Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
29437results about "Payment architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
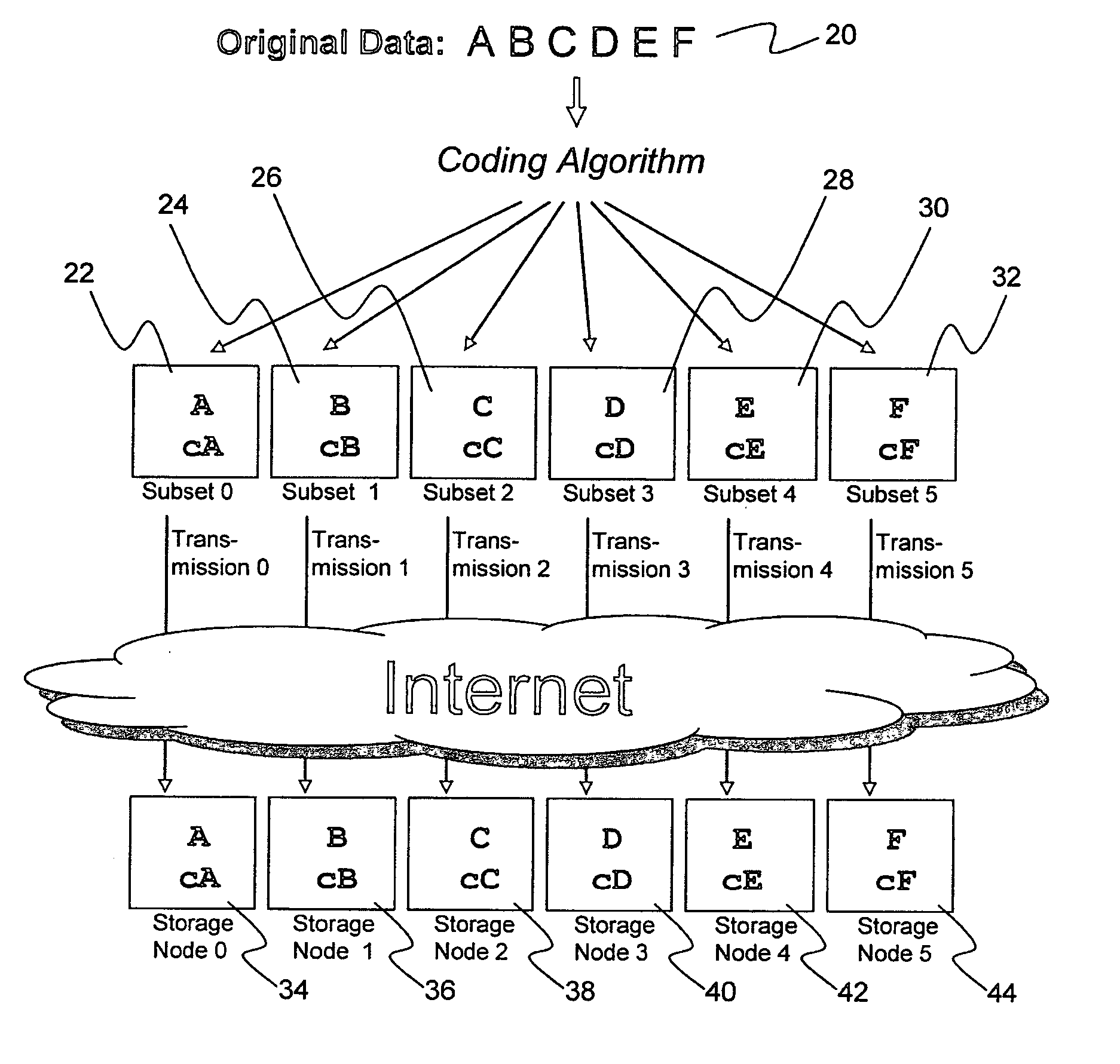
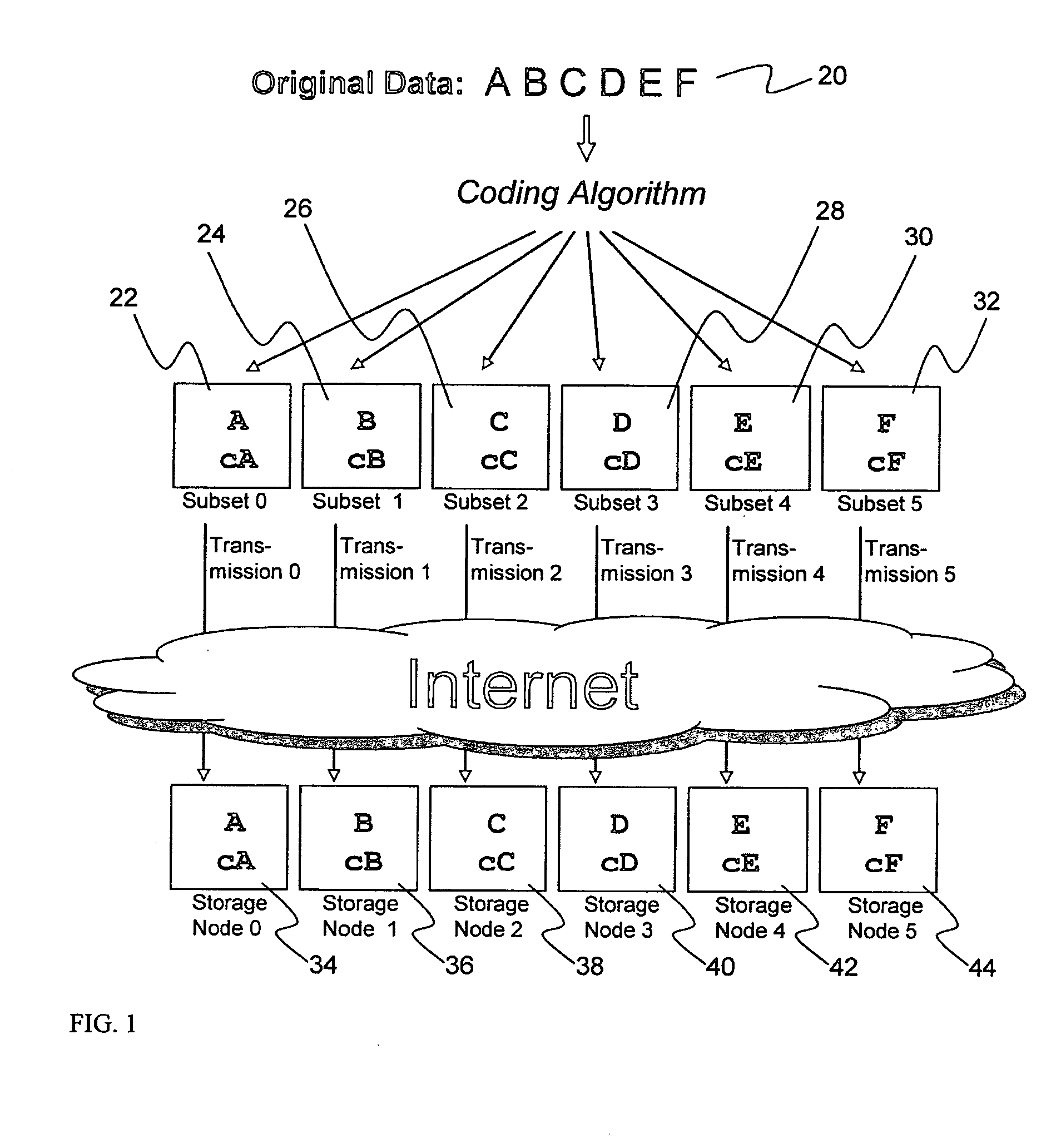
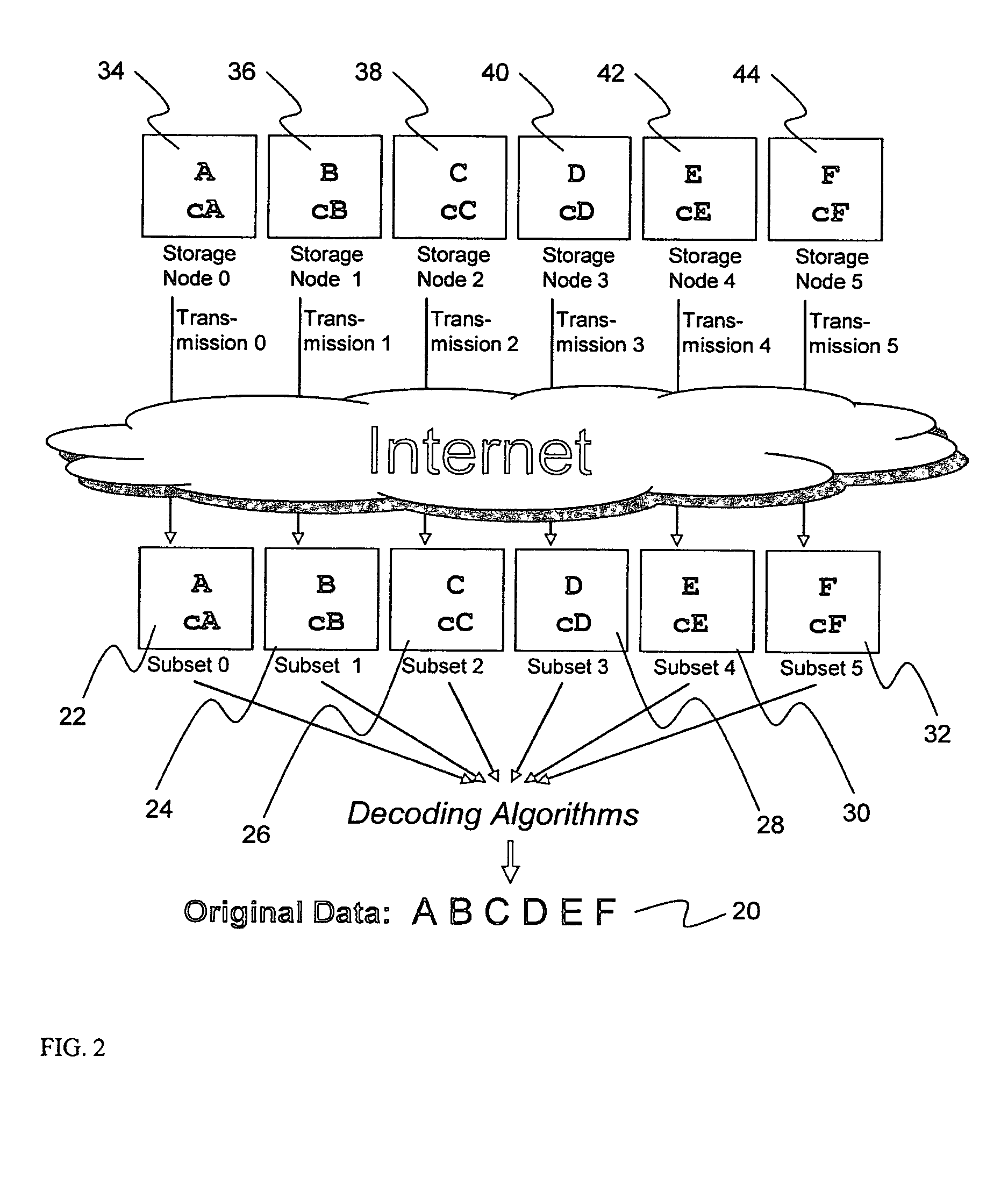
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
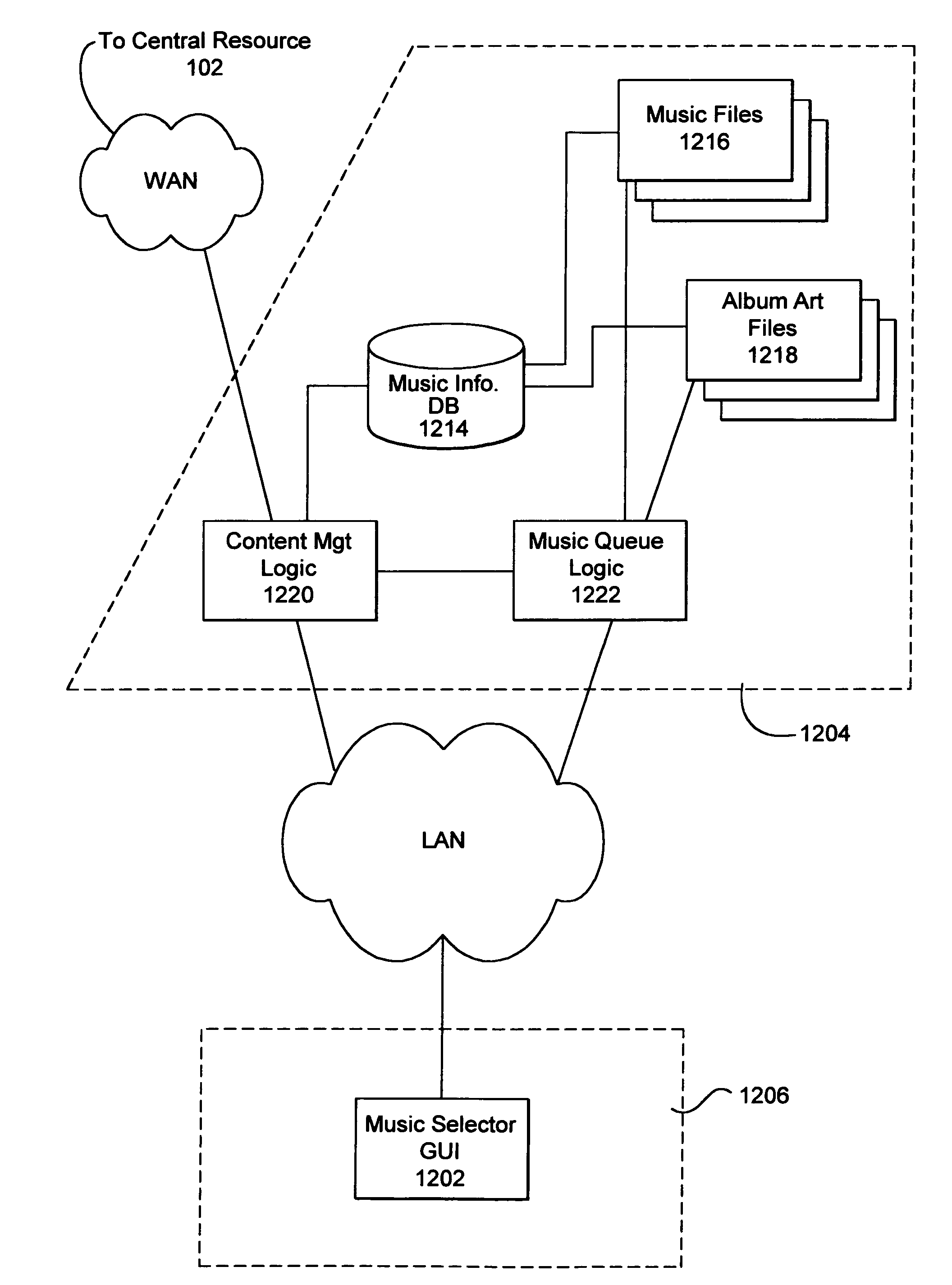
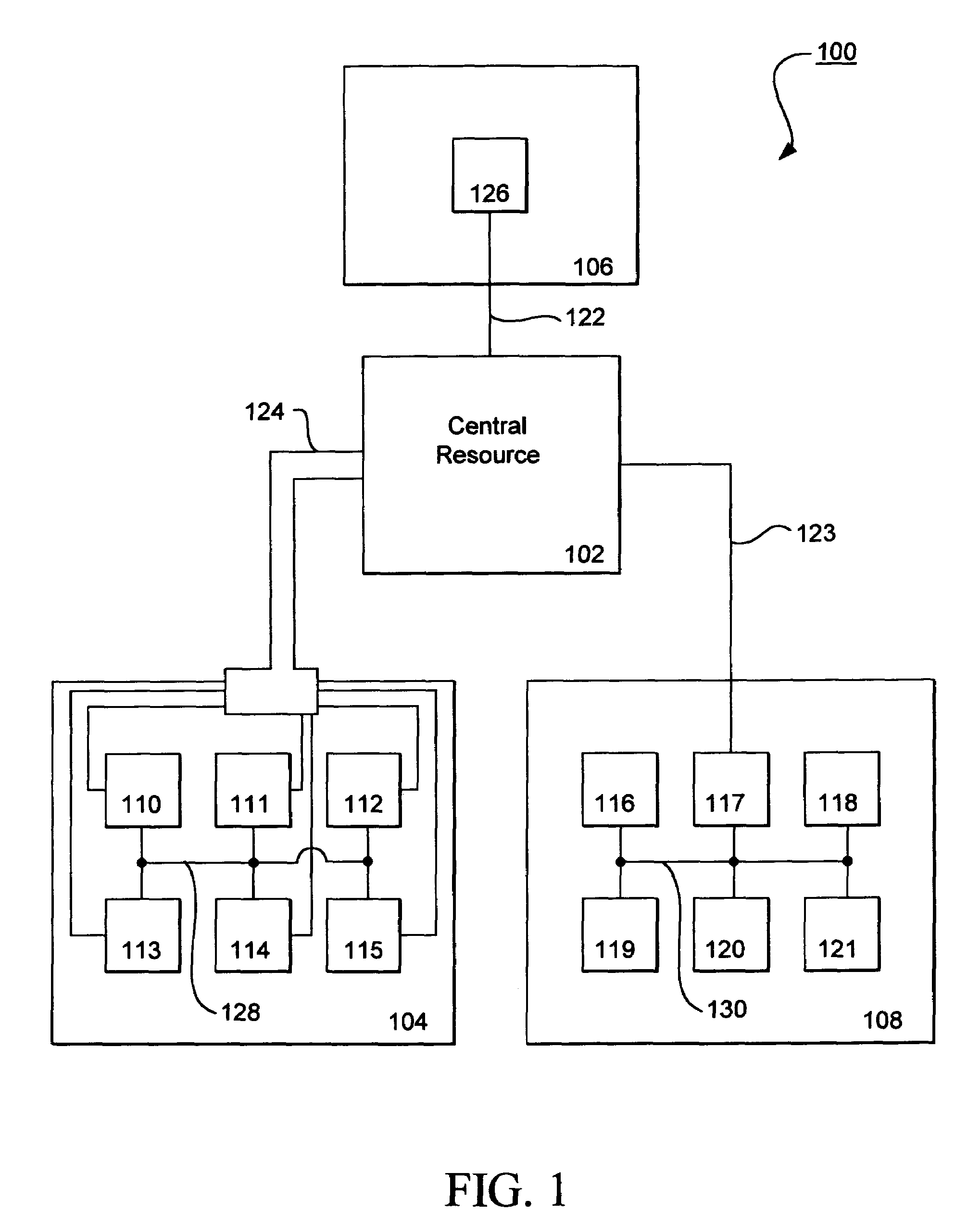
Distributed electronic entertainment method and apparatus
A distributed electronic entertainment method and apparatus are described. In one embodiment, a central management resource is coupled to multiple out-of-home venues through a wide area network (WAN). The central management resource stores content and performs management, monitoring and entertainment content delivery functions. At each venue at least one entertainment unit is coupled to the WAN. Multiple entertainment units in a venue are coupled to each other through a local area network (LAN). In one embodiment, an entertainment unit includes a user interface that comprises at least one graphical user interface (GUI). The entertainment unit further comprises a local memory device that stores entertainment content comprising music, a peripheral interface, and a user input device. A plurality of peripheral devices are coupled to the at least one entertainment unit via the peripheral interface, wherein a user, through the user input device and the user interface, performs at least one activity from a group comprising, playing music, playing electronic games, viewing television content, and browsing the Internet.
Owner:AMI ENTERTAINMENT NETWORK
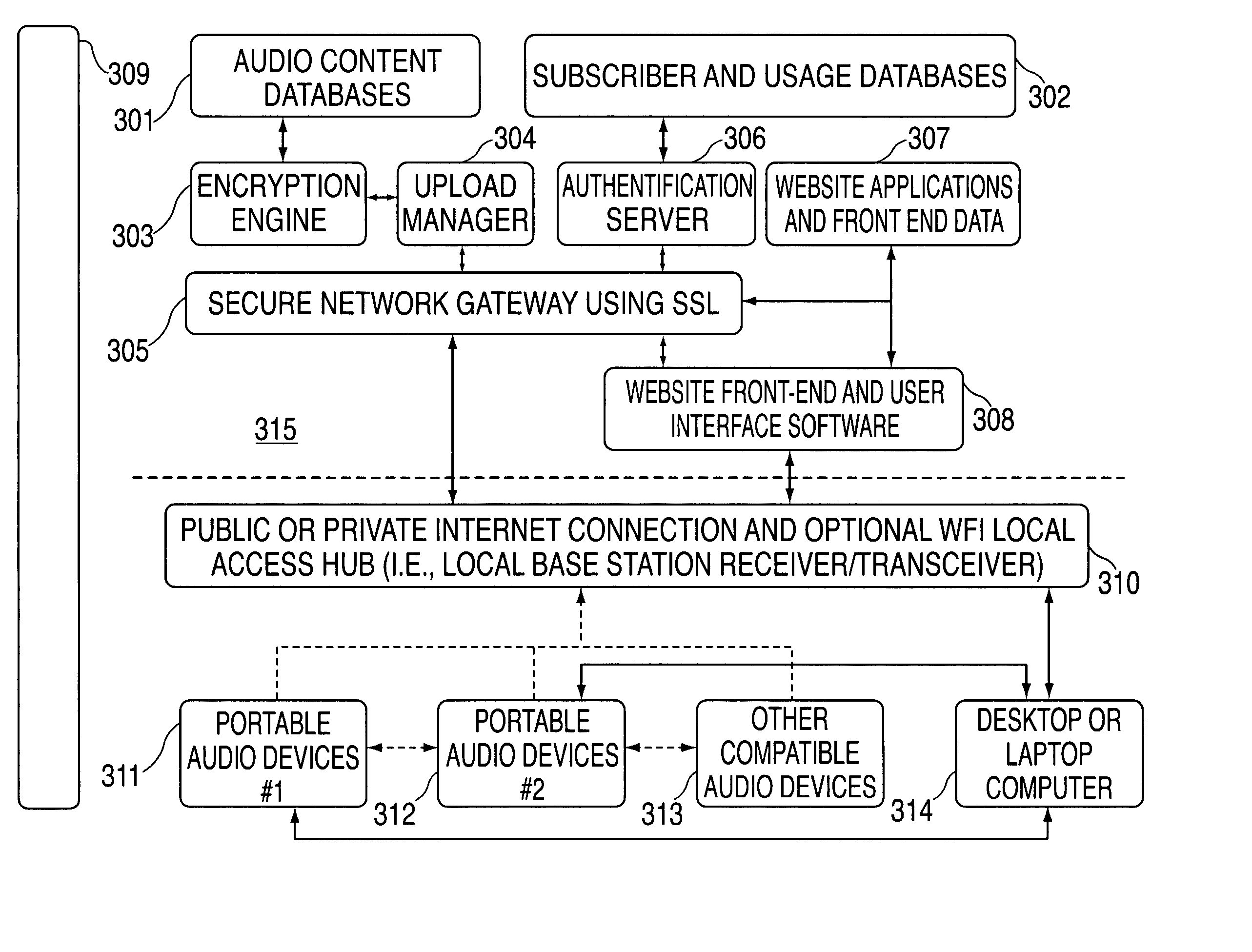
Audio visual player apparatus and system and method of content distribution using the same
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
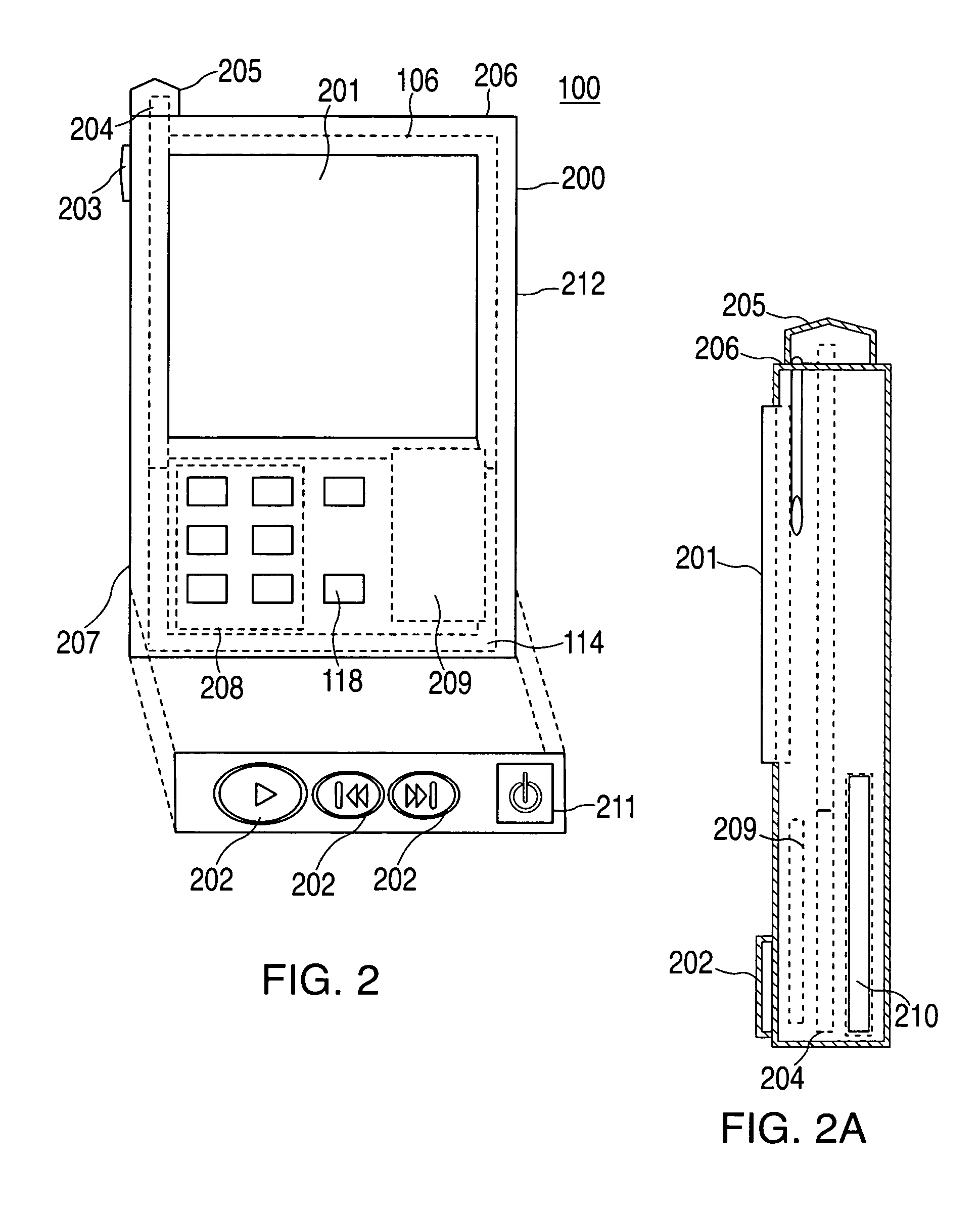
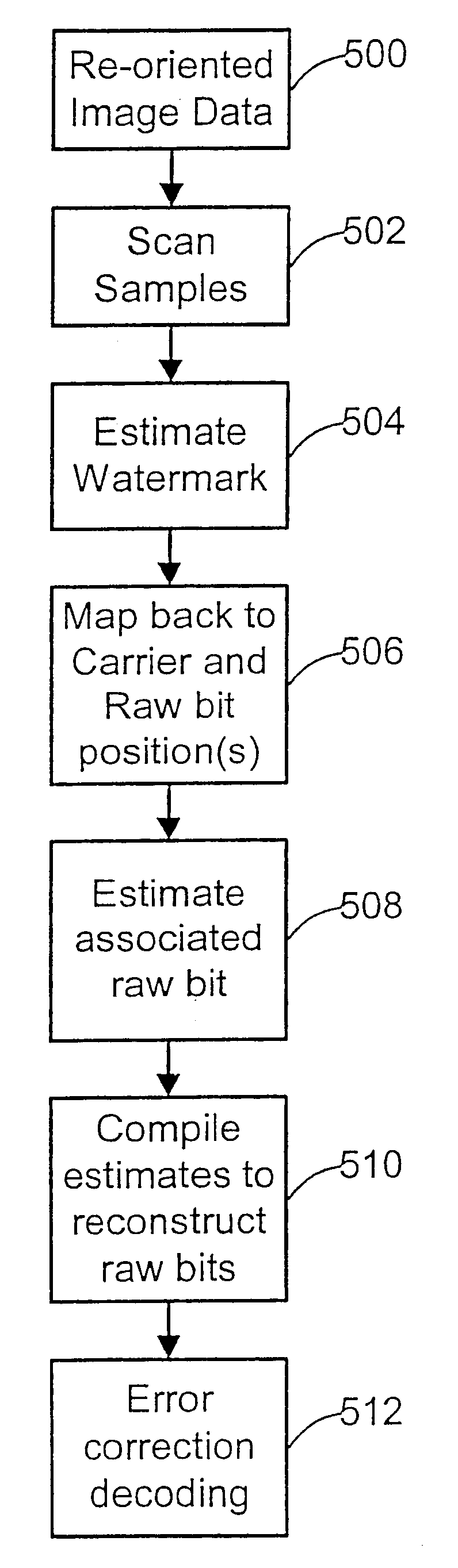
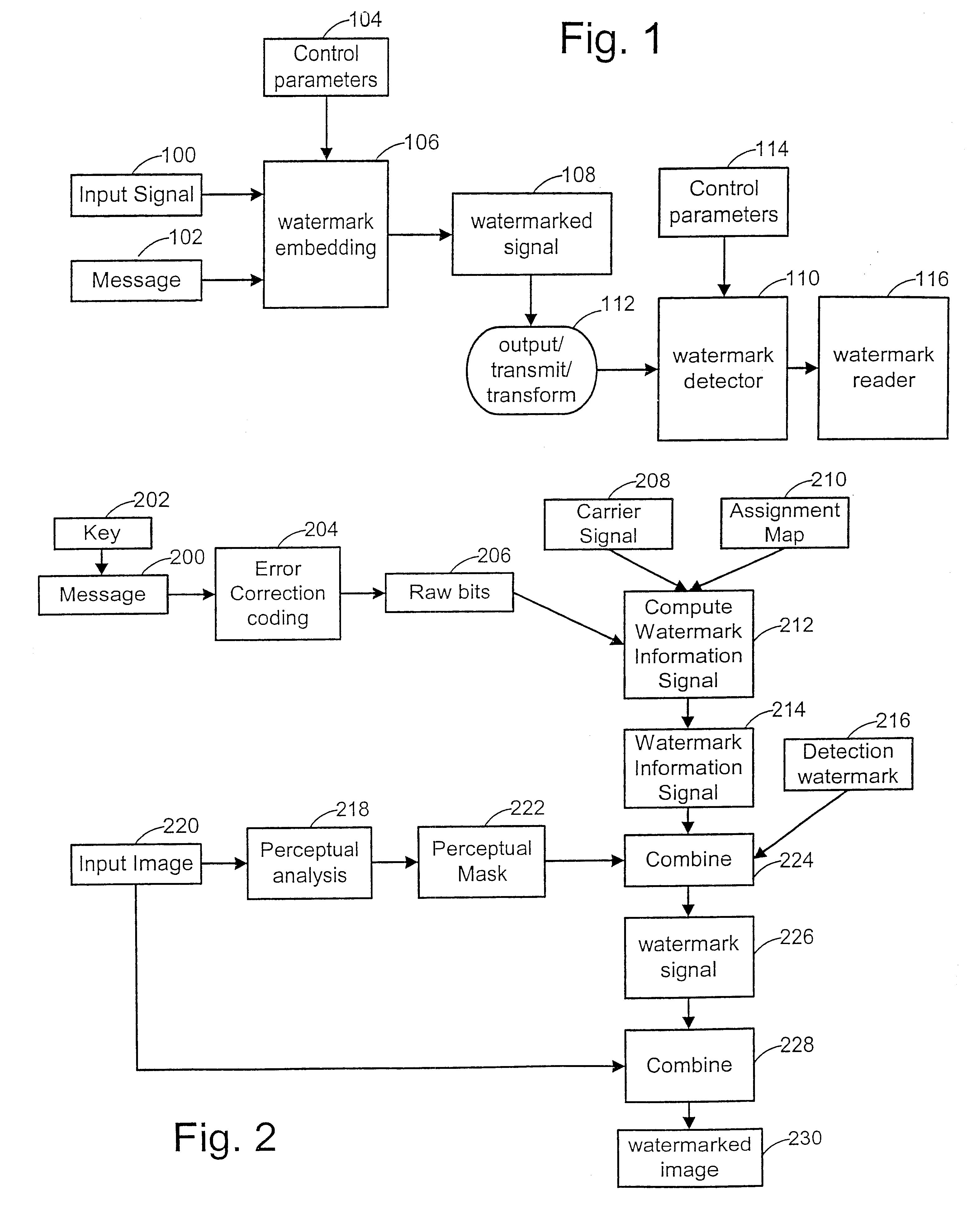
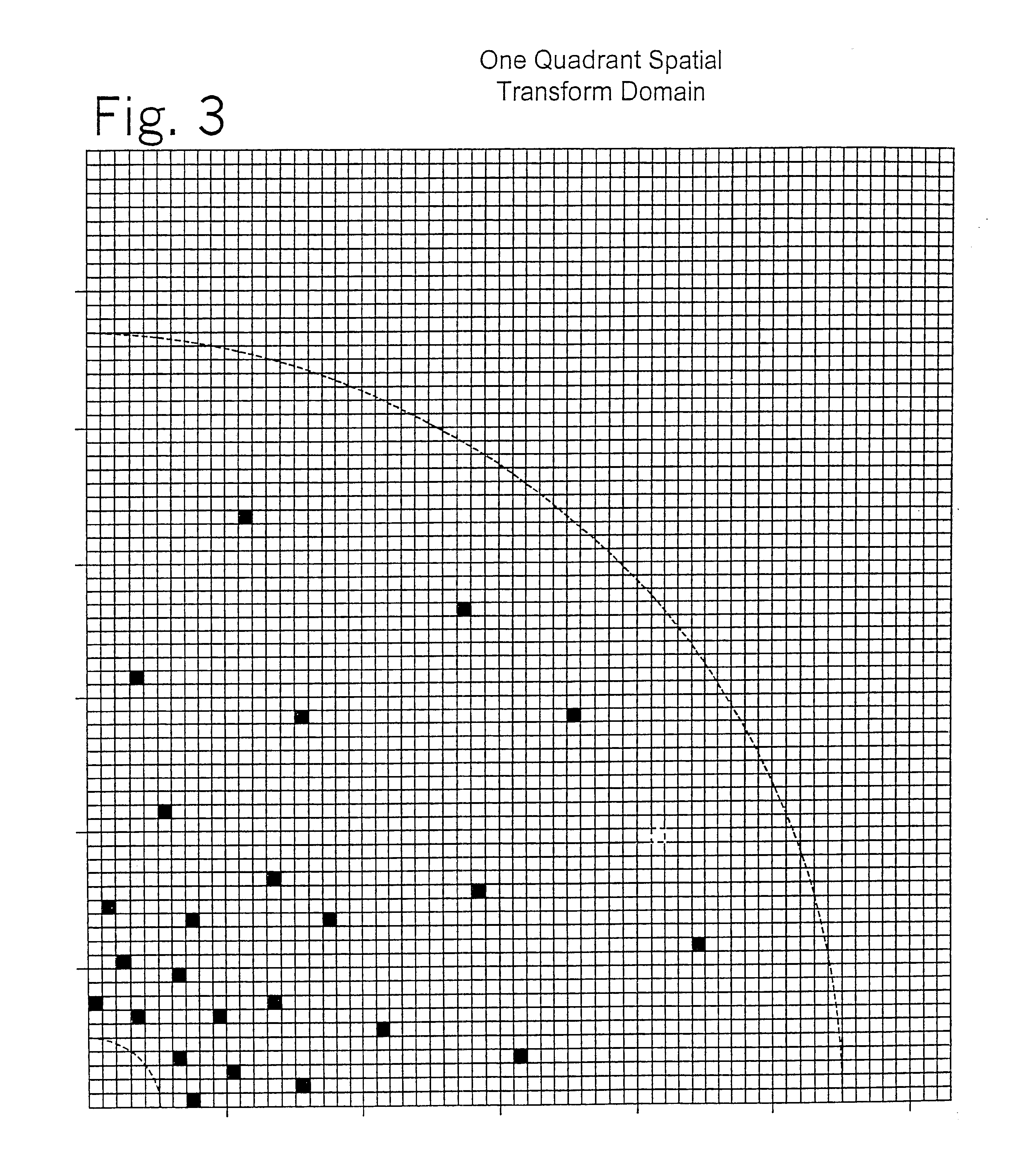
Watermark embedder and reader
InactiveUS6614914B1Mitigates effect of printingEasy to detectCoin-freed apparatusRecord information storageGraphicsComputer hardware
A watermark system includes an embedder, detector, and reader. The watermark embedder encodes a watermark signal in a host signal to create a combined signal. The detector looks for the watermark signal in a potentially corrupted version of the combined signal, and computes its orientation. Finally, a reader extracts a message in the watermark signal from the combined signal using the orientation to approximate the original state of the combined signal. While adapted for images, video and audio, the watermark system applies to other electronic and physical media. For example, it can be applied to mark graphical models, blank paper, film and other substrates, texturing objects for ID purposes, etc.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
