiveSpeech recognitionSpeech synthesisConcatenationInformation handling system
A method and system for providing efficient menu services for an information processing system that uses a telephone or other form of audio user interface. In one embodiment, the menu services provide effective support for novice users by providing a full listing of available keywords and rotating house advertisements which inform novice users of potential features and information. For experienced users, cues are rendered so that at any time the user can say a desired keyword to invoke the corresponding application. The menu is flat to facilitate its usage. Full keyword listings are rendered after the user is given a brief cue to say a keyword. Service messages rotate words and word prosody. When listening to receive information from the user, after the user has been cued, soft background music or other audible signals are rendered to inform the user that a response may now be spoken to the service. Other embodiments determine default cities, on which to report information, based on characteristics of the caller or based on cities that were previously selected by the caller. Other embodiments provide speech concatenation processes that have co-articulation and real-time subject-matter-based word selection which generate human sounding speech. Other embodiments reduce the occurrences of falsely triggered barge-ins during content delivery by only allowing interruption for certain special words. Other embodiments offer special services and modes for calls having voice recognition trouble. The special services are entered after predetermined criterion have been met by the call. Other embodiments provide special mechanisms for automatically recovering the address of a caller.
Owner:MICROSOFT TECH LICENSING LLC
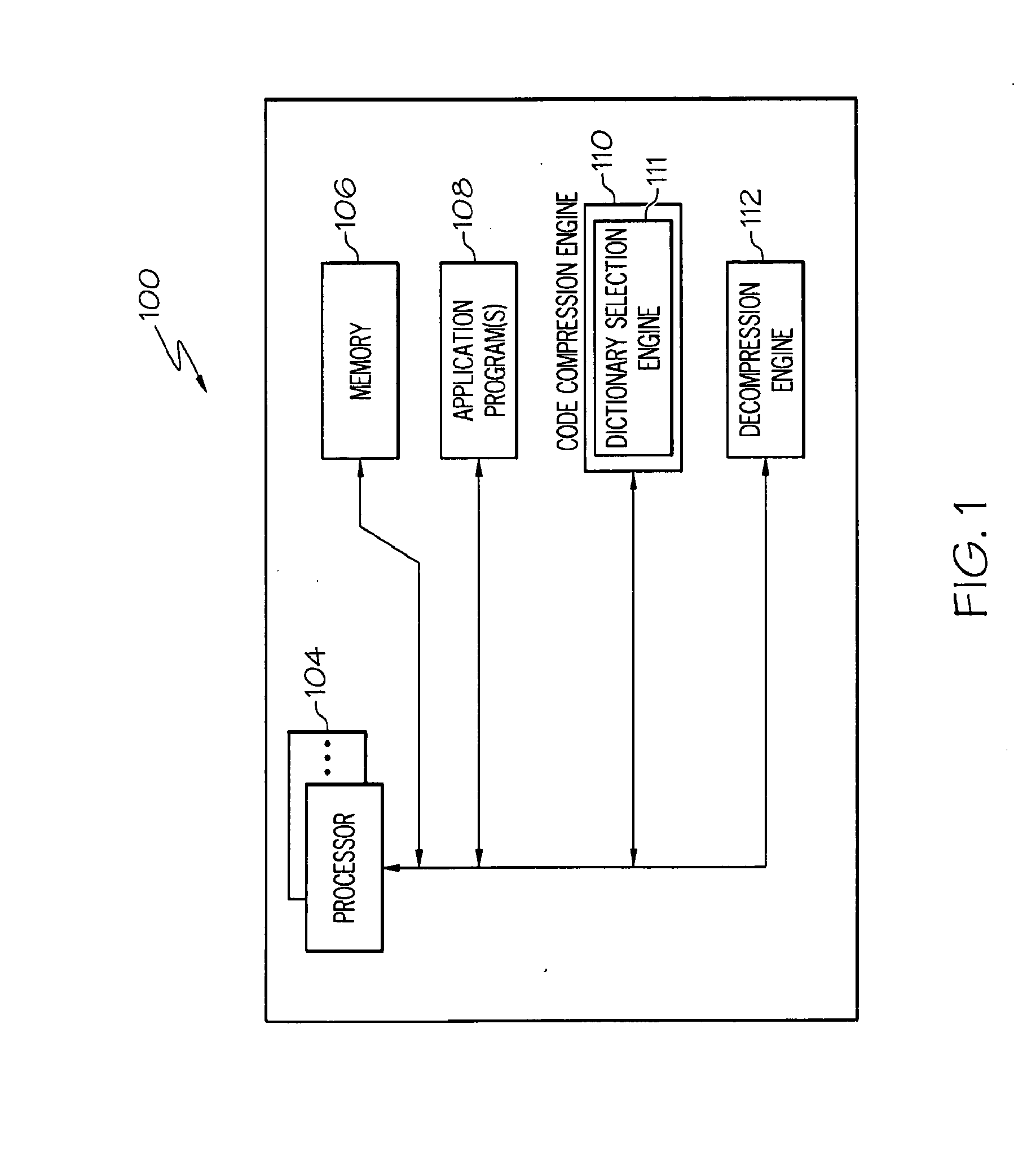
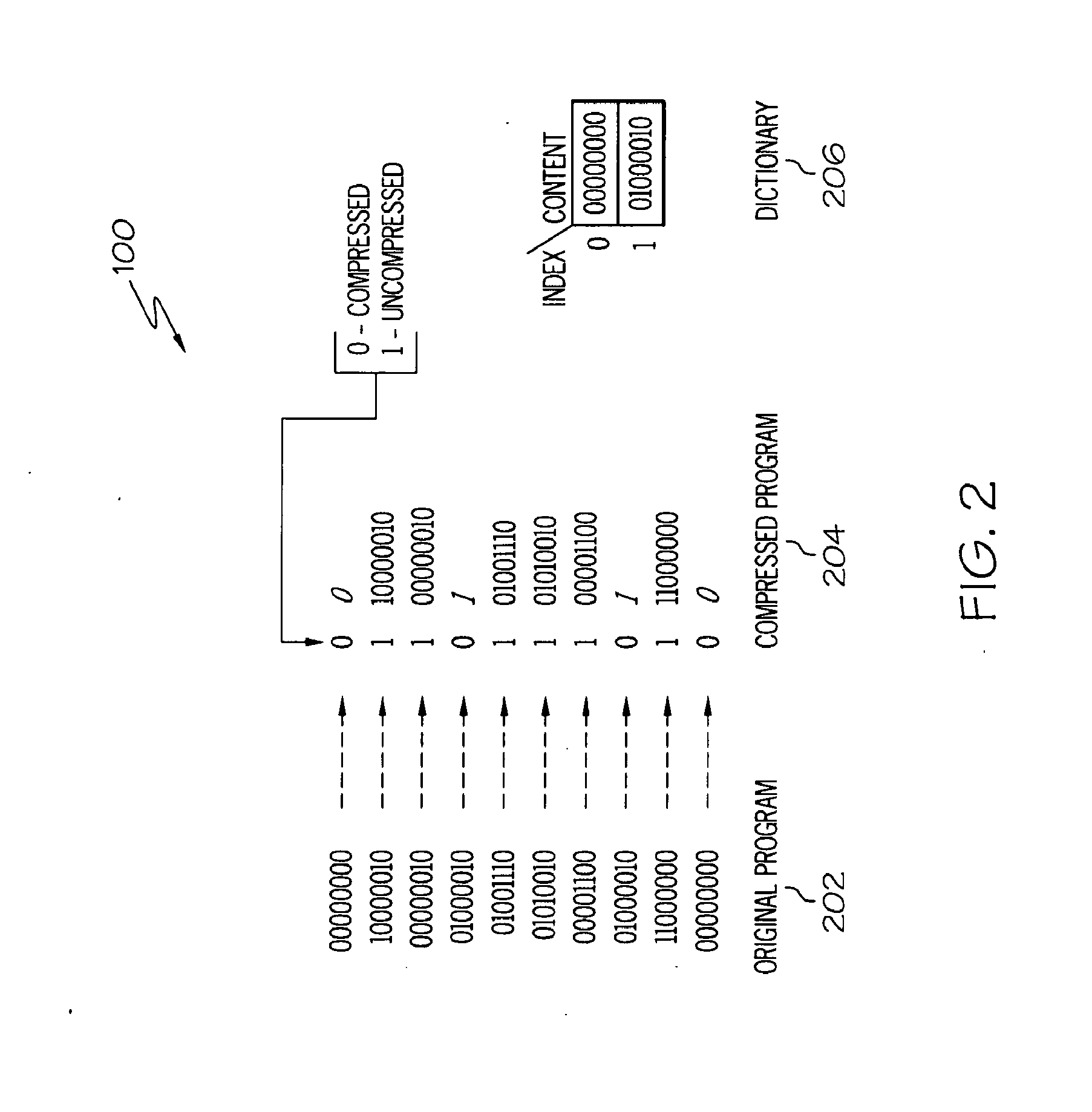
