Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3088results about How to "Effective distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
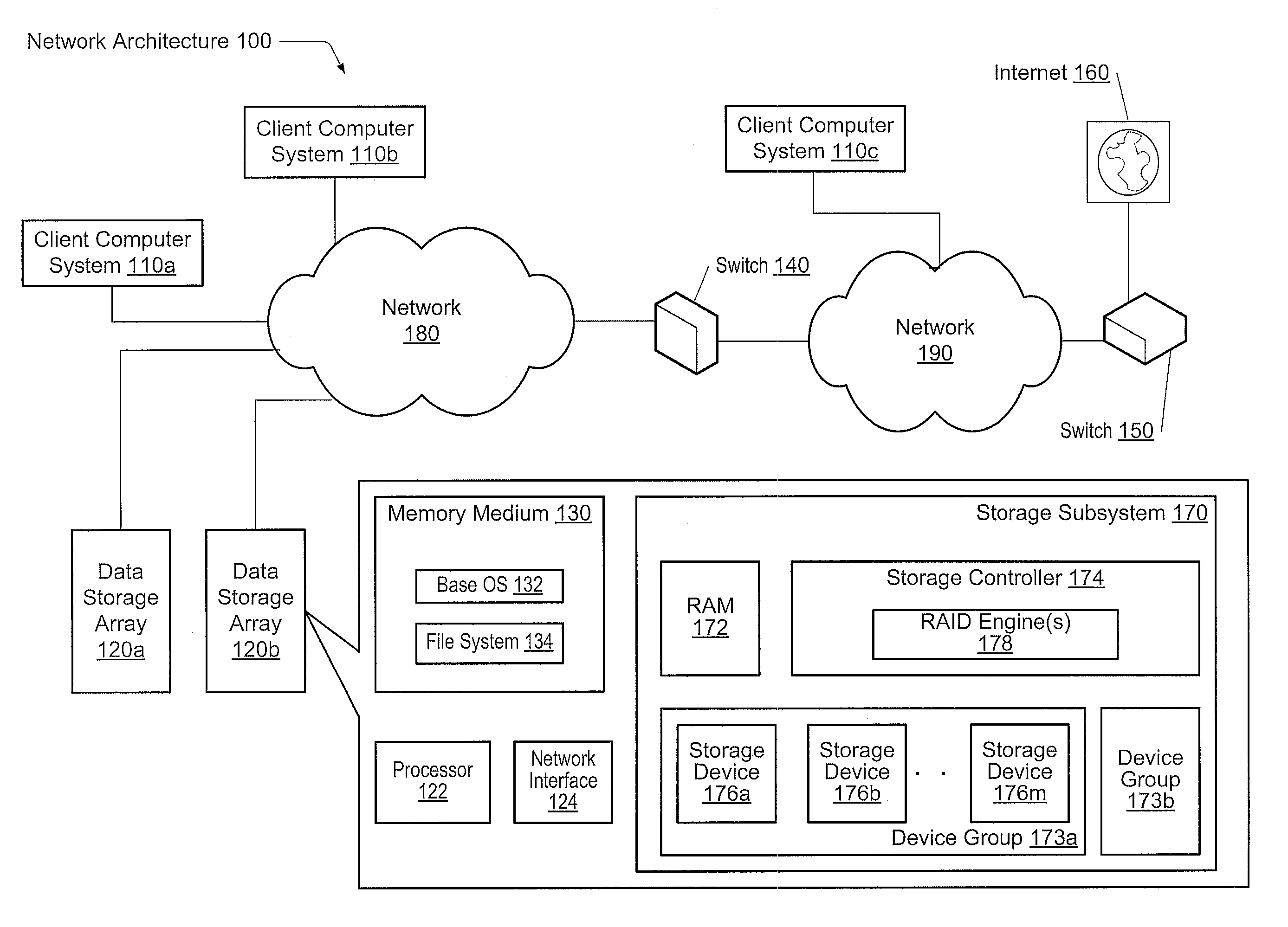
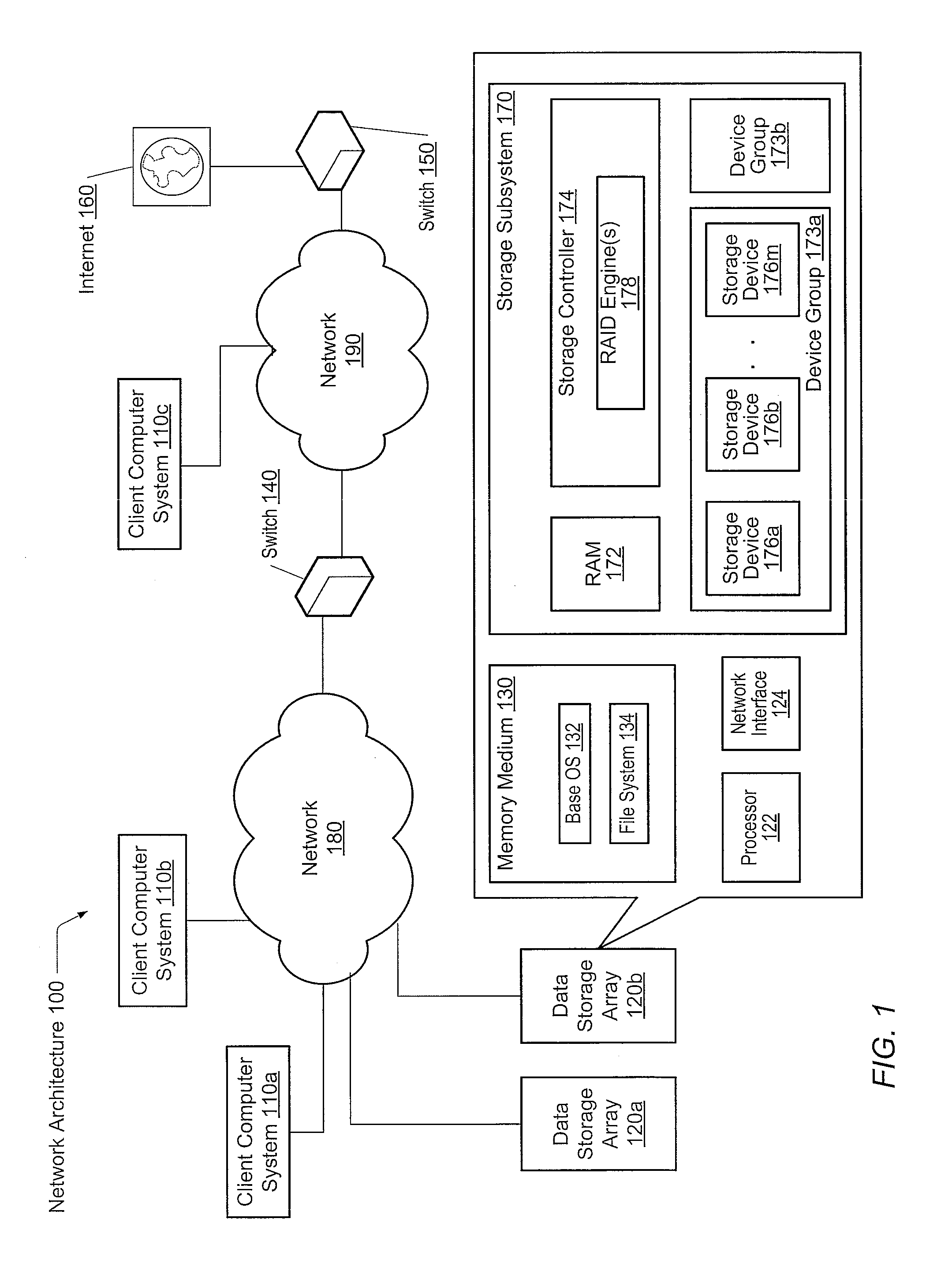
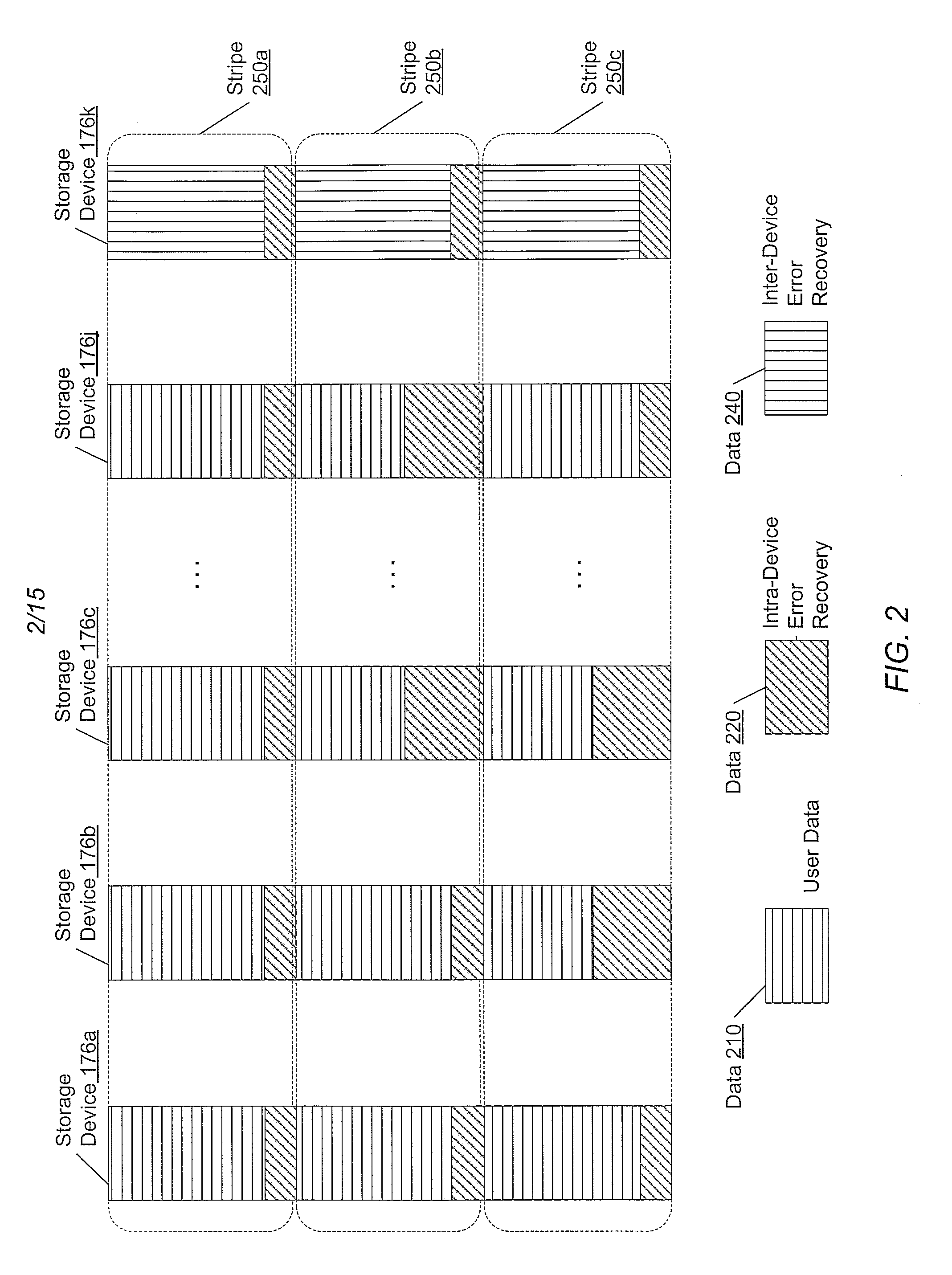
Adaptive raid for an SSD environment
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
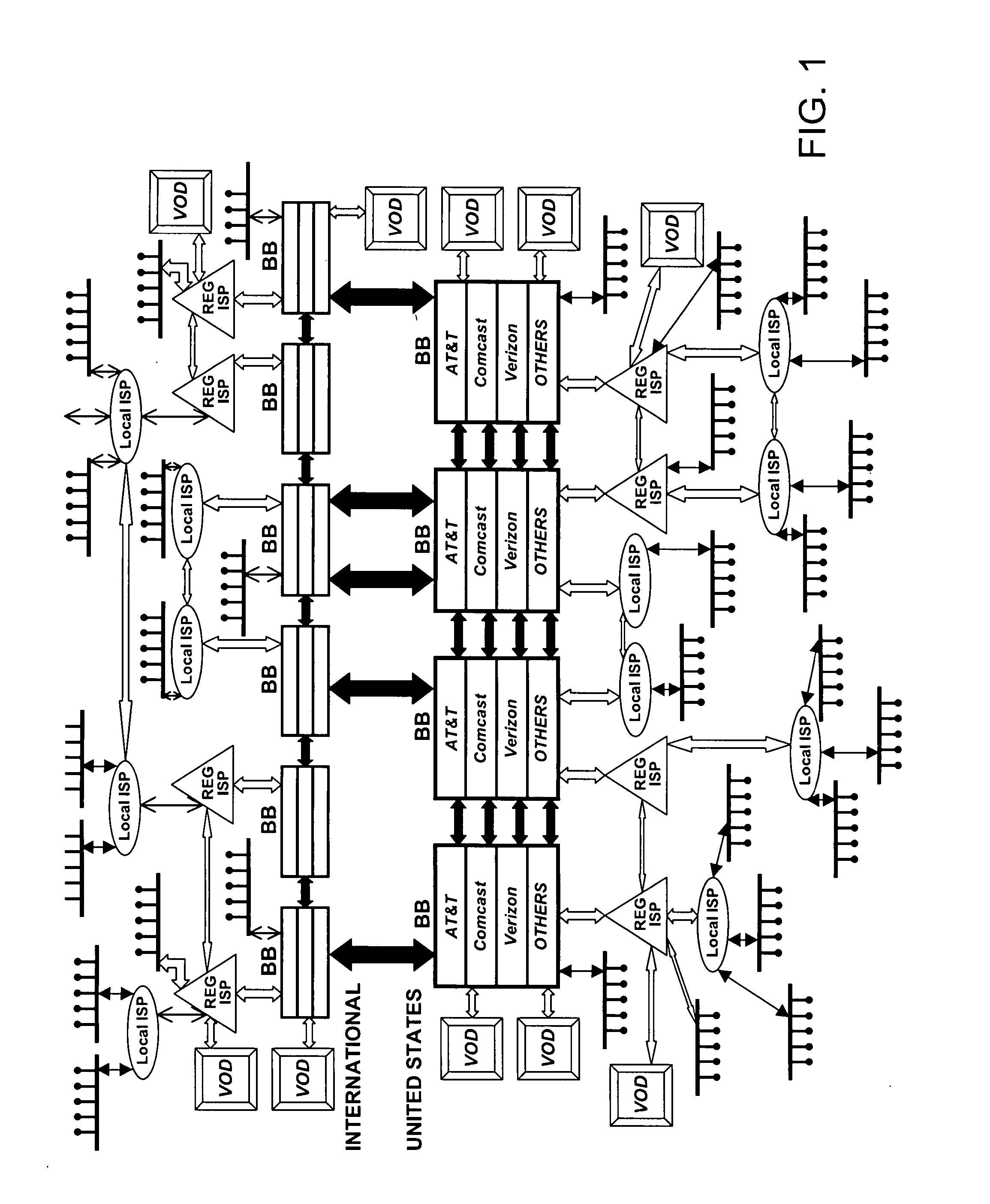
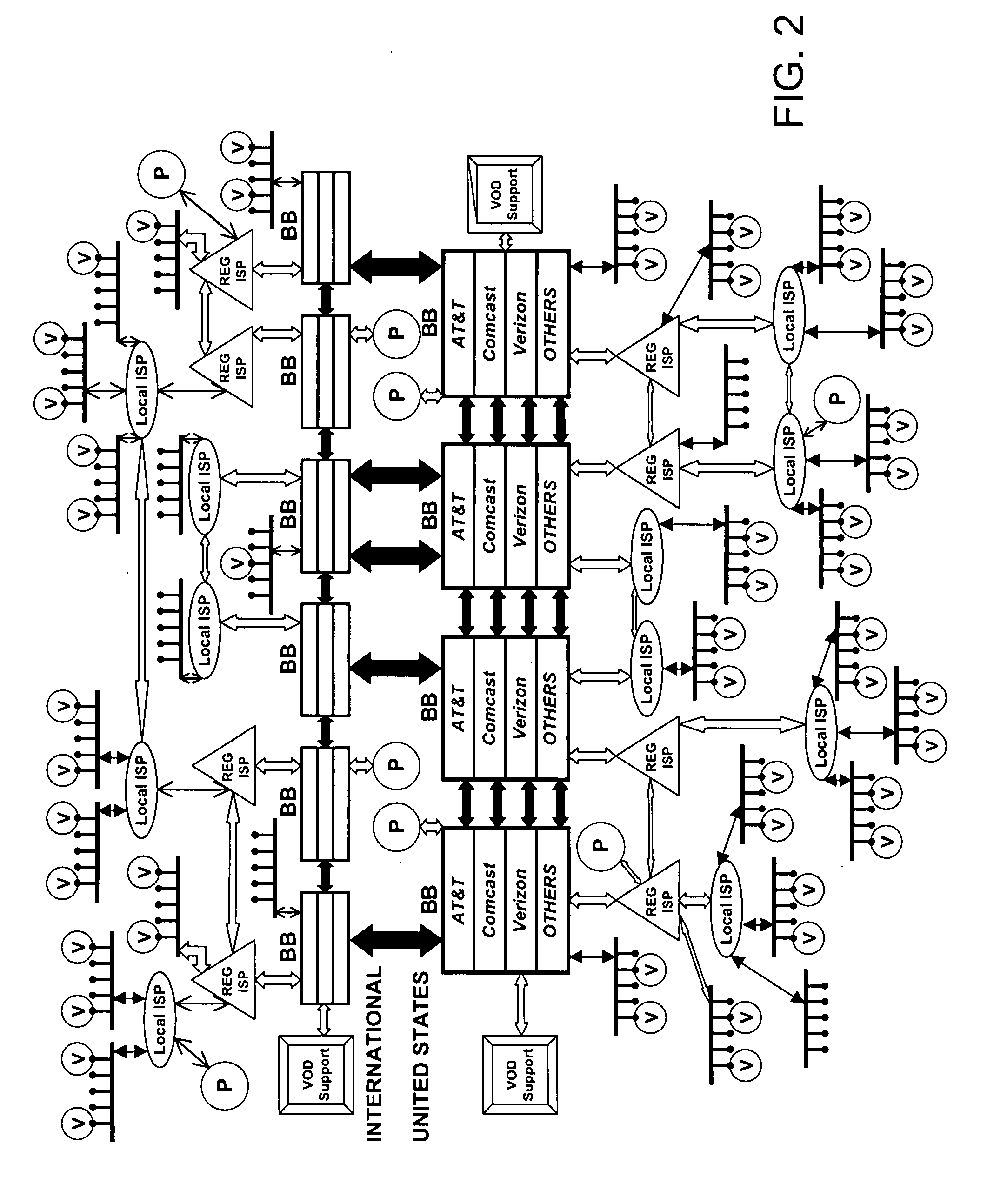
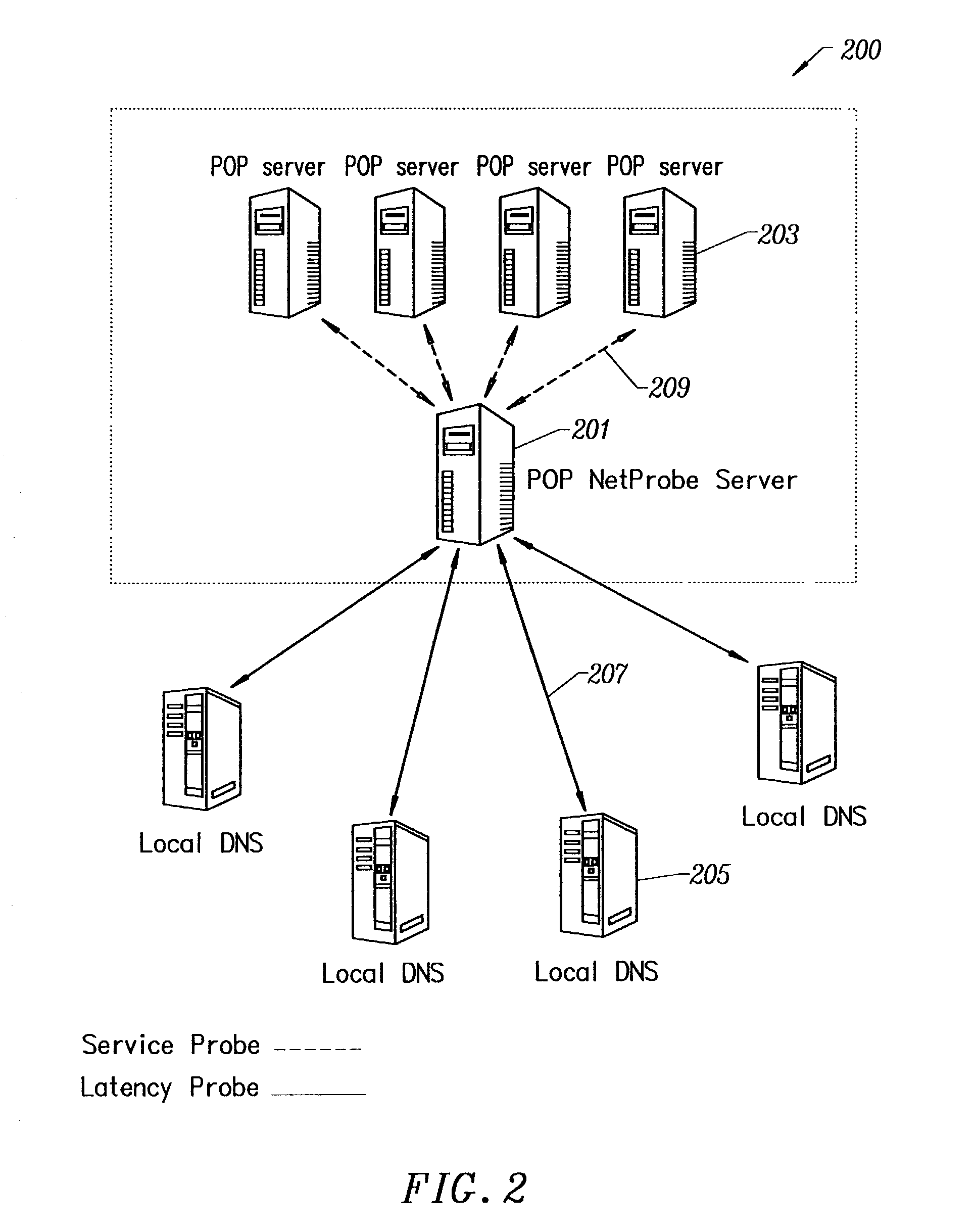
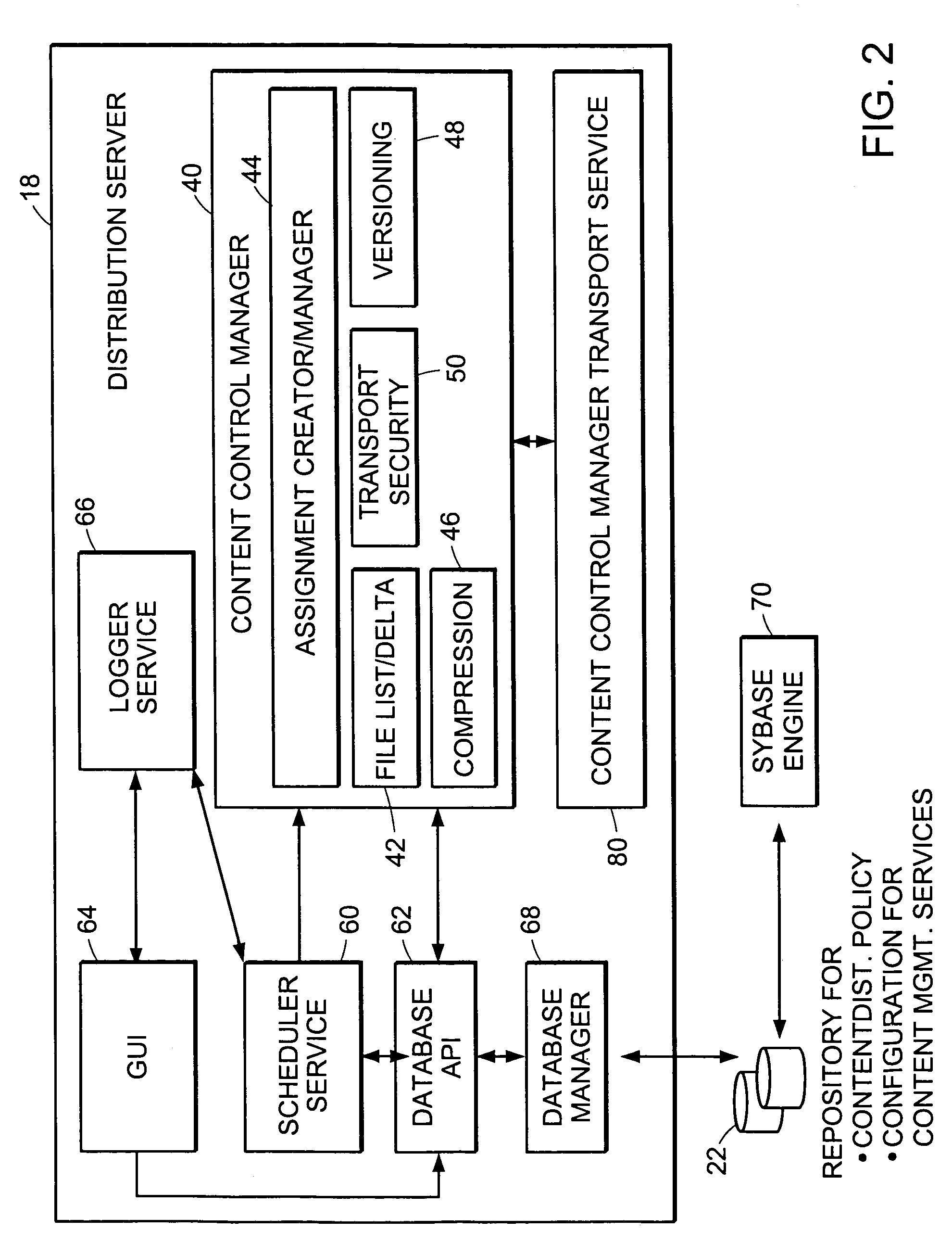
Push-Pull Based Content Delivery System
InactiveUS20080059631A1Maximize QoSImprove scalabilityDigital computer detailsTelevision systemsClosed loop feedbackPush pull
QoS is built into a peer network within existing Internet infrastructure itself lacking QoS, by enabling a network peer to continuously discern the network's ability to deliver to that peer a particular Content Object (distributed in groups of component Packages among neighboring VOD peers) within predetermined times. Content Objects are divided into groups of component Packages and distributed to Clusters of neighboring network peers, enhancing QoS upon subsequent retrieval. Tracking Files (lists of network peers storing Package groups) and Tracking Indexes (lists of network peers storing Tracking Files) are generated to facilitate “on demand” Content Objects retrieval. Dynamically monitoring network traffic (including VOD functionality, bandwidth and reliability) creates “distributed closed-loop feedback,” and in response, attributes of individual network peers (e.g., Trust Level and membership within a particular Cluster) are modified, and “content balancing” functions performed (e.g., redistribution of Package groups among network peers) enables maintaining high QoS.
