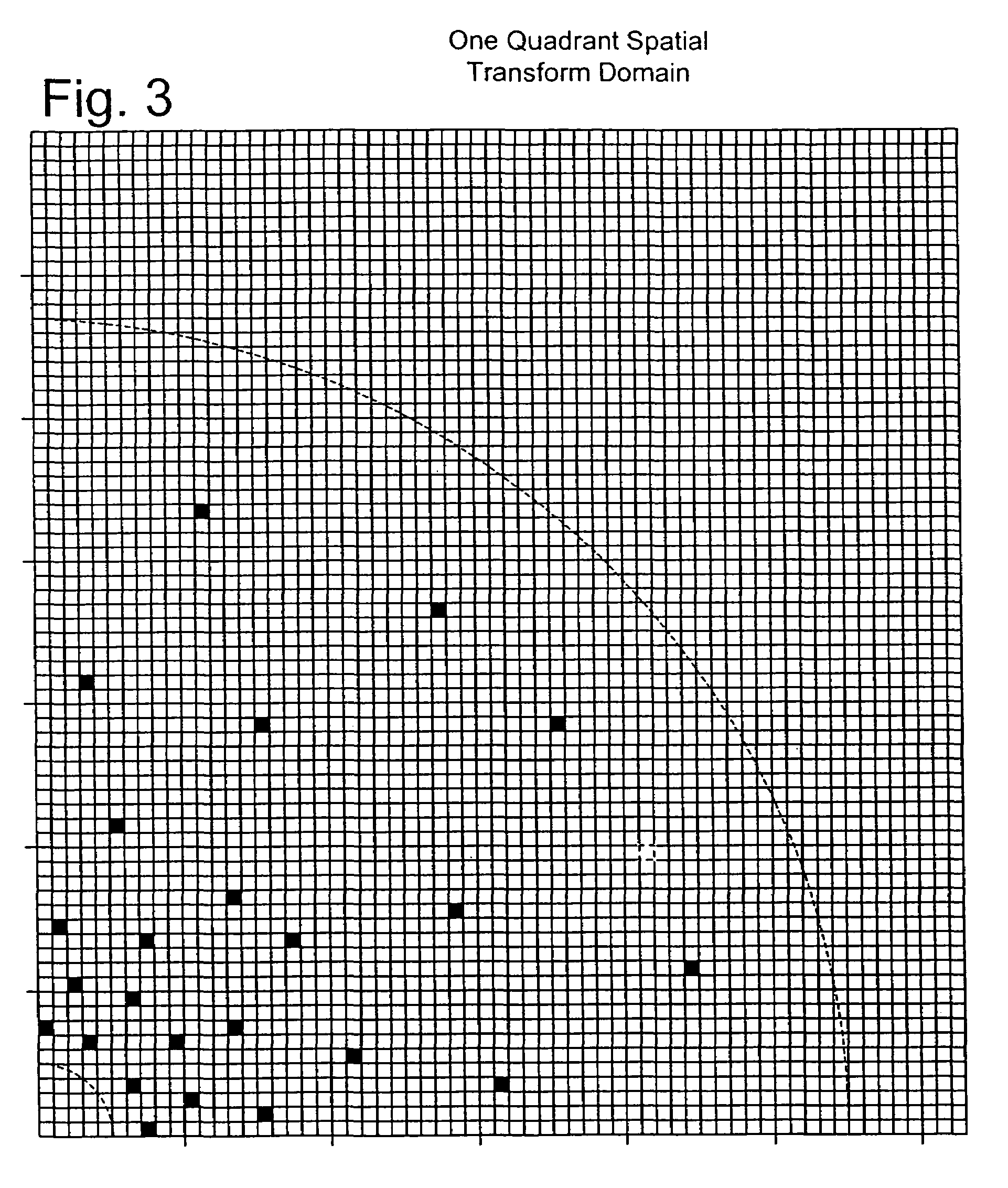
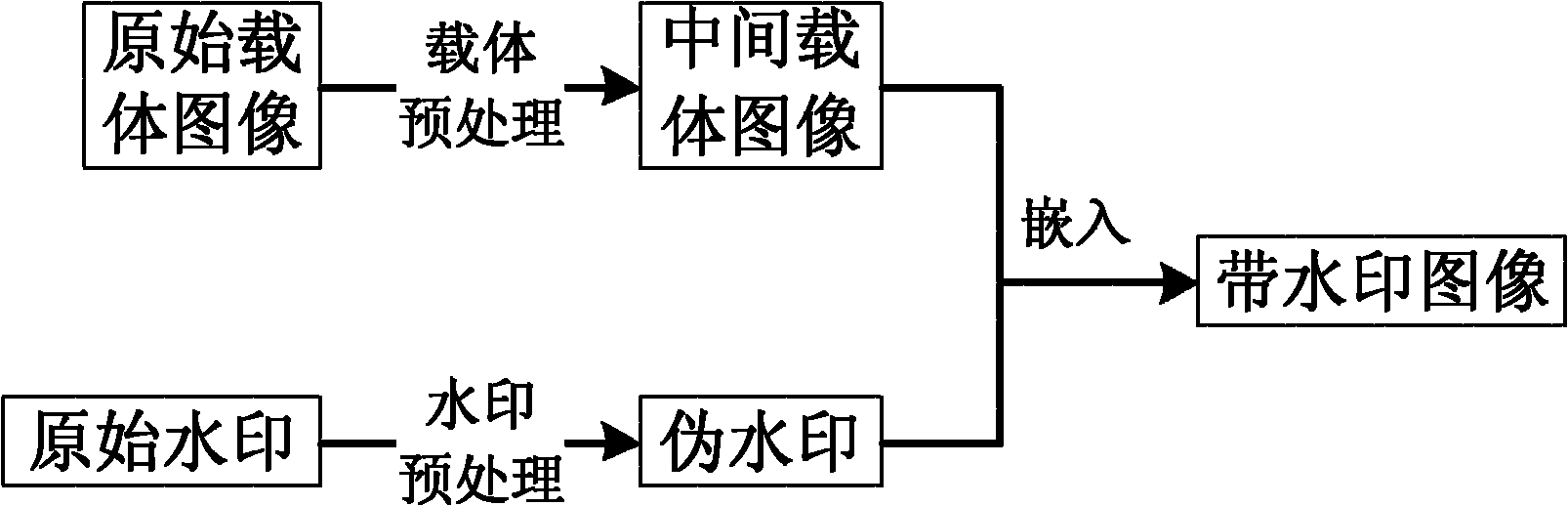
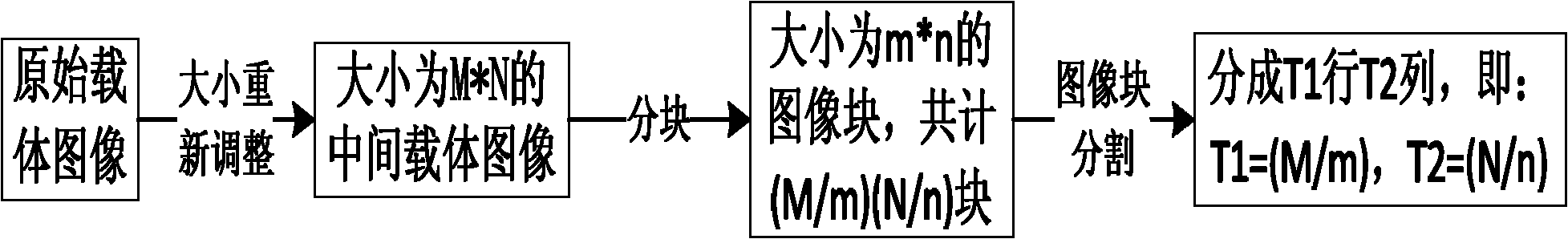
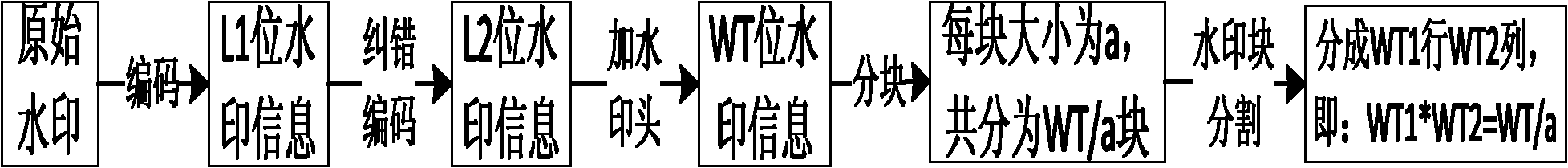
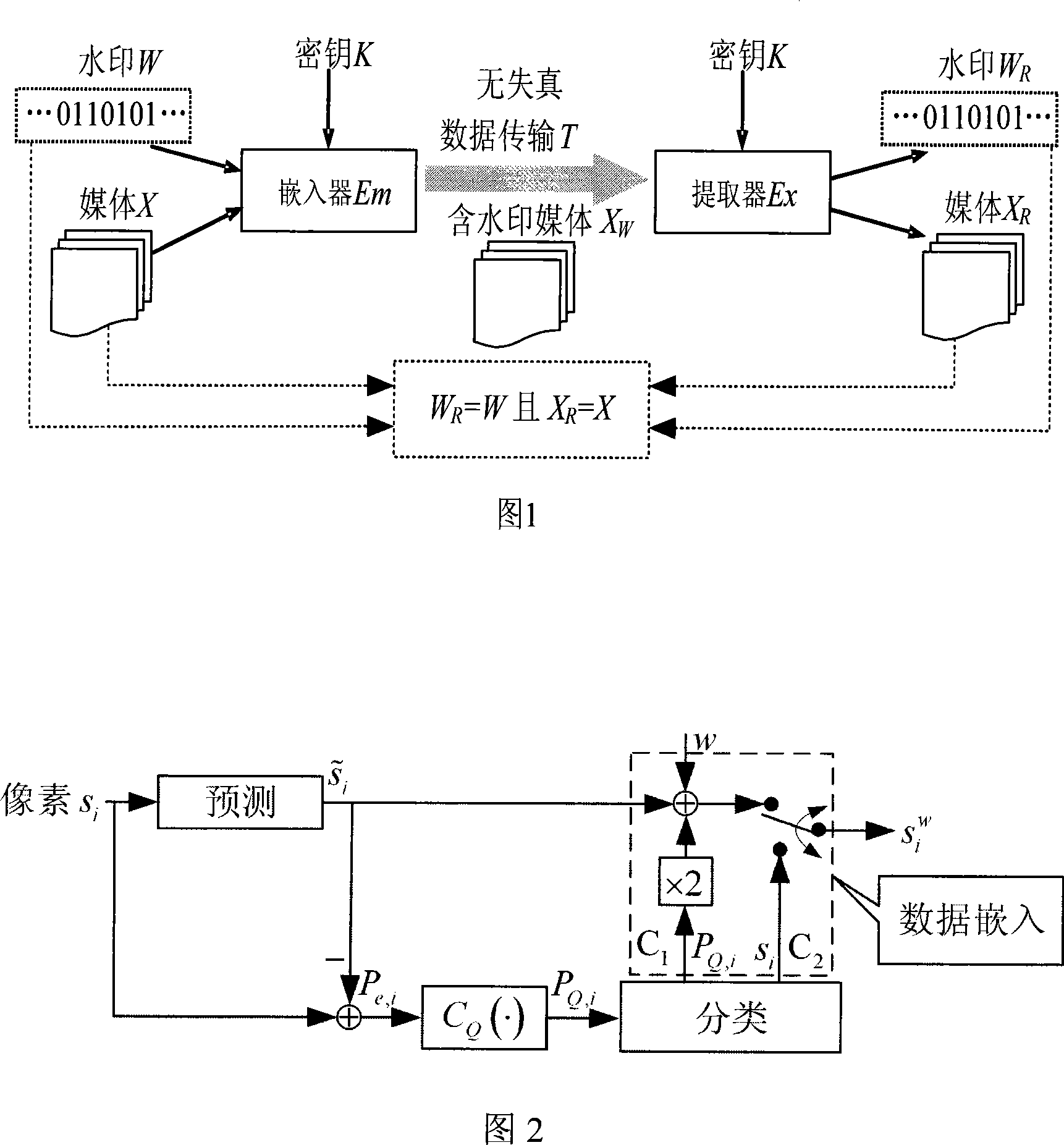
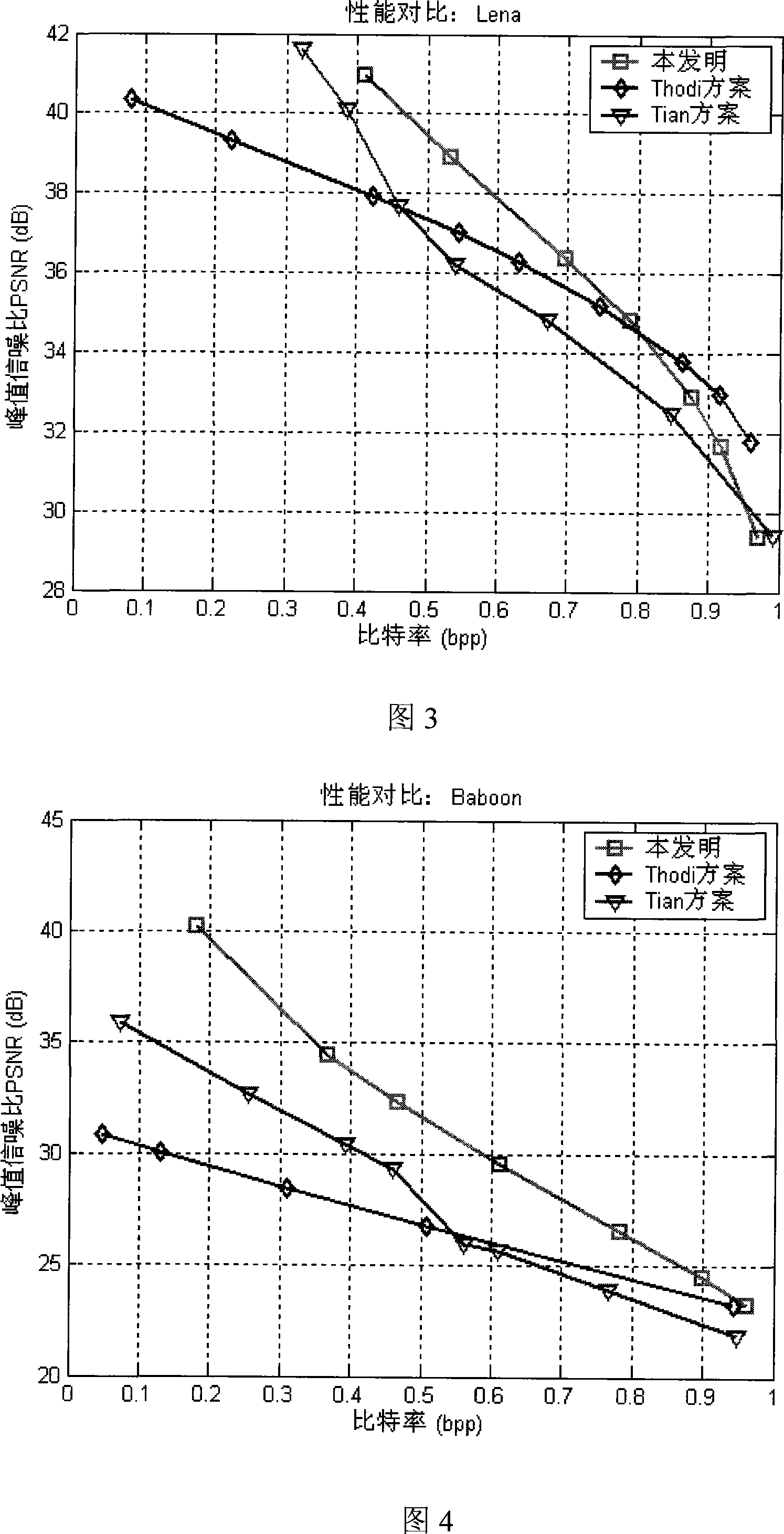
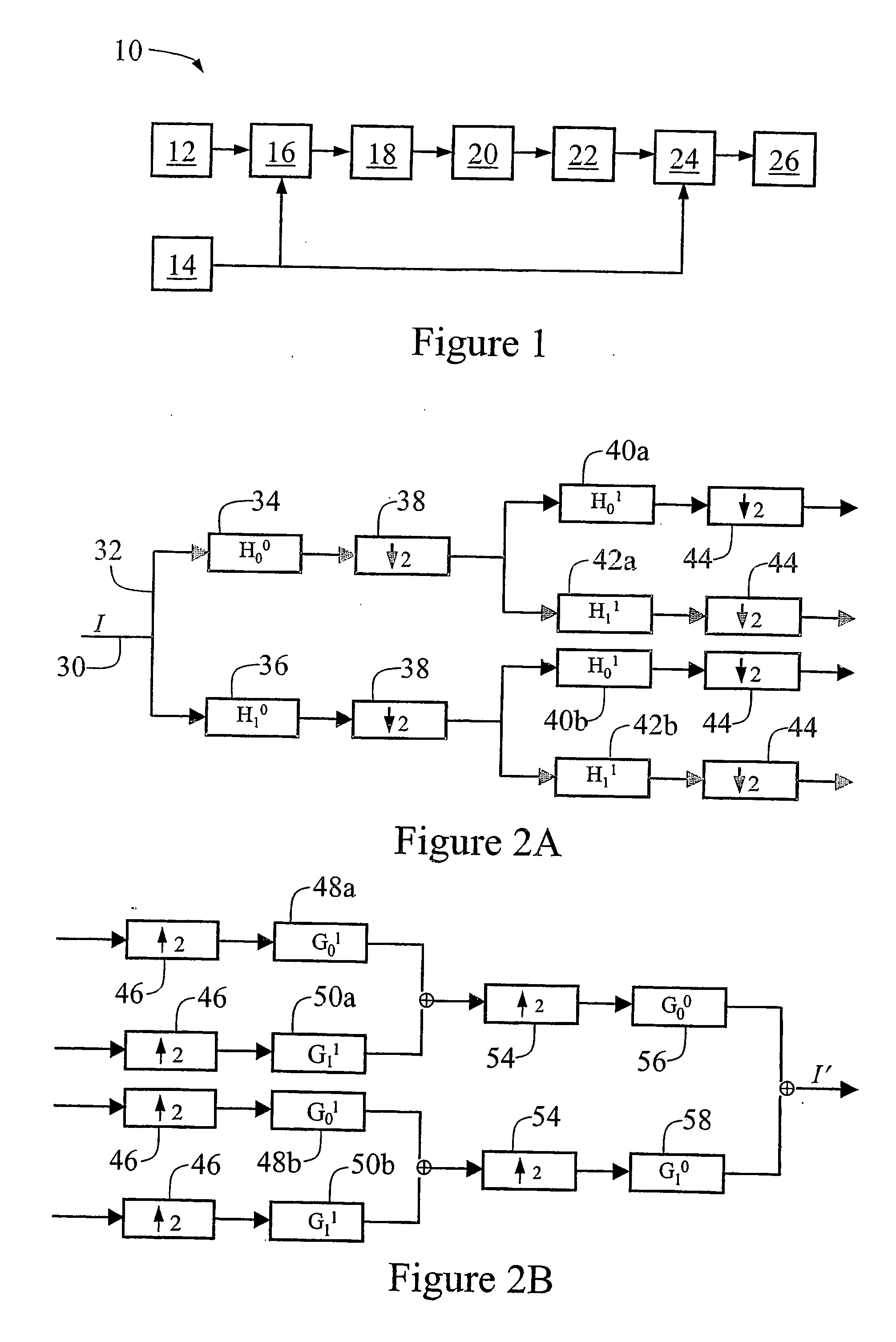
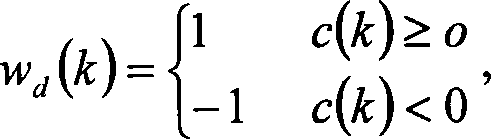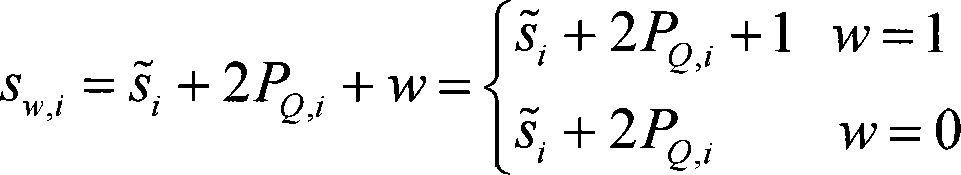Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
472 results about "Watermark method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
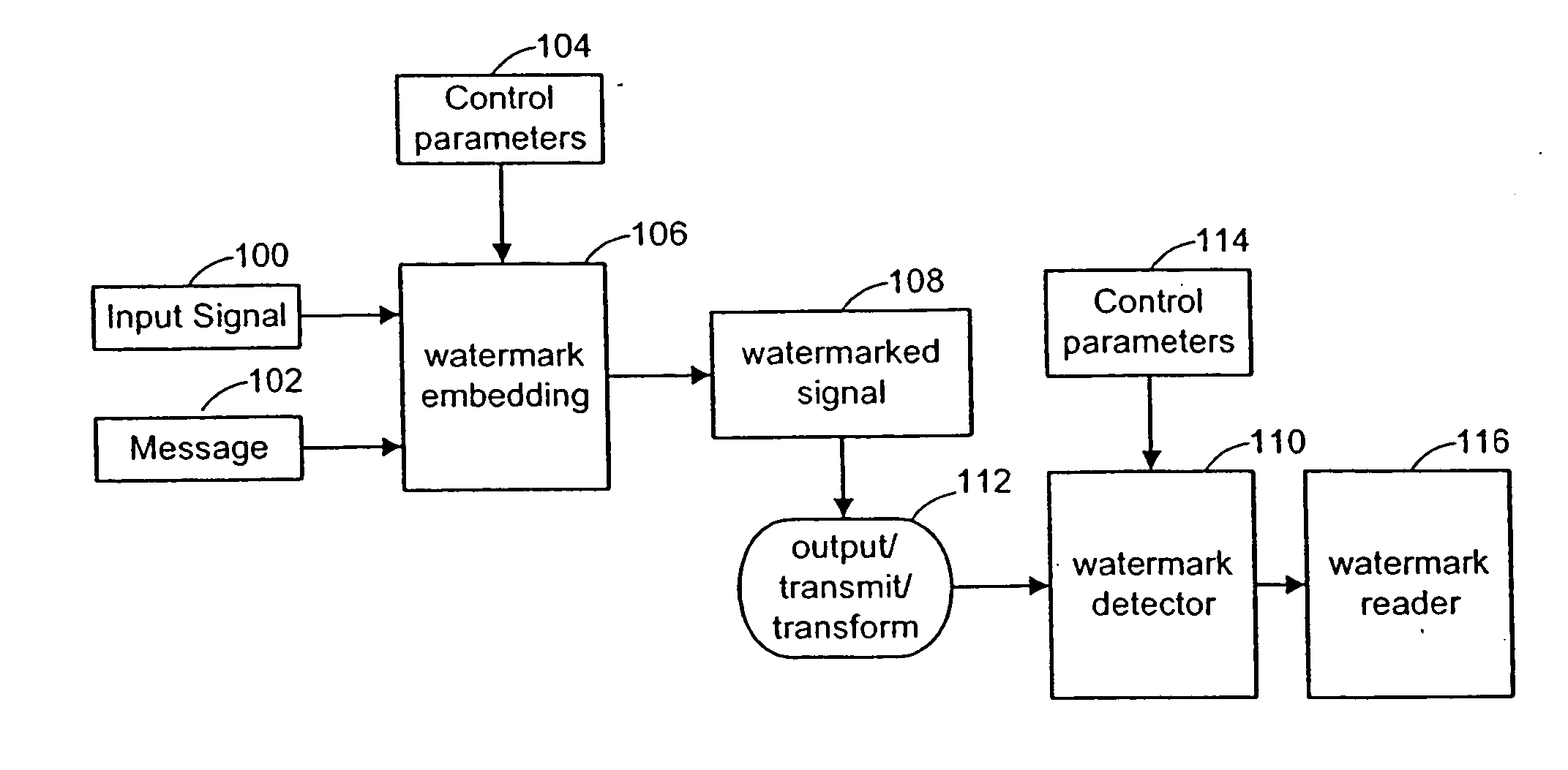
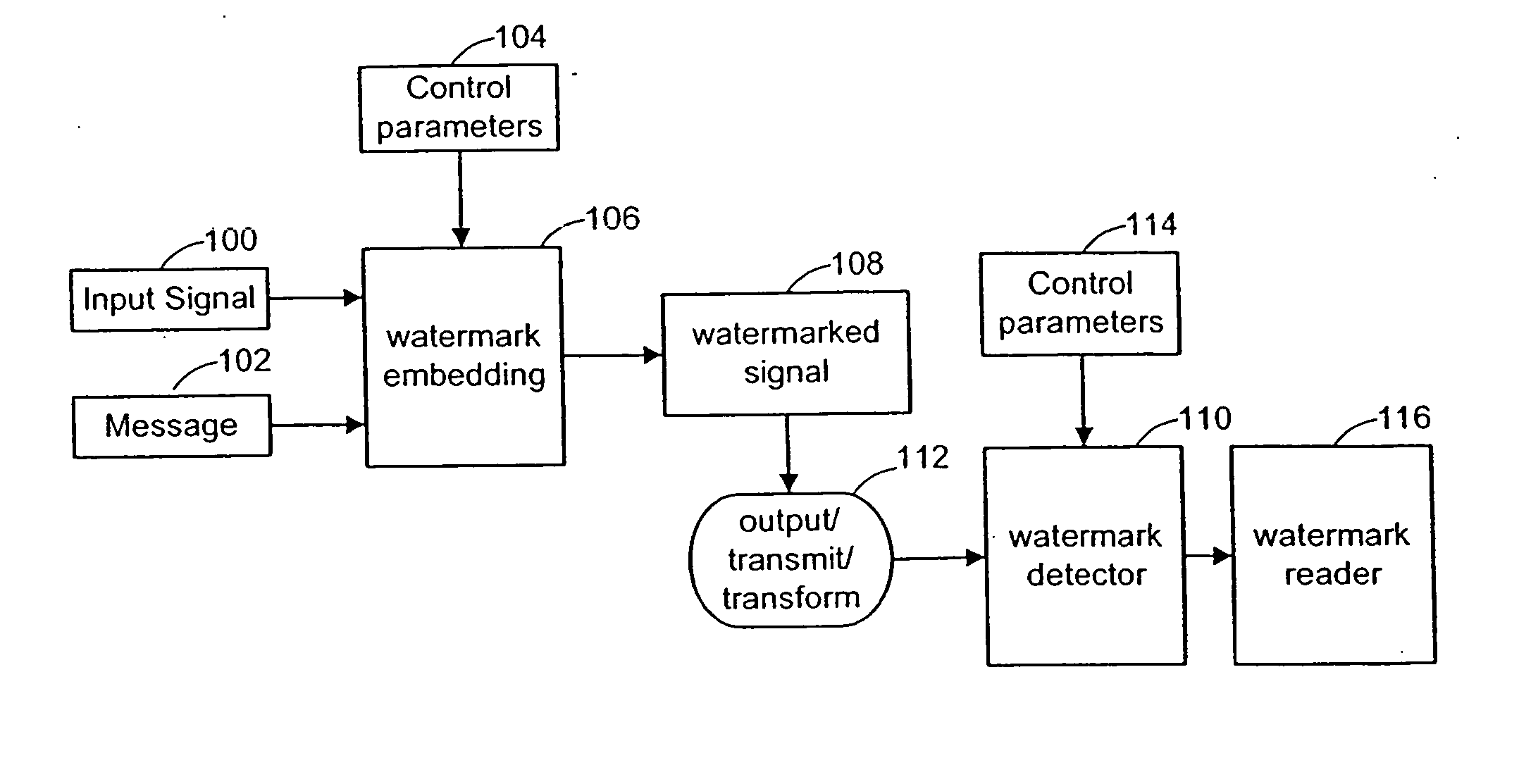
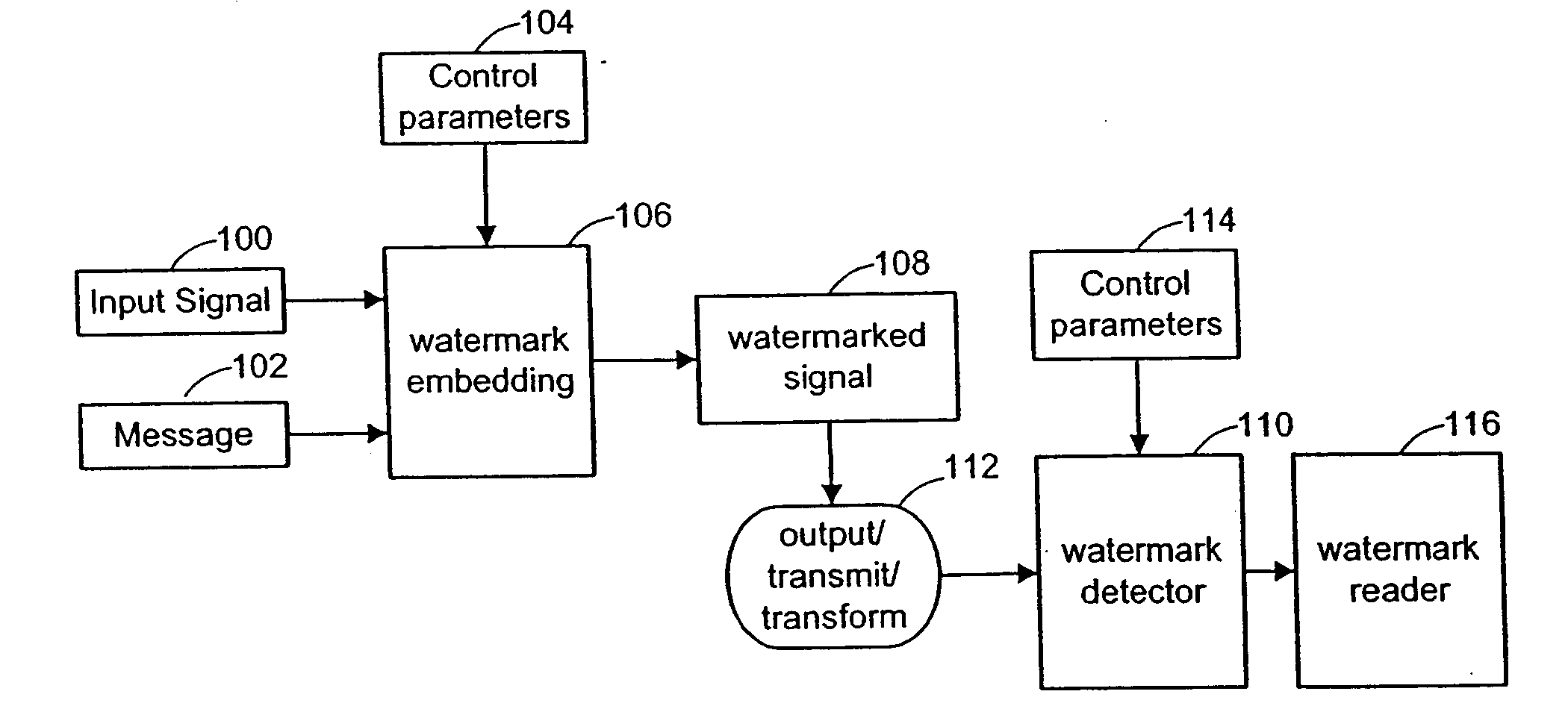
THE WATERMARK METHOD. Watermark has been, and continues to be, a catalyst for change. Through Watermark, you make the connections that lead to the growth of your businesses, learn valuable leadership skills that lead to promotions and find a community that supports you, educates you and shares your wisdom.
