Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1099results about How to "Avoid modification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
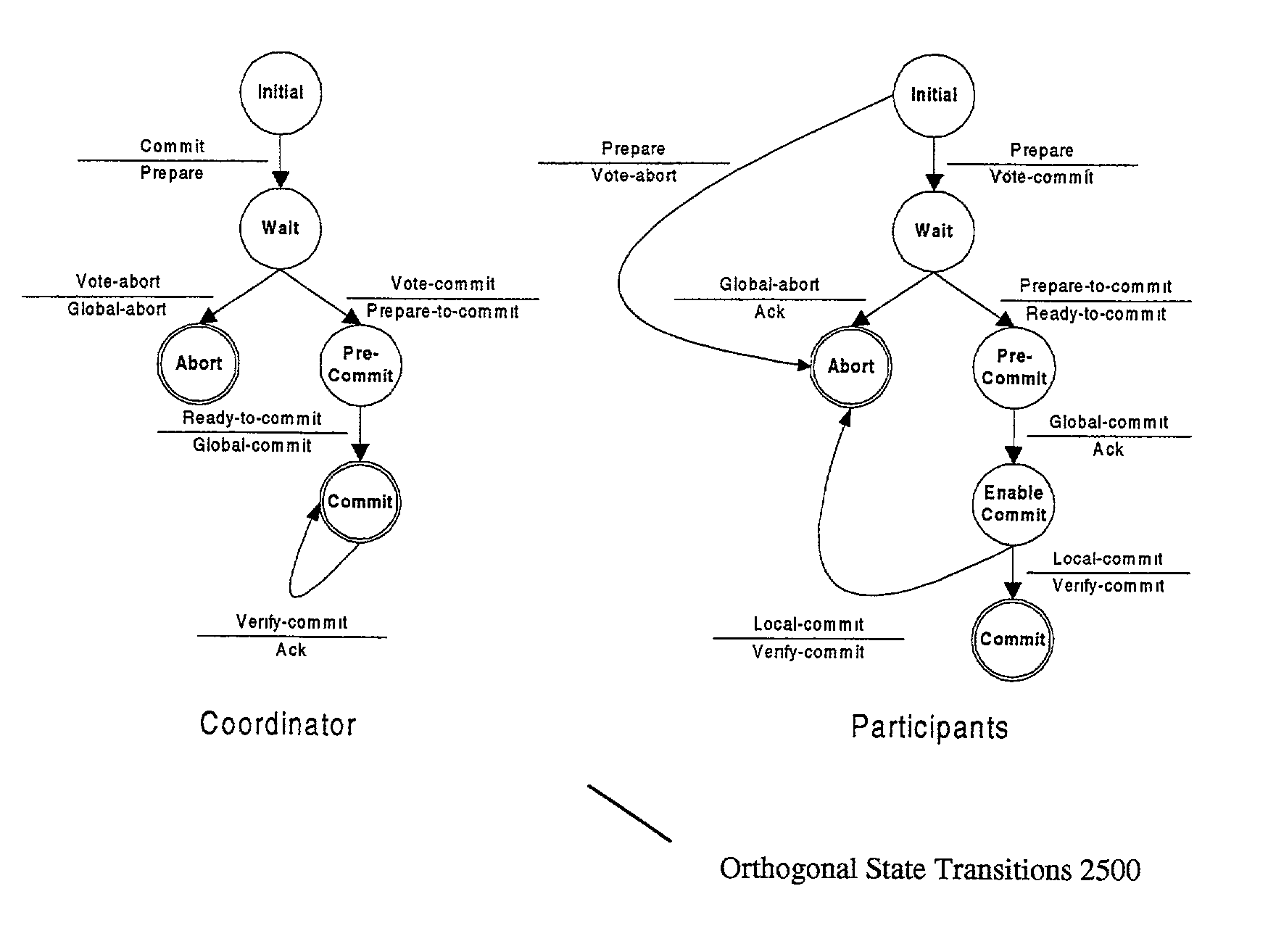
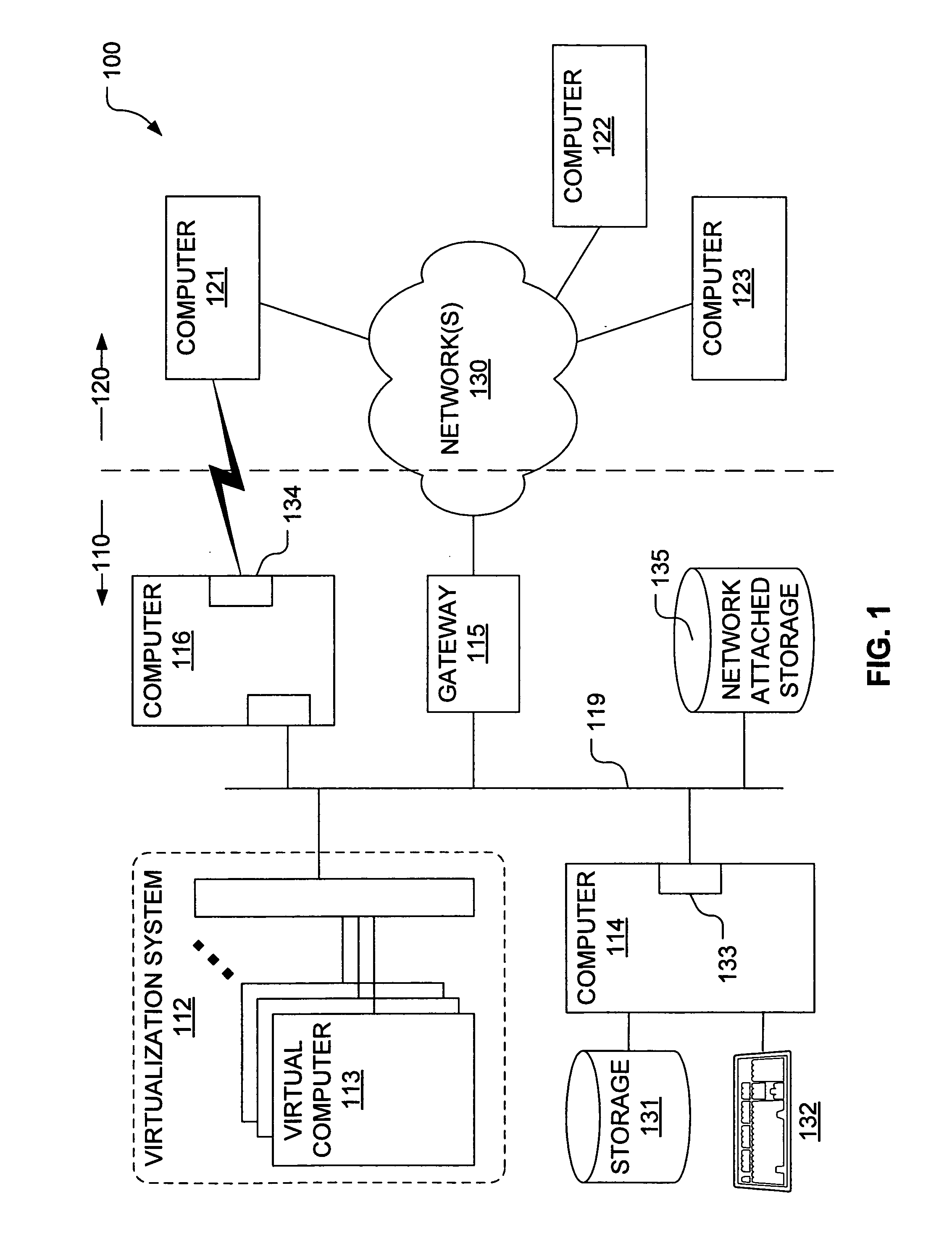
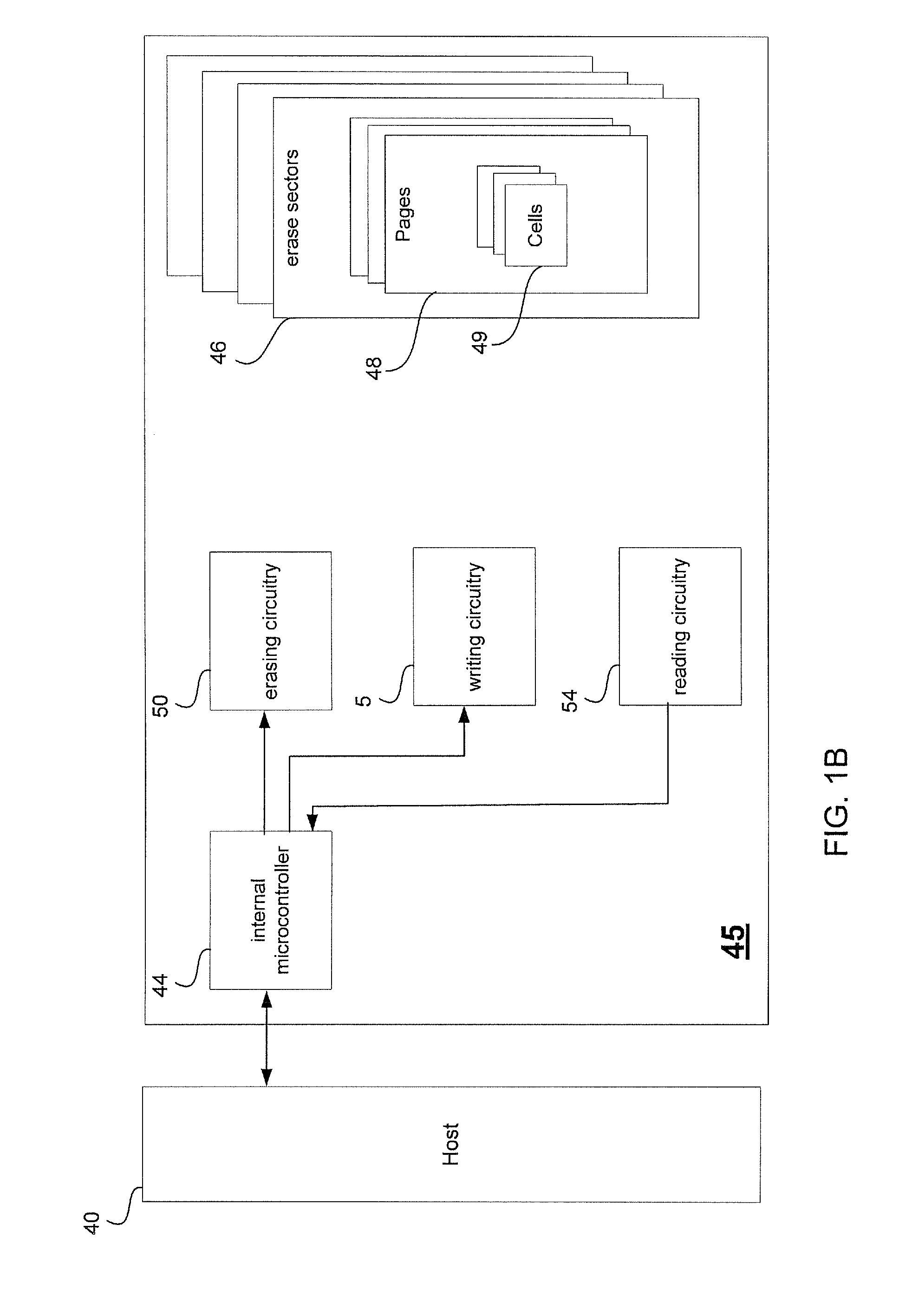
Asynchronous transcription object management system
ActiveUS7206805B1Avoid modificationReduce in quantityData processing applicationsMultiple digital computer combinationsManagement systemDistributed computing
Described herein is a system for executing distributed transactions. A coordinator and one or more participants cooperate to execute a distributed transaction, the distributed transaction including for each participant a transaction executed by the participant. To manage the transaction, the coordinator and the participant communicate over a network using, for example, a stateless protocol. Before each participant commits the transaction, the participants determine that the coordinator has committed the transaction. The coordinator commits the transaction after receiving acknowledgment from all the participants that they will commit the transaction. To determine whether the coordinator has committed the transaction, a participant transmits a message to the coordinator to acknowledge that it will commit the distributed transaction. The participant commits its respective transaction if it receives an acknowledgement from the coordinator. For the particular transaction being executed by a participant, the participant prevents other transactions from modifying a data item affected by the particular transaction. The participant will prevent such modifications until termination criteria for the particular transaction is satisfied, in which case the participant terminates the transaction.
