Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2972 results about "Semantics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Semantics (from Ancient Greek: σημαντικός sēmantikós, "significant") is the linguistic and philosophical study of meaning in language, programming languages, formal logics, and semiotics. It is concerned with the relationship between signifiers—like words, phrases, signs, and symbols—and what they stand for in reality, their denotation.
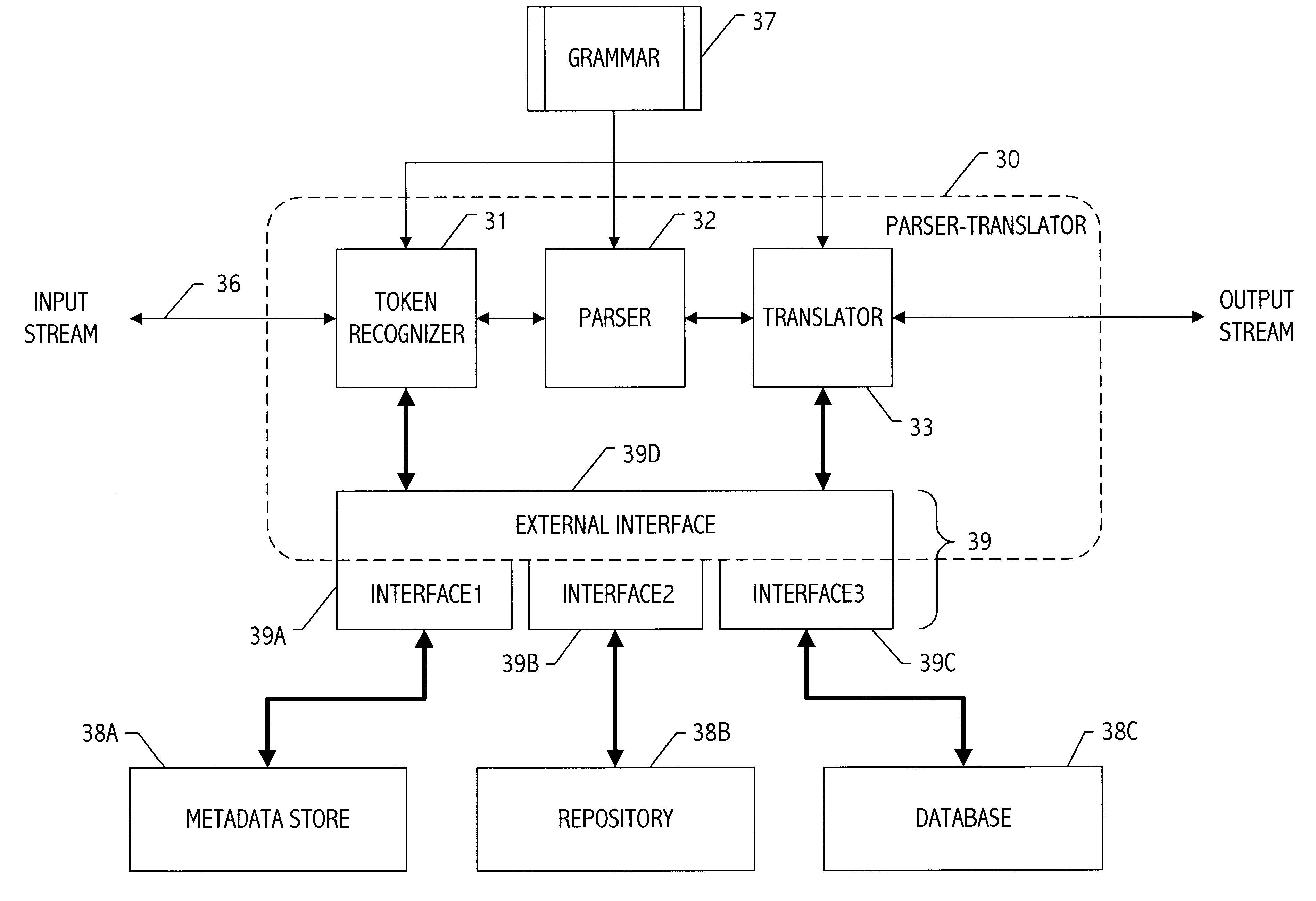
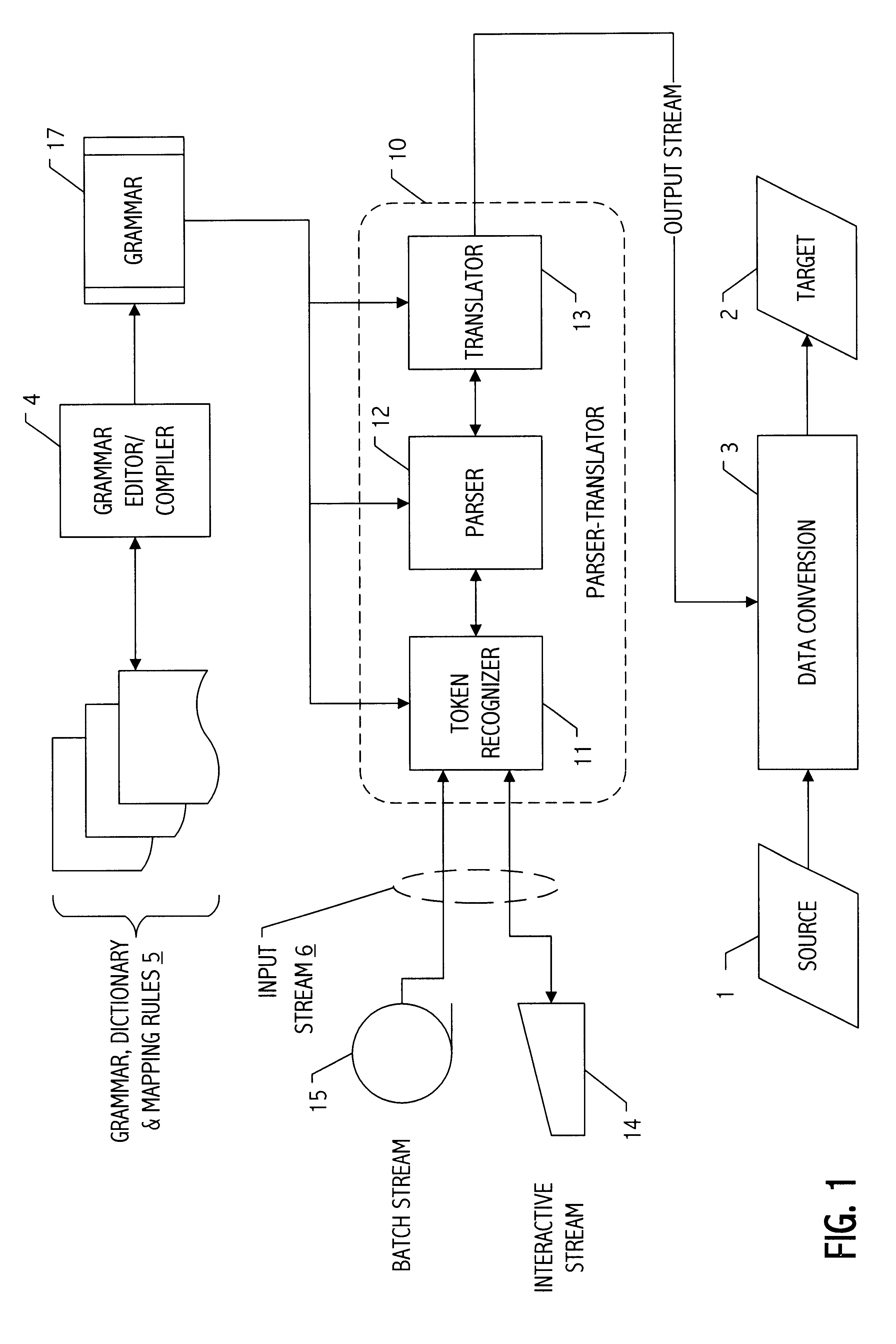
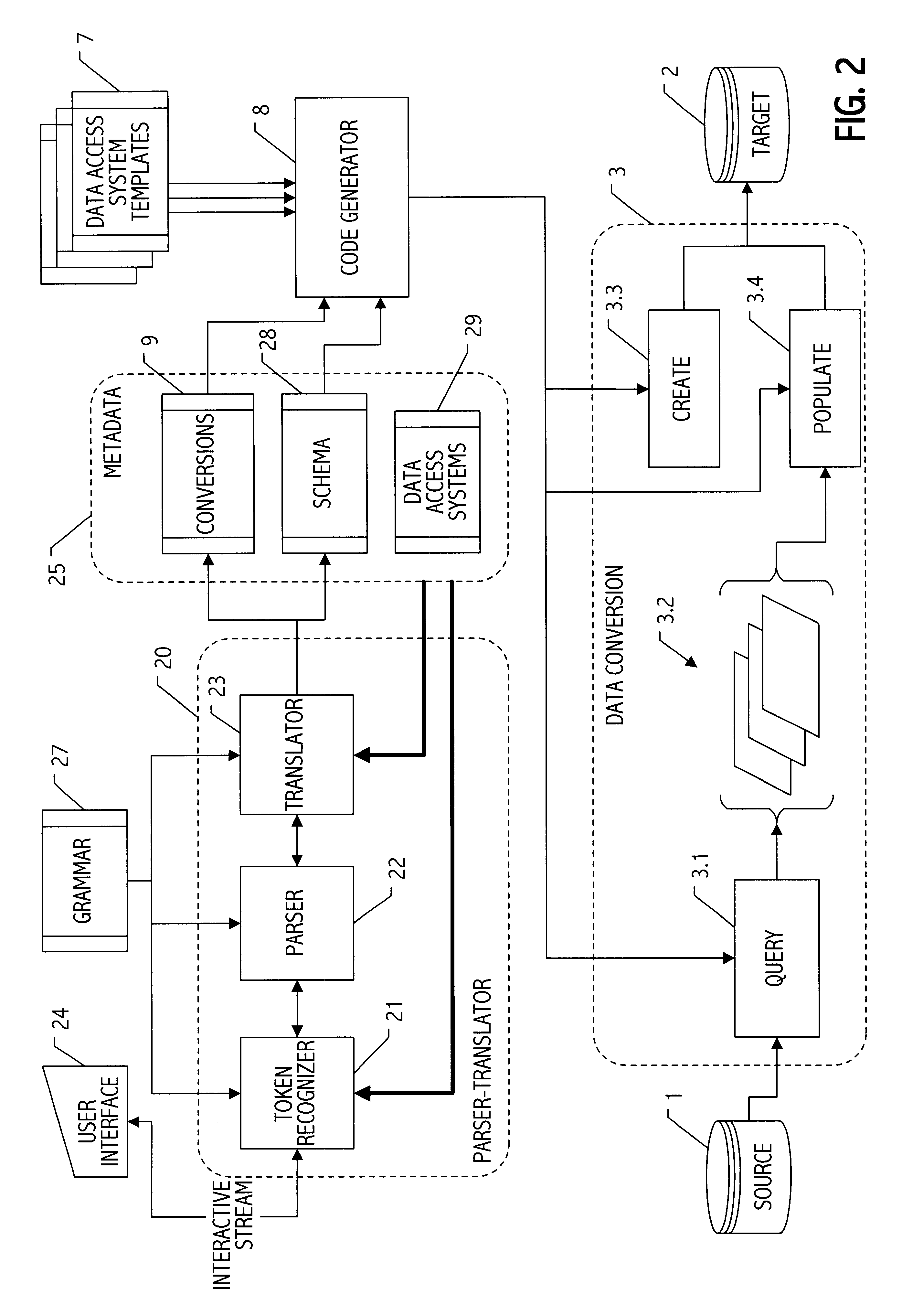
Parser translator system and method
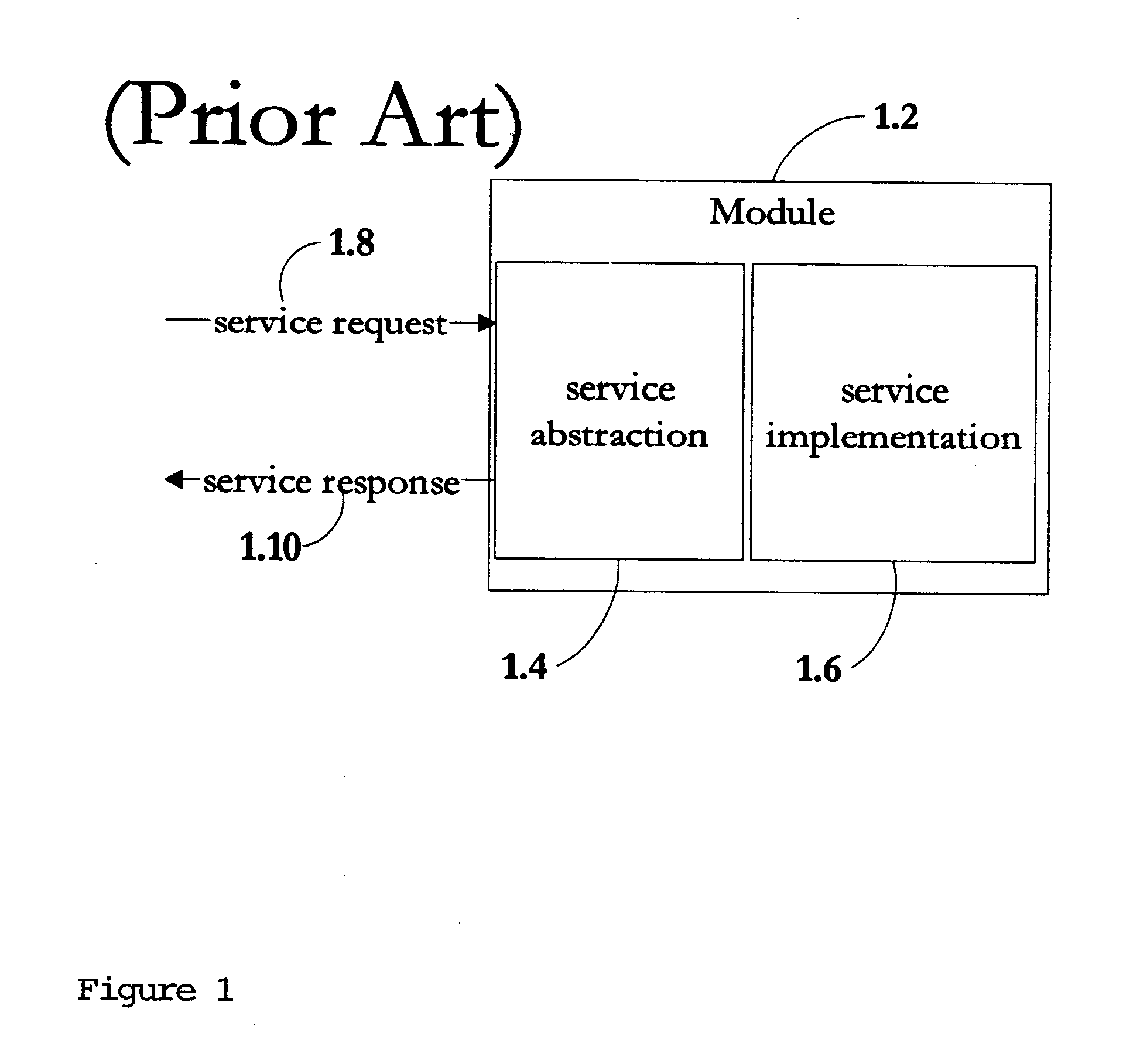
A parser-translator technology allows a user to specify complex test and / or transformation statements in a high-level user language, to ensure that such test and / or transformation statements are well-formed in accordance with a grammar defining legal statements in the user language, and to translate statements defined by the user into logically and syntactically correct directives for performing the desired data transformations or operations. Using the parser-translator technology, a user can focus on the semantics of the desired operations and need not be concerned with the proper syntax of a language for a particular system. Instead, grammars (i.e., data) define the behavior of a parser-translator implementation by encoding the universe of statements (e.g., legal test and / or transformation statements) and by encoding translations appropriate to a particular data processing application (e.g., a data conversion program, etc.). Some parser-translator implementations described herein interface dynamically with other systems and / or repositories to query for information about objects, systems and states represented therein, and / or their respective interfaces. Some grammars described herein encode sensitivity to an external context. In this way, context-sensitive prompting and validation of correct specification of statements is provided. A combination of parser technology and dynamic querying of external system state allows users to build complex statements (e.g., using natural languages within a user interface environment) and to translate those complex statements into statements or directives appropriate to a particular data processing application.
Owner:VERSATA
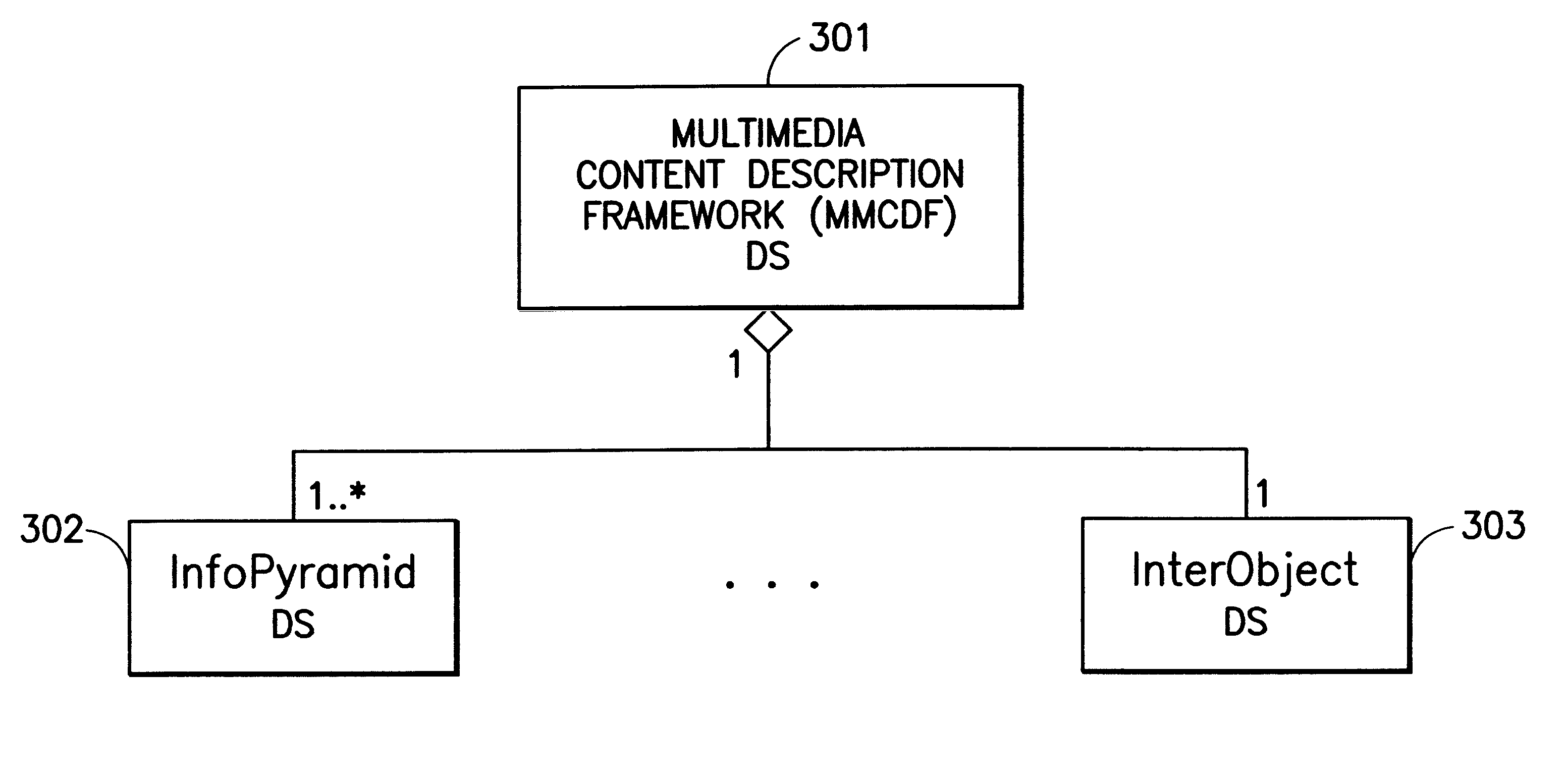
Multimedia content description framework
A framework is provided for describing multimedia content and a system in which a plurality of multimedia storage devices employing the content description methods of the present invention can interoperate. In accordance with one form of the present invention, the content description framework is a description scheme (DS) for describing streams or aggregations of multimedia objects, which may comprise audio, images, video, text, time series, and various other modalities. This description scheme can accommodate an essentially limitless number of descriptors in terms of features, semantics or metadata, and facilitate content-based search, index, and retrieval, among other capabilities, for both streamed or aggregated multimedia objects.
Owner:IBM CORP
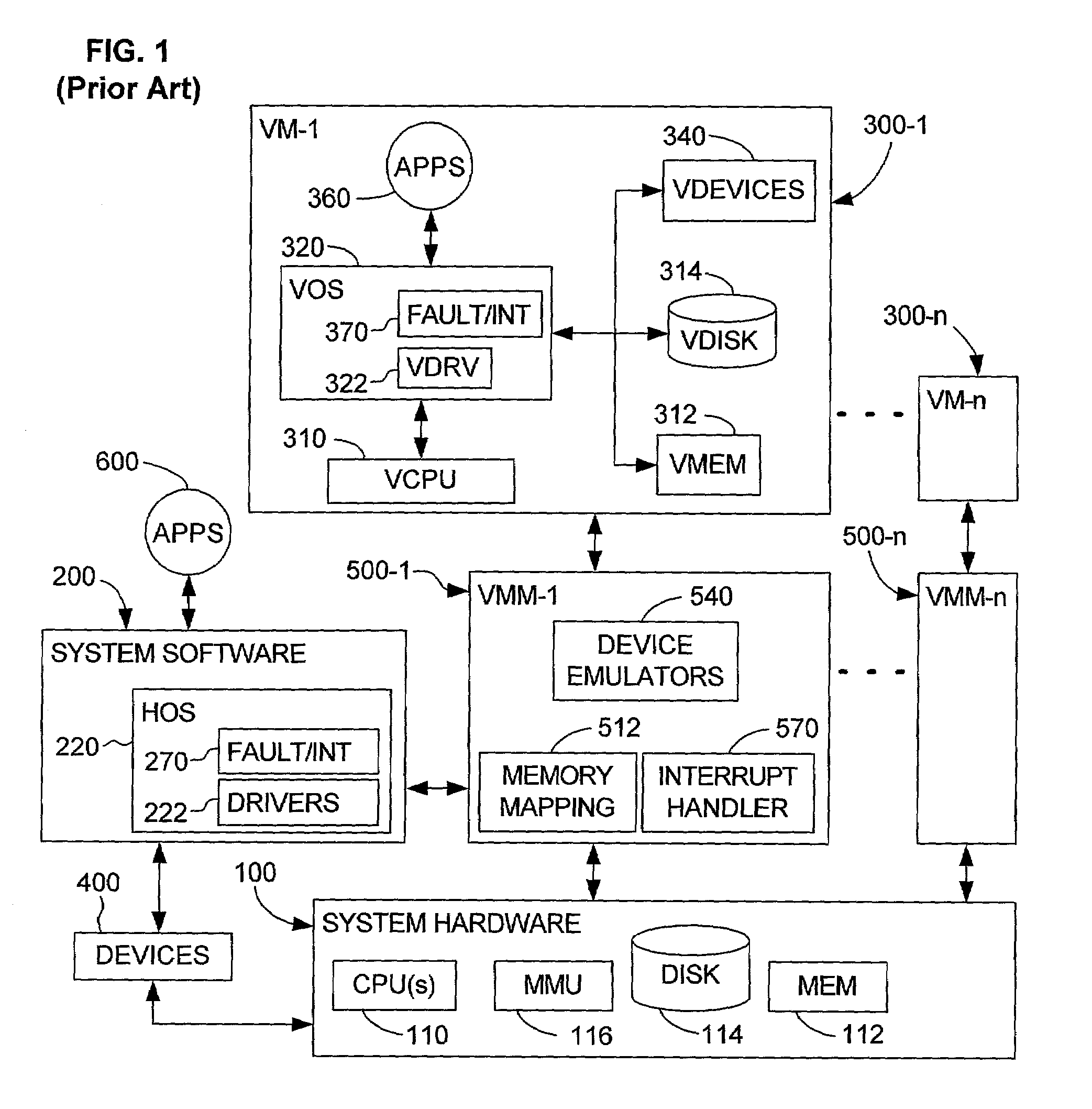
Transparent Memory-Mapped Emulation of I/O Calls
ActiveUS20090113425A1Memory architecture accessing/allocationError detection/correctionSemanticsMemory map
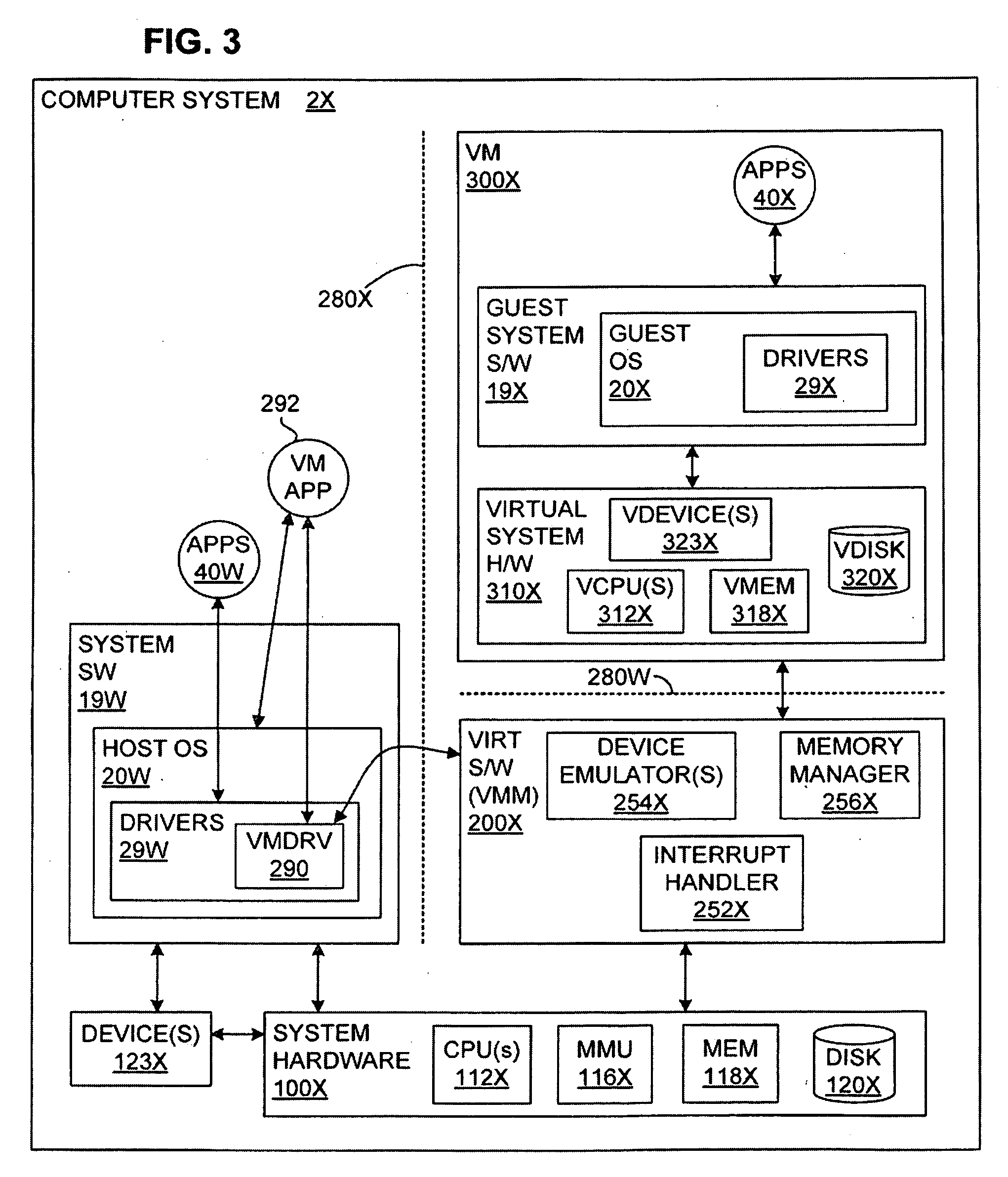
A virtual-machine-based system provides a mechanism to implement application file I / O operations of protected data by implementing the I / O operations semantics in a shim layer with memory-mapped regions. The semantics of these I / O operations are emulated in a shim layer with memory-mapped regions by using a mapping between a process' address space and a file or shared memory object. Data that is protected from viewing by a guest OS running in a virtual machine may nonetheless be accessed by the process.