System and methods for a micropayment-enabled marketplace with permission-based, self-service, precision-targeted delivery of advertising, entertainment and informational content and relationship marketing to anonymous internet users
InactiveUS20070067297A1Payment architectureSpecial data processing applicationsPersonalizationThird party
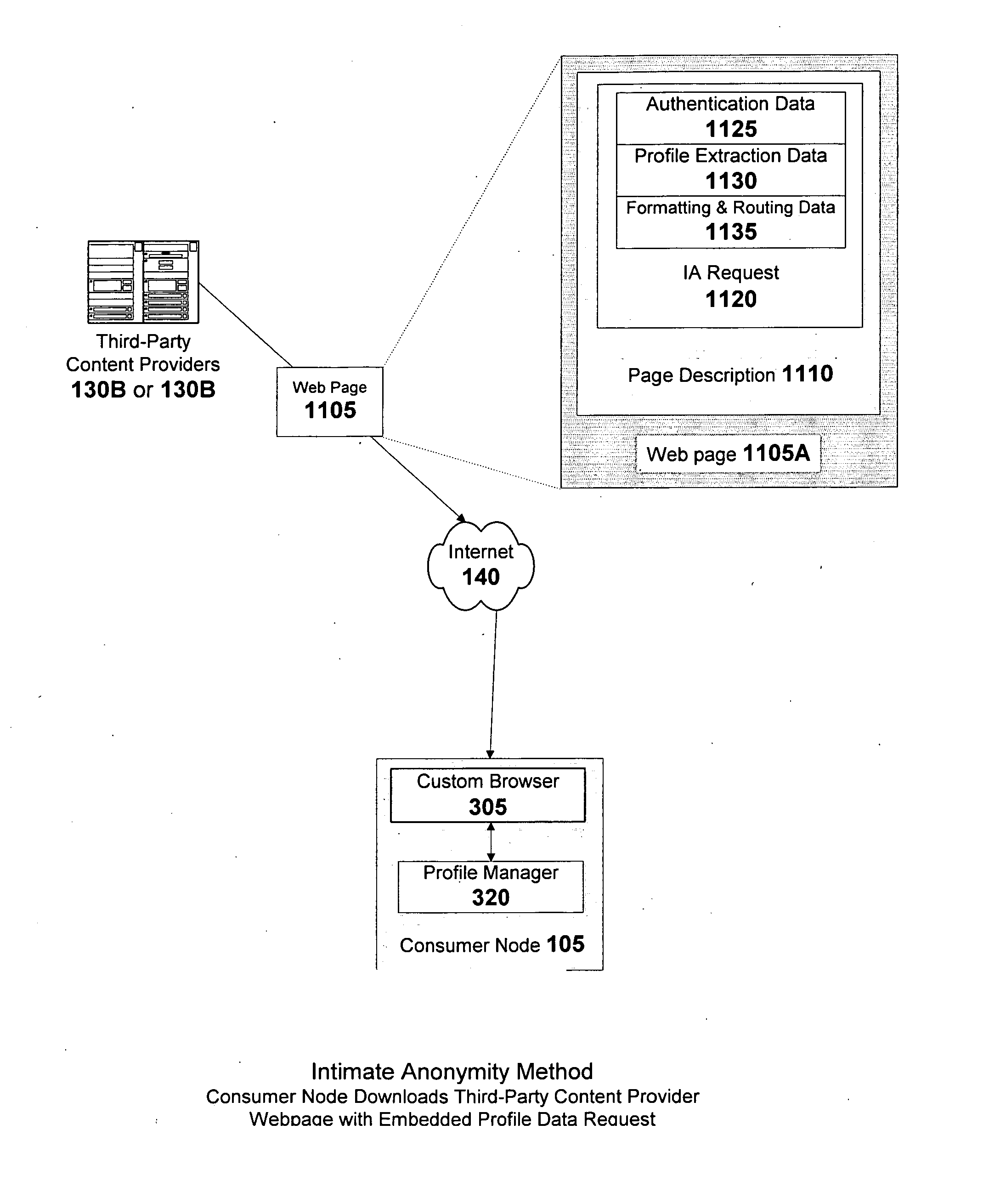
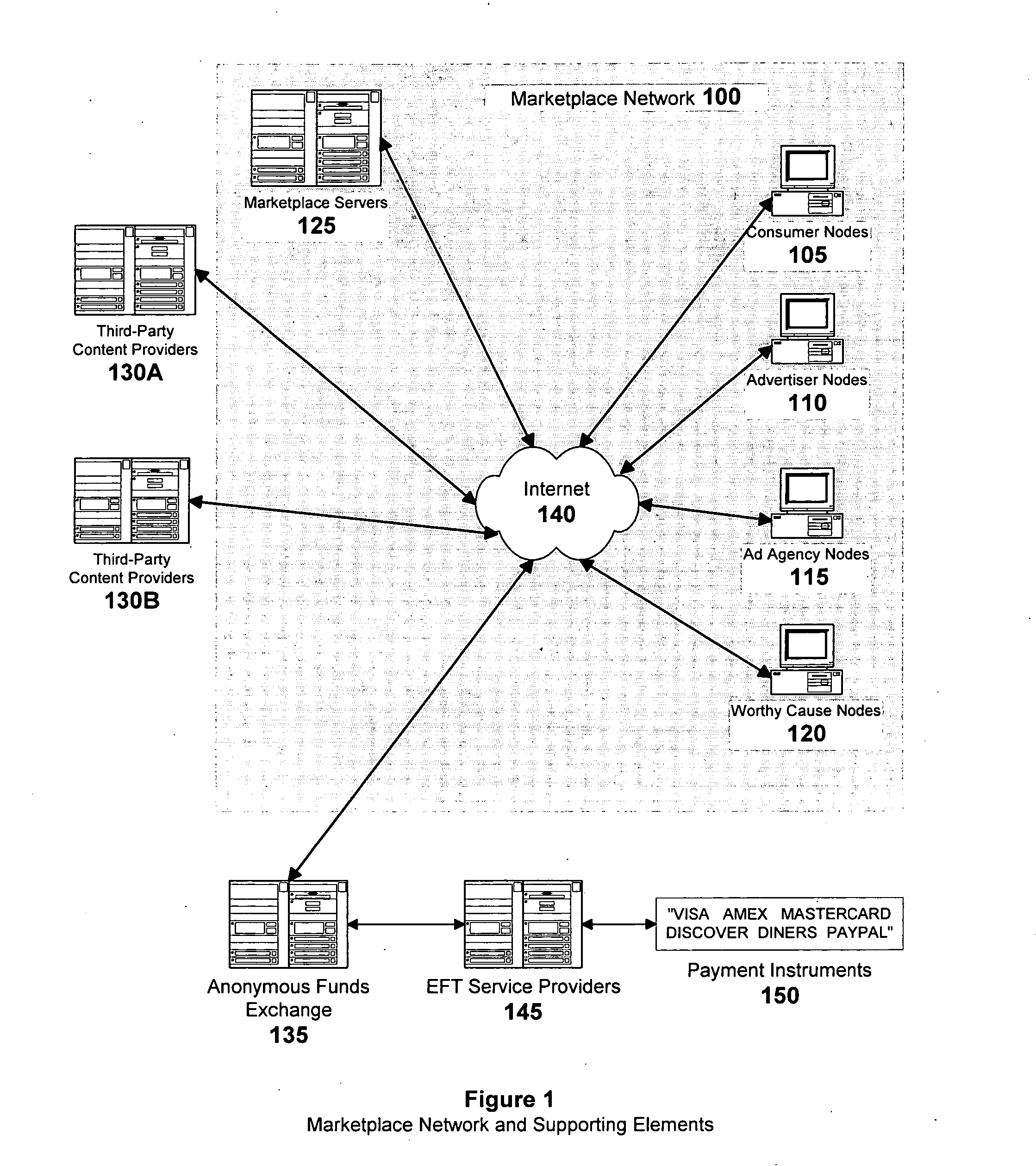
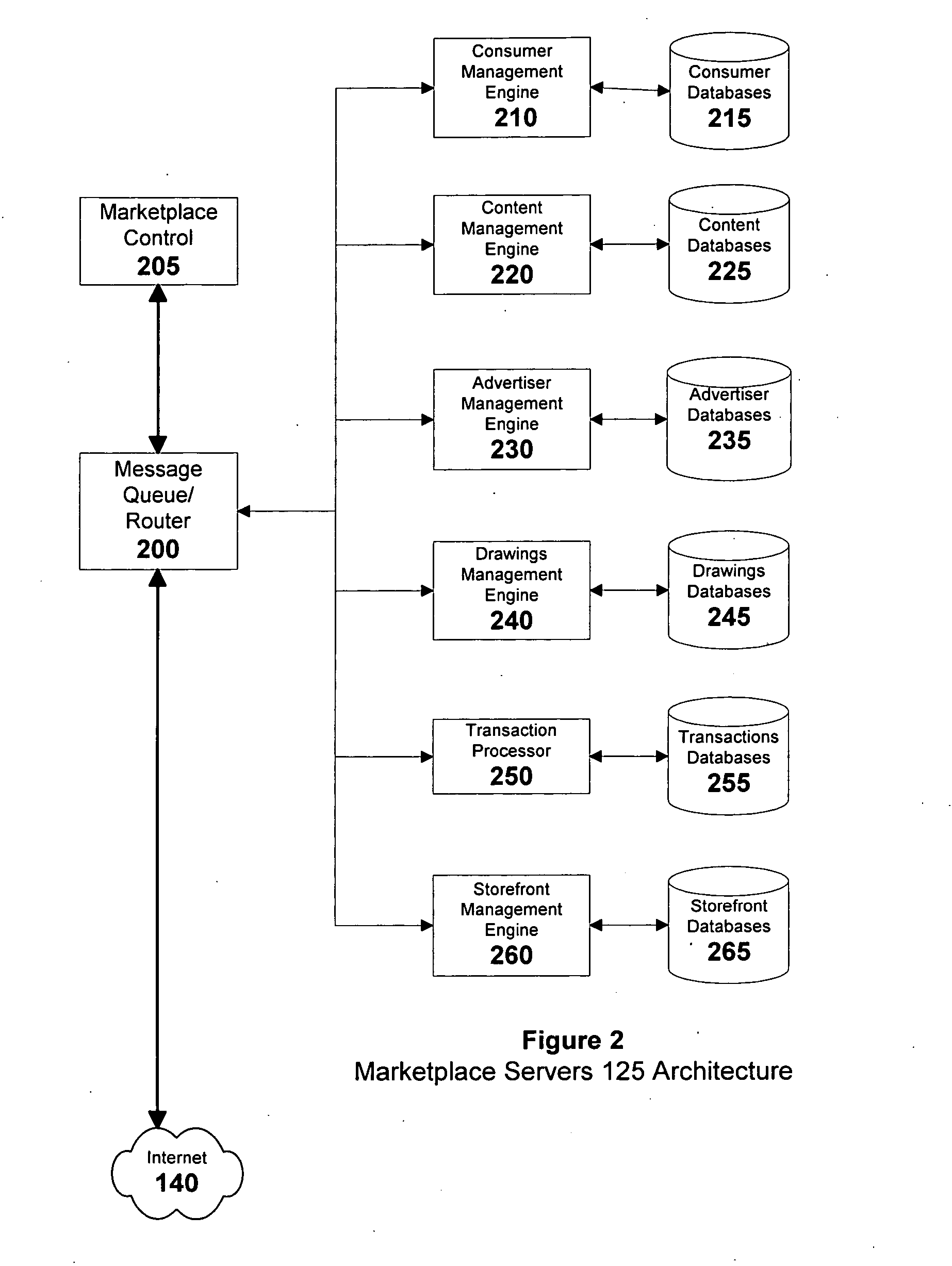
A method of enabling anonymous Internet users to publish and manage extensive, non-identifying personal data, including demographic, psychographic, needs, wants, interests, propensities, means to purchase, credibility and other data which in turn, enables a marketplace wherein such users, advertisers, websites, and other third-parties can mutually benefit from the commercial exploitation of such data. Advertisers can directly use the data to segregate the users into highly differentiated anonymous audiences for the purposes of targeting them with individualized marketing campaigns and then monitor user responses in near real-time. Websites can individualize their content to the profiles of visiting users. Users can share surface and deep web links with other users having similar profiles. Consumers participating in good faith are proportionately rewarded via revenue sharing, which they may withdraw from the marketplace or use to purchase and rent digital content offered in the marketplace's micropayment-enabled storefronts by other users and third-party content providers.
Owner:KUBLICKIS PETER JOSEPH
Linking of computers based on optical sensing of digital data
InactiveUS6311214B1Reduce businessLow costCoin-freed apparatusRecord information storageDigital dataBusiness card
A printed object, such as an item of postal mail, a book, printed advertising, a business card, product packaging, etc., is steganographically encoded with plural-bit data. When such an object is presented to an optical sensor, the plural-bit data is decoded and used to establish a link to an internet address corresponding to that object.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
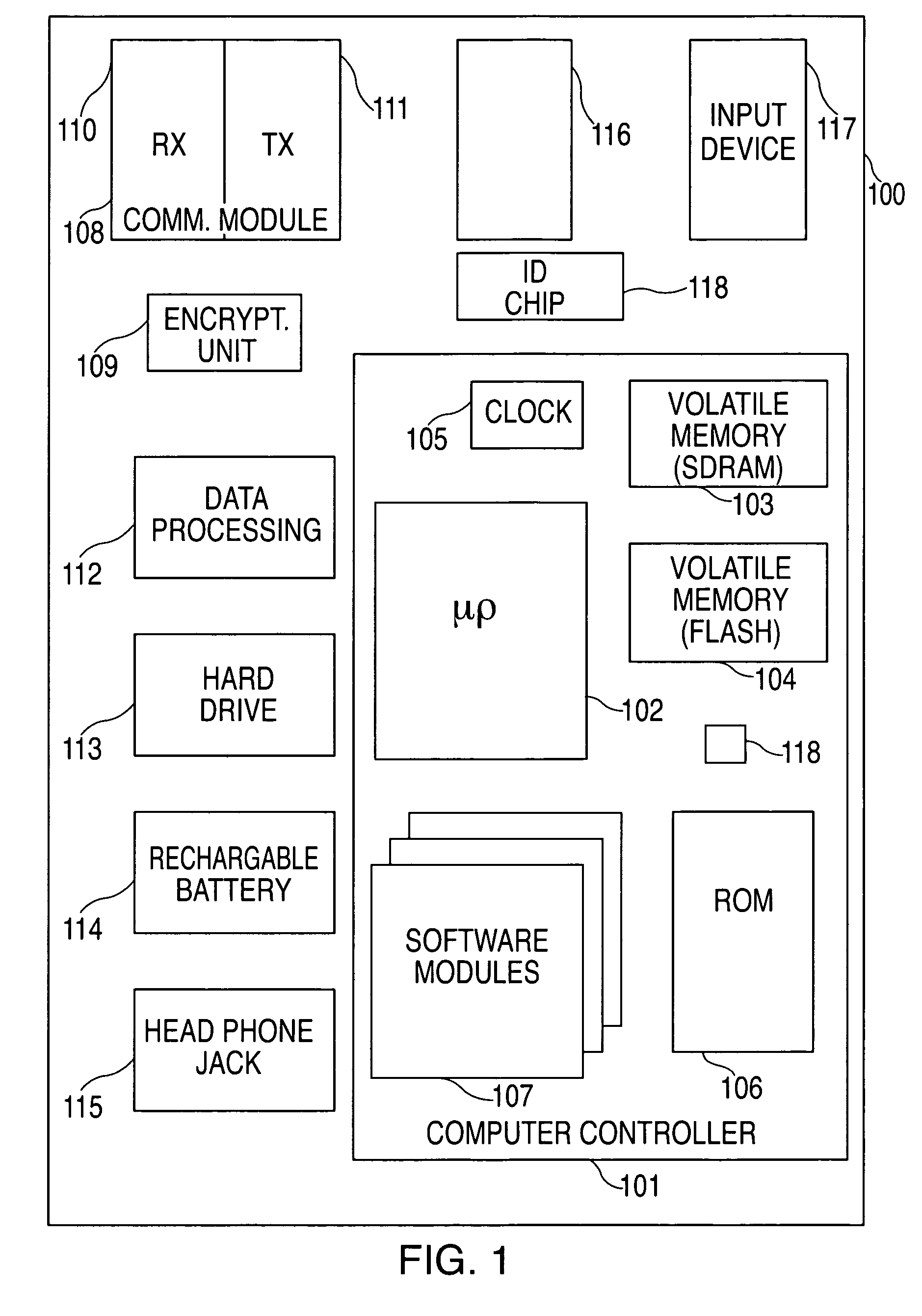
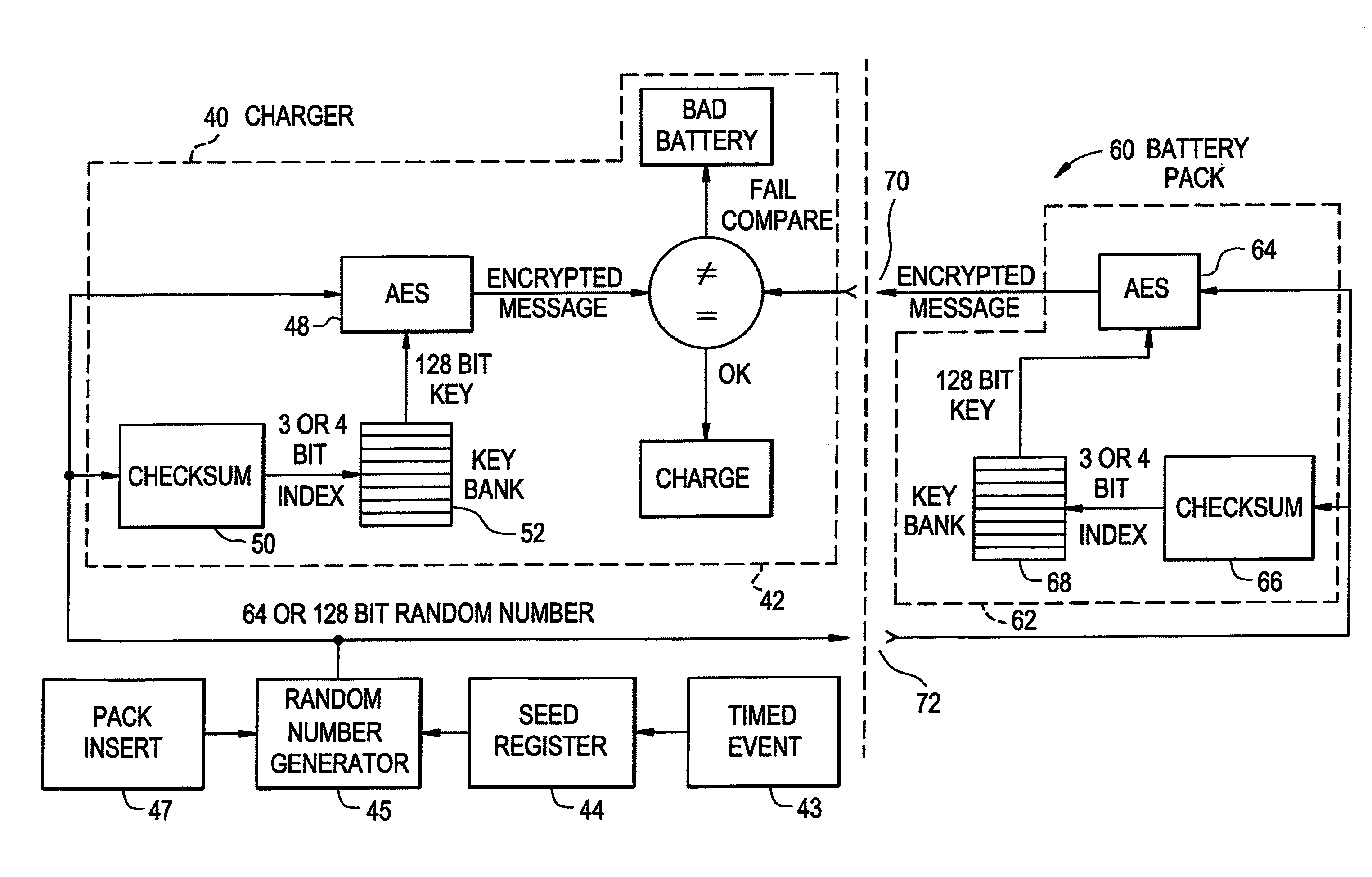
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
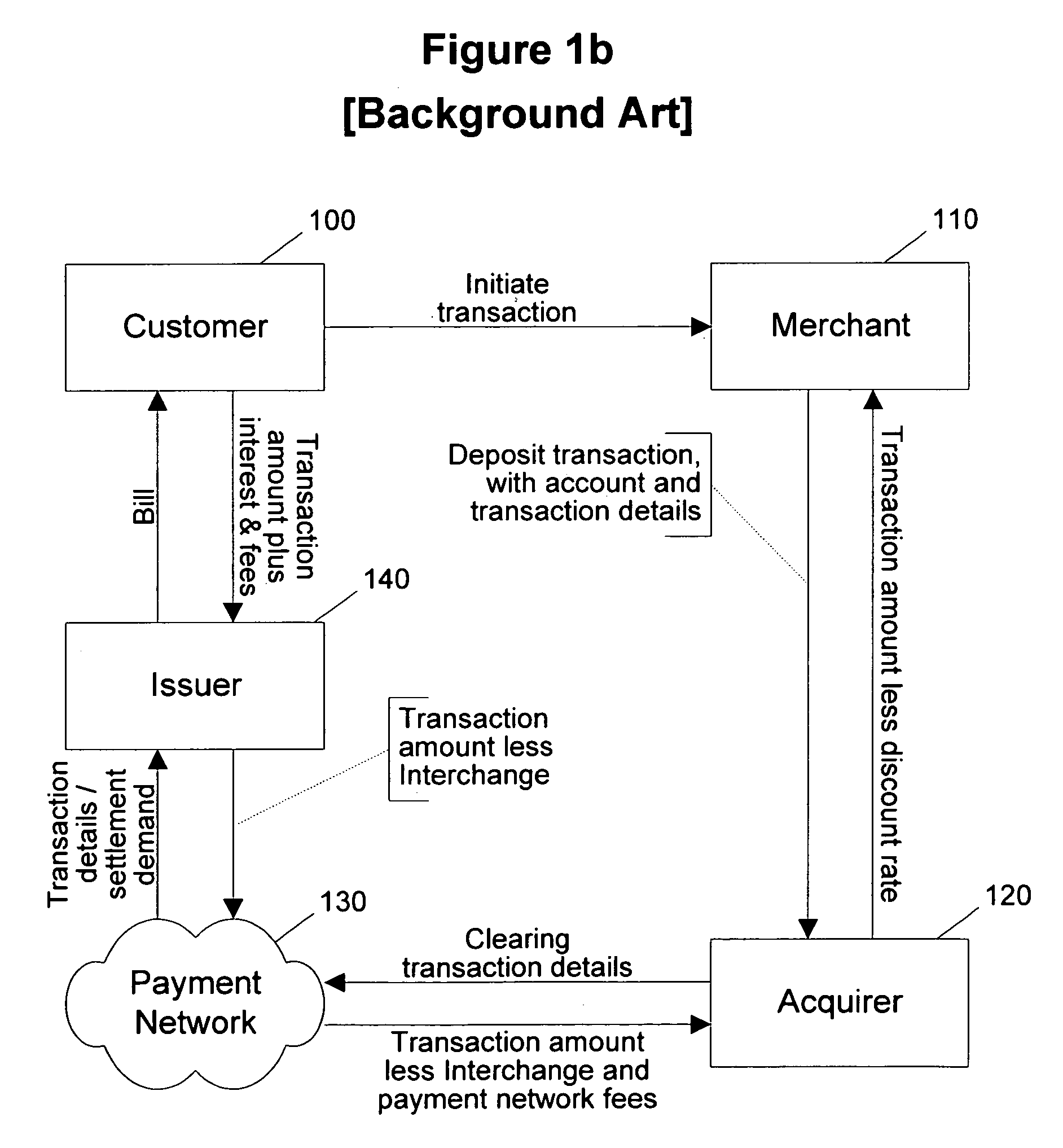
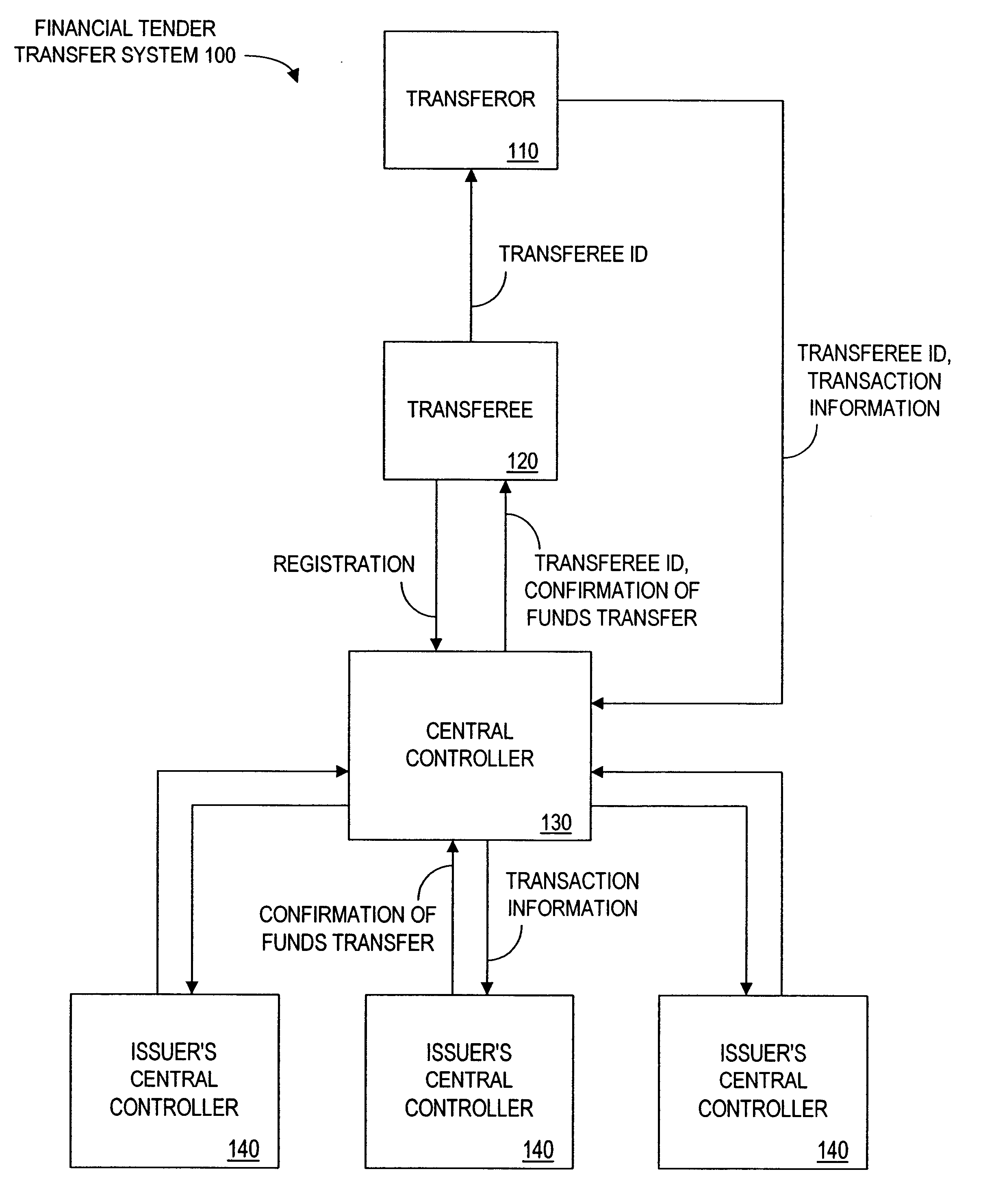
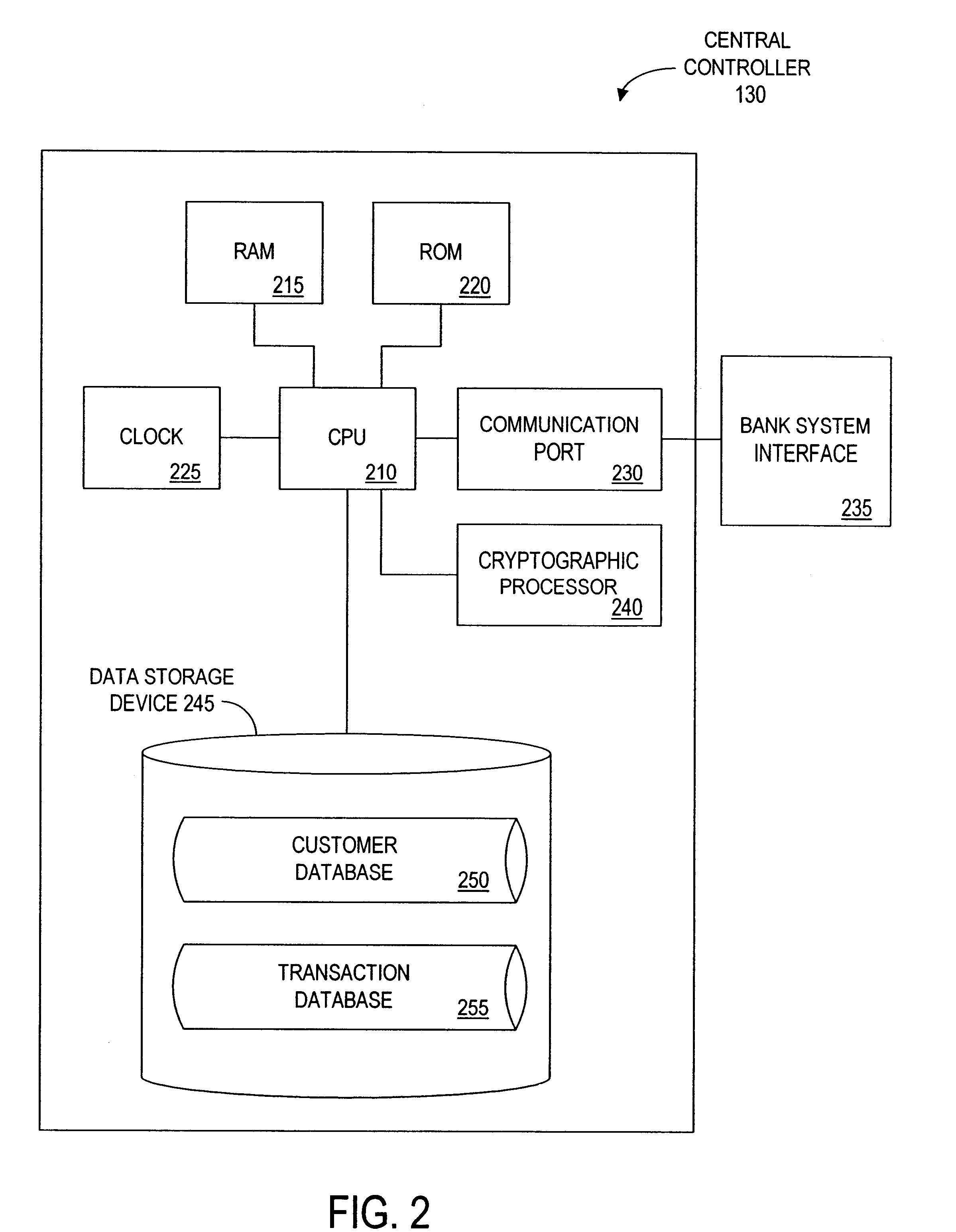
Method and apparatus for funds and credit line transfers
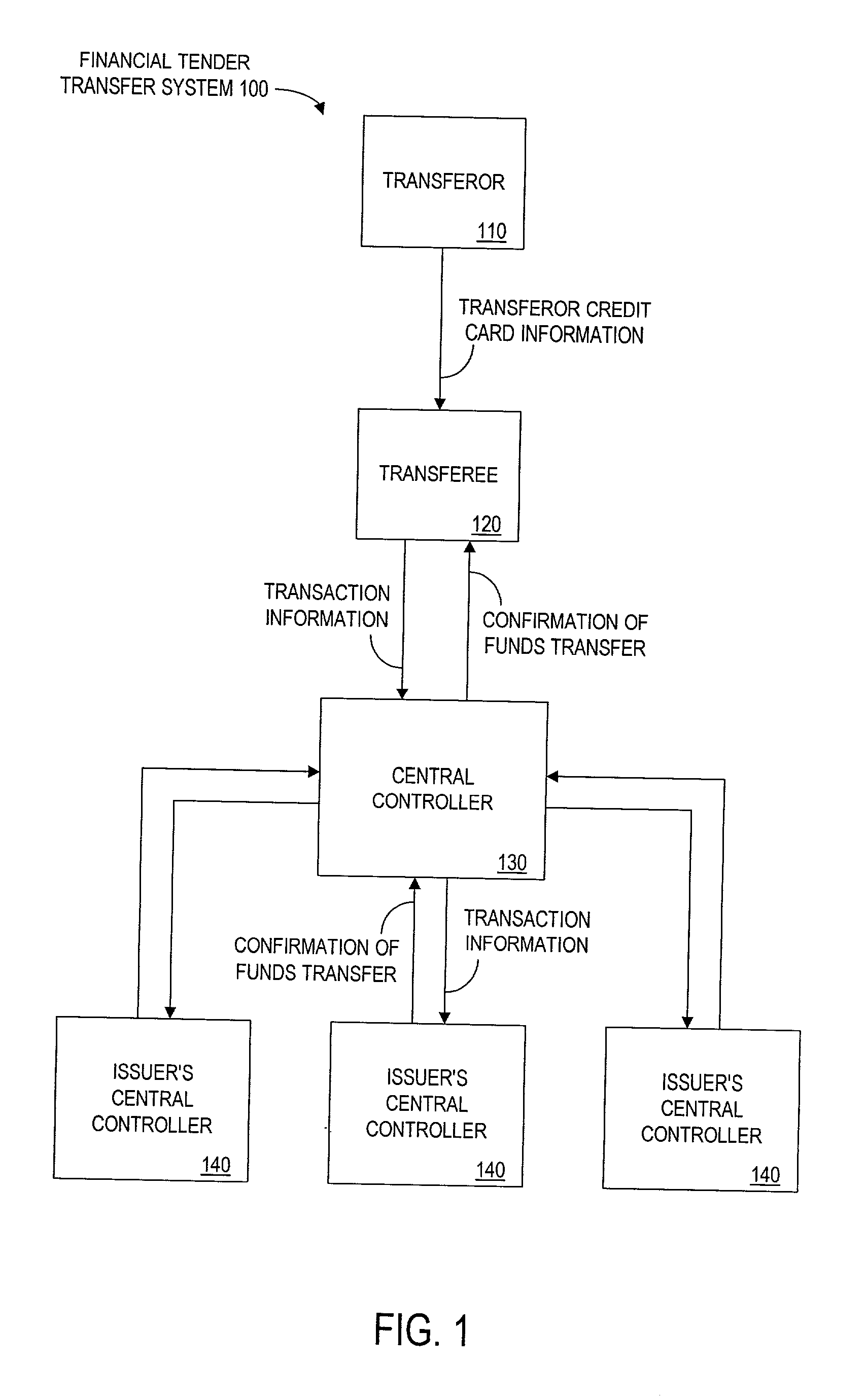
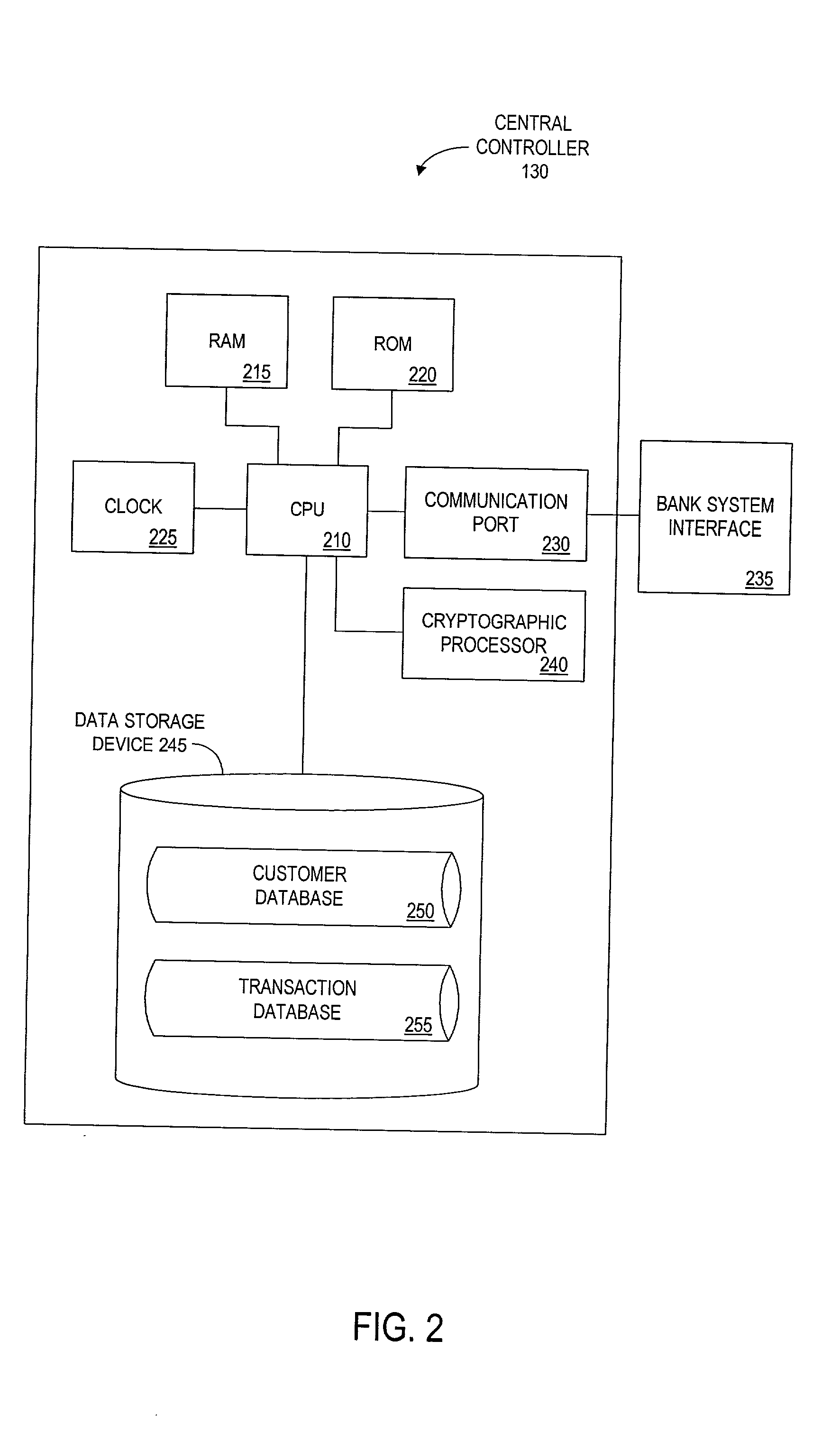
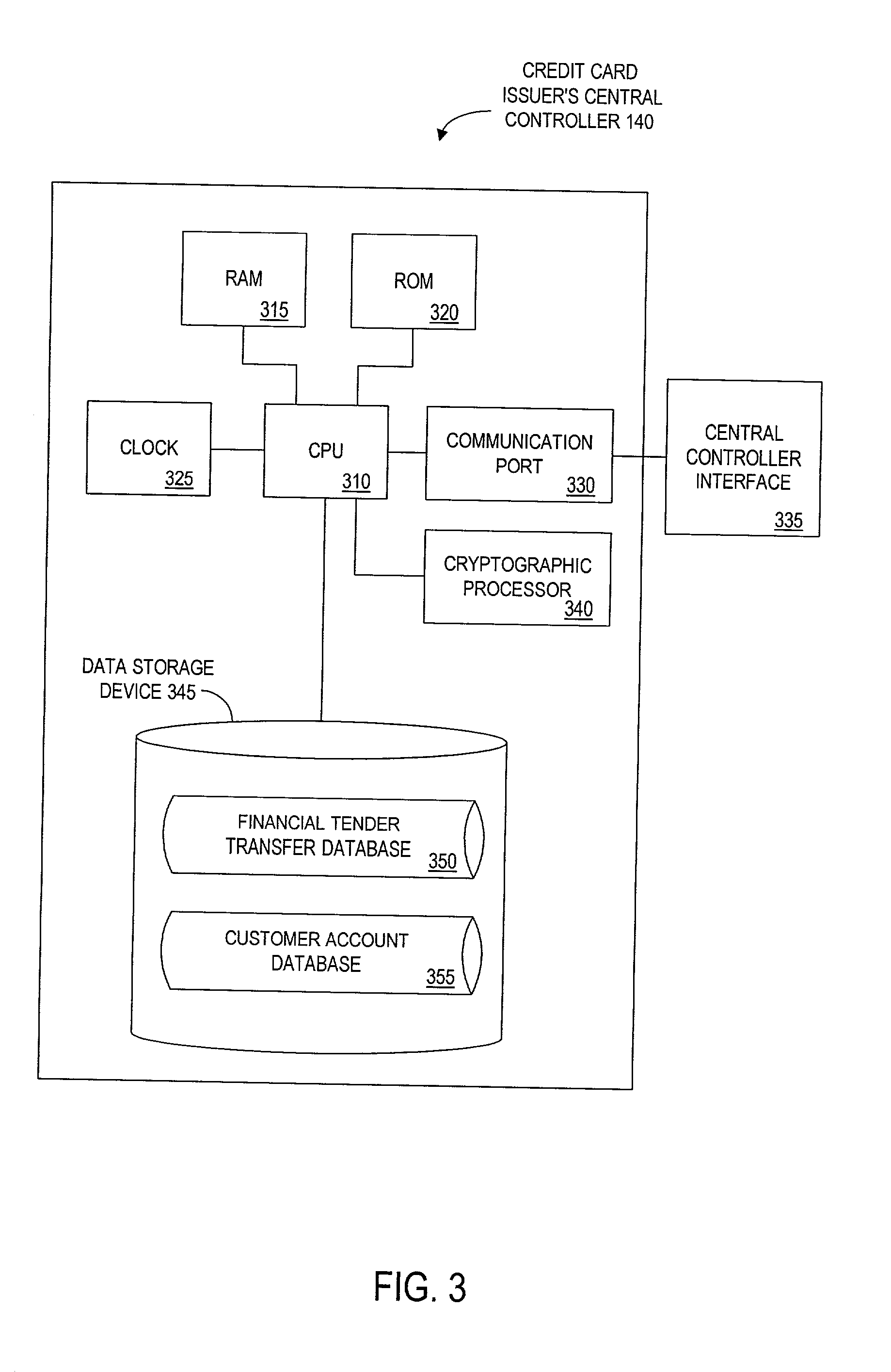
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
Mobile Person-to-Person Payment System
InactiveUS20070255653A1Easy to useFraudulent transaction is minimizedFinancePayment architectureBarcodeFinancial transaction
