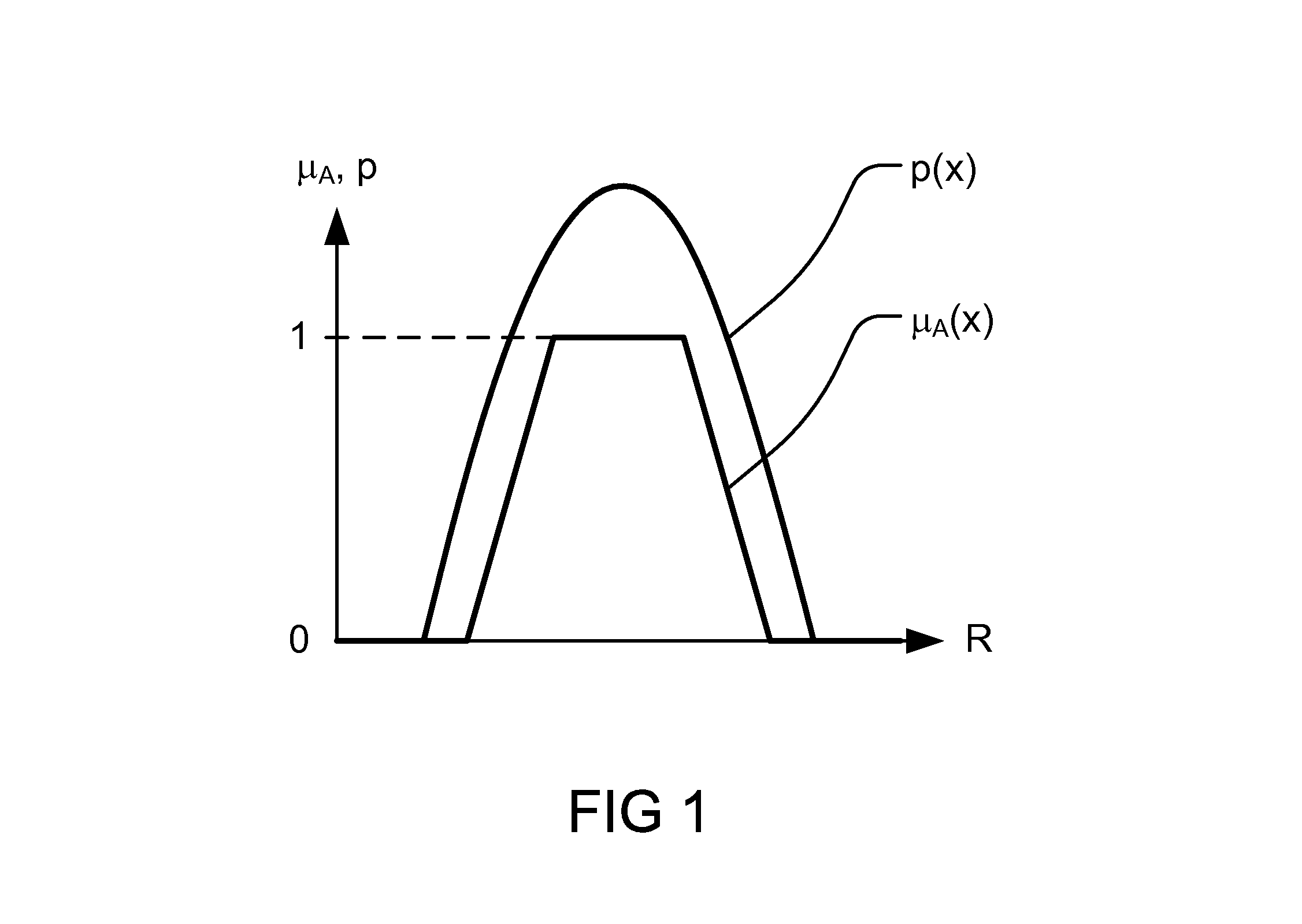
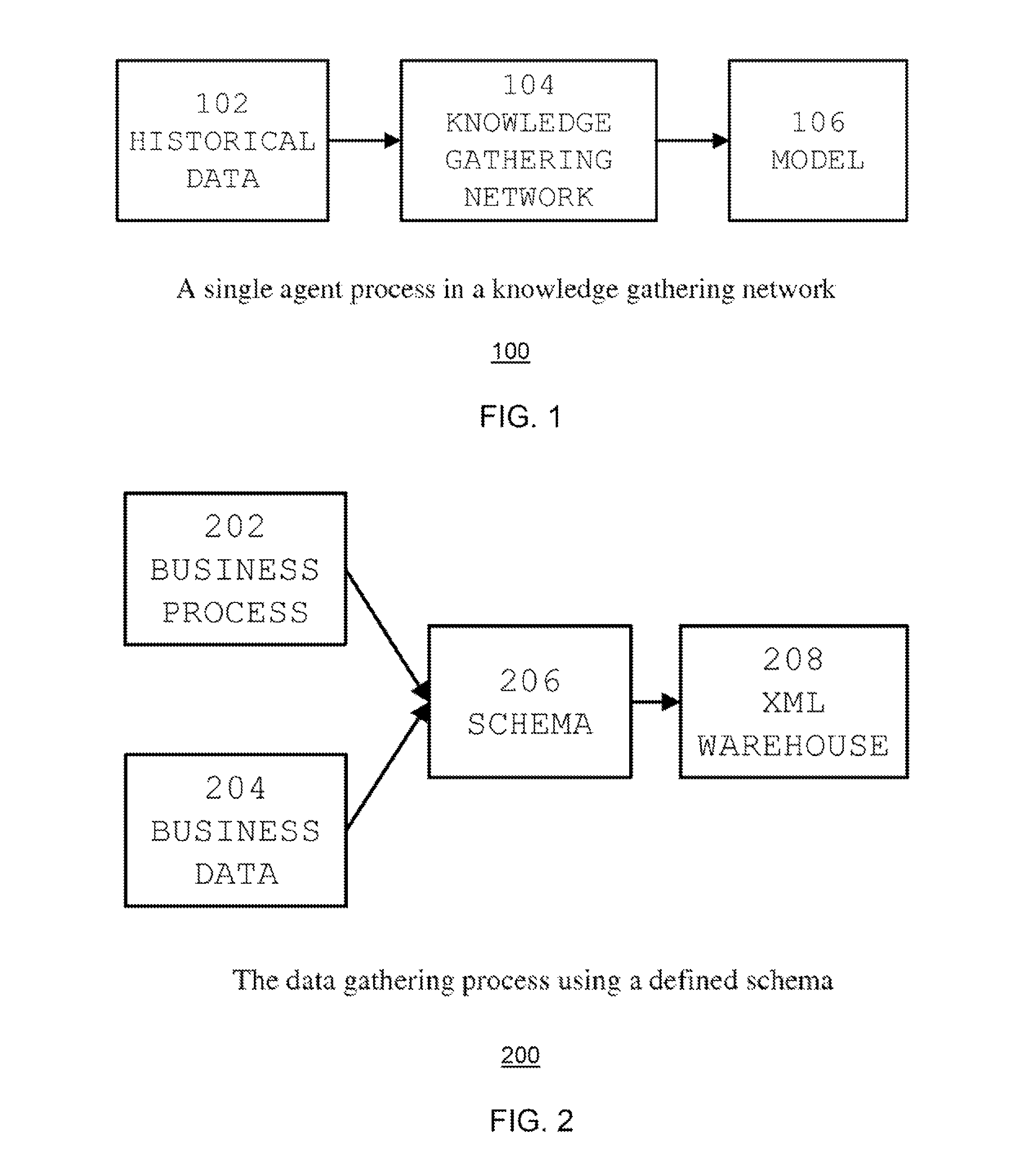
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30591 results about "Data analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data analysis is a process of inspecting, cleansing, transforming and modeling data with the goal of discovering useful information, informing conclusion and supporting decision-making. Data analysis has multiple facets and approaches, encompassing diverse techniques under a variety of names, and is used in different business, science, and social science domains. In today's business world, data analysis plays a role in making decisions more scientific and helping businesses operate more effectively.
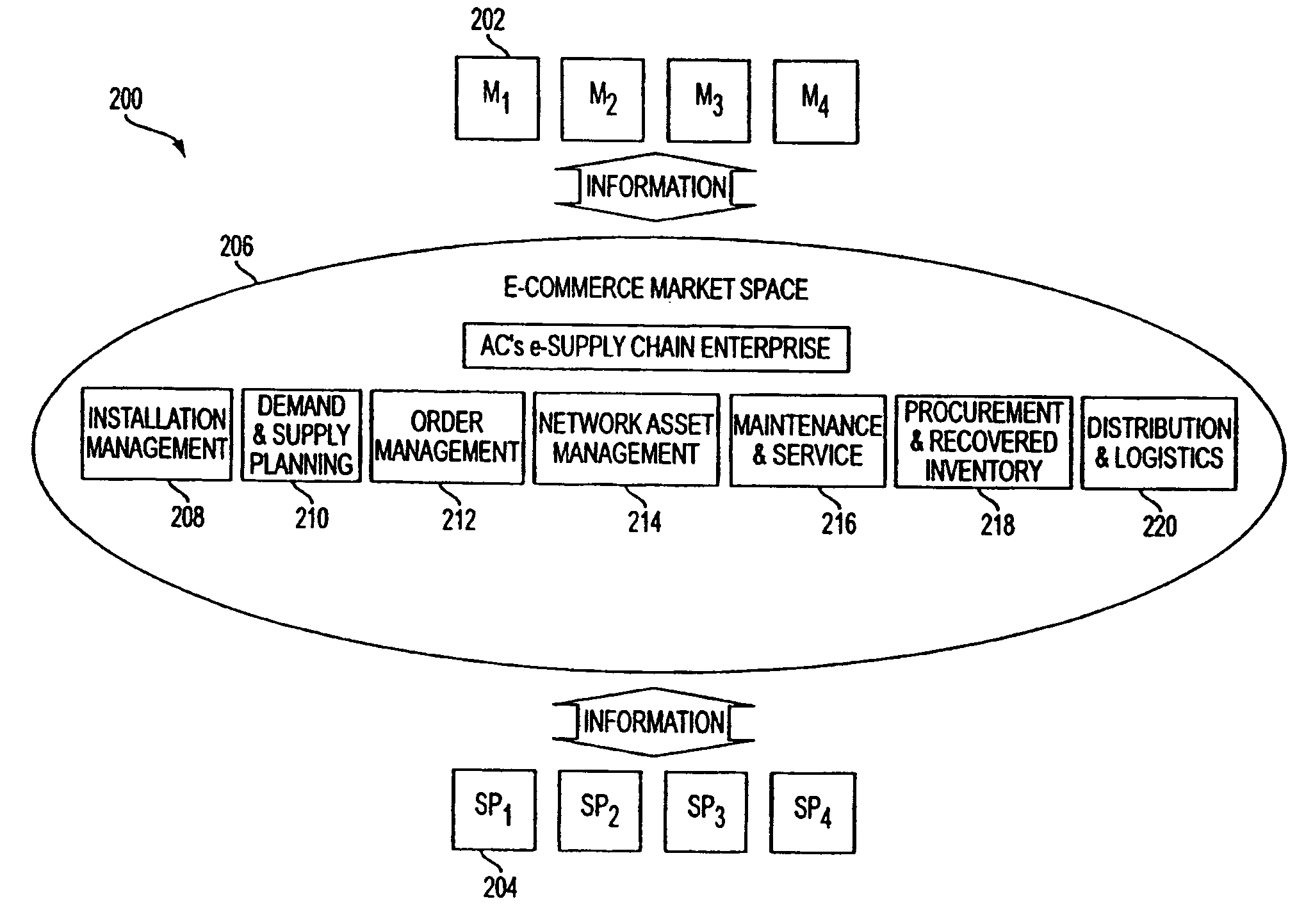
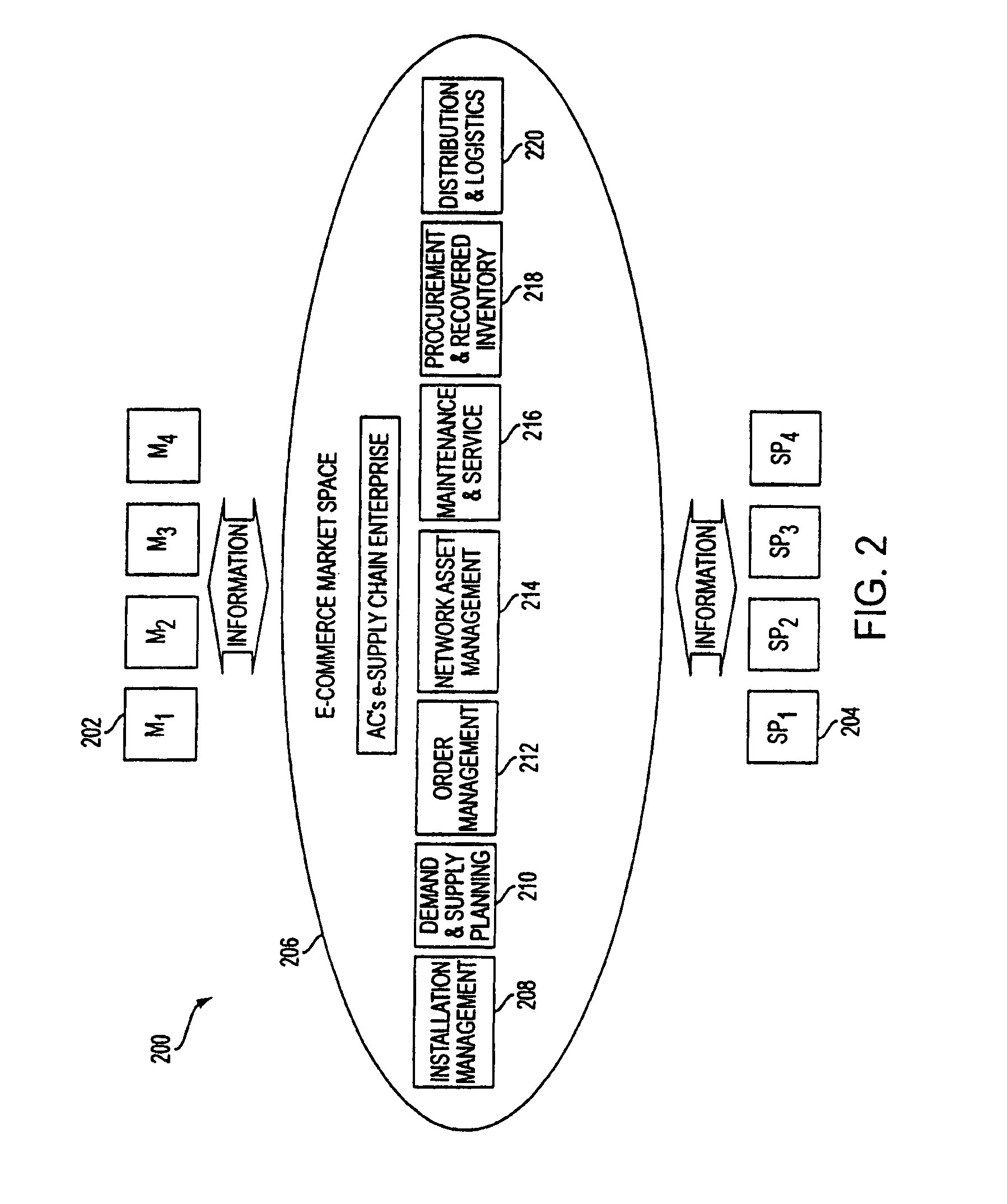
Technology sharing during demand and supply planning in a network-based supply chain environment
The present disclosure provides for supplying collaborative planning by a computerized framework manager. Steps include furnishing network connections and collecting supply and demand information from business entities. Such information is analyzed and used to facilitate planning among the business entites. The network provides data access for multiple data sources and the network is used to store capacity data. The computerized framework manager conducts reverse inventory management of the business entities through the collection of data; analysis of data is then used to predict future demand, and predicted future demand is used to forecast costs to manufacturers, from which suggestions regarding optimization is made.
Owner:ACCENTURE GLOBAL SERVICES LTD
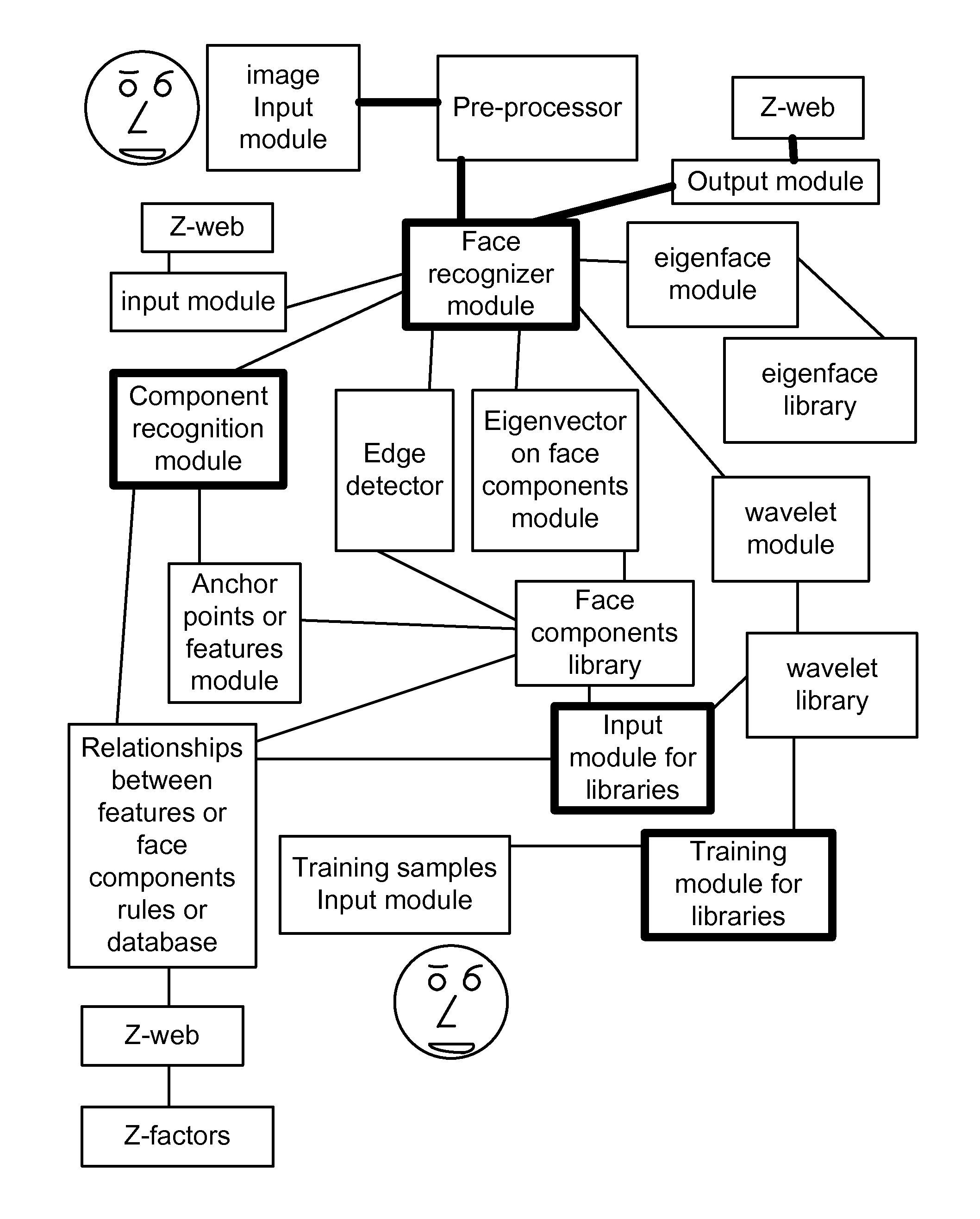
Application of Z-Webs and Z-factors to Analytics, Search Engine, Learning, Recognition, Natural Language, and Other Utilities
Here, we introduce Z-webs, including Z-factors and Z-nodes, for the understanding of relationships between objects, subjects, abstract ideas, concepts, or the like, including face, car, images, people, emotions, mood, text, natural language, voice, music, video, locations, formulas, facts, historical data, landmarks, personalities, ownership, family, friends, love, happiness, social behavior, voting behavior, and the like, to be used for many applications in our life, including on the search engine, analytics, Big Data processing, natural language processing, economy forecasting, face recognition, dealing with reliability and certainty, medical diagnosis, pattern recognition, object recognition, biometrics, security analysis, risk analysis, fraud detection, satellite image analysis, machine generated data analysis, machine learning, training samples, extracting data or patterns (from the video, images, and the like), editing video or images, and the like. Z-factors include reliability factor, confidence factor, expertise factor, bias factor, and the like, which is associated with each Z-node in the Z-web.