Owner:VODDLER GRP
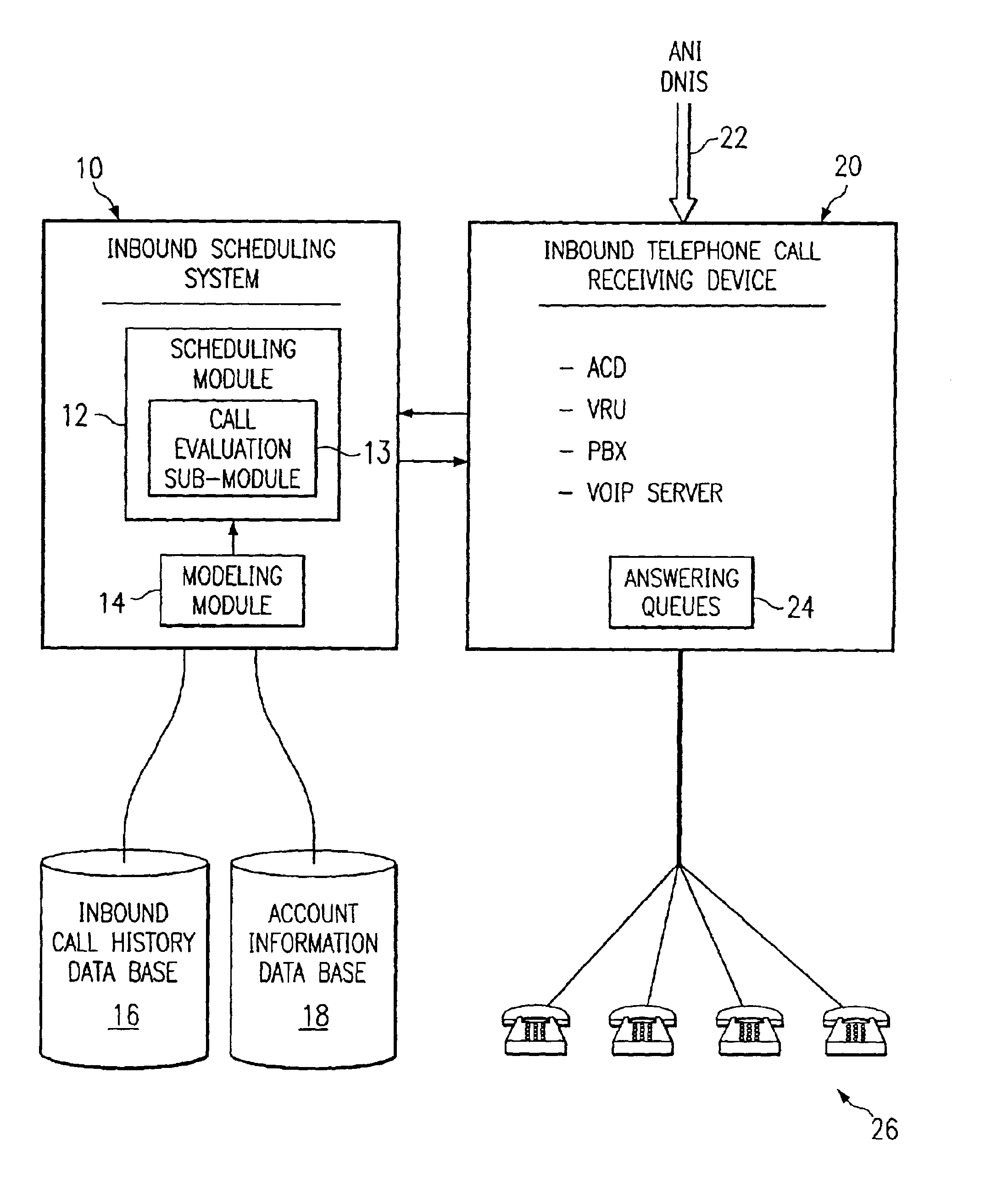
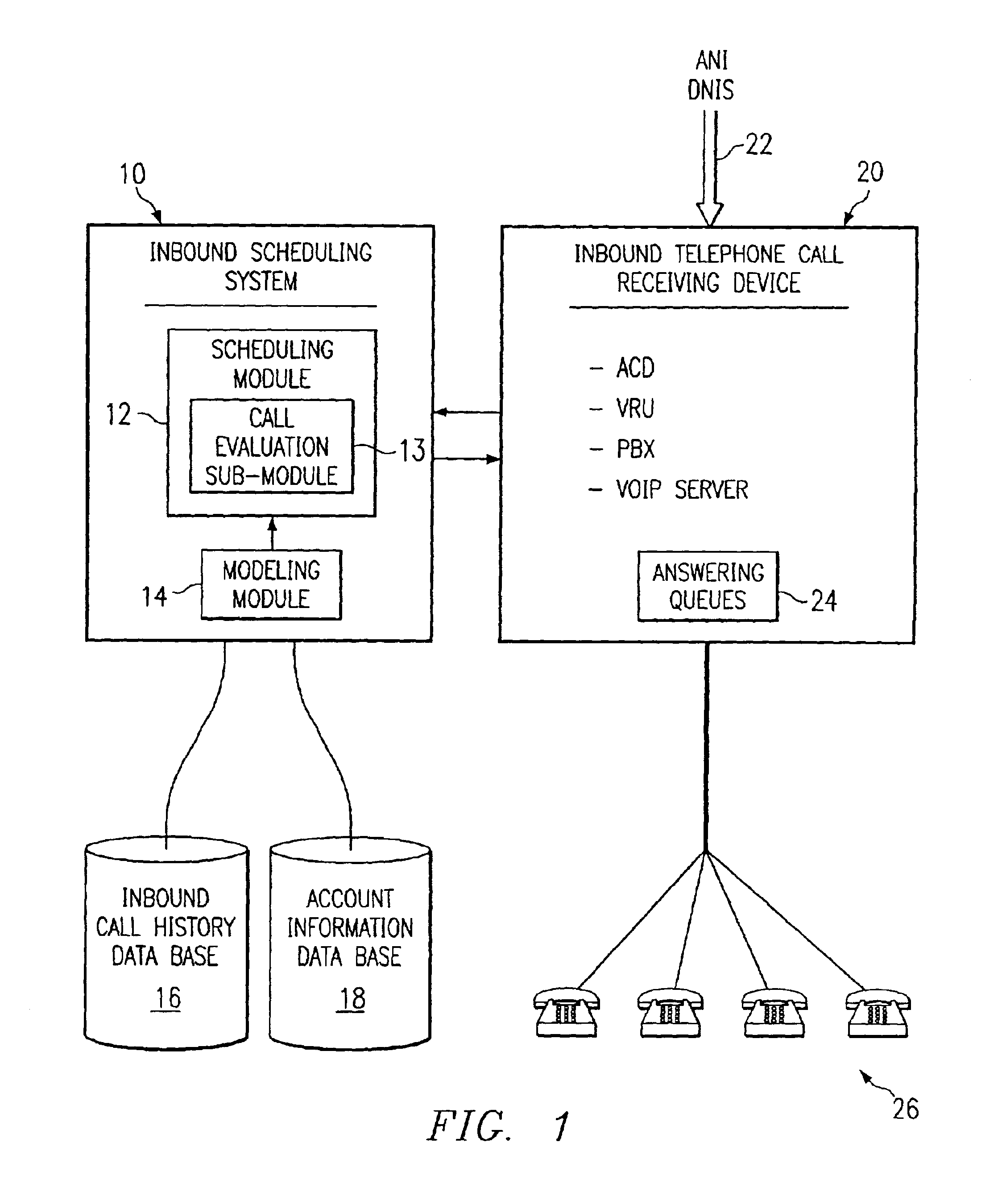
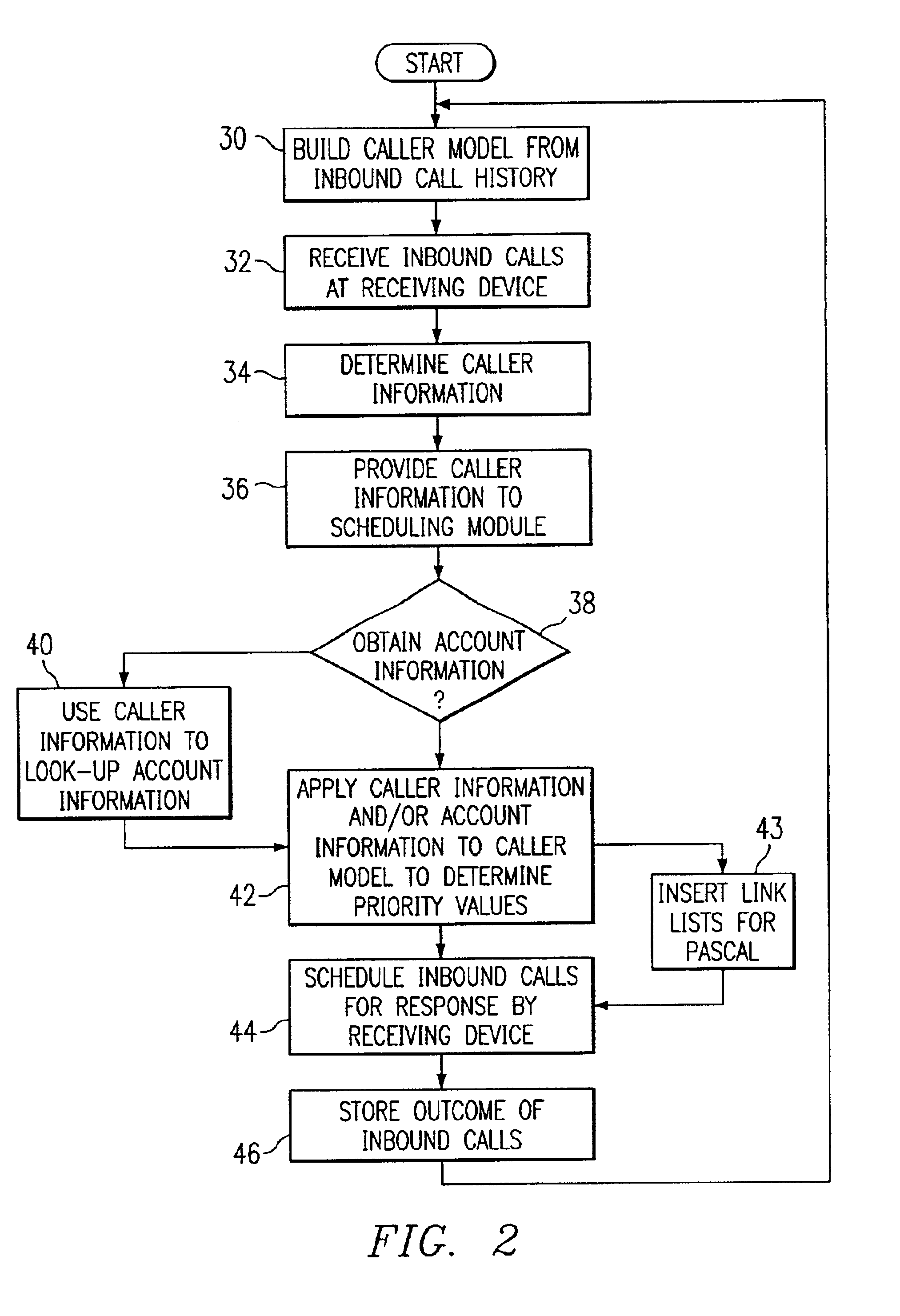
Method and system for self-service scheduling of inbound inquiries
InactiveUS6859529B2Accurate modelingMaximize useSpecial service for subscribersManual exchangesProduction rateRegression analysis
A method and system schedules inbound inquiries, such as inbound telephone calls, for response by agents in an order that is based in part on the forecasted outcome of the inbound inquiries. A scheduling module applies inquiry information to a model to forecast the outcome of an inbound inquiry. The forecasted outcome is used to set a priority value for ordering the inquiry. The priority value may be determined by solving a constrained optimization problem that seeks to maximize an objective function, such as maximizing an agent's productivity to produce sales or to minimize inbound call attrition. A modeling module generates models that forecast inquiry outcomes based on a history and inquiry information. Statistical analysis such as regression analysis determines the model with the outcome related to the nature of the inquiry. Operator wait time is regulated by forcing low priority and / or highly tolerant inbound inquiries to self service.
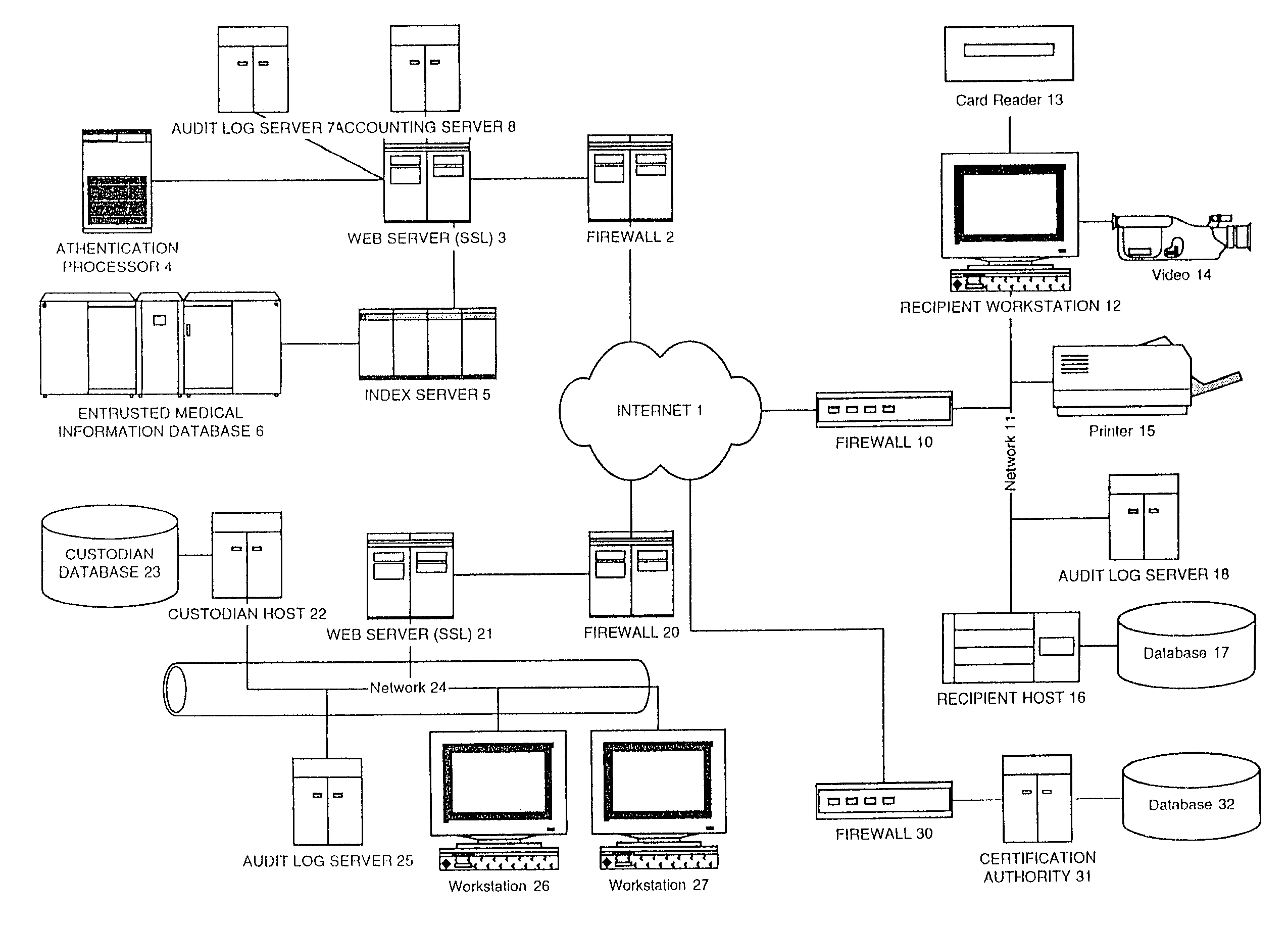
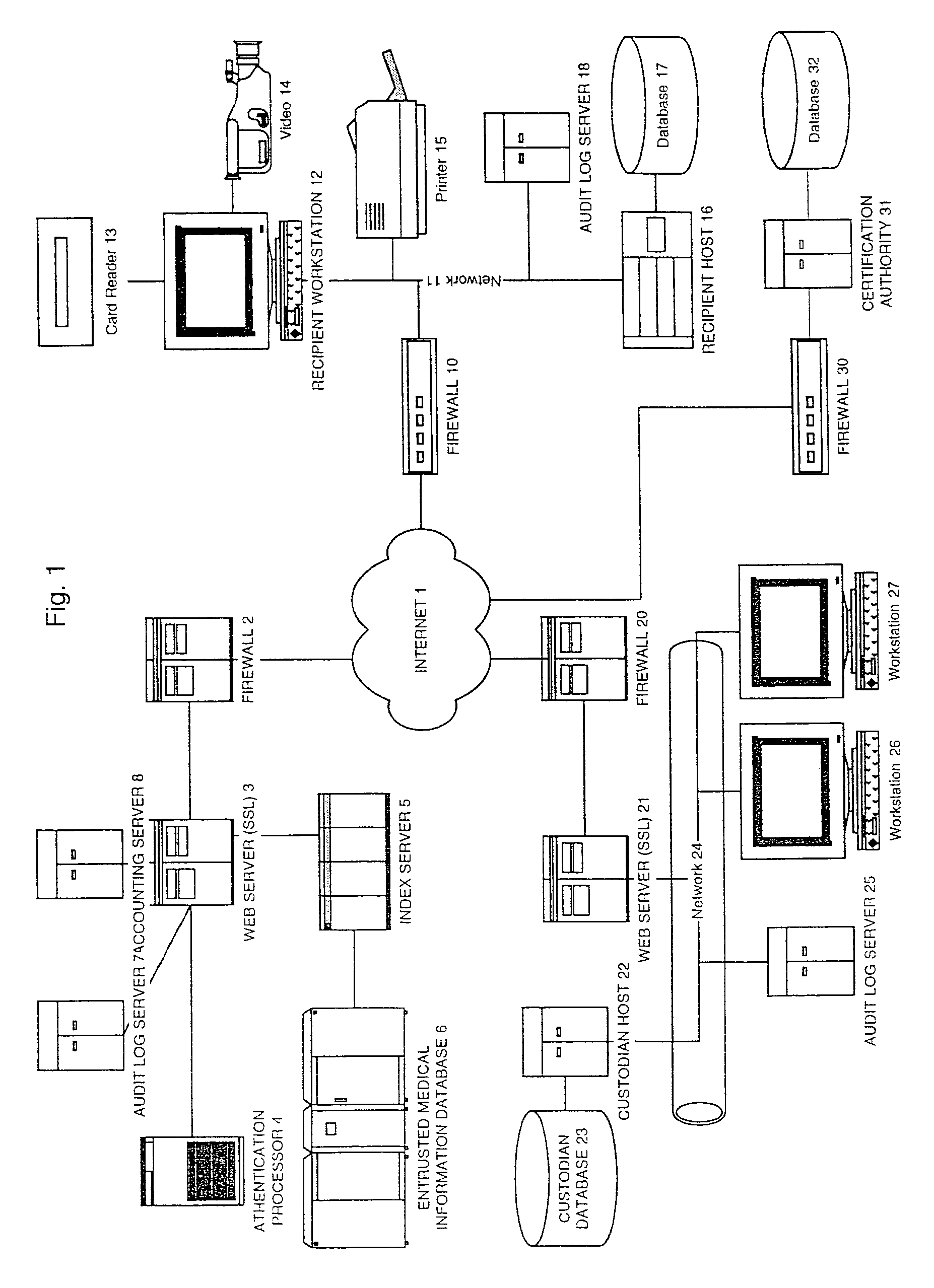
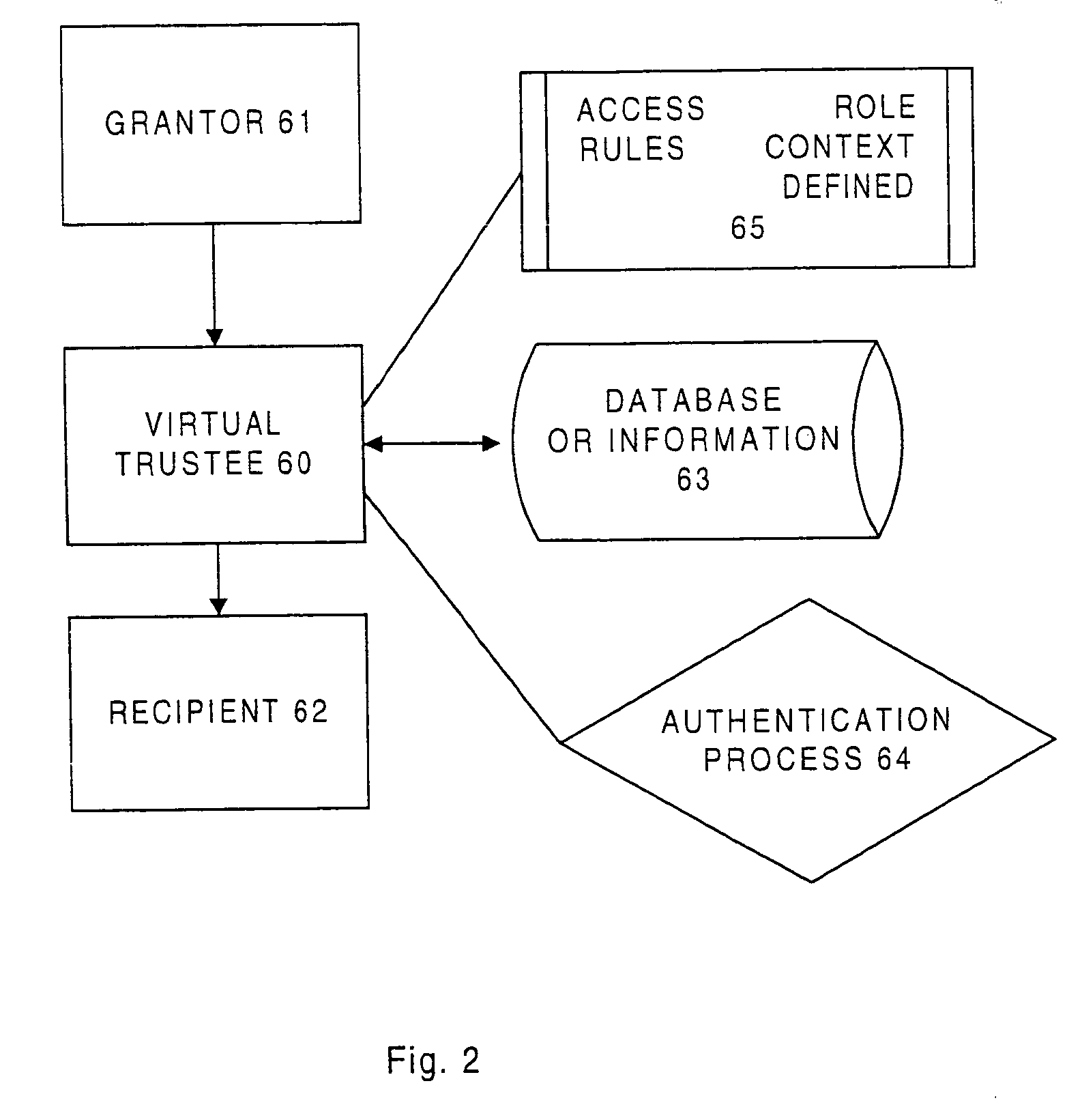
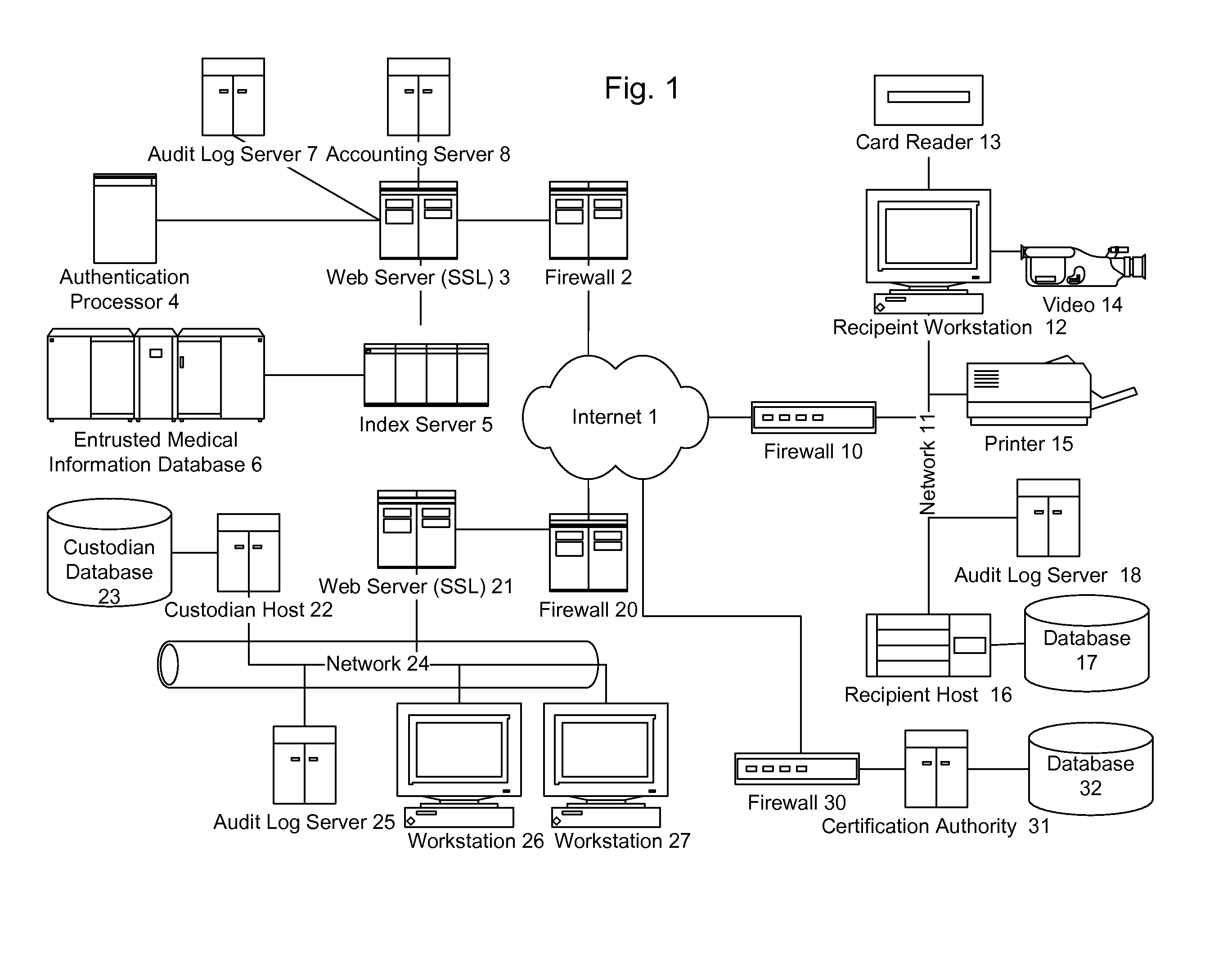
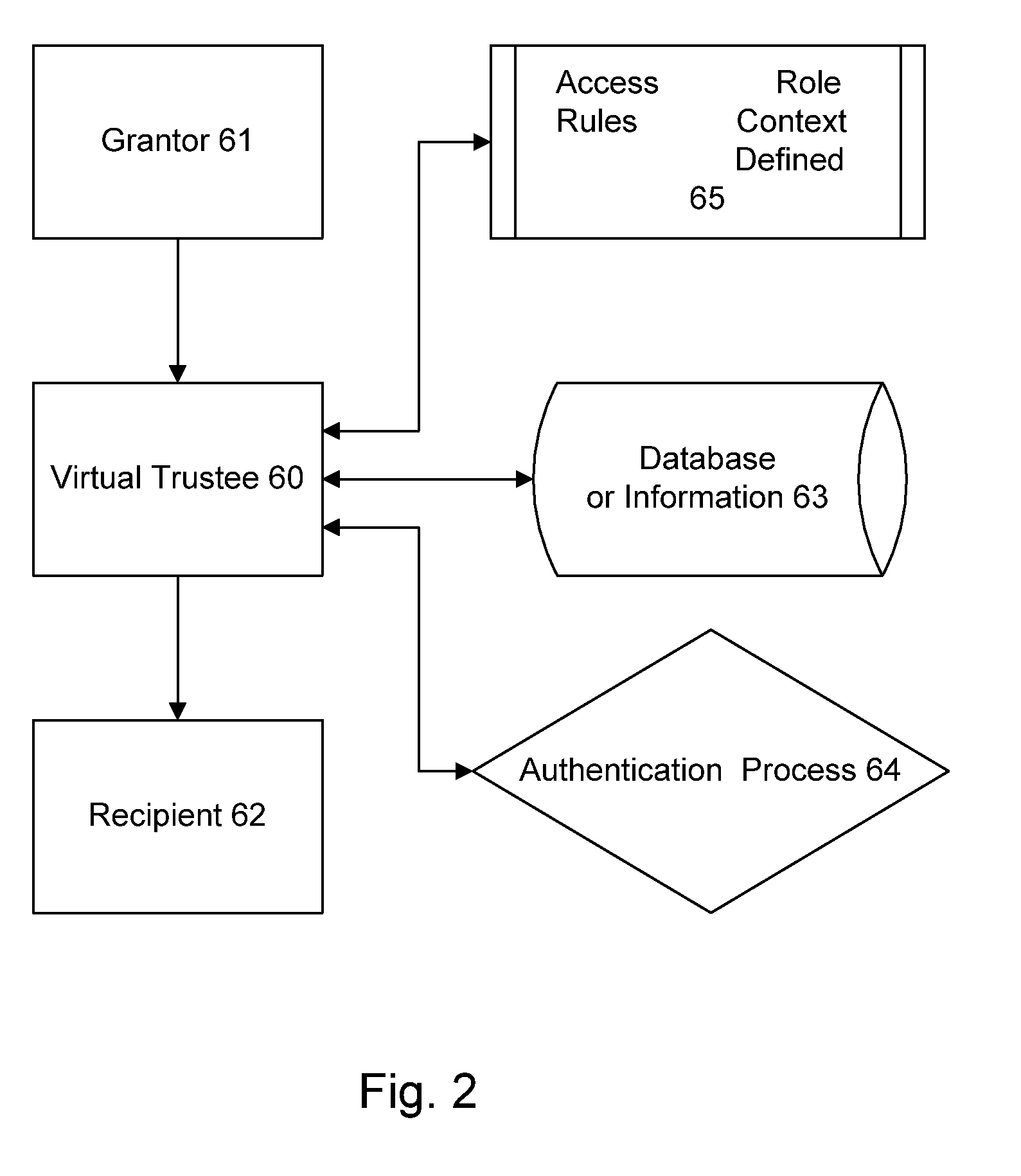
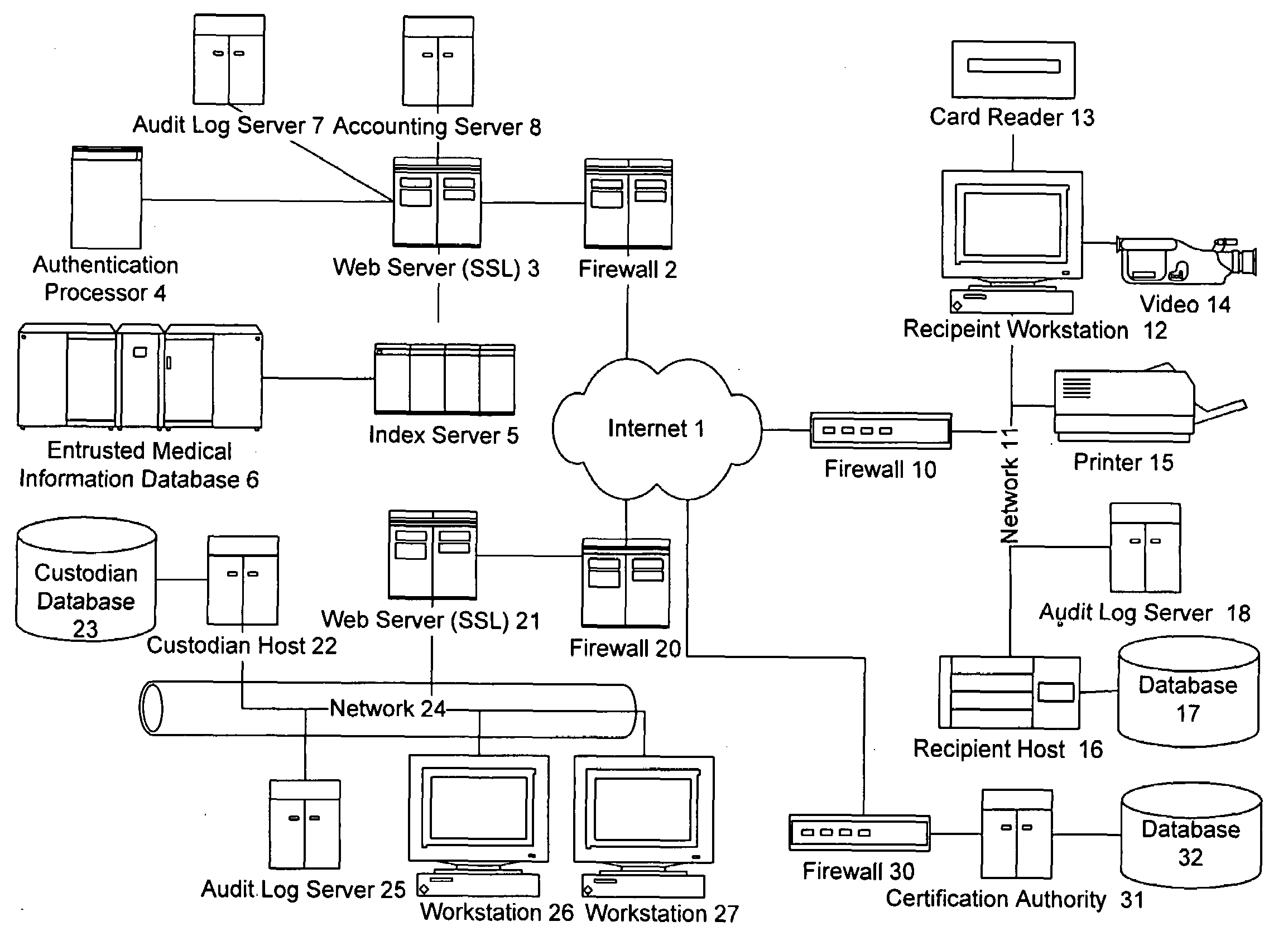
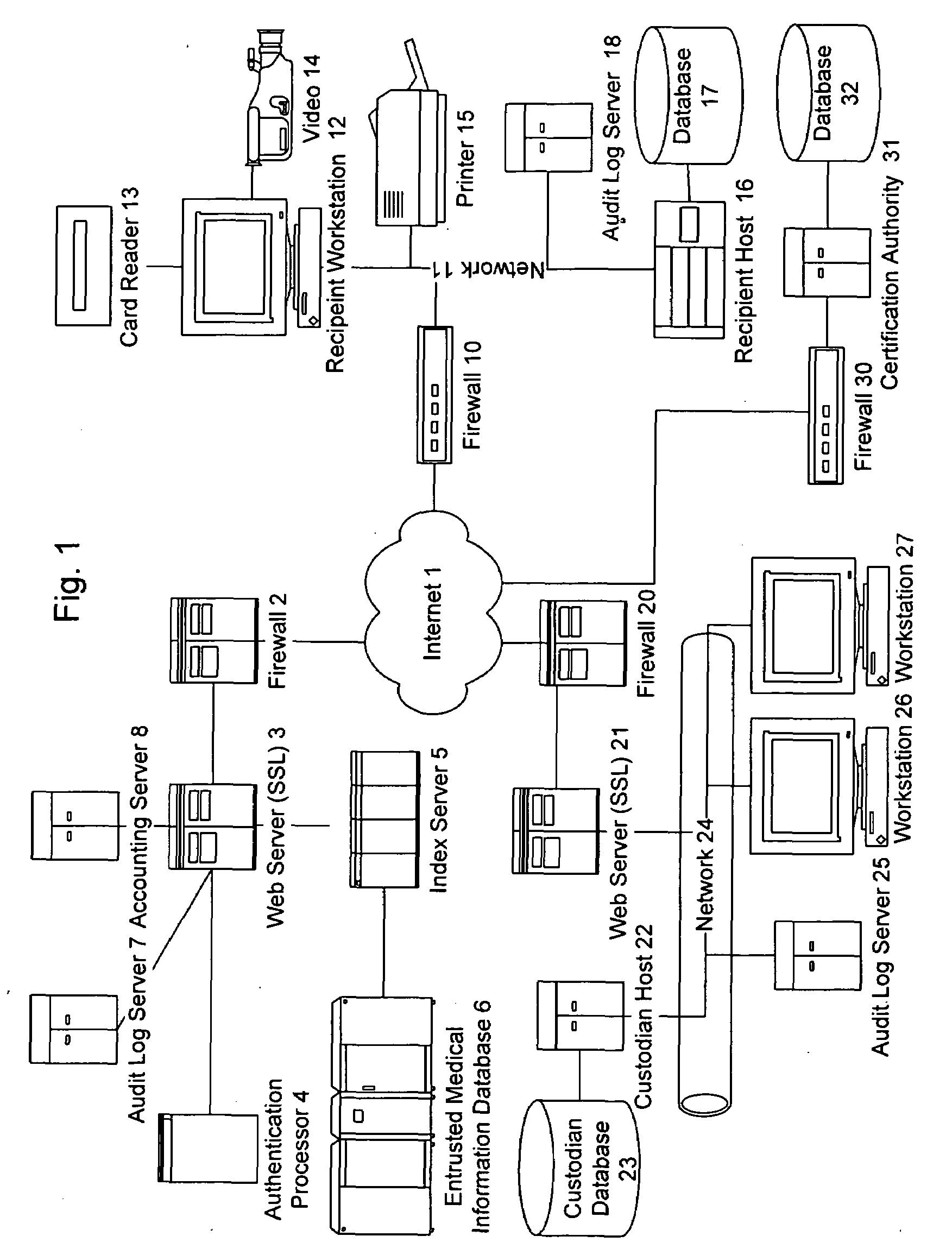
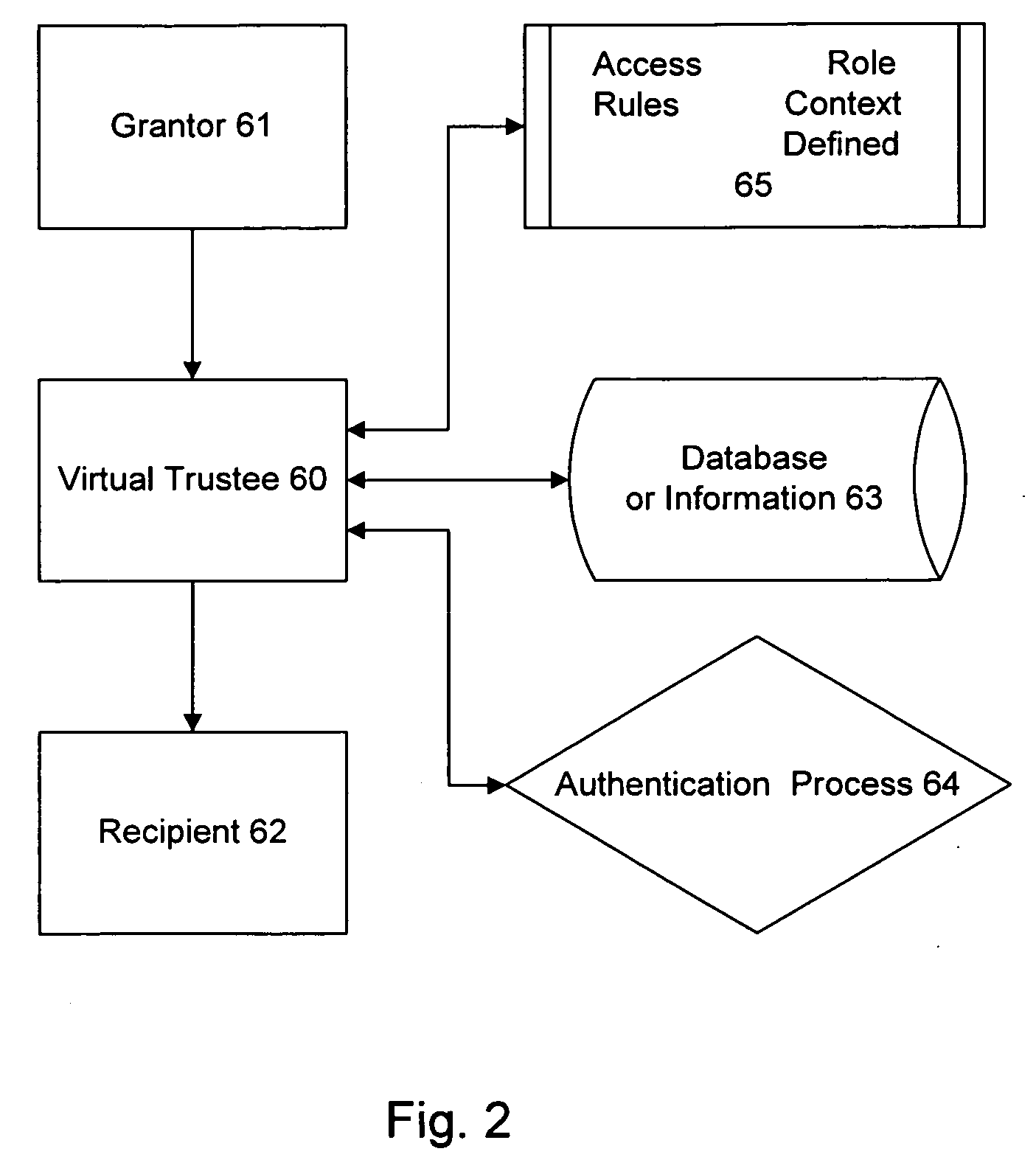
Information record infrastructure, system and method
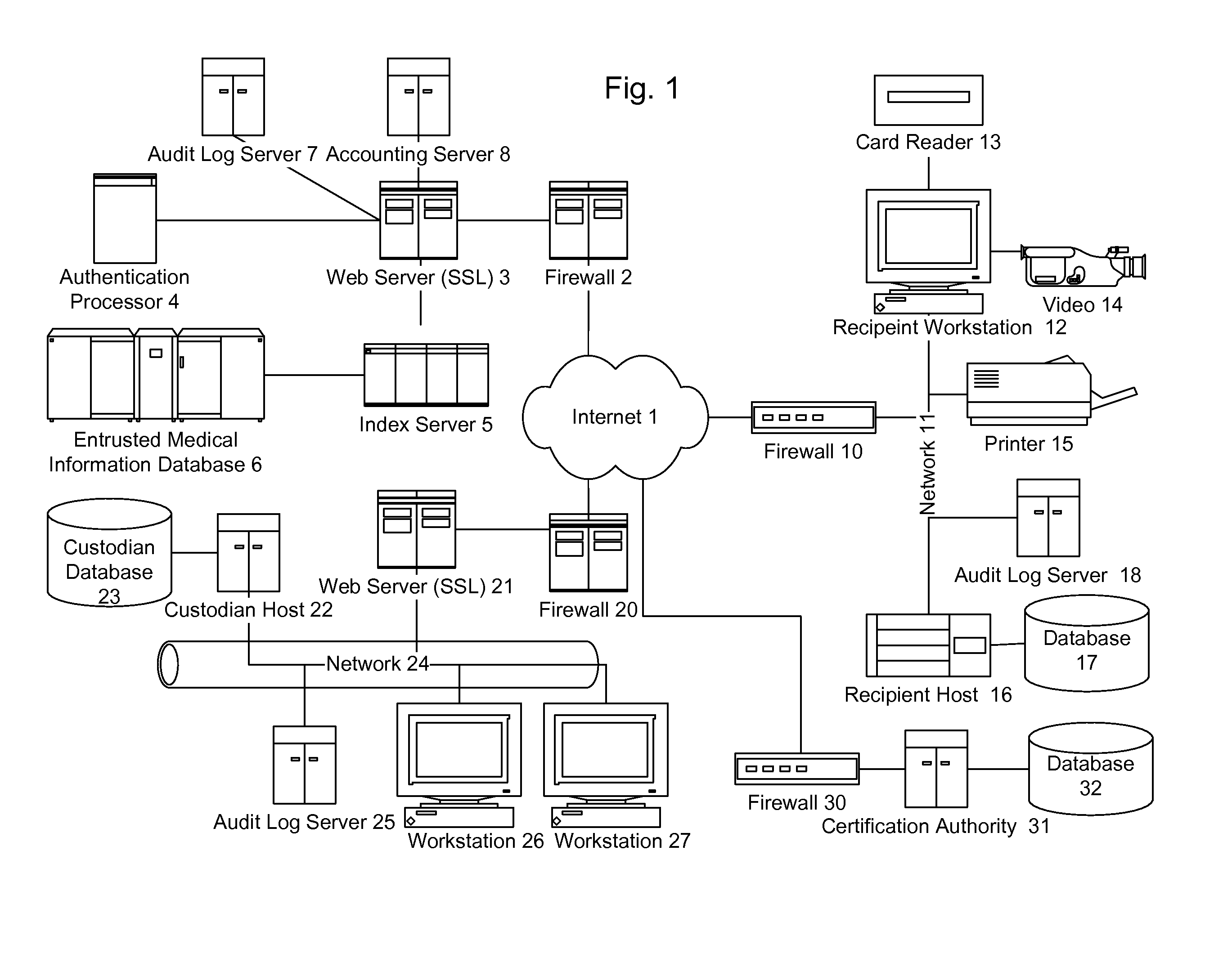
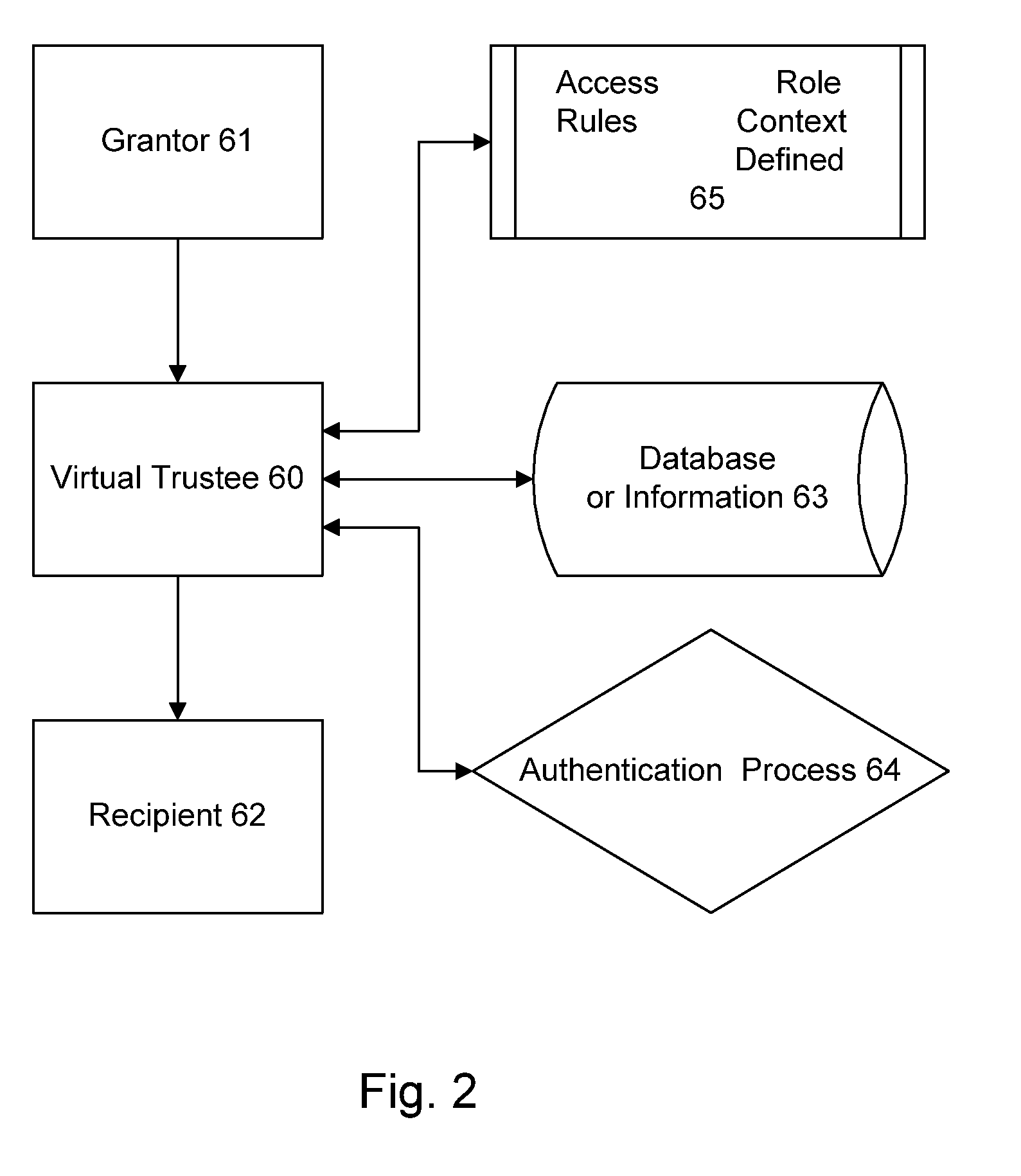
ActiveUS7587368B2Low costIncrease the number ofTelemedicineComputer security arrangementsMedical recordThird party
A method of maintaining electronic medical records, comprising the steps of receiving a medical transaction record, encrypted with an encryption key relating to a patient association of the file, accessing the encrypted medical transaction record according to a patient association; and further encrypting the encrypted accessed medical transaction record with an encryption key associated with an intended recipient of the medical record. The system and method according to the present invention presents a new business model for the creation, maintenance, transmission, and use of medical records, allowing financial burdens to be reallocated, for example more optimally or equitably, to decrease overall societal cost, or simply to provide a successful business model for a database proprietor. Secure entrusted medical records are held in trust by an independent third party on behalf of the patient, serving the medical community at large. Separately encrypted record elements may be aggregated as an information polymer.
Owner:RPX CORP
Watermarking scheme for image authentication
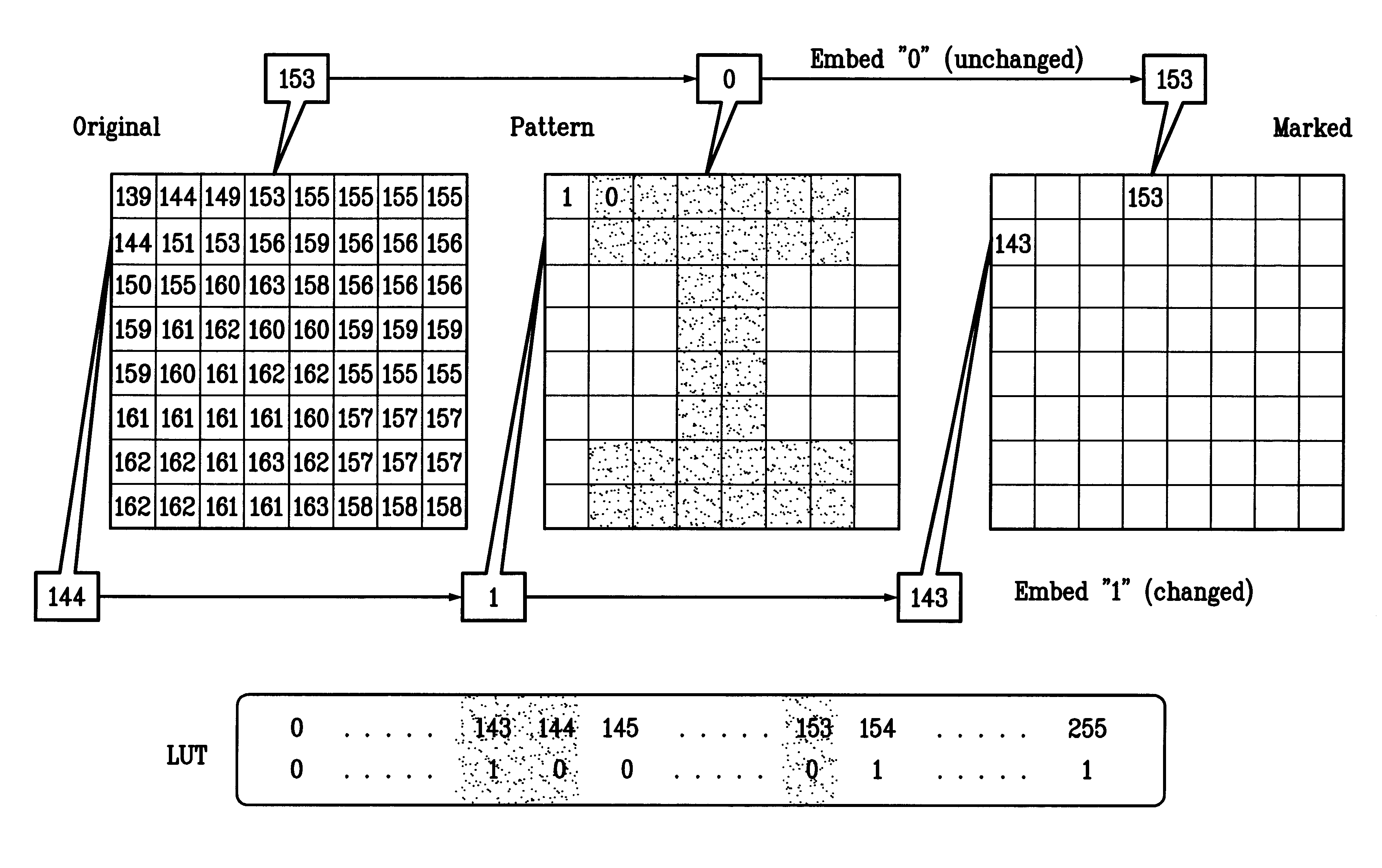
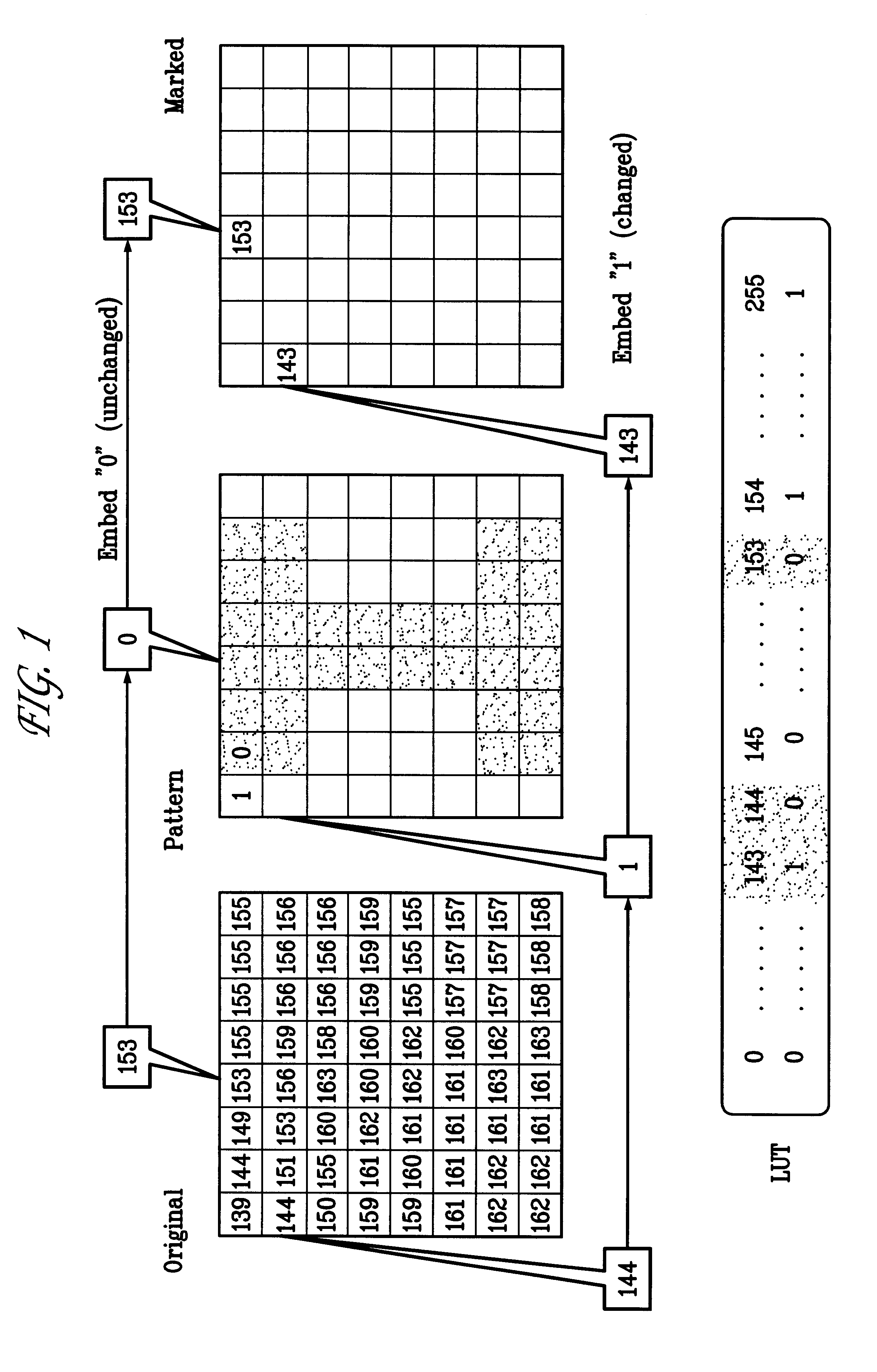
InactiveUS6285775B1Effective distributionQuick checkCharacter and pattern recognitionImage data processing detailsWatermark methodJPEG
A digital watermarking process whereby an invisible watermark inserted into a host image is utilized to determine whether or not the image has been altered and, if so, where in the image such alteration occurred. The watermarking method includes the steps of providing a look-up table containing a plurality of coefficients and corresponding values; transforming the image into a plurality of blocks, wherein each block contains coefficients matching coefficients in the look-up table; and embedding the watermark in the image by performing the following substeps for at least some of the blocks: First, a coefficient is selected for insertion