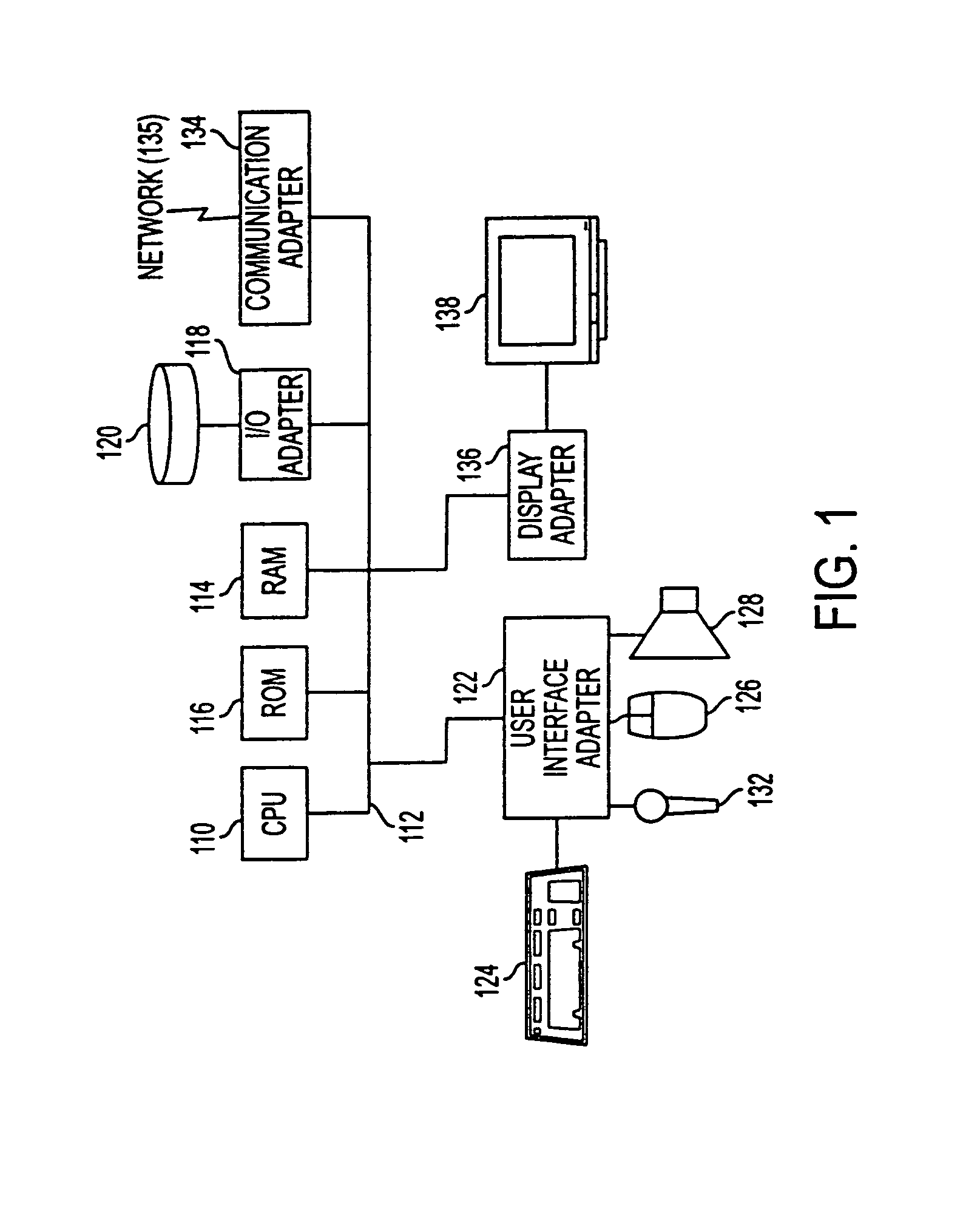
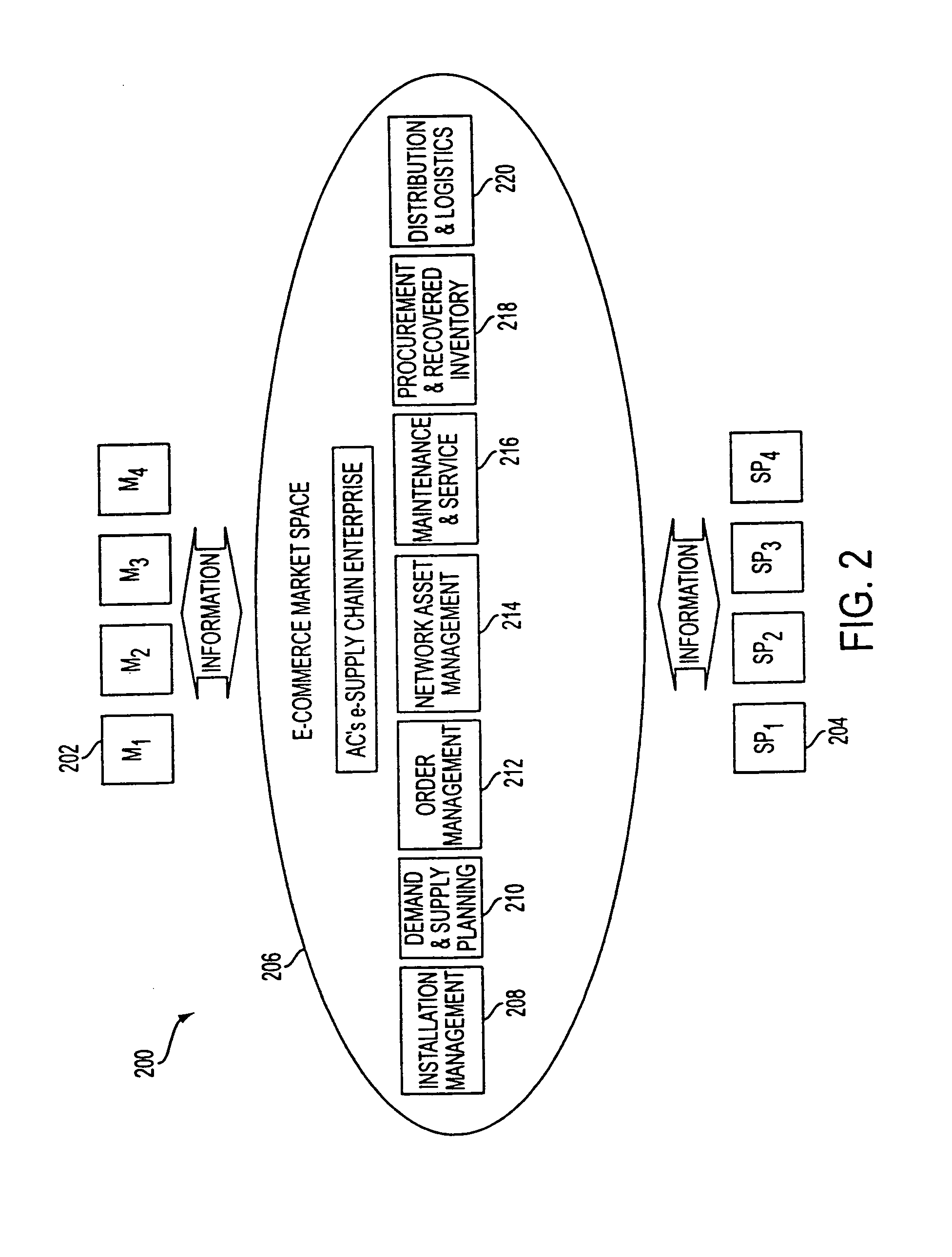
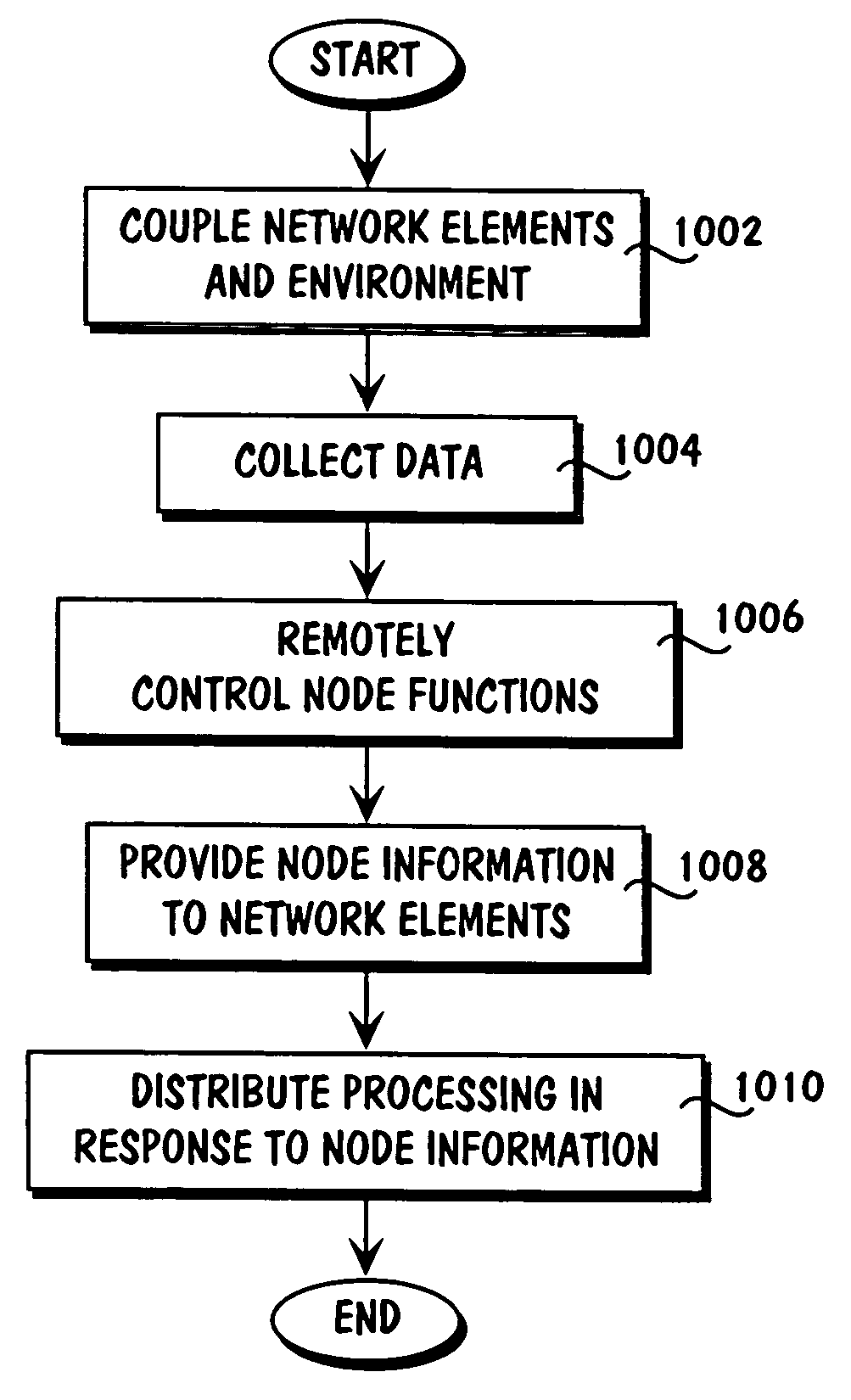
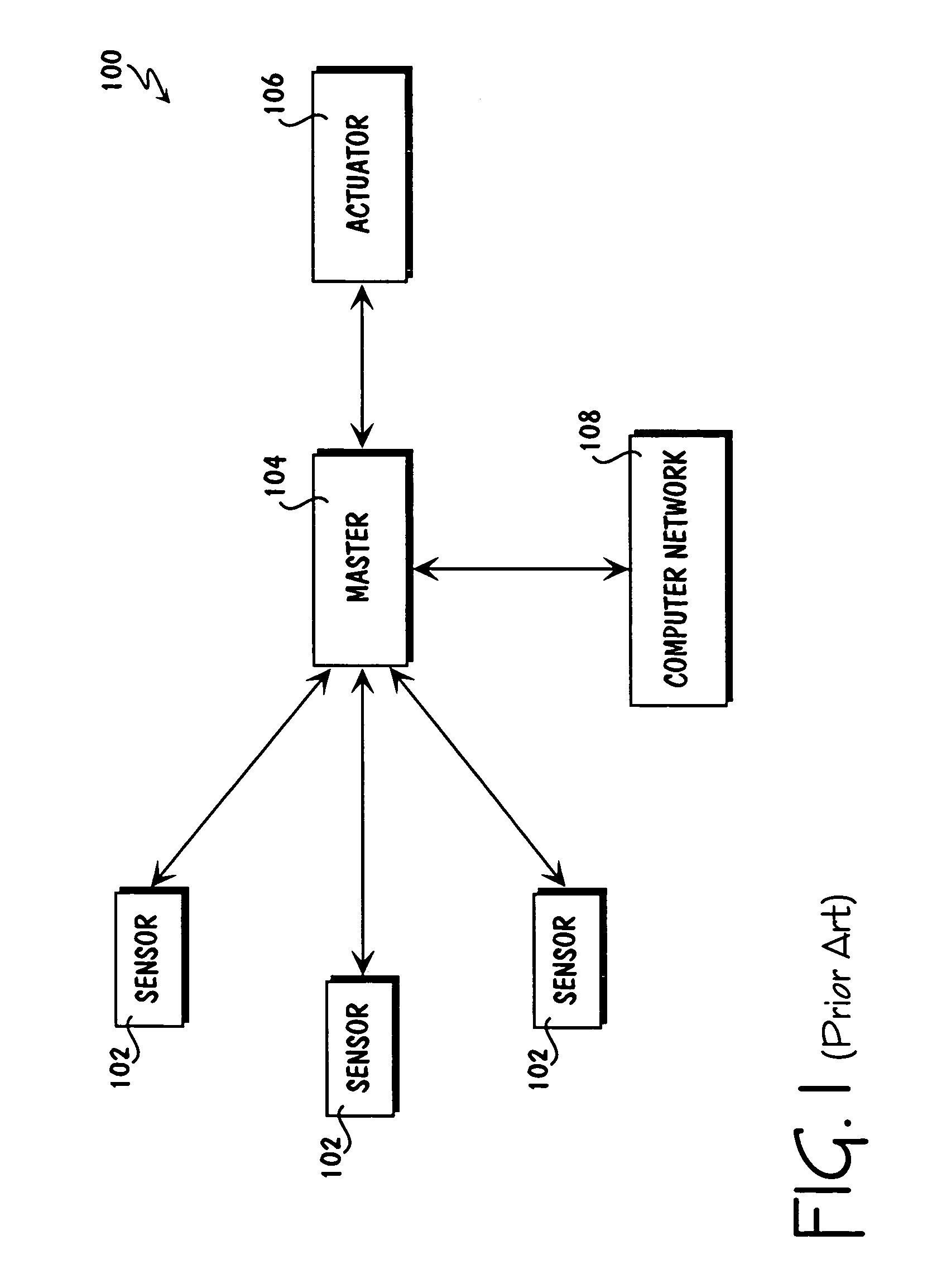
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
101560 results about "Distributed computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
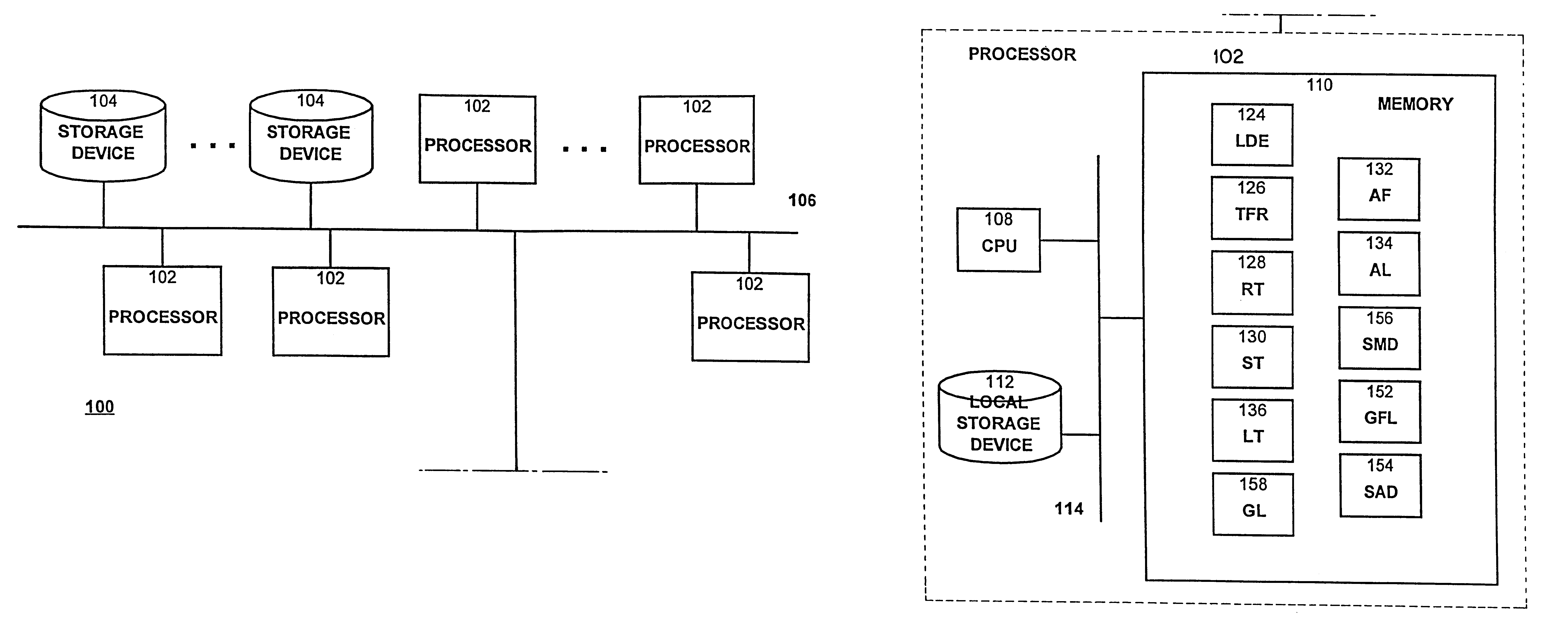
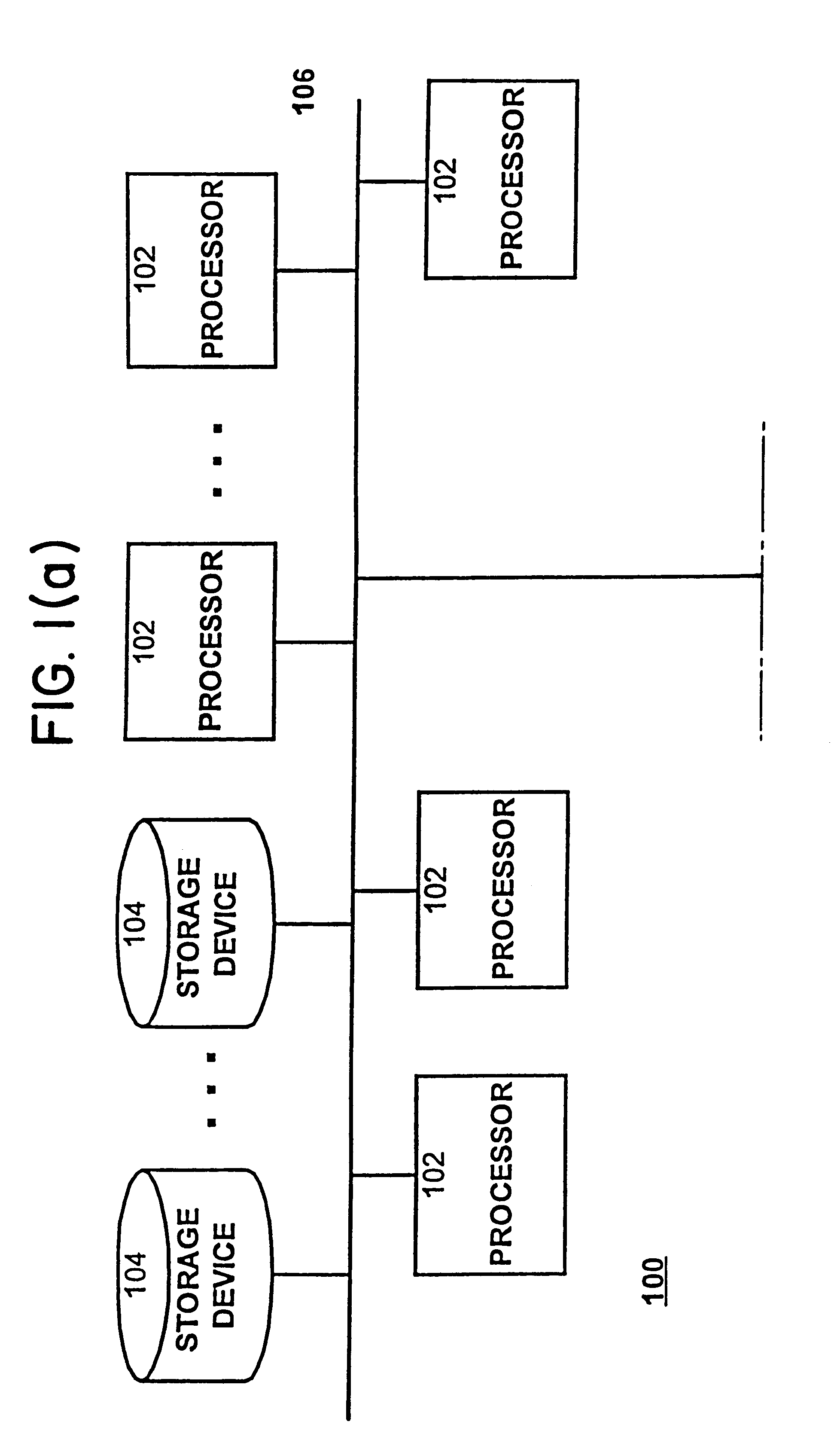
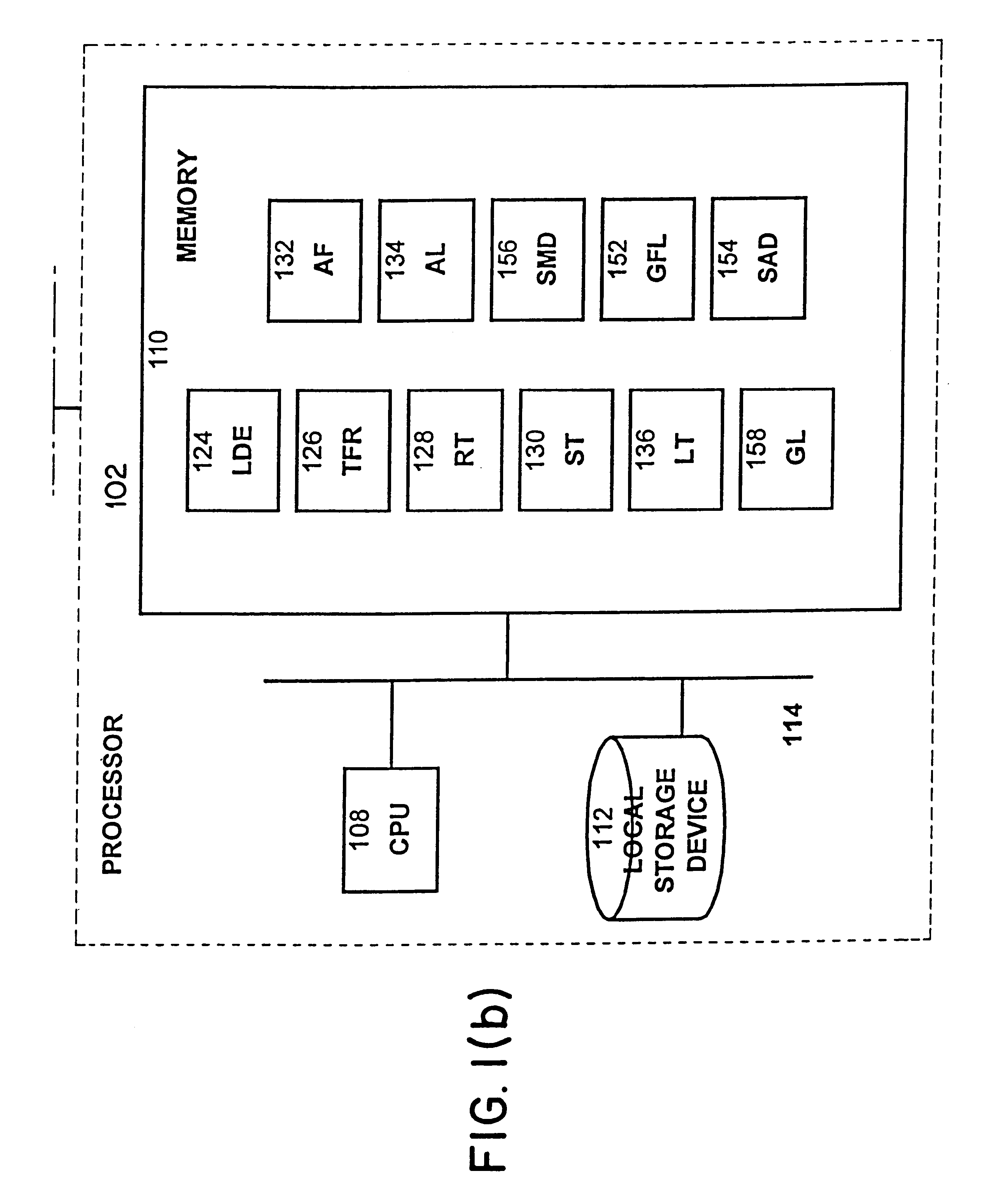
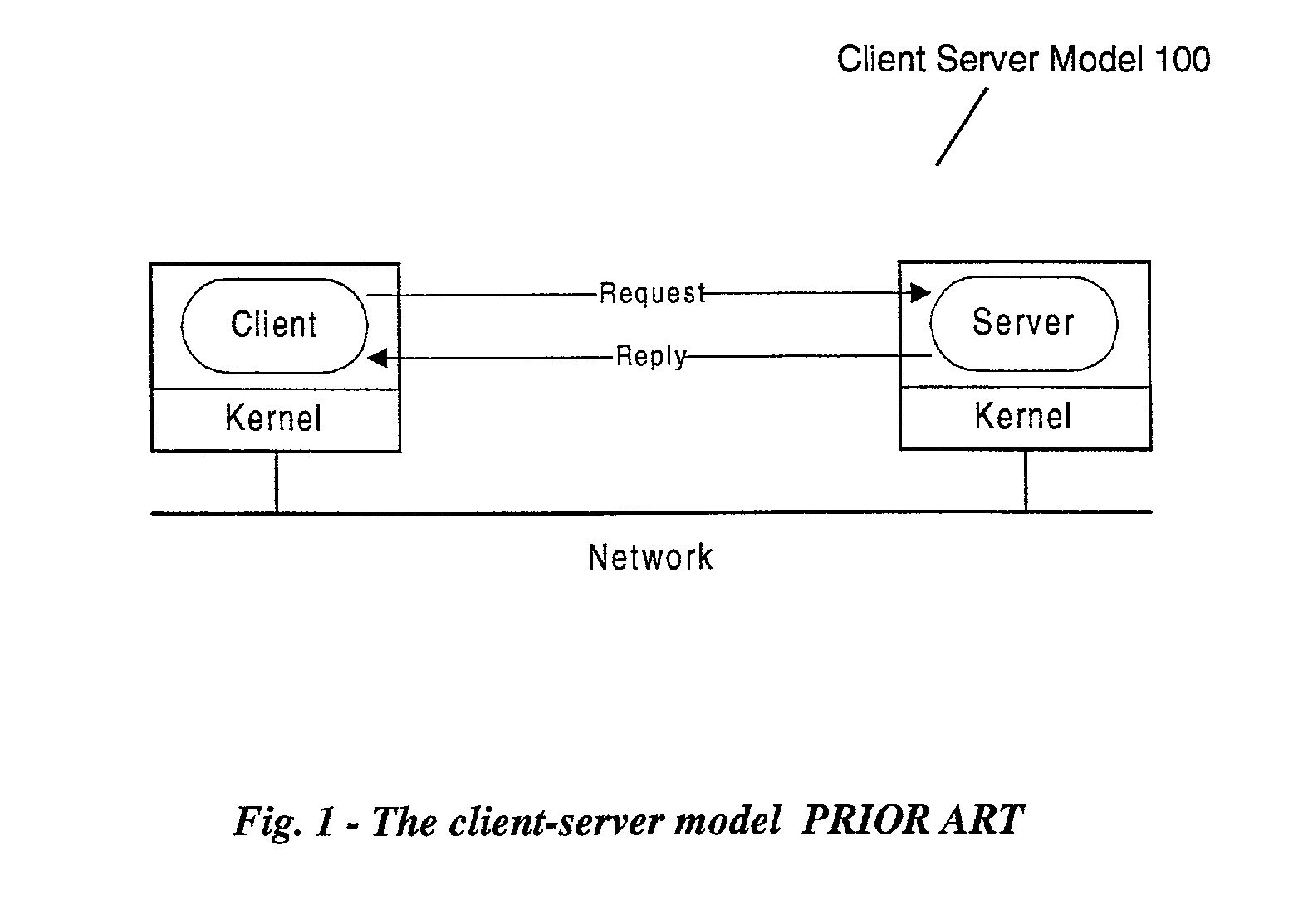
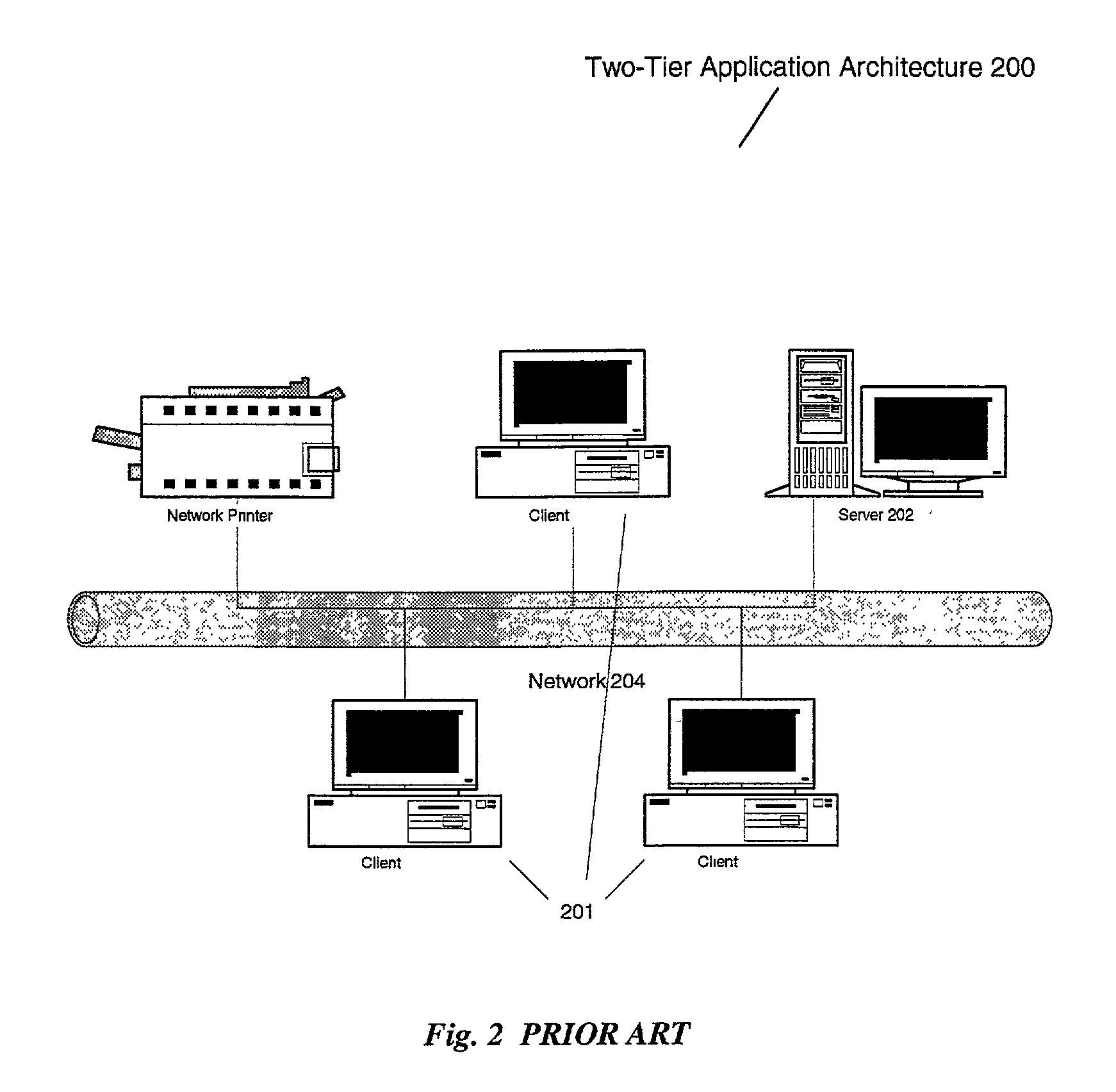
Distributed computing is a field of computer science that studies distributed systems. A distributed system is a system whose components are located on different networked computers, which communicate and coordinate their actions by passing messages to one another. The components interact with one another in order to achieve a common goal. Three significant characteristics of distributed systems are: concurrency of components, lack of a global clock, and independent failure of components. Examples of distributed systems vary from SOA-based systems to massively multiplayer online games to peer-to-peer applications.