Owner:ORACLE INT CORP
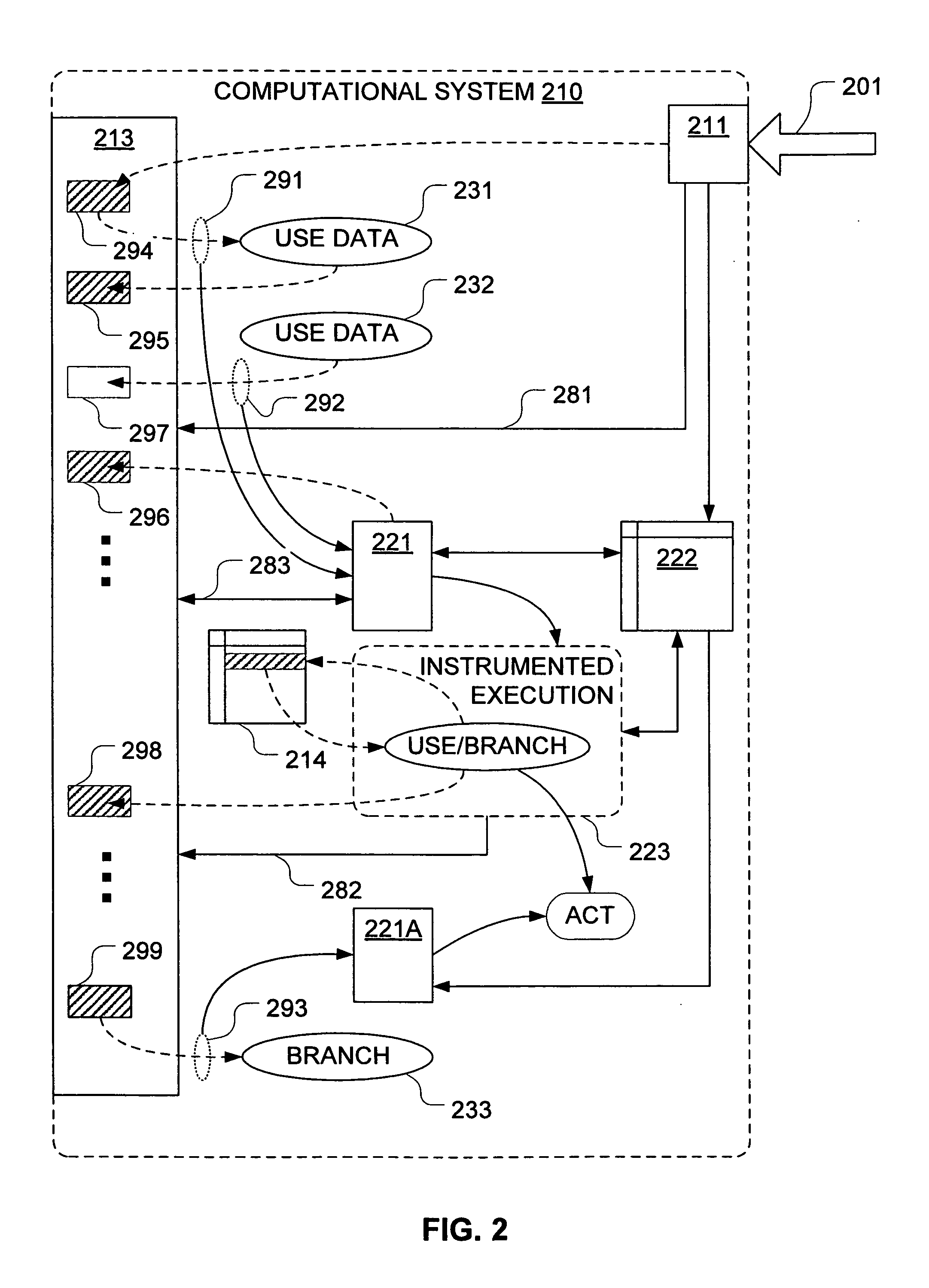
Taint tracking mechanism for computer security
ActiveUS8510827B1Easy to trackAvoid modificationMemory loss protectionDigital data processing detailsInformation dispersalOperation mode
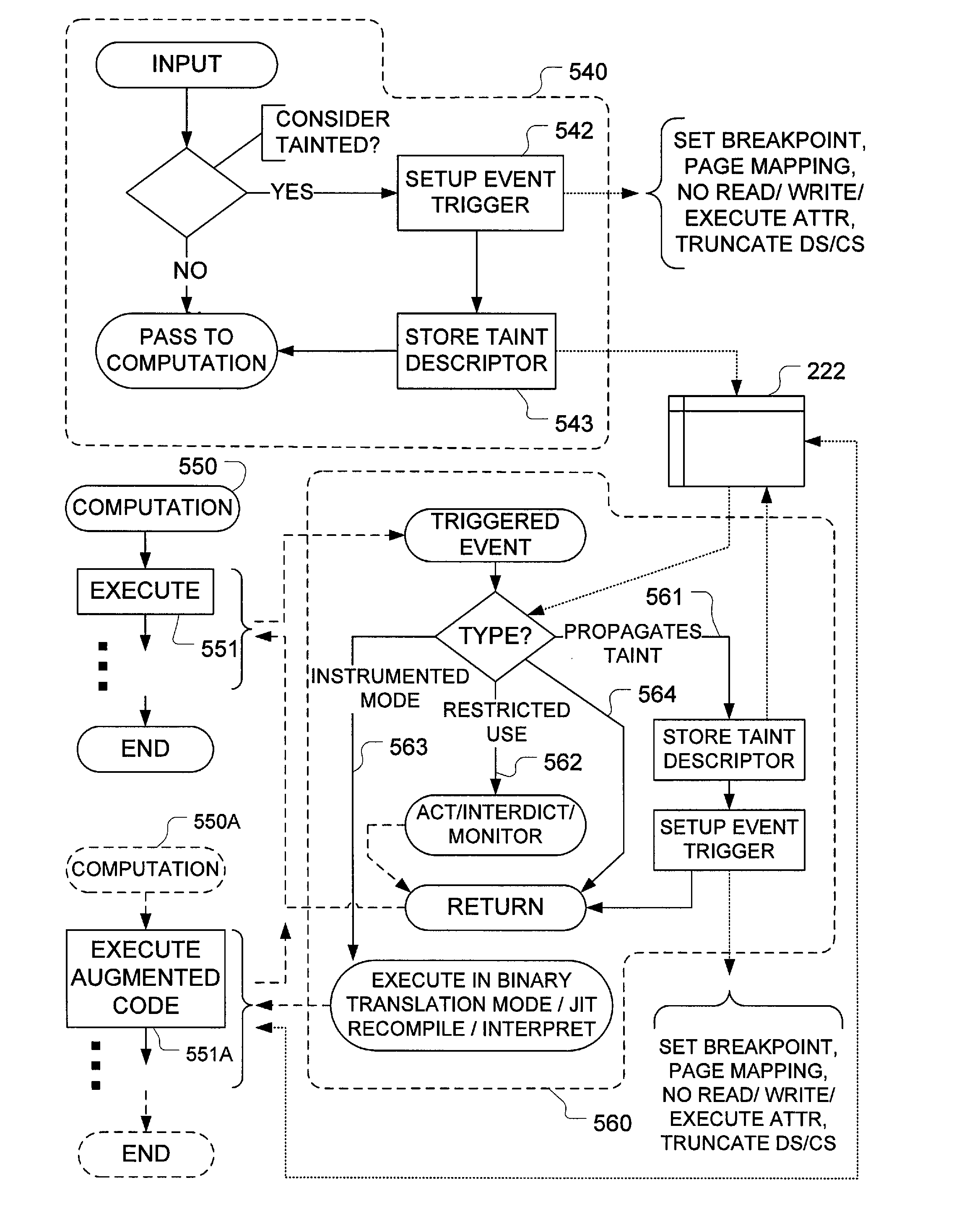
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and propagating taint status for memory locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security response if and when a control transfer (or other restricted use) is attempted based on tainted data. In some embodiments, memory management facilities and related exception handlers can be exploited to facilitate taint status propagation and / or security responses. Taint tracking through registers of a processor (or through other storage for which access is not conveniently mediated using a memory management facility) may be provided using an instrumented execution mode of operation. For example, the instrumented mode may be triggered by an attempt to propagate tainted information to a register. In some embodiments, an instrumented mode of operation may be more generally employed. For example, data received from an untrusted source or via an untrusted path is often transferred into a memory buffer for processing by a particular service, routine, process, thread or other computational unit. Code that implements the computational unit may be selectively executed in an instrumented mode that facilitates taint tracking. In general, instrumented execution modes may be supported using a variety of techniques including a binary translation (or rewriting) mode, just-in-time (JIT) compilation / re-compilation, interpreted mode execution, etc. Using an instrumented execution mode and / or exception handler techniques, modifications to CPU hardware can be avoided if desirable.
Owner:VMWARE INC
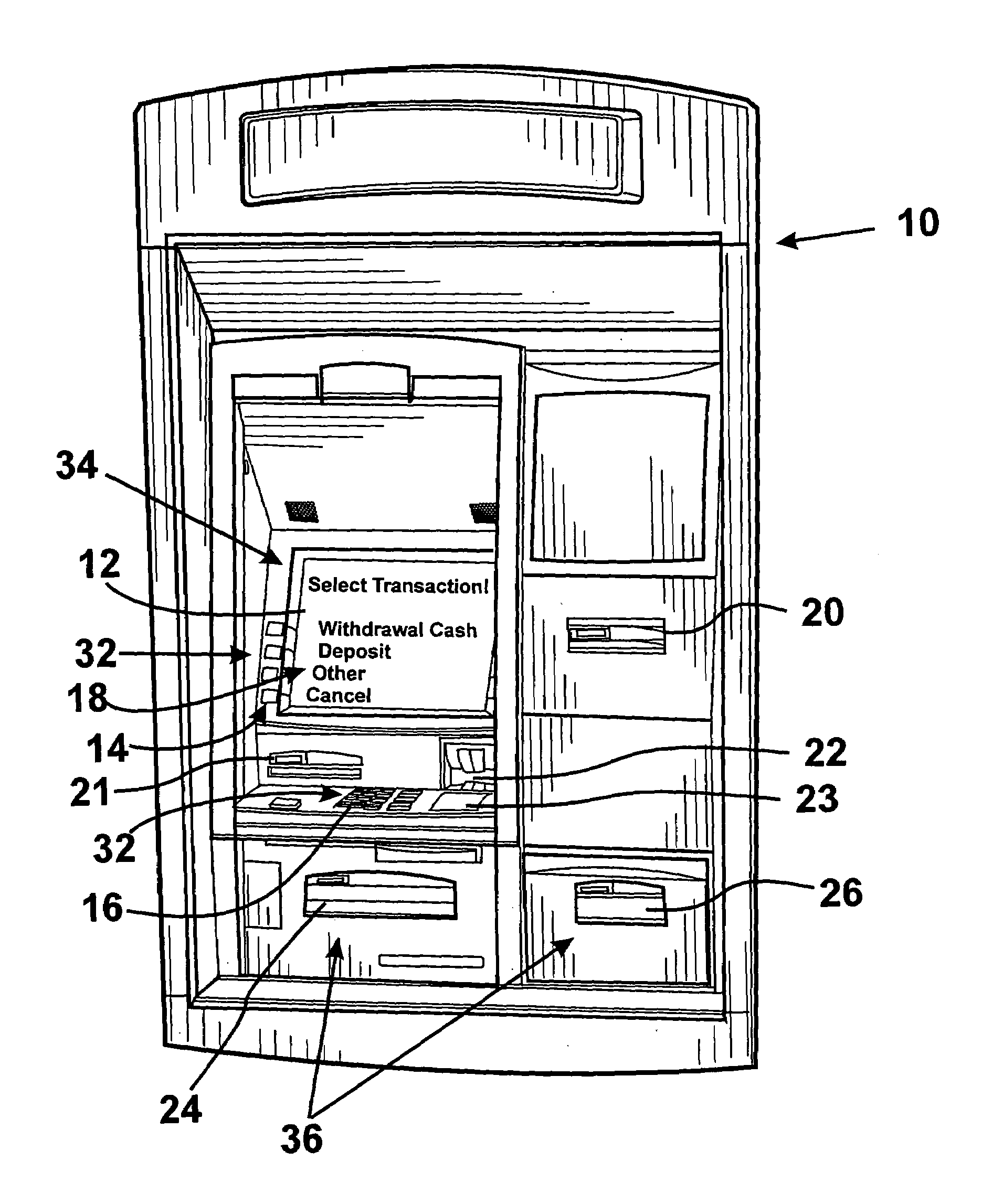
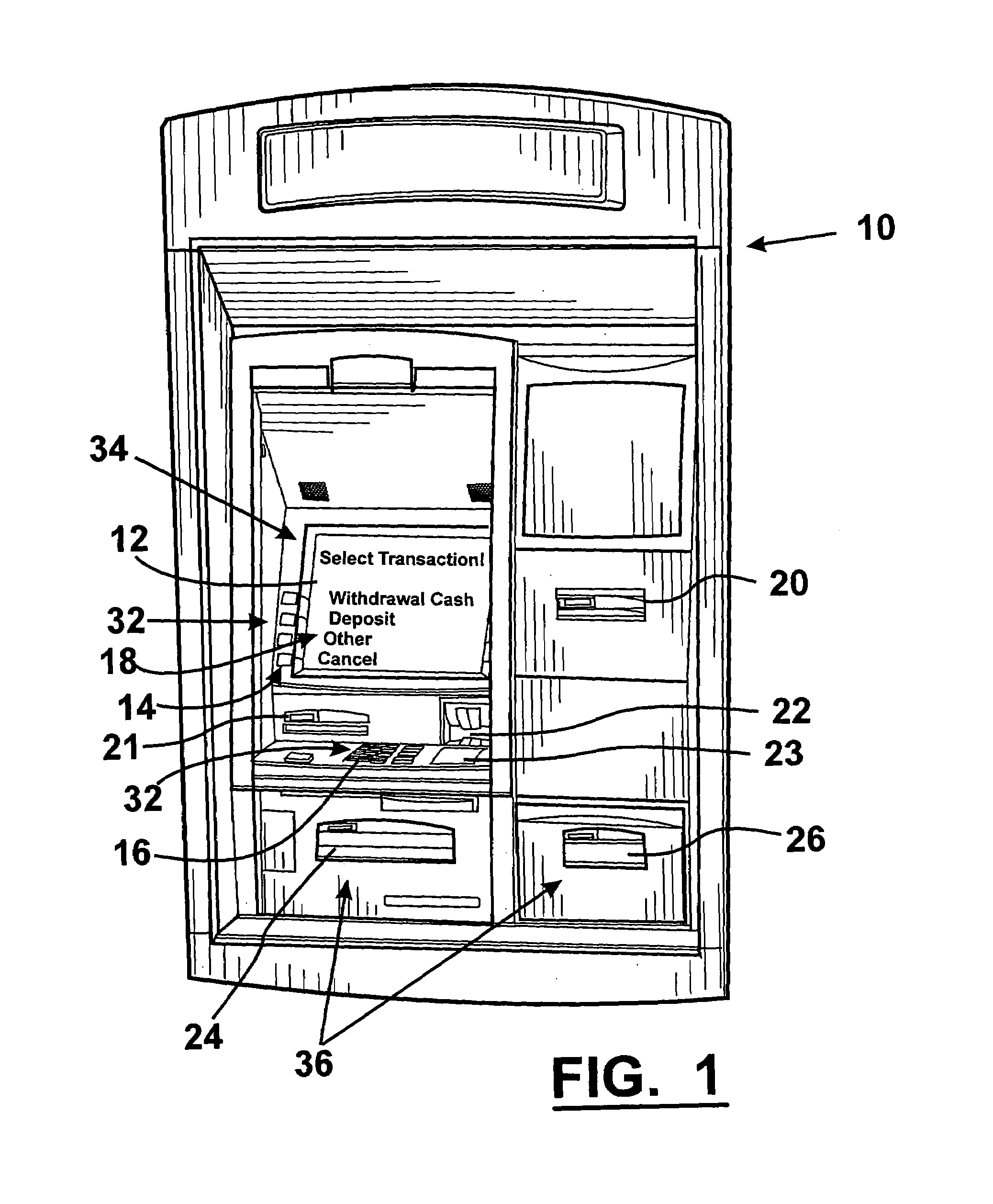
Automated banking machine component authentication system and method
ActiveUS7121460B1Increased resistenceAvoid modificationComplete banking machinesAcutation objectsComputer hardwareAuthentication system
An automated banking machine is provided which includes a first component and a second component. The first component is operative generate a first hash of a first identity data and a public key associated with the second component. The first component is operative to encrypt a randomly generated secret key using the public key associated with the second component. The second component is operative to receive at least one message from the first component which includes the encrypted secret key and the first hash. The second component is operative to decrypt the secret key with a private key that corresponds to the public key. The second component is operative to permit information associated with a transaction function to be communicated between the first and second components which is encrypted with the secret key when the first hash is determined by the second component to correspond to the first component.
