Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
230 results about "Binary translation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
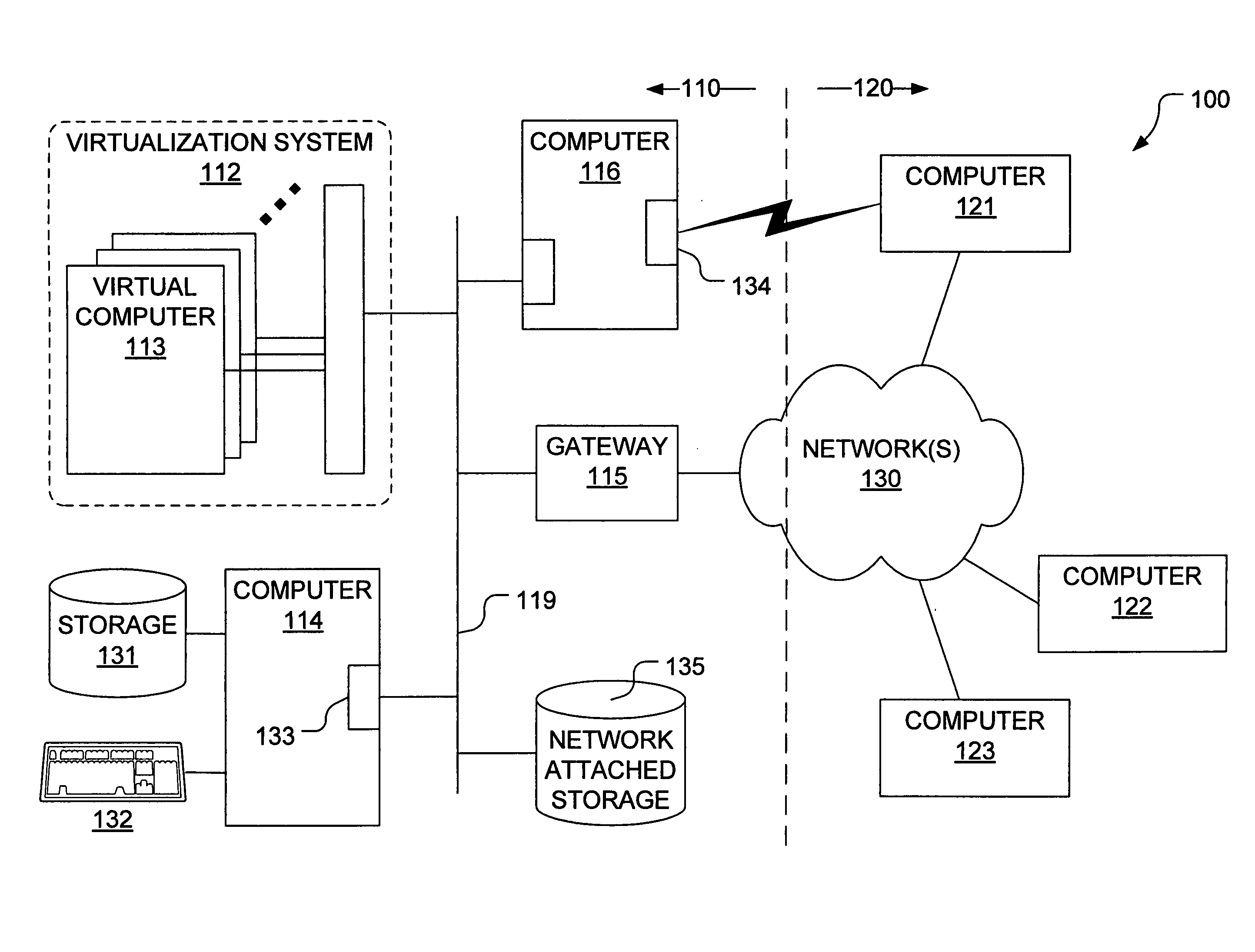
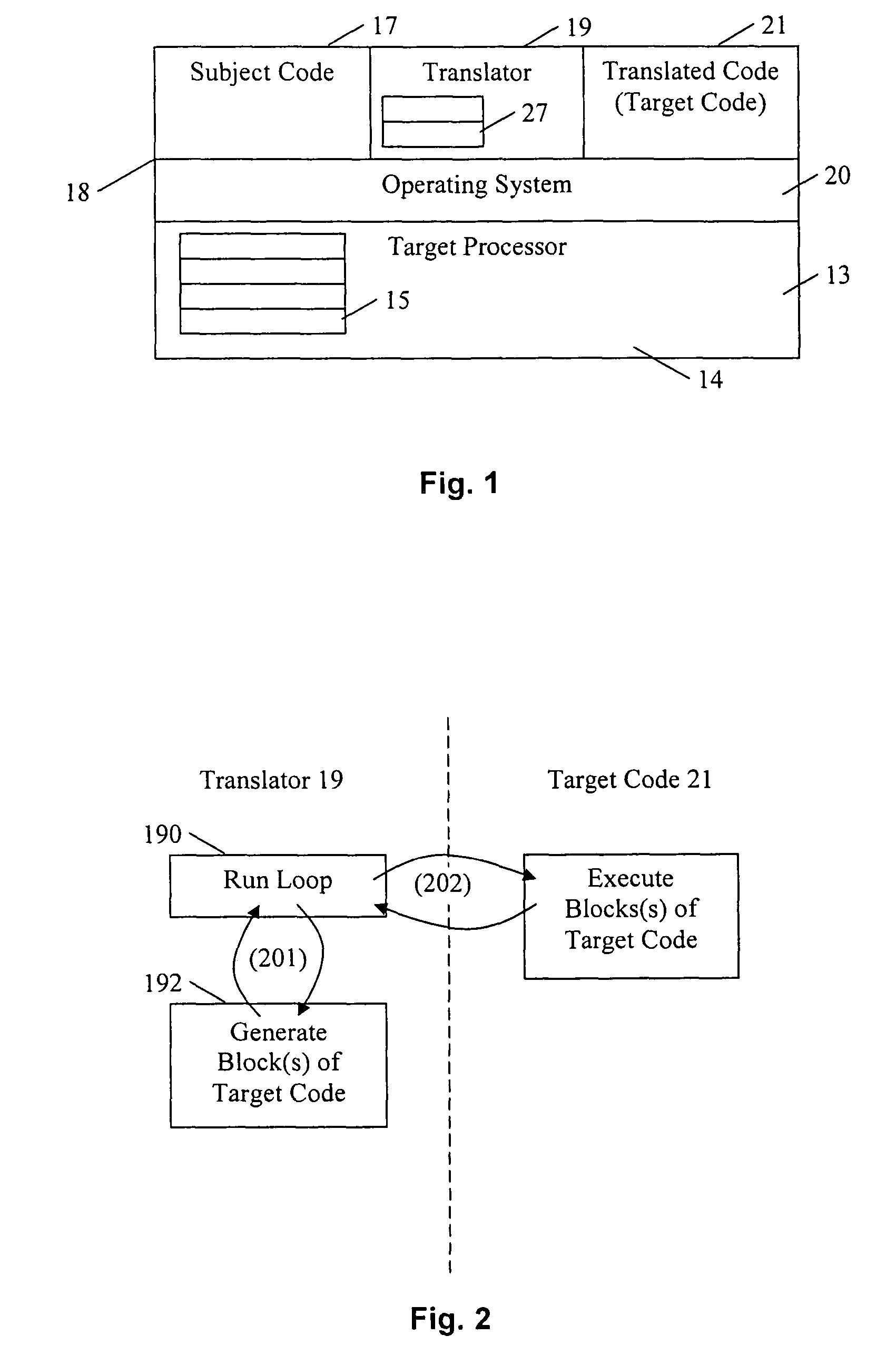
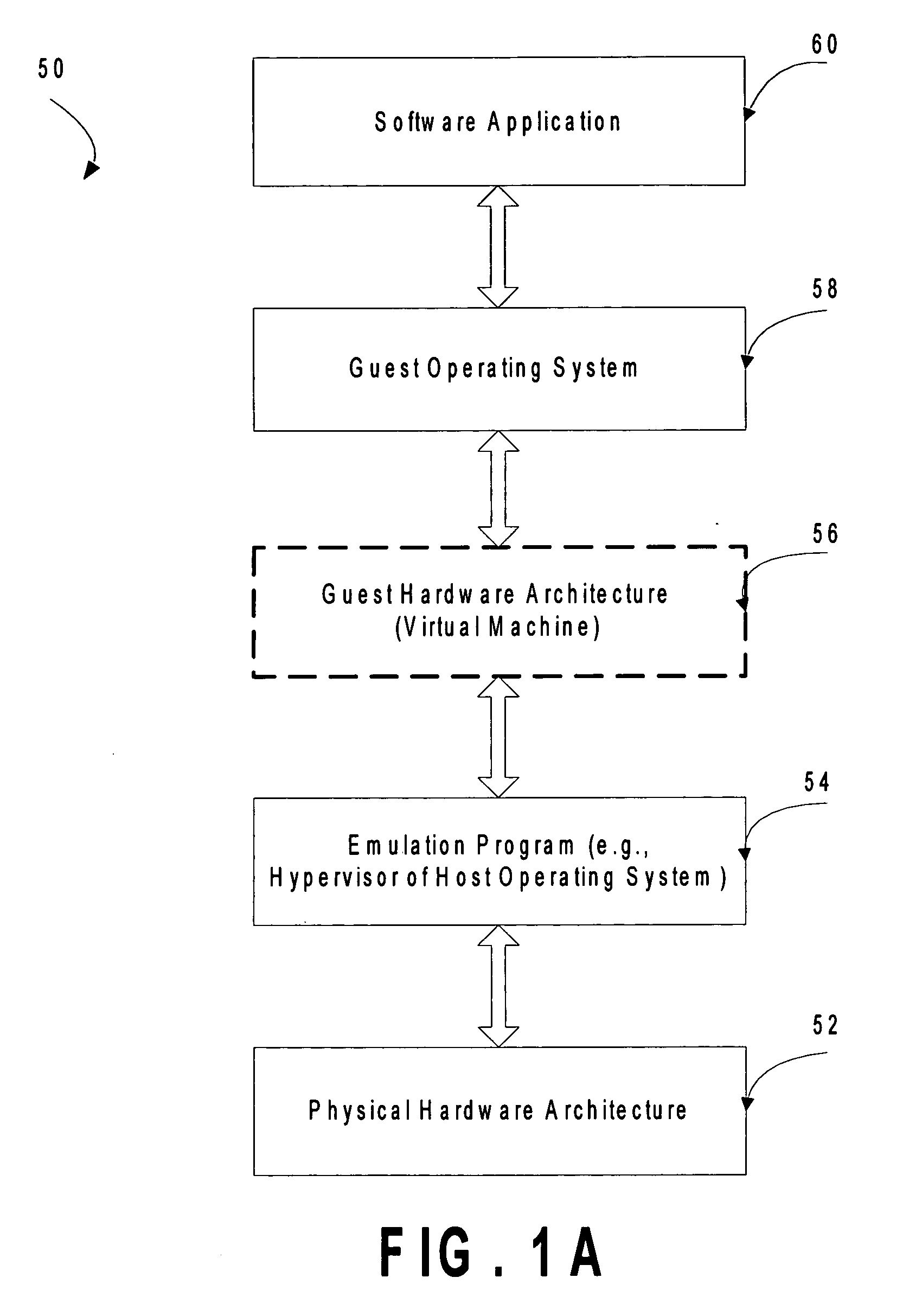
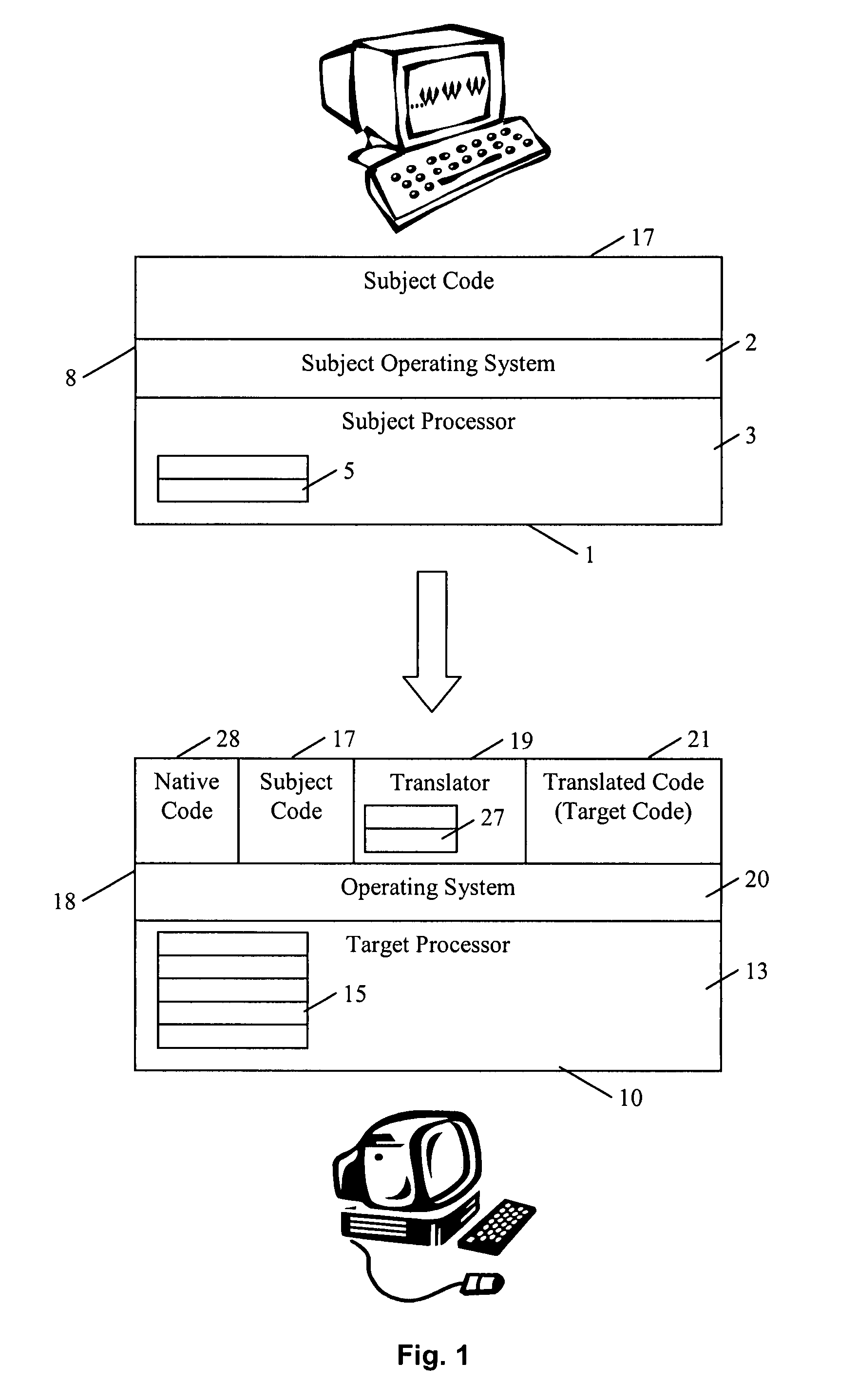
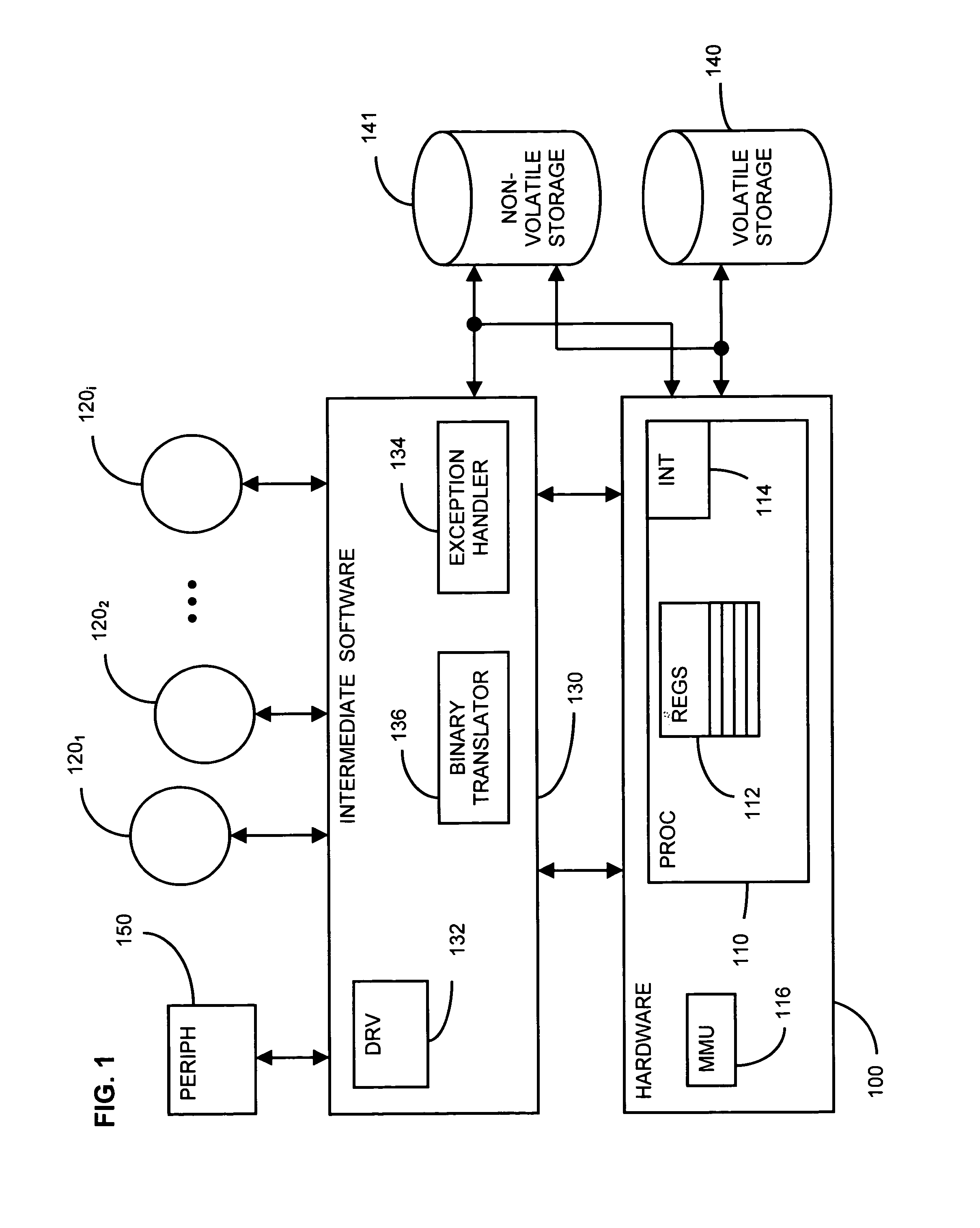
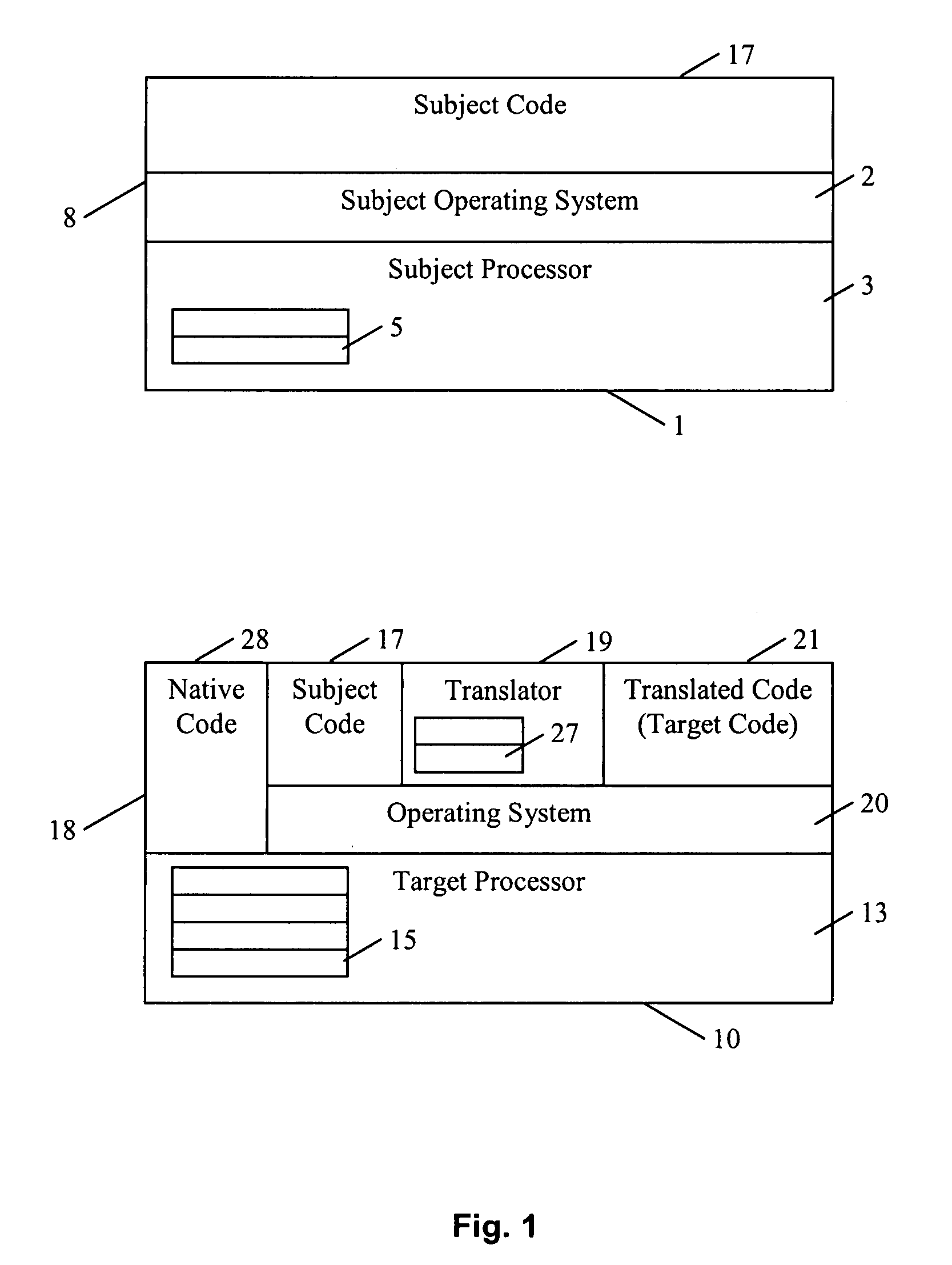
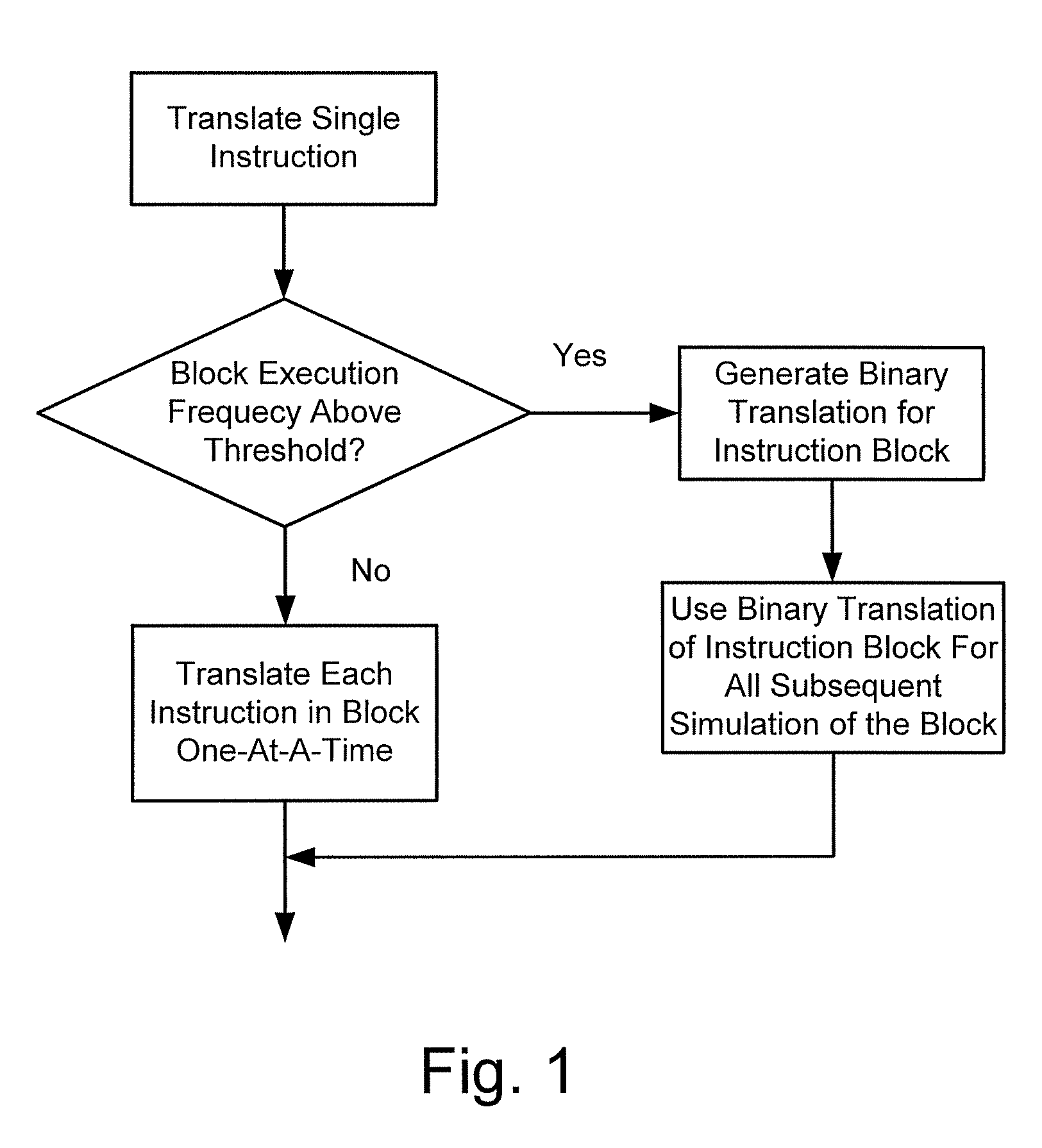
In computing, binary translation is a form of binary recompilation where sequences of instructions are translated from a source instruction set to the target instruction set. In some cases such as instruction set simulation, the target instruction set may be the same as the source instruction set, providing testing and debugging features such as instruction trace, conditional breakpoints and hot spot detection.