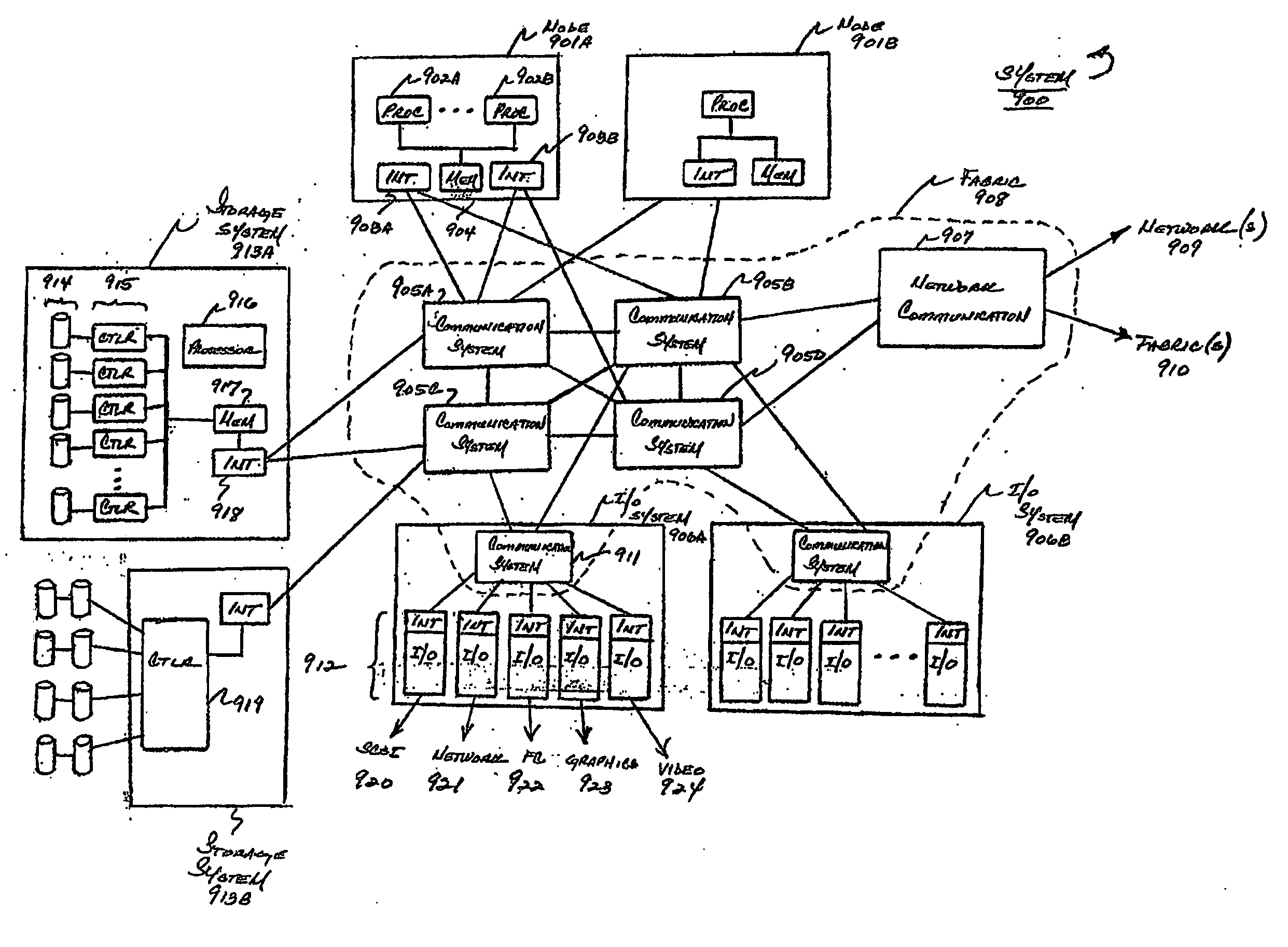
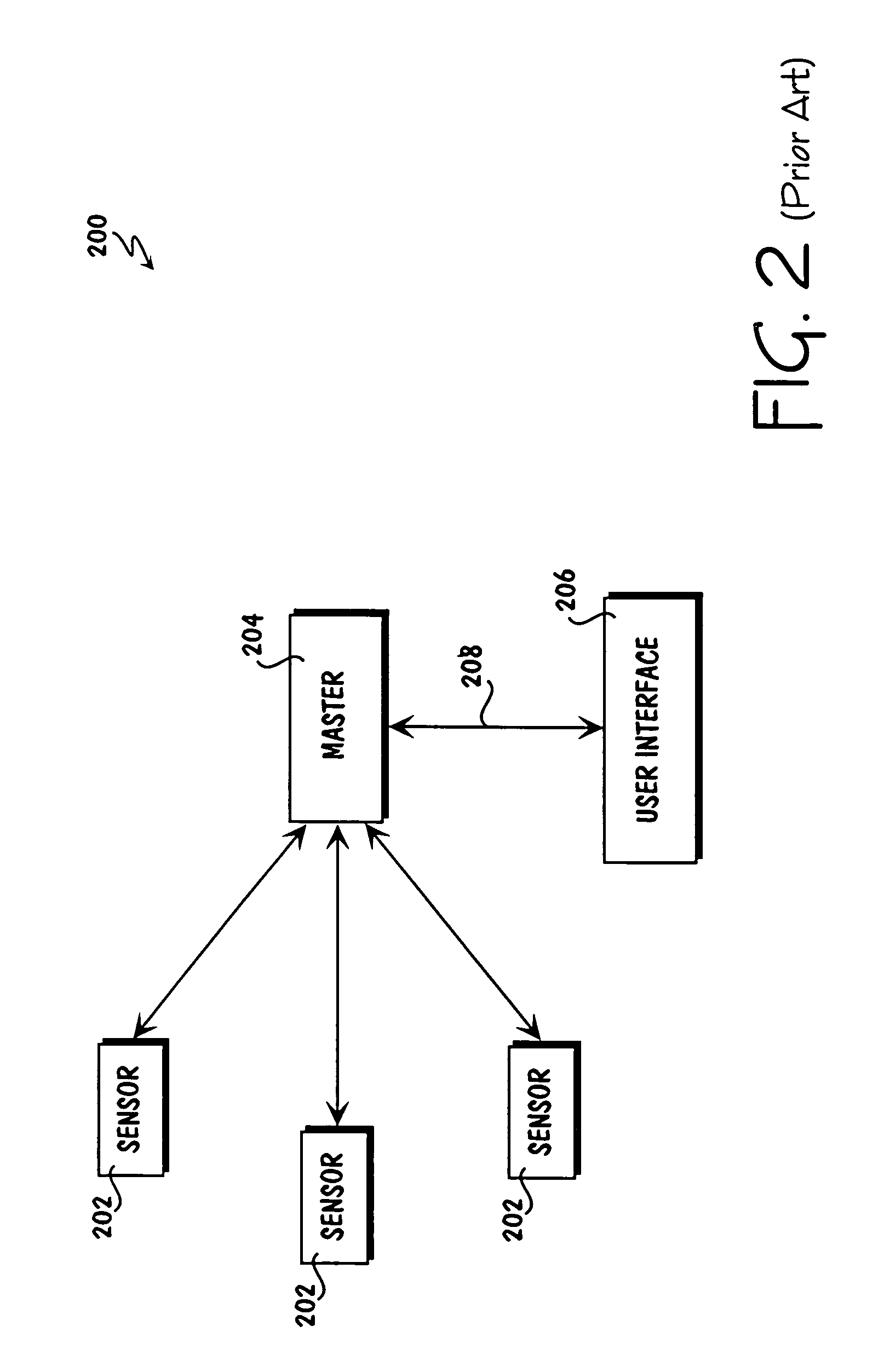
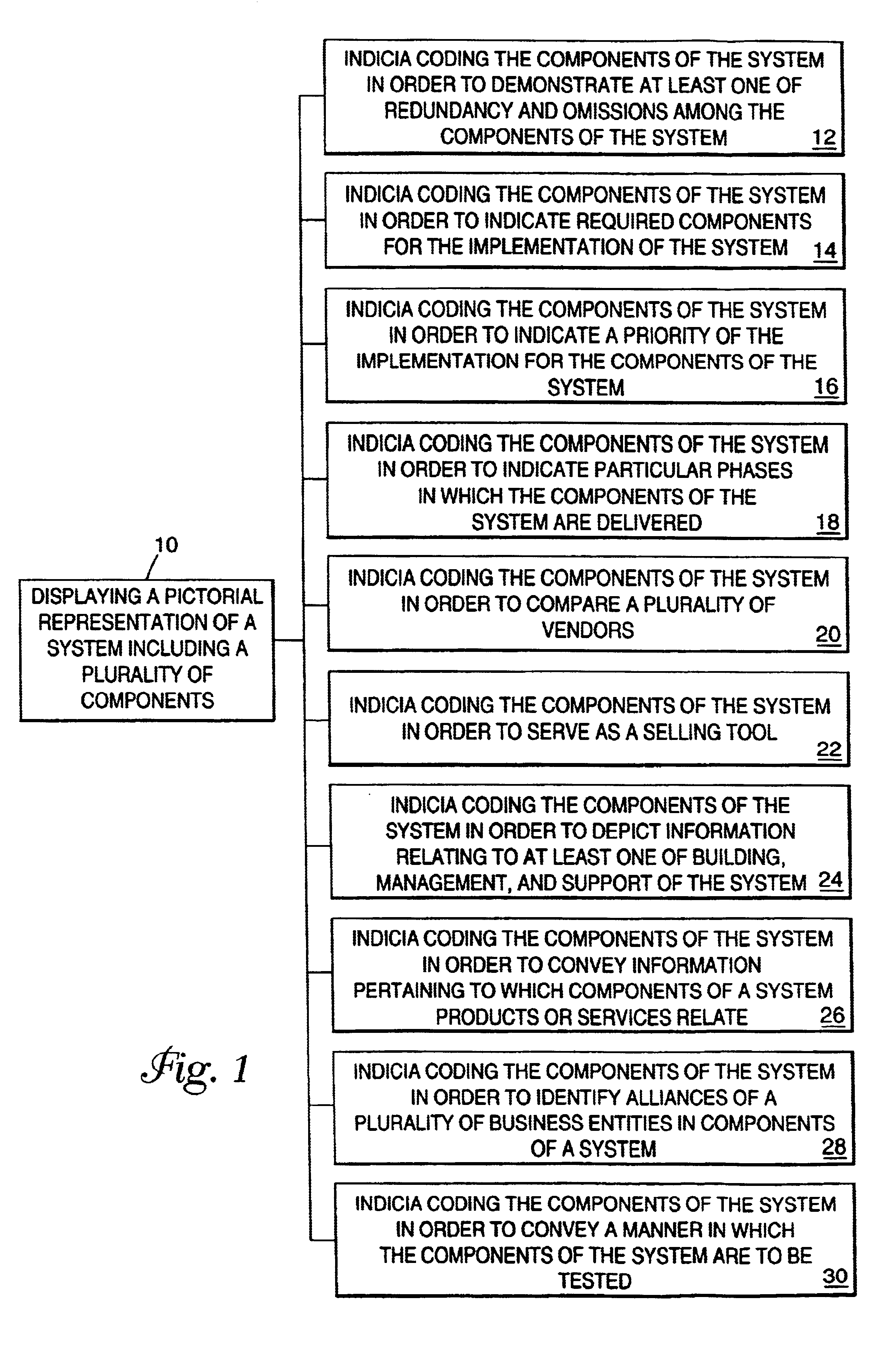
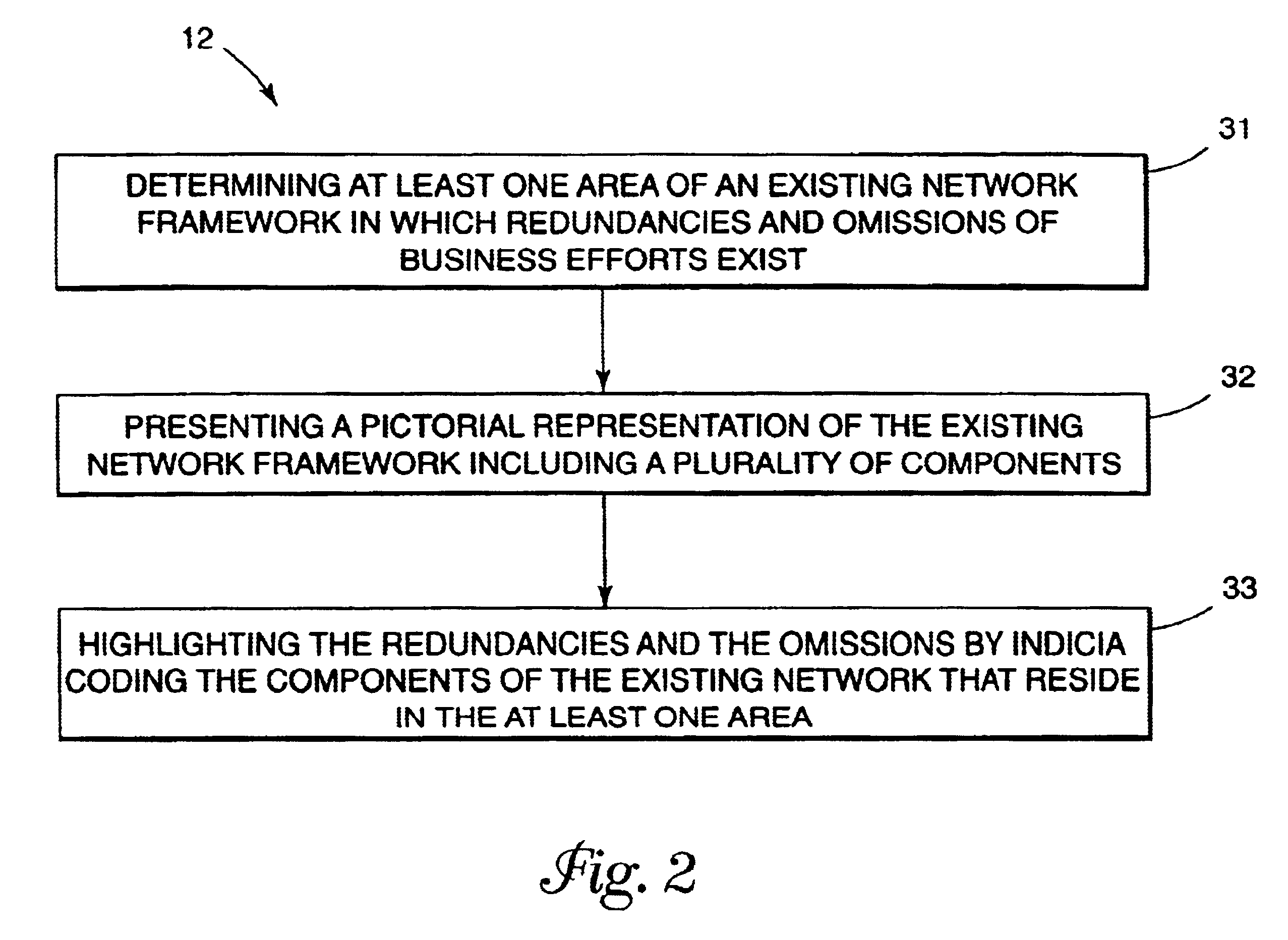
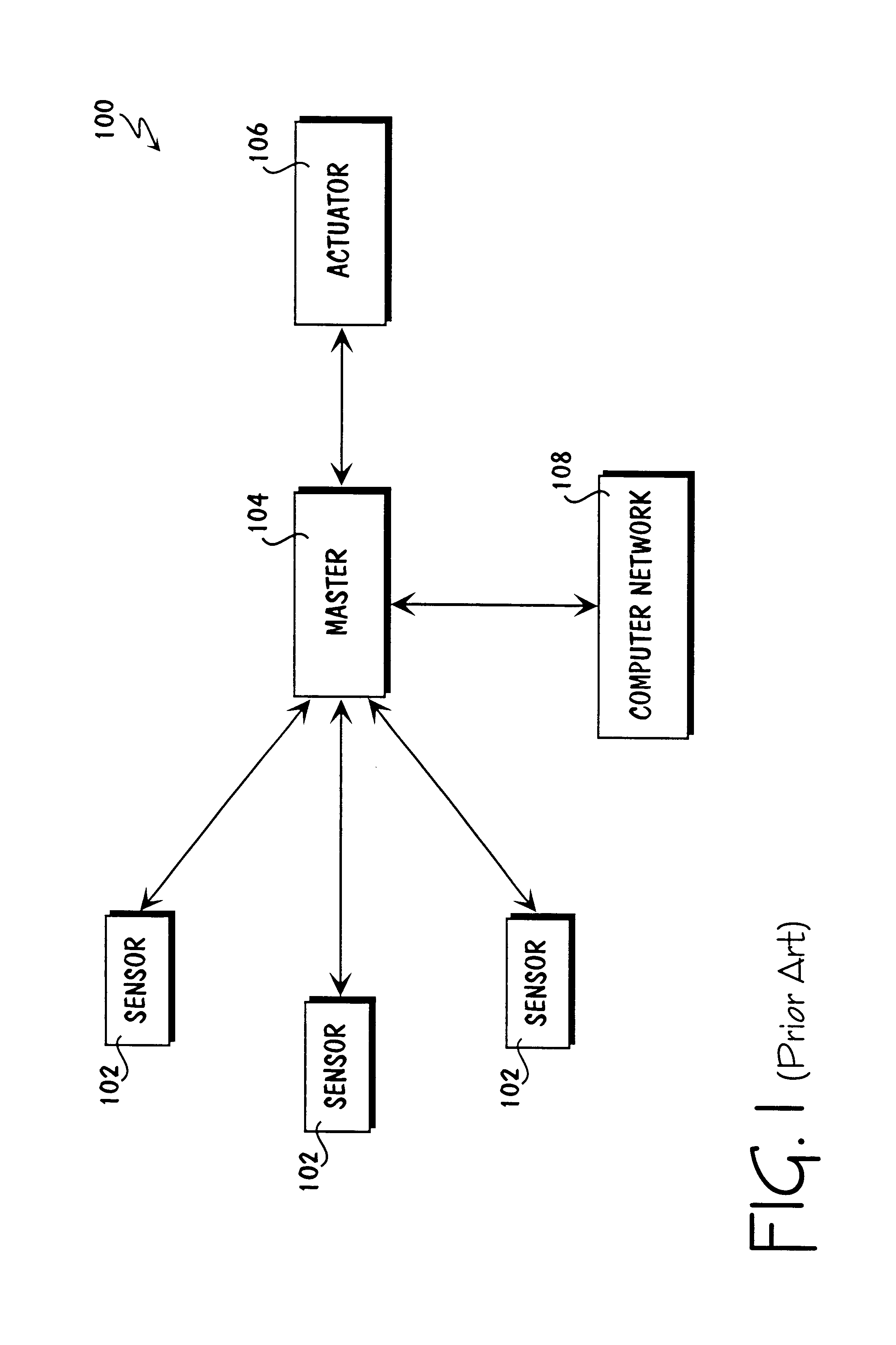
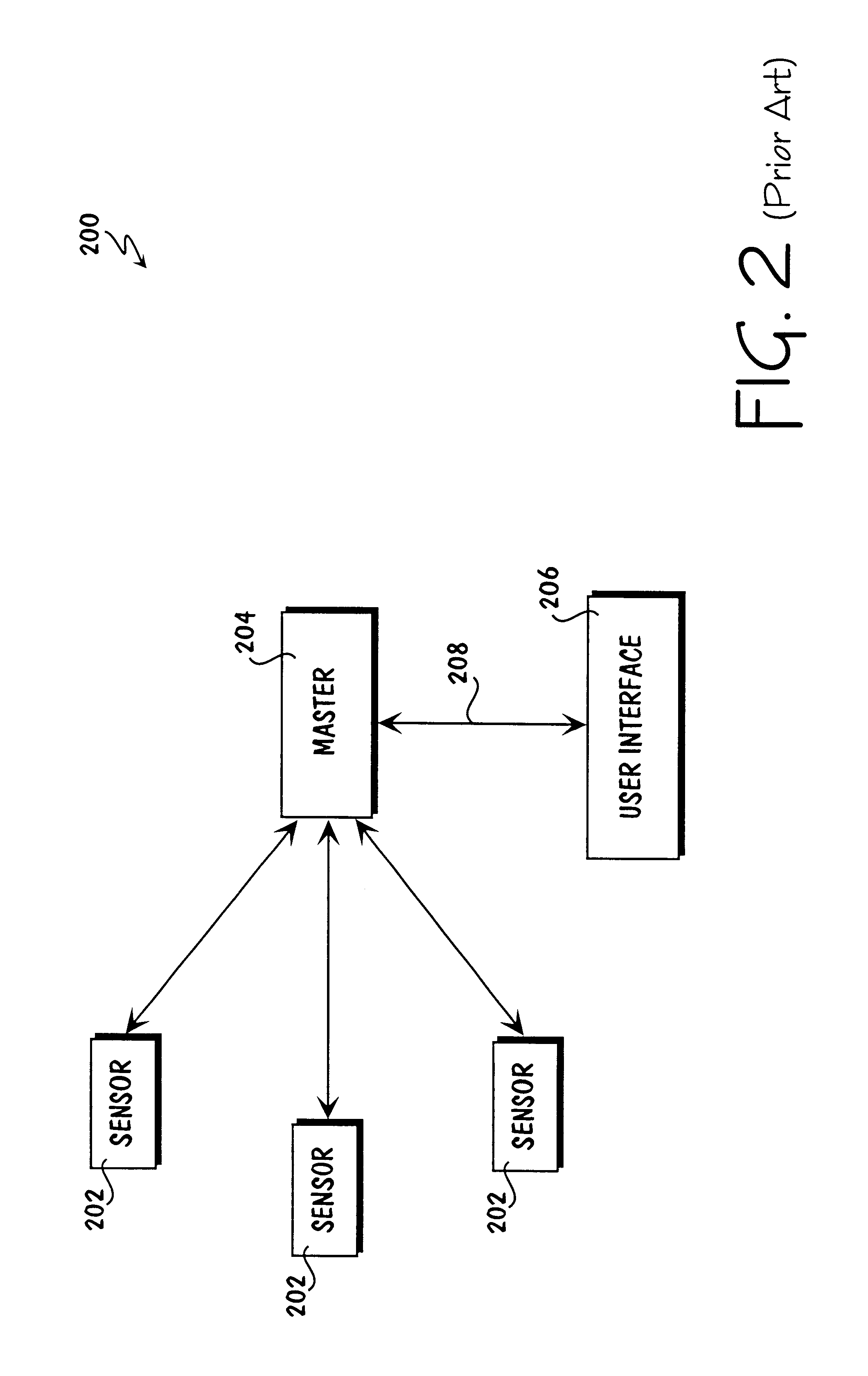
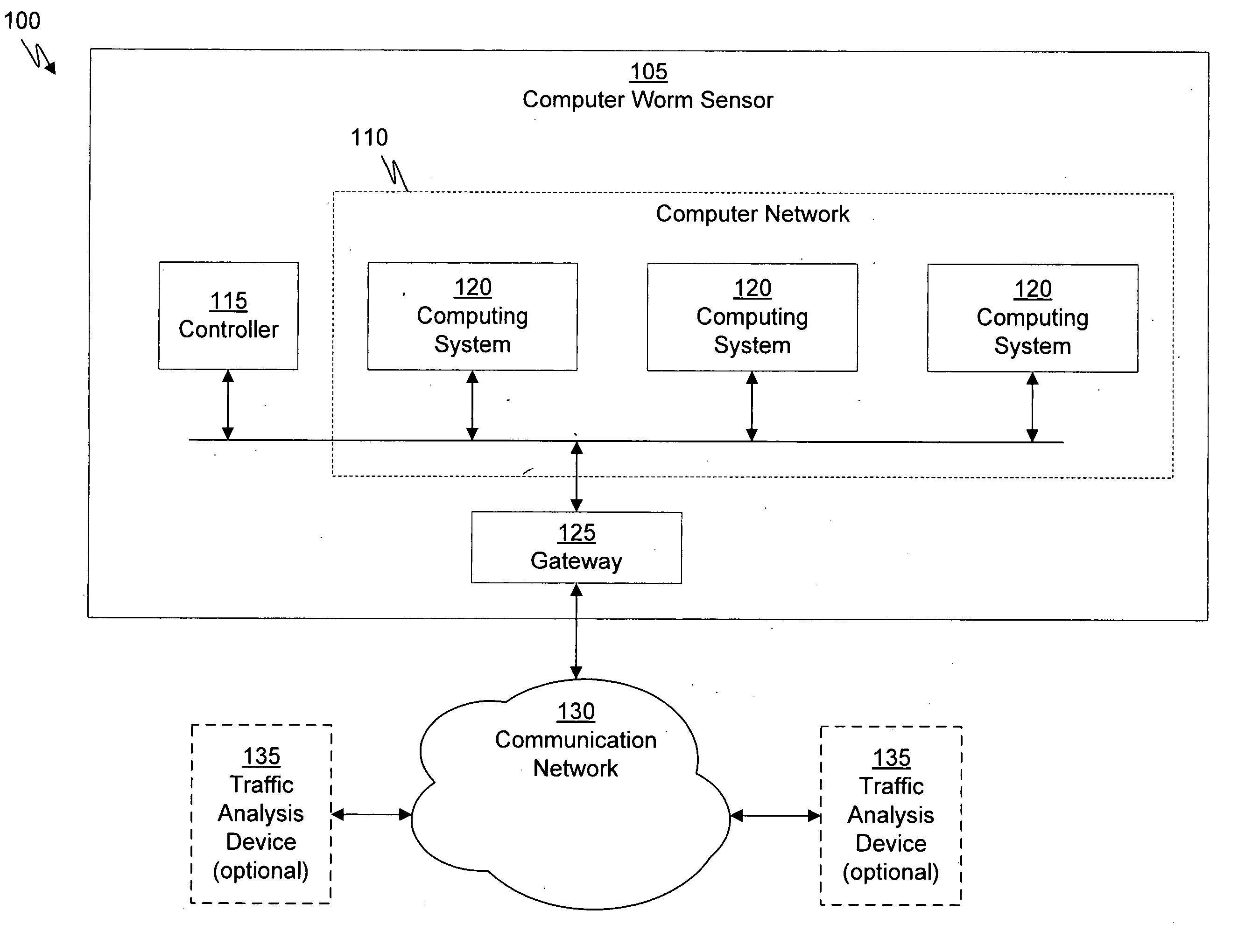
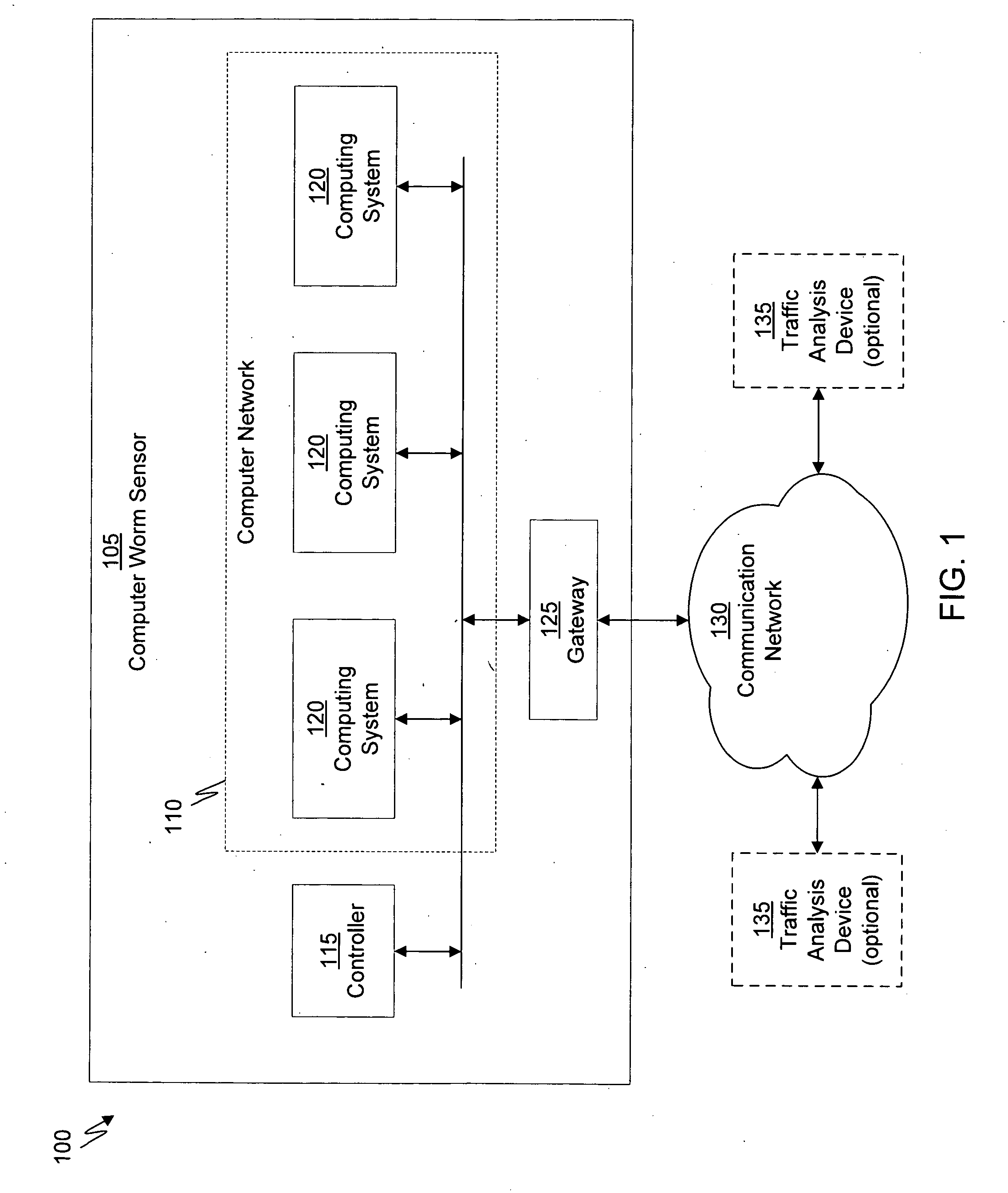
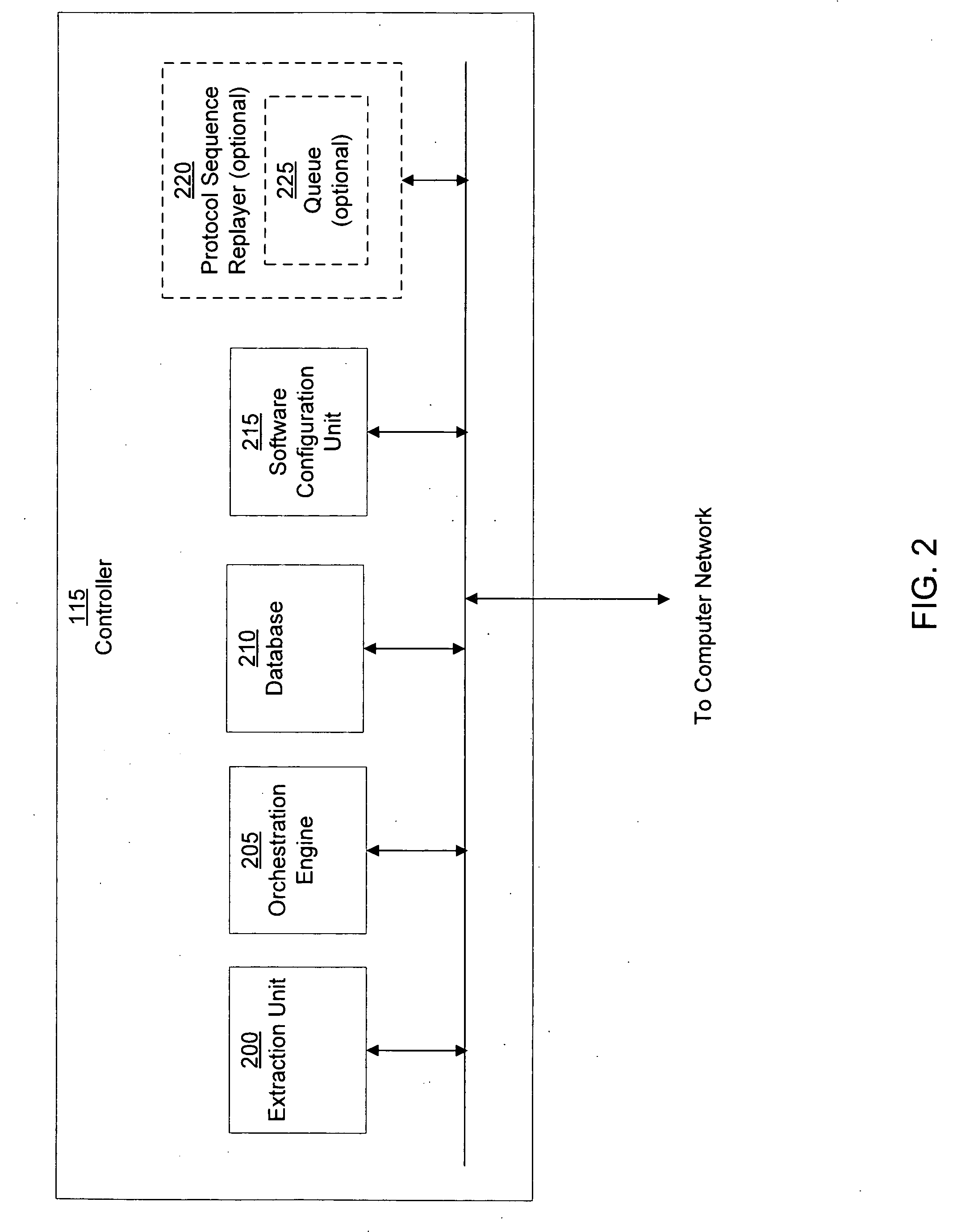
System for establishing plan to test components of web based framework by displaying pictorial representation and conveying indicia coded components of existing network framework
A system, method, and article of manufacture are provided for planning the testing of components of an existing network framework. First, a pictorial representation of an existing network framework is displayed along with a plurality of components of the existing network framework. Thereafter, the components of the existing network framework are indicia coded in order to convey a plan by which the components of the existing network framework are to be tested. The components may be indicia coded in order to convey an order of the testing or which components of the existing network framework are to be tested.
