Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5666 results about "Copying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
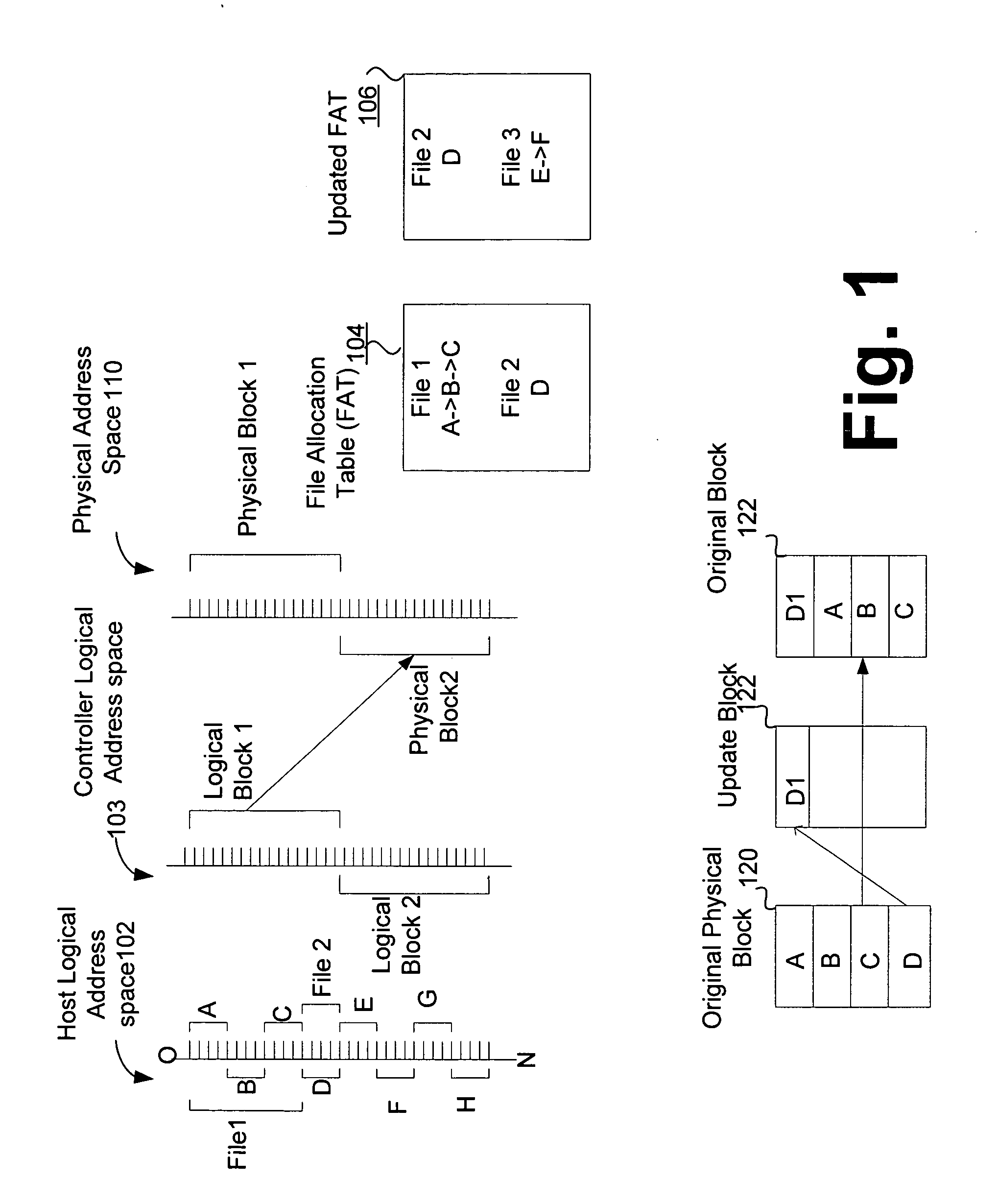
Copying is the duplication of information or an artifact based on an instance of that information or artifact, and not using the process that originally generated it. With analog forms of information, copying is only possible to a limited degree of accuracy, which depends on the quality of the equipment used and the skill of the operator. There is some inevitable generation loss, deterioration and accumulation of "noise" (random small changes, that have not sound) from original to copy when copies are made. This deterioration accumulates with each generation. With digital forms of information, copying is perfect. Copy and paste is frequently used by a computer user when they select and copy an area of text or content.
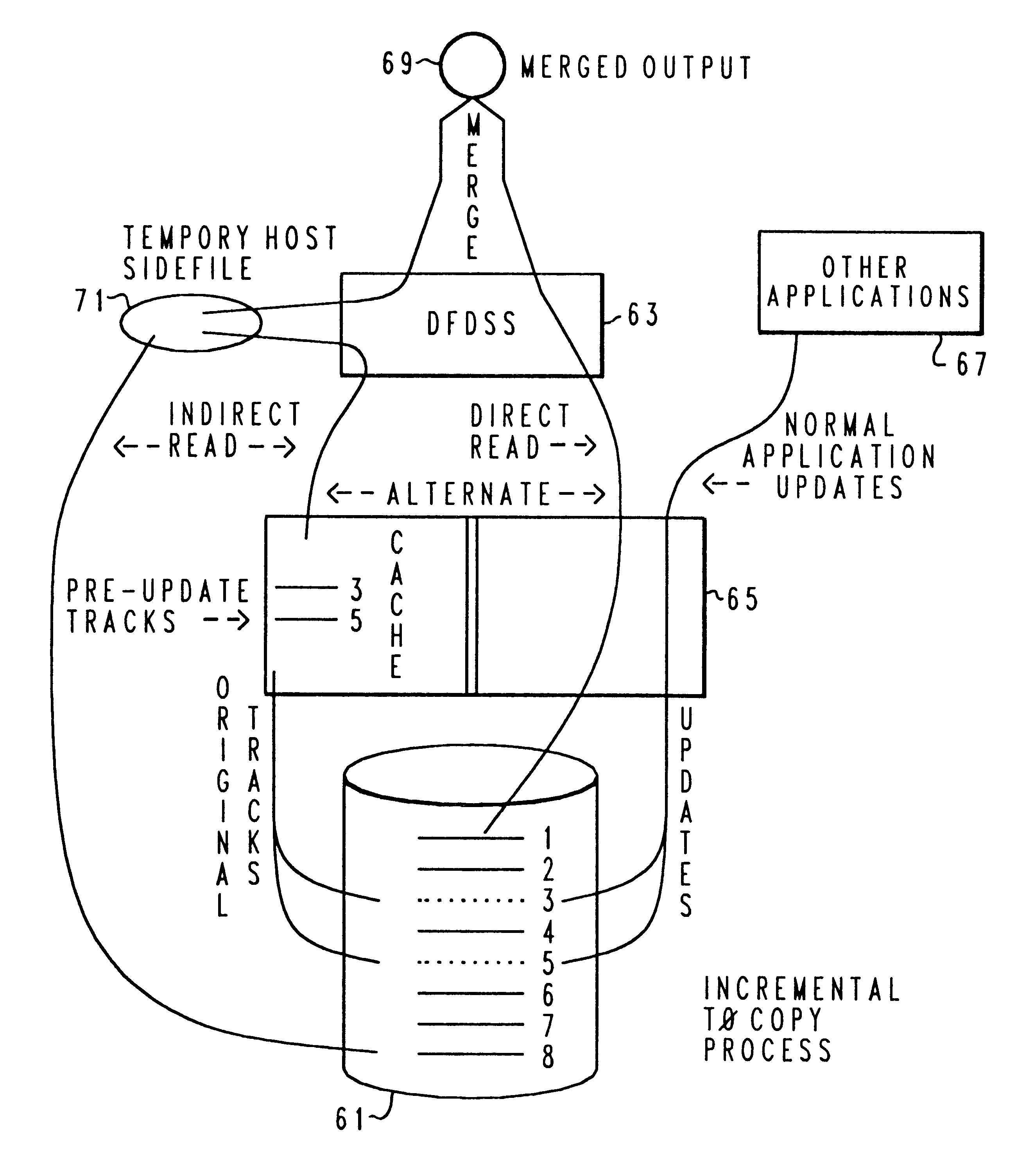
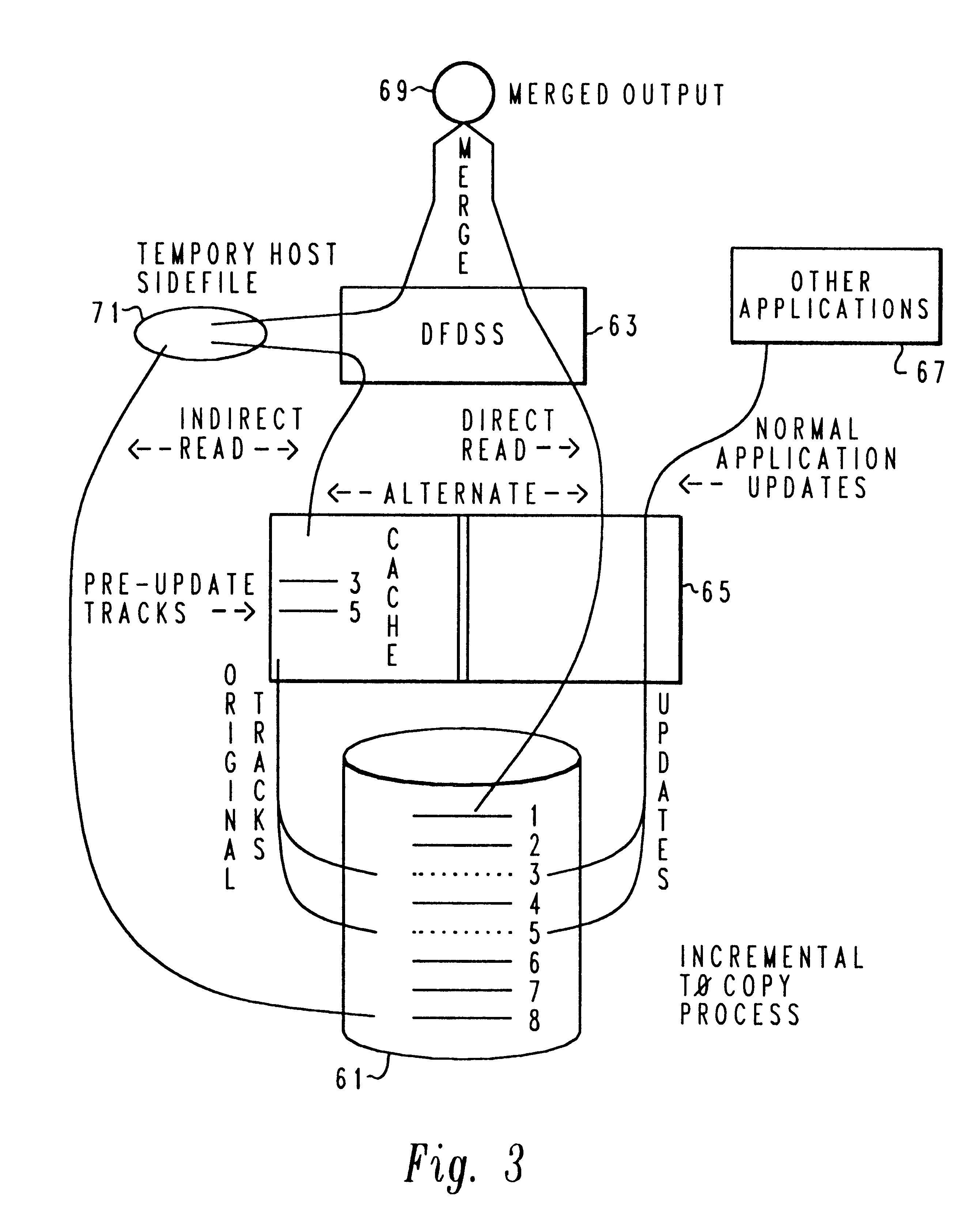
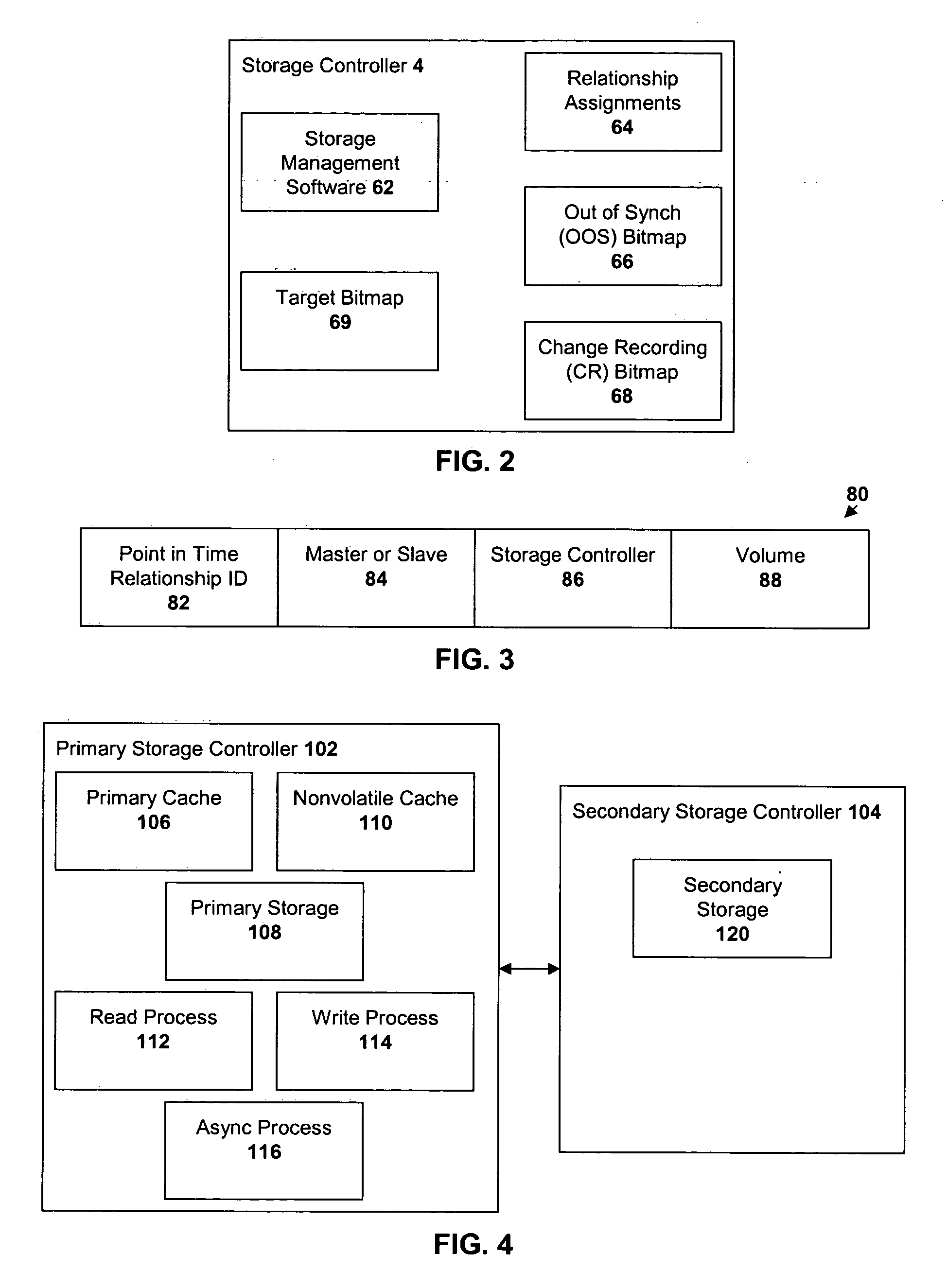
Method and system for incremental time zero backup copying of data
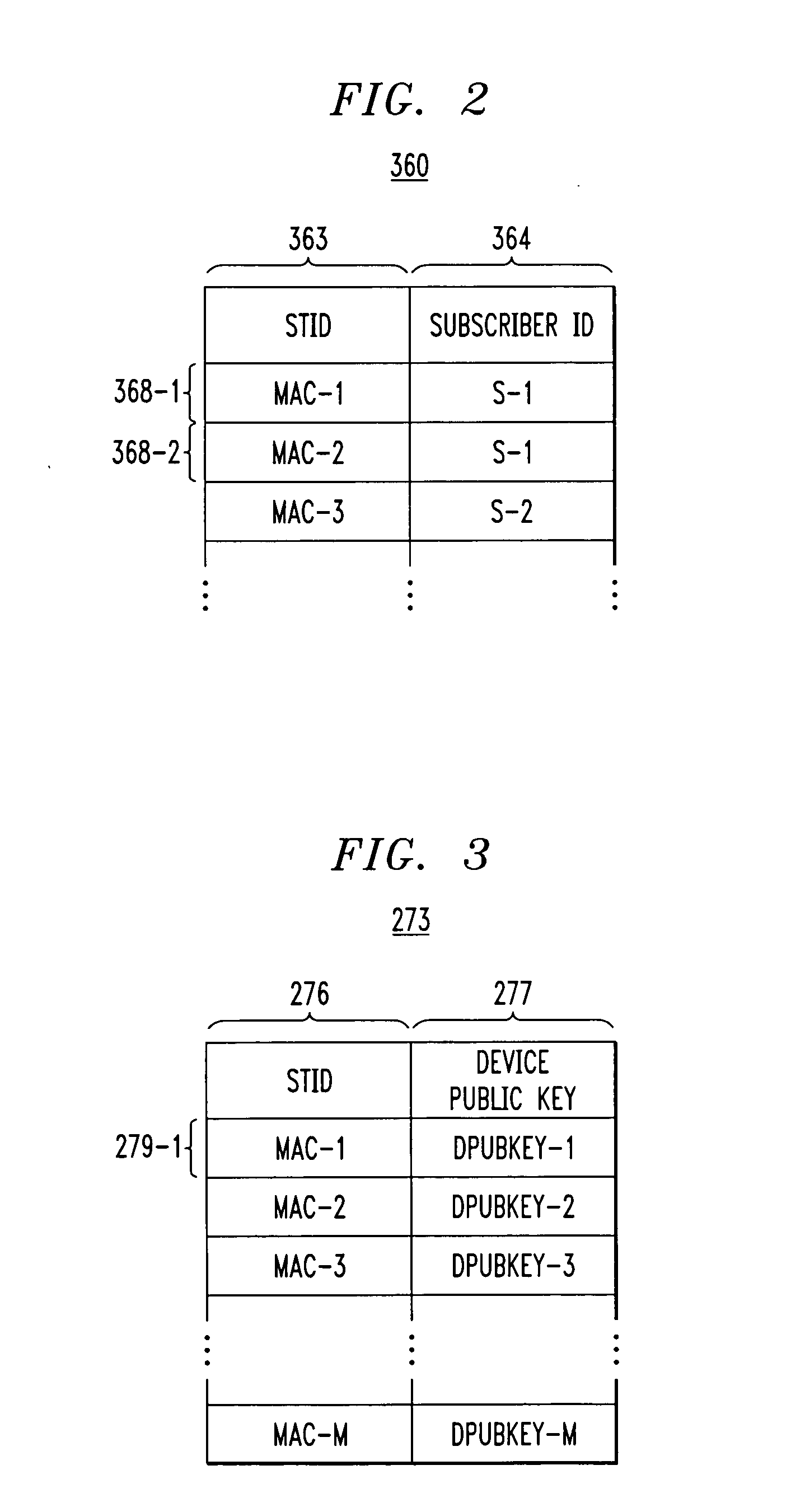
InactiveUSRE37601E1Maintaining continued availability of datasetsReduce suspensionRedundant operation error correctionMemory systemsData processing systemData set
Backup copying of designated datasets representing a first selected point in time consistency may be performed in a data processing system on an attached storage subsystem concurrent with data processing system application execution by first suspending application execution only long enough to form a logical-to-physical address concordance, and thereafter physically backing up the datasets on the storage subsystem on a scheduled or opportunistic basis. An indication of each update to a selected portion of the designated datasets which occurs after the first selected point in time is stored and application initiated updates to uncopied designated datasets are first buffered. Thereafter, sidefiles are made of the affected datasets, or portions thereof, the updates are then written through to the storage subsystem, and the sidefiles written to an alternate storage location in backup copy order, as controlled by the address concordance. At a subsequent point in time only those portions of the designated datasets which have been updated after the first selected period and time are copied, utilizing an identical technique.
Owner:IBM CORP
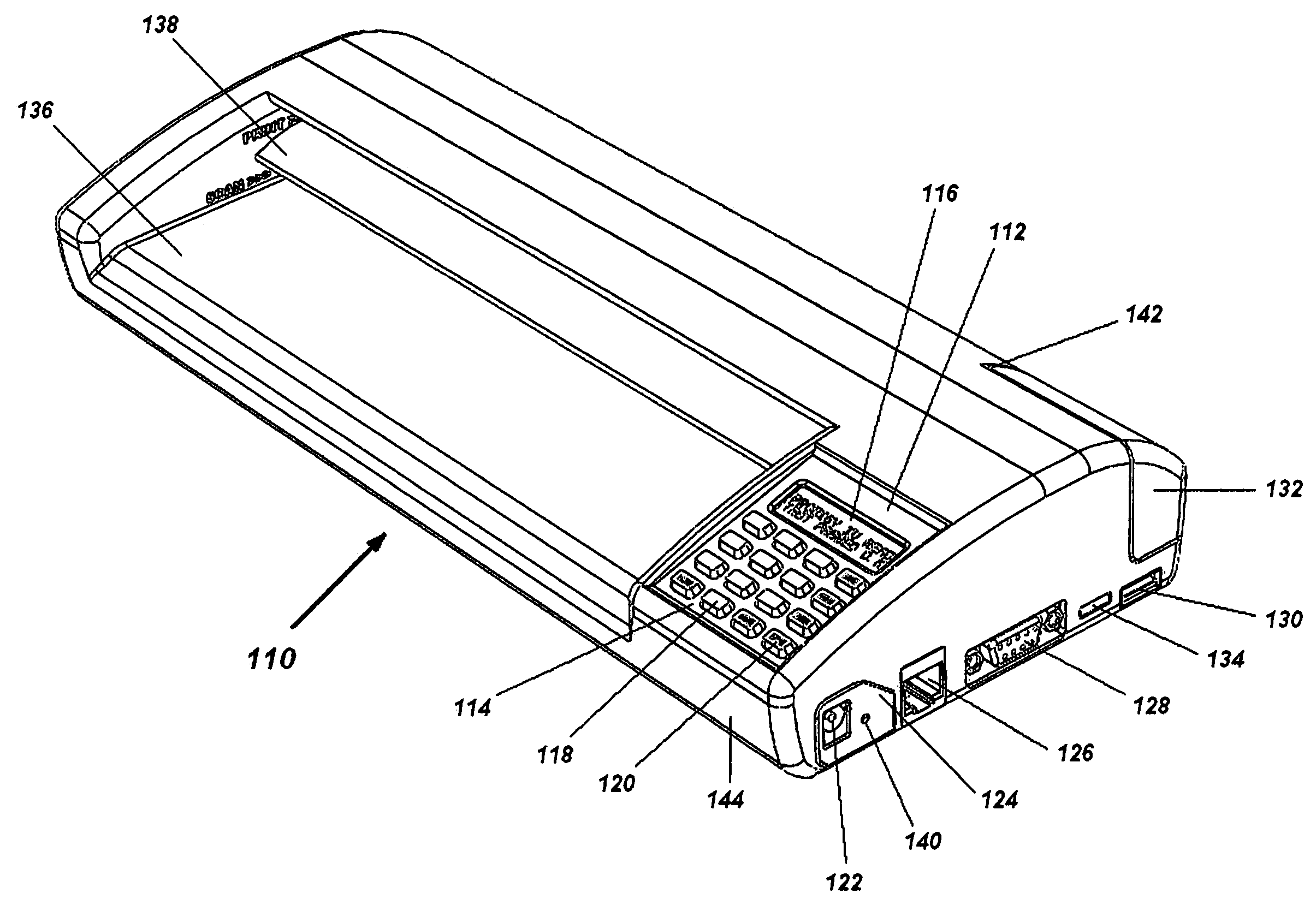
Portable electronic faxing, scanning, copying, and printing device
A lightweight, battery operated, portable, personal electronic device capable of faxing, scanning, printing and copying media as a standalone device or in cooperation with other electronic devices including PCs, mobile telephones, PDAs, etc. is provided. The device automatically detects the presence of fax-capable devices and reconfigures the software for compatibility with the fax-capable device eliminating the need for user programming. The device's ergonomic design, intrinsic physical stability, and same side paper feeds and user interface provide use in work areas having limited space. The device includes unidirectional, independent pathways for original and recording media such that paper jams are minimized. Portability is maximized through innovative power management software and hardware.
