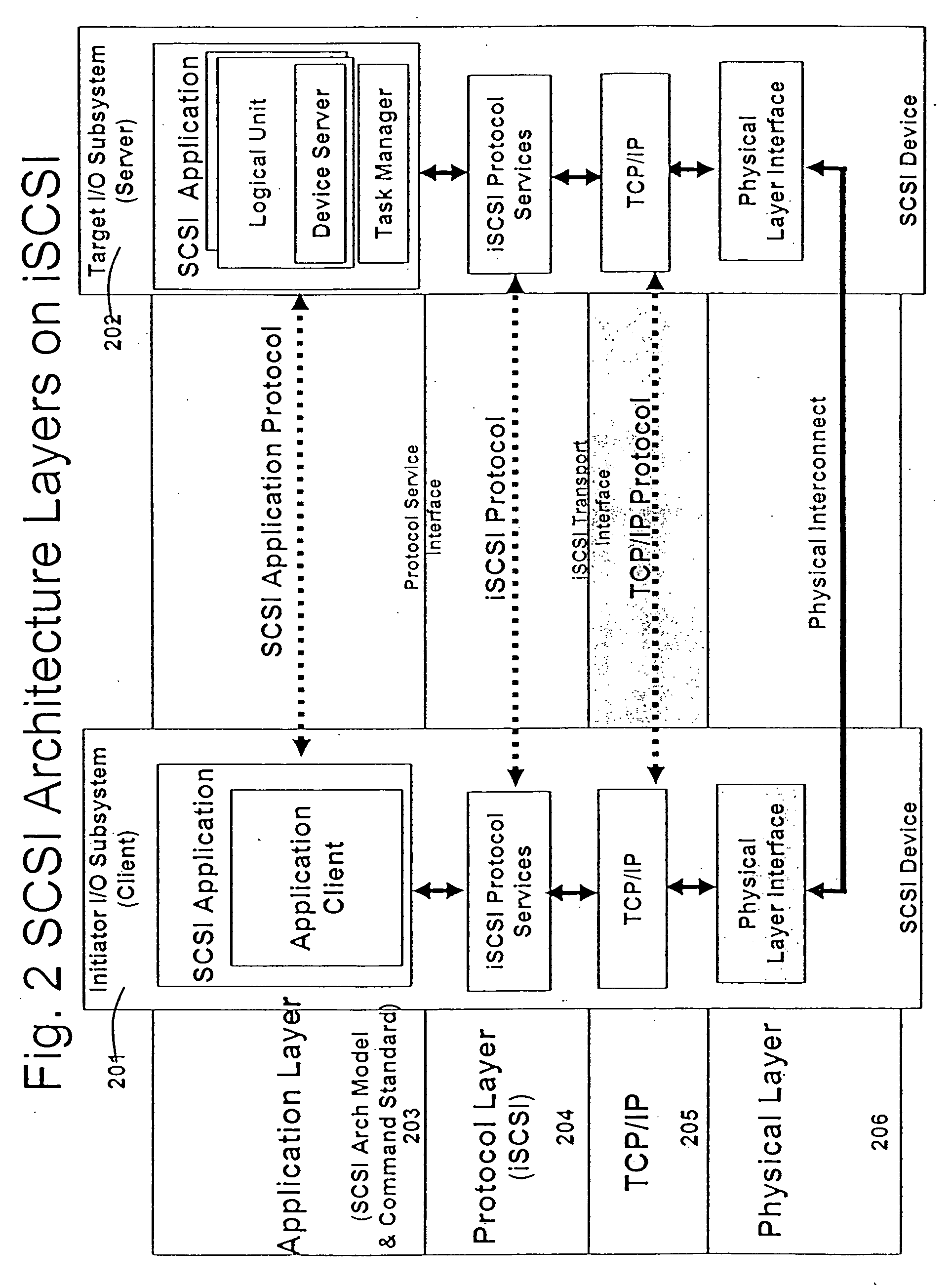
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
74298 results about "Self adaptive" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Self-Adaptive System. an automatic control system that preserves its operational capability under conditions of unforeseen change in the properties of the controlled system, in the control goal, or in the environment by changing its operation algorithm or searching for optimal states.
Intelligent electronic appliance system and method
InactiveUS6850252B1Minimize timeEasy to implementAnalogue secracy/subscription systemsCharacter and pattern recognitionAdaptive user interfaceDigital rights management
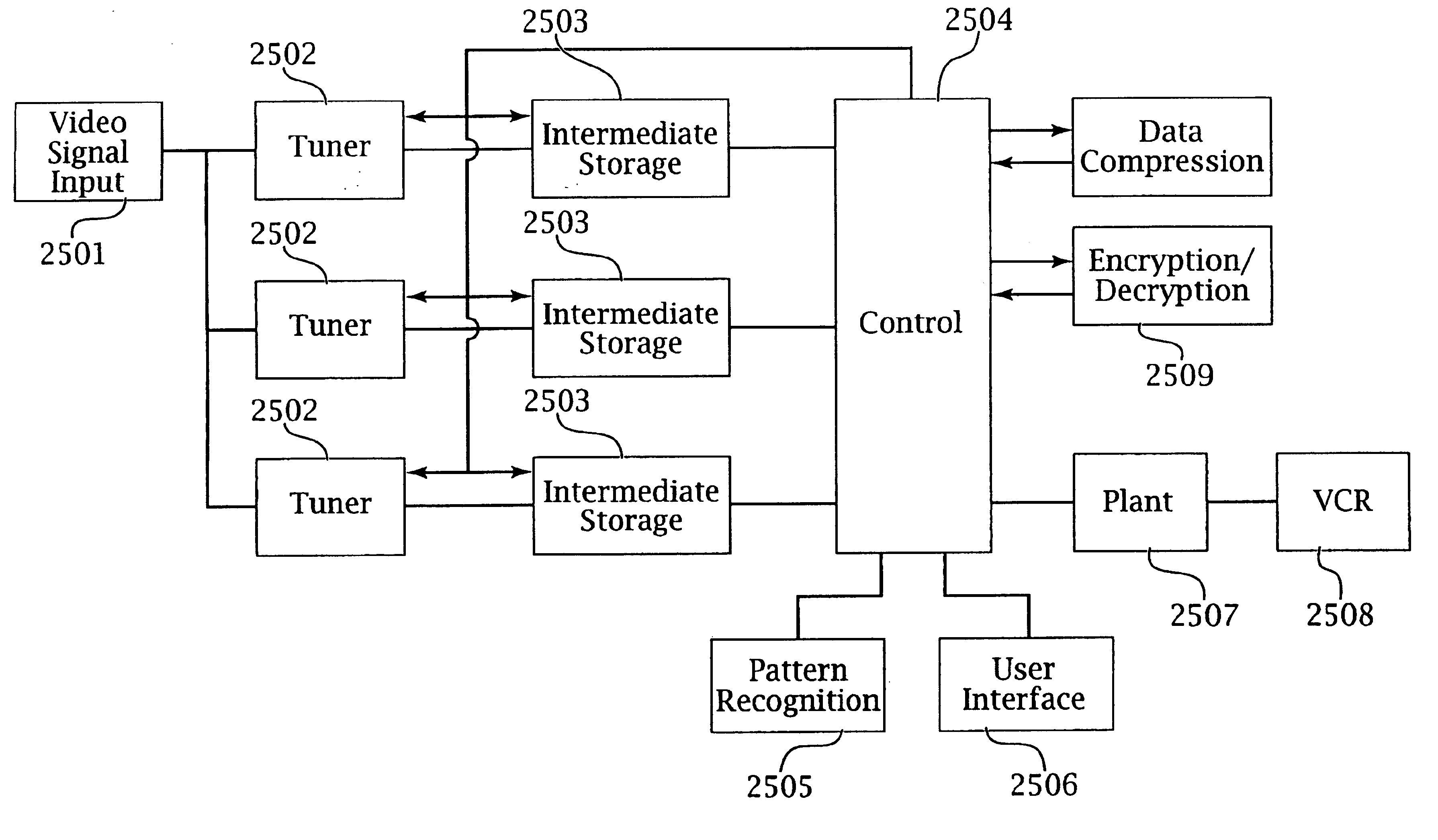
An intelligent electronic appliance preferably includes a user interface, data input and / or output port, and an intelligent processor. A preferred embodiment comprises a set top box for interacting with broadband media streams, with an adaptive user interface, content-based media processing and / or media metadata processing, and telecommunications integration. An adaptive user interface models the user, by observation, feedback, and / or explicit input, and presents a user interface and / or executes functions based on the user model. A content-based media processing system analyzes media content, for example audio and video, to understand the content, for example to generate content-descriptive metadata. A media metadata processing system operates on locally or remotely generated metadata to process the media in accordance with the metadata, which may be, for example, an electronic program guide, MPEG 7 data, and / or automatically generated format. A set top box preferably includes digital trick play effects, and incorporated digital rights management features.
Owner:BLANDING HOVENWEEP
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
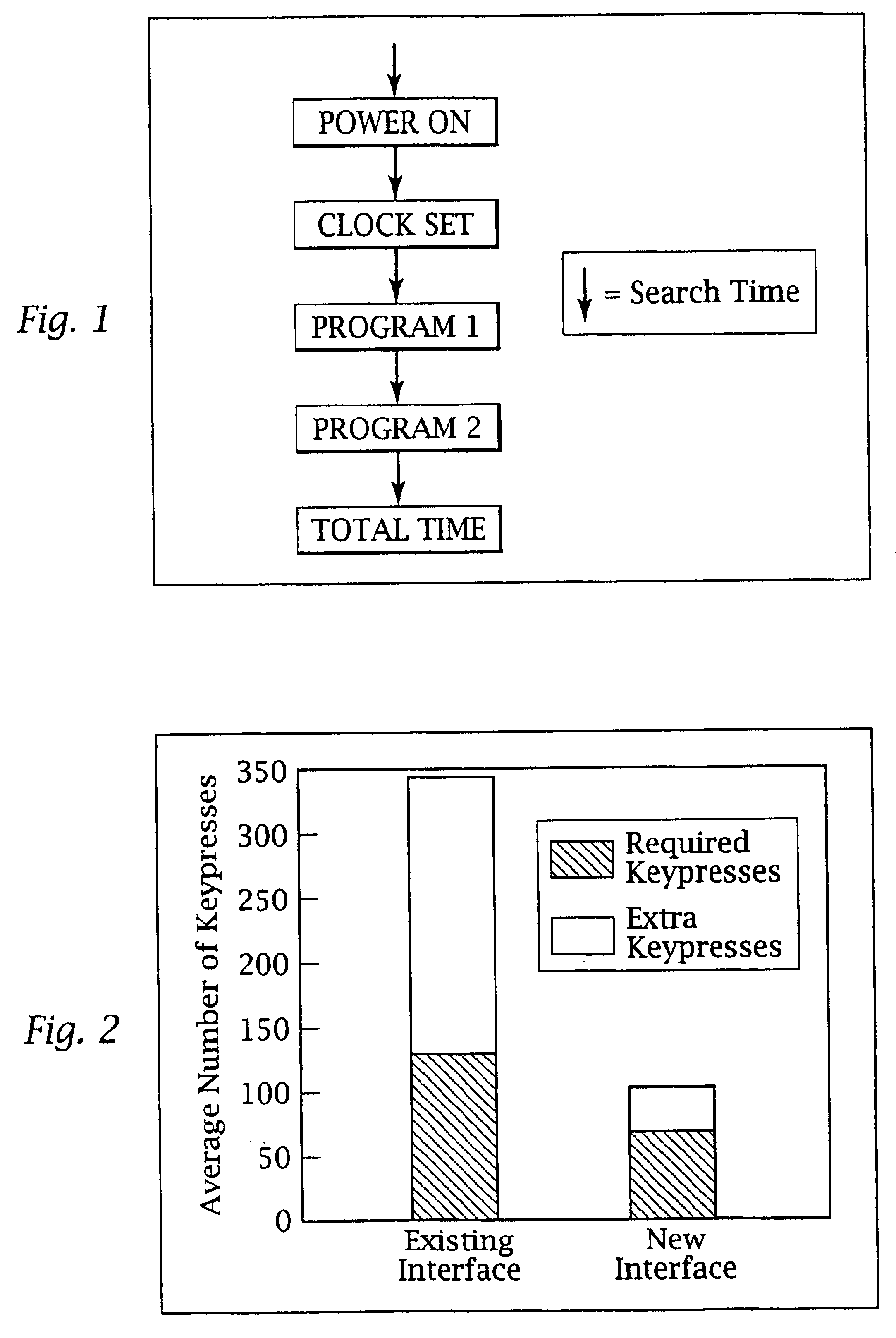
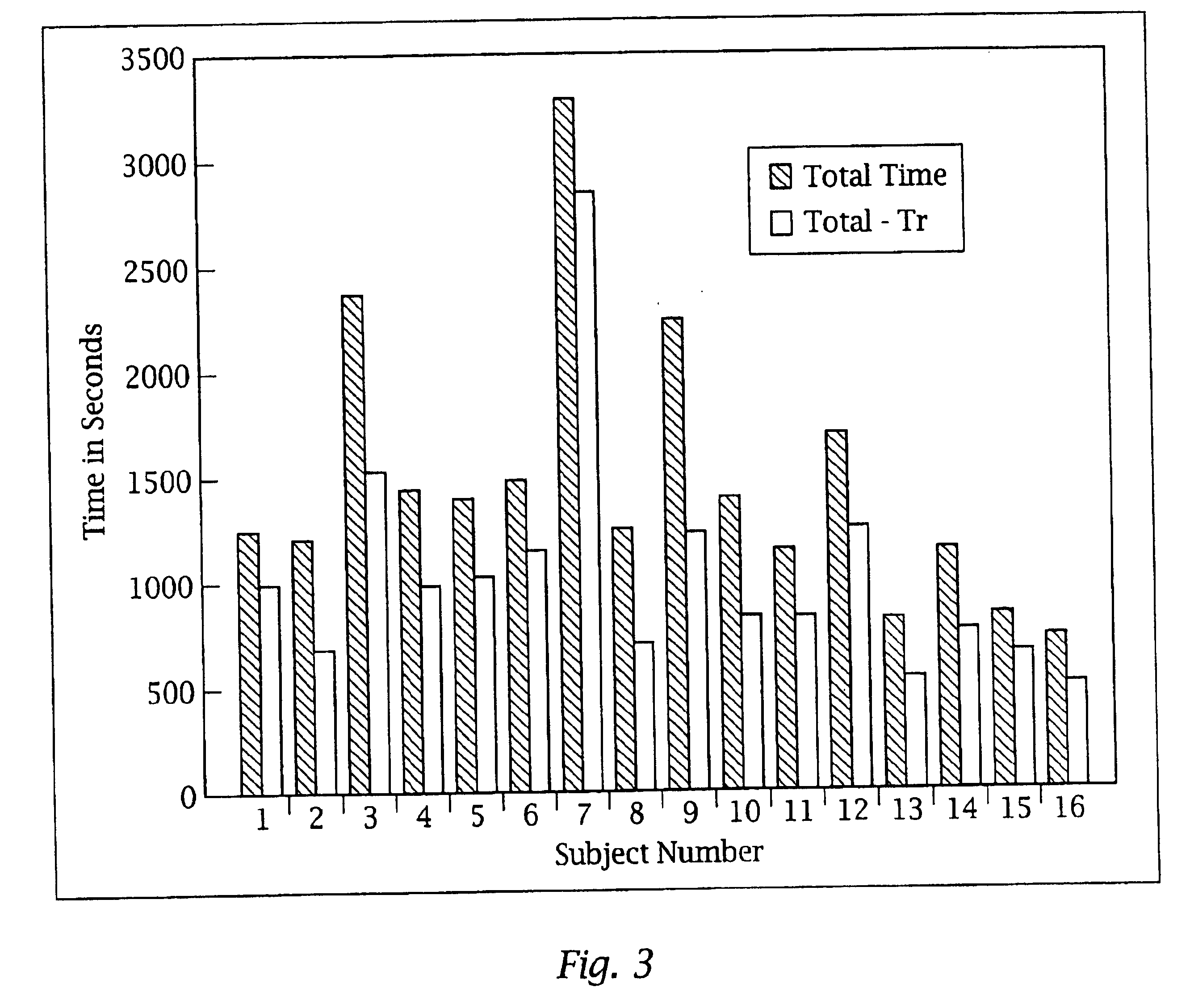
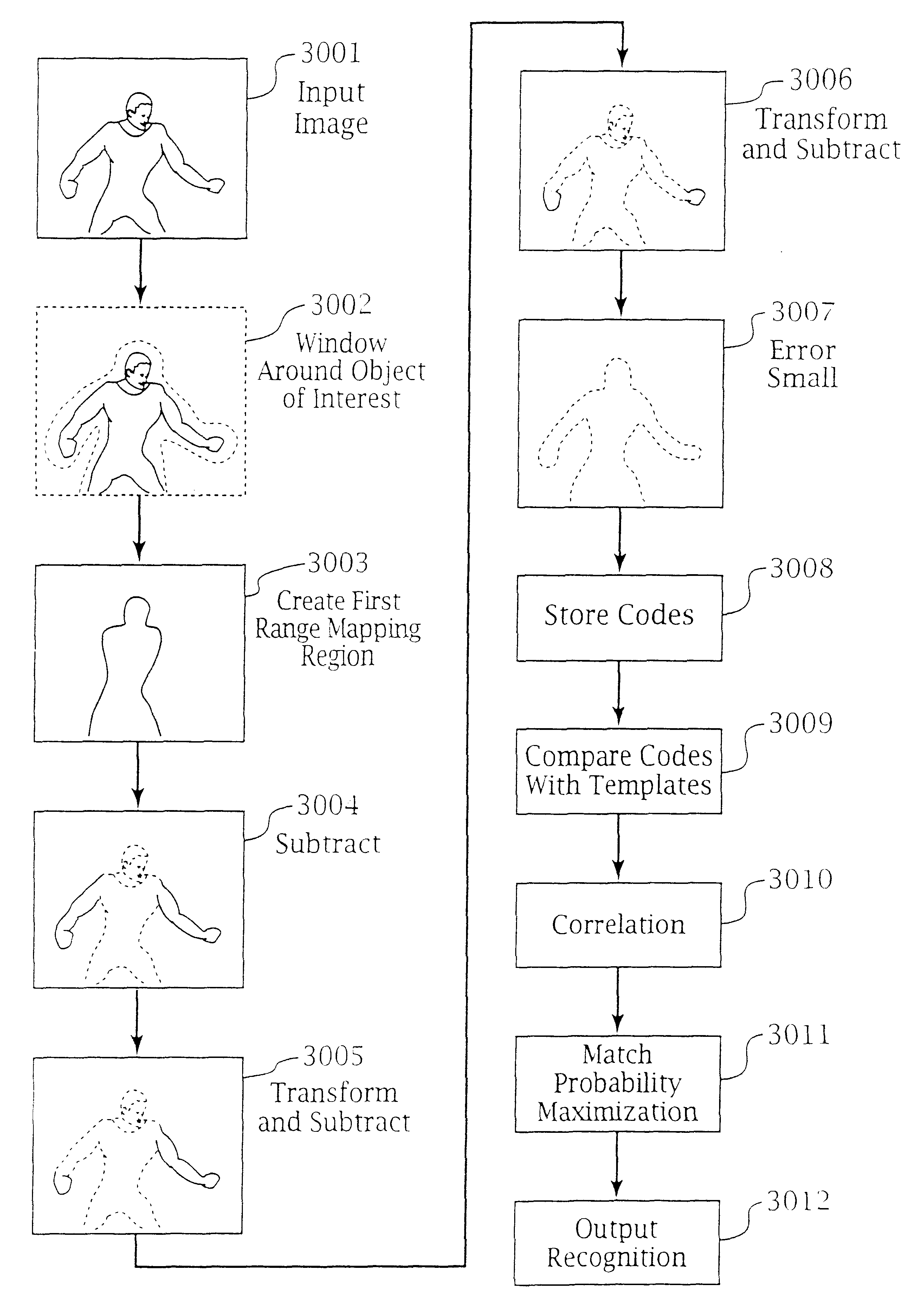
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
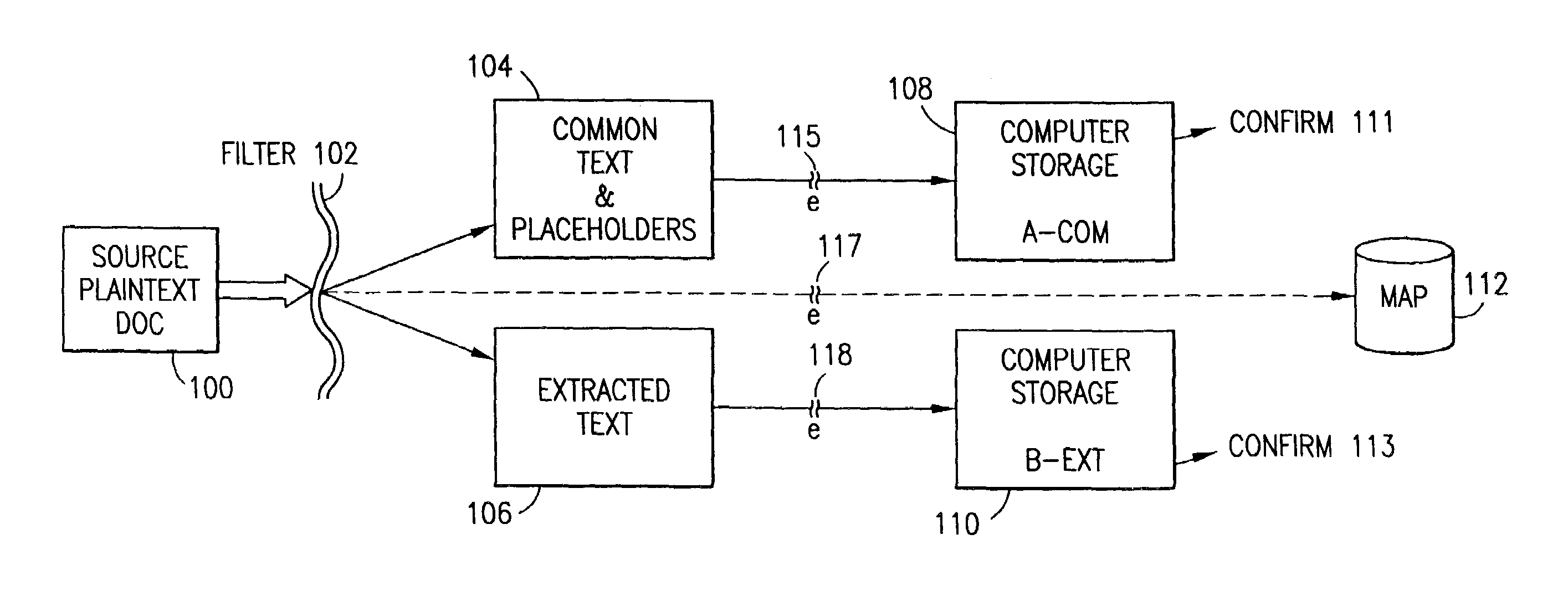
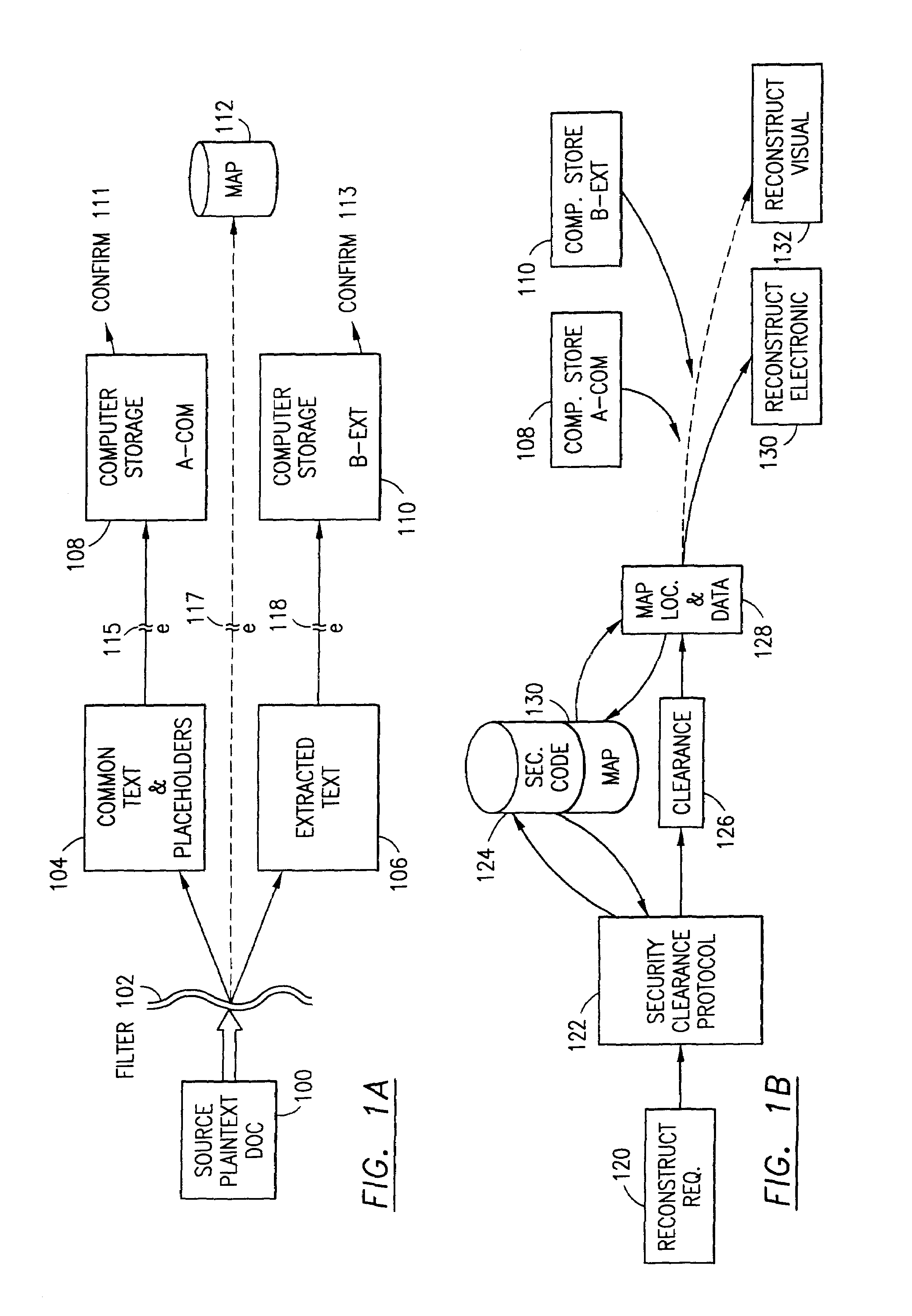
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
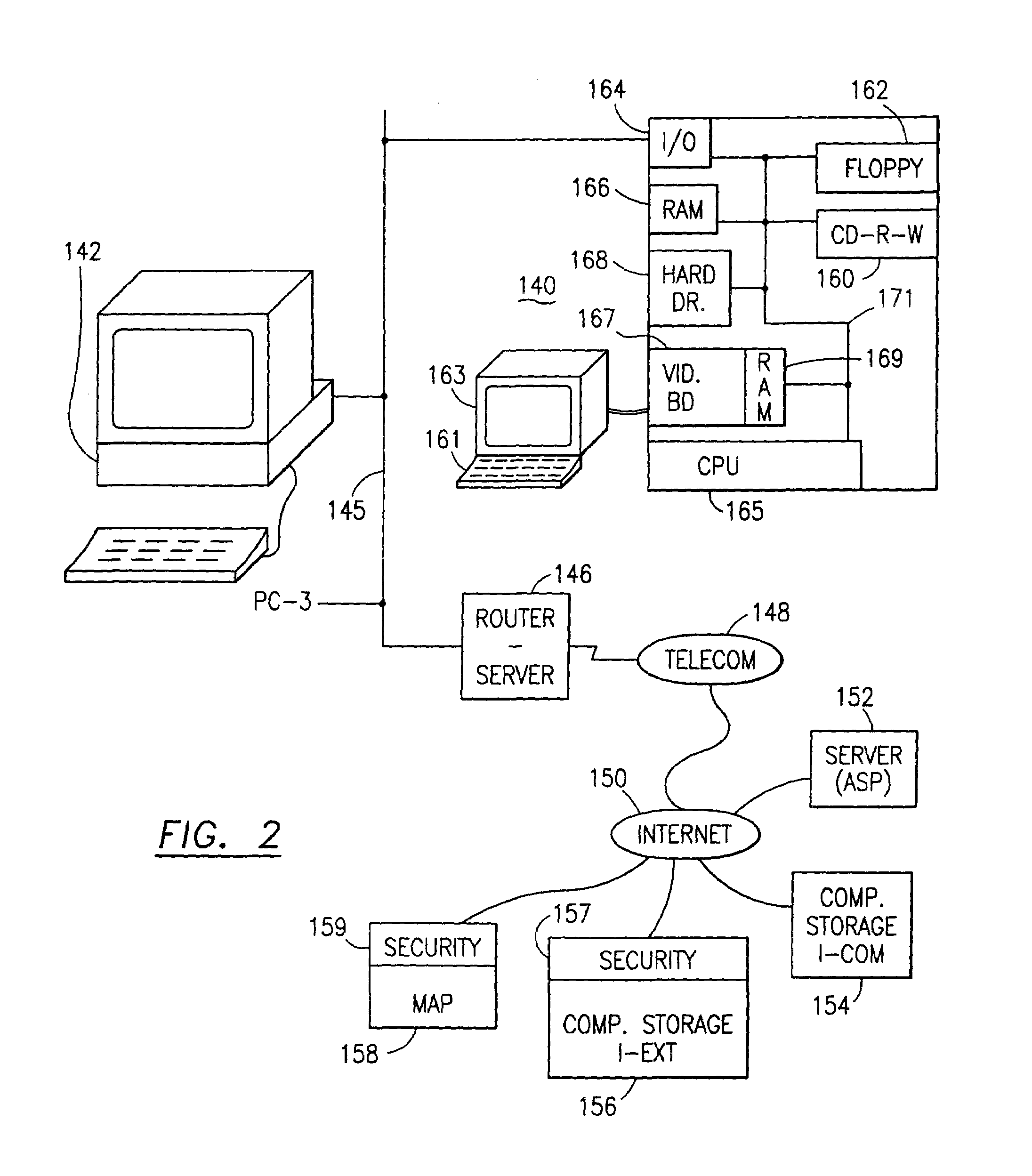
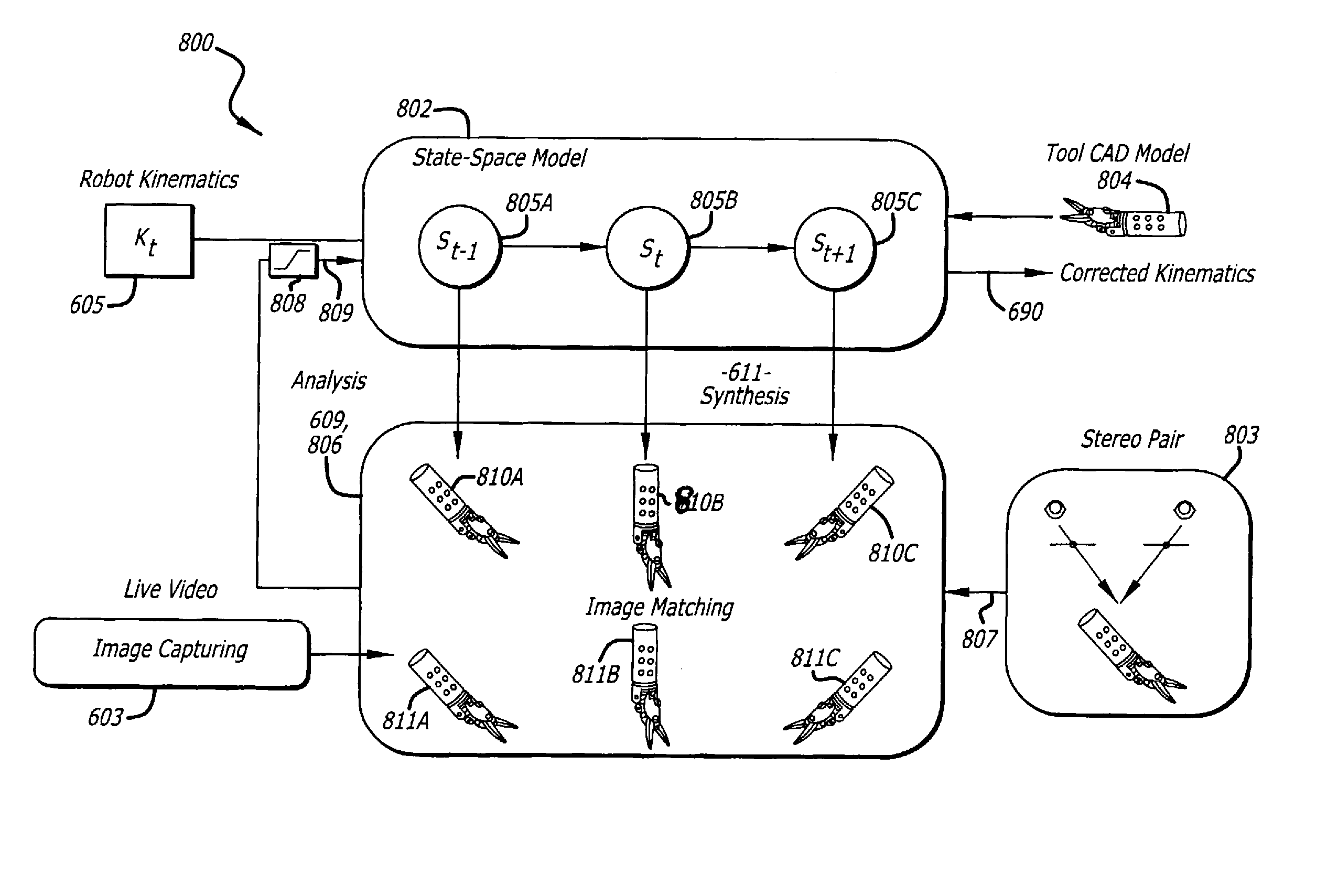
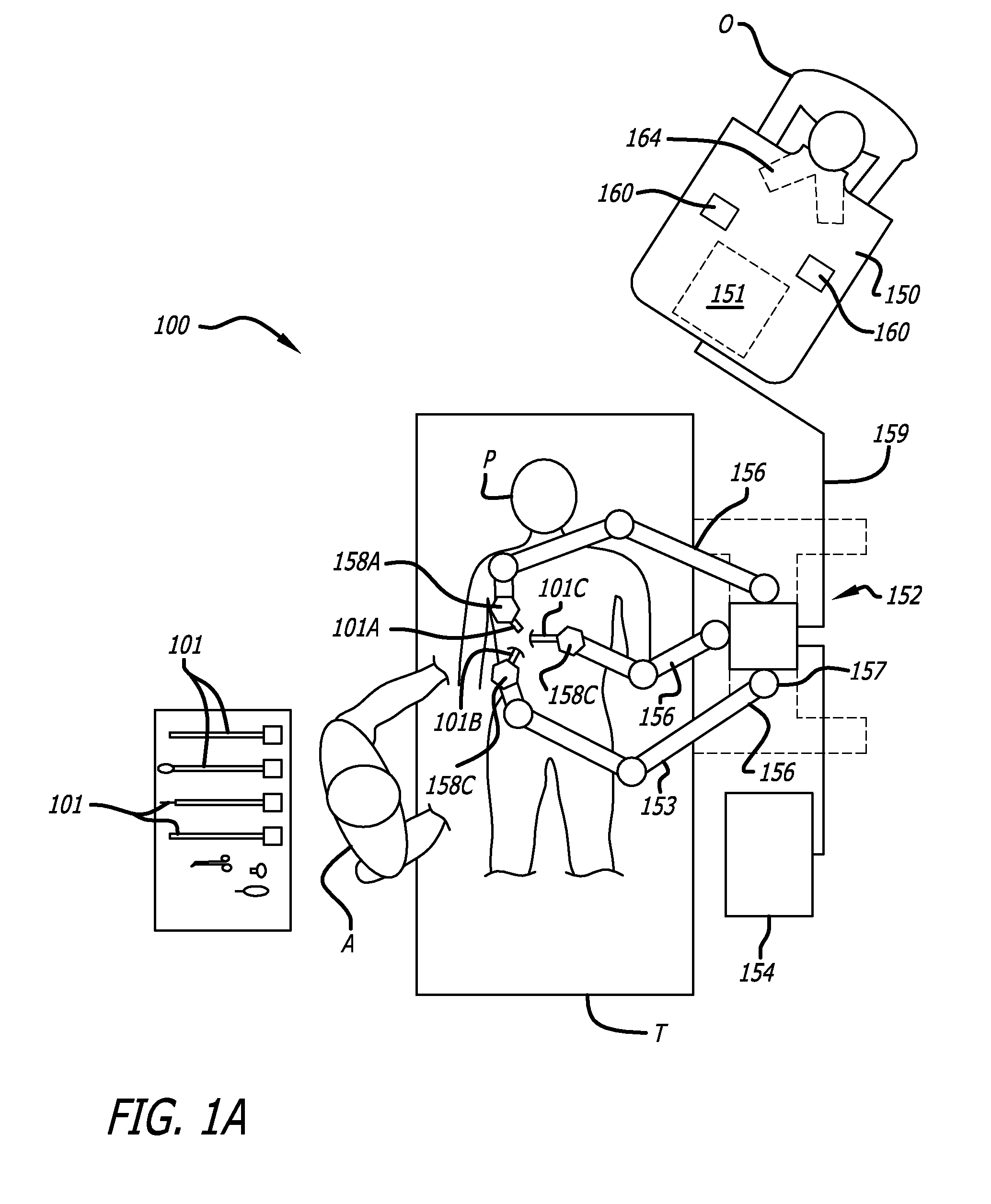
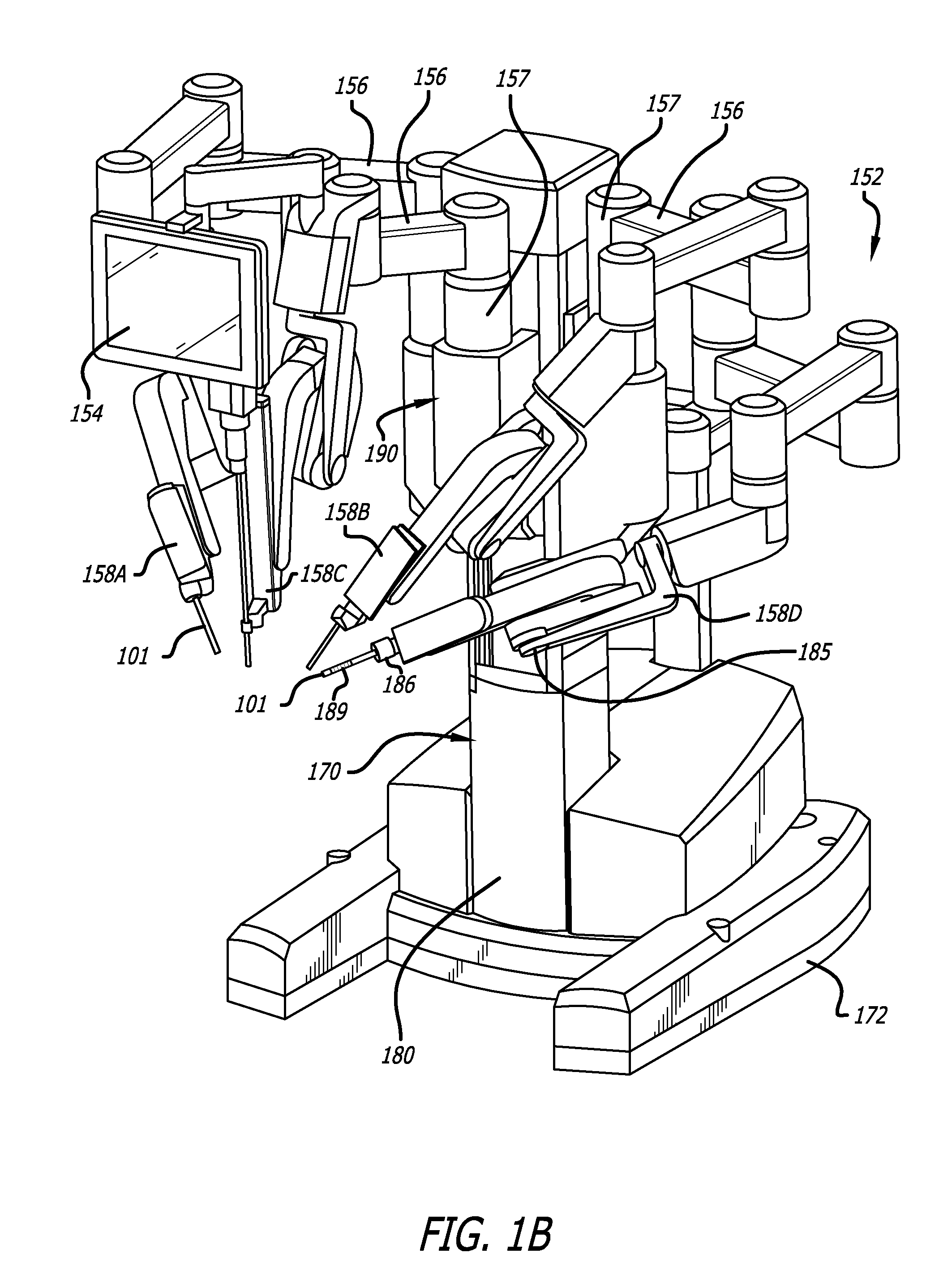
Methods and systems for robotic instrument tool tracking with adaptive fusion of kinematics information and image information
Owner:INTUITIVE SURGICAL OPERATIONS INC
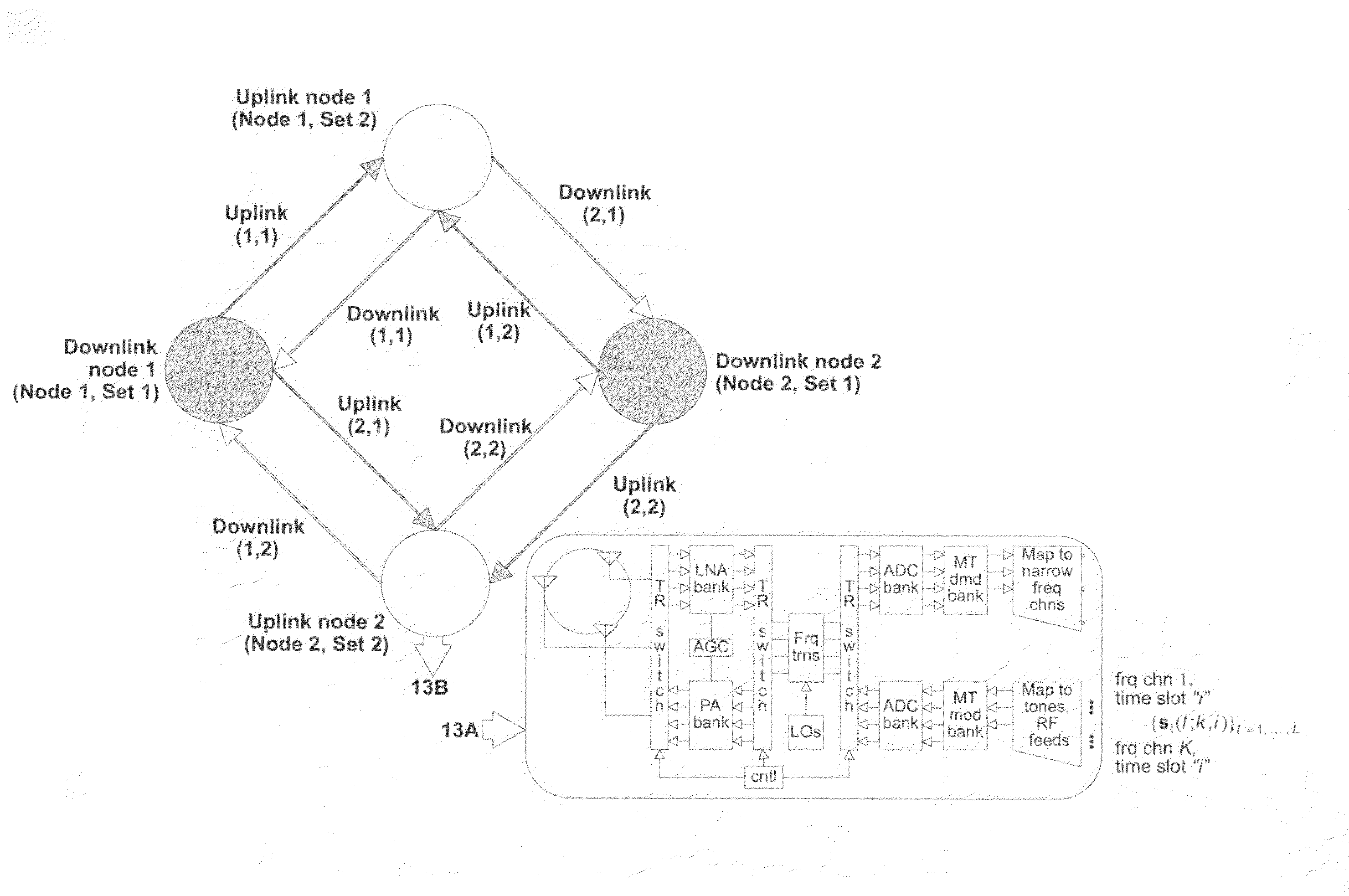