Owner:ACCENTURE GLOBAL SERVICES LTD
Multifactorial optimization system and method
A method for providing unequal allocation of rights among agents while operating according to fair principles, comprising assigning a hierarchal rank to each agent; providing a synthetic economic value to a first set of agents at the a high level of the hierarchy; allocating portions of the synthetic economic value by the first set of agents to a second set of agents at respectively different hierarchal rank than the first set of agents; and conducting an auction amongst agents using the synthetic economic value as the currency. A method for allocation among agents, comprising assigning a wealth generation function for generating future wealth to each of a plurality of agents, communicating subjective market information between agents, and transferring wealth generated by the secure wealth generation function between agents in consideration of a market transaction. The method may further comprise the step of transferring at least a portion of the wealth generation function between agents.
Owner:MEADWESTVACO CORP
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
Asset tracking in a network-based supply chain environment
The present disclosure controls the network and manages resources for managing network assets through in a network-based supply chain framework. Network assets are available to network users. One user may submit information reguarding potential for growth, the capacity, or the technological level of one of the network assets. Another user may submit similar information about another network asset. Based on the information from the users, the system may determine the optimal set of network assets. When network events about the assets are recieved, the events can be filtered, correlated and isolated. These events can then be translated into a standard object form for facilitating the determination of the problem causing the network event.
Owner:ACCENTURE GLOBAL SERVICES LTD
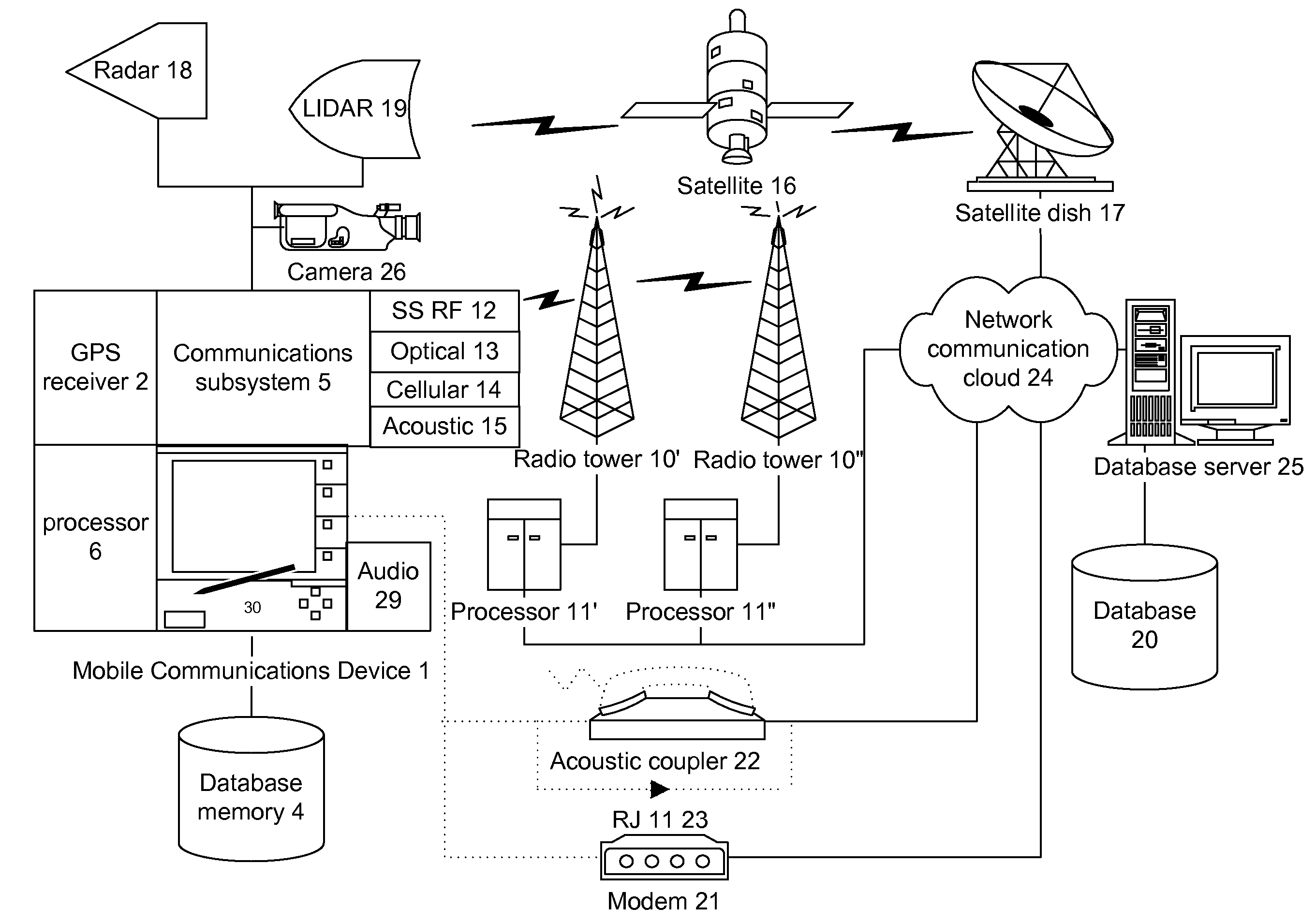
Method for collecting and processing data using internetworked wireless integrated network sensors (WINS)
InactiveUS7020701B1High reliability accessEasy to operateEnergy efficient ICTPower managementReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
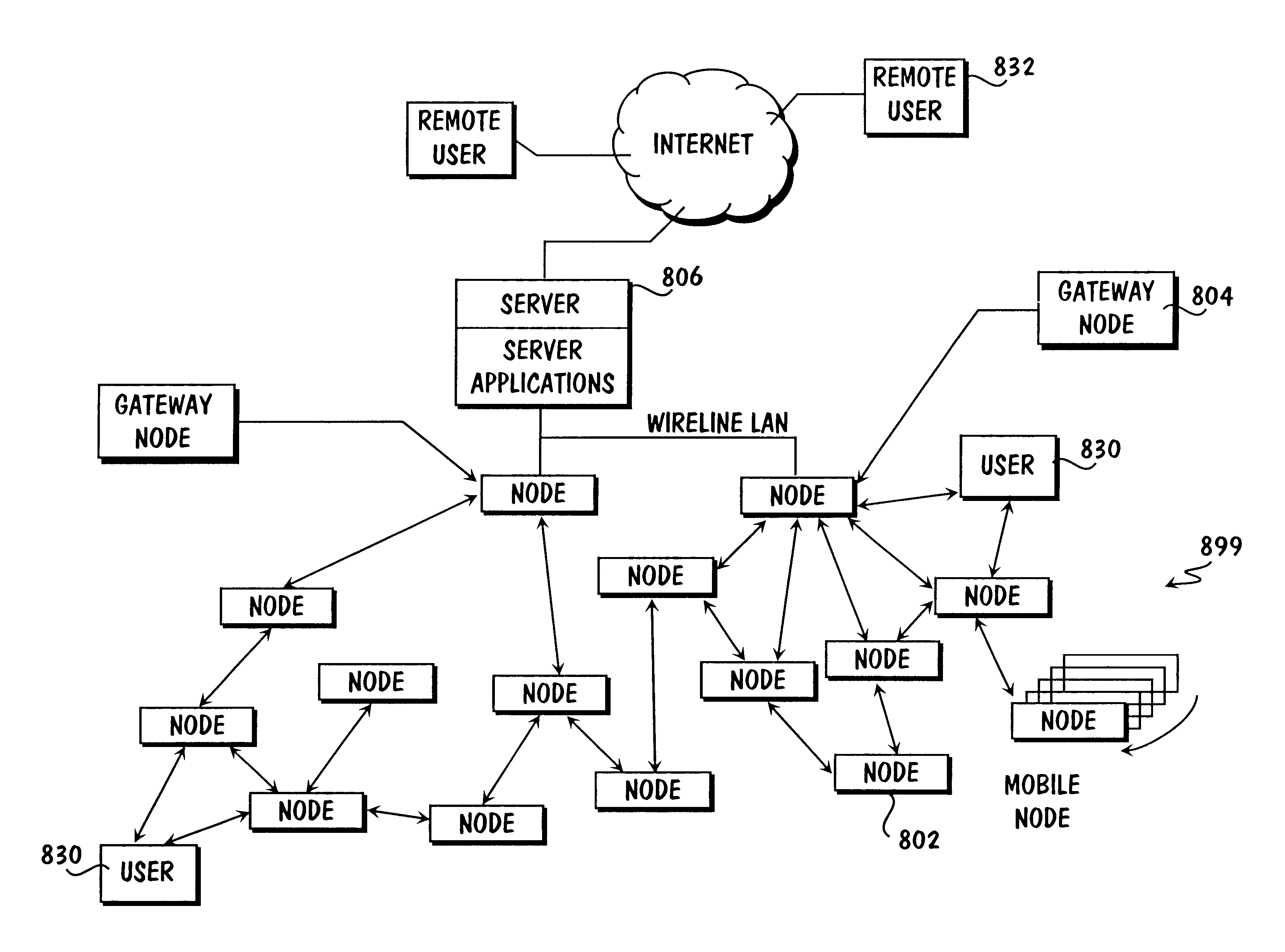
Business alliance identification in a web architecture framework
InactiveUS6721713B1Convenient verificationEasy to controlData processing applicationsDigital computer detailsBusiness entityDistributed computing
A system, method and article of manufacture are provided for identifying alliances among a plurality of business entities in components of a network framework. First, alliances are identified among a plurality of business entities in terms of components of a current network framework. Next, a pictorial representation is displayed of the current network framework and the components. The alliances are then conveyed by indicia coding the components of the current network framework in which the alliances exist.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method and apparatus for internetworked wireless integrated network sensor (WINS) nodes
InactiveUS6859831B1Ease real-time operating system issueImprove adaptabilitySpecific access rightsAnti-theft devicesReconfigurabilityMonitoring and control
The Wireless Integrated Network Sensor Next Generation (WINS NG) nodes provide distributed network and Internet access to sensors, controls, and processors that are deeply embedded in equipment, facilities, and the environment. The WINS NG network is a new monitoring and control capability for applications in transportation, manufacturing, health care, environmental monitoring, and safety and security. The WINS NG nodes combine microsensor technology, low power distributed signal processing, low power computation, and low power, low cost wireless and / or wired networking capability in a compact system. The WINS NG networks provide sensing, local control, remote reconfigurability, and embedded intelligent systems in structures, materials, and environments.
Owner:INTELLECTUAL VENTURES I LLC
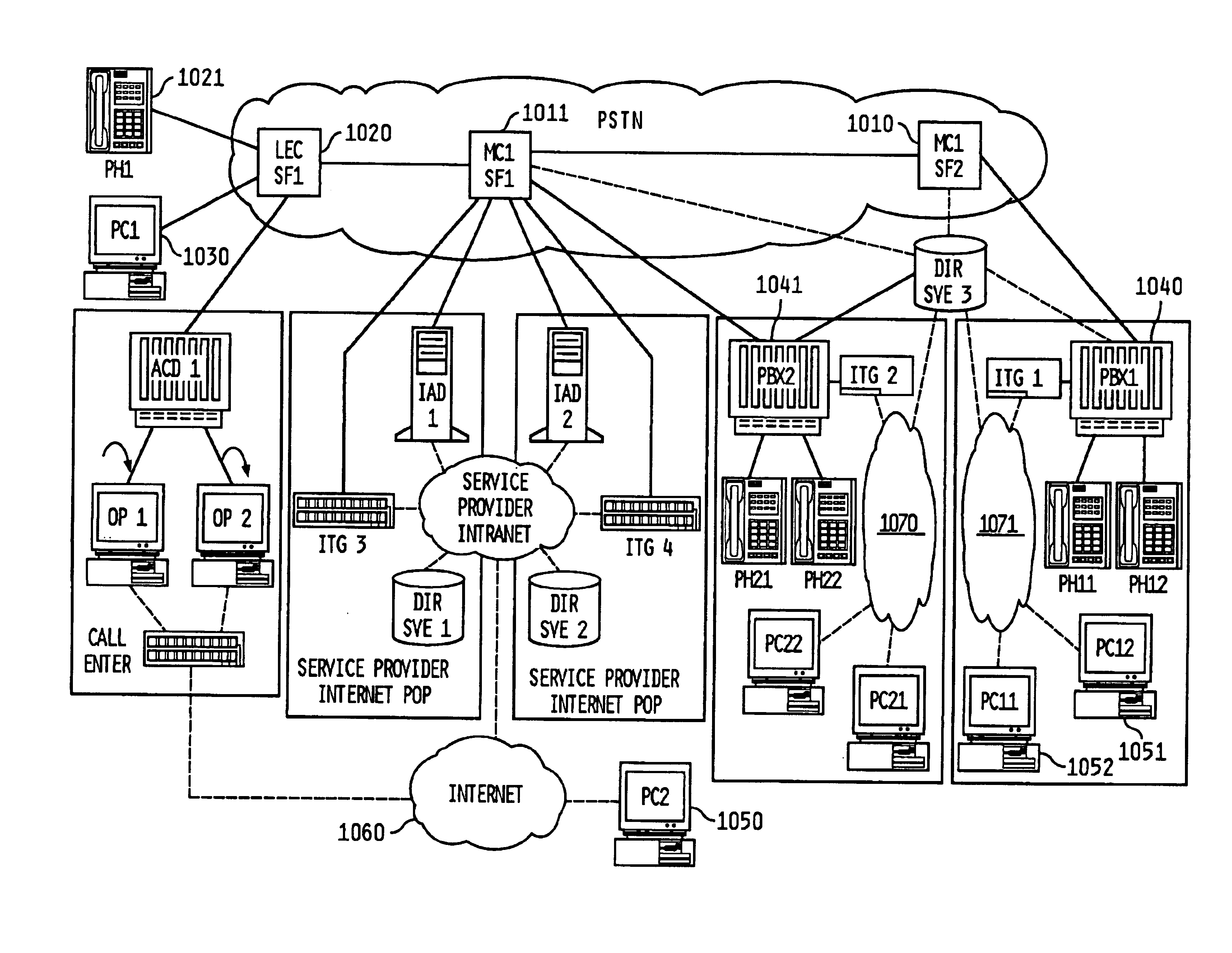
System, method and article of manufacture for selecting a gateway of a hybrid communication system architecture
