Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
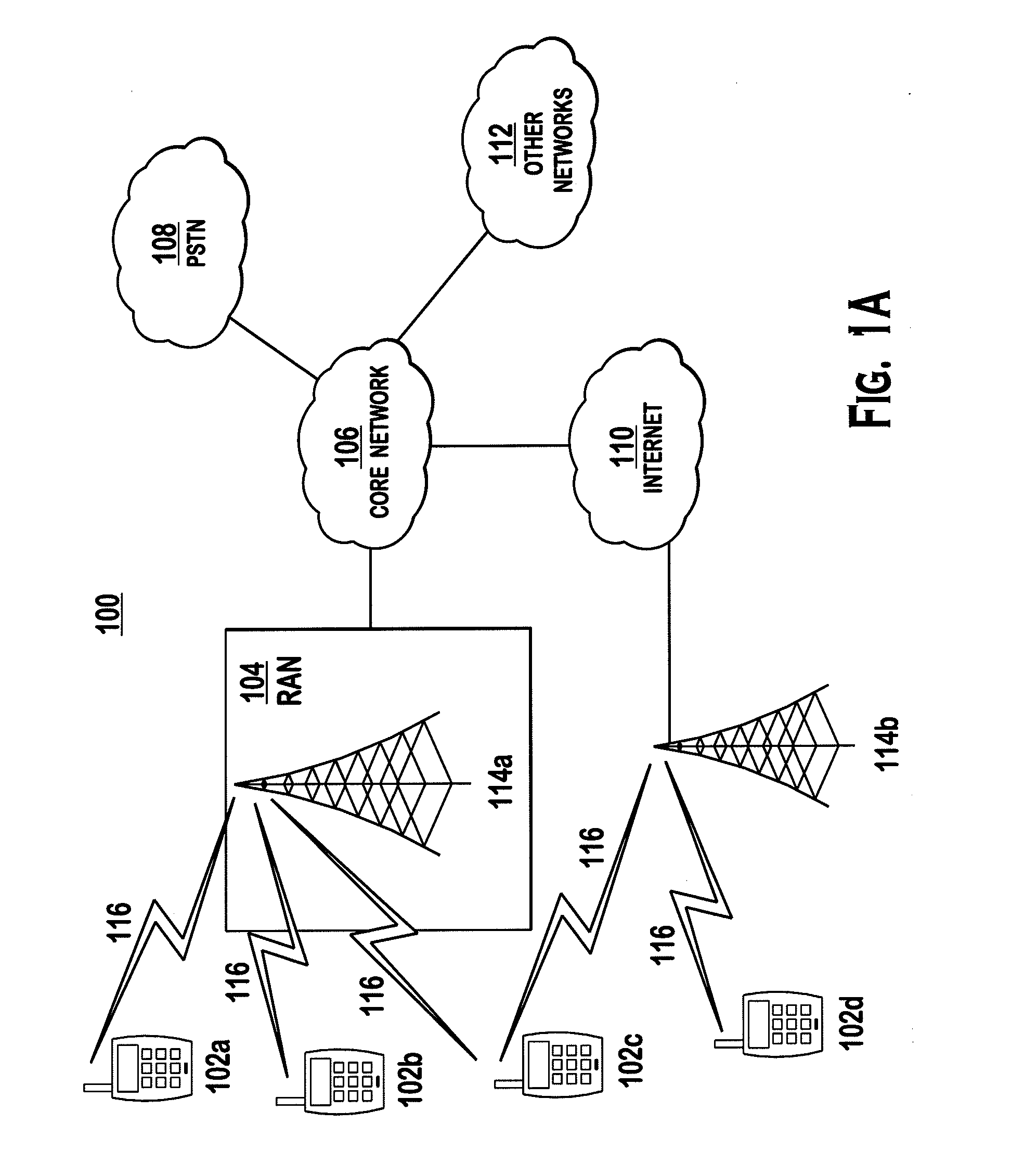
324 results about "Internet address" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet address (plural Internet addresses) (computing, Internet) Any address used to identify a place or resource on the Internet, such as a URL, an IP address, or a domain name. Generally used as a catch-all term by those without specific technical knowledge.
Linking of computers based on optical sensing of digital data
InactiveUS6311214B1Reduce businessLow costCoin-freed apparatusRecord information storageDigital dataBusiness card
A printed object, such as an item of postal mail, a book, printed advertising, a business card, product packaging, etc., is steganographically encoded with plural-bit data. When such an object is presented to an optical sensor, the plural-bit data is decoded and used to establish a link to an internet address corresponding to that object.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
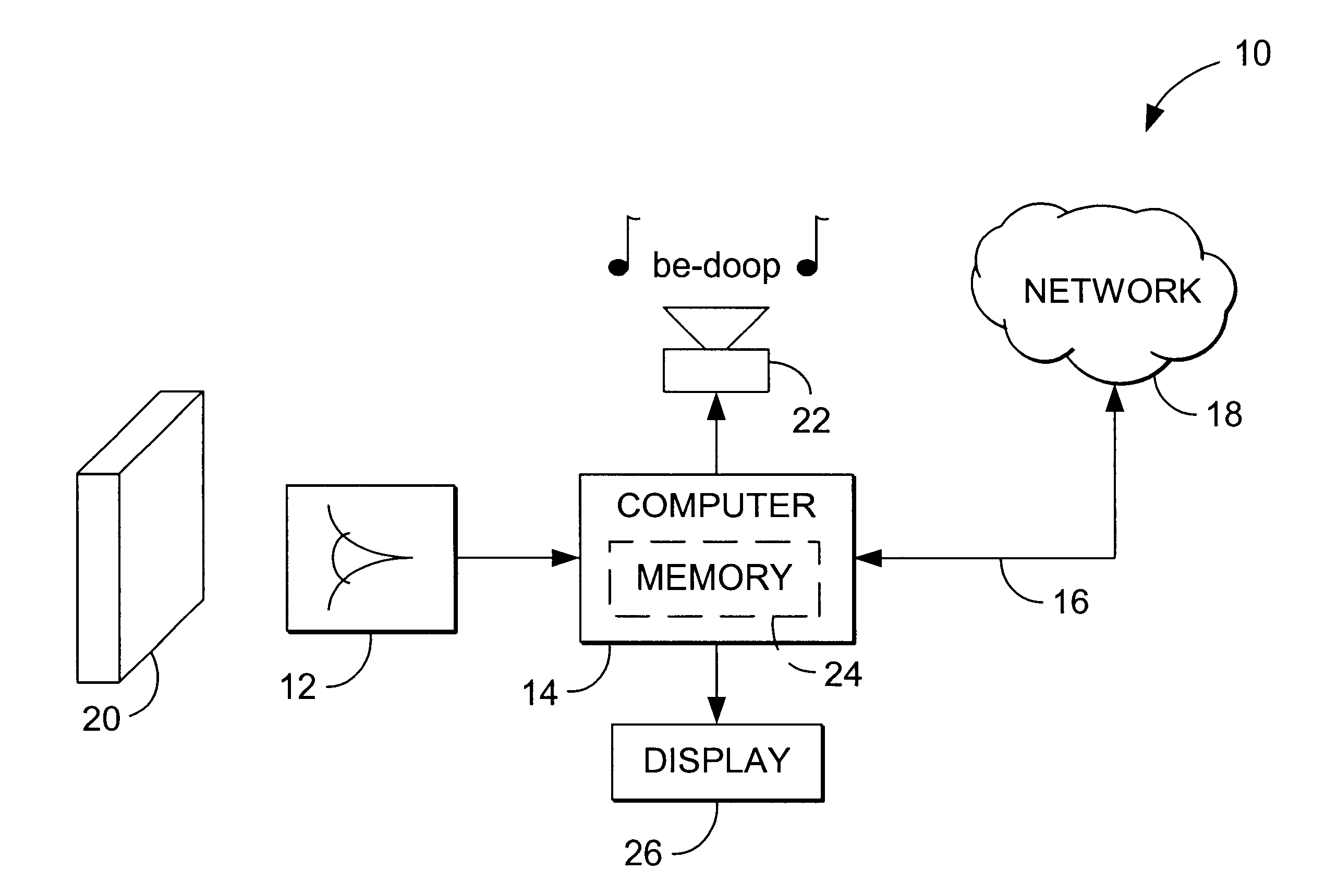
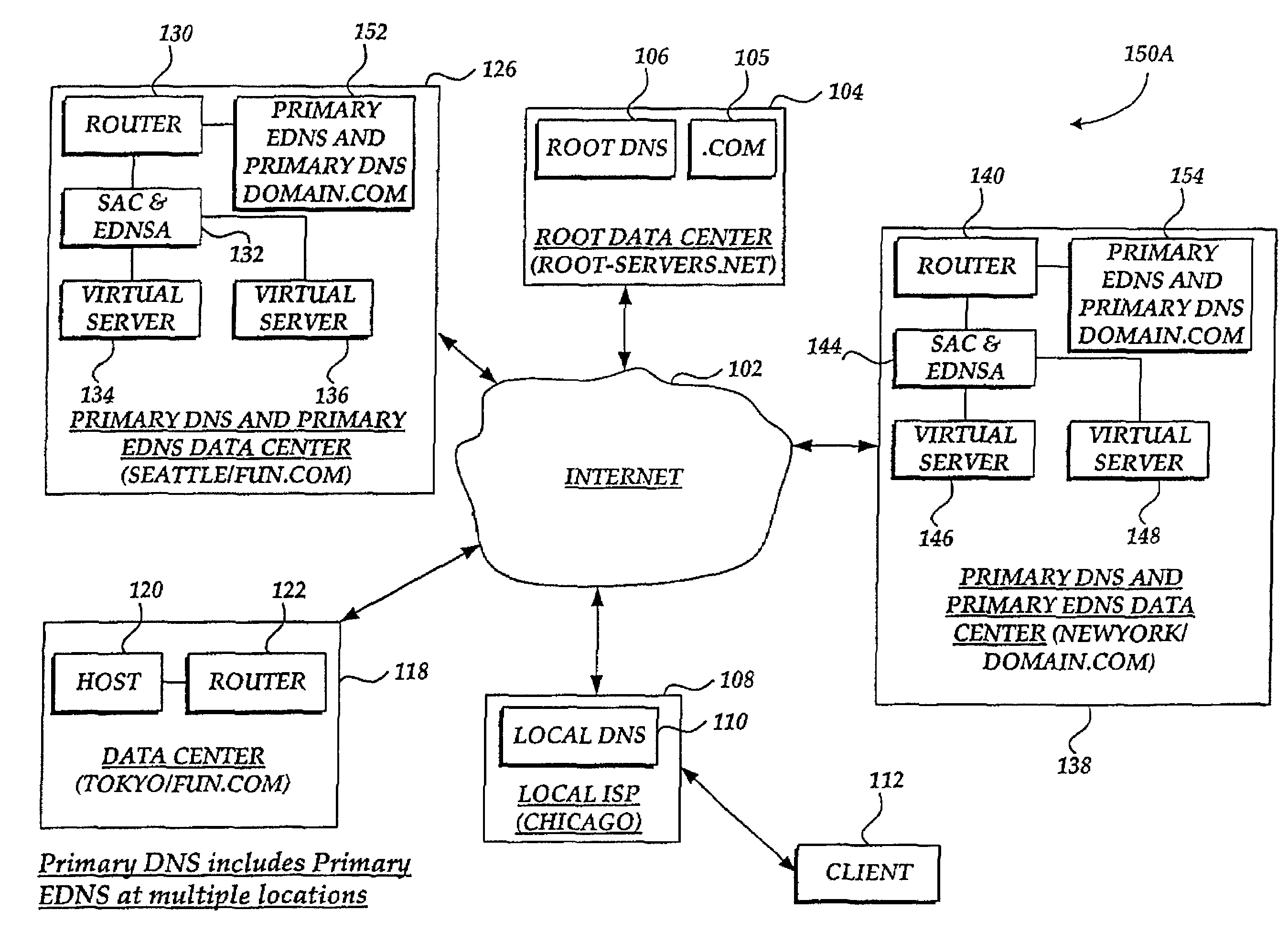
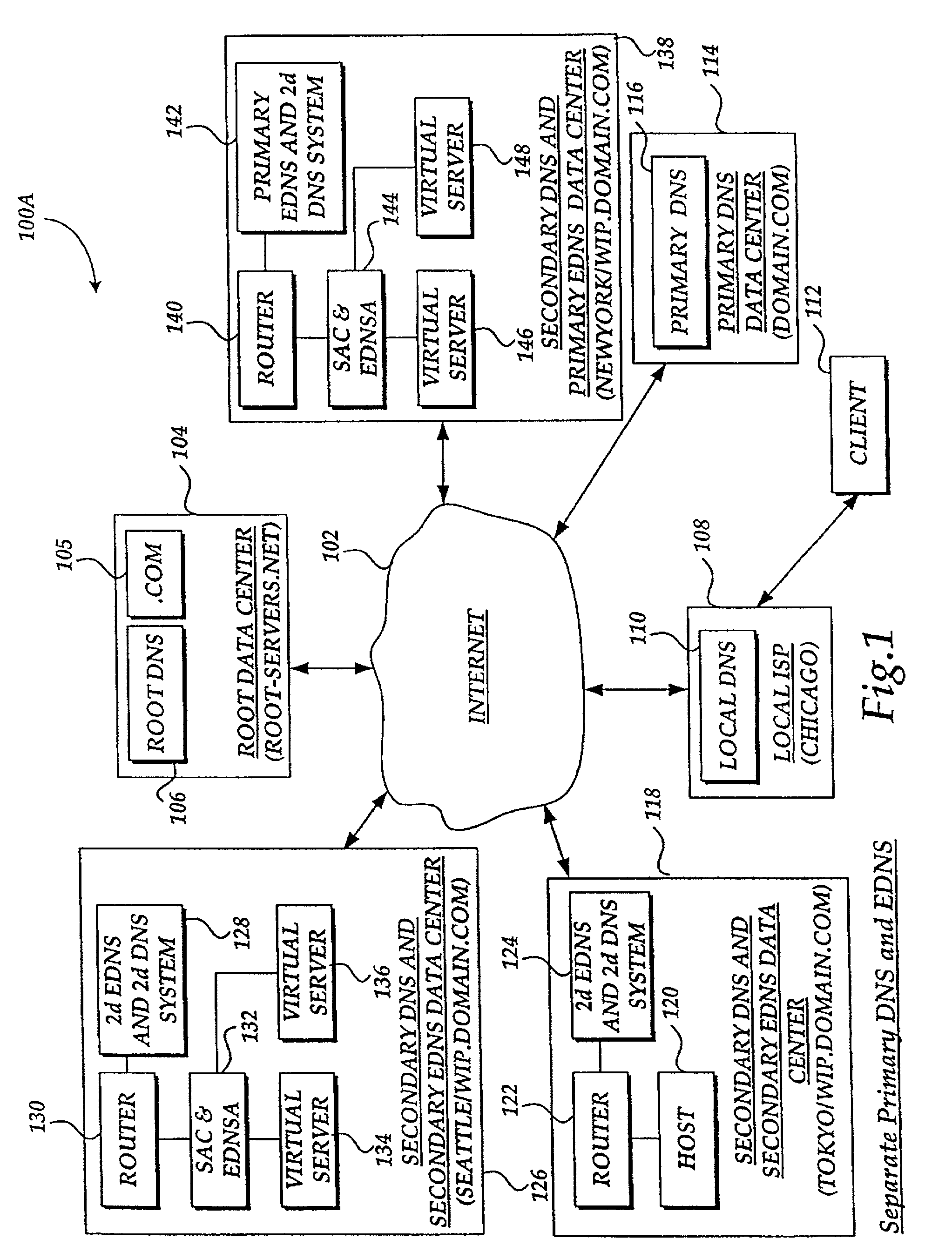
Method and system for balancing load distribution on a wide area network
InactiveUS7441045B2Close contactResource allocationMultiple digital computer combinationsDomain nameIp address
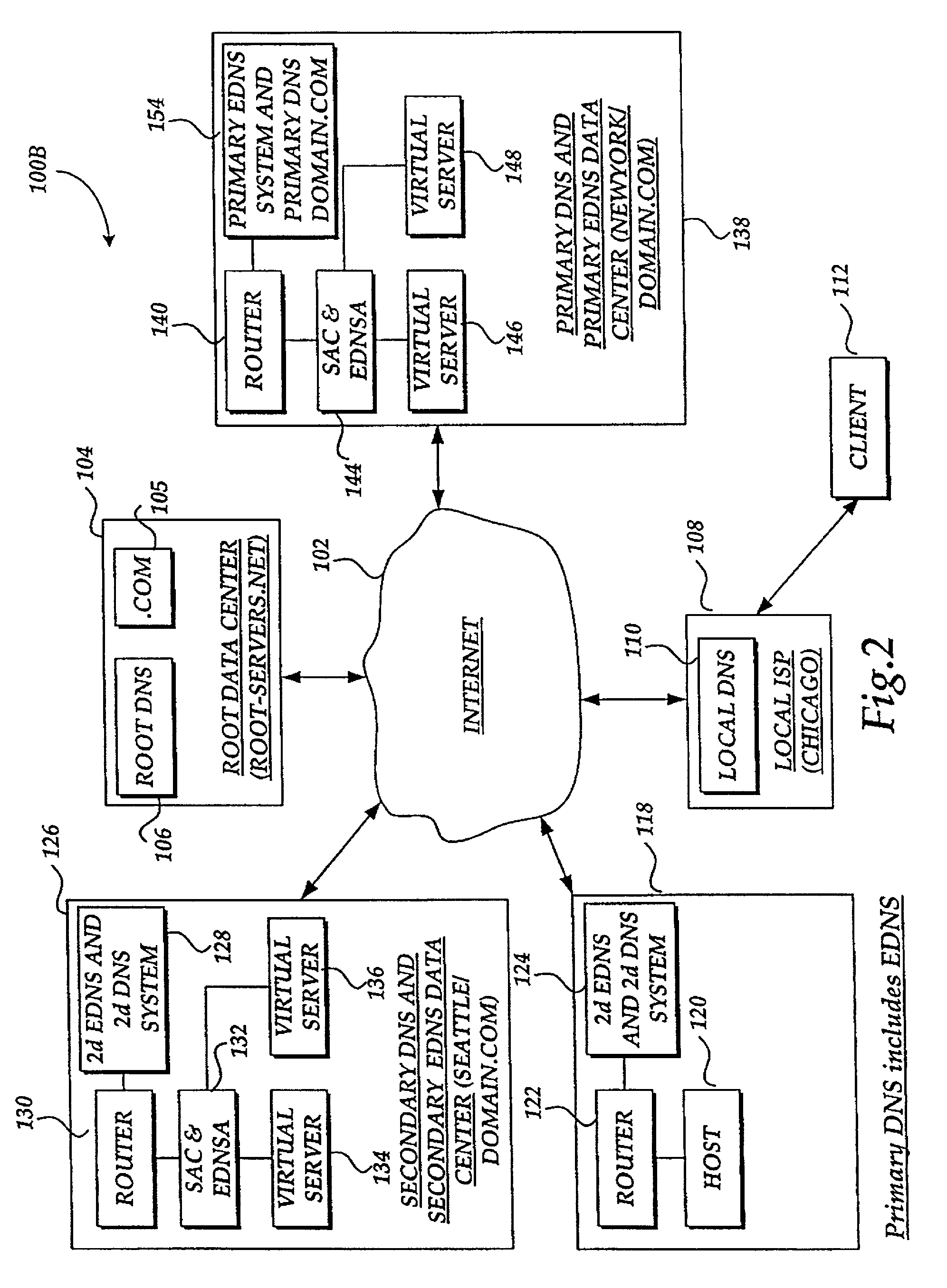
A system and method for balancing the load on virtual servers managed by server array controllers at separate data centers that are geographically distributed on a wide area network such as the Internet is described. The virtual servers provide access to resources associated with a domain name request by a client program. When a Primary Domain Name System (DNS) determined the requested domain name is delegated to a EDNS, the EDNS employs metric information and statistics to resolve an IP address for a virtual server that is selected by the EDNS to optimally balance the load and provide access to resources associated with the domain name. The EDNS may load balance name servers. Additionally, the name server load balancing system may bridge disparate content delivery networks. Internet addresses are divided into geographical information that is used to delegate traffic. Also, metric information is collected and analyzed to help distribute the traffic.
Owner:F5 NETWORKS INC
Content delivery and global traffic management network system
InactiveUS20020052942A1Meet cutting requirementsReduce trafficMetering/charging/biilling arrangementsError preventionWeb serviceCache server
Owner:AKAMAI TECH INC
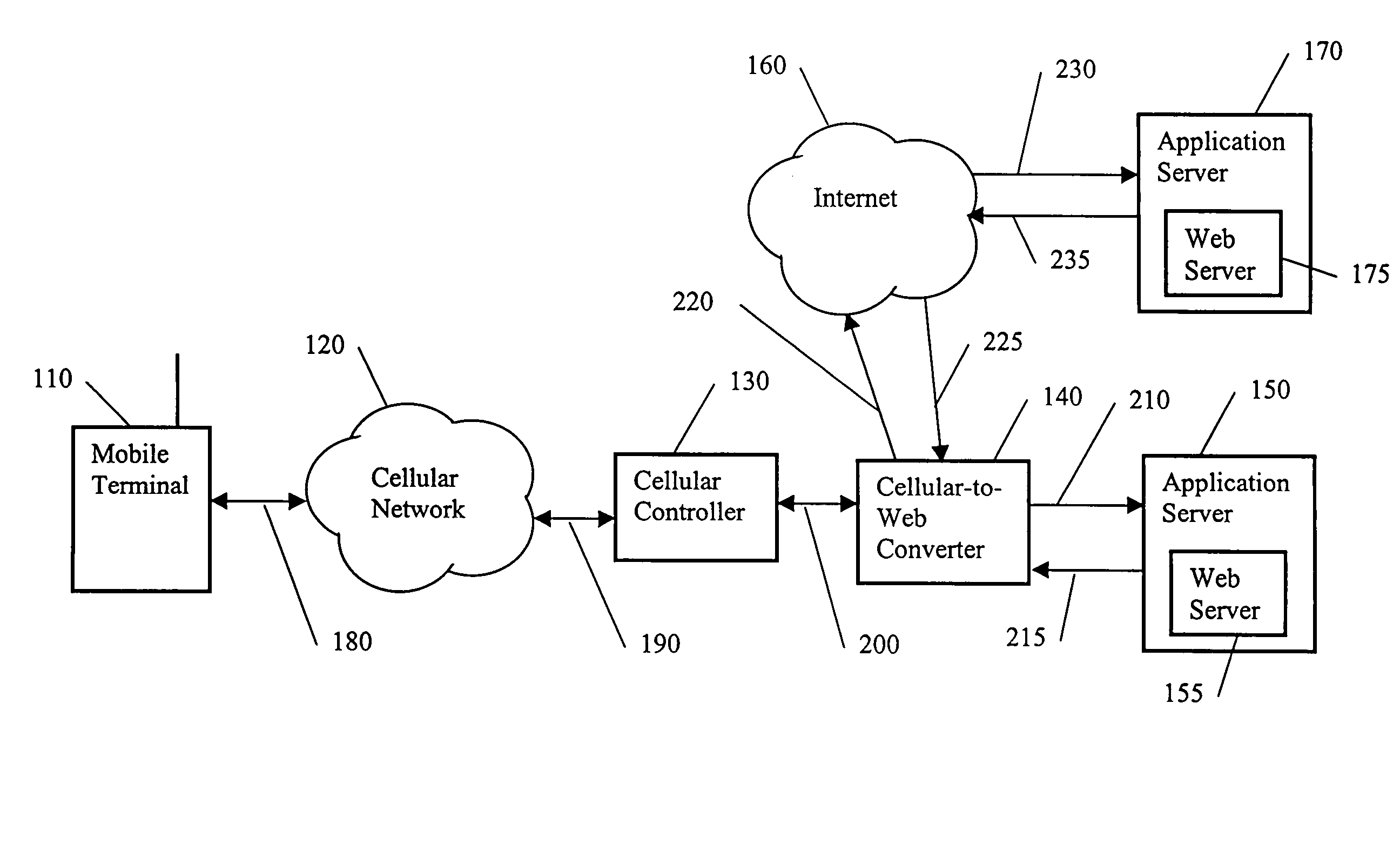
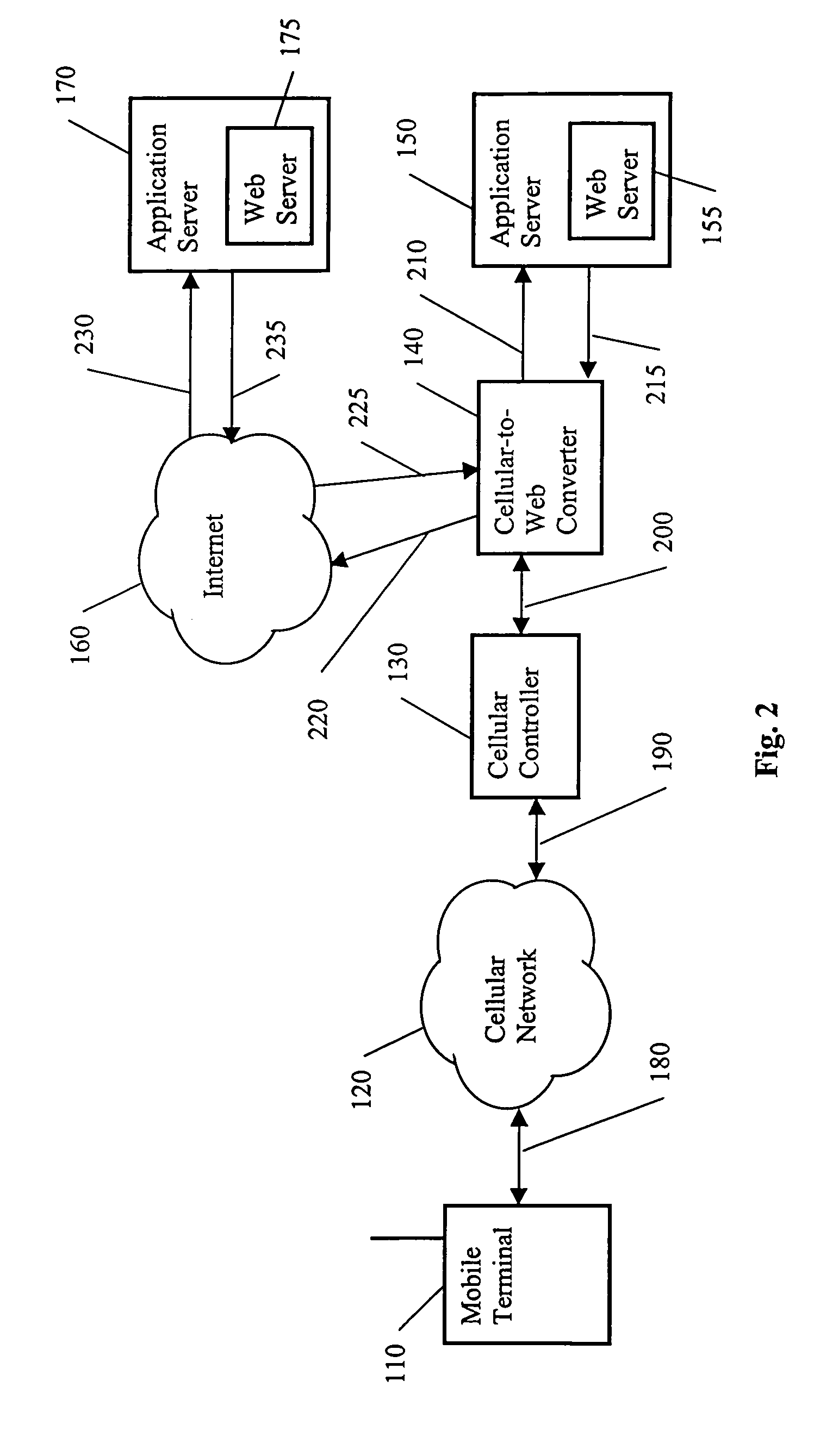
Web development and deployment using SMS and USSD
InactiveUS6961330B1Overcome disadvantagesIncrease chanceHybrid switching systemsInformation formatCommunications systemWeb development
A communication system contains a protocol converting controller. The controller receives an upstream mobile terminal message from a mobile terminal and converts the upstream mobile terminal message into an upstream Internet message to be used by an Internet server. Also, the controller receives a downstream Internet message from the Internet server and converts the downstream Internet message into a downstream mobile terminal message to be used by the mobile terminal. In one implementation, the downstream Internet message is output by an Internet application and contains an Internet page having mobile terminal data for creating the downstream mobile terminal message. The Internet page contains potentially responsive mobile terminal messages and Internet addresses that respectively correspond to the potentially responsive mobile terminal messages.
Owner:COMVERSE
Method and apparatus for machine-to-machine communication registration
ActiveUS20110128911A1Network traffic/resource managementBroadcast service distributionControl channelComputer science
Methods and apparatus are disclosed for Machine to Machine (M2M) communication registration. The methods provide single and periodic registration and may be device or network based. The devices in the system may be divided into groups. A single device member may perform the basic access steps for the group. Other devices may receive related access information on a control channel and use the information to access the system. The devices may send data, get updates, and then go to sleep. Internet addresses may be released or maintained. During a control cycle, the devices may wake up and listen to the control channel for any paging messages. Individual devices or the entire group may access the system. During a reporting cycle, all the devices may wake up and access the system to connect to the M2M system to upload data.