Owner:Z ADVANCED COMPUTING
Detecting and preventing bots and cheating in online gaming
ActiveUS20080004107A1Detecting and preventing cheatingEasy to explainApparatus for meter-controlled dispensingOffice automationCentralized computingHuman–computer interaction
Methods and devices are provided for detecting and / or preventing cheating in online gaming. Some implementations provide gaming information in formats that are difficult for a bot to interpret, but which are preferably easy for humans to interpret. Some implementations of the invention involve the tracking and analysis of players' gaming activities. Some implementations of the invention provide a multi-tier approach to data analysis. Some analyses may be performed, for example, by a centralized computing device such as a server, whereas other analyses may be performed by a host device. In some implementations, “challenge and response” measures will be employed. Some implementations of the invention involve detection and prevention of collaboration between players.
Owner:IGT
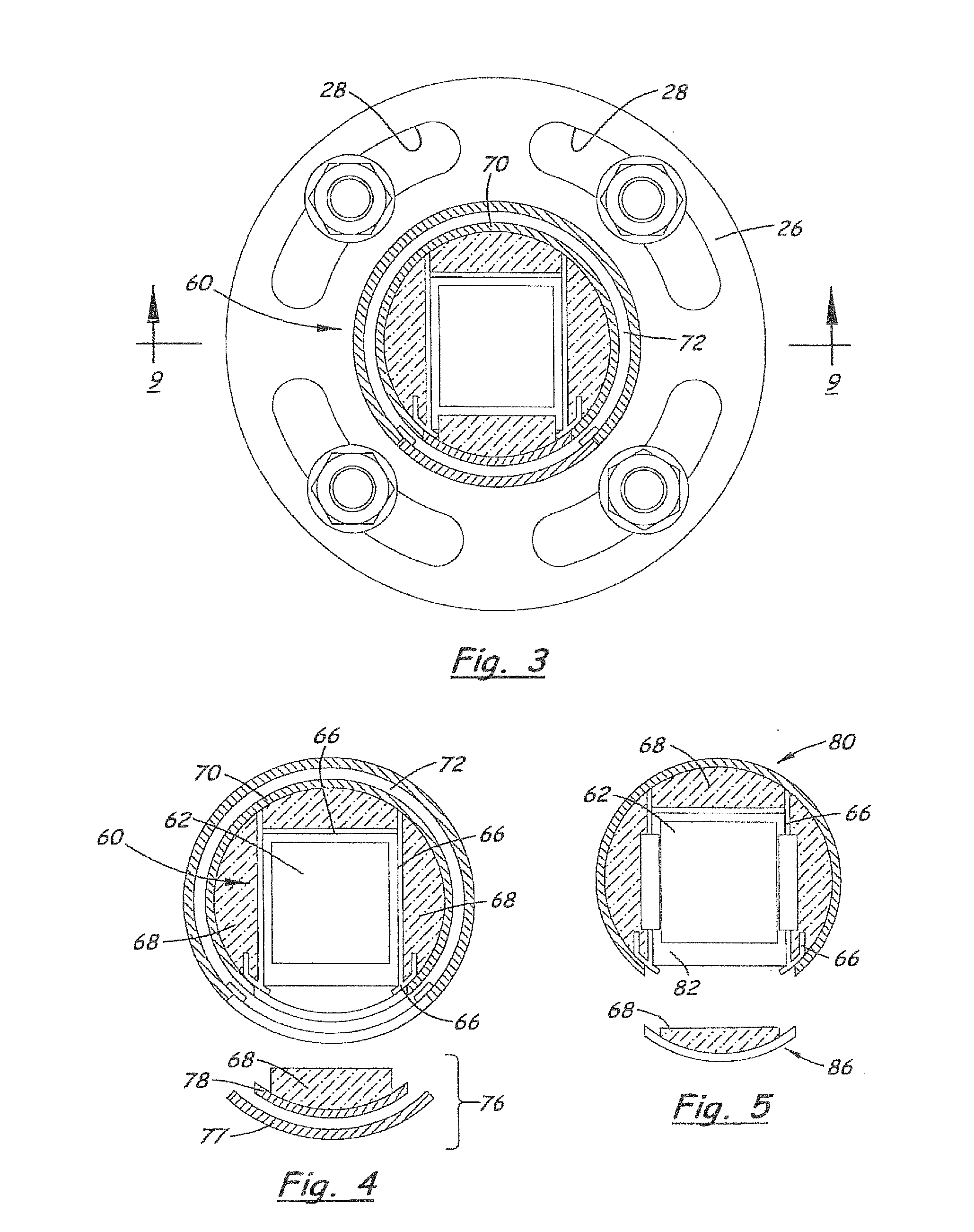
Smart instrument tray RFID reader
ActiveUS7362228B2Accurate and rapid trackingReduce processing costsSurgical furnitureDispensing apparatusEngineeringWorkstation
A radio frequency identification (RFID) workstation reader for RFID-enabled surgical instruments and surgical instrument trays and a method of using a RFID workstation reader to read RFID-enabled surgical instruments and surgical instrument trays is disclosed. The method, apparatus, and system enable individual instruments or a surgical instrument tray containing several surgical instruments to be quickly and efficiently inventoried and tracked. An instrument or instrument tray is placed on the workstation reader. An RF field generated by a plurality of antennae, causes RFID tags embedded in or attached to the instrument or instrument tray to emit a signal containing item specific identification information stored in the tags. The information is received by a control circuit and passed to a computer for data analysis. A status LED is illuminated on the workstation reader based on the results of the data analysis. The method, apparatus, and system can track, inspect, and verify inbound and outbound surgical instrument kits, and help to assess the surgical instruments' and trays' duty life cycle usage.
Owner:WARSAW ORTHOPEDIC INC
Method and apparatus for capturing and filtering datagrams for network security monitoring
ActiveUS7467408B1Improve network securityReduce network trafficMemory loss protectionUnauthorized memory use protectionTraffic capacitySecurity monitoring
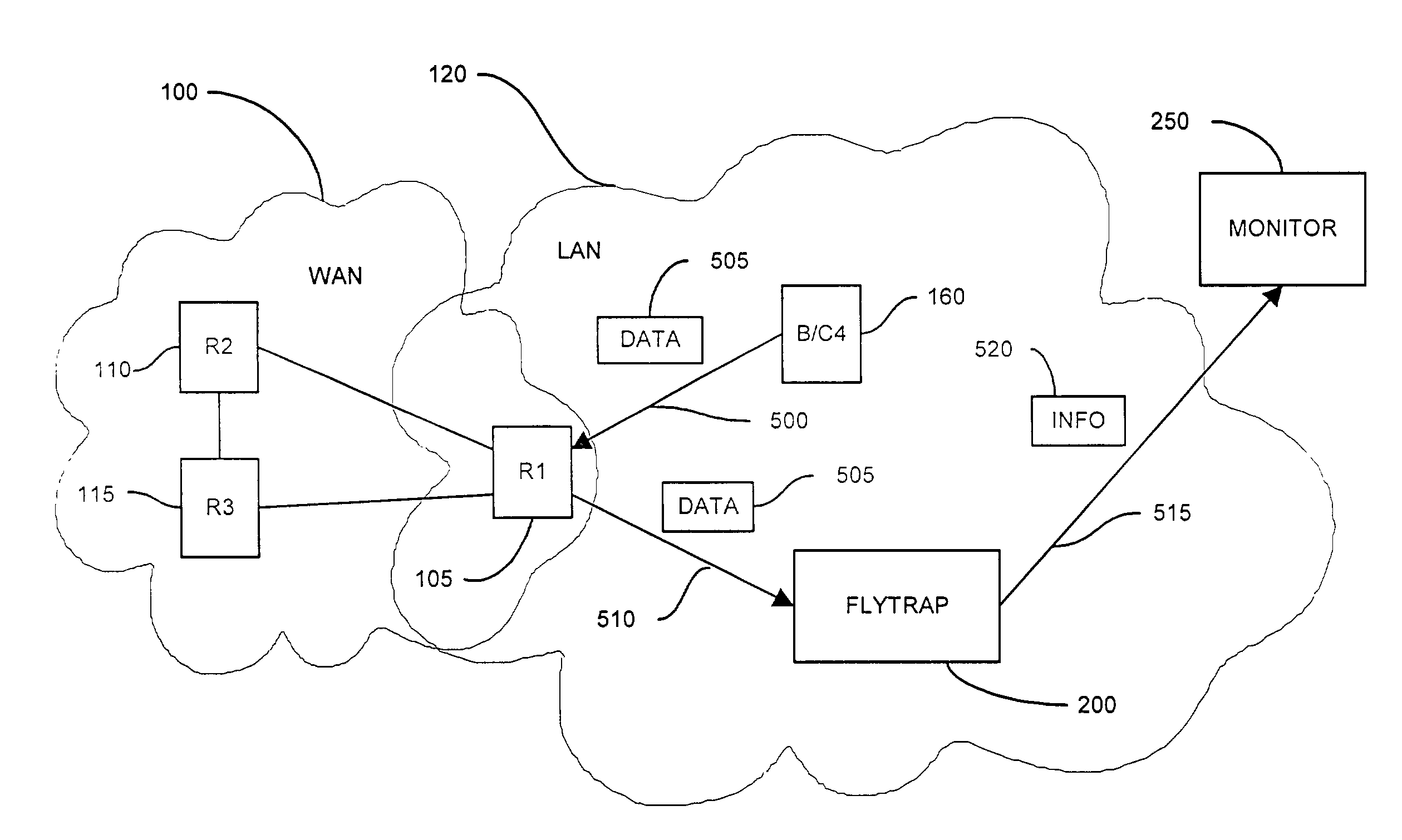
A method and system for security monitoring in a computer network has a packet sink with filtering and data analysis capabilities. The packet sink is a default destination for data packets having an address unrecognized by the network routers. At the packet sink, the packets are filtered and statistical summaries about the data traffic are created. The packet sink then forwards the data to a monitor, the information content depending on the level of traffic in the network.
Owner:CISCO TECH INC
Frequency encoding of resonant mass sensors
InactiveUS20050016276A1Sufficient ring timeImprove stabilityVibration measurement in solidsAnalysing fluids using sonic/ultrasonic/infrasonic wavesSensor arrayFrequency spectrum