of a marking value representative of a corresponding portion of the watermark. Next, the value of the selected coefficient to used to identify a corresponding value in the look-up table. Finally, the identified coefficient is left unchanged if the corresponding value is the same as the marking value, and is changed if the corresponding value is different from the marking value. After the insertion of the watermark, the image may be stored in a lossy-compression form, thus permitting efficient storage and distribution. Moreover, the method may be used to produce two output signals for authentication: (1) a meaningful pattern to facilitate a quick visual check, and (2) an additional signal to detect unauthorized alteration. The method can be applied to an image compressed using JPEG or other techniques, such as Wavelet compression, and the marked image can be kept in the compressed format. Any alteration made on the marked image can be localized, making the method suitable for use in a "trustworthy" digital camera or camcorder.
Owner:TRUSTEES OF THE UNIV OF PRINCETON THE
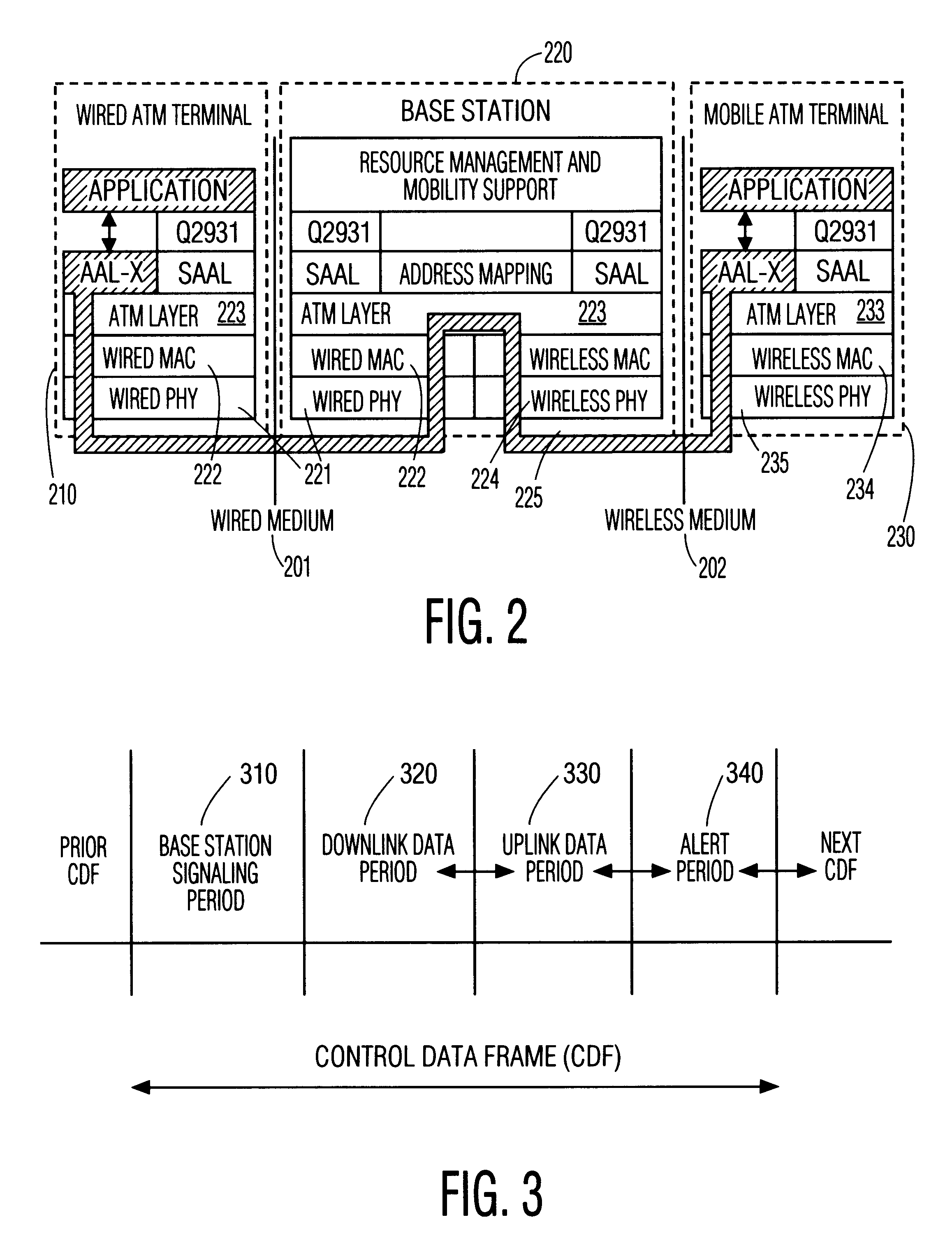
Medium access control (MAC) protocol for wireless ATM
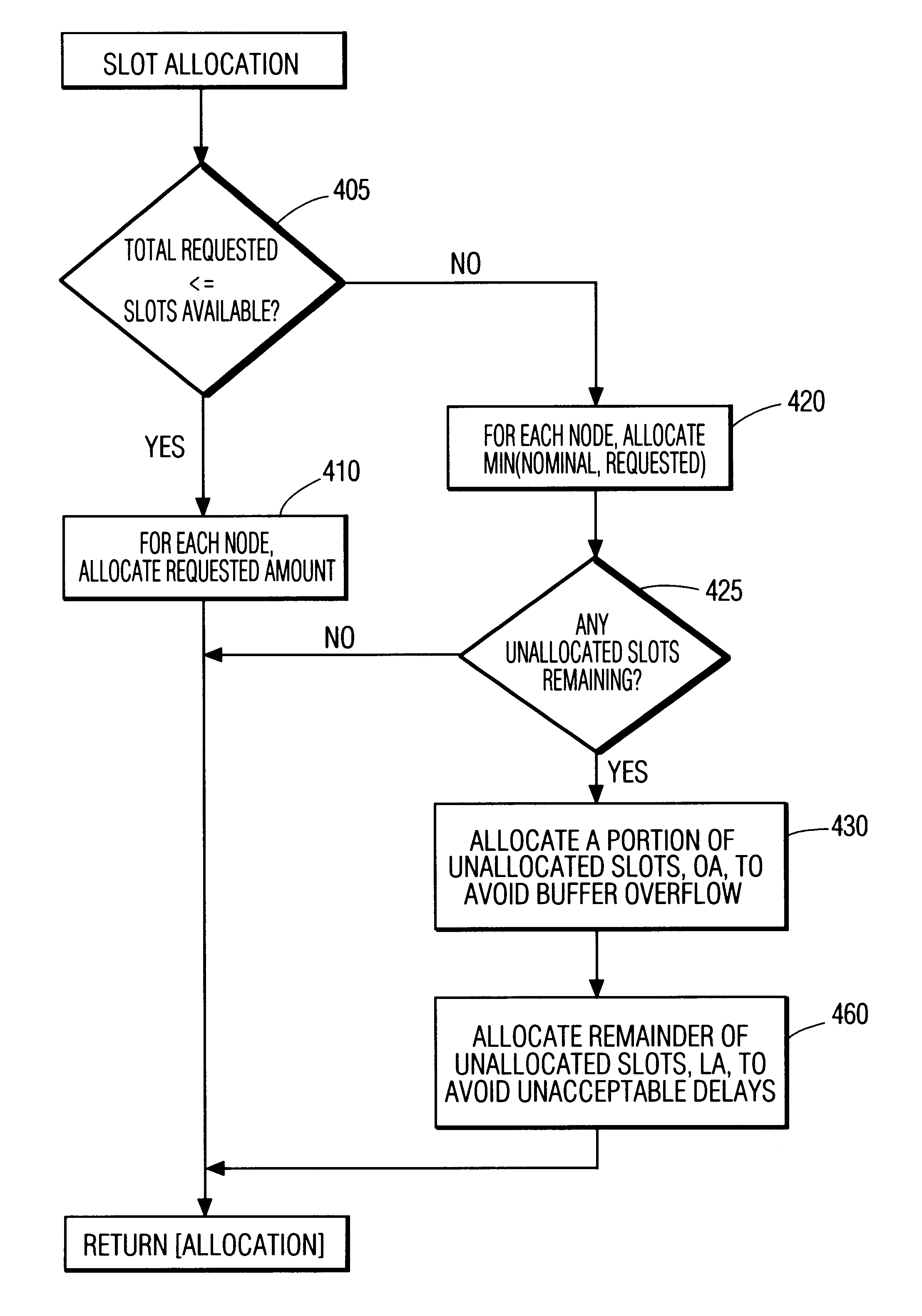
InactiveUS6198728B1Structure is limitedMinimize timePower managementNetwork traffic/resource managementNetwork communicationMedia access control
A protocol, method, and apparatus for managing network communications which are particularly well suited for ATM communications across a wireless medium. Contiguous time slots within a frame are allocated to each node having traffic to send. Each node is assured a nominal bandwidth, and excess bandwidth is distributed by demand. The allocation of excess bandwidth can be dependent upon the size of the buffer at each node, as well as the time-criticality of each message. Nodes communicate their requests for allocation by appending such control information to the first of their transmitted packets. The allocation, of each node's transmit and receive time slots, is transmitted to all the nodes at the beginning of each frame. Thereafter, each node need not participate on the network until their allocated time periods, thereby allowing portable devices to enter inactive states to conserve power. The network is operated in a connection mode; connections are established in a relatively non-interfering manner by the use of periodically occurring beacons. Inactive, unconnected, nodes need only monitor the network during these beacon periods, further allowing for power conservation.
Owner:UNILOC 2017 LLC
System for redirecting requests for data to servers having sufficient processing power to transcast streams of data in a desired format
InactiveUS6981045B1Attenuation bandwidthReduce deliveryMultiple digital computer combinationsTwo-way working systemsBandwidth requirementDistributed computing
A method includes polling a first plurality of one-hop gateway serves for available bandwidth and available number of CPU cycles for each respective one-hop gateway server, receiving a request to provide data to a media sink in a desired format, determining a bandwidth requirement and an estimated number of CPU cycles required for servicing the media sink, determining a second plurality of one-hop gateway servers having an available bandwidth greater or equal to the bandwidth requirement and an available number of CPU cycles greater or equal to the estimated number of CPU cycles, determining a one-hop gateway server from the second plurality of one-hop gateway servers appropriate for providing the data to the media sink and configured to receive data in a second format, and transcoding the data from a first format to the second format. An example gateway server and a computer program product usable therewith are also provided.