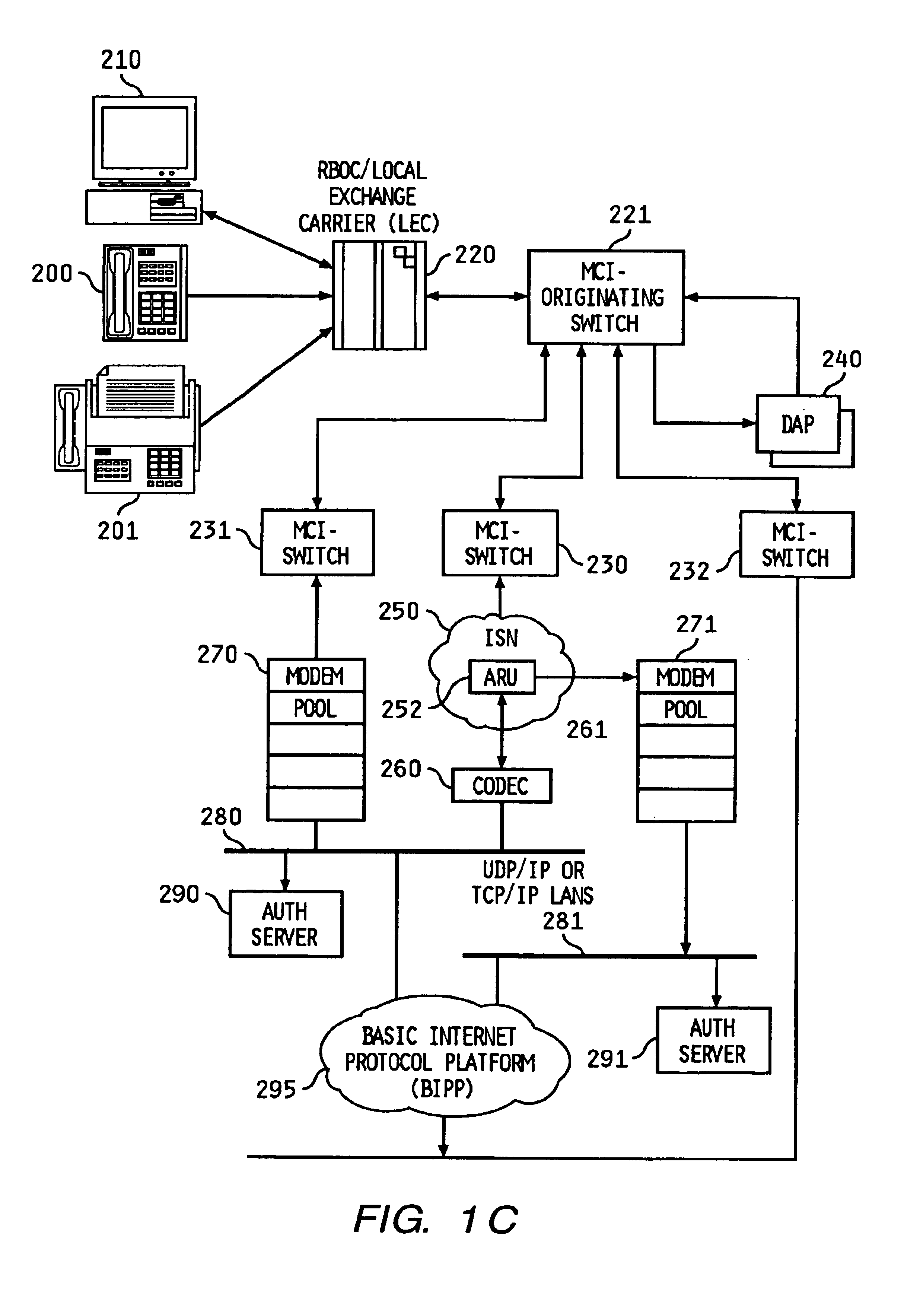
Telephone calls, data and other multimedia information is routed through a hybrid network which includes transfer of information across the internet utilizing telephony routing information and internet protocol address information. A media order entry captures complete user profile information for a user. This profile information is utilized by the system throughout the media experience for routing, billing, monitoring, reporting and other media control functions. Users can manage more aspects of a network than previously possible, and control network activities from a central site. A directory service that supports a hybrid communication system architecture is provided for routing traffic over the hybrid network and the internet and selecting a network proximal to the origination of the call.
Owner:VERIZON PATENT & LICENSING INC
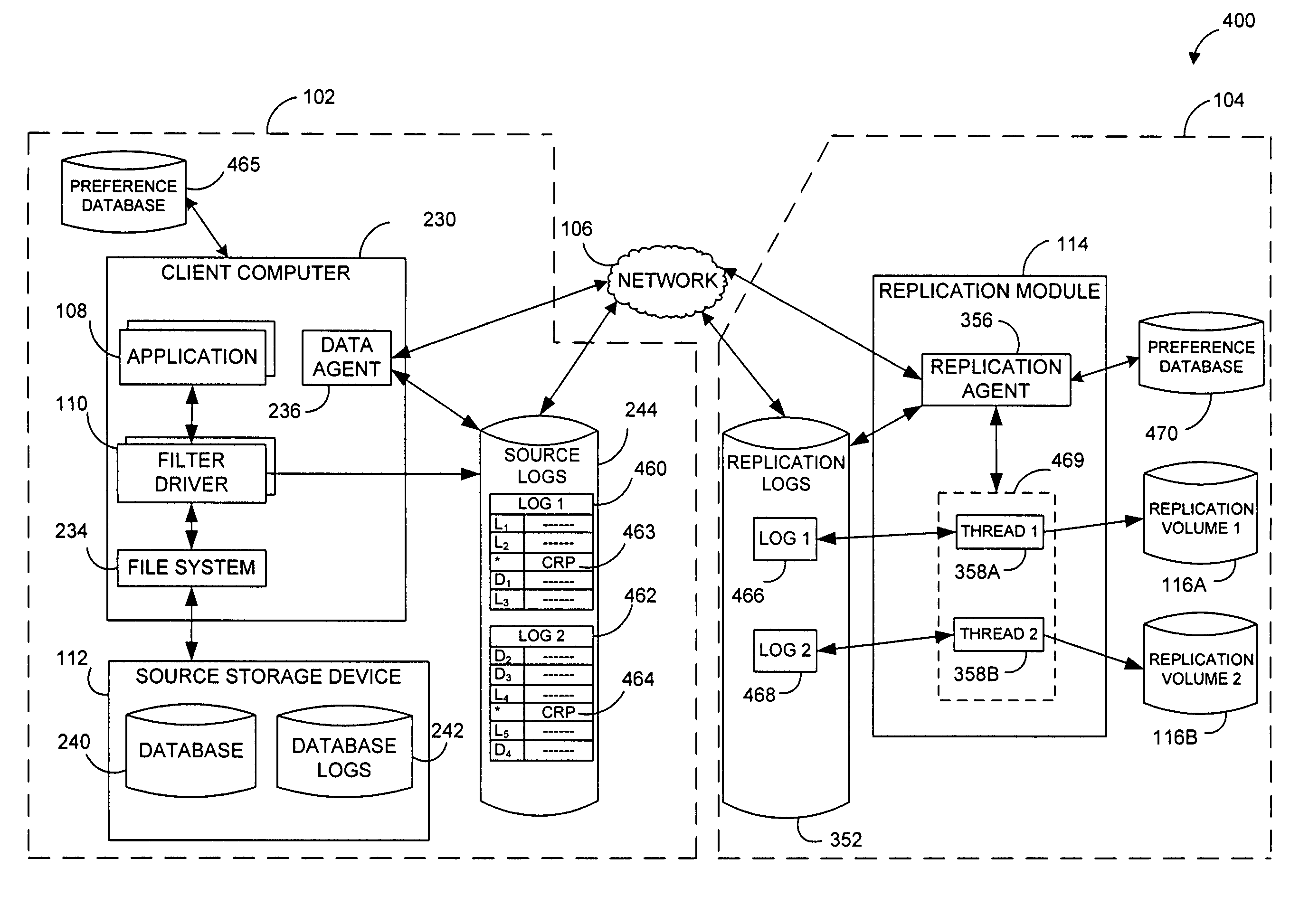
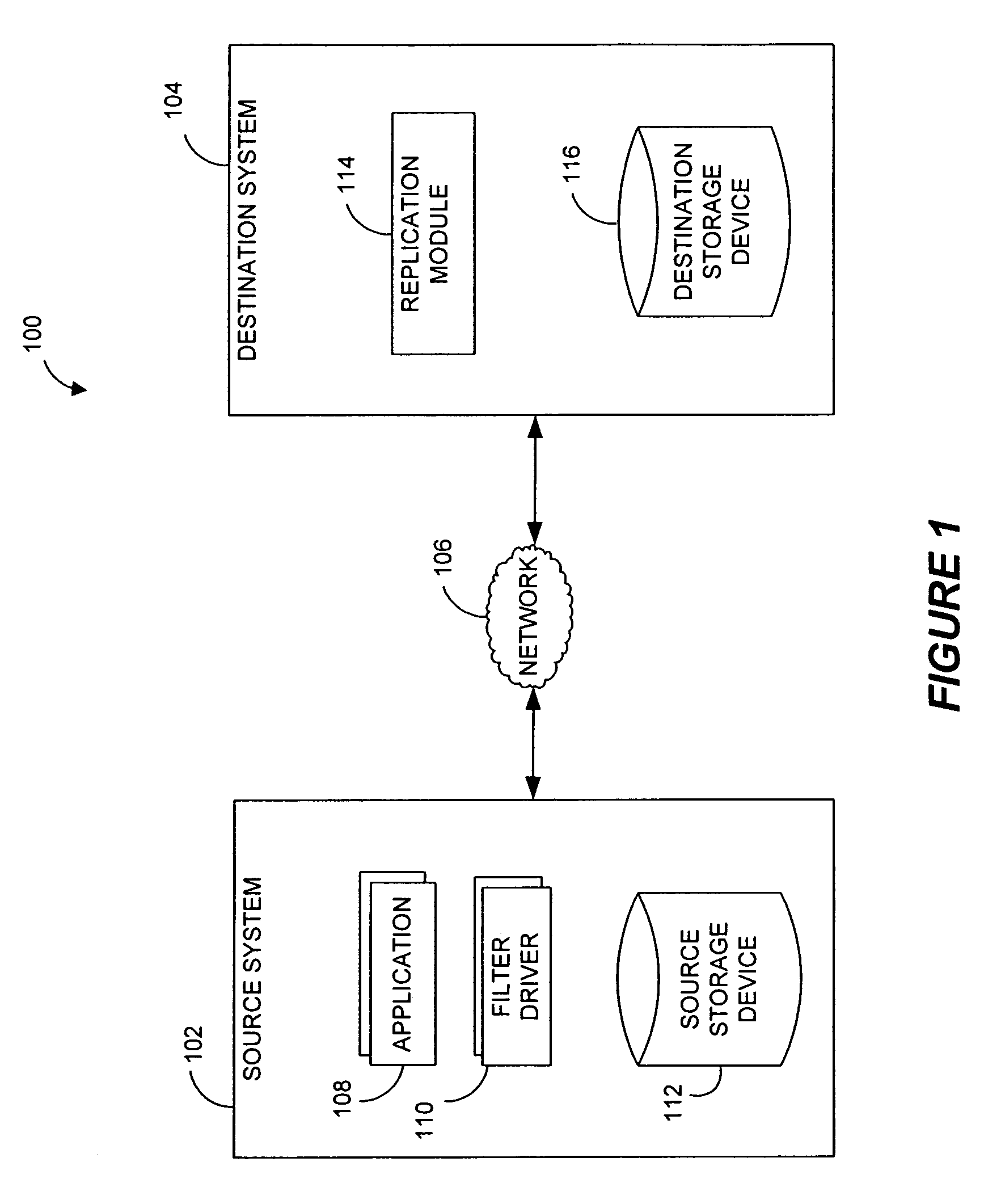
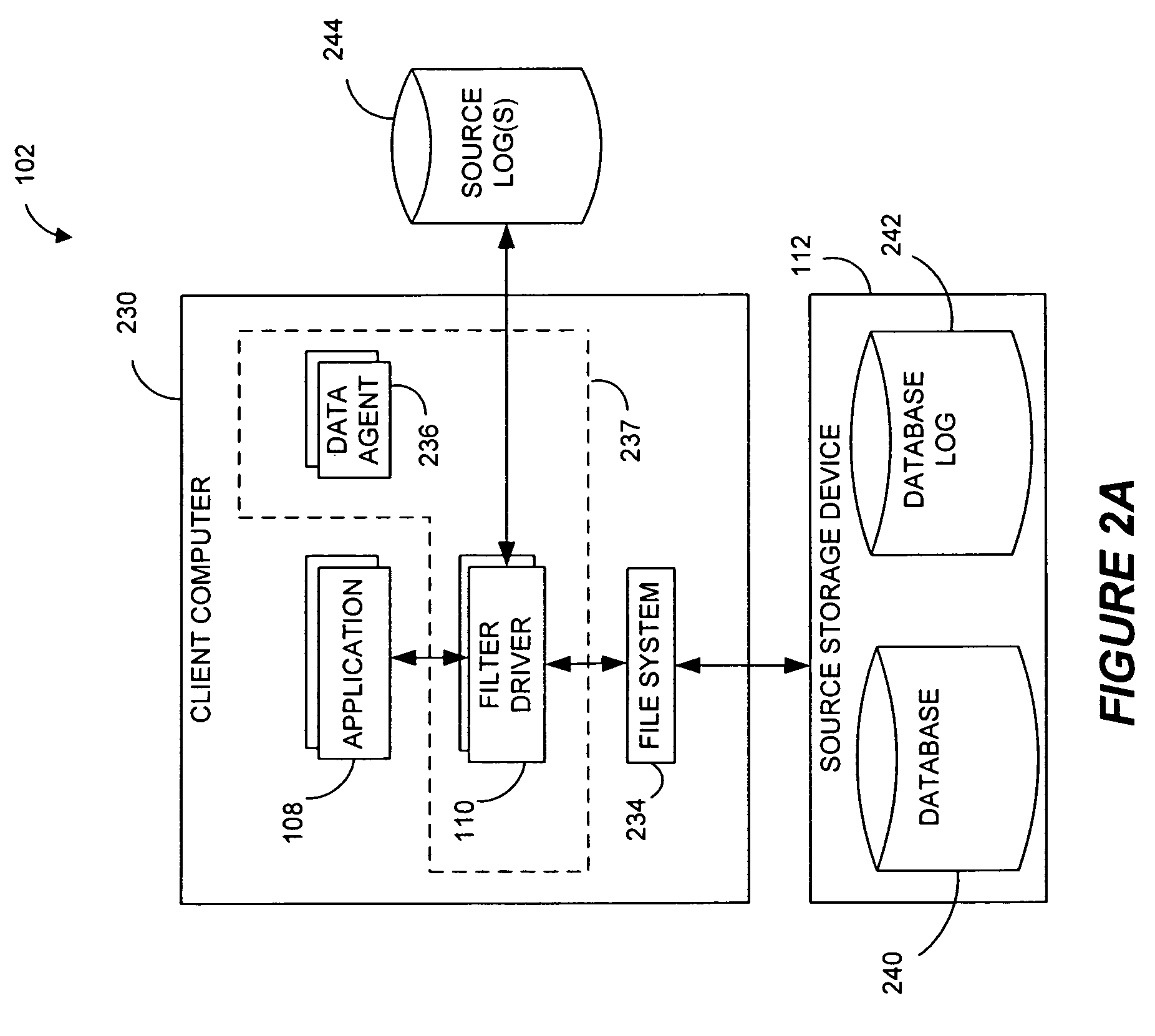
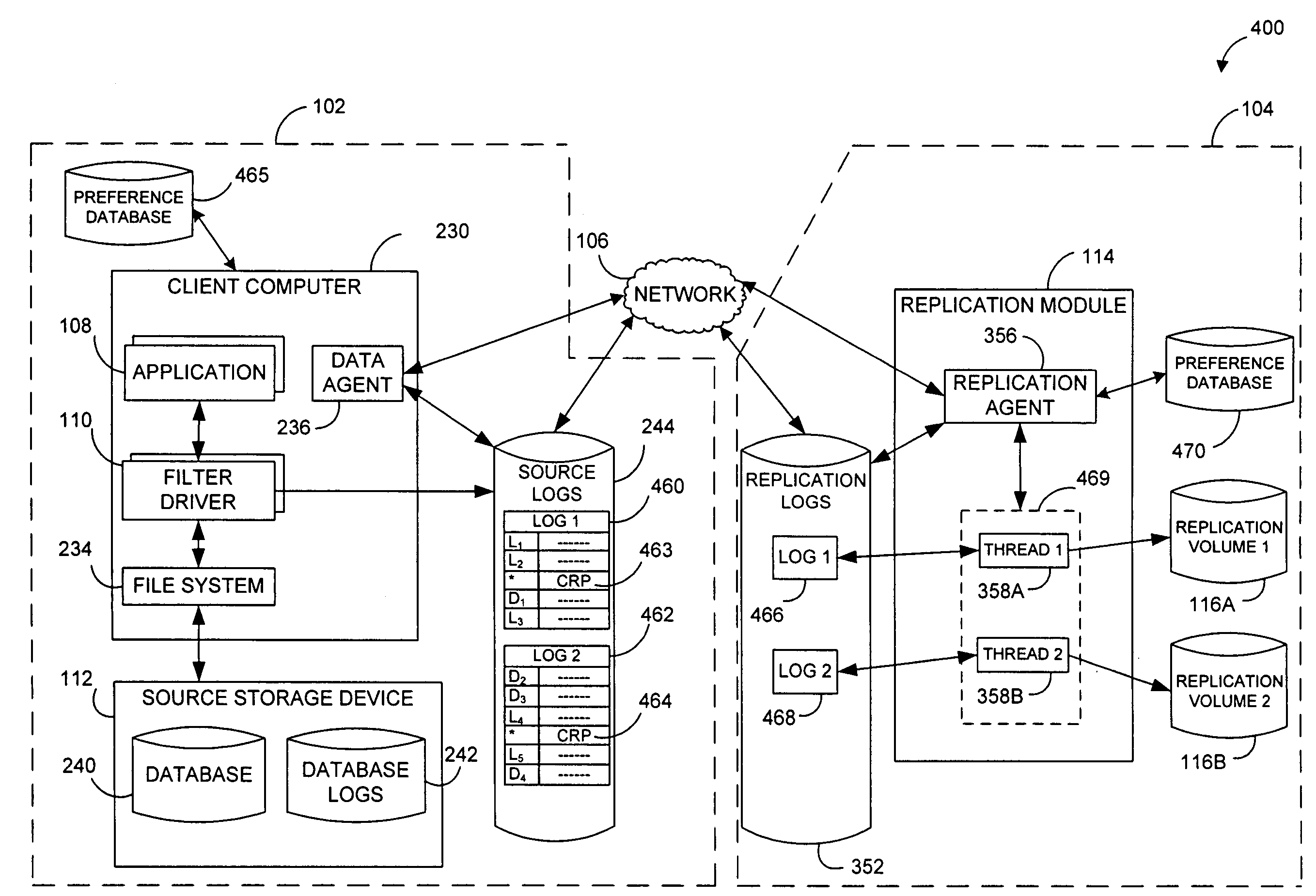
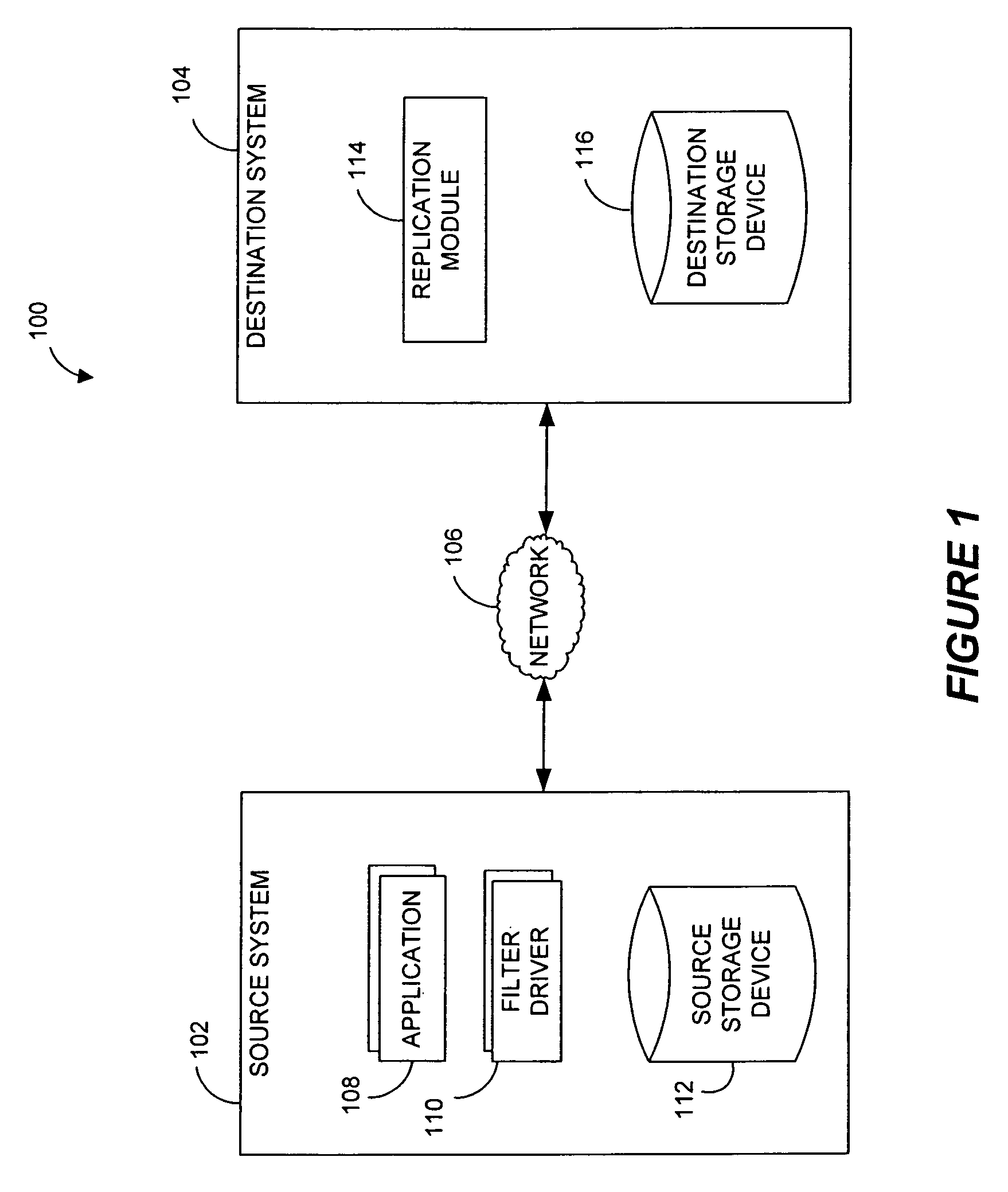
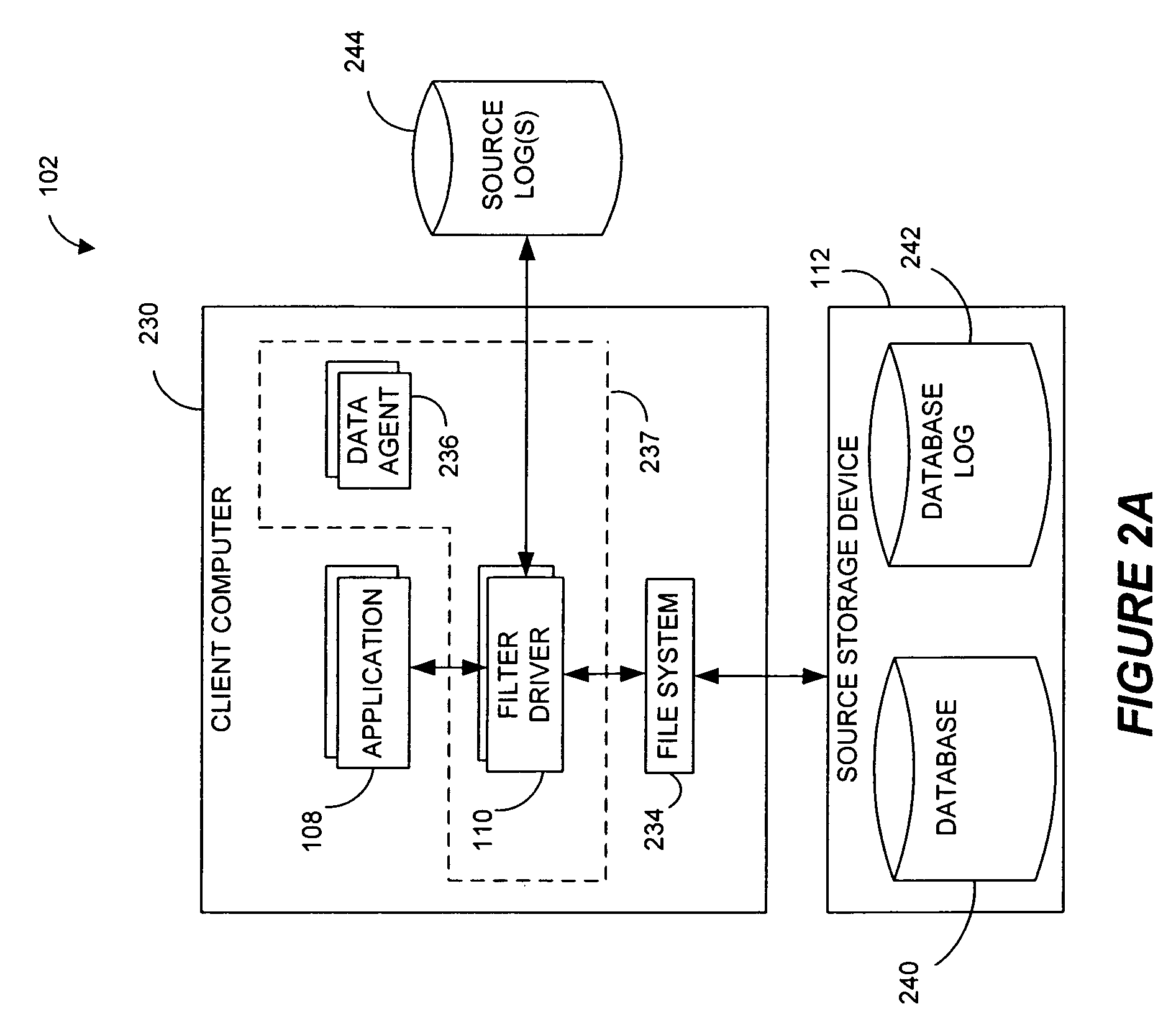
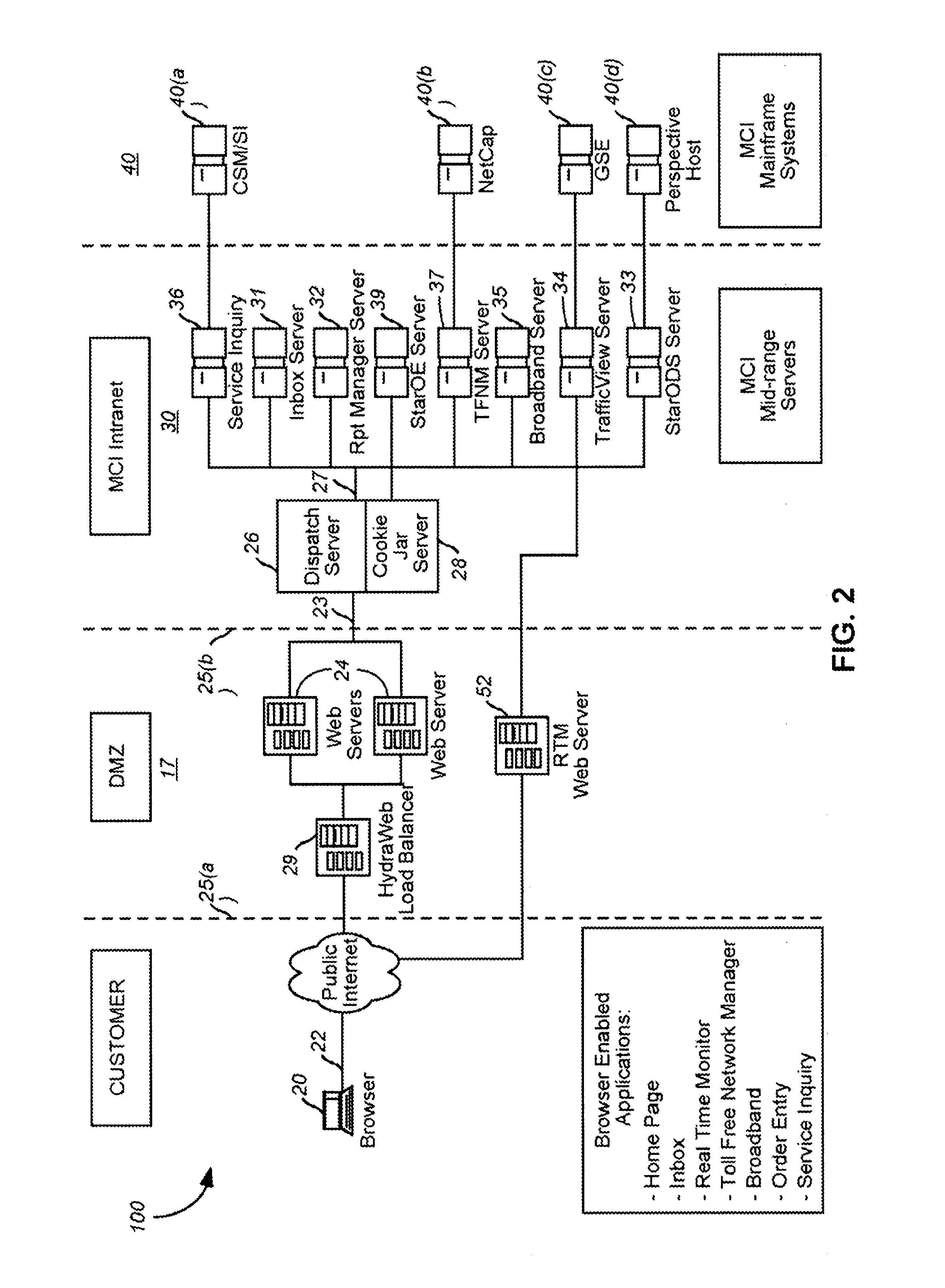
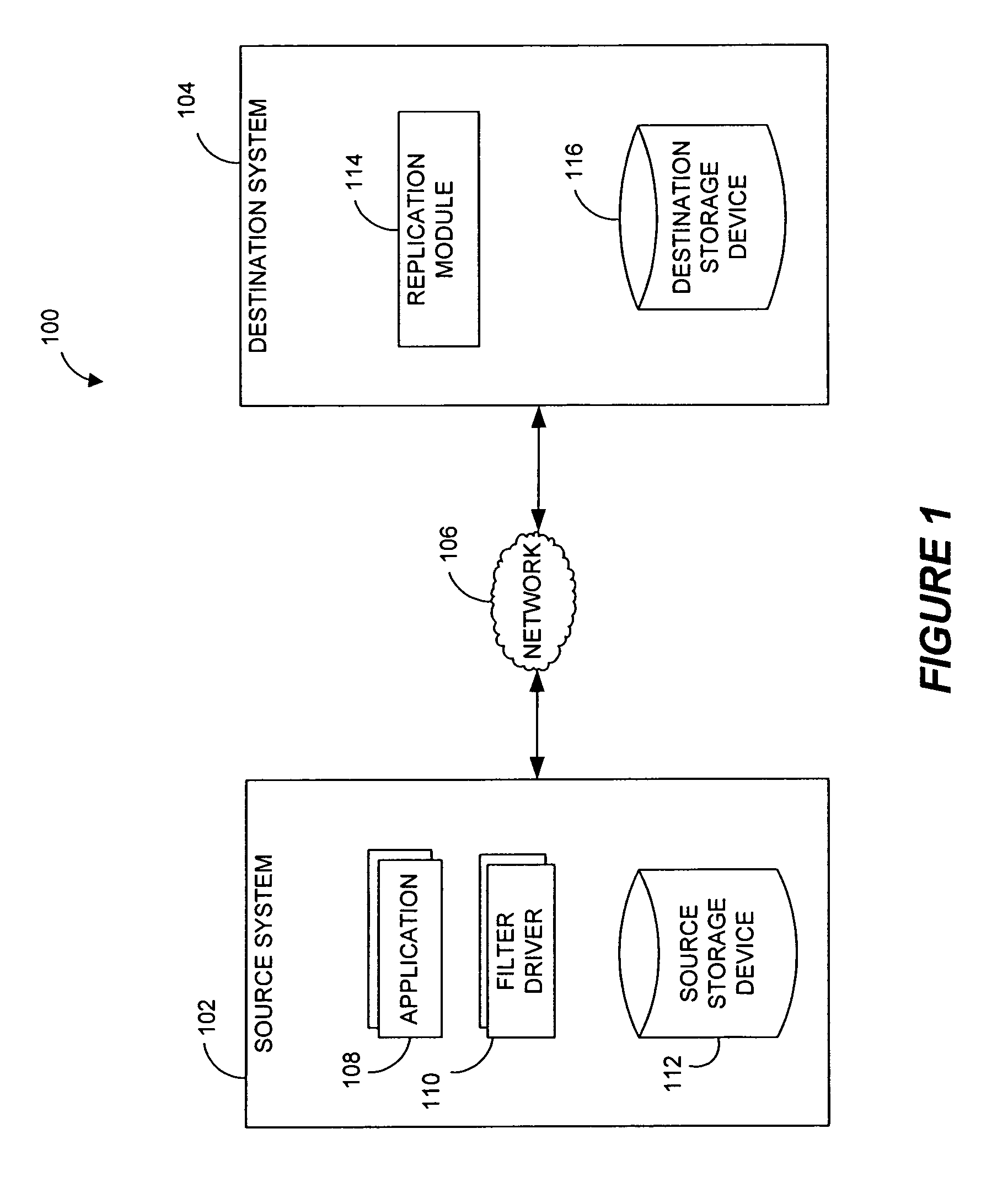
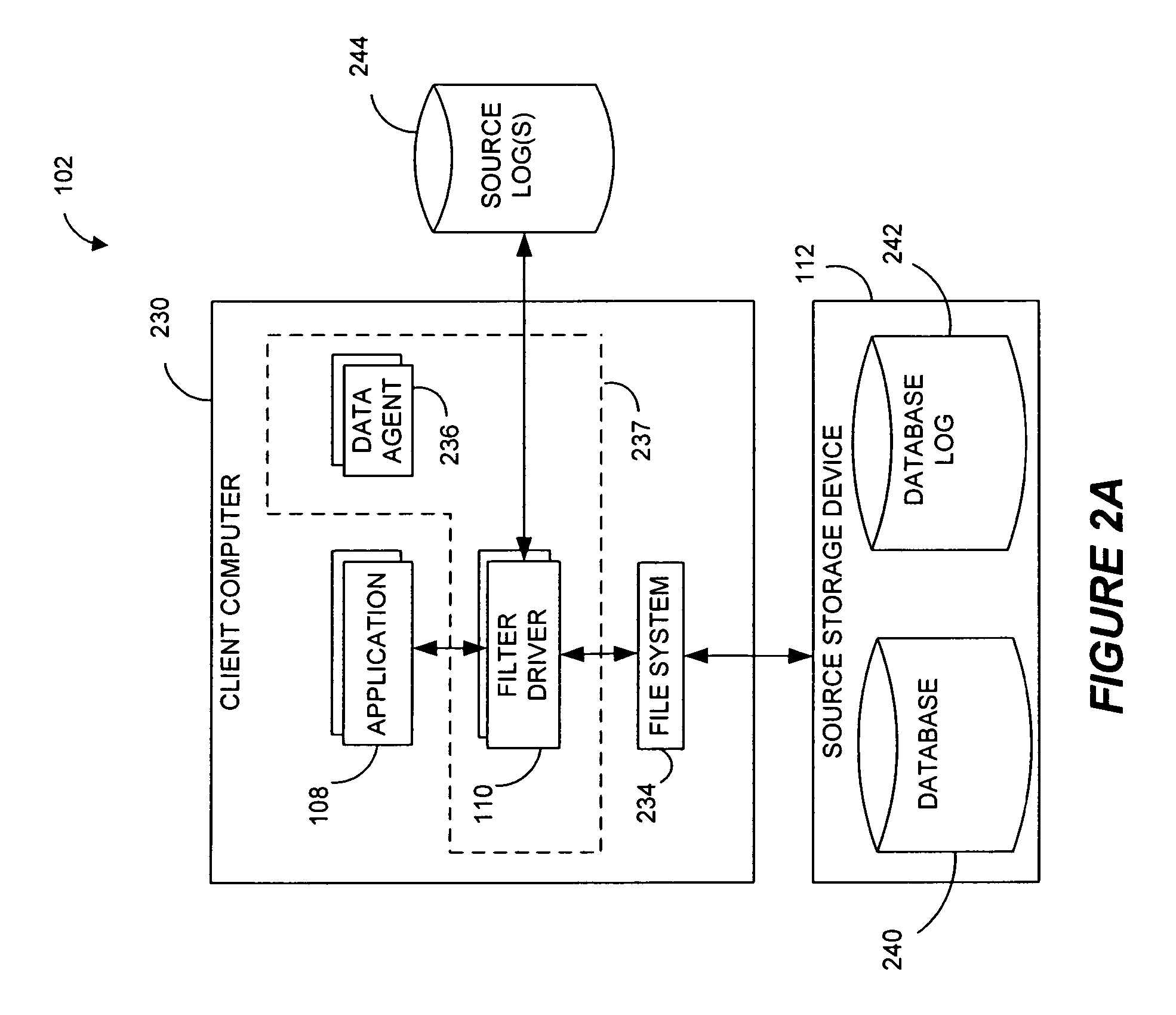
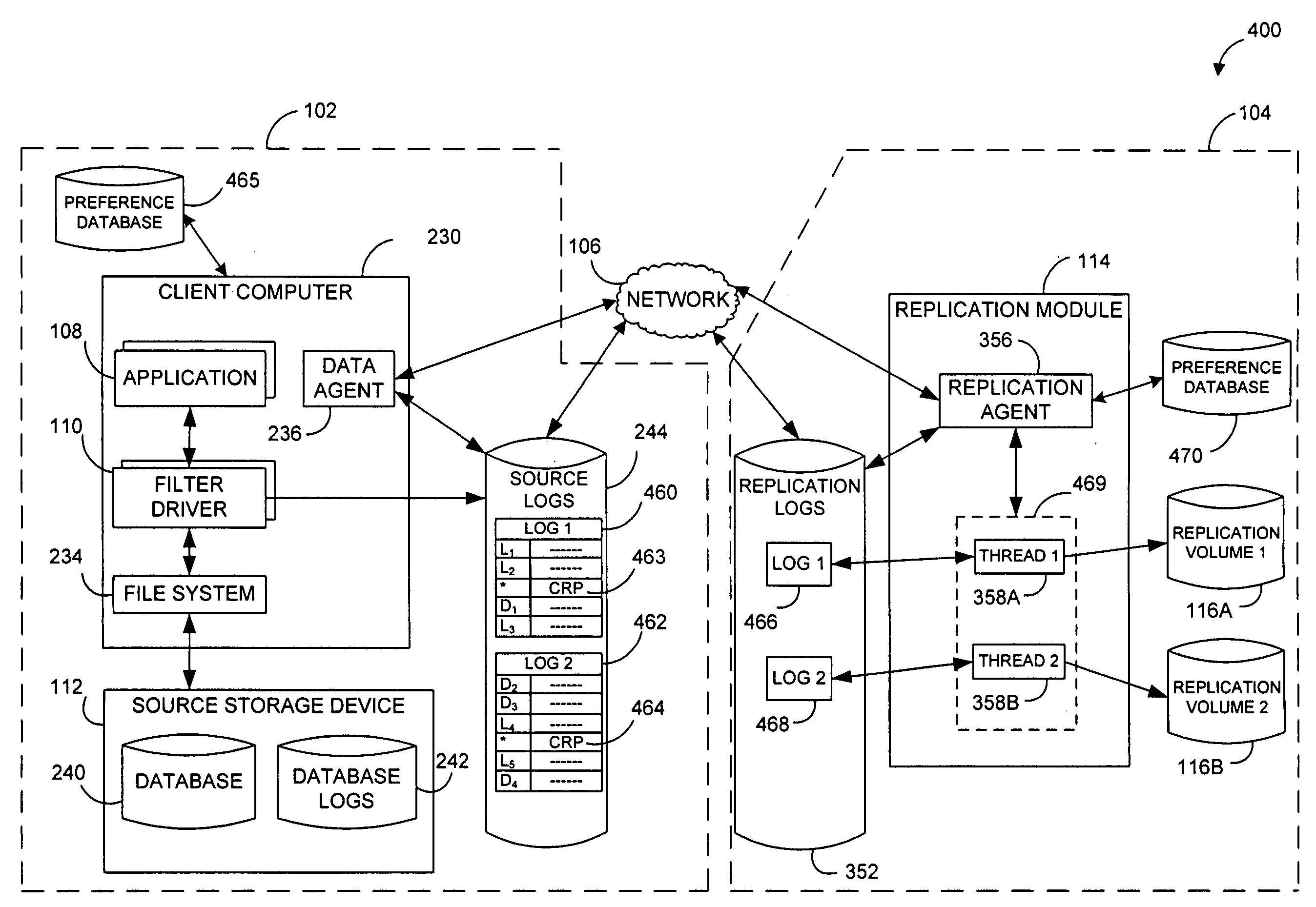
Systems and methods for monitoring application data in a data replication system
InactiveUS7617262B2Reduce impactReduce memory requirementsDigital data information retrievalData processing applicationsTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
Identifying and requesting data in network using identifiers which are based on contents of data
InactiveUS6415280B1Improve efficiencyImprove integrityData processing applicationsDigital data processing detailsHash functionData content
In a system in which a set of data items are distributed across a network of servers, at least some of the data items being cached versions of data items from a source server, a content delivery method includes determining a data identifier for a particular data item, the data identifier being determined using a given function of the data comprising the particular data item; and responsive to a request for the particular data item, the request including at least the data identifier of the particular data item, providing the particular data item from a given one of the servers of the network of servers. The request for the particular data item may be resolved based on a measure of availability of at least one of the servers, where the measure of availability may be a measurement of bandwidth to the server; a measurement of a cost of a connection to the server, and / or a measurement of a reliability of a connection to the server. The function used to determine the identifier may be a message digest function or a hash function.
Owner:LEVEL 3 COMM LLC +1
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
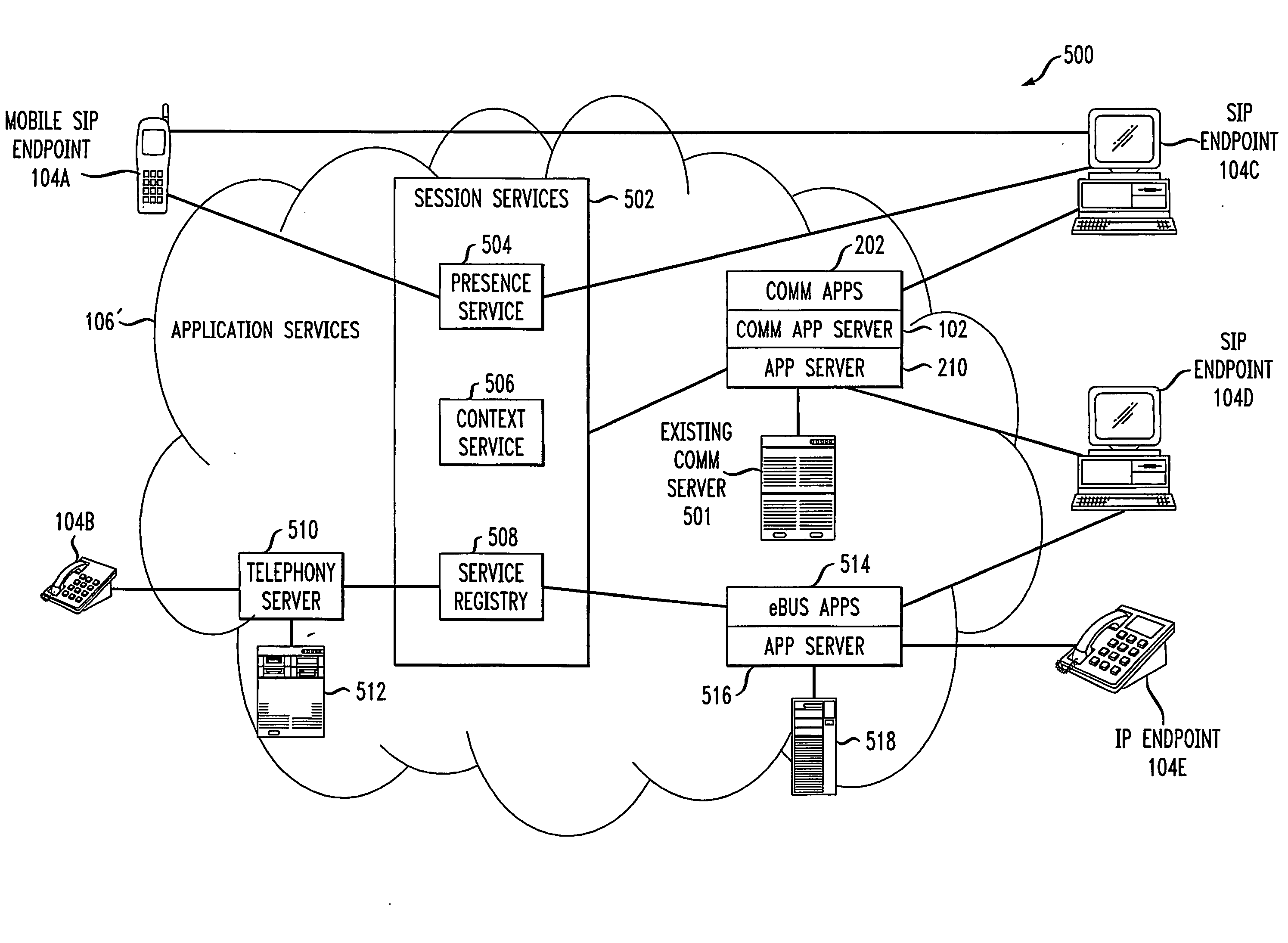
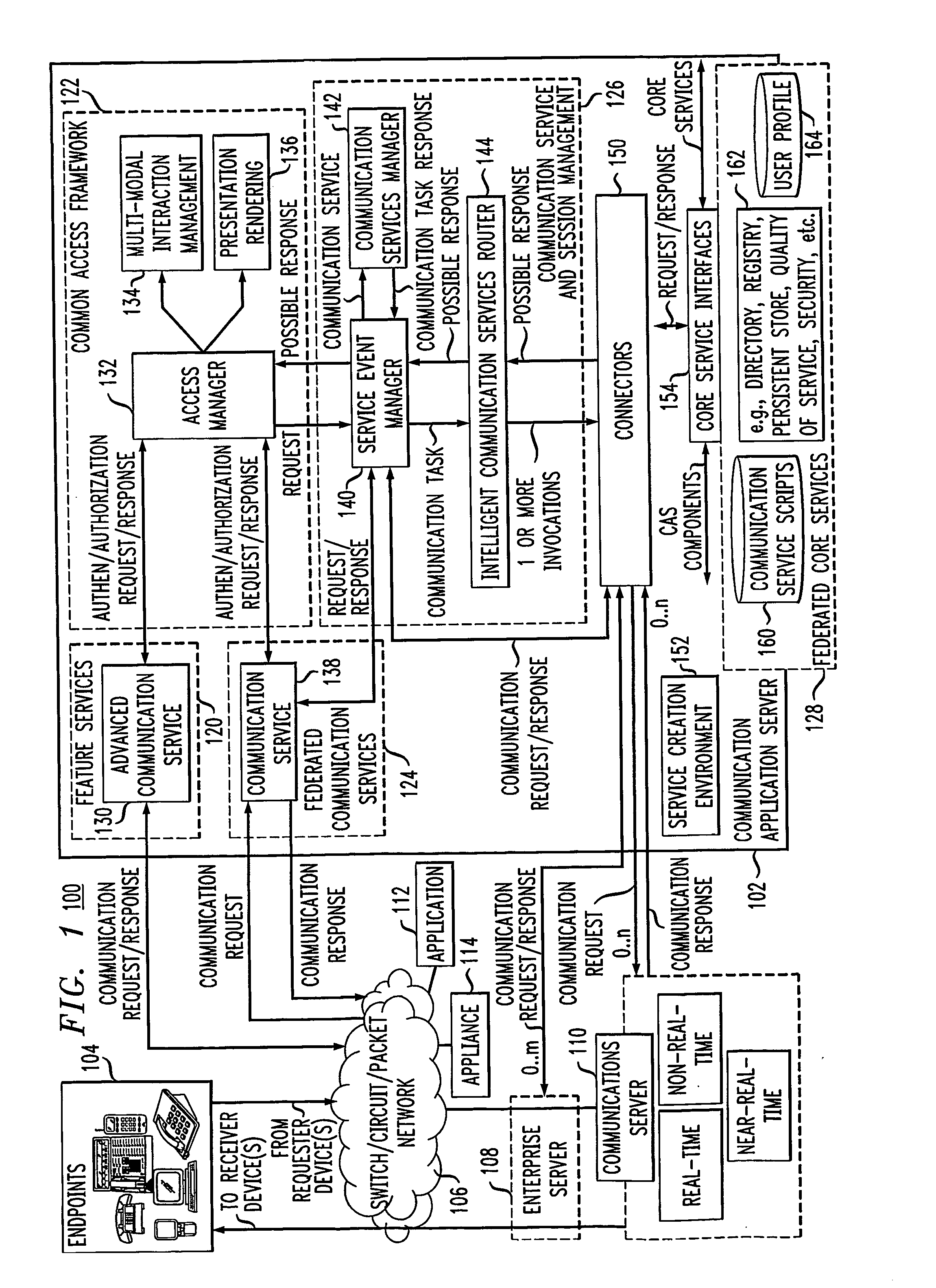
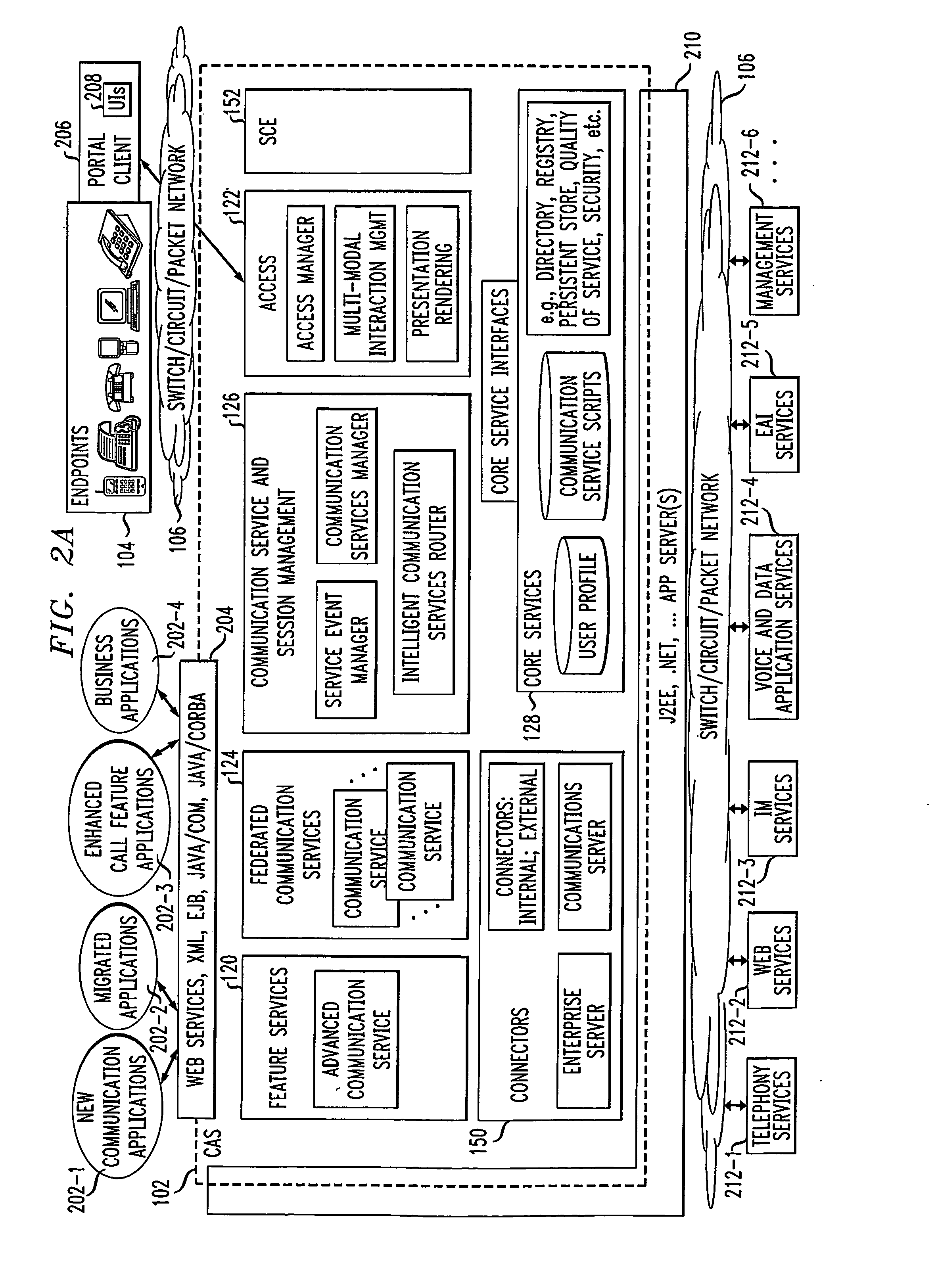
Communication application server for converged communication services
ActiveUS20080086564A1Multiple digital computer combinationsAutomatic exchangesApplication serverCommunications system
A communication application server for supporting converged communications in a communication system. The communication application server is responsive to communication service requests from external endpoints, applications or other c requesting entities, and in one embodiment comprises at least first and second components. The first component is operative: (i) to process a given one of the communication service requests to identify at least one corresponding communication service supported by the communication application server, (ii) to determine one or more executable communication tasks associated with the identified communication service; and (iii) to establish communication with one or more external servers to carry out execution of at least a subset of the one or more executable communication taks associated with the communication service. The second component is coupled between the first component and the one or more external servers, and provides, for each of the external servers, a corresponding interface for connecting the communication application server to the external server.