Owner:INTERDIGITAL PATENT HLDG INC
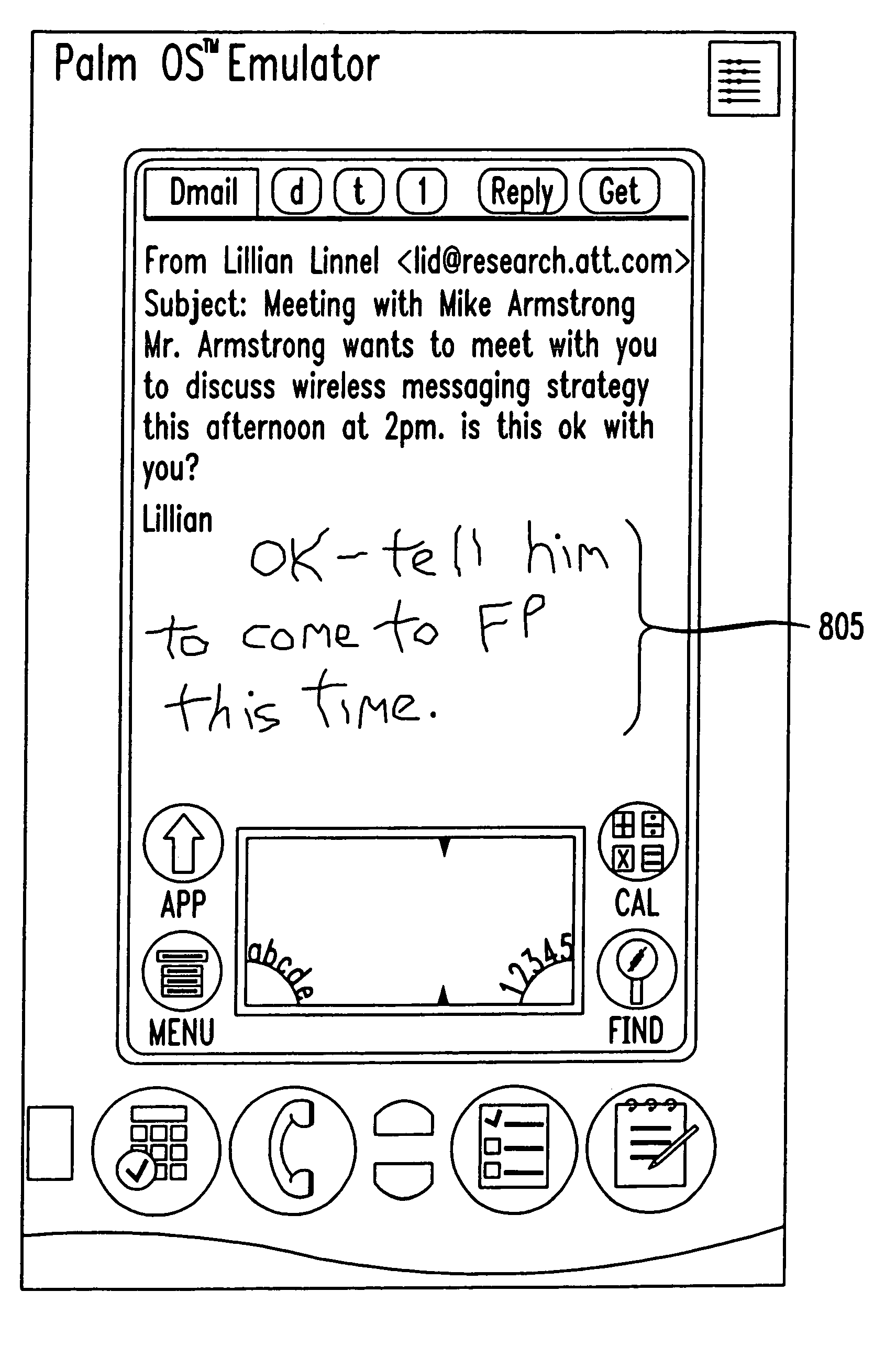
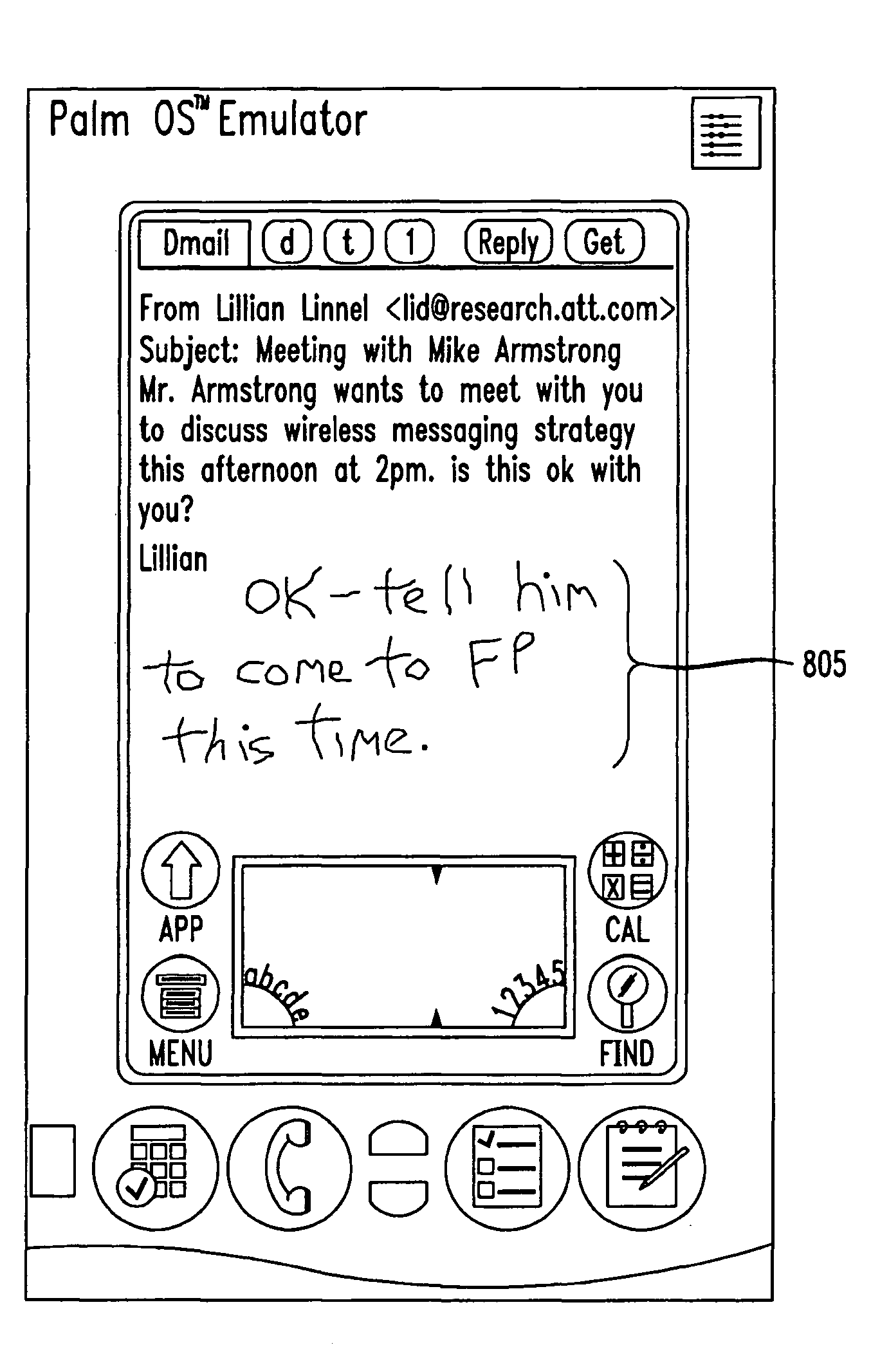
Method and system for handwritten electronic messaging
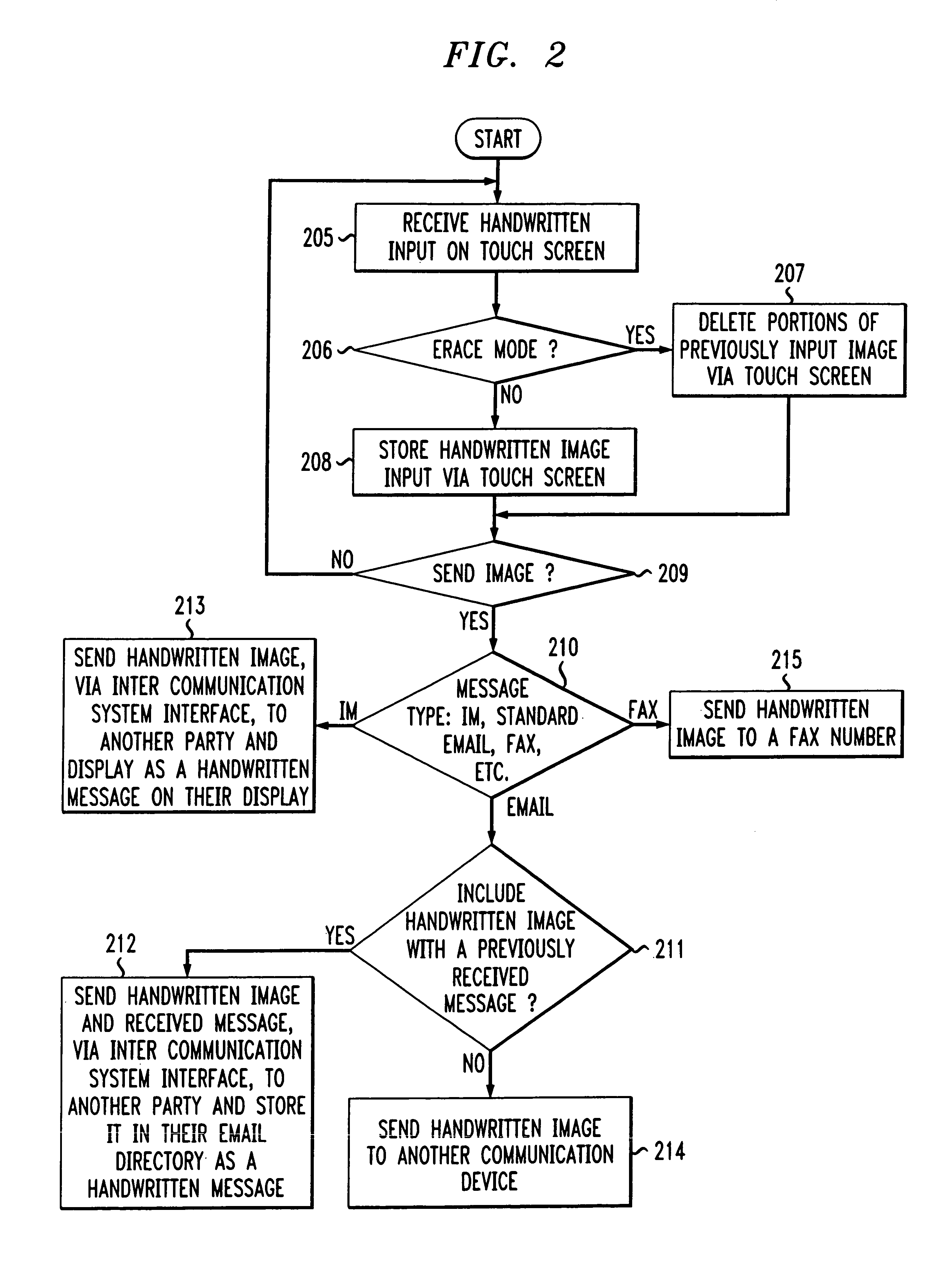
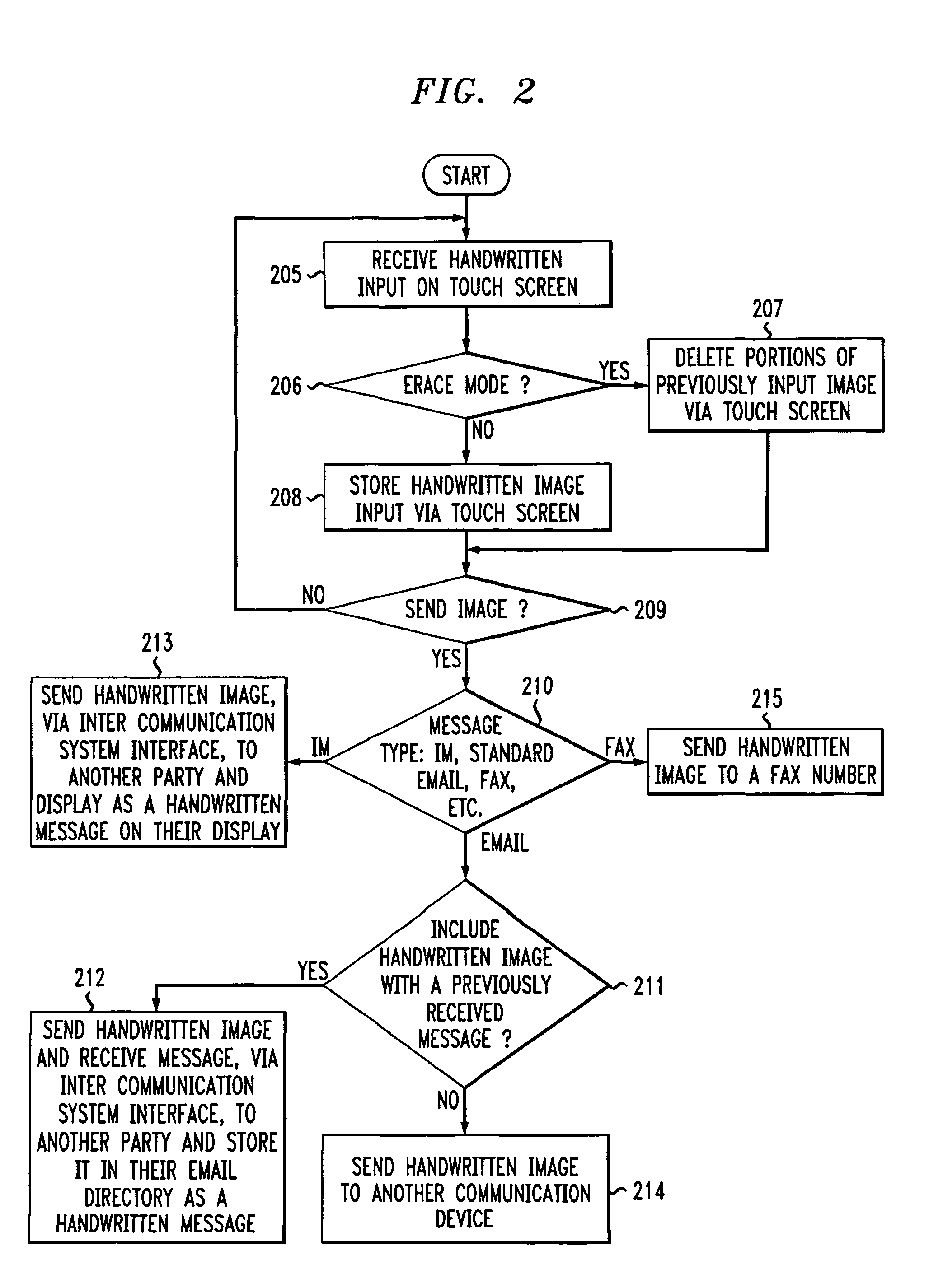
The present invention provides a system and method for providing handwritten messages with electronic communication devices. For example the electronic communication device may be a mobile communication device and may include a touch screen, screen buffer memory, processor, and transceiver. In preferred embodiments, the mobile communication device may be a personal digital assistant (PDA), a two-way pager, or a mobile telephone. The mobile communication device user may create a handwritten message on the touch screen using, for example, a stylus. In one exemplary embodiment, the handwritten message displayed on the touch screen may be stored to the buffer memory as an image, directed by the processor to the transceiver, and transmitted via a wireless connection to, for example, a wireless base station and the Internet. The Internet may route the handwritten message image to a desired Internet address. The handwritten message may be displayed in real time on the recipient's display, e.g., an instant message (IM) session, or stored in their email mailbox for later retrieval and display. The recipient may type in a text message in response to the hand written message, and this message will be transmitted to mobile communication device and displayed on the mobile communication device. In another embodiment, the receiving party may also have handwritten messaging capabilities (included with, for example, a PC, PDA or a mobile phone) and may respond with a handwritten message.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
System and method for placing orders via the internet
InactiveUS20100030662A1Simple and easily enteredFor direct connectionDigital computer detailsMarketingDomain nameWeb service
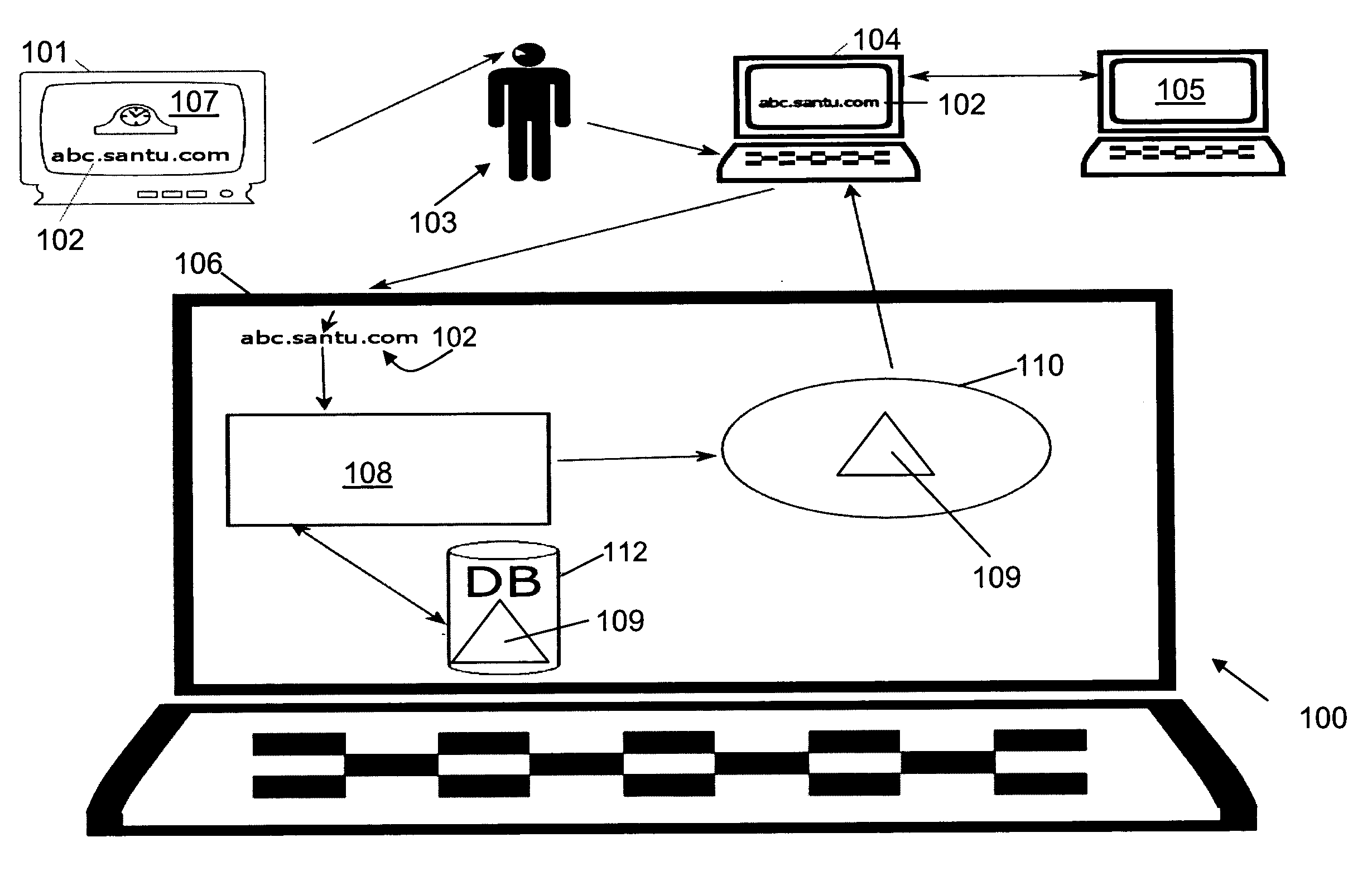
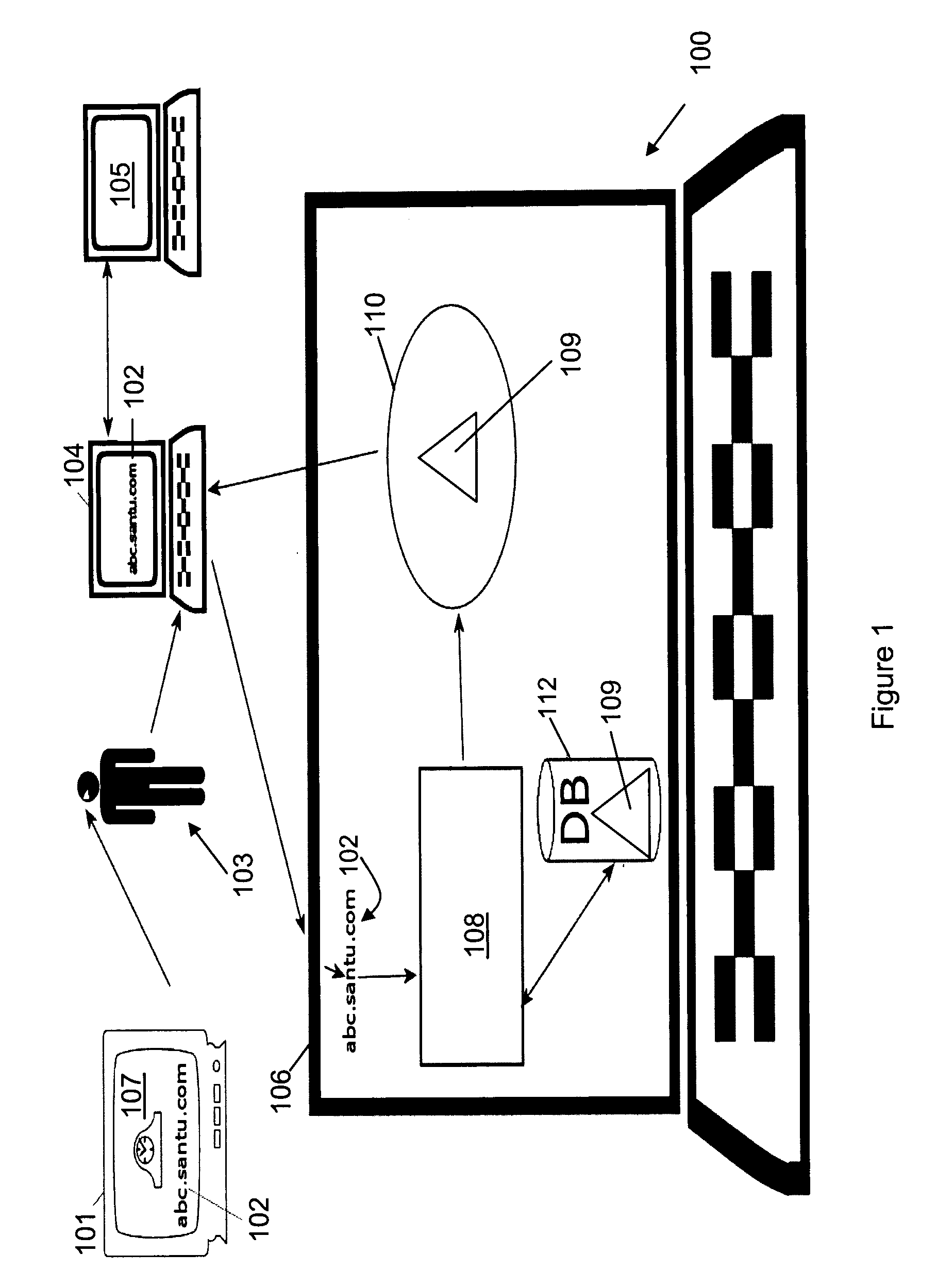
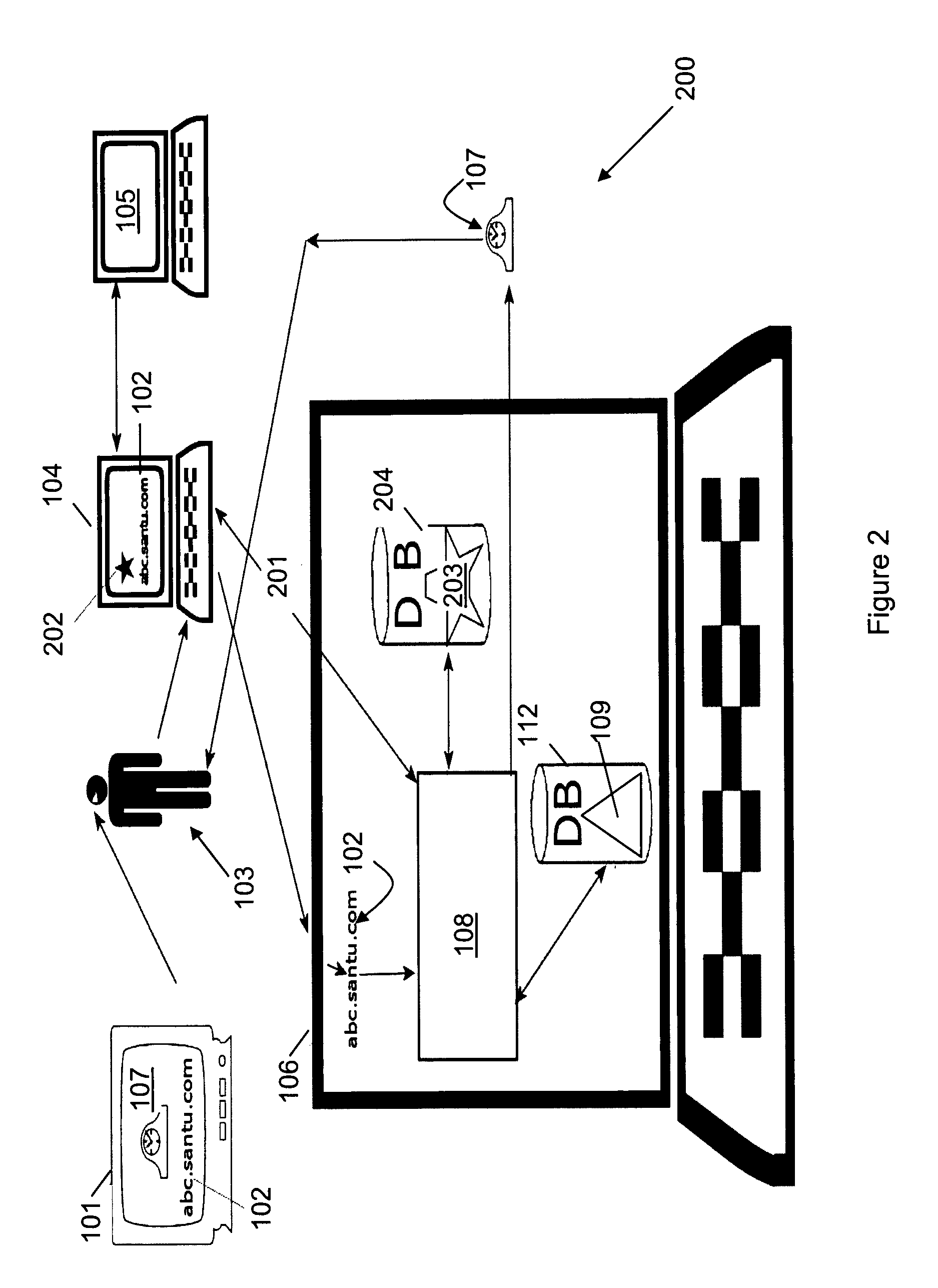
A system (100) enables a customer (103) to order goods via the Internet using a browsing device (104). The system includes at least one web server (106). The system further includes at least one DNS server (105) within a DNS system, which is configured to establish an association between goods (107), at least one corresponding domain name (102), and the web server (106). A request issued to the DNS server (105) to resolve the domain name (102) results in a response providing an Internet address of the web server (106). The web server (106) is configured to respond to a connection request initiated using the Internet address and a corresponding network resource locator including the domain name (102) by executing an ordering process. In various embodiments, the network resource locator may include a product identifier within the domain name, or within a distinct component thereof. The ordering process may proceed directly and automatically to the final placement of an order on behalf of the customer (103), or may include a check-out process prior to the final placement of an order.
Owner:GLOBECHARGE
Internet linking from image content
InactiveUS7058697B2Commercial value is not compromisedMaximization of identification signal energyCoin-freed apparatusRecord information storageGraphicsThe Internet
Address information is steganographically encoded into audio or graphic data, and thereafter decoded to permit linking to the internet. The address information can be a literal URL, or may be an index to a database from which a corresponding URL can be obtained.