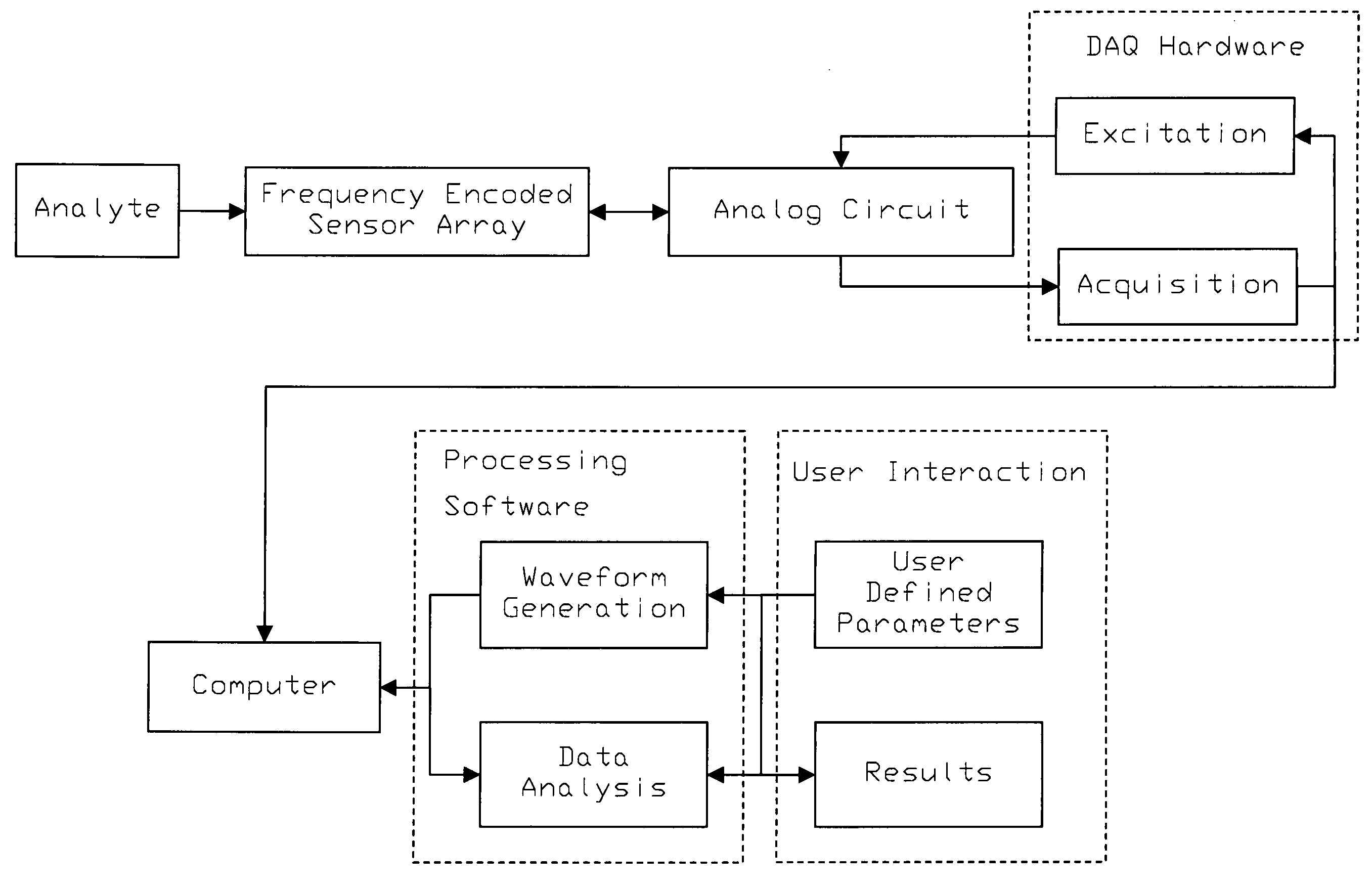
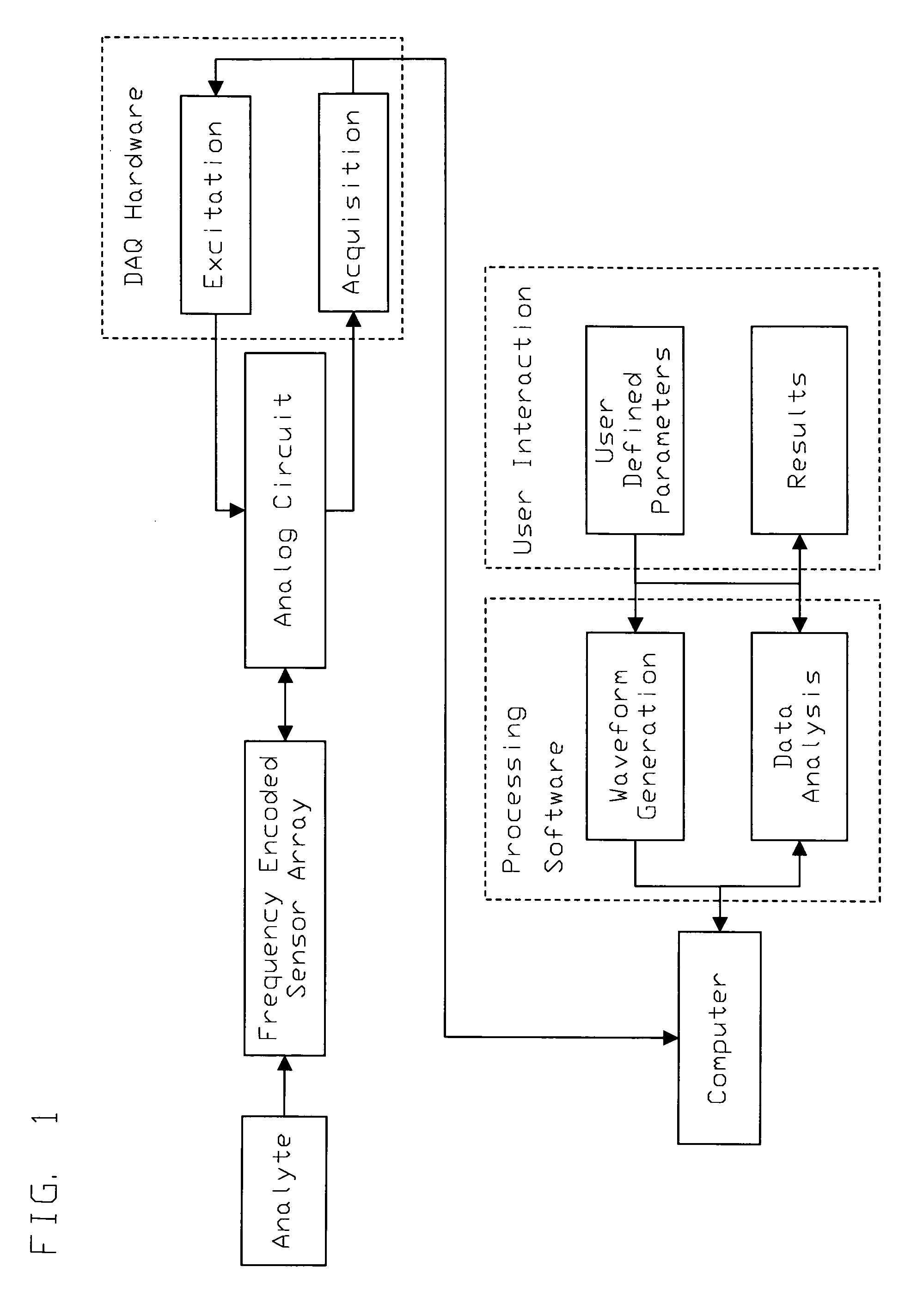
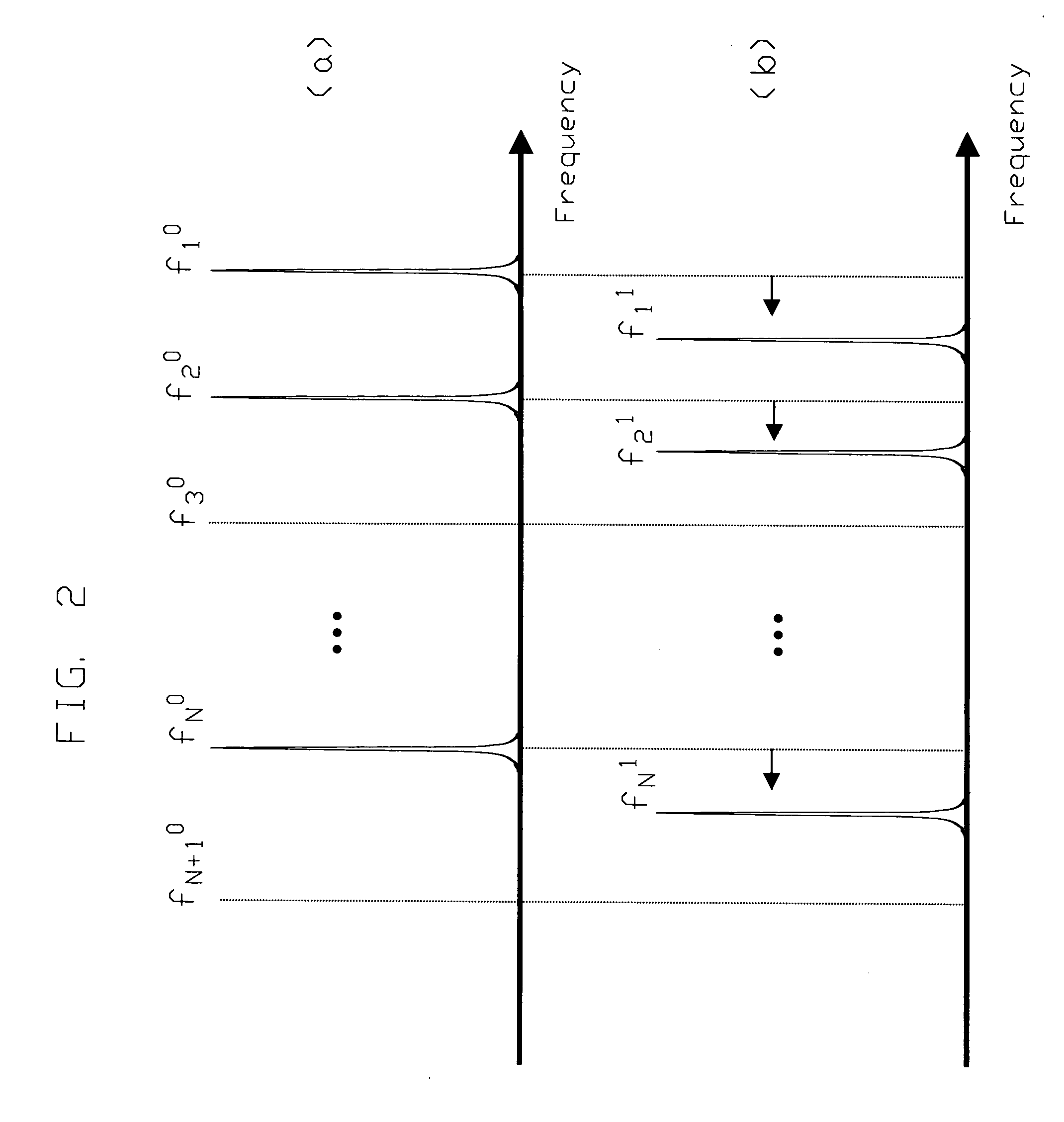
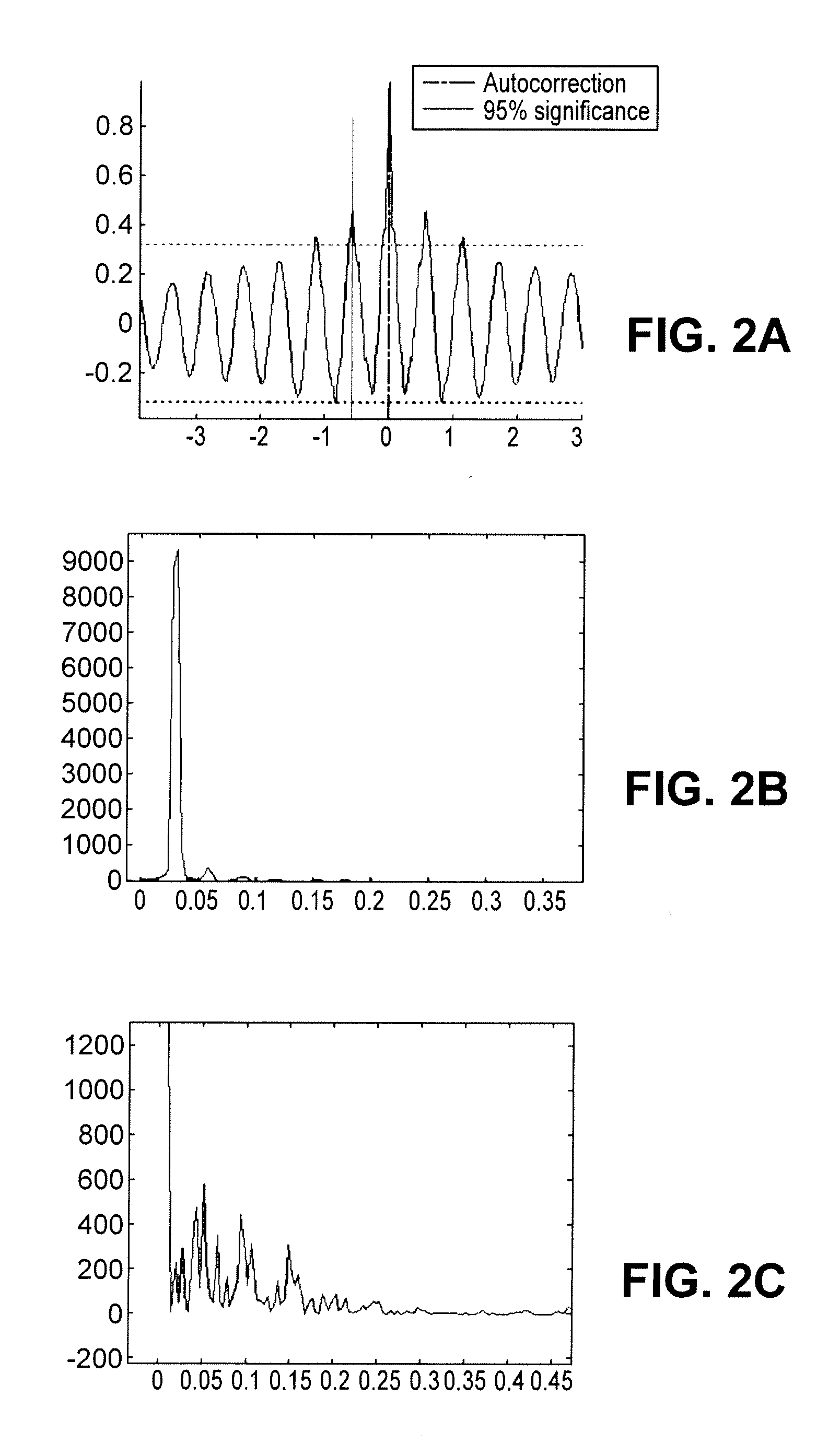
A method for the detection of analytes using resonant mass sensors or sensor arrays comprises frequency encoding each sensor element, acquiring a time-domain resonance signal from the sensor or sensor array as it is exposed to analyte, detecting change in the frequency or resonant properties of each sensor element using a Fourier transform or other spectral analysis method, and classifying, identifying, and / or quantifying analyte using an appropriate data analysis procedure. Frequency encoded sensors or sensor arrays comprise sensor elements with frequency domain resonance signals that can be uniquely identified under a defined range of operating conditions. Frequency encoding can be realized either by fabricating individual sensor elements with unique resonant frequencies or by tuning or modifying identical resonant devices to unique frequencies by adding or removing mass from individual sensor elements. The array of sensor elements comprises multiple resonant structures that may have identical or unique sensing layers. The sensing layers influence the sensor elements' response to analyte. Time-domain signal is acquired, typically in a single data acquisition channel, and typically using either (1) a pulsed excitation followed by acquisition of the free oscillatory decay of the entire array or (2) a rapid scan acquisition of signal from the entire array in a direct or heterodyne configuration. Spectrum analysis of the time domain data is typically accomplished with Fourier transform analysis. The methods and sensor arrays of the invention enable rapid and sensitive analyte detection, classification and / or identification of complex mixtures and unknown compounds, and quantification of known analytes, using sensor element design and signal detection hardware that are robust, simple and low cost.
Owner:PALO ALTO SENSOR TECH INNOVATION
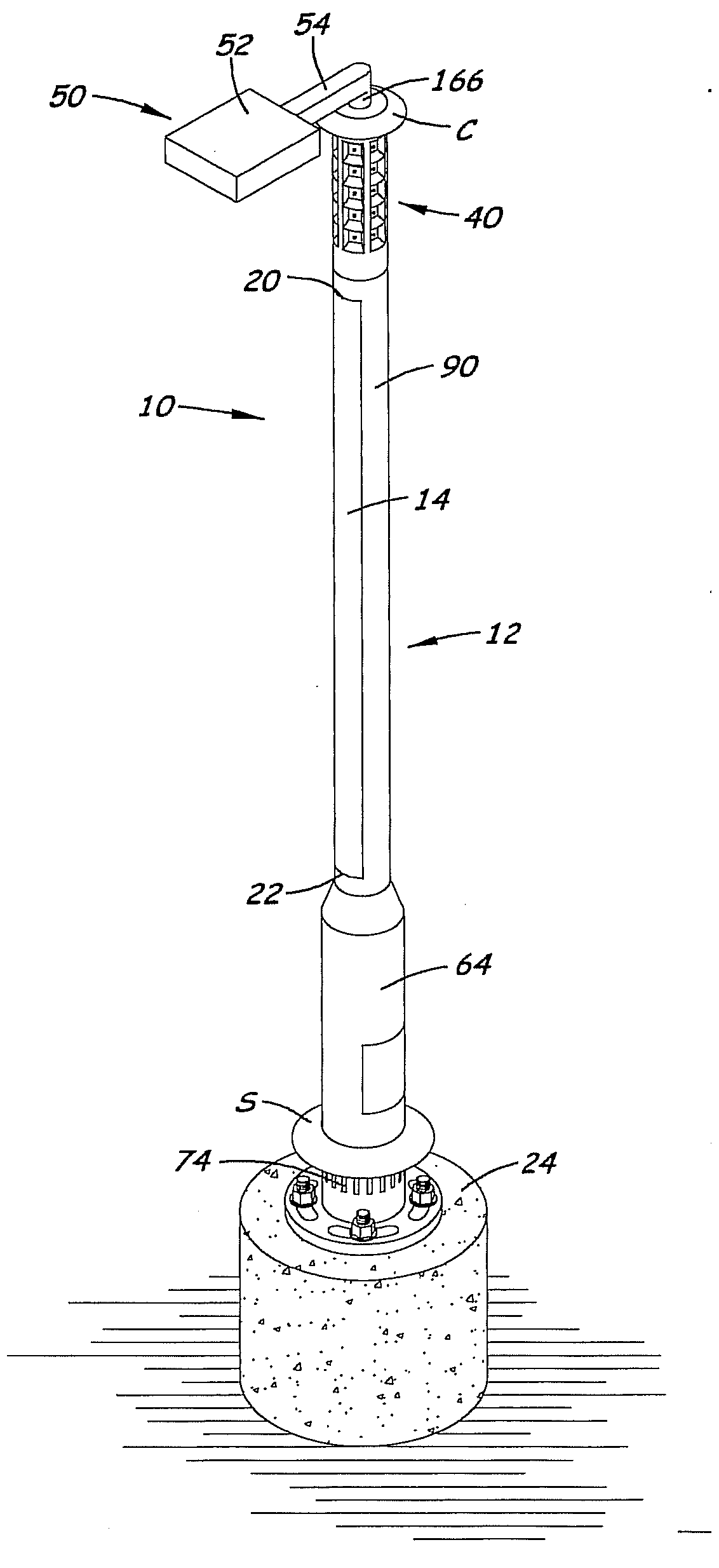
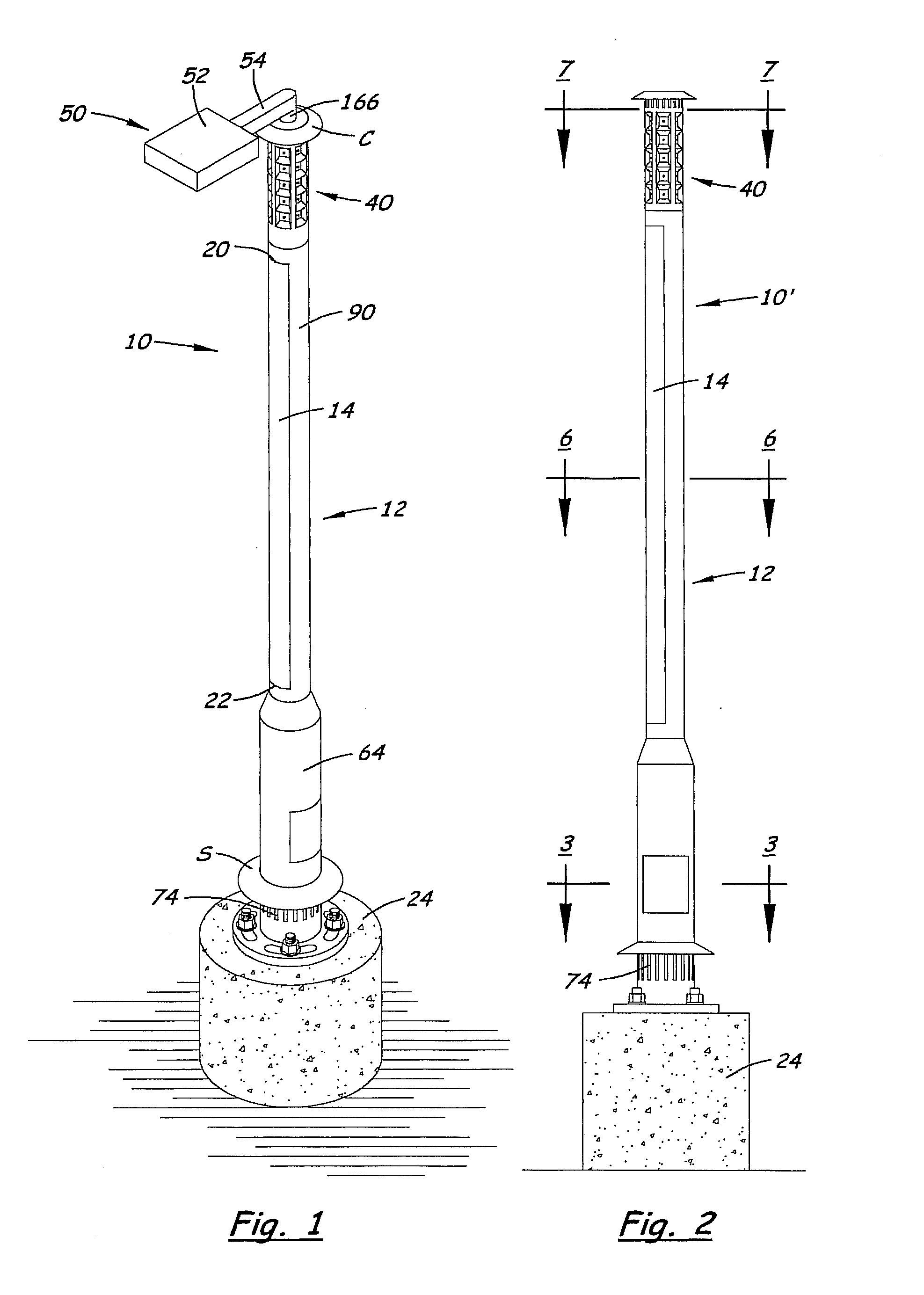
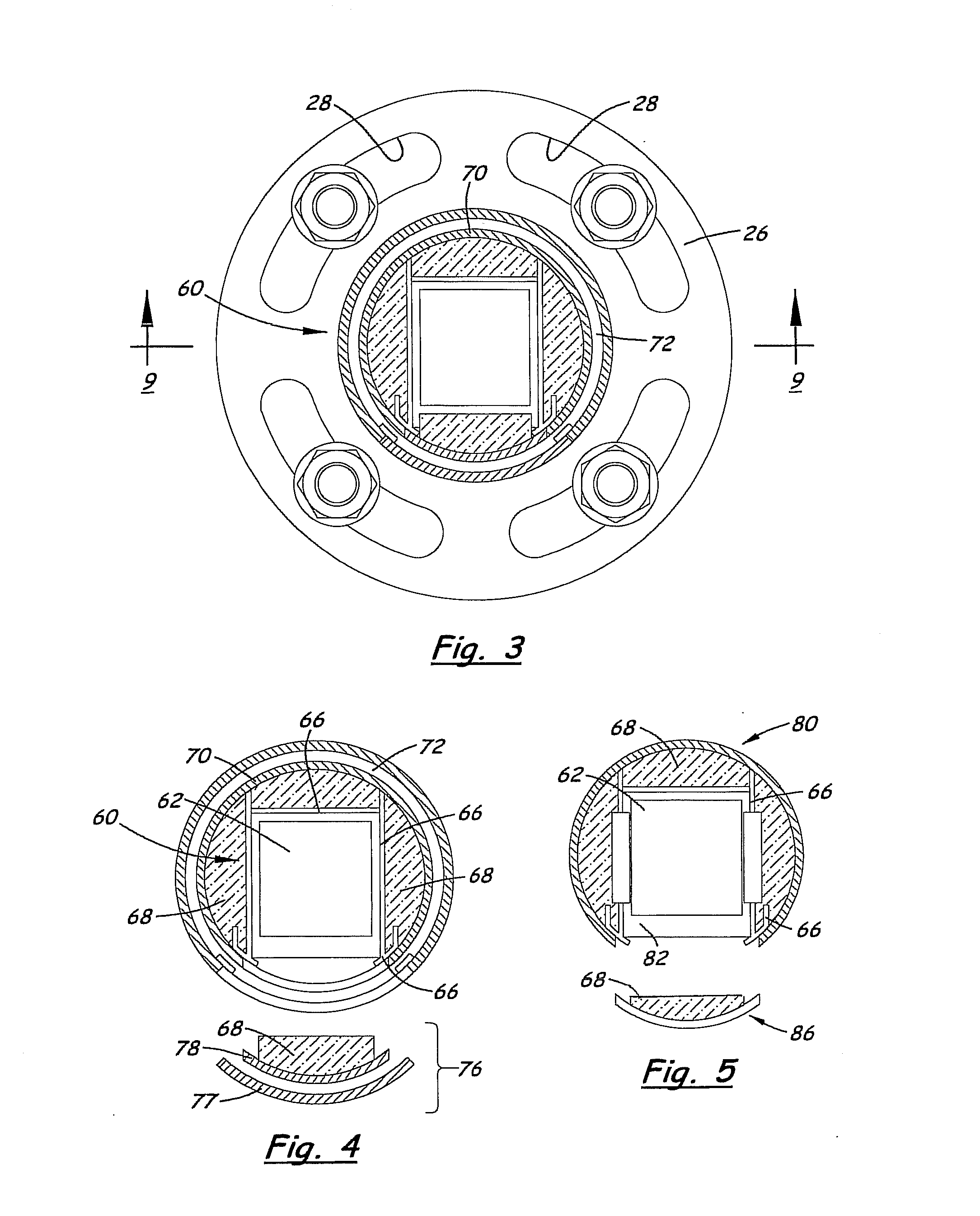
Energy-efficient solar-powered outdoor lighting
InactiveUS20150021990A1Guaranteed uptimeEffectively serveLighting support devicesPoint-like light sourceEffect lightEngineering
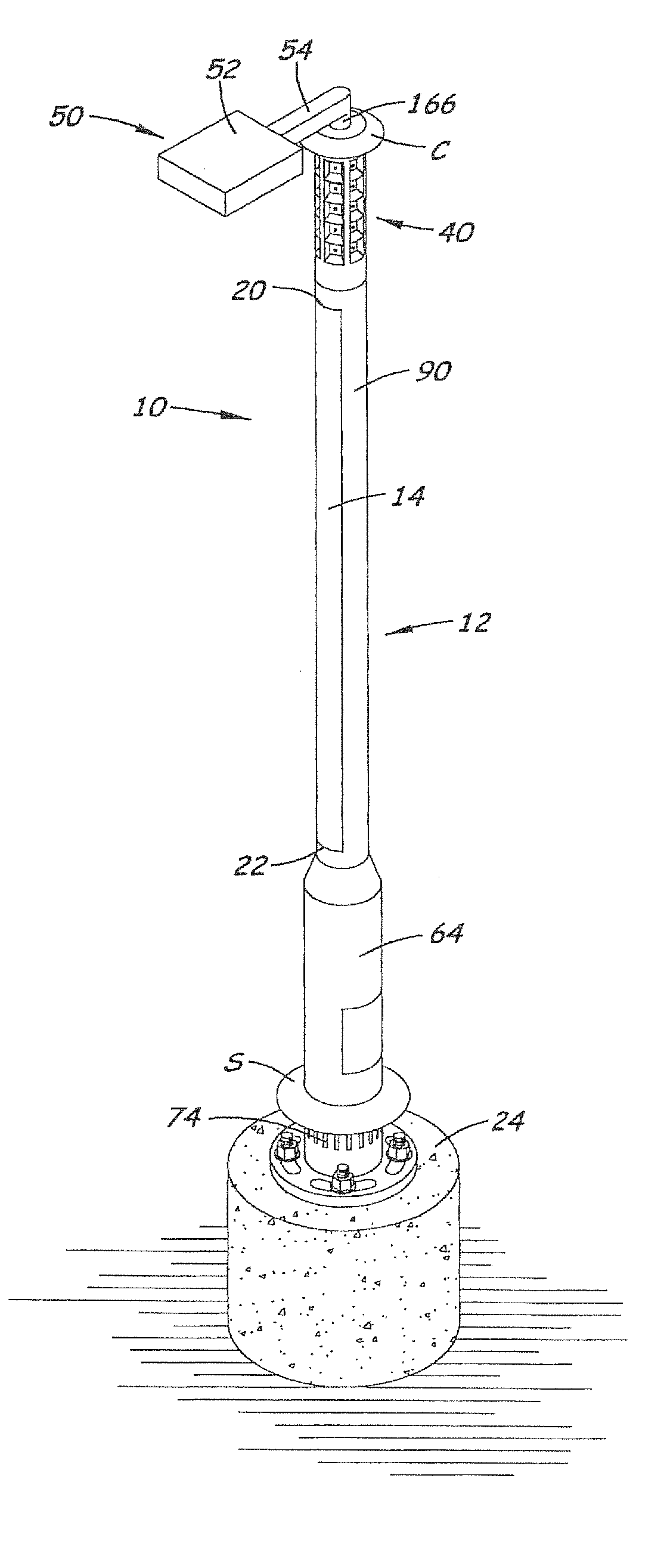
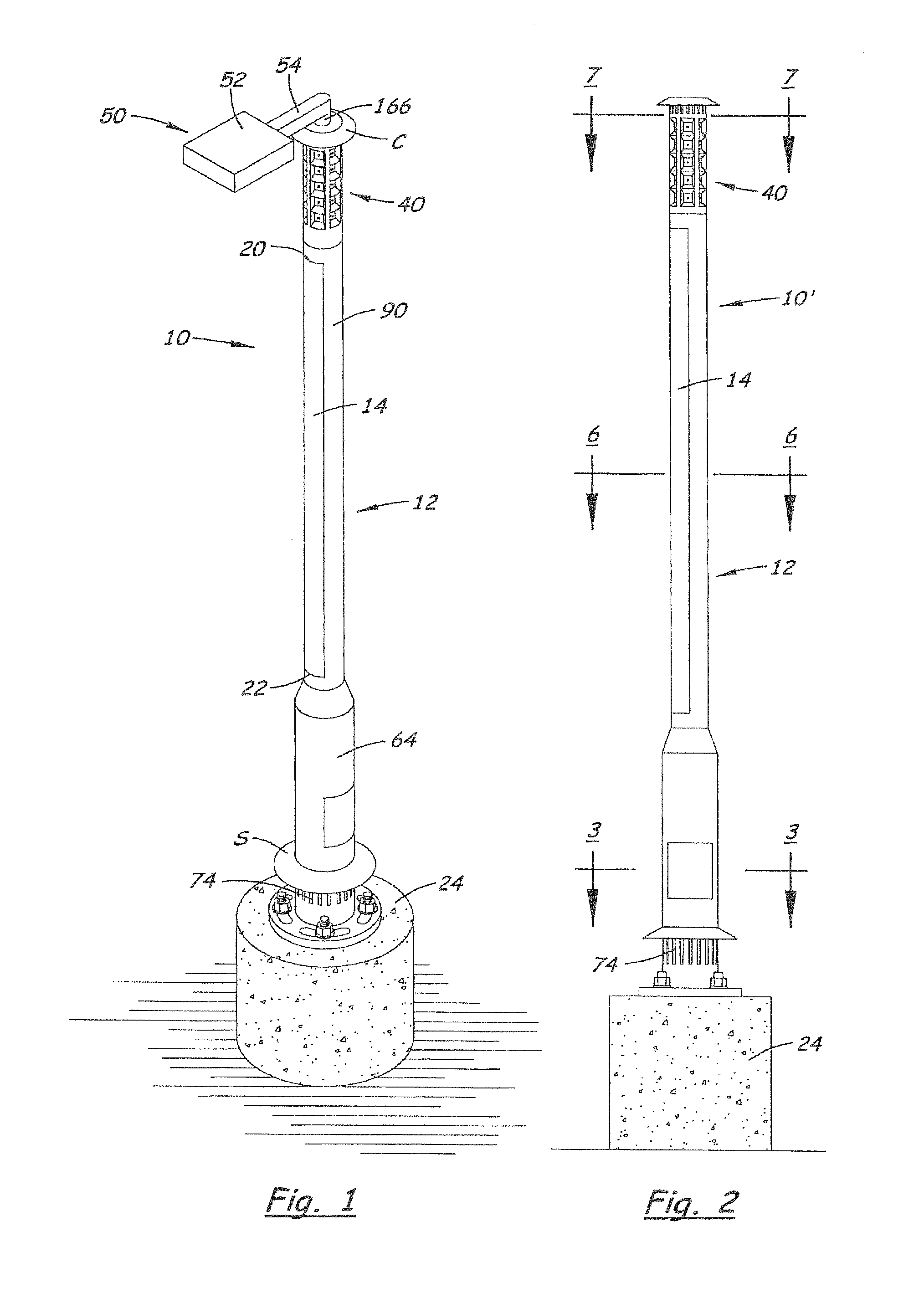
One or more outdoor lights may operate independently with sensing and control processes mainly on-pole, or may communicate as a networked array of poles, wherein a master / coordinating pole / node transmits signals from the networked array to a control station, and receive signals from the control station for the networked array, via call phone and / or satellite. Independent poles and / or the networked array of poles may be adapted for energy-saving processes; cooperation with the grid; renewable power production and storage by means of solar panels and associated batteries; and / or to provide Wi-Fi hot-spots, public safety alarms, information or data-analysis to the public or customers. An energy-saving active control system controls charging of the batteries and distribution of energy from the solar panel and / or the batteries, so that the batteries remain undamaged, and the light(s) remain operation even during the winter or other long periods of clouds and diffuse light. The active control of energy distribution by a load controller function may include dimming during the night, except when sensors detect motion, and, in extreme cloudy or diffuse-light periods, increasing increments of dimming and / or load shedding, to preserve the batteries and operability.