Taint tracking mechanism for computer security
ActiveUS8510827B1Easy to trackAvoid modificationMemory loss protectionDigital data processing detailsInformation dispersalOperation mode
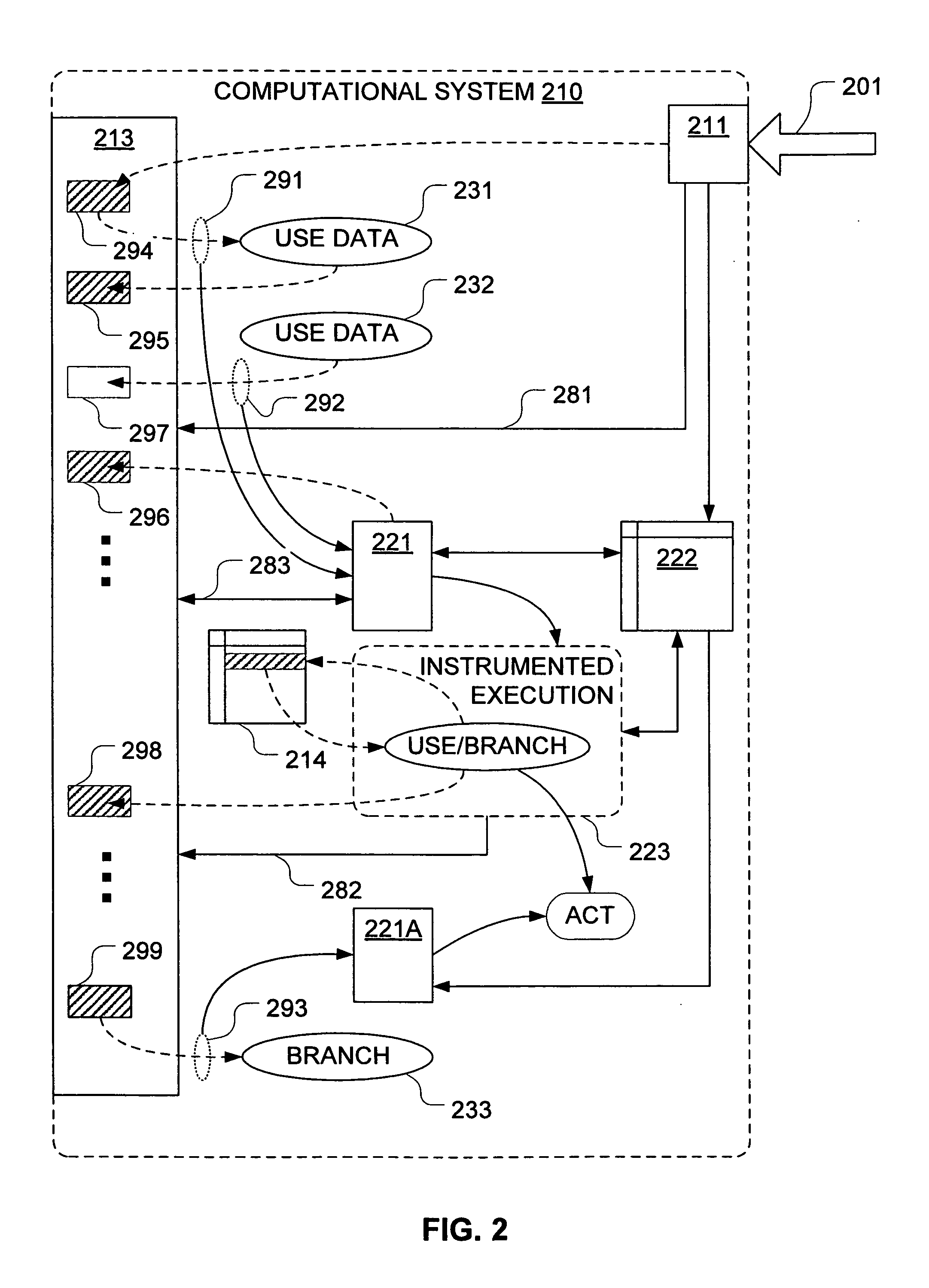
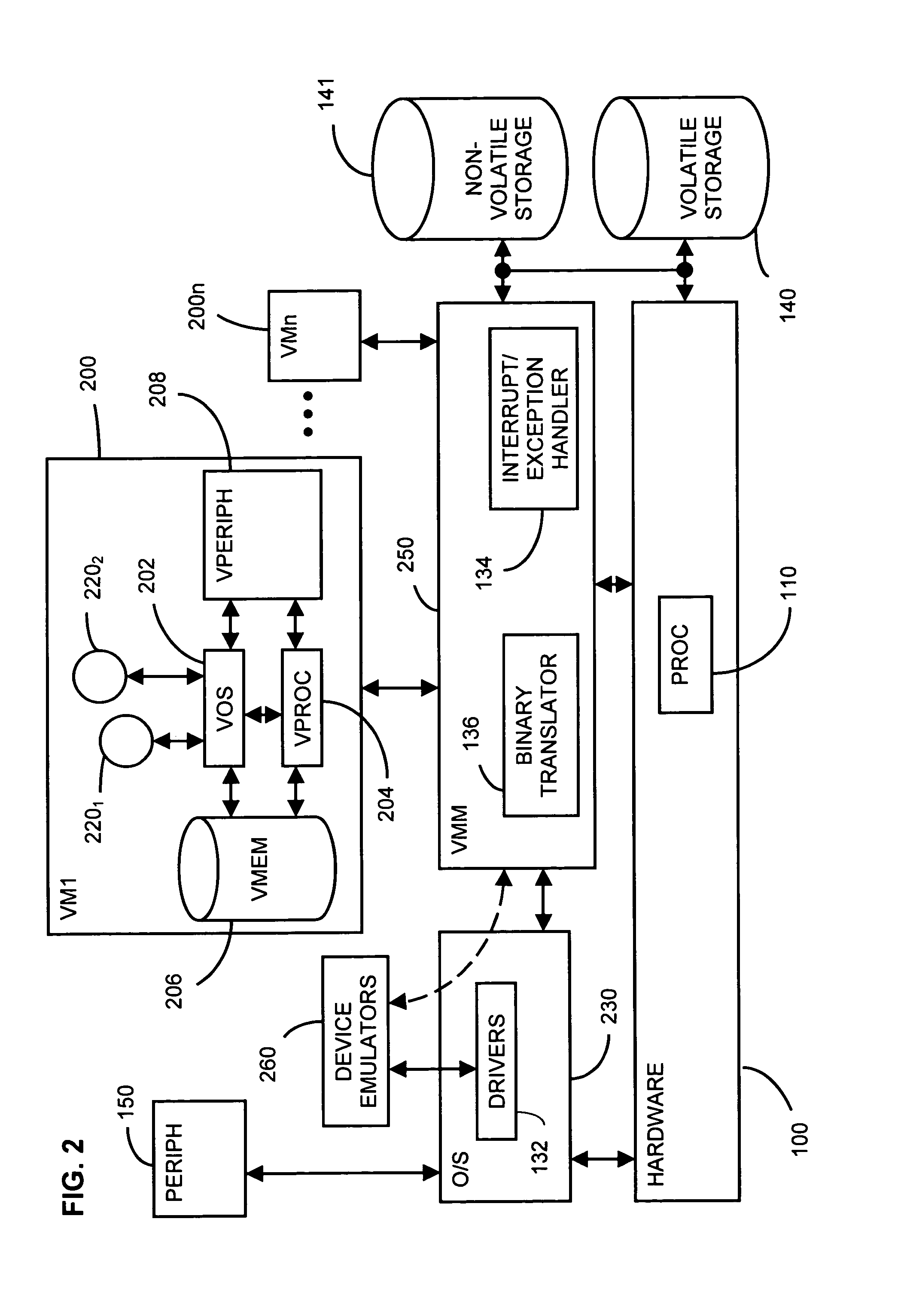
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and propagating taint status for memory locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security response if and when a control transfer (or other restricted use) is attempted based on tainted data. In some embodiments, memory management facilities and related exception handlers can be exploited to facilitate taint status propagation and / or security responses. Taint tracking through registers of a processor (or through other storage for which access is not conveniently mediated using a memory management facility) may be provided using an instrumented execution mode of operation. For example, the instrumented mode may be triggered by an attempt to propagate tainted information to a register. In some embodiments, an instrumented mode of operation may be more generally employed. For example, data received from an untrusted source or via an untrusted path is often transferred into a memory buffer for processing by a particular service, routine, process, thread or other computational unit. Code that implements the computational unit may be selectively executed in an instrumented mode that facilitates taint tracking. In general, instrumented execution modes may be supported using a variety of techniques including a binary translation (or rewriting) mode, just-in-time (JIT) compilation / re-compilation, interpreted mode execution, etc. Using an instrumented execution mode and / or exception handler techniques, modifications to CPU hardware can be avoided if desirable.
Owner:VMWARE INC
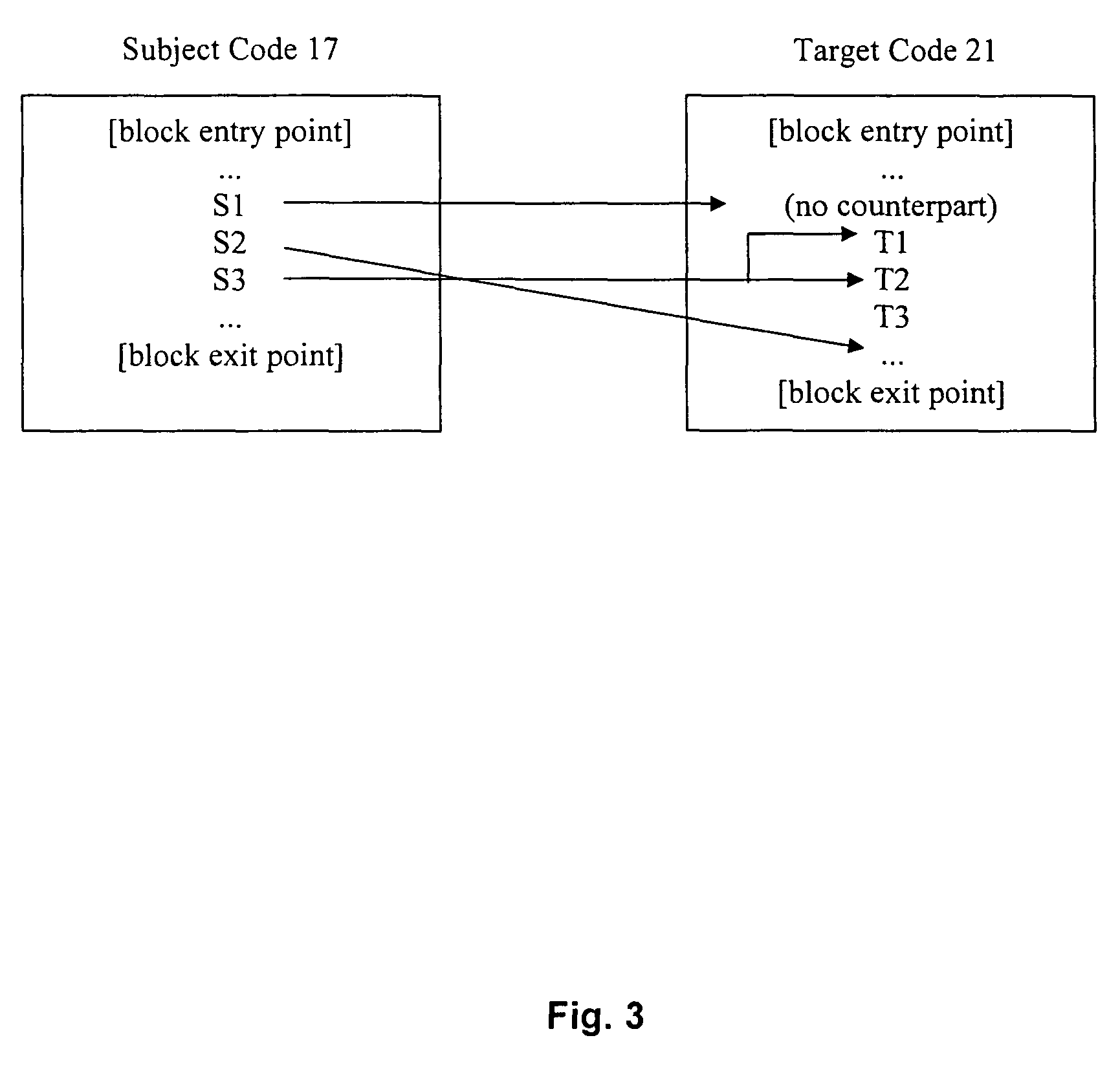
Converting program code with access coordination for a shared memory
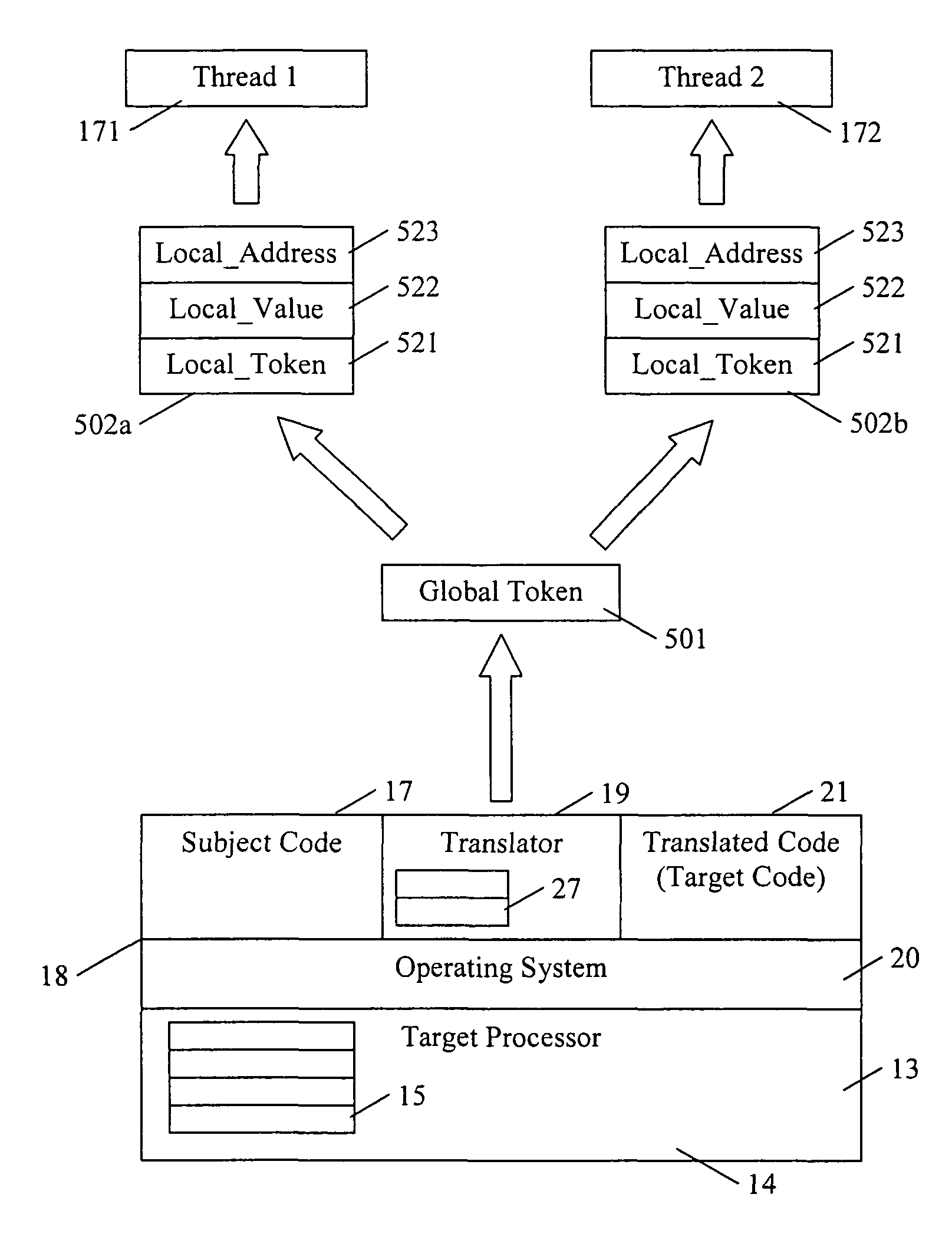
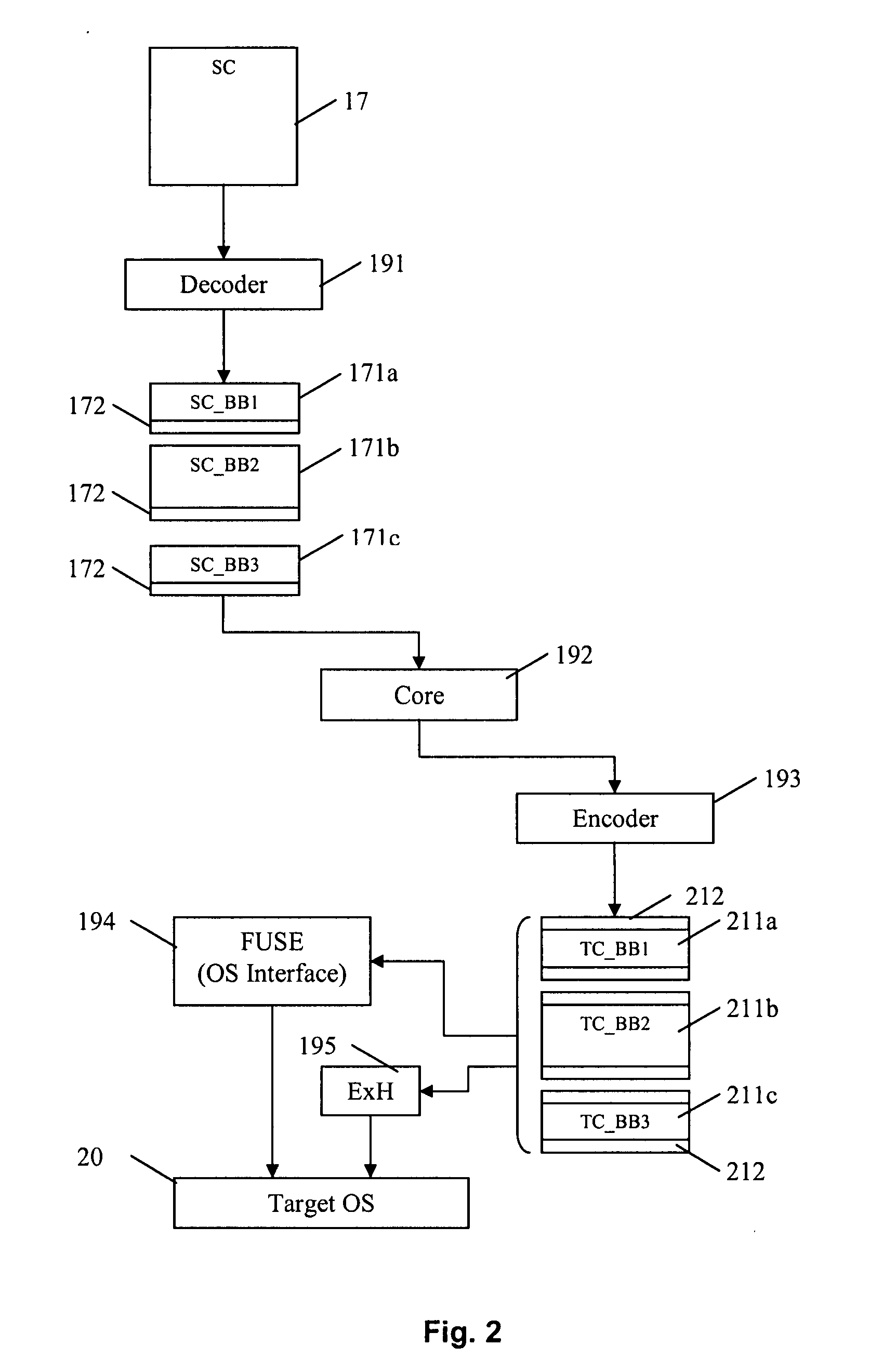
A dynamic binary translator 19 converts a subject program 17 into target code 21 on a target processor 13. For a multi-threaded subject environment, the translator 19 provides a global token 501 common to each thread 171, 172, and one or more sets of local data 502, which together are employed to coordinate access to a memory 18 as a shared resource. Adjusting the global token 501 allows the local datastructures 502a,b in each thread to detect potential interference with the shared resource 18.