Owner:SCI FORGE
File system shell
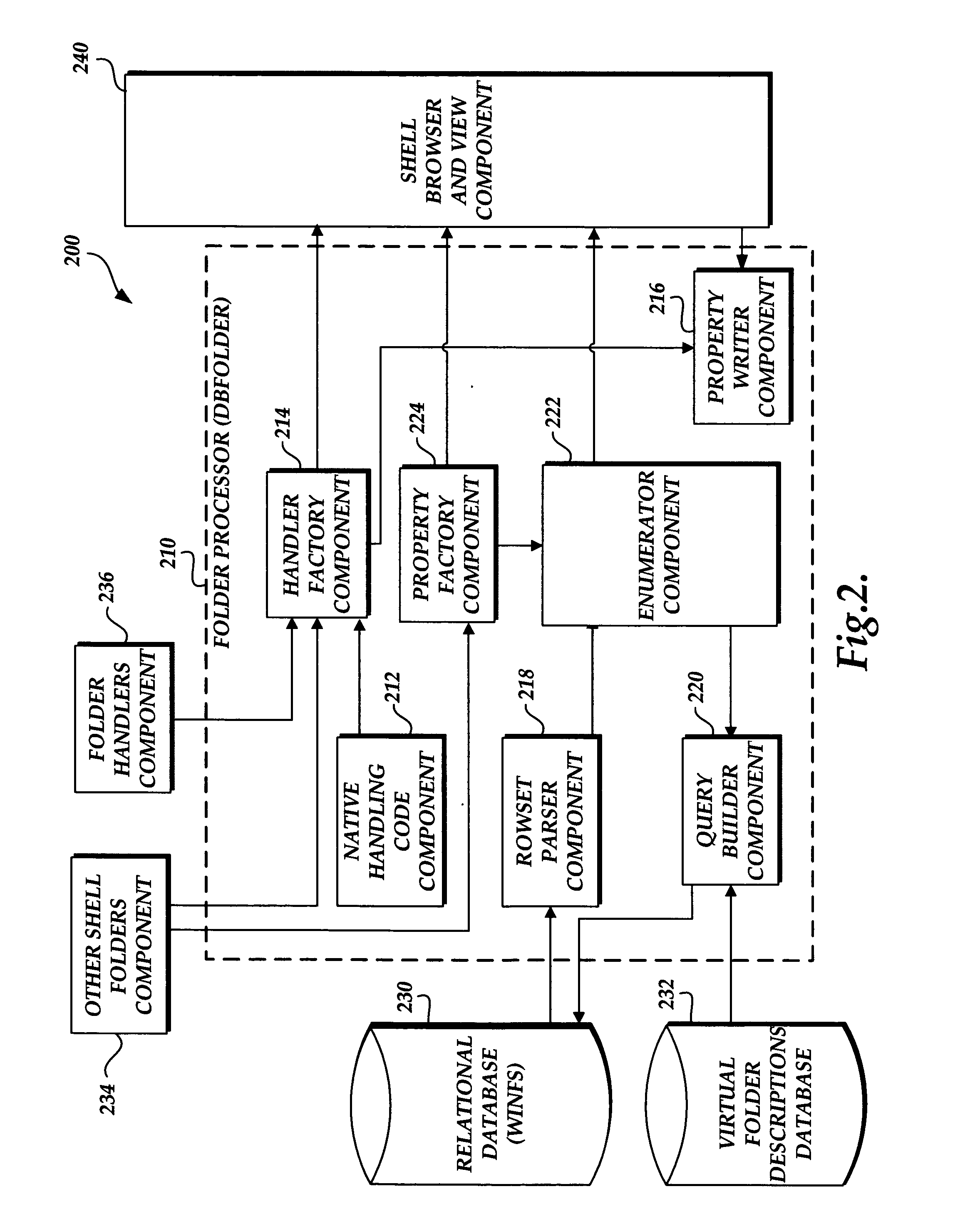
InactiveUS20060036568A1Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedProject type
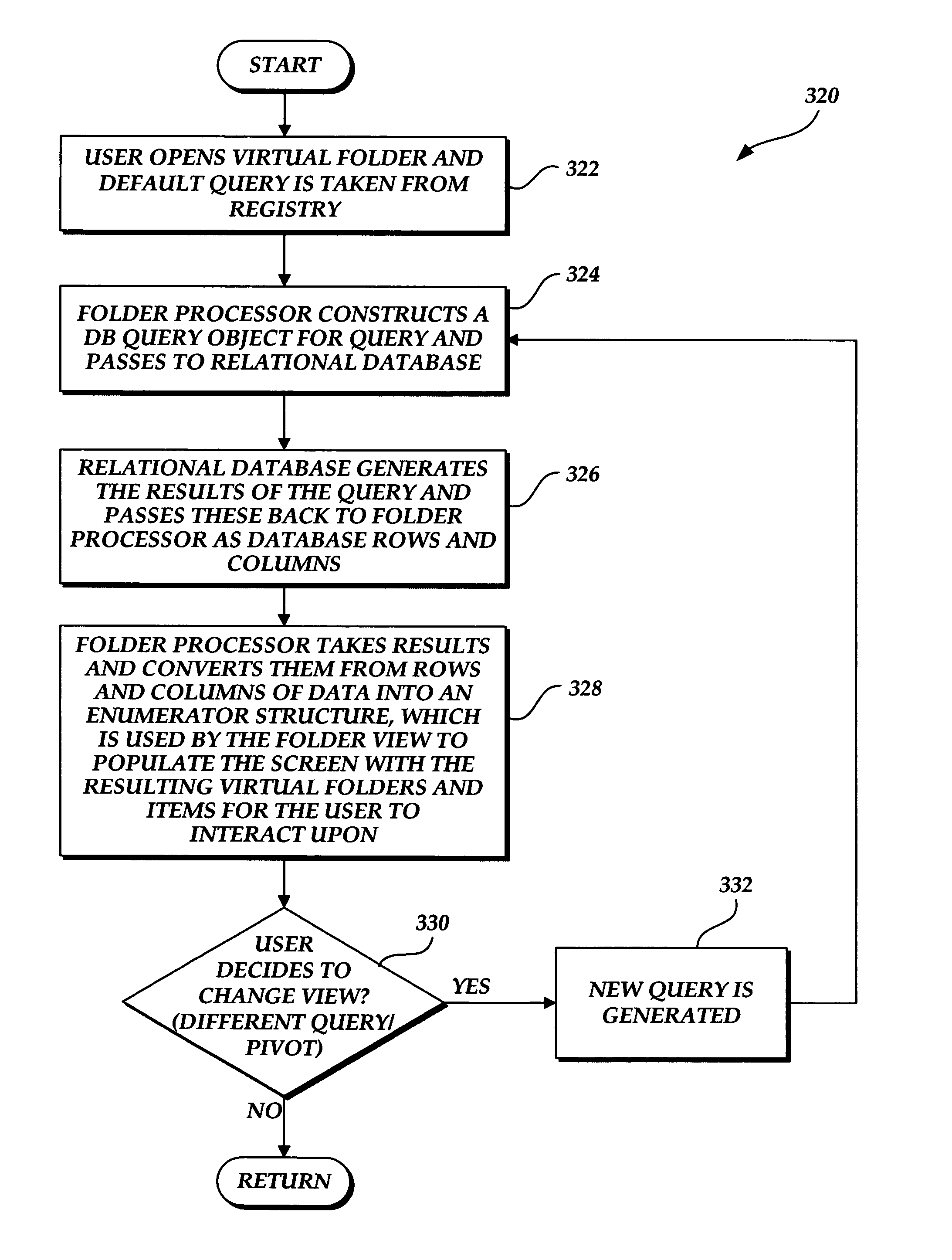
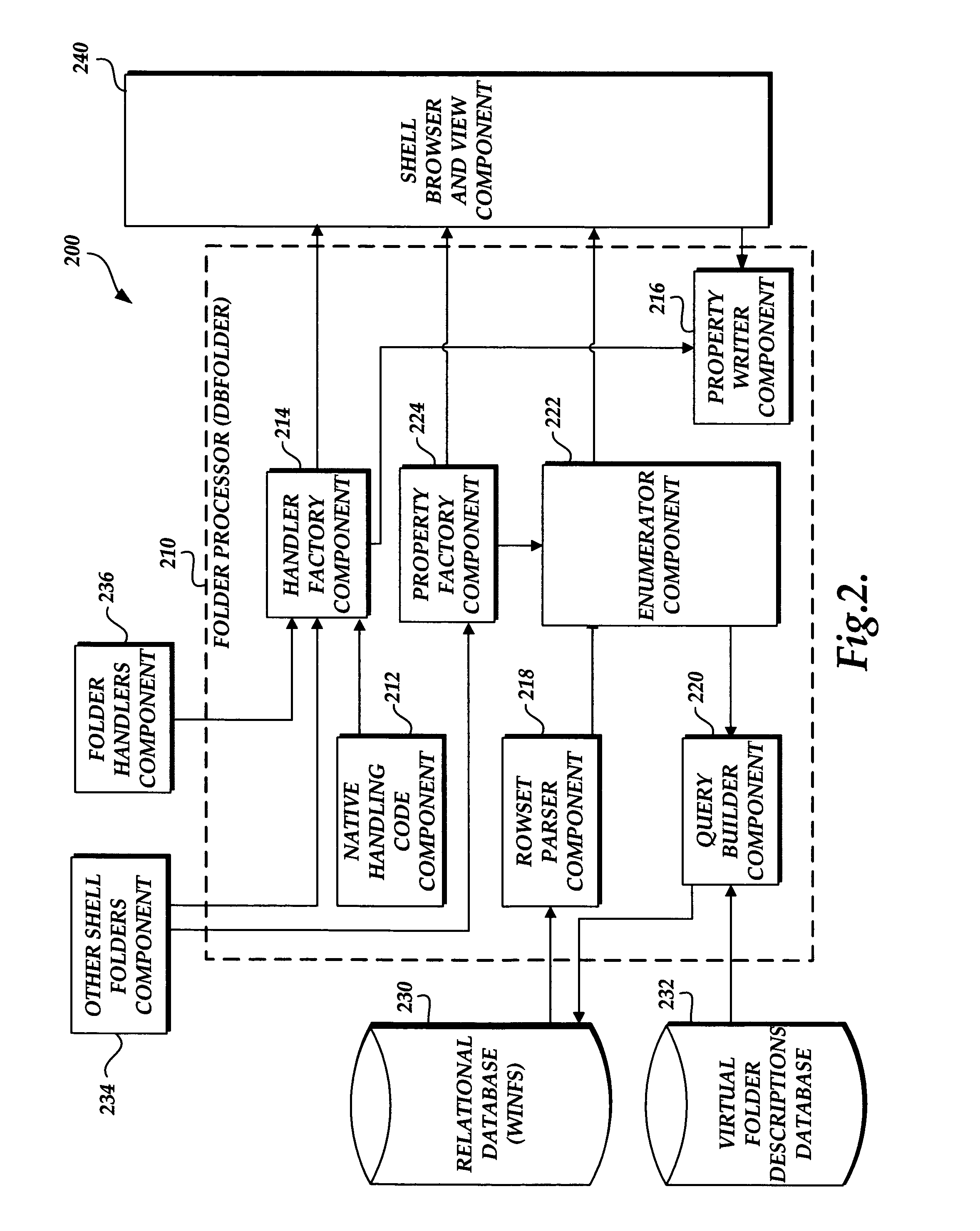
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
Cryptographic methods, apparatus and systems for storage media electronic rights management in closed and connected appliances
InactiveUS20010042043A1Low costGuaranteed to continue to useTelevision system detailsDigital data processing detailsControl setGeneral purpose
A rights management arrangement for storage media such as optical digital video disks (DVDs, also called digital versatile disks) provides adequate copy protection in a limited, inexpensive mass-produceable, low-capability platform such as a dedicated home consumer disk player and also provides enhanced, more flexible security techniques and methods when the same media are used with platforms having higher security capabilities. A control object (or set) defines plural rights management rules for instance, price for performance or rules governing redistribution. Low capability platforms may enable only a subset of the control rules such as controls on copying or marking of played material. Higher capability platforms may enable all (or different subsets) of the rules. Cryptographically strong security is provided by encrypting at least some of the information carried by the media and enabling decryption based on the control set and / or other limitations. A secure "software container" can be used to protectively encapsulate (e.g., by cryptographic techniques) various digital property content (e.g., audio, video, game, etc.) and control object (i.e., set of rules) information. A standardized container format is provided for general use on / with various mediums and platforms. In addition, a special purpose container may be provided for DVD medium and appliances (e.g., recorders, players, etc.) that contains DVD program content (digital property) and DVD medium specific rules. The techniques, systems and methods disclosed herein are capable of achieving compatibility with other protection standards, such as for example, CGMA and Matsushita data protection standards adopted for DVDs. Cooperative rights management may also be provided, where plural networked rights management arrangements collectively control a rights management event on one or more of such arrangements.
Owner:INTERTRUST TECH CORP
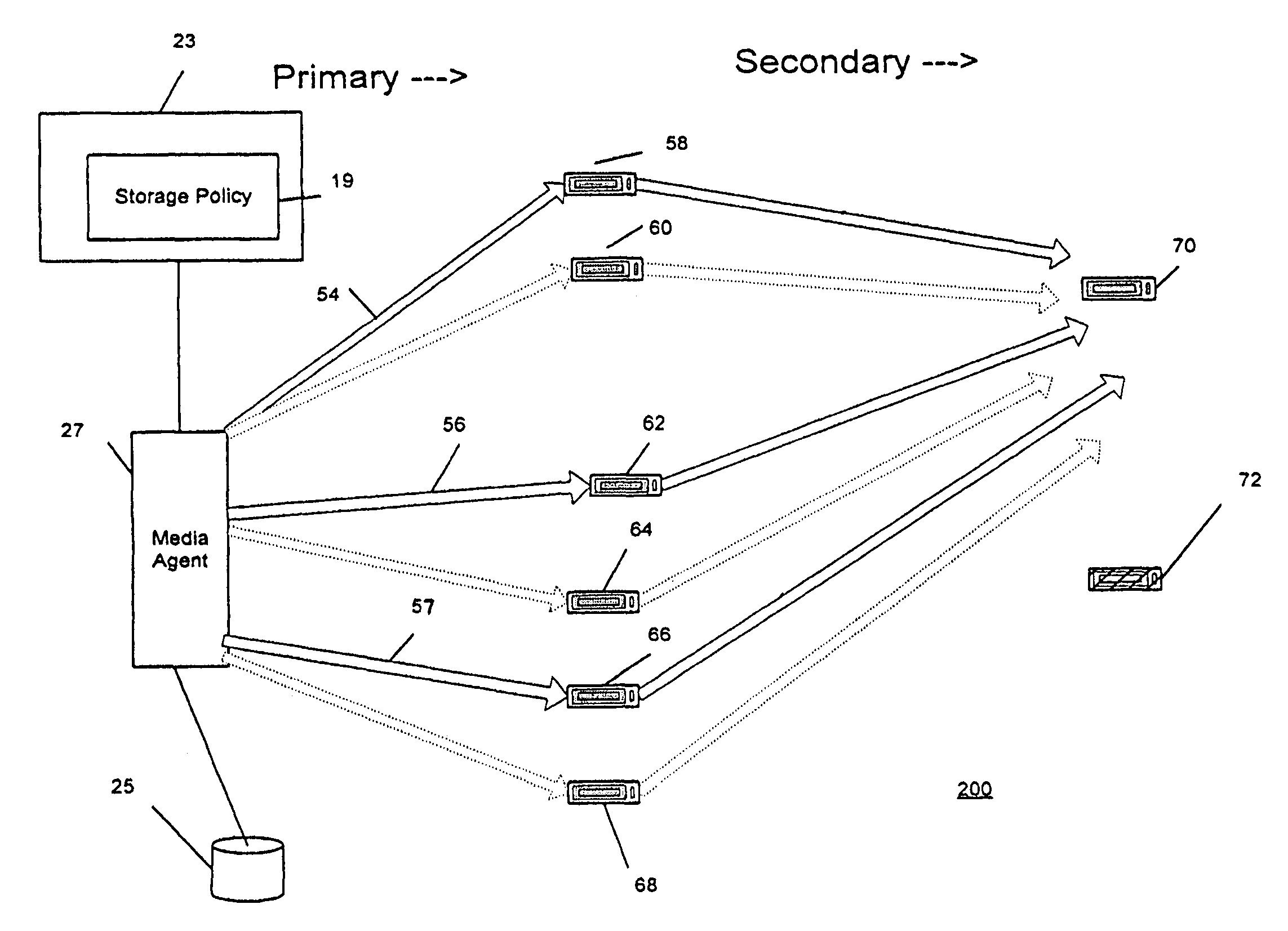
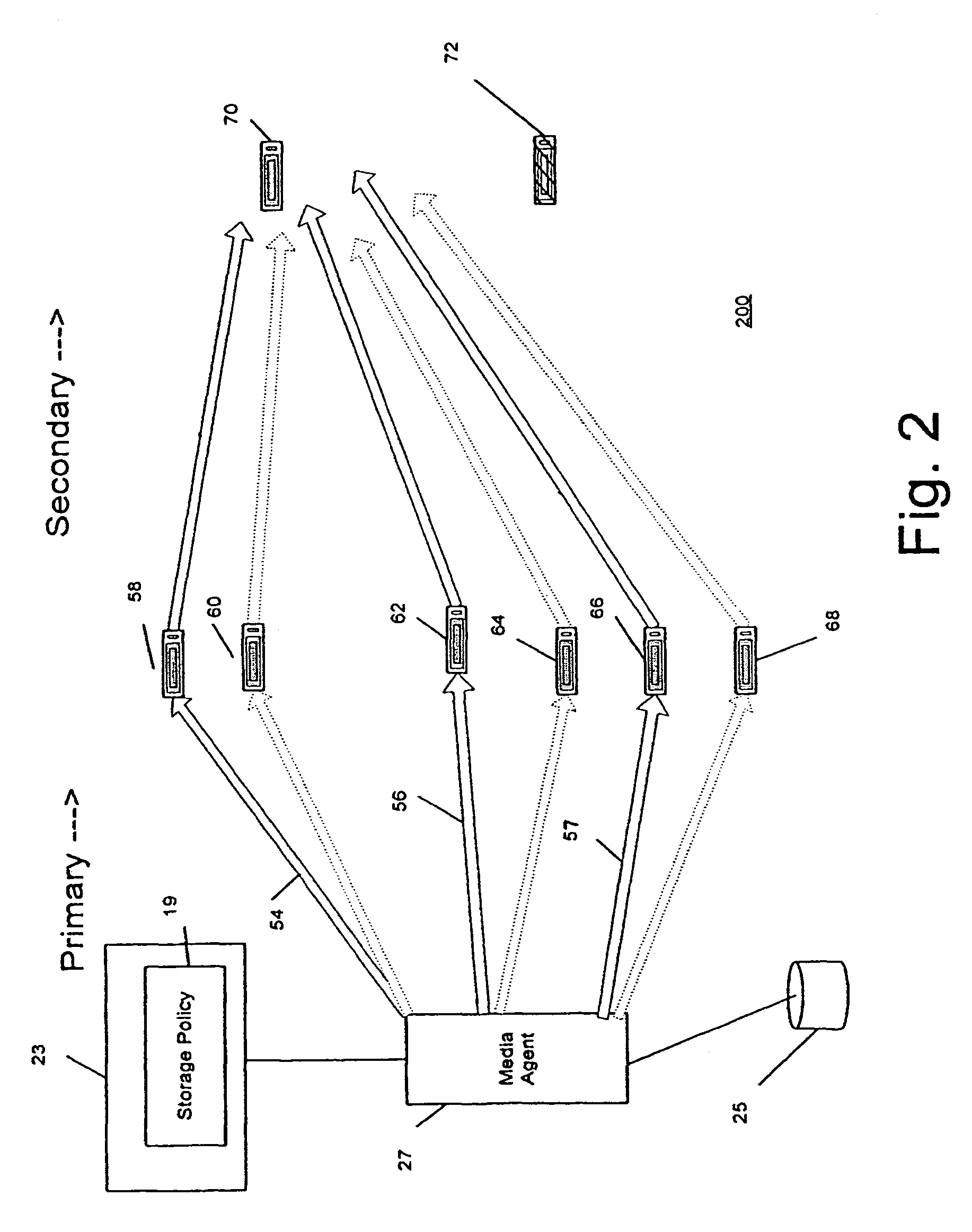
Combined stream auxiliary copy system and method
A system and method for transferring data in a library storage system. The library storage system comprises a management server including a storage policy. A media agent is connected to the management server. A plurality of storage media and a data source are connected to the media agent. The data source is divided into at least a first and a second portion of data. The portions of data are transferred from the data source to a first and second primary storage medium using a first and a second data stream respectively. The media agent then causes the first and second portion of data to be transferred from the first and second storage medium to a third auxiliary storage medium using a third combined data stream. Auxiliary copying is performed in chunks and multiple streams are copied in parallel.
Owner:COMMVAULT SYST INC
Automatic deletion of electronic messages
InactiveUS20110213845A1Memory loss protectionError detection/correctionComputer hardwareElectronic information
A system and method are provided for automatically deleting messages such as e-mail upon consumption by the recipient. Consumption by the recipient may include viewing the message, forwarding or replying to the message, or archiving, saving, copying, or moving the message. An indicator is inserted in the message, for example in the message header or body, indicating that the message is to be deleted upon detection of a triggering consumption action. Upon receipt at the recipient's mail client, the client determines whether the indicator is present, and, upon detection of a triggering consumption action, automatically closes any views of the message displayed by the recipient's mail client and deletes the message. Optionally a warning is provided to the recipient prior to deletion.
Owner:BLACKBERRY LTD
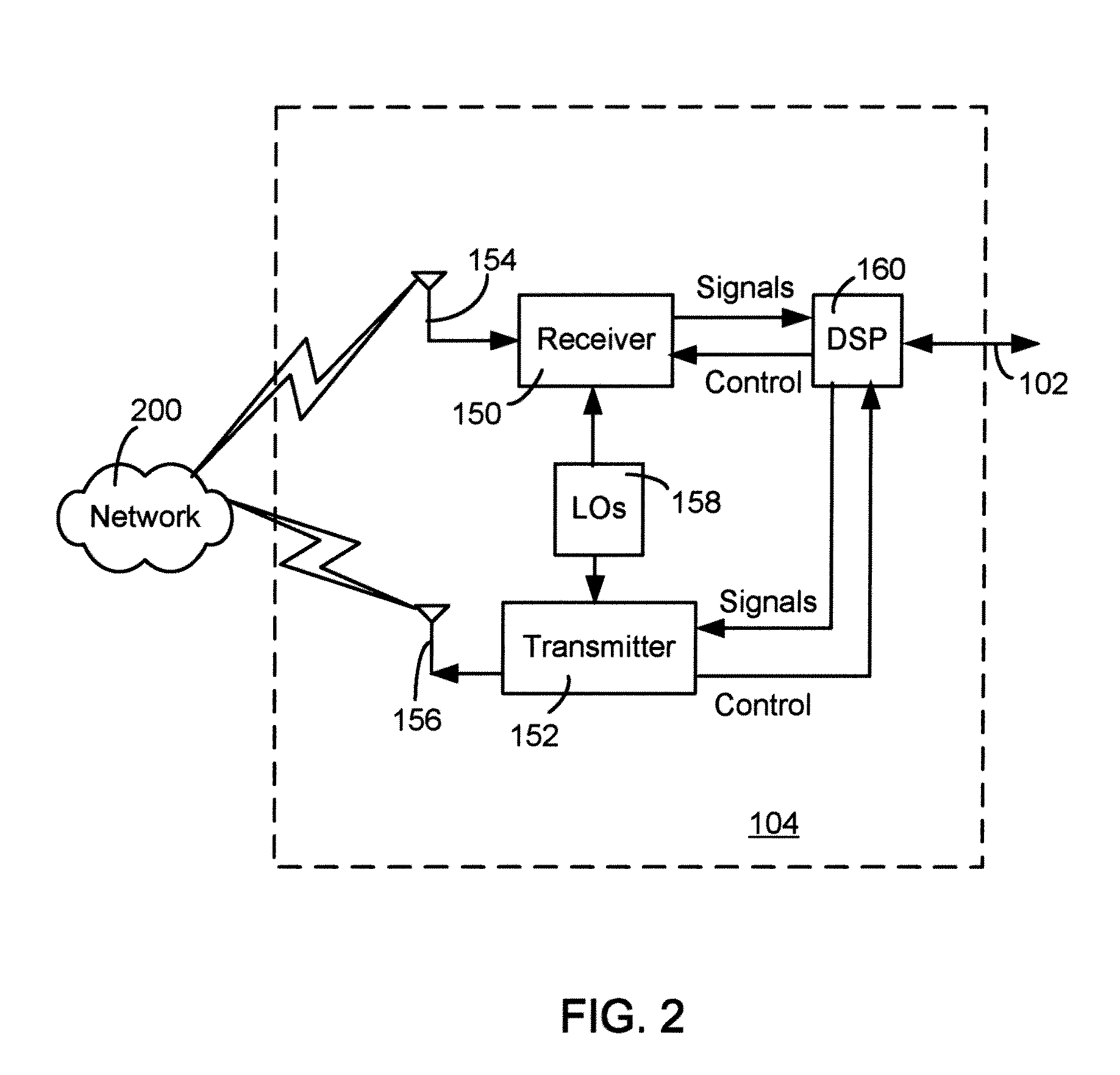
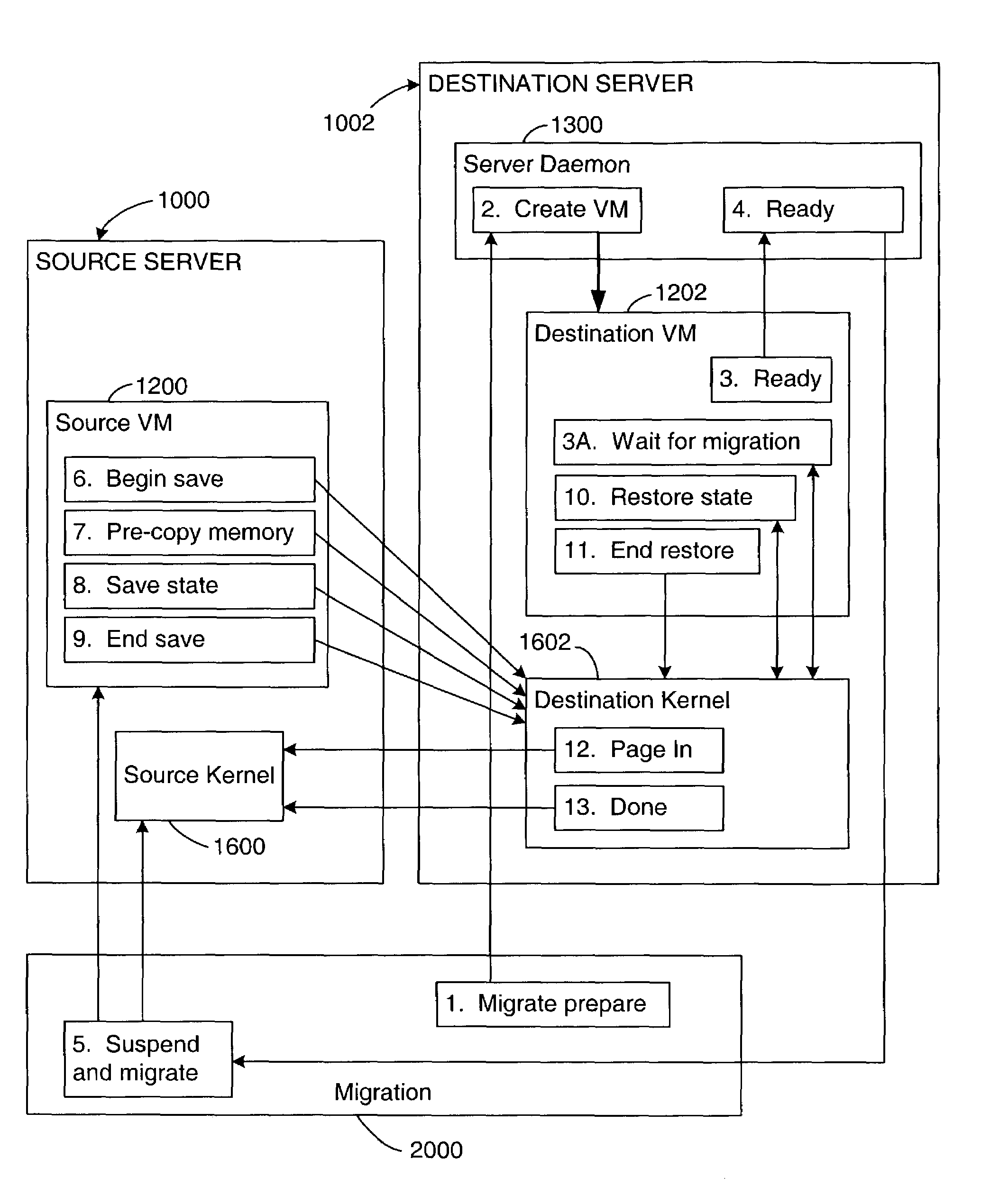
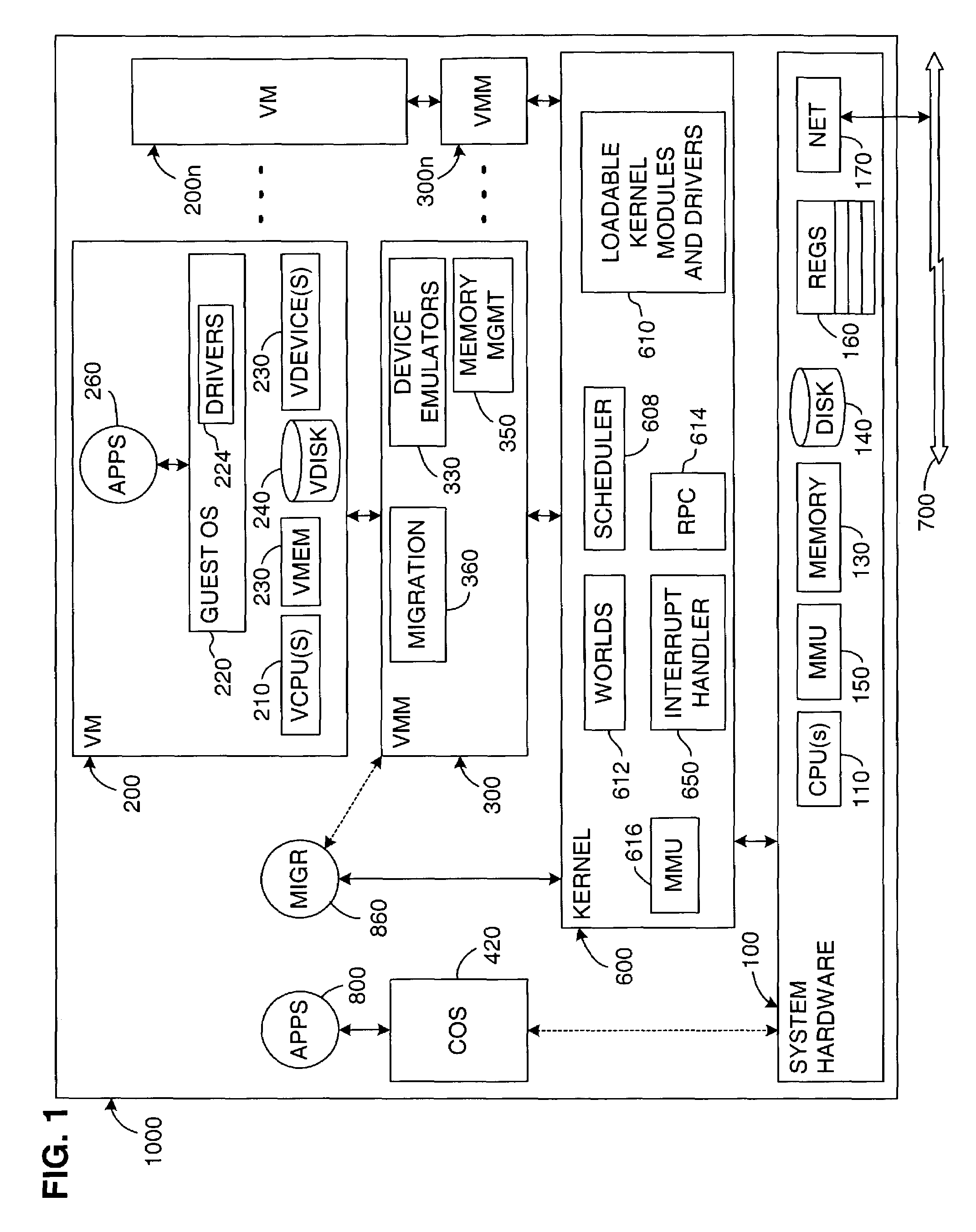
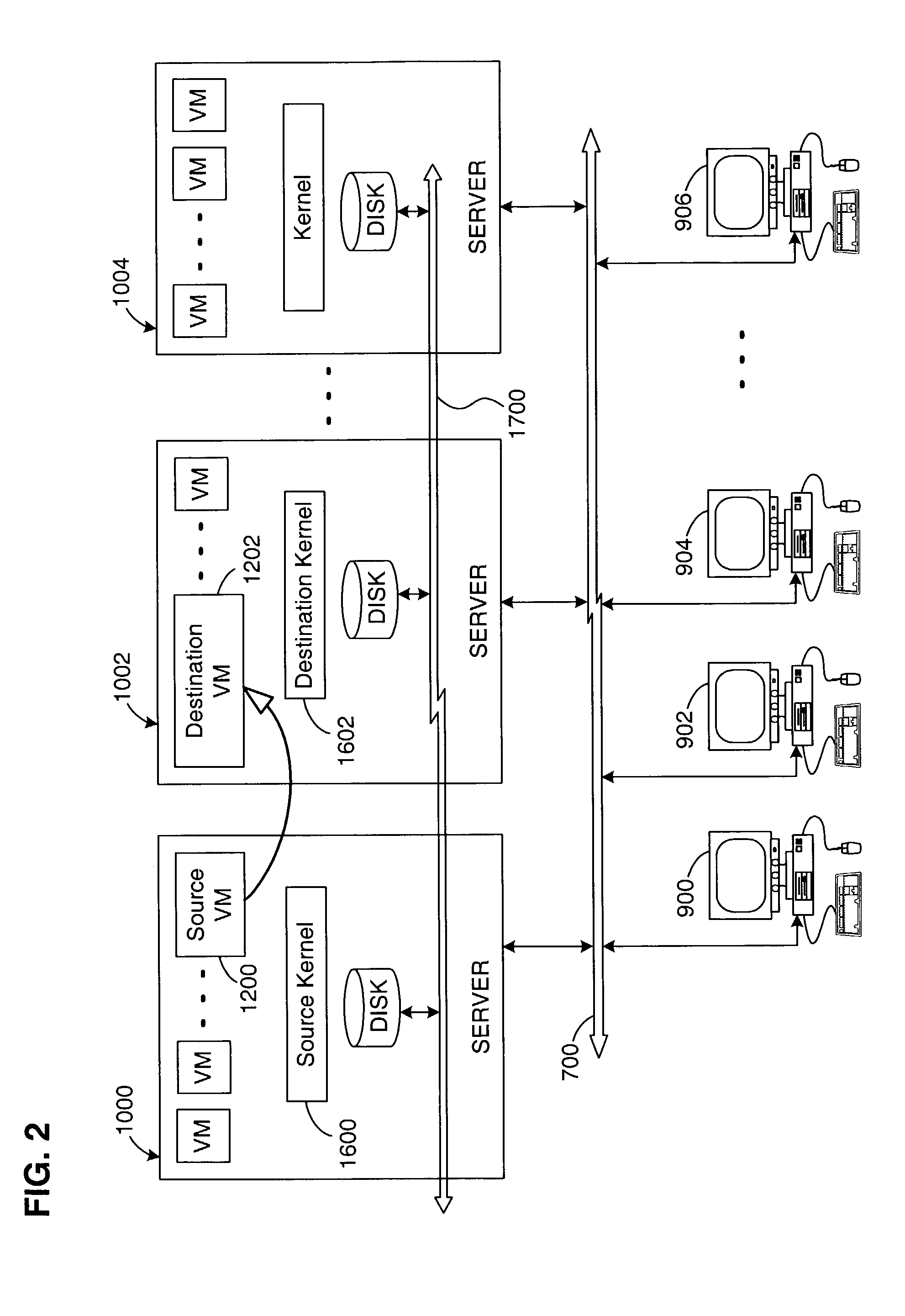
Virtual machine migration
A source virtual machine (VM) hosted on a source server is migrated to a destination VM on a destination server without first powering down the source VM. After optional pre-copying of the source VM's memory to the destination VM, the source VM is suspended and its non-memory state is transferred to the destination VM; the destination VM is then resumed from the transferred state. The source VM memory is either paged in to the destination VM on demand, or is transferred asynchronously by pre-copying and write-protecting the source VM memory, and then later transferring only the modified pages after the destination VM is resumed. The source and destination servers preferably share common storage, in which the source VM's virtual disk is stored; this avoids the need to transfer the virtual disk contents. Network connectivity is preferably also made transparent to the user by arranging the servers on a common subnet, with virtual network connection addresses generated from a common name space of physical addresses.