Owner:AVAYA INC
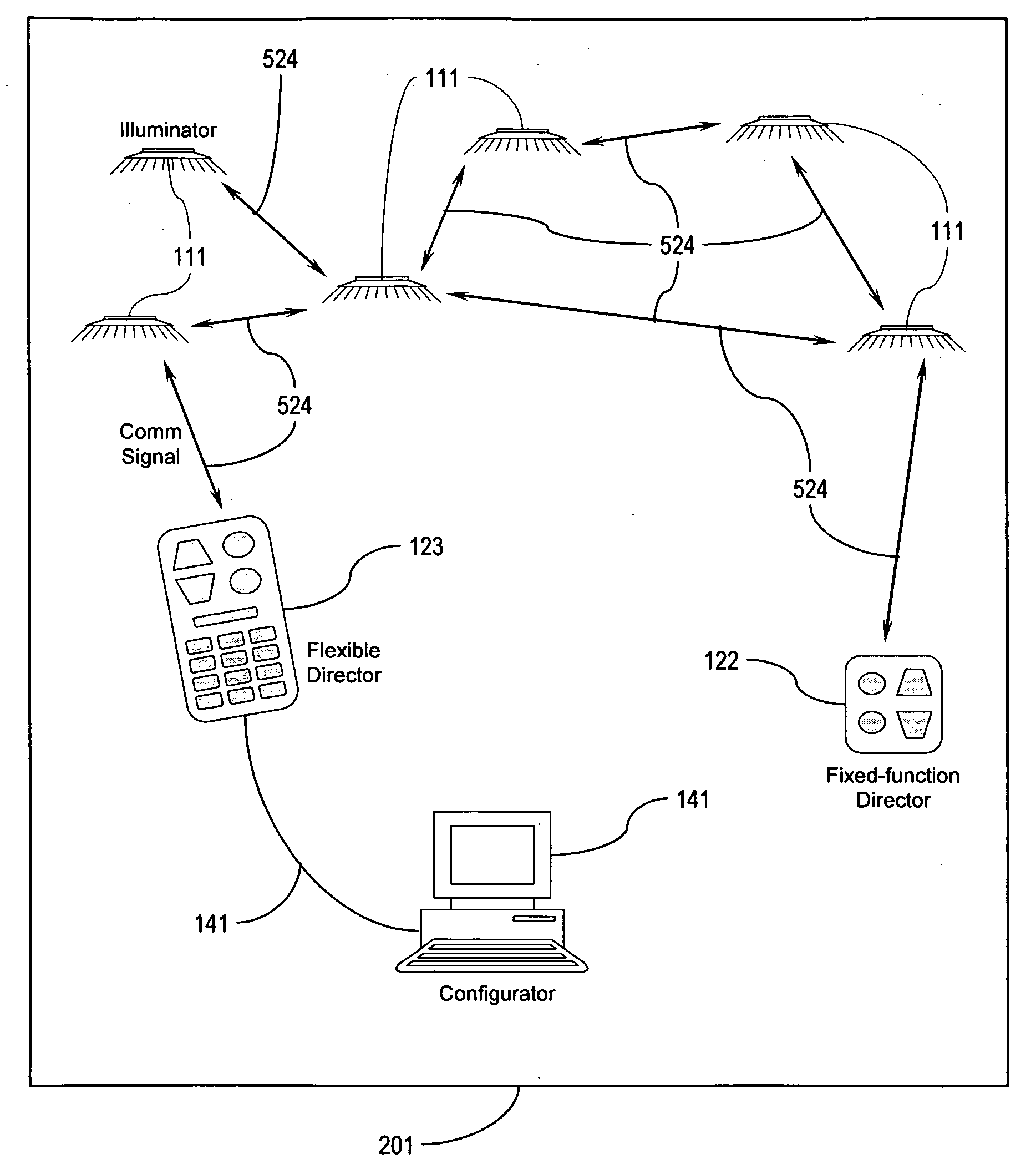
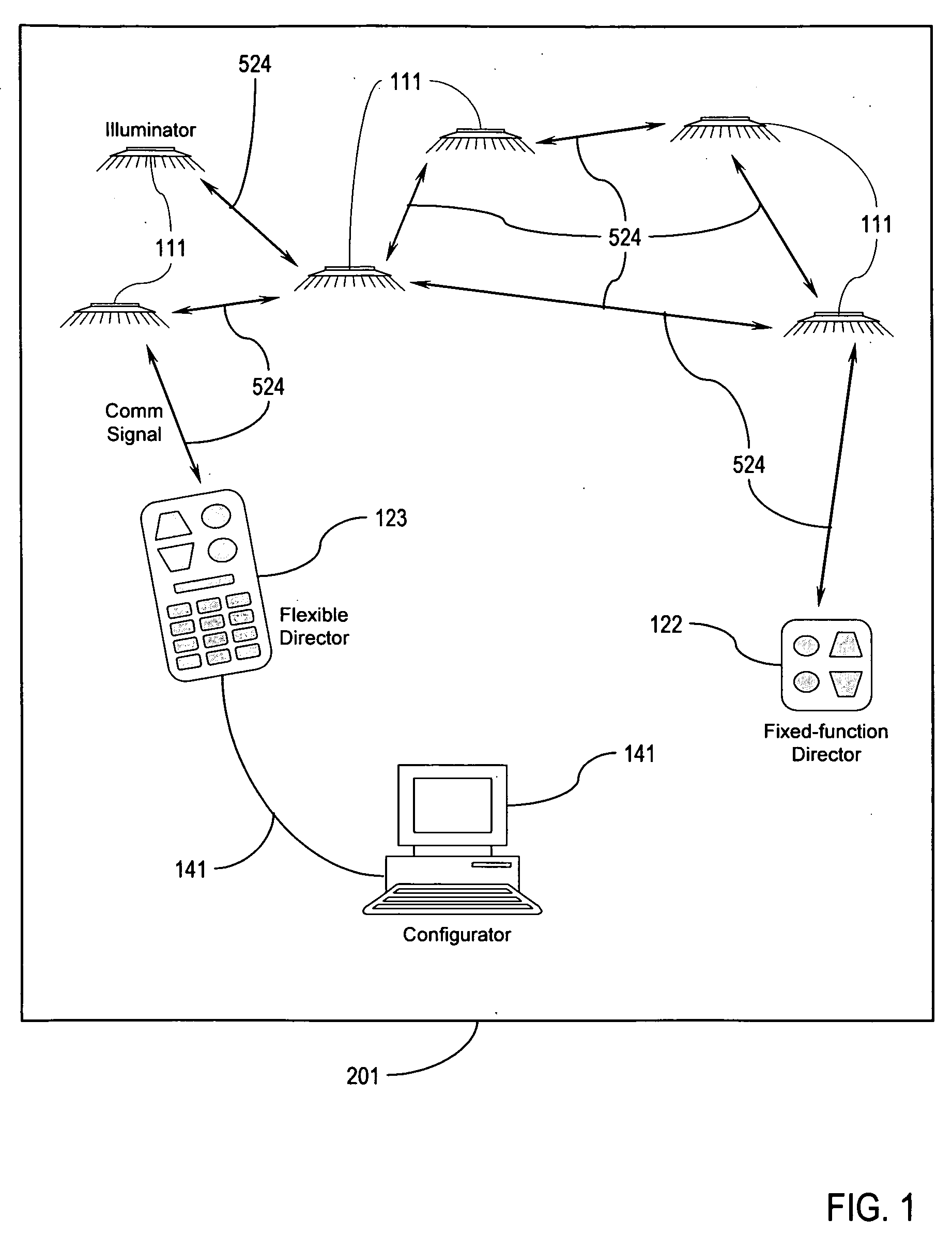
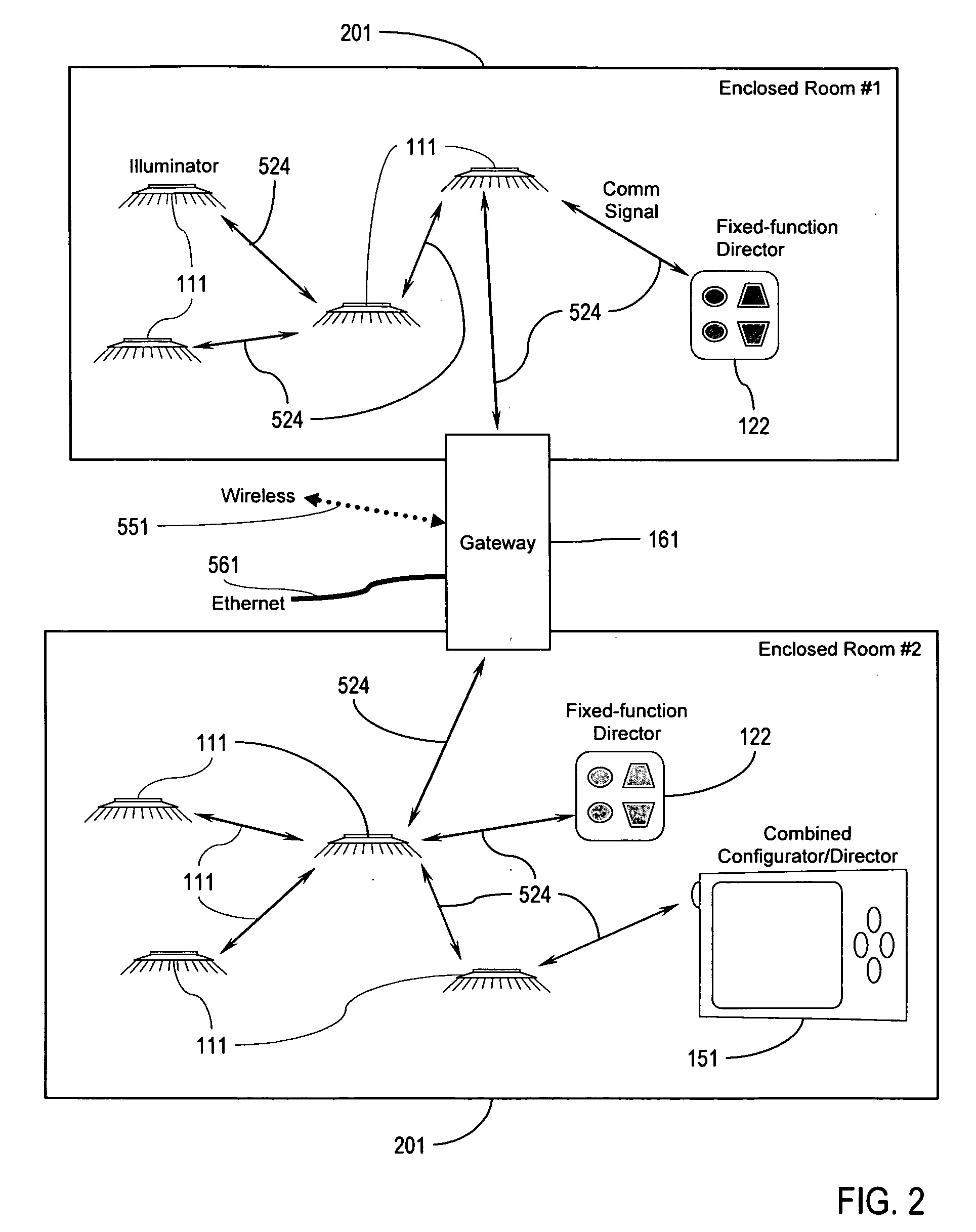
Illumination control network
ActiveUS20080265799A1Easy to adjustCost-effectiveElectrical apparatusElectric light circuit arrangementNetwork controlMovement control
The present invention addresses the problem of providing illumination in a manner that is energy efficient and intelligent. In particular, the present invention uses distributed processing across a network of illuminators to control the illumination for a given environment. The network controls the illumination level and pattern in response to light, sound, and motion. The network may also be trained according to uploaded software behavior modules, and subsets of the network may be organized into groups for illumination control and maintenance reporting.
Owner:SIBERT JULIE CLAIRE +1
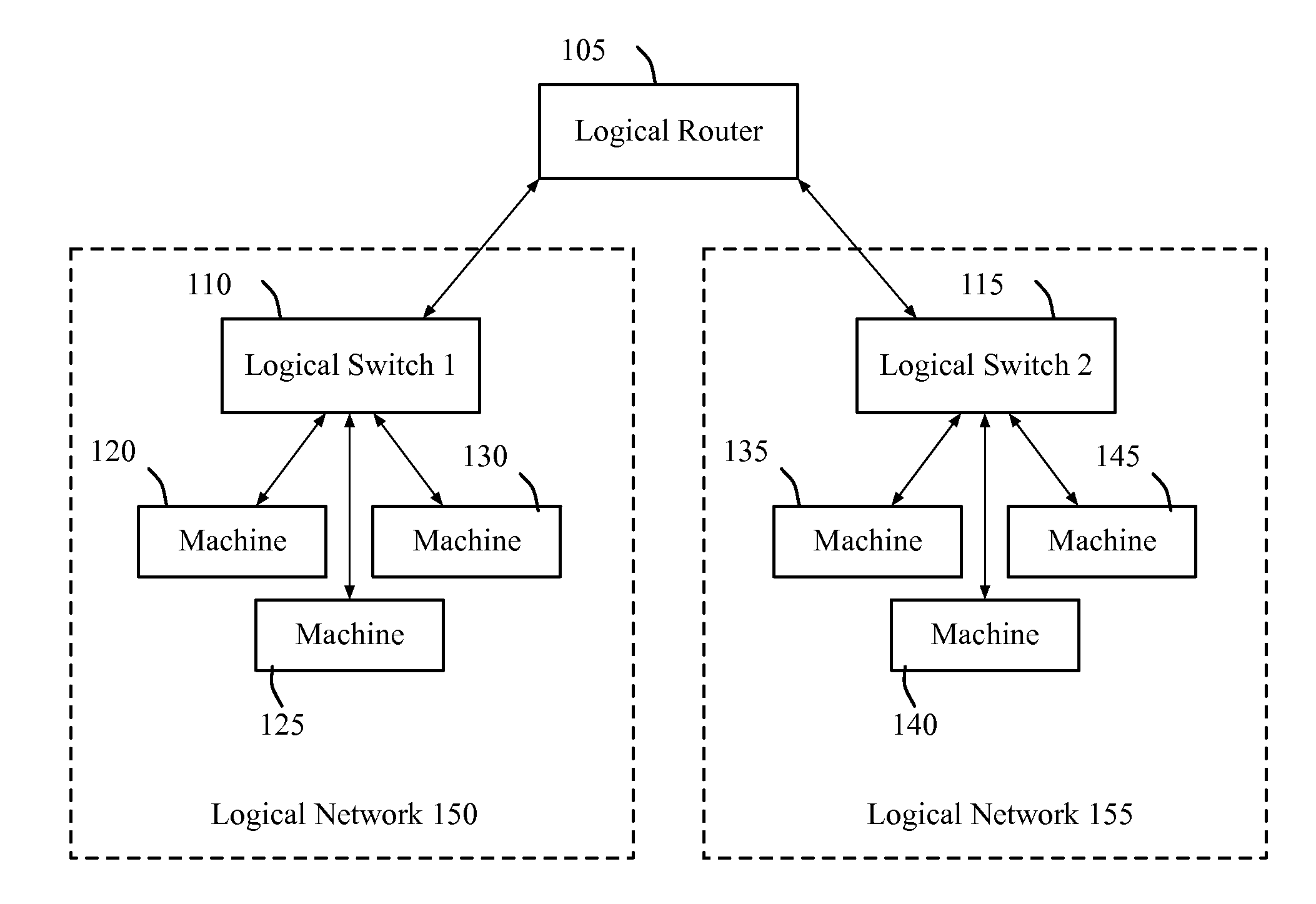
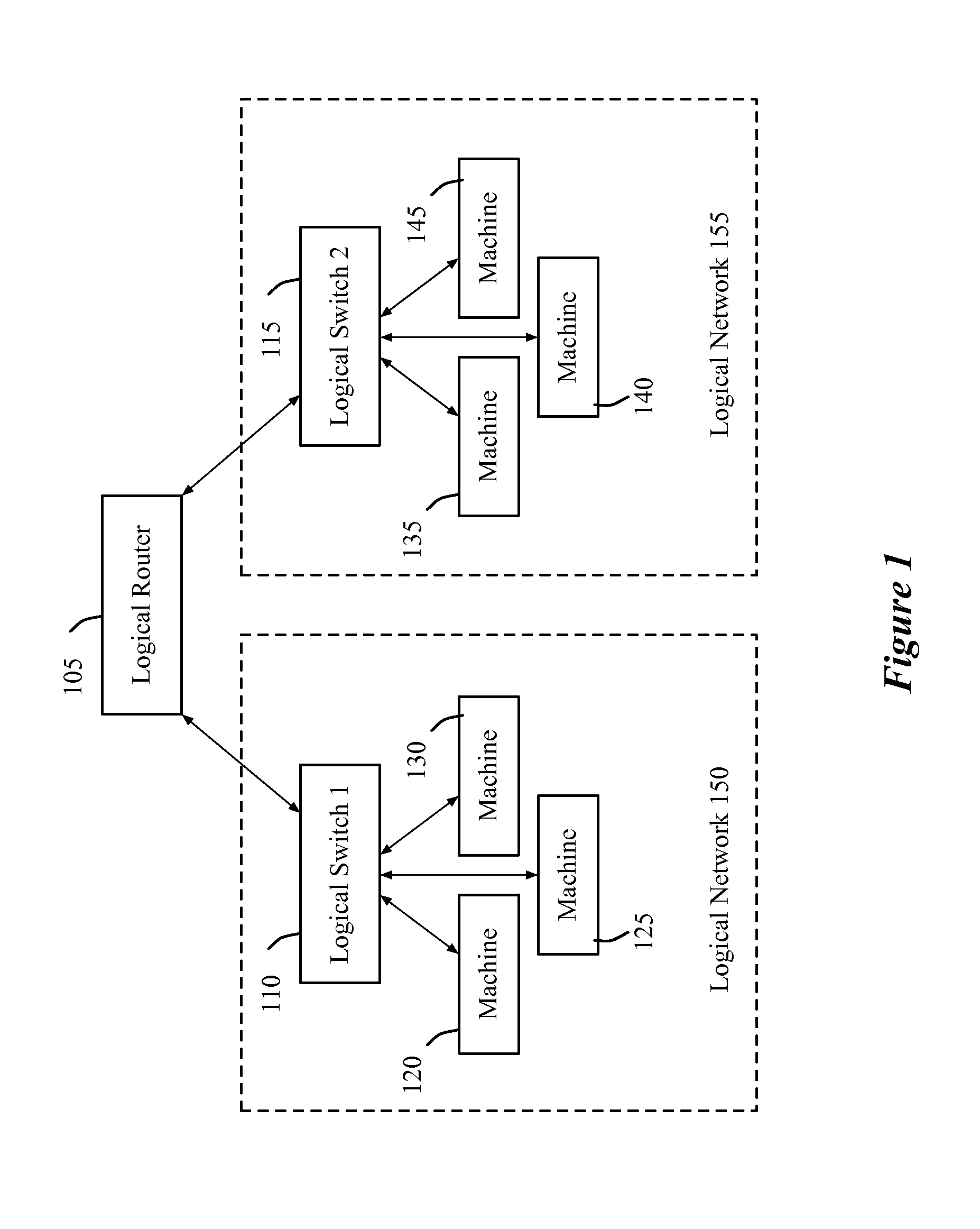
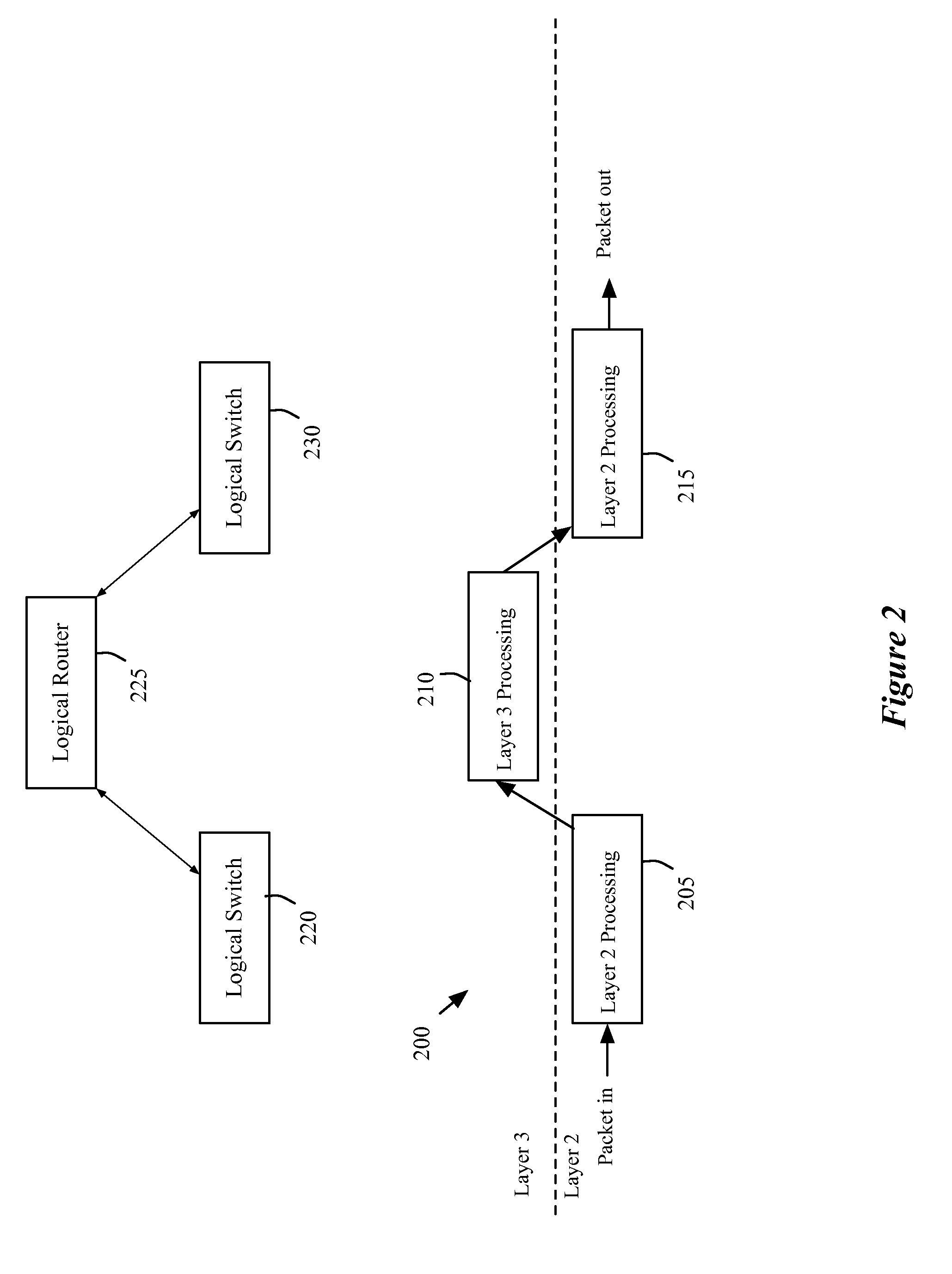
Distributed logical l3 routing
A novel method for configuring first and second managed forwarding elements to perform logical L2 switching and L3 routing is described. The method generates a first set of flow entries for configuring the first managed forwarding element to perform logical L2 ingress processing and L3 routing processing. The method generates a second set of flow entries for configuring the second managed forwarding element to performing logical L2 egress processing.
Owner:NICIRA
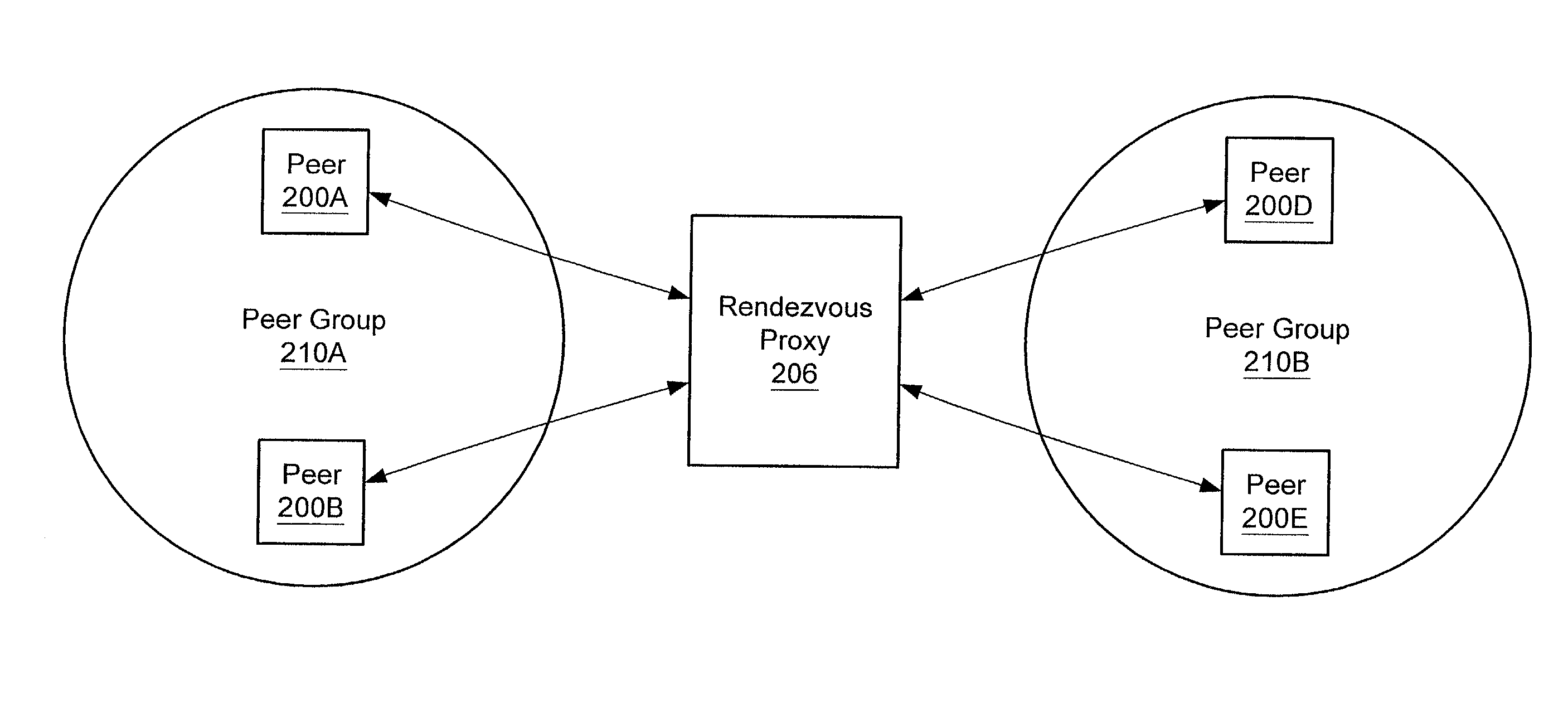
Relay peers for extending peer availability in a peer-to-peer networking environment
ActiveUS20020143855A1Multiprogramming arrangementsMultiple digital computer combinationsDistributed computingPeer-to-peer
A system and method for allowing peers to exchange messages with other peers independently of their network location in a peer-to-peer environment. Messages may be transparently routed, potentially traversing partitions (e.g. firewalls and NATs), and using different protocols to reach the destination peers. In one embodiment, any peer node may serve as a relay peer that allows peers inside a partition to have a presence outside the partition and provides a mechanism for peers outside partitions to discover and communicate with peers inside the partitions. In one embodiment, a relay peer may maintain information on routes to other peers and assist in relaying messages to other peers. In one embodiment, any peer may query a relay peer for route information. In one embodiment, messages may include routing information as part of their payloads.
Owner:ORACLE INT CORP
Integrated systems for providing communications network management services and interactive generating invoice documents
InactiveUS7225249B1Easy and convenient accessTelephonic communicationCathode-ray tube indicatorsWeb serviceInvoice
A integrated customer interface for providing telecommunications management to a customer at a browser involves a web server and a client application. The web server manages a client session supports communication of request messages received from the browser to a network management resource. The client application is integrated for use within the browser, downloadable from the web server in accordance with a predetermined customer entitlement, and programmed to be in interactive communications with the network management resource.
Owner:VERIZON PATENT & LICENSING INC
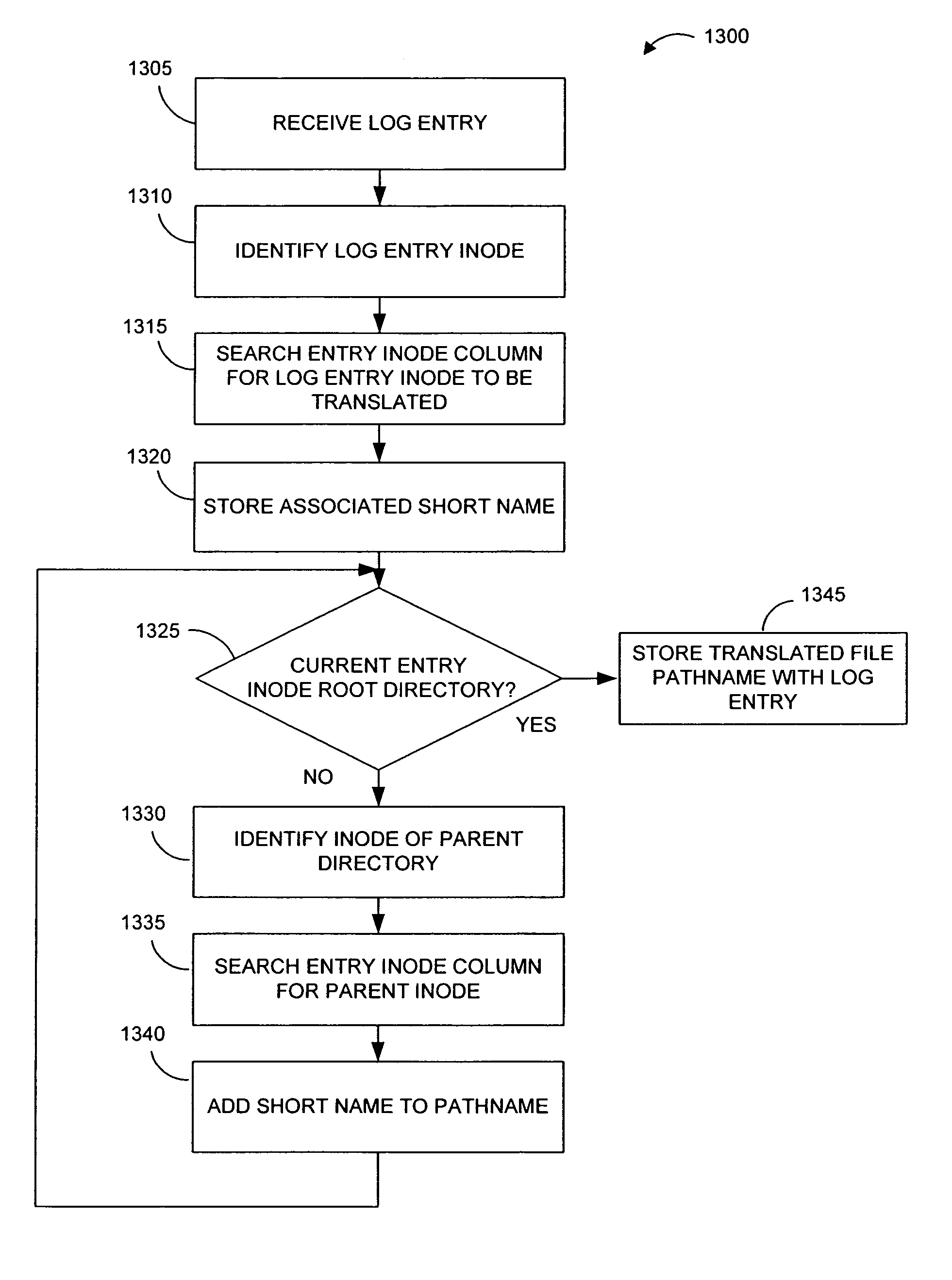
Pathname translation in a data replication system
InactiveUS7636743B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Owner:COMMVAULT SYST INC
System and method for transaction services patterns in a netcentric environment
InactiveUS7289964B1Reduce network trafficOffice automationProgram controlTraffic capacityTransaction service
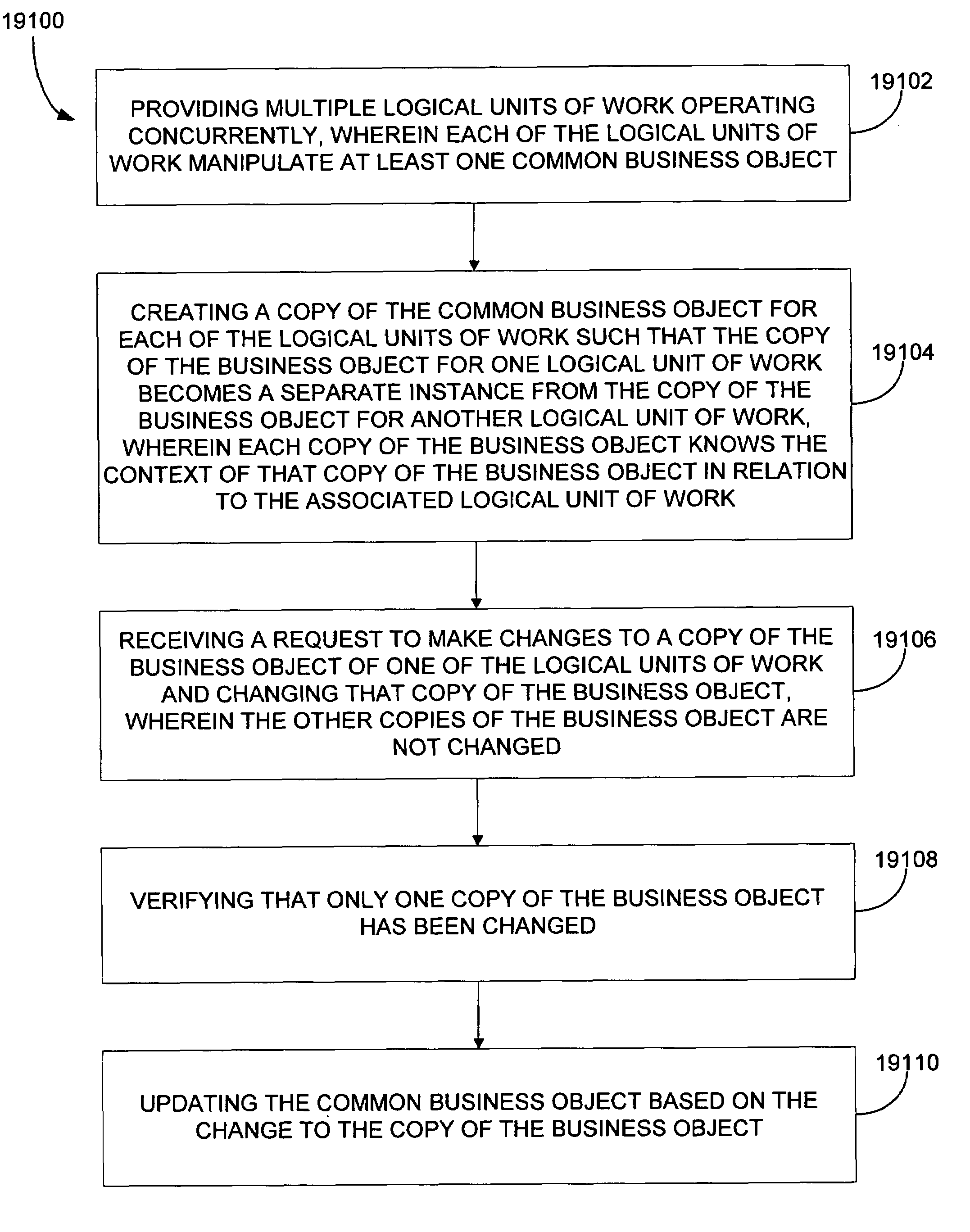
The present disclosure provides for implementing transaction services patterns. Logical requests are batched for reducing network traffic. A batched request is allowed to indicate that it depends on the response to another request. A single message is sent to all objects in a logical unit of work. Requests that are being unbatched from a batched message are sorted. Independent copies of business data are assigned to concurrent logical units of work for helping prevent the logical units of work from interfering with each other.