Owner:ADAPTIVE STREAMING INC
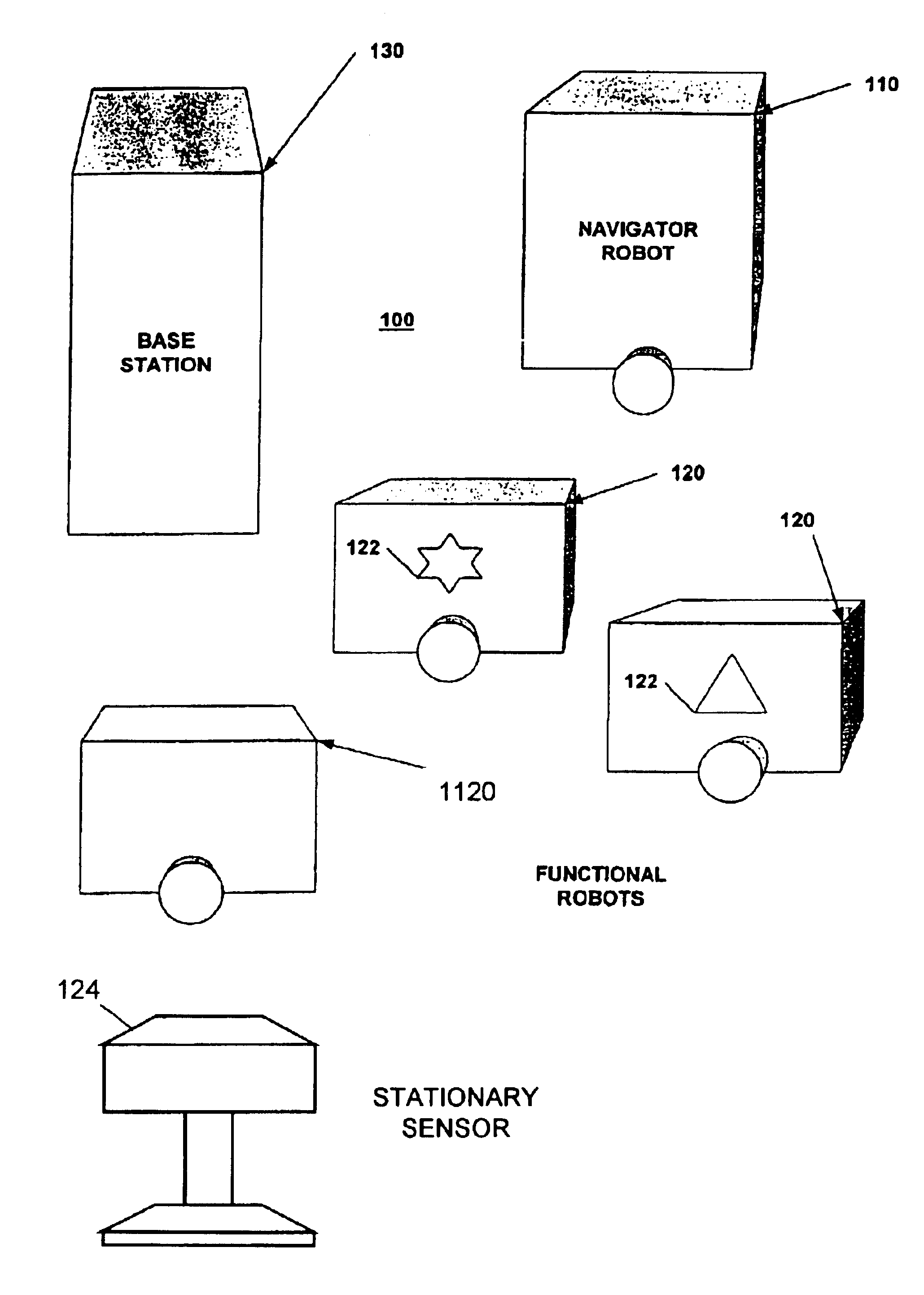
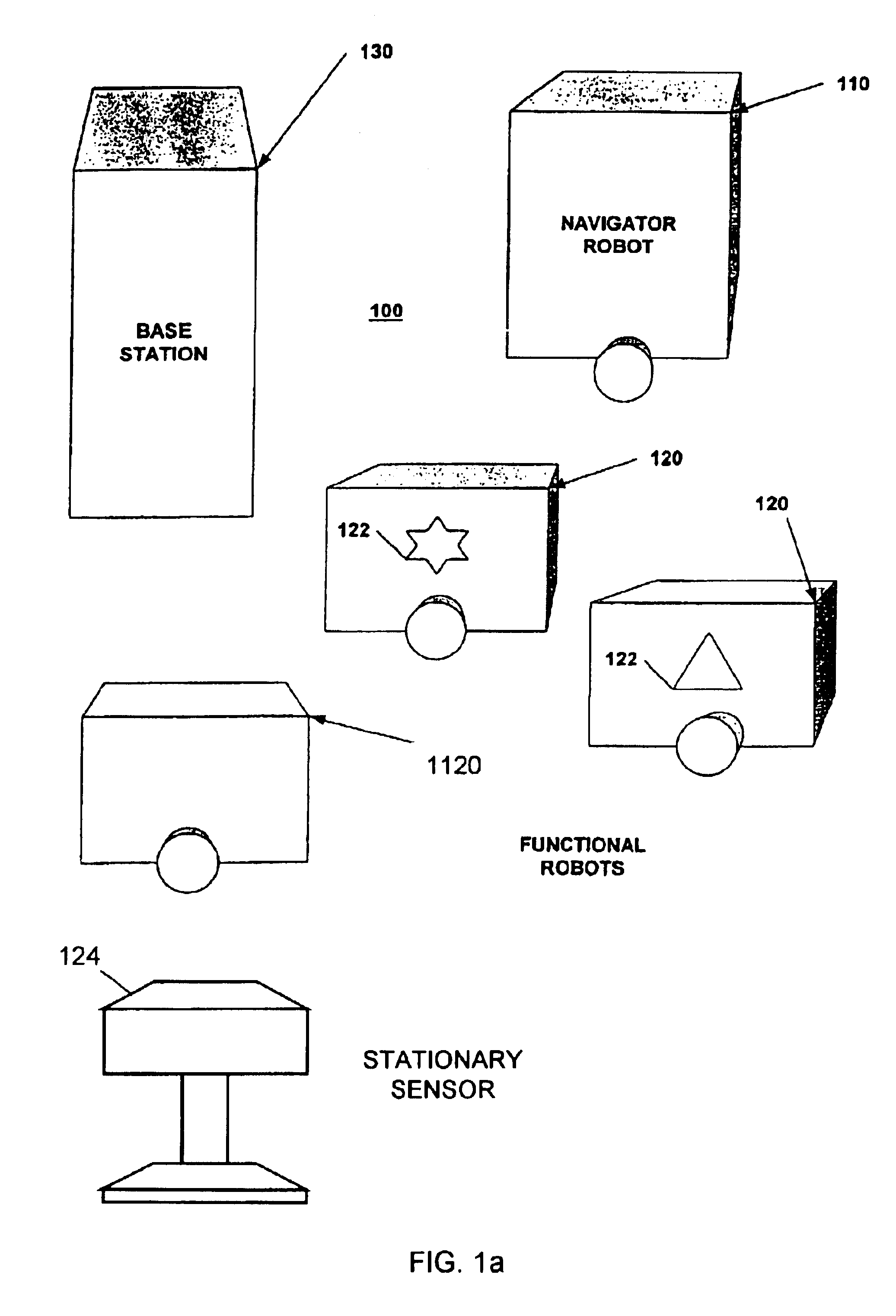
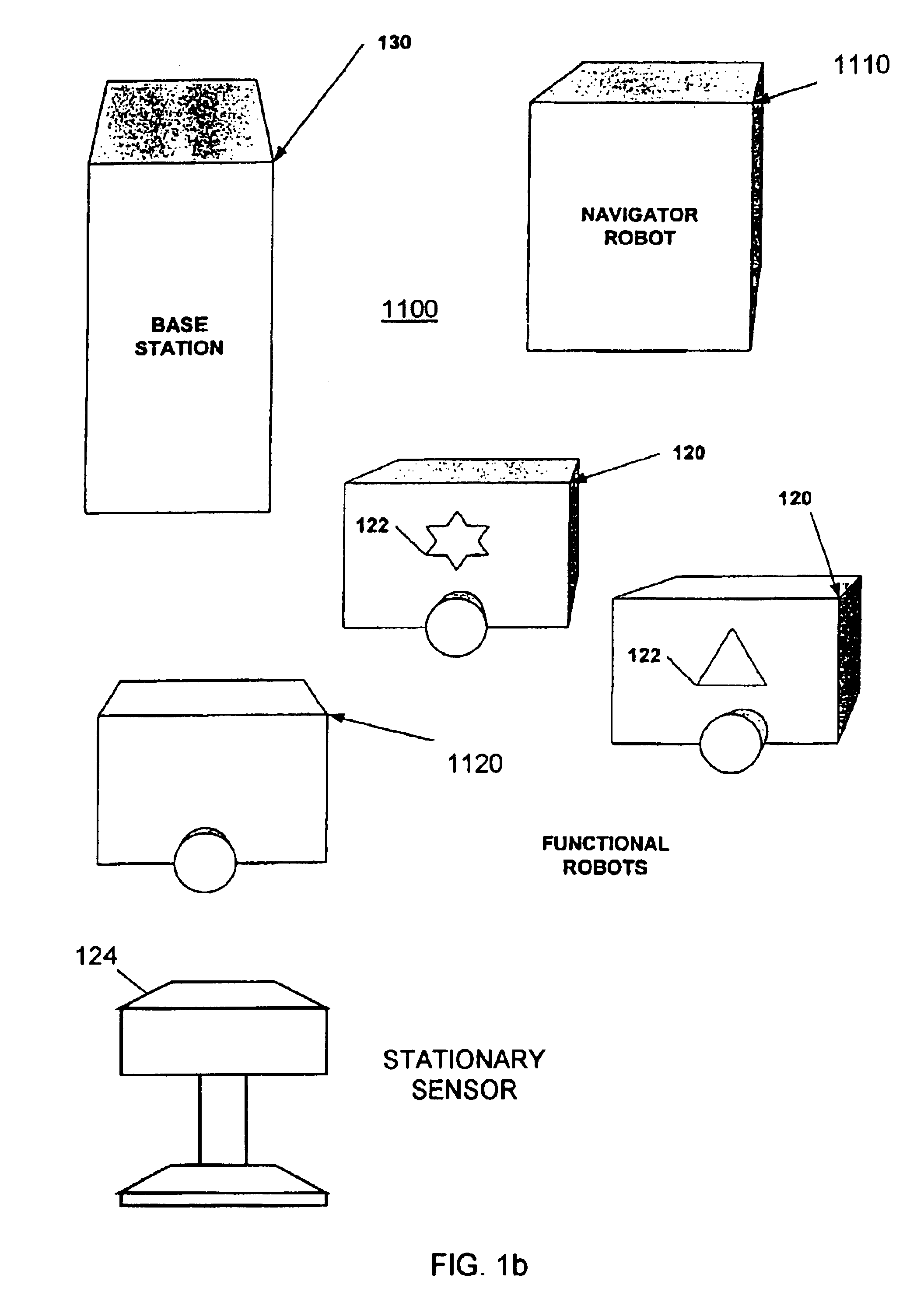
Autonomous multi-platform robotic system
InactiveUS6836701B2Fast and accurate and cost-effective mapping and localizationImprove overall senseProgramme-controlled manipulatorDigital data processing detailsRobotic systemsMulti platform
An autonomous multi-platform robot system (100, 1100) for performing at least one functional task in an environment is provided. The system includes at least one navigator platform (110, 1110) providing mapping, localization, planning, and control functions for itself and at least one other platform within the environment and at least one functional robot platform (120, 1120) in communication with one or more navigator platforms for performing one or more functional tasks. In one embodiment, one or more navigator platforms (1110) are stationary and include sensors (202) for sensing information about the environment. In another embodiment, one or more functional robot platforms (1120) include sensors (304) for sending information about the environment. In still another embodiment, the system includes one or more stationary platforms (124) with sensors (310) for sensing information about the environment.
Owner:ROYAL APPLIANCE MFG
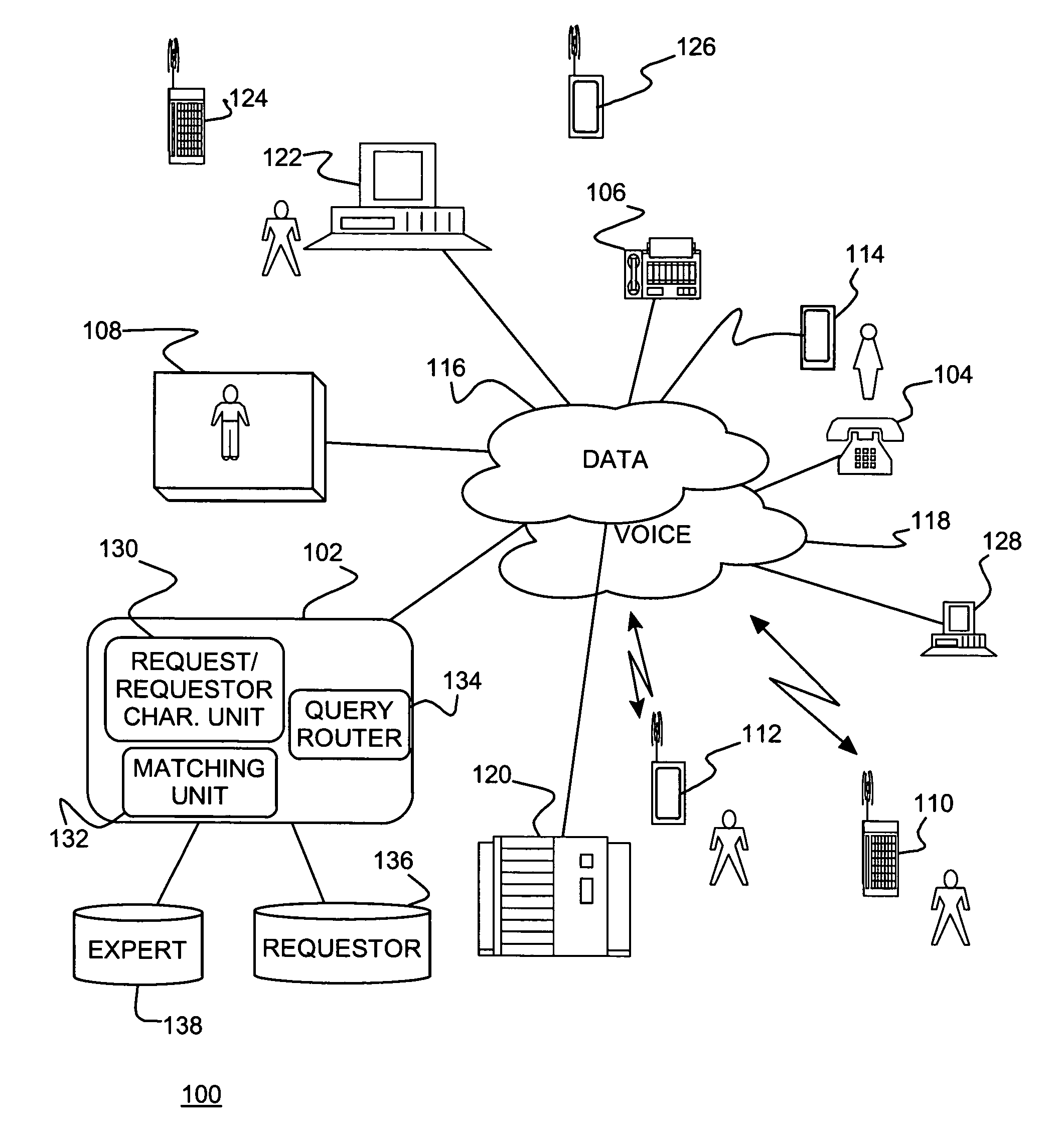
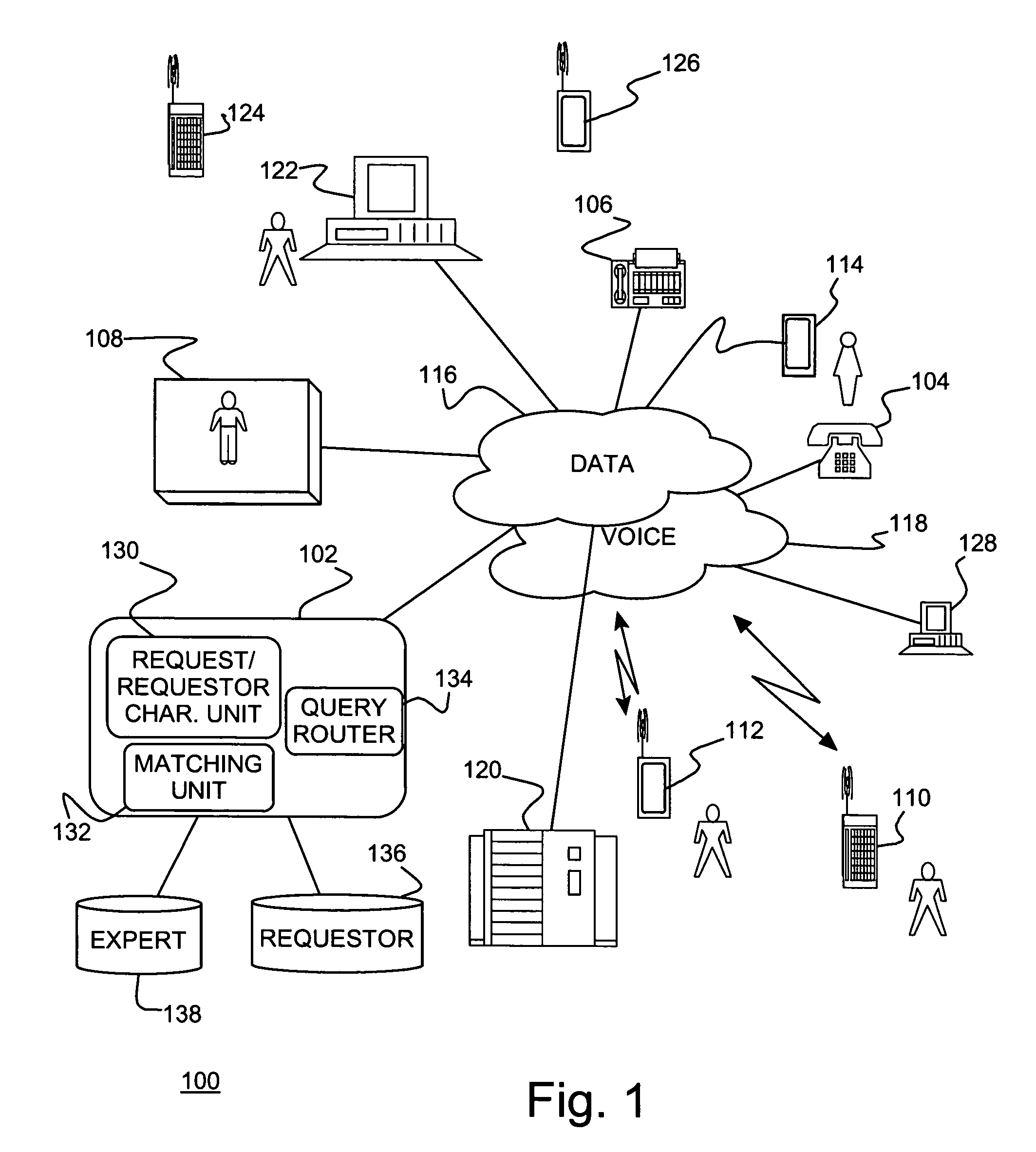
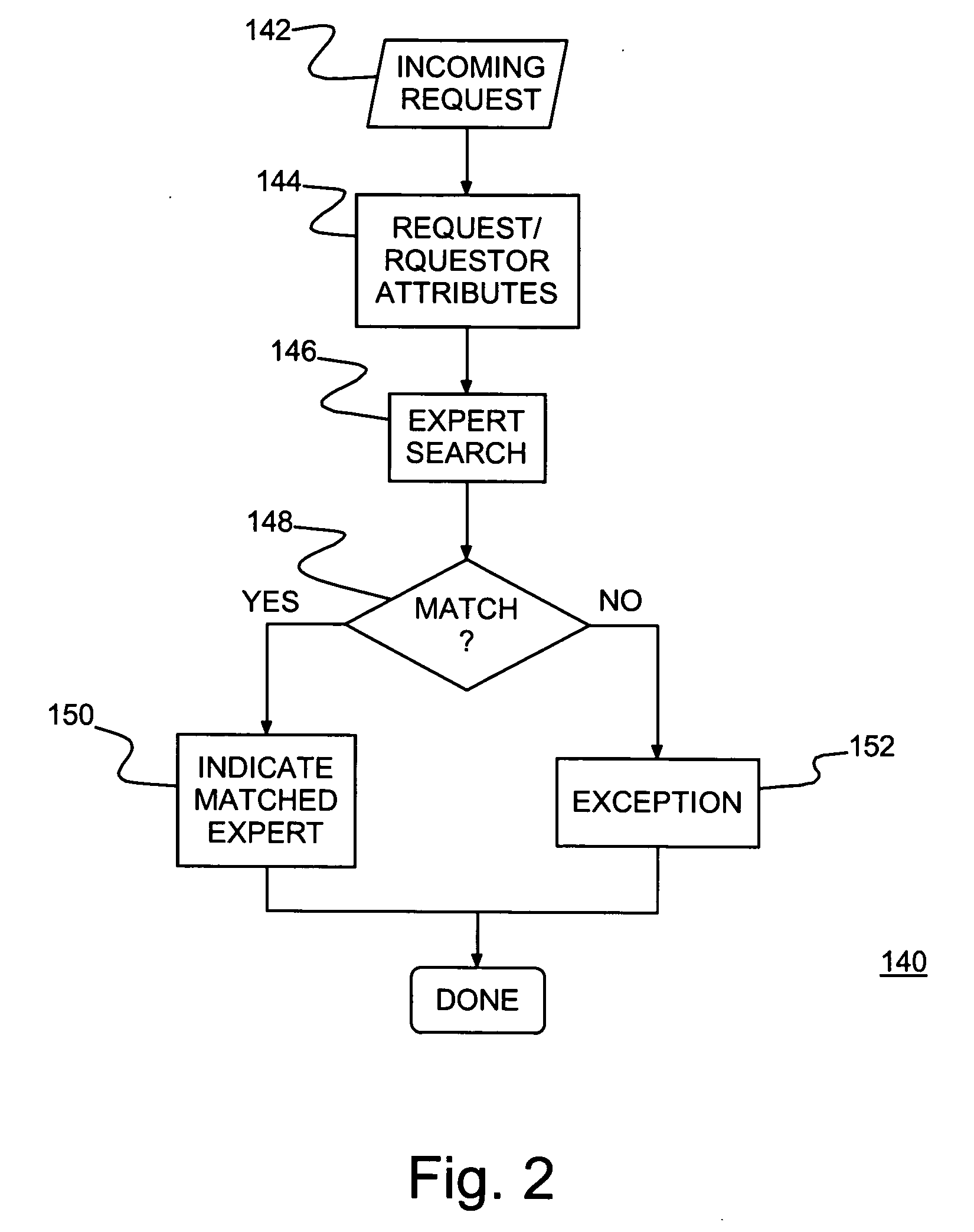
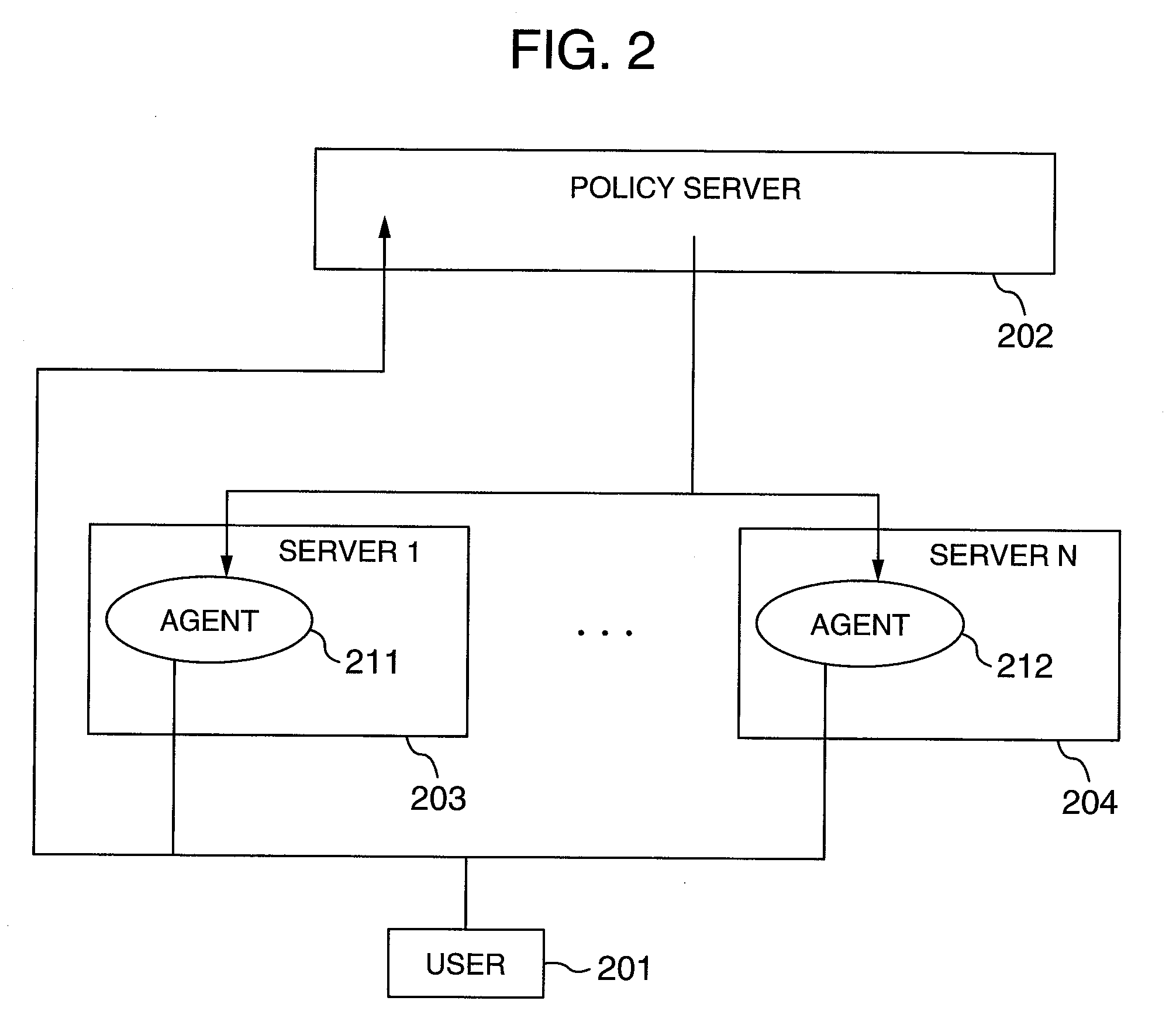
Knowledge management system automatically allocating expert resources
ActiveUS20060047615A1Effective distributionResource optimizationData processing applicationsKnowledge representationComputer scienceSpeech sound
A knowledge management system allocating expert resources, method of allocating expert resources and program product therefor. Information requests are provided over networked devices, e.g., over voice and data networks. Data on experts may be stored in an expert database and data on requesters stored in a requestor database. A pairing unit identifies an appropriate expert matched to each request and requestor. The pairing unit includes a request / requestor characterization unit collecting request / requestor attributes, a matching unit matching request / requestor attributes with an expert, and a routing unit routing each incoming request to a selected matching expert.
Owner:GOOGLE LLC
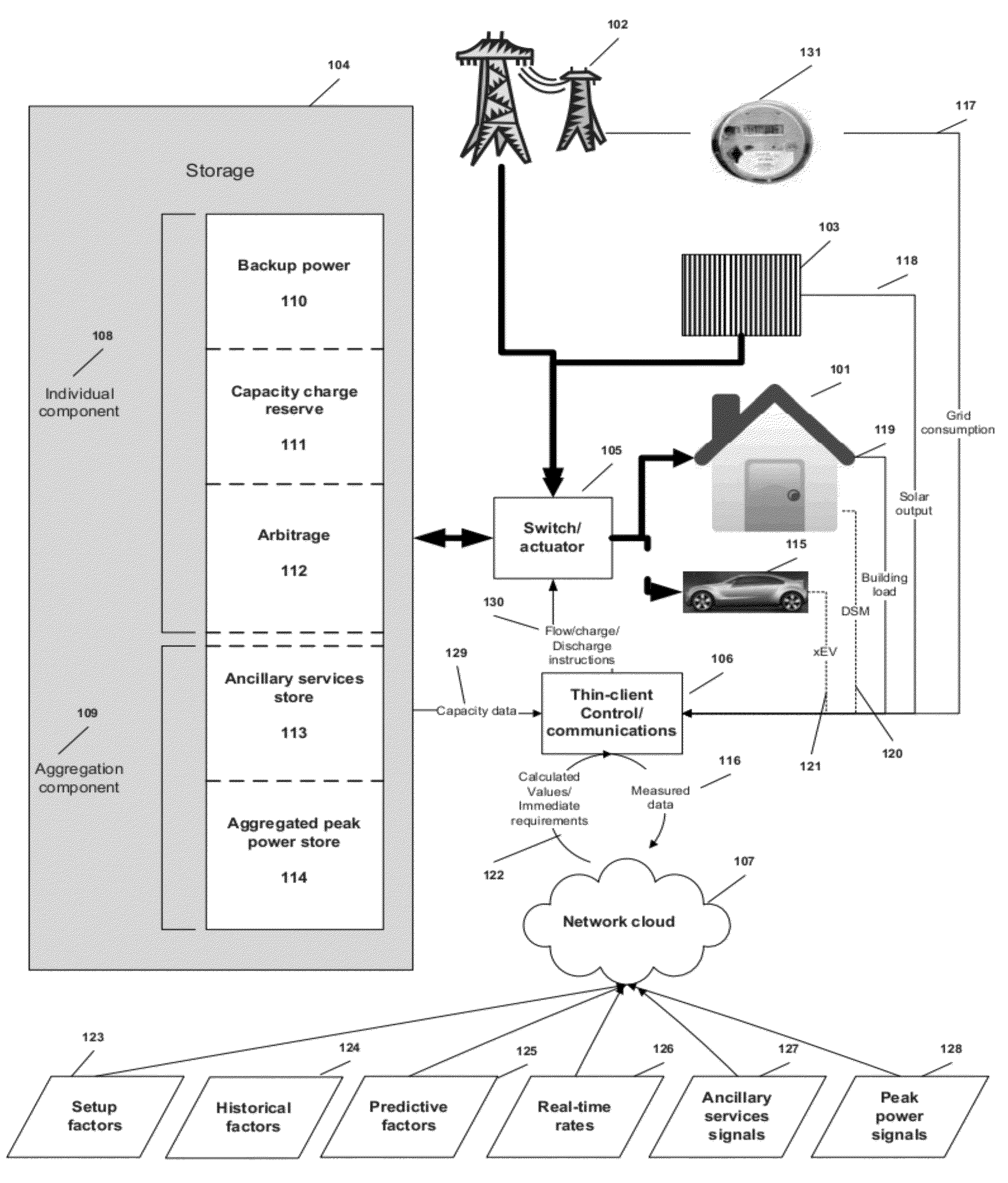
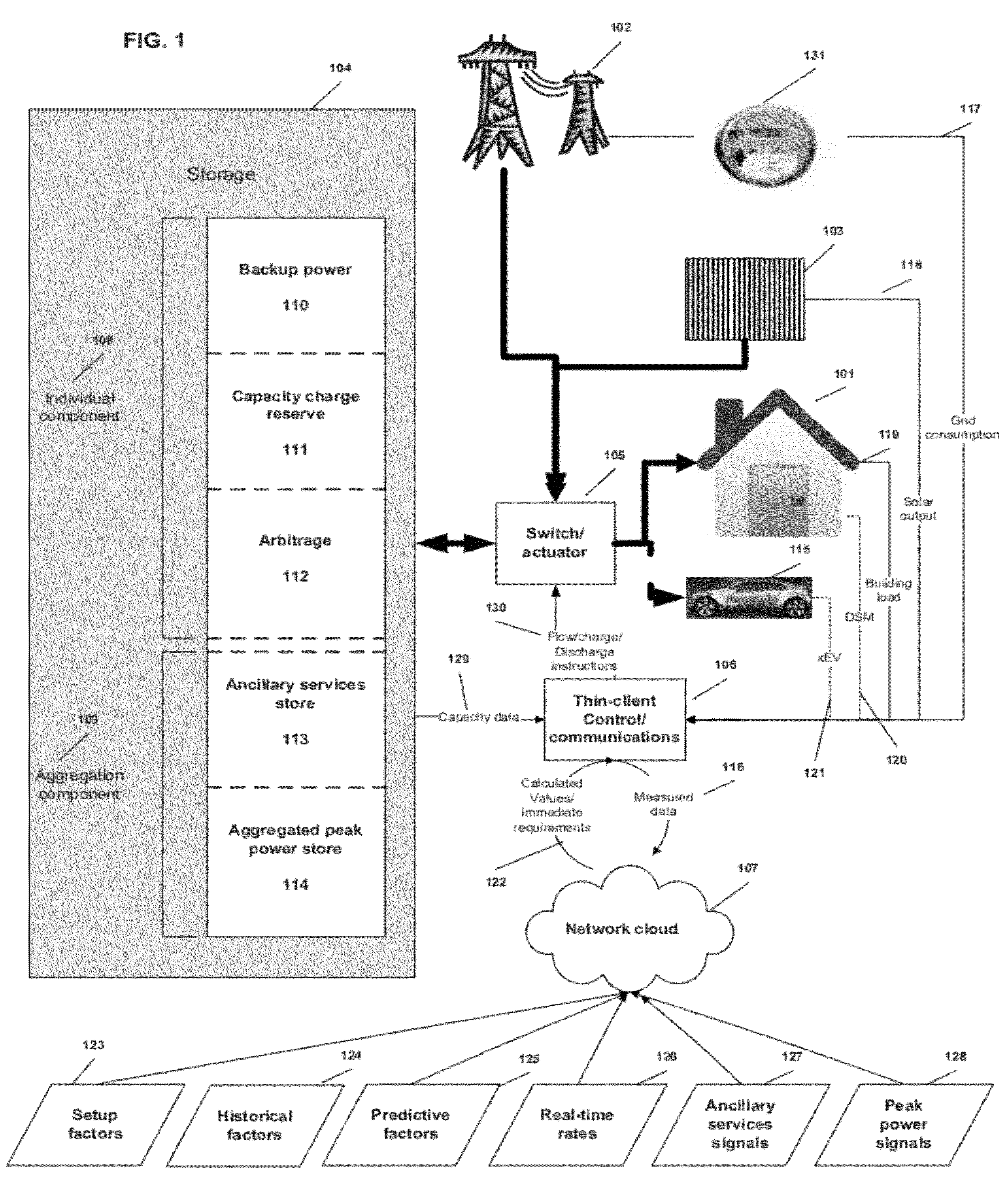
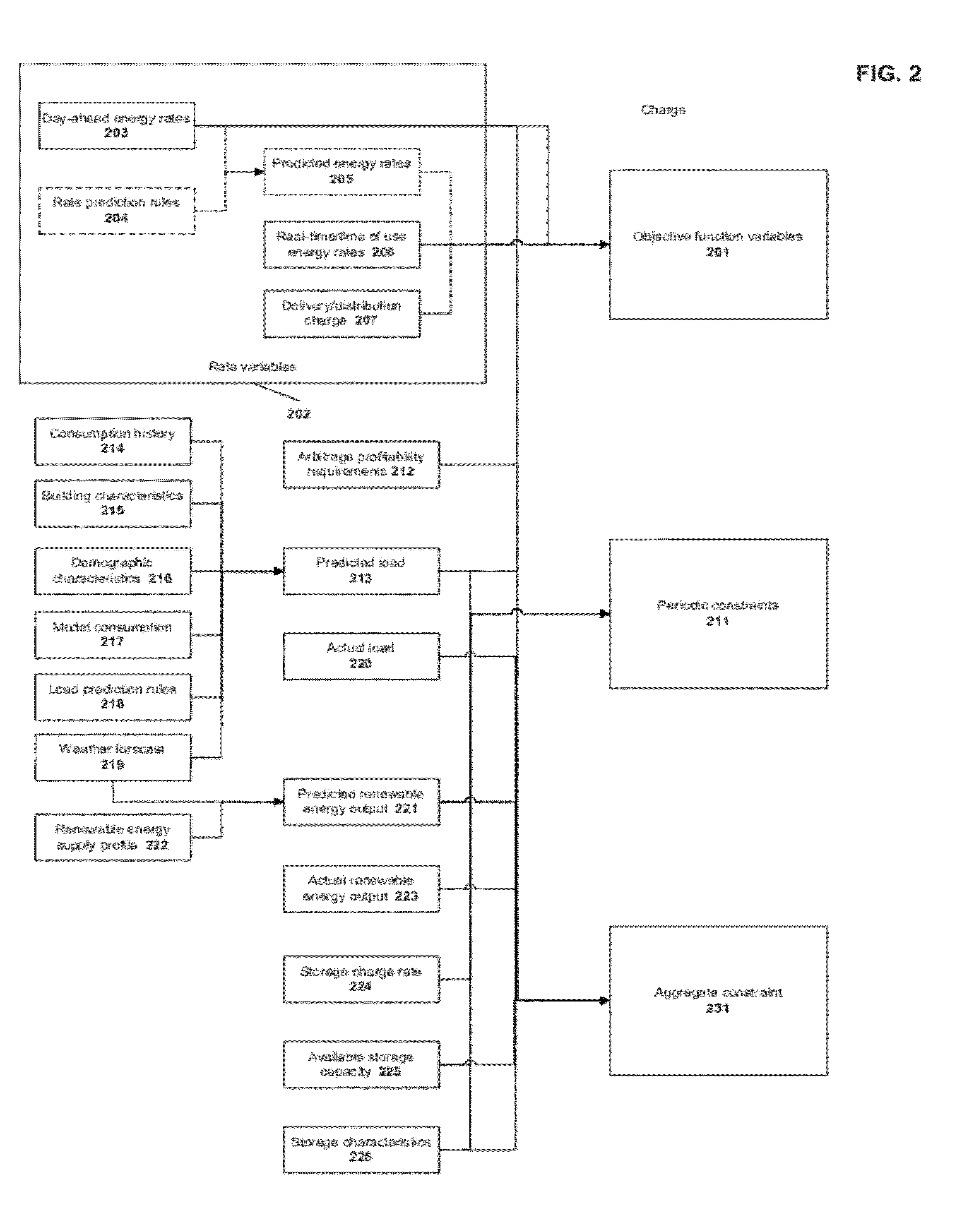
Virtual power plant system and method incorporating renewal energy, storage and scalable value-based optimization
ActiveUS20120130556A1Effective distributionLow costLevel controlWind energy generationCapital investmentPredictive factor
Methods and systems provided for creating a scalable building block for a virtual power plant, where individual buildings can incorporate on-site renewable energy assets and energy storage and optimize the acquisition, storage and consumption of energy in accordance with a value hierarchy. Each building block can be aggregated into a virtual power plant, in which centralized control of load shifting in selected buildings, based on predictive factors or price signals, can provide bulk power for ancillary services or peak demand situations. Aggregation can occur at multiple levels, including developments consisting of both individual and common renewable energy and storage assets. The methods used to optimize the system can also be applied to “right size” the amount of renewable energy and storage capacity at each site to maximize return on the capital investment.