Owner:DIGIMARC CORP
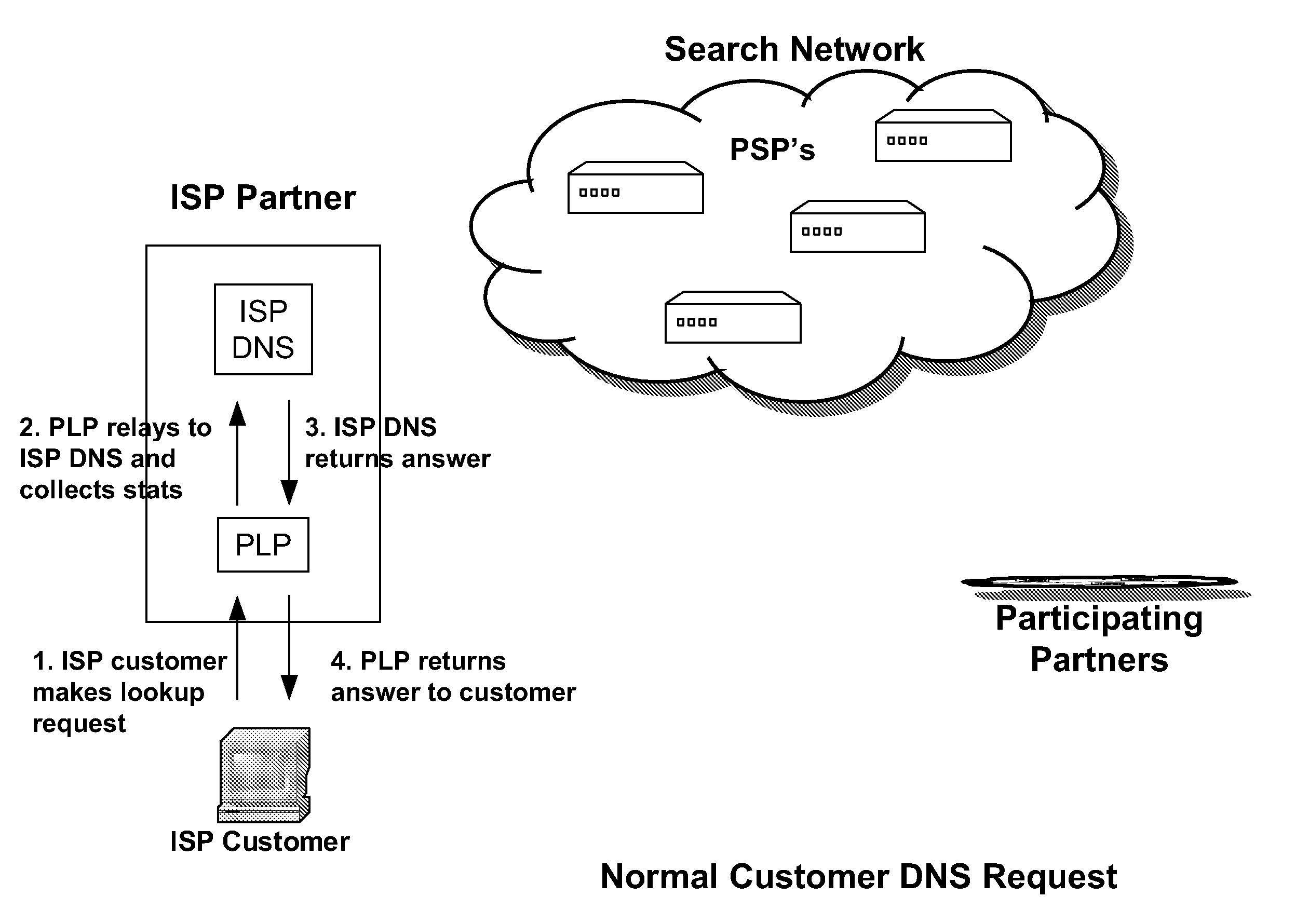
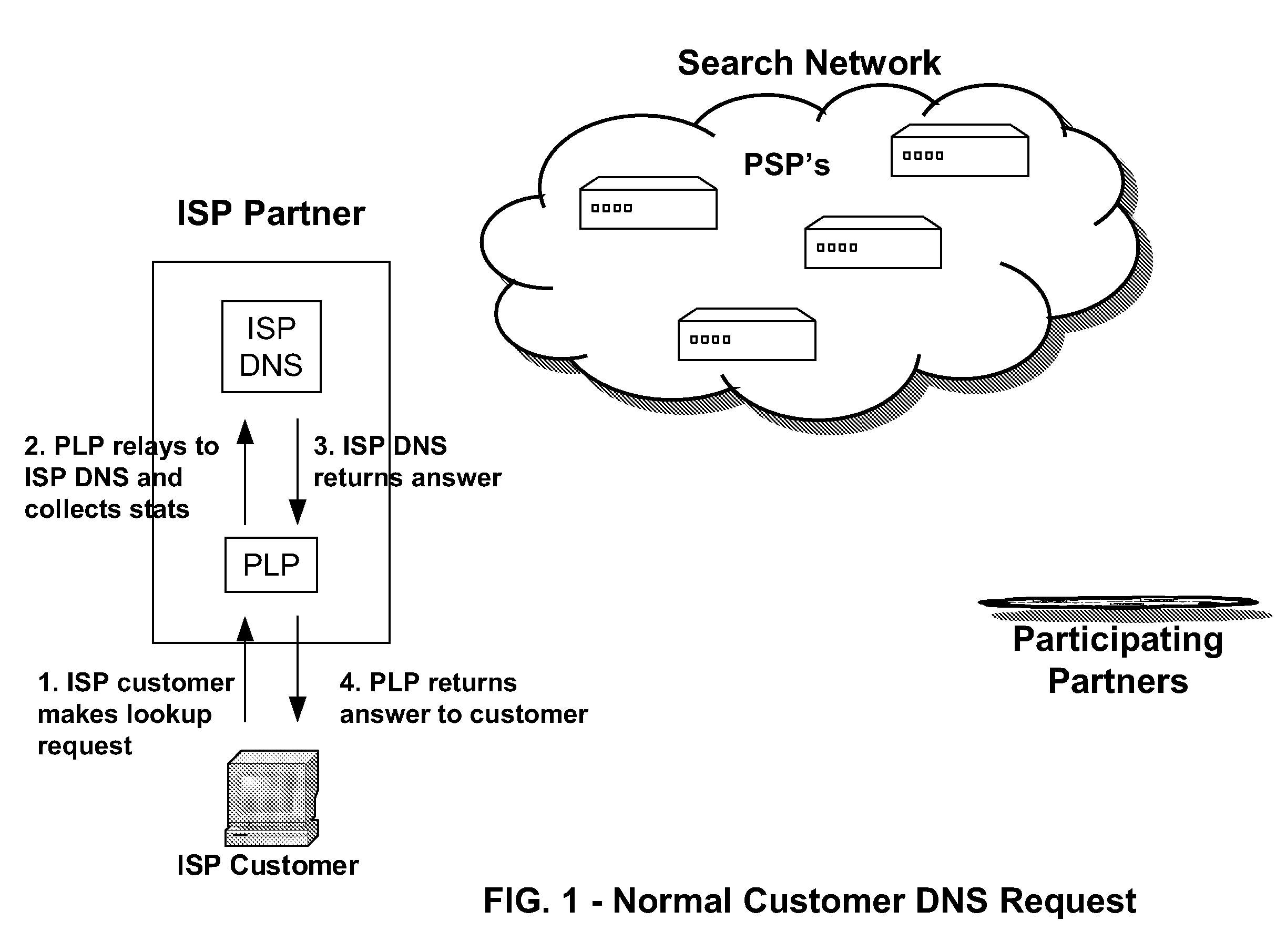
Systems and methods for direction of communication traffic
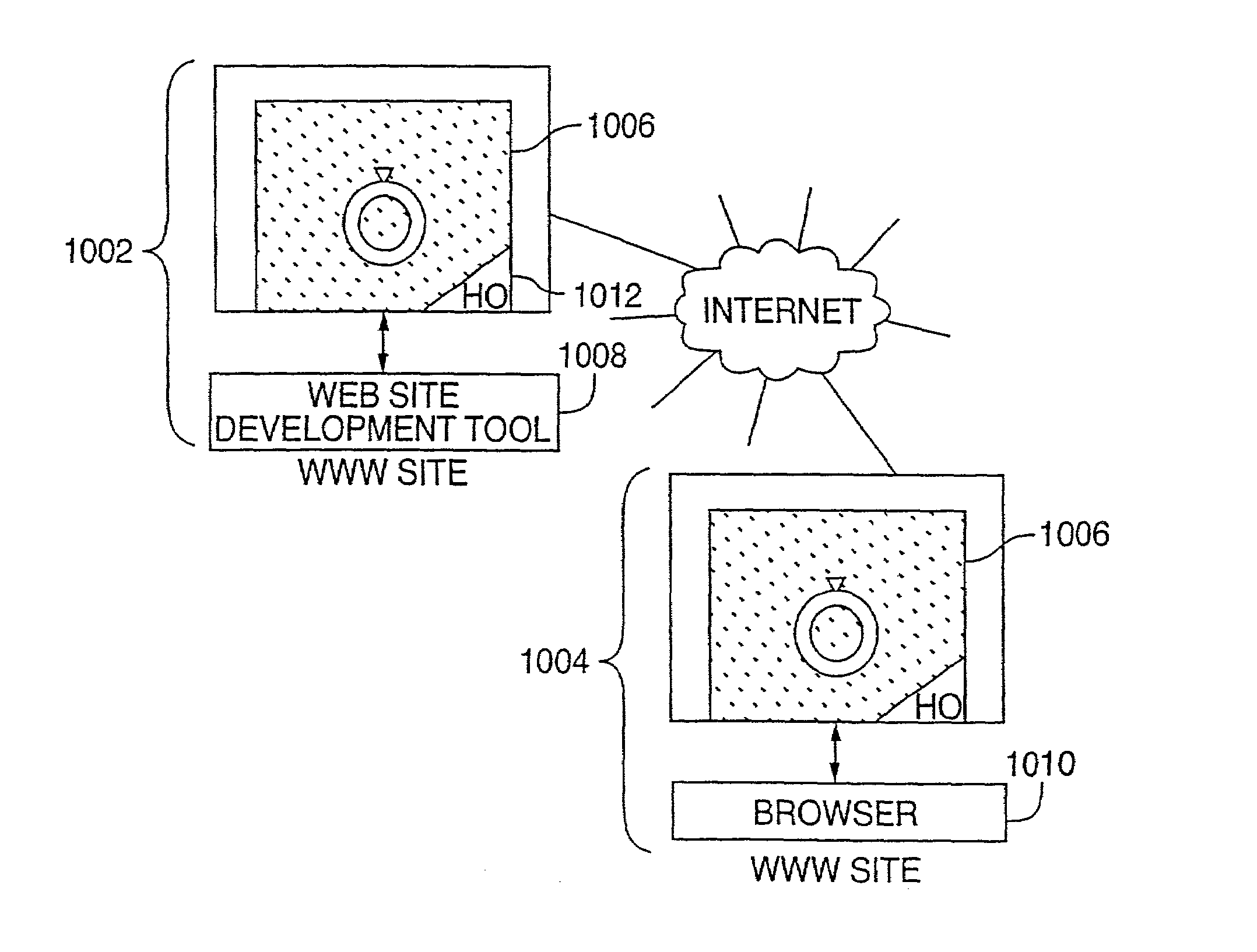
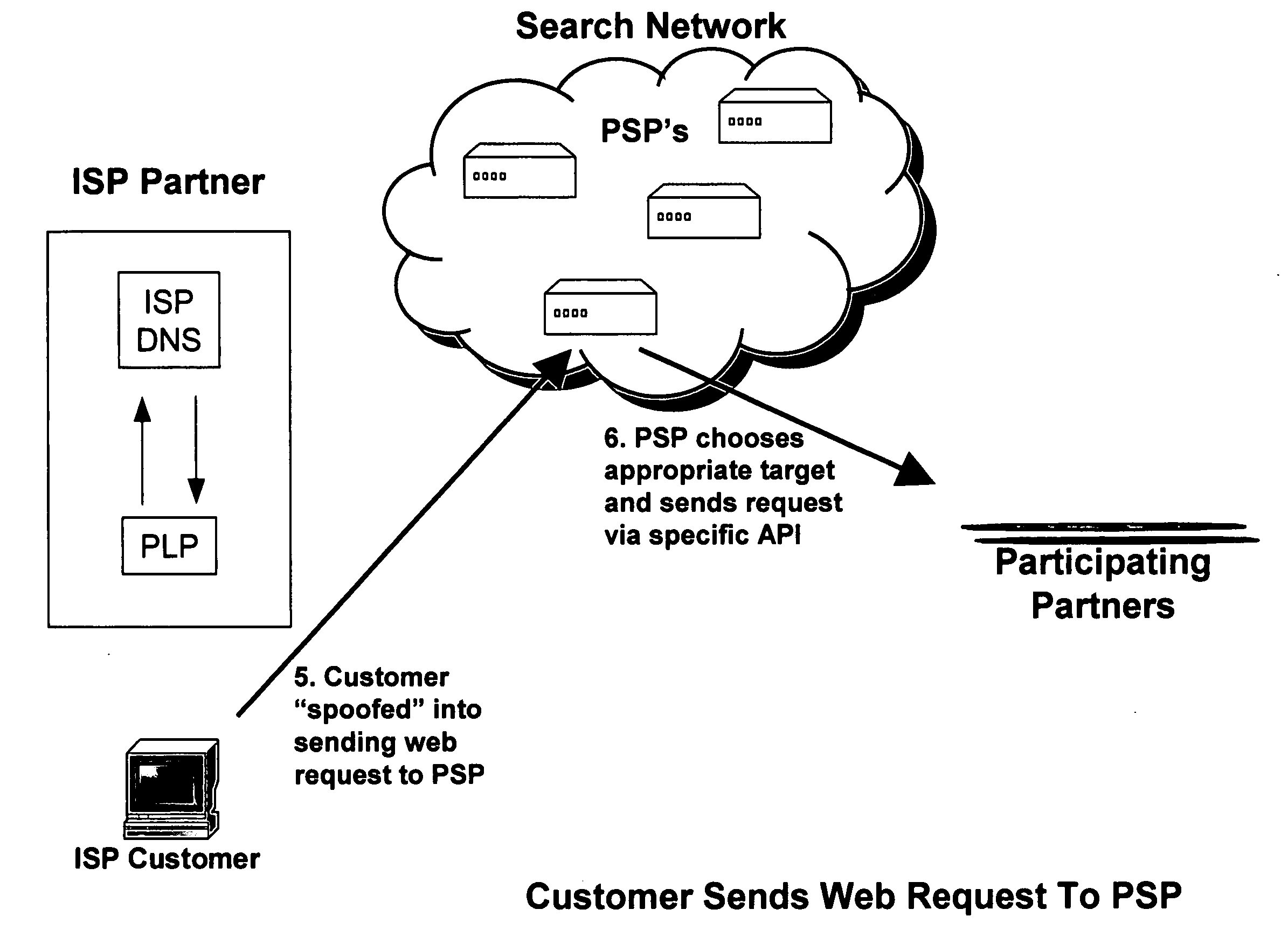
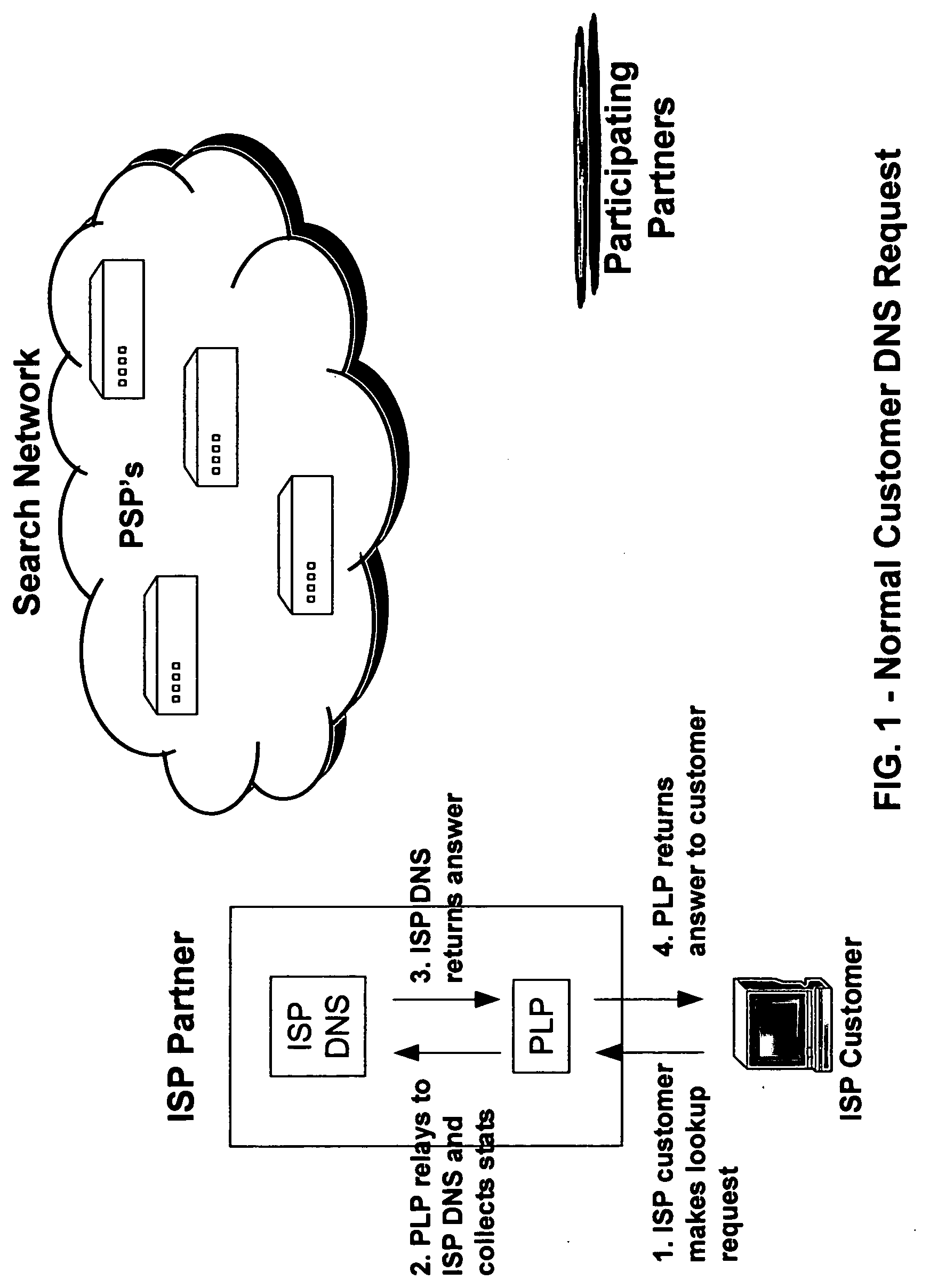
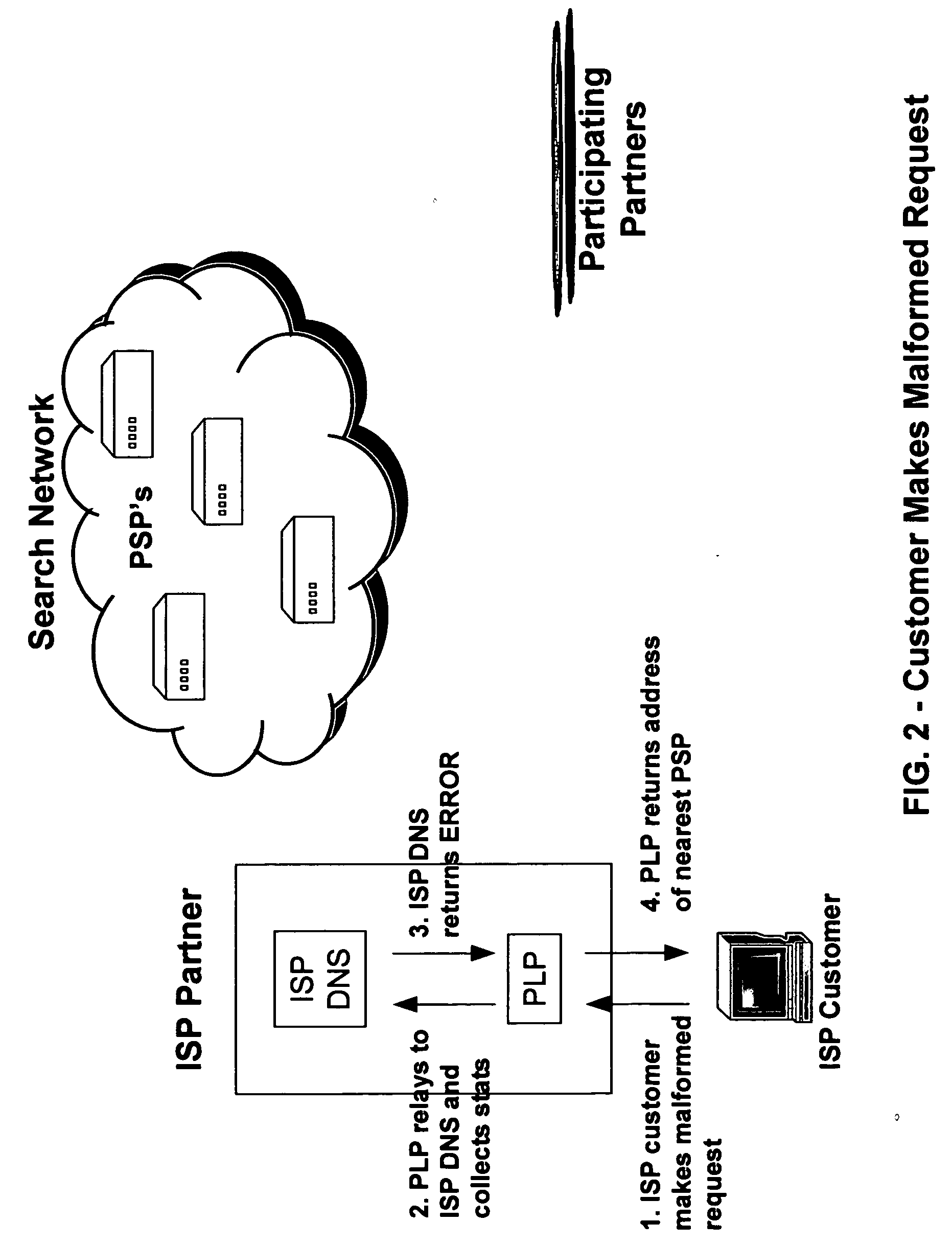
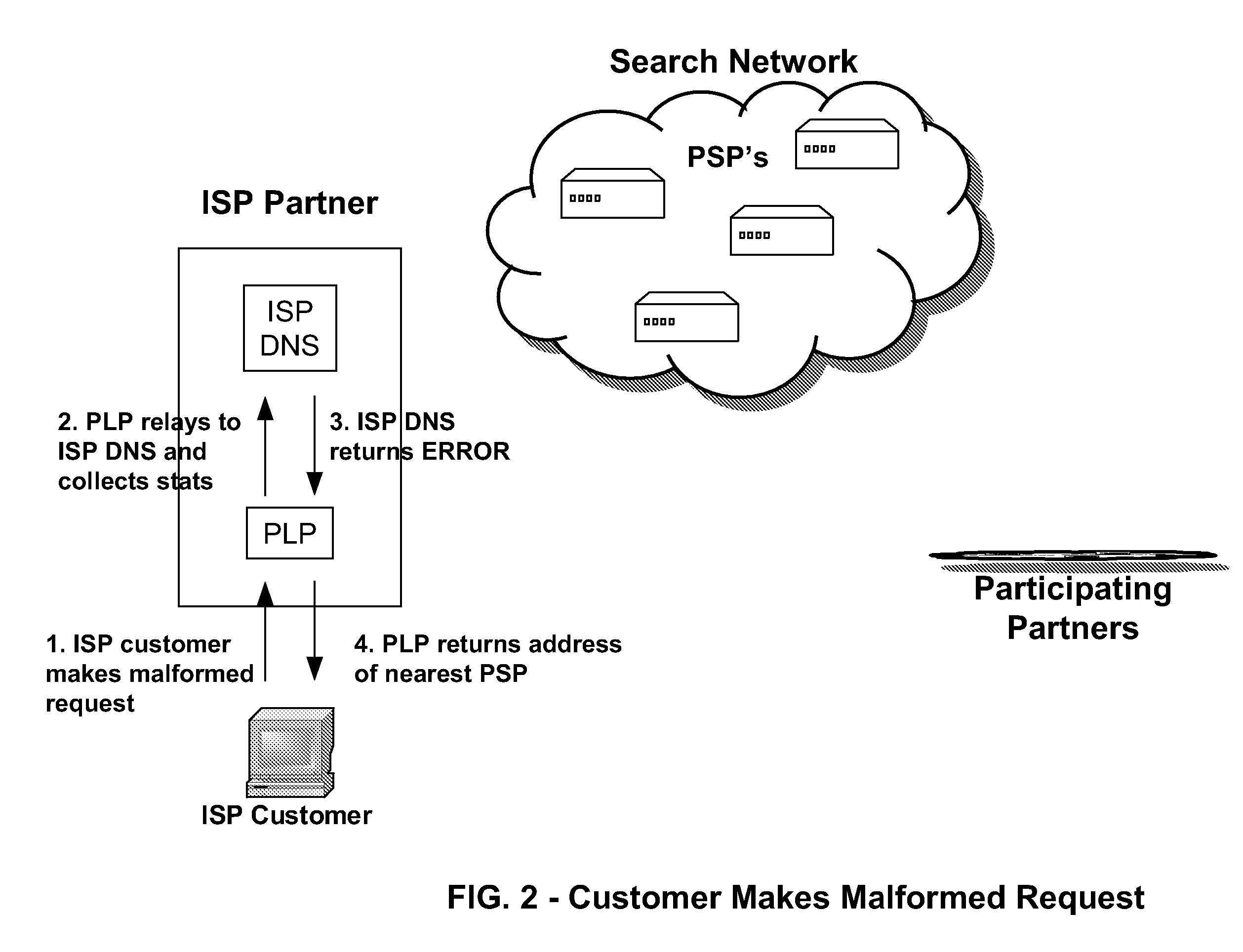
An Internet traffic redirection architecture is disclosed that allows for directing of trash traffic to specified sites. The system or method allows a controller, such as an ISP, to benefit from mistyped Internet addresses so that participating partners of the ISP are presented to the customer when the requests a web site that is not found or does not exist. The system decreases lost traffic by means of capturing unresolved “trash” traffic on the Internet and redirecting said traffic to a search engine partner and / or other partners.
Owner:PAXFIRE
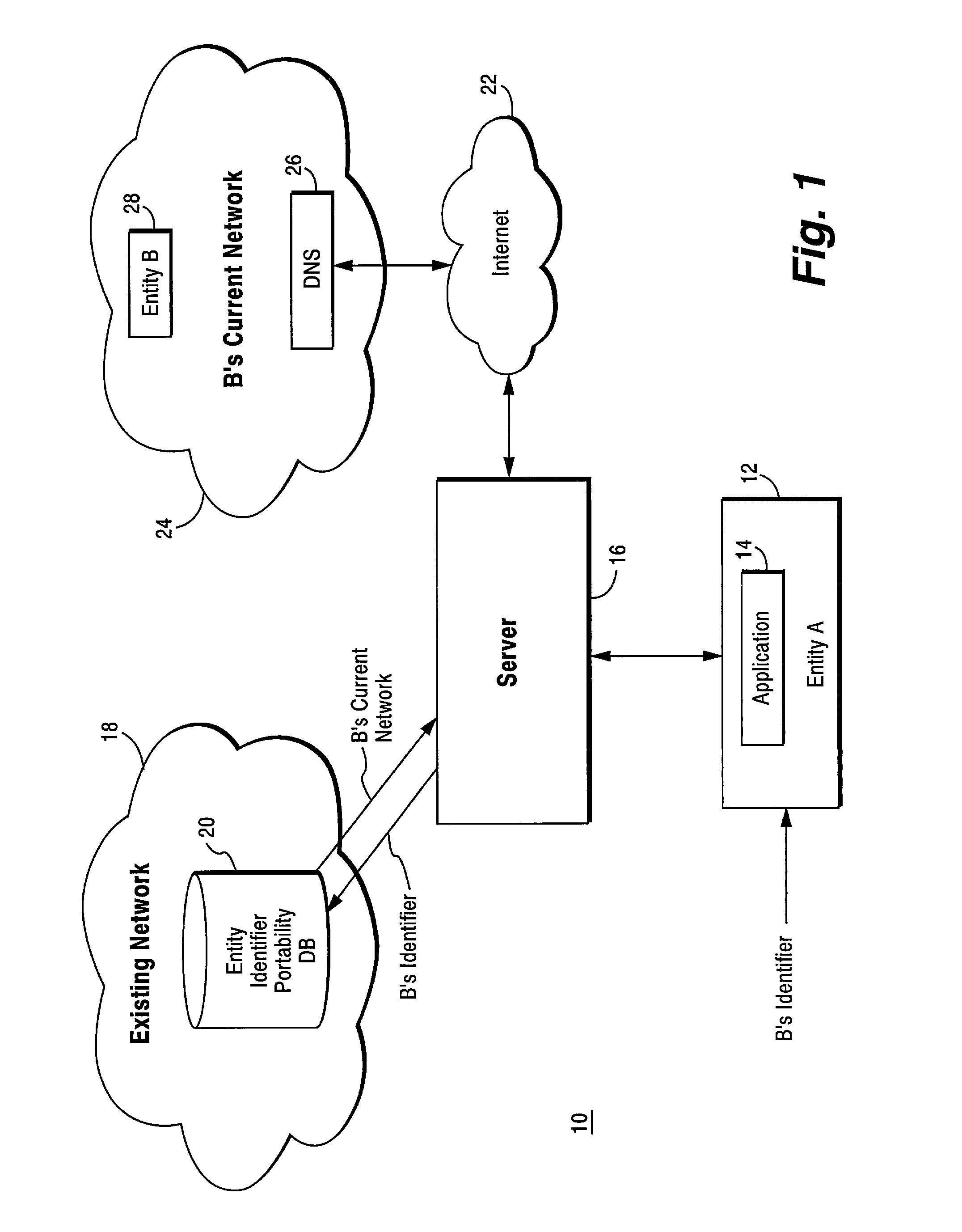
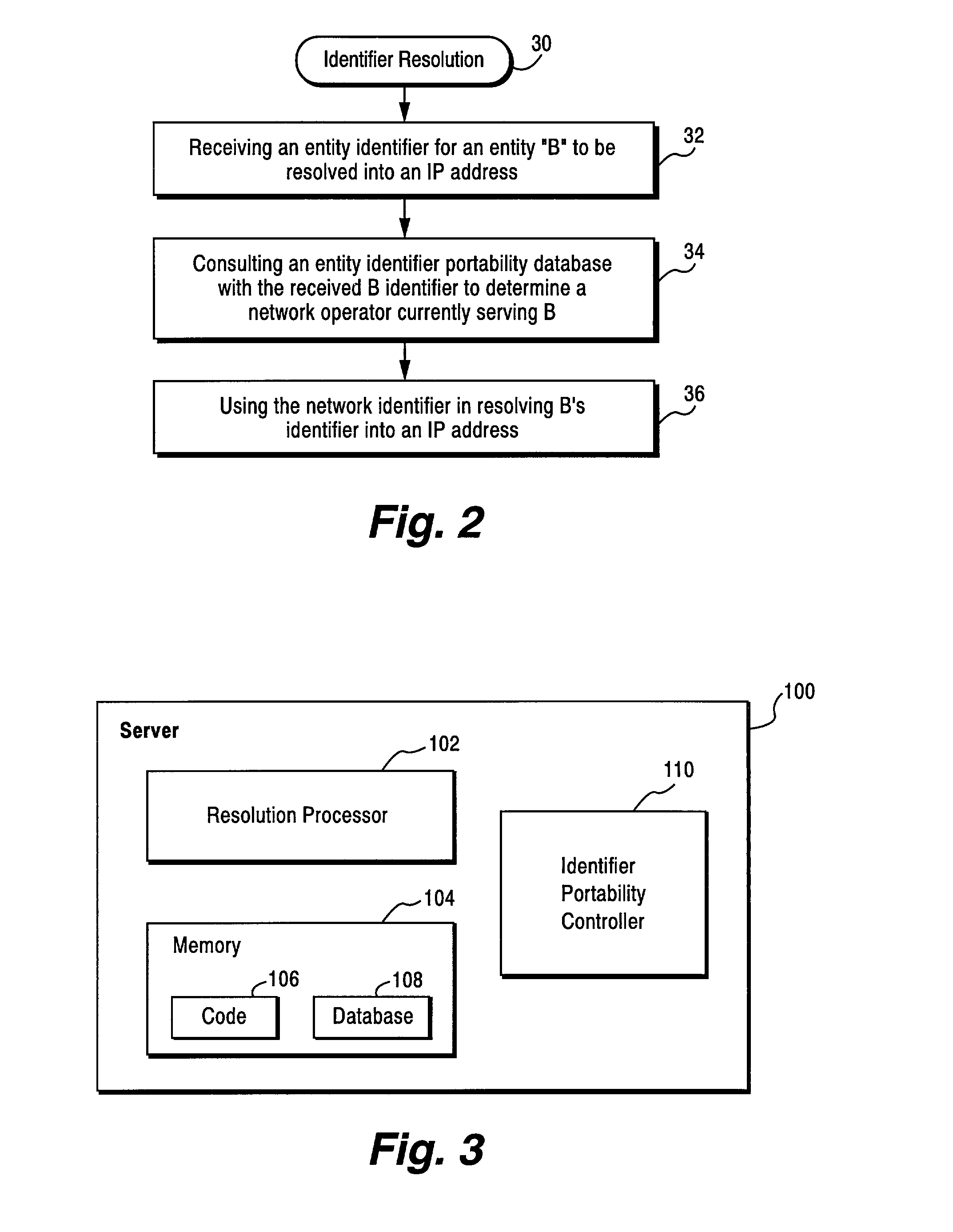
Method and apparatus for resolving an entity identifier into an internet address using a domain name system (DNS) server and an entity identifier portability database
ActiveUS7027582B2Faster and more efficient processingEasy to handleMultiplex system selection arrangementsSpecial service provision for substationDomain nameEntity identifier
The present invention provides an efficient way of resolving telephone numbers and other entity / device identifiers into Internet addresses as well as accommodating portability of those telephone numbers and other entity / device identifiers without having to substantially modify or rework the domain naming system (DNS) infrastructure or established number portability schemes. Self-contained, additional functionality is implemented on a DNS server which allows smooth IP address resolution of telephone numbers or other entity / device identifiers by taking advantage of existing portability databases without impacting the existing networks that create and maintain such portability databases.