A mobile payment platform and service provides a fast, easy way to make payments by users of mobile devices. The platform also interfaces with nonmobile channels and devices such as e-mail, instant messenger, and Web. In an implementation, funds are accessed from an account holder's mobile device such as a mobile phone or a personal digital assistant to make or receive payments. Financial transactions can be conducted on a person-to-person (P2P) or person-to-merchant (P2M) basis where each party is identified by a unique indicator such as a telephone number or bar code. Transactions can be requested through any number of means including SMS messaging, Web, e-mail, instant messenger, a mobile client application, an instant messaging plug-in application or “widget.” The mobile client application, resident on the mobile device, simplifies access and performing financial transactions in a fast, secure manner.
Owner:OBOPAY MOBILE TECH INDIA PTE LTD
System and method for an automated benefit recognition, acquisition, value exchange, and transaction settlement system using multivariable linear and nonlinear modeling
A system and process that provides an on-line, interactive, and fully integrated benefit-driven value exchange and settlement program that monitors, evaluates, and manages economic and personal benefits and executes functions to produce and acquire the maximum or preferred benefit items for users by guiding and automating appropriate payment and settlement actions. The present invention finds useful patterns in data; produces conclusions based on rules and experience; responds to environmental changes with or without human intervention; and, may evolve through selecting the best results from random mutations all of which are intended to maximise user value.
Owner:IANNACCI GREGORY FX
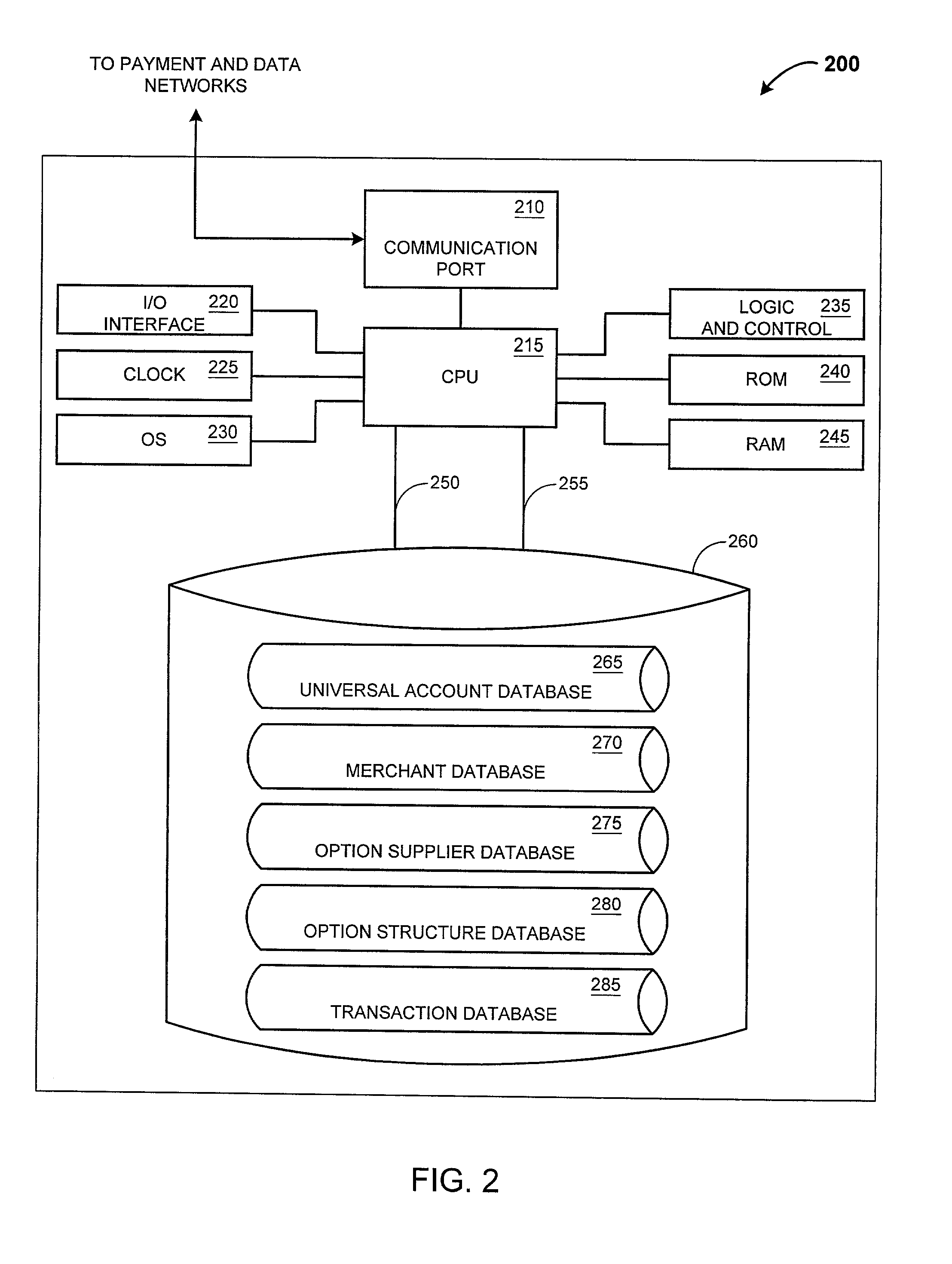
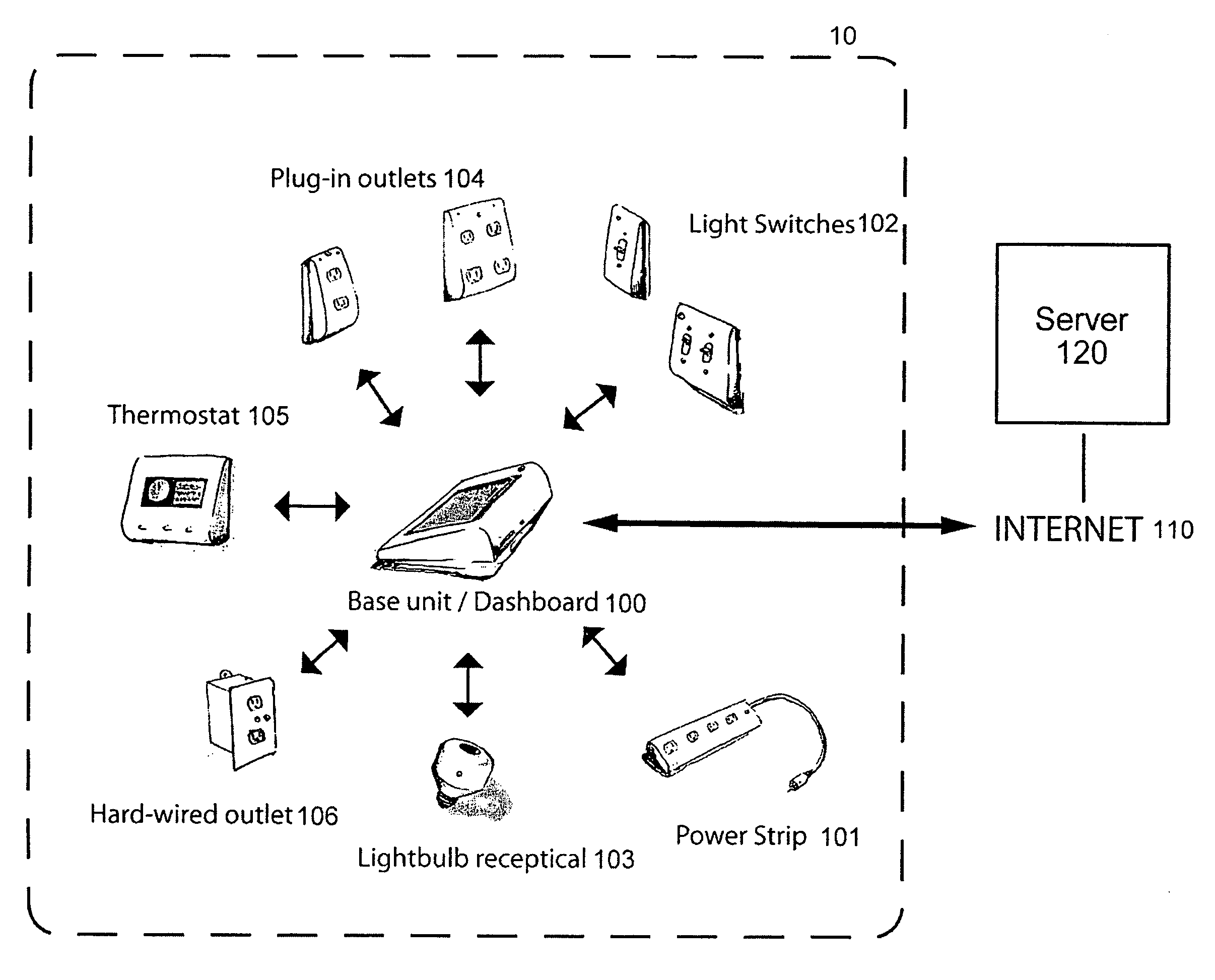
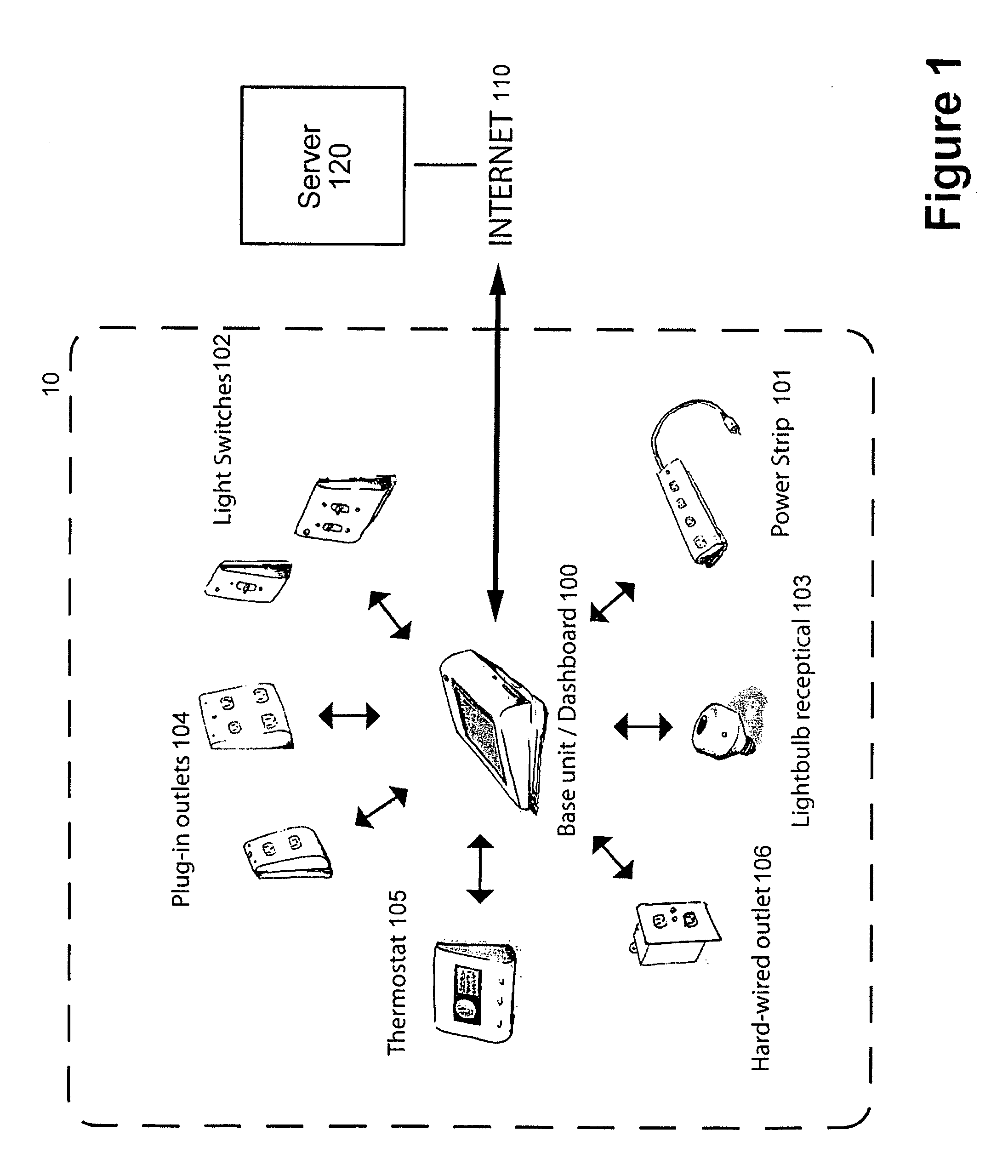
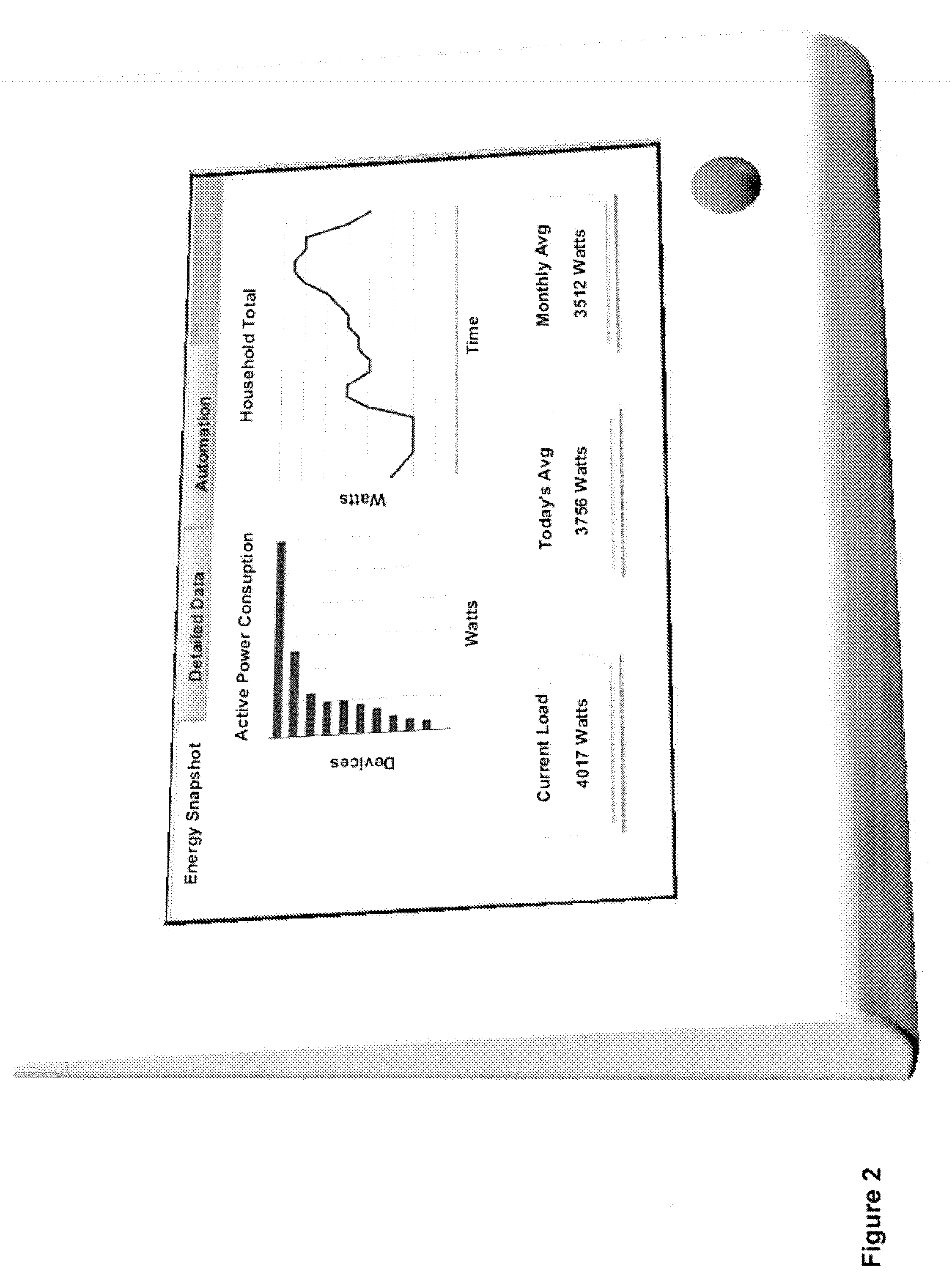
System and method for home energy monitor and control
ActiveUS20090195349A1Increase powerEfficient managementLevel controlPayment architectureCommunity basedMonitoring system
The invention generally concerns systems and methods for monitoring and controlling the power consumption of a power-consuming device. The system and method may connect to a power source and a power-consuming device, connecting the power-consuming device to the power source. The power usage of the power-consuming device may then be measured and monitored. This monitoring data may then be stored and optionally sent to a controlling device on a data network. The location of the power-consuming device may also be determined, recorded, and sent to a controlling device. The system may also control the power usage of the power-consuming device. In some cases, a remote server may connect multiple energy monitoring systems in order to gain additional efficiencies and foster a community-based social network.