Owner:IBM CORP
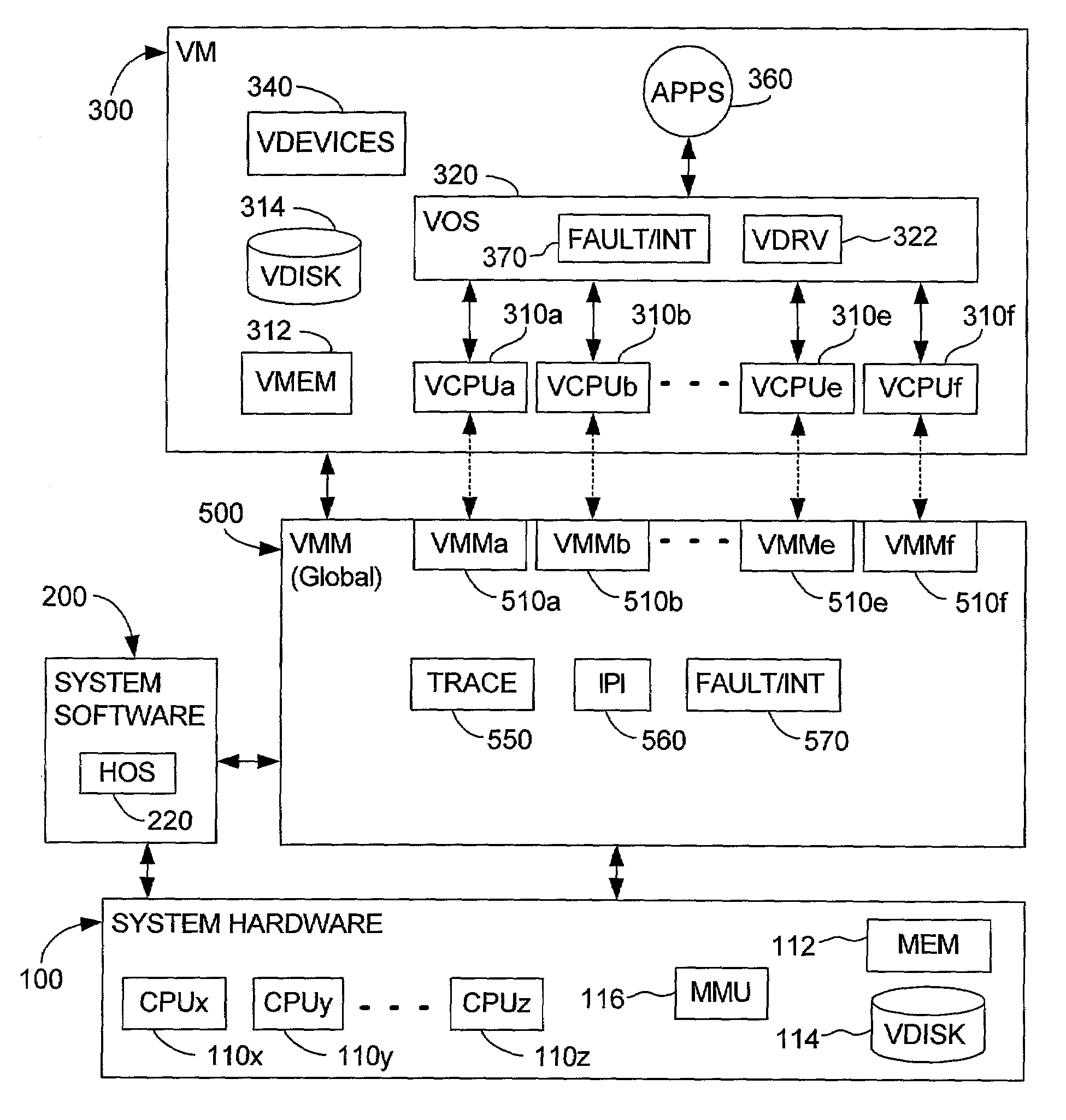
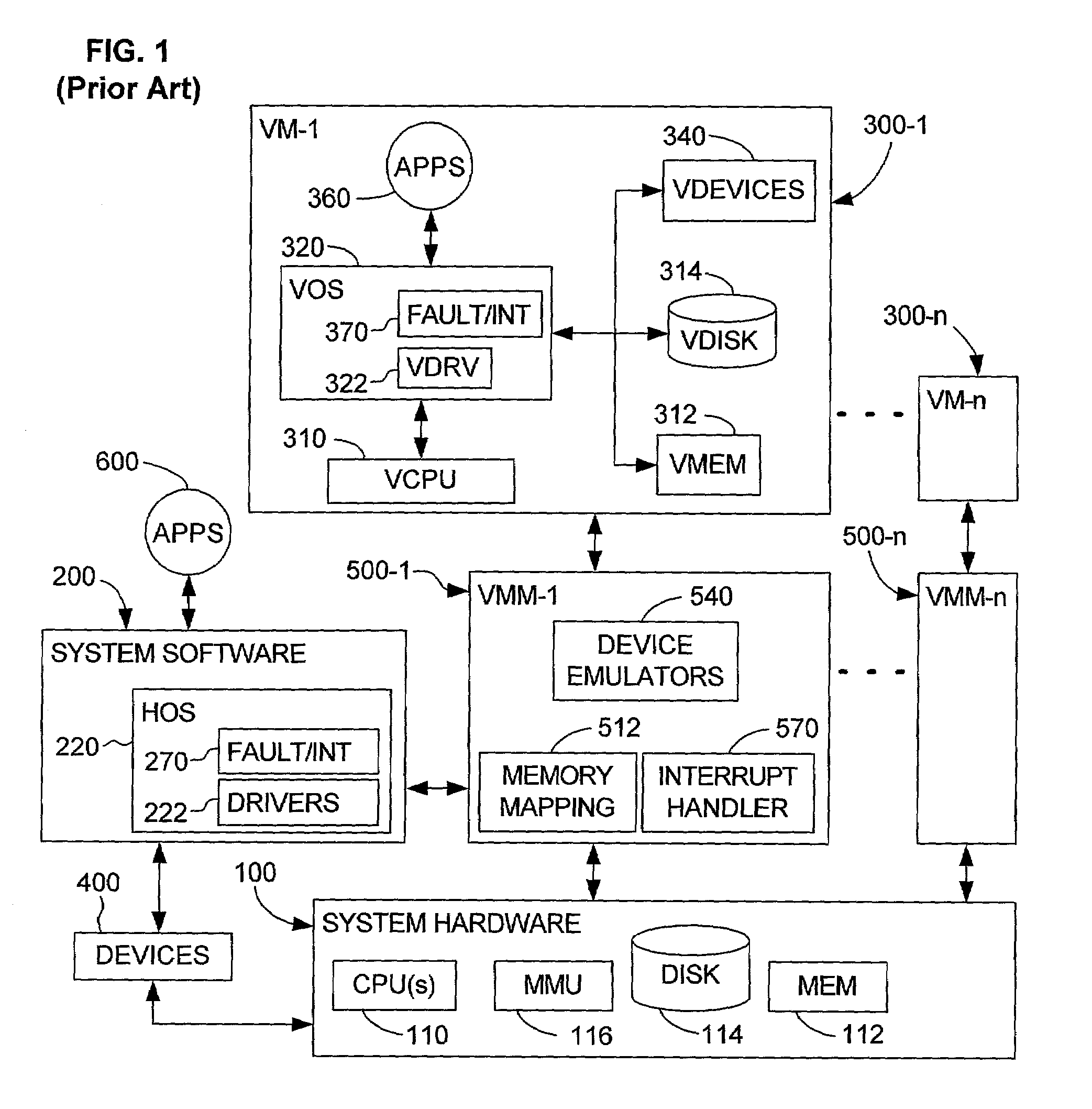
System and method for detecting access to shared structures and for maintaining coherence of derived structures in virtualized multiprocessor systems
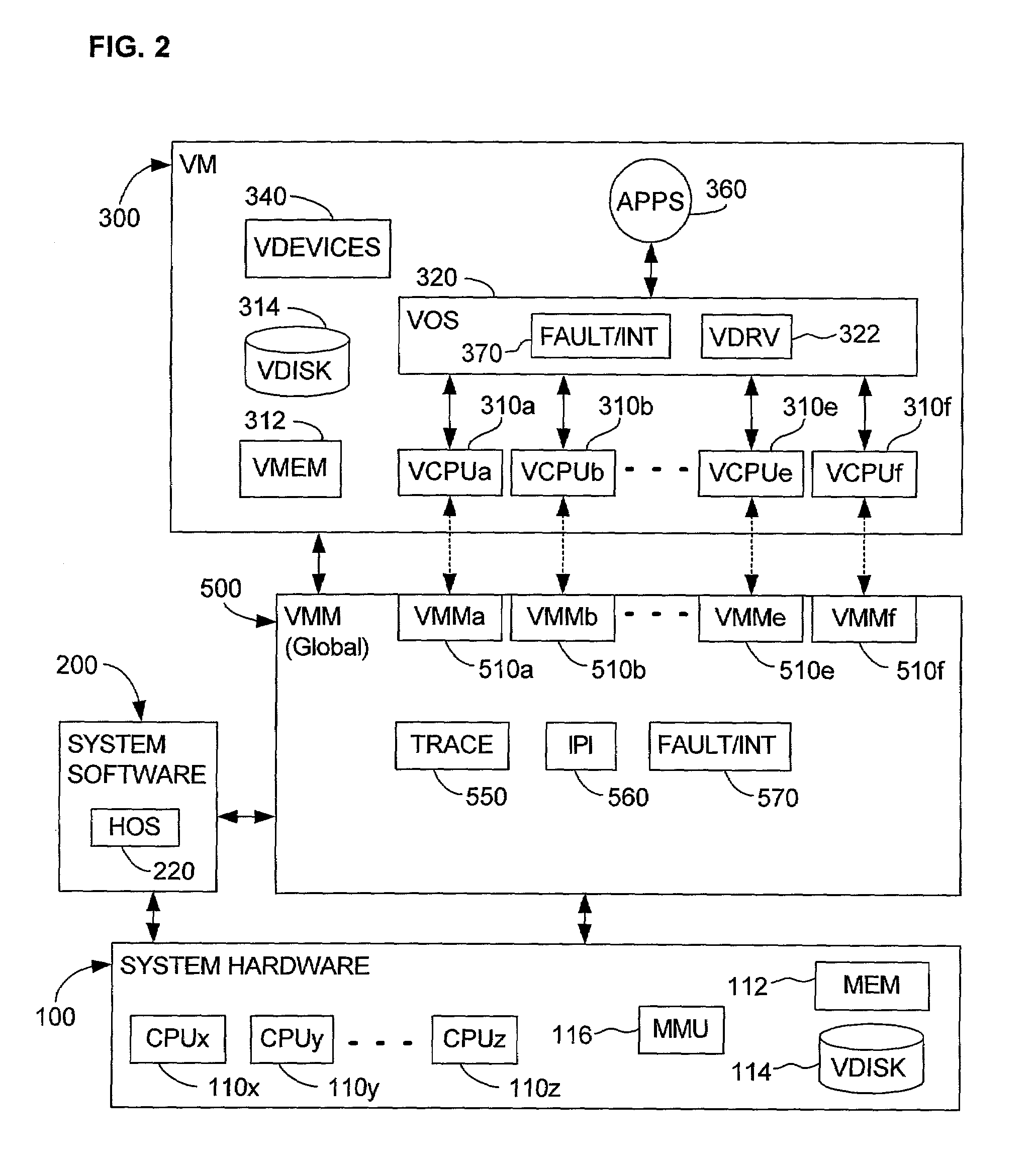
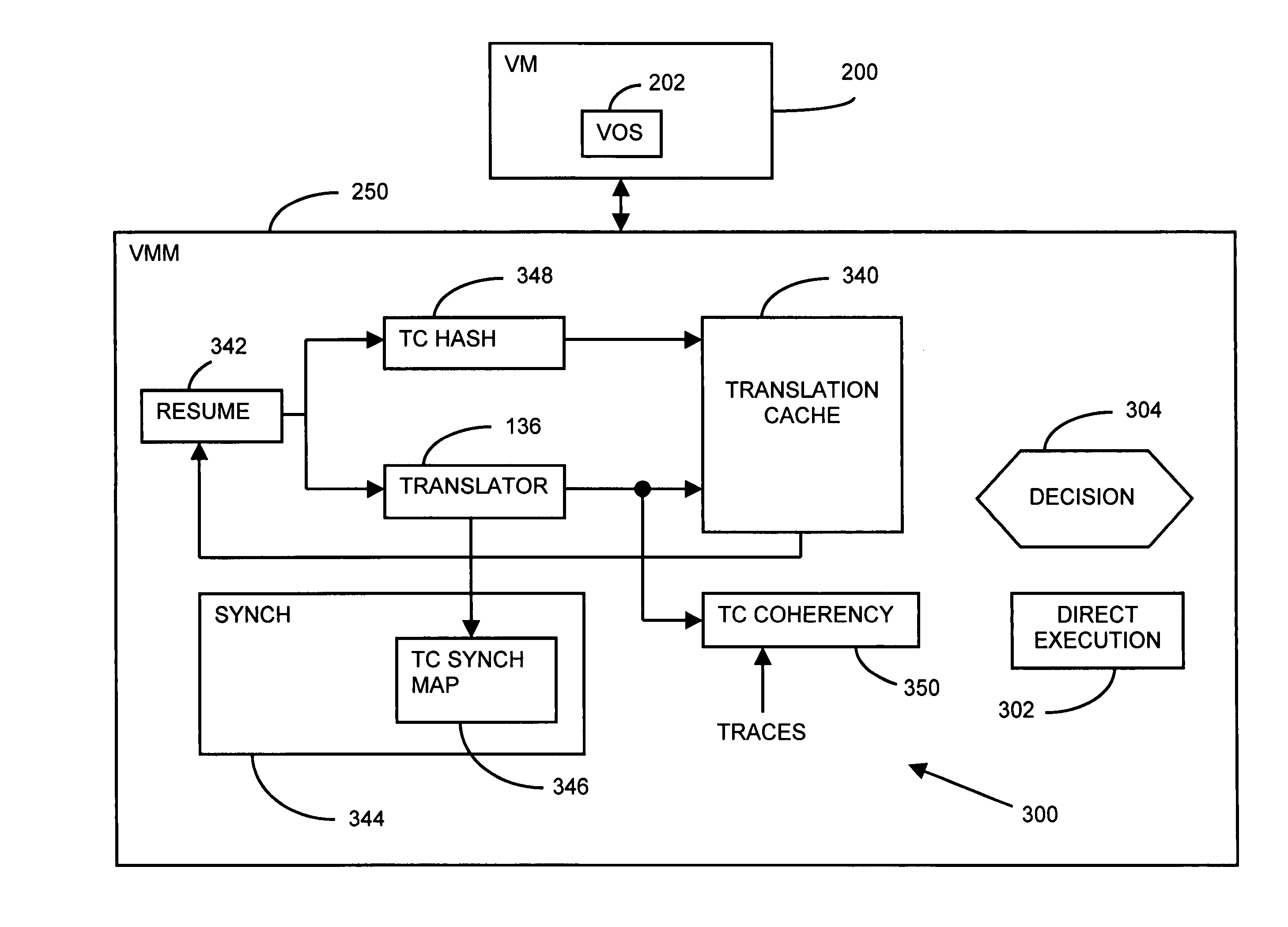
A computer system includes at least one virtual machine that has a plurality of virtual processors all running on an underlying hardware platform. A software interface layer such as a virtual machine monitor establishes traces on primary structures located in a common memory space as needed for the different virtual processors. Whenever any one of the virtual processors generates a trace event, such as accessing a traced structure, then a notification is sent to at least the other virtual processors that have a trace on the accessed primary structure. In some applications, the VMM derives and maintains secondary structures corresponding to the primary structures, such as where the VMM converts, through binary translation, original code intended to run on a virtual processor into code that can be run on an underlying physical processor of the hardware platform. In these applications, the VMM may rederive or invalidate the secondary structures as needed upon receipt of the notification of the trace event. Different semantics are provided for the notification, providing different choices of performance versus guaranteed consistency between primary and secondary structures. In the preferred embodiment of the invention, a dedicated sub-system is included within the VMM for each virtual processor; each sub-system establishes traces, senses trace events, issues the notification, and performs other operations relating specifically to its respective virtual processor.
Owner:VMWARE INC
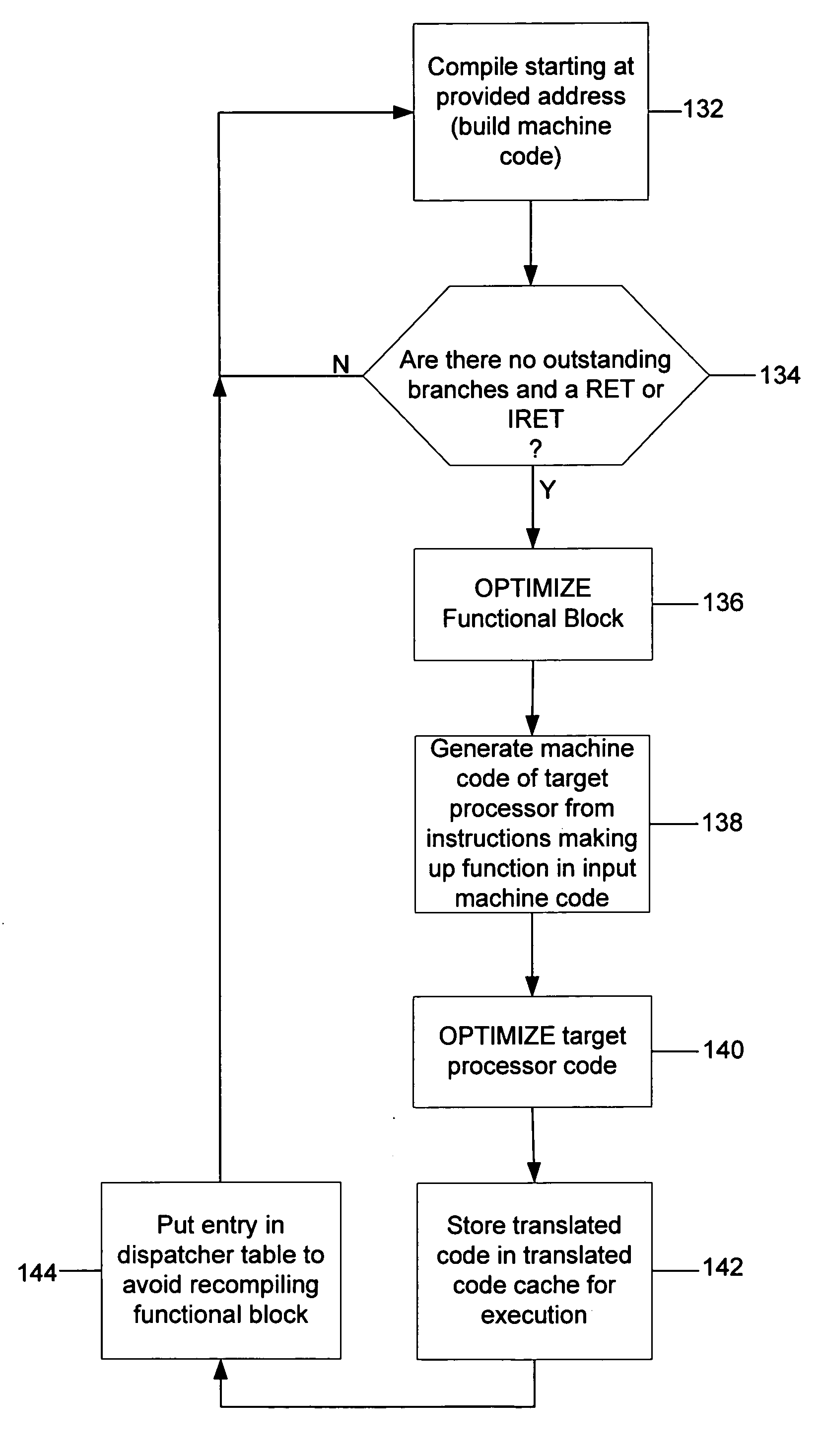
Function-level just-in-time translation engine with multiple pass optimization
InactiveUS20070006178A1Improve translationReduce context switchingBinary to binaryProgram controlCode TranslationSoftware emulation
A JIT binary translator translates code at a function level of the source code rather than at an opcode level. The JIT binary translator of the invention grabs an entire x86 function out of the source stream, rather than an instruction, translates the whole function into an equivalent function of the target processor, and executes that function all at once before returning to the source stream, thereby reducing context switching. Also, since the JIT binary translator sees the entire source code function context at once the software emulator may optimize the code translation. For example, the JIT binary translator might decide to translate a sequence of x86 instructions into an efficient PPC equivalent sequence. Many such optimizations result in a tighter emulated binary.
Owner:MICROSOFT TECH LICENSING LLC
Memory consistency protection in a multiprocessor computing system
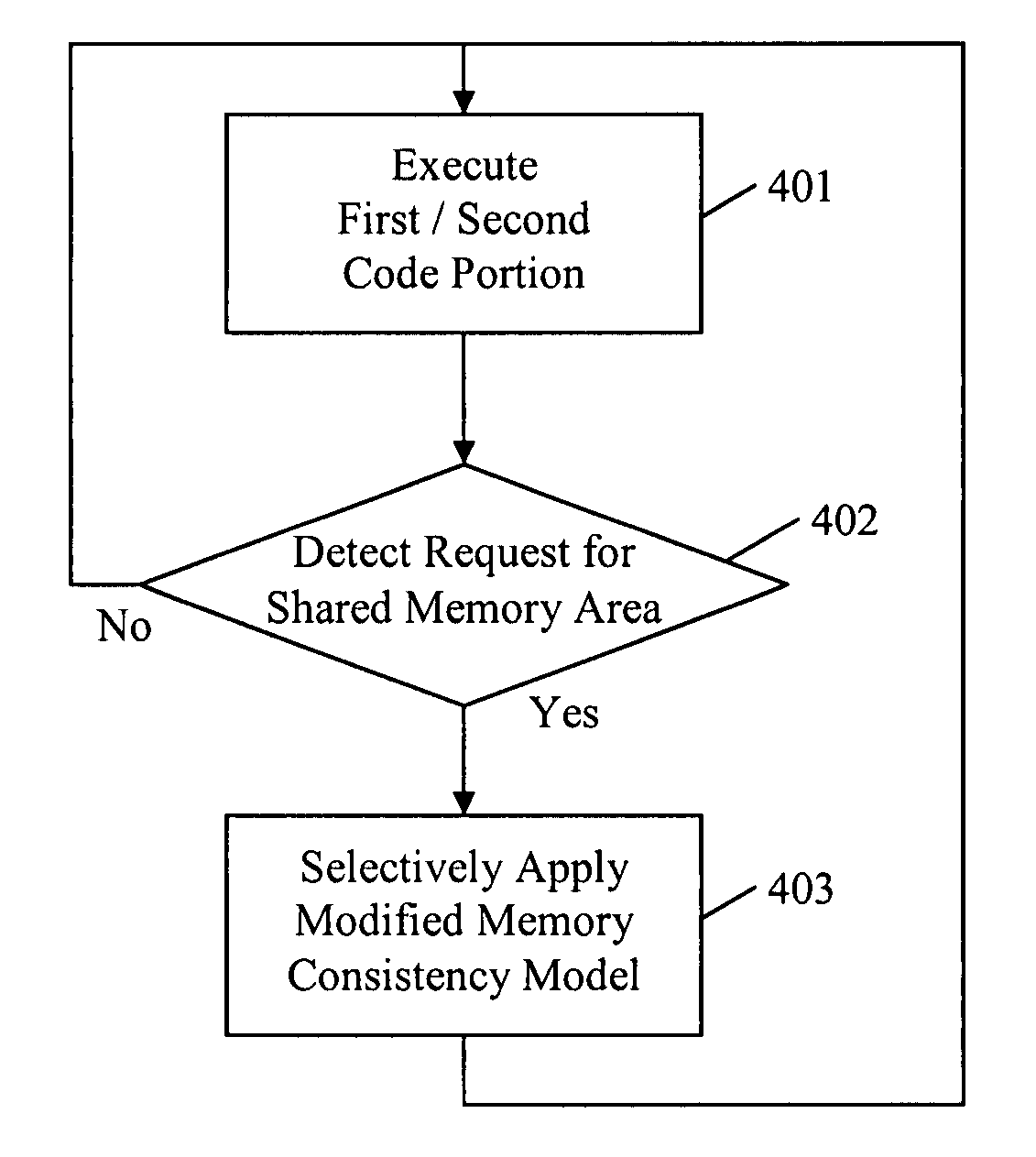
InactiveUS20080140971A1Low-cost and effectiveImproved memory consistencyResource allocationMemory adressing/allocation/relocationMulti processorObject code
A method and apparatus to protect memory consistency in a multiprocessor computing system are described, in particular relating to program code conversion such as dynamic binary translation. The exemplary system provides a memory, processors and a controller / translator unit (CTU) arranged to convert subject code into at least first and second target code portions executable on the processors. The CTU comprises an address space allocation unit to provide virtual address space regions and direct the target code portions to access the memory therethough; a shared memory detection unit to detect a request to access a shared memory area, accessible by both target code portions, and to identify at least one group of instructions in the first target code portion which access the shared memory area; and a memory protection unit to selectively apply memory consistency protection in relation to accesses to the shared memory area by the identified group of instructions.