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
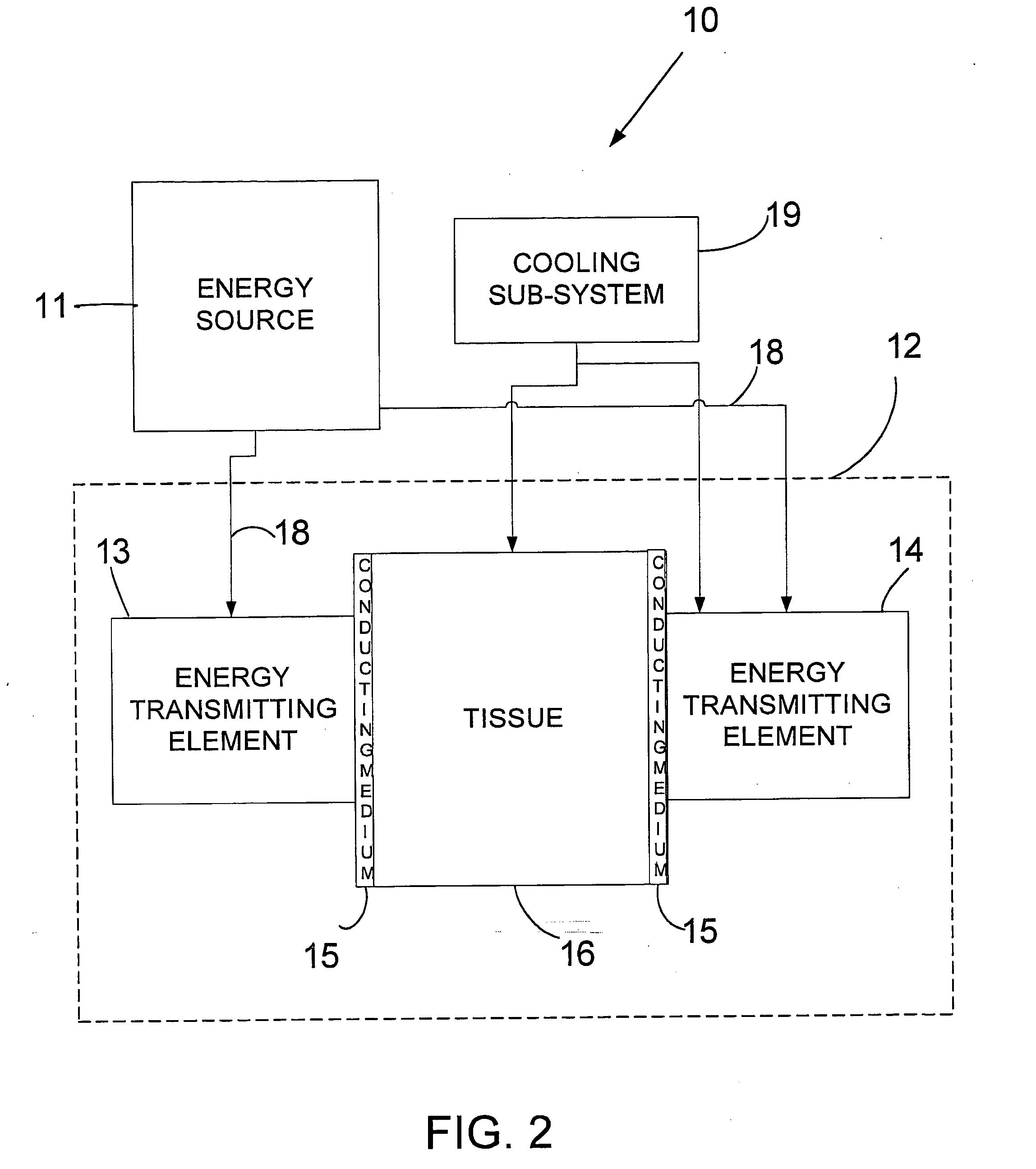
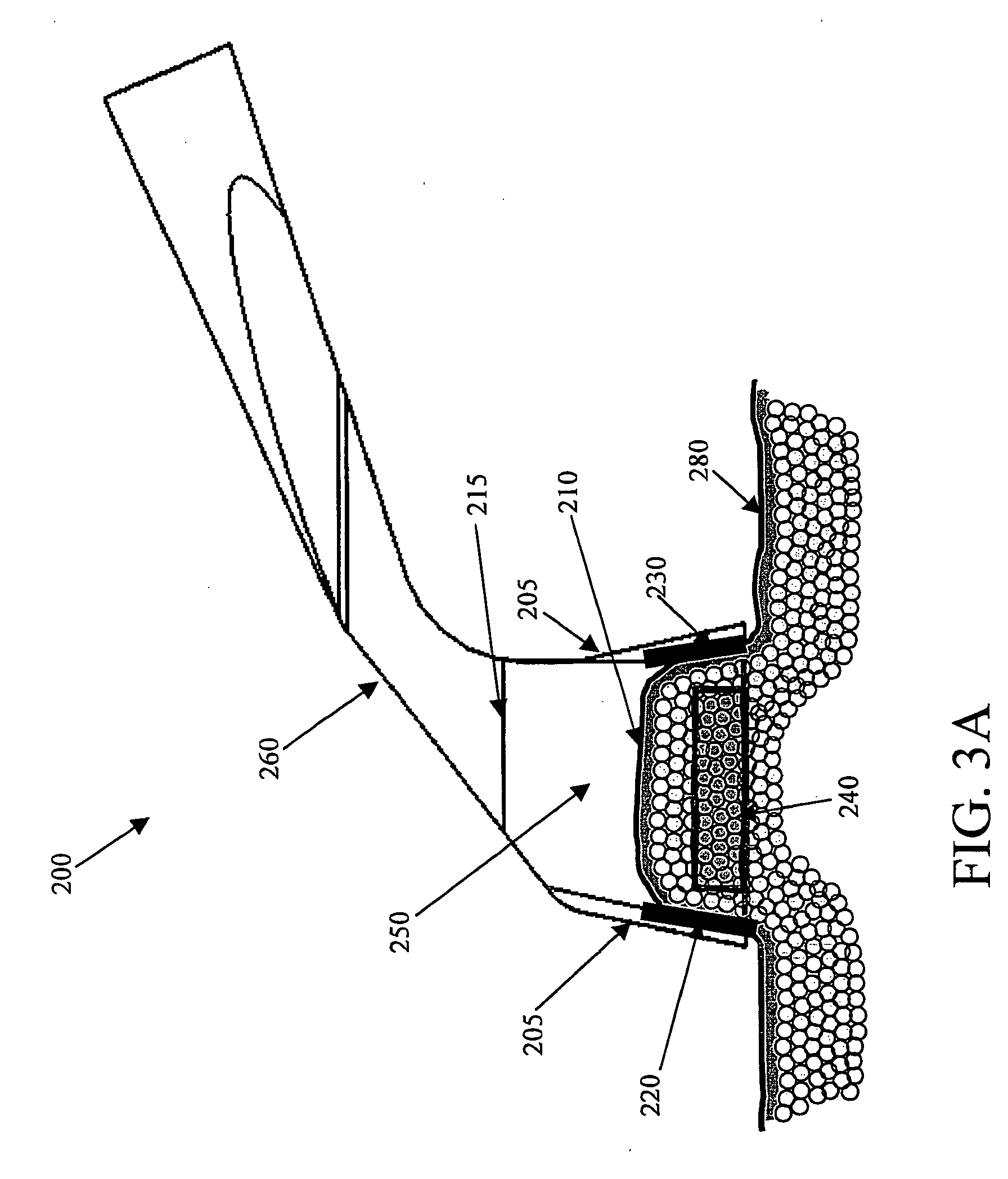
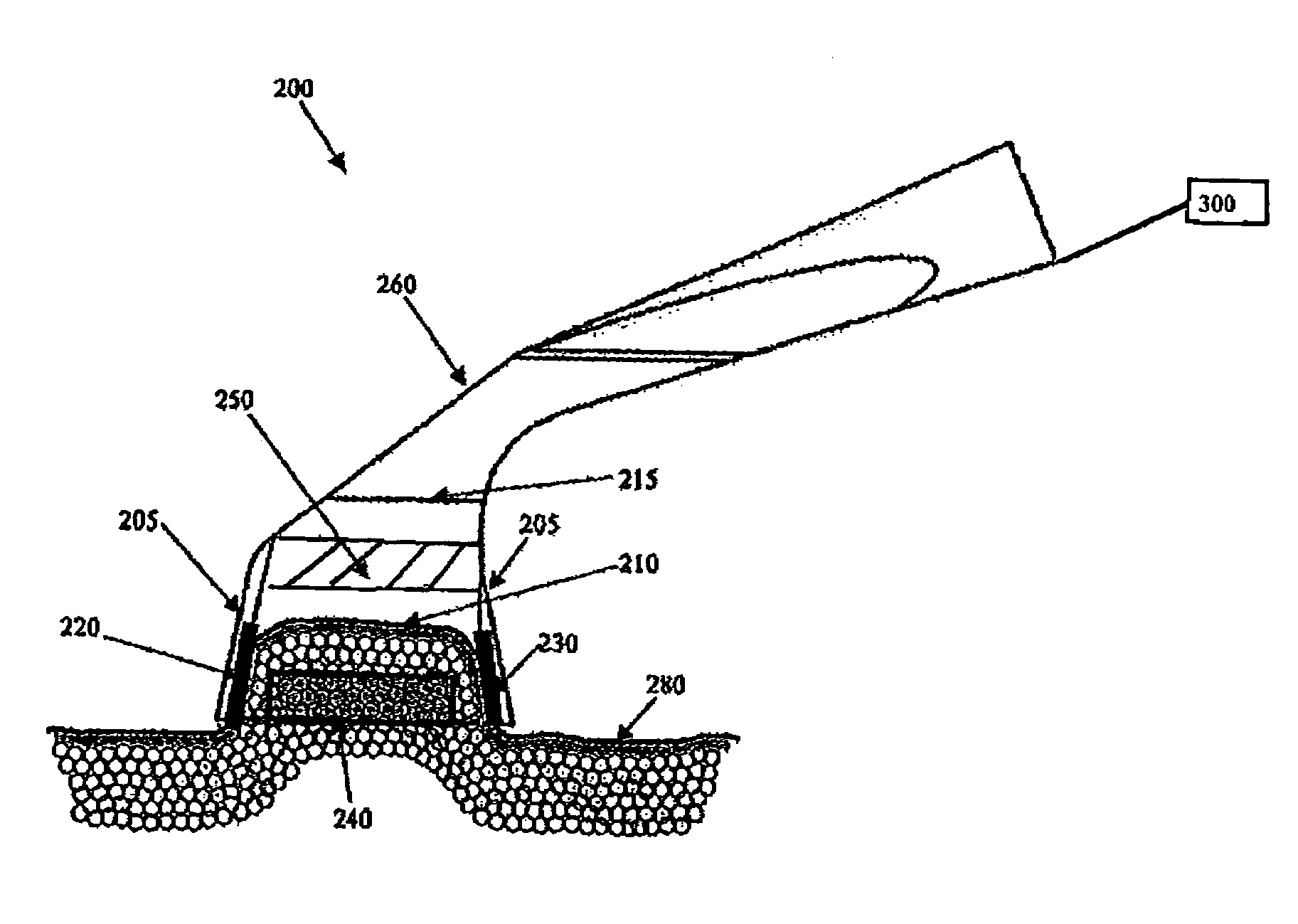
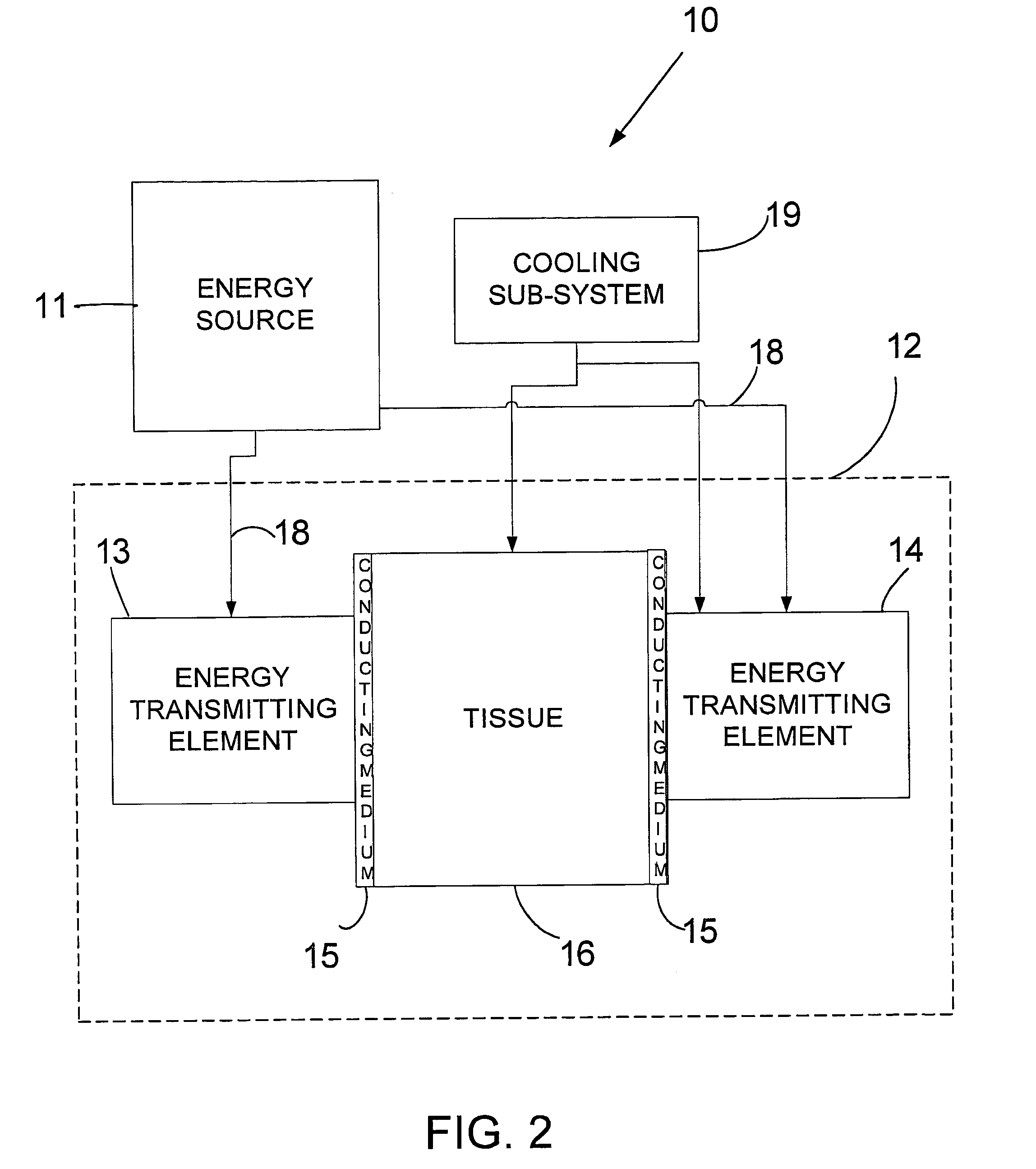
System and method for treating tissue
ActiveUS20050049543A1Prevent minimize damageImprove conductivityUltrasound therapyElectrotherapyTattoo removalElectromagnetic radiation
A method, device, and system for modifying or destroying selected tissue, by selecting an area of tissue for treatment, collecting the area between a plurality of energy transmitting elements, applying an electric current and / or electromagnetic radiation between the energy transmitting elements, and applying the electric current and / or electromagnetic radiation until, for example, the cells are modified or destroyed. Cooling may be applied to prevent unwanted modification. Conducting mediums may be applied to control tissue modification. Embodiments of the present invention may be used for treatment of fat cells, acne, lesions, tattoo removals etc.
Owner:LUMENIS BE LTD
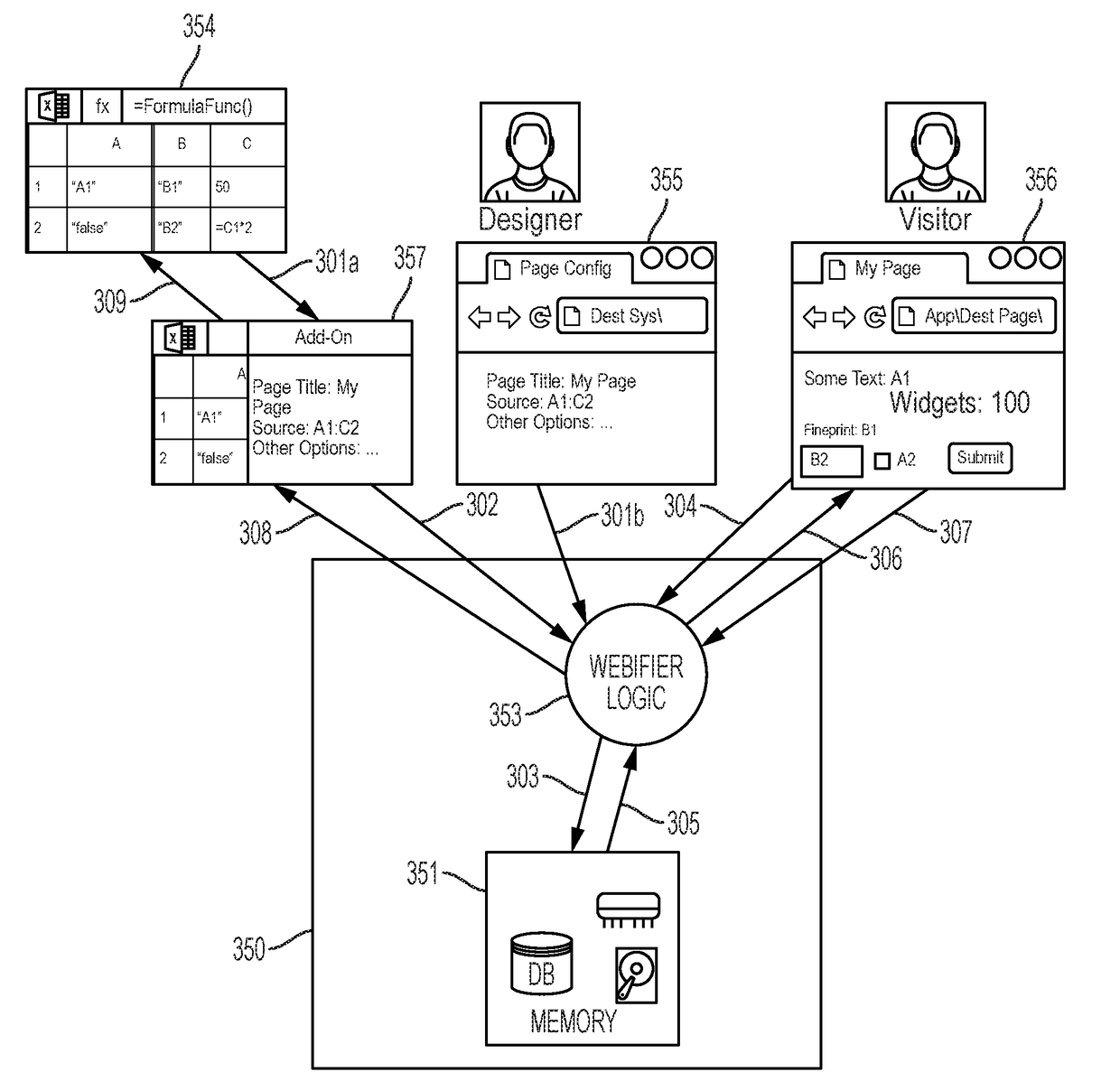
Spreadsheet-Based Software Application Development
ActiveUS20180157468A1Easy to createLimited abilityText processingVisual/graphical programmingElectronic formSoftware engineering
Aspects described herein may be used with local spreadsheet applications, web, and / or cloud-based spreadsheet solutions, to create complex custom software applications. Spreadsheets themselves lack the conceptual framework to be used as a platform tool to build custom or complex software applications. Using the methods and systems described herein using low-code / no-code techniques, a designer can create custom and / or complex software applications using one or more spreadsheets as the underlying blueprints for the software application. The resultant software application may be static / read-only, or may be interactive to allow users to dynamically add, delete, edit, or otherwise amend application data, e.g., via one or more online web pages or via a mobile application. Data transfer may be one-way or bi-directional between the blueprint spreadsheets and the resultant software application, thereby allowing amended data to be transferred from the software application back into spreadsheet form.