Lossless data compression and real-time decompression
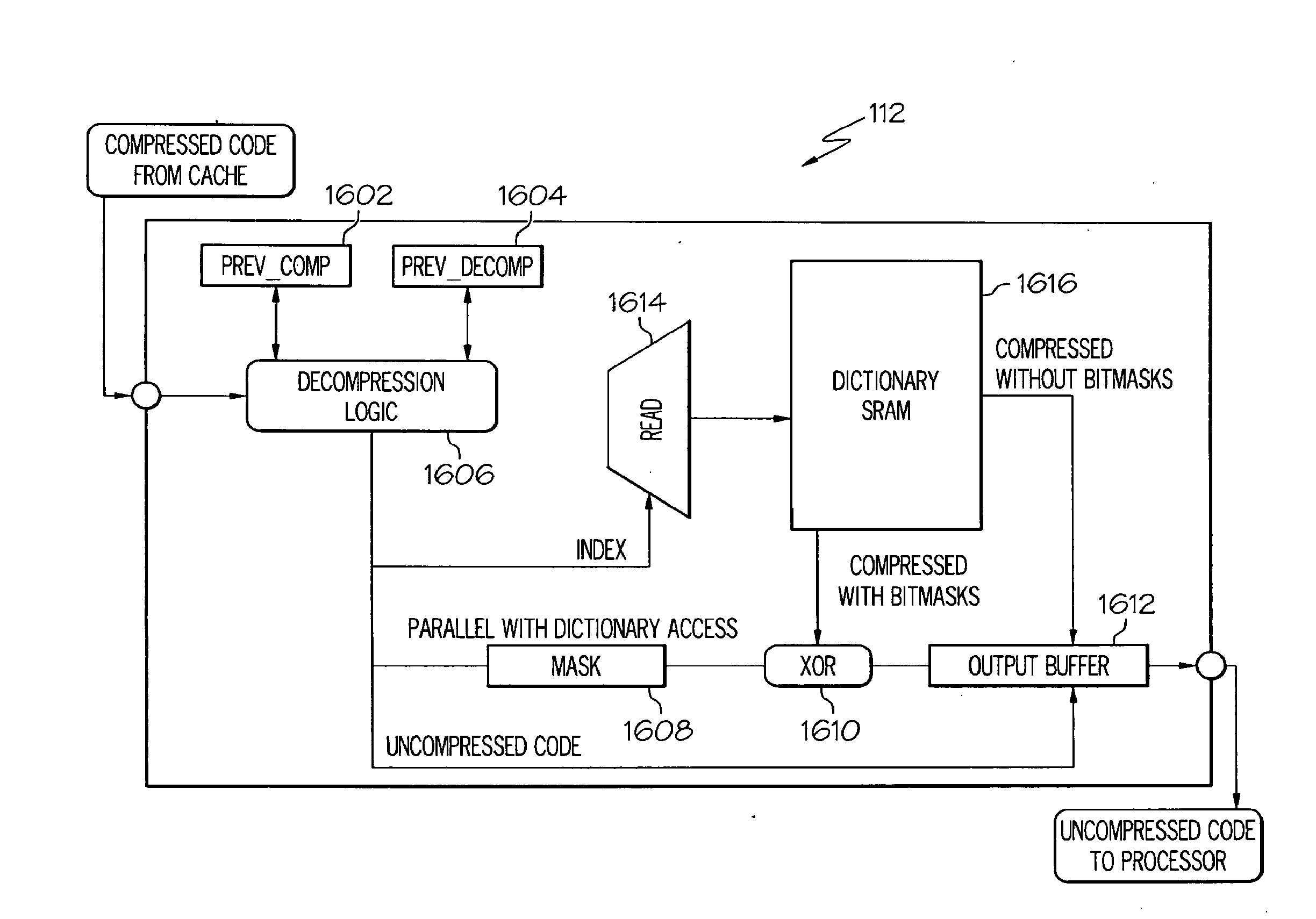
InactiveUS20100223237A1Maximizing compressing efficiencyMinimizes decompression penaltyDigital data processing detailsCode conversionInformation processingMaximal set
A method, information processing system, and computer program storage product store data in an information processing system. Uncompressed data is received and the uncompressed data is divided into a series of vectors. A sequence of profitable bitmask patterns is identified for the vectors that maximizes compression efficiency while minimizes decompression penalty. Matching patterns are created using multiple bit masks based on a set of maximum values of the frequency distribution of the vectors. A dictionary is built based upon the set of maximum values in the frequency distribution and a bit mask savings which is a number of bits reduced using each of the multiple bit masks. Each of the vectors is