Owner:INTERDIGITAL PATENT HLDG INC
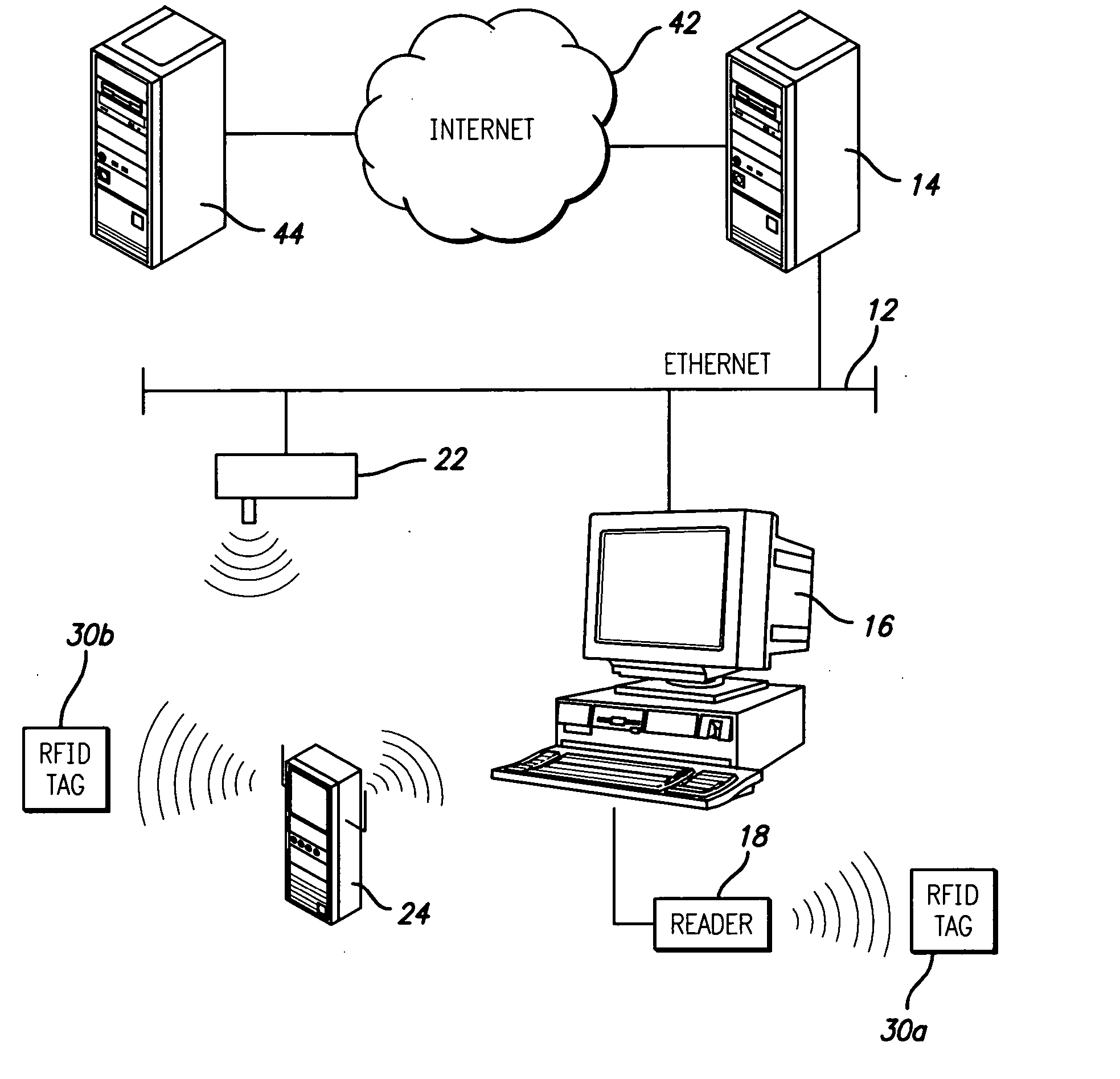
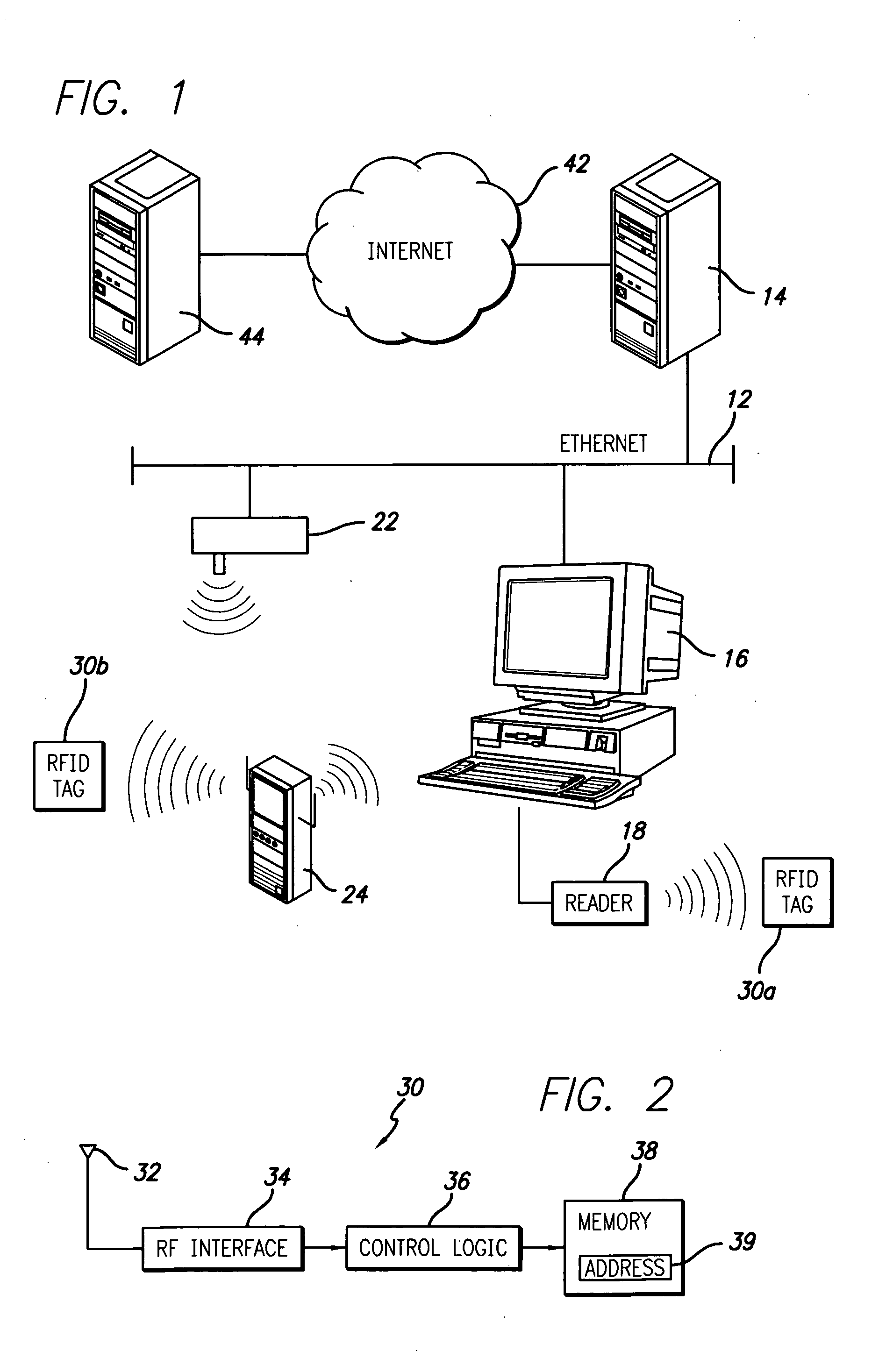
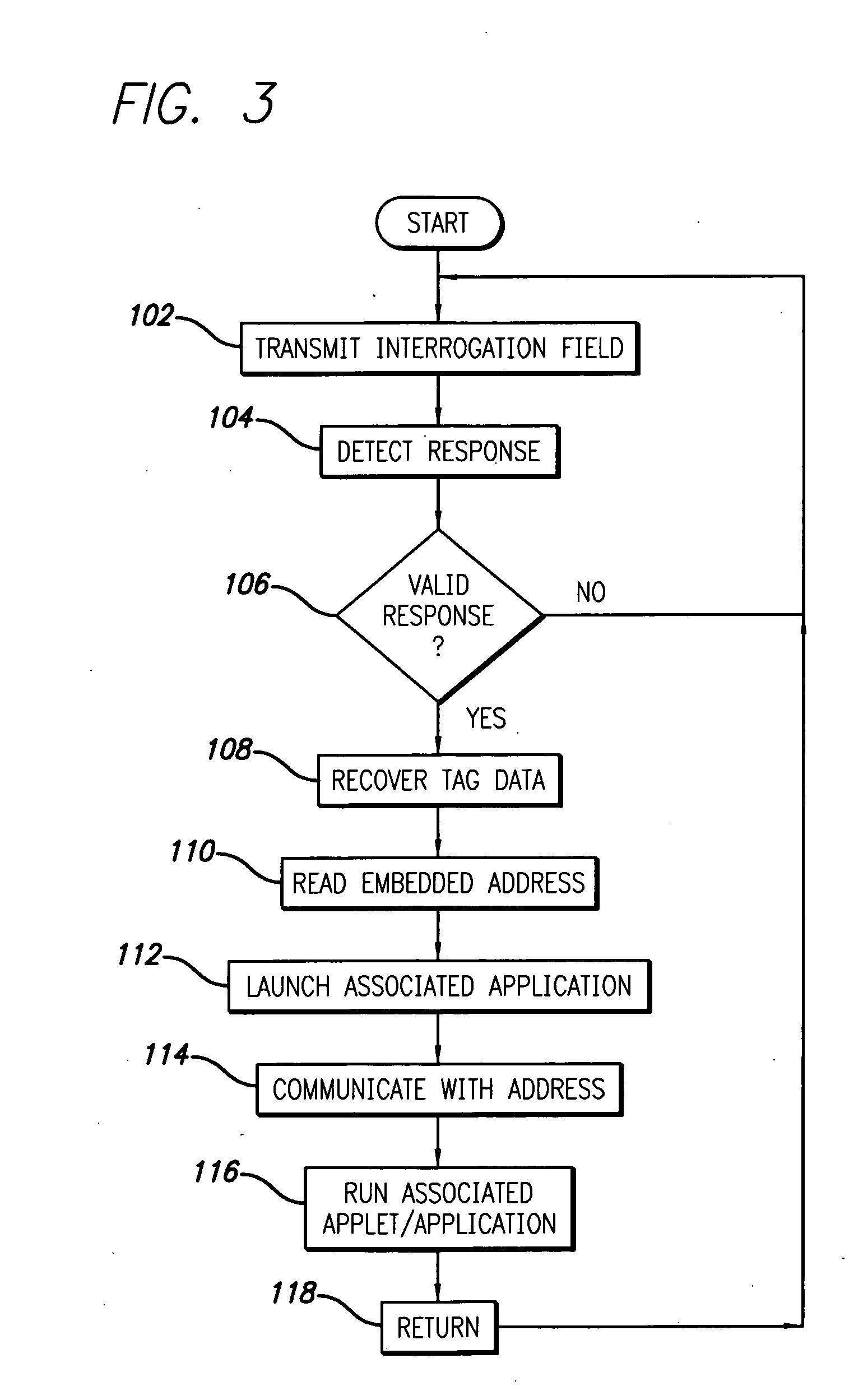
RFID tag with embedded Internet address
InactiveUS20060168644A1Easy to implementDigital data processing detailsUser identity/authority verificationEmail addressData field
A radio frequency identification (RFID) transponder comprises a memory space having a predetermined data field for storing a destination address identifying a location on the Internet corresponding to the RFID transponder. The Internet address may further comprise an e-mail address or Uniform Resource Locator (URL). In an embodiment of the invention, a computer network comprises a client computer having an application executing thereon, an RFID tag having a memory containing an Internet address corresponding to the RFID tag, and an RFID reader connected to the client computer and adapted to communicate with the RFID tag. The RFID reader recovers the Internet address from the RFID tag and provides the Internet address to the client computer. The client computer thereby communicates with the location defined by the Internet address corresponding to the RFID tag using the application. A host server is connected to the client computer, and may be further connected to the Internet. The client computer thereby can access the Internet location by operation of the application through the host server.
Owner:INTERMEC IP
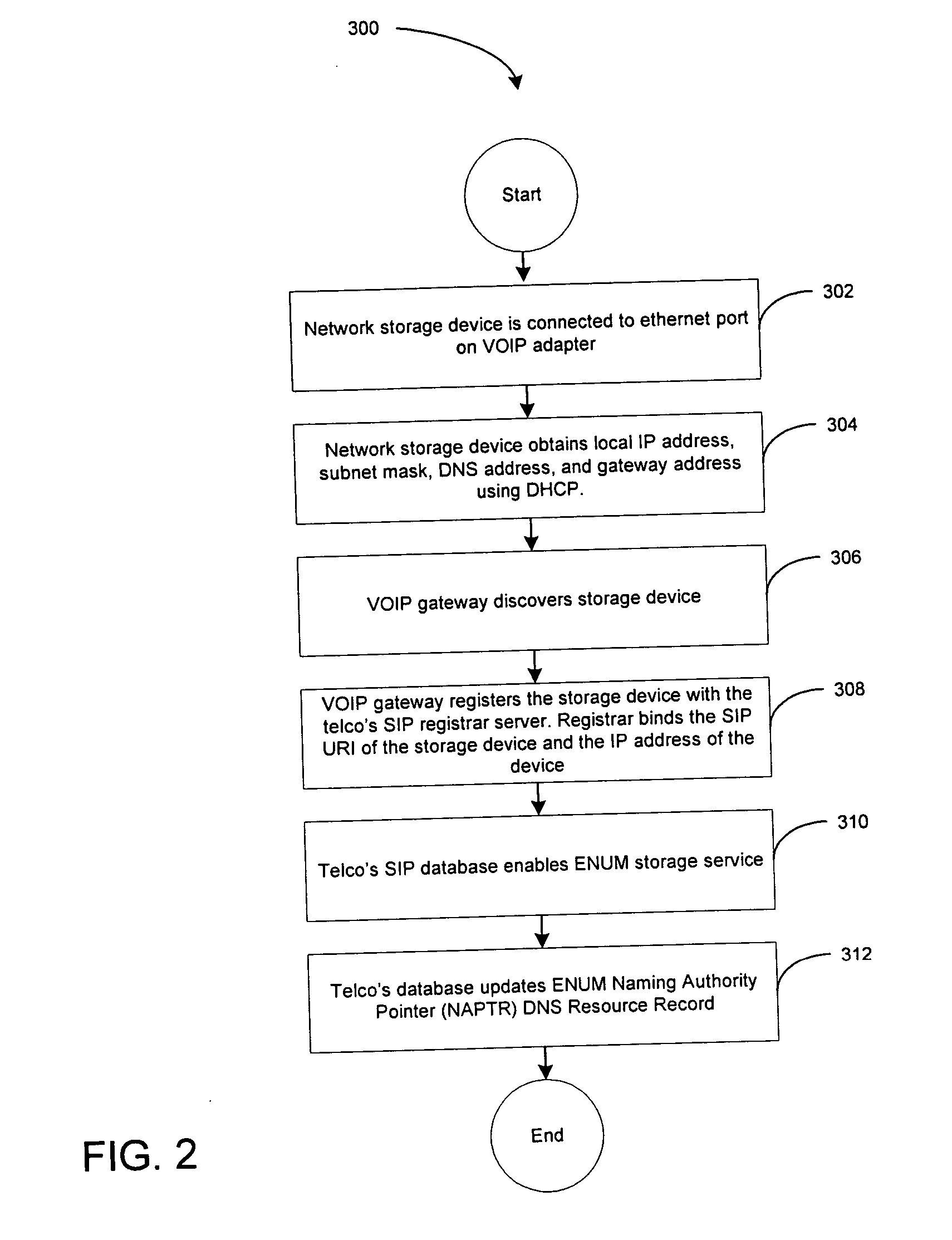
Method and system for accessing a storage or computing device via the Internet
InactiveUS20070043829A1Easy to implementConvenient and efficient and secure accessMultiple digital computer combinationsTransmissionDomain nameDomain Name System
A system and method for accessing a storage or computing device via the Internet using a Domain Name System (DNS)-based infrastructure is disclosed. One aspect of the methodology pertains to registering a storage device with a SIP registration server and associating it with an E.164 phone number. In one embodiment, a media device uses an ENUM engine to translate an E.164 number associated with a target storage device into a routable Internet address by using a Domain Name System (DNS)-based infrastructure. The routable Internet address is further used to establish real-time communication between the media device and the target device.
Owner:EQUISPAN LLC
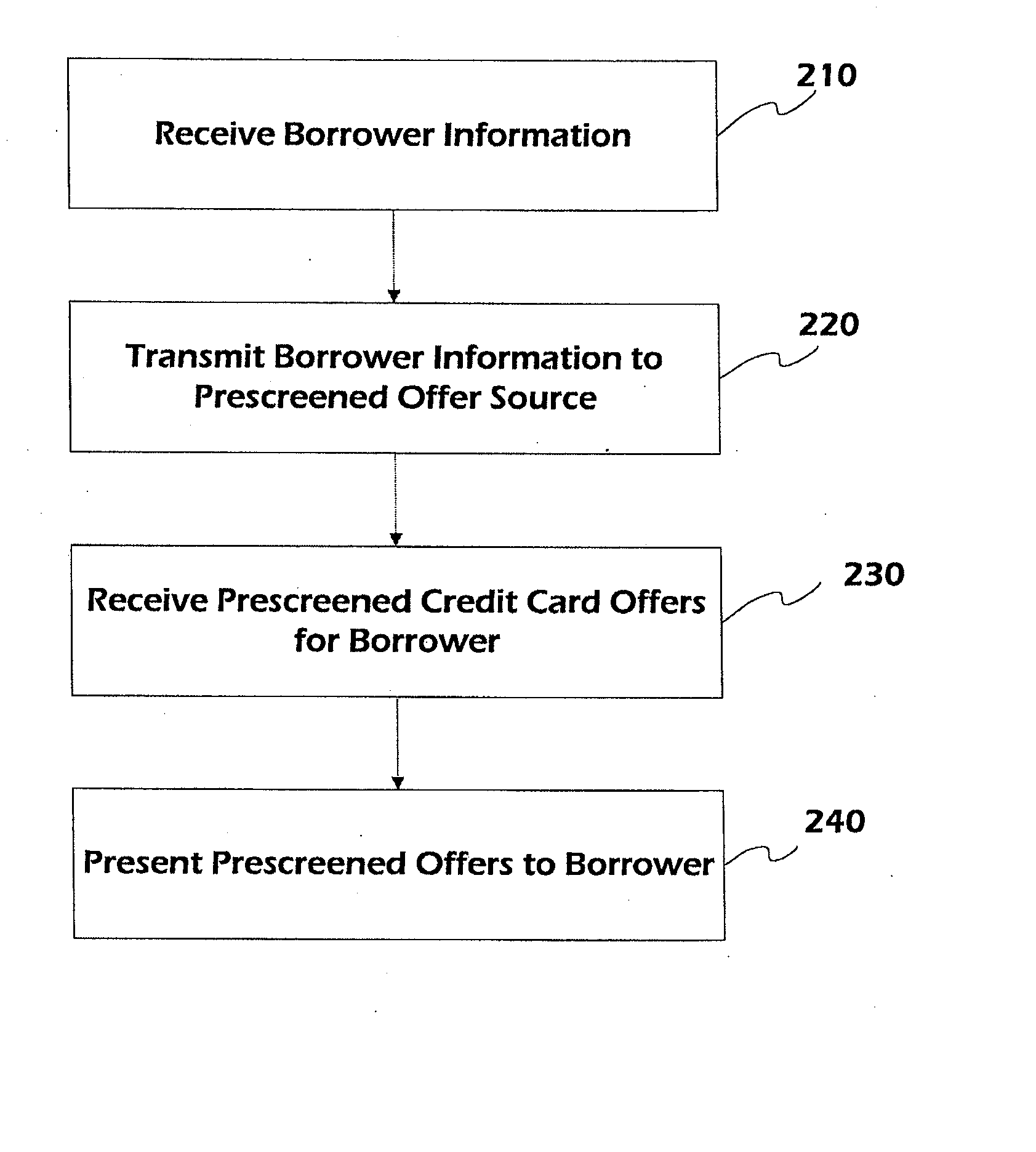
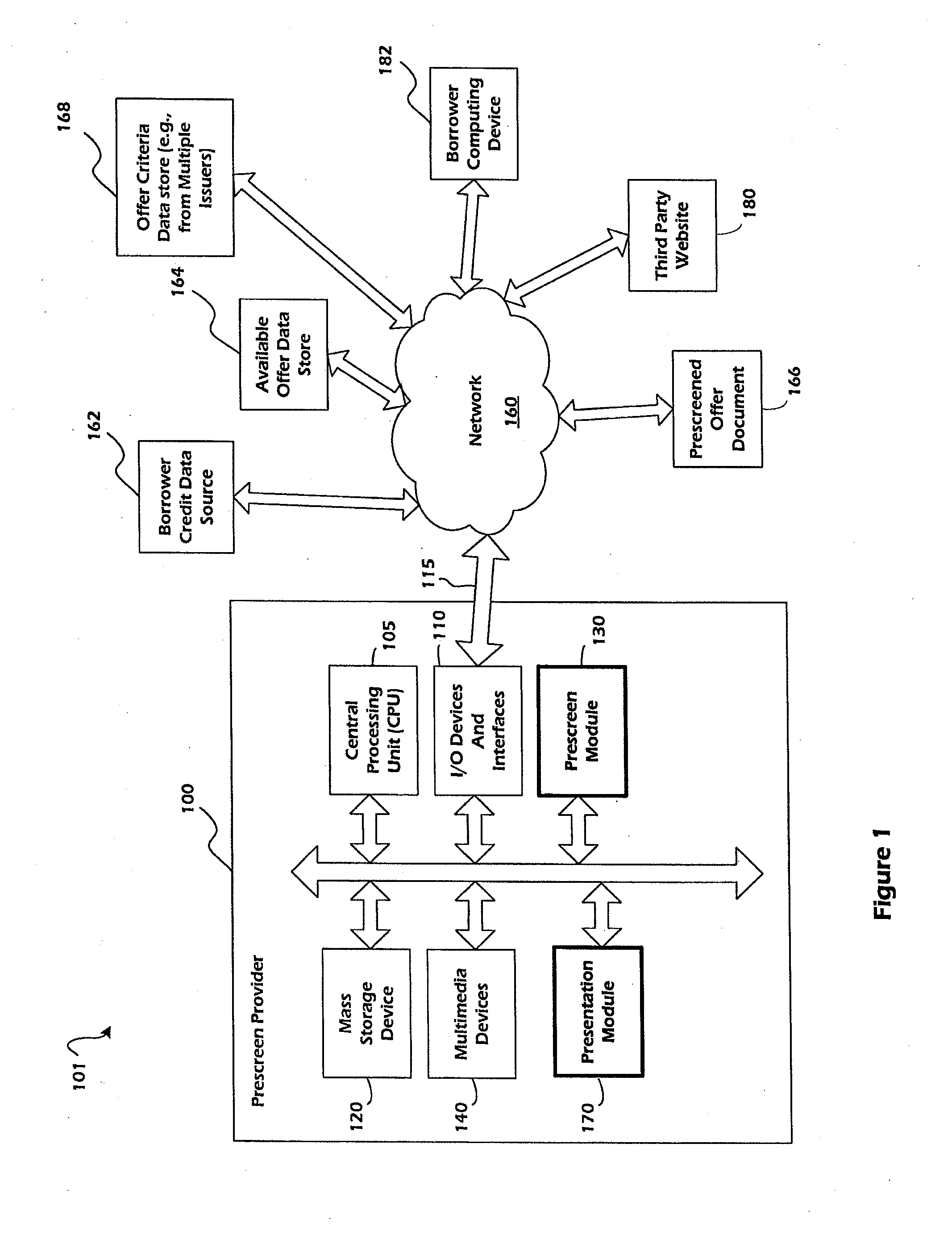
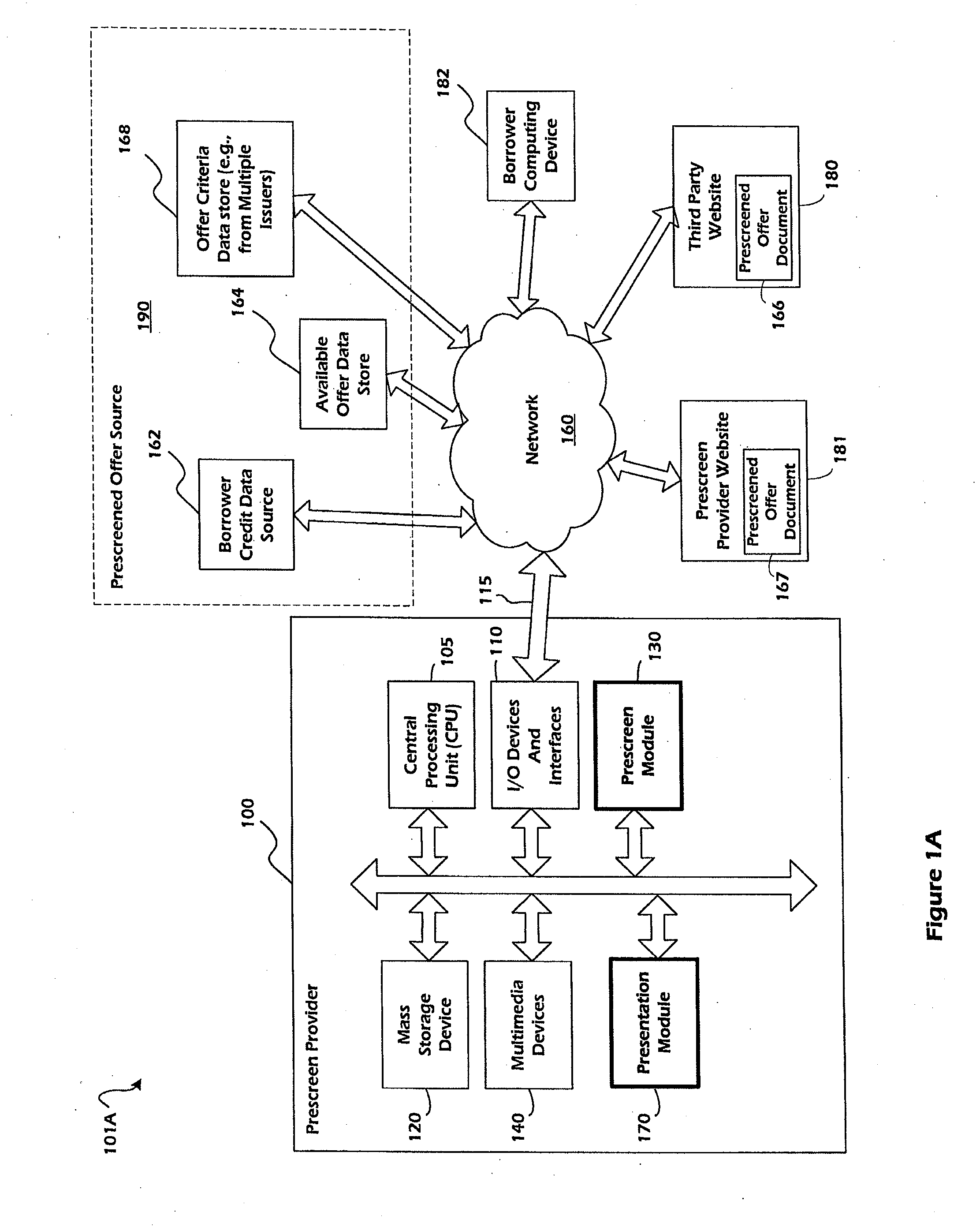
Online credit card prescreen systems and methods
In one embodiment, prescreened credit card offers, which are associated with credit cards that a particular borrower would be accepted upon application with the respective issuer, are provided to a borrower via a prescreen provider website and / or a referrer website. In one embodiment, a referrer provides borrower information to a prescreen provider. The prescreen provider initiates and / or performs a prescreening process, which includes accessing credit related information regarding the borrower. The prescreen provider matches the borrower with one or more credit cards that the borrower would like be accepted for, and provides a prescreened offer document to the referrer, or an Internet address of the prescreened offer document. The referrer may then provide the borrower with the prescreened credit card offers by presenting the prescreened offer document to the borrower. The prescreened credit card offers may additionally be filtered according to issuer criteria, referrer criteria, and / or borrower preferences.