Owner:ENERGYHUB
RFID reader with multiple interfaces
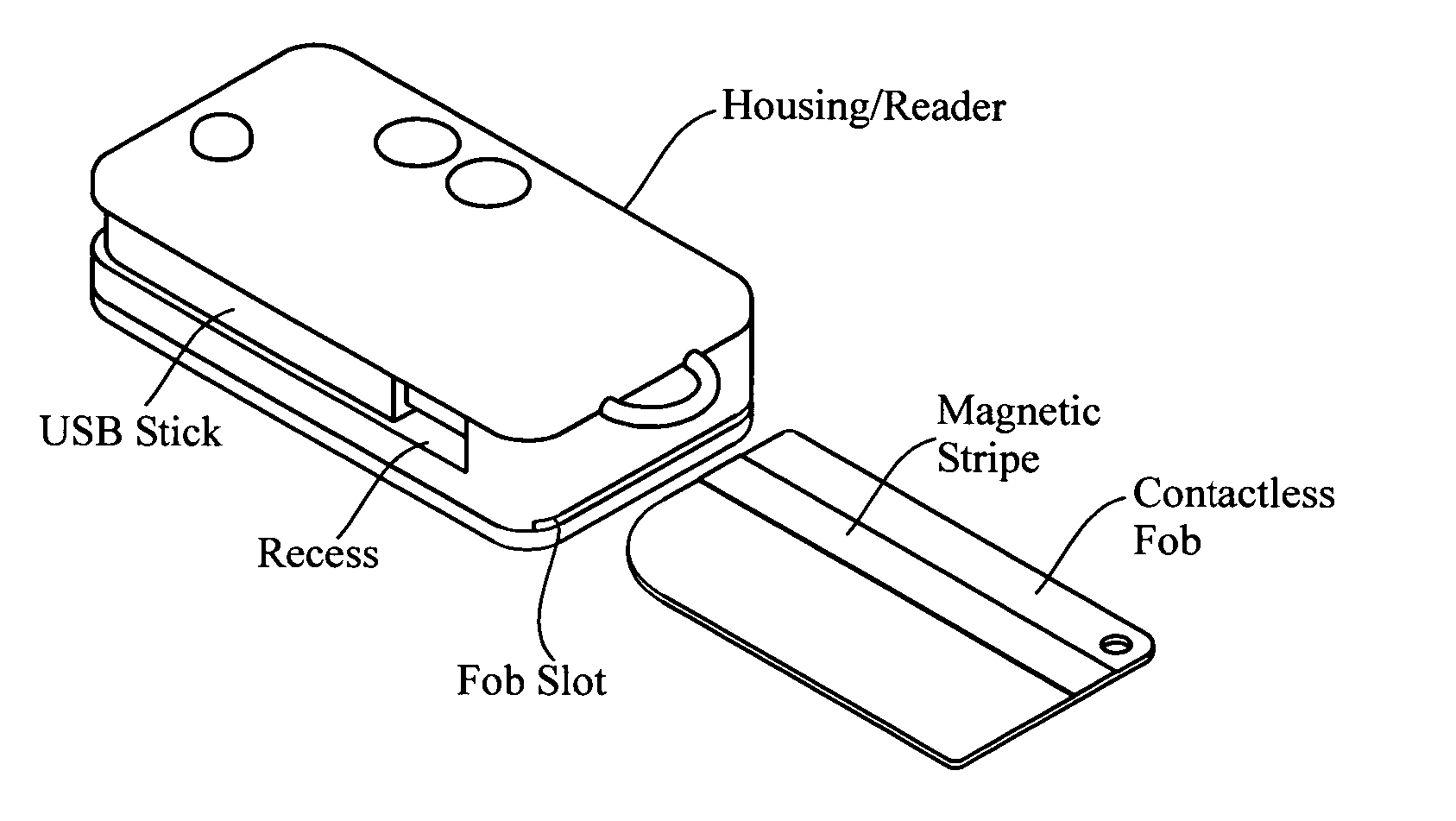
InactiveUS20060219776A1Anti-theft devicesSensing by galvanic contactsPersonalizationContactless smart card
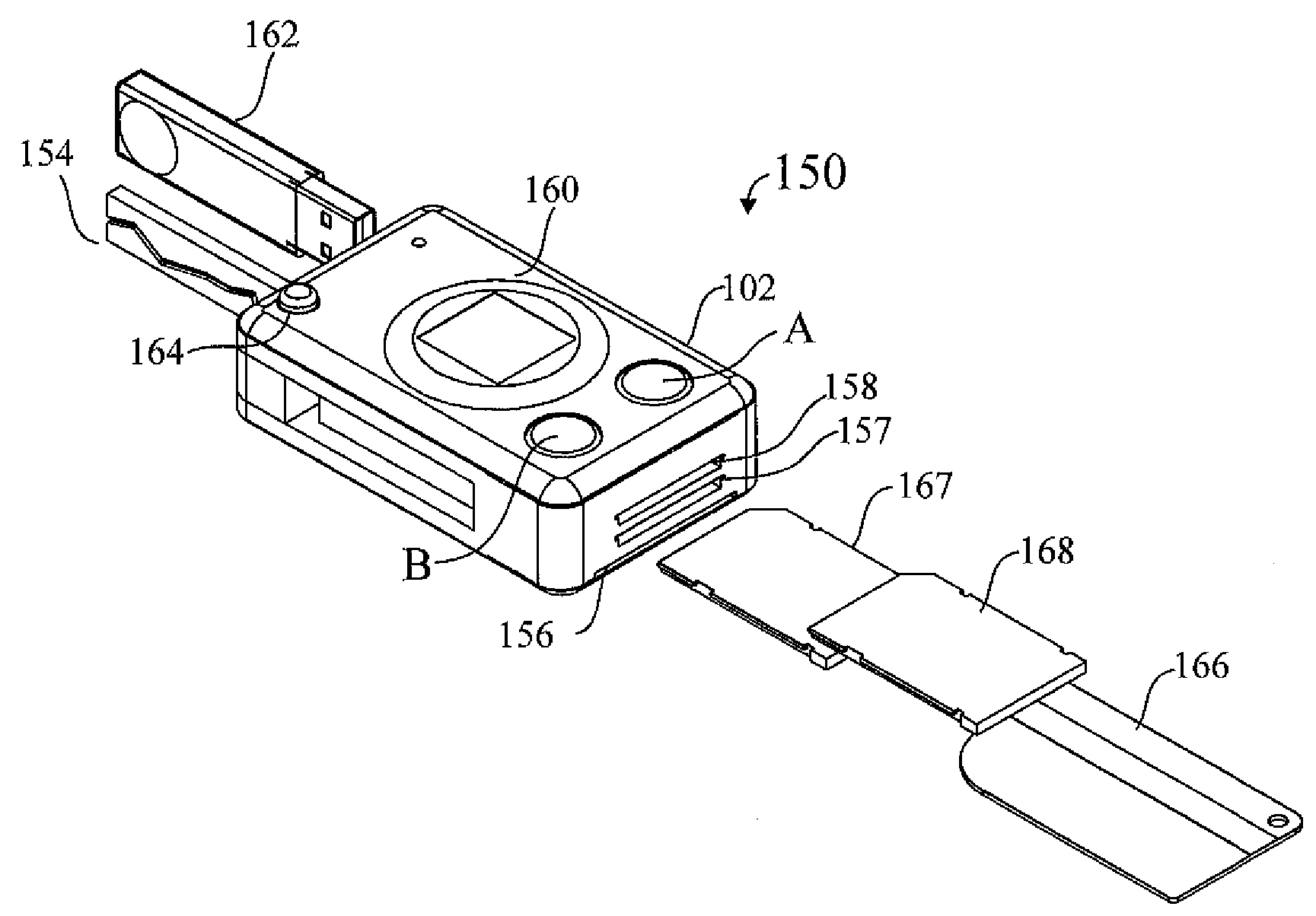
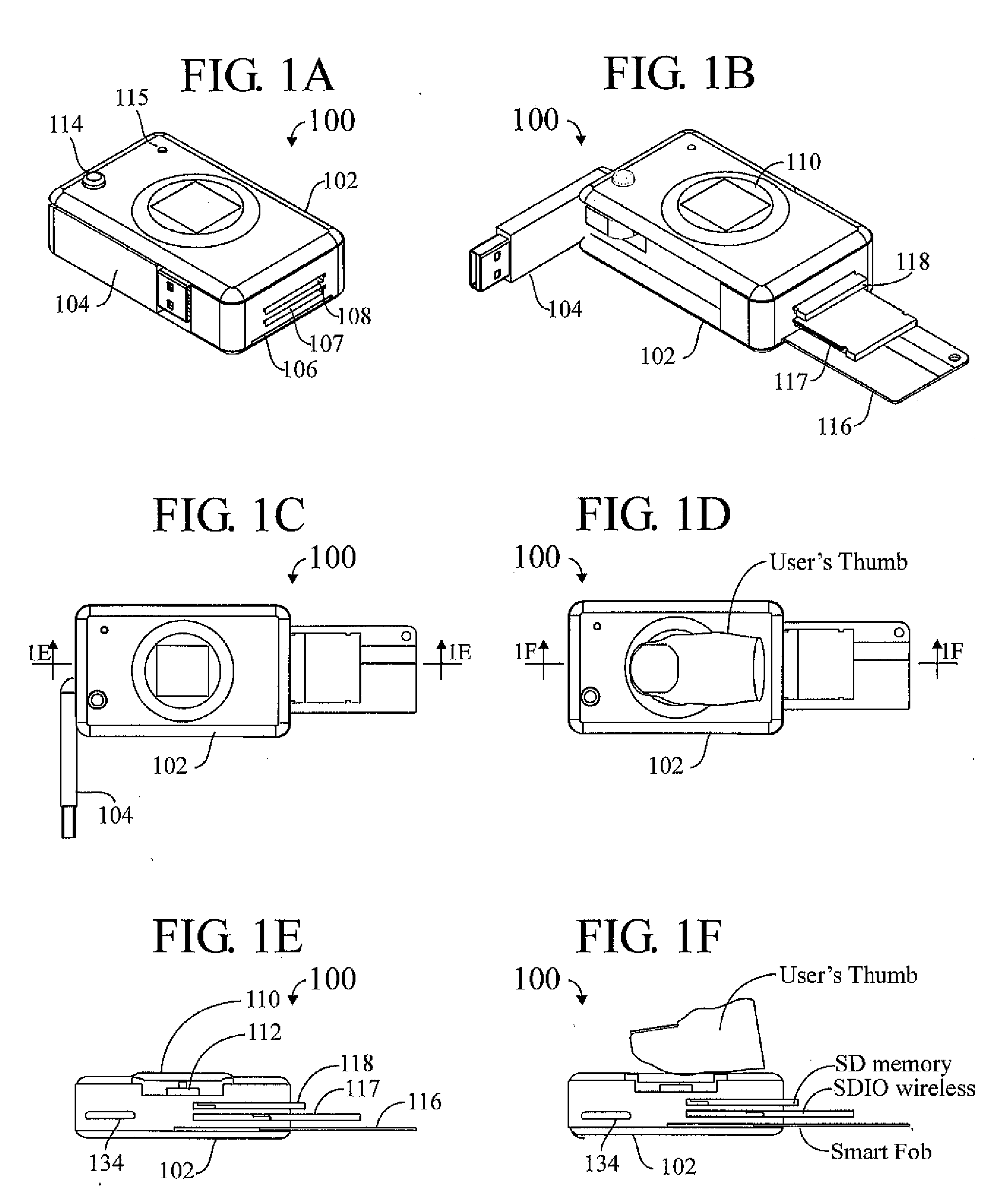
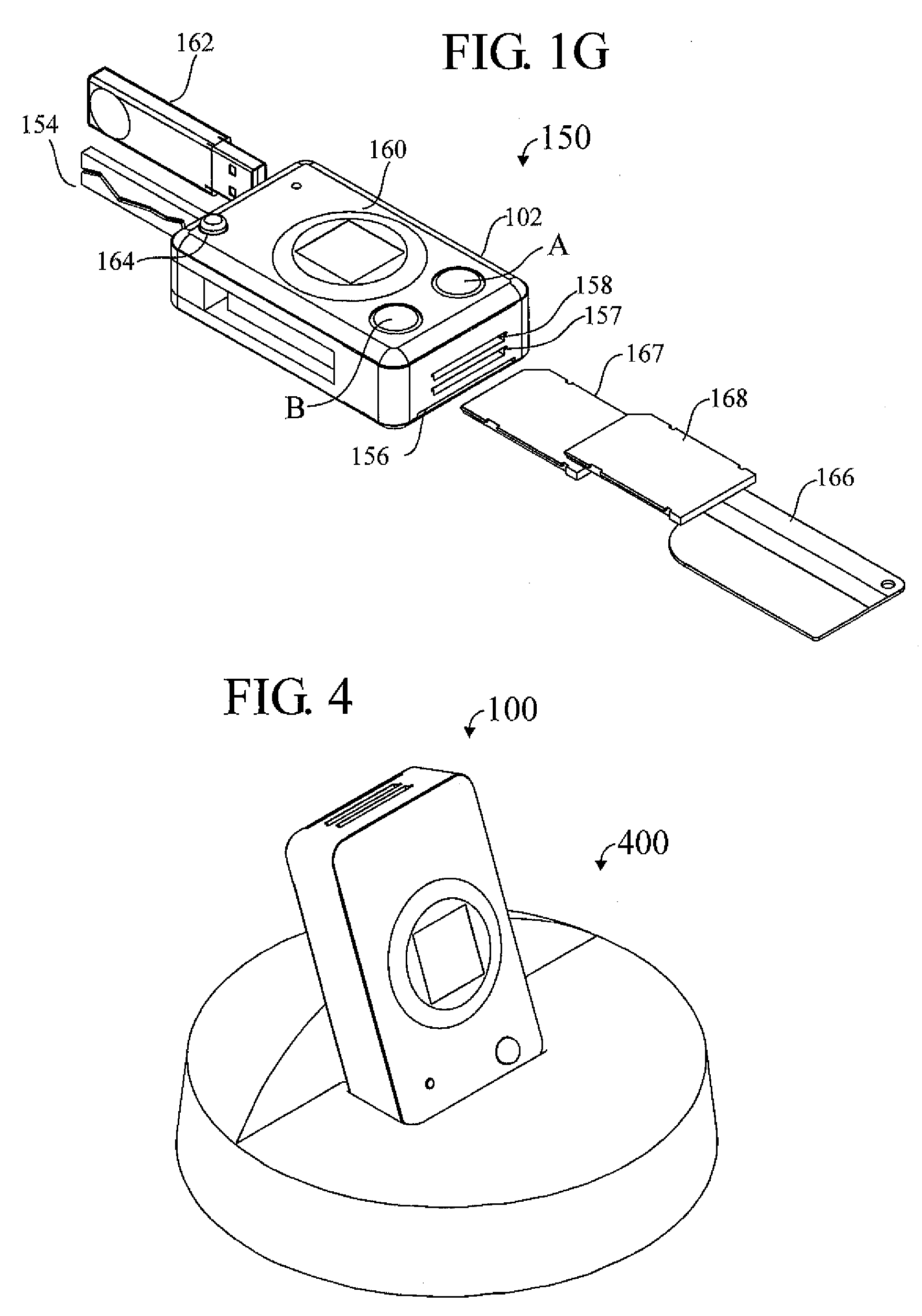
A pocket-size RFID reader apparatus having a contactless interface and a slot for insertion of a contactless smart card fob, and having a biometric sensor, thereby providing two levels of personalization. The apparatus may have a wireless interface; and a slot for insertion of a wireless SD I / O device. The apparatus may have a slot for insertion of an external memory device. The apparatus may have a mechanical connection (contact) interface. The apparatus may also have an RF interface for reading an electronic immobilizer within the apparatus.
Owner:DPD PATENT TRUST
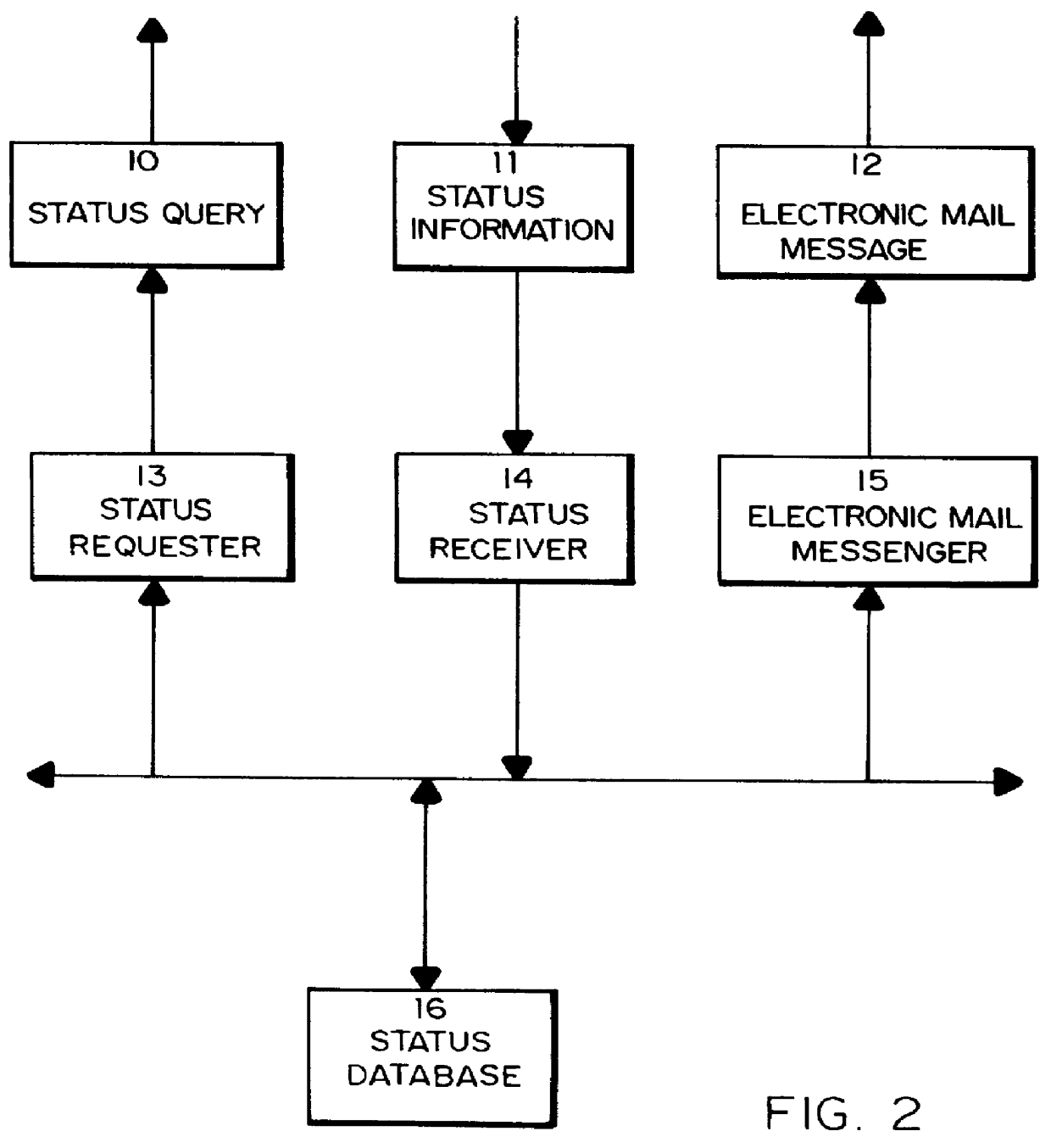
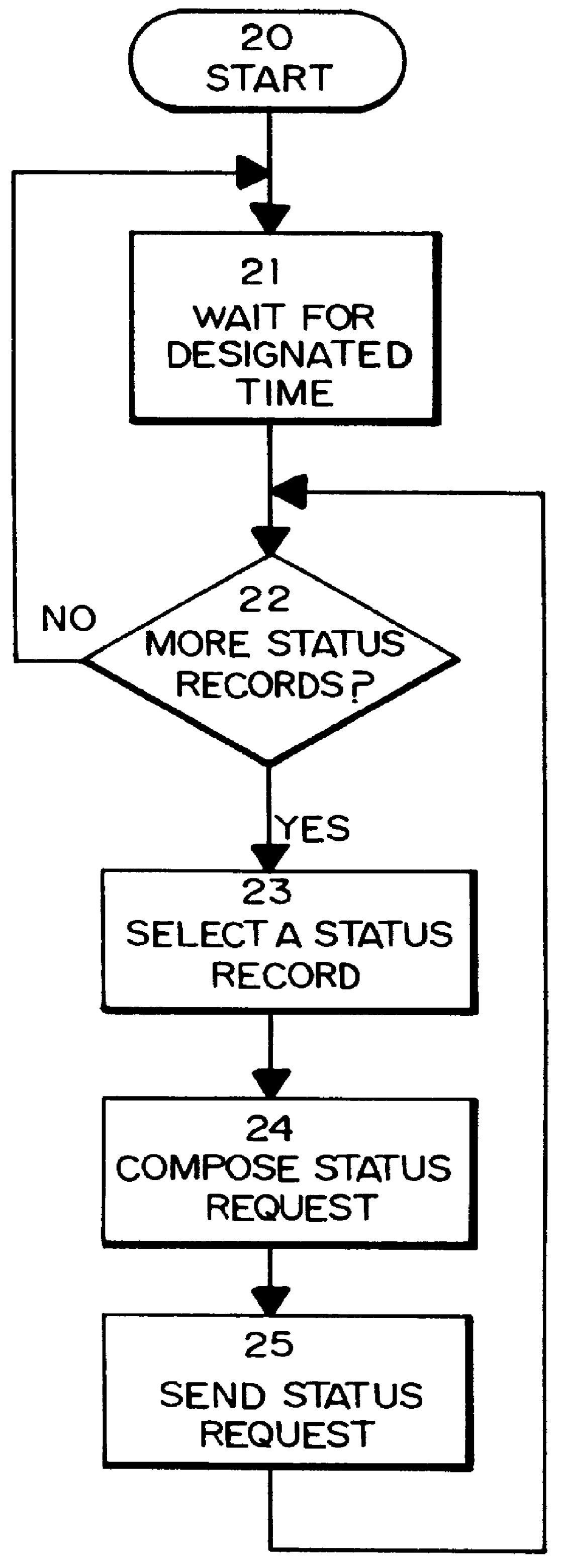
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
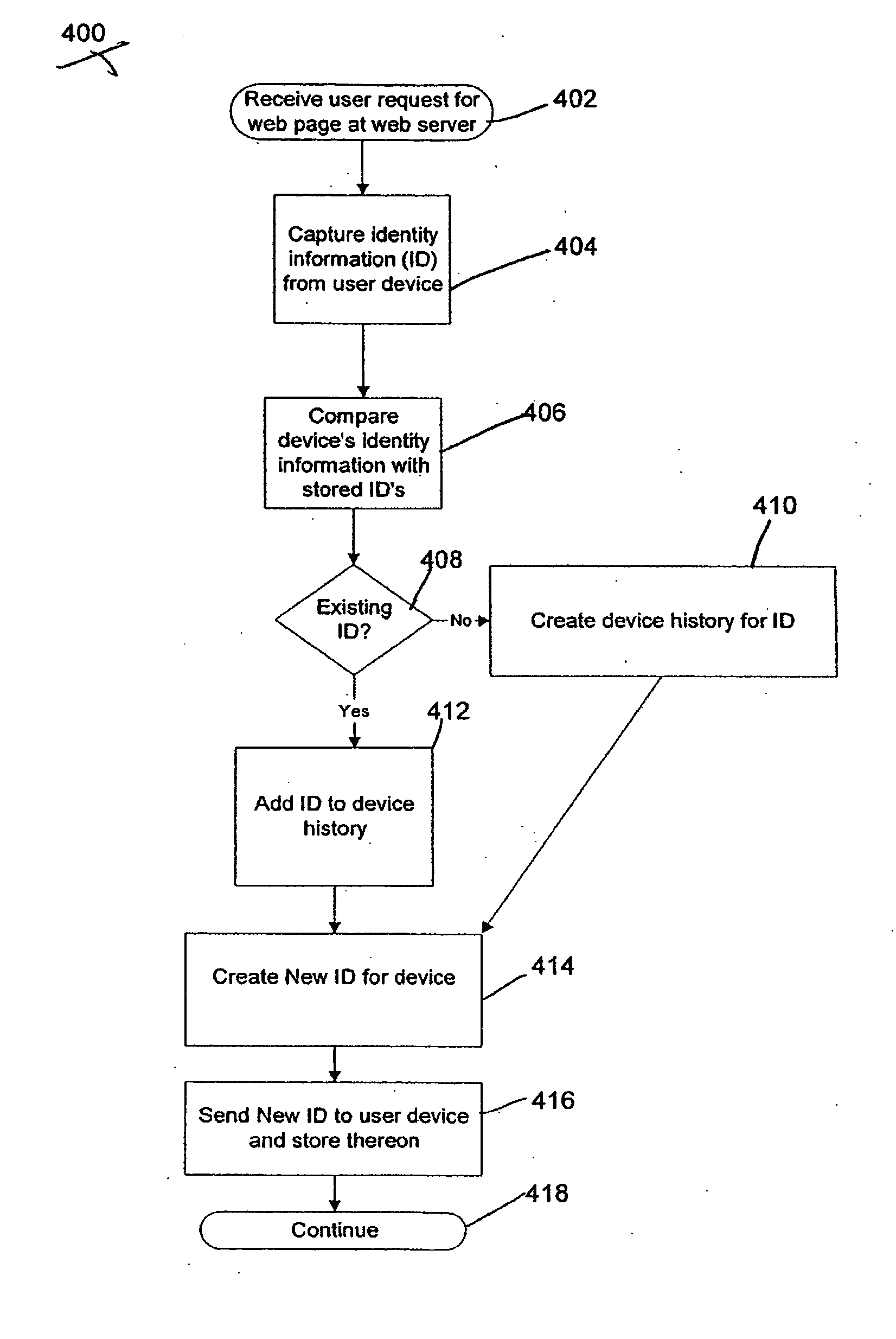
System and method for fraud monitoring, detection, and tiered user authentication
The present invention provides systems and methods for authenticating access requests from user devices by presenting one of a plurality of graphical user interfaces selected depending on a perceived risk of fraud associated with the devices. User devices are identified with fingerprinting information, and their associated risks of fraud are determined from past experience with the device or with similar devices and from third party information. In preferred embodiments, different graphical user interfaces are presented based on both fraud risk and, in the case of a known user, usability. In preferred embodiments, this invention is implemented as a number of communicating modules that identify user devices, assess their risk of fraud, present selected user interfaces, and maintain databases of fraud experiences. This invention also includes systems providing these authentication services.