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS20040095907A1Improve signal qualityReduce interference energyPower managementSpatial transmit diversityGlobal optimizationDiversity scheme
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitione encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6081750ADecrease productivityImprove the environmentComputer controlSimulator controlHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
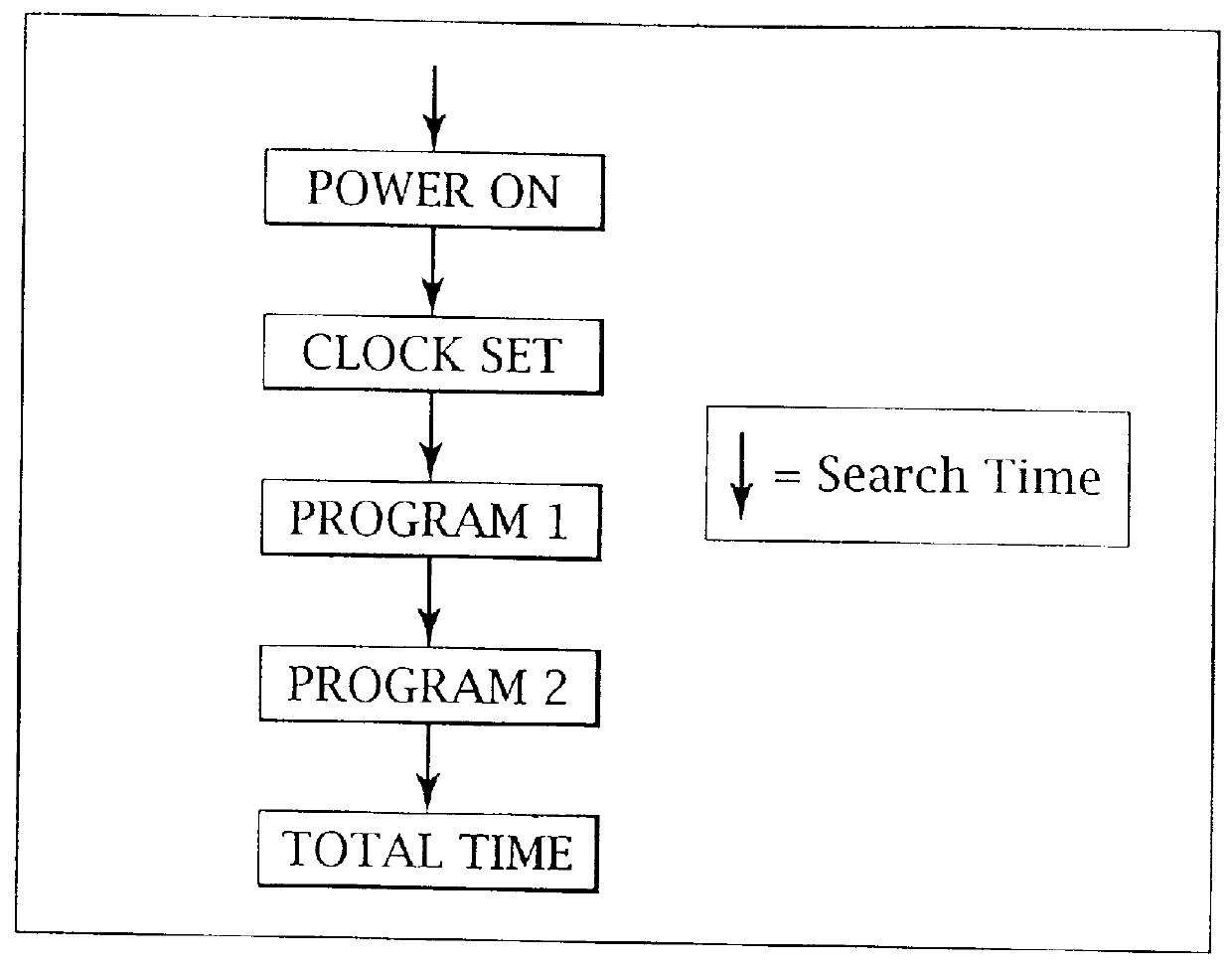
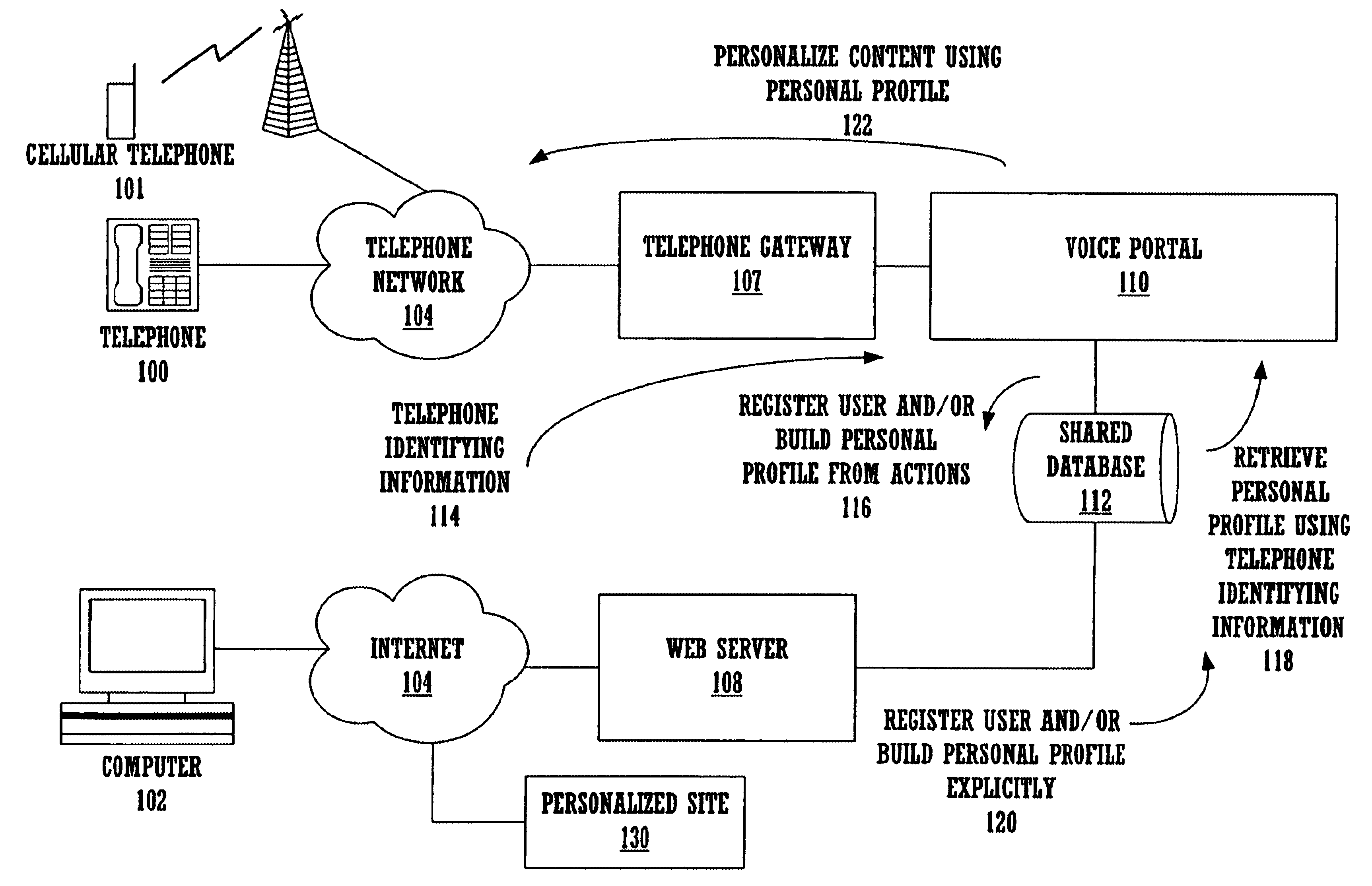
Method and apparatus for content personalization over a telephone interface with adaptive personalization
InactiveUS6842767B1Shorten speedIncrease volumeMultiple digital computer combinationsAutomatic exchangesPersonalizationHuman language
A method and apparatus for providing personalized information content over telephones is described. The creation of a voice portal is supported by the invention. Embodiments of the invention use telephone identifying information such as the calling party's number to identify, or create, user profiles for customization. The personalized content is specific to that user based on her / his telephone identifying information and may be further customized based on the current time, current date, the calling party's locales, and / or the calling party's dialect and speech patterns. Also, the telephone identifying information may support targeted advertising, content, and purchasing recommendations specific to that user. The system may use a voice password and / or touch-tone login system when appropriate to distinguish the caller or verify the caller's identity for specific activities. Typically, embodiments of the invention will immediately present a caller personalized content based on her / his profile using the appropriate dialect as well as the caller's preferred content. Profiles can be constructed as the caller uses embodiments of the invention as well as through explicit designation of preferences. For example, as the user selects topics, as well as particular content, a record of actions can be maintained. This record of actions can be used to provide suggestions and direct the personalization of the system for the user.
Owner:MICROSOFT TECH LICENSING LLC
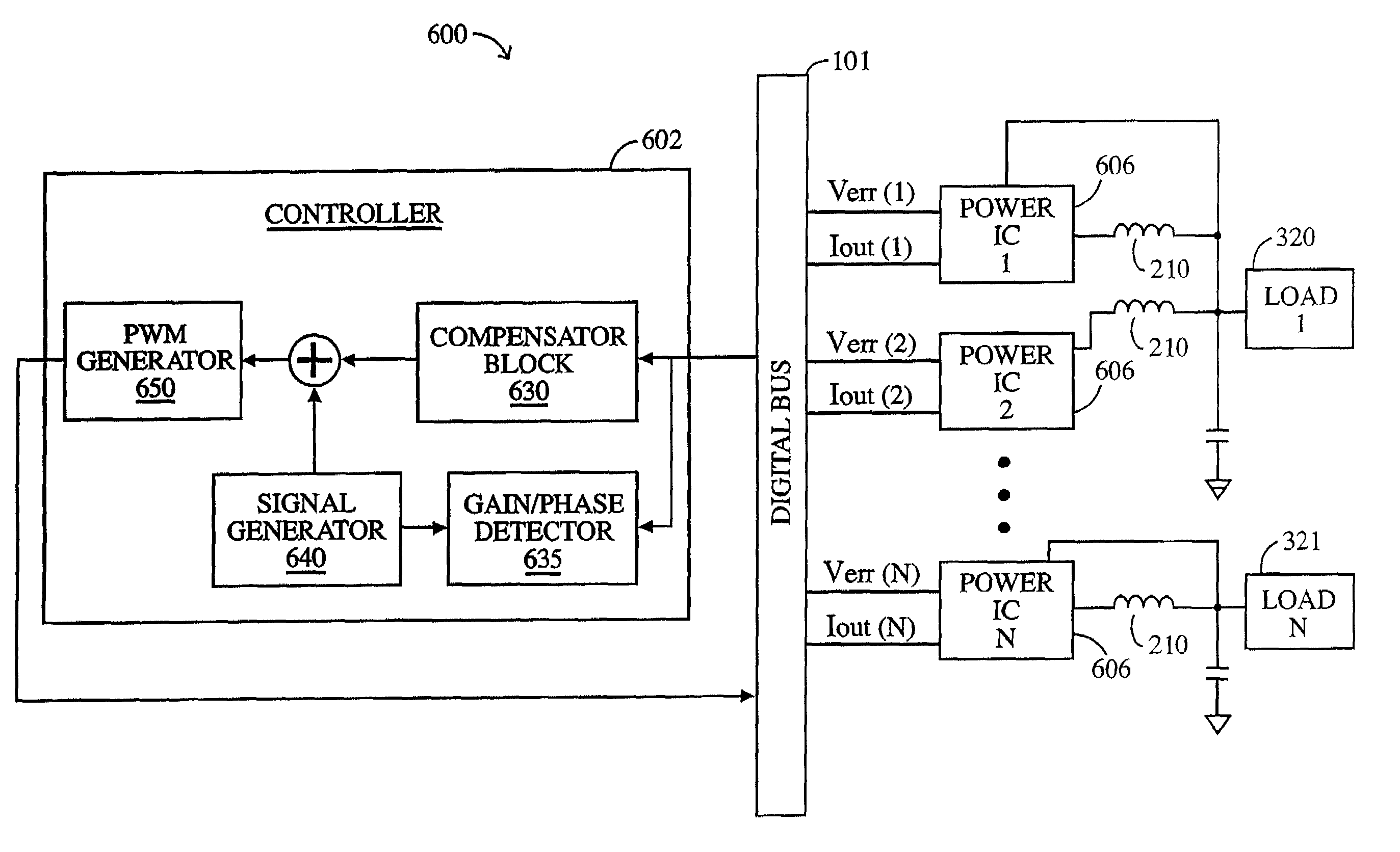
System and method for highly phased power regulation using adaptive compensation control
InactiveUS7007176B2Improved power regulation systemAdd control functionVolume/mass flow measurementDc-dc conversionComputer moduleEngineering