Owner:CPL ASSETS LLC +1
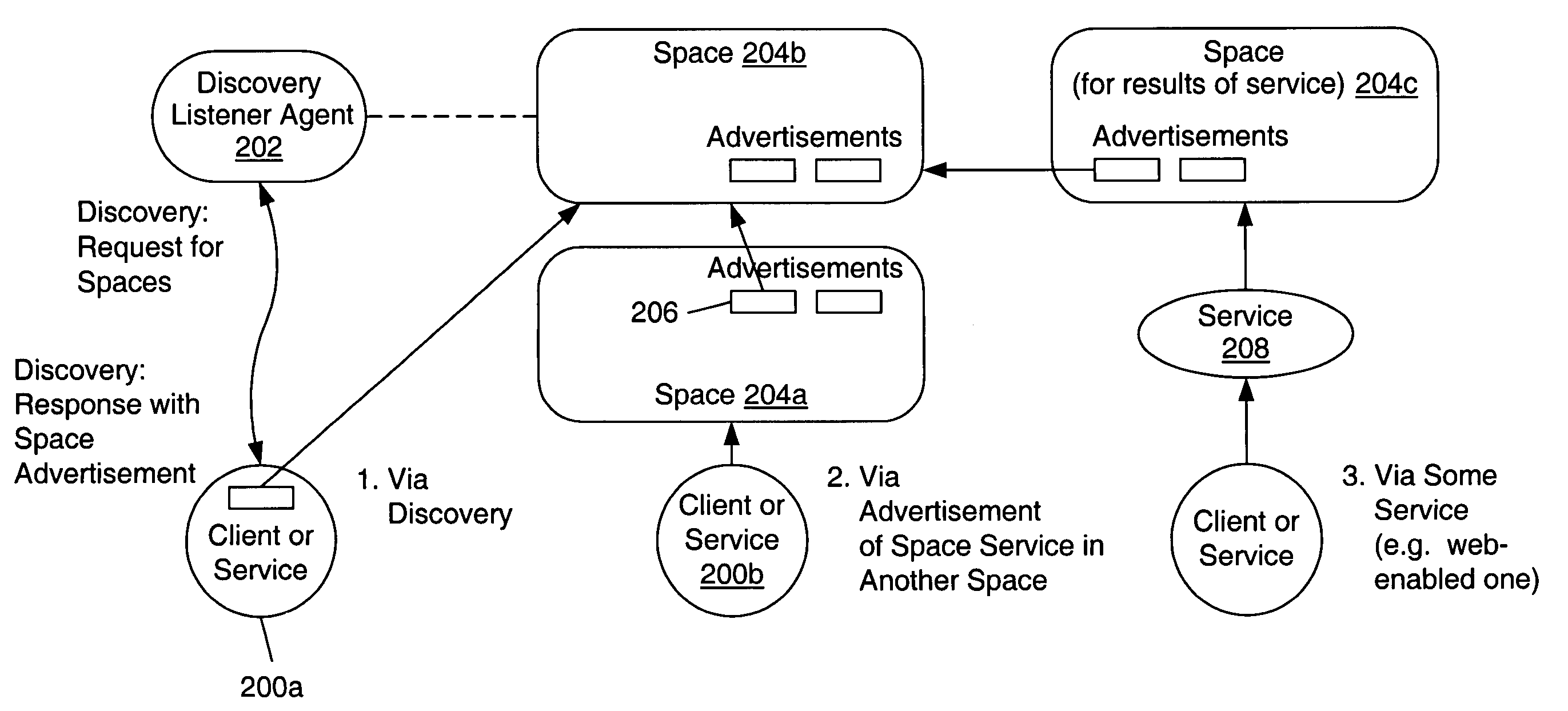
Mechanism and apparatus for URI-addressable repositories of service advertisements and other content in a distributed computing environment
InactiveUS7080078B1Save spaceCreate efficientlyWeb data indexingBuying/selling/leasing transactionsXML schemaInformation space
A system and method for interaction and access to shared content among clients and services in a distributed computing environment. A client may access a space service. The space service may store one or more XML service advertisements and / or other XML content in a space, and each of the service advertisements may include information which is usable to access and execute a corresponding service. The space service may include an XML schema which specifies one or more messages usable to invoke functions of the space service. For example, the schema may specify methods for reading advertisements from the space and publishing advertisements in the space. In accessing the space service, the client may send information such as an XML message (as specified in the schema) to the space service at an Internet address. In accessing the space service, the client may search the one or more service advertisements stored in the space. The client may select one of the service advertisements from the space. The desired service may be executed on behalf of the client. Upon execution, the service may generate a set of results. In one embodiment, these results may be published in a new space which may be accessed by the client for whose benefit the service was executed.
Owner:ORACLE INT CORP
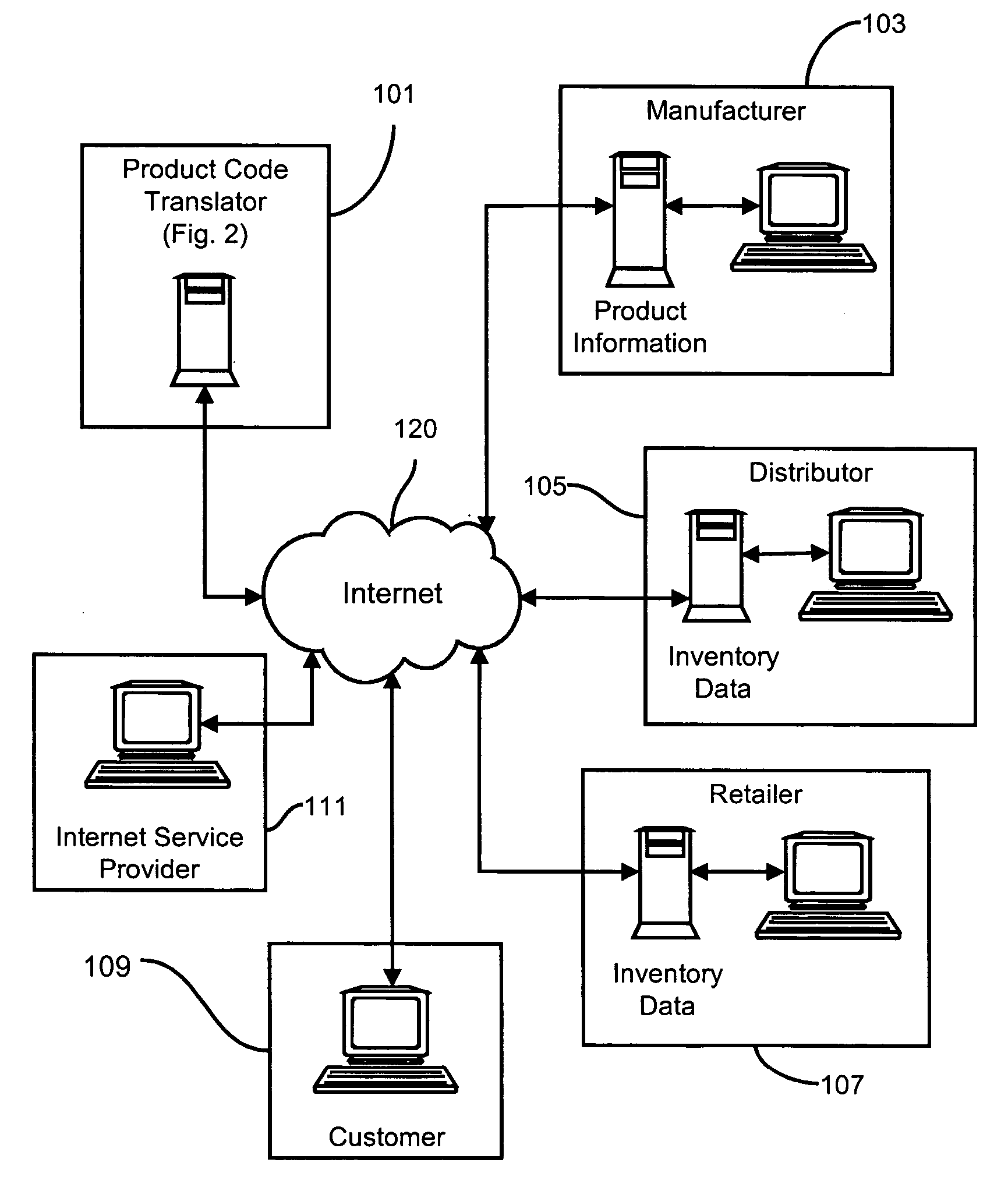
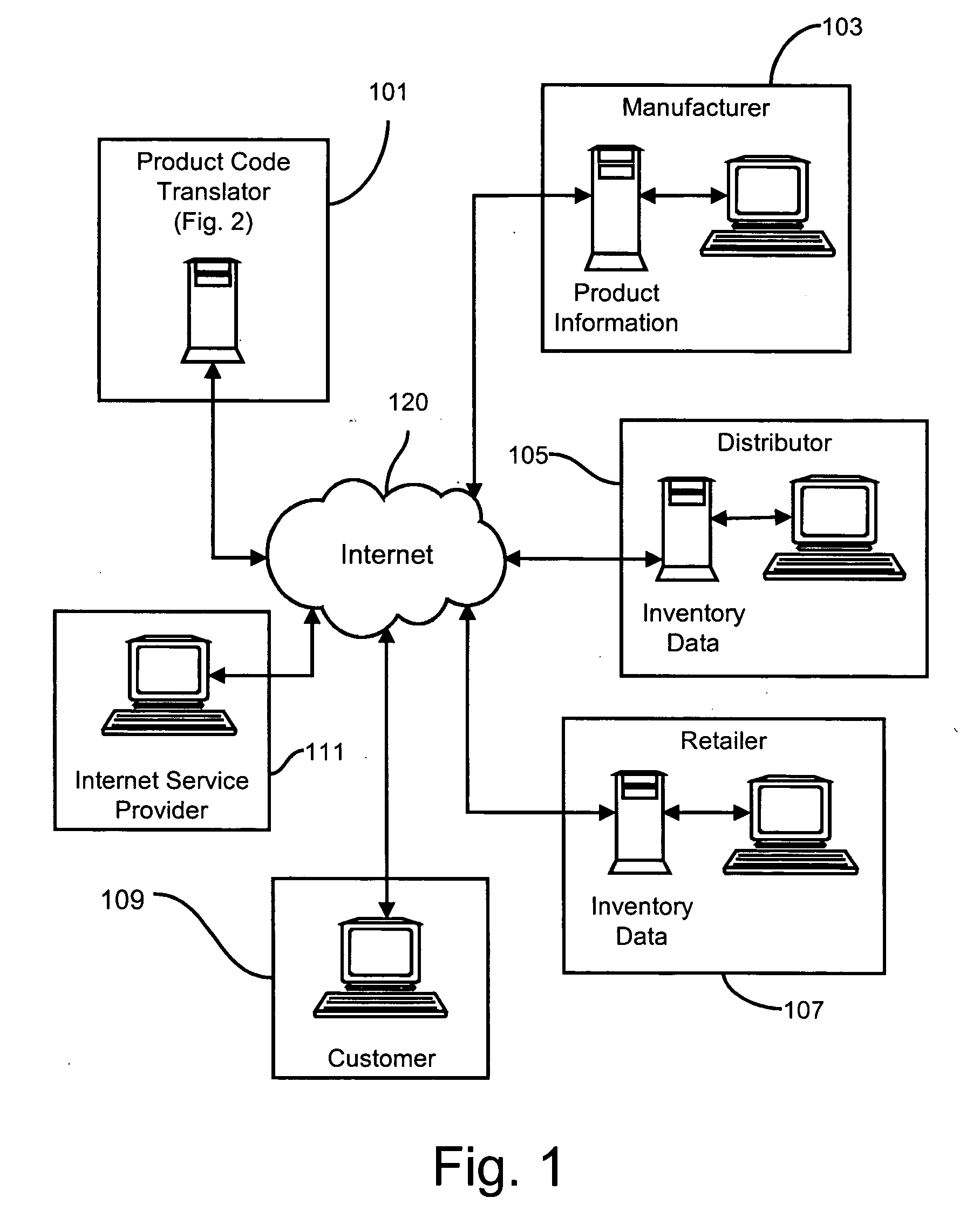
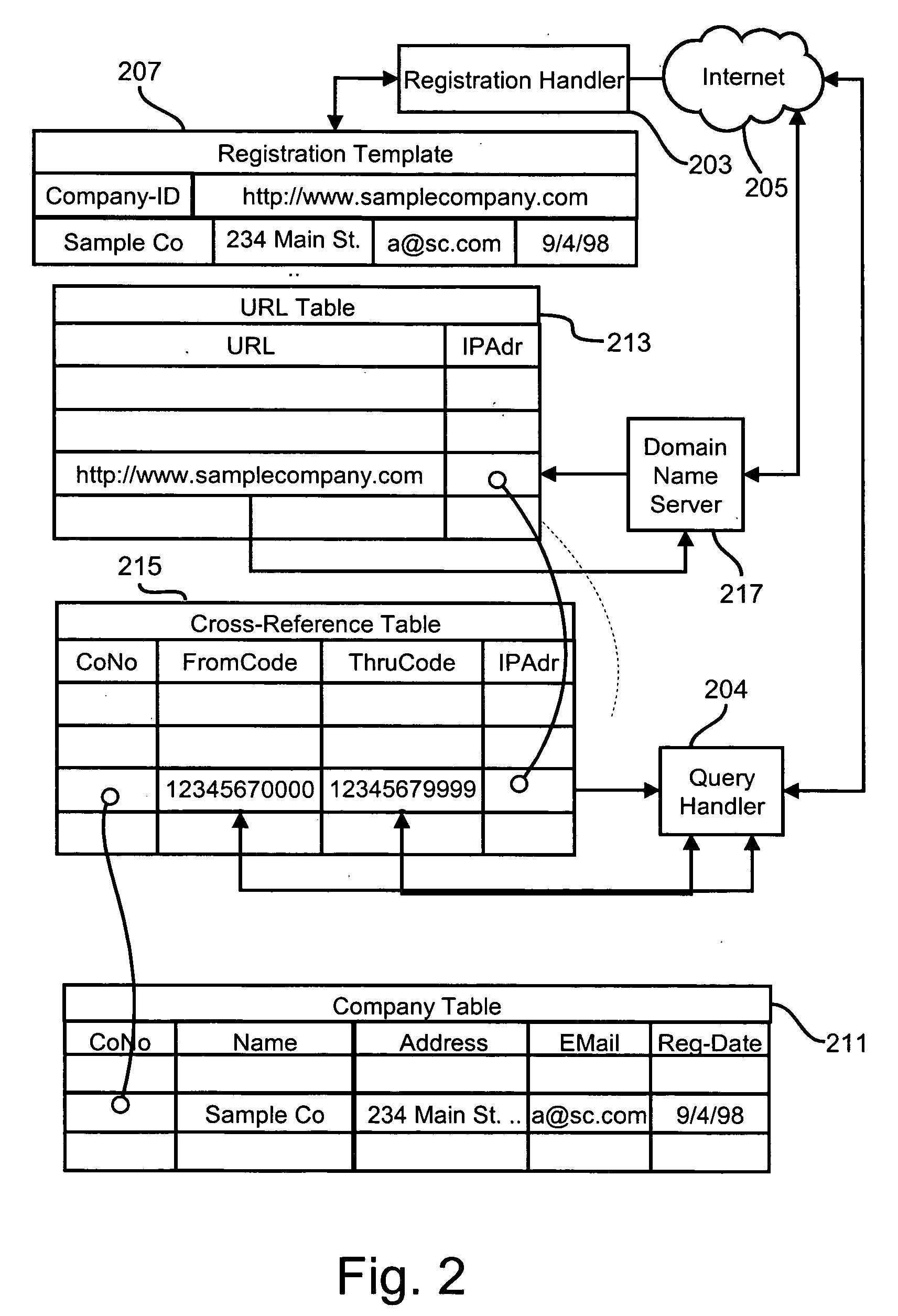
Methods and apparatus for transferring product information from manufacturers to retailers and distributors via the Internet
InactiveUS20060011720A1Digital data information retrievalVisual presentationUniversal Product CodeDomain name
Methods and apparatus for disseminating over the Internet product information produced and maintained by product manufacturers using existing universal product codes (bar codes) as access keys. A cross-referencing resource preferably implemented by the existing Internet Domain Name System (DNS) receives Internet request messages containing all or part of a universal product code value and returns the Internet address at which data or services relating to the identified product, or to the manufacturer of that product, may be obtained. By using preferred Web data storage formats and protocol which conform to XML, XLS, XLink, Xpointer, RDF and Web service standards specifications, product and company information may be seamlessly identified, retrieved and integrated with information from other sources. A “web register” module can be employed to provide an Internet interface between a shared sales Internet server and an otherwise conventional inventory control system, and operates in conjunction with the cross-referencing server to provide detailed product information to Internet shoppers who may purchase goods from existing stores via the Internet.
Owner:PROD ASSOC TECH LLC +1
Systems and methods for direction of communication traffic
Owner:BUSHNELL HAWTHORNE +1
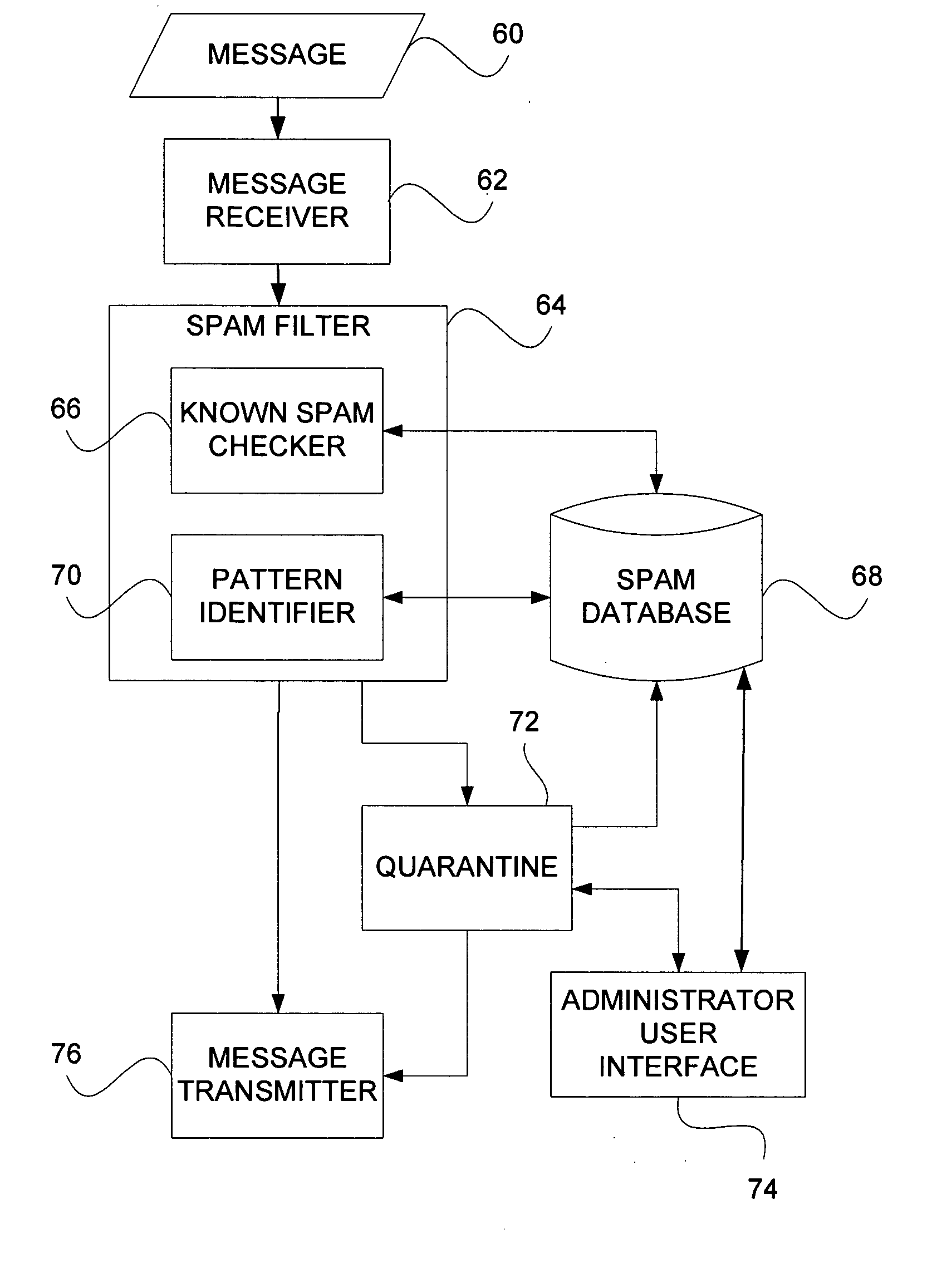
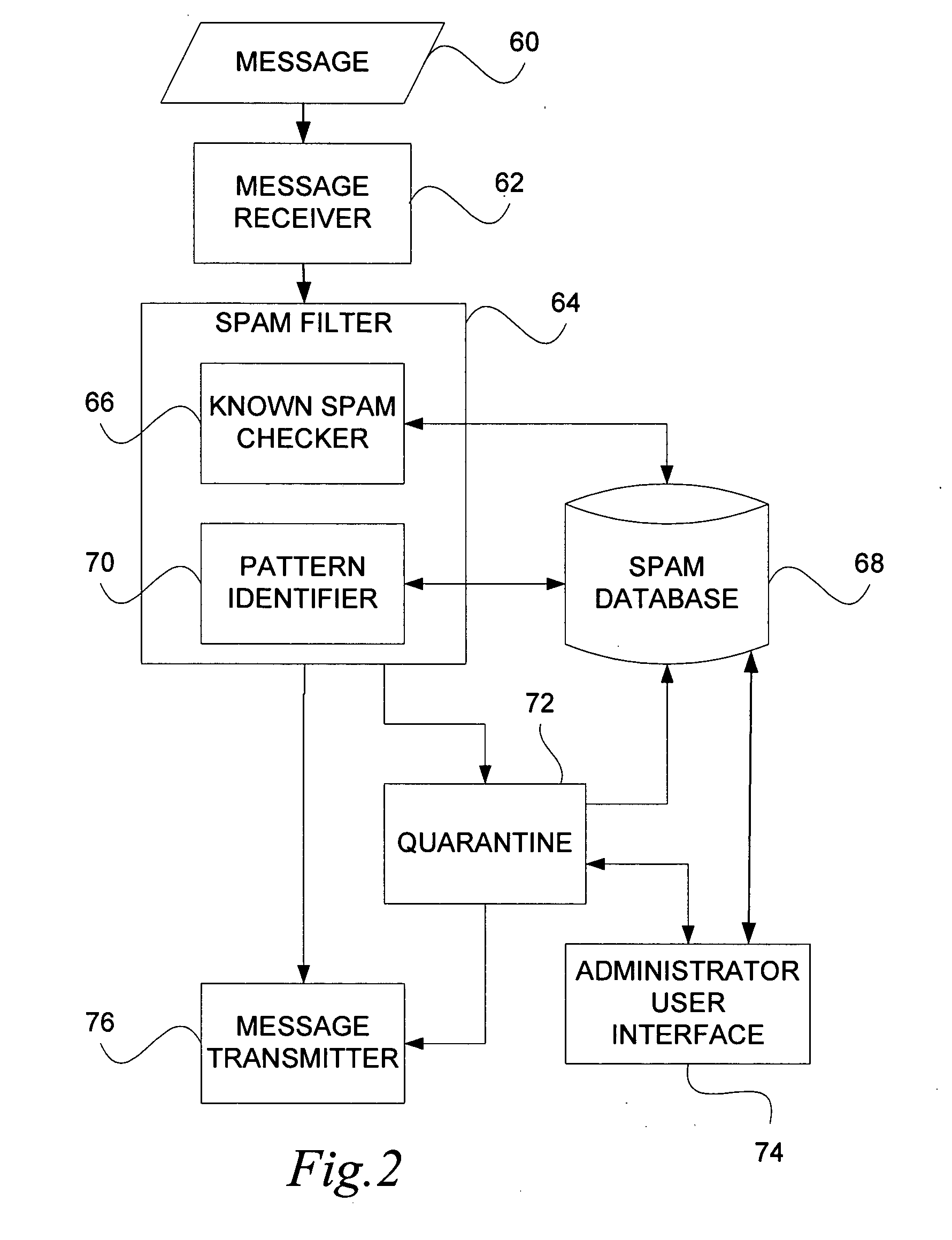
Messaging spam detection
InactiveUS20060026242A1Multiple digital computer combinationsData switching networksEmail addressTelecommunications
Detecting unsolicited messages (spam) by aggregating information across multiple recipients and / or across the same or differing messaging protocols. Multiple messages are analyzed to detect a call to action pattern that specifies a target communication address with which the recipients are requested to communicate, such as an email address, an Internet address, a telephone number, and the like. Once a frequency threshold of messages containing the call to action pattern is reached, subsequent messages are temporarily quarantined for evaluation by a human operator. If the human determines that the messages are not spam, the human can release the quarantined messages, and indicate that future messages with the call to action pattern are not to be delayed. Conversely, if the human determines that the messages are spam, the human can delete the messages in quarantine, and indicate that all future messages with that call to action pattern are to be deleted automatically.
Owner:WIRELESS SERVICES CORP
System server for channel-based internet network
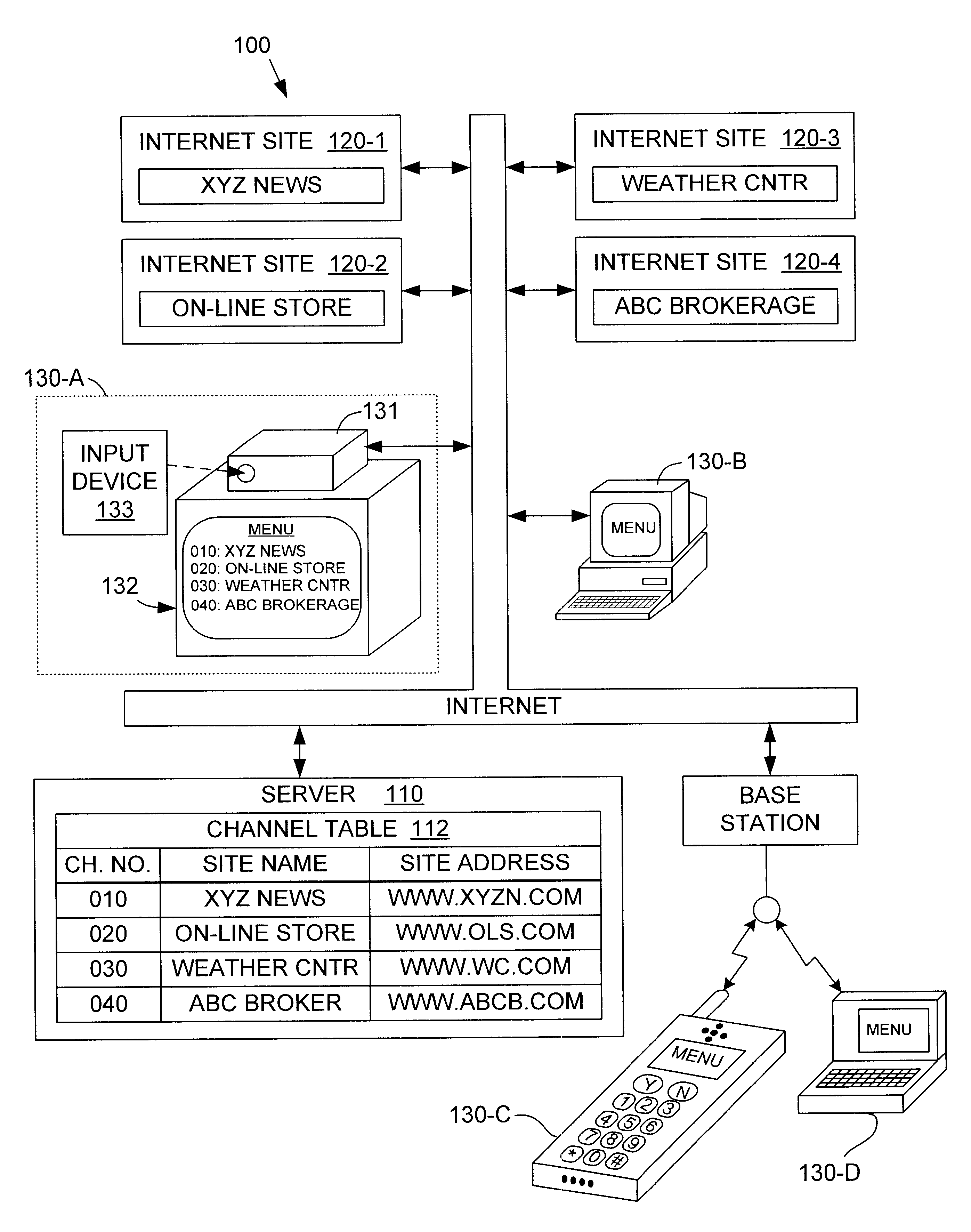
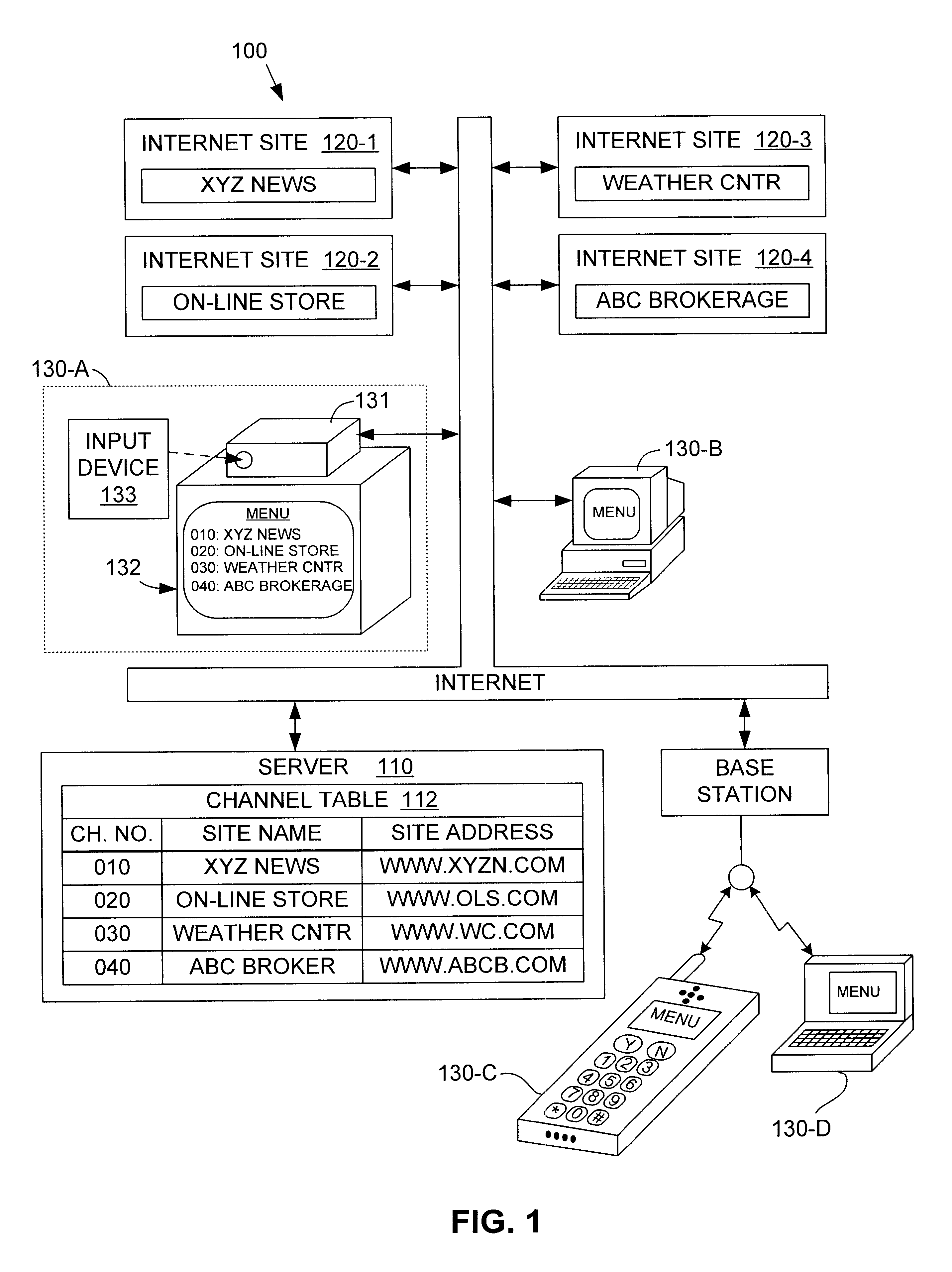
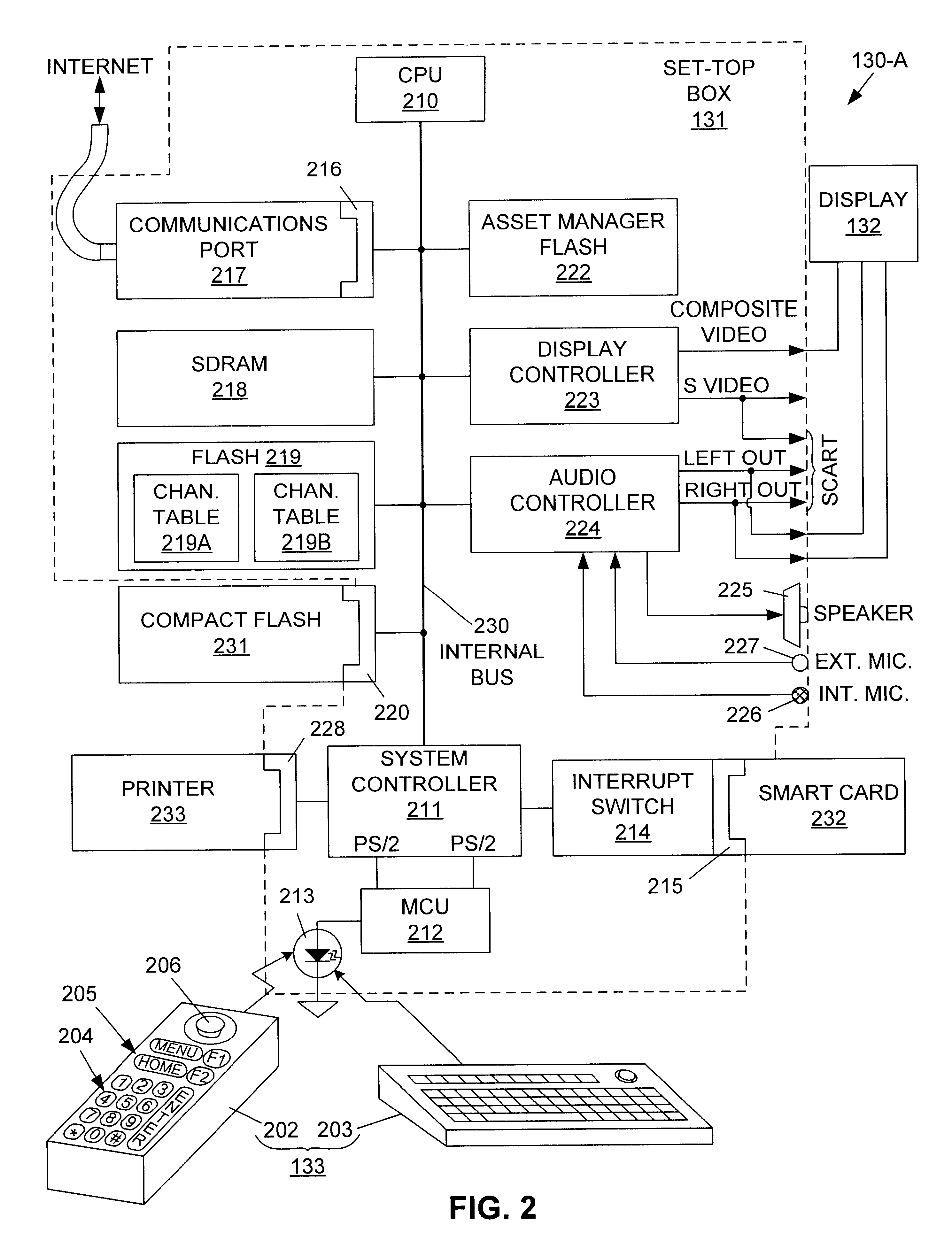
InactiveUS6587873B1Prevent unauthorized accessLess expensiveTelevision system detailsAnalogue secracy/subscription systemsWeb siteInternet network
A system server for a channel-based network including one or more Internet sites and one or more user terminals. The system server includes a channel table database storing a master channel table that includes a list of channel numbers, each channel number having an associated Internet address and an associated Internet site name. Each Internet site of the network is addressable by an associated Internet address stored in the master channel table. The system server includes a network database and an update manager database. The system server identifies each user terminal requesting service by comparing transmitted identification information with authorized user information stored in the network database. The system server also compares a channel table version number from the requesting user terminal with a version number stored in the update manager database that is associated with the master channel table, and notifies each requesting user terminal when updated channel table information is available. At each user terminal, a user reads the channel numbers and associated Internet site names from a menu displaying the downloaded channel table, selects an Internet site name from the displayed menu, and enters the channel number associated with the selected Internet site name using an input device that is similar to a television remote control.