Owner:INTELLIGENT GENERATION
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
ActiveUS7287275B2Speeding routingFine granularityError preventionFrequency-division multiplex detailsData streamNetwork packet
Disclosed herein are methods and systems for transmitting streams of data. In one embodiment, a method comprises the steps of: receiving a stream of data; organizing the stream of data into a plurality of packets; generating a packet watermark associated with the stream of data; combining the packet watermark with each of the plurality of packets to form watermarked packets; and transmitting at least one of the watermarked packets across a network. The present invention also relates to: receiving at least one packet that has been transmitted across a network; analyzing at least one packet for a watermark; and authenticating the at least one packet using at least a portion of the watermark. The present invention also relates to generating packet watermarks and packet watermark keys.
Owner:WISTARIA TRADING INC
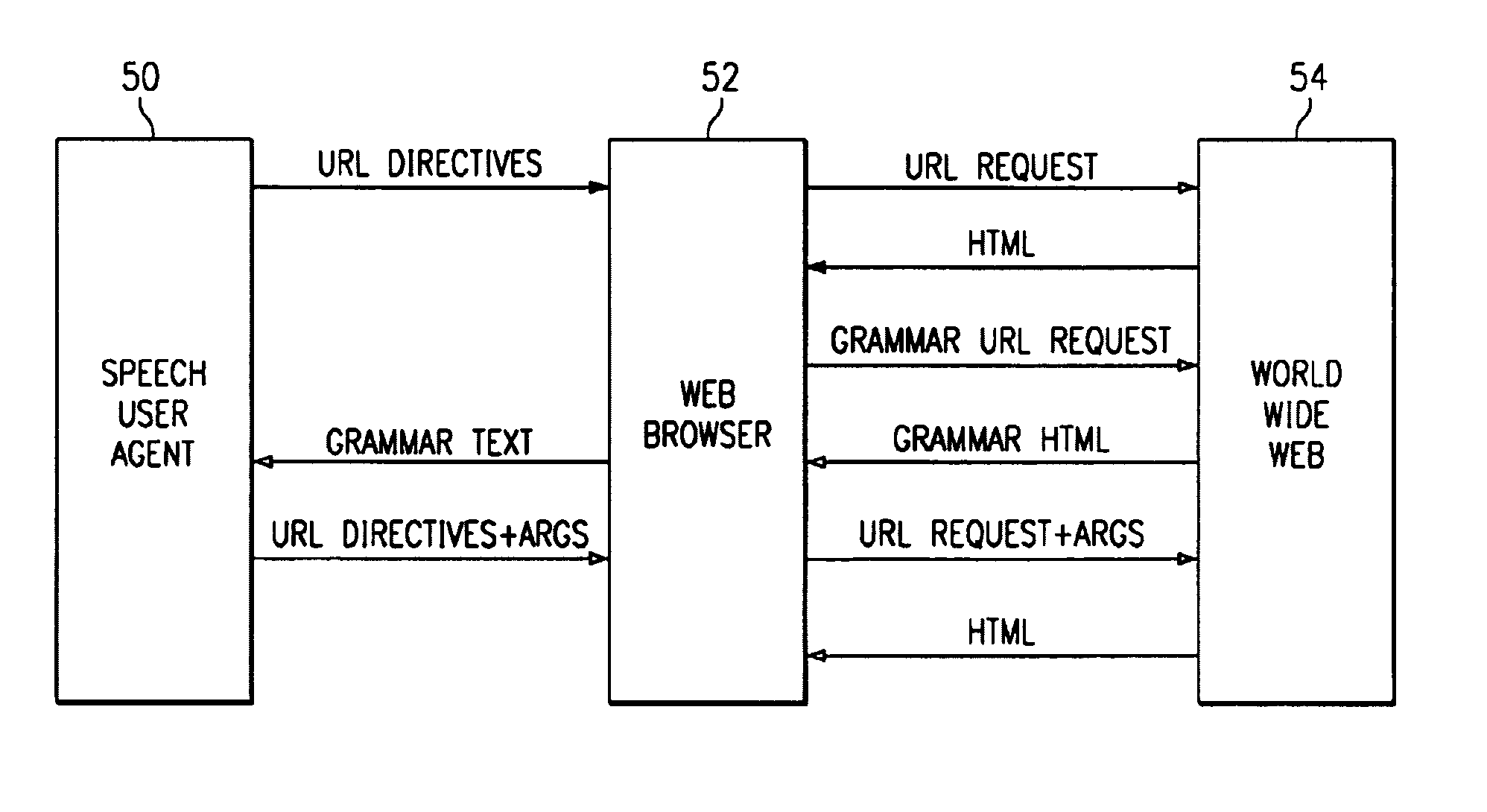
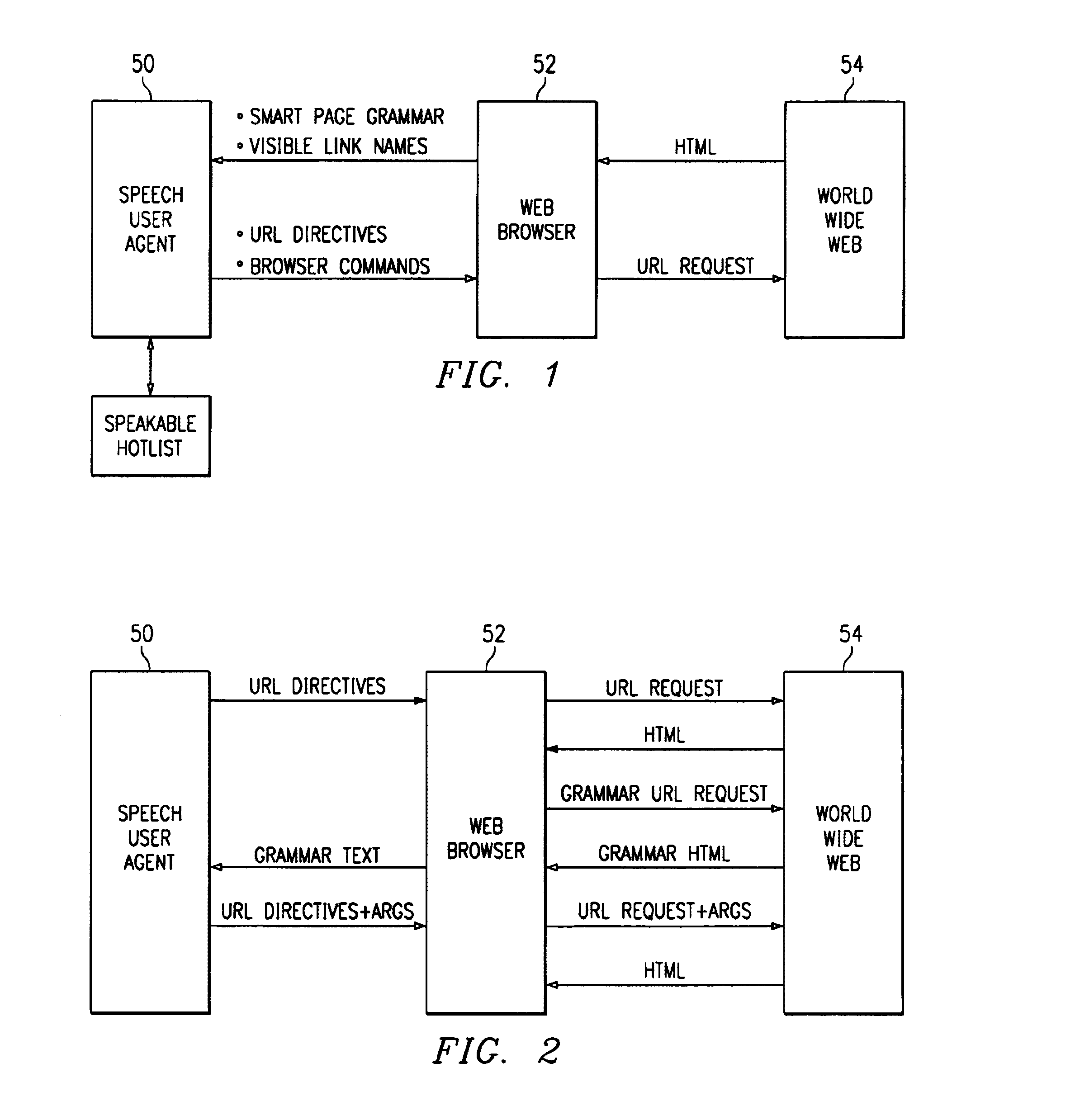
Voice activated apparatus for accessing information on the World Wide Web
InactiveUS7020609B2Easy accessAvoid overwritingAutomatic exchangesSpeech recognitionInformation resourceComputer module
This is a voice activated Hypermedia system using grammatical metadata, the system comprising: a speech user agent; a browsing module; and an information resource. The system may include: embedded intelligence in hypermedia source; a means for processing the actions of a user based on the embedded intelligence; a means for returning a result of the actions to the user. In addition, the hypermedia source maybe a HTML page or an instructional module for communicating allowed actions by a user. The system may also include embedded intelligence as a grammar or reference to a grammar. The grammar may be dynamically added to a speech recognizer. In addition, the actions can come from a speech recognizer. Furthermore, the system may include voice activated hypermedia links and intelligent modules that process information from the information resources for allowing actions from the user. Other devices, systems and methods are also disclosed.
Owner:TEXAS INSTR INC
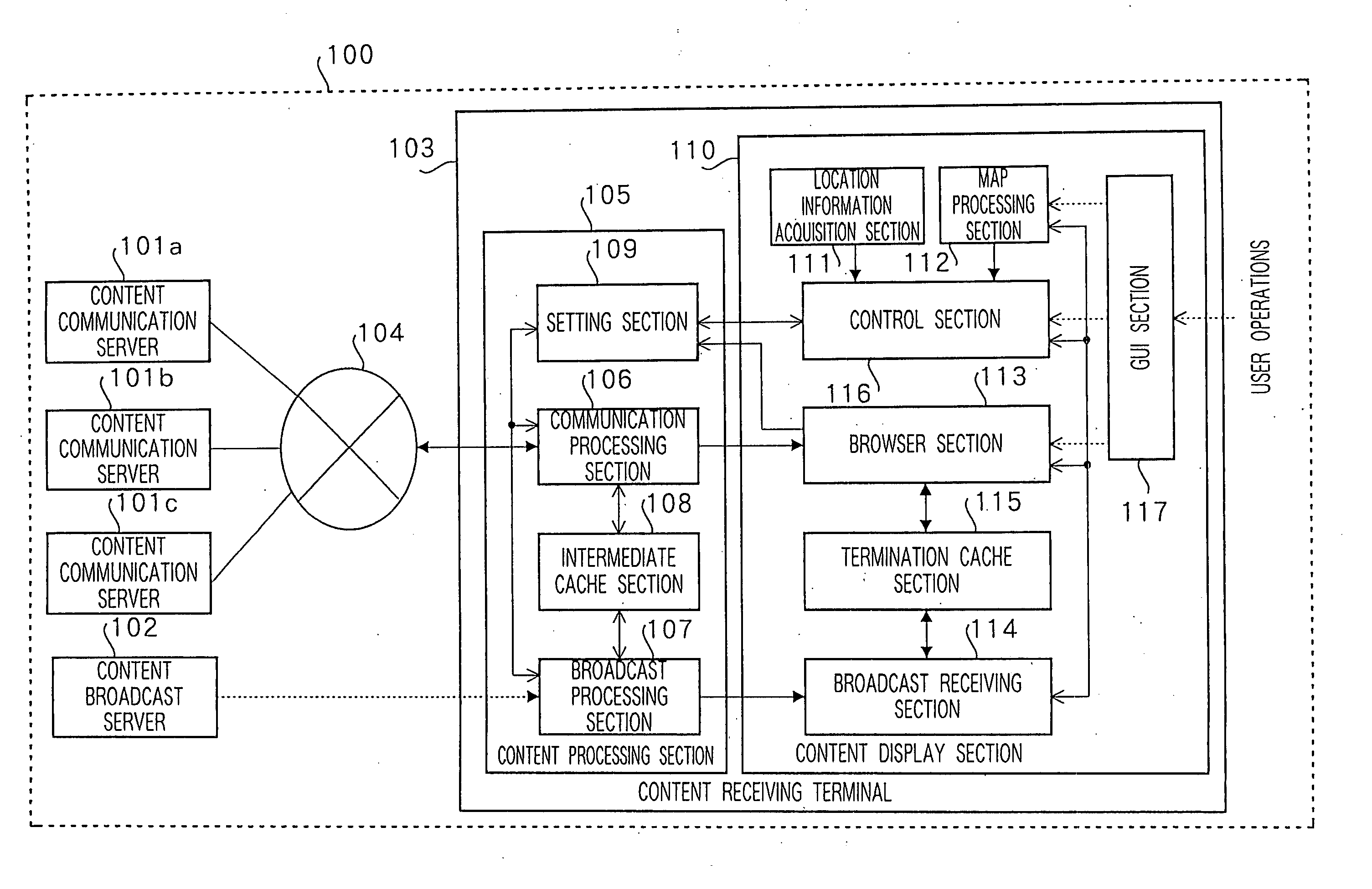
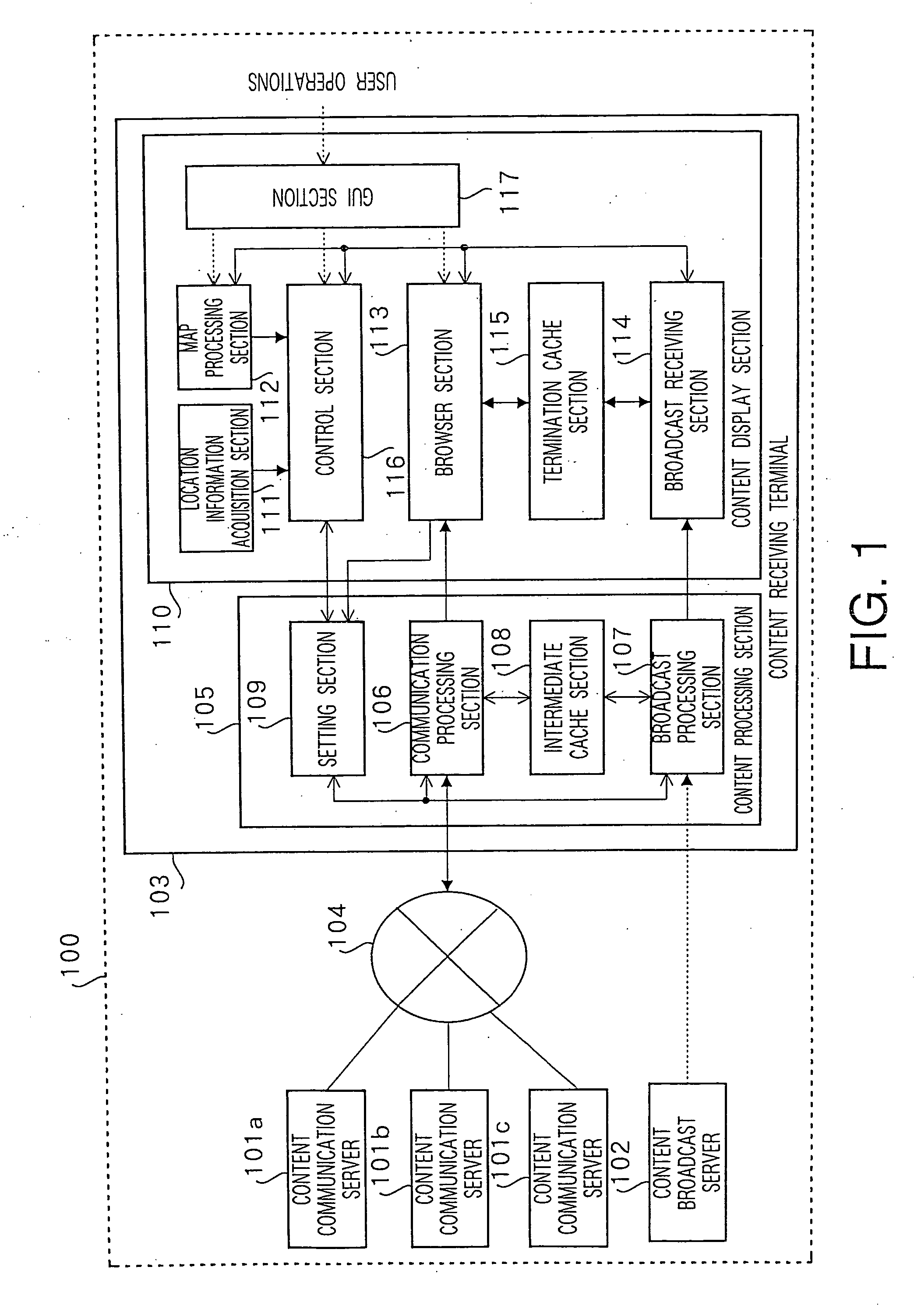
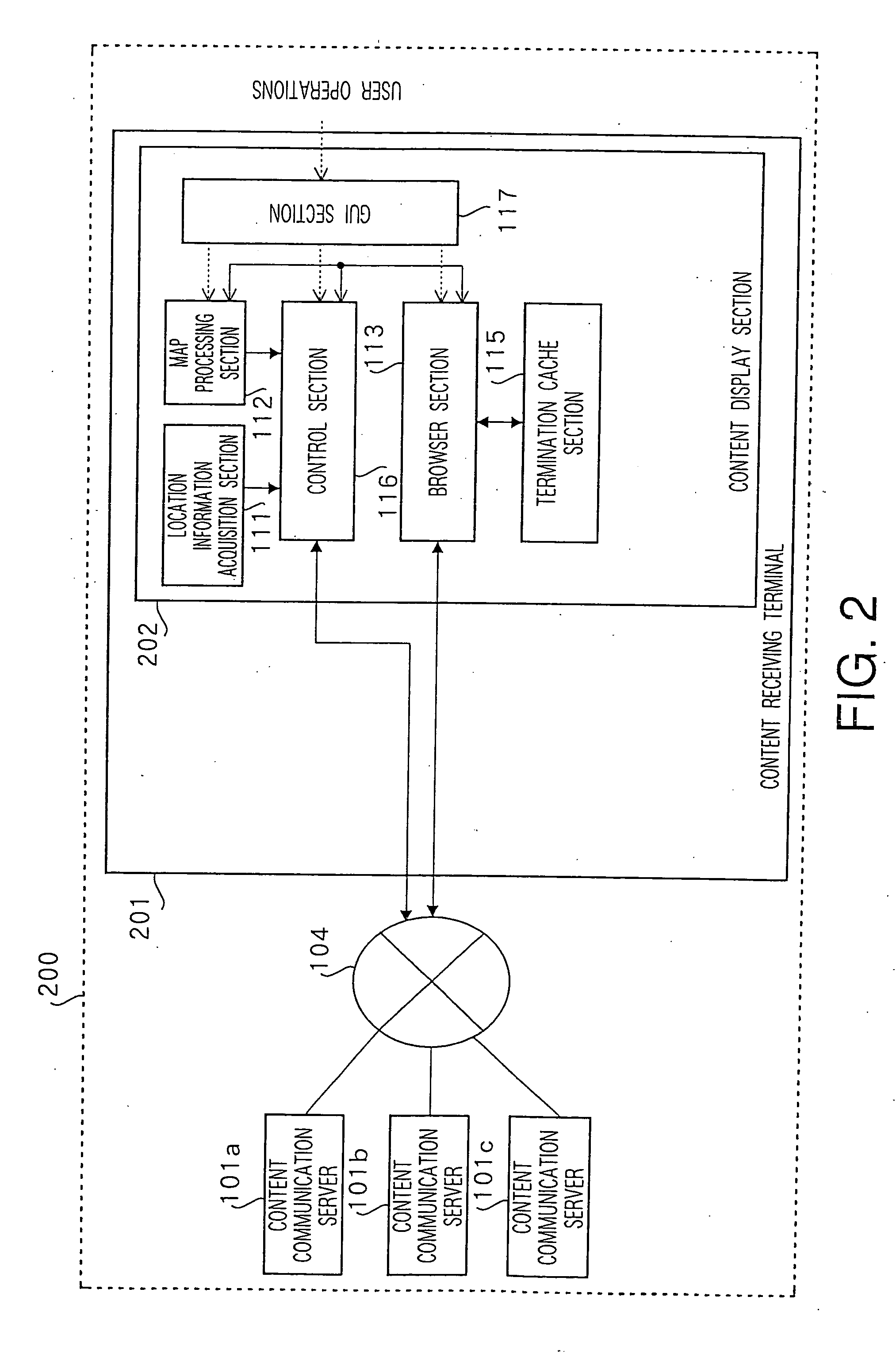
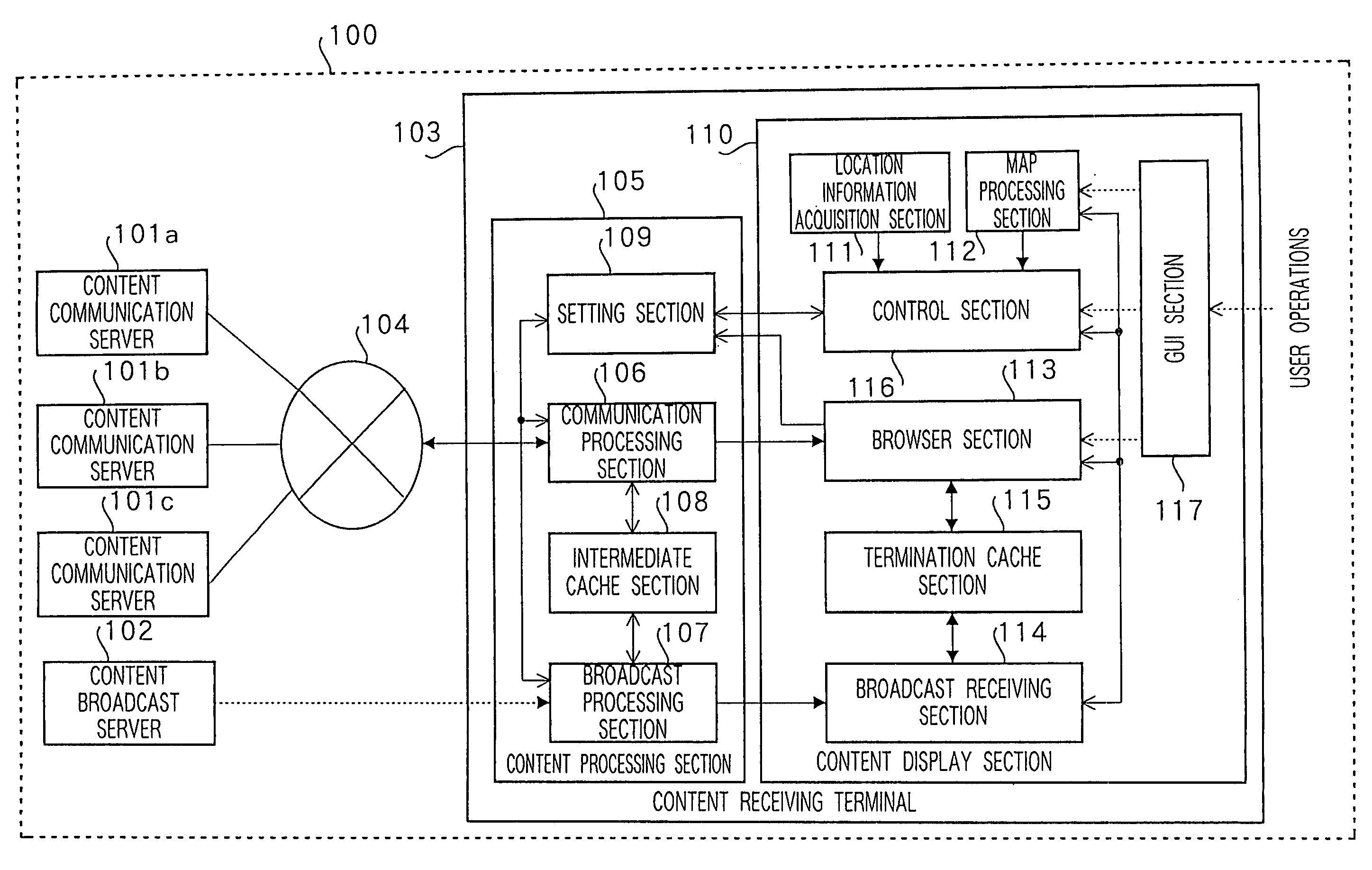
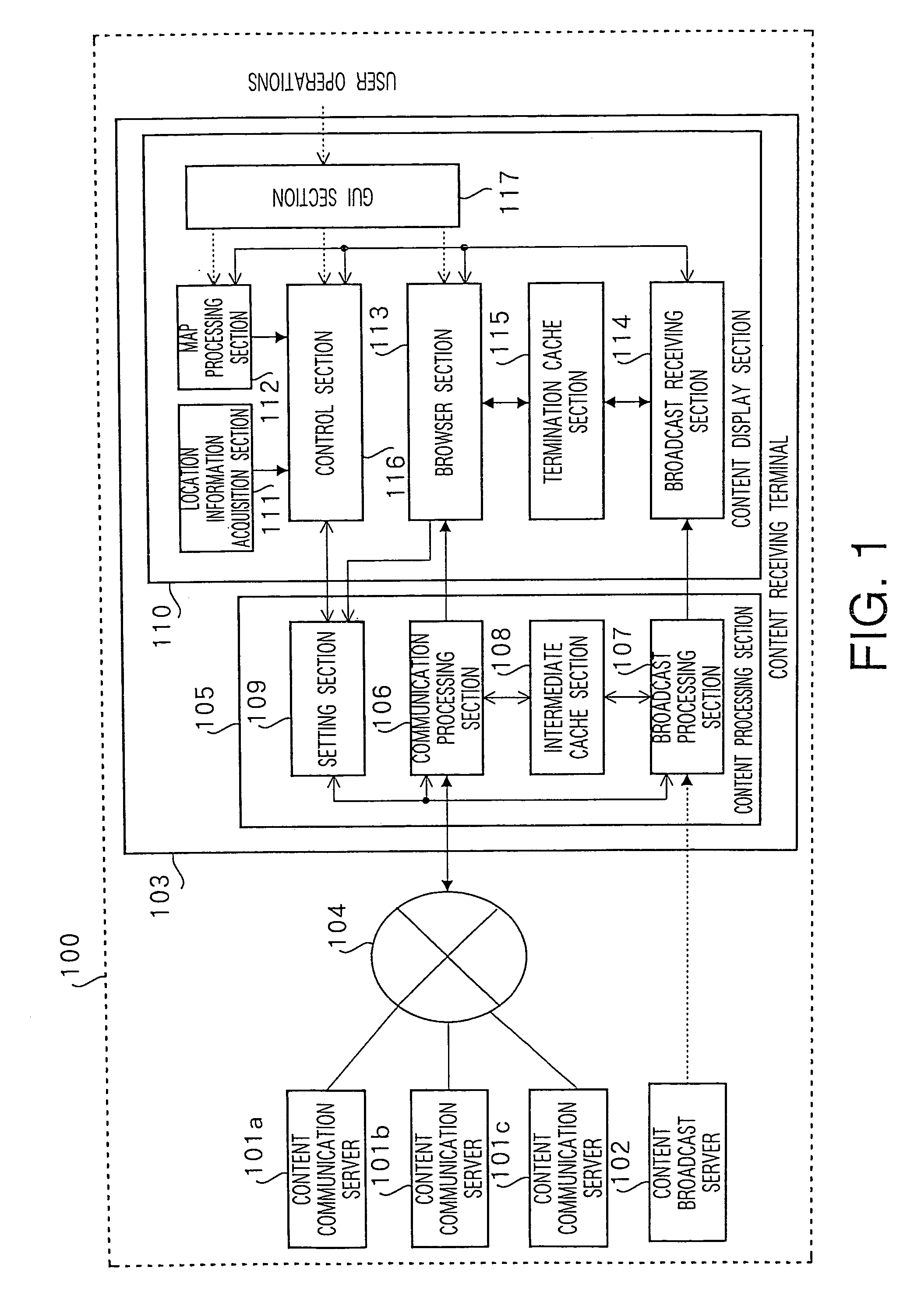
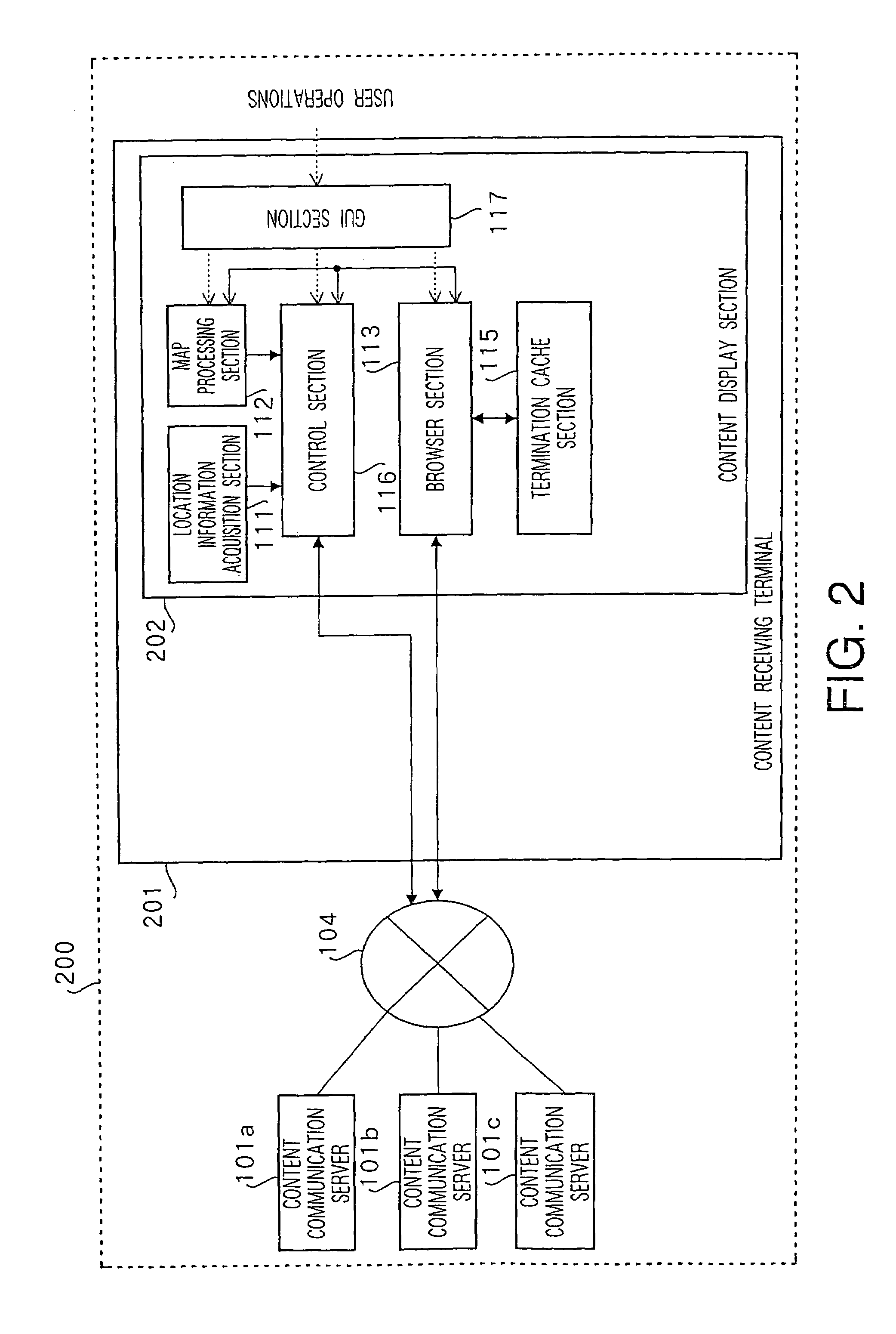
Content processing apparatus and content display apparatus based on location information
ActiveUS20060041556A1Effective distributionInstruments for road network navigationDigital data information retrievalPosition dependentGeolocation
The present invention receives list content providing location conditions in a list organized by location conditions in which a reference destination of location-dependent content, being content assigned correspondence to geographical location information, is compiled for each location condition, sent from a content communication server; receives the sent location information; generates area-specific list content comprising information on location-dependent content corresponding to location information, by extracting a list organized by location conditions, in which location conditions matching location information are provided, from the list content; and outputs the area-specific list content.