Owner:IBM CORP
Binary translator with precise exception synchronization mechanism
InactiveUS7516453B1Digital computer detailsConcurrent instruction executionComputerized systemGoal system
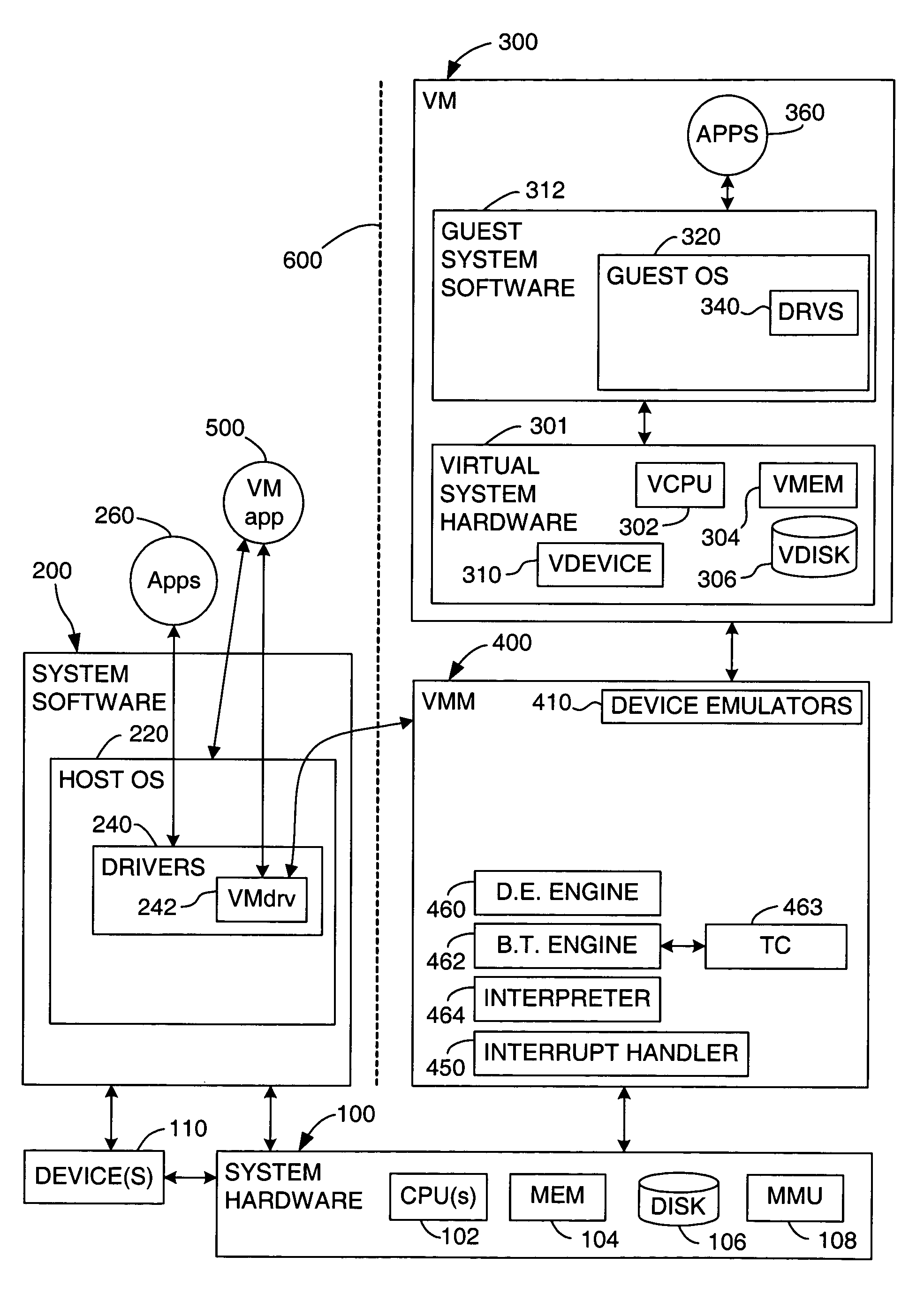
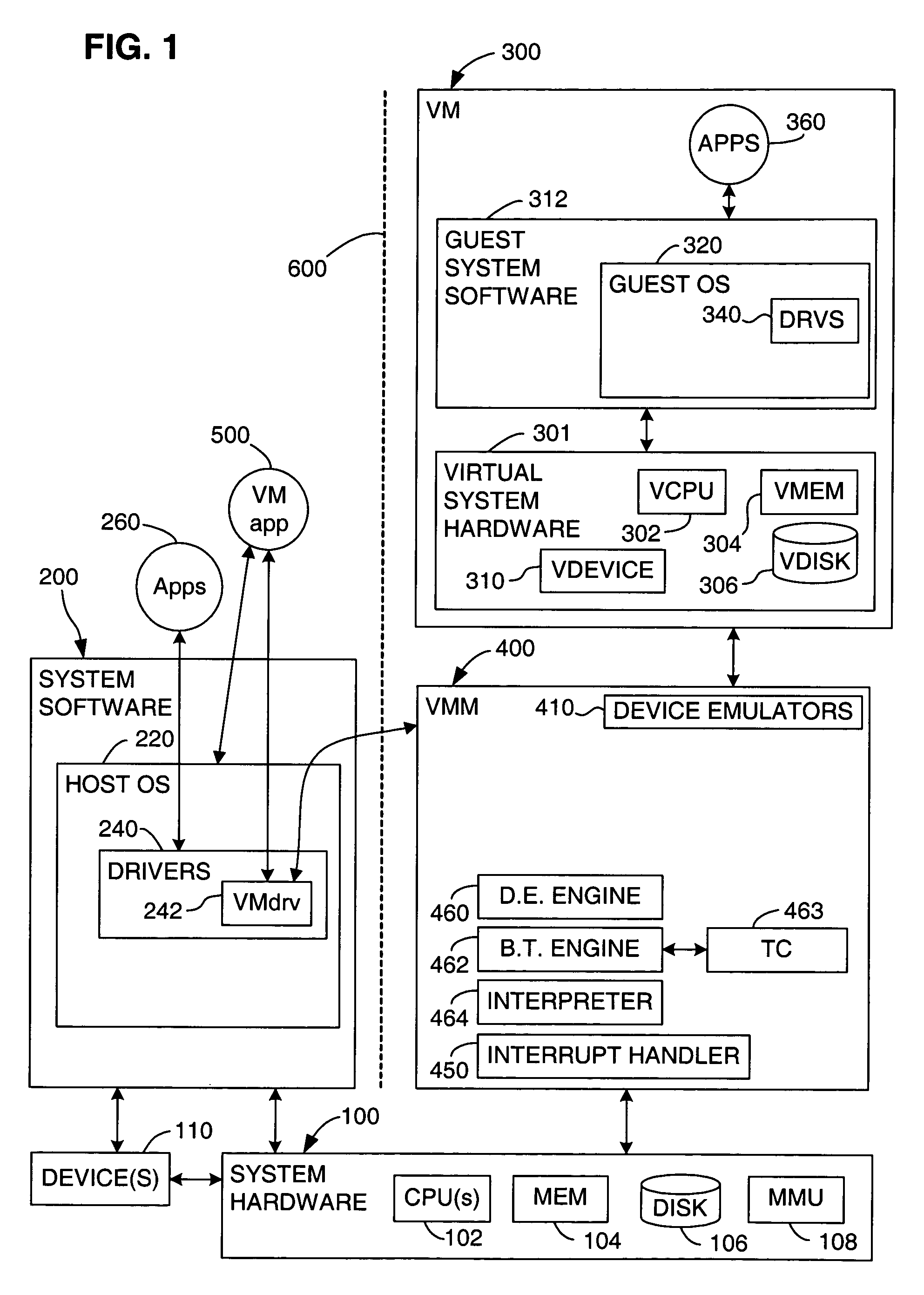
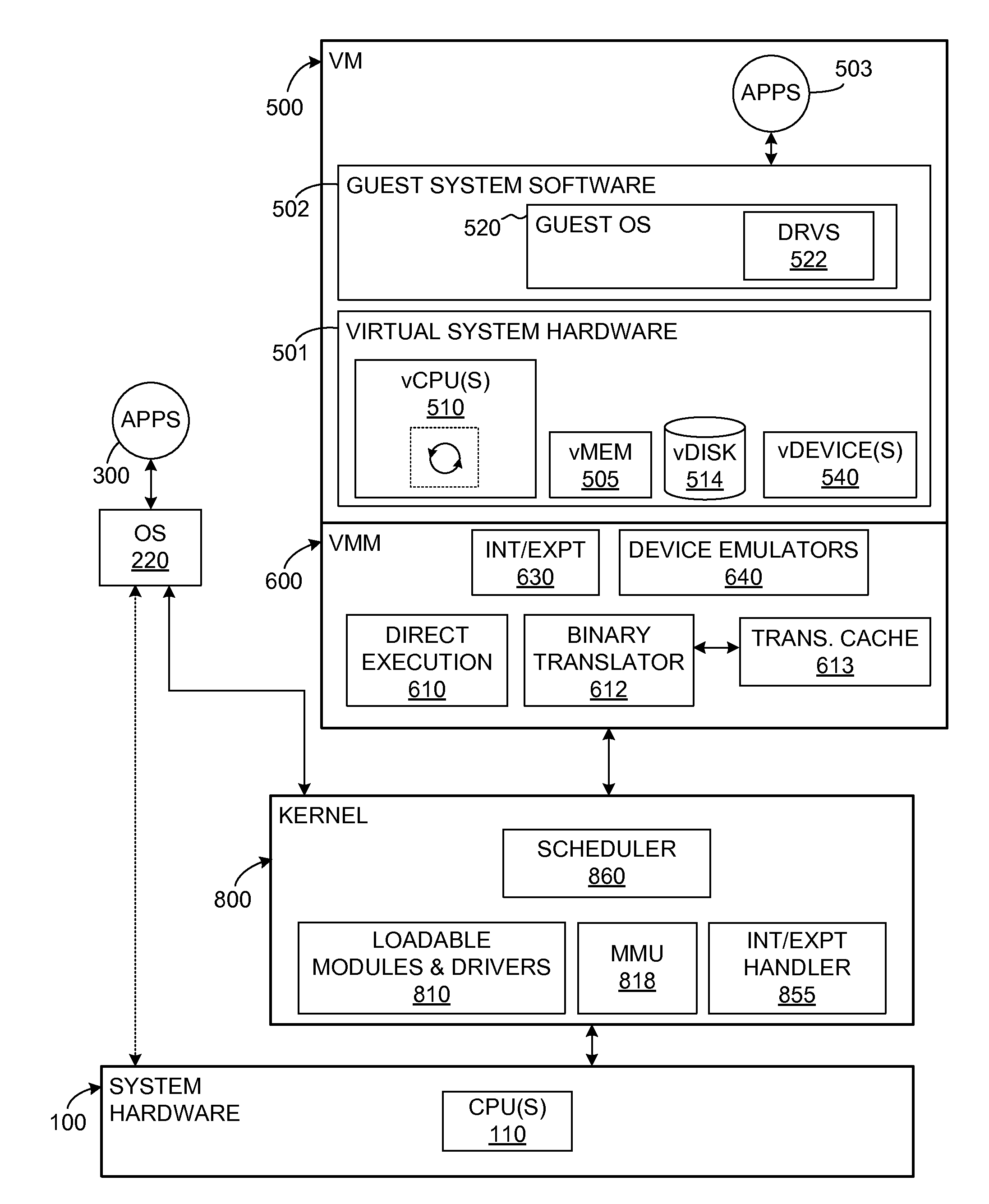
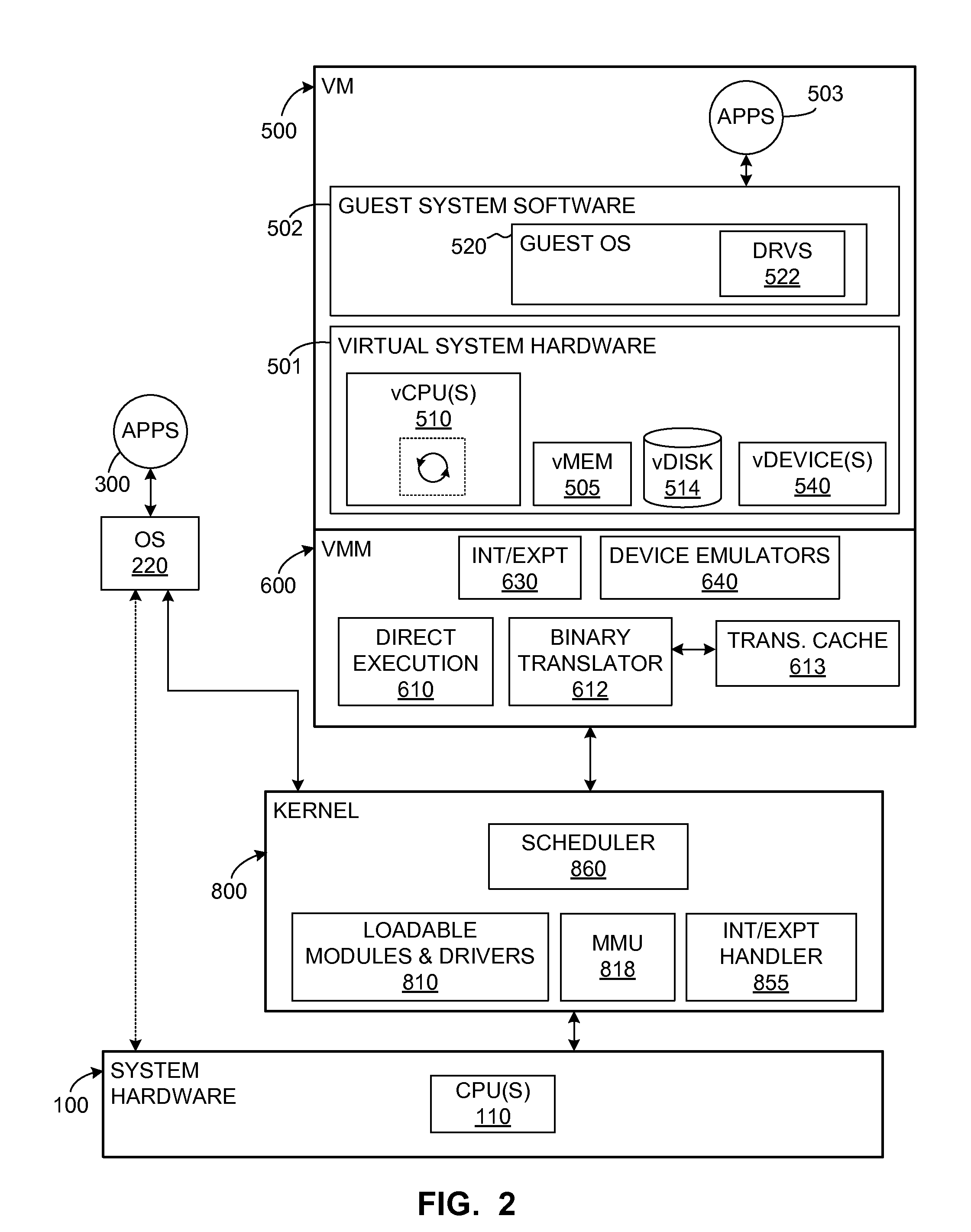
A source computer system with one instruction set architecture (ISA) is configured to run on a target hardware system that has its own ISA, which may be the same as the source ISA. In cases where the source instructions cannot be executed directly on the target system, the invention provides binary translation system. During execution from binary translation, however, both synchronous and asynchronous exceptions may arise. Synchronous exceptions may be either transparent (requiring processing action wholly within the target computer system) or non-transparent (requiring processing that alters a visible state of the source system). Asynchronous exceptions may also be either transparent or non-transparent, in which case an action that alters a visible state of the computer system needs to be applied. The invention includes subsystems, and related methods of operation, for detecting the occurrence of all of these types of exceptions, to handle them, and to do so with precise reentry into the interrupted instruction stream; by “precise” is meant that the atomic execution of the source instructions is guaranteed, and that the application of actions, including those that originate from asynchronous exceptions, occurs at the latest at the completion of the current source instruction at the time of the request for the action. The binary translation and exception-handling subsystems are preferably included as components of a virtual machine monitor which is installed between the target hardware system and the source system, which is preferably a virtual machine.
Owner:VMWARE INC
Method and apparatus for managing registers in a binary translator
ActiveUS7260815B1Specific program execution arrangementsMemory systemsProcessor registerParallel computing
The invention relates to managing registers during a binary translation mode in a virtual computing system. A set of registers is saved to memory before beginning to execute a series of blocks of translated code, and the contents of the set of registers are restored from memory later. A status register is maintained for tracking the status of each register within the set, the status indicating whether the contents are valid and whether the contents are saved in memory. Before the execution of each block, a determination is made as to whether the actions taken within the block relative to the registers are compatible with the current status of the registers. If the actions are not compatible, additional registers are saved to memory or restored from memory, so that the translation block can be executed.
Owner:VMWARE INC
Detecting conditions for transfer of execution from one computer instruction stream to another and executing transfer on satisfaction of the conditions
InactiveUS8121828B2Efficiently tailoredEasy to operateGeneral purpose stored program computerSoftware simulation/interpretation/emulationInstruction pipelineInstruction stream
A computer has instruction pipeline circuitry capable of executing two instruction set architectures (ISA's). A binary translator translates at least a selected portion of a computer program from a lower-performance one of the ISA's to a higher-performance one of the ISA's. Hardware initiates a query when about to execute a program region coded in the lower-performance ISA, to determine whether a higher-performance translation exists. If so, the about-to-be-executed instruction is aborted, and control transfers to the higher-performance translation. After execution of the higher-performance translation, execution of the lower-performance region is reestablished at a point downstream from the aborted instruction, in a context logically equivalent to that which would have prevailed had the code of the lower-performance region been allowed to proceed.
Owner:ADVANCED SILICON TECH
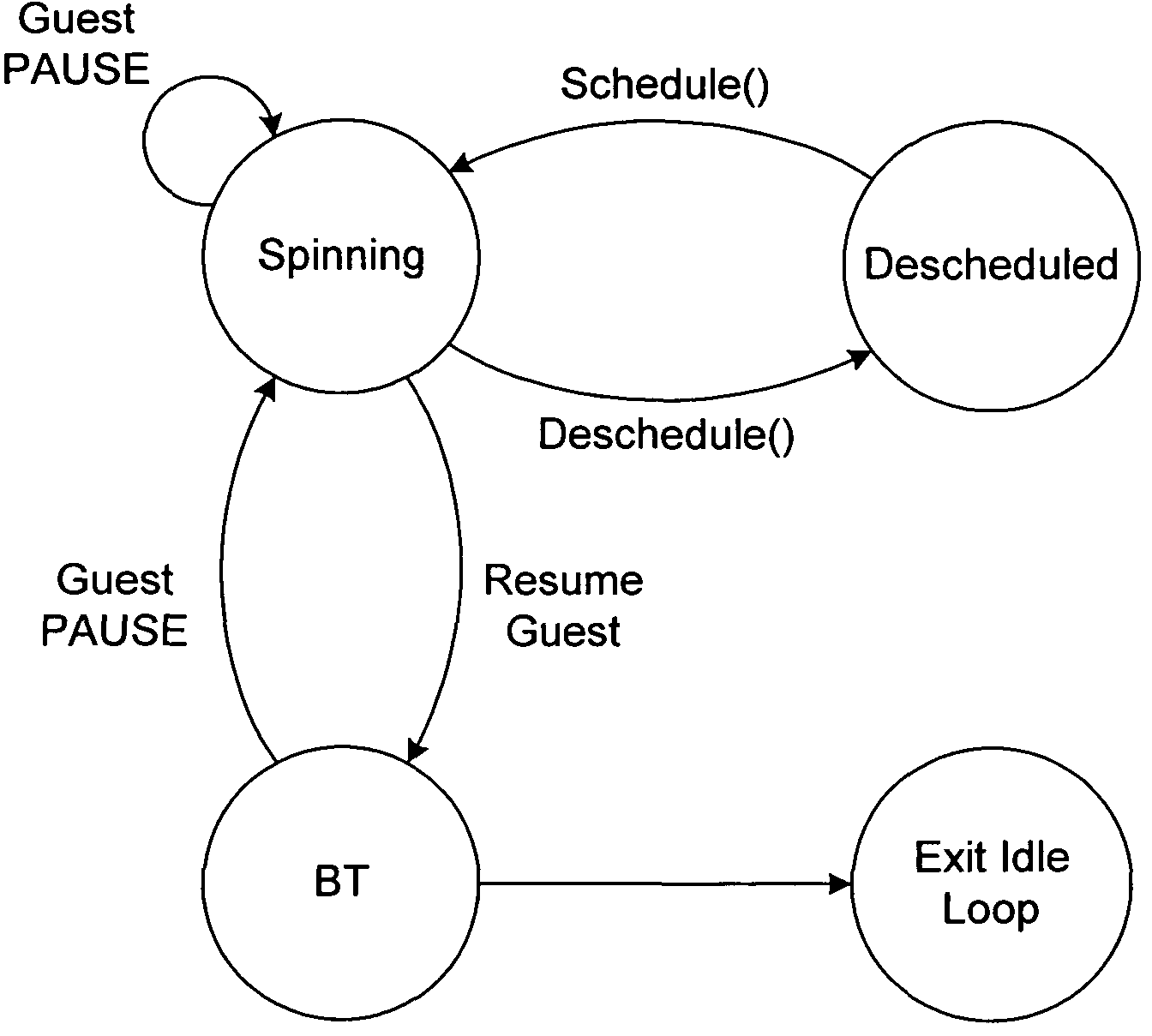
Selective descheduling of idling guests running on a host computer system
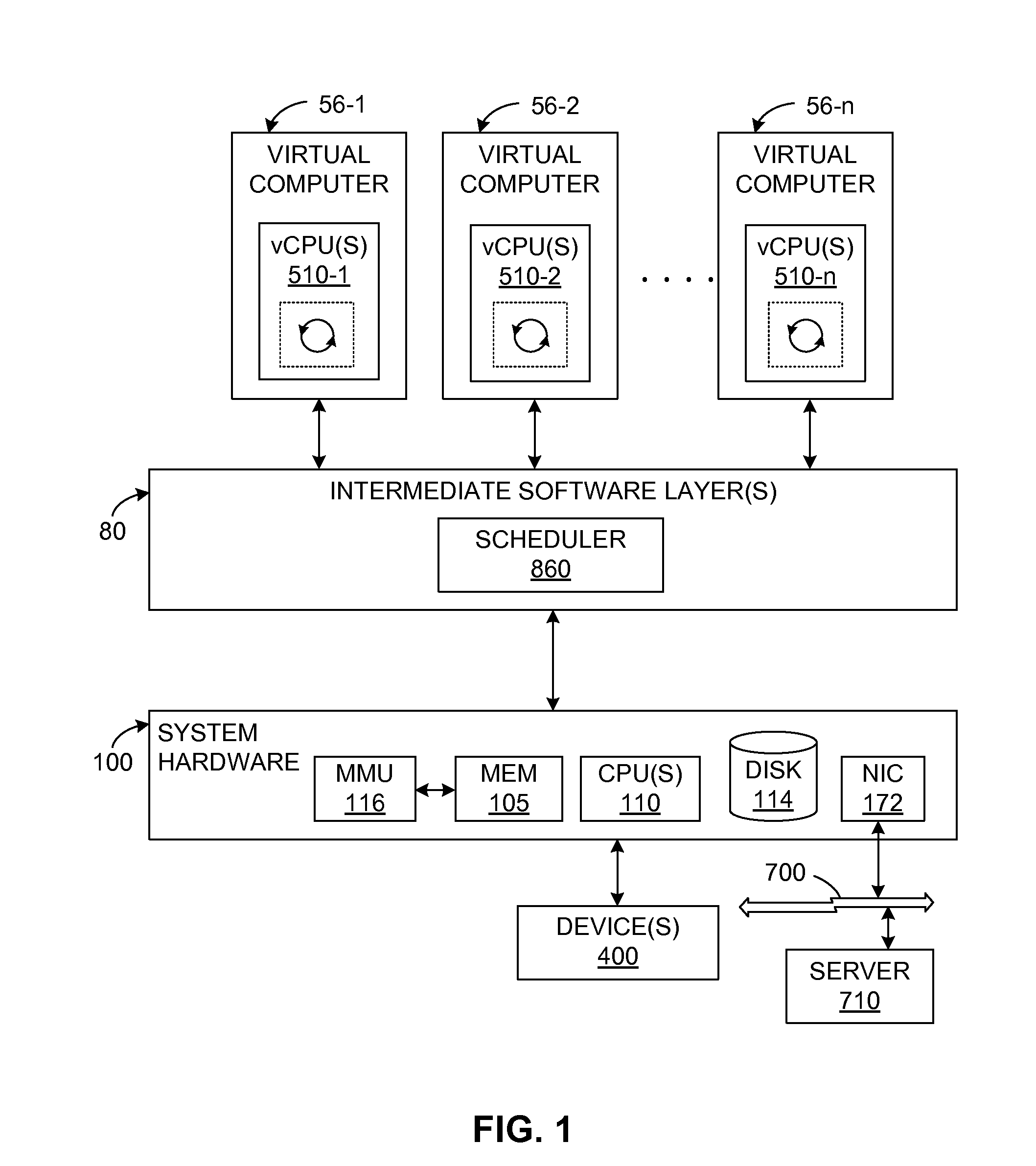
Guests, such as virtual machines, that are running on a host hardware platform are selectively descheduled when an idling condition is detected. An example of the idling condition is that the guest has been executing instructions in an idle loop for more than a threshold period. Guest instructions may be evaluated for the idling condition in conjunction with binary translation.