Owner:VIACLIX
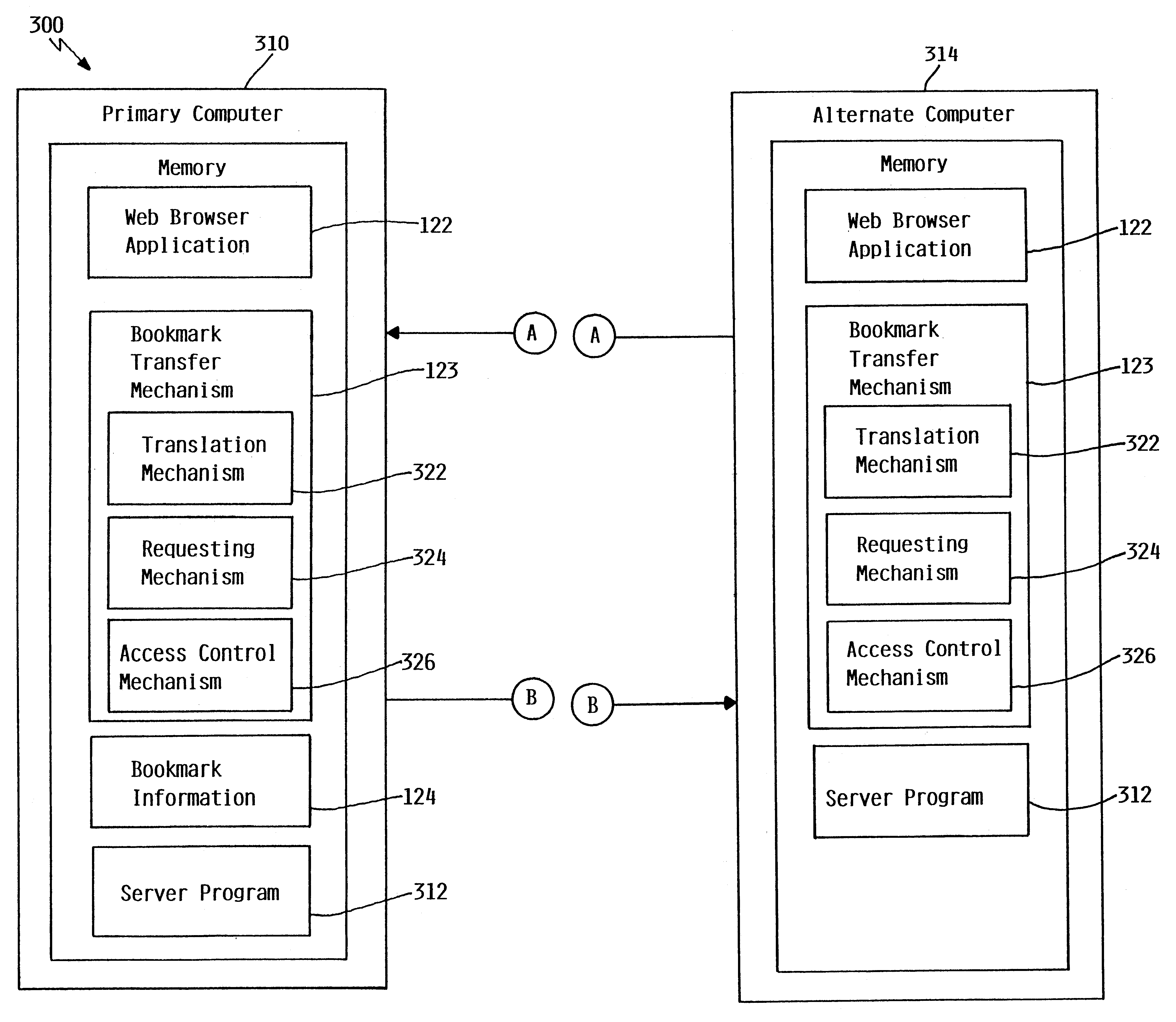
Method and apparatus for automatic downloading of URLs and internet addresses
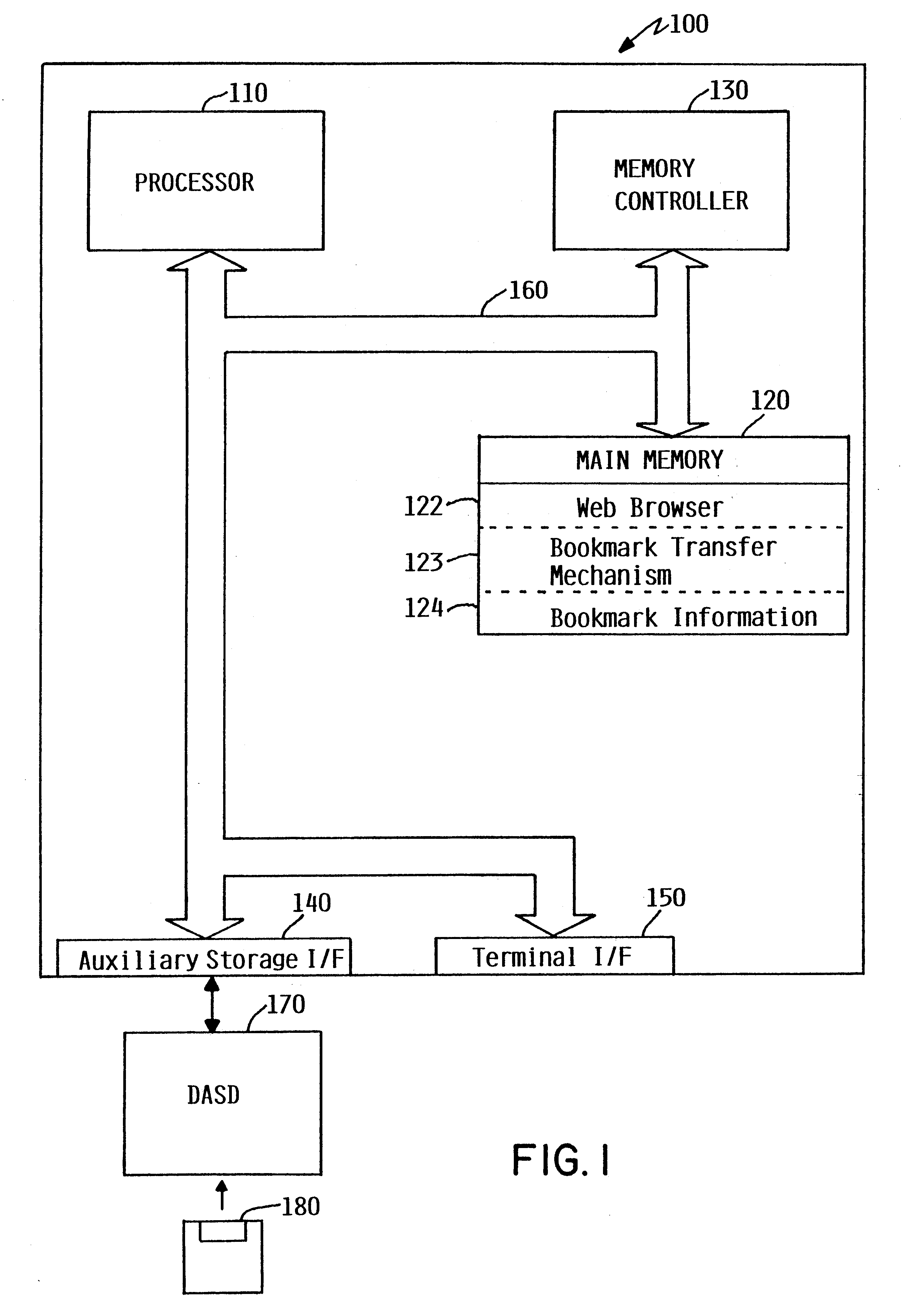
InactiveUS6393462B1Data processing applicationsDigital data information retrievalWeb browserUser input
A bookmark transfer mechanism allows a user to transfer bookmark information from a primary computer to an alternate computer to customize a bookmarks menu on a web browser displayed on the alternate computer. The alternate computer prompts the user for a base address which is used by the web browser on the alternate computer to locate the primary computer where bookmark information is stored. The base address should correspond to a primary computer that has been configured for automatic download of bookmark information. Once the primary computer is located, the alternate computer transfers the base address and prompts the user for security information. The alternate computer then delivers the security information to the primary computer. The primary computer then authenticates the security information. If the security information is not valid, the primary computer delivers an error message to the alternate computer indicating that access to the primary computer has been denied. If the security information is valid, the primary computer transfers the bookmark information to the alternate computer. If necessary, the alternate computer translates the received bookmark information to the proper web browser format and updates the bookmarks menu on the web browser to include the transferred bookmark information. The bookmark information may be either temporarily or permanently incorporated into the web browser.
Owner:IBM CORP
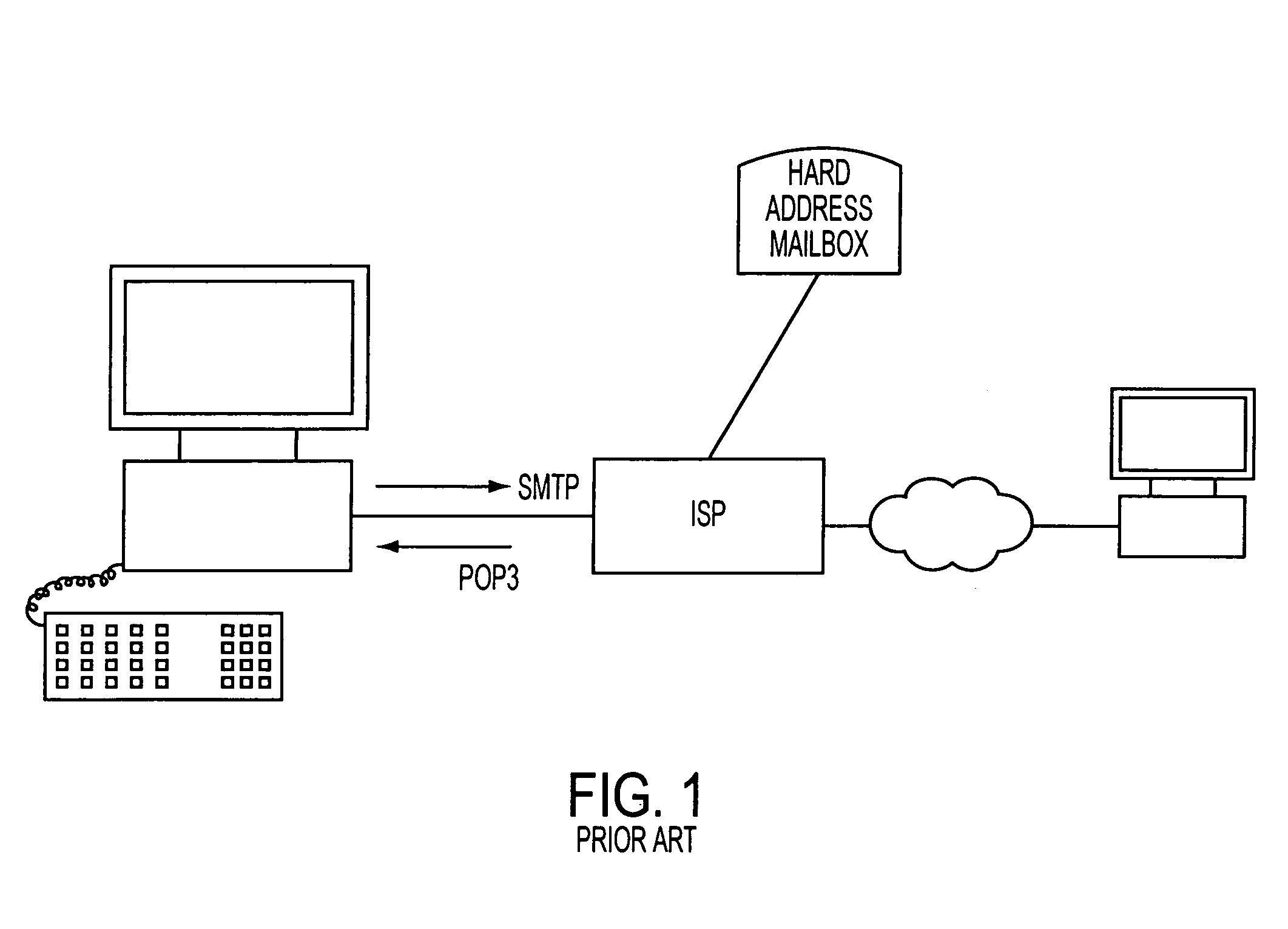
System and method for integrated management of electronic messages
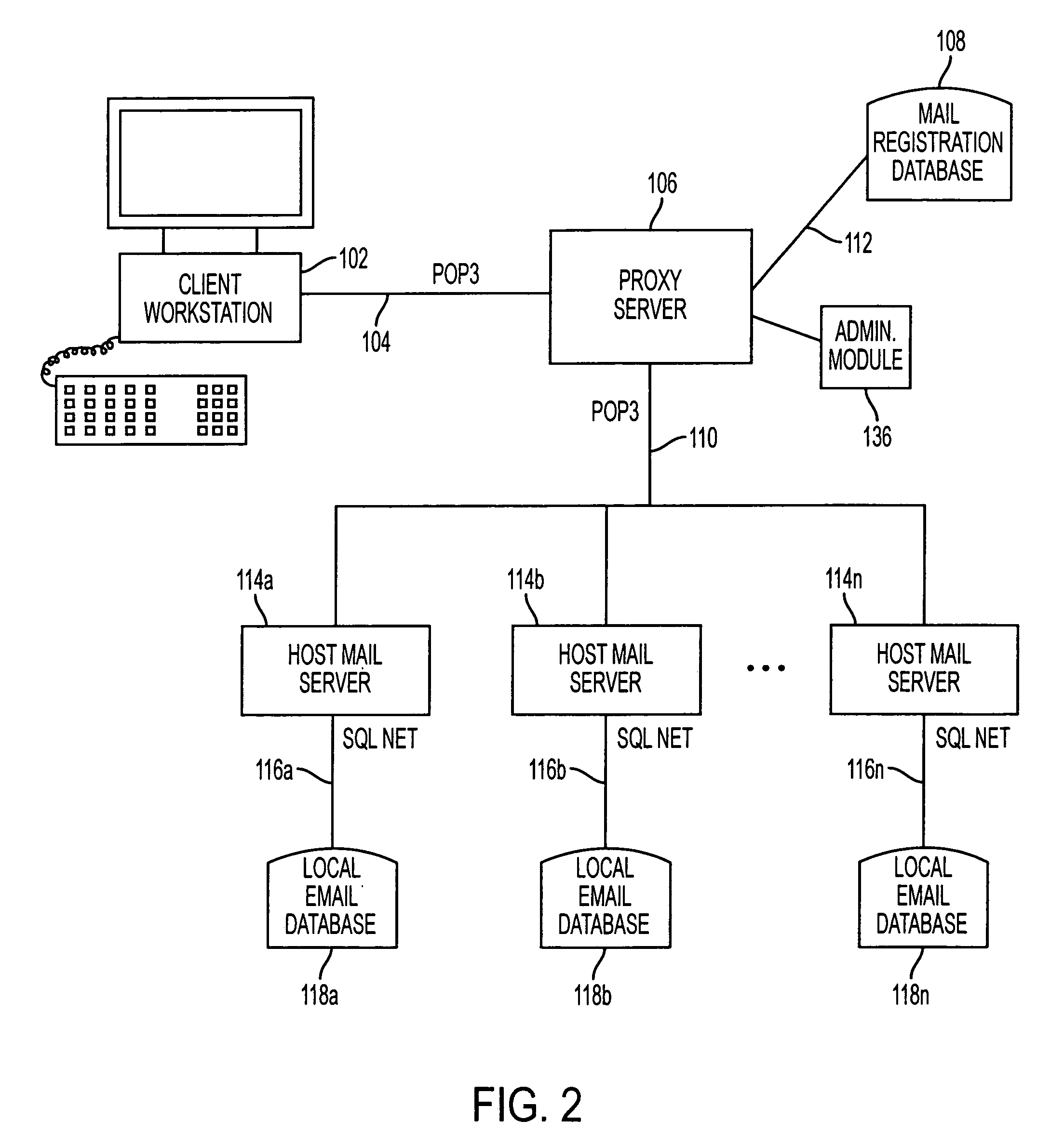
InactiveUS6965918B1Painless and transparent migrationGreat latitudeMultiple digital computer combinationsTransmissionClient-sideProxy server
An email proxy server system gives the user access to all of their email accounts through a unified port. The proxy server maintains a mail registration database associating the user's ID with multiple email accounts, which may be hosted on different Internet providers and otherwise. The email messages stored on the email hosts may be in POP3 format, which configuration the proxy server imitates to give the user an impression of transparent access to all of their email accounts. Because the ability to access individual mail boxes is unbound from particular internet addresses, one user may maintain any number of email mail boxes at different hosting servers, and change those addresses, without having to reprogram client, server, and other software. Moreover, the presentation of the integrated interface of the invention permits system administrators to attach service modules, such as billing and other packages directly to the proxy server to serve each of the different email accounts, without having to tailor those individual services to individual hosts hardware.
Owner:IBM CORP
System and method for disseminating information over a communication network according to predefined consumer profiles
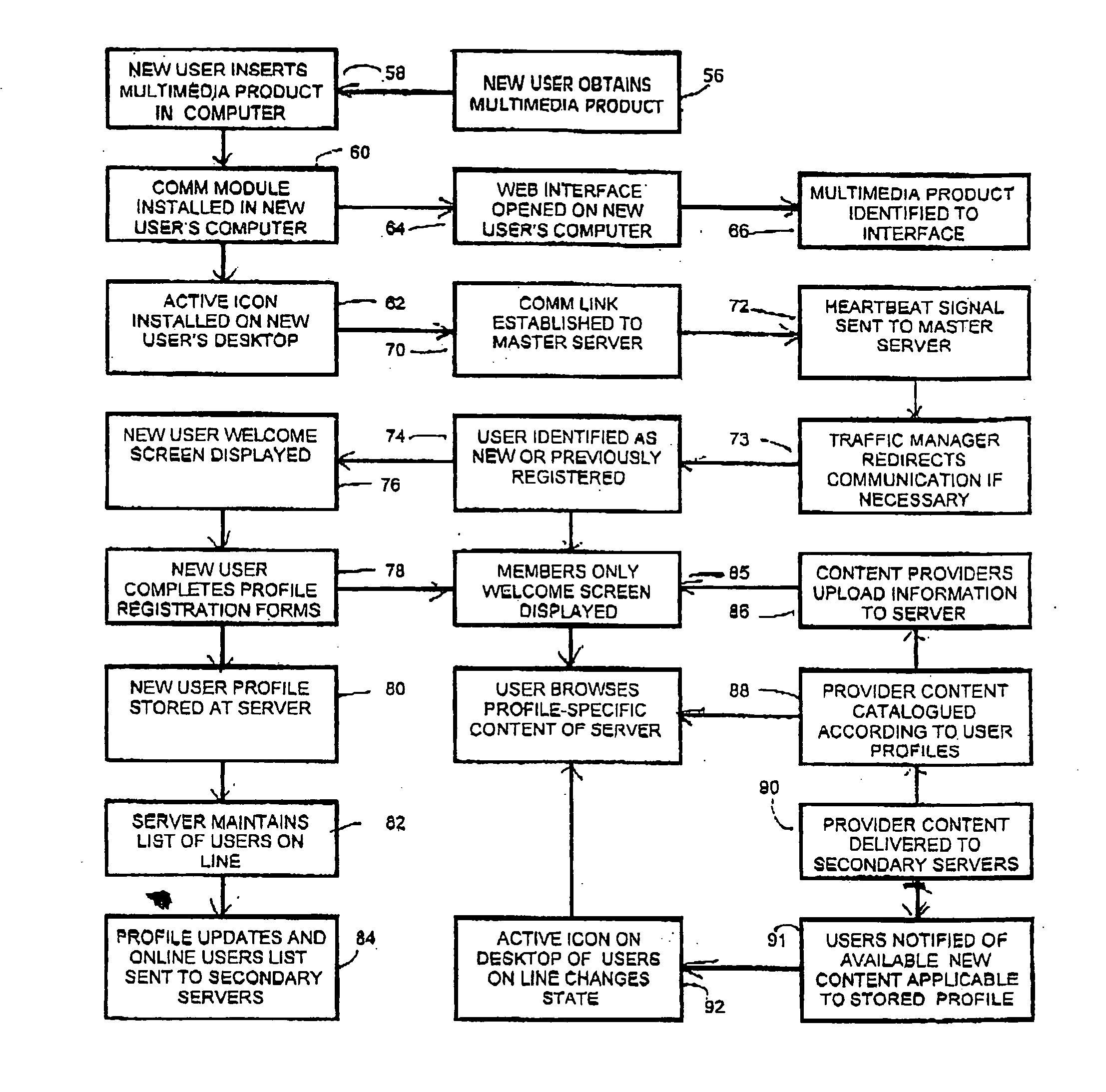
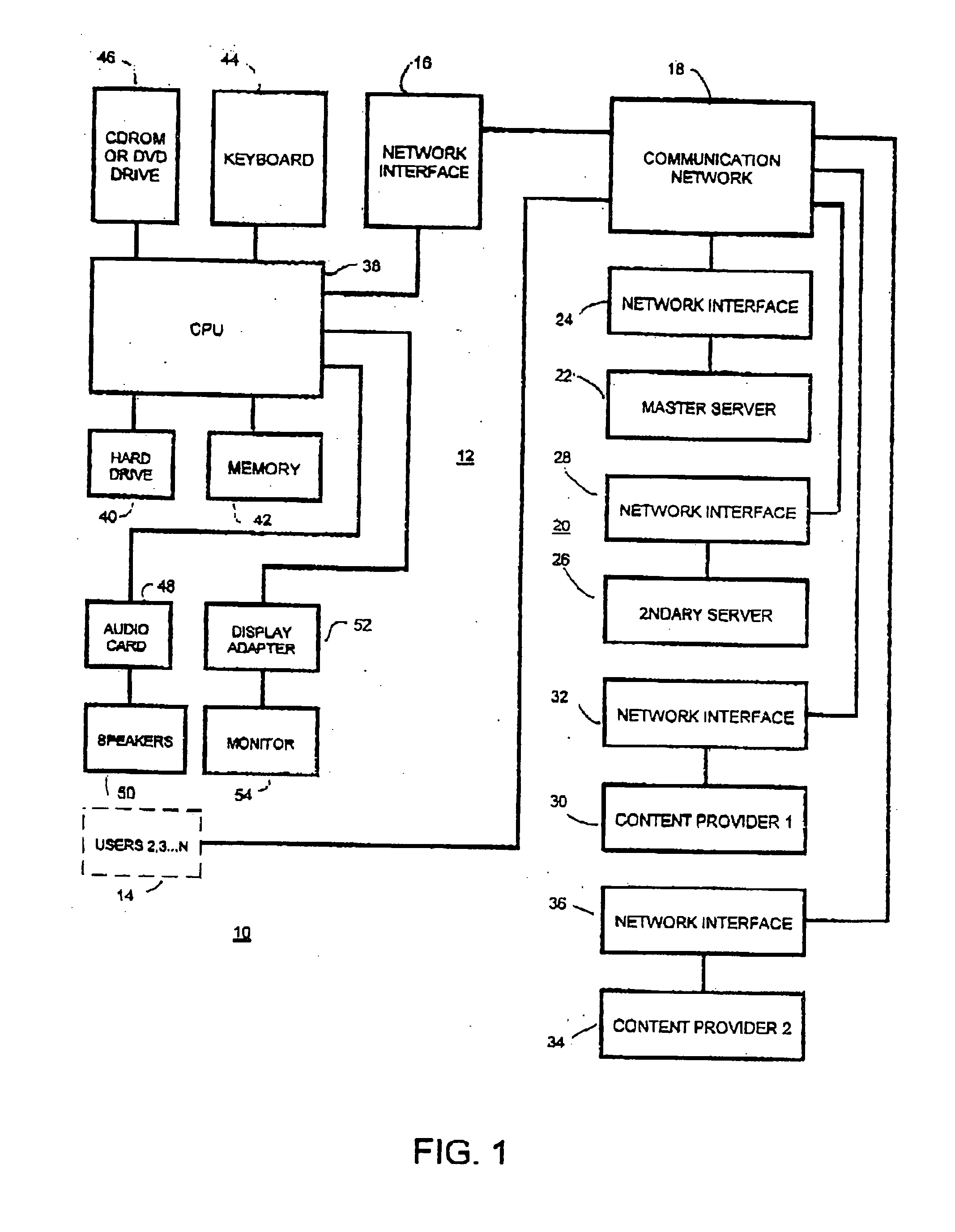
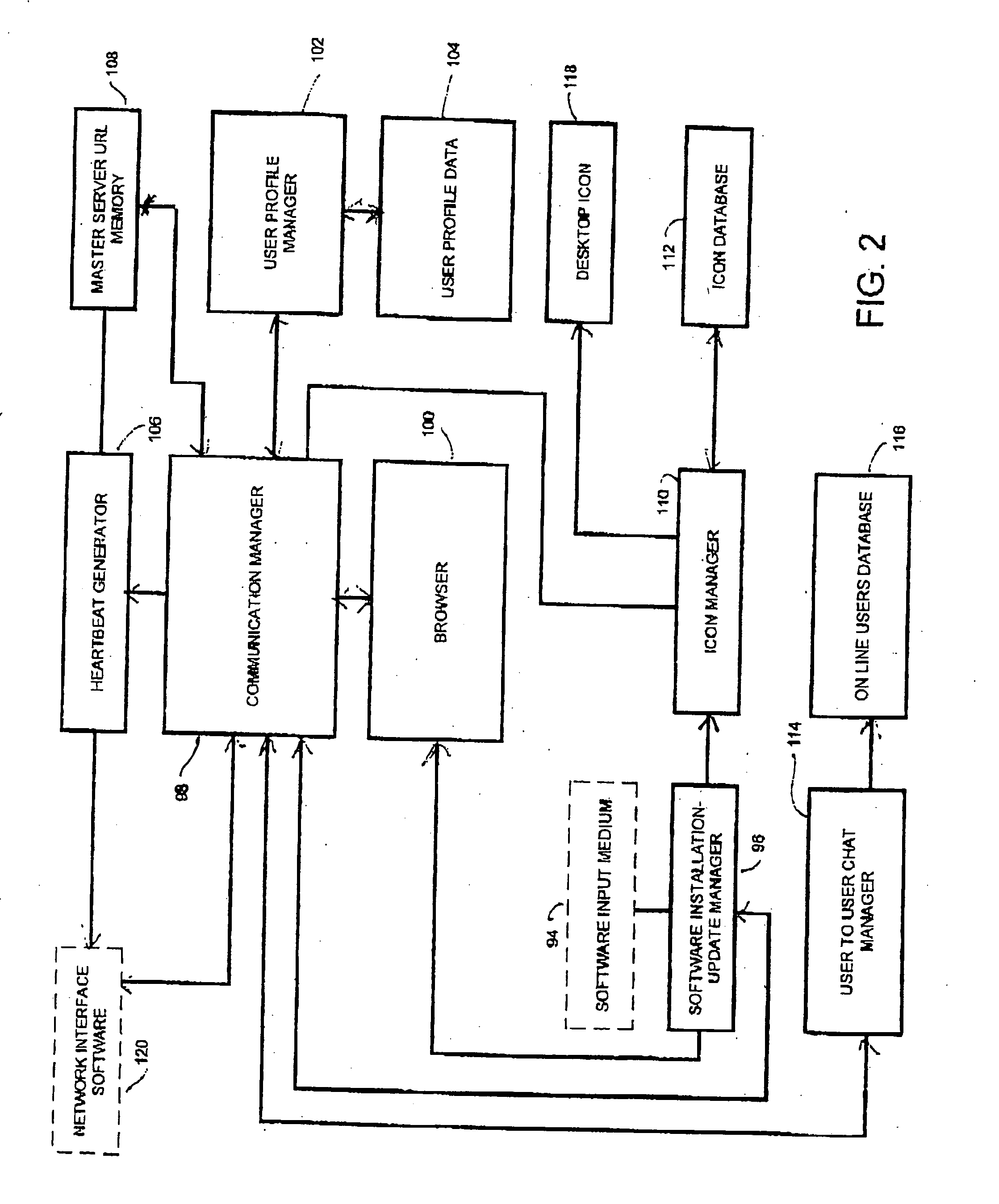
InactiveUS20040098449A1Facilitates a unique and highly personalized deliveryImprove targetingMultiple digital computer combinationsTransmissionOperational systemWeb browser
A system and method for distributing information to interested users according to predefined preferences over the Internet. The invention provides improved techniques for reaching potential recipients, for simplifying the initial response by interested individuals, and for facilitating the gathering and organizing of information from those individuals. The communication structure includes one or more servers and a plurality of dedicated client-side communication modules ("comm modules"). The servers store multimedia entertainment, advertising, or other information content and as well as profile information for the users of the comm modules. The stored information is organized according to the user profiles and is selectively made available for downloading on demand. The comm modules are preferably made available for installation on the client-side computers by distribution as an adjunct to the information, advertising or entertainment content of a multimedia product such as a CDROM or DVD. Profile information is developed the first time a user goes on line after installing the software. The comm module displays a small icon on the user's desktop which changes state whenever there is new information on the server corresponding to the user's profile. Users may then access the information at their convenience. The comm module includes a mini Web browser programmed for display of full-featured Web pages. It is compatible with operating systems commonly in use, and is runtime configurable and upgradable via server configuration messages. When the user goes online, the comm module connects directly to a routing server at a predetermined Internet address.