Watermarking scheme for image authentication
InactiveUS6285775B1Effective distributionQuick checkCharacter and pattern recognitionImage data processing detailsWatermark methodJPEG
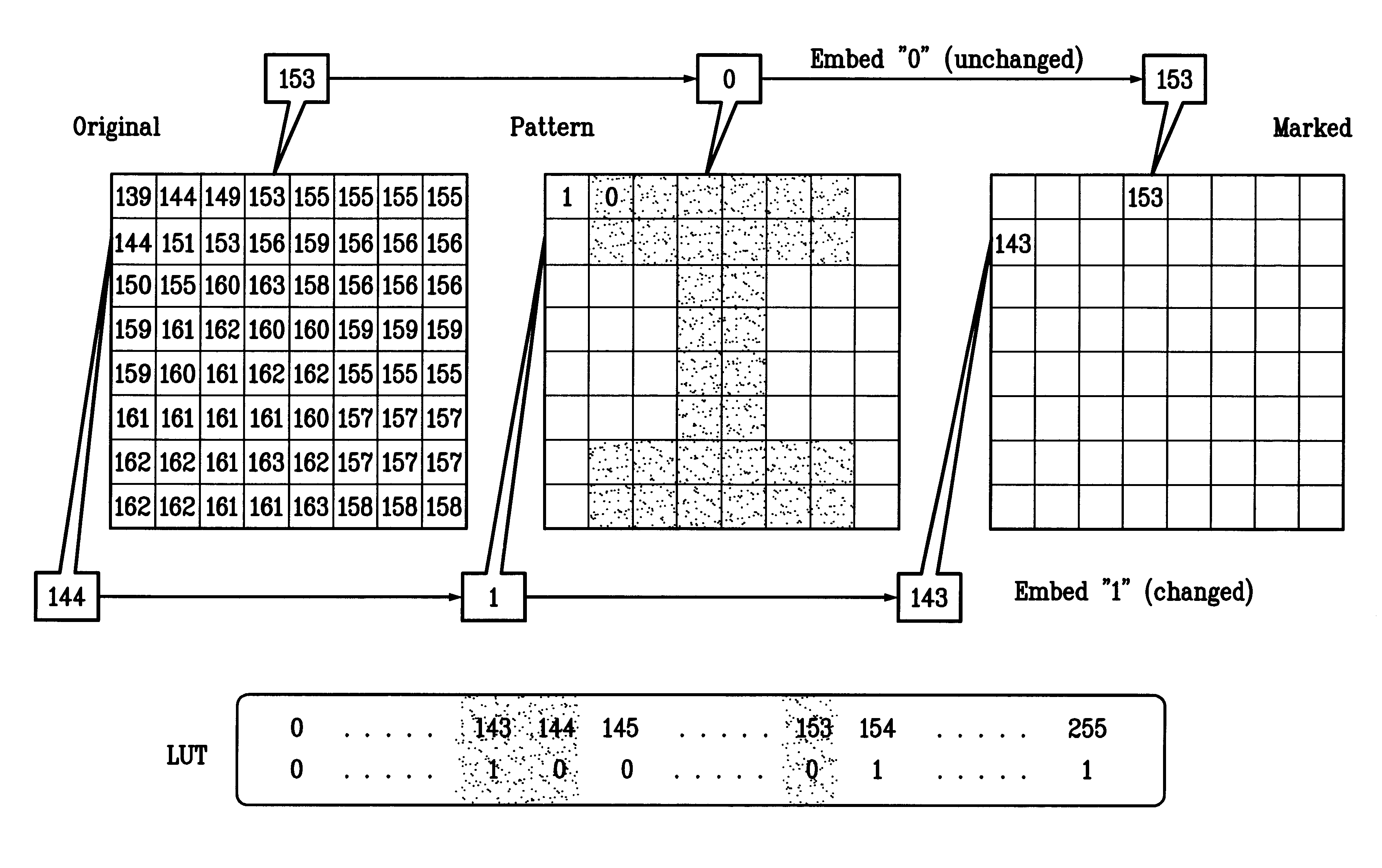
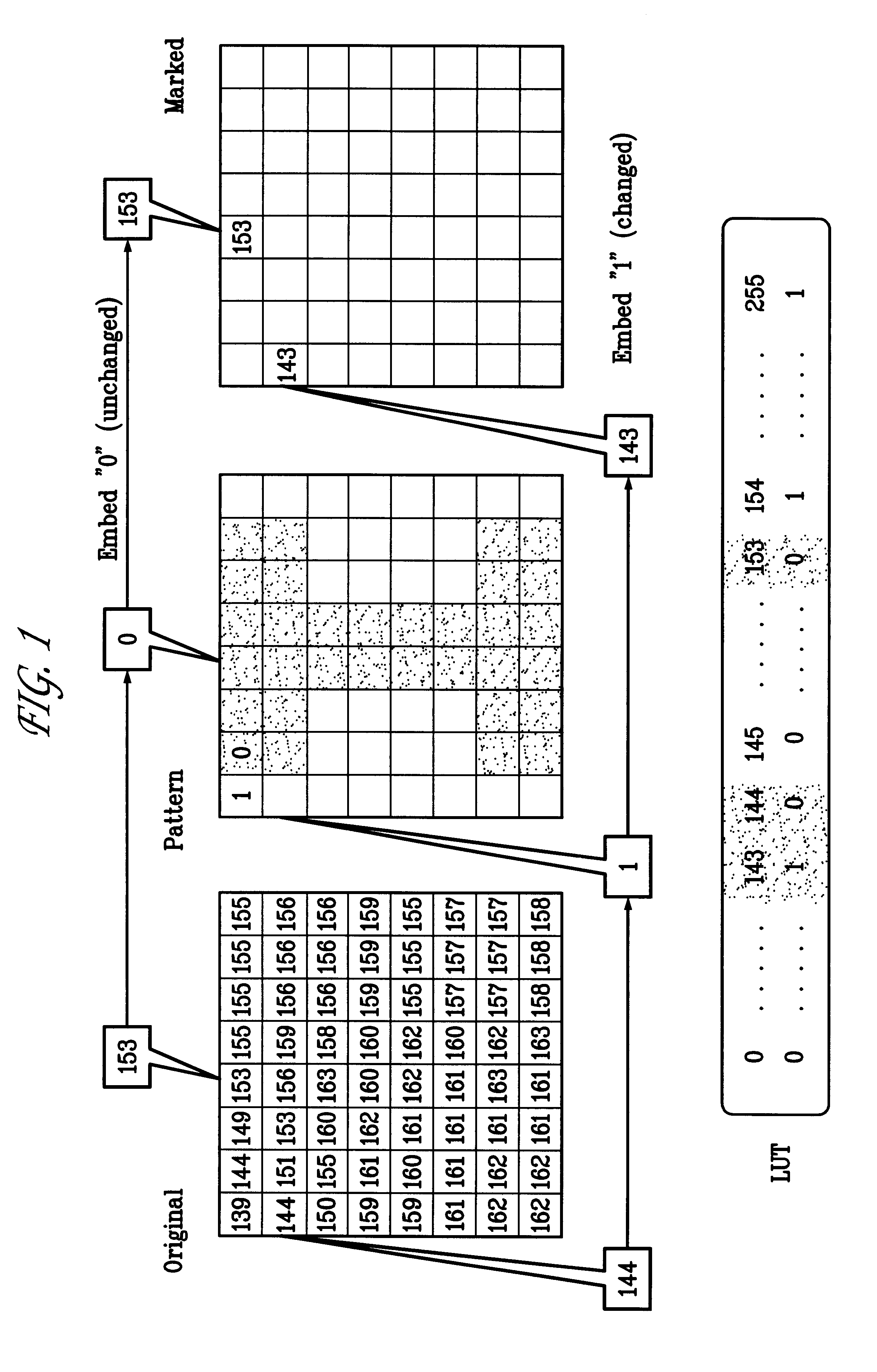
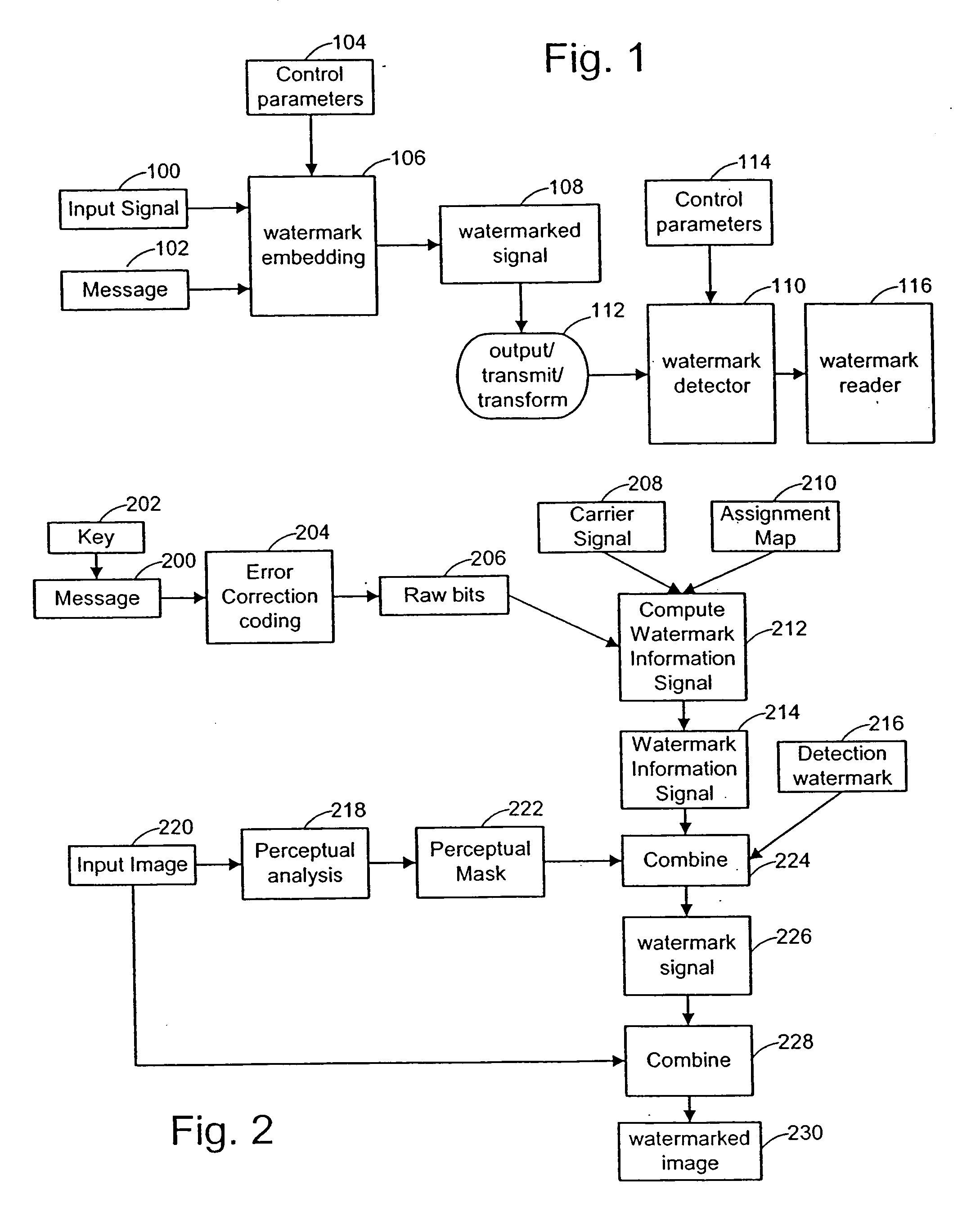
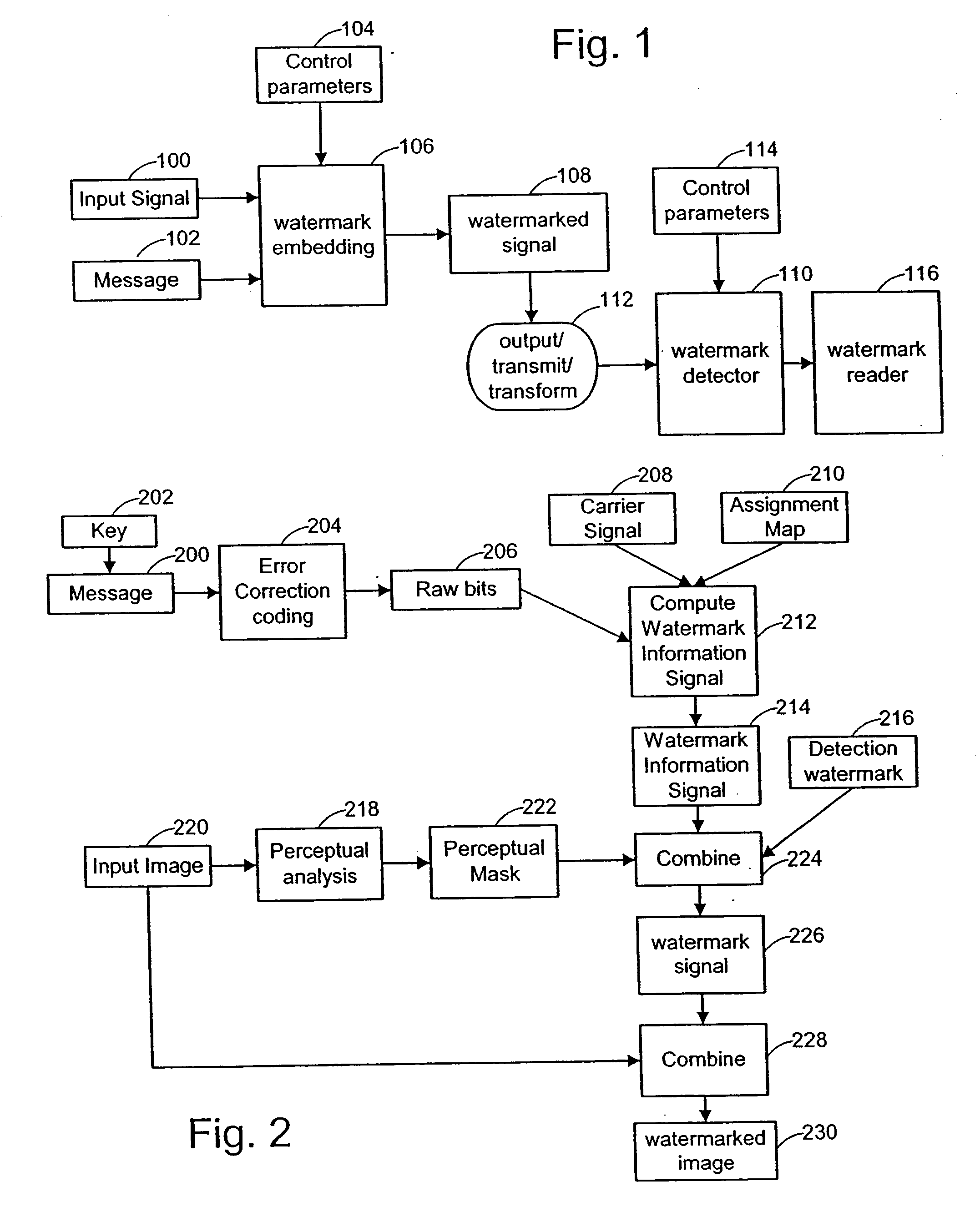
A digital watermarking process whereby an invisible watermark inserted into a host image is utilized to determine whether or not the image has been altered and, if so, where in the image such alteration occurred. The watermarking method includes the steps of providing a look-up table containing a plurality of coefficients and corresponding values; transforming the image into a plurality of blocks, wherein each block contains coefficients matching coefficients in the look-up table; and embedding the watermark in the image by performing the following substeps for at least some of the blocks: First, a coefficient is selected for insertion of a marking value representative of a corresponding portion of the watermark. Next, the value of the selected coefficient to used to identify a corresponding value in the look-up table. Finally, the identified coefficient is left unchanged if the corresponding value is the same as the marking value, and is changed if the corresponding value is different from the marking value. After the insertion of the watermark, the image may be stored in a lossy-compression form, thus permitting efficient storage and distribution. Moreover, the method may be used to produce two output signals for authentication: (1) a meaningful pattern to facilitate a quick visual check, and (2) an additional signal to detect unauthorized alteration. The method can be applied to an image compressed using JPEG or other techniques, such as Wavelet compression, and the marked image can be kept in the compressed format. Any alteration made on the marked image can be localized, making the method suitable for use in a "trustworthy" digital camera or camcorder.
Owner:TRUSTEES OF THE UNIV OF PRINCETON THE
Method for robust watermarking of content
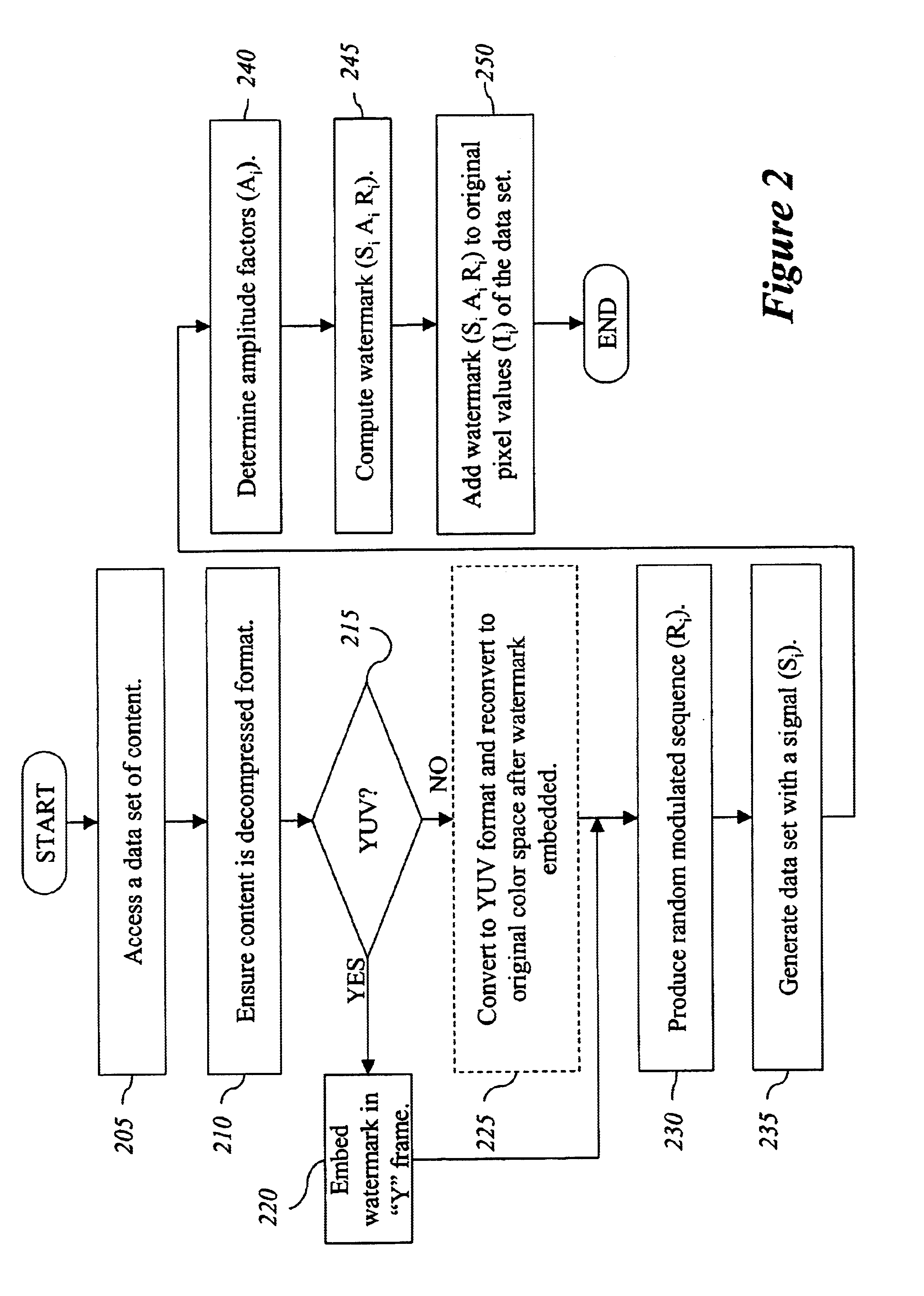
One inventive aspect pertains to a watermarking mechanism that allows a watermark to be determined from only a part of the video sequence without human intervention and without reference to the original watermarked frames. This watermark has improved invisibility, detection reliability and robustness. Invisibility is improved through the inclusion of frame difference parameters to calculate the amplitude of the watermark. Detection reliability and robustness can be improved by assuring that opposite signed values for the pseudo-random number sequence are spatially near each other and using data blocks forming the data sets, respectively. Another inventive aspect pertains to a watermarking mechanism that is exclusively dependent on the data contained in the data sets and is completely interoperable between spatial and compressed domains.