Owner:VMWARE INC
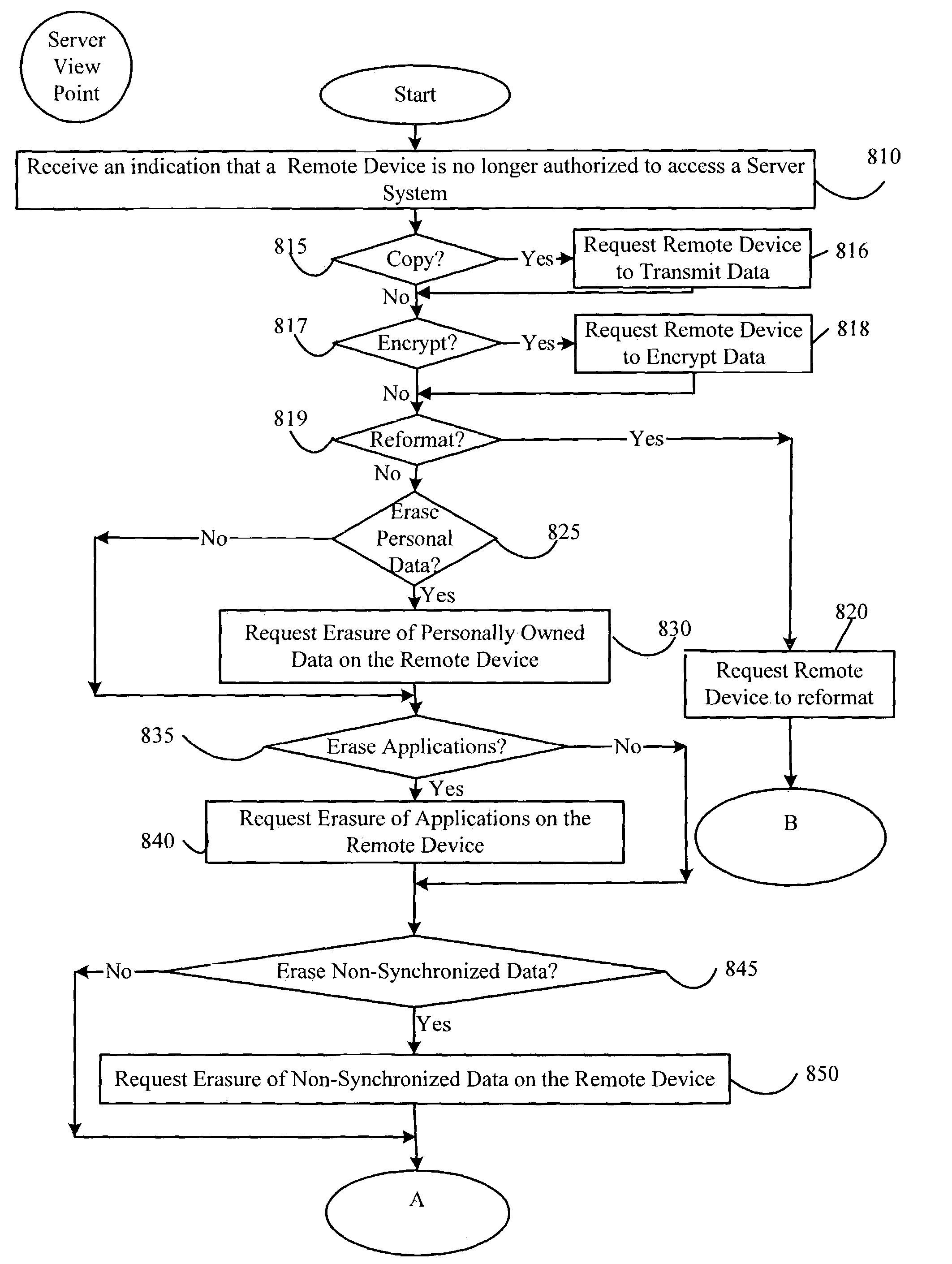
System and method for preventing access to data on a compromised remote device
ActiveUS8012219B2Avoid misuseVolume/mass flow measurementUser identity/authority verificationAuthorizationEncryption
Owner:BLACKBERRY LTD
Maintenance of a file version set including read-only and read-write snapshot copies of a production file
Read-only and read-write snapshot copies of a production file in a Unix-based file system are organized as a version set of file inodes and shared file blocks. Version pointers and branch pointers link the inodes. Initially the production file can have all its blocks preallocated or it can be a sparse file having only an inode and its last data block. A protocol is provided for creating read-only and read-write snapshots, deleting snapshots, restoring the production file with a specified snapshot, refreshing a specified snapshot, and naming the snapshots. Block pointers are marked with a flag indicating whether or not the pointed-to block is owned by the parent inode. A non-owner marking is inherited by all of the block's descendants. The block ownership controls the copying of indirect blocks when writing to the production file, and also controls deallocation and passing of blocks when deleting a read-only snapshot.
Owner:EMC IP HLDG CO LLC
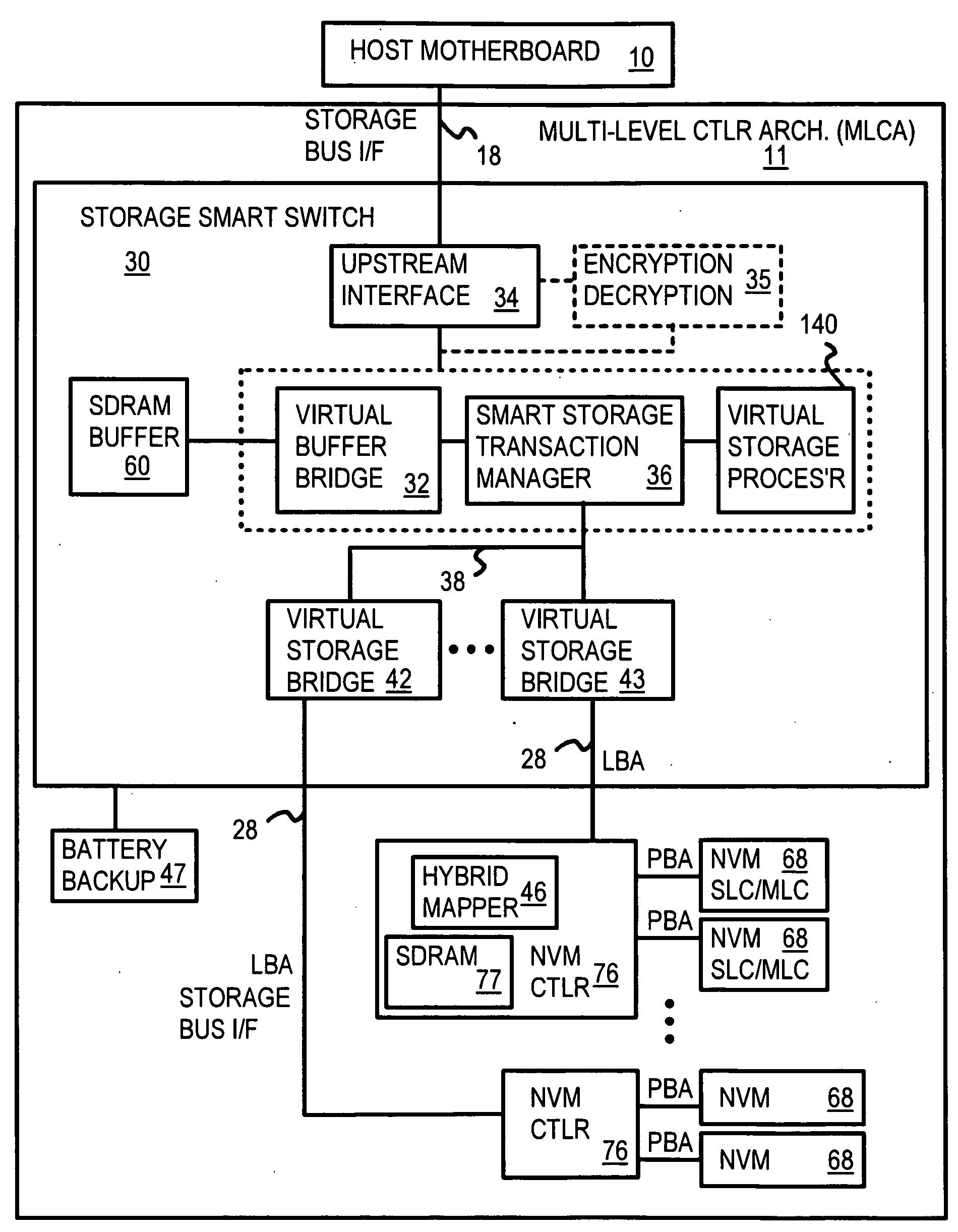
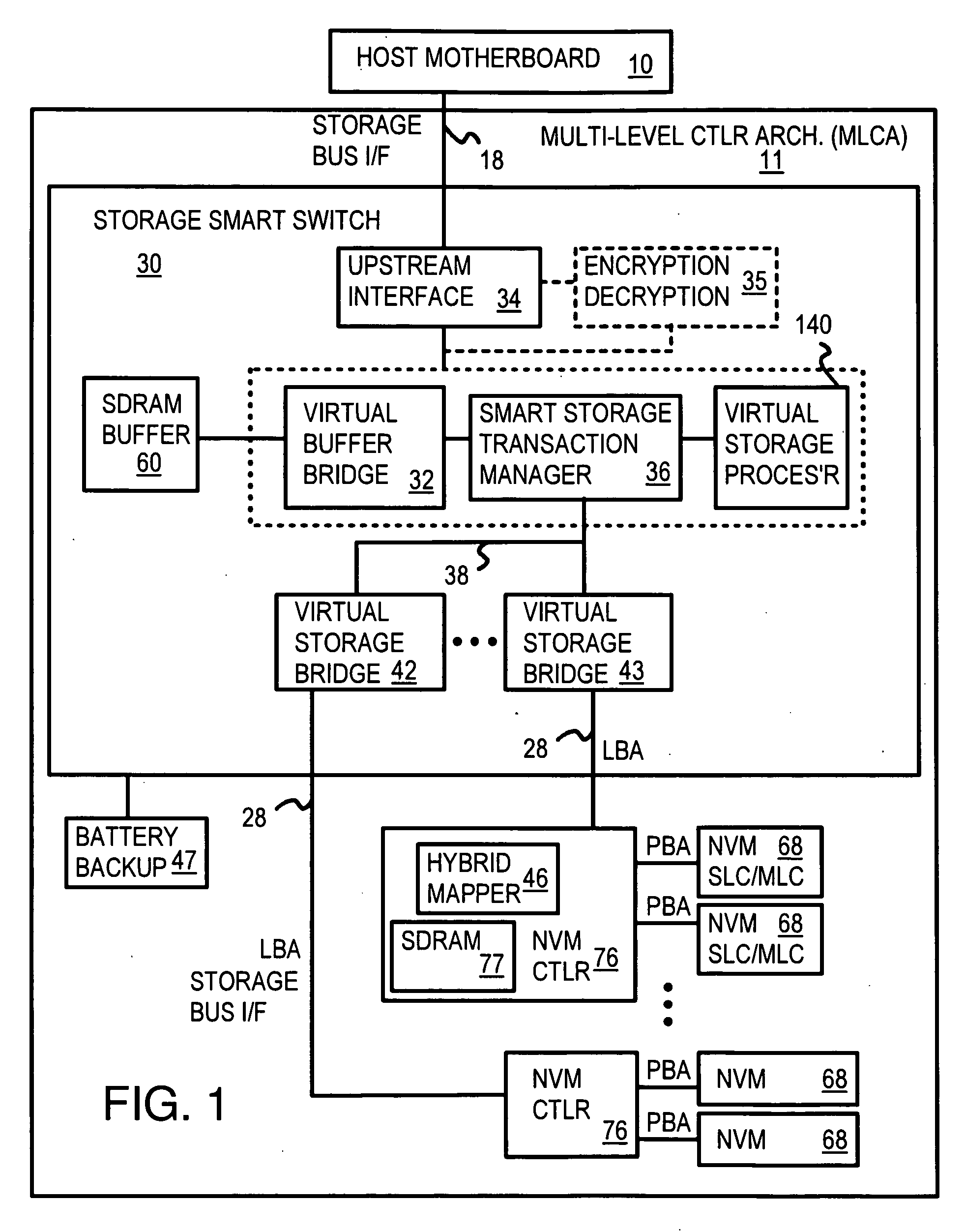
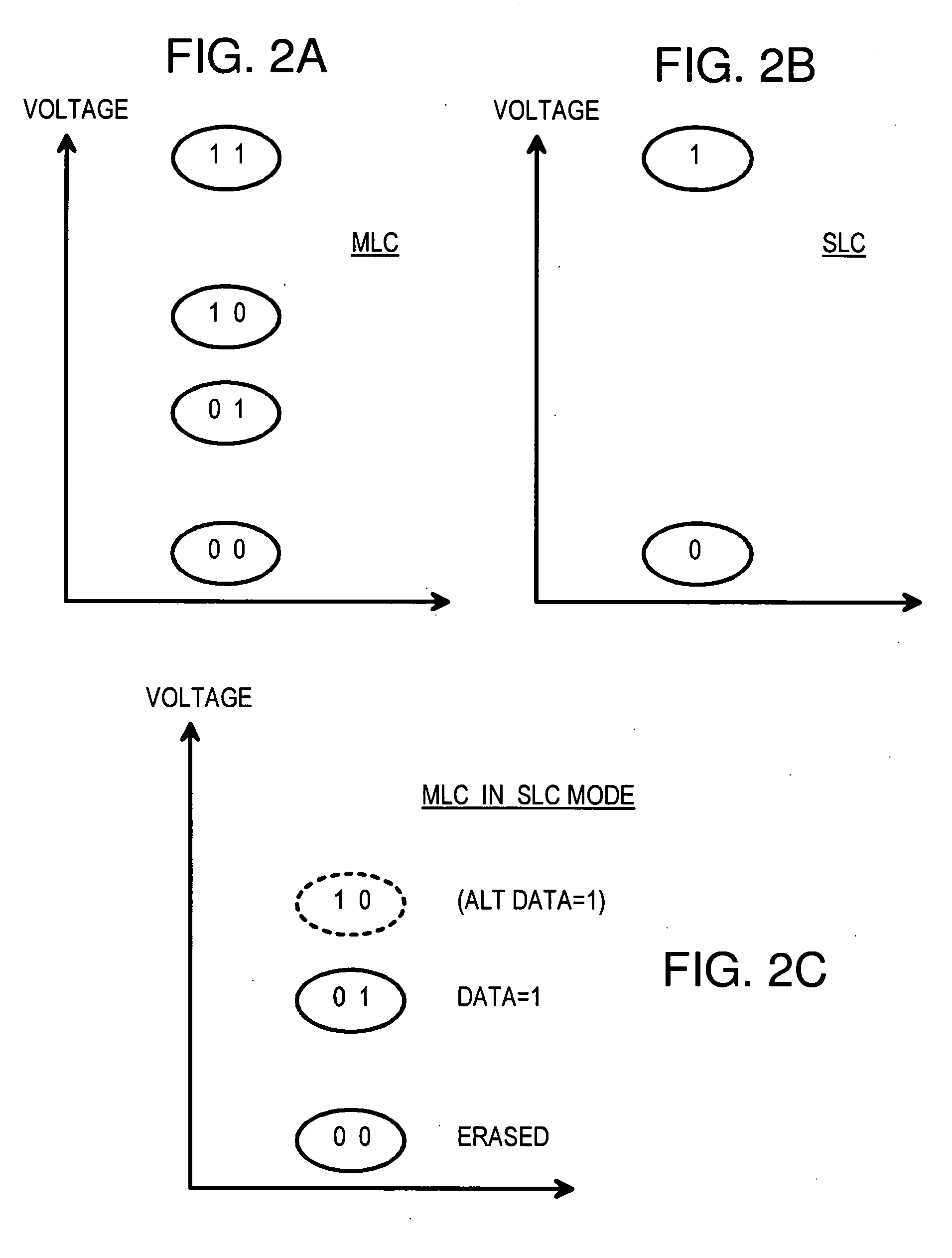
Hybrid 2-Level Mapping Tables for Hybrid Block- and Page-Mode Flash-Memory System
InactiveUS20090193184A1Memory architecture accessing/allocationMemory adressing/allocation/relocationVirtual fieldFrequency counter
A hybrid solid-state disk (SSD) has multi-level-cell (MLC) or single-level-cell (SLC) flash memory, or both. SLC flash may be emulated by MLC that uses fewer cell states. A NVM controller converts logical block addresses (LBA) to physical block addresses (PBA). Most data is block-mapped and stored in MLC flash, but some critical or high-frequency data is page-mapped to reduce block-relocation copying. A hybrid mapping table has a first-level and a second level. Only the first level is used for block-mapped data, but both levels are used for page-mapped data. The first level contains a block-page bit that indicates if the data is block-mapped or page-mapped. A PBA field in the first-level table maps block-mapped data, while a virtual field points to the second-level table where the PBA and page number is stored for page-mapped data. Page-mapped data is identified by a frequency counter or sector count. SRAM space is reduced.
Owner:SUPER TALENT ELECTRONICS
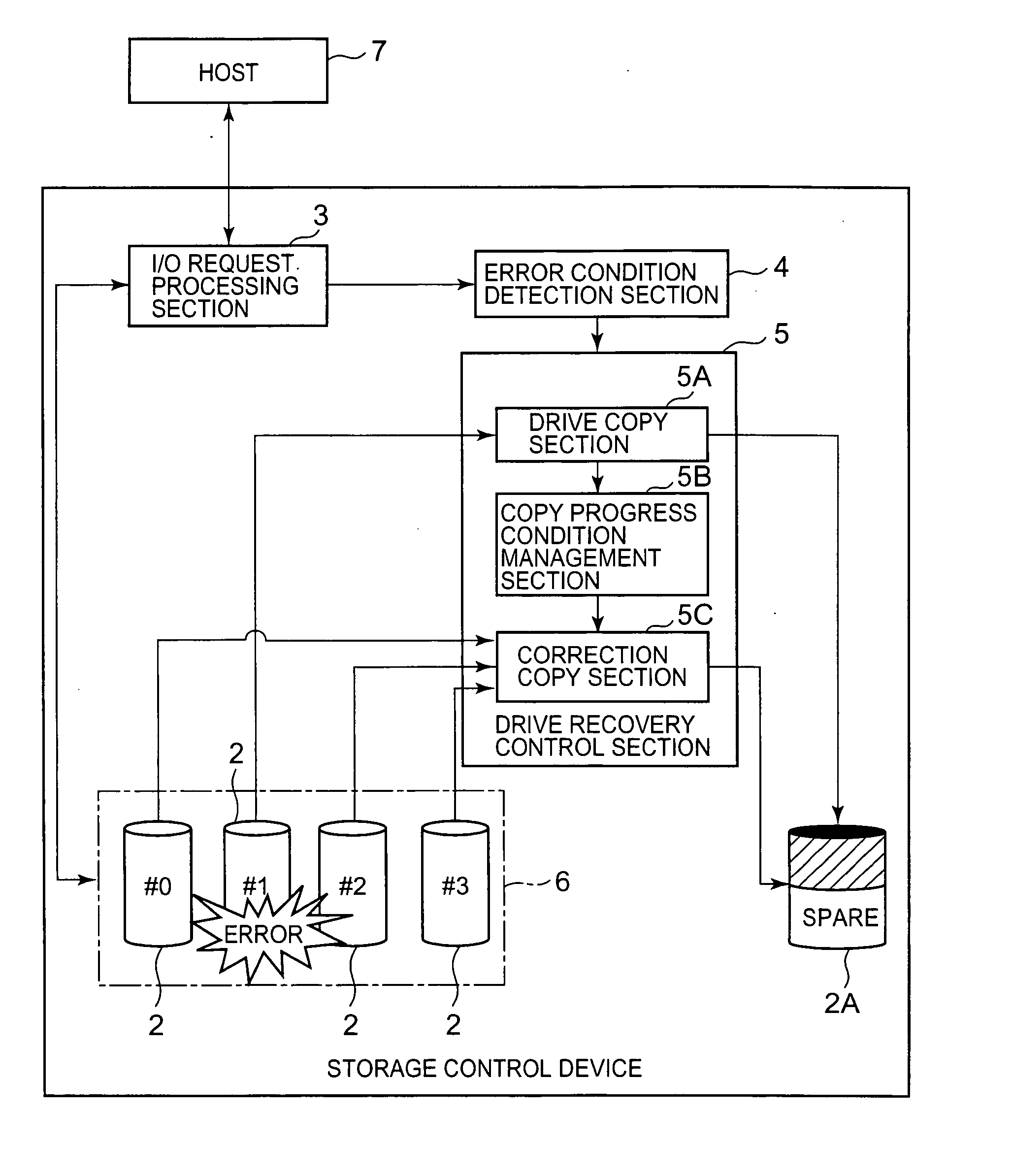
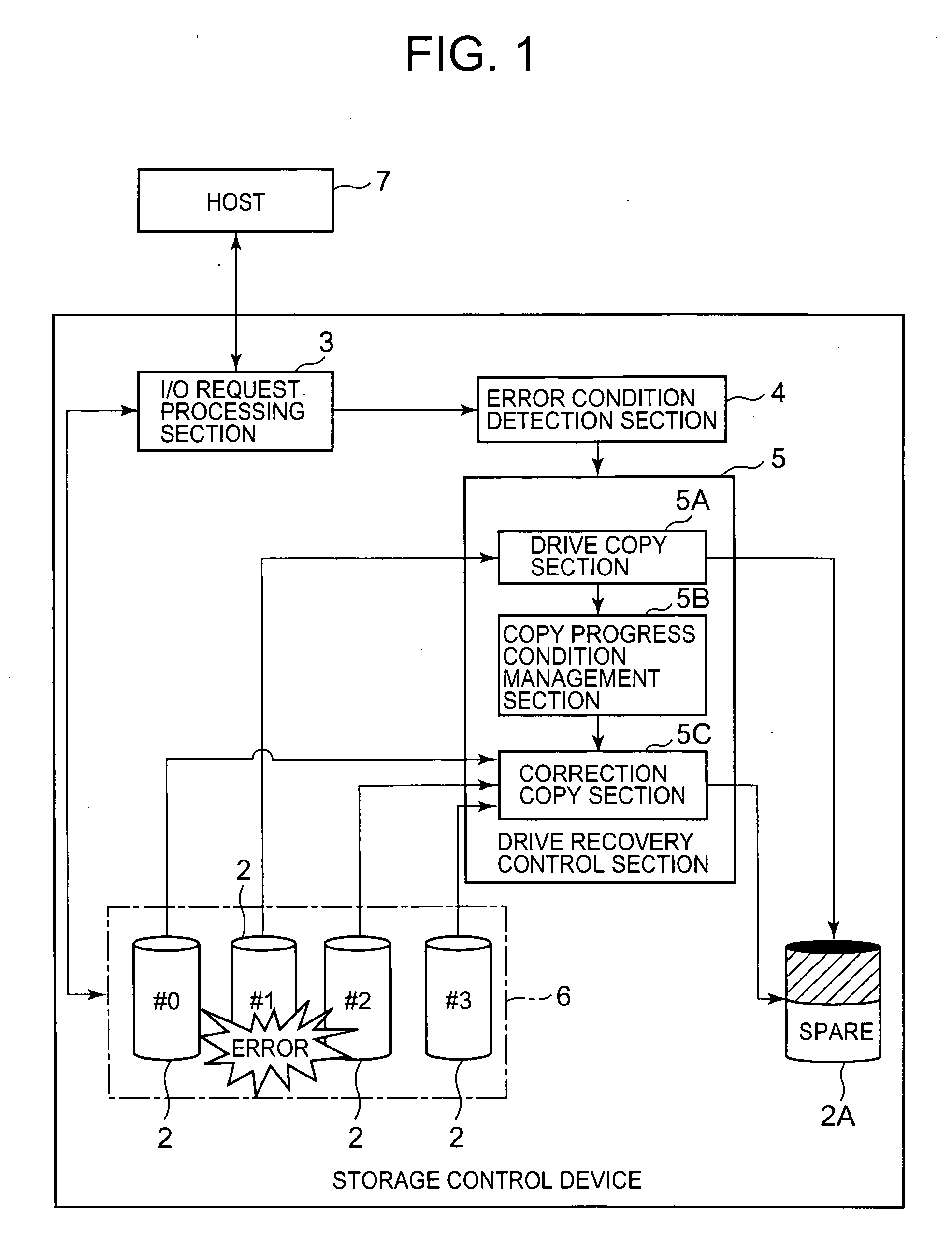
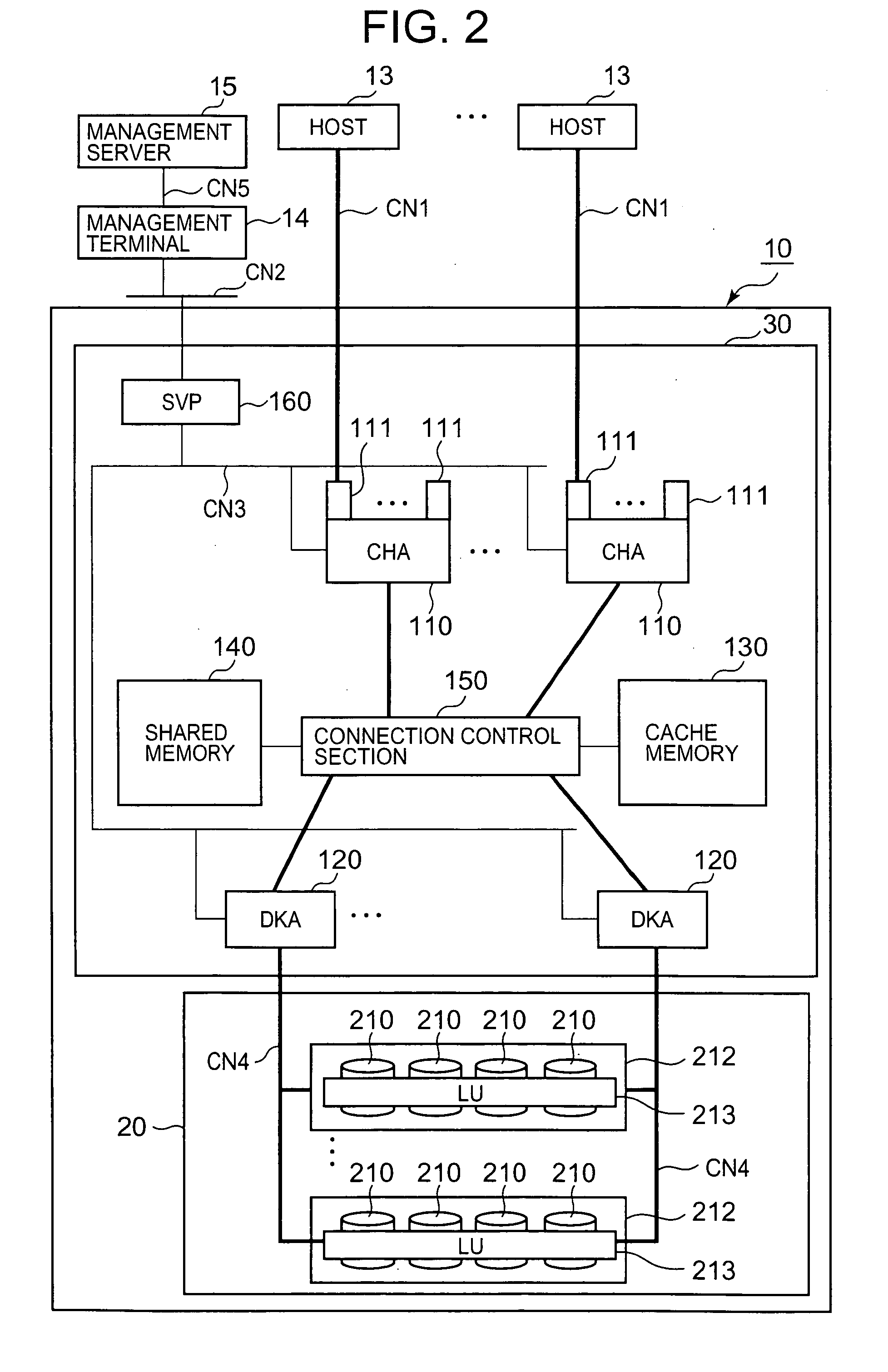
Storage control device and data recovery method for storage control device
The present invention efficiently recovers an error drive by suppressing futile copying. When the number of errors of the disk drive is equal to or more than a first threshold, data stored in the disk drive is copied to a spare drive by a drive copy section. When the number of errors of the disk drive is equal to or more than a second threshold prior to completion of the drive copy, the disk drive is closed, and a correction copy by a correction copy section is started in place of the drive copy. The correction copy section starts the correction copy from the position where the drive copy is interrupted by taking over the drive copy completion position (copy interrupt position) managed by a copy progress condition management section.
