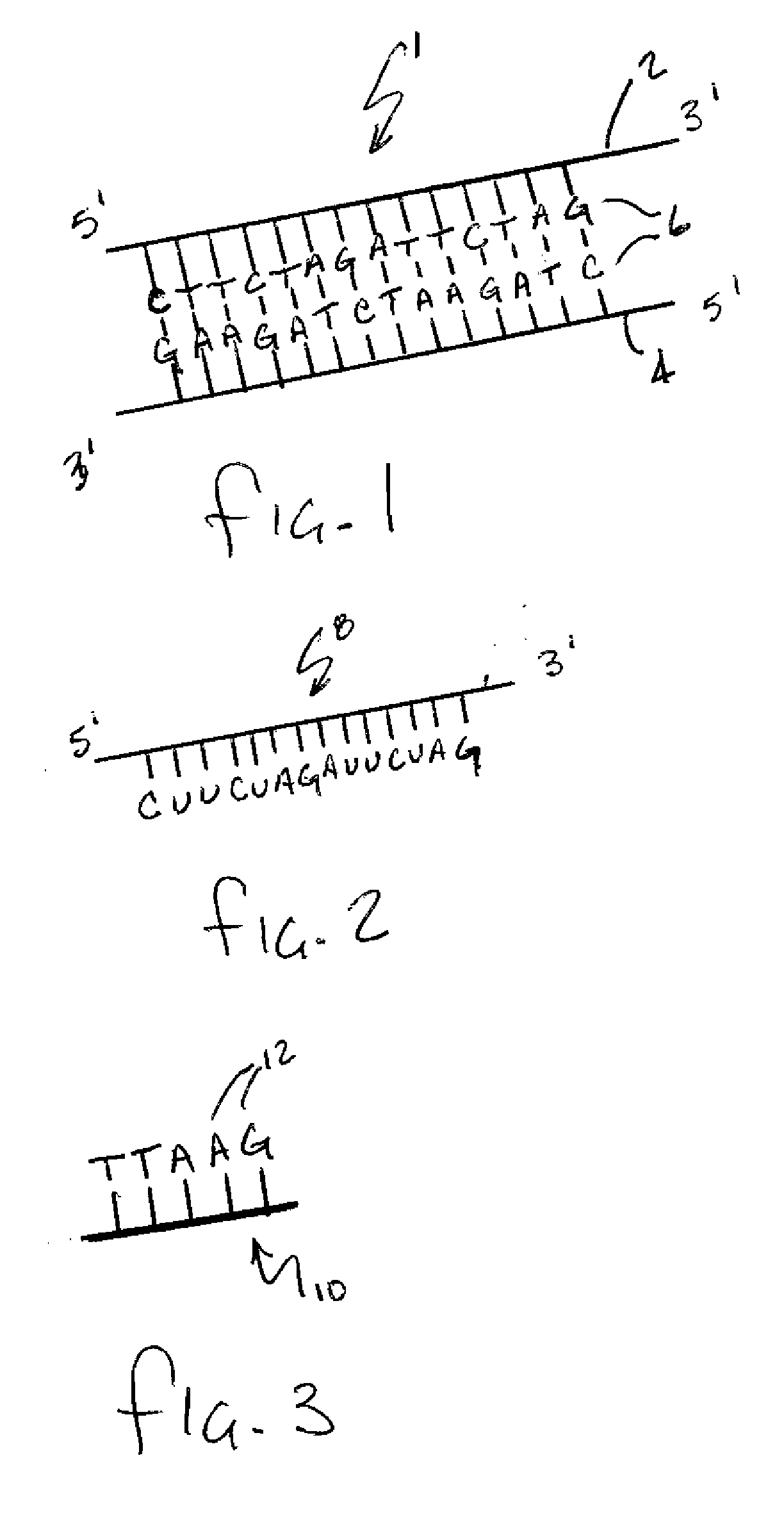Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
12254results about How to "Easy to analyze" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
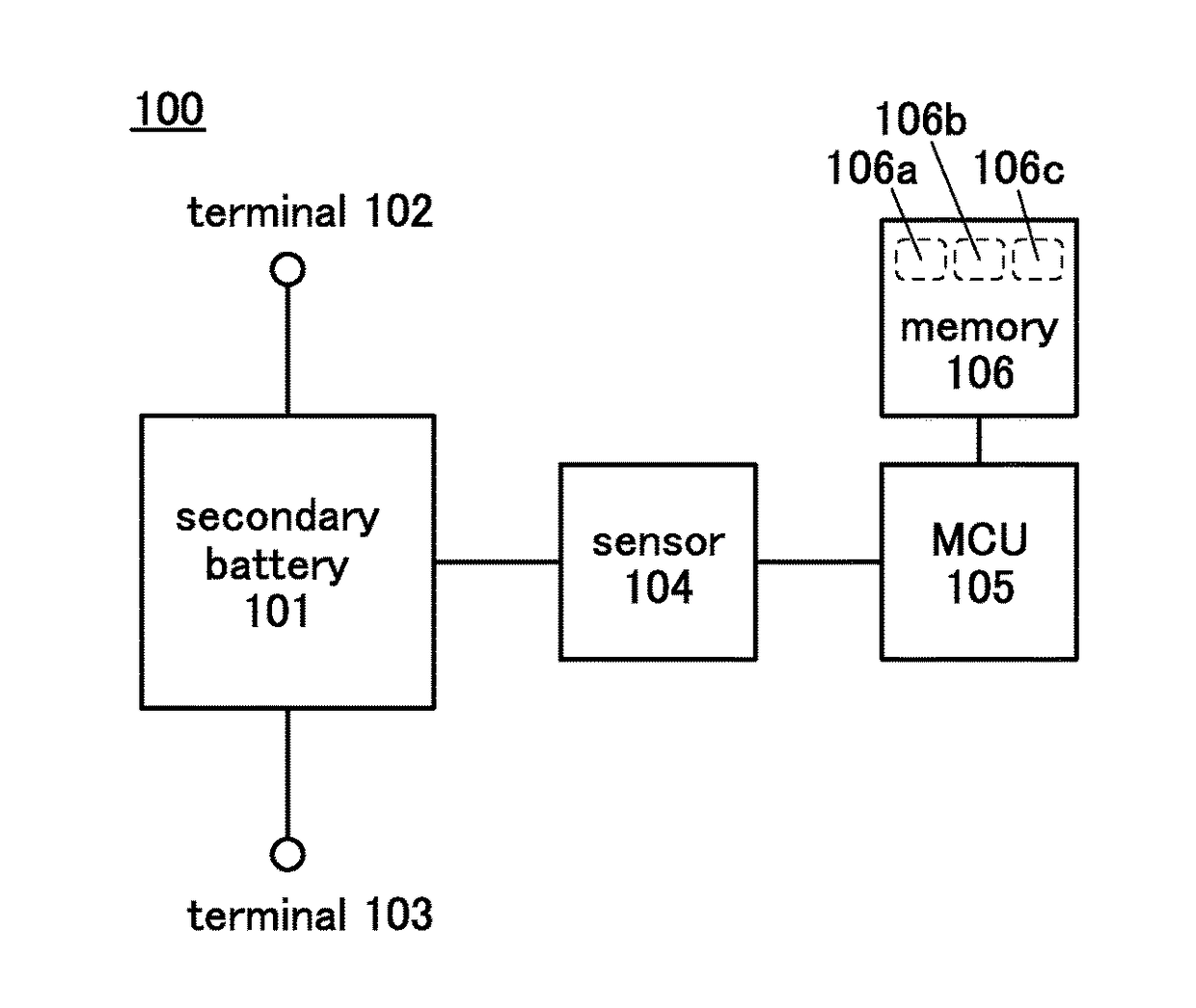
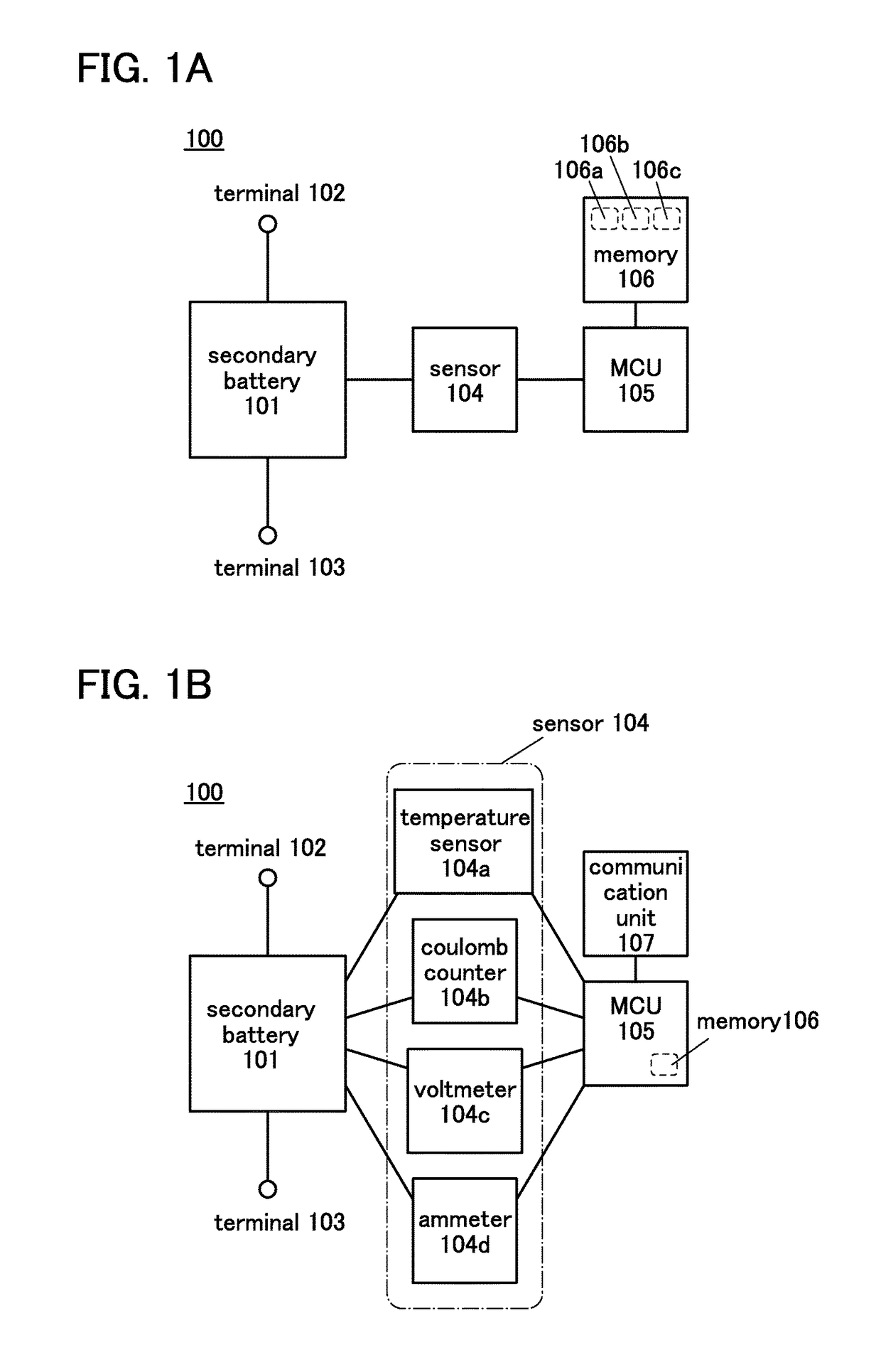
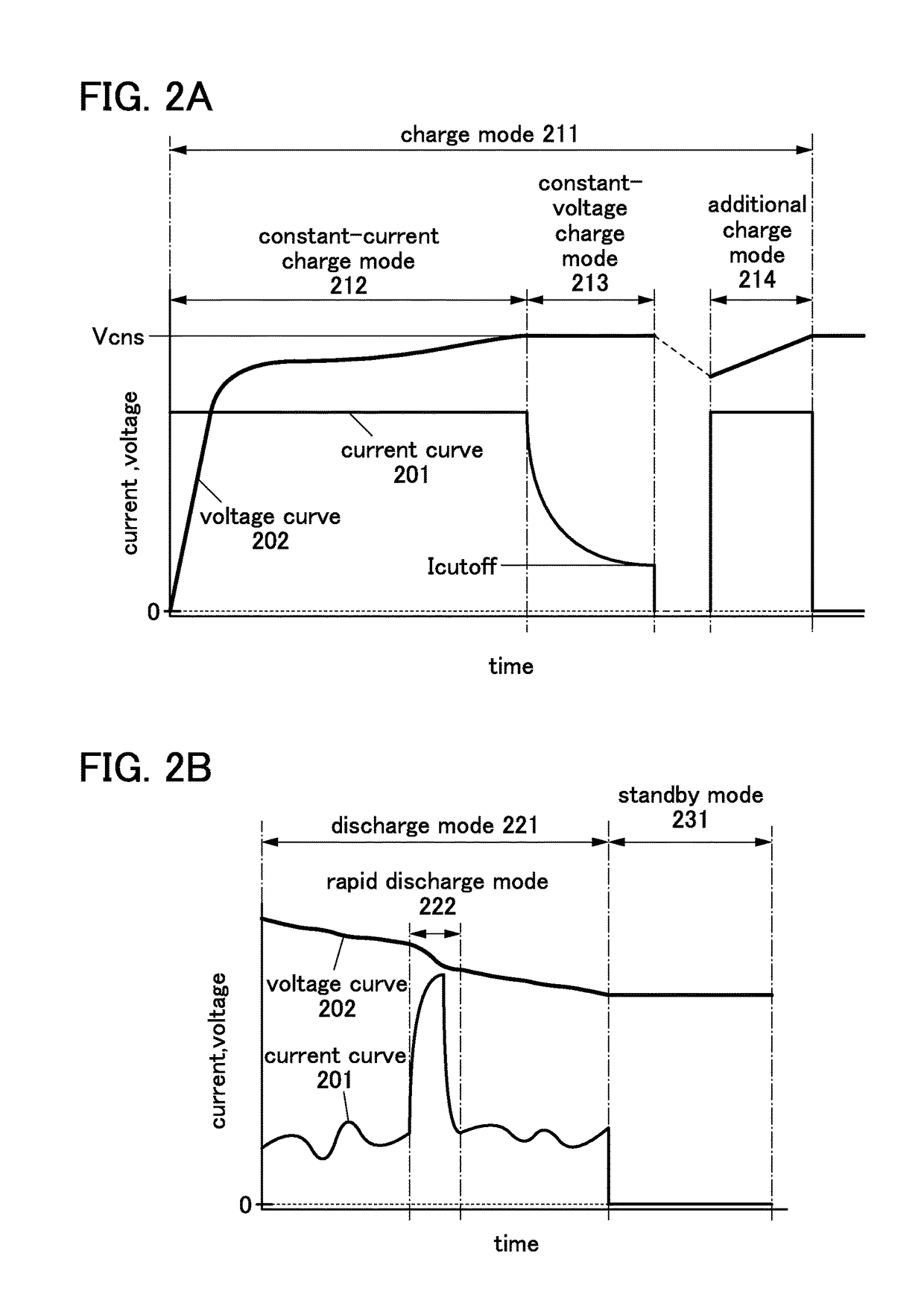
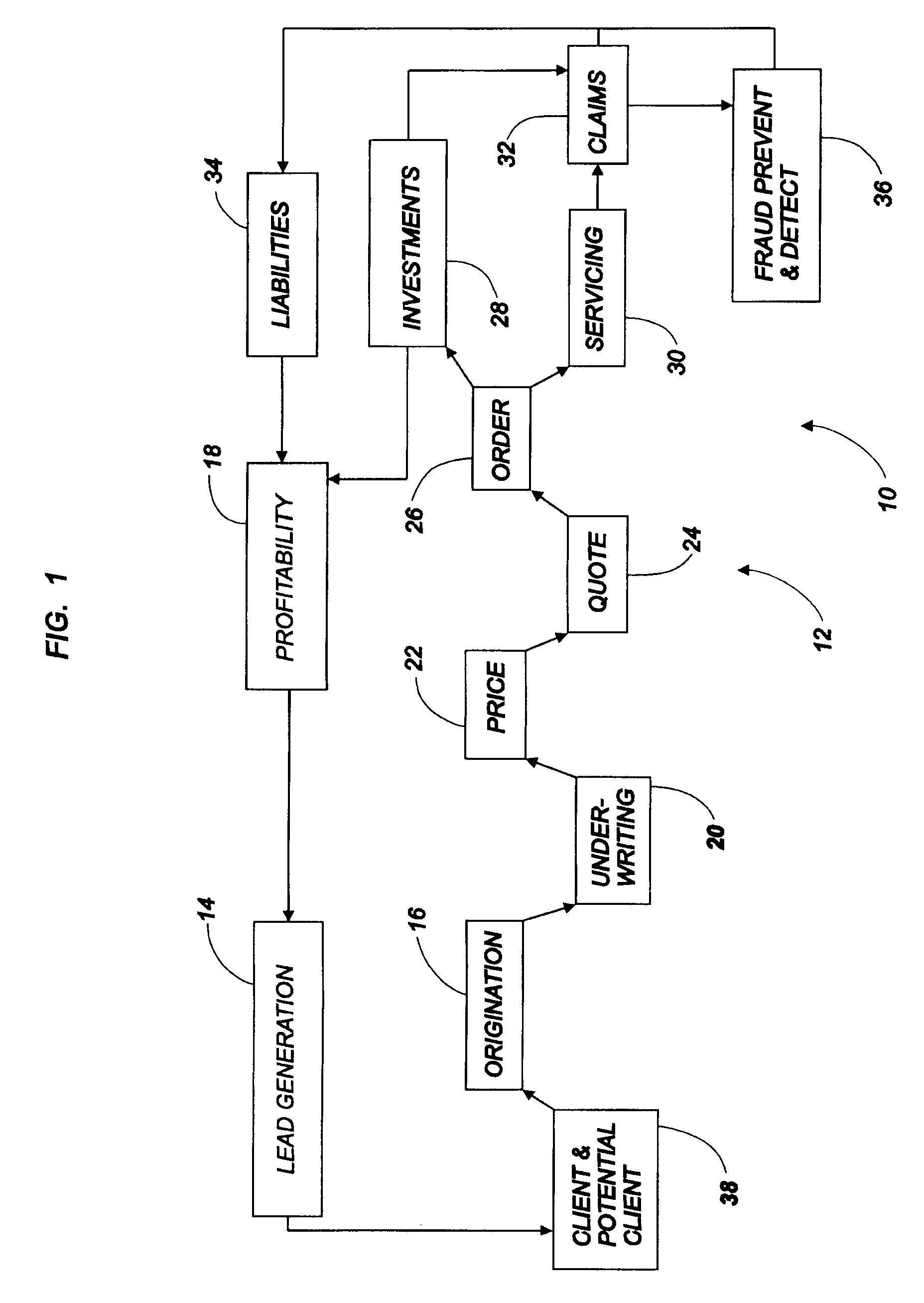
Power storage device and power storage system
ActiveUS9614258B2Easy to analyzeData retention time is longBatteries circuit arrangementsElectrical testingMicrocontrollerElectrical battery
To provide a power storage device, an operation condition of which is easily analyzed. A secondary battery includes a sensor that is a measurement unit, a microcontroller unit that is a determination unit, and a memory that is a memory unit. With the sensor, conditions of the secondary battery such as the remaining battery power, the voltage, the current, and the temperature are measured. The microcontroller unit performs arithmetic processing of the measurement results and determines the operation condition of the secondary battery. Further, the microcontroller unit stores the measurement result in the memory in accordance with the operation condition of the secondary battery.
Owner:SEMICON ENERGY LAB CO LTD
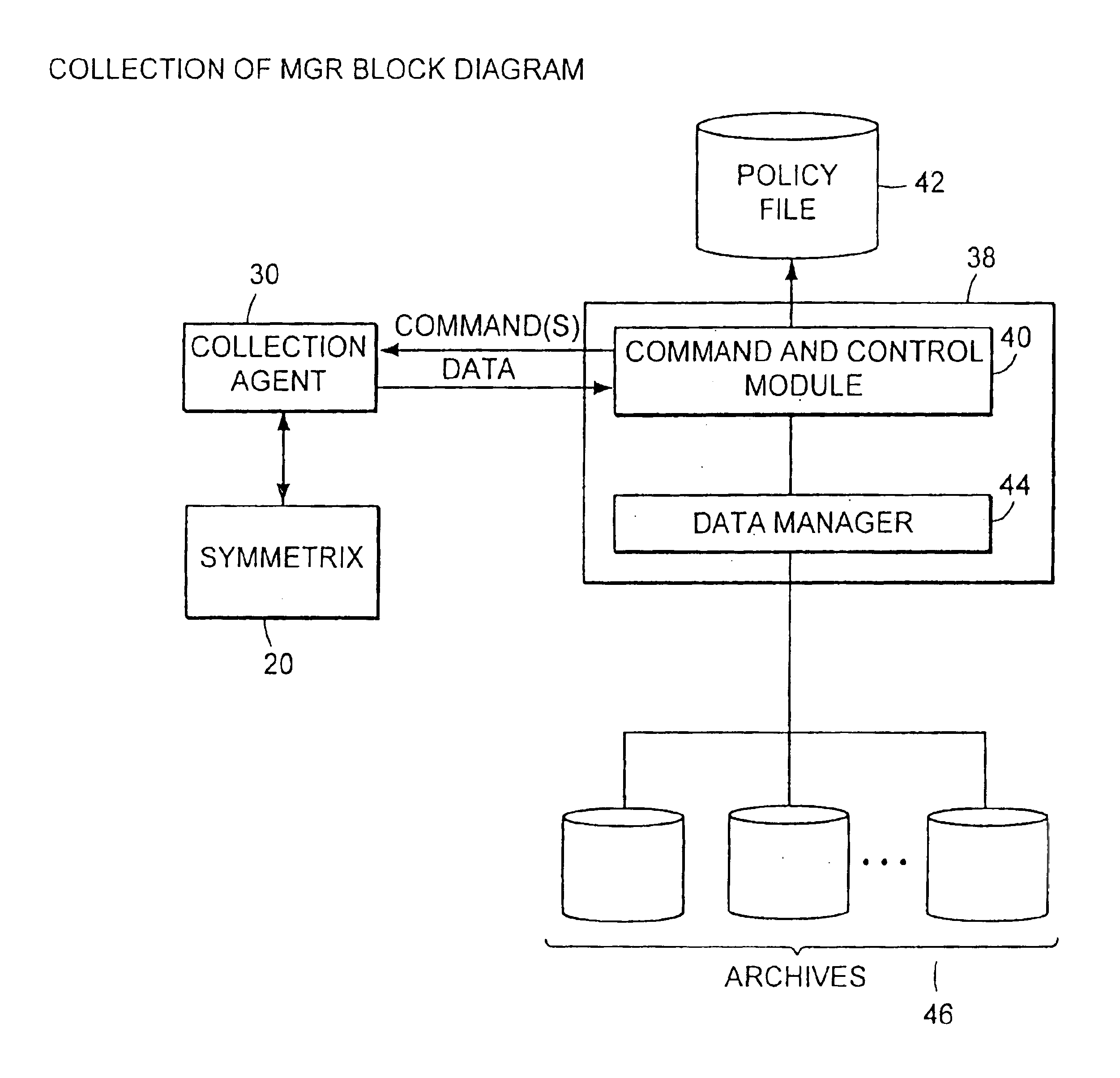
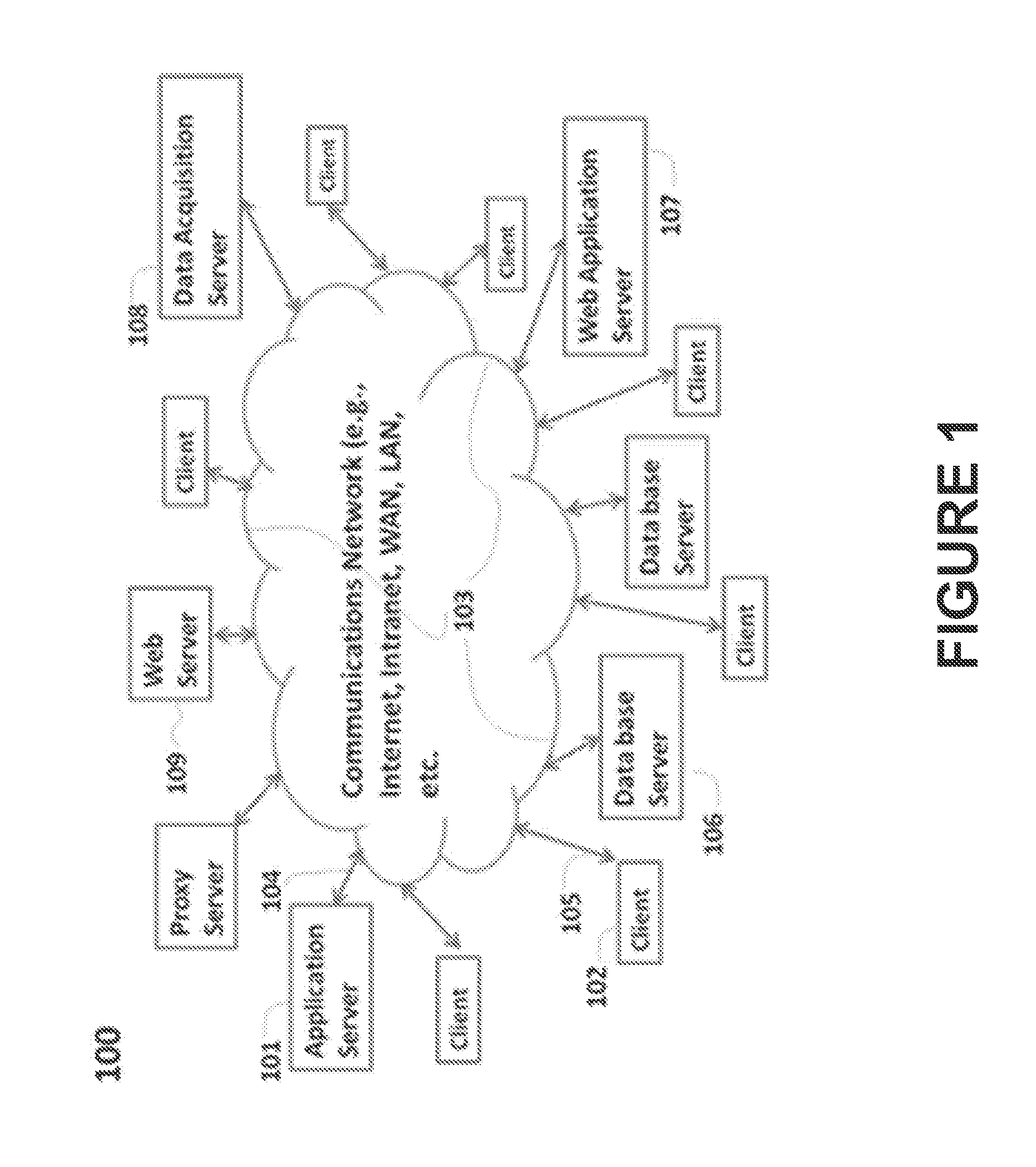
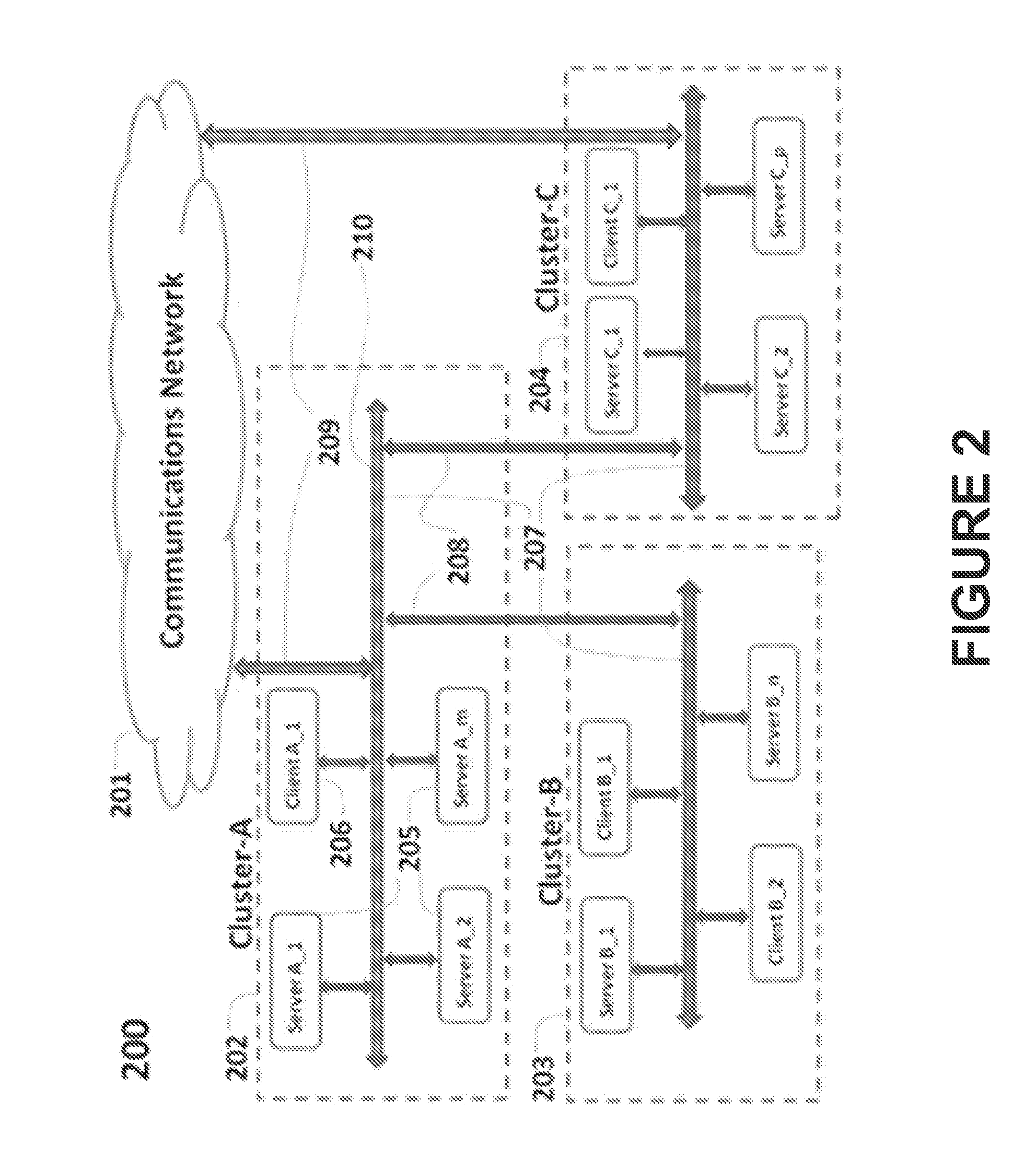
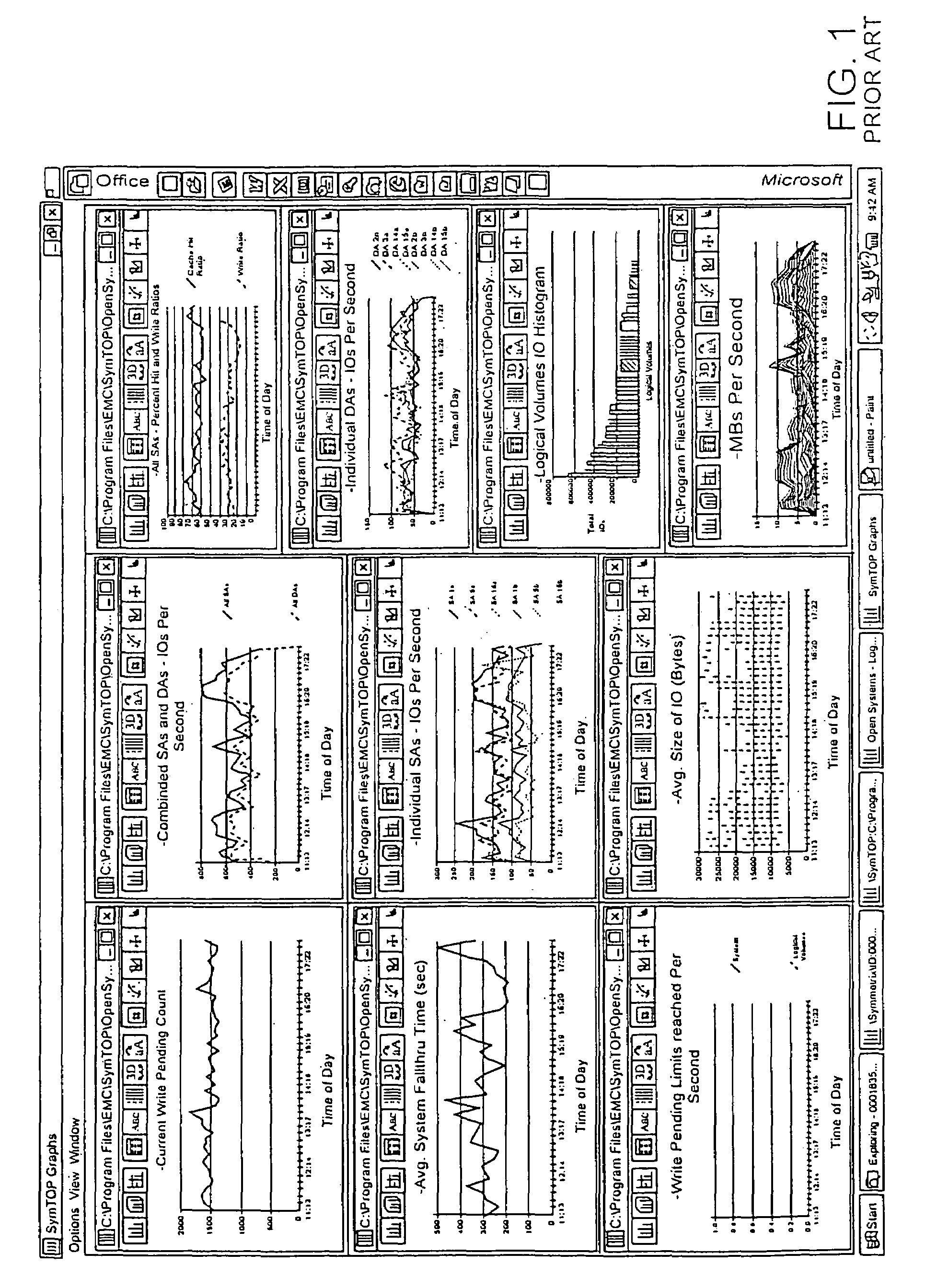
Method and apparatus for storage system metrics management and archive
InactiveUS6886020B1Promote generationEasy accessData processing applicationsDigital data information retrievalCommand and controlData management
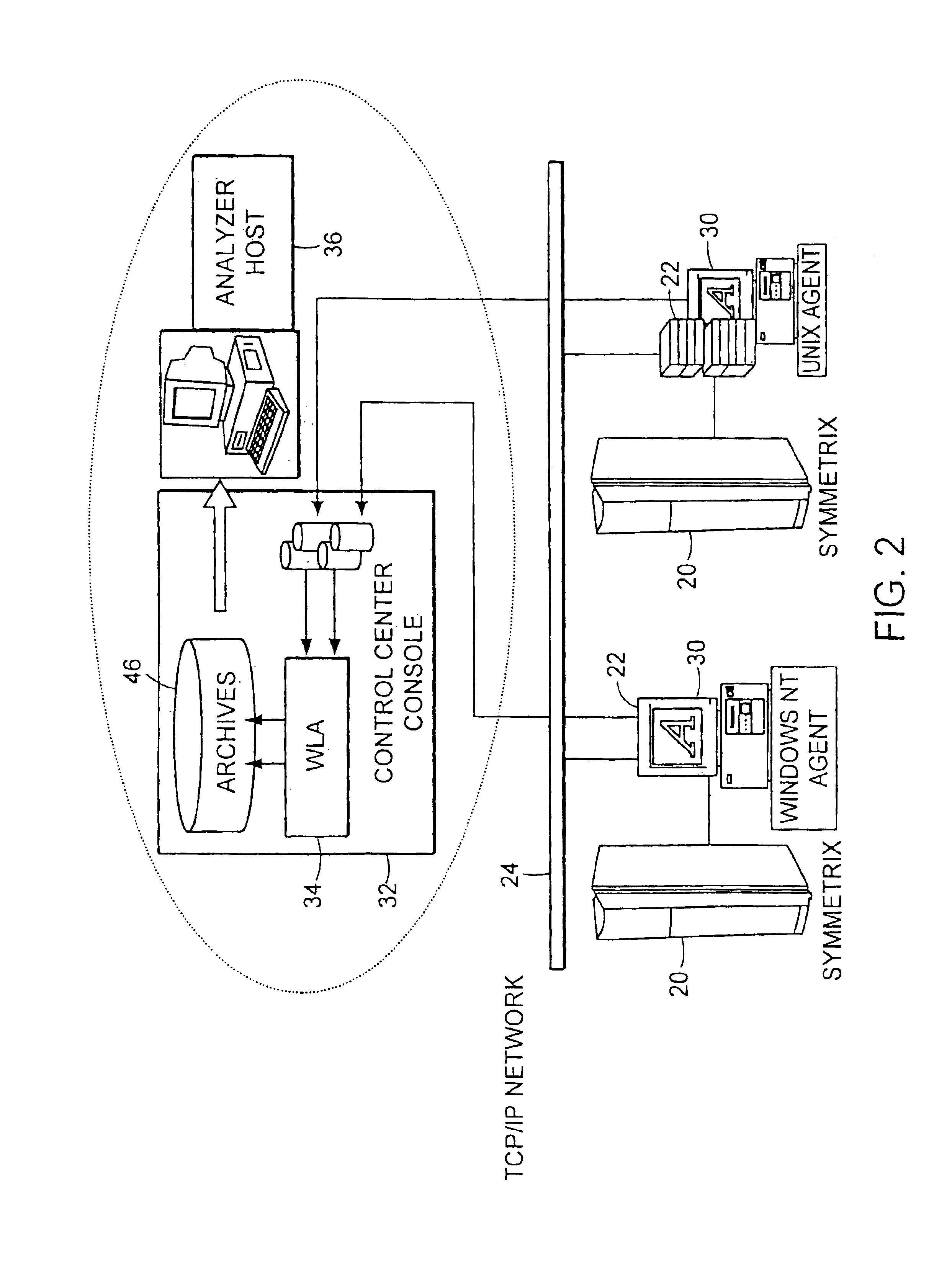
A data management and archive method and apparatus, such as for implementation in an automated system to monitor and manage status, performance and configuration data for a plurality of networked storage components. Analysis and cross-correlation of data related to the plurality of storage components can be done individually, collectively and / or comparatively. A collection manager component of a workload analyzer is implemented to start and stop data collection in the context of a system comprising at least one storage component (or at least two networked storage components). The collection manager includes a command and control module that coordinates requests of data from at least one collection agent configured on at least one host connected to the storage component(s).