Owner:STACHURA THOMAS
Dynamic e-mail system and method
InactiveUS20070244977A1Difficult to saveAvoid modificationMultiple digital computer combinationsTransmissionHyperlinkElectronic mail
A computer program product and method of sending an electronic message. The program allows the content of the message to be changed dynamically after the message is sent. Changes can be made by the sender after the message has been transmitted or by predetermined user preferences. The program provides embedded links within the message that are associated to the content. The content associated with the hyperlink can be changed after the message is sent. The invention is preferably practiced as an e-mail system. The sender selects media stored on a sever such as music, picture, or video files. The user can also optionally enter text. The e-mail message contains embedded hyperlinks that automatically access the media or text, and display them within the recipients e-mail. The sender can later decide to change the content of the e-mail by changing the files that are associated with the hyperlink. The file associated with the hyperlink can also be changed automatically according to predetermined preferences.
Owner:ATKINS QUIXOTE
Encoding method and system, decoding method and system
ActiveUS20100253555A1Correction errorAvoid modificationError detection/correctionCode conversionDecoding methodsComputer architecture
A decoder, an encoder, a decoding method and an encoding method are provided. The encoding method includes receiving data; generating a set of first codewords by applying a first encoding process on the received data; and performing a second encoding process on a folded version of each first codeword to provide a set of second codewords, wherein a folded version of a first codeword is representative of a storage of the first codeword in a two dimensional memory space, wherein the second codeword comprises redundancy bits.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for treating tissue
ActiveUS7250047B2Improve conductivityAvoid modificationUltrasound therapyElectrotherapyPower flowTattoo removal
A method, device, and system for modifying or destroying selected tissue, by selecting an area of tissue for treatment, collecting the area between a plurality of energy transmitting elements, applying an electric current and / or electromagnetic radiation between the energy transmitting elements, and applying the electric current and / or electromagnetic radiation until, for example, the cells are modified or destroyed. Cooling may be applied to prevent unwanted modification. Conducting mediums may be applied to control tissue modification. Embodiments of the present invention may be used for treatment of fat cells, acne, lesions, tattoo removals etc.
Owner:LUMENIS BE LTD
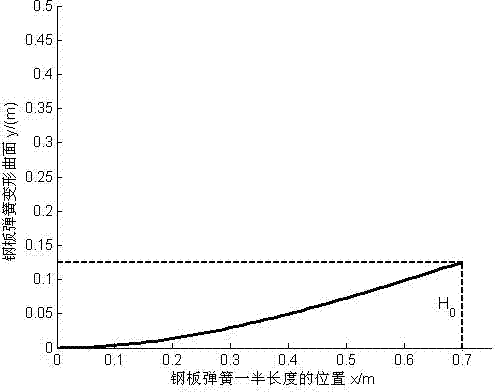
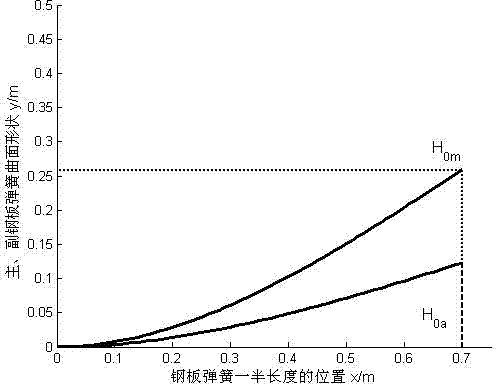
Analytical design method of camber and surface shape of automobile plate spring
InactiveCN102734364AAccurate and reliable designAvoid trial and error and modificationLeaf springsAutomotive engineeringSurface shape