Owner:VMWARE INC
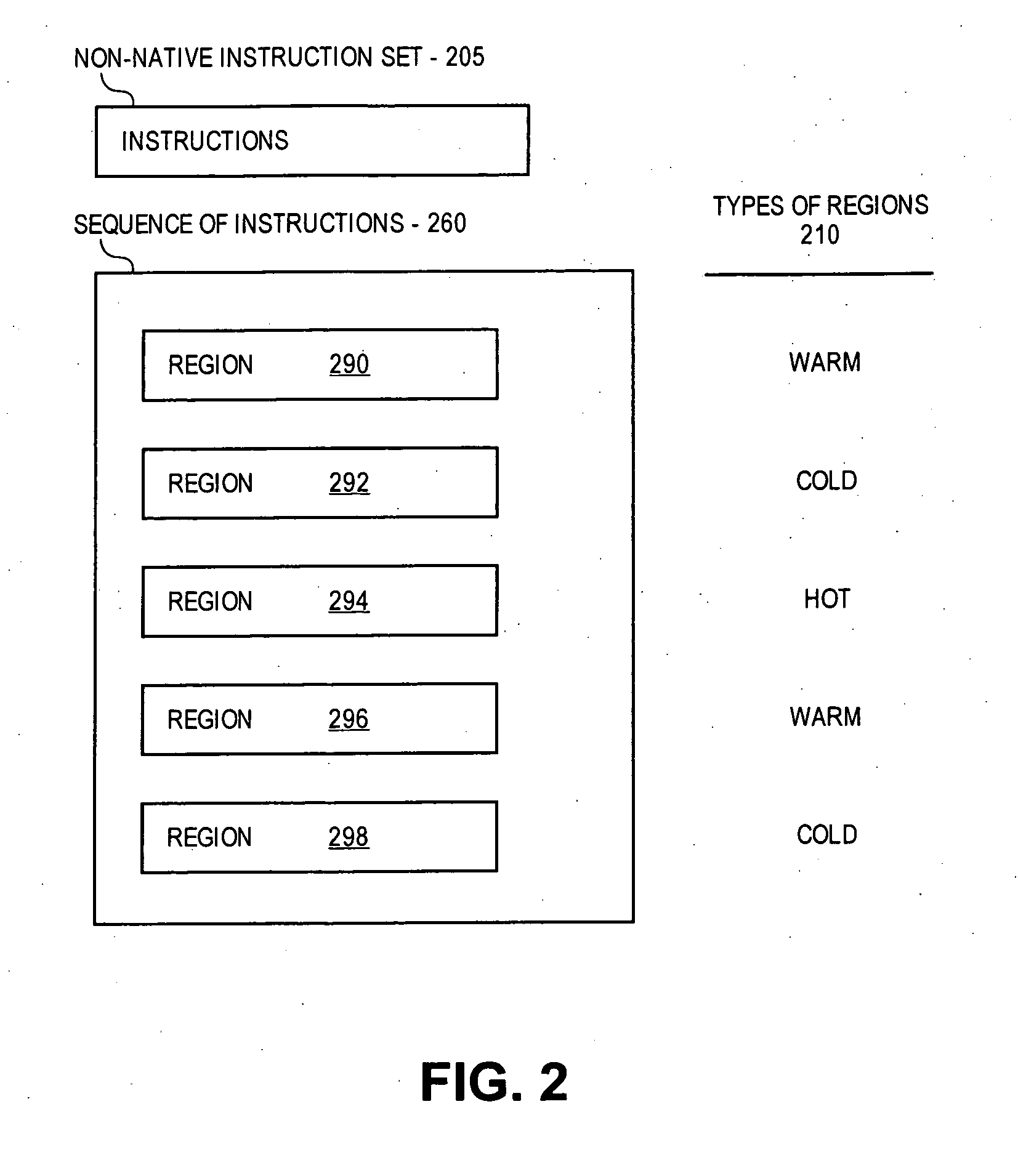
Compressing "warm" code in a dynamic binary translation environment
Selected regions of native instructions translated in a DBT environment from non-native instructions are compressed based on the independent compression of different fields of selected instructions using compression tables to reduce a length of selected fields. The regions of compressed instructions are stored and de-compressed into the native instructions during subsequent execution using de-compression tables. Specifically, for native instructions of a selected region, selected types of opcodes and / or operands may be compressed independently. The types may be selected by profiling the opcodes using benchmark programs and creating an opcode conversion table prior to compression, and scanning of the operands and creating an operand conversion table during compression of the opcodes.
Owner:INTEL CORP
Extreme pipeline and optimized reordering technology
ActiveUS20040181785A1More efficientDisable portionBinary to binaryTransportation and packagingOperational systemParallel computing
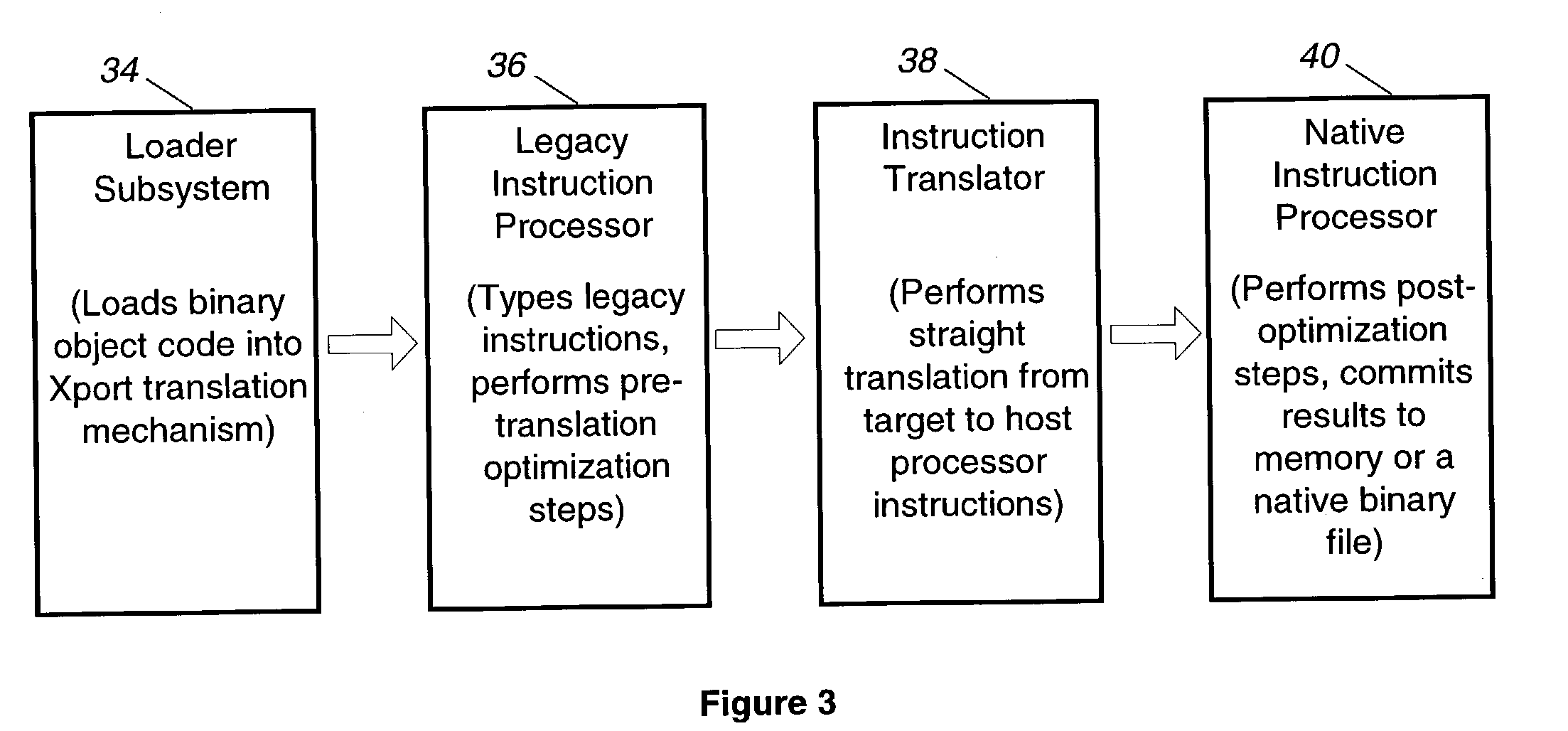
The present invention relates to a binary translator for directly translating binary instructions written for a legacy processor to executable binary instructions for a native processor. In accordance with an important aspect of the invention the binary translator is configured as a reconfigurable translator, which enables the binary translator to be used with different legacy processors and / or operating systems and native processors. The binary translators also optimize to take advantage of more efficient native processor instructions and allows portions of the legacy binary code to be disabled and / or new native instructions to be added to the application program without modification of the legacy binary code.
Owner:NORTHROP GRUMMAN SYST CORP
Apparatus and method for efficiently implementing a processor pipeline
ActiveUS20150378731A1General purpose stored program computerMultiprogramming arrangementsParallel computingCode Morphing Software
Various different embodiments of the invention are described including: (1) a method and apparatus for intelligently allocating threads within a binary translation system; (2) data cache way prediction guided by binary translation code morphing software; (3) fast interpreter hardware support on the data-side; (4) out-of-order retirement; (5) decoupled load retirement in an atomic OOO processor; (6) handling transactional and atomic memory in an out-of-order binary translation based processor; and (7) speculative memory management in a binary translation based out of order processor.
Owner:INTEL CORP
System and method for binary translation to improve parameter passing
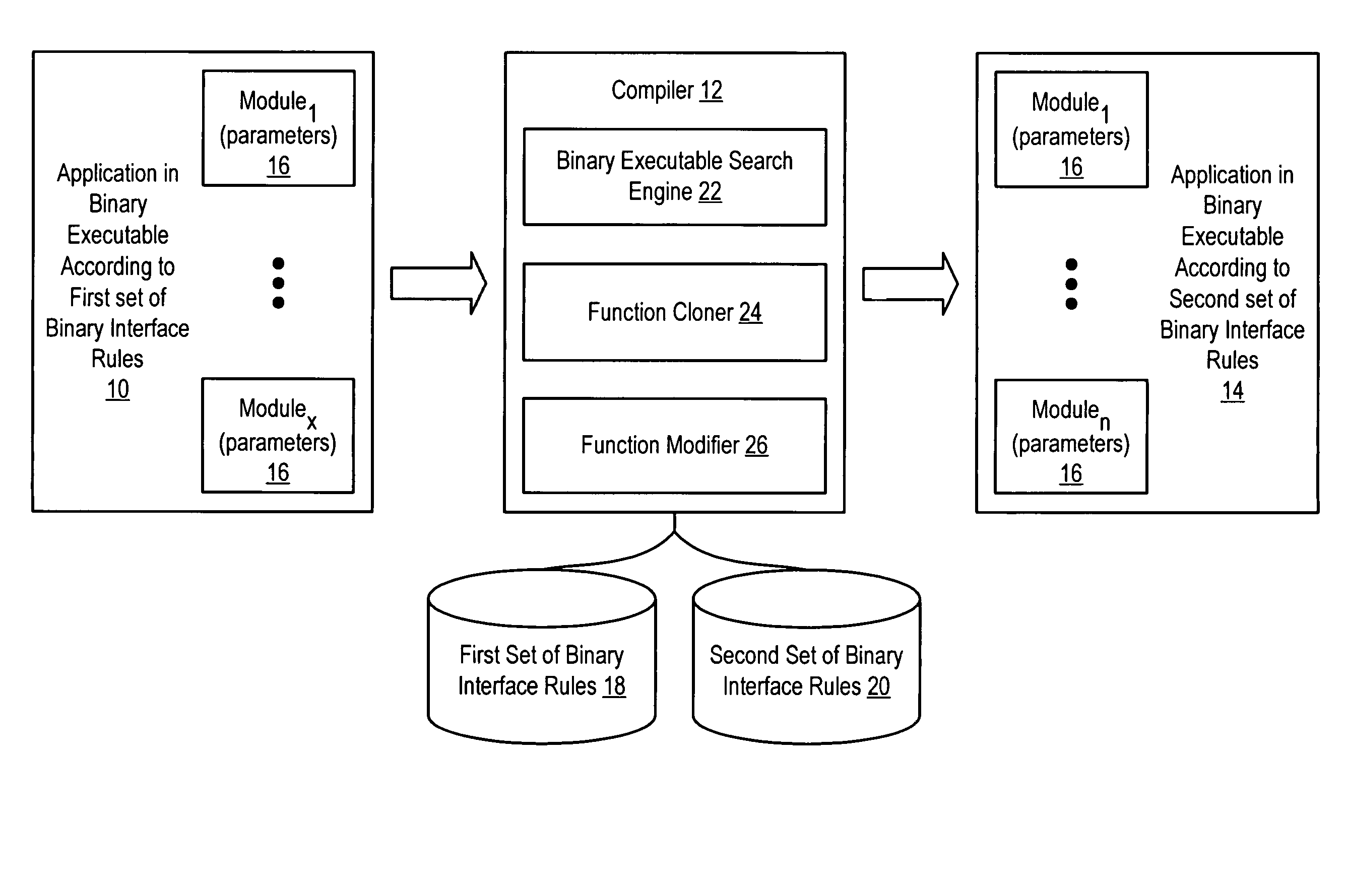
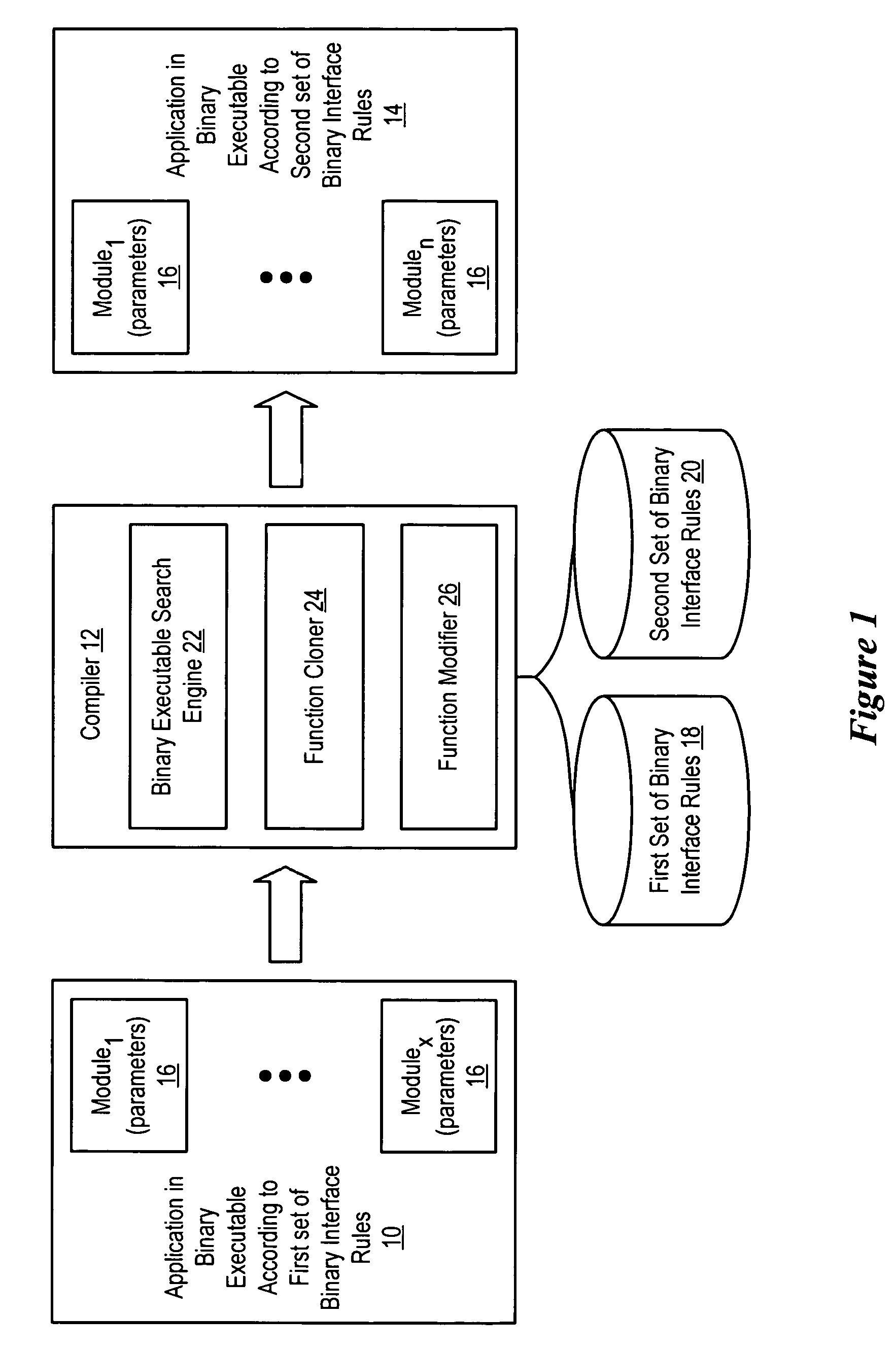
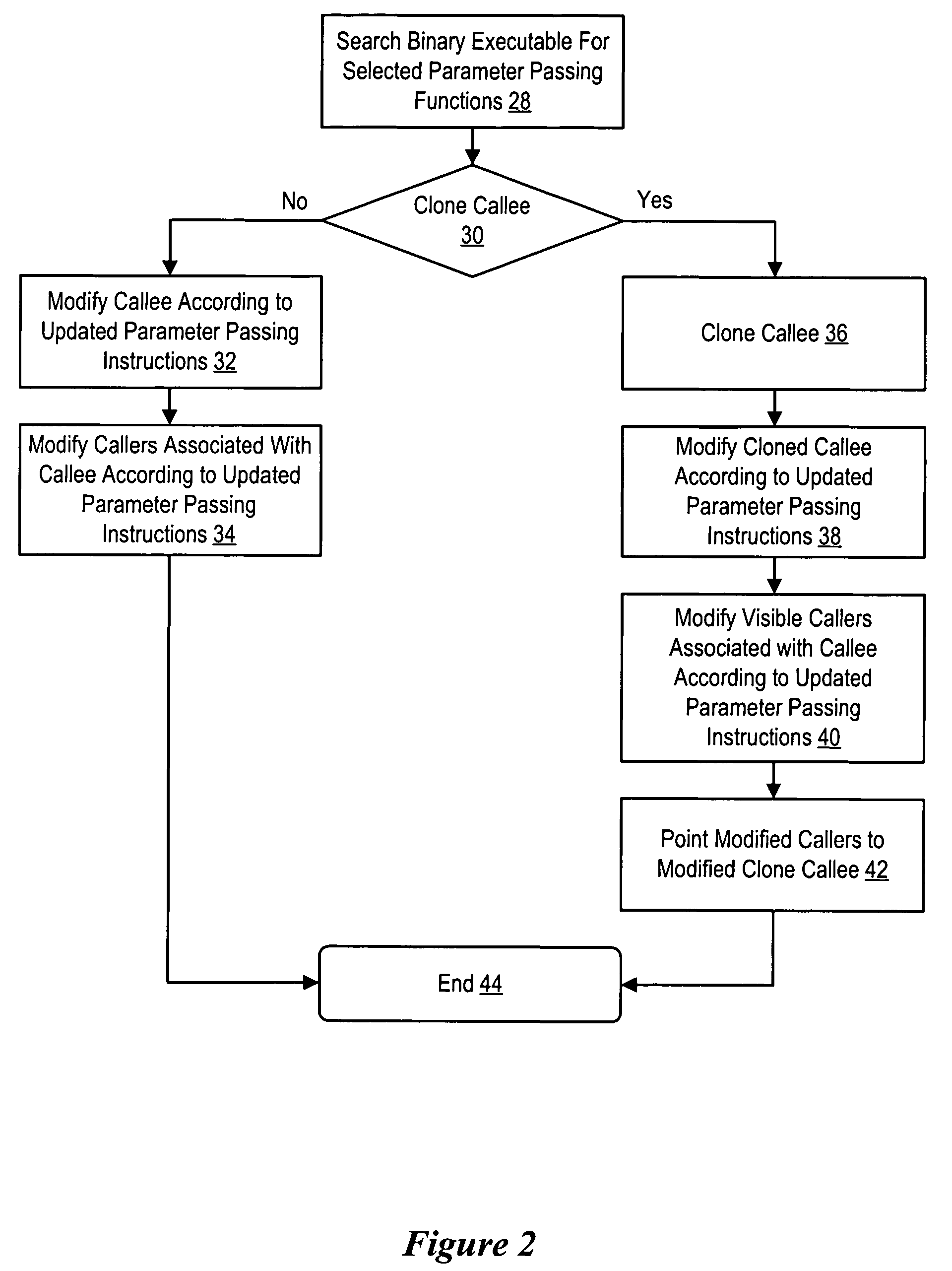
ActiveUS7861234B1Improve efficiencyReduce disadvantagesBinary to binaryProgram controlAlgorithmApplication software
An application compiled to a binary executable according to a first set of binary interface rules has selected caller / callee pairs that present parameter passing improvement possibilities modified from compliance with the first set of binary interface rules to compliance with a second set of binary interface rules to improve the efficiency of parameter passing, such as by reducing the number of instructions used to pass the parameters. A binary executable search engine searches the binary executable to locate functions having parameter passing improvement possibilities. Identified caller / callee function pairs are updated with a function modifier to pass the parameters more efficiently. Selected of the identified callee functions are cloned so that a cloned function is modified instead of the original function, thus leaving the original function to pass parameters with functions beyond the view of the binary executable search engine.
Owner:ORACLE INT CORP
Multiprocessor computing system with multi-mode memory consistency protection
ActiveUS20090210649A1Memory architecture accessing/allocationMemory adressing/allocation/relocationMulti processorActive memory
Disclosed are a method and apparatus for protecting memory consistency in a multiprocessor computing system, relating to program code conversion such as dynamic binary translation. The exemplary multiprocessor computing system provides memory and multiple processors, and a set of controller / translator units TX1, TX2, TX3 arranged to convert respective application programs into program threads T1, T2, etc., which are executed by the processors. Each controller / translator unit sets a first mode where a single thread T1 executes on a single processor P1, orders a second mode for two or more threads T1, T2 that are forced to execute one at a time on a single processor P2 such as by setting affinity with that processor, and orders a third mode to selectively apply active memory consistency protection in relation to accesses to explicit or implicit shared memory while allowing the multiple threads T1, T2, T3, T4 to execute on the multiple processors.