Owner:EMC IP HLDG CO LLC
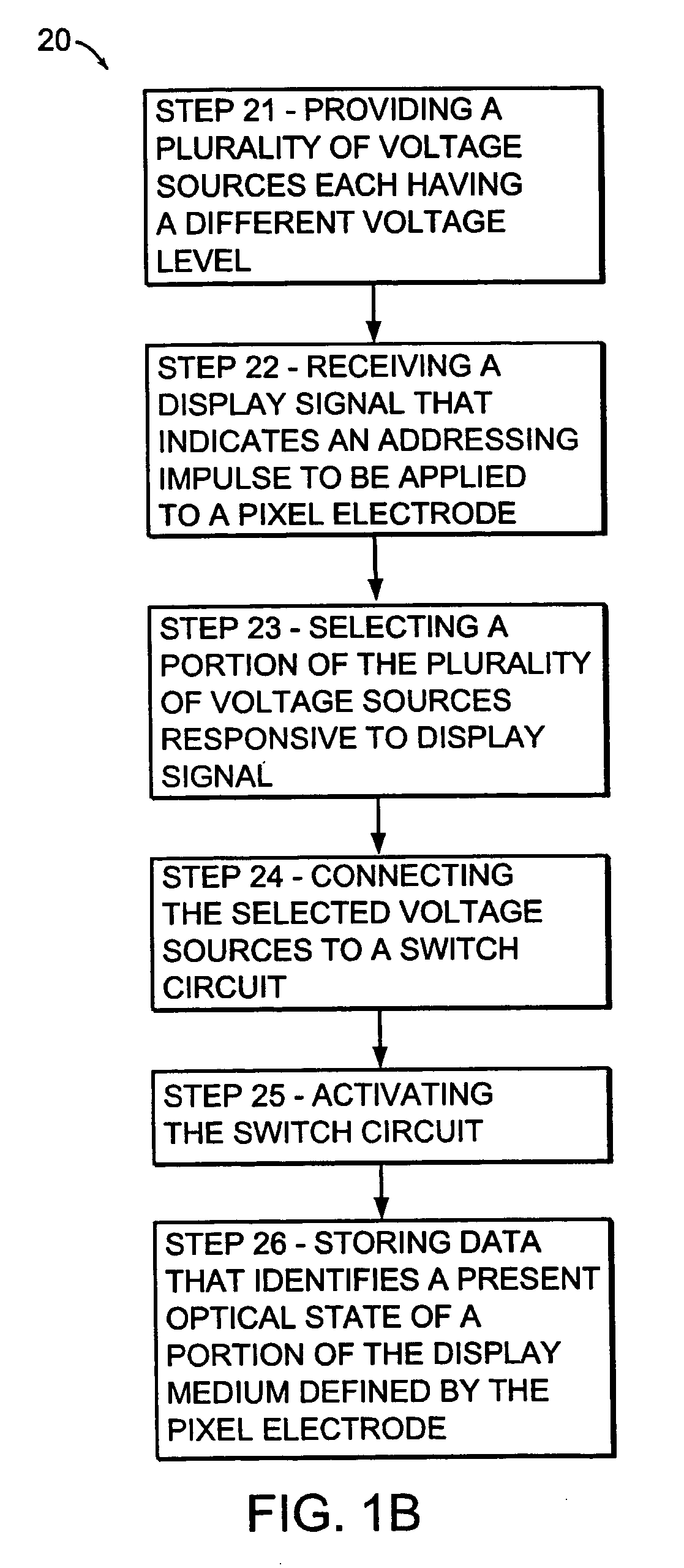
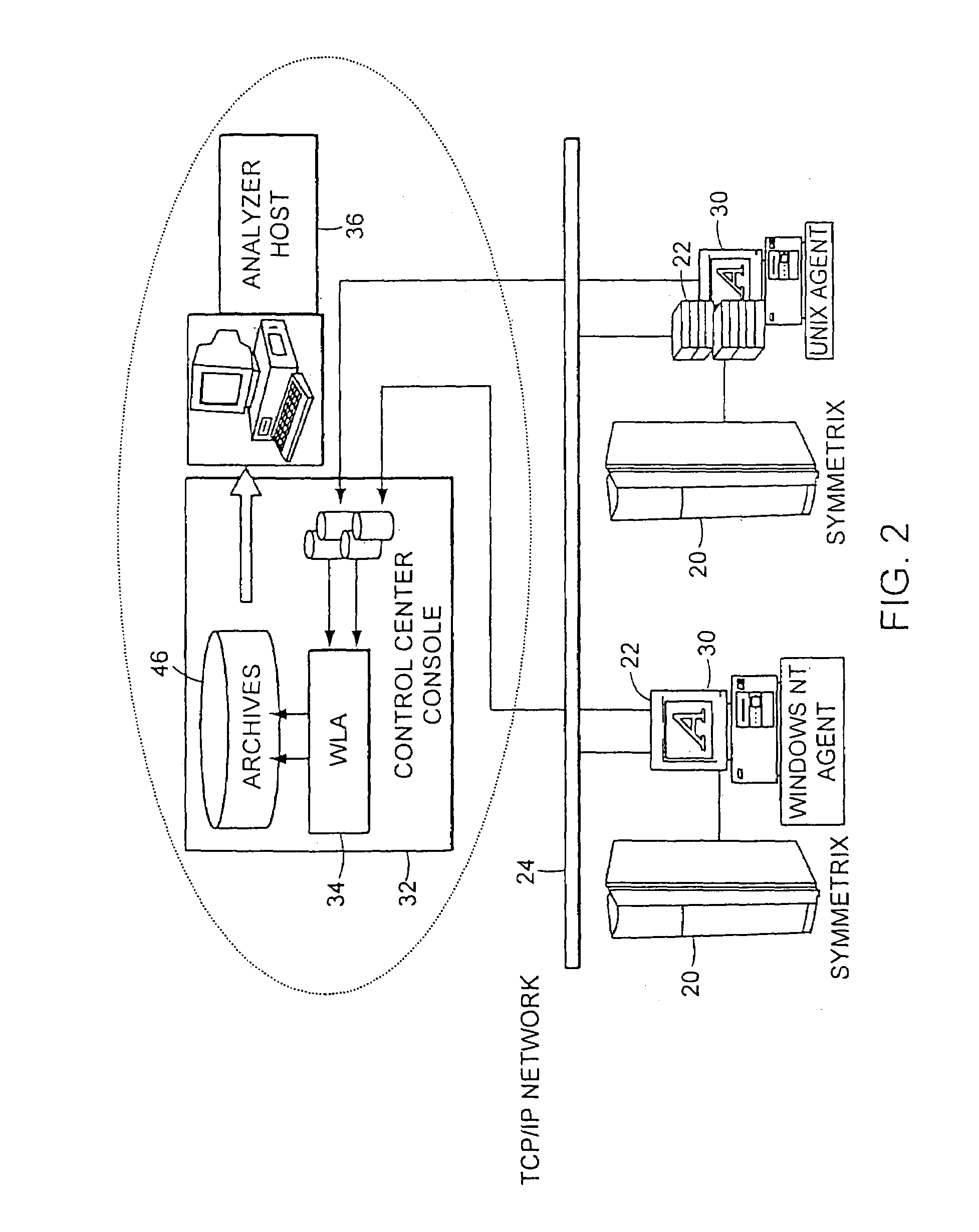
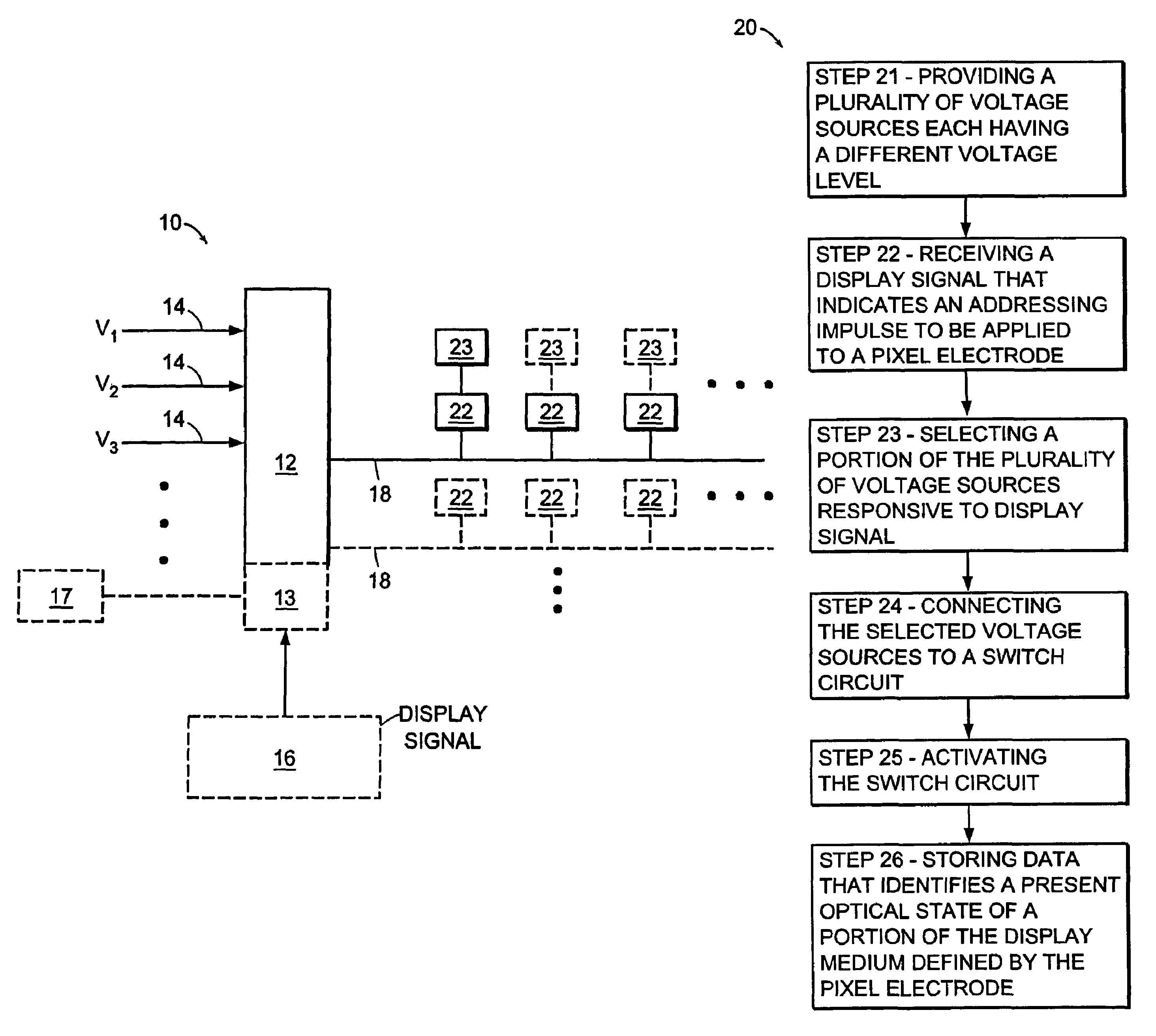
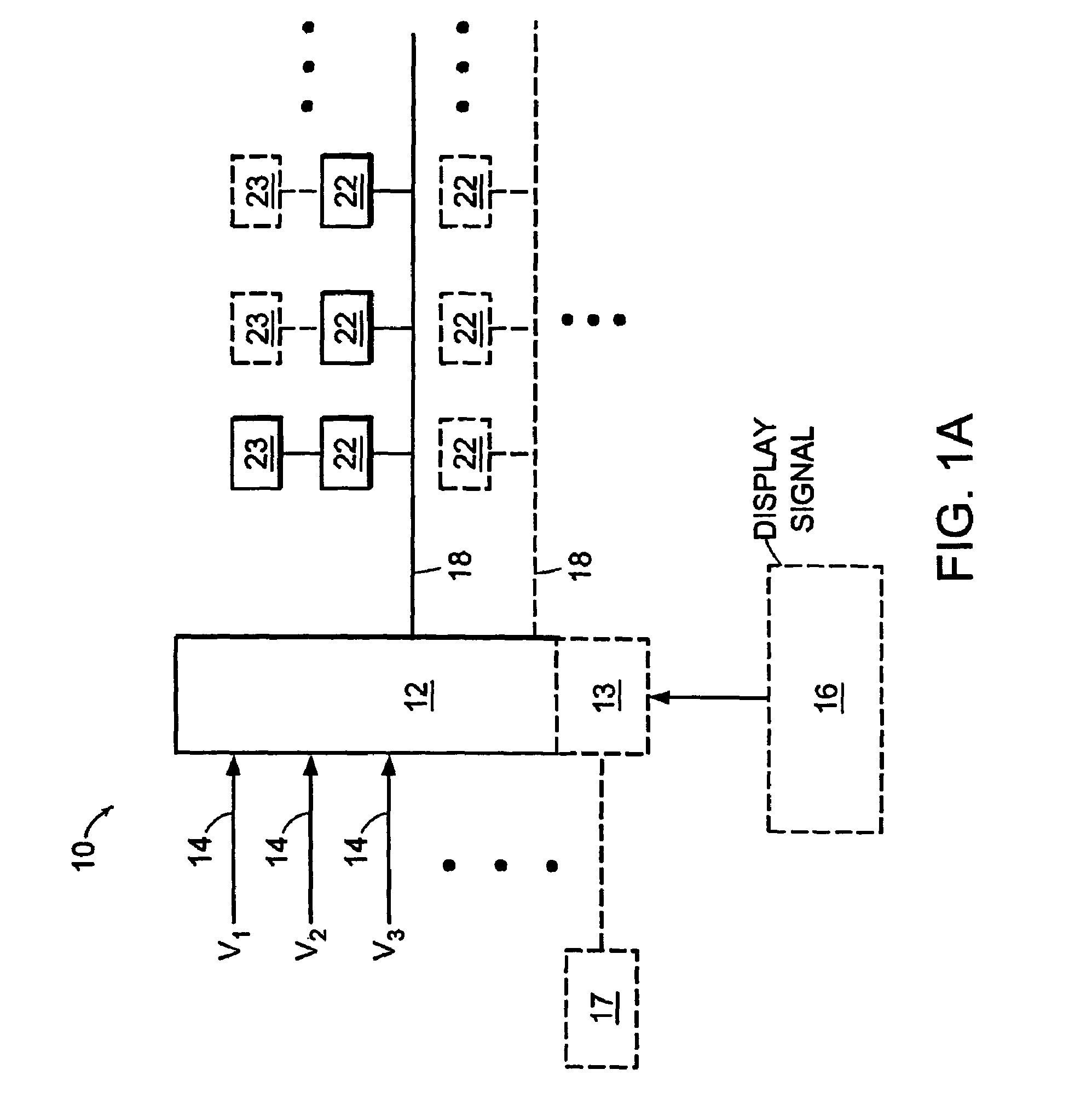
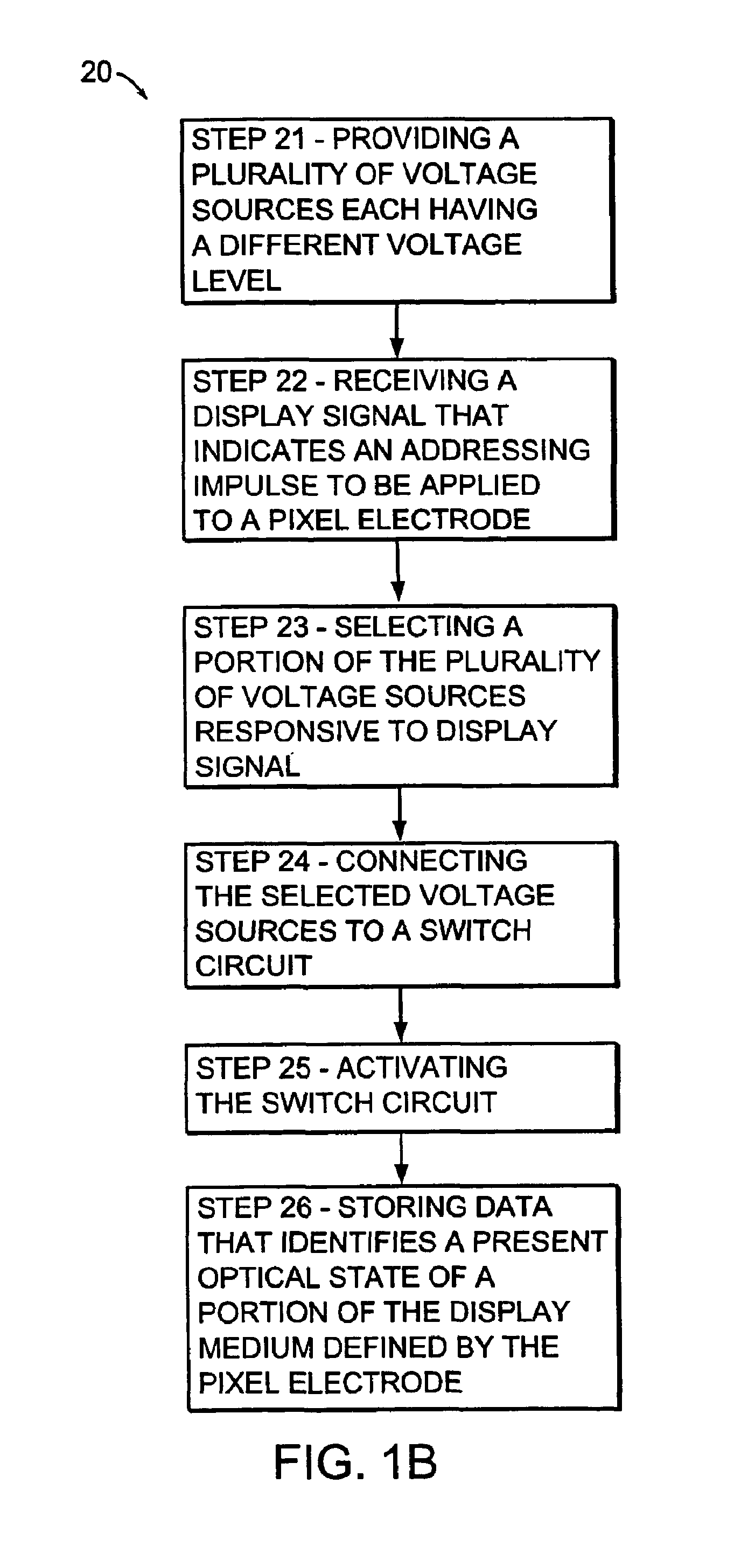
Voltage modulated driver circuits for electro-optic displays
ActiveUS7202847B2Low implementation costFaster design timeCathode-ray tube indicatorsNon-linear opticsDriver circuitElectricity
A method and system for applying addressing voltages to pixels of a display involves receiving input data. The input data includes an indication of an addressing voltage impulse to be applied to a pixel via an electrode. One or more voltage sources are selected, to provide the addressing voltage impulse. The one or more voltage sources each have a pre-selected voltage. The selected one or more voltage sources are electrically connected to an electrode to apply the addressing voltage impulse to the pixel.