Owner:ORACLE INT CORP
Wireless media system and player and method of operation
ActiveUS20060258289A1Easy to useMultimedia data browsing/visualisationPayment architectureUltra-widebandSecure communication
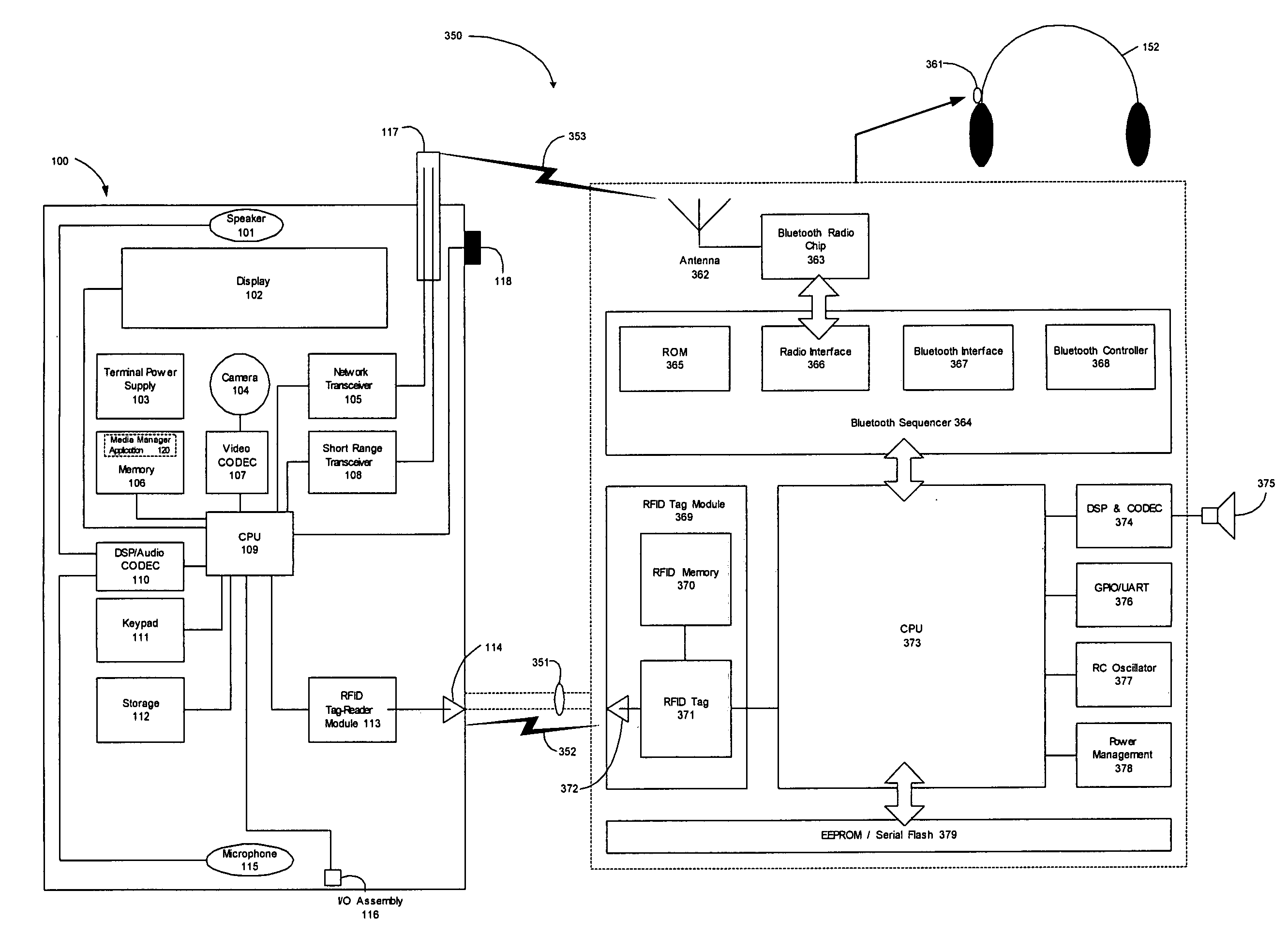
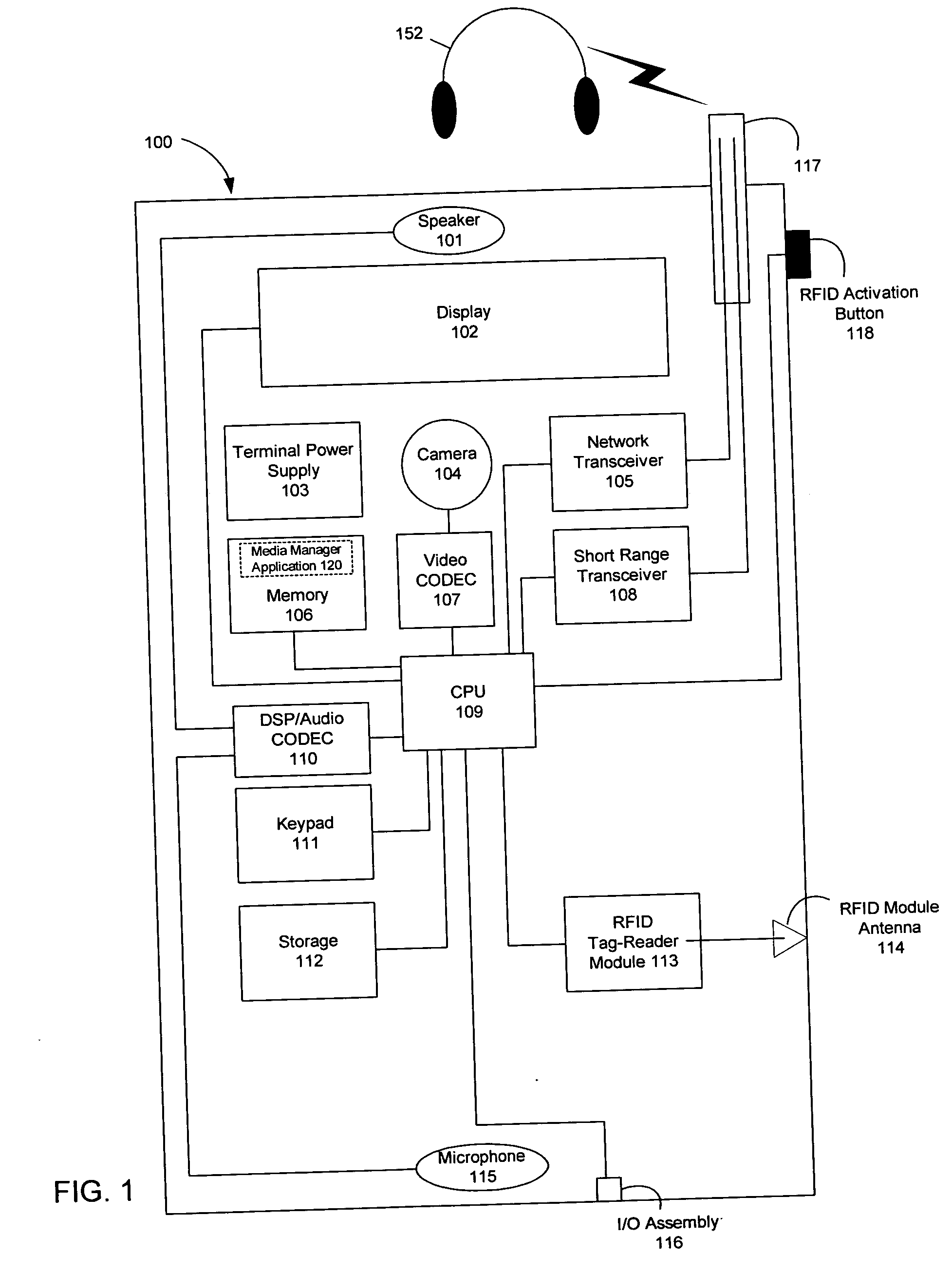
A wireless media player and a related system and methodology are disclosed. One aspect of the wireless media player system pertains to a virtual connector system, apparatus, and method for the automatic establishment of wireless connectivity with other electronic devices. In one embodiment, the media player device employs the use of integrated Radio Frequency Identification (RFID) technology to exchange communication settings, media capability, and other parameters with an external device that also has integrated RFID technology. The automatic exchange of settings and other information via a proximity-based RFID data exchange allows a media player to quickly establish a secure communication link with another device via a commonly supported wireless protocol such as Ultra Wideband (UWB) or Bluetooth. Another aspect of the media player system pertains to a method of using the captured media capability of the connecting device to customize certain menu options and software parameters in the media player.
Owner:SYNDEFENSE
Game theoretic prioritization scheme for mobile ad hoc networks permitting hierarchal deference
Owner:HOFFBERG STEVEN M
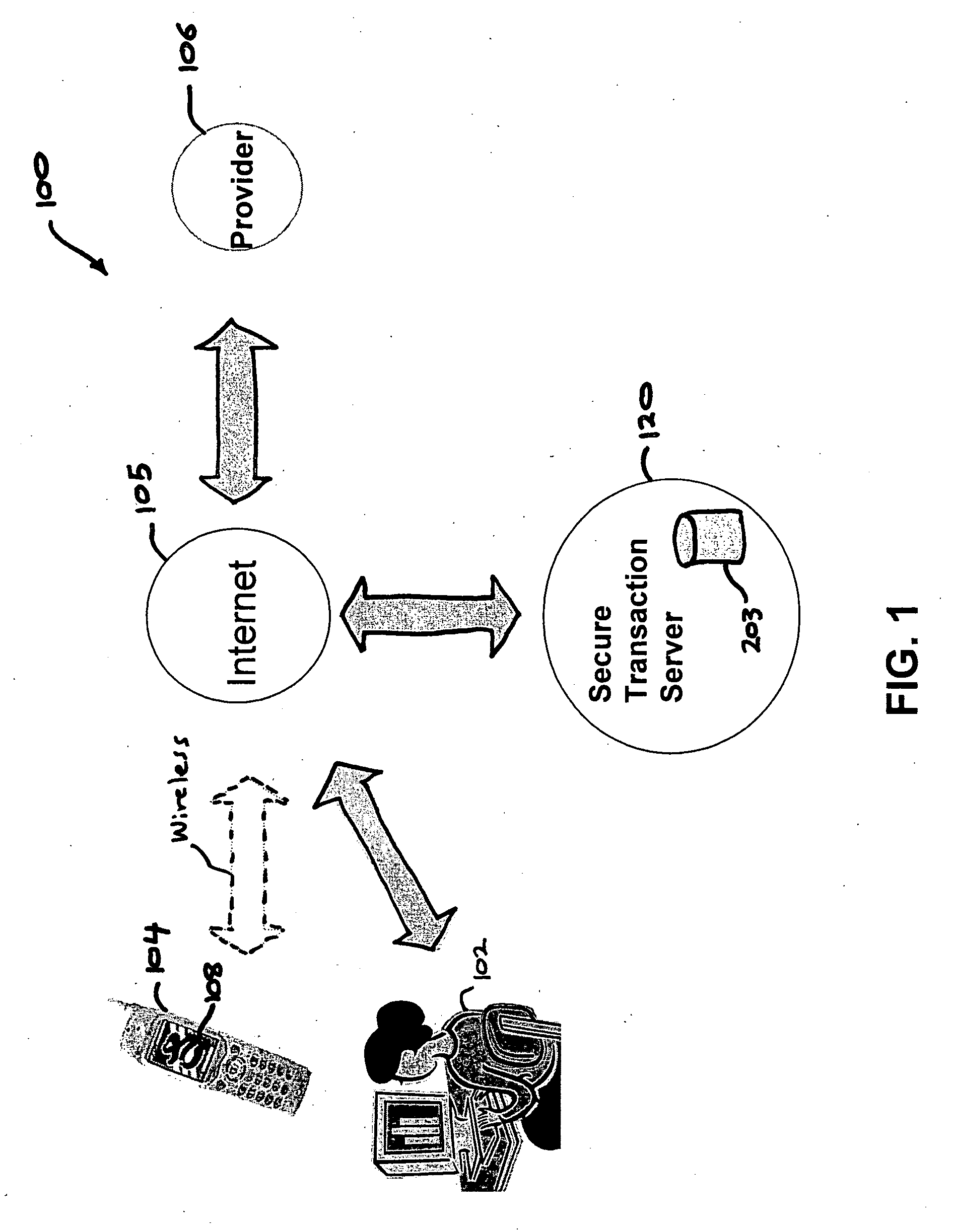
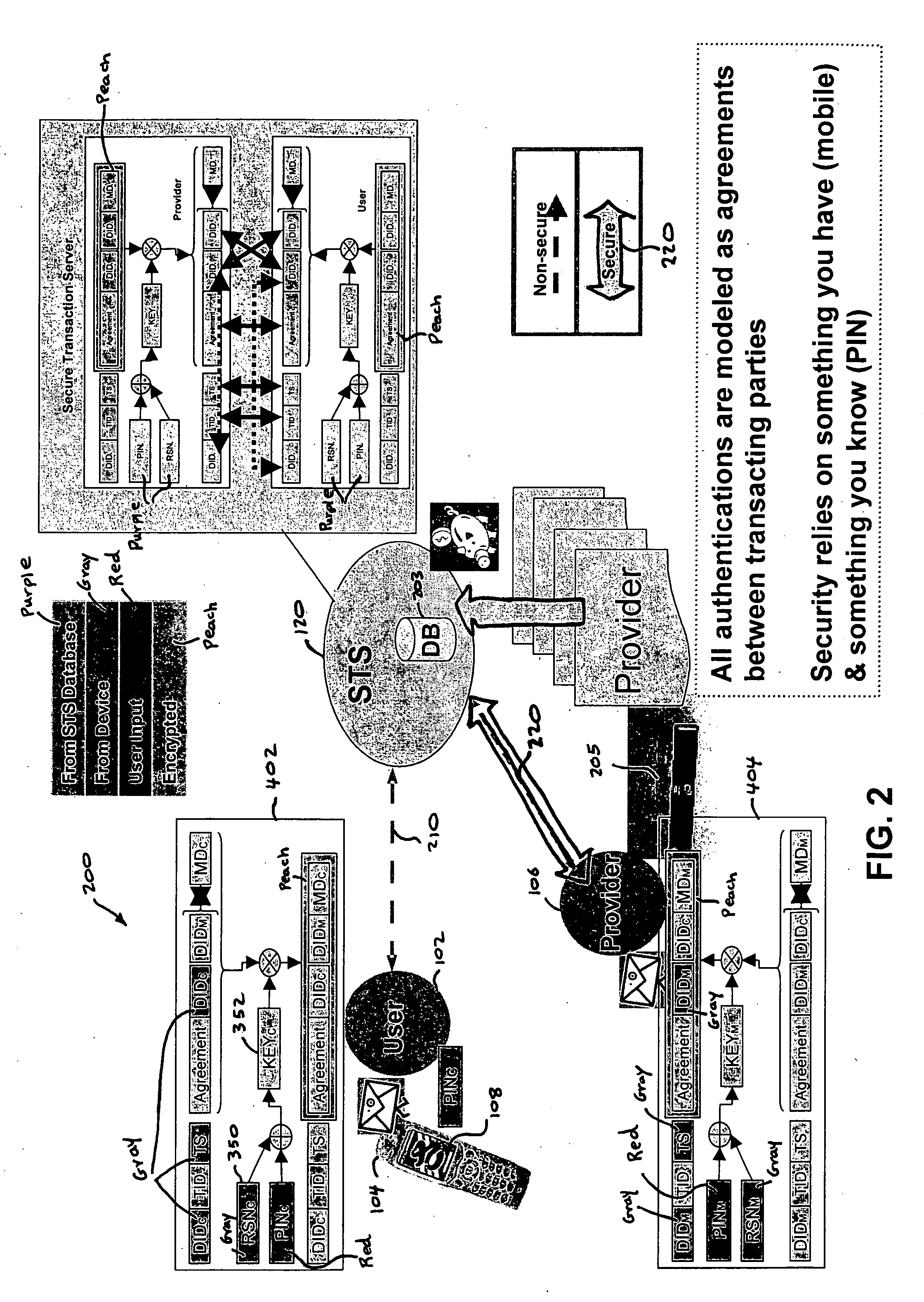
Authentication services using mobile device
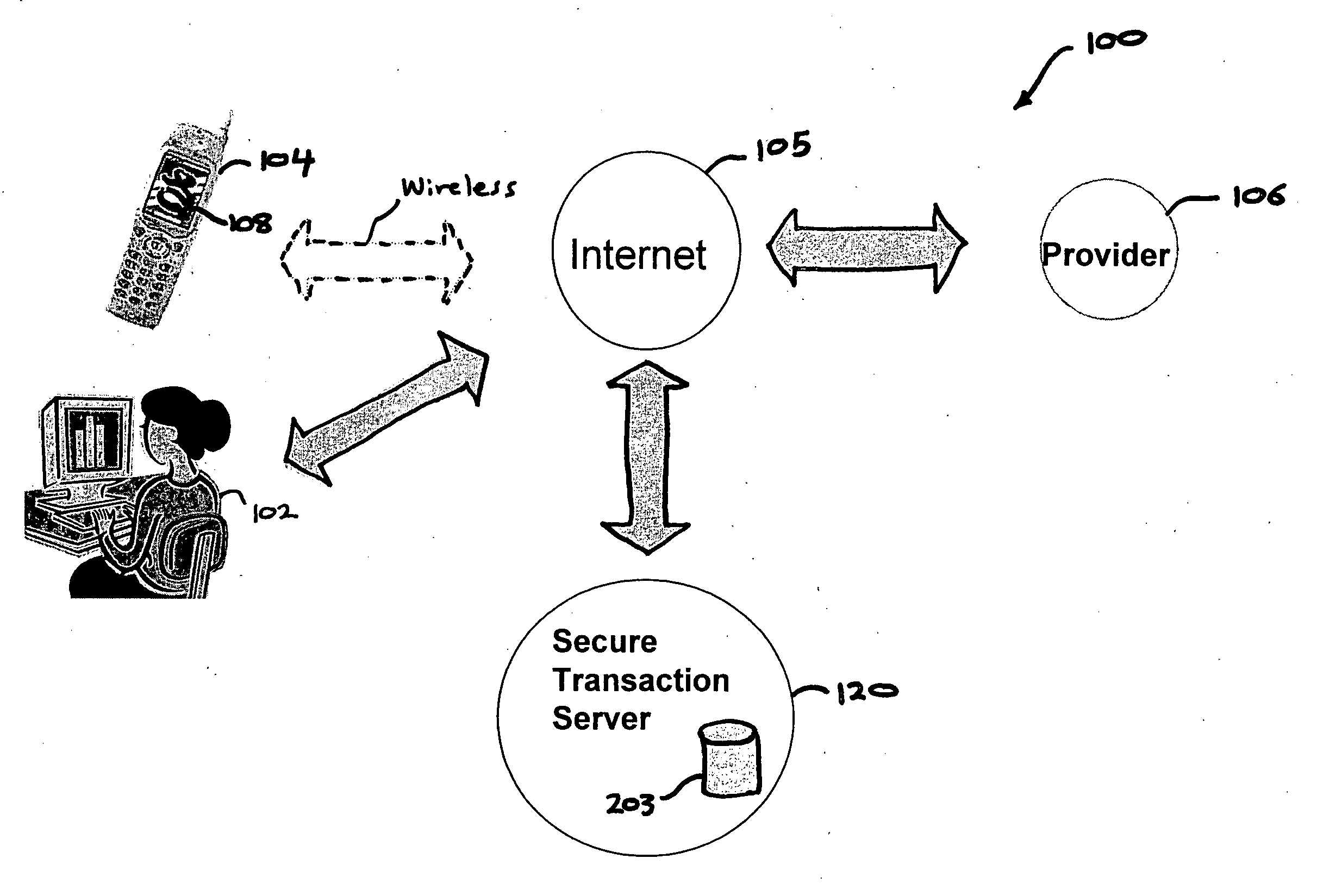
InactiveUS20060206709A1Payment architectureATM softwaresInternet Authentication ServiceMobile device
A method, and an apparatus performing the method, is provided by authenticating a mobile device communicably connectable to a wireless network by an authentication parameter from a secure transaction server (STS), as a mobile device authenticator; providing an STS correlation between a personal identification entry (PIE) and the mobile device authenticator; and inputting, by a user, the PIE and a provider action, to the mobile device authenticator to transmit a transformed secure user authenticable authorization request to the STS over the wireless network to authorize an action with a provider.
Owner:PCMS HOLDINGS INC
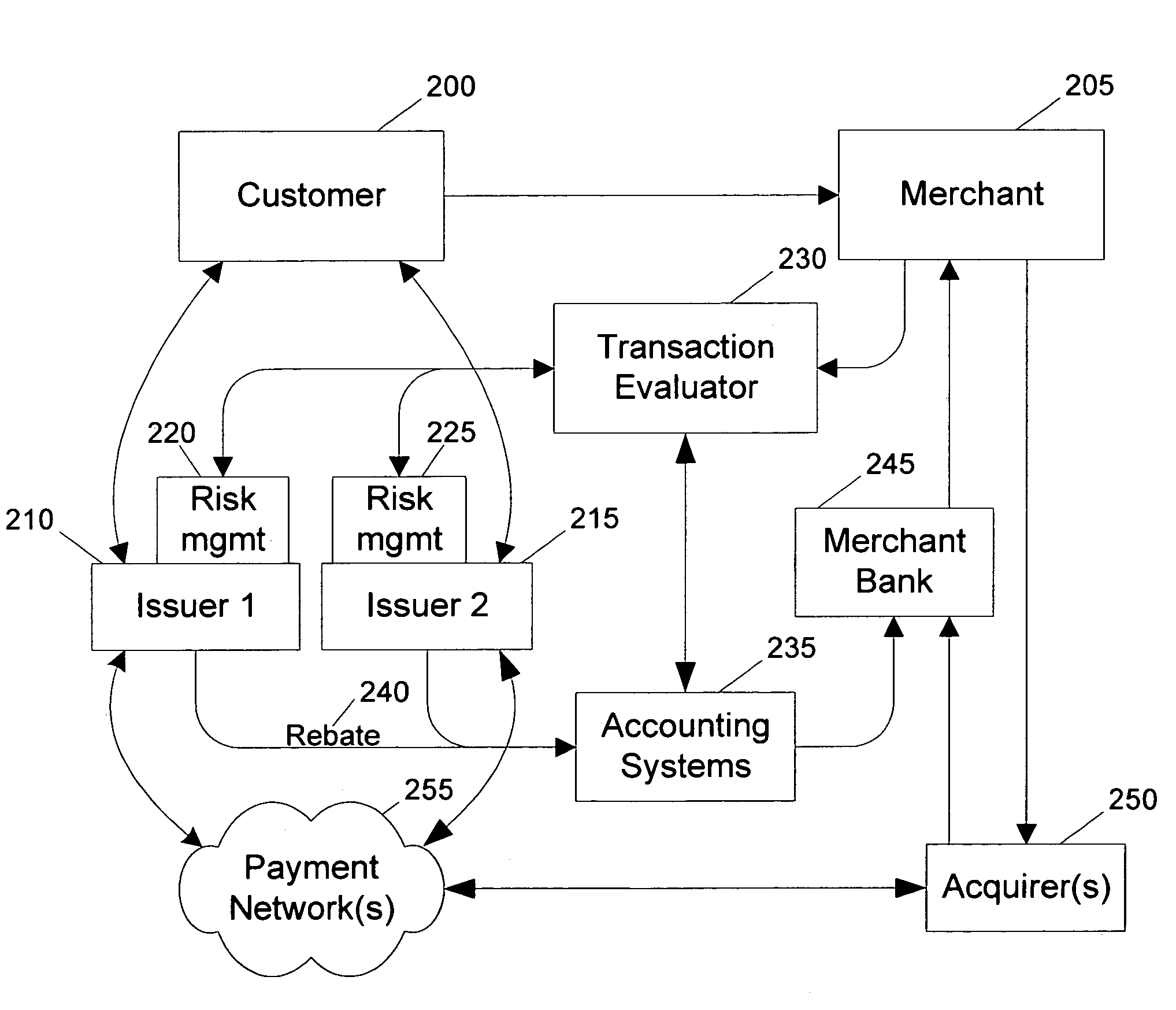
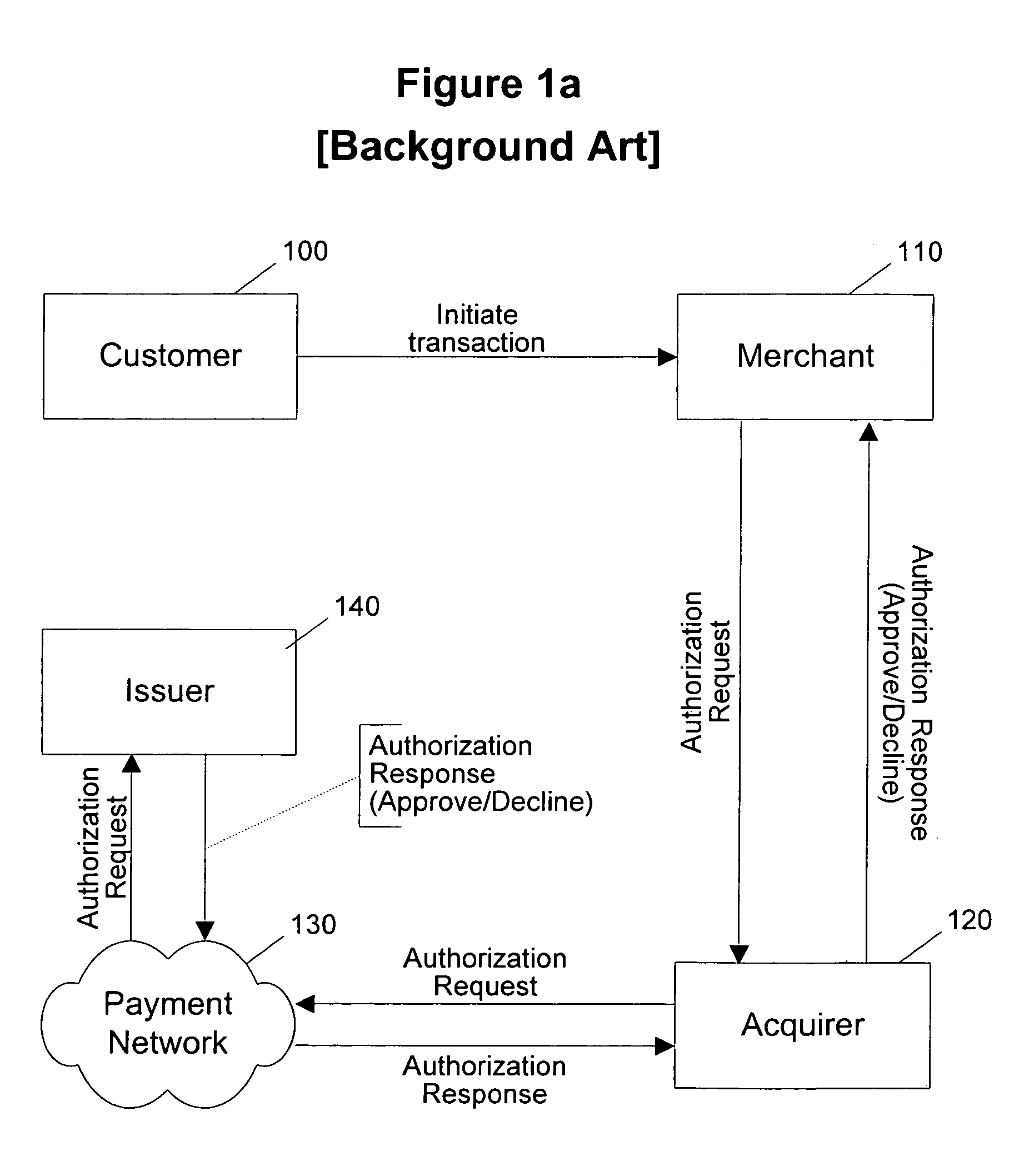
Routing methods and systems for increasing payment transaction volume and profitability
InactiveUS6999943B1More transactionEfficient routingFinancePayment architecturePayment transactionBenefit analysis
Customers often have access to multiple payment methods for any given transaction. In one embodiment of the invention, a merchant obtains information regarding multiple payment methods from a customer, and sends said information to a transaction evaluator. Via computer networks, the transaction evaluator sends information about the transaction to the issuers of one or more of the payment methods. The issuers perform a cost / benefit analysis of the transactions and respond with a description of the terms under which they are willing to process the transaction. Based on the issuer response, the transaction evaluator selects one of the payment methods. By enabling participating issuers to select favorable transactions and avoid unprofitable ones, the invention can thus improve issuer profitability by directing profitable transactions to participating issuers while directing unprofitable transactions away from participating issuers or to alternate transaction methods that are more profitable or less costly.