Owner:HITACHI LTD
Method and apparatus for maintaining data on non-volatile memory systems
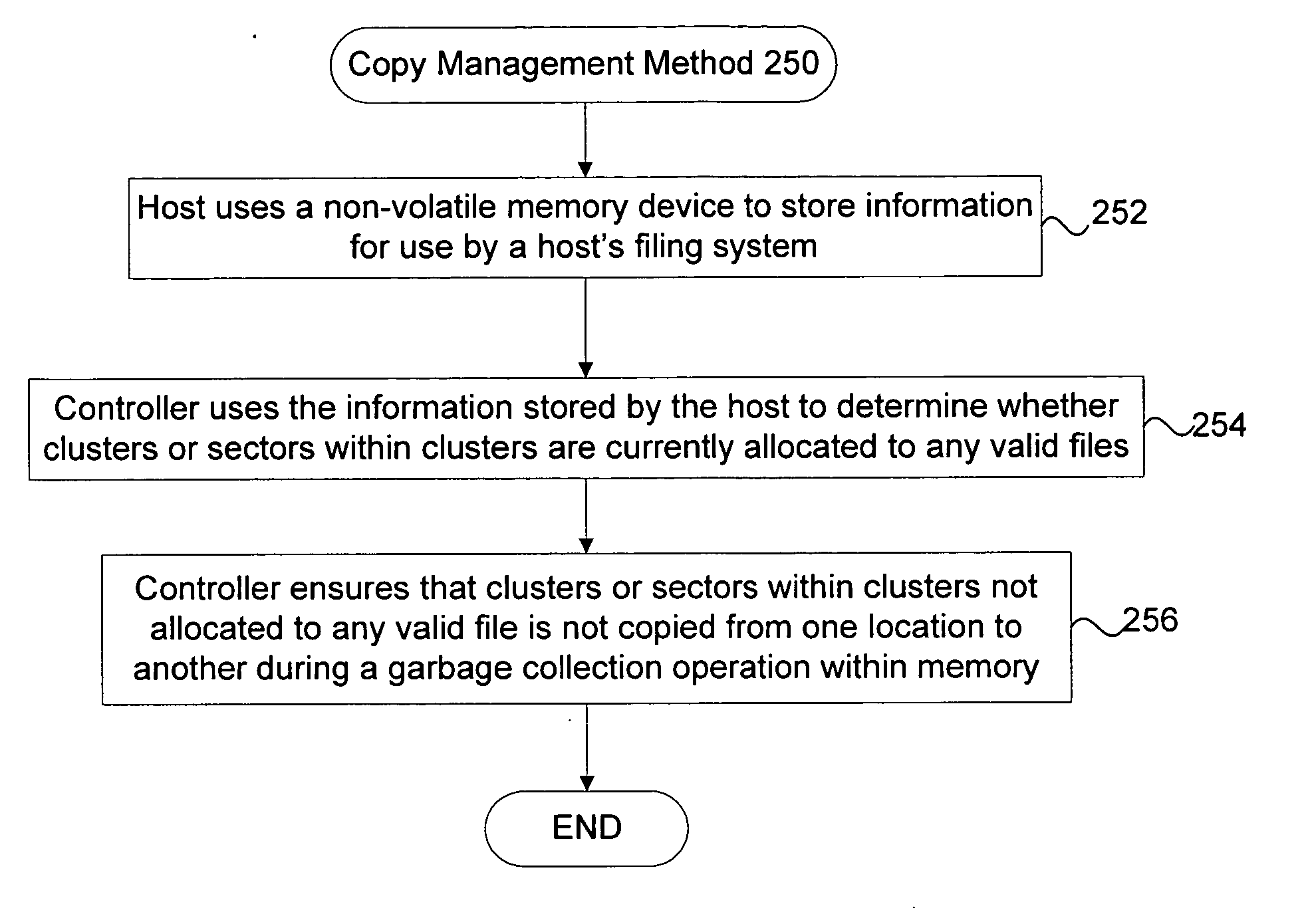
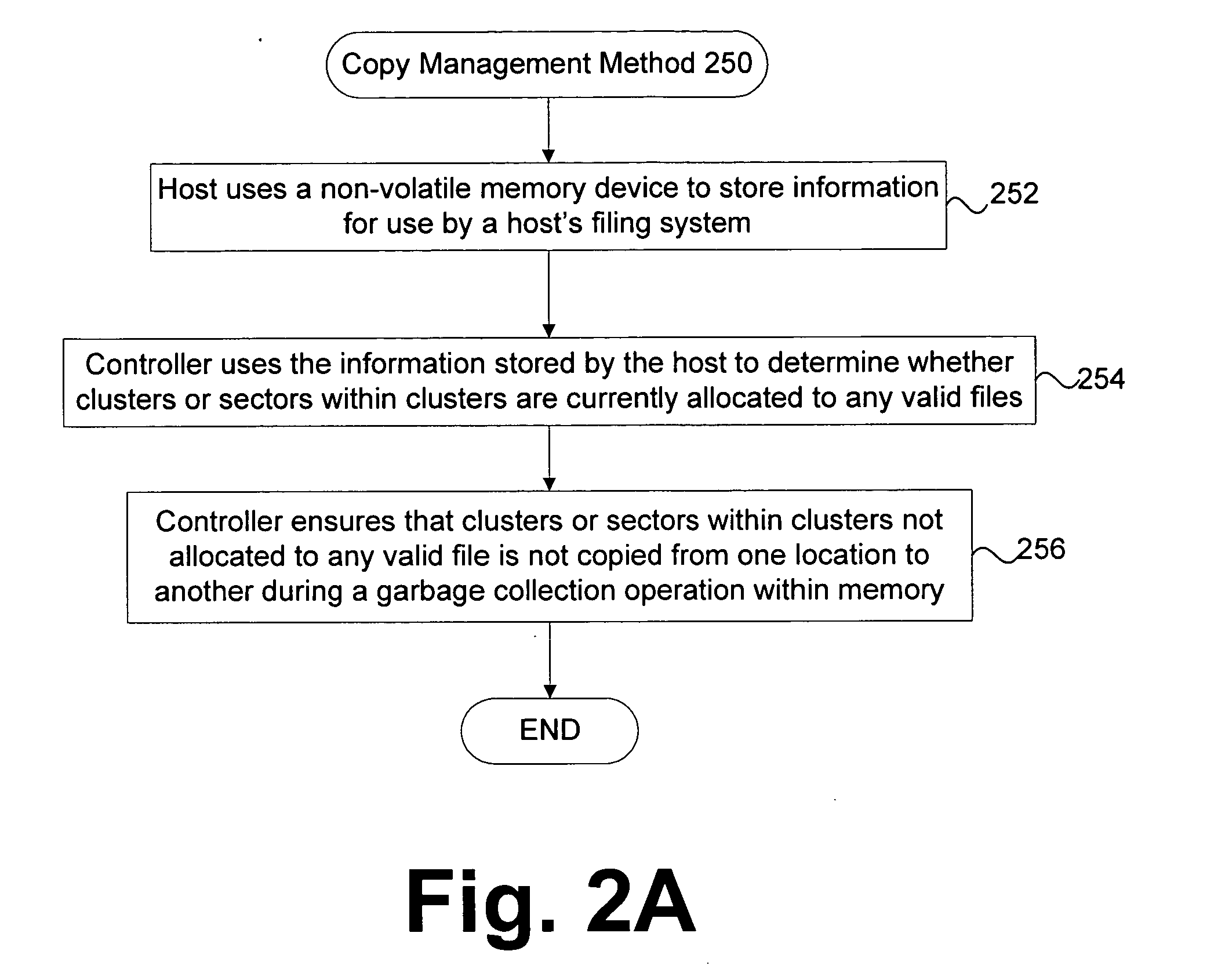
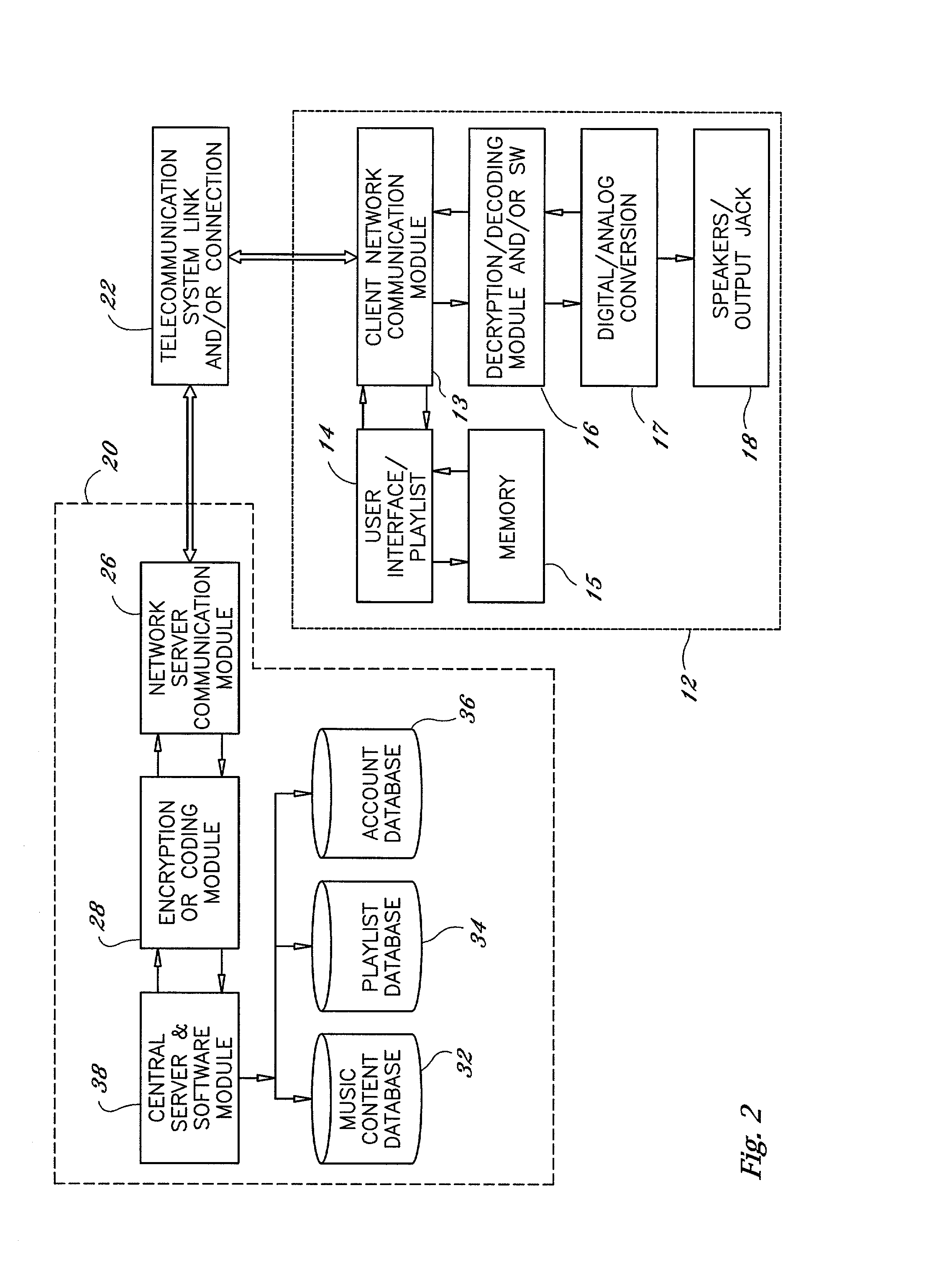
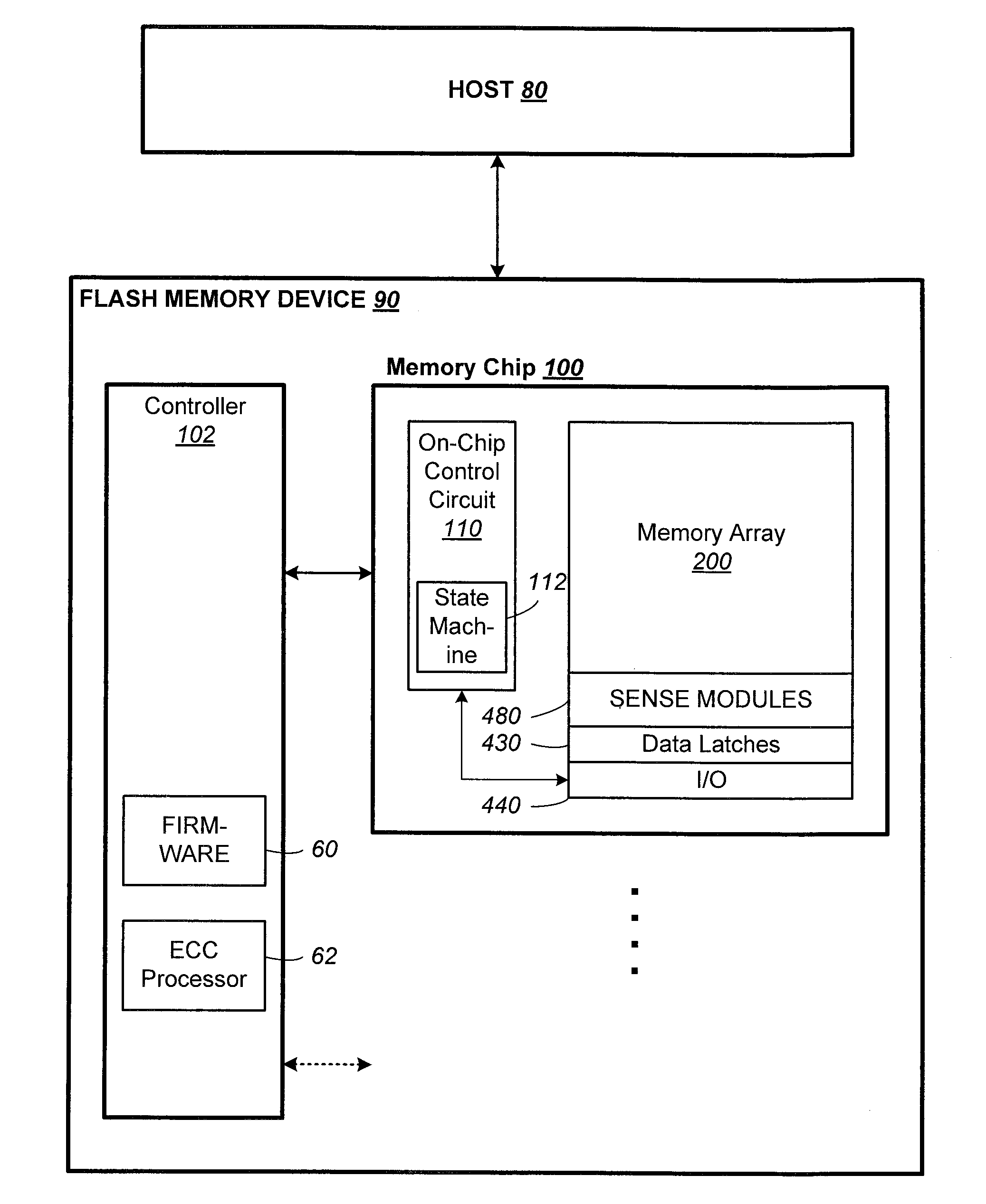
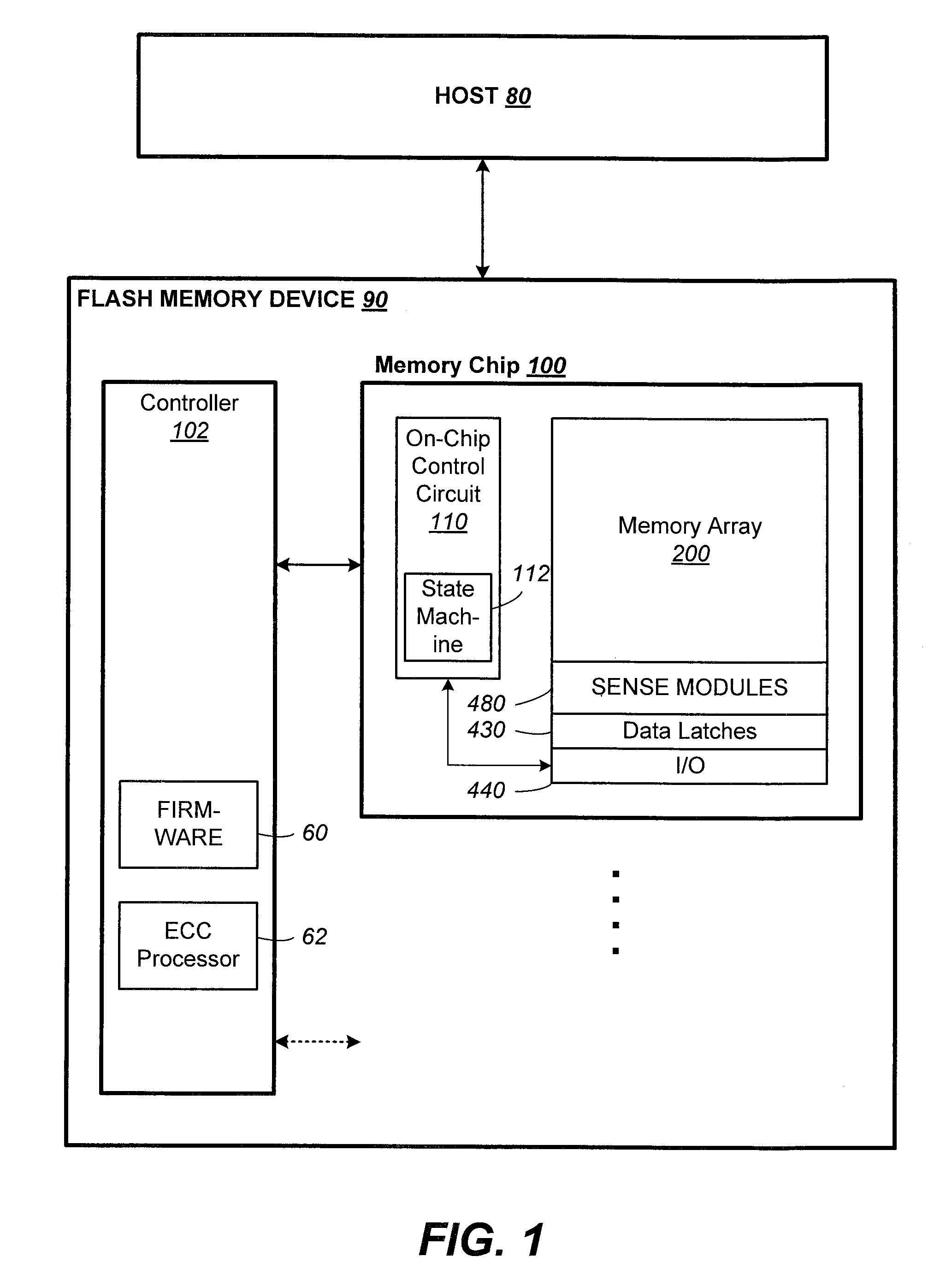
ActiveUS20060020744A1Improve system performanceUnnecessary operationMemory architecture accessing/allocationData processing applicationsCopyingVolatile memory
Techniques for managing data in a non-volatile memory system (e.g., Flash Memory) are disclosed. A controller can use information relating to a host's filing system, which is stored by the host on non-volatile memory, to determine if one or more clusters (or sectors with clusters) are currently allocated. The controller can use the information relating to the host's filing system to ensure that one or more clusters (or one or more sectors within a cluster) are not copied from one location to another location in the memory during a garbage collection cycle. As a result, some unnecessary operations (e.g., copying data) which are conventionally performed can be avoided and system performance can be enhanced.
Owner:SANDISK TECH LLC
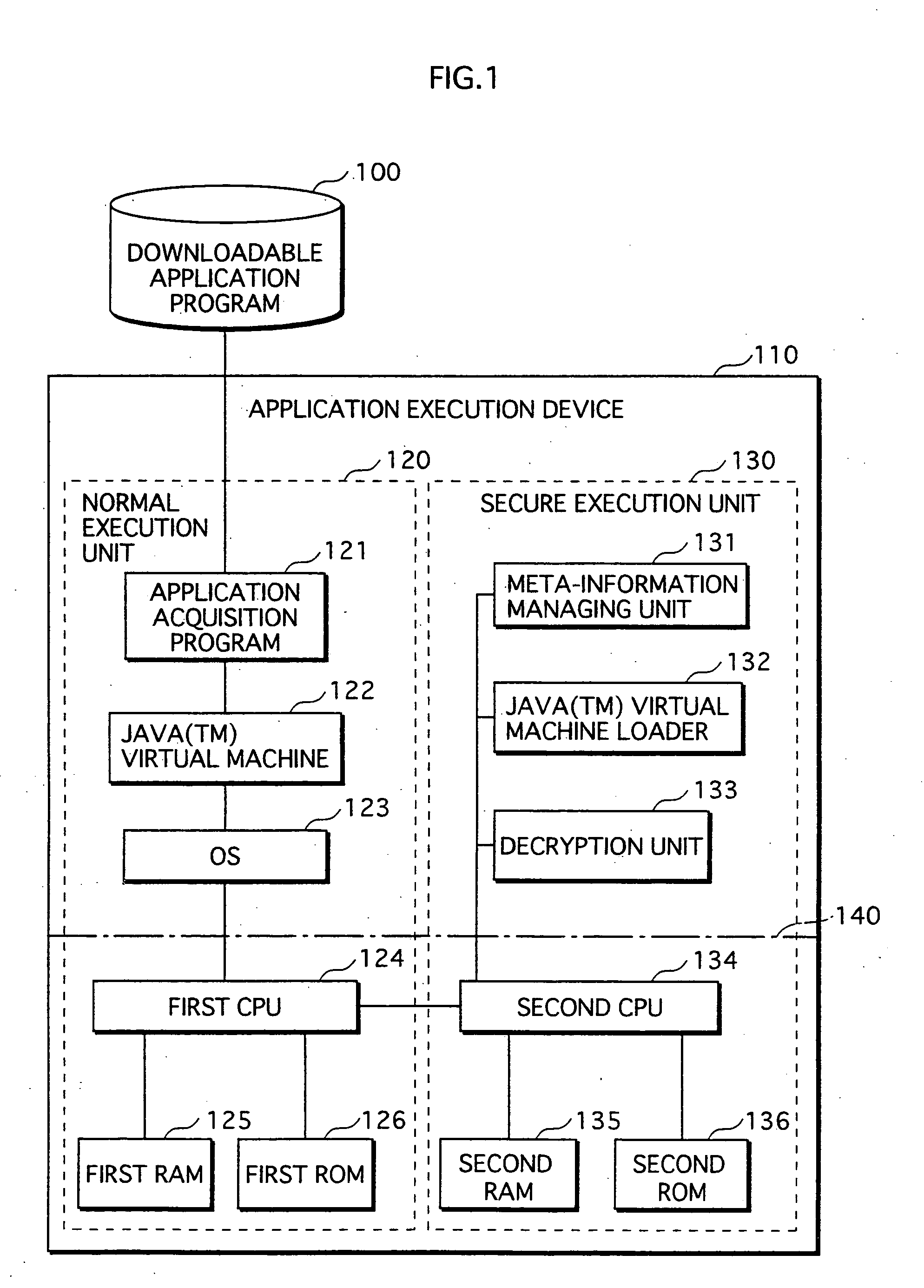
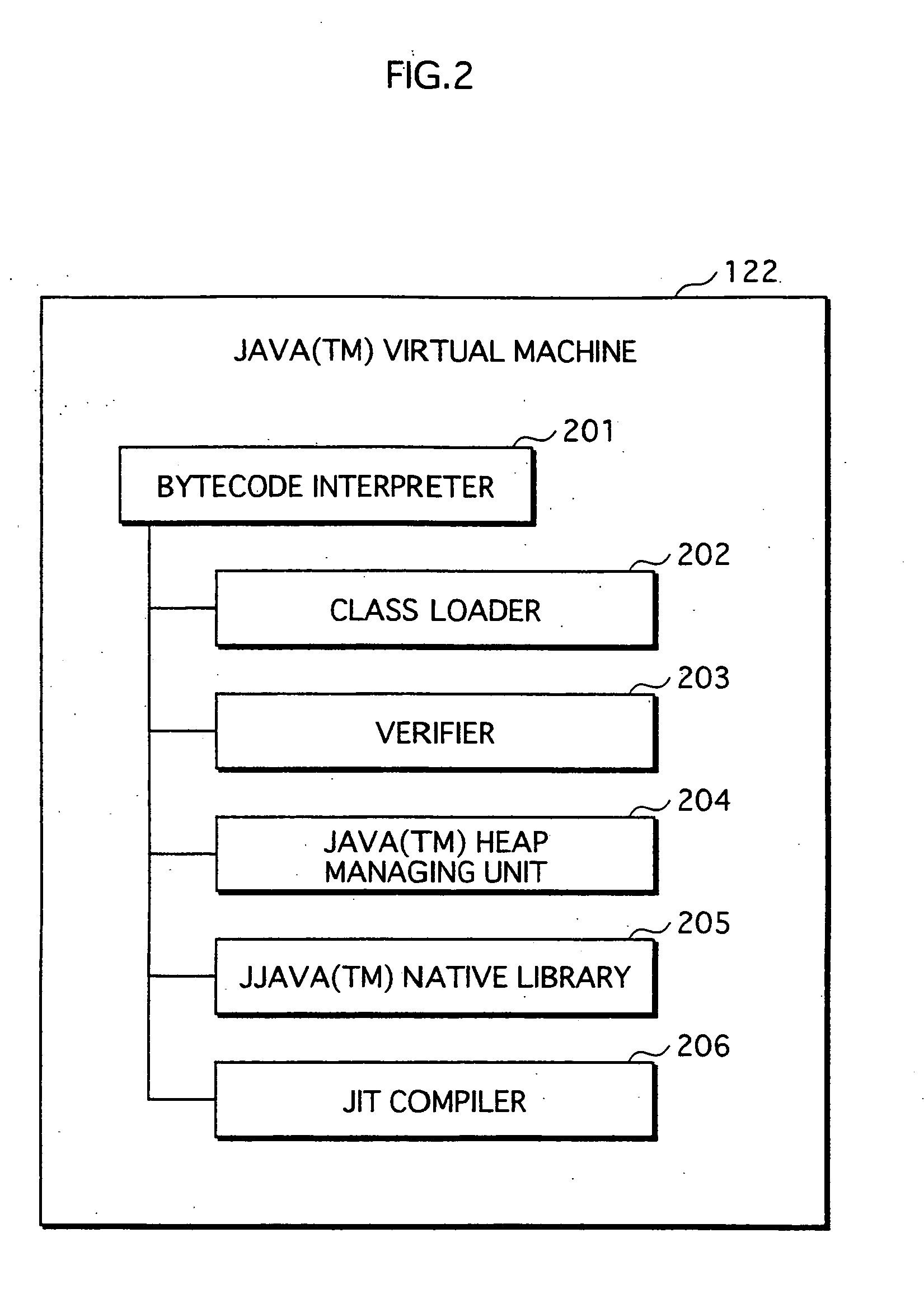
Application Execution Device and Application Execution Device Application Execution Method
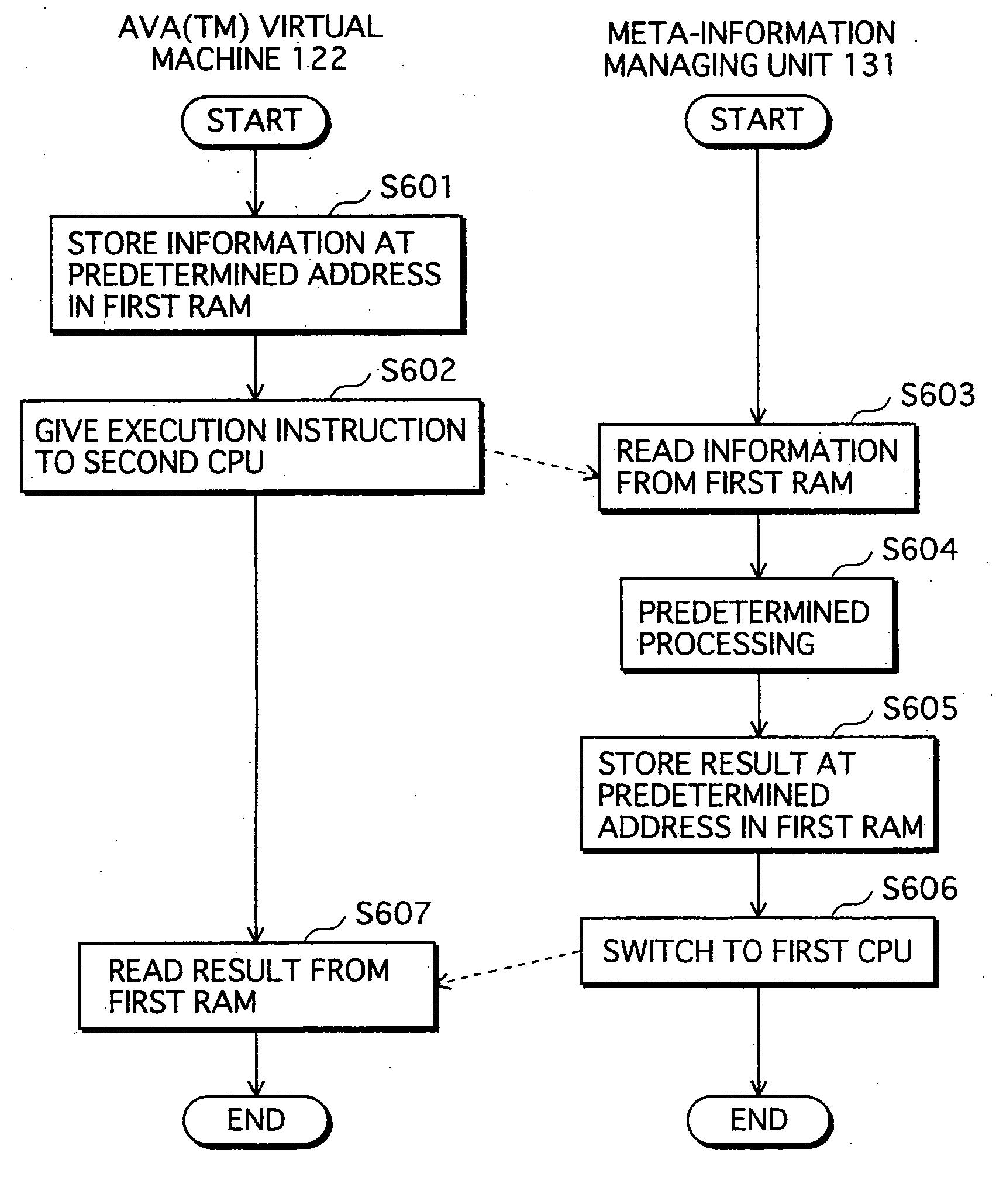
InactiveUS20070271446A1High protection levelDigital computer detailsPlatform integrity maintainanceExecution unitOperating system
The conventional application protection technique complicates an application to make it difficult to analyze the application. However, with such a complication method, the complicate program can be analyzed sooner or later by taking a lot of time no matter how the degree of the complication is high. Also, it is impossible to protect the application from unauthorized copying. The meta-information managing unit that is to be executed in the secure execution unit stores the meta-information of the application in an area that can not be accessed by a debugger. When the meta-information is required by the normal execution unit to execute the application, a result of predetermined calculation using the meta-information is notified to the normal execution unit. In this way, the meta-information of the application can be kept secret.