Owner:PANASONIC CORP
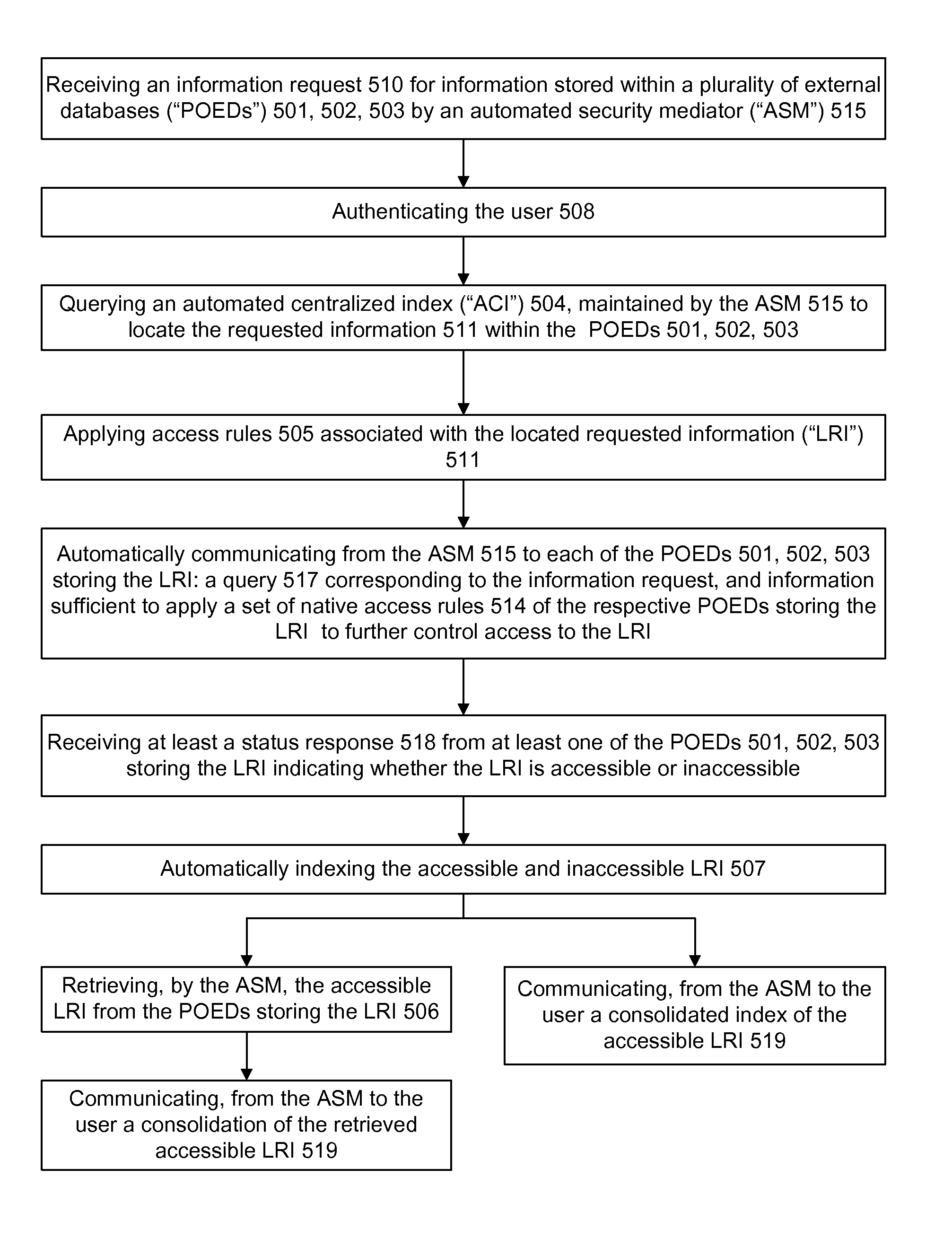
Information record infrastructure, system and method
InactiveUS20100241595A1Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
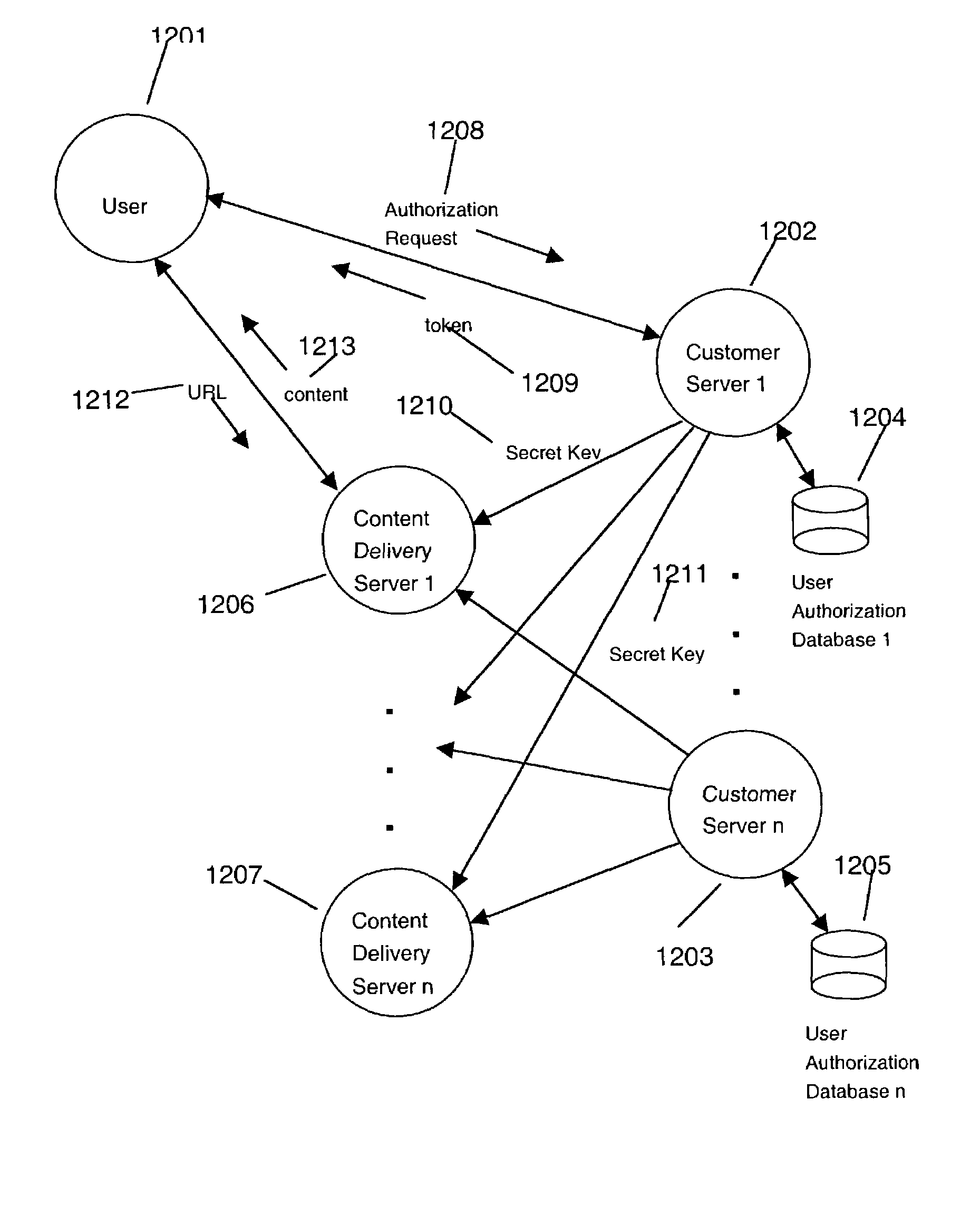
Secure content delivery system
InactiveUS7363361B2Effective distributionFast response timeMetering/charging/biilling arrangementsUser identity/authority verificationUniform resource locatorAuthorization
A secure streaming content delivery system provides a plurality of content servers connected to a network that host customer content that can be cached and / or stored, e.g., images, video, text, and / or software. The content servers respond to requests for customer content from users. The invention load balances user requests for cached customer content to the appropriate content server. A user makes a request to a customer's server / authorization server for delivery of the customer's content. The authorization server checks if the user is authorized to view the requested content. If the user is authorized, then the authorization server generates a hash value and embeds it into the URL which is passed to the user. A content server receives a URL request from the user for customer content cached on the content server. The request is verified by the content server.
Owner:AKAMAI TECH INC
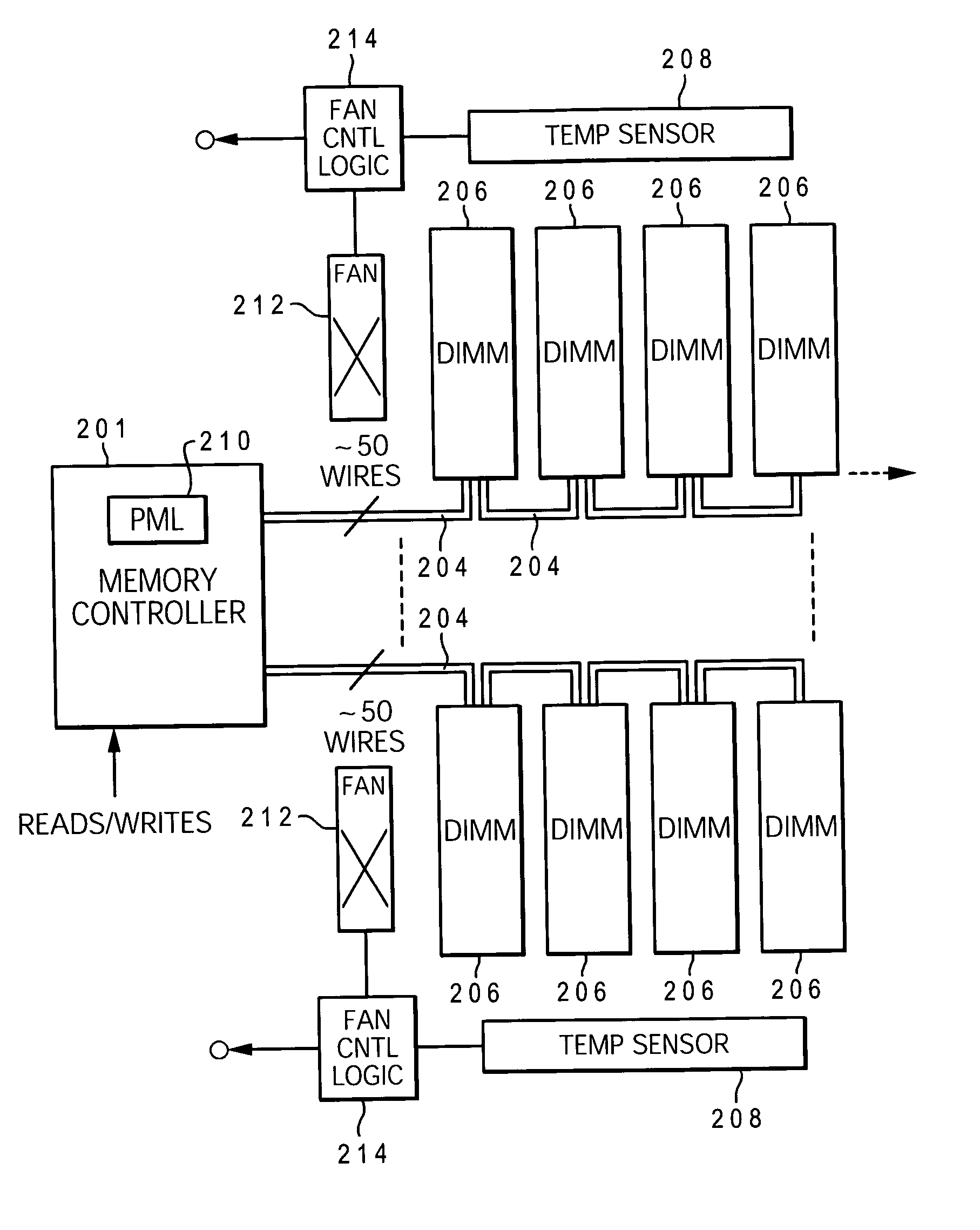
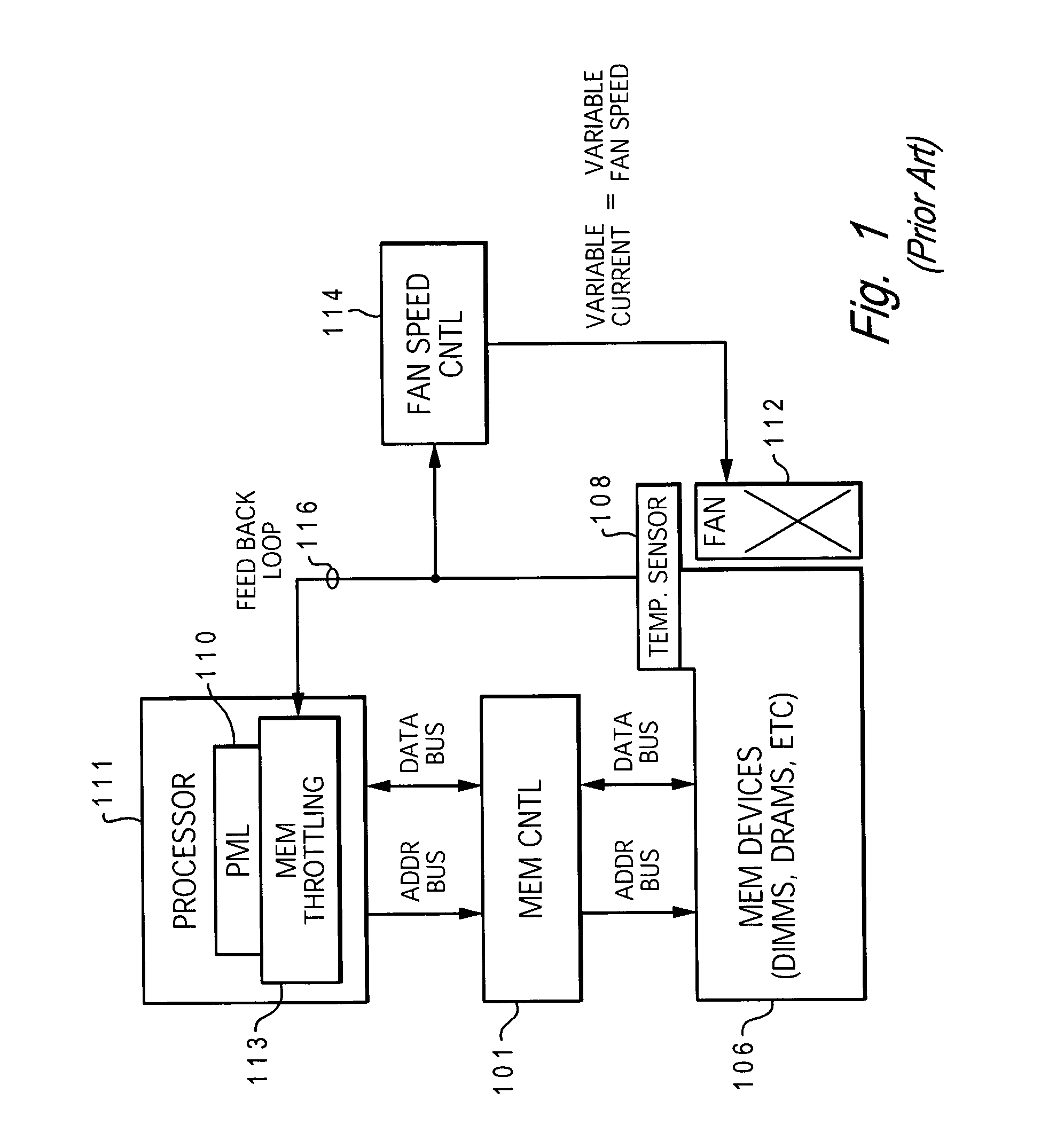
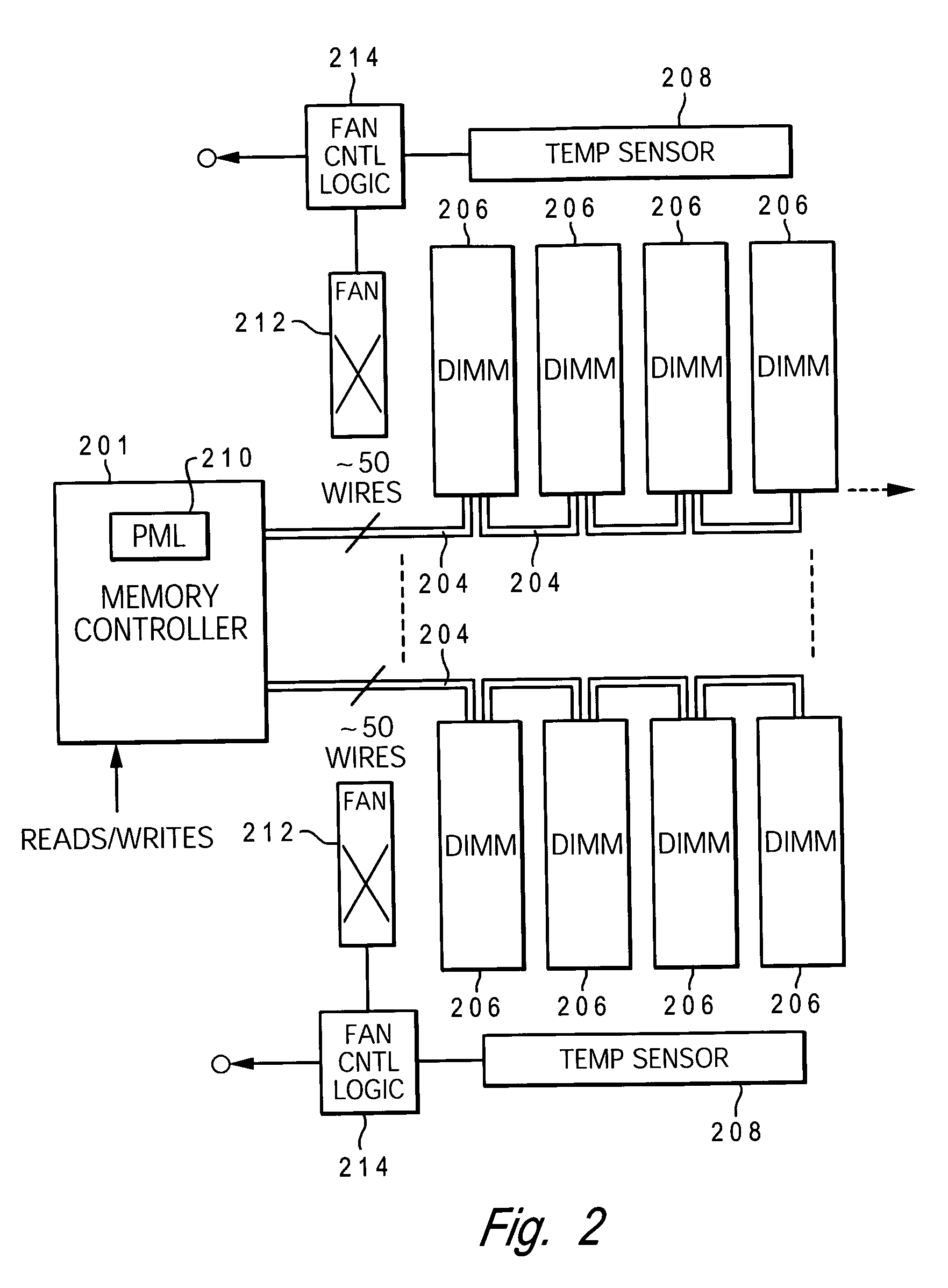
Dynamic power management via DIMM read operation limiter
InactiveUS20060179334A1Little or no usePower usageEnergy efficient ICTVolume/mass flow measurementDIMMDynamic power management
A method and system for enabling directed temperature / power management at the DIMM-level and / or DRAM-level utilizing intelligent scheduling of memory access operations received at the memory controller. Hot spots within the memory subsystem, caused by operating the DIMMs / DRAMs above predetermined / preset threshold power / temperature values for operating a DIMM and / or a DRAM, are avoided / controlled by logic within the memory controller. The memory controller logic throttles the number / frequency at which commands (read / write operations) are issued to the specific DIMM / DRAM based on feedback data received from the specific DIMM / DRAM reaching the preset threshold power usage value.
Owner:IBM CORP
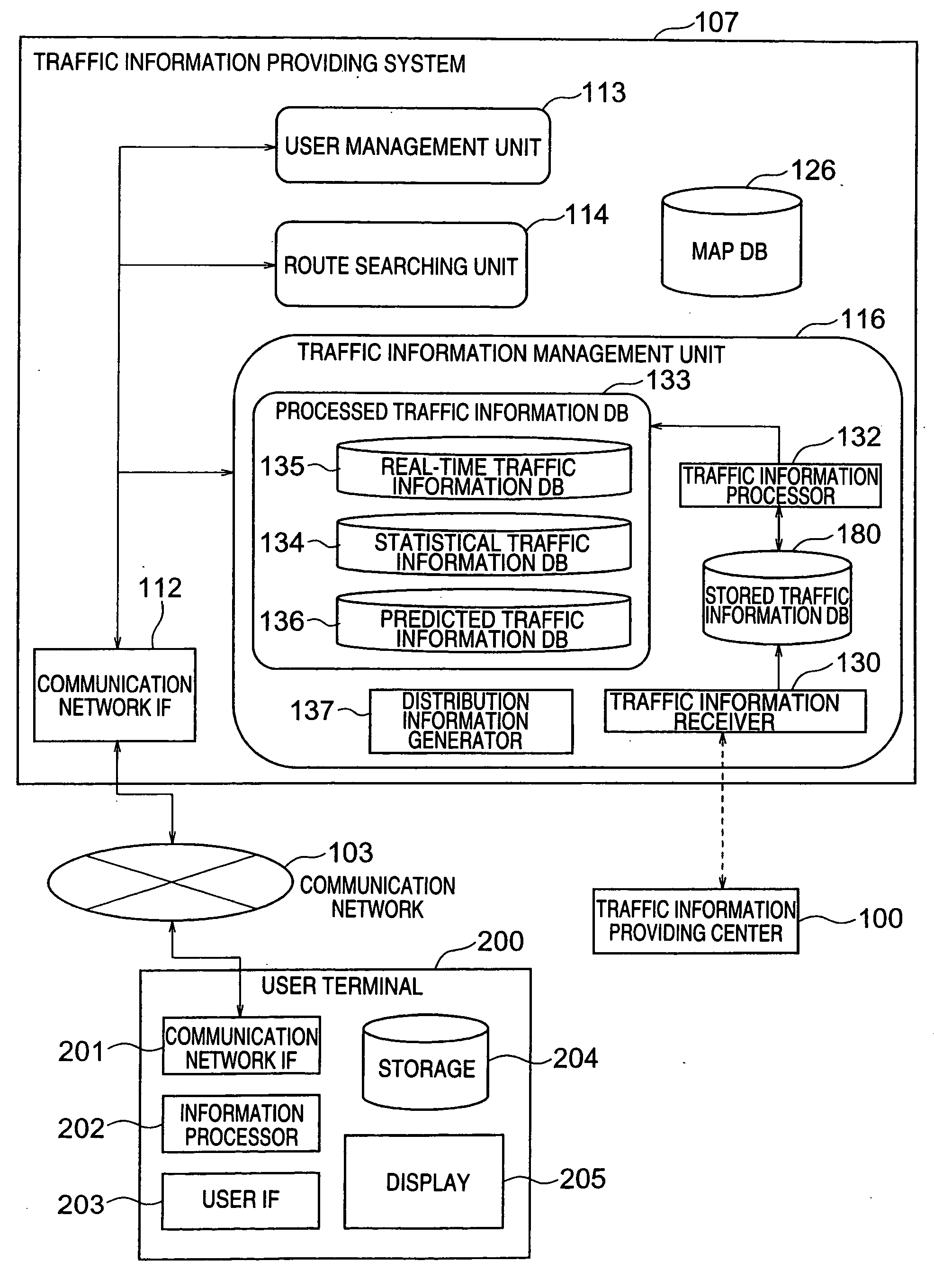
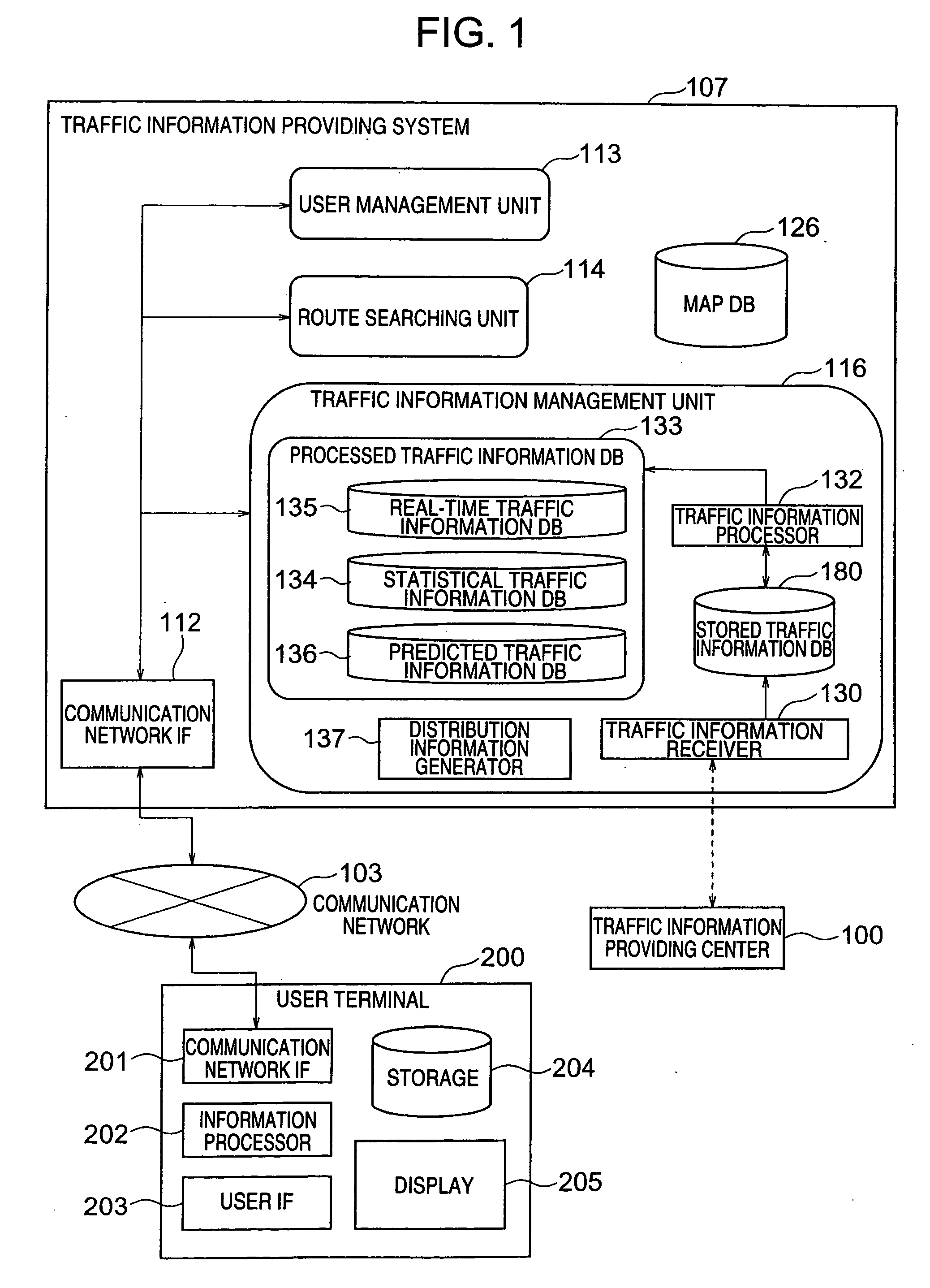
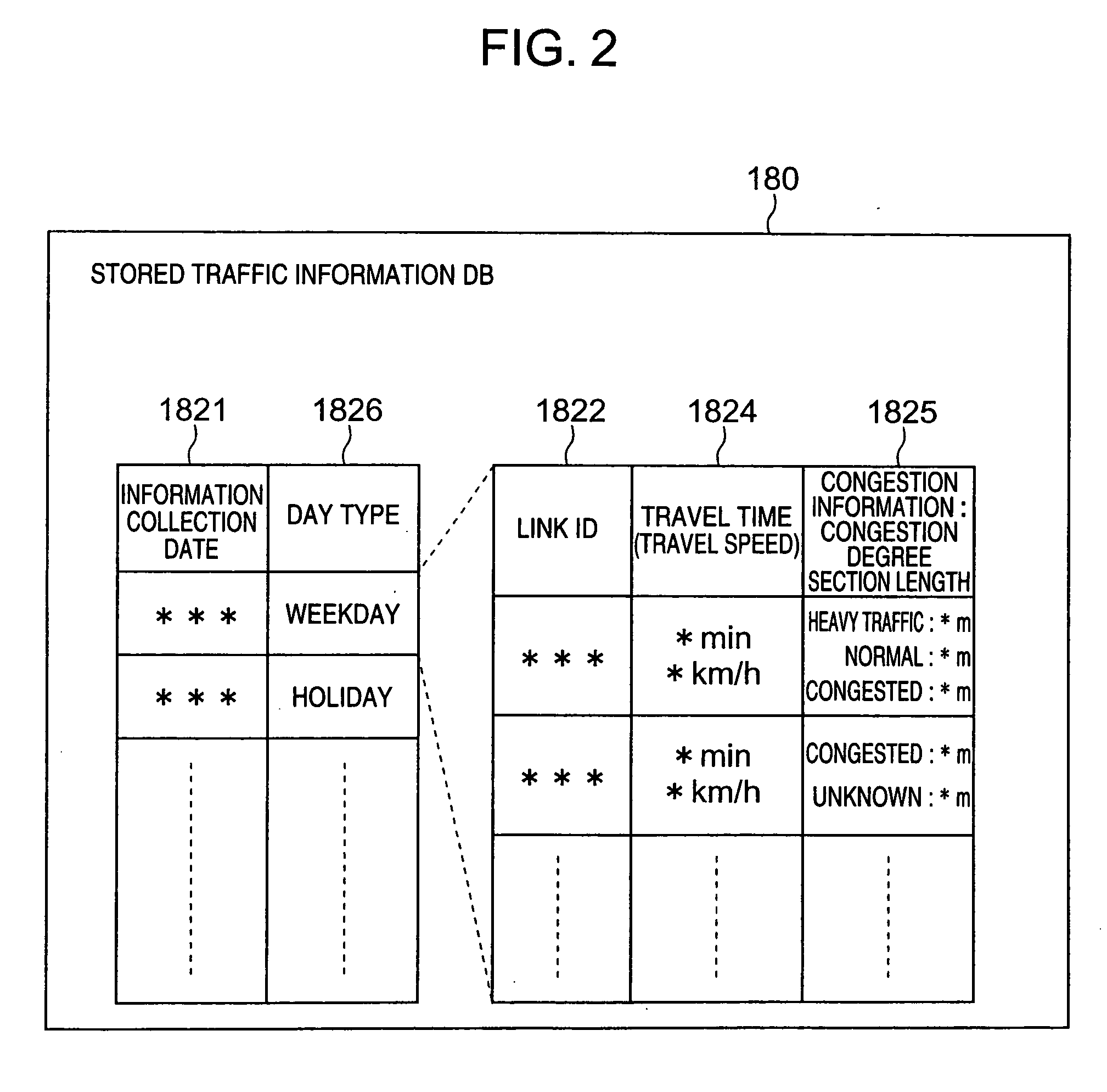
Traffic information providing system and car navigation system
InactiveUS20050093720A1Shorten communication timeReduce in quantityAnalogue computers for vehiclesInstruments for road network navigationComputer scienceCar navigation systems
A traffic information providing system externally acquires traffic information including information relating to the travel time of a link, calculates a travel time for a non-provision link to which no travel time is provided through estimate / complement operation. The estimate / complement operation is carried out with use of travel times, emergencies, travel times of links in the vicinity of the non-provision link, and so on, obtained in the near past. The system stores and statistically processes the externally-acquired traffic information, and also estimates a travel time in the near future. When there is an abnormality in the acquired traffic information, the system deletes the abnormality, regards the information as a non-provision link, calculates a probability distribution of travel times of links, calculates a probability distribution of travel times of the entire route made up of a plurality of links, and also calculates a probability for a specific travel time range.