Owner:VMWARE INC
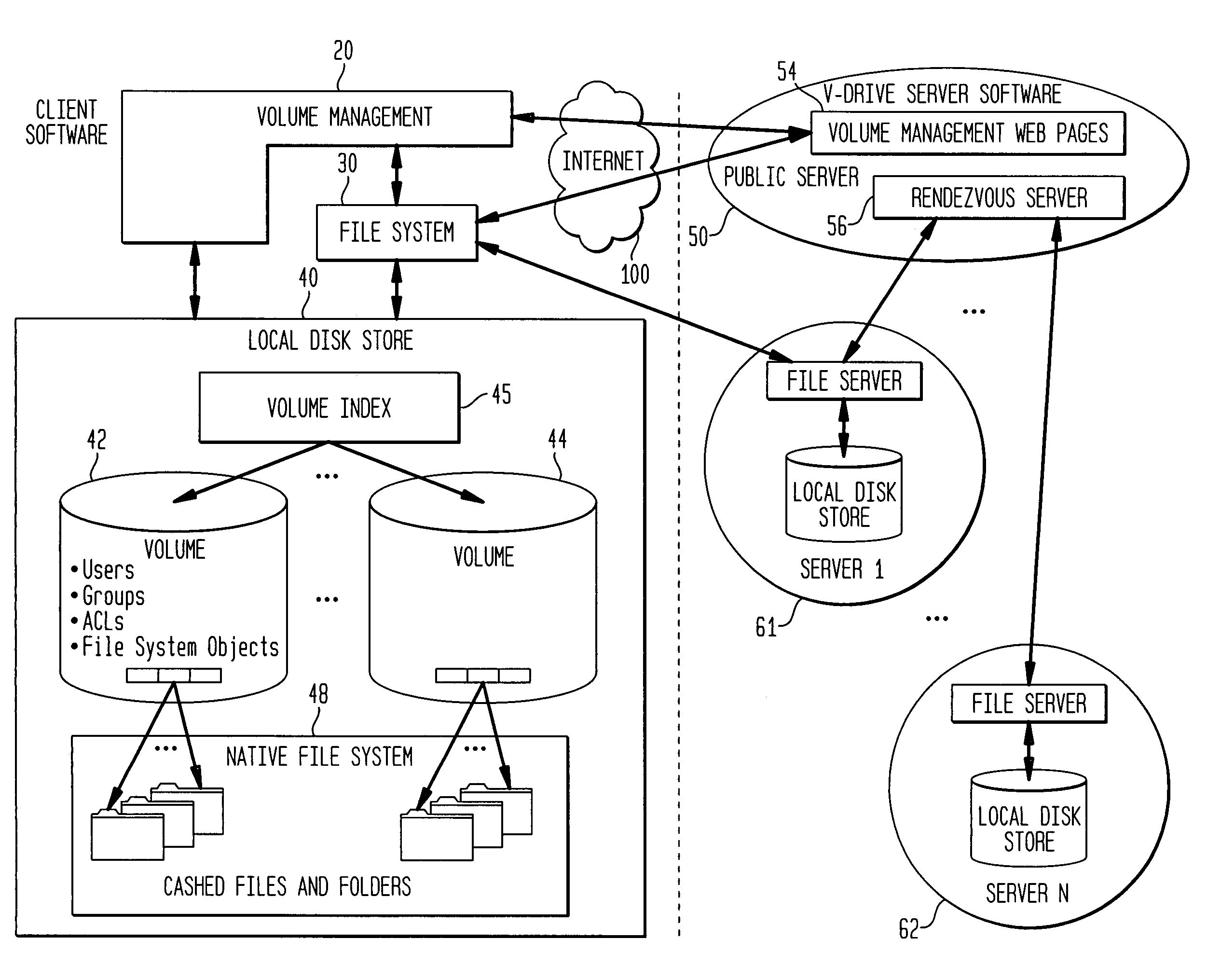
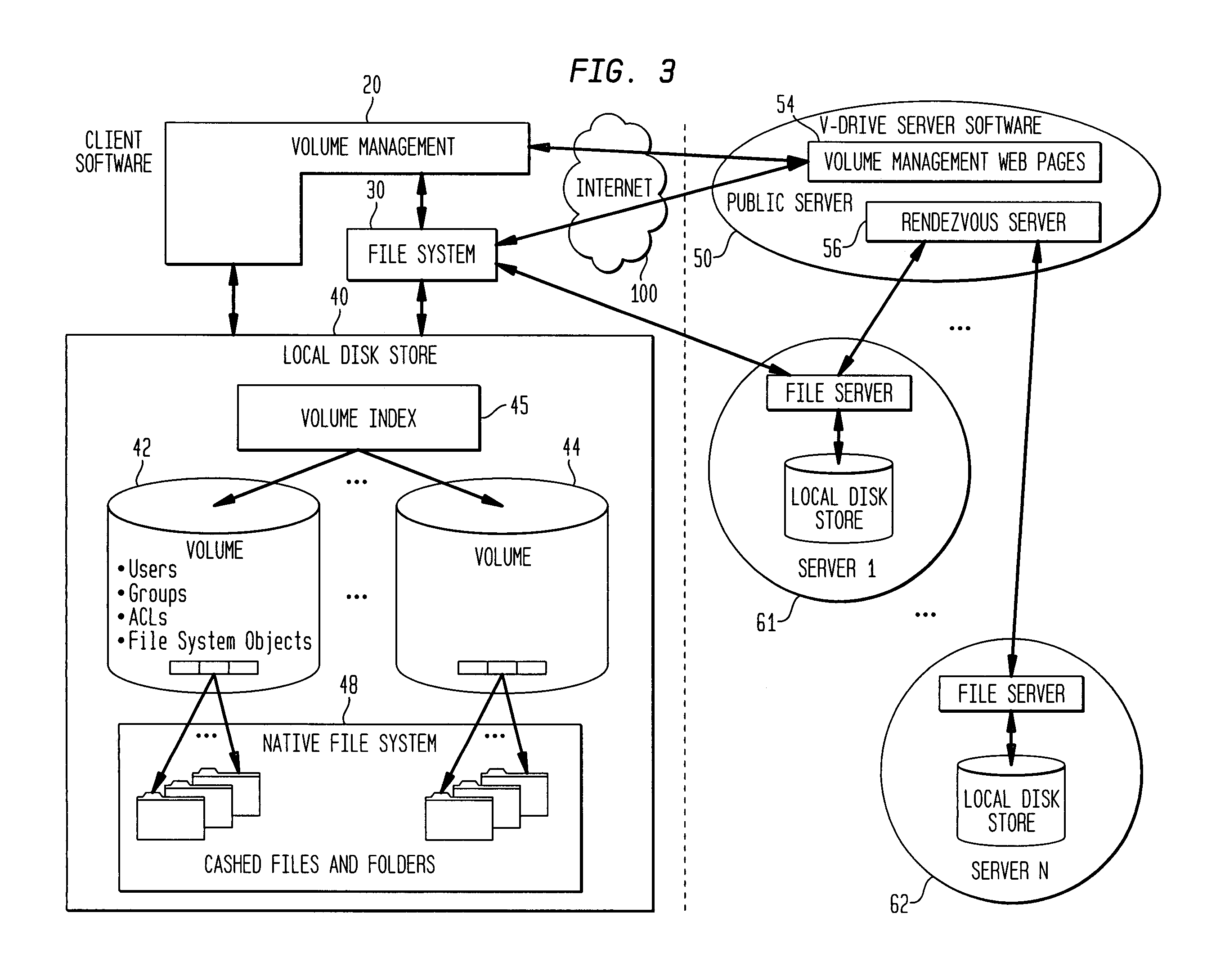
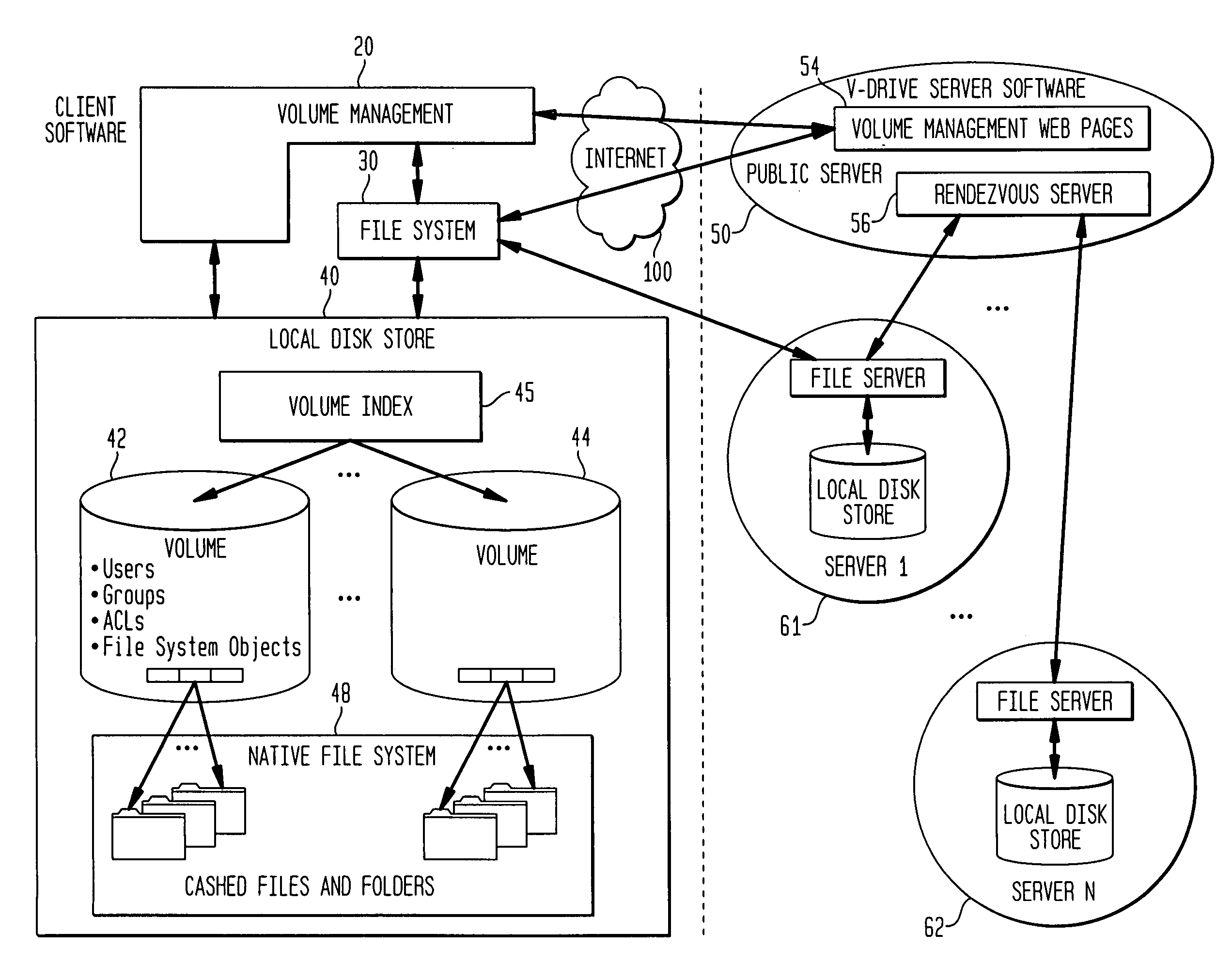
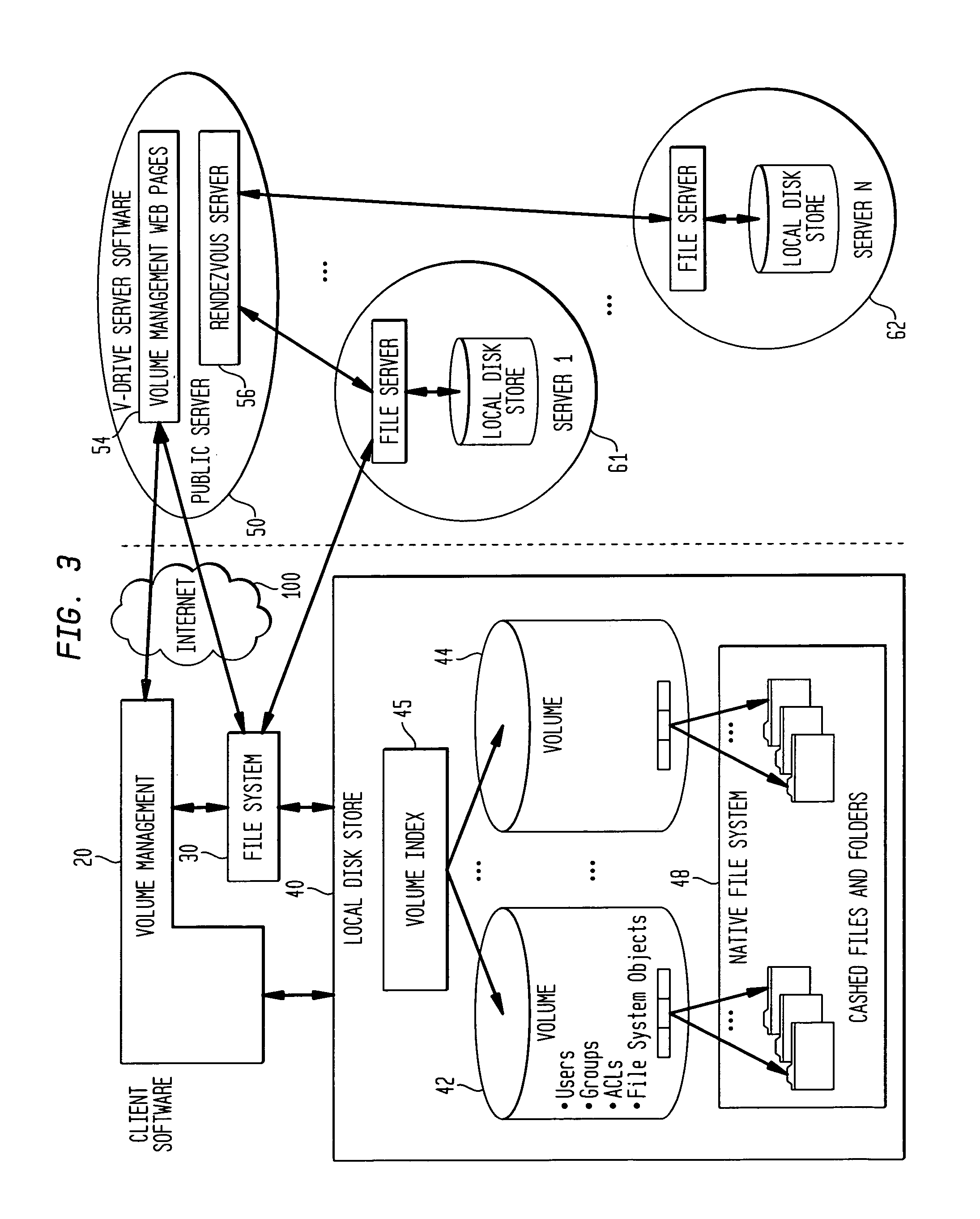
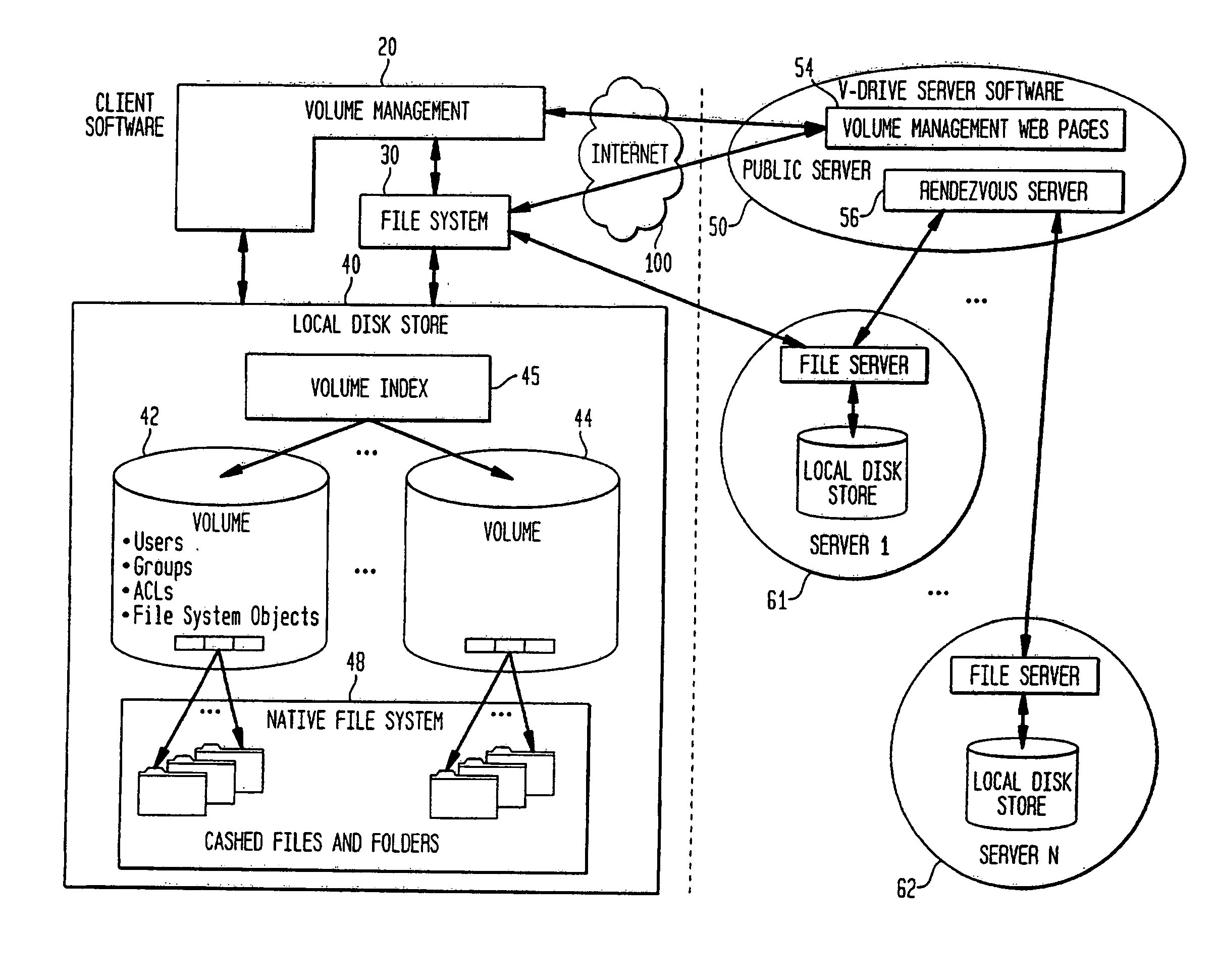
Internet-based shared file service with native PC client access and semantics and distributed access control
InactiveUS7136903B1Web data retrievalPublic key for secure communicationWide area networkAccess control
A multi-user file storage service and system enable each user of a pre-subscribed user group to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Additionally, an encrypted key is transferred from the file server node to a particular client node via a secure channel. The encrypted key uses an encryption function and a decryption function not known locally at the remote file server. Furthermore, both privileged access control rights and file sharing mode access control to a particular file of the group of files are delegated to one or more distributed nodes other than the remote file server node which provides the data.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics
A multi-user file storage service and system enables each user of a user group to operate an arbitrary client node at an arbitrary geographic location to communicate with a remote file server node via a wide area network. More than one user of the user group is permitted to access the file group at the remote file server node simultaneously, but the integrity of the files is maintained by controlling access so that each access to one of the files at the remote file server is performed, if at all, on a respective portion of that file as most recently updated at the remote file server node.
Owner:GOOGLE LLC
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
Method and apparatus for semantic discovery and mapping between data sources
ActiveUS20050055369A1Data processing applicationsDigital data information retrievalSemanticsData source
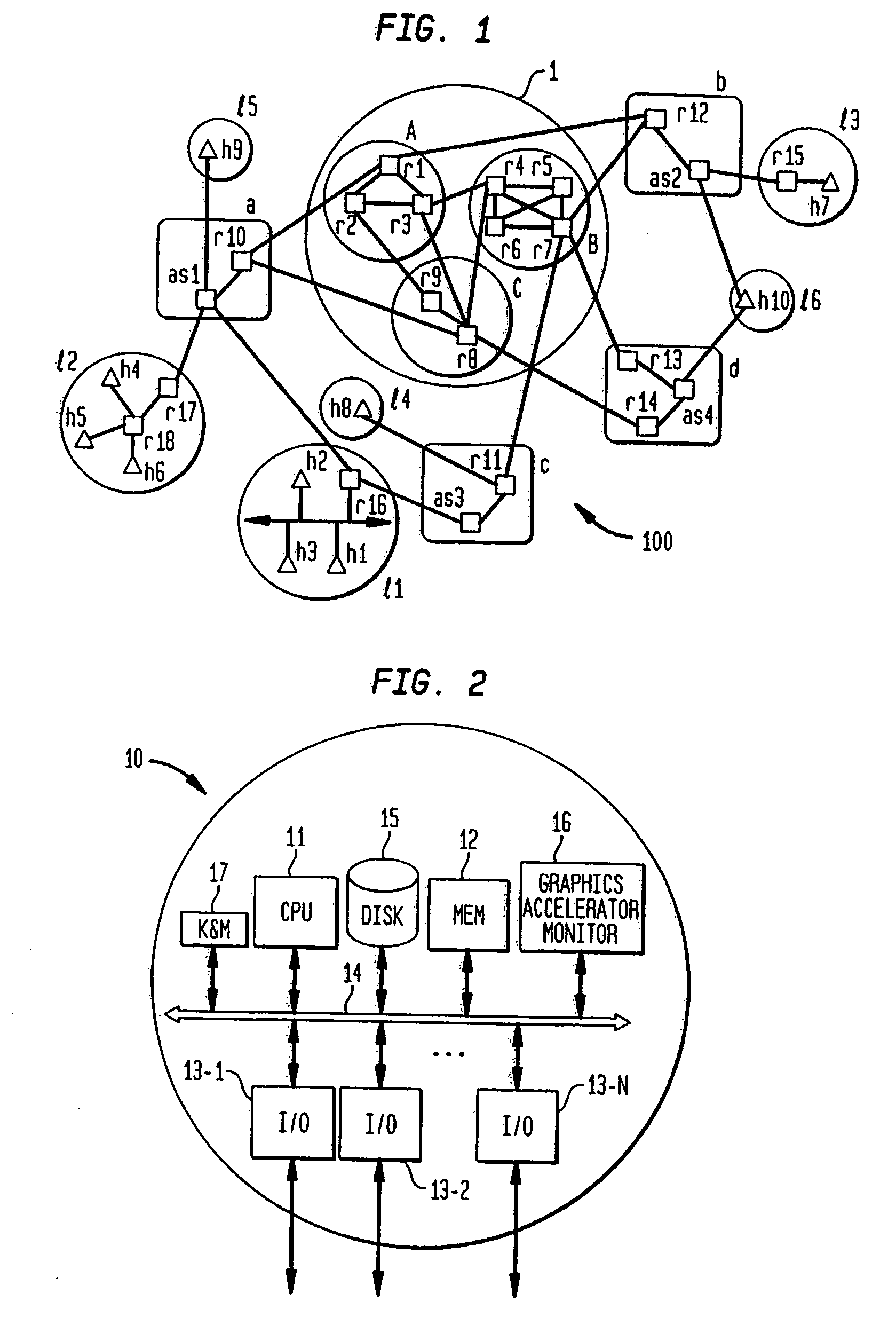
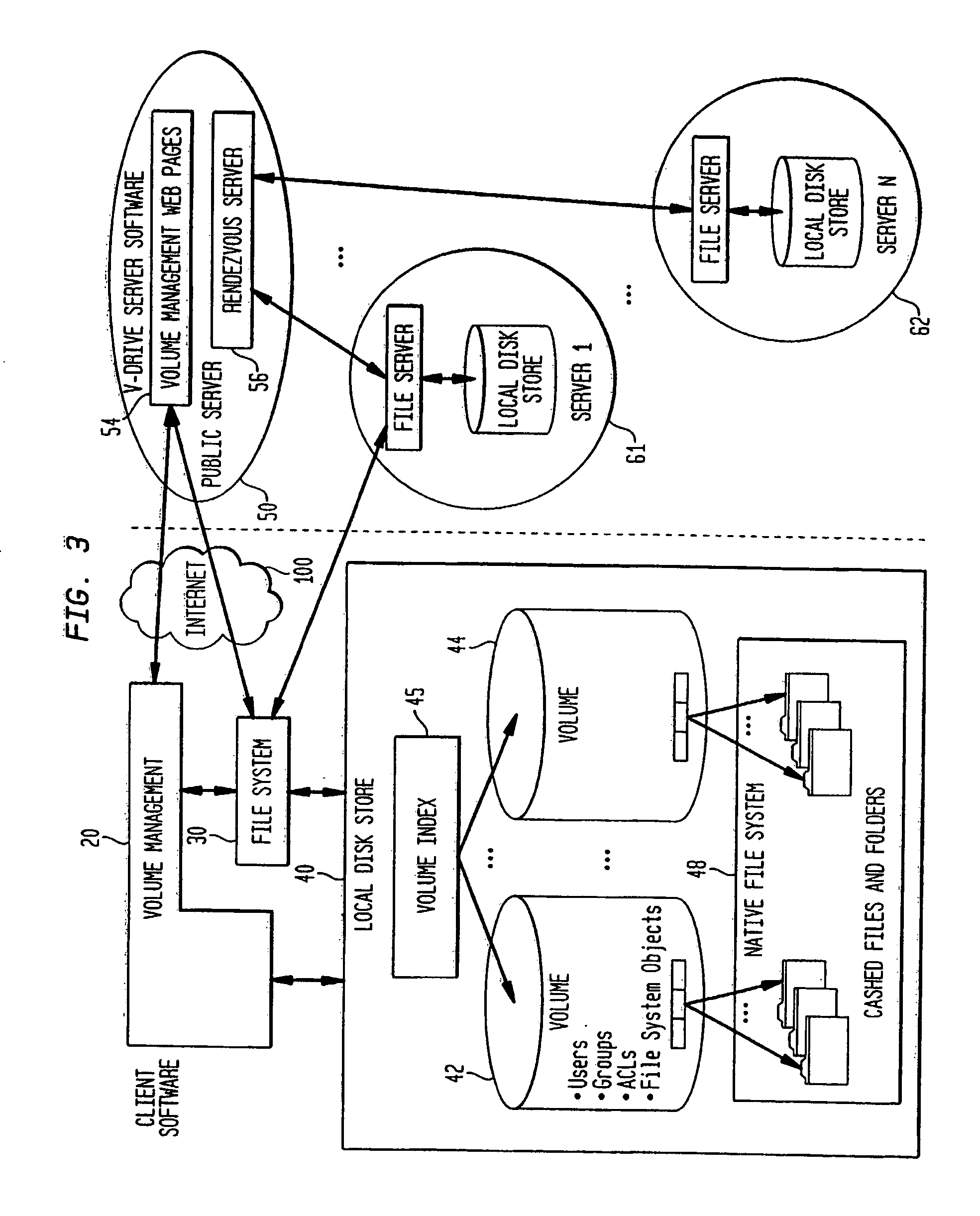
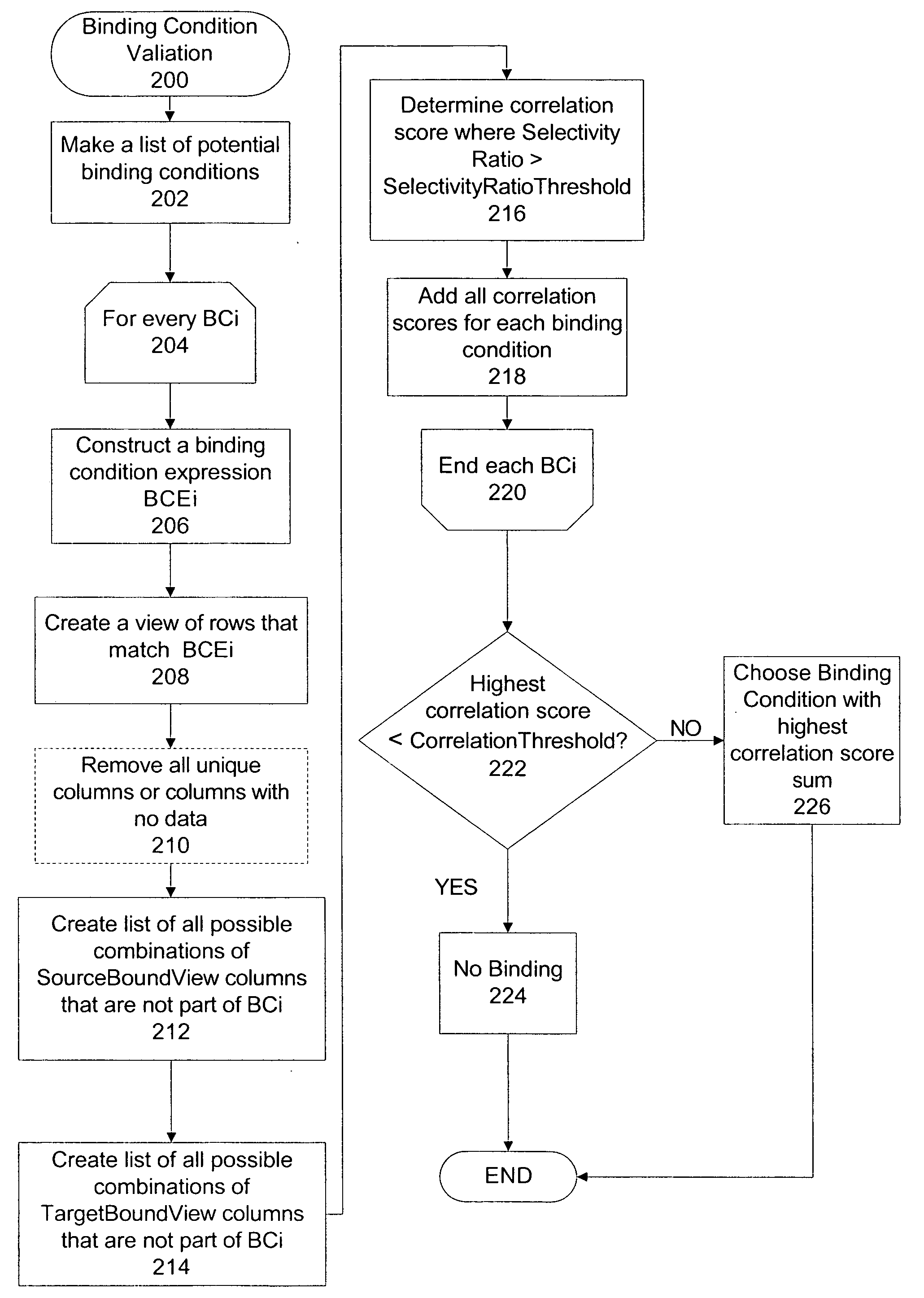
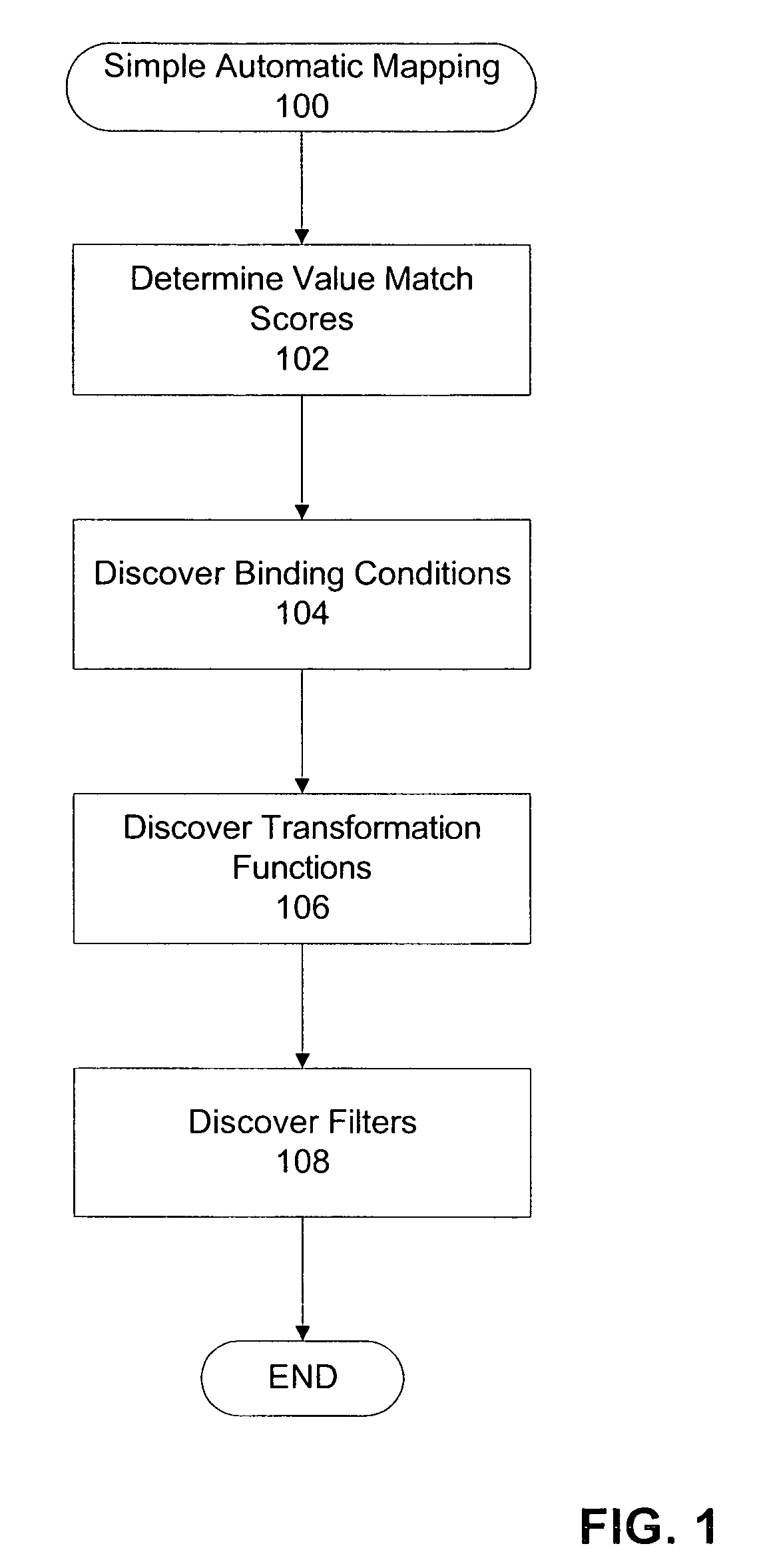
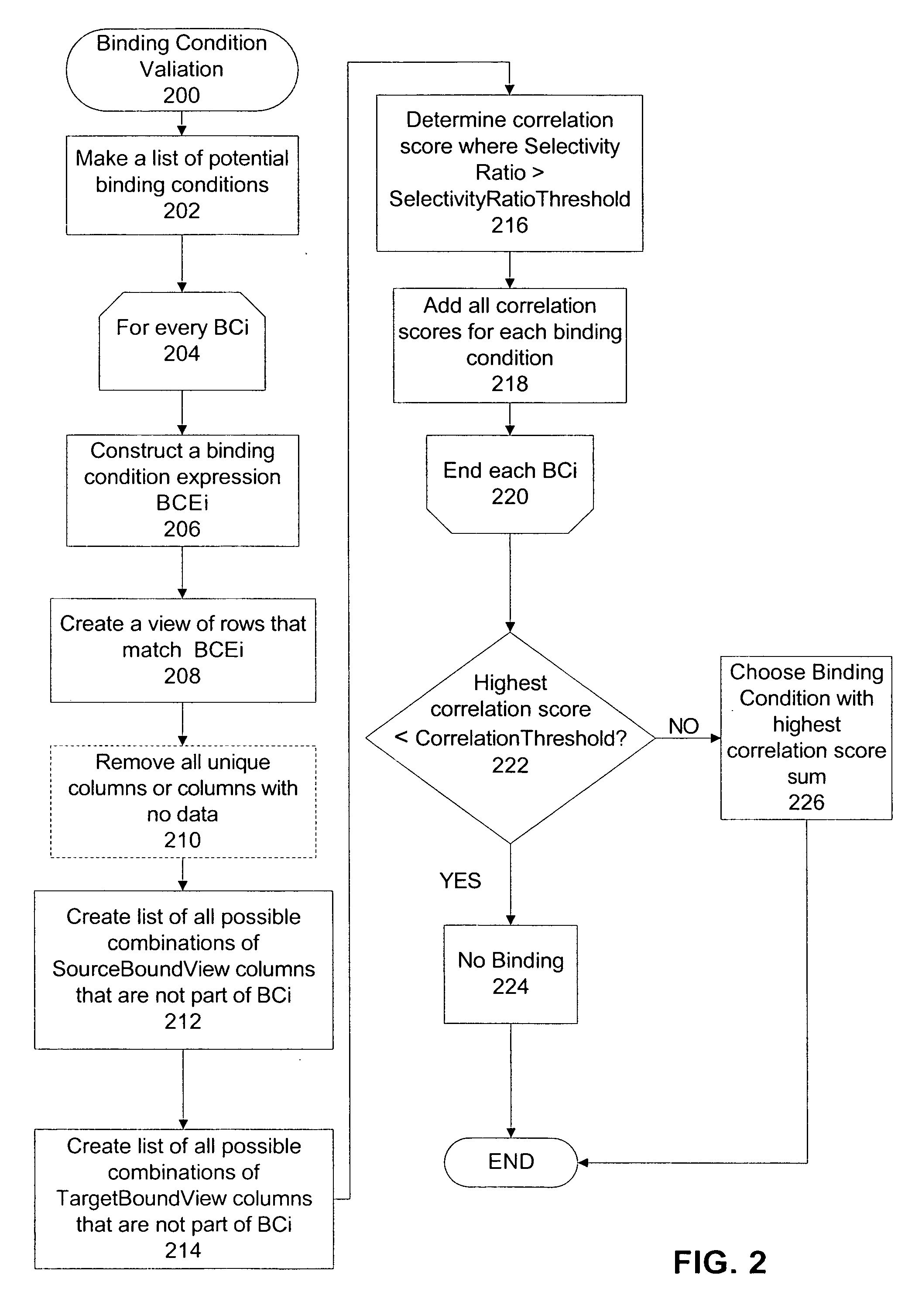
An apparatus and method are described for the discovery of semantics, relationships and mappings between data in different software applications, databases, files, reports, messages, or systems. In one aspect, semantics and relationships and mappings are identified between a first and a second data source. A binding condition is discovered between portions of data in the first and the second data source. The binding condition is used to discover correlations between portions of data in the first and the second data source. The binding condition and the correlations are used to discover a transformation function between portions of data in the first and the second data source.