Owner:E INK CORPORATION
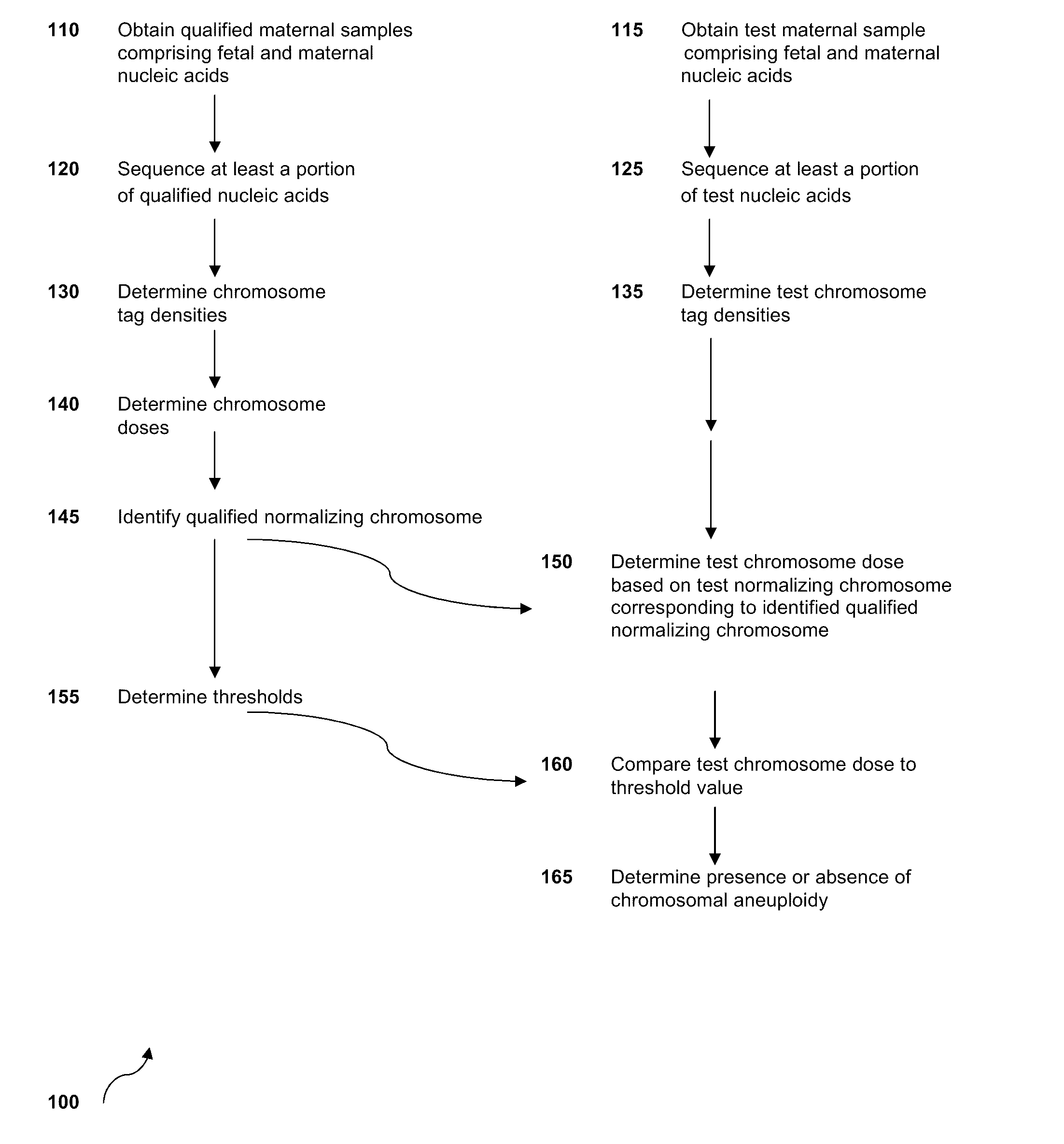
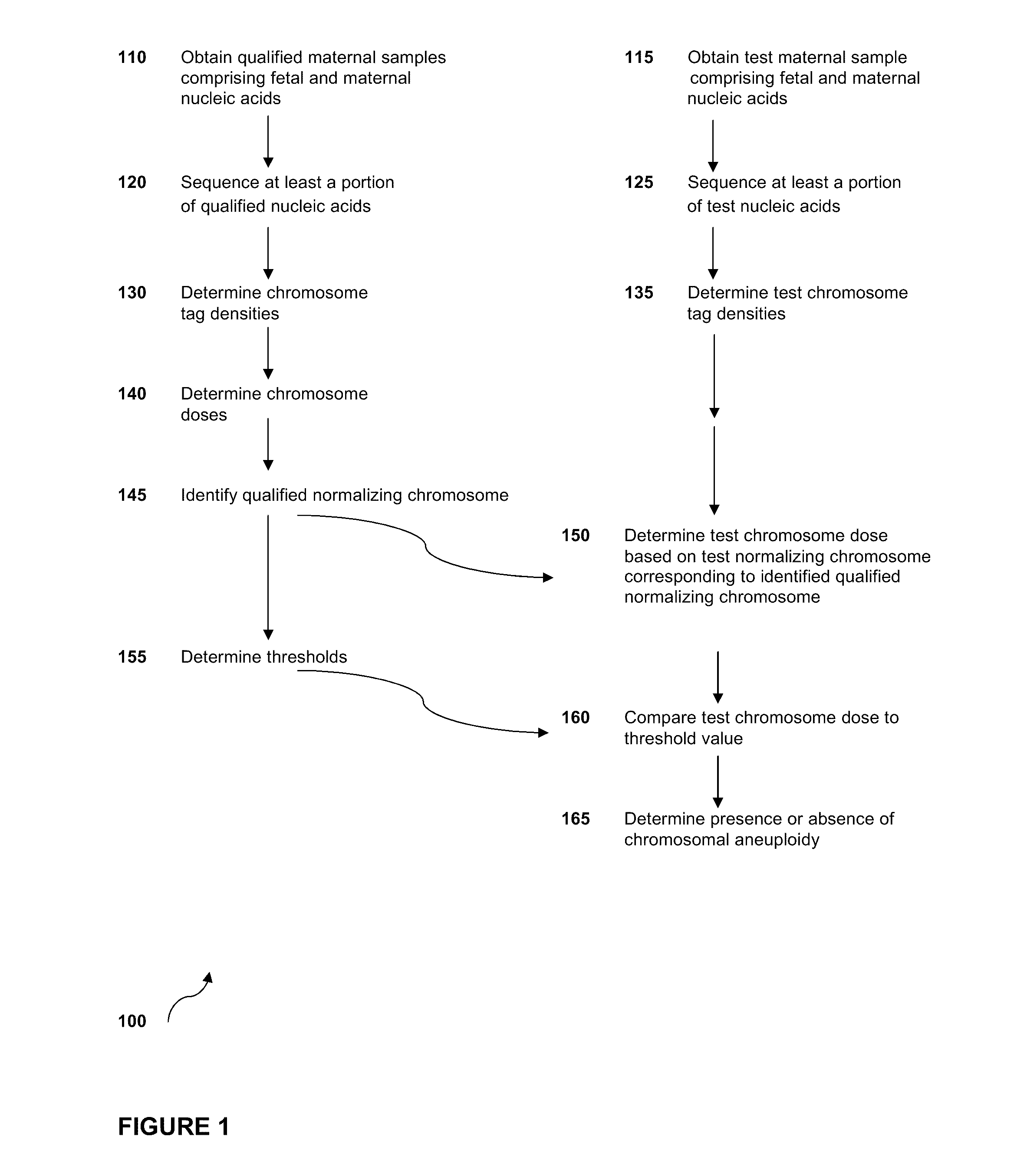
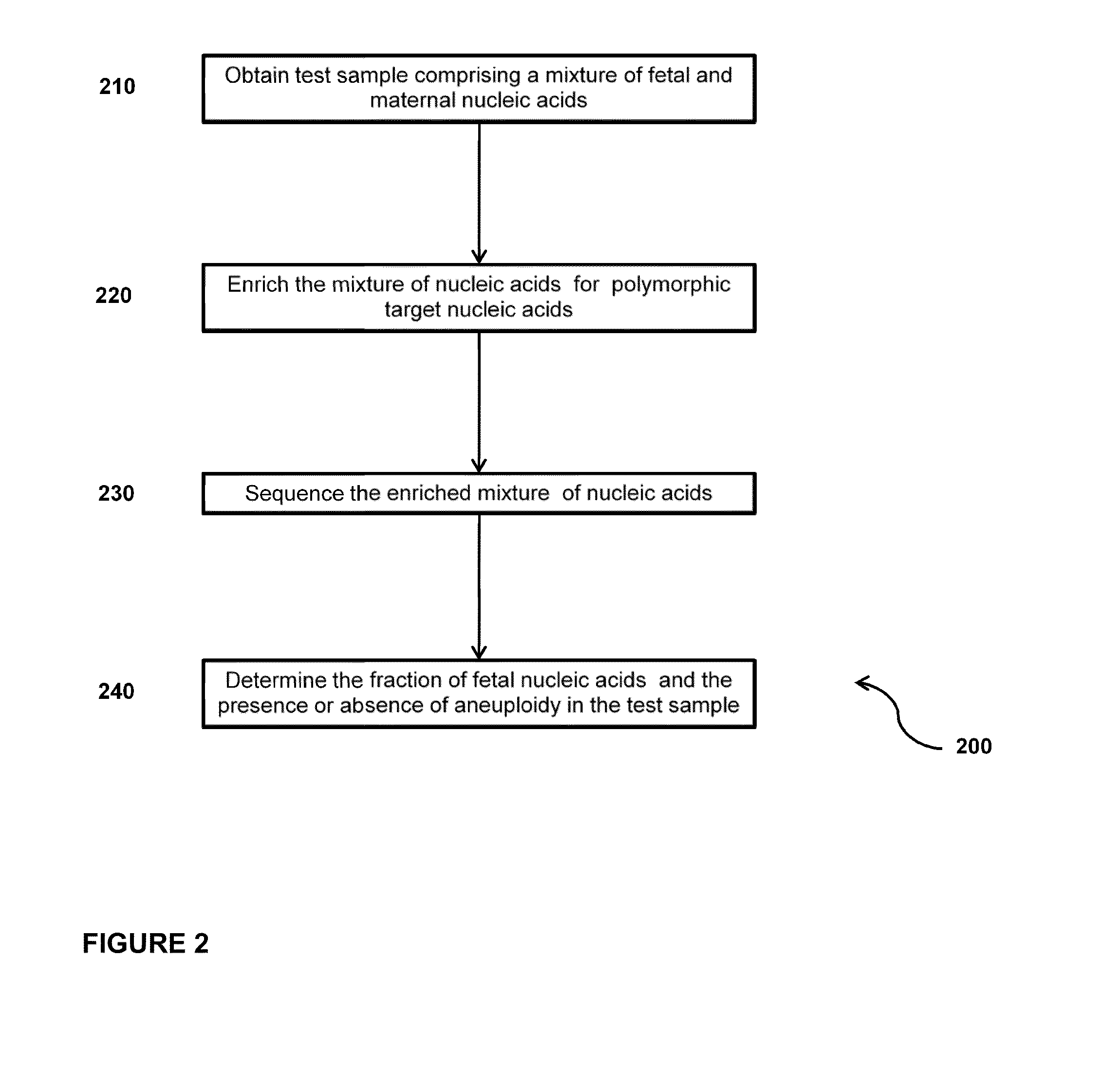
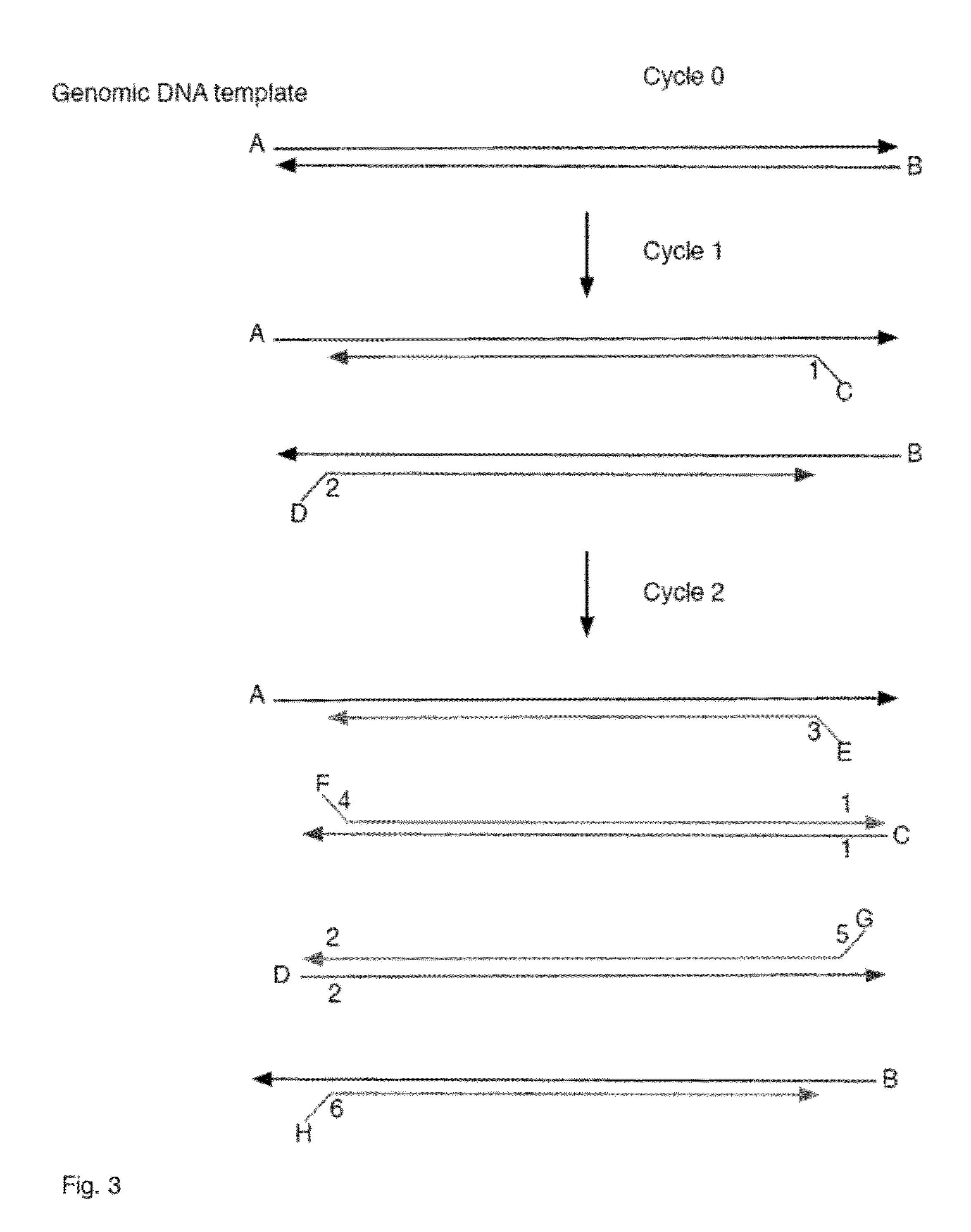
Sequencing methods and compositions for prenatal diagnoses
ActiveUS20110201507A1Quality improvementEasy to analyzeMicrobiological testing/measurementLibrary screeningPrenatal diagnosisGenetics
The invention provides methods for determining aneuploidy and / or fetal fraction in maternal samples comprising fetal and maternal cfDNA by massively parallel sequencing. The method comprises a novel protocol for preparing sequencing libraries that unexpectedly improves the quality of library DNA while expediting the process of analysis of samples for prenatal diagnoses.
Owner:VERINATA HEALTH INC
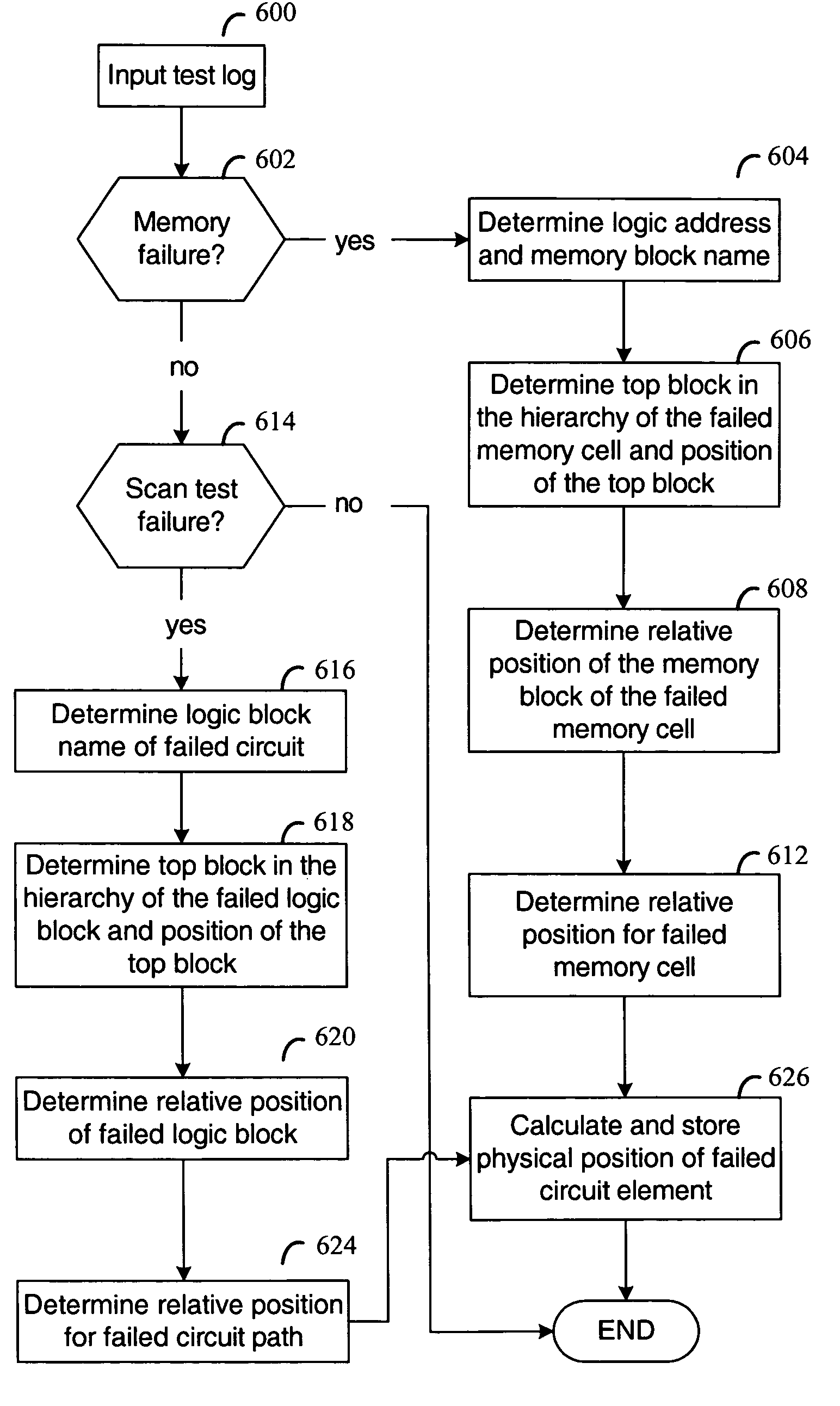
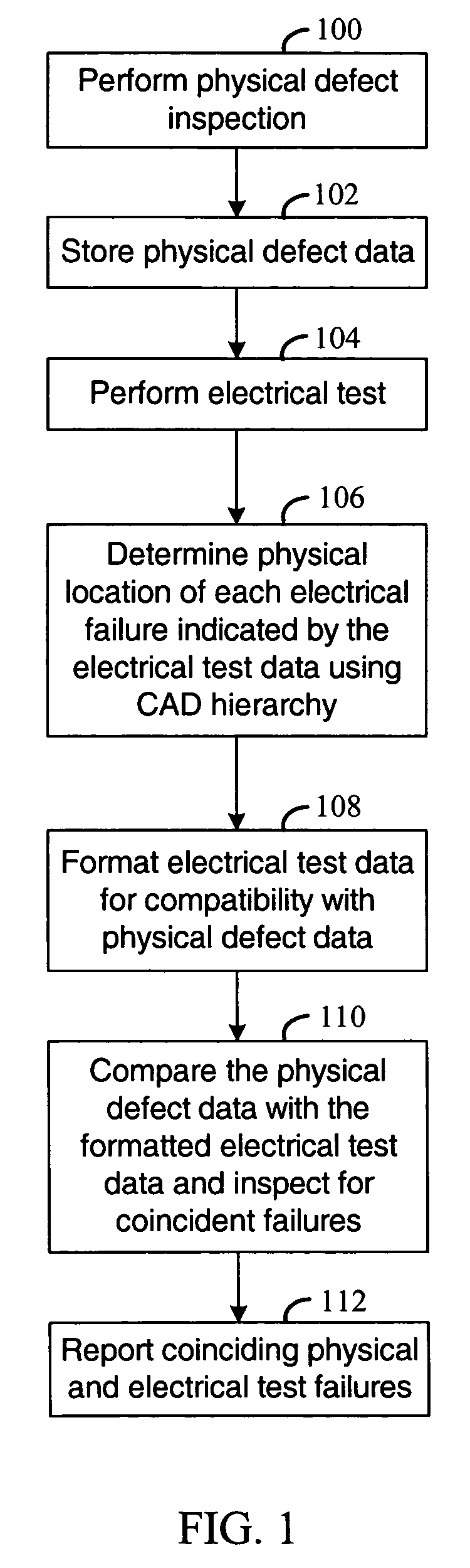
Correlation of electrical test data with physical defect data
ActiveUS6950771B1Improve yield analysisEasy to analyzeResistance/reactance/impedenceElectronic circuit testingData setDesign testing
Method and apparatus are disclosed for analyzing defect data produced in testing a semiconductor chip from a logic design. In various embodiments, input for processing is a first inspection data set that identifies a first set of physical locations that are associated with defects detected during fabrication of the chip. Also input is a second test data set that includes one or more identifiers associated with failing circuitry in the chip. A second set of physical locations is determined from the one or more identifiers of failing circuitry, hierarchical relationships between blocks of the design, and placement information associated with the blocks. Each of the one or more identifiers is associated with at least one of the blocks. Correspondences are identified between physical locations in the first inspection data set and the second set of physical locations.
Owner:XILINX INC
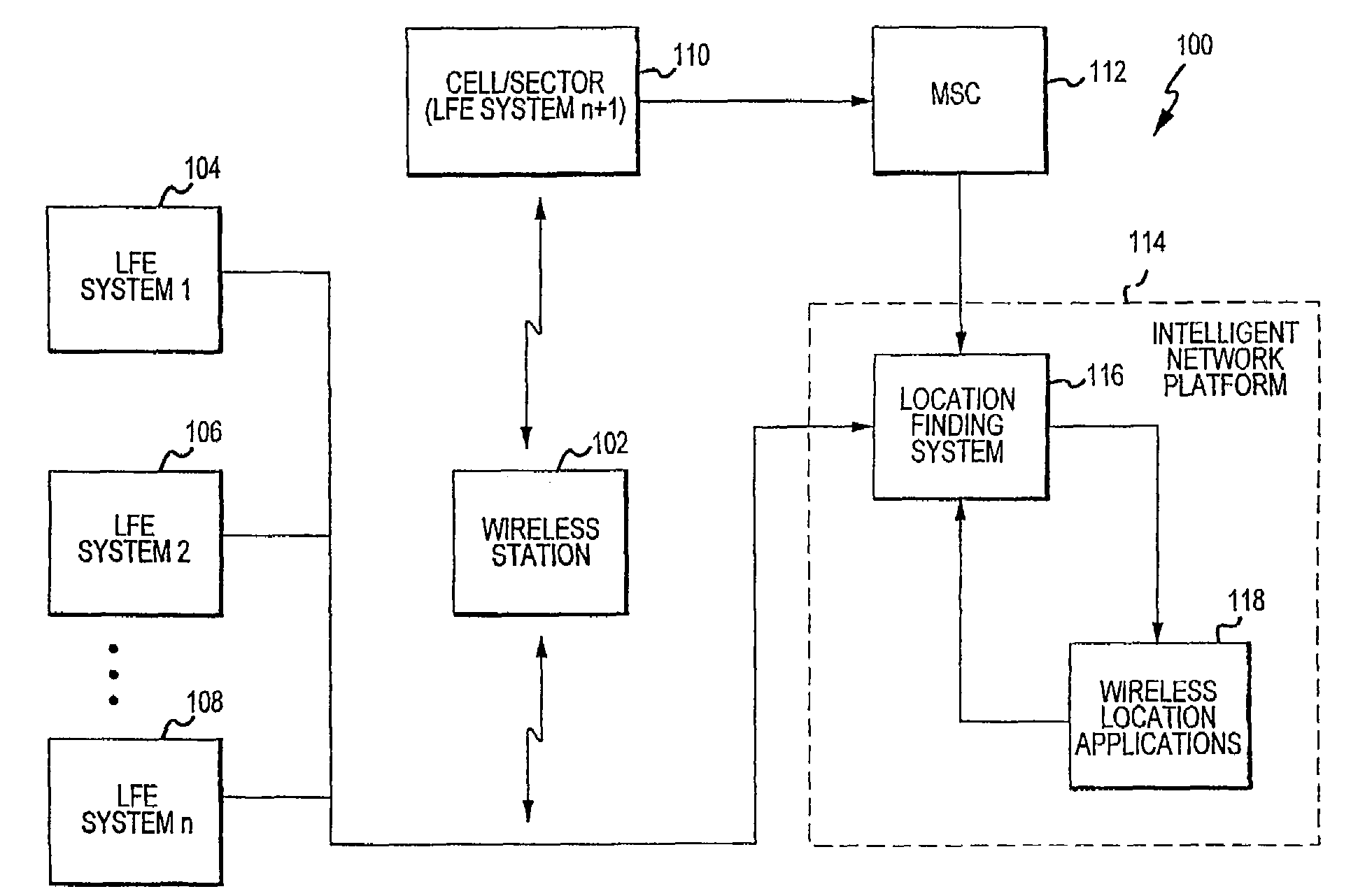
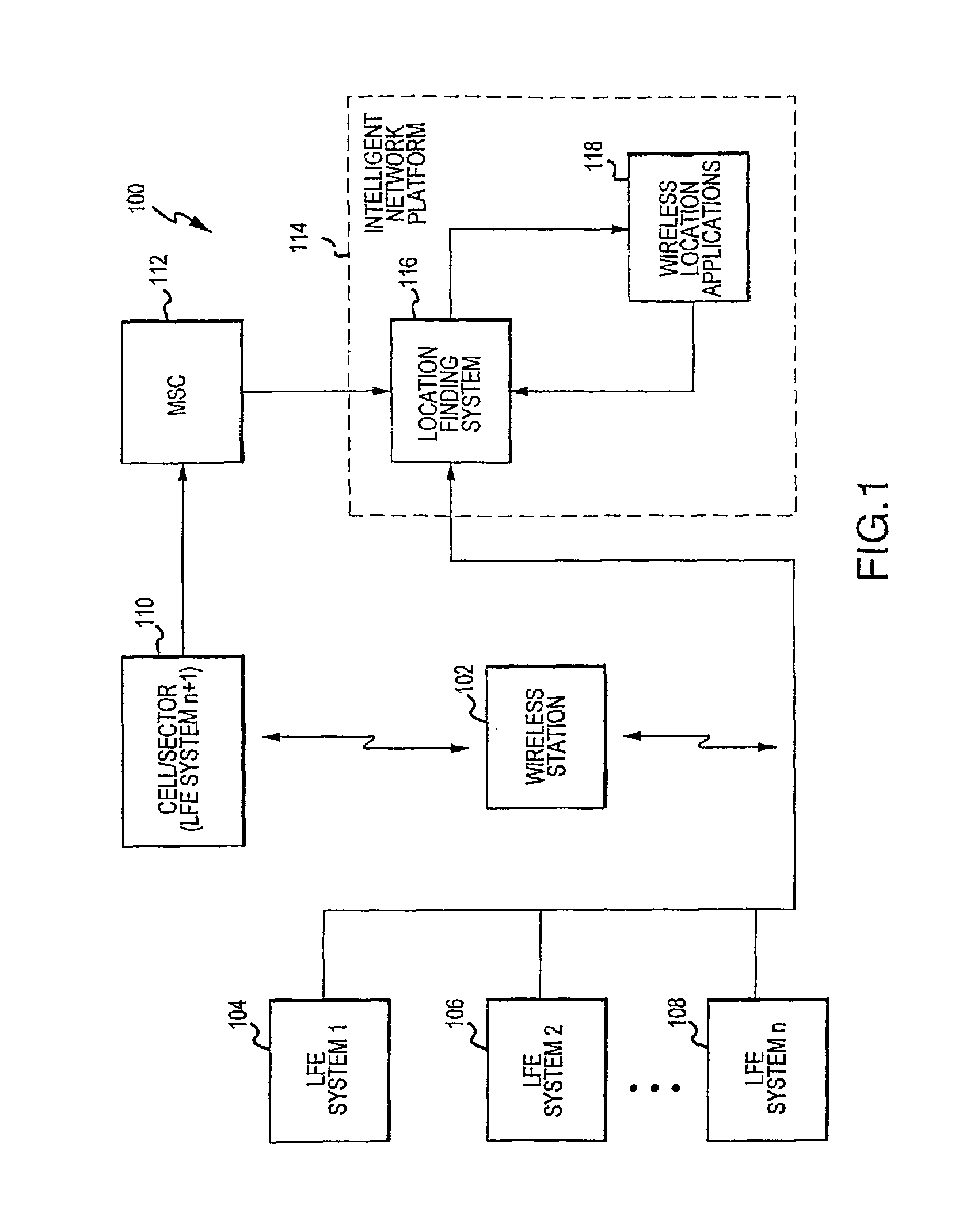
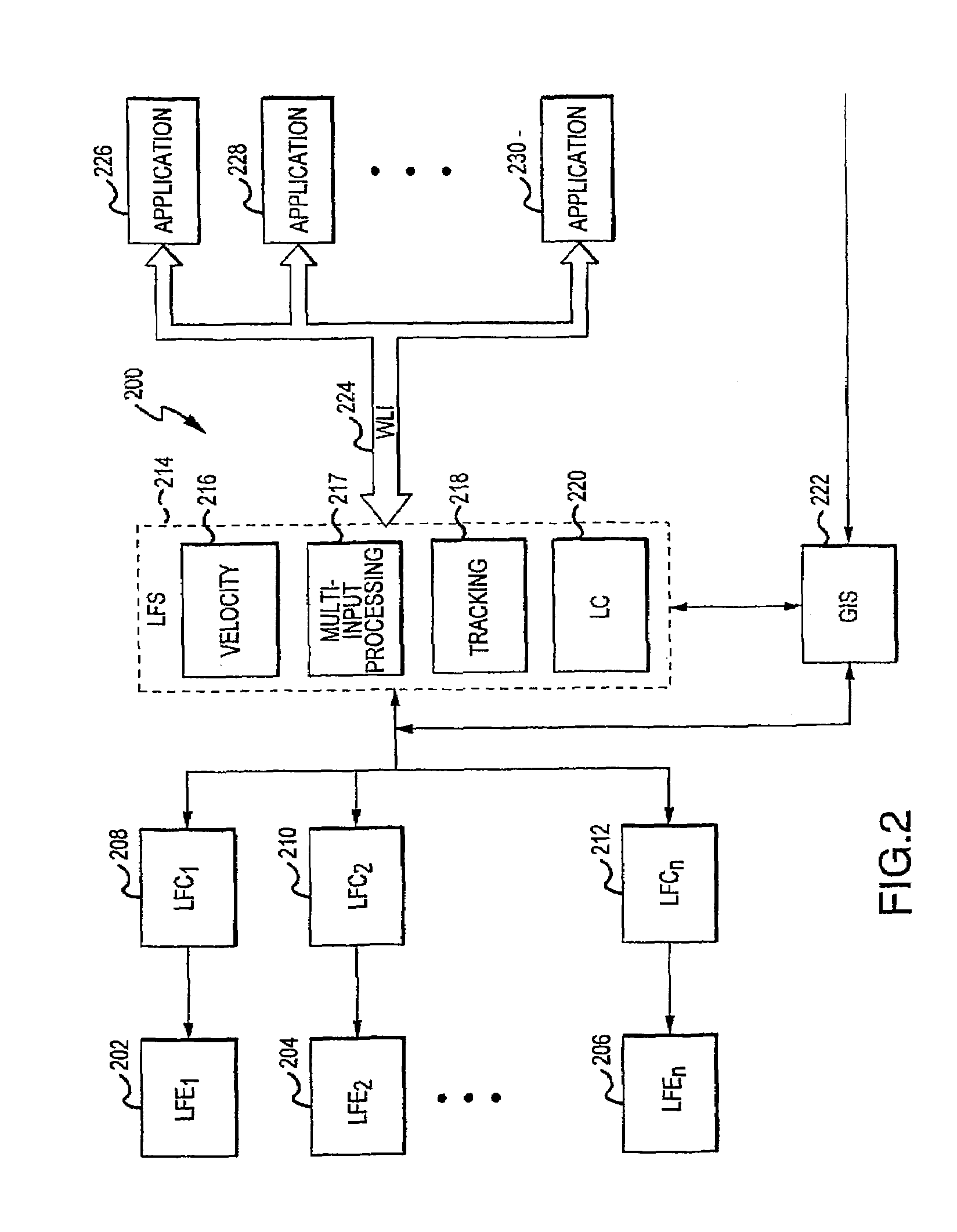
Interface for wireless location information
InactiveUS7522927B2Enhanced informationEnhancing timeliness and accuracy and reliabilityError preventionFrequency-division multiplex detailsLocation EquipmentComputer science
Multiple location finding equipment (LFE) inputs are used to enhance location information made available to wireless location-based applications. A wireless network utilizes a mobile switching center to route communications between wireless stations, a network platform, and a variety of LFE systems. A Location Finding System (LFS), resident on the network platform, receives location information from the LFEs and provides location information to wireless location based applications. In this regard, the LFS can receive input information at varying time intervals of varying accuracies and in various formats, and can provide standardized outputs to the applications, for example, depending on the needs of the applications. Multiple inputs may also be co-processed for enhanced accuracy. A specification can be used to ensure that location information at least meets certain minimum criteria, such as geographical accuracy, allowable age, acceptable response time, and confidence.