Owner:DOUBLECREDIT CORP
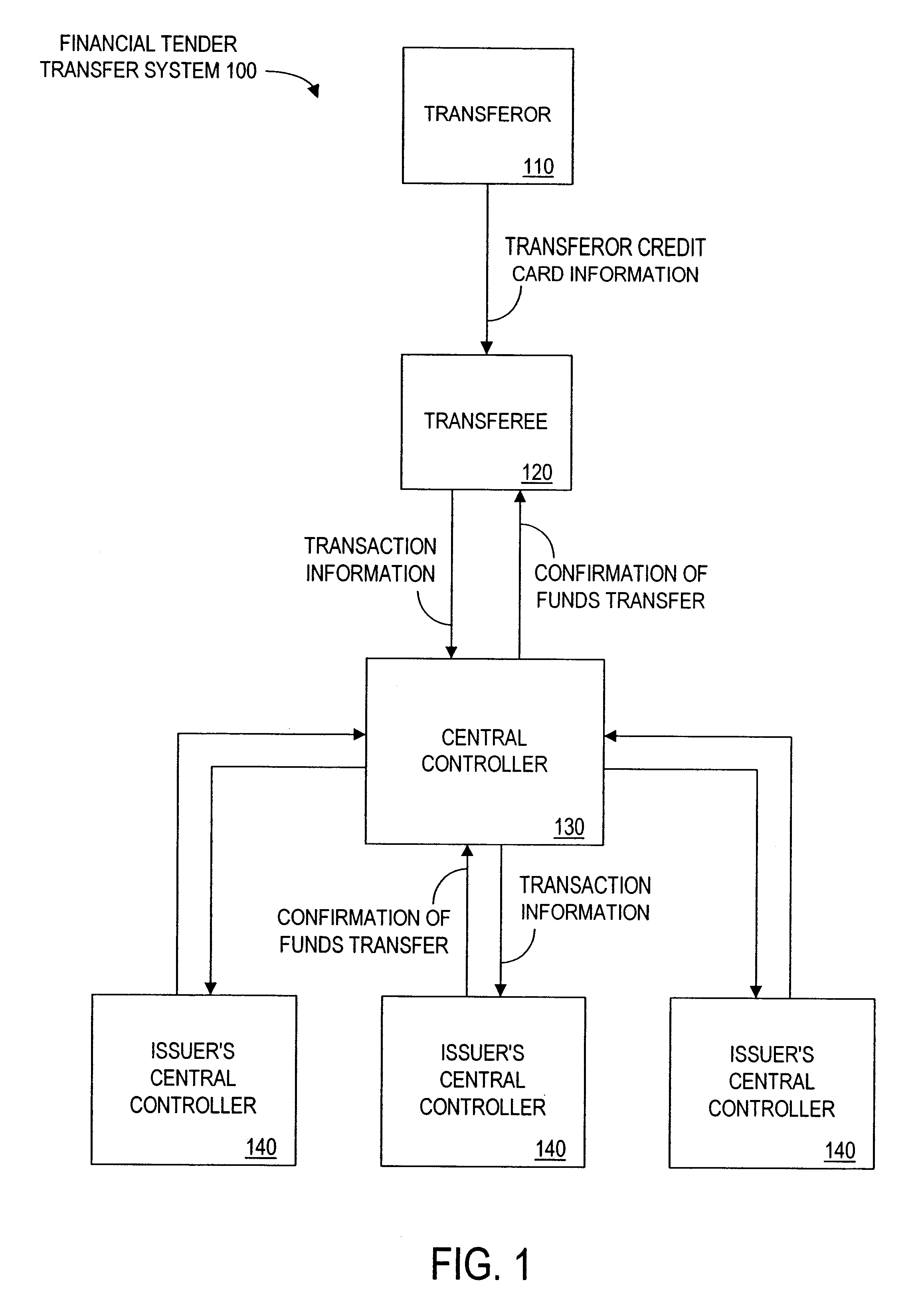
Method and apparatus for funds and credit line transfers
A financial tender transfer system allows a transferor to transfer credit or make payment to a transferee by debiting the credit card of the transferor and crediting the credit card of the transferee. The financial tender transfer system gives the transferee immediate access to the transferred money and ensures the transferor's credit card is valid. Neither party needs to give their credit card number to the other, so security is preserved. Any amount of value up to the full credit line of the transferor can be transferred to the transferee.
Owner:PAYPAL INC
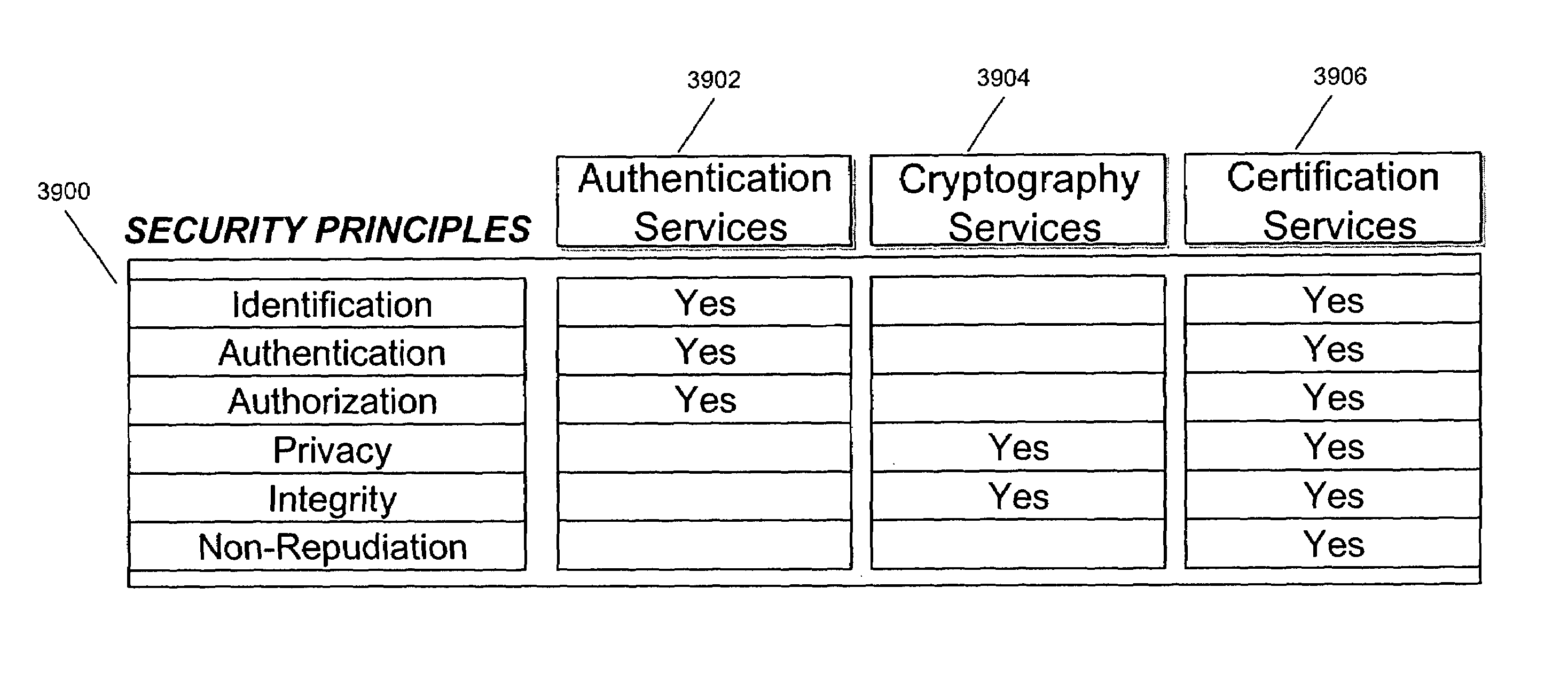
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
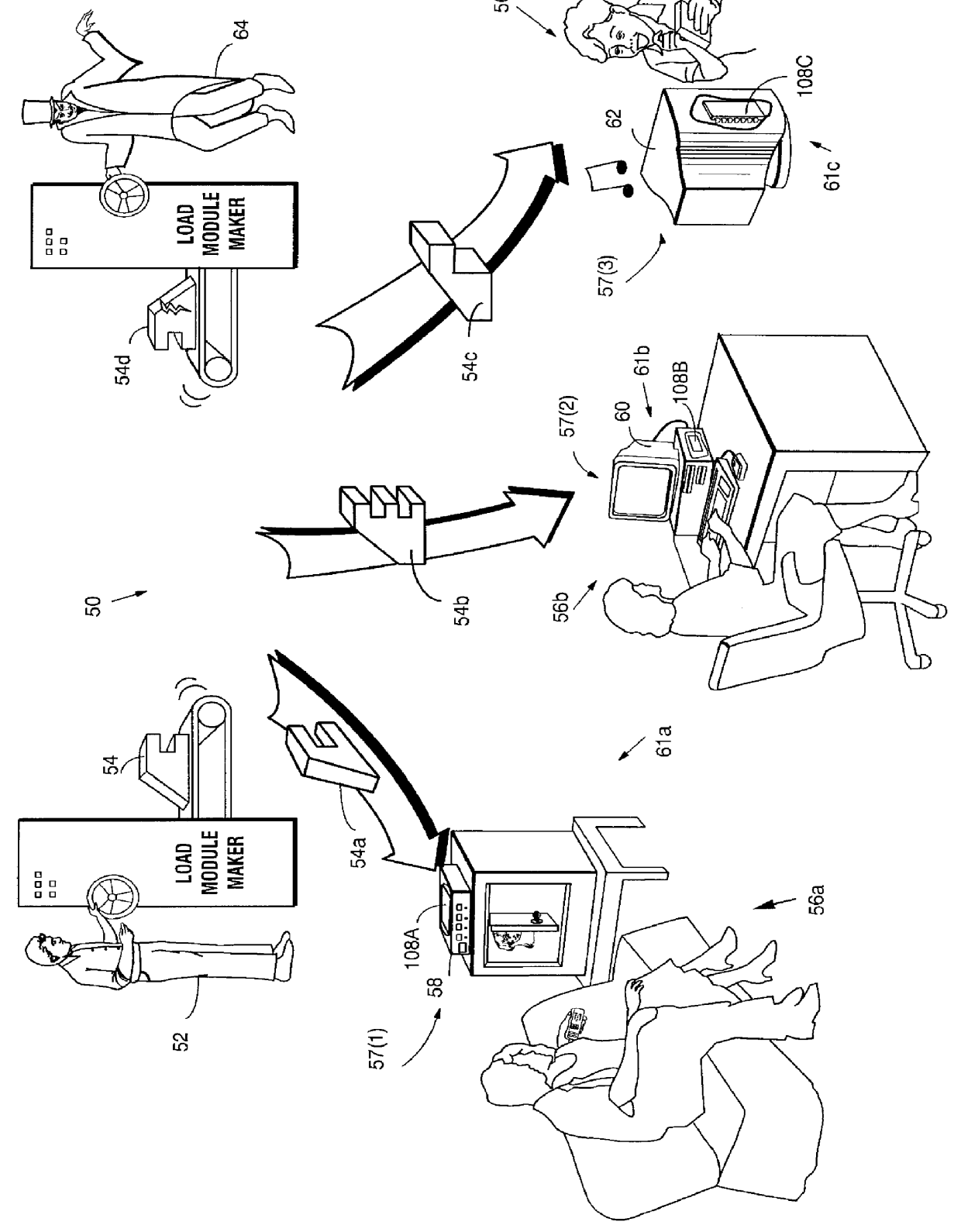
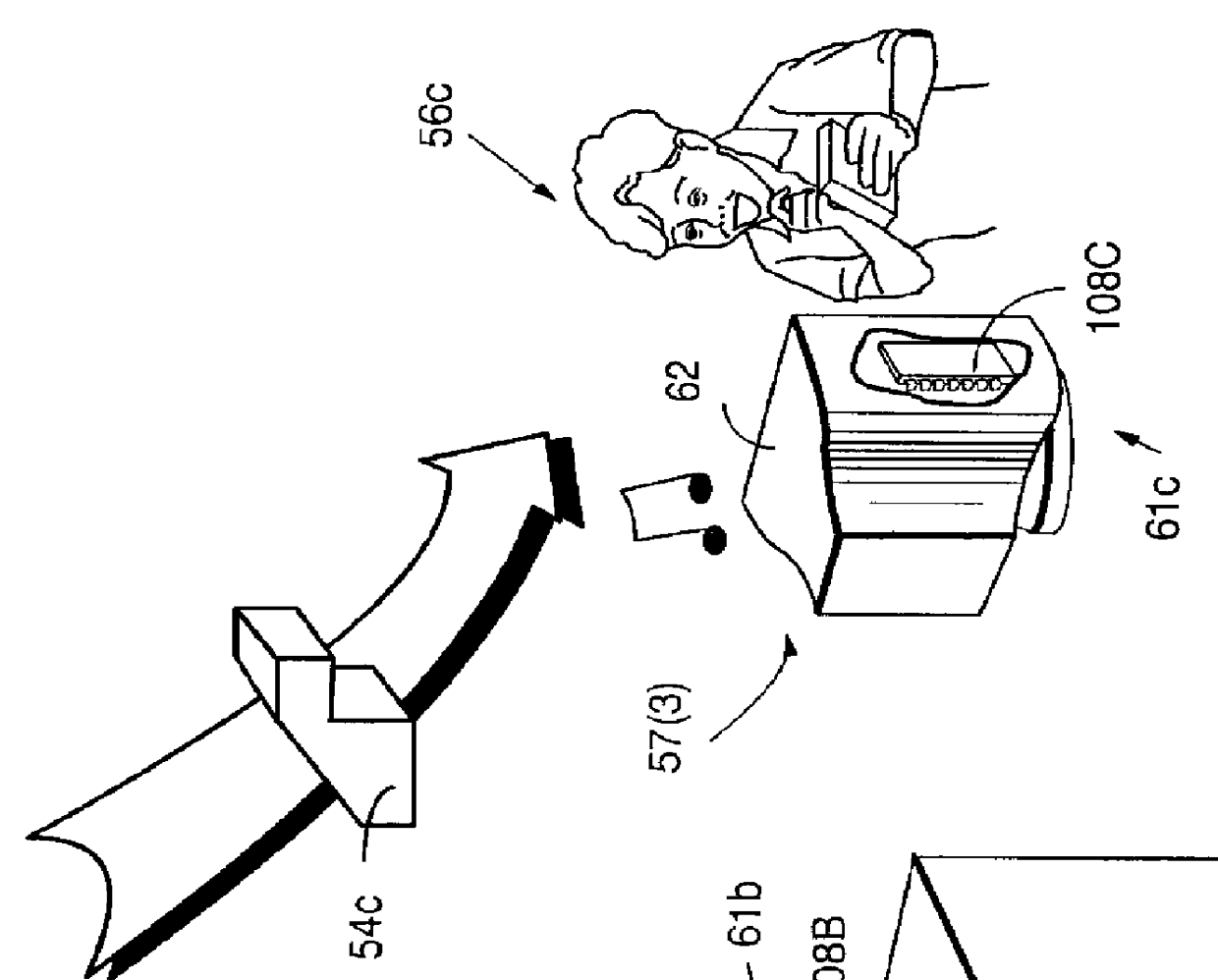
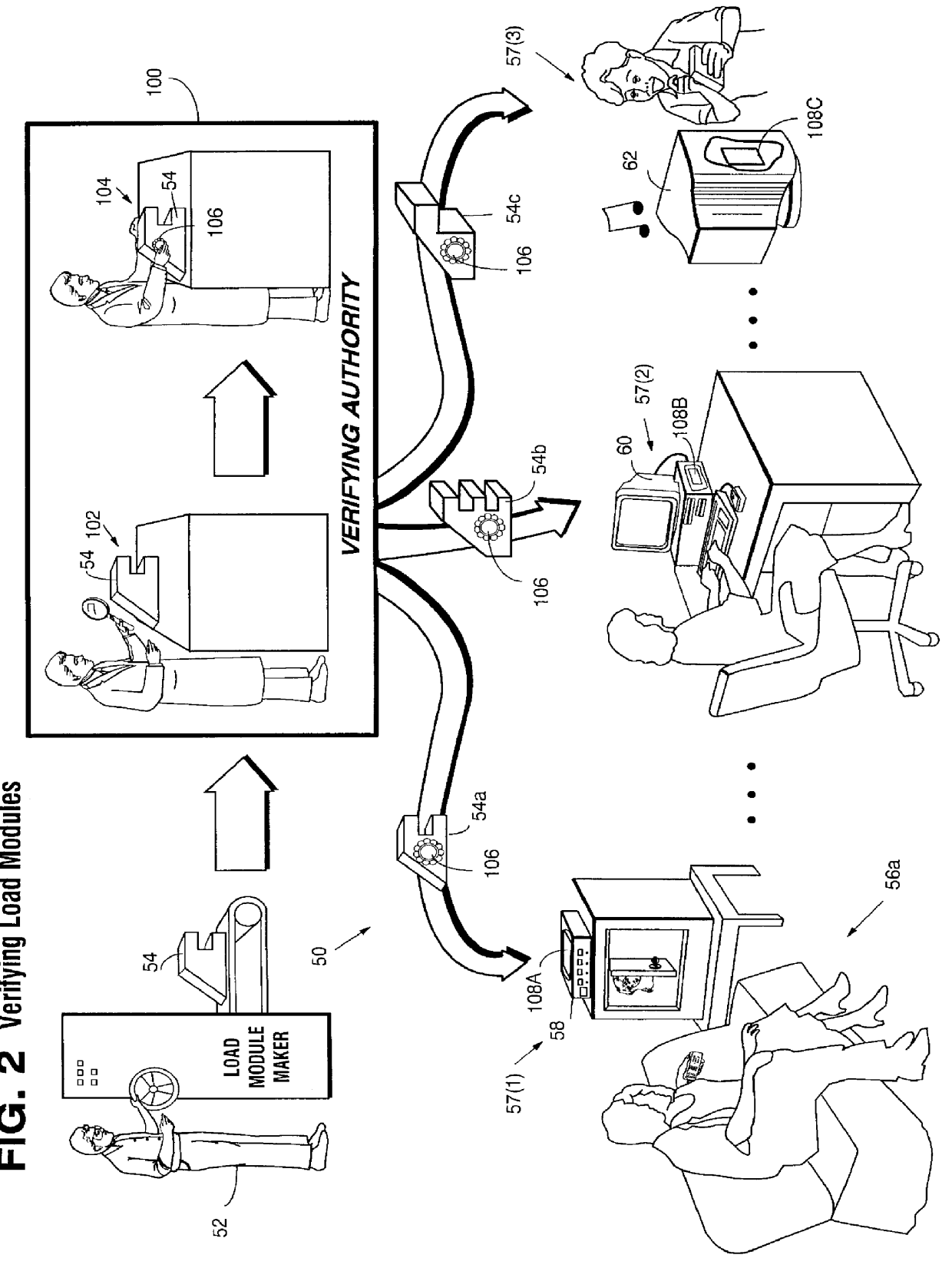
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
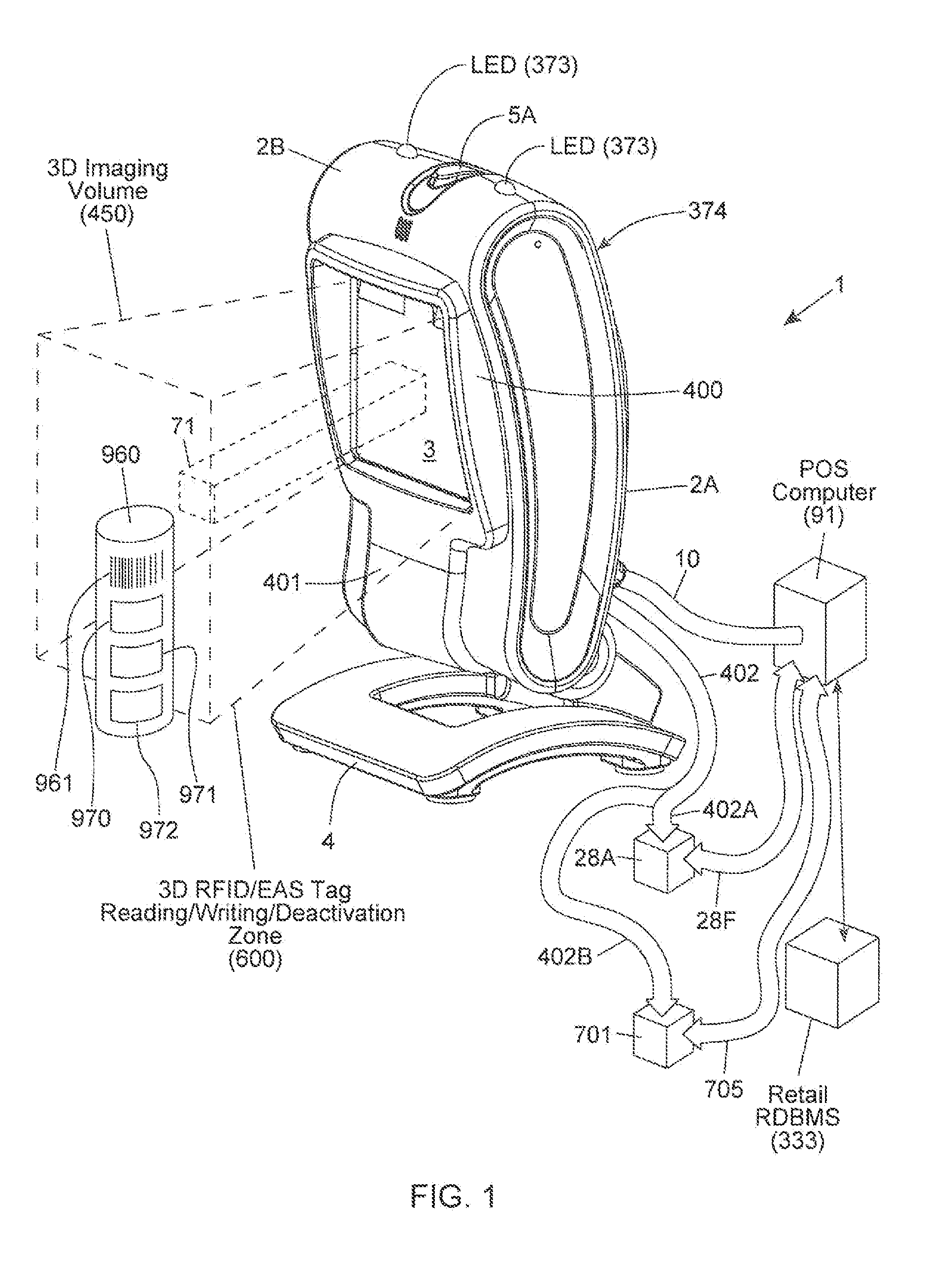
Method of and system for uniquely responding to code data captured from products so as to alert the product handler to carry out exception handling procedures
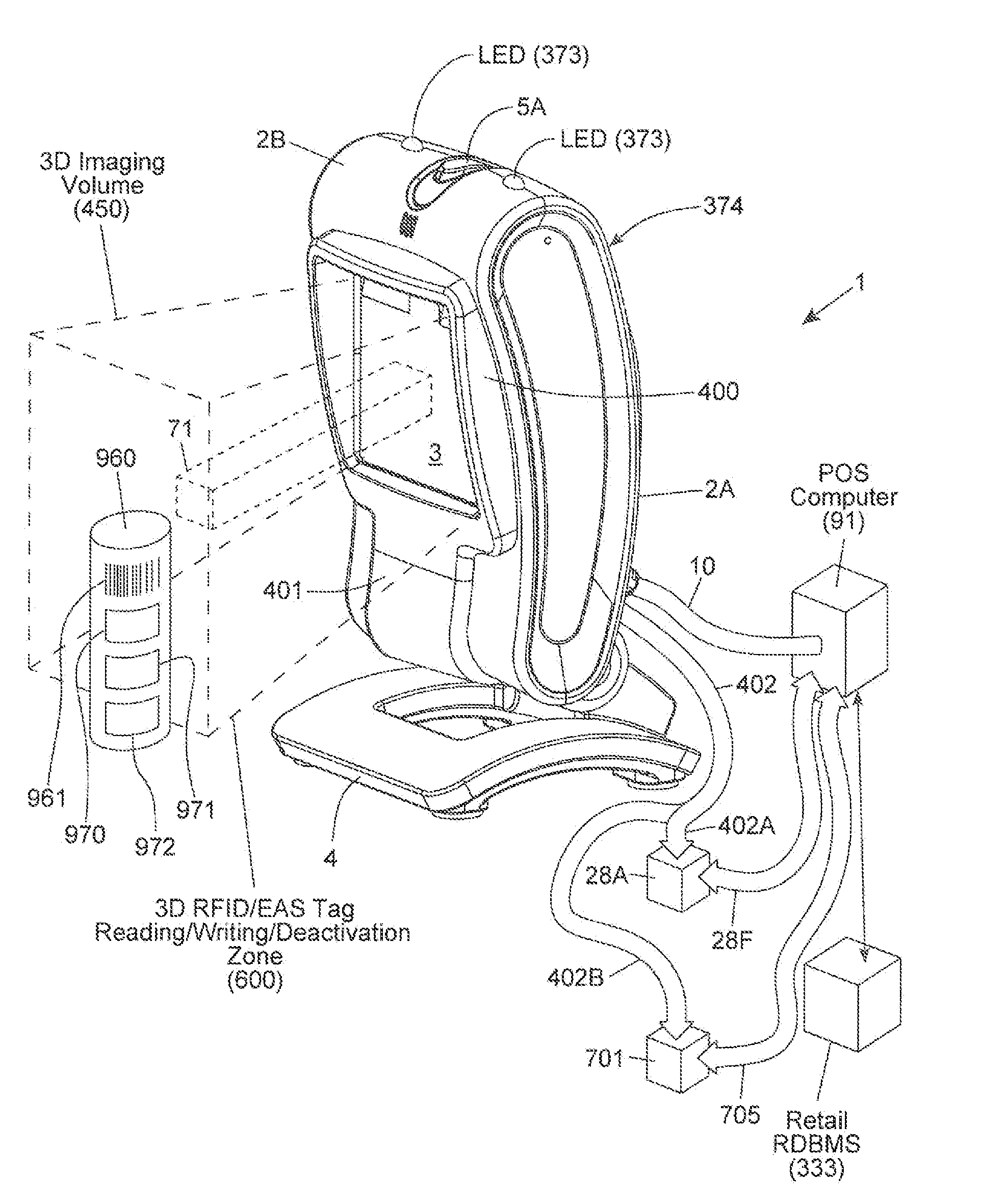
InactiveUS20120203647A1Avoid disadvantagesEffectively reliably informCash registersPayment architectureLogistics managementSoftware engineering
A code reading system capable of signaling exception handling procedures for products being handled in a work environment, such as, for example, consumer product being purchased in a retail store or a product or package being sorted by a logistics company. The system includes a system housing containing one or more one or more signal sources for generating distinctive visual and / or audible exception handling signals for special classes of products identified in the environment. Such special products may include: EAS tagged products requiring EAS tag deactivation: alcohol and tobacco products requiring proof of age; controlled products requiring additional customer tracking; age restricted products requiring identification; product purchases requiring personnel to show up and approve or assist in a product transaction; and the like.