Owner:IBM CORP
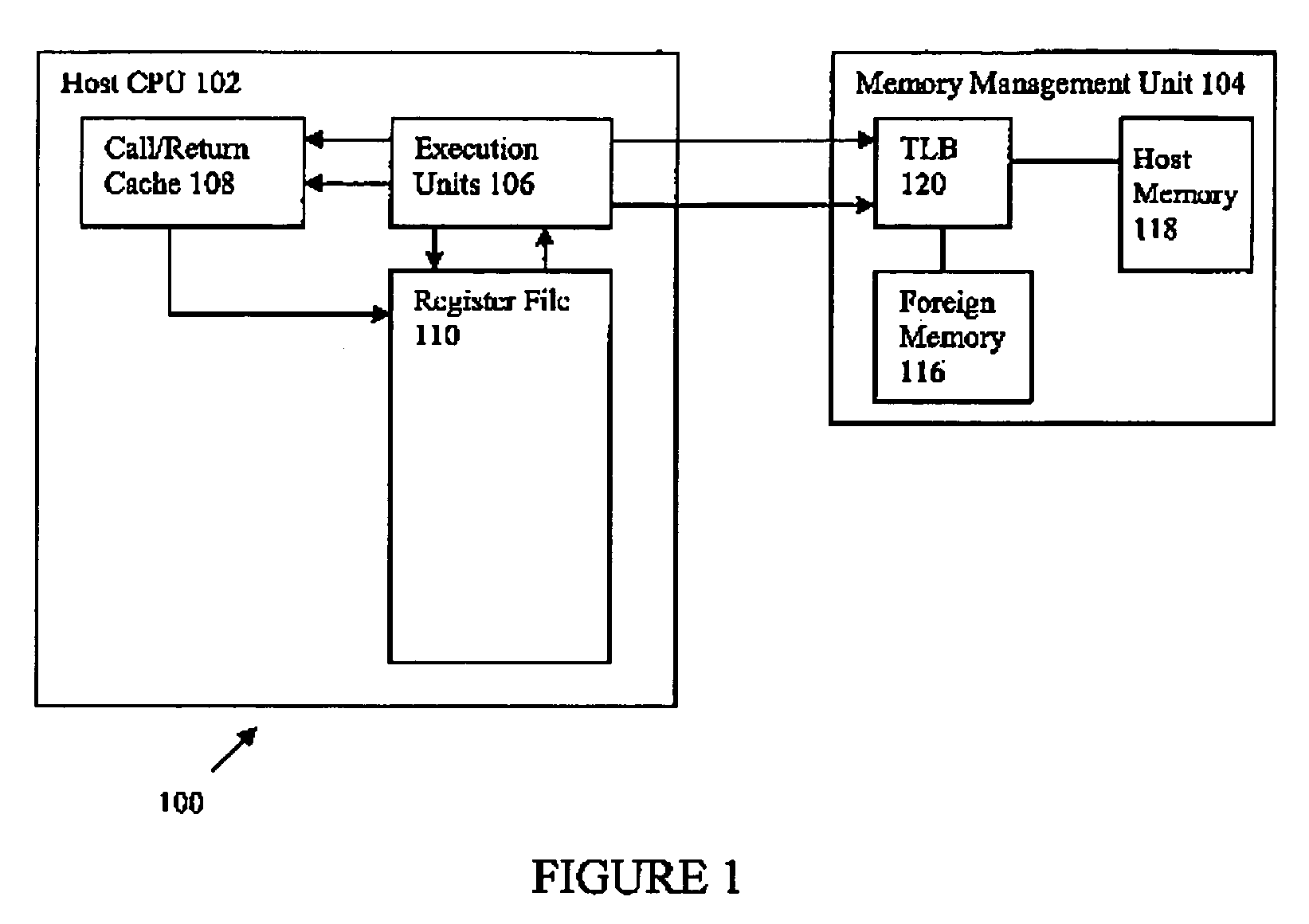
Prediction Mechanism for Subroutine Returns in Binary Translation Sub-Systems of Computers
Owner:VMWARE INC
Binary translation using peephole translation rules
InactiveUS20080172657A1Valid encodingEffective applicationBinary to binaryDigital computer detailsTheoretical computer scienceSoftware engineering
An efficient binary translator uses peephole translation rules to directly translate executable code from one instruction set to another. In a preferred embodiment, the translation rules are generated using superoptimization techniques that enable the translator to automatically learn translation rules for translating code from the source to target instruction set architecture.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
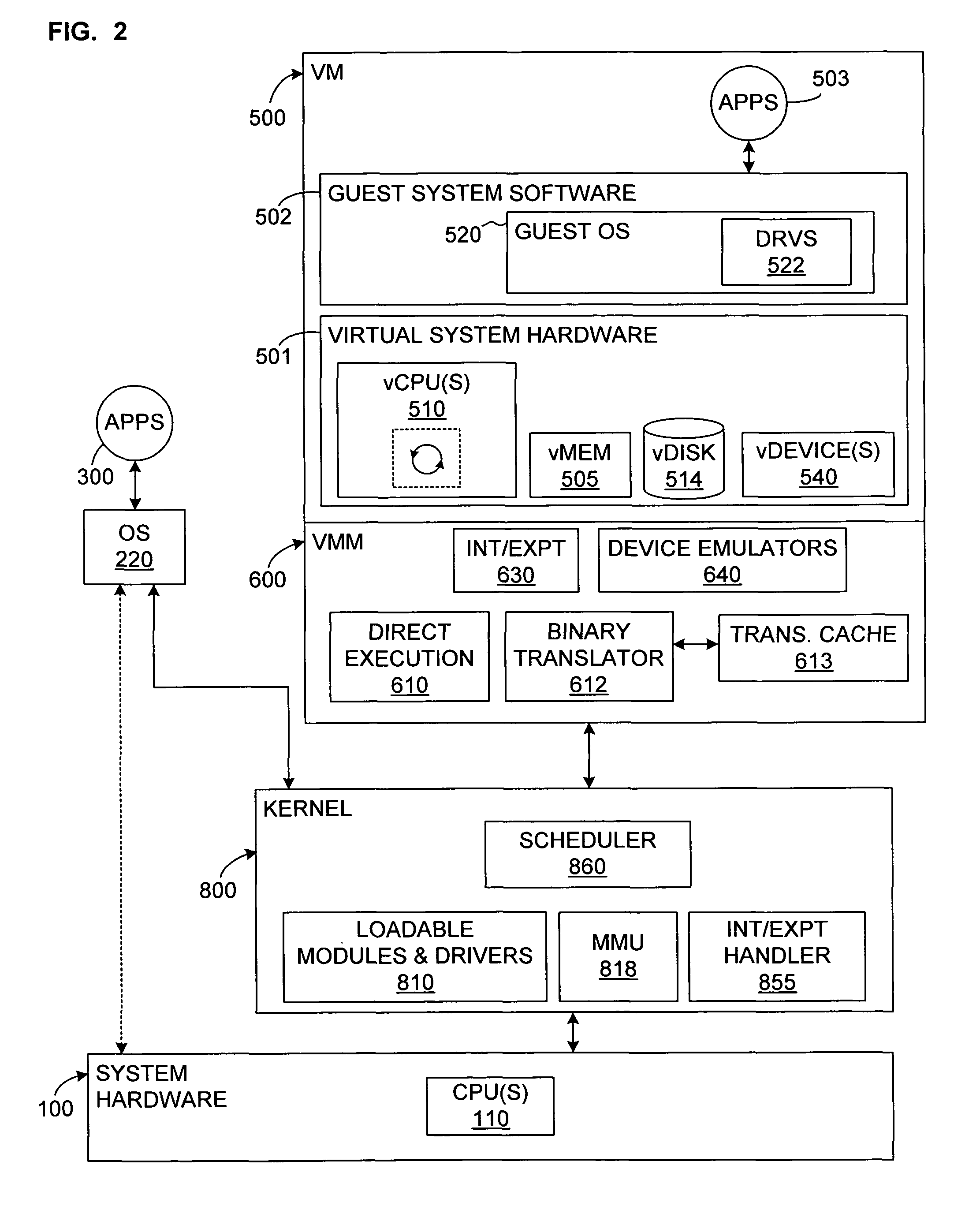
System and method for virtualizing processor and interrupt priorities
ActiveUS7590982B1Multiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationProcessor scheduling
Dispatching of interrupts to a processor is conditionally suppressed, that is, only if an old priority value and a new priority value are either both less than or both greater than a maximum pending priority value. This conditional avoidance of dispatching is preferably implemented by a virtual priority module within a binary translator in a virtualized computer system and relates to interrupts directed to a virtualized processor by a virtualized local APIC.
Owner:VMWARE INC
Simulator and simulating method for running guest program in host
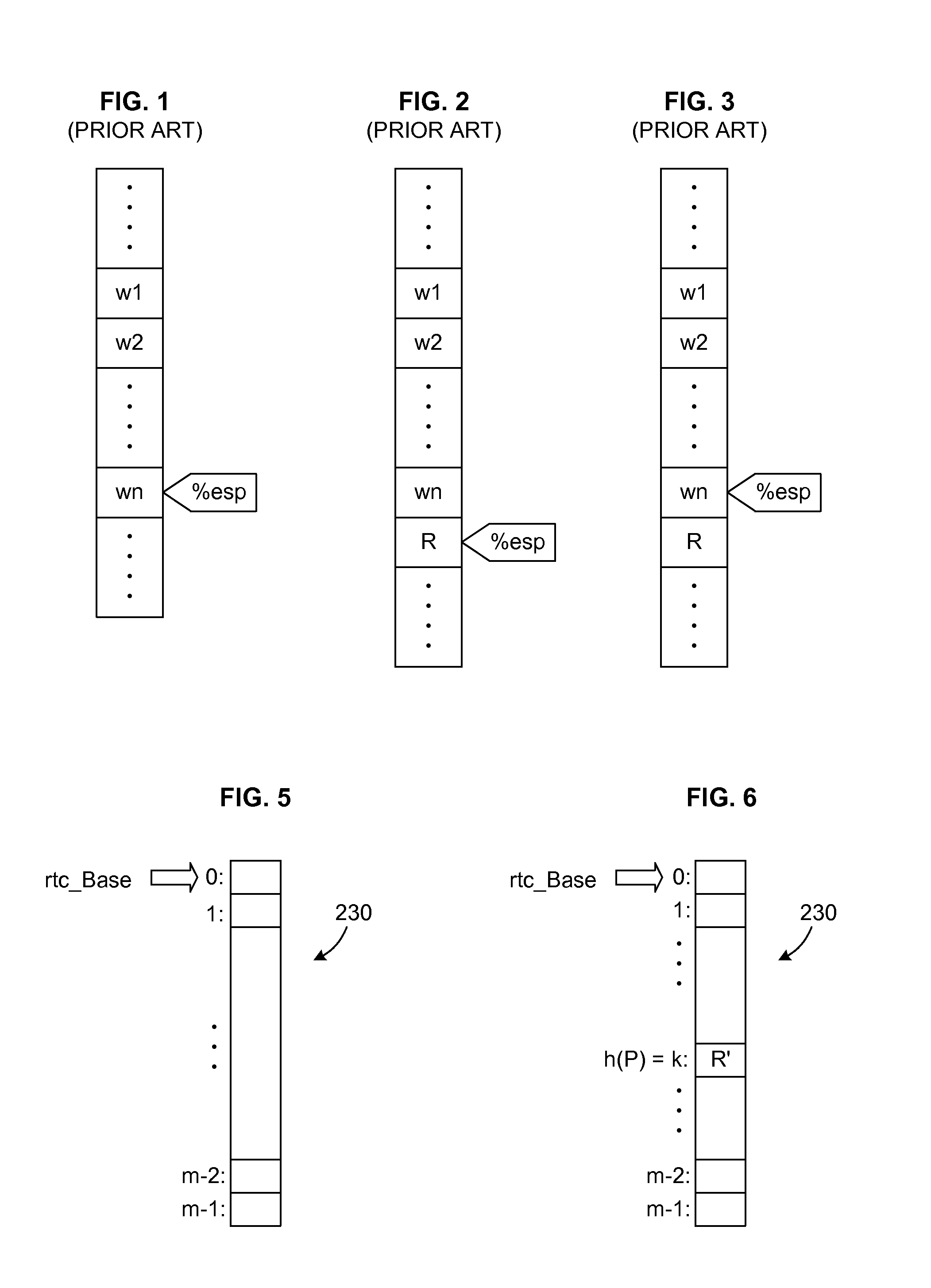
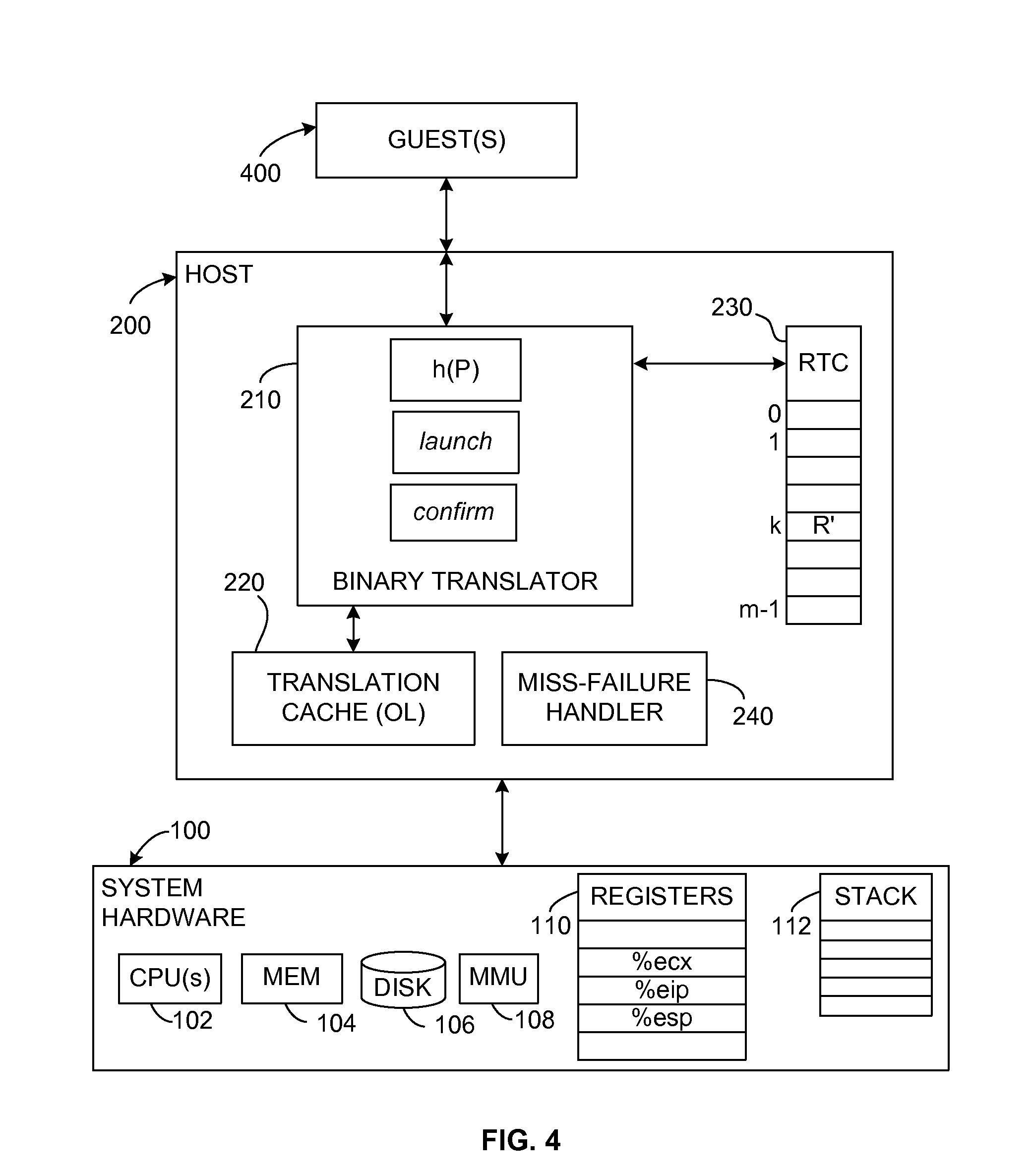
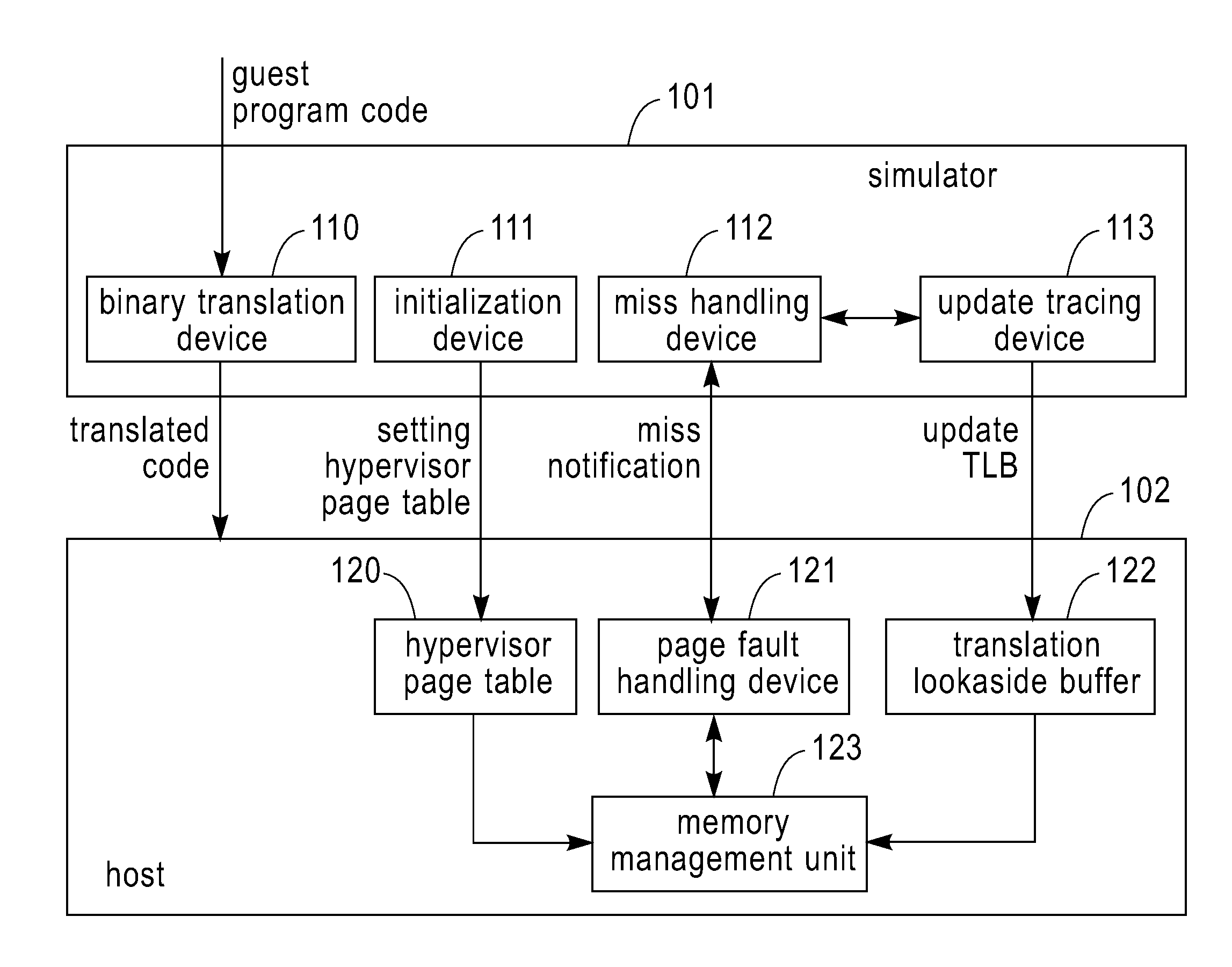
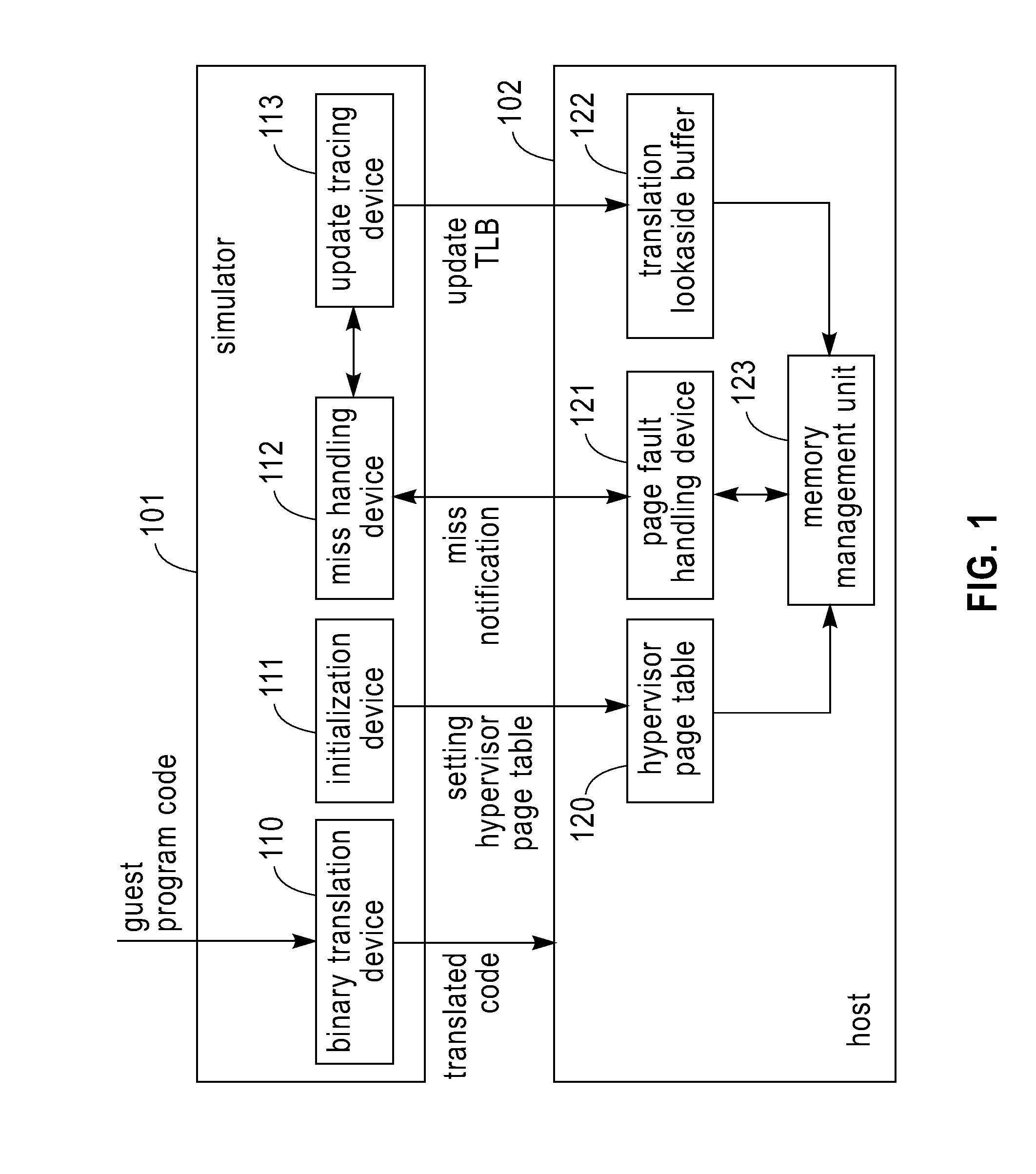
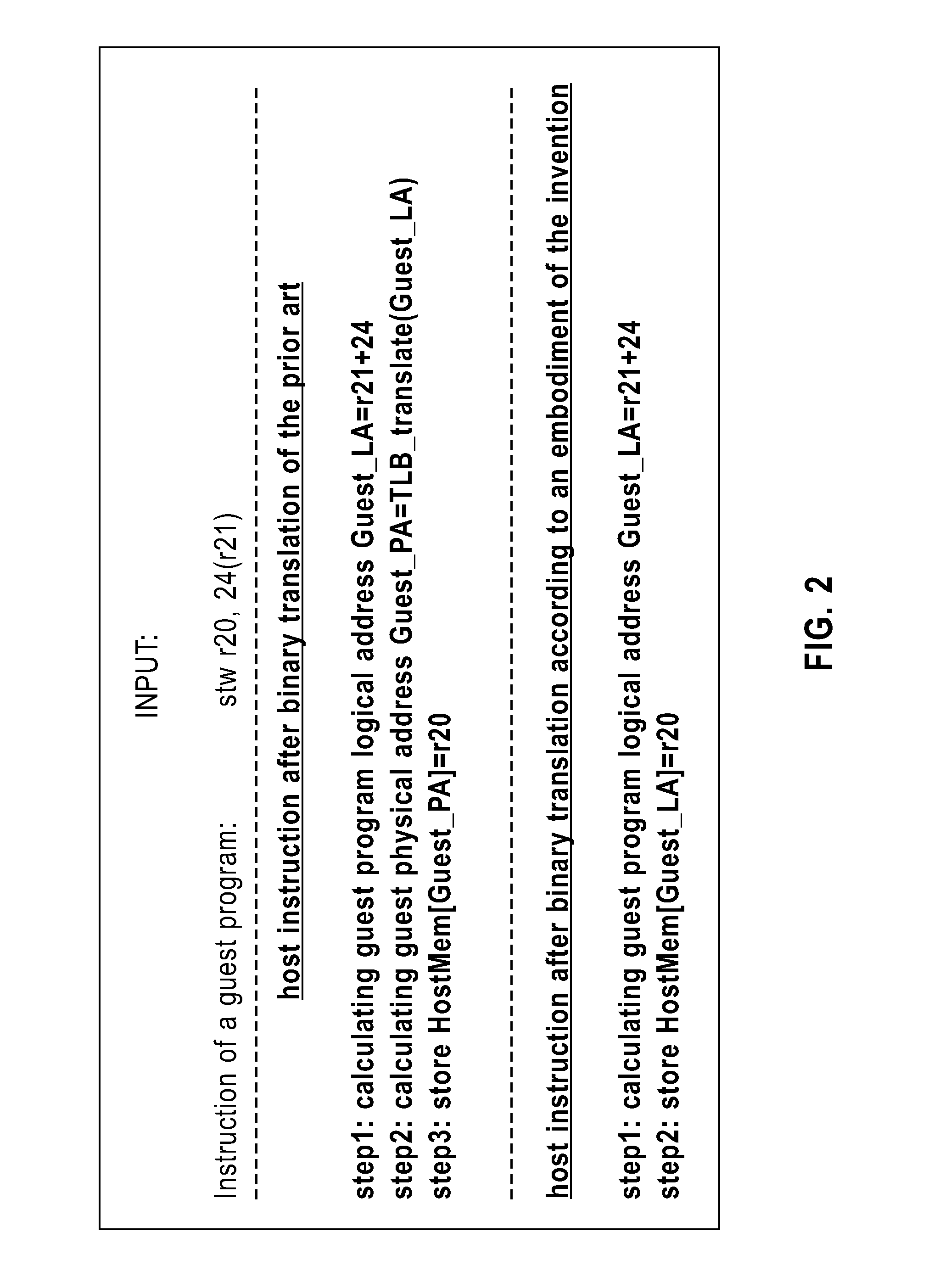
ActiveUS20100161875A1Improve executionEfficient executionMemory adressing/allocation/relocationComputer security arrangementsCode TranslationPage table
A Simulator and a simulating method for running a guest program in a host are disclosed. The simulator includes: an initialization device configured for setting content of a hypervisor page table in the host, the hypervisor page table mapping a guest physical address space to a host physical address space. The simulator further includes a binary translation device configured for employing a program logical address to perform a memory access in code translation. The simulator also includes a miss handling device configured for updating a guest translation look-aside buffer by treating a miss in a host translation look-aside buffer caused by the execution of the translated code as a miss in the guest translation look-aside buffer, wherein the host translation look-aside buffer is configured to buffer entries for mapping addresses in a guest program logical address space to addresses in the guest physical address space. The simulator further includes an update tracing device configured for, in response to the update to the guest translation look-aside buffer, perform the update to the host translation look-aside buffer. Also disclosed is a method for running a guest program in a host.