Owner:UNWIRED PLANET
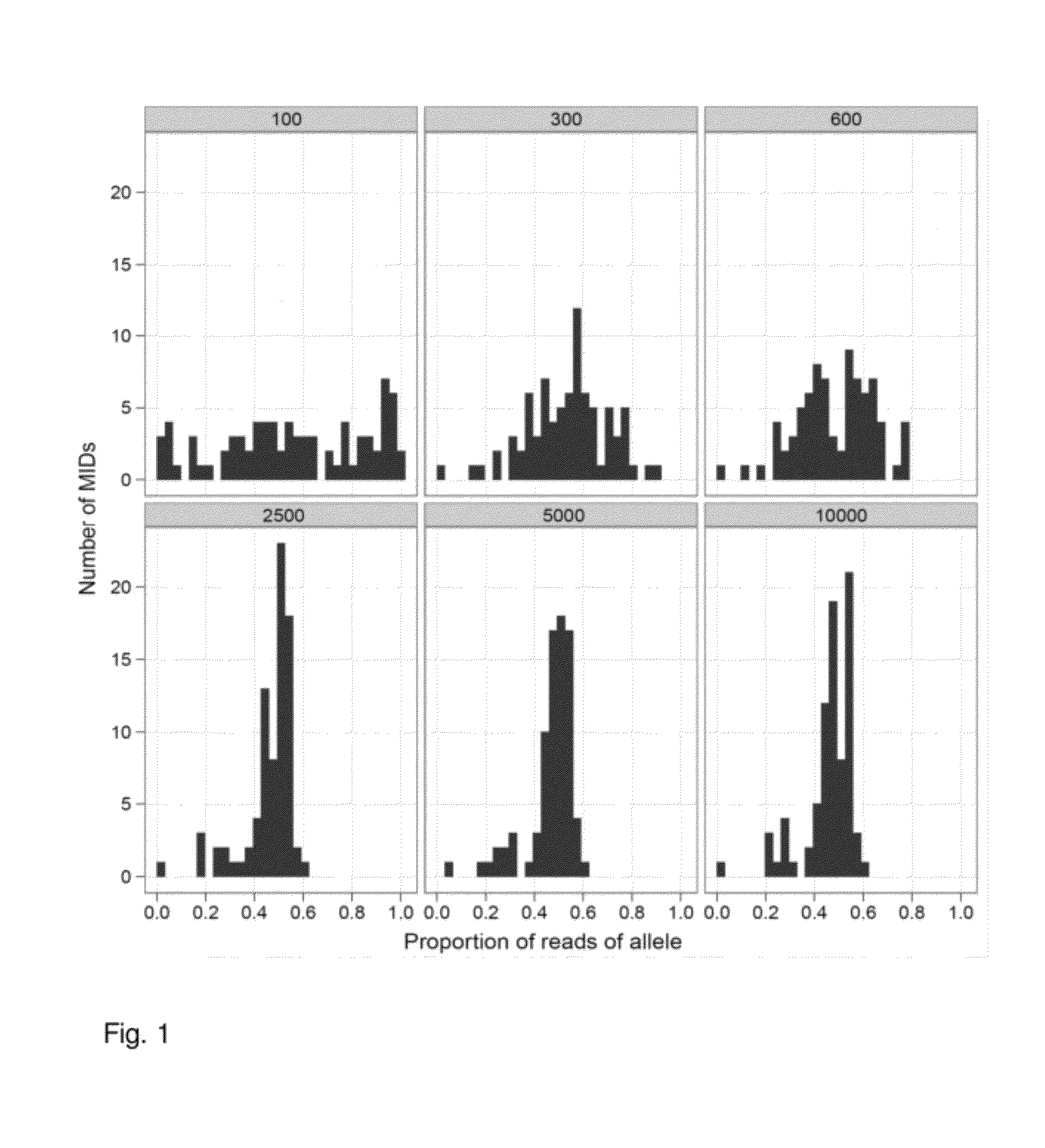
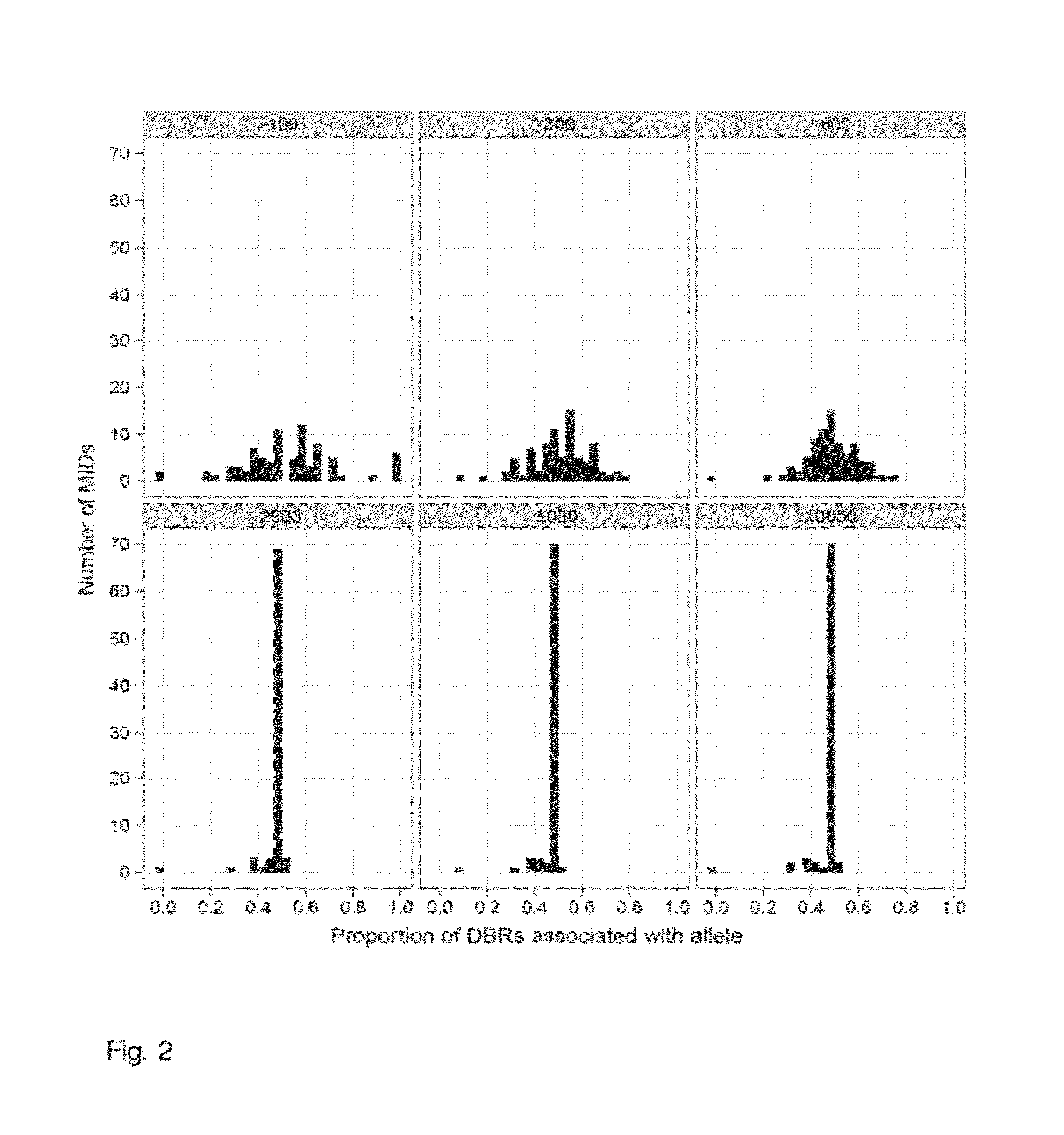
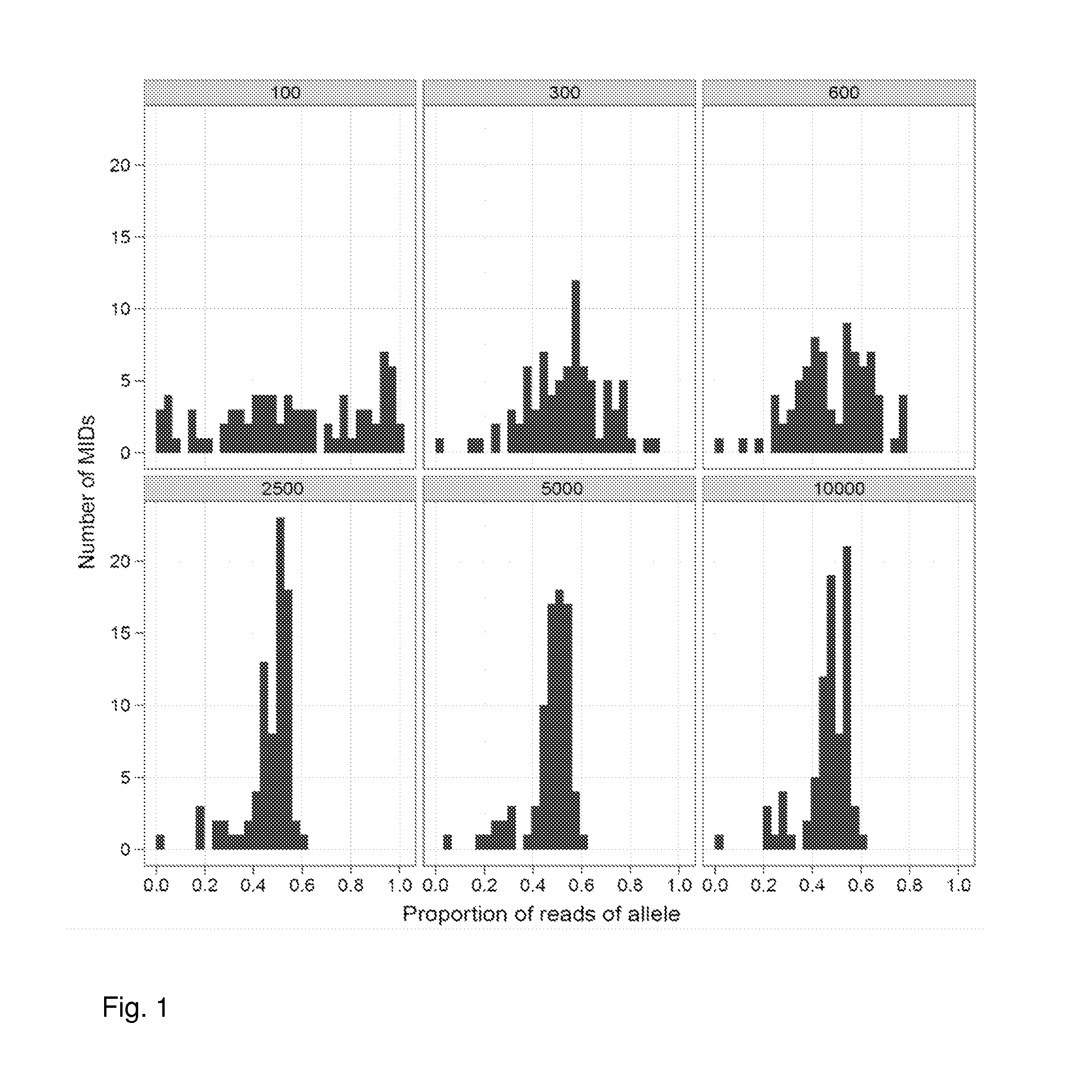
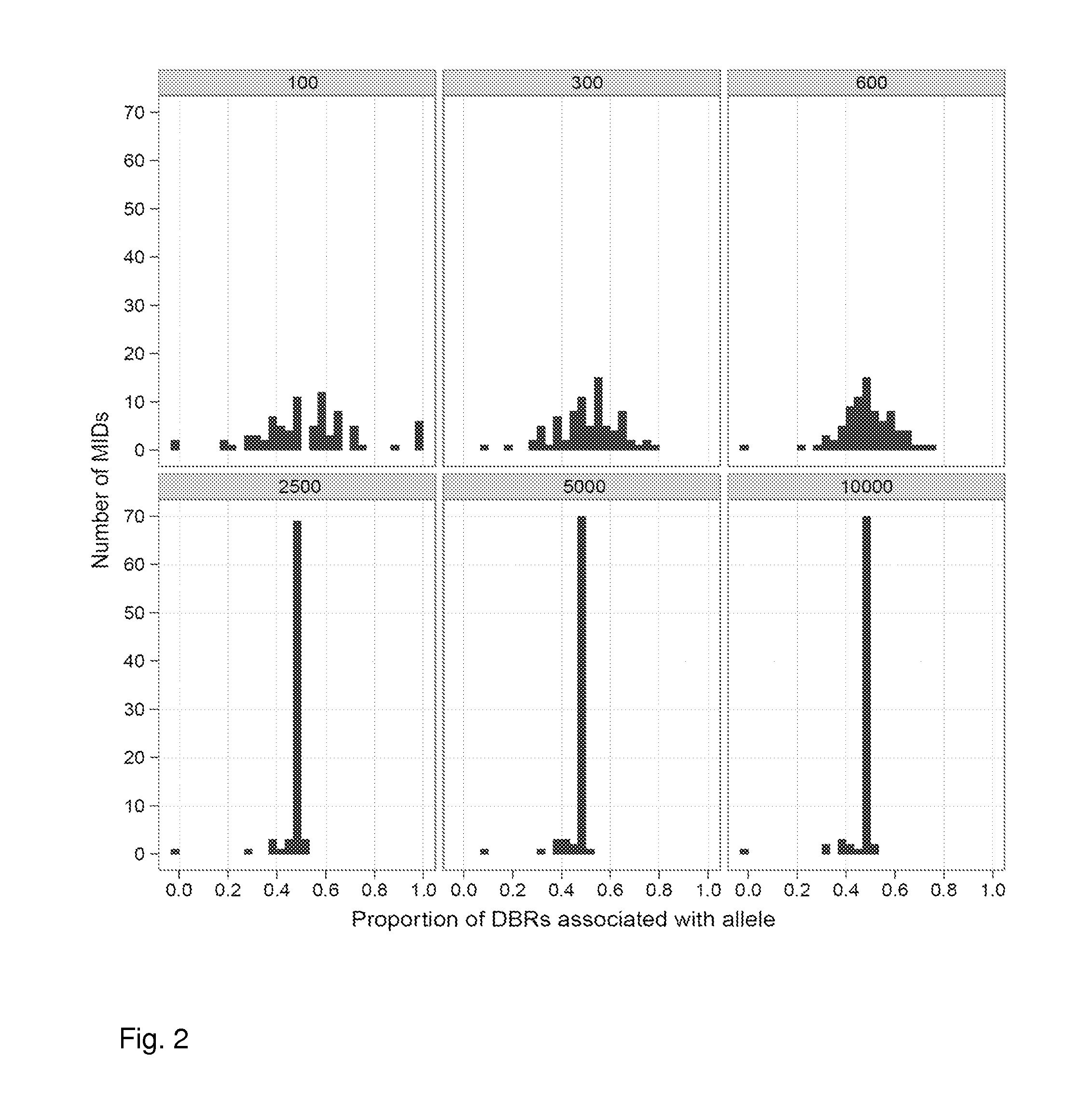
Increasing confidence of allele calls with molecular counting
ActiveUS8481292B2Easy to analyzeSugar derivativesMicrobiological testing/measurementSequence analysisNucleotide
Aspects of the present invention include methods and compositions for determining the number of individual polynucleotide molecules originating from the same genomic region of the same original sample that have been sequenced in a particular sequence analysis configuration or process. In these aspects of the invention, a degenerate base region (DBR) is attached to the starting polynucleotide molecules that are subsequently sequenced (e.g., after certain process steps are performed, e.g., amplification and / or enrichment). The number of different DBR sequences present in a sequencing run can be used to determine / estimate the number of different starting polynucleotides that have been sequenced. DBRs can be used to enhance numerous different nucleic acid sequence analysis applications, including allowing higher confidence allele call determinations in genotyping applications.
Owner:AGILENT TECH INC
System and method for obtaining information relating to an item of commerce using a portable imaging device
ActiveUS20050198095A1Facilitate sale forecasting analysisAccurate predictionMultiple digital computer combinationsBuying/selling/leasing transactionsBarcodePurchasing
A method, system, and apparatus are provided for allowing users to readily obtain information associated with a selected item from a remote location. More specifically, a user at the location of the first entity operates a portable imaging device to capture an image of identifying data, such as a barcode, that identifies a selected item. The captured image is then communicated to a server operated by a second entity that is different than the first entity to obtain item information (e.g., price, availability, etc.) associated with the selected item. The item information is communicated back to the portable imaging device for display to the user while the user remains at the location of the first entity. In other embodiments, the information extracted from the captured image may also be used to forecast future purchasing activity for the selected item.
Owner:AMAZON TECH INC
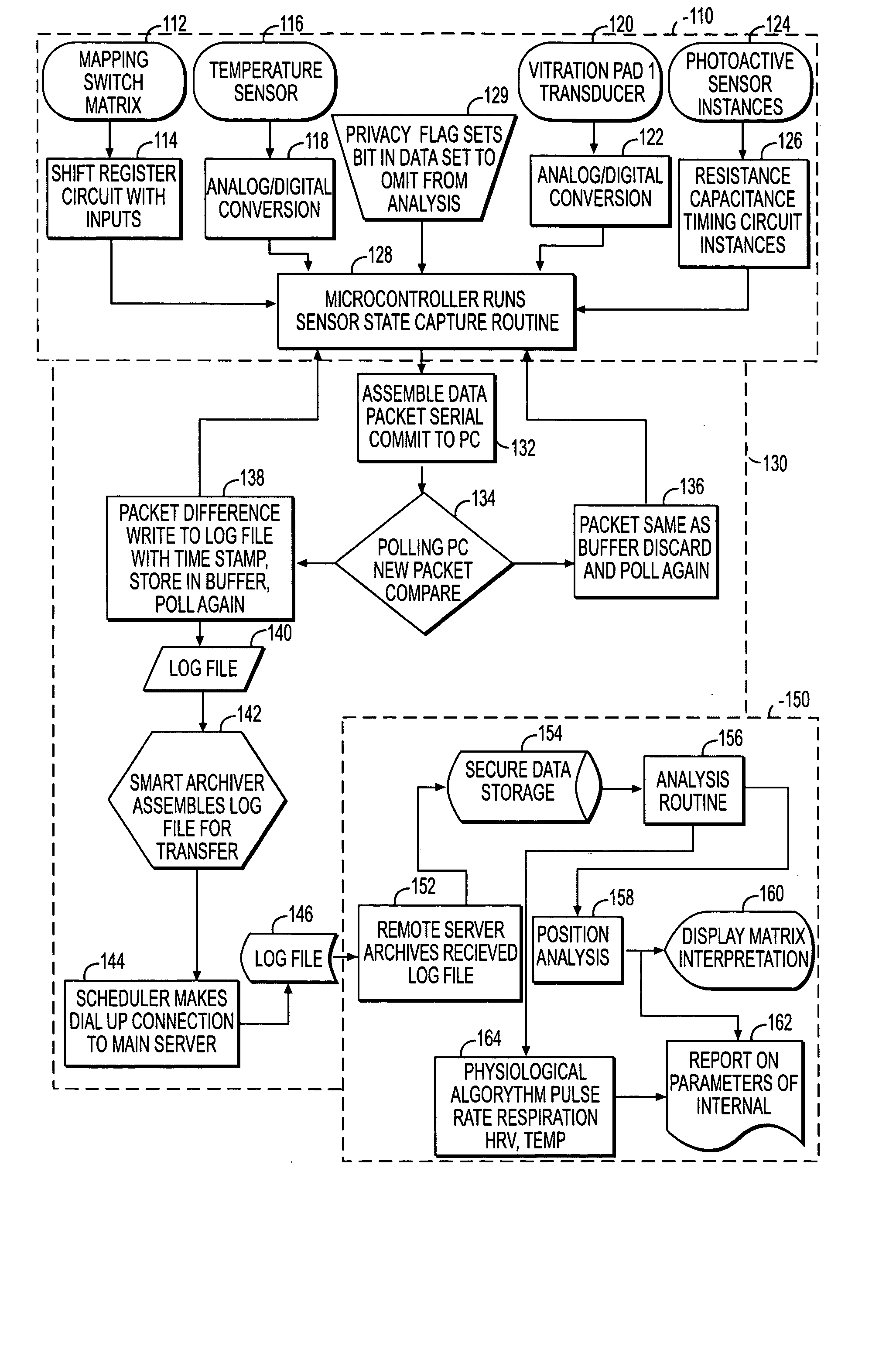
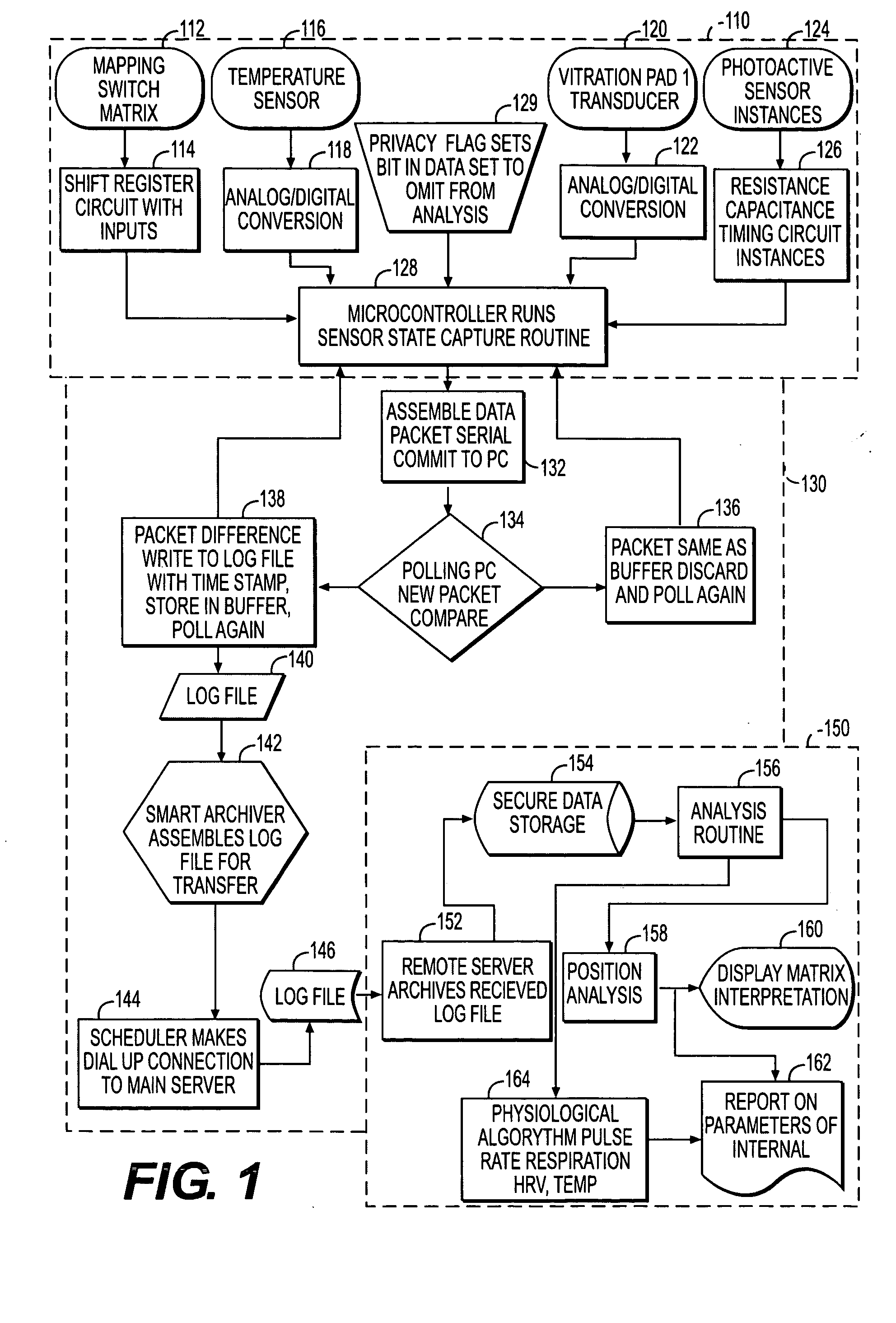
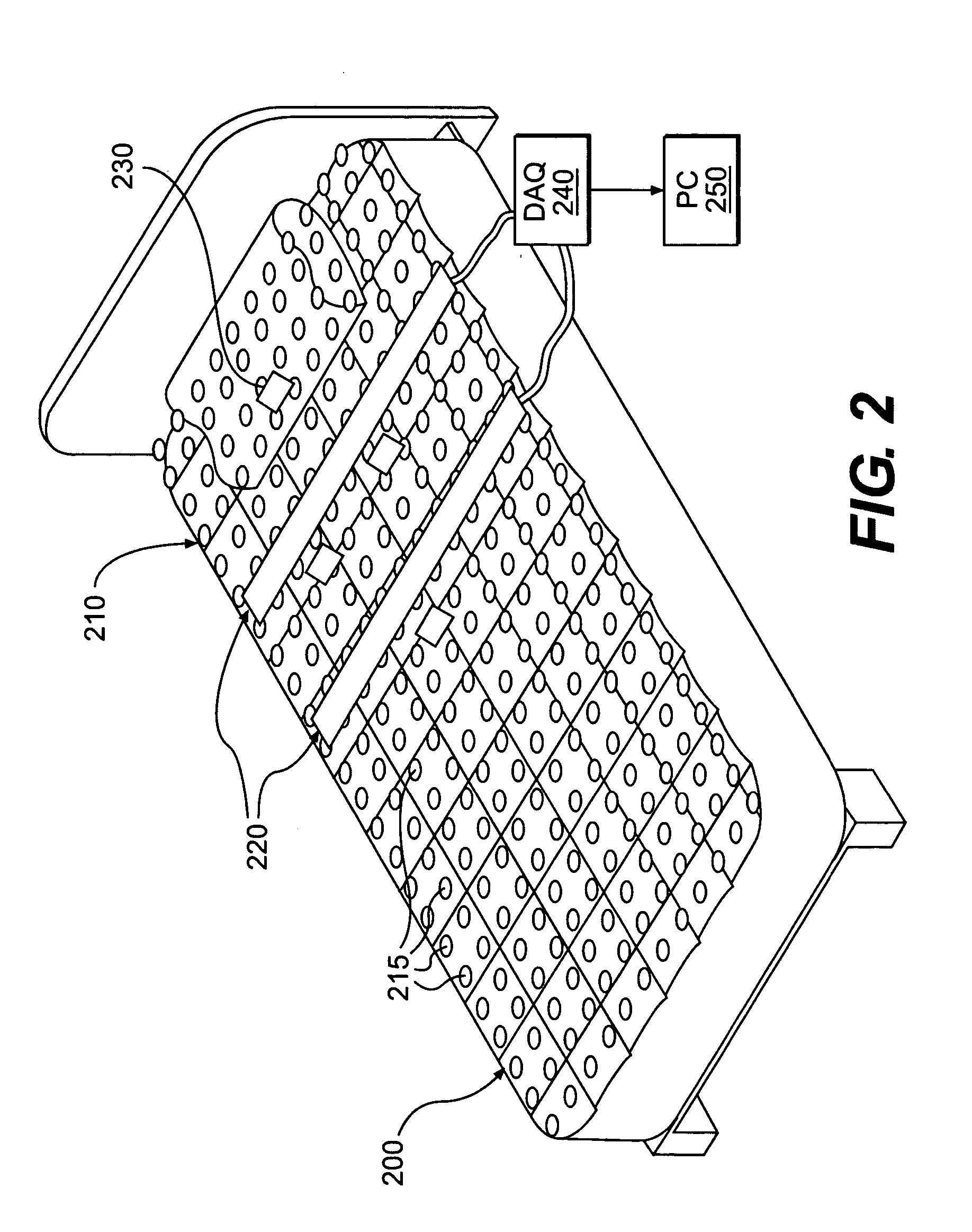
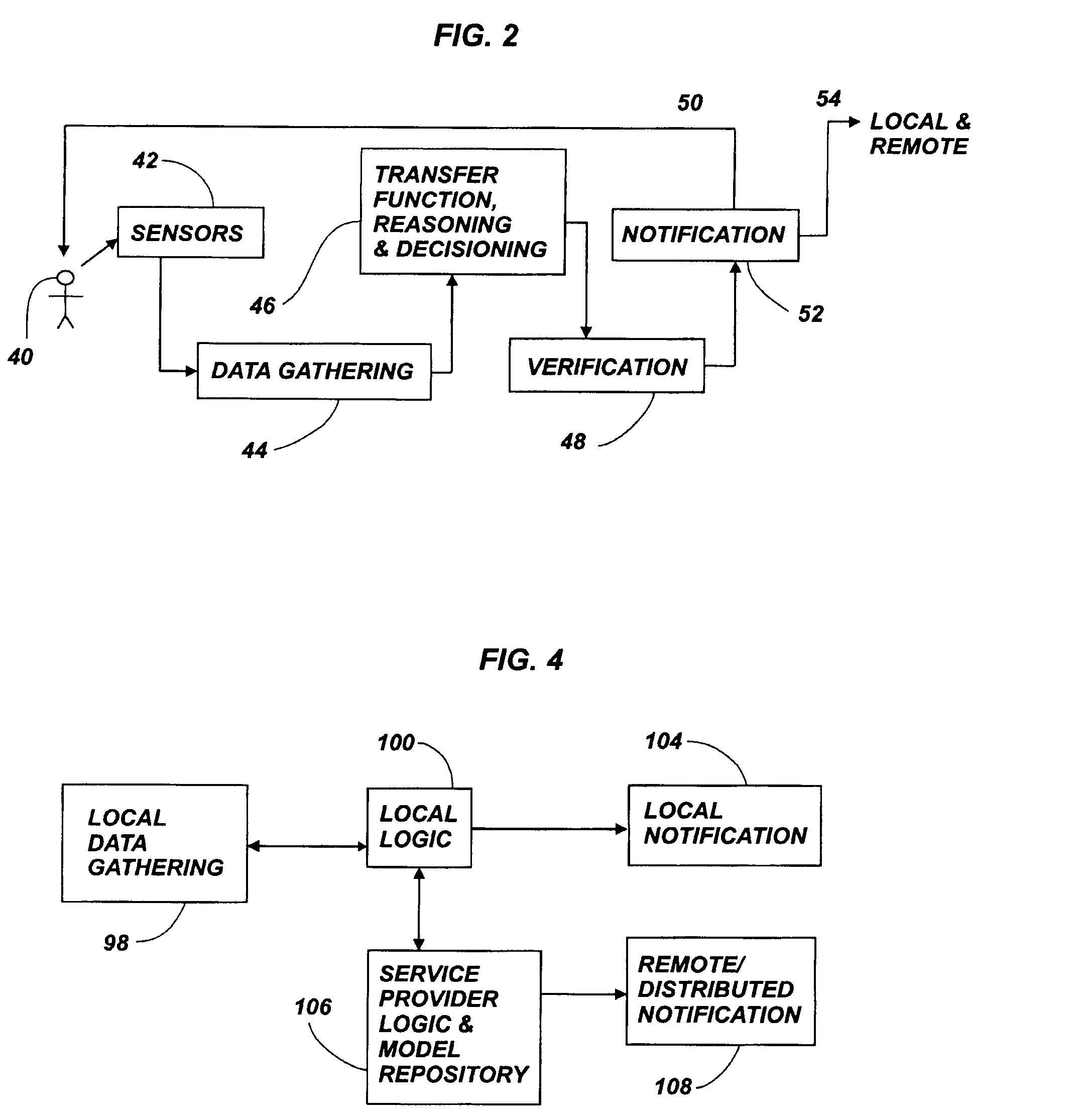
System and process for non-invasive collection and analysis of physiological signals
ActiveUS20050124864A1Simple signal processingCost-effectivePerson identificationCatheterDiseaseSleep Walking
A system and method for detecting, monitoring and analyzing physiological characteristics. Signals from a subject are acquired from a suite of sensors, such as temperature, carbon dioxide, humidity, light, movement, electromagnetic and vibration sensors, in a passive, non-invasive manner. The signals are processed, and physiological characteristics are isolated for analysis. The system and method are to analyze sleep patterns, as well as to prevent bed sores or detect conditions such as illness, restless leg syndrome, periodic leg movement, sleep walking, or sleep apnea. However, numerous other applications of the invention are also disclosed.