Owner:METROLOGIC INSTR
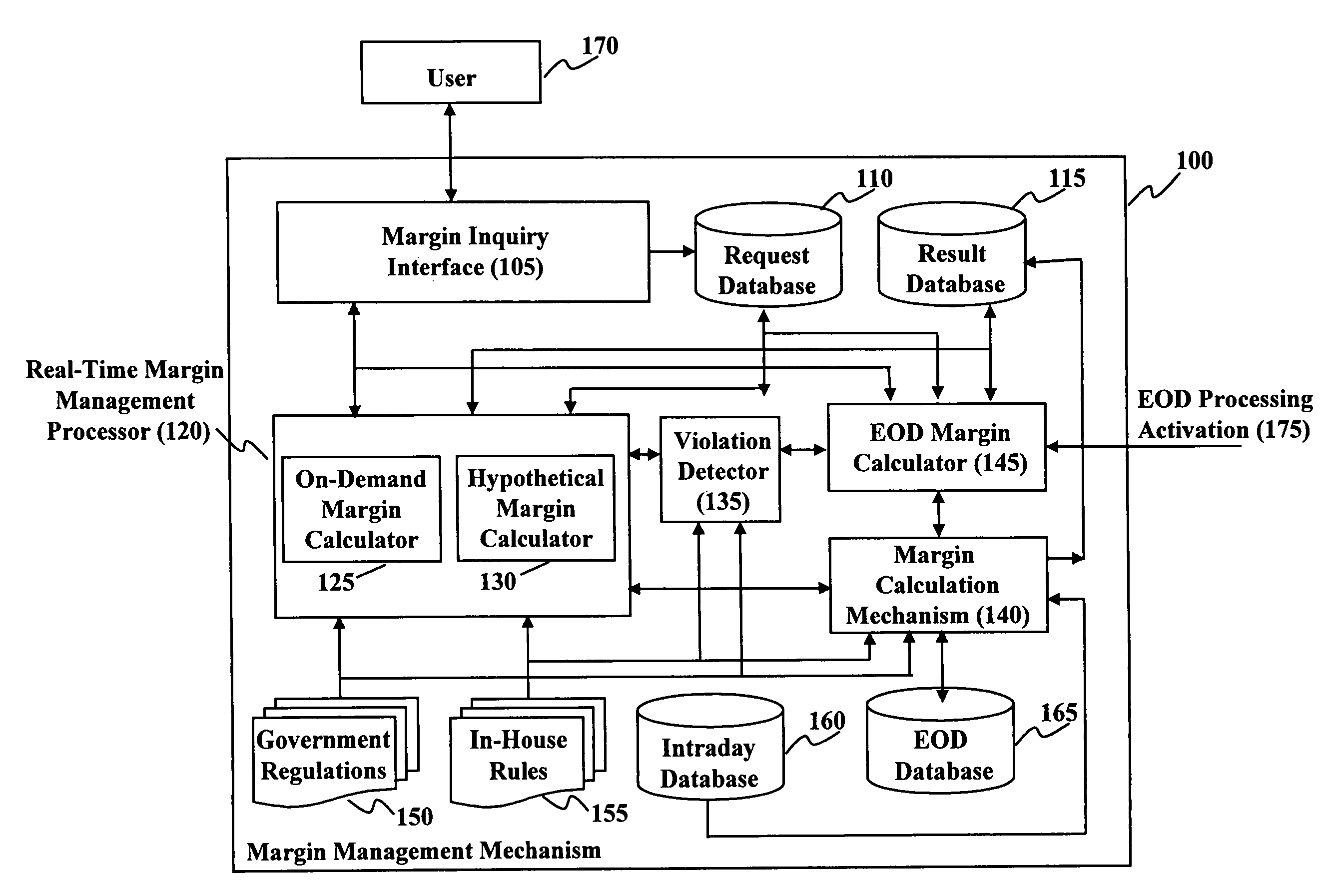
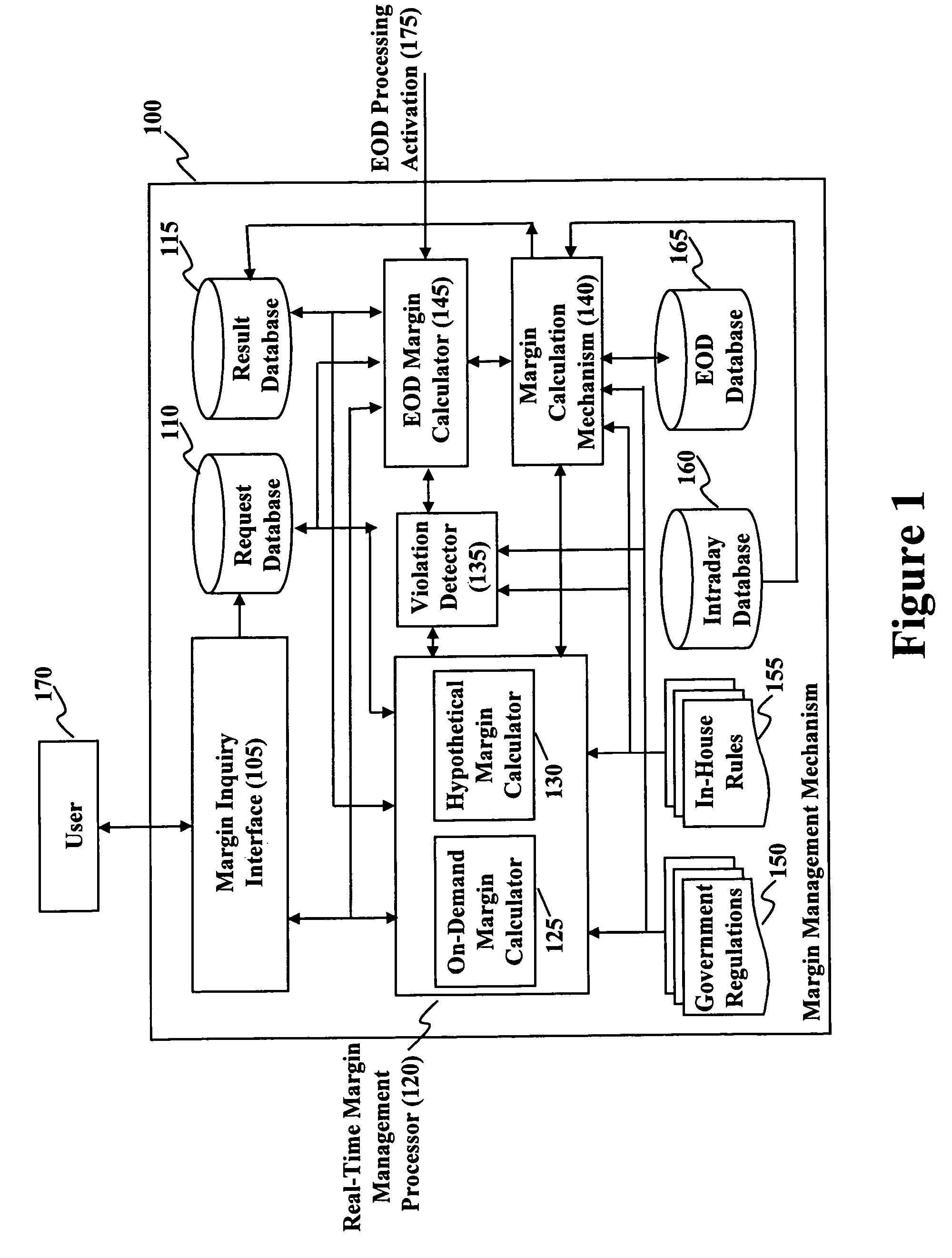
Method and system for real time margin calculation
Owner:UBS BUSINESS SOLUTIONS AG
Transaction terminal and adaptor therefor
Owner:HAND HELD PRODS
RFID token with multiple interface controller
InactiveUS20060208066A1Acutation objectsBroadcast information characterisationComputer moduleSmart card
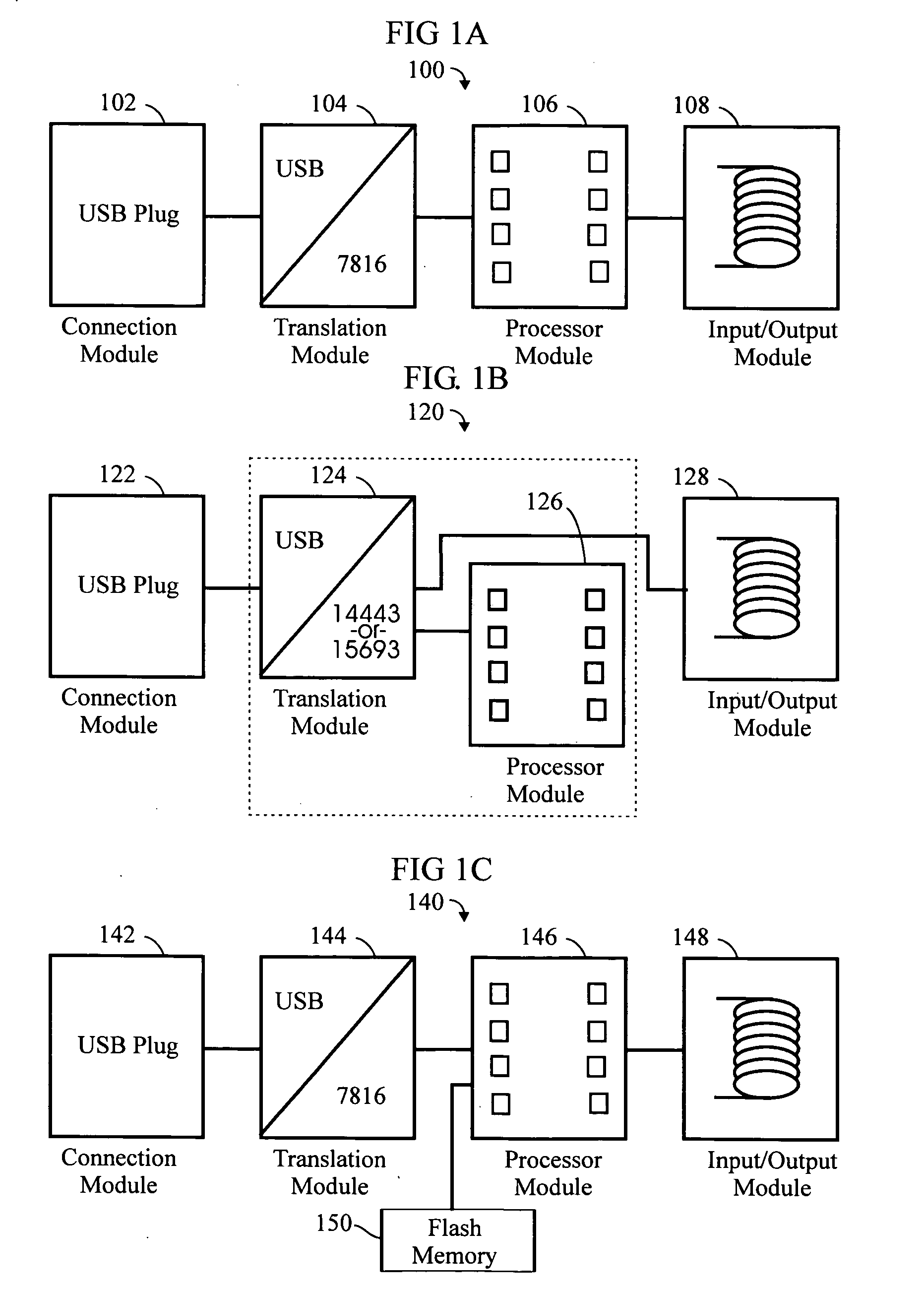
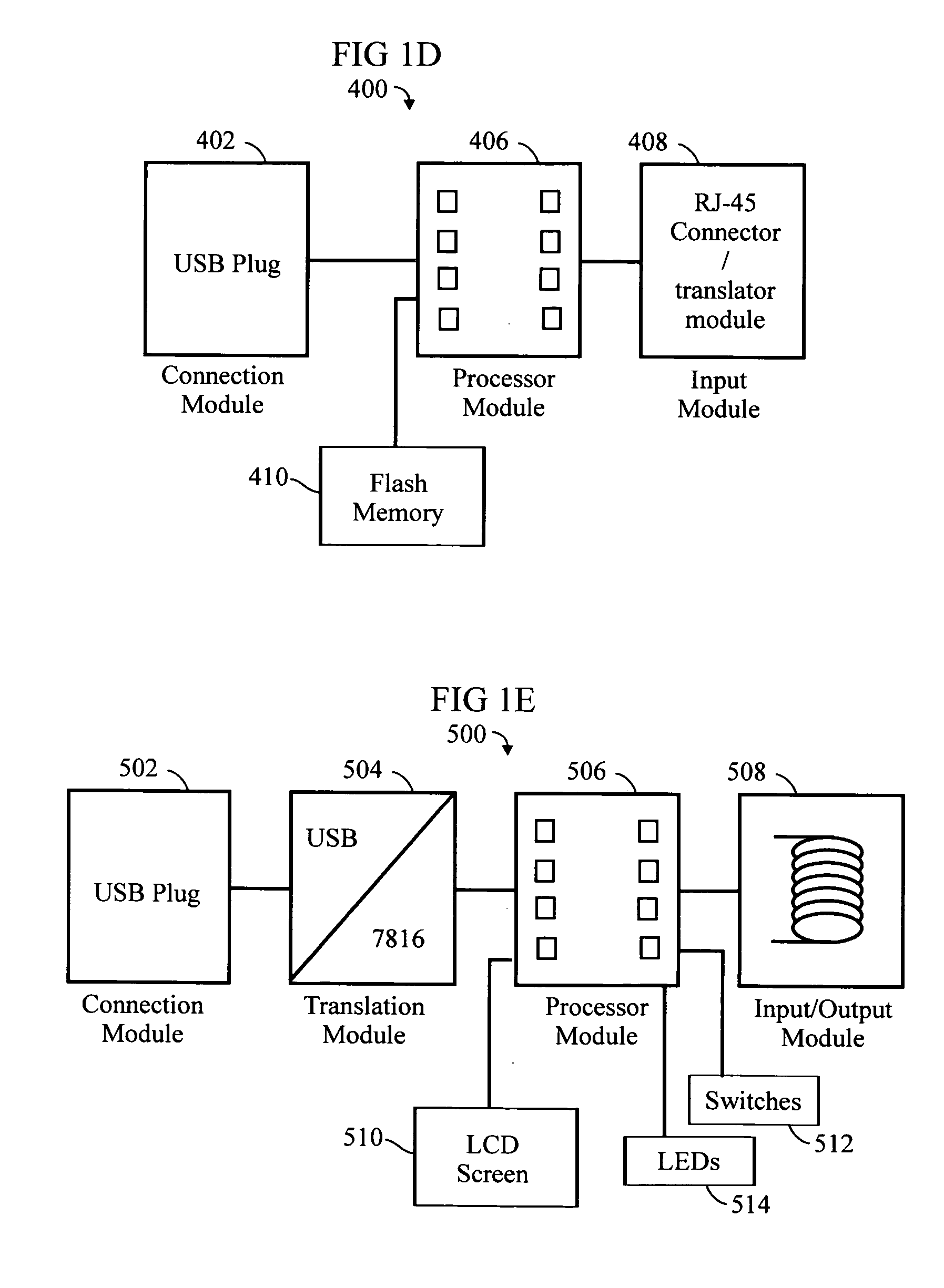
An RFID token apparatus has a connection module for interfacing with an appliance capable of communicating and interacting with remote servers and networks, a translation module for moving signals between a USB interface and a smart card interface, a processor module which may be capable of operating as a dual-interface (DI) chip; and an input / output module having at least one RF antenna and a modulator. An RFID-contactless interface according to ISO 14443 & ISO 15693 and / or NFC. A wireless interface according to Zigbee, Bluetooth, WLAN 802.11, UWB, USB wireless and / or any similar interface. An RFID reader apparatus has a housing; a slot for a contact or contactless fob; and a USB stick alternately protruding from the housing and retracted within the housing.
Owner:DPD PATENT TRUST
Electronic menu document creator in a virtual financial environment
The disclosure provides for creating a finalized document relating to a transaction. A buyer selects documents associated with a proposed transaction and indicates trade terms of an agreement relating to the documents selected. The trade terms are presented to a seller on an electronic form via an electronic document platform. The electronic form includes a combined purchase order proforma invoice, a transportation document, and a shipping document. The seller can amend the trade terms on the form, and each amendment creates a new version of the form. Negotiations of the trade terms between the buyer and the seller are conducted electronically and the negotiated fonn detailing the negotiation of the trade terms is generated and displayed electronically, also. A compliance check is performed and is triggered in response to a digital signature of the form. Payment is initiated to the seller after a verification of credit of the buyer.
Owner:ACCENTURE GLOBAL SERVICES LTD
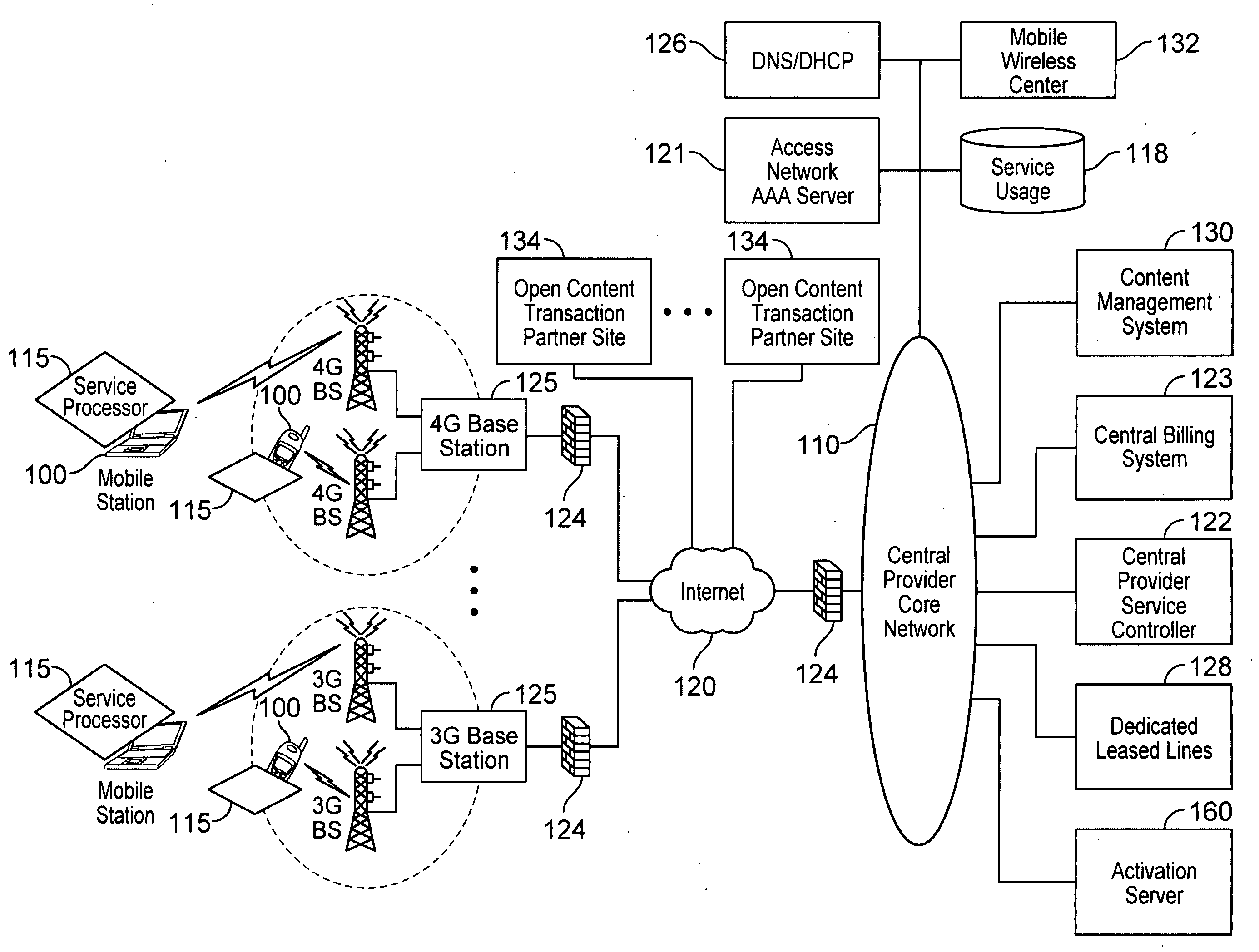
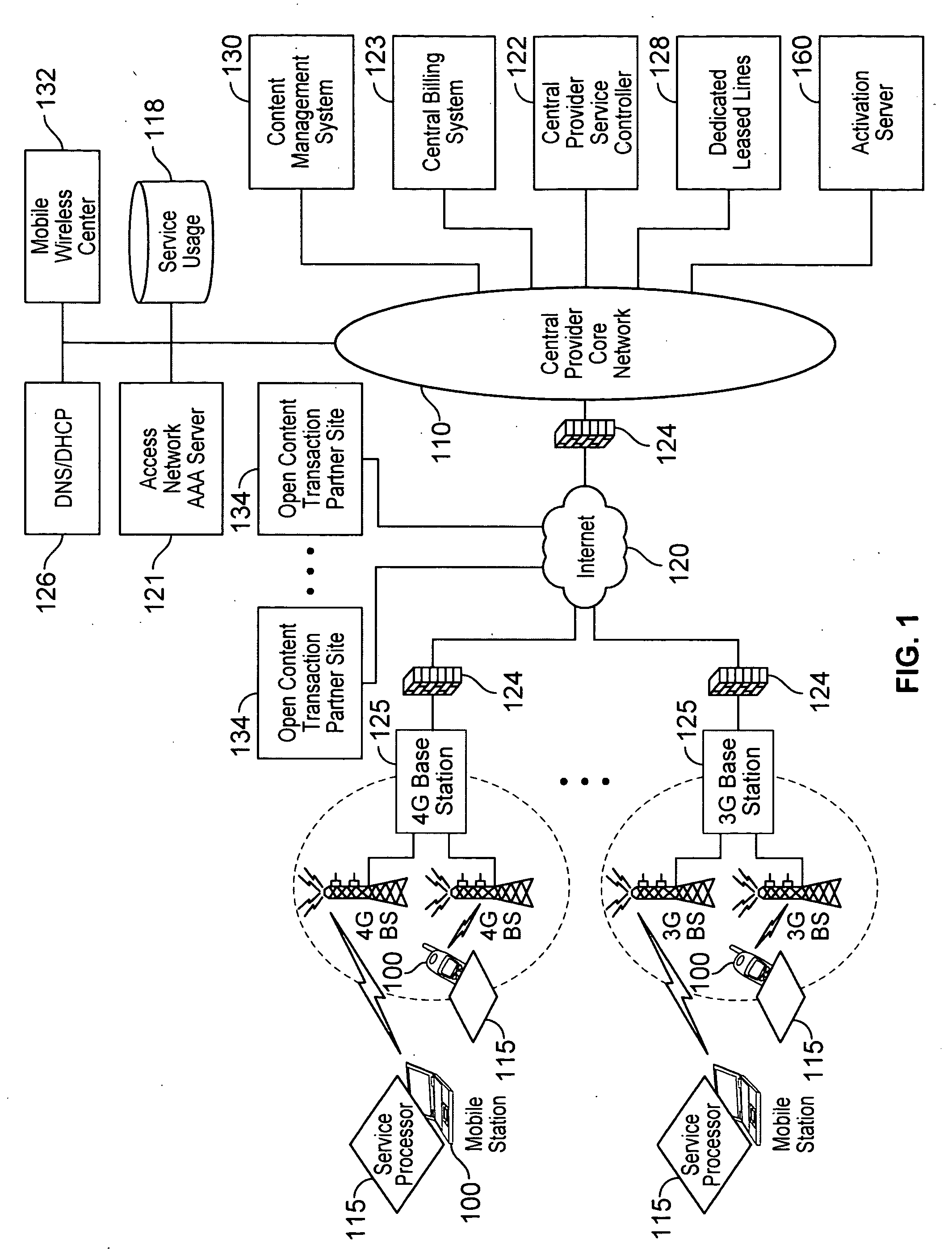
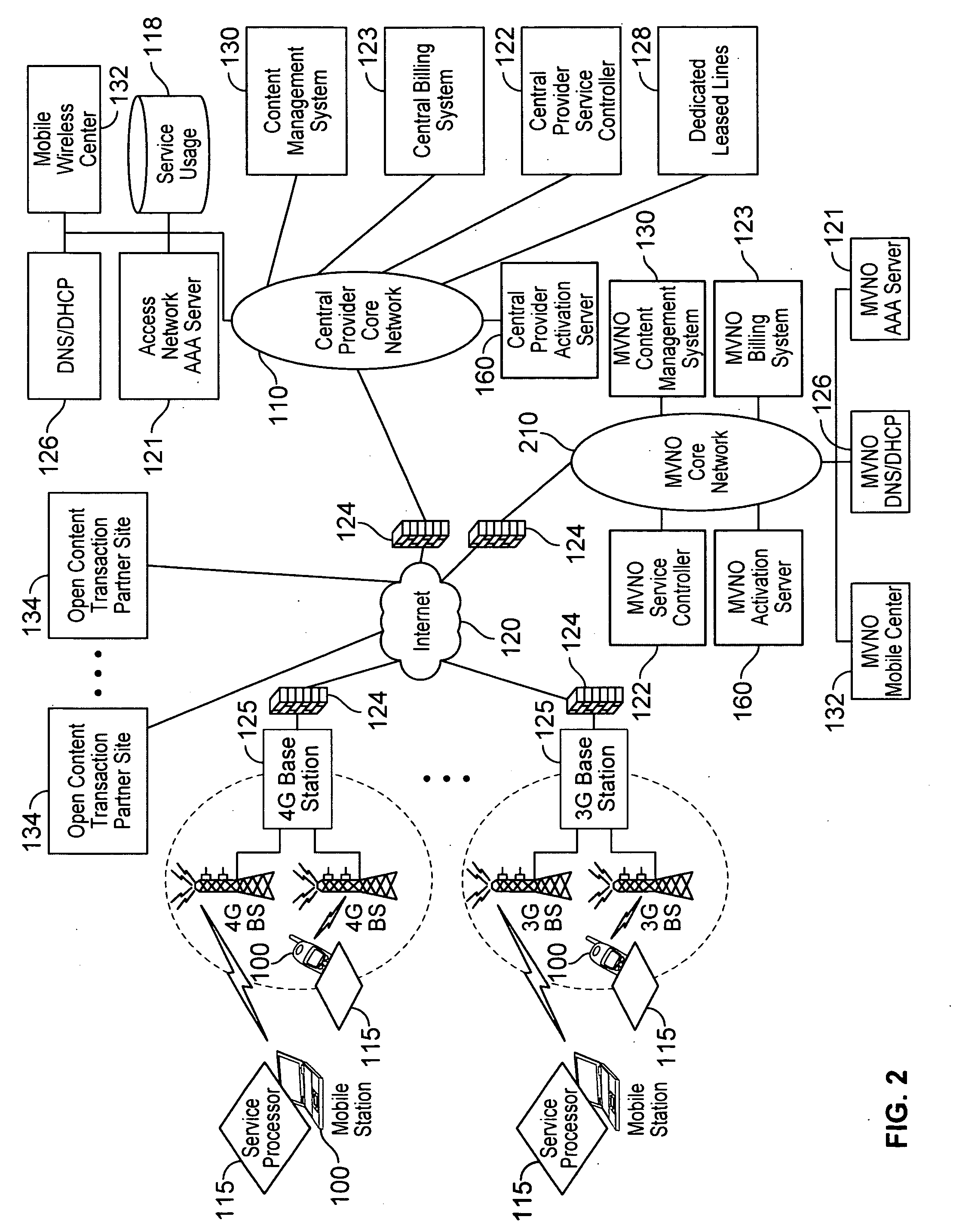
Automated device provisioning and activation
ActiveUS20100192212A1Digital data processing detailsTechnology managementCommunications systemBiological activation
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device stores a set of device credentials for activating the communications device for a service on a network; and sends an access request to the network, the access request including the set of device credentials.