Owner:IBM CORP
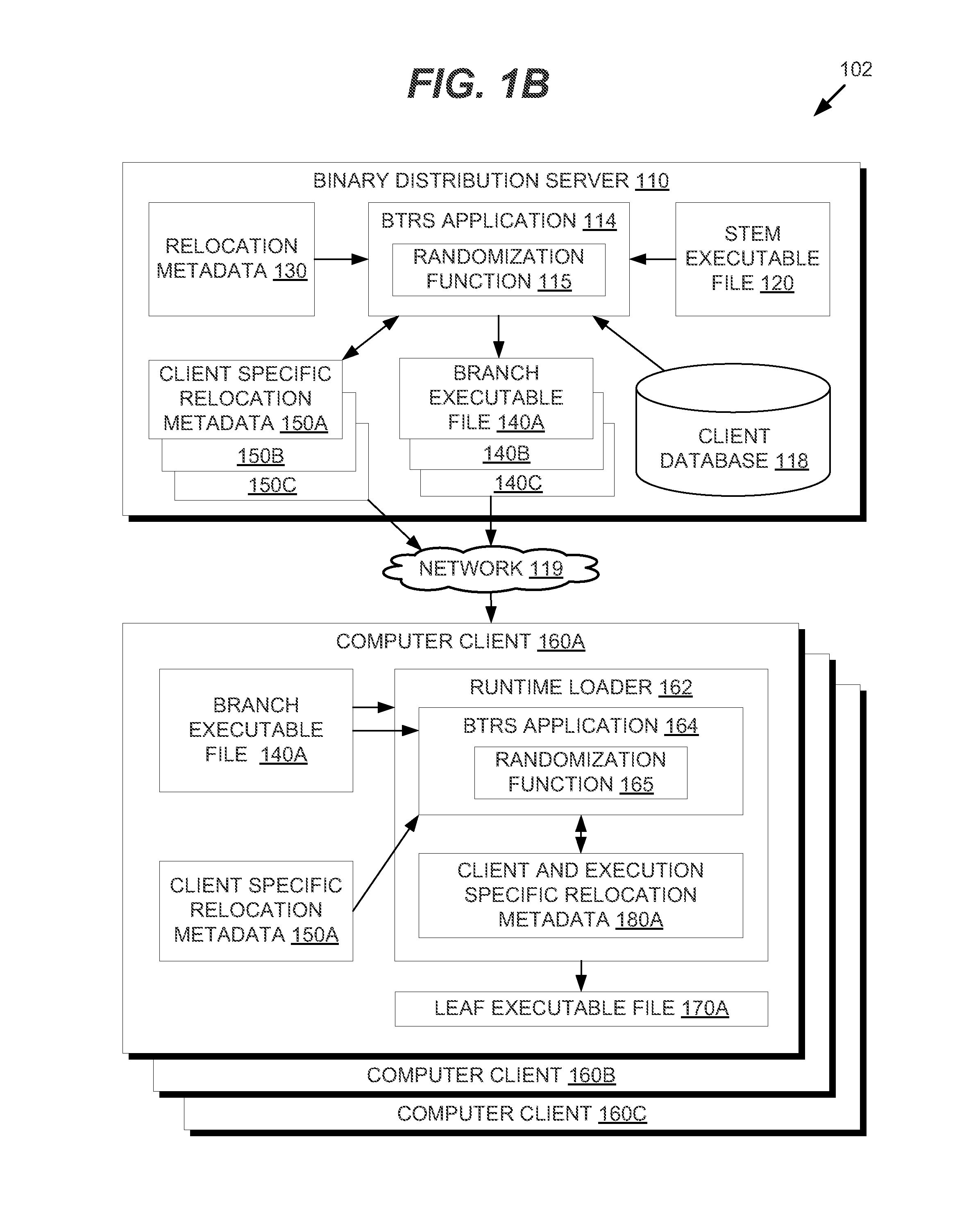
Binary Translation and Randomization System for Application Security
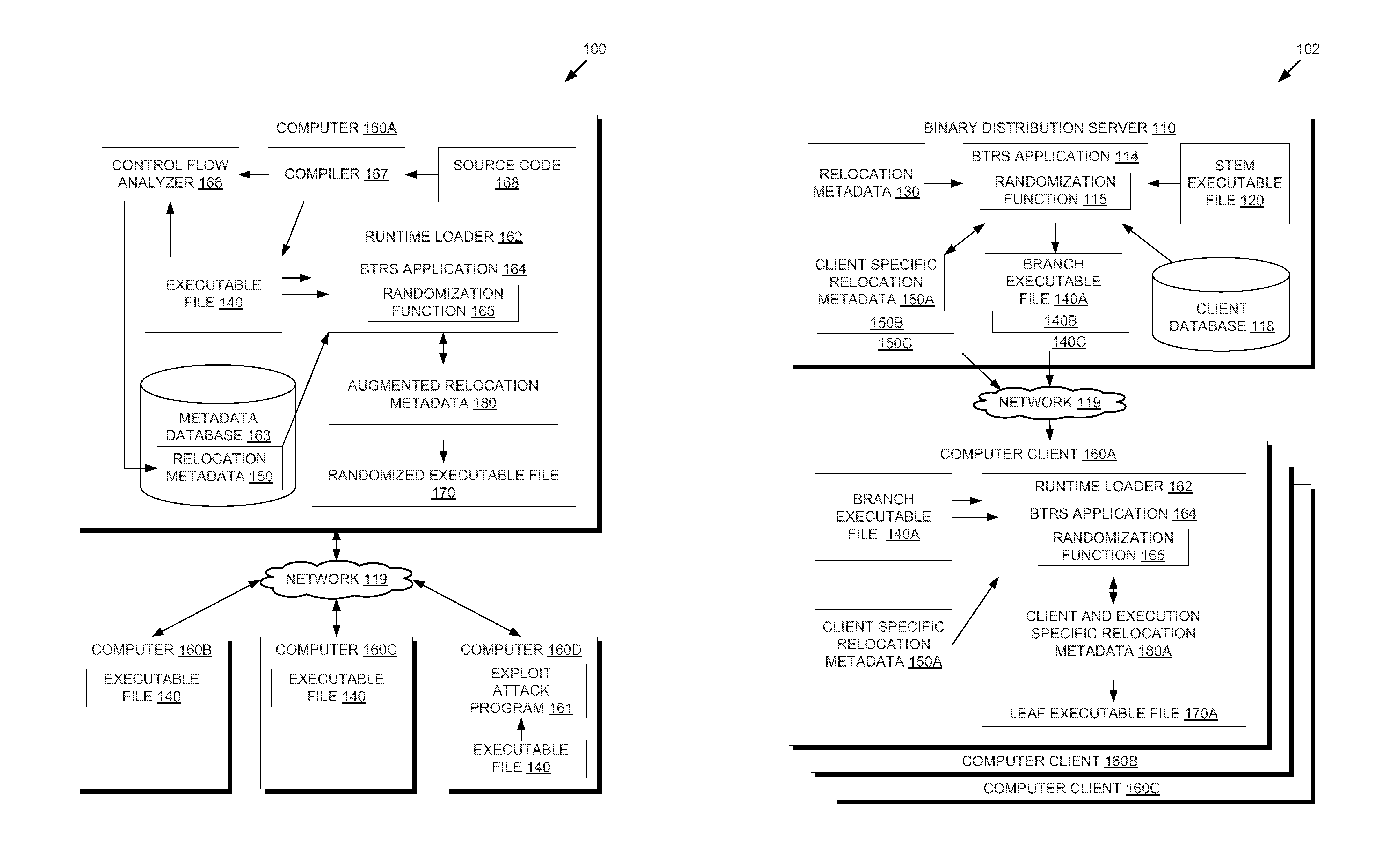
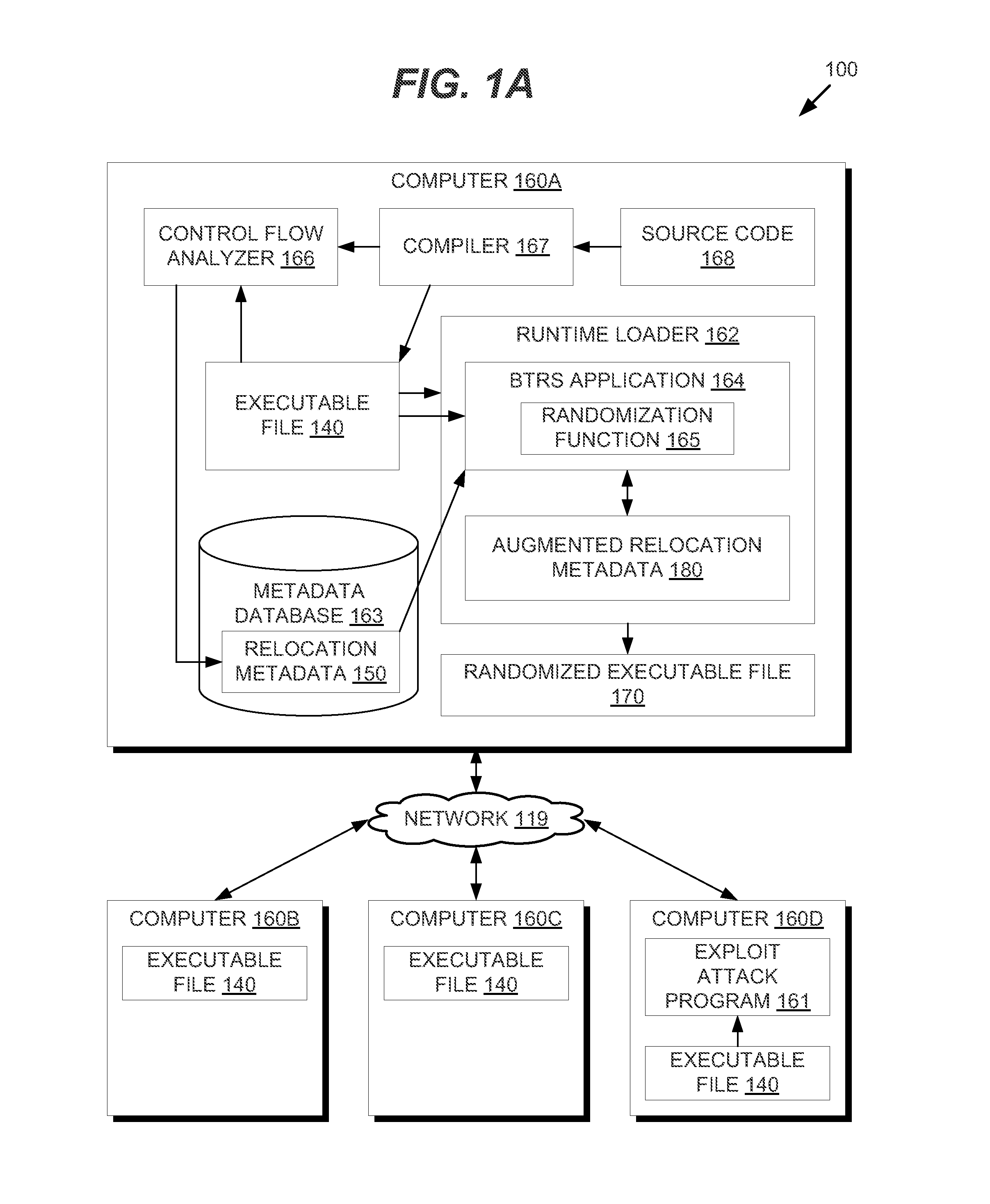
ActiveUS20150047049A1Digital data processing detailsAnalogue secracy/subscription systemsParallel computingExecution unit
In one embodiment, methods are described to provide a binary translation and randomization system. Relocation metadata is received, which comprises, for each of a plurality of execution units in an executable file, a mapping from the executable file into an address space range. For at least one of the plurality of execution units, the mapping is modified to replace instructions within the address space range with a relocated copy of the instructions at a randomly located address space range. An order of the plurality of execution units may thus be modified. An image is generated from the executable file using the relocation metadata, and an execution of the image is caused. The randomization may be carried out in two passes to provide executable files that are uniquely randomized for each computer and for each execution.
Owner:CISCO TECH INC
Restricting memory access to protect data when sharing a common address space
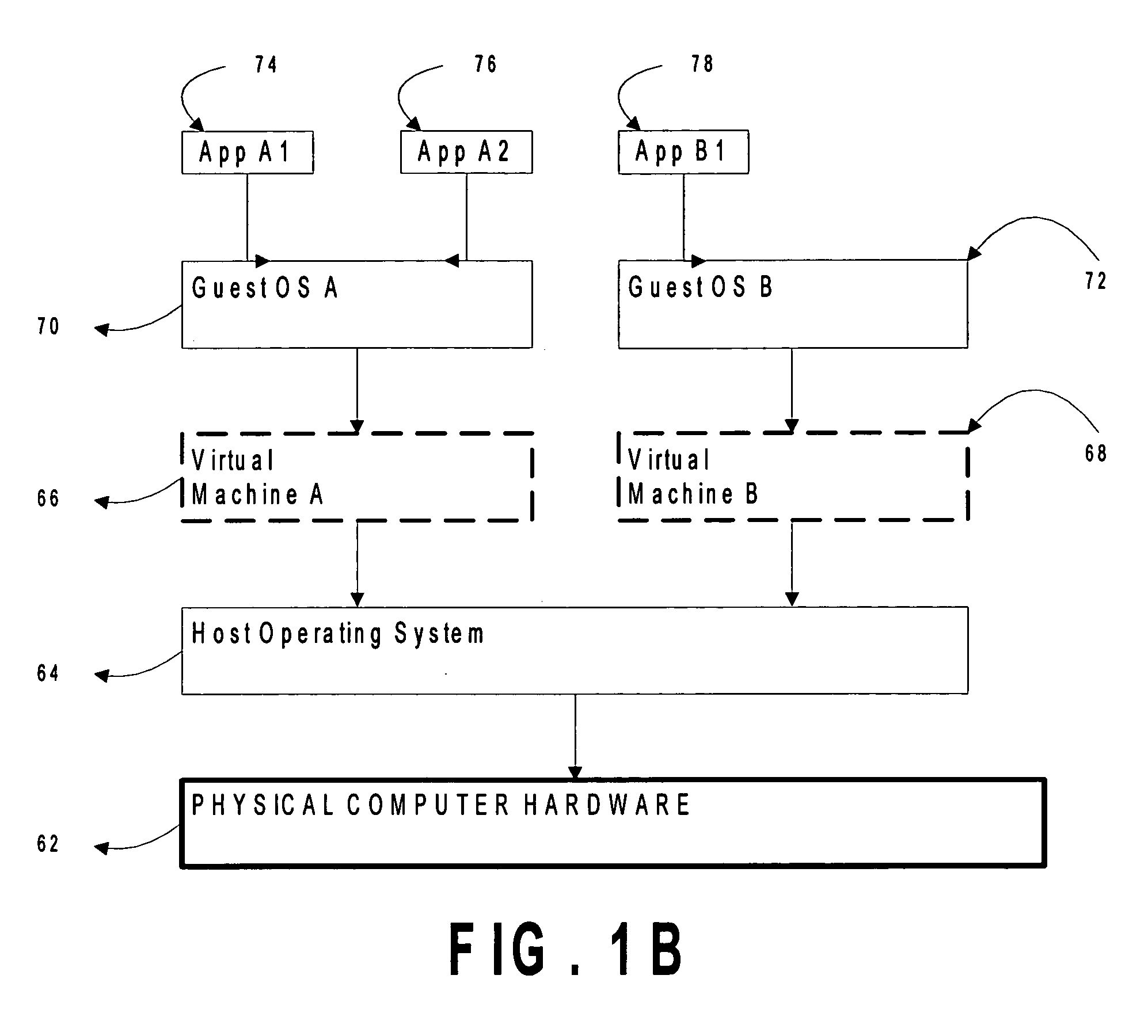
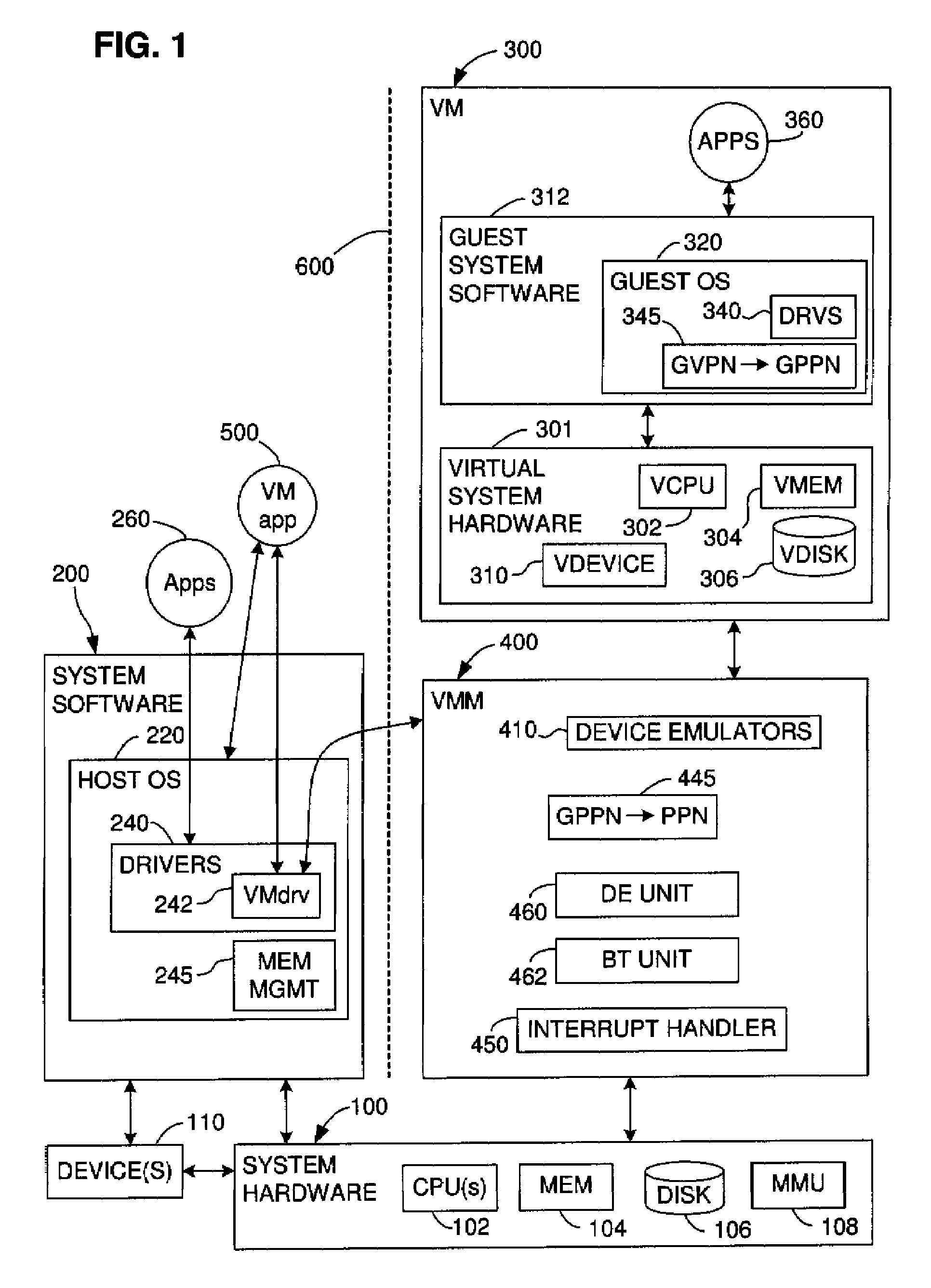
ActiveUS7281102B1Avoid accessMemory architecture accessing/allocationComputer security arrangementsVirtual computingDirect execution
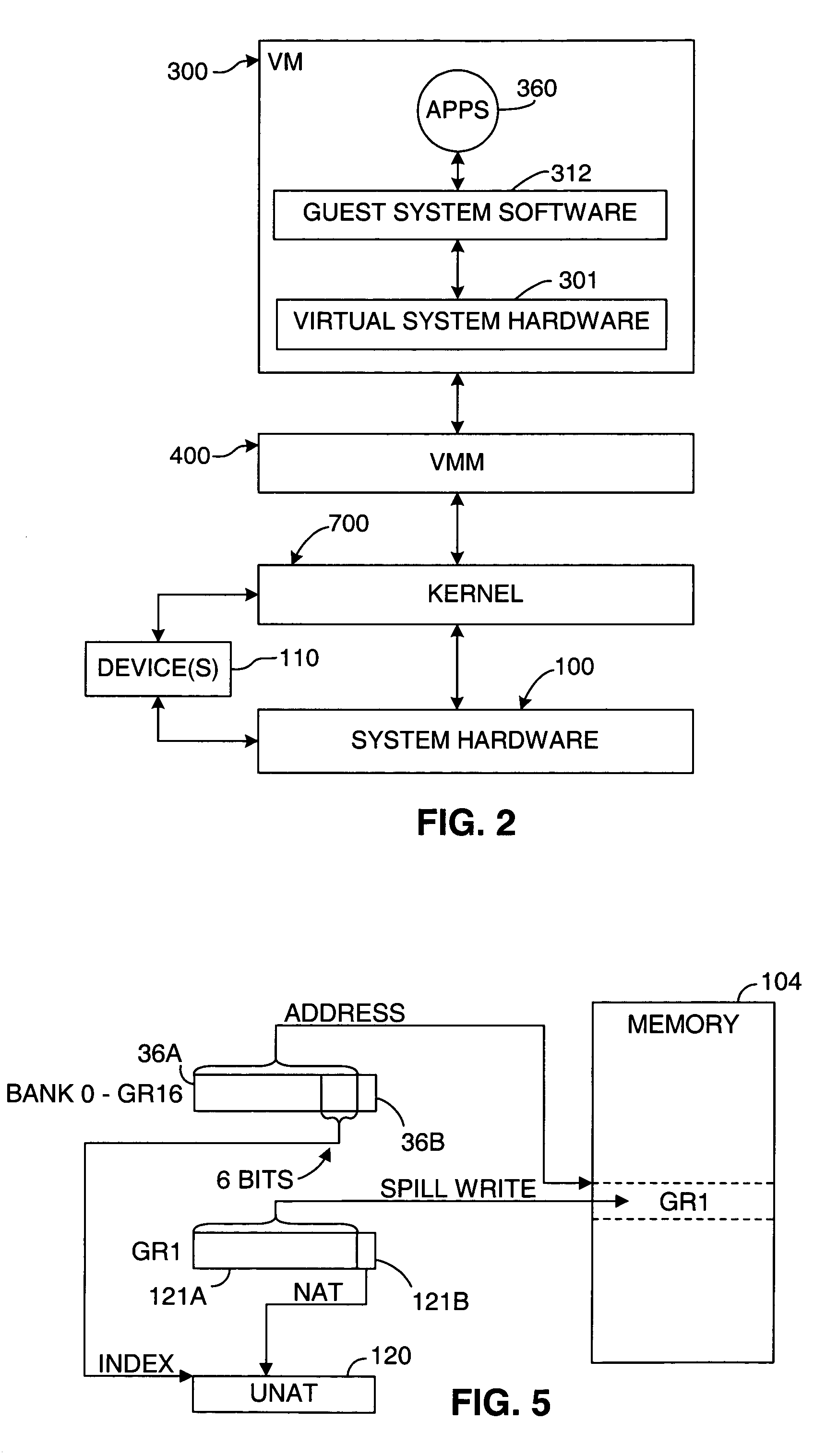
A first software entity occupies a portion of a linear address space of a second software entity and prevents the second software entity from accessing the memory of the first software entity. For example, in one embodiment of the invention, the first software entity is a virtual machine monitor (VMM), which supports a virtual machine (VM), the second software entity. The VMM sometimes directly executes guest instructions from the VM and, at other times, the VMM executes binary translated instructions derived from guest instructions. When executing binary translated instructions, the VMM uses memory segmentation to protect its memory. When directly executing guest instructions, the VMM may use either memory segmentation or a memory paging mechanism to protect its memory. When the memory paging mechanism is active during direct execution, the protection from the memory segmentation mechanism may be selectively deactivated to improve the efficiency of the virtual computer system.