Owner:BEST BUY HEALTH INC
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS20130104236A1Reduce analysisLower control priorityMemory loss protectionError detection/correctionApplication softwareBusiness process
Real time security, integrity, and reliability postures of operational (OT), information (IT), and security (ST) systems, as well as slower changing security and operational blueprint, policies, processes, and rules governing the enterprise security and business risk management process, dynamically evolve and adapt to domain, context, and situational awareness, as well as the controls implemented across the operational and information systems that are controlled. Embodiments of the invention are systematized and pervasively applied across interconnected, interdependent, and diverse operational, information, and security systems to mitigate system-wide business risk, to improve efficiency and effectiveness of business processes and to enhance security control which conventional perimeter, network, or host based control and protection schemes cannot successfully perform.
Owner:ALBEADO
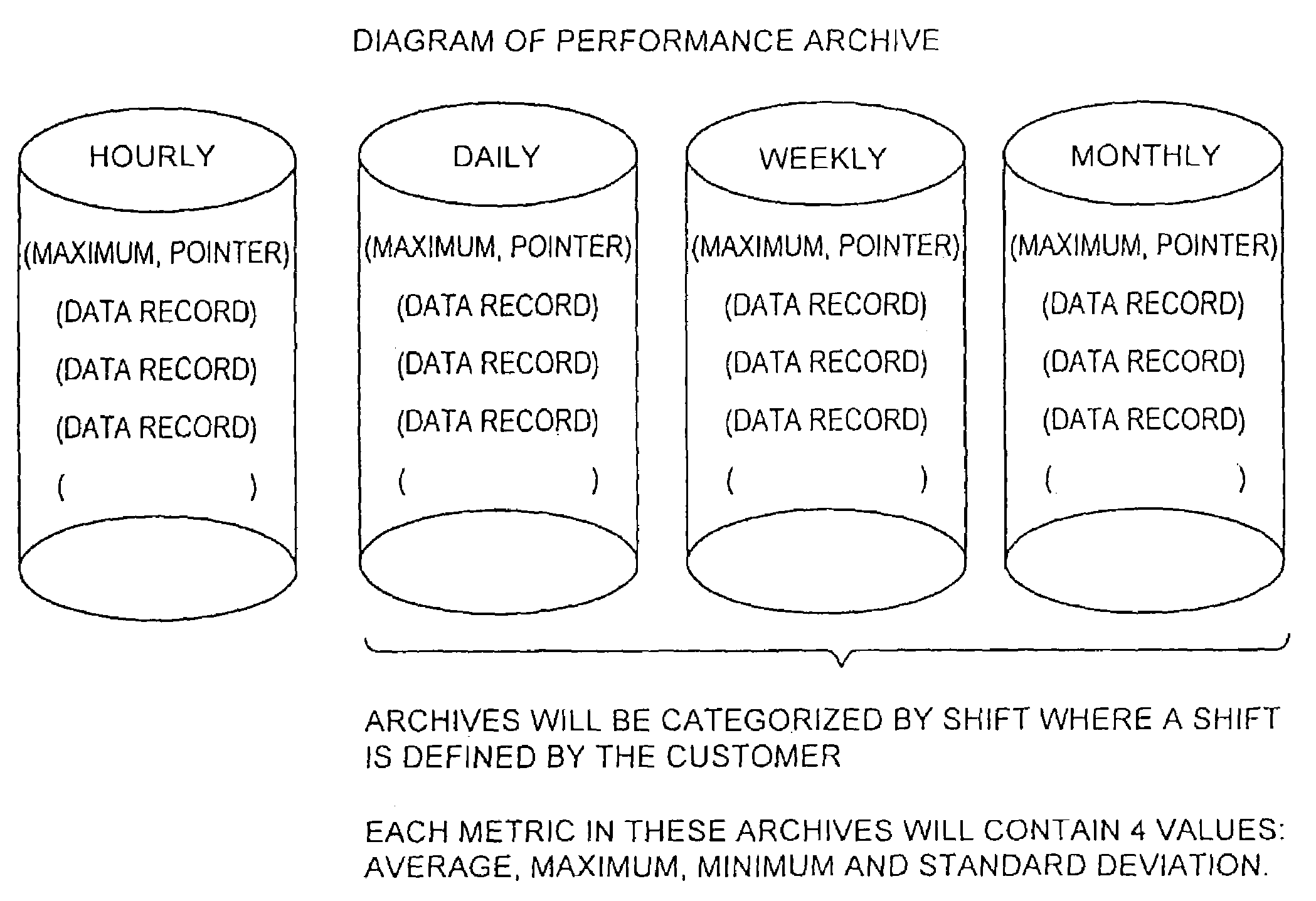
Method and storage and manipulation of storage system metrics
InactiveUS7082441B1Promote generationEasy accessData processing applicationsError detection/correctionData operationsData description
A method for storage and manipulation of storage system metrics incorporates a self-describing format wherein each data file includes a header block that contains the description and order of the periodic data. The header block is followed by a data block in which the data items are presented in the order that they appear in the data description block for that category. Two types of data are managed, including Base Metrics and Derived Metrics. Base Metrics are metrics that appear in the data file sent by an agent. Derived Metrics are computed based on a set of functions that derive new metrics from the base metrics as well as from previously defined derived metrics. A subset of the data block or file describes the configuration of the storage system at the time that the data file was created. Thus the data file contains a header section that in addition to describing the metrics also describes the configuration. A performance view component a user interface that facilitates access to the archives, and data manipulation effecting enhanced performance analysis, workload characterization and capacity planning. The performance view component facilitates generation of factory and user defined views of monitored metrics / parameters. Metrics from a storage system can be correlated using the performance view features, and parameters across machines can be correlated as well. System configuration(s) can be viewed and changed via the performance view user interface.
Owner:EMC IP HLDG CO LLC
Voltage modulated driver circuits for electro-optic displays
ActiveUS8125501B2Low implementation costFaster design timeCathode-ray tube indicatorsInput/output processes for data processingElectricityDriver circuit
A method and system for applying addressing voltages to pixels of a display involves receiving input data. The input data includes an indication of an addressing voltage impulse to be applied to a pixel via an electrode. One or more voltage sources are selected, to provide the addressing voltage impulse. The one or more voltage sources each have a pre-selected voltage, The selected one or more voltage sources are electrically connected to an electrode to apply the addressing voltage impulse to the pixel. The invention also provides a method of driving an electro-optic display which uses an intermediate image of reduced bit depth, and a method of driving an electro-optic display which uses a limited number of differing drive voltages, with higher voltage pulses being used before lower voltage pulses.
Owner:E INK CORPORATION
Increasing confidence of allele calls with molecular counting
ActiveUS20120071331A1Easy to analyzeMicrobiological testing/measurementLibrary member identificationSequence analysisAllele
Aspects of the present invention include methods and compositions for determining the number of individual polynucleotide molecules originating from the same genomic region of the same original sample that have been sequenced in a particular sequence analysis configuration or process. In these aspects of the invention, a degenerate base region (DBR) is attached to the starting polynucleotide molecules that are subsequently sequenced (e.g., after certain process steps are performed, e.g., amplification and / or enrichment). The number of different DBR sequences present in a sequencing run can be used to determine / estimate the number of different starting polynucleotides that have been sequenced. DBRs can be used to enhance numerous different nucleic acid sequence analysis applications, including allowing higher confidence allele call determinations in genotyping applications.
Owner:AGILENT TECH INC
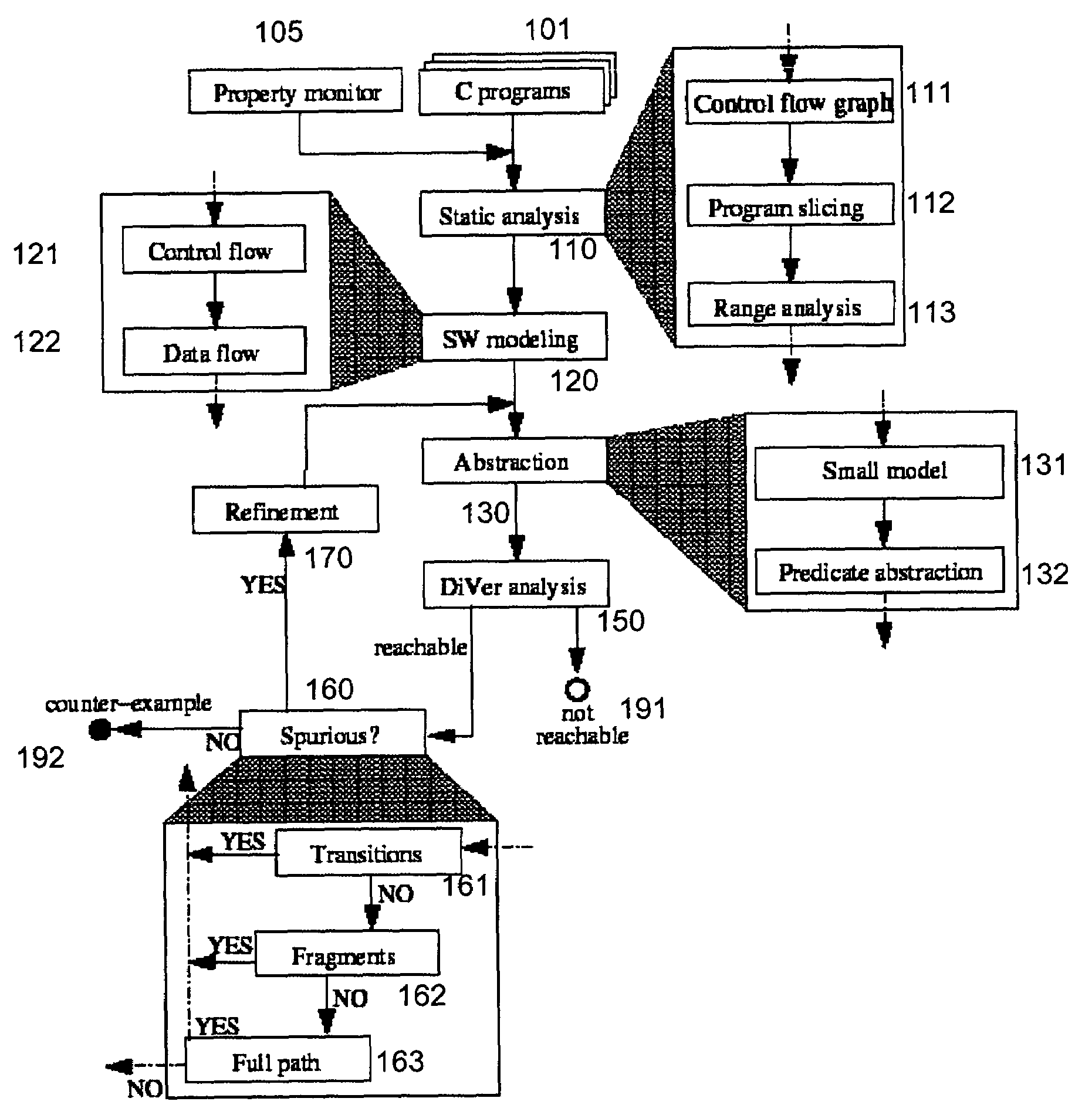
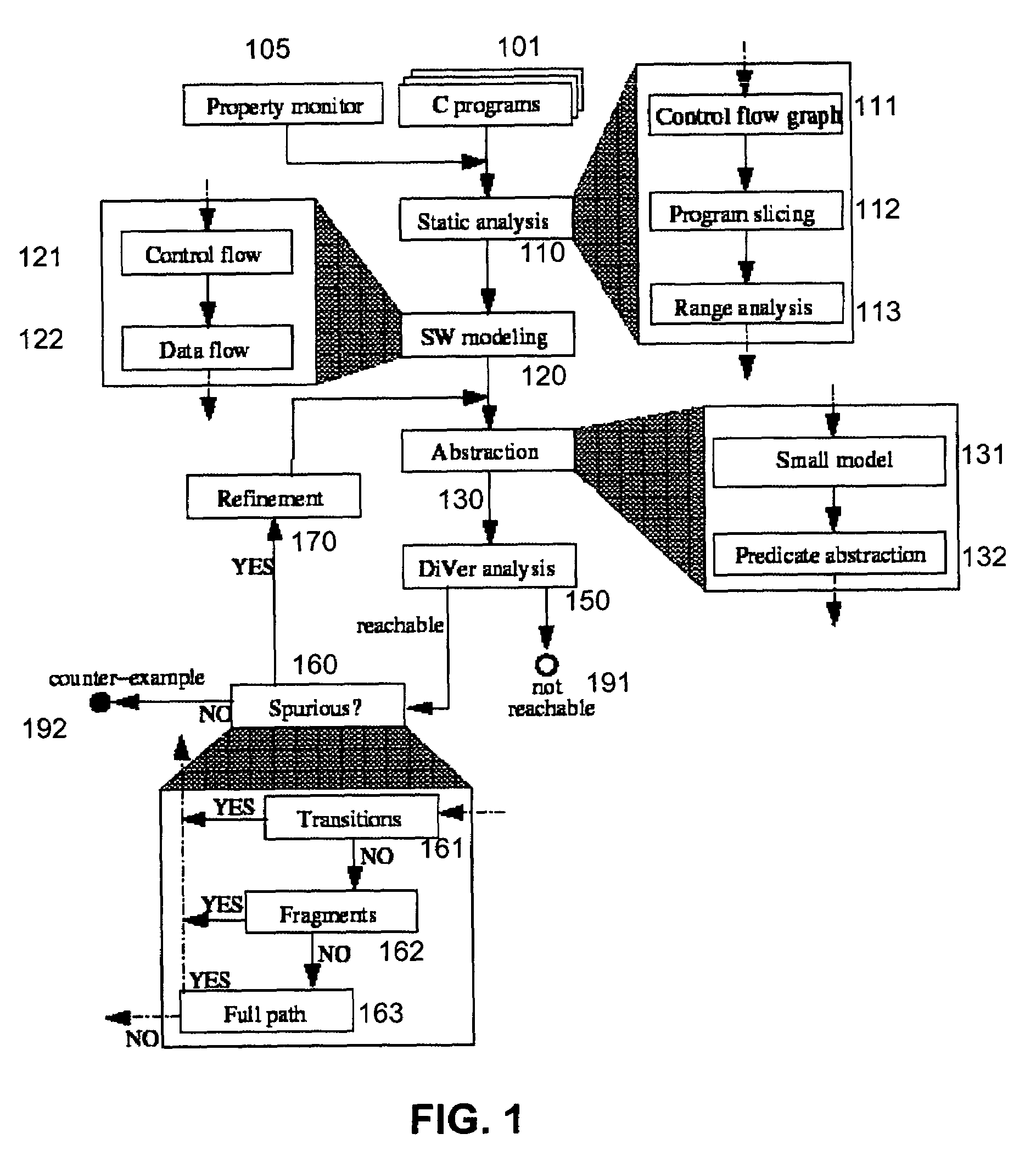
System and method for modeling, abstraction, and analysis of software
ActiveUS7346486B2Improve verification efficiencyImprove translationError detection/correctionComputation using non-denominational number representationBasic blockSoftware
A system and method is disclosed for formal verification of software programs that advantageously translates the software, which can have bounded recursion, into a Boolean representation comprised of basic blocks and which applies SAT-based model checking to the Boolean representation.
Owner:NEC CORP
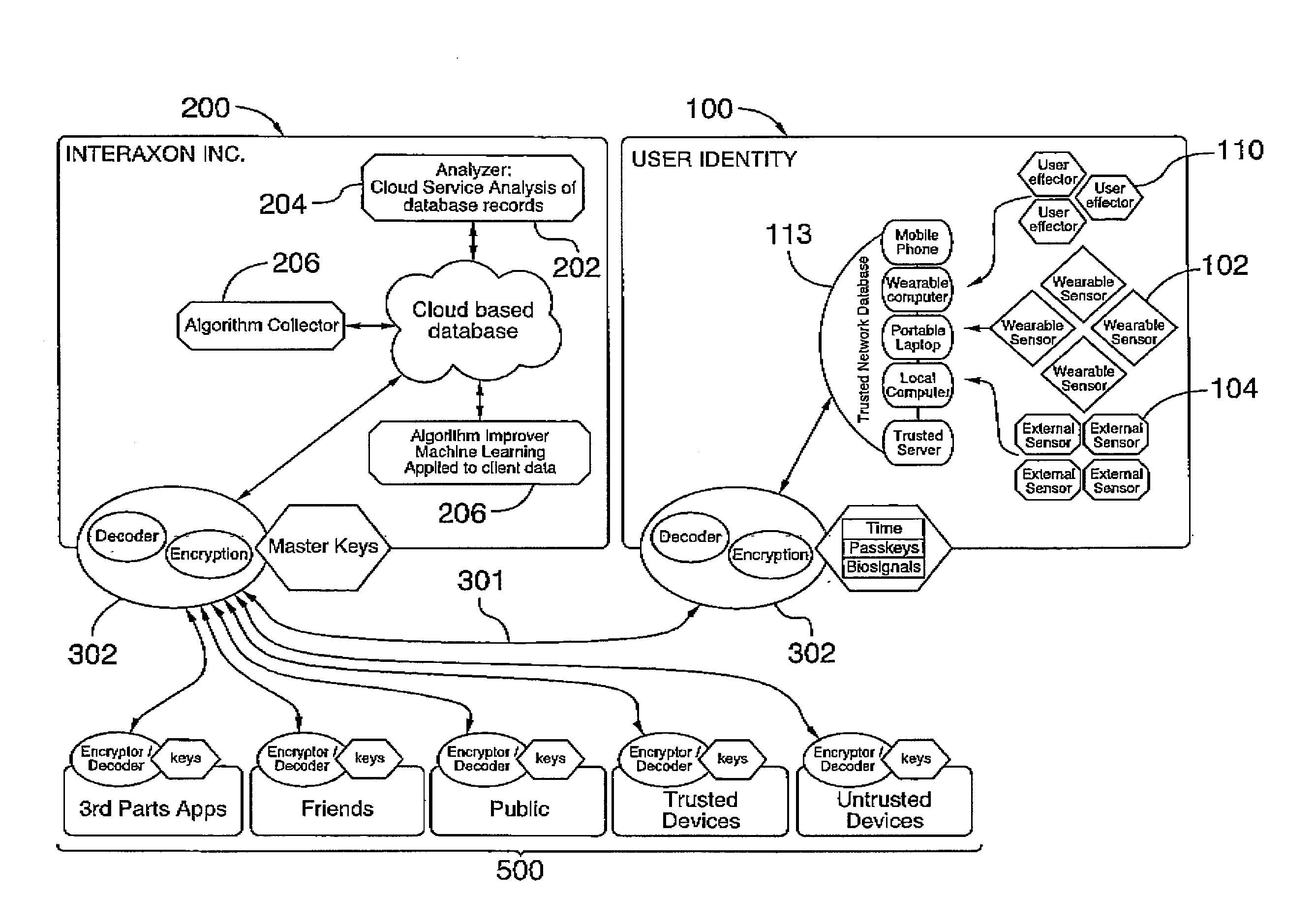
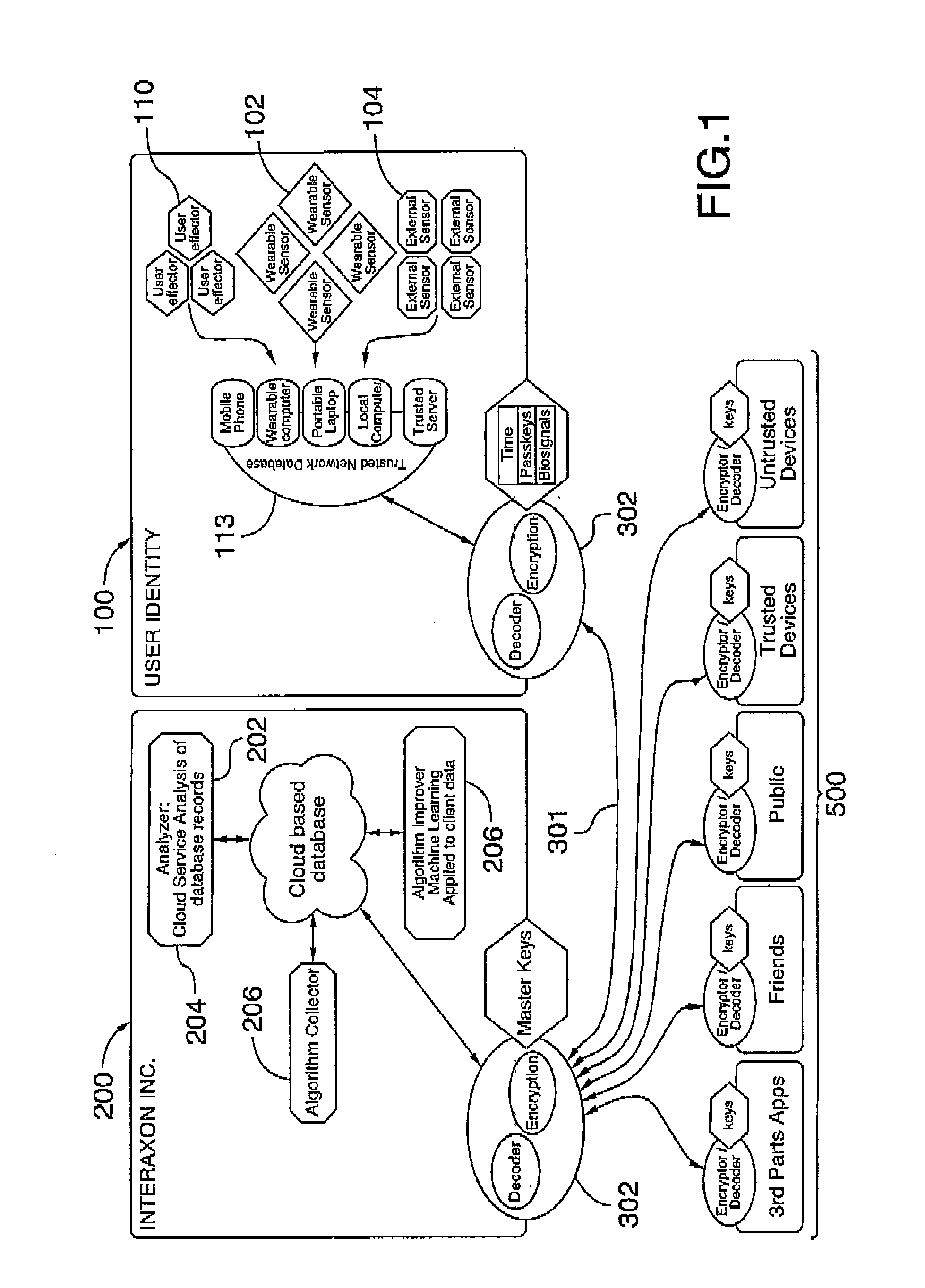
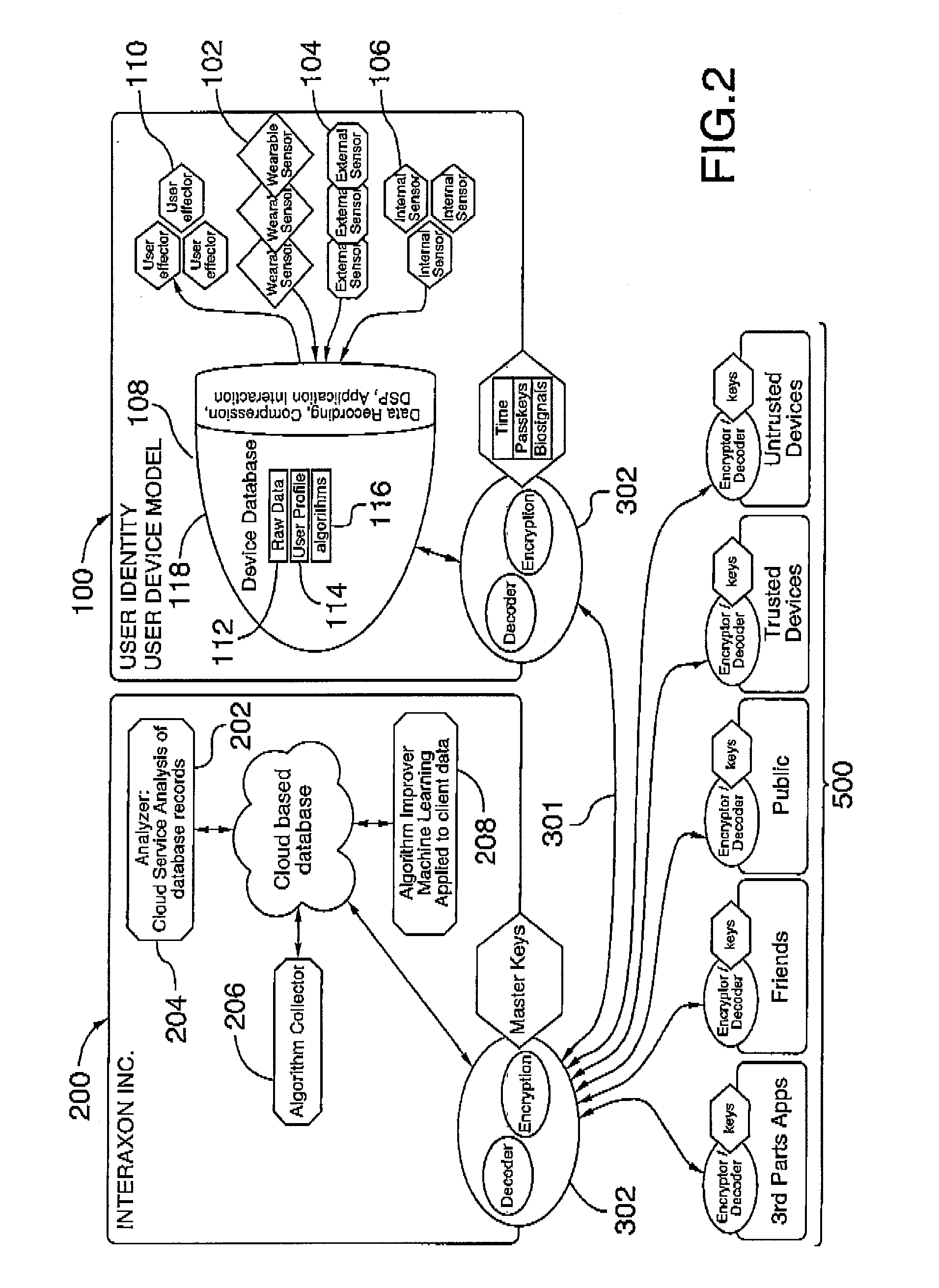
Systems and methods for collecting, analyzing, and sharing bio-signal and non-bio-signal data
ActiveUS20150199010A1Decreases learning curveSimple methodInput/output for user-computer interactionSpecial service provision for substationHuman–computer interactionBiofeedback
A computer network implemented system for improving the operation of one or more biofeedback computer systems is provided. The system includes an intelligent bio-signal processing system that is operable to: capture bio-signal data and in addition optionally non-bio-signal data; and analyze the bio-signal data and non-bio-signal data, if any, so as to: extract one or more features related to at least one individual interacting with the biofeedback computer system; classify the individual based on the features by establishing one or more brain wave interaction profiles for the individual for improving the interaction of the individual with the one or more biofeedback computer systems, and initiate the storage of the brain waive interaction profiles to a database; and access one or more machine learning components or processes for further improving the interaction of the individual with the one or more biofeedback computer systems by updating automatically the brain wave interaction profiles based on detecting one or more defined interactions between the individual and the one or more of the biofeedback computer systems. A number of additional system and computer implemented method features are also provided.