A highly phased power regulation (converter) system having an improved control feature is provided. A controller, such as a digital signal processor or microprocessor, receives digital information from a plurality of power conversion blocks and transmits control commands in response to the information. The controller is able to change the mode of operation of the system and / or re-phase the power blocks to accommodate a dynamic load requirement, occasions of high transient response or detection of a fault. A compensation block within the controller is used to regulate the output voltage and provide stability to the system. In one embodiment, the controller is implemented as a PID compensator controller. In another embodiment, a microprocessor is able to receive feedback on its own operation thus providing enabling the controller to anticipate and predict conditions by analyzing precursor data.
Owner:INFINEON TECH AUSTRIA AG
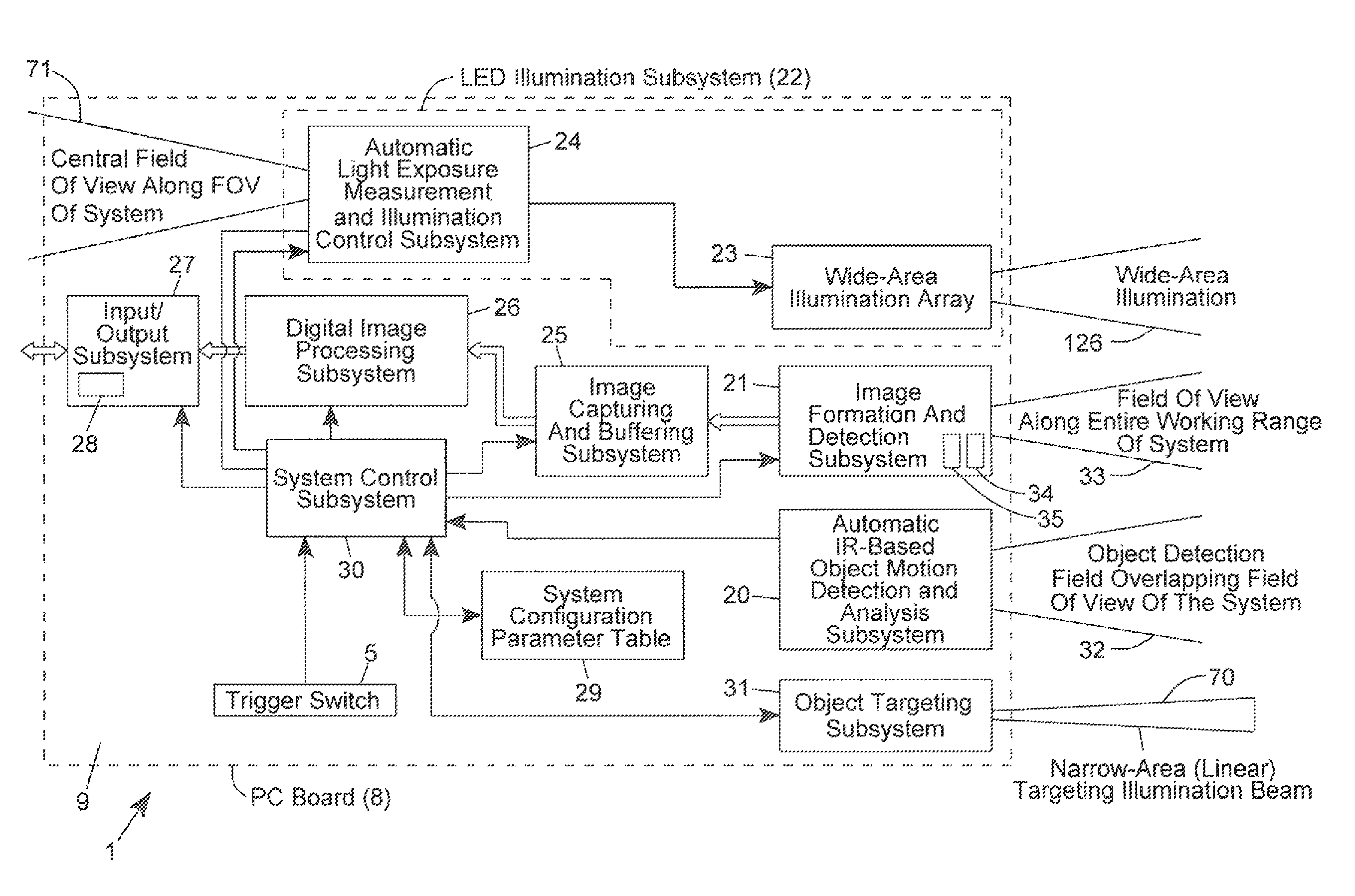
Auto-exposure method using continuous video frames under controlled illumination
ActiveUS8408464B2Improve the level ofCapture performanceTelevision system detailsMechanical apparatusGraphicsReal time analysis
An adaptive strobe illumination control process for use in a digital image capture and processing system. In general, the process involves: (i) illuminating an object in the field of view (FOV) with several different pulses of strobe (i.e. stroboscopic) illumination over a pair of consecutive video image frames; (ii) detecting digital images of the illuminated object over these consecutive image frames; and (iii) decode processing the digital images in an effort to read a code symbol graphically encoded therein. In a first illustrative embodiment, upon failure to read a code symbol graphically encoded in one of the first and second images, these digital images are analyzed in real-time, and based on the results of this real-time image analysis, the exposure time (i.e. photonic integration time interval) is automatically adjusted during subsequent image frames (i.e. image acquisition cycles) according to the principles of the present disclosure. In a second illustrative embodiment, upon failure to read a code symbol graphically encoded in one of the first and second images, these digital images are analyzed in real-time, and based on the results of this real-time image analysis, the energy level of the strobe illumination is automatically adjusted during subsequent image frames (i.e. image acquisition cycles) according to the principles of the present disclosure.