Owner:INTEL CORP
Authentication of identification documents using digital watermarks
InactiveUS7305104B2Character and pattern recognitionSecret communicationComputer hardwareWatermark method
Owner:DIGIMARC CORP
Signal continuity assessment using embedded watermarks
ActiveUS20080002854A1Fine granularitySpeech analysisCharacter and pattern recognitionWatermark methodVolumetric Mass Density
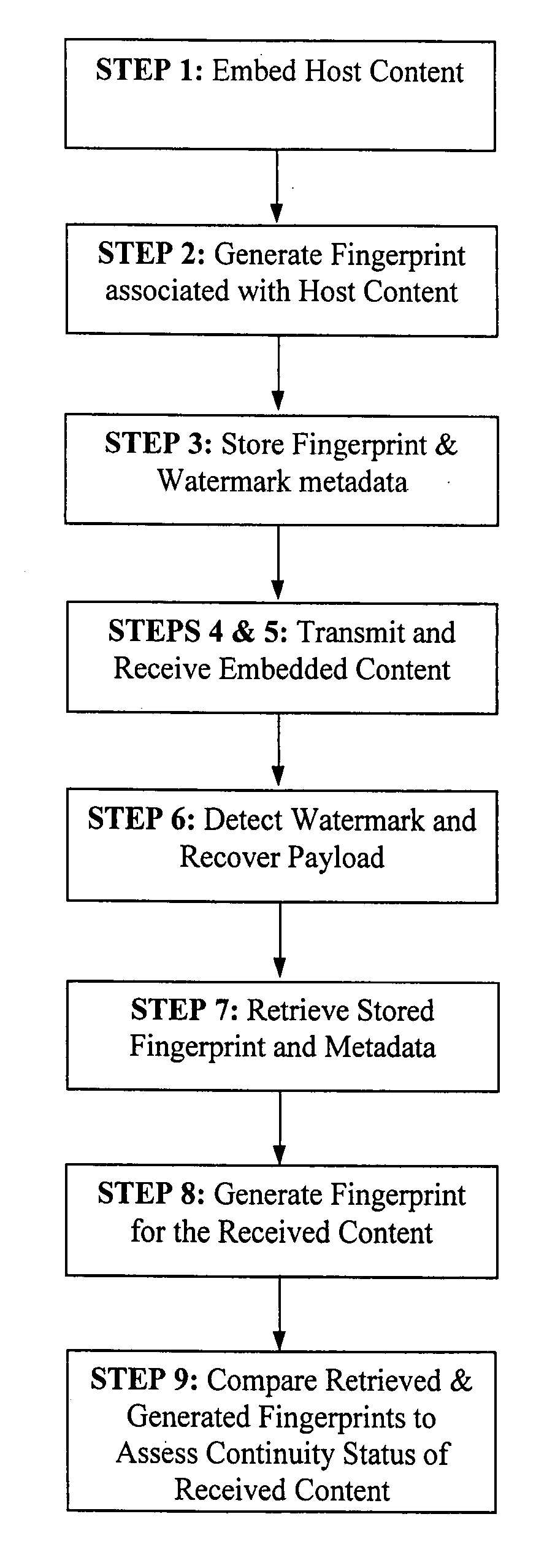
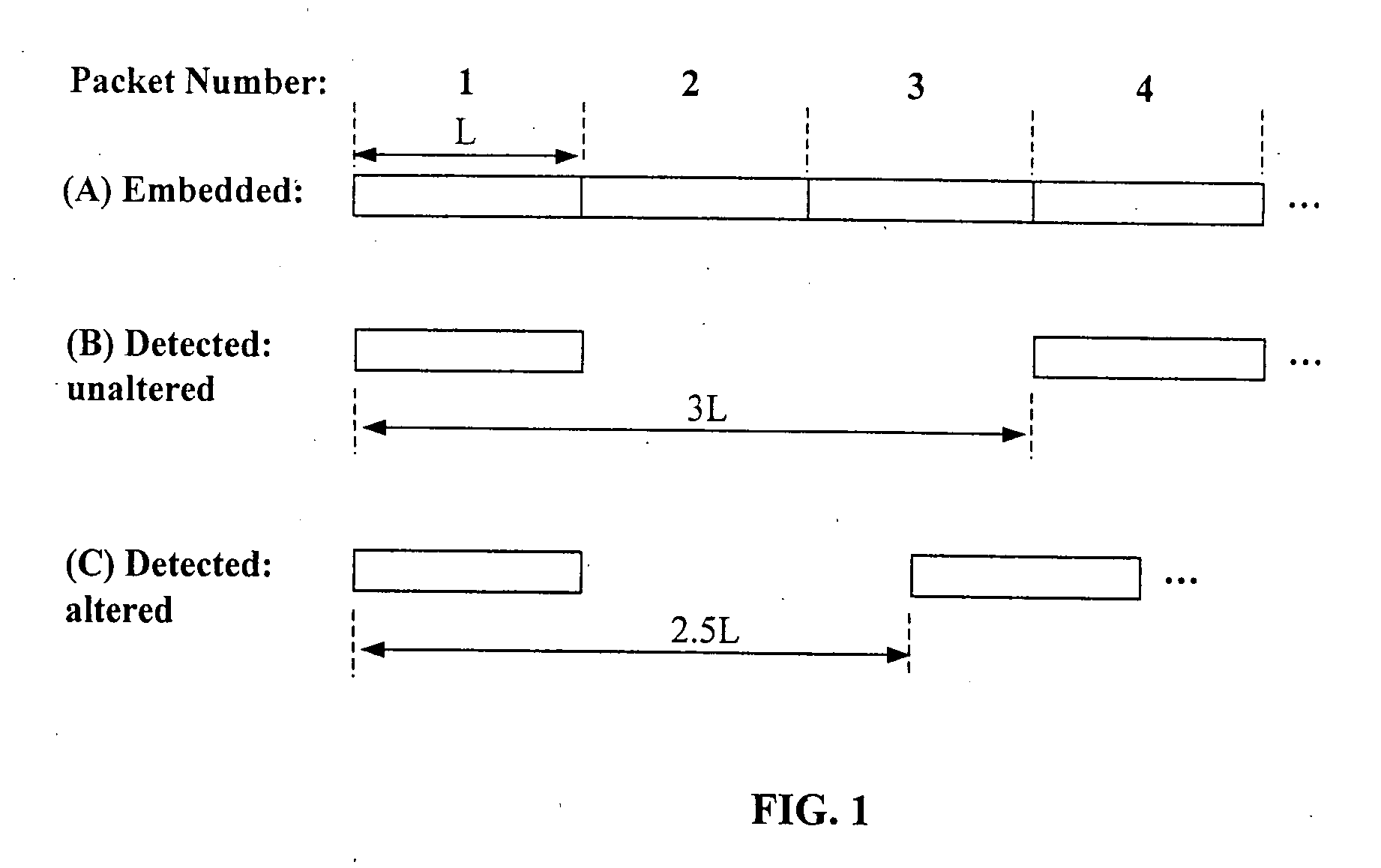
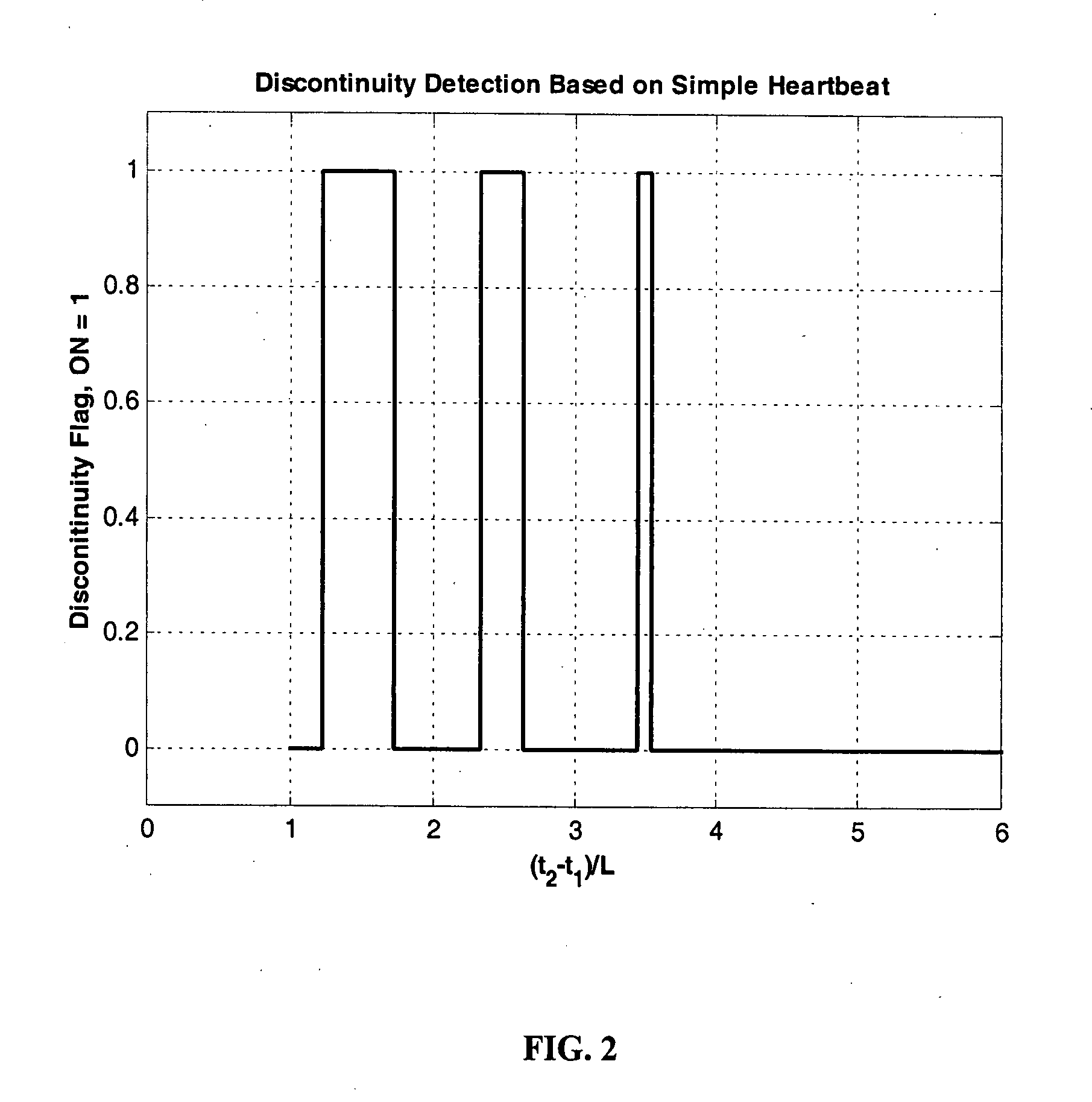
Methods, apparatus, and systems for signal continuity assessment using embedded watermarks are provided. The embedded watermarks are recovered from the content and one or more attributes associated with the recovered watermarks are identified. A continuity of the content can then be assessed in accordance with the one or more attributes. The continuity assessment may be based on a variety of factors, including but not limited to a determined heartbeat of the recovered watermarks, a density, separation, location, or extent, of the recovered watermarks, as well as information associated with the watermarks, such as a stego key, channel bits, packet numbers, a fingerprint, or the like.
Owner:IP ACQUISITIONS LLC
Authentication of physical and electronic media objects using digital watermarks
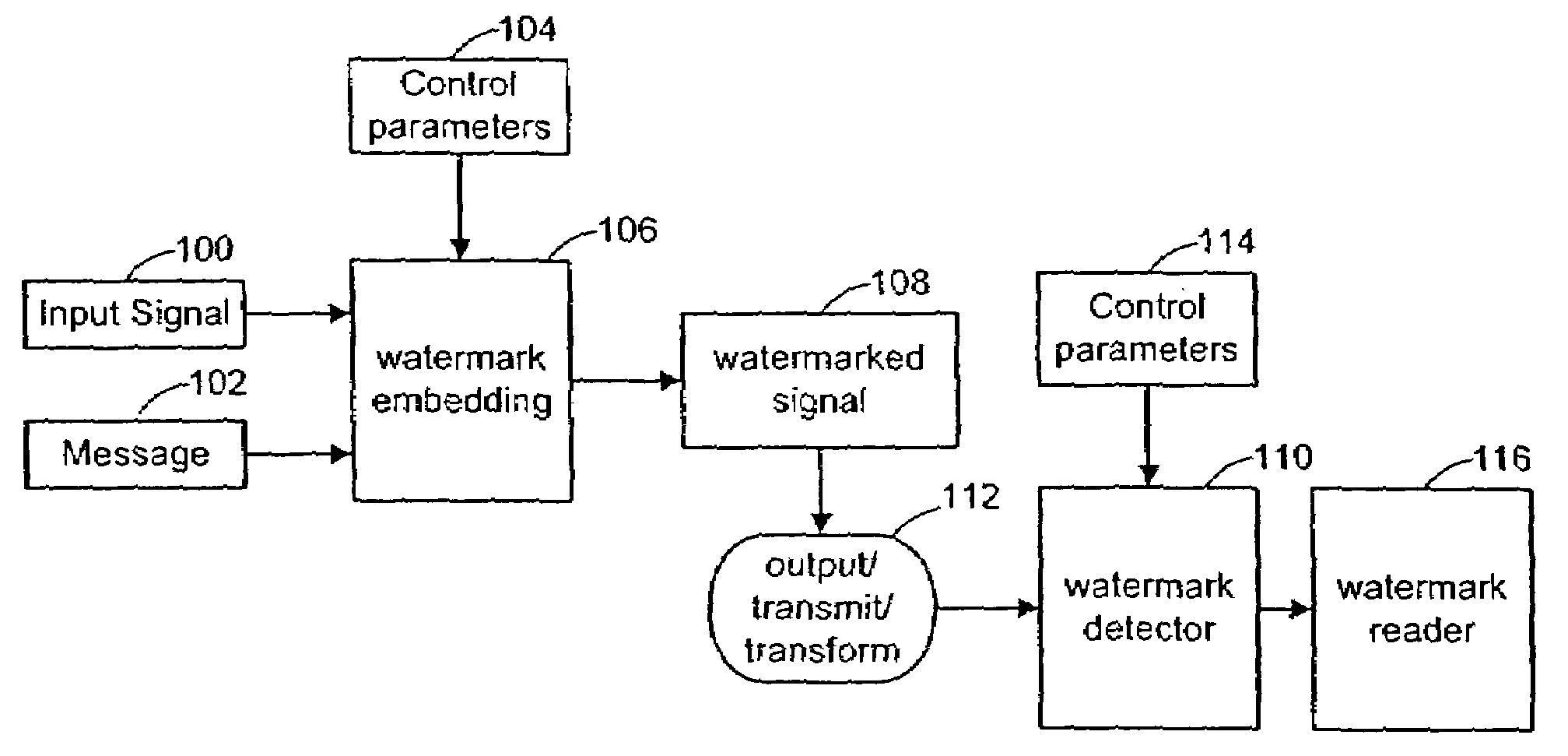
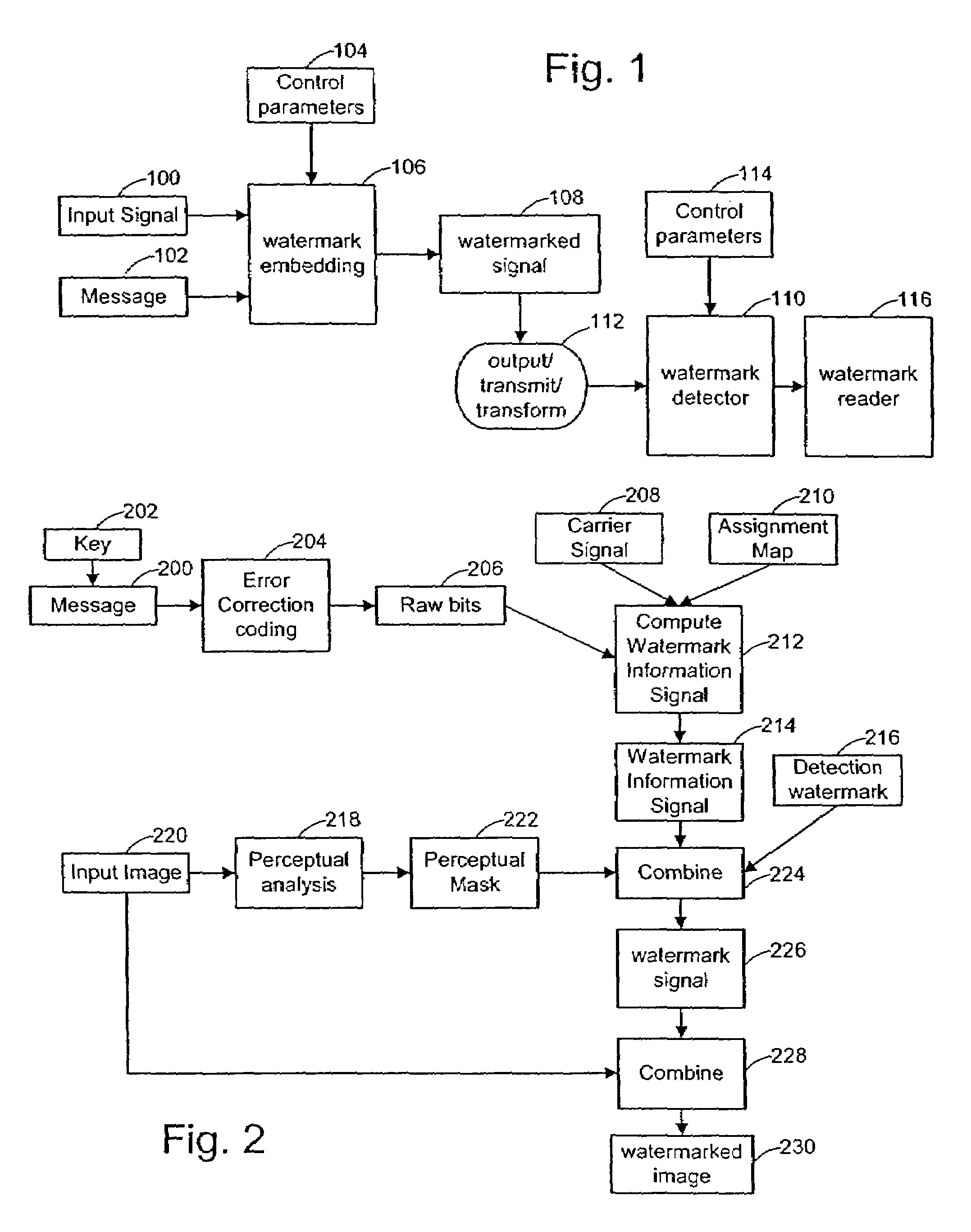
Digital watermark methods for encoding auxiliary data into a host signal are used to authenticate physical and electronic objects. One such method computes a content specific message dependent on the host signal, encodes the content specific message into a watermark signal, and embeds the watermark in the host signal such that the watermark signal is substantially imperceptible in the host signal. One specific implementation embeds data representing salient features of the host signal into the watermark. For example, for photo IDs, the method embeds the spatial location of salient features of the photo into the watermark. Another implementation computes a semi-sensitive hash of the host signal, such as a low pass filtering of the signal, and embeds the hash into the watermark. The watermark signal may be content dependent by making the watermark key dependent on some attribute of the signal in which the watermark is embedded. Another approach is to make the watermark key dependent on a user or an attribute of the user. Yet another approach is to use multiple watermark components and multiple watermark detection stages that help identify and screen out invalid watermark signals. Another digital watermarking method for authenticating a media object transforms a media signal to a frequency domain comprising an array of frequency coefficients. It selects a first set of frequency coefficients, and alters the selected first set of frequency coefficients so that values of the coefficients in the set correspond to a pattern. The pattern of the media signal is authenticated by comparing a pattern of the values of the frequency coefficients in the set with an expected pattern.
Owner:DIGIMARC CORP
Embedding supplemental data in an encoded signal, such as audio / video watermarks
InactiveUS6157330AReplicaImprove signal-to-noise ratioAnalogue conversionRecord information storageSignal-to-noise ratio (imaging)Watermark method
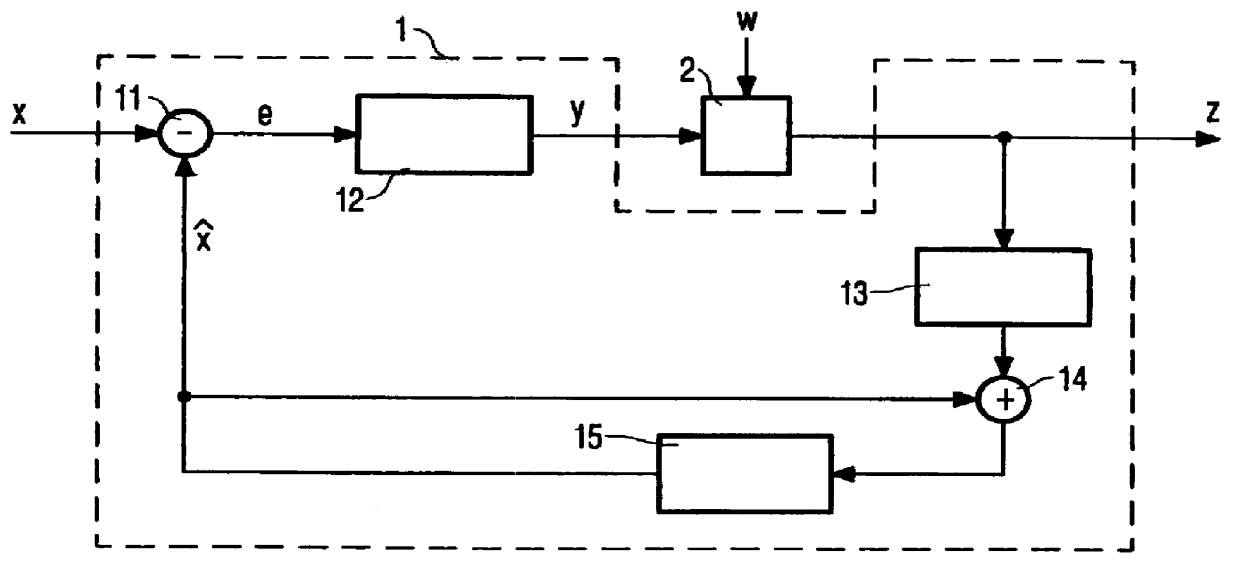
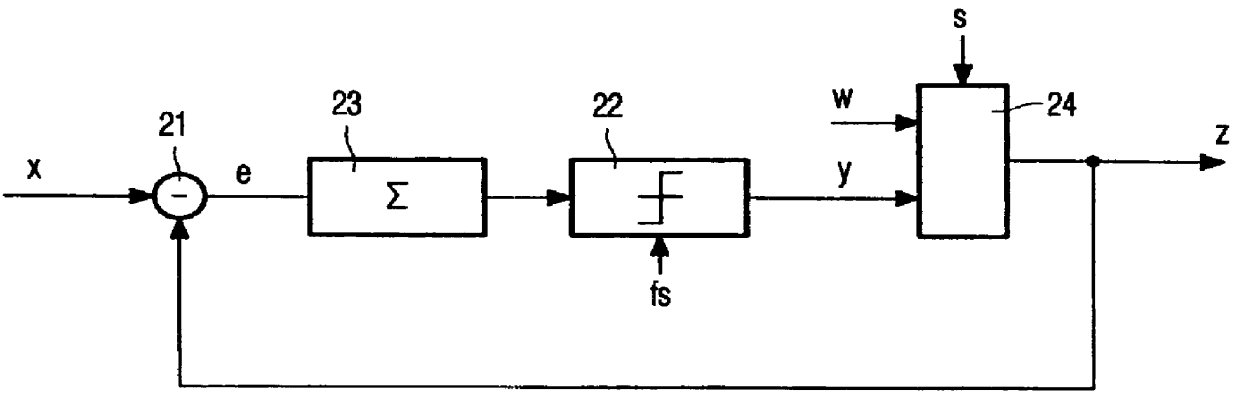
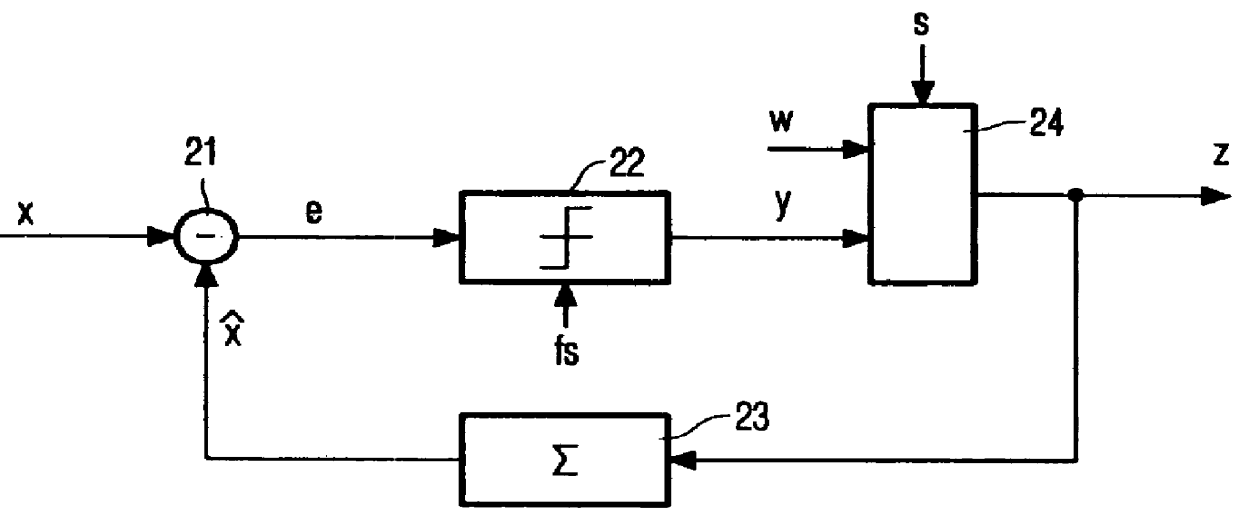
Method of embedding watermarks in a signal encoded by an encoder having a feedback loop, for example, a sigma-delta modulator (21,22,23). A digital watermark pattern (w) is embedded in the signal (z) by modifying selected samples (for example, replacing every 100th bit) of the encoded signal (y) by samples of the watermark pattern. The circuit (24) for modifying the samples is located inside the loop of the encoder. The effect of watermarking is thus compensated in subsequent encoding steps and the signal-to-noise ratio is only slightly affected.
Owner:U S PHILIPS CORP
Authentication of identification documents using digital watermarks
InactiveUS20050094848A1Character and pattern recognitionImage data processing detailsComputer hardwareWatermark method
Digital watermark methods for encoding auxiliary data into a host signal are used to authenticate physical and electronic objects. In one implementation, an identification document includes electronic circuitry. The electronic circuitry includes an image of an authorized bearer of the identification document. The image includes first digital watermarking having a plural-bit identifier. In some cases, the identification document includes a printed image of the authorized bearer of the identification document. The printed image includes second digital watermarking therein. The first digital watermarking and the second digital watermarking can be cross-correlated for authentication of the identification document.
Owner:DIGIMARC CORP +1
Authentication of physical and electronic media objects using digital watermarks
InactiveUS20050135656A1Coin-freed apparatusRecord information storageComputer hardwareWatermark method
Digital watermark methods for encoding auxiliary data into a host signal are used to authenticate physical and electronic objects. One such method computes a content specific message dependent on the host signal, encodes the content specific message into a watermark signal, and embeds the watermark in the host signal such that the watermark signal is substantially imperceptible in the host signal. One specific implementation embeds data representing salient features of the host signal into the watermark. For example, for photo IDs, the method embeds the spatial location of salient features of the photo into the watermark. Another implementation computes a semi-sensitive hash of the host signal, such as a low pass filtering of the signal, and embeds the hash into the watermark. The watermark signal may be content dependent by making the watermark key dependent on some attribute of the signal in which the watermark is embedded. Another approach is to make the watermark key dependent on a user or an attribute of the user. Yet another approach is to use multiple watermark components and multiple watermark detection stages that help identify and screen out invalid watermark signals. Another digital watermarking method for authenticating a media object transforms a media signal to a frequency domain comprising an array of frequency coefficients. It selects a first set of frequency coefficients, and alters the selected first set of frequency coefficients so that values of the coefficients in the set correspond to a pattern. The pattern of the media signal is authenticated by comparing a pattern of the values of the frequency coefficients in the set with an expected pattern.