Owner:ACCENTURE GLOBAL SERVICES LTD
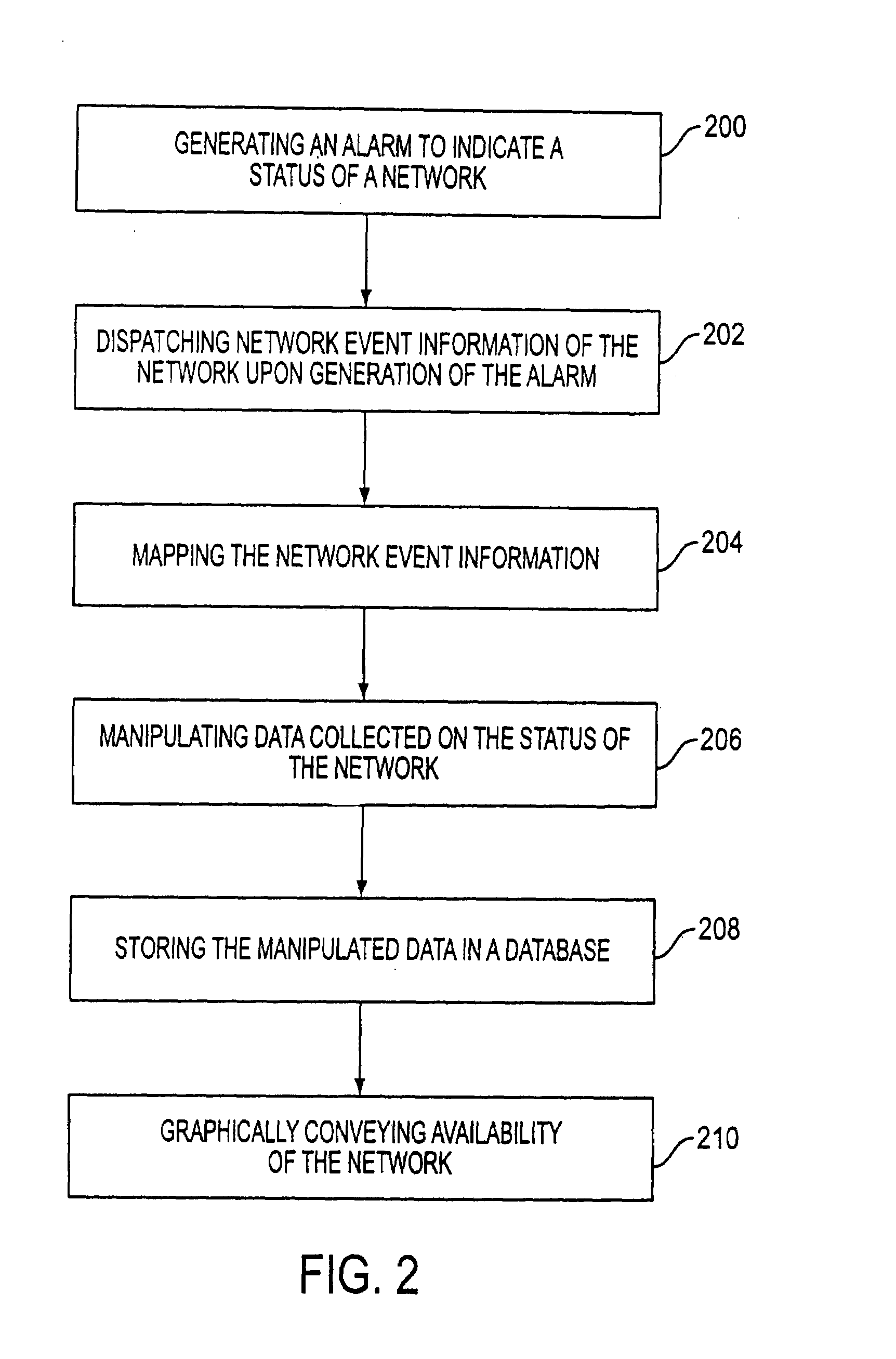
Controlling data collection, manipulation and storage on a network with service assurance capabilities
InactiveUS6985901B1Data processing applicationsDigital computer detailsEvent dataBiological activation
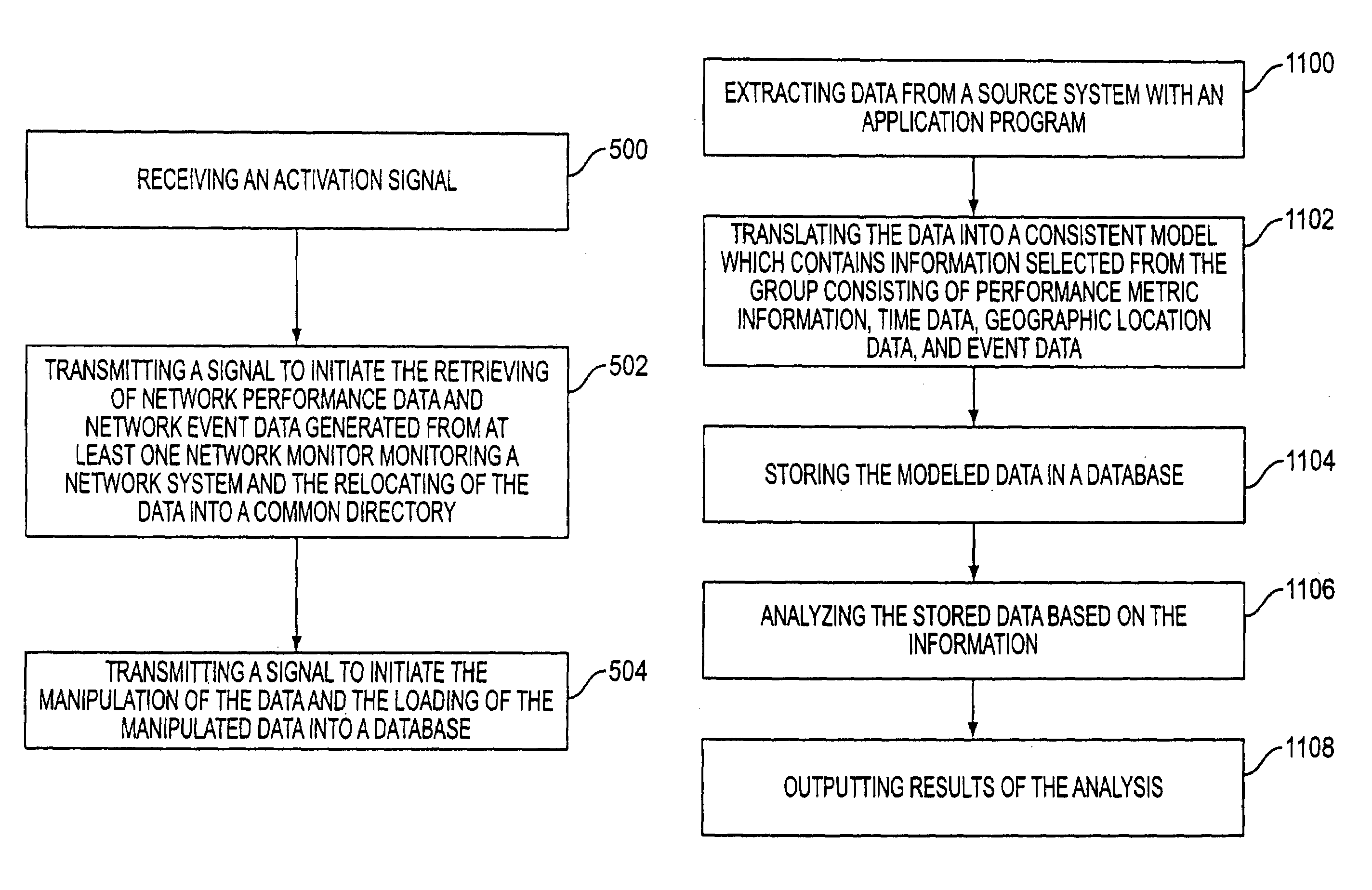
The present disclosure provides for controlling the collection, manipulation and storage of network performance data and network even data of a network with service assurance capabilities. Upon the receipt of an activation signal, a signal is transmitted to initiate the retrieving of network performance data and network event data generated from at least one network monitor. Such network monitor is adapted for monitoring a network system and the relocating of the data into a common directory. A signal is then transmitted to initiate the manipulation of the data and the loading of the manipulated data into a database.
Owner:ACCENTURE GLOBAL SERVICES LTD
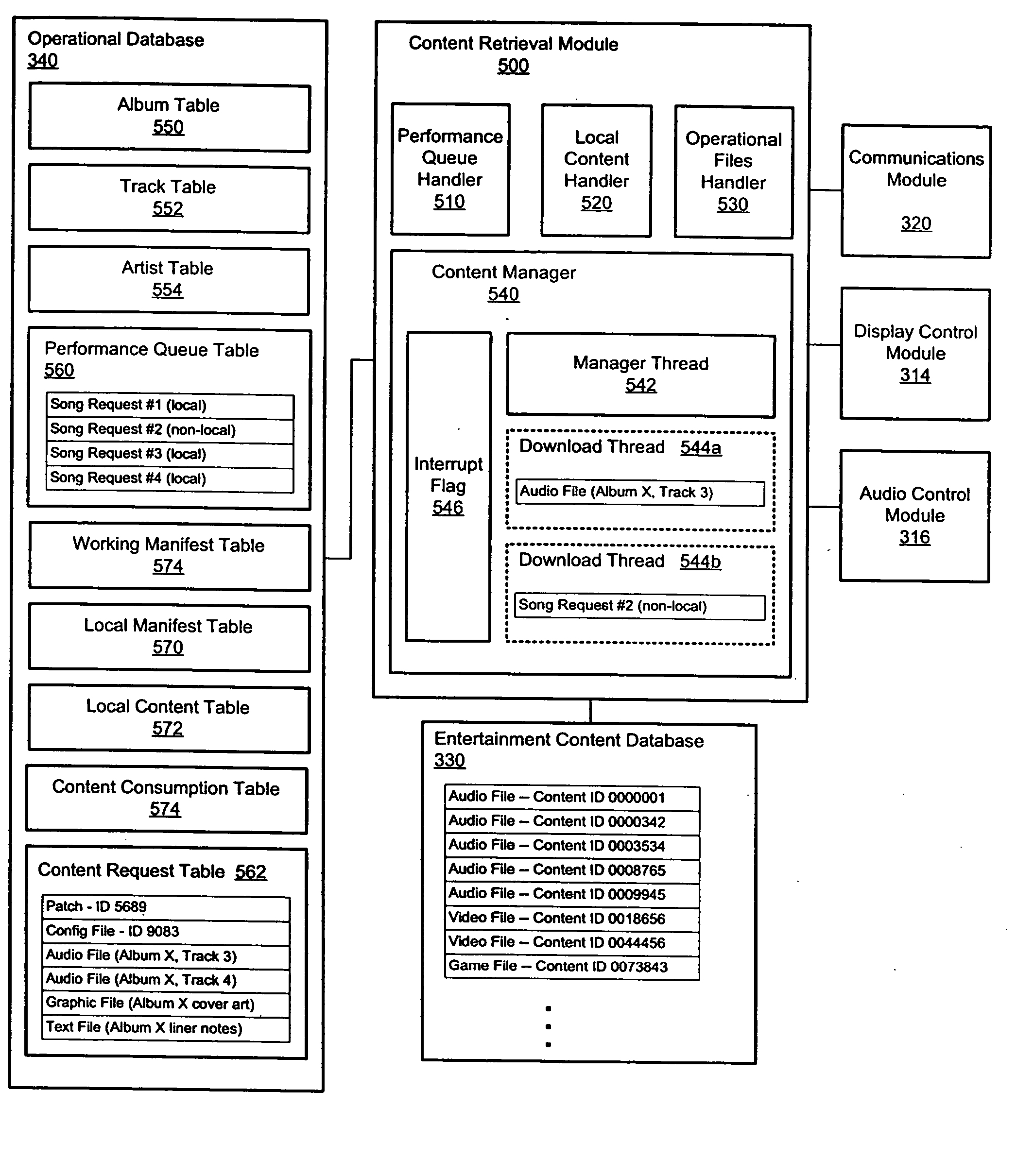
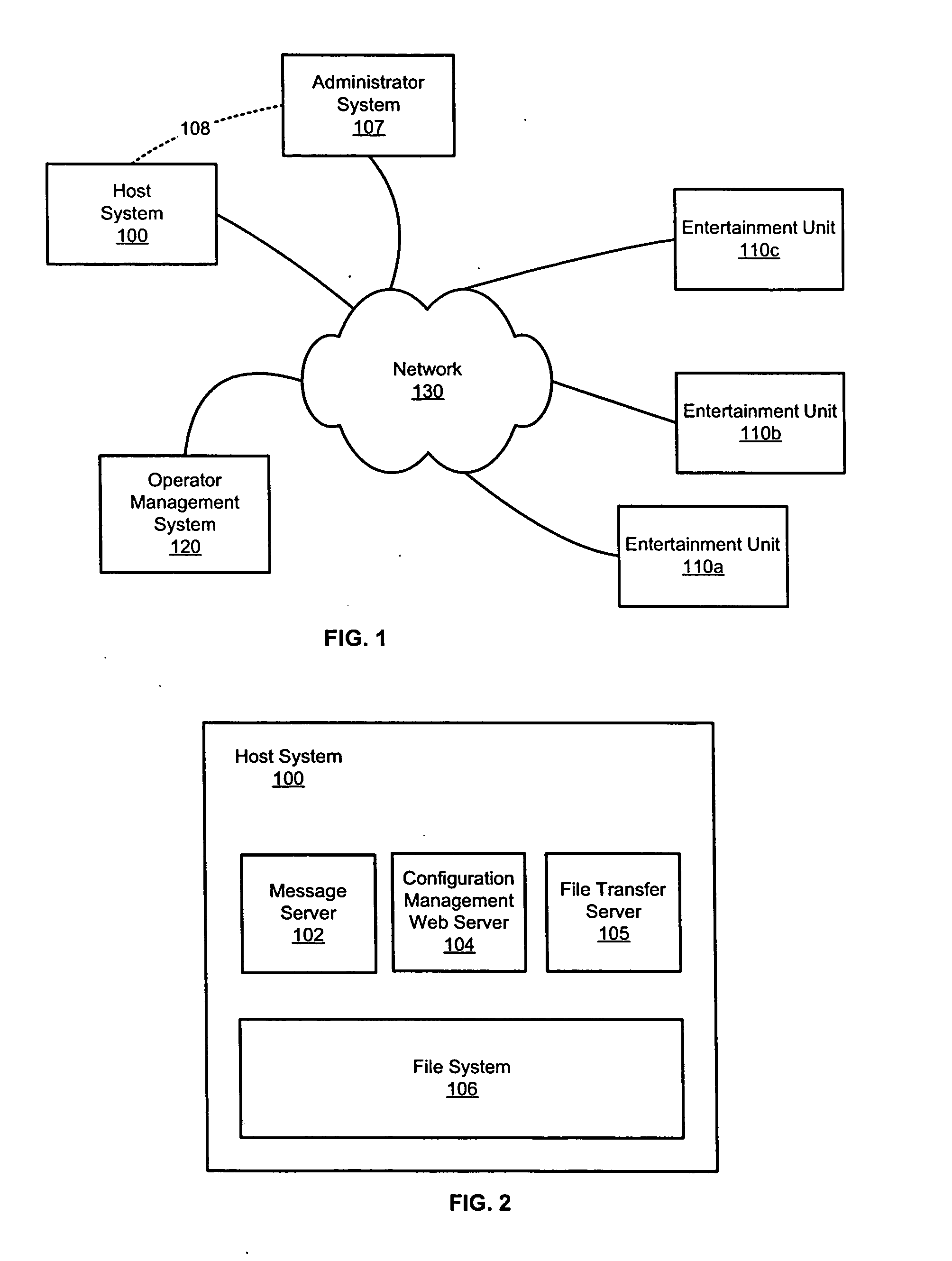
Prioritized content download for an entertainment device
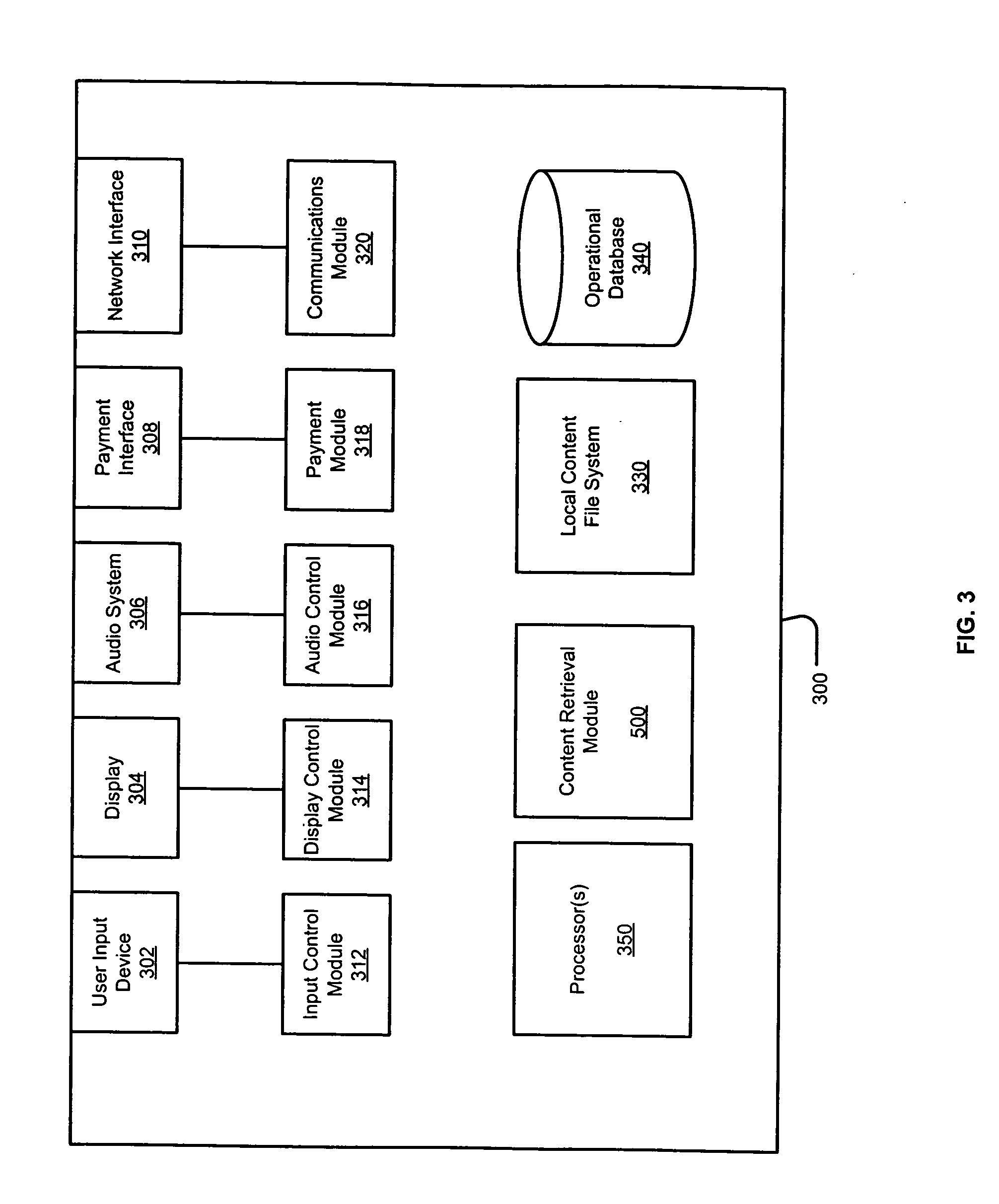
ActiveUS20060074750A1Multiprogramming arrangementsCash registersContent retrievalDistributed computing
Priority-based content retrieval mechanisms for digital entertainment devices are provided. In various embodiments, the download prioritizations may be interrupt-based, sequence-based, or a combination of the two. In interrupt-based prioritizations, a higher priority download request will interrupt a lower-priority download that is already in progress. In sequence-based prioritizations, a plurality of file download requests may be ordered in a download queue depending on the priority of the request, with higher priority requests being positioned towards the top of the queue and lower priority requests being positioned towards the bottom of the queue.
Owner:AMI ENTERTAINMENT NETWORK
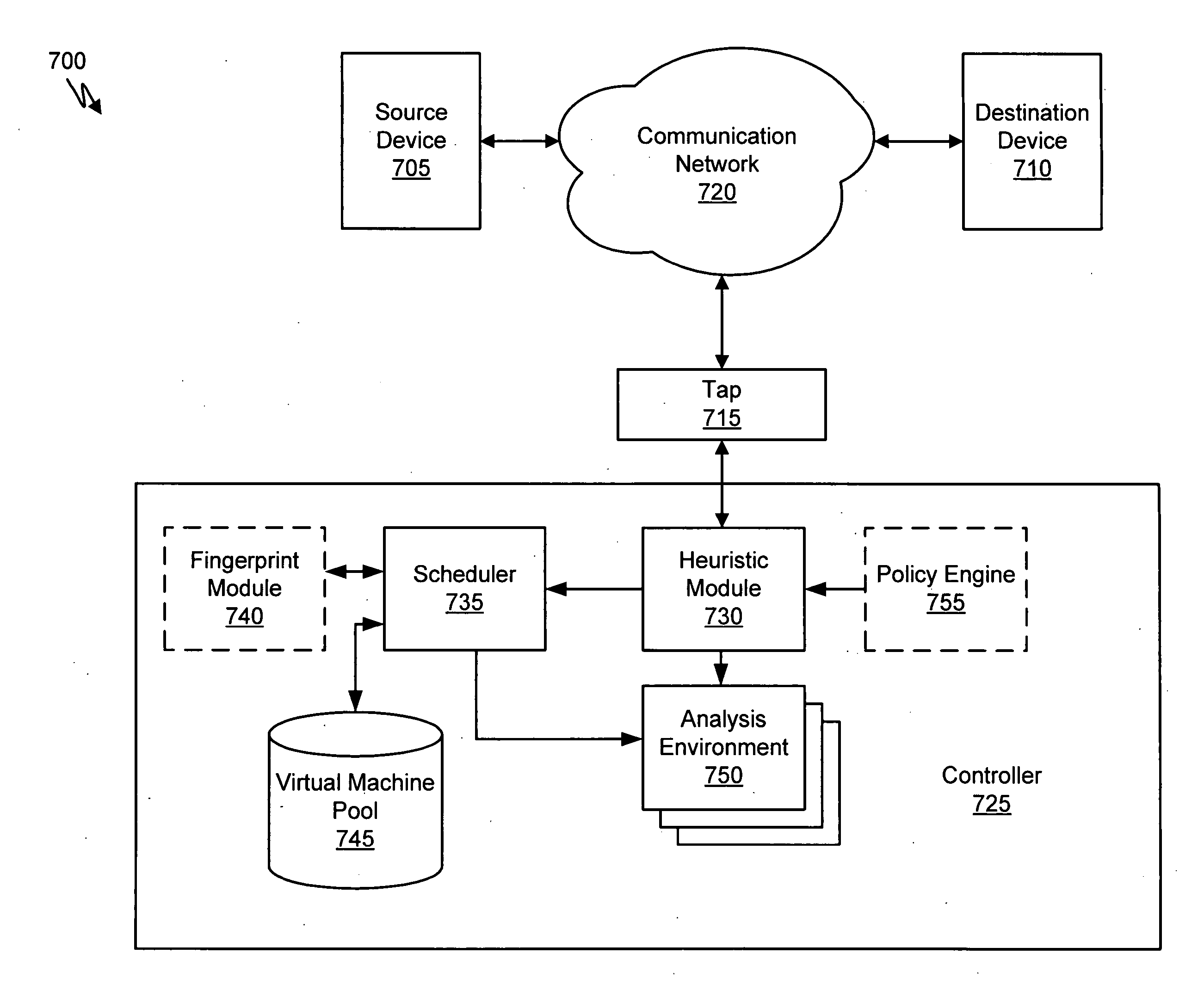
Virtual machine with dynamic data flow analysis
ActiveUS20070250930A1Memory loss protectionUnauthorized memory use protectionDynamic data flow analysisNetwork data
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to determine if the network data is suspicious, flag the network data as suspicious based on the heuristic determination, and concurrently simulate transmission of the network data to a plurality of destination devices.
Owner:FIREEYE SECURITY HLDG US LLC
Destination systems and methods for performing data replication
InactiveUS7617253B2Reduce impactReduce memory requirementsData processing applicationsDigital data information retrievalTemporal informationData management
Performing data management operations on replicated data in a computer network. Log entries are generated for data management operations of an application executing on a source system. Consistency point entries are used to indicate a time of a known good, or recoverable, state of the application. A destination system is configured to process a copy of the log and consistency point entries to replicate data in a replication volume, the replicated data being a copy of the application data on the source system. When the replicated data represents a known good state of the application, as determined by the consistency point entries, the destination system(s) may perform a storage operation (e.g., snapshot, backup) to copy the replicated data and to logically associate the copied data with a time information (e.g., time stamp) indicative of the source system time when the application was in the known good state.
Owner:COMMVAULT SYST INC
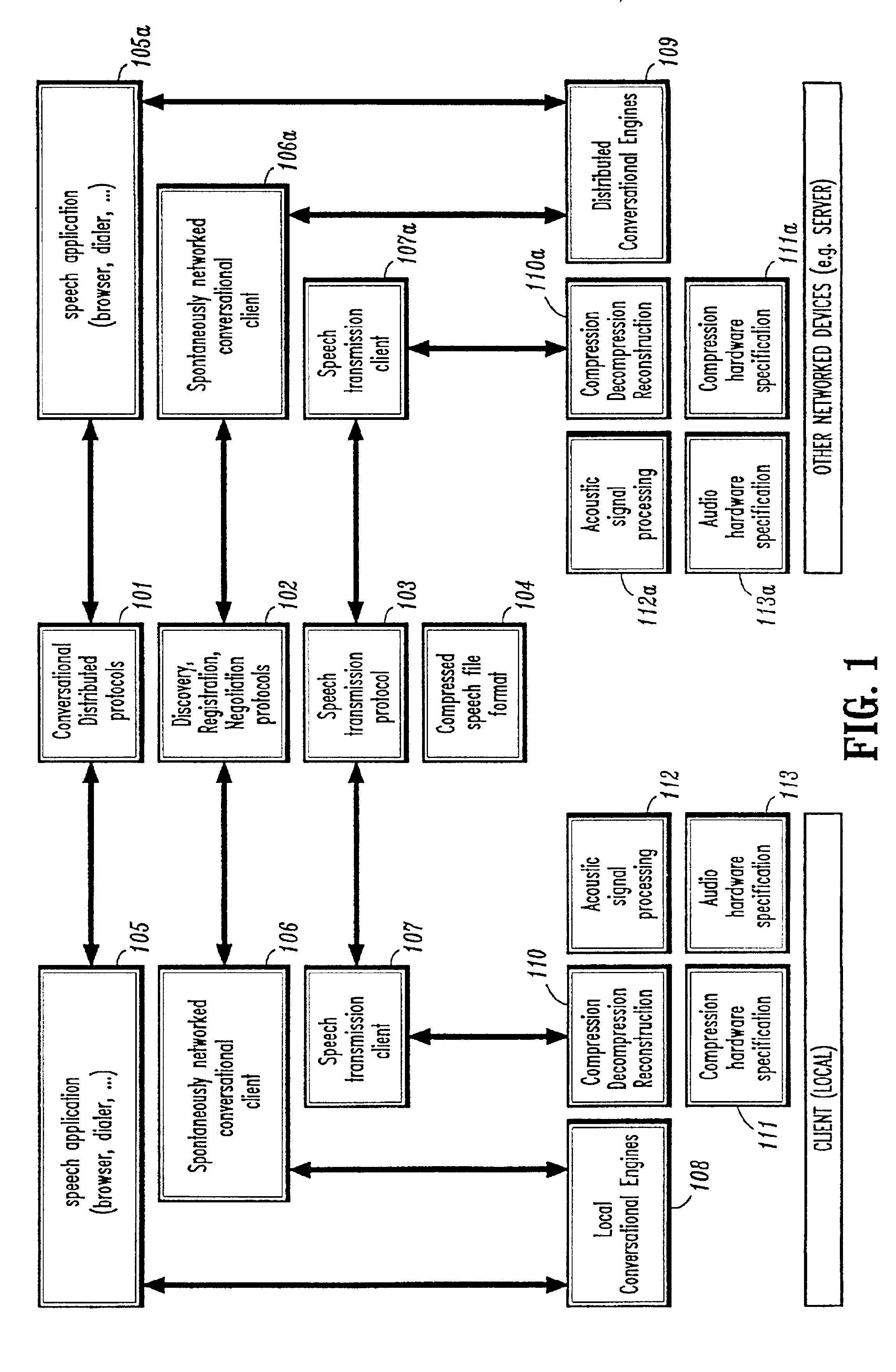
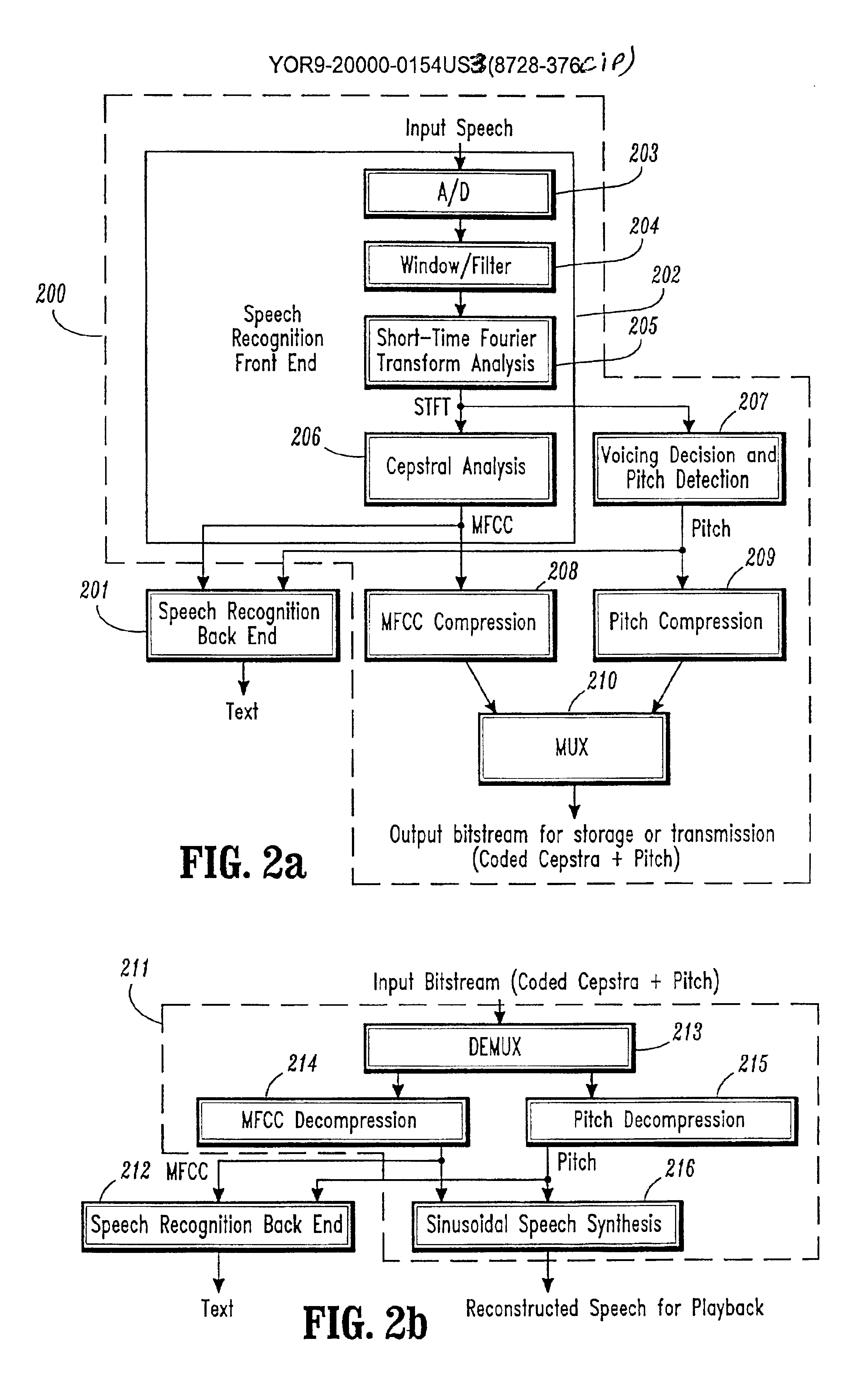
Conversational networking via transport, coding and control conversational protocols
InactiveUS6934756B2Broadcast transmission systemsMultiple digital computer combinationsSession controlRemote control
A system and method for implementing conversational protocols for distributed conversational networking architectures and / or distributed conversational applications, as well as real-time conversational computing between network-connected pervasive computing devices and / or servers over a computer network. The implementation of distributed conversational systems / applications according to the present invention is based, in part, on a suitably defined conversational coding, transport and control protocols. The control protocols include session control protocols, protocols for exchanging of speech meta-information, and speech engine remote control protocols.