Owner:VMWARE INC
Method and apparatus for handling dynamically linked function calls with respect to program code conversion
ActiveUS20080092151A1Reduce processReduce memory overheadInterprogram communicationMemory systemsControl flowObject code
A technique is provided for handling dynamically linked subject function calls arranged pass subject control flow to an intermediate control structure such as a procedure linkage table, then to subject linker code for modifying link information associated with the subject function calls during translation of subject code into target code in a dynamic binary translator. The subject code for execution on a subject processor is received by a translator, and corresponding target code for execution on the target processor is generated. The translator is arranged to build a function linkage table containing an entry giving the location of each function called by the subject code, so that code can be generated by the translator in which subject function calls are associated with code for performing the function, without generating target code corresponding to the intermediate control structure.
Owner:IBM CORP
Controlling compatibility levels of binary translations between instruction set architectures
In an embodiment, a method includes receiving a binary of a program code. The binary is based on a first instruction set architecture. The method also includes translating the binary, wherein the translated binary is based on a combination of the first instruction set architecture and a second instruction set architecture.
Owner:INTEL CORP
Selective omission of endian translation to enhance emulator performance
A JIT binary translator examines code to determine if a conversion from big-endian to little-endian can be omitted. For example, the conversion may be omitted when data is merely being loaded and stored. The conversion from big-endian to little-endian may also be omitted when storing certain constructs and numbers. A third example is loading of floating point values. If a conversion from big-endian to little-endian is performed, this could result in four instructions in PowerPC, seven if double precision. However, if floating point values are access consistently as big-endian, the result is only one PowerPC instruction. Optimizations, such as these result in a tighter emulated binary.
Owner:MICROSOFT TECH LICENSING LLC
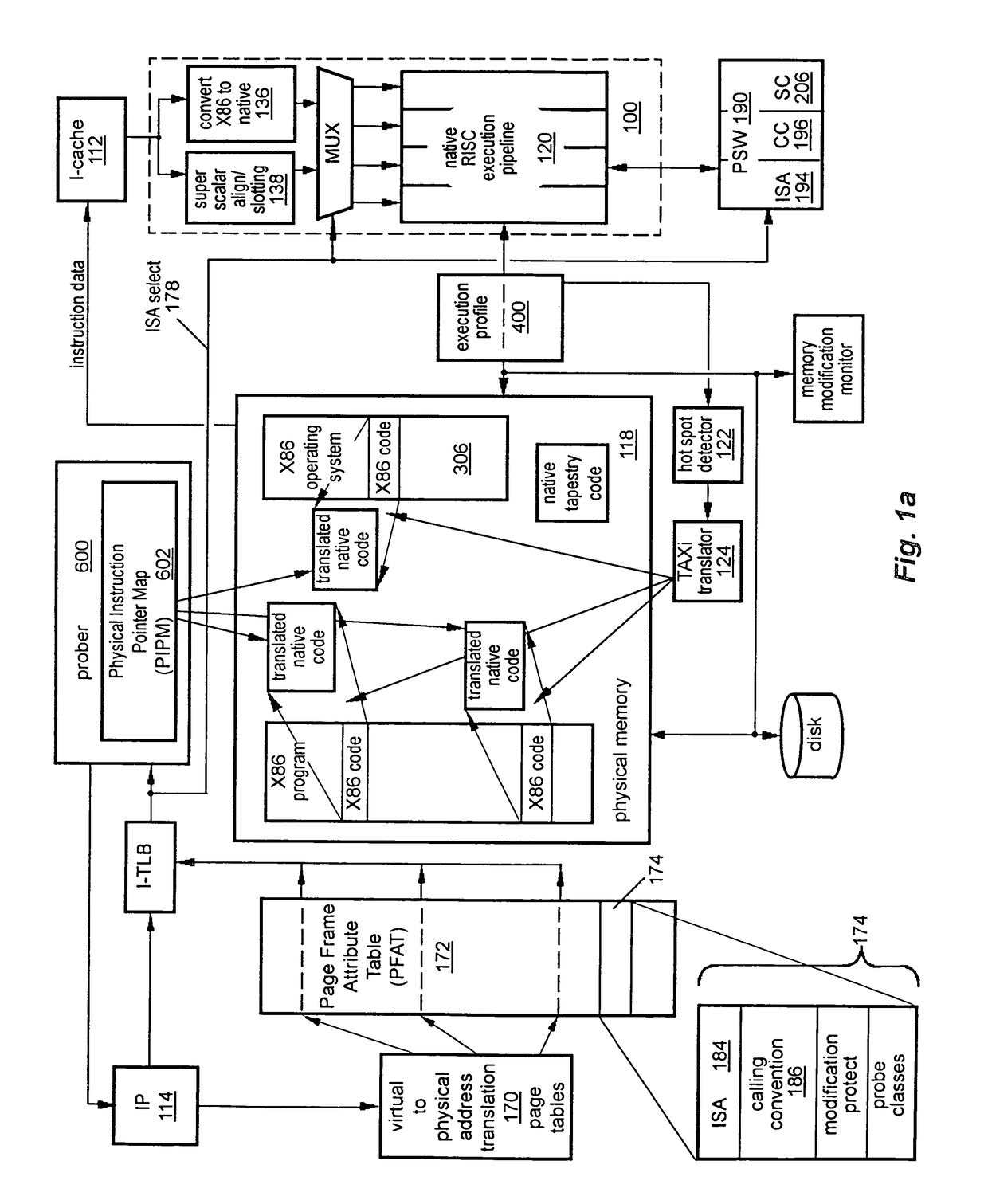
Instruction and logic to perform dynamic binary translation
A micro-architecture may provide a hardware and software co-designed dynamic binary translation. The micro-architecture may invoke a method to perform a dynamic binary translation. The method may comprise executing original software code compiled targeting a first instruction set, using processor hardware to detect a hot spot in the software code and passing control to a binary translation translator, determining a hot spot region for translation, generating the translated code using a second instruction set, placing the translated code in a translation cache, executing the translated code from the translated cache, and transitioning back to the original software code after the translated code finishes execution.
Owner:INTEL CORP
Method and system for multimode simulator generation from an instruction set architecture specification
InactiveUS20050015754A1Improve performanceReduce overheadSoftware simulation/interpretation/emulationMemory systemsGlobal simulationInstruction set
The present invention discloses method and system for a multimode simulator having an emulation core with improved performance. In an embodiment of the invention, the overhead caused by the exclusive use of the simulation technique using one instruction-at-a-time interpretation is reduced by additionally using binary translation for executed blocks of interpreted instructions (i.e. that contain no jumps out of the block) from the same instruction set architecture description. Since performing translations too frequently can undesirably increase overhead by overloading the cache, the binary translation is only performed for blocks that are executed frequently. Once the blocks are translated e.g. by forming the block from instructions via templates and generating the collective code, the overall simulator performance is significantly improved by running the blocks instead of running the instructions one-at-a-time.
Owner:VIRTUTECH
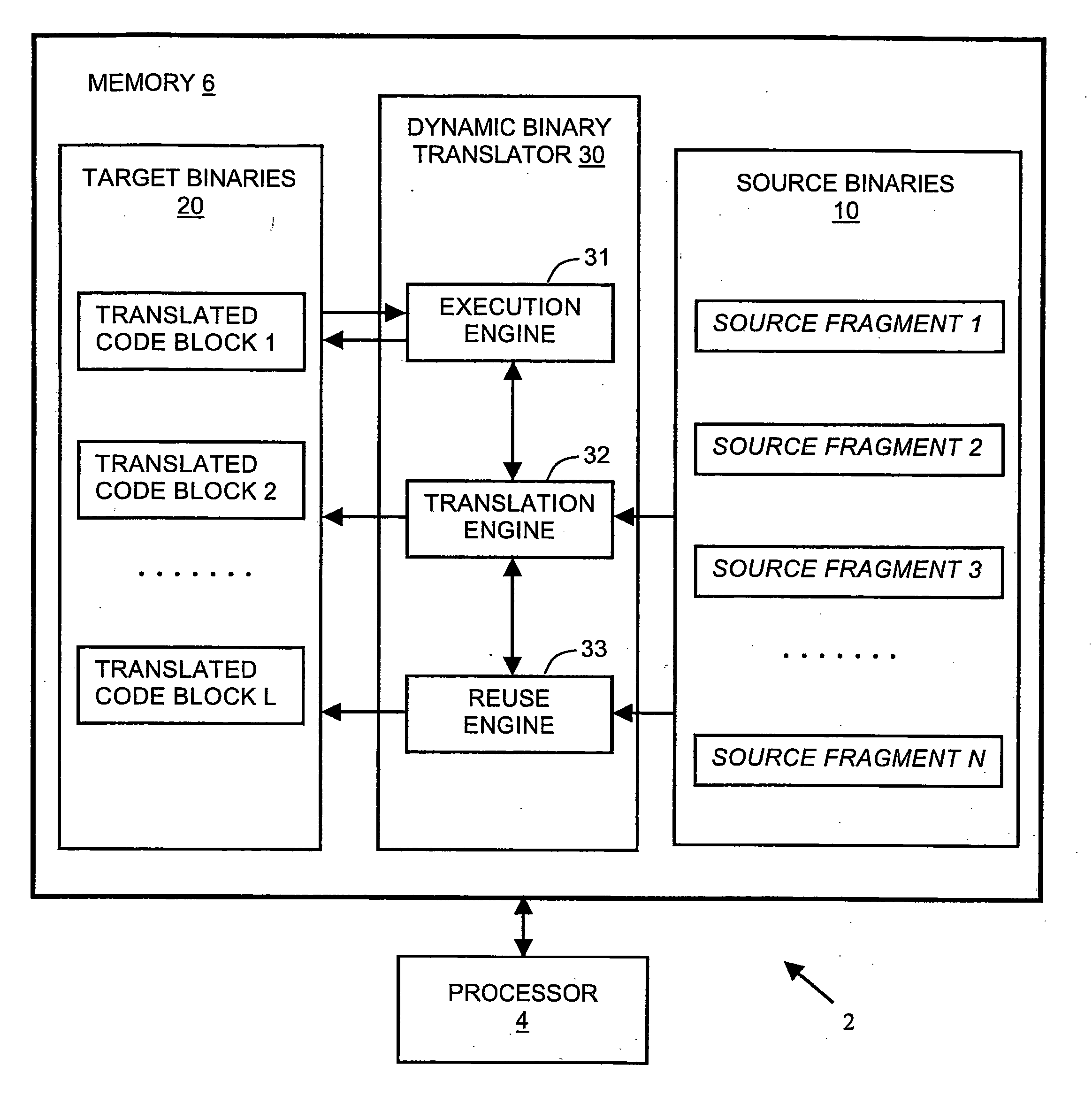
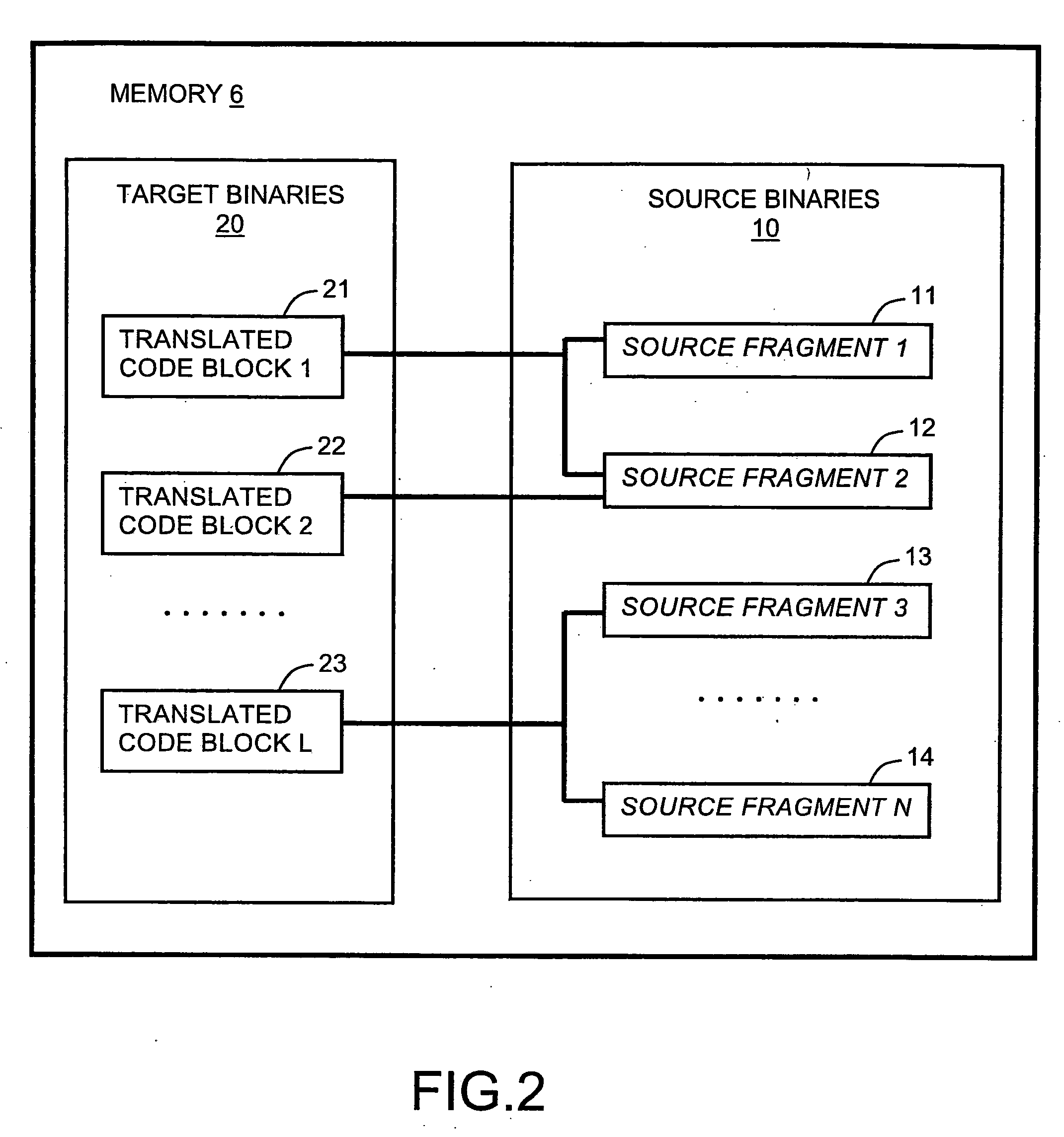
Apparatus, system, and method of dynamic binary translation with translation reuse
Embodiments of the invention disclose a method, apparatus and system of translating a source binary code into a target binary code. The translation according to embodiments of the invention may include determining whether or not a previously translated code block that relates to a source fragment to be currently translated may be reused for execution by a target processor. A reusability status of the previously translated code block may be determined based on a reusability status of a group of previously translated code blocks. In some embodiments, when no previously translated code blocks relating to the currently translated source fragment are found, the source fragment may be translated into a new target code block, which may be executed by the target processor. The new target code block may then be added to a group of previously translated code blocks.
Owner:INTEL CORP
Method for realizing virtual execution environment of central processing unit (CPU)/graphics processing unit (GPU) heterogeneous platform
ActiveCN101963918AMultiple digital computer combinationsSoftware simulation/interpretation/emulationData streamMulticore architecture
The invention relates to a method for realizing a virtual execution environment of a central processing unit (CPU) / graphics processing unit (GPU) heterogeneous platform, which belongs to the technical field of telecommunication. In the method, programs can be run on an X86CPU and NVIDIA GPU hybrid architecture by a dynamic binary translation technique; static information and dynamic information of the programs are acquired by the dynamic binary translation technique; program execution nested loops, a dependency relationship among the loops and data streams of inlet and outlet hot blocks are searched through the information; and the execution is implemented by two steps of: 1, acquiring information, optimizing the hot blocks and storing the hot blocks into files; 2, and generating a hybridprogram comprising a serial instruction and a parallel instruction and executing the program comprising the hybrid instructions. The method has the advantages that: the traditional serial programs can be run a CPU / GPU heterogeneous multi-core architecture by the dynamic binary translation technique, without modifying program source codes; and the execution of the programs can be accelerated by the GPU.
Owner:SHANGHAI JIAO TONG UNIV
Selective descheduling of idling guests running on a host computer system
Guests, such as virtual machines, that are running on a host hardware platform are selectively descheduled when an idling condition is detected. An example of the idling condition is that the guest has been executing instructions in an idle loop for more than a threshold period. Guest instructions may be evaluated for the idling condition in conjunction with binary translation.
Owner:VMWARE INC
Restricting memory access to protect data when sharing a common address space
ActiveUS7506122B1Memory architecture accessing/allocationComputer security arrangementsTerm memoryLinearity
A first software entity occupies a portion of a linear address space of a second software entity and prevents the second software entity from accessing the memory of the first software entity. For example, in one embodiment of the invention, the first software entity is a virtual machine monitor (VMM), which supports a virtual machine (VM), the second software entity. The VMM sometimes directly executes guest instructions from the VM and, at other times, the VMM executes binary translated instructions derived from guest instructions. When executing binary translated instructions, the VMM uses memory segmentation to protect its memory. When directly executing guest instructions, the VMM may use either memory segmentation or a memory paging mechanism to protect its memory. When the memory paging mechanism is active during direct execution, the protection from the memory segmentation mechanism may be selectively deactivated to improve the efficiency of the virtual computer system.
Owner:VMWARE INC
Method and apparatus for preserving precise exceptions in binary translated code
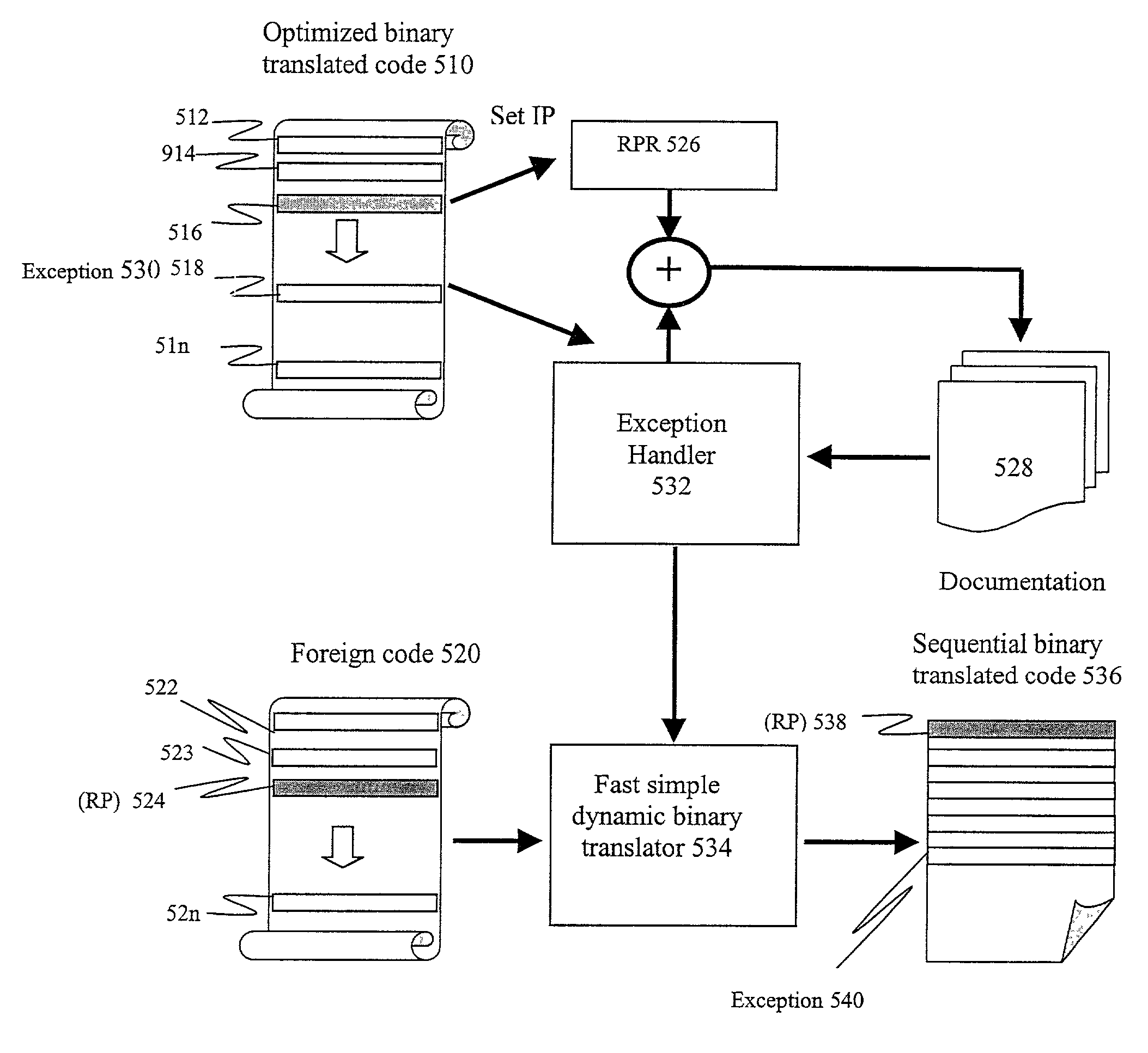
InactiveUS7065750B2Minimize the numberQuick fixMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationTheoretical computer scienceAdditional documentation
Precise exceptions handling in the optimized binary translated code is achieved by transitioning execution to the non-optimized step-by-step foreign code execution means in accordance with one of the several coherent foreign states designated during the optimized translation of the foreign code. A method to improve the operation by avoiding complete foreign state updates in the optimized code, an apparatus to track the switching between the states and a method to recompute the complete foreign state in accordance to the current state identification, execution context and additional documentation provided during the translation time are proposed.
Owner:ELBRUS INT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com