Owner:INOVUS SOLAR
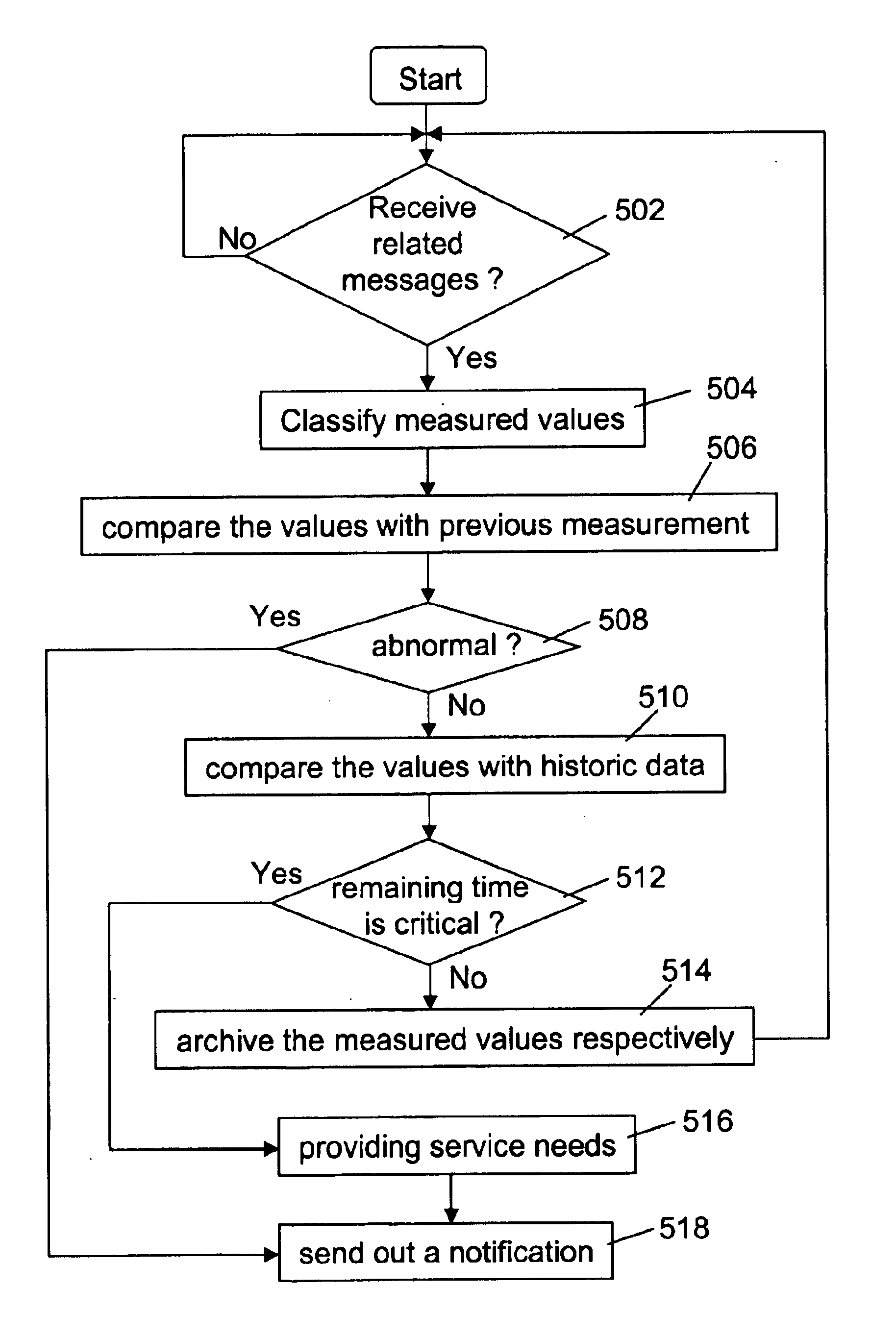
Method and architecture for monitoring the health of servers across data networks
InactiveUS6738811B1Sufficient detailError detection/correctionDigital computer detailsHealth conditionDiagnostic system
A health diagnostic system capable for monitoring the health condition of computing device on a network is disclosed. According to one aspect of the present invention, a computing device is installed a module that can provoke the monitoring process that periodically samples values representing the health condition of the computing device. The sampled values are then sent back to the monitoring server for analysis. Meanwhile a monitoring server receives the sampled values and performs data analysis to determine if the computing device is in a good / poor condition based on historic data that are further used to predicate what the remaining time is for the computing device to actually break down so that necessary measures may be taken to prevent an actual breakdown.
Owner:SUPER MICRO COMP
Systems and methods for client-based web crawling
InactiveUS20050071766A1The process is fast and accurateReducing server-client communication trafficData processing applicationsWeb data indexingData validationSource Data Verification
The present invention provides systems and methods for obtaining information from a networked system utilizing a distributed web crawler. The distributed nature of clients of a server is leveraged to provide fast and accurate web crawling data. Information gathered by a server's web crawler is compared to data retrieved by clients of the server to update the crawler's data. In one instance of the present invention, data comparison is achieved by utilizing information disseminated via a search engine results page. In another instance of the present invention, data validation is accomplished by client dictionaries, emanating from a server, that summarize web crawler data. The present invention also facilitates data analysis by providing a means to resist spoofing of a web crawler to increase data accuracy.
Owner:MICROSOFT TECH LICENSING LLC
Automatic and ambulatory monitoring of congestive heart failure patients
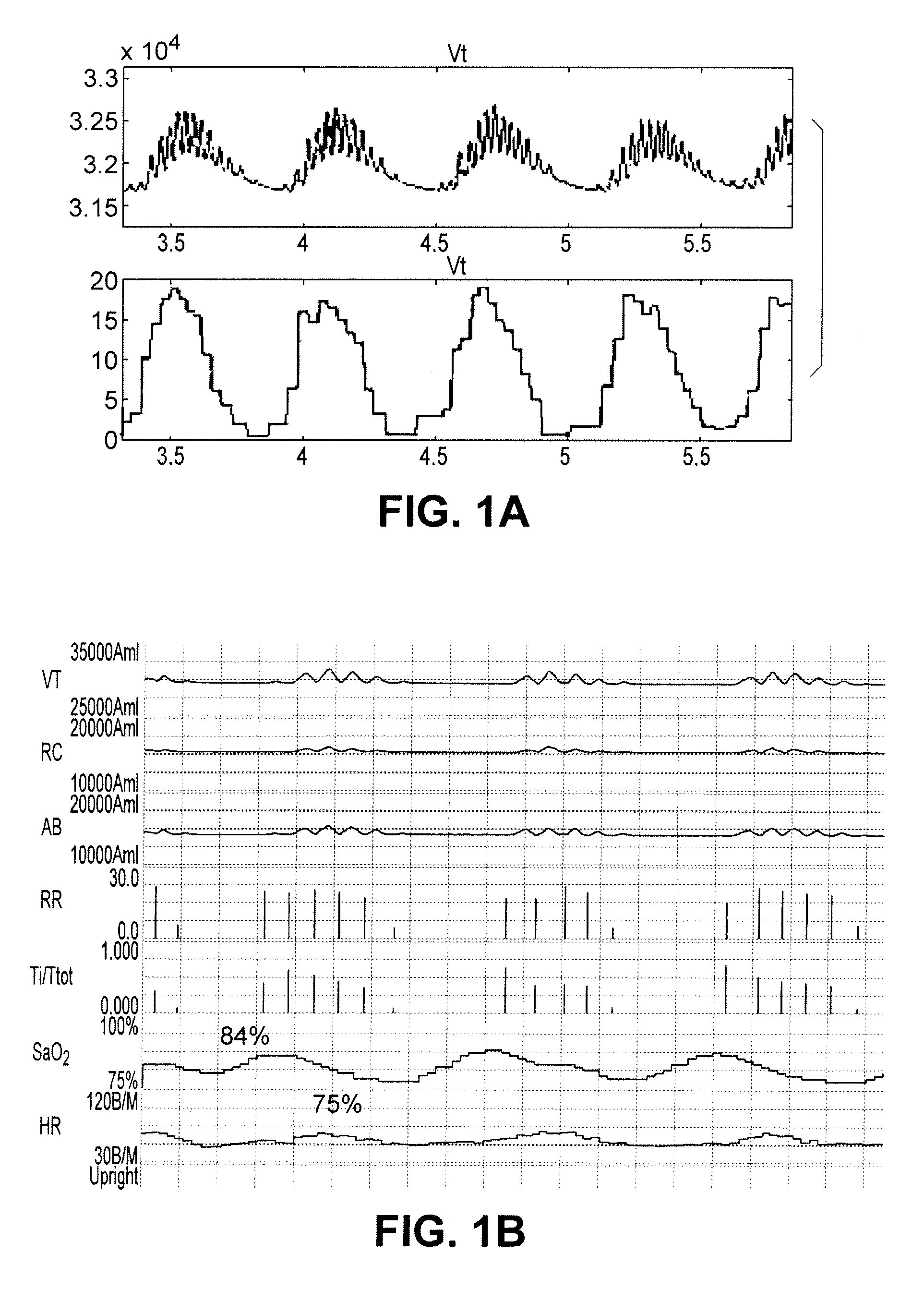
ActiveUS20080045815A1Rapid and targeted interventionImprove the quality of lifeElectrotherapyInertial sensorsRR intervalCongestive heart failure chf
This invention provides methods for non-invasively monitoring patients with congestive heart failure (CHF) and for reporting and / or warning of changes in the patients' status. The methods gather physiological data and combine the data into parameters by which the severity of CHF can be judged. Preferred parameters include periodic breathing and heart rate variability. This invention also provides systems for carrying out these methods which permit patients to engage in their normal daily activities. Preferably, physiological data analysis is performed by a portable electronic unit carried by the patients.