Owner:WORKDAY INC
Method and apparatus for automated video activity analysis
InactiveUS7200266B2Improving object extractionReduce dependenceBiometric pattern recognitionBurglar alarmHuman bodyPublic place
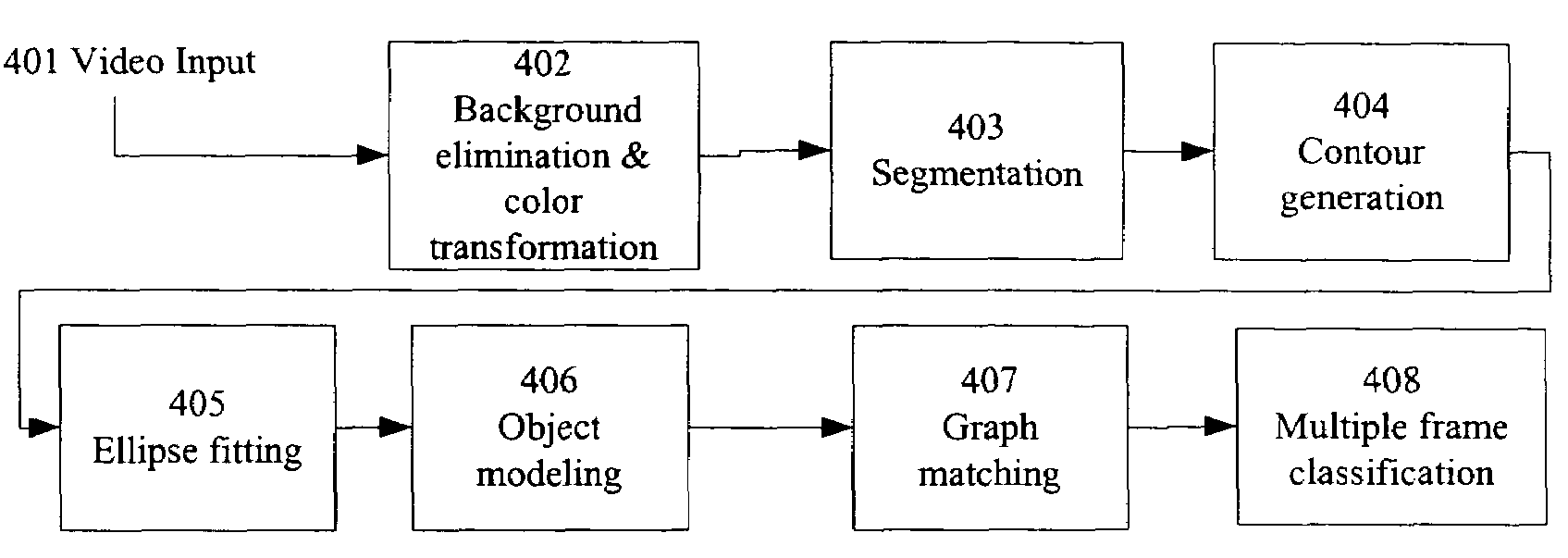
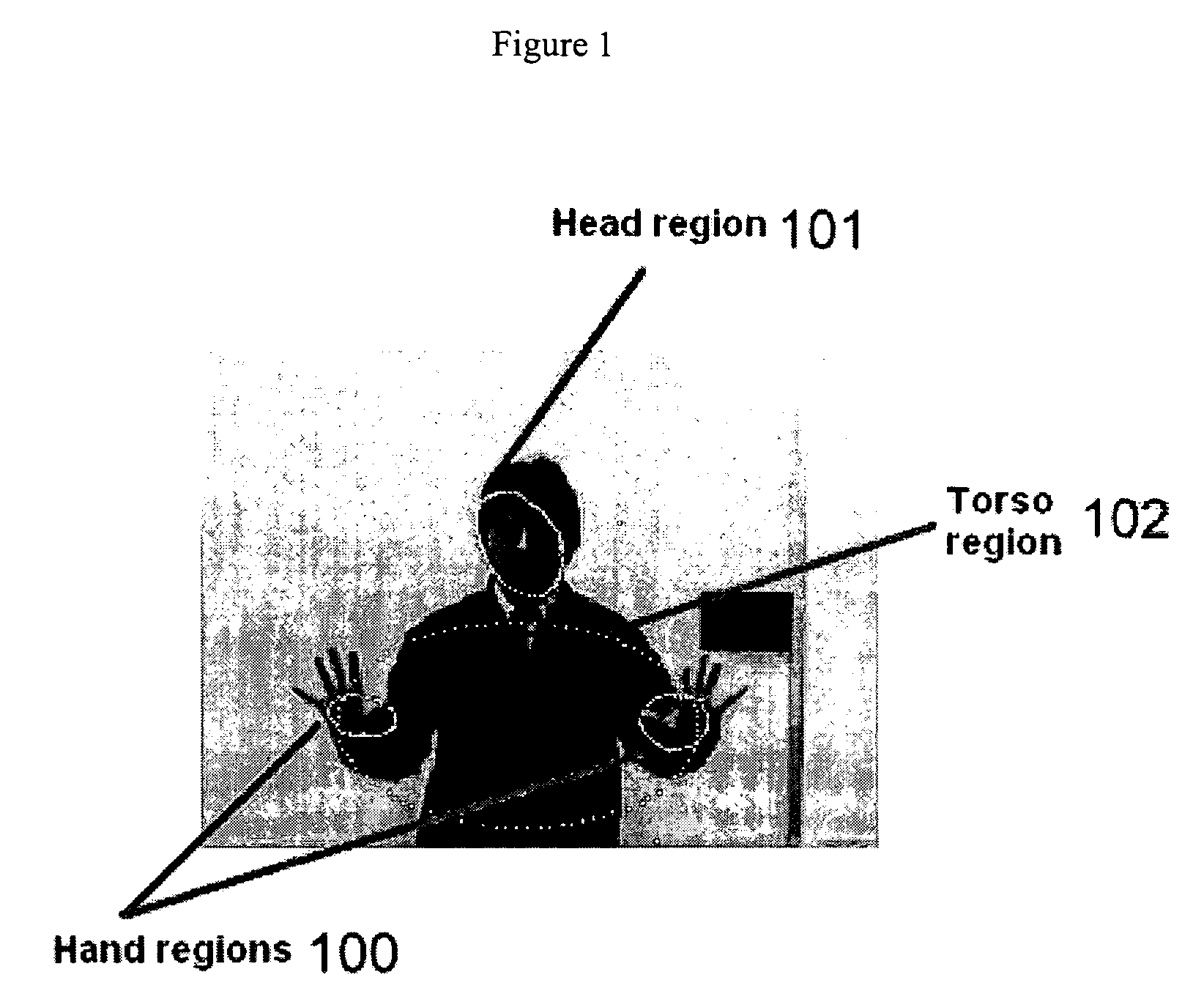
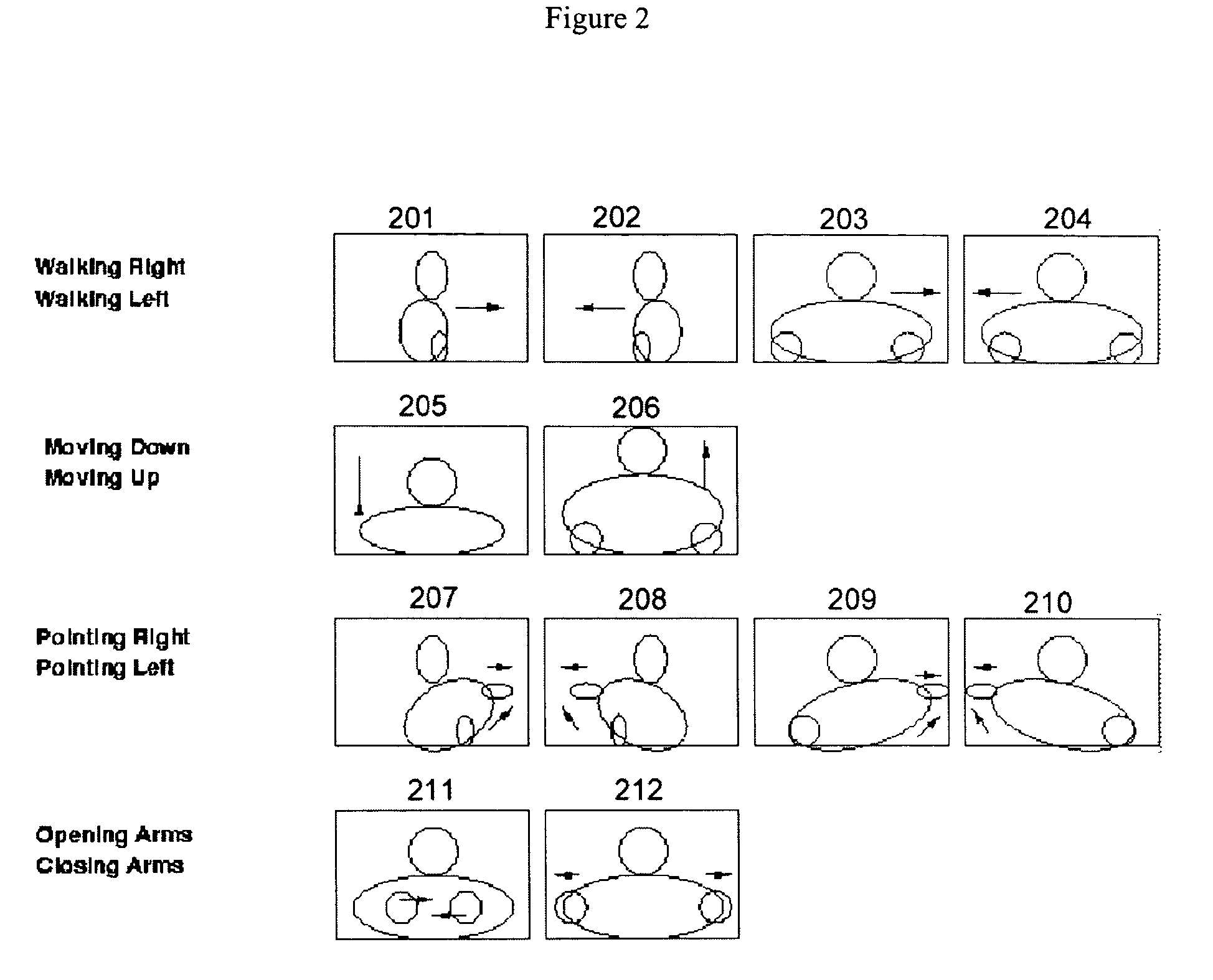
The invention is a new method and apparatus that can be used to detect, recognize, and analyze people or other objects in security checkpoints, public-places, parking lots, or in similar environments under surveillance to detect the presence of certain objects of interests (e.g., people), and to identify their activities for security and other purposes in real-time. The system can detect a wide range of activities for different applications. The method detects any new object introduced into a known environment and then classifies the object regions to human body parts or to other non-rigid and rigid objects. By comparing the detected objects with the graphs from a database in the system, the methodology is able to identify object parts and to decide on the presence of the object of interest (human, bag, dog, etc.) in video sequences. The system tracks the movement of different object parts in order to combine them at a later stage to high-level semantics. For example, the motion pattern of each human body part is compared to the motion pattern of the known activities. The recognized movements of the body parts are combined by a classifier to recognize the overall activity of the human body.
Owner:PRINCETON UNIV
Operating system abstraction and protection layer
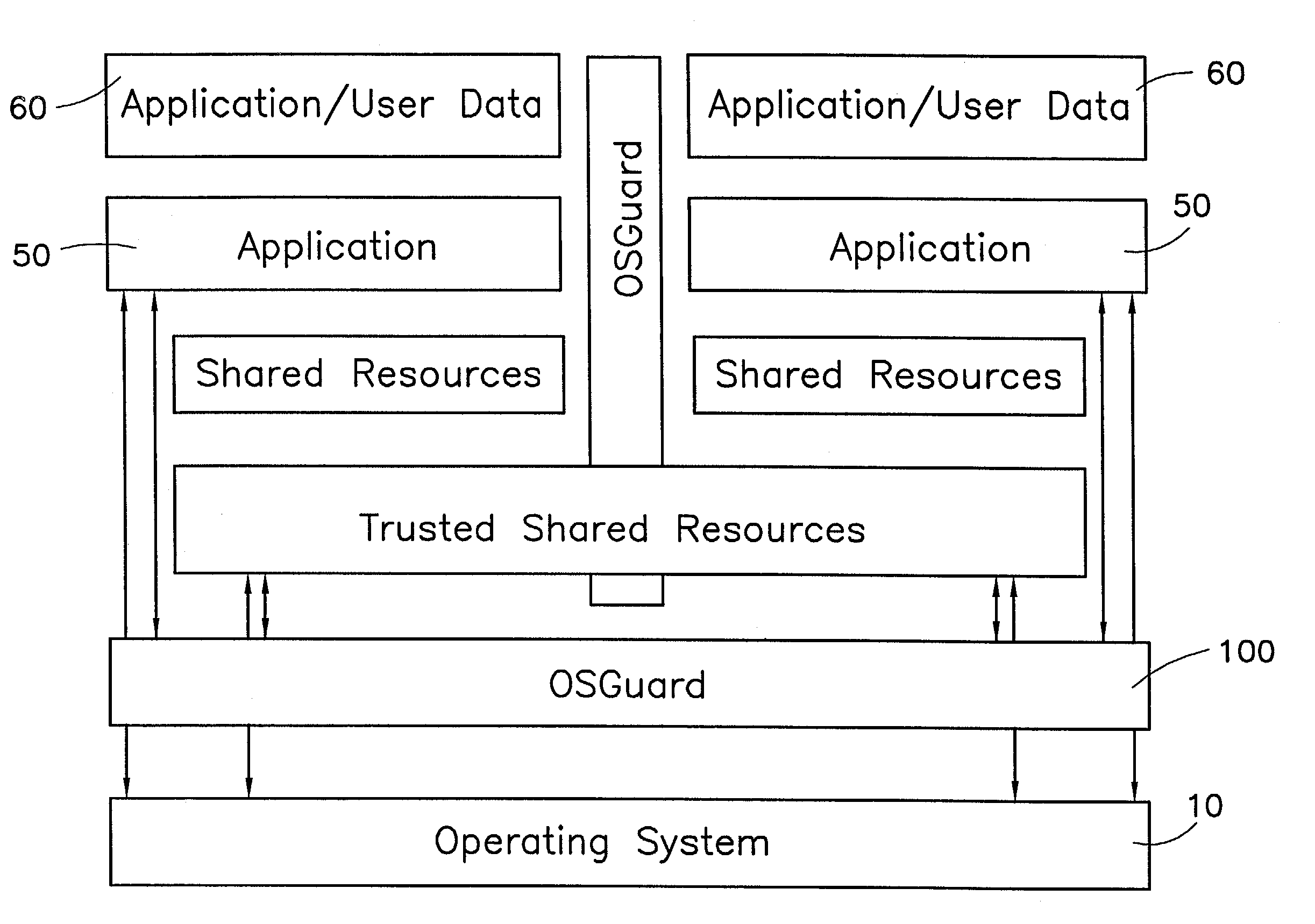
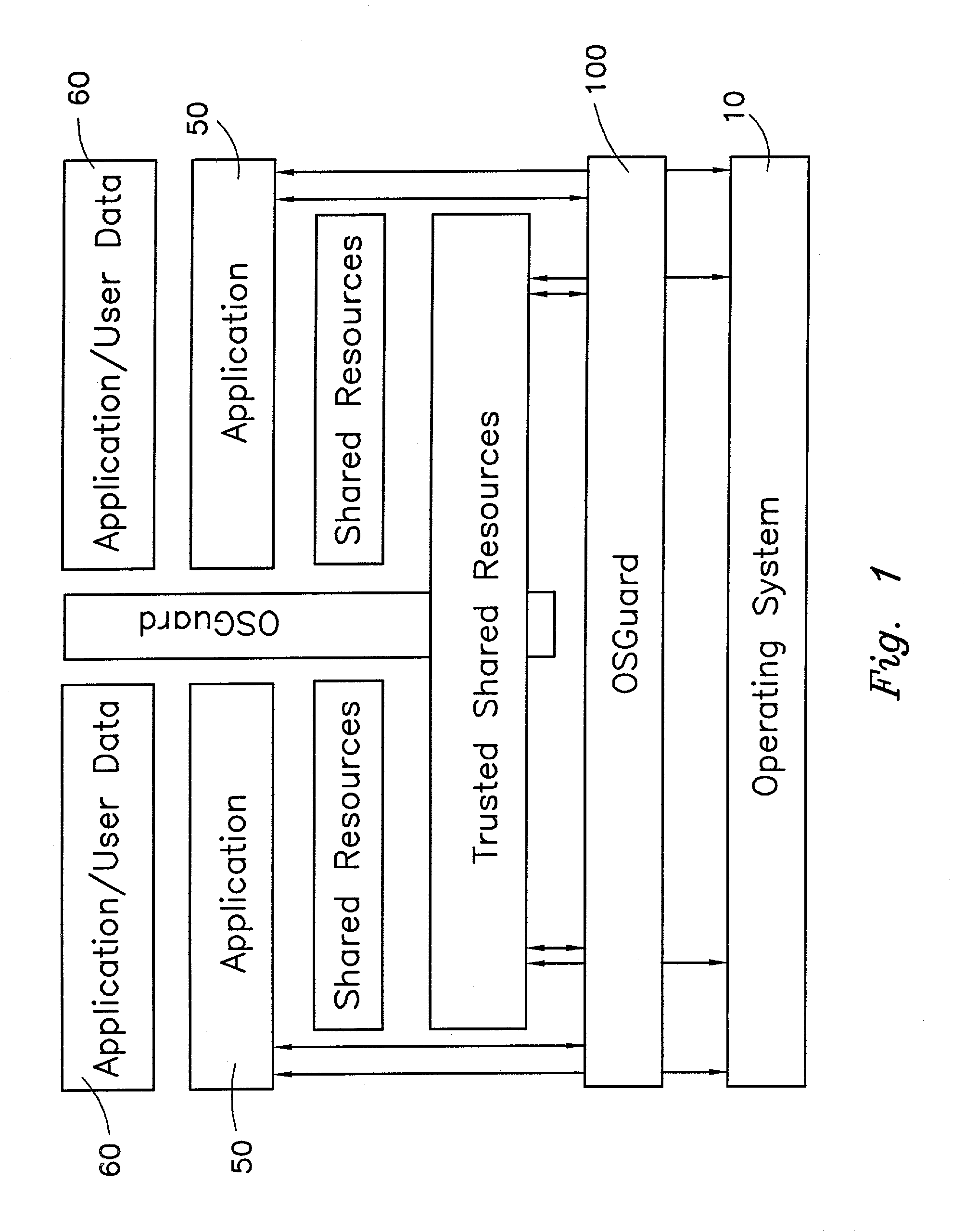
InactiveUS7028305B2Avoid changeInhibition of informationInterprogram communicationDigital computer detailsOperational systemConfiguration item
The present invention provides a system for creating an application software environment without changing an operating system of a client computer, the system comprising an operating system abstraction and protection layer, wherein said abstraction and protection layer is interposed between a running software application and said operating system, whereby a virtual environment in which an application may run is provided and application level interactions are substantially removed. Preferably, any changes directly to the operating system are selectively made within the context of the running application and the abstraction and protection layer dynamically changes the virtual environment according to administrative settings. Additionally, in certain embodiments, the system continually monitors the use of shared system resources and acts as a service to apply and remove changes to system components. The present thus invention defines an “Operating System Guard.” These components cover the protection semantics required by .DLLs and other shared library code as well as system device drivers, fonts, registries and other configuration items, files, and environment variables.
Owner:MICROSOFT TECH LICENSING LLC
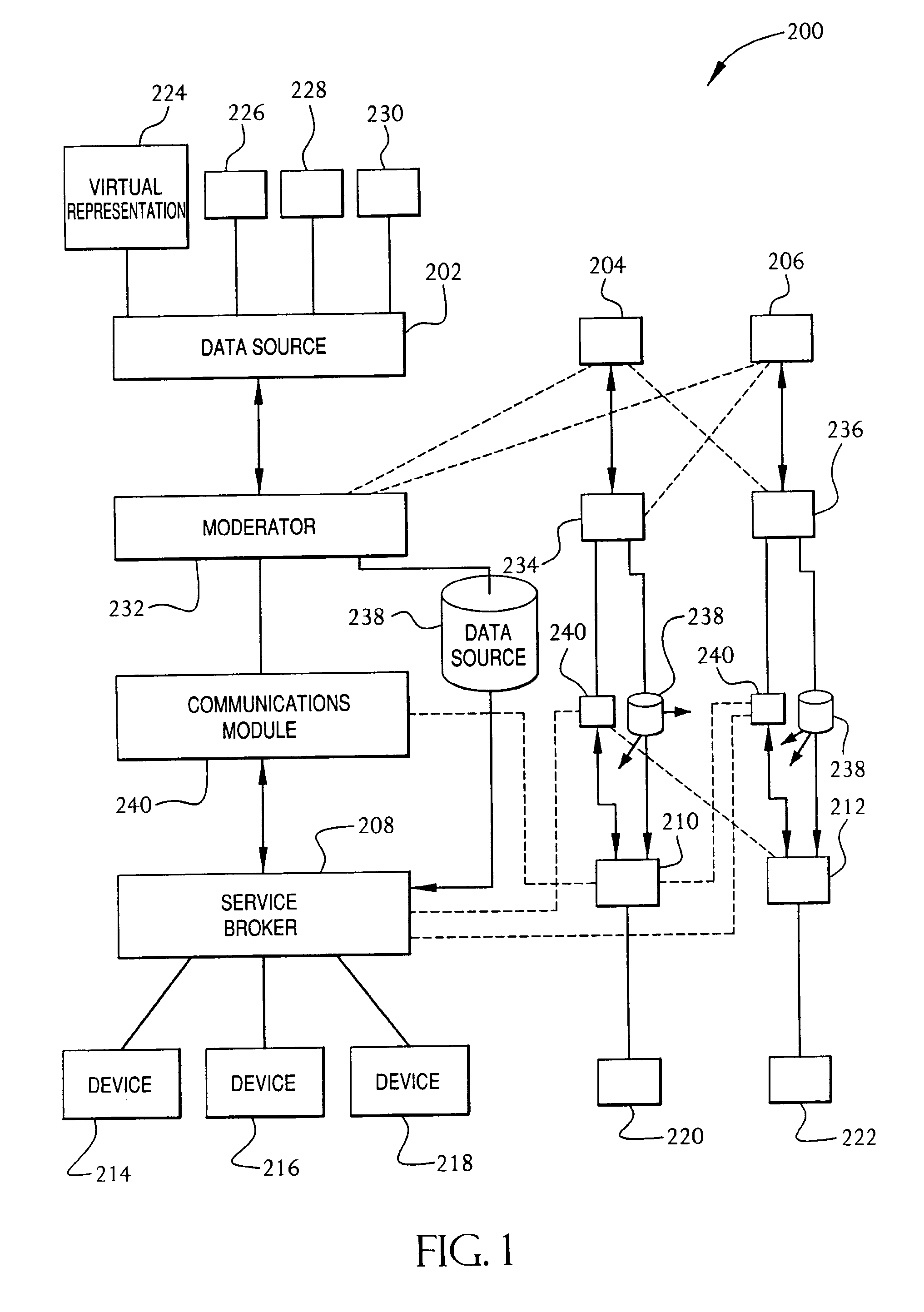
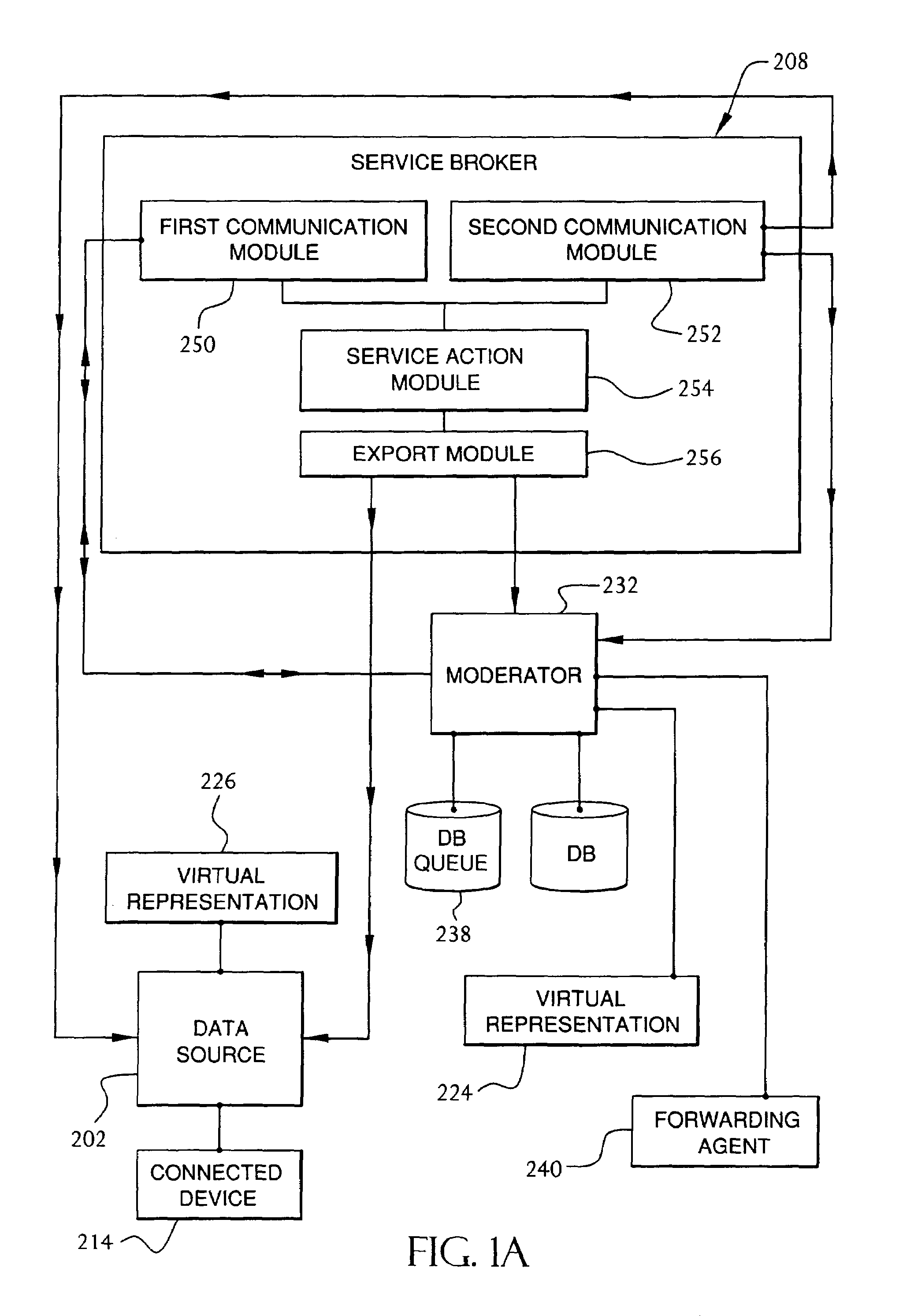
Service broker for processing data from a data network
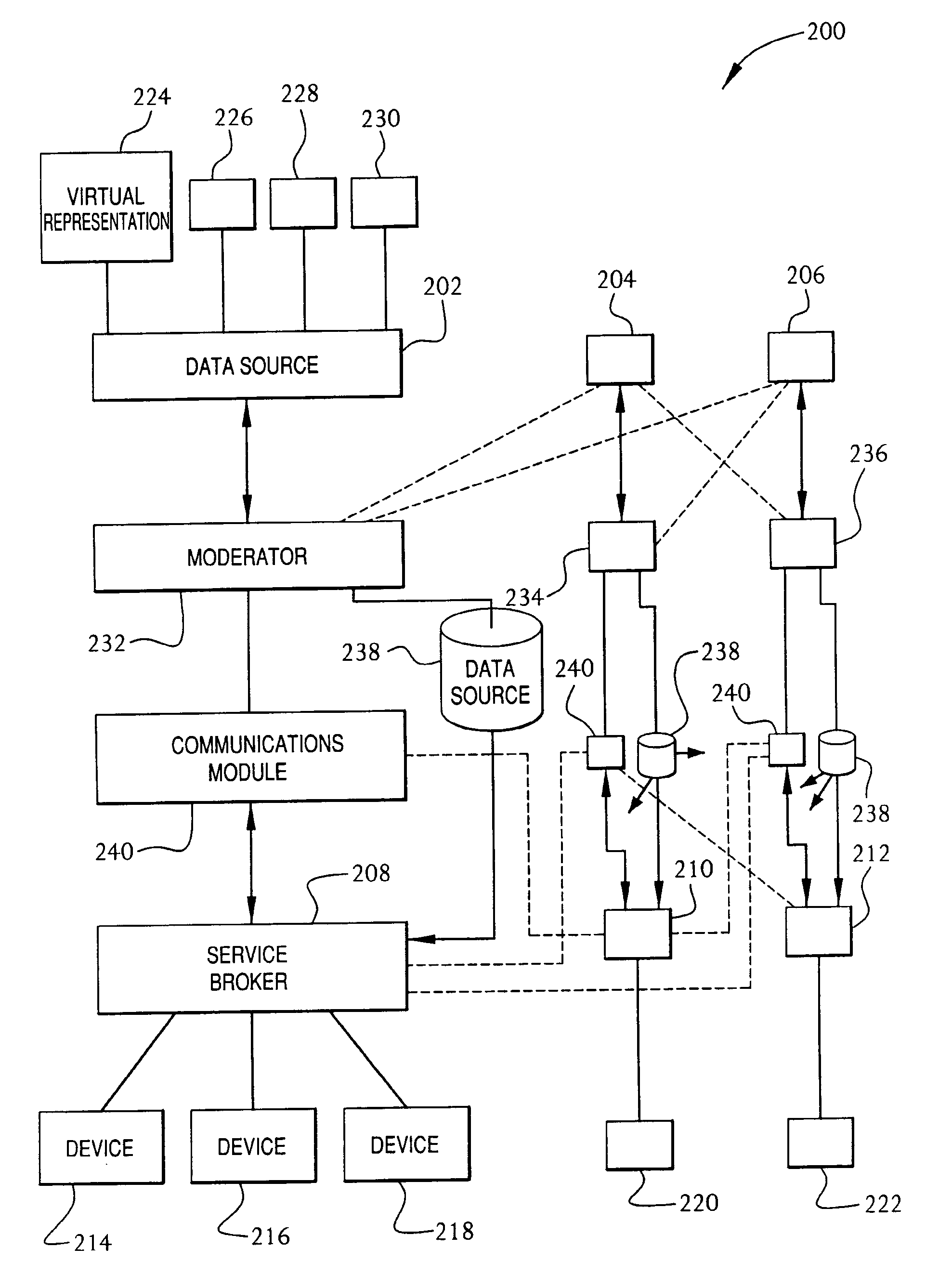
InactiveUS7032002B1Multiple digital computer combinationsStore-and-forward switching systemsCommand languageServer appliance
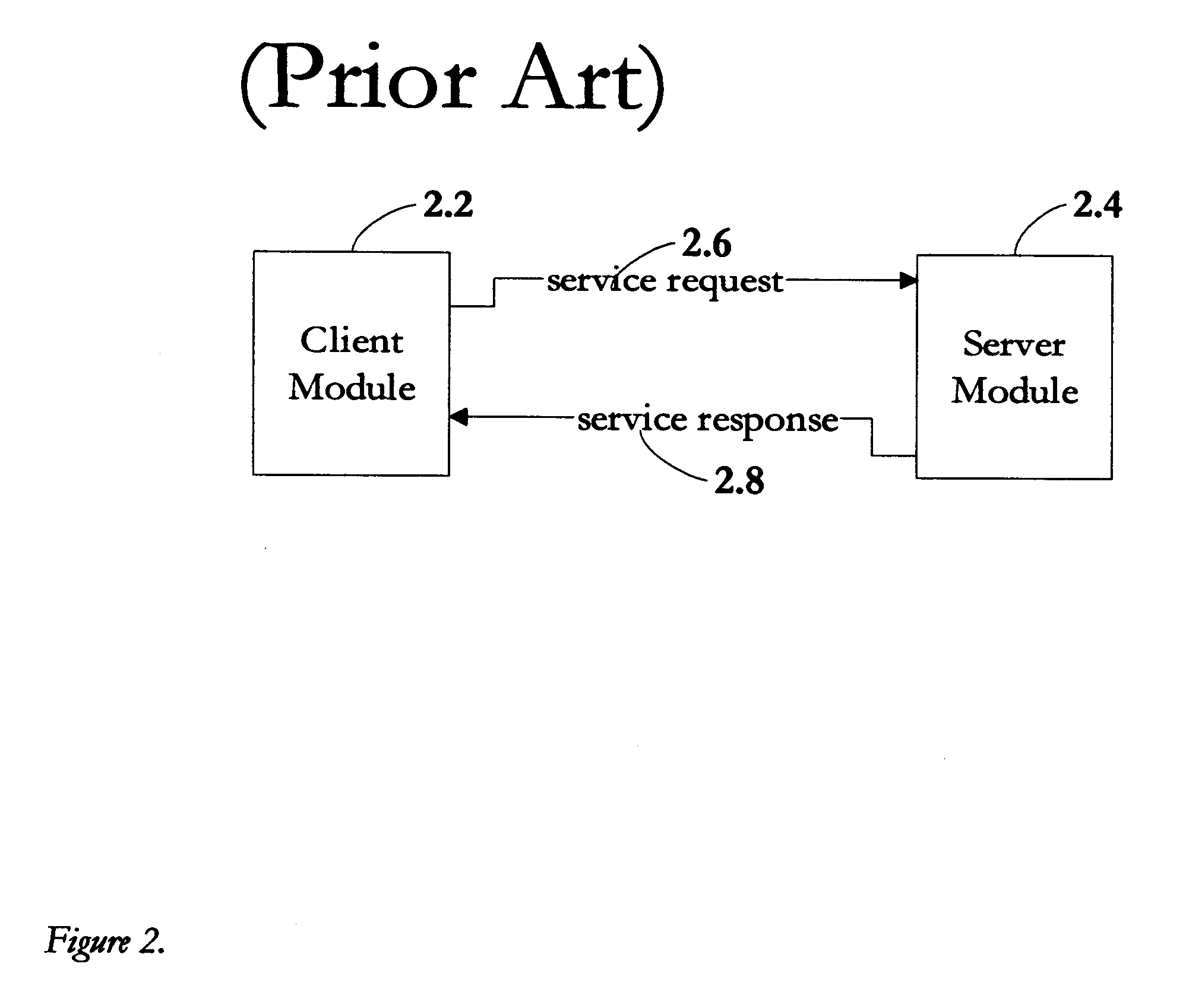
A method and system for communication between server-less computing devices or clients in computers communicating over networks, such as the World Wide Web (WWW) using stateless protocols, e.g., HTTP. In this scheme, there are two classes of clients which can operate independently or can be combined in computers communicating over the network: a) clients that issue commands and request status or data, and b) clients that function as service brokers for providing services and processing commands, updating status and providing specific data—resembleing a server device but without accessible TCP / IP ports. Each service providing device is authenticated, retains a unique identity and establishes a soft state with the globally accessible server or servers. All devices and clients can compile and process a globally common command language established between all communicating network clients. The central server includes a CGI processing program and a database to retain client specific information. The server database represents a collection of queues, each having a client unique identifiable status, pending commands and / or data components. In this scheme, commands and signaling transmitted between the servers and clients utilize standard HTTP protocol semantics and HTML or standard markup language syntax. Clients encapsulate or embed information as parameters passed to HTTP CGI as a set of standard HTTP conversations. A CGI processing program converts, parses or processes each conversation and passes arguments with or without data to queues.