Owner:BAR LAVI SHAI +2
Dual transaction authorization system and method
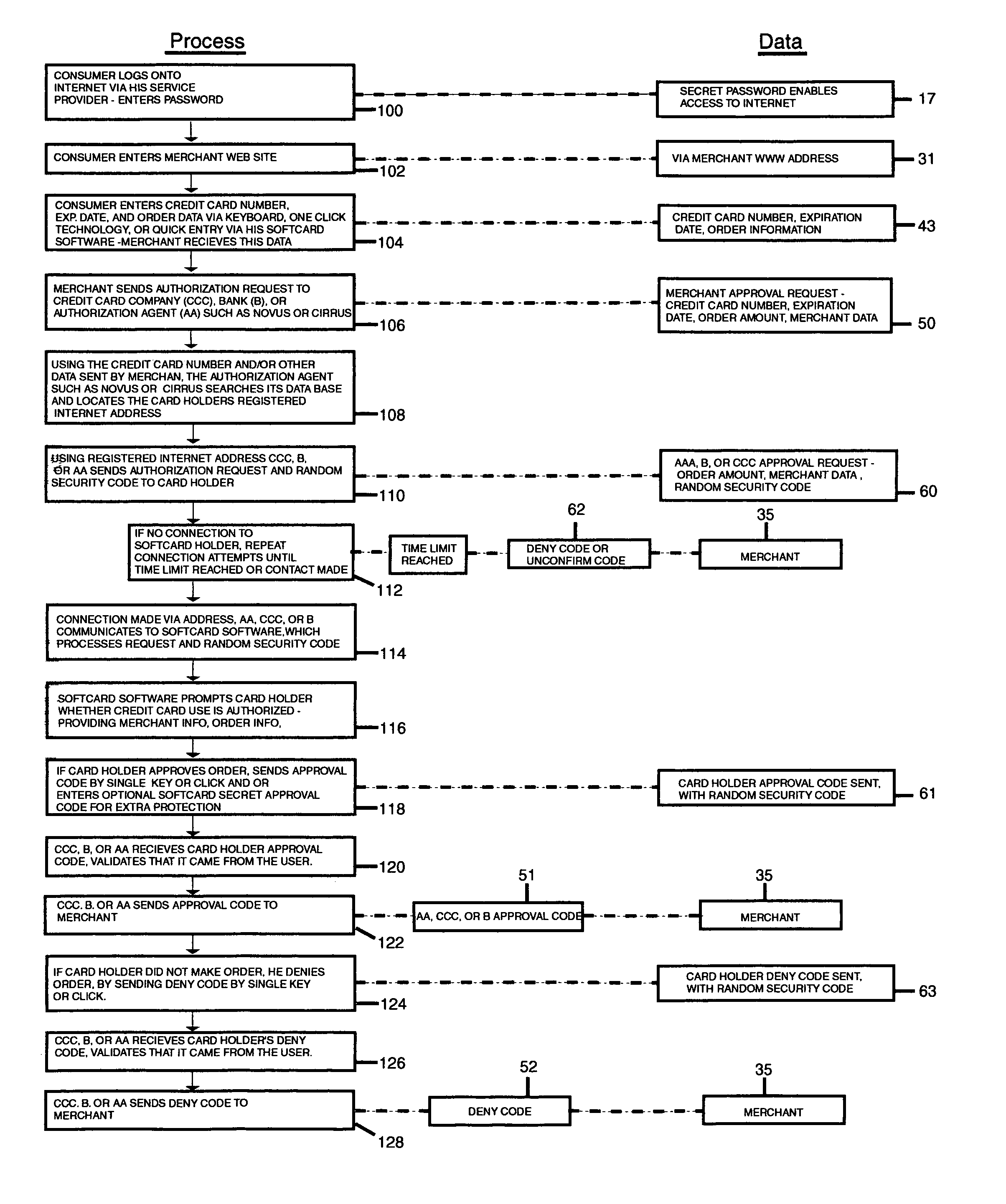
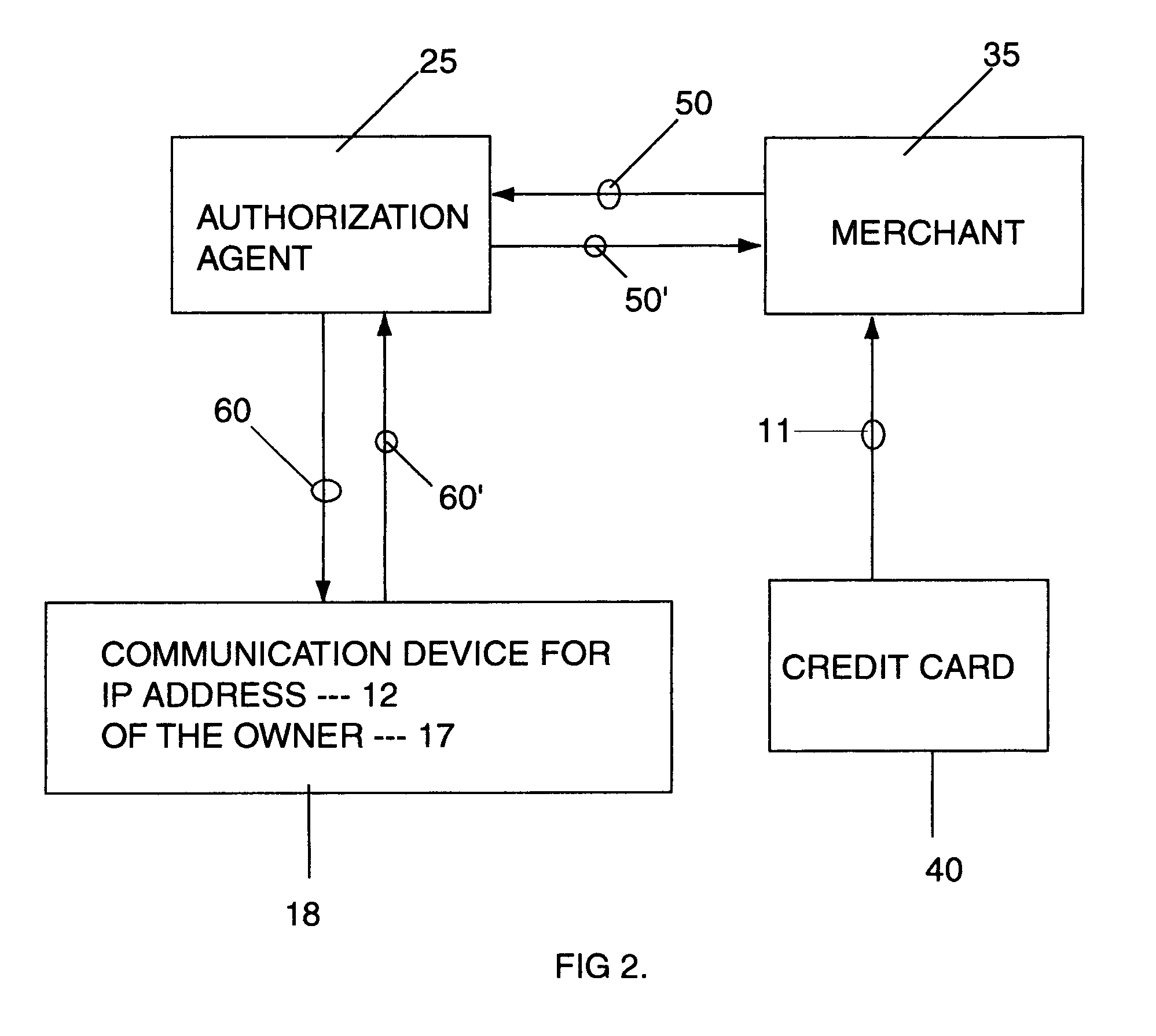
A general feature of the present invention is to provide a dual authorizing system and method to prevent fraudulent use of credit cards and E-signature. To do so, a third party verifier is provided to ensure that the rightful owner of the credit card or E-signature approves of the transaction before the purchase is completed between the merchant and the credit card user. This is accomplished by linking the owner's Internet address or addresses or other communication device address to the credit card number, and storing this information with the third party verifier, such as an Authorization agent. Once the card is used to make a purchase, the Authorization agent is notified of the purchase. The Authorization agent then pulls the corresponding Internet address or communication address for the credit card number, then sends an approval request message to the owner at the owner's Internet address or communication device. This way, only the owner who had previously registered the credit card number with the Authorization agent is notified of the pending purchase and can approve or deny the purchase and, thereby preventing unauthorized user from making purchase using the owner's credit card.
Owner:KLOOR HARRY THOMAS
Method and apparatus for an interactive Web Radio system that broadcasts a digital markup language
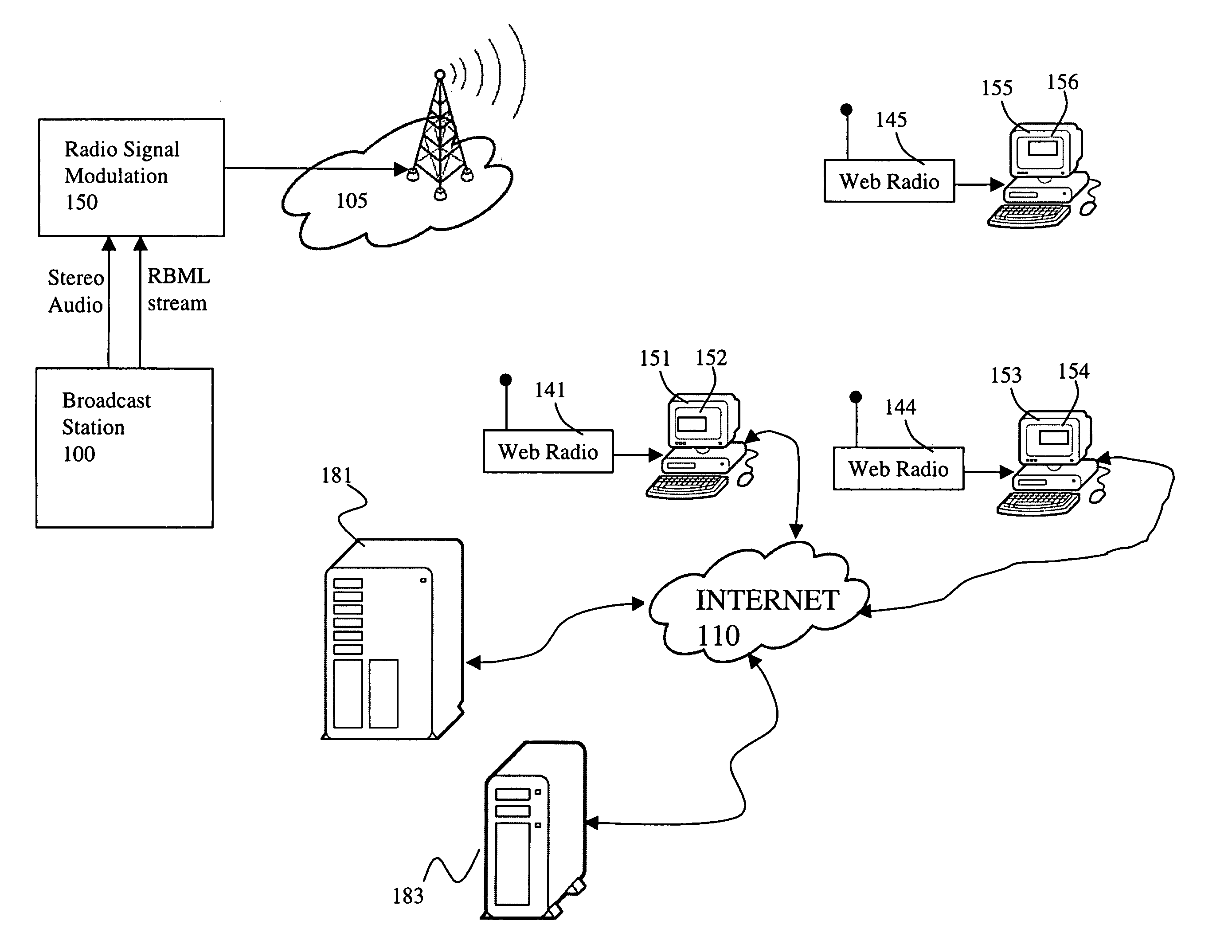
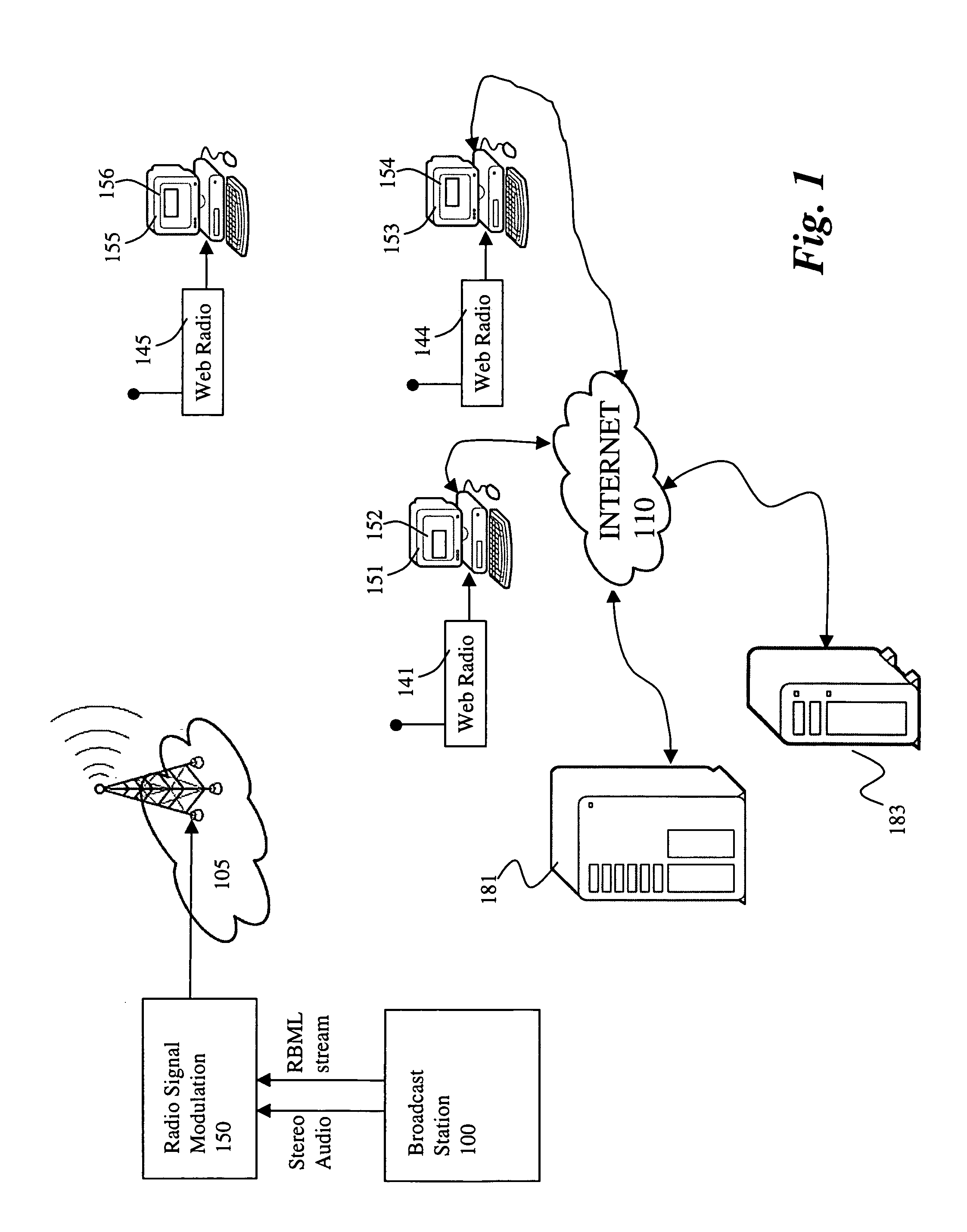
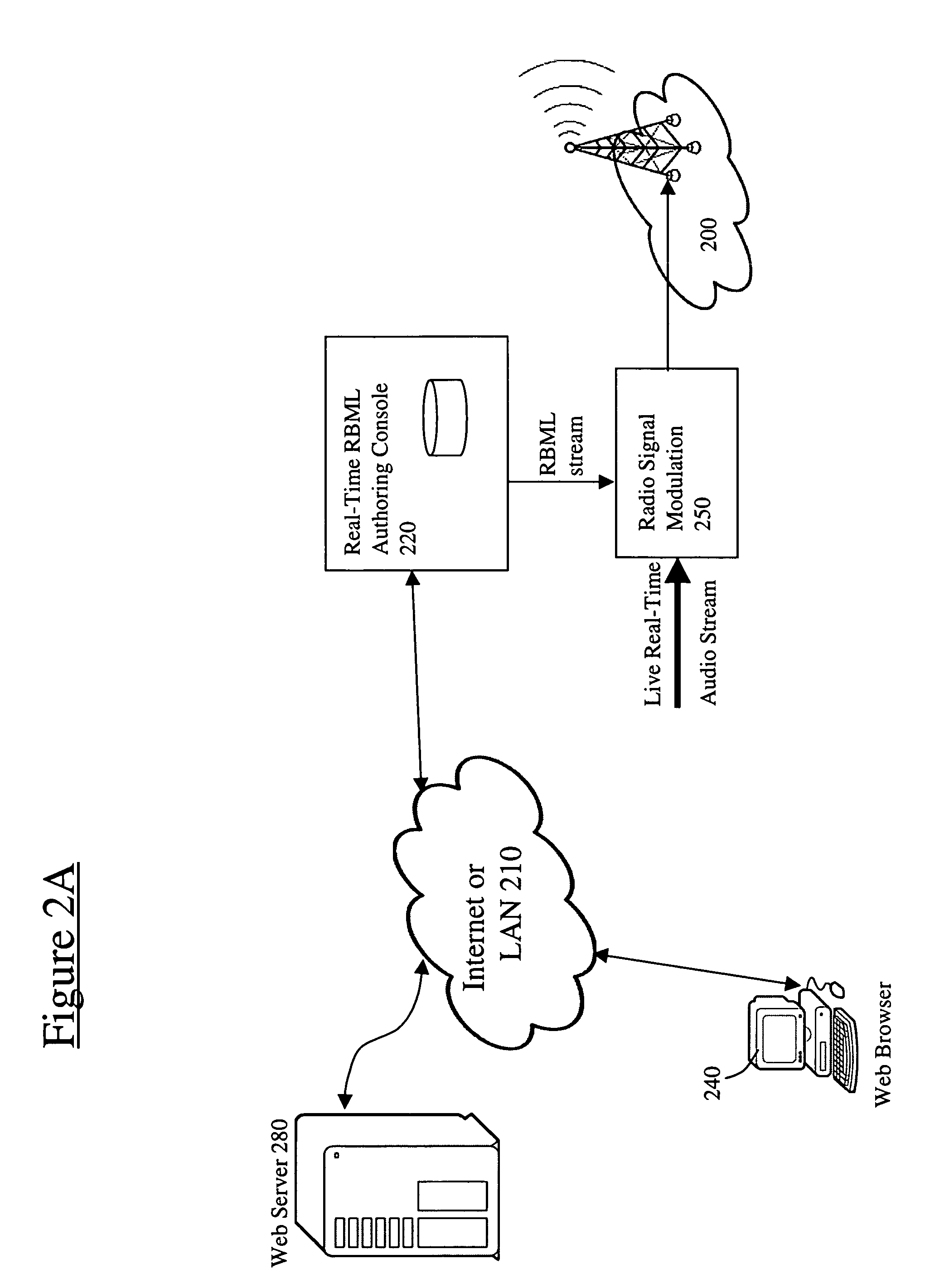
InactiveUS6975835B1Enhance radio broadcastEnhance radio broadcastsBroadcast information characterisationRadio data system/radio broadcast data systemRadio receiverRadio reception
An interactive radio system is disclosed. The overall architecture of the interactive radio system includes a broadcast system for broadcasting digital information across a radio signal to web radio receiver units. An interactive broadcast reception system includes a general purpose computer having a processor, display, and storage and internet connection, a broadcast receiver to communicate with the general purpose computer and to decode digital subcarrier data formatted as a broadcast markup language document, and application software that runs on the processor of the computer and communicates with the broadcast receiver to control the operation of the broadcast receiver and to respond to broadcast markup language commands in said broadcast markup language document by connecting to an internet address referenced in said digital subcarrier data.
Owner:SONIGISTIX CORP +1
User-transparent system for uniquely identifying network-distributed devices without explicitly provided device or user identifying information
InactiveUS20100057843A1Overcome deficienciesEasy to catchMultiple digital computer combinationsTransmissionUnique device identifierUnique identifier
A technique for uniquely identifying devices without explicitly provided device or user identifying information in a networked client-server environment, e.g., the Mobile Internet, in which content is downloaded from a server to a device browser executing at a client device, and using static XML markup tags embedded in the content in a manner transparent to a user situated at the device browser, derives a globally unique device identifier. Device identifying information is captured and maintained in a device profile database associated with a globally unique device identifier. Specifically, mark up code embedded into a referring content page effectively downloads software from a distribution server, and then instantiates the software in the client device browser. The software transparently and dynamically inserts an Internet address request to a device identification management system. The device identification management system selects a device profile associated with a previously detected request from the device and retrieves its globally unique identifier from a database of all profiles for all previous devices requesting unique device identifications. If a matching profile is not found in the database, the device identifying information associated with the request is entered as a new device profile along with a globally unique identifier associated with that specific device in the database. The globally unique identifier is delivered back to the device or external systems for their own use, e.g., mobile Internet advertising management systems.
Owner:MEDIA STAMP
System and method for identifying individual users accessing a web site
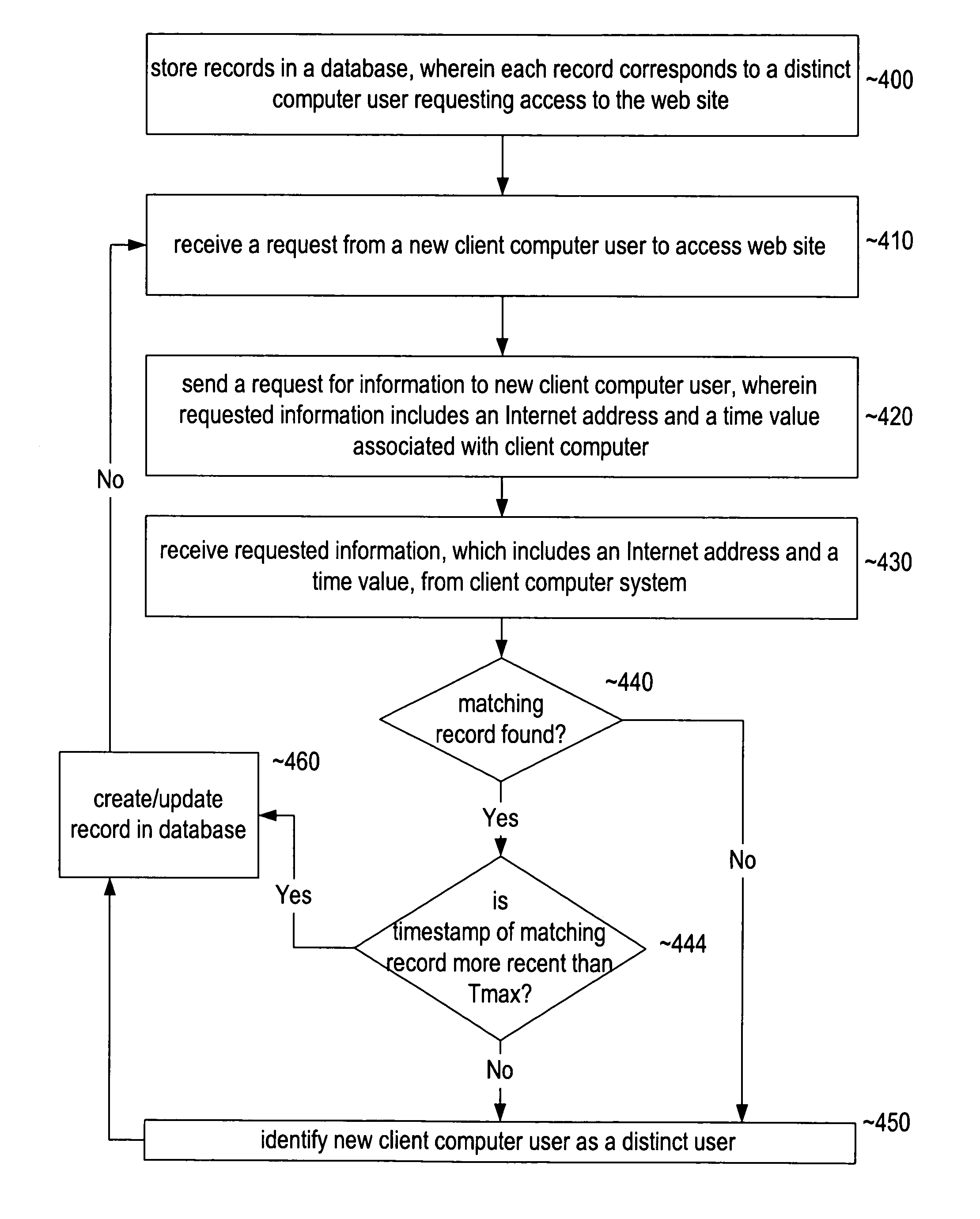
ActiveUS7962603B1Digital computer detailsWebsite content managementUser identifierApplication software
An improved method and system for identifying individual users accessing a web site. A web site server is able to identify distinct users by using a unique identifier associated with each client computer system requesting access to the web site. The unique identifier comprises an Internet address, such as an Internet Protocol (IP) address, and a time value associated with each client computer system requesting access to the web site. On starting up a web browser, an application program or browser plug-in may synchronize the internal clock included with the client computer system with a global time standard. The synchronized time value may be based on an event associated with the client computer system, such as the start of a web browser. A web site server may determine the uniqueness of the client computer system by comparing unique identifier records of users accessing the web site. A user may be identified as distinct if no matching record exists in the database. Multiple client computer systems having a common Internet address may be identified by using this method. Users privacy is also protected as the unique identifiers are erased when the client computer system's user exits the web browser or powers down the computer.