Owner:ADIDAS
Systems and/or methods for enabling cooperatively-completed rules-based data analytics of potentially sensitive data
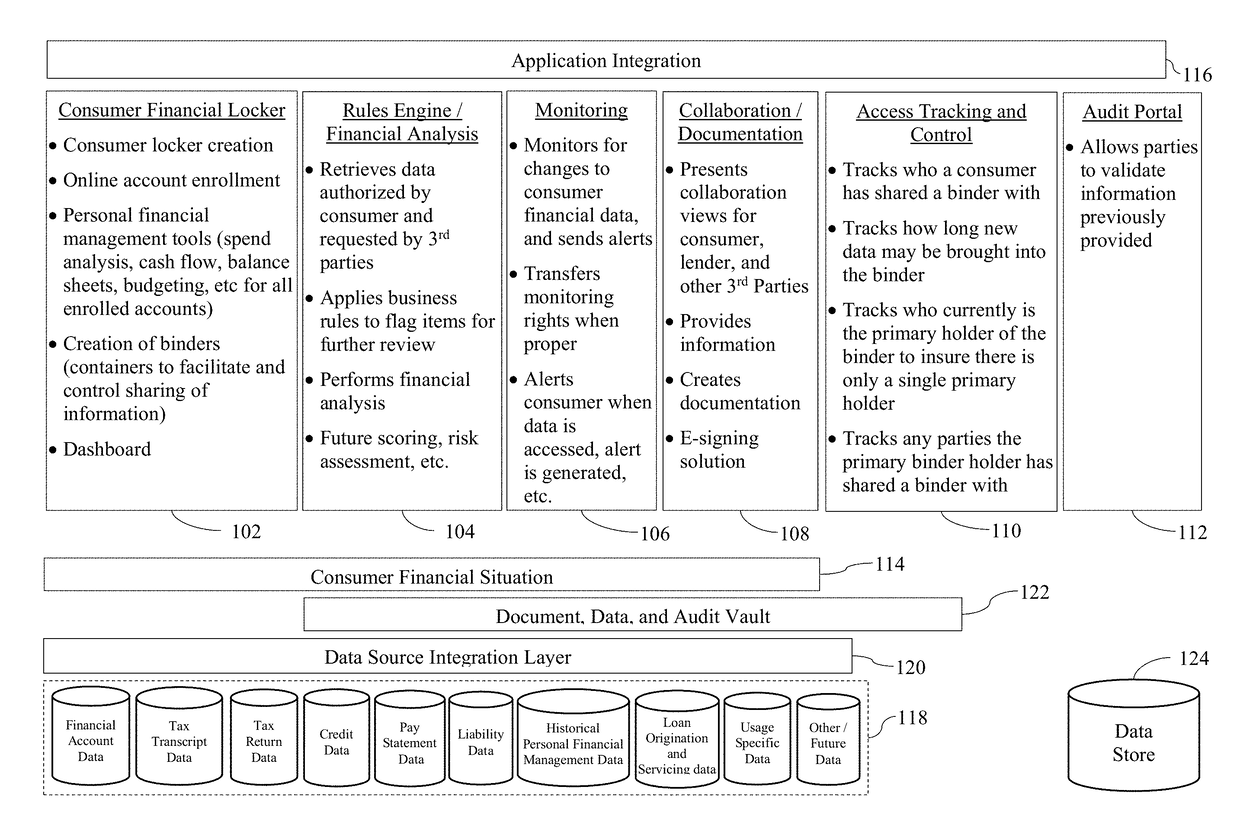
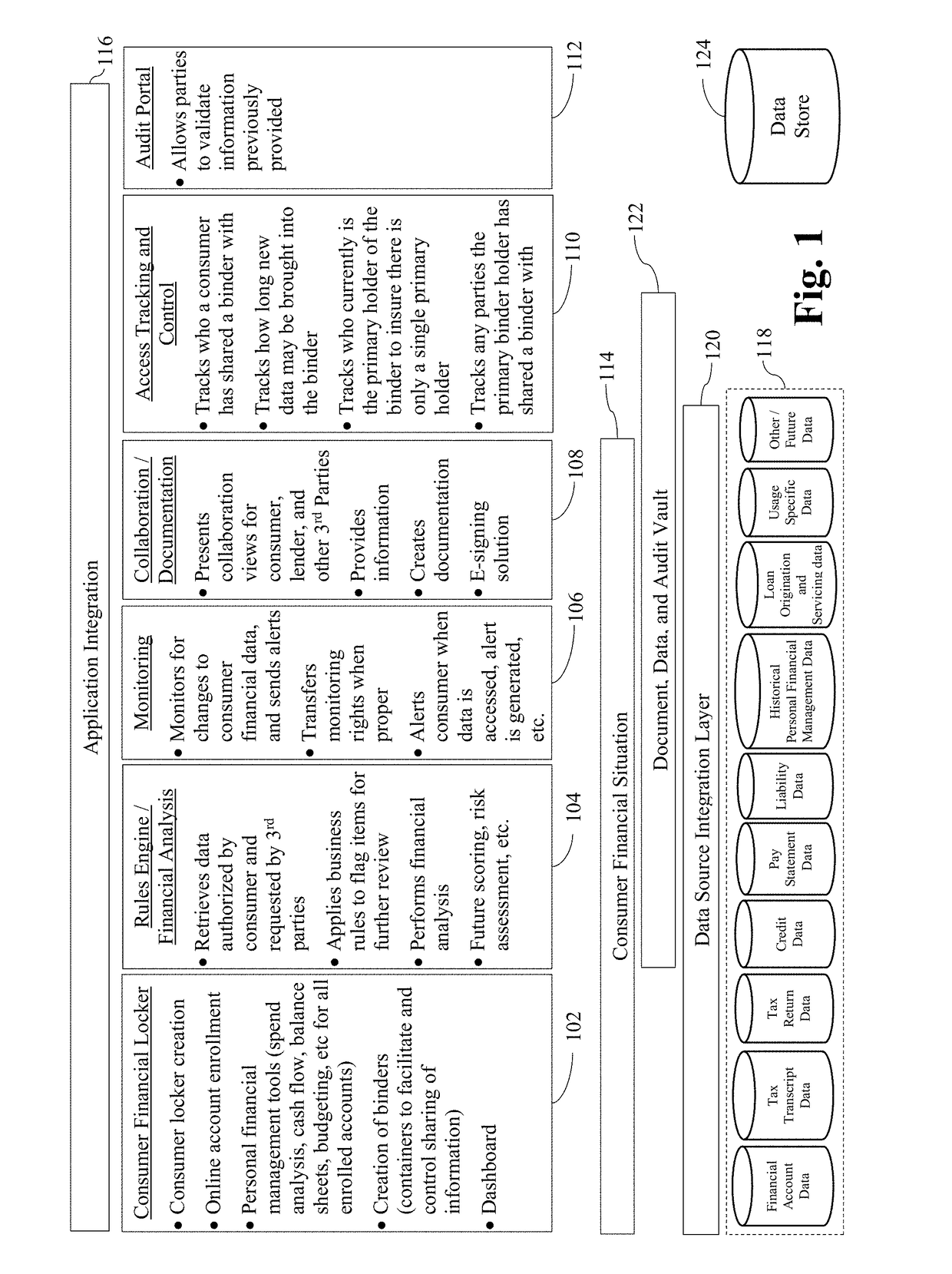
Certain example embodiments relate to systems and / or methods for providing enhanced control over potentially sensitive data sharable among and / or between different parties. For example, certain example embodiments provide views into computer-enabled workflows managed by external parties, including views into what sensitive data has been accessed, who has accessed it, etc., e.g., throughout the lifecycle of a product granted on the basis of an analysis of such data. A computer-enabled system for automatically assessing received sensitive data in accordance with one or more digitized rule sets also is provided in certain example embodiments, as are computer-mediated tools for helping to automatically, semi-automatically, and / or manually resolve issues detected in the assessments, e.g., via enhanced communication and collaboration, among and / or between parties to a transaction, as well as third-parties who indirectly are involved in the transaction. The data remains secure and traceable, e.g., in accordance with its provider's specifications.
Owner:FINLOCKER LLC
Tolerant and extensible discovery of relationships in data using structural information and data analysis
InactiveUS20060282429A1Relational databasesSpecial data processing applicationsMetric selectionData analysis
Various embodiments of a method, system and article of manufacture to discover relationships among a first set of elements and a second set of elements are provided. At least one metric algorithm is identified based on a metric selection parameter. A raw result is determined based on the at least one metric algorithm, a first specified structural description of the first set of elements and a second specified structural description of the second set of elements. The raw result comprises a plurality of relationship measurements and the raw result is ordered. In some embodiments, a balanced result is produced based on the raw result and a matching strategy algorithm. In other embodiments, the matching strategy algorithm is identified based on a matching strategy selection parameter.
Owner:IBM CORP
Systems for time-series predictive data analytics, and related methods and apparatus
ActiveUS20180046926A1Easy to understandPrediction is accurateResource allocationEnsemble learningAlgorithmData profiling
A predictive modeling method may include determining a time interval of time-series data; identifying one or more variables of the data as targets; determining a forecast range and a skip range associated with a prediction problem represented by the data; generating training data and testing data from the time-series data; fitting a predictive model to the training data; and testing the fitted model on the testing data. The forecast range may indicate a duration of a period for which values of the targets are to be predicted. The skip range may indicate a temporal lag between the time period corresponding to the data used to make predictions and the time period corresponding to the predictions. The skip range may separate input data subsets representing model inputs from subsets representing model outputs, and separate test data subsets representing model inputs from subsets representing validation data.
Owner:DATAROBOT INC
Energy-efficient solar-powered outdoor lighting
InactiveUS20120020060A1Guaranteed uptimeEffectively serveLighting support devicesPoint-like light sourceElectrical batteryOperability
One or more outdoor lights may operate independently with sensing and control processes mainly on-pole, or may communicate as a networked array of poles, wherein a master / coordinating pole / node transmits signals from the networked array to a control station, and receive signals from the control station for the networked array, via call phone and / or satellite. Independent poles and / or the networked array of poles may be adapted for energy-saving processes; cooperation with the grid; renewable power production and storage by means of solar panels and associated batteries; and / or to provide Wi-Fi hot-spots, public safety alarms, information or data-analysis to the public or customers. An energy-saving active control system controls charging of the batteries and distribution of energy from the solar panel and / or the batteries, so that the batteries remain undamaged, and the light(s) remain operation even during the winter or other long periods of clouds and diffuse light. The active control of energy distribution by a load controller function may include dimming during the night, except when sensors detect motion, and, in extreme cloudy or diffuse-light periods, increasing increments of dimming and / or load shedding, to preserve the batteries and operability.
Owner:INOVUS SOLAR
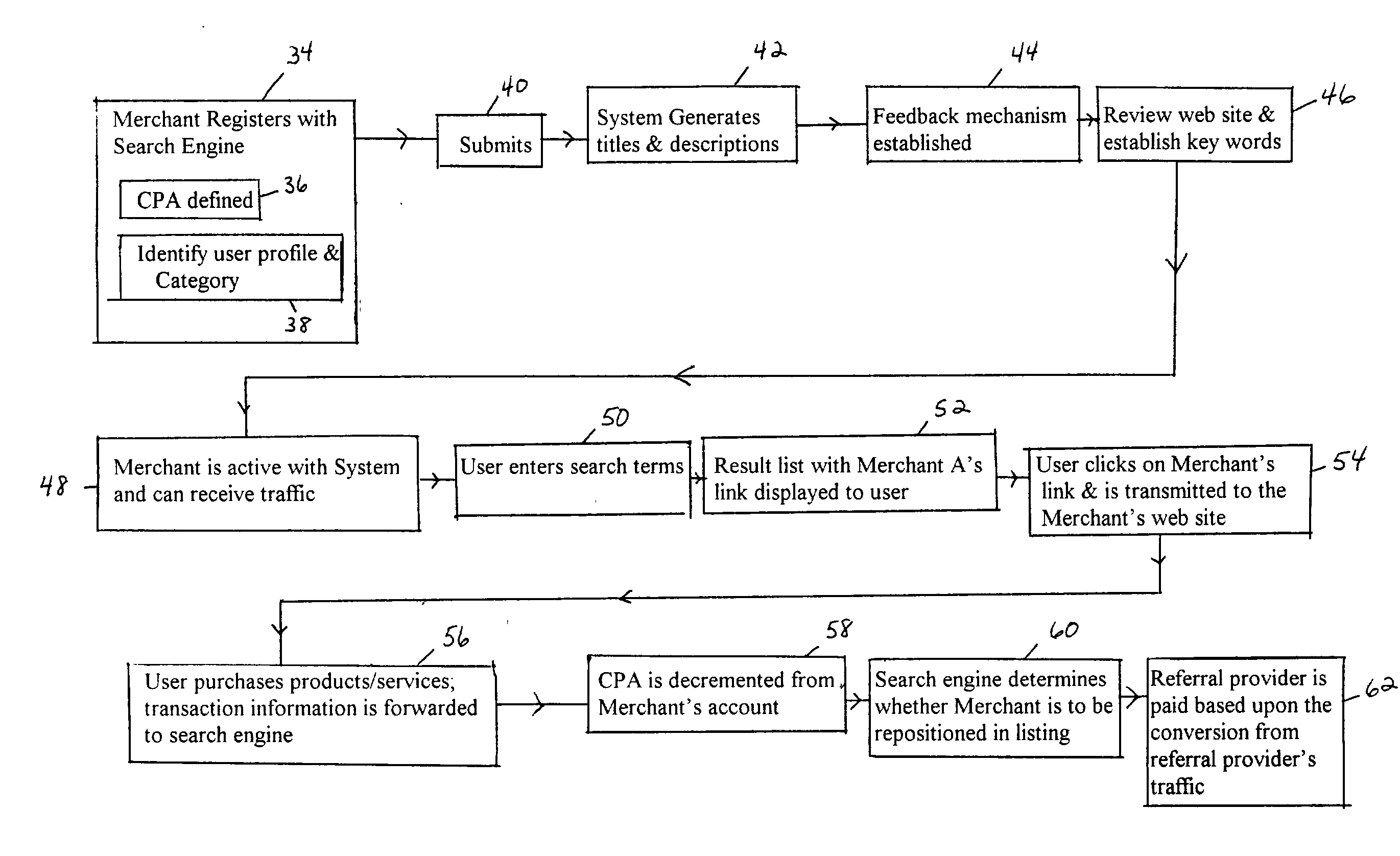
Cost-per-action search engine system, method and apparatus
InactiveUS20030216930A1Free advertiserIncreased its relevancyAdvertisementsBuying/selling/leasing transactionsRelevant informationDisplay list
Embodiments of the present invention are directed to a search engine system, method and apparatus comprising a search engine, a participant management system, at least one storage database, a listing database and at least one feedback mechanism. The search engine accepts input data and utilizes the input data to search for information related to the search terms. Upon retrieval of relevant information, the data analysis module organizes the data related to the search terms into a search results list. To determine the placement of listings upon a search request, the data analysis module determines the probability, for each relevant listing, that the user will ultimately complete the desired action if the listing is shown, wherein the probability of action is determined by a plurality of factors. This probability is then combined with the specific CPA for the advertiser. Transaction information derived from a search and click is returned through the feedback mechanism to the search engine for revised calculation of listing placement.
Owner:VALUE CLICK
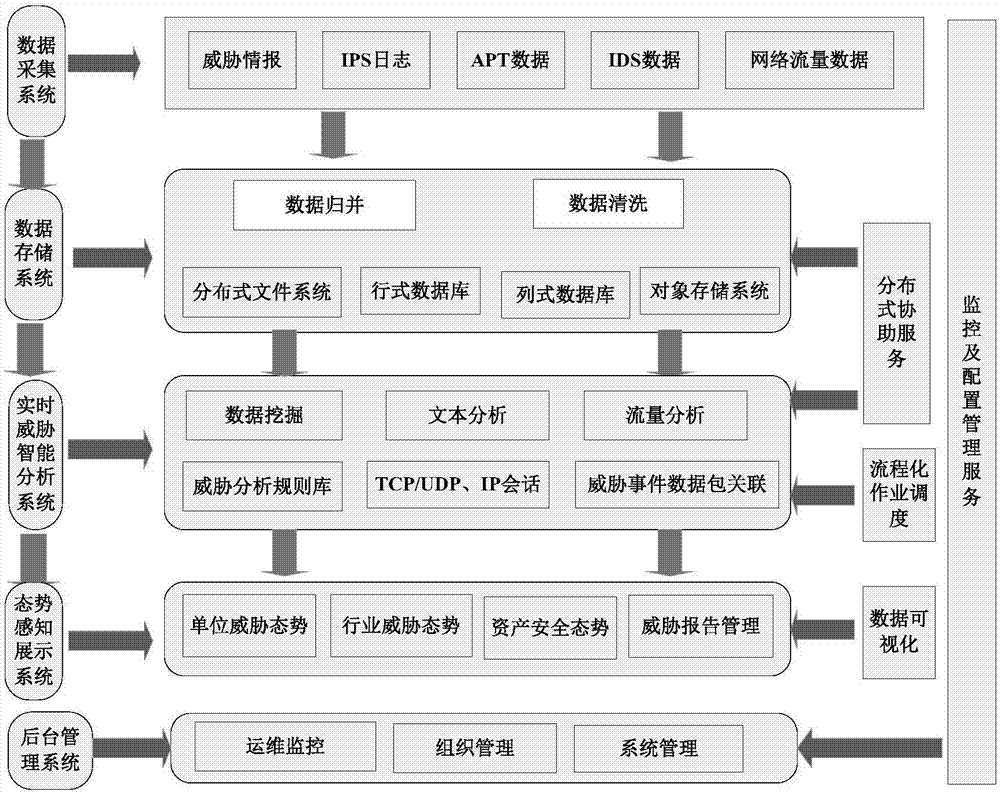
Threat early warning and monitoring system and method based on big data analysis and deployment architecture
ActiveCN107196910ARealize acquisitionRealize multi-dimensional graphical and intuitive displayData switching networksFull text searchTime processing
The invention discloses a threat early warning and monitoring system and method based on big data analysis and a deployment architecture. The system comprises a data acquisition system module, which is used for carrying out real-time data acquisition on original network traffic; a data storage system module, which is used for carrying out data merging and data cleaning on the data collected by the data acquisition system module, and then, carrying out storage management; a real-time threat intelligent analysis system module, which is used for carrying out deep analysis and mining on security data through data mining, text analysis, traffic analysis, full-text search engine and real-time processing, and identifying unknown security threats in real time by combining an intrusion detection module, a network abnormal behavior module and a device abnormal behavior module; and a situation awareness display system module, which is used for carrying out comprehensive display on security threat situations stereoscopically in real time through a data visualization tool library. The threat early warning and monitoring system and method based on big data analysis and the deployment architecture are used for network security threat situation awareness and deep analysis under a plurality of service scenarios, and realize comprehensive abilities from attack early warning, attack identification to analysis and evidence obtaining.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
Automated research systems and methods for researching systems
InactiveUS20090138415A1Improve understandingEasy to controlKnowledge representationInference methodsResearch softwareUser input
Systems and methods that provide for automated research into the workings of one or more studied systems include automated research software modules that communicate with domain knowledge bases, research professionals, automated laboratories experiment objects, and data analysis processes, wherein automatically selected experiment objects can be run at an automated laboratory to produce experimental results, and the subsequent data-processing providing automated guidance to a next round of experiment choice and automated research. An Experiment Director rules engine chooses Experiment Objects based on user input through a Query Manager.