Owner:AT&T DIGITAL LIFE
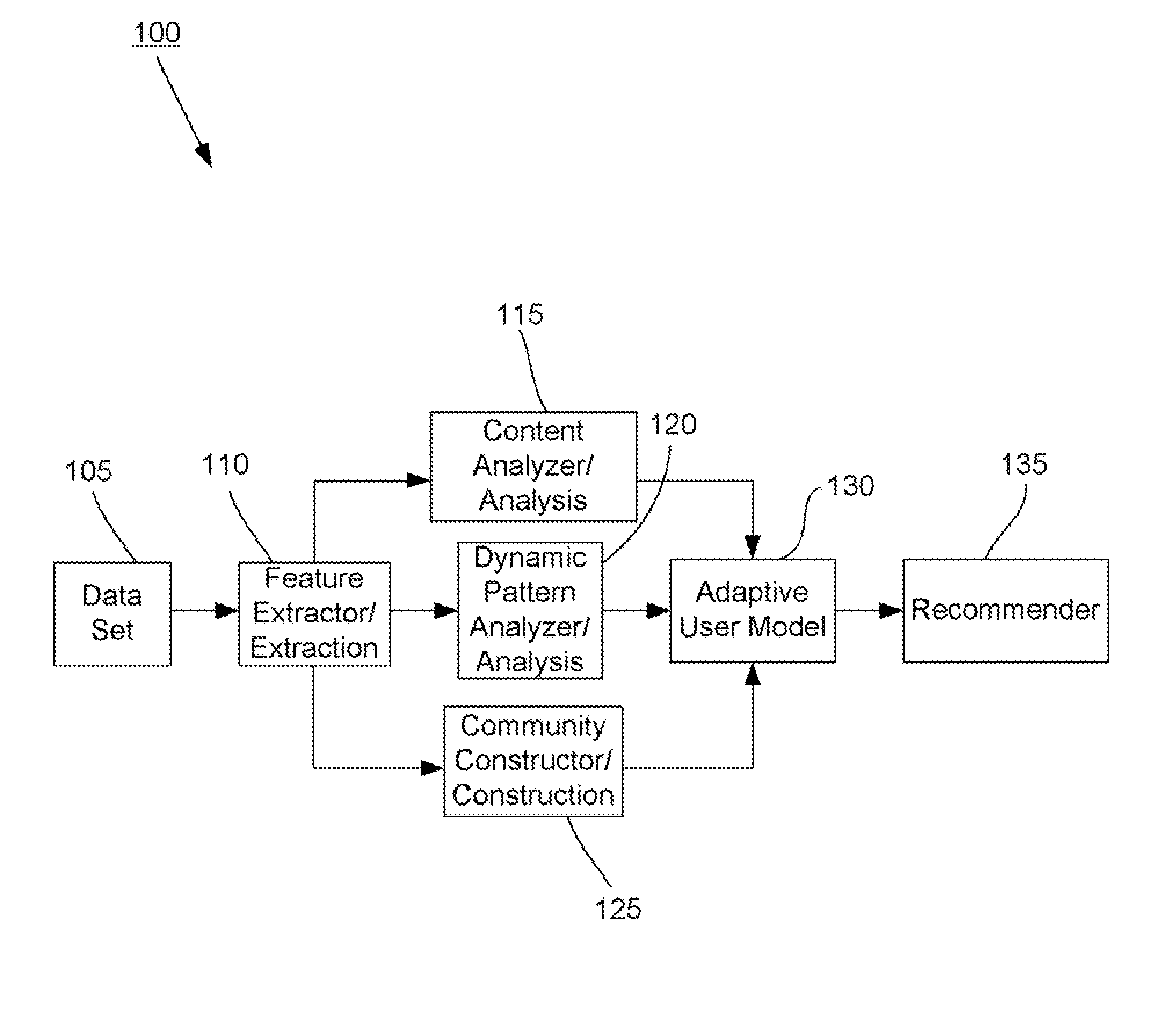
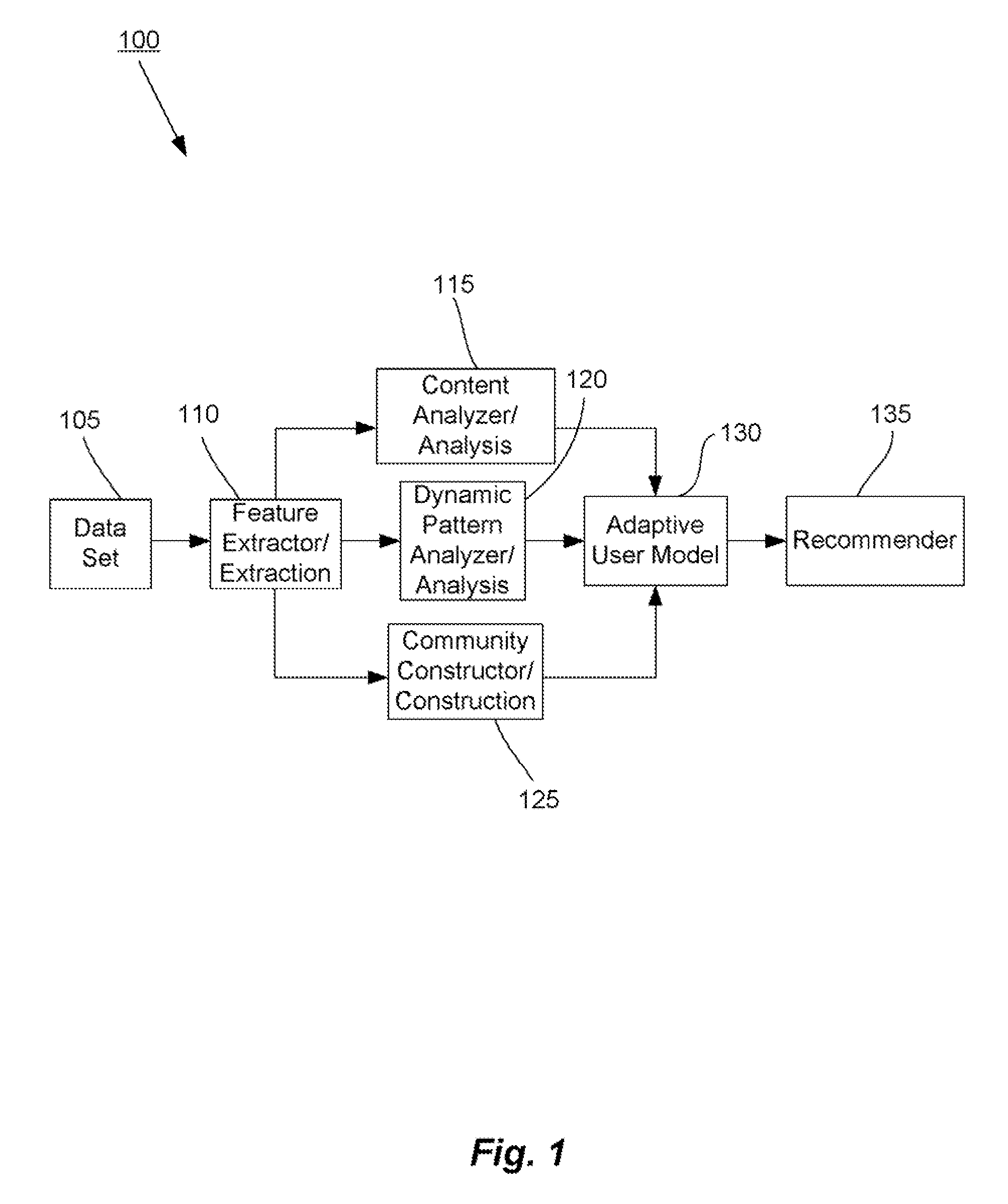
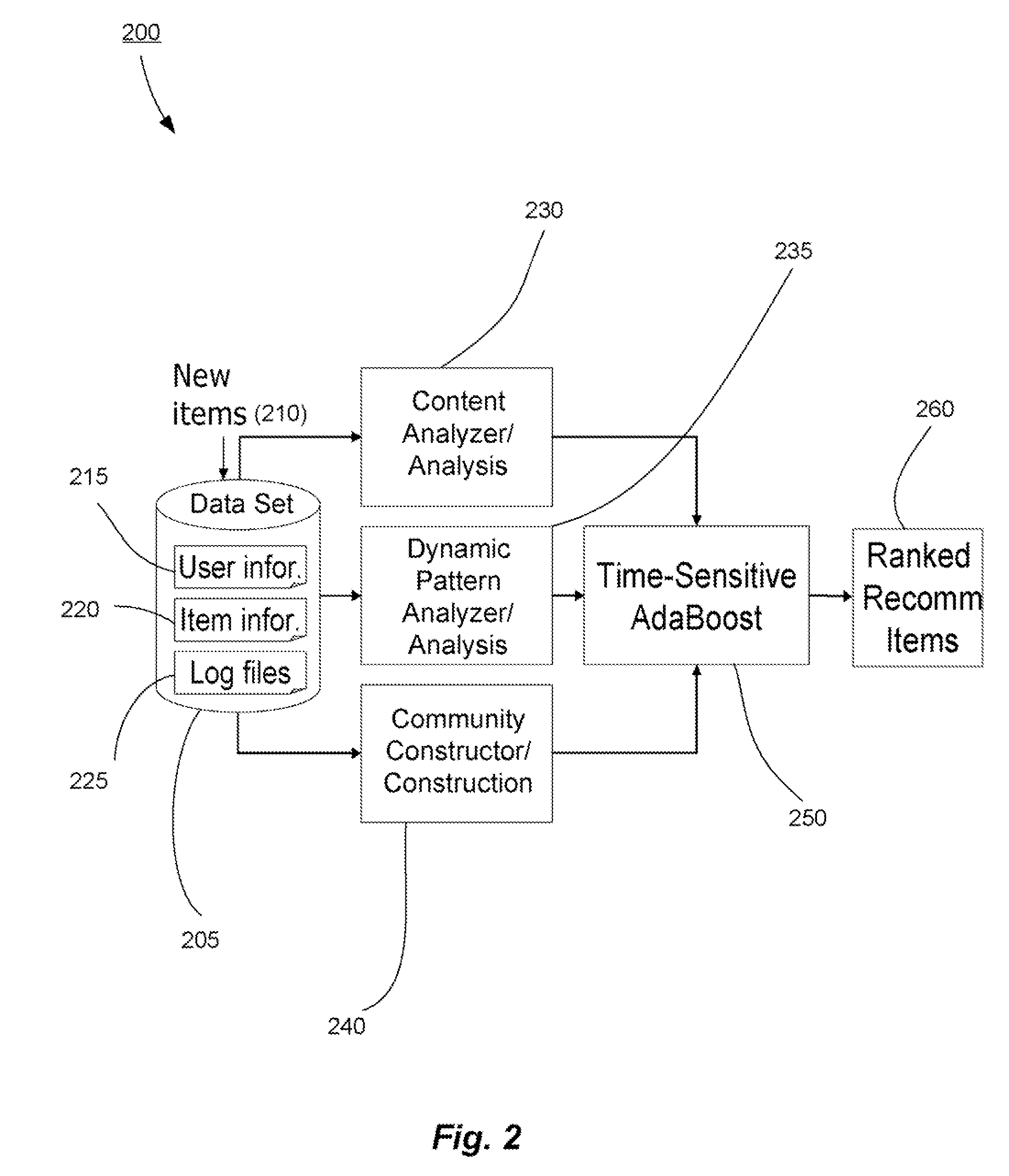
Methods and systems for utilizing content, dynamic patterns, and/or relational information for data analysis
InactiveUS20070118498A1Avoid problemsCommerceSpecial data processing applicationsTemporal changeAnalysis data
The present invention is directed generally to providing systems and methods for data analysis. More specifically, embodiments may provide system(s) and method(s) including dynamic user modeling techniques to capture the relational and dynamic patterns of information content and / or users' or entities' interests. Various embodiments may include system(s) and method(s) that are based on, for example, the past history of content semantics, temporal changes, and / or user community relationship. Various embodiments may include modeling and / or analysis of the dynamic nature of an item of interest's value to a user(s) / entity(ies) over time. The dynamic factors may be consider in any manner, such as, individually or combined, sequentially or simultaneously, etc. Further, some embodiments may include, for example, system(s) and method(s) relating to analyzing data to capture user / entity interests and / or characteristics, consider content semantics and evolutionary information, and / or using community relationships of users / entities to thereby analyze information and provide dynamic conclusion(s) (e.g., recommendation(s)).
Owner:NEC CORP
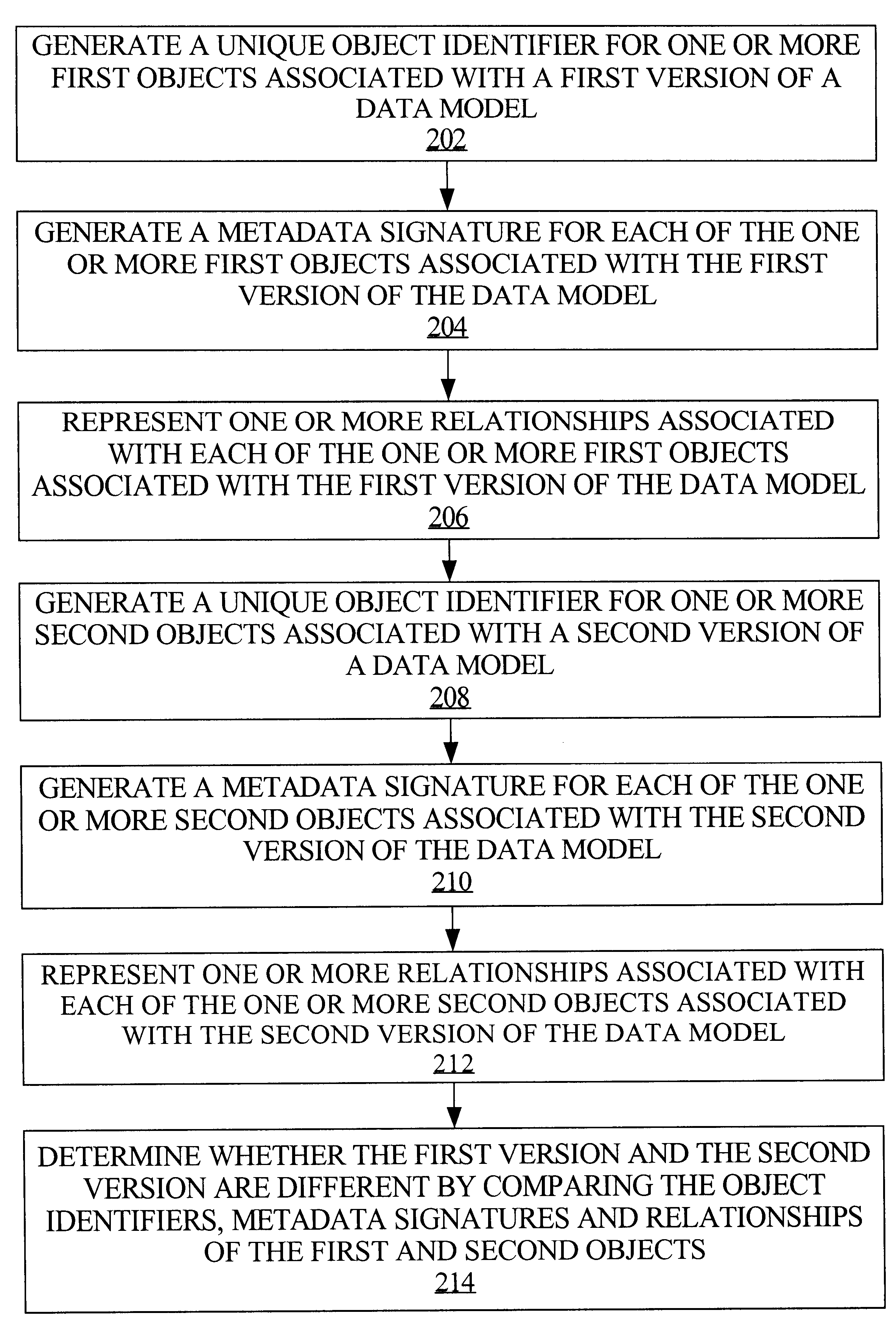
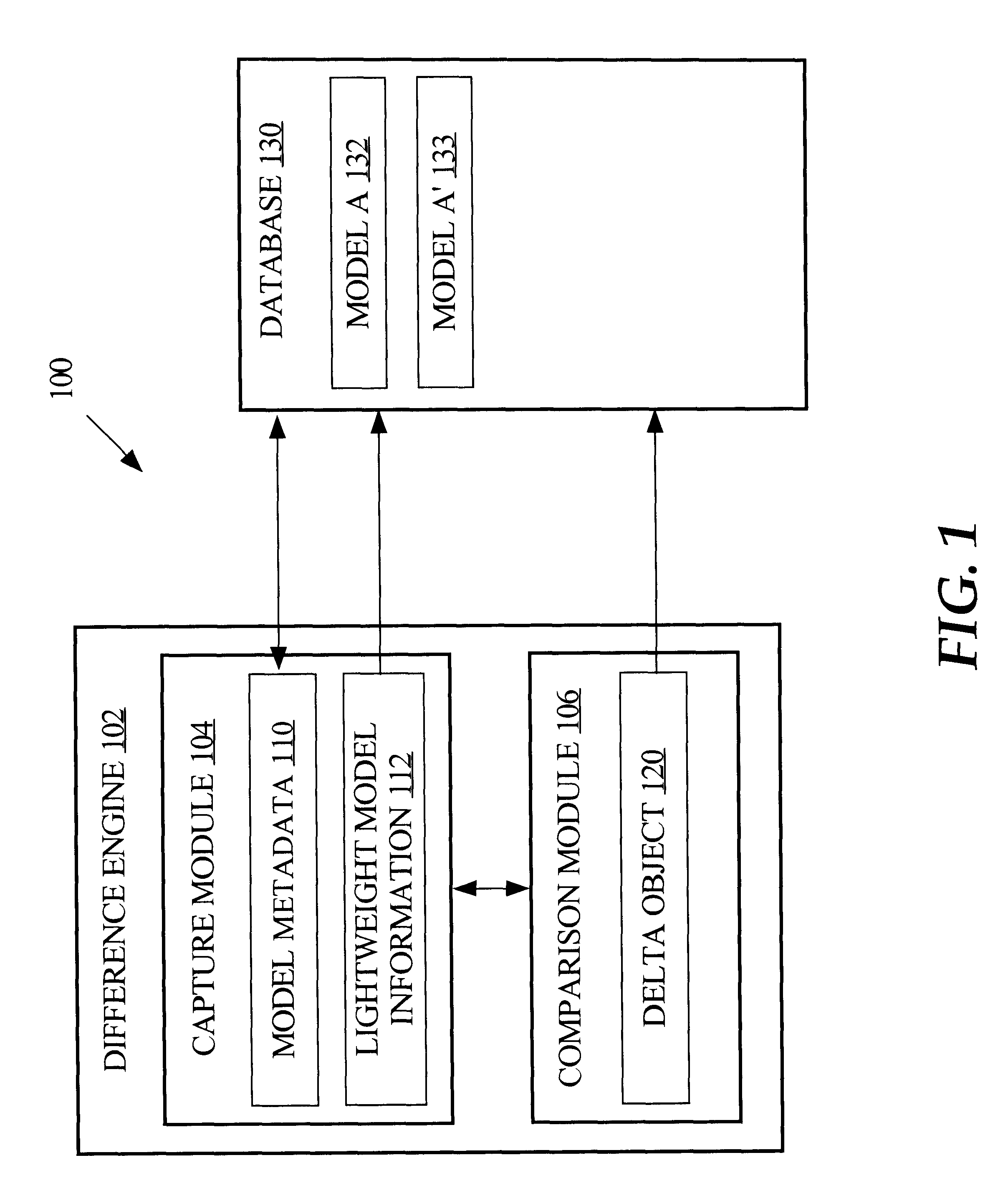
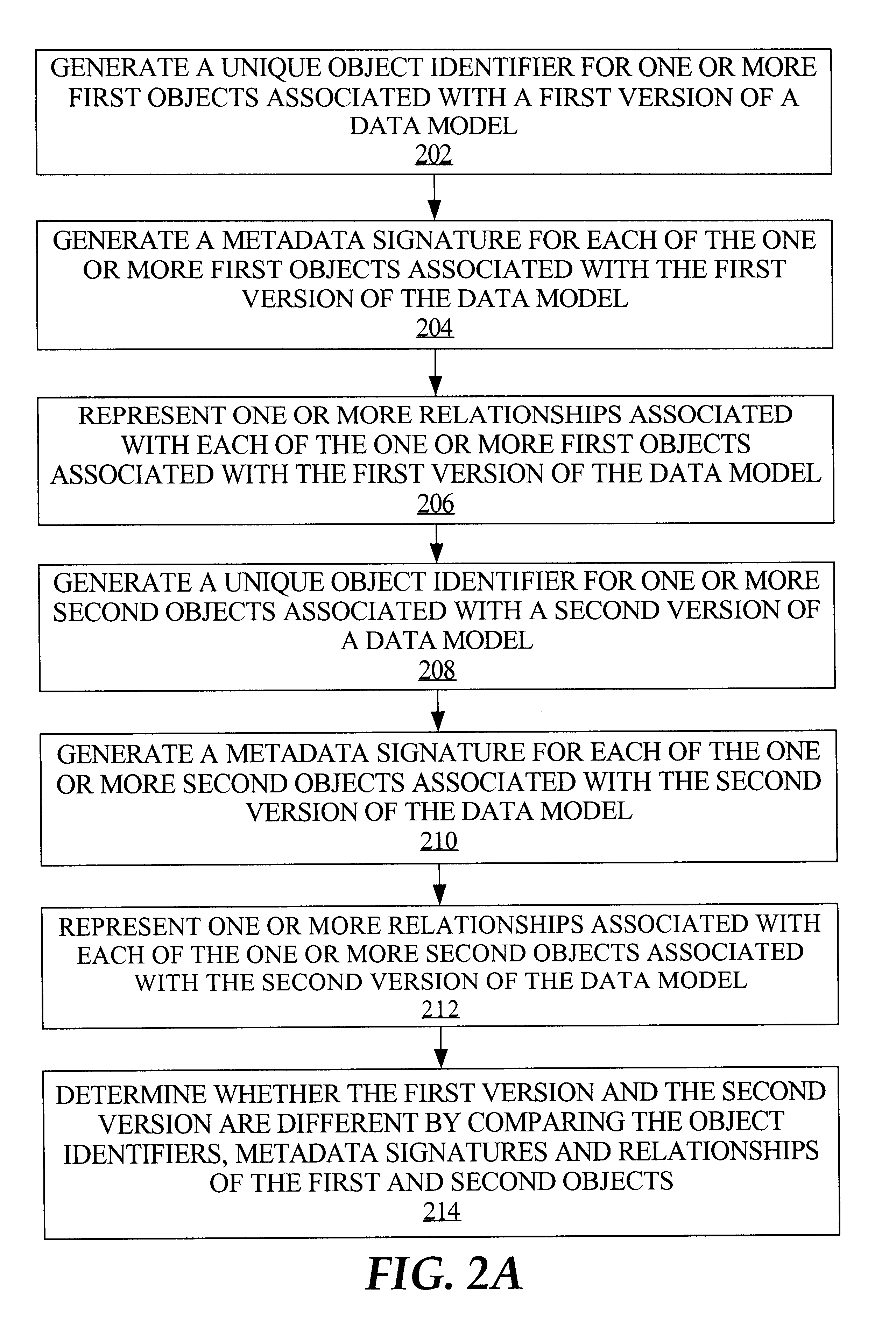
Metamodel-based metadata change management
InactiveUS6839724B2Data processing applicationsDigital data processing detailsChange managementData warehouse
A framework is provided for management of models. Management of data models or other types of models includes model change comparison and change implementation. For example, in the context of data warehouse models, model components and their process interactions are captured in a form such that different versions of a model can be automatically compared and any changes between versions determined. The framework provides the capability of capturing a model definition down to the level of an individual object and the semantics and relationships of each object. A model is represented and stored as a set of (1) unique object identifiers, (2) object metadata signatures that represent the semantics of objects, and (3) object relationships. Such model information can be stored in a relational database, against which a query, such as an SQL (Structured Query Language) query, can be executed to determine whether two models differ.
Owner:ORACLE INT CORP
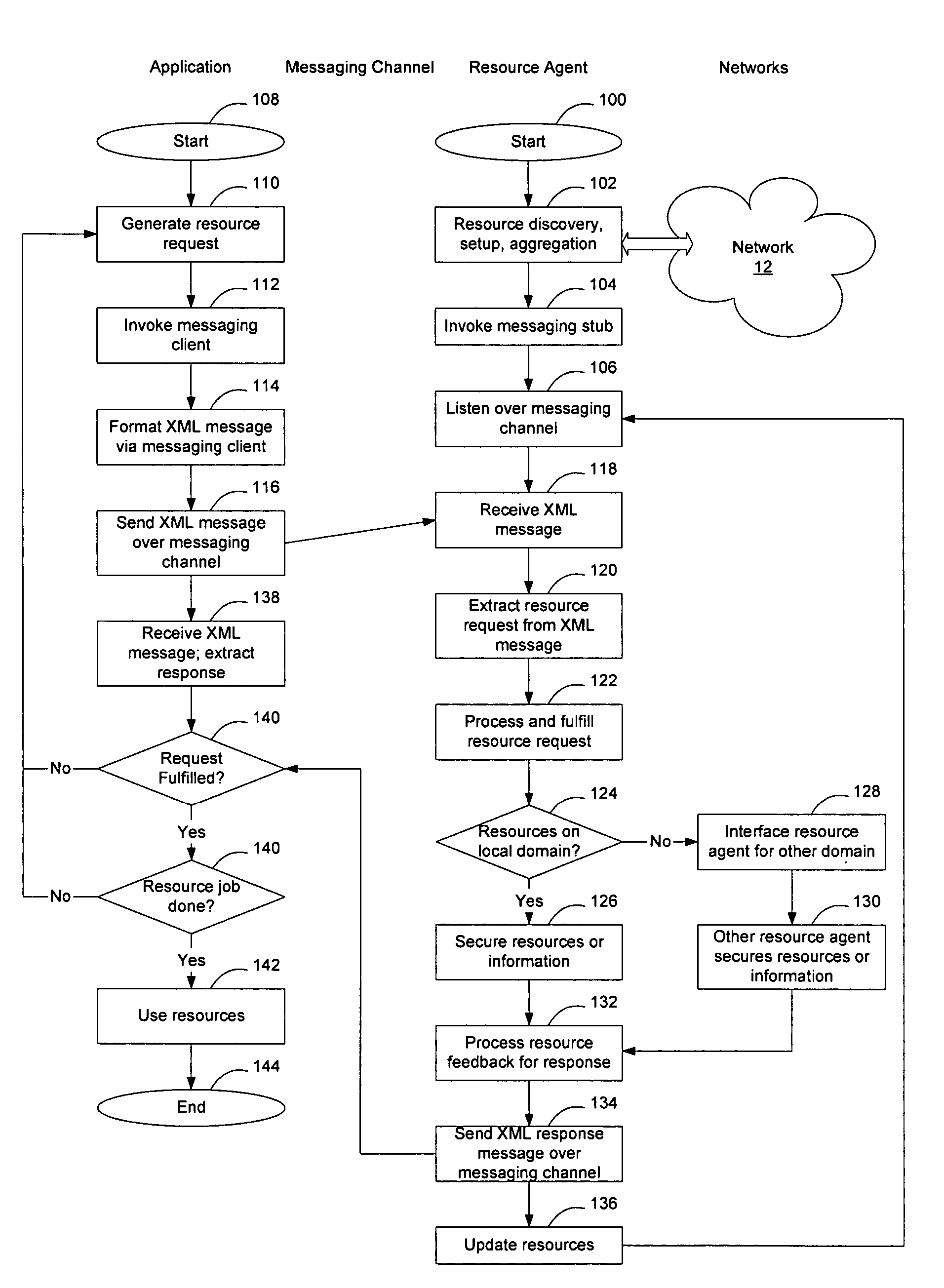
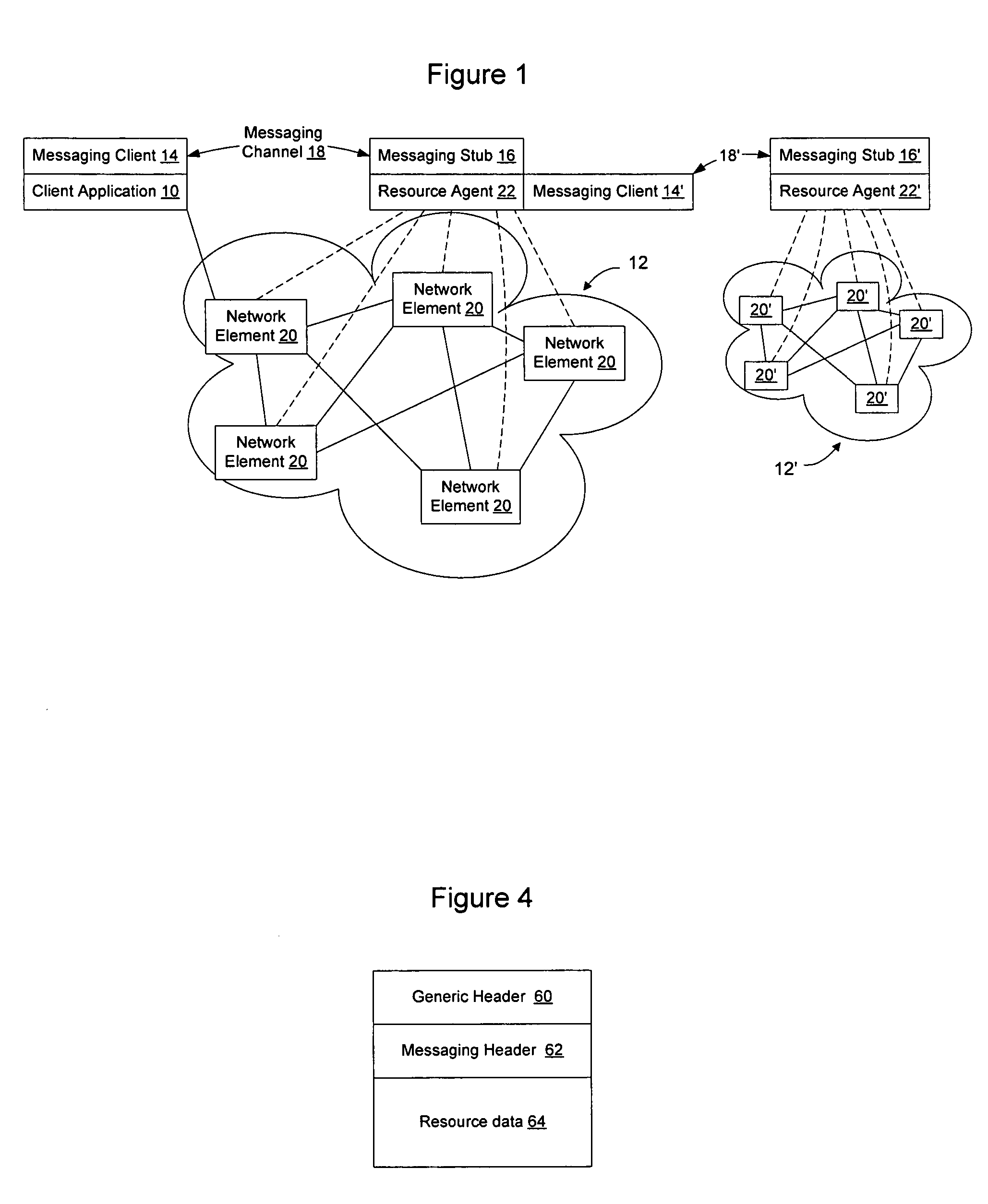
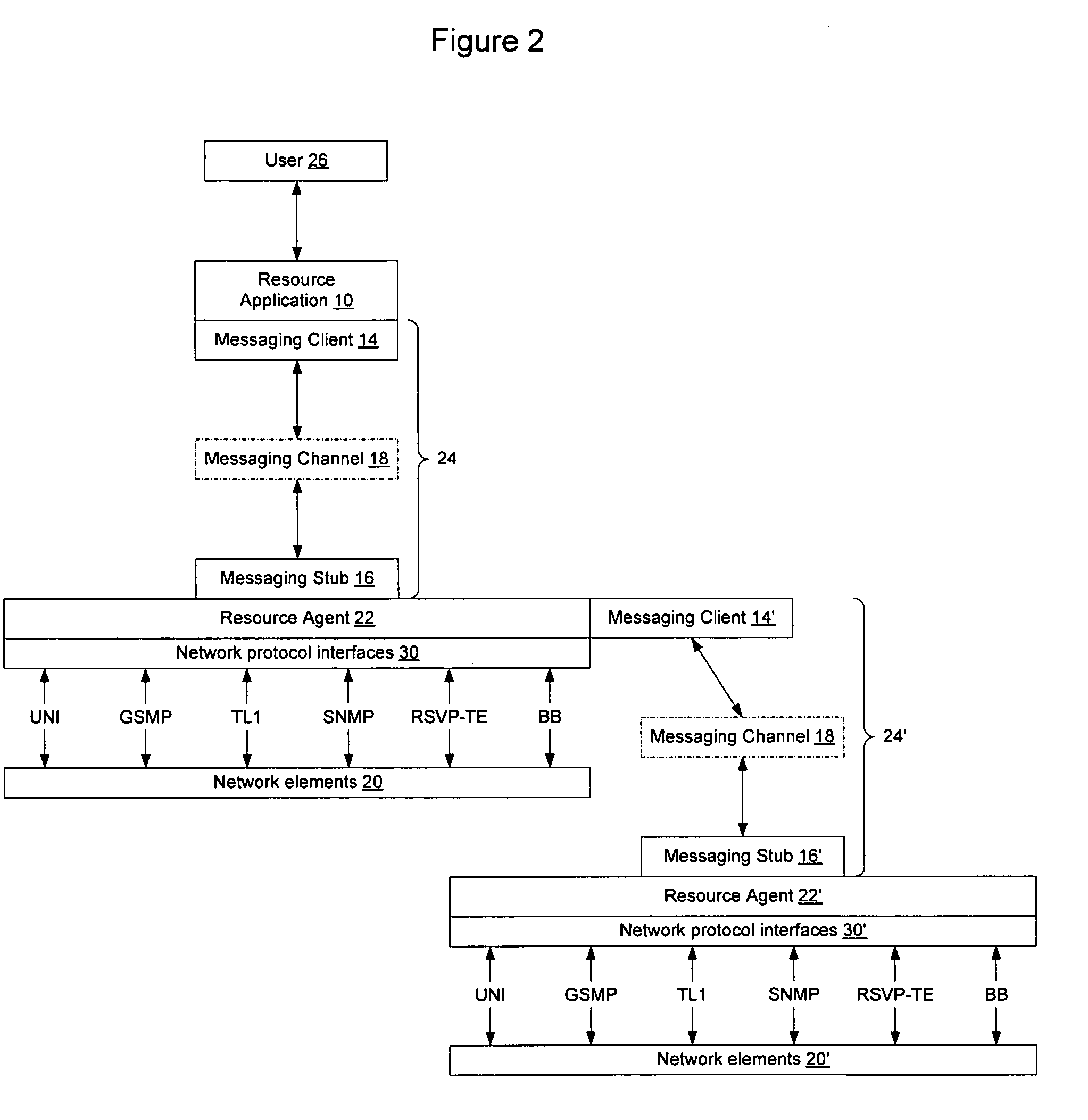
Extensible resource messaging between user applications and network elements in a communication network
InactiveUS20060075042A1Easily use new network resourceAvoid resourcesMultiple digital computer combinationsTransmissionXML schemaMessage passing
Extensible resource messaging in a communication network is provided through creation of a flexible, extensible, and secure messaging environment. A client-server architecture may be implemented in which user applications employ messaging clients to send resource requests for network information, allocation and other operations and receive resource responses, and in which network elements, through resource agents, may use messaging servers to accept resource requests and return resource responses. Resource agents in different network domains may interact through the messaging environment and work together to fulfill resource requests. An XML-based messaging mechanism may be built with a defined message format that can provide flexible message contexts. Network resource semantics may be specified using XML schemas so that network resources are expressed as resource-specific XML elements and network updates can be implemented by updating the XML resource schemas. Secure enhancements may be realized by secure transport, message verification and other means.