Owner:METROLOGIC INSTR
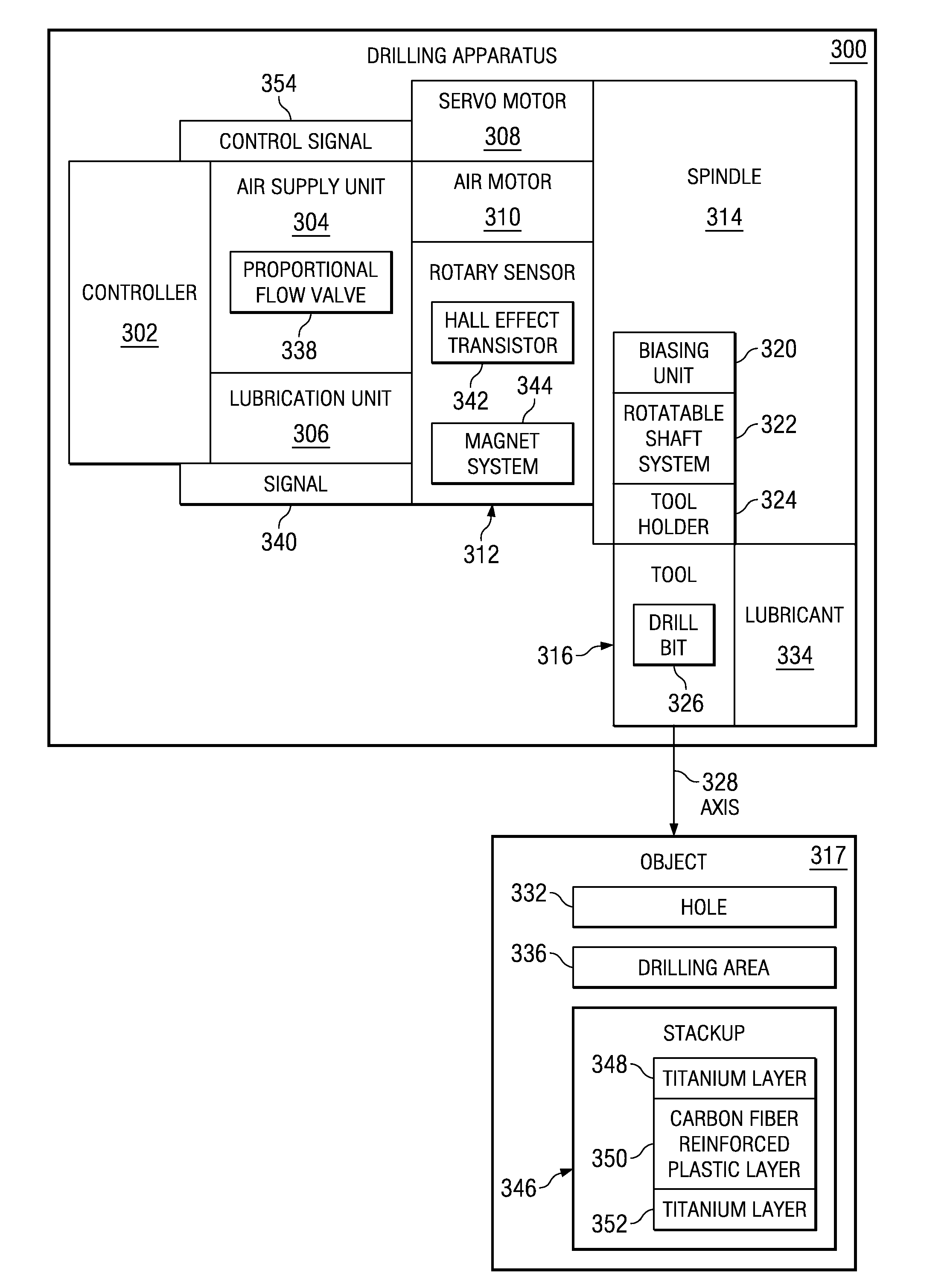
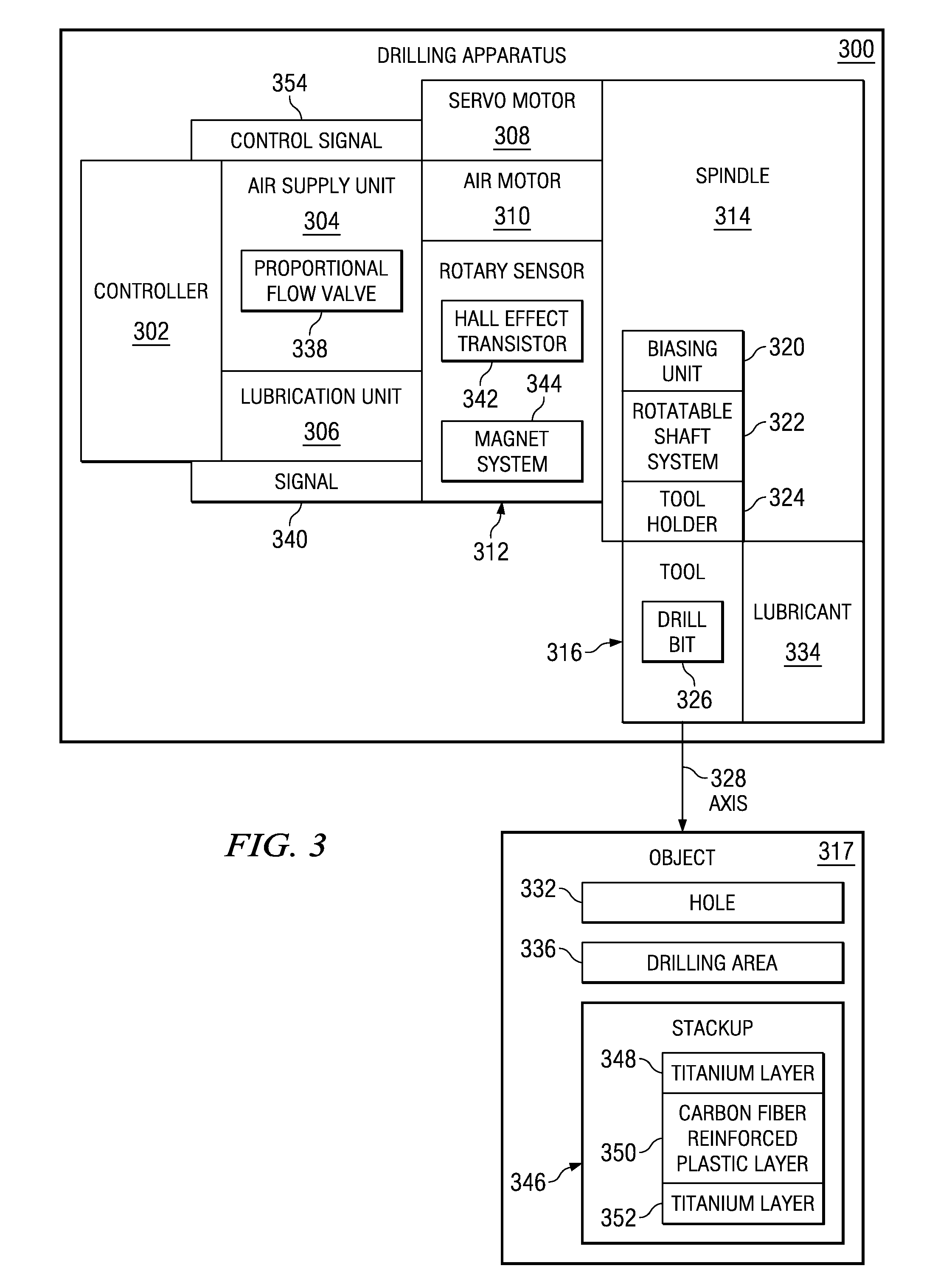
Adaptive positive feed drilling system
An apparatus for a drilling operation. In one advantageous embodiment, the drilling operation includes a motor, a rotary sensor, and a controller connected to the rotary sensor. The rotary sensor may be capable of generating a signal in response to rotary movement of the drill motor. The controller may be capable of monitoring a speed of the air motor from the signal generated by the rotary sensor and may be capable of identifying a change from a current layer in a stackup to a new layer in the stackup using the signal.
Owner:THE BOEING CO
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6418424B1Minimal costAvoid the needTelevision system detailsDigital data processing detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
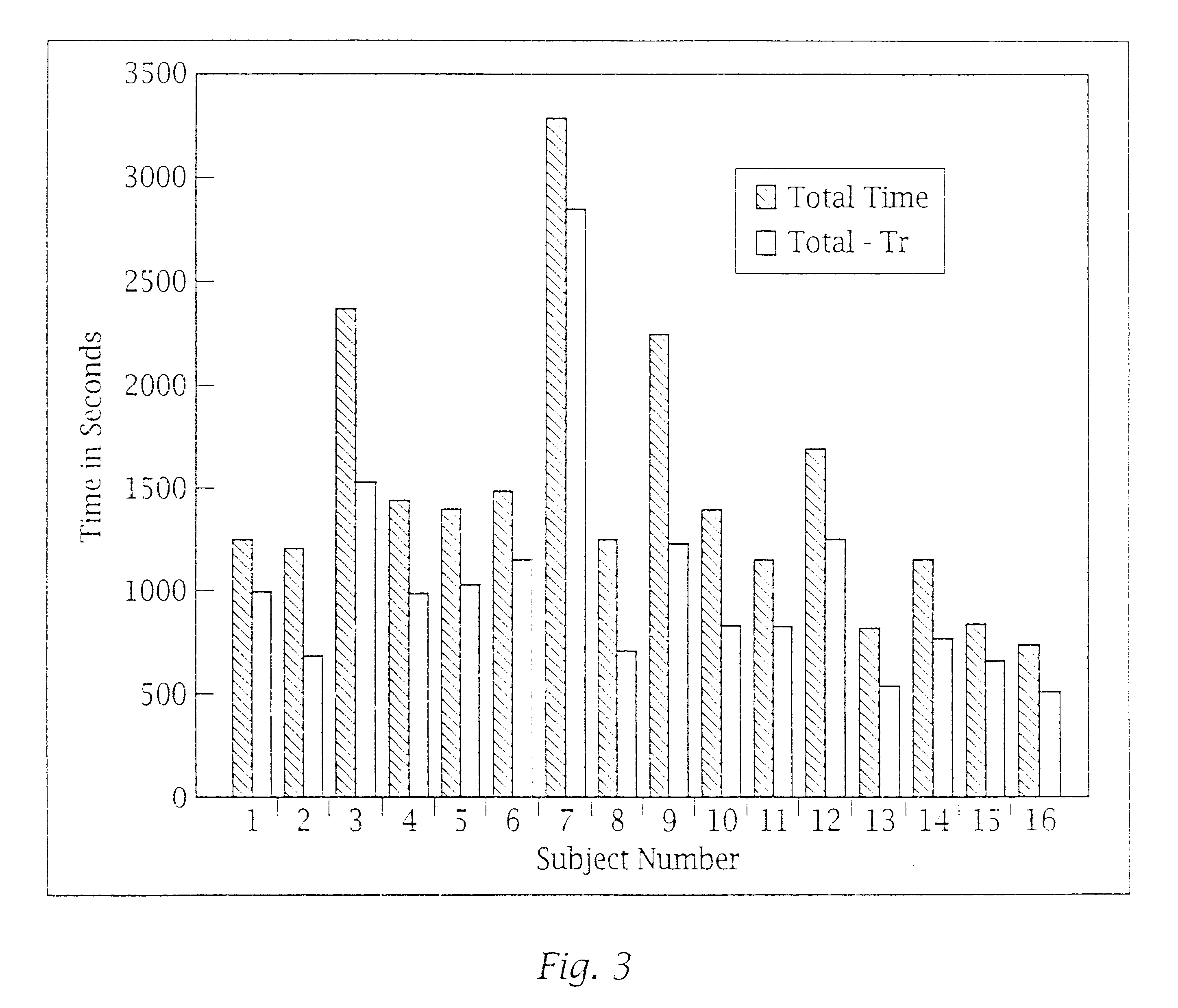
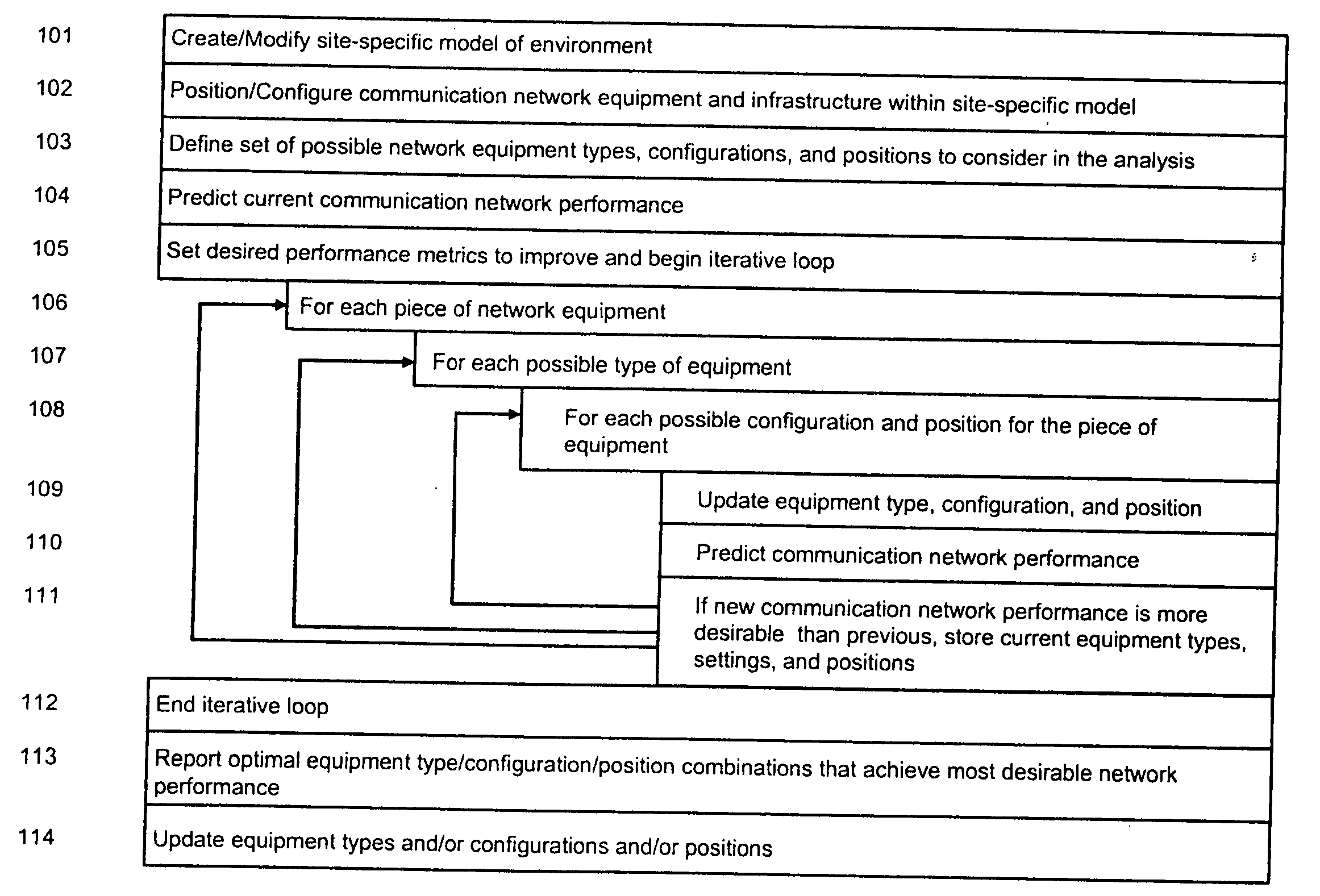
System and method for automated placement or configuration of equipment for obtaining desired network performance objectives and for security, RF tags, and bandwidth provisioning
ActiveUS20040236547A1Significant valueEasy to explainGeometric CADData taking preventionHard disc driveThe Internet
A method is presented for determining optimal or preferred configuration settings for wireless or wired network equipment in order to obtain a desirable level of network performance. A site-specific network model is used with adaptive processing to perform efficient design and on-going management of network performance. The invention iteratively determines overall network performance and cost, and further iterates equipment settings, locations and orientations. Real time control is between a site-specific Computer Aided Design (CAD) software application and the physical components of the network allows the invention to display, store, and iteratively adapt any network to constantly varying traffic and interference conditions. Alarms provide rapid adaptation of network parameters, and alerts and preprogrammed network shutdown actions may be taken autonomously. A wireless post-it note device and network allows massive data such as book contents or hard drive memory to be accessed within a room by a wide bandwidth reader device, and this can further be interconnected to the internet or Ethernet backbone in order to provide worldwide access and remote retrieval to wireless post-it devices.
Owner:EXTREME NETWORKS INC
Coding method and apparatus for multiple channels of audio information representing three-dimensional sound fields
InactiveUS6021386AConserve substantial bandwidthConveniently implementedBroadcast information characterisationSpeech analysisFrequency spectrumBit allocation
In an encoder, multiple channels of audio information representing multidimensional sound fields are split into subband signals and the subband signals in one or more subbands are combined to form composite signals. The composite signals, the subband signals not combined into a composite signal and information describing the spectral levels of subband signals combined into composite signals are assembled into an encoded output signal. The spectral level information conveys either the amplitude or power of the combined subband signals or the apparent direction of the sound field represented by the combined subband signals. In digital implementations, adaptive bit allocation may be used to reduce the informational requirements of the encoded signal.