Owner:HITACHI LTD
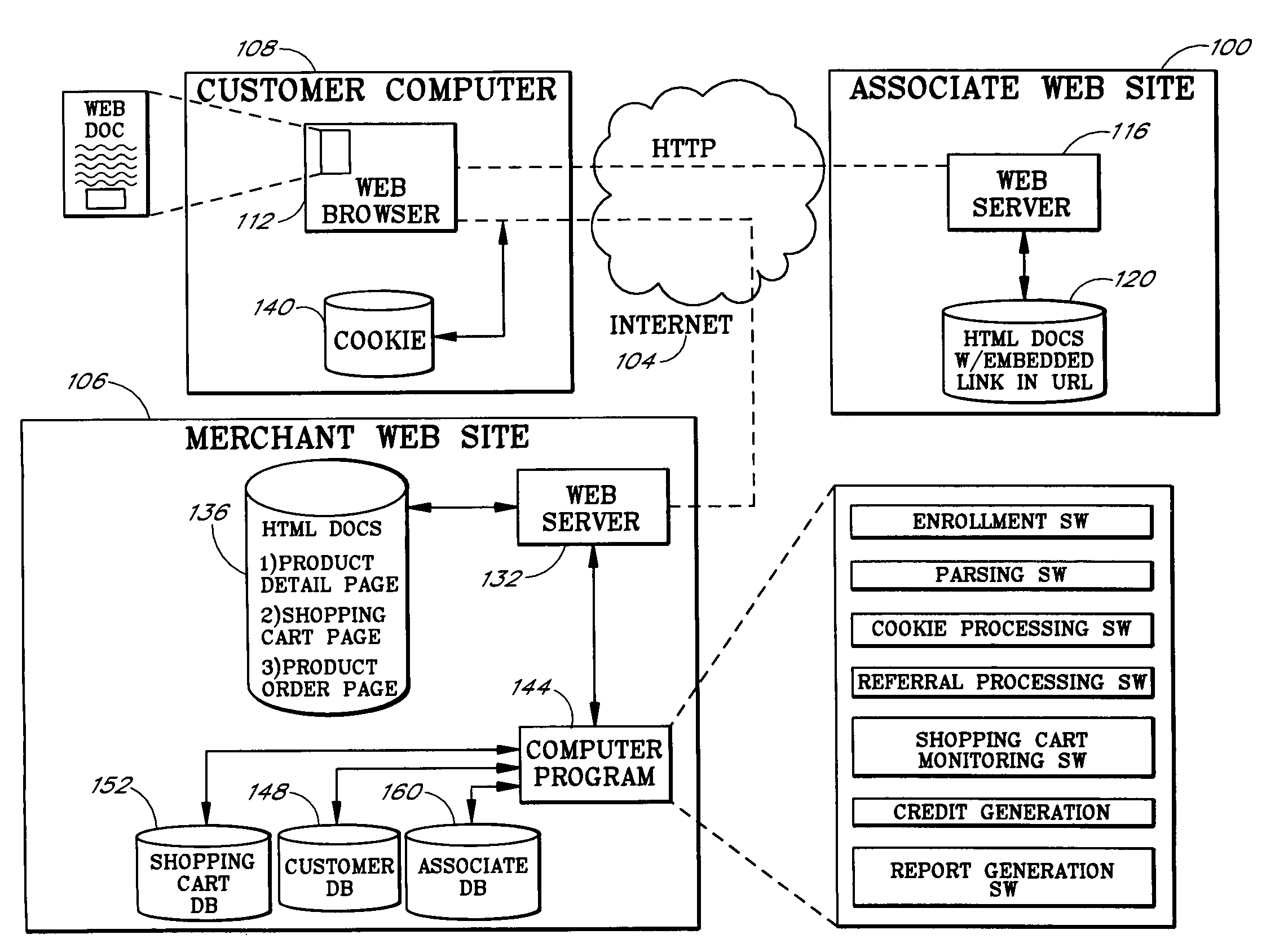
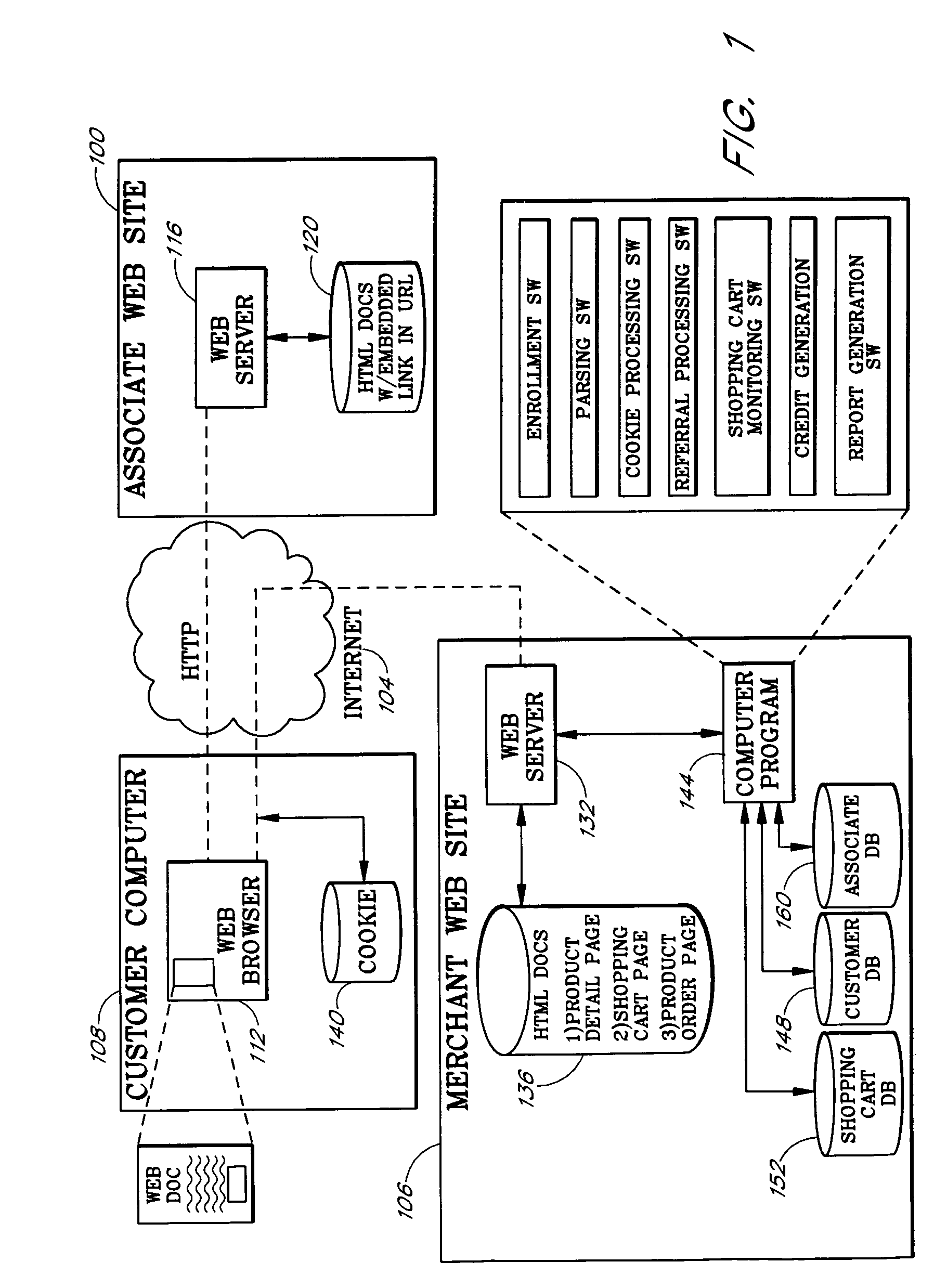
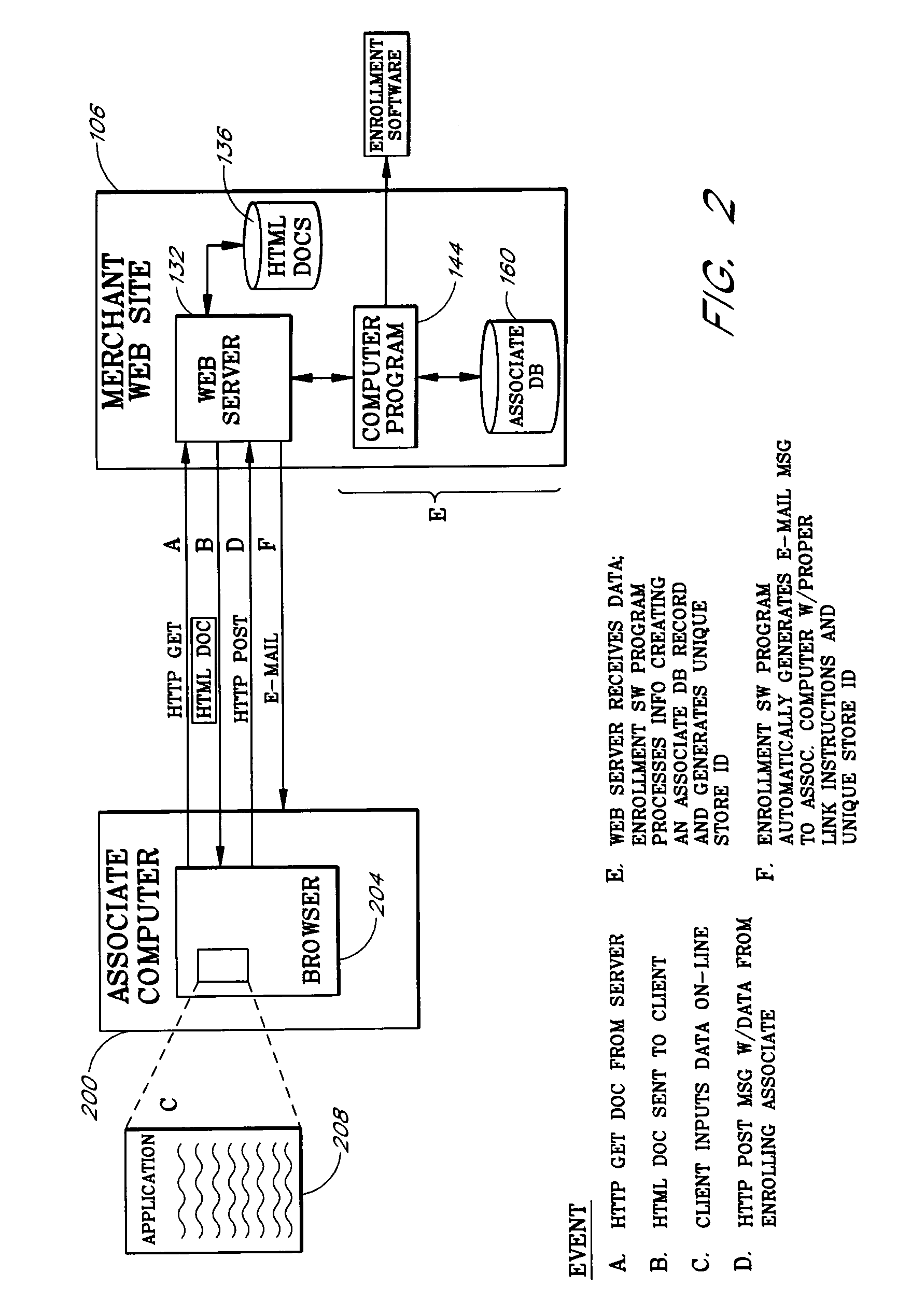
Internet-based customer referral system
InactiveUS7337133B1Effective marketingEfficiently sellMarket predictionsFinanceWeb siteInformation Dissemination
An Internet-based customer referral system enables individuals and other business entities (“associates”) to refer customers to a merchant's web site in return for compensation, such as commissions on resulting sales. Entities initially register with the merchant web site as associates, and are provided with instructions for creating links to the merchant web site. An associate may, for example, set up an associate web site (or other information dissemination system) with reviews, recommendations, and / or editorials of specific products in the merchant's online catalog, together with links to associated pages in the catalog. When a user follows such a link and then makes a purchase (as tracked by the merchant web site), the system preferably awards a commission to the associate. The system also preferably generates feedback reports that provide each associate with data regarding the effectiveness of each link provided by that associate.
Owner:AMAZON TECH INC
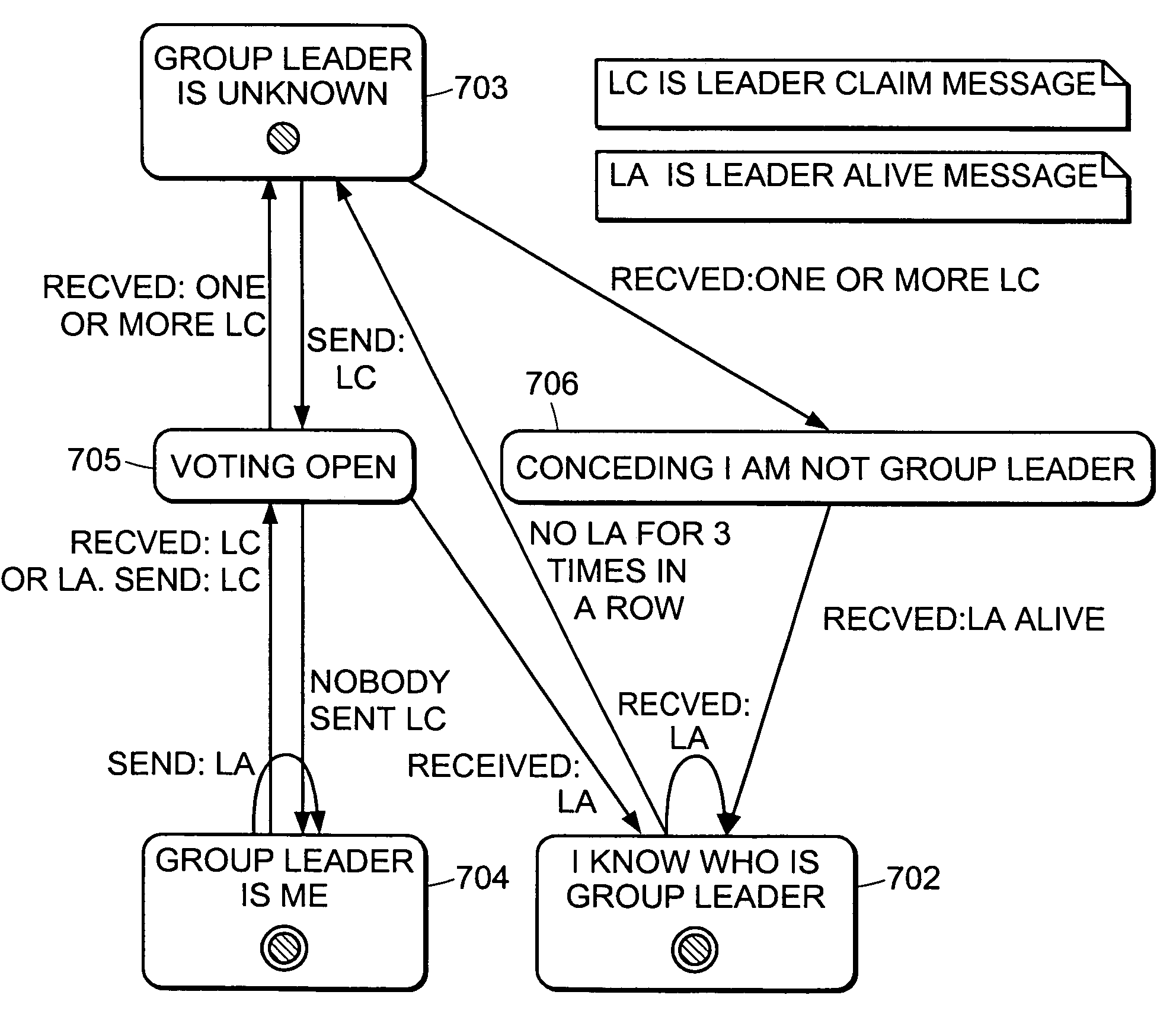
Method and apparatus for election of group leaders in a distributed network
InactiveUS6993587B1Effective controlEffective distributionMultiple digital computer combinationsTransmissionData fileMulticast network
The present invention provides a system and apparatus for efficient and reliable, control and distribution of data files in large-scale distributed networks. The members of a group of servers in a multicast network elect a group leader whenever a new group leader is required, as when the prior group leader become unavailable, as detected by absence of a periodic heartbeat message published by the leader. The election is carried out by a system of voting by each candidate whereby each candidate has a priority calculated from its configuration, and the server with the highest priority is configured to claim the leadership faster than the other candidates. As part of the claim, each candidate multicasts its priority. Each candidate that receives a multicast claim for leadership from another candidate compares its own priority against the claimant and only votes for itself if its own priority is higher. After a preconfigured period of hearing no other claimants with higher priority, the candidate with the highest priority becomes the new leader.
Owner:NETWORK APPLIANCE INC
Information record infrastructure, system and method
InactiveUS8380630B2Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
Adaptive load management: a system for incorporating customer electrical demand information for demand and supply side energy management
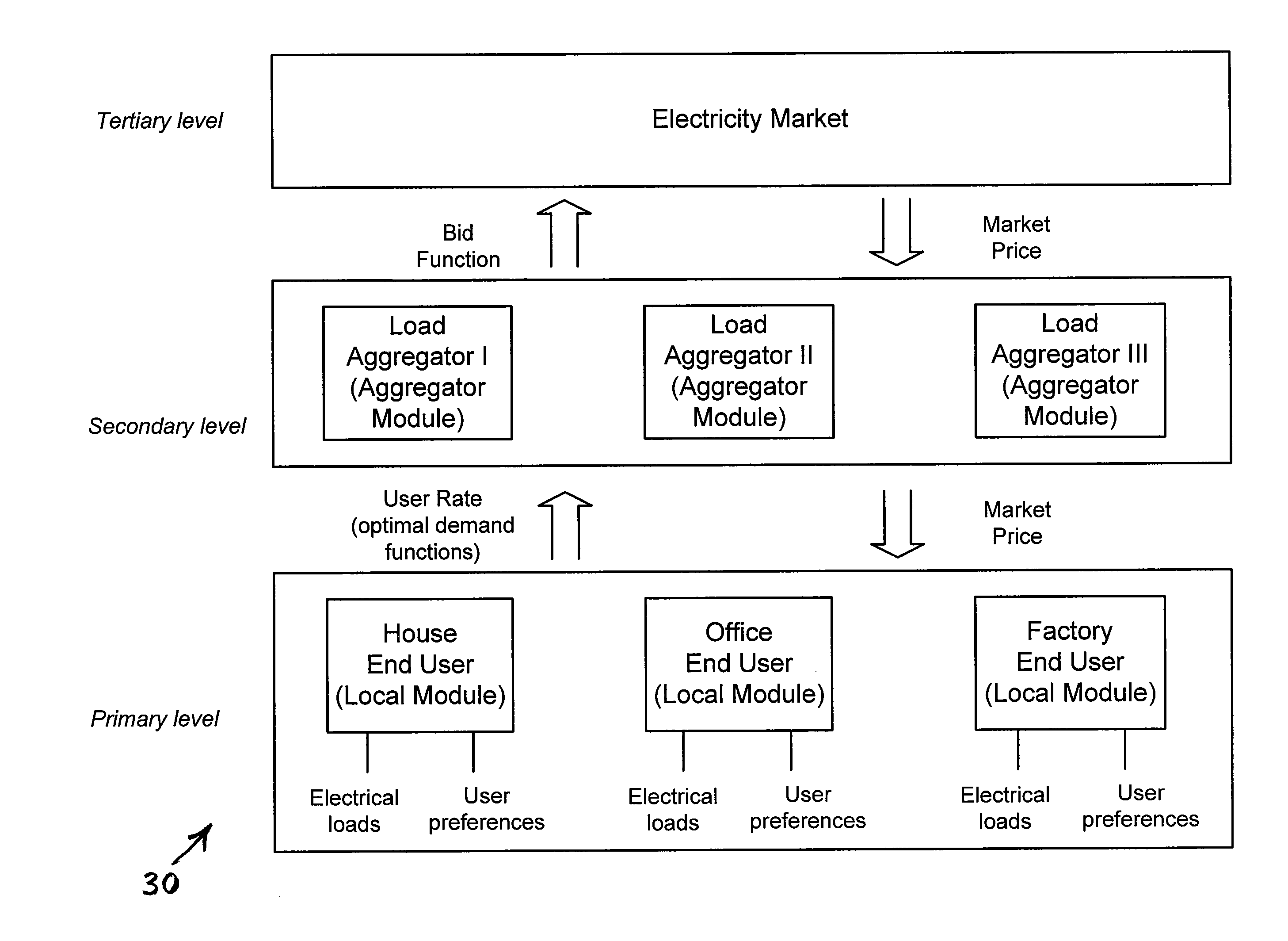
InactiveUS20120083930A1Efficiently allocatedEffective distributionMarket predictionsLevel controlElectricityEnergy management
A method for determining an amount of electricity to purchase includes determining electrical power consumption characteristics of an electrical load at an end user of the electricity. A preference of the end user for an output of the electrical load is ascertained. The output varies with a rate of electrical power consumption by the load. A mathematical model is created of an amount of electrical power to be consumed by the load as a function of time and of monetary cost of the electricity. The model is dependent upon the electrical power consumption characteristics of the electrical load and the preference of the end user for an output of the electrical load. An amount of electricity is purchased based on the mathematical model of an amount of electrical power to be consumed by the load, and based on the monetary cost of the electricity.
Owner:ROBERT BOSCH GMBH +1
System and method for enhancing distribution logistics and increasing surveillance ranges with unmanned aerial vehicles and a dock network
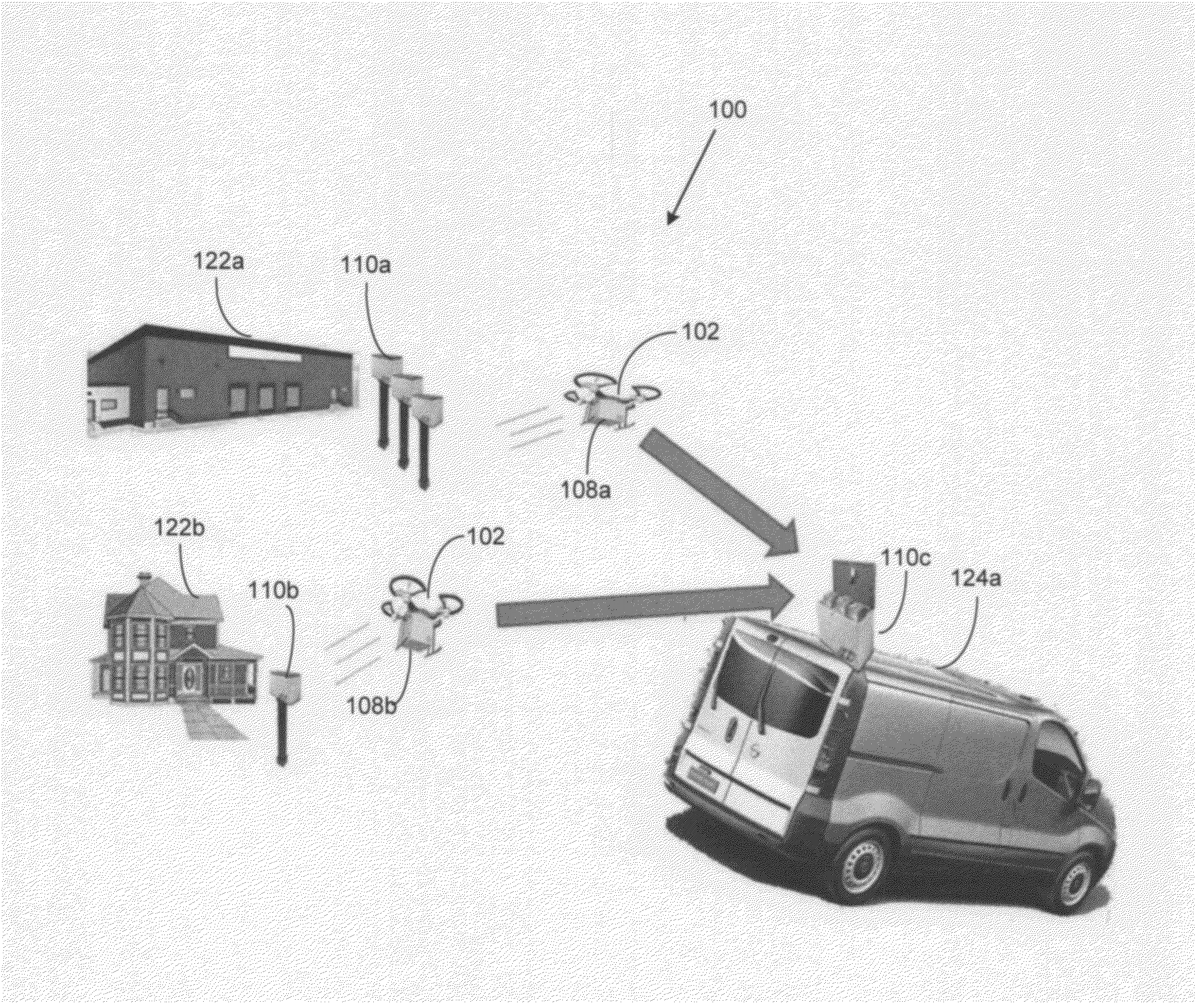
ActiveUS20160185466A1Enhancing distribution logisticsExpand the scope of surveillanceAircraft controlUnmanned aerial vehiclesMotion detectorLogistics management
A system and method for enhancing distribution logistics and surveillance ranges with unmanned aerial vehicles (UAV) and at least one dock in a dock network. The UAV remains in communication with the dock for enhancing distribution logistics of at least one package and increasing the range of surveillance for the unmanned aerial vehicle. From the dock, the UAV delivers the package to a destination point, obtains the package from a pick up point, recharges the unmanned aerial vehicle throughout the network of docks, and increases the range of distribution and surveillance. A logistics software controls the delivery and surveillance. A wireless communication device enables communication between the UAV and the dock. Light indicators indicate status of the package and the operational status of the UAV. A camera captures an image of the package in the dock. A motion detector detects the UAV for regulating access for loading / unloading and docking.
Owner:DREANO JR FRANK
Method and apparatus for election of group leaders in a distributed network
InactiveUS20050198359A1Effective controlEffective distributionMultiple digital computer combinationsTransmissionGroup controllerData file
A system and apparatus for control and distribution of data files in large-scale distributed networks. Members of a group of servers in a multicast network elect a group leader whenever a new group leader is required, as detected by absence of a periodic message published by the leader. Election is carried out by a system of voting by each candidate whereby each candidate has a priority calculated from its configuration, and the server with the highest priority is configured to claim the leadership faster than the other candidates. As part of the claim, each candidate multicasts its priority. Each candidate that receives a multicast claim for leadership from another candidate compares its own priority against the claimant and only votes for itself if its own priority is higher. After a preconfigured period of hearing no other claimants with higher priority, the candidate with the highest priority becomes the new leader.