Owner:NORTEL NETWORKS LTD
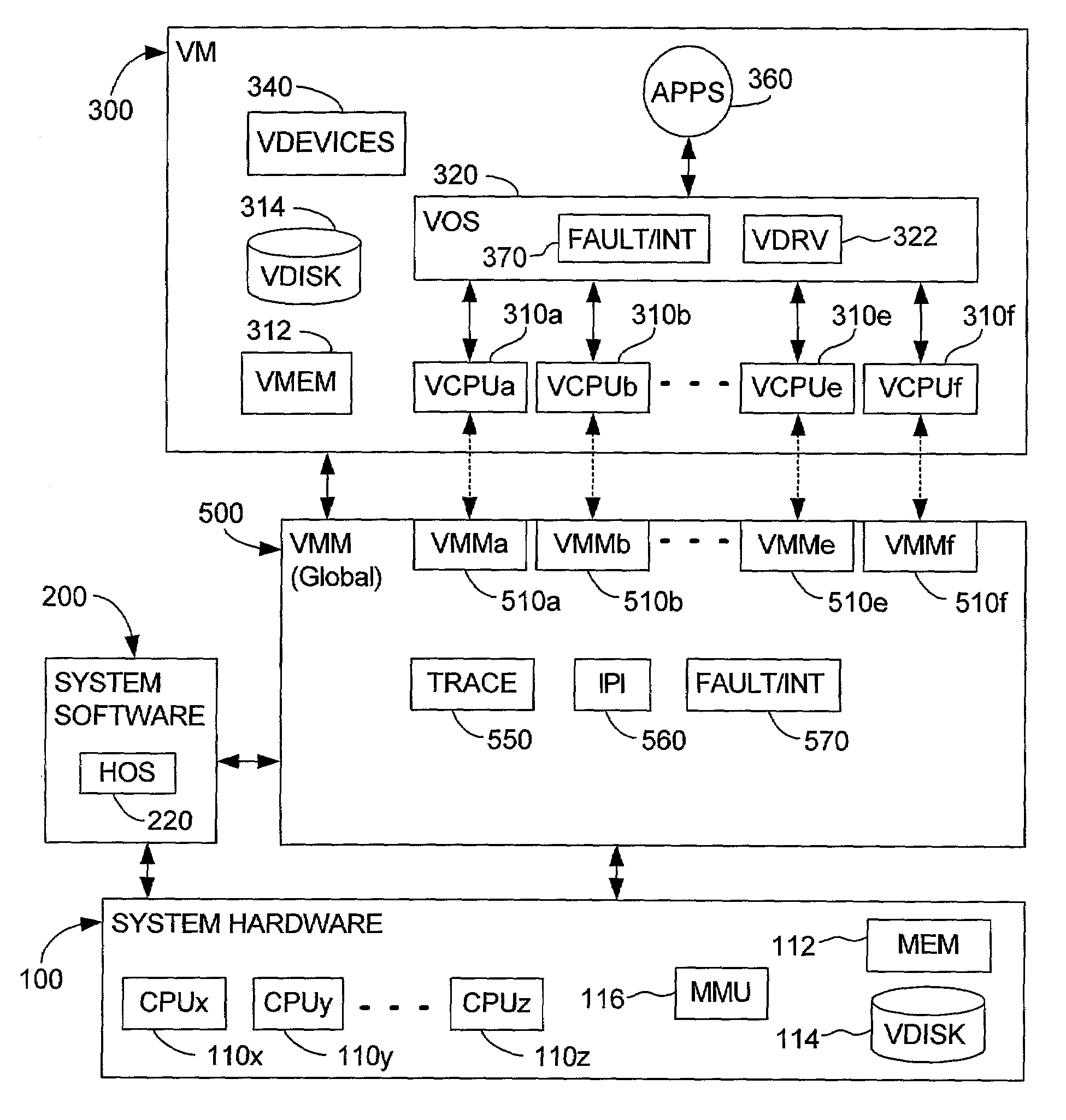
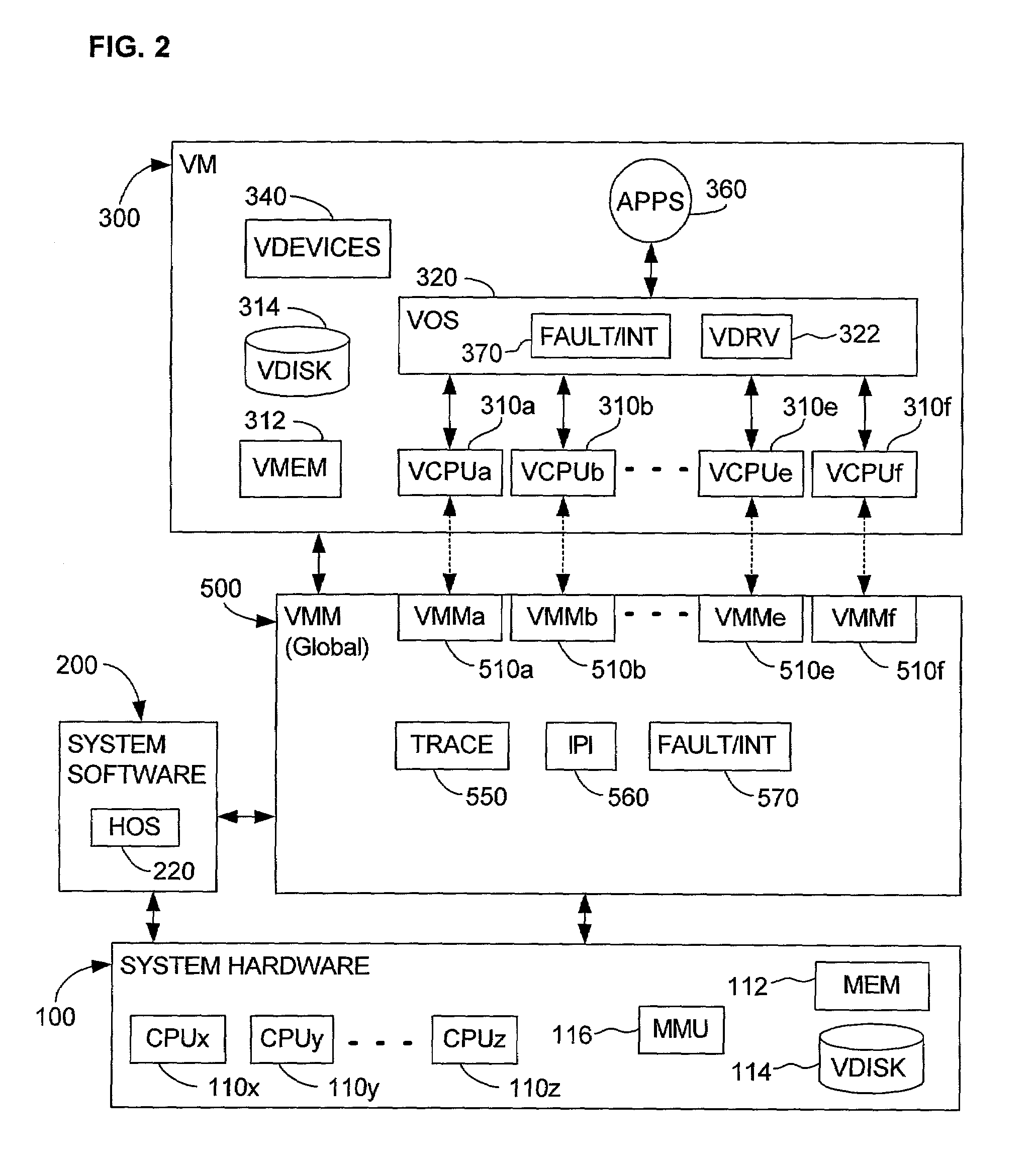
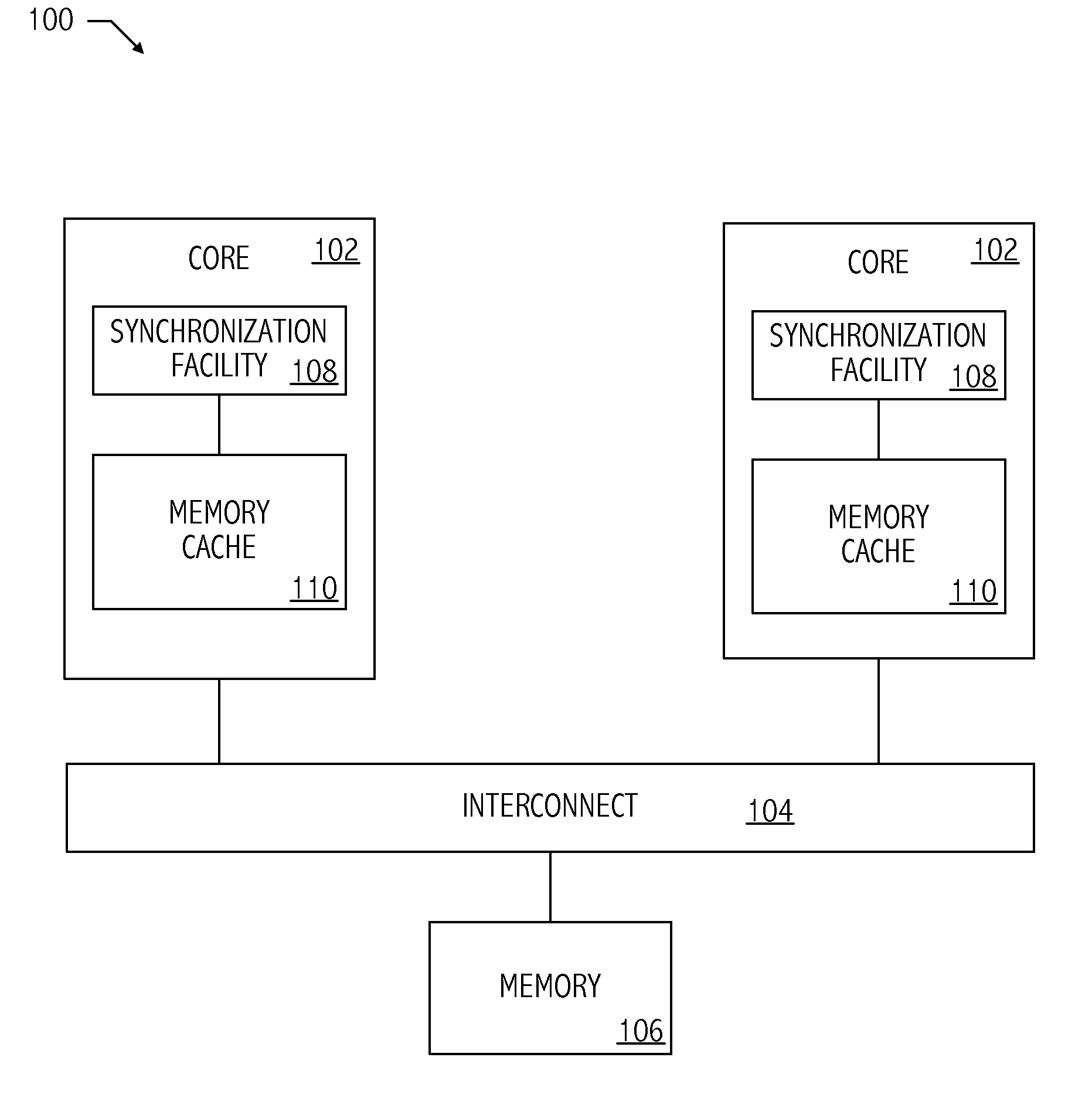
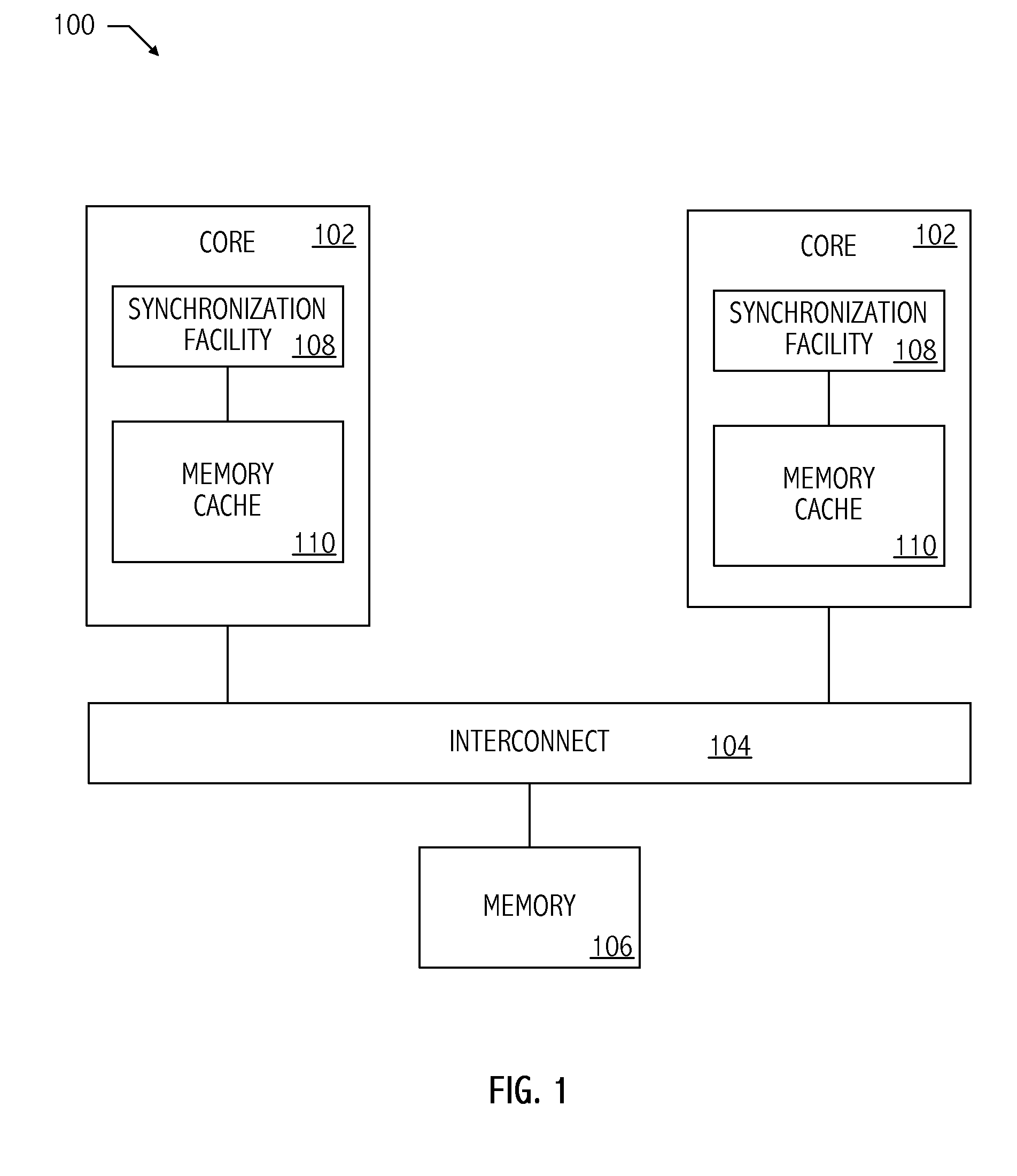
System and method for detecting access to shared structures and for maintaining coherence of derived structures in virtualized multiprocessor systems
A computer system includes at least one virtual machine that has a plurality of virtual processors all running on an underlying hardware platform. A software interface layer such as a virtual machine monitor establishes traces on primary structures located in a common memory space as needed for the different virtual processors. Whenever any one of the virtual processors generates a trace event, such as accessing a traced structure, then a notification is sent to at least the other virtual processors that have a trace on the accessed primary structure. In some applications, the VMM derives and maintains secondary structures corresponding to the primary structures, such as where the VMM converts, through binary translation, original code intended to run on a virtual processor into code that can be run on an underlying physical processor of the hardware platform. In these applications, the VMM may rederive or invalidate the secondary structures as needed upon receipt of the notification of the trace event. Different semantics are provided for the notification, providing different choices of performance versus guaranteed consistency between primary and secondary structures. In the preferred embodiment of the invention, a dedicated sub-system is included within the VMM for each virtual processor; each sub-system establishes traces, senses trace events, issues the notification, and performs other operations relating specifically to its respective virtual processor.
Owner:VMWARE INC
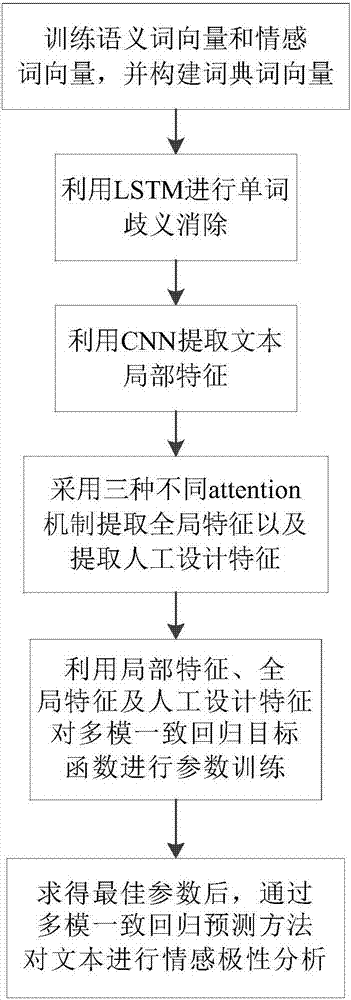
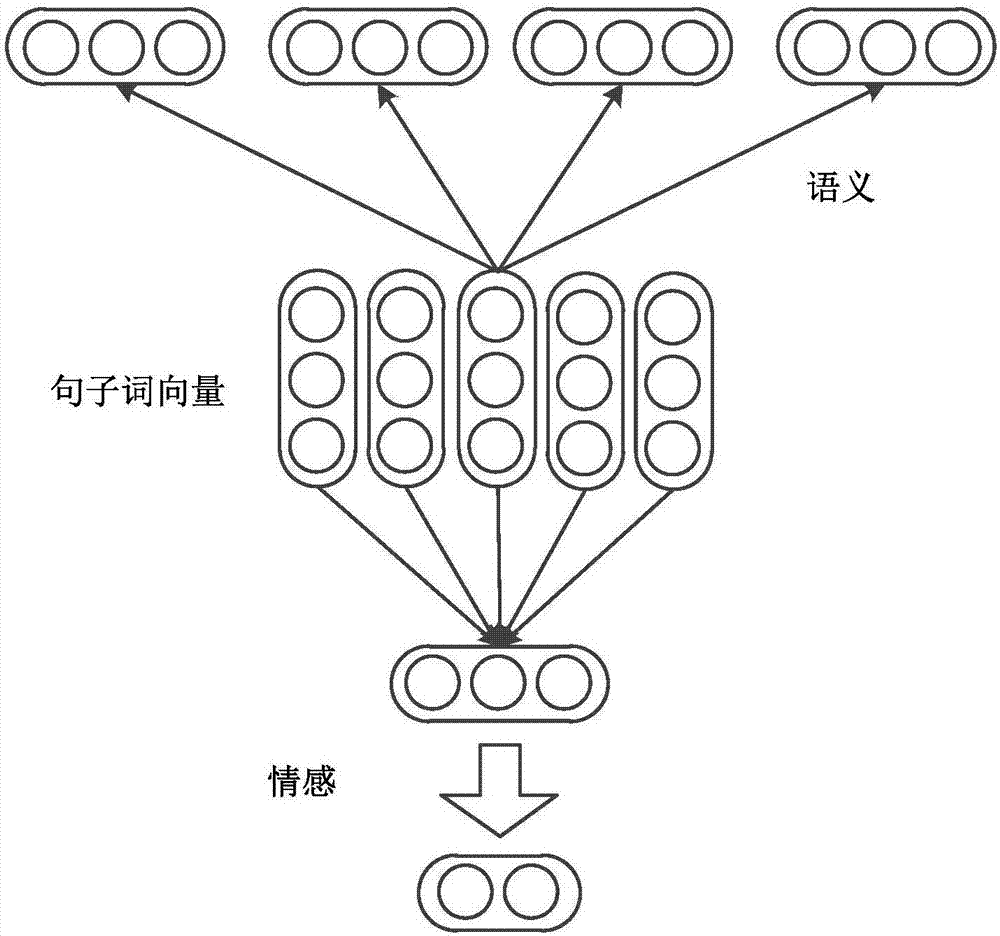
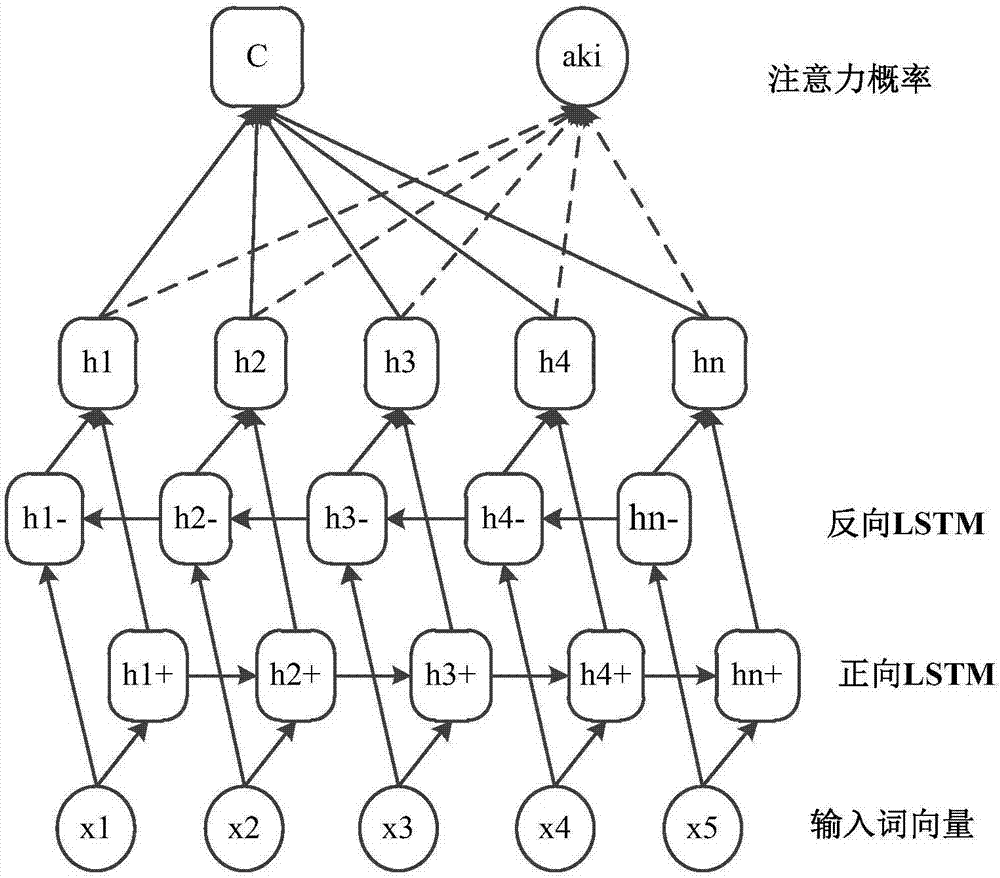
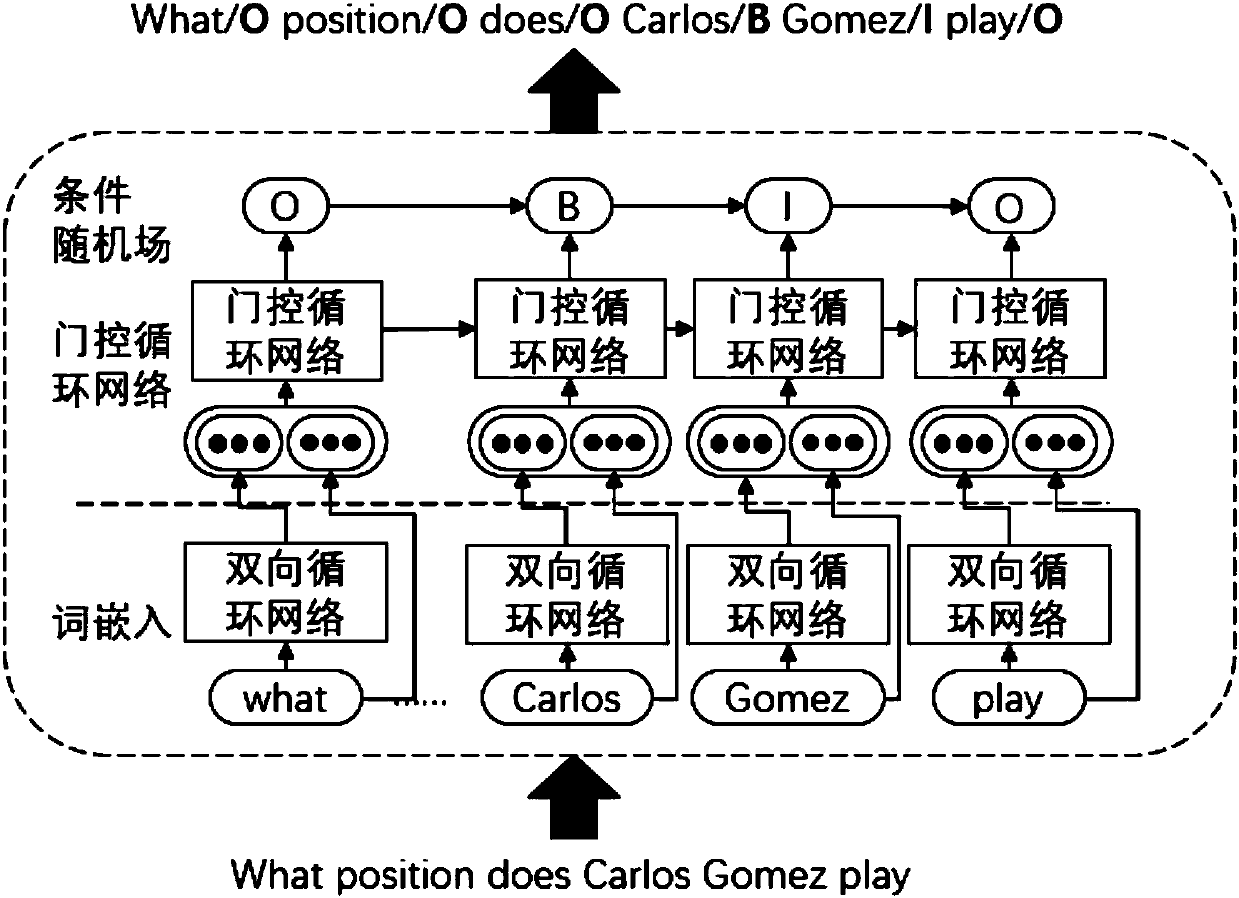
attention CNNs and CCR-based text sentiment analysis method
ActiveCN107092596AHigh precisionImprove classification accuracySemantic analysisNeural architecturesFeature extractionAmbiguity
The invention discloses an attention CNNs and CCR-based text sentiment analysis method and belongs to the field of natural language processing. The method comprises the following steps of 1, training a semantic word vector and a sentiment word vector by utilizing original text data and performing dictionary word vector establishment by utilizing a collected sentiment dictionary; 2, capturing context semantics of words by utilizing a long-short-term memory (LSTM) network to eliminate ambiguity; 3, extracting local features of a text in combination with convolution kernels with different filtering lengths by utilizing a convolutional neural network; 4, extracting global features by utilizing three different attention mechanisms; 5, performing artificial feature extraction on the original text data; 6, training a multimodal uniform regression target function by utilizing the local features, the global features and artificial features; and 7, performing sentiment polarity prediction by utilizing a multimodal uniform regression prediction method. Compared with a method adopting a single word vector, a method only extracting the local features of the text, or the like, the text sentiment analysis method can further improve the sentiment classification precision.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
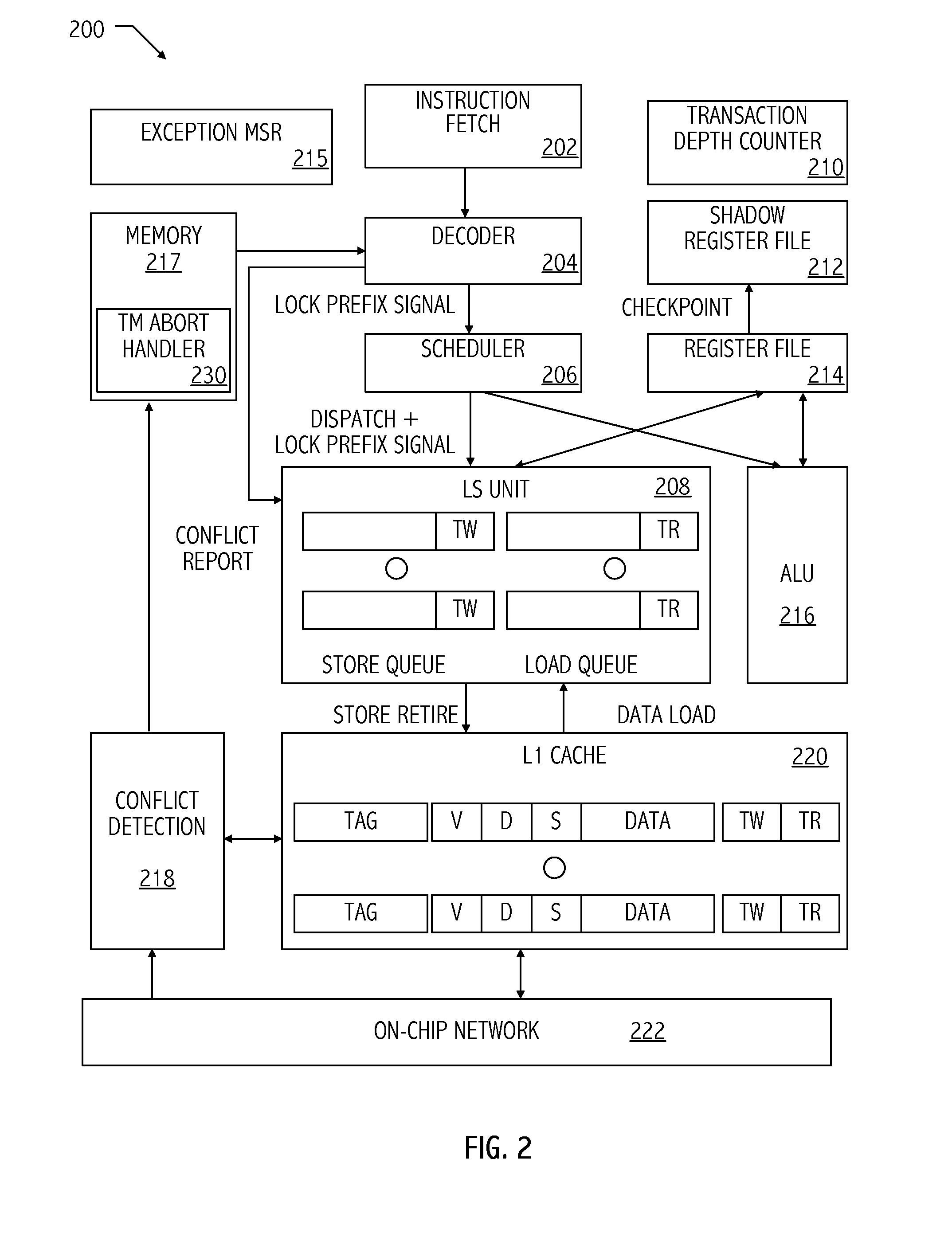
Inverted default semantics for in-speculative-region memory accesses
InactiveUS20110208921A1Unauthorized memory use protectionTransaction processingDirect memory accessMulti processor
A method for accessing memory by a first processor of a plurality of processors in a multi-processor system includes, responsive to a memory access instruction within a speculative region of a program, accessing contents of a memory location using a transactional memory access to the memory access instruction unless the memory access instruction indicates a non-transactional memory access. The method may include accessing contents of the memory location using a non-transactional memory access by the first processor according to the memory access instruction responsive to the instruction not being in the speculative region of the program. The method may include updating contents of the memory location responsive to the speculative region of the program executing successfully and the memory access instruction not being annotated to be a non-transactional memory access.