Owner:DOLBY LAB LICENSING CORP
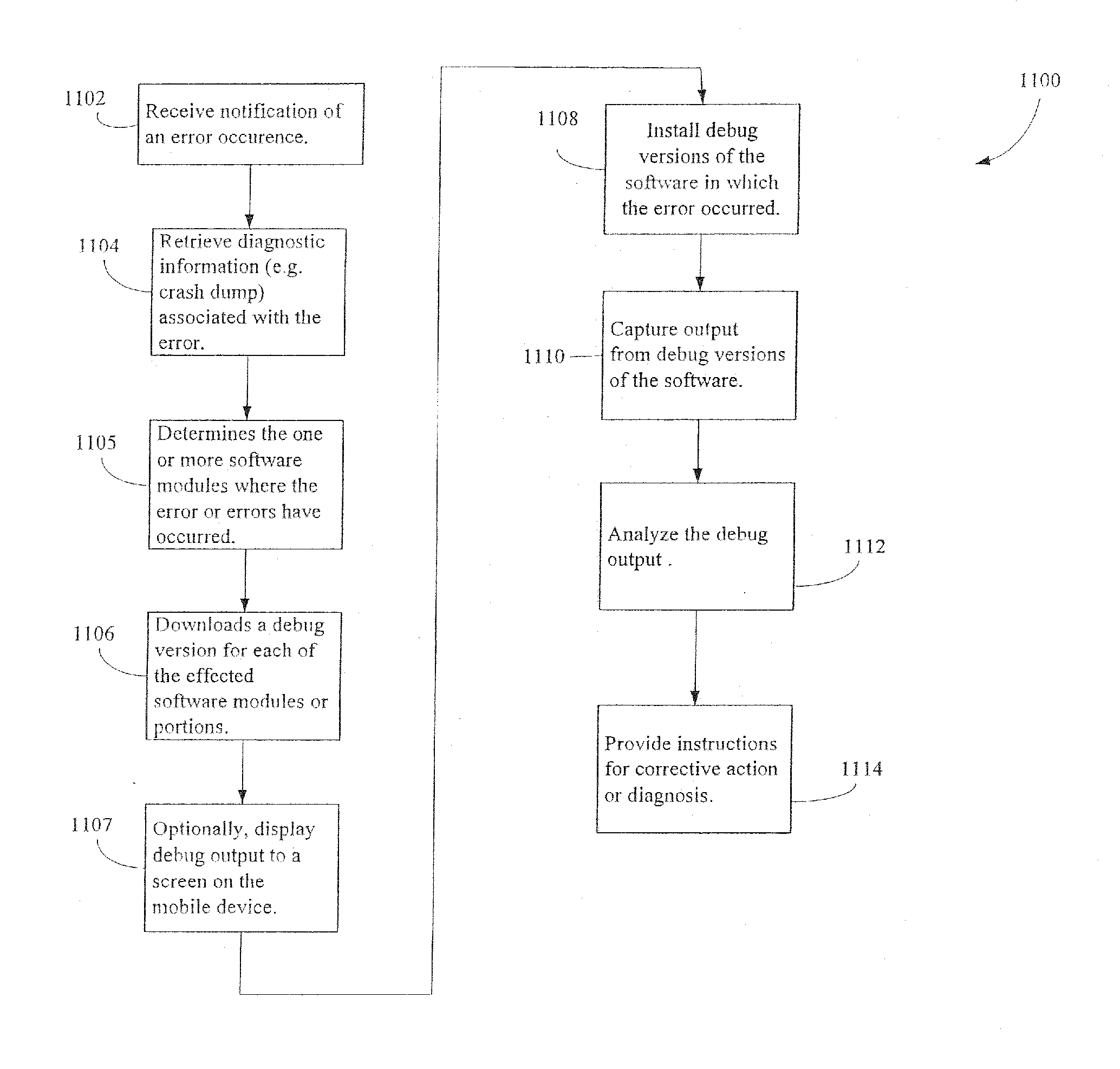
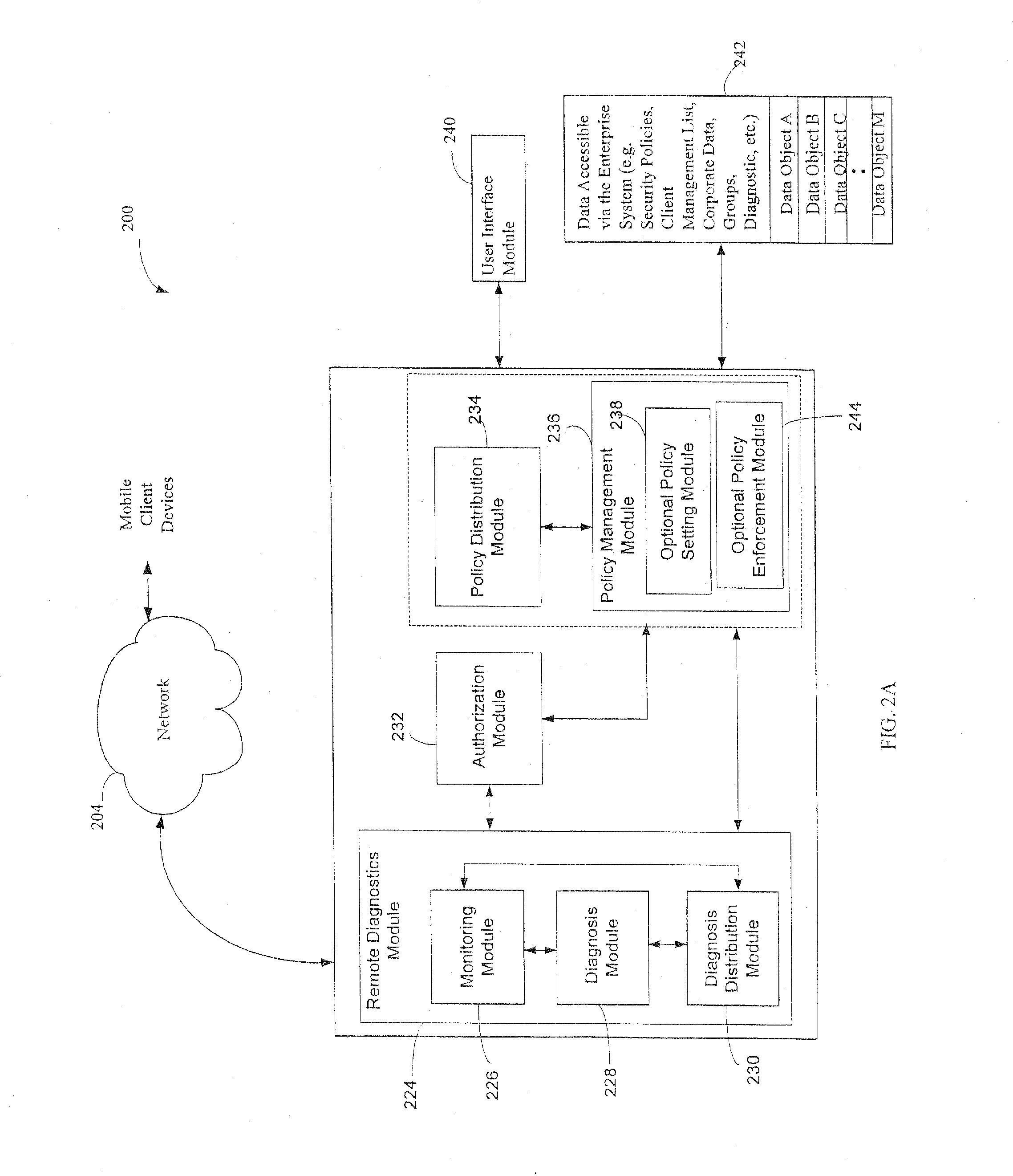
Administration of protection of data accessible by a mobile device
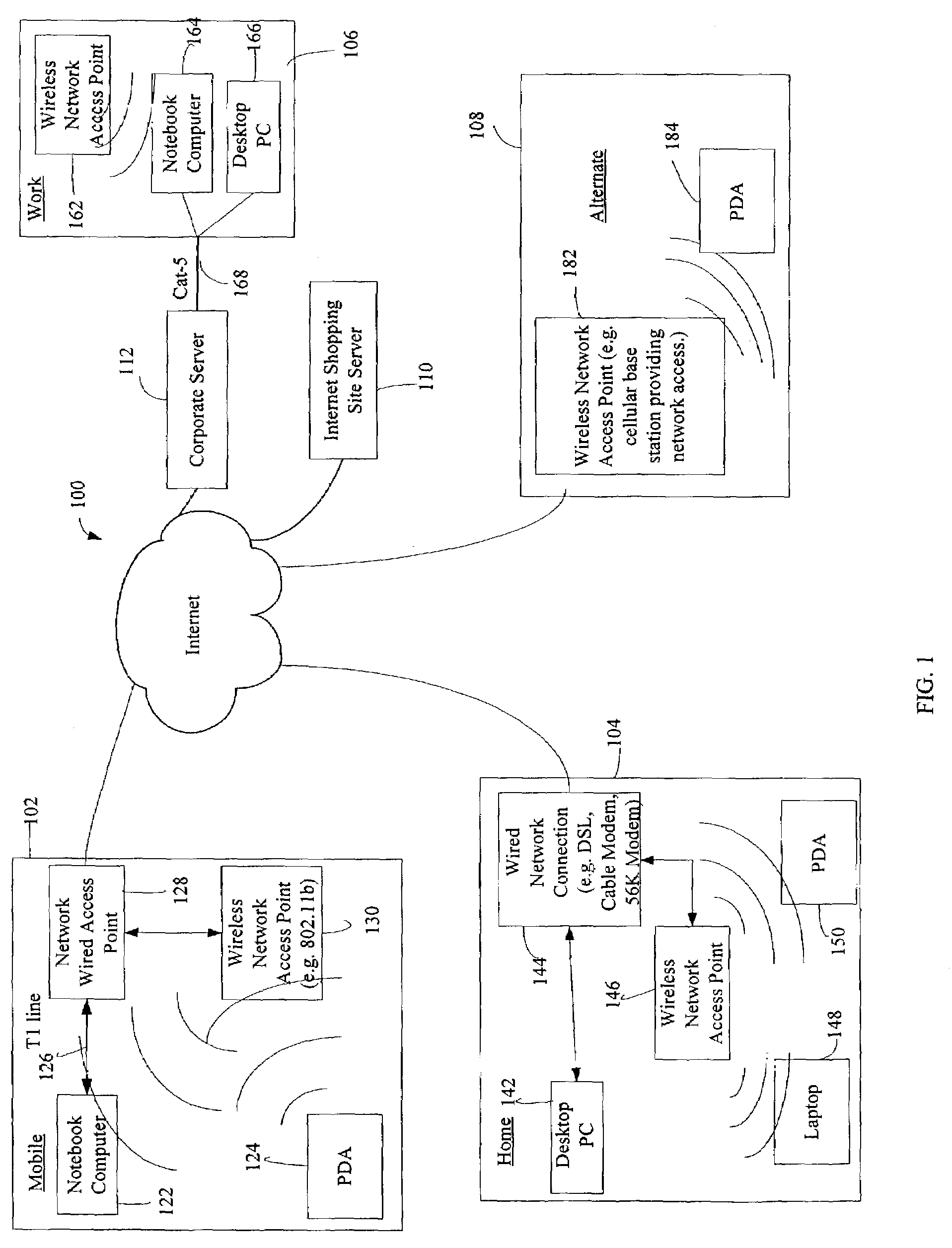
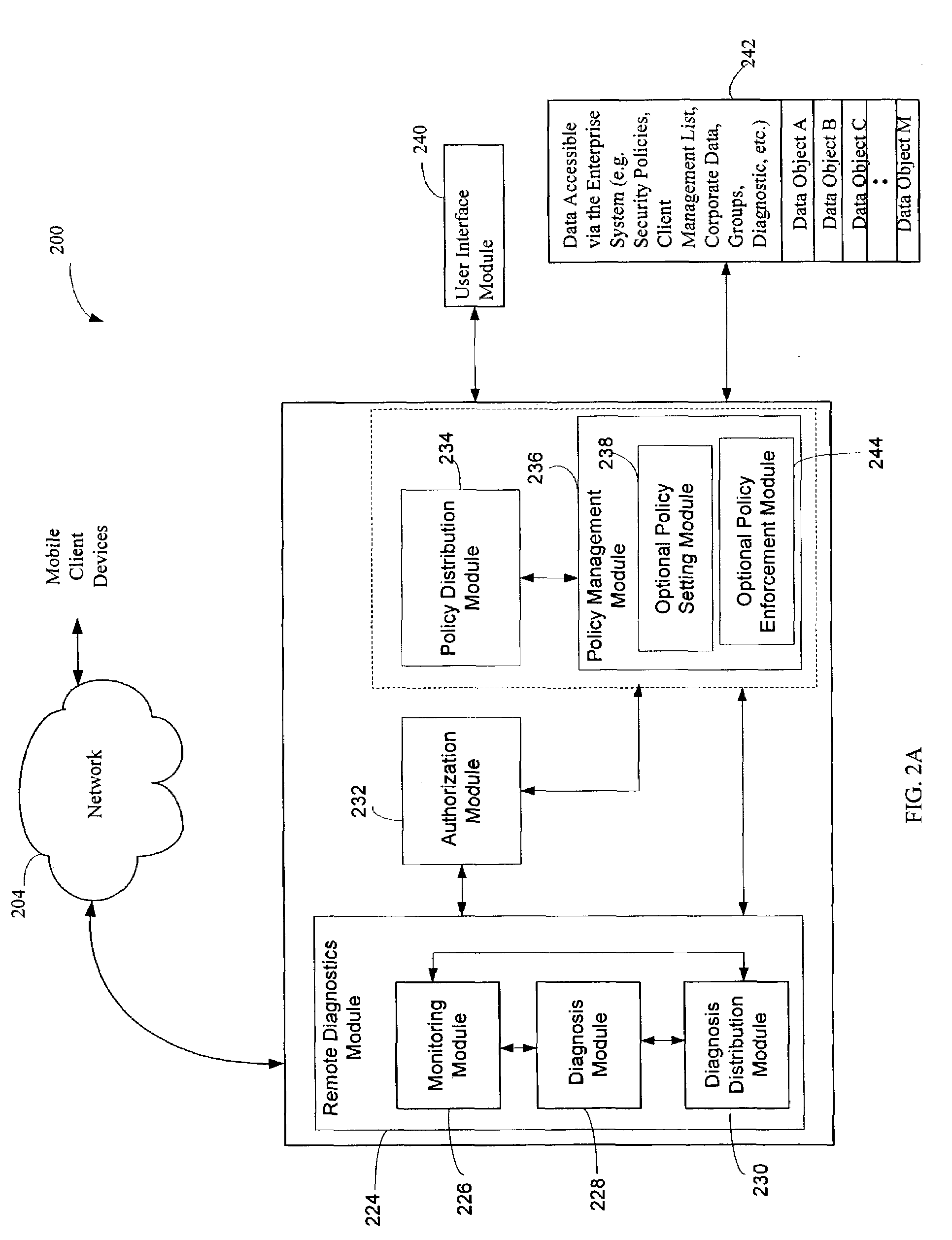
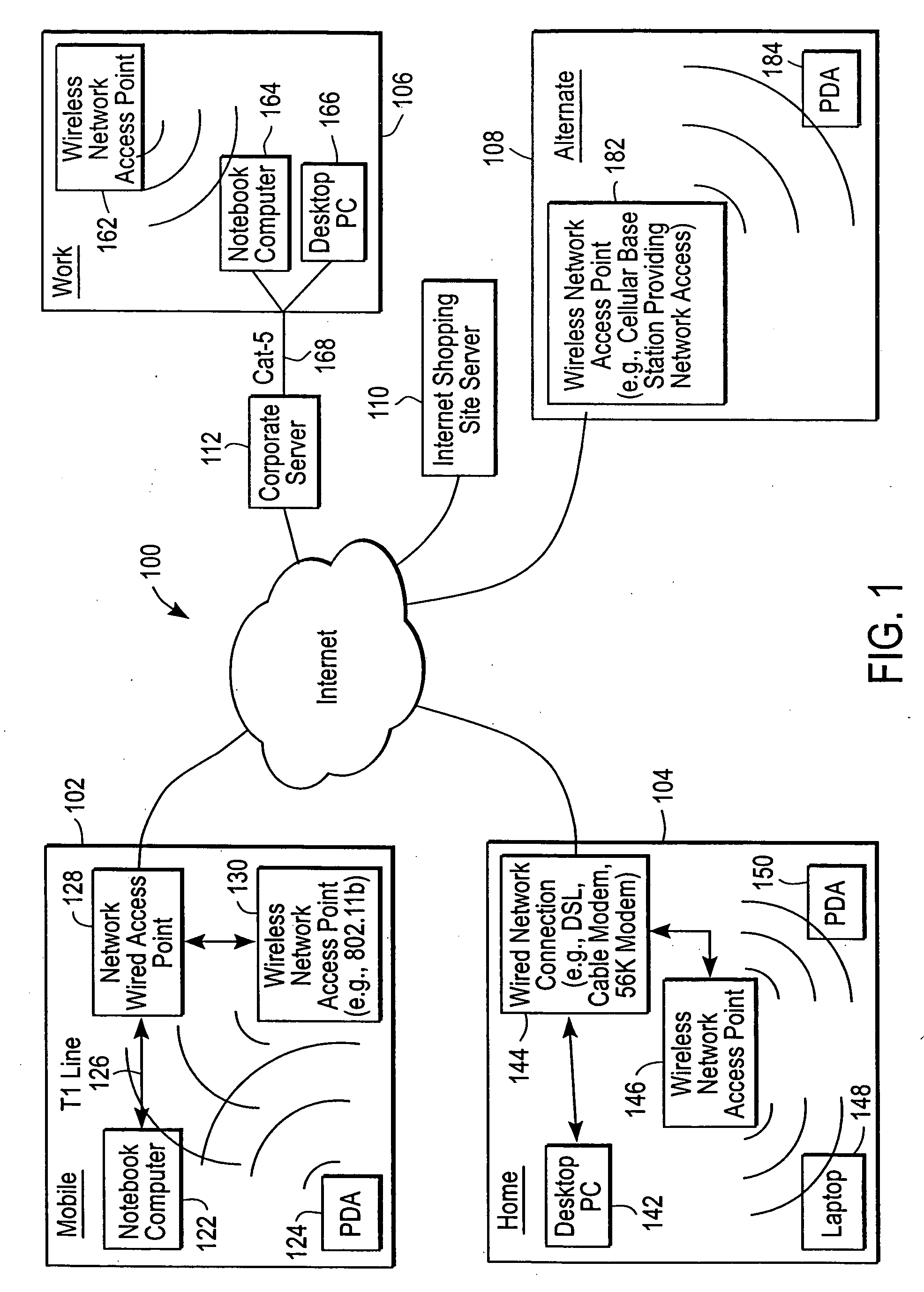
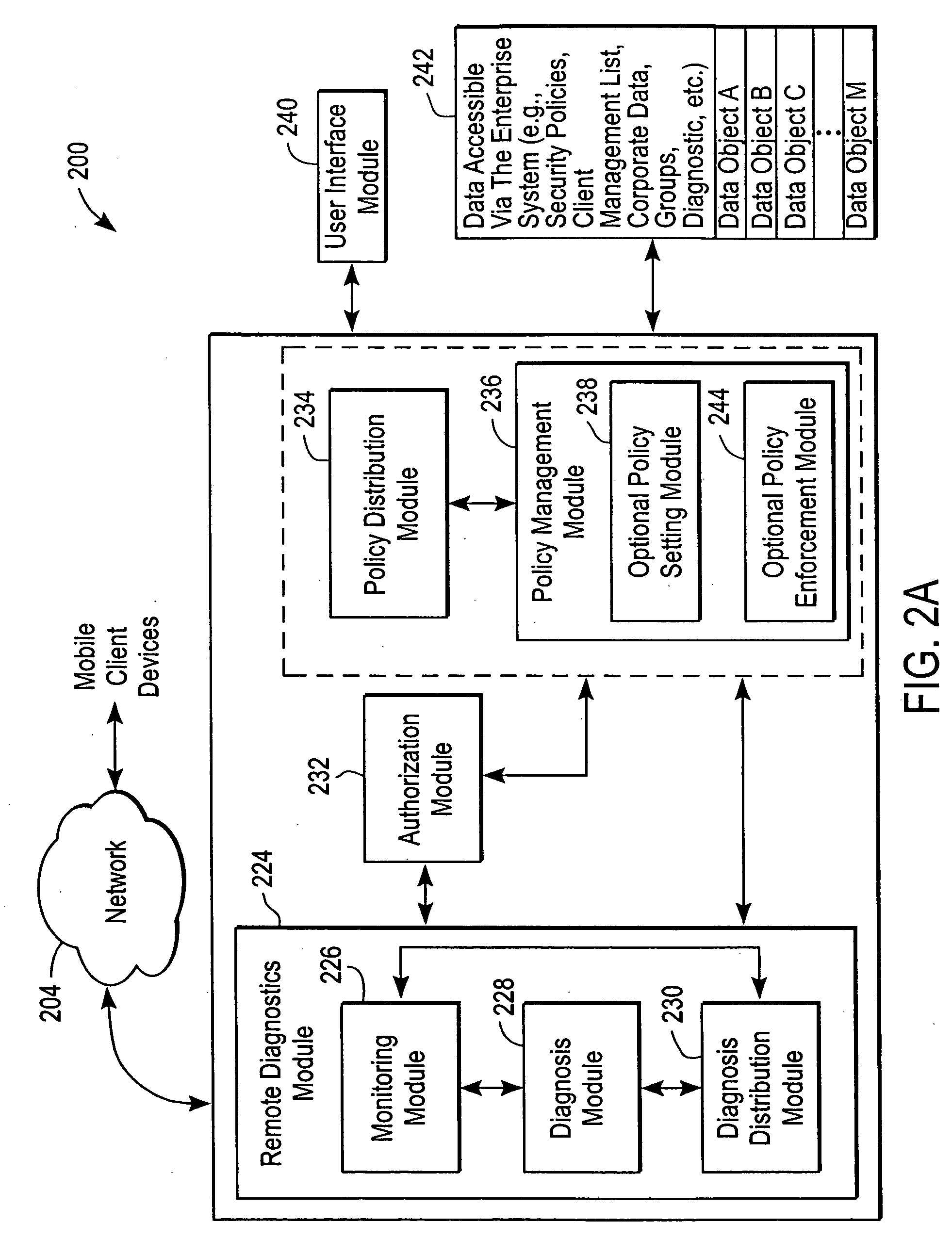
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
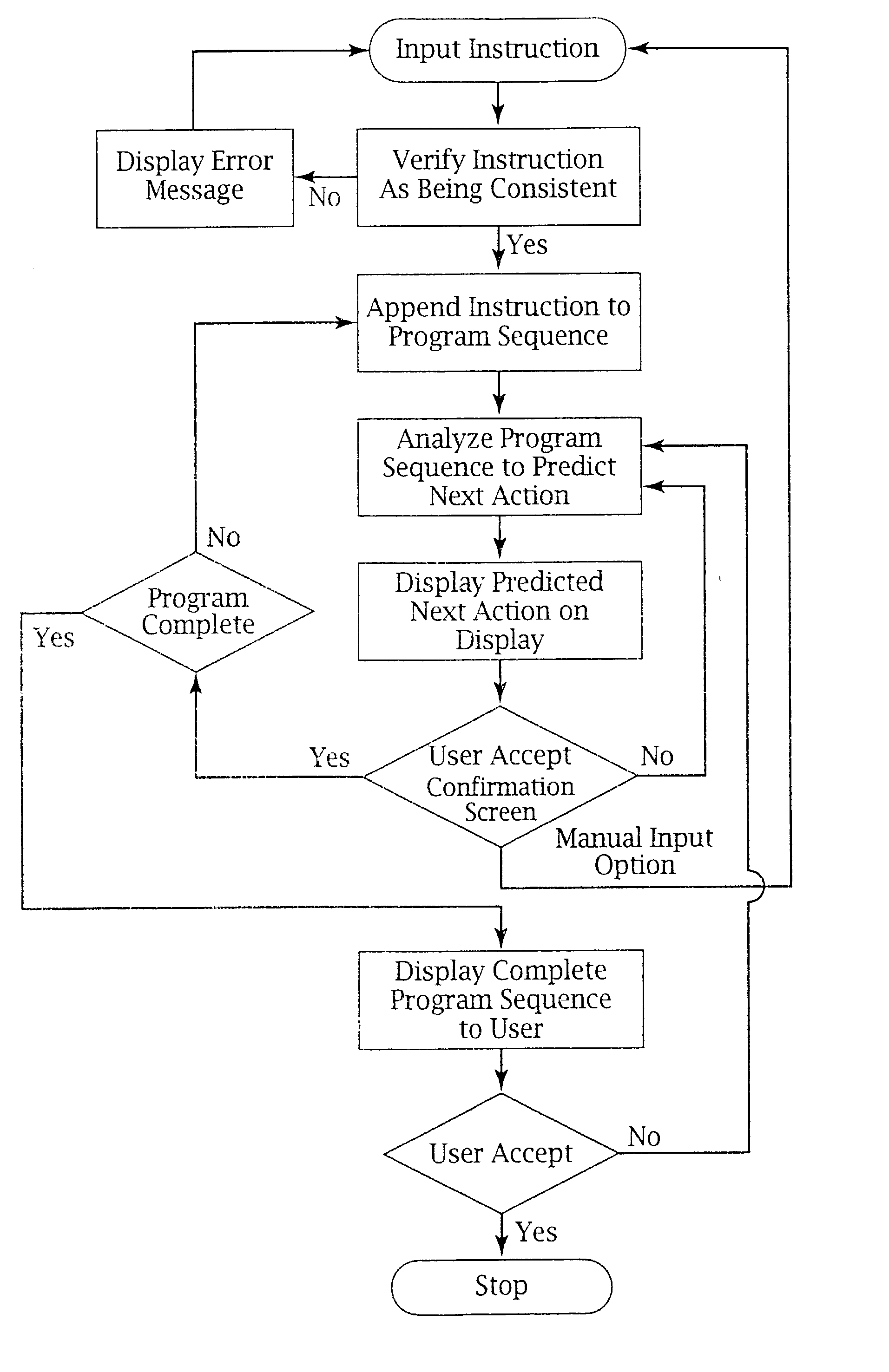
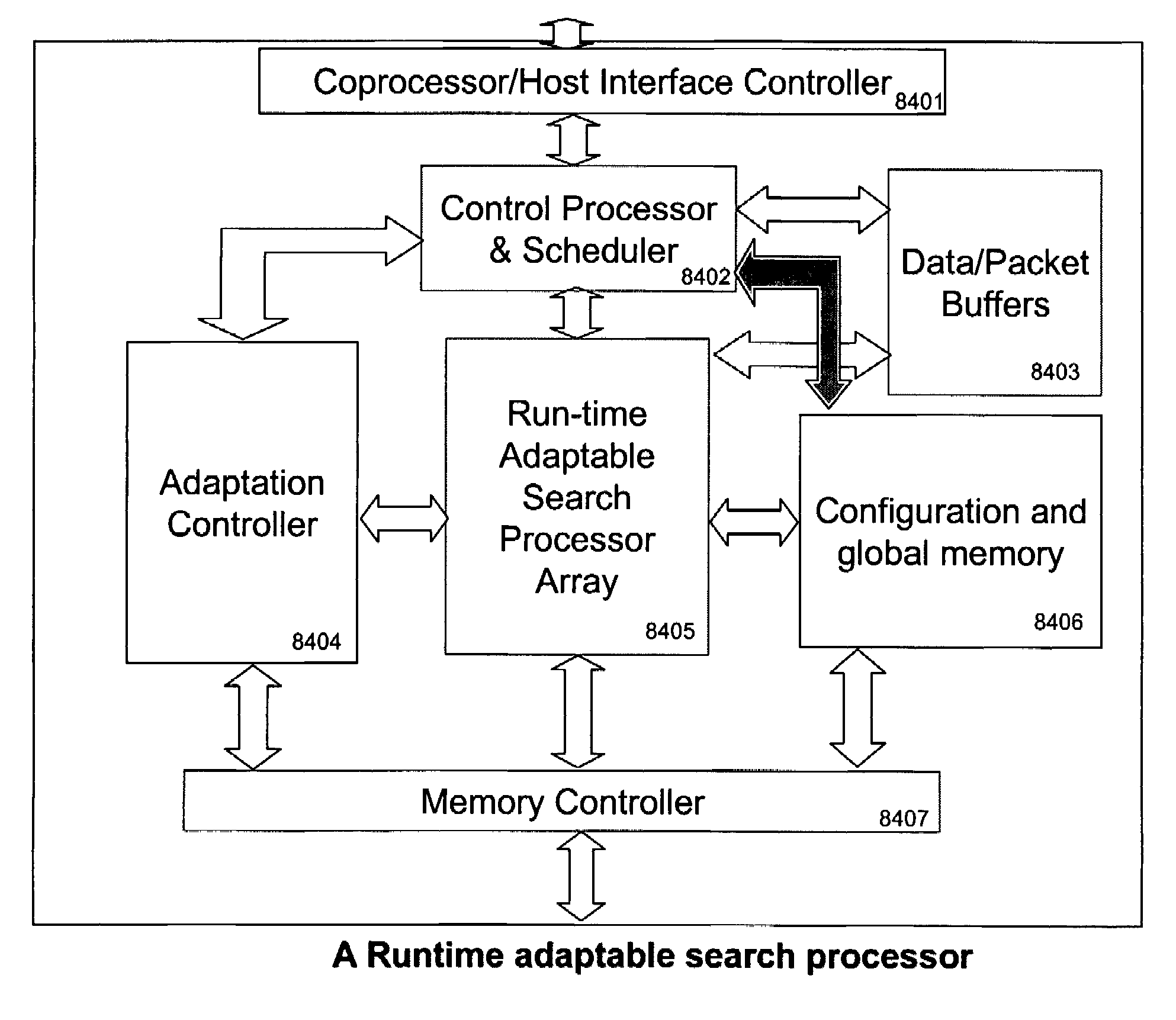
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
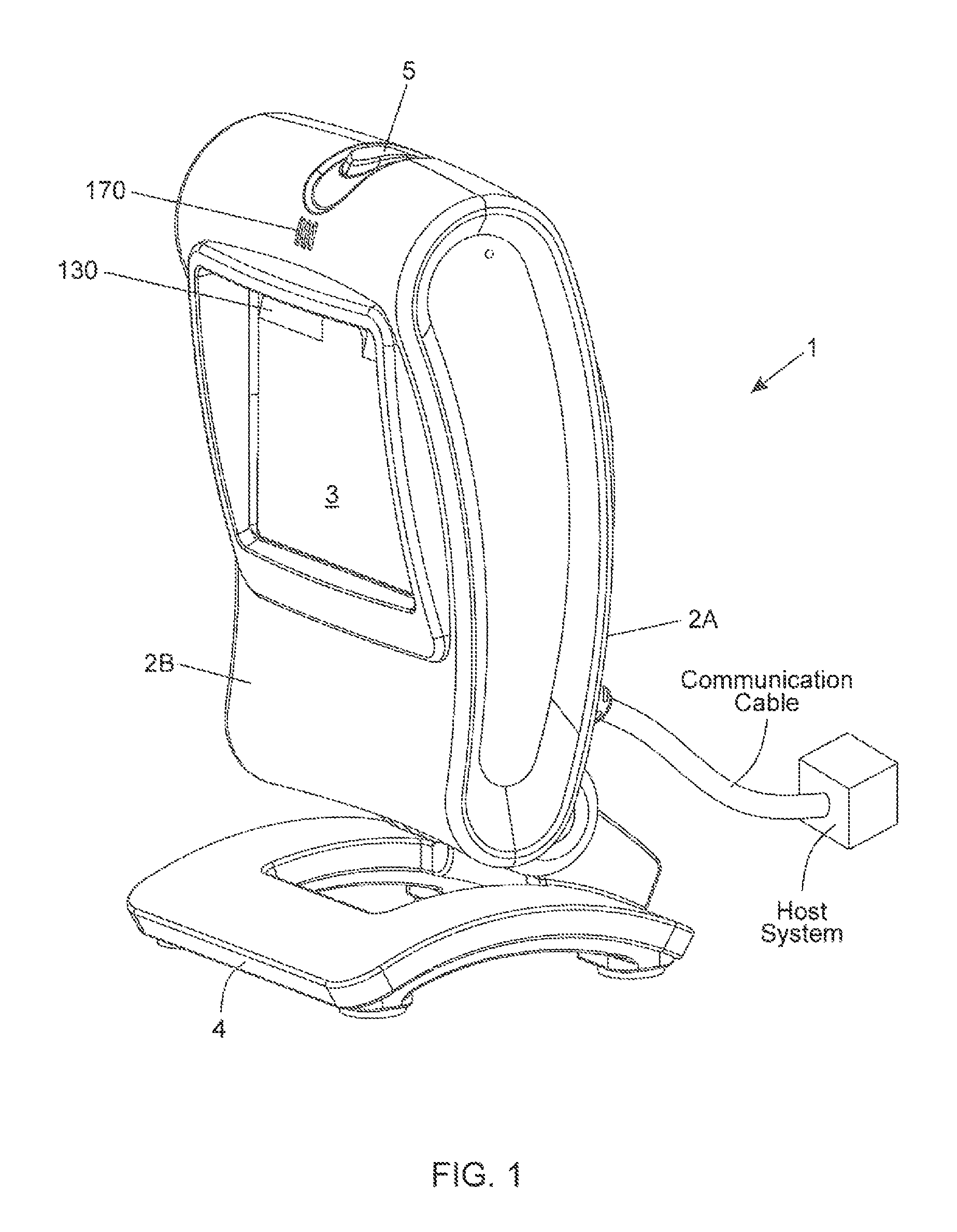
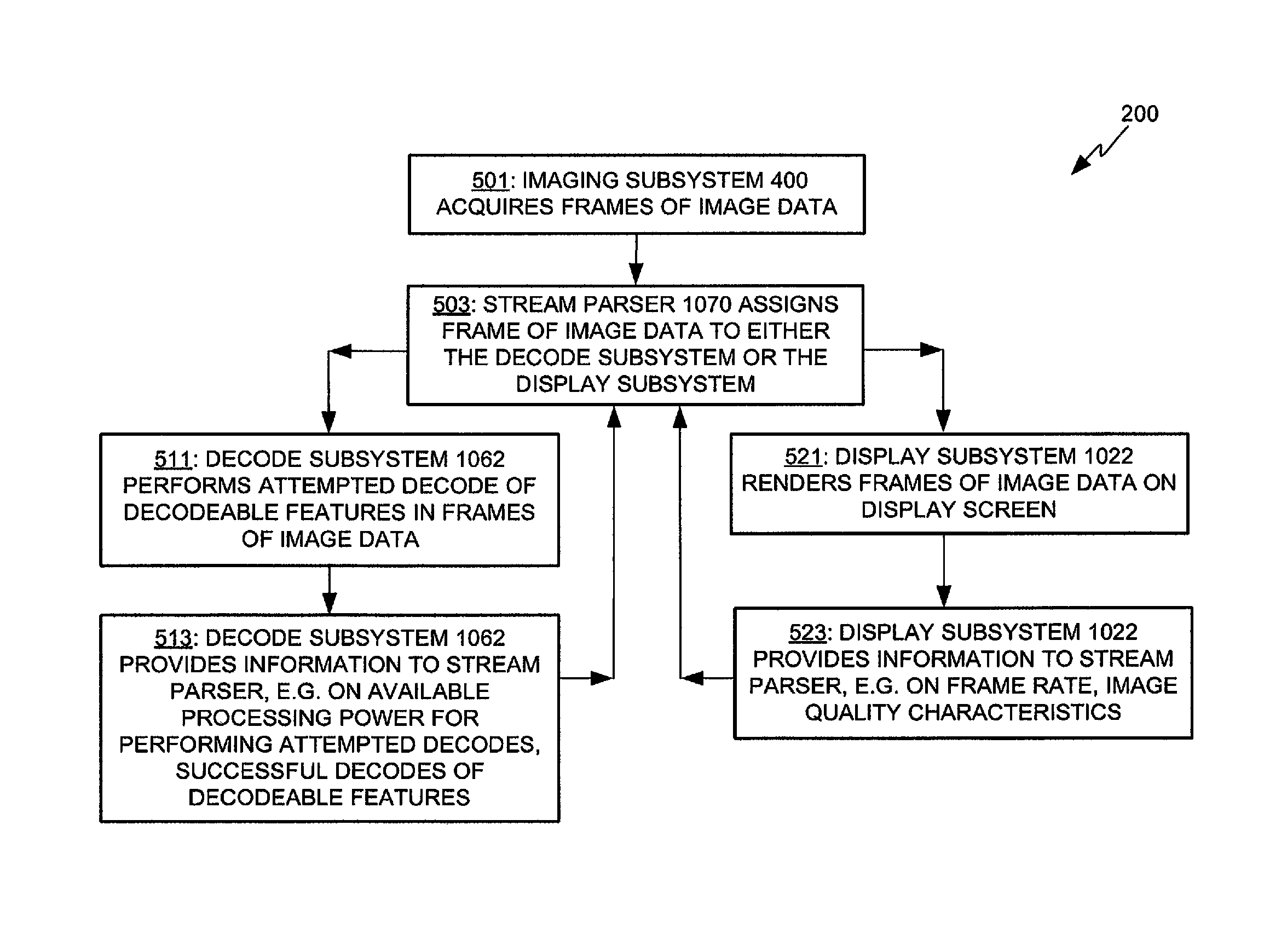
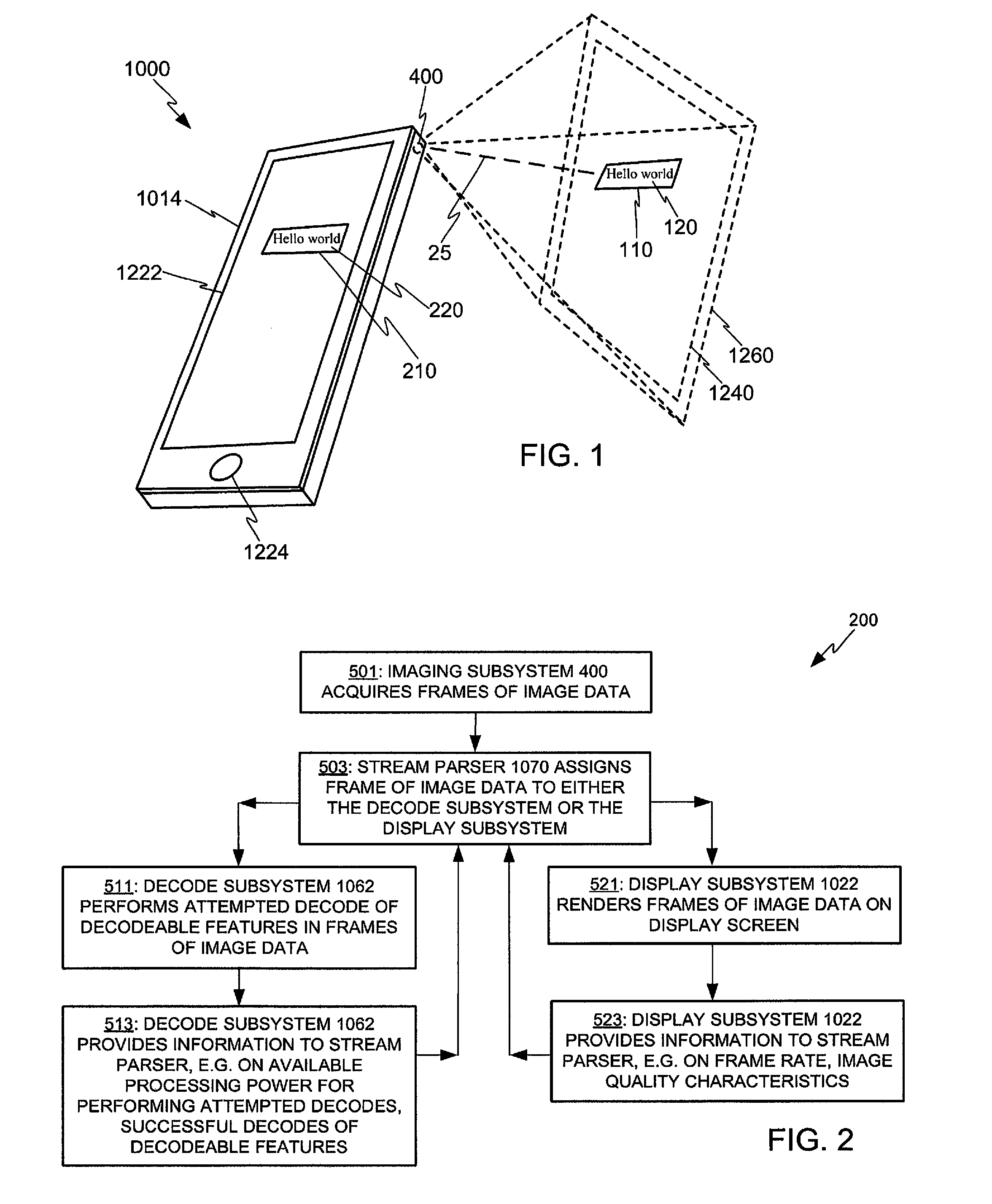
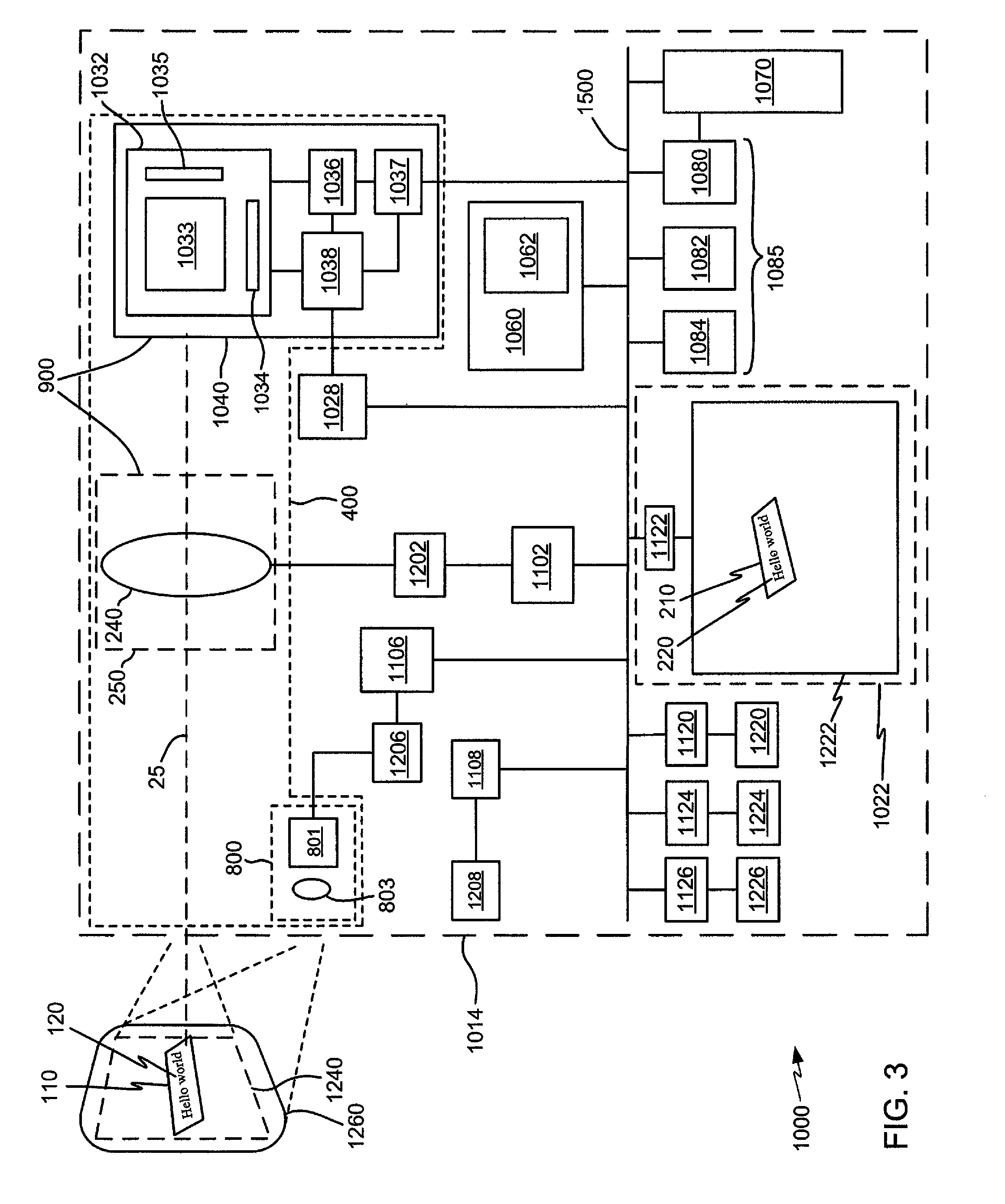
Adaptive video capture decode system
ActiveUS8879639B2Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer graphics (images)Adaptive video
Devices, methods, and software are disclosed for an adaptive video capture decode system that efficiently manages a stream of image frames between a device display screen and a processor performing decode attempts on decodable features in the image frames. In an illustrative embodiment, a device assigns frames of image data from a stream of frames of image data to either a display subsystem or a decode subsystem. The display subsystem is operative for rendering the frames of image data on a display screen. The decode subsystem is operative for receiving frames of image data and performing an attempted decode of a decodable indicia represented in at least one of the frames of image data. None of the frames of data are assigned to both the display subsystem and the decode subsystem.