Owner:DIGIMARC CORP
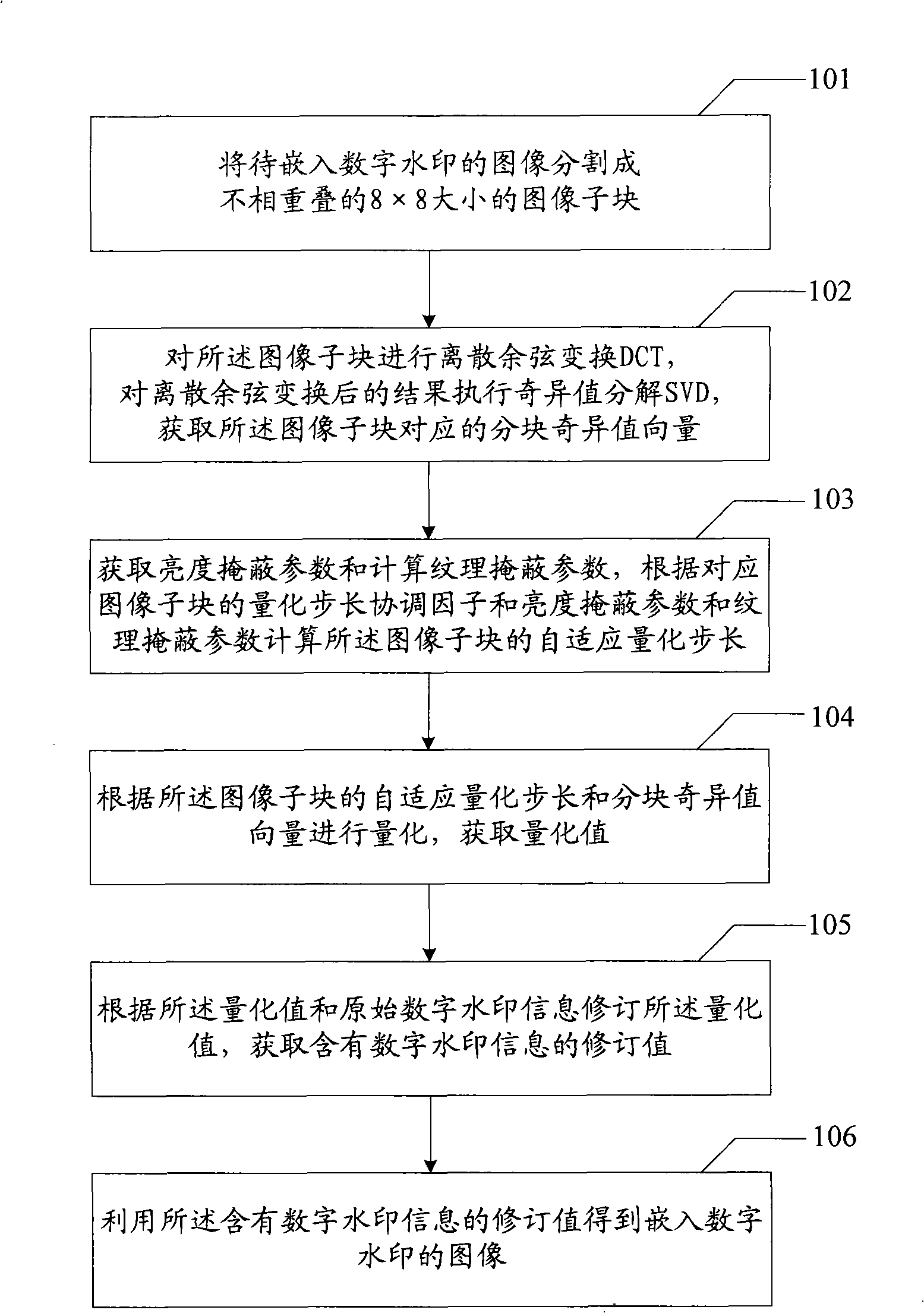
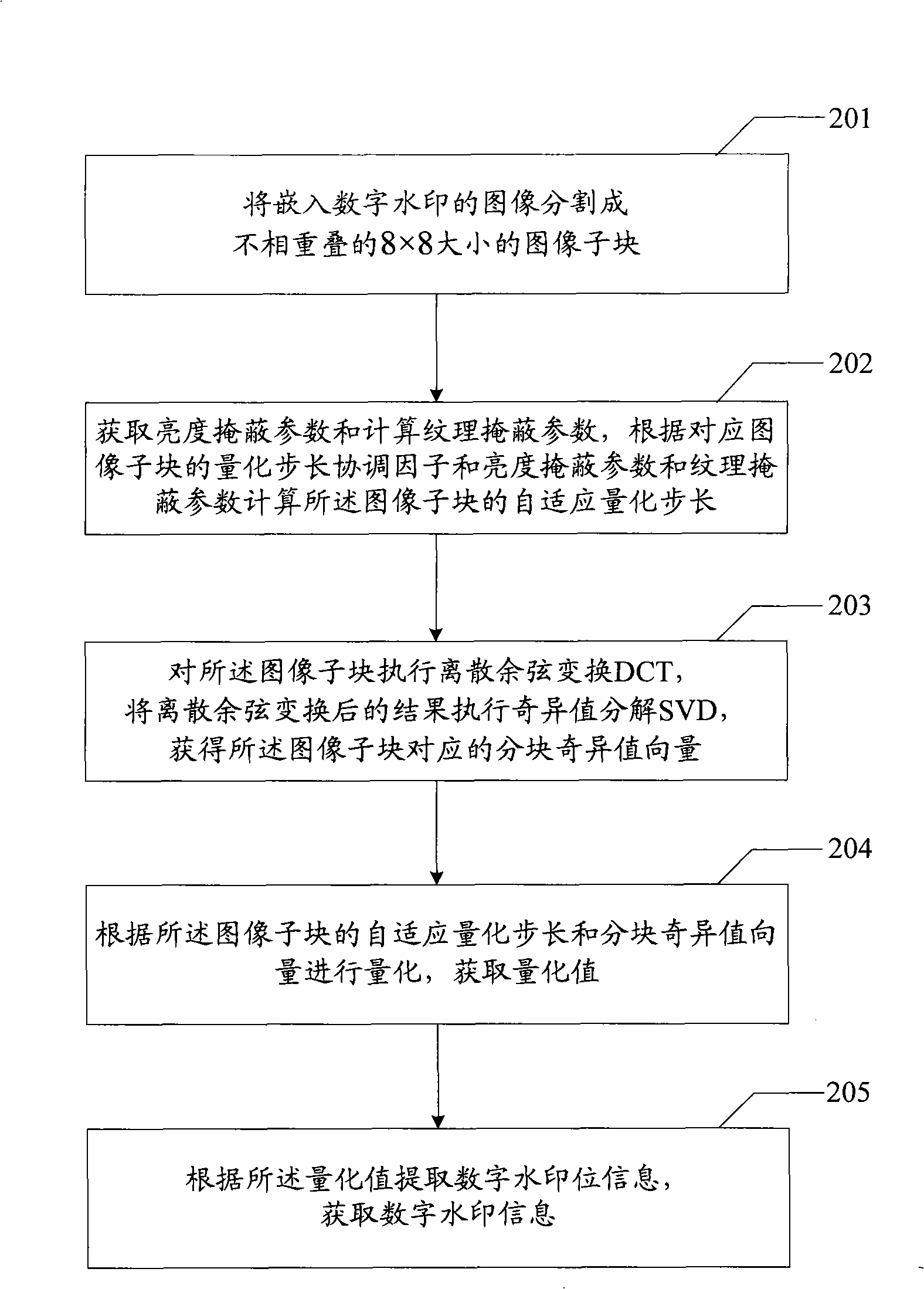
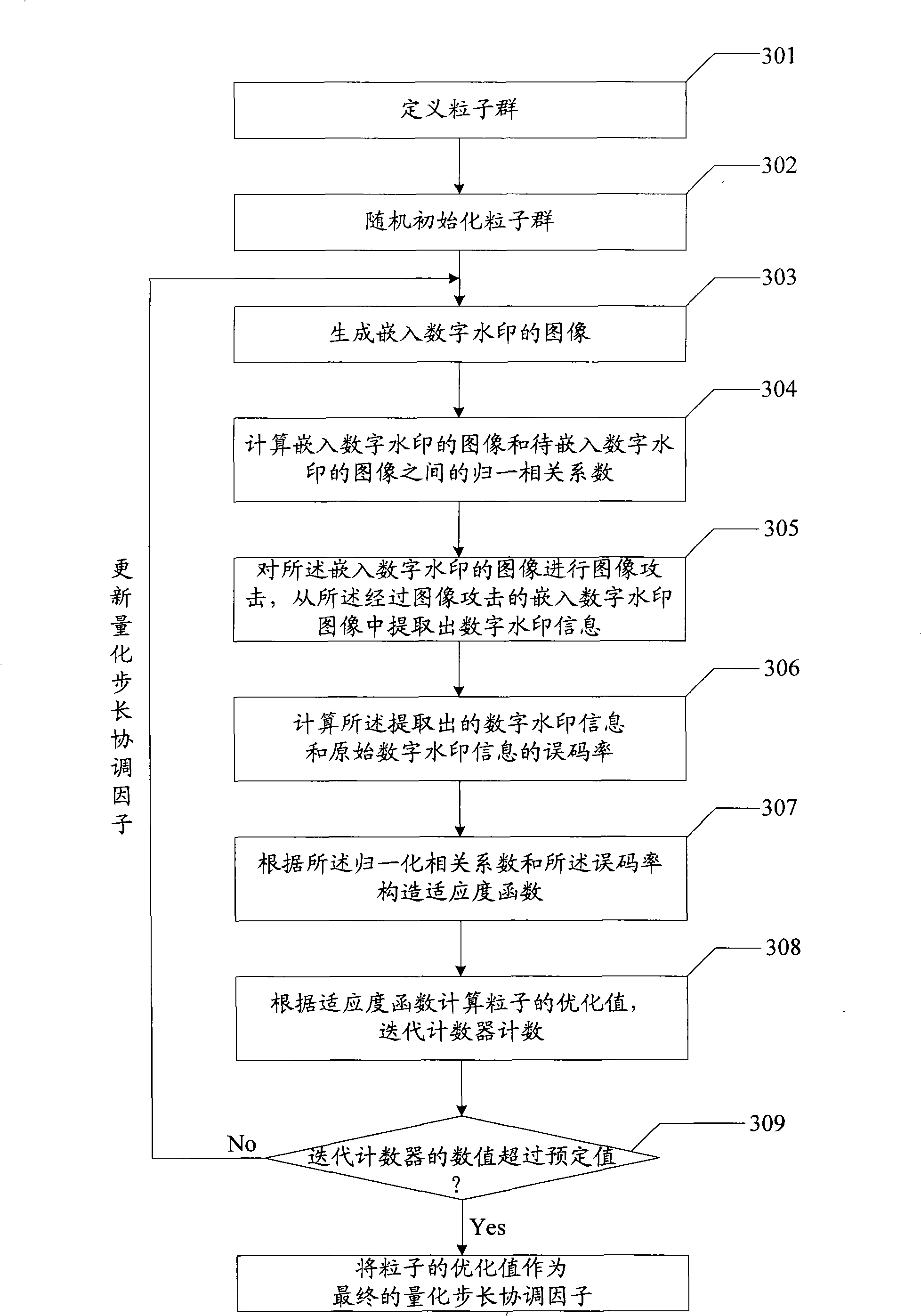
Digital watermarking embedding, extracting and quantizing step size coordinating factor optimizing method and device
The invention relates to an embedding, extracting and quantization step size coordination factor optimizing method of a digital watermark and a device thereof. The embodiment of an embedding method of the digital watermark comprises the steps that: an image to be embedded with the digital watermark is divided into image subblocks with preset size; DCT (discrete cosine transform) is executed to the image subblocks; SVD (singular value transform) is executed to the result after DCT so as to obtain a blocking singular value vector of the image subblocks; a texture masking parameter is calculated to obtain a brightness masking parameter; according to a quantization step size coordination factor, the brightness marking parameter and the texture masking parameter of the image subblocks, a self-adaptive quantization step size of the image subblocks is obtained; the self-adaptive quantization step size of the image subblocks and the blocking singular value vector are quantized to obtain a quantization value; amendment is carried out according to the quantization value and the information of the digital watermark to obtain an amendment value of the information of the digital watermark; and the amendment value containing the information of the digital watermark is utilized to obtain the image embedded with the digital watermark. The embodiment of the invention realizes the balance of the invisibility and the robustness of a digital watermarking method.
Owner:STATE GRID CORP OF CHINA +2
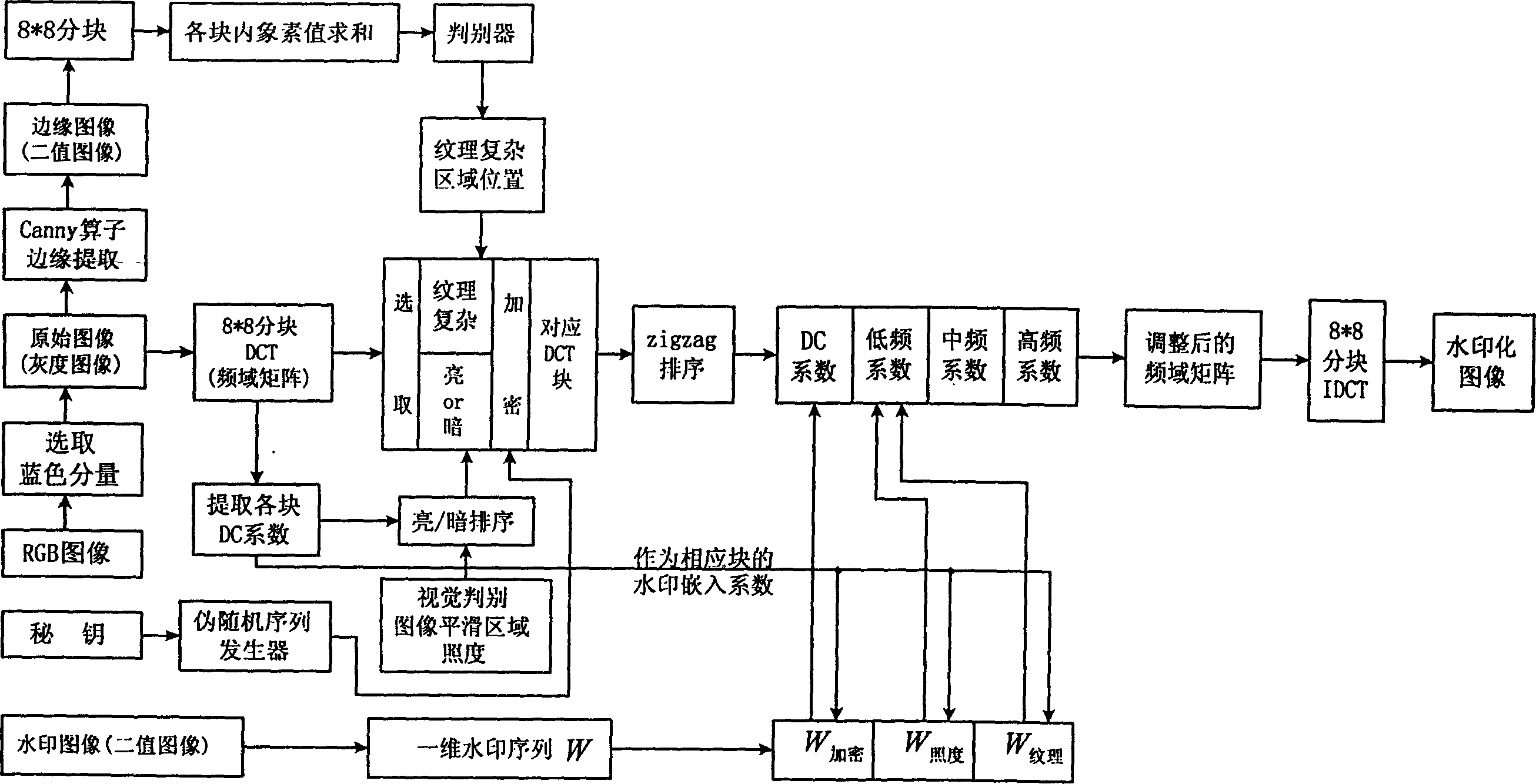
Image waterprint method for copyright protection
InactiveCN1455578AReduce the amount of calculationAvoid complexityTelevision system detailsColor television detailsPattern recognitionImage extraction
The present invention discloses an image watermark way applied to protecting copyright. It converts two-dimensional pels matrix to a two-value sequence group, splits the original image into 8*8 pels in the pels area, and processes discrete cosine conversion to (DCT) convert every pels area to frequency area. By fake radnom selecting block texture selecting block and illumination selecting block, it can conform which area block need to embed the watermark, and can sort them Zigzag. It embeds the encryption part of the watermark sequence group into the direct-current factor position of the random selecting block, also embeds the texture part and illumination part into respective low frequency factor position.
Owner:HEFEI UNIV OF TECH
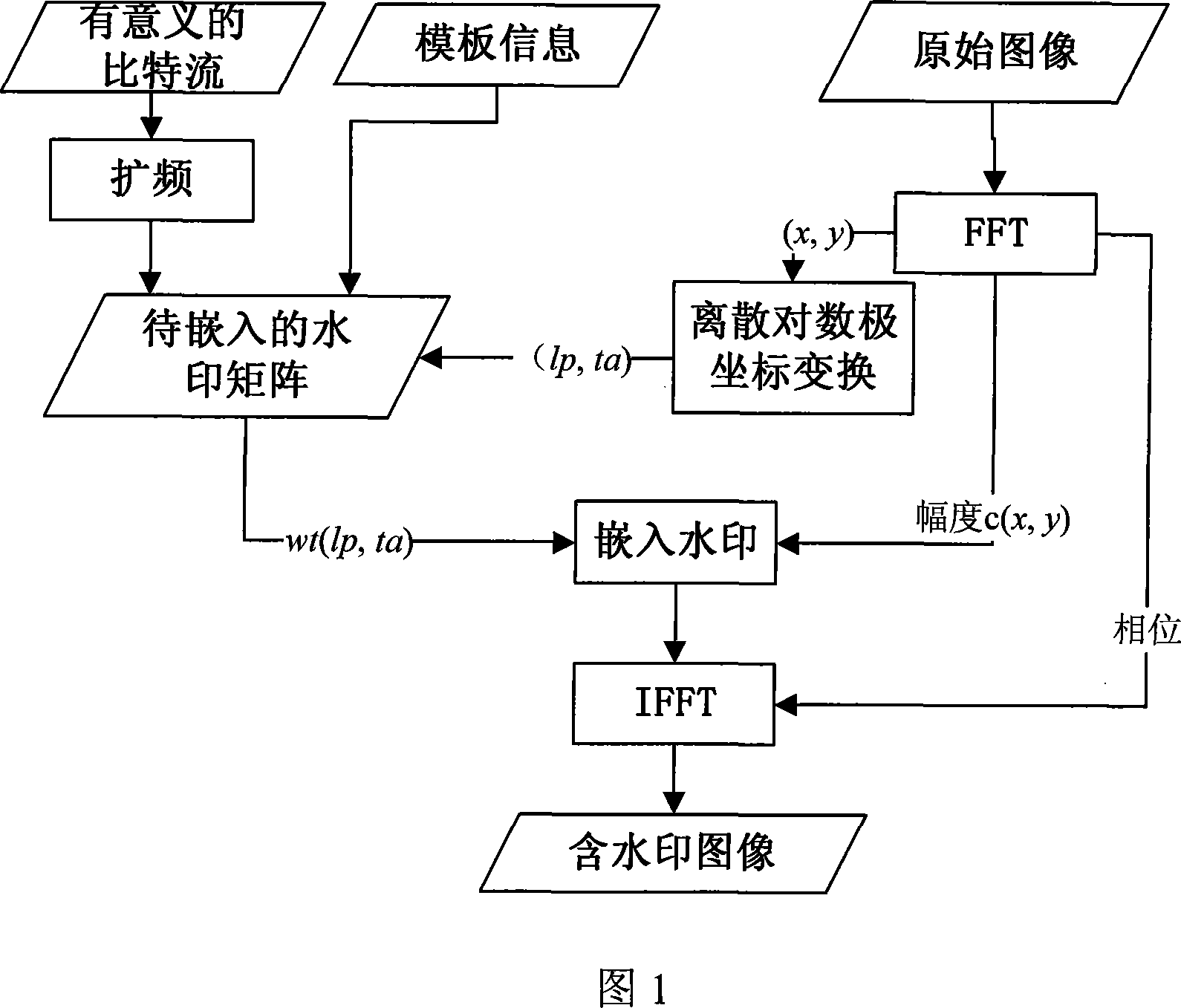
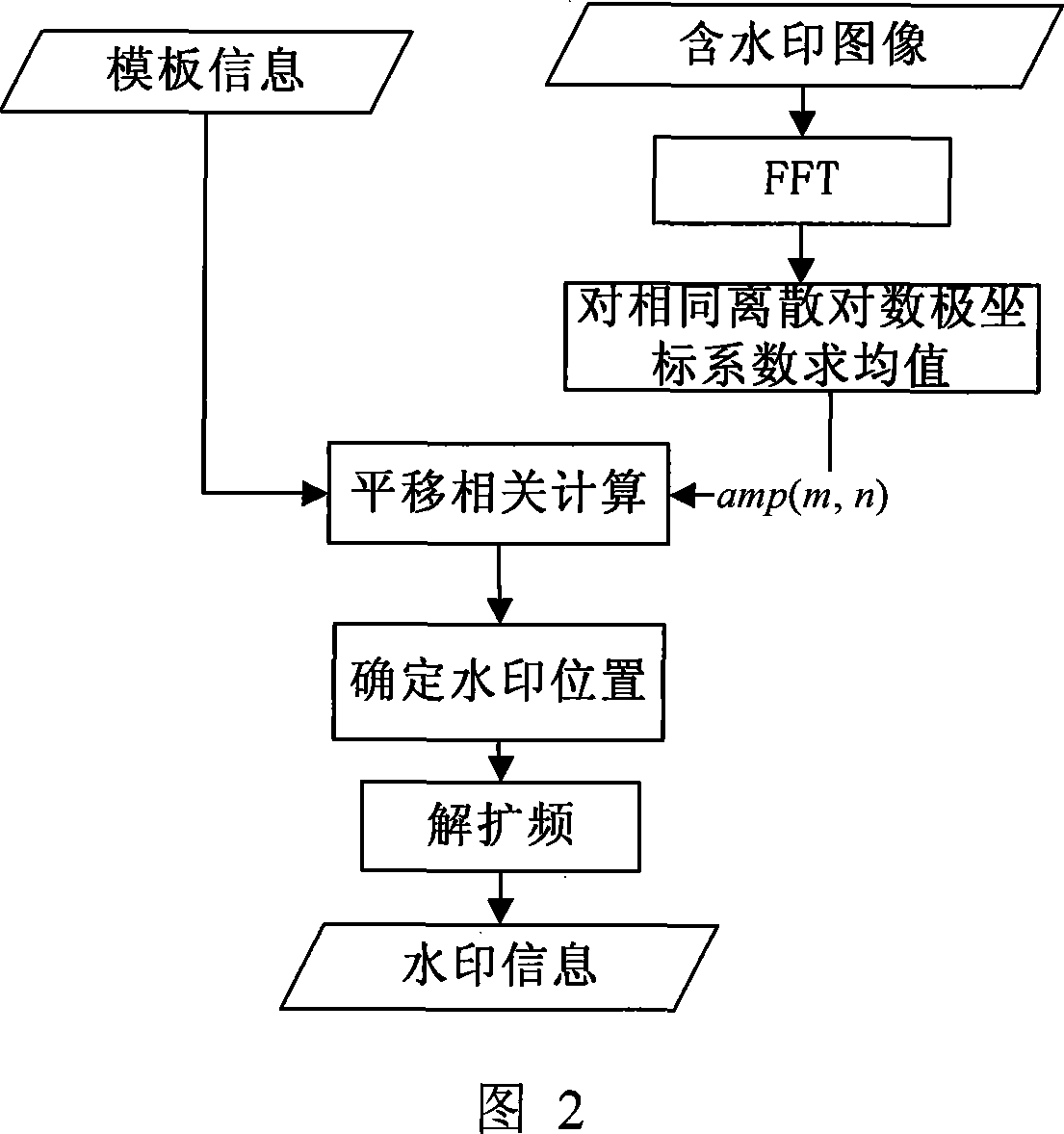
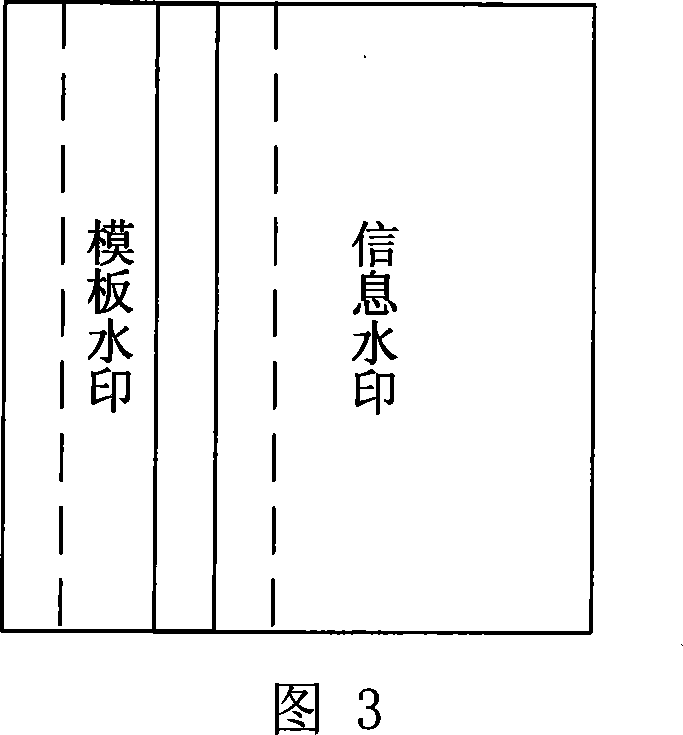
Multiple bit digital watermark method capable of resisting printing, scanning and geometric transformation
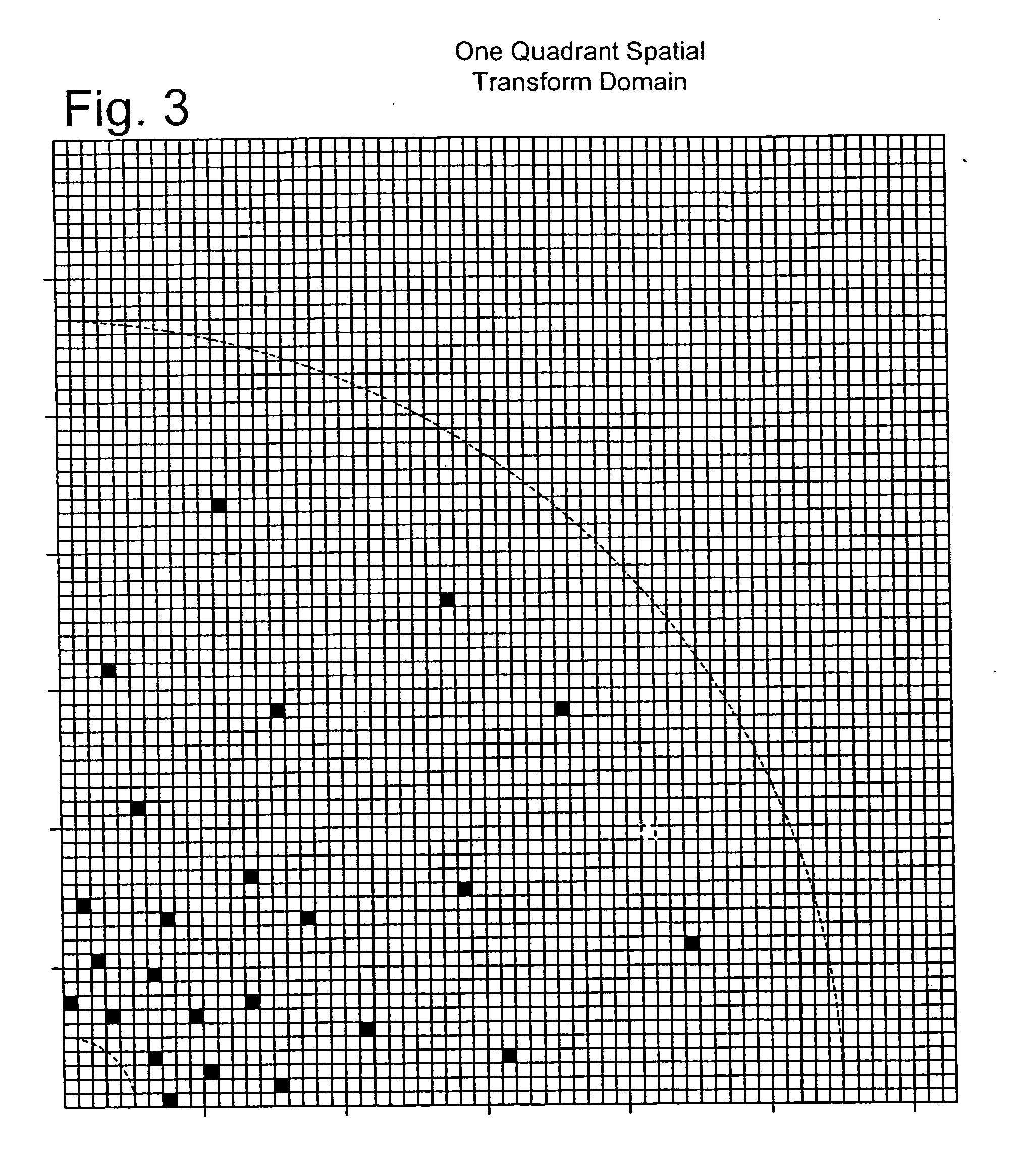
The invention discloses a multi-bit digital watermark method against the print scanning and the geometric transformation, which comprises the following steps: embedding the watermark in dispersion Fourier amplitude coefficient of the image; determining which Fourier amplitude coefficient every watermark bit embeds in according to the dispersion logarithmic polar coordinate of the Fourier amplitude coefficient; making the watermark detecting and extracting out-of-step when the image is carried out the geometric transformation of the pantographic rotating or the print scanning; synchronizing the information watermark according to the relation of the original mode and embedded mold when the watermark is detected and extracted because the pantograph and the rotating of the image corresponds with the translation of the Fourier logarithmic polar coordinate field at the radial and angel direction; extracting the meaning watermark information bit string; introducing the real interpolation and saving the time because the watermark embedding and detecting process doesn' t need the image interpolation arithmetic for the image and the Fourier amplitude coefficient; protecting the embedded mode. The invention can apply to the copyright protection of the digital image and video, false proof of the file and evidence, the monitoring of video broadcast.
Owner:SUN YAT SEN UNIV
Authentication of Physical and Electronic Media Objects Using Digital Watermarks
InactiveUS20090067671A1Character and pattern recognitionSecret communicationComputer hardwareWatermark method
Digital watermark methods for encoding auxiliary data into a host signal are used to authenticate physical and electronic objects. One such method computes a content specific message dependent on the host signal, encodes the content specific message into a watermark signal, and embeds the watermark in the host signal such that the watermark signal is substantially imperceptible in the host signal. One specific implementation embeds data representing salient features of the host signal into the watermark. For example, for photo IDs, the method embeds the spatial location of salient features of the photo into the watermark. Another implementation computes a semi-sensitive hash of the host signal, such as a low pass filtering of the signal, and embeds the hash into the watermark. The watermark signal may be content dependent by making the watermark key dependent on some attribute of the signal in which the watermark is embedded. Another approach is to make the watermark key dependent on a user or an attribute of the user. Yet another approach is to use multiple watermark components and multiple watermark detection stages that help identify and screen out invalid watermark signals. Another digital watermarking method for authenticating a media object transforms a media signal to a frequency domain comprising an array of frequency coefficients. It selects a first set of frequency coefficients, and alters the selected first set of frequency coefficients so that values of the coefficients in the set correspond to a pattern. The pattern of the media signal is authenticated by comparing a pattern of the values of the frequency coefficients in the set with an expected pattern.