Owner:PANASONIC CORP
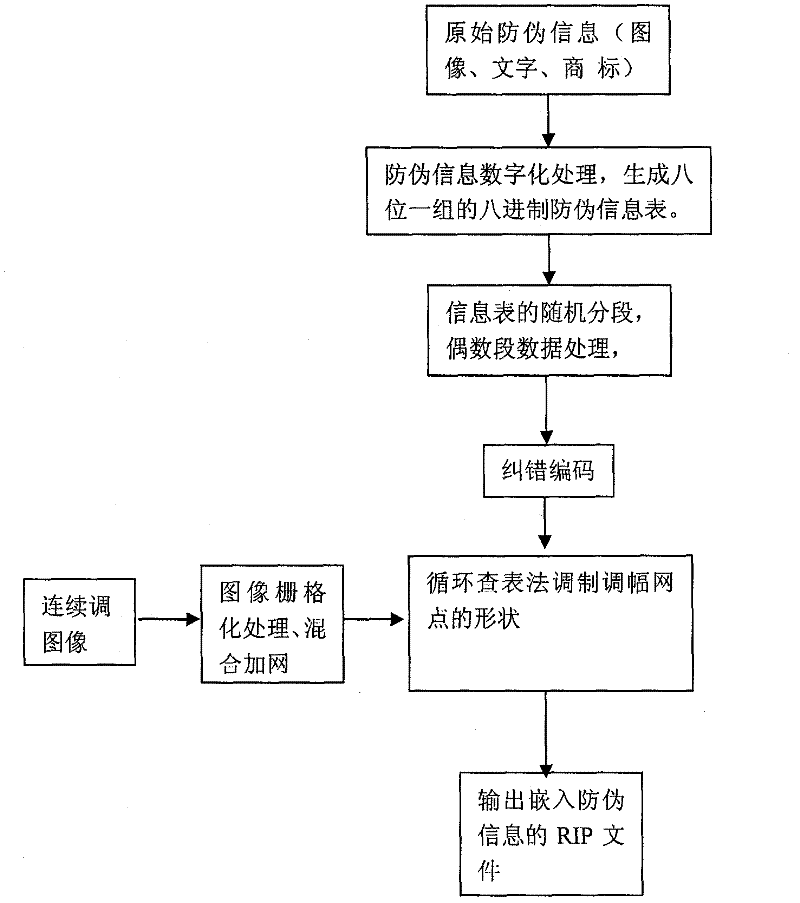
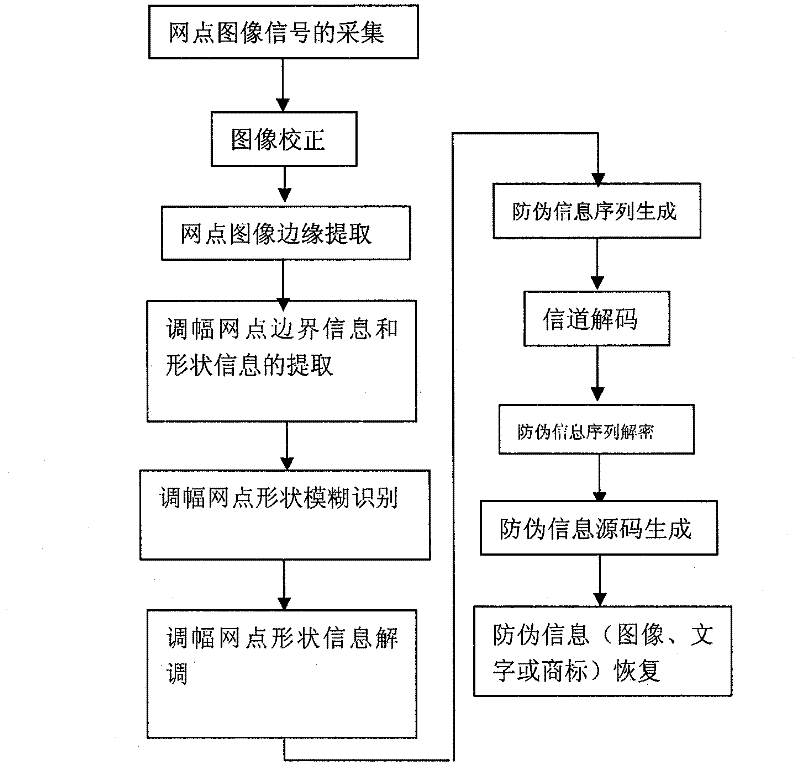
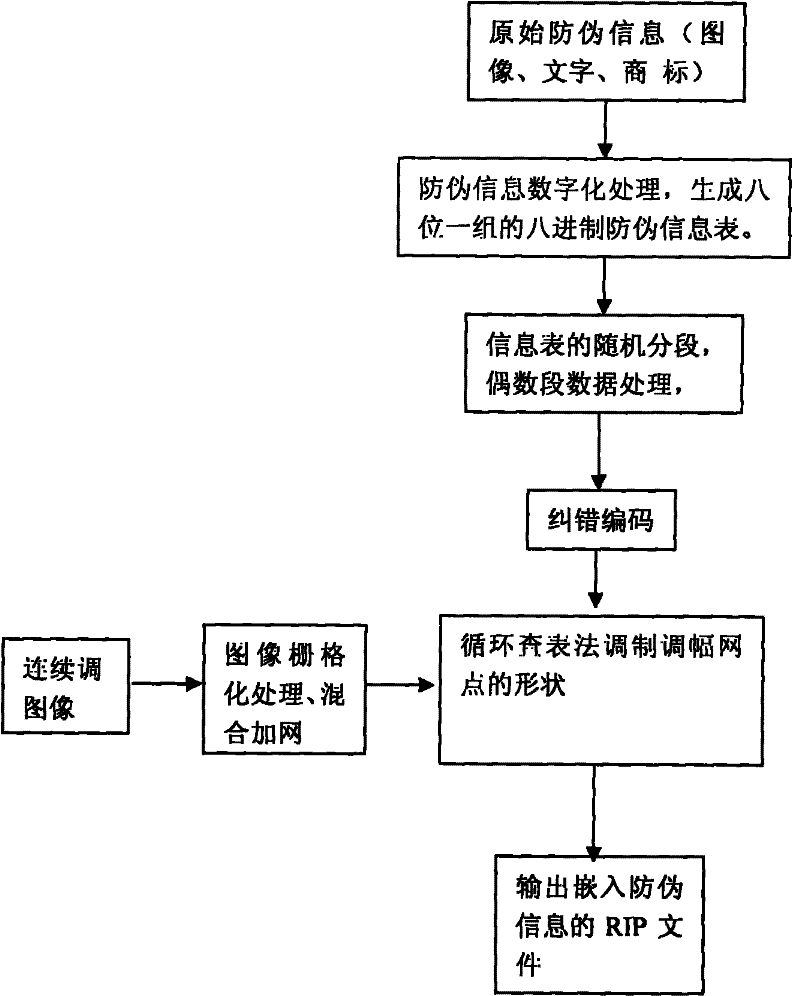
Multi-dimensional encryption anti-counterfeiting printing technology based on binary signals
InactiveCN102402696ACombating Illegal CopyingStrong anti-counterfeiting abilityVisual presentation using printersRecord carriers used with machinesElectronic documentMulti dimensional
The invention discloses a multi-dimensional encryption anti-counterfeiting printing technology based on binary signals. According to the anti-counterfeiting printing technology, two-dimensional encryption anti-counterfeiting information can be generated into binary modulation signals by encryption and channel coding, and the anti-counterfeiting information is orderly changed in an amplitude modulation screening form and embedded into a whole page in a modulation mode of a circulating table look-up method, so that the anti-counterfeiting information can be identified from a random fragment during presswork identification. The technology has strong fragment resistance, can resist illegal copying behaviors based on a camera, a scanner, an electronic document and the like more effectively, and can be widely applied in the anti-counterfeiting field of presswork.
Owner:BEIJING INSTITUTE OF GRAPHIC COMMUNICATION
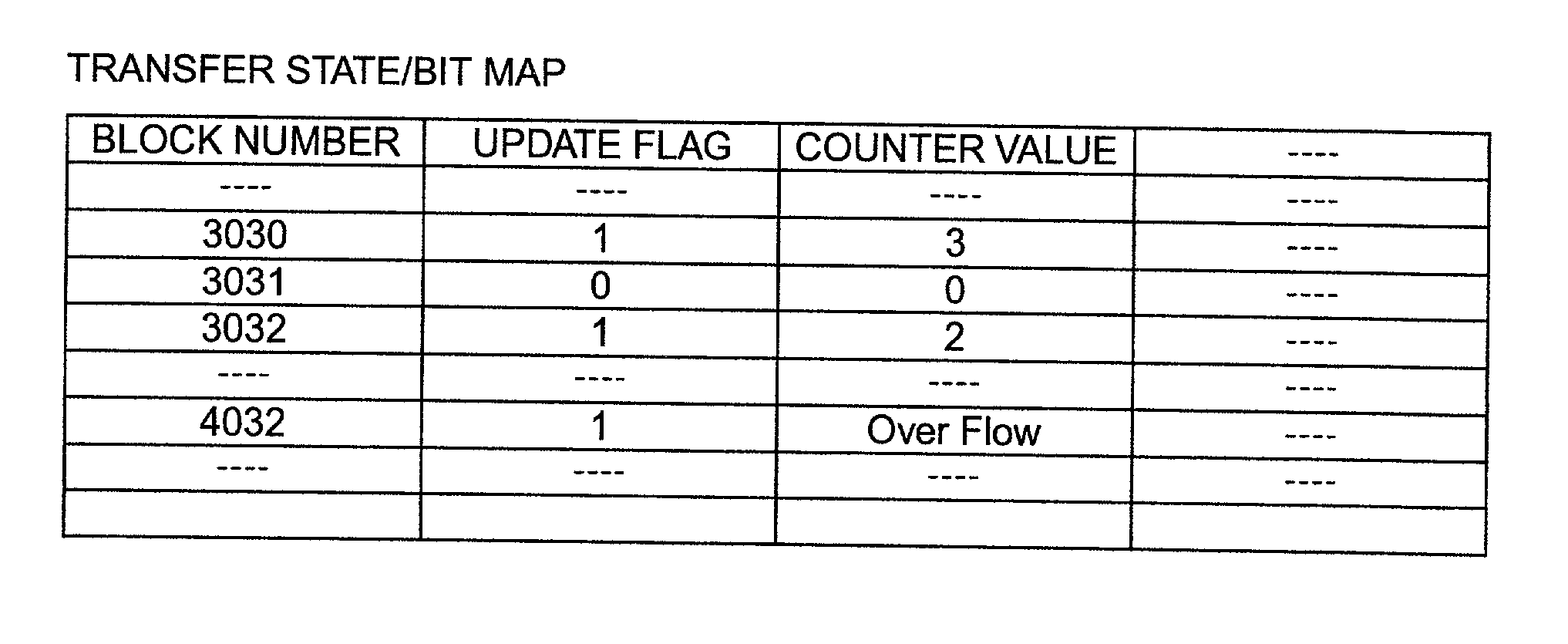
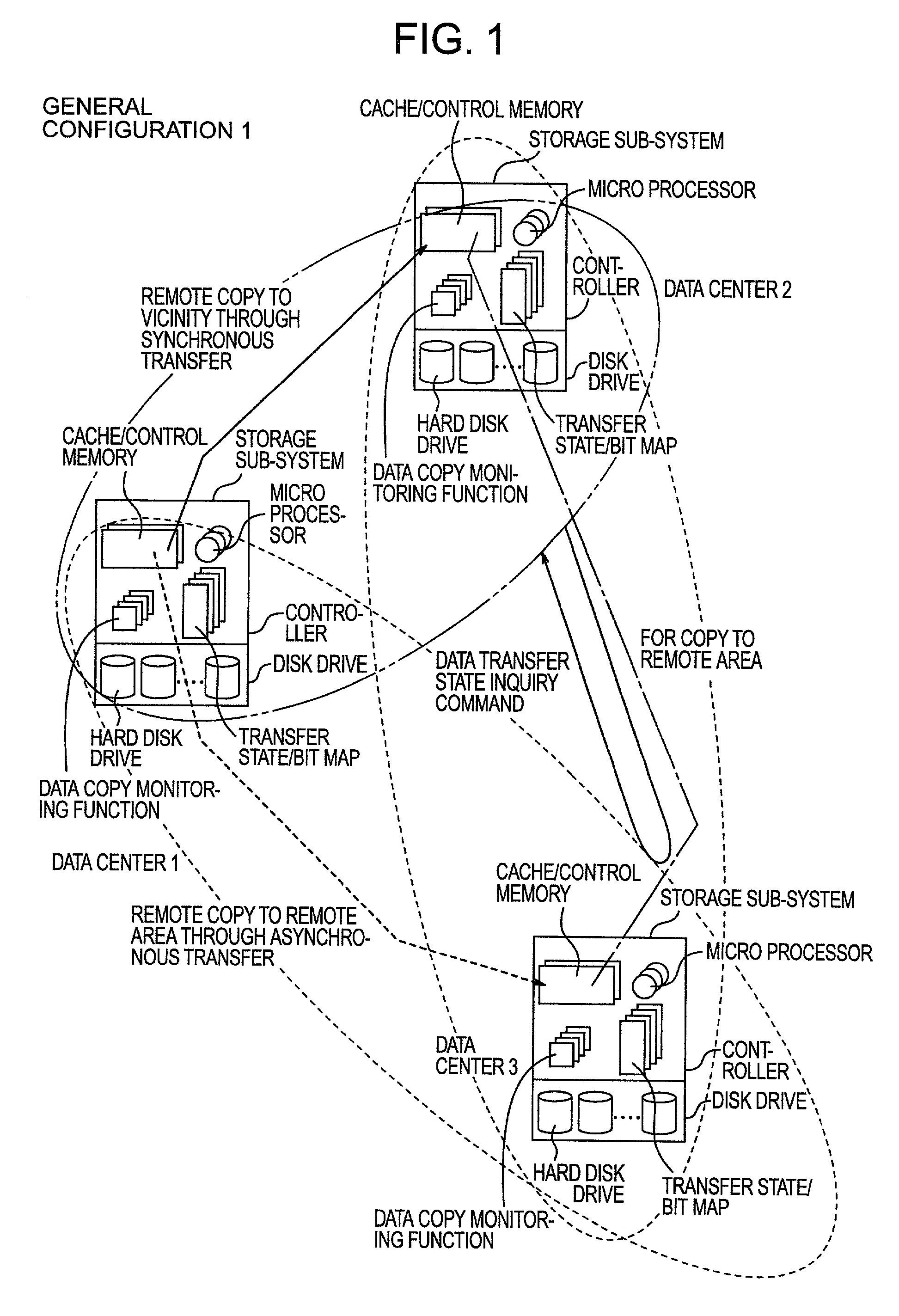
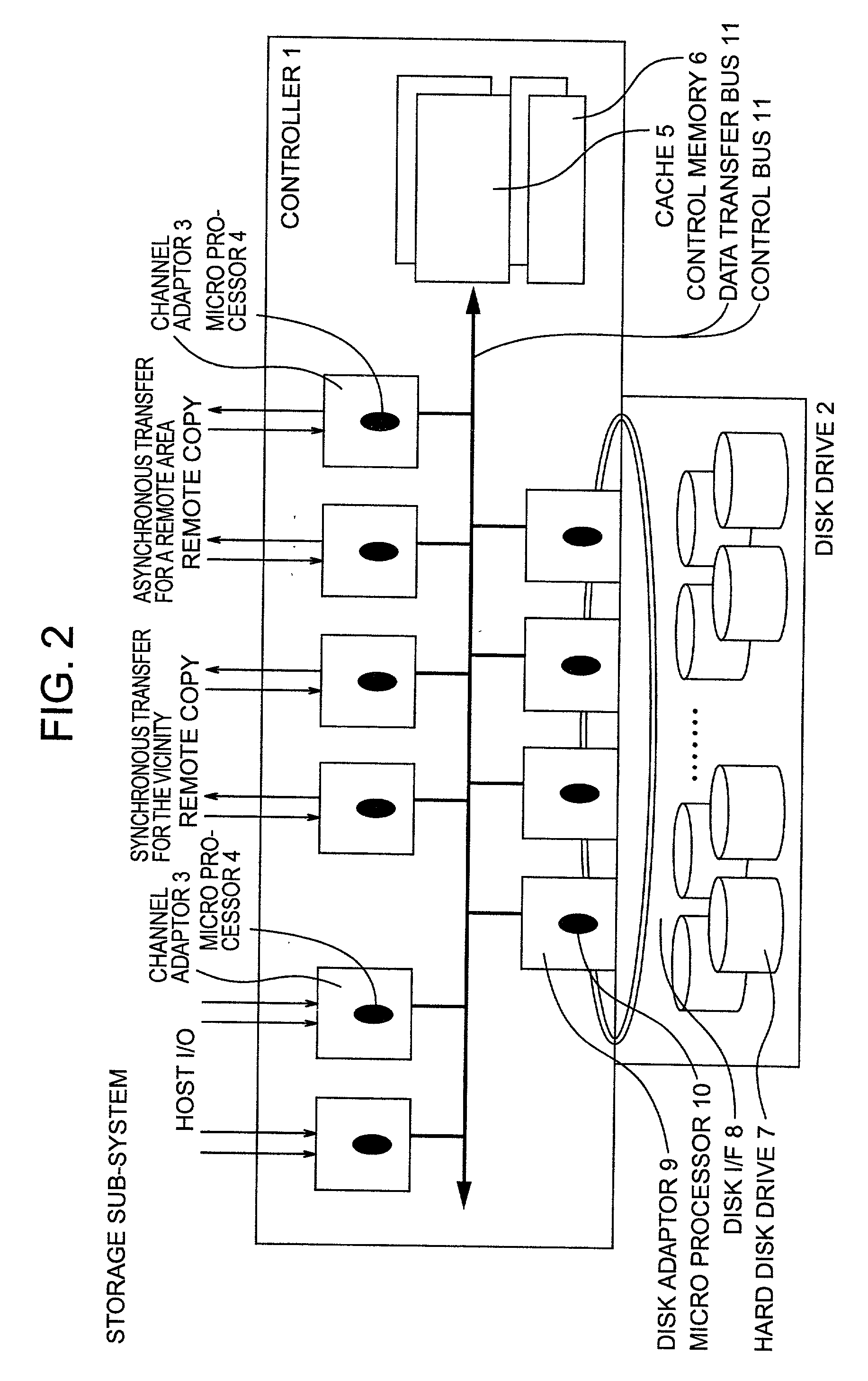
Remote copy control method, storage sub-system with the method, and large area data storage system using them
InactiveUS20030051111A1Data augmentationExtension of timeData processing applicationsInput/output to record carriersData centerData transmission
Two data centers located in the vicinity are connected using a synchronous transfer copy function, and one of the data centers is coupled with a third data center disposed at a remote location by an asynchronous remote copying function. The order whereat a storage sub-system located in the vicinity has received data from a host is consistently guaranteed, and the third data center holds the data. Further, each storage sub-system includes a function whereby, during normal operation, data can be exchanged and the data update state can be obtained by the storage sub-systems located in the two data centers that do not directly engage in data transmission.
Owner:HITACHI LTD
Apparatus and System for Managing Multiple Computers
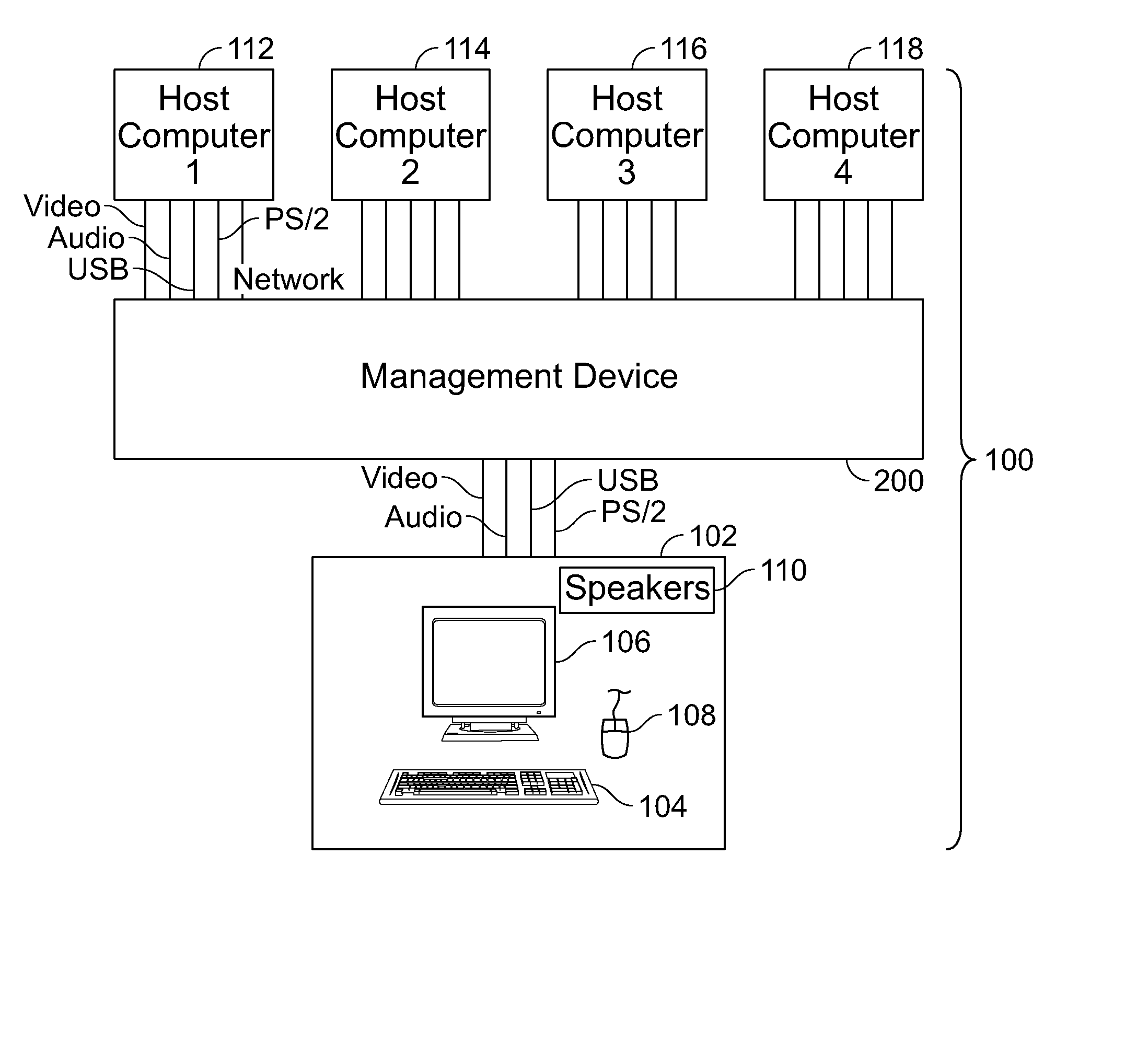
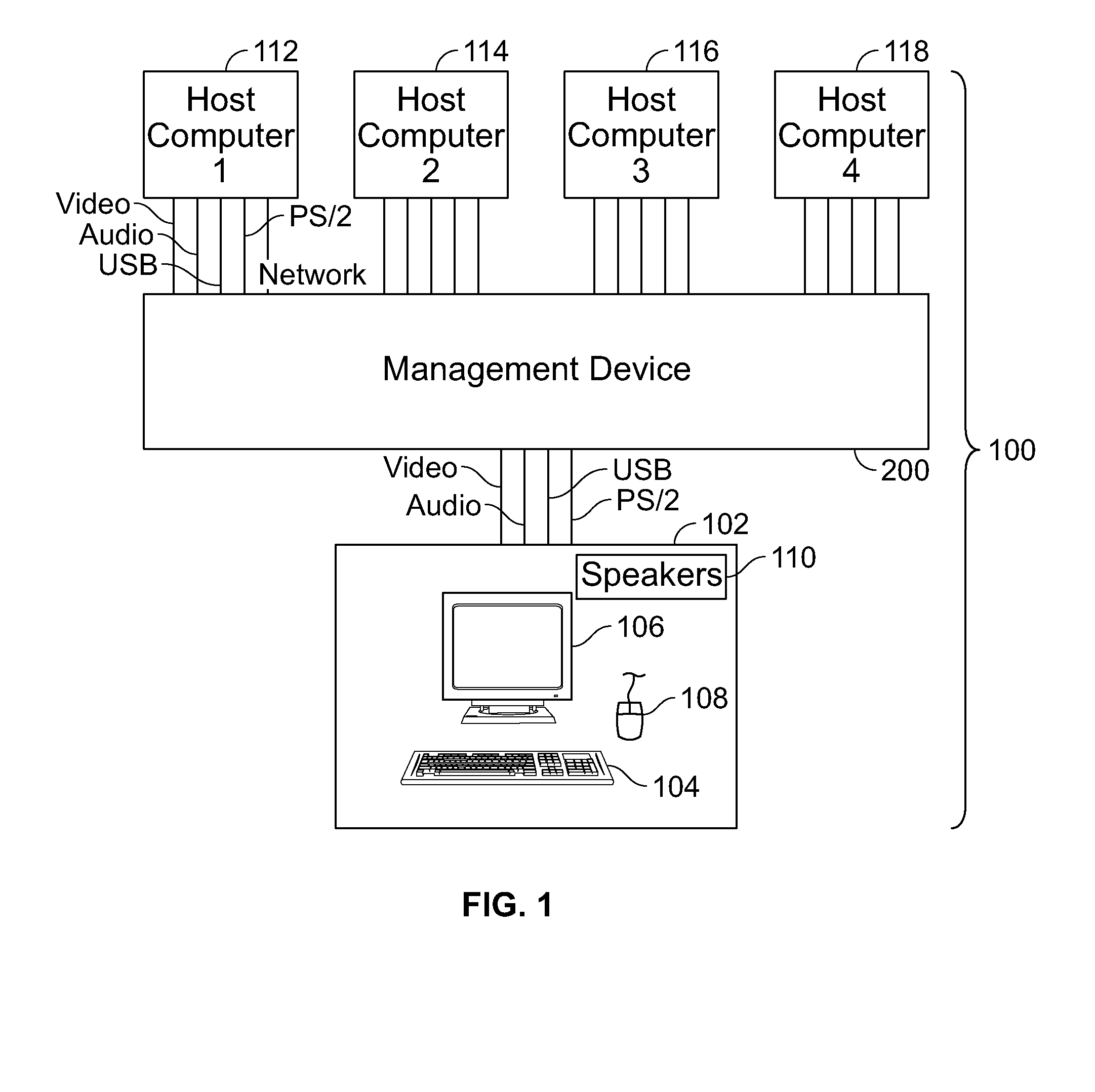
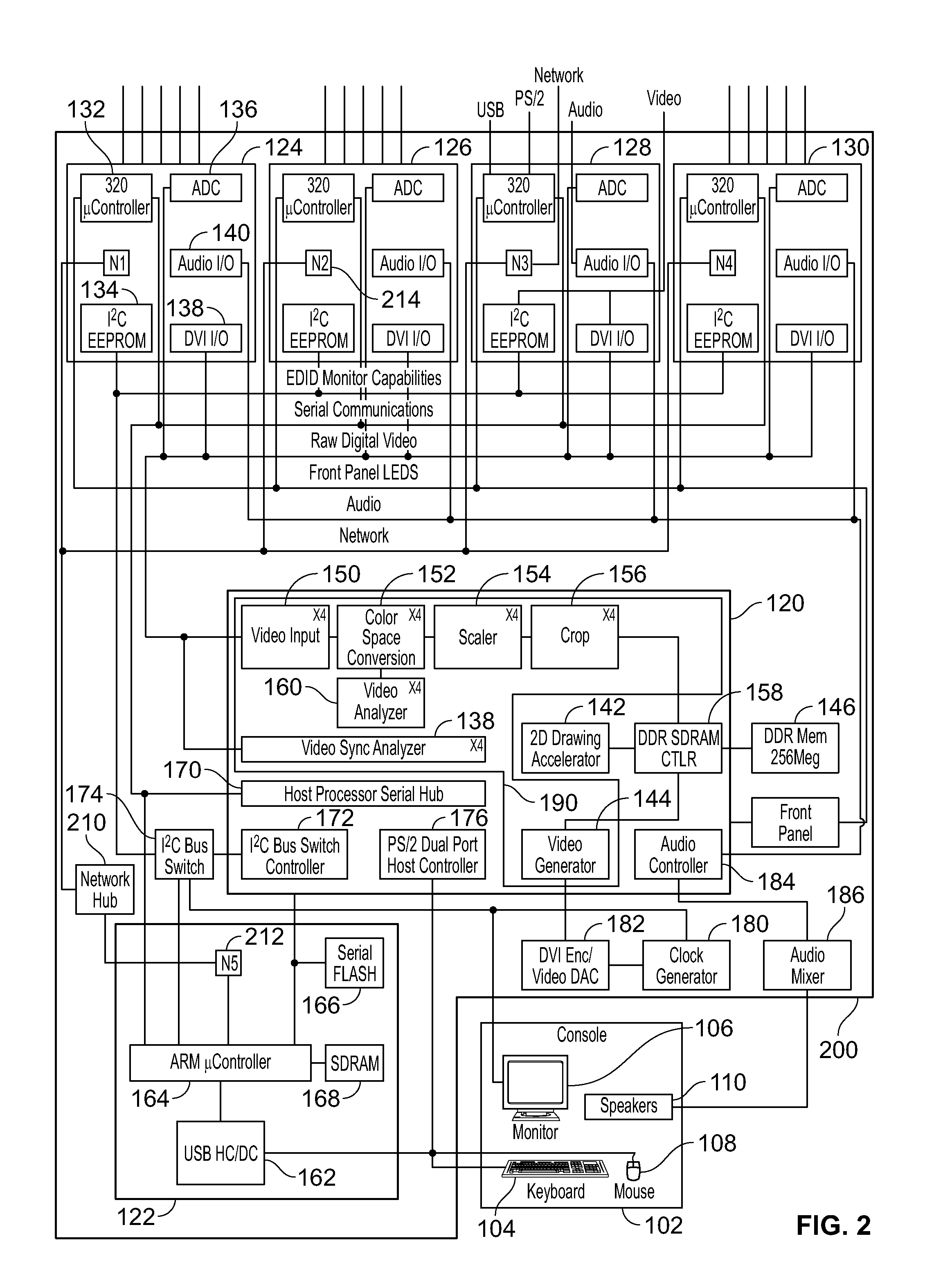
ActiveUS20080048975A1Suppress displayLow costCathode-ray tube indicatorsInput/output processes for data processingDrag and dropComputer graphics (images)
A system is presented for interconnecting a single user console having user interface devices, including a console keyboard, a console video display unit, a console mouse, and speakers, to a plurality of host computers each capable of using user interface devices, including a keyboard, a video display unit, and a mouse, and allowing the user to access one or more of the host computers from the single user console. The video output from each of the host computers is scaled and cropped as appropriate so that the video output of each host may be simultaneously displayed as host computer “windows” on the console video display unit or overlaid with the background suppressed to display application windows from multiple hosts on a single screen. The user may easily navigate between the host computers through a convenient and intuitive user interface that allows control of individual host computers, the transfer of files between computers using familiar a “drag and drop” interface, and copying and pasting of data between applications running on different computers. The audio output from each of the host computers may be mixed or switched for output to the speakers as desired.