Owner:HAND HELD PRODS
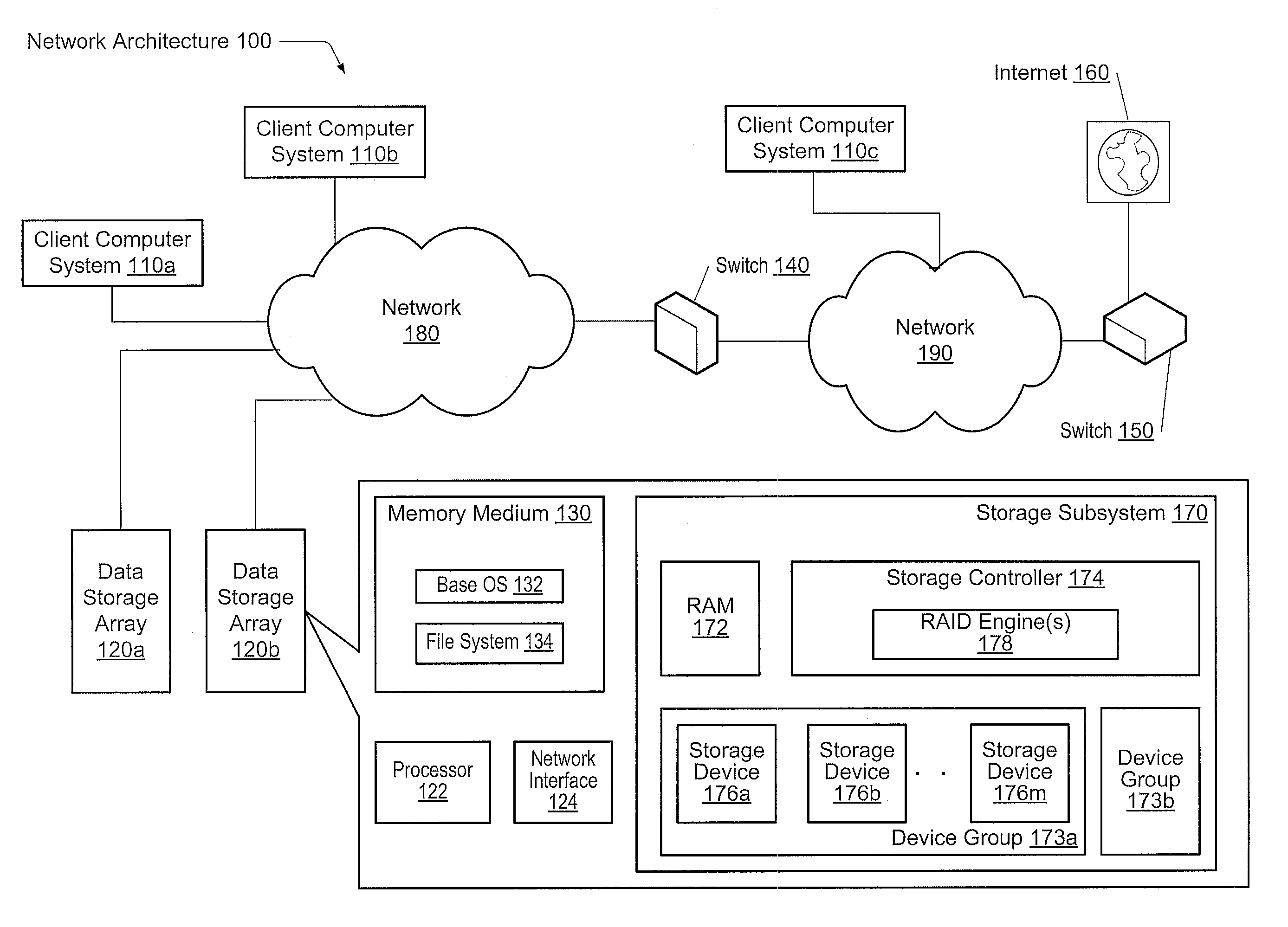
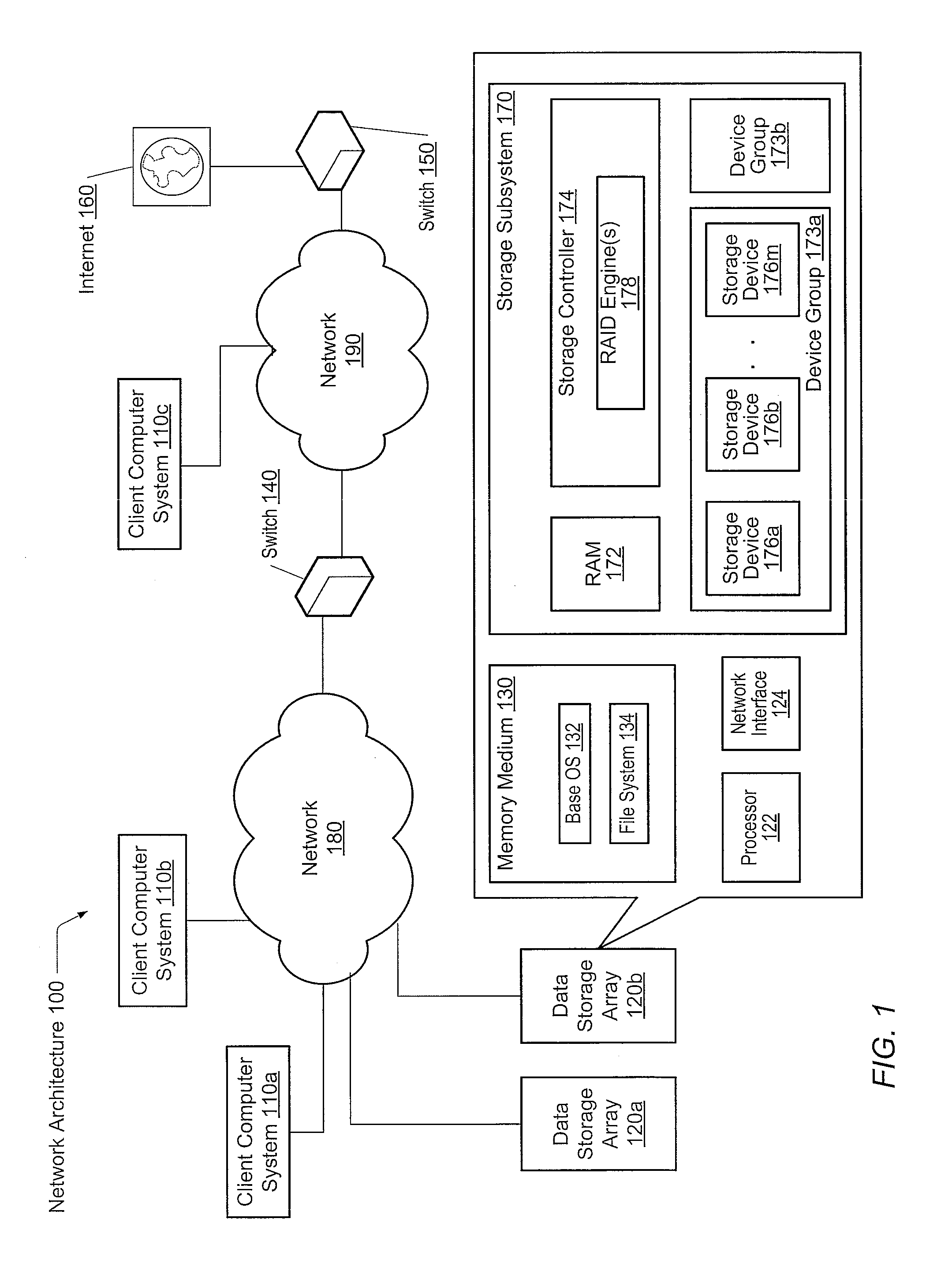
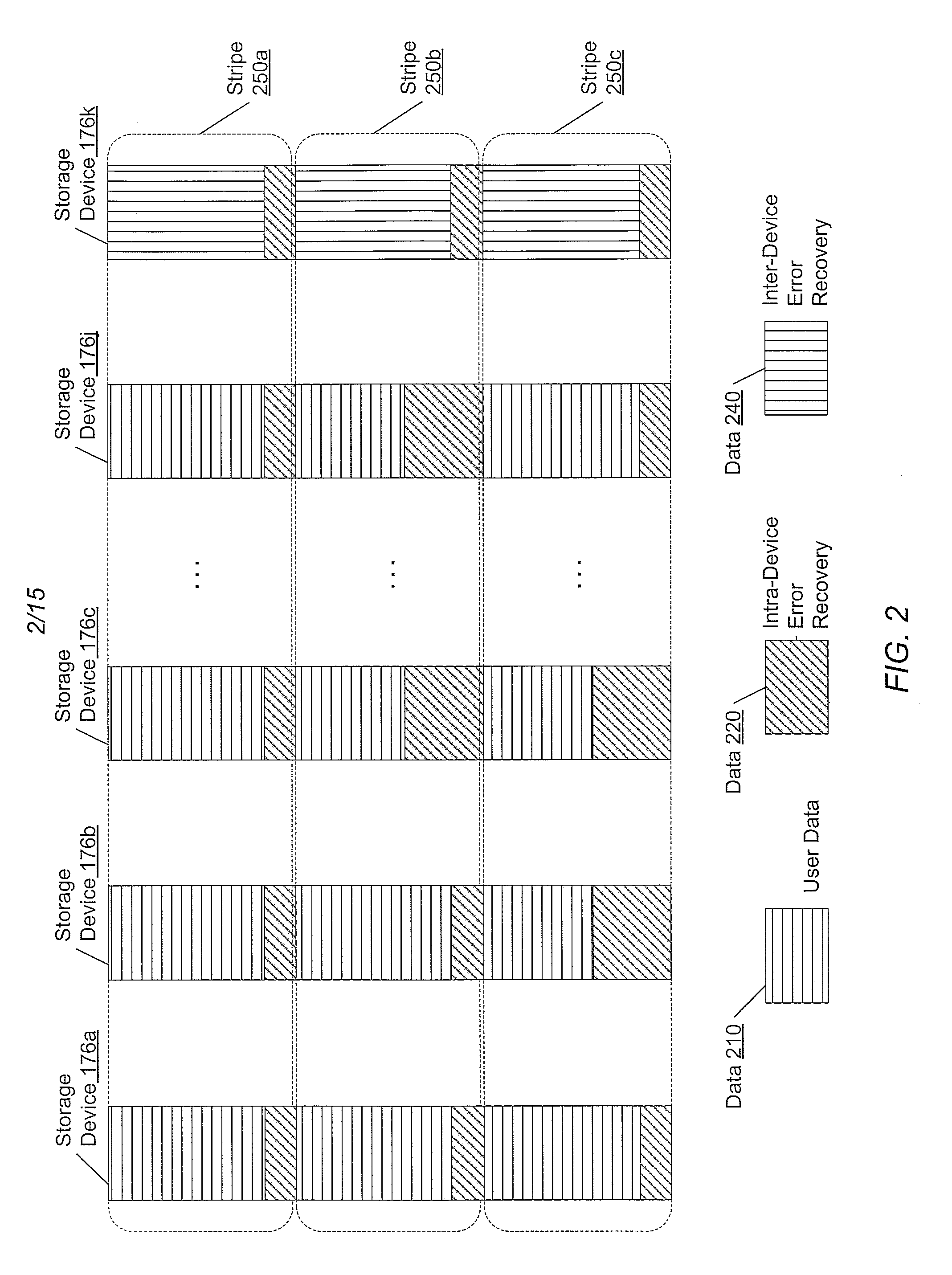
Adaptive raid for an SSD environment
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
Administration of protection of data accessible by a mobile device
ActiveUS20050055578A1Digital data processing detailsMultiple digital computer combinationsAnti virusEnterprise networking
The protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
System and method for autonomously generating heterogeneous data source interoperability bridges based on semantic modeling derived from self adapting ontology
InactiveUS20030172368A1Reduce dependenceImprove data securityVersion controlKnowledge representationTime errorData source
A system, including software components, that efficiently and dynamically analyzes changes to data sources, including application programs, within an integration environment and simultaneously re-codes dynamic adapters between the data sources is disclosed. The system also monitors at least two of said data sources to detect similarities within the data structures of said data sources and generates new dynamic adapters to integrate said at least two of said data sources. The system also provides real time error validation of dynamic adapters as well as performance optimization of newly created dynamic adapters that have been generated under changing environmental conditions.
Owner:COMPASS AL INC +1
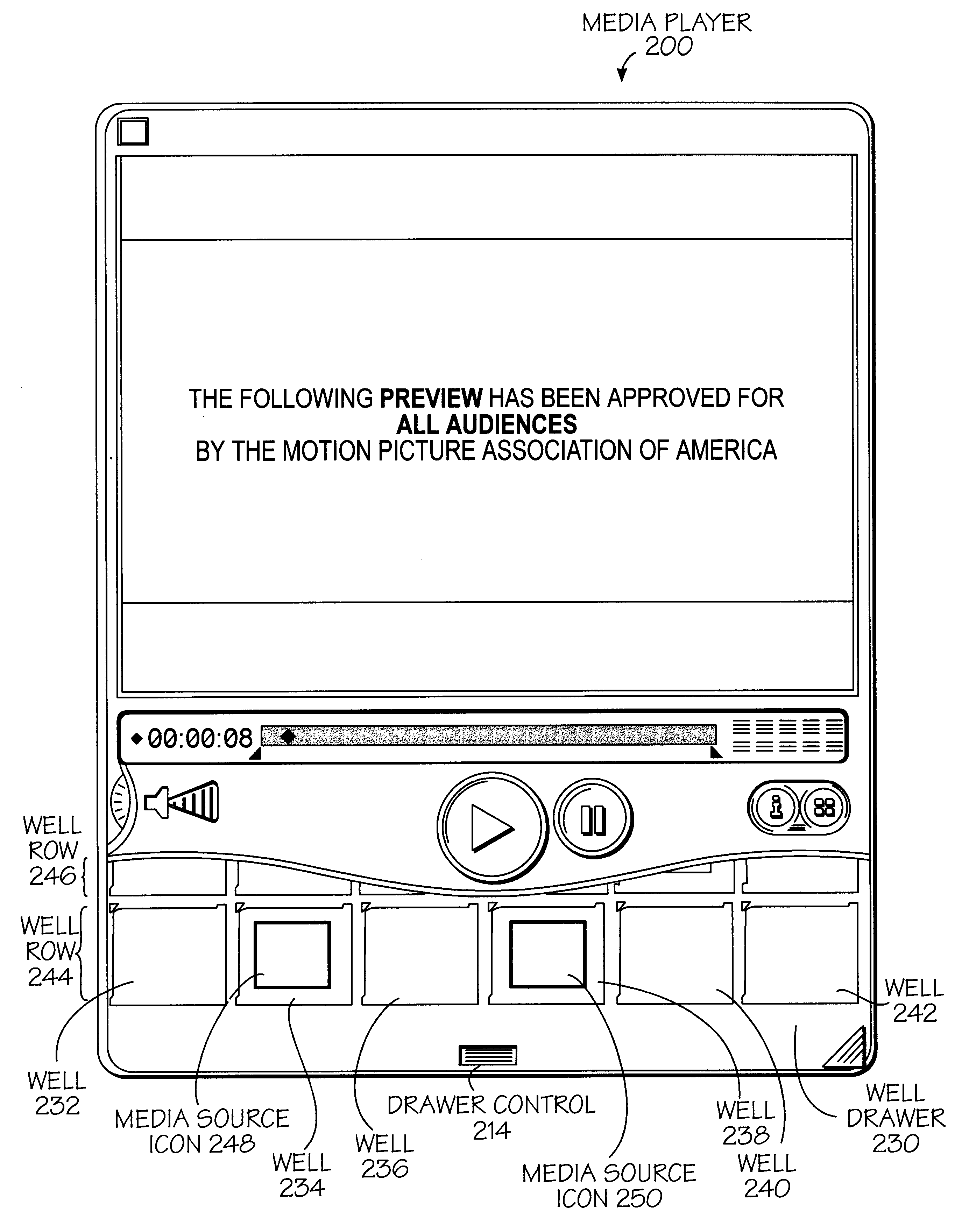
User interface for presenting media information
A user interface and methods for using a user interface for controlling processing of time-based media files. In one exemplary method, a graphical representation of a time line for a time-based media is displayed along with a graphical representation of a current time along the graphical representation of the time line. A start graphical indicator and a stop graphical indicator is also displayed along the graphical representation of the time line. A portion of the time-based media may be selected for presentation by dragging or positioning at least one of the start graphical indicator and the stop graphical indicator along the graphical representation of the time line. In another aspect of the invention, an exemplary method allows for the adaptive control of a portion of the interface which indicates time relating to a time-based media. An input speed is determined where this input is to change the portion and the rate at which the change to this portion occurs is dependent upon the input speed. Other aspects of the present invention relating to the interface for controlling the processing of time-based media files are also described.