Owner:HYDROJOULE LLC
Nanodosimeter based on single ion detection
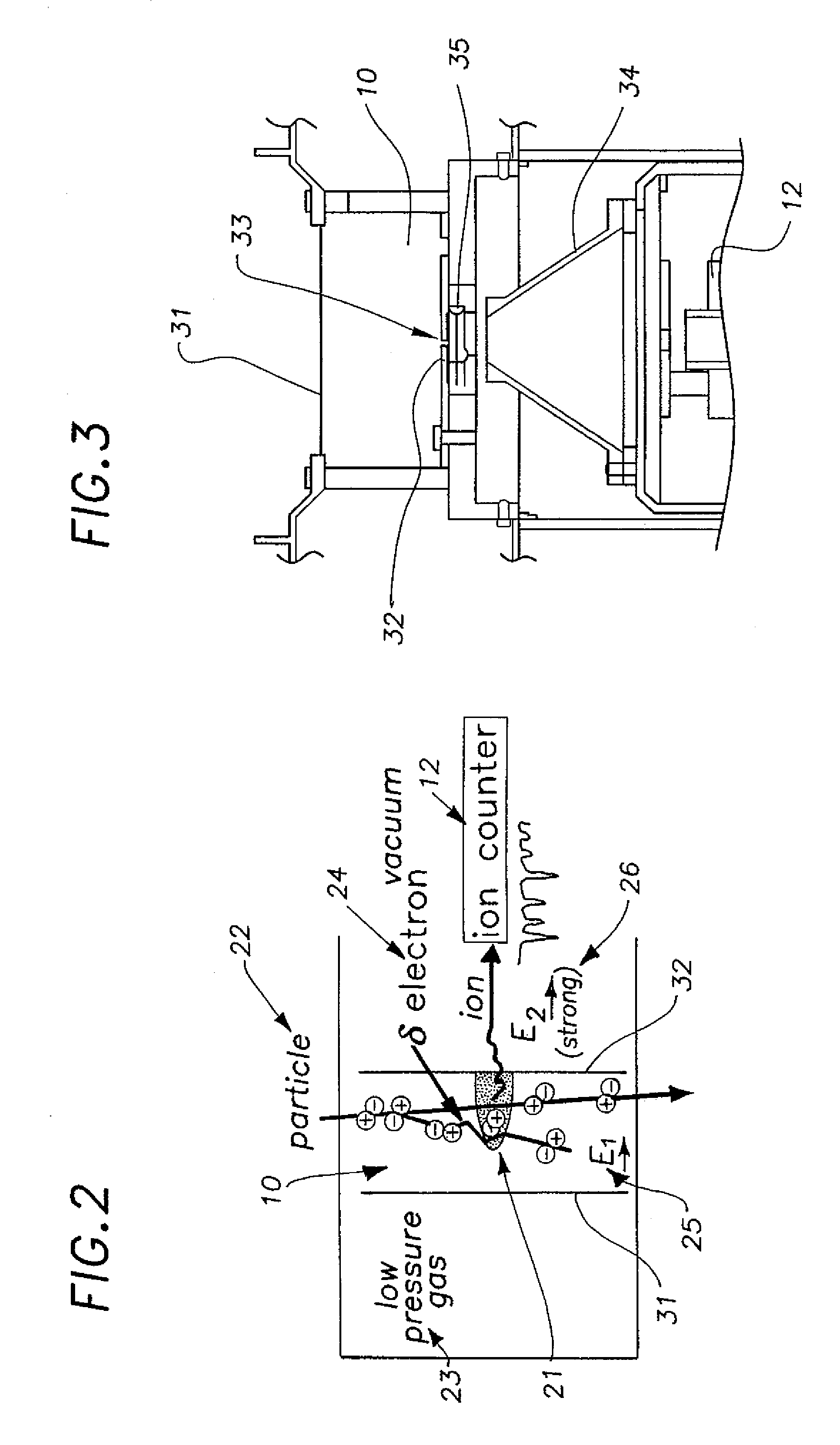
InactiveUS7081619B2Time-of-flight spectrometersMaterial analysis by electric/magnetic meansFluenceDosimeter
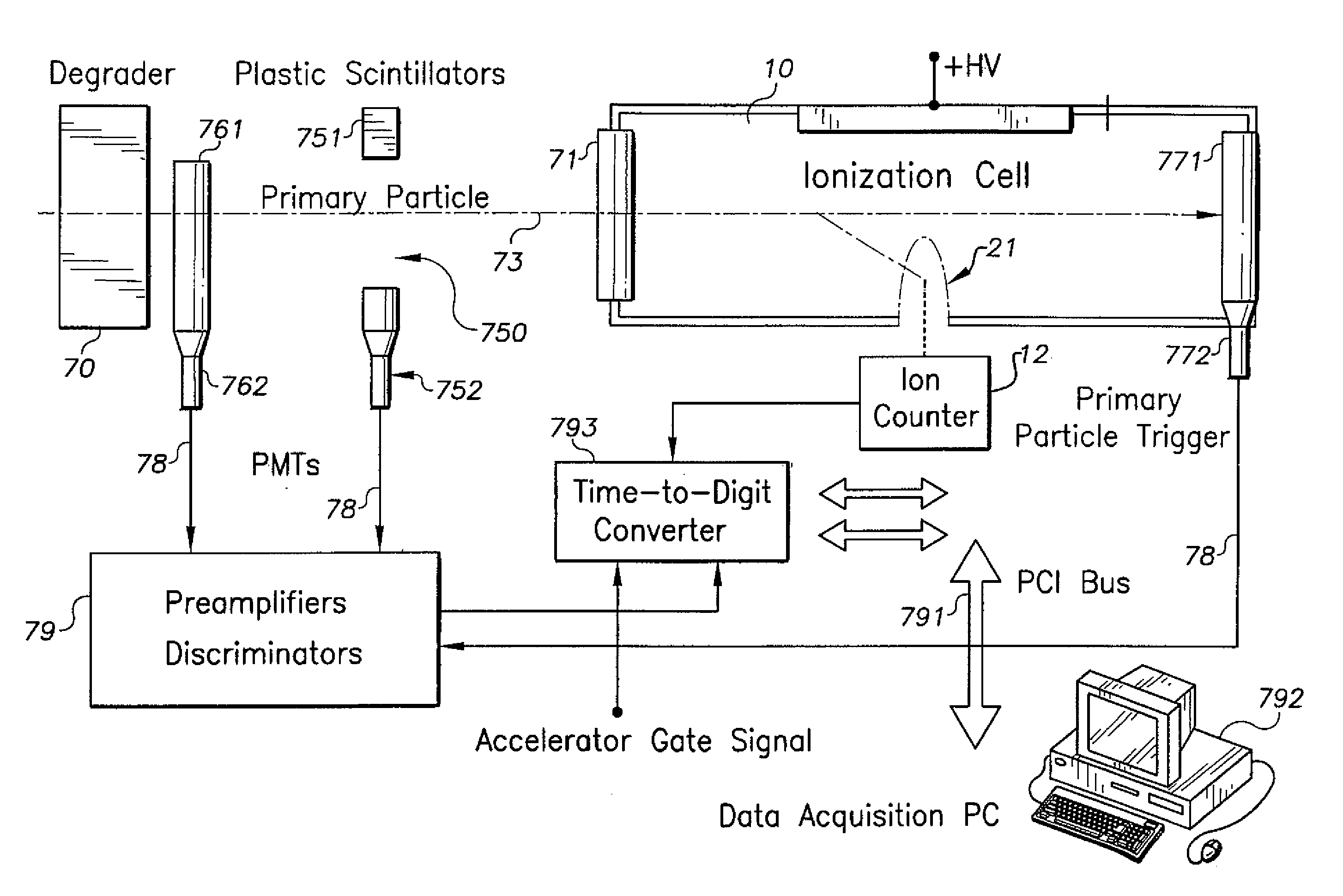
A nanodosimeter device (15) for detecting positive ions induced in a sensitive gas volume by a radiation field of primary particle, comprising an ionization chamber (10) for holding the sensitive gas volume to be irradiated by the radiation field of primary particles; an ion counter system connected to the ionization chamber (10) for detecting the positive ions which pass through the aperture opening and arrive at the ion counter (12) at an arrival time; a particle tracking system for position-sensitive detection of the primary particles passing through the sensitive gas volume; and a data acquisition system capable of coordinating the readout of all data signals and of performing data analysis correlating the arrival time of the positive ions detected by the ion counter system relative to the position sensitive data of primary particles detected by the particle tracking system. The invention further includes the use of the nanodosimeter for method of calibrating radiation exposure with damage to a nucleic acid within a sample. A volume of tissue-equivalent gas is radiated with a radiation field to induce positive ions. The resulting positive ions are measured and compared with a determination of presence or extent of damage resulting from irradiating a nucleic acid sample with an equivalent dose of radiation.
Owner:LOMA LINDA UNIVERSITY +1
System and method for providing unified workflows integrating multiple computer network resources
A computer network implemented system is provided comprising a workflow designer that is operable to enable the design of one or more workflows that utilize information or functions from one or more (i) business systems, (ii) applications, or (iii) databases; and an application programming interface (API) that is configured to connect to the (i) business systems, (ii) applications or (iii) databases so as to monitor user actions, and based on such user interactions applying one or more workflow overlays that incorporate one or more intelligent features for enhancing functions of the business systems and the applications. A related computer implemented method is also provided. A computer network service is also provided that acquires information relevant to sales processes and processes the information to generate insights for improving sales performance. A sales forecasting utility is provided that applies data analysis operations to information elements relevant to a sales process. Insights may be presented to a sales representative on a real time or near real time basis so as to guide sales related activities.
Owner:SALESCHOICE INC
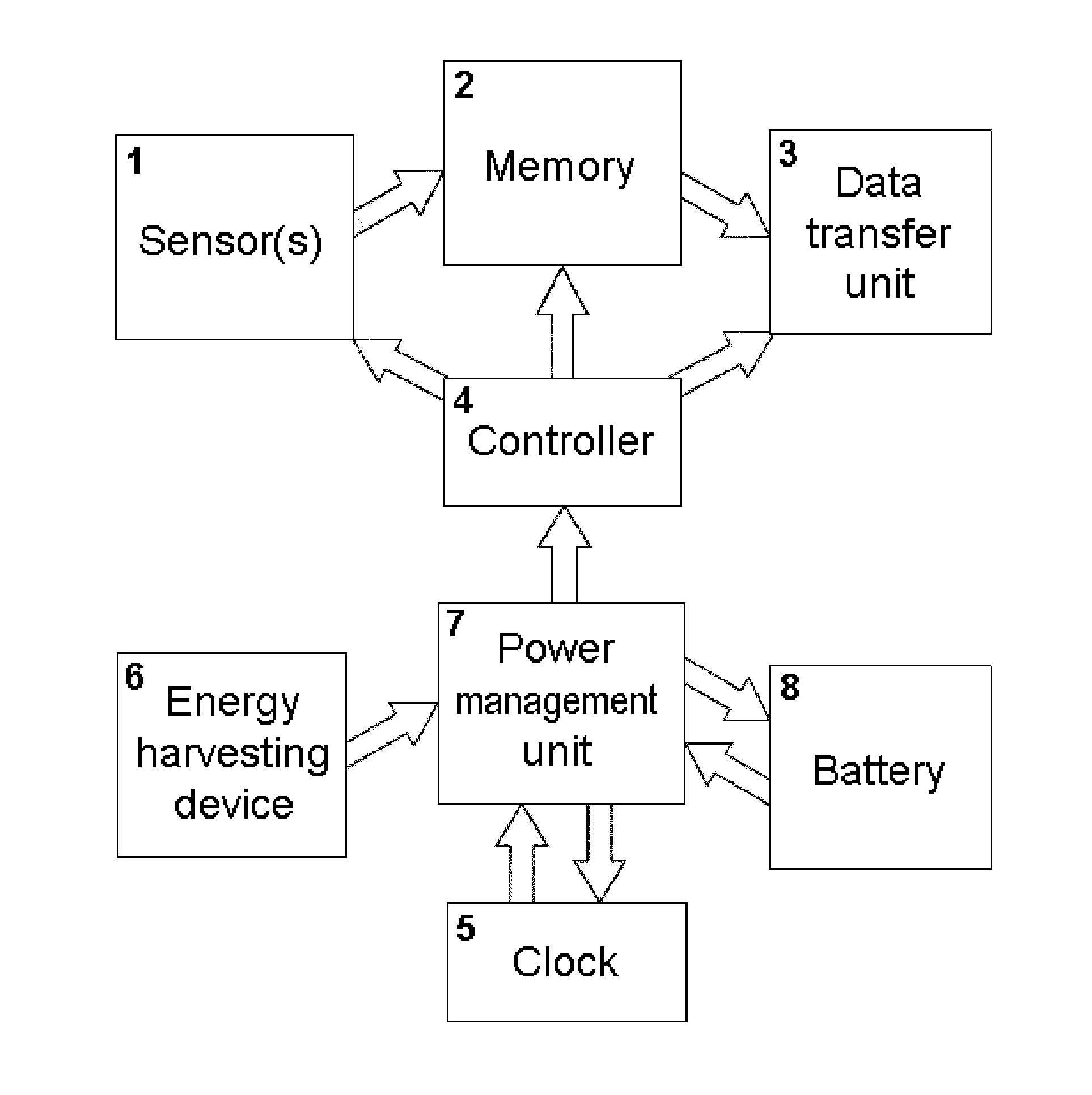
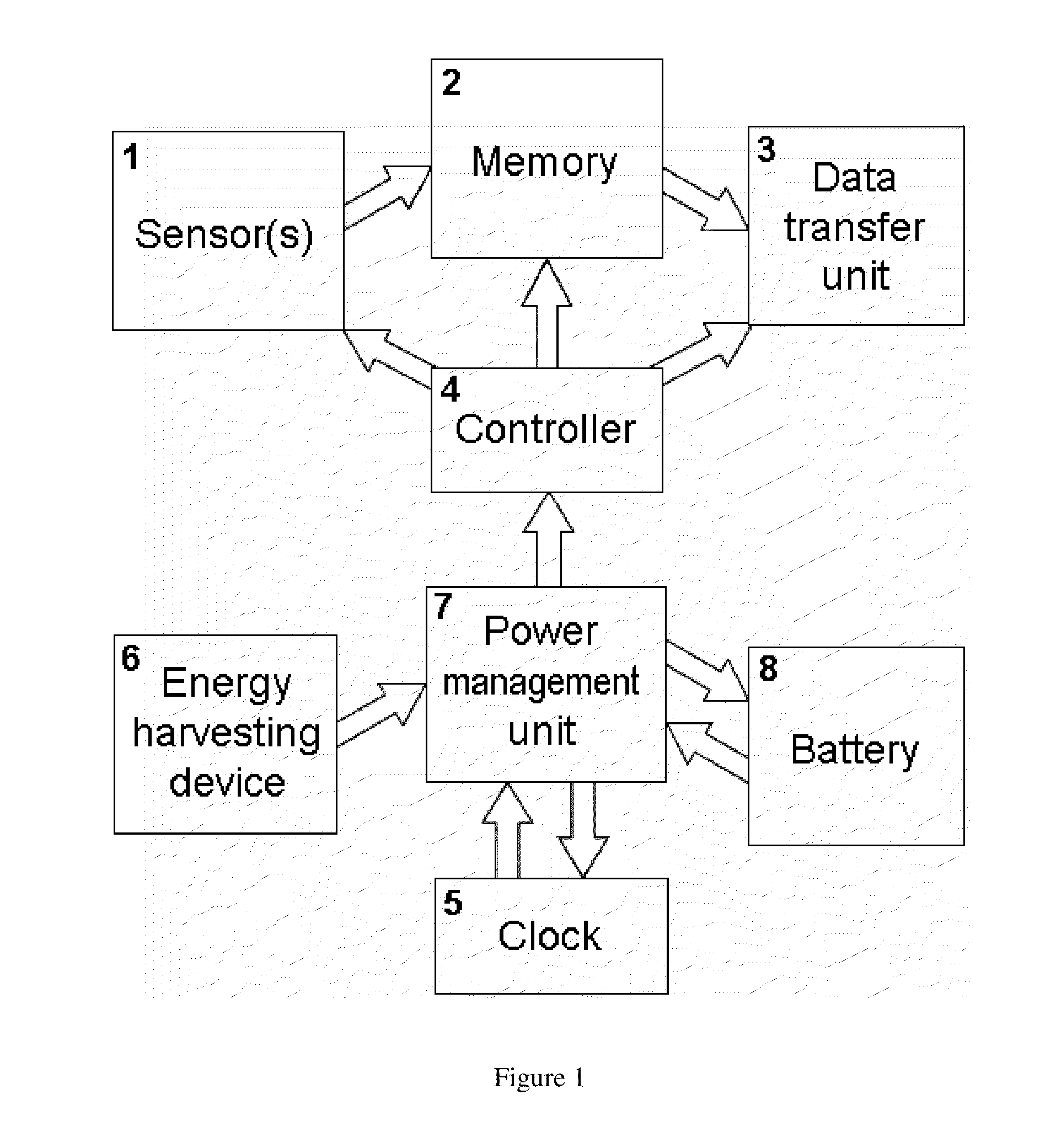
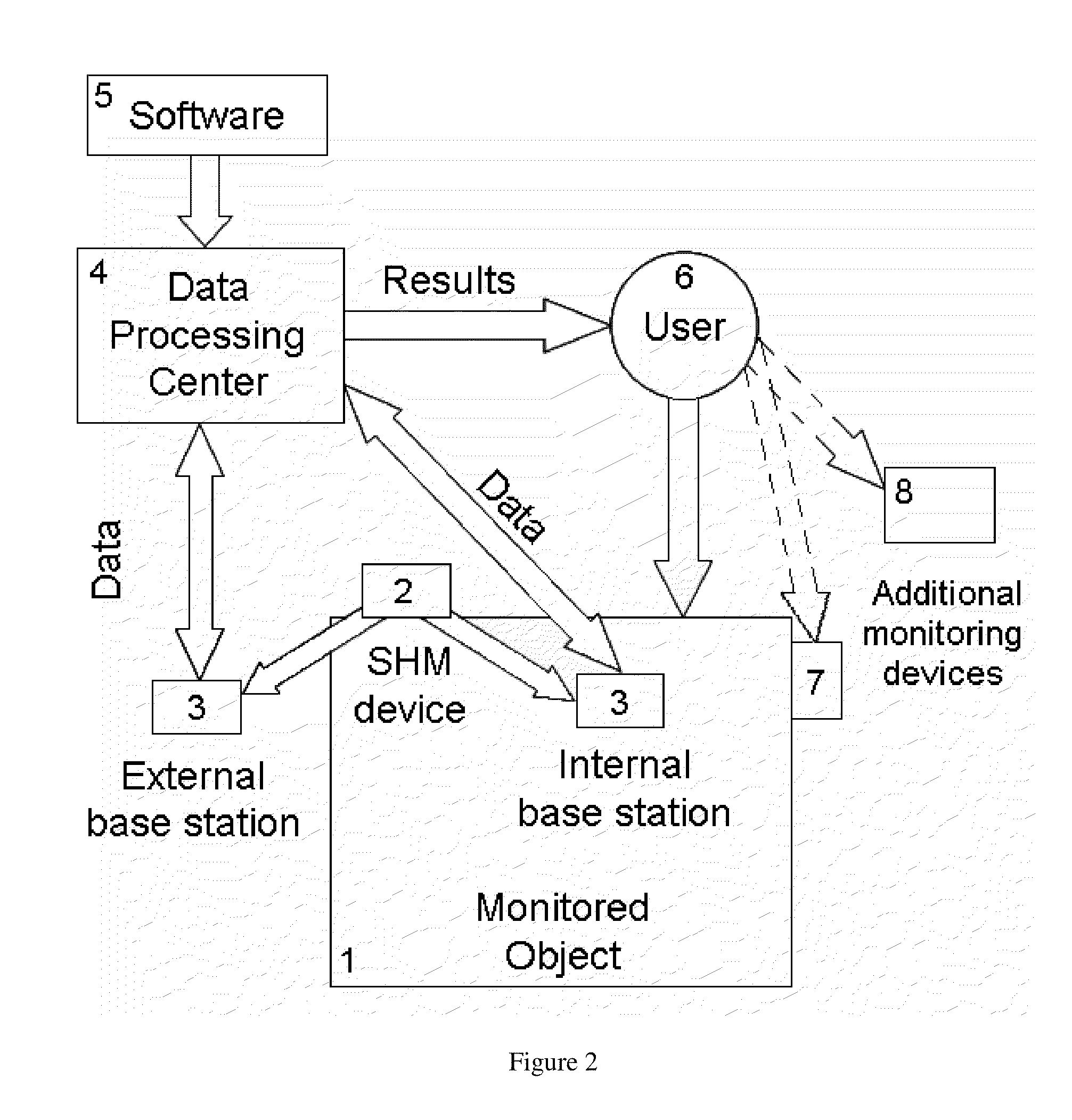
Autonomous Sensing Module, a System and a Method of Long-Term Condition Monitoring of Structures
InactiveUS20100271199A1Sufficient protectionEasy to useMaterial analysis using wave/particle radiationAnti-theft devicesPower Management UnitDependability
A system and a method of long-term condition monitoring of structures are based on use of autonomous sensing modules, centers for storing and processing data and software for data analysis. An autonomous sensing module contains a set of sensors for measurements of parameters related to the condition of a monitored structure, a non-volatile memory, a wireless data transfer unit, a controller, a clock circuit, a battery, an energy harvesting device and a power management unit. The autonomous sensing module provides a very long-term (40 years or more) functionality and reliability due to both use of at least near hermetic packages for the controller, the non-volatile memory, the battery, the clock circuit and the power management unit and choosing the duration of periods when the sensing module works in active mode in such a way that the average energy consumed by the autonomous sensing module is fully compensated by the average energy harvested by the energy harvesting device.
Owner:KOLOS INT
Systems and Methods for Visualization of Data Analysis
Exemplary systems and methods for visualization of data analysis are provided. In various embodiments, a method comprises accessing a database, analyzing the database to identify clusters of data, generating an interactive visualization comprising a plurality of nodes and a plurality of edges wherein a first node of the plurality of nodes represents a cluster and an edge of the plurality of edges represents an intersection of nodes of the plurality of nodes, selecting and dragging the first node in response to a user action, and reorienting the interactive visualization in response to the user action of selecting and dragging the first node.