Owner:NIHON DOT COM
Method and system for handwritten electronic messaging
The present invention provides a system and method for providing handwritten messages with electronic communication devices. For example the electronic communication device may be a mobile communication device and may include a touch screen, screen buffer memory, processor, and transceiver. In preferred embodiments, the mobile communication device may be a personal digital assistant (PDA), a two-way pager, or a mobile telephone. The mobile communication device user may create a handwritten message on the touch screen using, for example, a stylus. In one exemplary embodiment, the handwritten message displayed on the touch screen may be stored to the buffer memory as an image, directed by the processor to the transceiver, and transmitted via a wireless connection to, for example, a wireless base station and the Internet. The Internet may route the handwritten message image to a desired Internet address. The handwritten message may be displayed in real time on the recipient's display, e.g., an instant message (IM) session, or stored in their email mailbox for later retrieval and display. The recipient may type in a text message in response to the hand written message, and this message will be transmitted to mobile communication device and displayed on the mobile communication device. In another embodiment, the receiving party may also have handwritten messaging capabilities (included with, for example, a PC, PDA or a mobile phone) and may respond with a handwritten message.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Predictive malware scanning of internet data
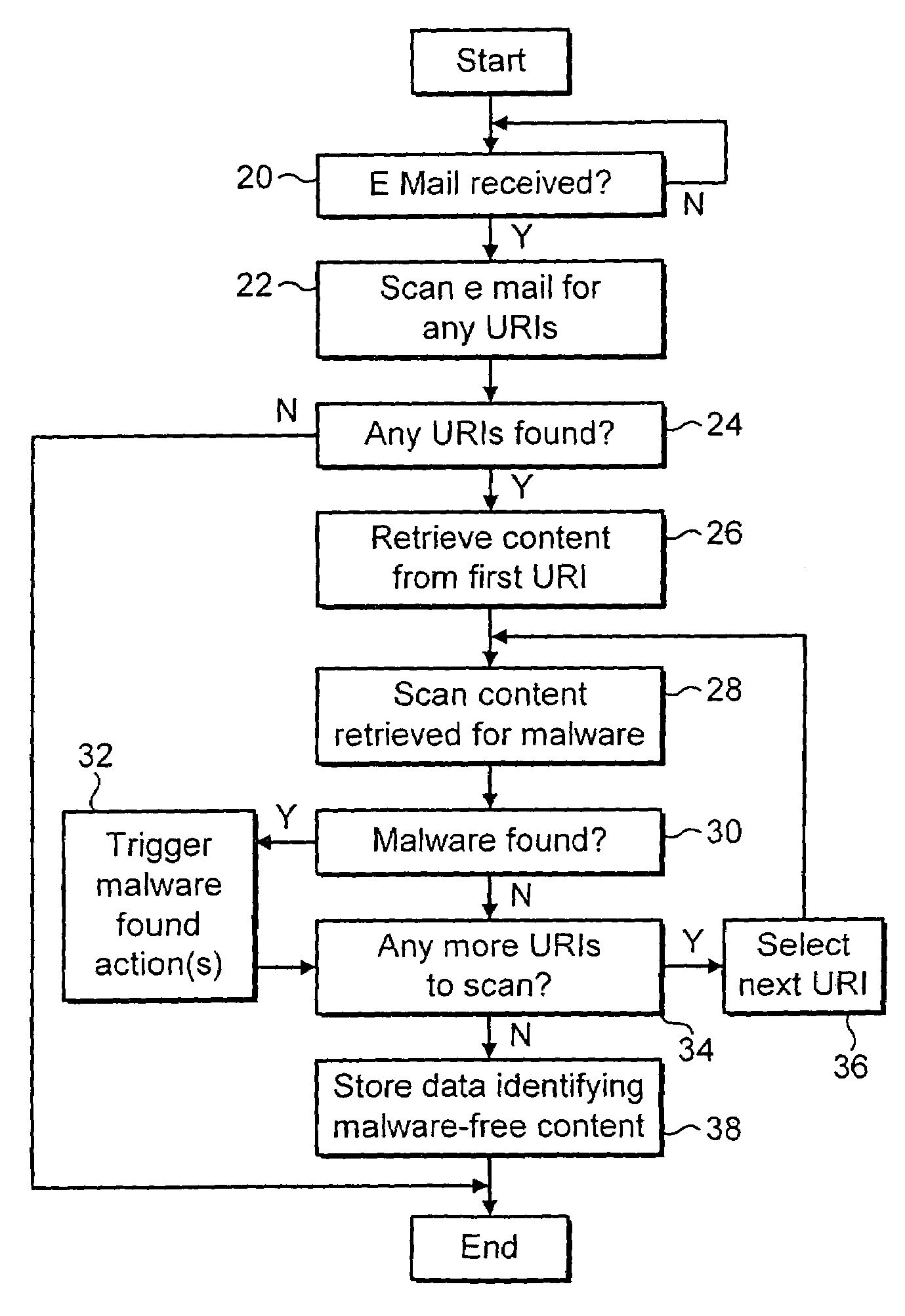
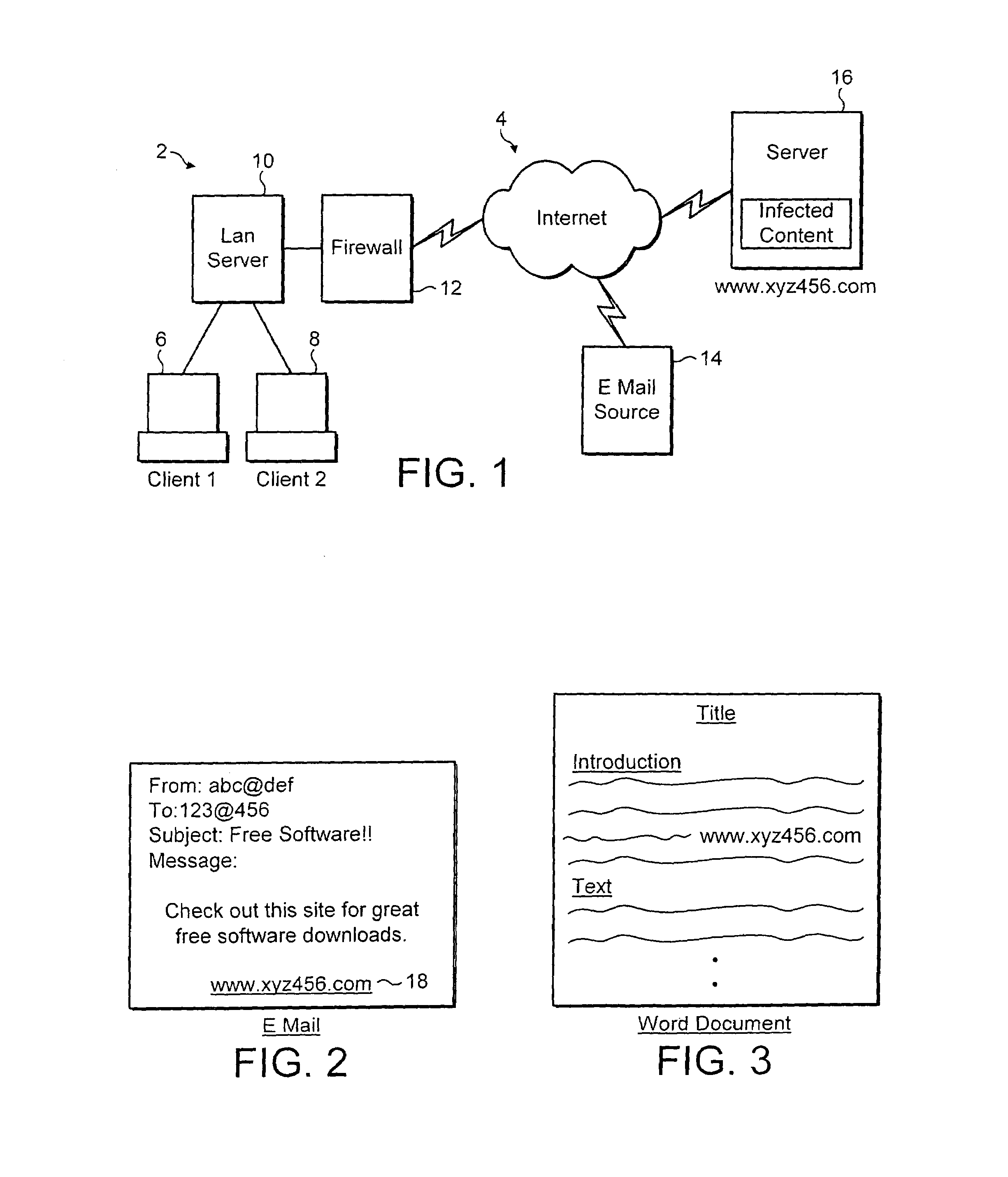
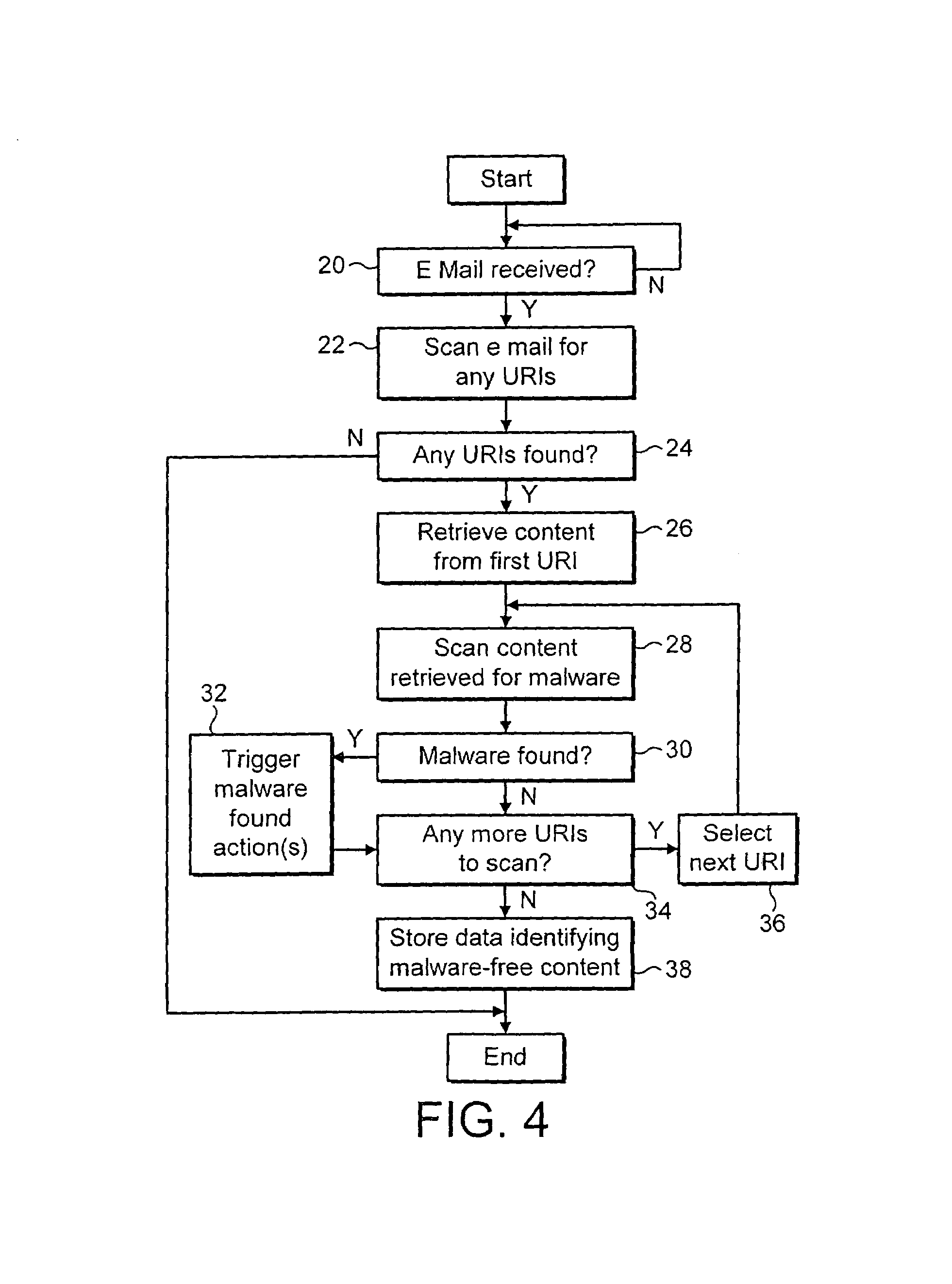
InactiveUS7096500B2Reduce the possibilityAccess to the data may be provided more rapidlyMemory loss protectionDetecting faulty computer hardwareMalwareInternet address
E-mail messages or computer files are scanned to identify embedded internet addresses. These embedded internet address 18 refer to data that may be retrieved via the internet. This data is pre-emptively retrieved and scanned for malware even though it has not been requested by a user. If the data is found to be malware-free, then a record of this is kept. If a user subsequently seeks to access the data associated with the embedded internet address, then the stored data may be referred to and if the internet address is found and the data associated with that address is unchanged since it was previously scanned, then that data may be supplied to the user without the need to be rescanned.
Owner:MCAFEE LLC
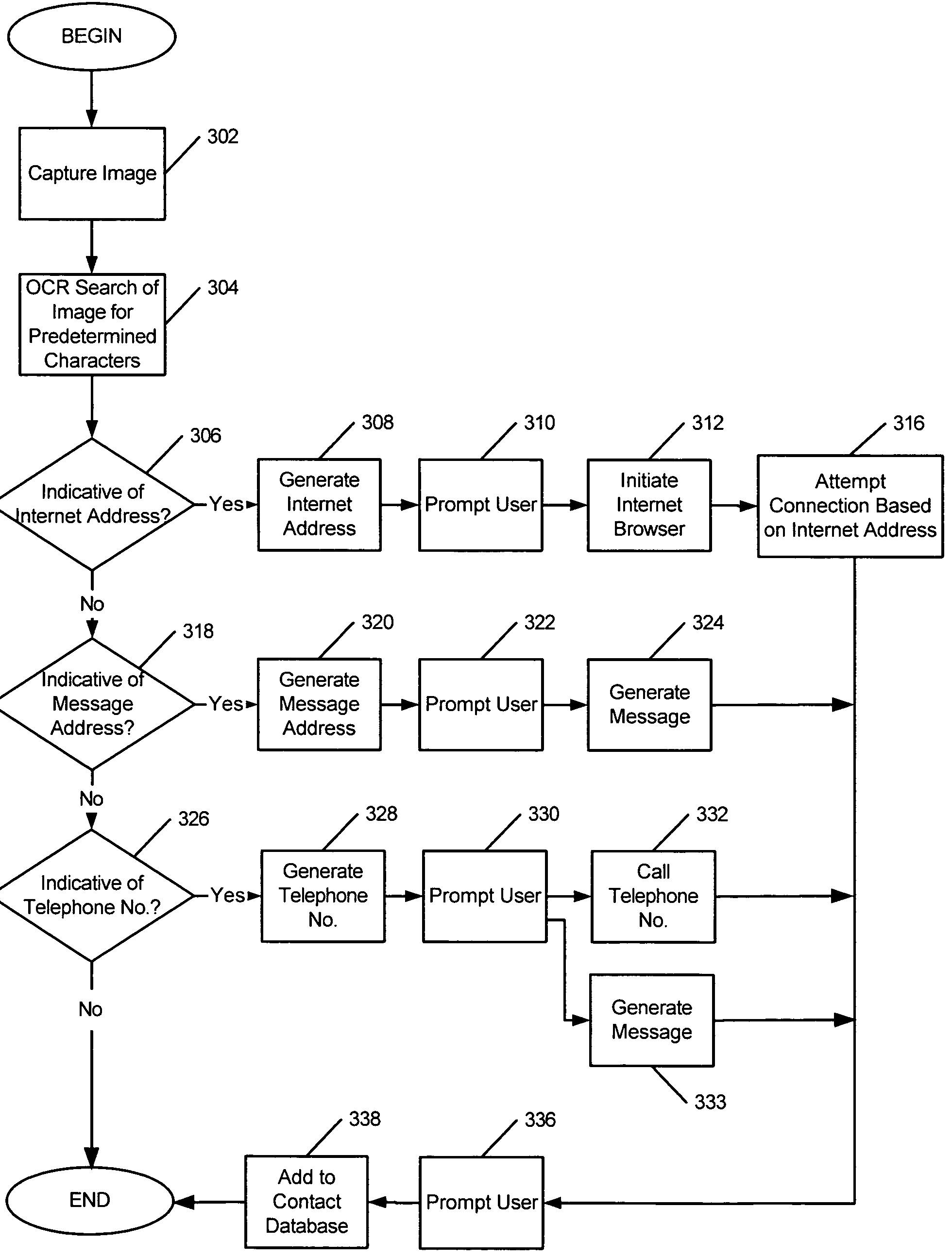
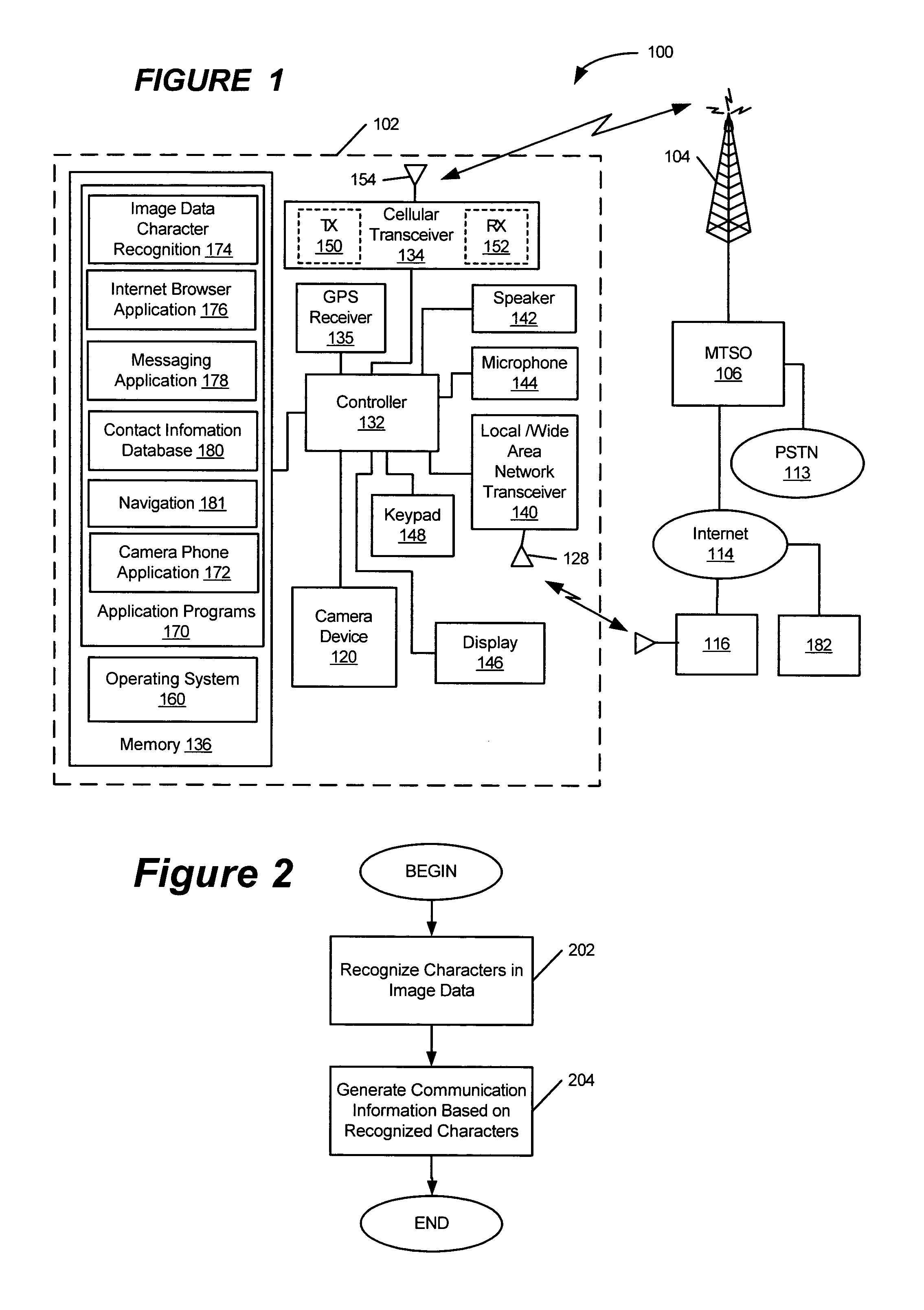
Mobile terminals, methods, and program products that generate communication information based on characters recognized in image data
InactiveUS7558595B2Television system detailsInstruments for road network navigationComputer terminalInternet address
Mobile terminals, methods, and program products generate information for communication from a mobile terminal. The mobile terminal can include a camera device and a controller. The camera device is configured to capture image data based on incident light. The controller is configured to recognize characters in the image data, and to generate the information that is to be communicated from the mobile terminal based on the recognized characters. The controller may determine that the recognized characters are indicative of an Internet address, a message address, a telephone number, a street address, and / or contact information.
Owner:SONY CORP
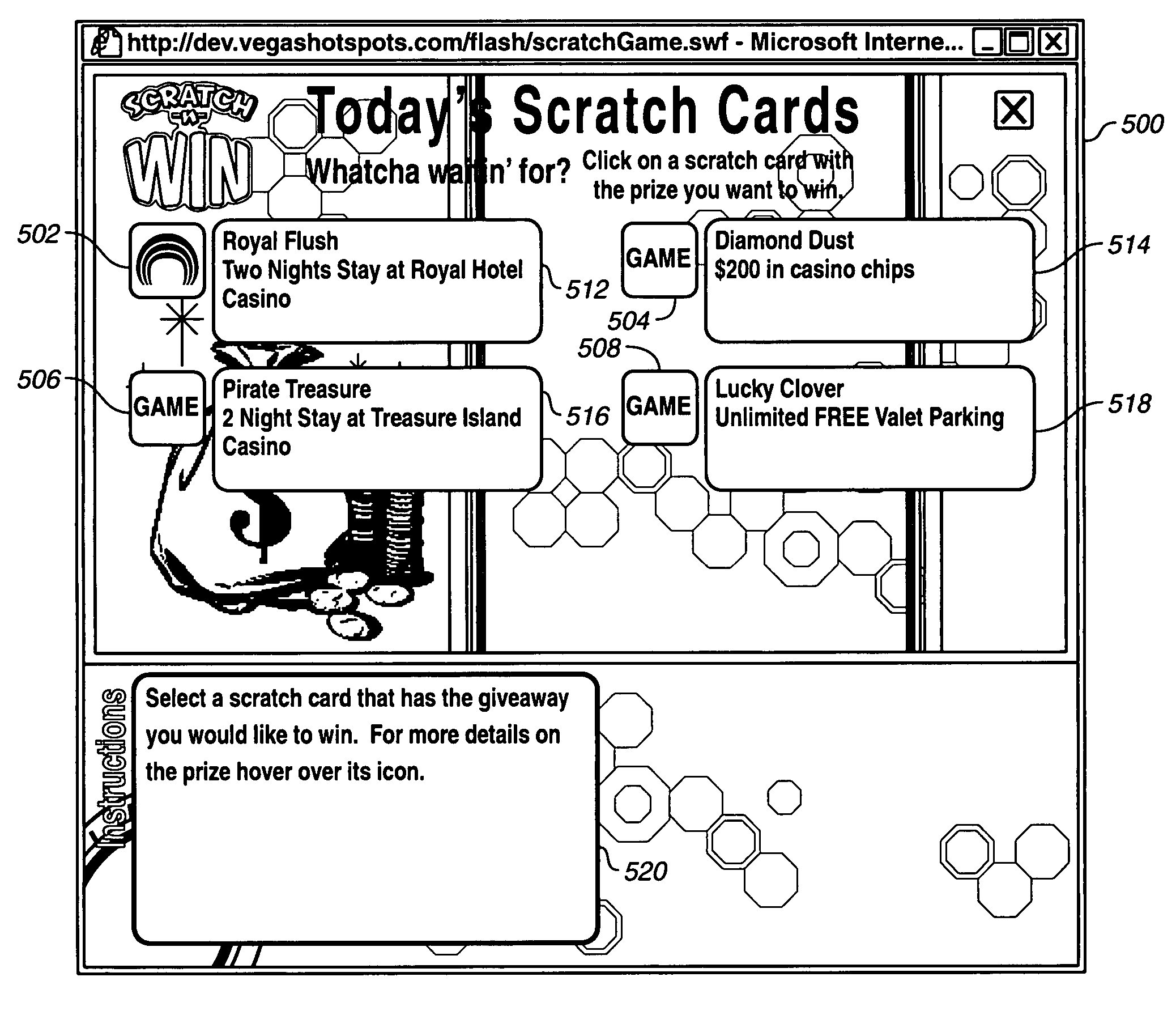
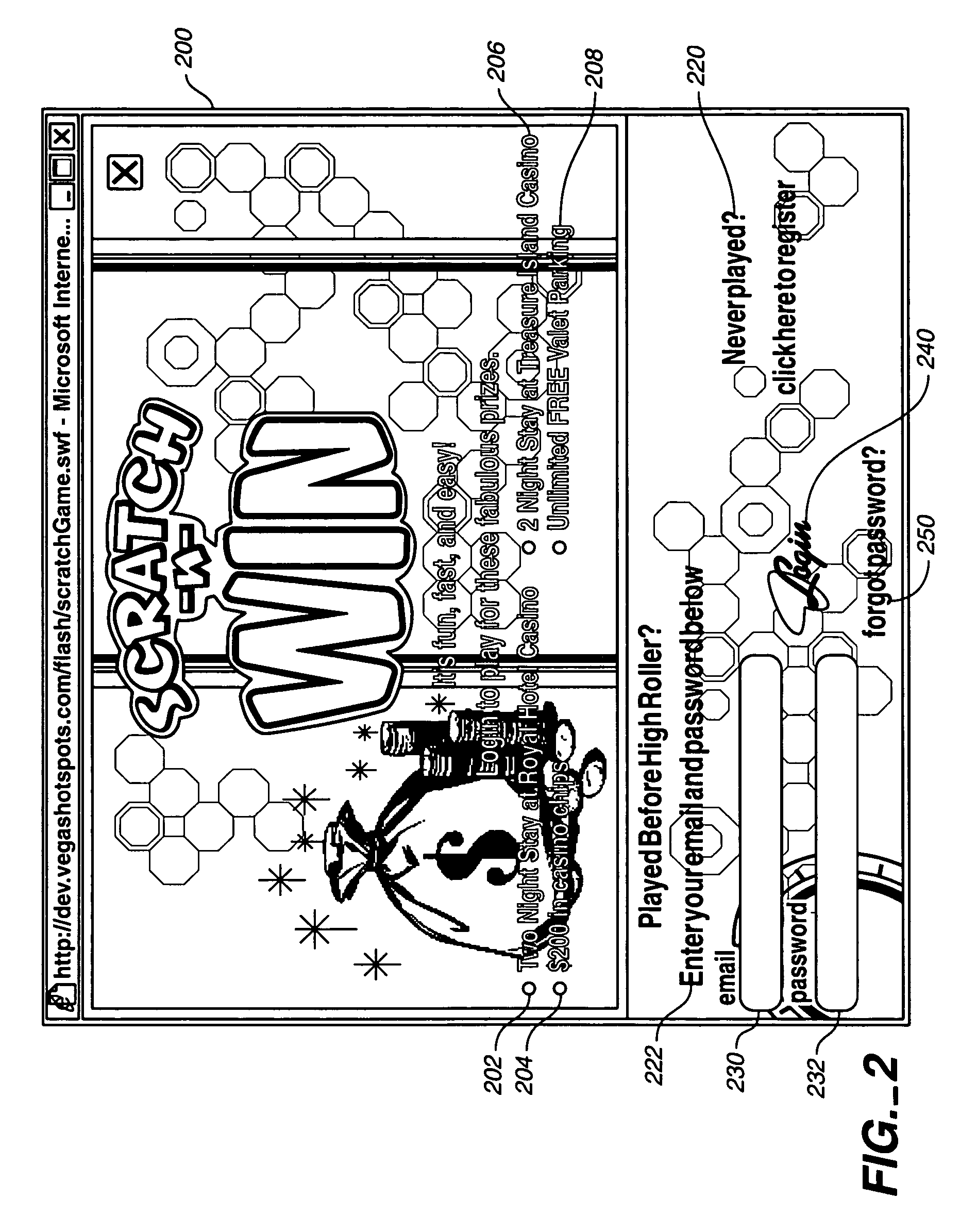
Method and system for online game and interactive marketing
InactiveUS20050091108A1Discounts/incentivesApparatus for meter-controlled dispensingEmail addressGame player
A method combines the use of an Internet address containing a word or phrase that conveys a known destination to a self-selected online user with an opportunity to play a game and to win valuable prizes. A first: time game player is asked to register and to input at least an e-mail address, and preferably to answer at least one destination-oriented question to have an opportunity to win at least one destination-oriented prize.
Owner:VEGASHOTSPOTS
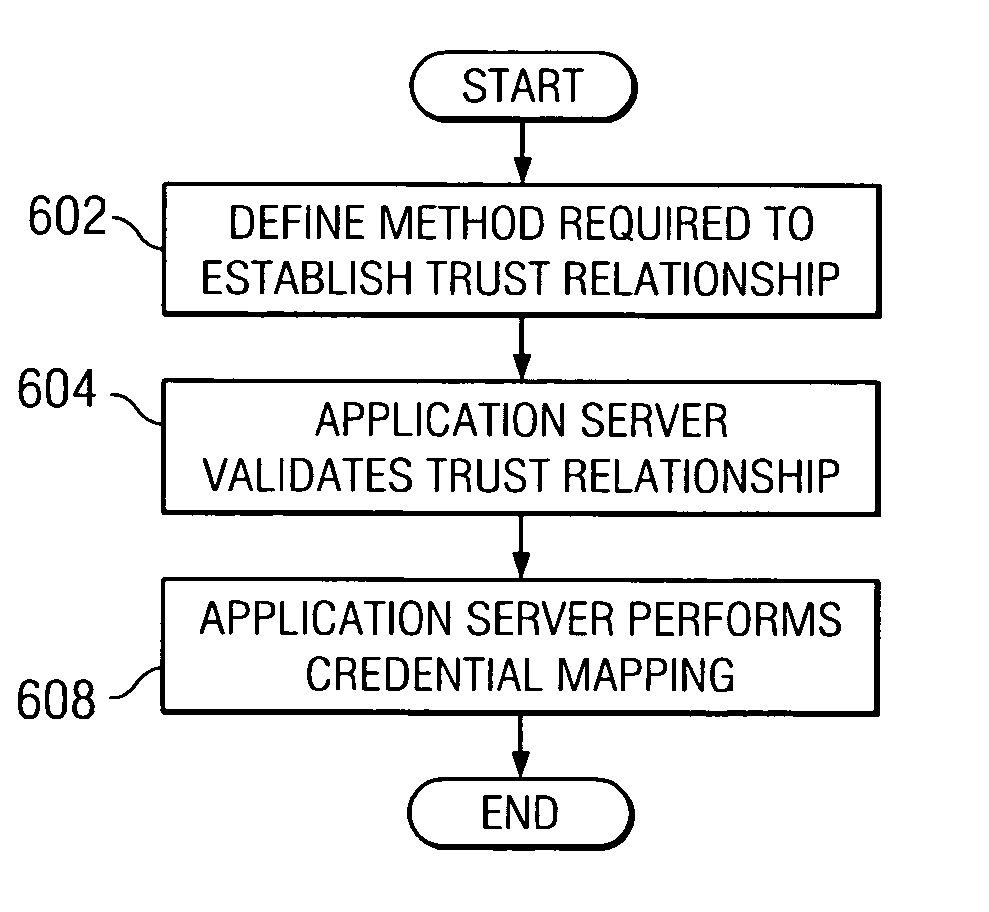
Declarative trust model between reverse proxy server and websphere application server
A method and system for providing a declarative trust association model that formalizes the way trust is established and requires corresponding authentication information to be presented in a standard format. Consequently, the application server may provide a guaranteed level of protection. The mechanism of the present invention provides a framework that allows an application server to enforce a trust evaluation and allows reverse proxy security server to assert a client's security identity, as well as other client security credential information. A known trust association interceptor model is extended to allow the reverse proxy security server to assert the authenticated user's security attributes. Such security attributes include, for example, group information, authentication strength, and location (i.e., where does the user enter the request, intranet vs. internet, IP address, etc.,). The security attributes can be used in making authorization decisions.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com