Owner:INTERAXON
Analytics-based security monitoring system and method
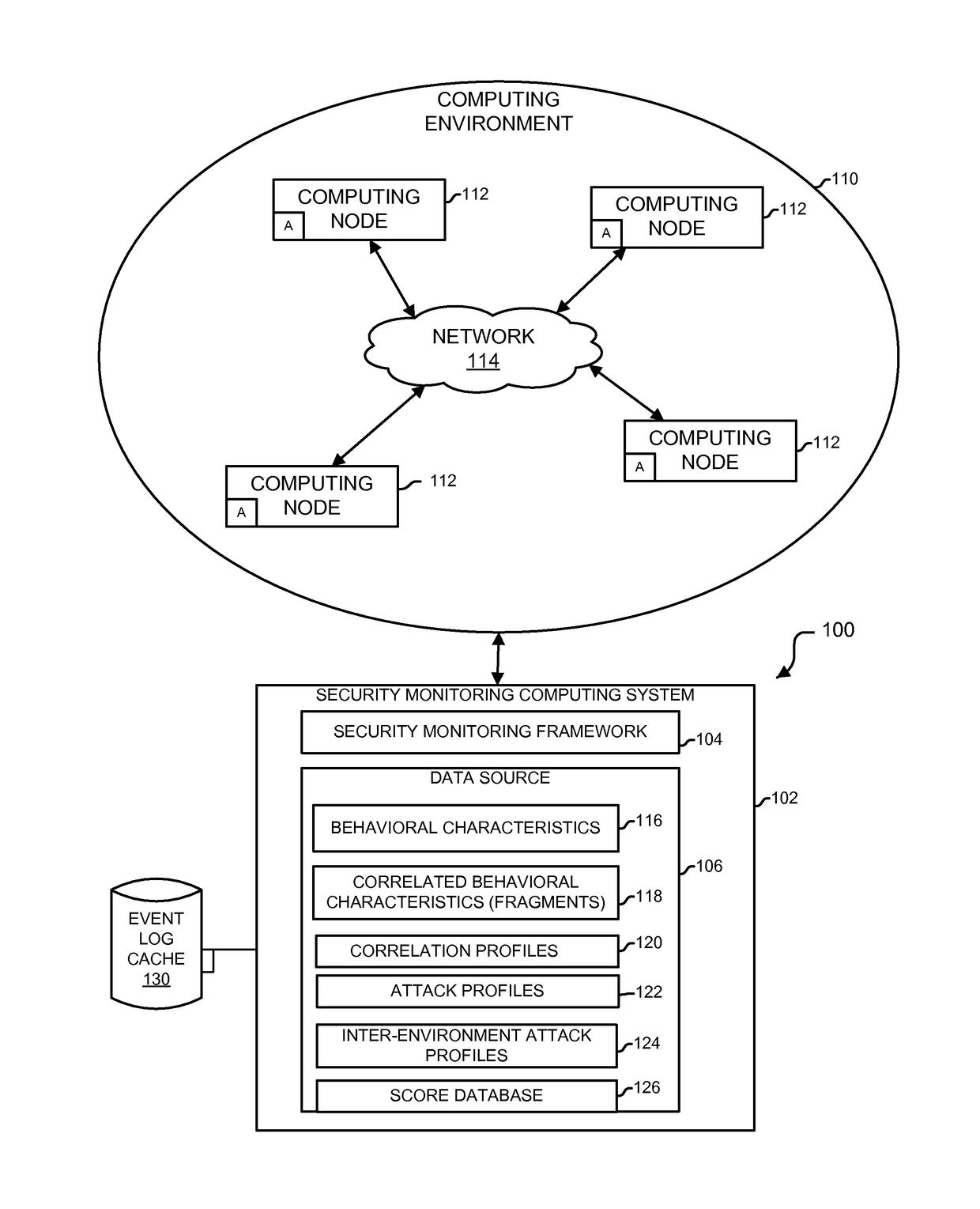
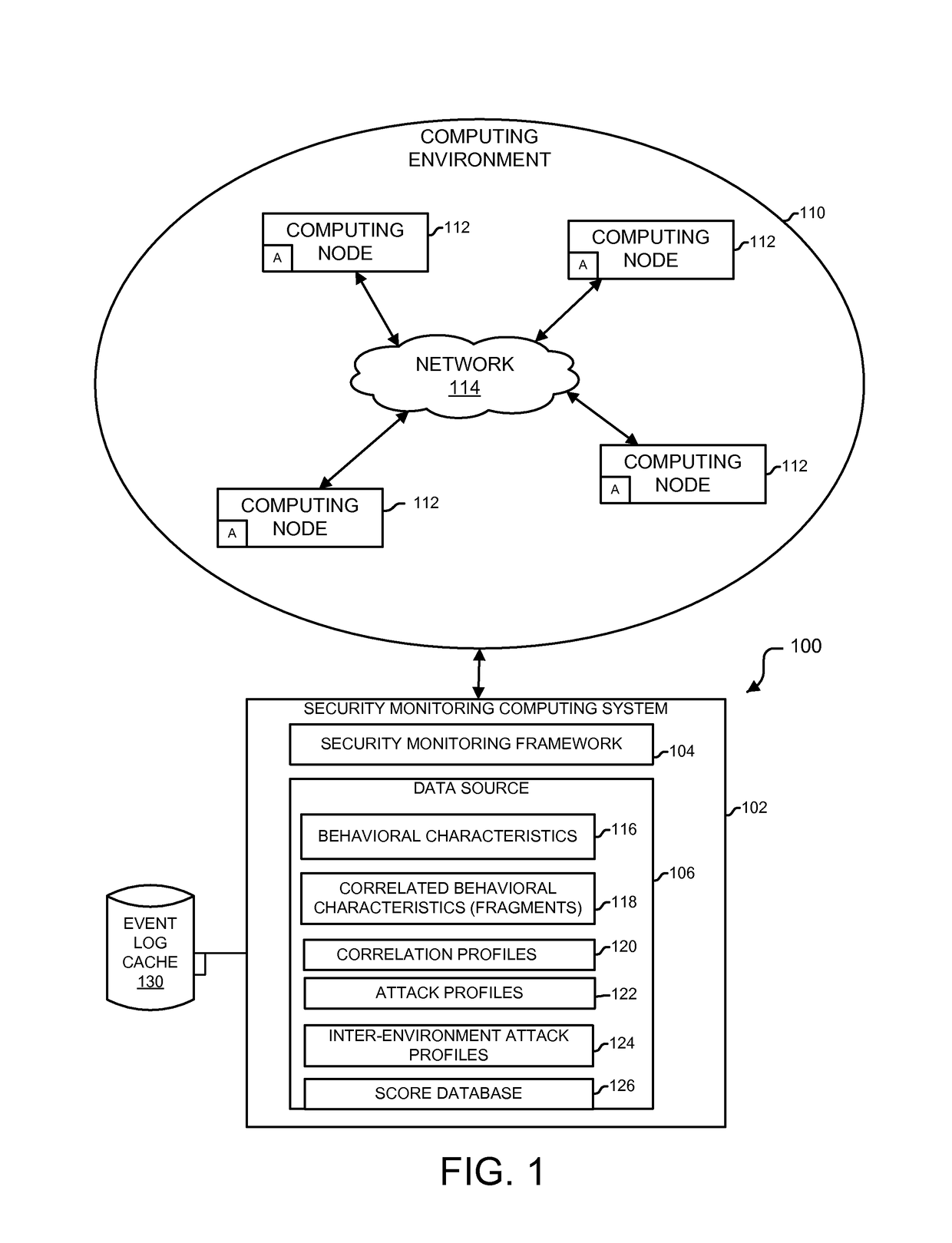
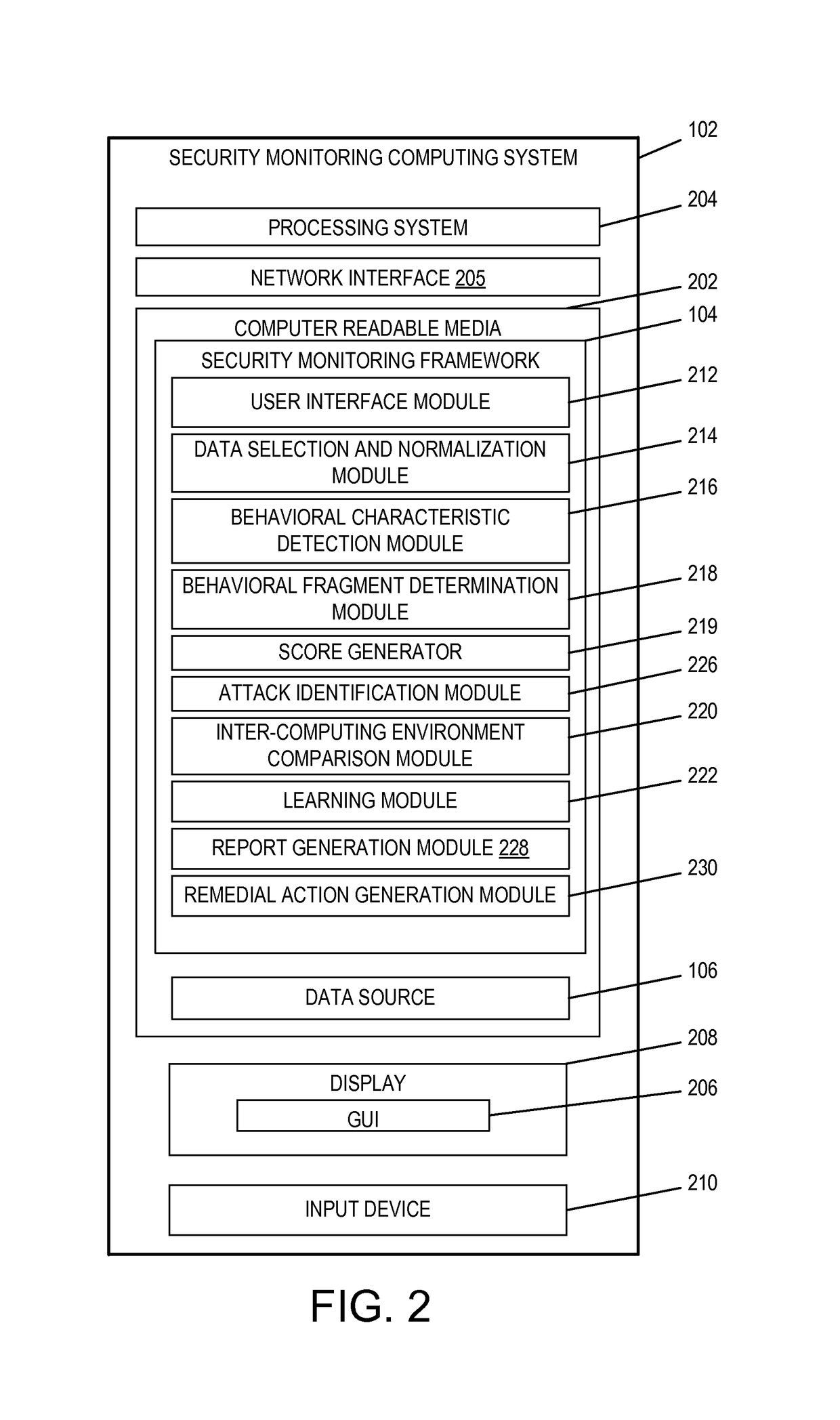
ActiveUS9654485B1Reduce size (quantity)Easy to analyzeMemory loss protectionError detection/correctionRemedial actionSecurity monitoring
An analytics-based security monitoring system includes instructions that may be executed by a computing system to receive data in the form of event logs from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:MANDIANT +1
Digital assurance method and system to extend in-home living
InactiveUS20060033625A1Overcome deficienciesOvercomes drawbackFinanceMedical automated diagnosisLife qualityEngineering
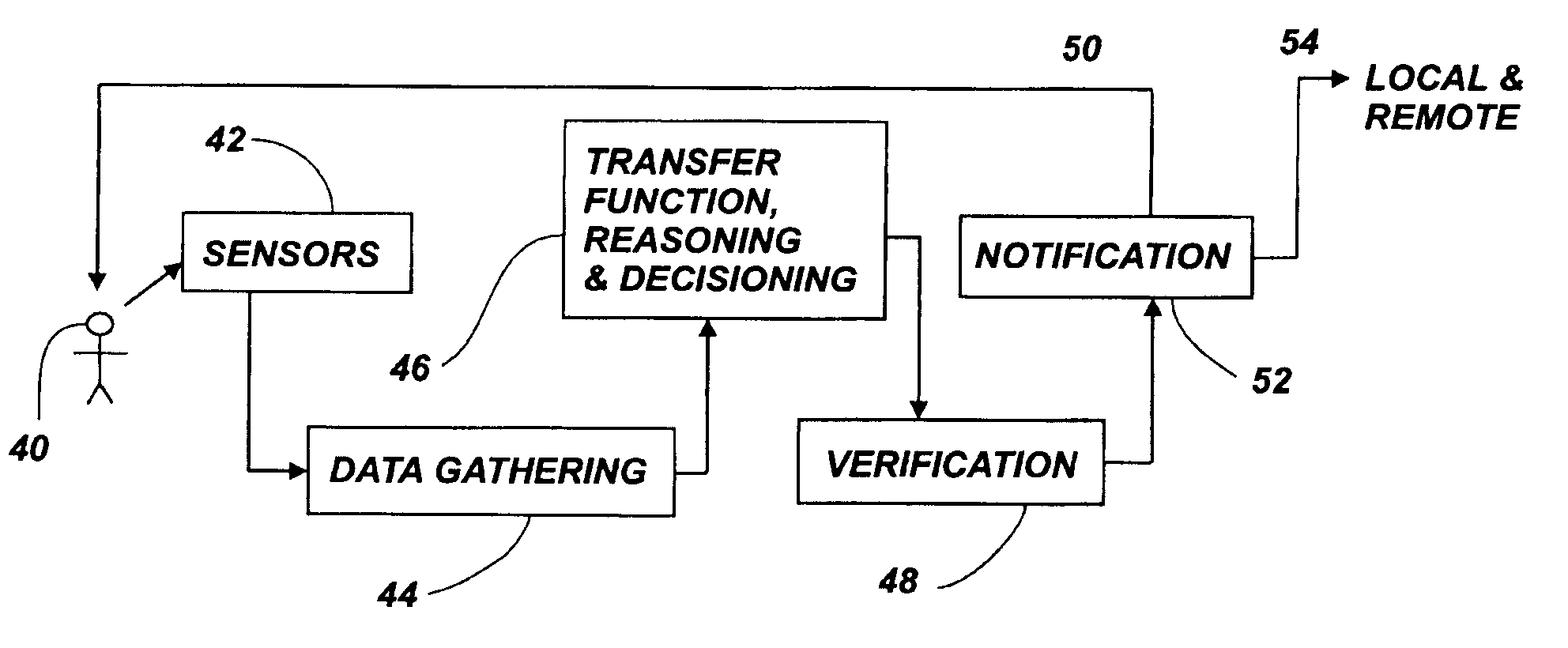
A system and method for facilitating in-home living by monitoring and analyzing in-home activities, and thereby implementing services for facilitating such living. The system includes an integrated portfolio of active and / or passive sensors for monitoring activities of an individual, and an analyzing system for synthesizing and analyzing signals from the sensors for thereby assessing a status of the individual and inferring the individual's quality of life. The system further includes a decision making system for generating an output based upon the assessment, and an activation system for activating processes to respond to the decision making.
Owner:GENERAL ELECTRIC CO
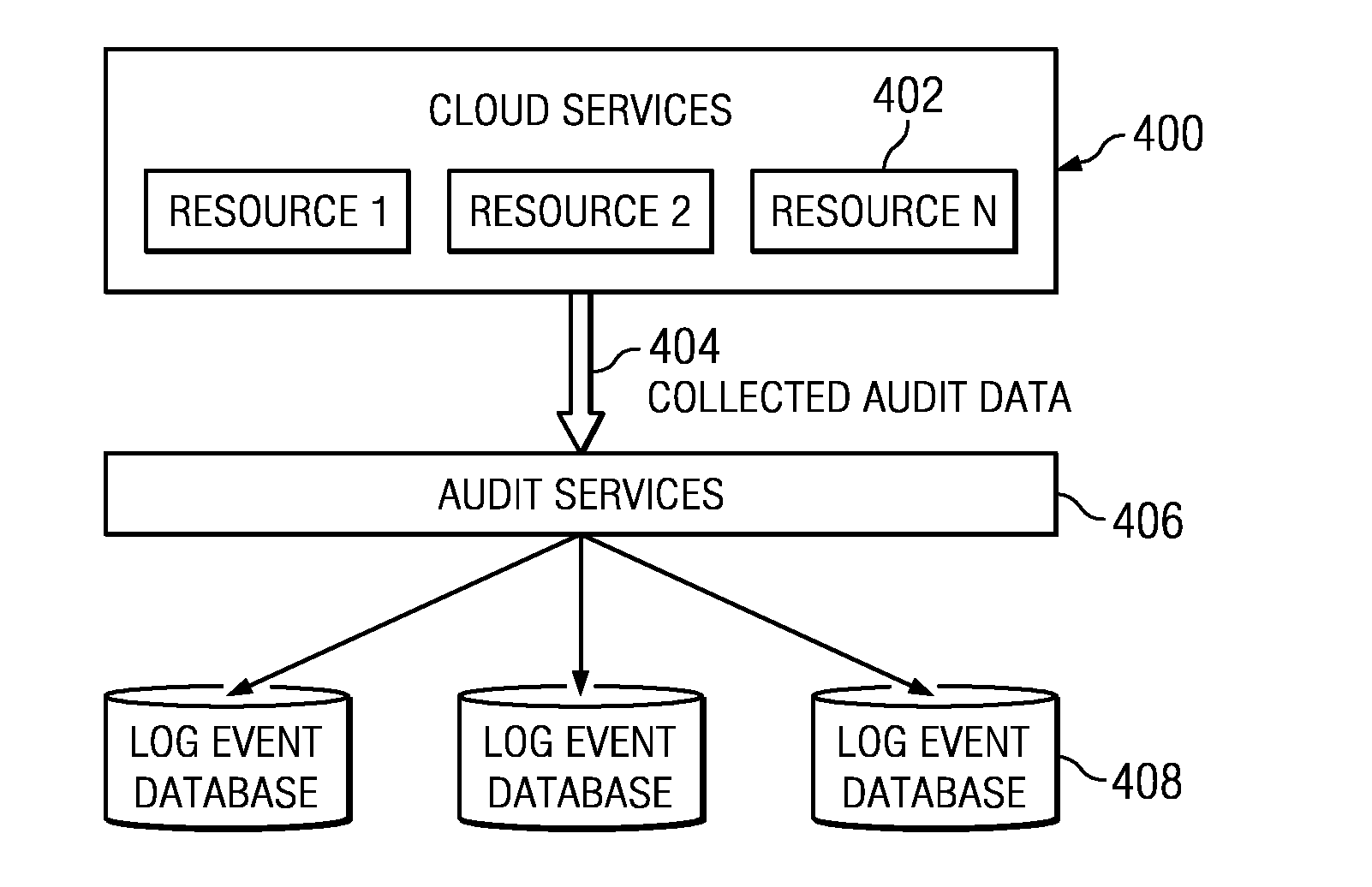
Multi-tenant audit awareness in support of cloud environments
ActiveUS20120179646A1Facilitate compliance analysisEasy to analyzeDatabase management systemsDigital data processing detailsData miningComputer science
A cloud enablement aggregation proxy (CEAP) receives and processes audit data from audited resources before such data is stored in a database. The CEAP manages log data for resources hosted in a multi-tenant shared pool of configurable computing resources (e.g., a compute cloud). A method for managing log data begins by the proxy aggregating and normalizing log information received from a plurality of the resources. The aggregated and normalized log information is then parsed to identify a tenant associated with each of a set of transactions. For each of the set of transactions, the CEAP annotates log data associated with the tenant and the particular transaction to include a tenant-specific identifier. An optional tenant separation proxy (TSP) separates the annotated log data on a per tenant basis prior to storage, and the tenant-specific log data may be stored in per tenant data structures or dedicated tenant log event databases to facilitate subsequent compliance or other analysis.
Owner:IBM CORP
Techniques for facilitating on-line contextual analysis and advertising
InactiveUS20100138452A1Easy to analyzeEasy to operateDigital data processing detailsSpecial data processing applicationsRelevant informationReal time analysis
Various techniques are disclosed for facilitating on-line contextual analysis and / or advertising operations implemented in a computer network. According to some embodiments, various aspects may be used for enabling advertisers to provide contextual advertising promotions to end-users based upon real-time analysis of web page content which may be served to an end-user's computer system. In at least one embodiment, the information obtained from the real-time analysis may be used to select, in real-time, contextually relevant information, advertisements, and / or other content which may then be displayed to the end-user, for example, via real-time insertion of textual markup objects and / or dynamic content. According to specific embodiments, various operations may be performed for adapting or modifying a conventional context-based advertising systems to improve various features such as, for example, ad relevance estimation, click-through rate estimation, advertisement selection and layout, balancing exploration and exploitation, etc.
Owner:AMOBEE
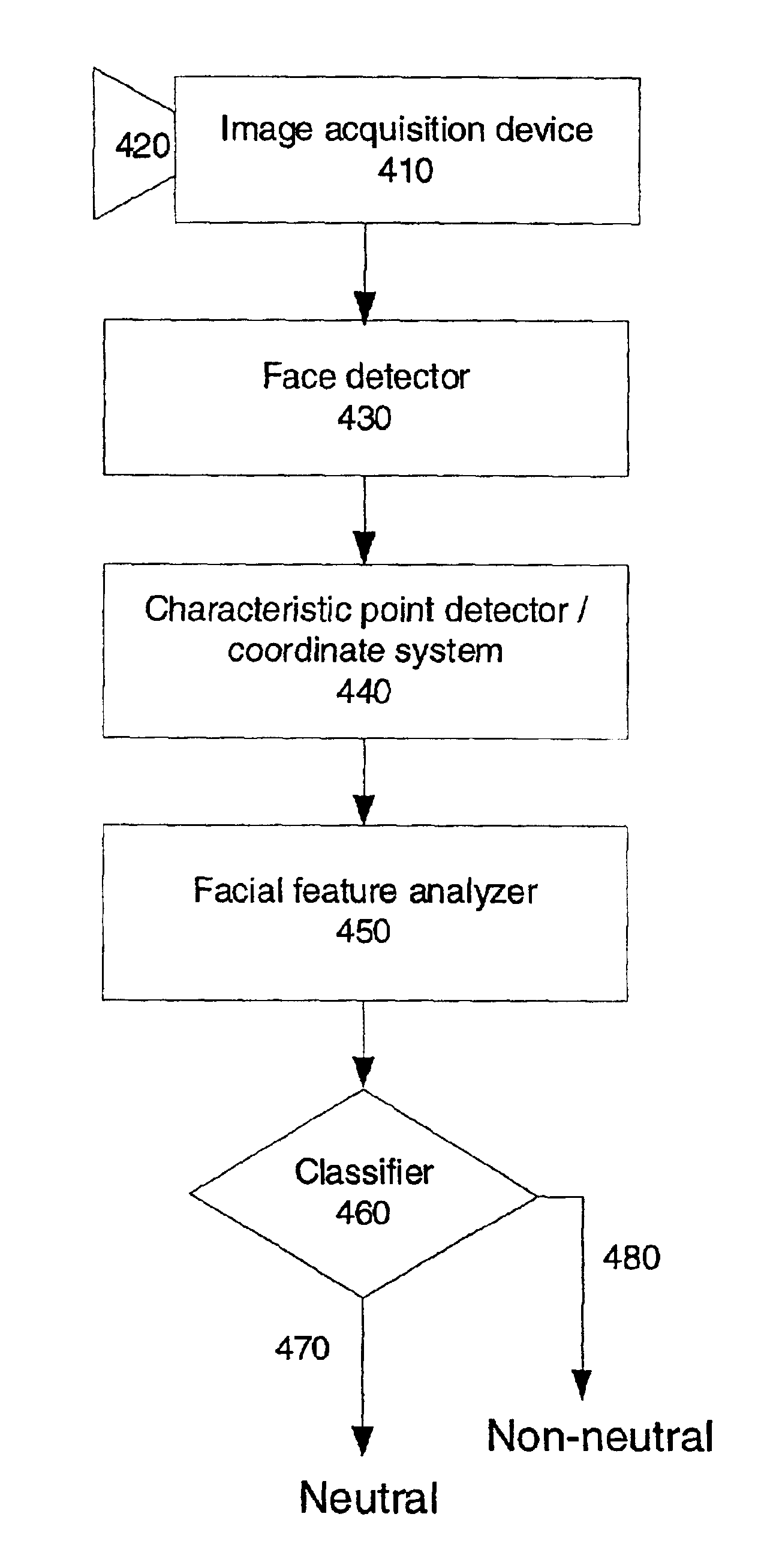
System and method for automatically detecting neutral expressionless faces in digital images
ActiveUS6879709B2Improve facial expression analysisEasy to analyzeProgramme controlElectric signal transmission systemsFace detectionDigital image
A system and method for automatic detecting neutral expressionless faces in digital images and video is described. First a face detector is used to detect the pose and position of a face and find the facial components. Second, the detected face is normalized to a standard size face. Then a set of geometrical facial features and three histograms in zones of mouth are extracted. Finally, by feeding these features to a classifier, the system detects if there is the neutral expressionless face or not.
Owner:SAMSUNG ELECTRONICS CO LTD
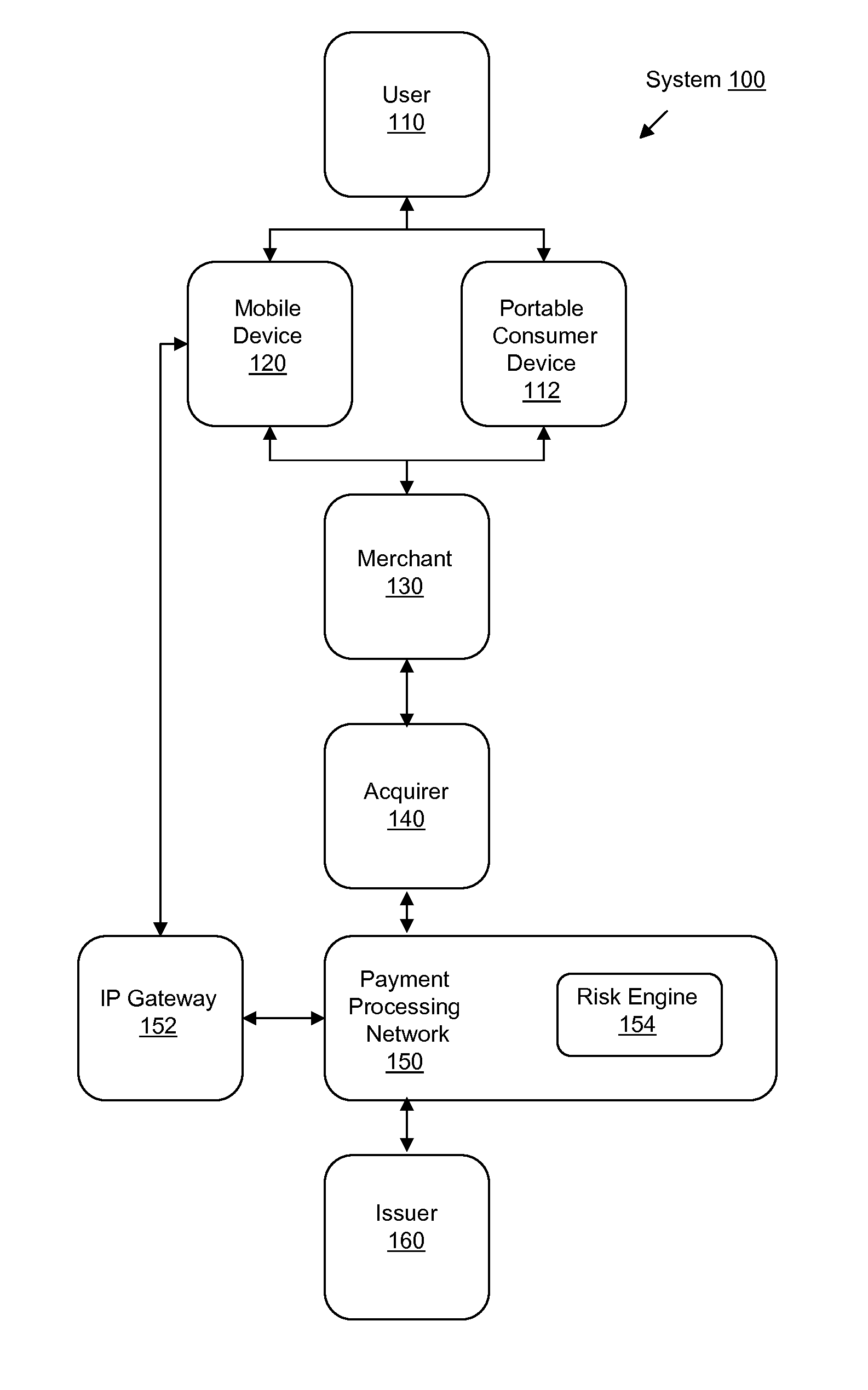
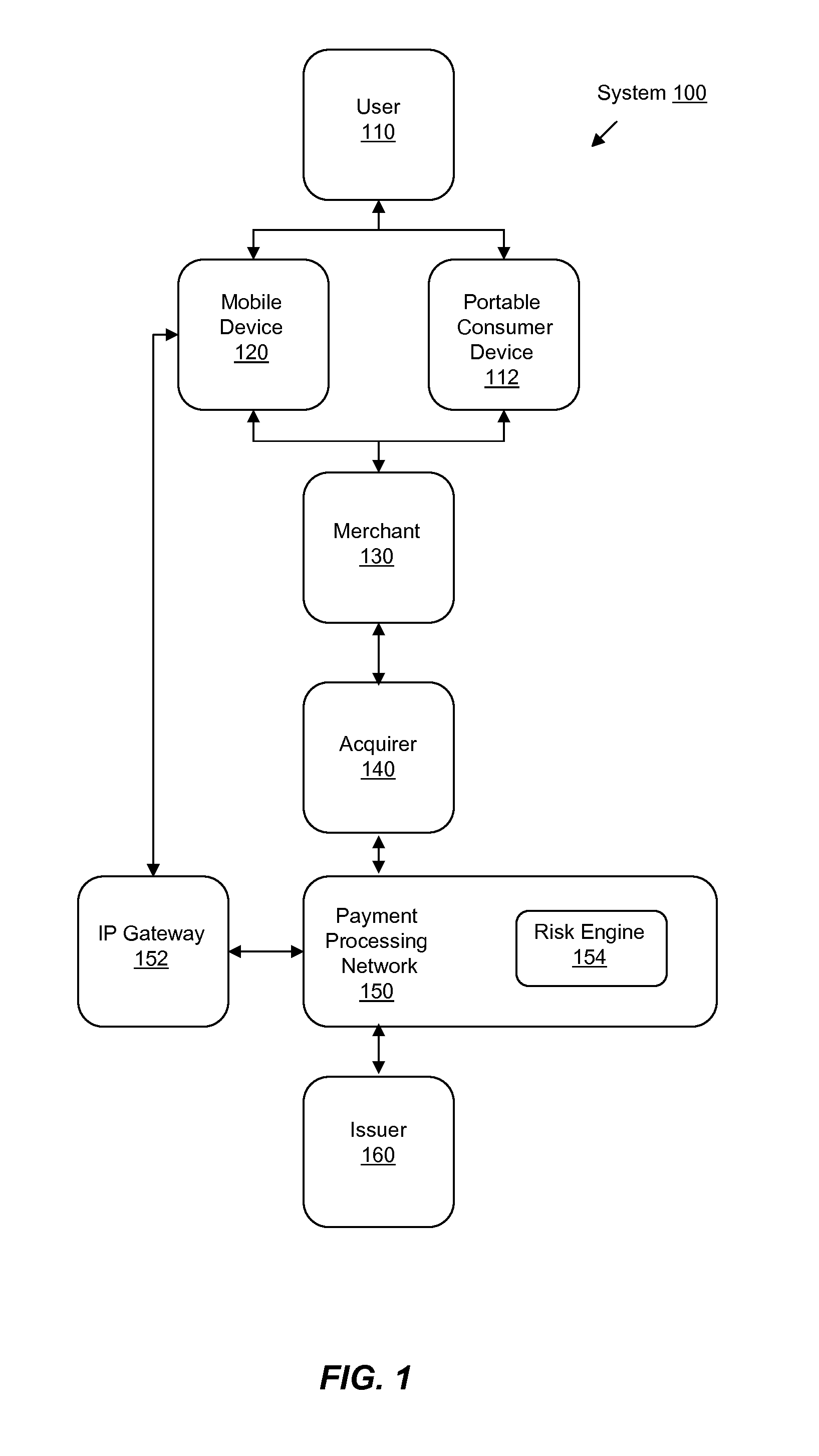
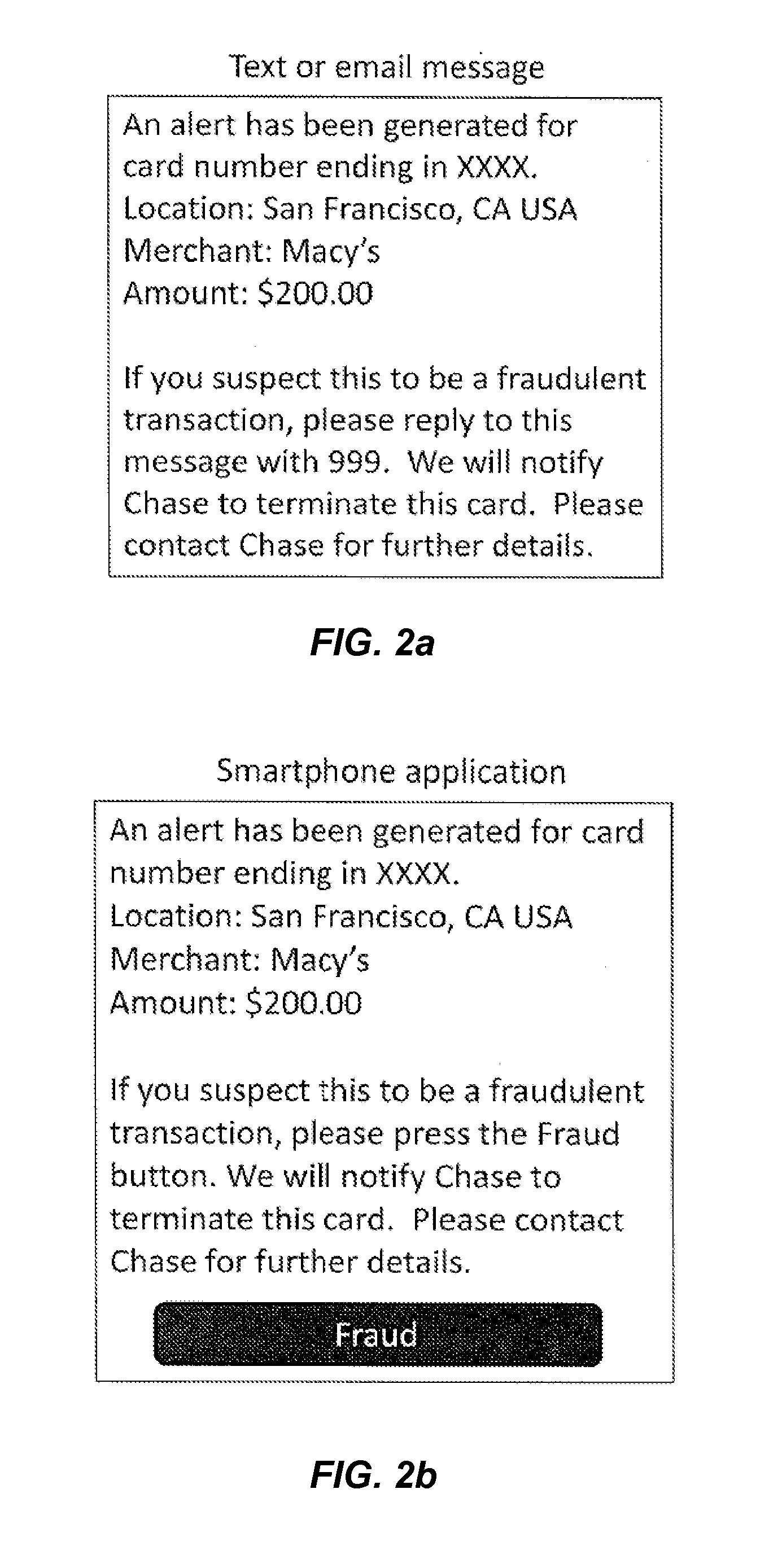
System and Method for Early Detection of Fraudulent Transactions
InactiveUS20110238564A1Faster and efficient useEasy to detectFinancePayment architectureMobile deviceFraudulent transaction
Systems, methods, and computer-readable media are disclosed for improved early detection and alerts related to fraudulent transactions. Certain embodiments involve sending an alert message to a mobile device associated with a portable consumer device. The alert includes notification of a recent transaction related to an account that is associated with the portable consumer device. A reply message is then received in response to the alert message. The response may indicate that the recent transaction is fraudulent. A risk engine is then updated with data associated with the reply message. In one potential additional embodiments, analysis and projections of potential future fraud are created or updated based on the reply message.