The invention relates to an analytical design method of a camber and a surface shape of an automobile plate spring, belonging to the field of automobile springs. According to the invention, the performances of a suspension are influenced by the camber and the surface shape of the plate spring, but an accurate design method for the camber and the surface shape is not provided. According to the performance requirements of the automobile suspension on the plate spring, the analytical design method of the camber and the surface shape of the automobile plate spring can be established by using elastic mechanical theory. The analytical design method of the camber and the surface shape of the automobile plate spring, provided by the invention, is simple and reliable, and requirements of precise design of the thickness of the automobile plate spring can be satisfied by utilizing the analytical design method. The analytical design method can be used for design of the vehicle suspension plate spring.
Owner:SHANDONG UNIV OF TECH
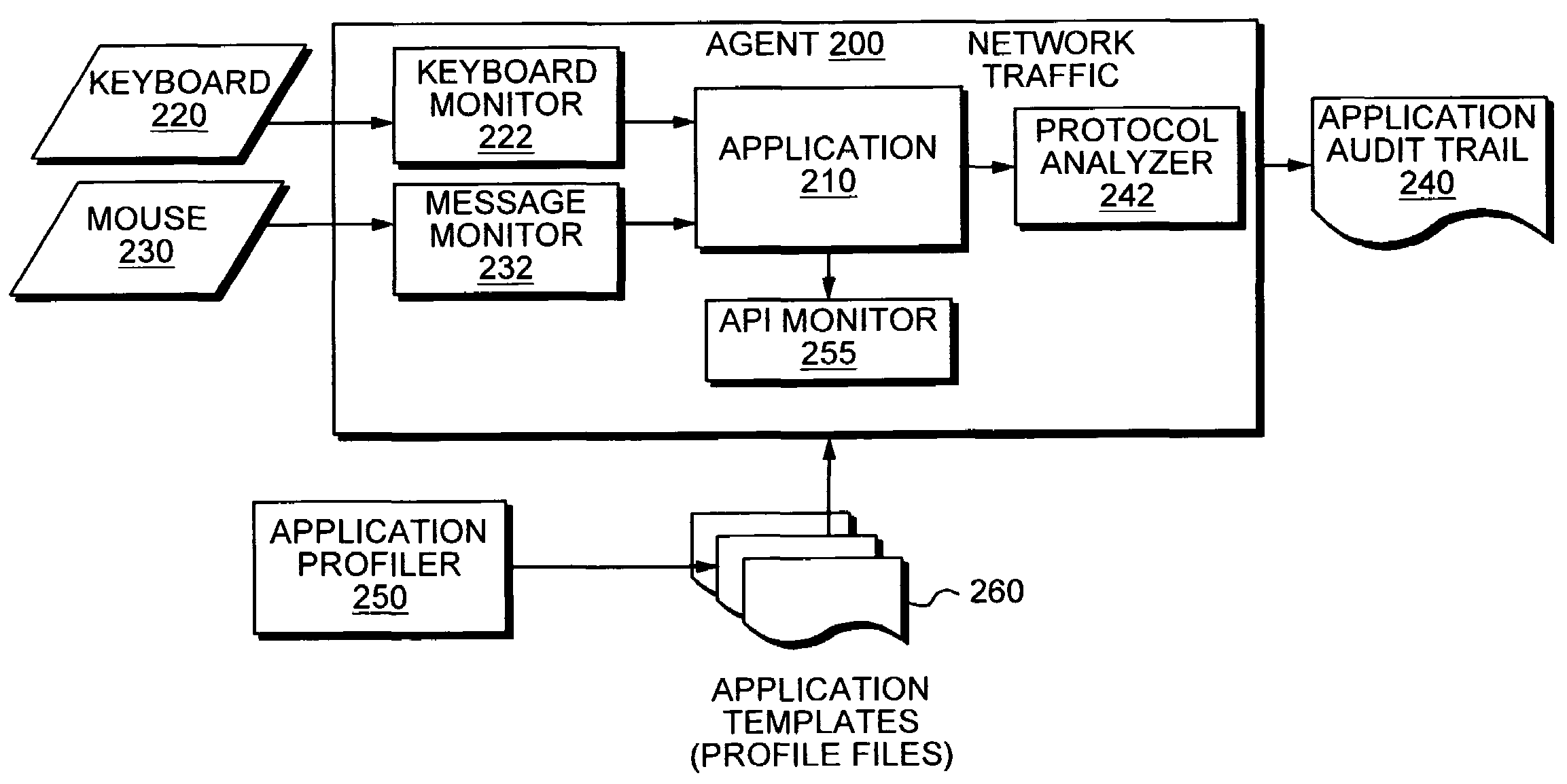
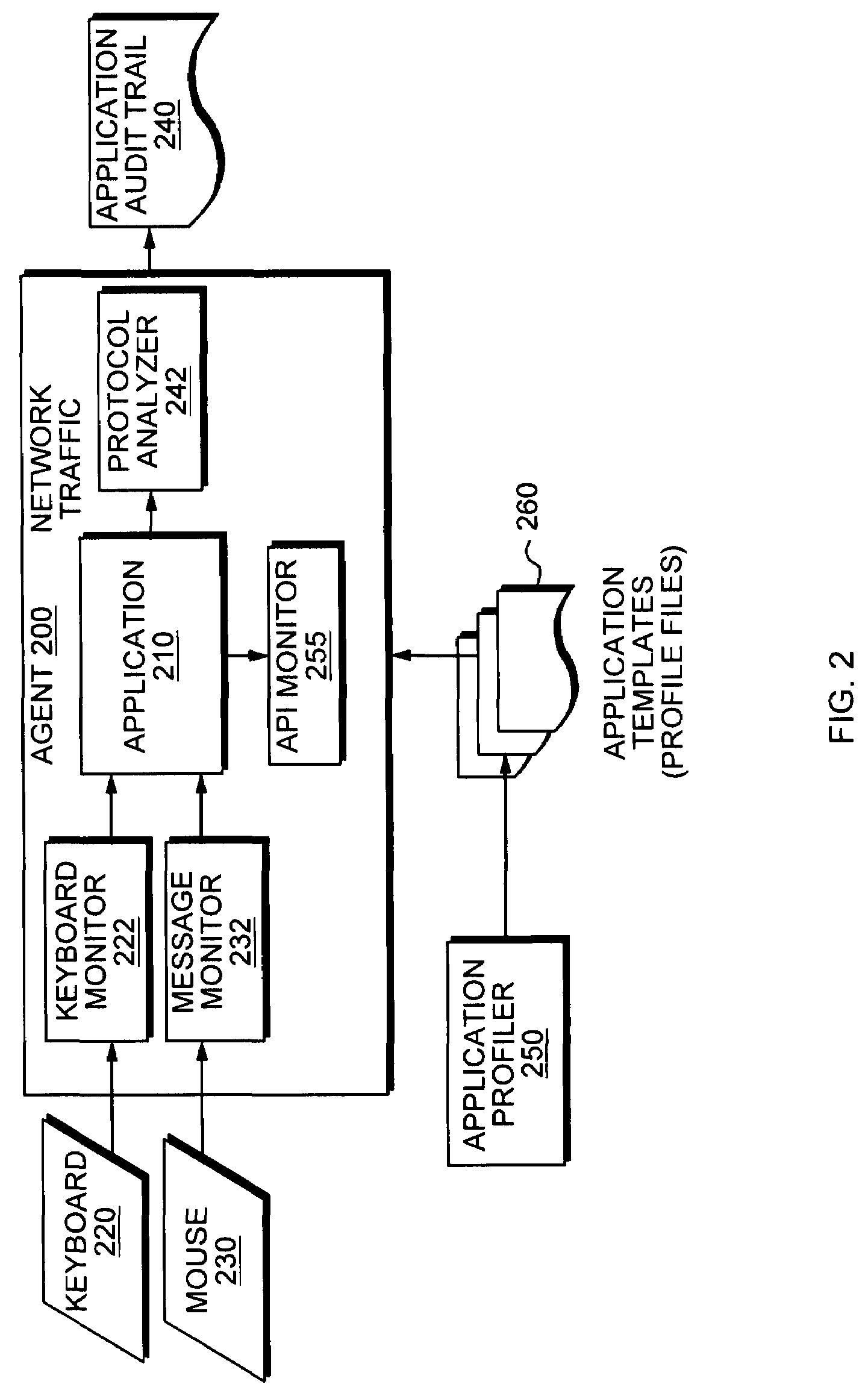
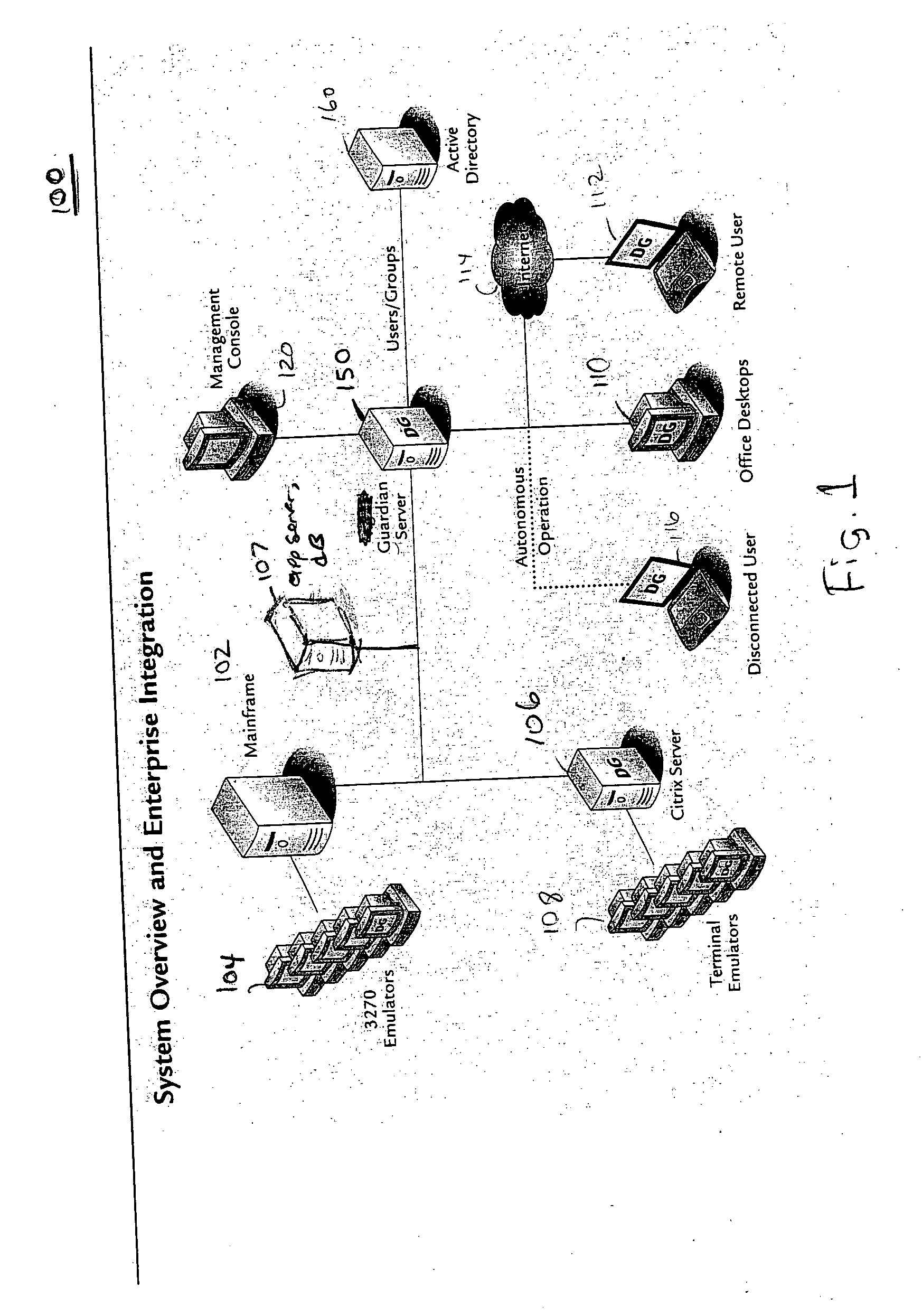
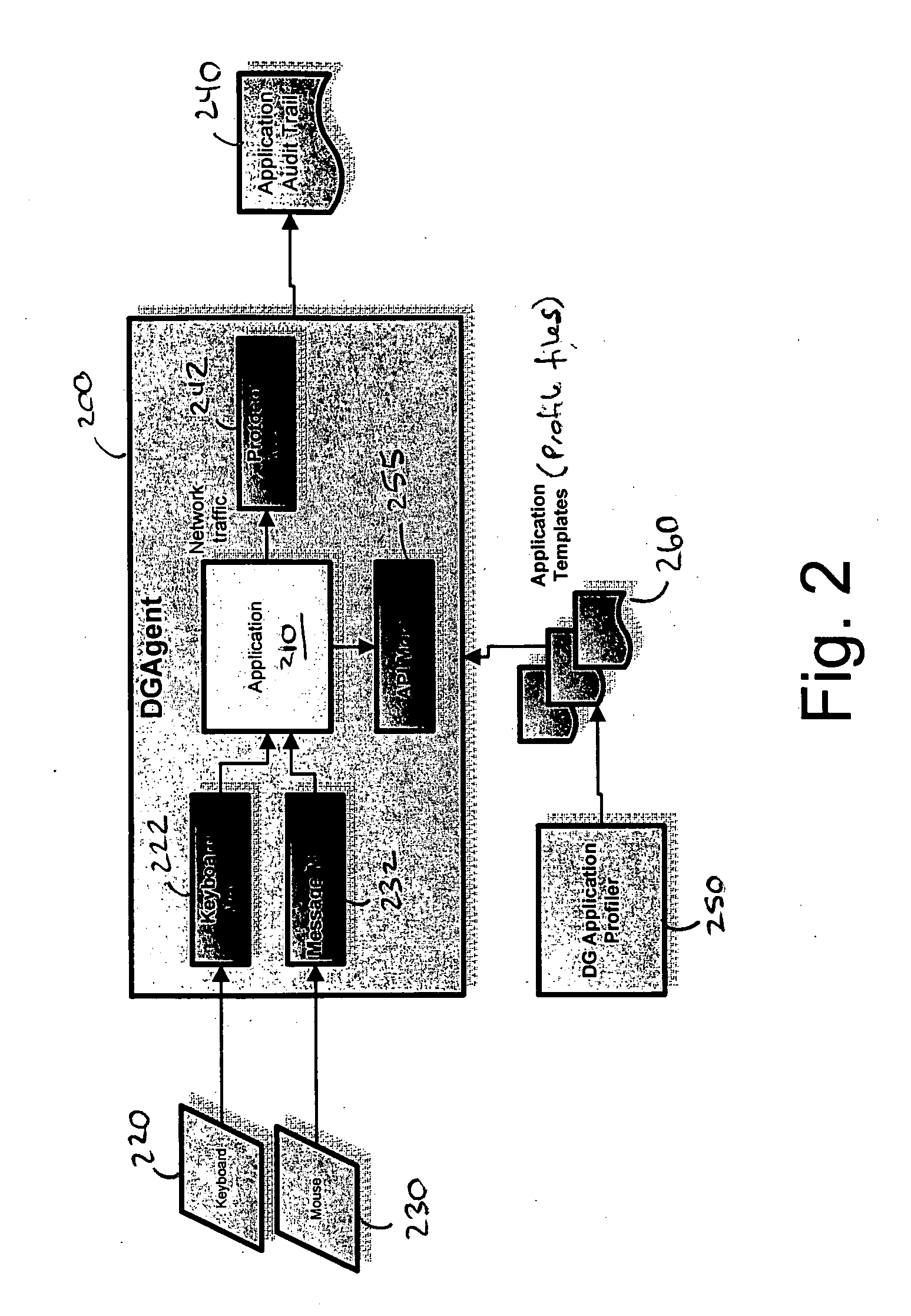
Application instrumentation and monitoring
ActiveUS7496575B2Cost effectiveAvoid the needDigital data processing detailsDigital computer detailsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
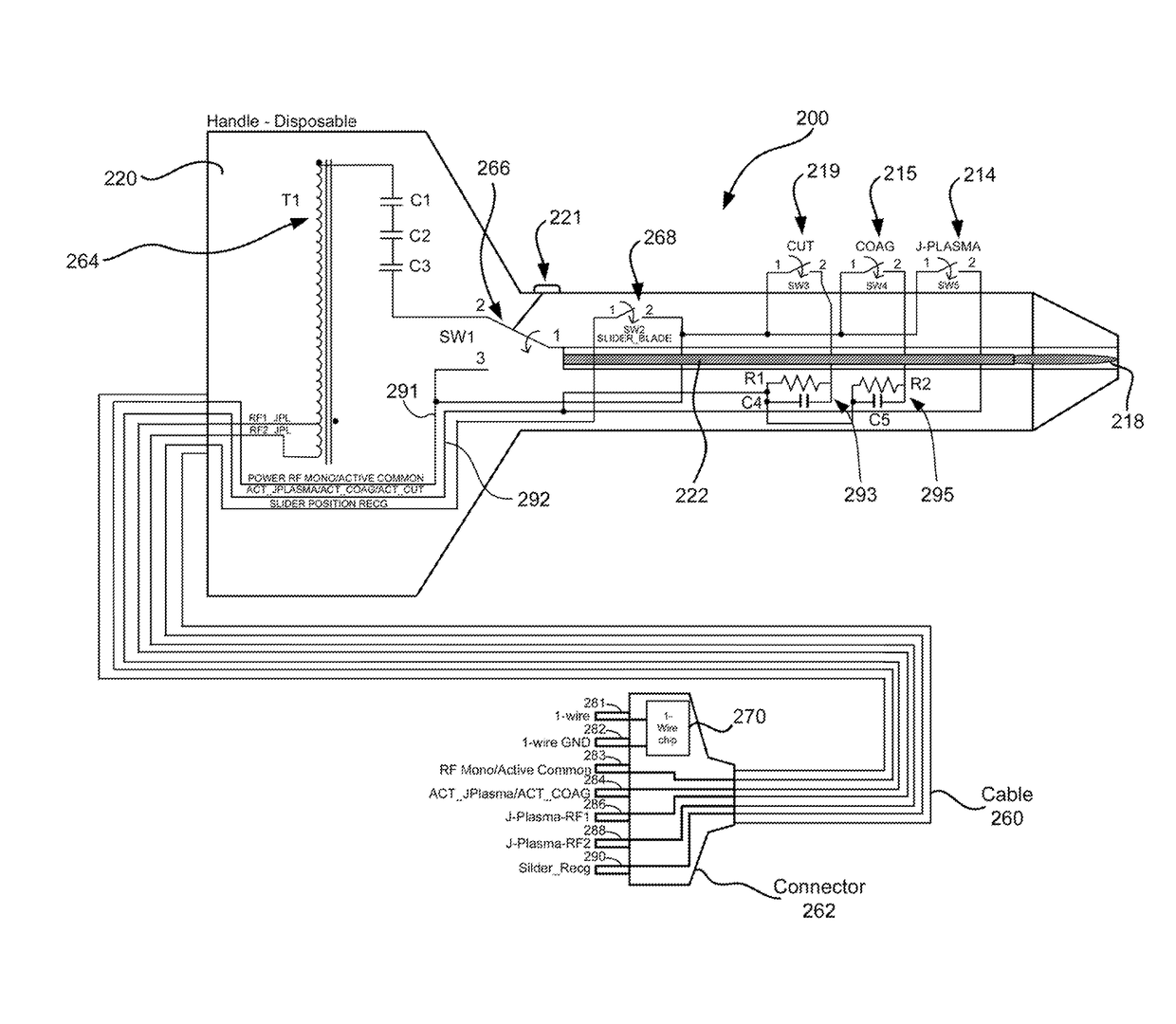
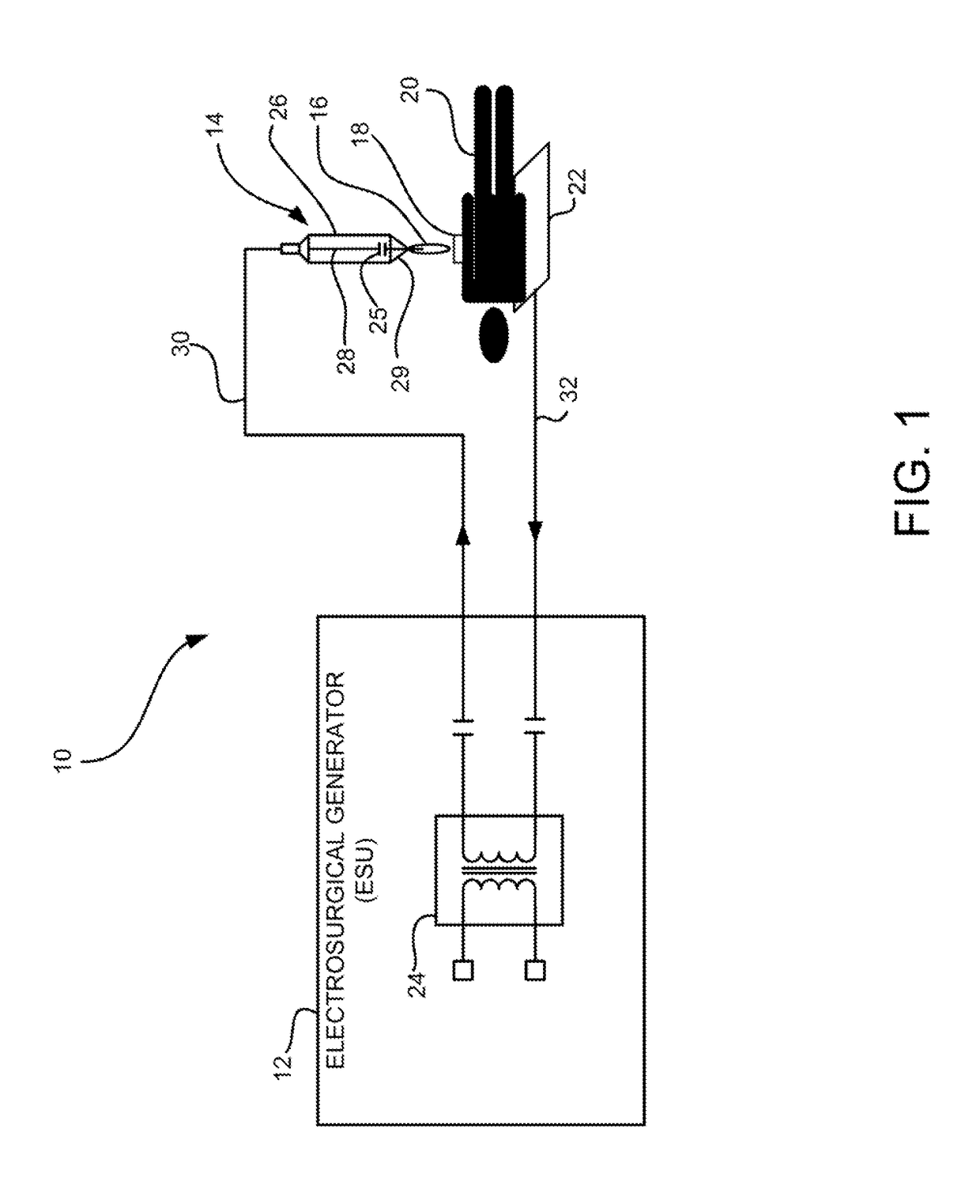
System and method for identifying and controlling an electrosurgical apparatus
ActiveUS9770285B2Avoid modificationImprove effectivenessIncision instrumentsDiagnosticsBiomedical engineeringELECTROSURGICAL DEVICE
Owner:BOVIE MEDICAL CORP
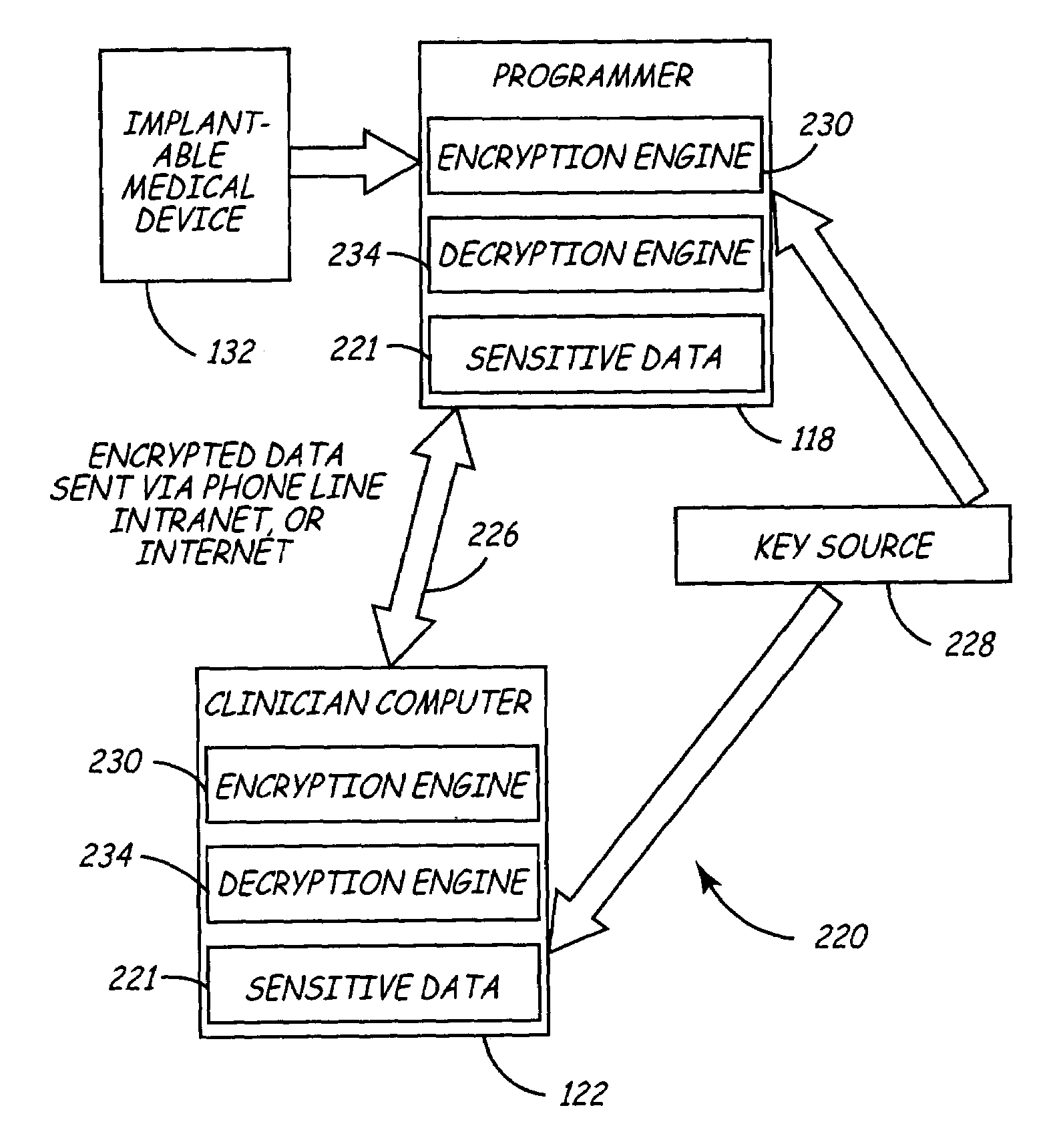
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
Spreadsheet-Based Software Application Development
ActiveUS20180157467A1Easy to createLimited abilityText processingVisual/graphical programmingData transmissionWeb application development
Aspects described herein may be used with local spreadsheet applications, web, and / or cloud-based spreadsheet solutions, to create complex custom software applications. Spreadsheets themselves lack the conceptual framework to be used as a platform tool to build custom or complex software applications. Using the methods and systems described herein using low-code / no-code techniques, a designer can create custom and / or complex software applications using one or more spreadsheets as the underlying blueprints for the software application. The resultant software application may be static / read-only, or may be interactive to allow users to dynamically add, delete, edit, or otherwise amend application data, e.g., via one or more online web pages or via a mobile application. Data transfer may be one-way or bi-directional between the blueprint spreadsheets and the resultant software application, thereby allowing amended data to be transferred from the software application back into spreadsheet form.