Owner:HEADWATER RES LLC
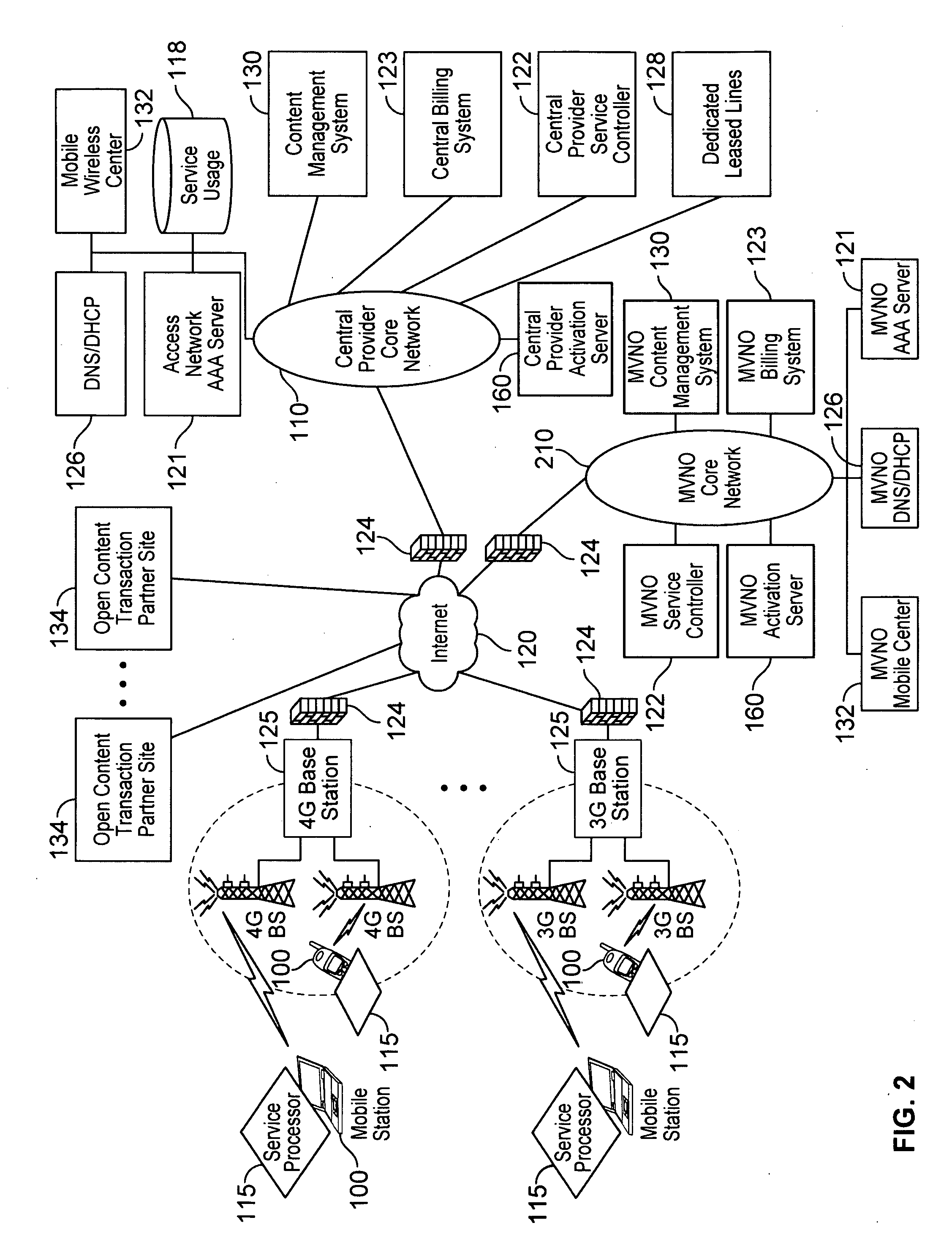
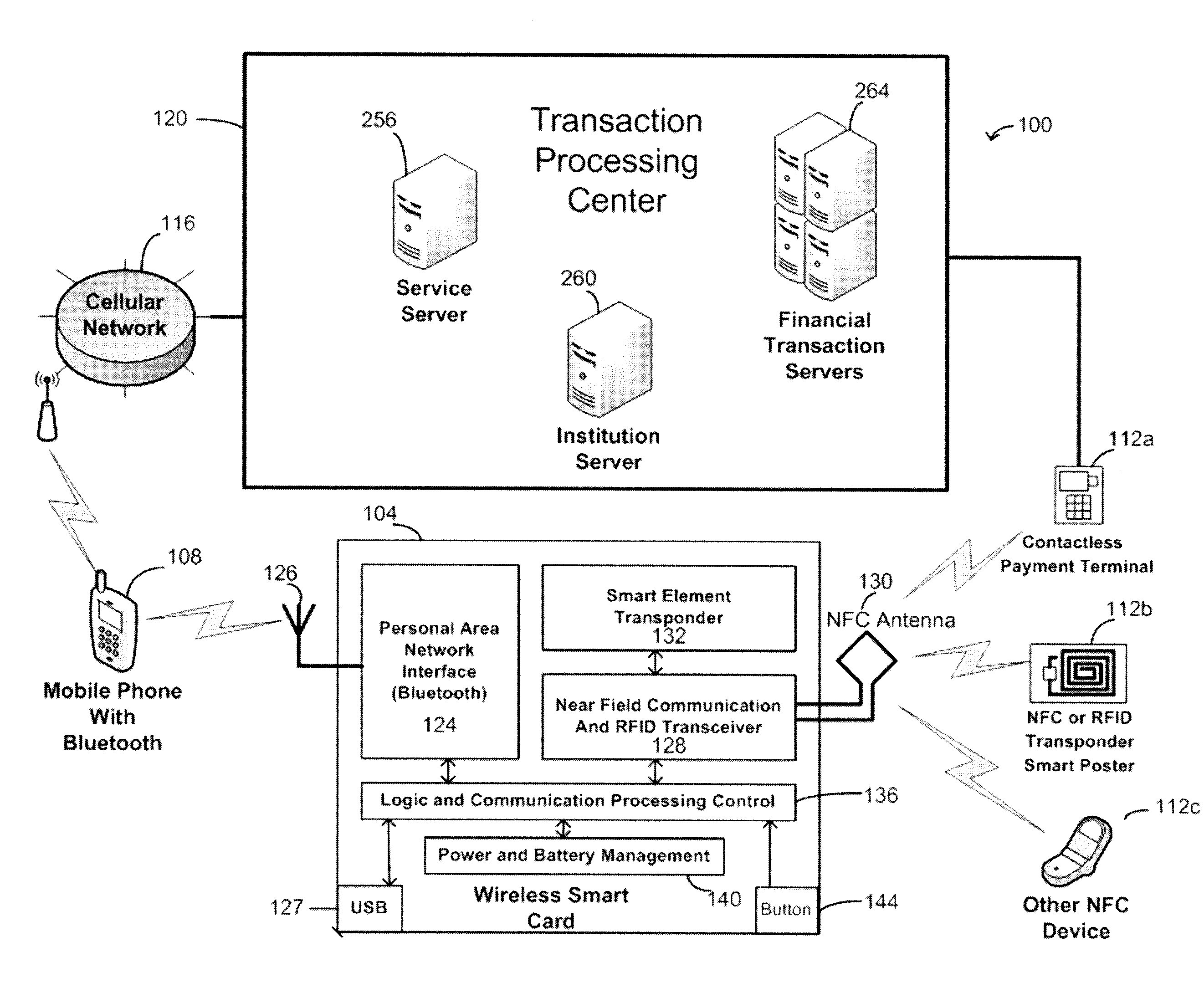
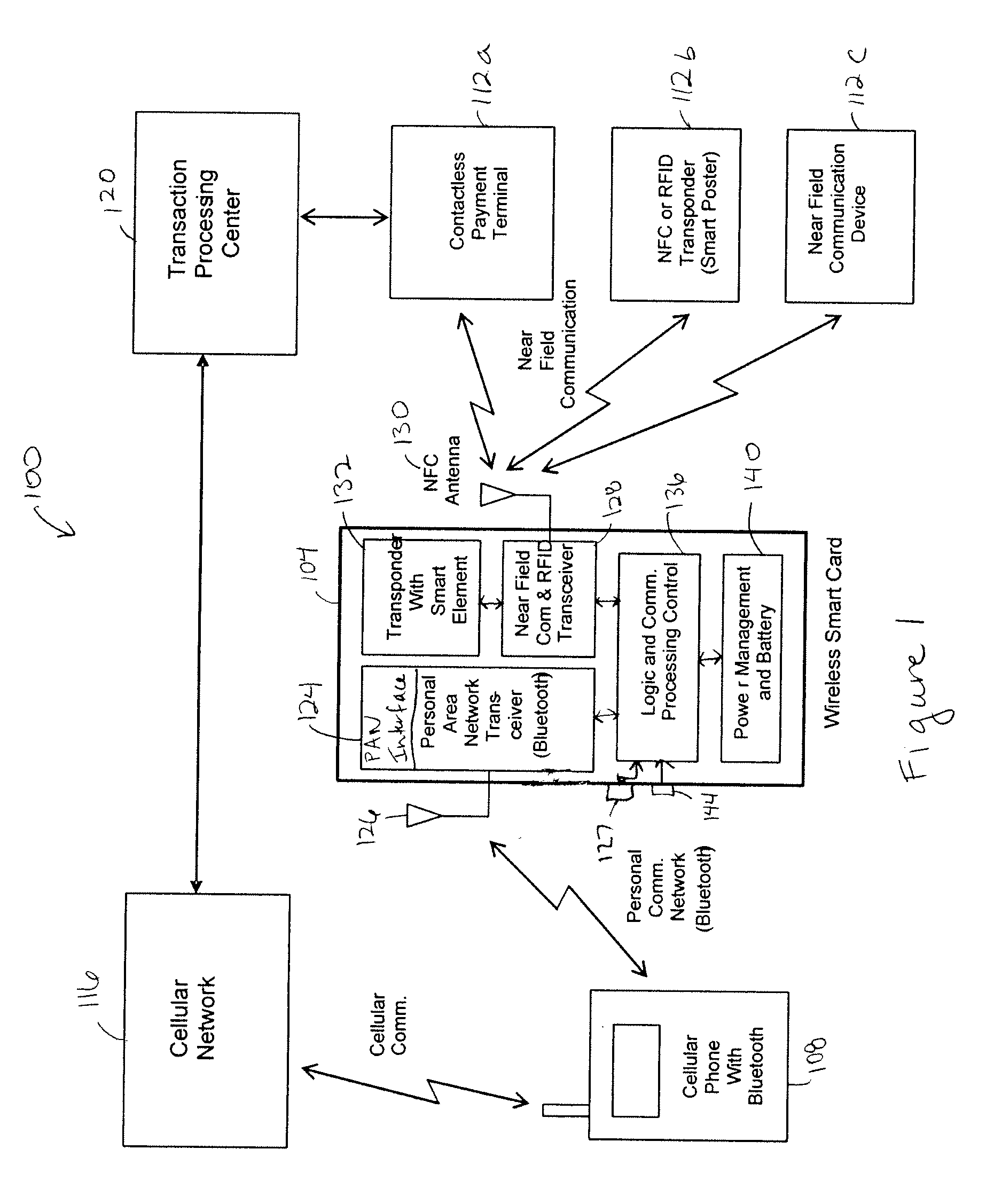
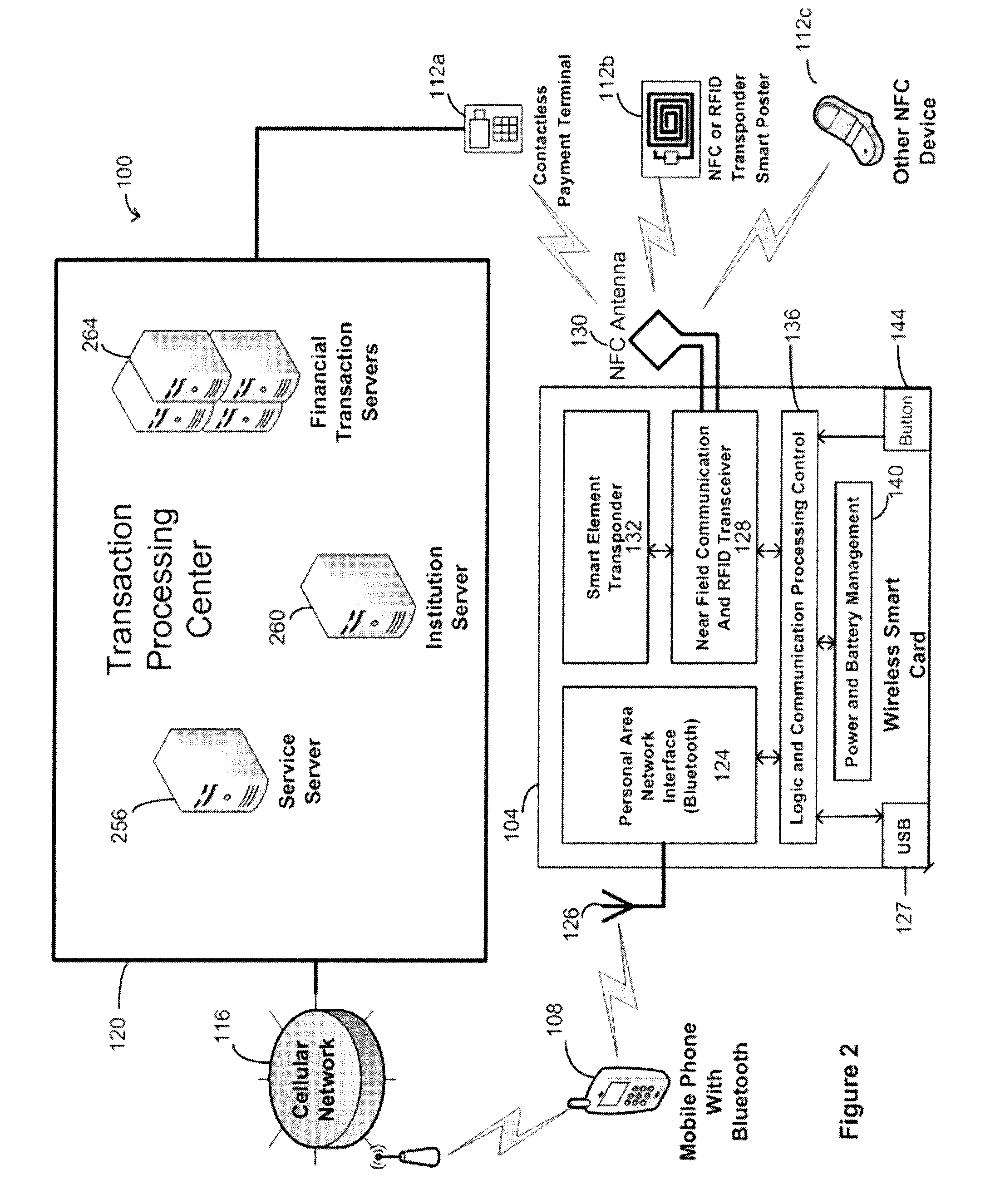
Wireless smart card and integrated personal area network, near field communication and contactless payment system
A wireless smart card having a personal area network transceiver, such as a Bluetooth transceiver, to couple the wireless smart card with a mobile communication device, and a near field communication (NFC) and radio-frequency identification (RFID) transceiver to couple the wireless smart card to a wireless transaction device, and a transponder with a secure element to allow secure communications between the mobile communication device with the wireless smart card and the wireless smart card and the wireless transaction device is described. The wireless smart card allows, for example, contactless payment through a Bluetooth-enabled mobile communication device without modification to the mobile communication device.
Owner:WIRELESS DYNAMICS
Verifiable device assisted service policy implementation
ActiveUS20100188975A1Error preventionFrequency-division multiplex detailsCommunications systemCommunication device
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting control of the communications device use of a service on a network; and monitors use of the service based on the service policy, in which the implementation of the service policy is verified.
Owner:HEADWATER RES LLC
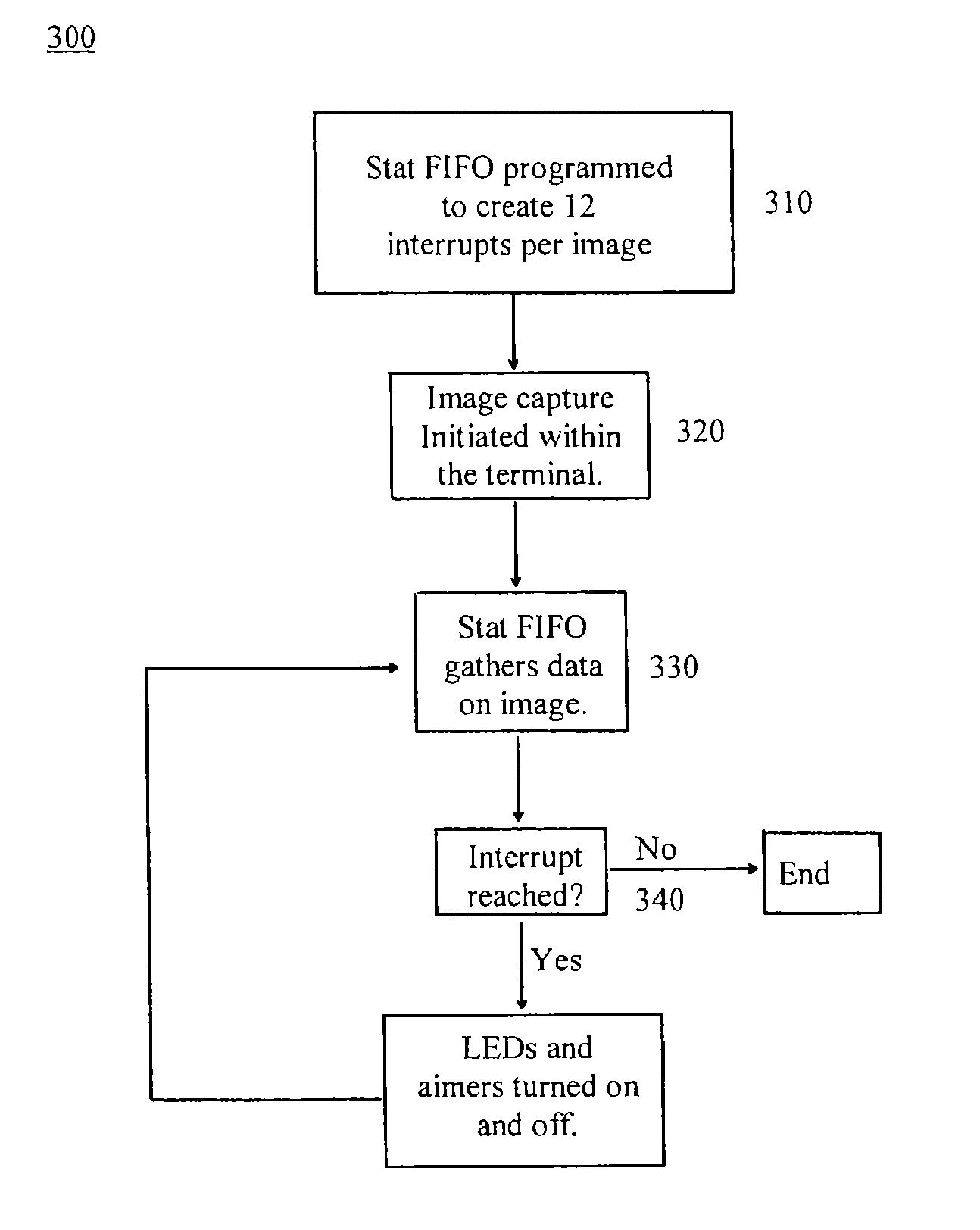
Cell phone reading mode using image timer
InactiveUS8777108B2Increase speed and efficiencyImprove compatibilityVisual representatino by photographic printingRecord information storageComputer graphics (images)Timer
An EIR terminal containing an image capture device configured to scan an image. The EIR terminal includes a lighting and exposure mechanism. The EIR terminal also includes a camera sensor interface with a stat FIFO. The stat FIFO is configured to receive data from the image capture device. When the stat FIFO, during image scanning, receives a pre-determined amount of image data, it fires an interrupt, which times the lighting and exposure mechanism in the EIR terminal.
Owner:HONEYWELL INT INC
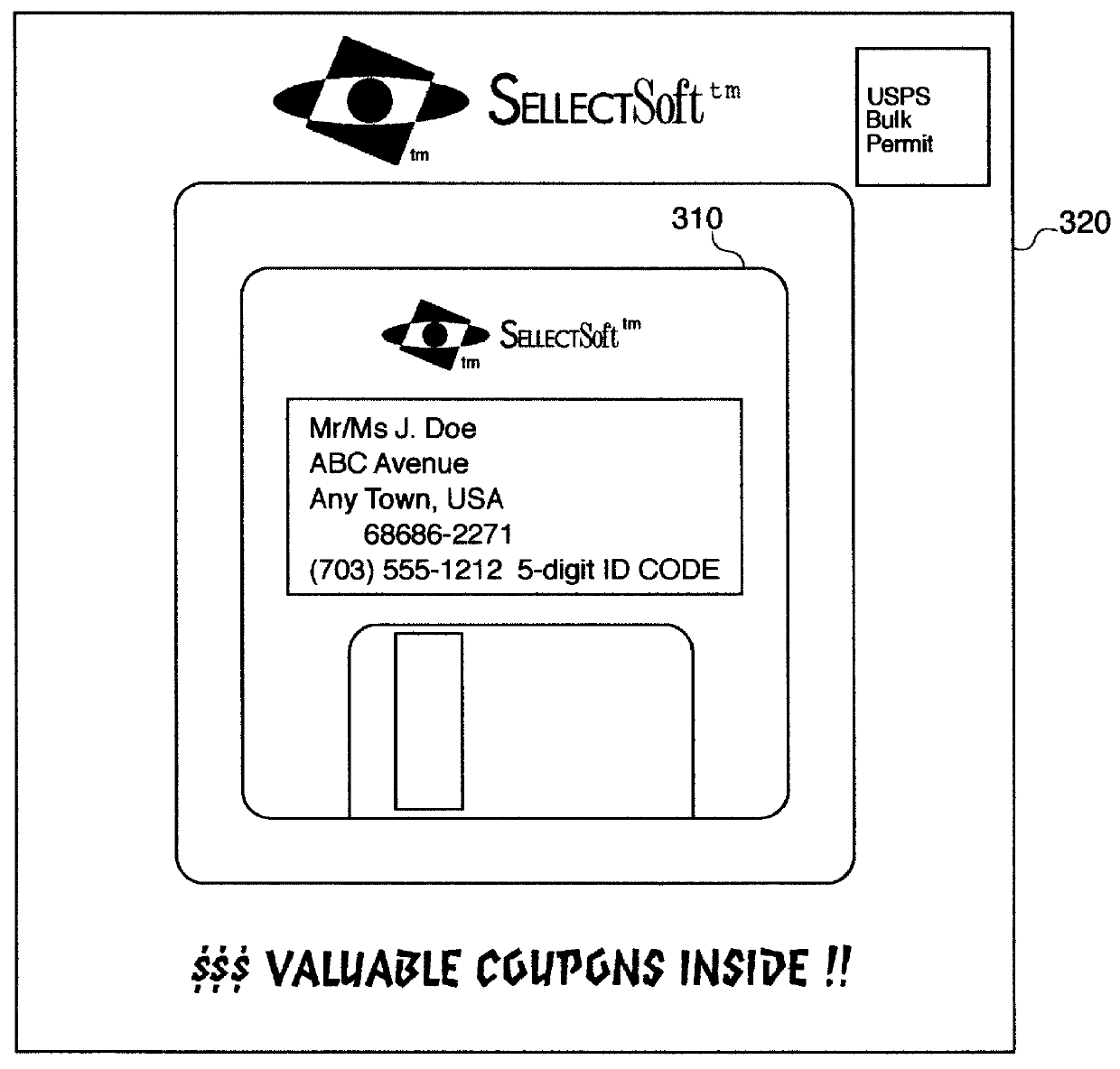
Electronic discount couponing method and apparatus for generating an electronic list of coupons
InactiveUS6035280AReduce the possibilityEliminate needPublic buildingsDigital computer detailsGraphicsGraphical user interface
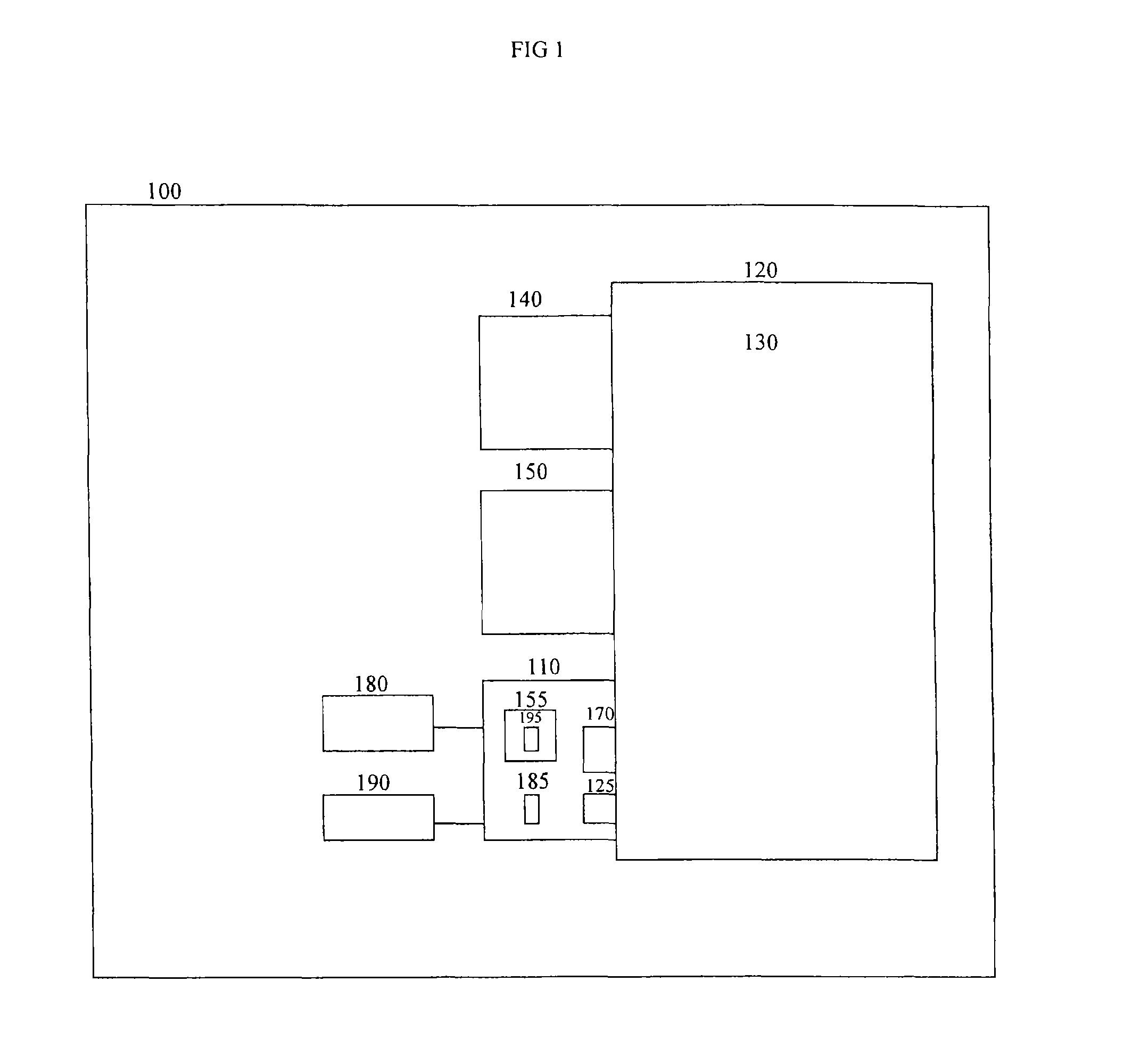
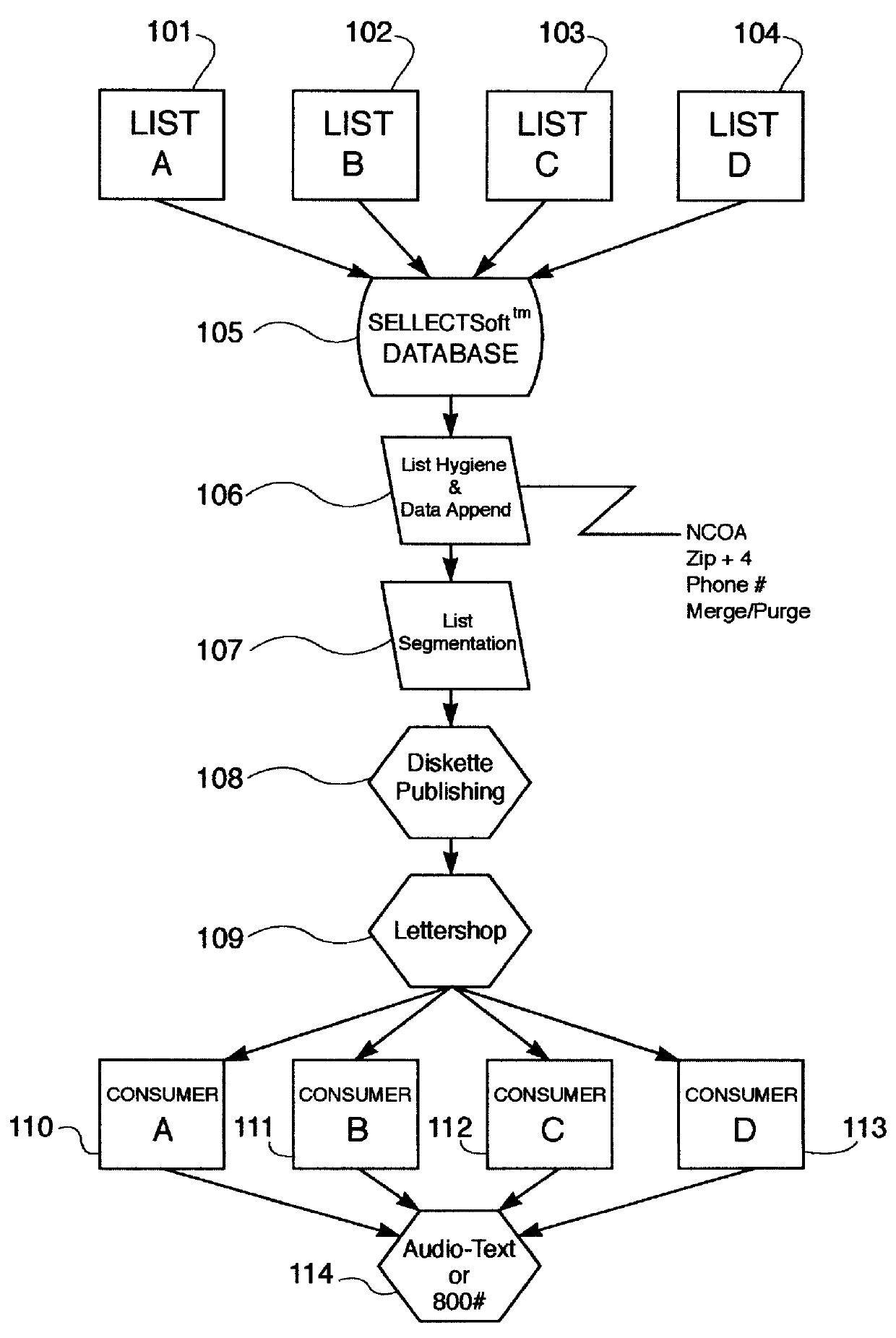
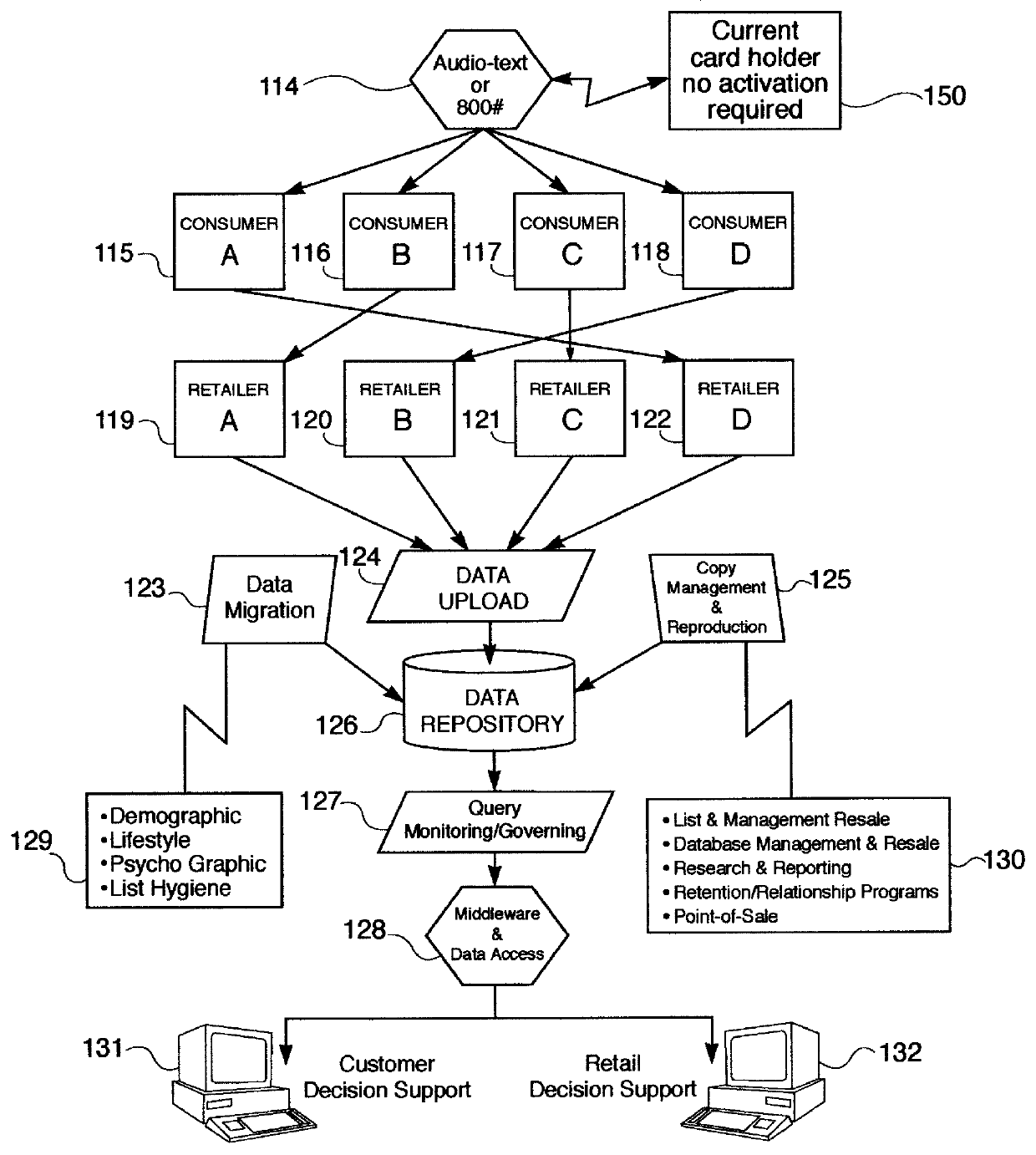
A method and apparatus for distributing, generating, and redeeming discount Virtual Coupons TM , rebate or gift certificates or the like which may be used on conjunction with a frequency card program or the like. Virtual Coupons TM may be distributed electronically, for example, in the form of a diskette or CD-ROM software. Software on the diskette or CD-ROM may prompt a consumer to call a 1-800 number for a validation number or code. During the phone call, telemarketing personnel may request consumer demographic and or identification information which may be entered into a centralized database. Once the software is validated, a consumer may print out a list selected Virtual Coupons TM displayed on a Graphical User Interface (GUI). When a product is purchased, the UPC code of the product may be compared electronically with a list of Virtual Coupons TM authorized for a particular consumer. An appropriate coupon discount may then be applied and the Virtual Coupon TM may be considered "redeemed". Once redeemed, consumer ID information and Virtual Coupon TM information may be retrieved electronically and used to update a central database. Accurate data may then be produced illustrating which consumers or groups of consumers are redeeming which Virtual Coupons TM . Such data may be used for marketing purposes or to generated further diskettes for distribution targeting specific consumers or groups of consumers with specific classes of Virtual Coupon TM offerings. The use of Virtual Coupons TM eliminates or reduces fraud, and allows a frequency card discount to be applied only a limited number of times.
Owner:CATALINA MARKETING CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com