Owner:VISA INT SERVICE ASSOC
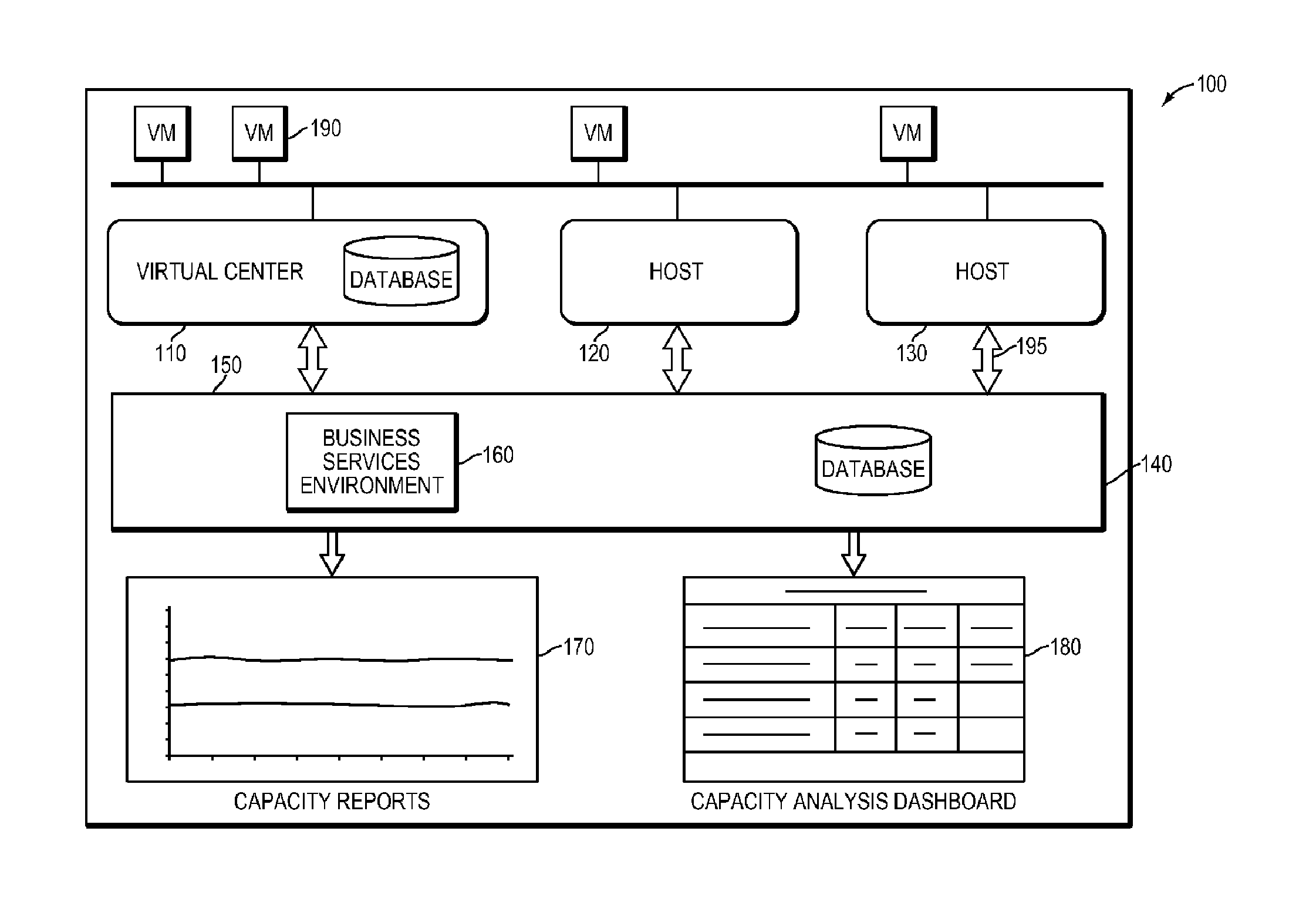
Systems and methods for real-time monitoring of virtualized environments
ActiveUS8738972B1Improve operationImprove performanceError detection/correctionSpecial data processing applicationsVirtualizationRoot cause
A method of root cause analysis in a virtual machine environment includes receiving a plurality of events from a system monitoring the virtualized environment. The events may include alarms or alerts, such as alarms or alerts associated with a resource reaching or exceeding a threshold. The capacity manager consumes these events and performs event correlation to produce a set of correlated events. The capacity manager performs a root cause analysis on the set of correlated events to identify one or more root causes. The capacity manager further performs an impact analysis to determine how the root cause impacts the system, such as other virtual machines, hosts or resource in the virtual environment. Based on the root cause and impact analysis, the capacity manager makes one or more recommendations to address issues with or to improve the operations and / or performance of the virtualized environment.
Owner:QUEST SOFTWARE INC
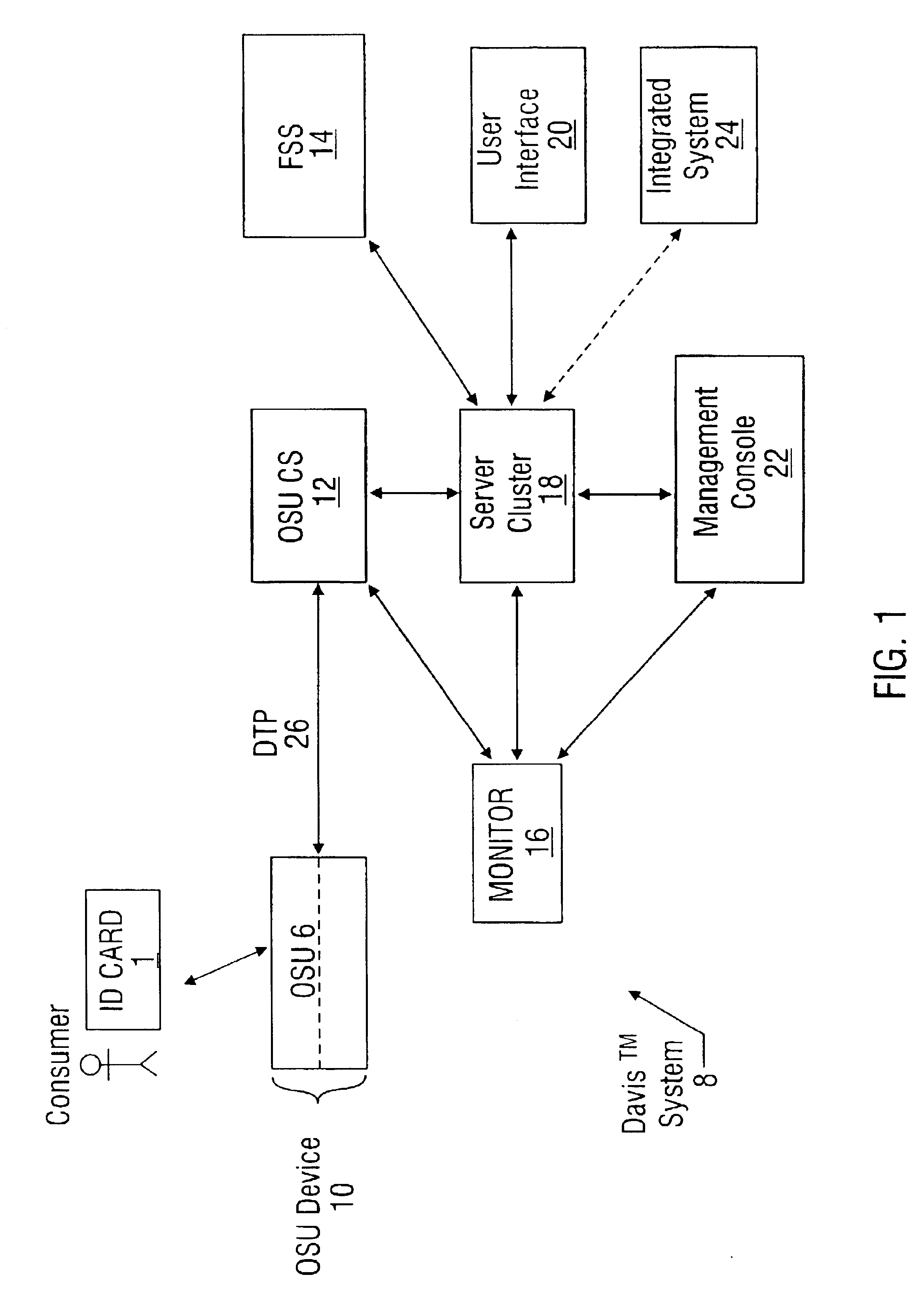
System for vending products and services using an identification card and associated methods
InactiveUS6854642B2Improve system performanceEasy to analyzeSpecial data processing applicationsVerifying markings correctnessComputer terminalDriver's license
A highly integrated and flexible system for vending products and services to consumers. The system receives information in advance of the vend by having the consumer insert an identification (ID) card, preferably a driver's license, into a point-of-purchase terminal (referred to as an OSU device). The OSU device preferably contains an Optical Scanning Unit (OSU), capable of scanning the textual information on the ID card. In one embodiment, the scanned information is compared against optical templates present in the system to discern or verify the information on the ID card, and is then used by the system to enable or disable the vending transaction, and / or to allow access to several preregistered system accounts.
Owner:CNT TECH
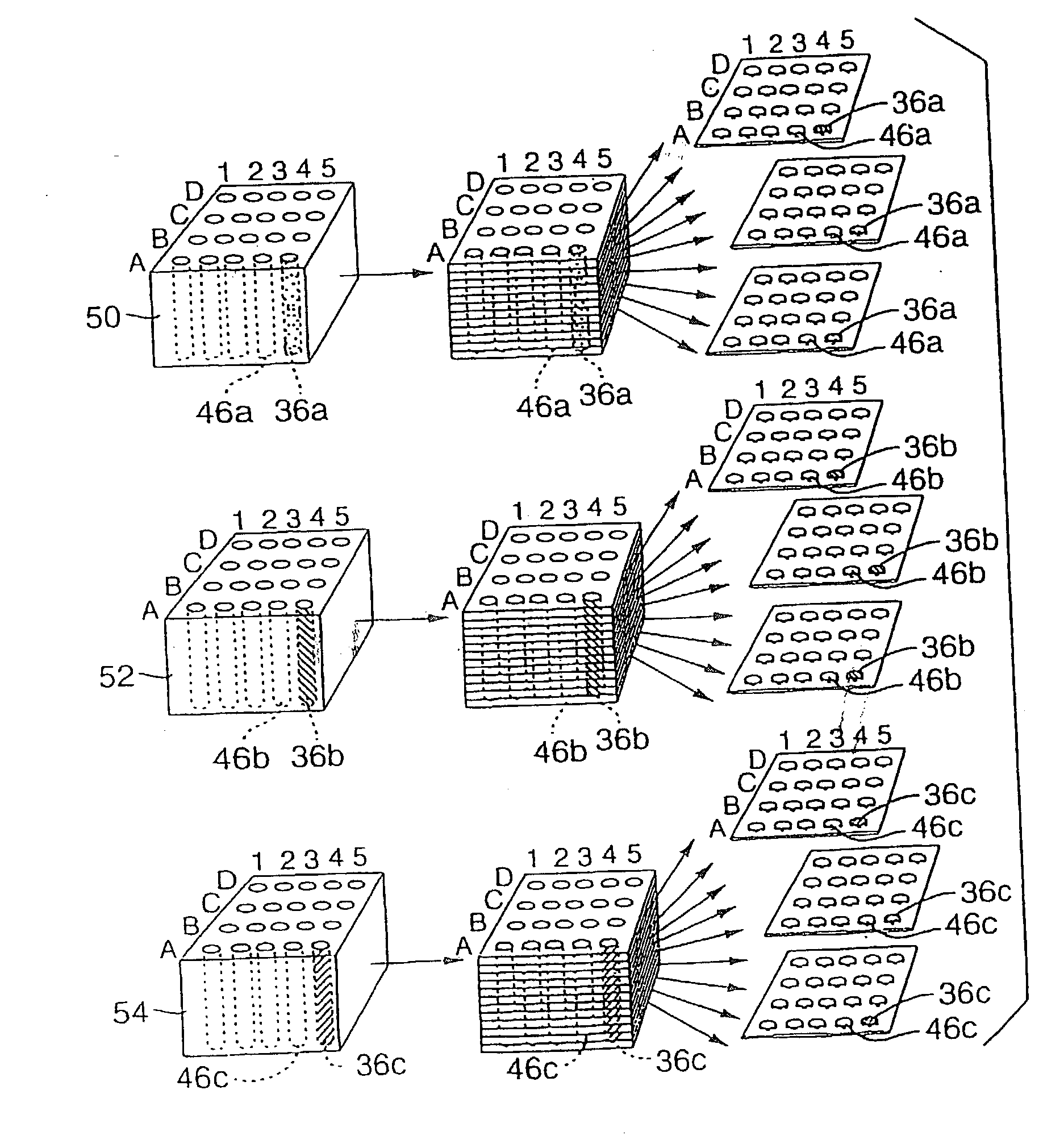
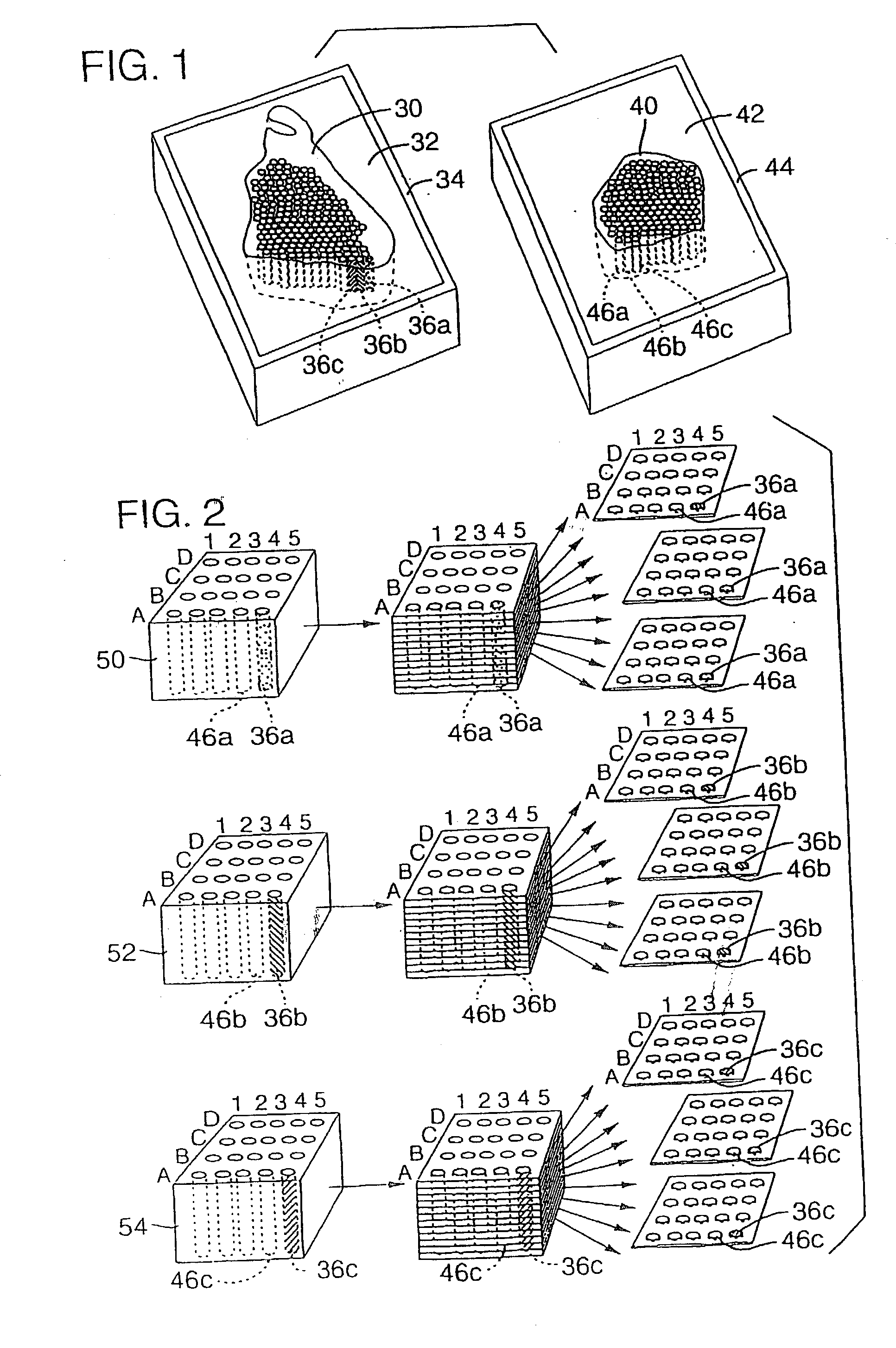
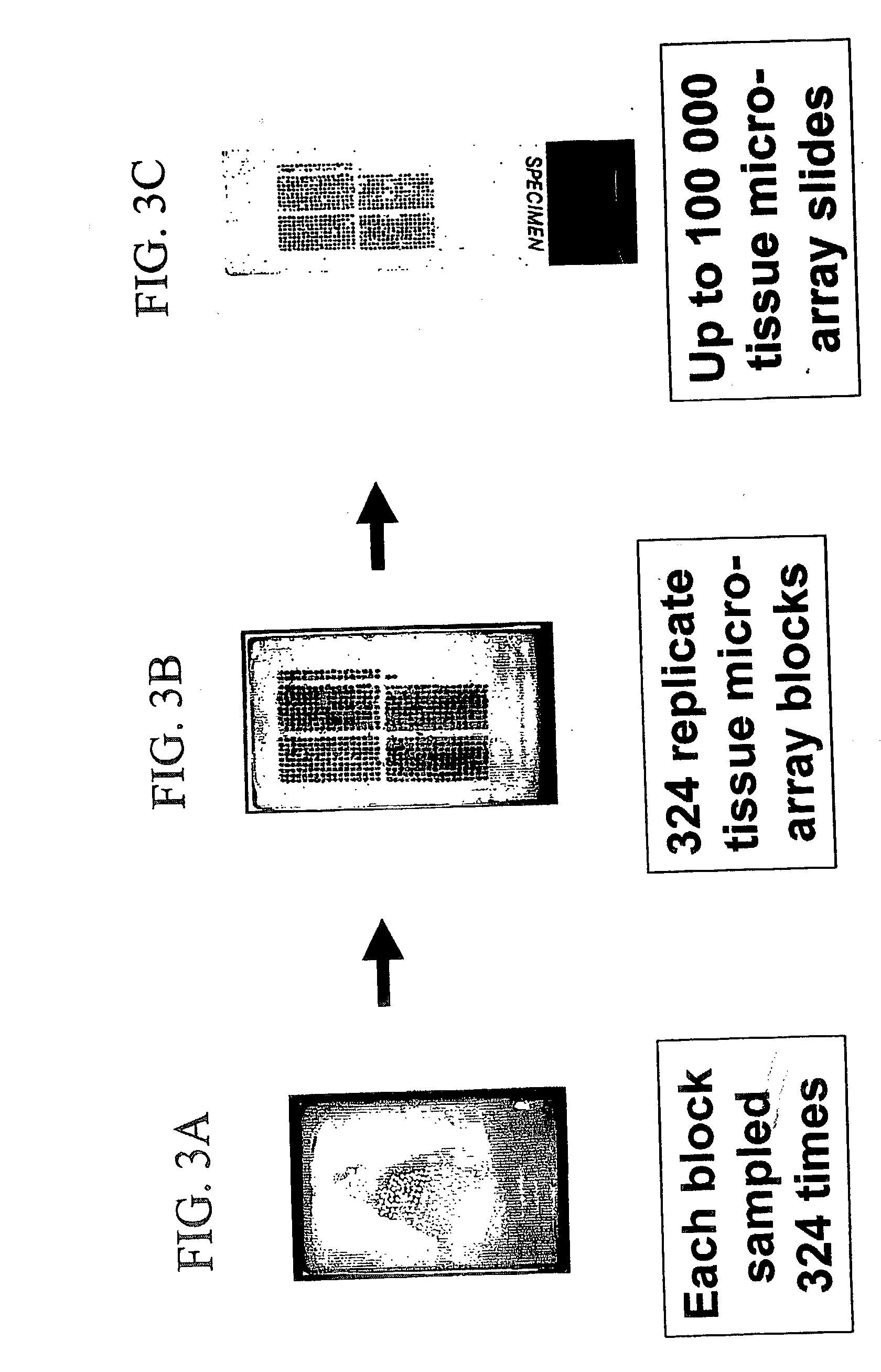
High-throughput tissue microarray technology and applications
InactiveUS20030215936A1Easy to analyzeGood for comparisonBioreactor/fermenter combinationsBiological substance pretreatmentsClinical informationTissue microarray
A method and apparatus are disclosed for a high-throughput, large-scale molecular profiling of tissue specimens by retrieving a donor tissue specimen from an array of donor specimens, placing a sample of the donor specimen in an assigned location in a recipient array, providing substantial copies of the array, performing a different biological analysis of each copy, and storing the results of the analysis. The results may be compared to determine if there are correlations or discrepancies between the results of different biological analyses at each assigned location, and also compared to clinical information about the human patient from which the tissue was obtained. The results of similar analyses on corresponding sections of the array can be used as quality control devices, for example by subjecting the arrays to a single simultaneous investigative procedure. Uniform interpretation of the arrays can be obtained, and compared to interpretations of different observers.
Owner:UNITED STATES OF AMERICA
Hybridization assisted nanopore sequencing
InactiveUS20070190542A1Eliminate needEasy to analyzeMicrobiological testing/measurementLaboratory glasswaresHybridization probeNucleic Acid Probes
A method of employing a nanopore structure in a manner that allows the detection of the positions (relative and / or absolute) of nucleic acid probes that are hybridized onto a single-stranded nucleic acid molecule. In accordance with the method the strand of interest is hybridized with a probe having a known sequence. The strand and hybridized probes are translocated through a nanopore. The fluctuations in current measured across the nanopore will vary as a function of time corresponding to the passing of a probe attachment point along the strand. These fluctuations in current are then used to determine the attachment positions of the probes along the strand of interest. This probe position data is then fed into a computer algorithm that returns the sequence of the strand of interest.
Owner:NABSYS 2 0 +1
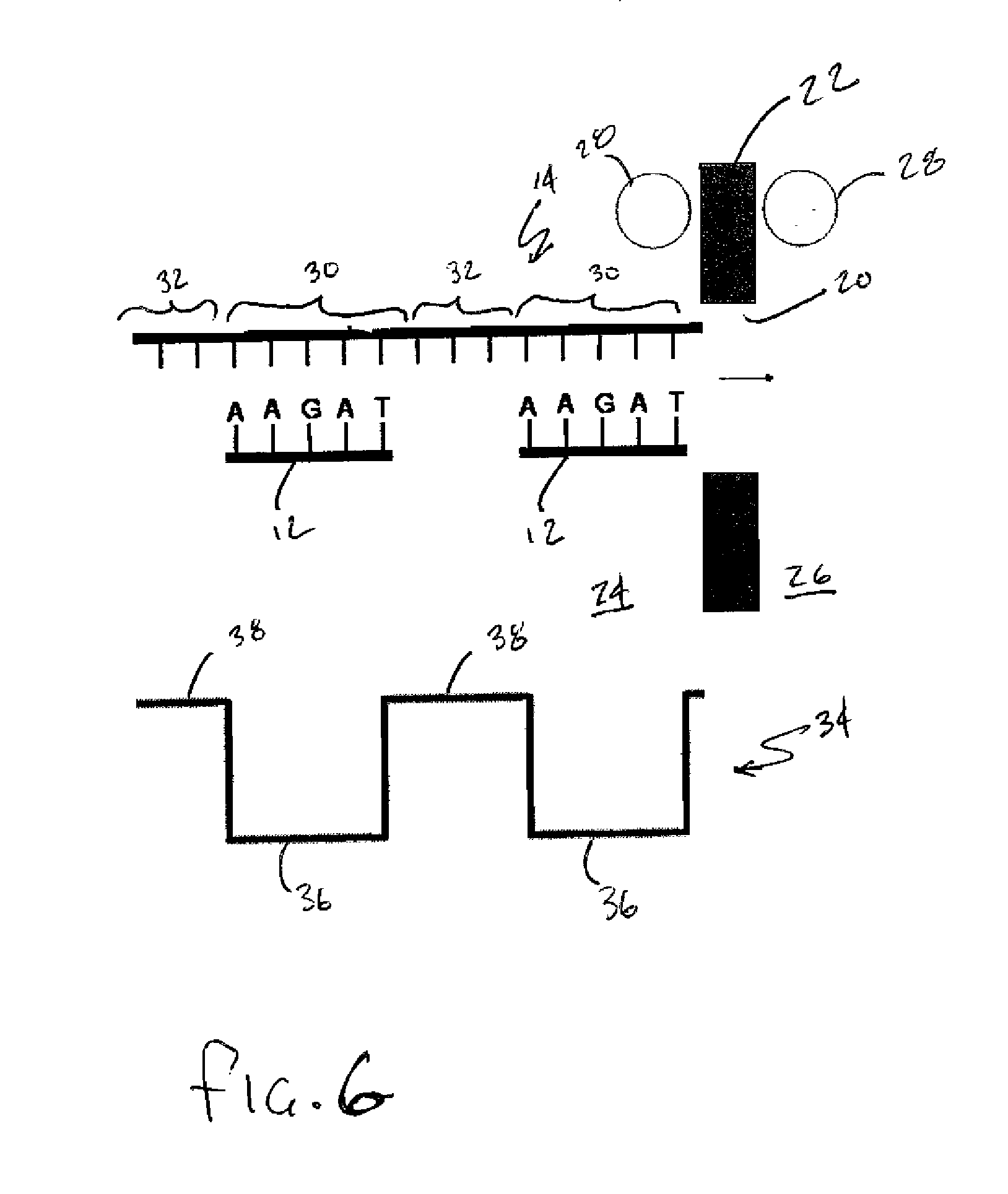
Consumer credit data storage system
InactiveUS7584146B1Rapid responseEasy to analyzeFinancePayment circuitsData informationComputerized system
A consumer credit information data base for storing current consumer credit information, as well as historical credit data information. On-line computerized systems can access the data base and present current and historical credit data information to users so that better assessments can be made as to the credit worthiness of a consumer.