Owner:DIGIMARC CORP
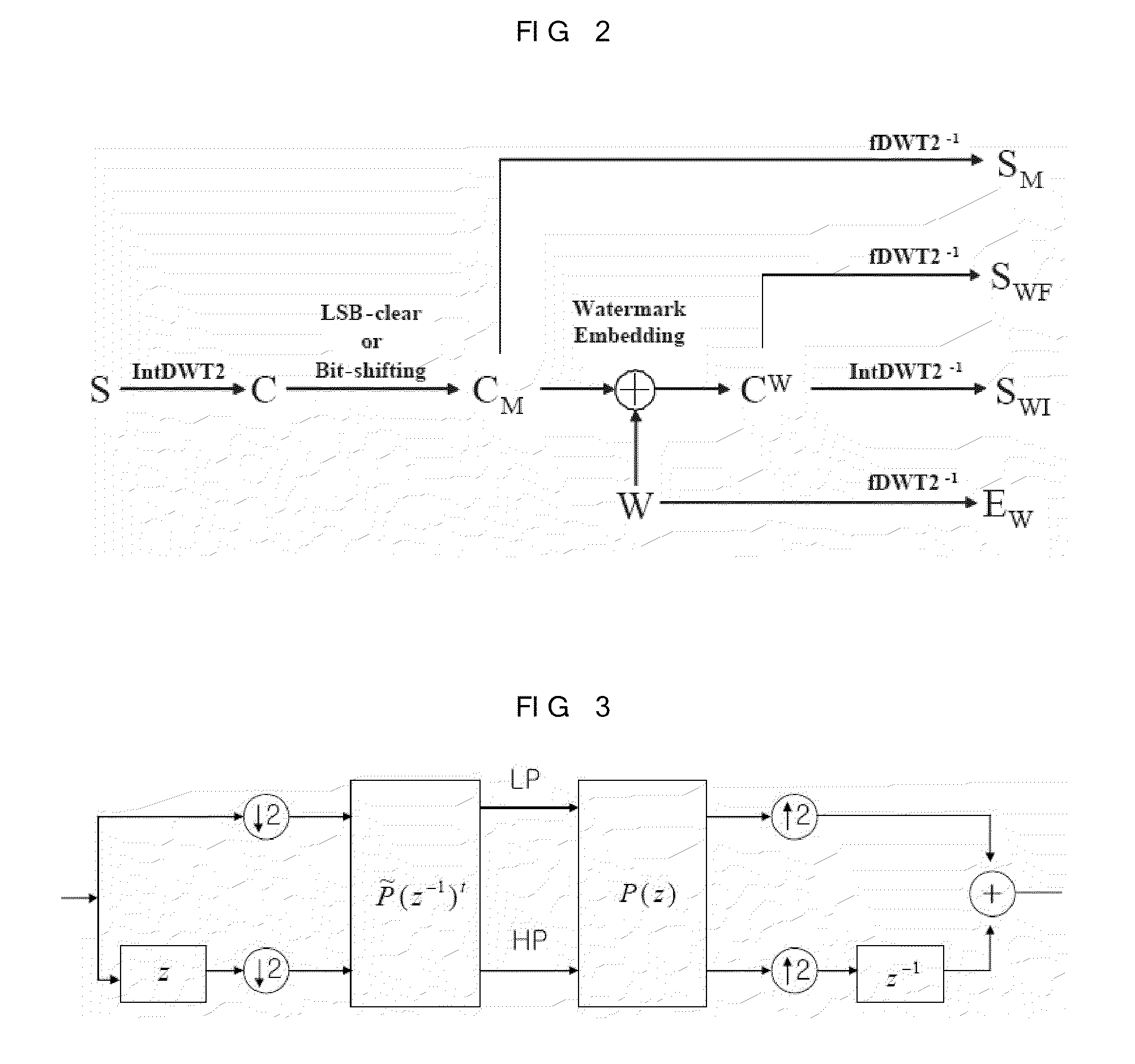
Method For Reversible Image Watermarking Based On Integer-to-Integer Wavelet Transform
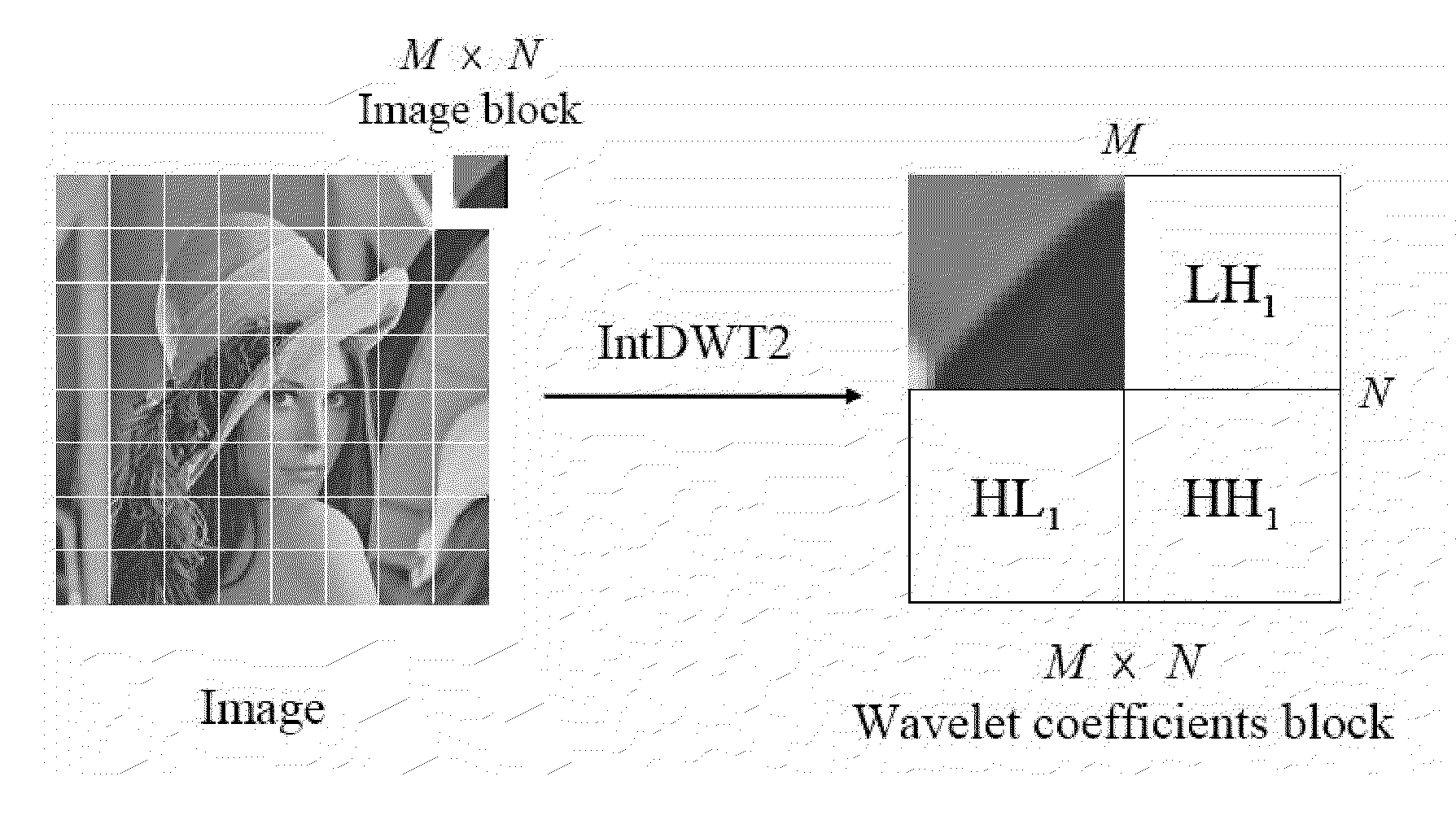
ActiveUS20090116685A1Increase embedding capacityImprove perceived qualityTelevision system detailsCharacter and pattern recognitionWaveletInteger wavelet transform
Enhanced method for embedding watermarks based on integer-to-integer wavelet transform is provided. The method according to the present invention includes the steps of: (A) dividing an original image (X×Y) to a plurality of image blocks (M×N); (B) selecting image blocks for embedding an location information that indicates image blocks to be watermarked;(C) embedding the location information into the image blocks selected in the step (B); and (D) embedding watermarks into remaining image blocks which are not selected in the step (B).
Owner:KOREA ADVANCED INST OF SCI & TECH
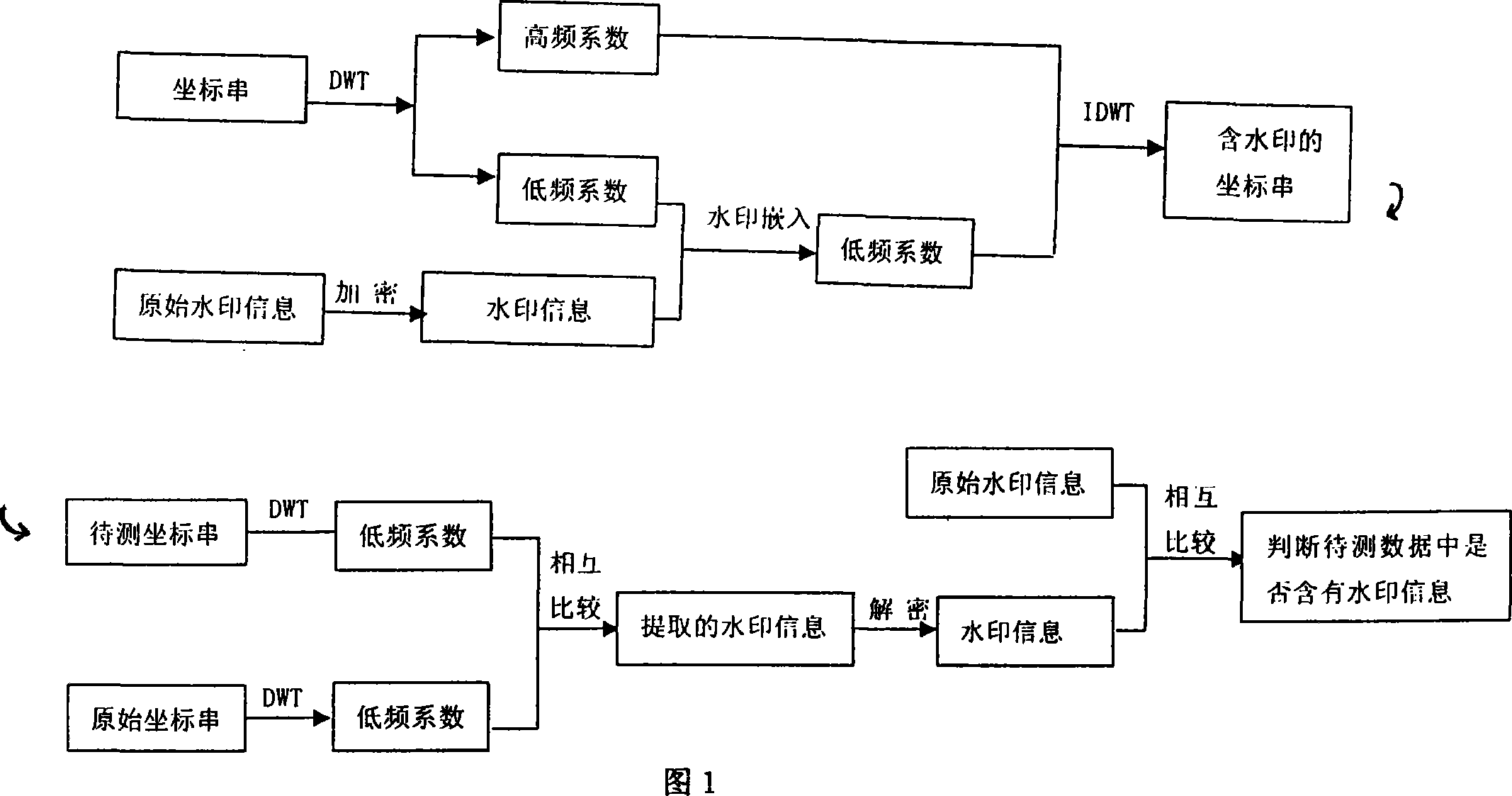
Watermark method of vectorial geographical spatial data based on integral wavelet transforms
InactiveCN101093574AImprove robustnessStrong anti-noise abilityImage data processing detailsWatermark methodGeographic space
A vector geographic space data watermarking-method based on integer wavelet transform includes fetching original vector geographic space data from mapping databank, enciphering watermark information with chaos sequence, carrying out integer wavelet transform on coordinate string of said geographic space data and embedding watermark information into low frequency coefficient of wavelet transform; picking up watermark information by comparing wavelet coefficient mutual relation of data string to be tested to original reference data string when watermark is required to be picked up.
Owner:THE PLA INFORMATION ENG UNIV
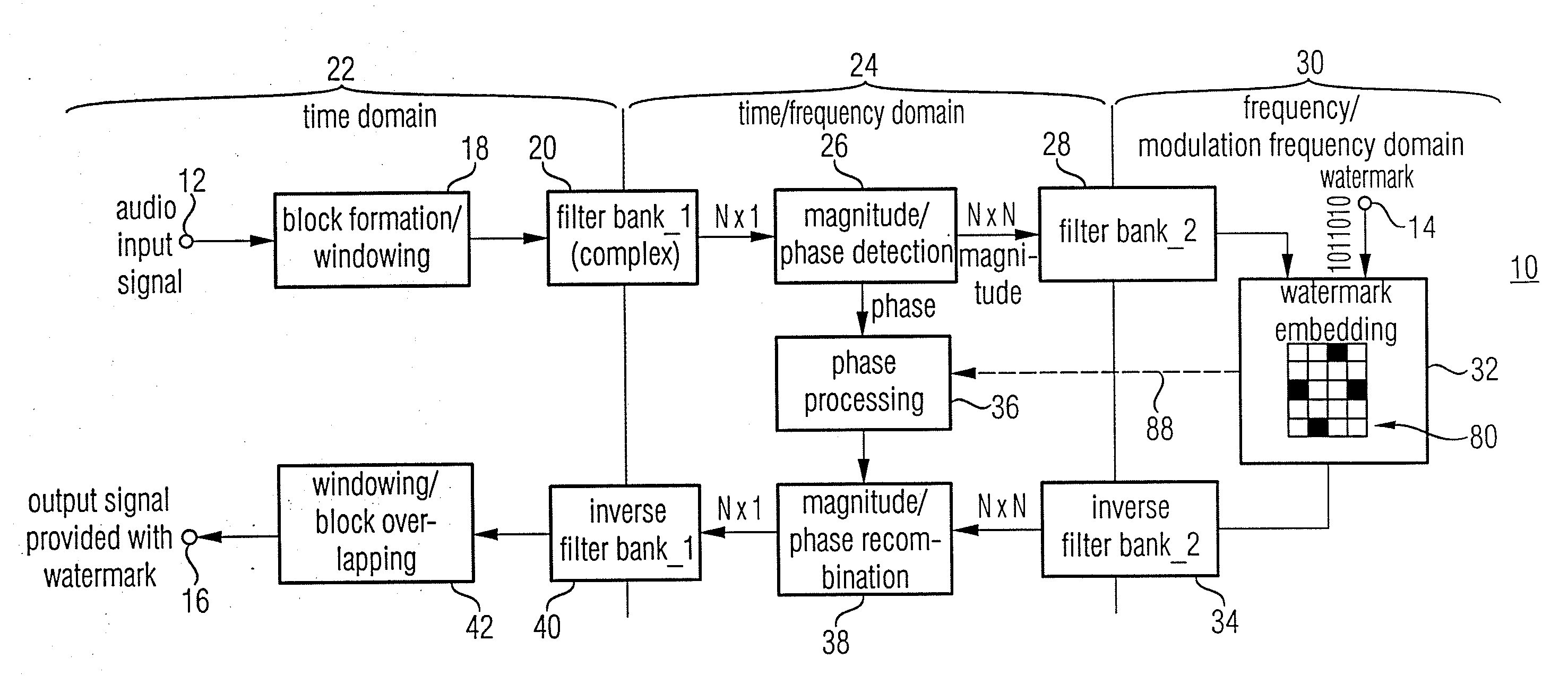
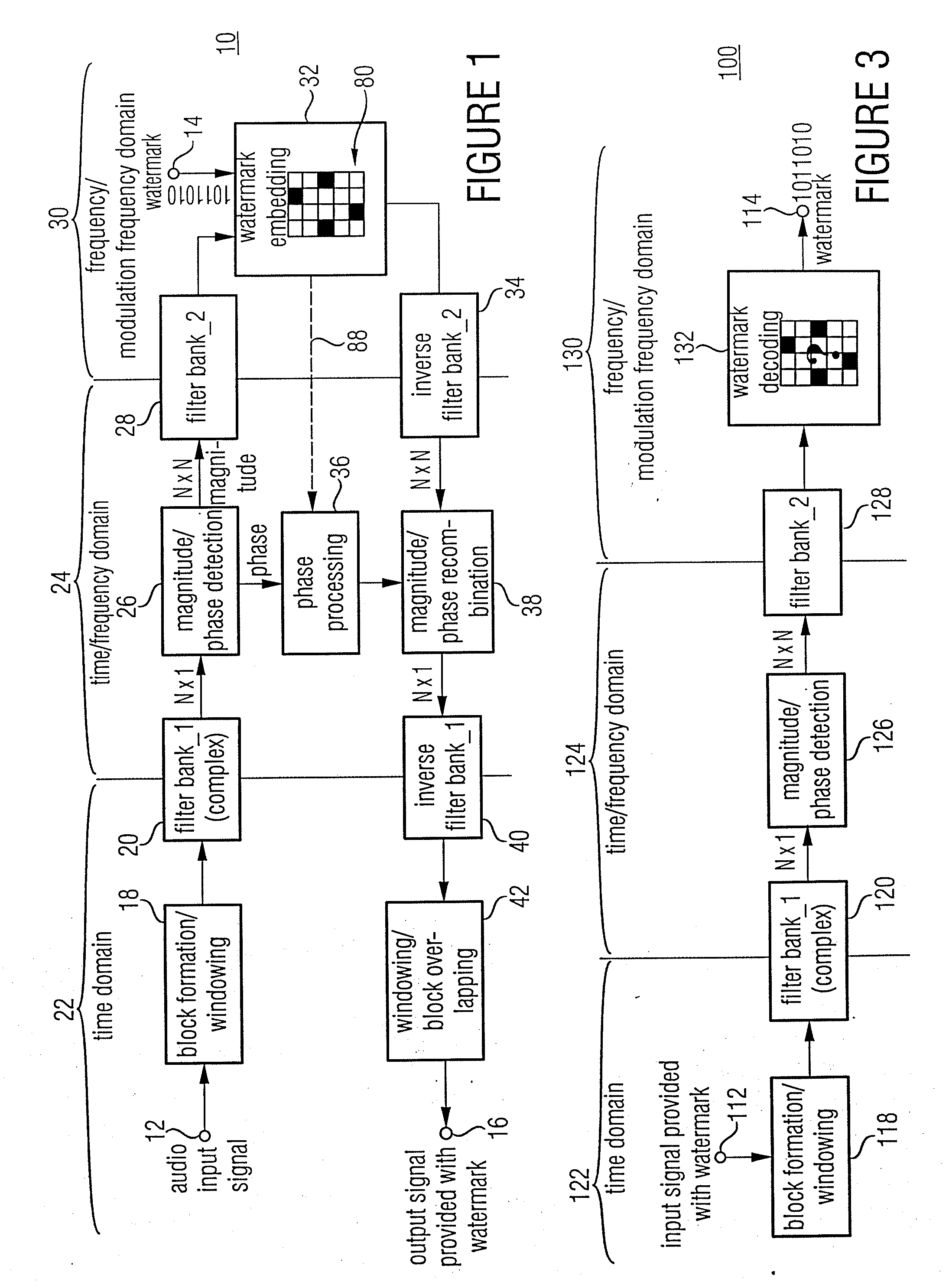
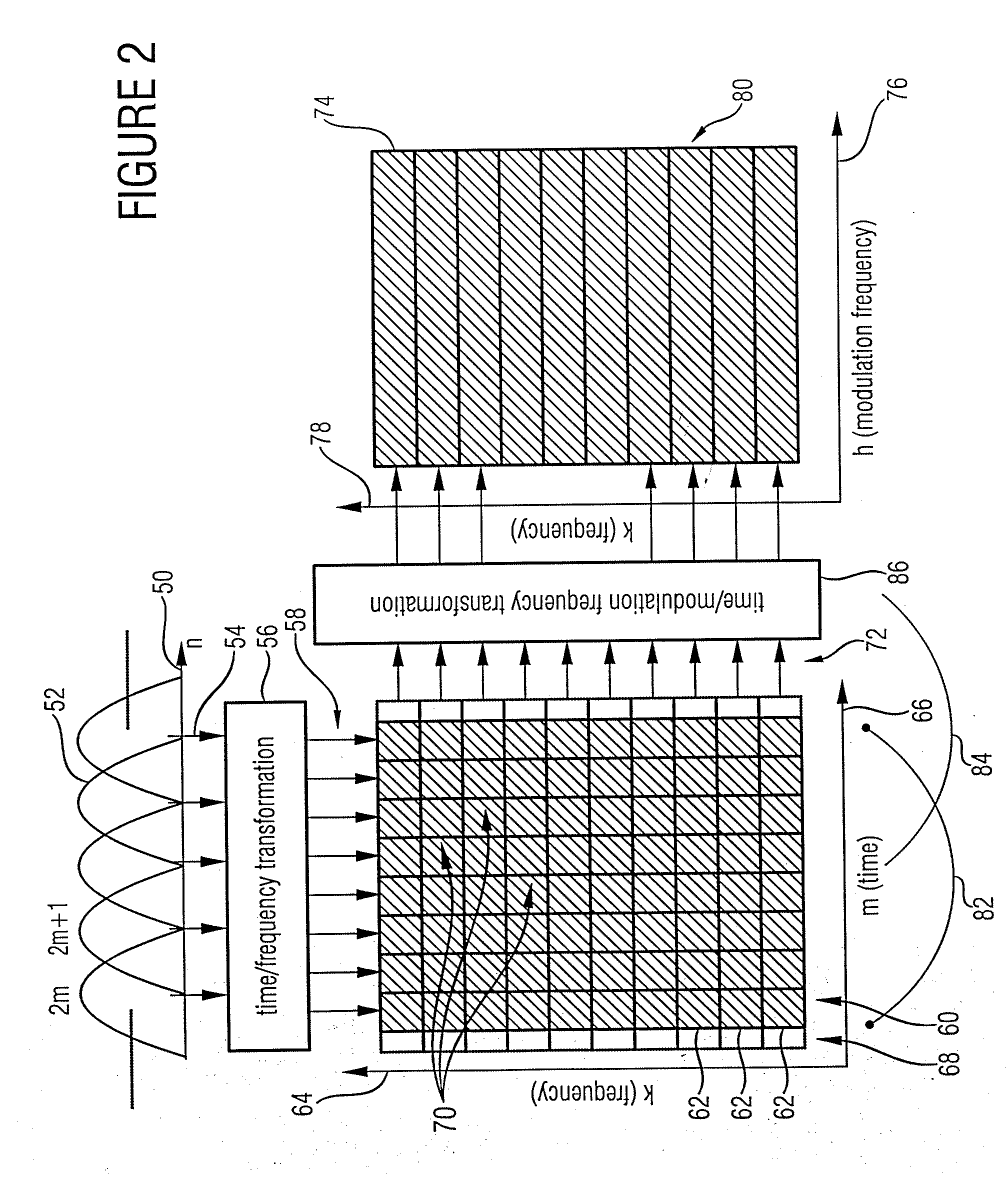
Watermark Embedding
ActiveUS20080027729A1Simple processSpectral/fourier analysisAmplifier modifications to reduce noise influenceFrequency spectrumWatermark method
According to an inventive scheme for introducing a watermark into an information signal, the information signal is at first transferred from a time representation to a spectral / modulation spectral representation). The information signal is then manipulated in the spectral / modulation spectral representation in dependence on the watermark to be introduced to obtain a modified spectral / modulation spectral representation, and subsequently an information signal provided with a watermark is formed based on the modified spectral / modulation spectral representation. An advantage is that, due to the fact that the watermark is embedded and / or derived in the spectral / modulation spectral representation or range, traditional correlation attacks as are used in watermark methods based on a spread-band modulation cannot succeed easily.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
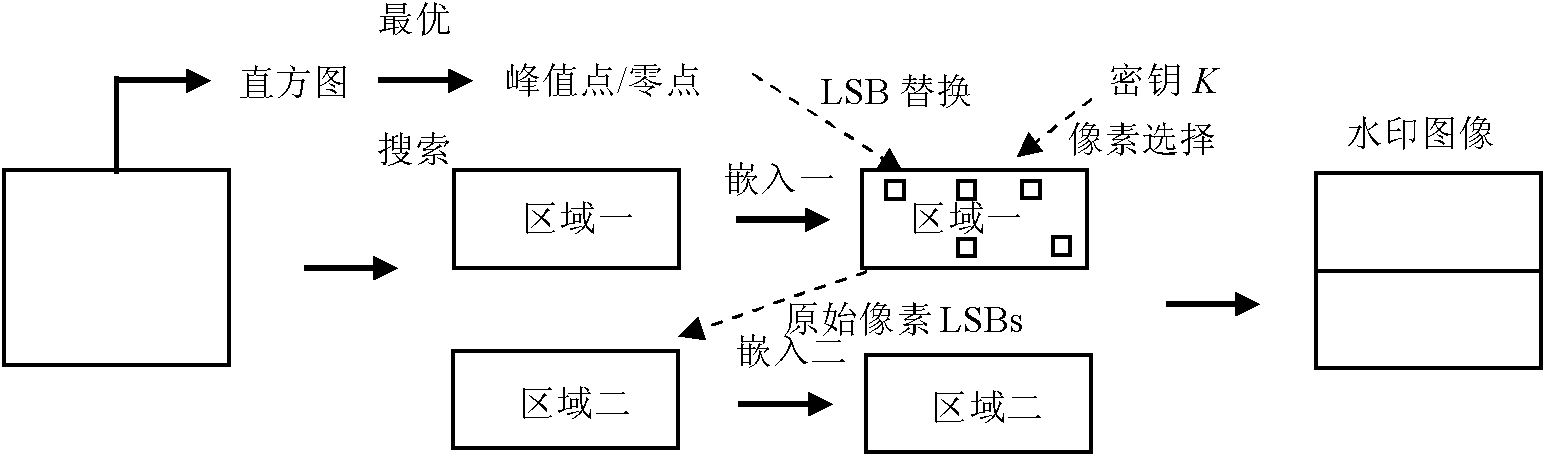
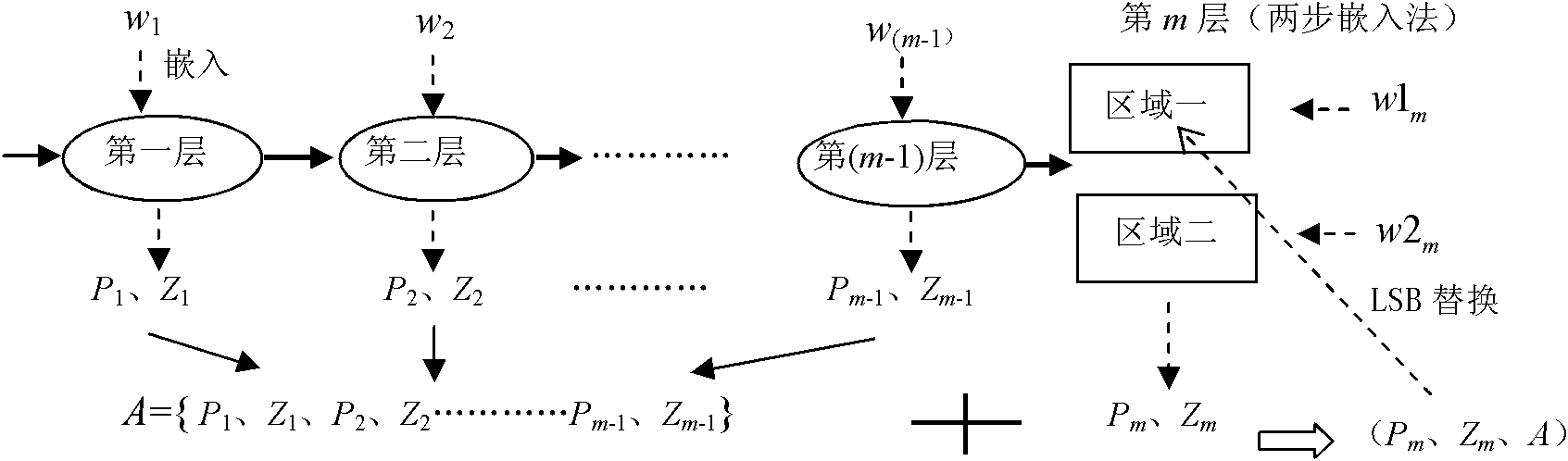
Reversible watermark method utilizing histogram shifting
InactiveCN102567942AReduce sizeEasy to compressImage data processing detailsProgram/content distribution protectionBit blitGeneration process
The invention provides a reversible watermark method based on histogram shifting and has significant practical values for protecting multimedia copyrights. By means of the reversible watermark method, traditional histogram shifting algorithms are improved in two aspects, firstly, 1 and 0 in a bite map are more imbalanced by arranging a generation process of the bit map on watermark embedding rather than in a non-pretreatment stage, so that compression is easier, and embedding capacity is improved; and secondly, the reversible watermark method is a two-step embedding method. The watermark blind extraction is achieved and troubles that the histogram shifting method needs extra side information transmitting are solved by dividing an image into an upper large area and a lower large area, subjecting the upper area to the watermark embedding, embedding the generated side information into the lowest significant bit containing watermark pixels in the area, and embedding the left watermark information and the replaced lowest significant information into the lower area.
Owner:SUN YAT SEN UNIV
Vector map watermark method based on object property characteristic
InactiveCN101458810AZero damageImprove the immunityImage data processing detailsObject basedGrid density
The invention provides a vector map watermark method based on object property characteristics, comprising: using user input to generate watermark codes needed to be embedded; according to watermark capacity, defining the scale of the watermark formed by watermark objects that embedded into object set; for the vector map of the object watermark, using a modified grid density spatial cluster analysis method to generate a watermark embedded target set; in the property document of the vector map, searching the property characteristic information corresponding to the vector object in the embedded target set; according to the watermark information generated in the step (1), randomly selecting the vector element in the generated watermark embedded target set, embedding watermark code into the property coordinate information of the element; disordering the vector formed by all vector object sequences embedded by watermark marks, storing iteration number as a key; reading vector map property document, using a watermark detection program to extract watermark information, and judging the watermark existence state of map carrier according to watermark similarity.