Owner:NETWORK APPLIANCE INC
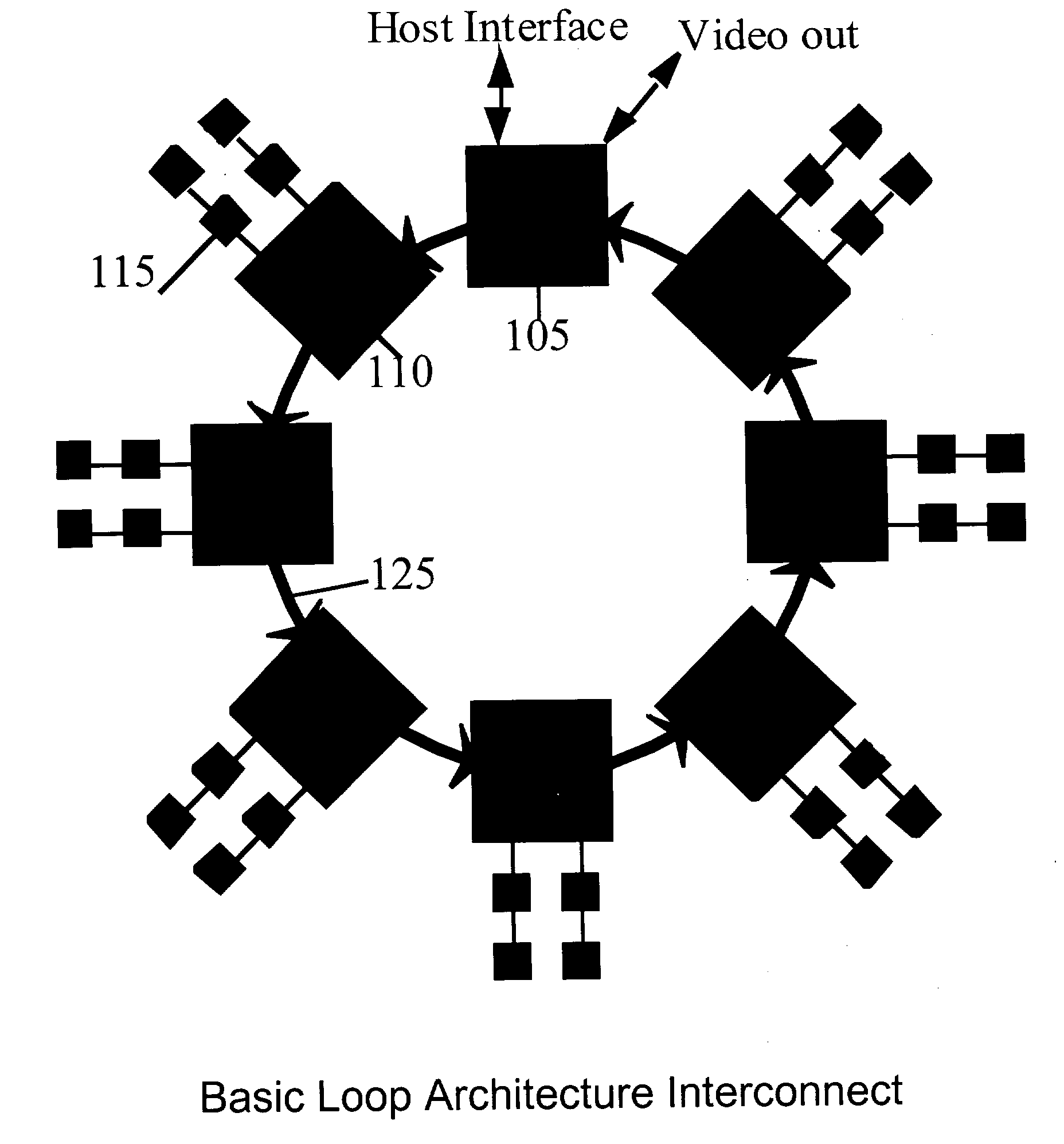
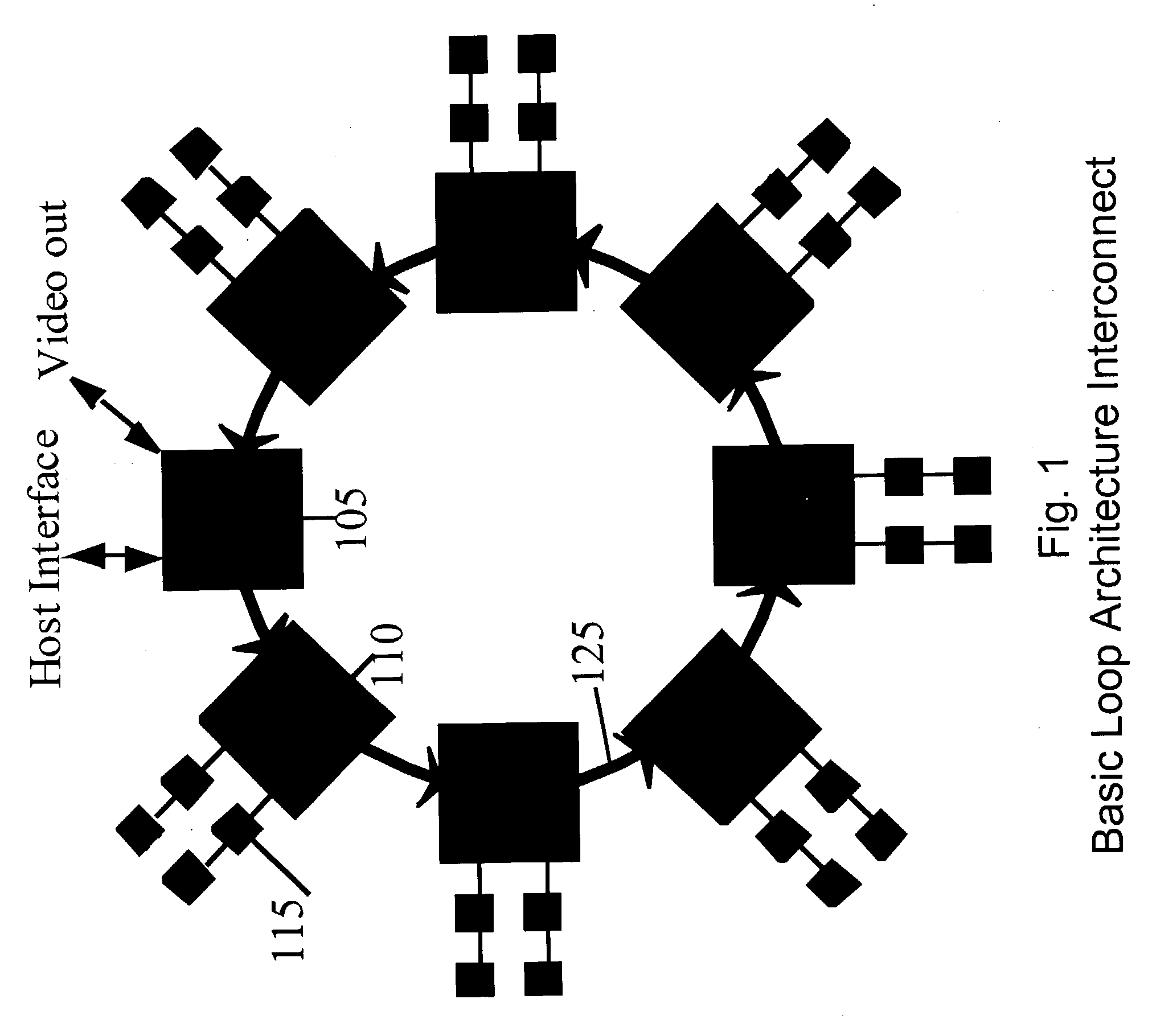
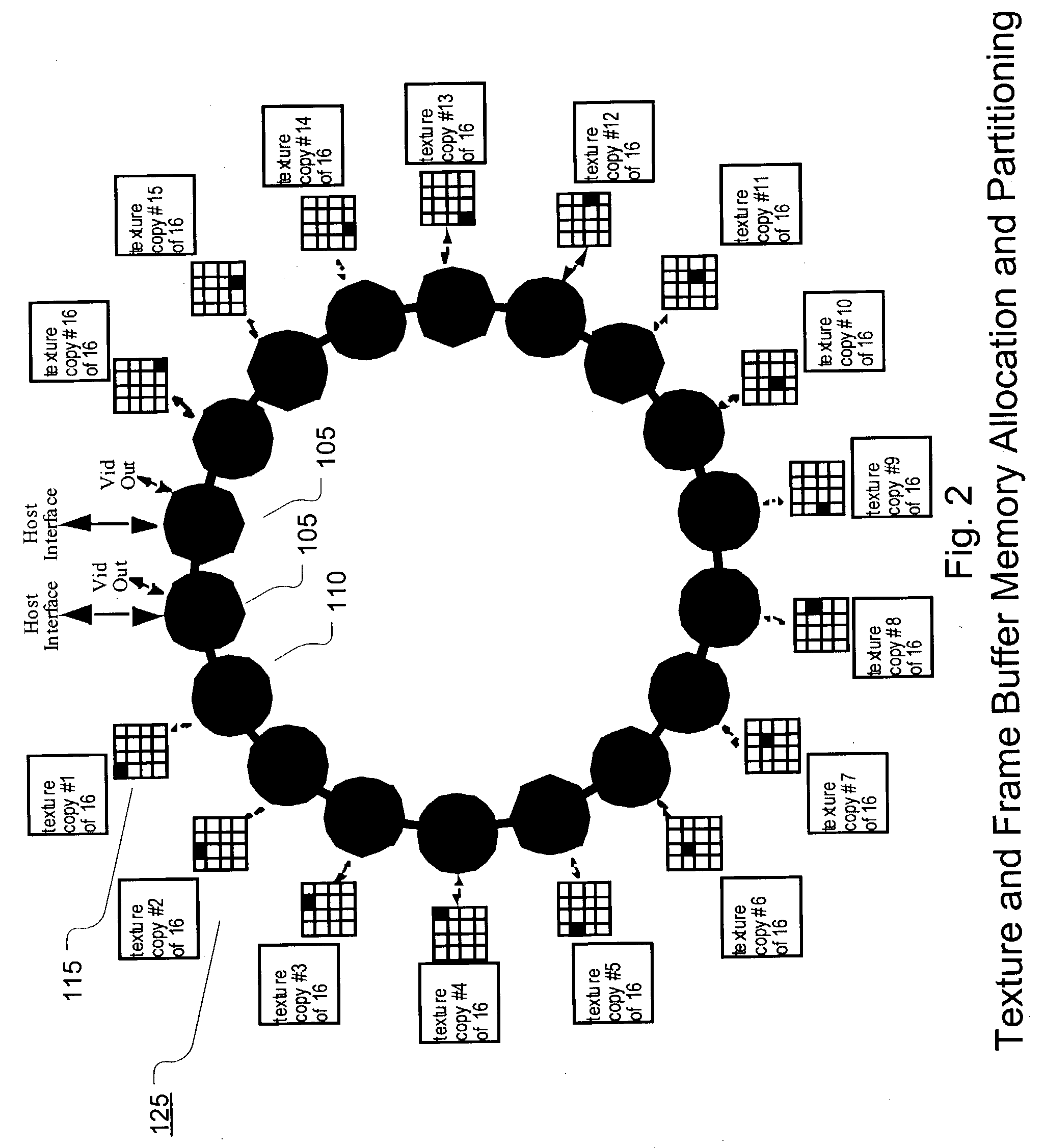
Scalable high performance 3d graphics
InactiveUS20040012600A1Minimizes cost and riskEasy to scaleImage enhancementImage memory managementGraphicsHigh bandwidth
A high-speed ring topology. In one embodiment, two base chip types are required: a "drawing" chip, LoopDraw, and an "interface" chip, LoopInterface. Each of these chips have a set of pins that supports an identical high speed point to point unidirectional input and output ring interconnect interface: the LoopLink. The LoopDraw chip uses additional pins to connect to several standard memories that form a high bandwidth local memory sub-system. The LoopInterface chip uses additional pins to support a high speed host computer host interface, at least one video output interface, and possibly also additional non-local interconnects to other LoopInterface chip(s).
Owner:DEERING MICHAEL F +2
Method for vector delivery
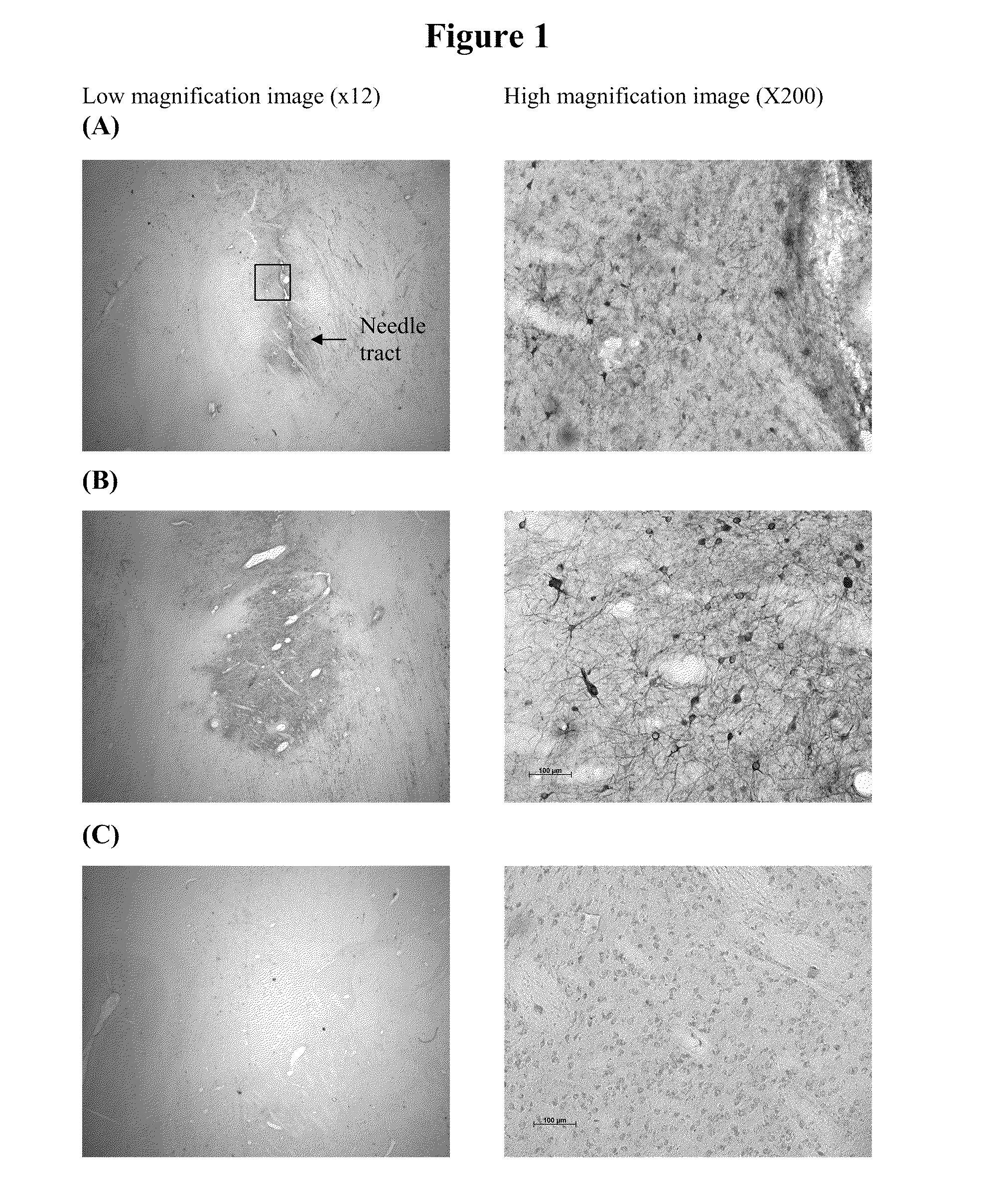
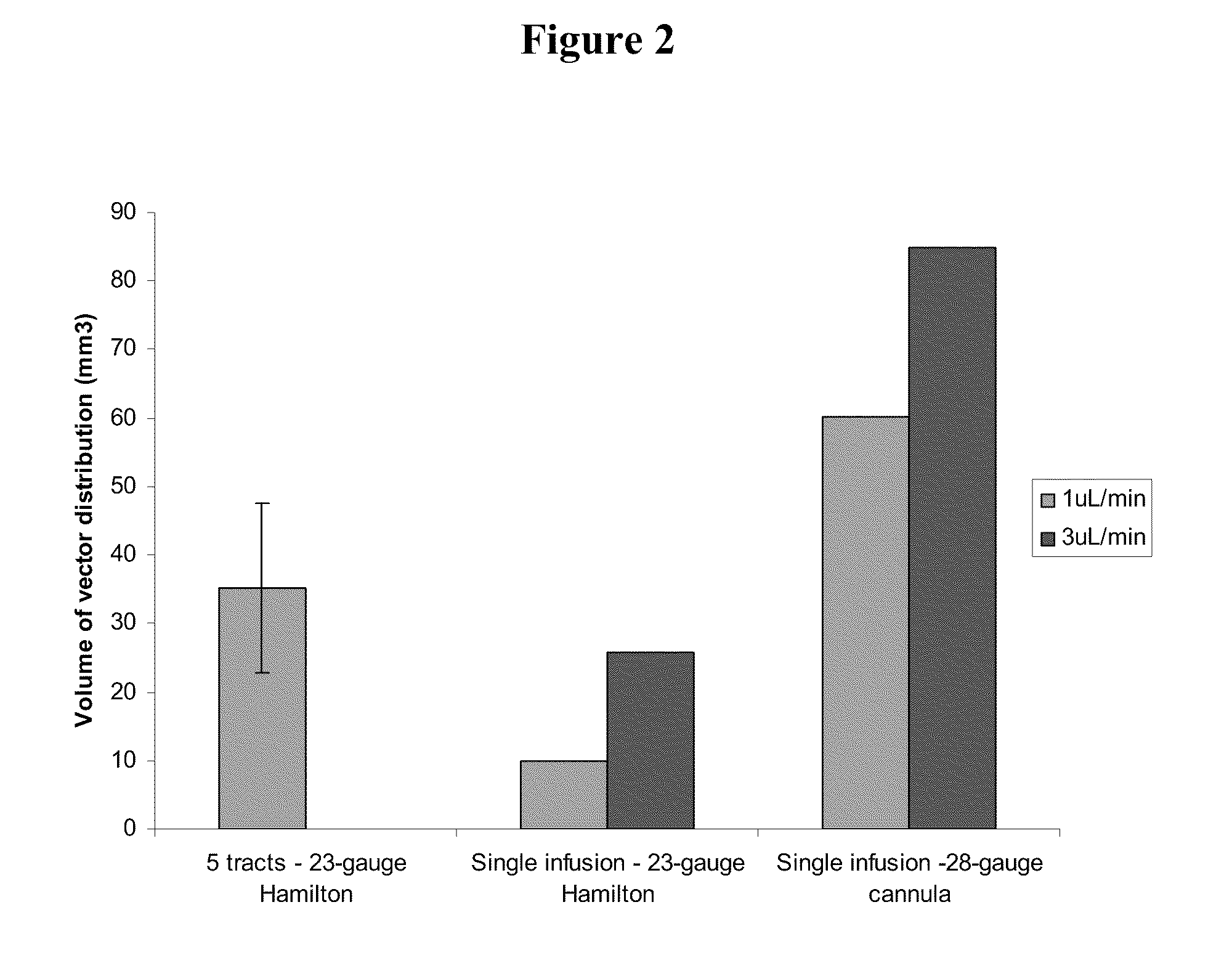
InactiveUS20110293571A1Optimize volumeTotal volume of vector distribution in the brain wasBiocideOrganic active ingredientsNeuroscience
Owner:OXFORD BIOMEDICA (UK) LTD
Computer resource distribution method based on prediciton
InactiveUS20090113056A1Reduce in quantityReduce maintenance costsResource allocationDigital computer detailsComputer resourcesDistribution method
Owner:HITACHI LTD
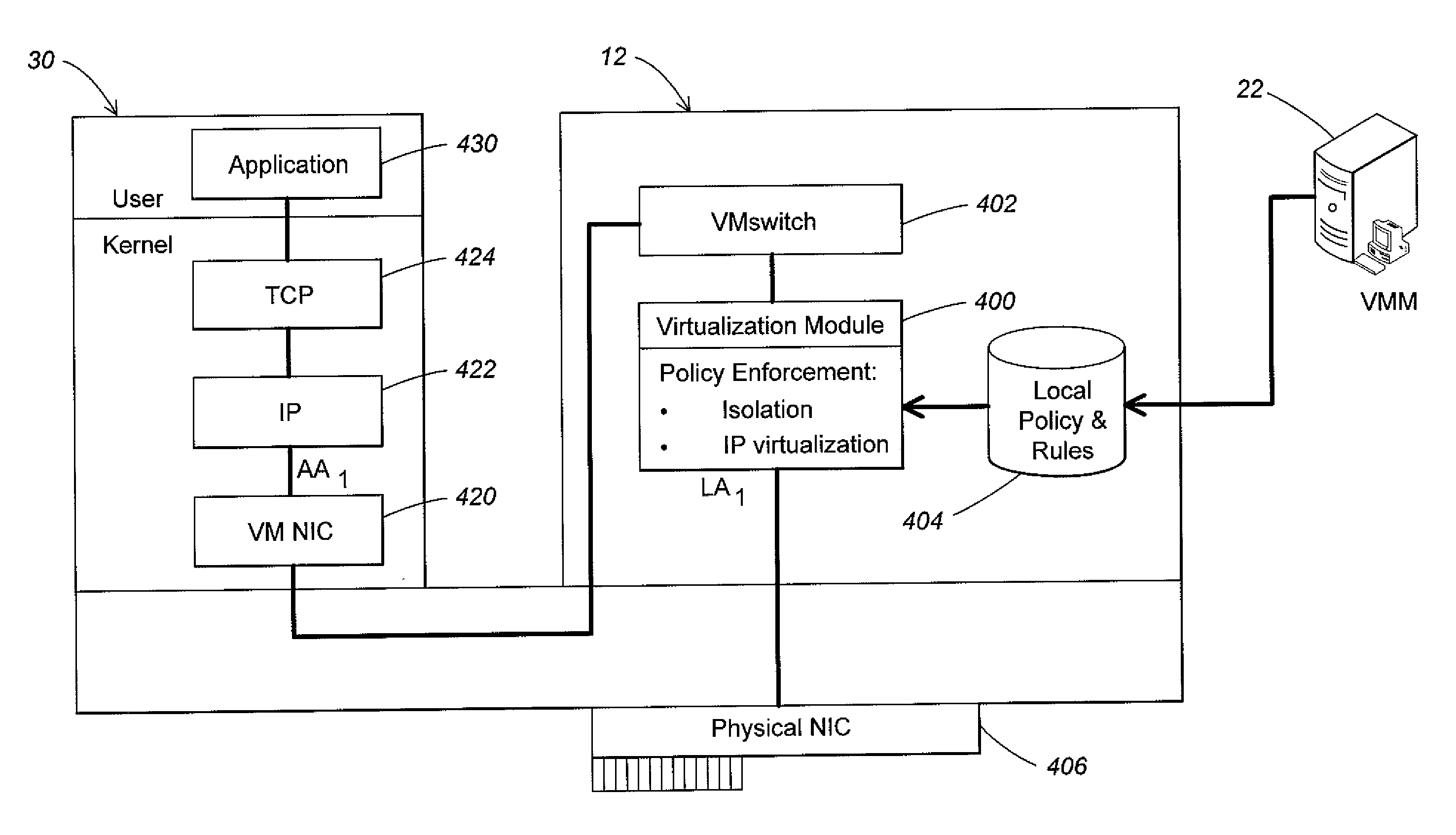
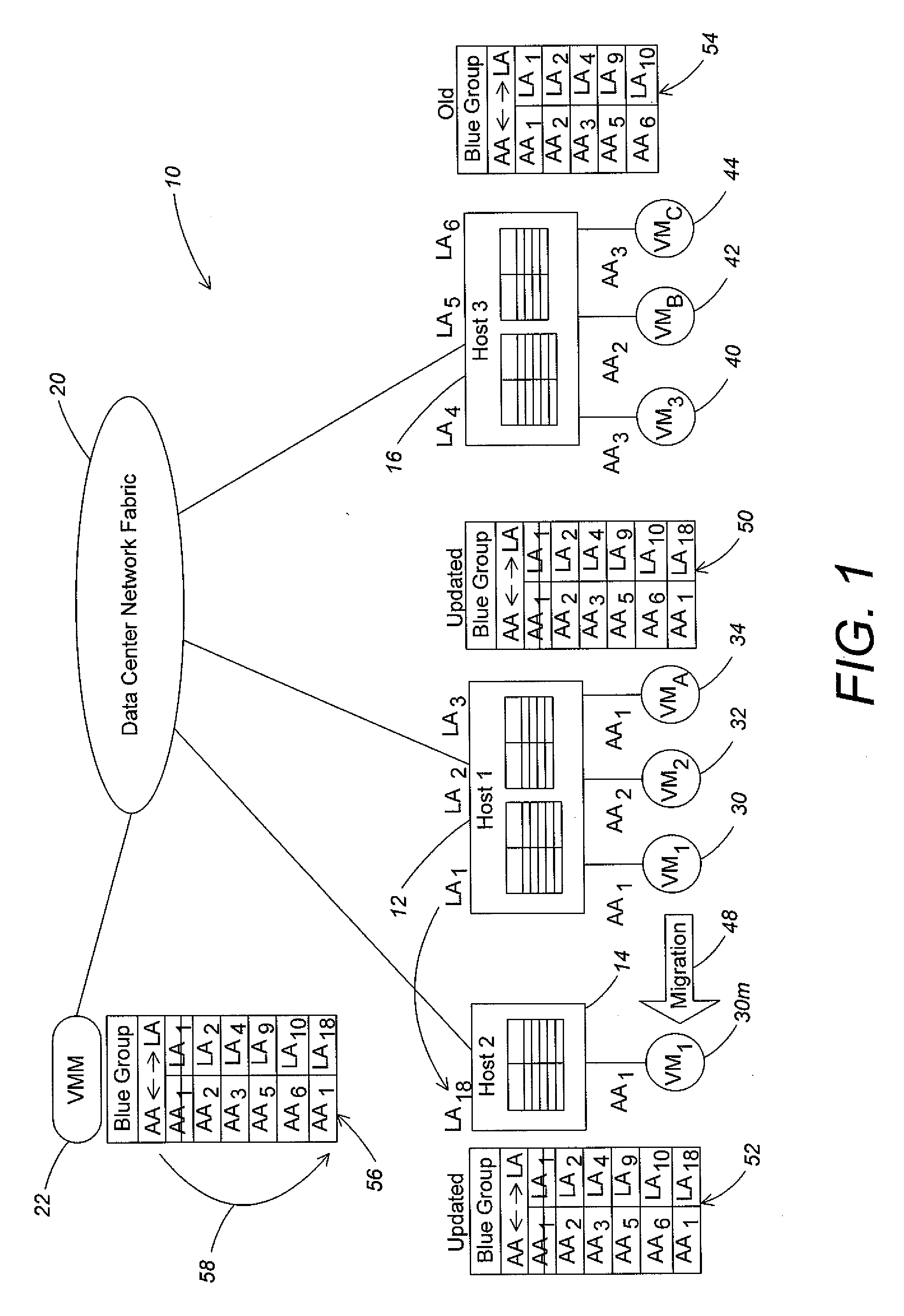
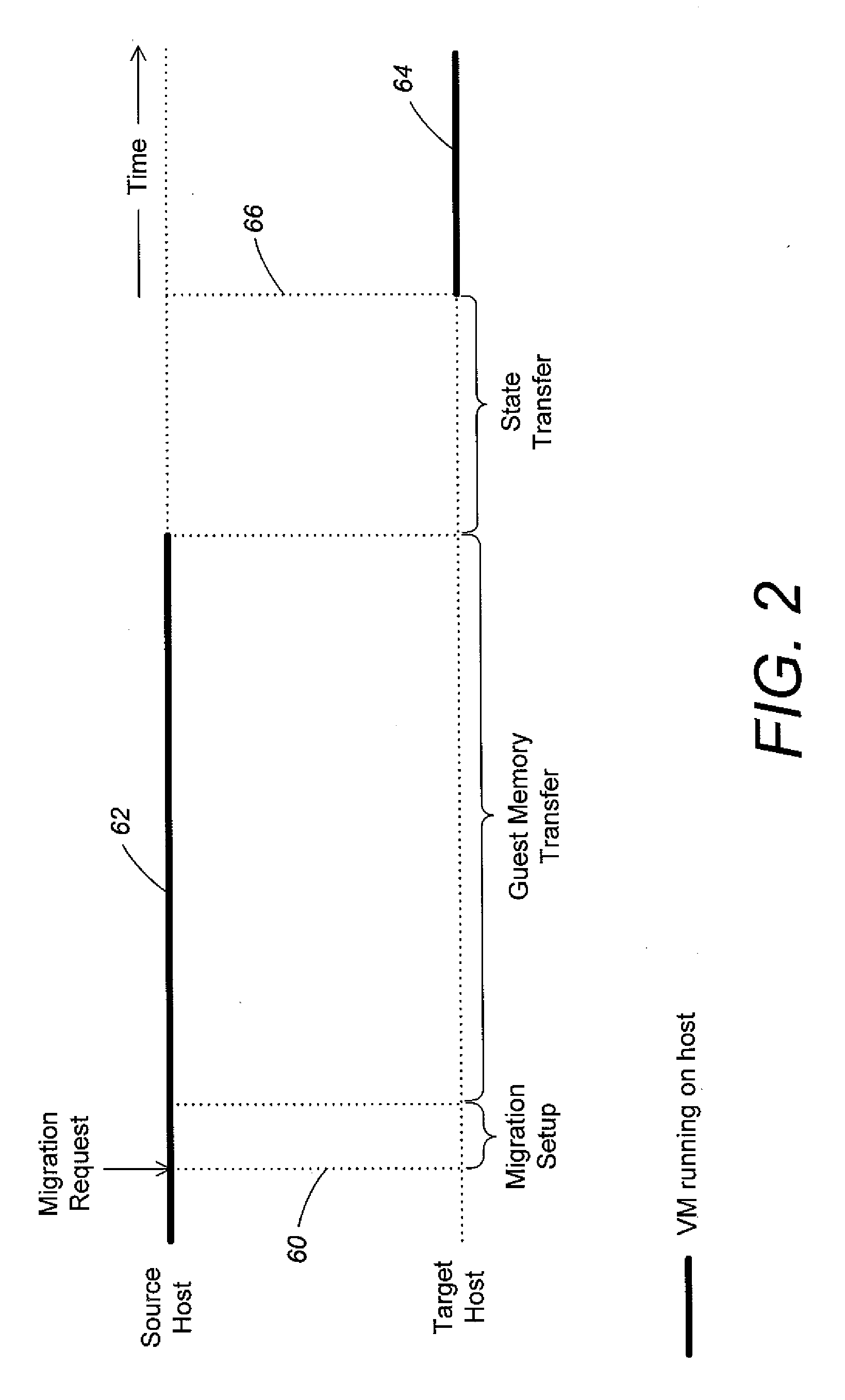
Virtual machine migration to minimize packet loss in virtualized network
ActiveUS20130031544A1Effective distributionError detection/correctionMultiprogramming arrangementsPacket lossData center
Methods and apparatus are provided for controlling live migration of a virtual machine from a first host to a second host in a data center. A virtual machine manager may distribute to at least one host in a virtual network an updated mapping policy that maps a customer address of the virtual machine to a provider address of the migrated virtual machine. The updated mapping policy enables hosts in the virtual network to communicate with the migrated virtual machine. The updated mapping policy can be a shadow policy. The shadow policy is transmitted to hosts in the virtual network by the virtual machine manager before live migration of the virtual machine completes and is maintained by recipient hosts in an inactive state until triggered. The virtual machine manager notifies hosts in the virtual network to activate the shadow policy when live migration completes.
Owner:MICROSOFT TECH LICENSING LLC
Content processing apparatus and content display apparatus based on location information
ActiveUS7461528B2Effective distributionInstruments for road network navigationDigital data information retrievalPosition dependentGeolocation
Owner:PANASONIC CORP
Information record infrastructure, system and method
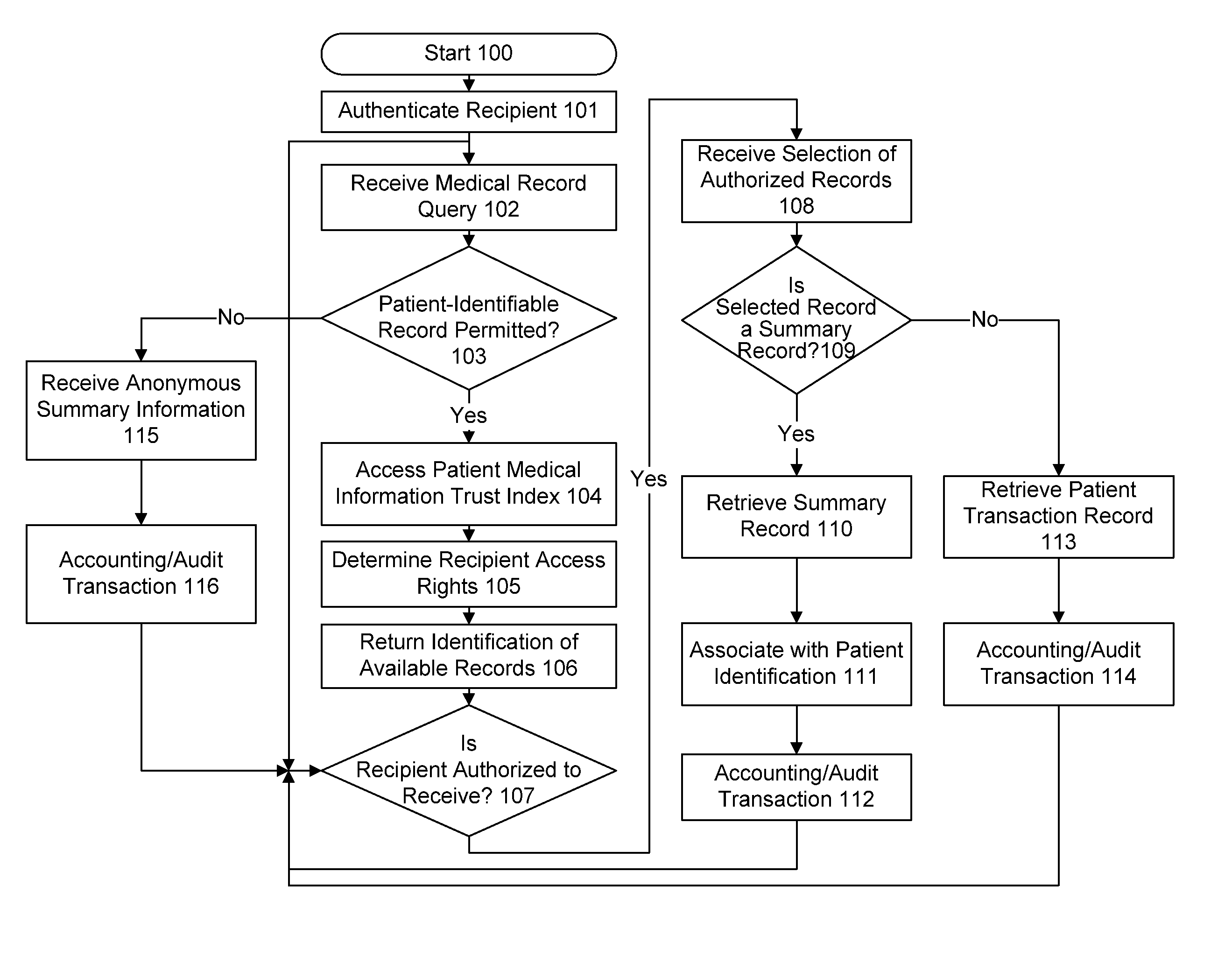
InactiveUS20080306872A1Low costIncrease the number ofUser identity/authority verificationTelemedicineMedical recordPayment
A method for controlling access to a medical record of a patient hosted by at least one medical record repository, comprising a plurality of sub-records, each sub-record having an associated different patient-controlled access control criteria, comprising: receiving, by an intermediary, a request for a medical record from a requester, said request comprising a medical record identifier, a requester identifier, requester authentication information, and patient-provided access control authorization; automatically processing, by the intermediary, the request for the medical record to authenticate the requester and determine sufficiency of the patient-provided access control authorization to meet the patient-controlled access control criteria for each respective sub-record encompassed by the request; and selectively communicating, from the intermediary to the at least one medical record repository, an identification of each sub-record for which access control criteria are determined to be sufficient for access by the requestor. An electronic payment authorization associated with the request may be generated, for compensation of at least one of the intermediary and a medical record repository.
Owner:RPX CORP
Implantable elastomeric depot compositions and uses thereof
InactiveUS20050079202A1Reduce dosing frequencyPatient compliance is goodProsthesisDrageesControlled releaseElastomer
Methods and compositions for systemically or locally administering a beneficial agent to a subject are described, and include, for example, implantable elastomeric depot compositions that can be injected into a desired location and which can provide controlled release of a beneficial agent over a prolonged duration of time. The compositions include a biocompatible, elastomeric polymer, a biocompatible solvent having low water miscibility that forms an elastomeric viscous gel with the polymer and limits water uptake by the implant, and a beneficial agent.
Owner:DURECT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com