Owner:INNOVIS DATA SOLUTIONS
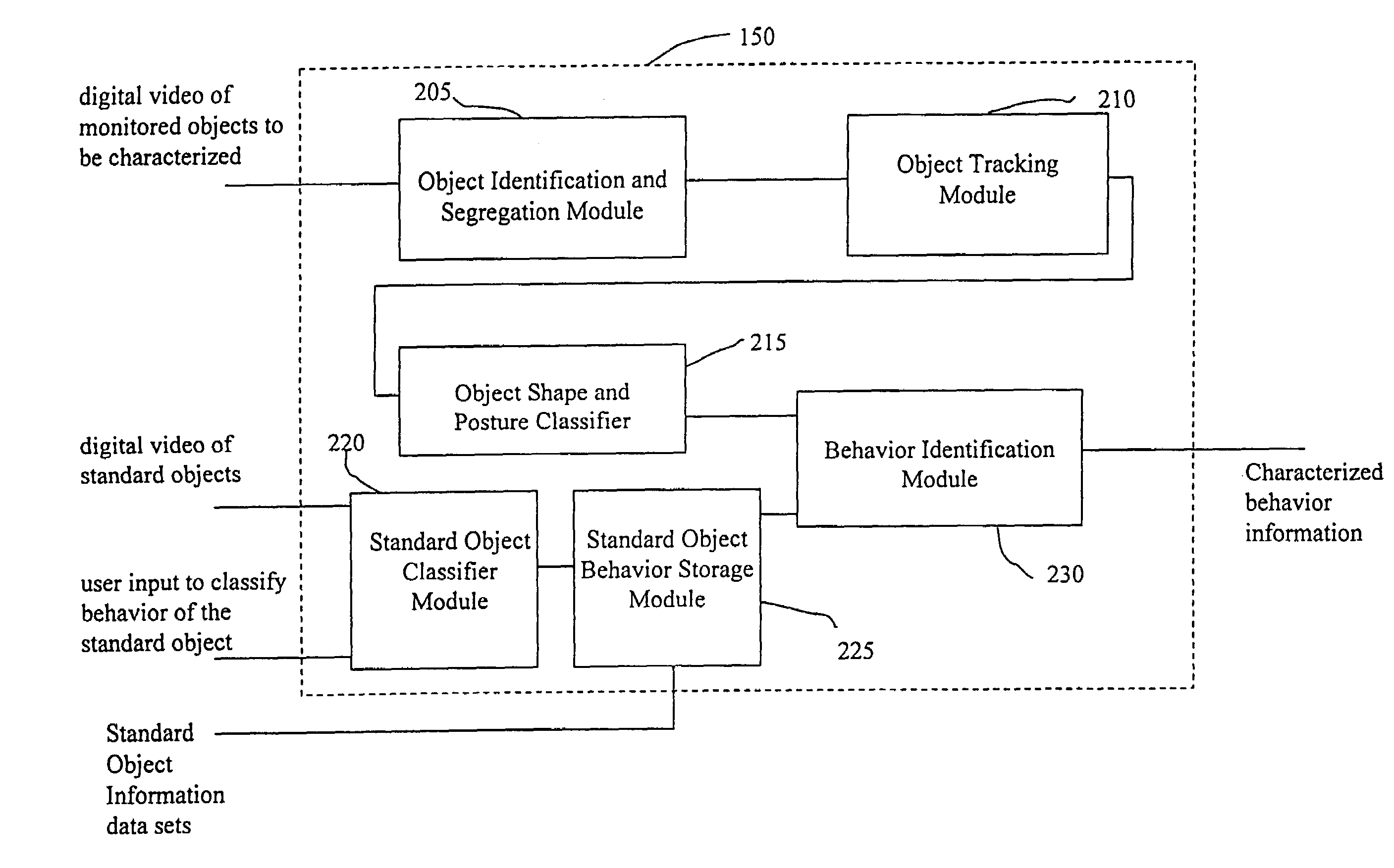
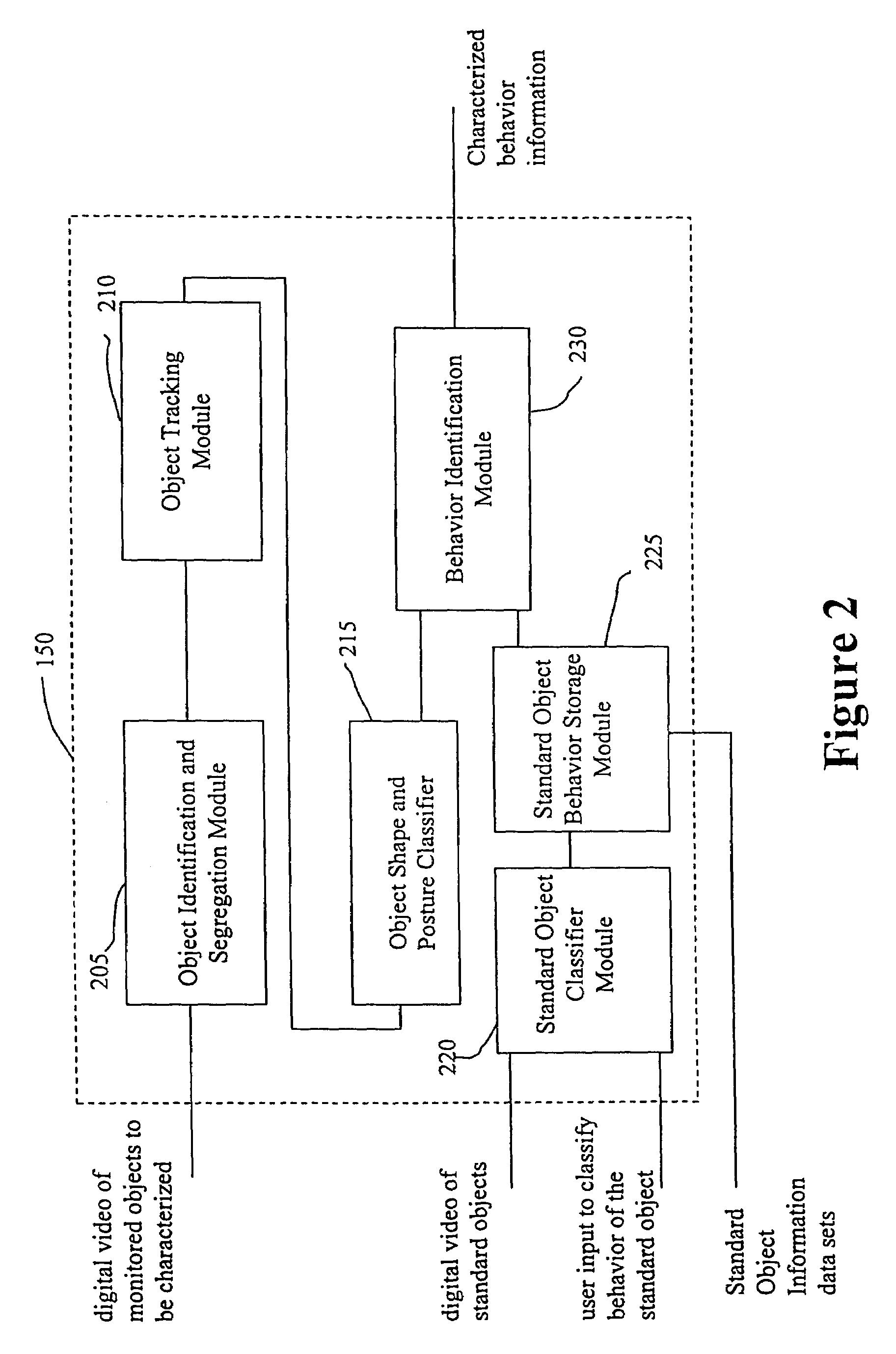
System and method for object identification and behavior characterization using video analysis
InactiveUS7068842B2Accurate identificationEfficient detectionImage enhancementImage analysisProbabilistic methodAnimal behavior
In general, the present invention is directed to systems and methods for finding the position and shape of an object using video. The invention includes a system with a video camera coupled to a computer in which the computer is configured to automatically provide object segmentation and identification, object motion tracking (for moving objects), object position classification, and behavior identification. In a preferred embodiment, the present invention may use background subtraction for object identification and tracking, probabilistic approach with expectation-maximization for tracking the motion detection and object classification, and decision tree classification for behavior identification. Thus, the present invention is capable of automatically monitoring a video image to identify, track and classify the actions of various objects and the object's movements within the image. The image may be provided in real time or from storage. The invention is particularly useful for monitoring and classifying animal behavior for testing drugs and genetic mutations, but may be used in any of a number of other surveillance applications.
Owner:CLEVER SYS
Health monitoring
InactiveUS6928370B2Facilitate acquisitionEasy to analyzeVibration measurement in solidsAnalysing solids using sonic/ultrasonic/infrasonic wavesVibration measurementMonitoring system
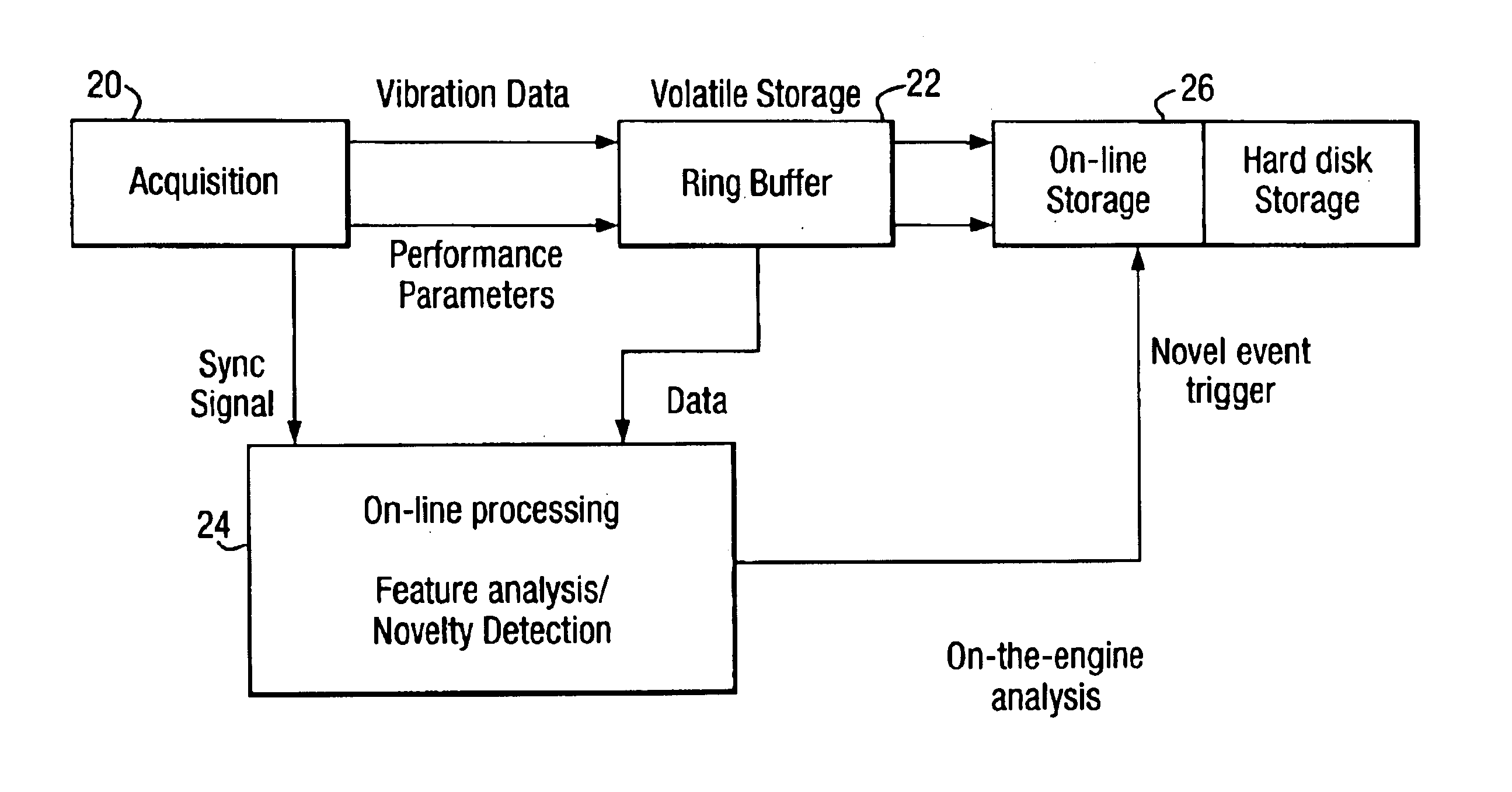
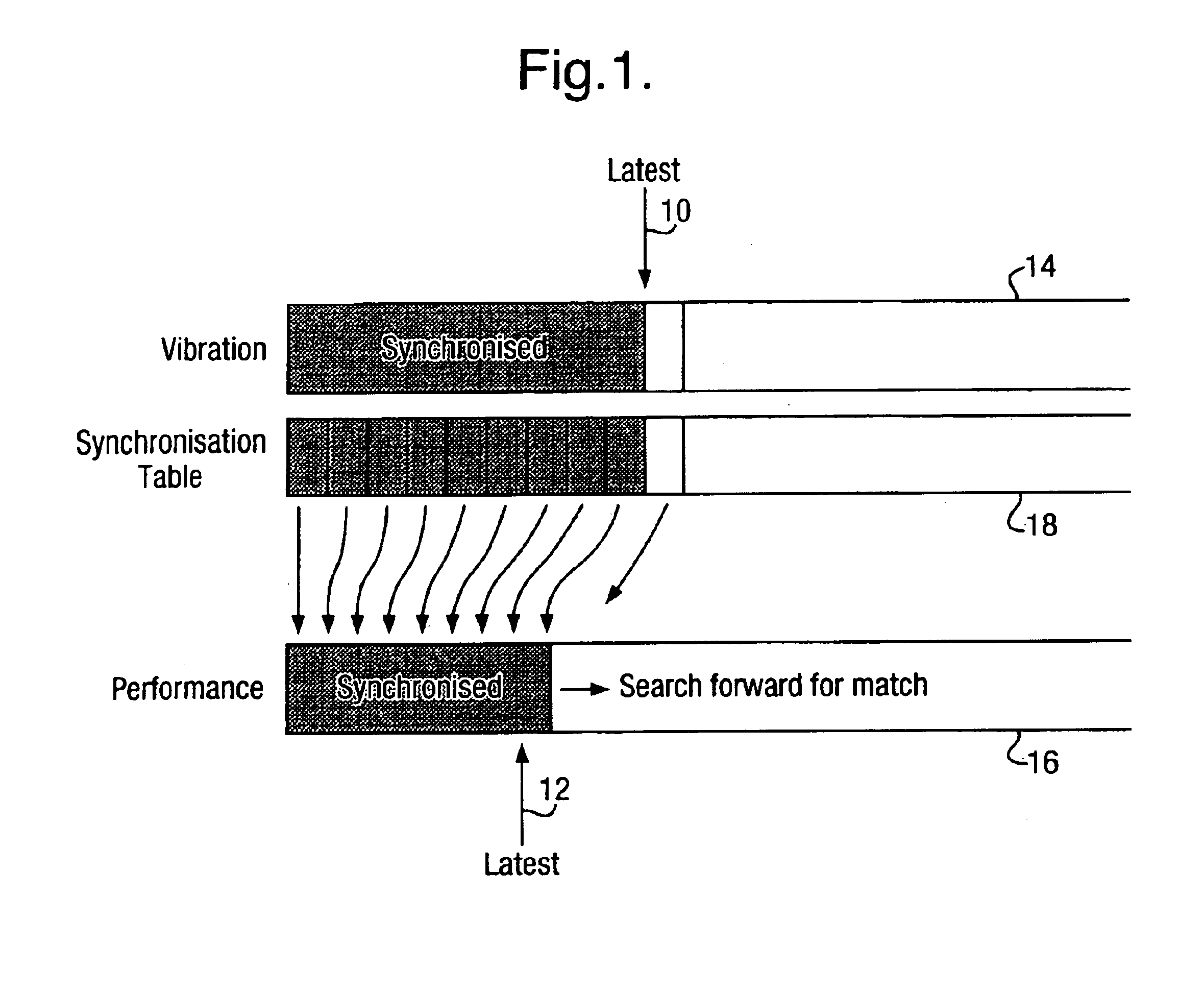
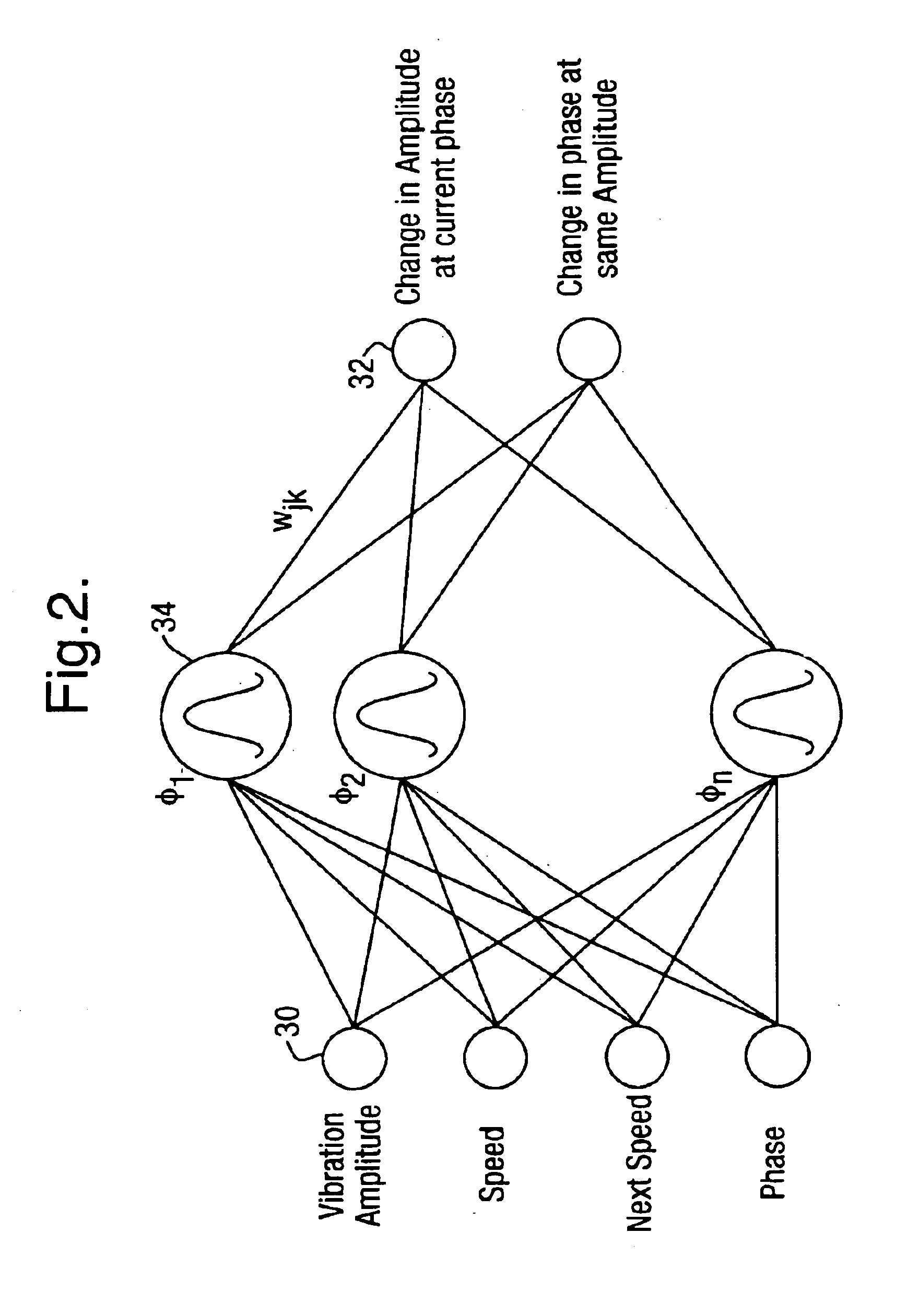
A method for monitoring the health of a system comprises performing at each of a plurality of times the steps of:constructing a condition signature from a plurality of condition indicators including (a) a plurality of vibration measurements acquired from the system or (b) one or more vibration measurements and one or more performance parameter measurements acquired from the system;predicting a normal signature from a model defining one or more inter-dependencies between said condition indicators, the normal signature corresponding to the condition signature for a healthy system;comparing the condition signature with the normal signature; andregistering an event if the condition signature differs from the normal signature by more than a predetermined threshold.
Owner:ROLLS ROYCE PLC
System and device for multi-scale analysis and representation of physiological data
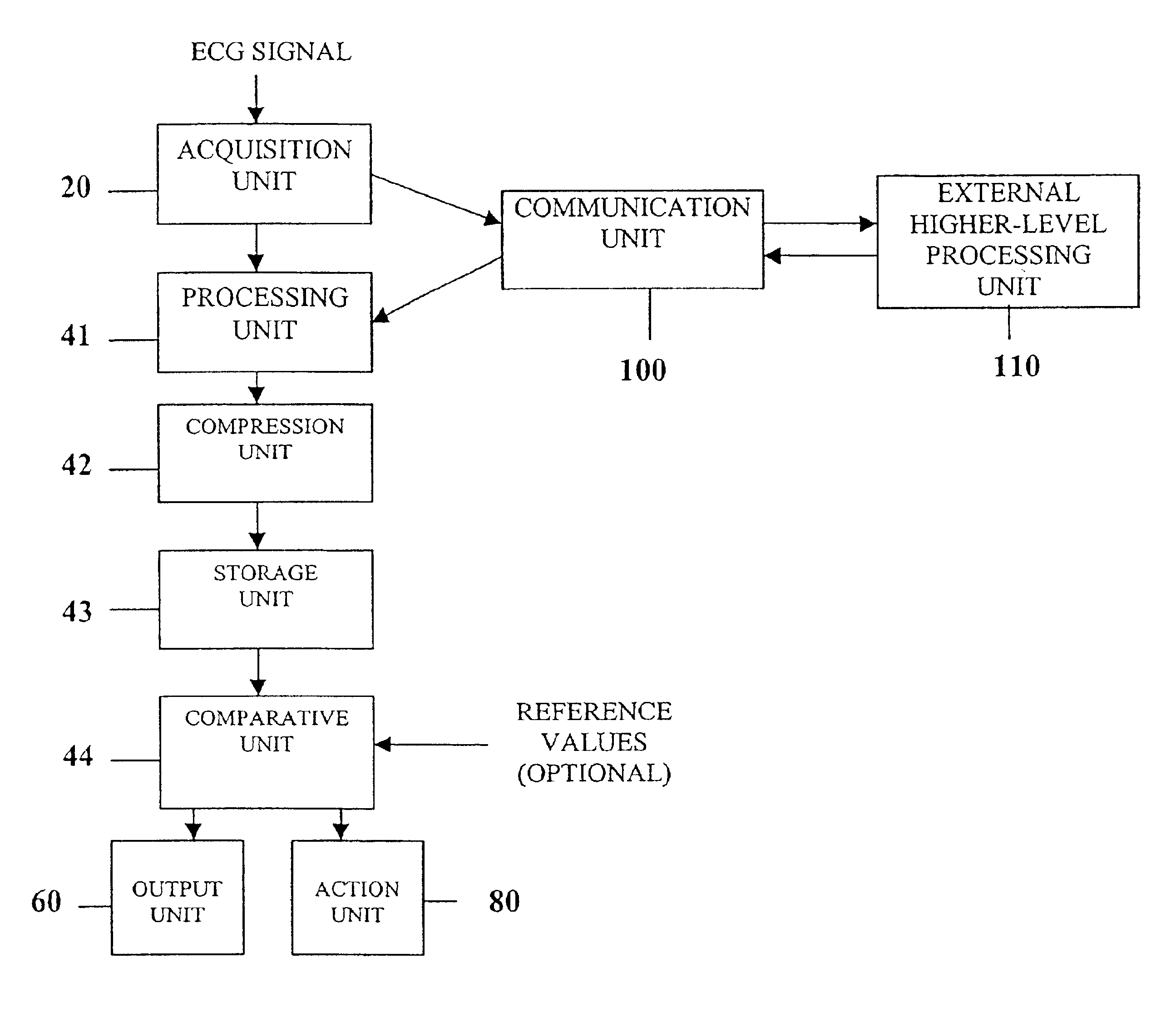
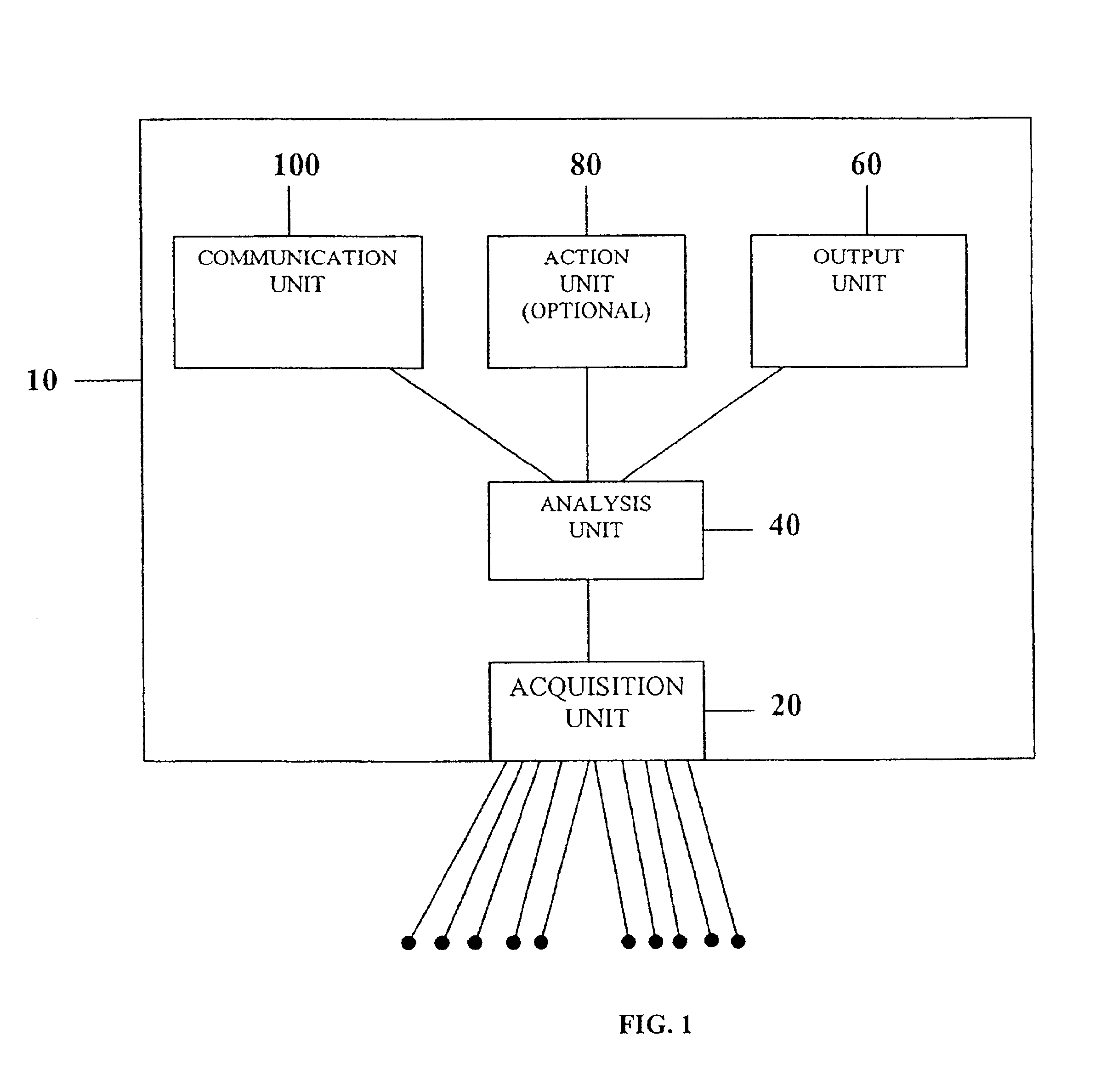
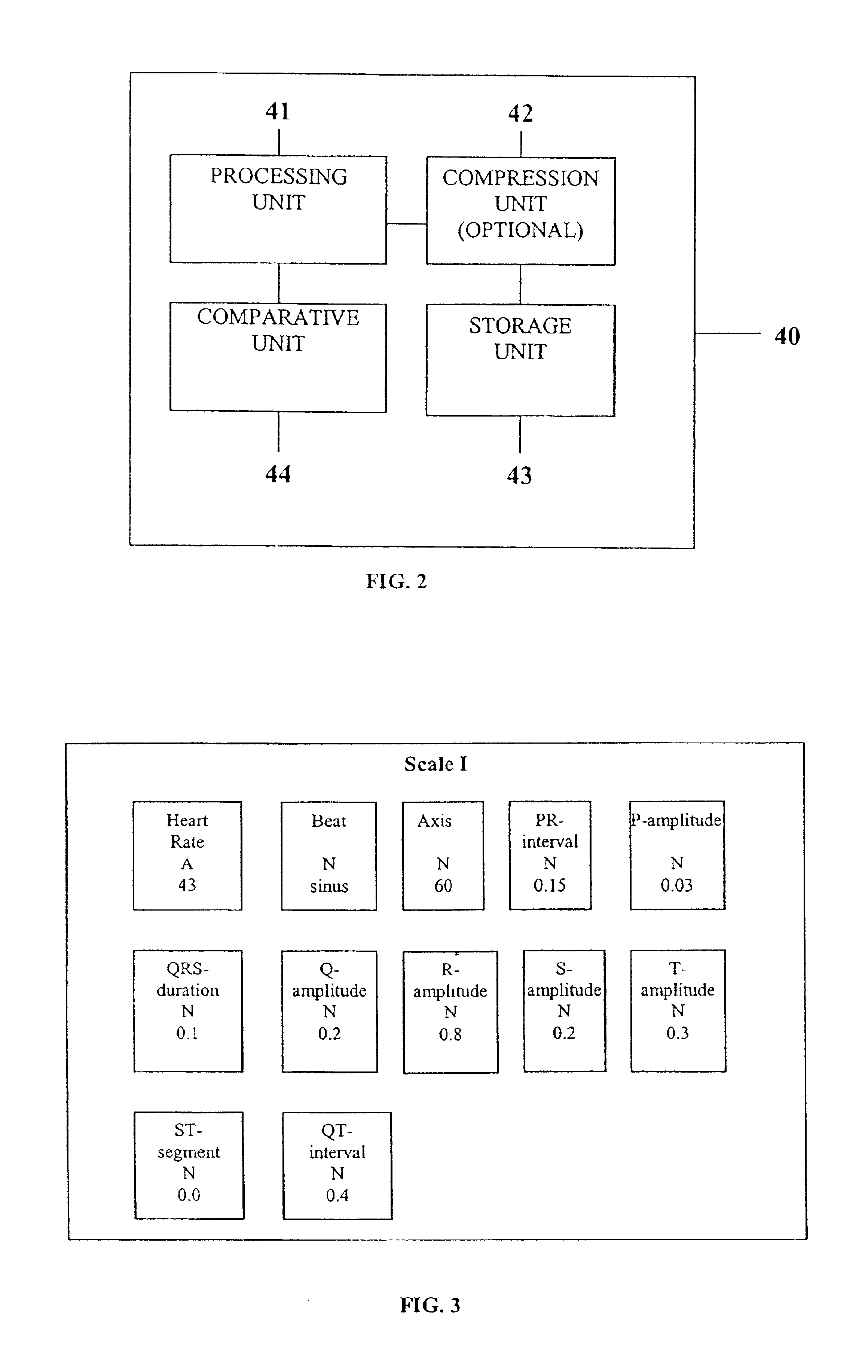
InactiveUS6925324B2Easy to analyzeIncrease computing resourcesElectrocardiographySensorsReal time analysisT wave
System comprised of a medical device and method for analyzing physiological and health data and representing the most significant parameters at different levels of detail which are understandable to a lay person and a medical professional. Low, intermediate and high-resolution scales can exchange information between each other for improving the analyses; the scales can be defined according to the corresponding software and hardware resources. A low-resolution Scale I represents a small number of primary elements such as intervals between the heart beats, duration of electrocardiographic PQ, QRS, and QT-intervals, amplitudes of P-, Q-, R-, S-, and T-waves. This real-time analysis is implemented in a portable device that requires minimum computational resources. The set of primary elements and their search criteria can be adjusted using intermediate or high-resolution levels. At the intermediate-resolution Scale II, serial changes in each of the said elements can be determined using a mathematical decomposition into series of basis functions and their coefficients. This scale can be implemented using a specialized processor or a computer organizer. At the high-resolution Scale III, combined serial changes in all primary elements can be determined to provide complete information about the dynamics of the signal. This scale can be implemented using a powerful processor, a network of computers or the Internet. The system can be used for personal or group self-evaluation, emergency or routine ECG analysis, or continuous event, stress-test or bed-side monitoring.
Owner:SHUSTERMAN VLADIMIR
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com