Owner:BELKIN INT
File system image transfer
InactiveUS7174352B2Data processing applicationsSpecial data processing applicationsFile systemImage transfer
Owner:NETWORK APPLIANCE INC
System, device and method for remotely providing, accessing and using personal entertainment media
InactiveUS20020091848A1Analogue secracy/subscription systemsComputer security arrangementsTangible objectComputer terminal
Systems and methods for permitting consumers to securely purchase, access, download and / or stream entertainment content such as musical and audio visual works, including a remote terminal or terminals. Consumers subscribe to the system and obtain a terminal or terminals. The terminals permit the subscribers to access the system to obtain content, either by downloading same to the terminal or by directly perceiving the content while streaming the content to the terminal. The invention prevents unauthorized copying, distribution and / or performance of protected works while at the same time eliminating the need for consumers to possess the tangible objects, e.g. CDS and DVDs, upon which detectable works normally reside. The software associated with the system regulates the transmission of content from the database(s) upon which it is stored, through a central server associated with the system, to the subscriber terminals for storage or immediate, i.e., "streaming", playback.
Owner:AGRESTA ROBERT +2
Non-Volatile Memory And Method With Post-Write Read And Adaptive Re-Write To Manage Errors
ActiveUS20110099460A1Small marginImprove performanceMemory loss protectionRead-only memoriesHigh densityLow density
Data errors in non-volatile memory inevitably increase with usage and with higher density of bits stored per cell. The memory is configured to have a first portion operating with less error but of lower density storage, and a second portion operating with a higher density but less robust storage. Input data is written and staged in the first portion before being copied to the second portion. An error management provides checking the quality of the copied data for excessive error bits. The copying and checking are repeated on a different location in the second portion until either a predetermined quality is satisfied or the number or repeats exceeds a predetermined limit. The error management is not started when a memory is new with little or no errors, but started after the memory has aged to a predetermined amount as determined by the number of erase / program cycling its has experienced.
Owner:SANDISK TECH LLC
File system image transfer
InactiveUS20010044807A1Data processing applicationsRedundant operation error correctionFile systemImage transfer
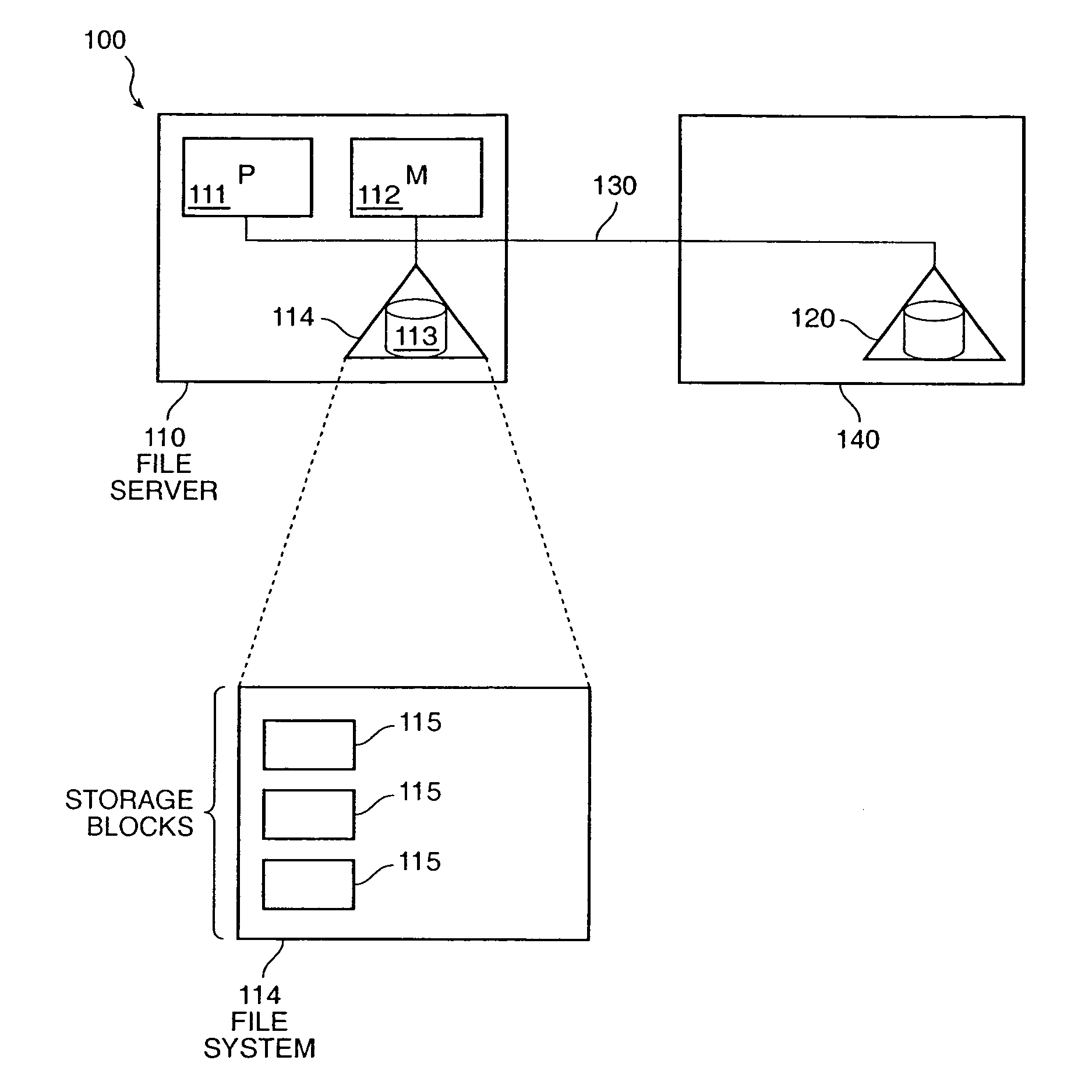
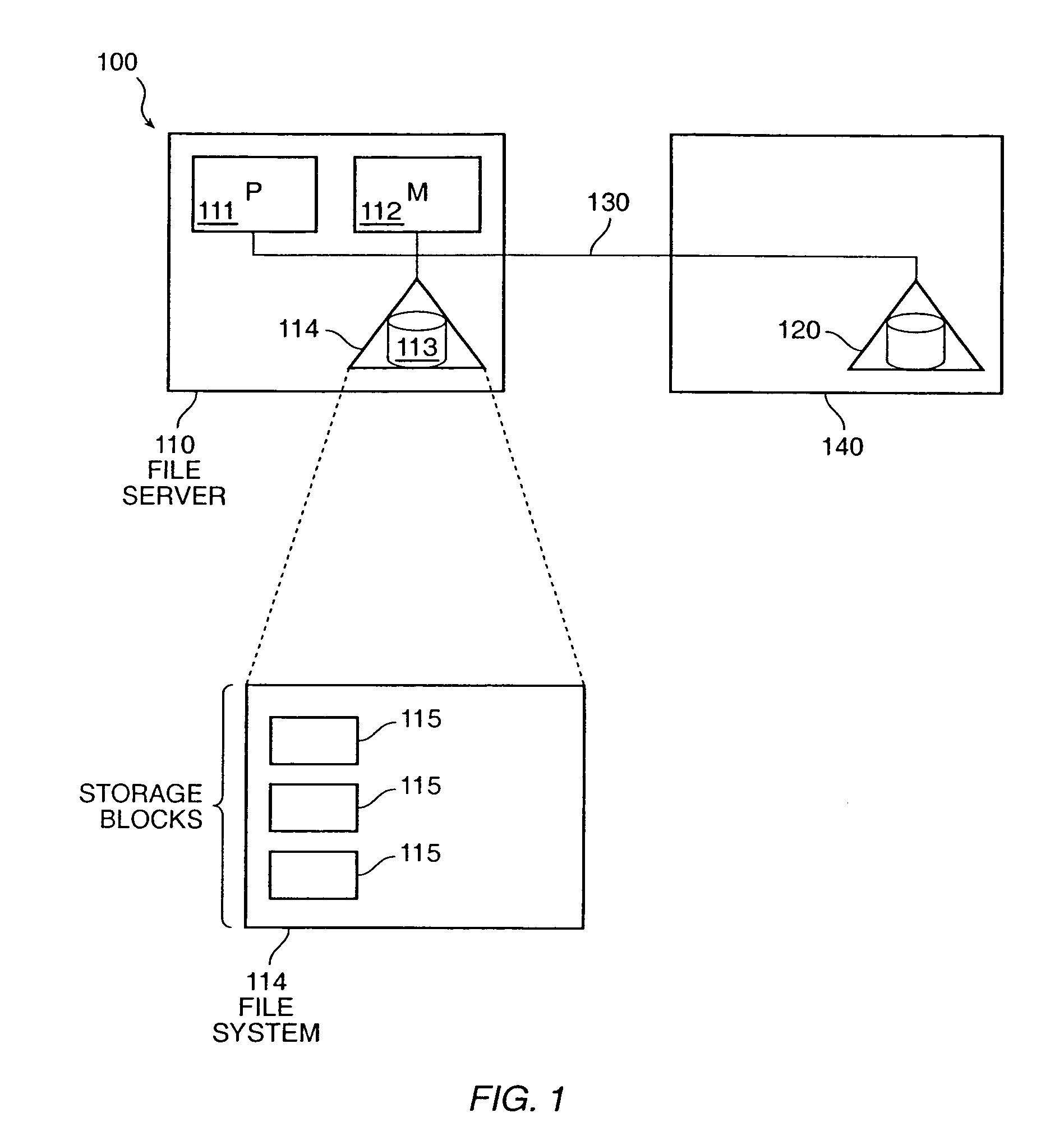
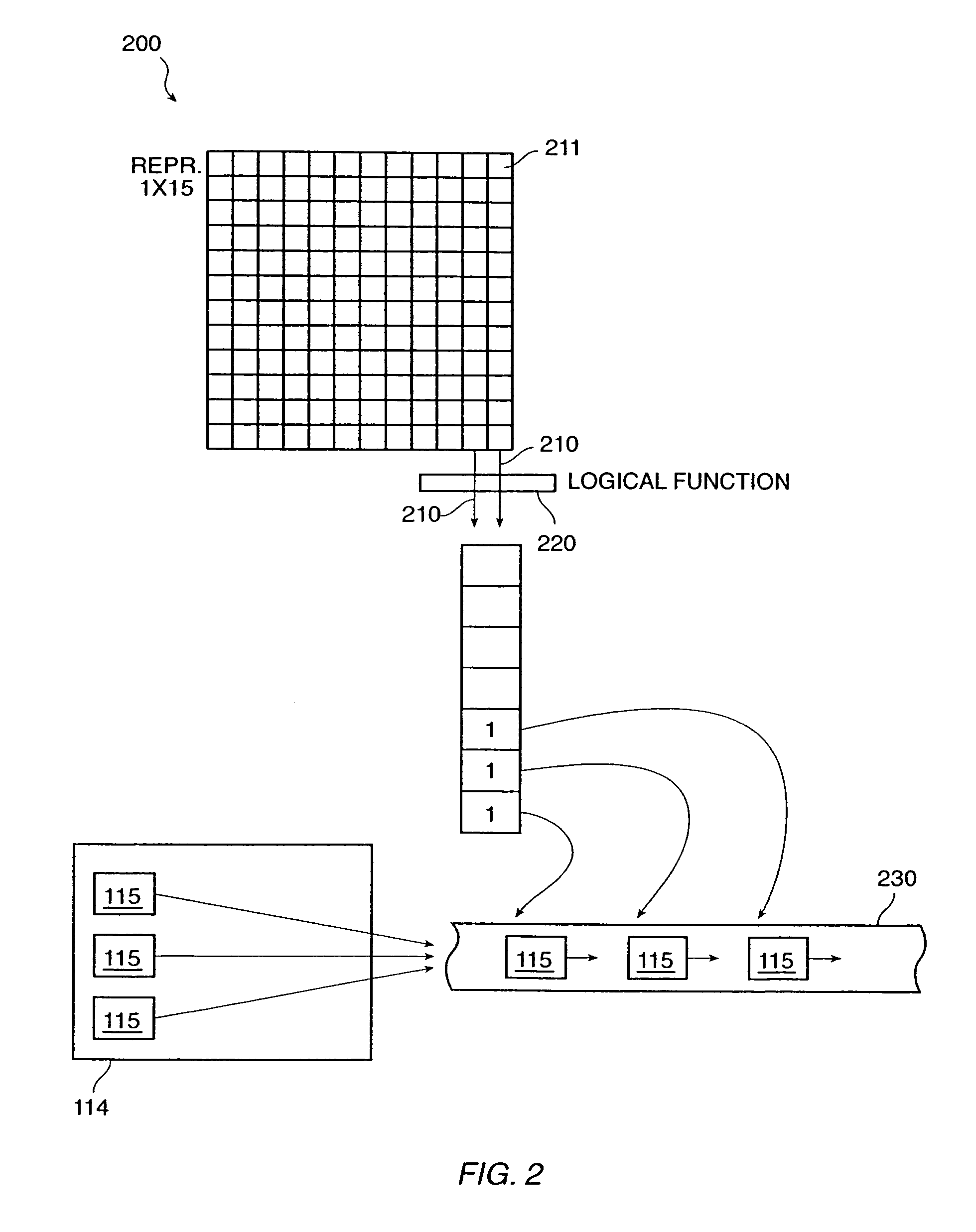
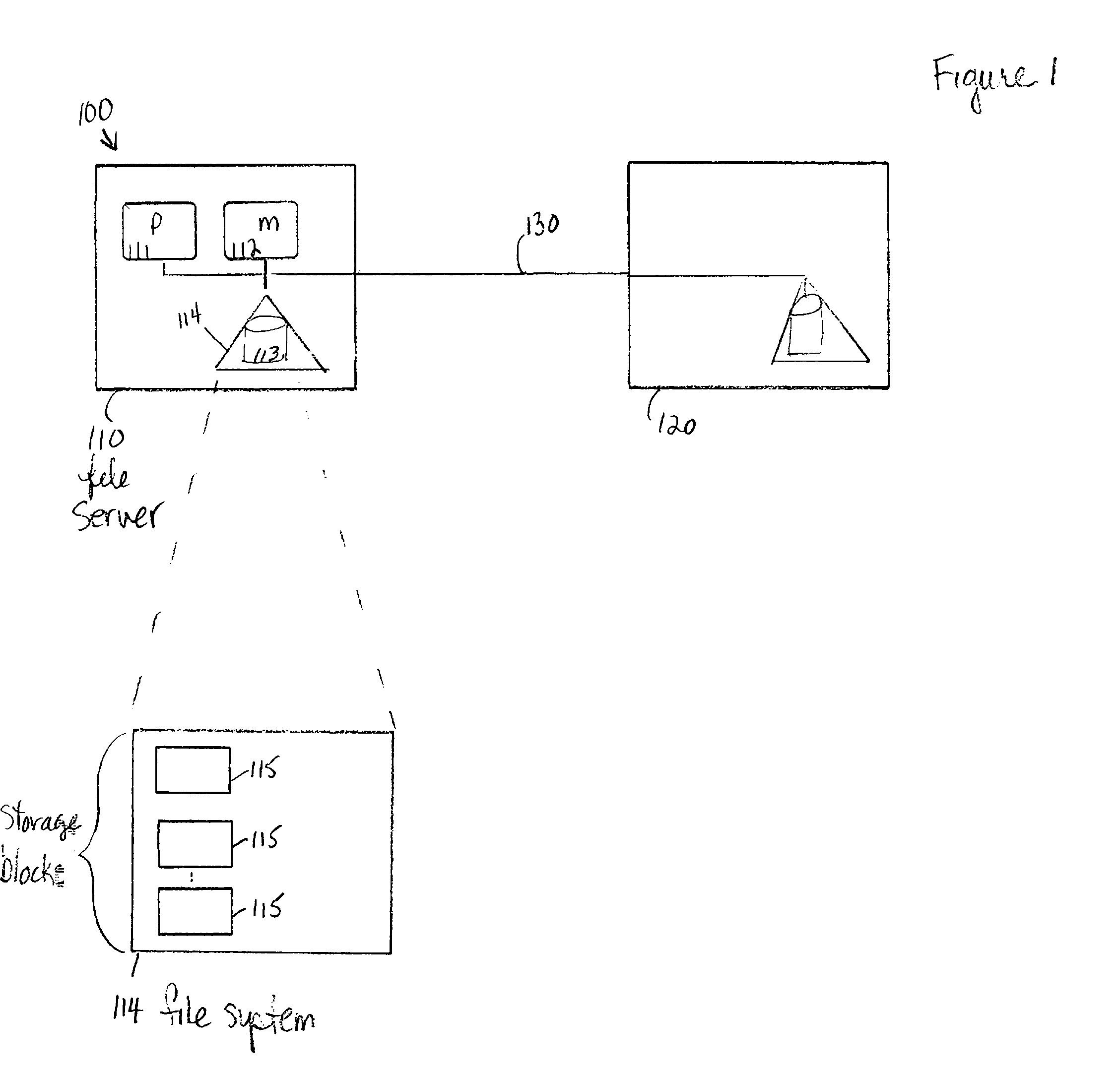
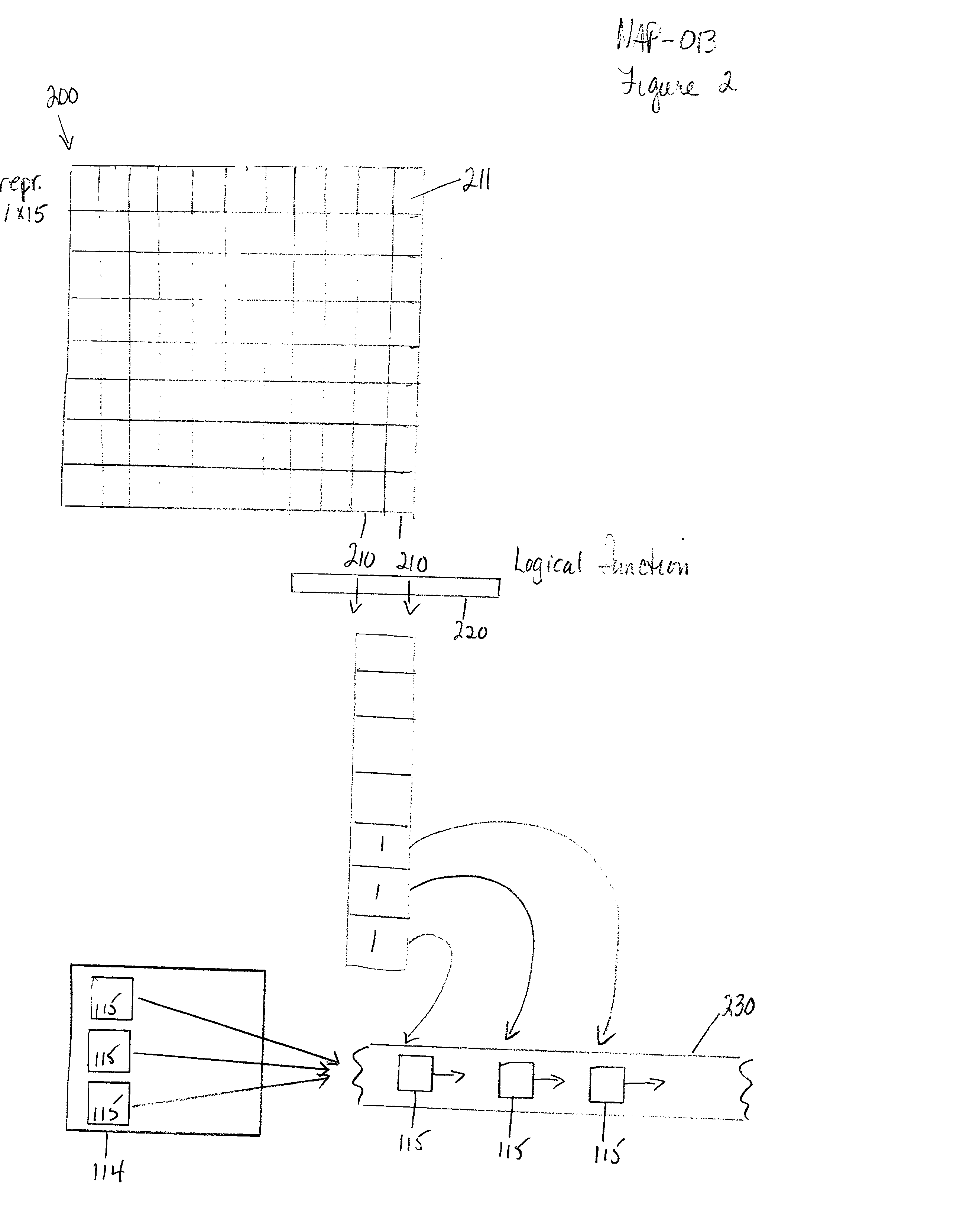
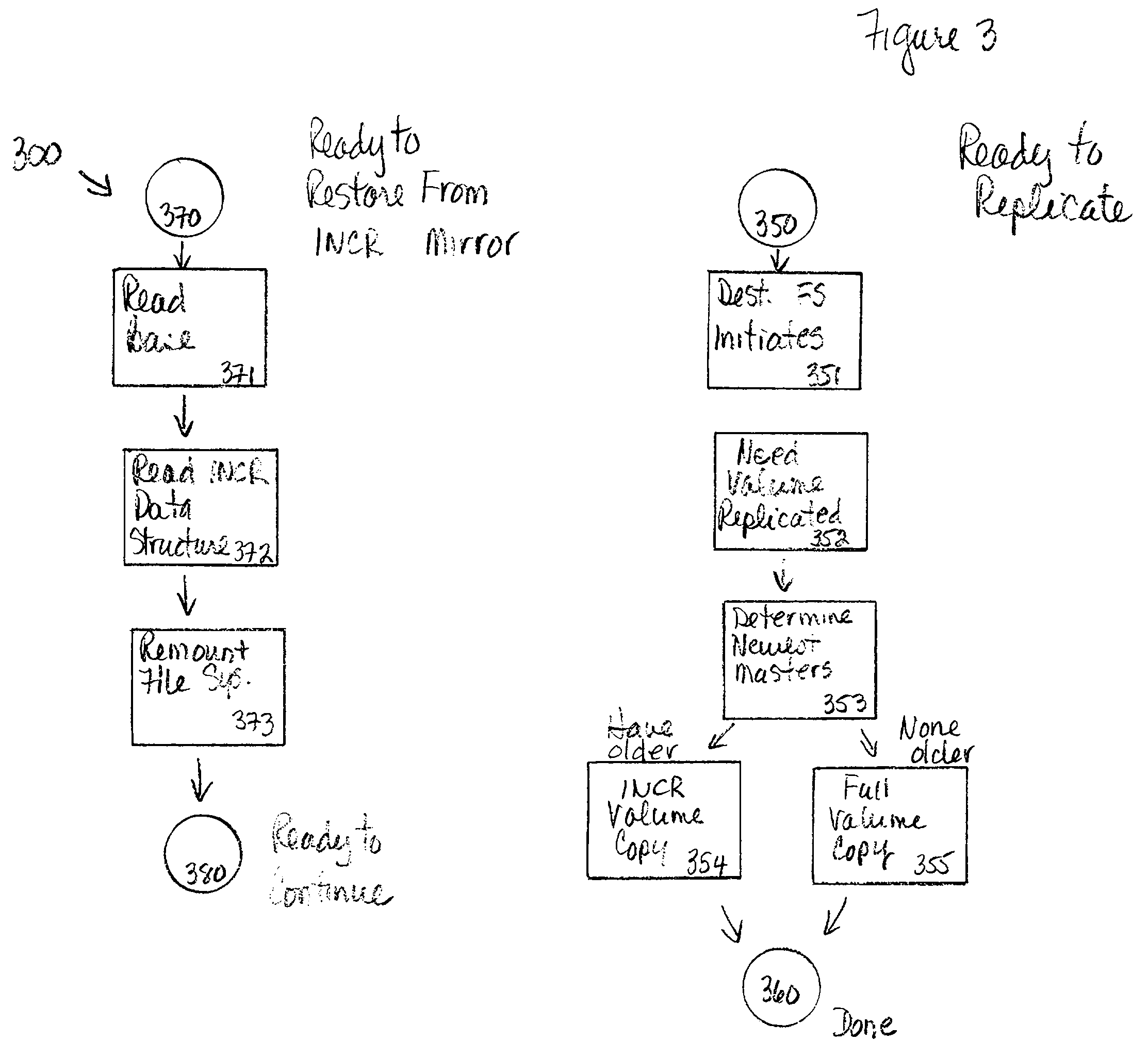
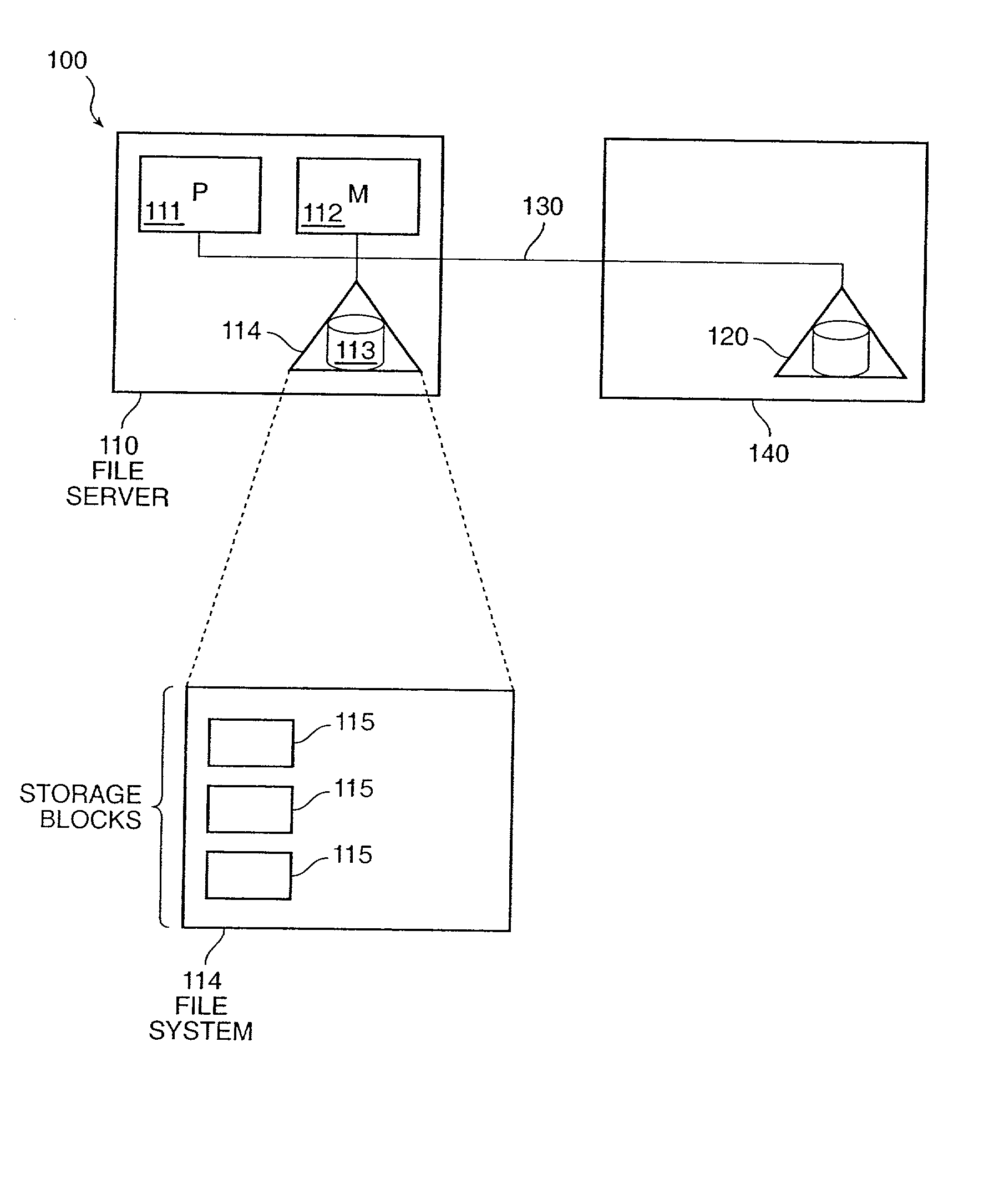
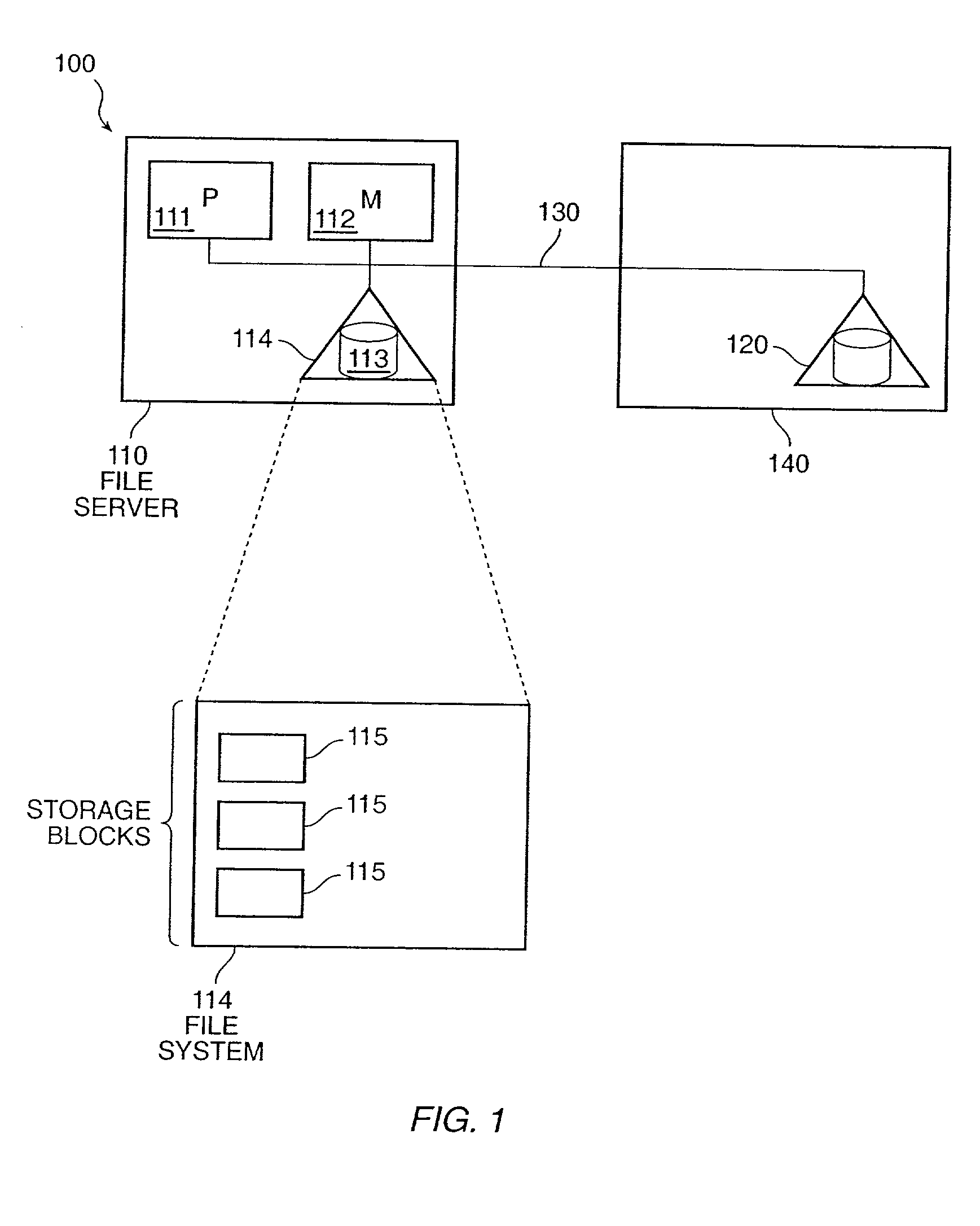
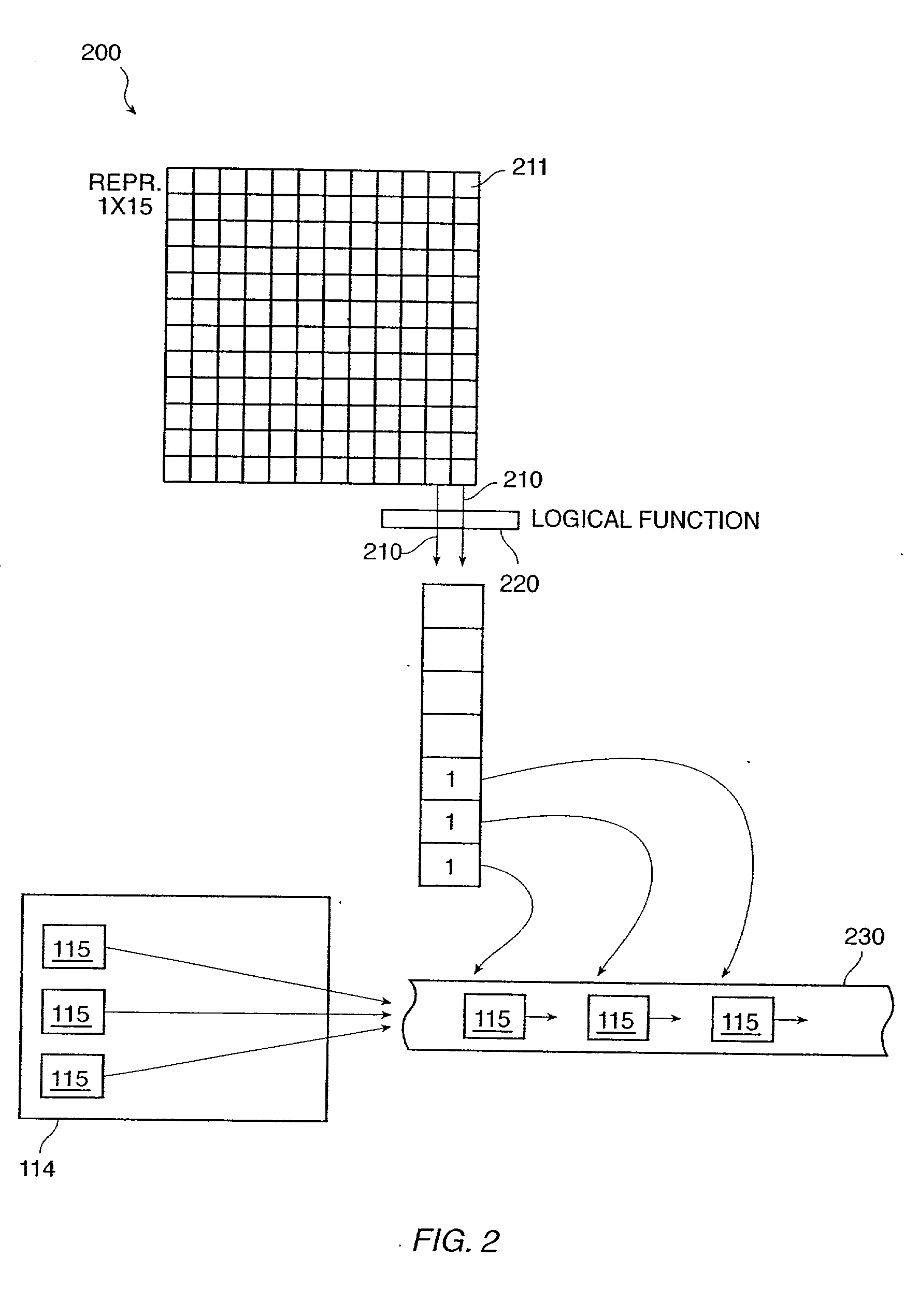
The invention provides a method and system for duplicating all or part of a file system while maintaining consistent copies of the file system. The file server maintains a set of snapshots, each indicating a set of storage blocks making up a consistent copy of the file system as it was at a known time. Each snapshot can be used for a purpose other than maintaining the coherency of the file system, such as duplicating or transferring a backup copy of the file system to a destination storage medium. In a preferred embodiment, the snapshots can be manipulated to identify sets of storage blocks in the file system for incremental backup or copying, or to provide a file system backup that is both complete and relatively inexpensive.