Owner:SYMPHONYAI SENSA LLC
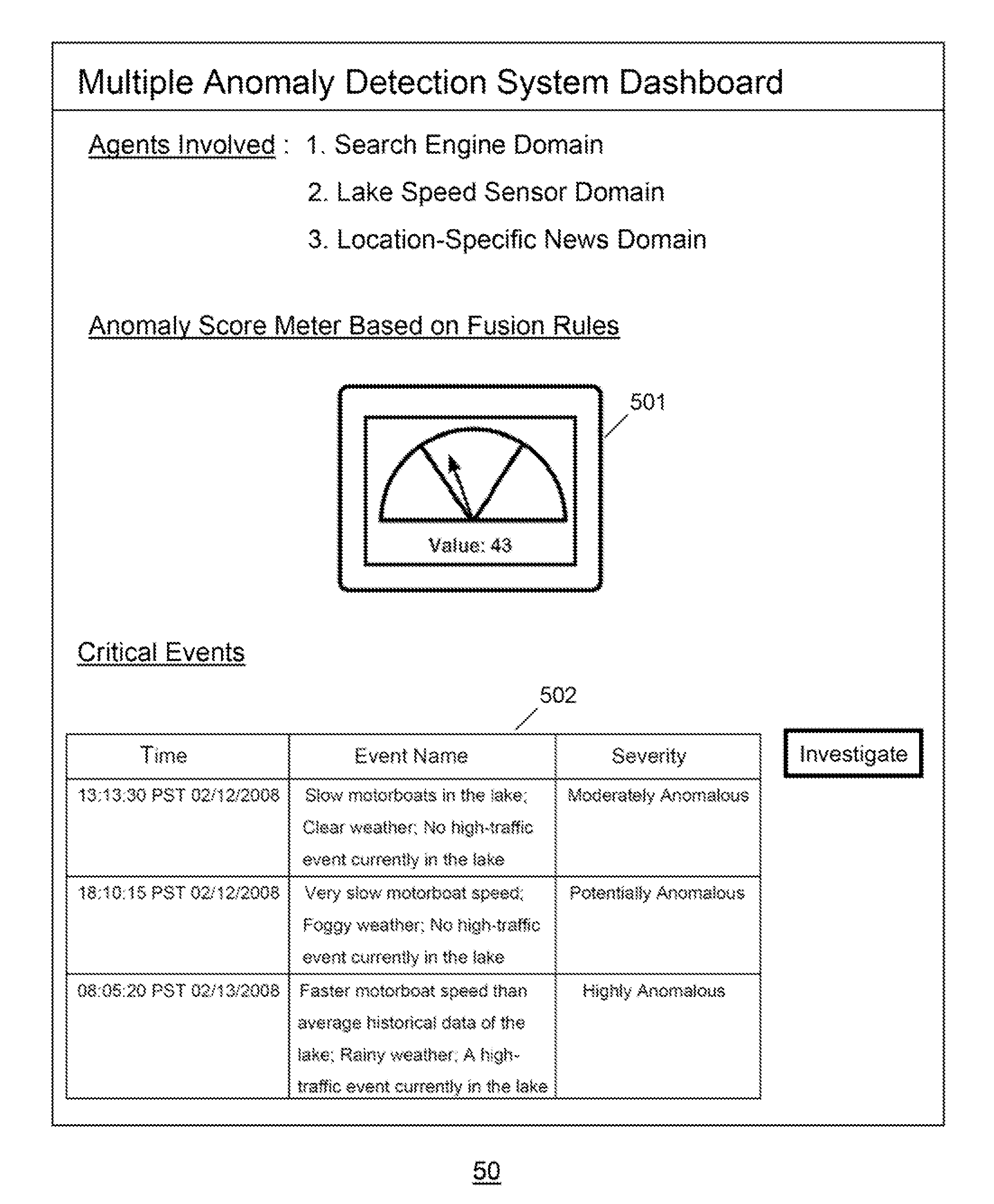
Multiple Domain Anomaly Detection System and Method Using Fusion Rule and Visualization
ActiveUS20110295783A1Digital data information retrievalDigital computer detailsAnomaly detectionDomain analysis
The present invention discloses various embodiments of multiple domain anomaly detection systems and methods. In one embodiment of the invention, a multiple domain anomaly detection system uses a generic learning procedure per domain to create a “normal data profile” for each domain based on observation of data per domain, wherein the normal data profile for each domain can be used to determine and compute domain-specific anomaly data per domain. Then, domain-specific anomaly data per domain can be analyzed together in a cross-domain fusion data analysis using one or more fusion rules. The fusion rules may involve comparison of domain-specific anomaly data from multiple domains to derive a multiple-domain anomaly score meter for a particular cross-domain analysis task. The multiple domain anomaly detection system and its related method may also utilize domain-specific anomaly indicators of each domain to derive a cross-domain anomaly indicator using the fusion rules.
Owner:ZHAO YING +2
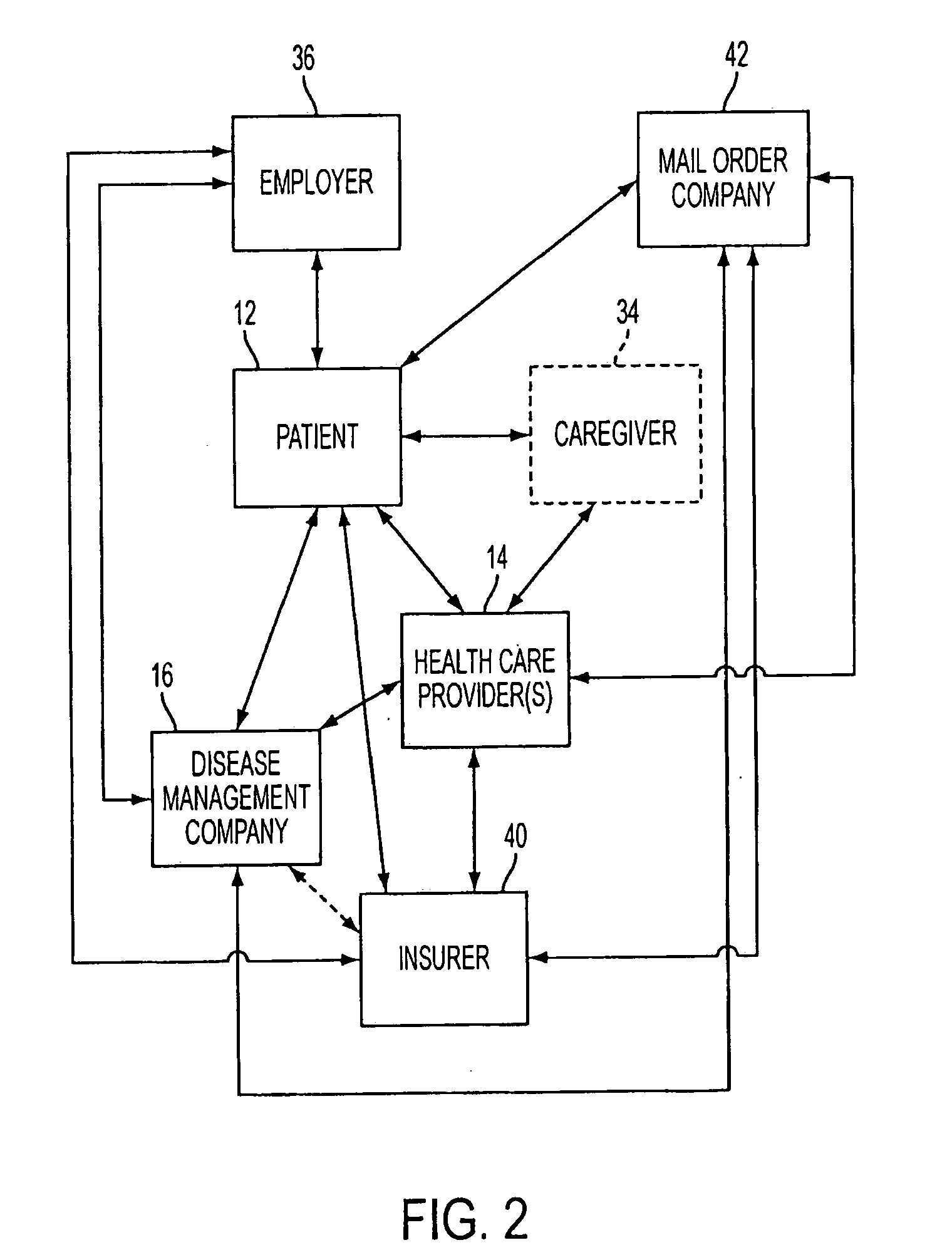
System and Methods for Improved Diabetes Data Management and Use Employing Wireless Connectivity Between Patients and Healthcare Providers and Repository of Diabetes Management Information
ActiveUS20100069730A1Shorten development timeExtended service lifePhysical therapies and activitiesDrug and medicationsDiseaseInformation repository
Methods, devices and a system for disease management are provided that employ diagnostic testing devices (e.g., blood glucose meters) and medication delivery devices (e.g., insulin delivery devices) for providing data to a repository in real-time and automatically. Repository data can be analyzed to determine such information as actual test strip use, patient health parameters to outside prescribed ranges, testing and medication delivery compliance, patient profiles or stakeholders to receive promotional items or incentives, and so on. Connected meters and medication delivery devices and repository data analysis are also employed to associate a diagnostic test to a mealtime based on timing of a therapeutic intervention performed by an individual.
Owner:EMBECTA CORP
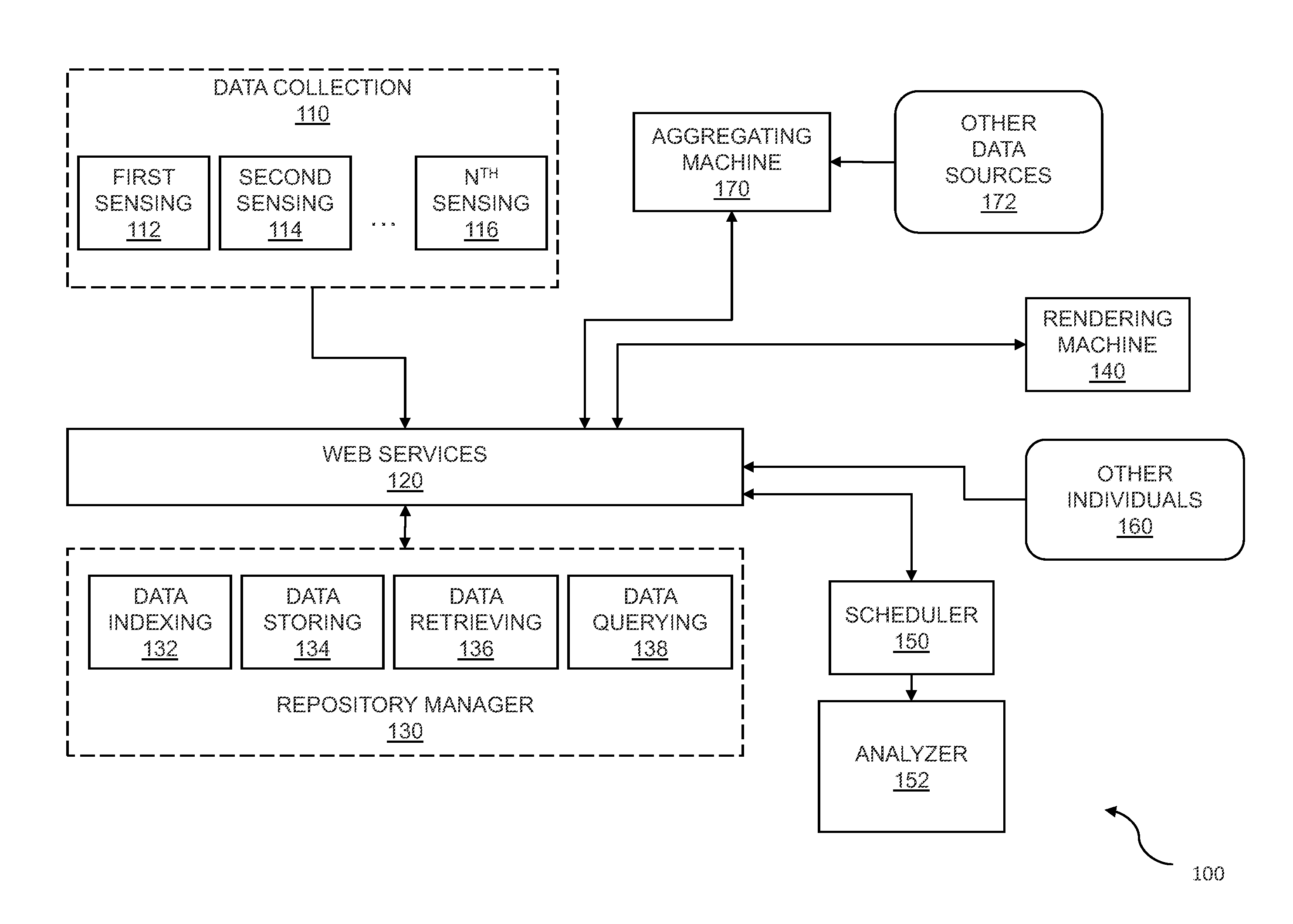
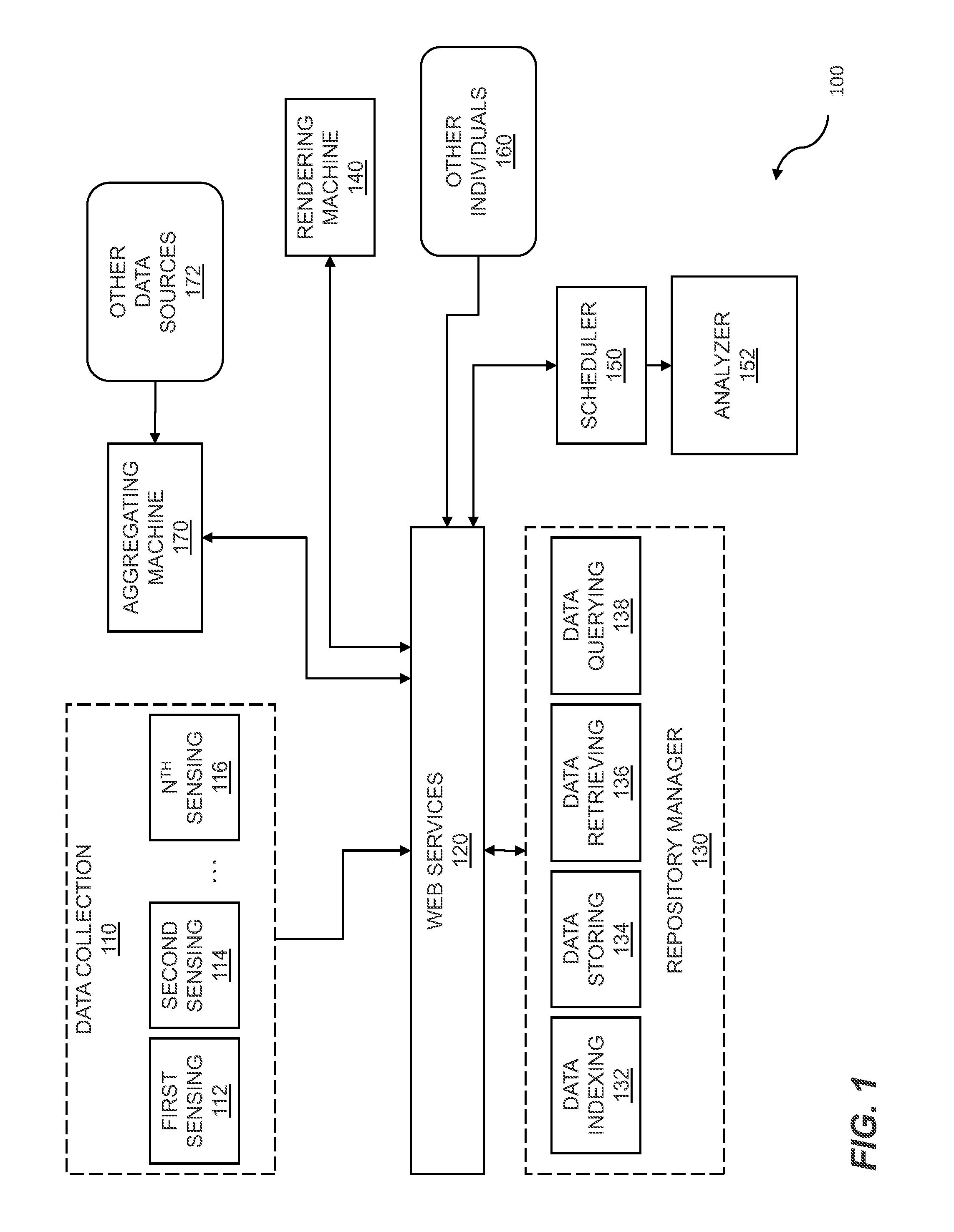
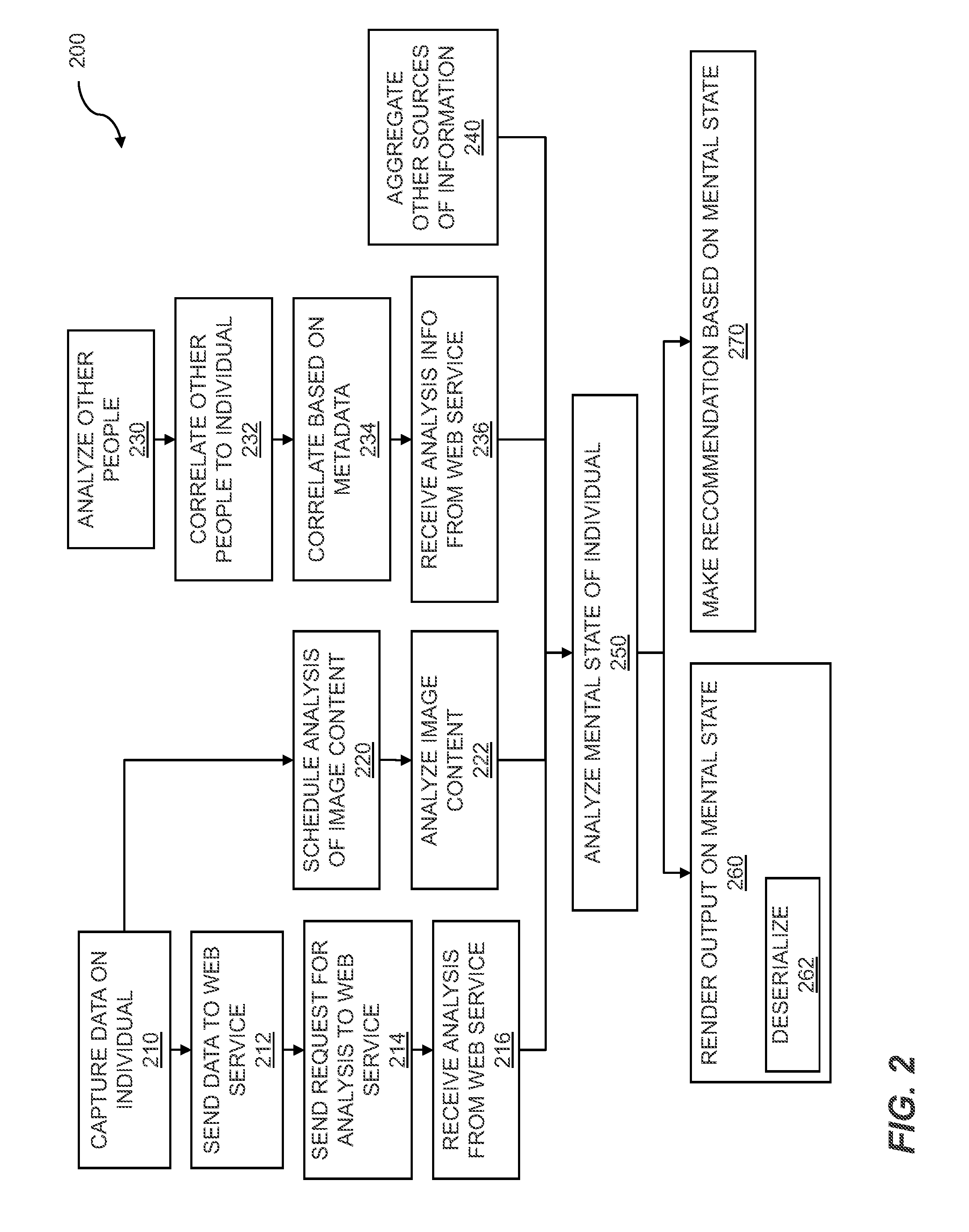
Mental state analysis using web services
Analysis of mental states is provided using web services to enable data analysis. Data is captured for an individual where the data includes facial information and physiological information. Analysis is performed on a web service and the analysis is received. The mental states of other people may be correlated to the mental state for the individual. Other sources of information may be aggregated where the information may be used to analyze the mental state of the individual. Analysis of the mental state of the individual or group of individuals is rendered for display.