Owner:HARBIN ENG UNIV
Image digital watermark method
InactiveCN1517855AOvercoming invisibilityOvercoming the Contradictions Between RobustnessImage enhancementTelevision system detailsTime domainWatermark method
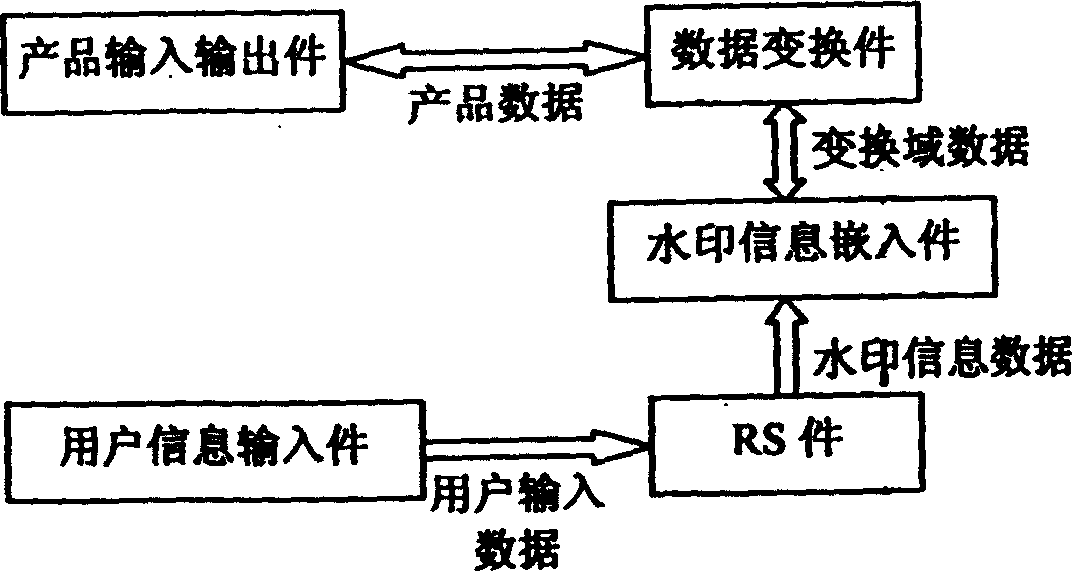
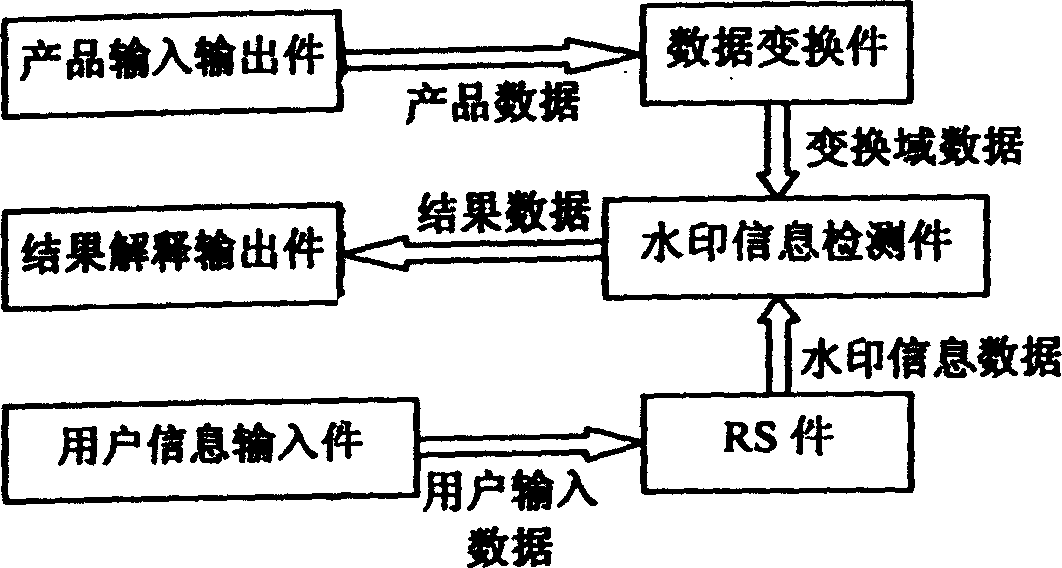
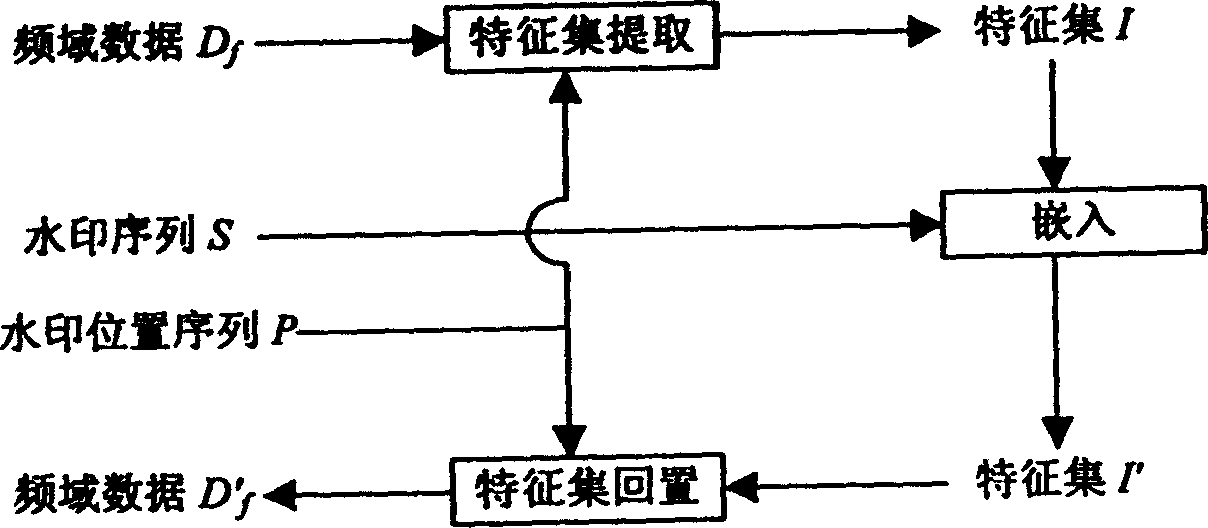
A digital watermark method for image includes such steps as inputting product data, converting it to frequency domain data, inputting private information of user, generating watermark information by RS unit, embedding the watermark into the frequency domain of product, converting it to airspace time domain to become product data, outputting the product with watermark. The watermark check includes converting the product data to frequency domain data, generating check information from private information, correlation analyzing between said frequency domain data and check information, and explaining.
Owner:成都市宇飞信息工程有限公司
Method and system for adding and detecting watermark
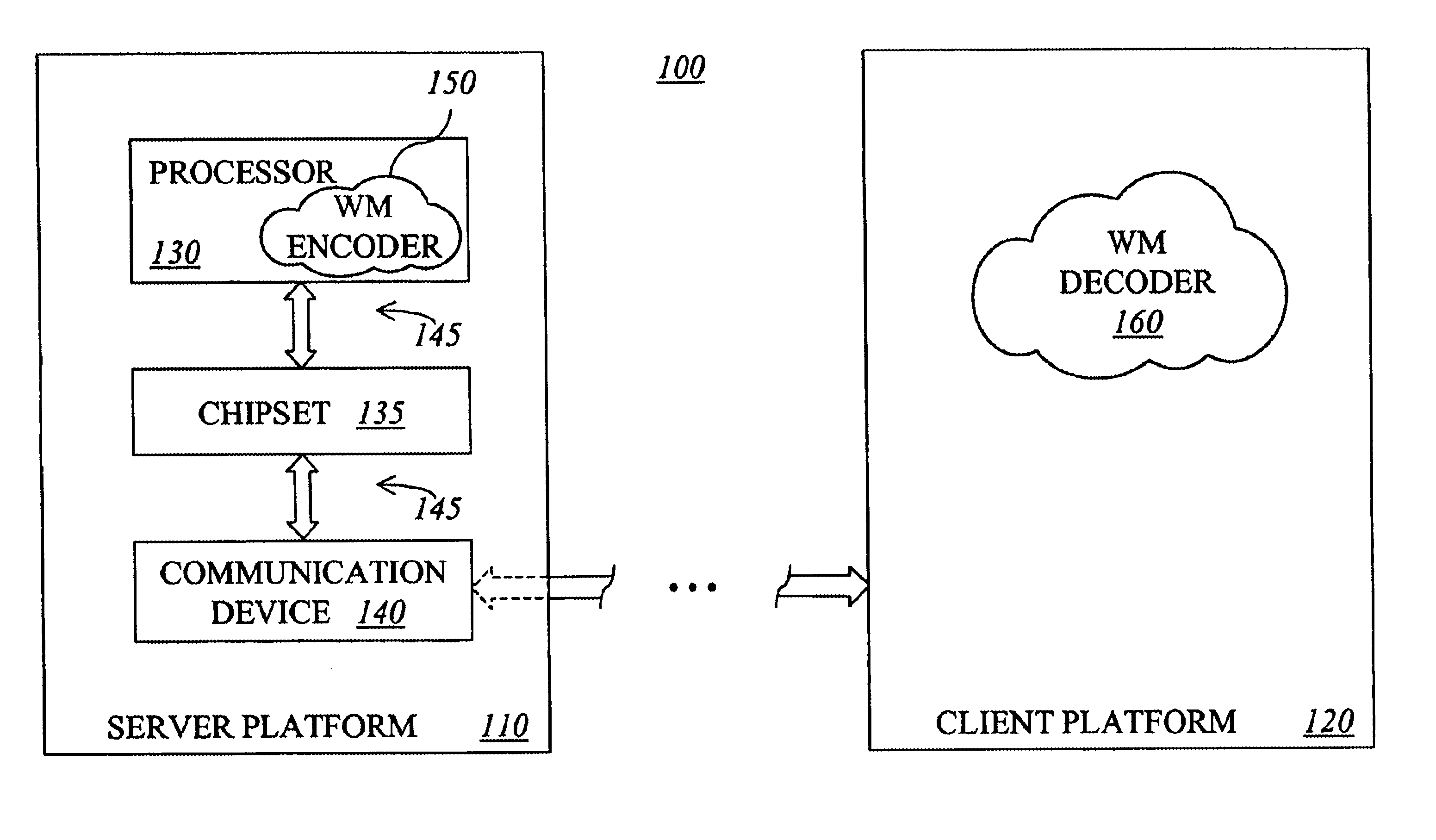
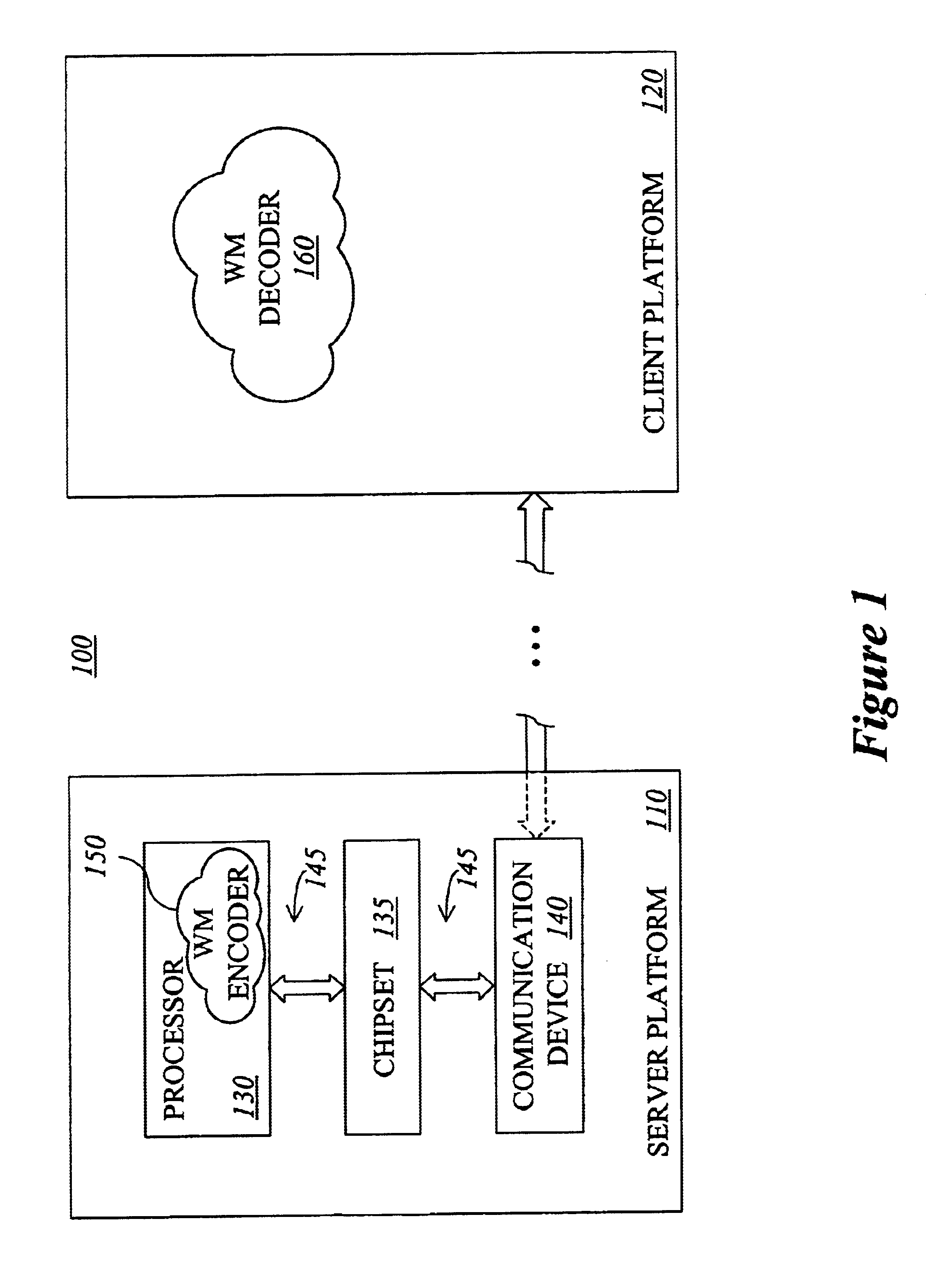
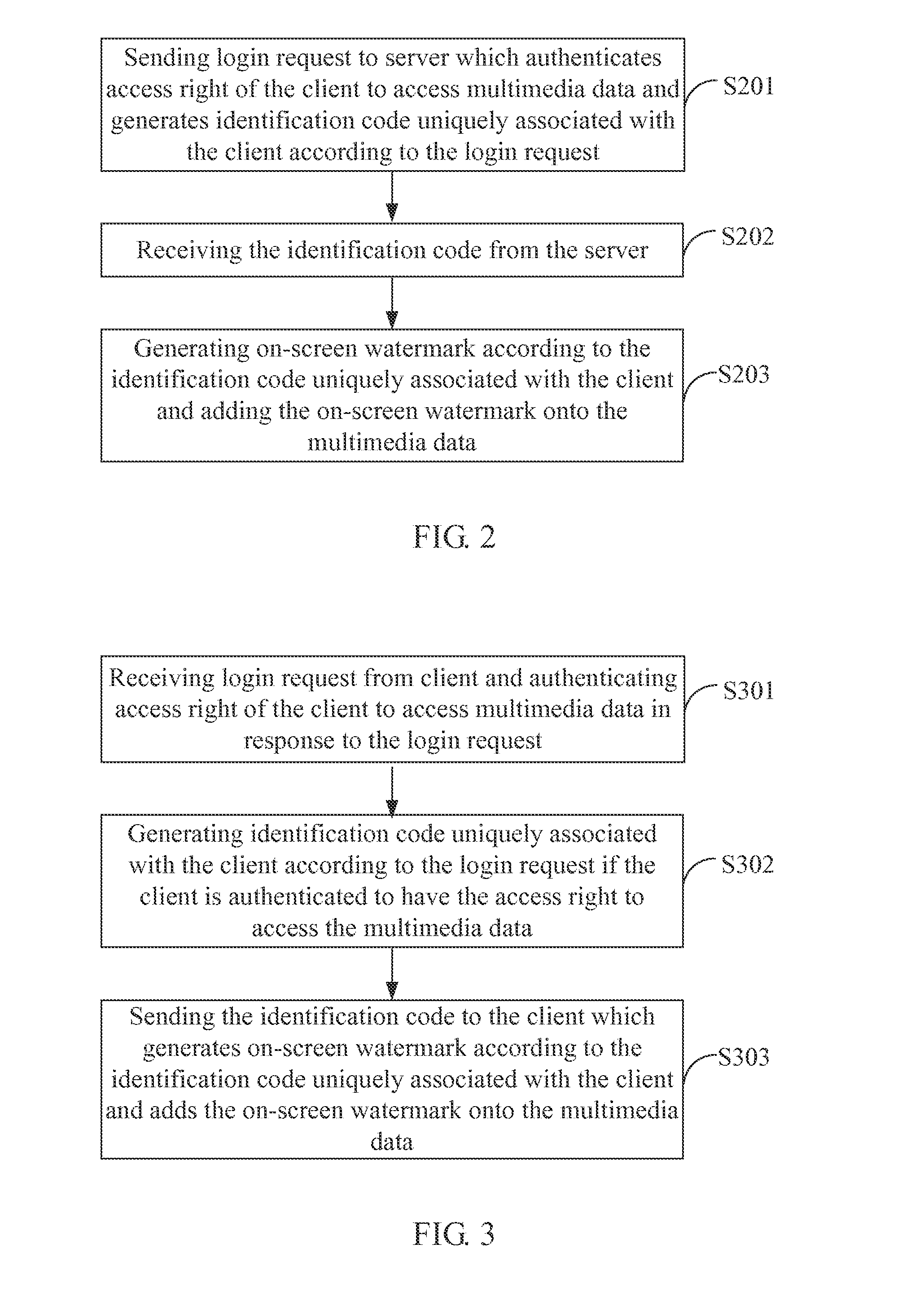
ActiveUS20140219495A1Character and pattern recognitionImage data processing detailsWatermark methodClient-side
A watermarking method and system are provided. The watermarking system includes a server and a client in communication with each other. At first, the client sends a login request to the server. The server authenticates an access right of the client to access specific multimedia data and generates an identification code uniquely associated with the client according to the login request if the client is authenticated to have the access right to access the multimedia data. An on-screen watermark is generated according to the identification code and added onto the multimedia data to be played. The watermark-generating and adding step may be performed by either the server or the client. The on-screen watermark can be detected by a watermark-detecting method and system to trace privacy source.
Owner:TENCENT TECH (SHENZHEN) CO LTD
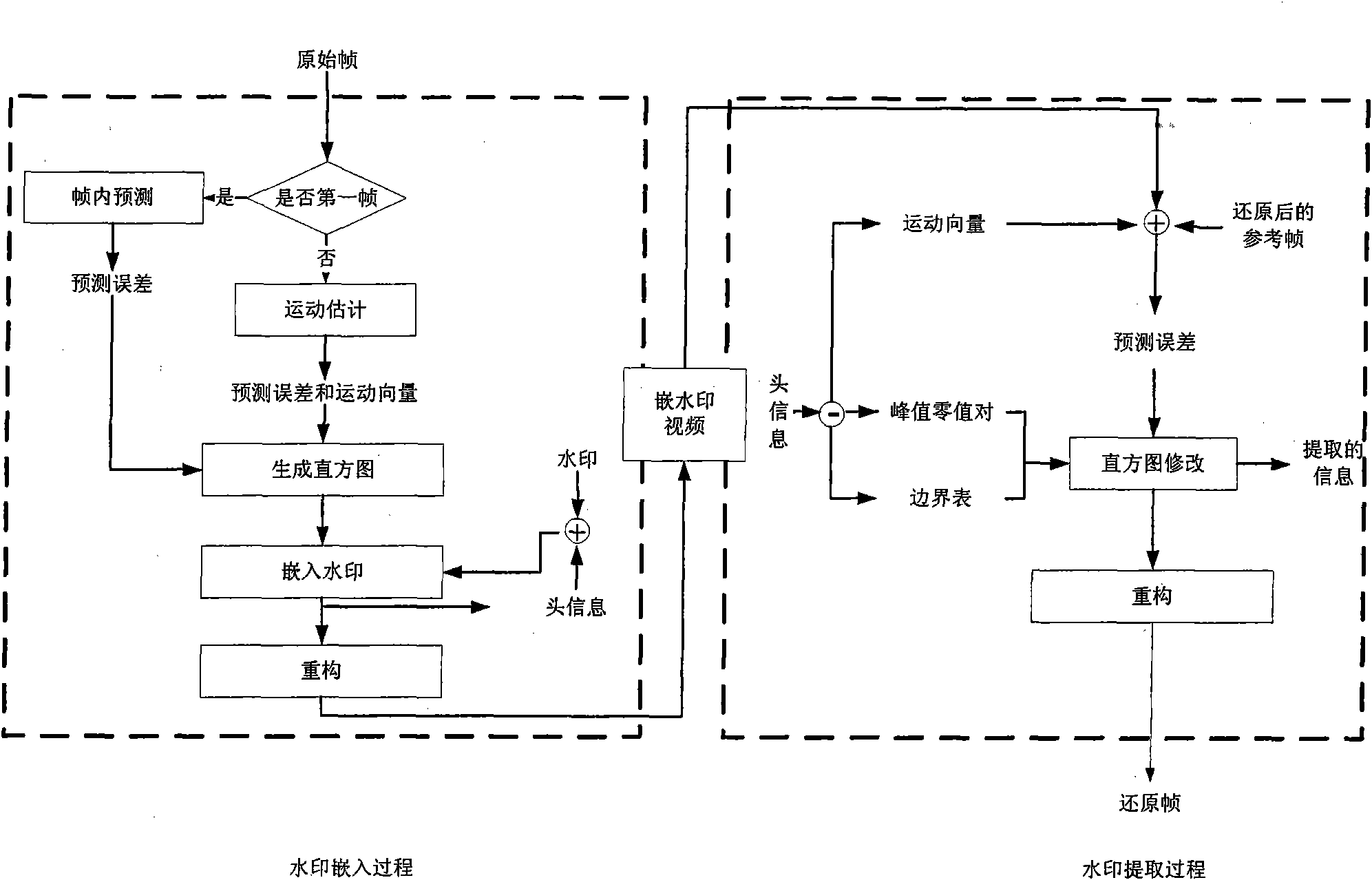
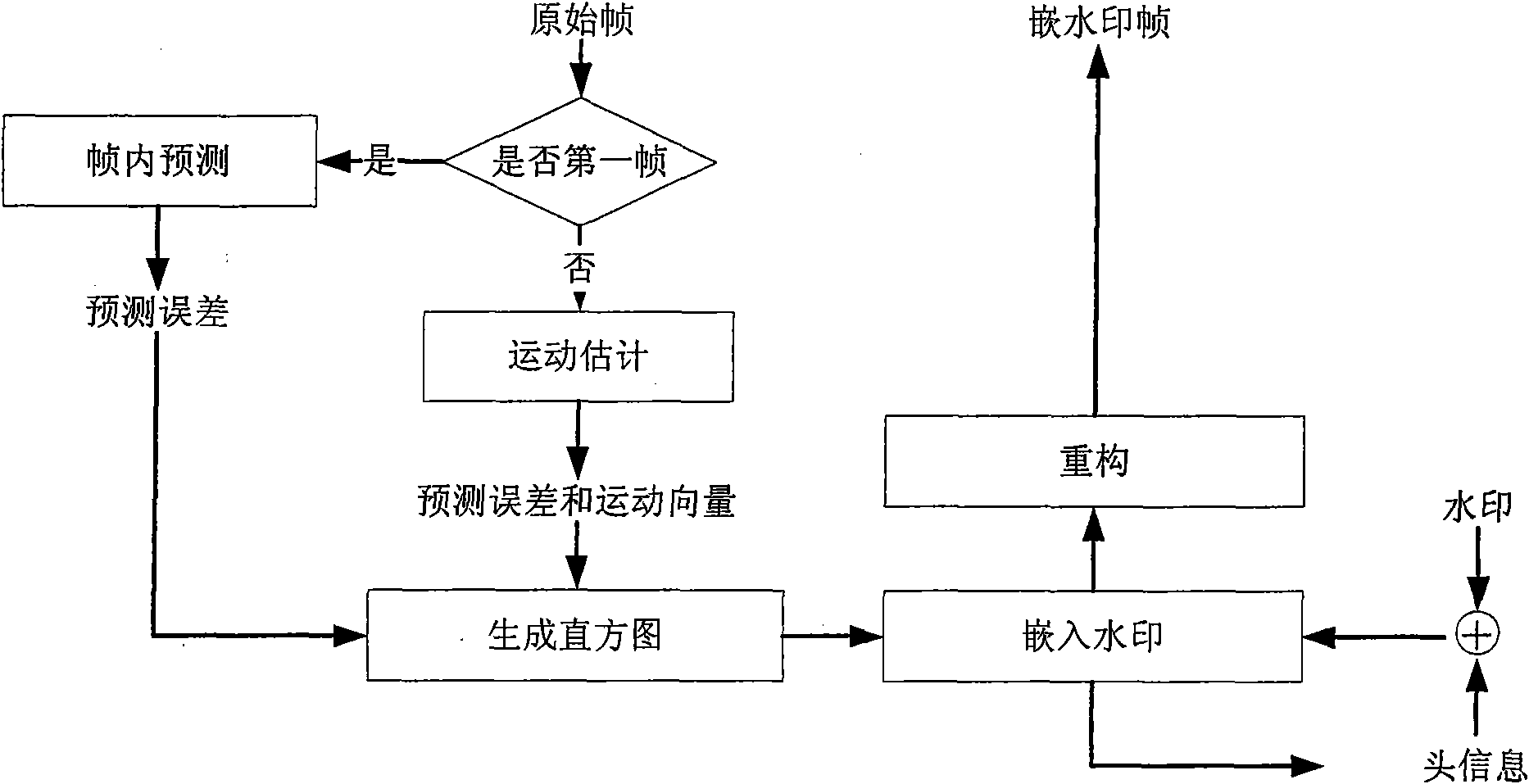
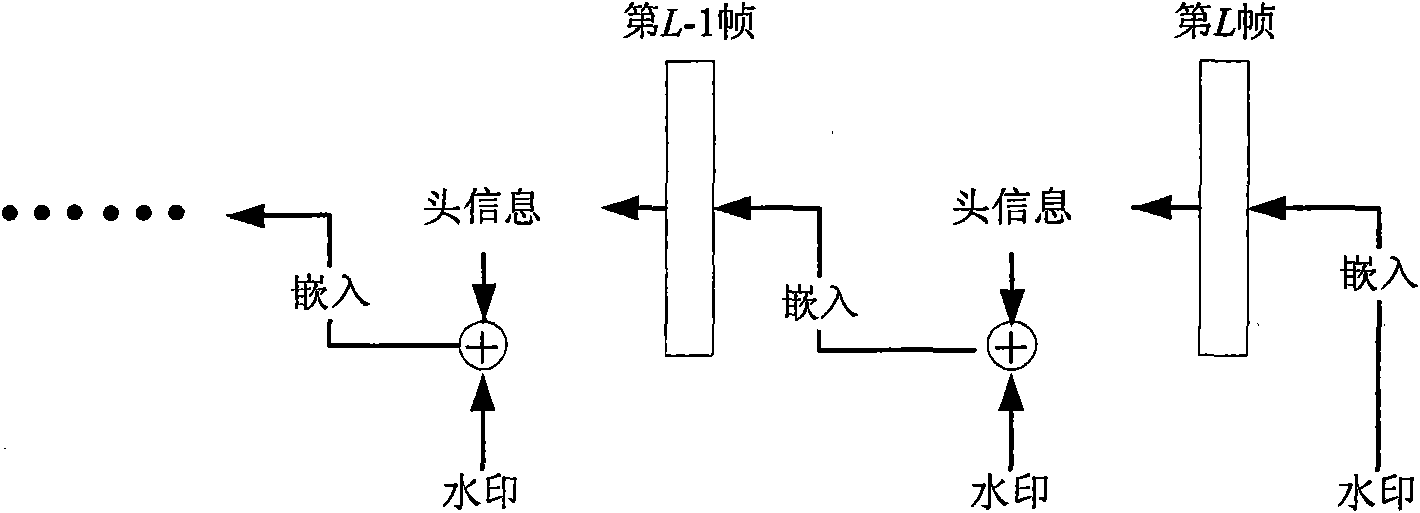
Reversible video frequency watermark method based on interframe forecast error histogram modification
InactiveCN101651837AIncrease embedding capacityImprove forecast accuracyAnalogue secracy/subscription systemsDigital video signal modificationWatermark methodQuality of vision
The invention relates to a reversible video frequency watermark method based on interframe forecast error histogram modification, comprising watermark embedding and watermark detection. The watermarkembedding process is carried out according to a video frequency negative sequence: firstly, utilizing the previous frame to carry out motion estimation to obtain an interframe forecast error, and thencarrying out the histogram modification on the interframe forecast error so as to embed a watermark. An extracting process is carried out according to a video frequency sequence mode: similarly, utilizing the previous frame to carry out the motion estimation to obtain a forecast error, and then extracting a watermark from the forecast error, and modifying a histogram to carry out the frame imagerecovery. The invention uses the mode of negative sequence embedding and sequence extracting, thereby an embedded video frequency frame can be recovered after the watermark is extracted, and the reversibility of the video frequency watermark is realized; the motion estimation is used according to the content relation of adjacent interframes to carry out prediction so as to enable the forecast error histogram to have the height centrality, and realize the bigger embedding content; in the embedding process, using the histogram modification enables that the influence on the frame image is small,and a watermark-embedded video frequency has high visual quality.