Owner:NETWORK APPLIANCE INC
File system image transfer
InactiveUS20020049718A1Data processing applicationsDigital data processing detailsImage transferFile system
The invention provides a method and system for duplicating all or part of a file system while maintaining consistent copies of the file system. The file server maintains a set of snapshots, each indicating a set of storage blocks making up a consistent copy of the file system as it was at a known time. Each snapshot can be used for a purpose other than maintaining the coherency of the file system, such as duplicating or transferring a backup copy of the file system to a destination storage medium. In a preferred embodiment, the snapshots can be manipulated to identify sets of storage blocks in the file system for incremental backup or copying, or to provide a file system backup that is both complete and relatively inexpensive. Also in a preferred embodiment, shadow snapshots can be maintained, with a shadow snapshot including a set of member storage blocks that formed a consistent file system other than an active file system, with a set of selected member storage blocks removed from the consistent file system.
Owner:NETWORK APPLIANCE INC
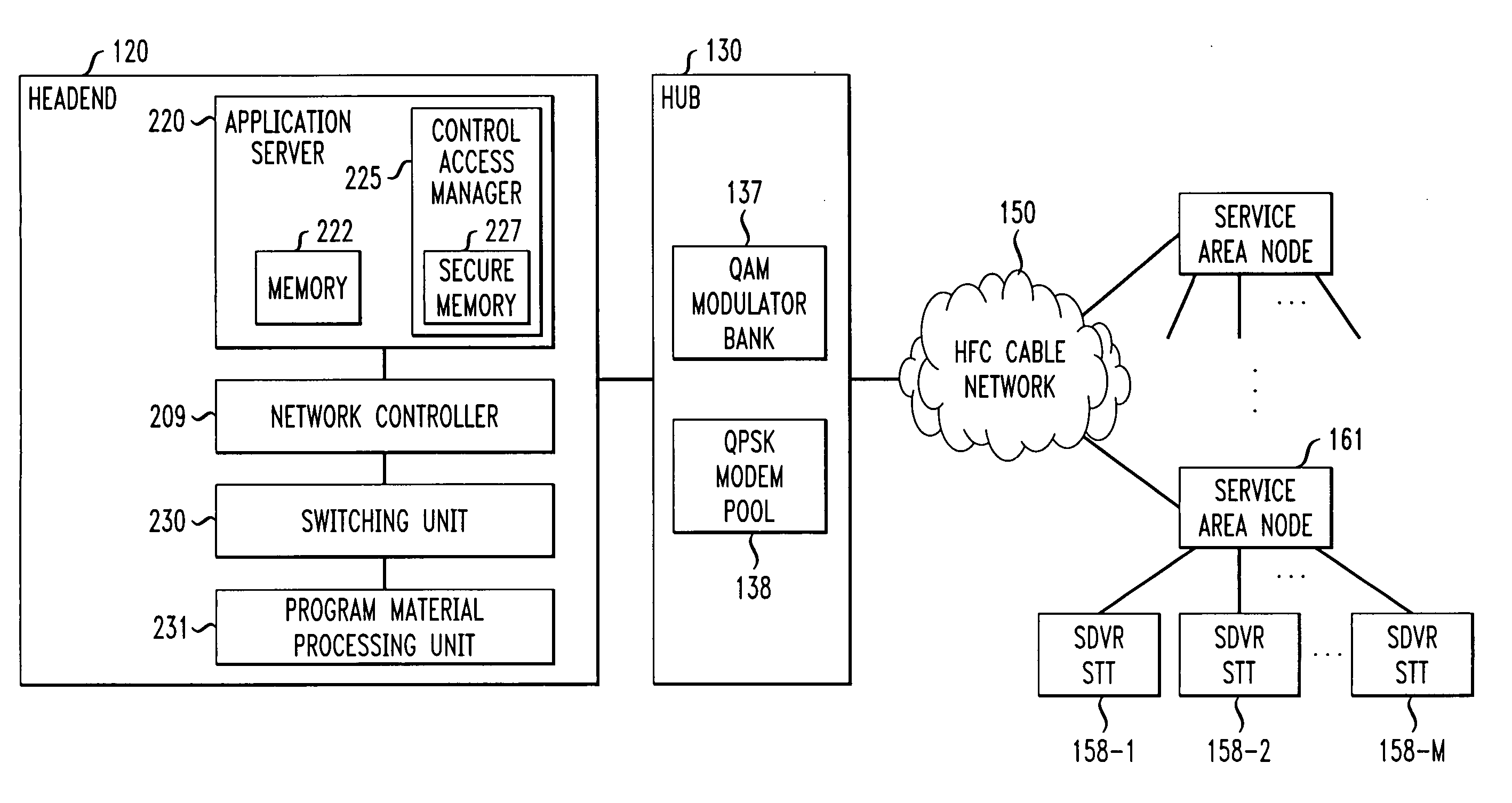
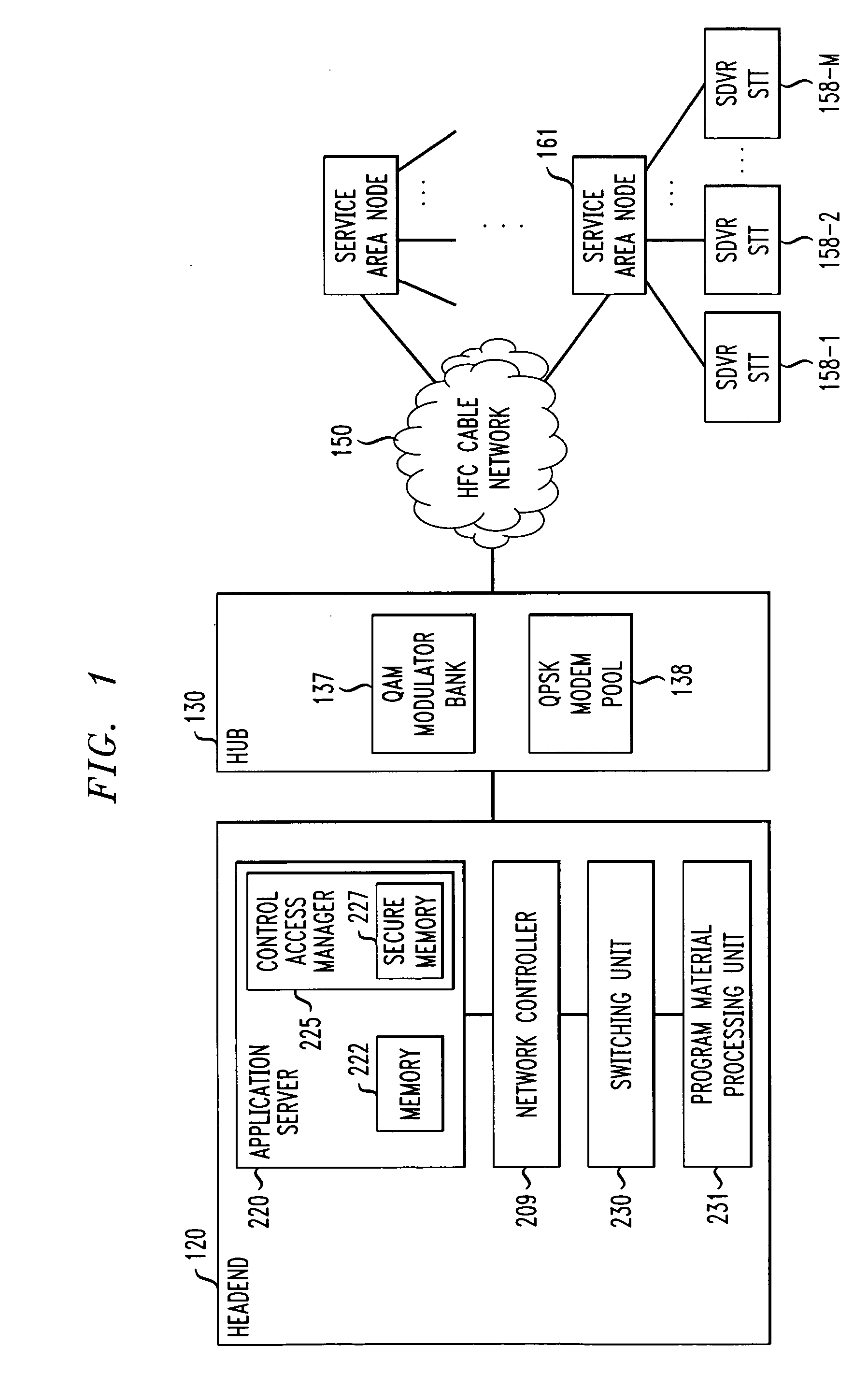
Technique for securely communicating and storing programming material in a trusted domain
A “trusted domain” is established within which content received from a communications network, e.g., a cable TV network, is protected from unauthorized copying thereof, in accordance with the invention. In an illustrative embodiment, the trusted domain includes a device associated with a user which receives content from the cable TV network. The content may be encrypted using a content key in accordance, e.g., with a 3DES encryption algorithm before it is stored in the device. In addition, a first encrypted content key version and a second encrypted content key version are generated by respectively encrypting the content key with a public key associated with the device and another public key associated with the user, in accordance with public key cryptography. The first and second encrypted content key versions are stored in association with the encrypted content in the device storage. The encrypted content can be migrated from a first device to a second device, and can be decrypted in the second device if the second device is associated with the same user, and also provided with the second encrypted content key version.
Owner:TIME WARNER CABLE ENTERPRISES LLC
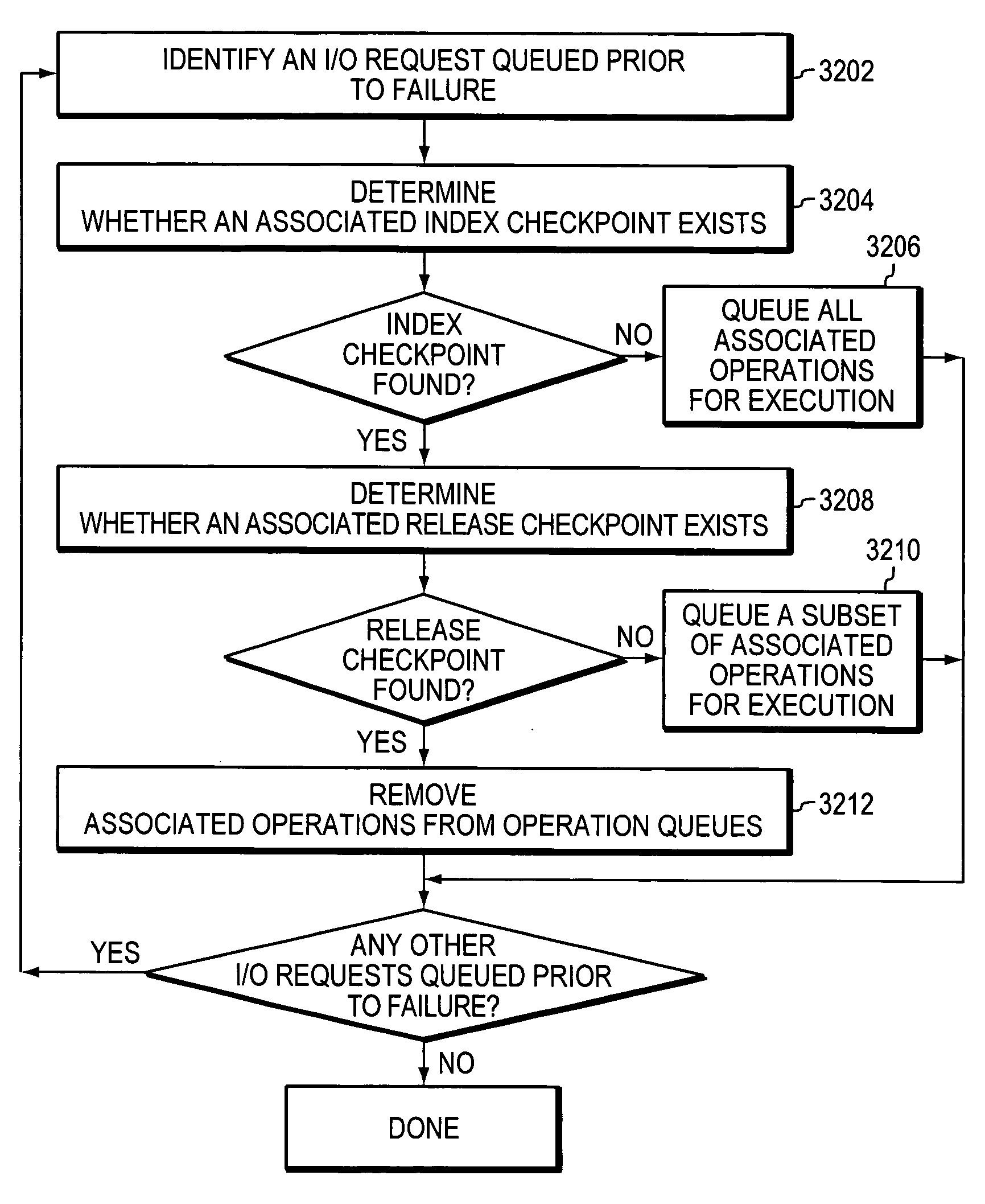
Recovering from storage transaction failures using checkpoints
ActiveUS20060047925A1Easy to useInformation can be usedMemory loss protectionError detection/correctionSuccessful completionOriginal data
The disclosed technology facilitates recovery from storage-related failures by checkpointing copy-on-write operation sequences. An operation sequence incorporating such checkpoints into a copy-on-write can include the following: receive a write request that identifies payload data to be written to a first data store, read original data associated with the first data store, copy the original data to a second data store, record transactional information associated with the write request, generate a first checkpoint to confirm the successful recordation of the transactional information and the successful copying of the original data to the second data store, write the payload data to the first data store, acknowledge a successful completion of the copy-on-write operation sequence, and generate a second checkpoint that confirms the successful completion of such operation sequence. The first and second checkpoints are used to form a pre-failure representation of one or more storage units (or parts thereof). The checkpoints can be stored with other transactional information, to facilitate recovery in the event of a failure, and can be used to facilitate the use of optimizations to process I / O operations.
Owner:SYMANTEC OPERATING CORP
User interface for a file system shell
InactiveUS7769794B2Adapt quicklyDigital data information retrievalSpecial data processing applicationsView basedFile system
A file system shell is provided. One aspect of the shell provides virtual folders which expose regular files and folders to users in different views based on their metadata instead of the actual physical underlying file system structure on the disk. Users are able to work with the virtual folders through direct manipulation (e.g., clicking and dragging, copying, pasting, etc.). Filters are provided for narrowing down sets of items. Quick links are provided which can be clicked on to generate useful views of the sets of items. Libraries are provided which consist of large groups of usable types of items that can be associated together, along with functions and tools related to the items. A virtual address bar is provided which comprises a plurality of segments, each segment corresponding to a filter for selecting content. A shell browser is provided with which users can readily identify an item based on the metadata associated with that item. An object previewer in a shell browser is provided which is configured to display a plurality of items representing multiple item types.
Owner:MICROSOFT TECH LICENSING LLC
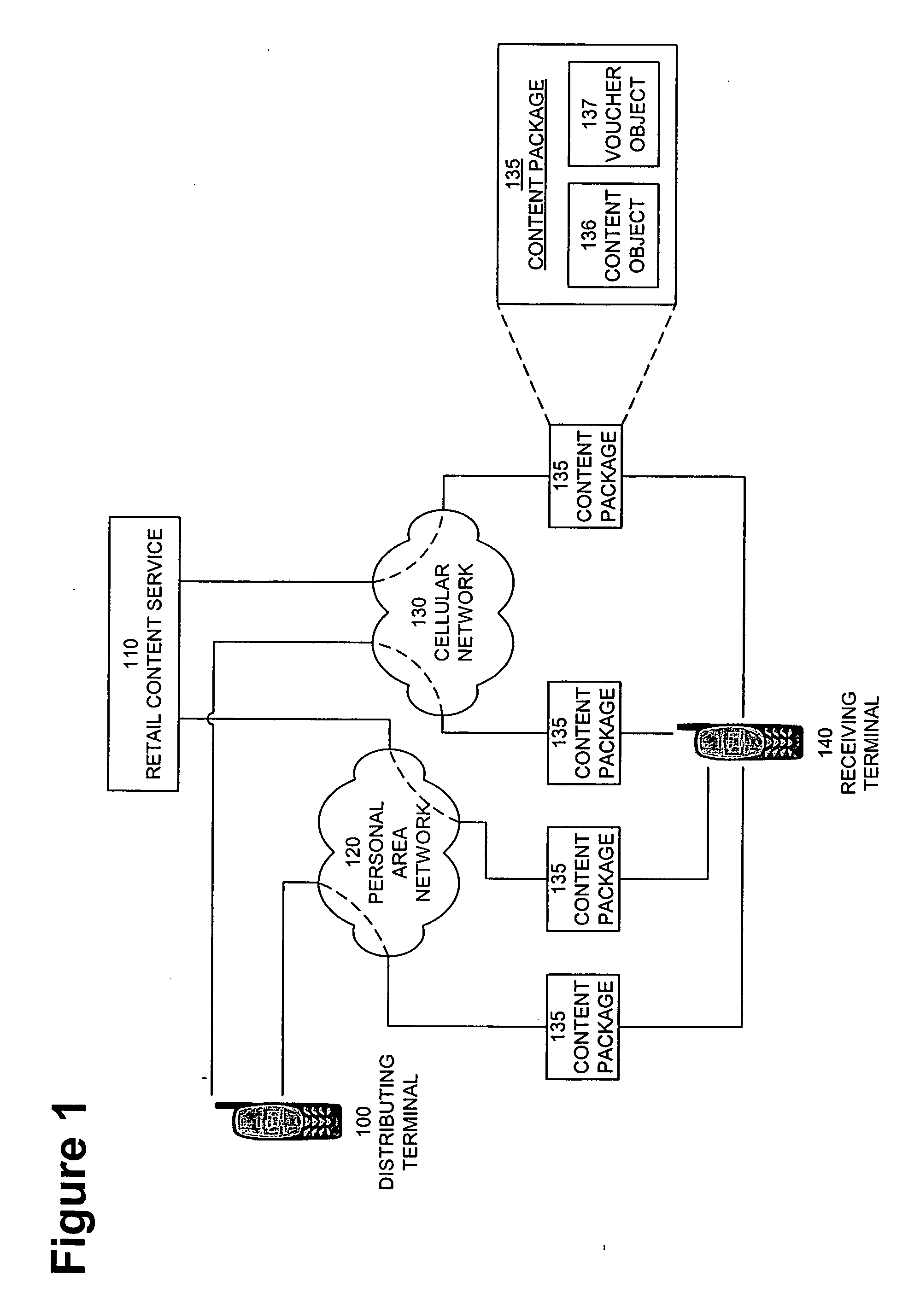
Digital rights management in a mobile communications environment
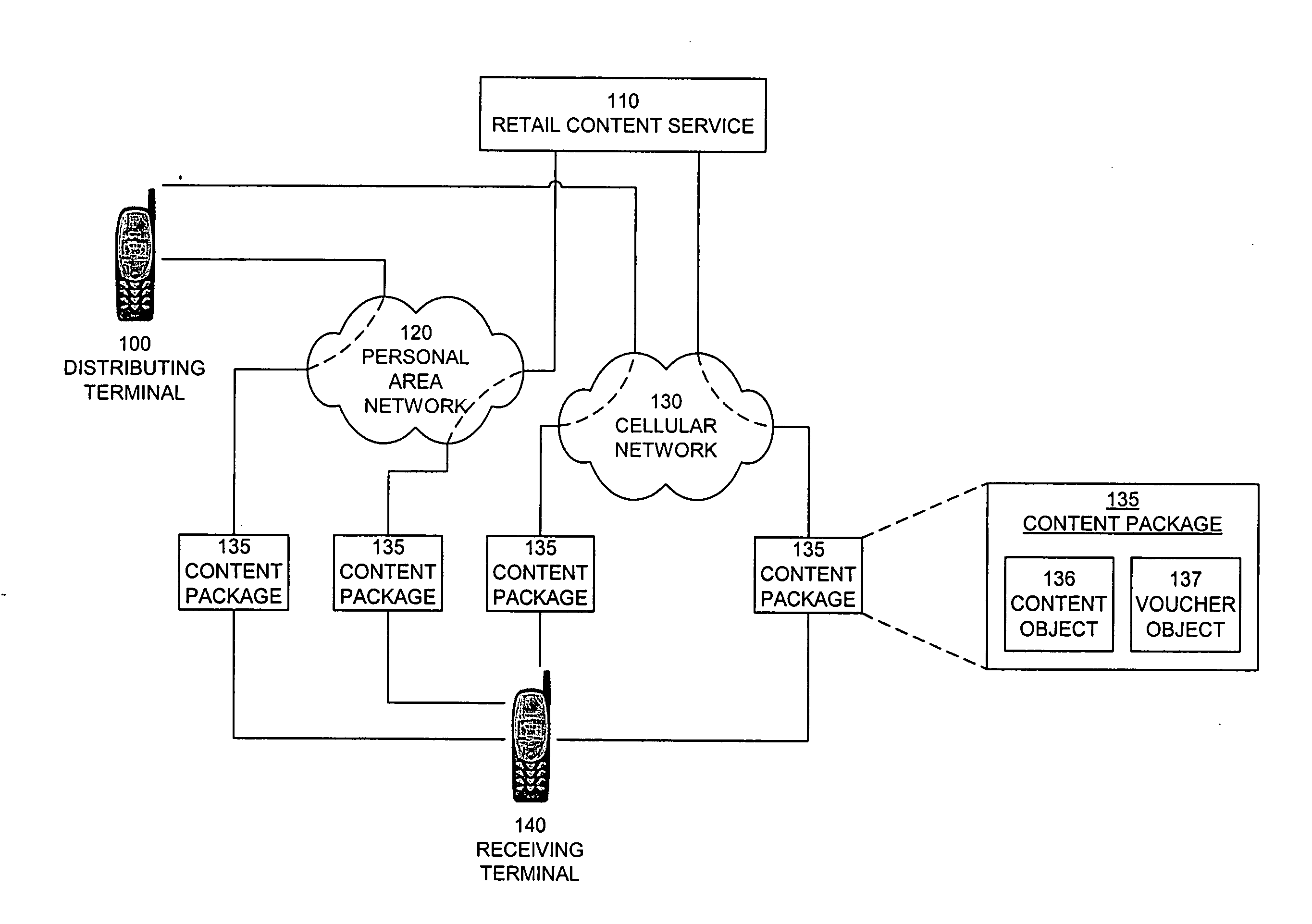
InactiveUS20070112676A1Payment architectureProgram/content distribution protectionDigital rights managementVoucher
The invention provides a method, system, and computer program product to control the access, copying, and / or transfer of a digital asset by mobile, wireless devices using a digital voucher. The digital voucher references a primary content that contains all of the expression for that particular asset and a secondary content that contains information that can be distilled out as a preview. The information in the primary content can be limited to a specified duration or a specific number of viewings. The author, owner, or possessor of the digital asset specifies the terms and conditions for distribution of the digital asset. The digital voucher authorizes the mobile, wireless device to access a specified primary or secondary content that may be located elsewhere in the network. The mobile, wireless device can download a copy of portions or all of the content depending on the terms specified in the voucher.