Owner:ADVANCED MICRO DEVICES INC
Method and apparatus for the development of dynamically configurable software systems
InactiveUS6269473B1Dynamic configurabilityImprove abilitiesData processing applicationsSoftware designSoftware systemSemantics
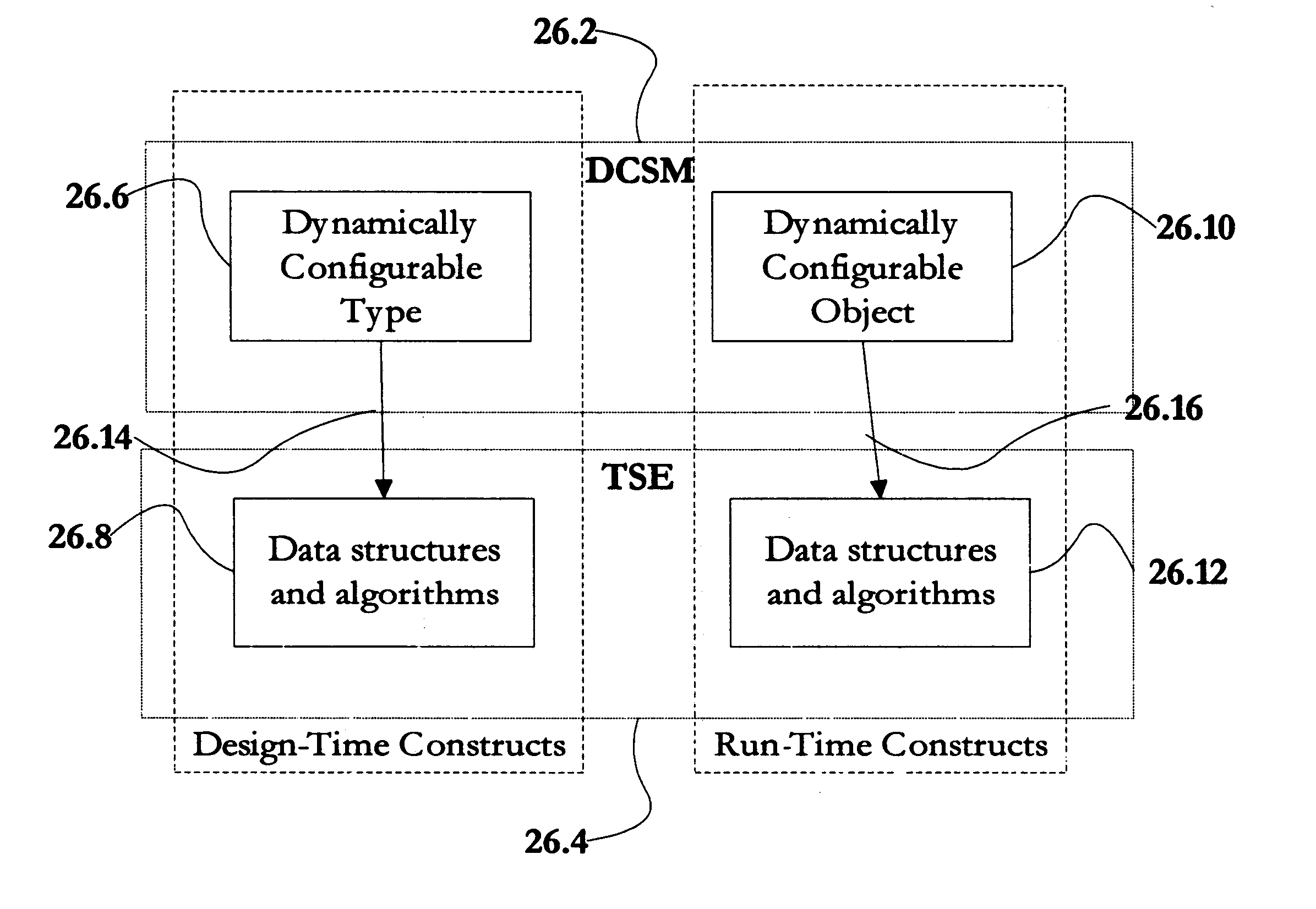
A software modeling environment is presented that supports the development and execution of software that can be dynamically configured. This is achieved by introducing a design-time object modeling construct called a dynamically configurable type (DCT) that supports the subdivision of an object into a plurality of subsets of semantics and allows dynamic merging of these semantic subsets together in different combinations in order to allow the resultant object to exhibit different semantics over time to serve different purposes. Specific process modeling constructs are included which take advantage of this semantic merging capability. Also included are other supporting design-time and run-time constructs and services. One embodiment of the present invention allows this software modeling environment to be integrated into a standard software development environment, enhancing the modeling capabilities already present.
Owner:EVOLVE SOFTWARE
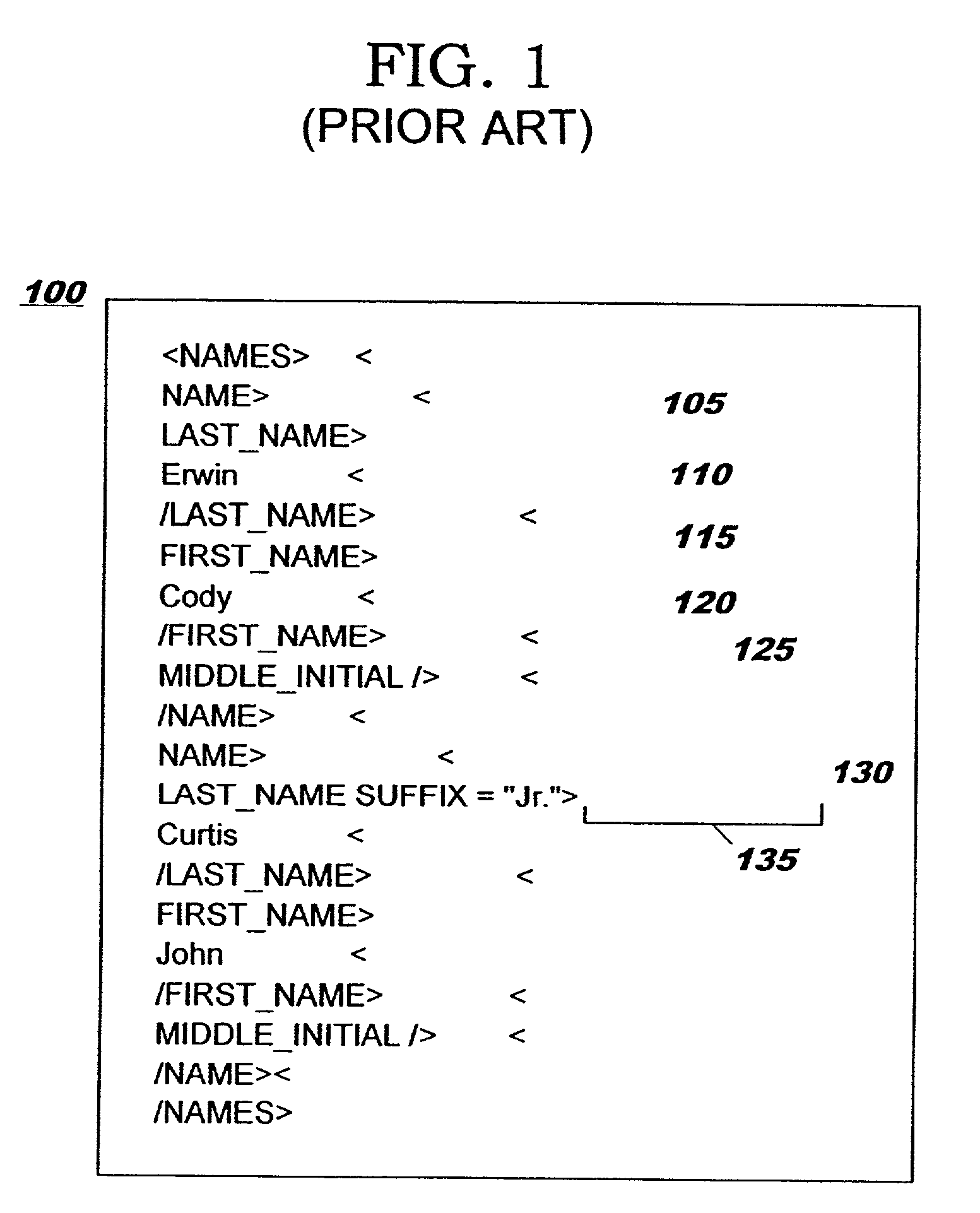
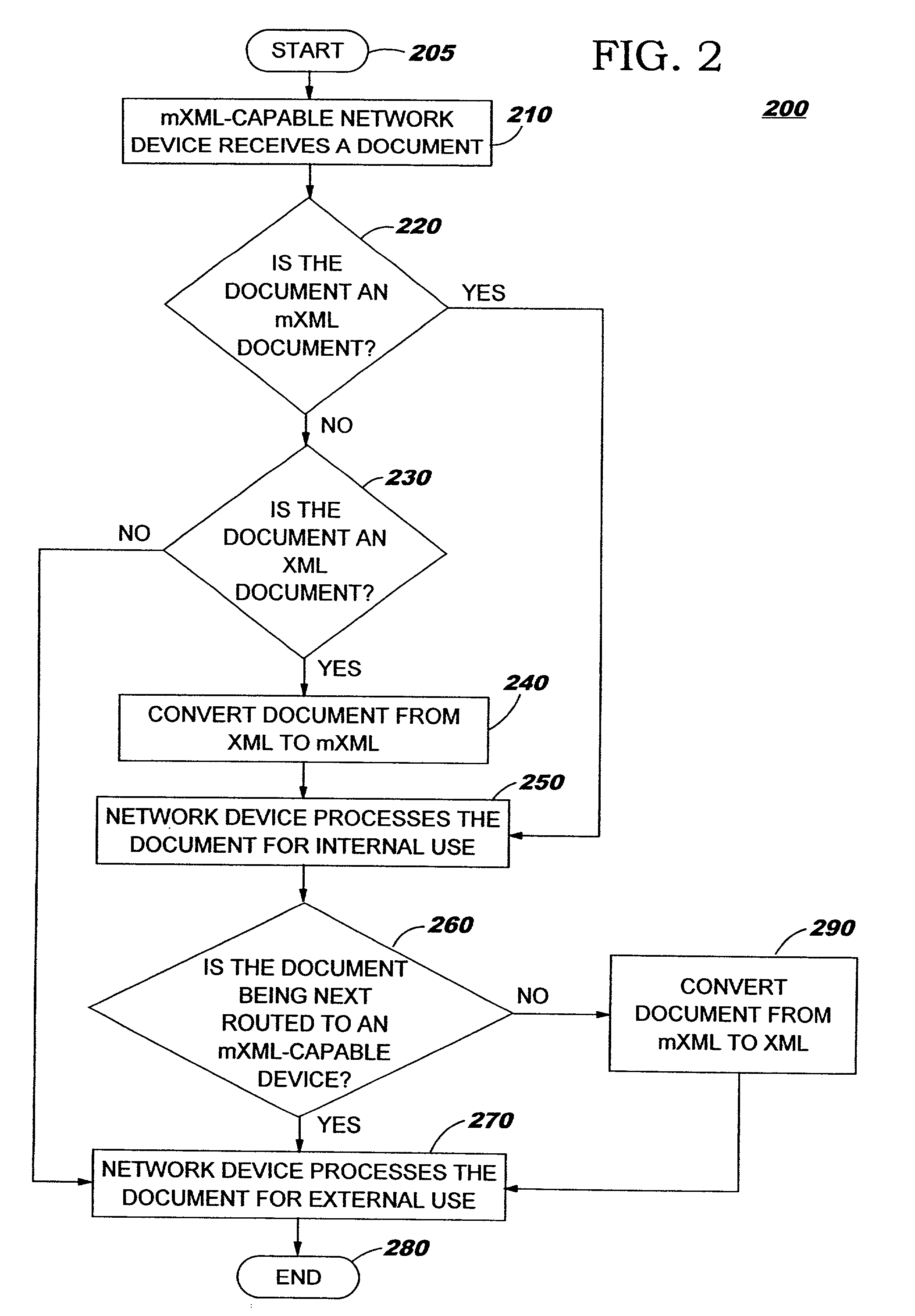
Conversion of documents between XML and processor efficient MXML in content based routing networks
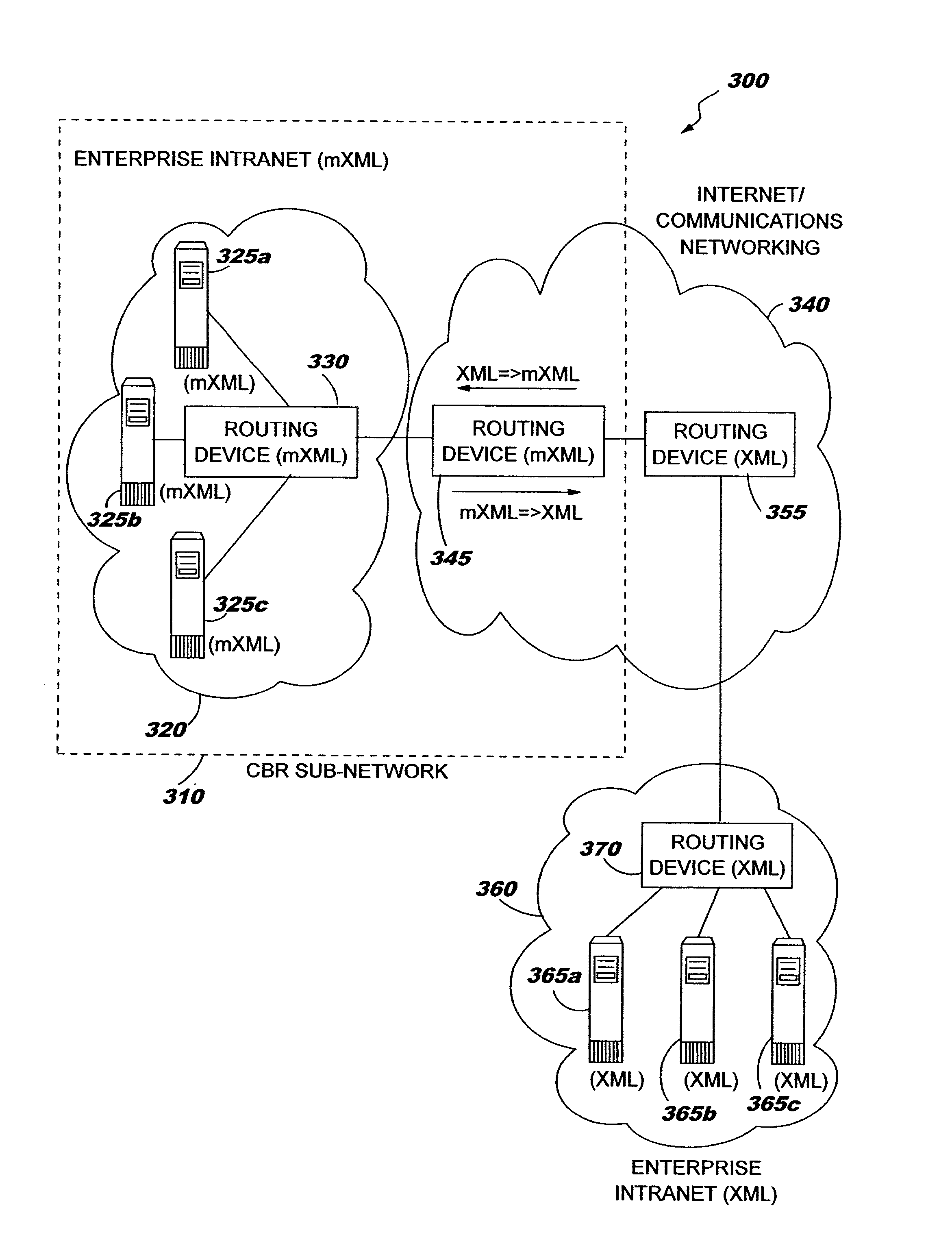
InactiveUS7134075B2Efficient processingImprove performanceNatural language data processingSpecial data processing applicationsSemanticsExtensible markup
A method, system, and computer program product for efficient processing of Extensible Markup Language (XML) documents in Content Based Routing (“CBR”) networks. Specifically, the method involves converting existing XML documents to a machine-oriented notation (“mXML”) which is significantly more compact than XML, while still conveying the content and semantics of the data and the structure of the document. Documents are converted from XML to mXML upon entering a CBR subnetwork and / or upon receipt by an mXML-capable device. The documents are then processed in mXML format. Devices within the inventive system are provided with an awareness of whether target devices or processes are mXML-capable. Documents being routed to a target which is mXML-capable are passed in mXML format while documents being routed to a target which is not mXML-capable are converted to XML before they are passed.
Owner:IBM CORP
Database query handler supporting querying of textual annotations of relations between data objects
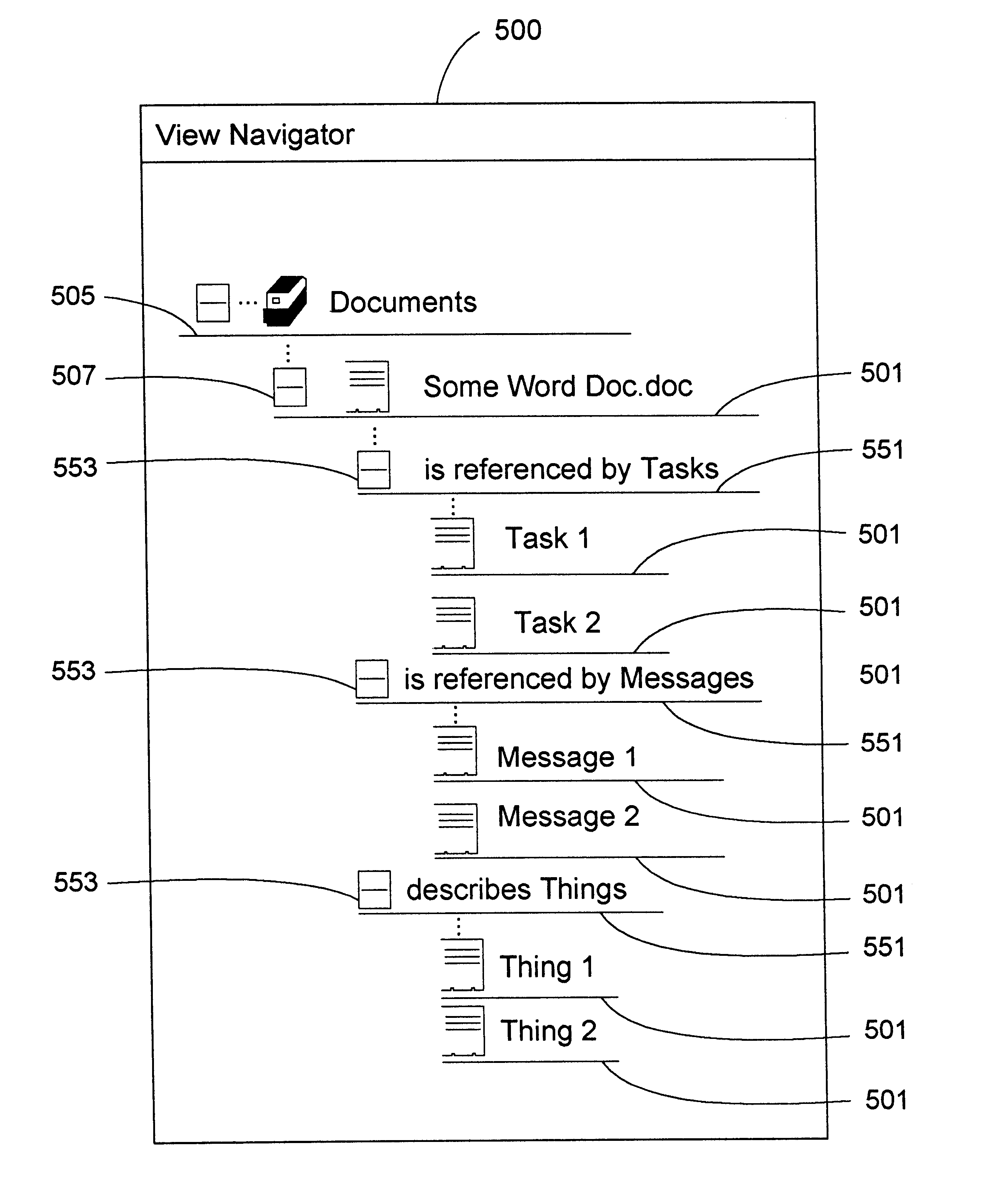
InactiveUS6618732B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsDatabase queryCustomer relationship management
An improved command handler (and database system utilizing the improved command handler) interfaces to a datastore storing item data for a plurality of items and bi-directional modifier data, corresponding to a relation between at least one first item and at least one second item, that represents first text characterizing semantics of a relationship of the at least one first item to the at least one second item, and represents second text characterizing semantics of a relationship of the at least one second item to the at least one first item. The command handler operates, in response to receiving a first-type query command that specifies at least one given item, to access the datastore to identify i) at least one related item that is related to the given item, and identify ii) either the first text or the second text characterizing semantics of the relation between the given item and the at least one related item. The command hander returns i) data corresponding to the at least one related item; and ii) data corresponding to the identified first text and or second text characterizing semantics of the relation between the given item and the at least one related item. Preferably, the data returned in response to the first-type query command identifies the at least one related item. and identifies the first text or second text characterizing semantics of the relation between the given item and the at least one related item. In addition, the command handler preferably supports additional commands that retrieve from the datastore information related to specified objects, object types, and relations.The command handler (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the command handler (and database system) provides an efficient mechanism to query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that efficient and readily adaptable to client-server database systems or other distributed database systems.
Owner:REVELINK
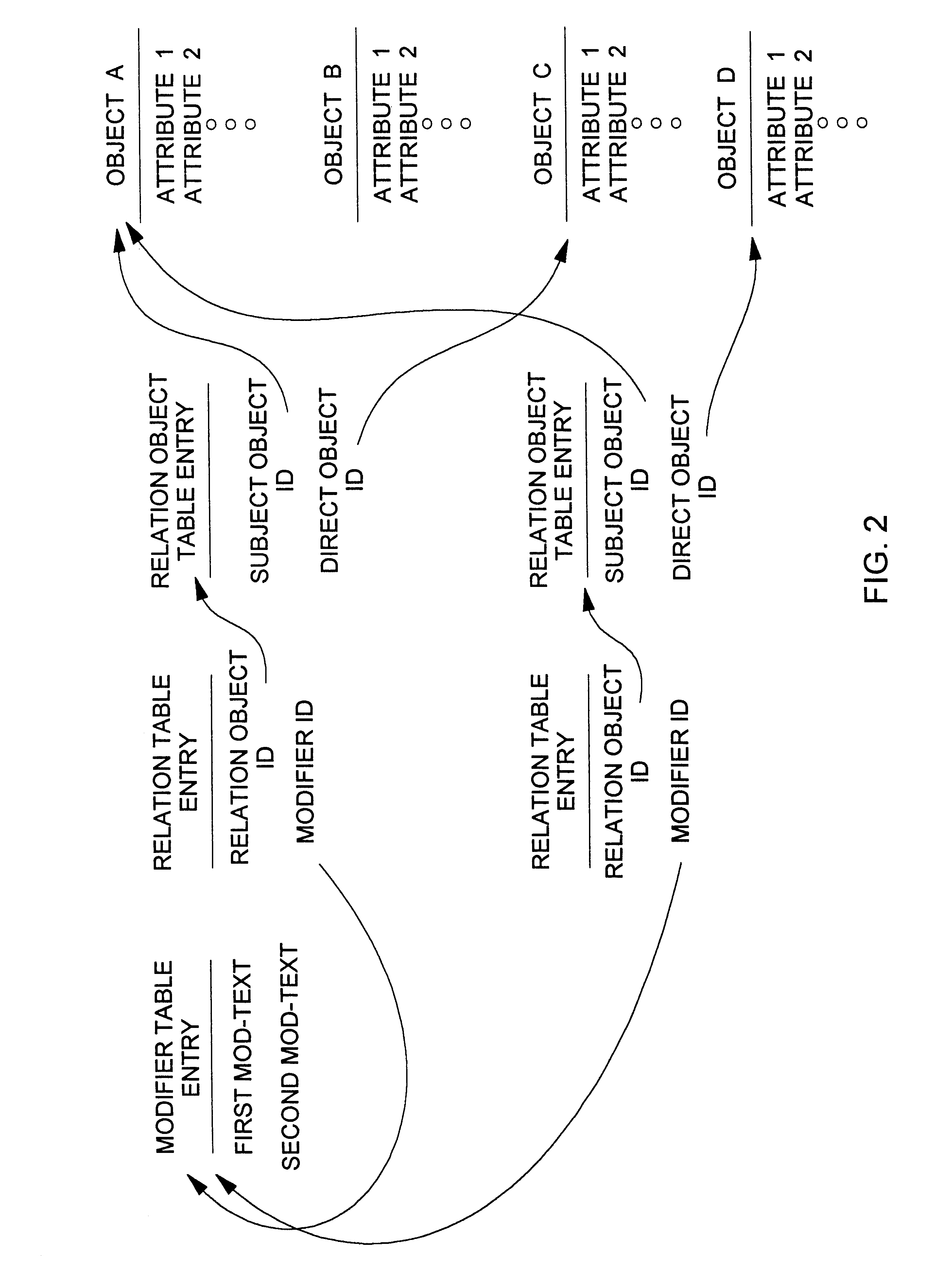
Method for generic object oriented description of structured data (GDL)
InactiveUS7092950B2Facilitate semanticFacilitate definitional information verificationData processing applicationsDigital data processing detailsText entryComputerized system
A method is provided for use in a computer system to describe and obtain arbitrary data relating to a subject. The method provides a meta-language “Generic Object Oriented Description of Structured Data (GDL)” and a Parser. GDL allows a user to organize, define and describe subjects through the use of a schema known as a Template. Templates can be used to define the semantics for each subject element as well as, to define how each element fits into a larger data framework. Through the concept of Inheritance, Templates can be extended and defined to various levels of nesting, while still having a common core of properties. GDL allows the features and attributes of a subject to be quickly and readily extended or modified by altering a source file. A GDL parser provides a structured and hierarchical representation of the information, validation of text-entry semantics and a means to traverse through information obtained from the source file.