Owner:STACHURA THOMAS
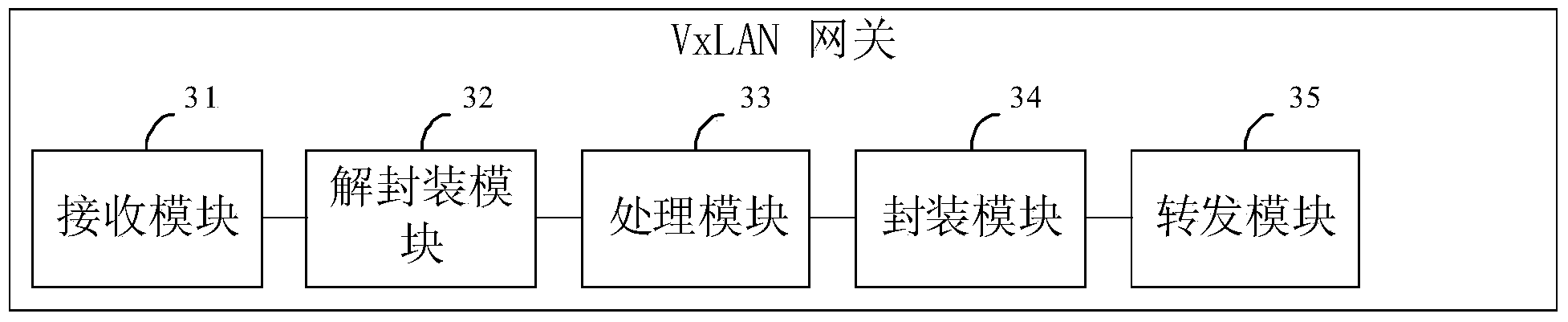
Packet forwarding method and VxLAN gateway
ActiveCN104350714AImprove forwarding efficiencyAvoid modificationNetworks interconnectionNetwork connectionsIp addressComputer science
The invention provides a packet forwarding method and a VxLAN gateway. The method comprises receiving a VxLAN packet, the load in which comprises a communication packet sent from a first VM to a second VM; determining a second VN1 of a subnetwork of next-hop equipment of the communication packet according to a first VN1 in the packet header of the VxLAn packet and the IP address of the second VM in the load; and packaging the communication packet according to the second VN1; and forwarding the packaged VxLAN packet to the next-hop equipment further through a tunnel corresponding to the second VN1. In this way, the condition that the forwarding of the VxLAN packet can be only realized after the VxLAN gateway corrects the communication packet in the load of the VxLAN is avoided, and the forwarding efficiency of the VxLAN packet is improved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
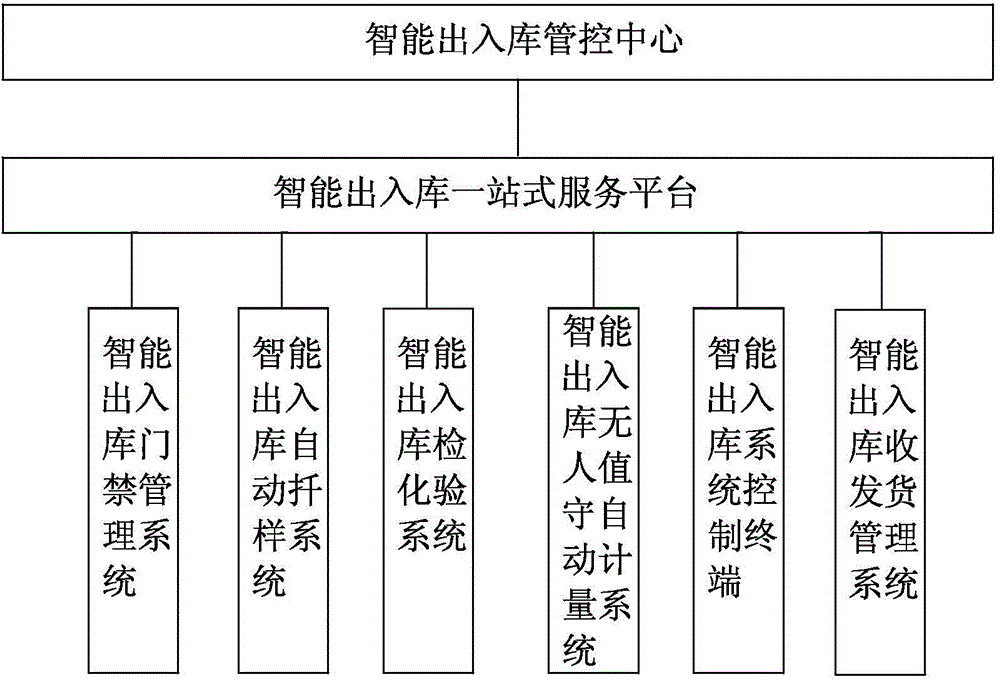
Intelligent depot output-input system of digital grain depot
ActiveCN103559605ASimplify business processesRealize paperless managementIndividual entry/exit registersLogisticsIntelligent managementComputer science
The invention discloses an intelligent depot output-input system of a digital grain depot. The intelligent depot output-input system of the digital gain depot comprises an intelligent depot output-input access control system, an intelligent depot output-input automatic sampling system, an intelligent depot output-input examination assay system, an intelligent depot output-input unattended operation automatic metering system, an intelligent depot output-input system control terminal, an intelligent depot output-input goods receiving-sending management system, an intelligent depot output-input system one-stop service platform and an intelligent depot output-input system control center. The intelligent depot output-input access control system, the intelligent depot output-input automatic sampling system, the intelligent depot output-input examination assay system, the intelligent depot output-input unattended operation automatic metering system, the intelligent depot output-input system control terminal, the intelligent depot output-input goods receiving-sending management system and the intelligent depot output-input system control center are connected with the intelligent depot output-input system one-stop service platform. According to the intelligent depot output-input system of the digital grain depot, a computer, the RFID internet of things technology, the communication technology and the information technology are converged together, networking, automation and intelligent management of the depot output and input are achieved, and labor participation is reduced.
Owner:JINAN JINZHONG ELECTRONICS SCALE +1
Hybrid contact lens system and method
InactiveUS20050018130A1Easy to createReduce penetrationOptical articlesEye diagnosticsChemical solutionPeripheral zone
A hybrid contact lens comprises a central zone comprising a substantially rigid, gas permeable material having a DK of at least 30, a relatively soft peripheral zone and an intermediate zone comprising a film or coating that is created around the central zone, and then cured. The film facilitates chemical bonding between the central zone and the peripheral zone, and also provides a protective barrier to prevent modification of the physical characteristics of the central zone. The film may be created by soaking the central zone in a chemical solution for a predetermined amount of soaking time.
Owner:SYNERGEYES
Application instrumentation and monitoring
ActiveUS20060123101A1Cost effectiveAvoid the needDigital computer detailsComputer security arrangementsApplication softwareData store
A data processing application logging, recording, and reporting process and infrastructure. Compliance with regulatory directives such as HIPAA, internal organizational and corporate, personal information privacy, and other security policies can thus be enforced without the need to recode legacy application software. In one preferred embodiment, a core agent process provides “listener” functionality that captures user input events, such as keyboard and mouse interactions, between a user and a legacy application of interest. The agent obtains instructions for how to deal with such events, accessing information that describes the application's behavior as already captured by an application profiler tool. Keyboard and mouse data entry sequences, screen controls and fields of interest are tagged during application profiling process. This data is stored in application profile developed for each mode of a legacy application. The technique can be implemented in various Information Technology (IT) environments including mainframe / terminal applications and / or client / server applications. Thus, full coverage of “fat” client, “thin” client, and legacy “mainframe” applications can be provided with a common approach across an enterprise.
Owner:DIGITAL GUARDIAN LLC
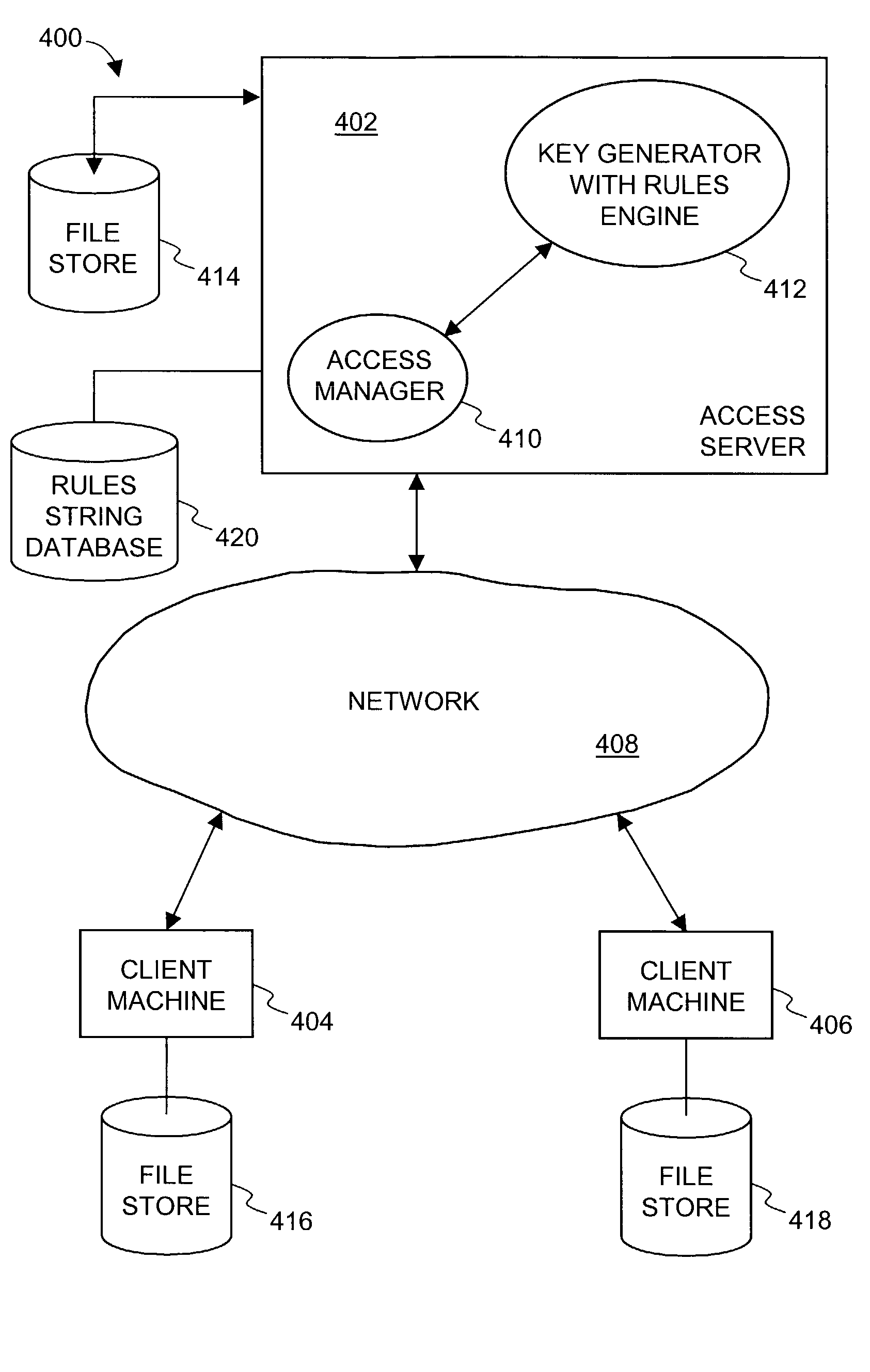
Security system using indirect key generation from access rules and methods therefor
ActiveUS7921450B1Improve approachLimited accessKey distribution for secure communicationDigital data processing detailsComputer scienceKey generation
Improved system and approaches for centralized storage of access restrictions which are associated with public keys are disclosed. The access restrictions serve to limit access to files secured by a security system. According to one aspect of the present invention, identifiers, or encoded versions thereof, are used as public keys to identify particular access restrictions. The identifiers to the access restrictions are used in a decentralized manner for public keys, while the access restrictions themselves are maintained in a centralized manner. As compared to the access restrictions, the public keys based on identifiers tend to be smaller and more uniform in size. The centralized storage of the access restrictions also facilitates subsequent changes to access restrictions for previously secured files. The improved system and approaches is particularly suitable in an enterprise environment.
Owner:INTELLECTUAL VENTURES I LLC
Jet nozzle mixer
InactiveUS6854260B2Reduce noiseAvoid problemsAircraft navigation controlCosmonautic vehiclesJet engineThrust efficiency
An external jet nozzle mixer (20) includes identically formed lobes (48), equal in number those of the internal mixer (42). External mixer (20) works with internal mixer (42), further to mix the engine internal bypass flow with the internal jet engine core flow, to level the disparate exhaust flow velocities, to reduce the peak velocities from the jet engine core and increase the lower bypass velocities of the engine internal bypass flow, and thereby to reduce noise. The internal lobe contours act as lifting flutes, causing mixing of the primary hot and cold flows before exiting the nozzle. The external lobe contours act as venturi chutes, accelerating the cooler ambient air secondary flow. The lobes thus act collectively as an injector to force the cooler ambient secondary flow into the previously mixed primary flow as it exits the nozzle. Also obtained is an increased thrust efficiency and a consequently decreased fuel consumption and engine emissions.
Owner:COMTRAN LTD
Method for Defining a Dental Framework Design Volume
InactiveUS20120088208A1Avoid further processingAvoid modificationProgramme controlDental implantsEngineeringImproved method
An improved method of a dental framework design and manufacturing, incorporating a dental framework design volume to eliminate framework or denture teeth modification post framework manufacturing.
Owner:CAGENIX
Security system for generating keys from access rules in a decentralized manner and methods therefor
ActiveUS8006280B1Easy accessAvoid modificationKey distribution for secure communicationMultiple keys/algorithms usageKey distributionKey generation
Improved system and approaches for decentralized key generation are disclosed. The keys that can be generated include both public keys and private keys. The public keys are arbitrary strings that embed or encode access restrictions. The access restrictions are used to enforce access control policies. The public keys are used to encrypt some or all portions of files. The private keys can be generated to decrypt the portions of the files that have been encrypted with the public keys. By generating keys in a decentralized manner, not only are key distribution burdens substantially eliminated but also off-line access to encrypted files is facilitated.
Owner:INTELLECTUAL VENTURES I LLC
Forensics tool for examination and recovery and computer data
InactiveUS20070226170A1Avoid modificationAvoid creatingData processing applicationsError detection/correctionElectronic discoveryFile size
The present invention concerns an electronic forensic tool for conducting electronic discovery and computer forensic analysis. The present invention allows a non-technical person such as a non-forensic expert to conduct electronic discovery and thereby obviate the need for an expert in many situations. The present invention allows for electronic discovery in a forensically sound manner. The present invention also concerns a business method for electronic discovery involving a software program and a command server for generating expanded functionality. The client software may be distributed at minimal or no cost, preferably as a CD. Using the client software, a user boots a target machine to determine whether a target machine contains data of interest. The client software will, however, only display limited data such as file information, date, last modified, and file size. To access and examine the actual underlying data, the user must obtain additional functionality, e.g. by purchasing a command block from the control server. The additional functionality will allow the client program to extract the data of interest or the entire contents of the target machine to an external device for further analysis.