Owner:NOKIA CORP
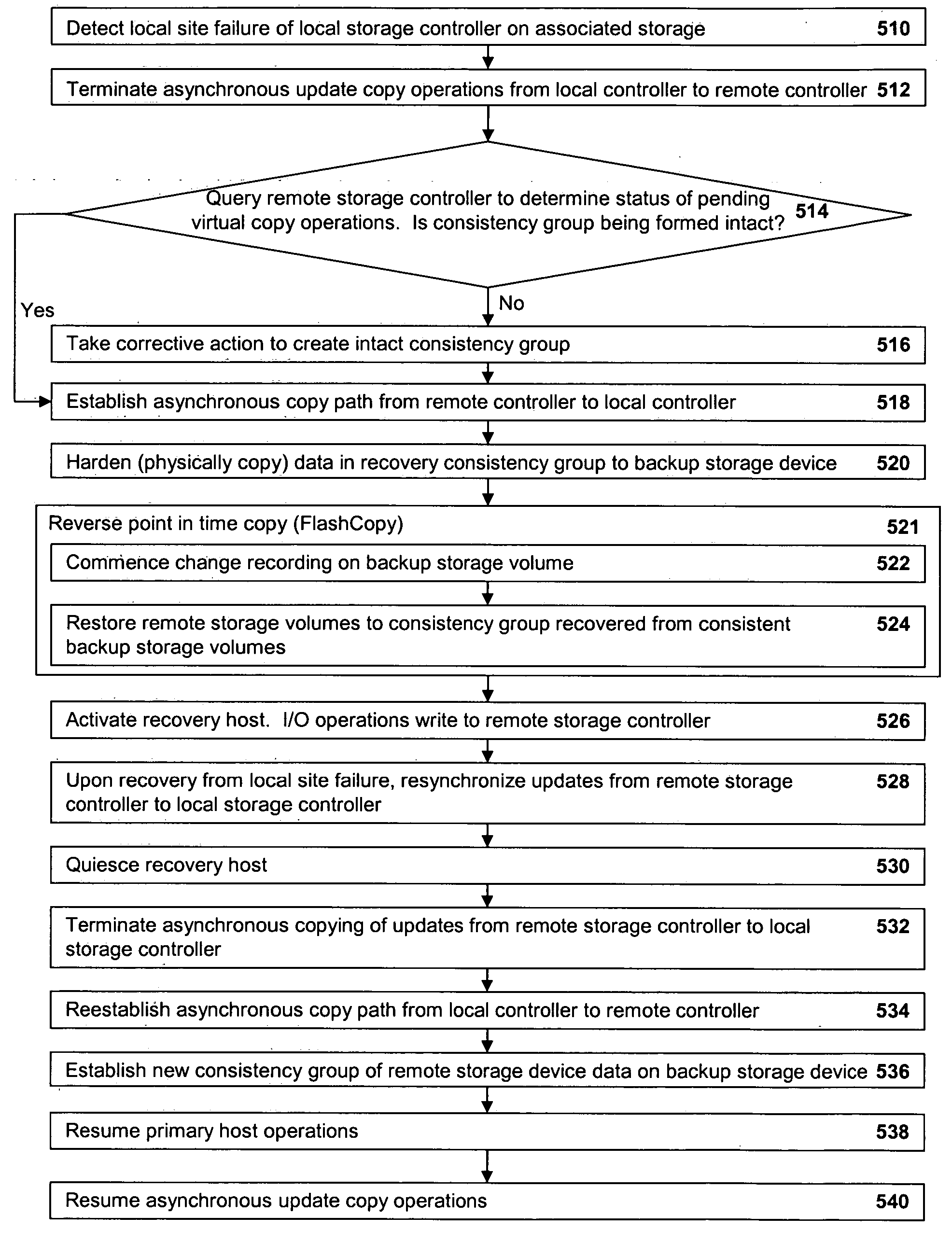
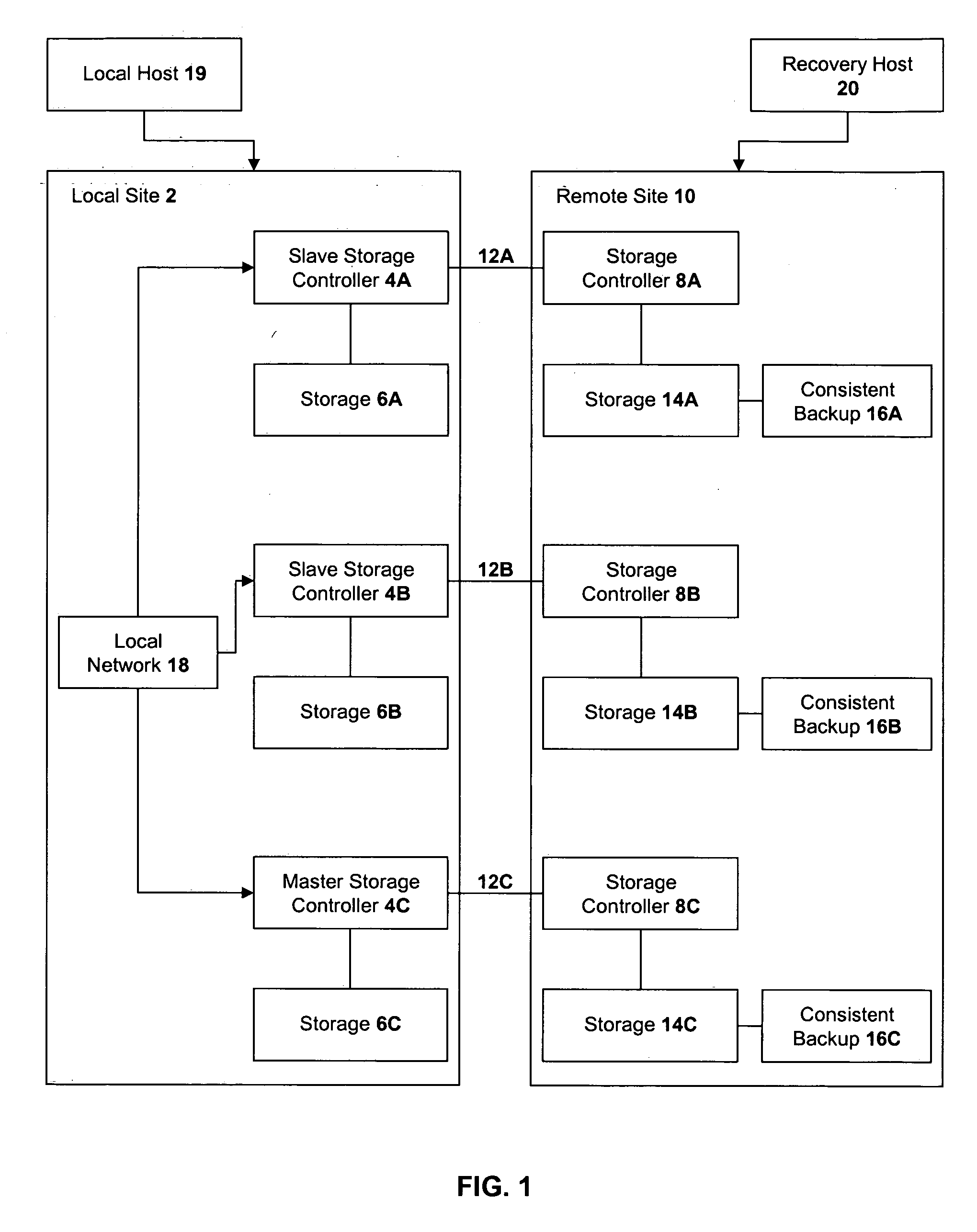
Method, system, and program for recovery from a failure in an asynchronous data copying system
InactiveUS20050071708A1Application downtime is minimizedMemory loss protectionUnauthorized memory use protectionRecovery methodDevice form
A method of recovery from a data storage system failure in a data storage system having a host computer writing data updates to a local storage controller at a local site. The local controller is associated with a local storage device. The local storage controller is also configured to asynchronously copy the updates to a remote storage controller associated with a remote storage device at a remote site. In addition, the remote storage controller is configured to store a consistent point in time copy of the updates on a backup storage device. The consistent point in time copy is known as a consistency group. Upon detection of a failure associated with the local site, a determination is made whether a group of updates pending for storage on the backup storage device form an intact consistency group. If an intact consistency group has not formed, corrective action may be taken to create an intact consistency group. The recovery method further consists of synchronizing the remote storage device, initiating recovery operations and, upon recovery of the local site, resynchronization of the local storage device and the backup storage device to recovery consistency group without the need for full volume storage copies and while minimizing application downtime.
Owner:IBM CORP
Generation isolation system and method for garbage collection
InactiveUS6098089AData processing applicationsMemory adressing/allocation/relocationProgramming languageWaste collection
Architectural support for generation isolation is provided through trapping of intergenerational pointer stores. Identification of pointer stores as intergenerational is performed by a store barrier responsive to an intergenerational pointer store trap matrix that is programmably encoded with store target object and store pointer data generation pairs to be trapped. The write barrier and intergenerational pointer store trap matrix provide a programmably-flexible definition of generation pairs to be trapped, affording a garbage collector implementer with support for a wide variety of generational garbage collection methods, including remembered set-based methods, card-marking type methods, write barrier based copying collector methods, etc., as well as combinations thereof and combinations including train algorithm type methods to managing mature portions of a generationally collected memory space. Pointer specific store instruction replacement allows implementations in accordance with this invention to provide an exact barrier to not only pointer stores, but to the specific intergenerational pointer stores of interest to a particular garbage collection method or combination of methods.
Owner:ORACLE INT CORP
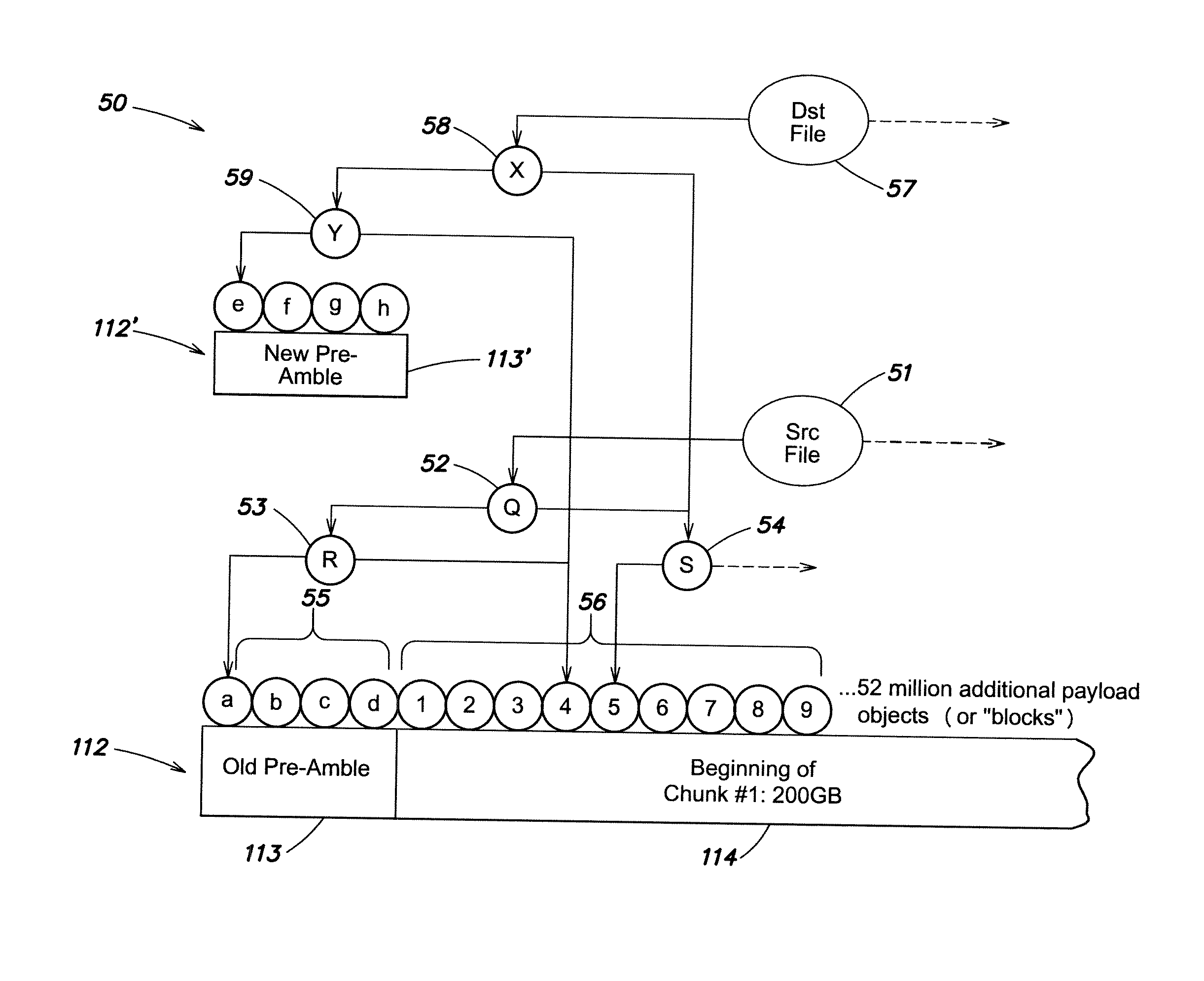
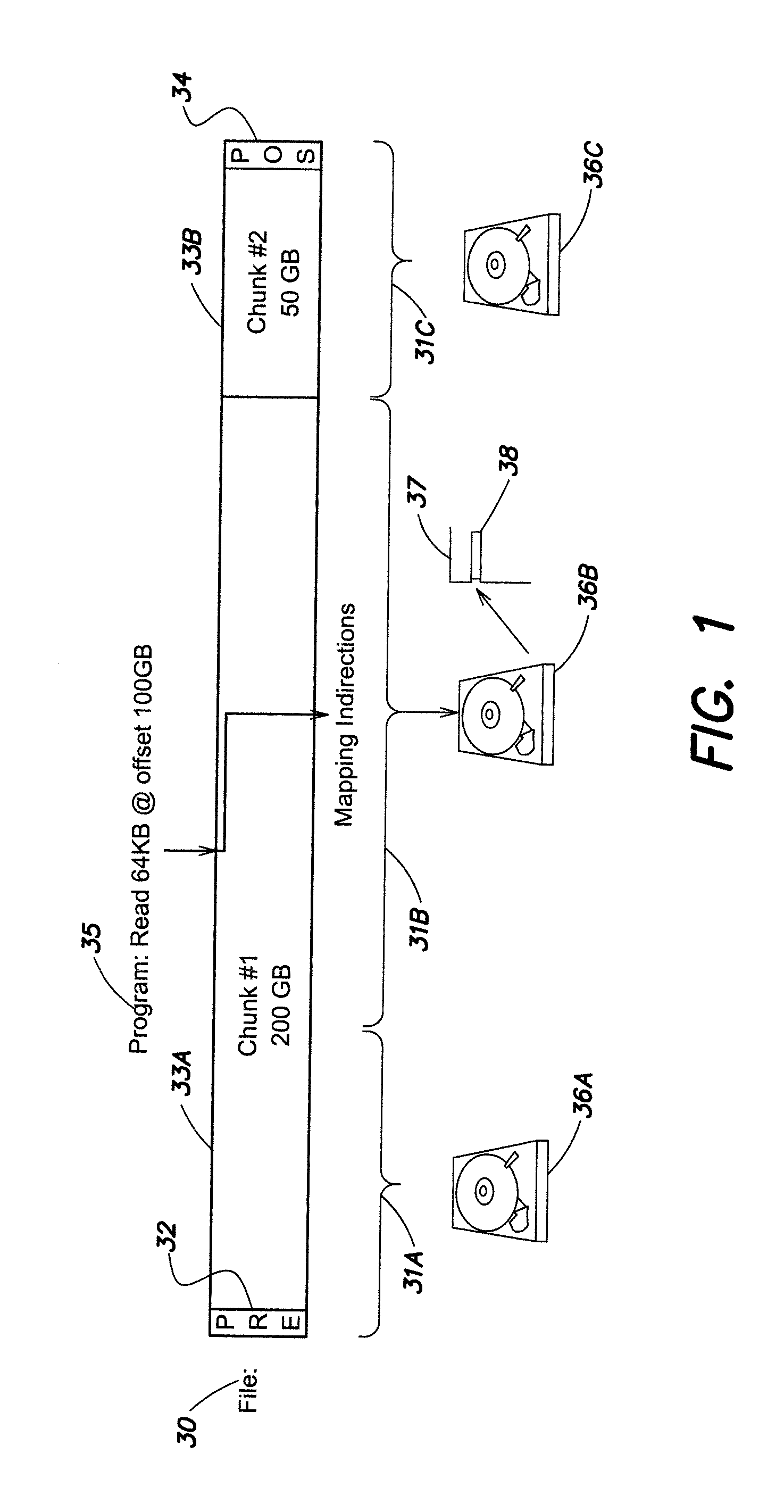
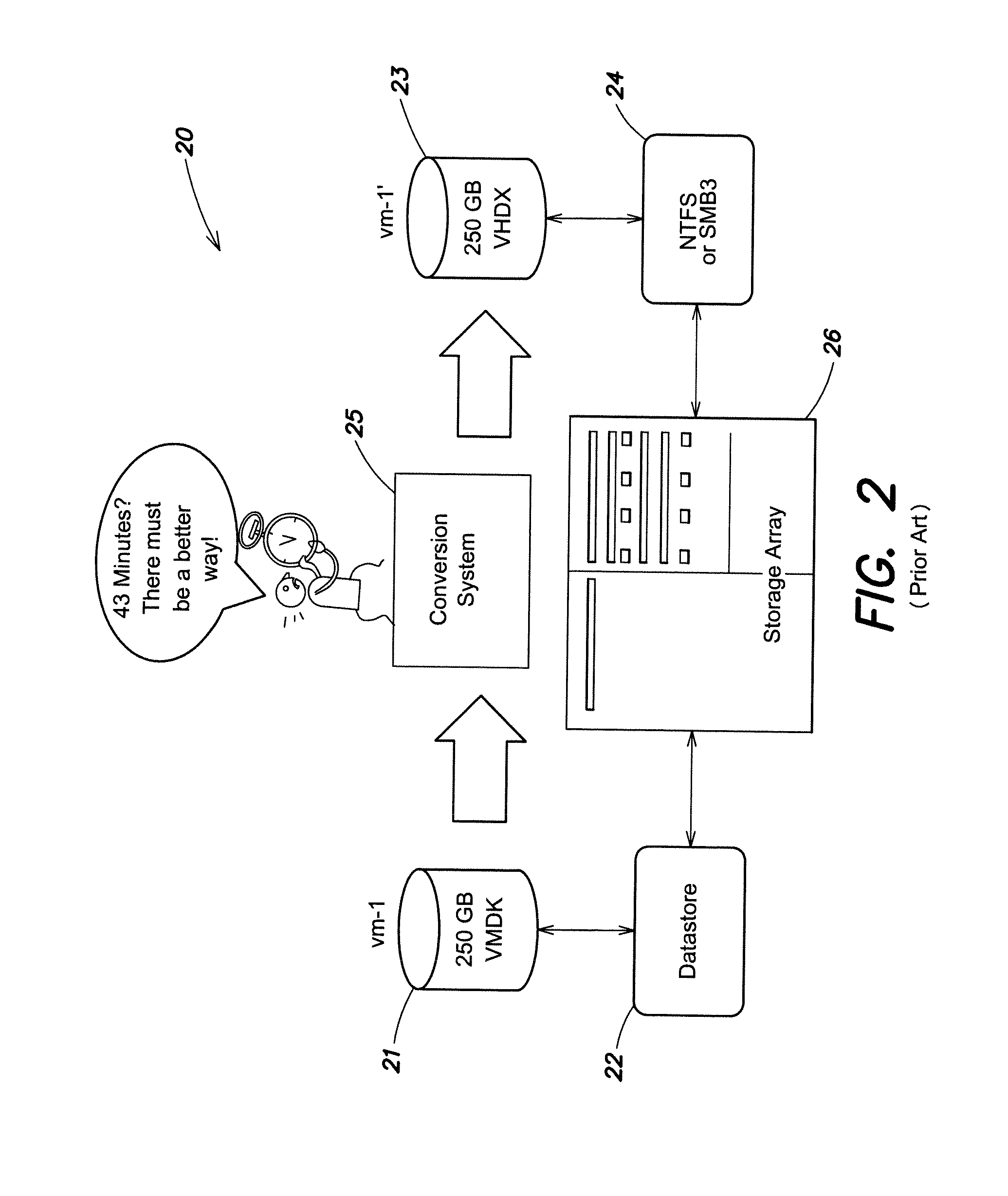
System and method for virtual machine conversion
ActiveUS20150058382A1Improve efficiencyDigital data information retrievalProgram controlFile systemData element
System and method for conversion of virtual machine files without requiring copying of the virtual machine payload (data) from one location to another location. By eliminating this step, applicant's invention significantly enhances the efficiency of the conversion process. In one embodiment, a file system or storage system provides indirections to locations of data elements stored on a persistent storage media. A source virtual machine file includes hypervisor metadata (HM) data elements in one hypervisor file format, and virtual machine payload (VMP) data elements. The source virtual machine file is converted by transforming the HM data elements of the source file to create destination HM data elements in a destination hypervisor format different from the source hypervisor format; maintaining the locations of the VMP data elements stored on the persistent storage media constant during the conversion from source to destination file formats without reading or writing the VMP data elements; and creating indirections to reference the destination HM data elements in the destination hypervisor format and the existing stored VMP data elements.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
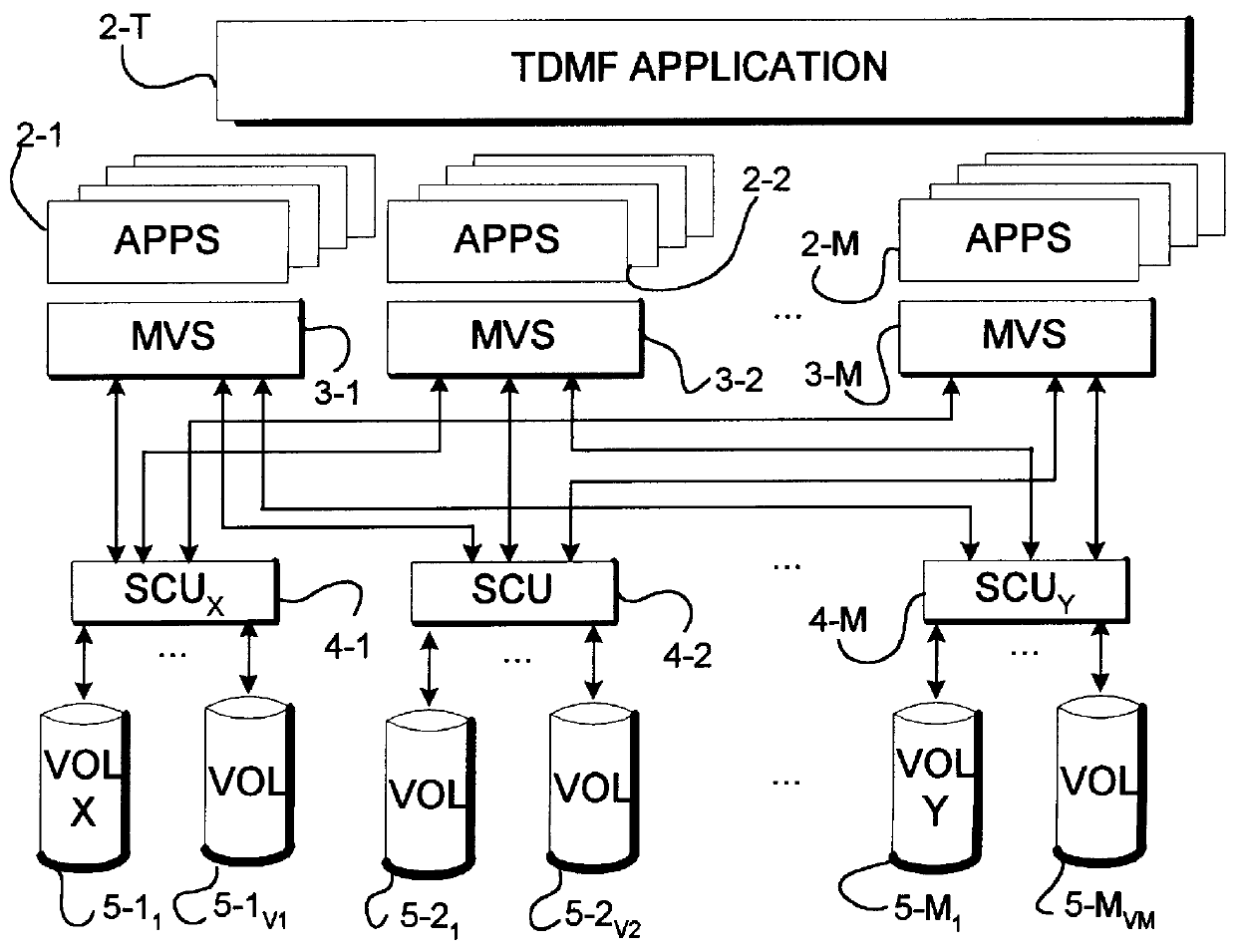
Computer system with transparent data migration between storage volumes
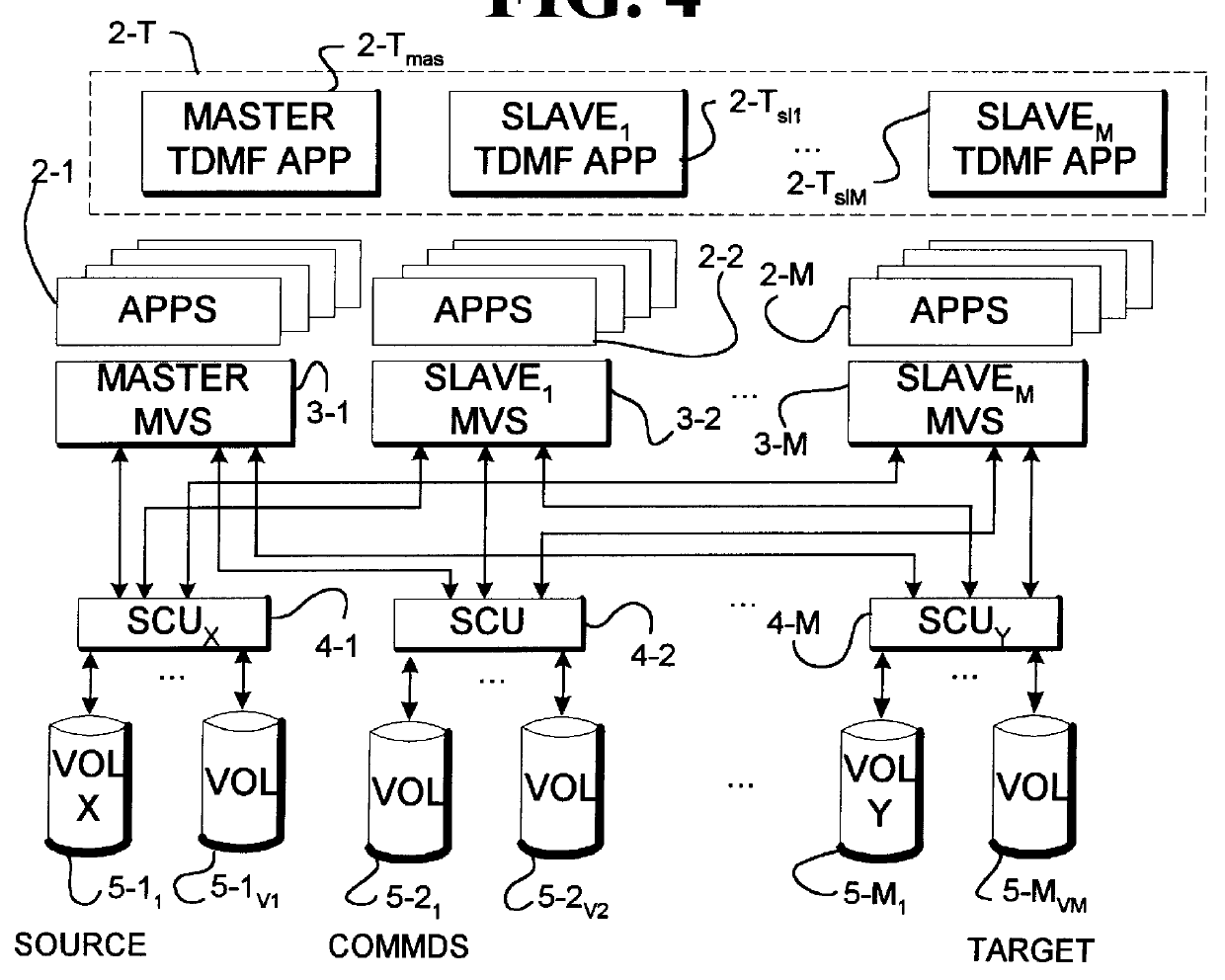
InactiveUS6145066AEnsures independenceMinimal disruptionInput/output to record carriersMemory adressing/allocation/relocationOperational systemComputerized system
A computer system includes a transparent data migration facility (TDNff) to accomplish automated movement of data (migration) from one location to another in the system. A data migration program includes a main module to control the start of a migration session when said application programs are using data accessed to and from the source volume, to migrate data from the source volume to the target volume, and to end the migration session whereby the application programs are using data accessed to and from the target volume. The data migration program includes a volume module to control the volumes during the migration session. The data migration program includes a copy module to control the copying of data from the source module to the target module during the migration session. The data migration program includes a monitor module for monitoring I / O transfers to the data volumes during the migration sessions. The computer system may have a plurality of operating systems associated with instances of the data migration program which allows for concurrent data migrations. The plurality of instances of the data migration program may also be controlled in a master slave relationship. A migration session may include a plurality of migration phases such as activation, copy, refresh, quiesce, synchronize, redirect, resume and termination phases.
Owner:SOFTEK STORAGE SOLUTIONS CORP
Optical disc having RFID tag, optical disc apparatus, and system for preventing unauthorized copying
InactiveUS7317396B2Reliable preventionInhibitory contentDigital data processing detailsMechanical recordingSecret codeInformation needs
In an optical disc having an RFID tag, disc control information needed for control of reproduction of the content recorded in the disc body of the optical disc is stored in the RFID tag. Thereby, even if the content recorded in the disc body is illegally copied in some way, common optical disc apparatus incapable of reading RFID tags cannot read and copy the disc control information stored in the RFID tag. Accordingly, unauthorized copying of the content recorded on the optical disc can be reliably prevented without the use of special cryptographic technology.
Owner:FUNAI ELECTRIC CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com