Owner:IBM CORP
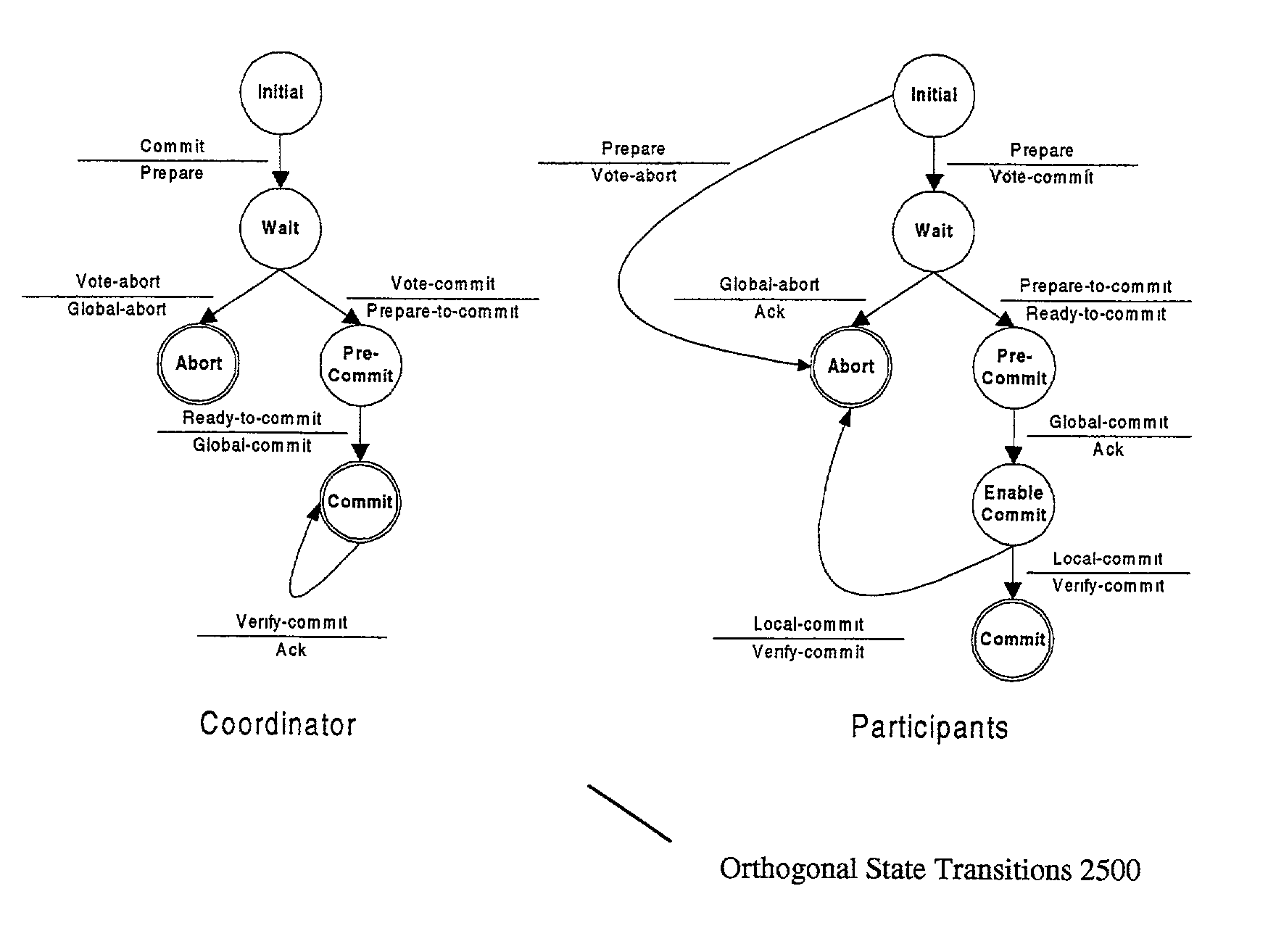
Asynchronous transcription object management system
ActiveUS7206805B1Avoid modificationReduce in quantityData processing applicationsMultiple digital computer combinationsManagement systemDistributed computing
Described herein is a system for executing distributed transactions. A coordinator and one or more participants cooperate to execute a distributed transaction, the distributed transaction including for each participant a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. Before each participant commits the transaction, the participants determine that the coordinator has committed the transaction. The coordinator commits the transaction after receiving acknowledgment from all the participants that they will commit the transaction. To determine whether the coordinator has committed the transaction, a participant transmits a message to the coordinator to acknowledge that it will commit the distributed transaction. The participant commits its respective transaction if it receives an acknowledgement from the coordinator. For the particular transaction being executed by a participant, the participant prevents other transactions from modifying a data item affected by the particular transaction. The participant will prevent such modifications until termination criteria for the particular transaction is satisfied, in which case the participant terminates the transaction.
Owner:ORACLE INT CORP
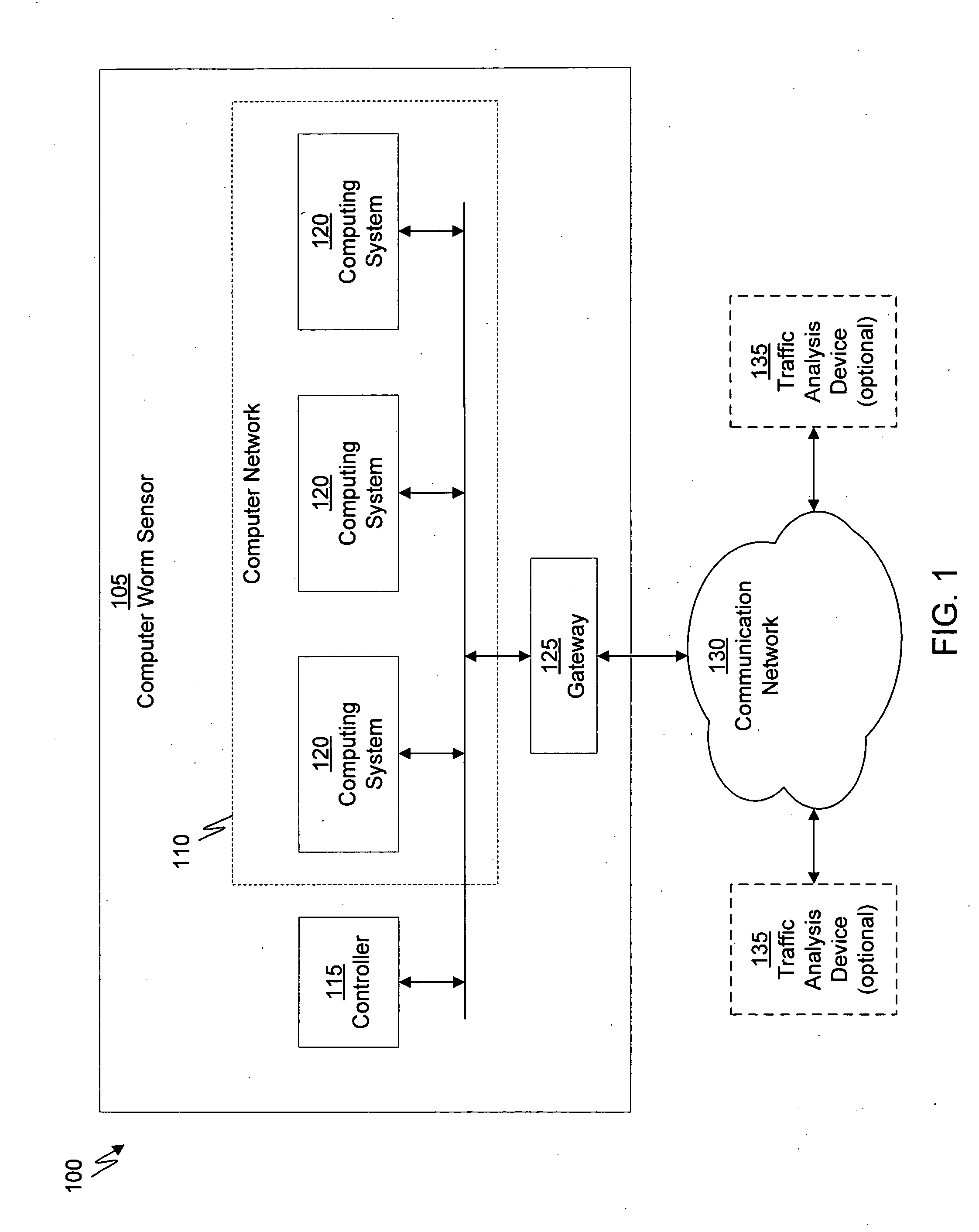
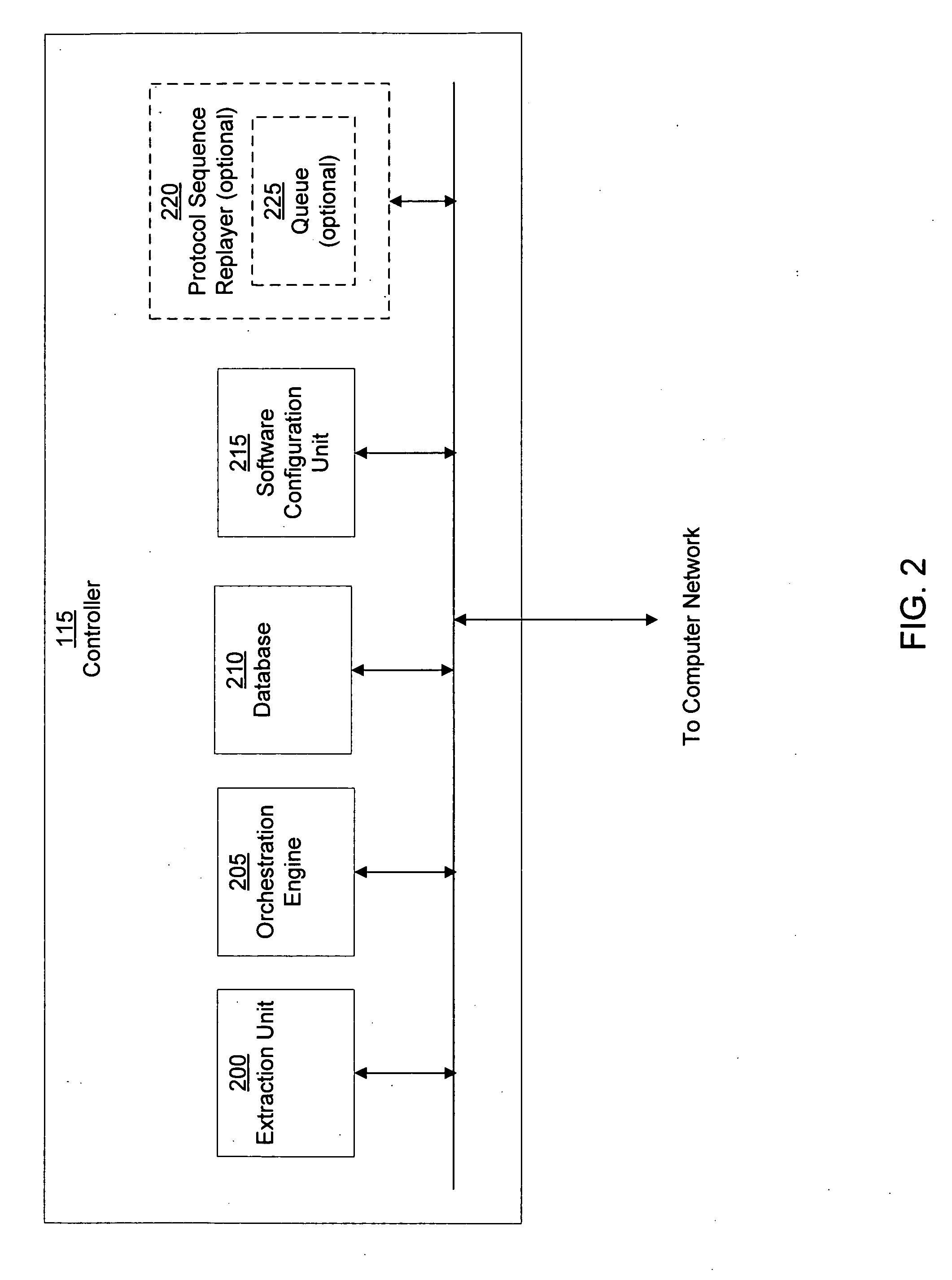
Method for detecting anomaly action within a computer network
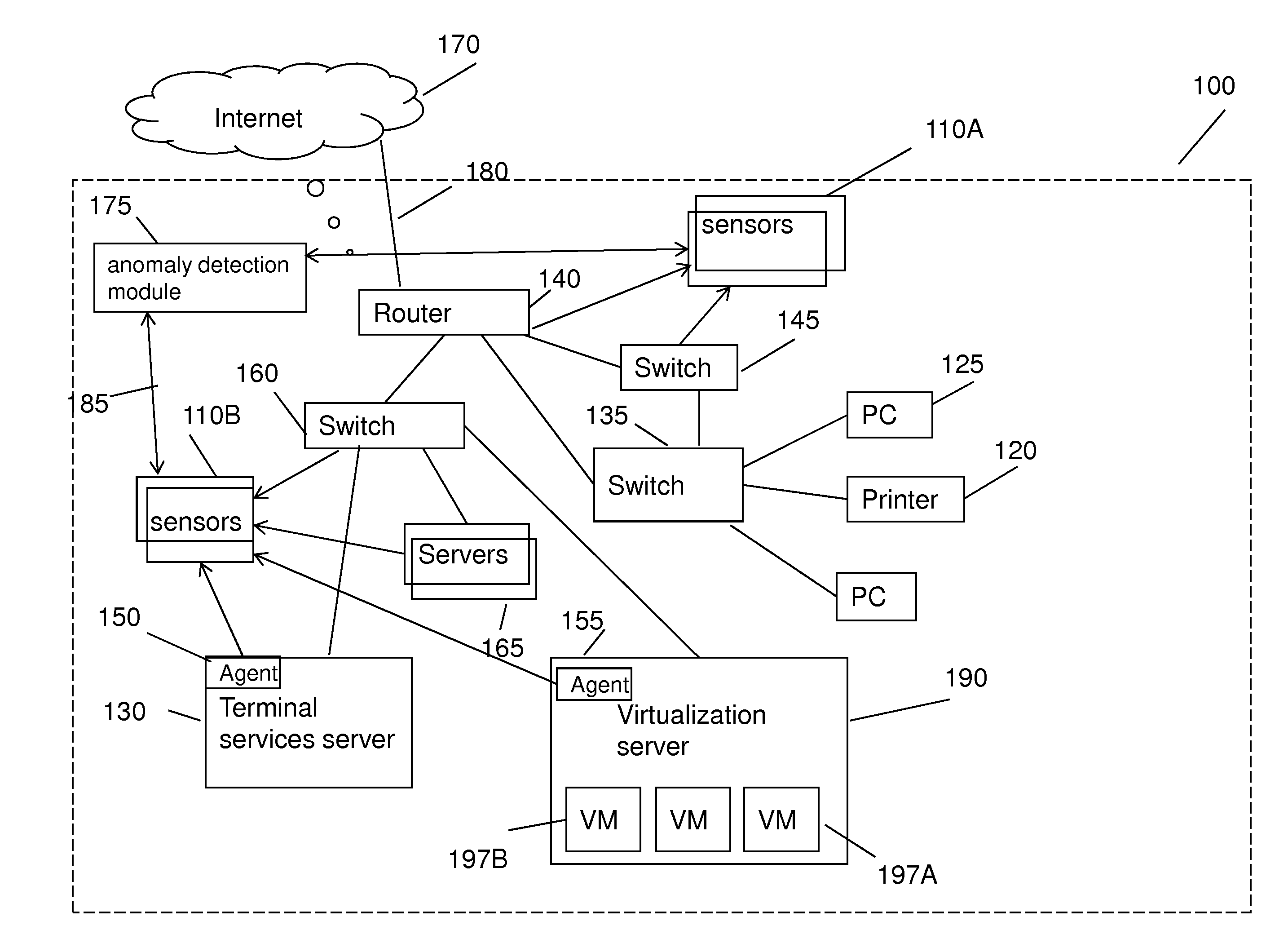
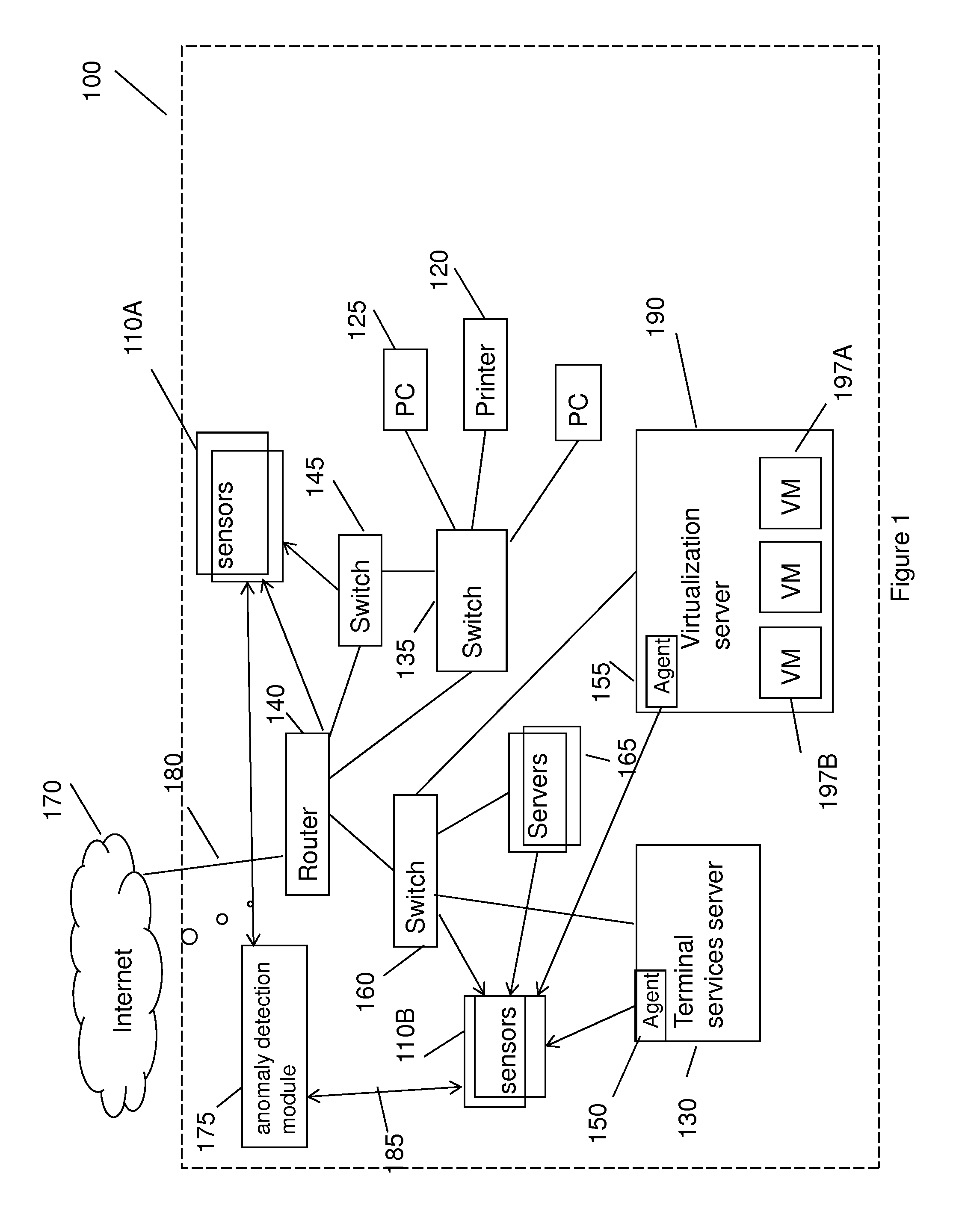
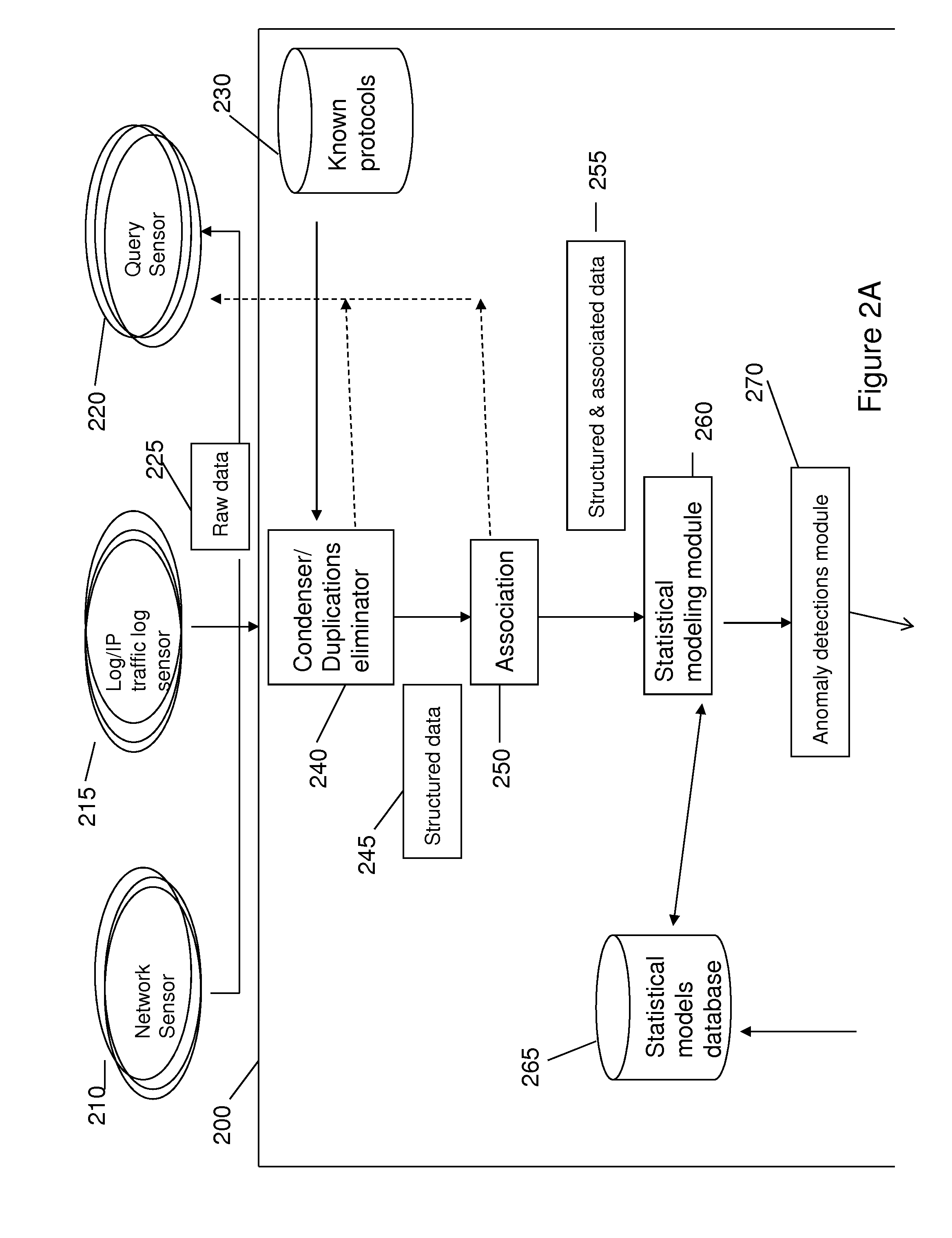
InactiveUS20140165207A1Eliminating duplication and processing dataMemory loss protectionError detection/correctionOriginal dataDistributed computing
A method and system for detecting anomalous action within a computer network is provided herein. The method starts with collecting raw data from at least one probe sensor that is associated with at least one router, switch or at least one server which are part of the computer network. Next, the raw data is being parsed and analyzed and meta-data is created from the raw data. Computer network actions are being identified based on existing knowledge about network protocols. The meta-data is associated with entities by analyzing the identified network actions and correlating between different computer network actions. Finally, creating at least one statistical model of the respective computer network said model including network actions' behavior pattern and online or batch detection of anomalous network actions associated with entities based on the statistical models.
Owner:LIGHT CYBER
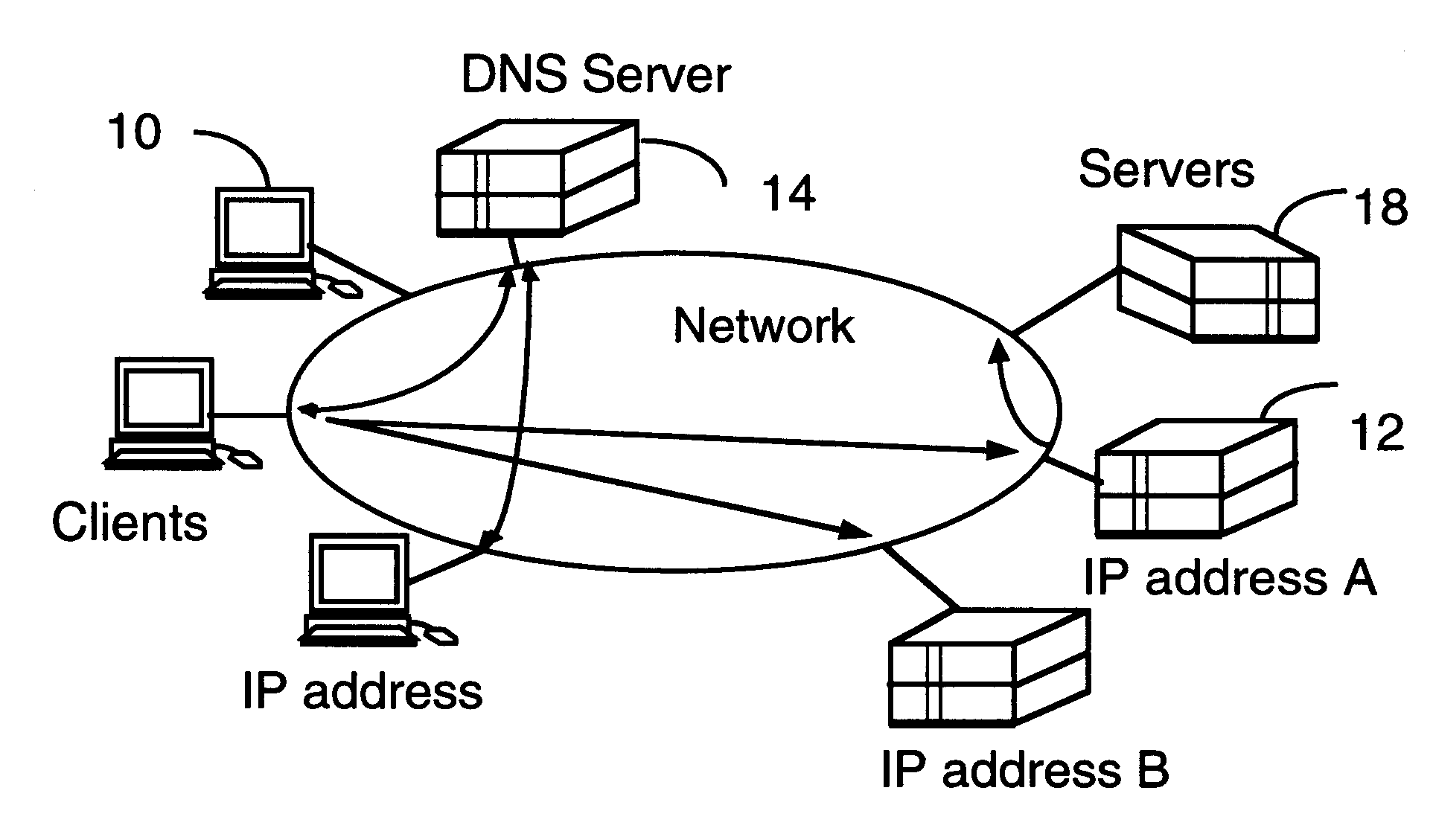
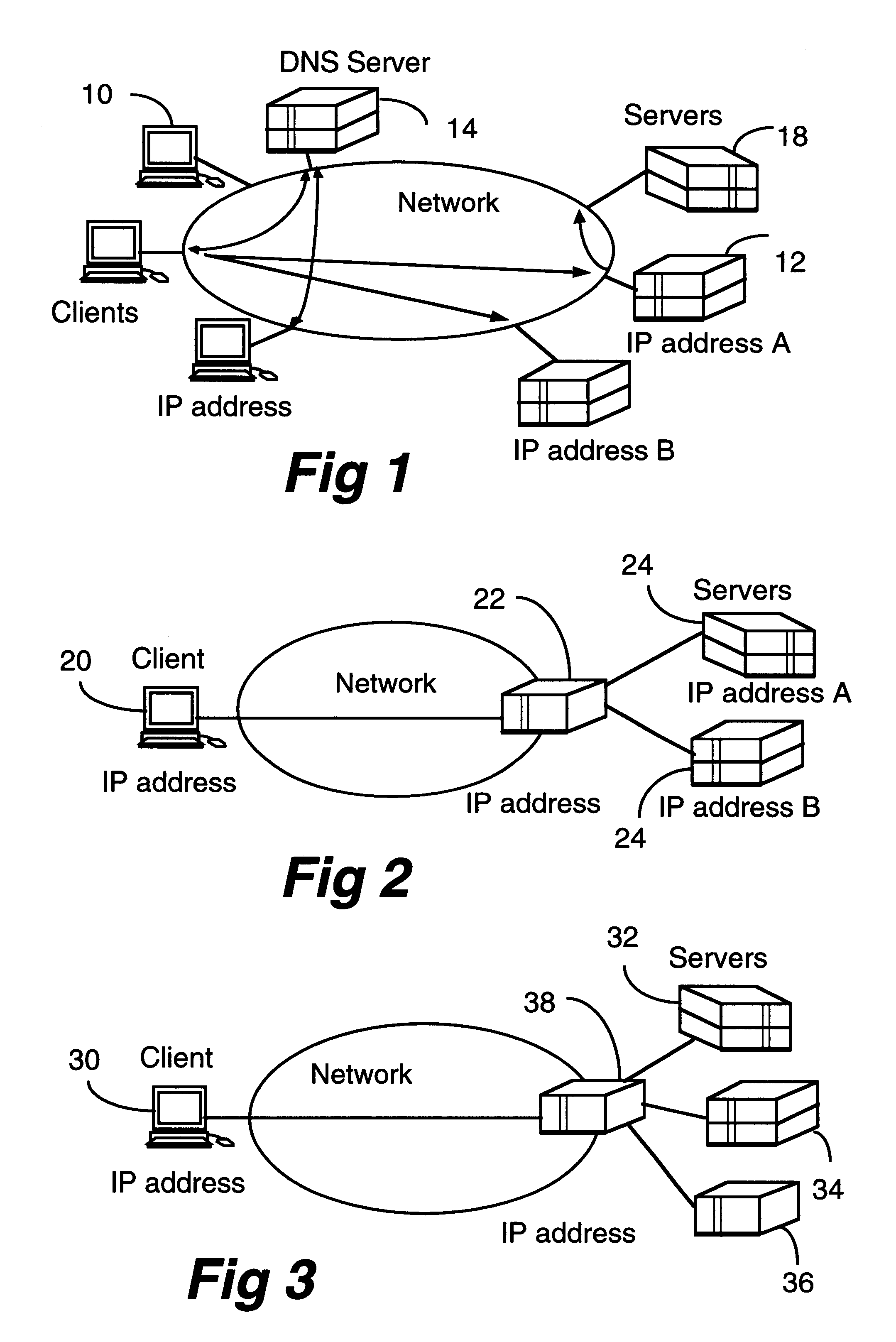
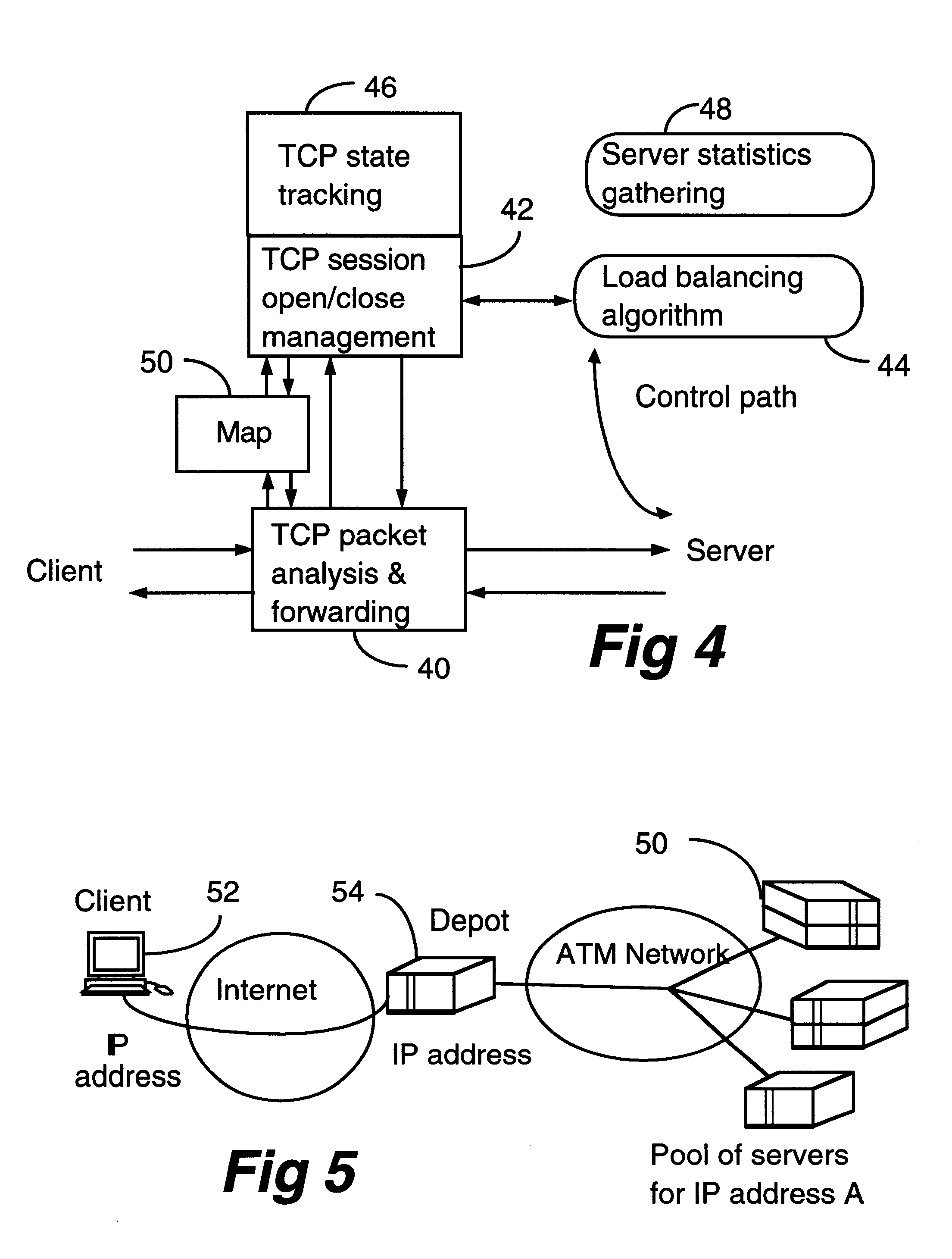
Scaleable web server and method of efficiently managing multiple servers
InactiveUS6330602B1Improve performanceEfficient managementData switching by path configurationMultiple digital computer combinationsInformation resourceWeb service
A client-server architecture includes a plurality of clients and a plurality of servers. Information resources are replicated among the servers. According to one aspect, the invention includes an intermediary device called a "depot" sitting transparently between a client and a pool of servers which have the replicated information resources. The depot dynamically distributes multiple sessions contained in a client request among the servers. This architecture realizes a good granular scaleability of servers, and improved server throughput with a good response time. Multiple depots also realize robustness.