Owner:SUN DAVID
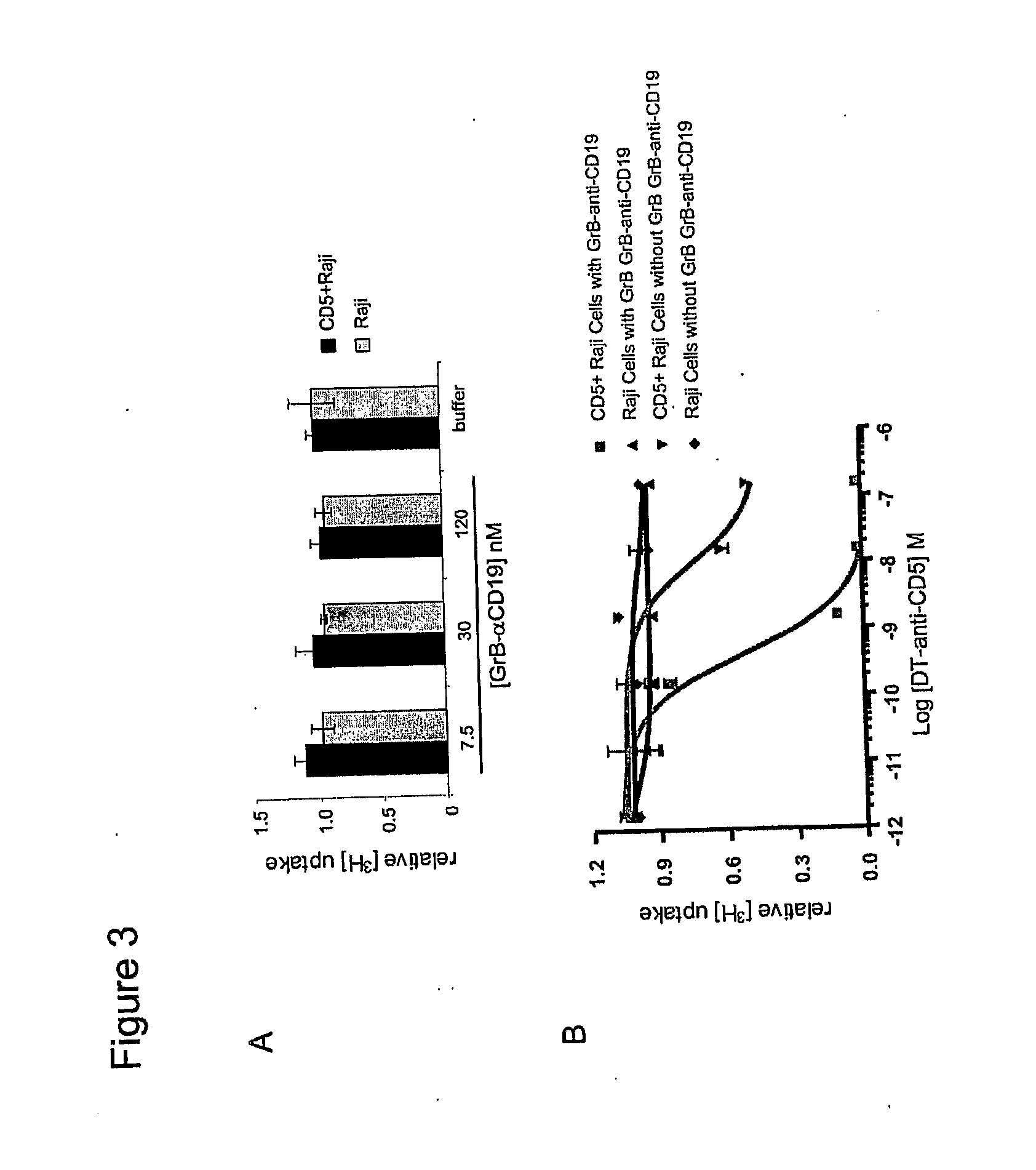
Methods, compositions, and kits for the selective activation of protoxins through combinatoral targeting
ActiveUS20100055761A1Promote their toxic effectStrong specificityAntibacterial agentsPeptide/protein ingredientsDiseaseBiological activation
The present invention provides methods and compositions for treating various diseases through selective killipg of targeted cells using a combinatorial targeting approach. The invention features protoxin fusion proteins containing a cell targeting moiety and, a modifiable activation moiety which is activated by an activation moiety not naturally operably found in, on, or in the vicinity of a target cell. These methods also include the combinatorial use of two or more therapeutic agents, at minimum comprising a protoxin and a protoxin activator, to target and destroy a specific cell population.
Owner:THE GENERAL HOSPITAL CORP
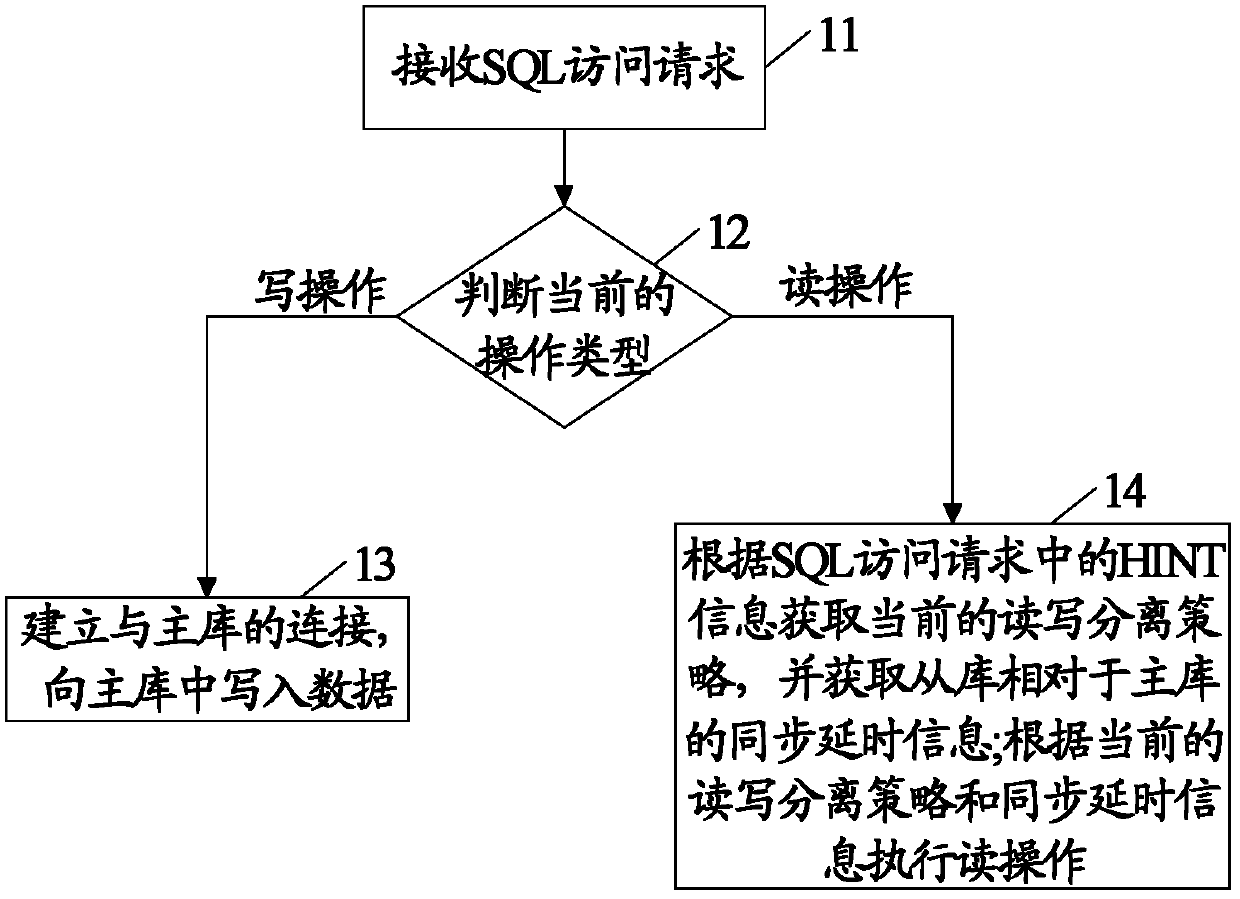
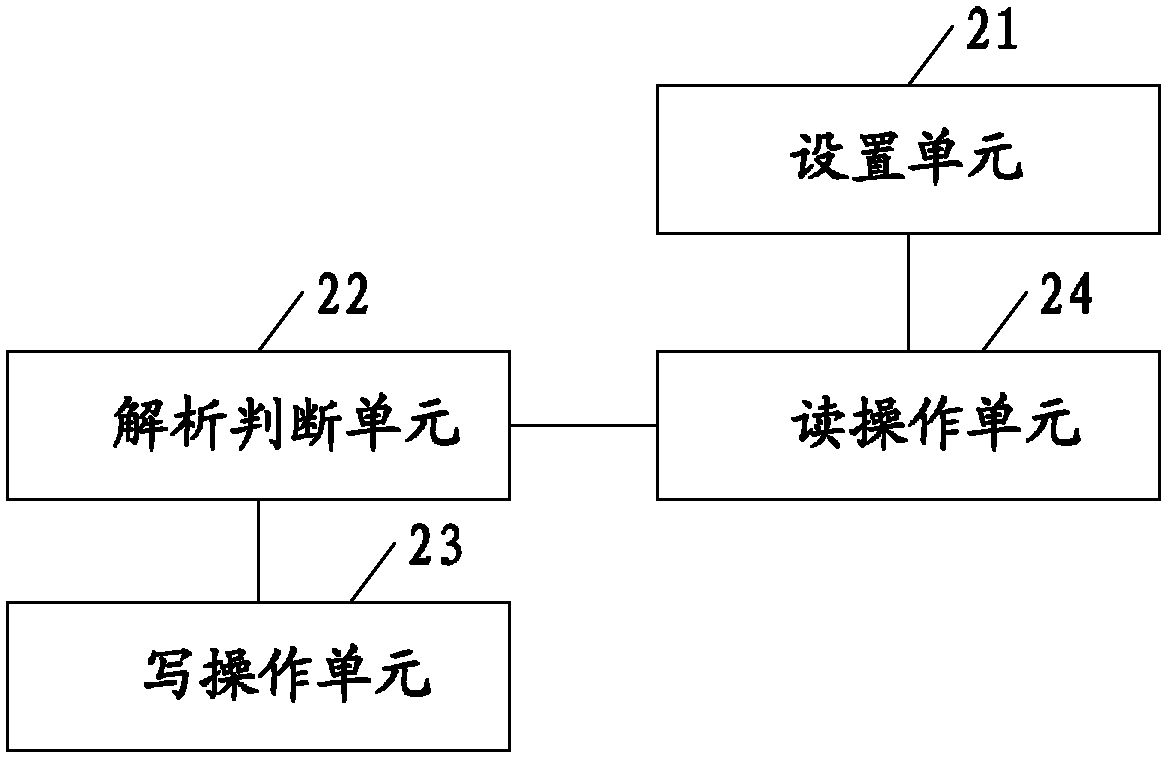
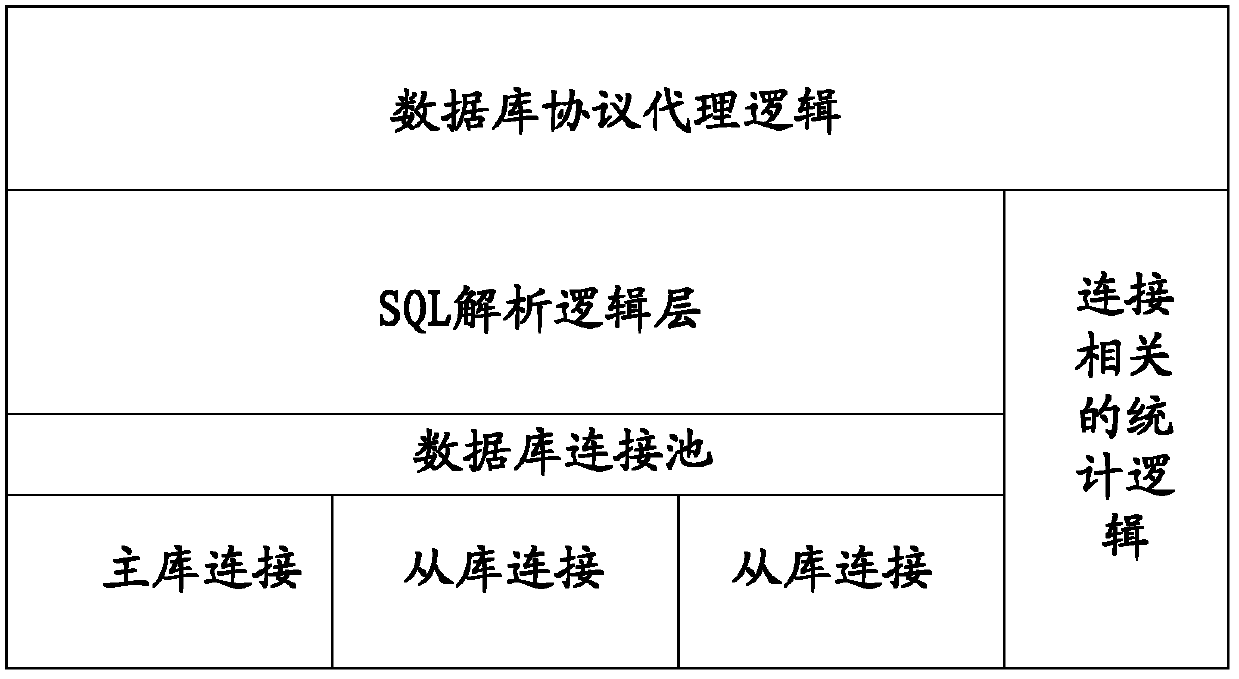
Implementation method and device for data reading-writing splitting system
ActiveCN102591964AIncrease flexibilityAvoid synchronous delay and cannot read dataSpecial data processing applicationsQuery languageSQL
The invention discloses an implementation method and a device for a data reading-writing splitting system. According to the implementation method for the data reading-writing splitting system provided by the embodiment of the invention, a piece of: HINT information indicating a reading-writing splitting strategy is set in an SQL (structured query language) access request of a reading operation. The method comprises the steps of analyzing a received SQL access request and judging the current operation type; if the current operation type is writing operation, establishing a connection with a master database and writing data into the master database; and if the current operation type is reading operation, acquiring the current reading-writing splitting strategy according to the HINT information in the SQL access request, acquiring the synchronization and time delay information from a slave database with respect to the master database, and executing the reading operation according to the current reading-writing splitting strategy and the synchronization and time delay information. According to the scheme, the needed trusted data can be read when time delay occurs in the slave database, the scheme is better compatible with the existing system resources and the utilization rate of the resources is increased.