Owner:AFFECTIVA
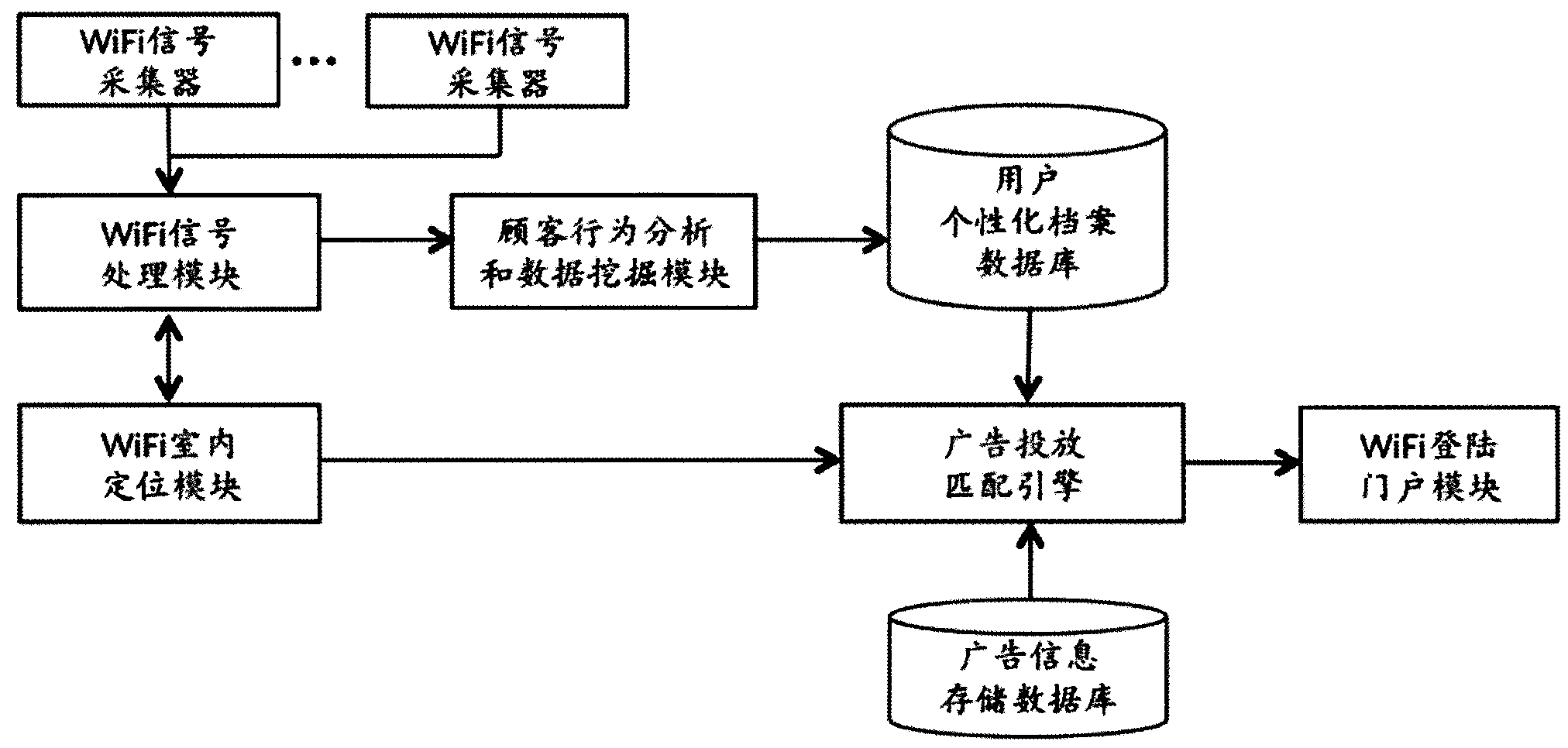
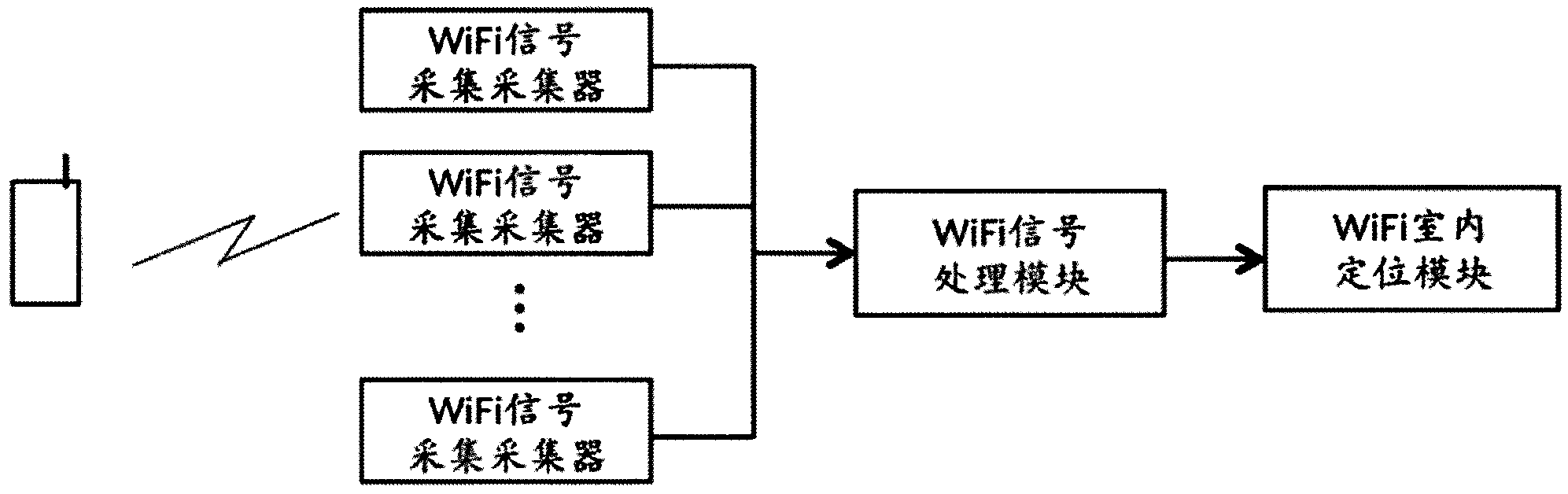
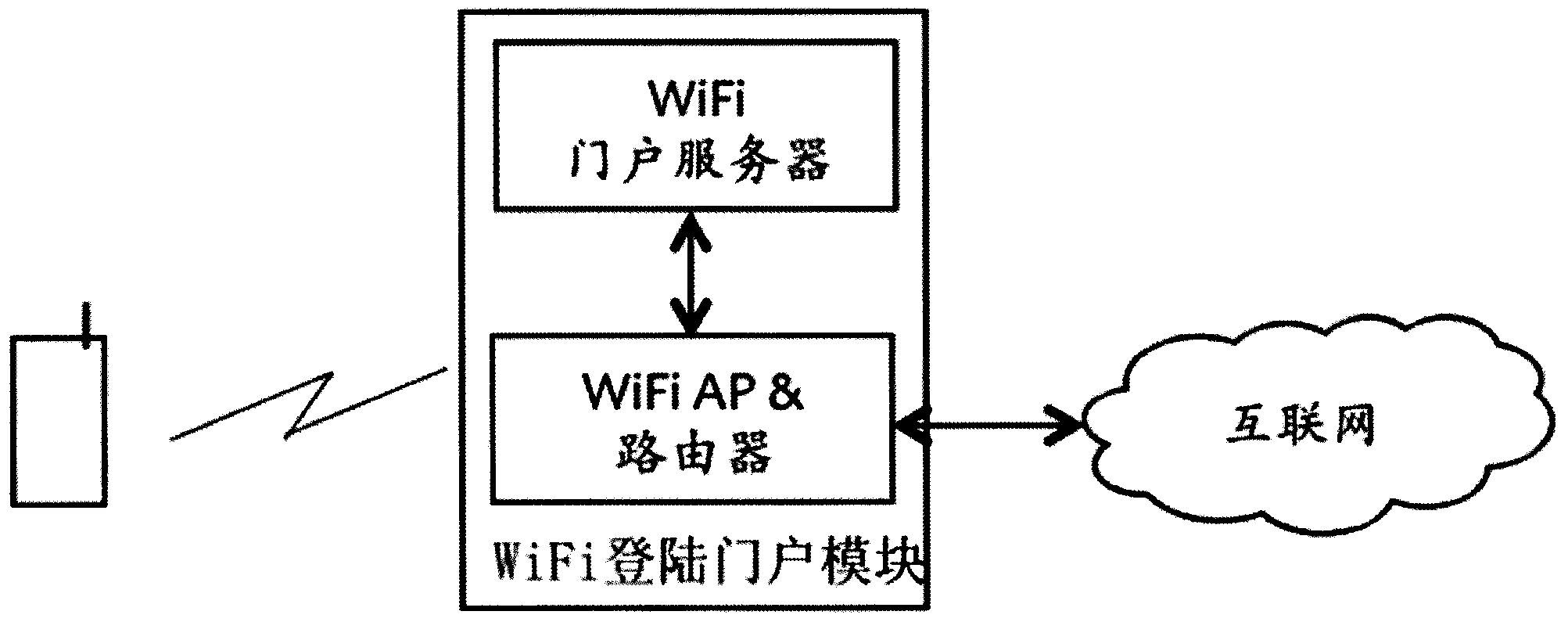
Information pushing system of WiFi (wireless fidelity) terminal and implementation method thereof
ActiveCN103402177AImprove experienceReal-time field precision marketingBroadcast service distributionMessaging/mailboxes/announcementsPersonalizationBehavioral analytics
The invention discloses an information pushing system of a WiFi (wireless fidelity) terminal and an implementation method thereof. The system comprises a WiFi signal collector, a WiFi signal processing module, a WiFi indoor positioning module, a customer activity analyzing and data mining module, a user personality file database, an advertisement information storage database, an advertisement putting and matching engine and a WiFi logging portal module. The system is suitable for all terminals with the WiFi function, such as mobile phones, PADs (personal access device) and PCs (personal computer), and different software platforms, such as Andriod, wP, iOS, Windows, MAC OS and Linux, the WiFi terminals do not need any software modification and updating, and the applicable range is wide. The possible hobby of a consumer is judged through data analysis and mining, and the real-time and on-site precise marketing is realized for target users, so on one hand, the experience of the user consuming in business places is improved, and on the other hand, the commercial value of sellers and factories is improved.
Owner:江苏数原信息技术有限公司
Application of Z-webs and Z-factors to analytics, search engine, learning, recognition, natural language, and other utilities
ActiveUS8873813B2Character and pattern recognitionFuzzy logic based systemsMedical diagnosisConfidence factor
Here, we introduce Z-webs, including Z-factors and Z-nodes, for the understanding of relationships between objects, subjects, abstract ideas, concepts, or the like, including face, car, images, people, emotions, mood, text, natural language, voice, music, video, locations, formulas, facts, historical data, landmarks, personalities, ownership, family, friends, love, happiness, social behavior, voting behavior, and the like, to be used for many applications in our life, including on the search engine, analytics, Big Data processing, natural language processing, economy forecasting, face recognition, dealing with reliability and certainty, medical diagnosis, pattern recognition, object recognition, biometrics, security analysis, risk analysis, fraud detection, satellite image analysis, machine generated data analysis, machine learning, training samples, extracting data or patterns (from the video, images, and the like), editing video or images, and the like. Z-factors include reliability factor, confidence factor, expertise factor, bias factor, and the like, which is associated with each Z-node in the Z-web.
Owner:Z ADVANCED COMPUTING
Distributed pattern recognition training method and system
ActiveUS20060015341A1Multiple digital computer combinationsSpeech recognitionPattern recognitionTraining methods
A distributed pattern recognition training method includes providing data communication between at least one central pattern analysis node and a plurality of peripheral data analysis sites. The method also includes communicating from the at least one central pattern analysis node to the plurality of peripheral data analysis a plurality of kernel-based pattern elements. The method further includes performing a plurality of iterations of pattern template training at each of the plurality of peripheral data analysis sites.
Owner:AURILAB
System and method for knowledge pattern search from networked agents
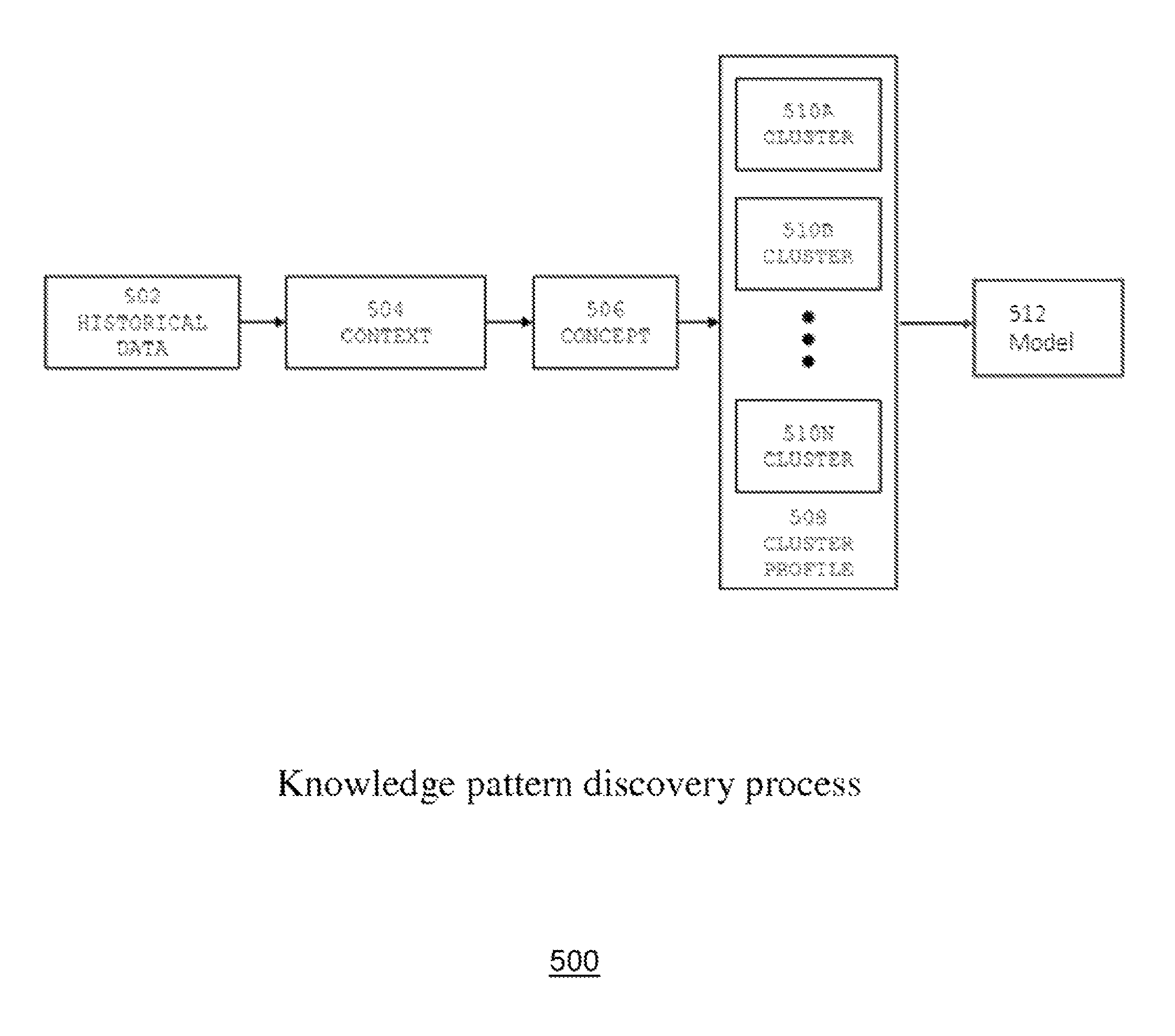
One or more systems and methods for knowledge pattern search from networked agents are disclosed in various embodiments of the invention. A system and a related method can utilizes a knowledge pattern discovery process, which involves analyzing historical data, contextualizing, conceptualizing, clustering, and modeling of data to pattern and discover information of interest. This process may involve constructing a pattern-identifying model using a computer system by applying a context-concept-cluster (CCC) data analysis method, and visualizing that information using a computer system interface. In one embodiment of the invention, once the pattern-identifying model is constructed, the real-time data can be gathered using multiple learning agent devices, and then analyzed by the pattern-identifying model to identify various patterns for gains analysis and derivation of an anomalousness score. This system can be useful for knowledge discovery applications in various industries, including business, competitive intelligence, and academic research.
Owner:ZHAO YING +1
Methods and apparatuses for medical imaging
InactiveUS20080051660A1Blood flow measurement devicesCharacter and pattern recognitionGratingUltrasound angiography
A set of intravascular ultrasound (IVUS) related systems, apparatuses and methods are disclosed. New catheter designs including contrast agent introduction subsystems and / or Doppler subsystems are disclosed. Methods for acquiring and analyzing Doppler data from intravascular ultrasound (IVUS) catheters are disclosed. RF-based detection of blood and / or contrast agents such as micro-bubbles are disclosed. Methods for frame-grating image data analysis permitting frame registration before, during and after a contrasting effect is imposed on a system being imaged are disclosed. Methods for difference imaging for contrast detection are disclosed. Methods for quantification and visualization of IVUS data are disclosed. And methods for IVUS imaging are disclosed.
Owner:UNIV HOUSTON SYST
System used for constructing user figure
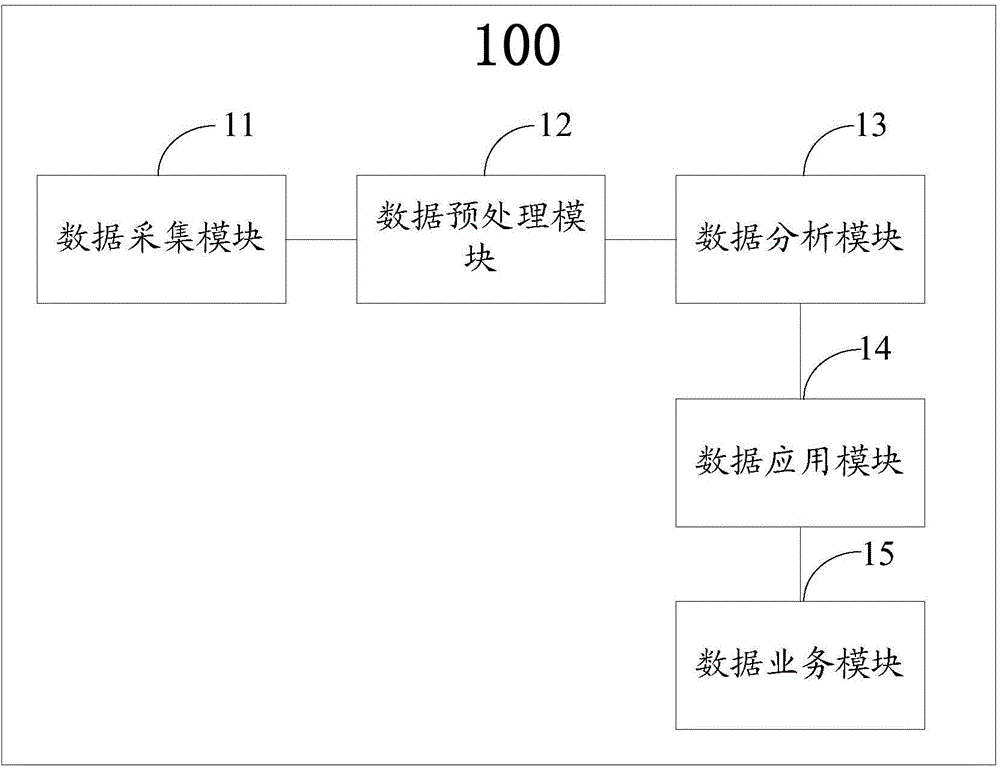
InactiveCN106504099AEasy to analyzeAccurate analysisData processing applicationsSpecial data processing applicationsFeature extractionData acquisition
The invention discloses a system used for constructing a user figure. The system comprises a data acquisition module used for acquiring the Internet surfing log data of a user, a data pre-processing module used for pre-processing the Internet surfing log data of the user, a data analysis module used for carrying out characteristic extraction for the Internet surfing log data after pre-processing to acquire attribute characteristics of the user, a data application module used for matching in a multi-dimensional database on the basis of label classification trained by an established multi-dimensional characteristic database according to the attribute characteristics of the user to acquire multi-dimensional attribute labels of the user, and a data business module used for constructing the user figure according to the multi-dimensional attribute labels. The system is advantaged in that the holographic multi-dimensional user figure can be constructed, and rapid precise advertisement delivery of service providers / enterprises / companies and consumption behavior recommendation of use groups can be satisfied.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com