Owner:AVAYA INC
Network caching system for streamed applications
InactiveUS20030009538A1Data processing applicationsMultiple digital computer combinationsApplication serverNetwork packet
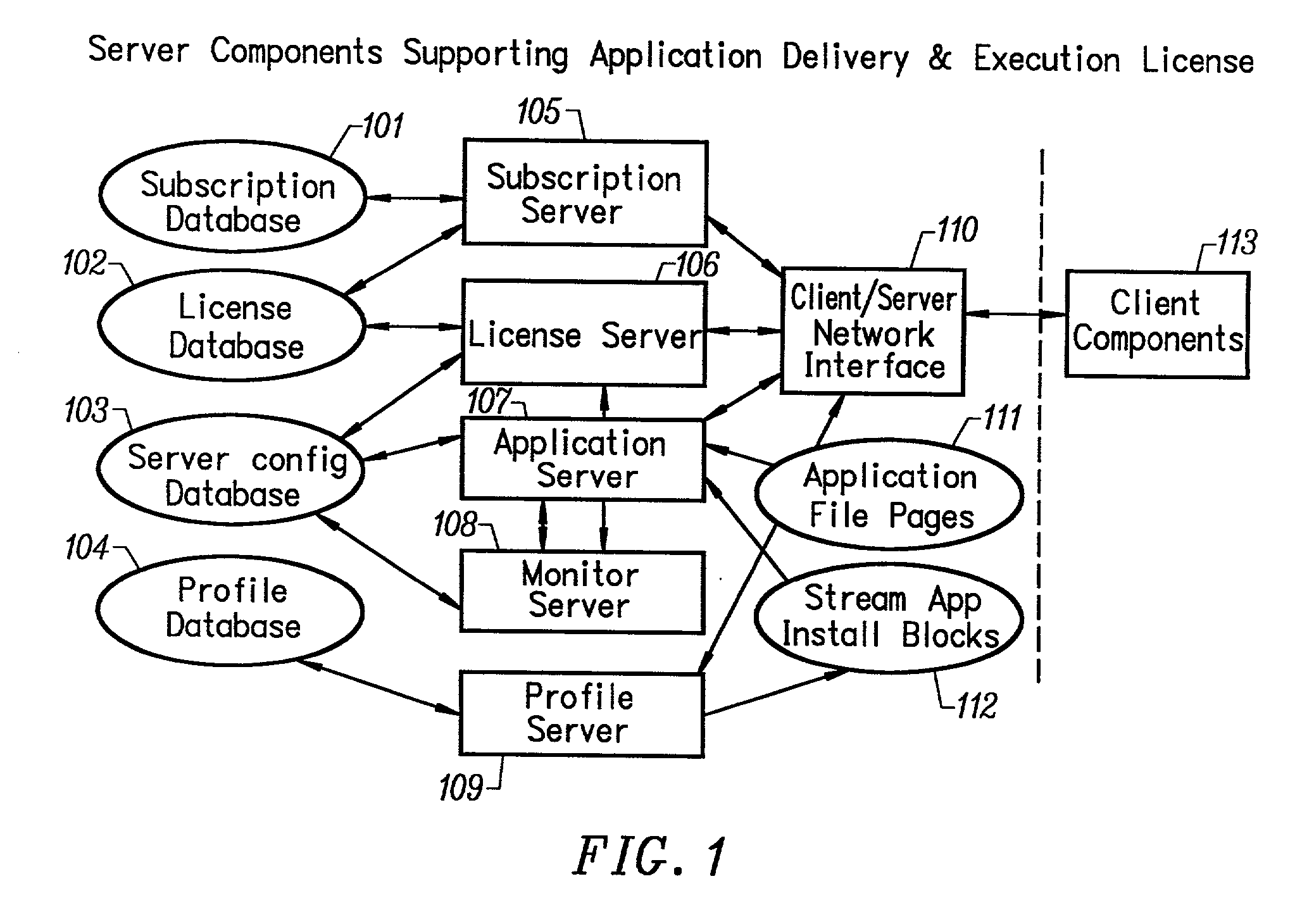
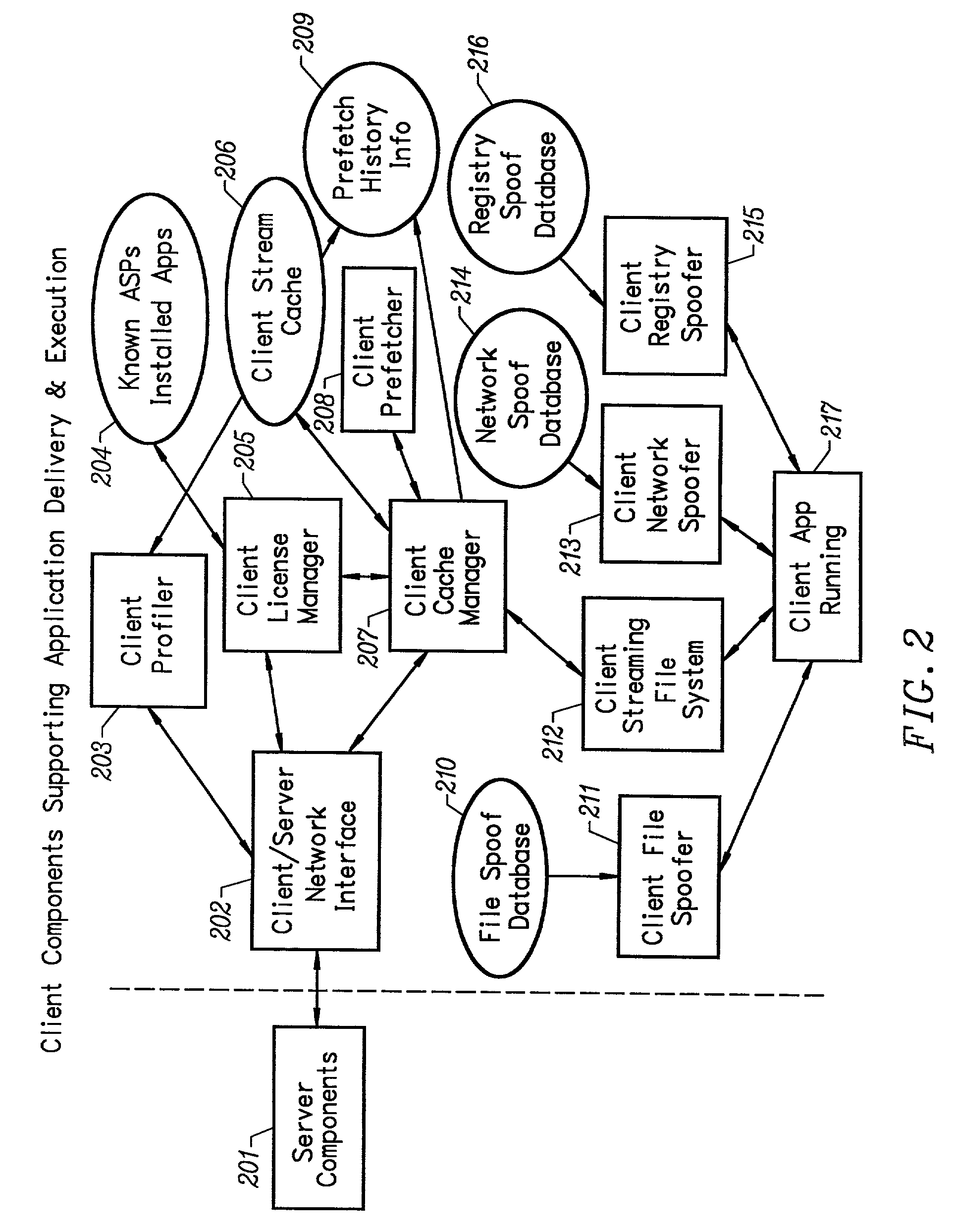
A network caching system for streamed applications provides for the caching of streamed applications within a computer network that are accessible by client systems within the network. Clients request streamed application file pages from other client systems, proxy servers, and application servers as each streamed application file is stored in a cache and used. Streamed application file page requests are broadcast to other clients using a multicast packet. Proxy servers are provided in the network that store a select set of streamed application file pages and respond to client requests by sending a response packet containing the requested streamed application file page if the streamed application file page is stored on the proxy server. Streamed application servers store all of the streamed application file pages. Clients try to send requests to streamed application servers as a last resort. Clients can concurrently send requests to other clients, to a proxy server, and to a streamed application server. Clients measure the response time to the clients requests placing a positive weighting on the more responsive request path and sending subsequent requests to the more positively weighted request path first.
Owner:NUMECENT HLDG
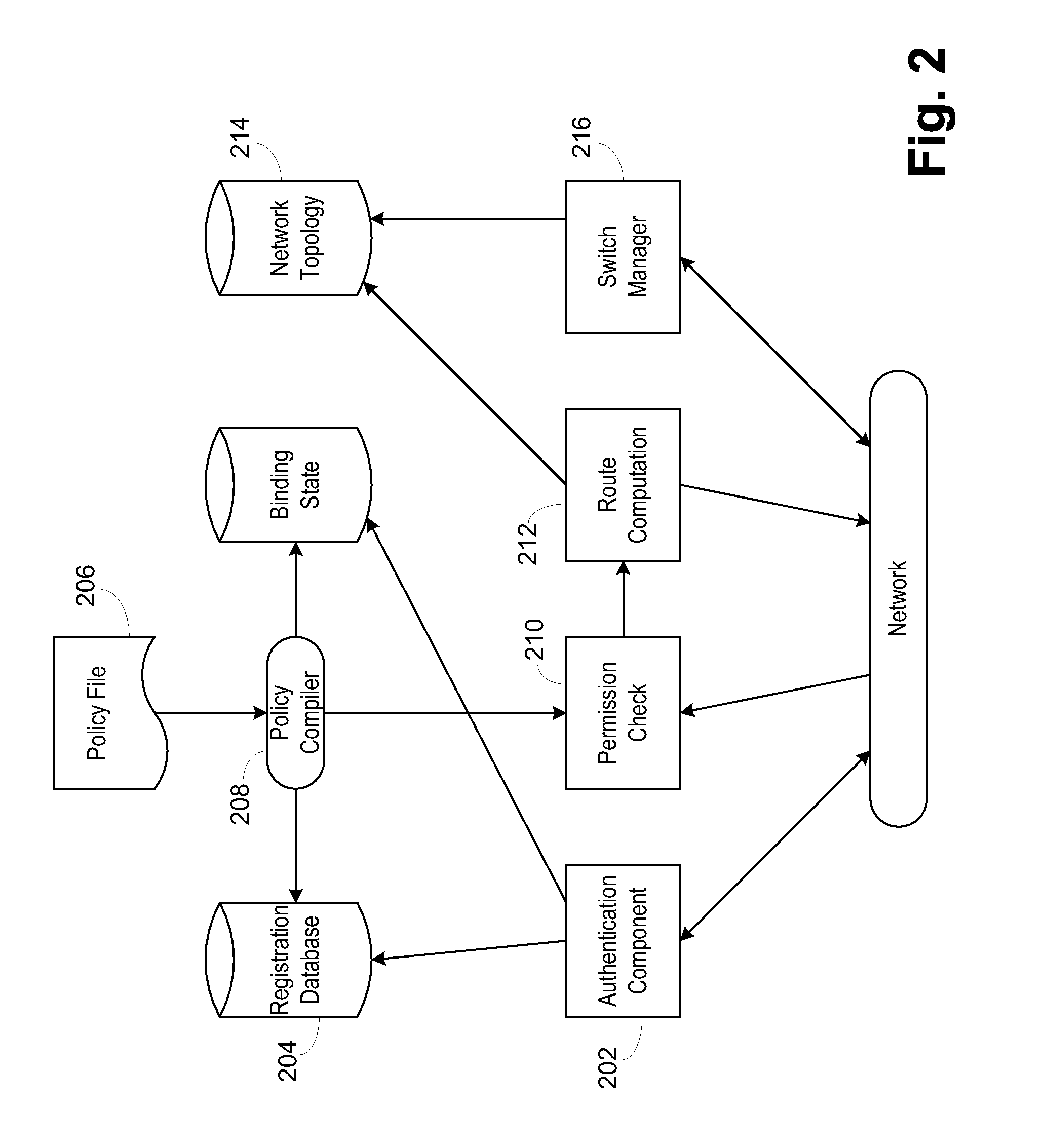
Secure network switching infrastructure
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
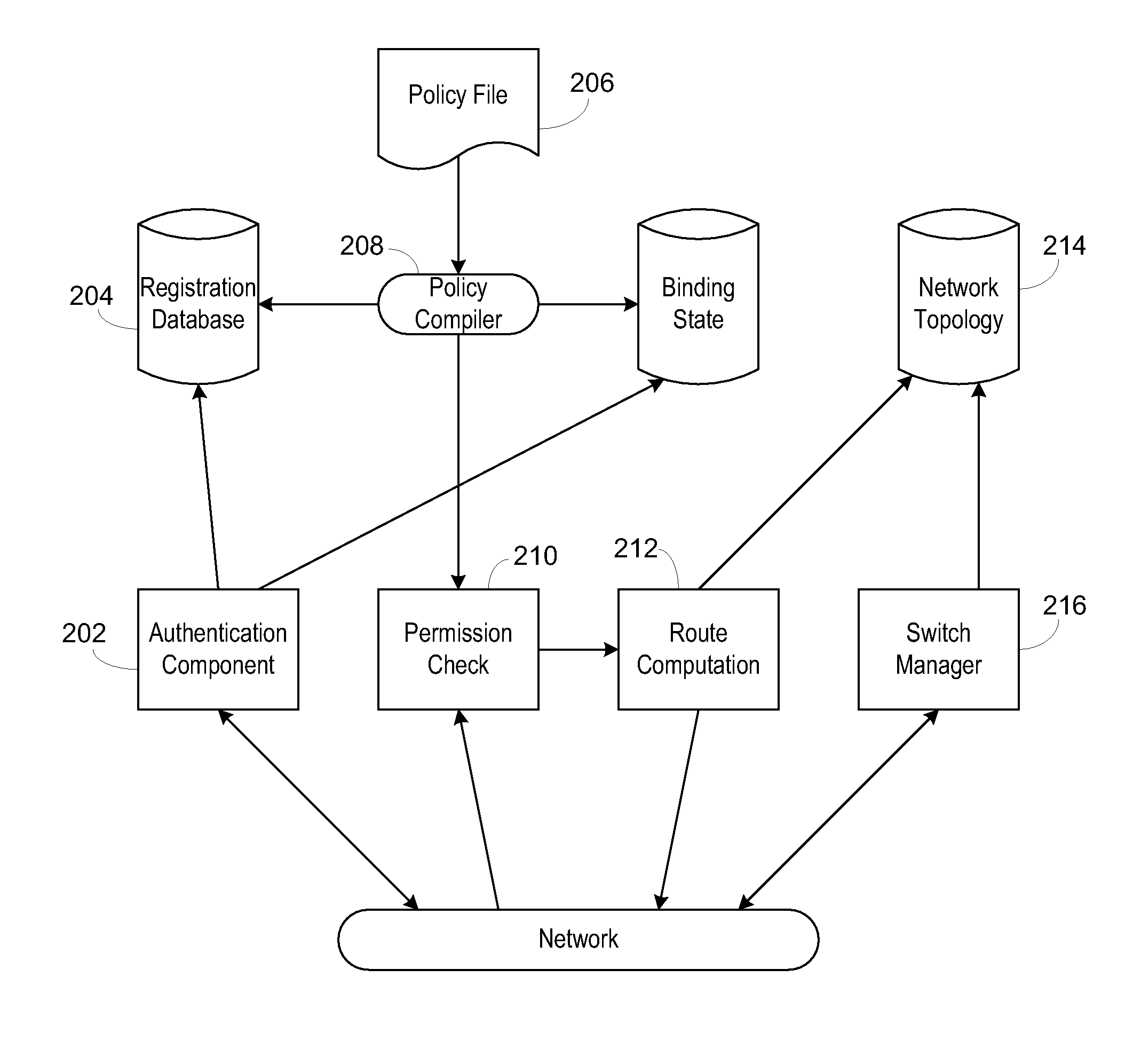
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Heuristic based capture with replay to virtual machine
A suspicious activity capture system can comprise a tap configured to copy network data from a communication network, and a controller coupled to the tap. The controller is coupled to the tap and is configured to receive the copy of the network data from the tap, analyze the copy of the network data with a heuristic to flag the network data as suspicious, and simulate transmission of the network data to a destination device.
Owner:FIREEYE SECURITY HLDG US LLC
Dynamic Network Connection System and Method
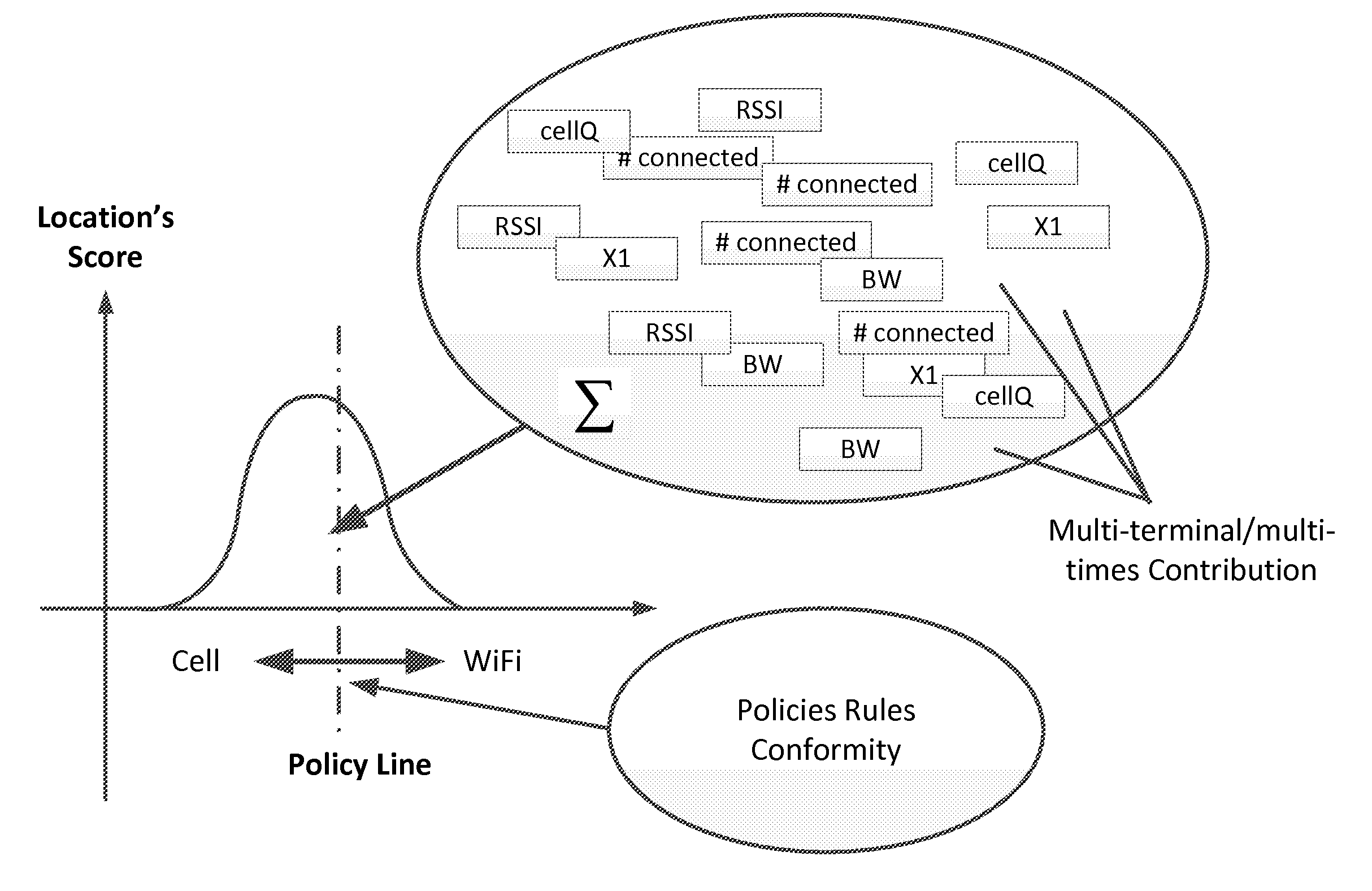
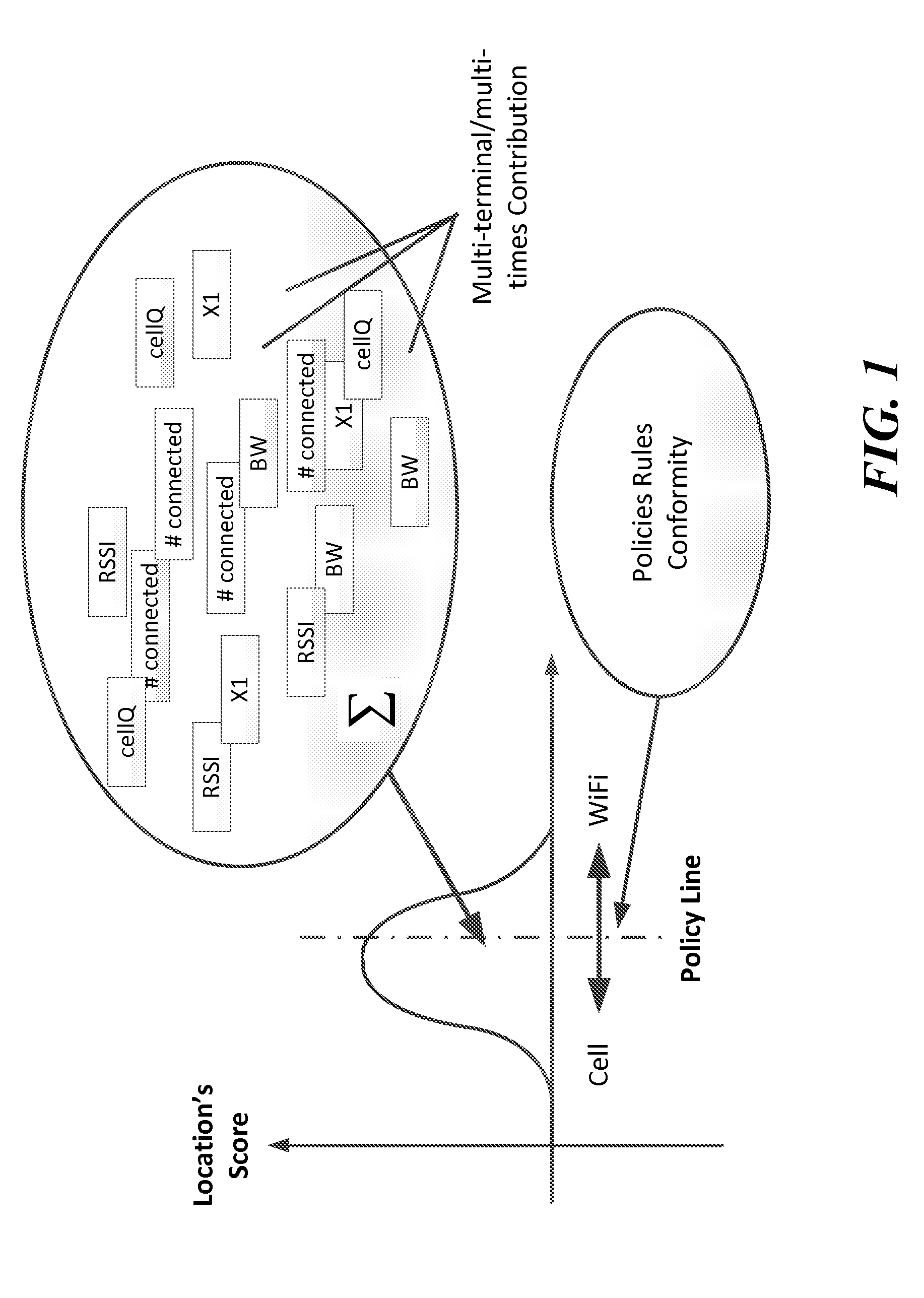
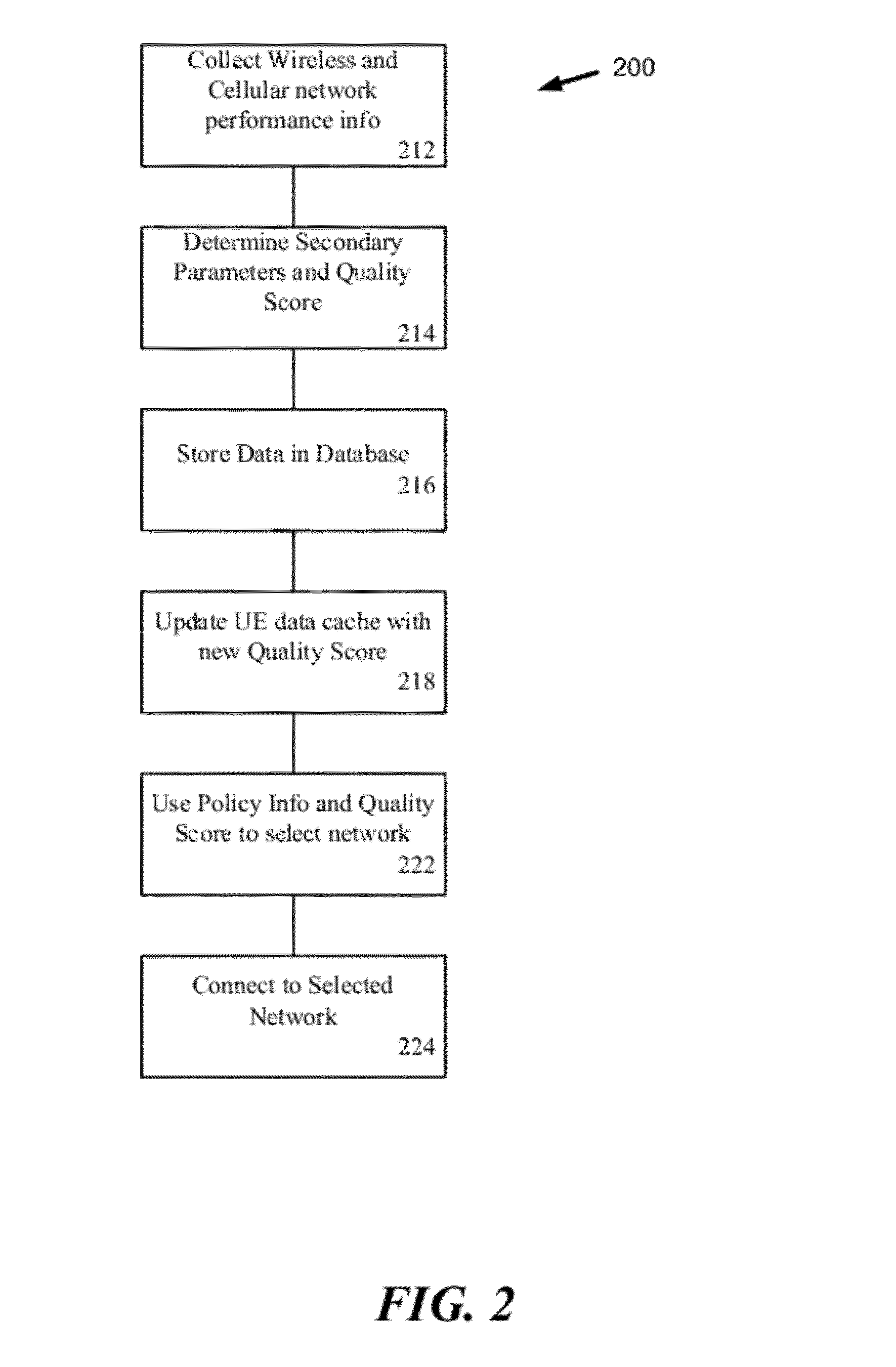
ActiveUS20120196644A1Reduce error rateReduce noiseAssess restrictionRadio transmissionNetwork connectionChoice making
A method and system for selecting a network to establish a connection to from a set of available network includes a network database providing historical information about each of the networks and sends the database information to end user terminals. The end user terminals monitor real-time performance information about each of the available networks and can send this information to the network database. The end user terminals also include network connection policy information which can be used to make the selection decision. The end user terminal determines a network quality score for each available network as a function of the historical information from the network database, the real-time performance information about each available network and the network connection policy information. The end user terminal can select the available network as a function of the network quality score, for example, selecting the available network with the highest network quality score.
Owner:WEFI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com