Owner:APPLE INC
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS7248841B2Strong advantageReduced Power RequirementsPower managementSpatial transmit diversityGlobal optimizationRandom delay
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitone encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
Method and apparatus for controlling transmissions of a communications systems
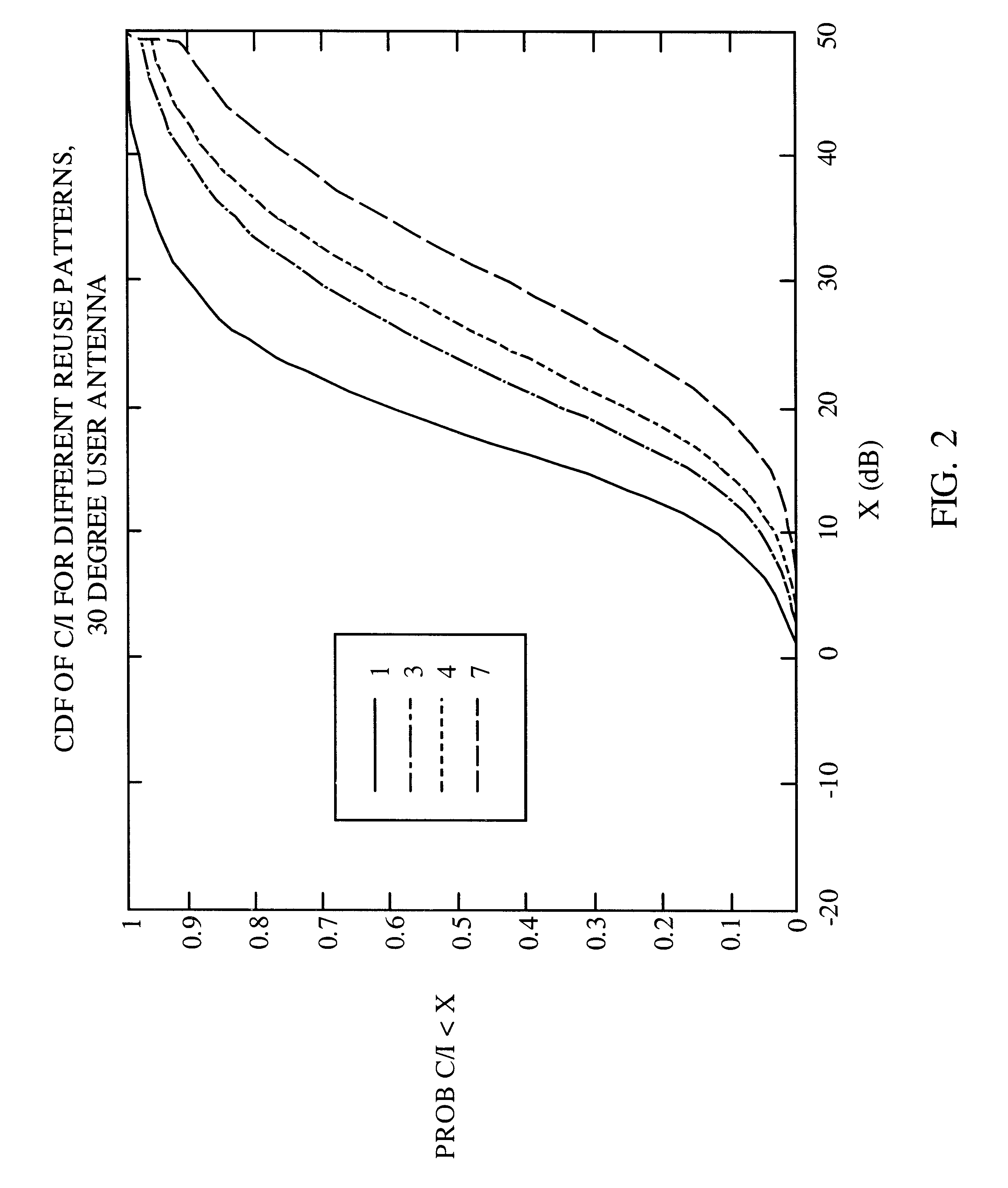
InactiveUS6493331B1Reduce the amount of noiseLower Level RequirementsEnergy efficient ICTPower managementControl communicationsSystem requirements
In some aspects, each cell in the communications system can be designed to operate in accordance with a set of back-off factors that identify the reductions in peak transmit power levels for the channels associated with the back-off factors. The back-off factors are defined to provide the required power to a large percentage of the users while reducing the amount of interference. In some other aspects, the cells operate using an adaptive reuse scheme that allows the cells to efficiently allocate and reallocate the system resources to reflect changes in the system. A reuse scheme is initially defined and resources are allocated to the cells. During operation, changes in the operating conditions of the system are detected and the reuse scheme is redefined as necessary based on the detected changes. For example, the loading conditions of the cells can be detected, and the resources can be reallocated and / or the reuse scheme can be redefined. In yet other aspects, techniques are provided to efficiency schedule data transmissions and to assign channels to users. Data transmissions can be scheduled based on user priorities, some fairness criteria, system requirements, and other factors. Users are assigned to available channels based on a number of channel assignment schemes. Channel metrics are also provided, which can be used to prioritize users and for channel assignments.
Owner:QUALCOMM INC
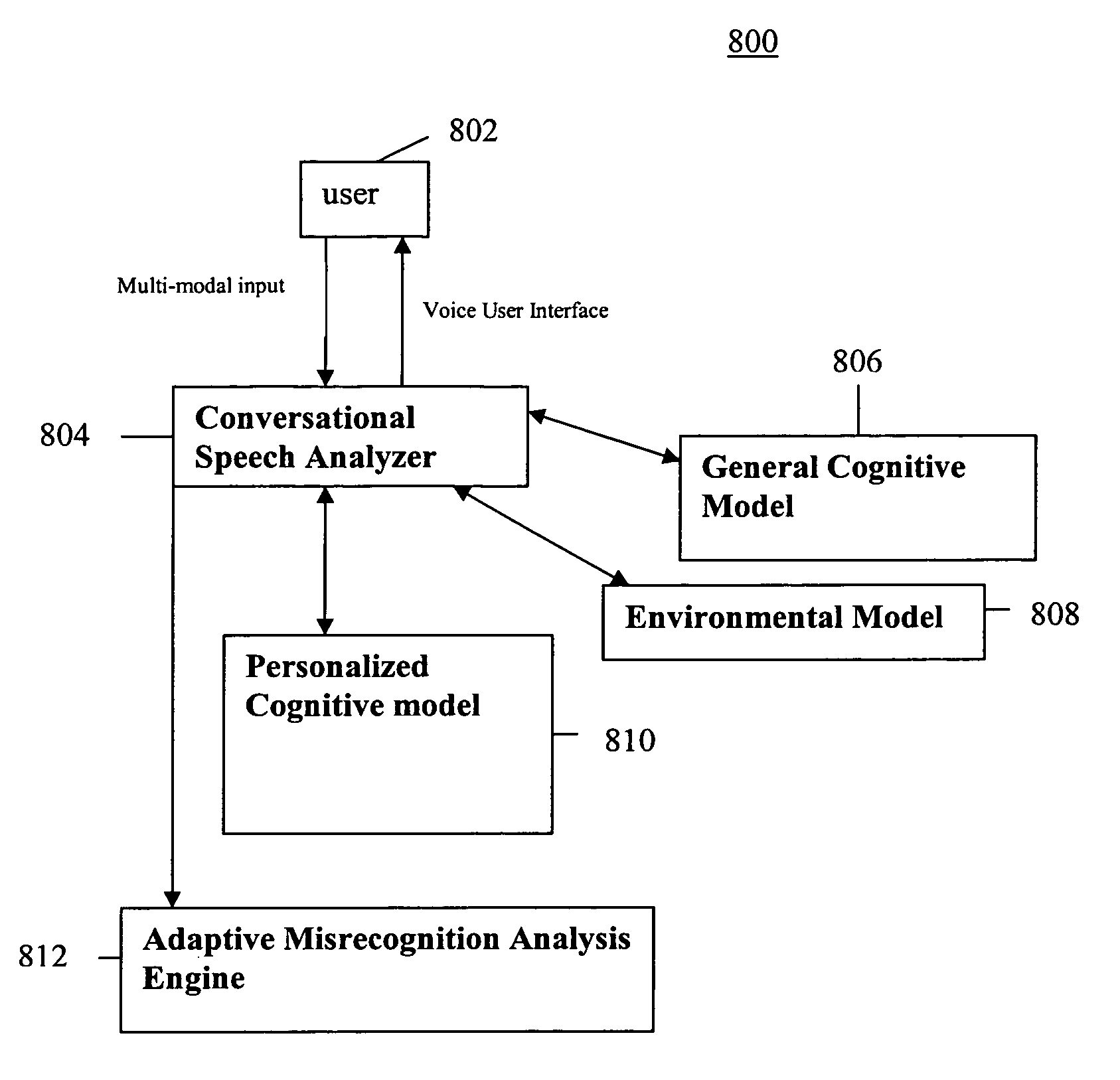
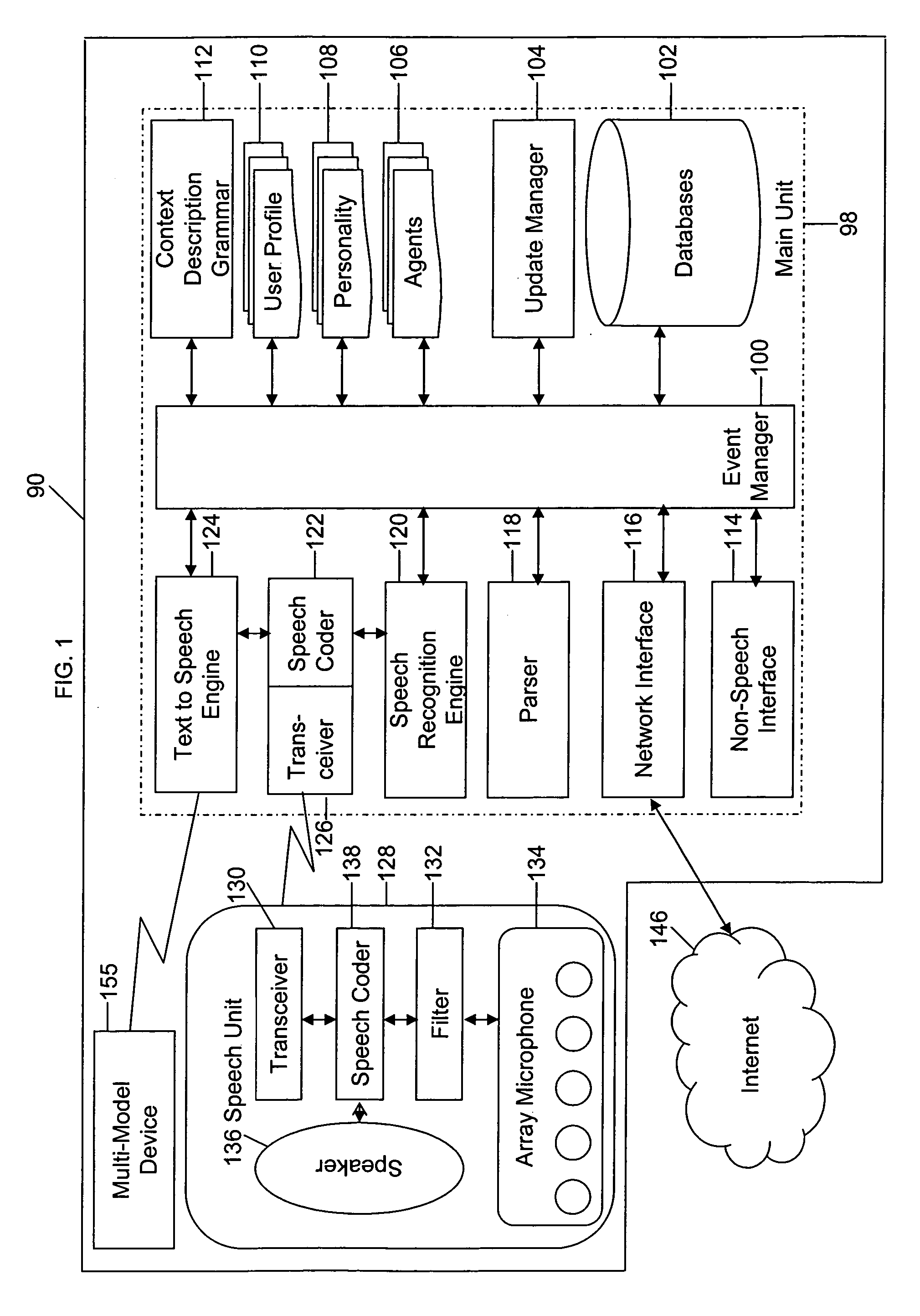
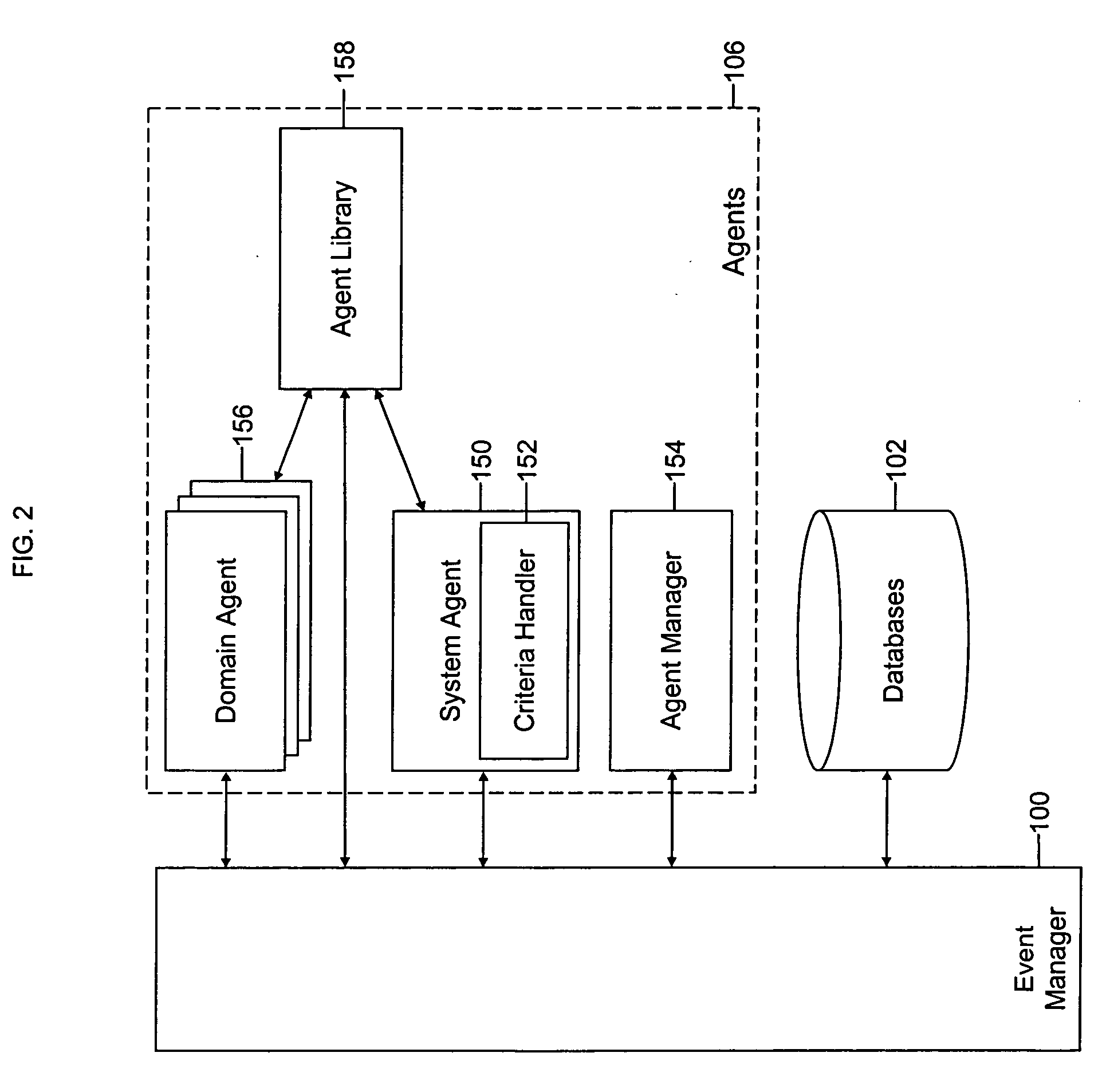
System and method of supporting adaptive misrecognition in conversational speech
ActiveUS20070038436A1Improve maximizationHigh bandwidthNatural language data processingSpeech recognitionPersonalizationSpoken language
A system and method are provided for receiving speech and / or non-speech communications of natural language questions and / or commands and executing the questions and / or commands. The invention provides a conversational human-machine interface that includes a conversational speech analyzer, a general cognitive model, an environmental model, and a personalized cognitive model to determine context, domain knowledge, and invoke prior information to interpret a spoken utterance or a received non-spoken message. The system and method creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context of the speech or non-speech communication and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
System and method for a cooperative conversational voice user interface
Owner:VB ASSETS LLC
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
ActiveUS7136710B1Significant to useImprove computing powerComputer controlAnalogue secracy/subscription systemsConceptual basisHuman–machine interface
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP +1
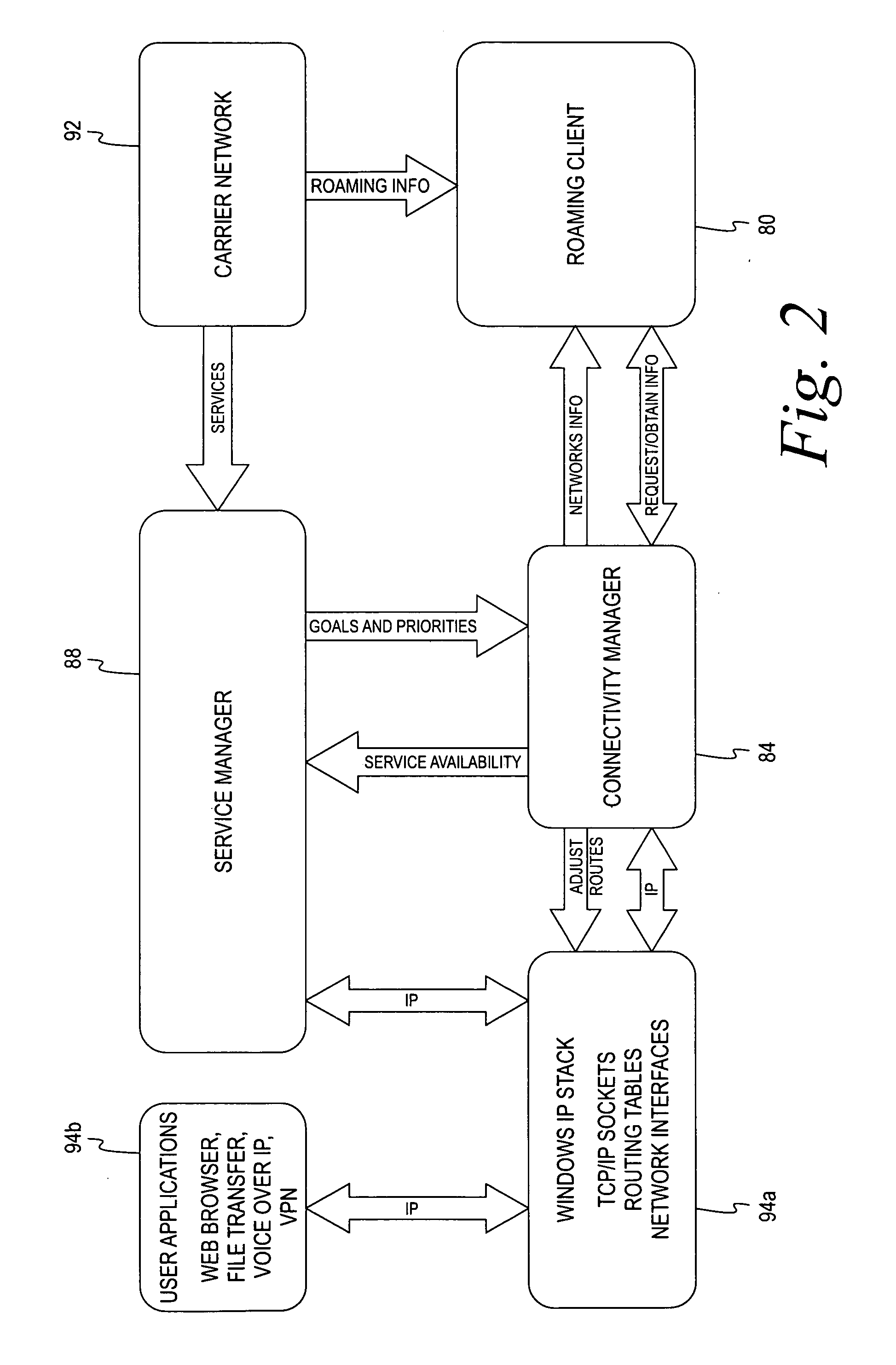
Mobile connectivity solution
A method and application for selecting a network from one or more candidate networks is disclosed. Information is gathered from one or more database relating to each of the one or more candidate networks and is harmonized in relation to an associated network type. The harmonized information is evaluated to allocate a weight to each of the candidate networks. The weight represents the desirability of each of the candidate networks. The required resources to connect to each of the candidate networks are determined from information contained within the service-provider database, from information obtained by the end-user, and by self-adaptive learning algorithms. At least one of the candidate networks is selected based on the allocated weight of the candidate network and the application attempts to connect to the candidate network. The method and application incorporates the ability to control and integrate a plurality of services on a user device via the candidate network.
Owner:DELL MARKETING CORP
Administration of protection of data accessible by a mobile device
The administration of protection of data on a client mobile computing device by a server computer system such as within an enterprise network or on a separate mobile computing device is described. Security tools are described that provide different security policies to be enforced based on a location associated with a network environment in which a mobile device is operating. Methods for detecting the location of the mobile device are described. Additionally, the security tools may also provide for enforcing different policies based on security features. Examples of security features include the type of connection, wired or wireless, over which data is being transferred, the operation of anti-virus software, or the type of network adapter card. The different security policies provide enforcement mechanisms that may be tailored based upon the detected location and / or active security features associated with the mobile device. Examples of enforcement mechanisms are adaptive port blocking, file hiding and file encryption.
Owner:APPLE INC
Media recording device with packet data interface
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Runtime adaptable search processor
ActiveUS7685254B2Improve application performanceLarge capacityWeb data indexingMemory adressing/allocation/relocationPacket schedulingSchema for Object-Oriented XML
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. The search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. Scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com