Owner:MICROSOFT TECH LICENSING LLC
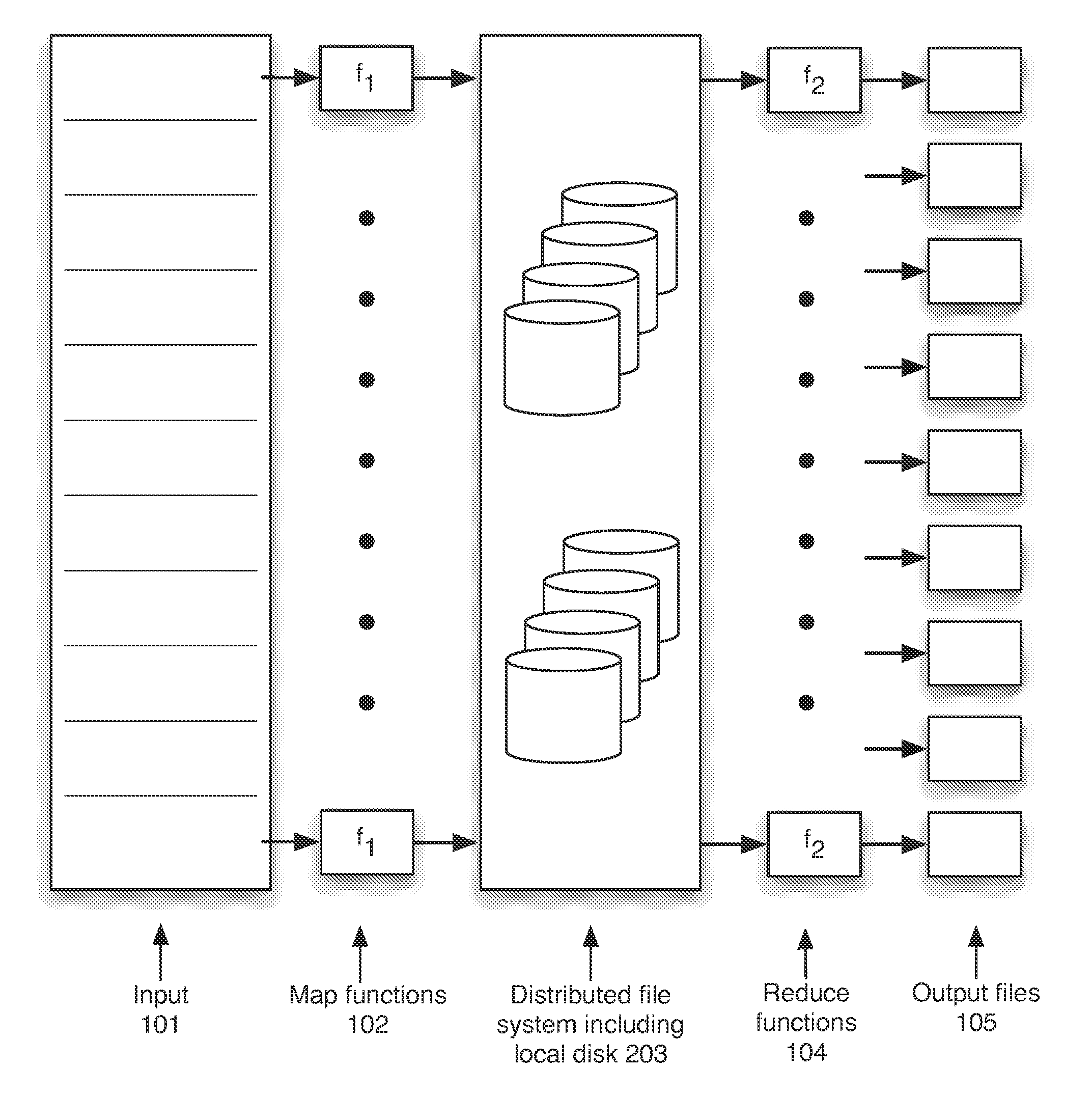
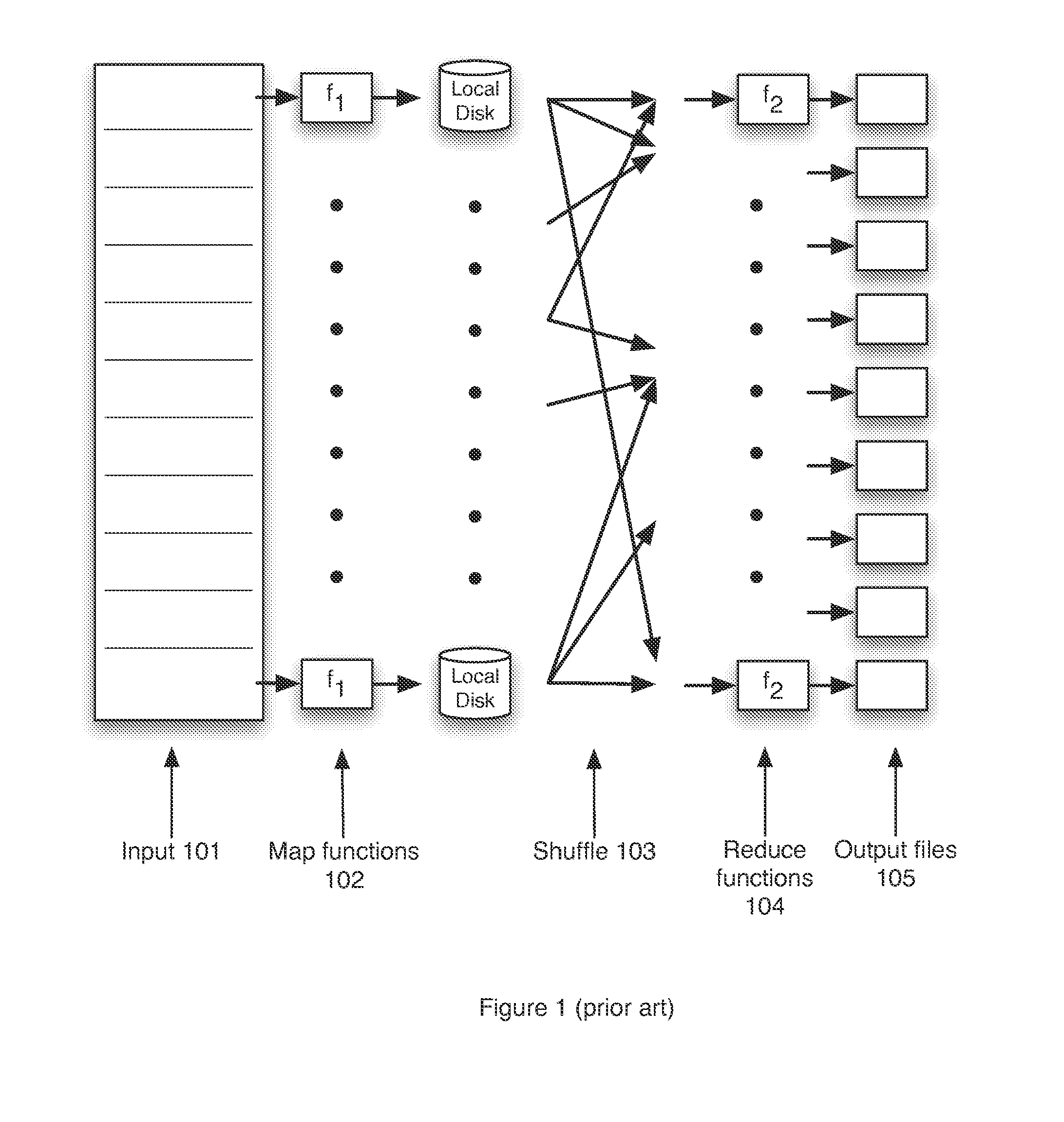
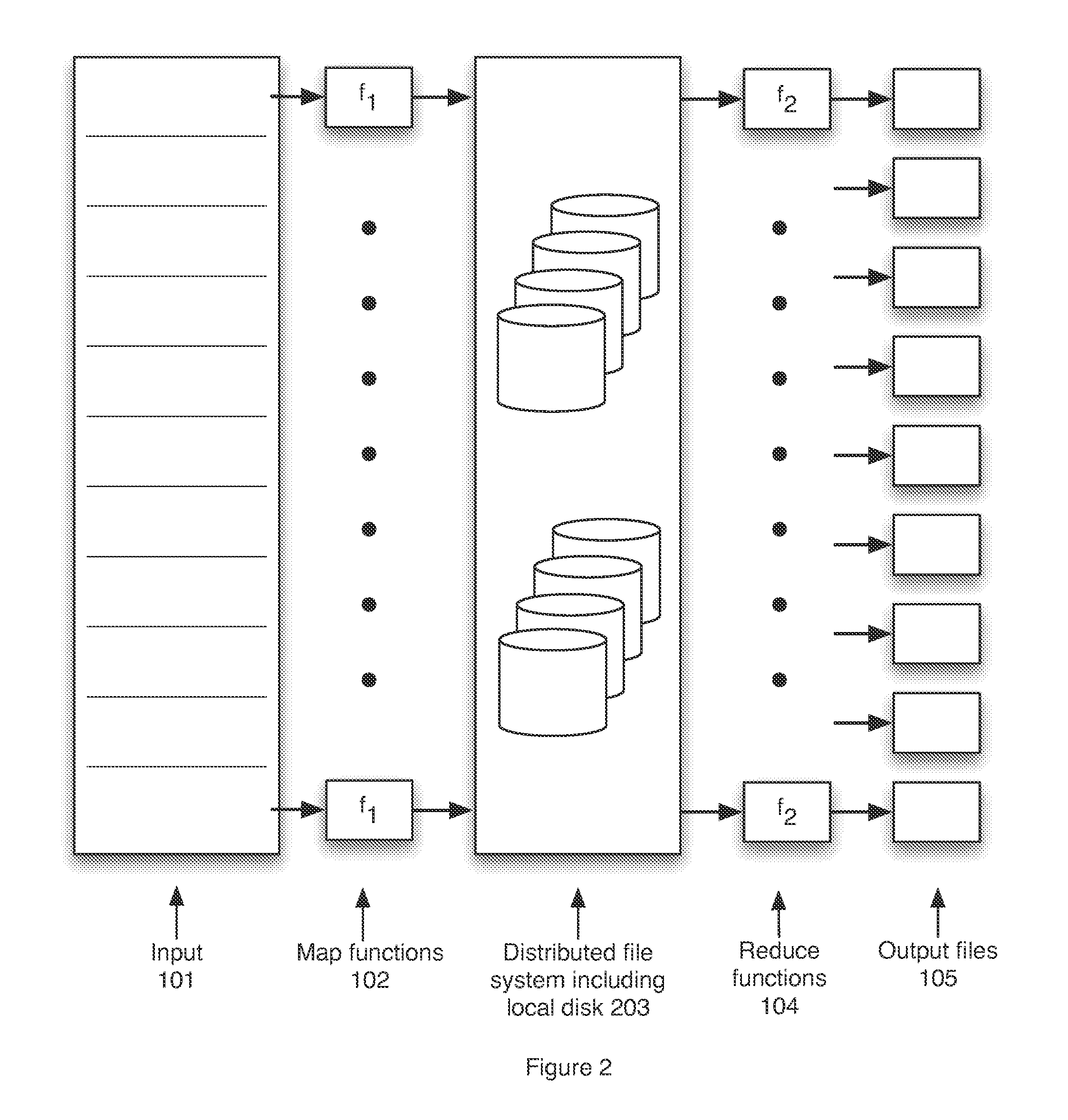
Map-Reduce Ready Distributed File System
A map-reduce compatible distributed file system that consists of successive component layers that each provide the basis on which the next layer is built provides transactional read-write-update semantics with file chunk replication and huge file-create rates. A primitive storage layer (storage pools) knits together raw block stores and provides a storage mechanism for containers and transaction logs. Storage pools are manipulated by individual file servers. Containers provide the fundamental basis for data replication, relocation, and transactional updates. A container location database allows containers to be found among all file servers, as well as defining precedence among replicas of containers to organize transactional updates of container contents. Volumes facilitate control of data placement, creation of snapshots and mirrors, and retention of a variety of control and policy information. Key-value stores relate keys to data for such purposes as directories, container location maps, and offset maps in compressed files.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
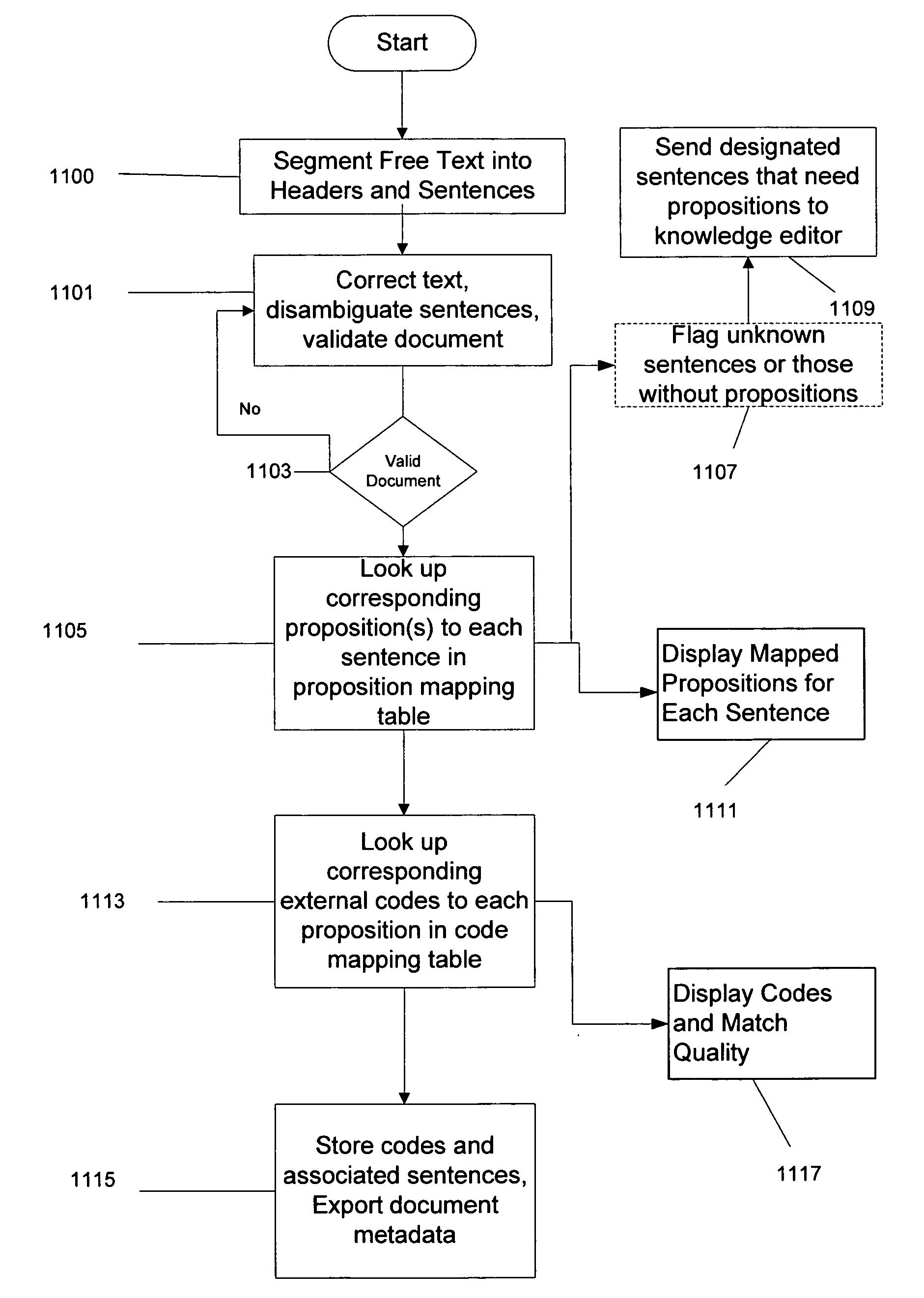
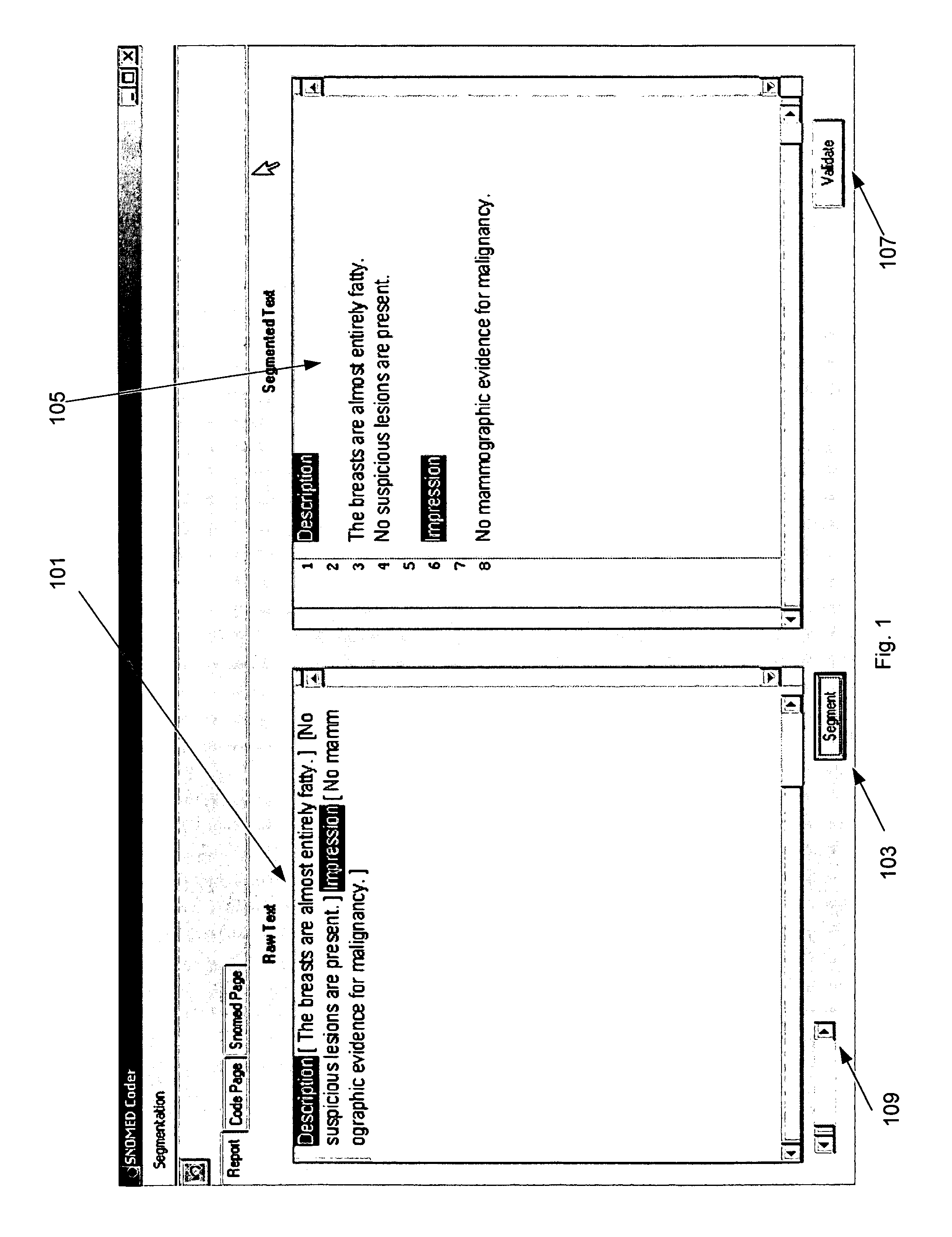
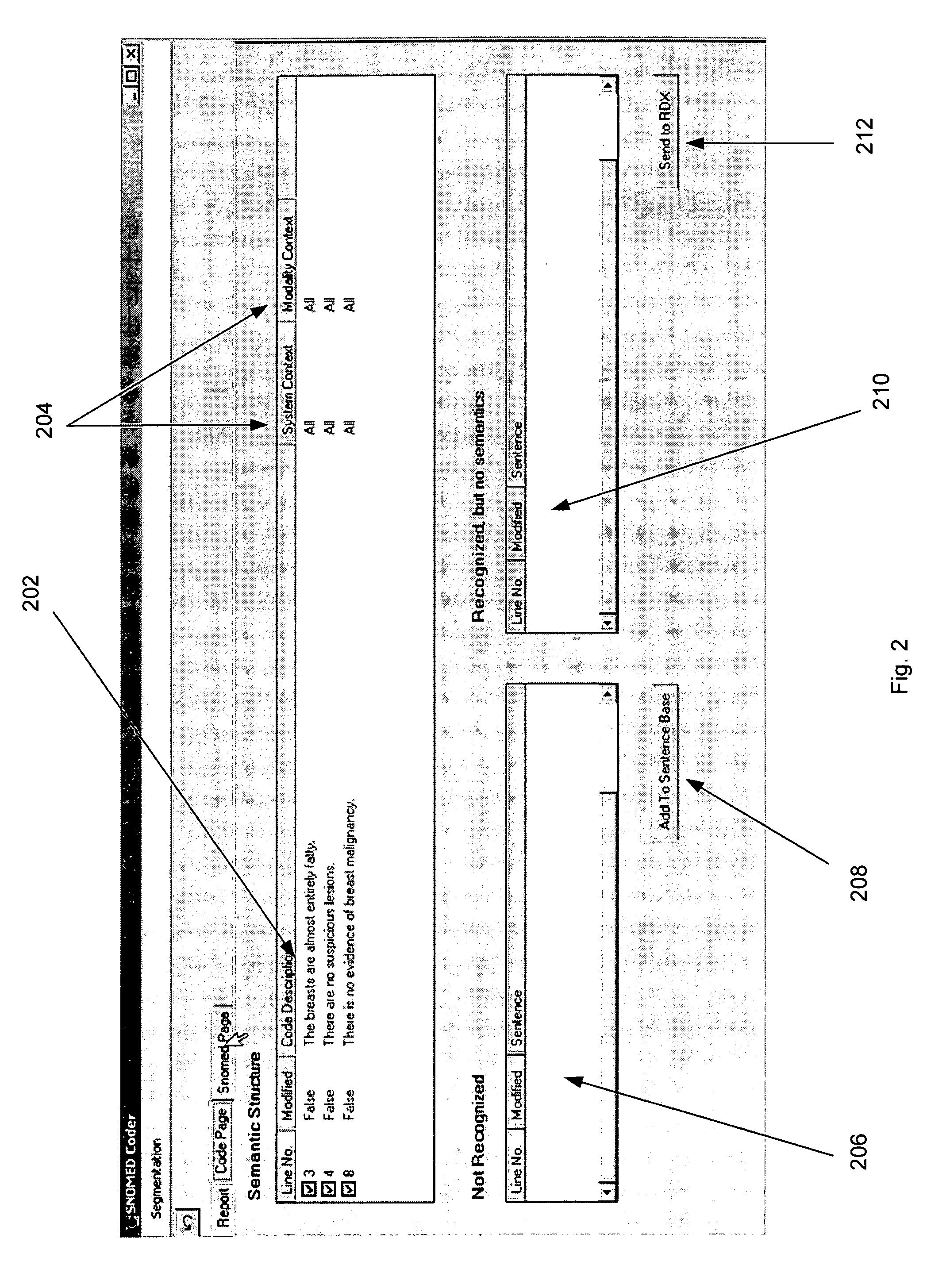
Process and system for high precision coding of free text documents against a standard lexicon
InactiveUS7610192B1Minimal effortFinanceDigital data processing detailsMedical recordElectronic medical record
Coding free text documents, especially in medicine, has become an urgent priority as electronic medical records (EMR) mature, and the need to exchange data between EMRs becomes more acute. However, only a few automated coding systems exist, and they can only code a small portion of the free text against a limited number of codes. The precision of these systems is low and code quality is not measured. The present invention discloses a process and system which implements semantic coding against standard lexicon(s) with high precision. The standard lexicon can come from a number of different sources, but is usually developed by a standard's body. The system is semi-automated to enable medical coders or others to process free text documents at a rapid rate and with high precision. The system performs the steps of segmenting a document, flagging the need for corrections, validating the document against a data type definition, and looking up both the semantics and standard codes which correspond to the document's sentences. The coder has the option to intervene at any step in the process to fix mistakes made by the system. A knowledge base, consisting of propositions, represents the semantic knowledge in the domain. When sentences with unknown semantics are discovered they can be easily added to the knowledge base. The propositions in the knowledge base are associated with codes in the standard lexicon. The quality of each match is rated by a professional who understands the knowledge domain. The system uses this information to perform high precision coding and measure the quality of the match.
Owner:JAMIESON PATRICK WILLIAM
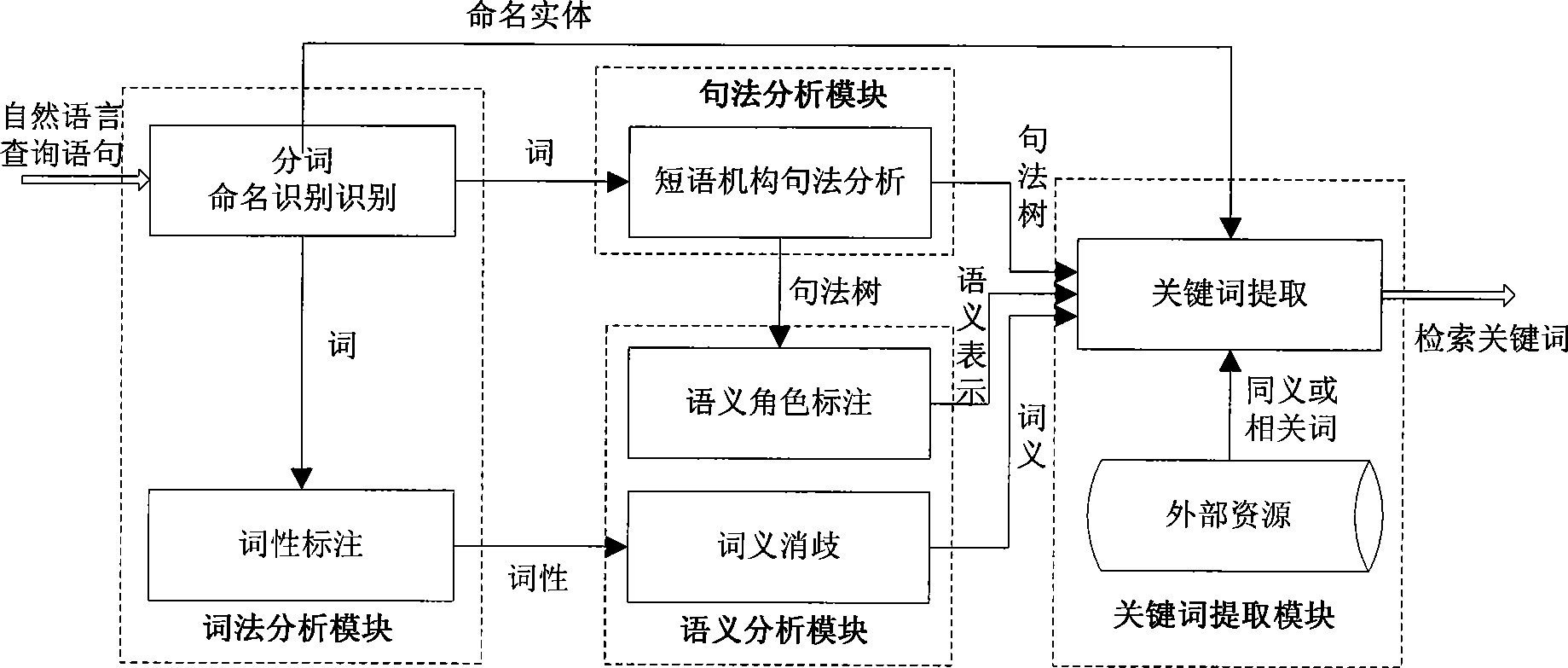
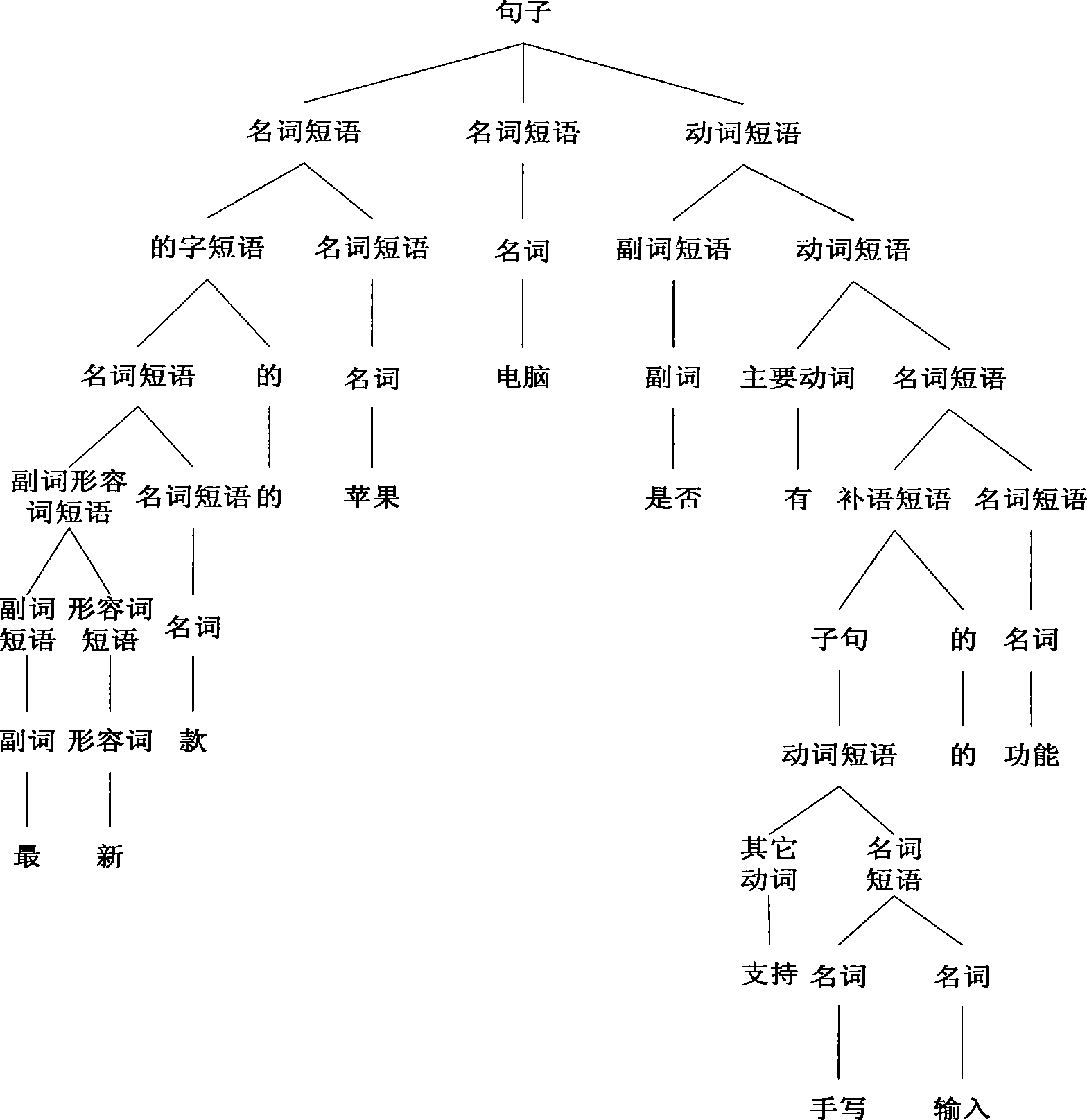
Enquiry statement analytical method and system for information retrieval
InactiveCN101510221ASearch results are accurateExact matchNatural language data processingSpecial data processing applicationsNamed-entity recognitionLexical analysis
The invention discloses a query sentence analyzing method based on understanding of natural languages and a system thereof, and belongs to the technical field of information retrieval. The query sentence analyzing method comprises the following steps: (1) automatic segmenting, named entity identification and part-of-speech tagging of an input Chinese query sentence are implemented; (2) syntax structure of the segmented sentence is analyzed so as to obtain a syntax structural tree, and meaning of each word is determined according to the sentence after the part-of-speech tagging; (3) according to the syntax structure and the meaning of each word, semantic roles of predicates in the sentence are tagged; and (4) according to the analyzed result of the sentence from the levels of syntactics, syntax and semantics, keywords are expanded and the keywords that can reflect user information retrieval requirements are extracted. The query sentence analyzing system of the invention comprises a syntactic analyzing module, a syntax analyzing module, a semantic analyzing module and a keyword extracting module. The query sentence analyzing method and system can greatly improve the accuracy of query results and provide desired query results for users.
Owner:PEKING UNIV
Managing dependencies between operations in a distributed system
InactiveUS20150172412A1Reduce transaction overheadSaving synchronizationFile access structuresTransmissionSemanticsSerialization
An efficient fault-tolerant event ordering service as well as a simplified approach to transaction processing based on global event ordering determines the order of interdependent operations in a distributed system. The fault-tolerant event ordering service externalizes the task of tracking dependencies to capture a global view of dependencies between a set of distributed operations in a distributed system. A novel protocol referred to as linear transactions coordinates distributed transactions with Atomicity, Consistency, Isolation, Durability (ACID) semantics on top of a sharded data store. The linear transactions protocol achieves scalability by distributing the coordination task to only those servers that hold relevant data for each transaction and achieves high performance by serializing only those transactions whose concurrent execution could potentially yield a violation of ACID semantics.
Owner:CORNELL UNIVERSITY
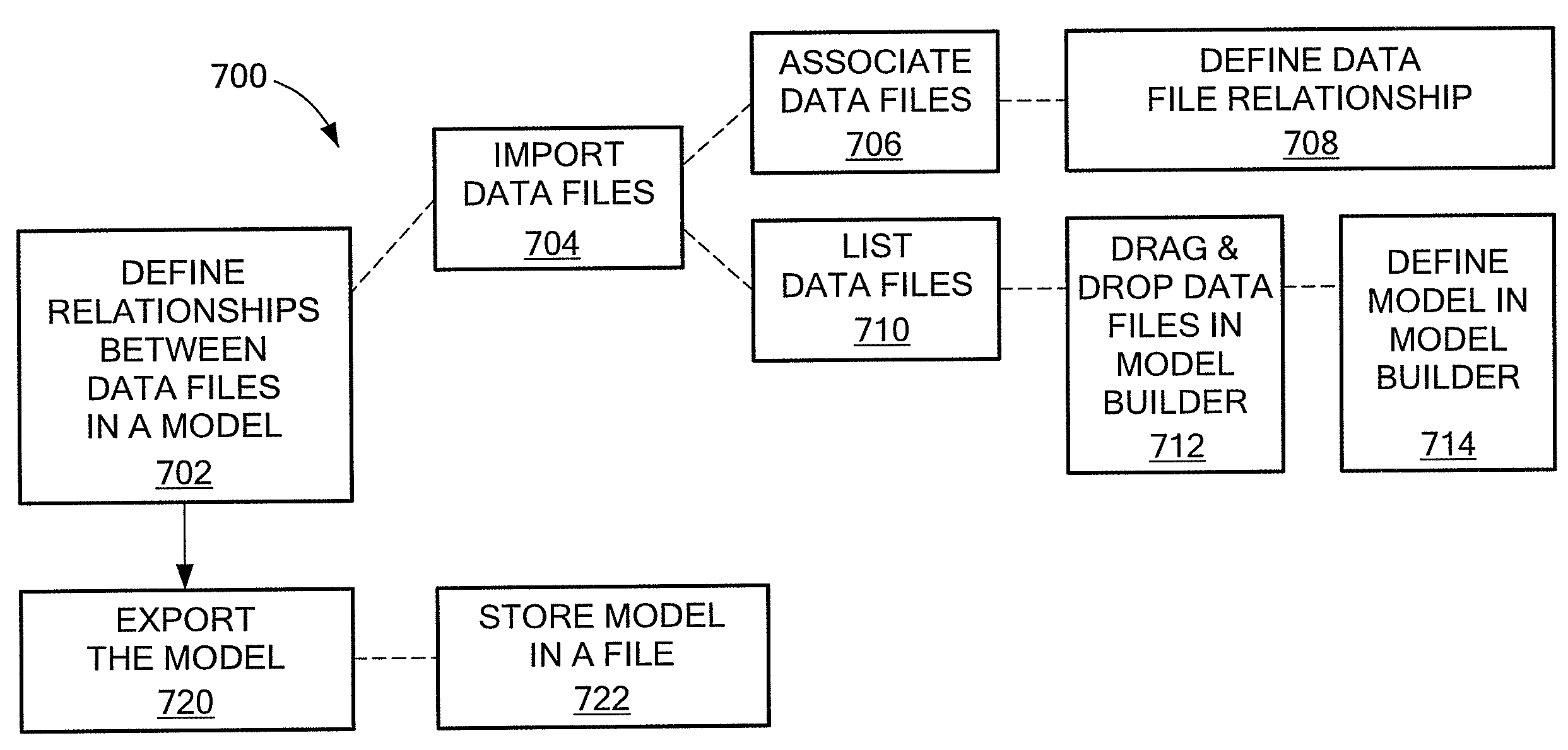
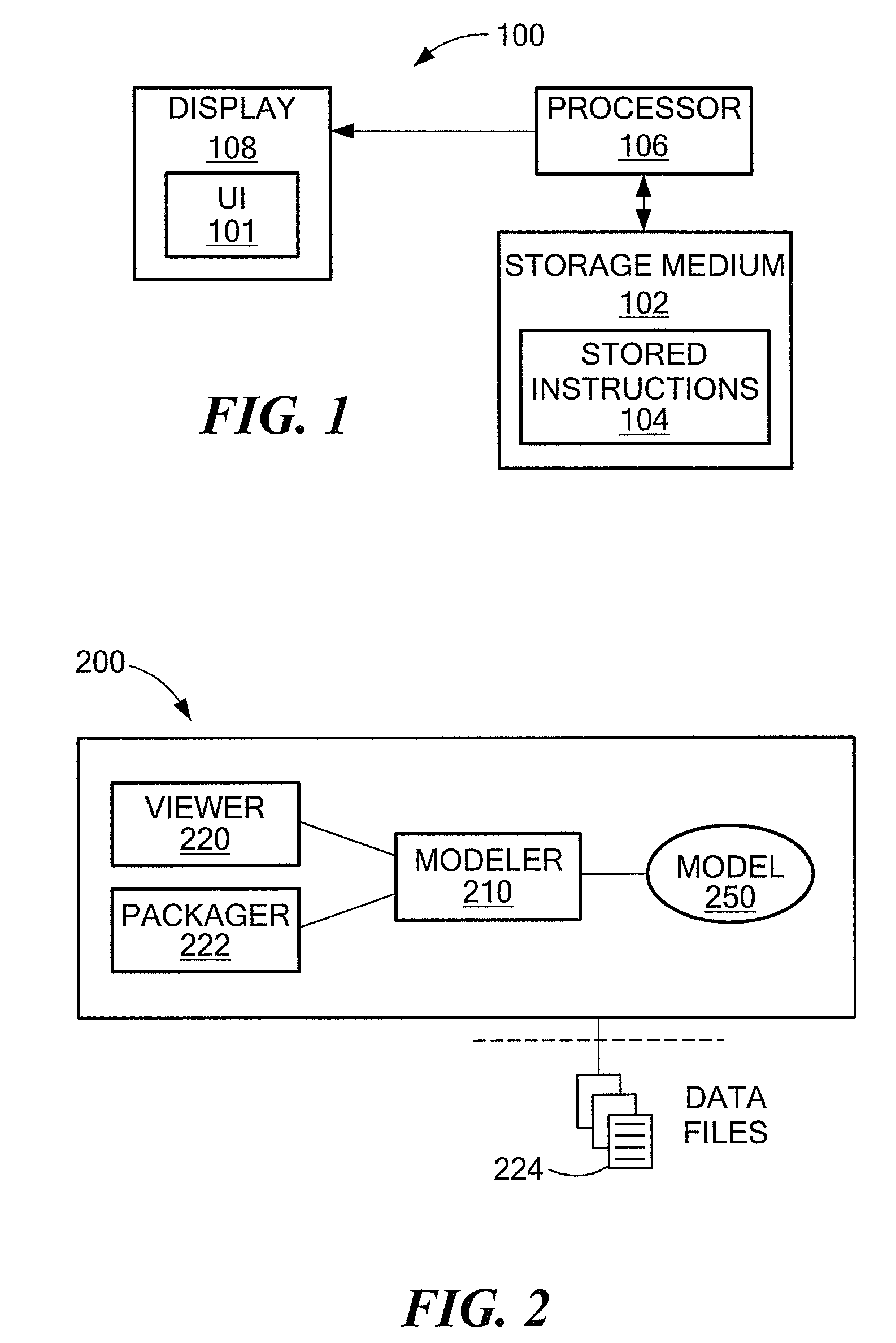
Semantic packager
InactiveUS20090282068A1Avoiding file name conflictsEliminate structureSpecial data processing applicationsDocument management systemsData fileSemantics
A system includes a storage medium having stored instructions thereon that when executed by a machine result in the following: a semantic modeler component to define relationships between data files in a semantic model; a viewer component coupled to the semantic modeler component to view the semantic model; and a packager component coupled to the semantic modeler component to export the semantic model and the data files.
Owner:RAYTHEON CO
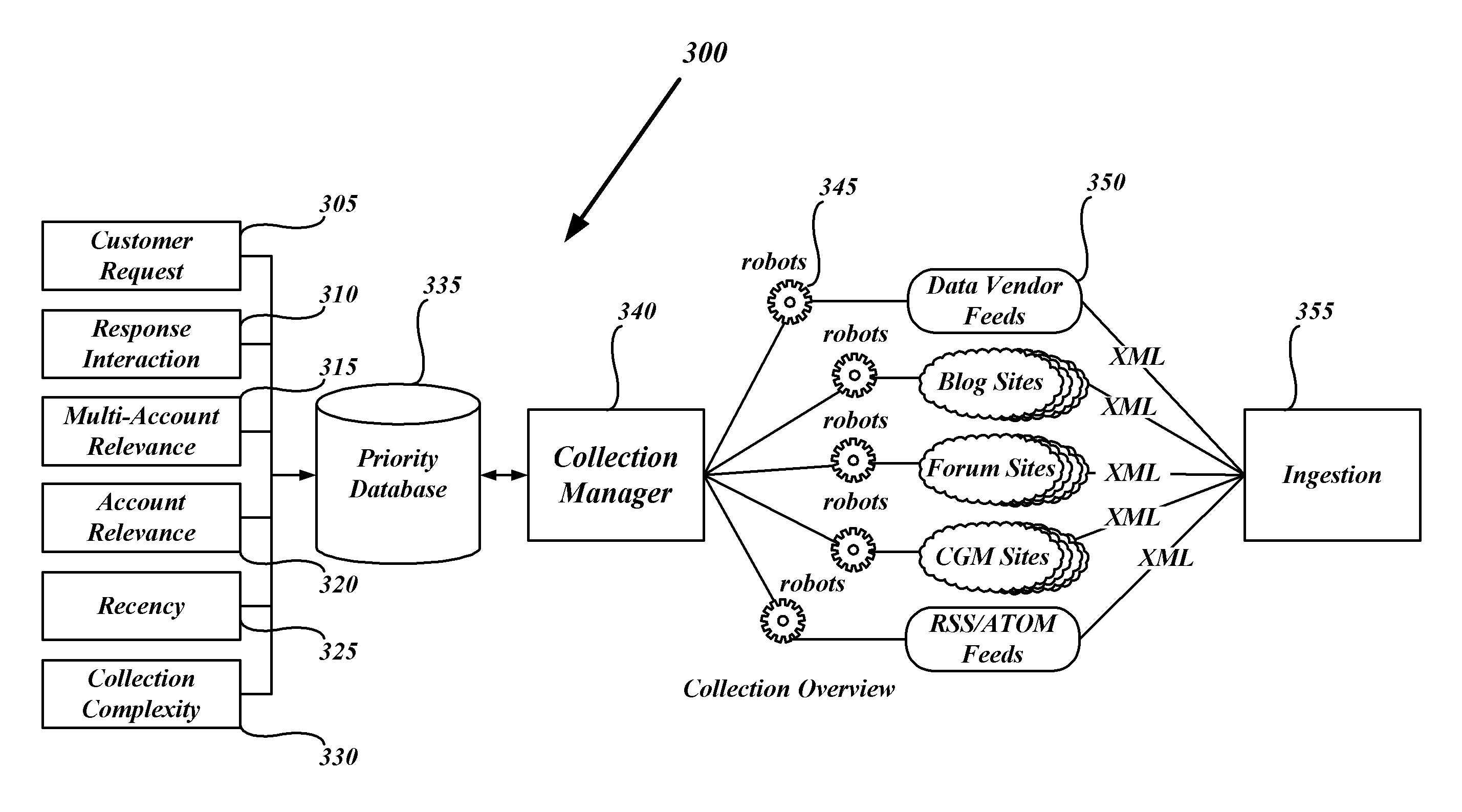
Systems and methods for consumer-generated media reputation management
ActiveUS20100275128A1Input/output for user-computer interactionOffice automationGraphicsGraphical user interface
Methods and systems for monitoring consumer generated media are disclosed herein. Consumer generated media (CGM) is discovered using a plurality of keywords from a set of keywords configured to return consumer generated media embedded in a digital location. CGM is collected from a plurality of sources using a plurality of robots configured to collect media from the discovered CGM. CGM is normalized for statistical analysis. CGM is tested for conceptual relevance to the predetermined topic using the series of keywords. Sentiment is determined of the collected consumer generated media based on the semantics of the language in the collected CGM. A graphical user interface is generated having collected consumer generated media and statistical information related to at least one of the conceptual relevance and the determined sentiment. The graphical user interface is displayed and a reply is enabled to at least one of the collected consumer generated media, displayed within the graphical user interface, such that when selected a reply is posted to the source of the CGM.