Owner:BEIJING FEINNO COMM TECH
Automatic adjustment of image quality according to type of light source
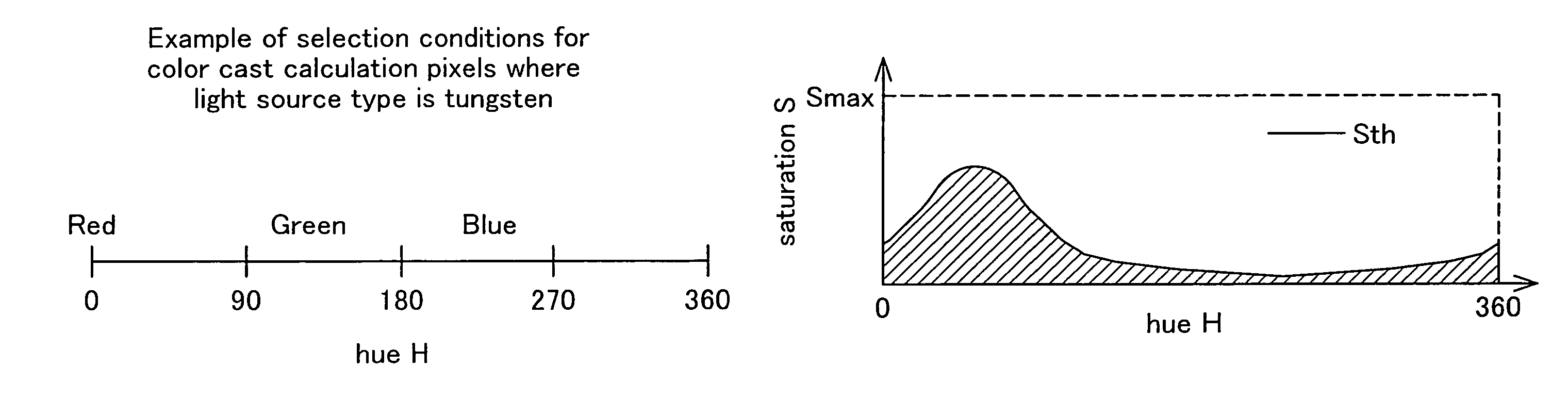
InactiveUS7532239B2Minimize impactAvoid modificationColor signal processing circuitsPicture reproducers using projection devicesPattern recognitionColor shift
There is provided an output device for outputting an image using image data generated by an image generating device, and image generation record information that is associated with the image data and that includes at least information relating to shooting conditions at the time of generation of the image data, comprising an image quality adjuster that, in the event that the image generation record information contains light source information relating to color shift of a light source at the time of generation of the image data, is able to execute the white balance adjustment process of the image data on the basis of the color of the light source obtained using the light source information; and an image output unit for outputting an image according to the image quality-adjusted image data.
Owner:138 EAST LCD ADVANCEMENTS LTD
Methods, software, and systems for knowledge base coordination
ActiveUS20070299799A1Avoid modificationDigital computer detailsComputation using non-denominational number representationKnowledge managementKnowledge base
The present invention provides computer program products, systems, and related methods of coordinating a knowledge base.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
High-speed automatic medicine packing machine
The invention relates to a high-speed automatic medicine packing machine, comprising a machine frame, wherein the machine frame is provided with a medicine board conveying belt and a packaging box conveying belt; the medicine board conveying belt and the packaging box conveying belt are arranged in parallel, and parts of the medicine board conveying belt and the packaging box conveying belt are overlapped; the overlapped part of the medicine board conveying belt and the packaging box conveying belt is provided with a medicine board pushing device which is used for pushing the semi-finished products to the packaging box conveying belt from the medicine board conveying belt; a medicine adding device and a paper adding device are sequentially arranged from one end of the medicine board conveying belt, which is far away from the packaging box conveying belt to one end of the medicine board conveying belt, which is close to the packaging box conveying belt; and a box unfolding device and a sealing device are sequentially arranged from one end of the packaging box conveying belt, which is close to the medicine board conveying belt to one end of the packaging box conveying belt, which is far away from the medicine board conveying belt. The medicine adding device, the paper adding device, the box unfolding device, the sealing device, the medicine board pushing device, the medicine board conveying belt and the packaging box conveying belt are controlled by a controller through a circuit. After adopting the scheme, the high-speed automatic medicine packing machine provided by the invention is high in efficiency and attractive in appearance.
Owner:瑞安市华科包装机械有限公司
Computational system including mechanisms for tracking propagation of information with aging
ActiveUS7958558B1Control overheadEasy to trackMemory loss protectionError detection/correctionInternet privacyControl transfer
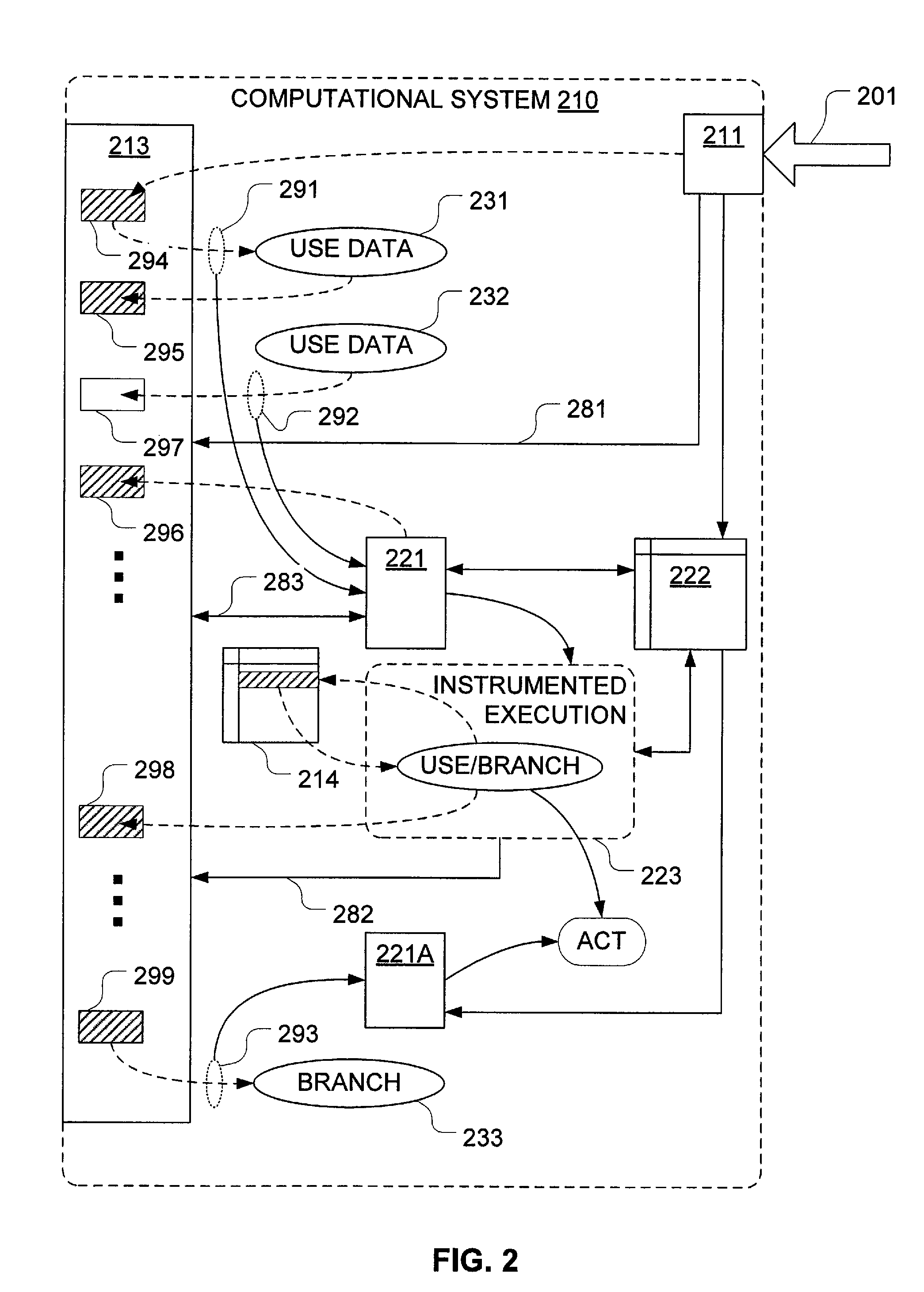
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and selectively propagating taint status for storage locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security (or other appropriate) response if and when a control transfer (or other restricted use) is attempted based on tainted data. By employing aging in decisions to propagate, it is possible limit overheads associated with such tracking. In some embodiments, a decay oriented metric is applied and further propagation of taints is interrupted once aging reaches a predetermined decay threshold. In some embodiments, more generalized labels may be maintained and selectively propagated based on an aging metric. For example, in some embodiments, labels may be employed to code source designation or classification, aging, popularity / frequency of access or taint.
Owner:VMWARE INC
Control function implementing selective transparent data authentication within an integrated system
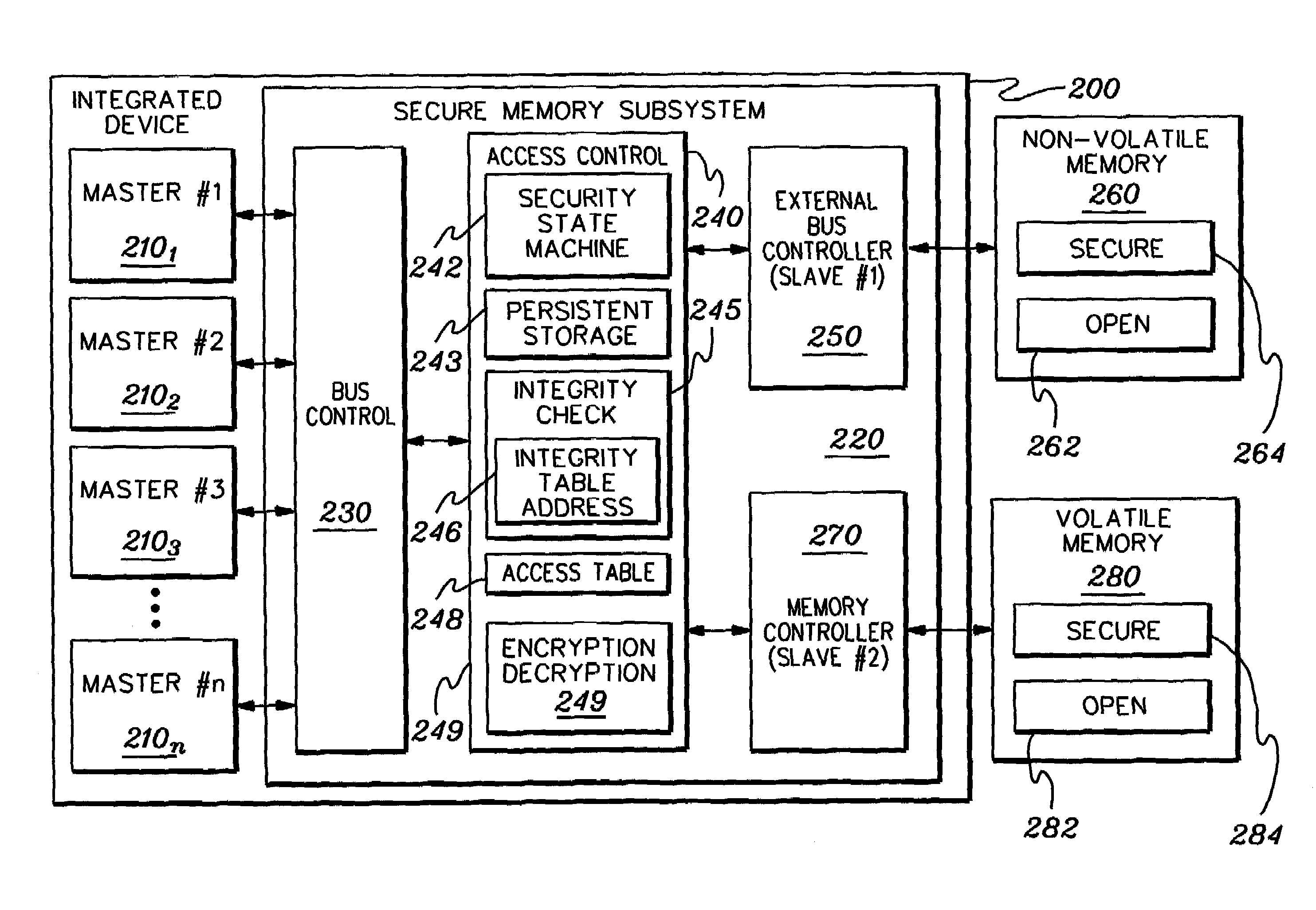
InactiveUS7266842B2Simplified integrity value calculationCode latency be minimizedRandom number generatorsUser identity/authority verificationData access controlData request
A data authentication technique is provided for a data access control function of an integrated system. The technique includes passing a data request from a functional master of the integrated system through the data access control function, and responsive to the data request, selectively authenticating requested data. The selective authentication, which can occur transparent to the functional master initiating the data request, includes employing integrity value generation on the requested data when originally stored and when retrieved, in combination with encryption and decryption thereof to ensure the authenticity of the requested data. As an enhancement, cascading integrity values may be employed to facilitate data authentication.
Owner:IBM CORP
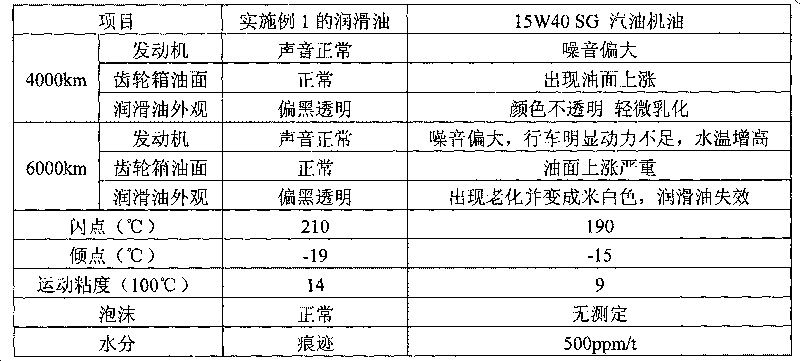
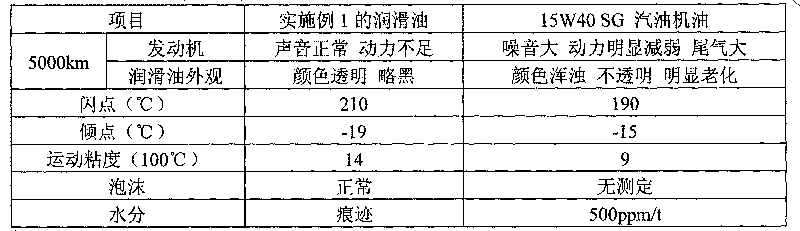
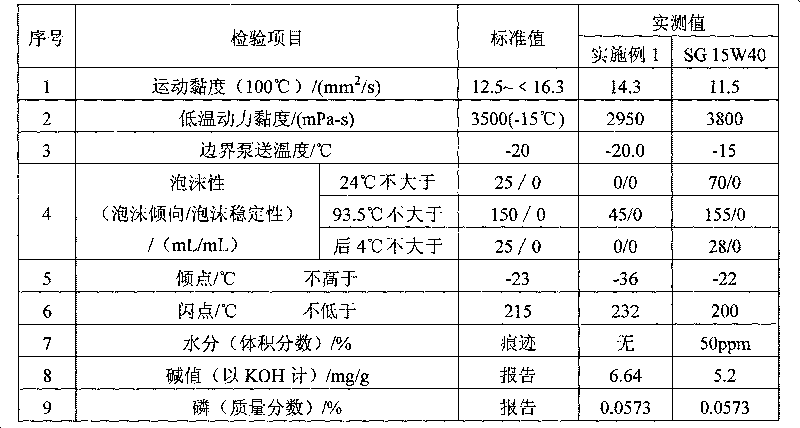
Lubricating oil for methanol fuel engine and preparation method thereof
InactiveCN101705144AAnti-agingResistance to emulsification damageAdditivesAntioxidantBULK ACTIVE INGREDIENT
The invention provides lubricating oil for a methanol fuel engine, which comprises the following components in percentage by weight: metal detergent 2.2-5.2, ashless dispersant 3.5-6.8, antioxidant and anticorrosion agent 0.5-1.6, high-temperature antioxidant 0.3-0.8, viscosity index improver 6-11, oiliness solvent 2.8-6, anti-foaming agent 120ppm, metal anti-rust agent 0.3-0.7, base oil 62.7-83, demulsifying agent 0.1-0.3, metal extreme pressure anti-wear agent 1.0-4 and pour point depressant 0.3-0.9. The lubricating oil of the invention has functions of preventing wear and rust of the engine, can prevent the active ingredients thereof from being extracted and emulsified by methanol and is particularly suitable for engines using M85 or M100 methanol gasoline as a fuel.
Owner:王恩臣 +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com