Owner:BEIHANG UNIV
Digital watermark method capable of simultaneously resisting various attacks
InactiveCN102122385AResistant to clipping attacksResistant to scaling attacksImage data processing detailsWatermark methodBinary information
The invention discloses a digital watermark method capable of simultaneously resisting various attacks, belonging to the field of digital watermark. The invention particularly relates to a digital watermark method capable of simultaneously resisting attacks, such as clipping, scaling, filtering, noise and the like. At present, the most published digital watermark technologies only can resist certain common geometric attacks, noise attacks and filtering attacks, wherein geometric attacks do not contain clipping attacks, only one attack can be resisted once, and the combined attack of various attacks can not be resisted. The invention relates to the digital watermark method which is characterized in that different types of watermark information are embedded into a carrier image, specifically comprising the steps of embedding and extracting the watermark; the watermark can be converted into binary information with a specific length; the watermark becomes a 'pseudo watermark' by coding, correcting errors and adding a watermark head; then, the obtained 'pseudo watermark' is embedded into the carrier image; in the extraction process, the 'pseudo watermark' is obtained firstly; and then an original watermark is obtained. With the method, clipping attack and image scaling attack can be effectively resisted.
Owner:BEIJING UNIV OF TECH
High capacity reversible water mark method based on predication and companding technology
InactiveCN101105857AExcellent Peak Signal to Noise RatioReduce computational complexityImage data processing detailsSignal-to-noise ratio (imaging)High peak
The invention discloses a high-capacity reversible watermark method based on predication and companding technique. Through the introduction of the companding technique, the invention includes two processes: watermark embedding and watermark extracting. The invention effectively solves the problem of capacity consumption of position drawing in reversible watermark algorithm, and achieves high embedding capacity even in the situation of low threshold value. Meanwhile, due to the operation of data re-embedding after the compression of high predication errors, the invention still can maintain high peak signal to noise ratio (PSNR value).
Owner:BEIJING JIAOTONG UNIV
Watermarking method and apparatus
InactiveUS20070172094A1Reduce correlationUser identity/authority verificationCharacter and pattern recognitionWatermark methodComputer vision
Owner:ST ELECTRONICS INFO SECURITY
Method and apparatus for enhanced audio/video services with two watermarks
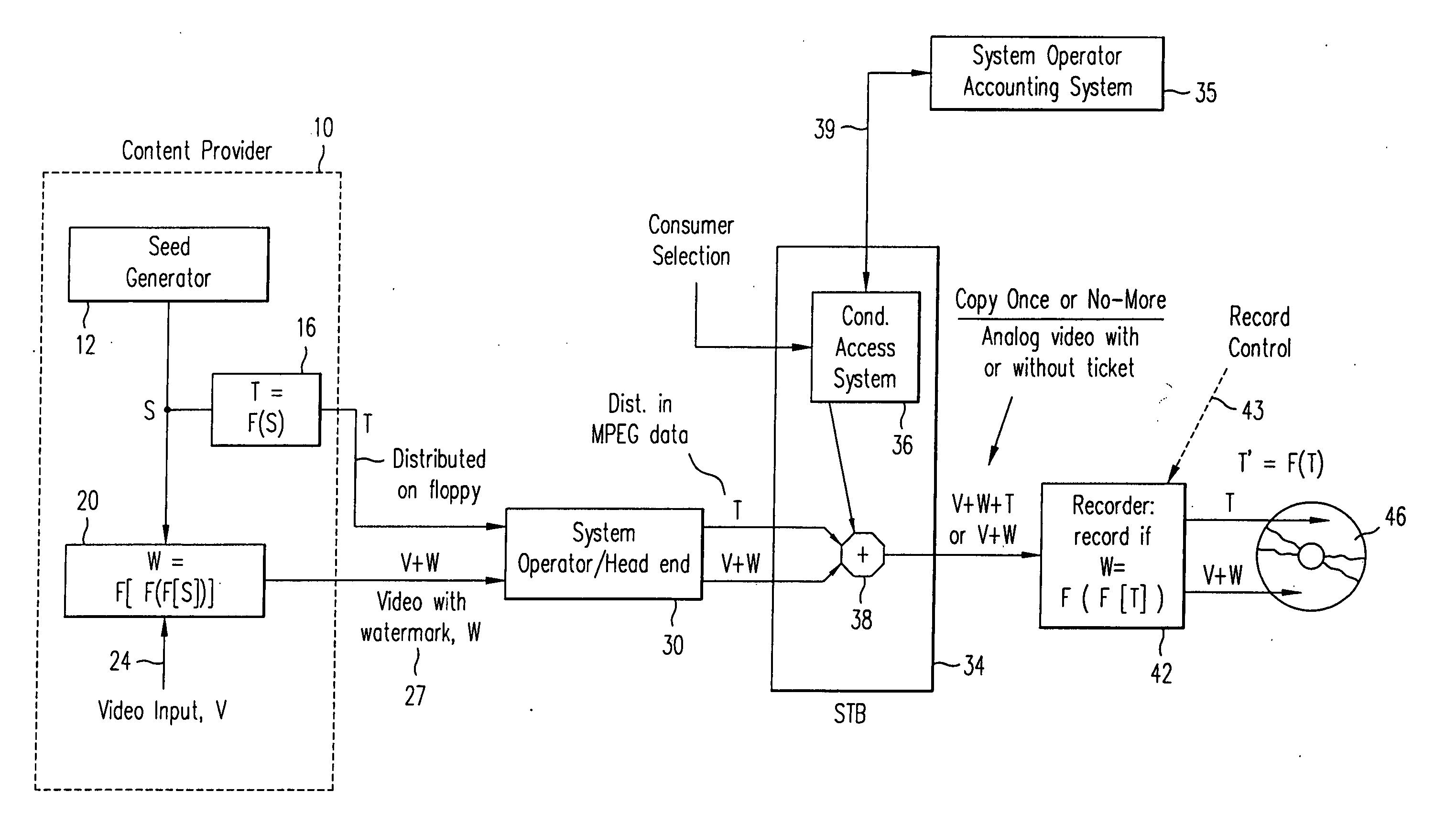
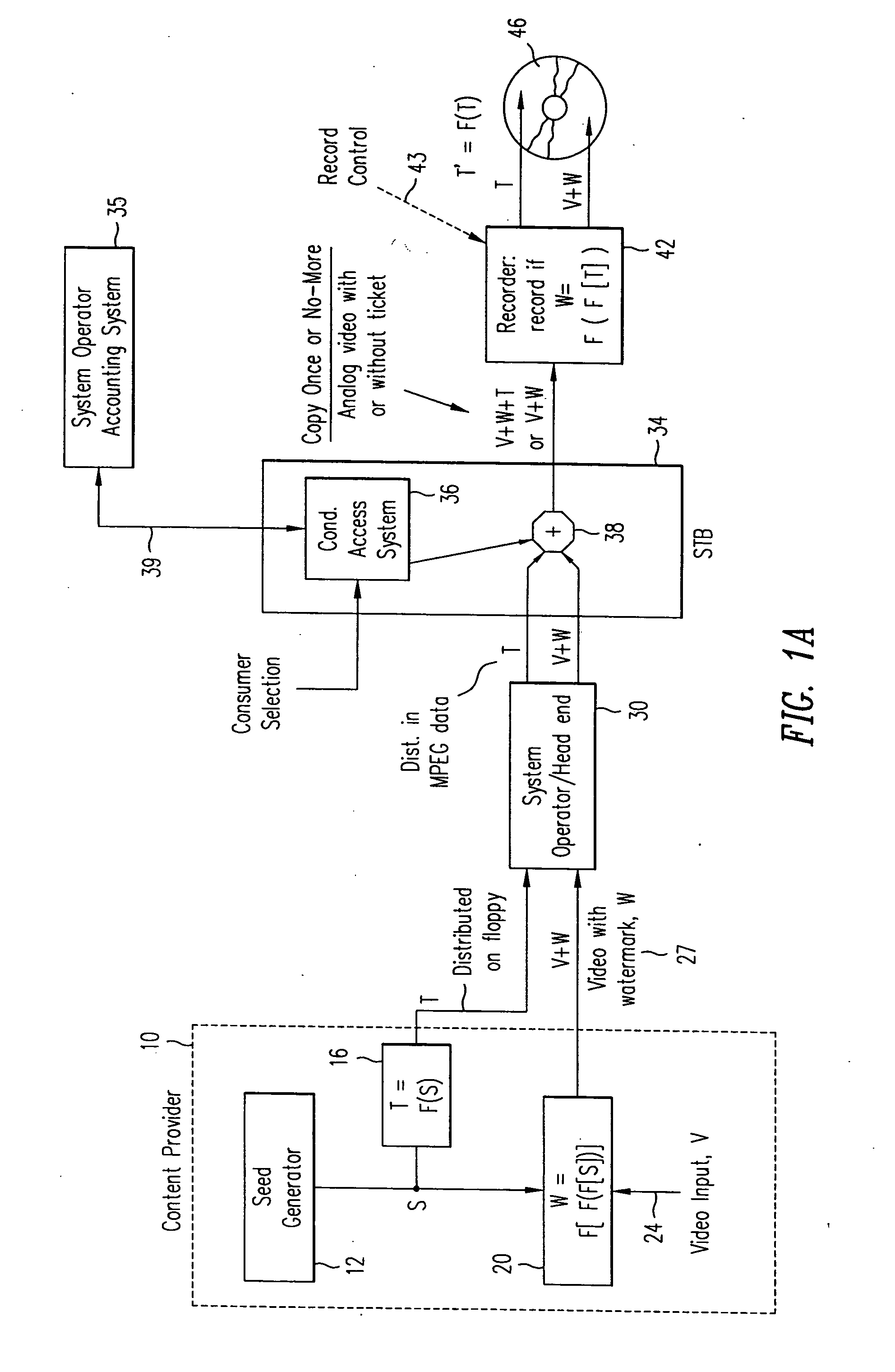
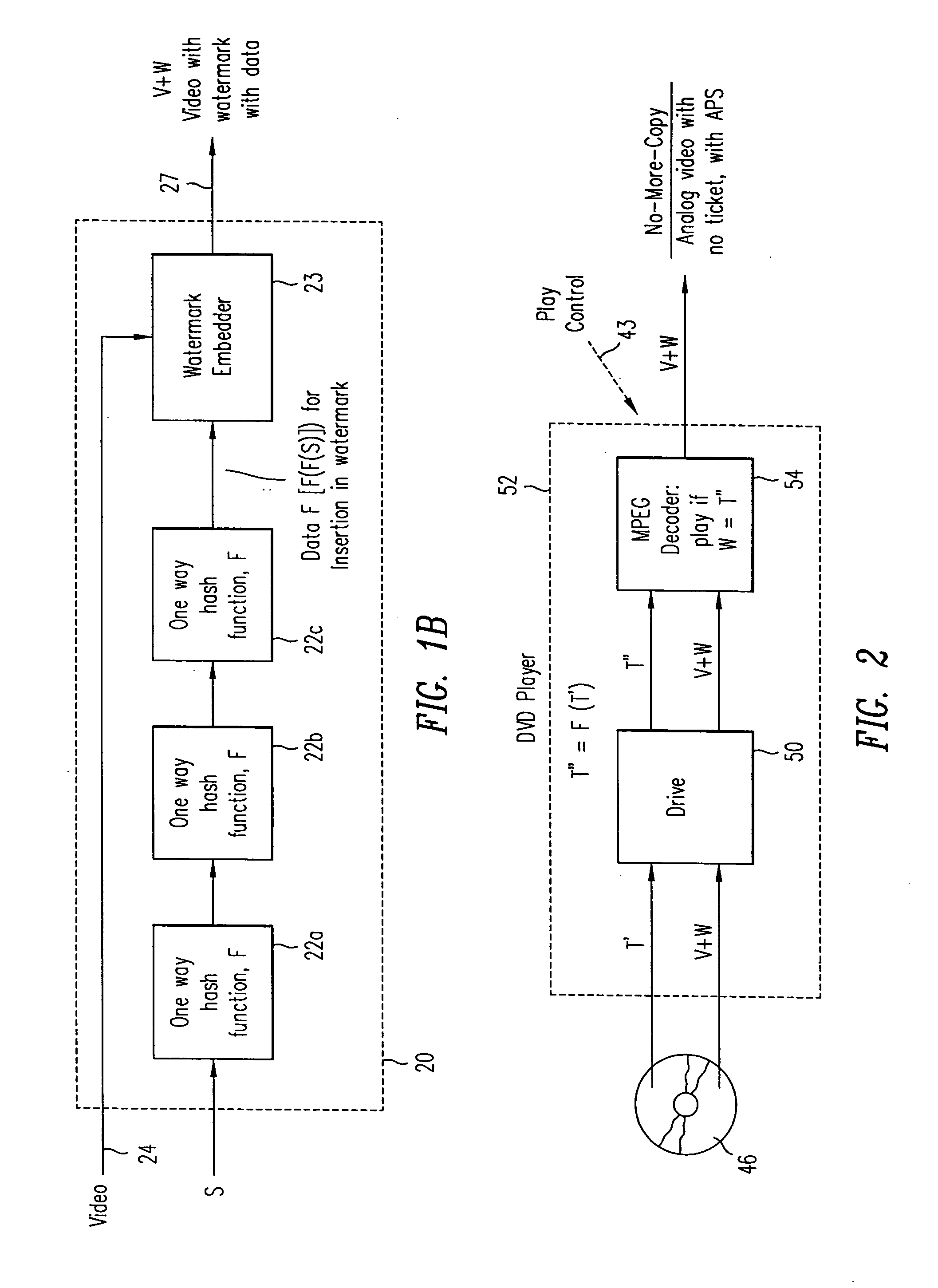
InactiveUS20050135614A1Add featureChange is minimalTelevision system detailsData taking preventionComputer hardwareWatermark method
Method and apparatus for controlling copying (recording) of an audio or video signal transmitted over a cable television or direct satellite broadcast system or the internet. Copyrighted (or other) audio or video material is protected from unwanted copying (recording) by the combination of a watermark embedded in the audio or video signal at the cable television head end together with additional copy protection data inserted in the audio or video signal, the data being a second watermark. The watermarks are audio or video watermarks embedded in active portions of the audio or video signal. The watermarks are, e.g., predetermined function s of the active video or audio. Only if the consumer is willing to pay a fee is the video or audio signal with both the watermarks transmitted to his recording device which then compares the watermarks, and only if they match is the recording permitted.
Owner:ALL MEDIA GUIDE +10
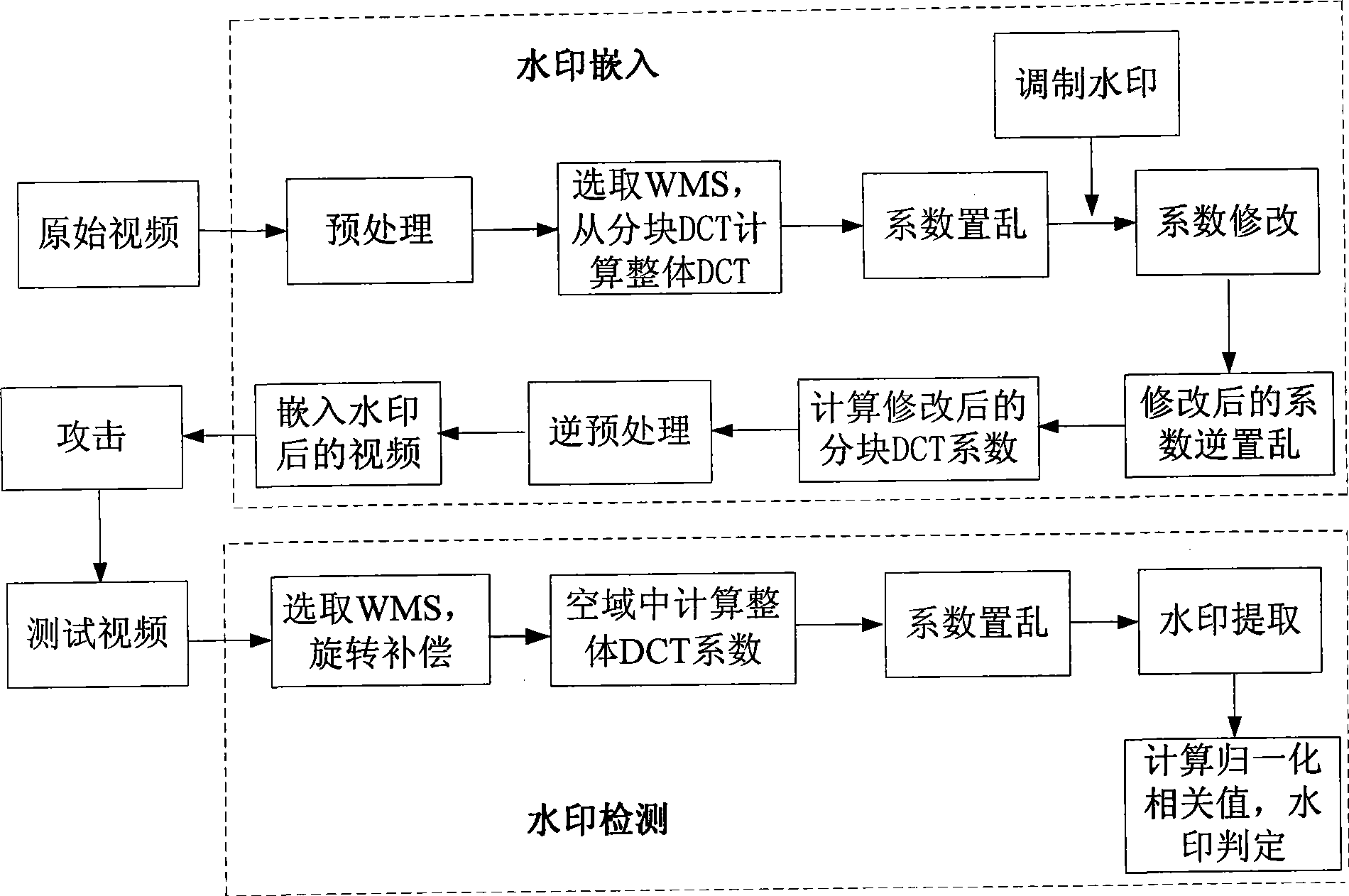
Geometric attack resisting real-time video watermarking method
InactiveCN101489133AImprove robustnessPerceived transparency is goodTelevision systemsDigital video signal modificationWatermark methodSignal processing
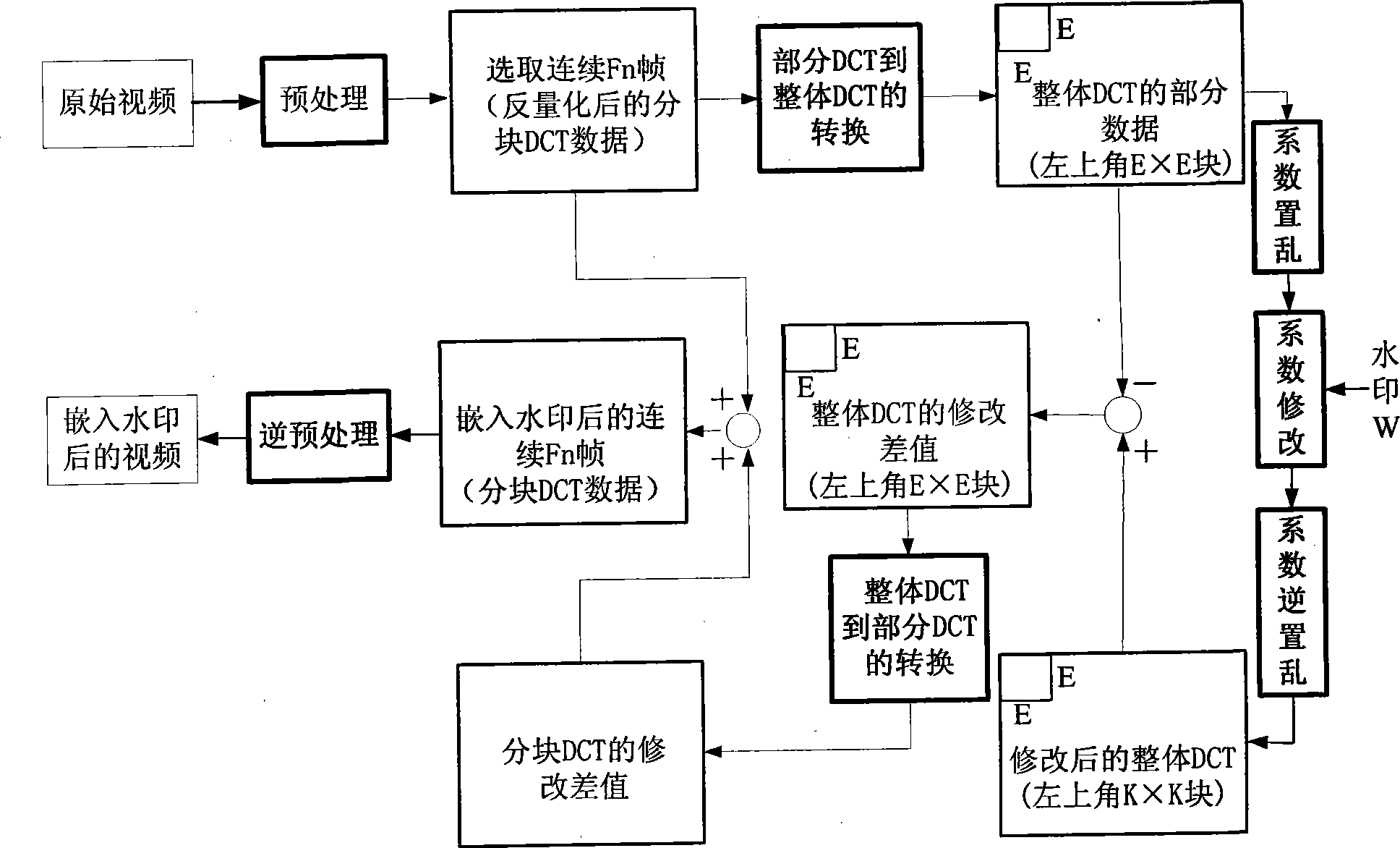
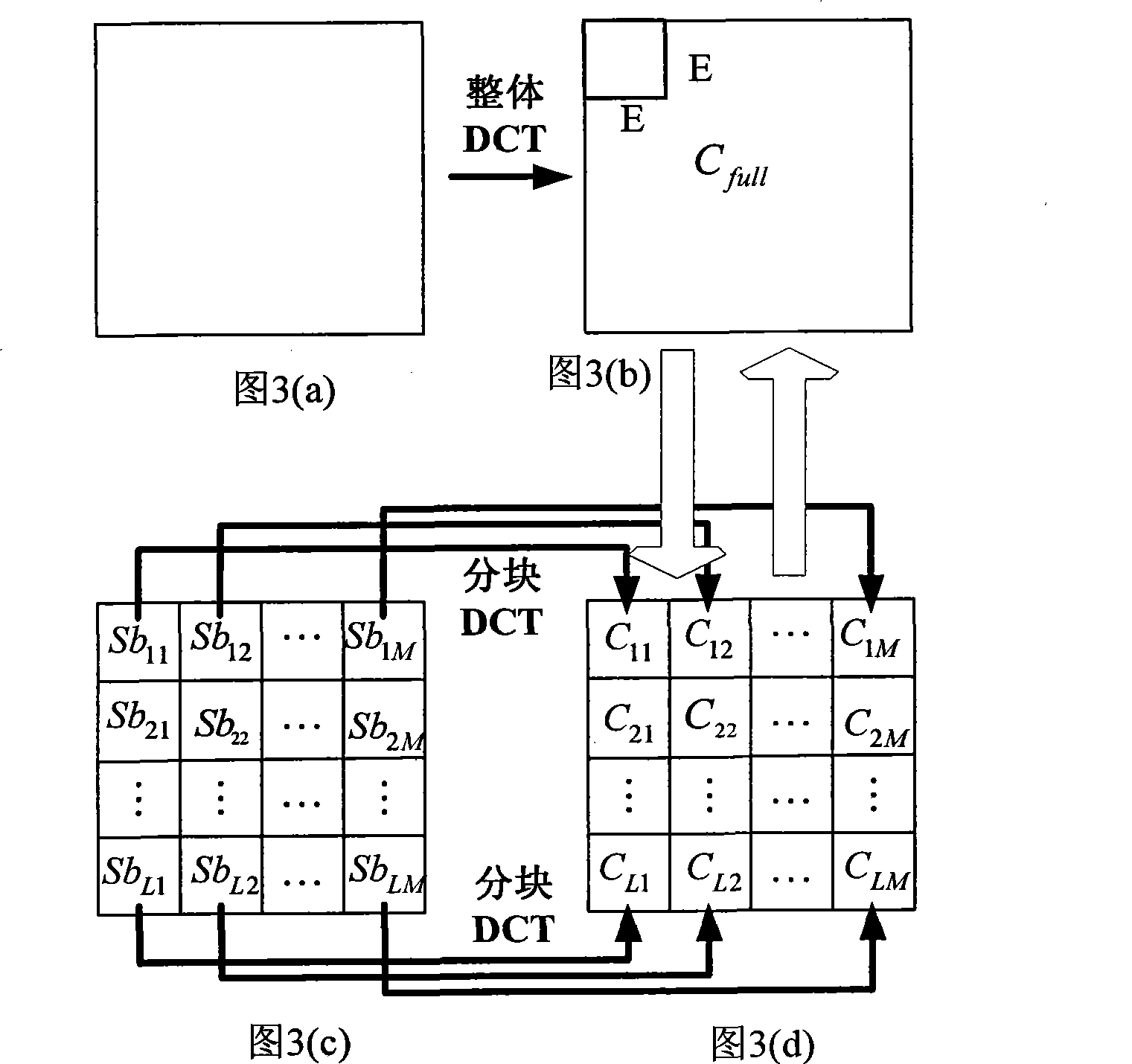
The invention provides a real-time video watermark method resisting geometric attacks mainly suitable for a video file based on coding. The method directly transforms a partitioning DCT coefficient to an integral DCT coefficient through a quick speed change method, then self-adaptingly modifies a low frequency coefficient value in the integral DCT domain to embedding a watermark signal, transforms a difference value between the watermark embedded integral DCT coefficient and an original coefficient to a difference value of the partitioning DCT coefficient, then rewriting the different value to the partitioning DCT coefficient. The watermark detection is performed in an air space, because a detection process is performed with a video play back, at the same time the video is fully decoded, and is directly performed the integral DCT transformation from the air space, then in order to resist rotary attacks, the detection video is performed a rotary compensation, and is performed a watermark pick-up according to a rule at the embedding time. The results show that the method has very good robustness to a common signal treatment and the conventional geometric attacks (row-column removal, rotation, equal proportion scaling, aspect ratio attack, linear transform, random distortion, cutting and several coalition attacks or the like).
Owner:HUAZHONG UNIV OF SCI & TECH
H.264 compression bit stream oriented video watermark method
InactiveCN101841700AReduce difficultyIncrease the difficultyPulse modulation television signal transmissionDigital video signal modificationVariable-length codeVideo bitstream
The invention discloses an H.264 compression bit stream oriented video watermark method. The method comprises the following steps of: generating an authentication code according to a predictive mode of a 4*4 brightness block in an I film; and embedding the authentication code in the film-grade bit stream by modulating variable-length code words of some motion sub-blocks of a B film and a P film, wherein the modulation is performed based on a mapping rule between the variable-length code words and the bits to be embedded, and the mapped variable-length code words is extremely similar to the original variable-length code words. Because in the method, the video bit stream is unnecessarily pre-processed, and comparison and replacement operations are performed by selecting the proper variable-length code words only from the H.264 / AVC compression bit stream in the watermark embedding process without a huge number of operations, so that the method has the advantages of low computing complexity, high safety and high practicability, and can better meet the requirements of the real-time video processing.
Owner:NINGBO UNIV
Digital watermark method against geometrical attack based on image characteristic region
InactiveCN101030293ALocalizedDoes not affect feature pointsImage data processing detailsWatermark methodDigital image
A digital watermark method resisting against geometric attack includes relating watermark information to image character region, generating local character region with invariance on geometric attack by utilizing most stable Harris character point in image, making said region to be round character region by image normalization, carrying out two-stages of wavelet transforms on these round character regions, selecting revision coefficient regions to embed watermark at the second stage wavelet transform and realizing watermark-embedding. The method for picking up watermark is also disclosed.