compressed using the dictionary and the matching patterns with having high bit mask savings. The compressed vectors are stored into memory. Also, an efficient placement is developed to enable parallel decompression of the compressed codes.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
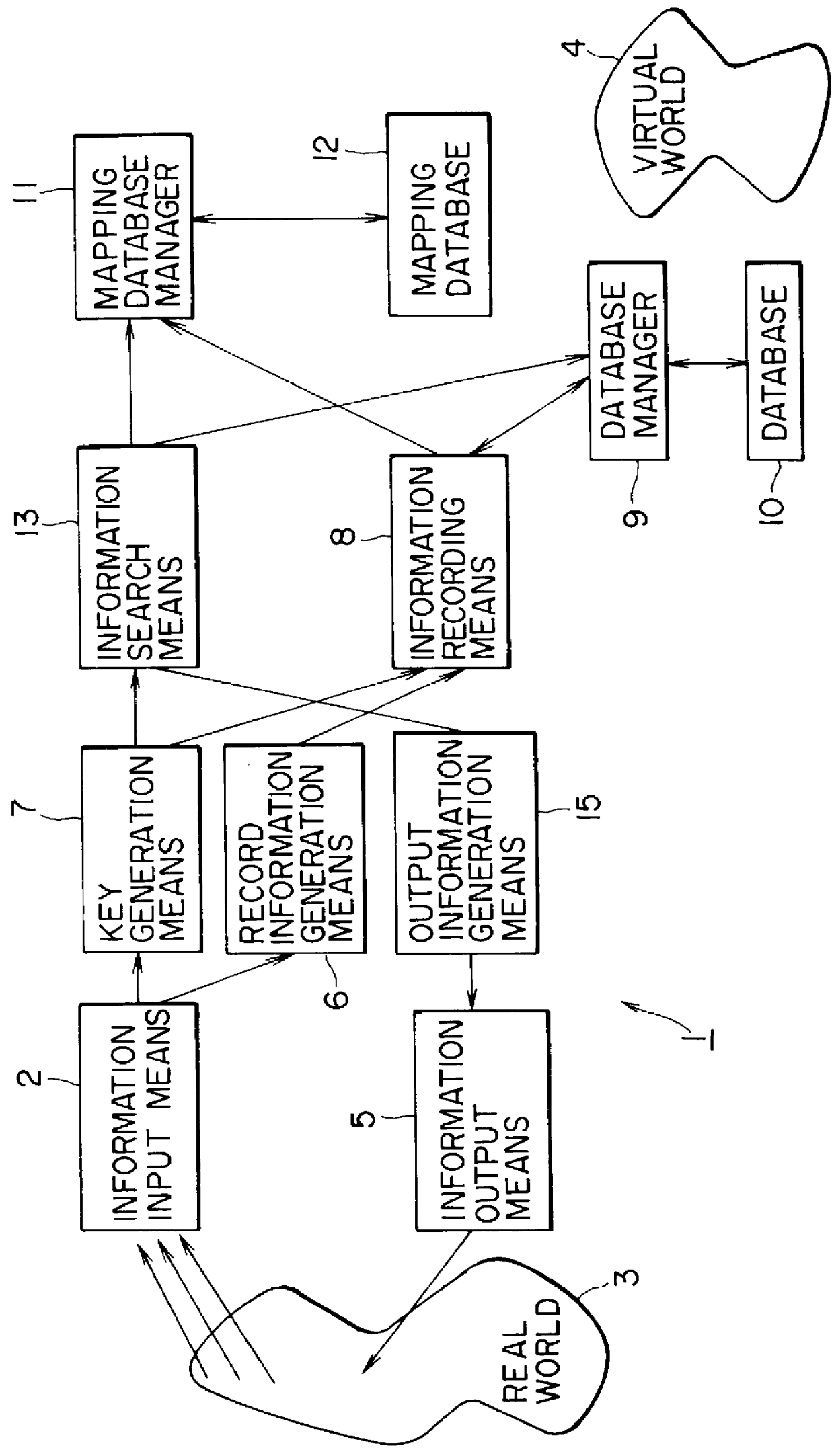
Information processing apparatus and information processing method
InactiveUS6055536AEasy accessWeb data indexingBuying/selling/leasing transactionsInformation processingVirtual world
An information processing system stores information of various types, which is obtained in the real world, in connection with keys indicative of the attribute and feature of the information so that the real-world information is stored quickly and surely in the virtual world which is formed of the linkage of information and stored information of various types is retrieved easily.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com