Owner:CISION US INC
Systems, methods and apparatus for distributed decision processing
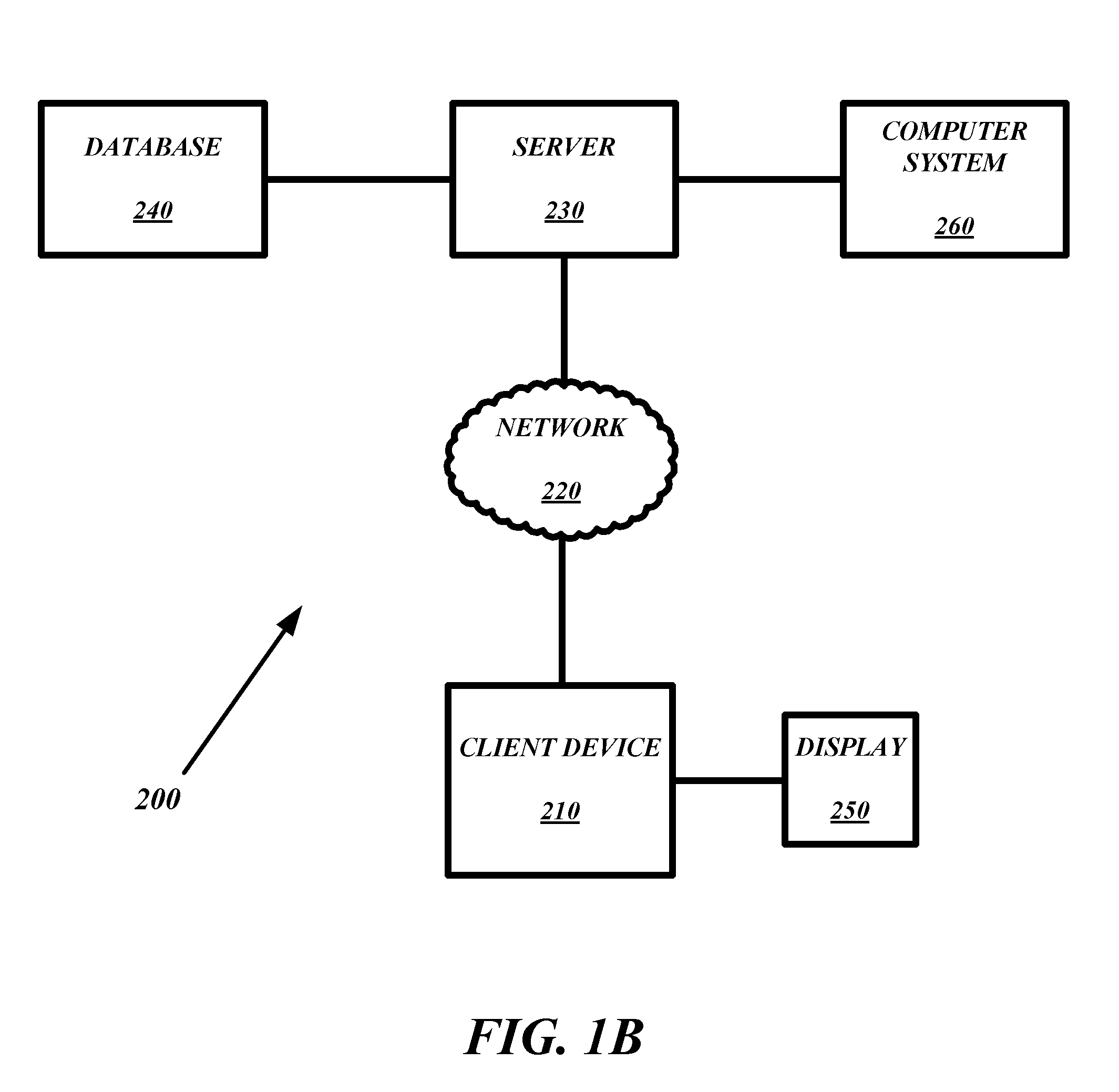
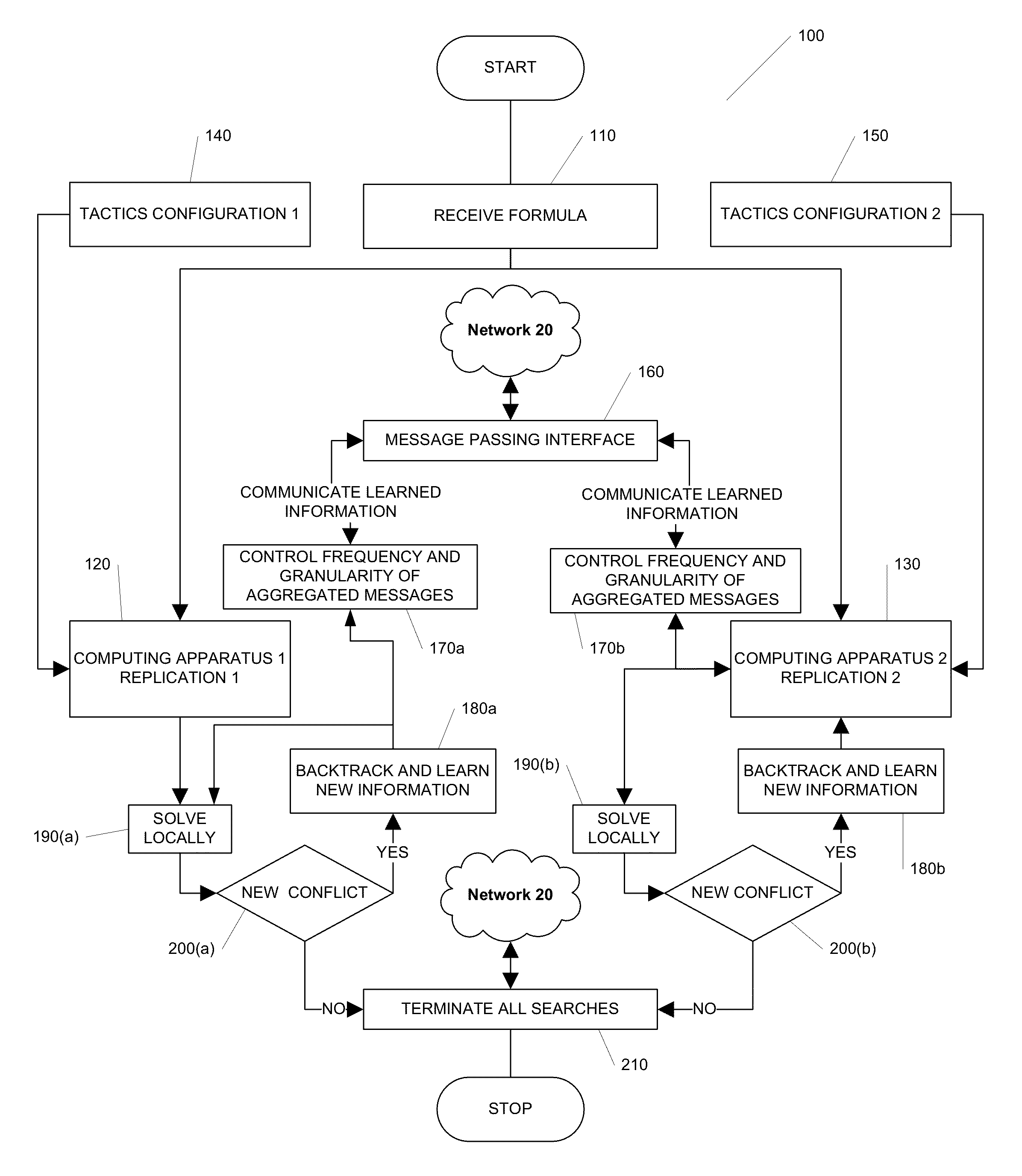
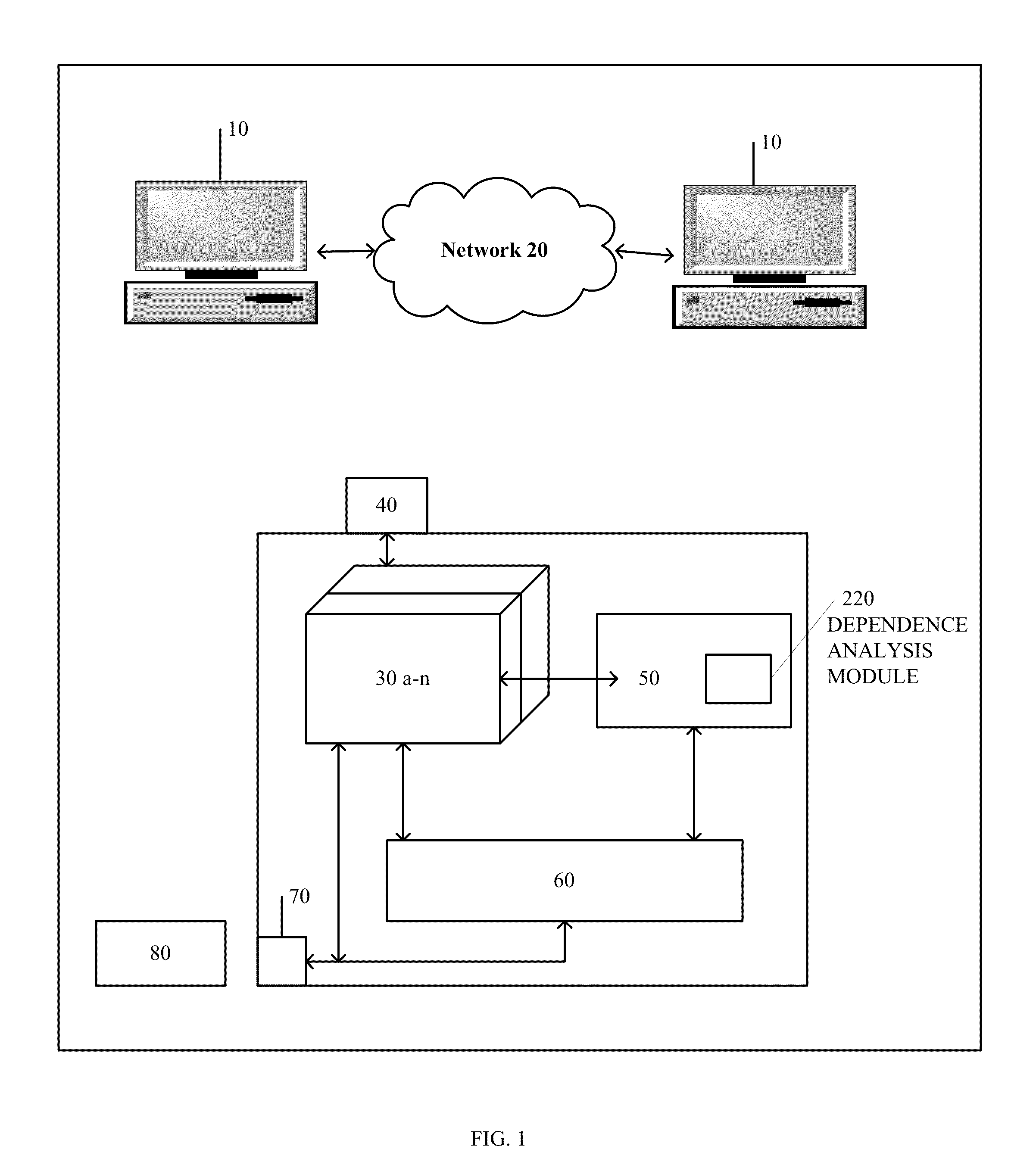
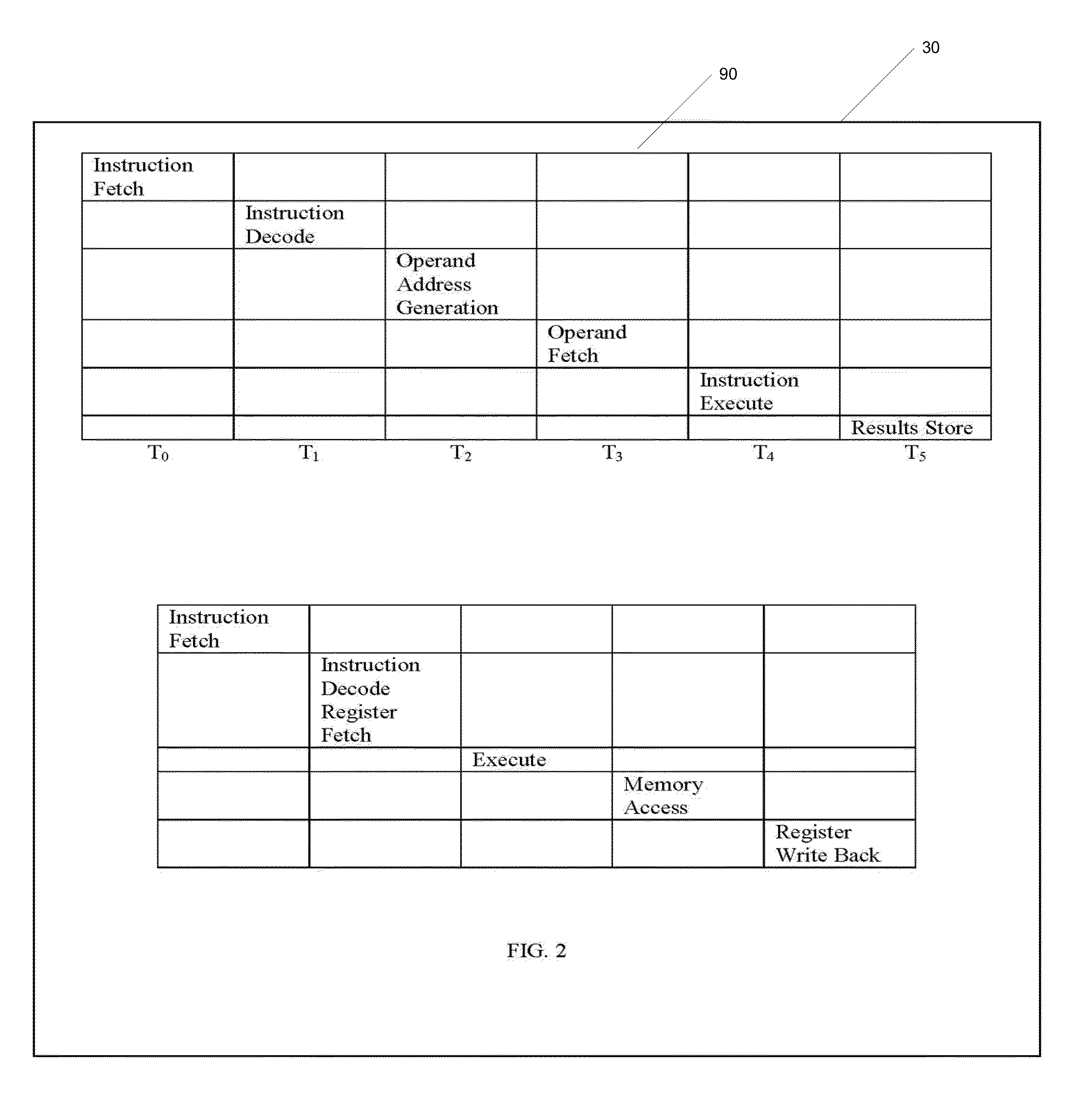
Methods, apparatus, and computer software product for making a decision based on the semantics of formal logic are provided. In an exemplary embodiment, two custom computing apparatuses are used to resolve the satisfiability of a logical formula and provide an example. In this embodiment, the two custom computing apparatuses operate in concert to explore the space of possible satisfying examples. This Abstract is provided for the sole purpose of complying with the Abstract requirement rules. This Abstract is submitted with the explicit understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:QUALCOMM TECHNOLOGIES INC
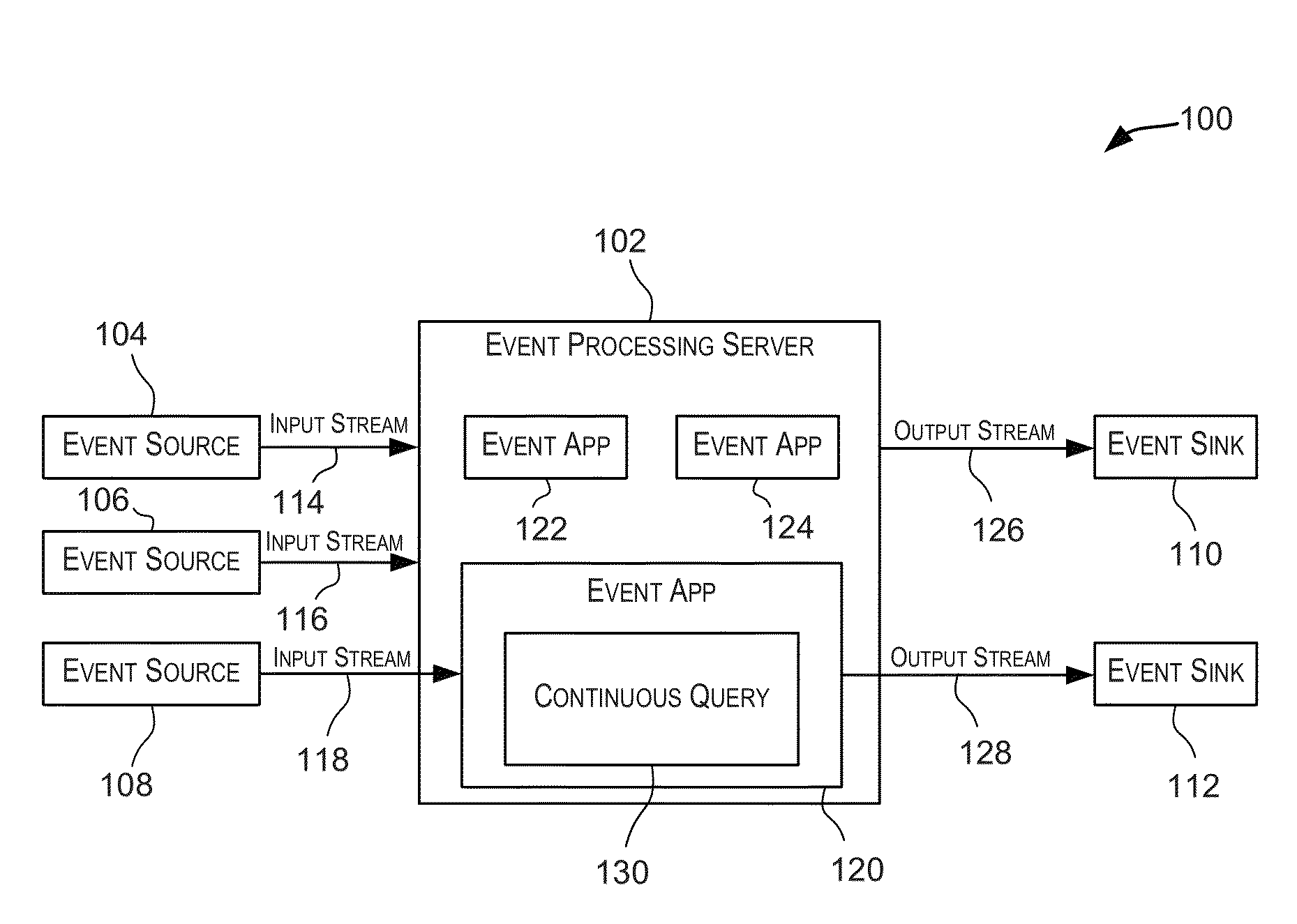
Scaling event processing using distributed flows and map-reduce operations
Some event ordering requirements can be determined based on continuous event processing queries. Other event ordering requirements can be determined based on distribution flow types being used to distribute events from event streams to node executing the queries. Events from event streams can be ordered according to ordering semantics that are based on a combination of all of these event ordering requirements. Additionally, virtual computing nodes can be associated with constraints, and computing processors can be associated with capabilities. Virtual computing nodes for processing event streams can be assigned to execute on various computing processors based on both these constraints and capabilities. Additionally, for each of several events in an event stream, a ratio between a total latency and a communication latency can be for determined. Based on an average of these ratios, a quantity of reducing nodes that will be involved in a map-reduce operation can be selected.
Owner:ORACLE INT CORP
Question and answer method based on knowledge map
ActiveCN107748757ANatural language data processingSpecial data processing applicationsEntity linkingNatural language understanding
The invention provides a question and answer method based on a knowledge map. The question and answer method based on a knowledge map provided in the invention is realized by subject entity matching,relationship matching and answer determination. The subject entity matching mainly comprises naming entity identification and entity linking. The naming entity identification is aimed at identifying naming entities such as names of people, names of places, and names of organizations in natural language questions q. The entity linking corresponds the identified naming entity to a certain entity inthe knowledge base, that is, finding out an entity s in triples; Relationship matching is to understand the semantics expressed by question q through natural language understanding technology, and match the relationship p in the triples (s, p, o) in the search space in order to determine the semantics of the question and its corresponding relationship with the knowledge base. The candidate subjectentity is obtained through entity identification and entity linking, and the relationship matching can obtain the candidate relationship, thereby obtaining several candidate triples; the answer determination is to rank the candidate triples according to entity recognition score, relationship match score, etc. to determine the final answer.
Owner:BEIHANG UNIV
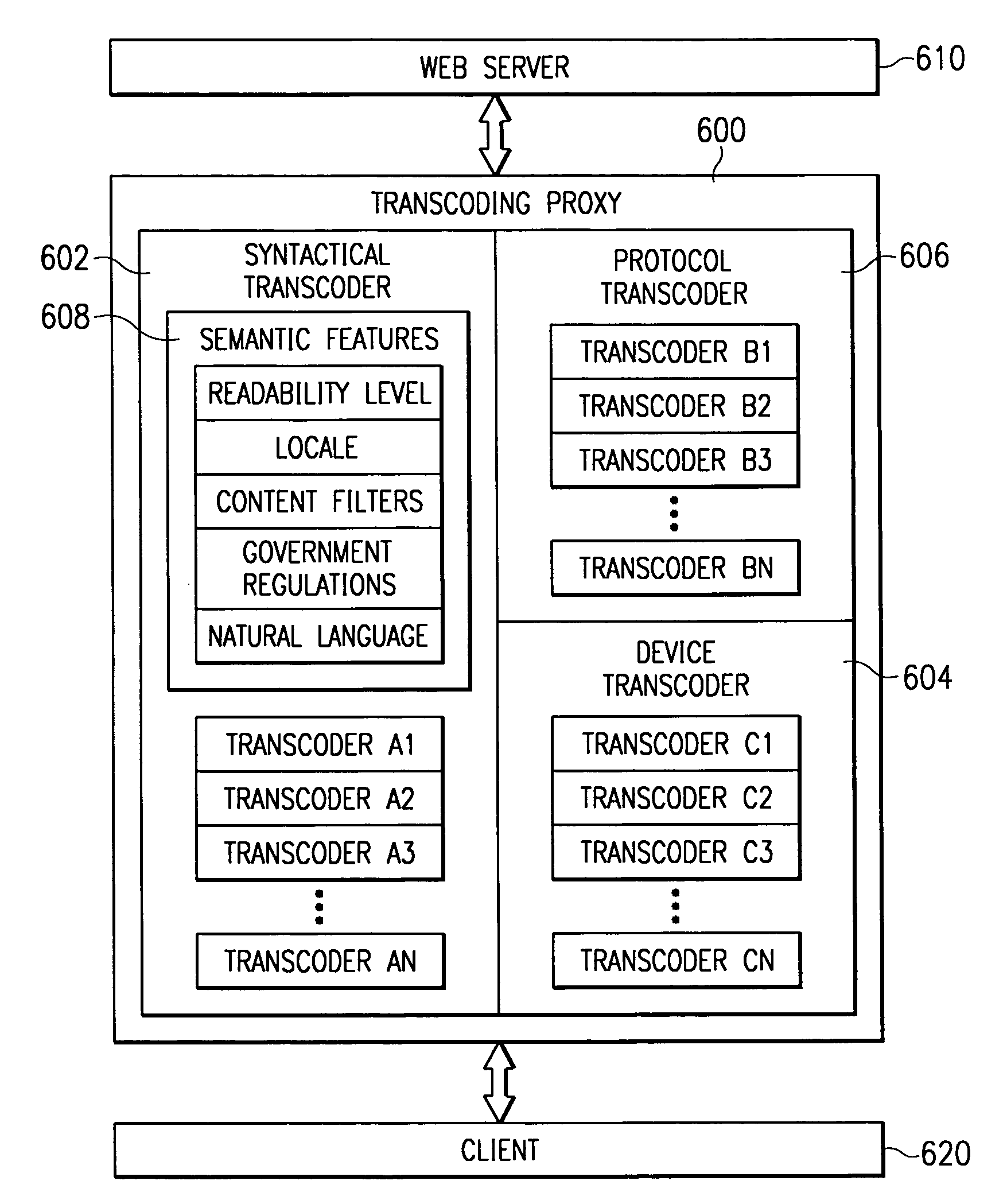
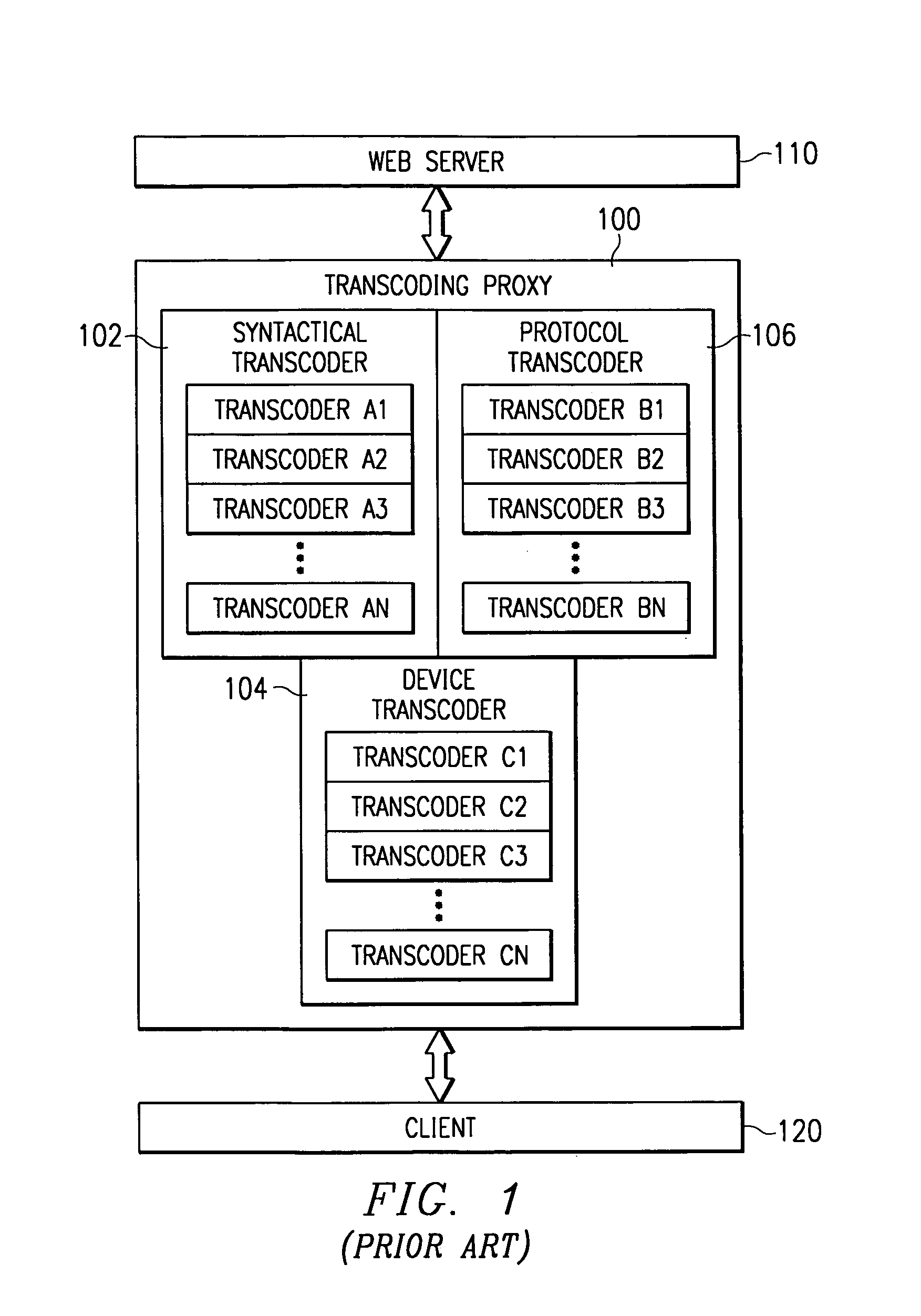
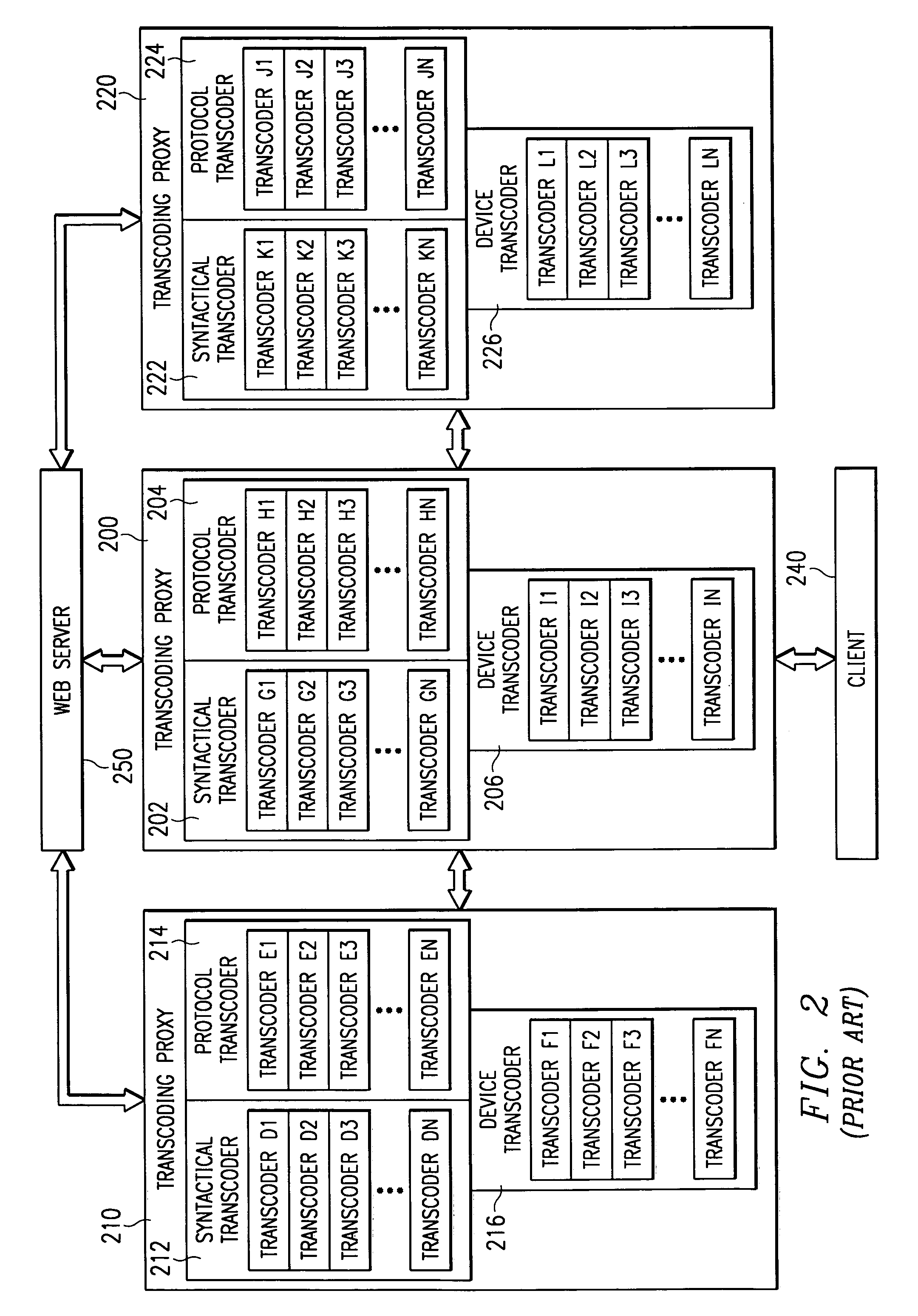
System and method for incorporating semantic characteristics into the format-driven syntactic document transcoding framework
InactiveUS6993476B1Digital data information retrievalMultiple digital computer combinationsSemanticsSemantic feature
Initially, a client requests a specific document and provides the preferences, including readability level preferences of the document, locale preferences, content filtering instructions preferences, governmental regulations preferences, natural language preferences, and document syntactic format preferences. The transcoding proxy requests and receives the document from the origin server, with the document having origin semantic characteristics. The document from the origin server has an origin readability level and origin locale, is conformant with origin content filtering instructions and origin governmental regulations, and is in origin natural language and in origin document syntactic format. Using the client semantics preferences, the transcoding proxy revises the document in a sequential or parallel fashion. The origin semantics characteristics of the document are, thus, revised to the semantic preferences specified by the client.
Owner:NUANCE COMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com