Owner:XIDIAN UNIV
Digital watermark imbedding and detecting method and device
ActiveCN101482965AImprove concealmentImprove robustnessImage data processing detailsWatermark methodDigital watermarking
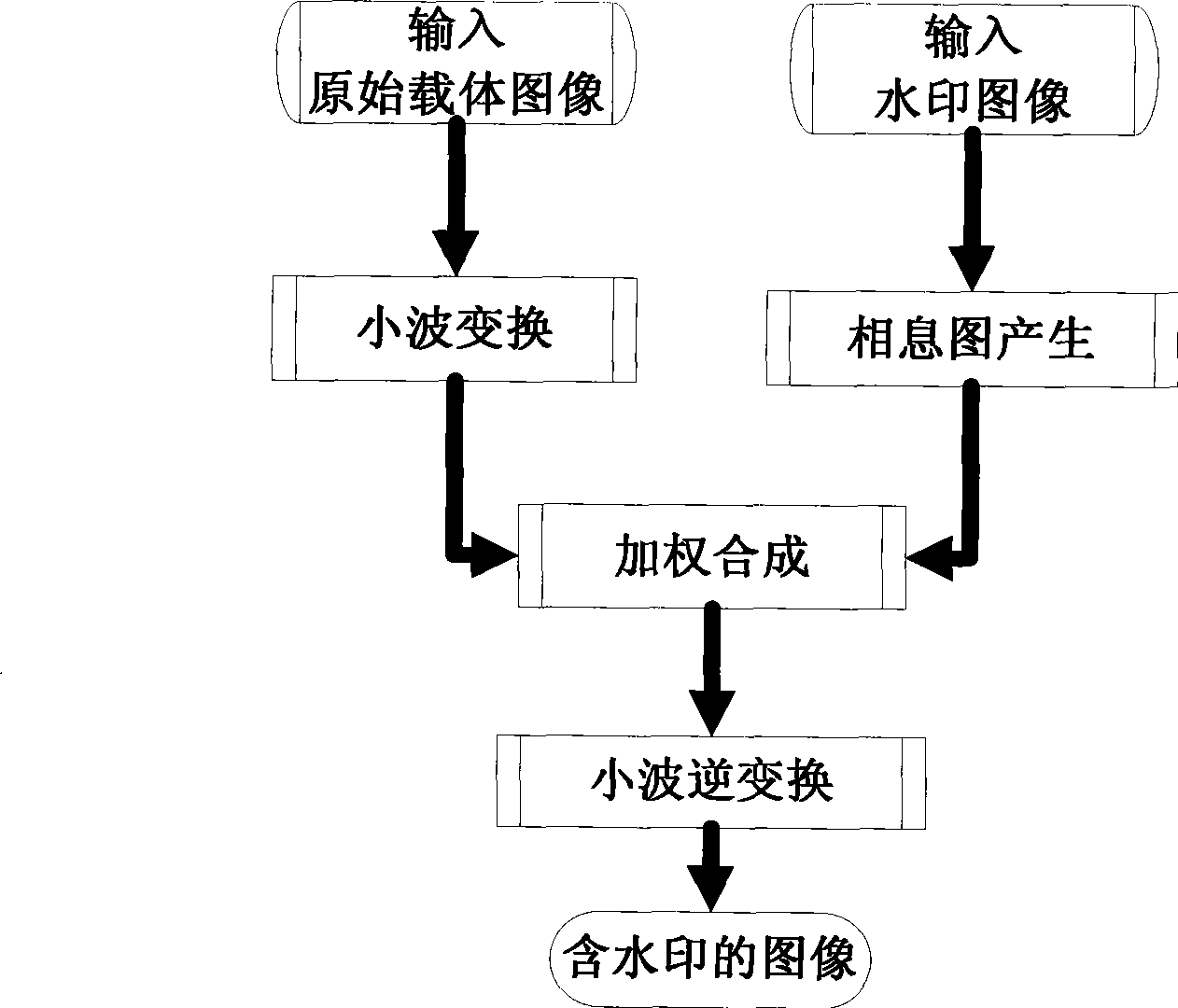
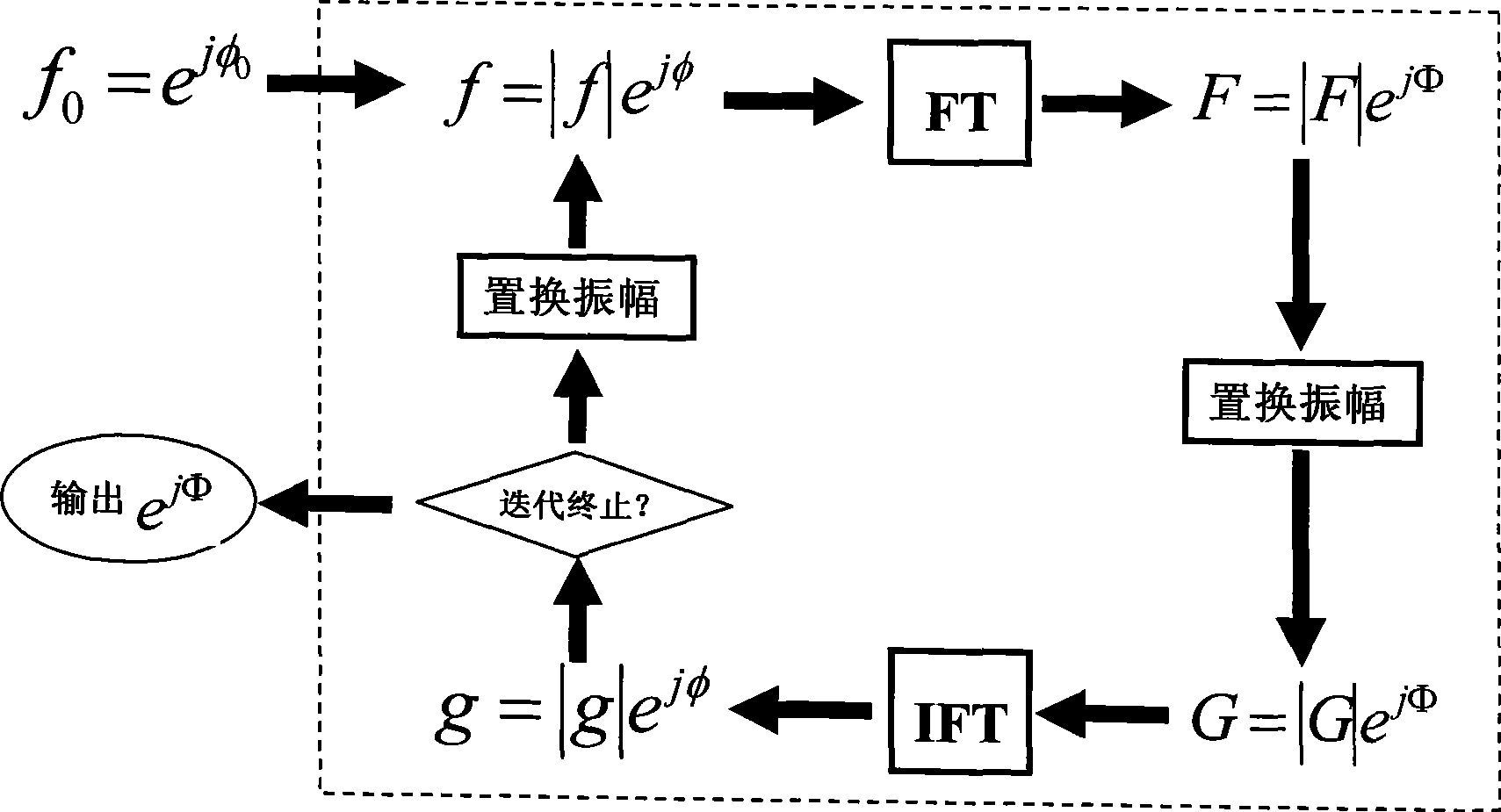
The invention discloses a method for inlaying a digital watermark, comprising step A1 of transforming a watermark image to generate a phase holographic image; step B1 of transforming a digital carrier image by means of wavelet; step C1 of synthesizing the phase holographic image after being weighted with a wavelet low-frequency coefficient obtained by transforming a digital carrier image by means of wavelet; step D1 of inversely transforming the synthesized wavelet low-frequency coefficient to generate an image having a watermark. The invention also discloses a corresponding digital watermark detecting method and a digital watermark inlaying and detecting device used to implement the inlaying and detecting method. Compared with the prior digital watermark method, concealment and robustness of the invention are obviously improved. Furthermore, the invention has the shear resistance of the holographic watermark scheme and avoids problem of interference between conjugate images.
Owner:SHENZHEN ESUN DISPLAY
Robust image watermark method based on local Tchebichef moment
InactiveCN101556686AImprove detection accuracyOvercoming the problem of low detection rateImage data processing detailsImaging processingWatermark method
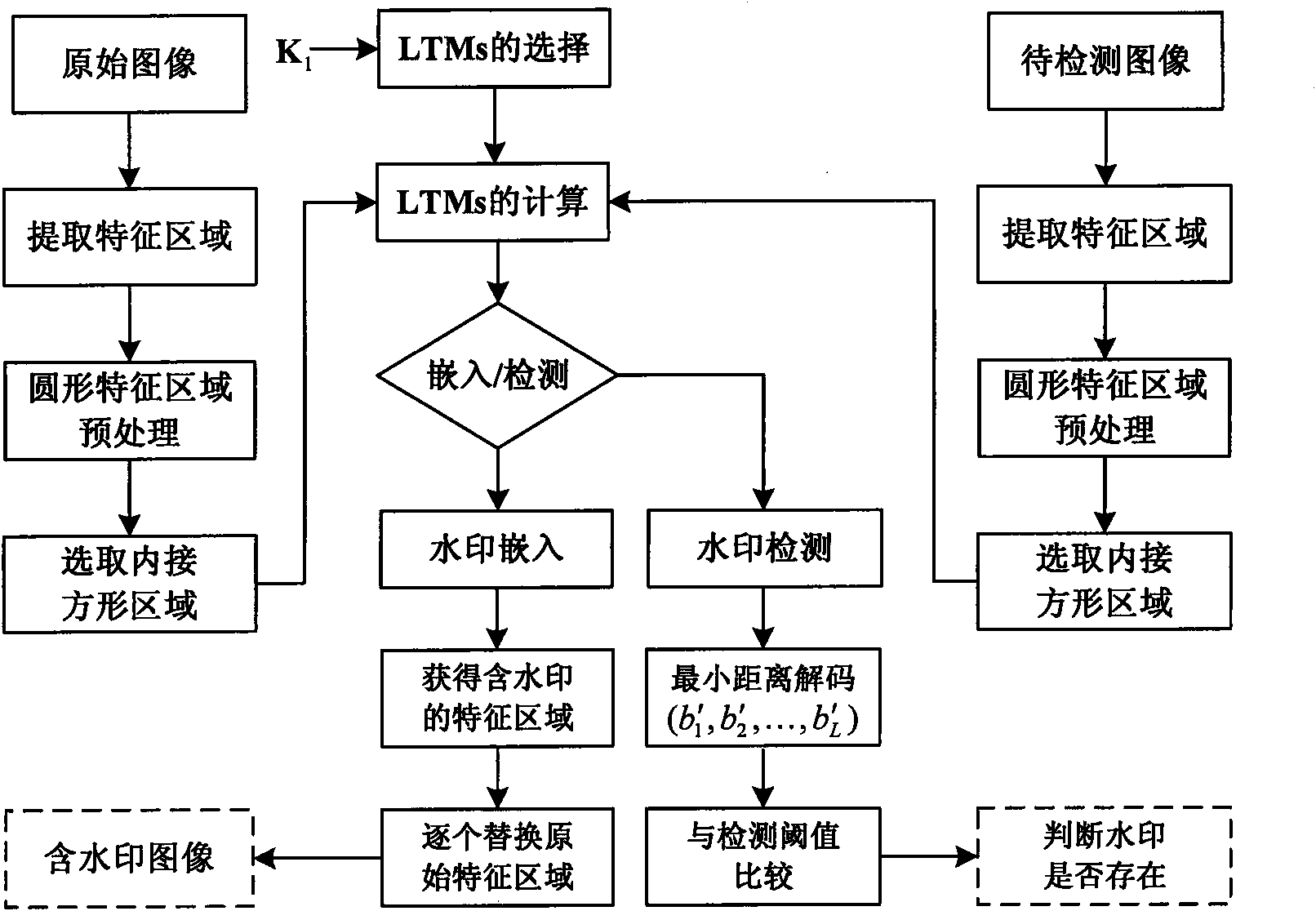
The invention discloses a robust image watermark new method based on a local Tchebichef moment, mainly solving the problem that a watermark arithmetic based on image characteristic at present can not effectively resist general image processing and geometry attack simultaneously. The method comprises the steps as follows: firstly, extracting characteristic points of an original image by utilizing a Harris-Laplace detection operator, and obtaining a group of stable and mutually independent round characteristic areas through characteristic selection; then obtaining a geometrically unchanged round characteristic area through principle direction alignment; and finally, calculating the Tchebichef moment in an inscribed square image block of the round characteristic area, and embedding a watermark through dithering quantized modulation to modify an amplitude value with low-level Tchebichef moment. In detection, the modified low-level Tchebichef moment is obtained through the dithering quantized modulation, and a minimum distance is utilized to realize the blind extraction of the watermark. The invention has favorable nonvisibility, excellent robust performance for general image processing, geometry attach and combined attach and superior performance to similar methods and can be used for copyright protection for different images.
Owner:XIDIAN UNIV
High-robustness dual transform domain image zero watermarking method
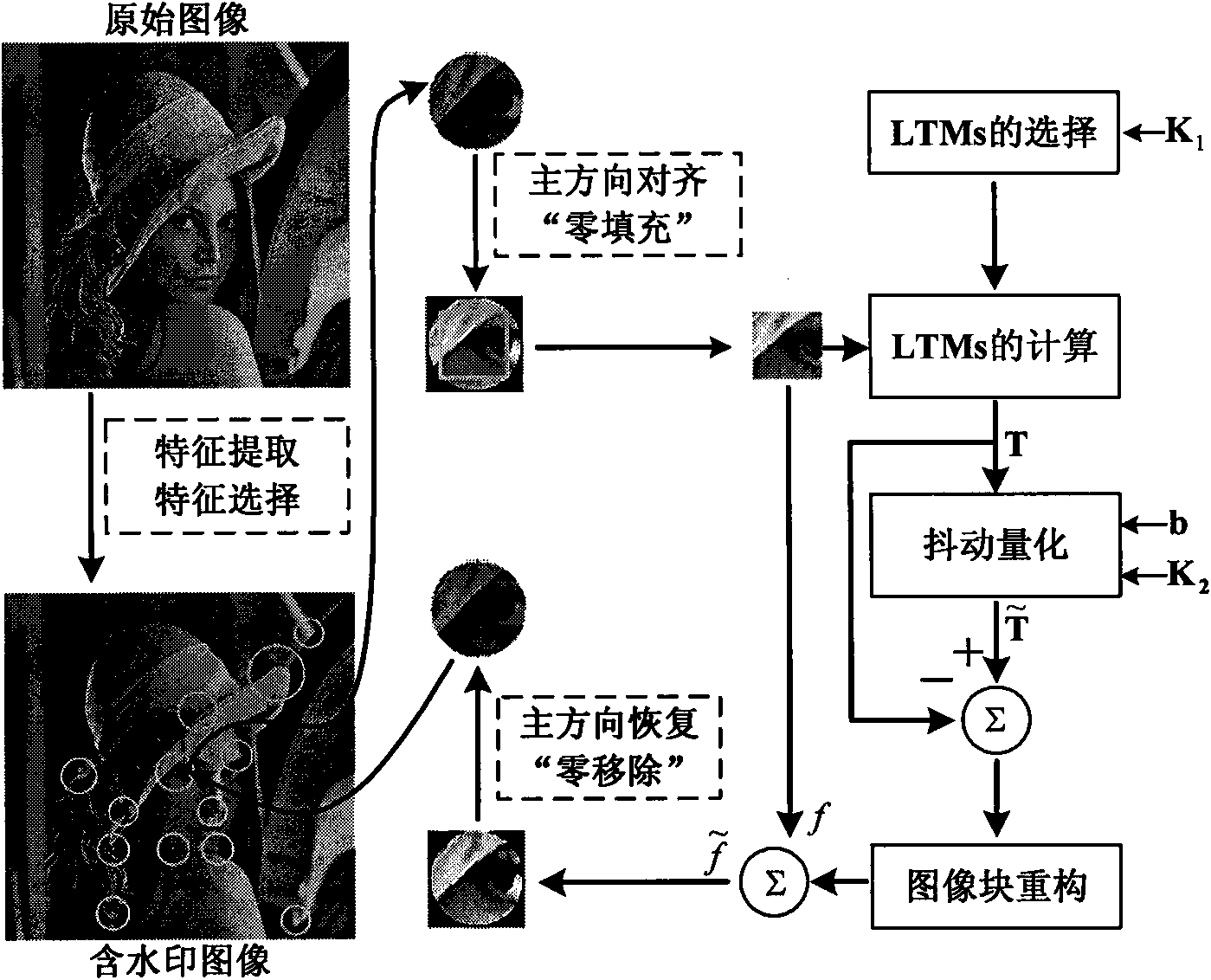
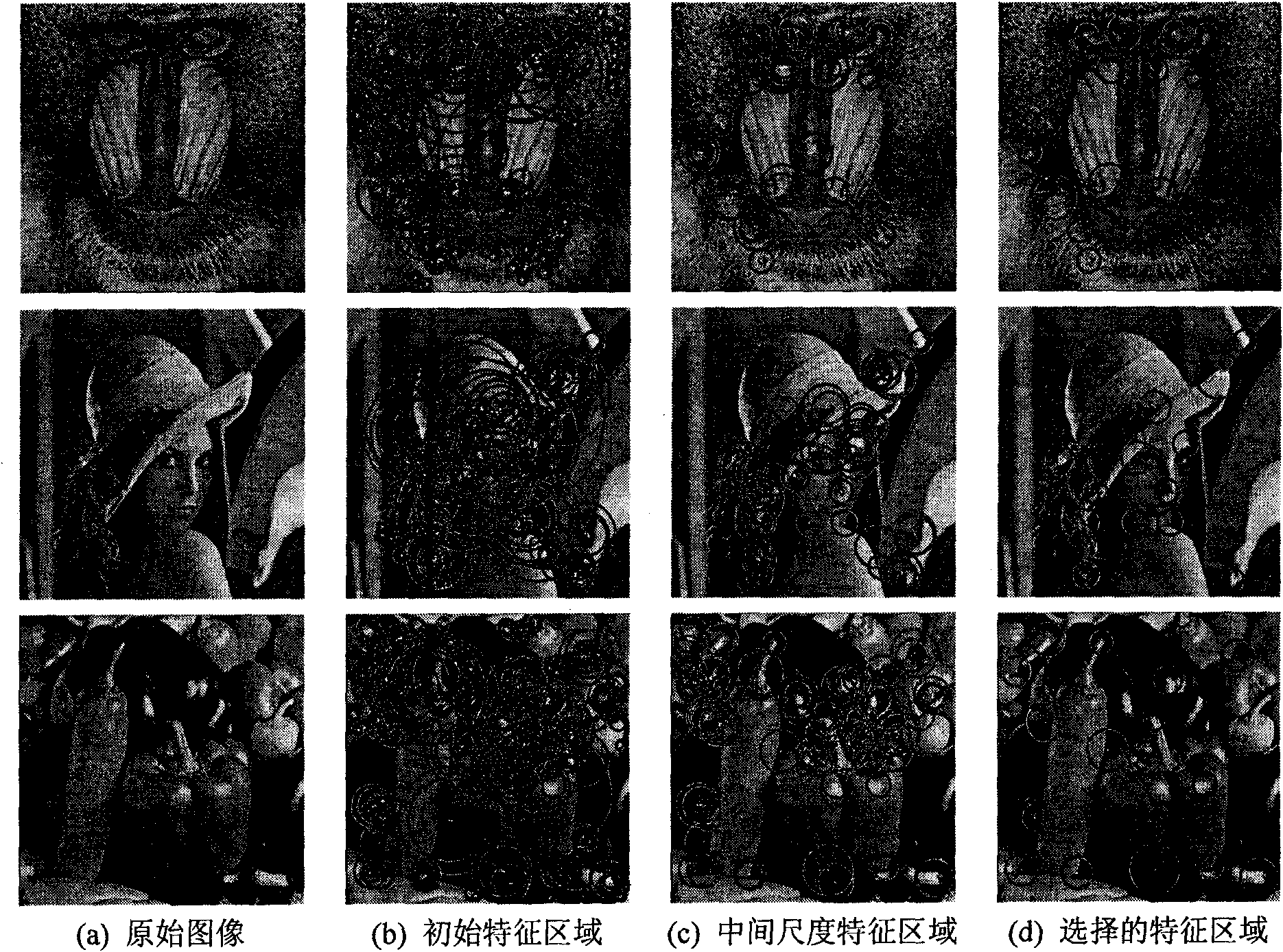
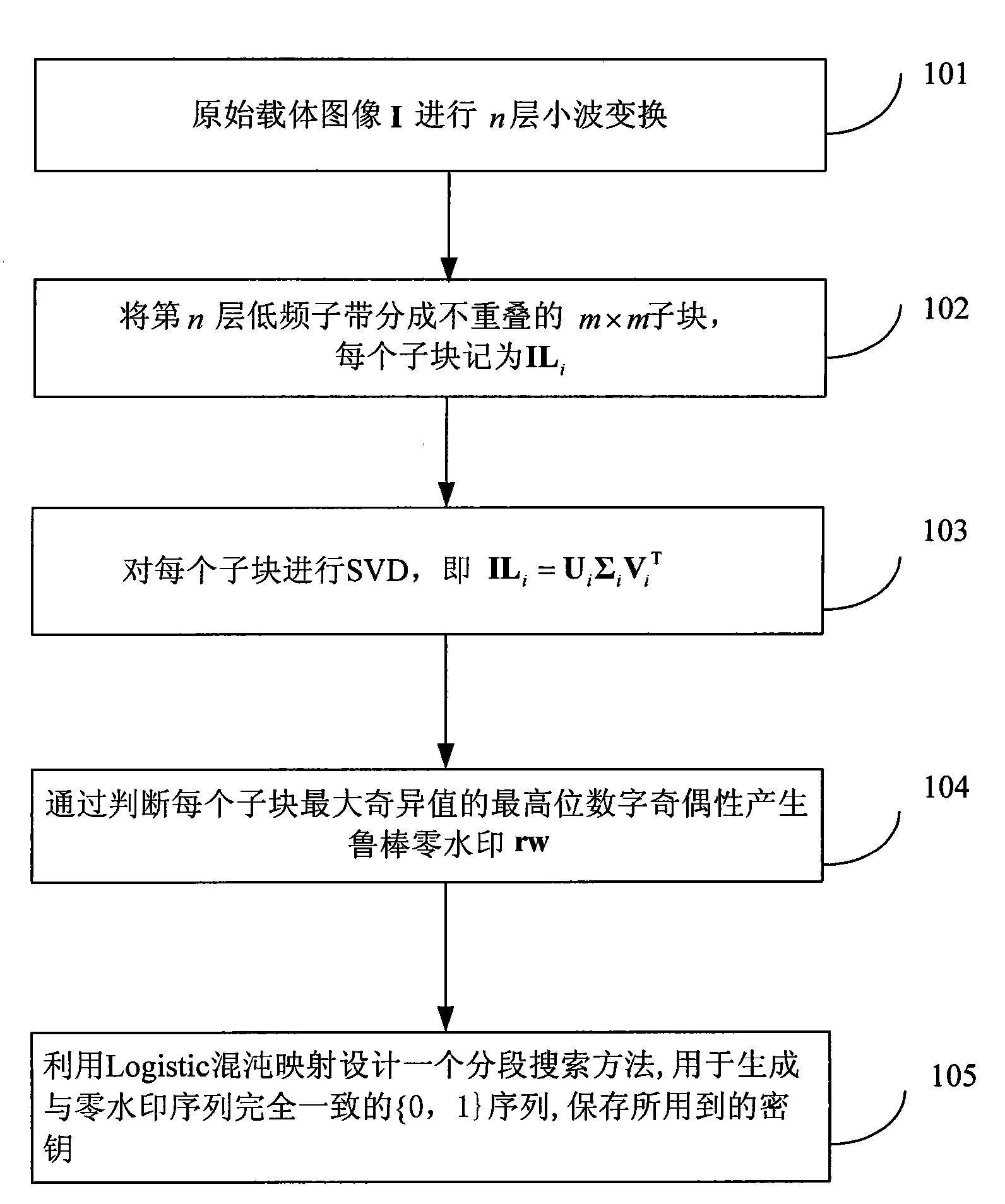
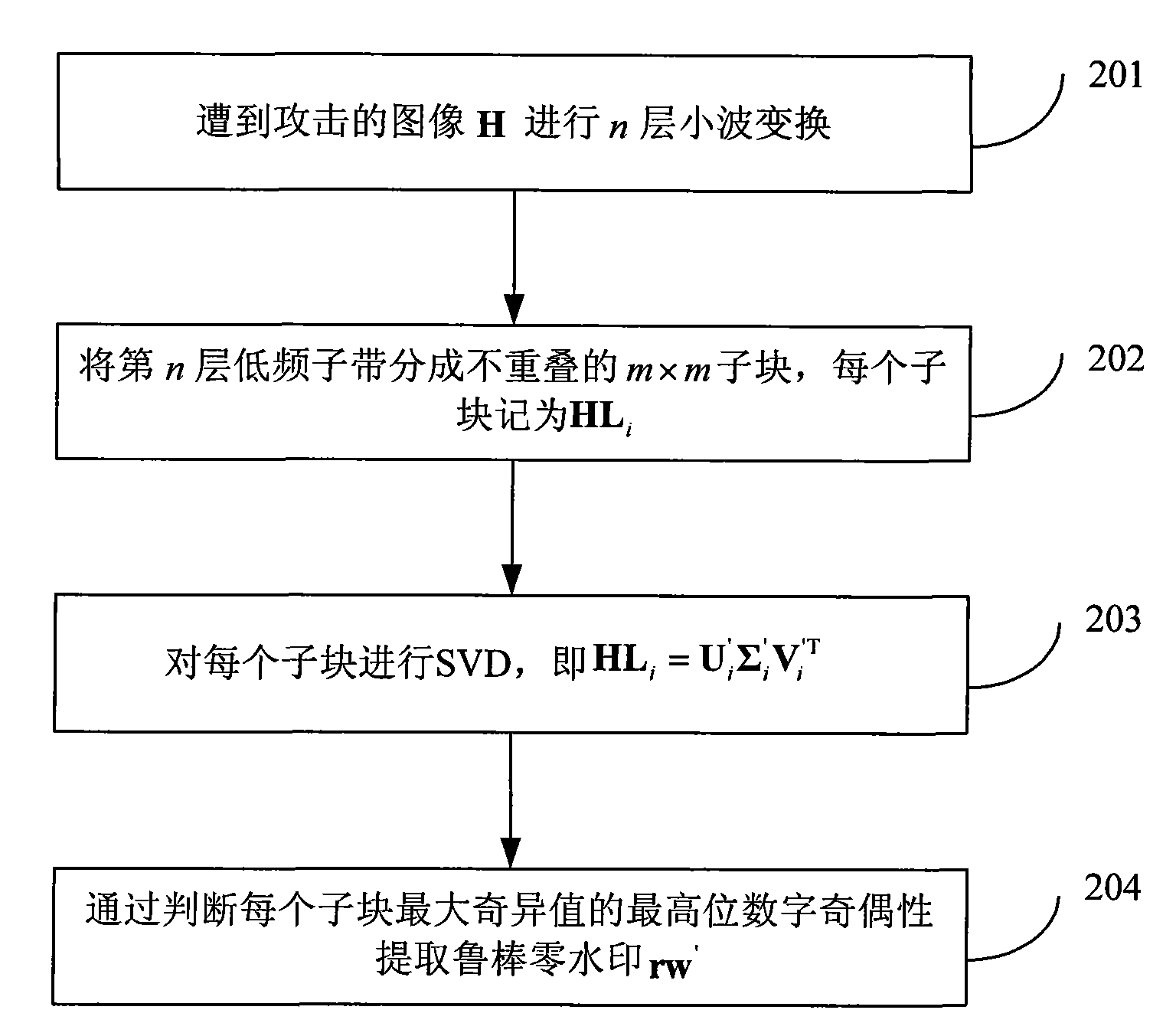
InactiveCN101604441AAchieve copyright certificationTo achieve the purpose of copyright protectionImage codingImage data processing detailsSingular value decompositionInvisibility
A robustness watermarking method plays a significant role in the field of copyright certification. A main problem to be considered in the design of the robustness watermarking method is how to improve the robustness as high as possible on the basis of ensuring excellent invisibility of a watermark. The invention designs a high-robustness dual transform domain image zero watermarking method by using an energy concentration effect of low-frequency sub-bands of a wavelet transformed image and the singular value stability of singular value decomposition. The method comprises the following steps: firstly, subjecting an original image to discrete wavelet transform; secondly, selecting a low-frequency subband for block singular value decomposition; and finally, generating a robustness watermark by judging the parity of a number in the top digit of a maximum singular value of each subblock. The method avoids any change in the original image, thereby having excellent invisibility. Compared with other overwhelming majority of robustness watermarking methods, the method has stronger anti-attack robustness. The method can realize blind copyright certification.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com